Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3417 results about "Decision tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
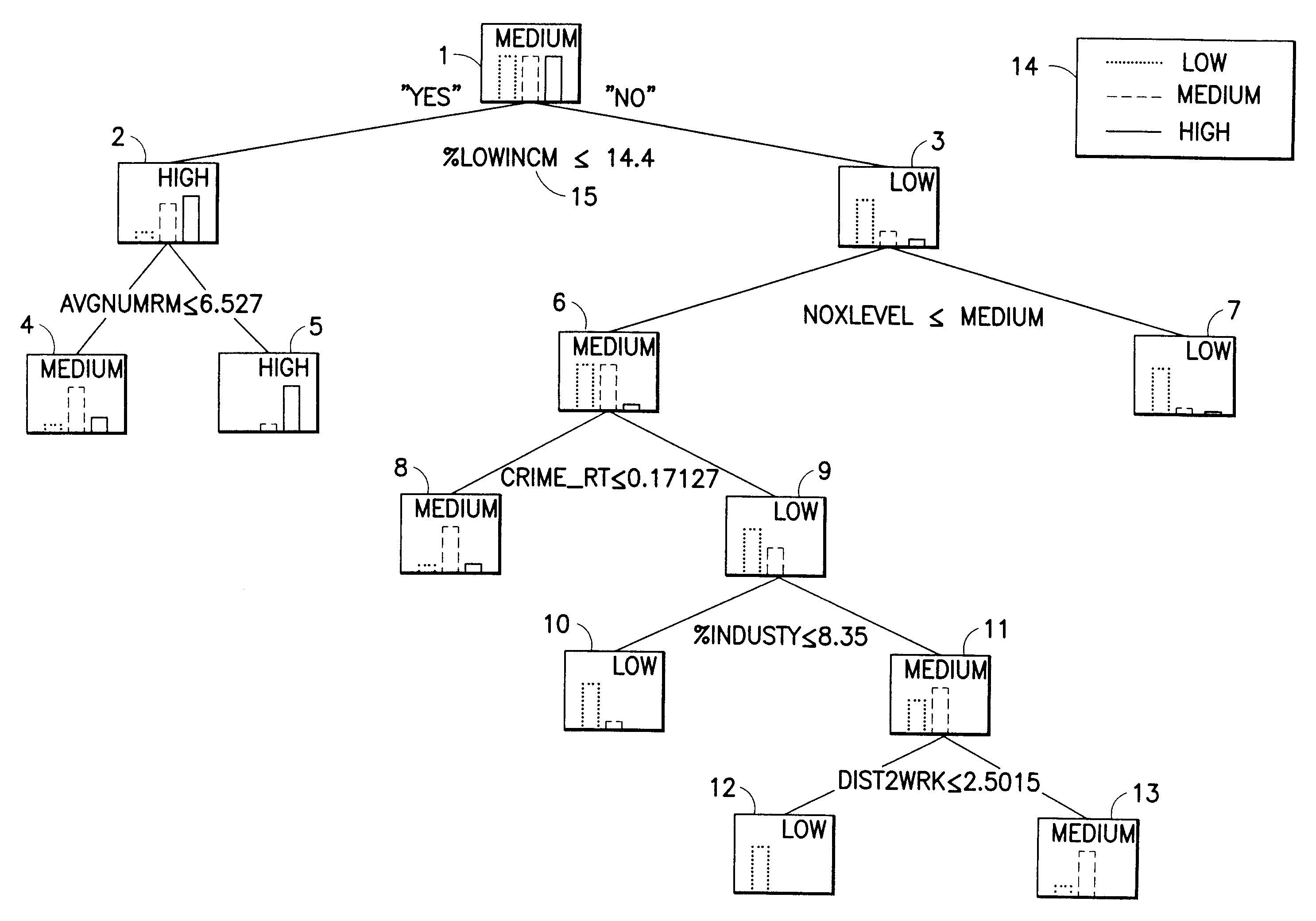
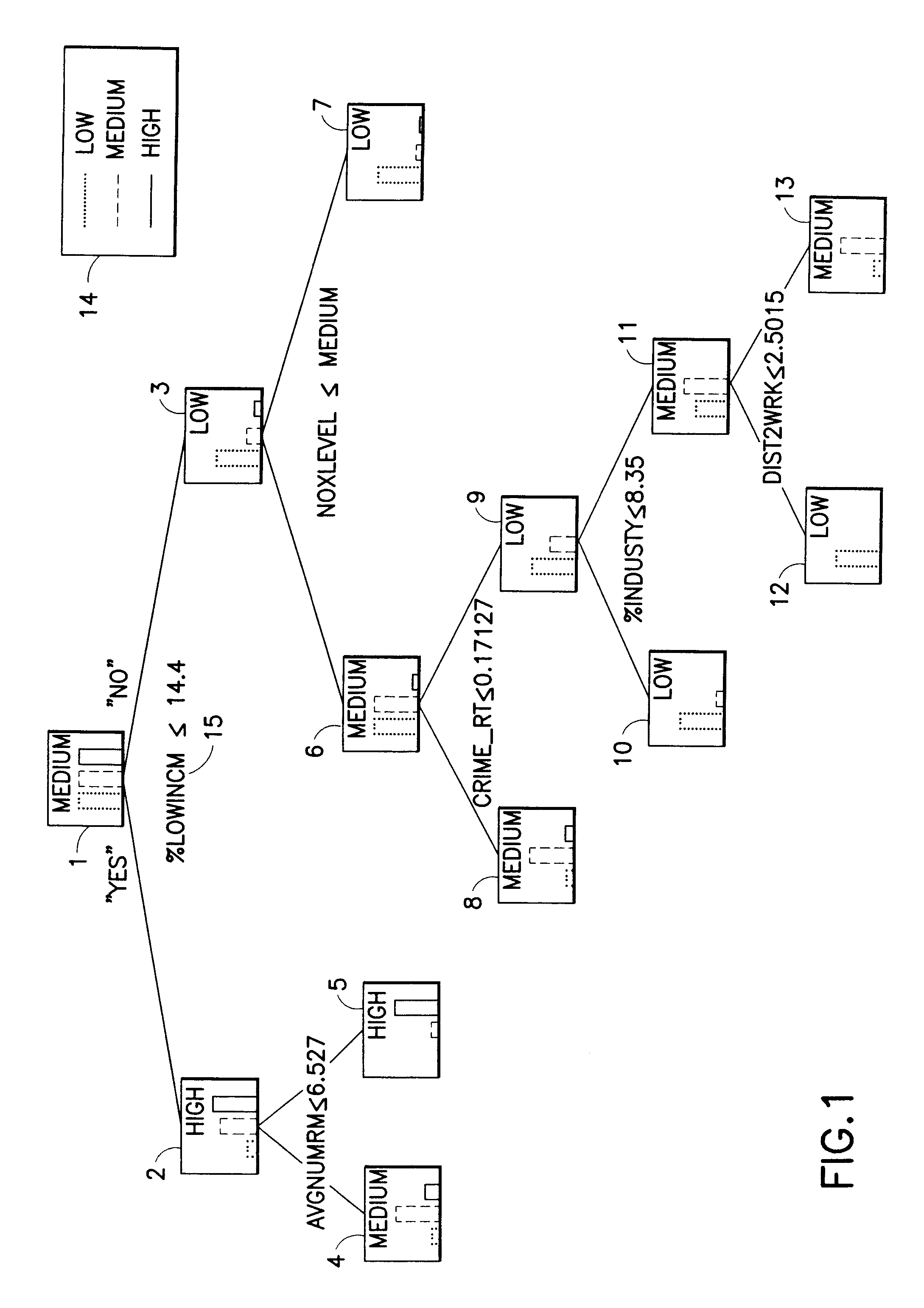
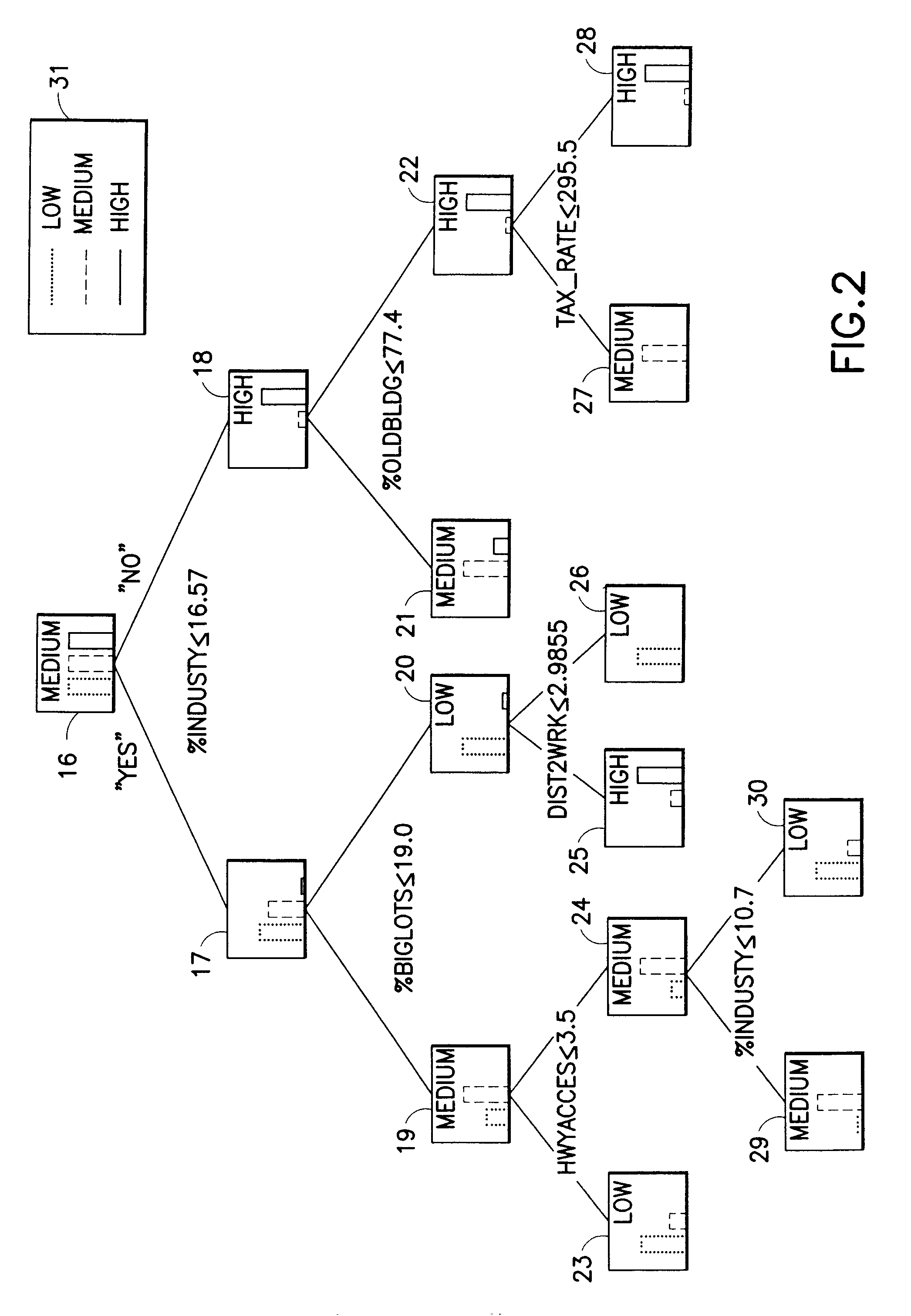
A decision tree is a decision support tool that uses a tree-like model of decisions and their possible consequences, including chance event outcomes, resource costs, and utility. It is one way to display an algorithm that only contains conditional control statements.
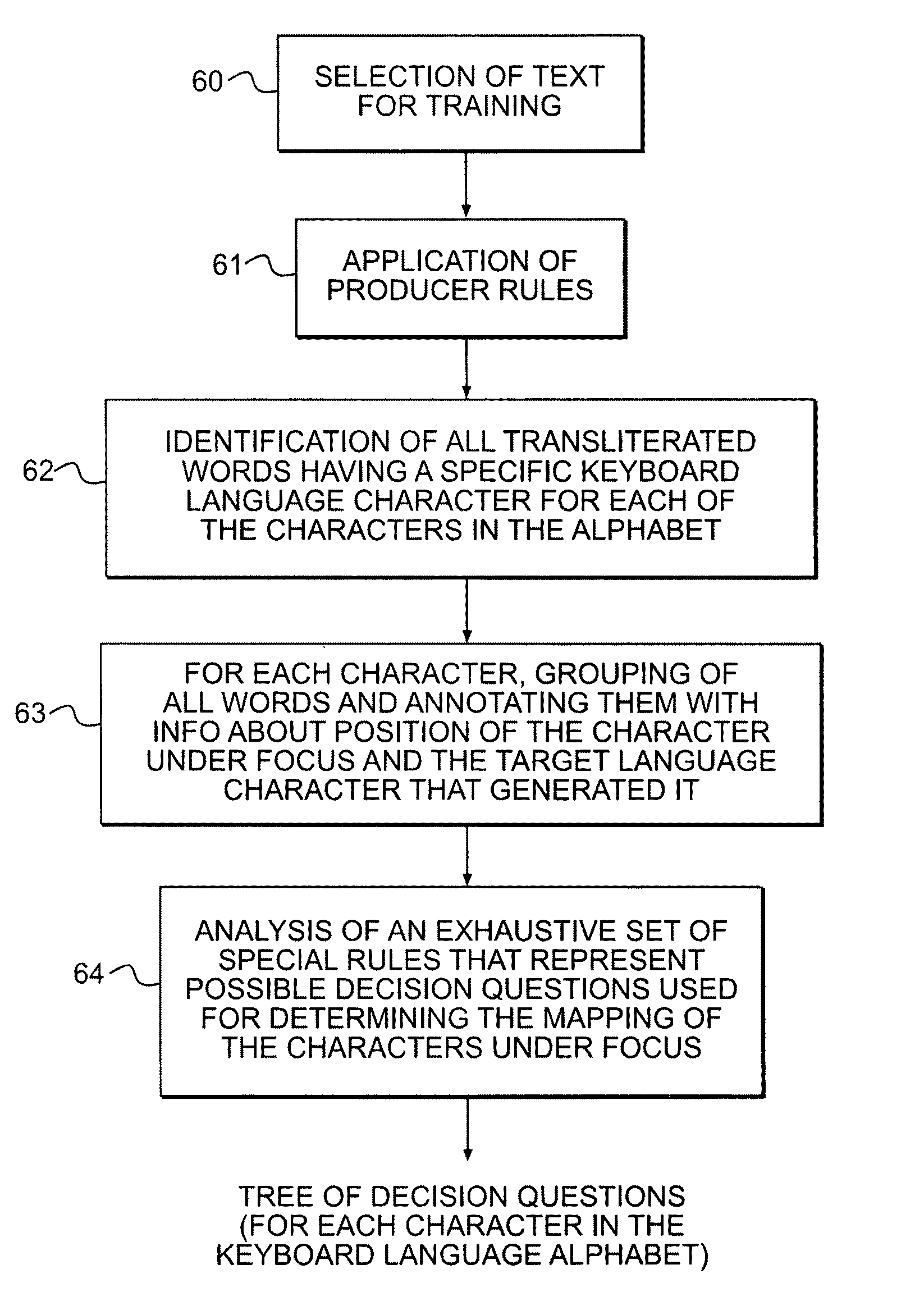
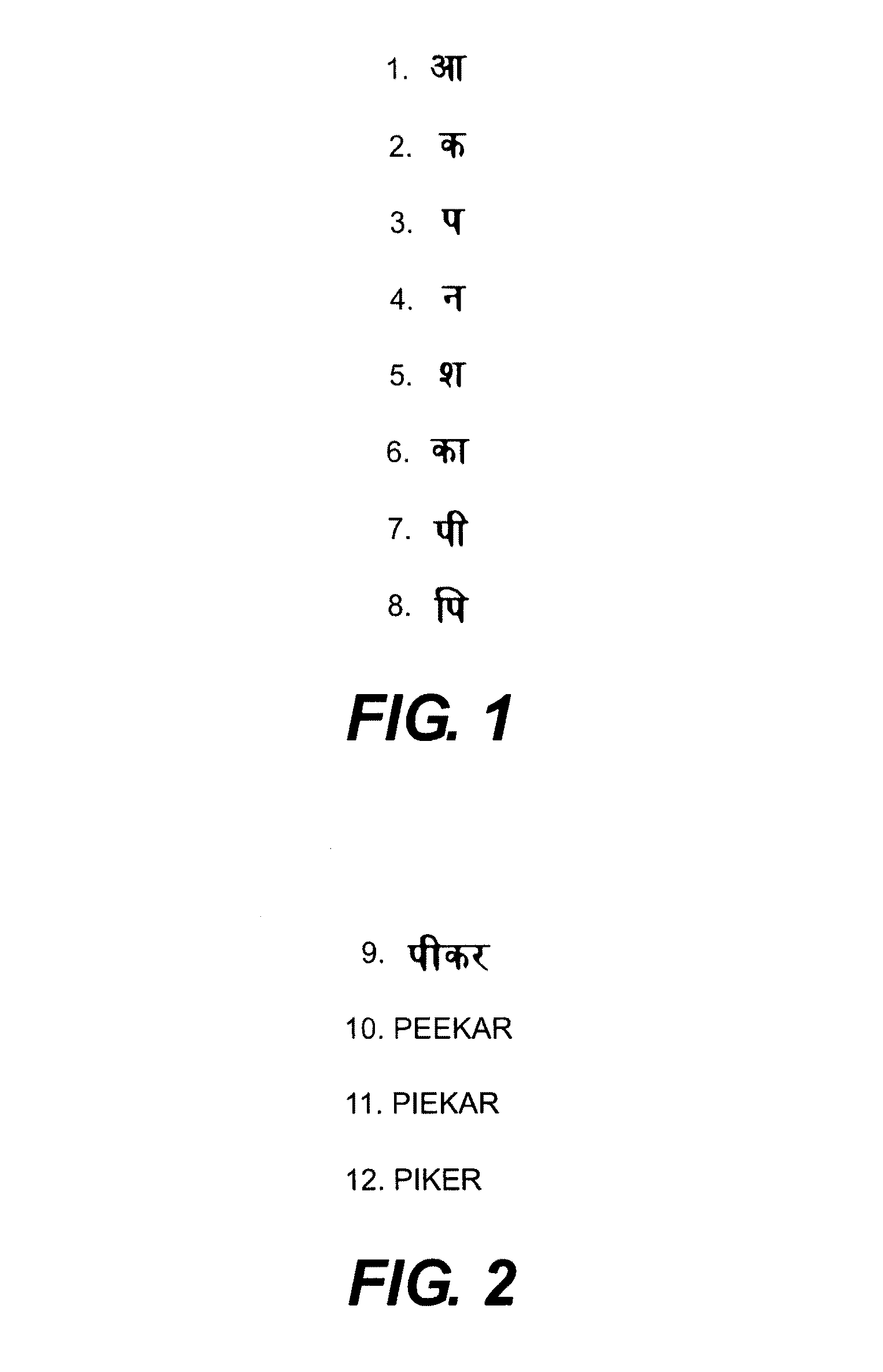
System, method to generate transliteration and method for generating decision tree to obtain transliteration
InactiveUS8005664B2Easily transliterateFast and efficient and accurate methodNatural language data processingSpecial data processing applicationsProgramming languageTransliteration
Owner:TACHYON TECH PVT
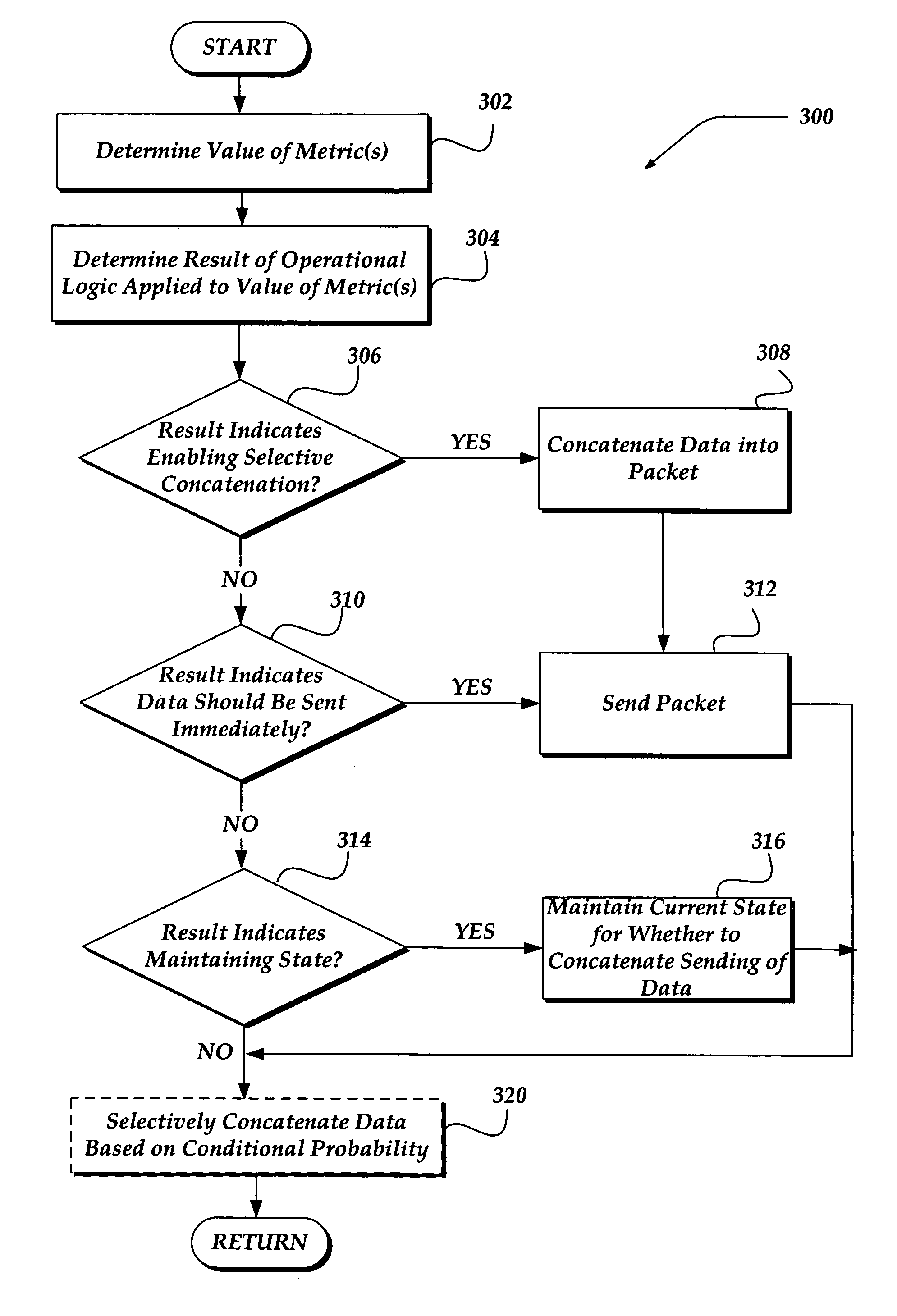
Selectively enabling network packet concatenation based on metrics
InactiveUS7873065B1Data switching by path configurationStore-and-forward switching systemsData connectionNetwork packet
A method, system, and apparatus are directed towards selectively concatenating data into a packet to modify a number of packets transmitted over a network based on a combination of network and / or send-queue metrics. In one embodiment, Nagle's algorithm is used for concatenating data into a packet. The concatenation may be selectively enabled based on heuristics applied to the combination of metrics. In one embodiment, the result may indicate that there should be a concatenation, or that data should be sent immediately, or that a current state for whether to concatenate or not should be maintained. The heuristics may include an expert system, decision tree, truth table, function, or the like. The heuristics may be provided by a user, or another computing device. In another embodiment, the concatenation may be enabled based on a conditional probability determined from the combination of metrics.
Owner:F5 NETWORKS INC
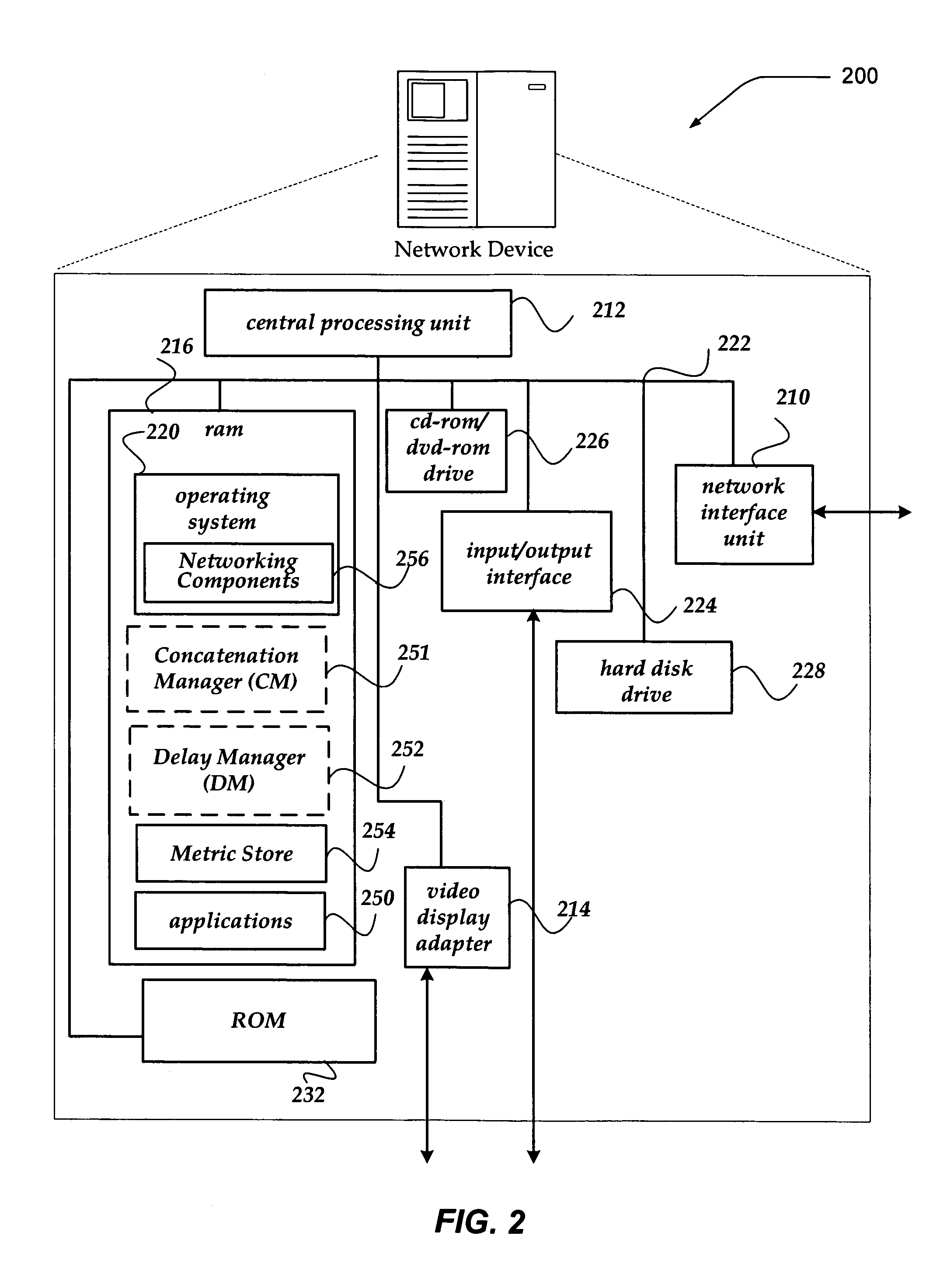
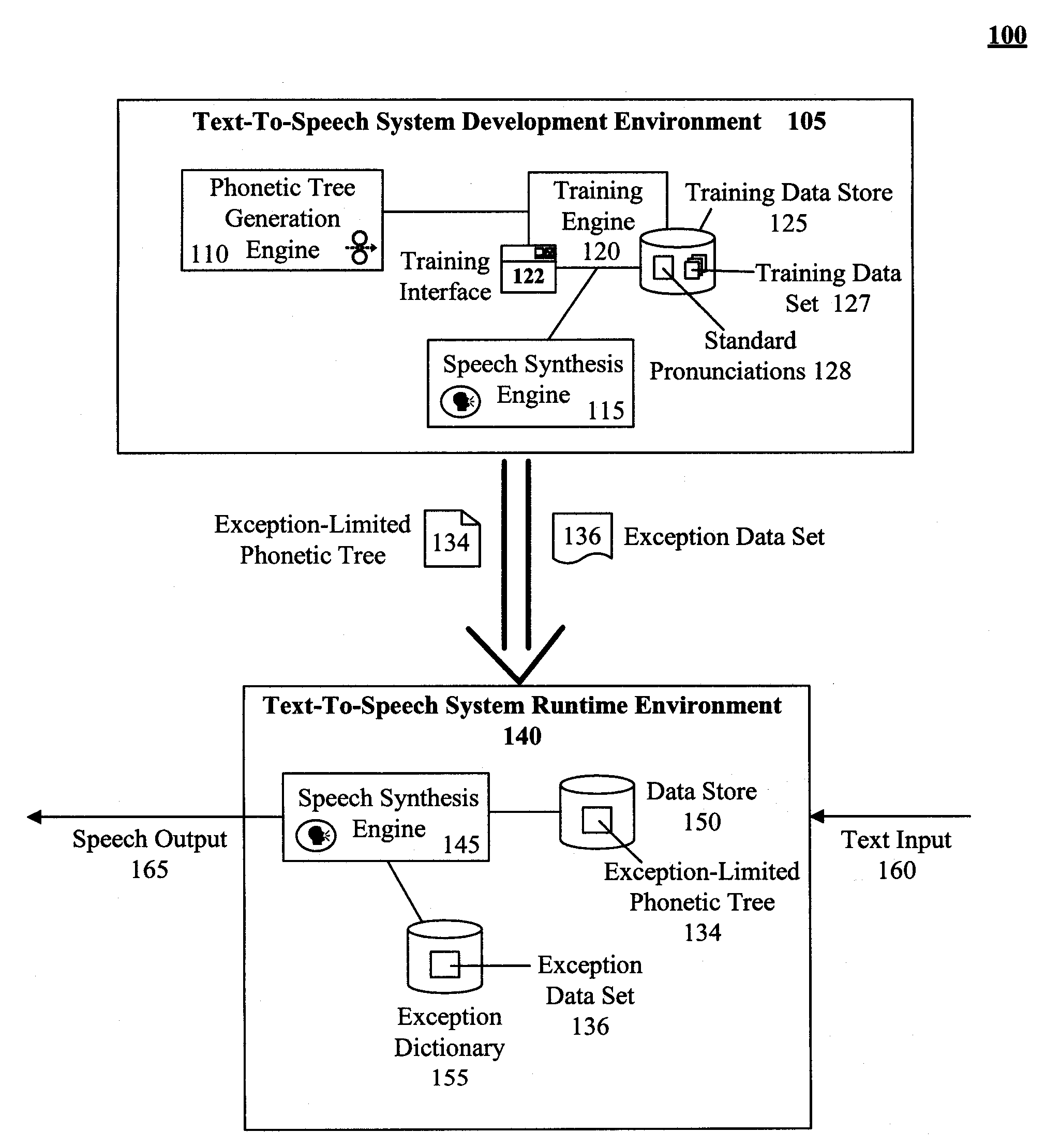
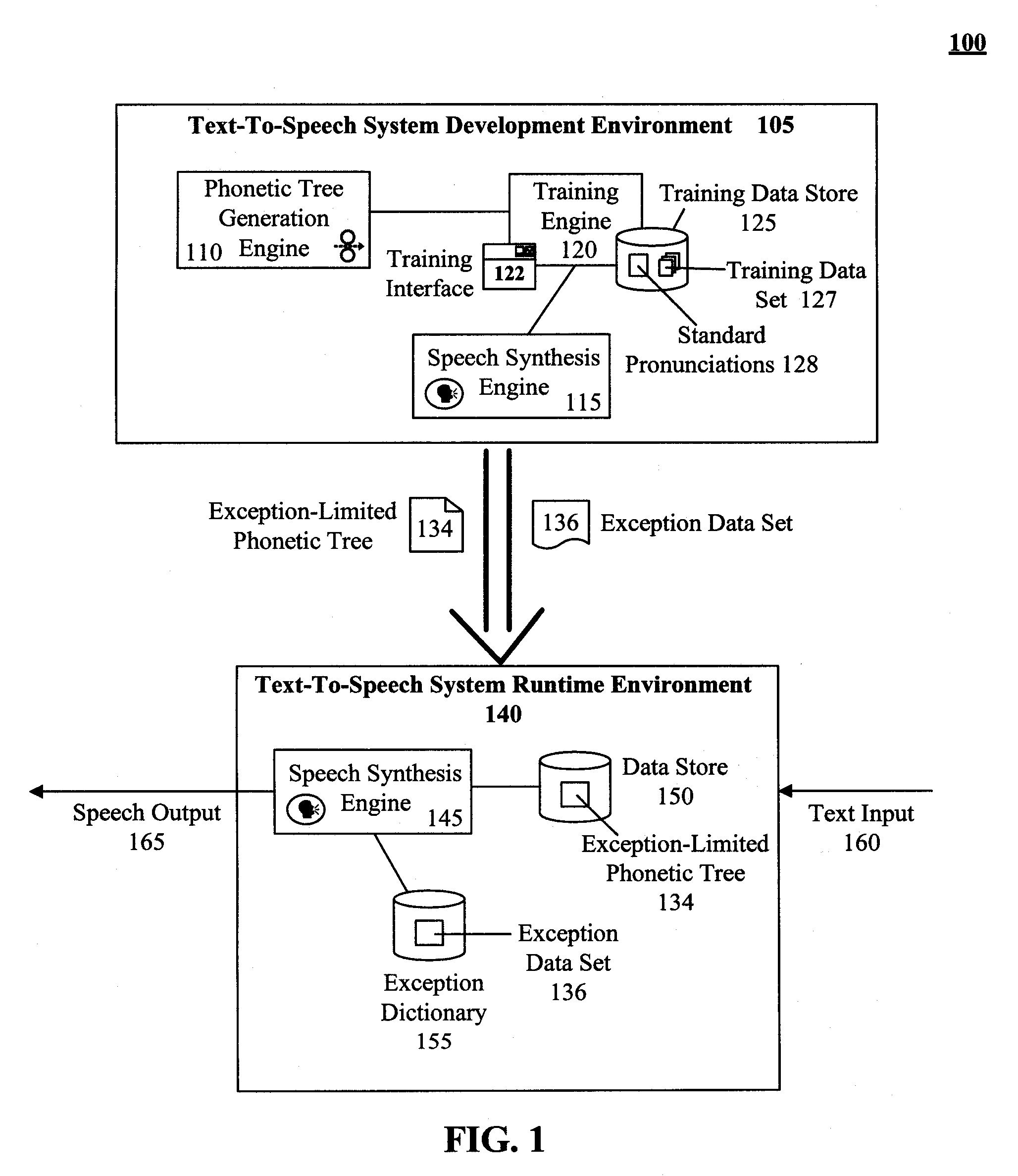
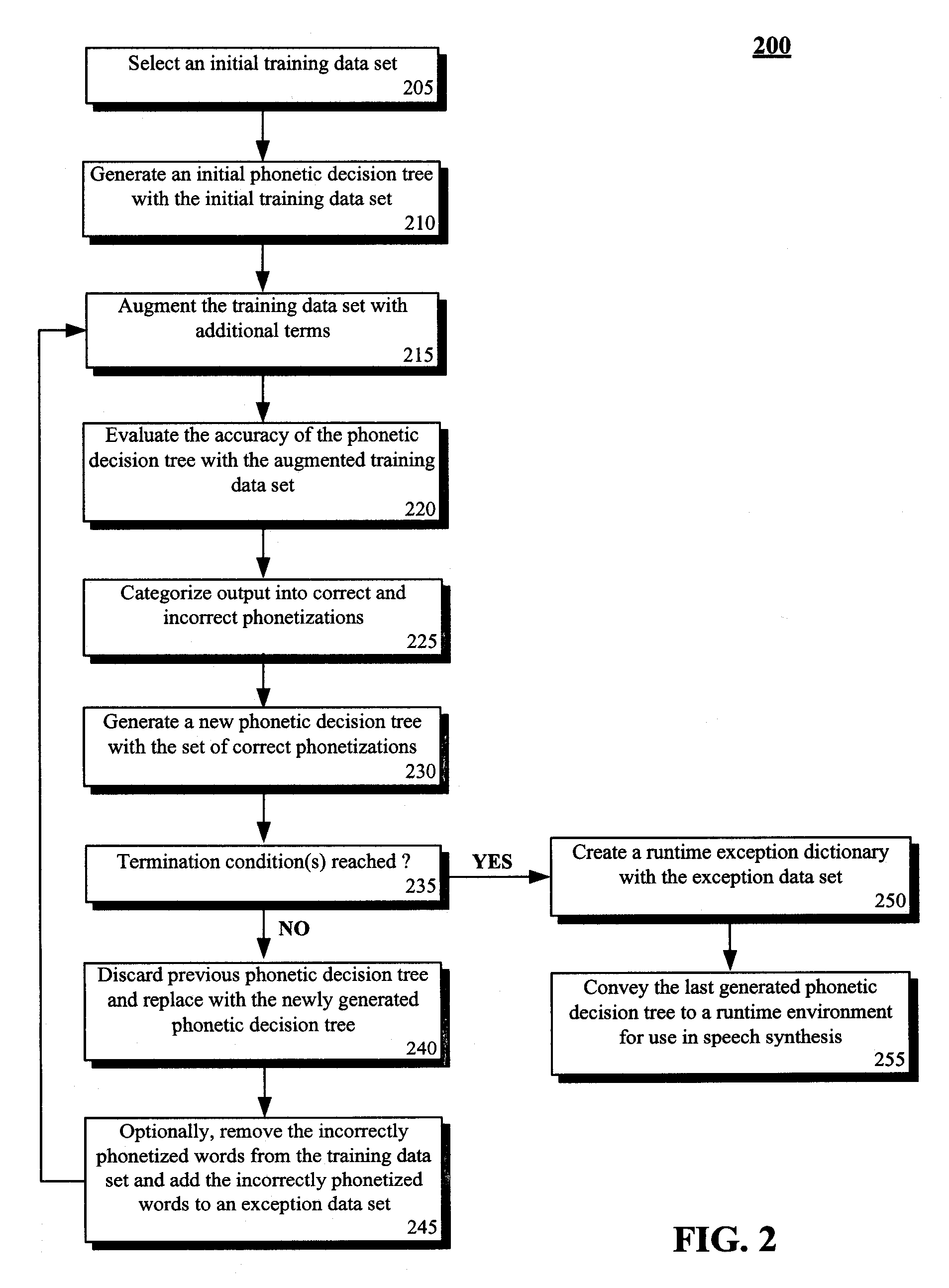
Technique for training a phonetic decision tree with limited phonetic exceptional terms
ActiveUS20080319753A1Exposure was also limitedSpeech recognitionSpeech synthesisTheoretical computer scienceSpeech sound
The present invention discloses a method for training an exception-limited phonetic decision tree. An initial subset of data can be selected and used for creating an initial phonetic decision tree. Additional terms can then be incorporated into the subset. The enlarged subset can be used to evaluate the phonetic decision tree with the results being categorized as either correctly or incorrectly phonetized. An exception-limited phonetic tree can be generated from the set of correctly phonetized terms. If the termination conditions for the method have been determined to be unsatisfactorily met, then steps of the method can be repeated.
Owner:CERENCE OPERATING CO
Predictive Analytics for Semi-Structured Case Oriented Processes
InactiveUS20120066166A1Probabilistic networksFuzzy logic based systemsNODALTheoretical computer science
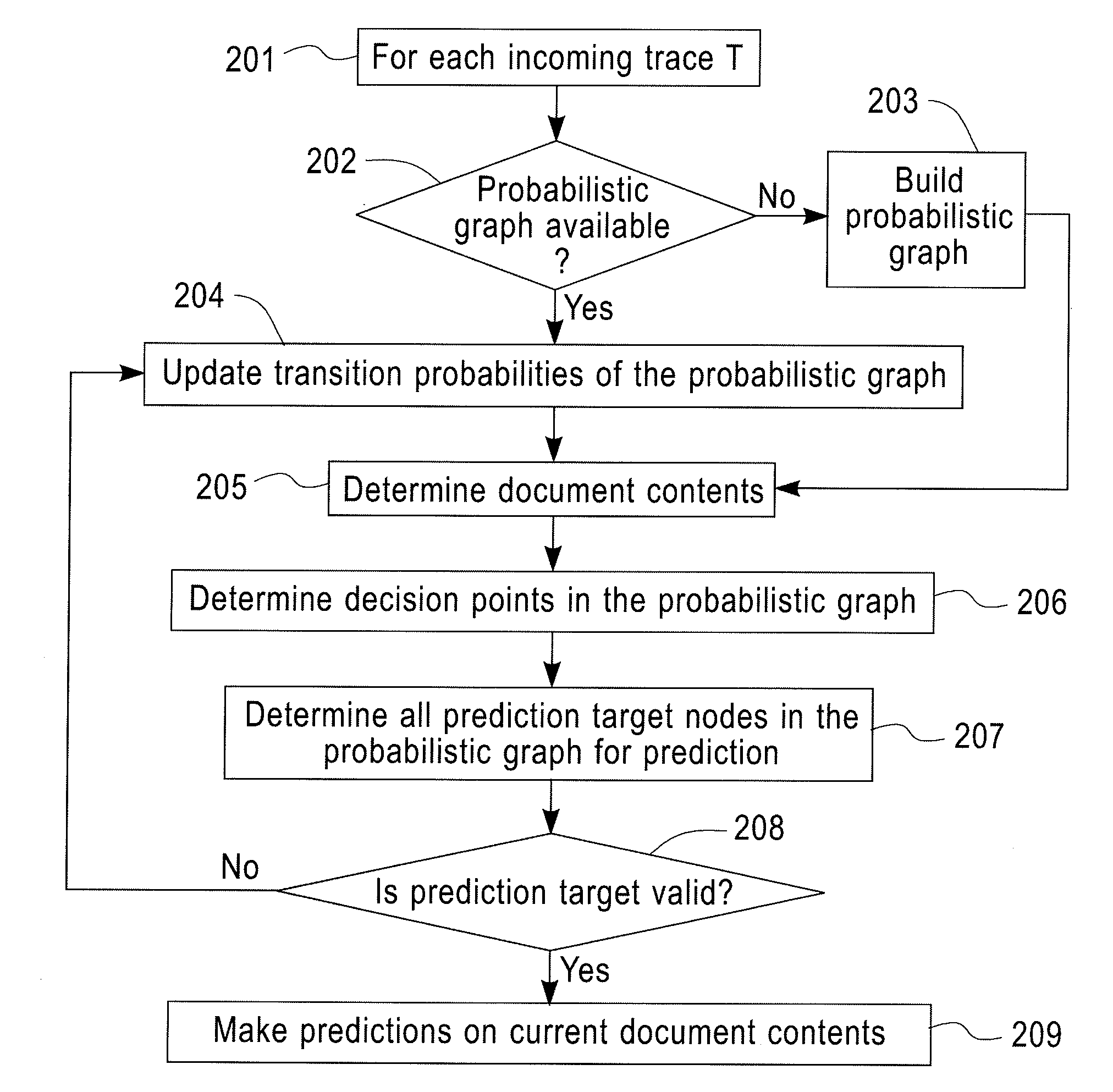
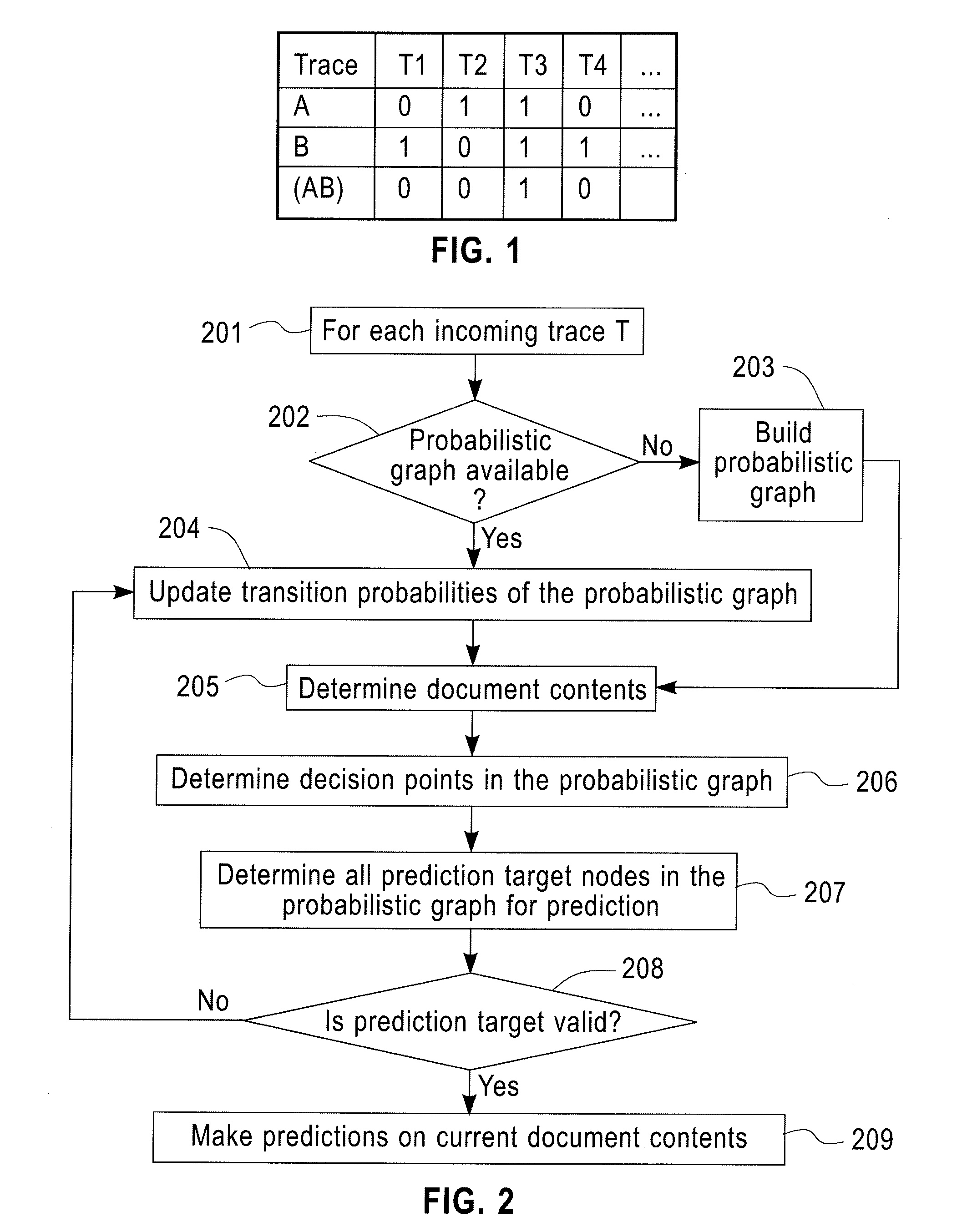
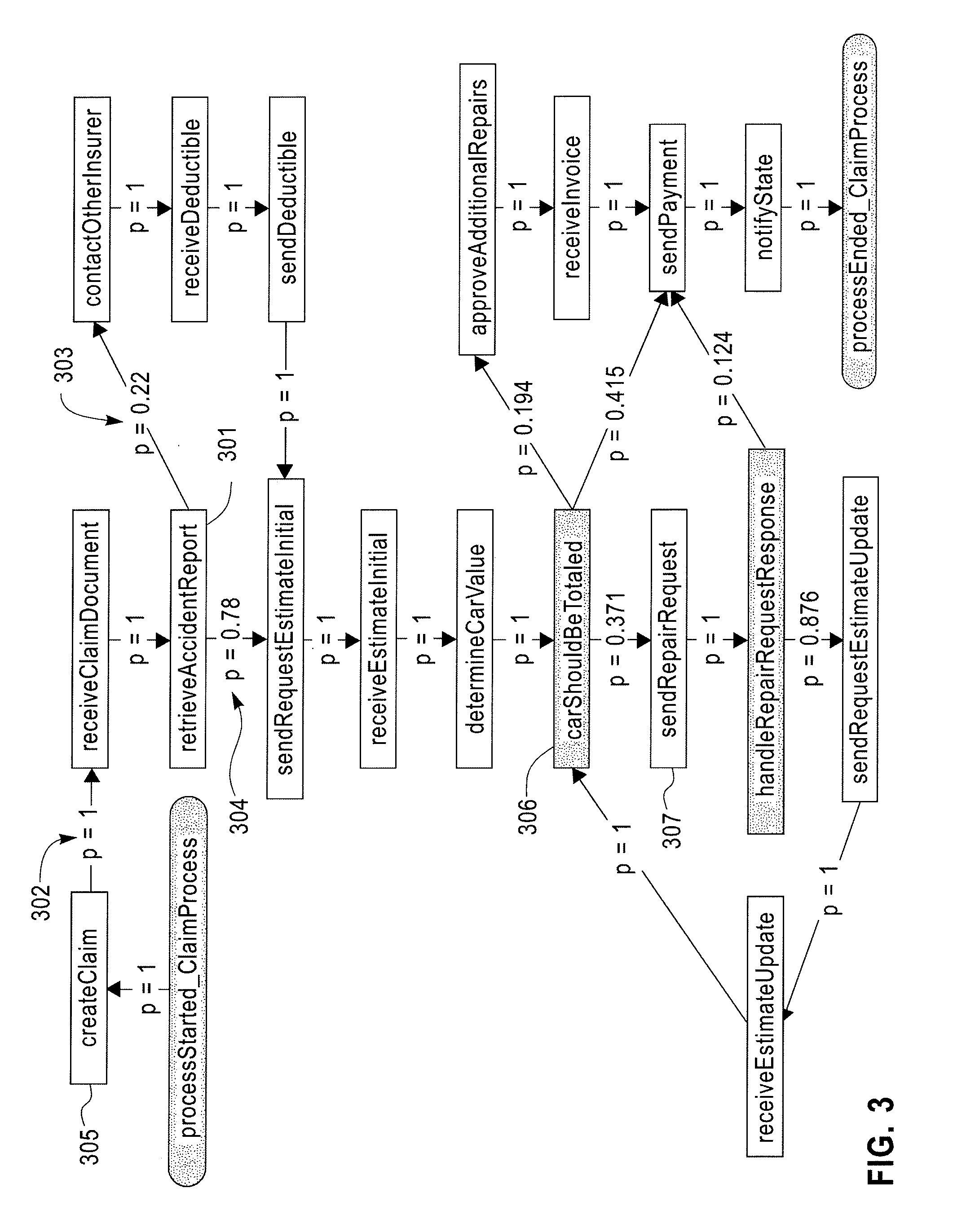
A method for predictive analytics for a process includes receiving at least one trace of the process, building a probabilistic graph modeling the at least one trace, determining content at each node of the probabilistic graph, wherein a node represents an activity of the process and at least one node is a decision node, modeling each decision node as a respective decision tree, and predicting, for an execution of the process, a path in the probabilistic graph from any decision node to a prediction target node of a plurality of prediction target nodes given the content.
Owner:IBM CORP
System and method for recommending items of interest to a user
ActiveUS20070078849A1Improve privacyDigital data information retrievalSelective content distributionPersonalizationDecision taking
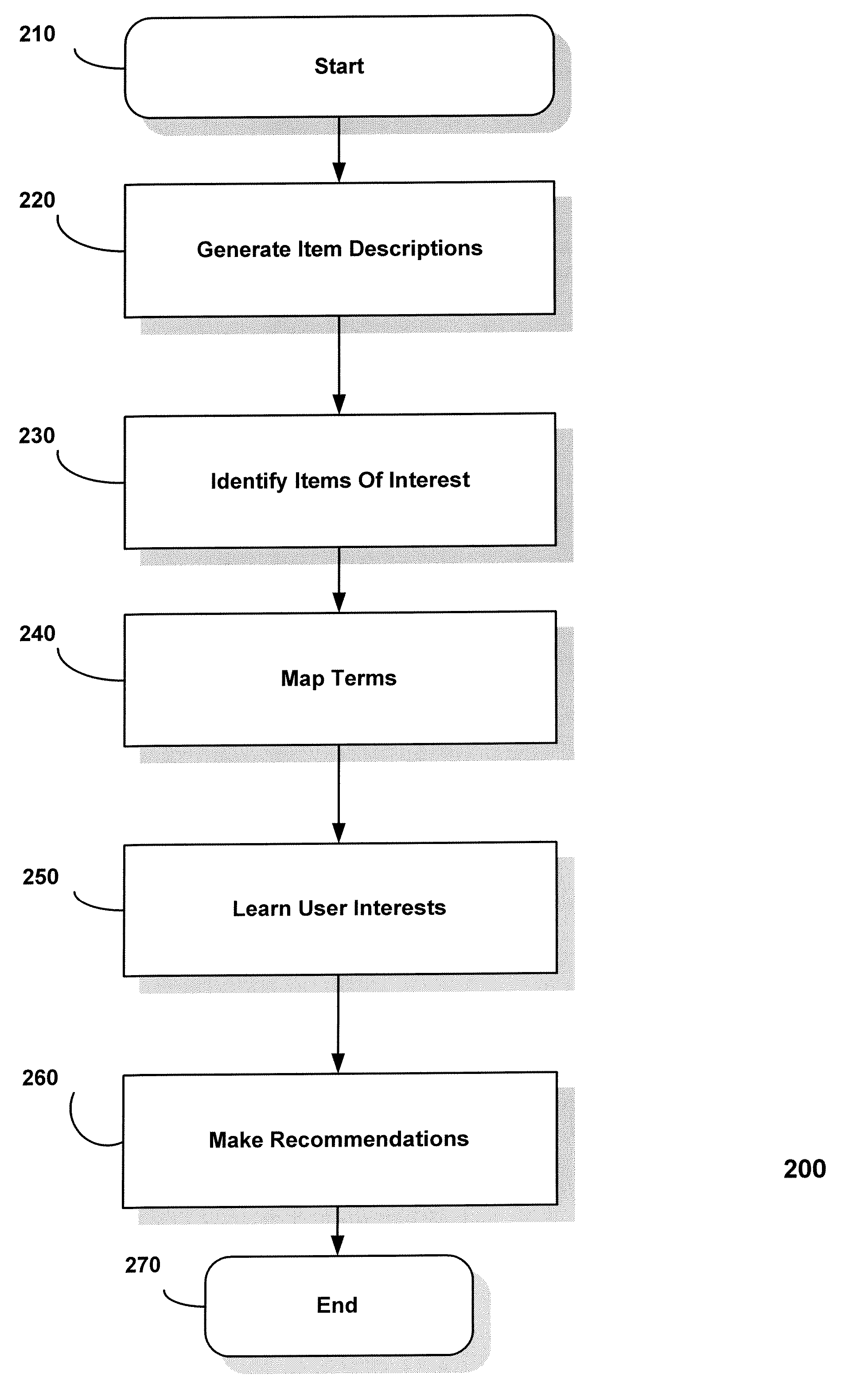
A system and method is disclosed for recommending items to individual users using a combination of clustering decision trees and frequency-based term mapping. The system and method of the present invention is configured to receive data based on user action, such as television remote control activity, or computer keyboard entry, and when a new item data is made available from sources such as television program guides, movie databases, deliverers of advertising data, on-line auction web sites, and electronic mail servers, the system and method analytically breaks down the new item data, compares it to ascertained attributes of item data that a user liked in the past, and produces numeric ranking of the new item data dynamically, and without subsequent user input, or data manipulation by item data deliverers, and is tailored to each individual user. A embodiment is disclosed for learning user interests based on user actions and then applying the learned knowledge to rank, recommend, and / or filter items, such as e-mail spam, based on the level of interest to a user. The embodiment may be used for automated personalized information learning, recommendation, and / or filtering systems in applications such as television programming, web-based auctions, targeted advertising, and electronic mail filtering. The embodiment may be structured to generate item descriptions, learn items of interest, learn terms that effectively describe the items, cluster similar items in a compact data structure, and then use the structure to rank new offerings. Embodiments of the present invention include, by way of non-limiting example: allowing the assignment of rank scores to candidate items so one can be recommended over another, building decision trees incrementally using unsupervised learning to cluster examples into categories automatically, consistency with “edge” (thick client) computing whereby certain data structures and most of the processing are localized to the set-top box or local PC, the ability to learn content attributes automatically on-the-fly, and the ability to store user preferences in opaque local data structures and are not easily traceable to individual users.
Owner:FOURTHWALL MEDIA
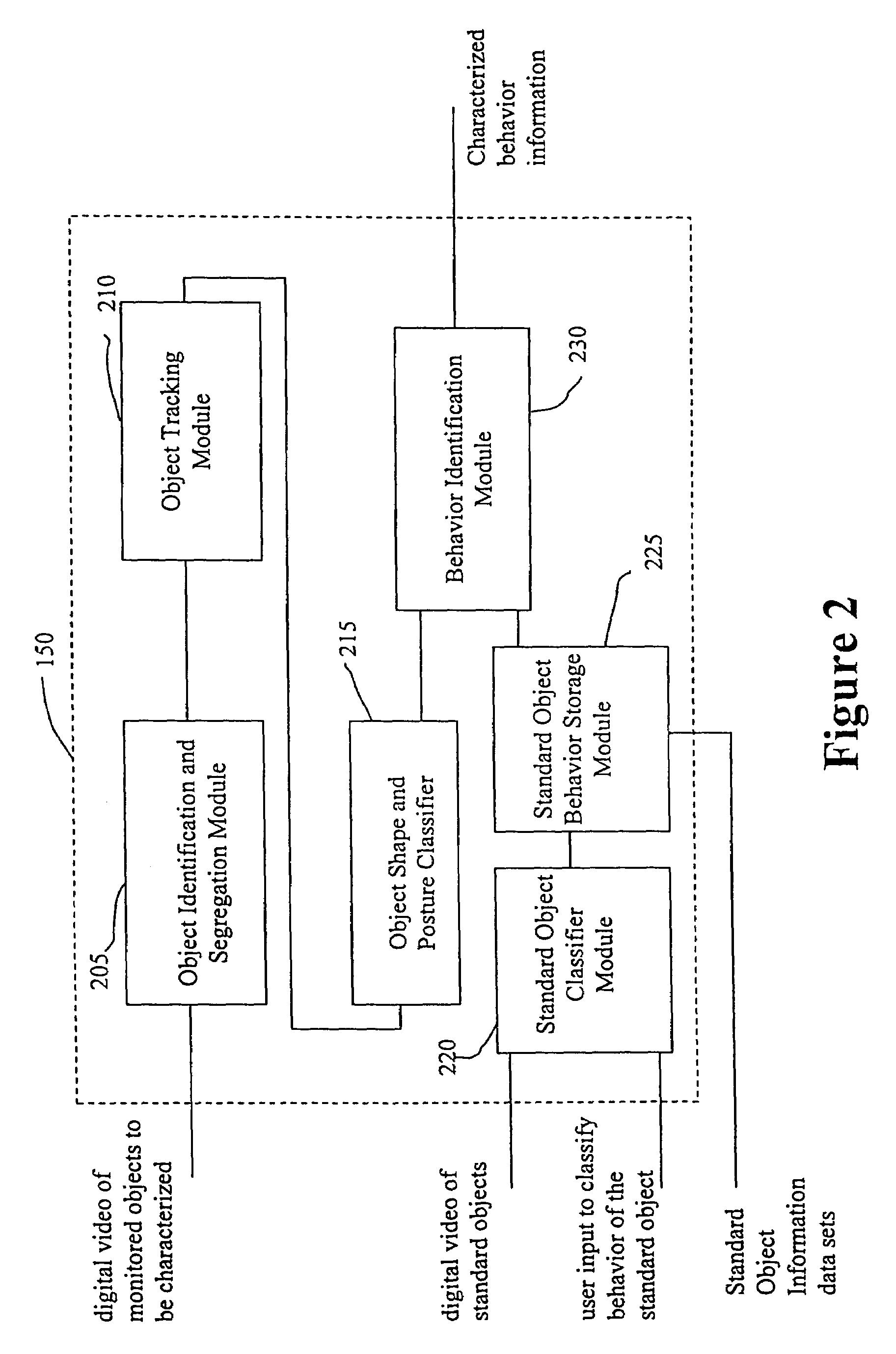
System and method for object identification and behavior characterization using video analysis
InactiveUS7068842B2Accurate identificationEfficient detectionImage enhancementImage analysisProbabilistic methodAnimal behavior
In general, the present invention is directed to systems and methods for finding the position and shape of an object using video. The invention includes a system with a video camera coupled to a computer in which the computer is configured to automatically provide object segmentation and identification, object motion tracking (for moving objects), object position classification, and behavior identification. In a preferred embodiment, the present invention may use background subtraction for object identification and tracking, probabilistic approach with expectation-maximization for tracking the motion detection and object classification, and decision tree classification for behavior identification. Thus, the present invention is capable of automatically monitoring a video image to identify, track and classify the actions of various objects and the object's movements within the image. The image may be provided in real time or from storage. The invention is particularly useful for monitoring and classifying animal behavior for testing drugs and genetic mutations, but may be used in any of a number of other surveillance applications.
Owner:CLEVER SYS
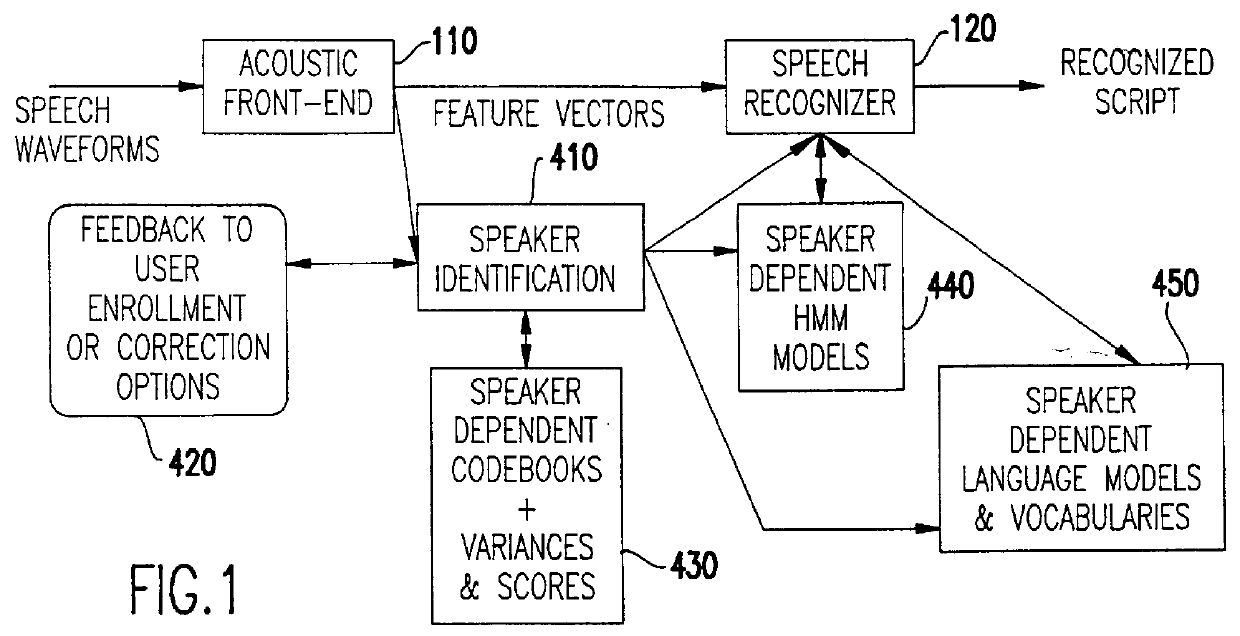
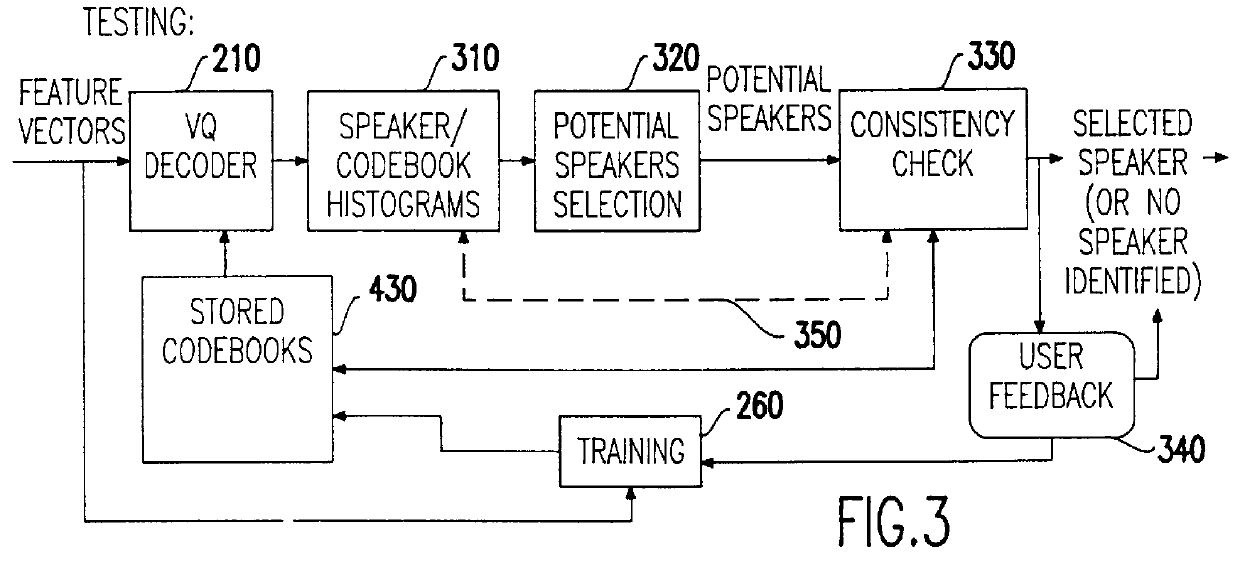
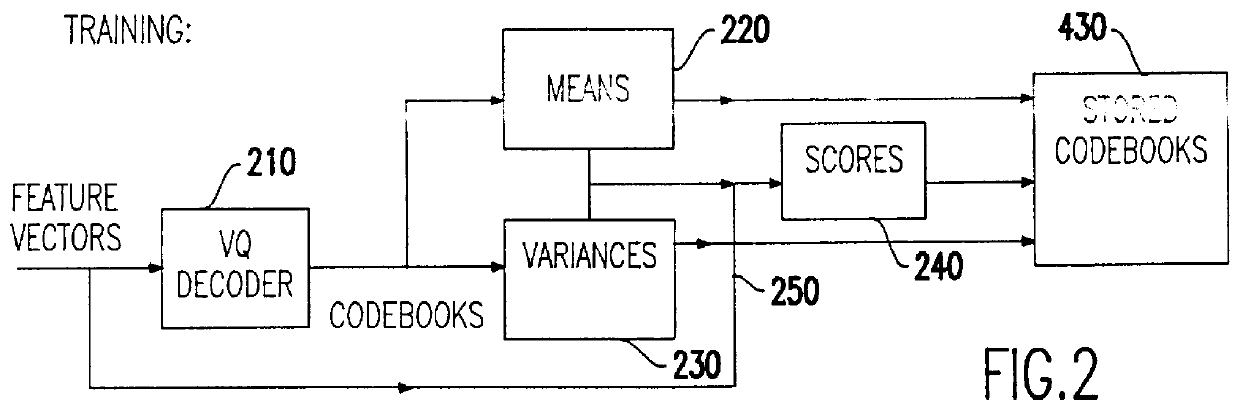
Speech recognition with attempted speaker recognition for speaker model prefetching or alternative speech modeling
Speaker recognition is attempted on input speech signals concurrently with provision of input speech signals to a speech recognition system. If a speaker is recognized, a speaker dependent model which has been trained on an enrolled speaker is supplied to the speech recognition system. If not recognized, then a speaker-independent recognition model is used or, alternatively, the new speaker is enrolled. Other speaker specific information such as a special language model, grammar, vocabulary, a dictionary, a list of names, a language and speaker dependent preferences can also be provided to improve the speech recognition function or even configure or customize the speech recognition system or the response of any system such as a computer or network controlled in response thereto. A consistency check in the form of a decision tree is preferably provided to accelerate the speaker recognition process and increase the accuracy thereof. Further training of a model and / or enrollment of additional speakers may be initiated upon completion of speaker recognition and / or adaptively upon each speaker utterance.
Owner:IBM CORP
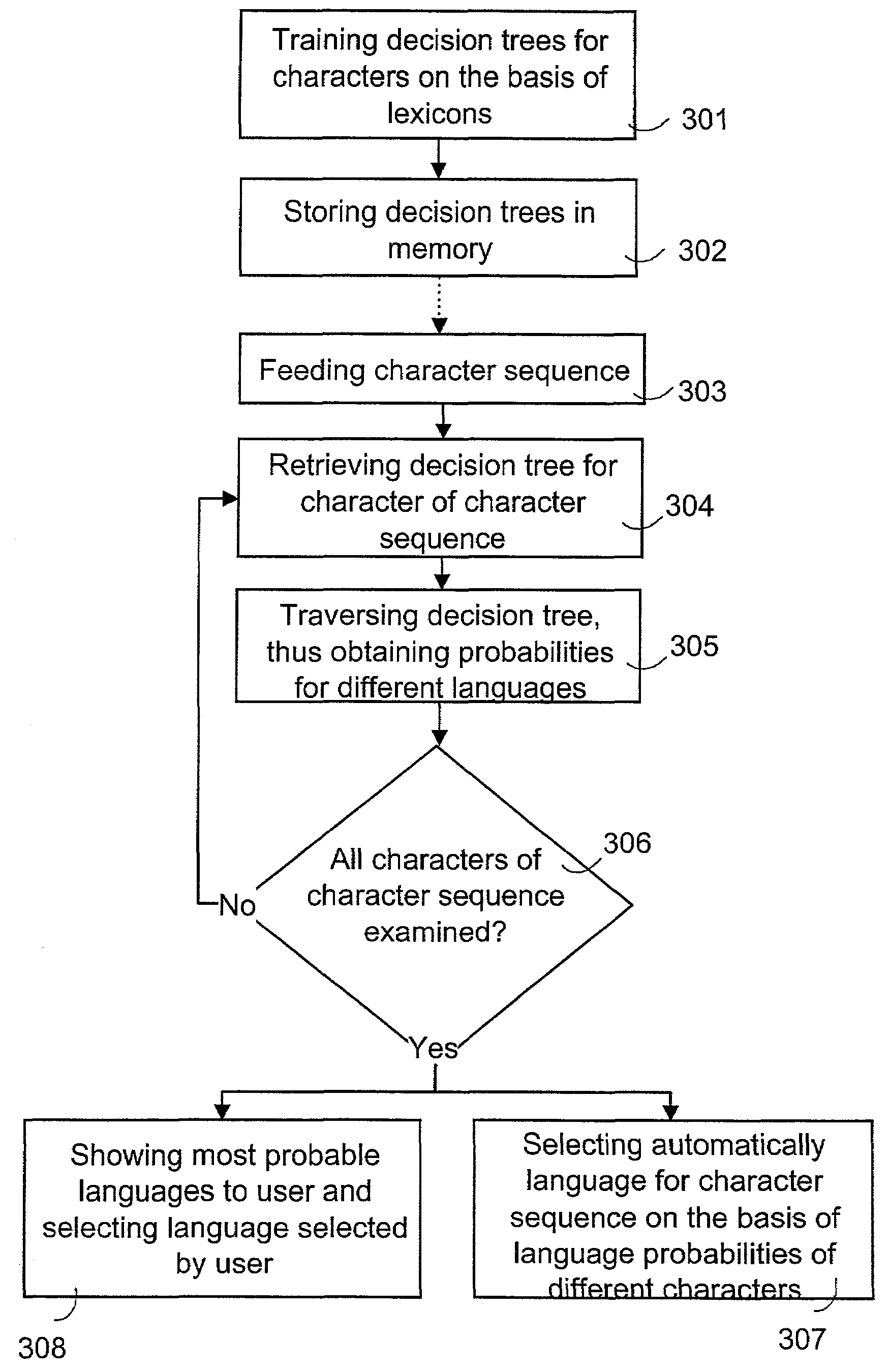
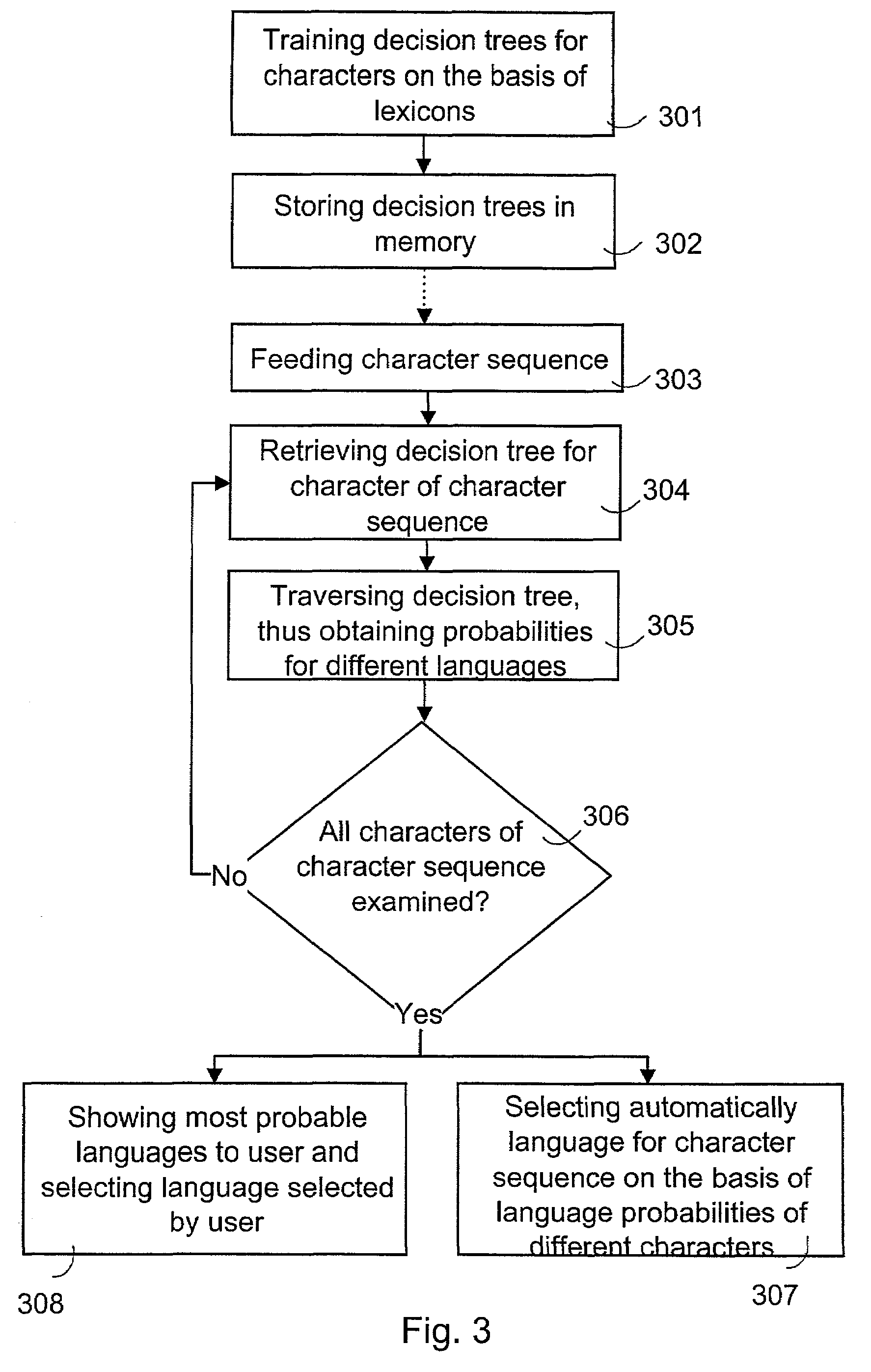
Determining language for character sequence
InactiveUS7139697B2Maximize information gainImprove efficiencyNatural language data processingSpecial data processing applicationsData treatmentDecision tree
A method for selecting the language for a character sequence fed into a data processing device, wherein decision trees are trained for different characters on the basis of lexicons of predetermined languages. The decision trees describe language probabilities on the basis of characters in the environments of the characters. The decision trees for at least some of the characters of the character sequence fed into the data processing device are traversed, thus obtaining a probability of at least one language for each character. The language for the character sequence is selected on the basis of the probabilities obtained.
Owner:WSOU INVESTMENTS LLC
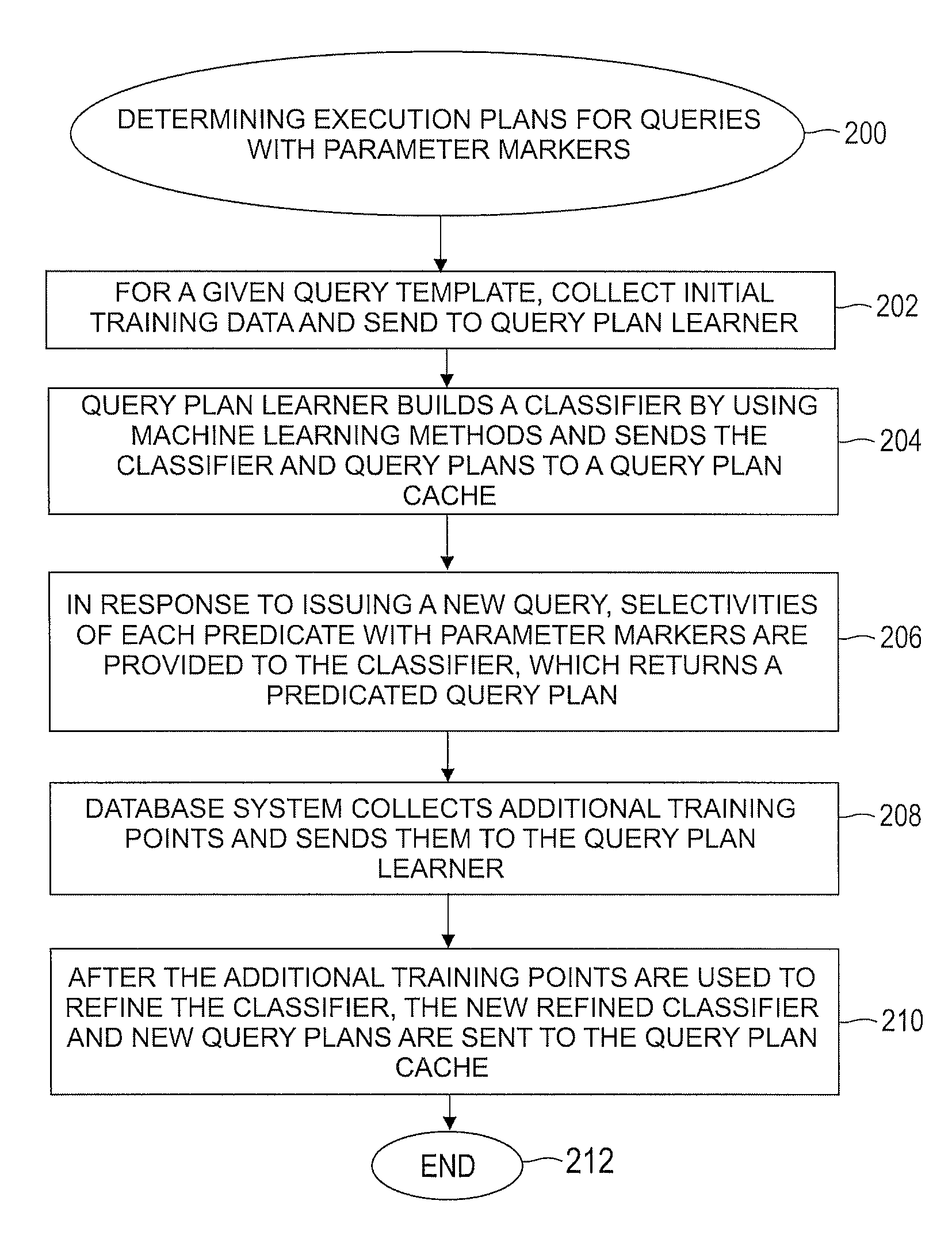
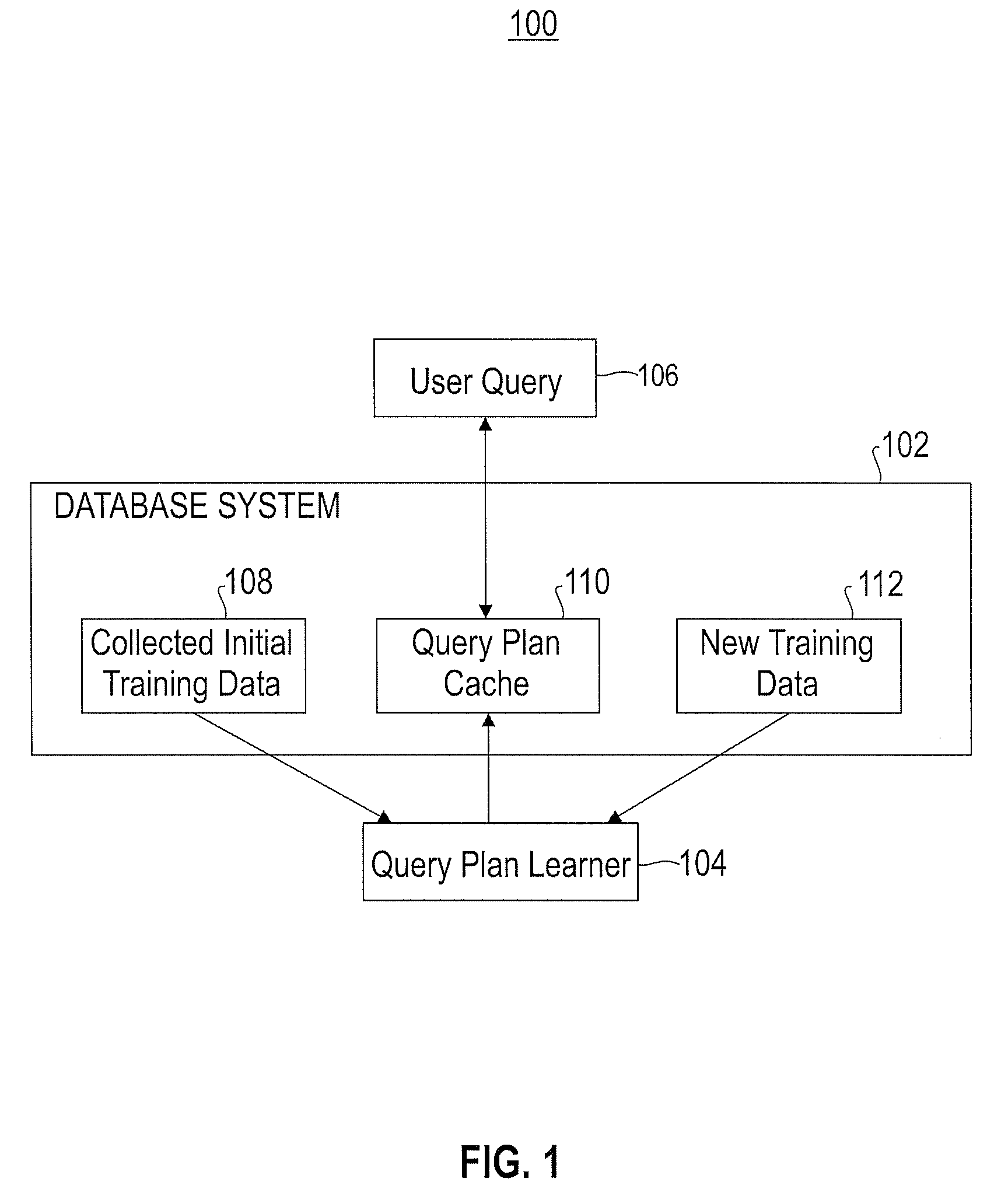
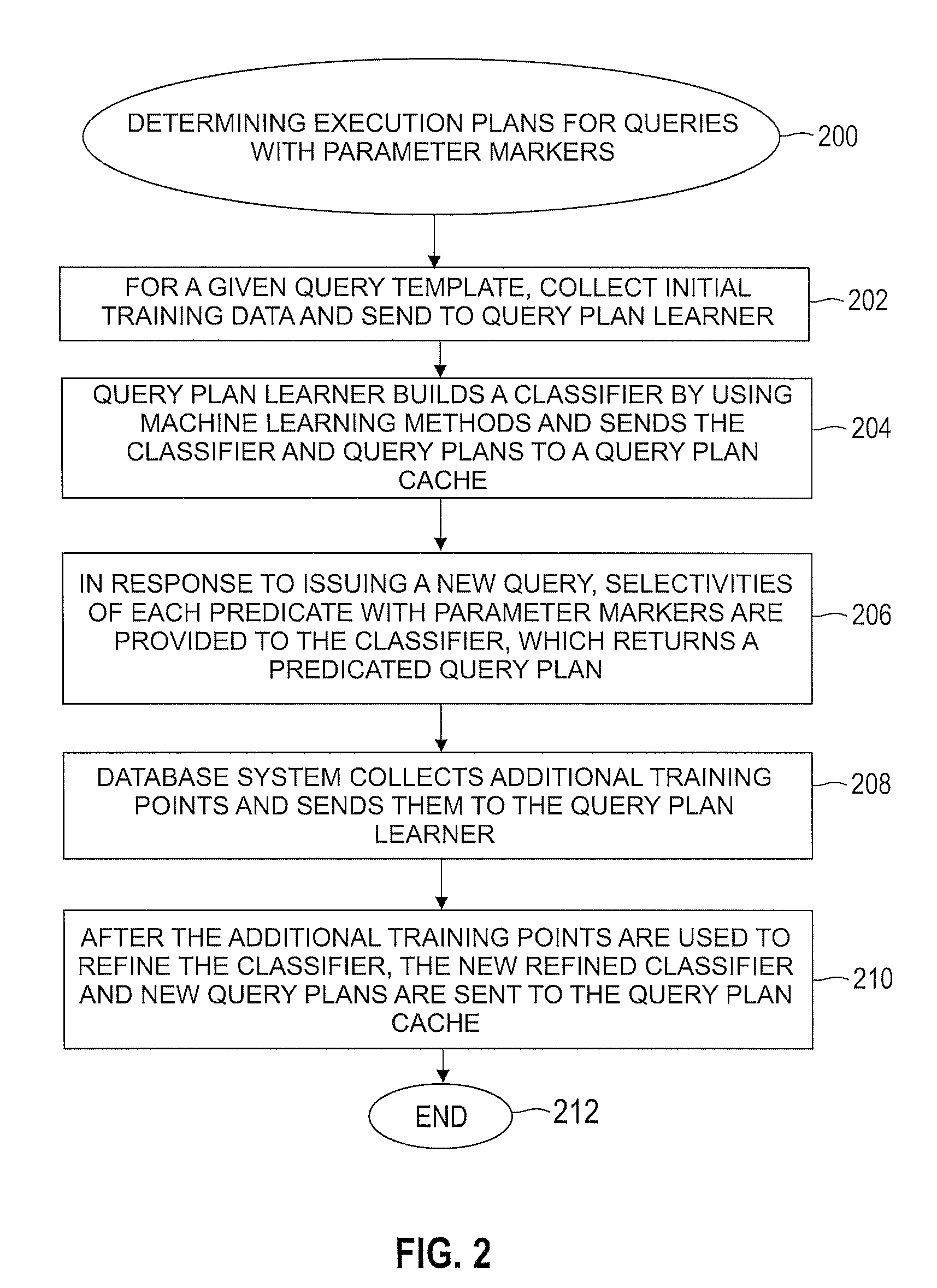
Automatically and adaptively determining execution plans for queries with parameter markers
InactiveUS20080195577A1Accurate modelingImprove forecast accuracyDigital data information retrievalSpecial data processing applicationsExecution planWorkload
A method for automatically and adaptively determining query execution plans for parametric queries. A first classifier trained by an initial set of training points is generated using a set of random decision trees (RDTs). A query workload and / or database statistics are dynamically updated. A new set of training points collected off-line is used to modify the first classifier into a second classifier. A database query is received at a runtime subsequent to the off line phase. The query includes predicates having parameter markers bound to actual values. The predicates are associated with selectivities. The query execution plan is determined by identifying an optimal average of posterior probabilities obtained across a set of RDTs and mapping the selectivities to a plan. The determined query execution plan is included in an augmented set of training points that includes the initial set and the new set.
Owner:IBM CORP
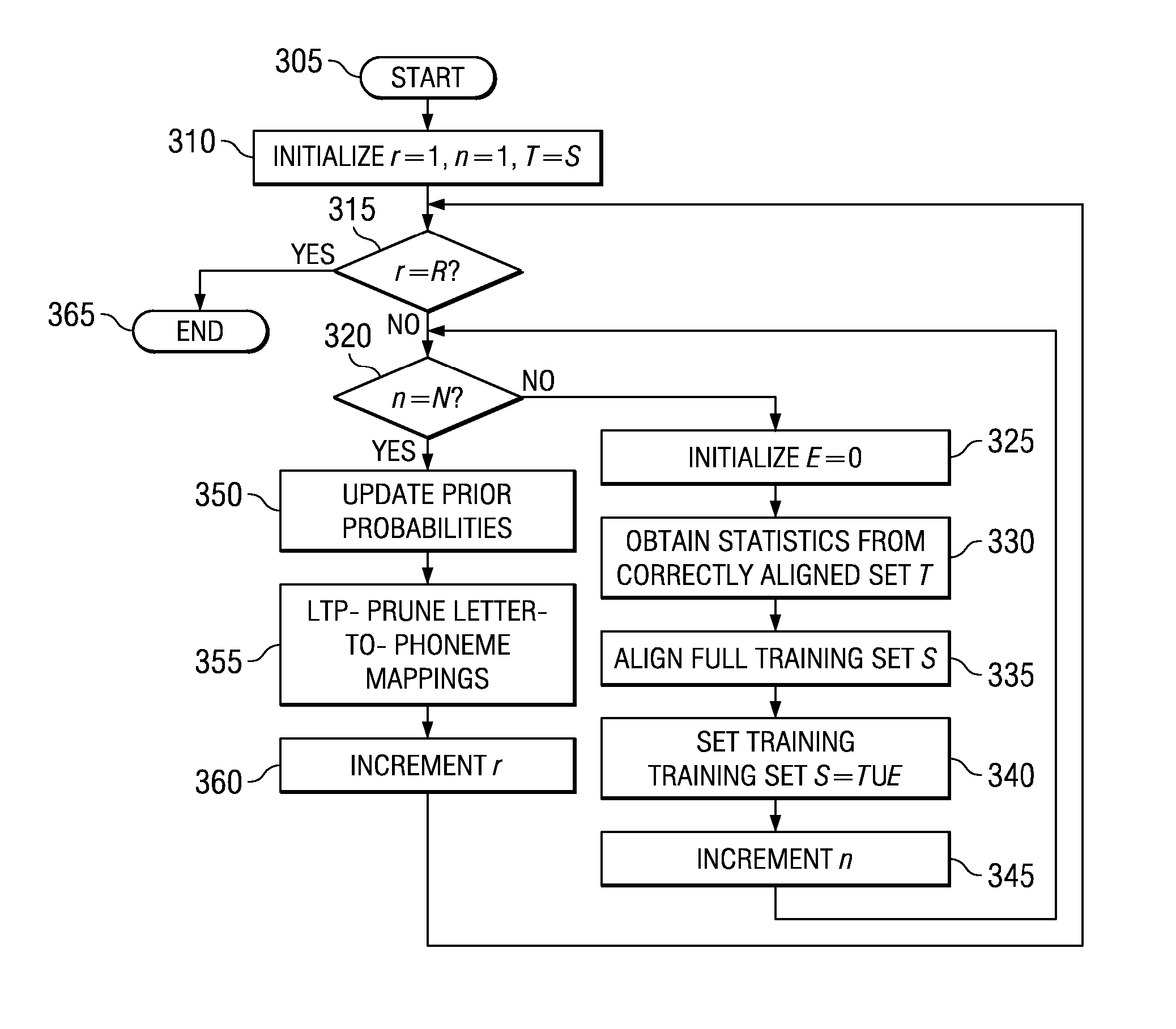
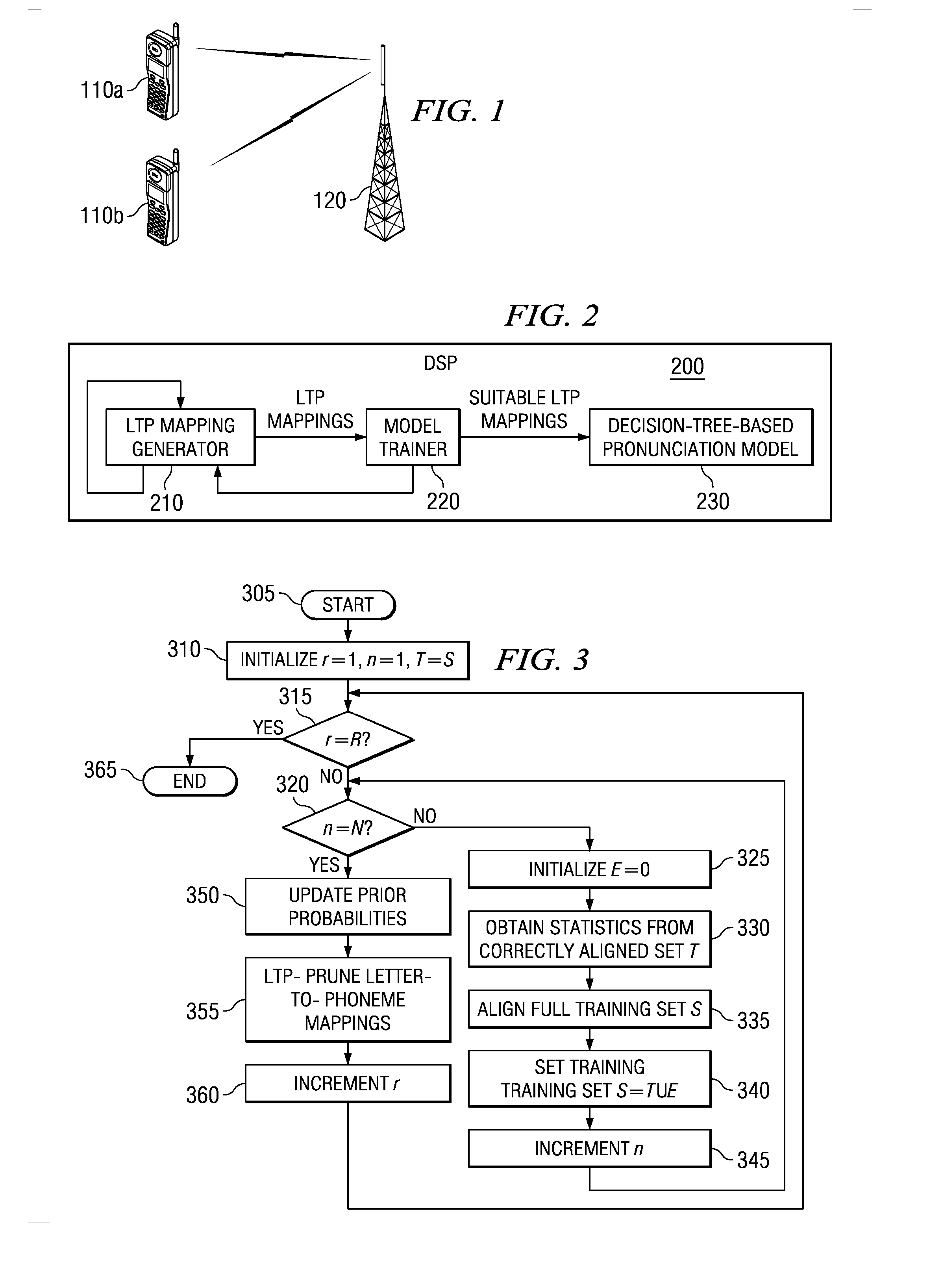
System and method for text-to-phoneme mapping with prior knowledge
A system for, and method of, text-to-phoneme (TTP) mapping and a digital signal processor (DSP) incorporating the system or the method. In one embodiment, the system includes: (1) a letter-to-phoneme (LTP) mapping generator configured to generate an LTP mapping by iteratively aligning a full training set with a set of correctly aligned entries based on statistics of phonemes and letters from the set of correctly aligned entries and redefining the full training set as a union of the set of correctly aligned entries and a set of incorrectly aligned entries created during the aligning and (2) a model trainer configured to update prior probabilities of LTP mappings generated by the LTP generator and evaluate whether the LTP mappings are suitable for training a decision-tree-based pronunciation model (DTPM).
Owner:TEXAS INSTR INC
Differentially private machine learning using a random forest classifier
A request from a client is received to generate a differentially private random forest classifier trained using a set of restricted data. The differentially private random forest classifier is generated in response to the request. Generating the differentially private random forest classifier includes determining a number of decision trees and generating the determined number of decision trees. Generating a decision tree includes generating a set of splits based on the restricted data, determining an information gain for each split, selecting a split from the set using an exponential mechanism, and adding the split to the decision tree. The differentially private random forest classifier is provided to the client.
Owner:SNOWFLAKE INC
Using sequencing and timing information of behavior events in machine learning to detect malware
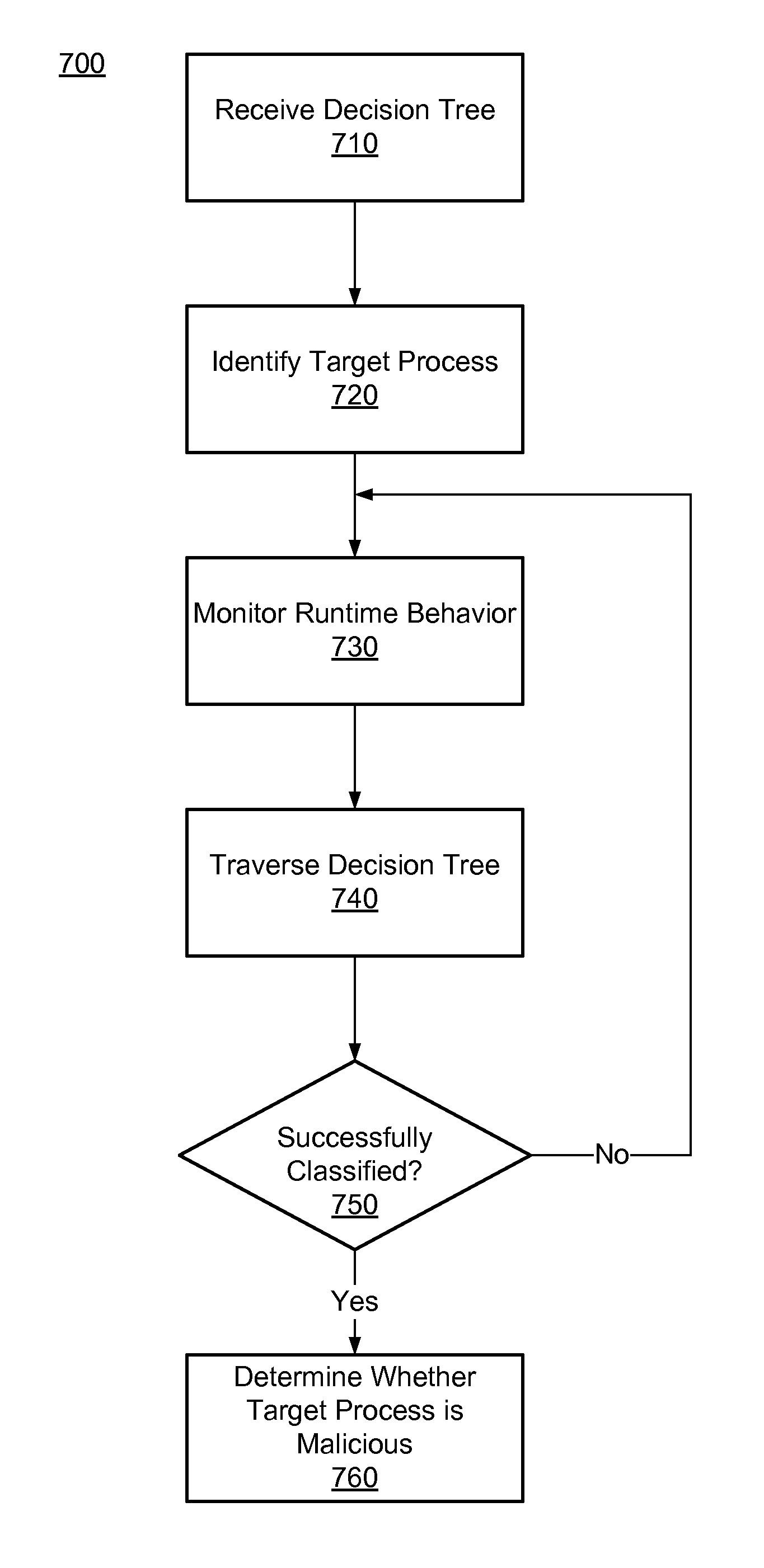
ActiveUS8401982B1Memory loss protectionError detection/correctionFeature vectorTheoretical computer science
A decision tree for classifying computer files is constructed. A set of training files known to be legitimate or malicious are executed and their runtime behaviors are monitored. When a behavior event is detected for one of the training file at a point in time, a feature vector is generated for that training file. Behavior sequencing and timing information for the training file at that point in time is identified and encoded in the feature vector. Feature vectors for each of the training files at various points in time are fed into a decision tree induction algorithm to construct a decision tree that takes into account of the sequencing and timing information.
Owner:NORTONLIFELOCK INC
Software solution management of problem loans
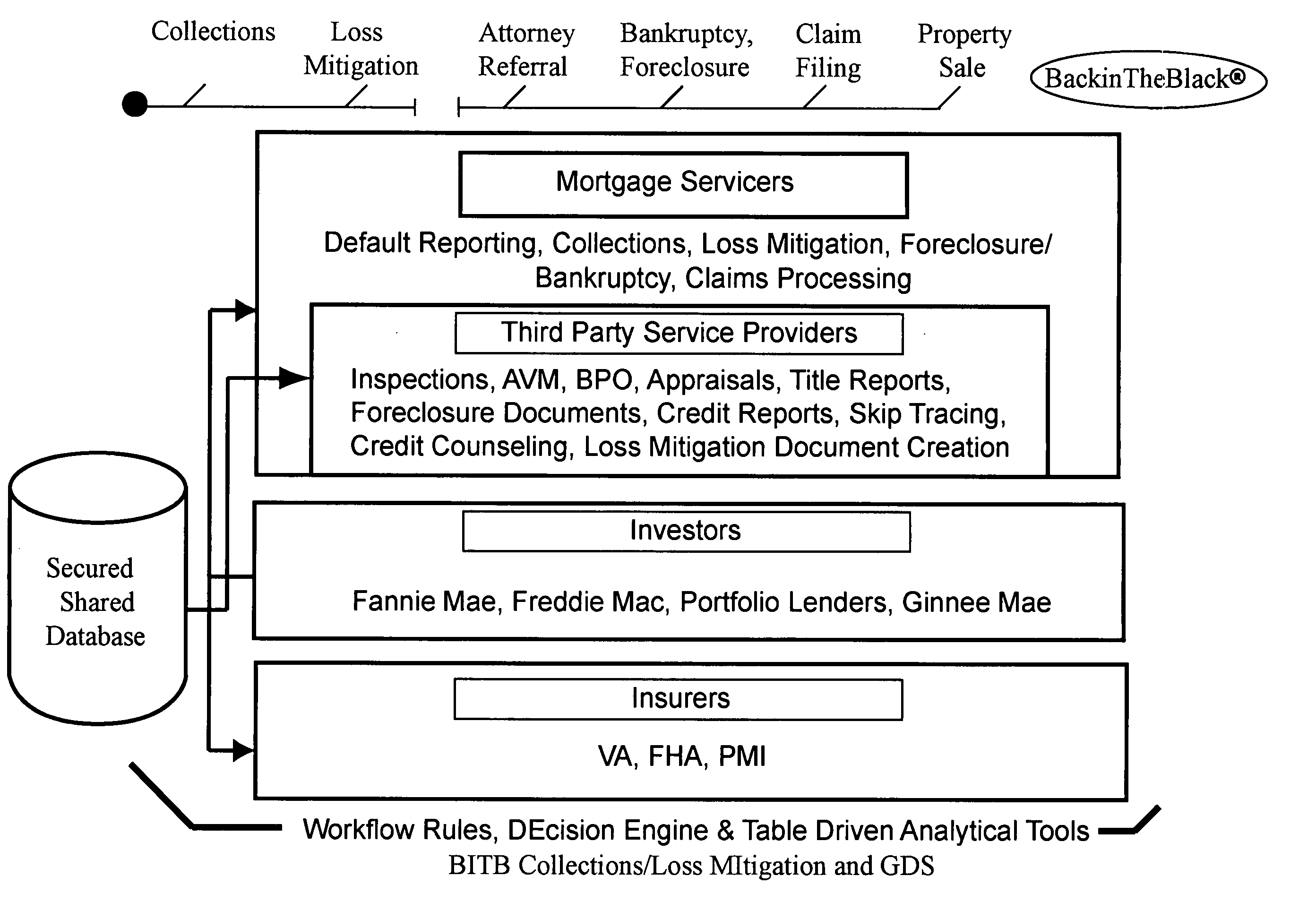
InactiveUS20050278246A1Increasing availability of resourceFacilitate dialogueFinanceSpecial data processing applicationsProcess lossComputer science
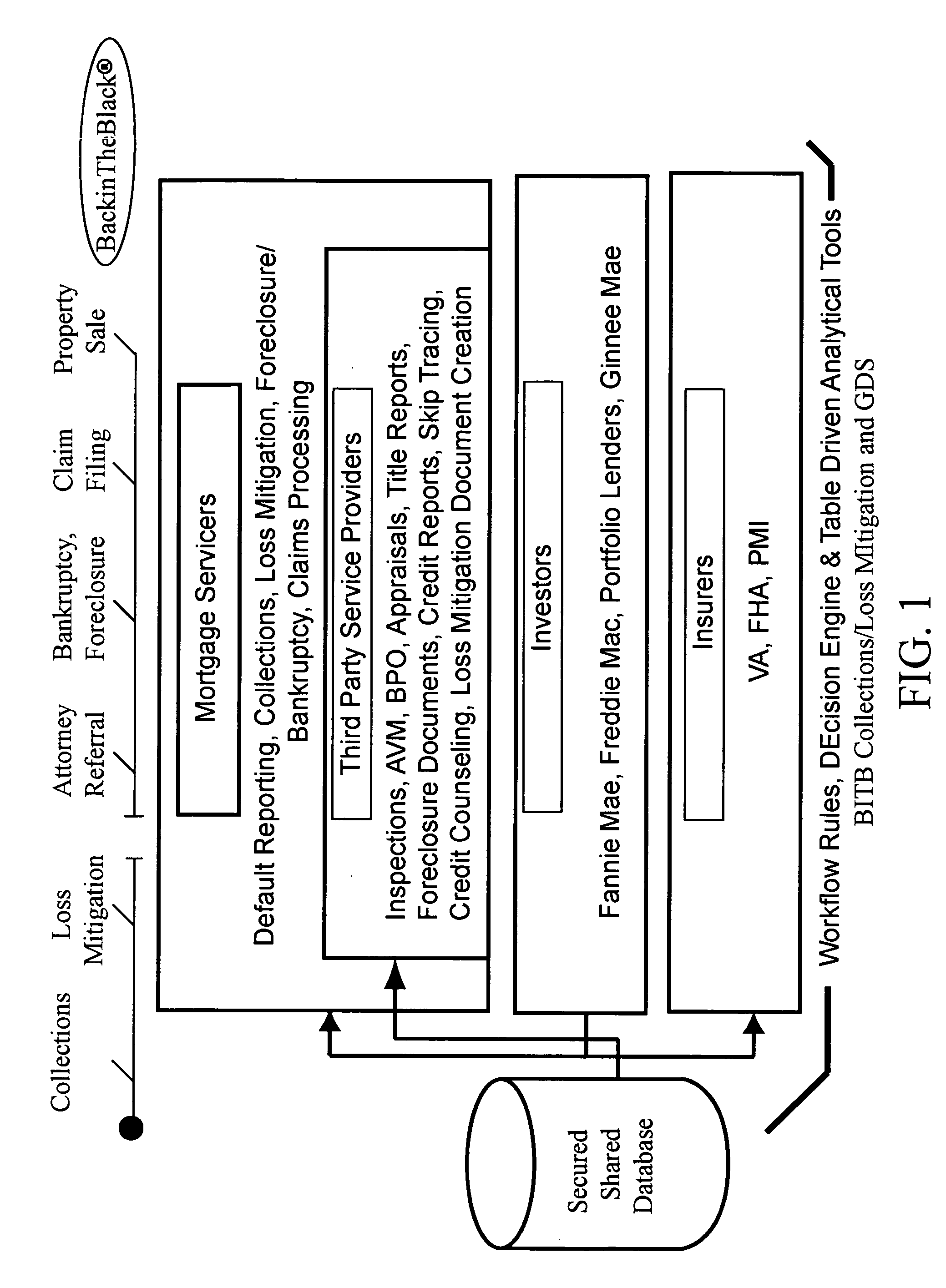
An improved and automated ASP-delivered loan workout system, inclusive of communication architecture and software method that assists a user in improving the dialogue and counseling sessions between user, borrower, and other involved parties, and which increases loan servicer efficiency while decreasing the time and expense necessary to process loss mitigation cases-including identification of an appropriate financial workout solution, via the use of logical decision tree-based interviews-increases the rate of identification of viable loss mitigation options, and selects and manages the best loss mitigation solution, all in real-time, and within investor and lender requirements, within loan guarantor and insurer conditions, and in compliance with rapidly changing industry standards and government rules.
Owner:MSTD
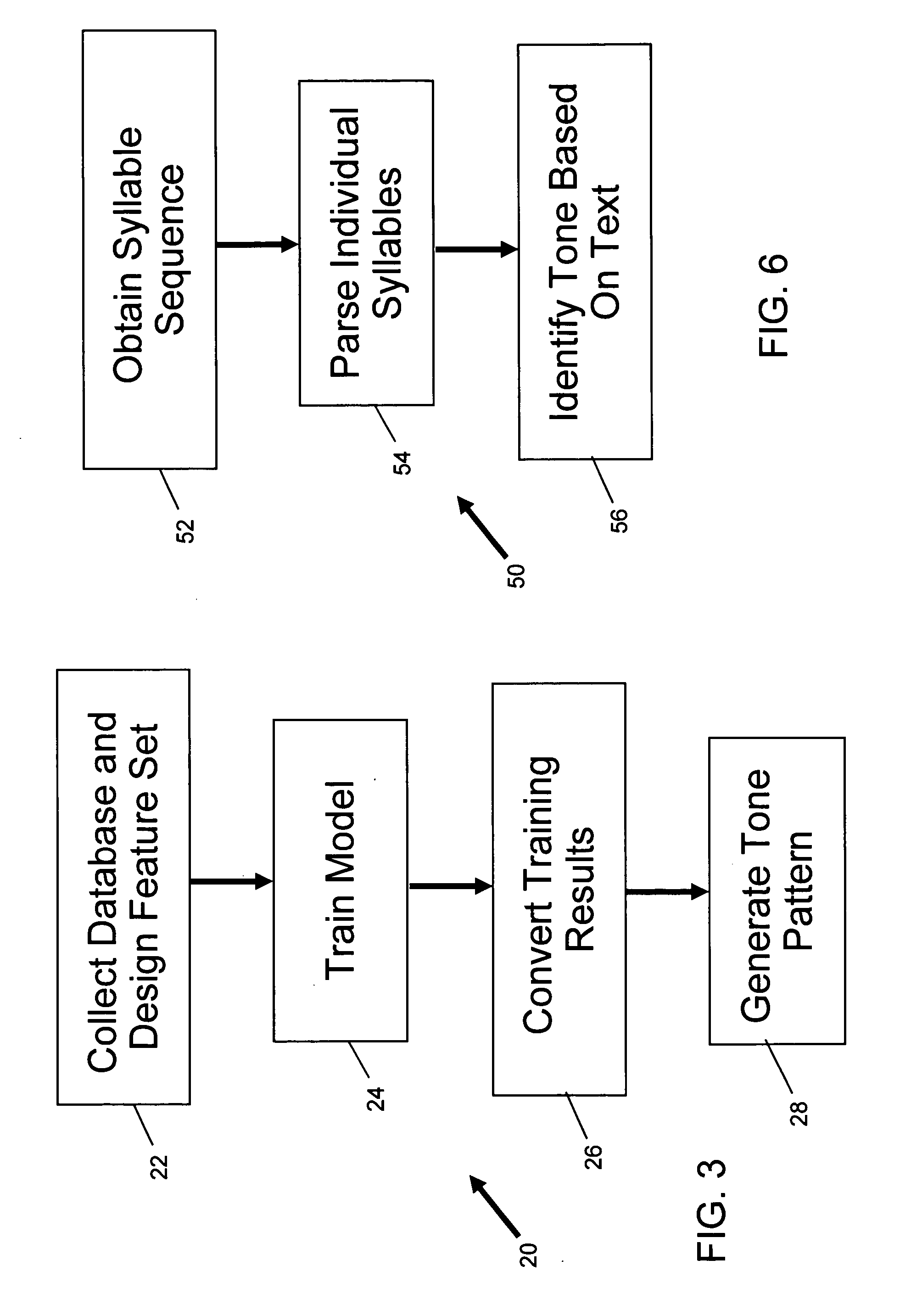
Predicting tone pattern information for textual information used in telecommunication systems
The techniques described include generating tonal information from a textual entry and, further, applying this tonal information to PINYIN sequences using decision trees. For example, a method of predicting tone pattern information for textual information used in telecommunication systems includes parsing a textual entry into segments and identifying tonal information for the textual entry using the parsed segments. The tonal information can be generated with a decision tree. The method can also be implemented in a distributed system where the conversion is done at a back-end server and the information is sent to a communication device after a request.
Owner:WSOU INVESTMENTS LLC
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20080184371A1Memory loss protectionError detection/correctionComputer wormTheoretical computer science
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. According to the proposed method, hardware and / or software parameters that can characterize known behavioral patterns in the computerized system are determined. Known malicious code samples are learned by a machine learning process, such as decision trees, Naïve Bayes, Bayesian Networks, and artificial neural networks, and the results of the machine learning process are analyzed in respect to these behavioral patterns. Then, known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
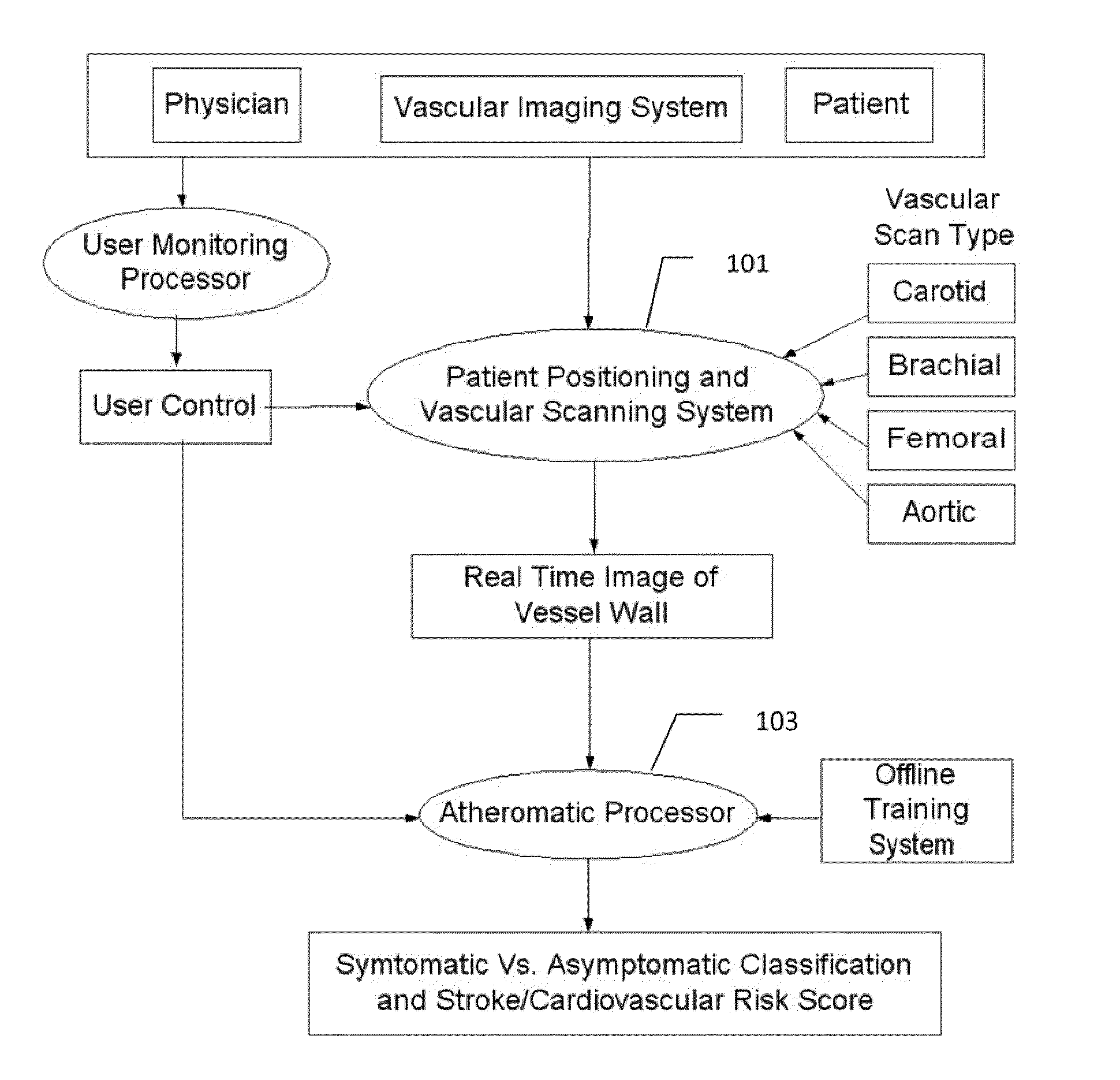
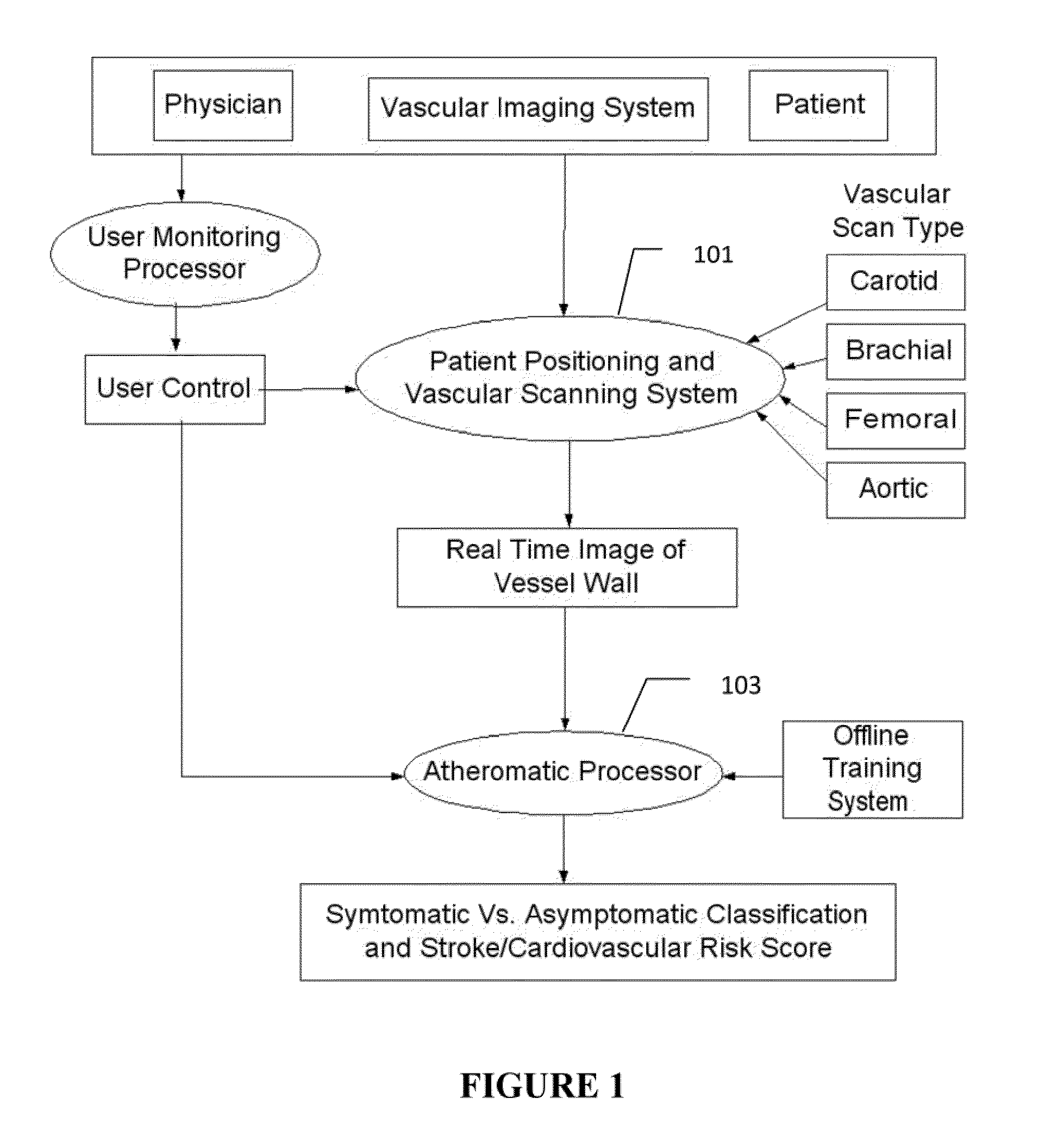
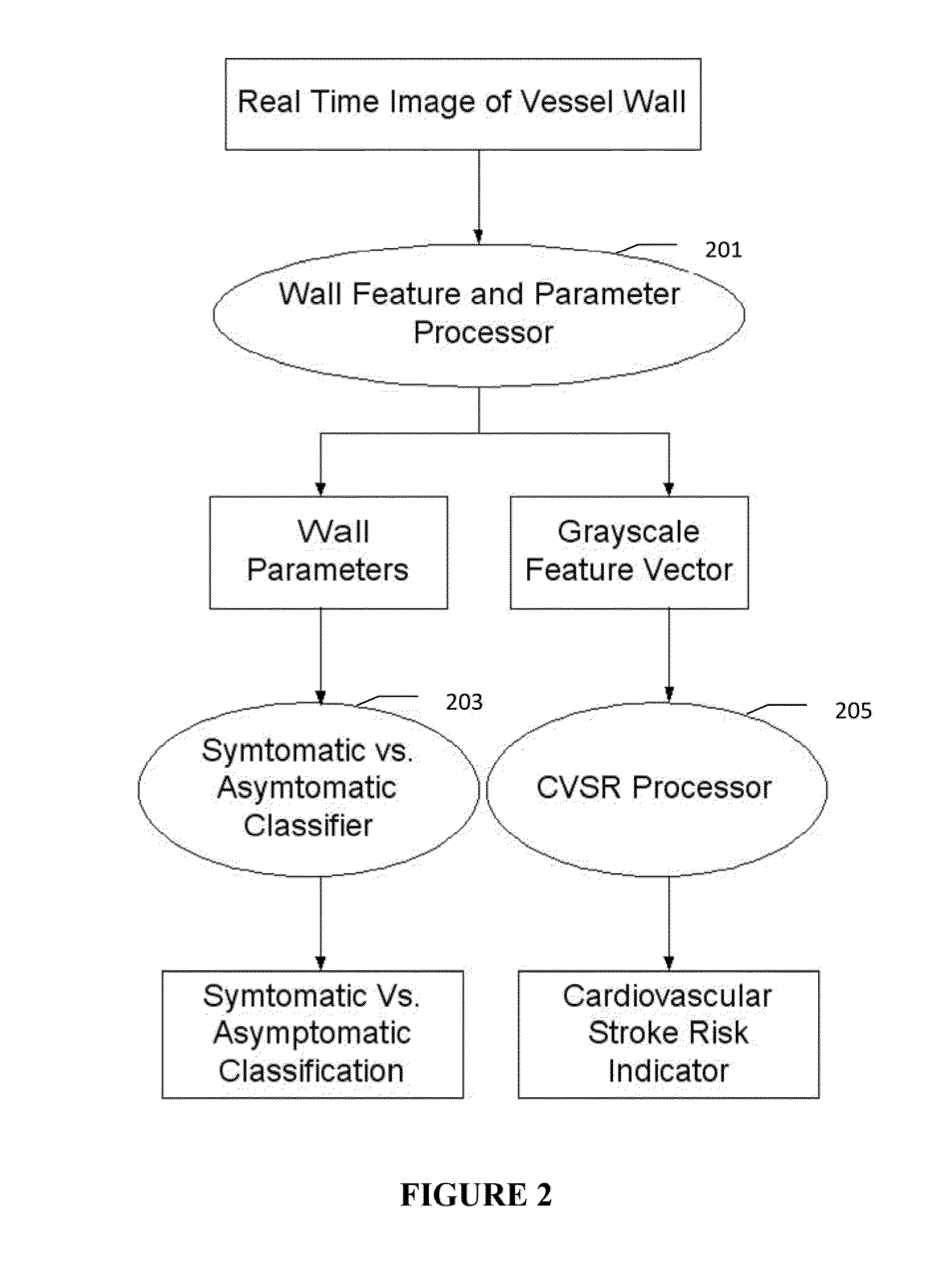
Imaging based symptomatic classification and cardiovascular stroke risk score estimation
InactiveUS20110257545A1Improve accuracyMaximum accuracyUltrasonic/sonic/infrasonic diagnosticsImage enhancementGround truthCross modality
Characterization of carotid atherosclerosis and classification of plaque into symptomatic or asymptomatic along with the risk score estimation are key steps necessary for allowing the vascular surgeons to decide if the patient has to definitely undergo risky treatment procedures that are needed to unblock the stenosis. This application describes a statistical (a) Computer Aided Diagnostic (CAD) technique for symptomatic versus asymptomatic plaque automated classification of carotid ultrasound images and (b) presents a cardiovascular stroke risk score computation. We demonstrate this for longitudinal Ultrasound, CT, MR modalities and extendable to 3D carotid Ultrasound. The on-line system consists of Atherosclerotic Wall Region estimation using AtheroEdge™ for longitudinal Ultrasound or Athero-CTView™ for CT or Athero-MRView from MR. This greyscale Wall Region is then fed to a feature extraction processor which computes: (a) Higher Order Spectra; (b) Discrete Wavelet Transform (DWT); (c) Texture and (d) Wall Variability. The output of the Feature Processor is fed to the Classifier which is trained off-line from the Database of similar Atherosclerotic Wall Region images. The off-line Classifier is trained from the significant features from (a) Higher Order Spectra; (b) Discrete Wavelet Transform (DWT); (c) Texture and (d) Wall Variability, selected using t-test. Symptomatic ground truth information about the training patients is drawn from cross modality imaging such as CT or MR or 3D ultrasound in the form of 0 or 1. Support Vector Machine (SVM) supervised classifier of varying kernel functions is used off-line for training. The Atheromatic™ system is also demonstrated for Radial Basis Probabilistic Neural Network (RBPNN), or Nearest Neighbor (KNN) classifier or Decision Trees (DT) Classifier for symptomatic versus asymptomatic plaque automated classification. The obtained training parameters are then used to evaluate the test set. The system also yields the cardiovascular stroke risk score value on the basis of the four set of wall features.
Owner:SURI JASJIT S
Method for constructing segmentation-based predictive models
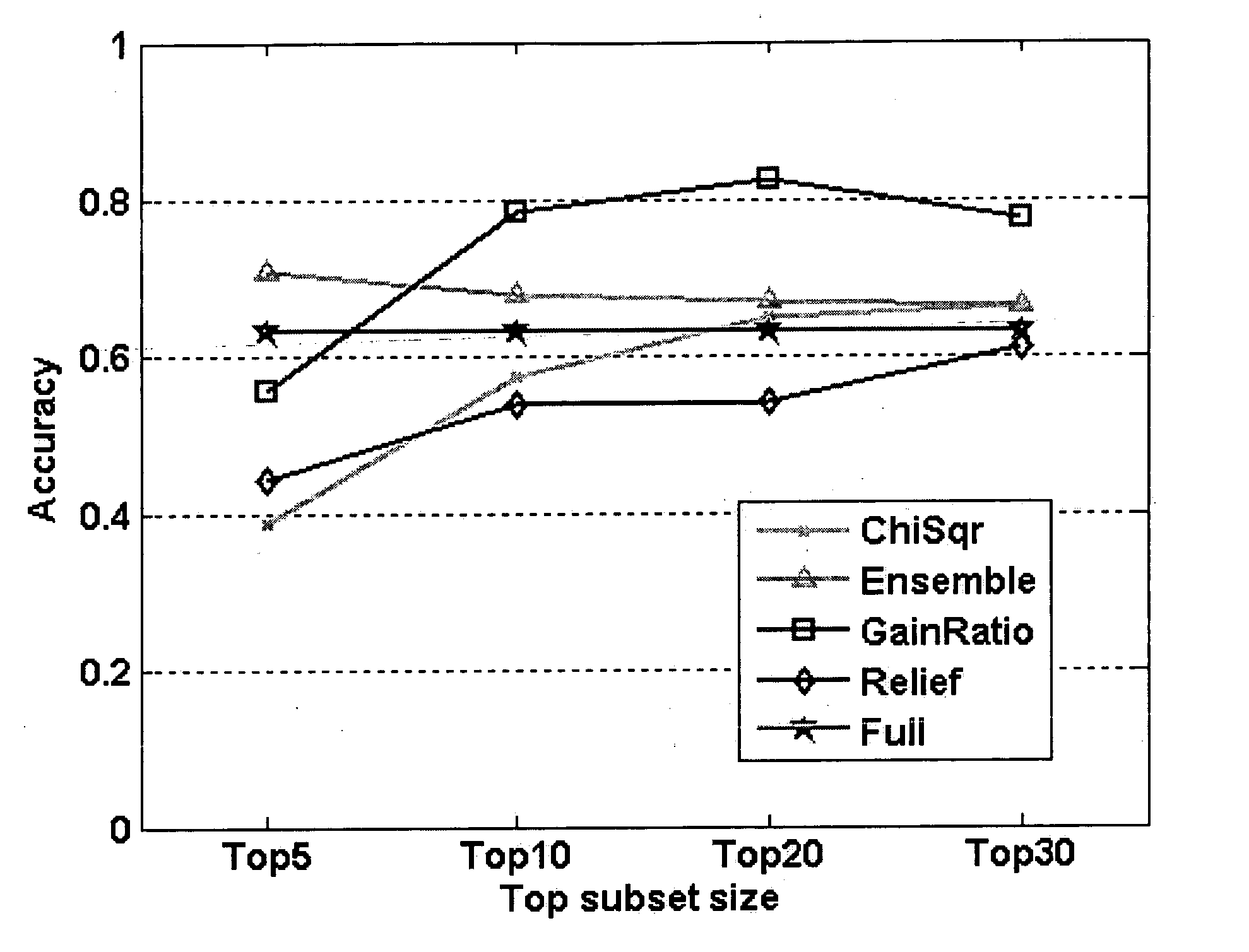
InactiveUS20090030864A1Improve abilitiesMathematical modelsData processing applicationsMultivariate statisticalEngineering
The present invention generally relates to computer databases and, more particularly, to data mining and knowledge discovery. The invention specifically relates to a method for constructing segmentation-based predictive models, such as decision-tree classifiers, wherein data records are partitioned into a plurality of segments and separate predictive models are constructed for each segment. The present invention contemplates a computerized method for automatically building segmentation-based predictive models that substantially improves upon the modeling capabilities of decision trees and related technologies, and that automatically produces models that are competitive with, if not better than, those produced by data analysts and applied statisticians using traditional, labor-intensive statistical techniques. The invention achieves these properties by performing segmentation and multivariate statistical modeling within each segment simultaneously. Segments are constructed so as to maximize the accuracies of the predictive models within each segment. Simultaneously, the multivariate statistical models within each segment are refined so as to maximize their respective predictive accuracies.
Owner:GLOBALFOUNDRIES INC
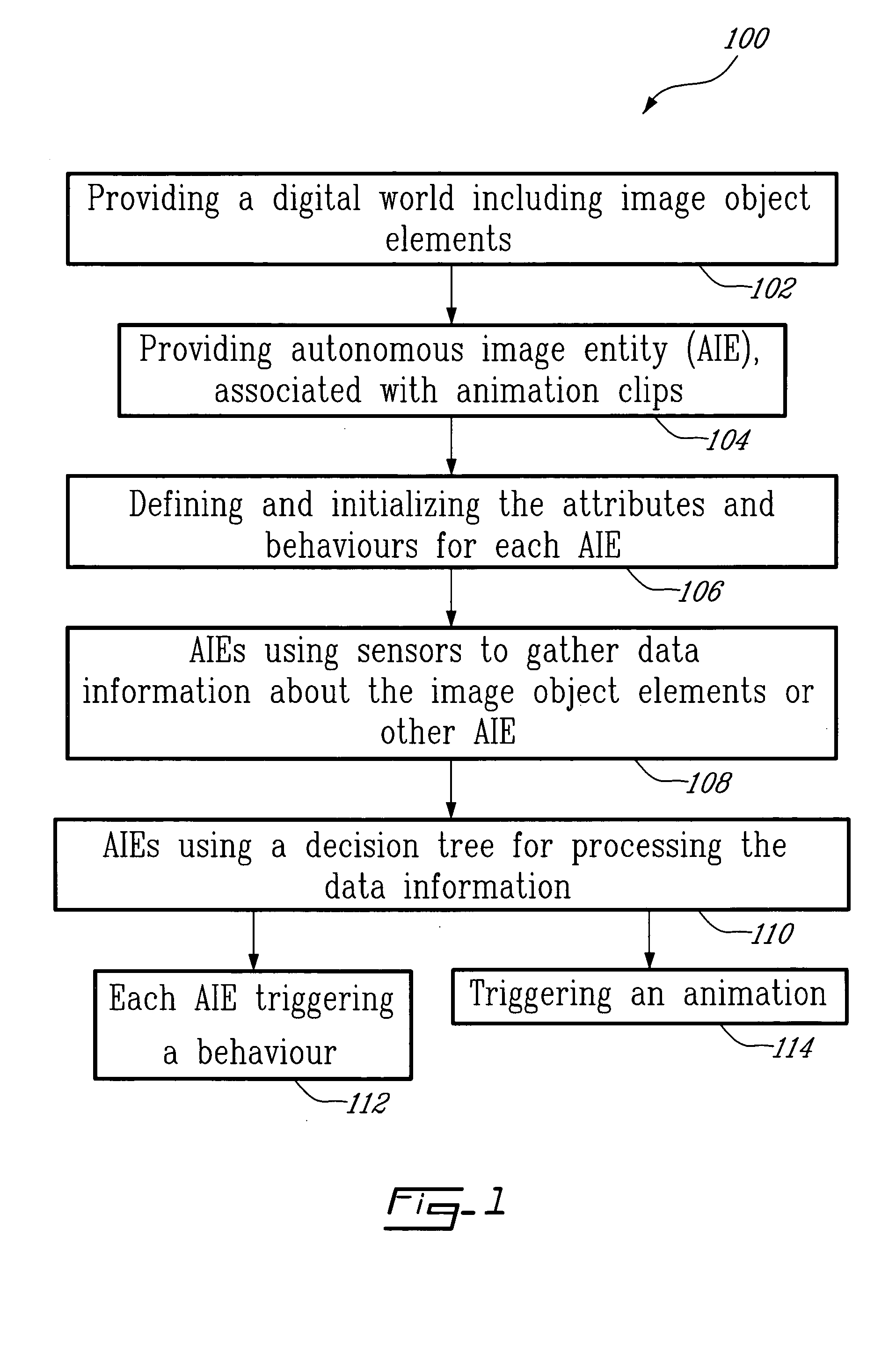
Method and system for on-screen animation of digital objects or characters
The method for on-screen animation includes providing a digital world including image object elements and defining autonomous image entities (AIE). Each AIE may represent a character or an object that is characterized by i) attributes defining the AIE relatively to the image objects elements of the digital world, and ii) behaviours for modifying some of the attributes. Each AIE is associated to animation clips allowing representing the AIE in movement in the digital world. Virtual sensors allow the AIE to gather data information about image object elements or other AIE within the digital world. Decision trees are used for processing the data information resulting in selecting and triggering one of the animation cycle or selecting a new behaviour. A system embodying the above method is also provided. The method and system for on-screen animation of digital entities according to the present invention can be used for creating animation for movies, for video games, and for simulation.
Owner:BGT BIOGRAPHIC TECH
Solution network decision trees
A method for searching potential solutions within a solution network. The method includes authoring a solution to solve an issue, storing the solution within a decision tree relating to the issue, and searching the solution network based upon the issue. The searching includes accessing the decision tree relating to the issue.
Owner:DELL PROD LP
Method and system of evaluating performance of a crop
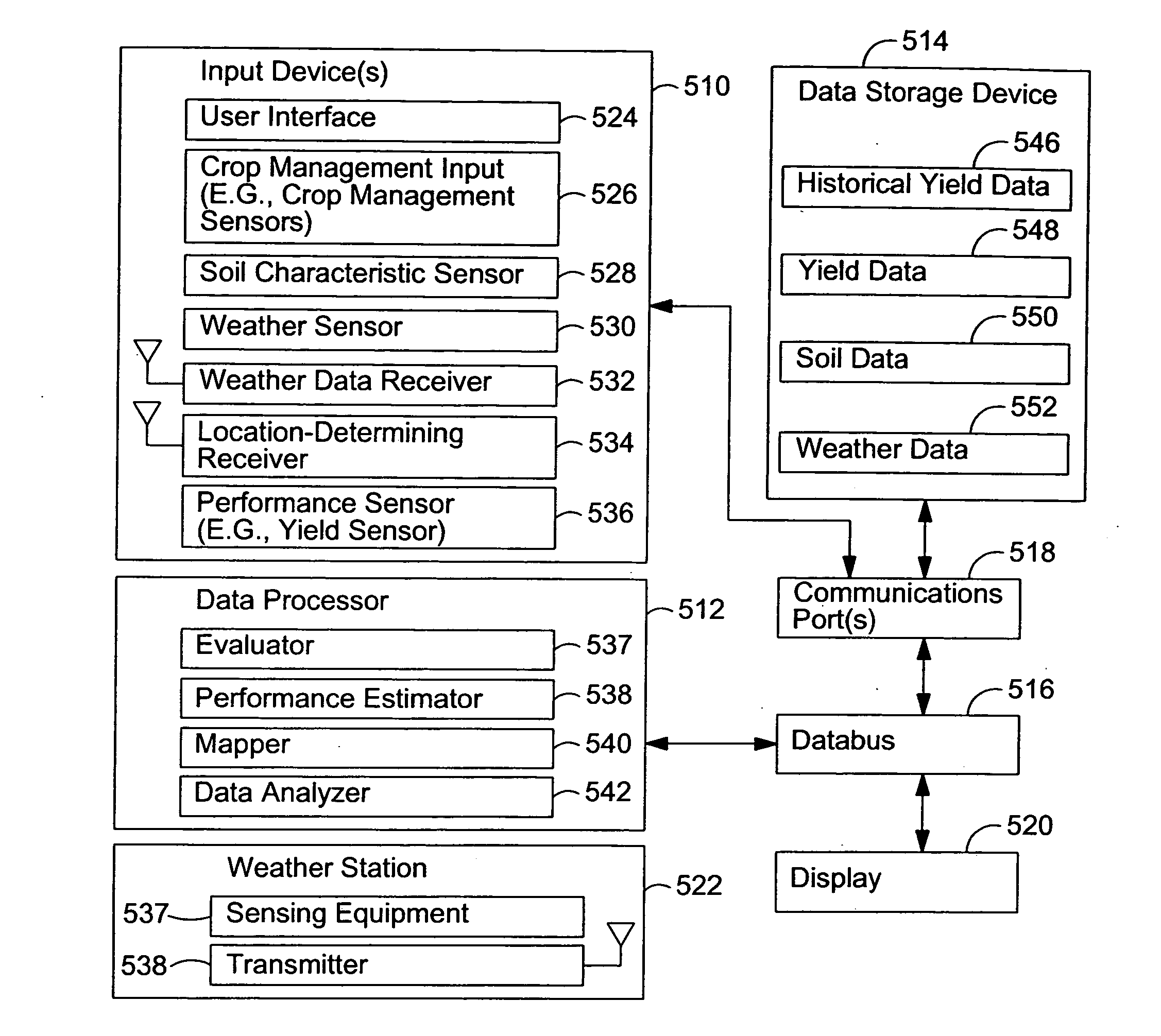
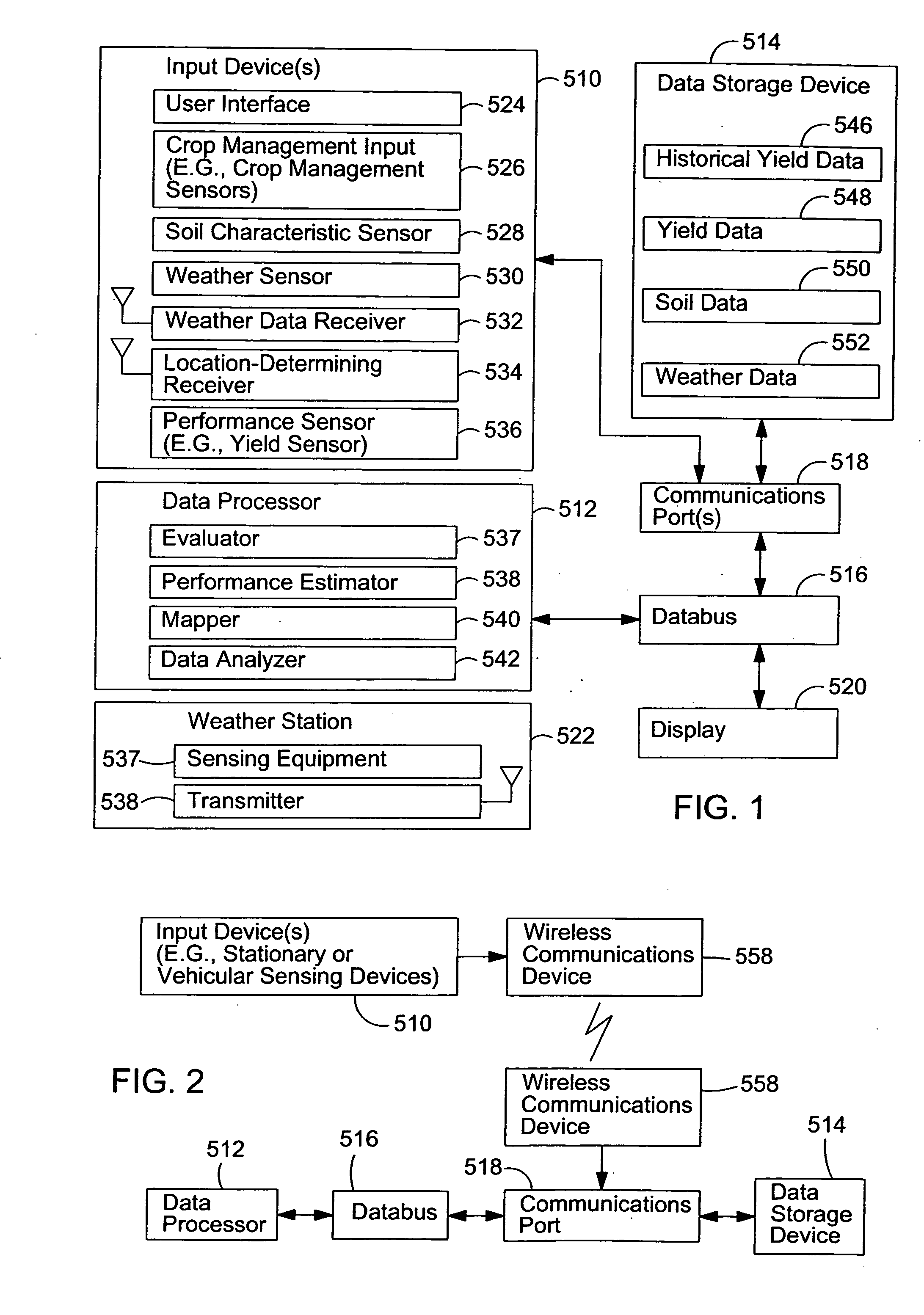
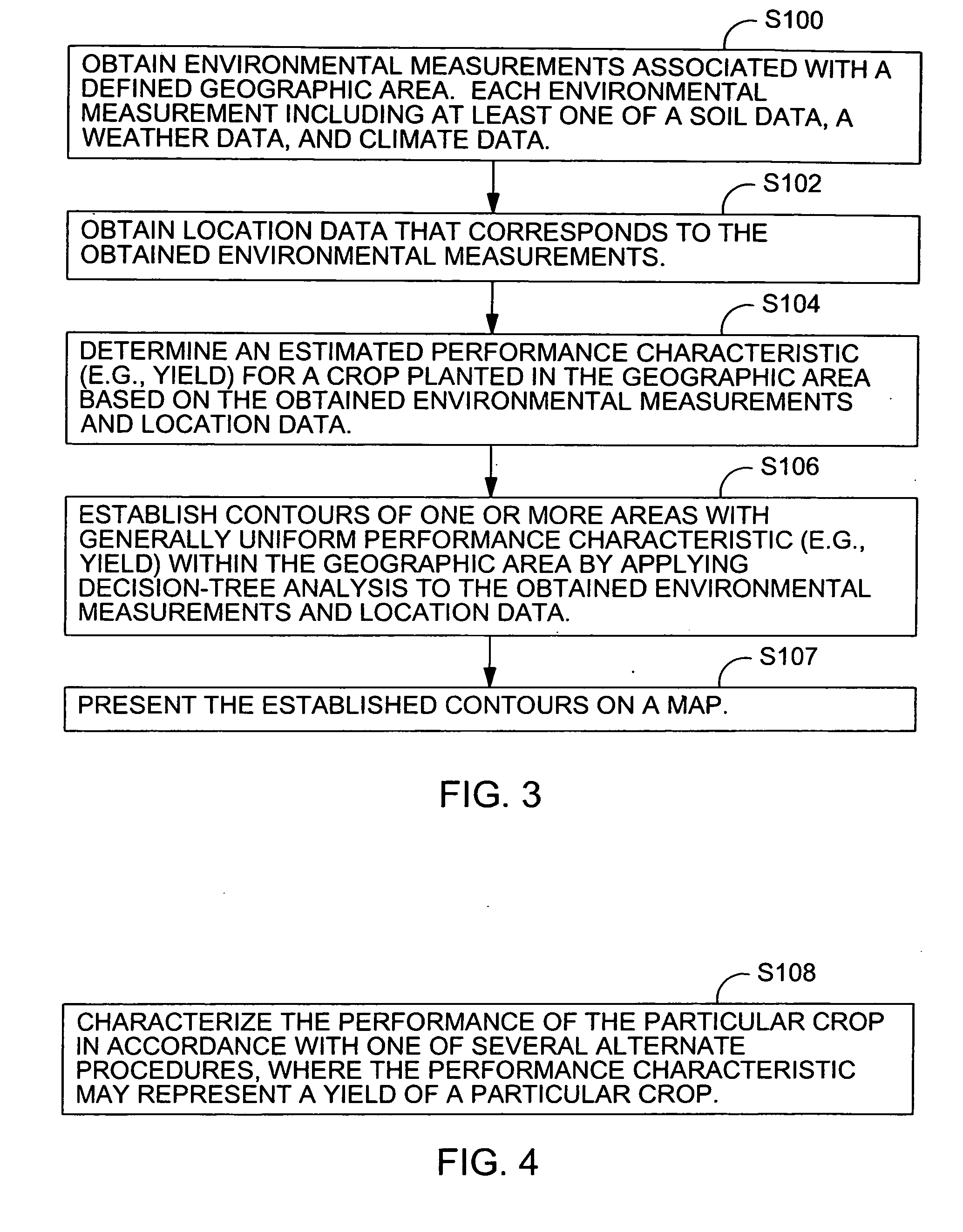
ActiveUS20060074560A1Well representedForecastingElectric/magnetic detectionEnvironmental resource managementGeographic regions
A method and system of evaluating crop performance facilitates characterization of the environmental impact of a geographic region or areas within the region for growing plant-life. Environmental measurements are obtained. The environmental measurements are associated with a geographic region. Each environmental measurement includes at least one of soil data and weather data. Respective location data is obtained. The location data is associated with corresponding environmental measurements. An estimated performance characteristic is determined for a particular crop planted in the geographic region based on the obtained environmental measurements and respective location data. Contours are established for one or more uniform performance areas with generally uniform performance characteristic within the geographic region by applying a decision-tree analysis to the obtained environmental measurements.
Owner:DEERE & CO
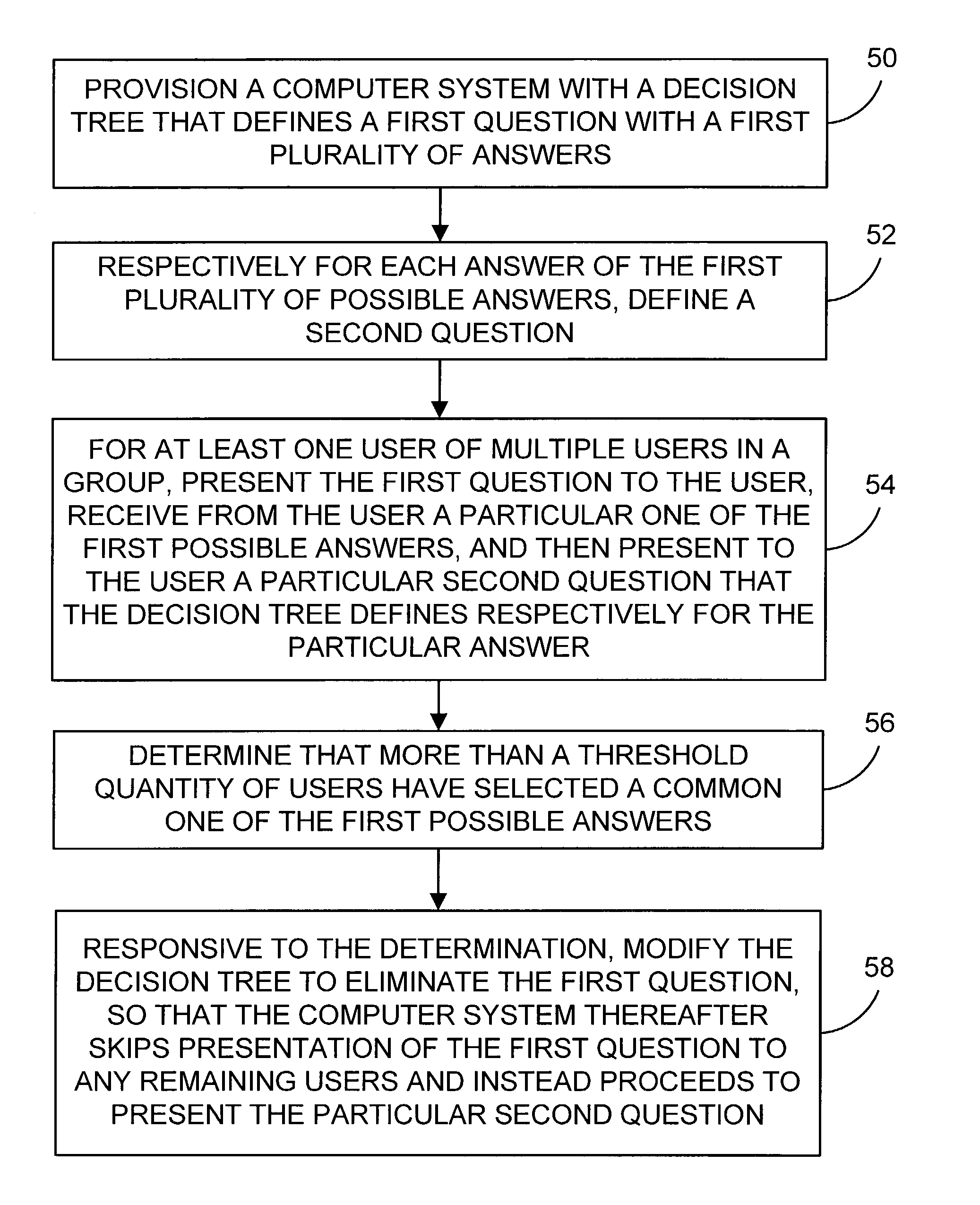
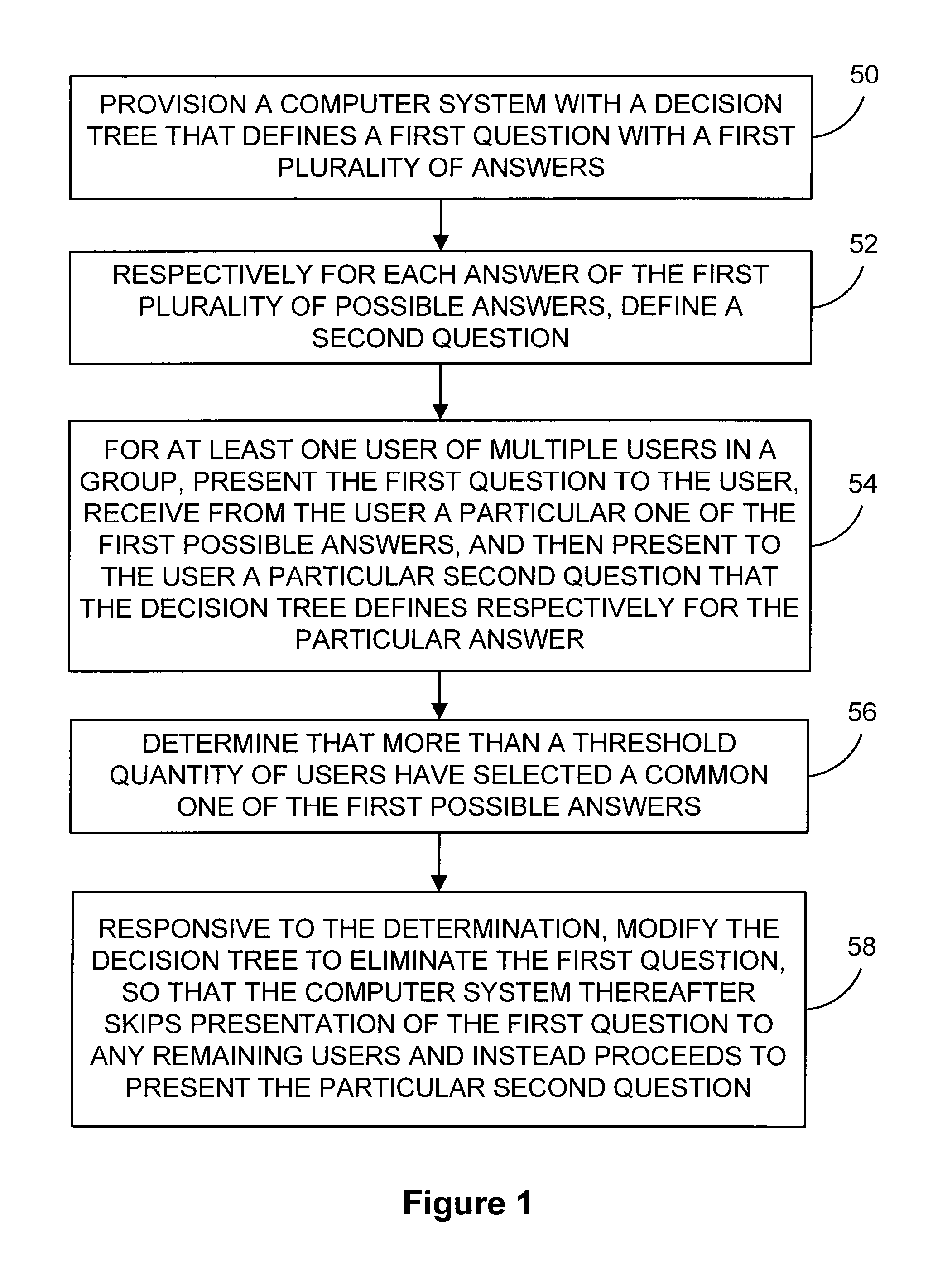
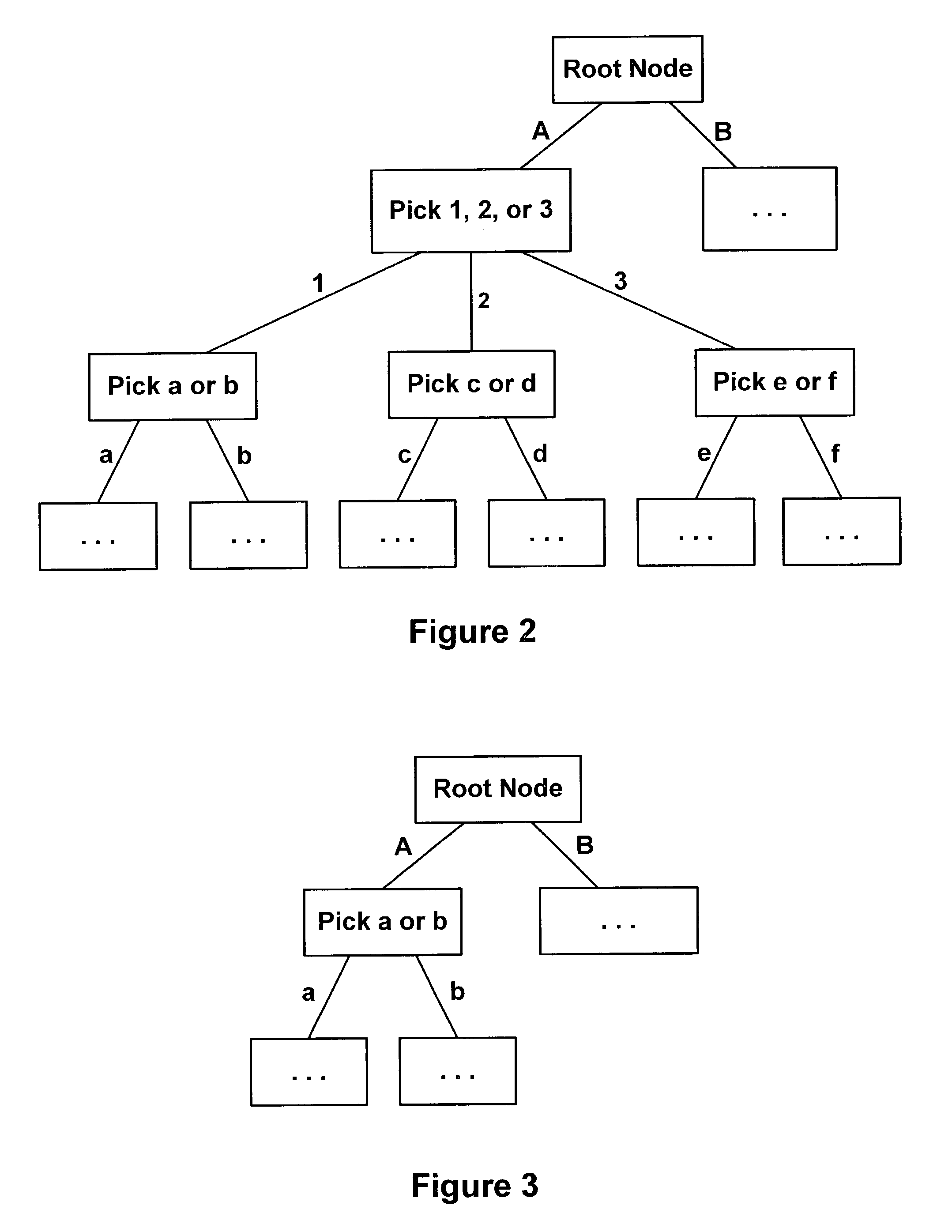
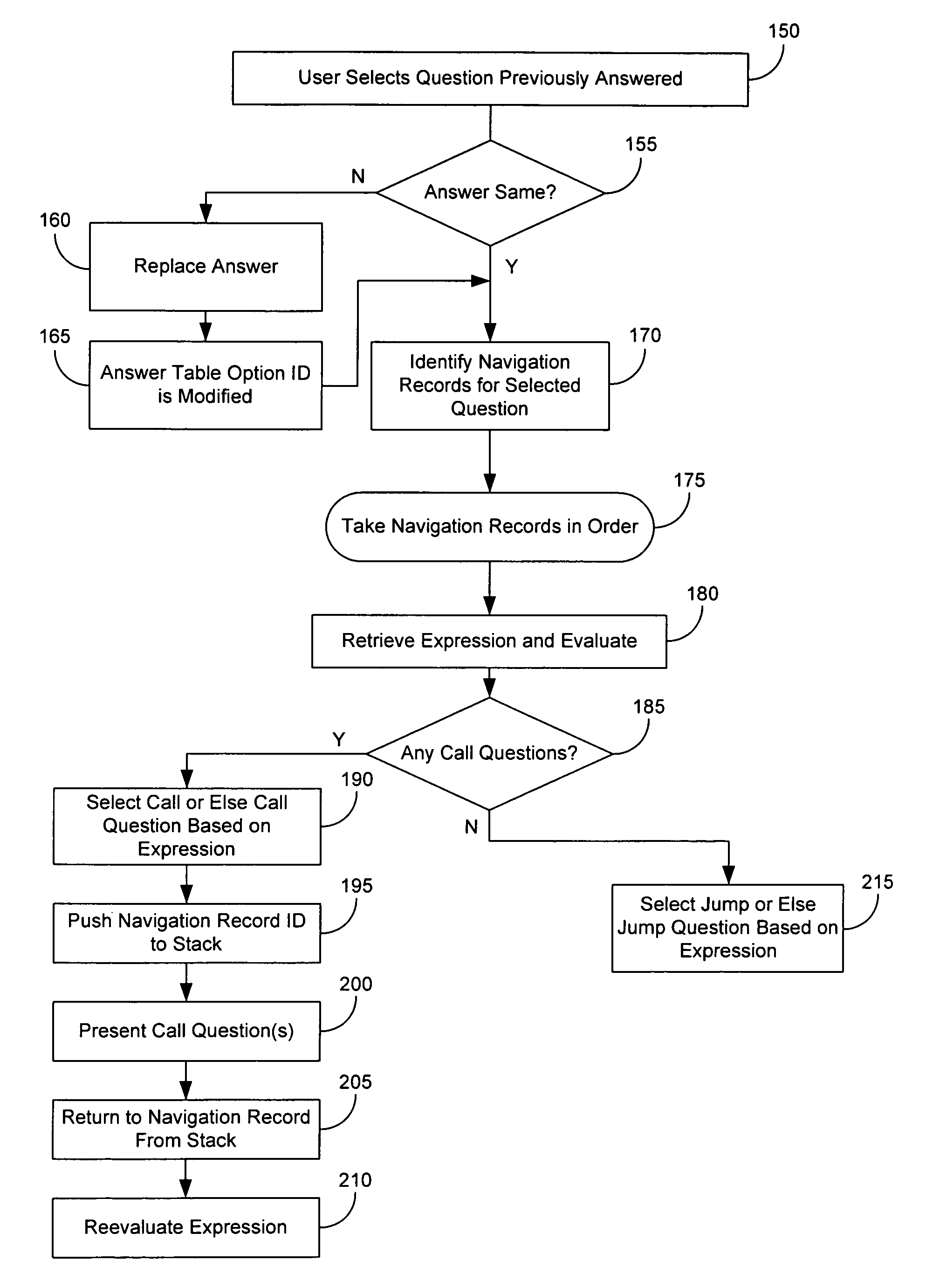
Method and system for dynamic variation of decision tree architecture
A method and system for selecting and presenting questions to users is provided. The method and system provides for a decision-tree architecture that functionally changes form as users traverse the tree, depending on the responses provided by the users.
Owner:SPRING SPECTRUM LP
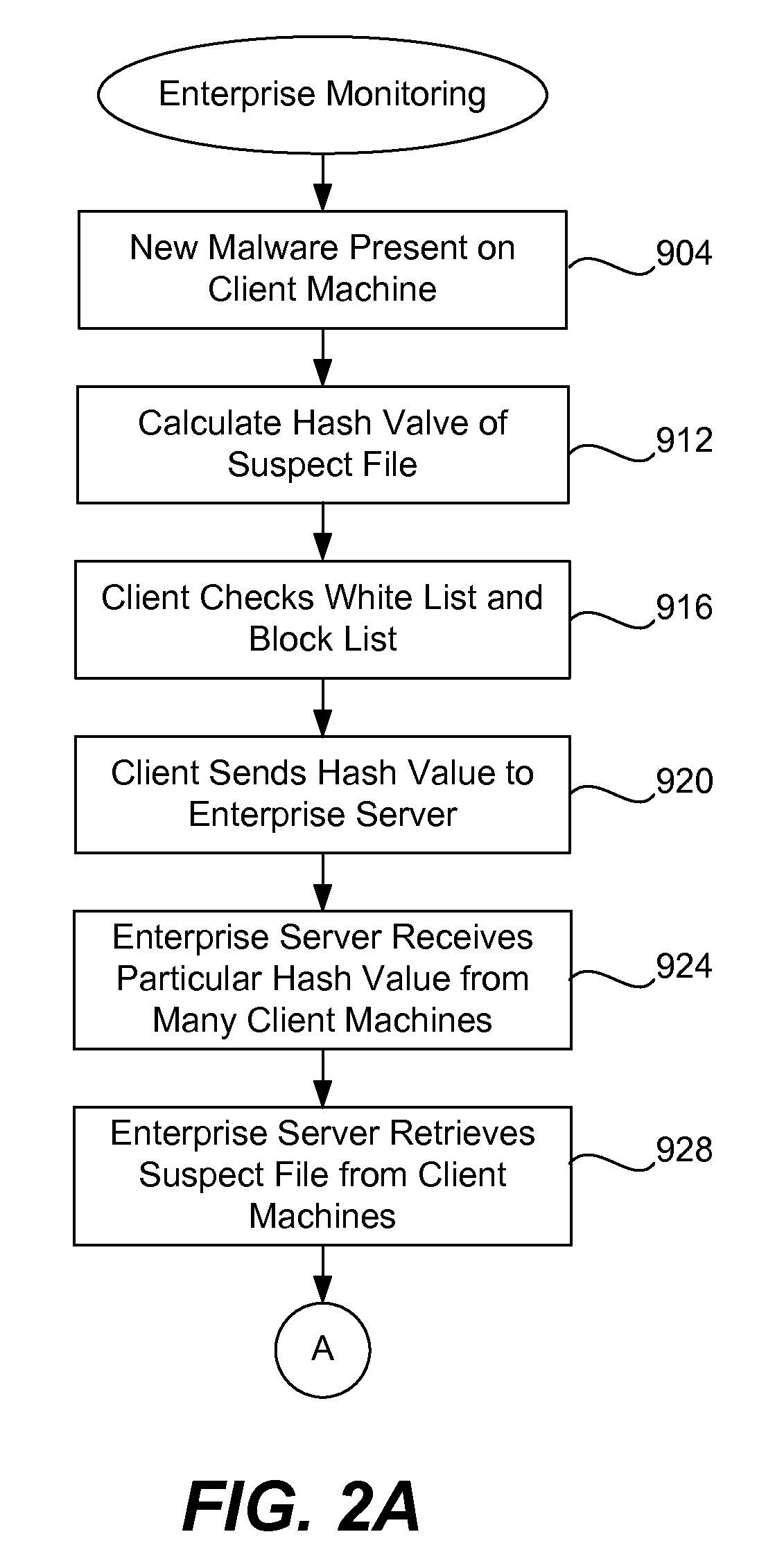
Zero day malware scanner
ActiveUS8375450B1Quick analysisReduce the amount of memoryMemory loss protectionUser identity/authority verificationClient-sideMalware
A training model for malware detection is developed using common substrings extracted from known malware samples. The probability of each substring occurring within a malware family is determined and a decision tree is constructed using the substrings. An enterprise server receives indications from client machines that a particular file is suspected of being malware. The suspect file is retrieved and the decision tree is walked using the suspect file. A leaf node is reached that identifies a particular common substring, a byte offset within the suspect file at which it is likely that the common substring begins, and a probability distribution that the common substring appears in a number of malware families. A hash value of the common substring is compared (exact or approximate) against the corresponding substring in the suspect file. If positive, a result is returned to the enterprise server indicating the probability that the suspect file is a member of a particular malware family.
Owner:TREND MICRO INC
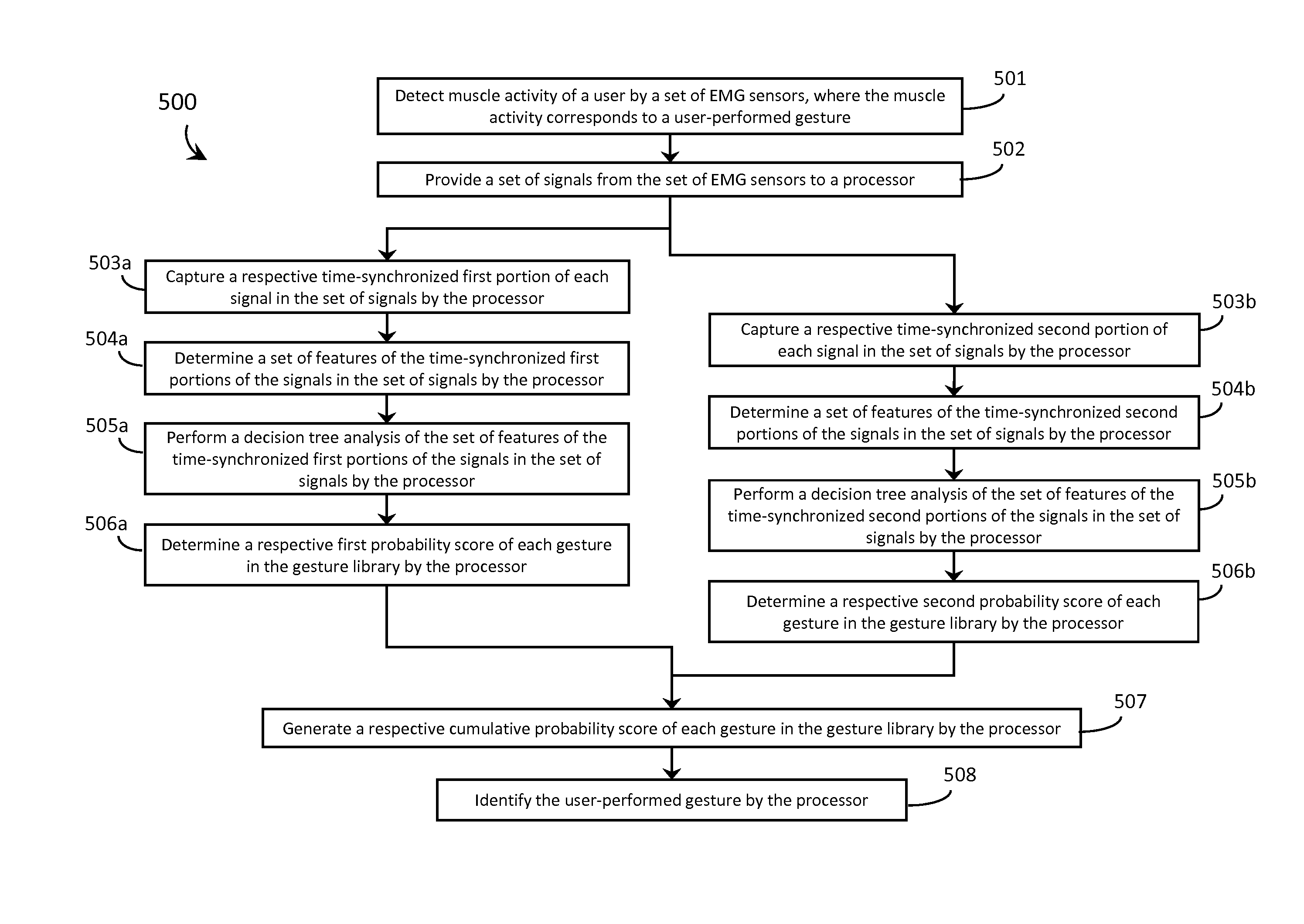
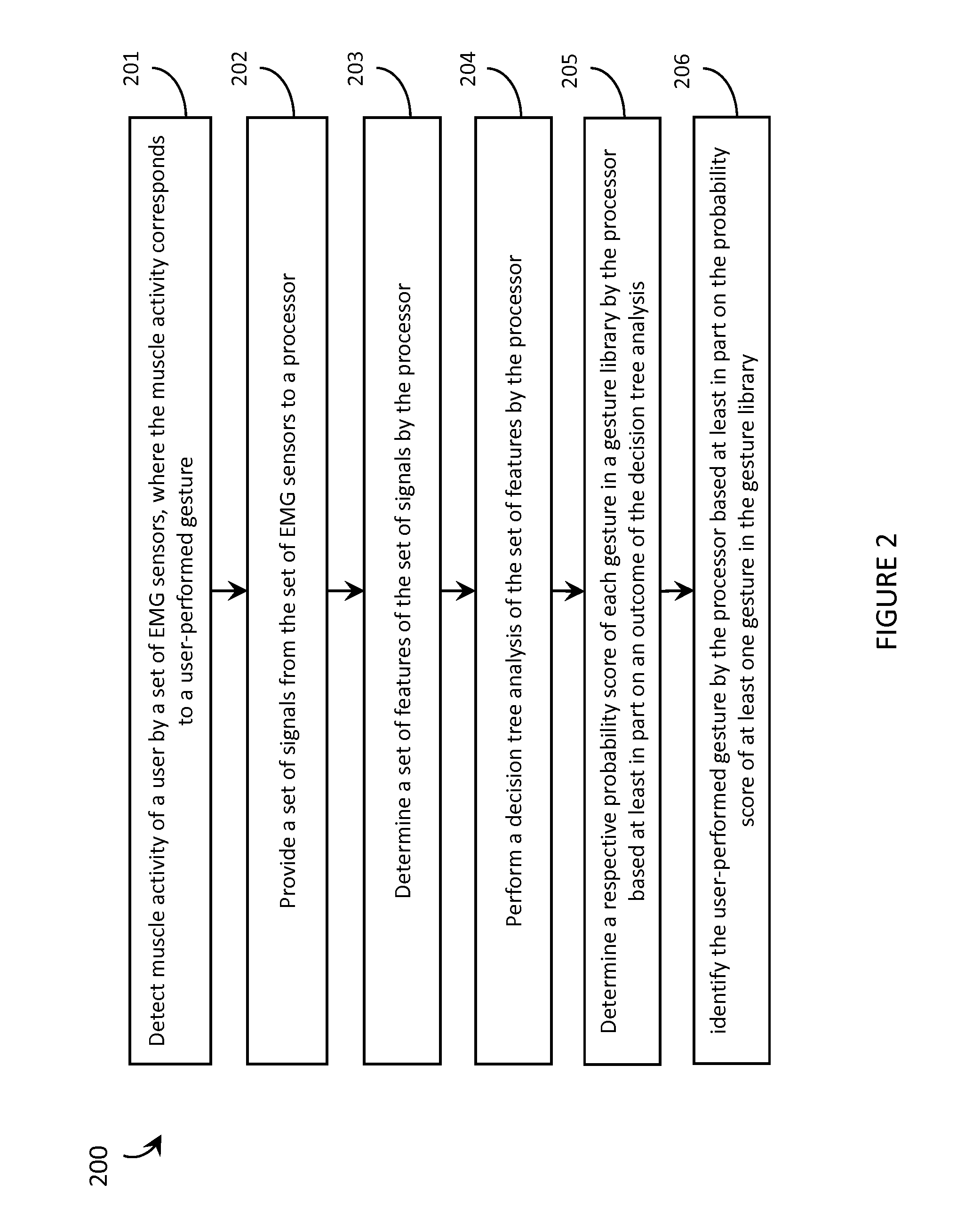
Systems, articles, and methods for gesture identification in wearable electromyography devices
ActiveUS20150109202A1Input/output for user-computer interactionMedical data miningEngineeringBoard processor
Systems, articles, and methods perform gesture identification with limited computational resources. A wearable electromyography (“EMG”) device includes multiple EMG sensors, an on-board processor, and a non-transitory processor-readable memory that stores data and / or processor-executable instructions for performing gesture identification. The wearable EMG device detects and determines features of signals when a user performs a physical gesture, and processes the features by performing a decision tree analysis. The decision tree analysis invokes a decision tree stored in the memory, where storing and executing the decision tree may be managed by limited computational resources. The outcome of the decision tree analysis is a probability vector that assigns a respective probability score to each gesture in a gesture library. The accuracy of the gesture identification may be enhanced by performing multiple iterations of the decision tree analysis across multiple time windows of the EMG signal data and combining the resulting probability vectors.
Owner:META PLATFORMS TECH LLC
Computer system and method for a self administered risk assessment
InactiveUS6334192B1SurgeryComputer-assisted medical data acquisitionComputer monitorComputerized system
A computer system for performing an interactive assessment of the risk of an event, has a computer monitor to present to a user of the system a series of questions and potential responses, and a keyboard or other device to select a response to the question. The system can administer complex inverted tree type decision algorithms, in which the questions that are presented to the user, depend upon the response to the previous question, and an assessment of the risk of an event is presented to the user whenever they reach the terminus point in the decision tree. The risk assessment algorithm is data driven and a risk assessment is defined by entries in a file, which is available over a network. The system provides options so each user may view the path through the sequence of questions and answers, and interact with the risk assessment, in a manner customized for their own interactive session.
Owner:KARPF RONALD S
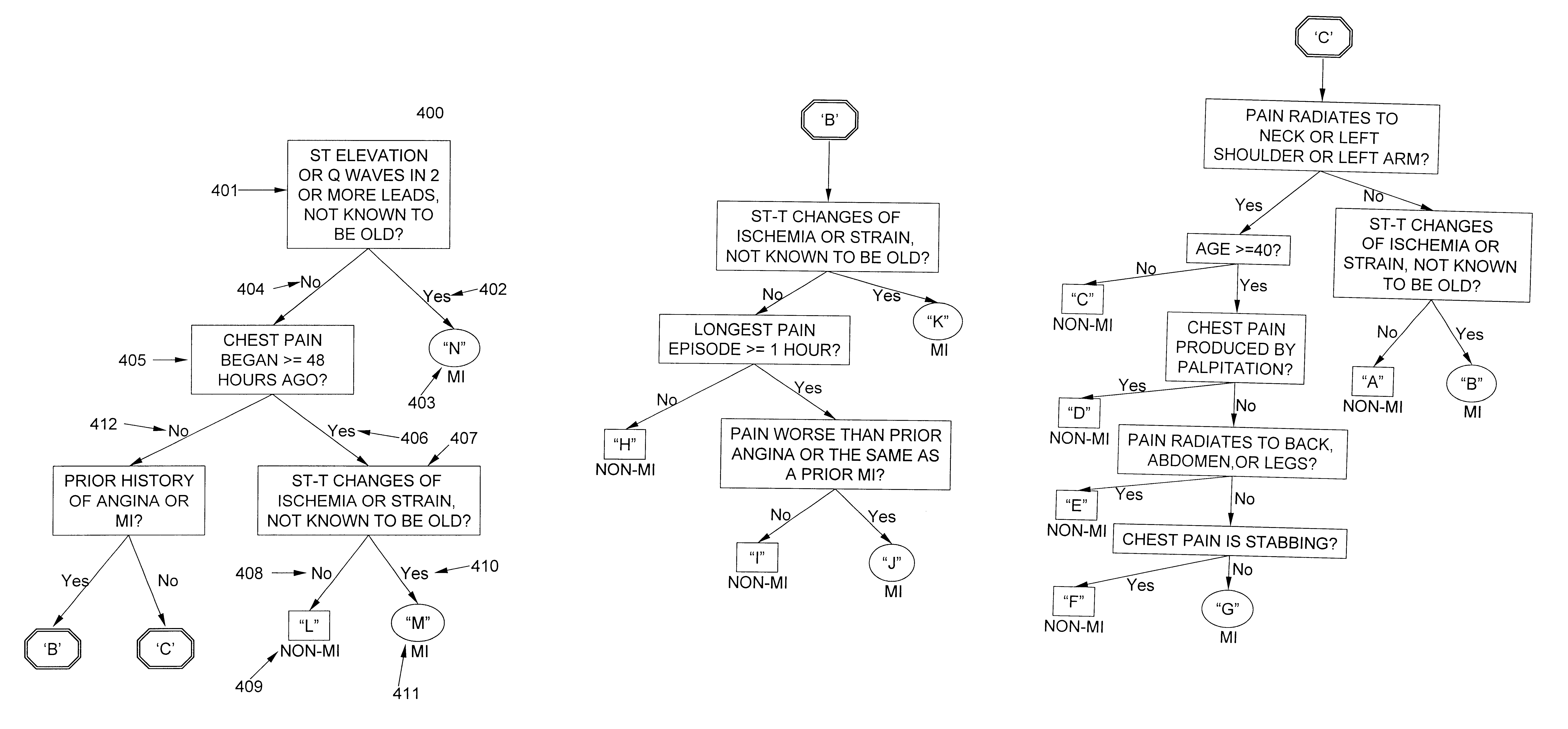
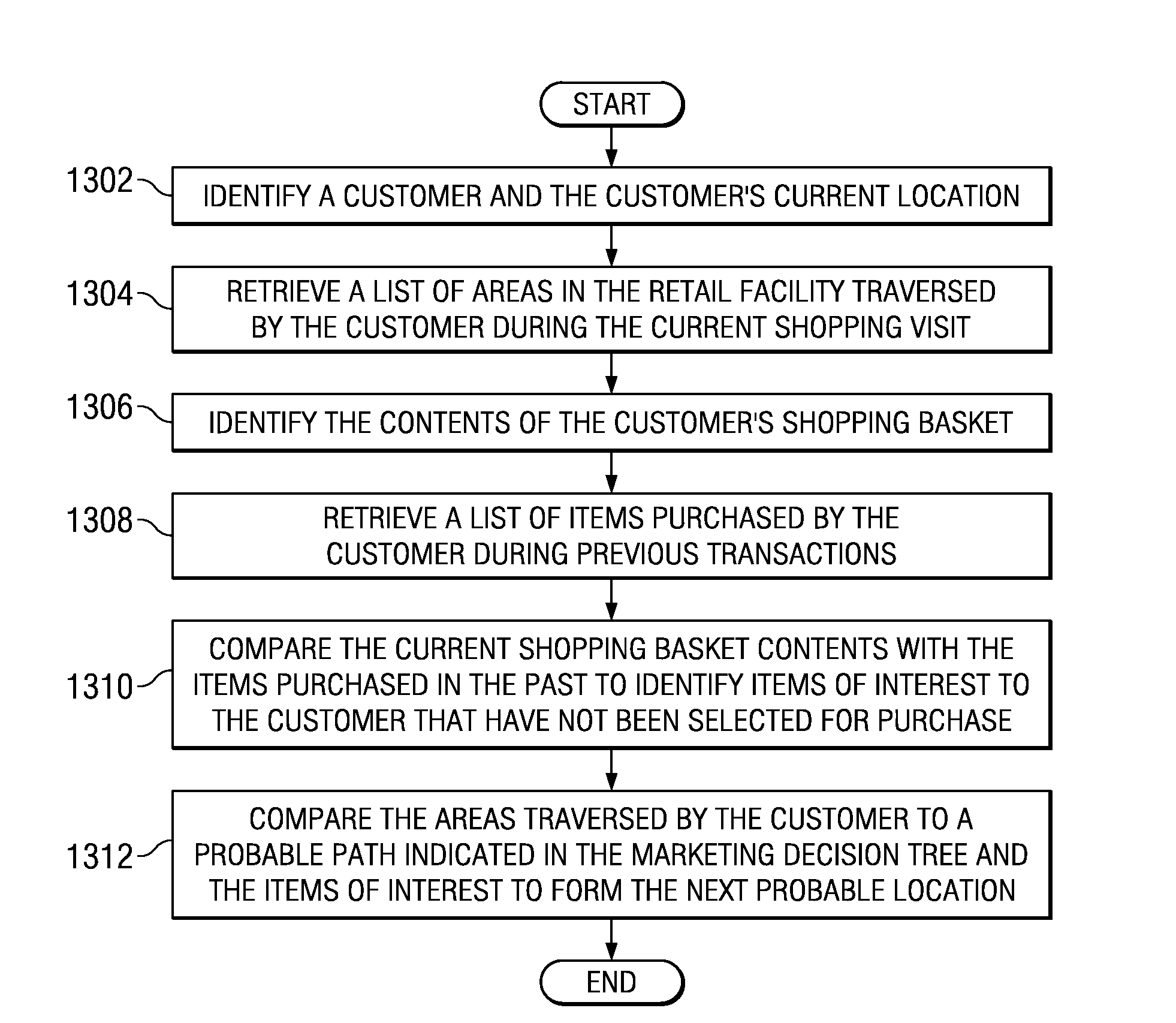
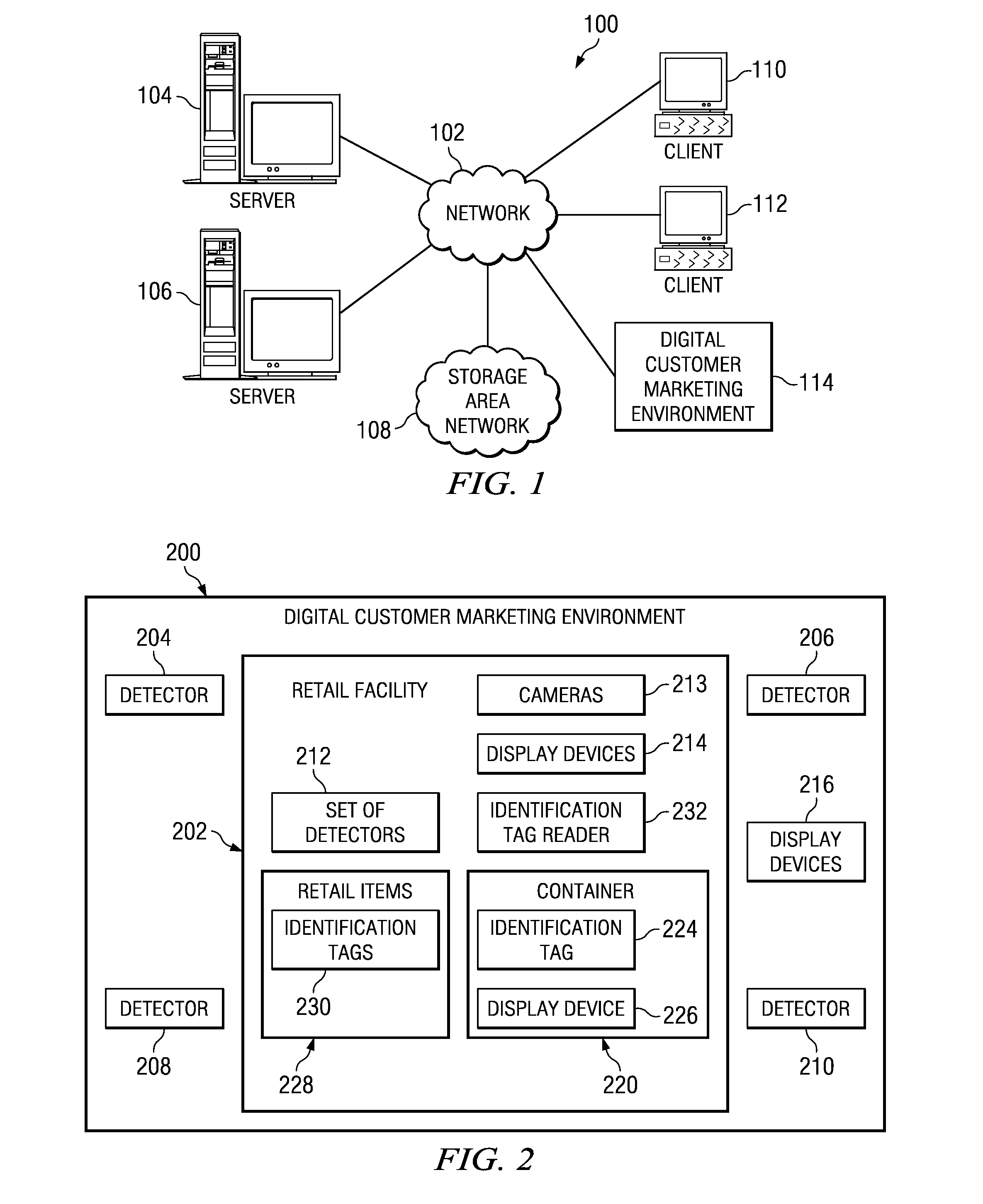
Method and apparatus for decision tree based marketing and selling for a retail store
A computer implemented method, apparatus, and computer usable program product for decision tree based marketing to a customer in a retail facility. In response to identifying a customer associated with the retail facility, a marketing decision tree for the customer is retrieved. The marketing decision tree indicates a set of paths through the retail facility that the customer will most likely follow while shopping. A next probable location of the customer is identified using a current location of the customer and the marketing decision tree. A customized marketing message for an item located in the next probable location is presented to the customer.
Owner:DAEDALUS BLUE LLC
Method and system for detecting malicious behavioral patterns in a computer, using machine learning
InactiveUS20070294768A1Memory loss protectionUnauthorized memory use protectionComputer wormComputerized system
Method for detecting malicious behavioral patterns which are related to malicious software such as a computer worm in computerized systems that include data exchange channels with other systems over a data network. Accordingly, hardware and / or software parameters are determined in the computerized system that is can characterize known behavioral patterns thereof. Known malicious code samples are learned by a machine learning process, such as decision trees and artificial neural networks, and the results of the machine learning process are analyzed in respect to the behavioral patterns of the computerized system. Then known and unknown malicious code samples are identified according to the results of the machine learning process.
Owner:DEUTSCHE TELEKOM AG
Process for creating service action data structures
InactiveUS20050060662A1ResourcesInput/output processes for data processingComputer assistanceDecision taking
A process for assisting a user to order the IT services the user wants even if the user is not familiar with the proper IT terminology or concepts. The process comprises: displaying an IT services catalog; determining if a user that wishes to order an IT service selects an option for computer assistance in selecting a service action; if a user requests assistance, displaying questions in an order dictated by a decision tree defined in advance by an IT professional, and traversing the decision tree based upon answers provided by the user via computer input devices until one or more recommendations for service actions have been encountered; gathering all recommended service actions and filling in fields in a data structure based upon answers given by said user; upon completion of step 3, or if said user does not request assistance in step 2, soliciting said user to fill in all unpopulated fields of a data structure defining one or more service actions which are either selected by the user or which have been recommended by processing the decision tree and validating all user data input.
Owner:GODUNOV ENTERPRISES
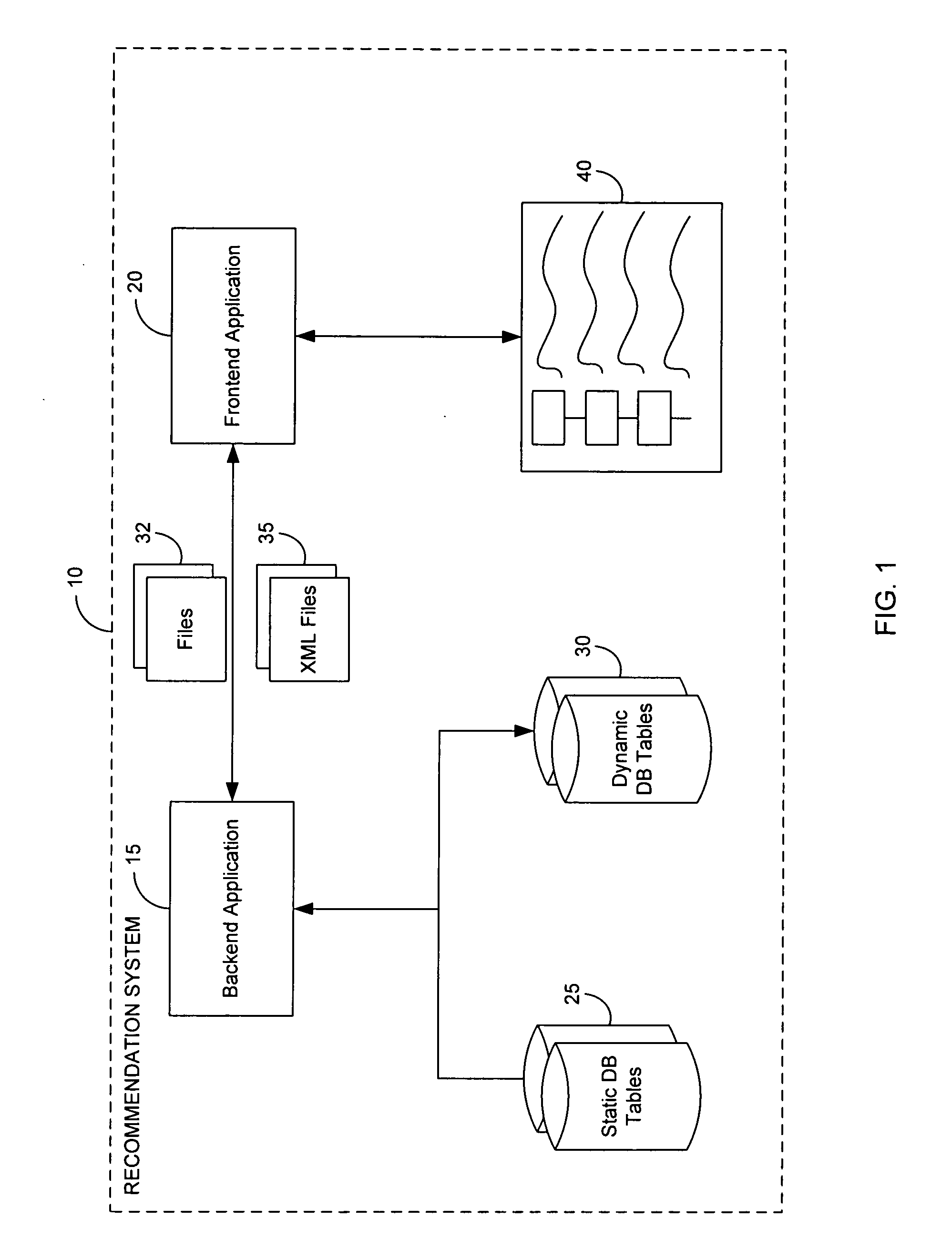
Extensible configuration engine system and method
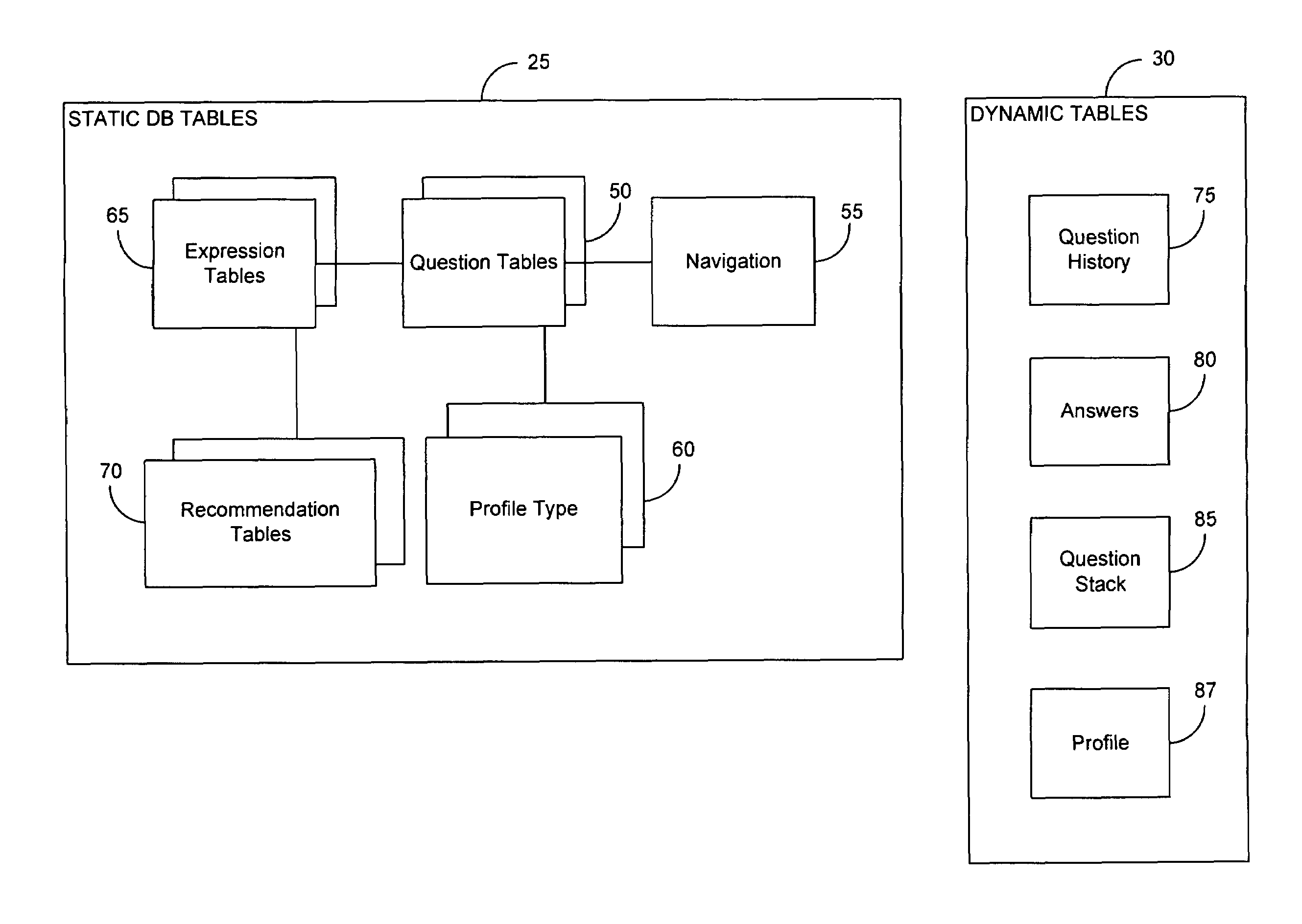
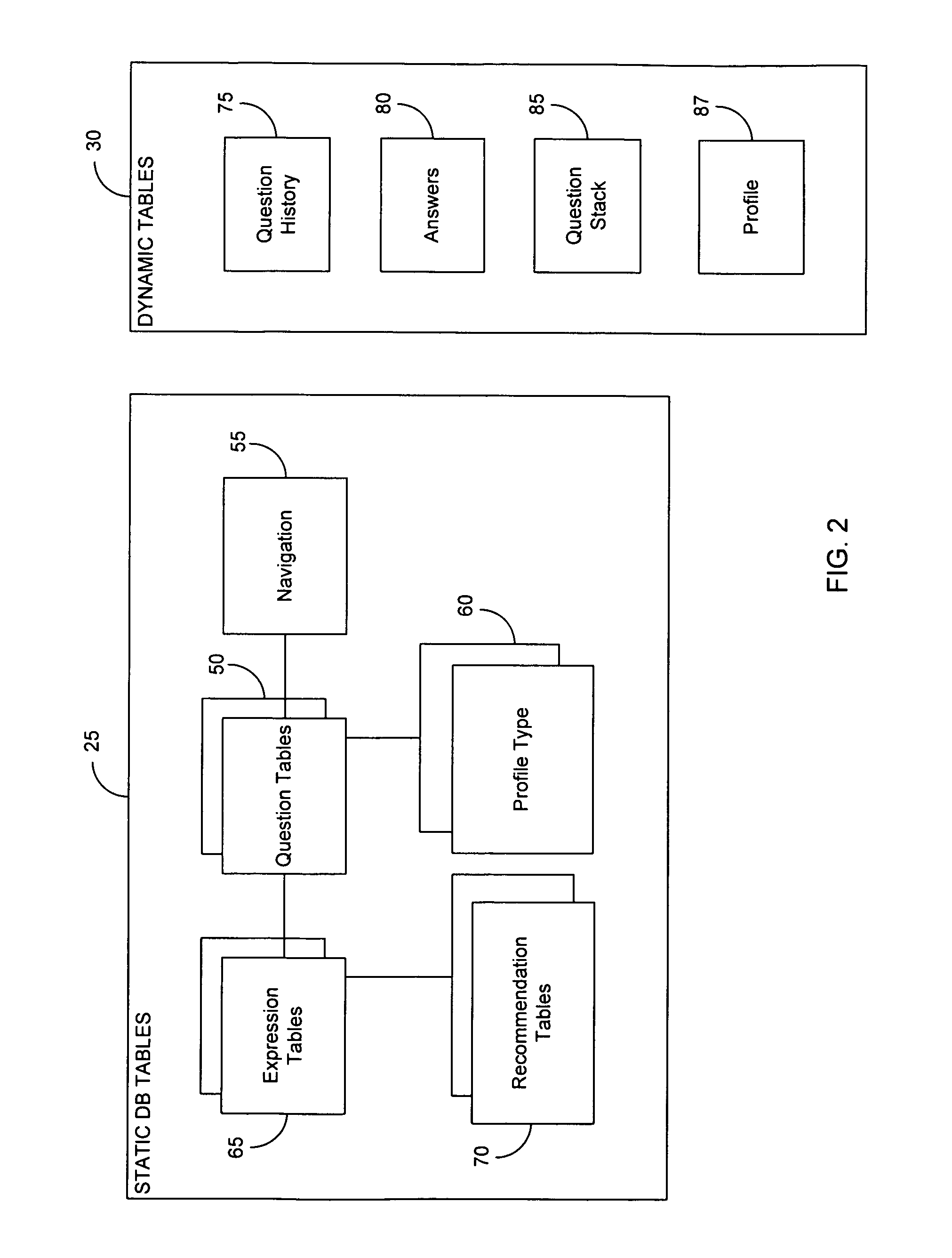
InactiveUS7457790B2Easy to manufactureDigital data processing detailsResourcesRelational databaseApplication software
Methods and systems are provided for facilitating decision making through an improved recommendation system. The data used in the system, such as the questions and business logic for navigating between questions, is stored in relational database tables that are easy to access and edit by users. A backend application program reads the data and processes the navigation logic depending upon answers received from users to automatically generate a decision tree. Users are allowed to select questions earlier in the tree, and the application can regenerate a tree from the point of the selected question and on. The application program stores the questions to be presented in a structured document which is handed off to a user interface generation program.
Owner:COMMVAULT SYST INC
Method and system for filtering sensitive web page based on multiple classifier amalgamation
ActiveCN101281521ASolve tight control problemsShort processing timeCharacter and pattern recognitionData switching networksData streamInternet content
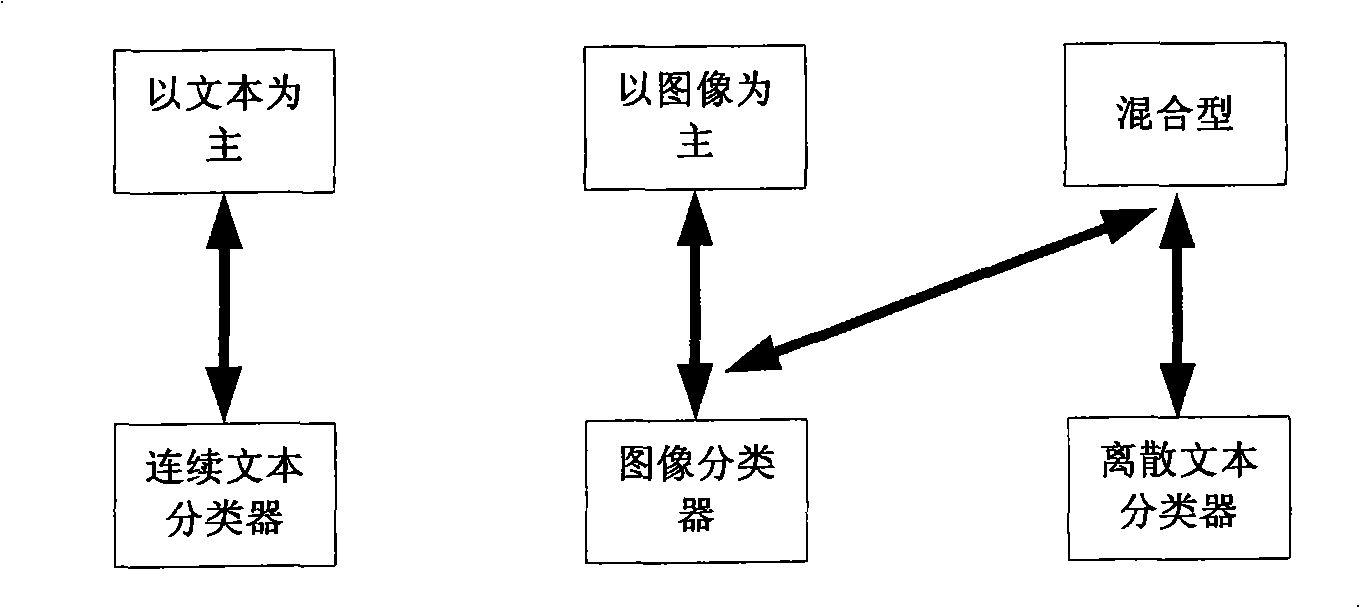
The invention discloses a system and a method for filtering sensitive webpage, which is based on multi-classifier fusion. The processing object is a webpage, and the processing result is whether the webpage contains sensitive content, which may be pornography, reaction, violence and other unhealthy Internet contents harmful to society. The system comprises a data stream obtaining and preprocessing unit, an image and text stream filtering unit and an information fusion unit of image filter and text filter, by the cooperation of multiple classifiers, the system acquires source code of a webpage by using the URL of the webpage, a text and an image are separated at preprocessing stage to obtain text information and effective image information; an input webpage is divided into three modes by decision tree algorithm; the webpage is recognized by using a consecutive text classifier, a discrete sensitive text classifier and an image classifier, the output result recognized by the classifiers is fused and calculated, then a judge factor is given, and the final result is returned to a browser.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Systems and methods for generating configuration metrics in a storage network
InactiveUS20070166674A1Facilitate decision-makingEasy to manufactureElectrical appliancesTeaching apparatusRelational databaseApplication software
Methods and systems are provided for facilitating decision making through an improved recommendation system. The data used in the system, such as the questions and business logic for navigating between questions, is stored in relational database tables that are easy to access and edit by users. A backend application program reads the data and processes the navigation logic depending upon answers received from users to automatically generate a decision tree. Users are allowed to select questions earlier in the tree, and the application can regenerate a tree from the point of the selected question and on. The application program stores the questions to be presented in a structured document which is handed off to a user interface generation program.
Owner:COMMVAULT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com