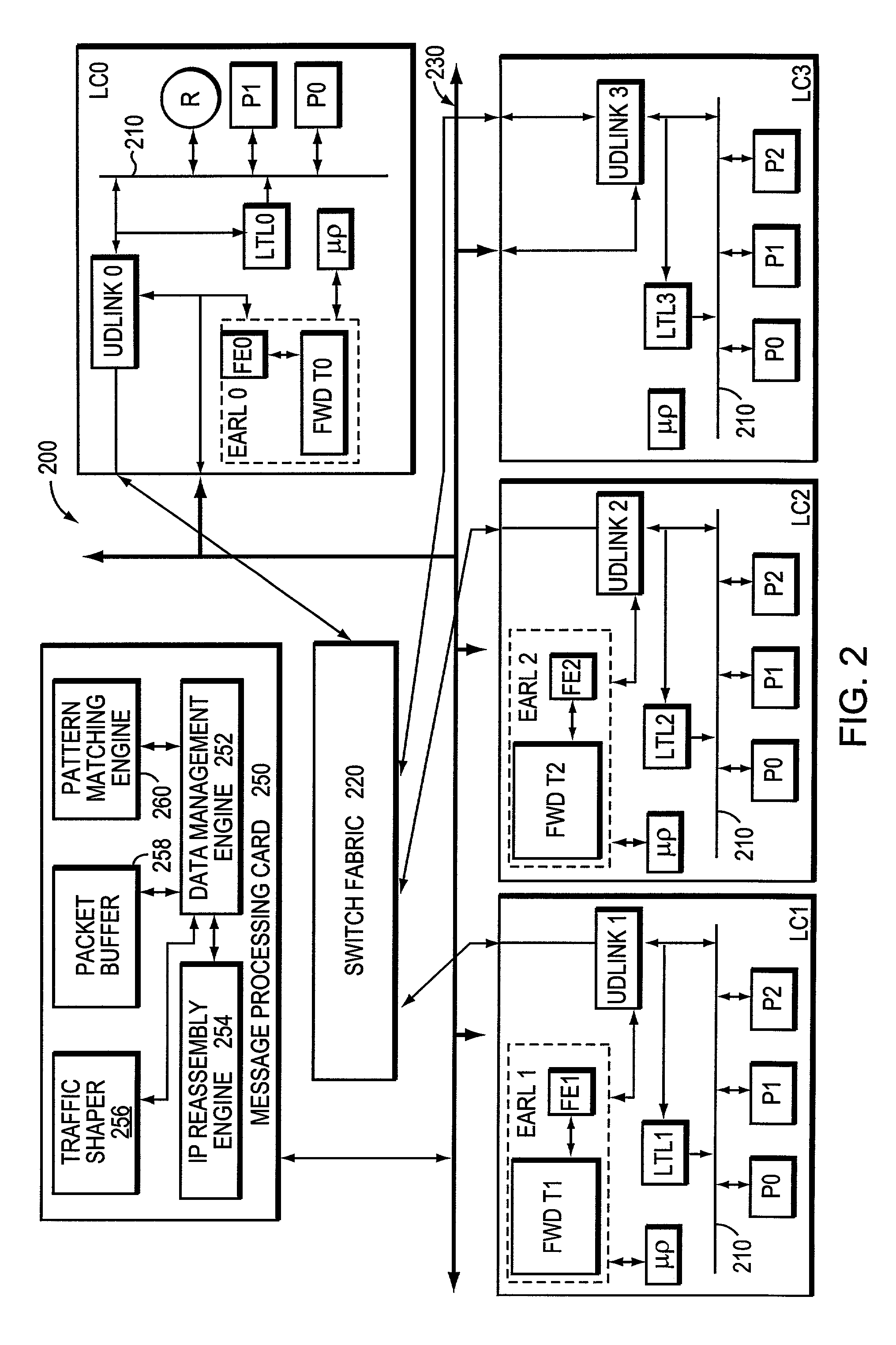
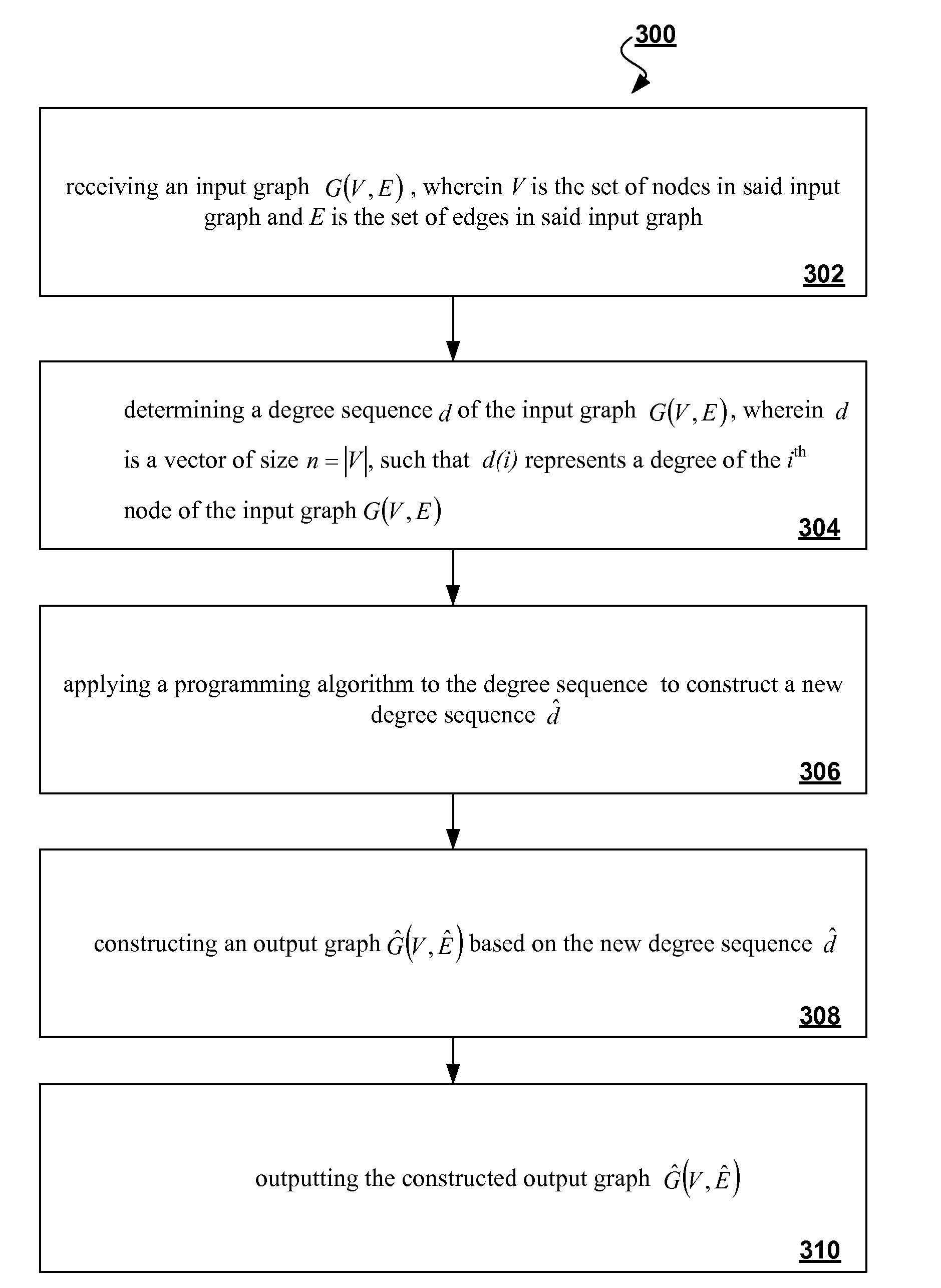
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52947 results about "Theoretical computer science" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Theoretical computer science (TCS) is a subset of general computer science and mathematics that focuses on more mathematical topics of computing and includes the theory of computation. It is difficult to circumscribe the theoretical areas precisely.
Methods and apparatus for interpreting user selections in the context of a relation distributed as a set of orthogonalized sub-relations
Owner:ORACLE INT CORP
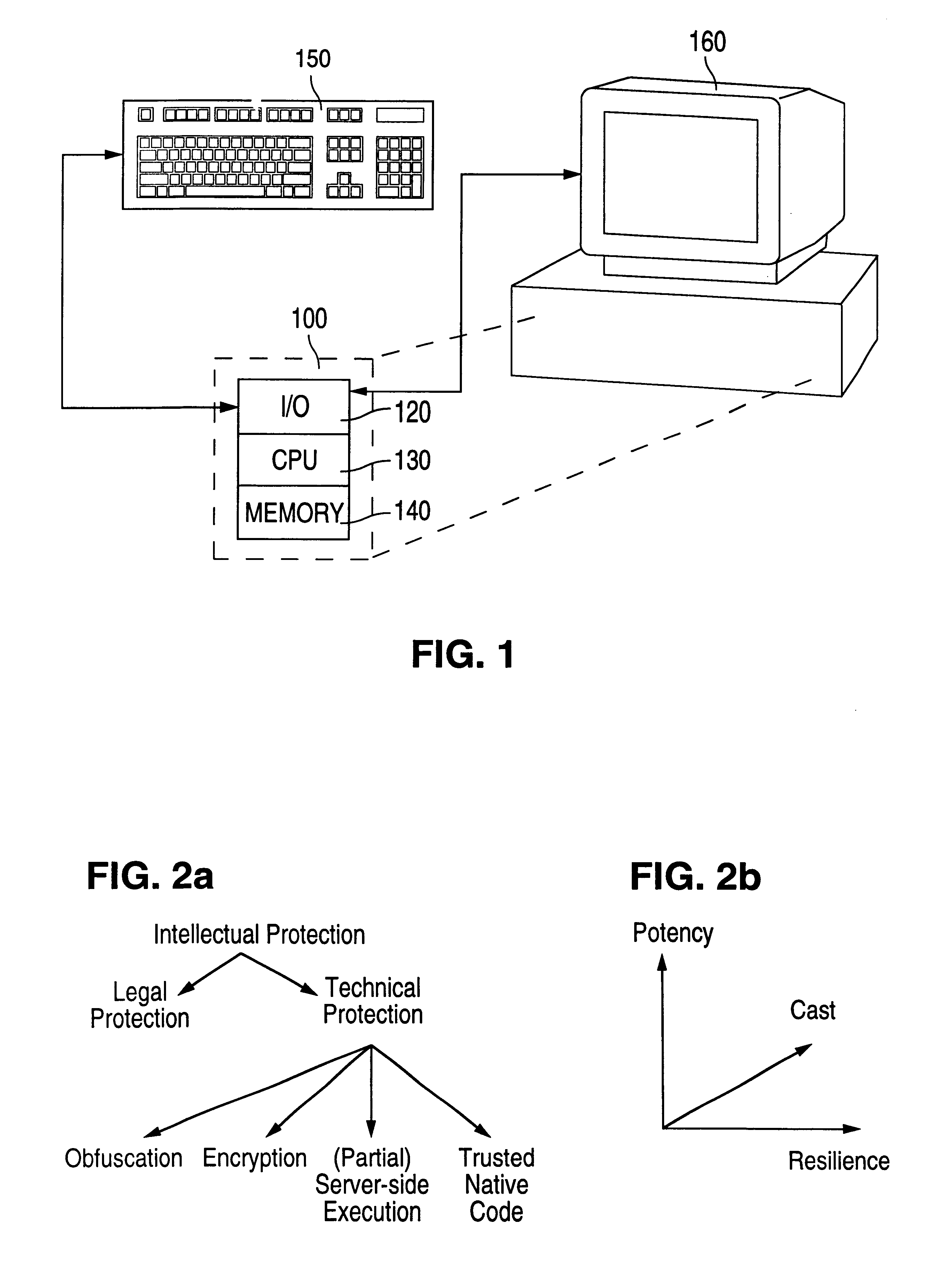
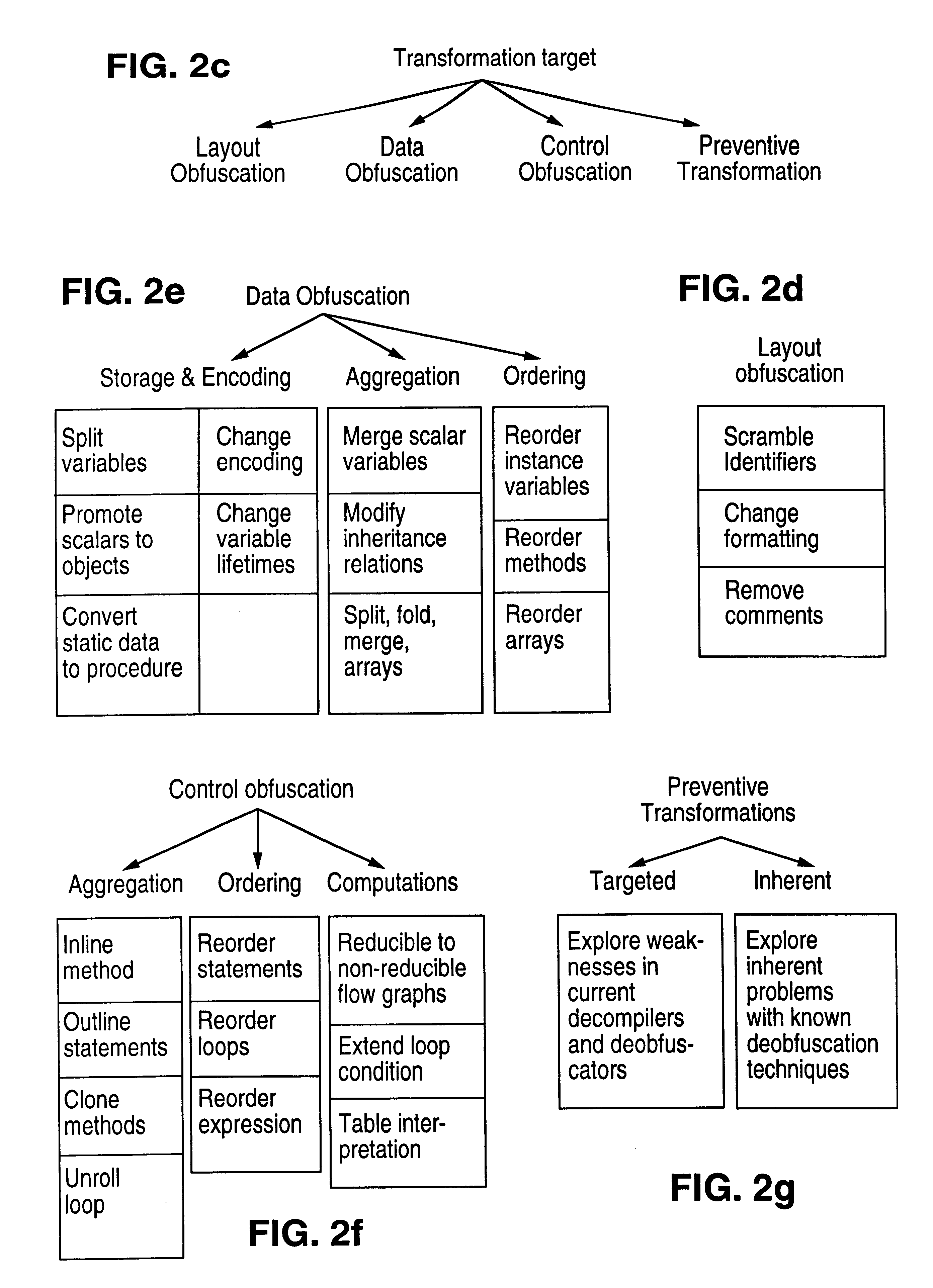
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
System and Methodology for Parallel Query Optimization Using Semantic-Based Partitioning
ActiveUS20060218123A1Improve query performanceLow costDigital data information retrievalDigital data processing detailsQuery optimizationTheoretical computer science
A system and methodology for parallel query optimization using semantic-based partitioning is described. In one embodiment, for example, in a database system comprising a database storing data in database tables, a method is described for improving query performance by dynamically partitioning the data, the method comprises steps of: receiving a query requesting data from the database; generating a plurality of subplans for executing the query, each subplan including one or more operators for performing relational operations; adding operators for partitioning data and performing a given relational operation in parallel to at least some of the plurality of subplans; and building a plan for execution of the query based, at least in part, upon selecting subplans having favorable execution costs
Owner:SYBASE INC
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
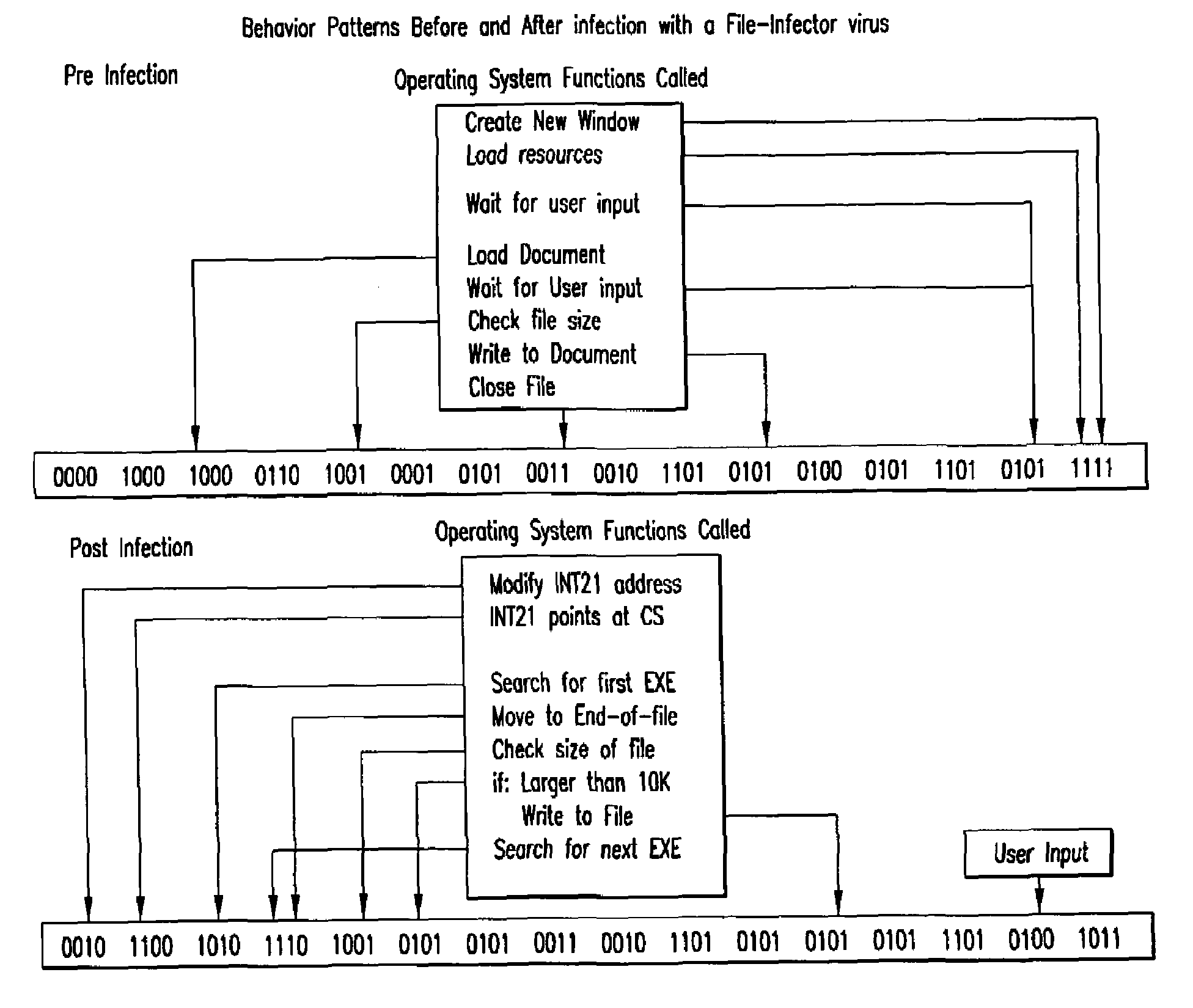
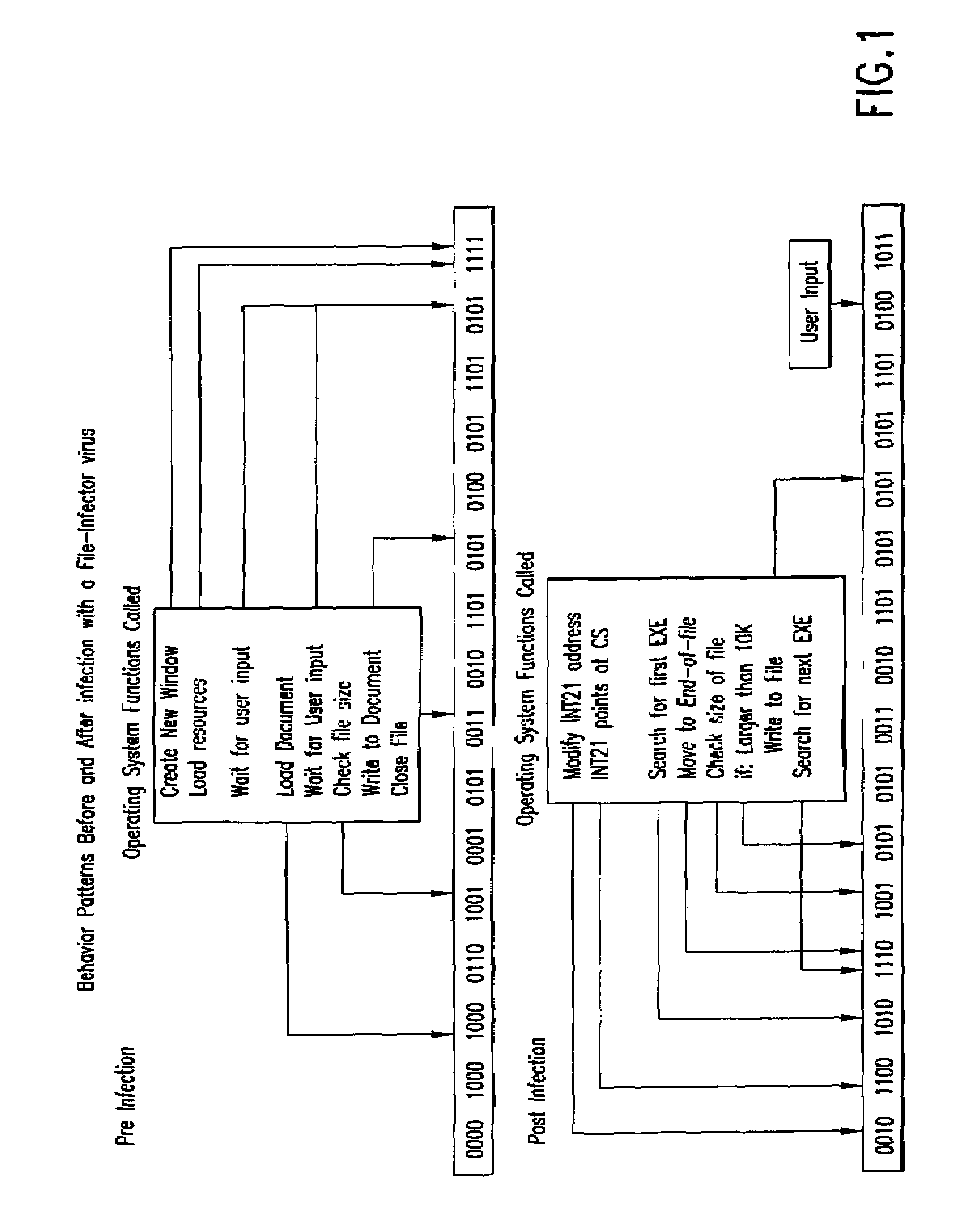
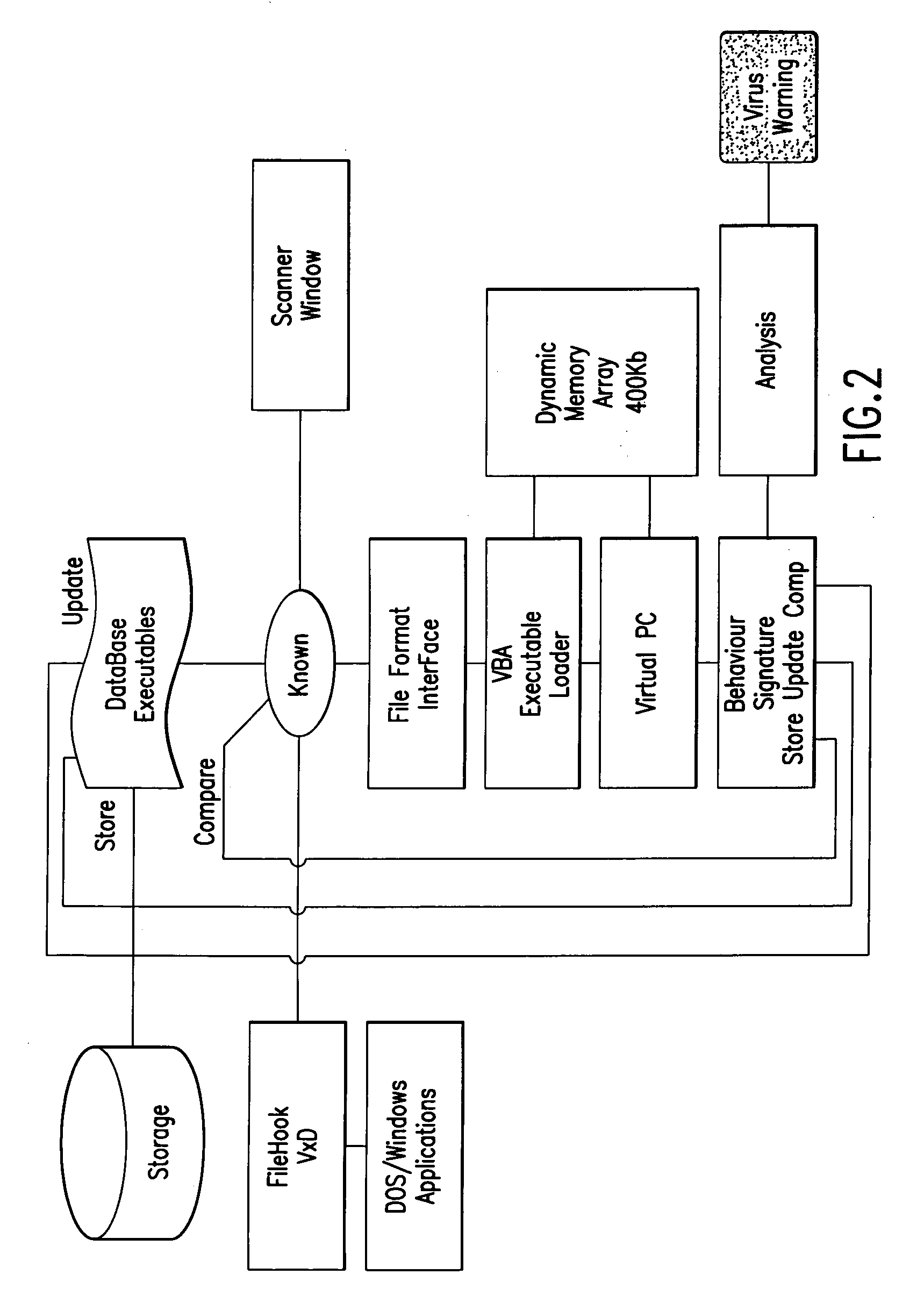
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
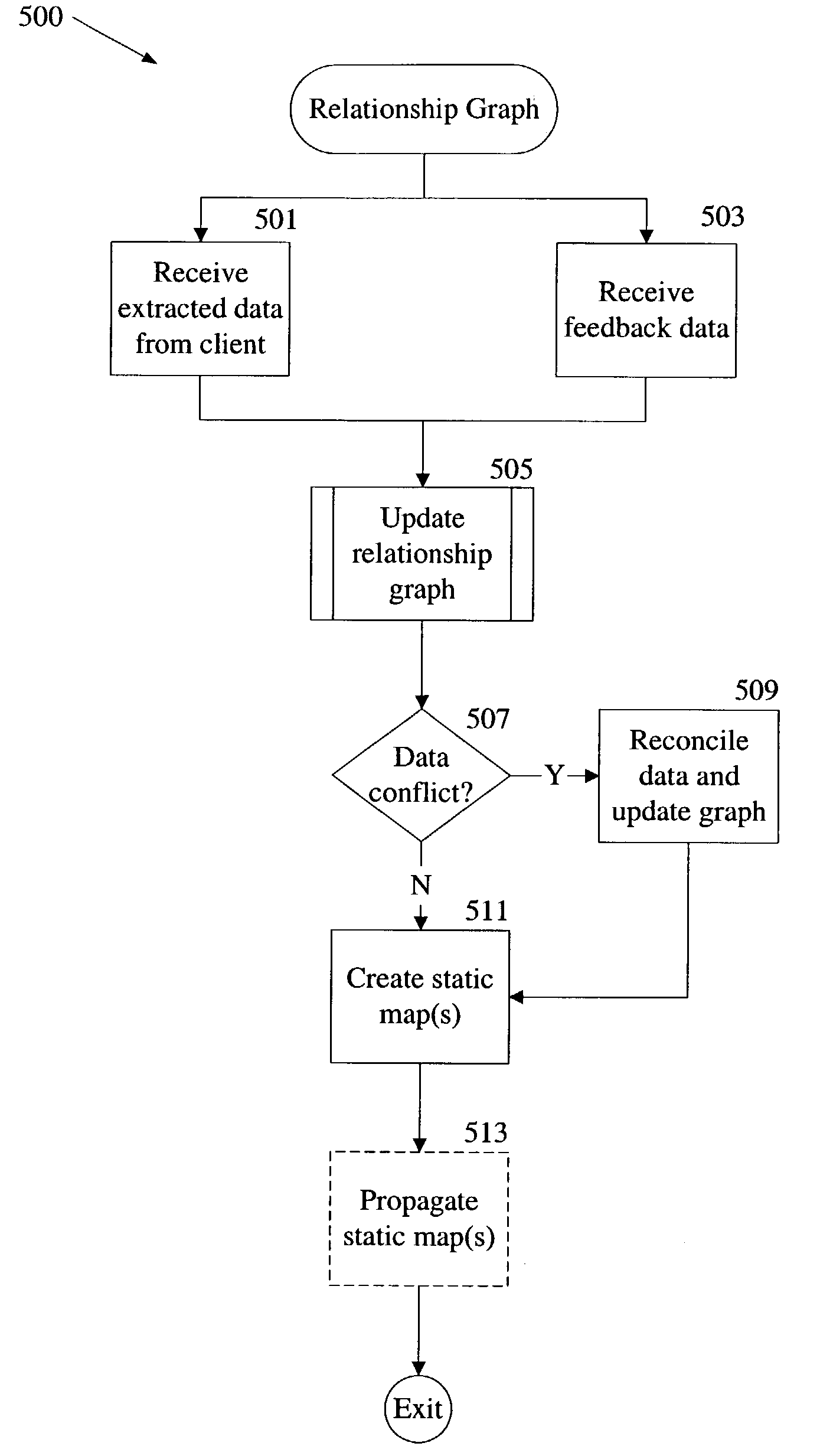
Creation and maintenance of social relationship network graphs
InactiveUS7539697B1Data processing applicationsDigital data information retrievalData sourceSocial web
A relationship graph representing a social network connecting multiple entities is created and maintained as nodes and edges. Data received for an entity is used to create a new node. A strength of relationship value is calculated for each relationship between the new entity and an entity represented by an existing node and assigned to an edge is created to represent each relationship. Data received for an existing node causes the node to be updated, and the strength of relationship values for each of its relationships to be recalculated and assigned to the appropriate edge. More than one node may exist for an entity and conflicts among the data of the multiple nodes are reconciled. The received data may be extracted from data sources owned by a user in accordance with privacy criteria for the user, or may result from processing data in the relationship graph.
Owner:SPOKE SOFTWARE
Method and system for generating a document representation
ActiveUS20100228693A1Without structureHighly to changeDigital data information retrievalSemantic analysisPart of speechGrammatical relation
A method, system and computer program product for generating a document representation are disclosed. The system includes a server and a client computer, and the method involves: receiving into memory a resource containing at least one sentence of text; producing a tree comprising tree elements indicating parts-of-speech and grammatical relations between the tree elements; producing semantic structures each having three tree elements to represent a simple clause (subject-predicate-object); and storing a semantic network of semantic structures and connections therebetween. The semantic network may be created from a user provided root concept. Output representations include concept maps, facts listings, text summaries, tag clouds, indices; and an annotated text. The system interactively modifies semantic networks in response to user feedback, and produces personal semantic networks and document use histories.
Owner:IFWE
Method for presenting hierarchical data
InactiveUS20050060647A1Easy to operateDatabase management systemsDigital computer detailsHyperlinkDisplay device
Methods, programs (120) and apparatus (100) are disclosed for accessing and heterogenous data sources (150-153) and presenting information obtained therefrom. Specifically, the data sources may have hierarchical data, which may be presented by identifying a context data node from the data, the context data node having one or more descendent data nodes. At least one data pattern is determined in the descendent data nodes. At least one display type is assigned to the current context data node on the basis of the at least one data pattern. Thereafter, the method presents at least a subset of the descendent data nodes according to one of the assigned display types. Also disclosed is a method of browsing an hierarchically-represented data source. A user operation is interpreted to identify a context data node from the data source, the context data node having one or more descendent data nodes. At least one data pattern in the descendent data nodes is then determined and at least one display type is assigned to the current context data node on the basis of the at least one data pattern. A subset of the descendent data nodes is then presented according to one of the assigned display types, the subset including at least one hyperlink (3401,3402) having as its target a descendant data node of the current context data node. A further user operation is then interpreted to select the at least one hyperlink, the selection resulting in the current context data node being replaced with the data node corresponding to the target of the selected hyperlink. These steps may be repeated until no further hyperlinks to descendent data nodes are included in the subset. Other methods associated with access and presentation are also disclosed.
Owner:CANON KK
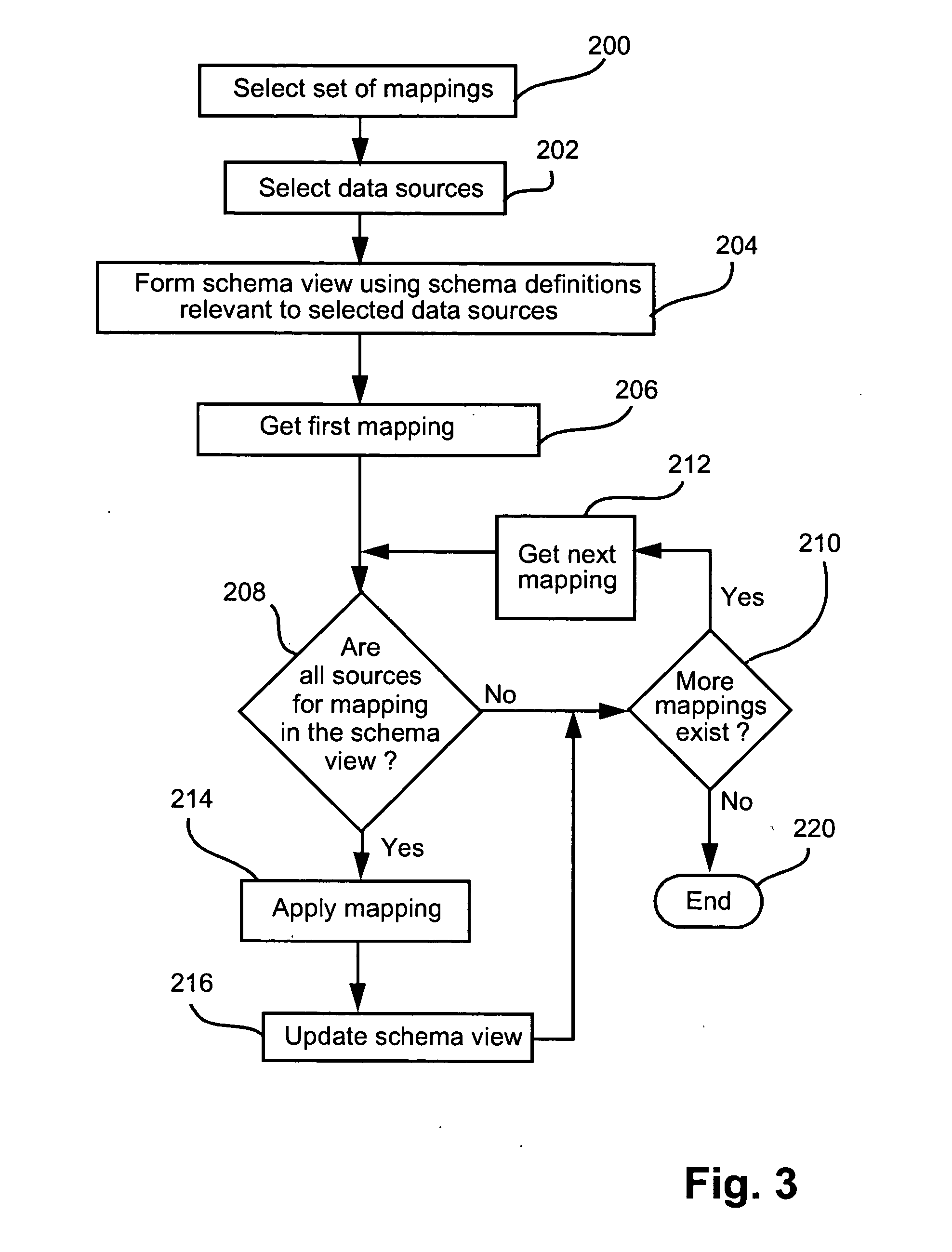
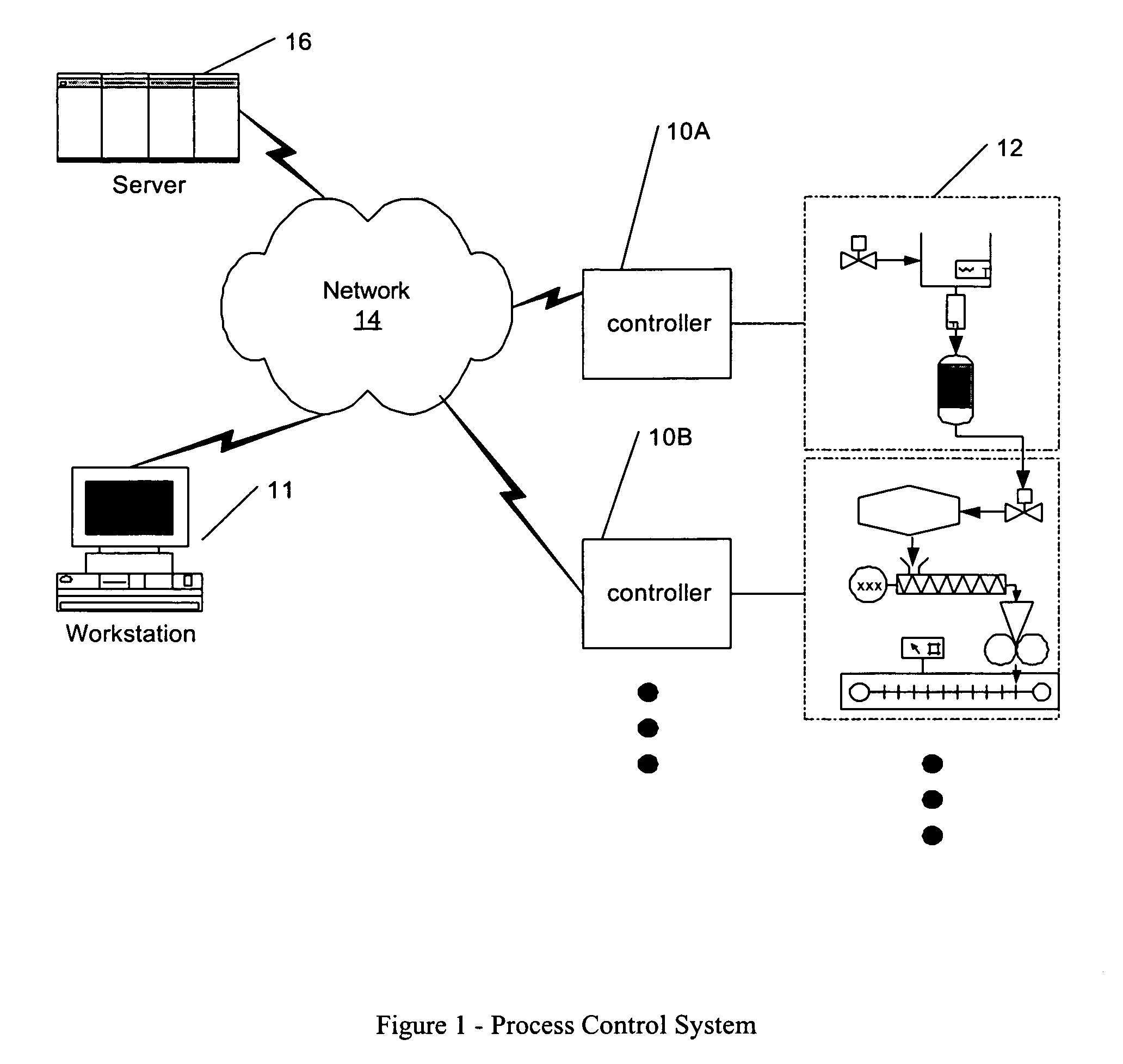
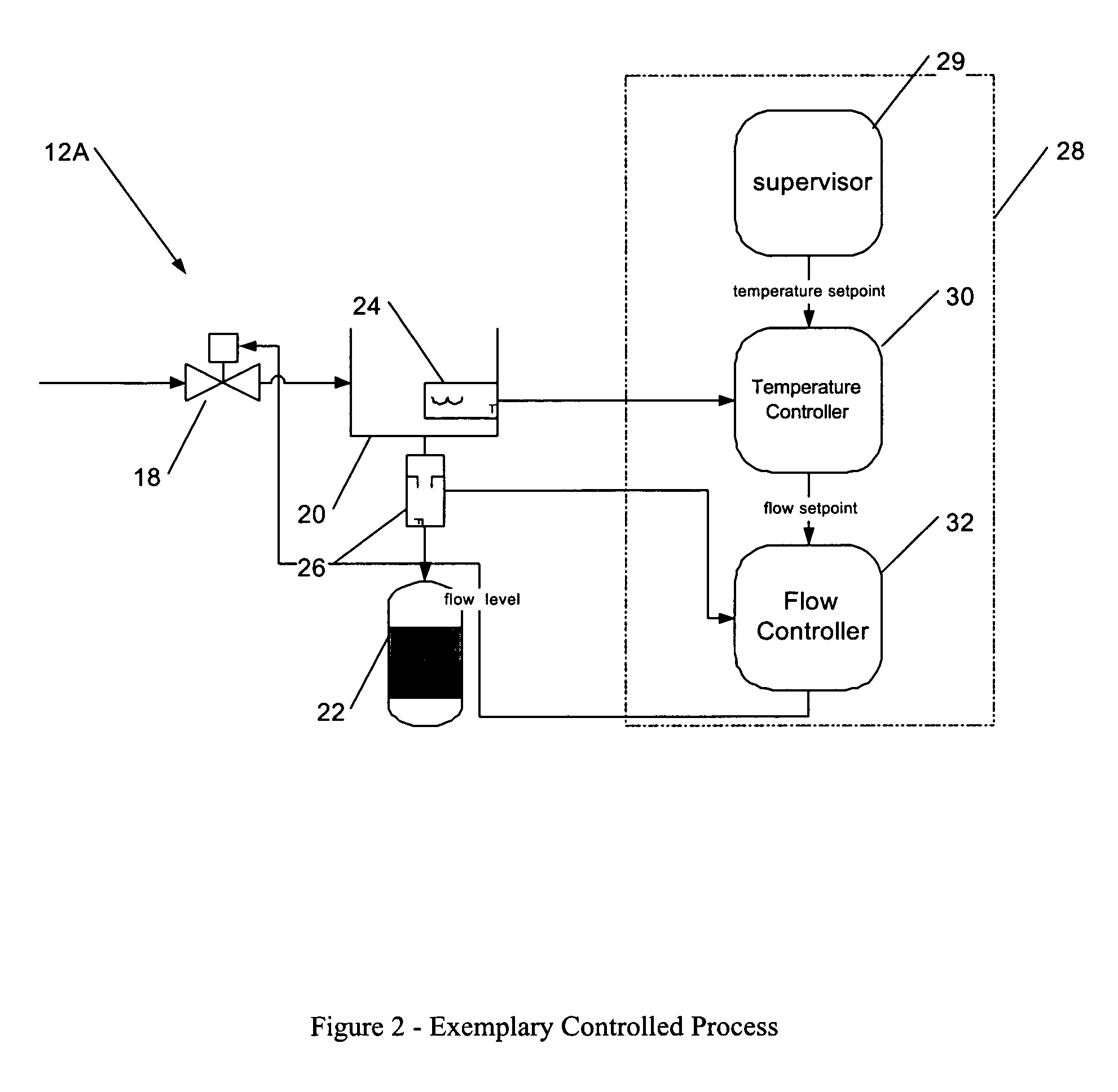
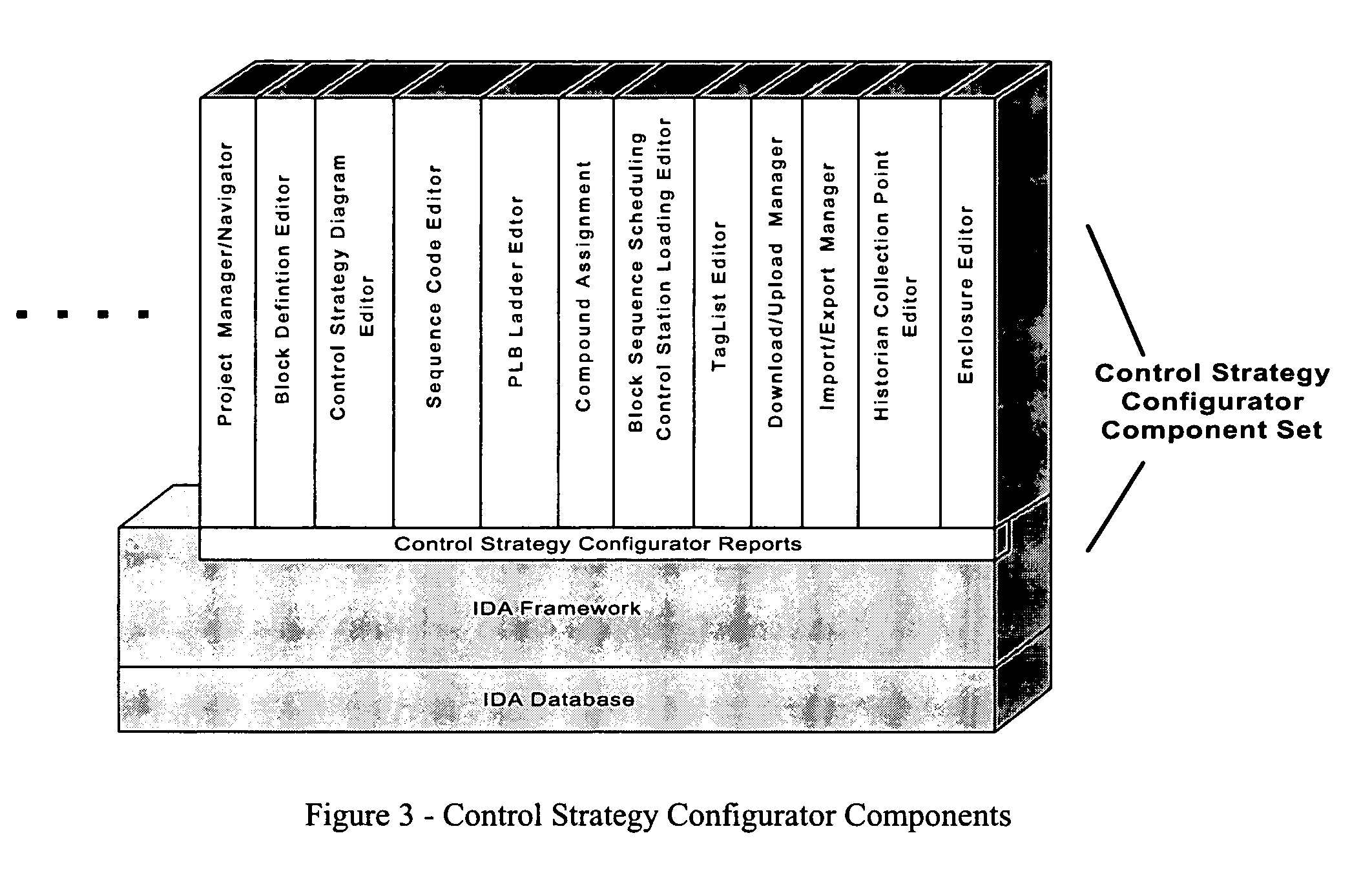
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Speed up big-number multiplication using single instruction multiple data (SIMD) architectures
InactiveUS20130332707A1Digital computer detailsSpecific program execution arrangementsMatrix multiplicationSIMD
A processing apparatus may be configured to include logic to generate a first set of vectors based on a first integer and a second set of vectors based on a second integer, logic to calculate sub products by multiplying the first set of vectors to the second set of vectors, logic to split each sub product into a first half and a second half and logic to generate a final result by adding together all first and second halves at respective digit positions.
Owner:INTEL CORP
System and method for DIDO precoding interpolation in multicarrier systems
ActiveUS20100316163A1Improve downlink throughputReduce distractionsSite diversityModulated-carrier systemsPrecodingTheoretical computer science
A system and machine-implemented method are described for performing precoding interpolation in a DIDO system which employs orthogonal frequency-division multiplexing (OFDM) and DIDO precoding to communicate with a plurality of distributed-input-distributed-output (DIDO) clients. For example, a system according to one embodiment of the invention comprises: selecting a first subset of ODFM tones to determine a first subset of precoding weights; deriving a second subset of precoding weights for a second subset of ODFM tones by interpolating between the first subset of precoding weights; and using a combination of the first subset of precoding weights and the second subset of precoding weights to precode a data stream prior to transmitting the data stream to a DIDO client.
Owner:REARDEN
Running-min and running-max instructions for processing vectors using a base value from a key element of an input vector
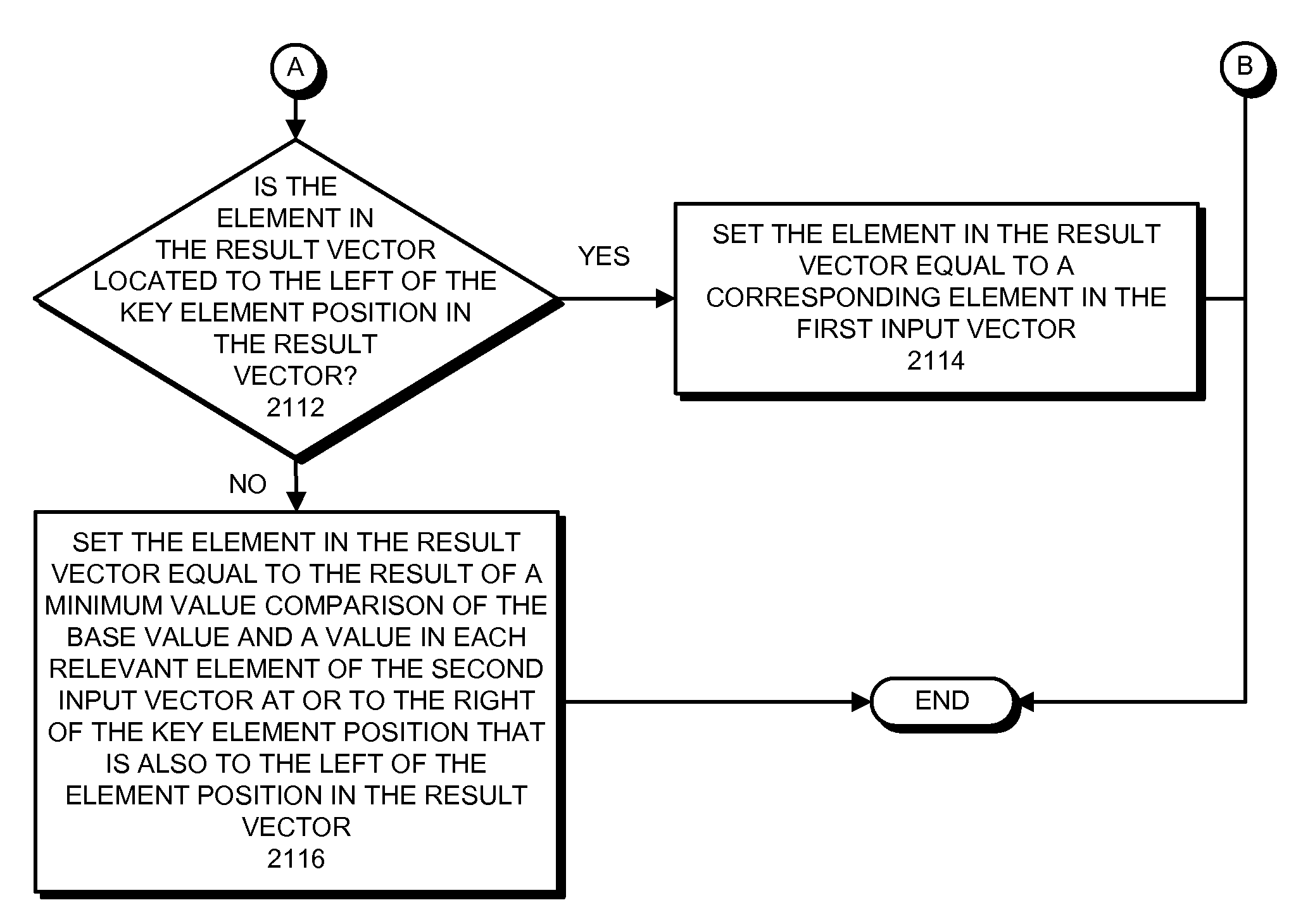
ActiveUS8417921B2Software engineeringGeneral purpose stored program computerControl vectorTheoretical computer science
The described embodiments provide a processor for generating a result vector that contains results from a comparison operation. During operation, the processor receives a first input vector, a second input vector, and a control vector. When subsequently generating a result vector, the processor first captures a base value from a key element position in the first input vector. For selected elements in the result vector, processor compares the base value and values from relevant elements to the left of a corresponding element in the second input vector, and writes the result into the element in the result vector. In the described embodiments, the key element position and the relevant elements can be defined by the control vector and an optional predicate vector.
Owner:APPLE INC
Method for finding local extrema of a set of values for a parallel processing element
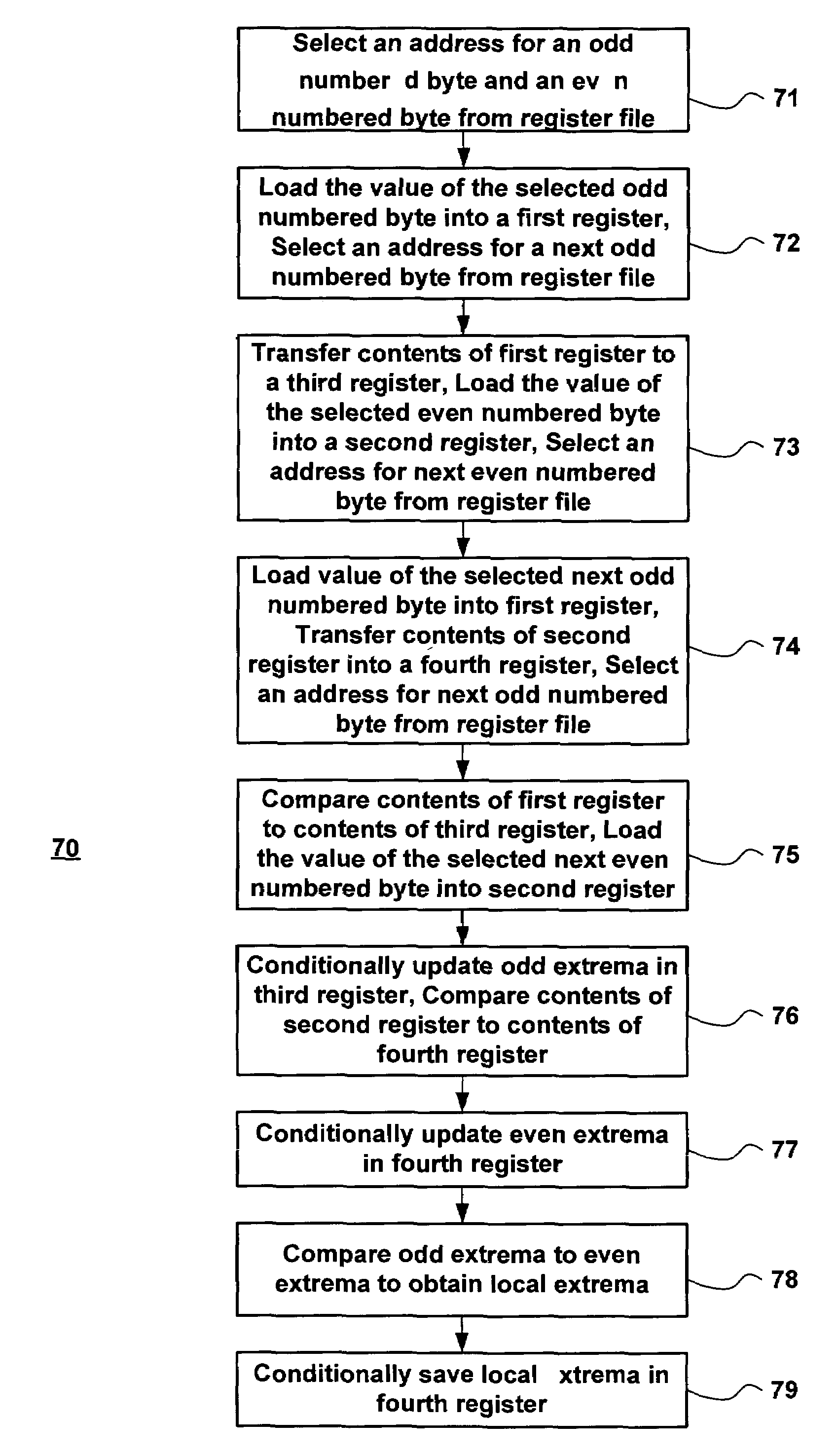
ActiveUS7454451B2Digital data processing detailsDigital computer detailsTheoretical computer scienceProcessing element
A method for finding a local extrema for a single processing element having a set of values associated therewith includes separating the set of values into an odd set of values and an even set of values, determining a first extrema from the odd set of values, determining a second extrema from the even set of values, and determining the local extrema from the first extrema and the second extrema. The first extrema is found by comparing each odd-numbered value in the set to each other odd-numbered value in the set and the second extrema is found by comparing each even-numbered value in the set to each other even-numbered value in the set.
Owner:MICRON TECH INC
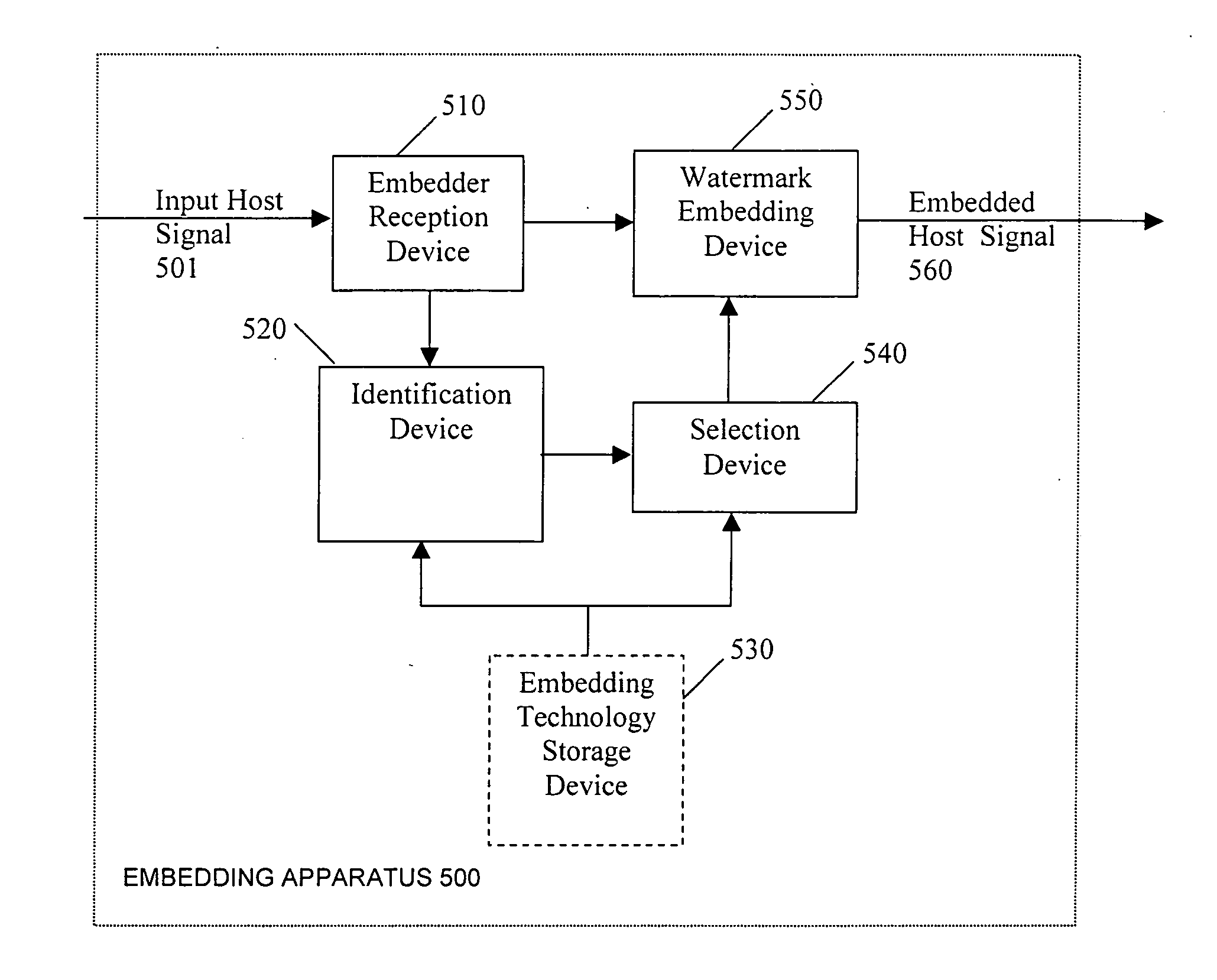
Security enhancements of digital watermarks for multi-media content
InactiveUS20060239501A1Reliable methodLow costUser identity/authority verificationSpeech analysisTheoretical computer scienceSecurity enhancement
Methods and apparatus for embedding digital watermarks into a digital host content are provided. A digital host content is received, e.g., at a receiver or other device incorporating a receiver. One or more watermark embedding technologies is selected. Multiple embedding opportunities are identified within the host content. A subset of the identified embedding opportunities is selected. A multiplicity of digital watermarks are then embedded into the host content in accordance with the selected subset of embedding opportunities utilizing the one or more selected watermark embedding technologies. The selecting of the subset of embedding opportunities may be adapted to provide a desired tradeoff between levels of robustness, security, and transparency of the watermark. A plurality of watermarking embedding technologies may be selected and used in the embedding step.
Owner:VERANCE
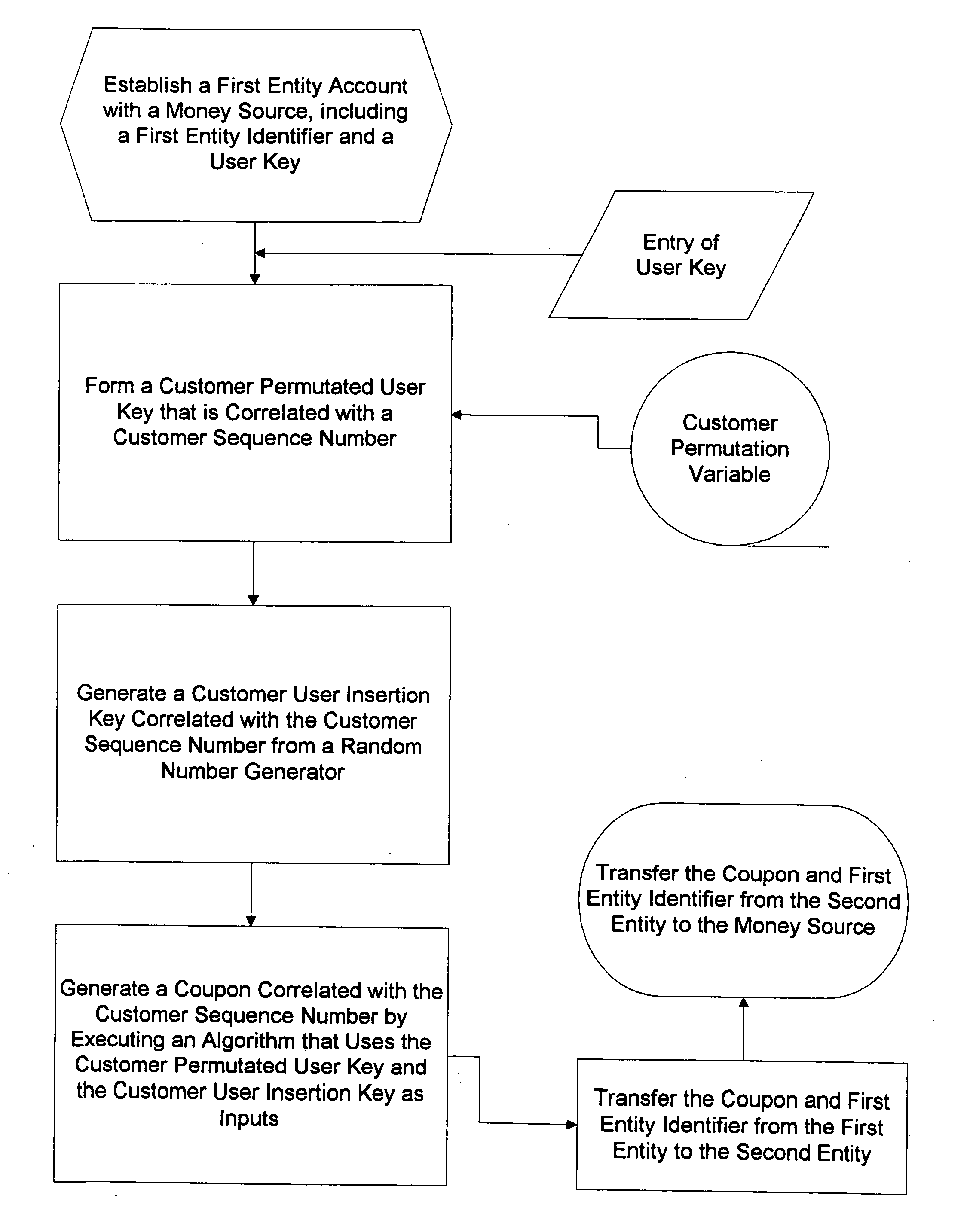
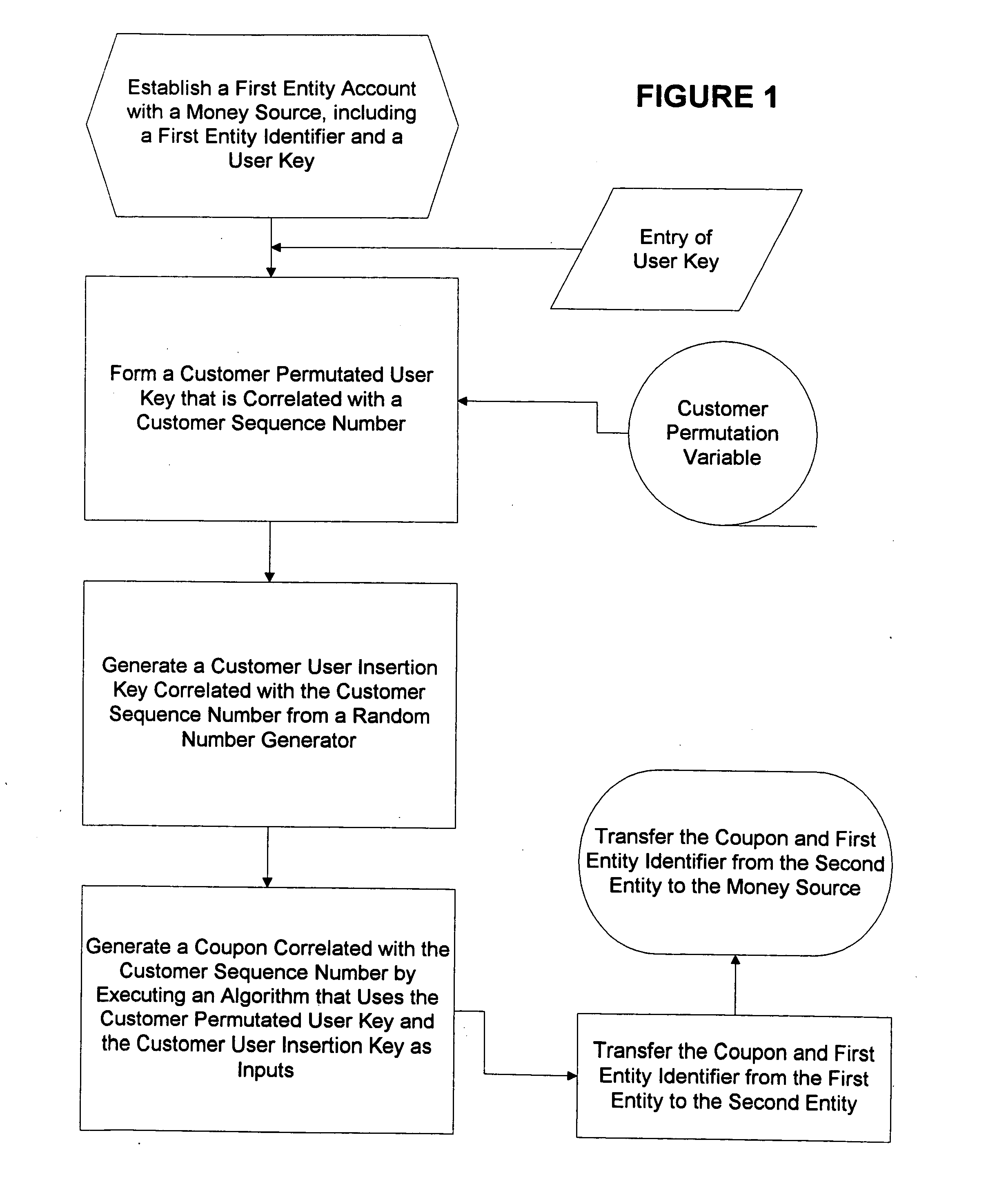
Method for generating customer one-time unique purchase order numbers
InactiveUS20050080747A1Anonymous user systemsRecord carriers used with machinesCredit cardPersonal identification number
Multiple secure transactions are provided through use of a method that uses customer one-time unique purchase order numbers (“Coupons”) generated by an algorithm that uses a permutated user key and a user insertion key as input variables. A user key (such as a Personal Identification Number, or “PIN”) is combined with a permutation variable that is correlated with a customer sequence number to create the permutated user key. A random number generator is used to generate the user insertion key correlated with the customer sequence number. The algorithm can insert the permutated user key into a user account number through use of the user insertion key. A Coupon is validated by confirming that it is contained in a set of money source Coupons generated by a money source using the user key and a random number generator that is synchronized with the random number used to generate Coupons. Once a Coupon is validated, the matching money source Coupon and all earlier generated money source Coupons are deleted from the set, and a new set is generated. If a preselected number of Coupons are not validated for a chosen entity, an invalid user account number will be set. Coupons can be used for credit card or bank card transactions, and they can be generated without changing fixed digits of traditional twenty digit account numbers.
Owner:PRIVASYS
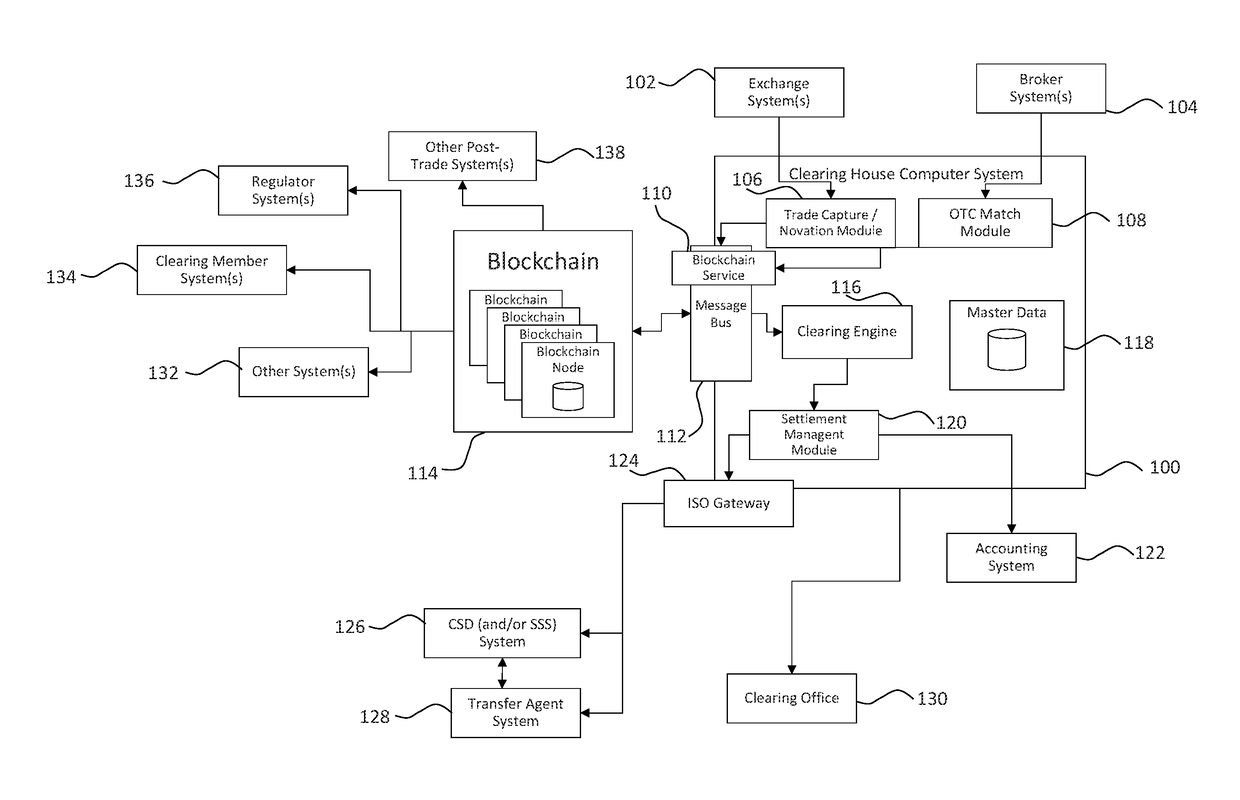
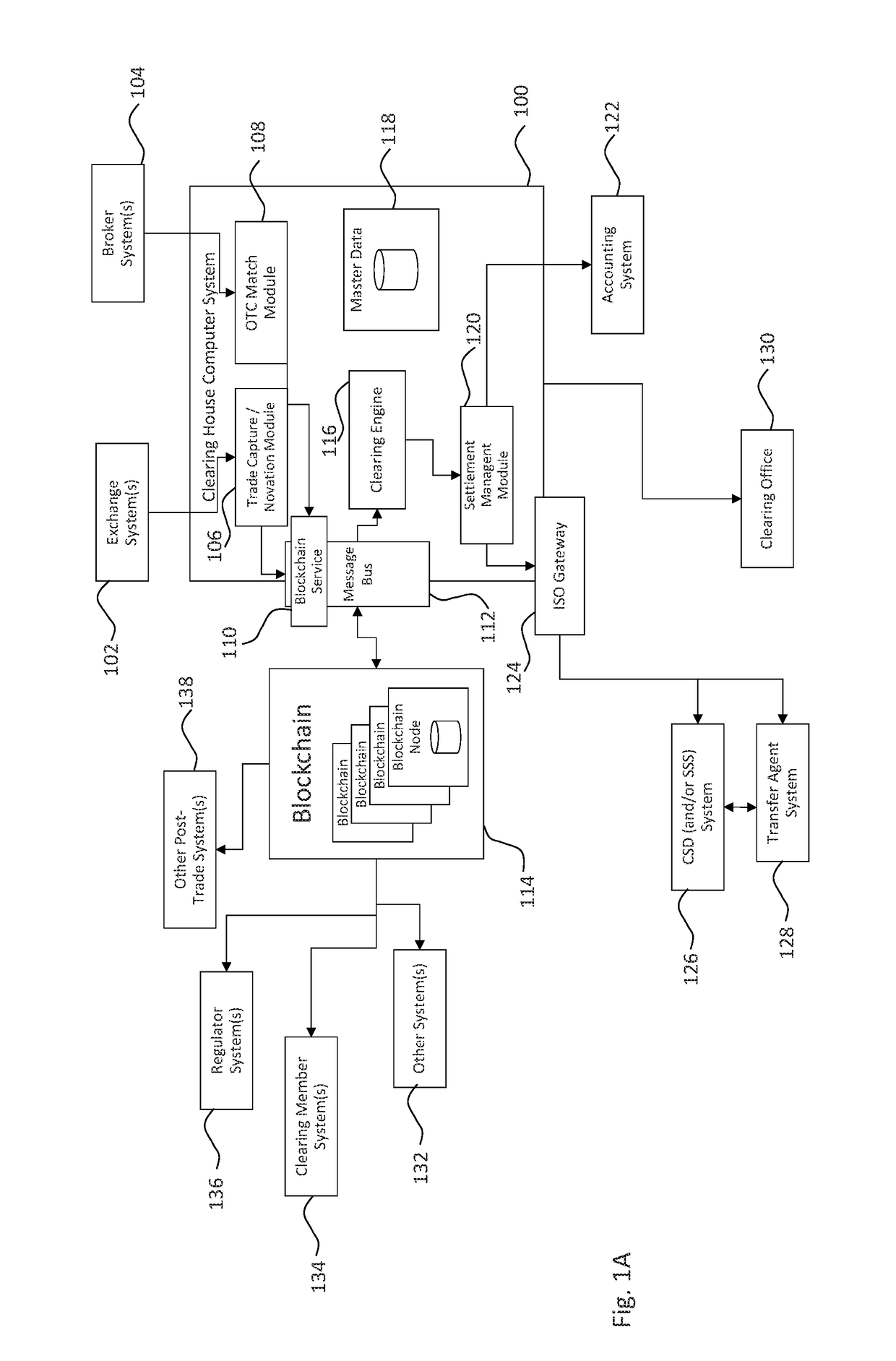
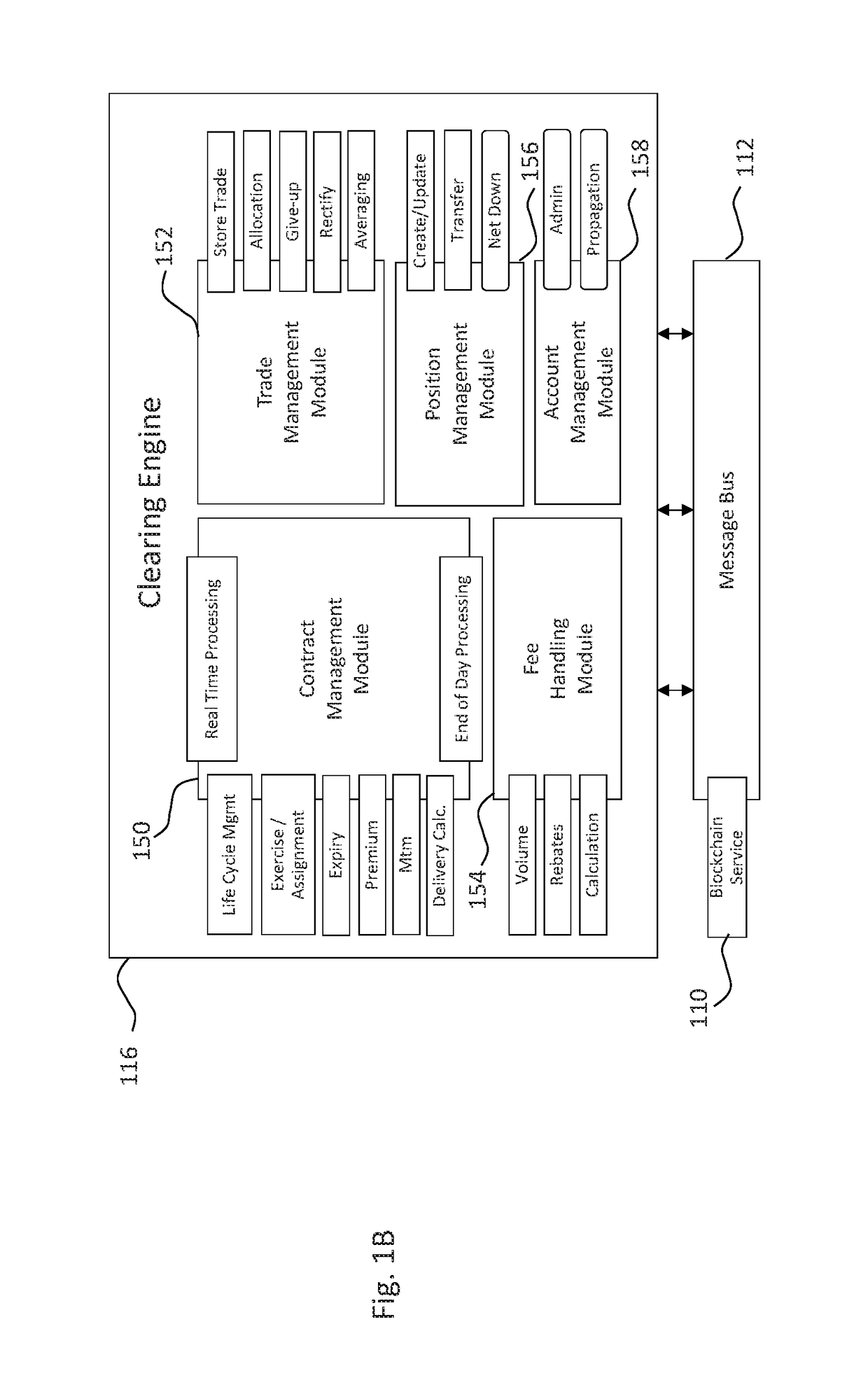
Systems and methods for storing and sharing transactional data using a distributed computing systems
ActiveUS20170230189A1FinanceEncryption apparatus with shift registers/memoriesComputerized systemComputing systems
A computer system that interfaces with a blockchain is provided. The computer system receives match data for a match between a first data transaction request that is associated with a first identifier and a second data transaction request that is associated with a second identifier. A first blockchain transaction is generated based on the match data and stored to a blockchain. At least one further blockchain transaction is generates that splits the match into two different transactions—one between the first identifier and an intermediary and the second between the intermediary. These are recorded to the blockchain via the further blockchain transactions.
Owner:NASDAQ TECHNOLOGY AB
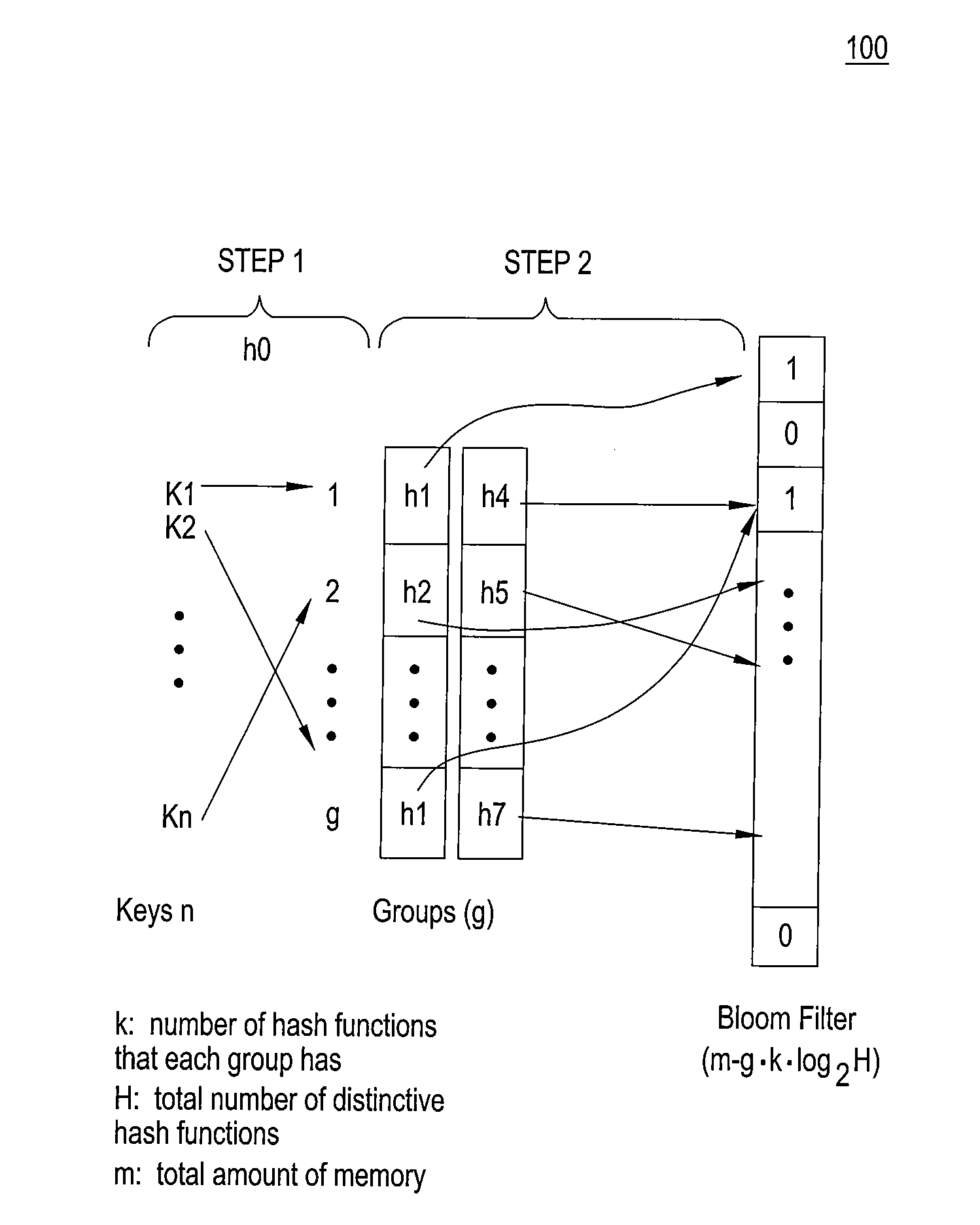
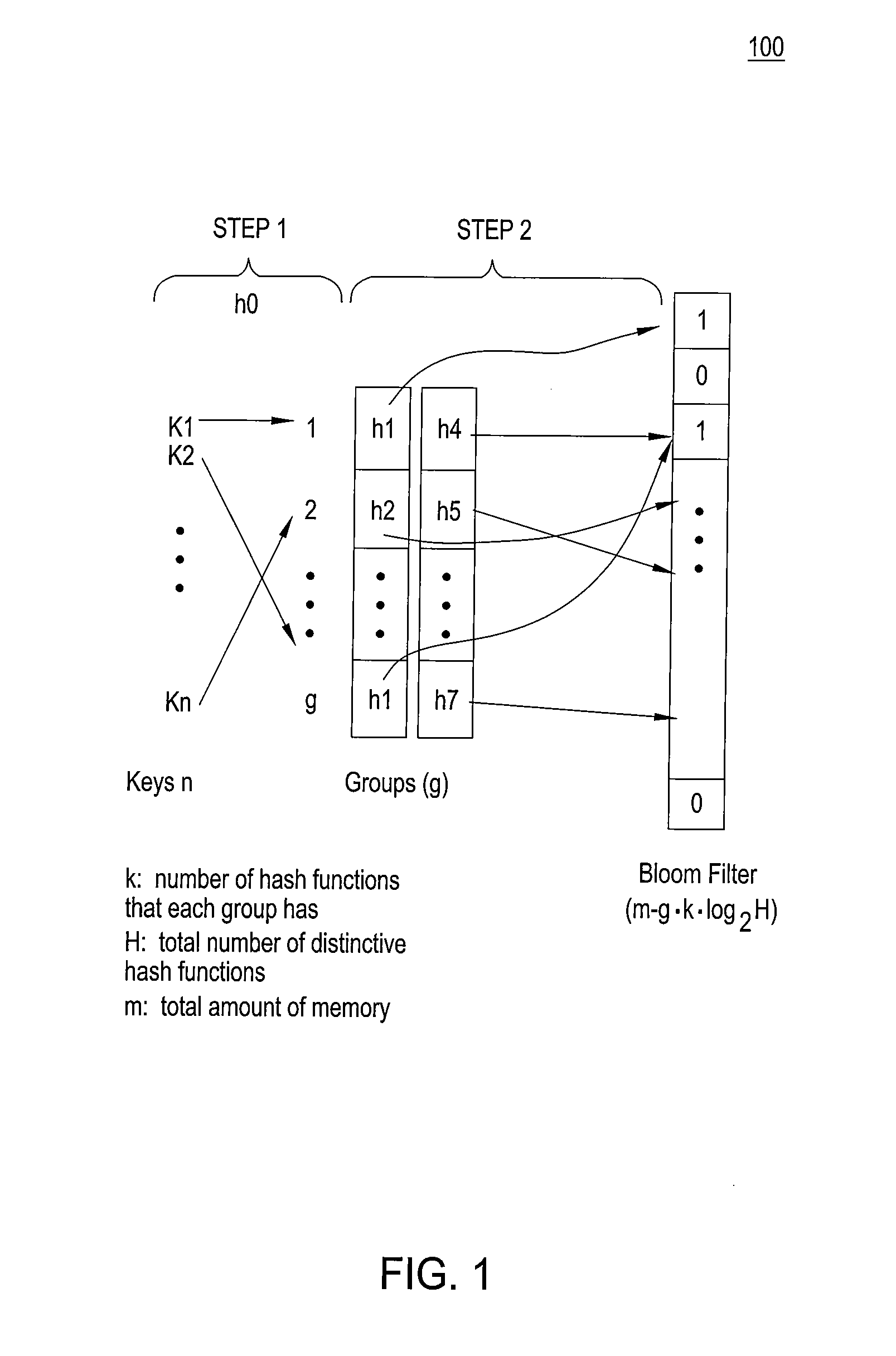
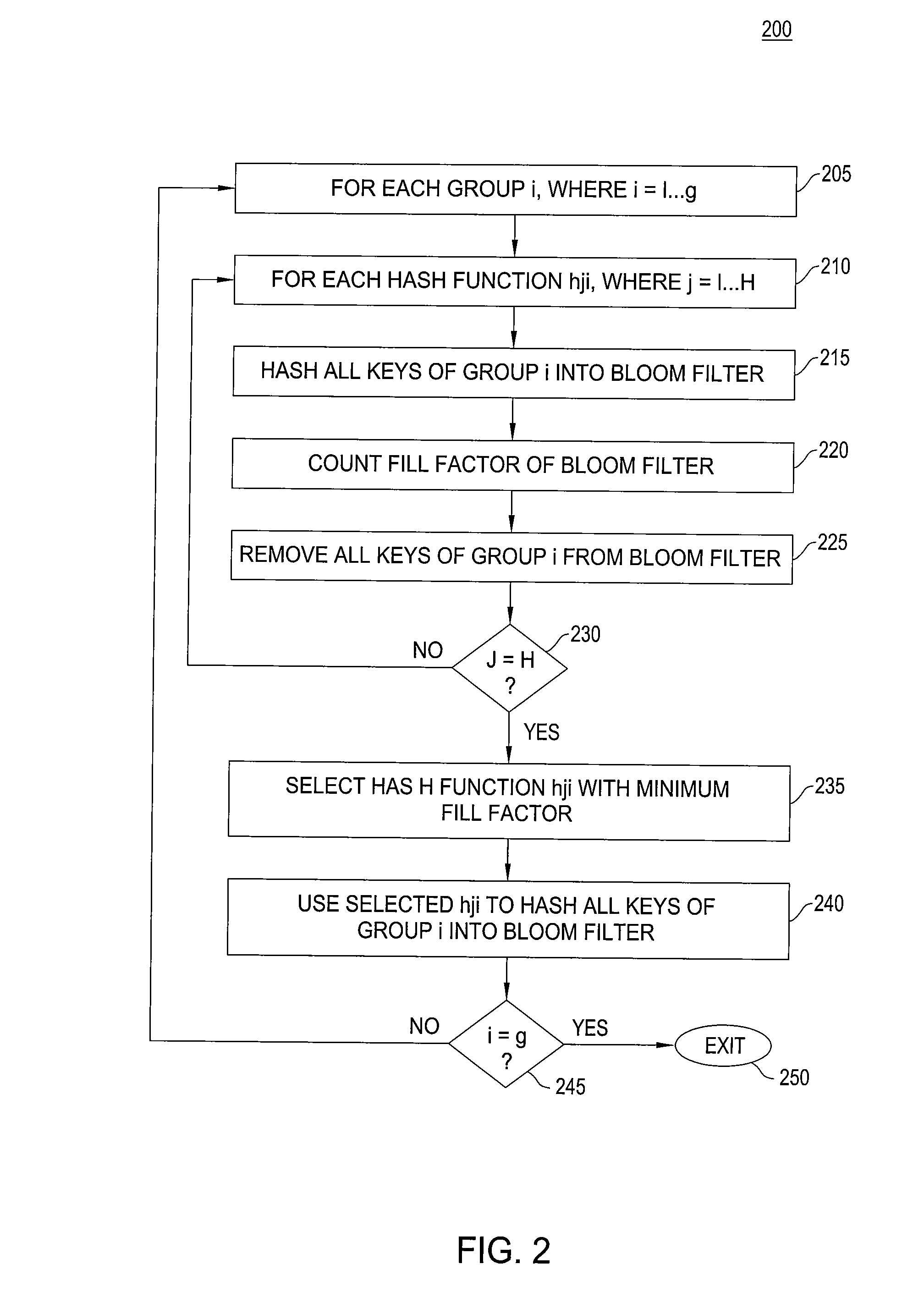
High accuracy bloom filter using partitioned hashing
ActiveUS20080313132A1Reduce false alarm rateReduce the probability of false positivesTransmissionSpecial data processing applicationsHash functionTheoretical computer science
A method and system for generating a bloom filter by mapping into respective groups each of a plurality of initial keys according to a first hash function and mapping each group hashed key into a bloom filter using k respective hash functions.
Owner:ALCATEL-LUCENT USA INC
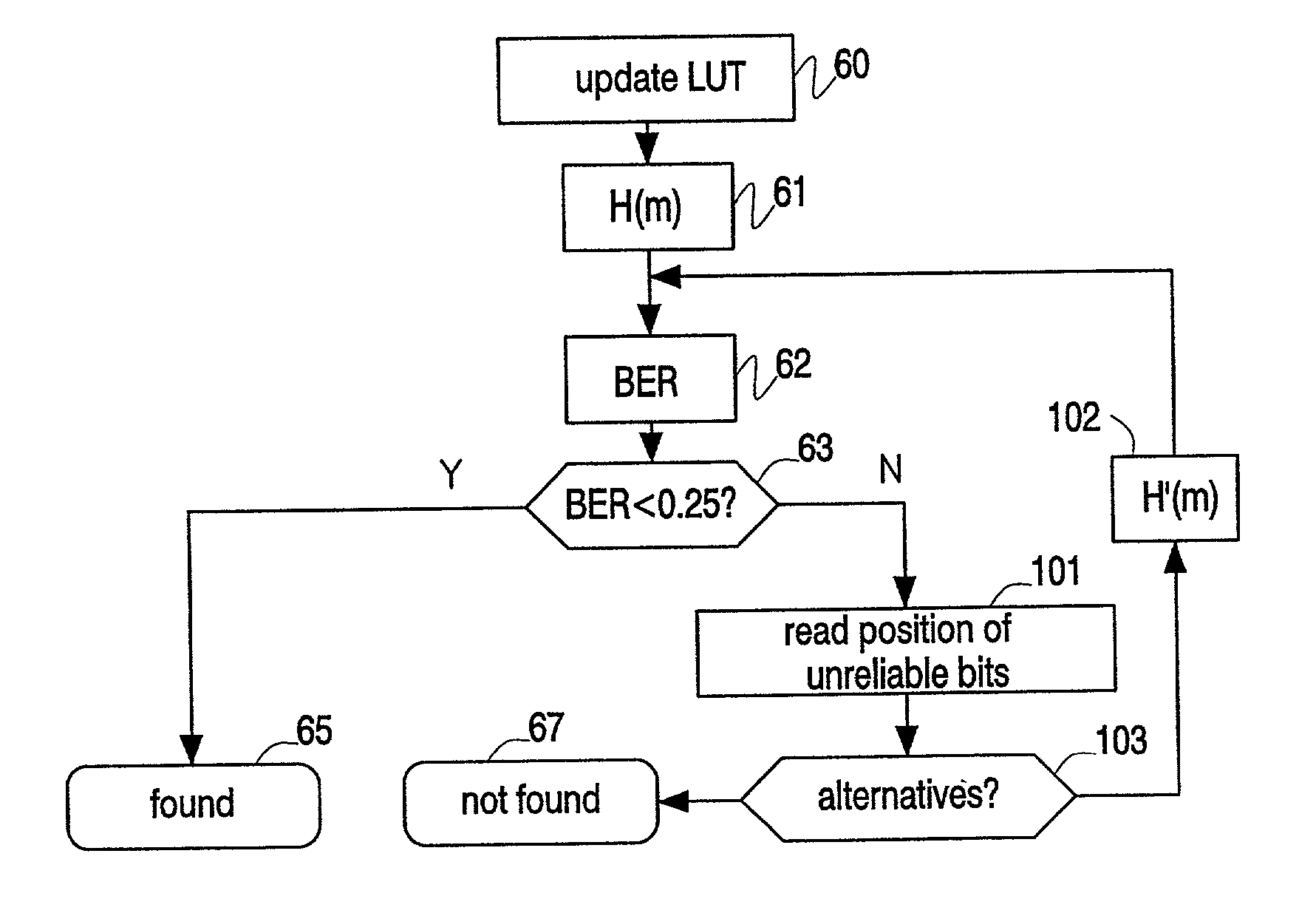
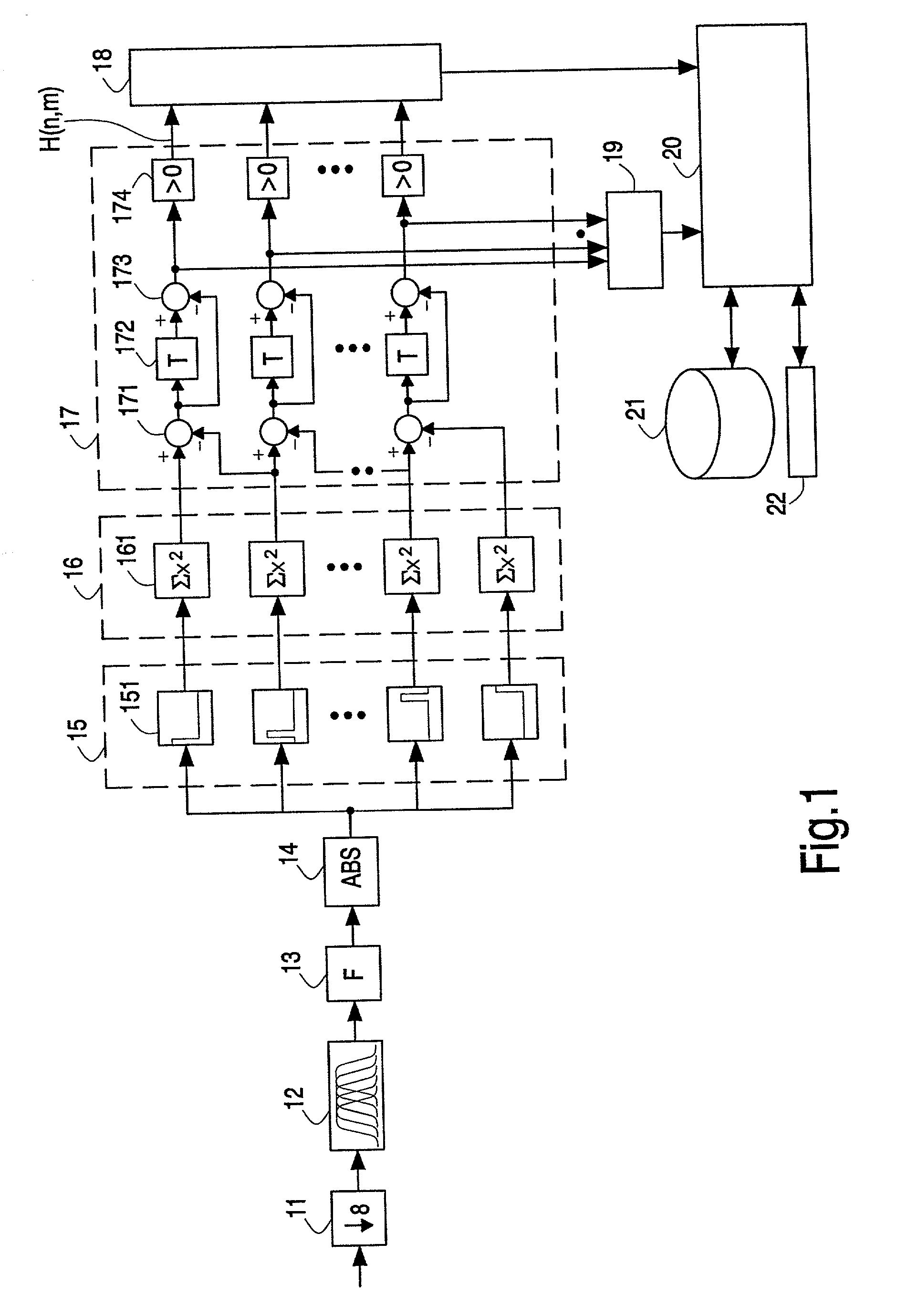
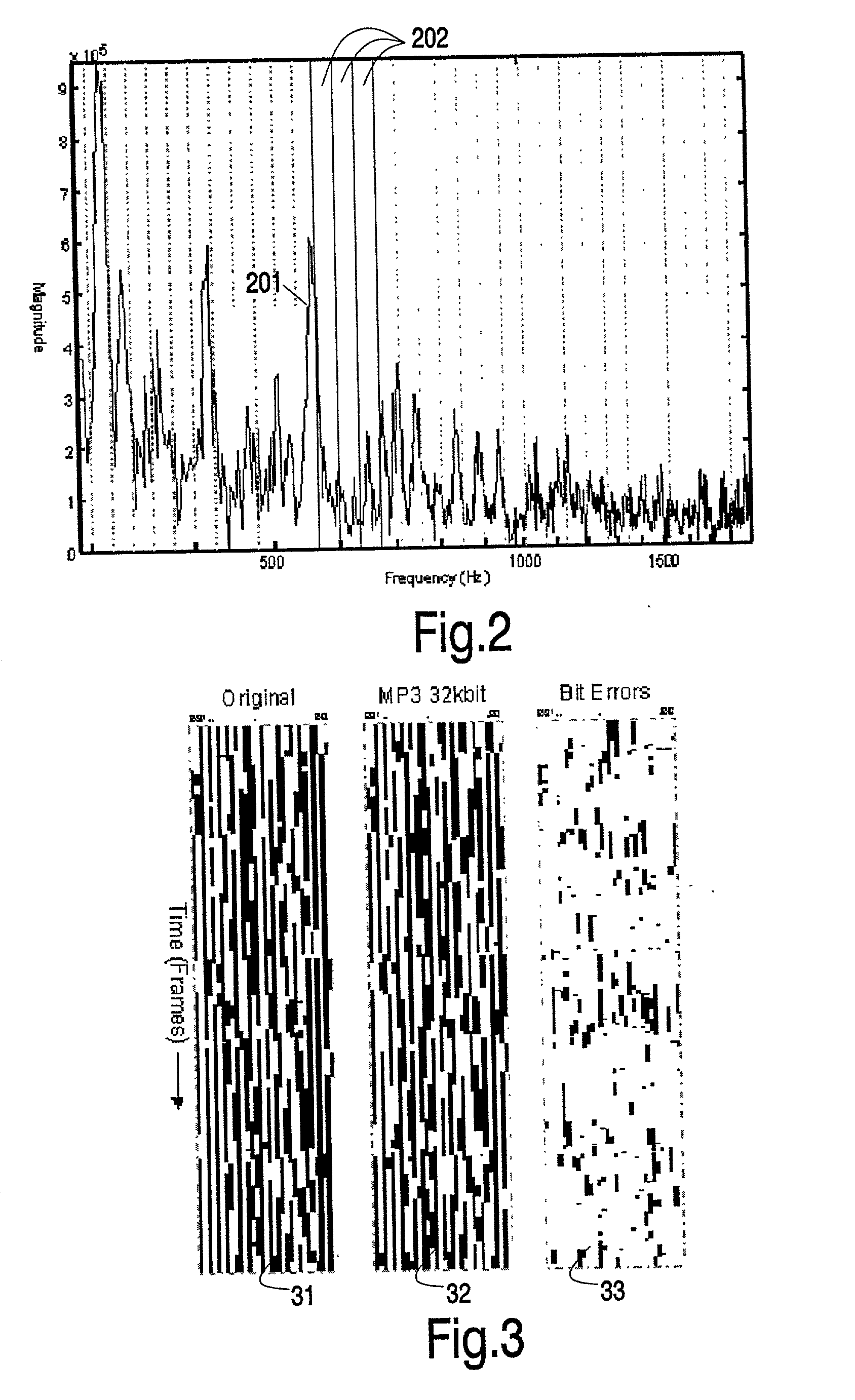
Generating and matching hashes of multimedia content
ActiveUS20020178410A1RobustRobust hashingElectrophonic musical instrumentsCode conversionFrequency spectrumAlgorithm
Hashes are short summaries or signatures of data files which can be used to identify the file. Hashing multimedia content (audio, video, images) is difficult because the hash of original content and processed (e.g. compressed) content may differ significantly. The disclosed method generates robust hashes for multimedia content, for example, audio clips. The audio clip is divided (12) into successive (preferably overlapping) frames. For each frame, the frequency spectrum is divided (15) into bands. A robust property of each band (e.g. energy) is computed (16) and represented (17) by a respective hash bit. An audio clip is thus represented by a concatenation of binary hash words, one for each frame. To identify a possibly compressed audio signal, a block of hash words derived therefrom is matched by a computer (20) with a large database (21). Such matching strategies are also disclosed. In an advantageous embodiment, the extraction process also provides information (19) as to which of the hash bits are the least reliable. Flipping these bits considerably improves the speed and performance of the matching process.
Owner:GRACENOTE
Method for storing multiple levels of design data in a common database
InactiveUS6505328B1Increase flexibilityEasy to integrateSemiconductor/solid-state device manufacturingCAD circuit designGraphicsLogic circuit design
Owner:MAGMA DESIGN AUTOMATION
Method and apparatus for low density parity check encoding of data
InactiveUS6895547B2Improve performanceError preventionError detection/correctionTheoretical computer scienceParity-check matrix
A method for low-density parity-check (LDPC) encoding of data comprises defining a first M×N parity check matrix; generating, based on the first parity check matrix, a second parity check matrix having an M×M triangular sub-matrix; and, mapping the data into an LDPC code word based on the second parity check matrix. The method is particularly useful for data communications applications, but may also be employed in other applications such as, for example, data storage.
Owner:GLOBALFOUNDRIES US INC
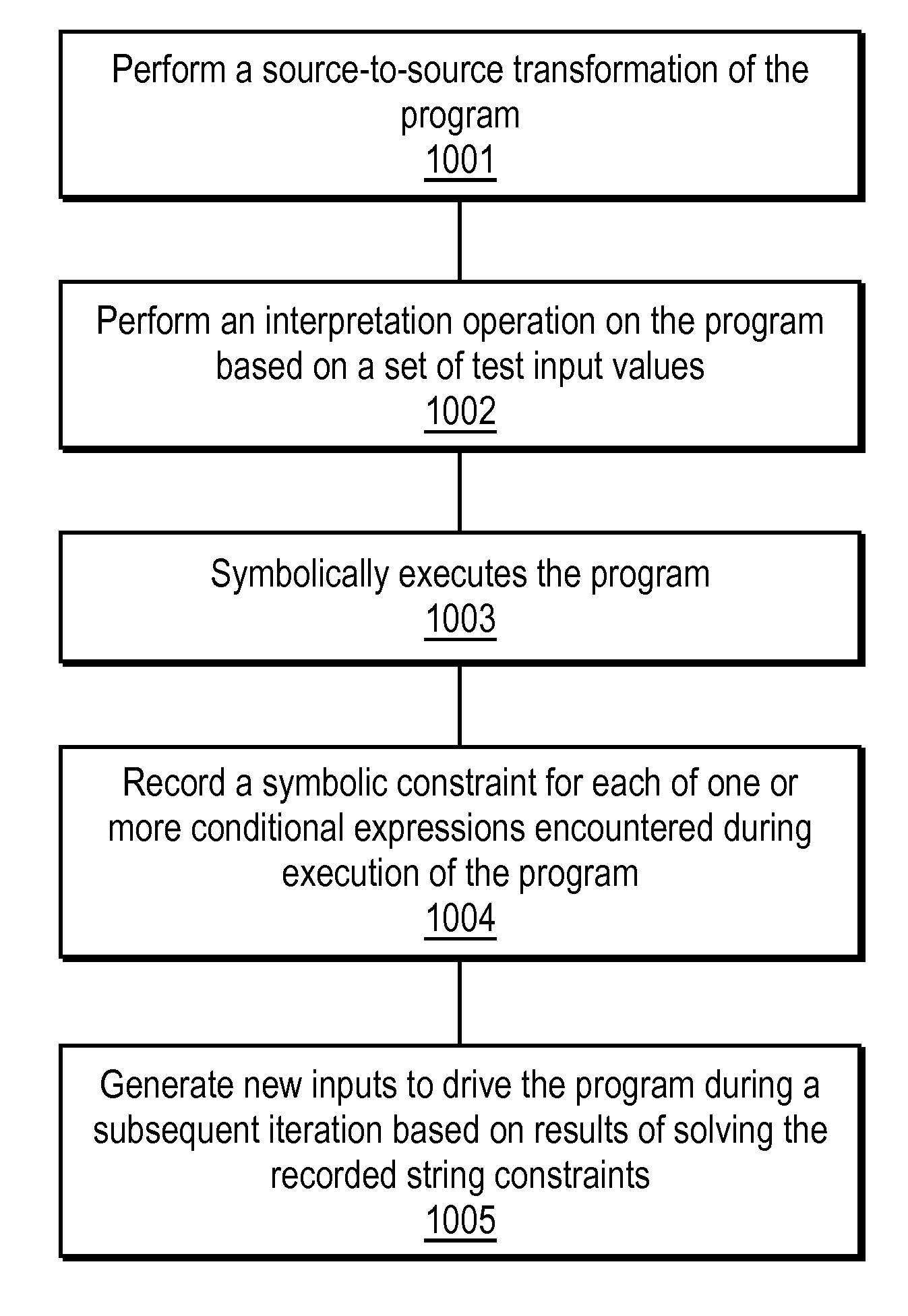
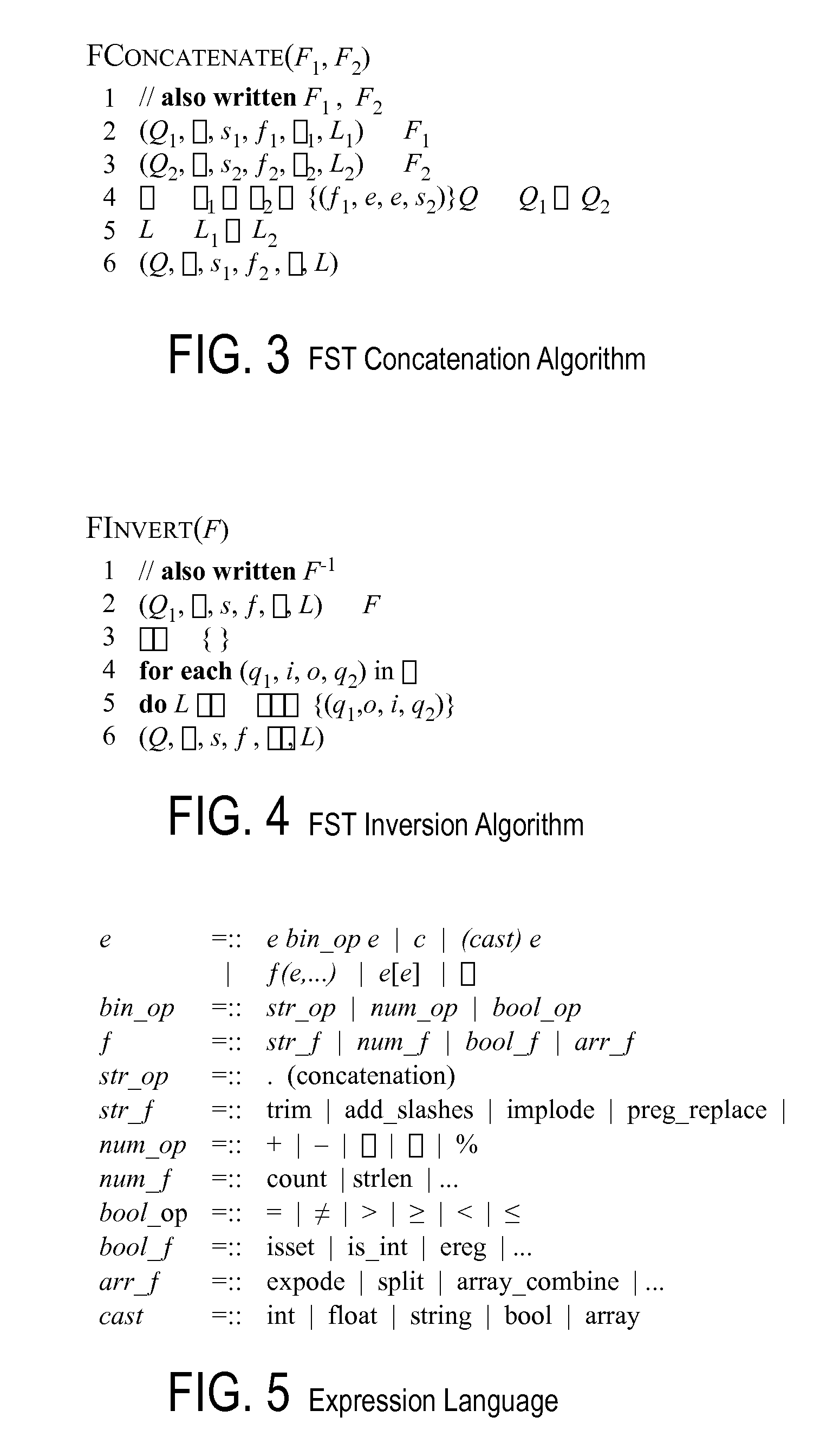
Automated test input generation for web applications
ActiveUS20090125976A1Error detection/correctionSoftware engineeringSource transformationString operations
A method and apparatus is disclosed herein for automated test input generation for web applications. In one embodiment, the method comprises performing a source-to-source transformation of the program; performing interpretation on the program based on a set of test input values; symbolically executing the program; recording a symbolic constraint for each of one or more conditional expressions encountered during execution of the program, including analyzing a string operation in the program to identify one or more possible execution paths, and generating symbolic inputs representing values of variables in each of the conditional expressions as a numeric expression and a string constraint including generating constraints on string values by modeling string operations using finite state transducers (FSTs) and supplying values from the program's execution in place of intractable sub-expressions; and generating new inputs to drive the program during a subsequent iteration based on results of solving the recorded string constraints.
Owner:NTT DOCOMO INC
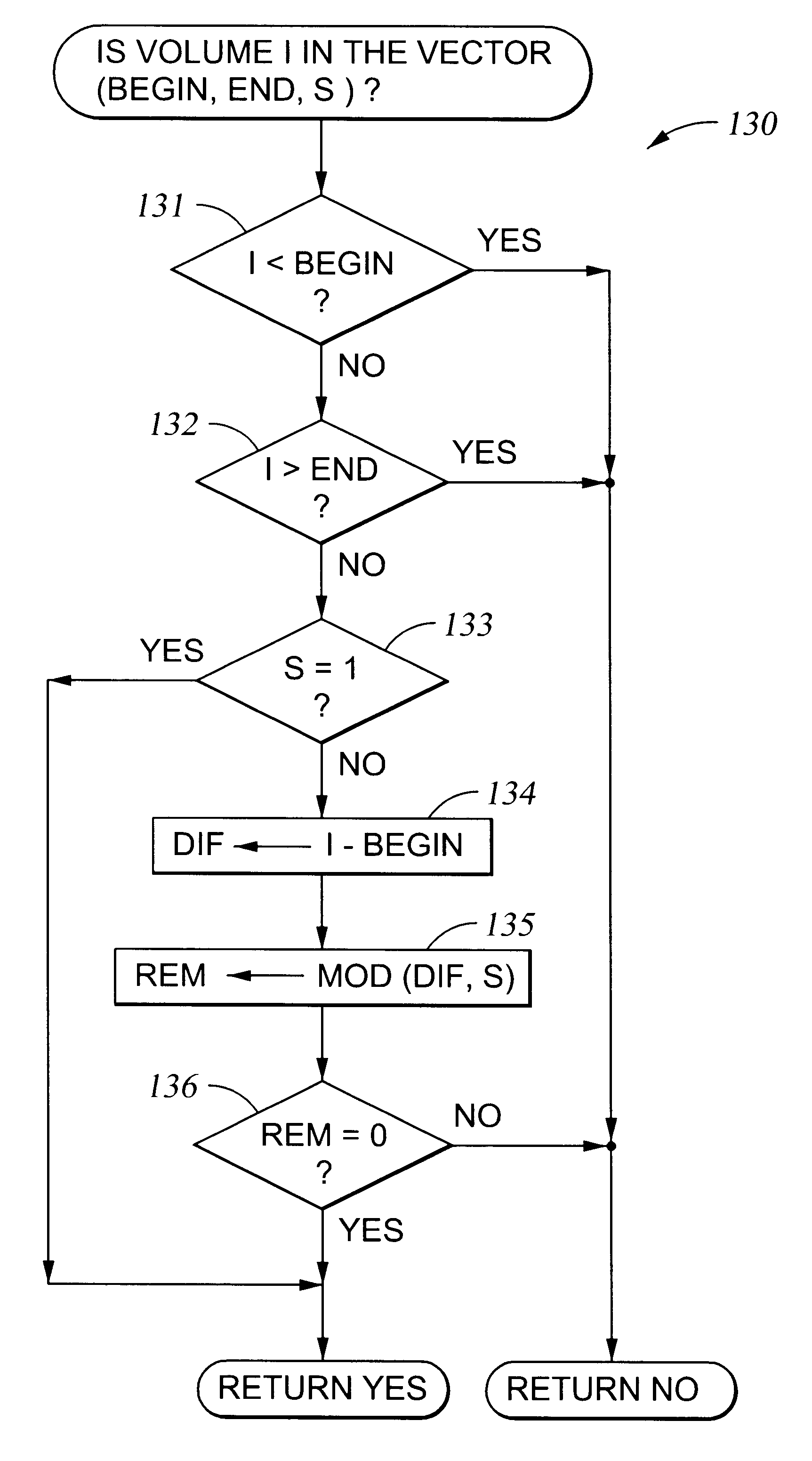
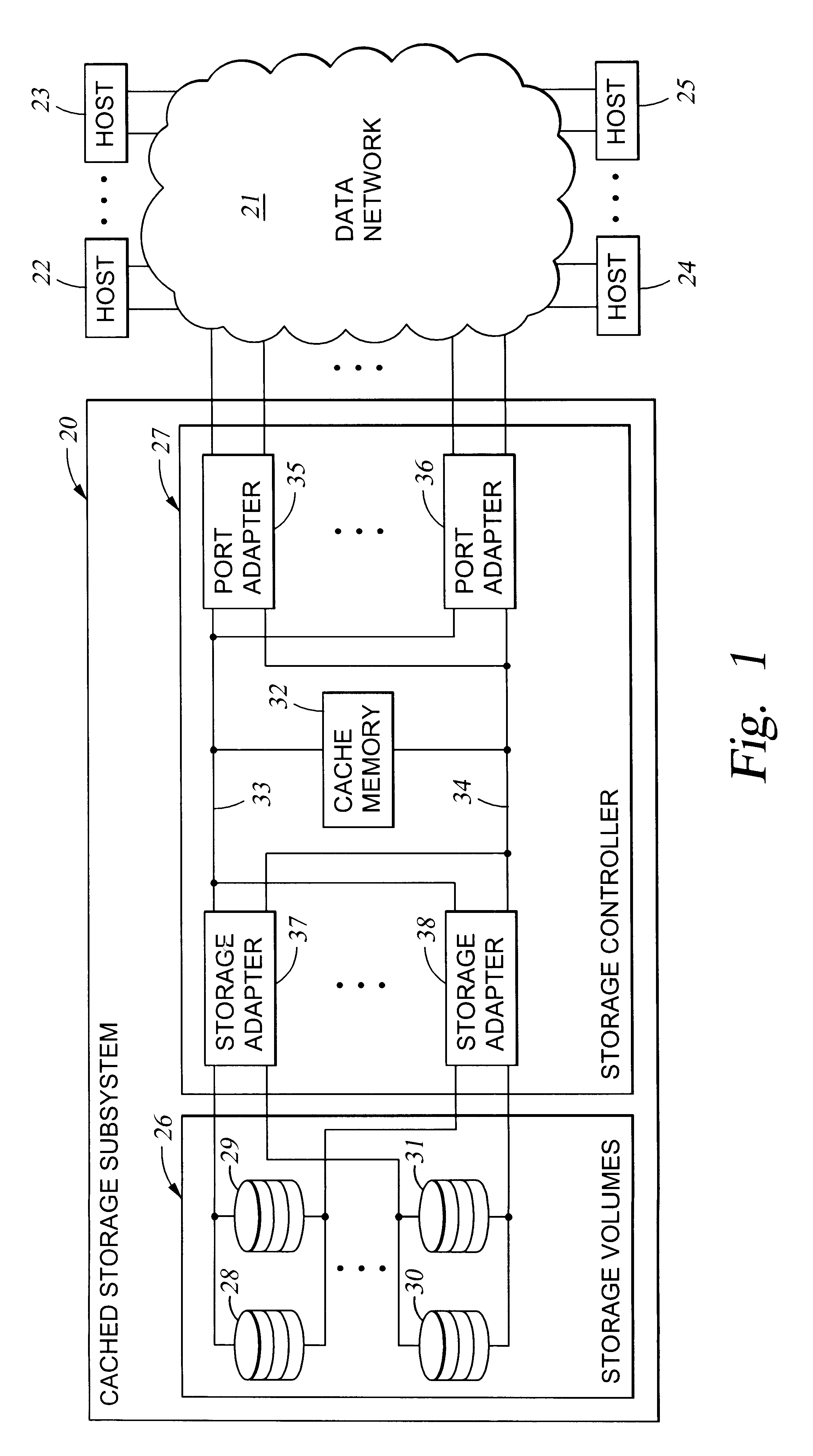
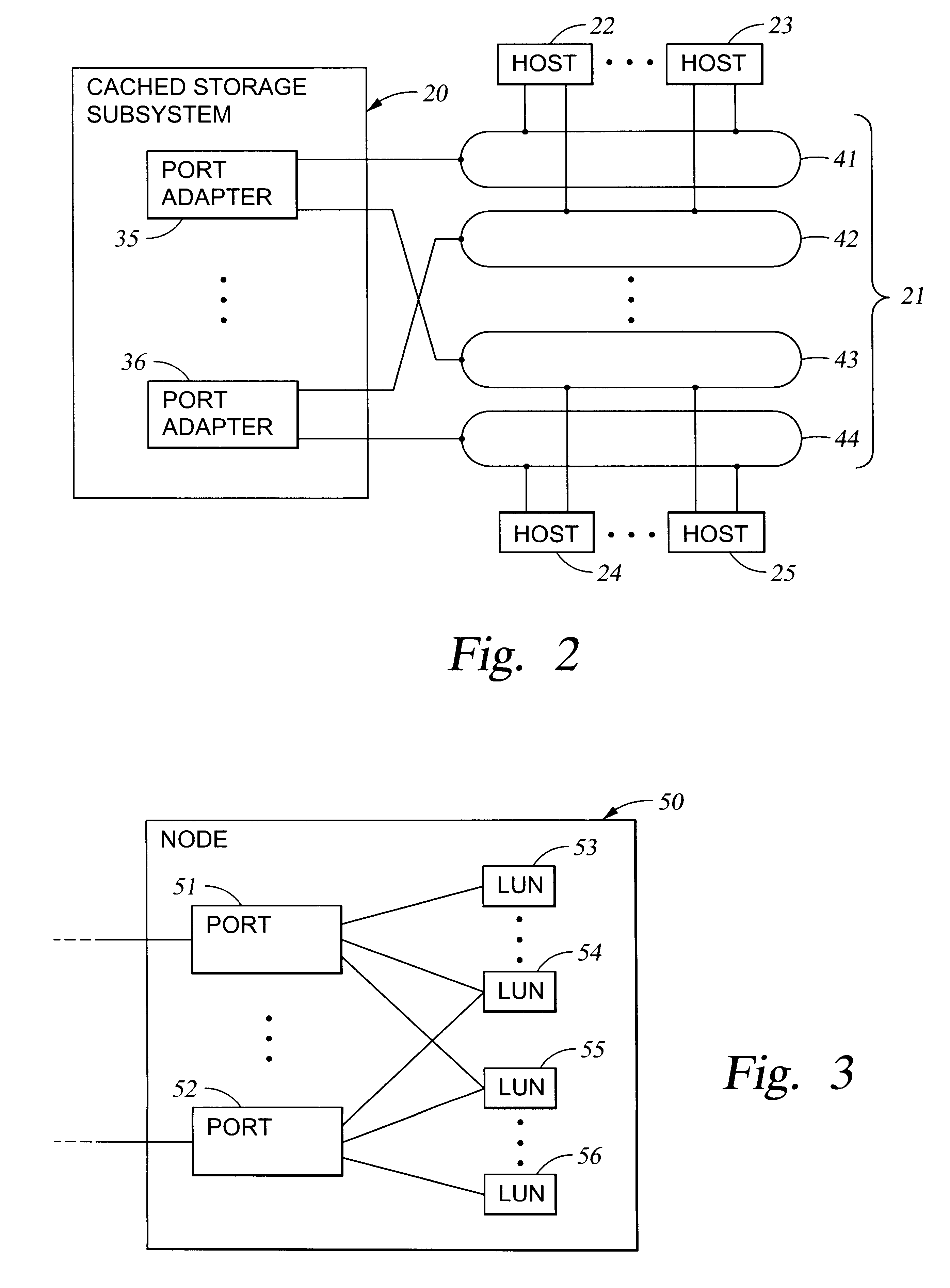
Configuring vectors of logical storage units for data storage partitioning and sharing
InactiveUS6295575B1Input/output to record carriersMemory adressing/allocation/relocationTheoretical computer scienceData store
In a data storage subsystem providing data storage to host processors, a process of configuration defines a subset of the data storage that each host may access. A vector specification is a convenient mechanism for specifying a set of storage volumes that a host may access. For example, for each host processor, there is stored in memory of the data storage subsystem a list of contiguous ranges or vectors of the storage volumes that the host may access. To determine whether or not a specified logical volume number is included in the vector, a modulus of the stride of the vector is computed from the difference between the address of the specified logical volume and the beginning address of the vector, and the modulus is compared to zero. To provide a mapping between logical unit numbers specified by the host and the logical volumes, a contiguous range of logical unit numbers may also be specified for each contiguous range or vector of storage volumes. The logical volume number is computed from a specified logical unit number by computing a difference between the specified logical unit number and the beginning logical unit number, multiplying the difference by the stride of the vector to produce a product, and adding the product to the beginning address of the vector.
Owner:EMC IP HLDG CO LLC
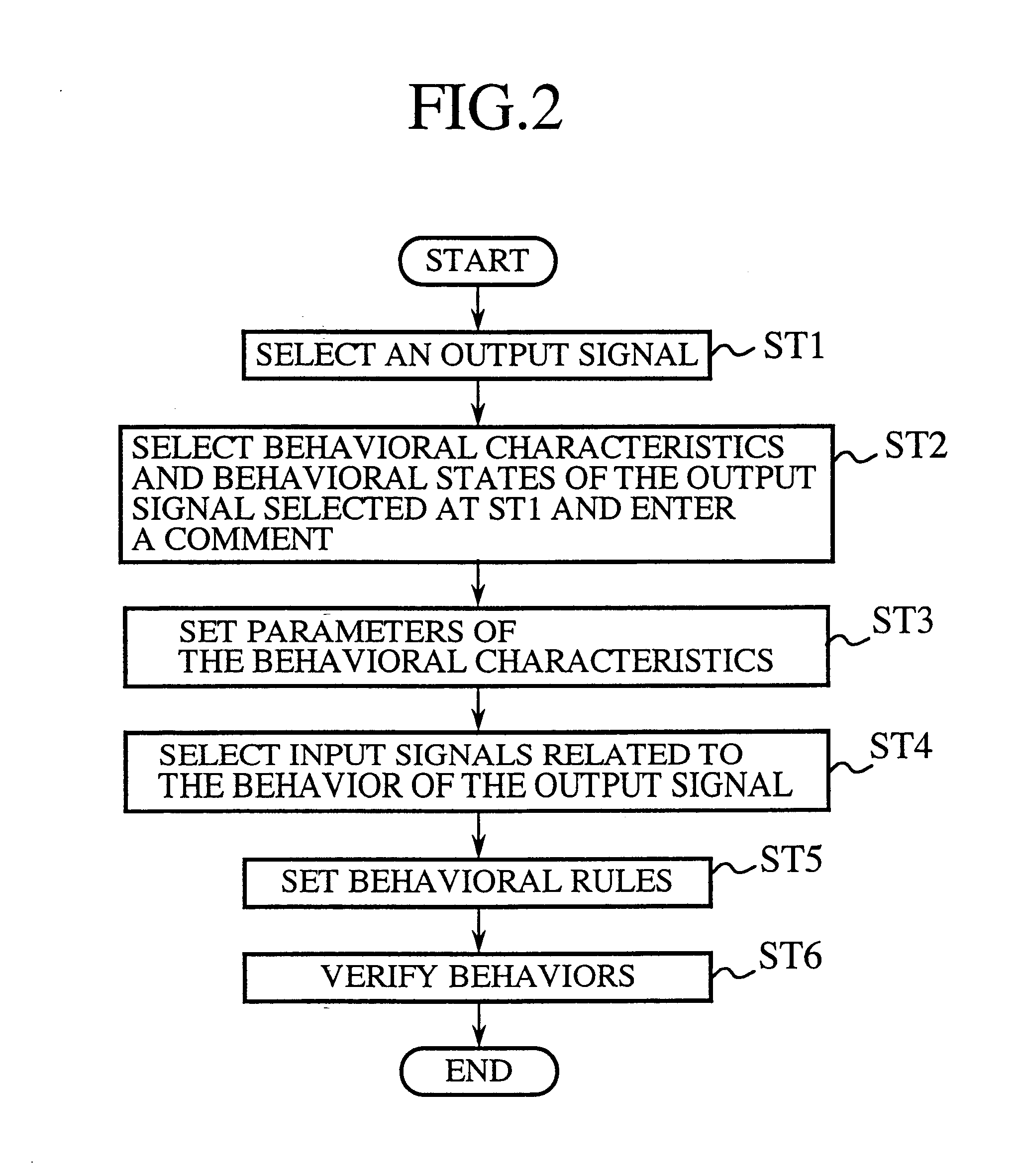
Visual programming method and its system
InactiveUS6366300B1Improve efficiencyReduce developmentProgramme controlData processing applicationsProgramming languageGraphics
The user is allowed to automatically generate a program by using a visual programming method and a system adopting the method for automatically generating a program wherein an object selection means 8 is used for selecting a behavioral graphical object defining the behavior of a load connected thereto, a behavior selection means 9 is used for selecting the type of the behavior of the behavioral graphical object, a relevant object selection means 10 is used for selecting relevant graphical objects related to the behavior of the behavioral graphical object and a behavioral rule setting means 11 is used for setting behavioral rules of the behavioral graphical object whereas a behavioral characteristic selection unit 3509 is used for selecting a behavior of a behavioral graphical object selected by using a behavioral object selection unit 3508, behavioral condition setting unit 3510 is used for setting conditions for the behavior of the behavioral graphical object and a relevant object selection unit 3511 is used for defining a relation.
Owner:MITSUBISHI ELECTRIC CORP
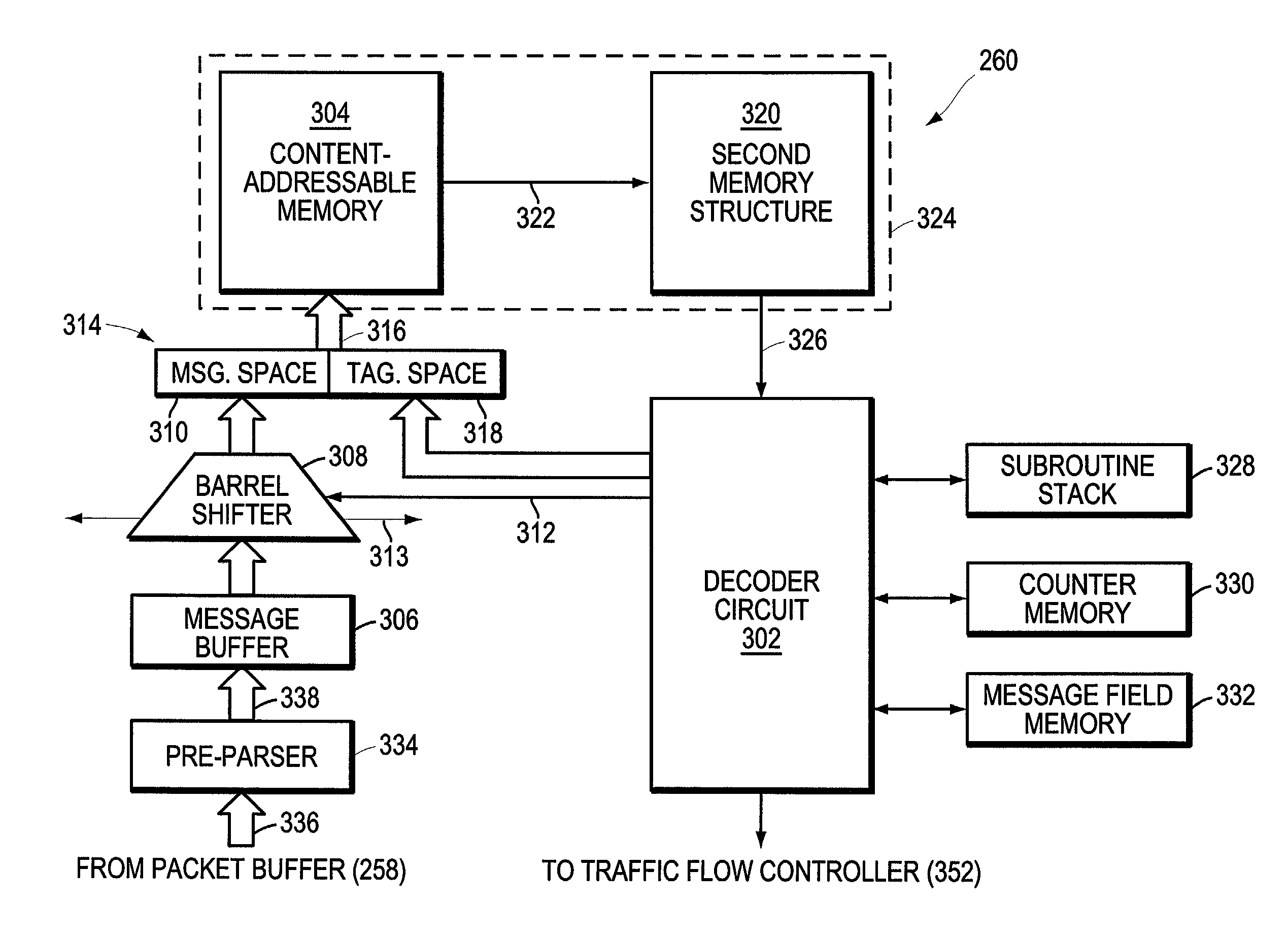
System and method for performing regular expression matching with high parallelism
InactiveUS7225188B1Digital data information retrievalData processing applicationsPattern matchingTheoretical computer science
A system and method for searching data strings, such as network messages, for one or more predefined regular expressions is provided. Regular expressions are programmed into a pattern matching engine so that multiple characters, e.g., 32, of the data strings can be searched at the same time. The pattern matching engine includes a regular expression storage device having one or more content-addressable memories (CAMs) whose rows may be divided into sections. Each predefined regular expression is analyzed so as to identify the “borders” within the regular expression. A border is preferably defined to exist at each occurrence of one or more predefined metacharacters, such as “.*”, which finds any character zero, one or more times. The borders separate the regular expression into a sequence of sub-expressions each of which may be one or more characters in length. Each sub-expression is preferably programmed into a corresponding section of the pattern matching engine. The system may also be configured so as to search multiple regular expressions in parallel.
Owner:CISCO TECH INC
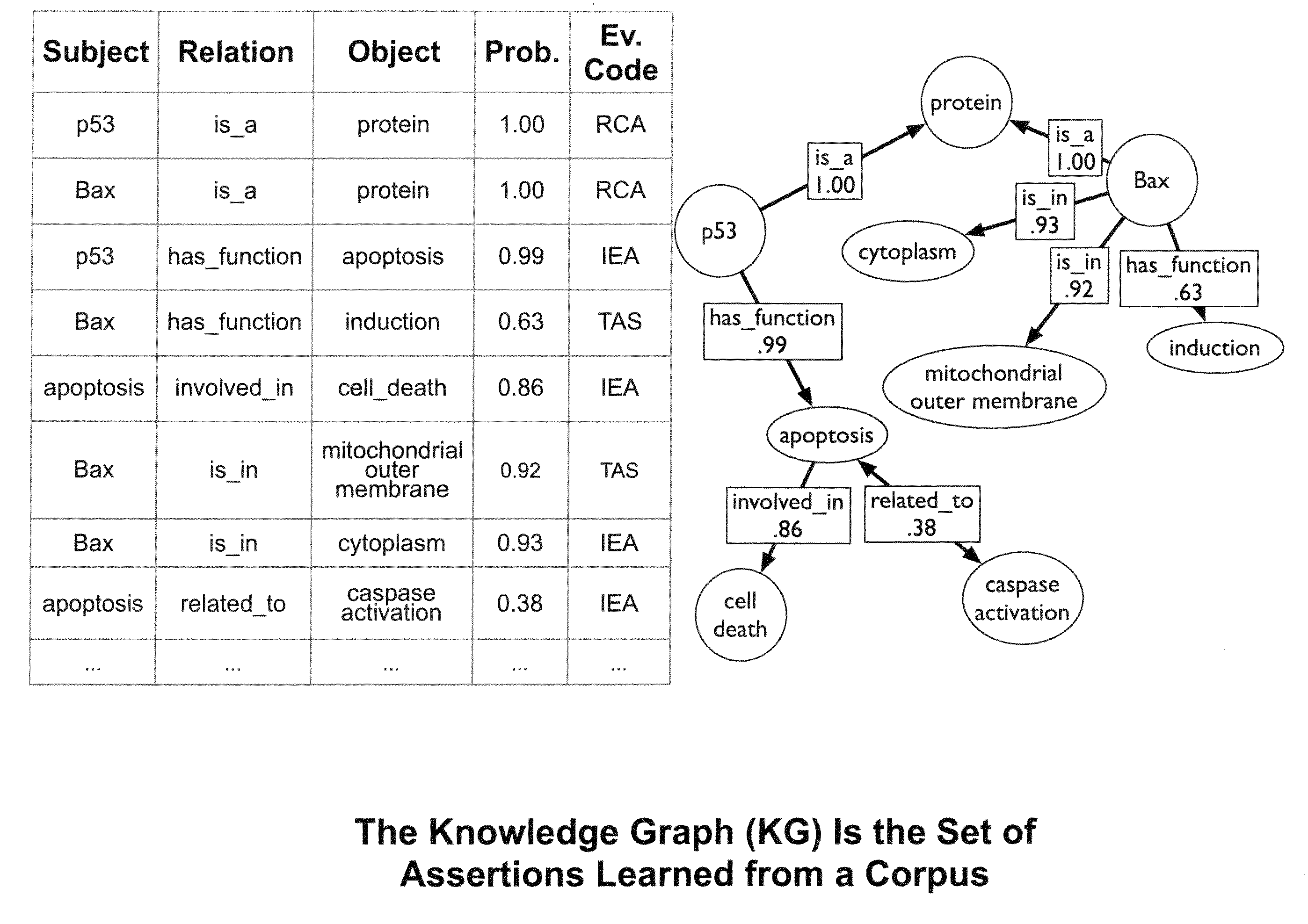
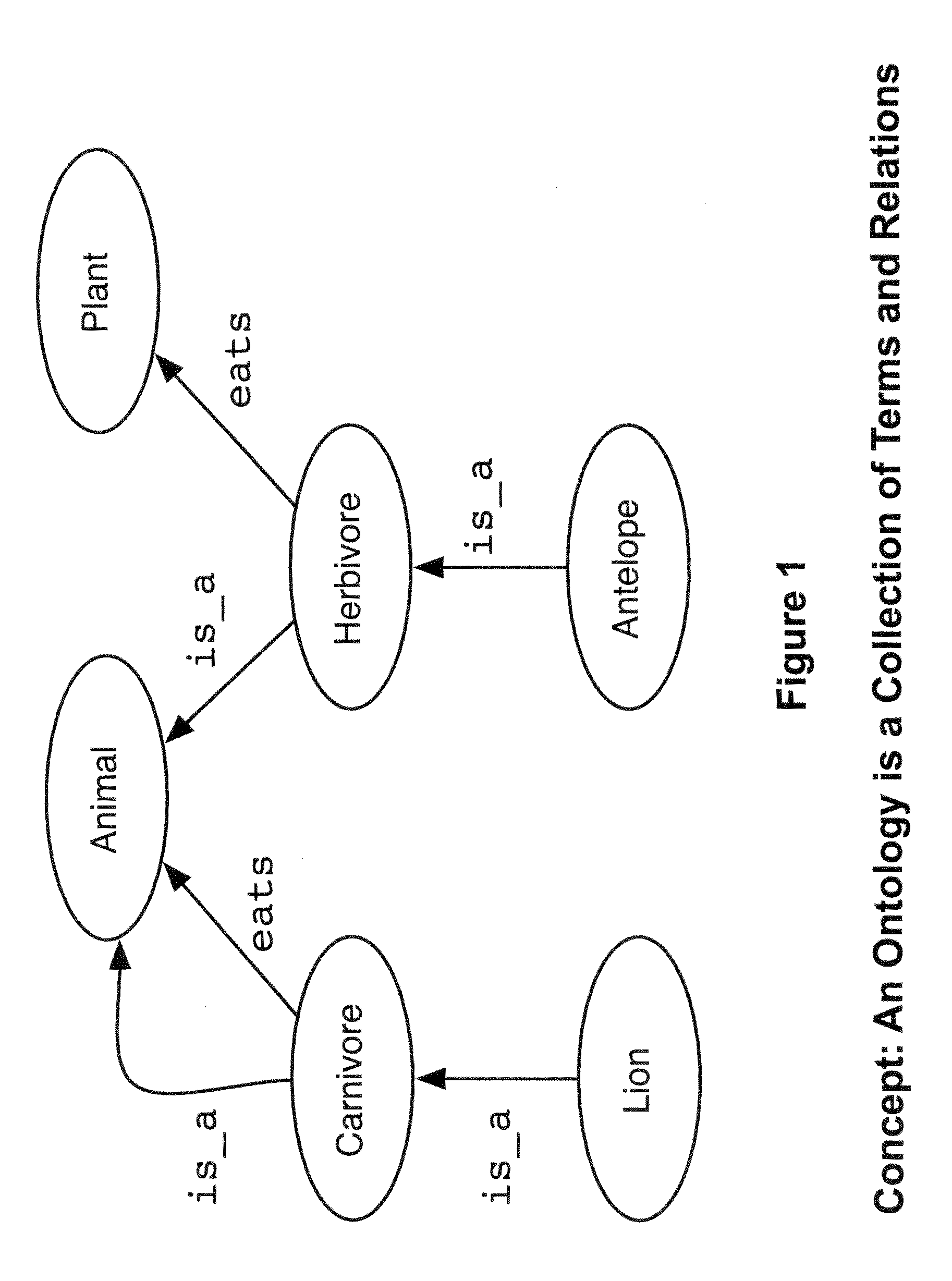
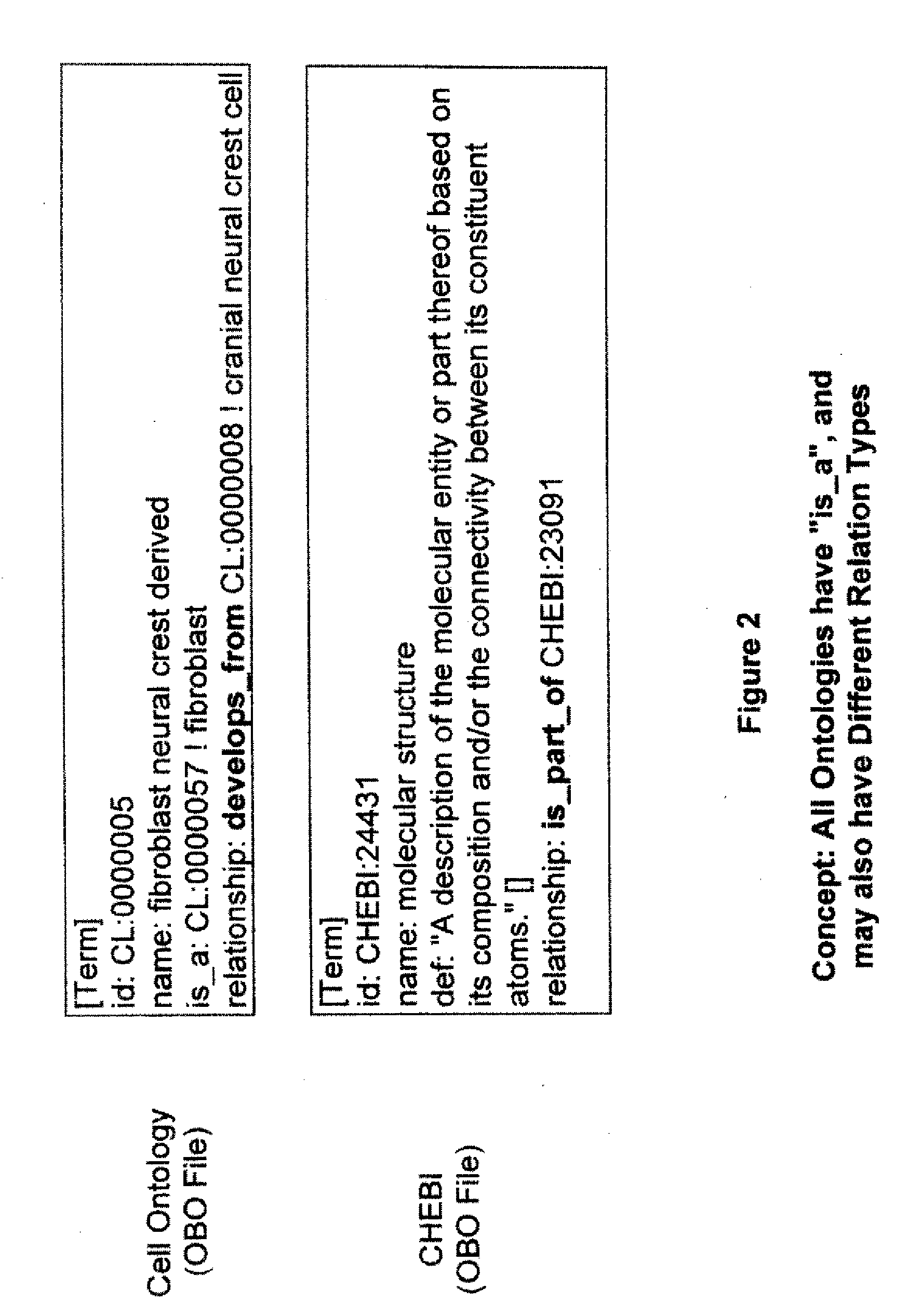
Methods and Systems of Automatic Ontology Population
Methods and systems for creating a knowledge graph that relates terms in a corpus of literature in the form of an assertion and provides a probability of the veracity of the assertion are disclosed herein. Various aspects of the invention are directed to and / or involve knowledge graphs and structured digital abstracts (SDAs) offering a machine readable representation of statements in a corpus of literature. Various methods and systems of the invention can automatically extract, structure, and visualize the statements. Such graphs and abstracts can be useful for a variety of applications including, but not necessarily limited to, semantic-based search tools for search of electronic medical records, specific content verticals (e.g. newswire, finance, history) and general internet searches.
Owner:COUNSYL INC
Efficient read/write algorithms and associated mapping for block-level data reduction processes
ActiveUS8140821B1Well formedFacilitates efficient read and write accessError detection/correctionDigital data processing detailsTheoretical computer scienceBlock level
A system configured to optimize access to stored chunks of data is provided. The system comprises a vLUN layer, a mapped LUN layer, and a mapping layer disposed between the vLUN and the mapped LUN. The vLUN provides a plurality of logical chunk addresses (LCAs) and the mapped LUN provides a plurality of physical chunk addresses (PCAs), where each LCA or PCA stores a respective chunk of data. The mapping layer defines a layout of the mapped LUN that facilitates efficient read and write access to the mapped LUN.
Owner:EMC IP HLDG CO LLC
Web application assessment based on intelligent generation of attack strings
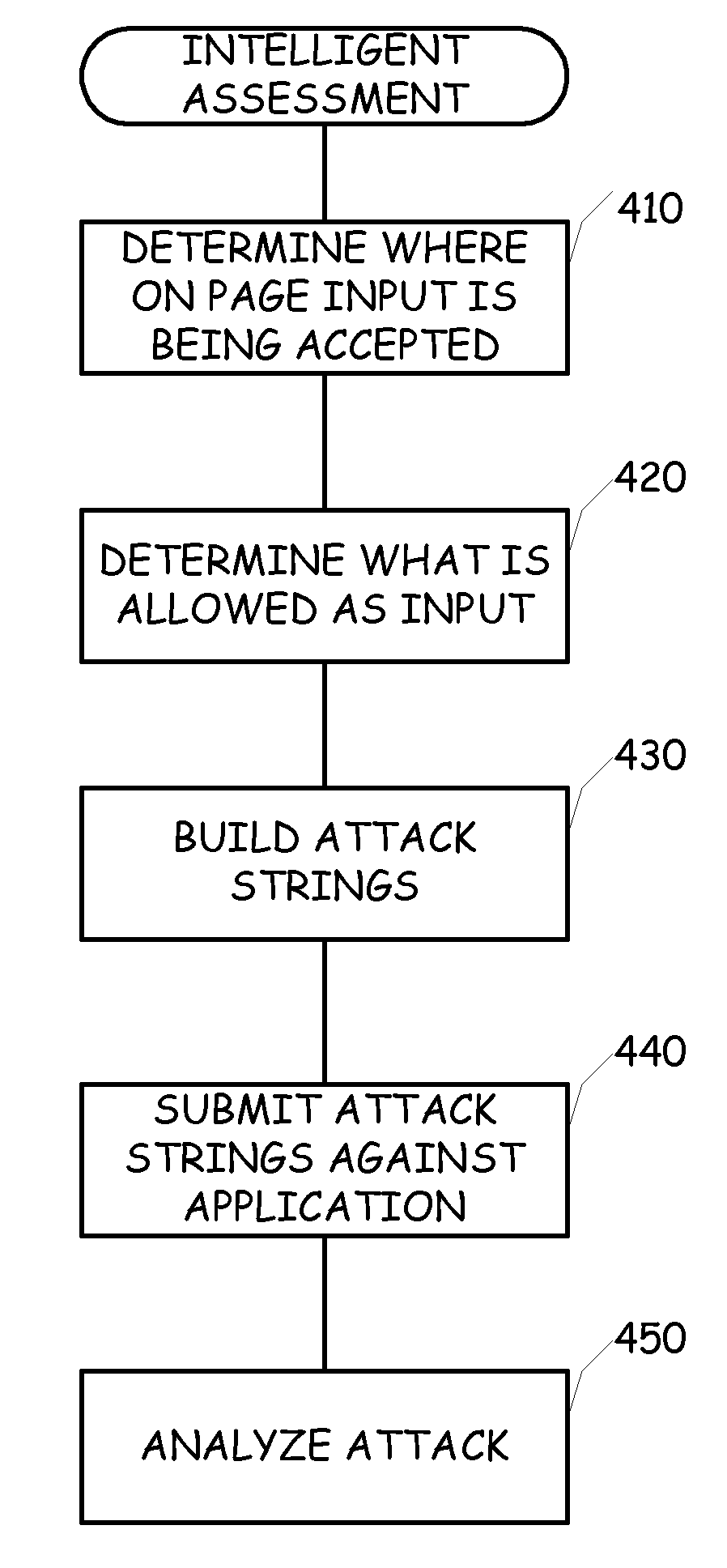
ActiveUS20080120722A1Easy to startImprove efficiencyMemory loss protectionError detection/correctionWeb siteWeb application
A web application is more efficiently analyzed by intelligently generating attack sequences to be used in the assessment. Rather than simply sending a canned list of static strings at a web application, the operation of the web application is analyzed to determine the filtering and acceptance characteristics of the web site. As this information is ascertained, a vocabulary of allowed symbols is created. This vocabulary is used in the building of attack strings and as such, the number of attack strings fired at the web application is greatly reduced, as well as the number of false positives.
Owner:MICRO FOCUS LLC
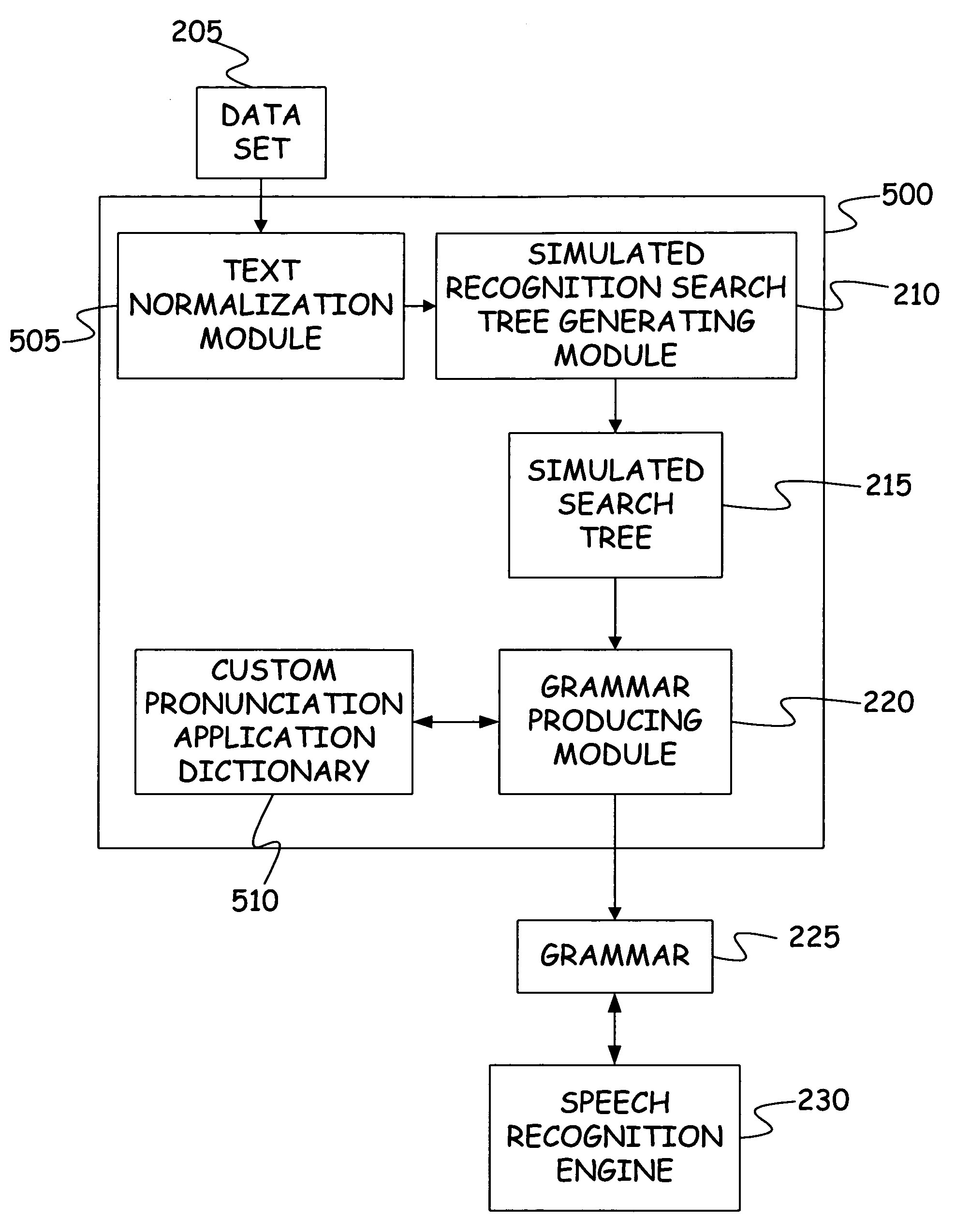
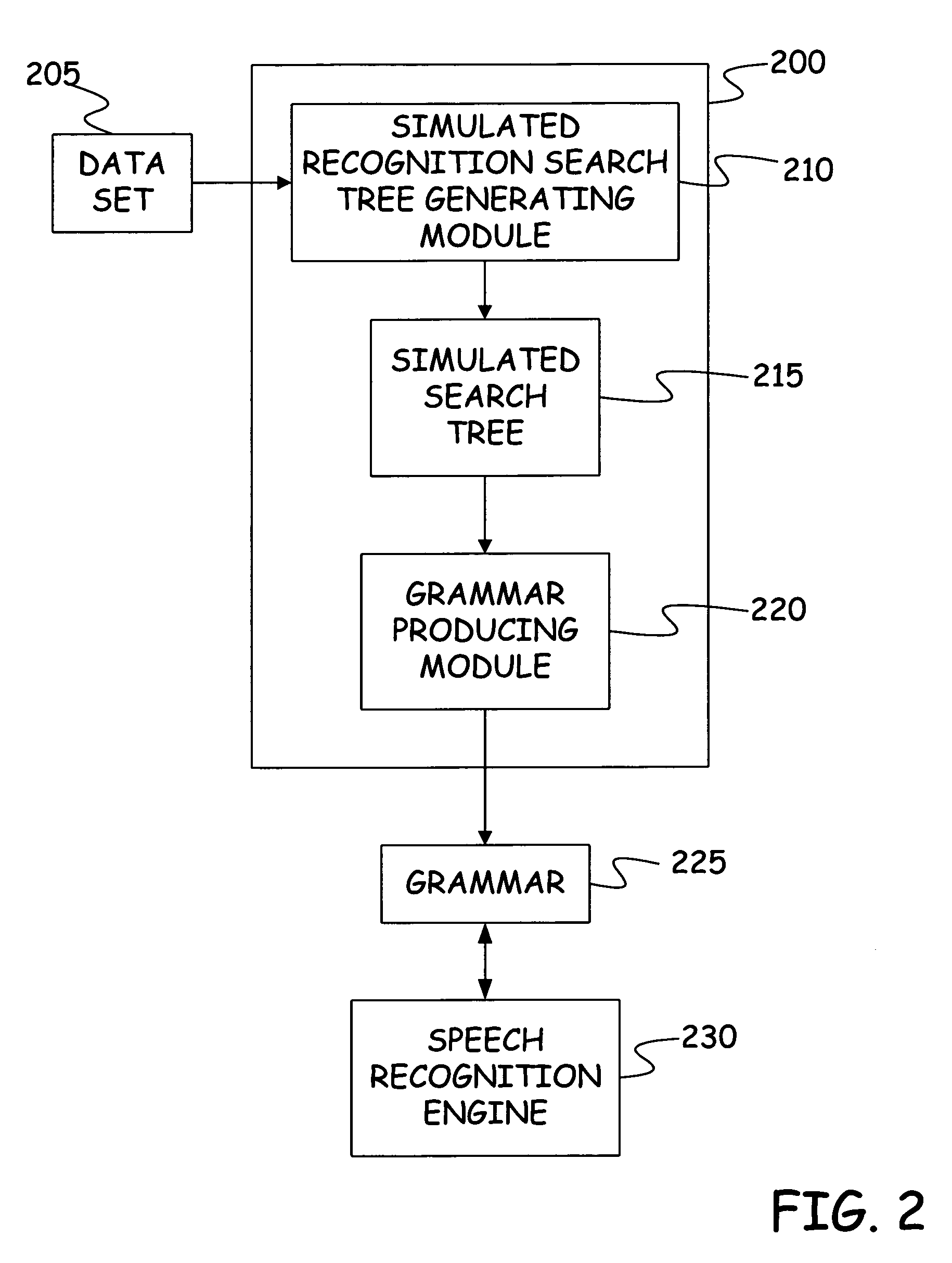
Method and apparatus for automatic grammar generation from data entries
InactiveUS7636657B2Speech recognitionSpecial data processing applicationsData setTheoretical computer science
Owner:MICROSOFT TECH LICENSING LLC
Algorithms for identity anonymization on graphs
InactiveUS20090303237A1Preserving individual privacy and basic structure of networkDrawing from basic elementsTransmissionGraphicsRe identification
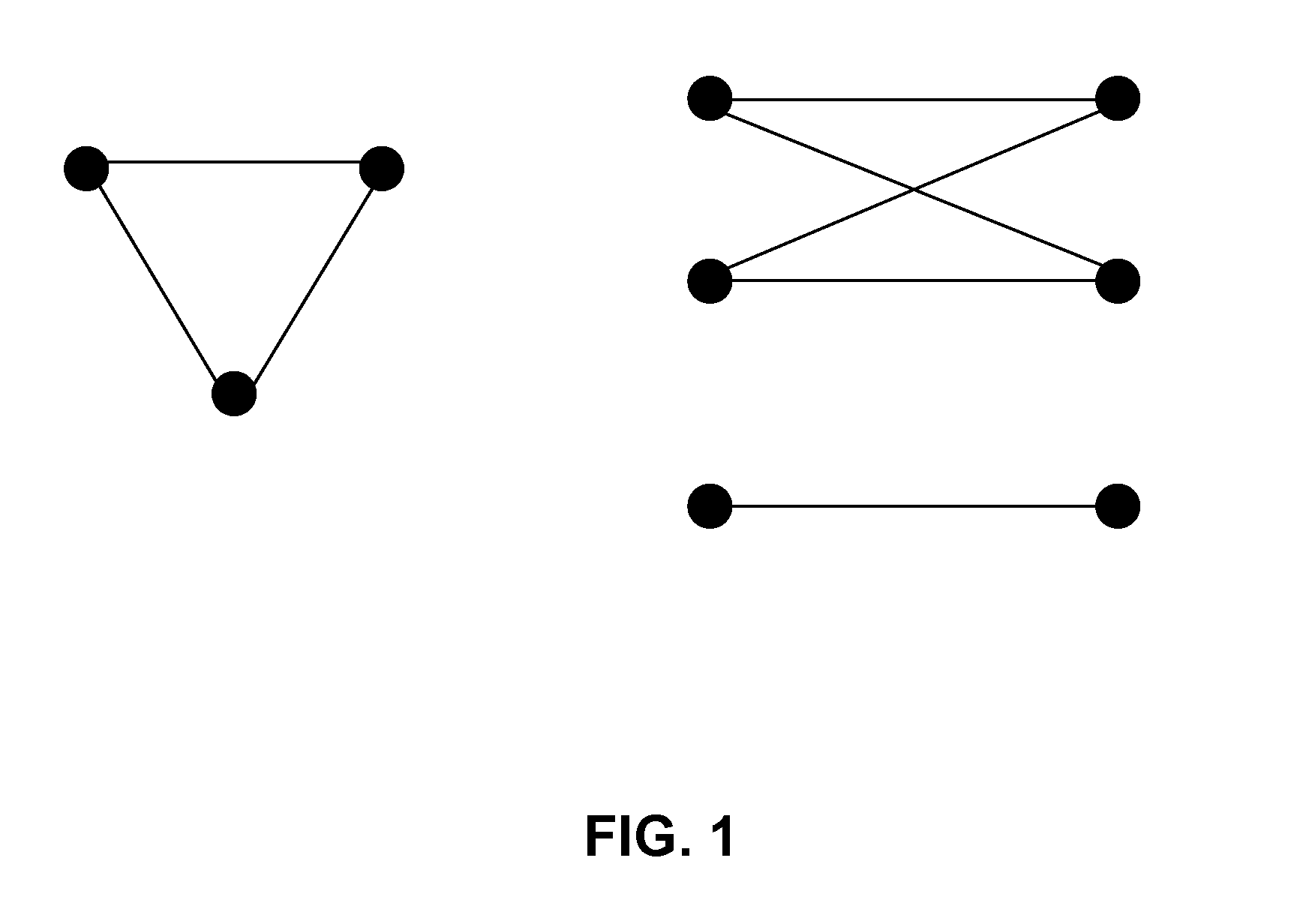
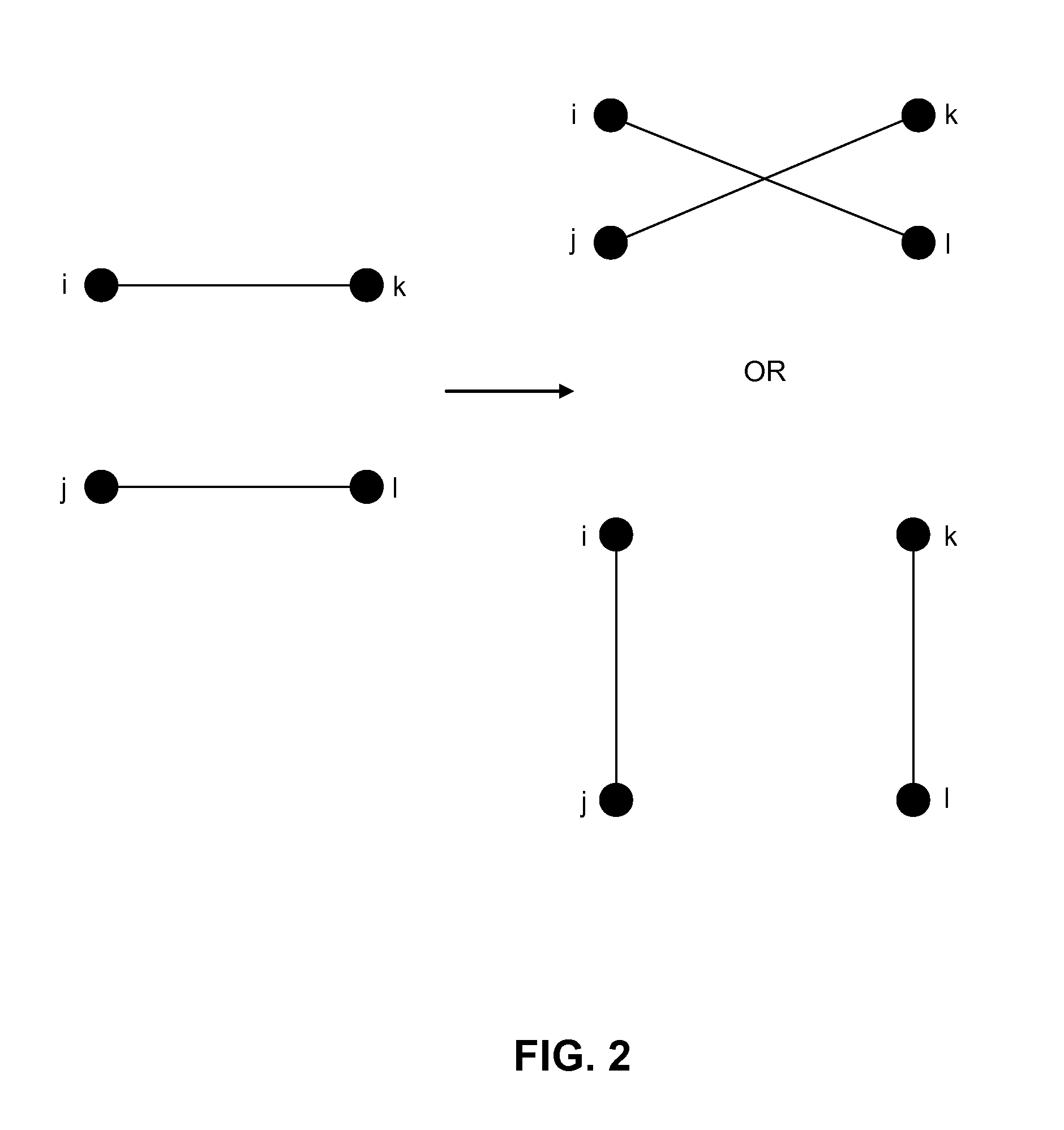
The proliferation of network data in various application domains has raised privacy concerns for the individuals involved. Recent studies show that simply removing the identities of the nodes before publishing the graph / social network data does not guarantee privacy. The structure of the graph itself, and in is basic form the degree of the nodes, can be revealing the identities of individuals. To address this issue, a specific graph-anonymization framework is proposed. A graph is called k-degree anonymous if for every node v, there exist at least k−1 other nodes in the graph with the same degree as v. This definition of anonymity prevents the re-identification of individuals by adversaries with a priori knowledge of the degree of certain nodes. Given a graph G, the proposed graph-anonymization problem asks for the k-degree anonymous graph that stems from G with the minimum number of graph-modification operations. Simple and efficient algorithms are devised for solving this problem, wherein these algorithms are based on principles related to the realizability of degree sequences.
Owner:IBM CORP
Methods for performing packet classification via prefix pair bit vectors
InactiveUS20060221956A1Data switching by path configurationPrefix headerTheoretical computer science
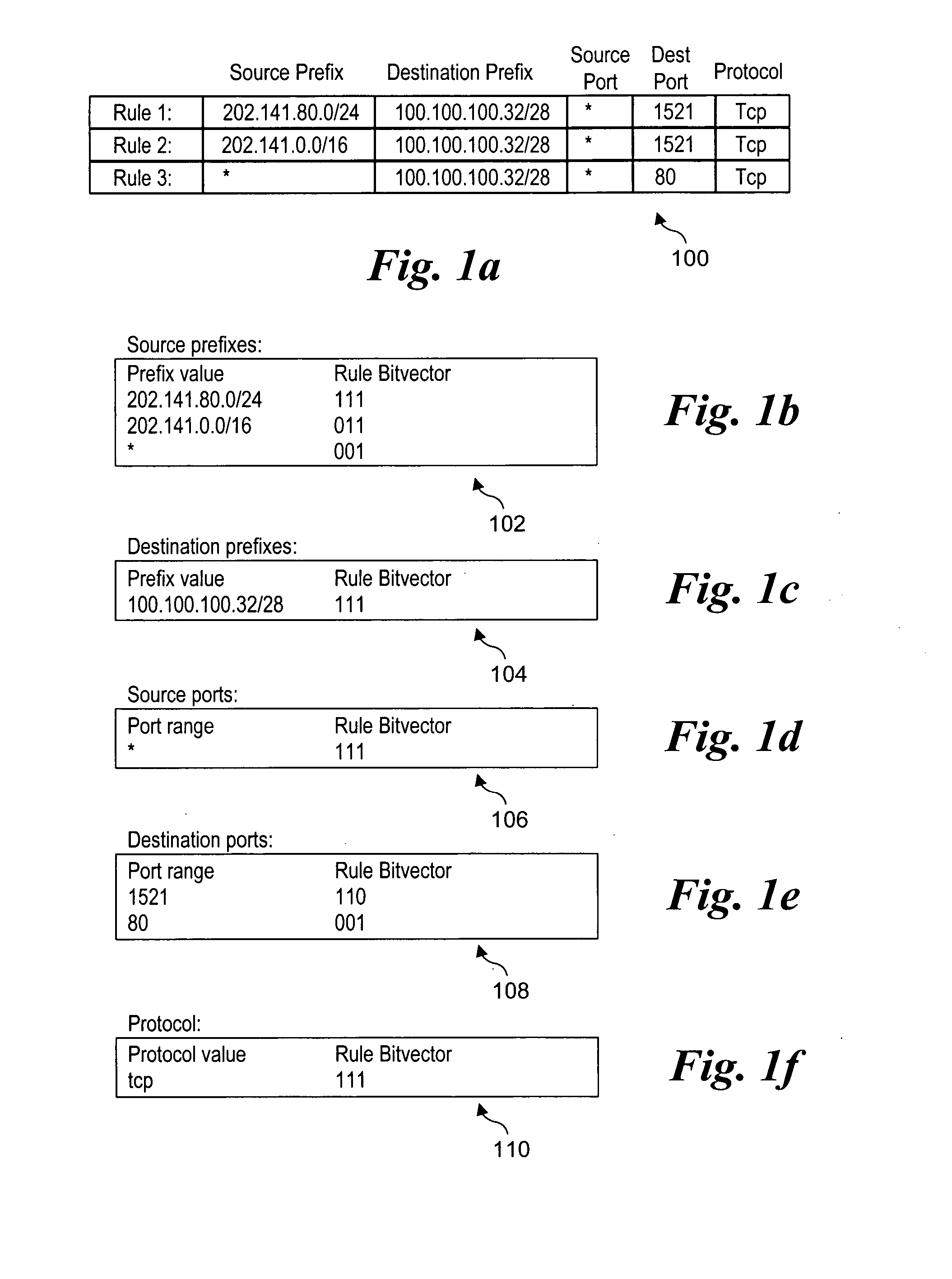
Methods for performing packet classification via prefix pair bit vectors. Unique prefix pairs in an access control list (ACL) are identified, with each prefix pair comprising a unique combination of a source prefix and a destination prefix. Corresponding prefix pair bit vectors (PPBVs) are defined for each unique source prefix and unique destination prefix in the ACL, with each PPBV including a string of bits and each bit position in the string associated with a corresponding prefix pair. A list of transport field value combinations are associated with each prefix pair based on corresponding entries in the ACL. During packet-processing operations, PPBV lookups are made using the source and destination prefix header values, and the PPBVs are logically ANDed to identify applicable prefix pairs. A search is then performed on transport field value combinations corresponding to the prefix pairs and the packet header to identify a highest priority rule.
Owner:INTEL CORP
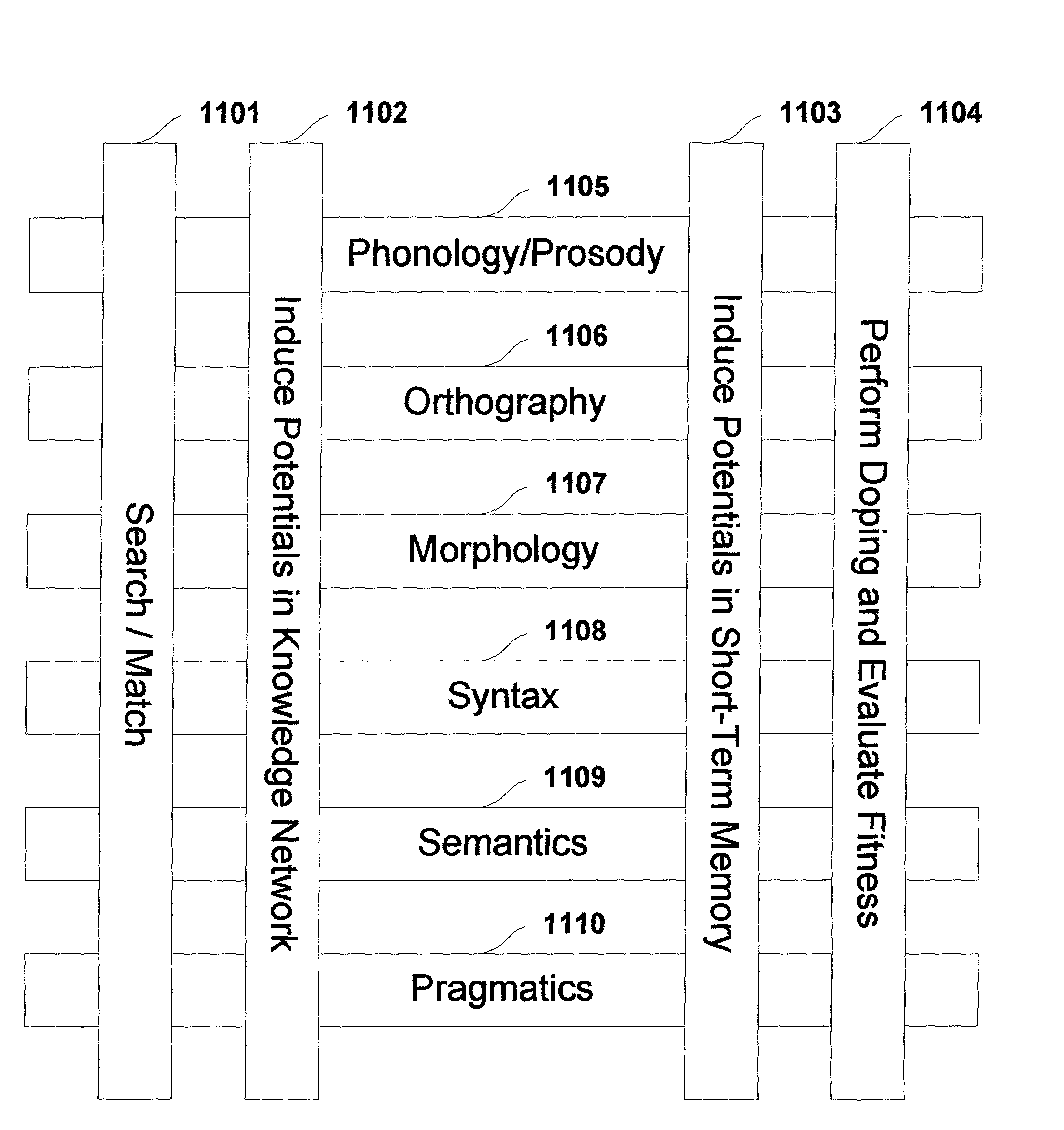
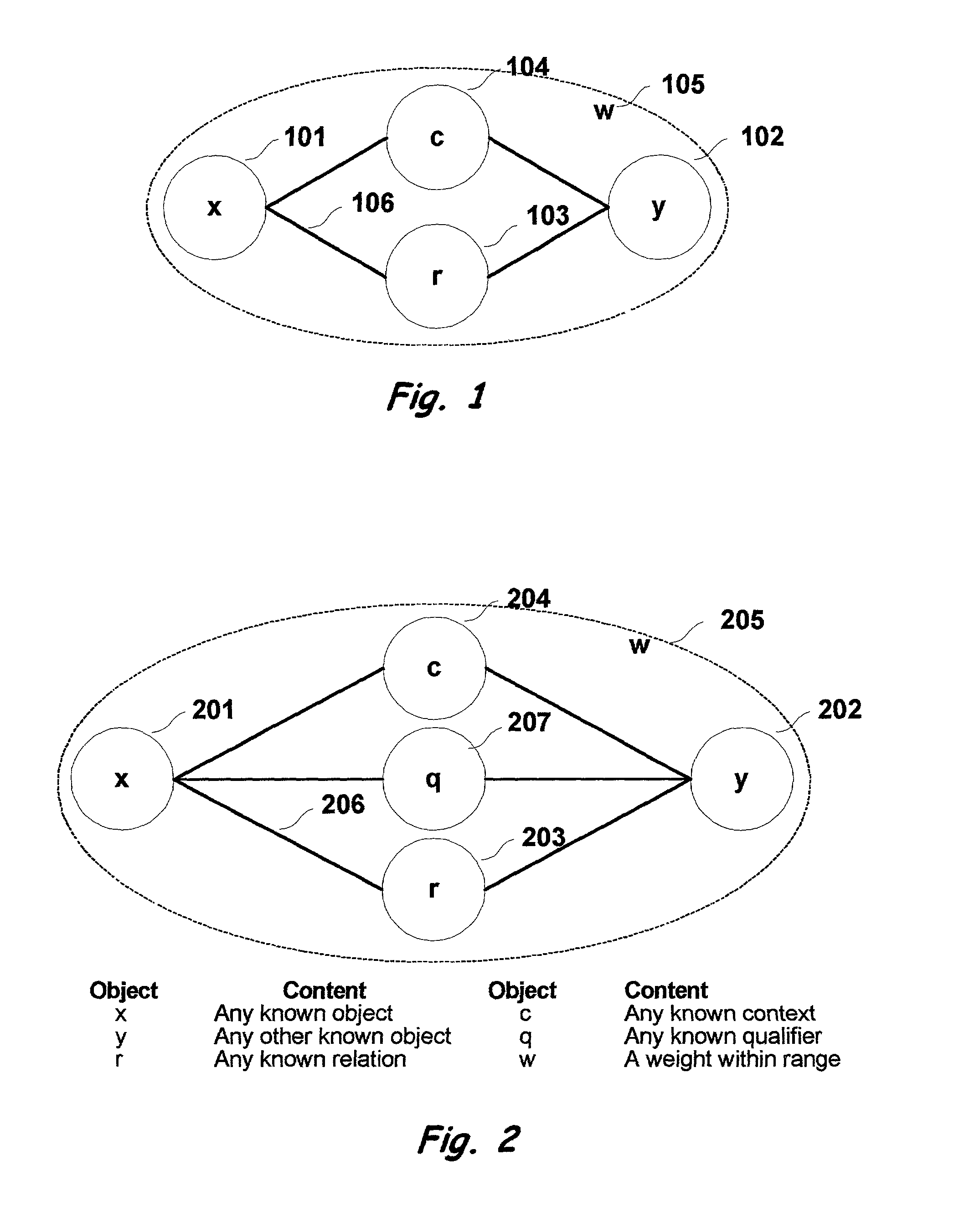
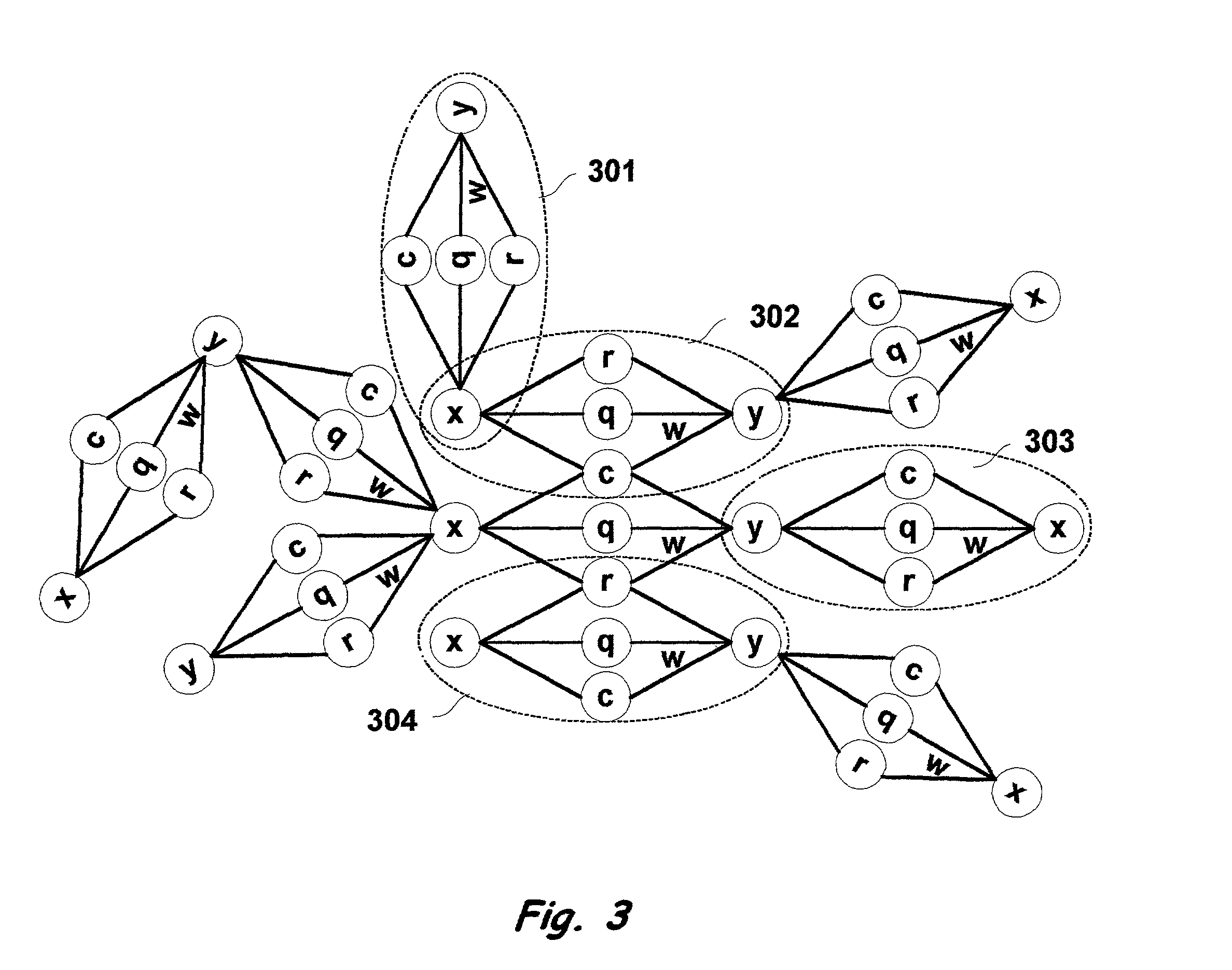
Multi-dimensional method and apparatus for automated language interpretation
A method and apparatus for natural language interpretation are described. The invention includes a schema and apparatus for storing, in digital, analog, or other machine-readable format, a network of propositions formed of a plurality of text and / or non-text objects, and the steps of retrieving a string of input text, and locating all associated propositions in the network for each word in the input string. Embodiments of the invention also include optimization steps for locating said propositions, and specialized structures for storing them in a ready access storage area simulating human short-term memory. The schema and steps may also include structures and processes for obtaining and adjusting the weights of said propositions to determine posterior probabilities representing the intended meaning. Embodiments of the invention also include an apparatus designed to apply an automated interpretation algorithm to automated voice response systems and portable knowledge appliance devices.
Owner:KNOWLEDGENETICA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com