Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1849 results about "Data node" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
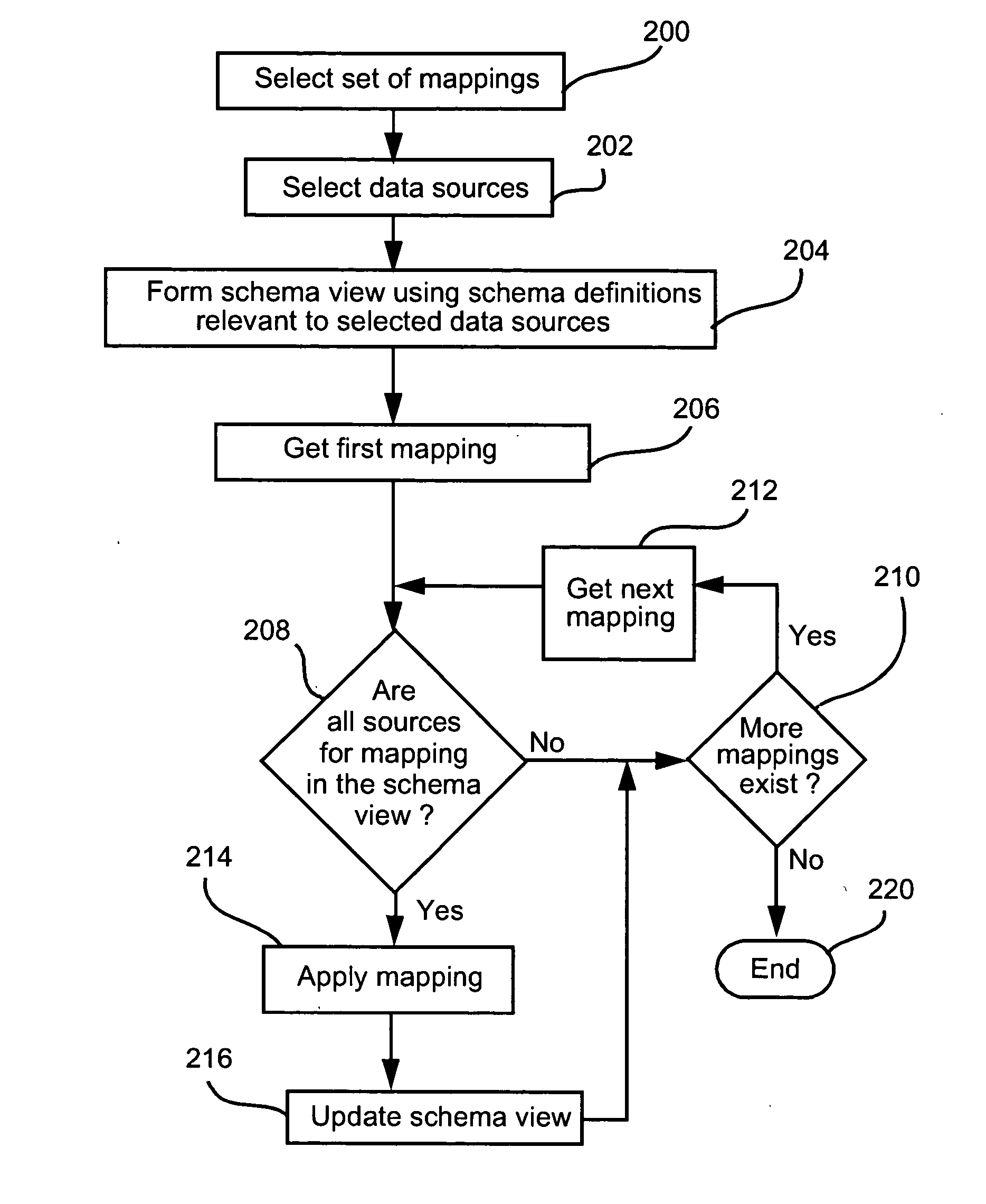
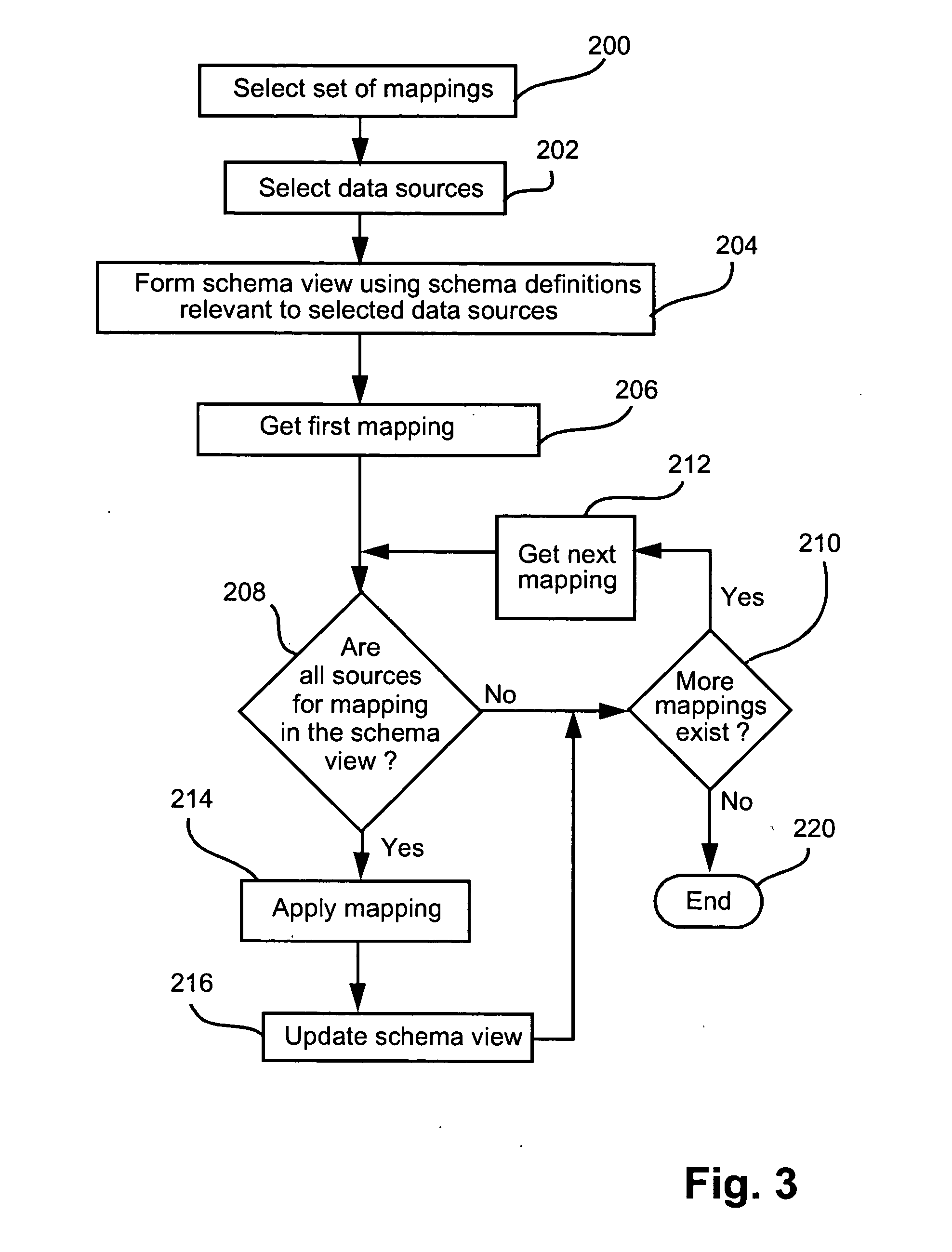
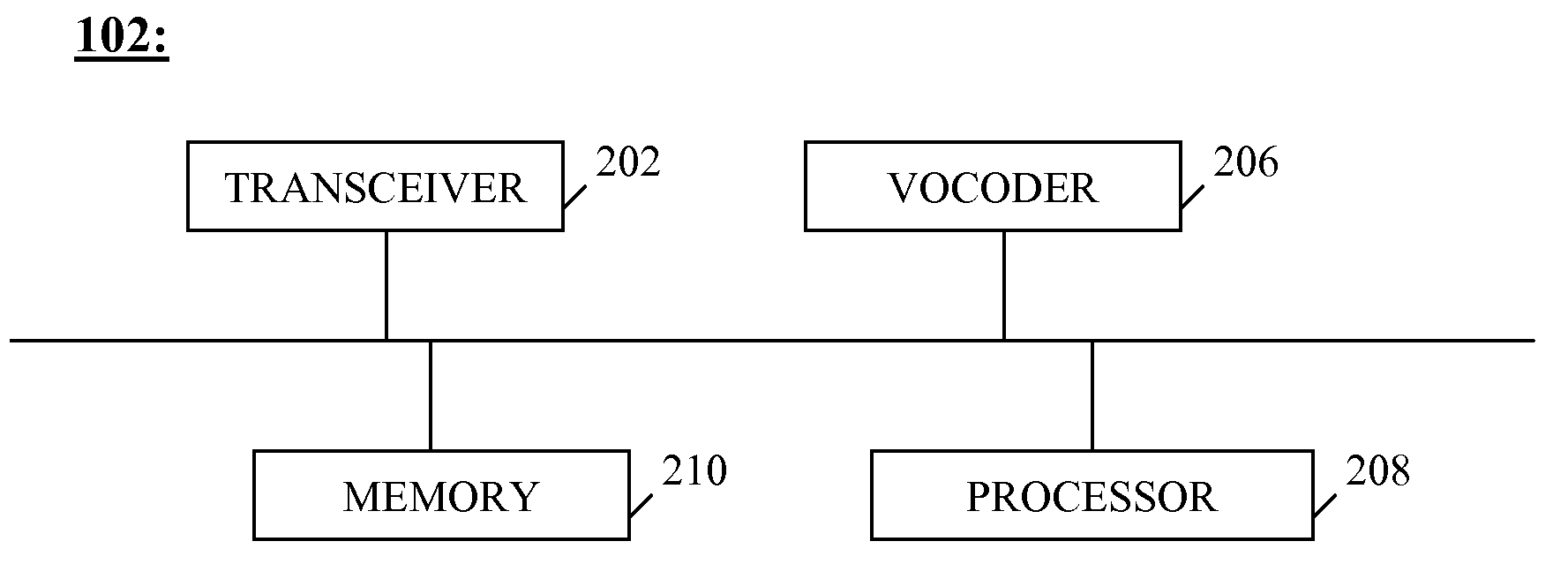
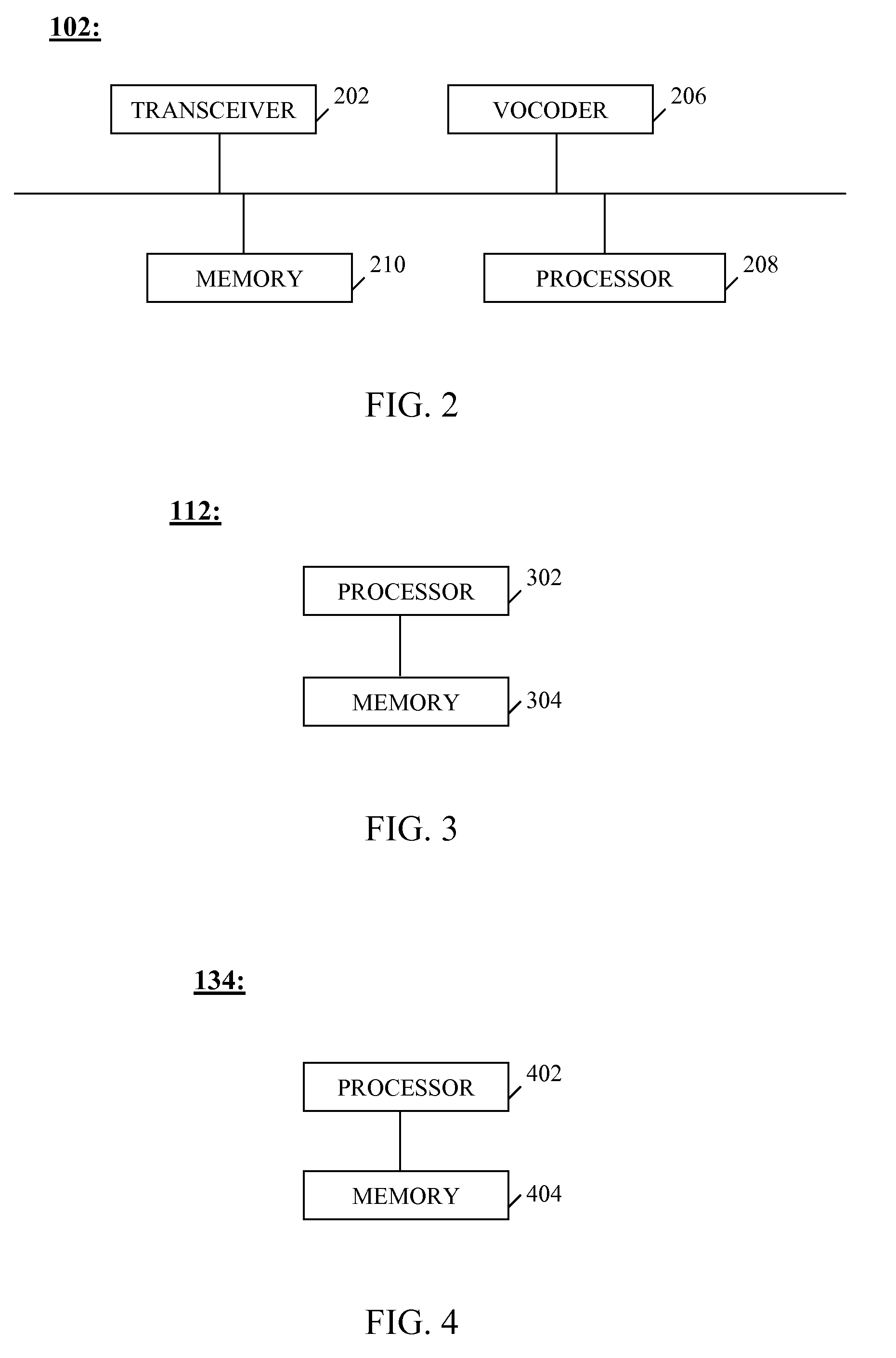
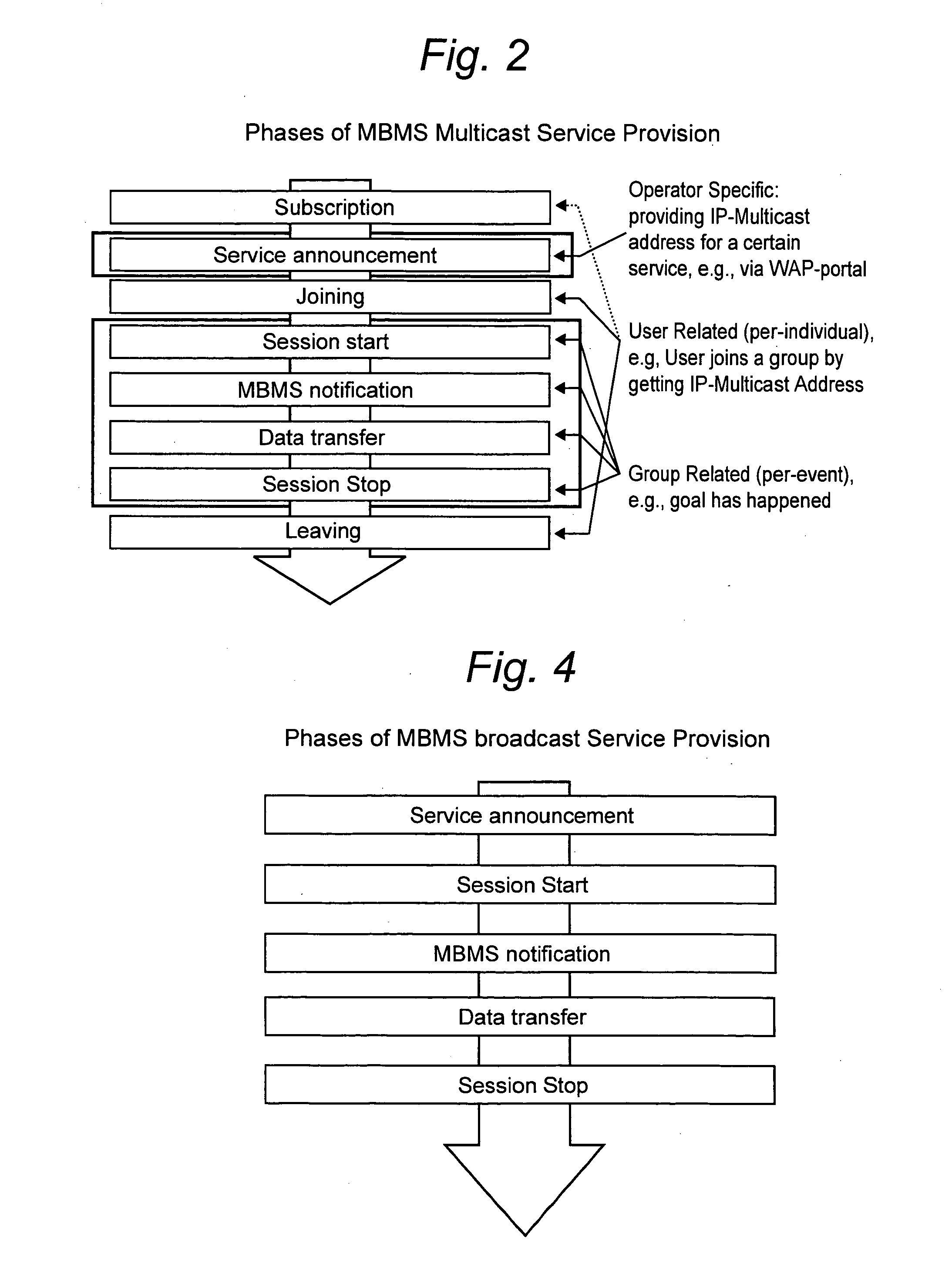
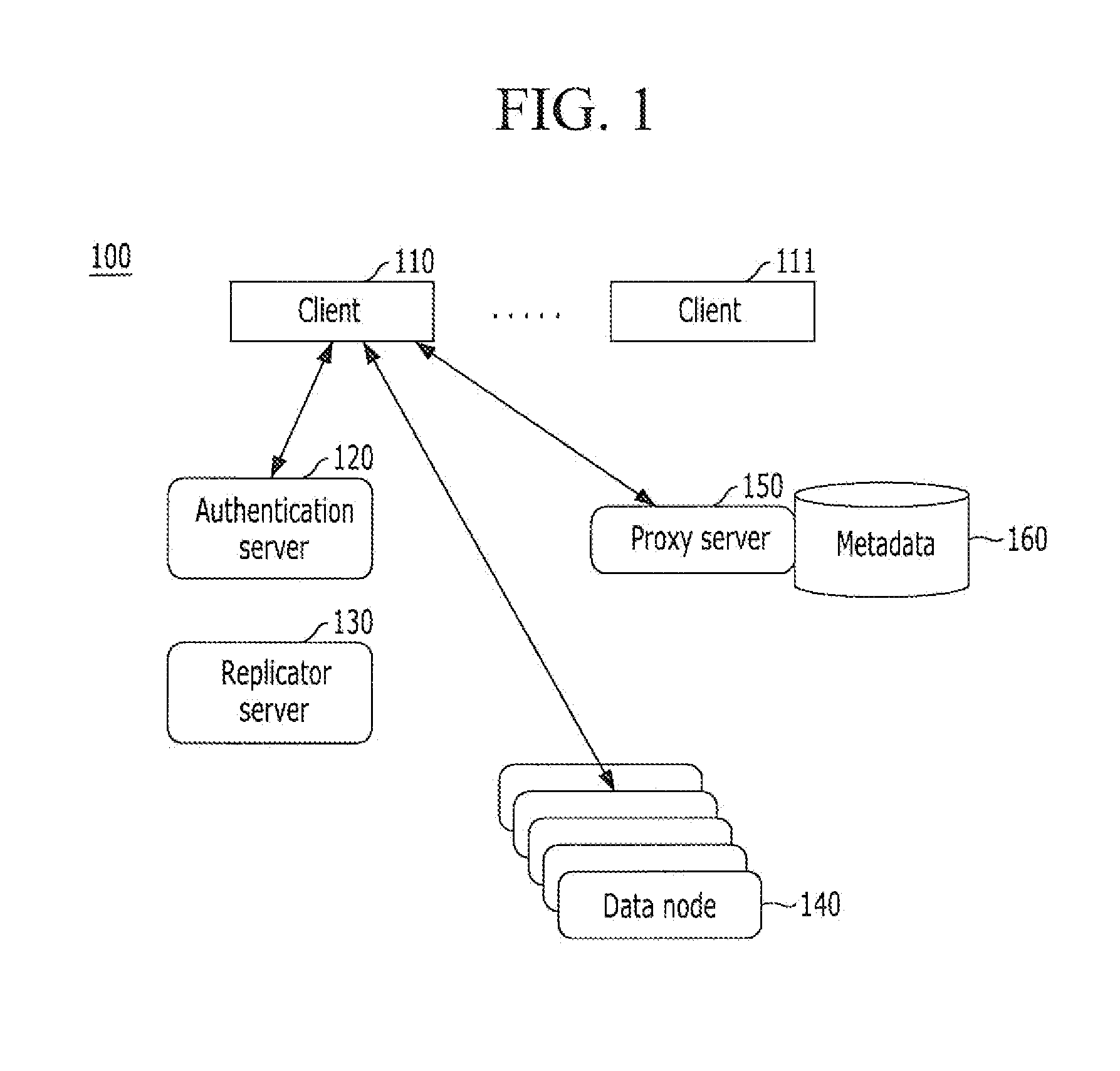
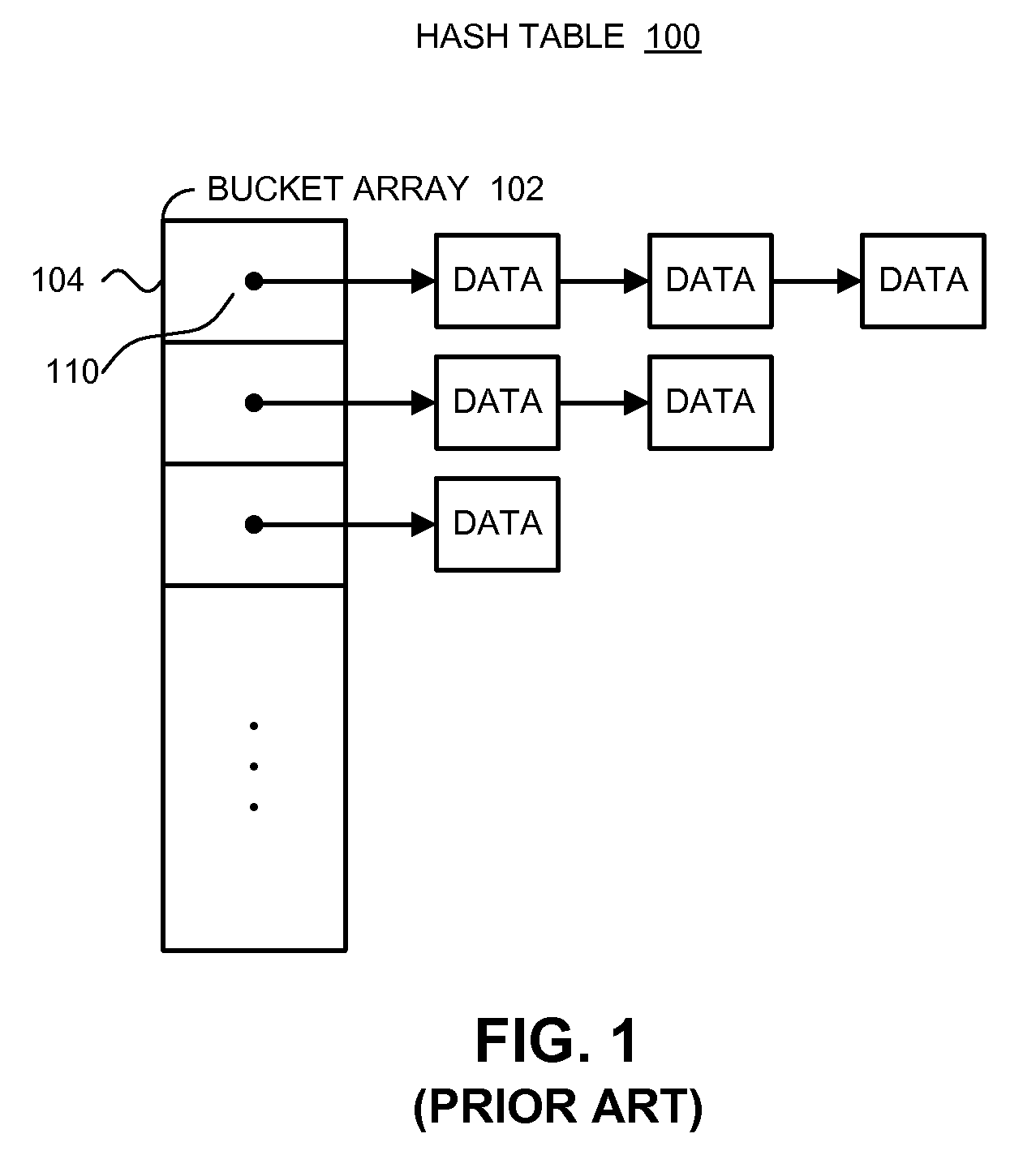
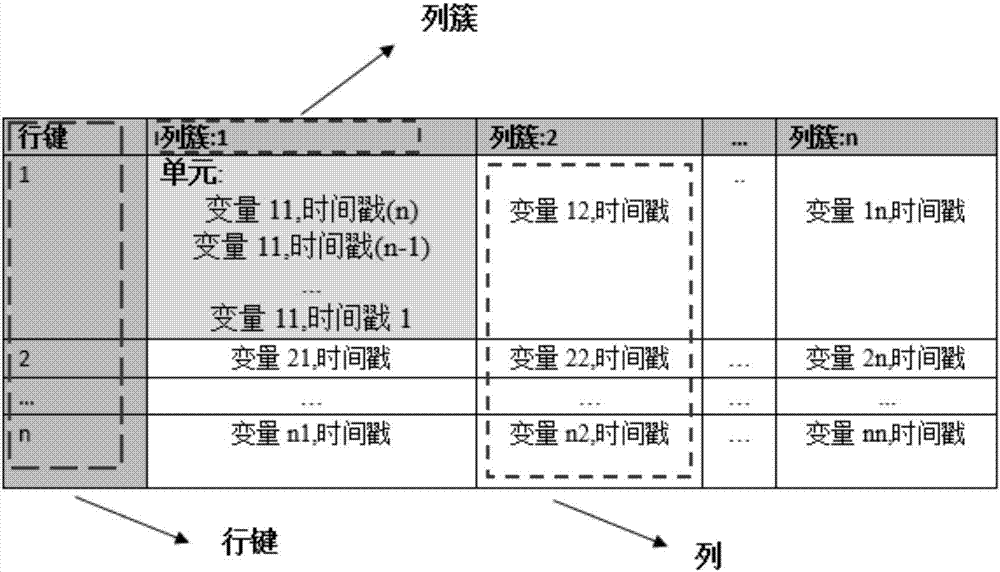
Data nodes. A data node is an appliance that you can add to your event and flow processors to increase storage capacity and improve search performance. You can add an unlimited number of data nodes to your IBM® Security QRadar® deployment, and they can be added at any time.
Method for presenting hierarchical data
InactiveUS20050060647A1Easy to operateDatabase management systemsDigital computer detailsHyperlinkDisplay device
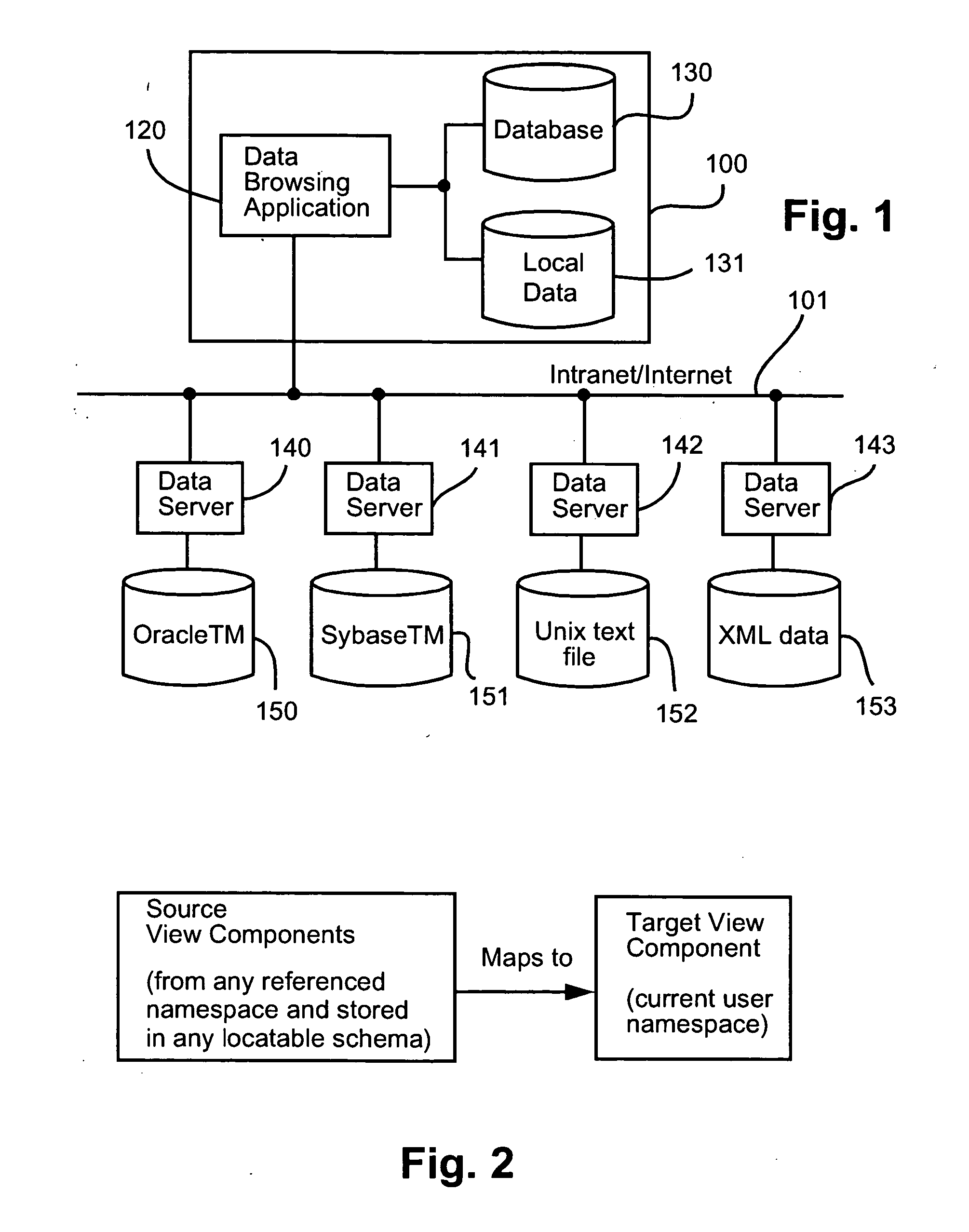
Methods, programs (120) and apparatus (100) are disclosed for accessing and heterogenous data sources (150-153) and presenting information obtained therefrom. Specifically, the data sources may have hierarchical data, which may be presented by identifying a context data node from the data, the context data node having one or more descendent data nodes. At least one data pattern is determined in the descendent data nodes. At least one display type is assigned to the current context data node on the basis of the at least one data pattern. Thereafter, the method presents at least a subset of the descendent data nodes according to one of the assigned display types. Also disclosed is a method of browsing an hierarchically-represented data source. A user operation is interpreted to identify a context data node from the data source, the context data node having one or more descendent data nodes. At least one data pattern in the descendent data nodes is then determined and at least one display type is assigned to the current context data node on the basis of the at least one data pattern. A subset of the descendent data nodes is then presented according to one of the assigned display types, the subset including at least one hyperlink (3401,3402) having as its target a descendant data node of the current context data node. A further user operation is then interpreted to select the at least one hyperlink, the selection resulting in the current context data node being replaced with the data node corresponding to the target of the selected hyperlink. These steps may be repeated until no further hyperlinks to descendent data nodes are included in the subset. Other methods associated with access and presentation are also disclosed.
Owner:CANON KK
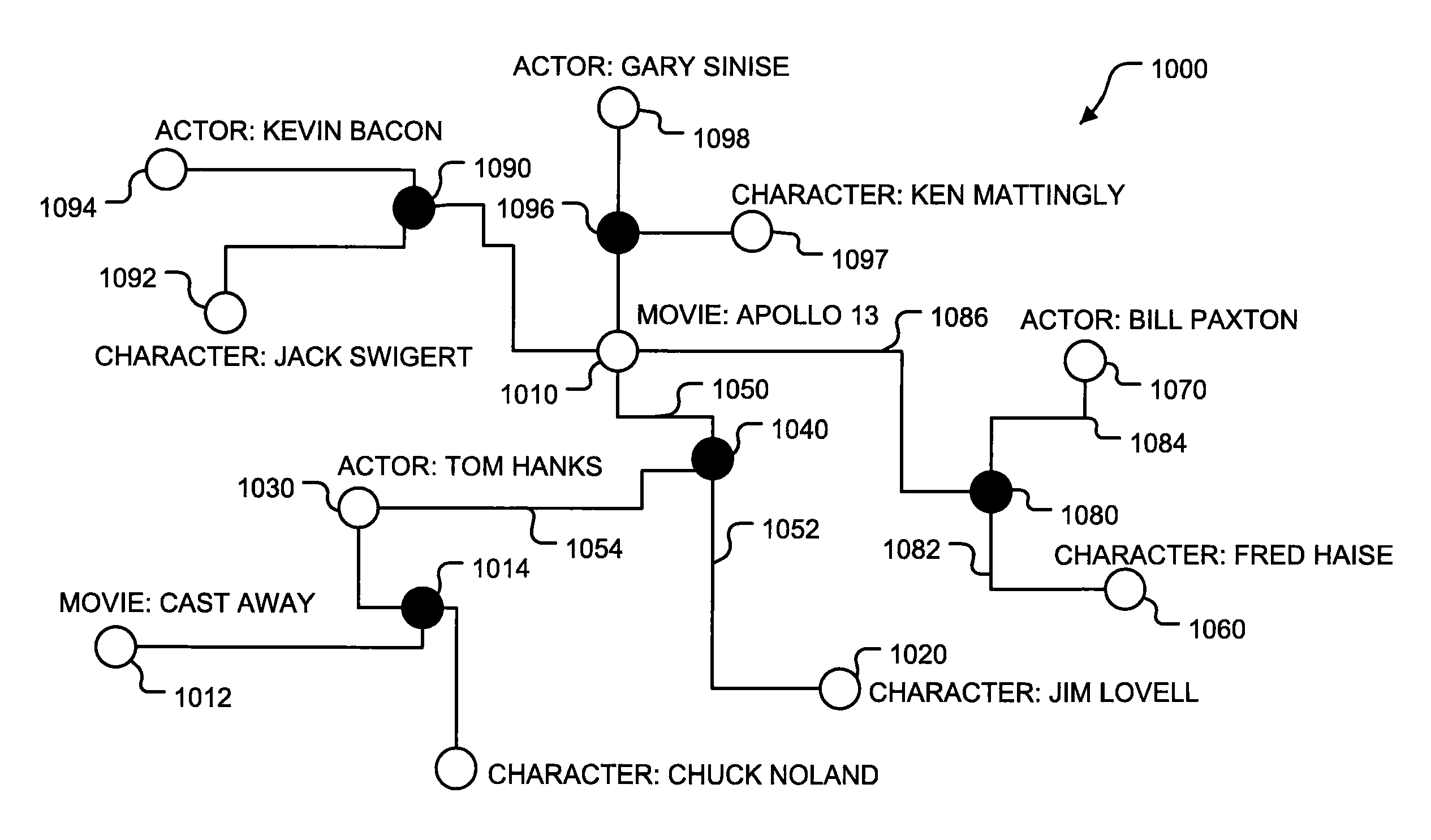
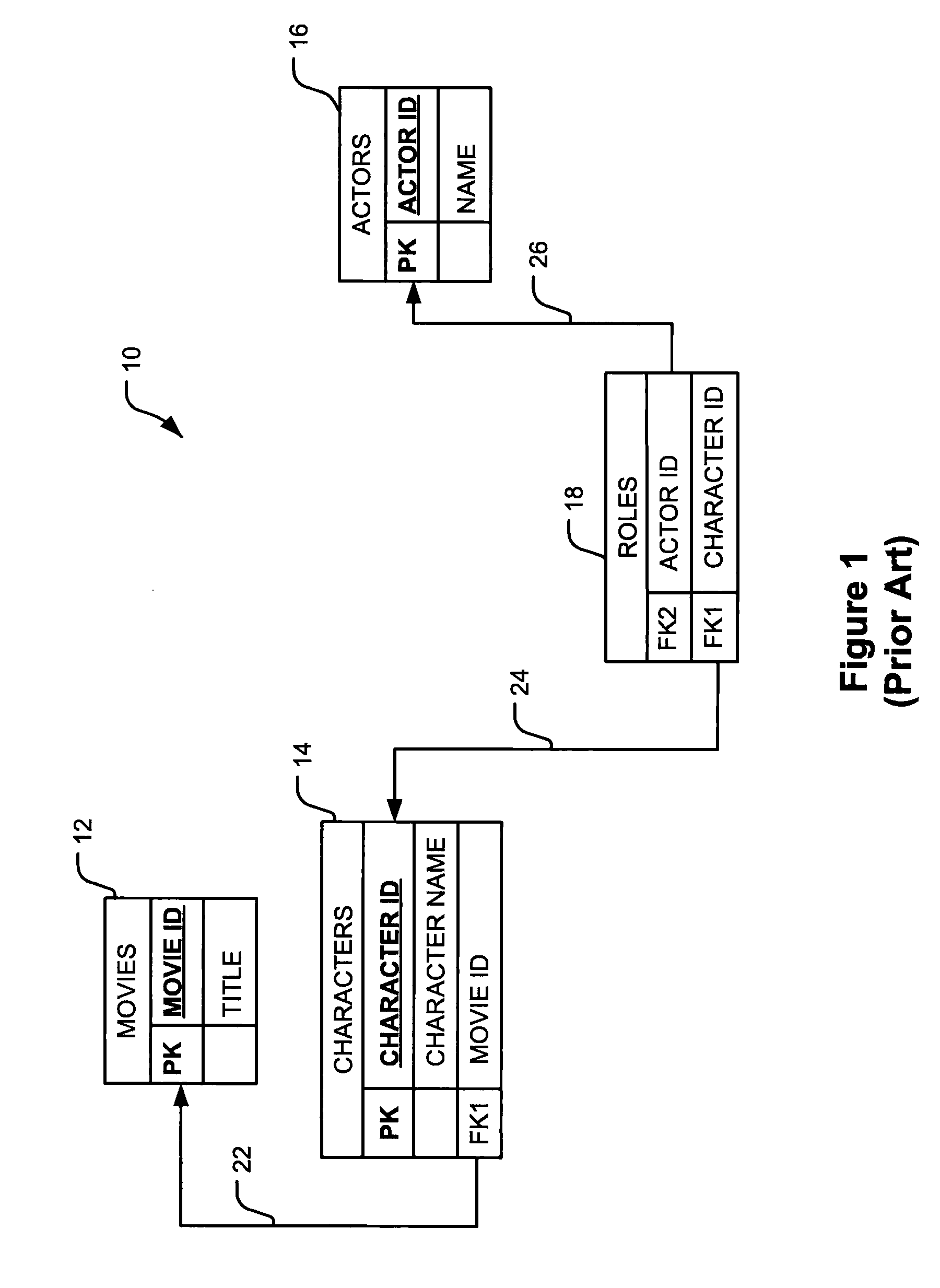
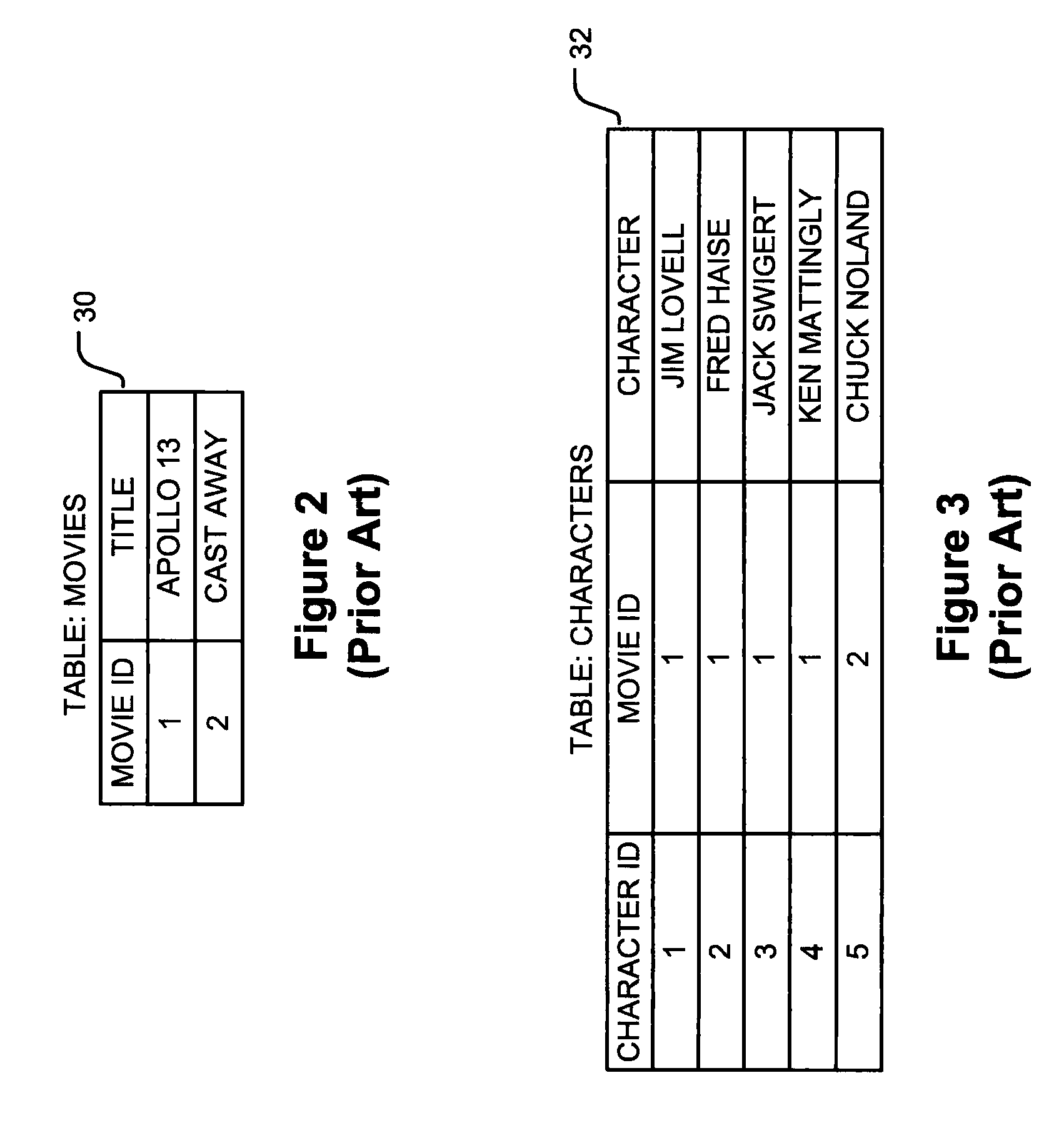
Database system and related method
A database system storing a data structure. The data structure includes a plurality of data nodes that each store a type and a value. None of the data nodes are linked directly to one another. The data structure also includes a plurality of context nodes that are each linked to at least two data nodes. The context nodes do not store data. Instead, each of the context nodes indicates a relationship exits between the data nodes connected to it.
Owner:APPLIED TECHN SYST
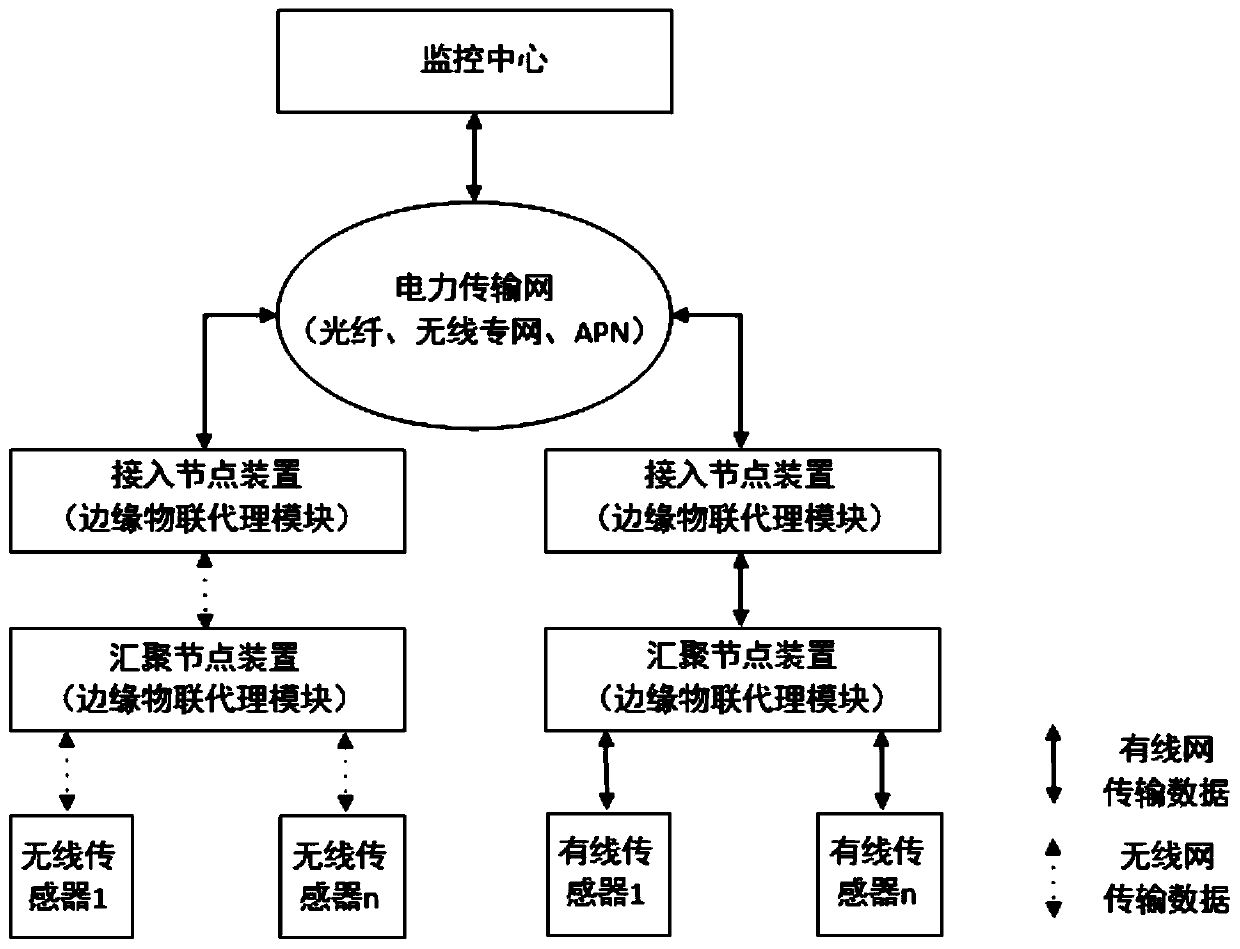
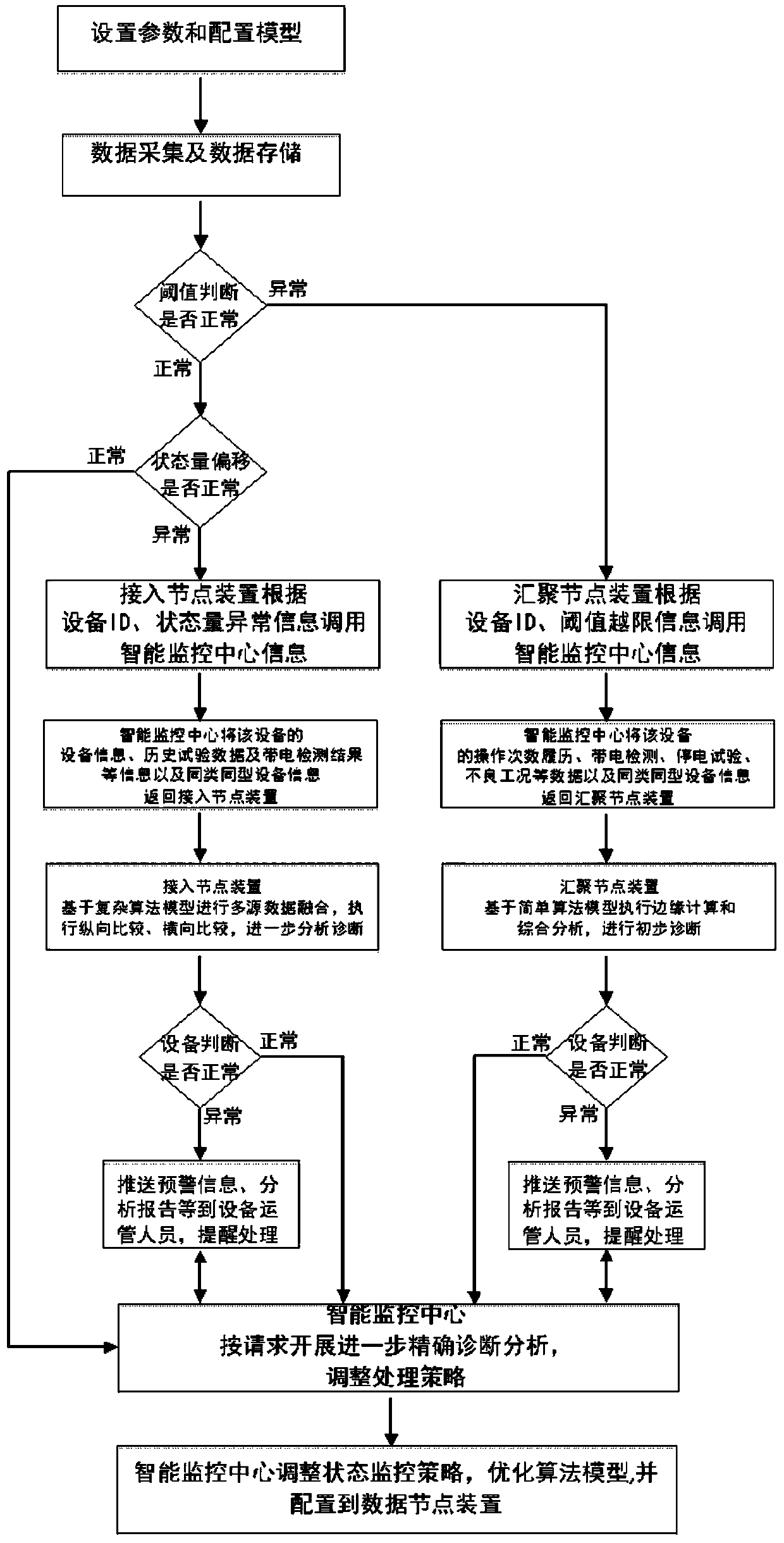
GIS device state intelligent monitoring system and method based on edge computing technology
ActiveCN110401262AImprove securityImprove efficiencyCircuit arrangementsData switching networksState parameterSmart surveillance
The invention relates to a GIS device state intelligent monitoring system and method based on the edge computing technology. The system includes a state sensor terminal, a data node device and an intelligent monitoring center, wherein the state sensor terminal is used for gathering collected state data to the data node device to perform power IoT edge calculation and is connected with the intelligent monitoring center through the transmission network, the condition monitoring sensor terminal is used for acquiring related state parameters in real time and receiving and performing limited edge calculation tasks, the data node device is used for collecting the data and receiving and performing the edge calculation tasks, and the intelligent monitoring center is used for performing equipment IoT management, intelligent evaluation analysis and advanced application for a GIS device state and configuring an optimized edge calculation algorithm model and an SG-CIM data model to the data node device. The system is advantaged in that a circuit breaker GIS equipment Internet of Things system of a substation is constructed, and the automation, informationization and intelligence level of equipment state evaluation and diagnosis can be improved.
Owner:BEIJING XJ ELECTRIC +1
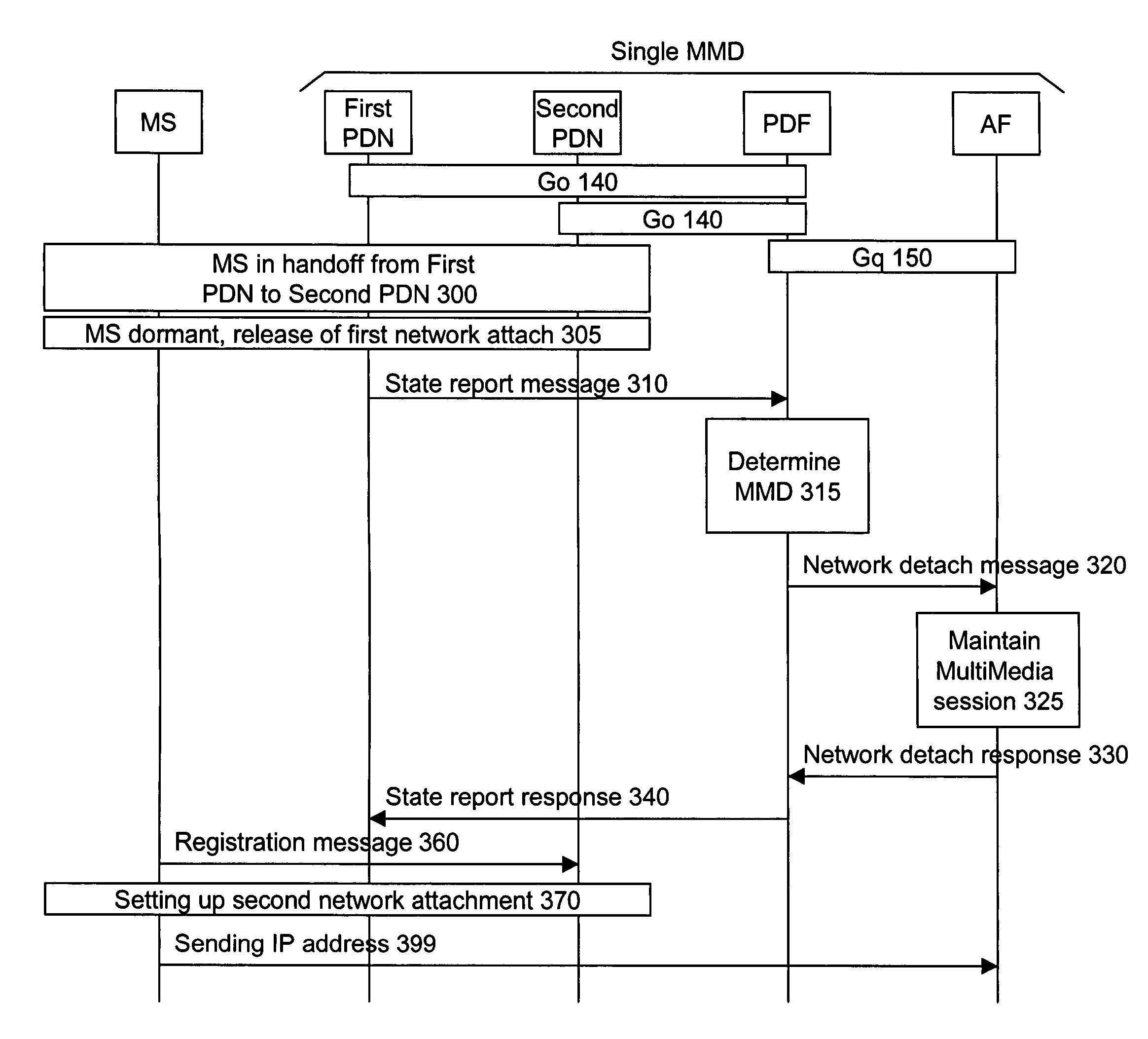
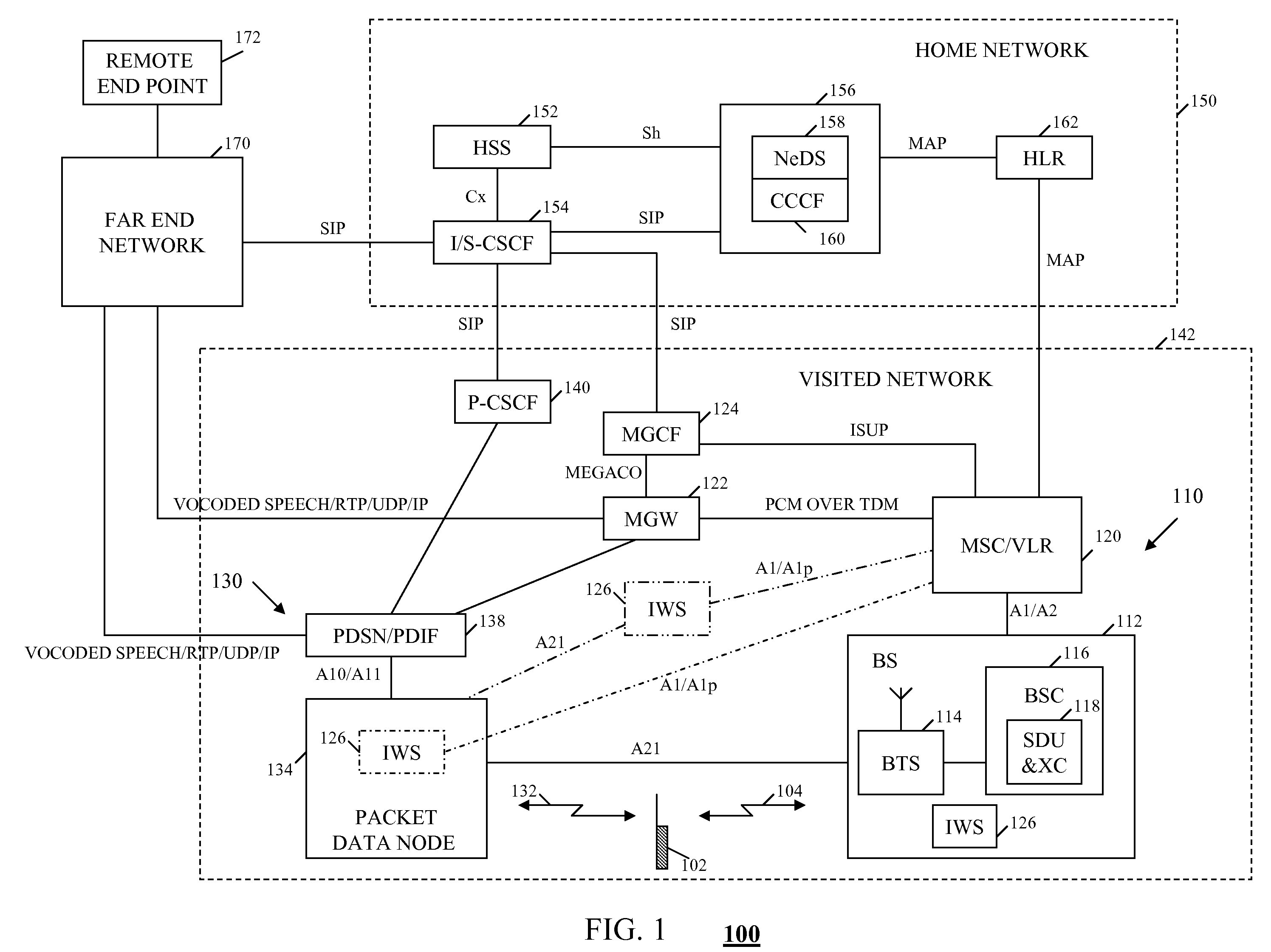
Seamless handoff for multimedia services
A method and Policy Decision Function node are provided for maintaining a multimedia session in an alive state for a mobile station following a release of a network attachment resulting from a handoff from a first Packet Data Node to a second Packet Data Node followed by a dormancy state of the mobile station. If both Packet Data Nodes are comprised into a same MultiMedia Domain, the Policy Decision Function informs an Application Function of the MultiMedia Domain that the multimedia session shall be maintained. Otherwise, if the two Packet Data Nodes are comprised into distinct MultiMedia Domains, a first Policy Decision Function, in addition to informing a first Application Function that the multimedia session shall be maintained, also fetches a context of the multimedia session. Further, the first Policy Decision Function transfers the context of the multimedia session to the first Packet Data Node, which in turn sends the context of the multimedia session to the second Packet Data Node. Subsequent to reactivation of the mobile station, a second Policy Decision Function transfers the context of the multimedia session from the second Packet Data Node to a second Application Function in a second MultiMedia Domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
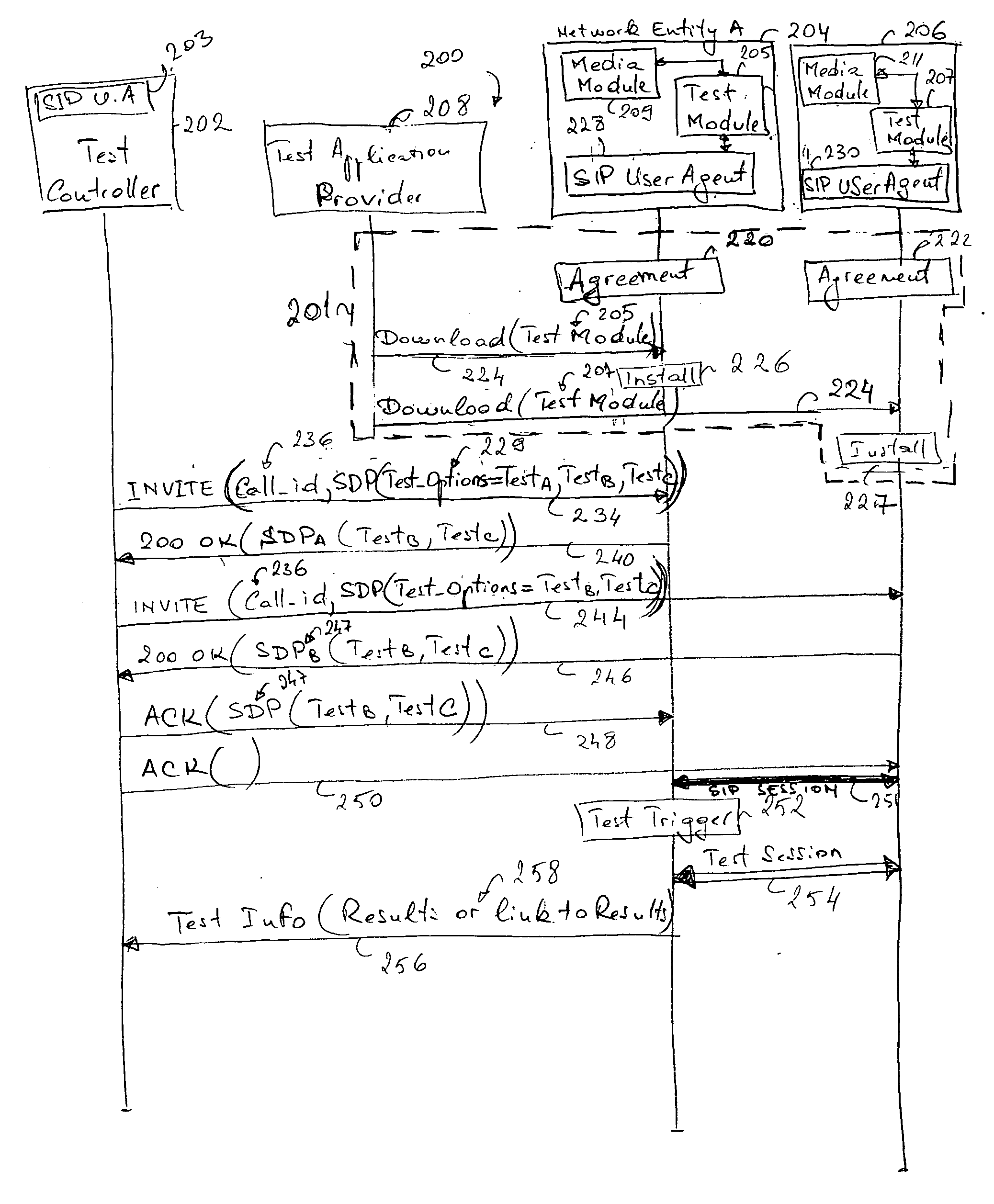
Method and network entity for session initiation protocol (SIP) based network traffic measurements
InactiveUS20060031522A1Multiple digital computer combinationsData switching networksComputer hardwareSession Initiation Protocol
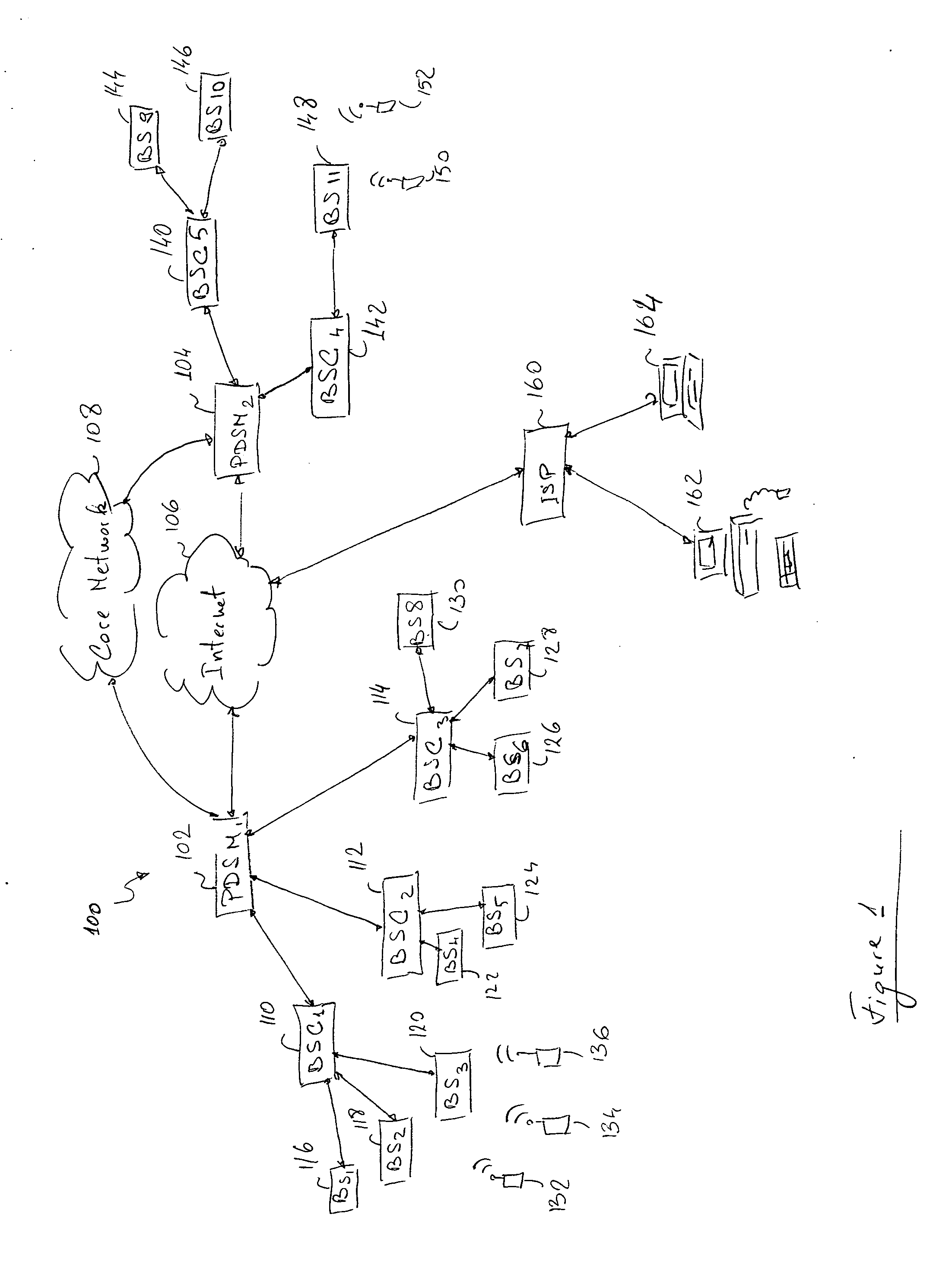
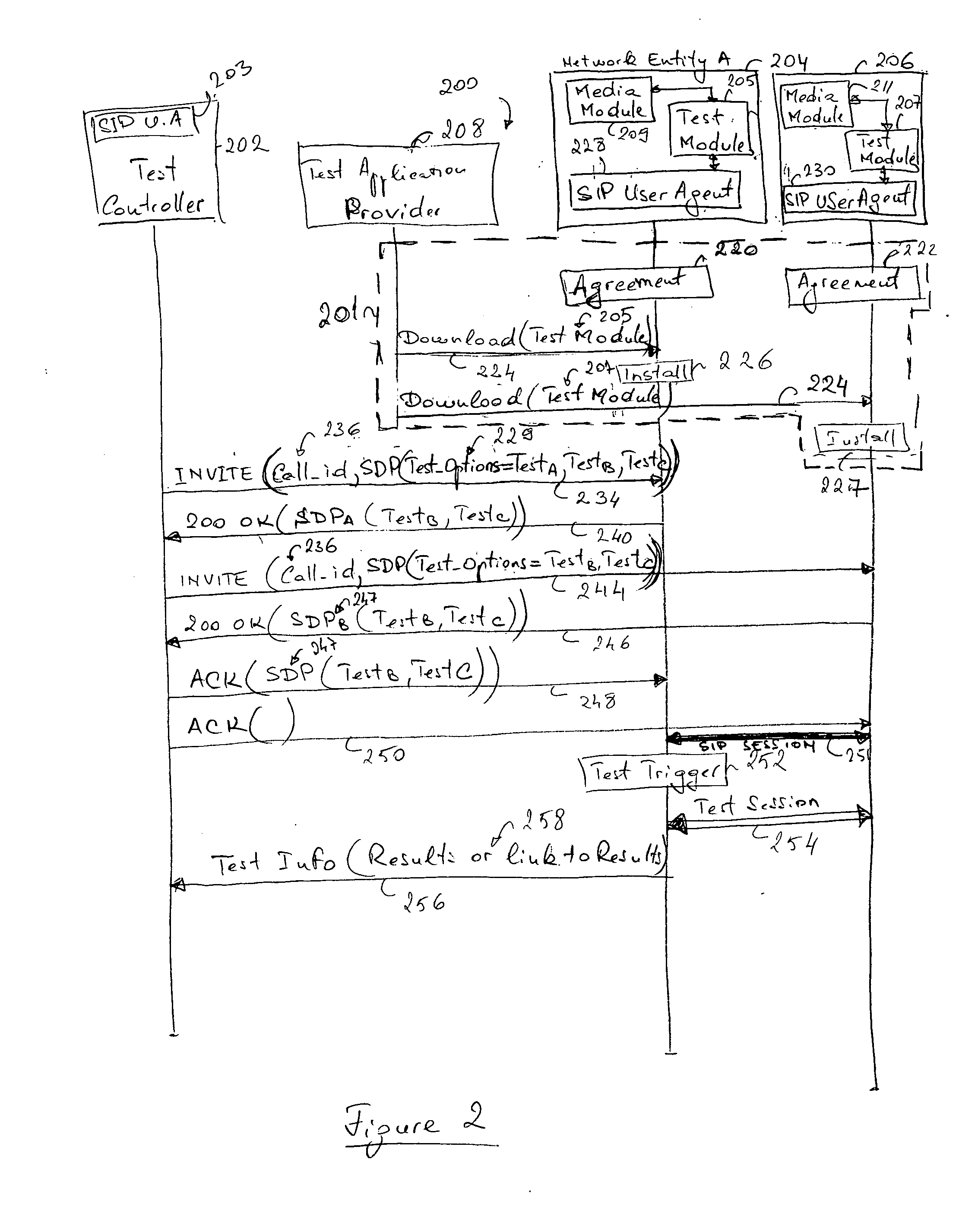
A method, network entity and test controller for establishing a Session Initiation Protocol (SIP) session between a plurality of SIP-based network entities and performing test measurements over the SIP session. The test controller instructs the network entities to establish the SIP session and specifies which test measurements are to be performed. The SIP session is established between the network entities, the test measurements are carried out, and the results are reported back to the test controller by at least one of the network entities, which may be terminals or packet data nodes such as a CDMA2000 Packet data Switched Node (PDSN) or Base Station Controller (BSC). The network entities may comprise SIP user agents and test modules in the forms of software and / or hardware.
Owner:TELEFON AB LM ERICSSON (PUBL)
Streaming XPath algorithm for XPath expressions with predicates
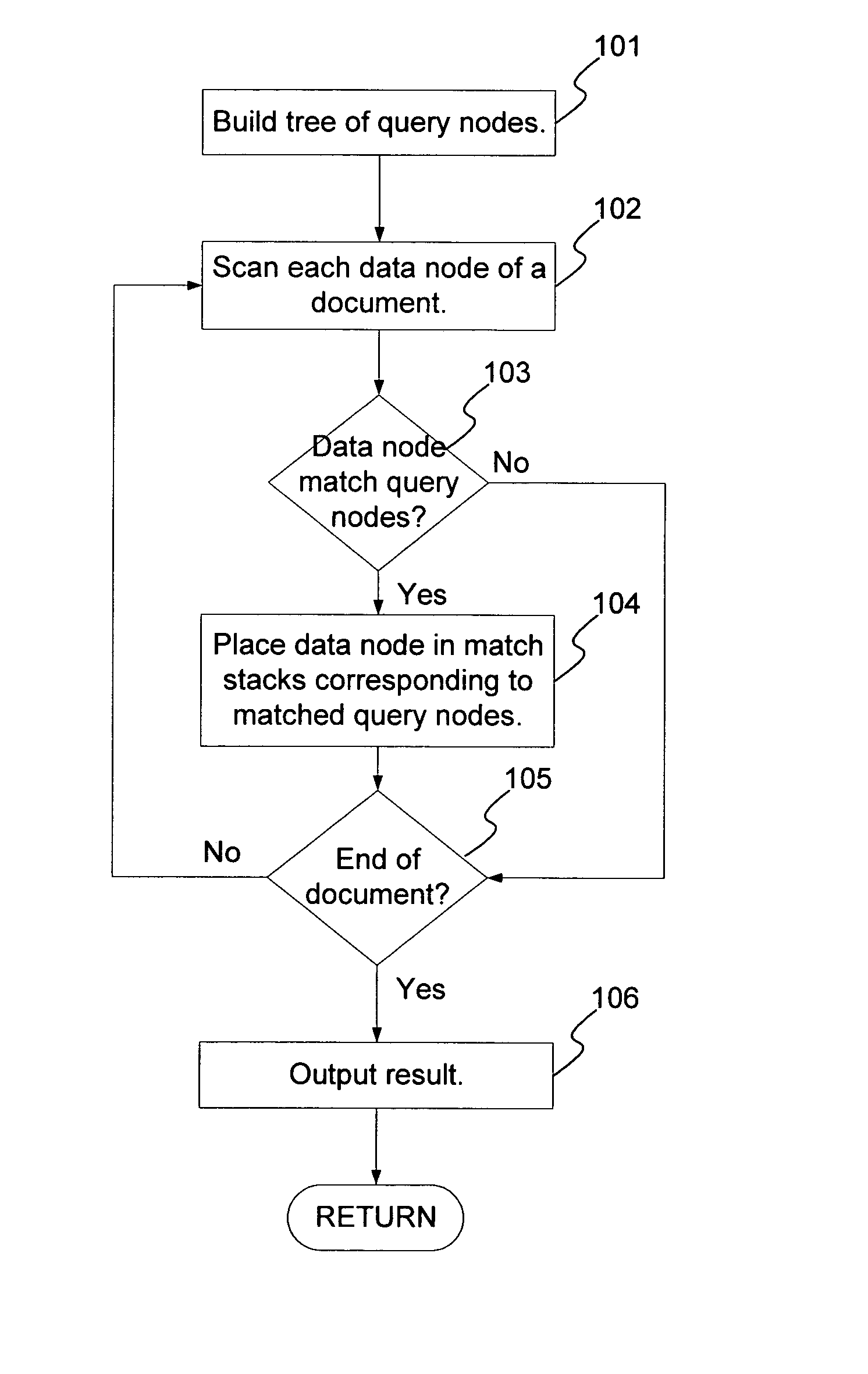
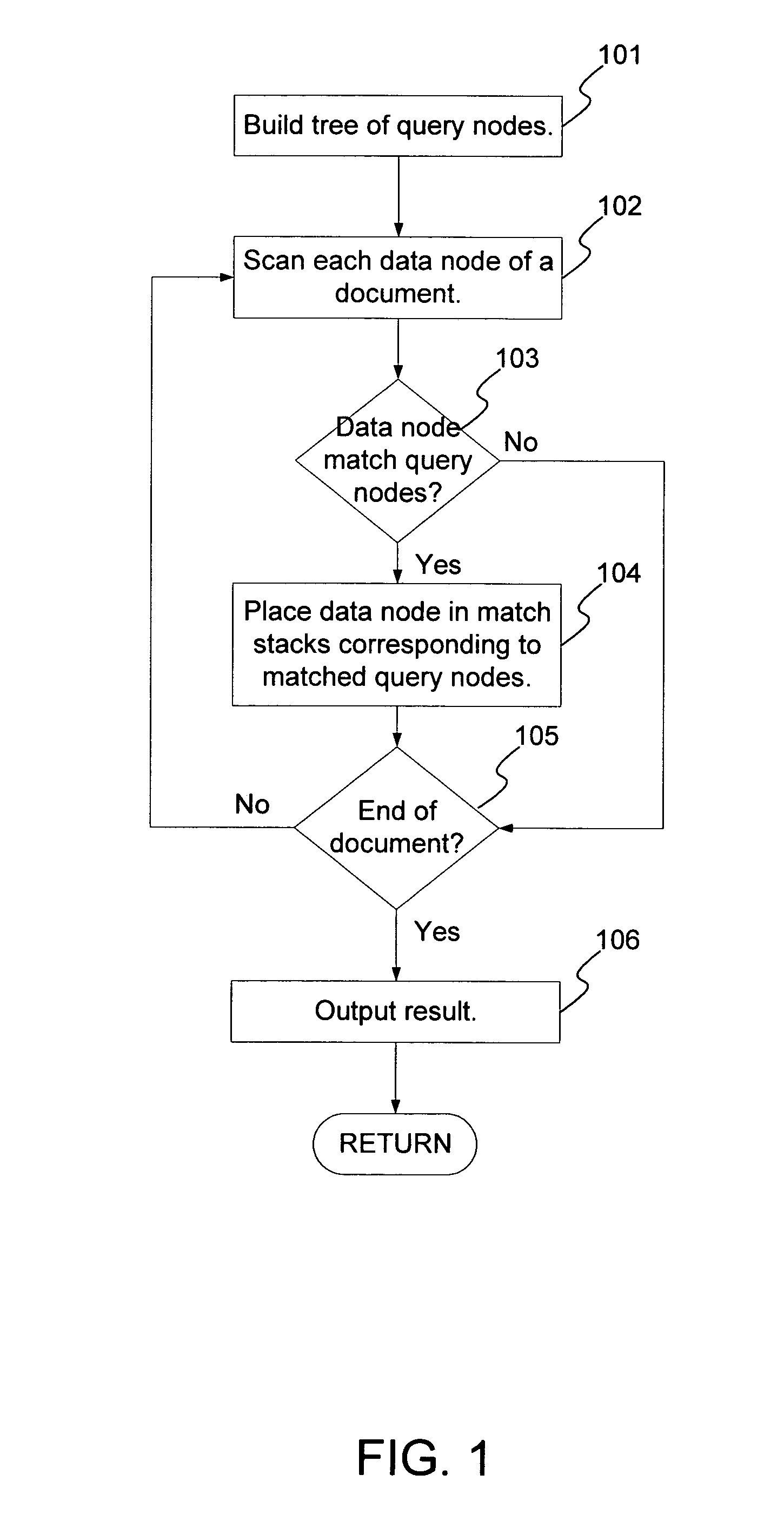
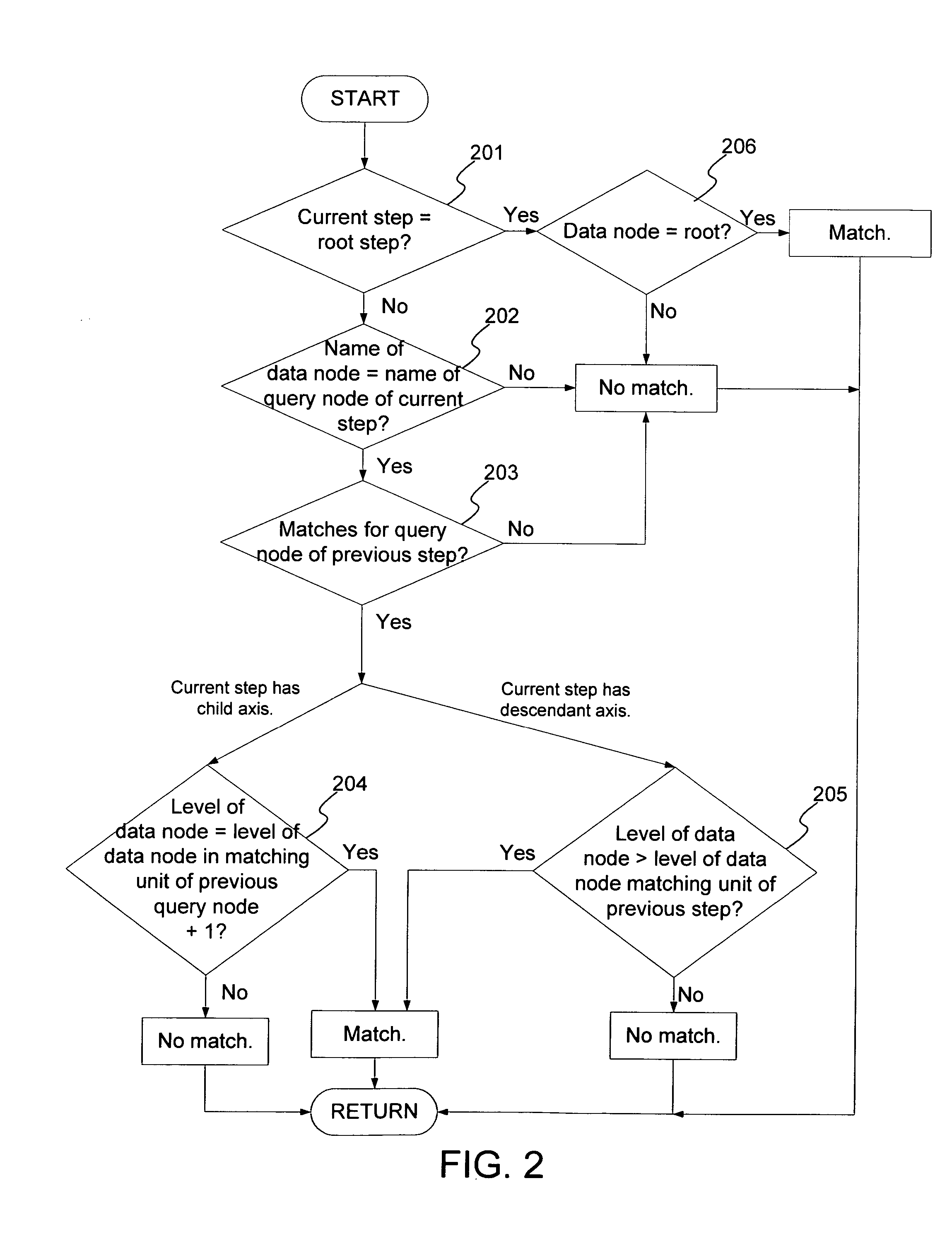
InactiveUS20070198479A1Digital data information retrievalSpecial data processing applicationsPaper documentData node
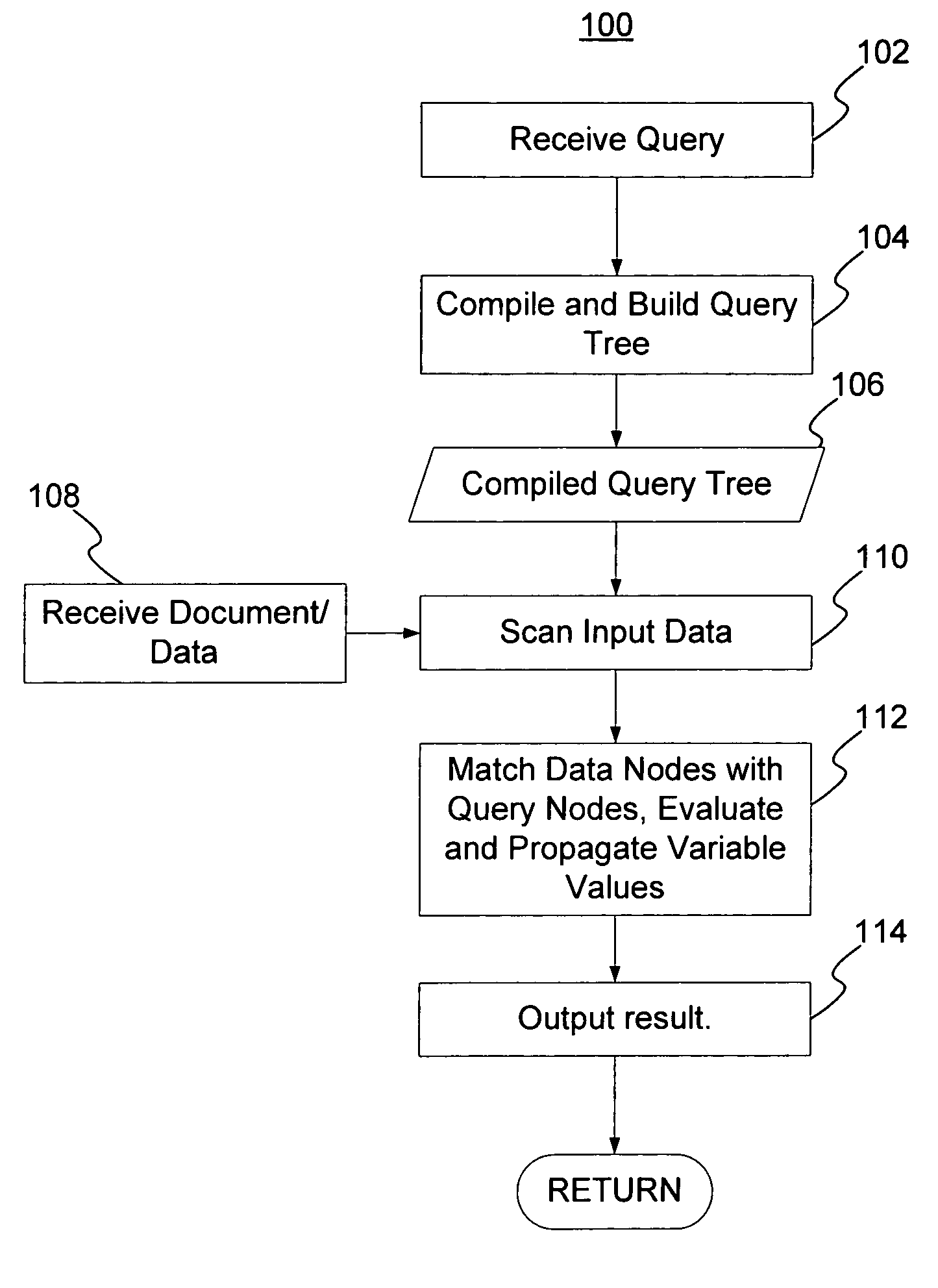
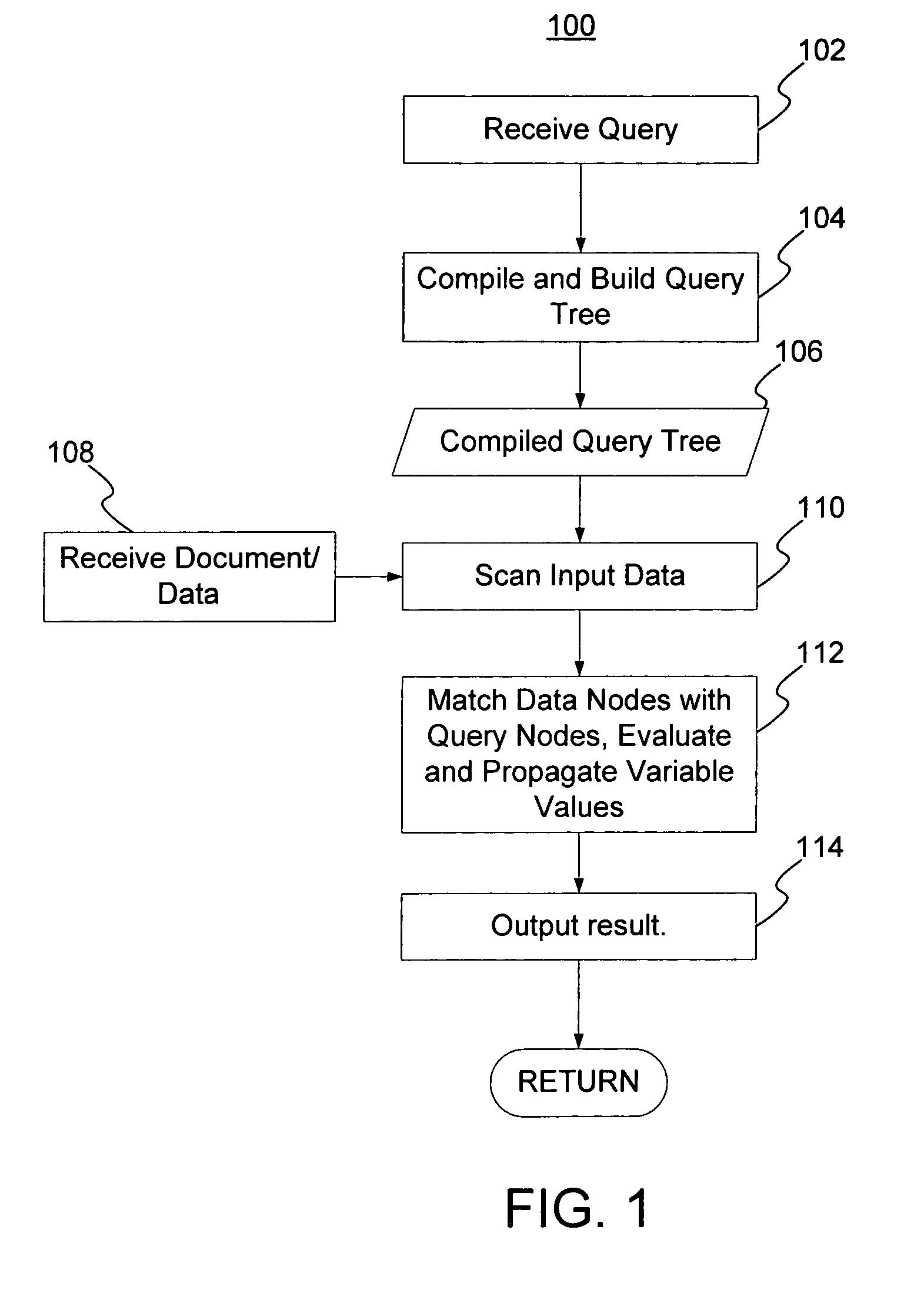
A method and system for evaluating a path query are disclosed. The path query corresponds to a query tree including a plurality of query nodes. At least one query node corresponds to at least one predicate and is at a level. The predicate(s) are evaluated for previous query node(s). The method and system include scanning data nodes of a document and determining if the data nodes match the query nodes. The method and system also include placing data related to the data node in match stacks corresponding to matched query nodes. The data for the query node(s) include attribute(s) corresponding to the predicate(s). The method and system further include propagating a matching of the at least one query node backward to a matching of the at least one previous query node.
Owner:IBM CORP
Cloud data storage system
InactiveUS20130151884A1Low costDigital data information retrievalSpecial data processing applicationsData accessData node
A cloud data storage system is provided for multiple clients to access data of files comprising at least one node connecting to a first storage means; at least one namenode module for processing file operations issued from the clients, namenode module issuing data access instructions to access and maintain the metadata on the first storage means; at least one datanode module respectively executing on at least one node, each datanode module functioning to scan and access a second storage means connected thereto; at least one data import module selectively executing on nodes in which datanode module are executing, the data import module scanning a second storage means newly connected to the cloud data storage system and obtaining a corresponding metadata, and executing data migration operation for the data in second storage means without actual physical uploading operation.
Owner:PROMISE TECHNOLOGY
Method and system for intertechnology handoff of a hybrid access terminal
ActiveUS20070280264A1Data switching by path configurationWireless network protocolsCommunications systemData node
A communication system utilizes an interface terminating at a base station (BS) of a circuit services network and a wireless packet data node in a packet data network and DOS over DBM signaling between the BS and an access terminal (AT), thereby permitting the communication system to tunnel SIP messaging between the AT and an IMS network via the BS and a packet data node and to tunnel HRPD traffic channel information and an HRPD identifier from the packet data network to the AT via the BS. Thus, a handoff of a voice call involving the AT may be initiated from the circuit services network to the paket data networking prior to the AT etablishing a call dialogue with the packet data network.
Owner:GOOGLE TECH HLDG LLC
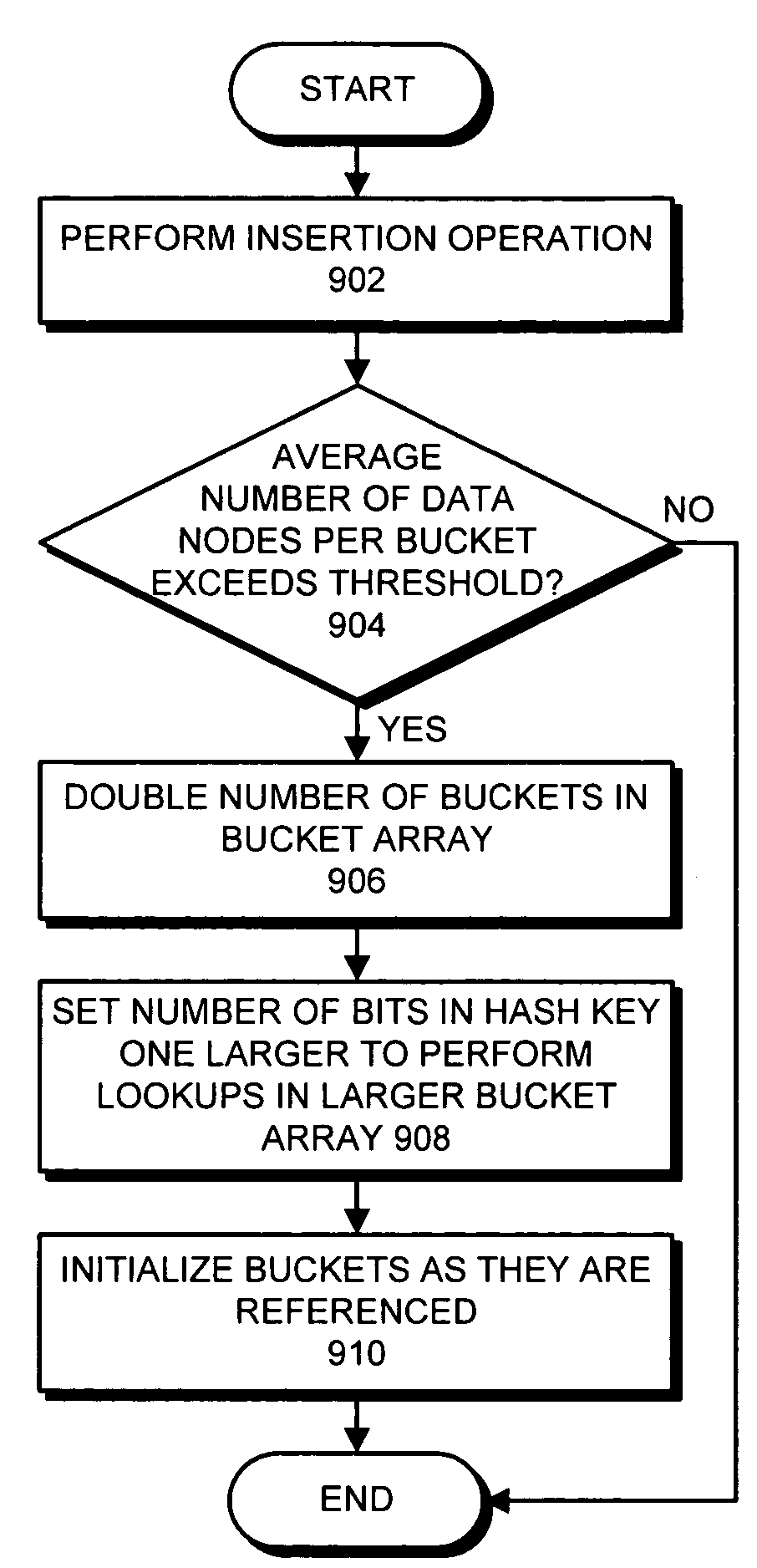
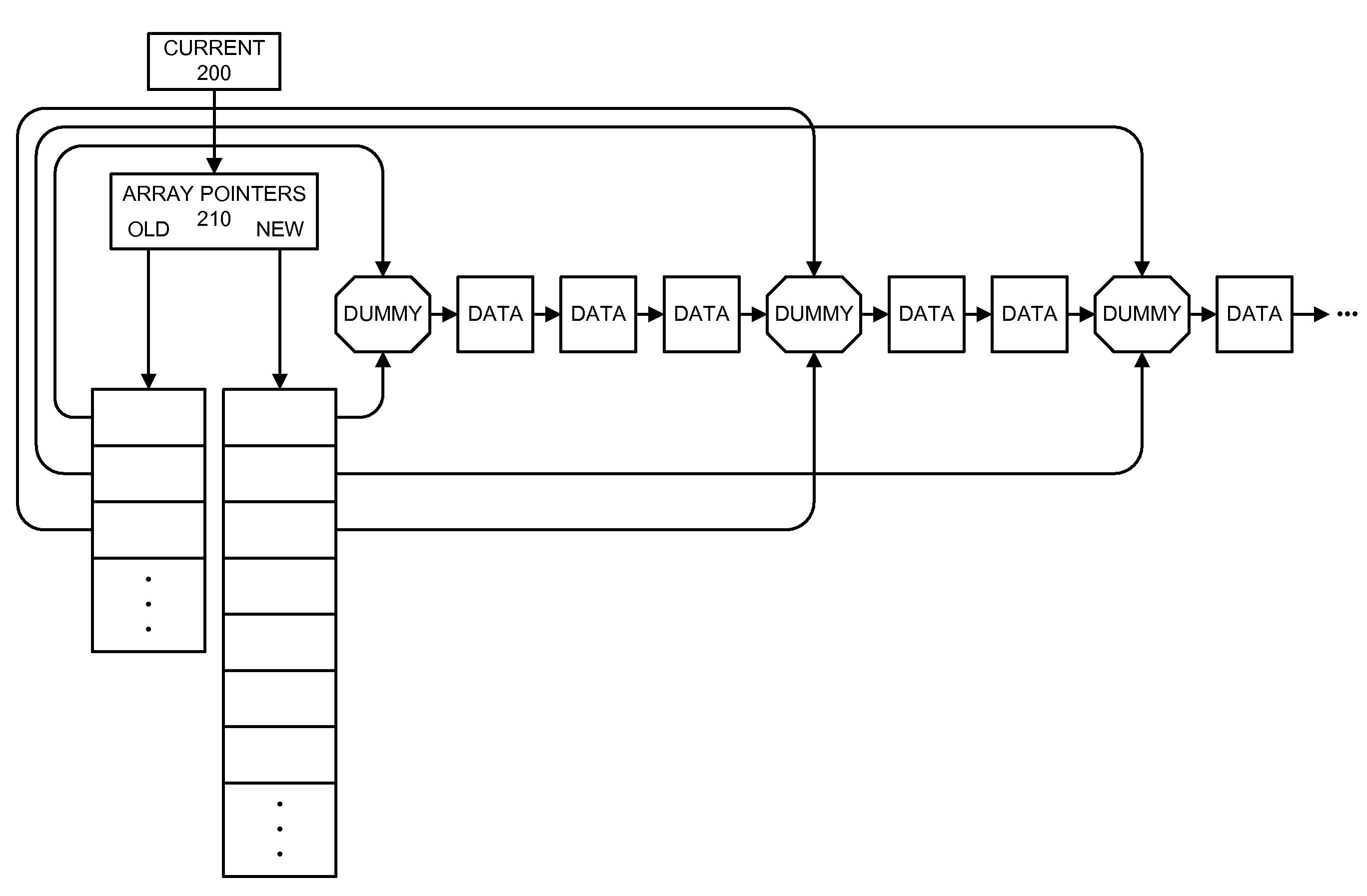
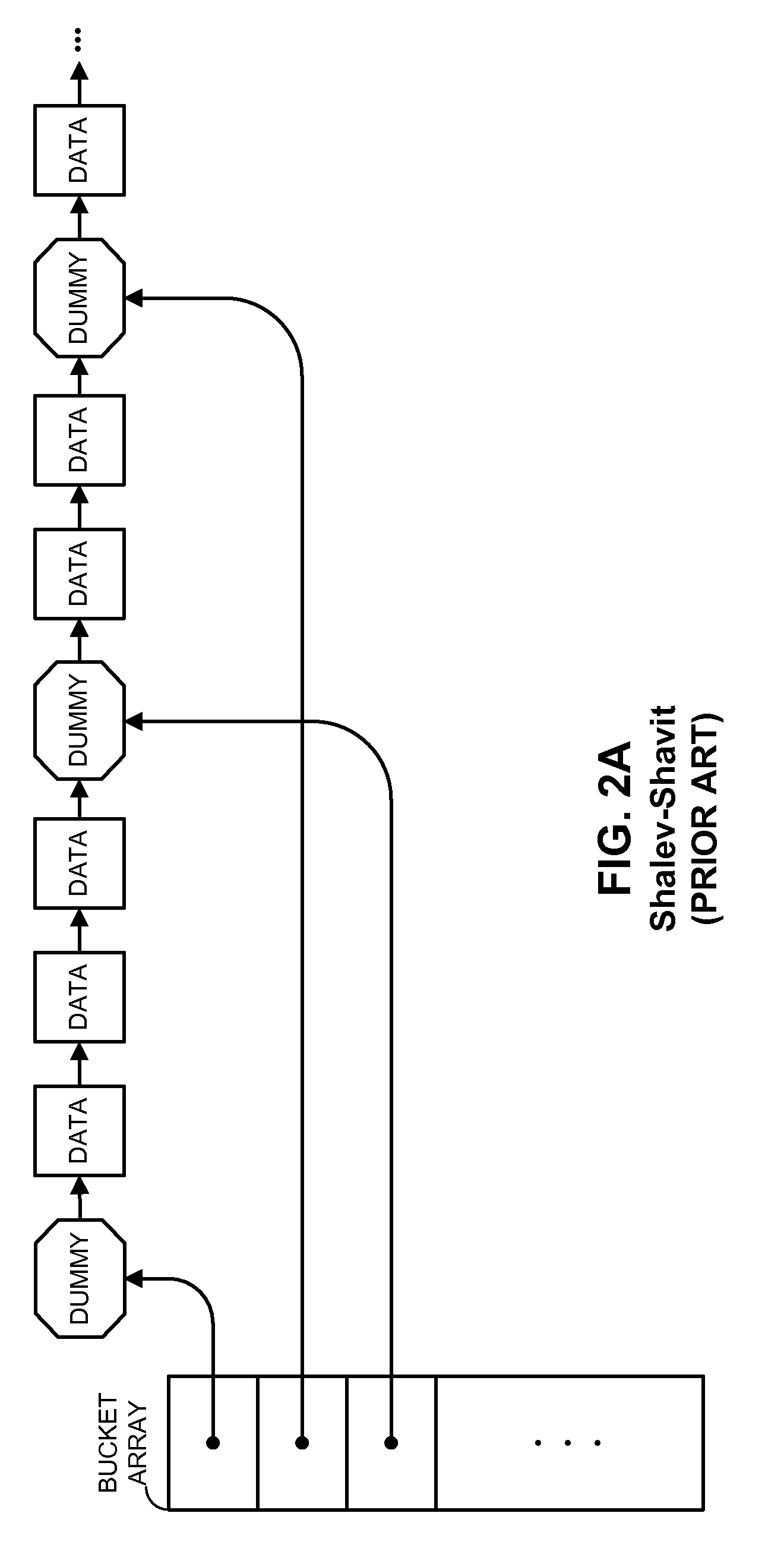
Method and apparatus for implementing a fully dynamic lock-free hash table
ActiveUS7287131B1Safely deletedData processing applicationsDigital data information retrievalTheoretical computer scienceData node
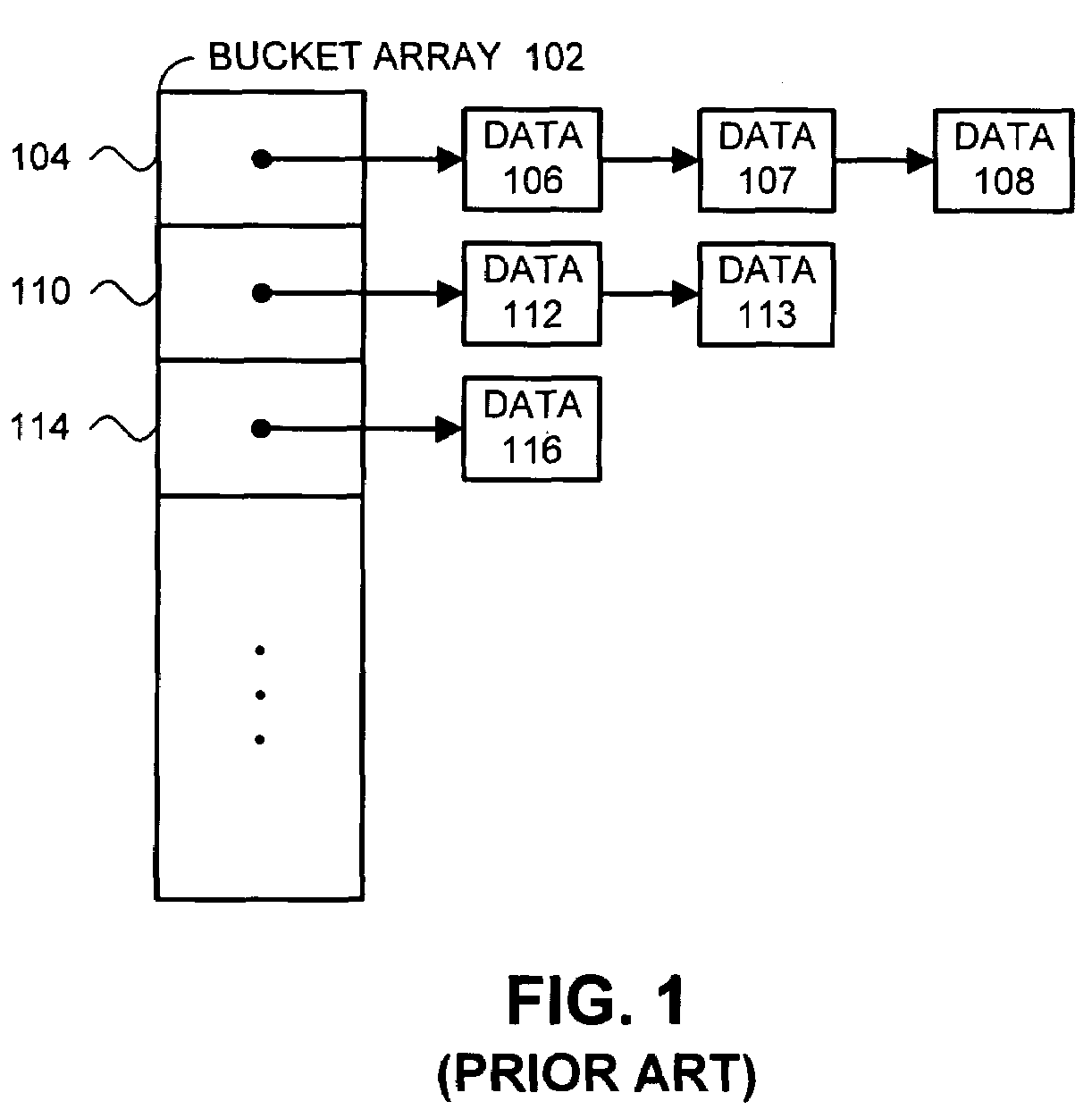
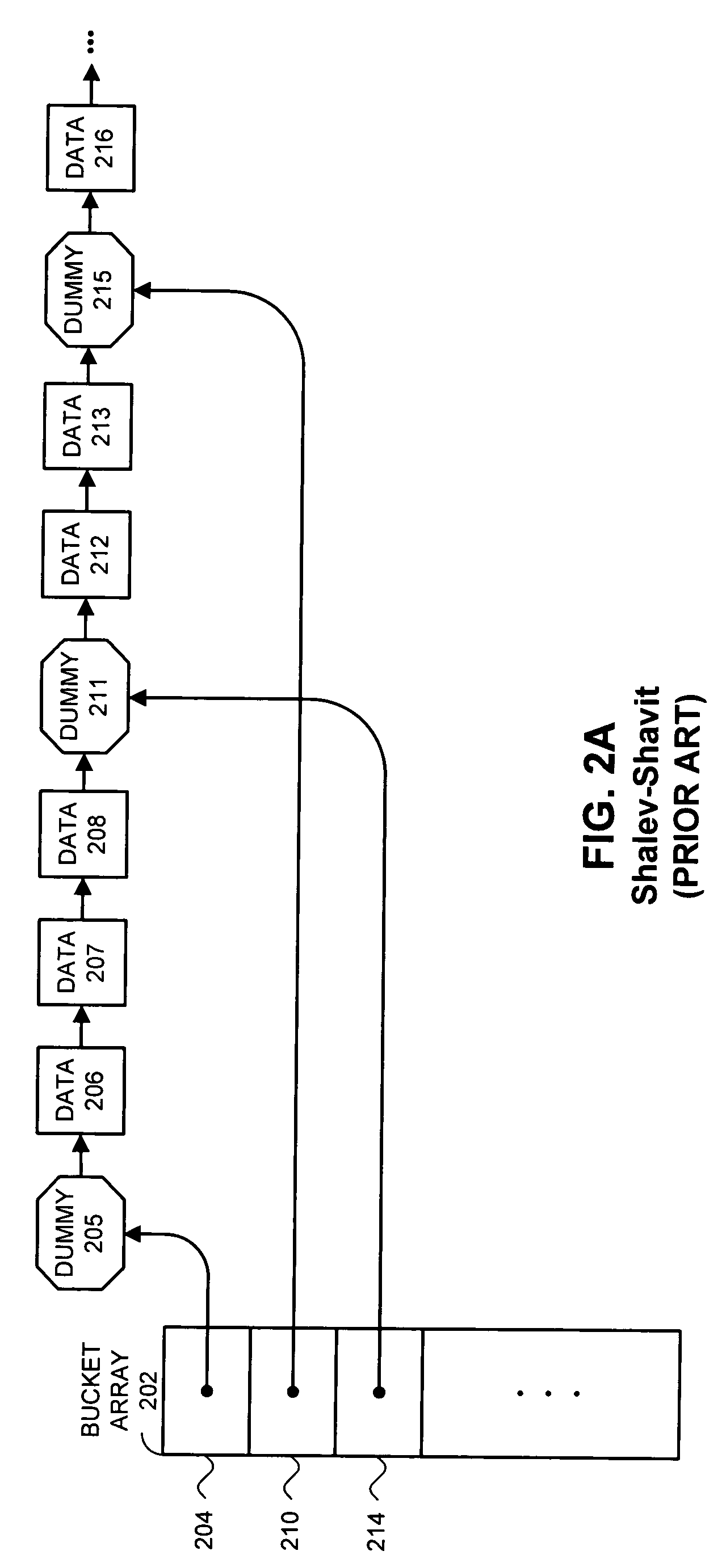
One embodiment of the present invention provides a system that implements a hash table that is fully dynamic and lock-free. During a lookup in the hash table the system first uses a hash key to lookup a bucket pointer in a bucket array. Next, the system follows the bucket pointer to a data node within a linked list that contains all of the data nodes in the hash table, wherein the linked list contains only data nodes and at most a constant number of dummy nodes. The system then searches from the data node through the linked list to locate a node that matches the hash key, if one exists.
Owner:ORACLE INT CORP
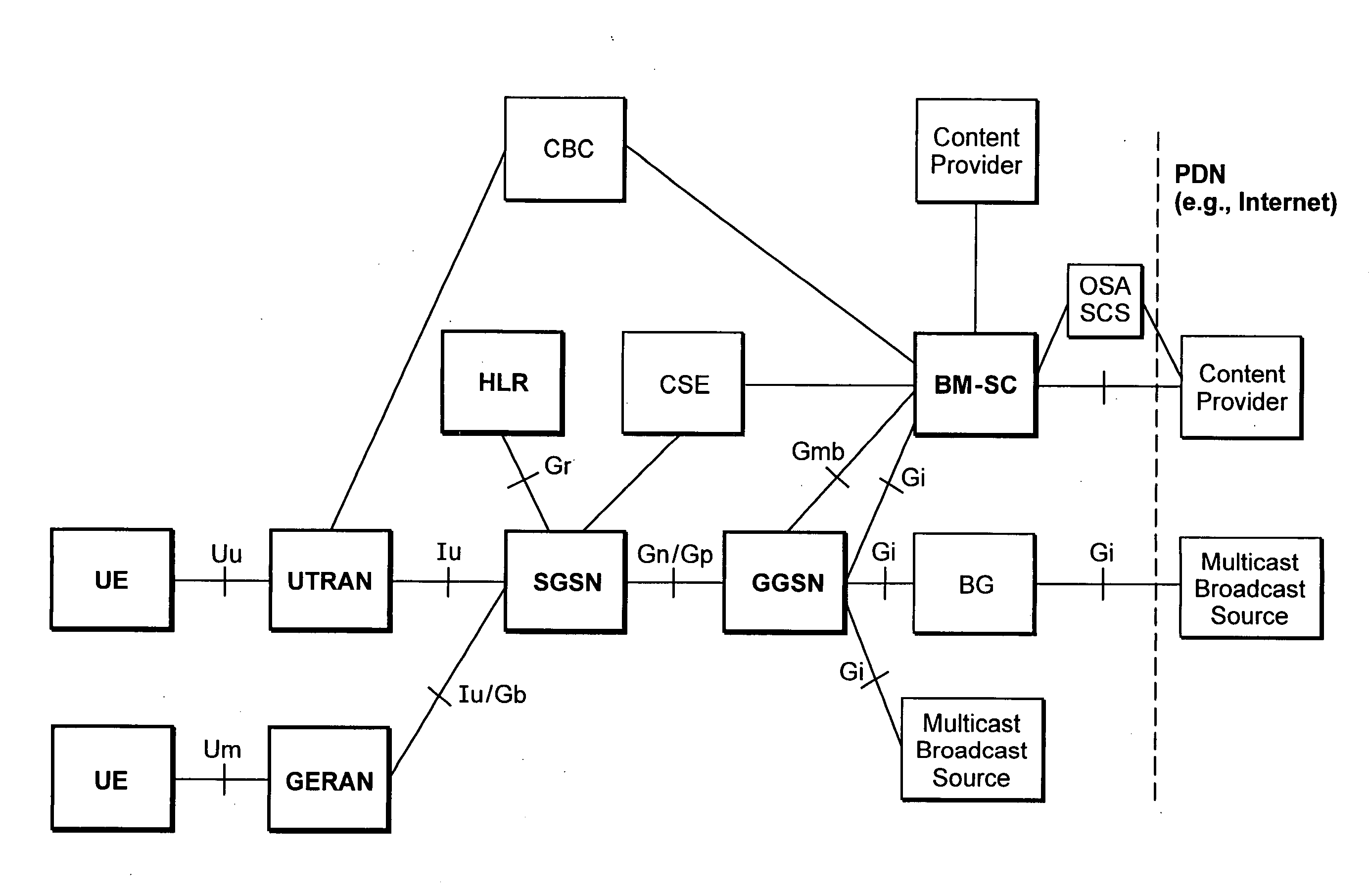
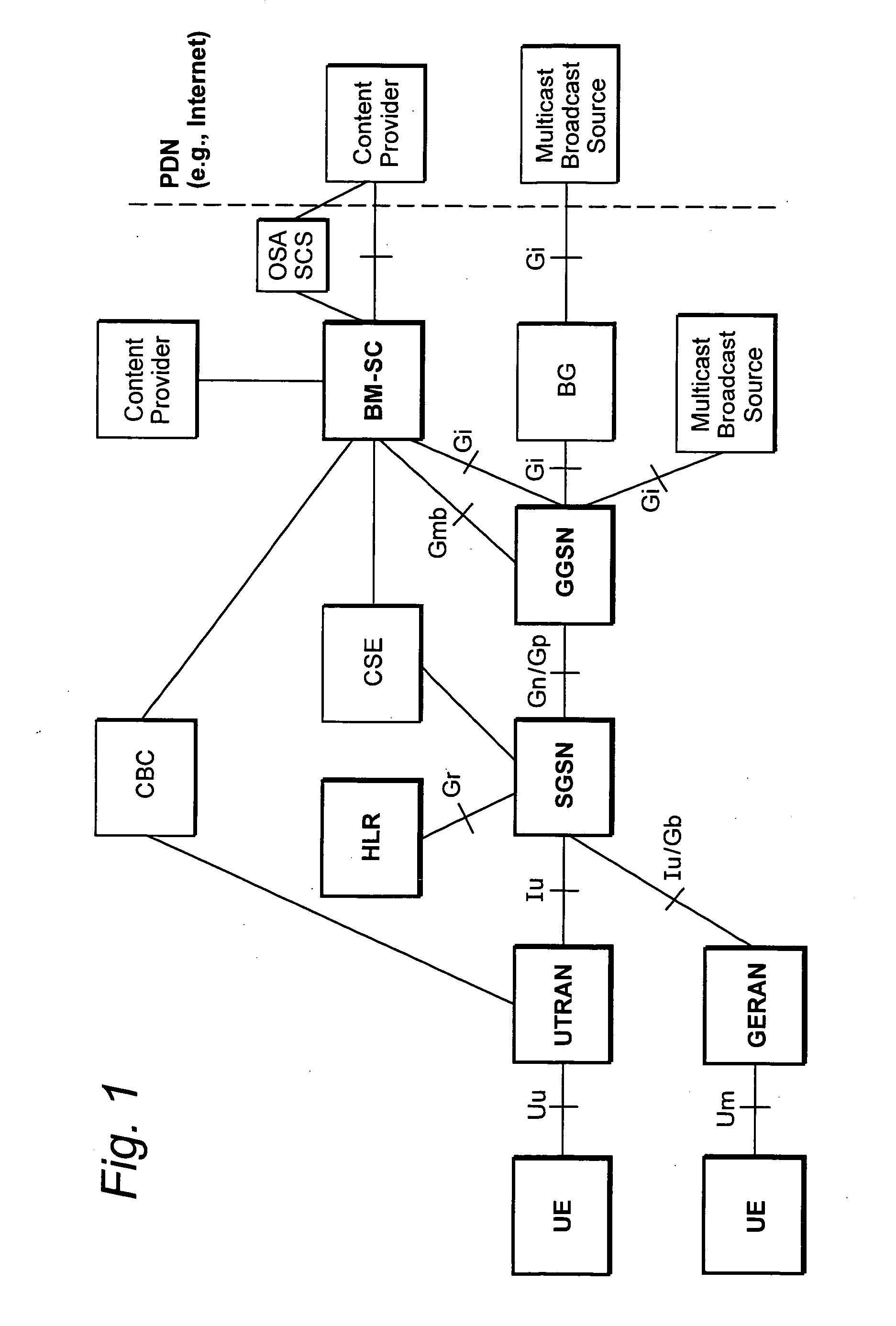
Resource utilization for multimedia broadcast multicast services (MBMS)
InactiveUS20060171369A1Network traffic/resource managementBroadcast specific applicationsData packResource utilization
A multimedia broadcast multicast type service (MBMS) is offered to mobile subscribers. A RAN node communicates with one or more radio base stations that transmit and receive information with mobile subscriber terminals, some of which subscribe to the MBMS. The RAN node communicates with multiple core network packet data nodes that receive MBMS data for delivery to the RAN node. One of the multiple core network packet data nodes is selected to provide the MBMS data associated with the MBMS to the RAN node. The others are instructed not to provide the MBMS data, but they still perform other MBMS support functions for their mobile terminals such as MBMS charging, etc.
Owner:TELEFON AB LM ERICSSON (PUBL)
Database system storing a data structure that includes data nodes connected by context nodes and related method
A database system storing a data structure. The data structure includes a plurality of data nodes that each store a type and a value. None of the data nodes are linked directly to one another. The data structure also includes a plurality of context nodes that are each linked to at least two data nodes. The context nodes do not store data. Instead, each of the context nodes indicates a relationship exits between the data nodes connected to it.
Owner:APPLIED TECHN SYST
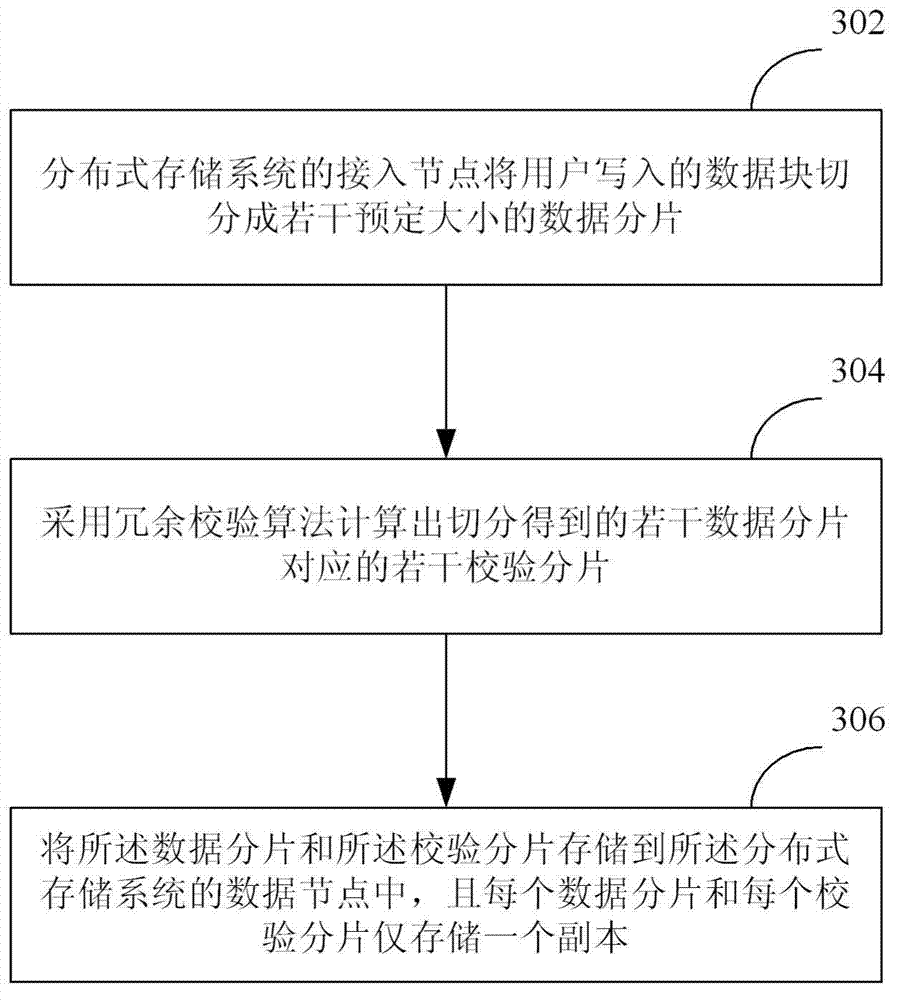
Data storage method, data storage equipment and distributed storage system
InactiveCN103699494AGuaranteed reliabilityReduce the proportionMemory adressing/allocation/relocationRedundant data error correctionData nodeData reliability
The invention discloses a data storage method, data storage equipment and a distributed storage system. The method, the equipment and the system belong to the technical field of computers. The data storage method comprises the steps that access nodes of the distributed storage system cut a data block which is written in by a user into a plurality of data fragments with preset sizes; a plurality of check fragments corresponding to the data fragments which are obtained by cutting are calculated through a redundancy check algorithm; the data fragments and the check fragments are stored into the data nodes of the distributed storage system, and each data fragment and each check fragment only store one copy. According to the data storage method, the data storage equipment and the distributed storage system, the proportion of redundant data can be reduced on the premise of ensuring data reliability, so as to save the storage space.
Owner:BEIJING QIHOO TECH CO LTD +1
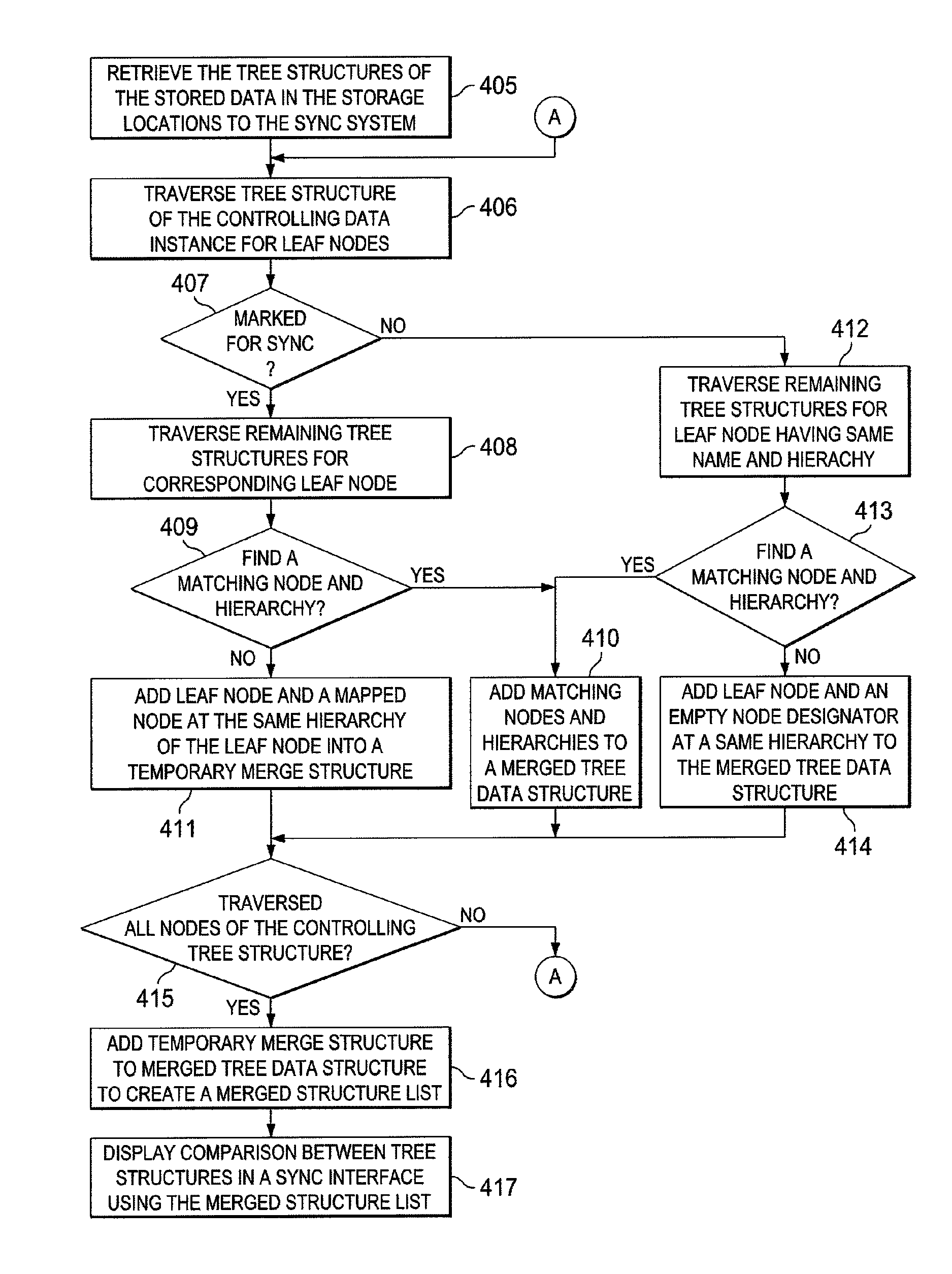
Synchronizing multiple hierarchal data structures
ActiveUS8301994B1Database distribution/replicationSpecial data processing applicationsData nodeData mining
Synchronization between multiple data repositories is described which retrieves tree structures that represent the hierarchical organization of the data repositories that will be or are synchronized. One of tree structures is parsed for data nodes, while the other tree structures are parsed for each such data node to find matching data nodes having corresponding hierarchies. Moved nodes are identified when a matching node is found that does not have the same hierarchy in its tree structure. Similarly, deleted nodes are identified when a node is found with no match in a controlling tree structure. Data structure lists are compiled noting matching relationships and hierarchies and also noting moved and deleted nodes and their relationships with the rest of the formerly corresponding nodes. Using these data structure lists, a synchronization interface is generated for display to a user that visually compares the synchronization of the multiple data repositories.
Owner:ADOBE INC
System and method for generating a lock-free dual queue
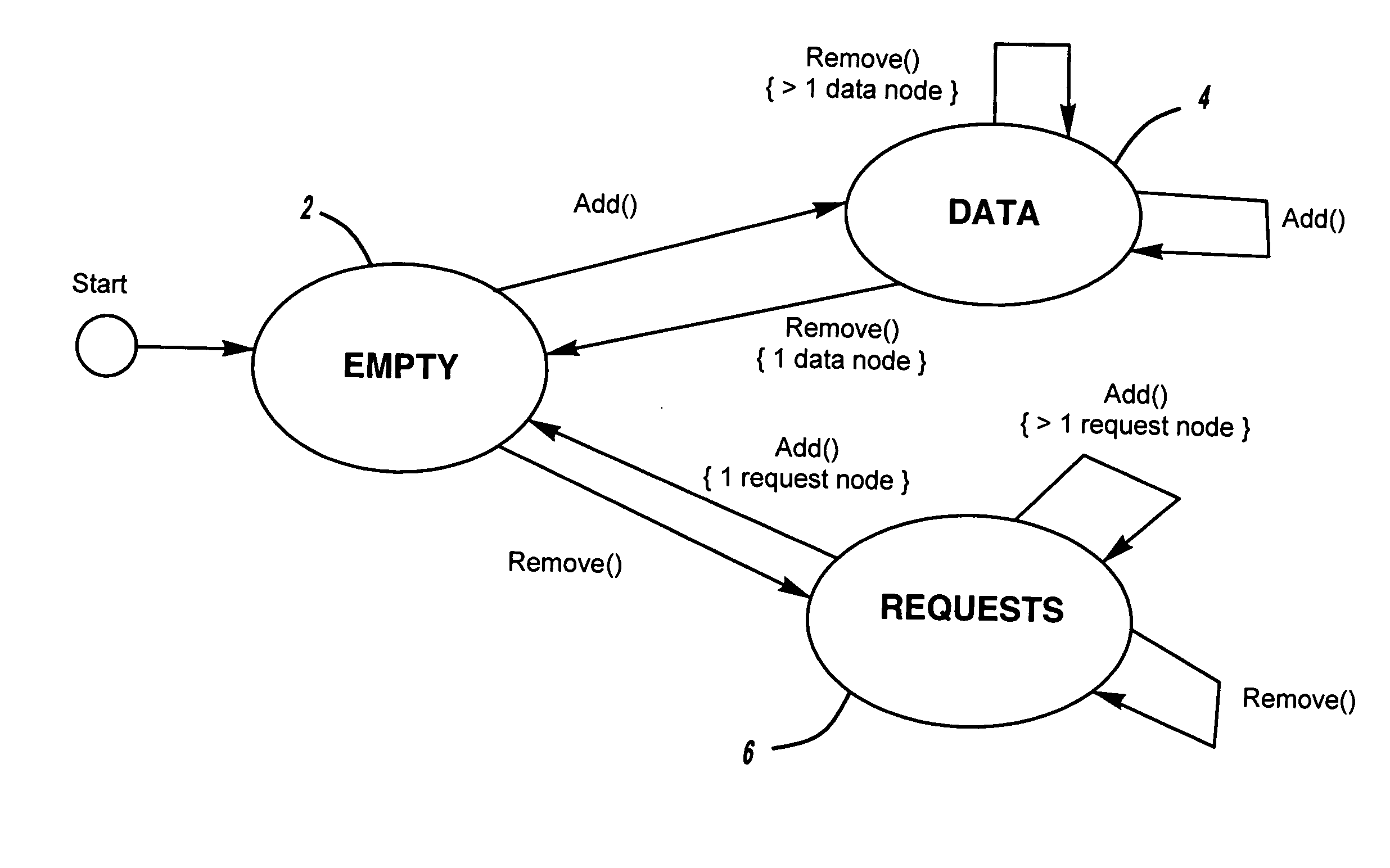
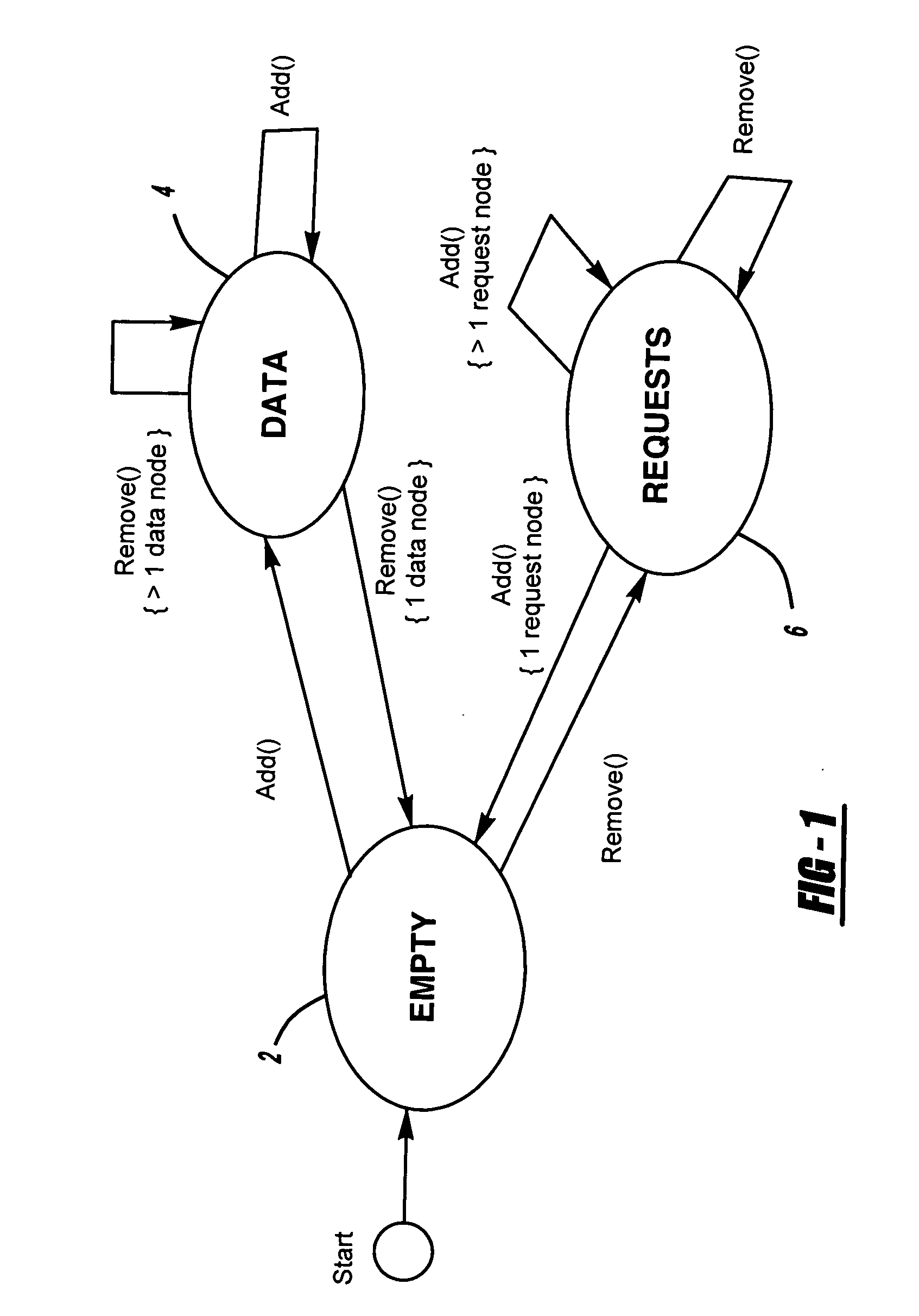
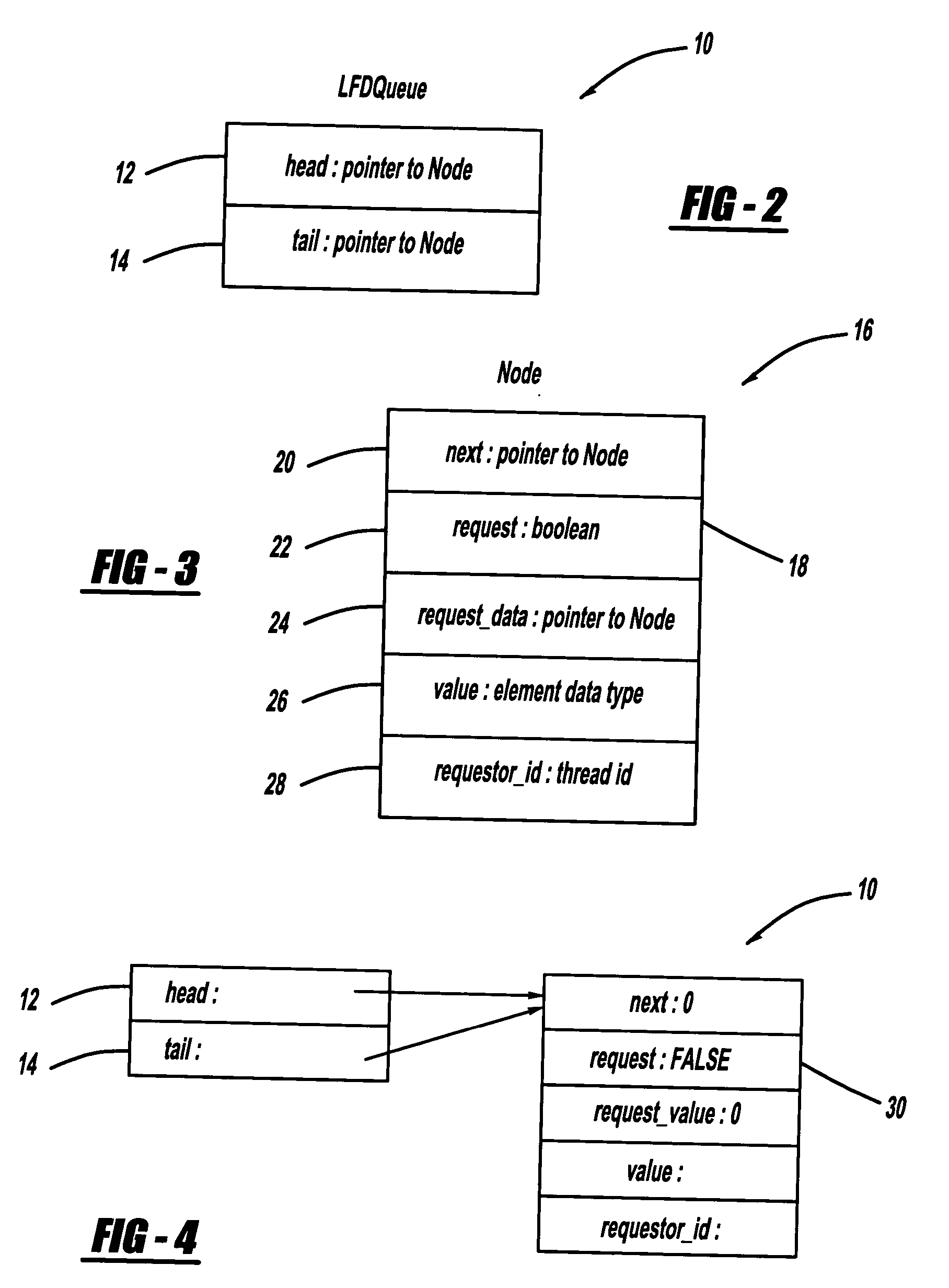
ActiveUS20070157200A1Eliminating contention costEliminating exclusive accessProgram synchronisationMemory systemsData nodeWaiting time
A method of supporting condition synchronization for a shared data structure so as to provide concurrent access. A protocol is provided between a thread creating a request as part of a remove operation and a thread fulfilling a request as part of an add operation. The protocol provides for the thread making such a request to check the request_value field of the request node and then wait on its own condition variable. A requesting thread sets a requestor_id field of a request node with a value that identifies the thread. A fulfilling thread sets a request_value field of a request node with the address of the data node with the value, and then signals the requesting thread as identified by the requestor_id field. Upon receiving the signal, the requesting thread wakes up and retrieves the value from the data node pointed to it by the request_value field of the request node. If a wait times out, the requesting thread attempts to signal that the wait timed out by performing a CAS operation on the request_value field to modify it from zero to non-zero. If the CAS operation succeeds, the request timed out and the remove operation return failure. If the CAS operation fails, the request was fulfilled since the fulfilling thread set the request_value field with the address of the data node.
Owner:LEVEL 3 COMM LLC
System and method for retransmitting uplink data from a mobile terminal in a soft handover region in an asynchronous CDMA mobile communication system servicing an enhanced uplink dedicated transport channel
InactiveUS7346035B2Error prevention/detection by using return channelNetwork traffic/resource managementAsynchronous cdmaCommunications system
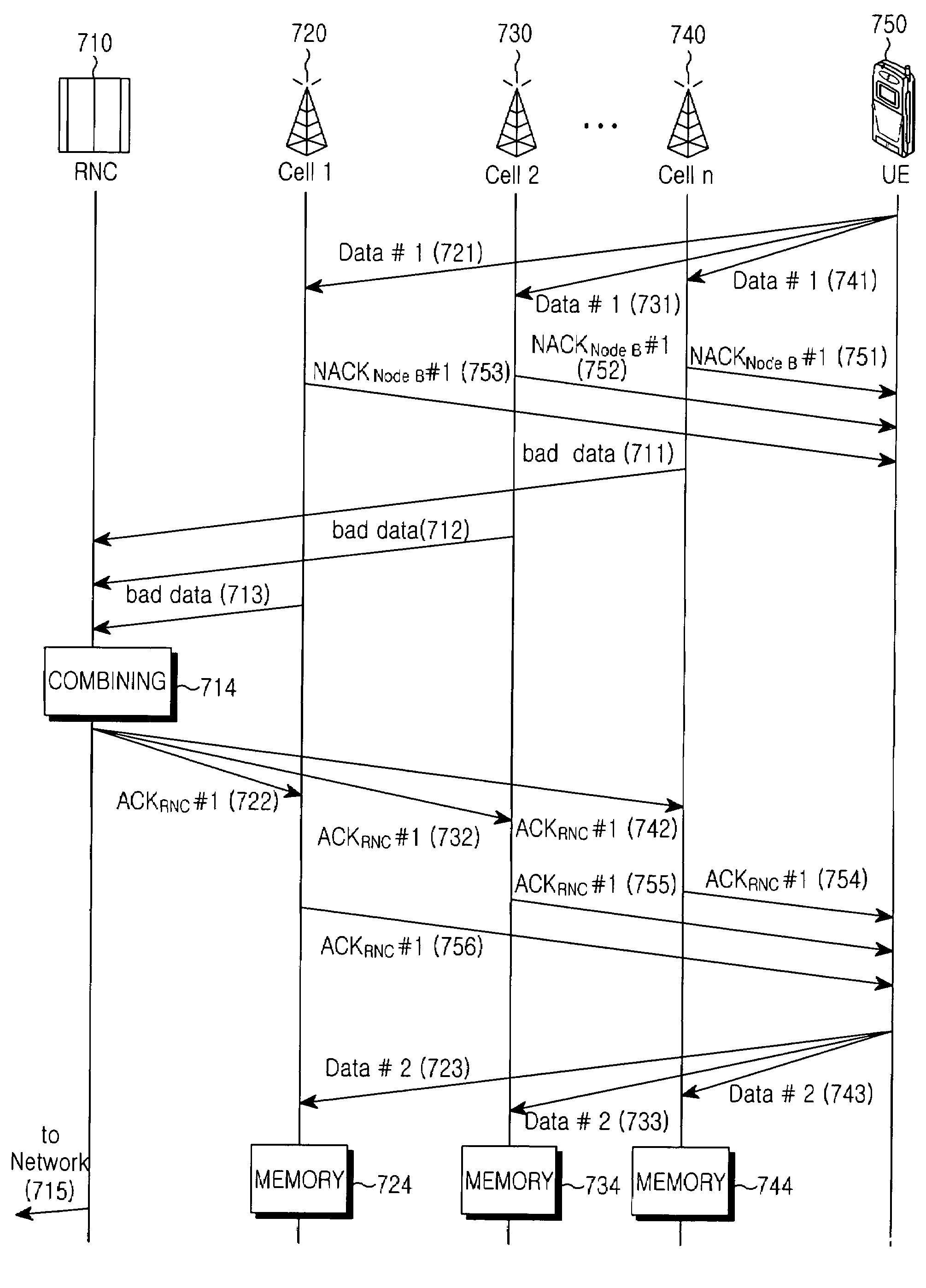
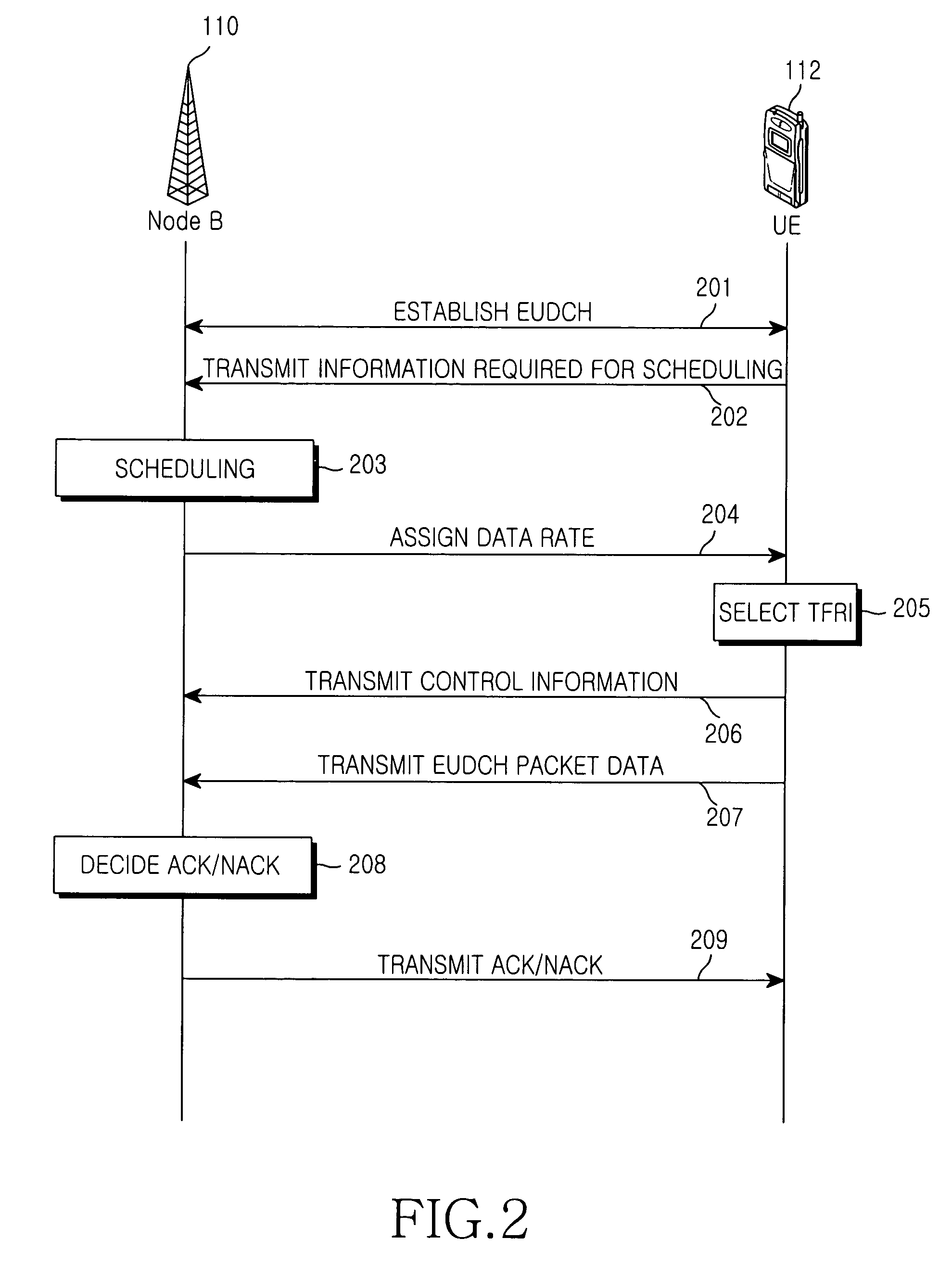
A method and system of retransmitting uplink packet data from a user equipment (UE) in a handover region to Node Bs. The UE transmits packet data to the Node Bs on an enhanced uplink dedicated transport channel (EUDCH). The Node Bs transmit to the UE first response fields indicating whether the Node Bs have received good packet data or bad packet data, and second response fields that the Node Bs received from an RNC indicating whether a radio network controller (RNC) has received good packet data or bad packet data. The UE then detects the first and second response fields and retransmits the uplink packet data according to the values of the response fields in the UE.
Owner:SAMSUNG ELECTRONICS CO LTD
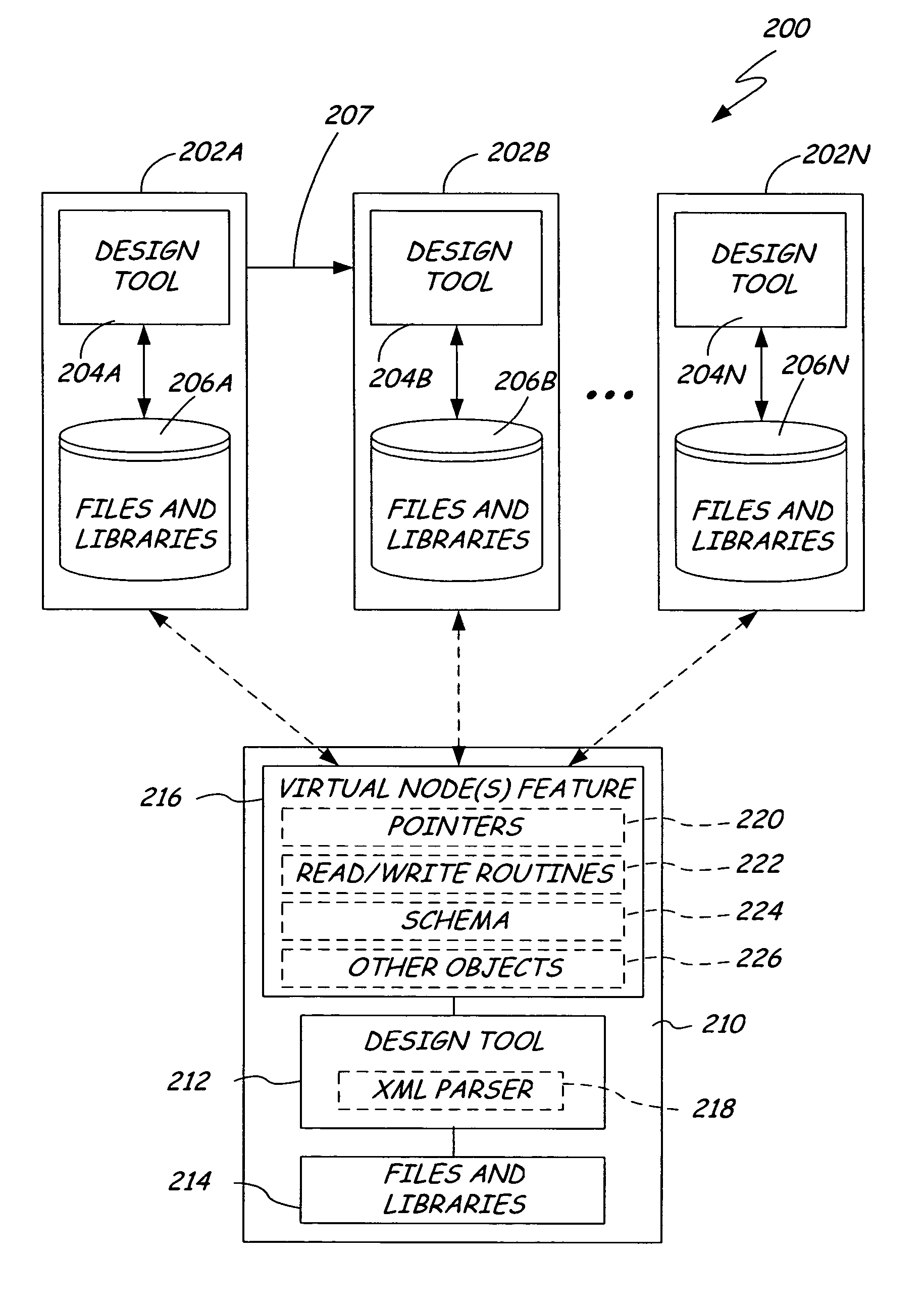
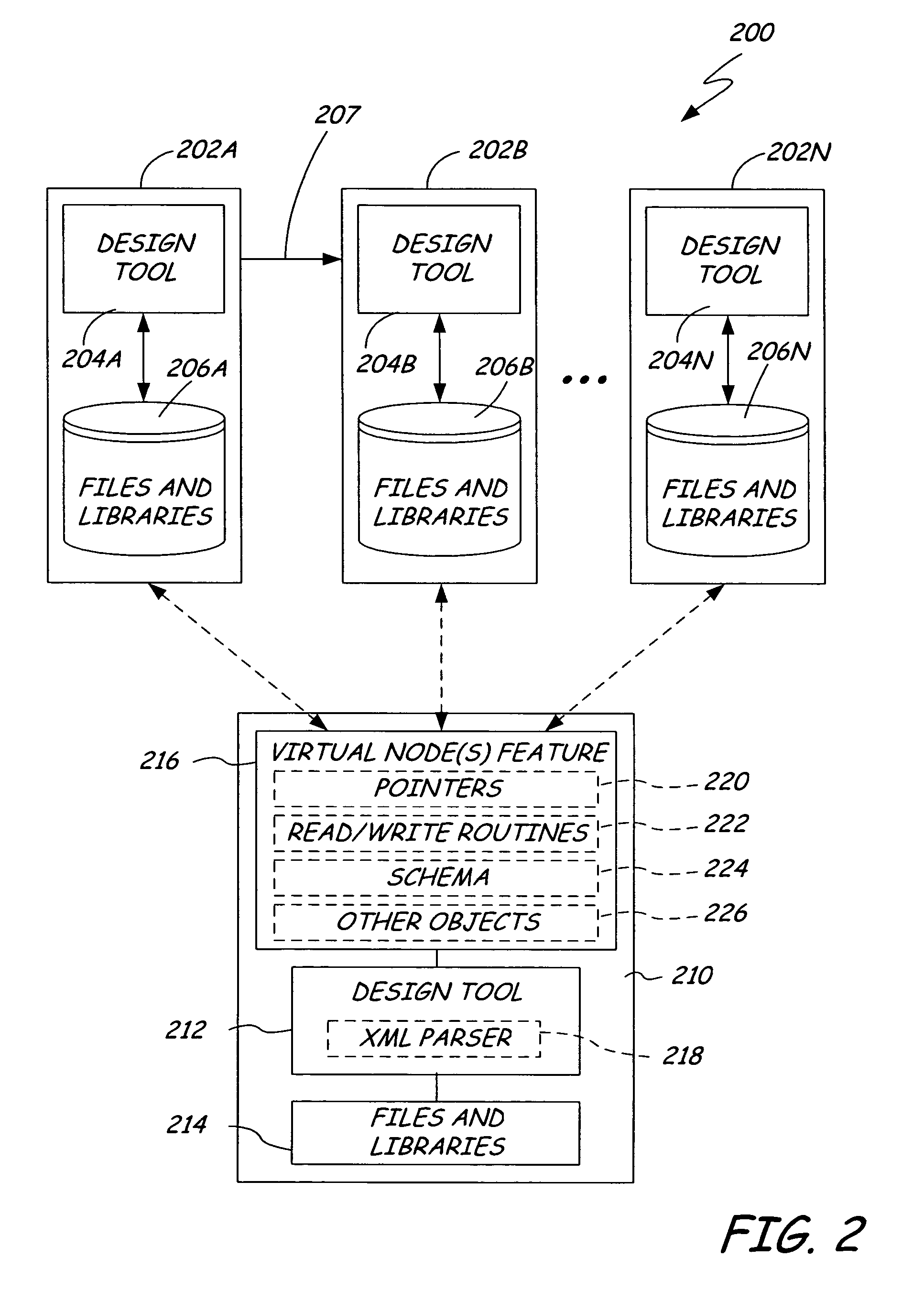
Virtual data representation through selective bidirectional translation
InactiveUS20060112376A1Software designProgram controlComputer architectureComputer aided circuit design
A computer-aided circuit design application has a virtual node feature and a design tool. The virtual node feature is adapted to access design specification information in a first data format and to represent the accessed design specification information as a virtual data node object within a list of node objects in a second data format. The design tool is operable on the list of node objects and the virtual data node object.
Owner:BELL SEMICON LLC
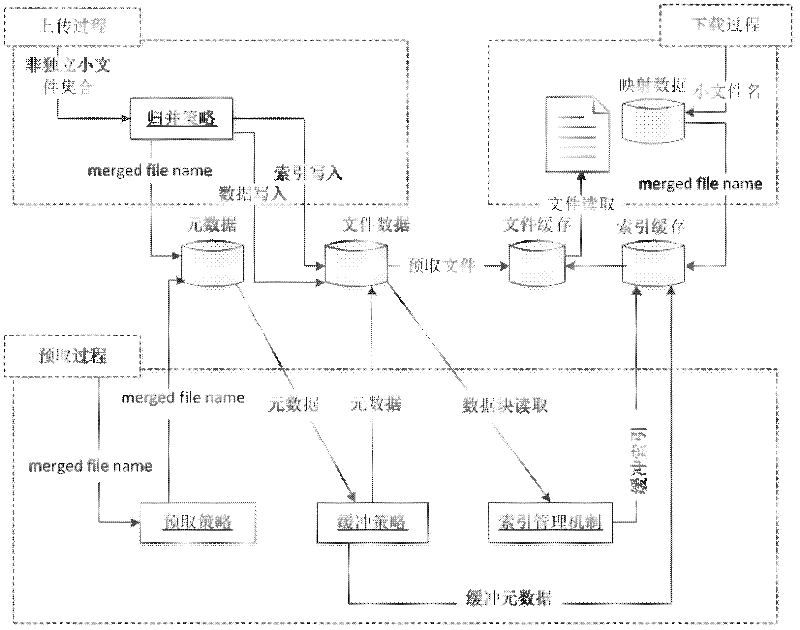
Mass non-independent small file associated storage method based on Hadoop
InactiveCN102332027AReduce interactionImprove storage efficiencySpecial data processing applicationsData nodeSmall files
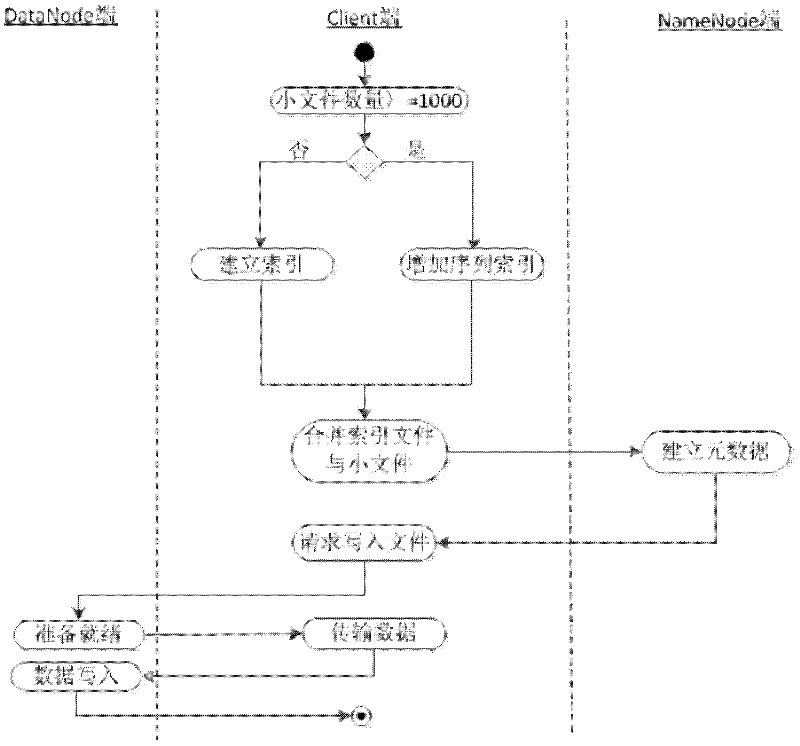
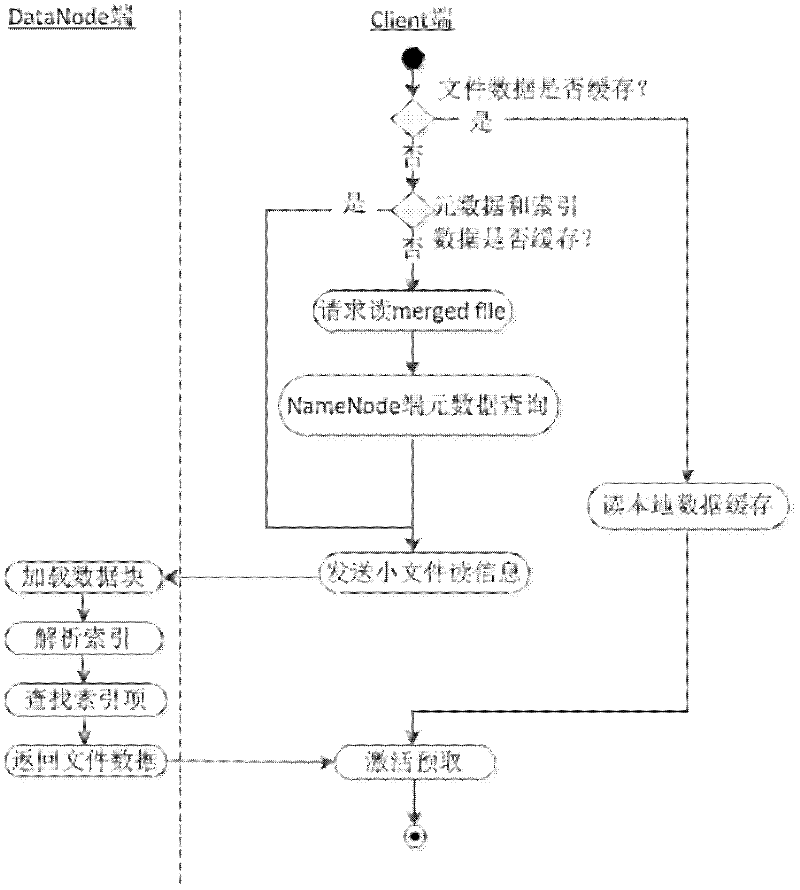
The invention discloses a mass non-independent small file associated storage method based on Hadoop. The method is mainly used for solving the problem of low mass non-independent small file access and reading efficiency and aims at a plurality of small files, namely non-independent small files obtained by cutting a big file. The method is characterized by comprising the following steps: (1) merging all the small files of the big file into one file which is named merged file; (2) establishing a local index for each merged file, and storing a local index file and a file entity onto a Data Node of a Hadoop system while updating; and (3) when the non-independent small files are read, improving the file reading efficiency by adopting metadata cache, local index file pre-fetching and associated file pre-fetching. By utilizing the method provided by the invention, the efficiency of the existing Hadoop system for storing and reading small files is improved. The method is suitable for the storage and management of the mass non-independent small files in universal scenes.
Owner:XI AN JIAOTONG UNIV
Block chain safety storage method
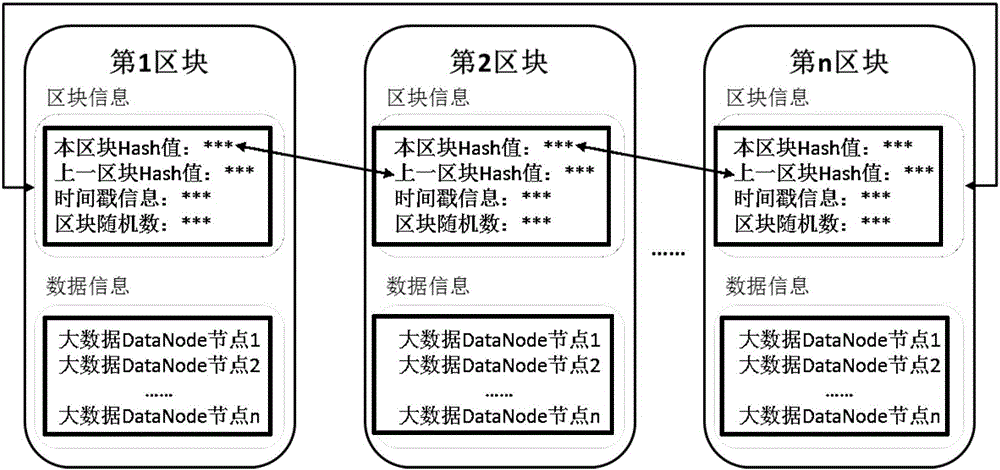
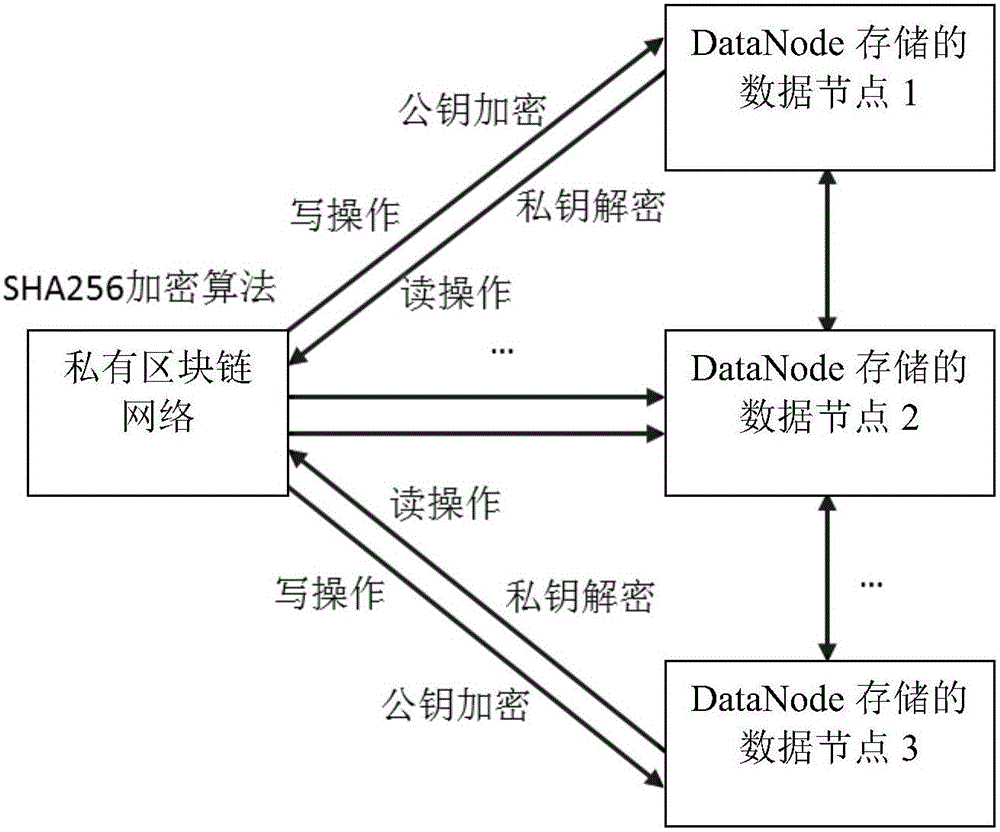
ActiveCN106503574AFully consider securityImprove securityDigital data protectionFile system administrationPlaintextData platform
The invention provides a block chain safety storage method. The method makes each client-side Client have a name node, the data storage safety of a big data platform is greatly improved, the pressure brought by a centralized server is effectively avoided by adopting decentration design, and common apportion is performed through a whole privately-owned block chain network; Data Node of each data block of Hadoop is encrypted, and the safety of each data in big data is fully guaranteed. A data storage and management mechanism of the big data platform is further improved, a single mode relying on a central node is converted into a network environment jointly maintained jointly by all participants, and the decentration design is really achieved. By setting PKI and user permission, the shortcoming of simple and extensive plaintext storage of important data is broken through, and a safe and encrypted storage process and method are deepened.
Owner:NO 32 RES INST OF CHINA ELECTRONICS TECH GRP
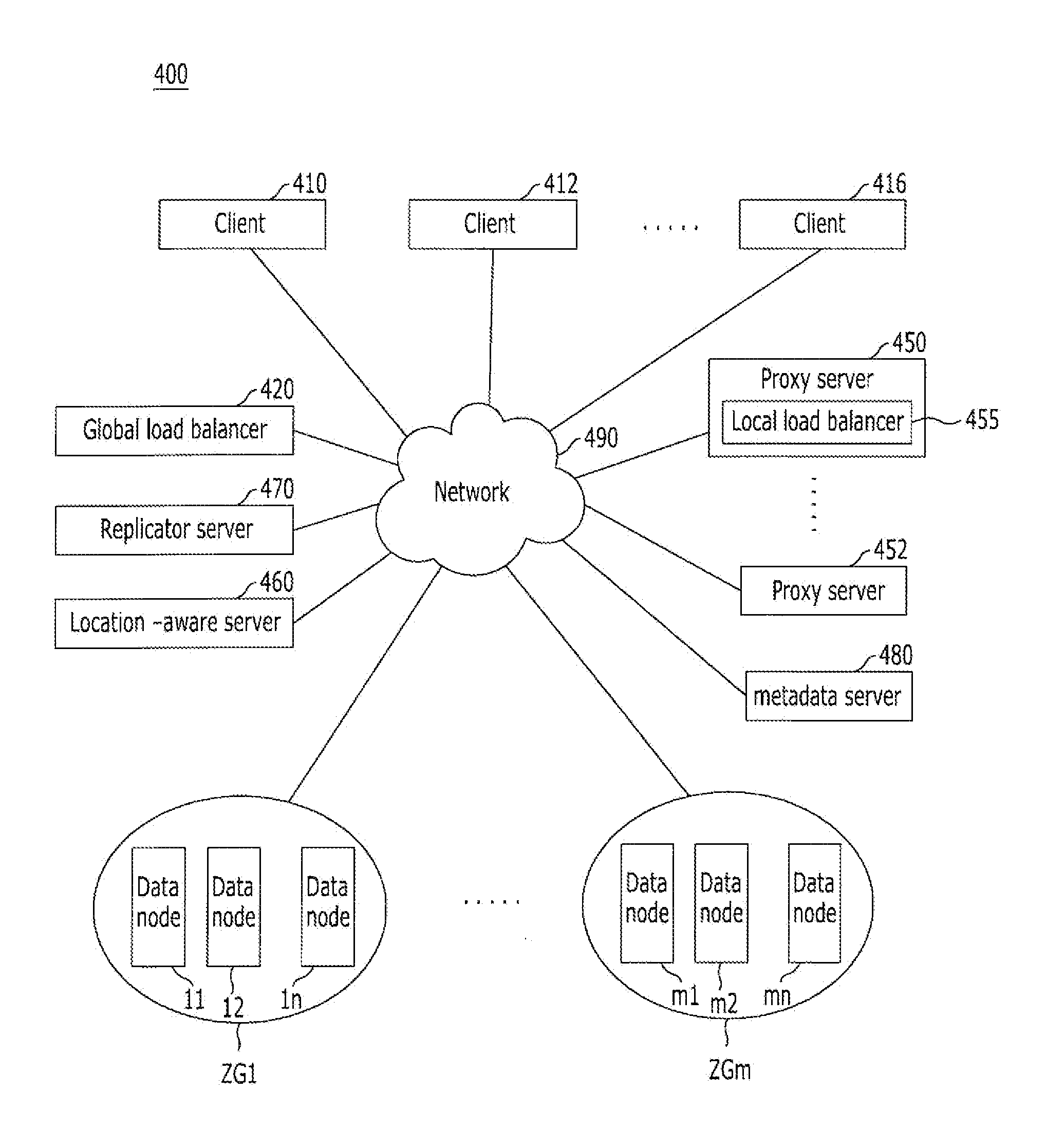
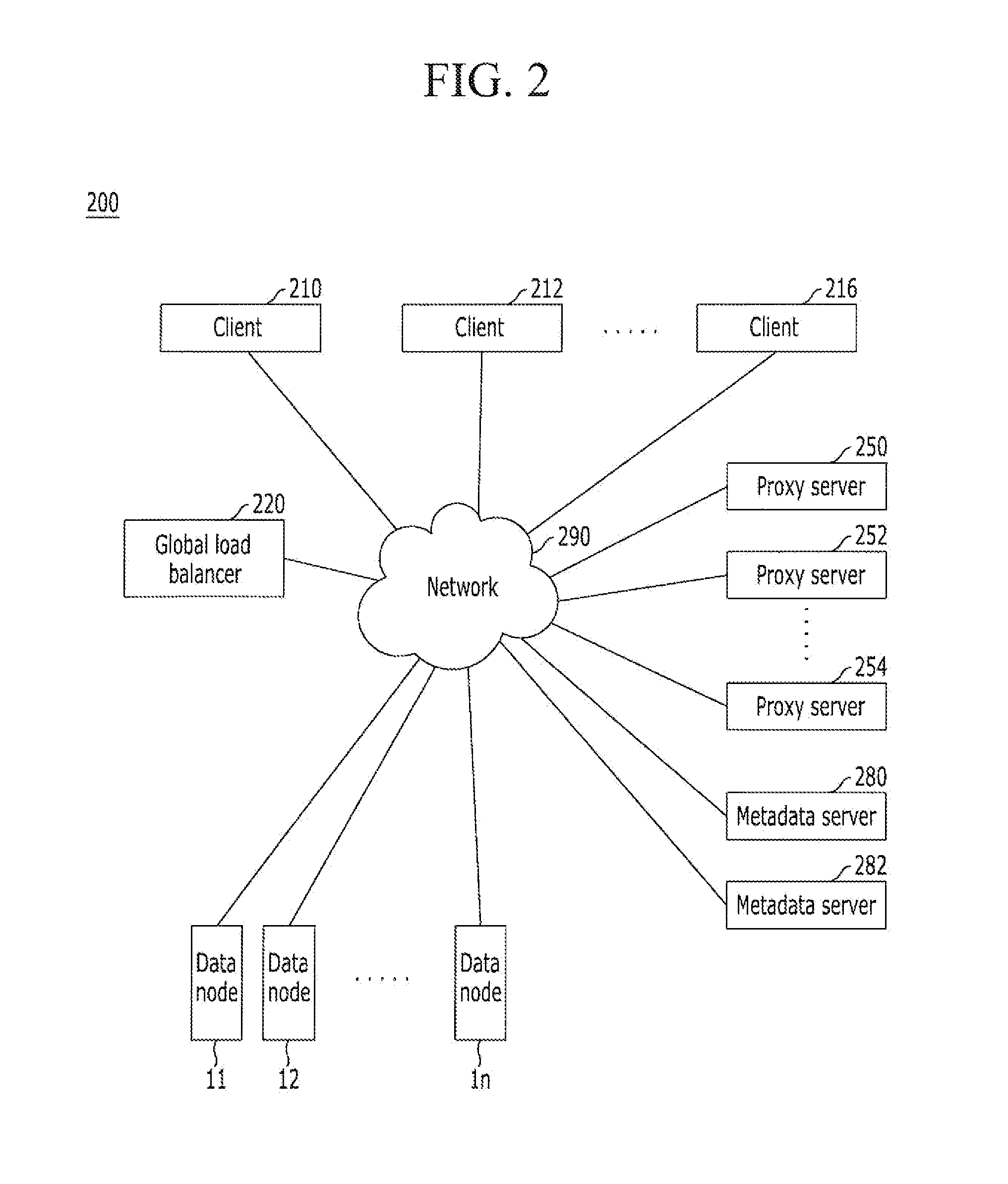
Distributed storage system including a plurality of proxy servers and method for managing objects
A distributed storage system including a plurality of proxy server and a method for managing objects. The distributed storage system may include a plurality of data nodes, a plurality of proxy server, and a global load balancer. Each one of the plurality of data nodes may be configured to perform at least one management operation and output an operation result. Each one of the plurality of proxy servers may be configured to perform operations for controlling the plurality of data nodes to perform the at least one management operation in response to an operation request from a respective client. The global load balancer may be configured to select one proxy server from the plurality of proxy servers and allocate the selected proxy server to the respective client as the responsible proxy server. The respective client may perform the management operation through the allocated responsible proxy server.
Owner:KT CORP
Data sharing method based on blockchain and related to private data
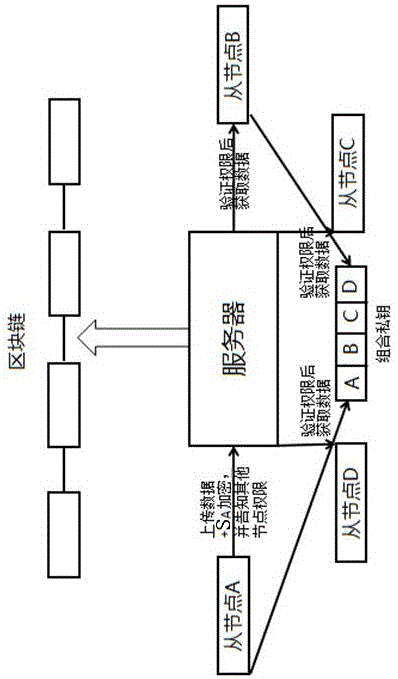
InactiveCN106778343AEnsure safetyImprove confidentialityDigital data protectionTransmissionData nodeData exchange
The invention relates to the technical field of information security and provides a data sharing method based on blockchain and related to private data. The method includes the steps that a private key S is allocated by the blockchain and held by four slave nodes A, B, C and D, when the private key S is generated, a piece of verification information is written into each part in the private key, and through comparison of the verification information, one certain node in the blockchain judges the identity of another node on the basis; the private data of each slave node uses the corresponding part of private key in an encrypted mode, and a network needs to be informed of which node can obtain what data during encryption; when one certain slave node intends to have access to the private data uploaded by other nodes, the network makes the verification information compared with verification information carried by part of the private key of an upload data node, and when the verification result is one of the nodes informed by the upload data node, the node applying at the moment can have access to the private data uploaded by another node. The method is capable of guaranteeing safety of exchange and obtaining of the private data in the blockchain.
Owner:苏州展识科技有限公司
Big data distributed storage method and system
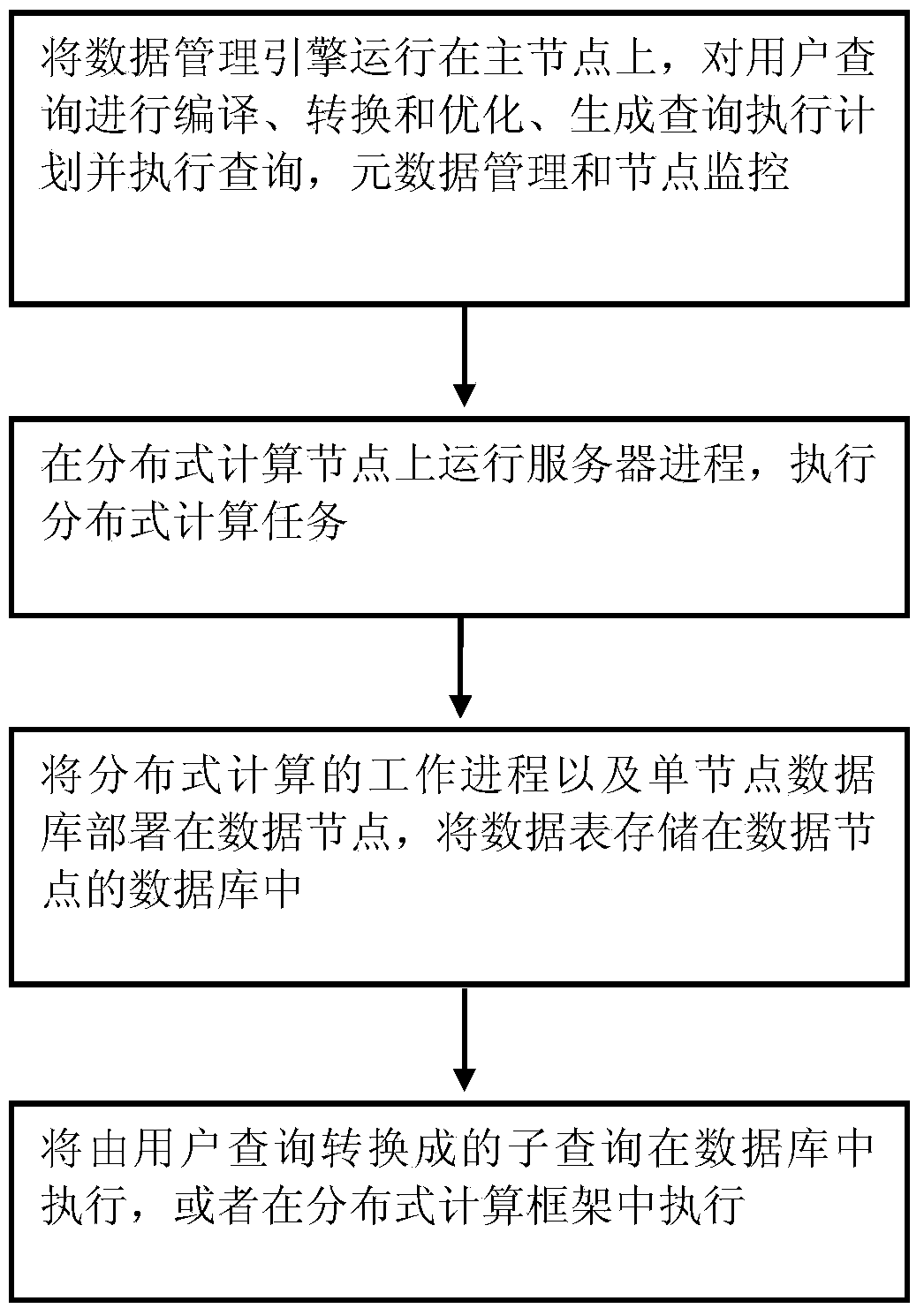
InactiveCN104063486AAvoid transmission costsImproved distributed storage methodSpecial data processing applicationsExecution planMetadata management
The invention provides a big data distributed storage method and system. The method comprises the steps of operating a data management engine on a main node, conducting compiling, conversion and optimization on user queries, generating and executing a query executing plan, and conducting metadata management and node monitoring; operating server processes on a distributed computational node and executing a distributed computation task; deploying the working processes of distributed computation and a single-node database on a data node; executing a subquery in the database or in a distributed computation frame. According to the big data distributed storage method and system, the opportunities that the queries are pushed down to the database to be executed are increased, data transmission cost caused by cross-node connection is avoided, and query performance is improved.
Owner:SICHUAN FEDSTORE TECH
Multi-tenant data management model for SAAS (software as a service) platform
InactiveCN103455512ASupport independent customizationSupport data unified managementSpecial data processing applicationsData accessData node
The invention provides a multi-tenant data management model for an SAAS (software as a service) platform. The multi-tenant data management model comprises a data storage unit, a data index unit and a data splitting and synchronous migration unit. According to the model, metadata are connected with user customized data in a data mapping mode, data indexes are built by the aid of position indexes and tenant logic indexes, the model provides complete customized data for tenants in a single node through the indexes, data of a single tenant are simultaneously operated in a plurality of nodes, independent customization of the tenants and unified data management can be effectively supported, data sharing among the nodes is facilitated, scalability of platform data nodes in the cloud is ensured, and uniformity, scalability and usability of data access patterns of the SaaS delivery platform are improved.
Owner:上海博腾信息科技(集团)有限公司
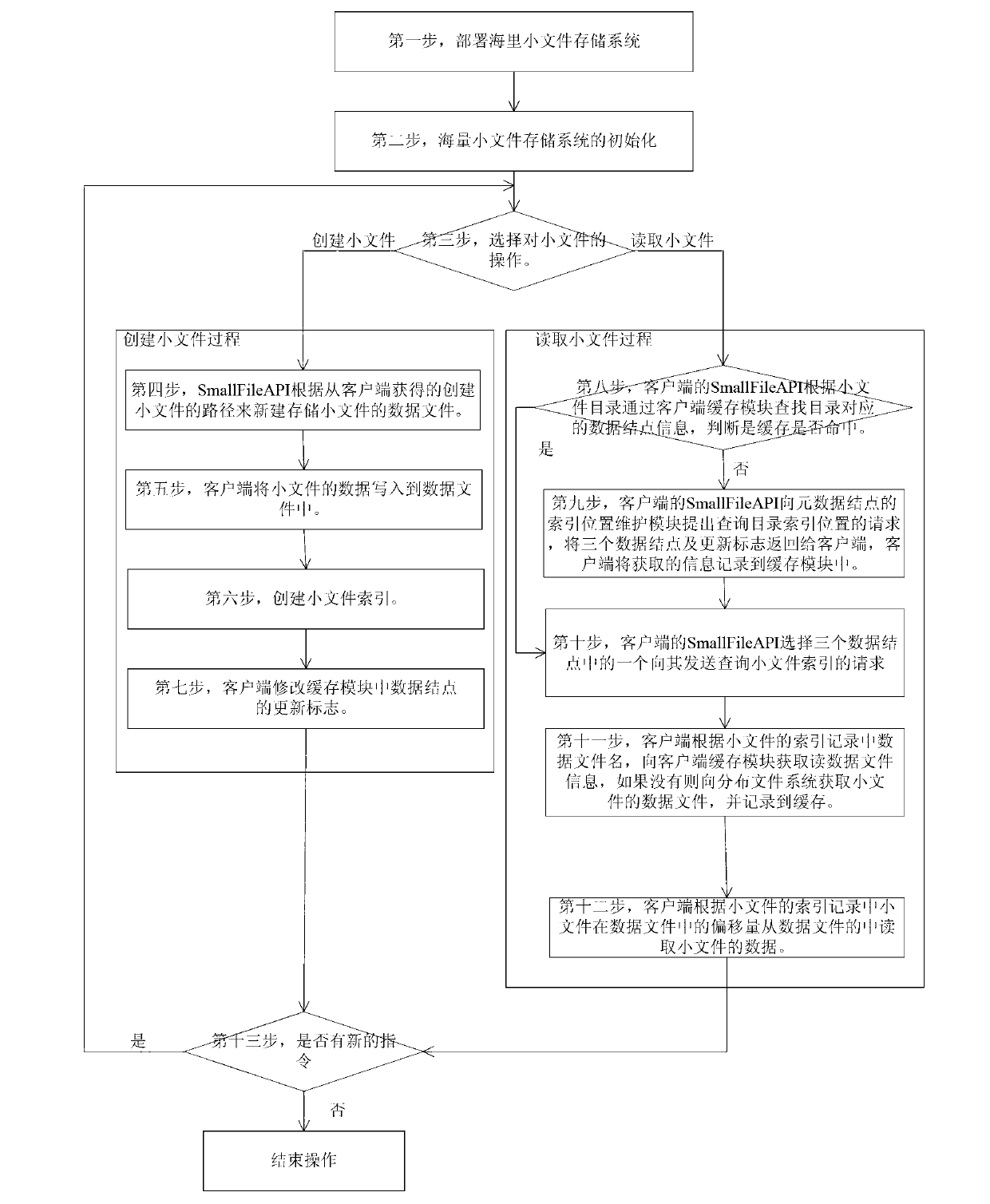
Method for storing mass of small files on basis of master-slave distributed file system
ActiveCN103020315ATo achieve fault toleranceSolve the problem when storing a large number of small filesSpecial data processing applicationsDistributed File SystemData file
The invention discloses a method for storing a mass of small files on the basis of a master-slave distributed file system, and aims to solve the problem about storing the mass small files in the master-slave distributed file system. The technical scheme includes that the method includes that a mass small file storage system is deployed and initialized, and then small files are created and read by a SmallFileAPI (small file-application program interface) of a client side according to a command received from a keyboard. When the small files are created by a system, the SmallFileAPI creates data files of the small files according to small file paths obtained from the client side, writes in small file data and simultaneously creates small file indexes at data nodes; when the small files are read by the system, data node information corresponding to a parent directory is acquired according to the small file paths, an index request is transmitted to any of the data nodes, and finally the small file data are read from the data files according to index information. By the aid of the method, the problem about mass of storage metadata of the mass of small files is solved, writing efficiency of the mass small file storage system is improved, and reliability of the system is guaranteed.
Owner:NAT UNIV OF DEFENSE TECH
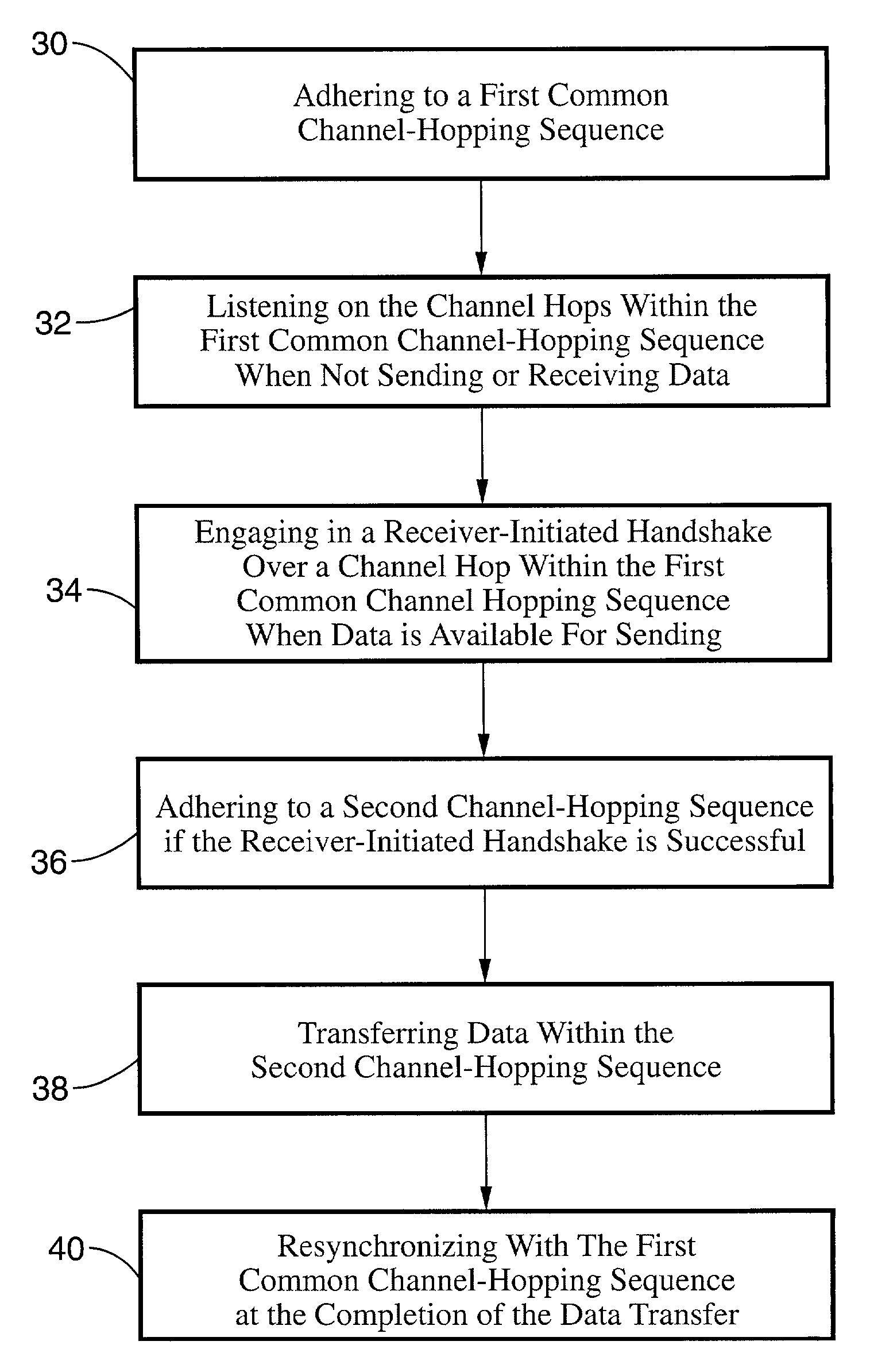
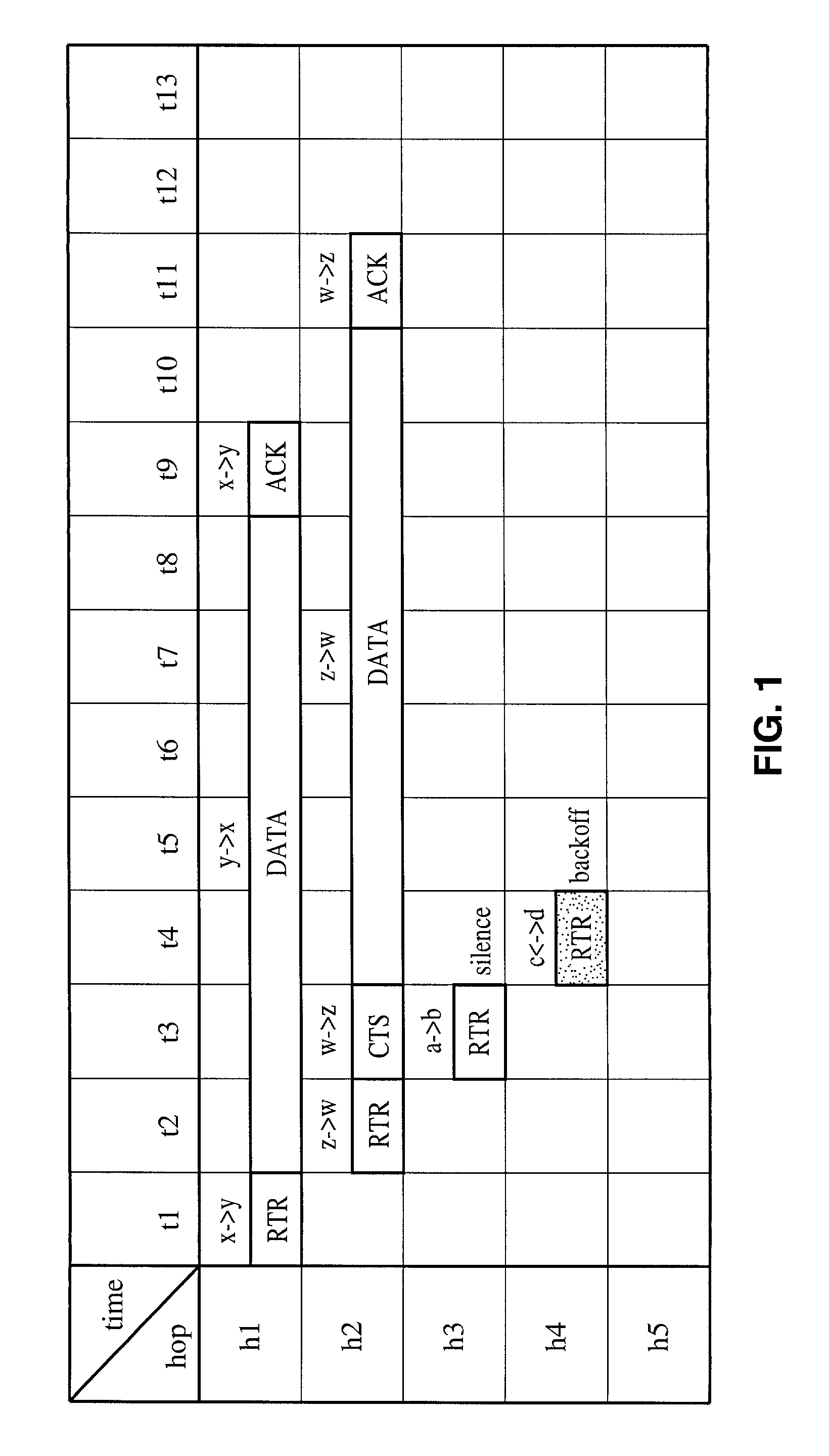
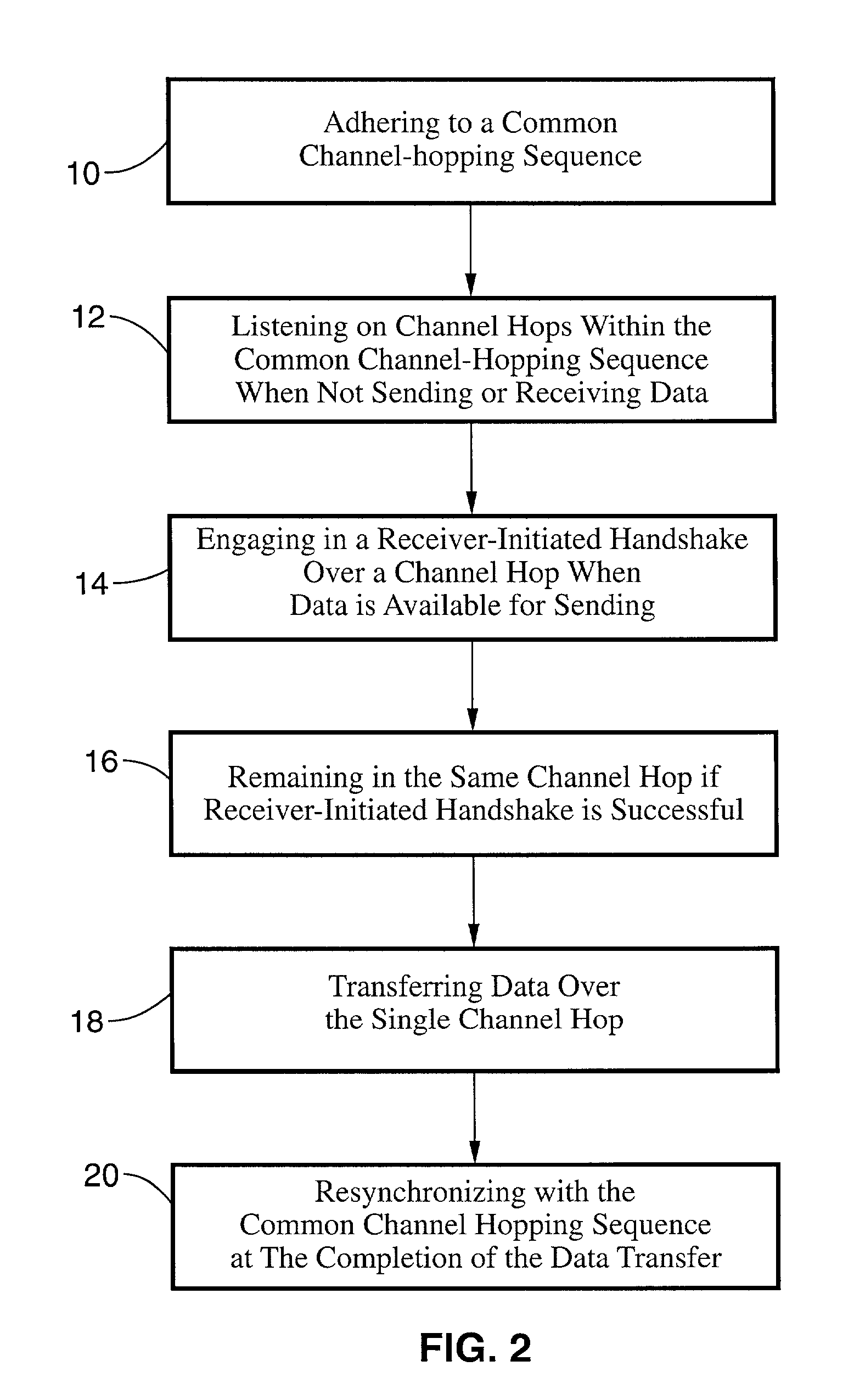
Receiver-initiated channel-hopping (RICH) method for wireless communication networks
ActiveUS7002910B2Improve communication throughputLow Latency FeaturesError preventionTransmission systemsData nodeData transmission
A family of medium-access (MAC) collision-avoidance receiver-initiated channel-hopping (RICH) protocols which do not rely on carrier-sensing, or unique codes to each node within the network. The RICH protocol requires that each network nodes adhere to a common channel-hopping sequence, and that nodes that are not in a state of sending or receiving data will listen on the common channel hop. To send data nodes enter into a receiver-initiated dialogue over the channel-hop at the time at which a data transmission is needed. Nodes which succeed in performing the collision-avoidance handshake remain in the same channel-hop for the remainder of the data transfer, while the remaining nodes continue with the common channel hopping sequence. The described RICH protocols are capable of providing collision-free operation even in the presence of hidden terminals.
Owner:RGT UNIV OF CALIFORNIA
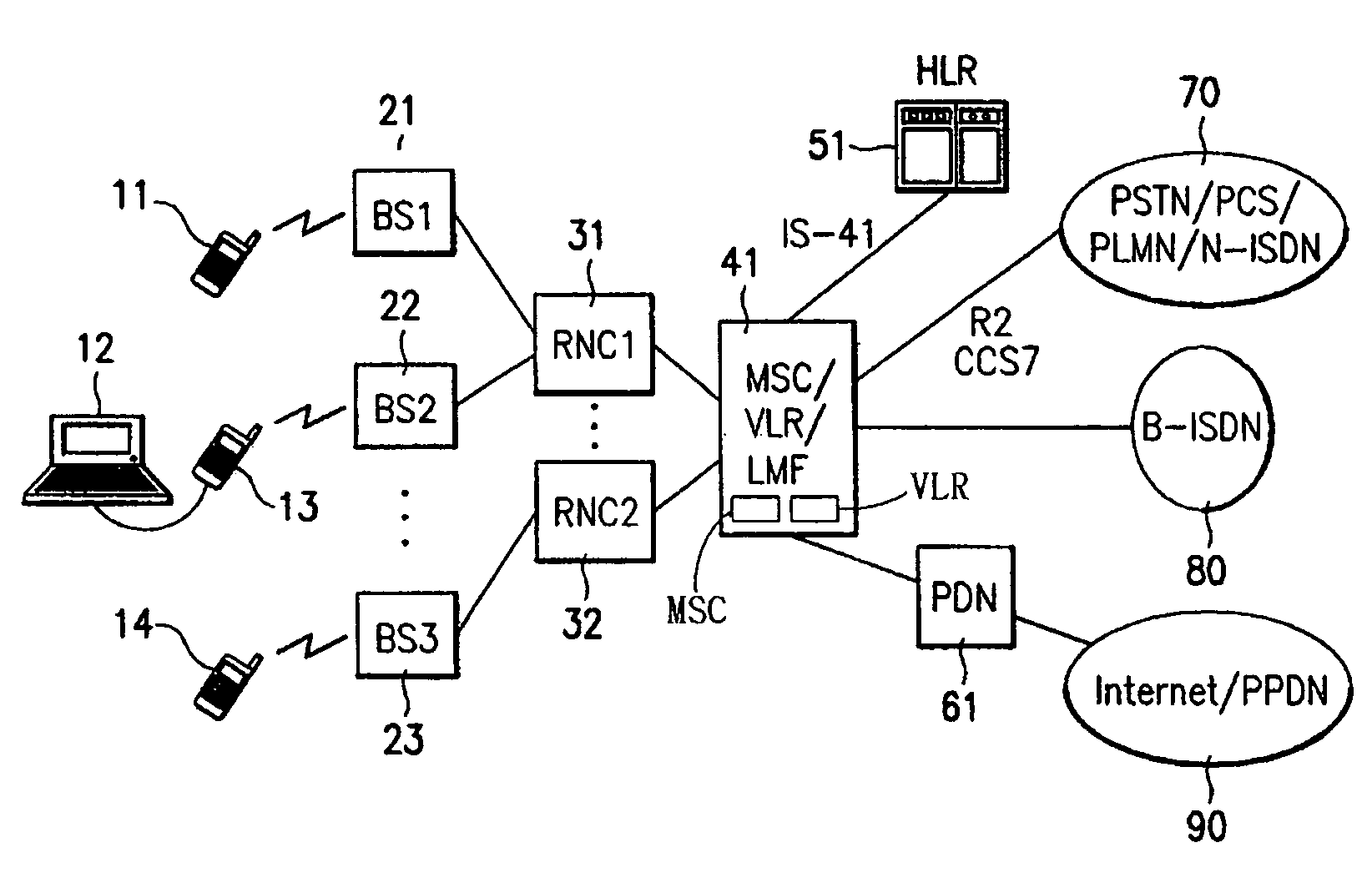
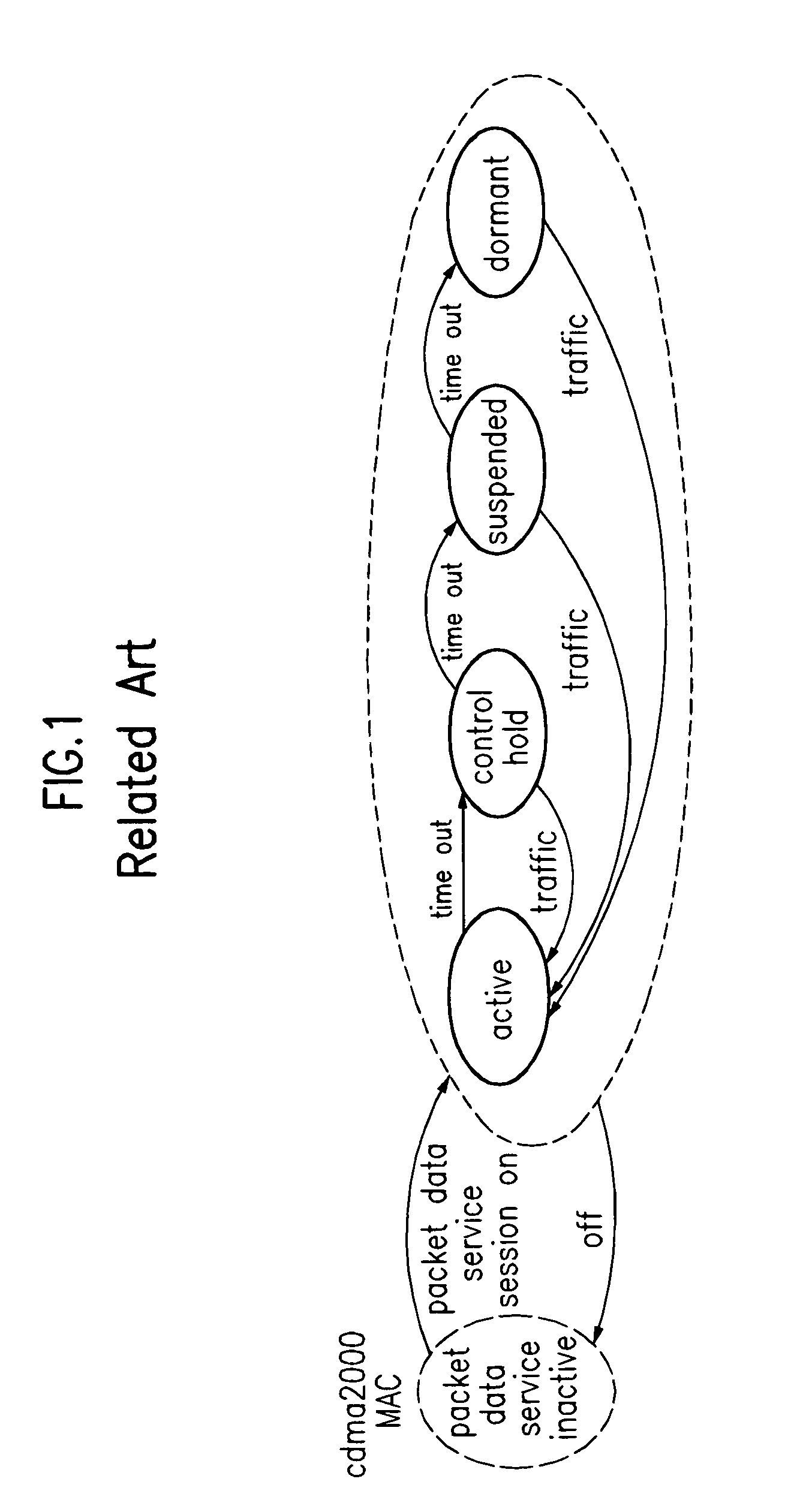
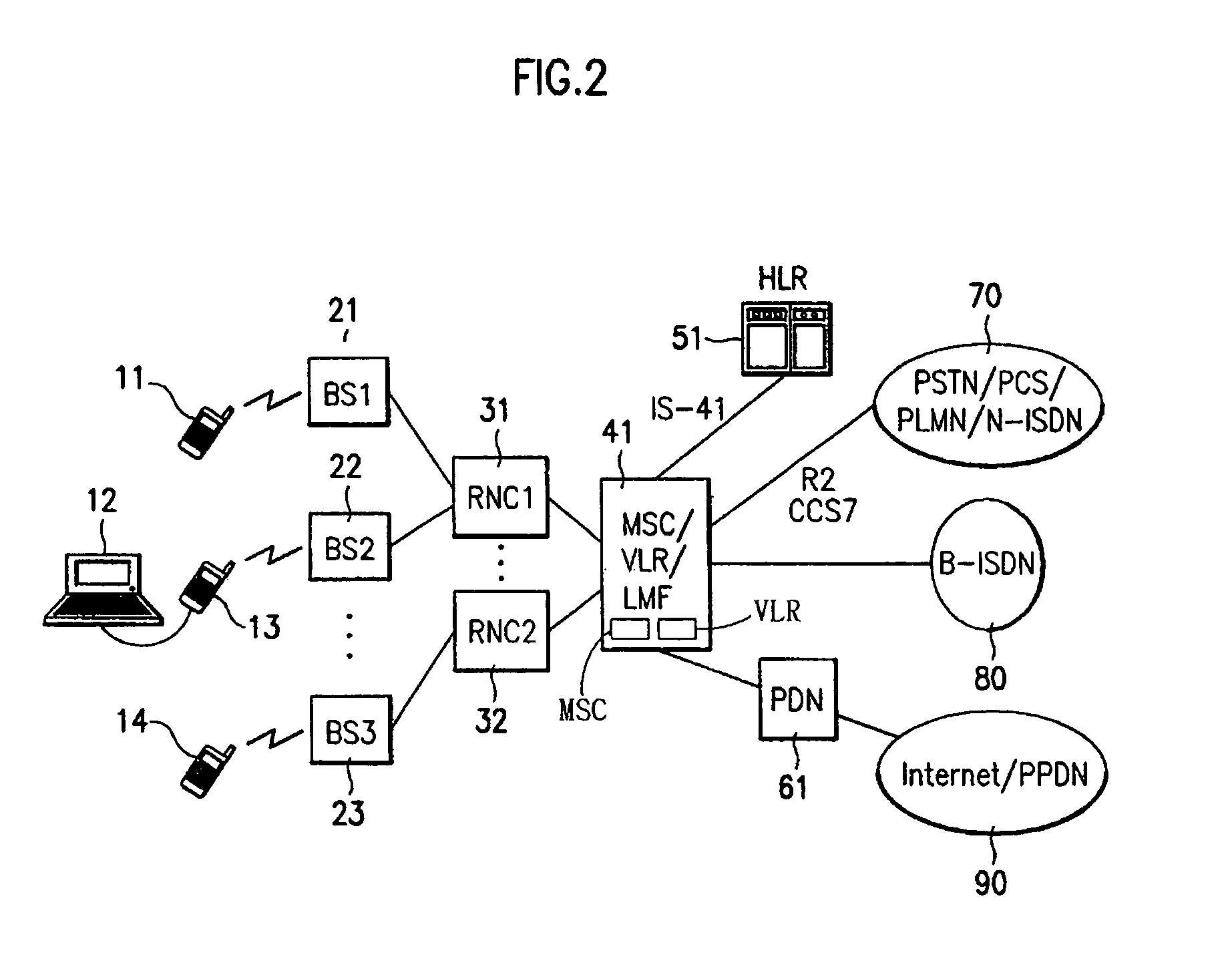
System and method for controlling packet data service in mobile communication network
InactiveUS7035636B1Eliminate the problemRadio/inductive link selection arrangementsRadio transmissionRadio networksPoint-to-Point Protocol
A system and method is provided for controlling a packet data service in a mobile communication network, in which, when a packet data service active terminal moves from an area of an old radio network controller to an area of a new radio network controller in either a suspended state or a dormant state, the same medium access control state information and the same radio resource control information are applied between the new radio network controller and the active terminal. Therefore, the packet data service can rapidly be resumed on the basis of an initially established point-to-point protocol link. If the active terminal moves from the old radio network controller to the new radio network controller under the condition that only a point-to-point protocol state is maintained between the active terminal and a packet data node, the active terminal detects a received pilot signal and checks a system overhead message. If the active terminal should perform a handoff operation in the suspended state, the active terminal requests the old radio network controller to permit its change to the dormant state or an active state.
Owner:SISVEL INT
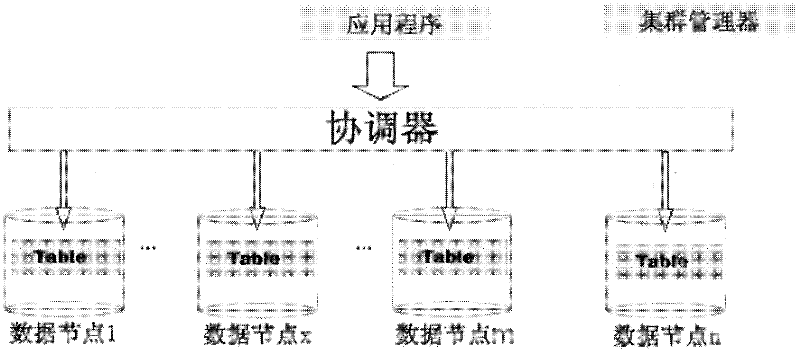
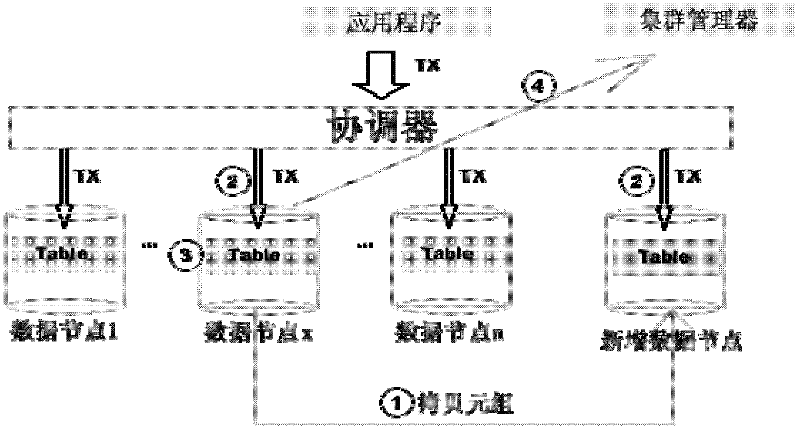
Method for achieving system dynamic expansion in shared-nothing database cluster
ActiveCN102521297ASolving the Dynamic Scalability ChallengeReduce the impactSpecial data processing applicationsHigh availabilityData node
The invention discloses a method for achieving system dynamic expansion in a shared-nothing database cluster, which includes the following steps: adding and detecting newly added data nodes and verifying connectivity of the newly added data nodes; initializing the newly added data nodes and synchronizing metadata information into the newly added data nodes; redistributing related tuples of a data table and distributed on the newly added data nodes in data nodes and the newly added data nodes, and leading operation on the data table in the redistributing process to be synchronous in the data nodes and the newly added data nodes; and modifying cluster configuration files in a cluster manager. The method solves the problem of difficulty in dynamic expansion of the shared-nothing database cluster, and greatly reduces influence on and loss of user service logic during expansion of the cluster. By means of the method, on-line expansion can be achieved, so that high expandability of a system can be ensured, and high availability of the system can further be ensured.
Owner:北京人大金仓信息技术股份有限公司
Streaming XPath algorithm for XPath value index key generation
InactiveUS20060106758A1Reduce in quantityEase of evaluationData processing applicationsRelational databasesPath expressionPaper document
A method generates hierarchical path index keys for single and multiple indexes with one scan of a document. Each data node of the document is scanned and matches to query nodes are identified. A data node matches a query node if the three conditions hold: if it is not the root step, there is a match for the query node in the previous step of the query; the data node matches the query node of the current step; and the edges of the data and query nodes match. A sub-tree of a data node can be skipped if the data node is not matched and its level is less than the fixed levels of the query. The matched data node is then placed in the match stacks corresponding to the match query nodes. The method uses transitivity properties among matching units to reduce the number of states that need to be tracked and to improve the evaluation of path expressions significantly.
Owner:GOOGLE LLC
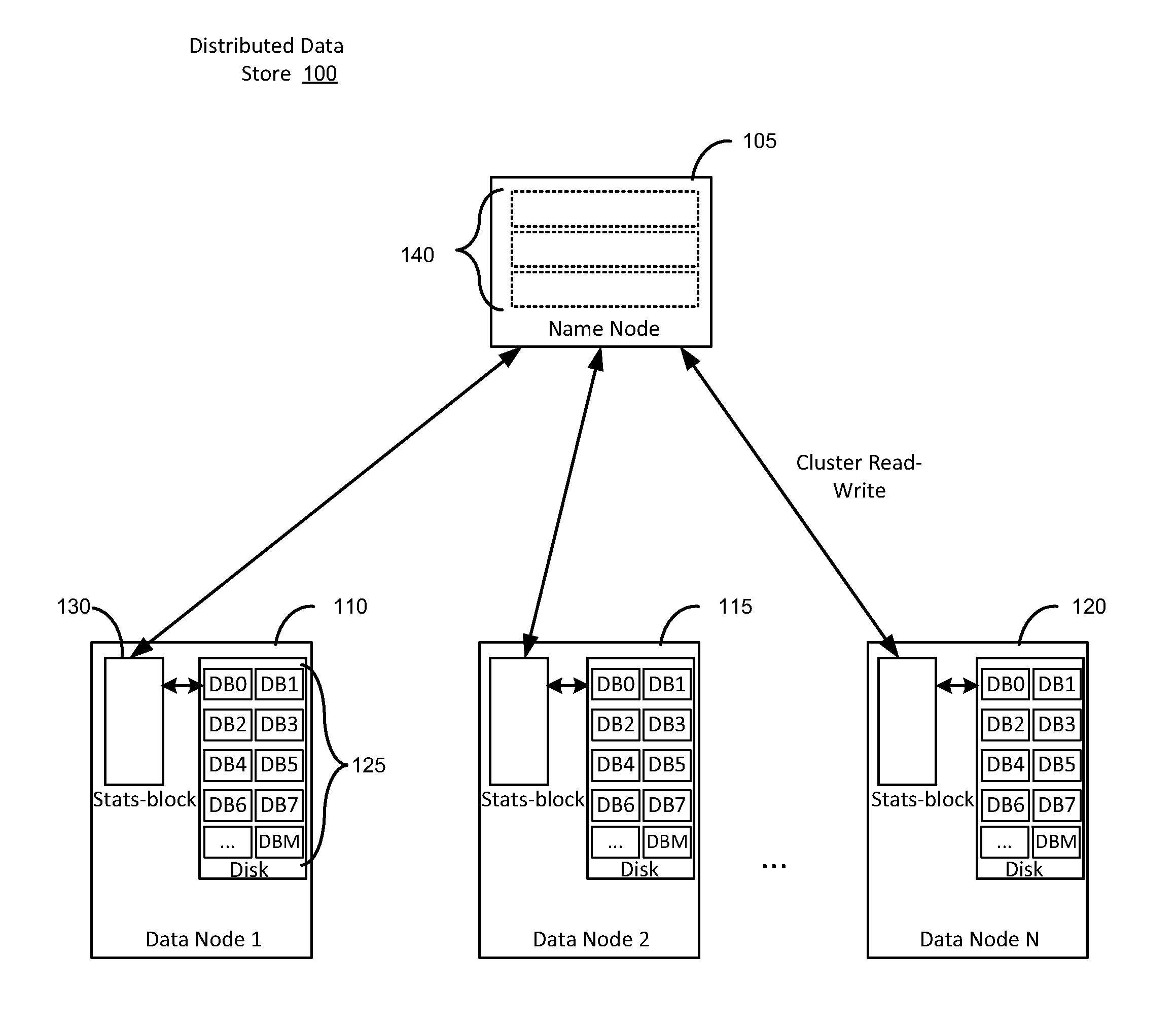
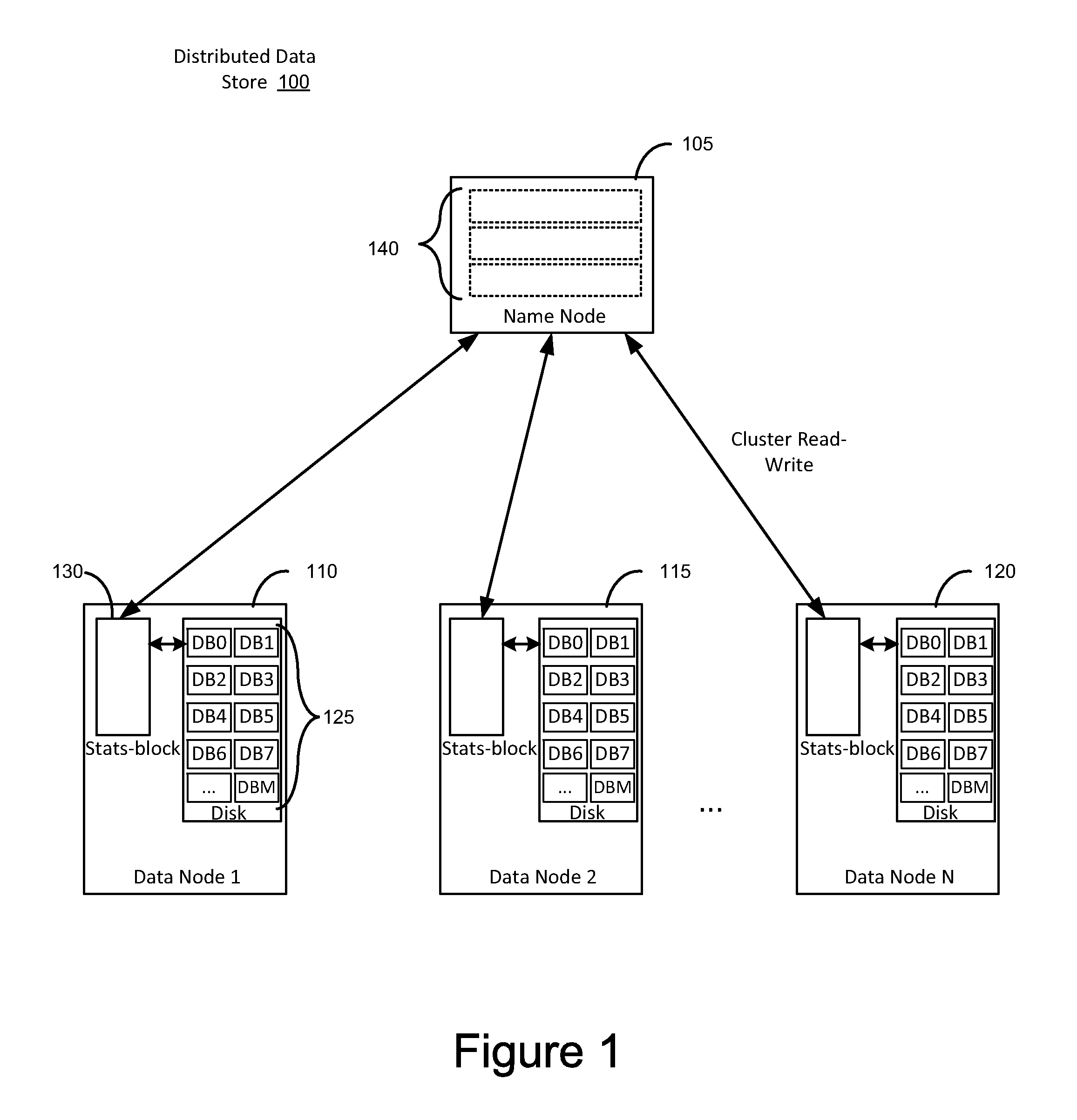
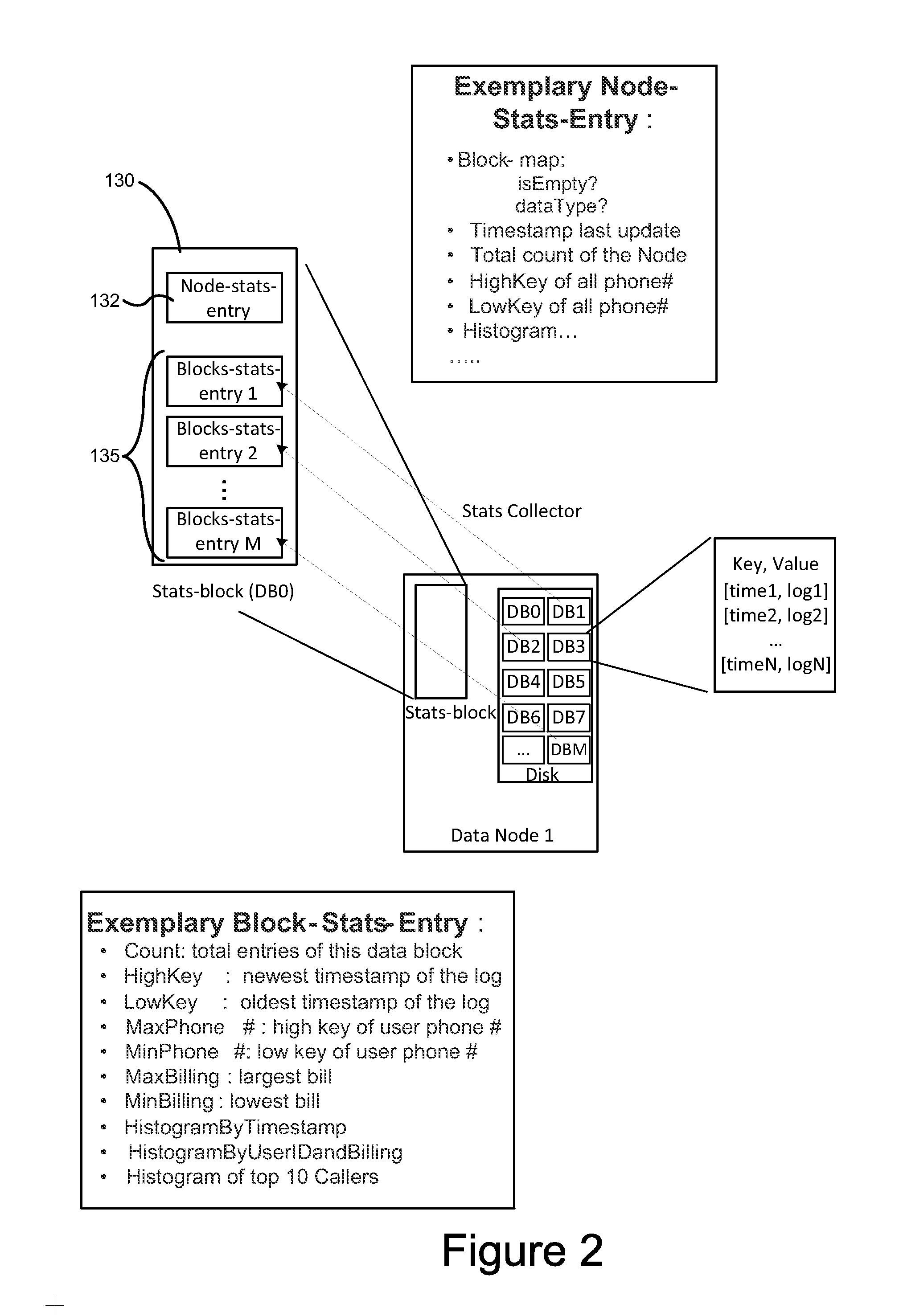
Big data statistics at data-block level
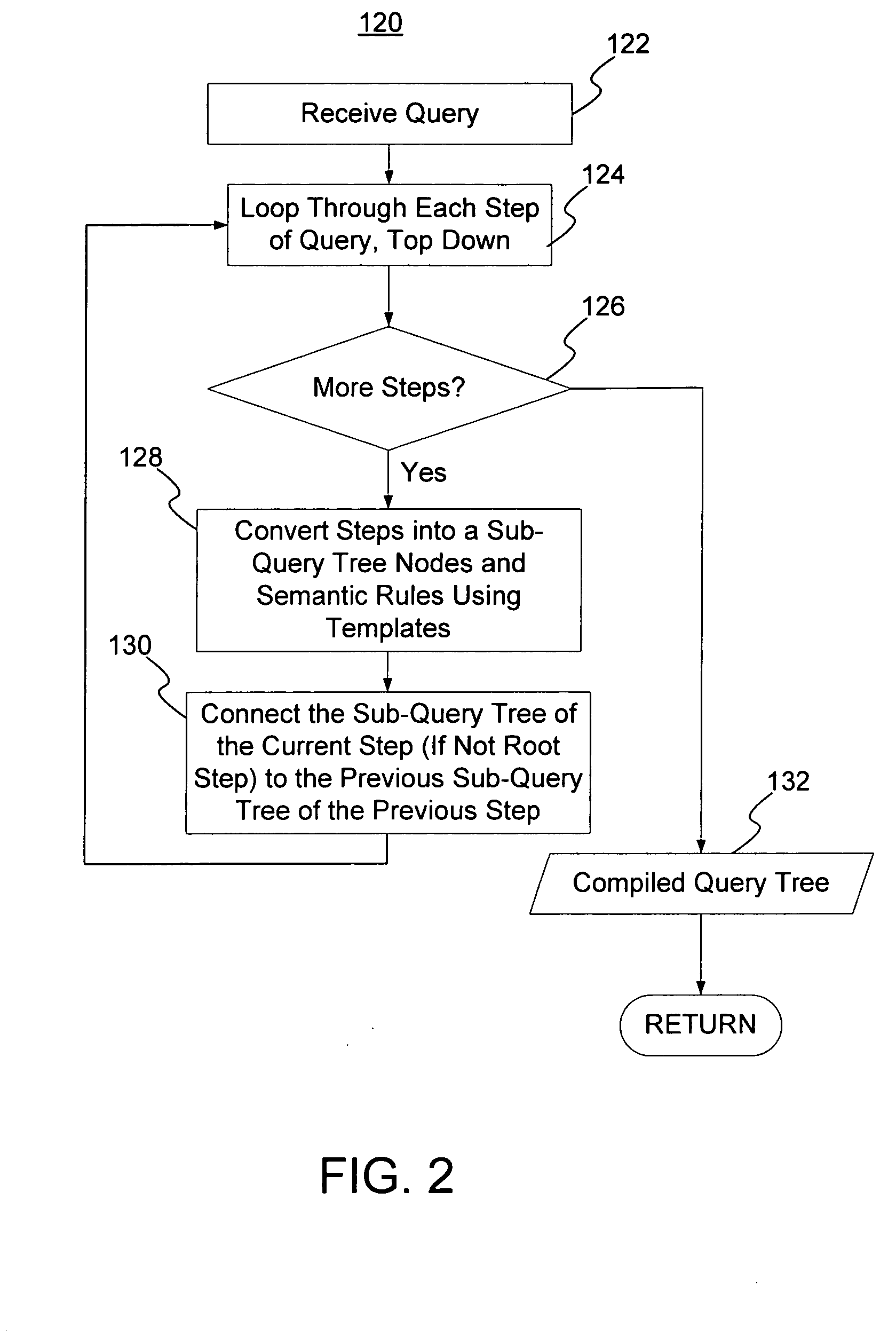
InactiveUS20160306810A1Reduce resource requirementsHigh bandwidth operationSpecial data processing applicationsDatabase indexingDistributed File SystemData node
System and method for storing statistical data of records stored in a distributed file system. In one aspect a statistical data block is allocated in a memory of a data node for storing statistical data of records stored in a storage disk of the data node. Each data block of the plurality of data blocks in the data node has a respective entry in the statistical data block, which is collocated with data blocks on the data node. Statistical data of records stored in the distributed file system are collected, and written to statistical data block in the memory of the data node.
Owner:FUTUREWEI TECH INC
Method and apparatus for indexing a hash table which is organized as a linked list
ActiveUS7370054B1Safely deletedData processing applicationsDigital data information retrievalTheoretical computer scienceData node
One embodiment of the present invention provides a system that implements a hash table that is fully dynamic and lock-free. During a lookup in the hash table the system first uses a hash key to lookup a bucket pointer in a bucket array. Next, the system follows the bucket pointer to a data node within a linked list that contains all of the data nodes in the hash table, wherein the linked list contains only data nodes and at most a constant number of dummy nodes. The system then searches from the data node through the linked list to locate a node that matches the hash key, if one exists.
Owner:SUN MICROSYSTEMS INC
Big-data parallel computing method and system based on distributed columnar storage
InactiveCN107329982AReduce the frequency of read and write operationsShort timeResource allocationSpecial data processing applicationsParallel computingLarge screen
The invention discloses a big-data parallel computing method and system based on distributed columnar storage. Data which is most often accessed currently is stored by using the NoSQL columnar storage based on a memory, the cache optimizing function is achieved, and quick data query is achieved; a distributed cluster architecture, big data storing demands are met, and the dynamic scalability of the data storage capacity is achieved; combined with a parallel computing framework based on Spark, the data analysis and the parallel operation of a business layer are achieved, and the computing speed is increased; the real-time data visual experience of the large-screen rolling analysis is achieved by using a graph and diagram engine. In the big-data parallel computing method and system, the memory processing performance and the parallel computing advantages of a distributed cloud server are given full play, the bottlenecks of a single server and serial computing performance are overcome, the redundant data transmission between data nodes is avoided, the real-time response speed of the system is increased, and quick big-data analysis is achieved.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com