Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6017 results about "File storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
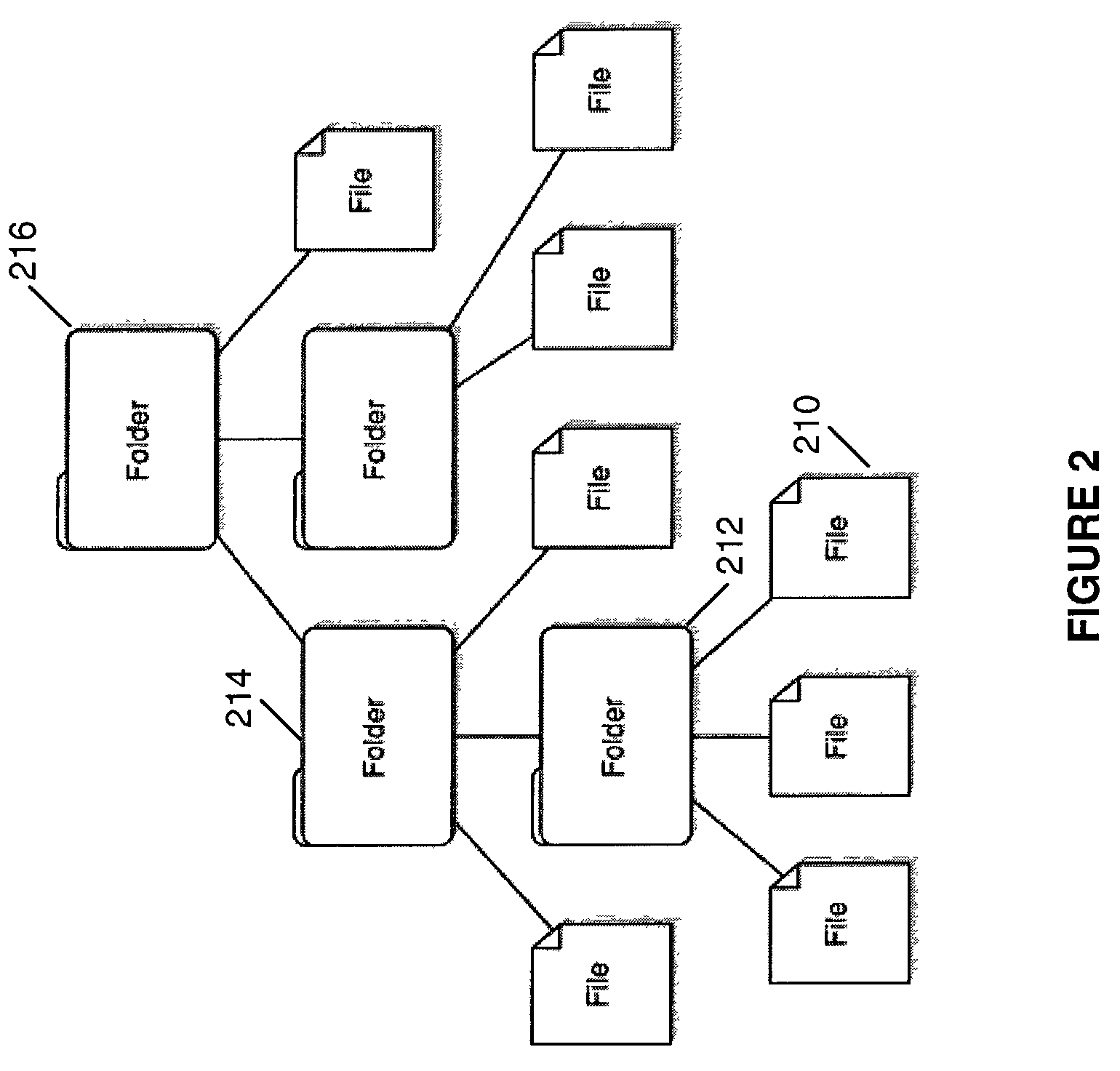
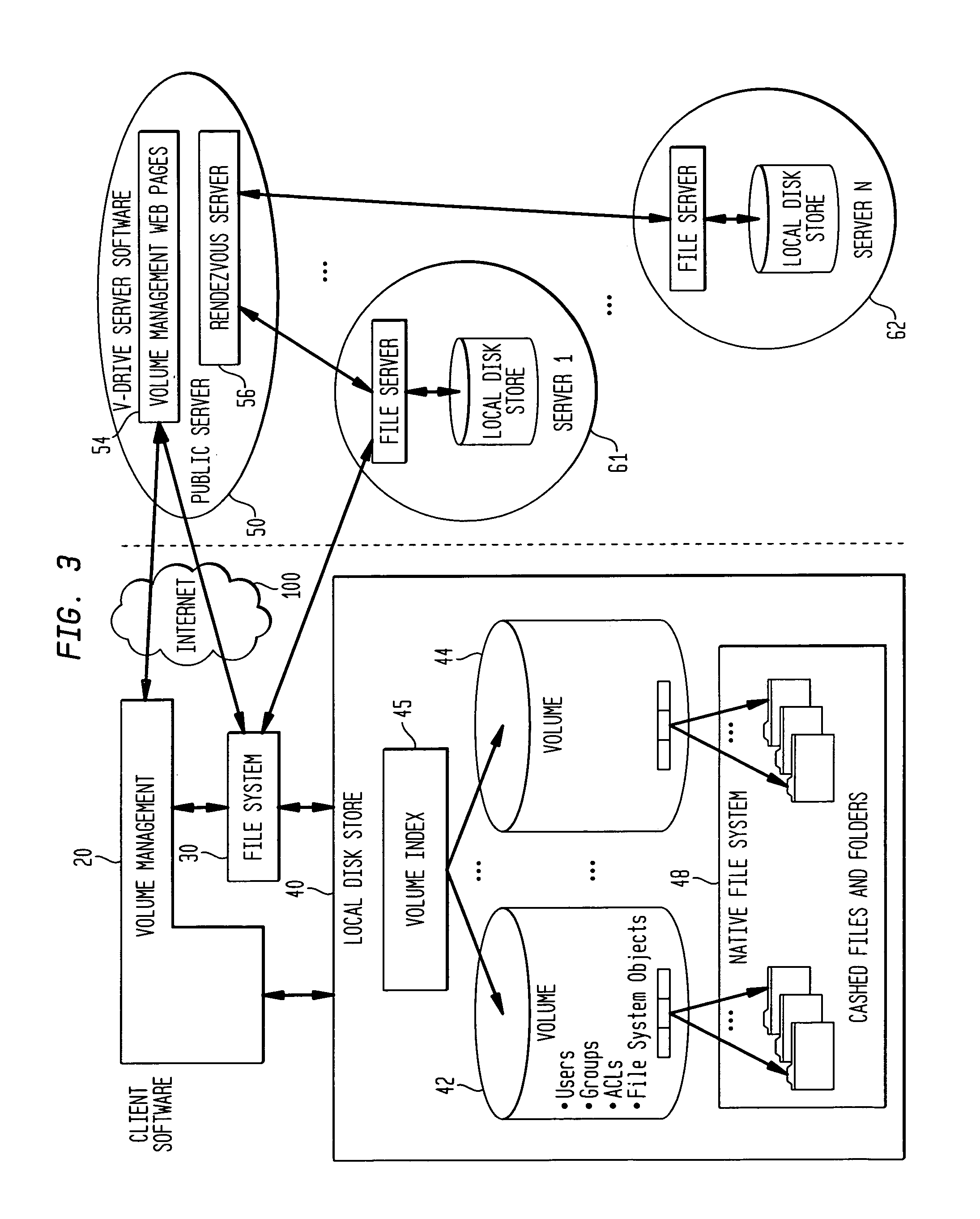
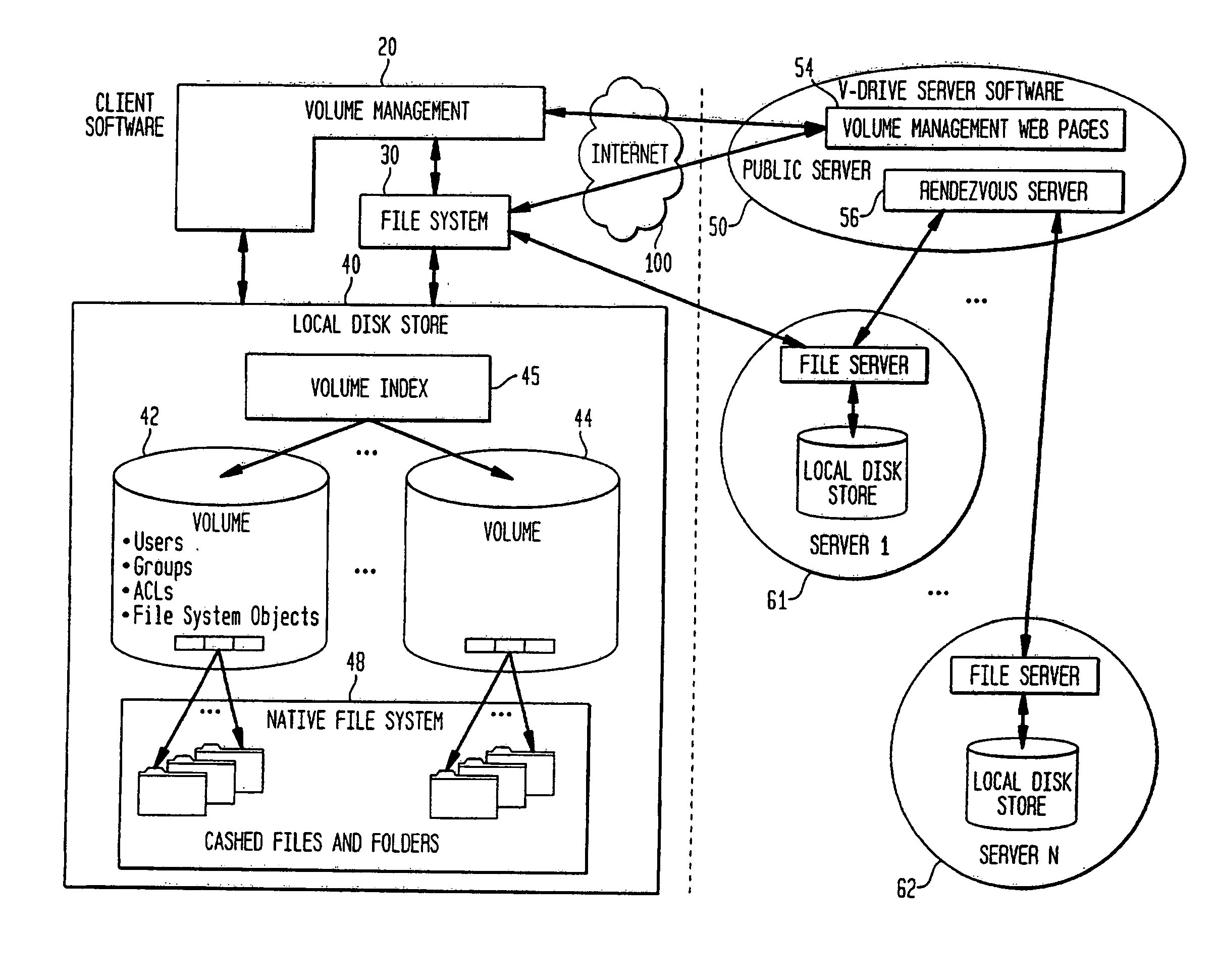
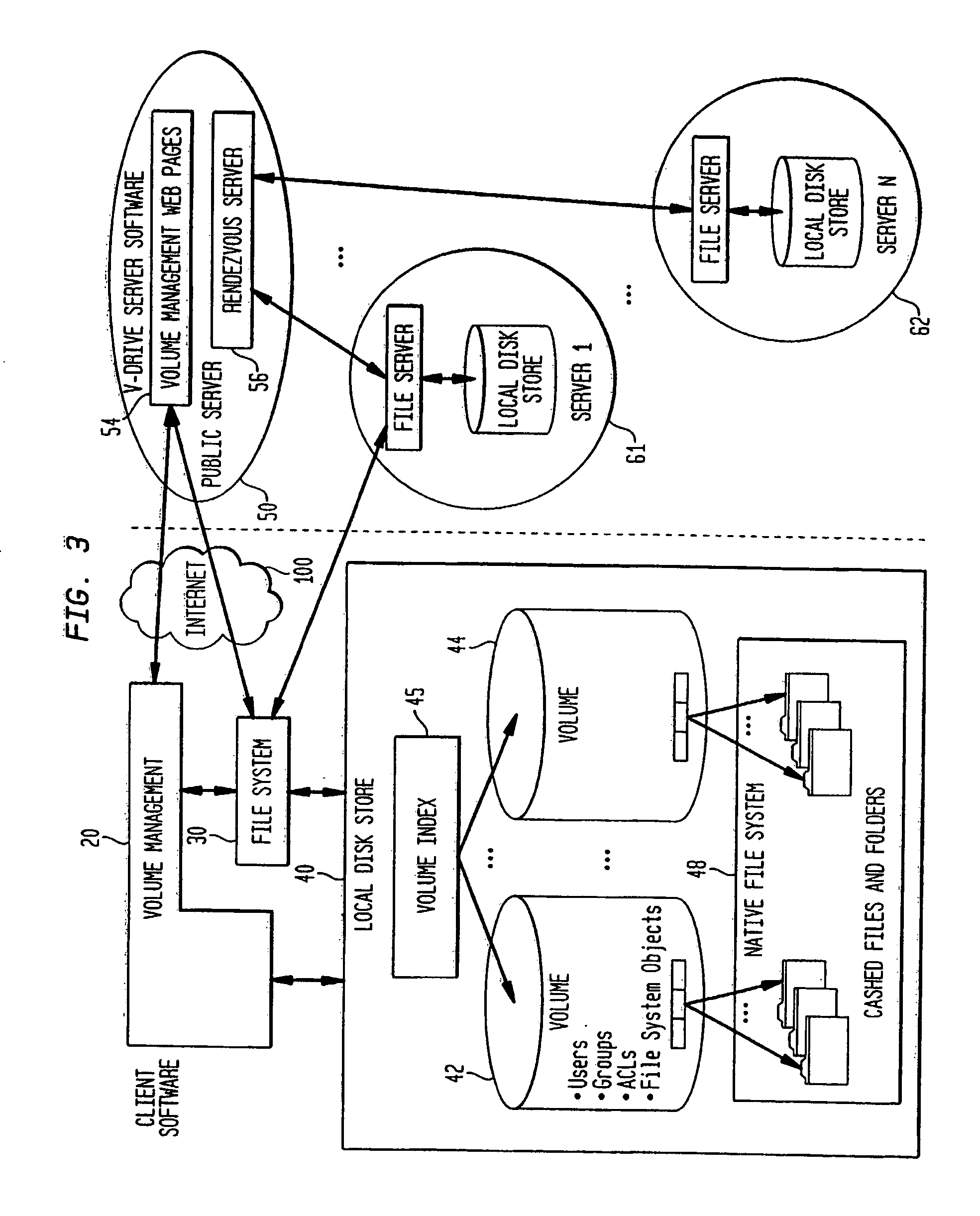
File storage, also called file-level or file-based storage, stores data in a hierarchical structure. The data is saved in files and folders, and presented to both the system storing it and the system retrieving it in the same format.
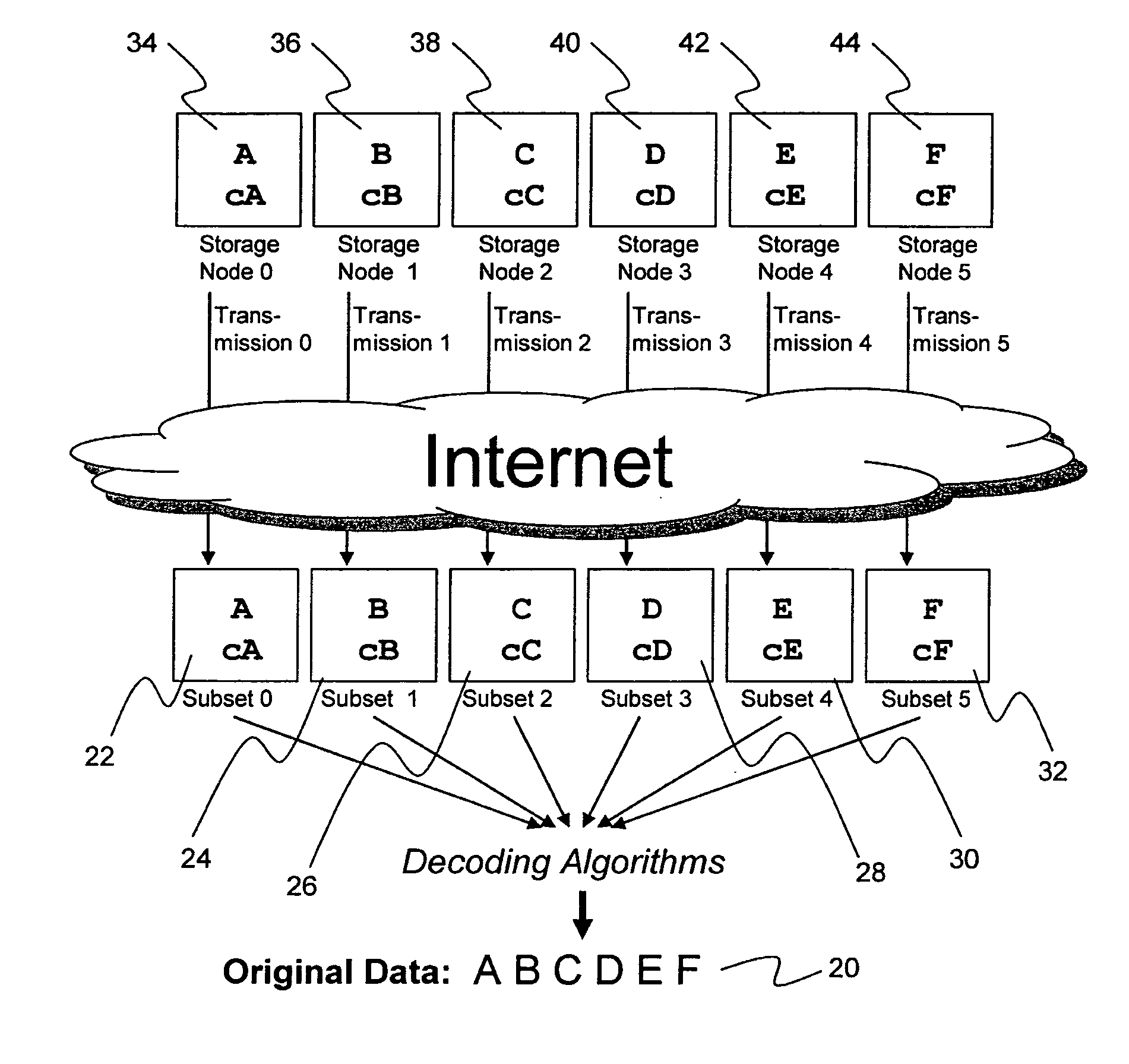
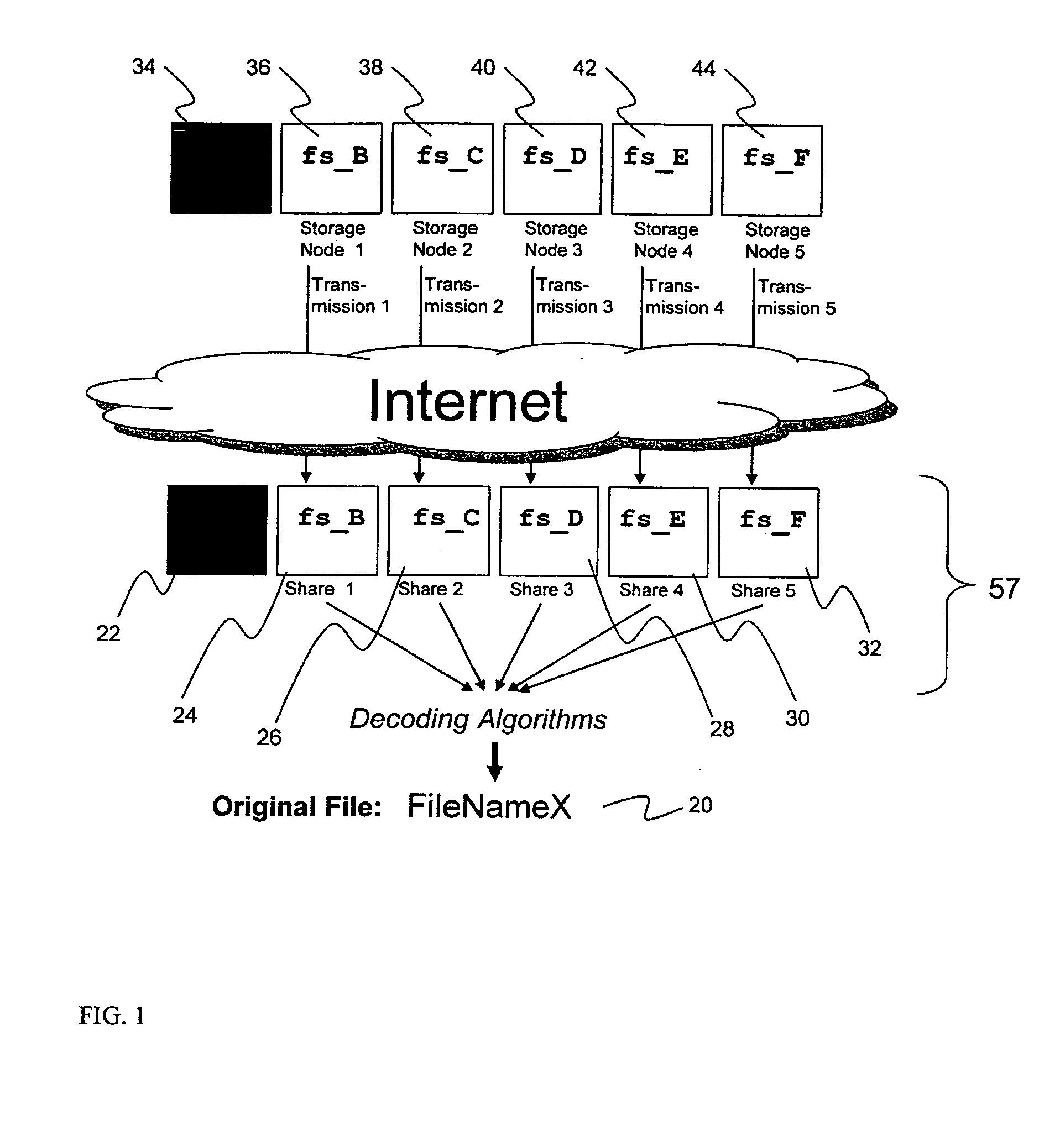
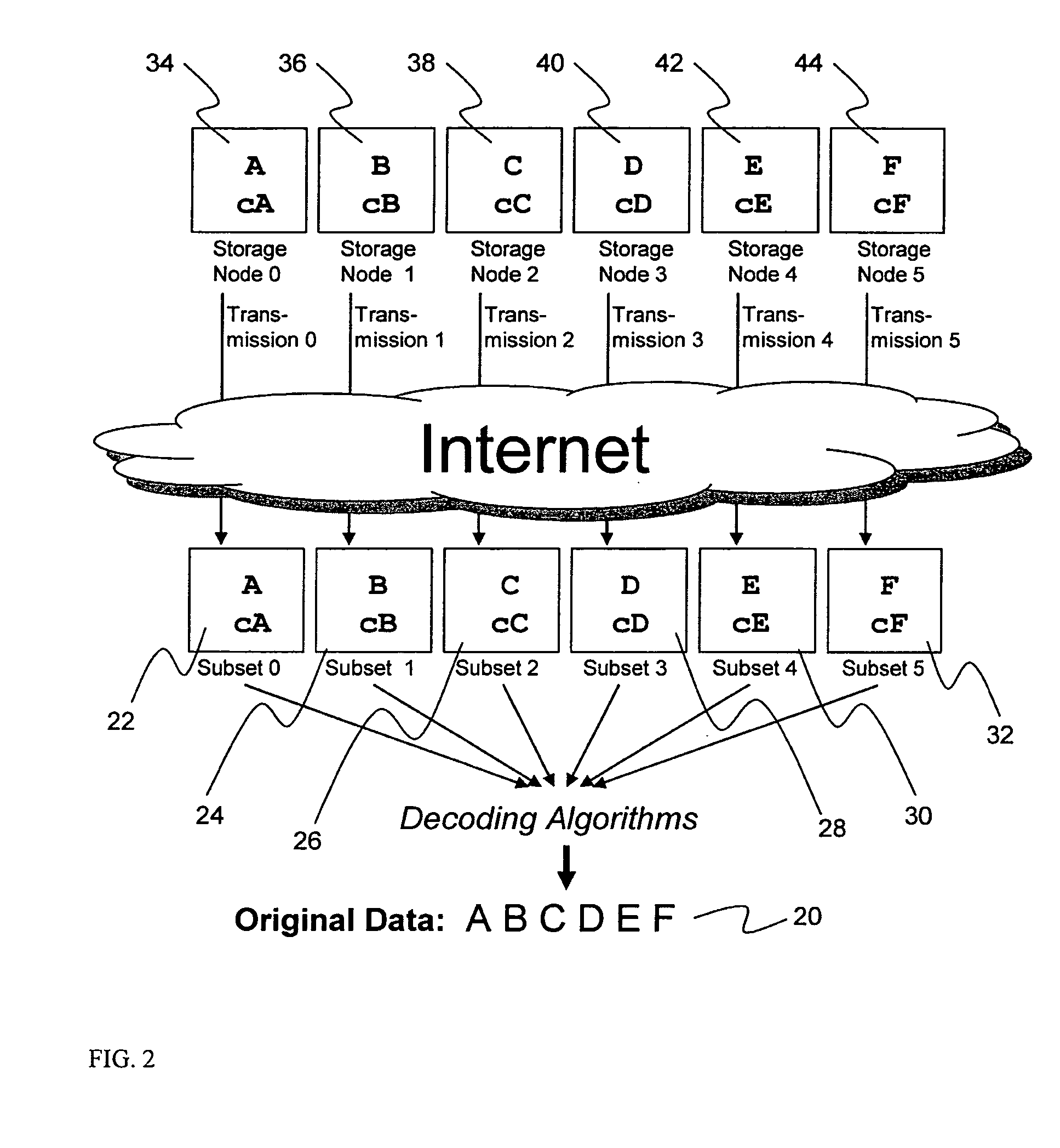
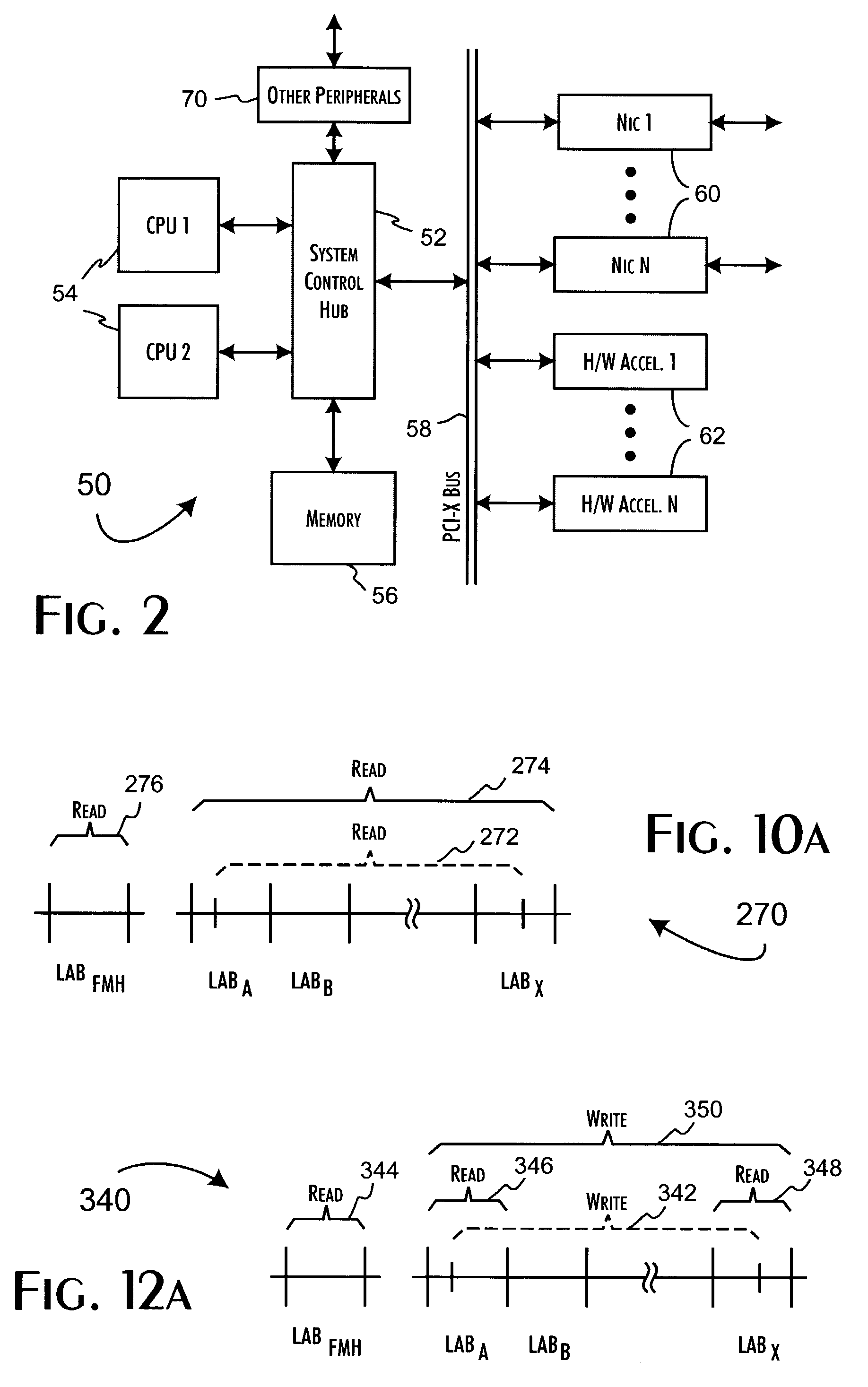
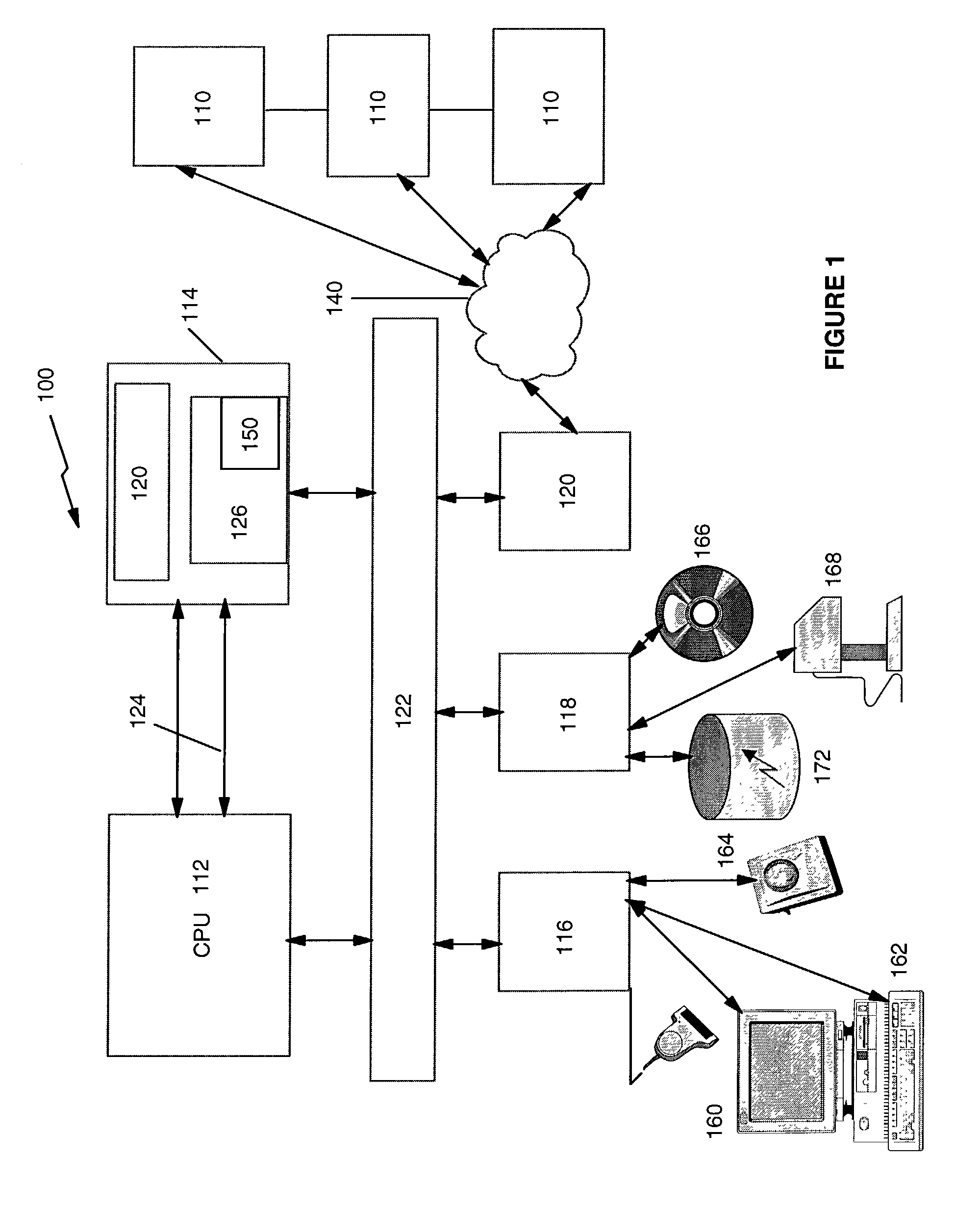
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
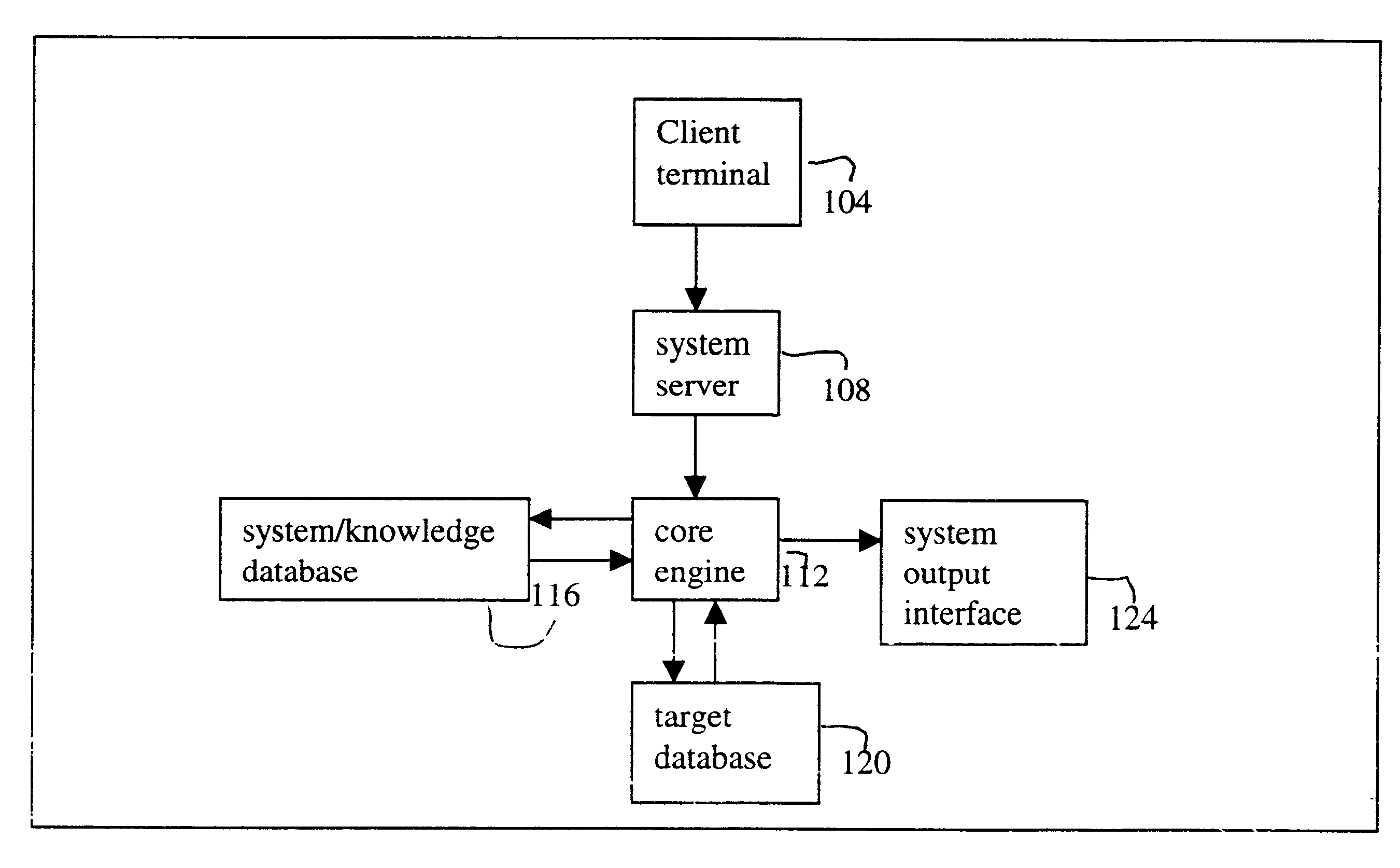
Natural language interface for searching database
InactiveUS6598039B1Data processing applicationsDigital data information retrievalSearch wordsSystems analysis
A system and method for searching information from a database using a natural language. In one embodiment, the system analyzes a natural language search request and converts the search request into one or more search words. The search words are further converted into a string of bytes, and a subset of a target database, referred to as the datasoup, is searched. If there is a match between the bytes and raw data in the datasoup, the searched data is retrieved from the target database. The searched data is then formatted and provided to a user. Optionally, the searched data can be provided to the user unformatted. In another embodiment, the system includes a system server configured to receive a natural language search request, a core engine coupled to the system server and to the target database, and a system database coupled to the core engine, where the core engine accesses the system database to analyze the search request. The system database stores global rules, one or more preference files, and one or more dictionaries, and the preference file stores information about the user.
Owner:GO ALBERT FRANCE
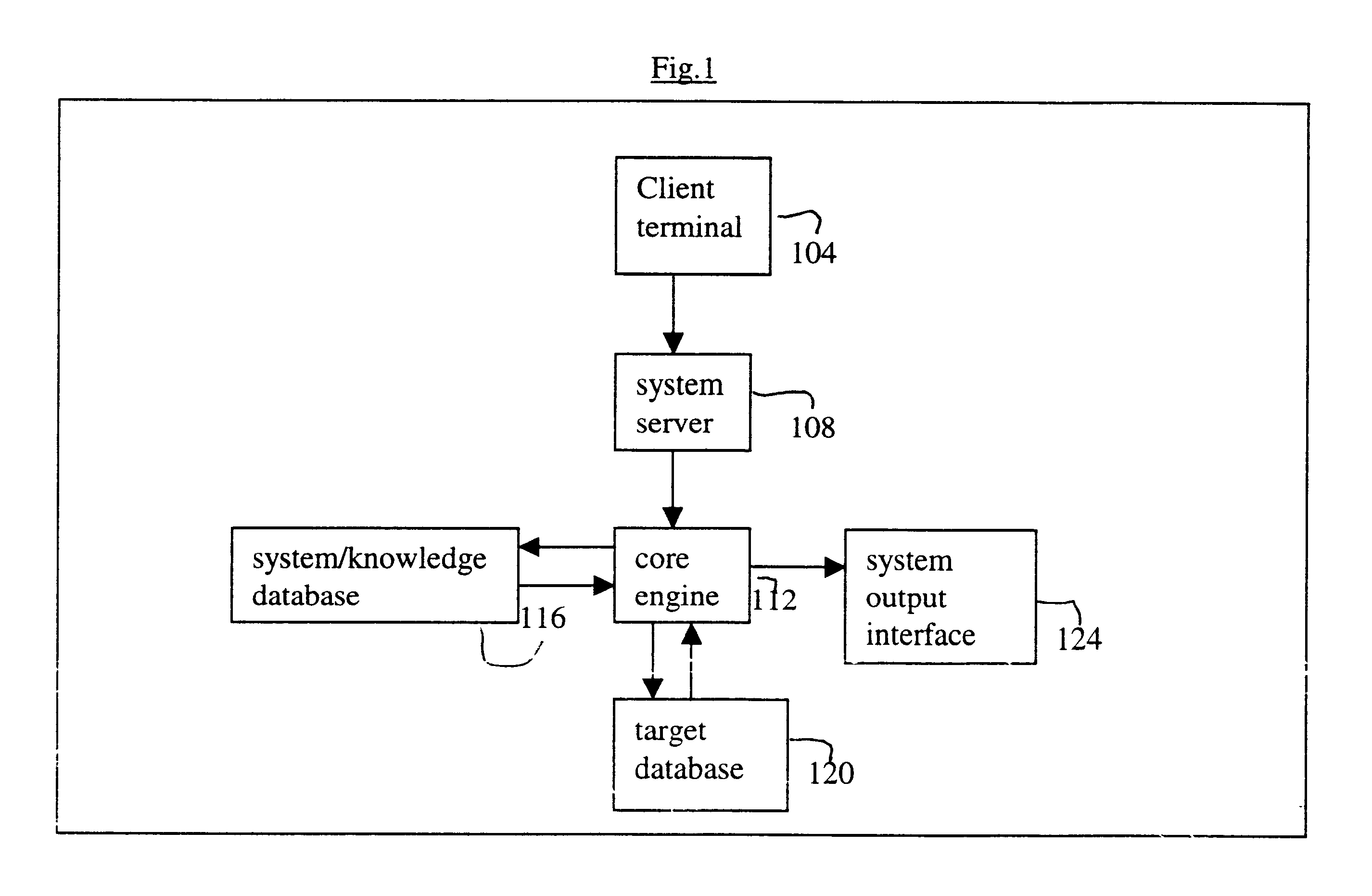
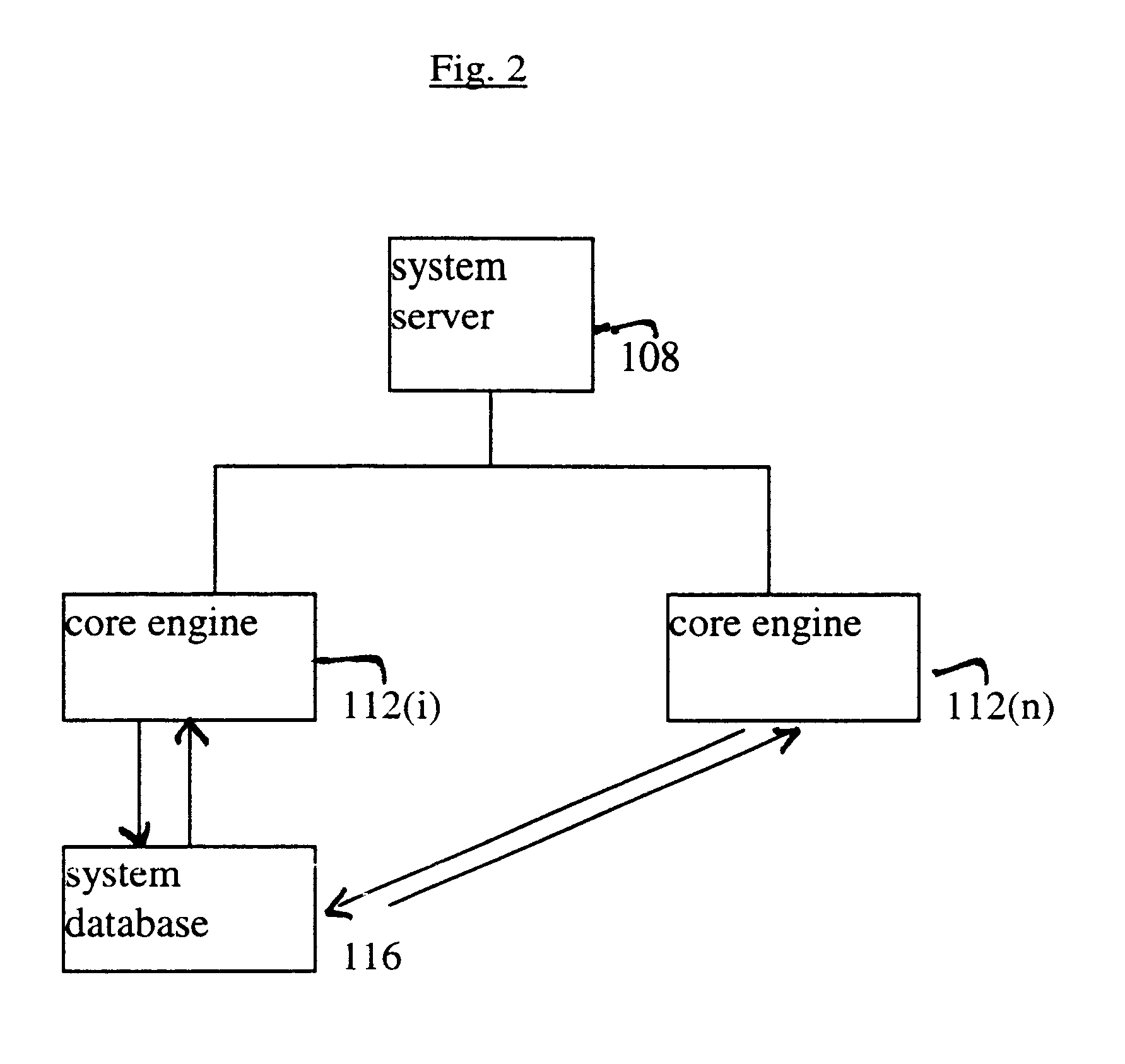
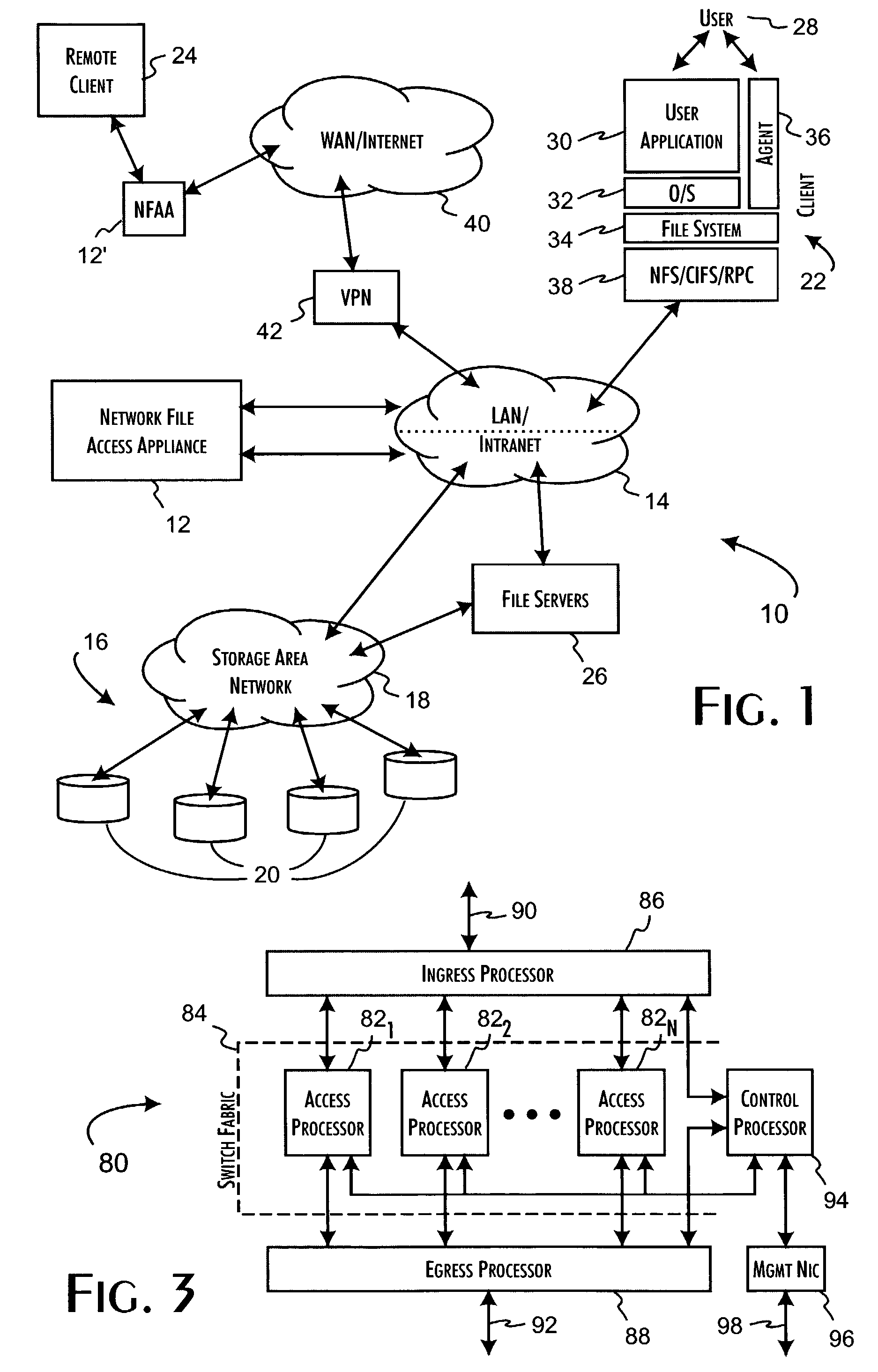
Logical access block processing protocol for transparent secure file storage
InactiveUS7334124B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationComputer hardwareDigital signature
Network data files are secure through the operation of an infrastructure gateway-based network file access appliance. Network file data, corresponding to network pocket payload data, are further reduced to a sequence of data blocks that are secured through any combination of block encryption, compression, and digital signatures. File meta-data, including encryption, compression and block-level digital signatures are persistently stored with the file data, either in-band in the file as stored or out-of-band key as a separately stored file or file policy record. File meta-data is recovered with accesses of the file data to support bidirectional encryption and compression and to detect tampering with the file data by comparison against block-level digital signatures.
Owner:THALES ESECURITY INC
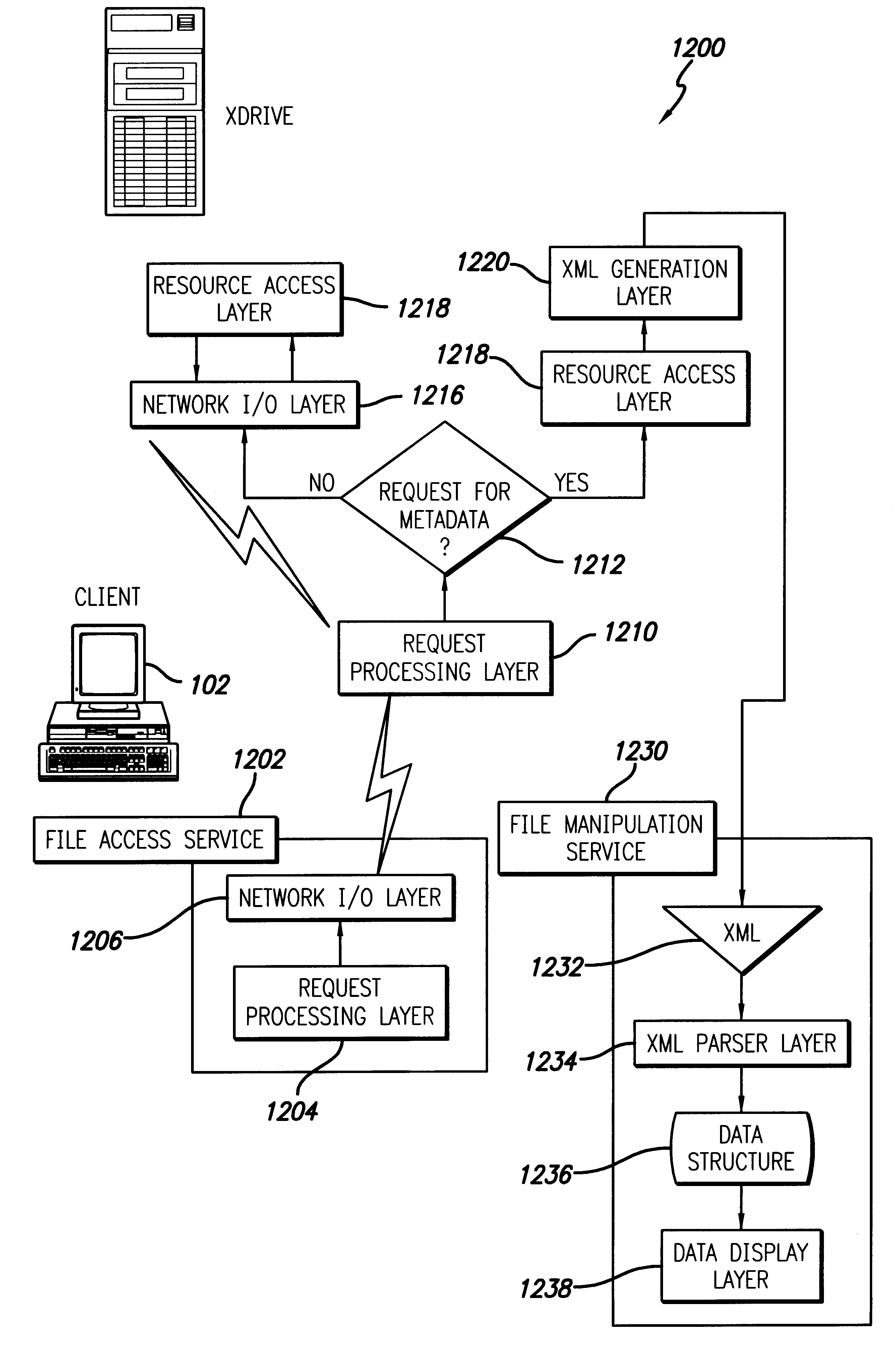
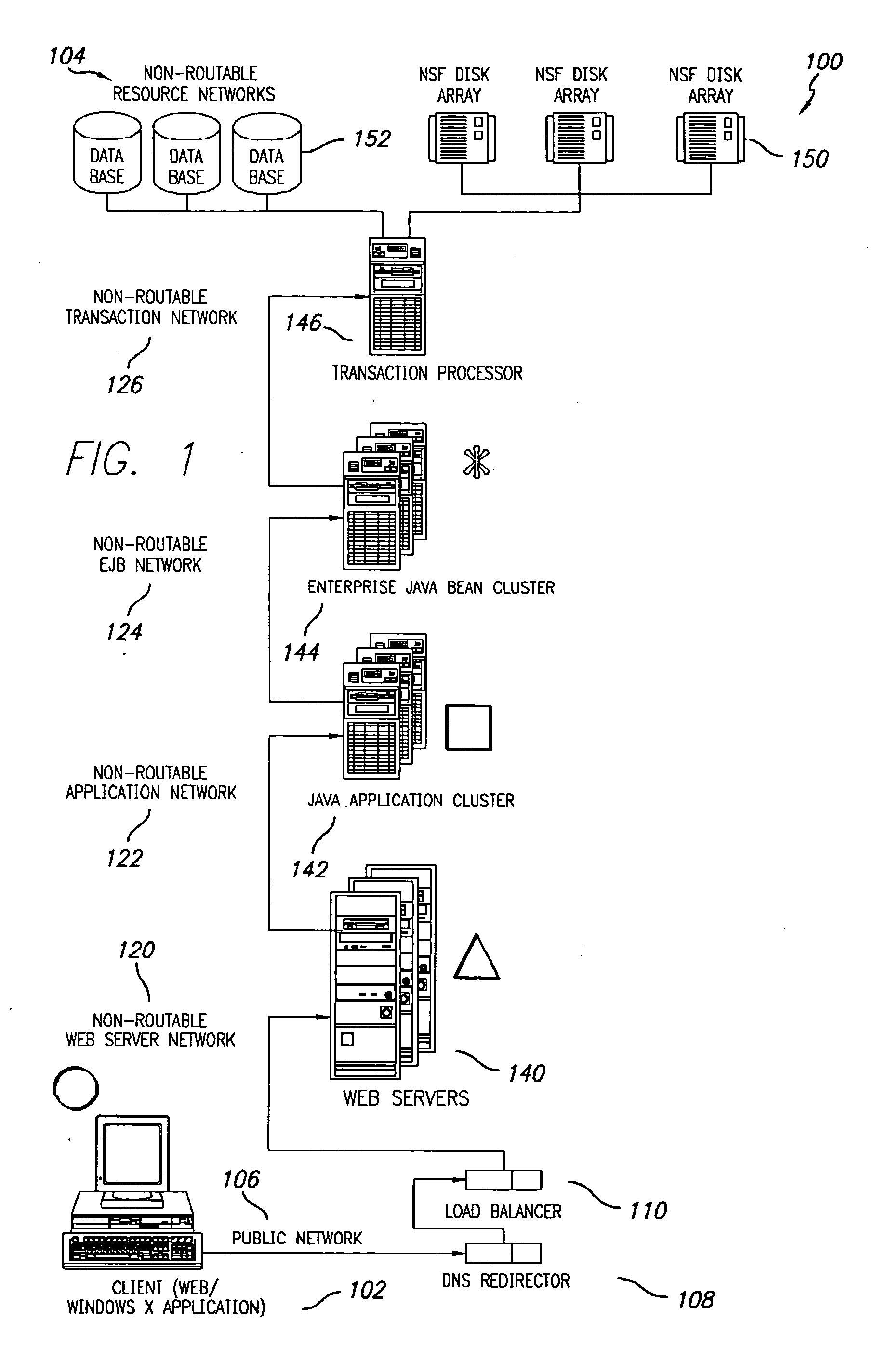
Shared internet storage resource, user interface system, and method
InactiveUS6351776B1Easy to understandData processing applicationsWeb data indexingData streamWeb service
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java(R)-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:TIME WARNER
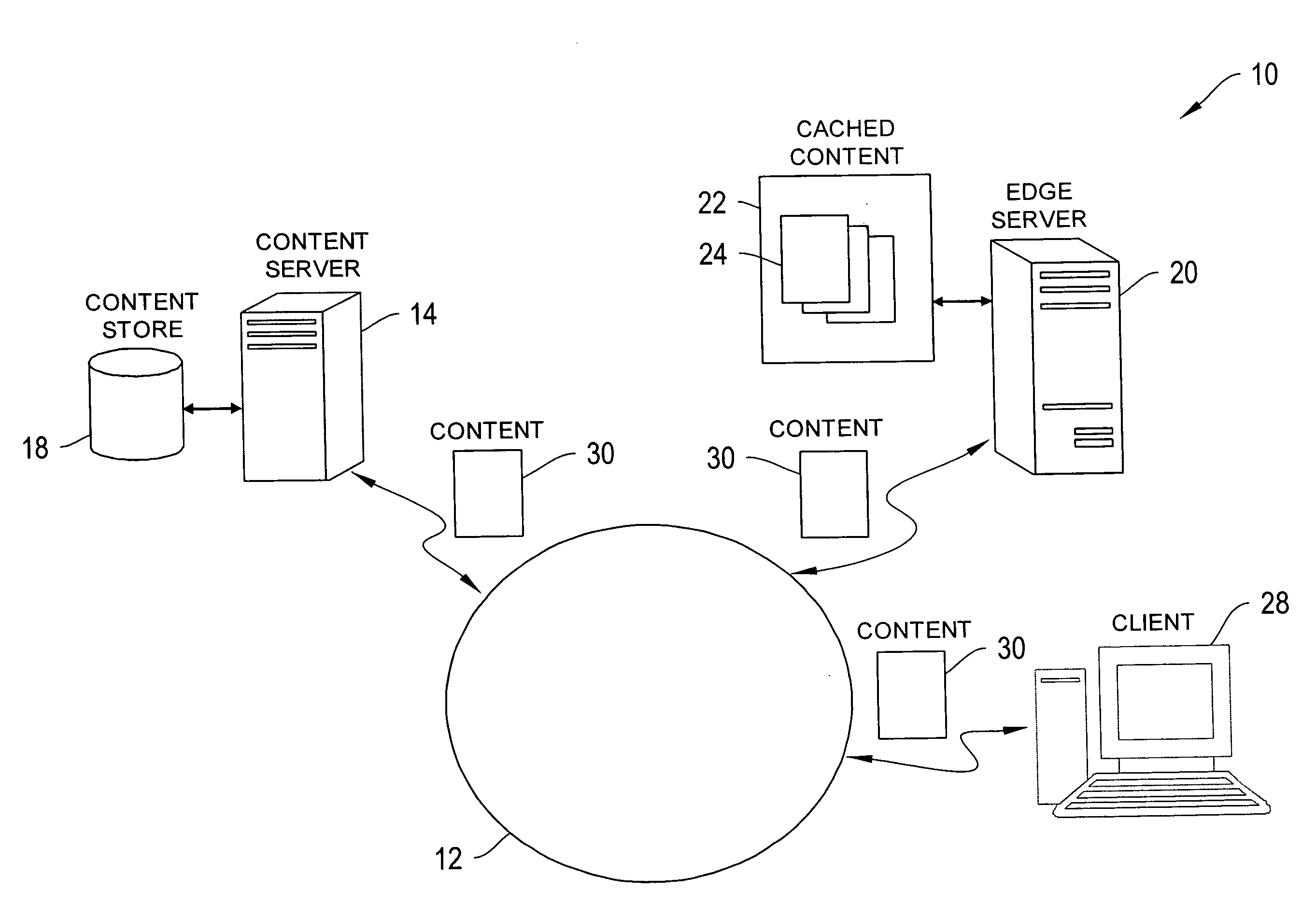
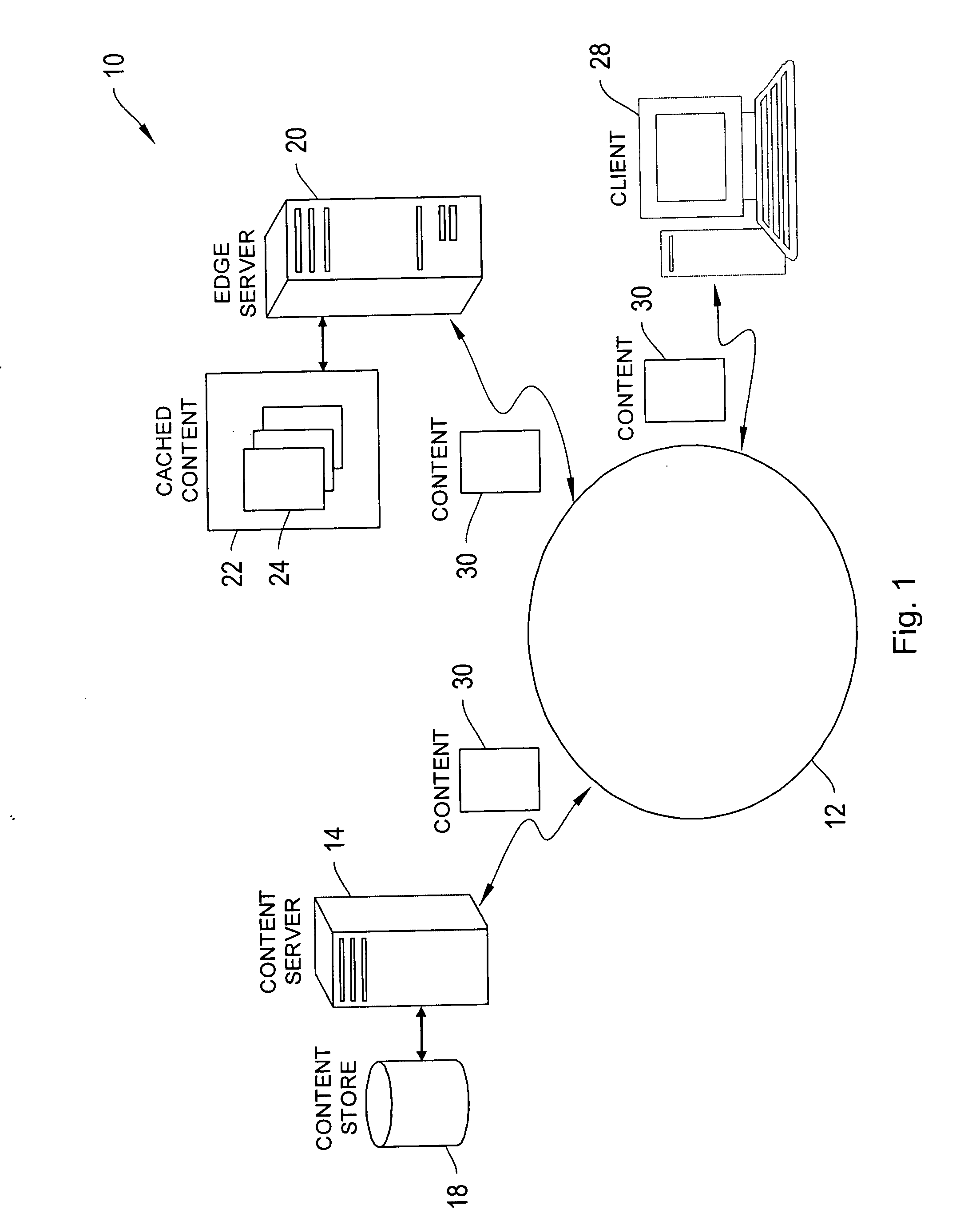
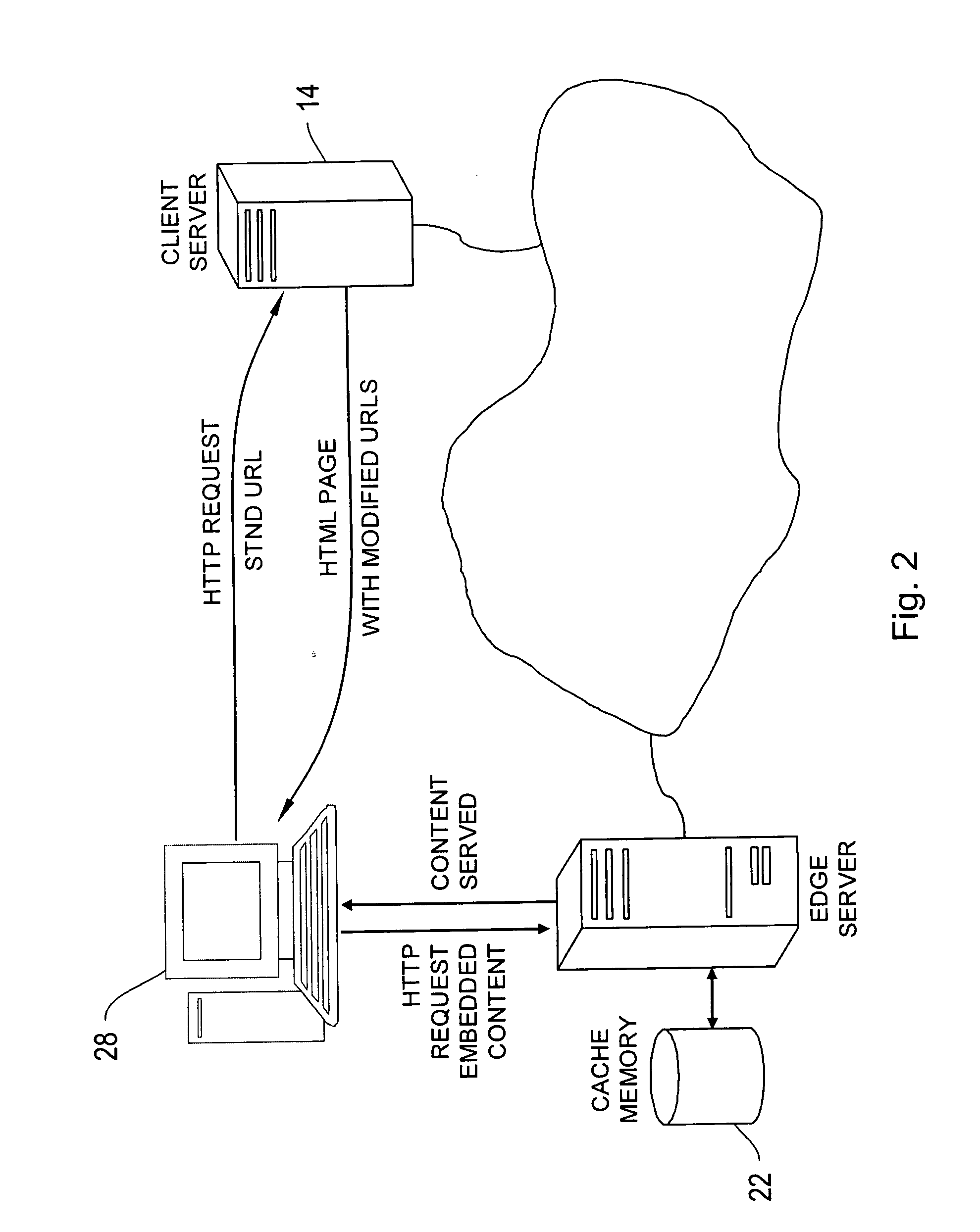
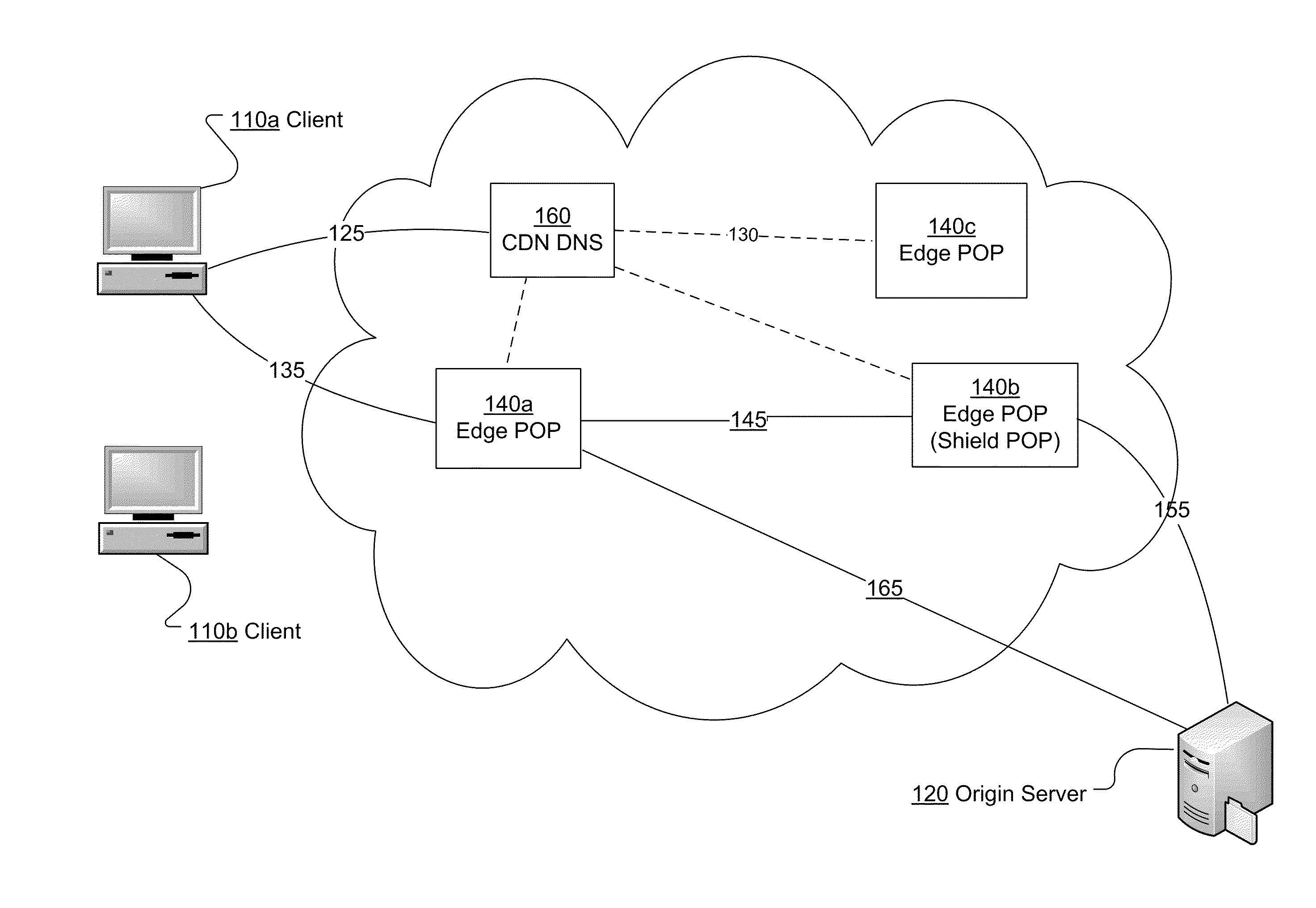
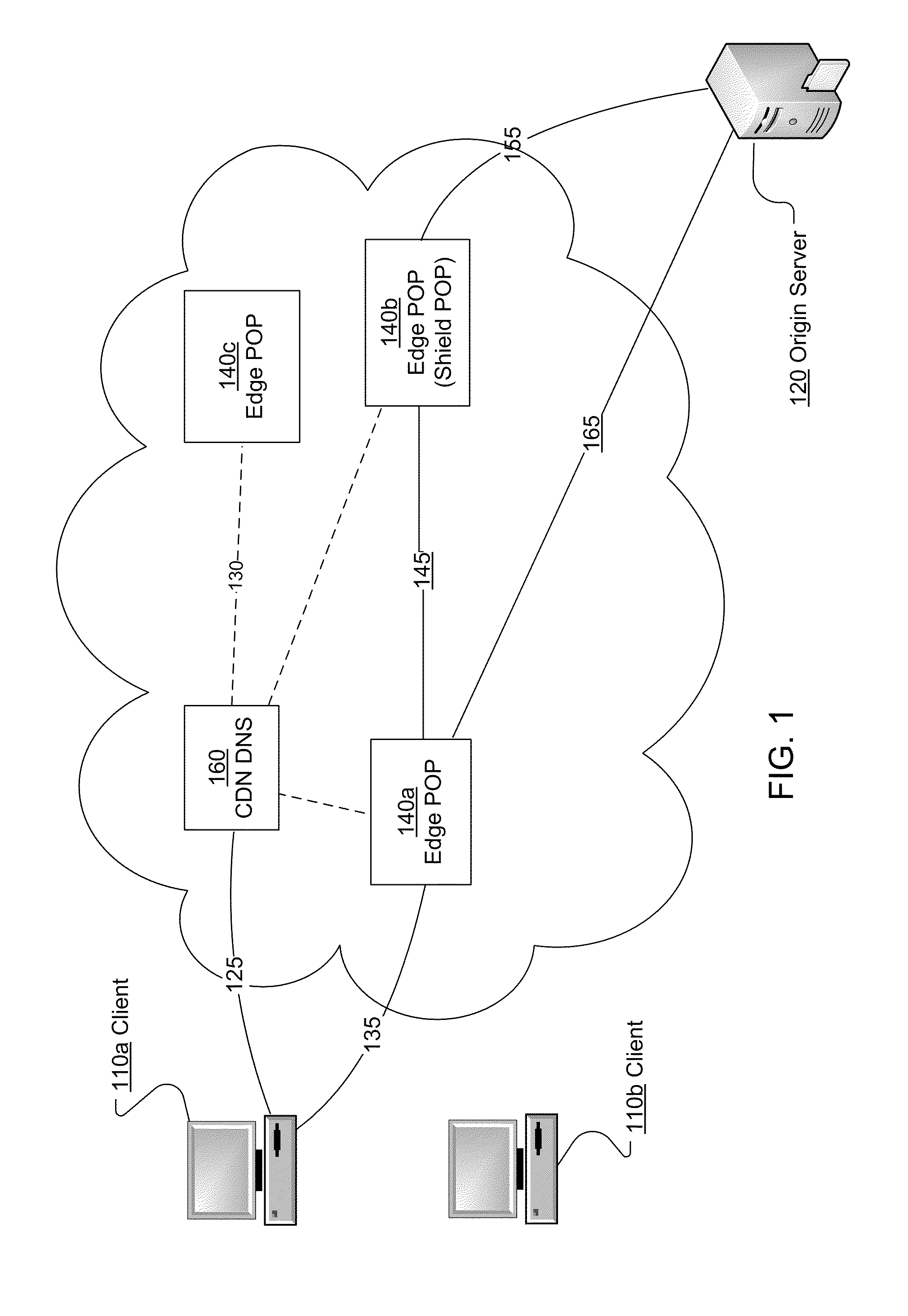
Content network global replacement policy
ActiveUS20090070533A1Efficiently and controllably deliverMemory adressing/allocation/relocationTransmissionEdge serverData store
This invention is related to content delivery systems and methods. In one aspect of the invention, a content provider controls a replacement process operating at an edge server. The edge server services content providers and has a data store for storing content associated with respective ones of the content providers. A content provider sets a replacement policy at the edge server that controls the movement of content associated with the content provider, into and out of the data store. In another aspect of the invention, a content delivery system includes a content server storing content files, an edge server having cache memory for storing content files, and a replacement policy module for managing content stored within the cache memory. The replacement policy module can store portions of the content files at the content server within the cache memory, as a function of a replacement policy set by a content owner.
Owner:EDGIO INC
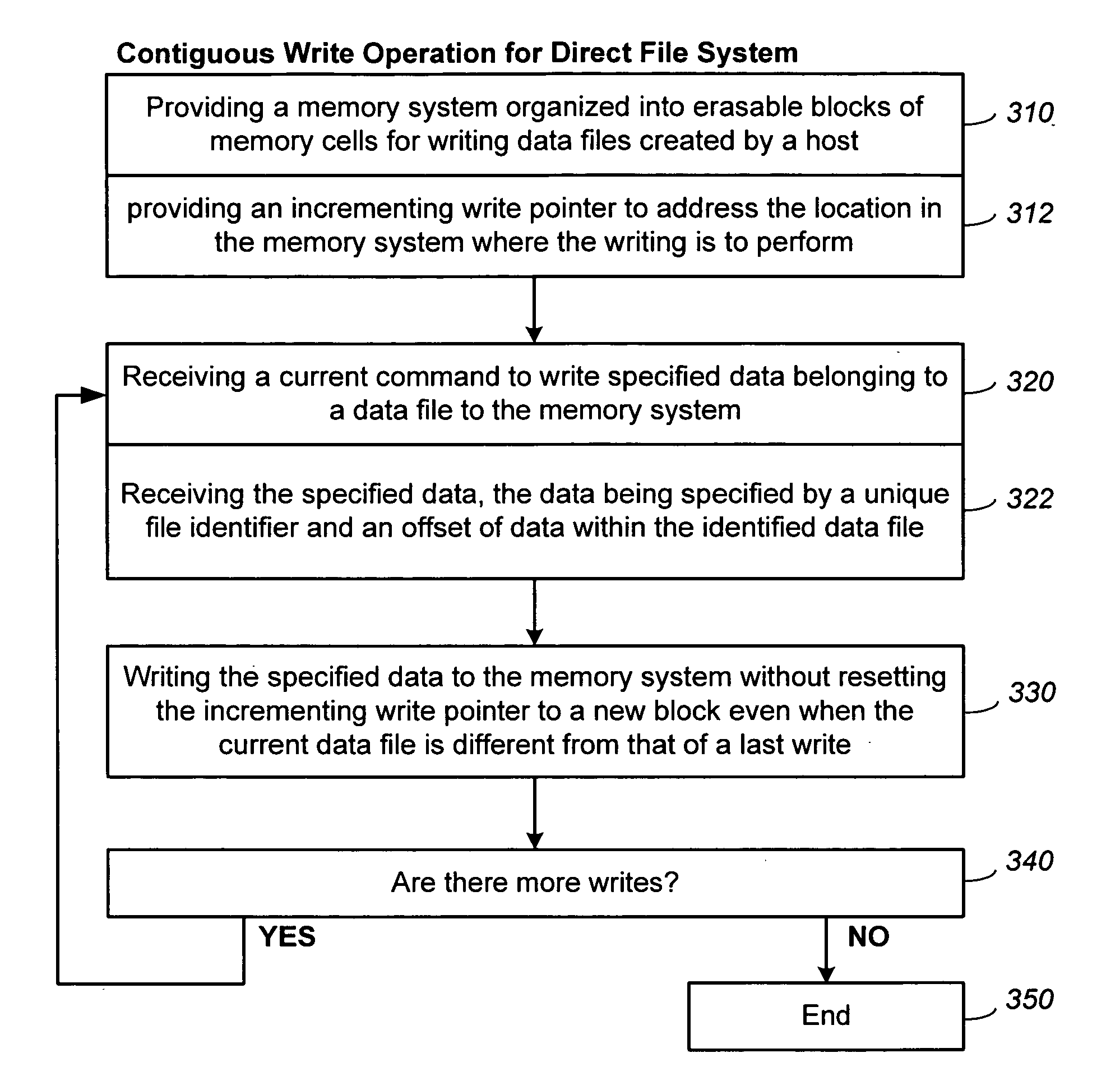
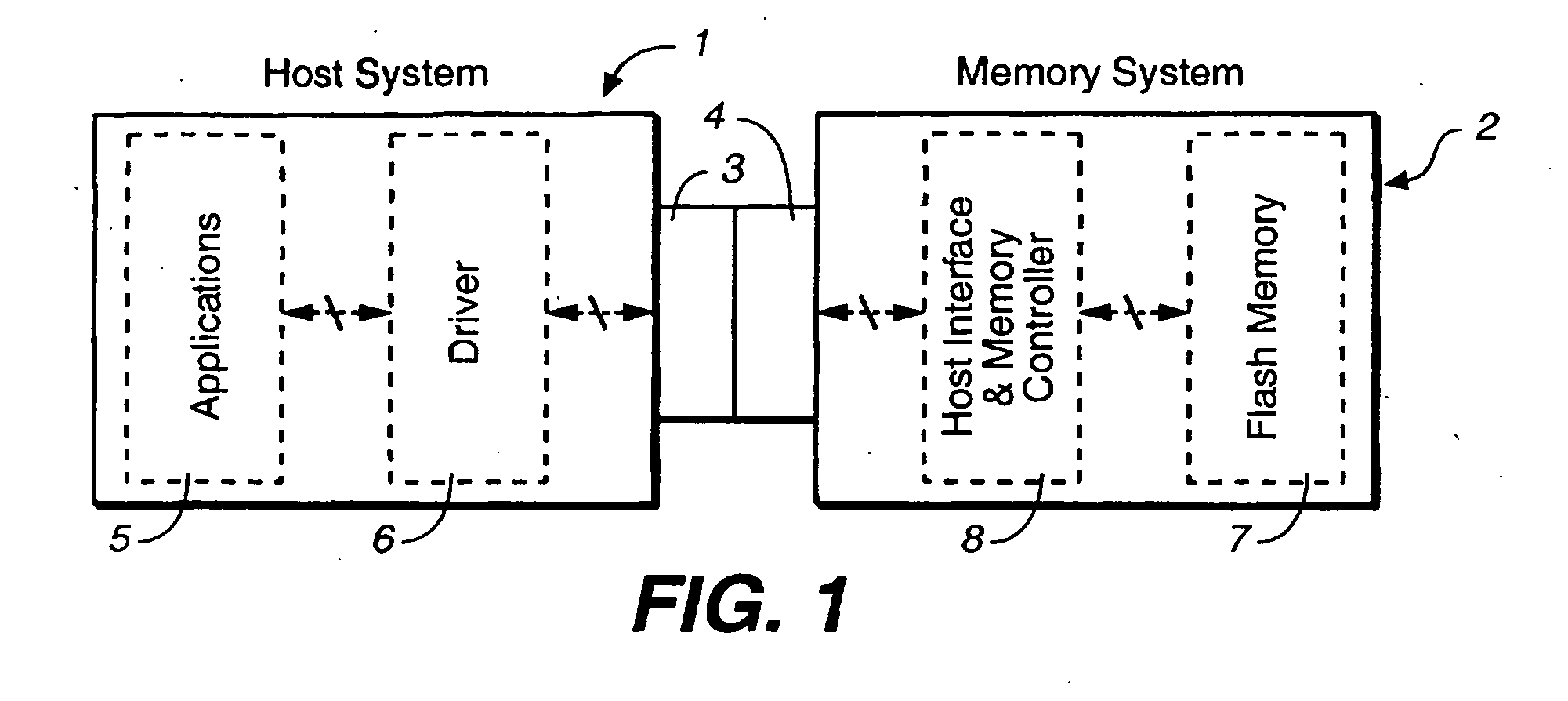
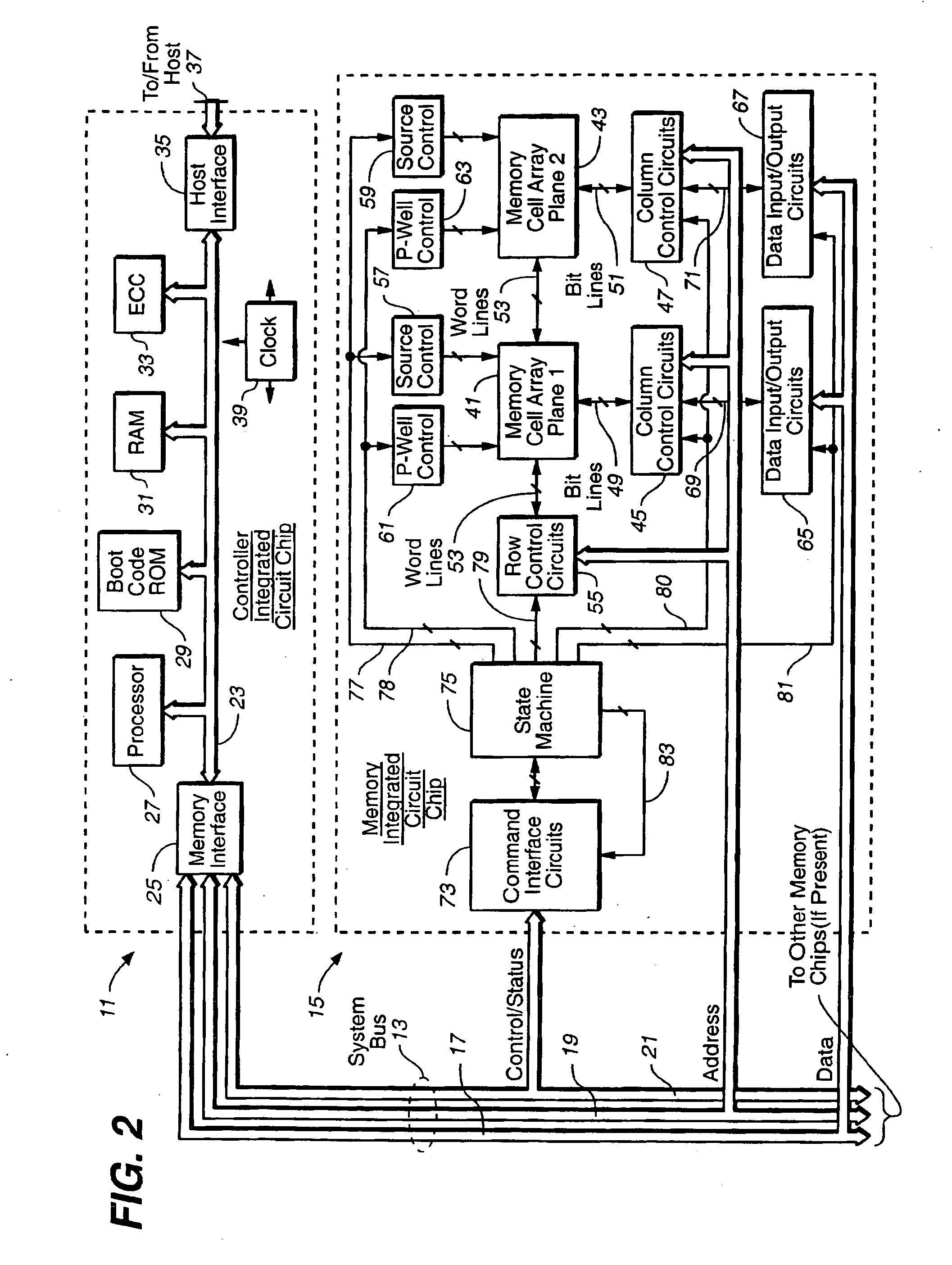
Methods for memory allocation in non-volatile memories with a directly mapped file storage system
InactiveUS20070156998A1Improve performanceEfficient packagingMemory architecture accessing/allocationMemory systemsData compressionWrite pointer
In a memory system with a file storage system, a scheme for allocating memory locations for a write operation is to write the files substantially contiguously in a memory block one after another rather than to start a new file in a new block. In this way, they are more efficiently packed into the blocks by being written contiguously one after another. In a preferred embodiment, an incrementing write pointer points to the write location in memory for the next data for a file, which is independent of the offset address of the data within the file. When a current write block becomes filled with file data, an erased block is allocated, and the write pointer is moved to this block. Similarly a relocation pointer is used for data relocation during garbage collection or data compaction operations.
Owner:SANDISK TECH LLC
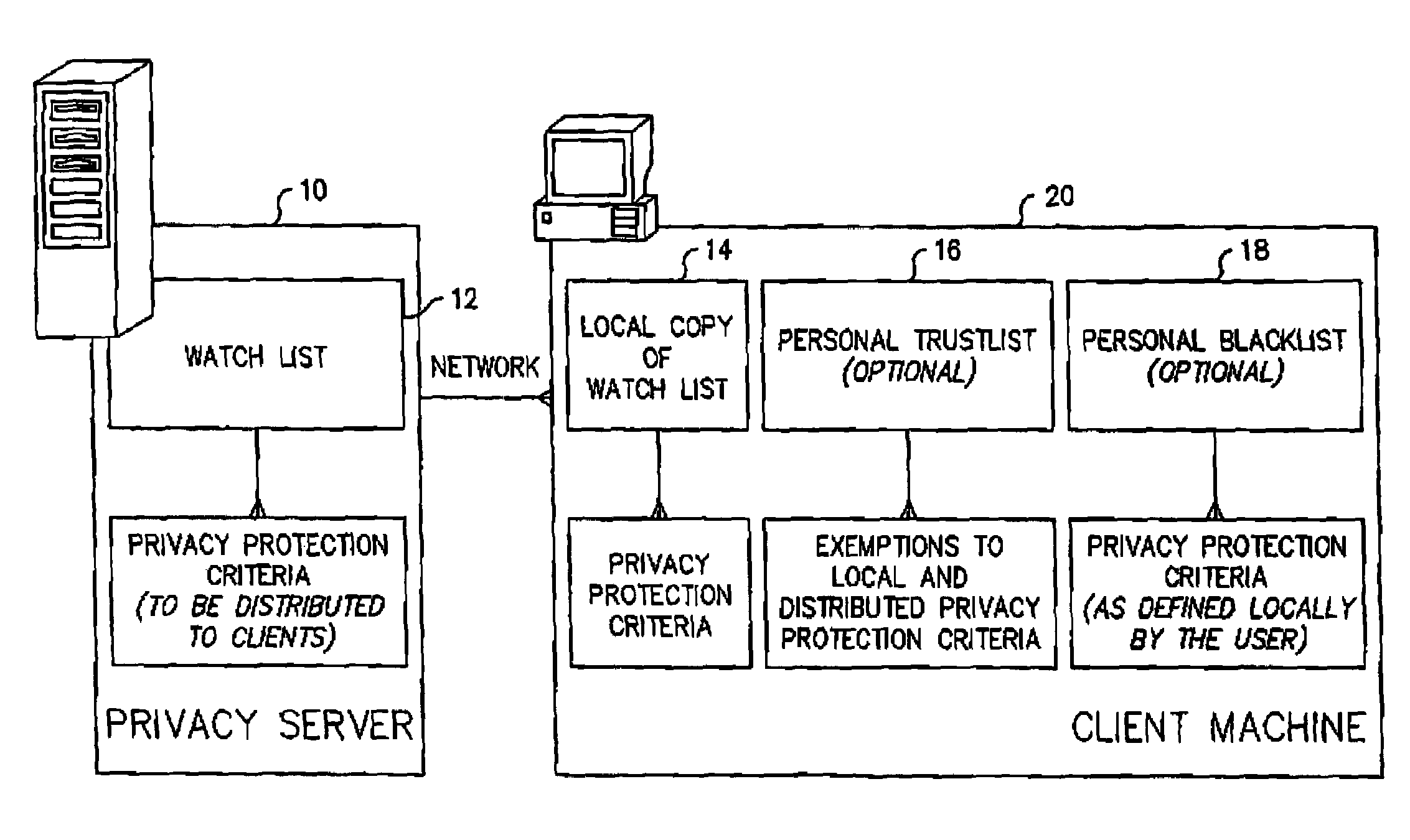
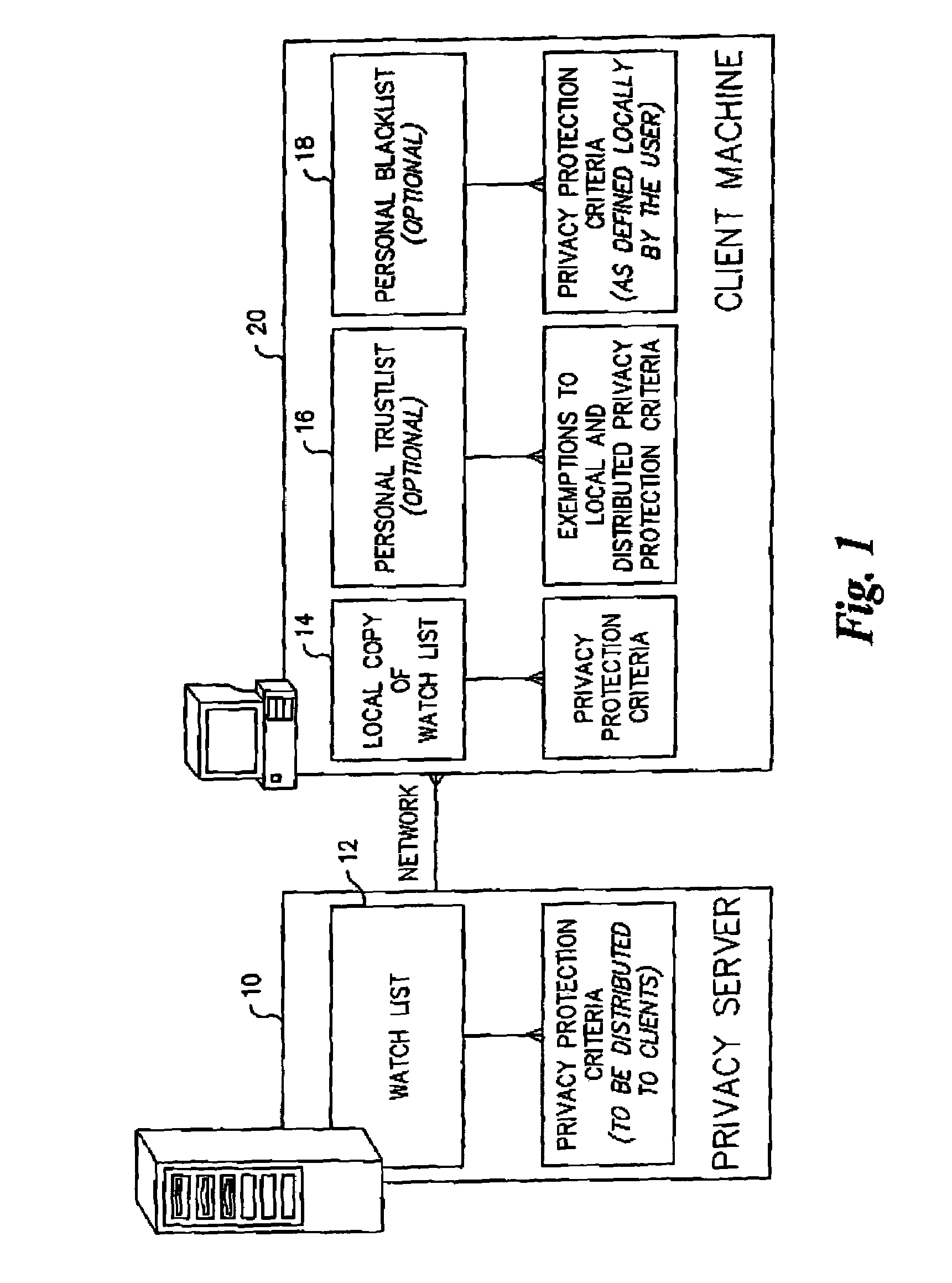
System and method for network administration and local administration of privacy protection criteria
InactiveUS7603356B2Computer security arrangementsSpecial data processing applicationsClient-sideContinuous mode
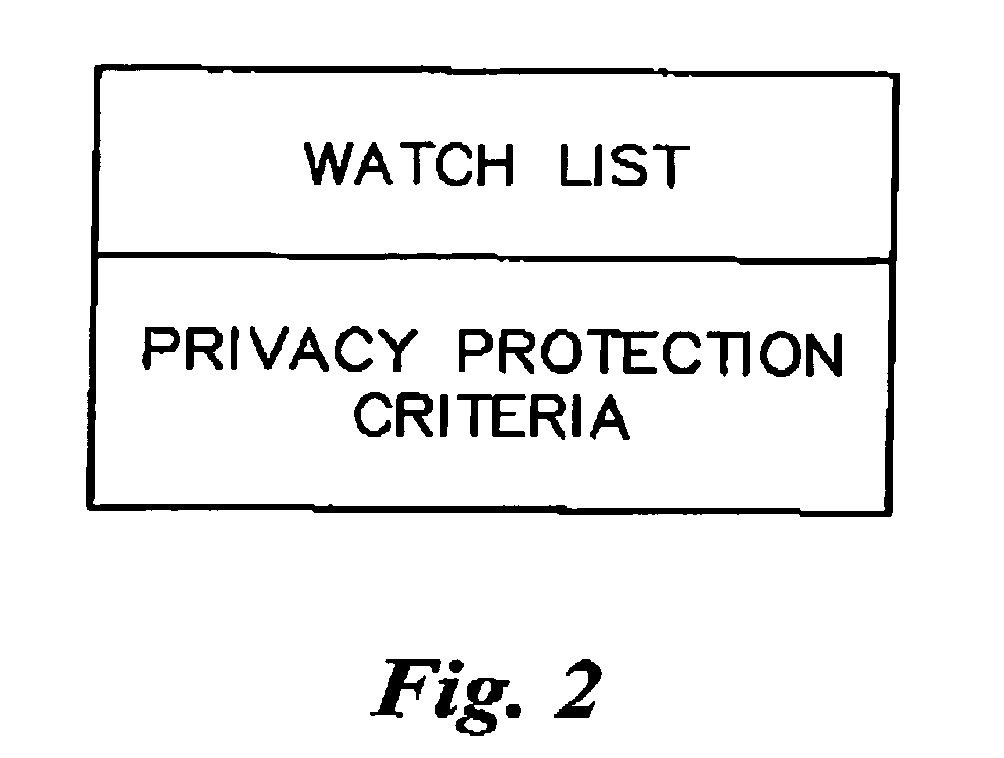
Cookie files received from cookie file sources (e.g., Internet websites) are screened based upon the recommendations of a service provider which downloads privacy protection criteria in the form of a “watch list” to a subscriber's client machine. A user-friendly interface allows the subscriber to optionally modify the watch list prior to it being used at the subscriber's client machine by assigning known cookie file sources to either a “trustlist” or a “blacklist.” A “composite list” is then generated and used by the client machine to screen cookie files. The subscriber receives updates from the service provider on either a periodic or “as-needed” basis using a “quick update algorithm.” A “privacy scanning algorithm” runs on the client machine and has two different modes of operation. The first is a continuous mode where unwanted cookie files are blocked from being stored at the client machine. The second is a periodic mode where the client machine is “scrubbed” of unwanted cookie files according to the privacy protection criteria.
Owner:ASCENTIVE
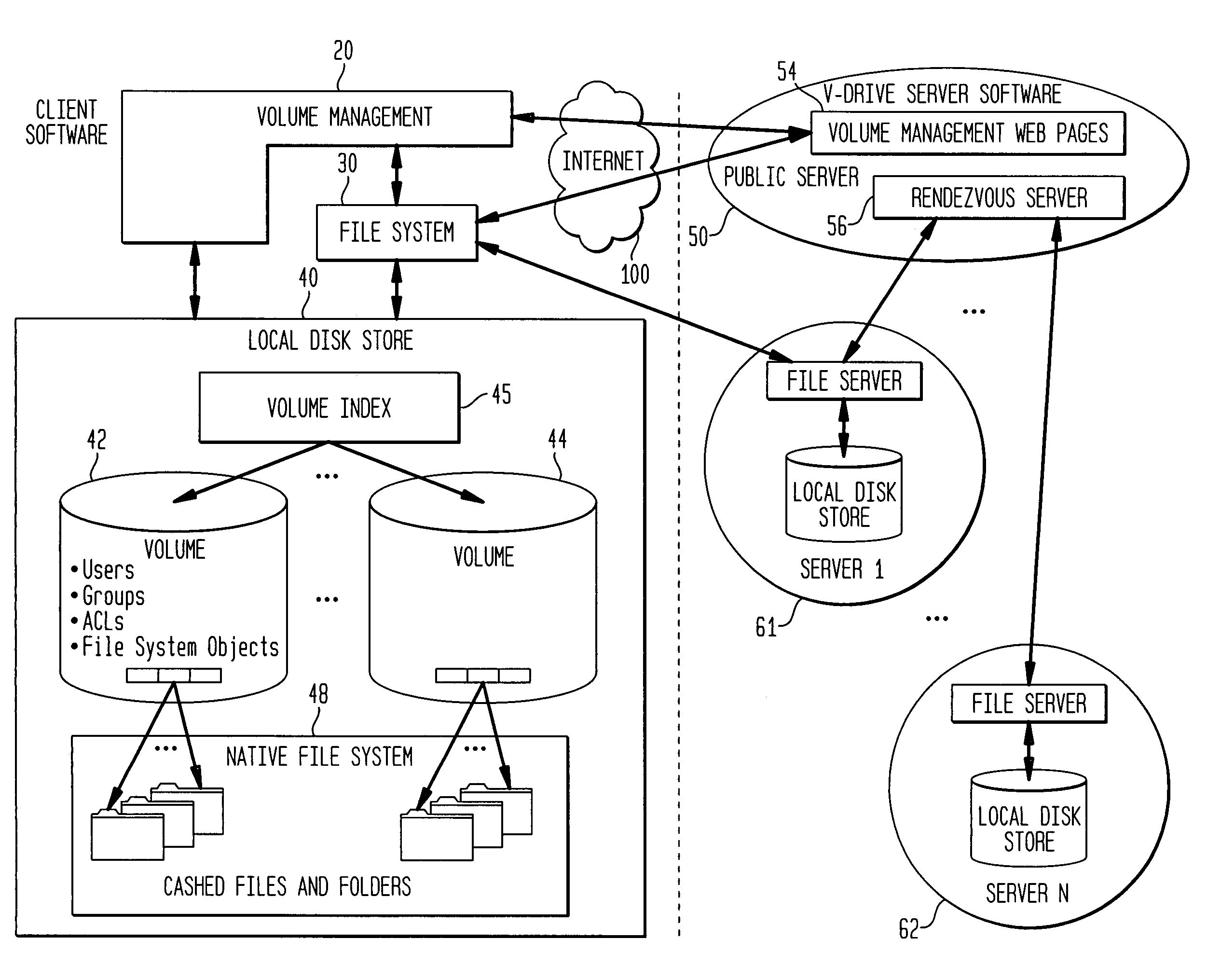
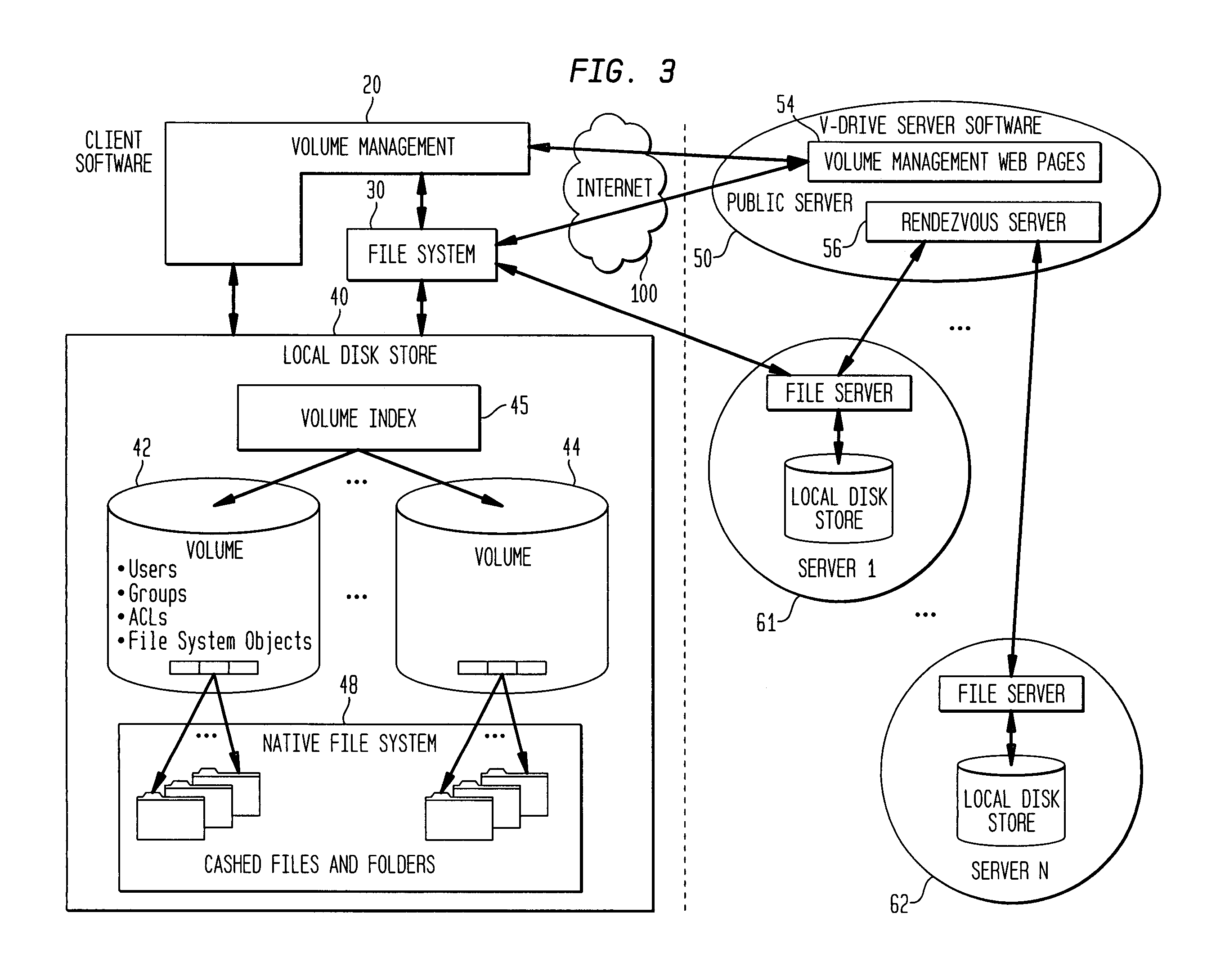
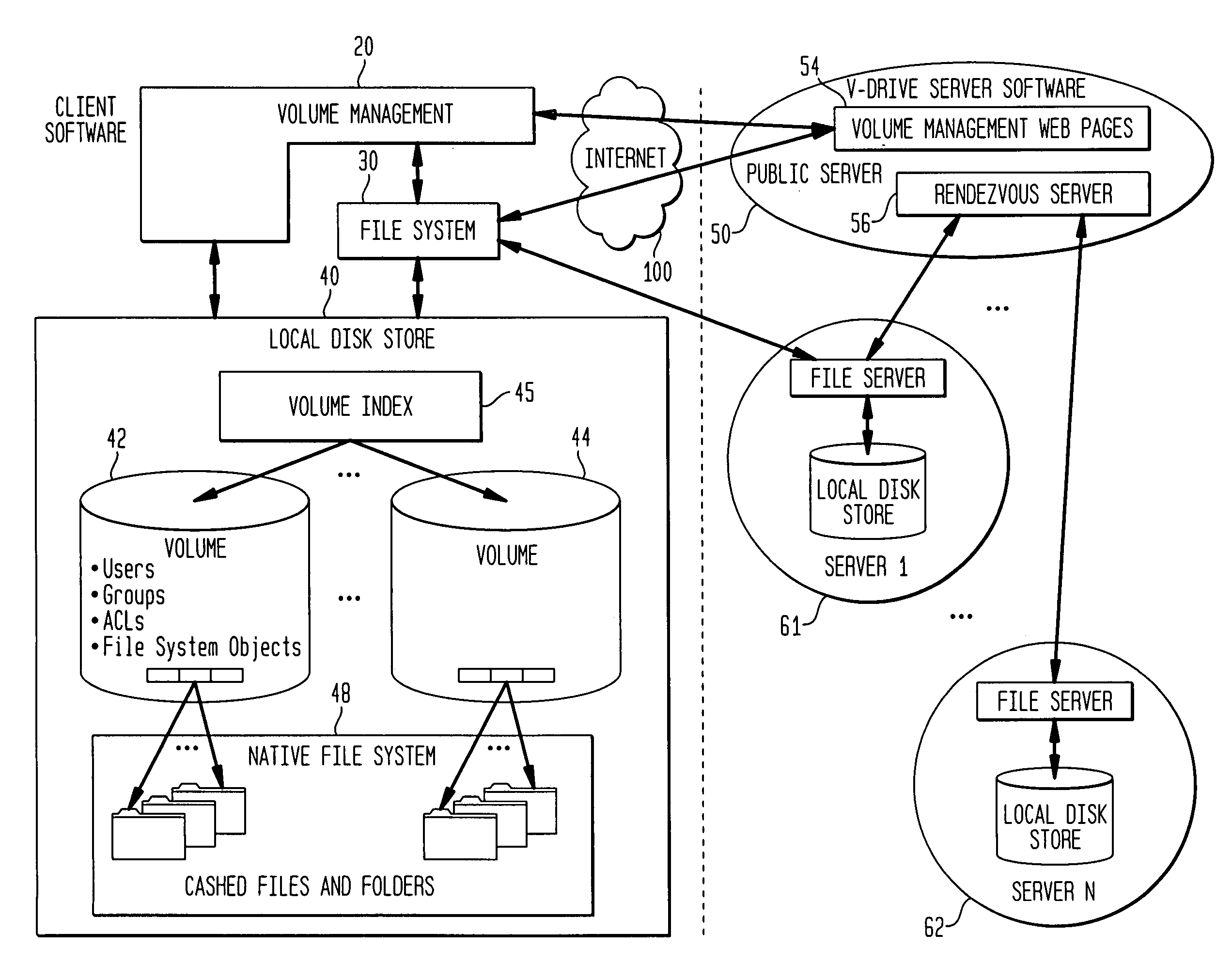
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
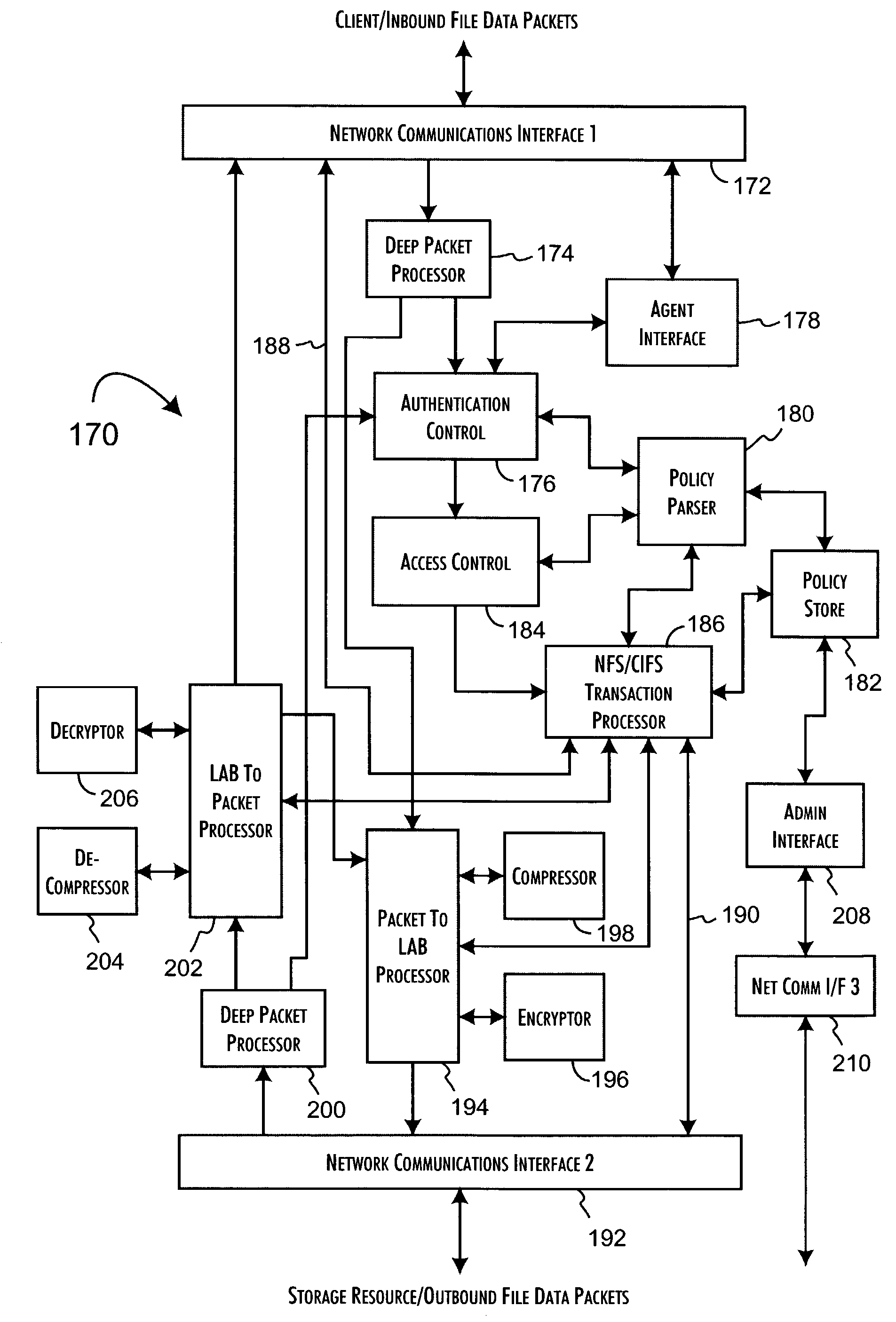
Handling of malware scanning of files stored within a file storage device of a computer network
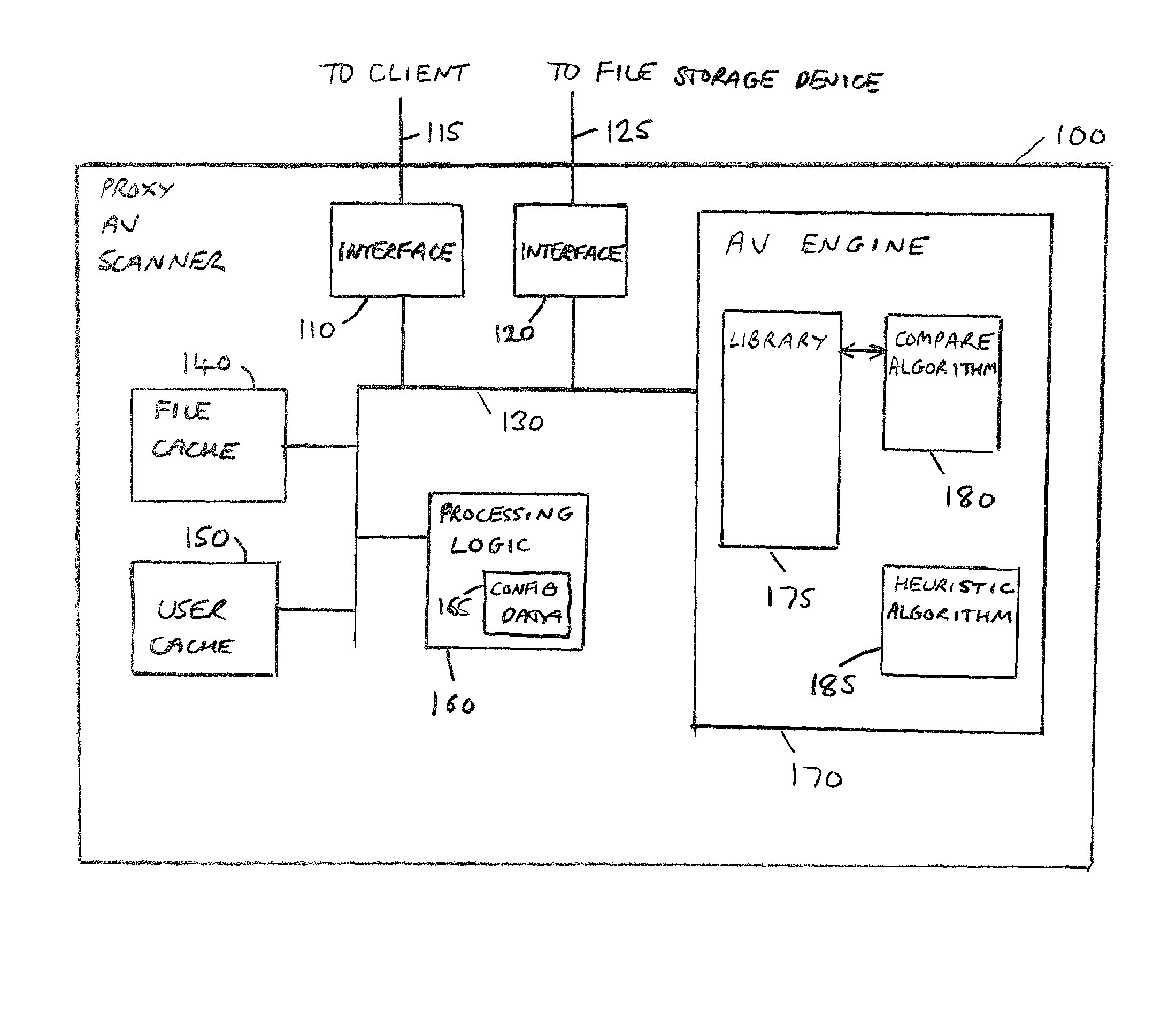
InactiveUS7093002B2Reduce the possibilityCost effectiveMemory loss protectionError detection/correctionOperational systemLaser scanning
The present invention provides a load balancing device, computer program product, and method for balancing the load across a plurality of proxy devices arranged to perform malware scanning of files stored within a file storage device of a computer network. The computer network has a plurality of client devices arranged to issue access requests using a dedicated file access protocol to the file storage device in order to access files stored on the file storage device. The load balancing device is arranged so as to intercept access requests issued to the file storage device, and comprises a client interface for receiving an access request issued to the file storage device using the dedicated file access protocol. Further, the load balancing device comprises load balancing logic for applying a predetermined load balancing routine to determine to which proxy device to direct the received access request, and a proxy device interface for sending the access request to the proxy device determined by the load balancing logic, each proxy device being coupled to the file storage device. This enables a very efficient system to be developed for performing malware scanning of files stored within the file storage device, whilst enabling that system to be developed independently of the particular file storage device being used in the computer network, or the operating system being run on that file storage device.
Owner:MCAFEE LLC
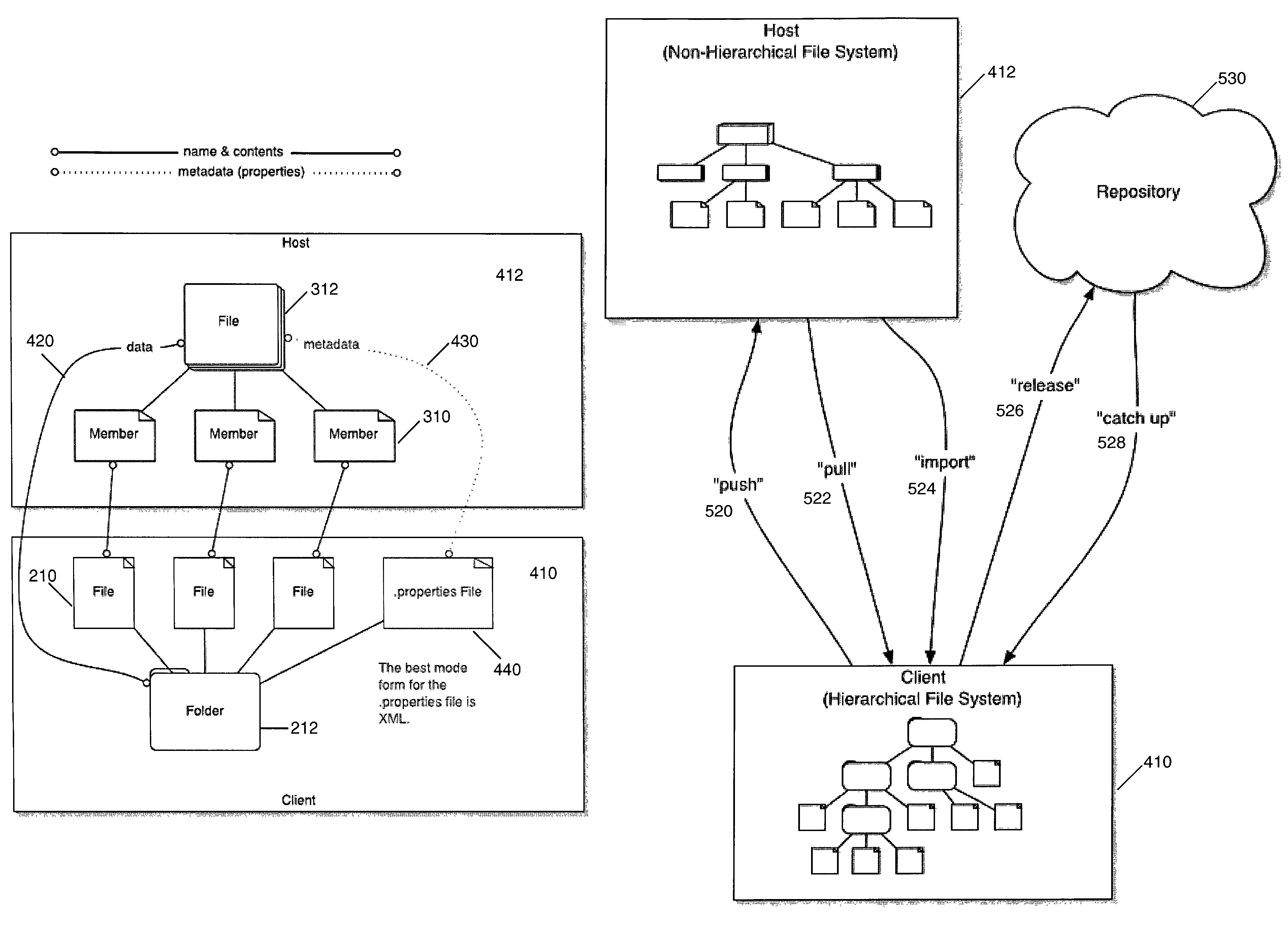
Transferring data and storing metadata across a network
InactiveUS7617222B2Improve flowData processing applicationsDigital data information retrievalFile systemThe Internet
Data is now able to be transferred back and forth between computer systems which have disparate file systems, e.g., between a computer having a hierarchical file system and a computer having a nonhierarchical file system. The differences, however, are not limited to the file storage system. Data may now be transferred across different platforms, different human and computer languages, different binary codes, etc. From one computer system the associated metadata is stored in a interpretable format on the second computer system so that when data and its associated metadata are transferred, the second computer system can interpret the transferred data. Data transfer can be accomplished in both directions. Thus, a tool writer or a software developer using a integrated development environment, such as Eclipse, on a Linux workstation with its hierarchical file system may download source files and other resources from an iSeries computer server with its OS / 400 nonhierarchical file system, modify the resources, and then put them back onto the iSeries machine for use on the iSeries. The metadata of the source file and other resources are stored in a .properties file which, if in XML format, supports the transfer of resources across the Internet.
Owner:IBM CORP
Internet-based shared file service with native PC client access and semantics
A multi-user file storage service and system enables each user of a user group to operate an arbitrary client node at an arbitrary geographic location to communicate with a remote file server node via a wide area network. More than one user of the user group is permitted to access the file group at the remote file server node simultaneously, but the integrity of the files is maintained by controlling access so that each access to one of the files at the remote file server is performed, if at all, on a respective portion of that file as most recently updated at the remote file server node.
Owner:GOOGLE LLC
Internet-based shared file service with native PC client access and semantics and distributed version control
InactiveUS20060129627A1Multiple digital computer combinationsTransmissionOperational systemWide area network
A multi-user file storage service and system enable each user of a pre-subscribed user group to operate an arbitrary client node at an arbitrary geographic location, to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node in communication with the remote file server node via the wide area network. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Illustratively, the integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Thus, all native operating system application programming interfaces operate as if all multi-user applications accessing the files function as if the remote server and client nodes were on the same local area network. Illustratively, an interface is provided for adapting file access one of the client nodes. The interface designates at the client node each accessible file of the group as stored on a virtual storage device. The interface enables access to the designated files in a fashion which is indistinguishable, by users of, and applications executing at, the client node, with access to one or more files stored on a physical storage device that is locally present at the client node. Illustratively, an encrypted key is transferred from the remote file server node to one of the client nodes via a secure channel. The key is encrypted using an encryption function not known locally at the remote file server node. The transferred key is decrypted at the client node. The key is used at the client node to decrypt information of the files downloaded from the remote file server node or to encrypt information of the files prior to uploading for storage at the remote file server node. Access control to a particular one of the files of the group can be delegated to an access control node.
Owner:GOOGLE LLC
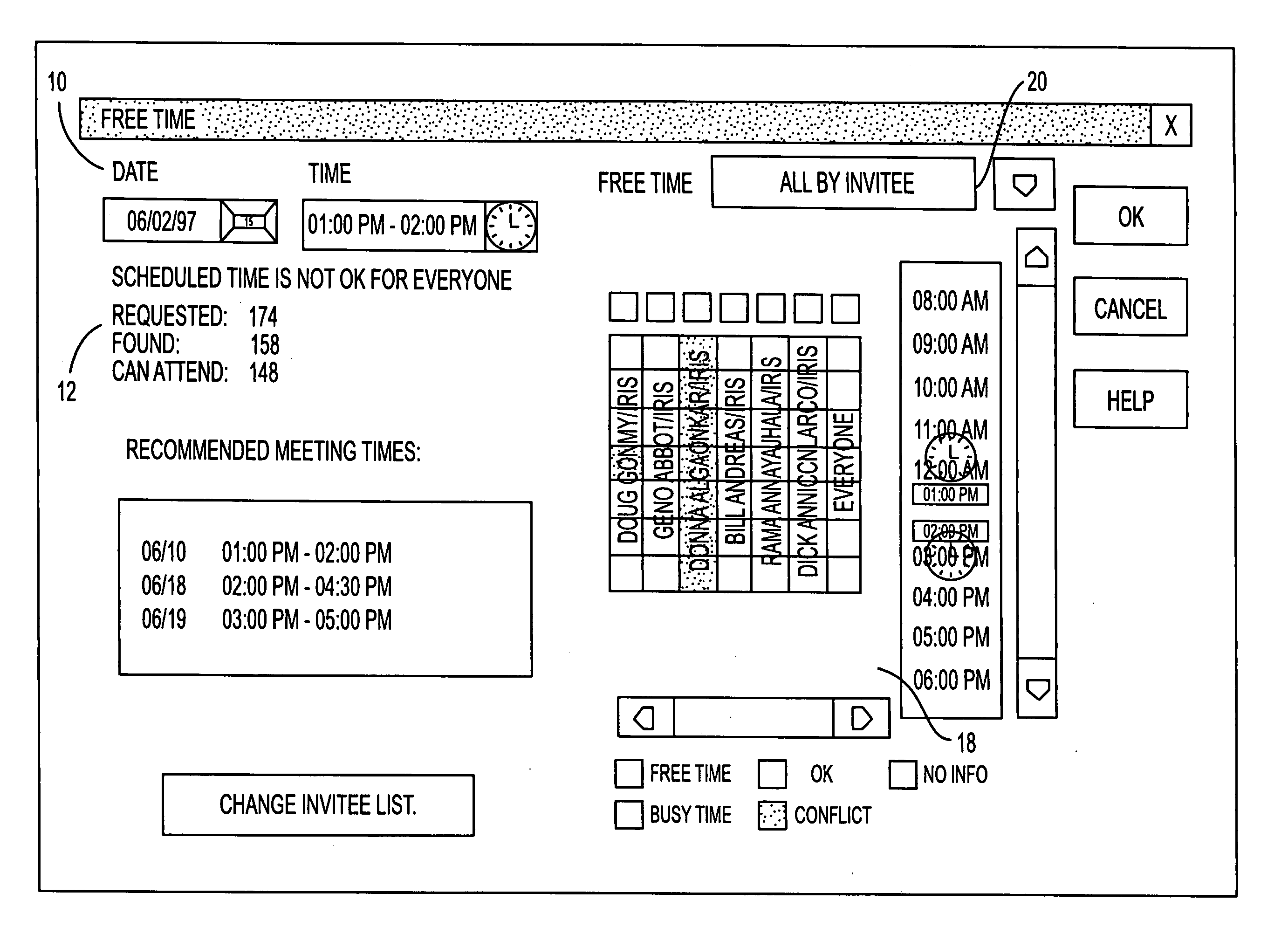
Electronic calendar with group scheduling and storage of user and resource profiles
InactiveUS7082402B2Convenient treatmentEnhanced information management capabilityText processingOffice automationBusy timeEmail address
A system for scheduling time intervals for a plurality of users comprises a database associated with one or more server means for storing a profile for each potential invitee of the system. Each invitee profile comprises user profiles that have information regarding available and unavailable times for that user and the electronic mail address for the user and resource profiles having information about the available times for a particular resource such as a room or equipment. A request generator connected over a network to the one or more server generates a request for allocation of a time interval for one or more of the plurality of invitees. The system then provides a busy time determination device that gathers the profiles for the plurality of invitees that were requested by the request generating means and that are available in the databases and determines whether those invitees are available during the time interval requested by the request generating means. For all available invitees, the electronic mail address in the profile is used to send each available requested invitee an invitation to attend at the requested time interval.
Owner:IBM CORP
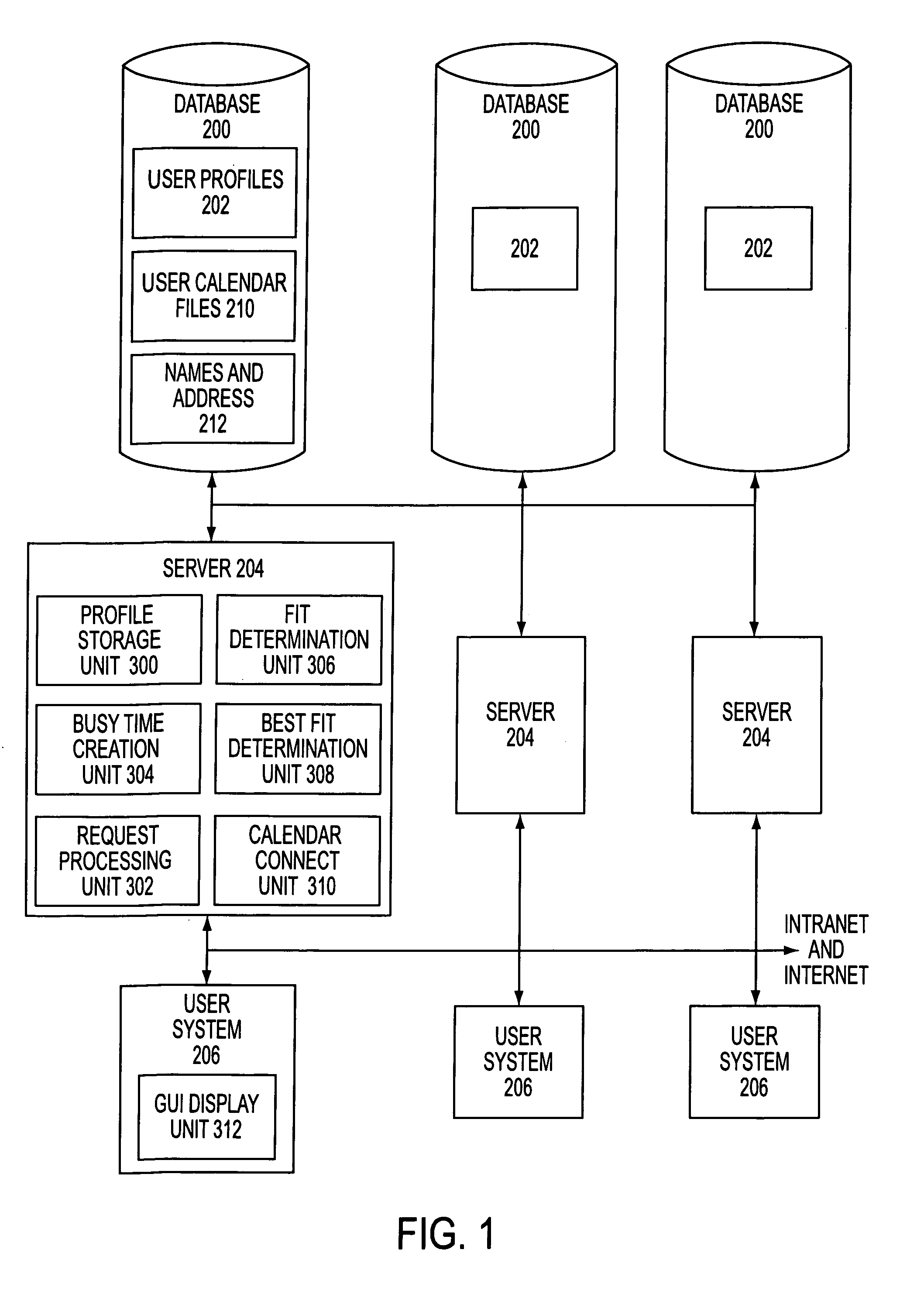
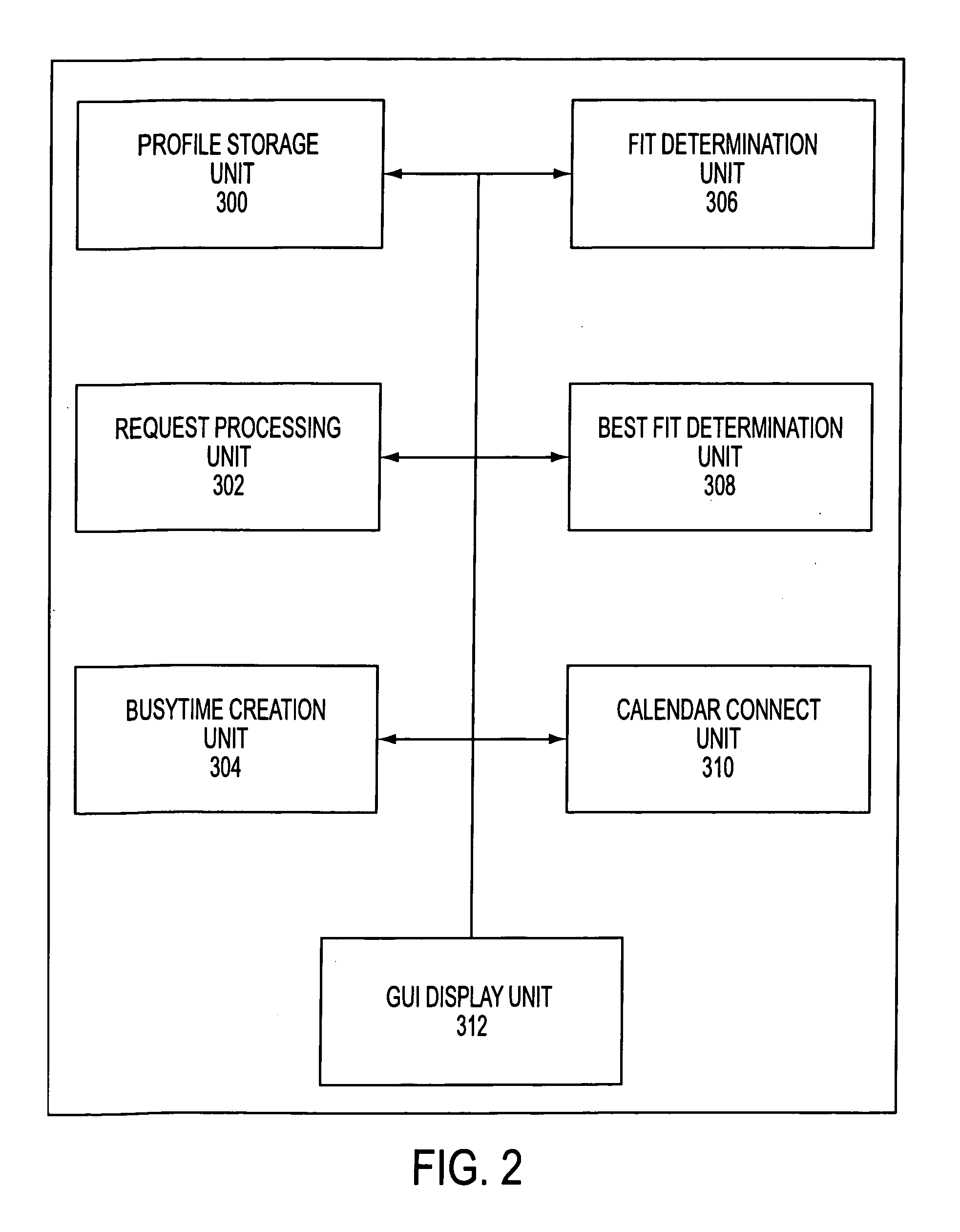
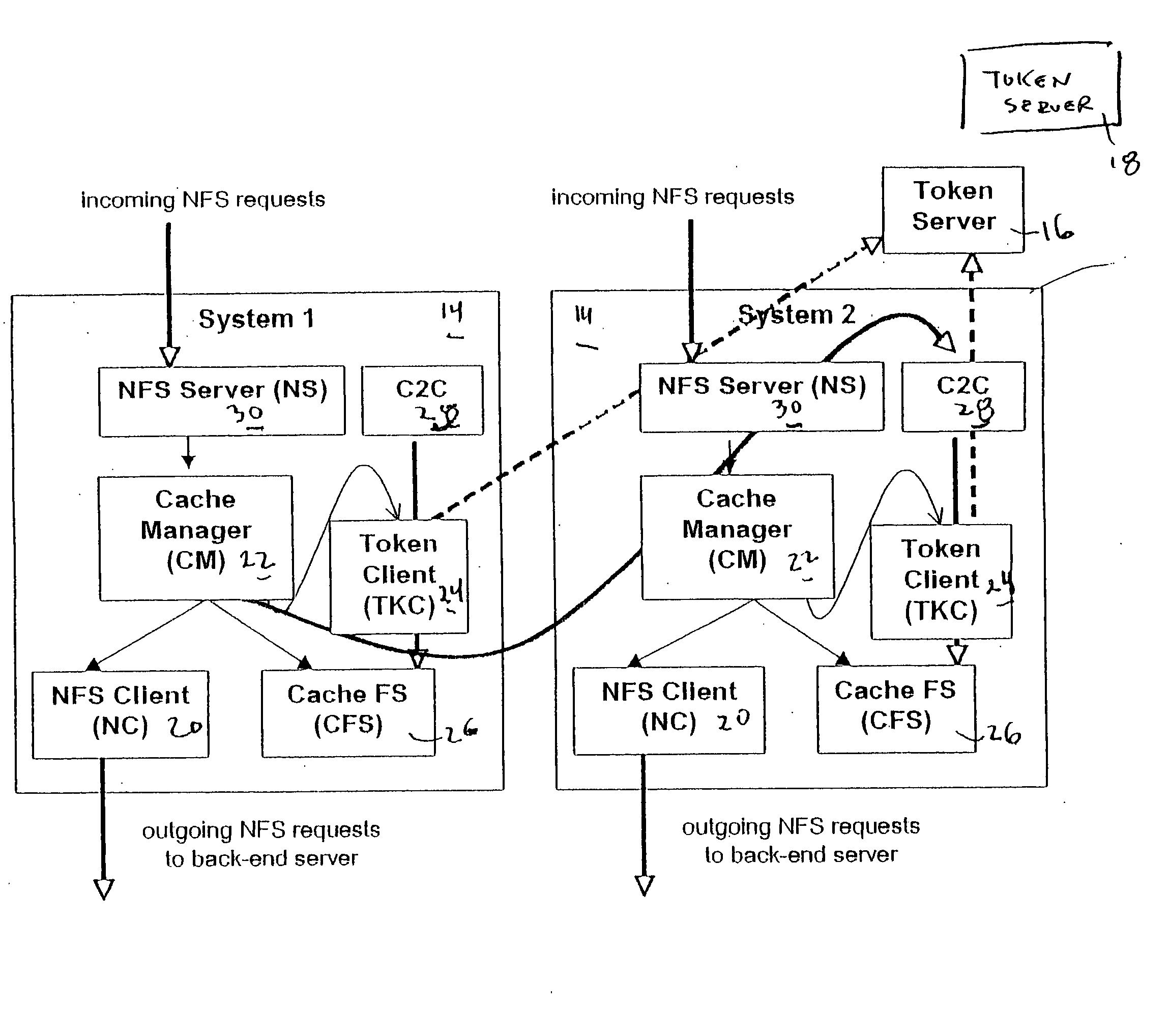
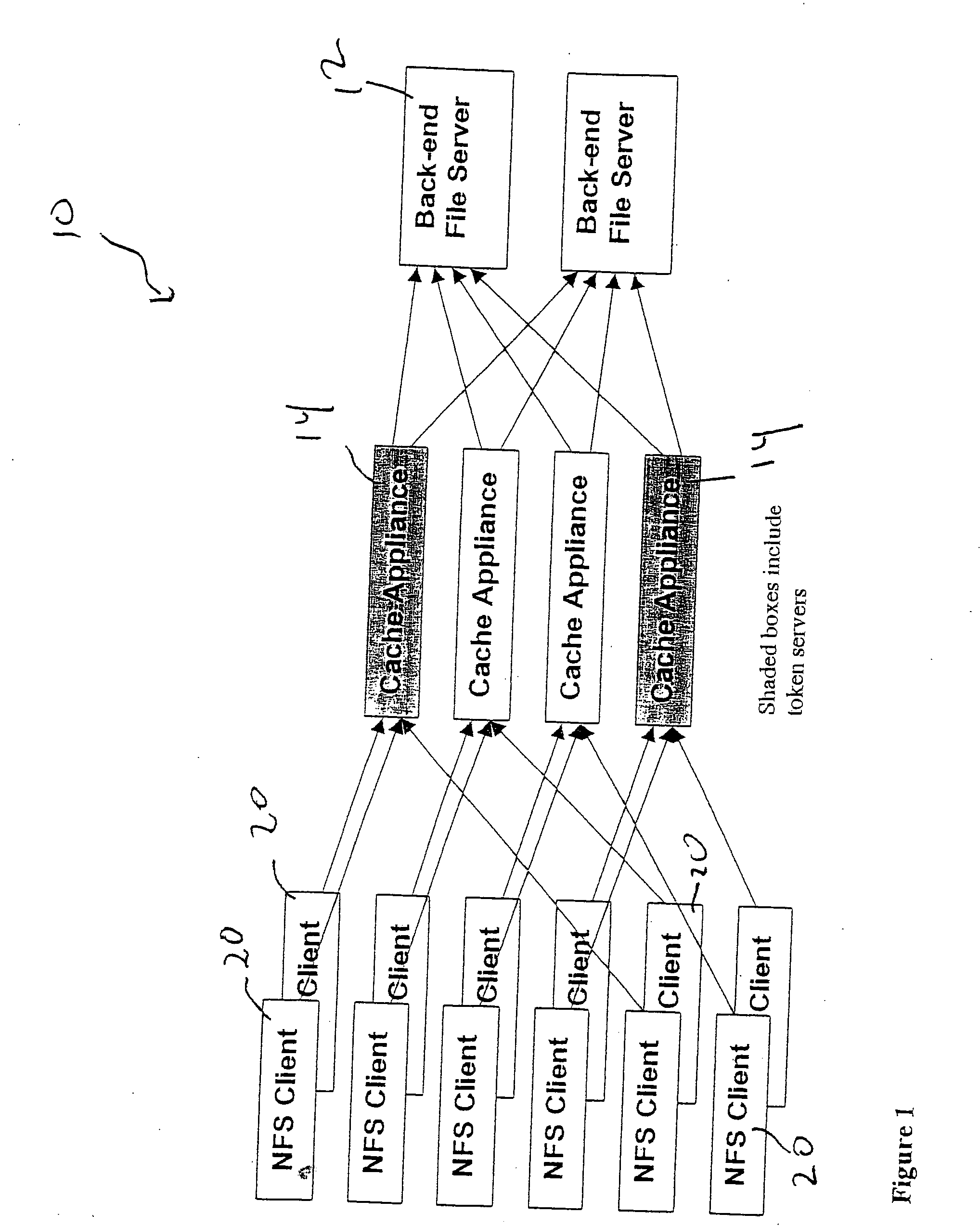
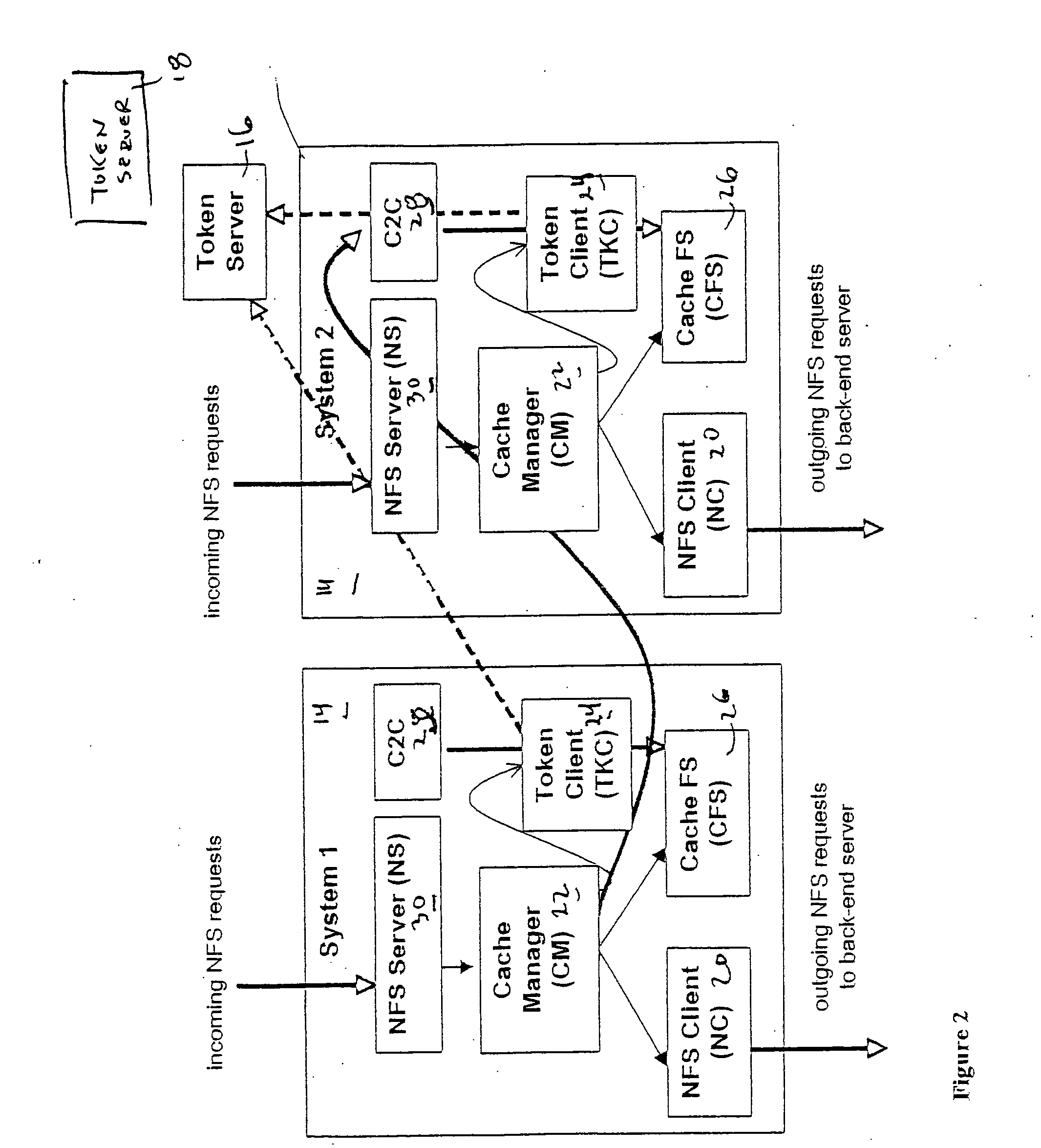
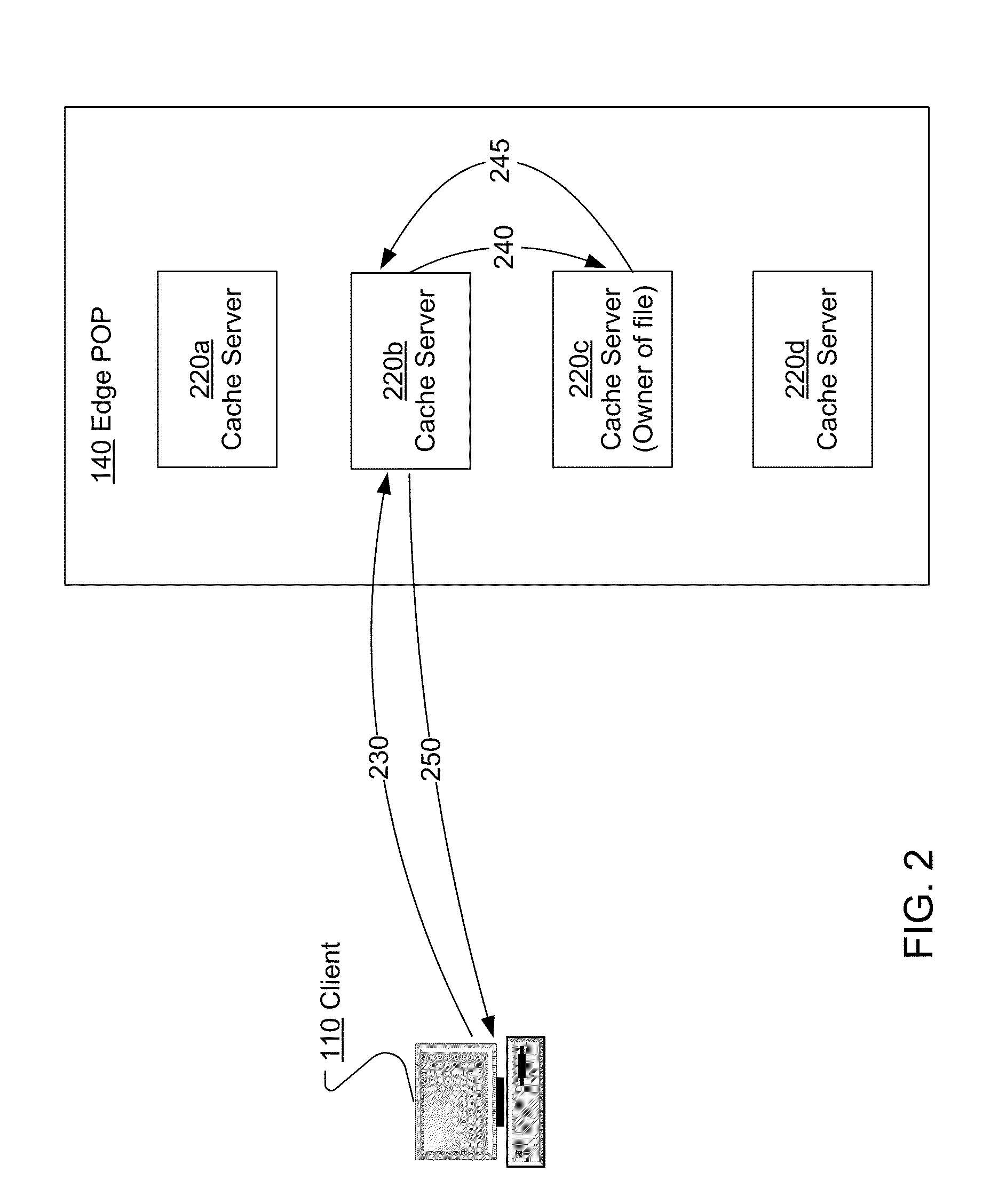
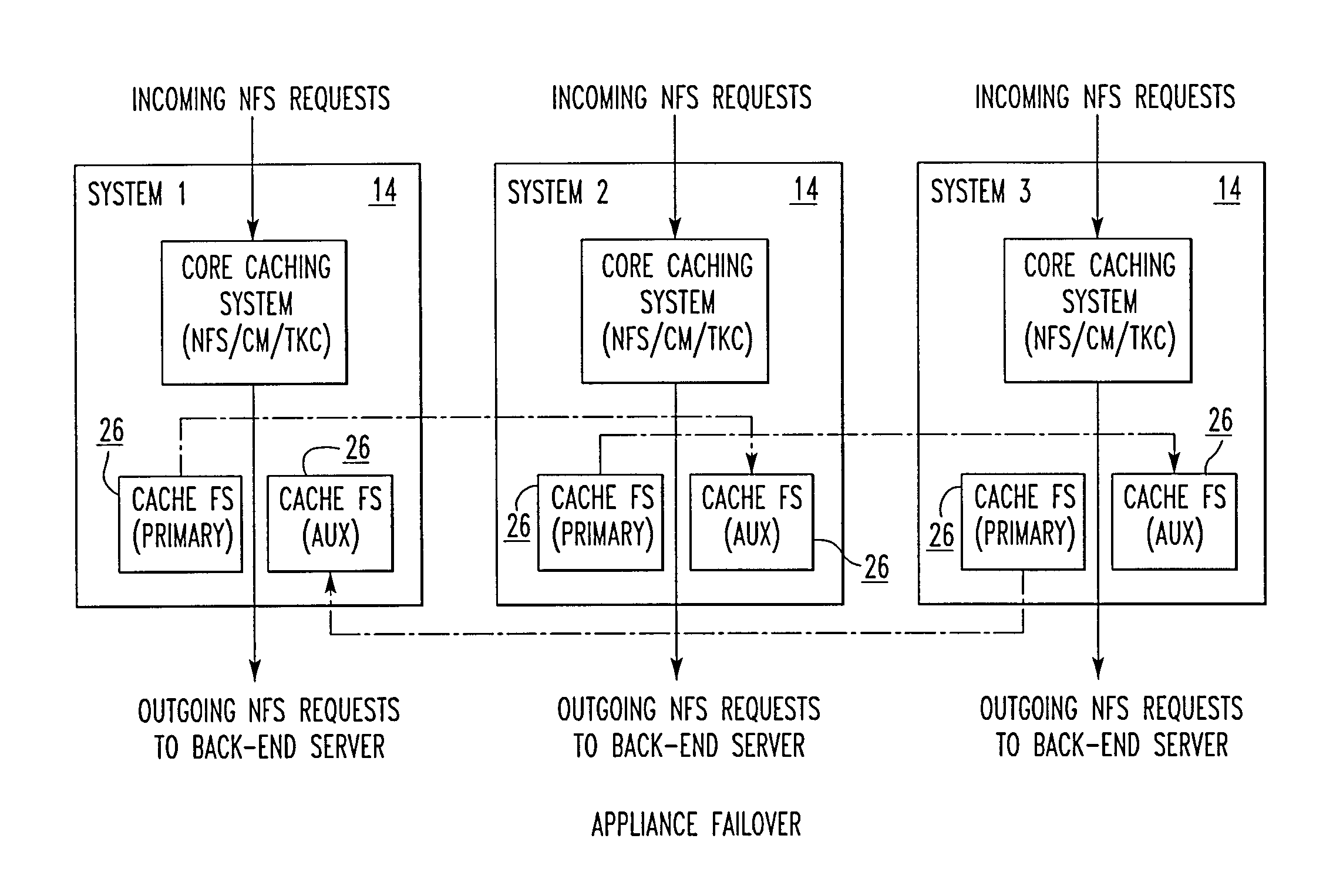
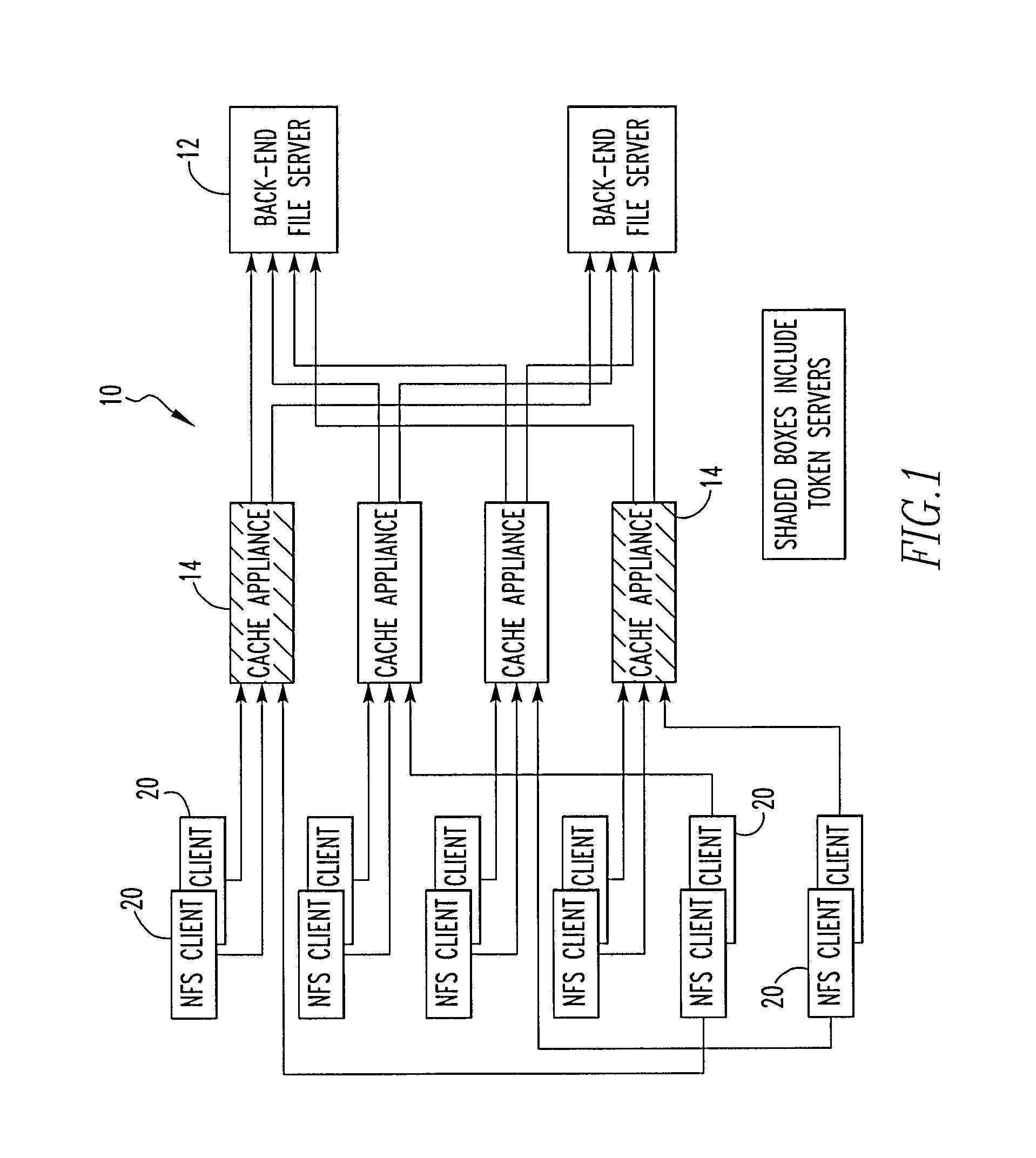
File storage system, cache appliance, and method
ActiveUS20100094806A1Increase profitLow costMemory architecture accessing/allocationDigital data processing detailsFile systemBack end server
A file storage system for storing data of a file received from a client includes a back-end file server in which the data is stored. The system includes a cache appliance in communication with the file server, such that the appliance stores portions of the data or attributes of the file, and uses the stored data or attributes to process file system requests received from the client, and which reads and writes data and attributes to the back-end file server independently. A system for responding to a file system protocol request in regard to a back-end server includes a token server. The system includes a plurality of cache appliances in communication with the token server, each of which receives tokens from the token server to synchronize access to data and attributes caches of the cache appliances, and reading and writing data and attributes to the back-end servers when tokens are revoked, the cache appliance having persistent storage in which data are stored, and the token server having persistent storage in which tokens are stored. A storage system includes a plurality of backend servers. The system includes a token server which grants permission to read and write file attributes and data system, and includes a plurality of cache appliances in communication with at least one of the backend servers and the token server for processing an incoming NFS request to the one backend server. Each cache appliance comprises an NFS server which converts incoming NFS requests into cache manager operations; a token client module in communication with the token server having a cache of tokens obtained from the token server; a cache manager that caches data and attributes and uses tokens from the token client module to ensure that the cached data or attributes are the most recent data or attributes, and an NFS client which sends outgoing NFS requests to the back-end file server. Methods for storing data of a file received from a client.
Owner:MICROSOFT TECH LICENSING LLC
File bundling for cache servers of content delivery networks
InactiveUS20110276623A1Easy data accessReduce read operationsDigital data information retrievalDigital data processing detailsHard disc driveCache server
Data access time in content delivery networks is improved by storing files in cache servers as file bundles. A cache server determines that multiple files are requested by the same client based on information available in the request including the IP address of the client, a URL of a webpage referring to the file, and / or a cookie stored at a client. The cache server stores multiple files requested by the same client on the hard drive as a file bundle with meta data associating the files with one another, such that they can be accessed together. A future request from the client for a file in a file bundle results in multiple files from the file bundle being loaded in the memory. If the client requests another file from the file bundle, the file is accessed directly from the memory instead of the hard drive, resulting in improved performance.
Owner:CDNETWORKS HLDG SINGAPORE PTE LTD
Shared Internet storage resource, user interface system, and method
InactiveUS20100185614A1Promote activeDigital data processing detailsMultiple digital computer combinationsData streamWeb service
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java®-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:OBRIEN BRETT +3
System and method for tracking and routing shipped items
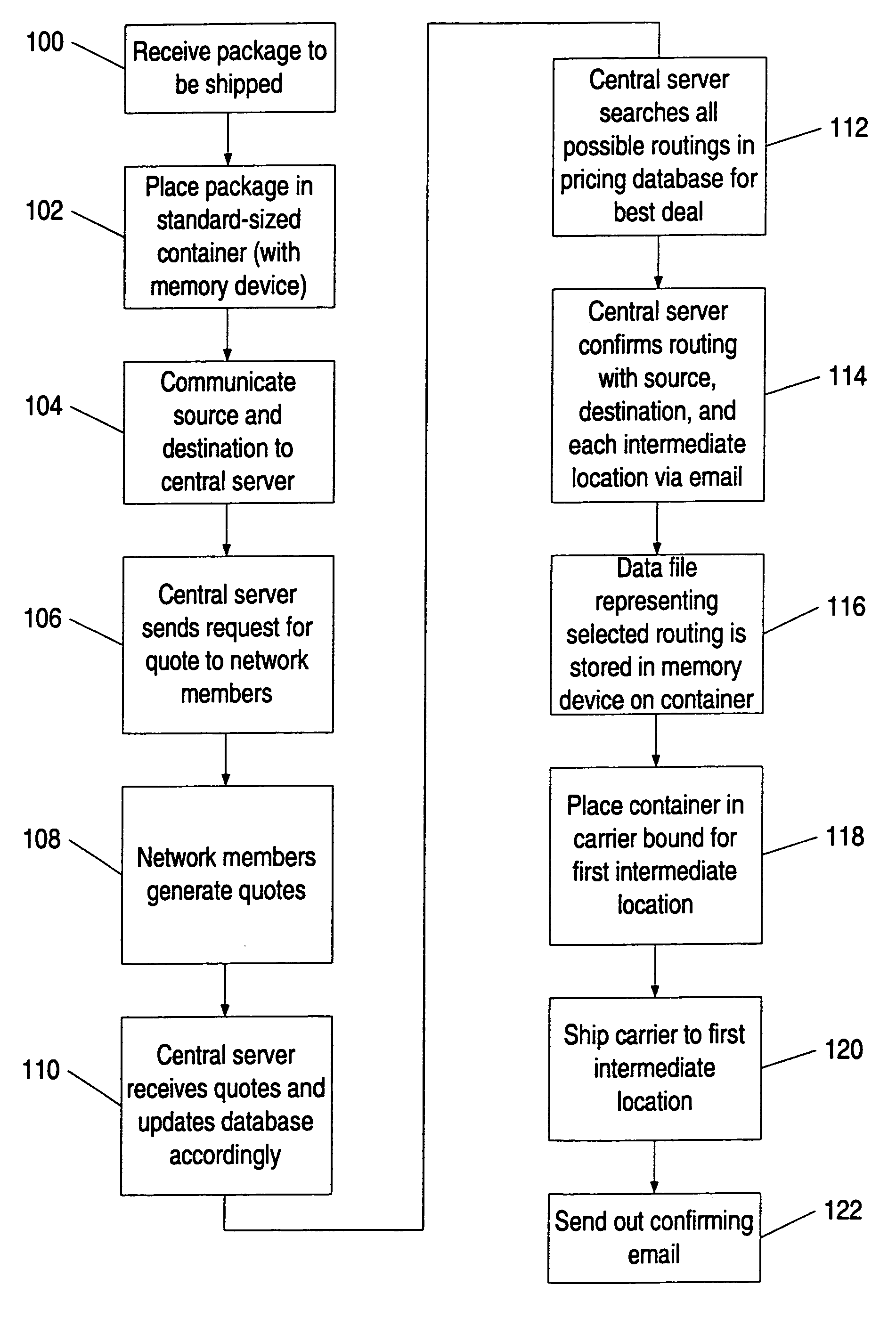
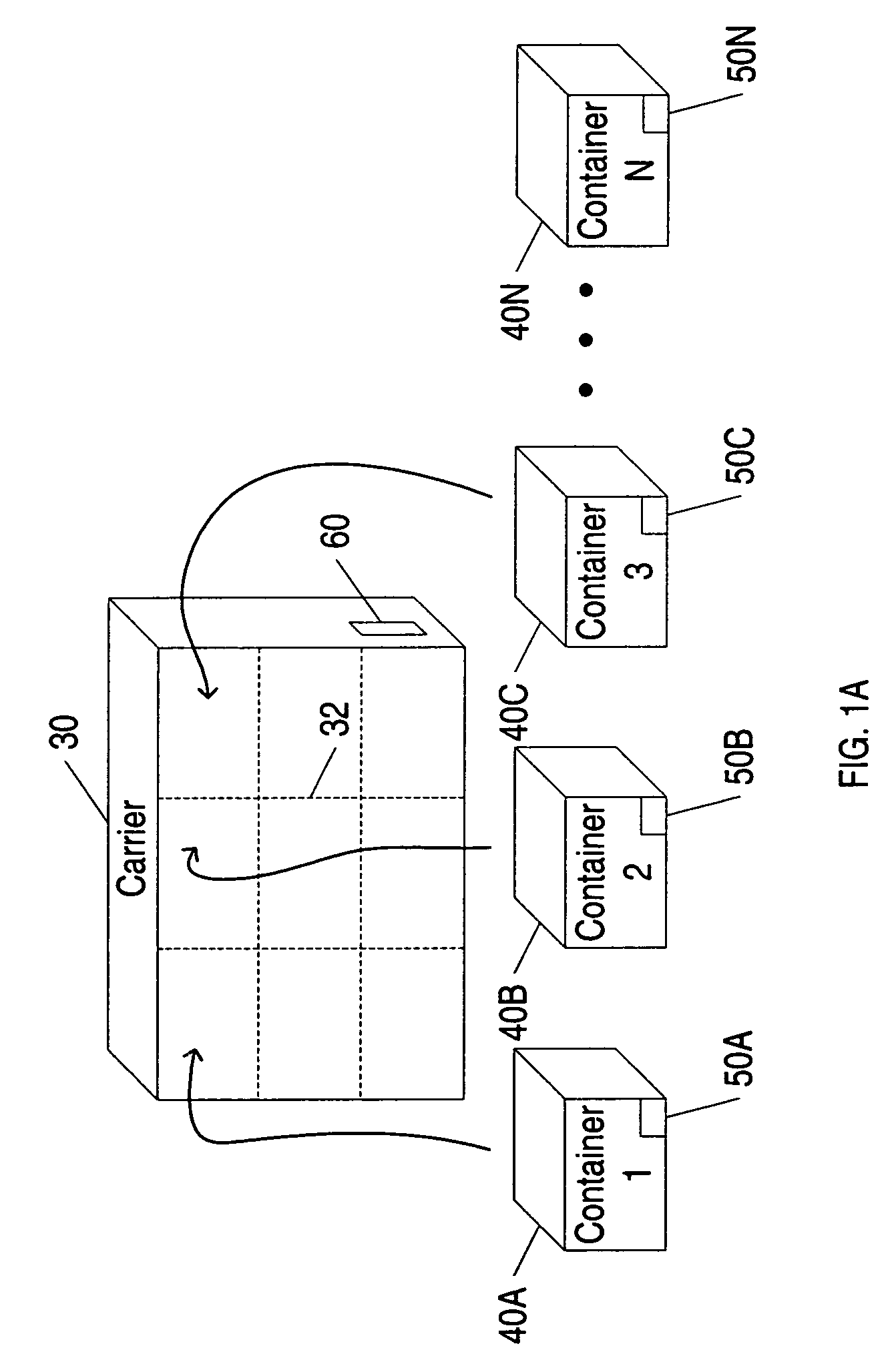
InactiveUS7035856B1Simplify the shipping processSimple processContainer decorationsLevel indicationsData fileFile storage
A method and system for shipping items. A server is configured to send out requests for quotes to a number of regional shipping companies using a network. The server receives responses from the network and selects a route based on the responses. The route may include shipping the item to one or more intermediate destinations before the item arrives at the final destination. The server may create a data file reflecting the selected route. The items are packed in one or more containers, wherein each container has a memory device. At least part of the data file is then stored into the memory device. The memory device may be accessed as needed during shipping to determine where the item is going and when the item needs to arrive. Additional information may also be stored in the memory device, and the device may be updated at intermediate destinations. Each container may take a different routing, and the server may actively search for better routings as the item proceeds along the selected route. The containers may be configured to be placed within carriers that hold multiple containers, and the carriers may also be configured with memory devices.
Owner:NIHON DOT COM
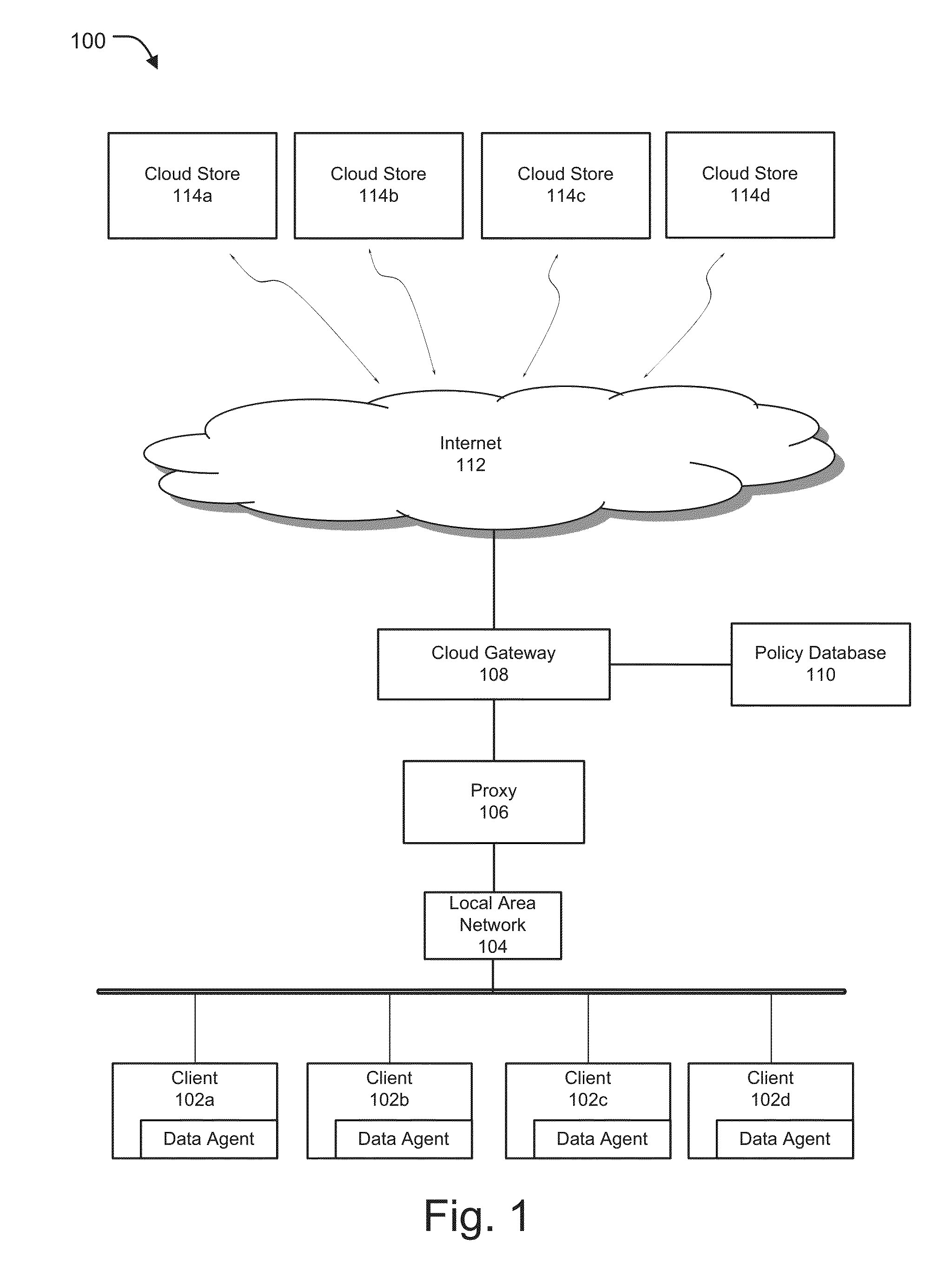
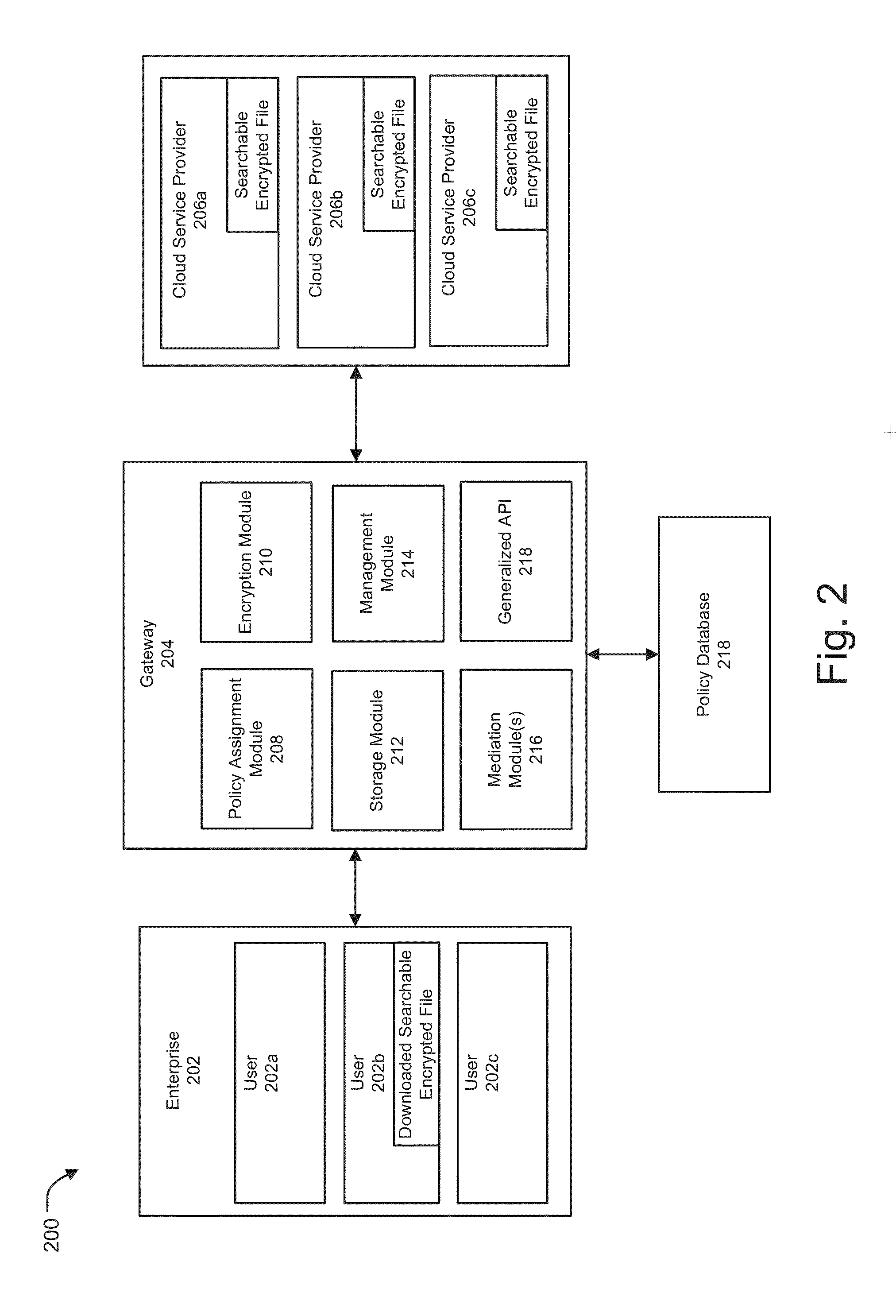
Secure cloud storage distribution and aggregation
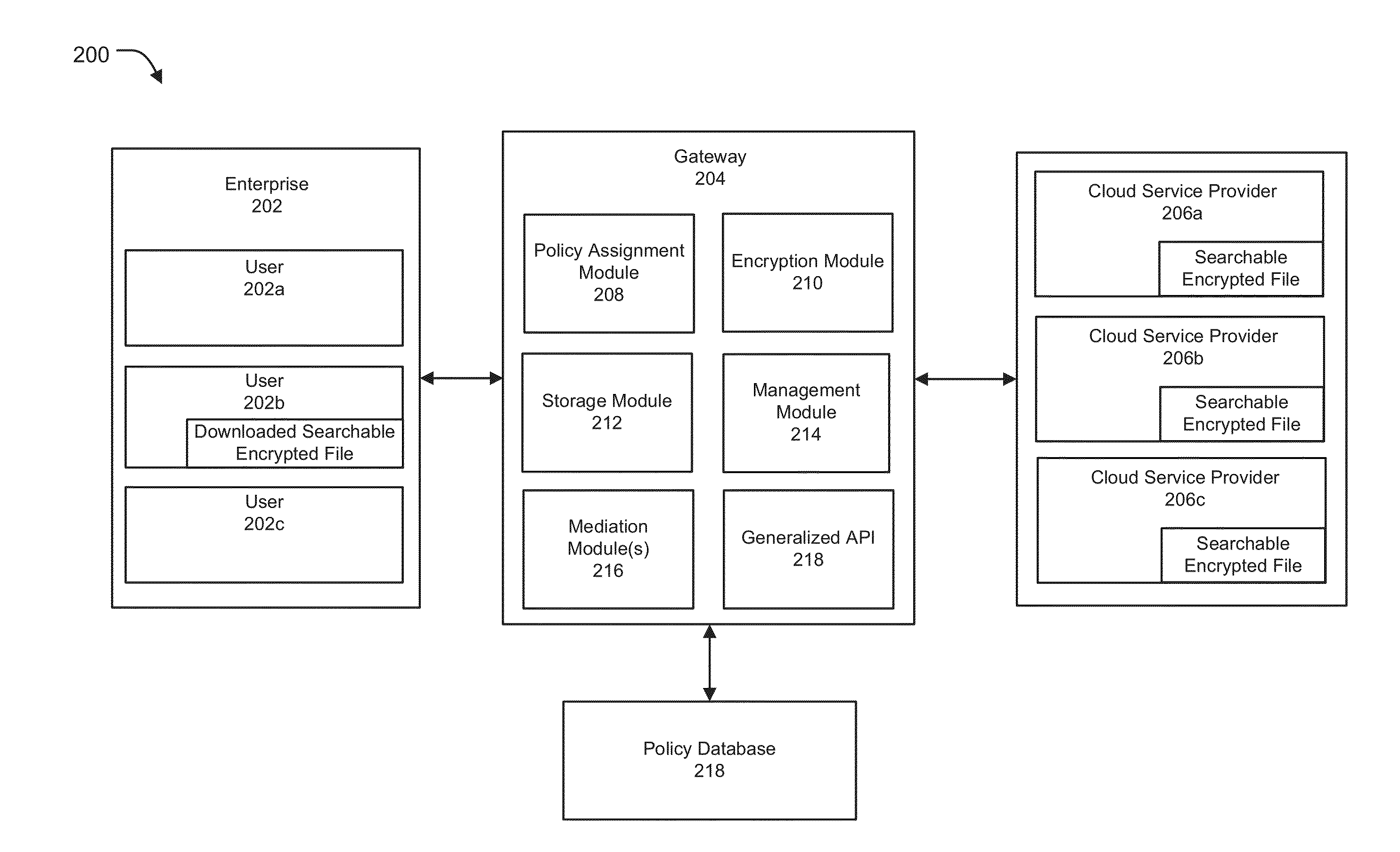
ActiveUS20150154418A1Easy to storeDigital data protectionSpecial data processing applicationsThird partyApplication programming interface
Methods and systems for vendor independent and secure cloud storage distribution and aggregation are provided. According to one embodiment, an application programming interface (API) is provided by a cloud storage gateway device logically interposed between third-party cloud storage platforms and users of an enterprise. The API facilitates storing of files, issuing of search requests against the files and retrieval of content of the files. A file storage policy is assigned to each user, which defines access rights, storage diversity requirements and a type of encryption to be applied to files. Responsive to receiving a request to store a file, (i) searchable encrypted data is created relating to content and / or metadata of the file based on the assigned file storage policy; and (ii) the searchable encrypted data is distributed among the third-party cloud storage platforms based on the storage diversity requirements defined by the assigned file storage policy.
Owner:FORTINET
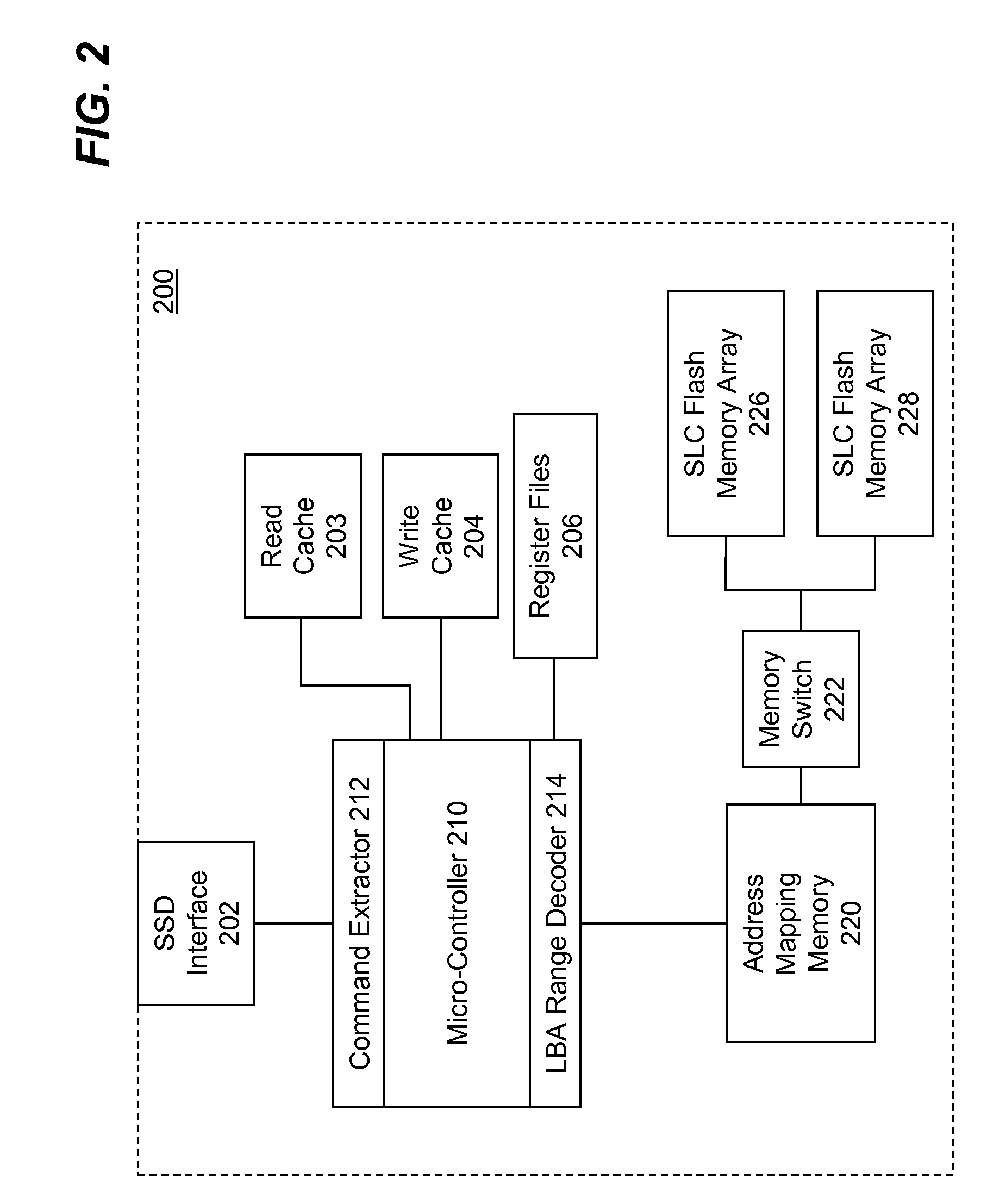
Hybrid SSD Using A Combination of SLC and MLC Flash Memory Arrays
InactiveUS20080215800A1Reduce manufacturing costAcceptable levelMemory architecture accessing/allocationInternal/peripheral component protectionData fileSingle level
Hybrid solid state drives (SSD) using a combination of single-level cell (SLC) and multi-level cell (MLC) flash memory arrays are described. According to one aspect of the present invention, a hybrid SSD is built using a combination SLC and MLC flash memory arrays. The SSD also includes a micro-controller to control and coordinate data transfer from a host computing device to either the SLC flash memory array of the MLC flash memory array. A memory selection indicator is determined by triaging data file based on one or more criteria, which include, but is not limited to, storing system files and user directories in the SLC flash memory array and storing user files in the MLC flash memory array; or storing more frequent access files in the SLC flash memory array, while less frequent accessed files in the MLC flash memory array.
Owner:SUPER TALENT TECH CORP
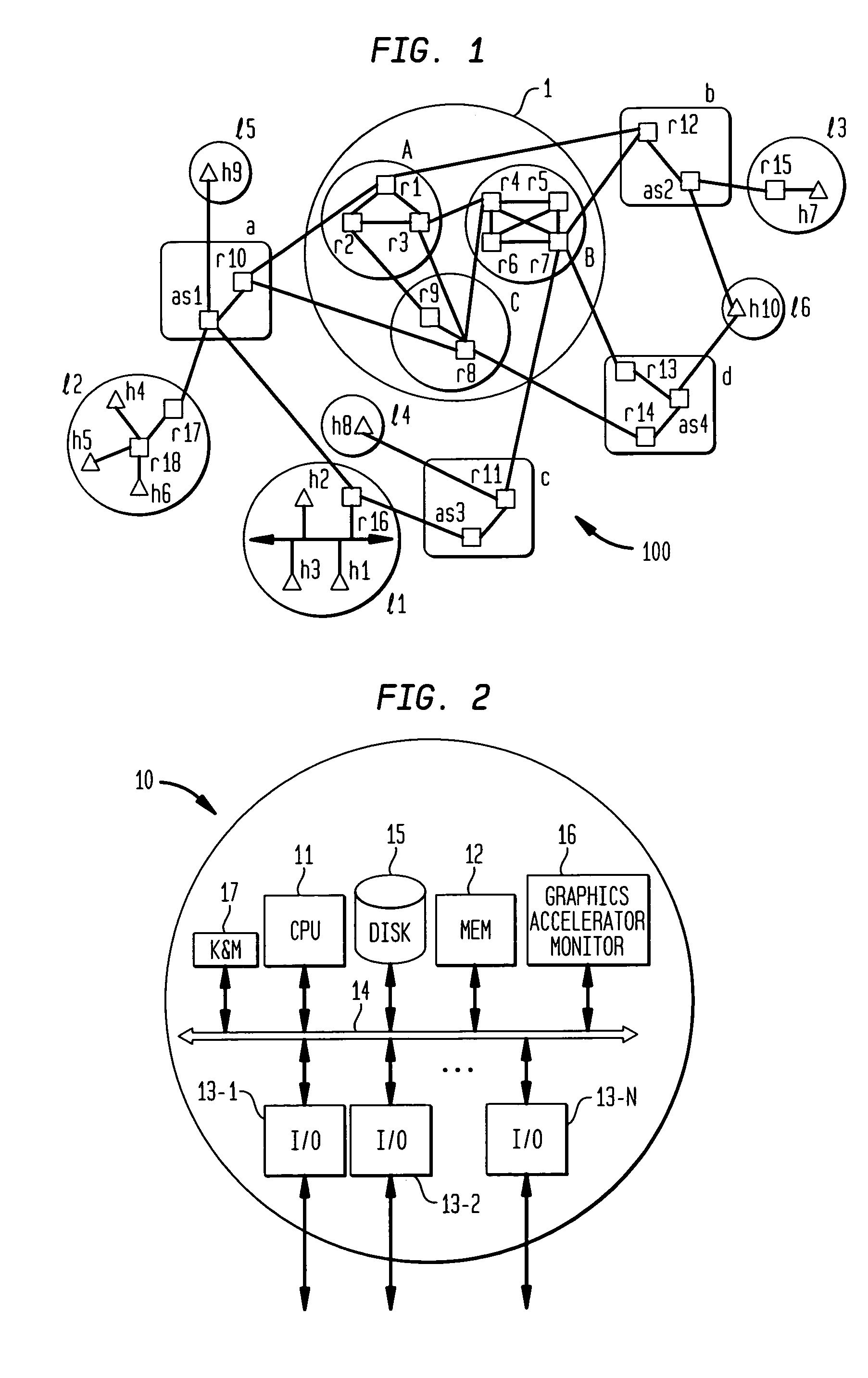
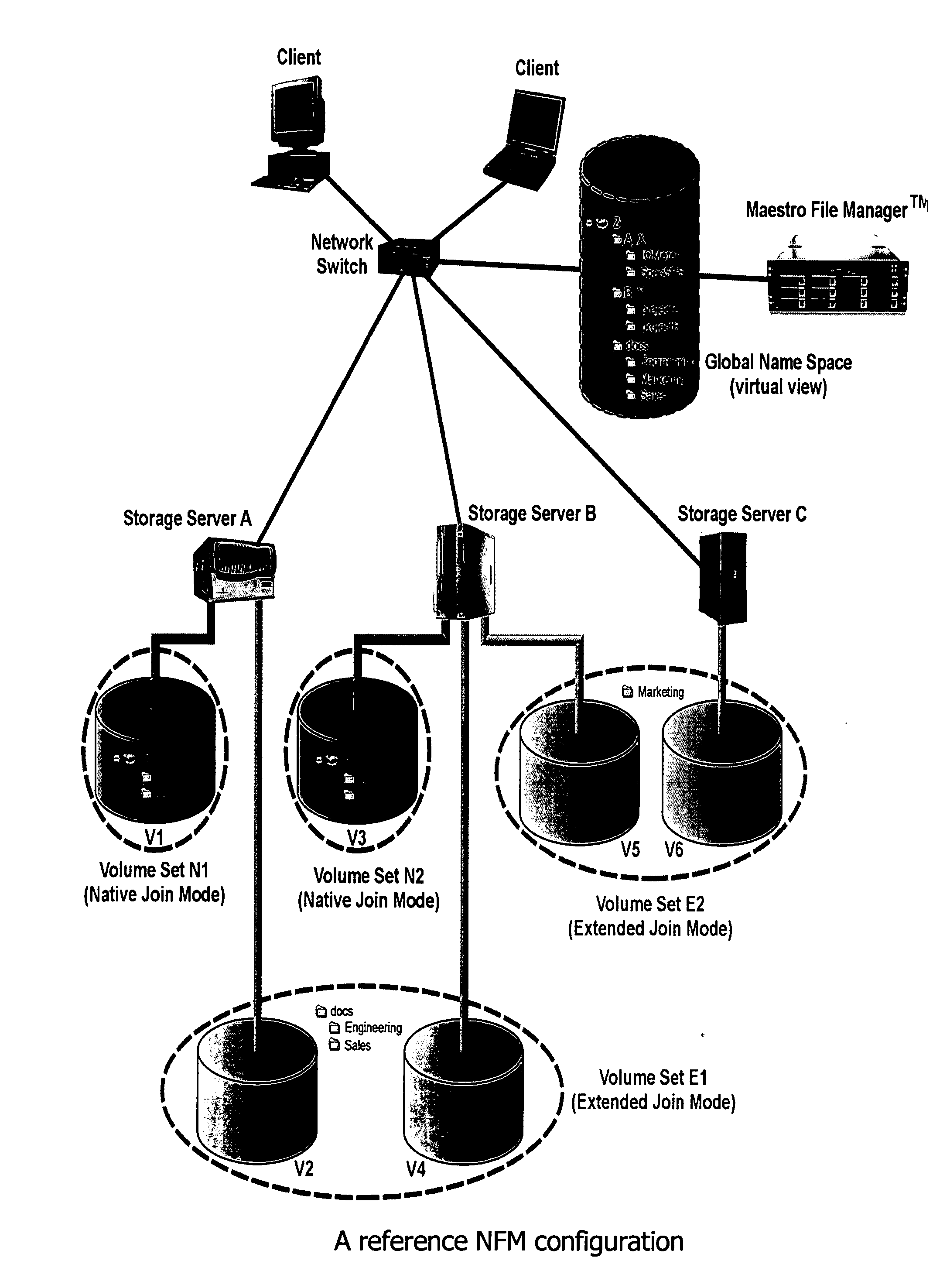
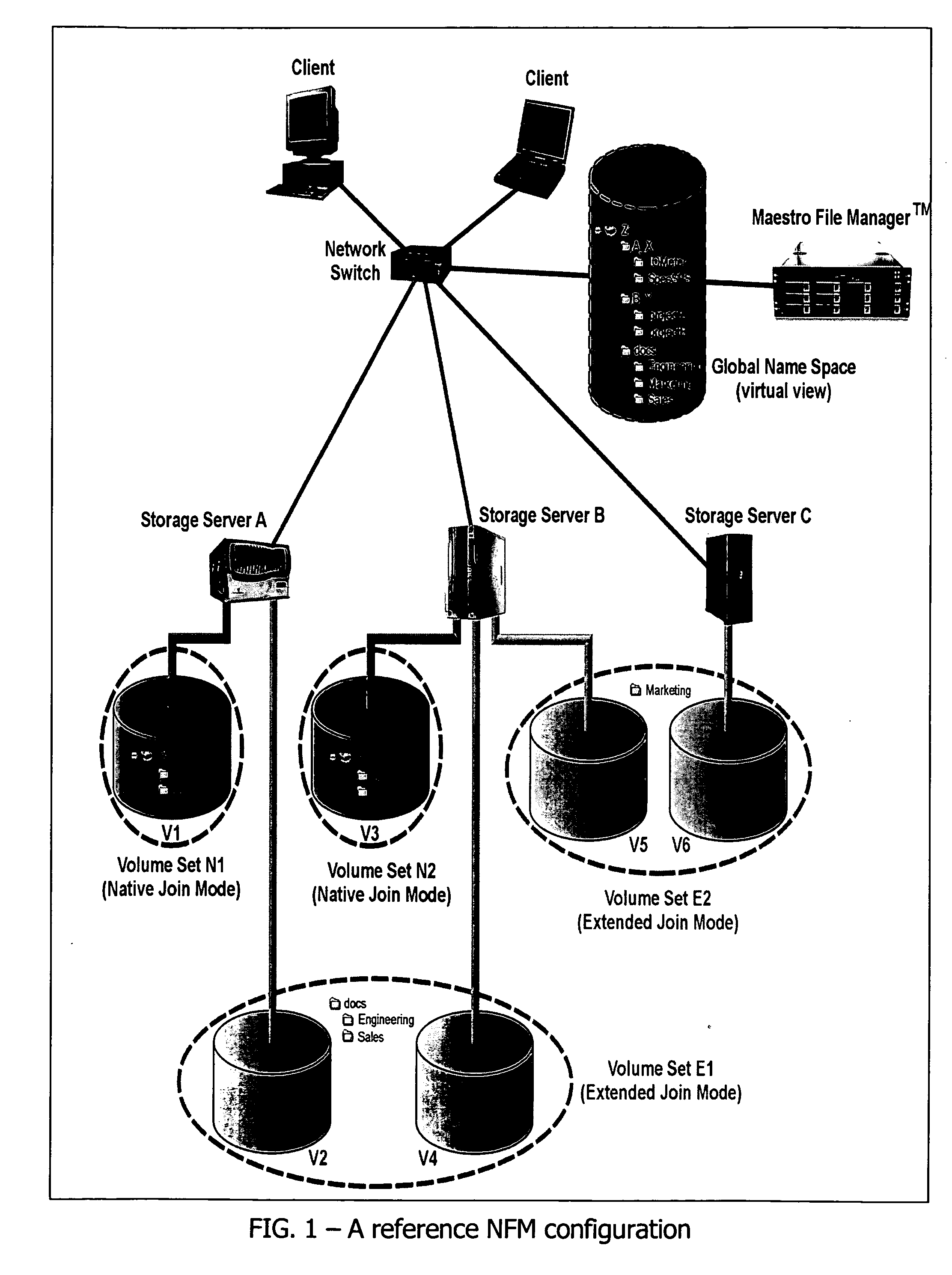
File Aggregation in a Switched File System
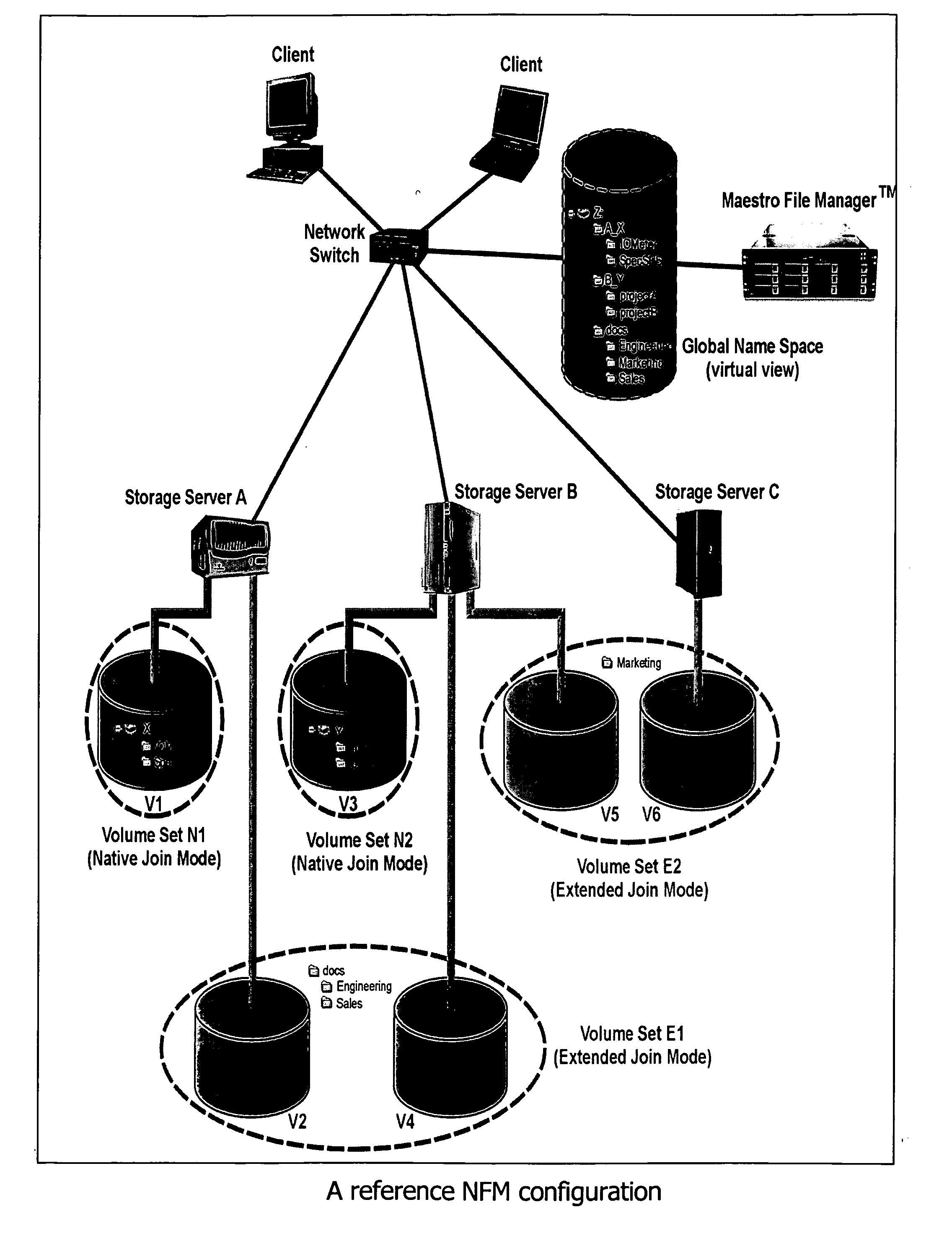
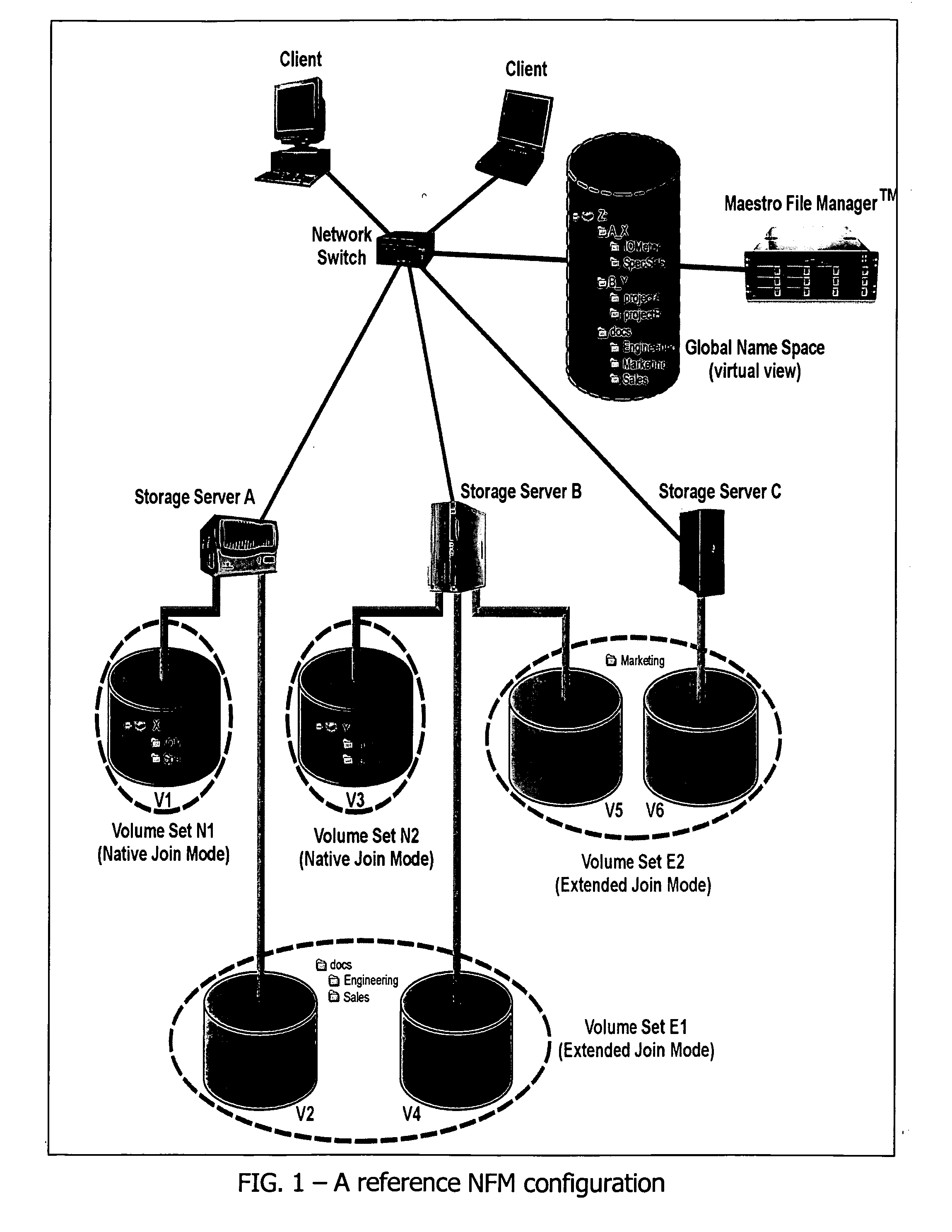
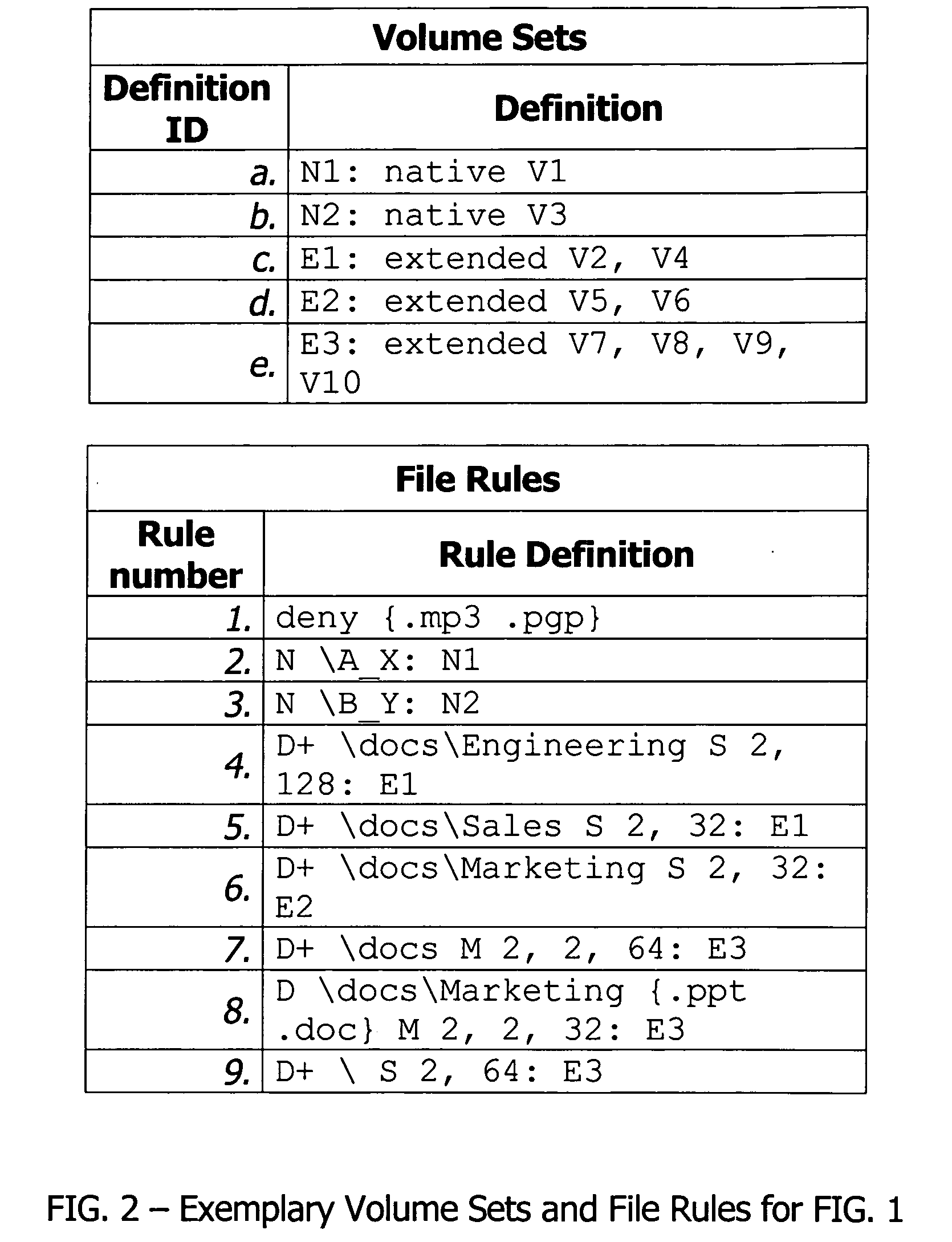
InactiveUS20090077097A1Digital data information retrievalMemory loss protectionFile systemGlobal file system
In a switched file system, a file switching device is logically positioned between clients and file servers and communicates with the clients and the file servers using standard network file protocols. The file switching device appears as a server to the client devices and as a client to the file servers. The file switching device aggregates storage from multiple file servers into a global filesystem and presents a global namespace to the client devices. The file switching device typically supports a “native” mode for integrating legacy files into the global namespace and an “extended” mode for actively managing files across one or more file servers. Typically, native-mode files may be accessed directly or indirectly via the file switching device, while extended-mode files may be accessed only through the file switching device. The file switching device may manage file storage using various types of rules, e.g., for managing multiple storage tiers or for applying different types of encoding schemes to files. Rules may be applied to pre-existing files.
Owner:RPX CORP
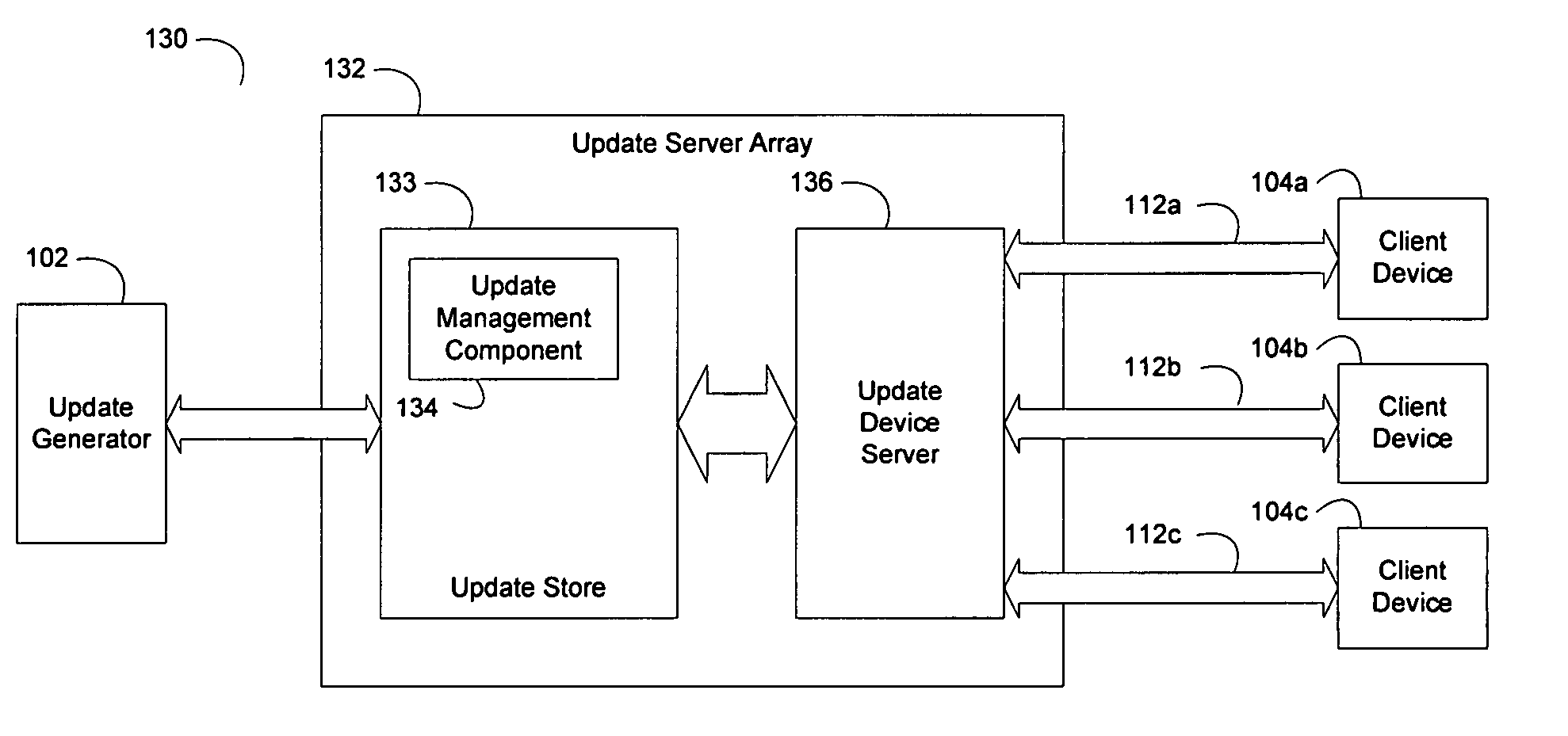
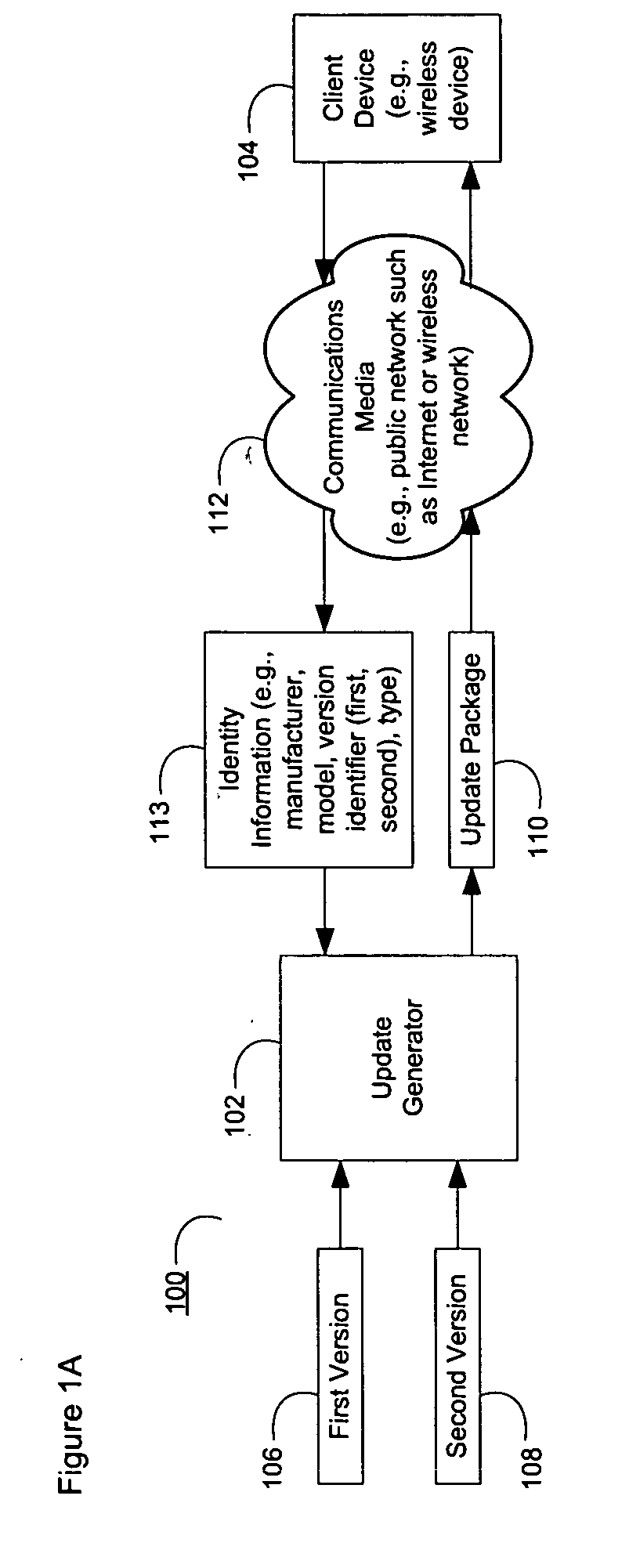
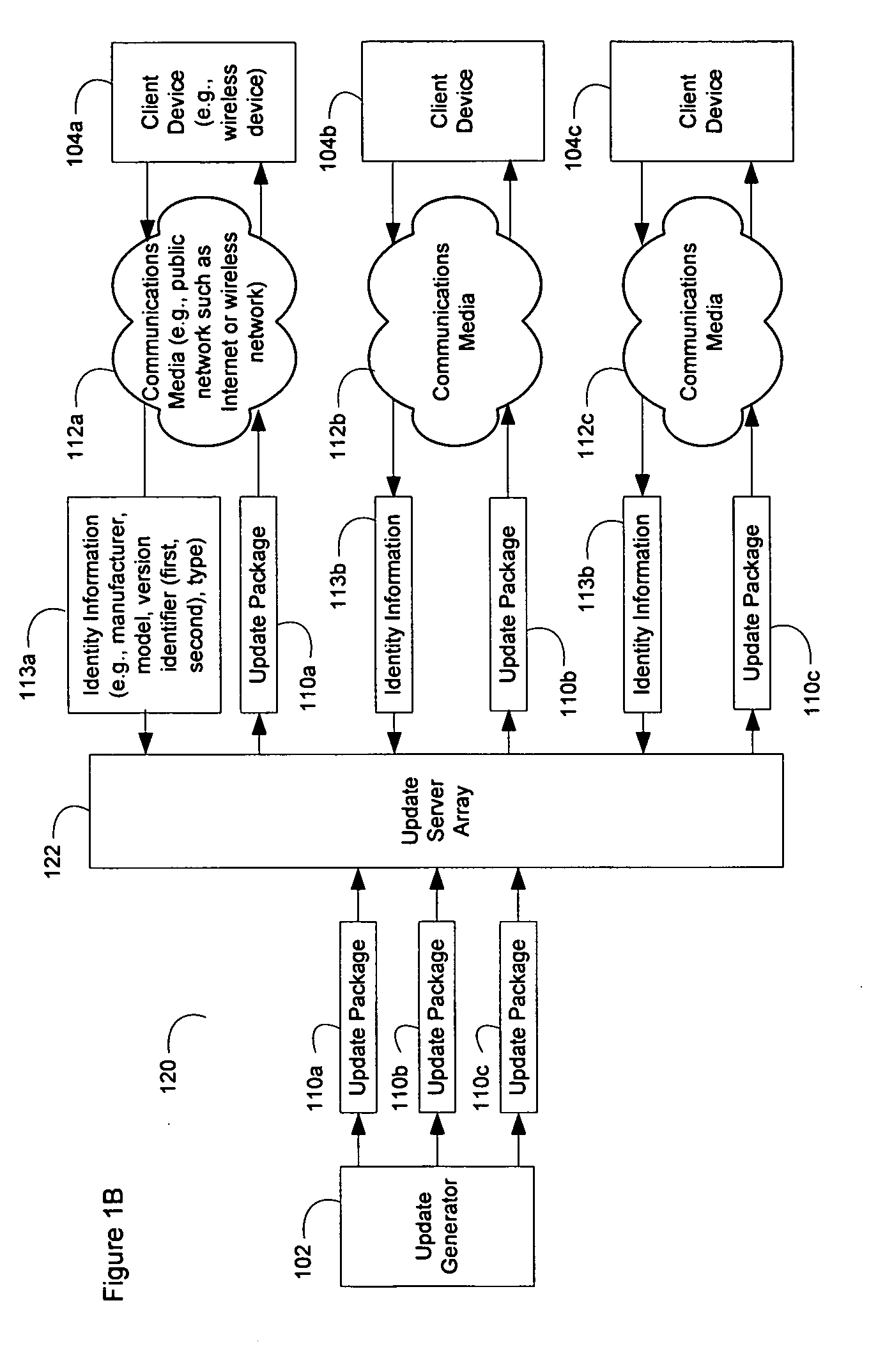
System and method for updating and distributing information
ActiveUS20060130046A1Addressing slow performanceEfficient updateDigital computer detailsProgram loading/initiatingSoftware engineeringDatabase
The present invention discloses efficient devices, systems, and methods for updating digital information sequences that are comprised by software (110a), devices (104a), and data (110c). In addition, these digital information sequences may be stored and used in various forms, including but not limited to files, memory locations, and / or embedded storage locations. The disclosed invention is thus suitable for updating many types of digital information sequences and in the context of updating software comprised of multiple files. Furthermore, the devices, systems, and methods described herein provide a developer skilled in the art with an improved ability to generate update information as needed and, additionally, allow users to proceed through a simplified update path, which is not error-prone, and may be performed more quickly than through the use of existing technologies.
Owner:HEWLETT PACKARD DEV CO LP
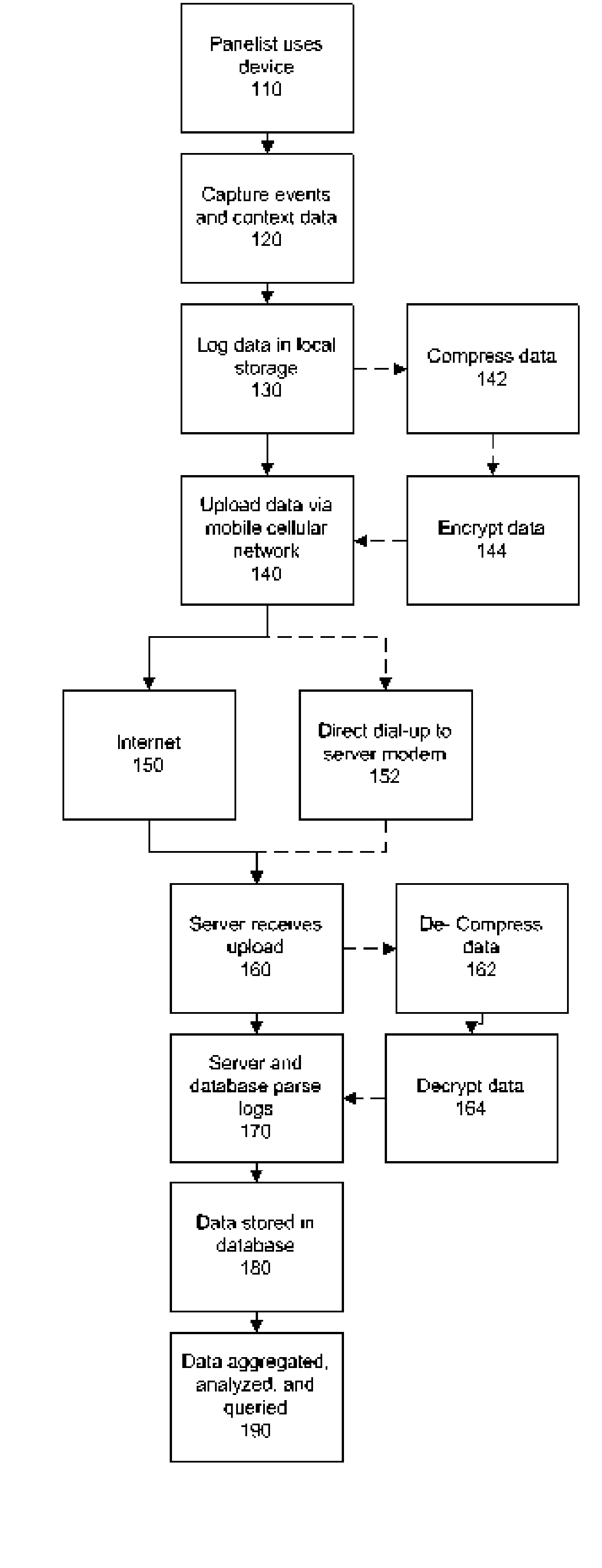
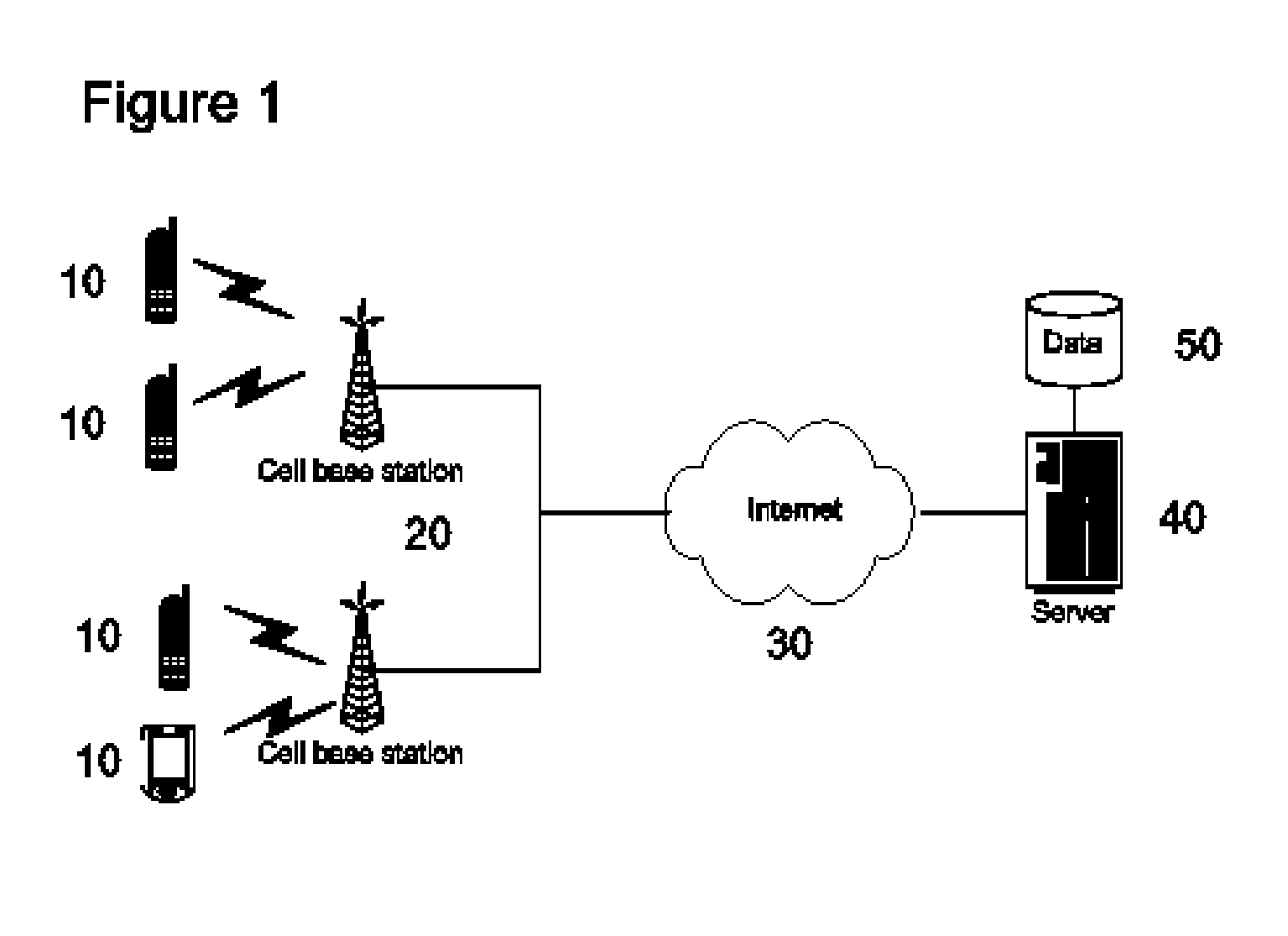
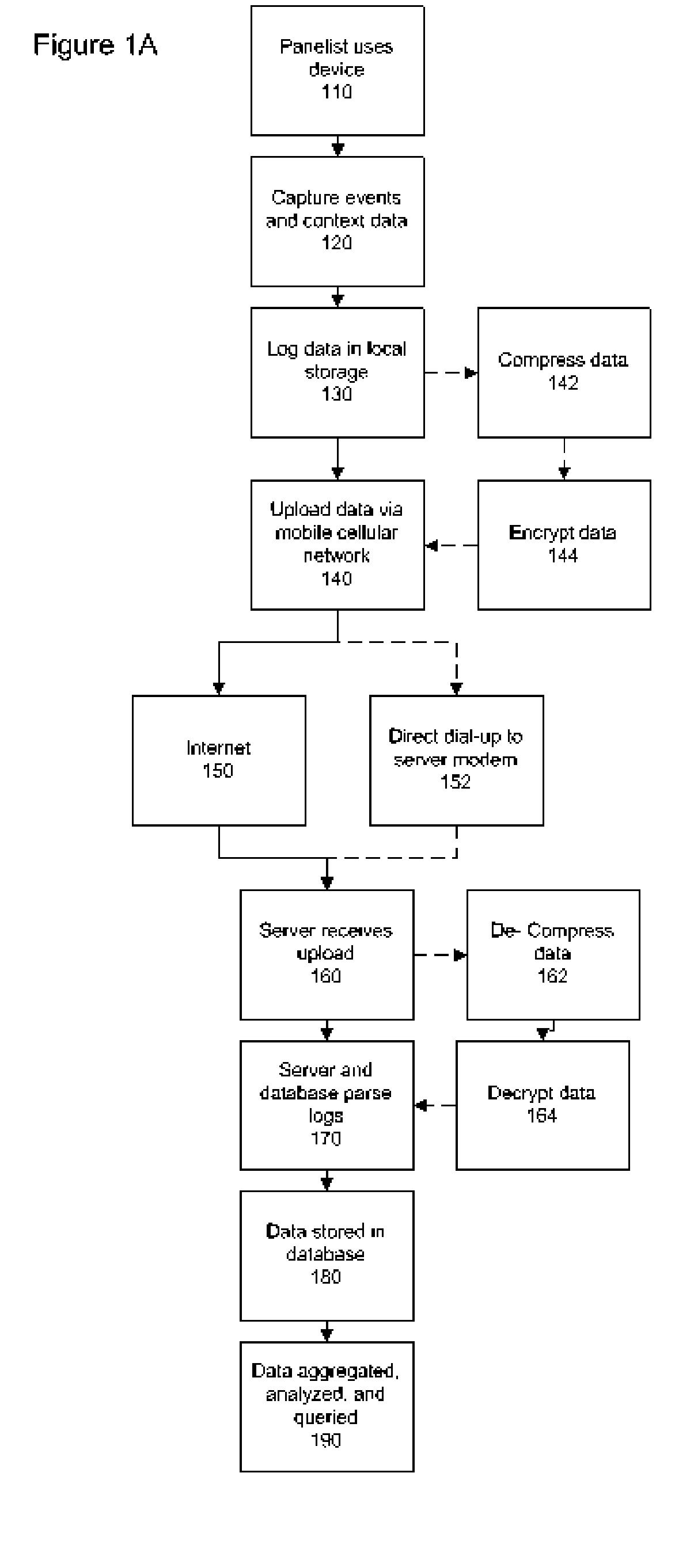
System and method to track wireless device and communications usage
InactiveUS20050213511A1Short timeLow costError preventionTransmission systemsCommunications systemSignal quality
A system and method for gathering and reporting user and device activity data from wireless communication devices through a log file. The log file stores entries related to user events including the use of communications and applications, as well as access to local and remote media resource files. The log file entries may include parameters critical to mobile device operation such as location, signal quality, and battery power. The data gathering system comprises a plurality of wireless communications devices, each of which sends the log files through an available wireless communications system to a central facility for processing and aggregation into a database. Stored data is analyzed to generate, display, and marketing information that may include historical trends and projections of future consumer preferences and activities.
Owner:MERLIN MOBILE MEDIA
File Aggregation in a Switched File System
InactiveUS20090106255A1Digital data information retrievalError detection/correctionGlobal file systemFile system
In a switched file system, a file switching device is logically positioned between clients and file servers and communicates with the clients and the file servers using standard network file protocols. The file switching device appears as a server to the client devices and as a client to the file servers. The file switching device aggregates storage from multiple file servers into a global filesystem and presents a global namespace to the client devices. The file switching device typically supports a “native” mode for integrating legacy files into the global namespace and an “extended” mode for actively managing files across one or more file servers. Typically, native-mode files may be accessed directly or indirectly via the file switching device, while extended-mode files may be accessed only through the file switching device. The file switching device may manage file storage using various types of rules, e.g., for managing multiple storage tiers or for applying different types of encoding schemes to files. Rules may be applied to pre-existing files.
Owner:RPX CORP
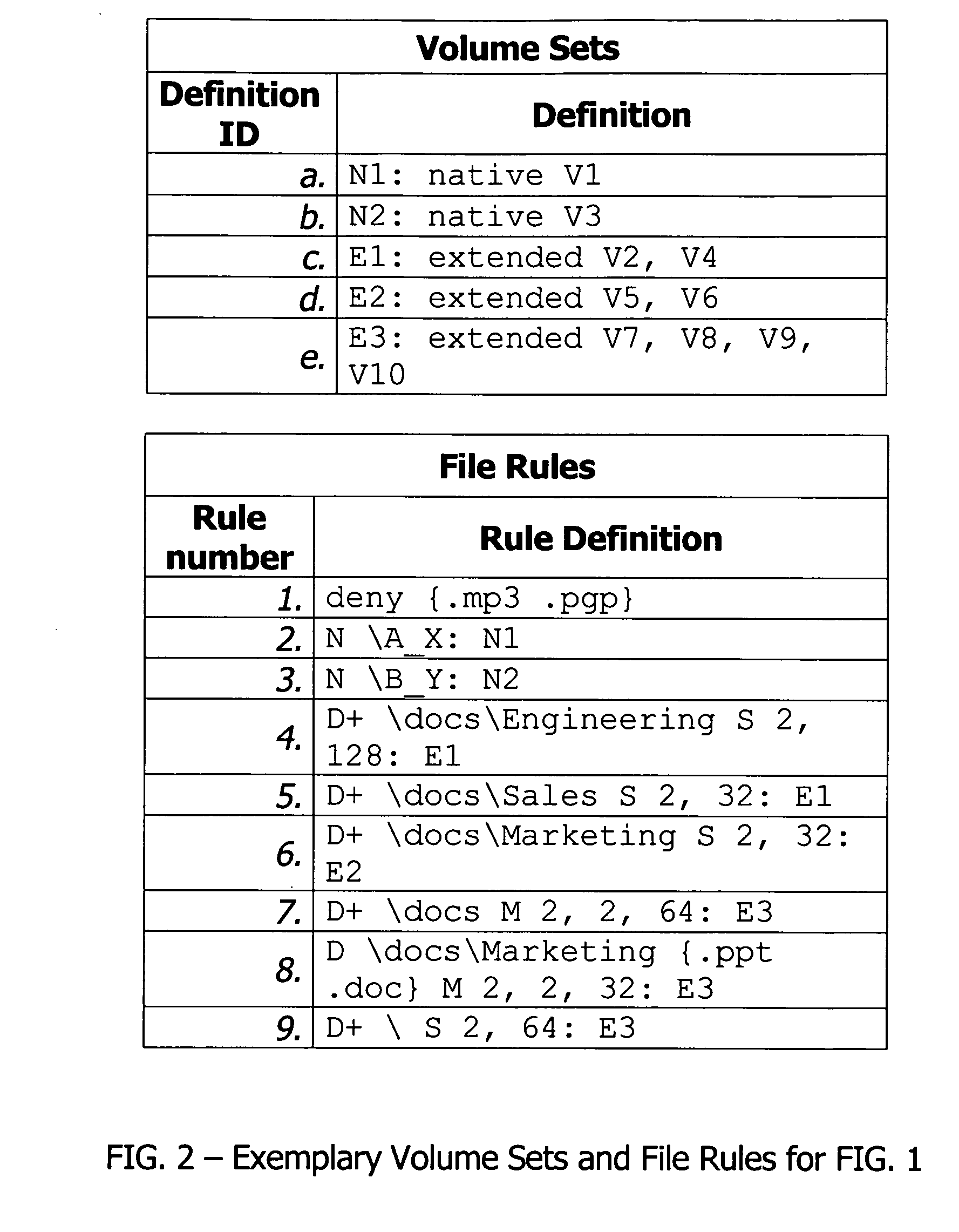
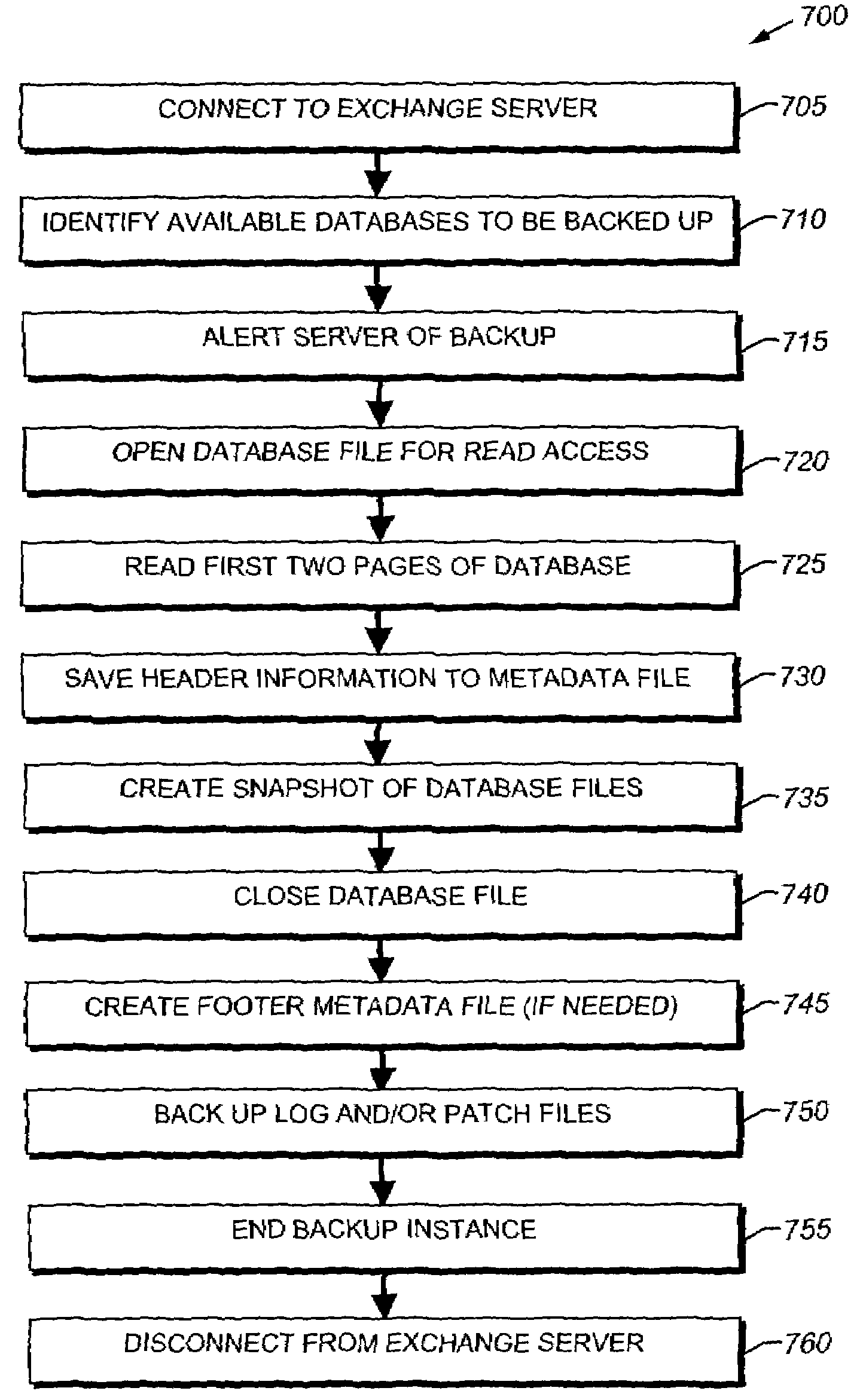
System and method for snapshot full backup and hard recovery of a database
ActiveUS7707184B1Overcome disadvantagesError detection/correctionDigital data processing detailsDatabase fileBackup
The present invention provides a method for generating a backup of a database file that is suitable for a hard recovery operation. A snapshot of the database file is generated and the log and / or patch files associated with the database are stored in a backup location. Additionally, the header and / or footer information of the database is stored, thereby enabling a restored snapshot of the database to be converted into a file suitable for a hard recovery operation.
Owner:NETWORK APPLIANCE INC
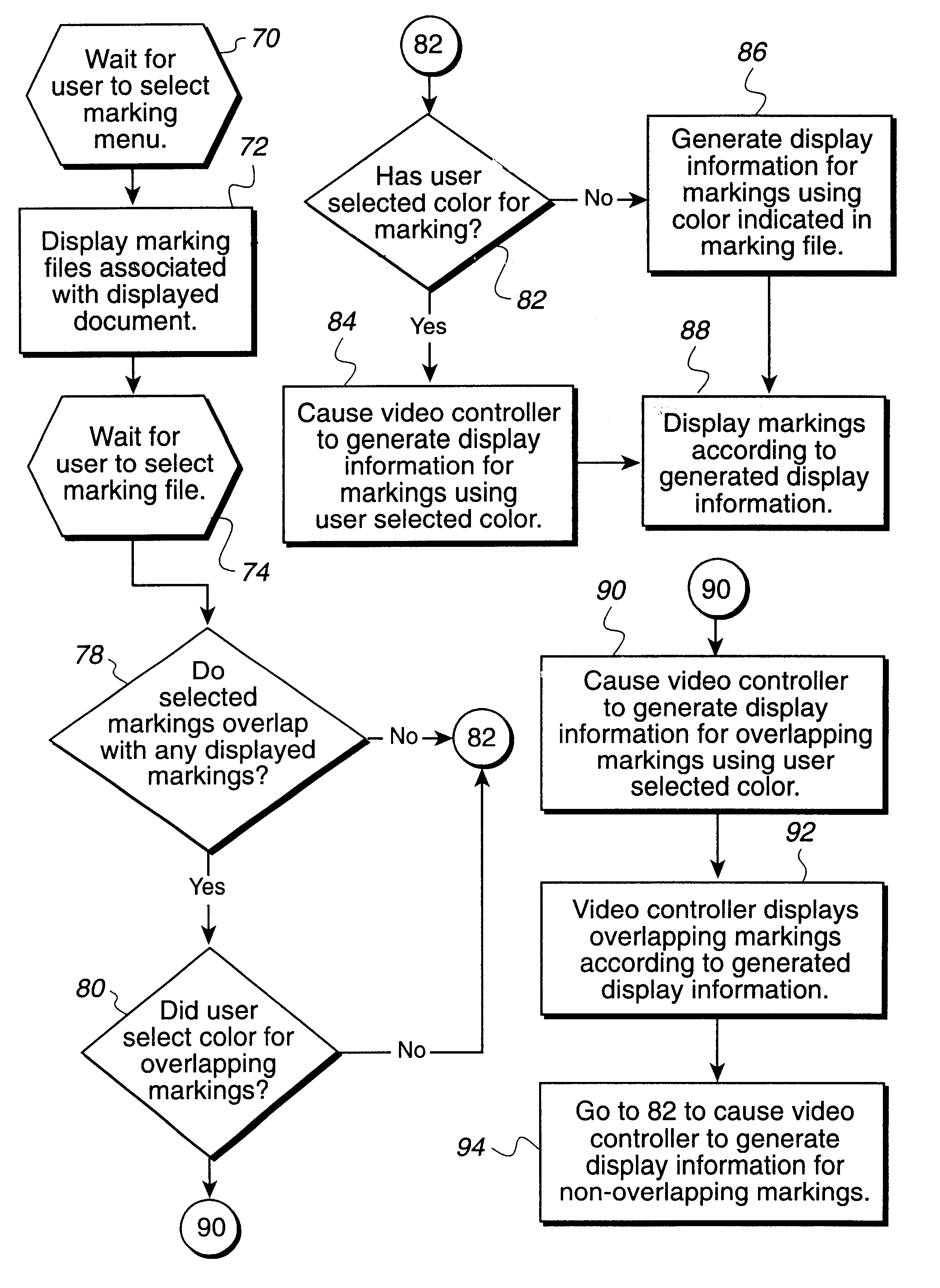
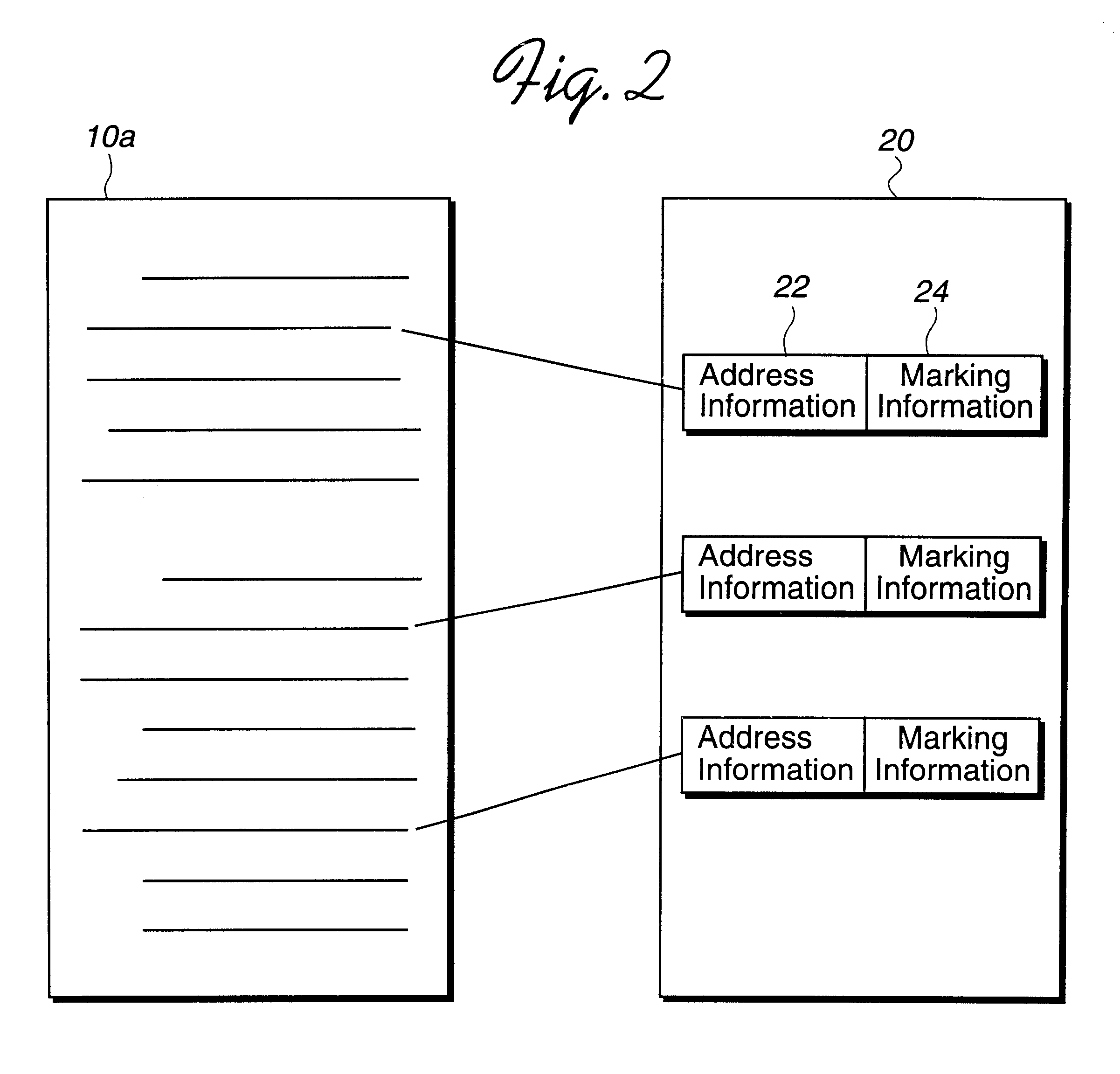
Method, system, and program for storing and retrieving markings for display to an electronic media file
InactiveUS6551357B1Digital computer detailsCathode-ray tube indicatorsGraphicsGraphical user interface
Disclosed is a method, system, and program for displaying markings to electronic media, such as text, images, video clips, audio clips, etc., in an electronic media file. A marking file includes markings and address information indicating locations of electronic media in the electronic media file to which the markings apply. The marking file is created by receiving marking input entered into a graphical user interface (GUI) window displaying the electronic media on a monitor attached to the computer. The marking file is then stored as a separate file from the electronic media file. The electronic media file and marking file are processed to display the markings indicated in the marking file superimposed on the electronic media from the electronic media file on the monitor.
Owner:IBM CORP
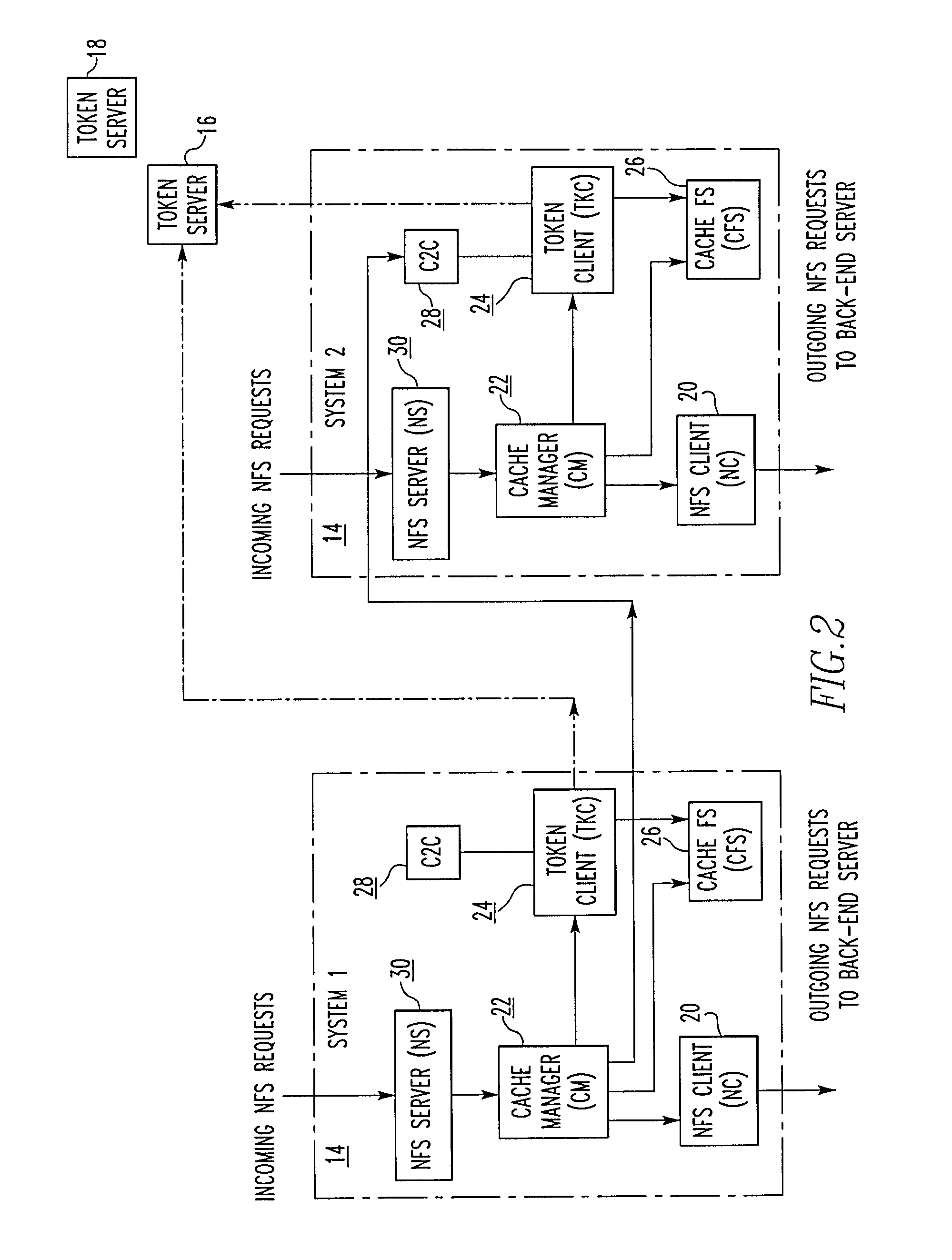
File storage system, cache appliance, and method
ActiveUS9323681B2Avoid the needMemory architecture accessing/allocationDigital data processing detailsFile systemBack end server
A file storage system for storing data of a file received from a client includes a back-end file server in which the data is stored. The system includes a cache appliance in communication with the file server, such that the appliance stores portions of the data or attributes of the file, and uses the stored data or attributes to process file system requests received from the client, and which reads and writes data and attributes to the back-end file server independently. A system for responding to a file system protocol request in regard to a back-end server includes a token server. The system includes a plurality of cache appliances in communication with the token server, each of which receives tokens from the token server to synchronize access to data and attributes caches of the cache appliances, and reading and writing data and attributes to the back-end servers when tokens are revoked, the cache appliance having persistent storage in which data are stored, and the token server having persistent storage in which tokens are stored. A storage system includes a plurality of backend servers. The system includes a token server which grants permission to read and write file attributes and data system, and includes a plurality of cache appliances in communication with at least one of the backend servers and the token server for processing an incoming NFS request to the one backend server. Each cache appliance comprises an NFS server which converts incoming NFS requests into cache manager operations; a token client module in communication with the token server having a cache of tokens obtained from the token server; a cache manager that caches data and attributes and uses tokens from the token client module to ensure that the cached data or attributes are the most recent data or attributes, and an NFS client which sends outgoing NFS requests to the back-end file server. Methods for storing data of a file received from a client.
Owner:MICROSOFT TECH LICENSING LLC
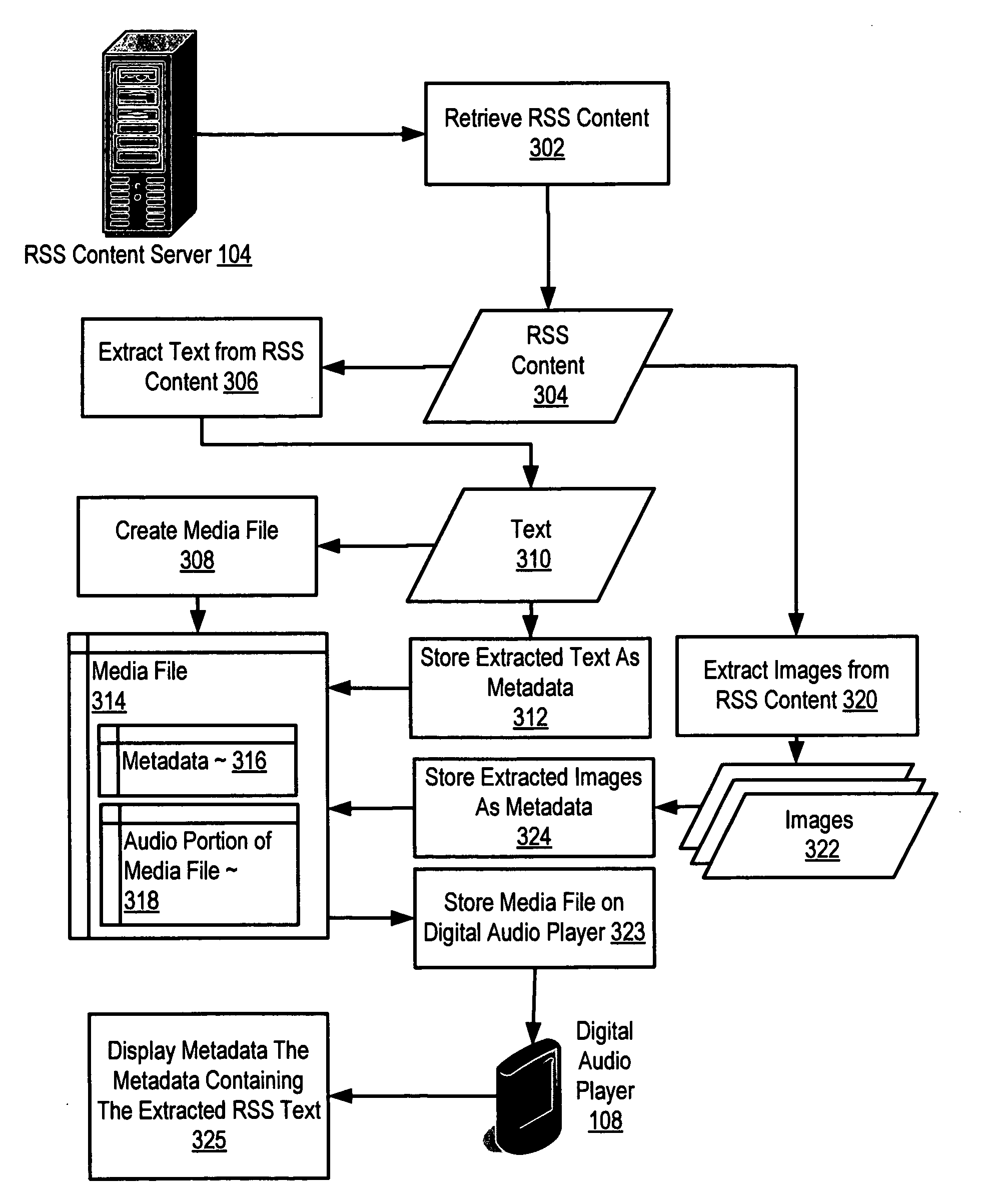
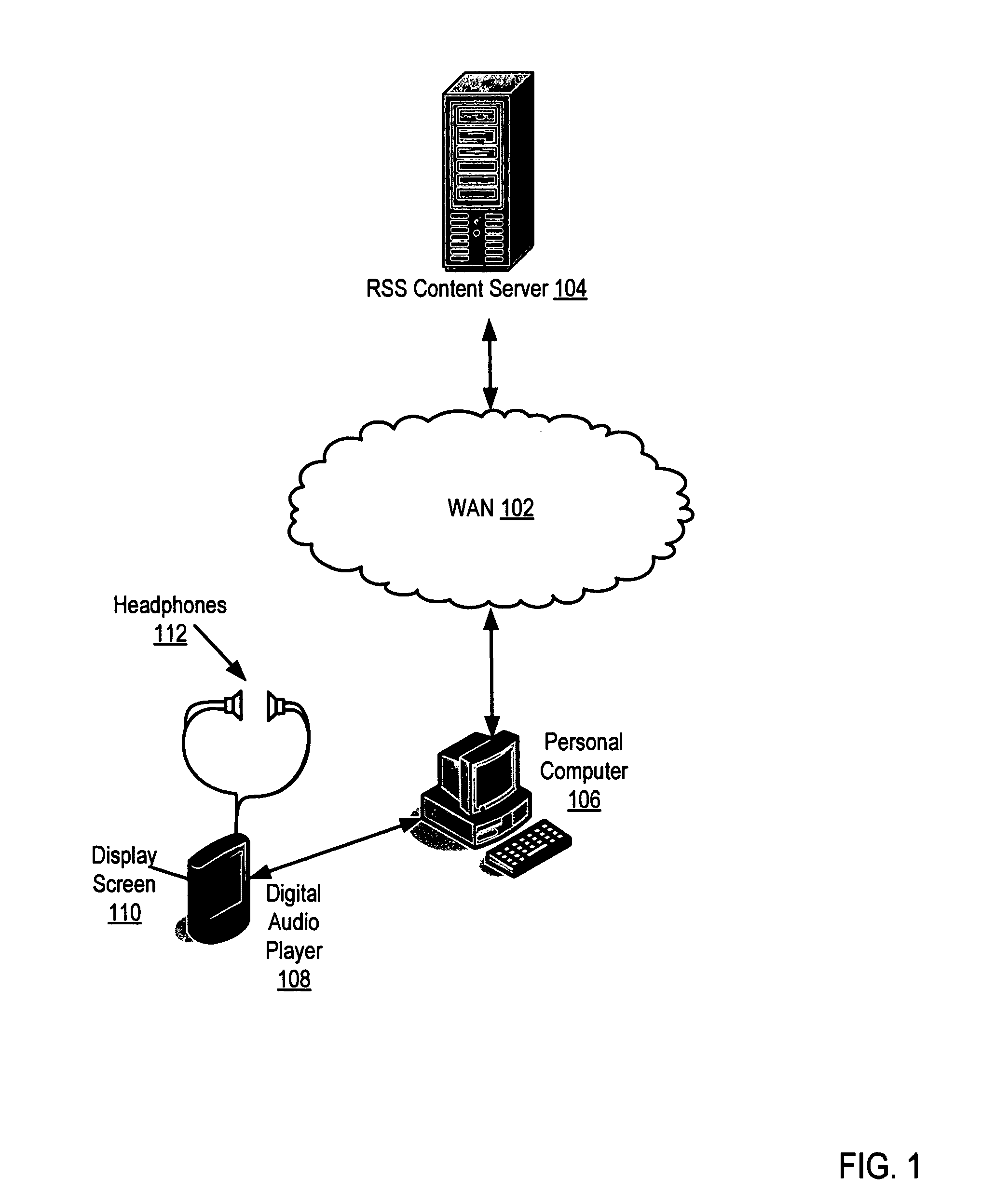
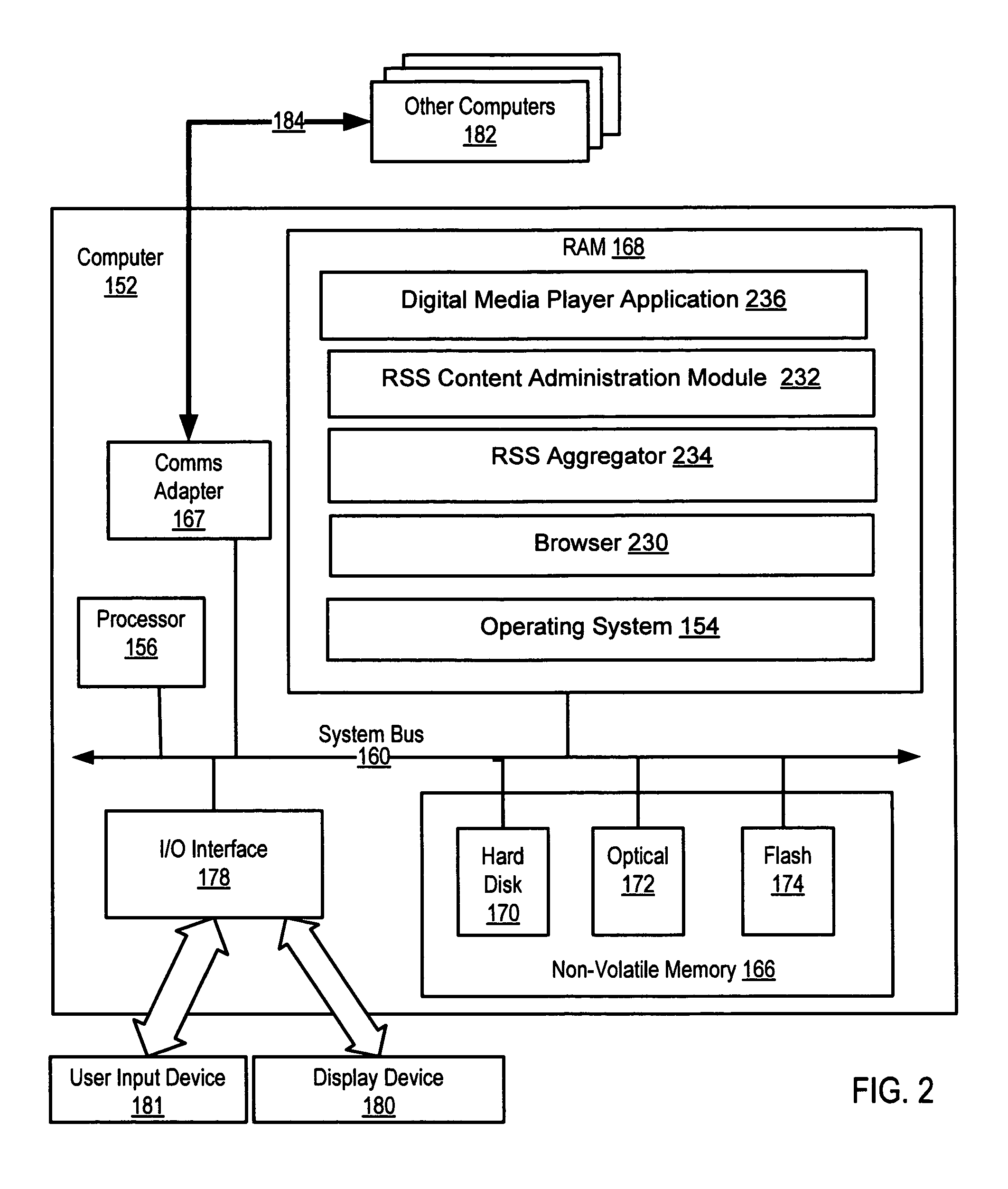
RSS content administration for rendering RSS content on a digital audio player
Methods, systems, and computer program products are provided for RSS content administration for rendering RSS content on a digital audio player. Embodiments include retrieving, through an RSS feed, RSS content; extracting text from the RSS content; creating a media file; and storing the extracted text of the RSS content as metadata associated with the media file. Embodiments also typically include extracting one or more images from the RSS content; and storing the extracted images as metadata associated with the media file. Embodiments also typically include extracting text from the RSS content for audio rendering on the digital audio player; converting the text to speech; and recording the speech in the audio portion of the media file. Many embodiments also include storing the media file on a digital audio player; displaying the metadata describing the media file; and playing the audio portion containing the speech.
Owner:IBM CORP
IC card file system
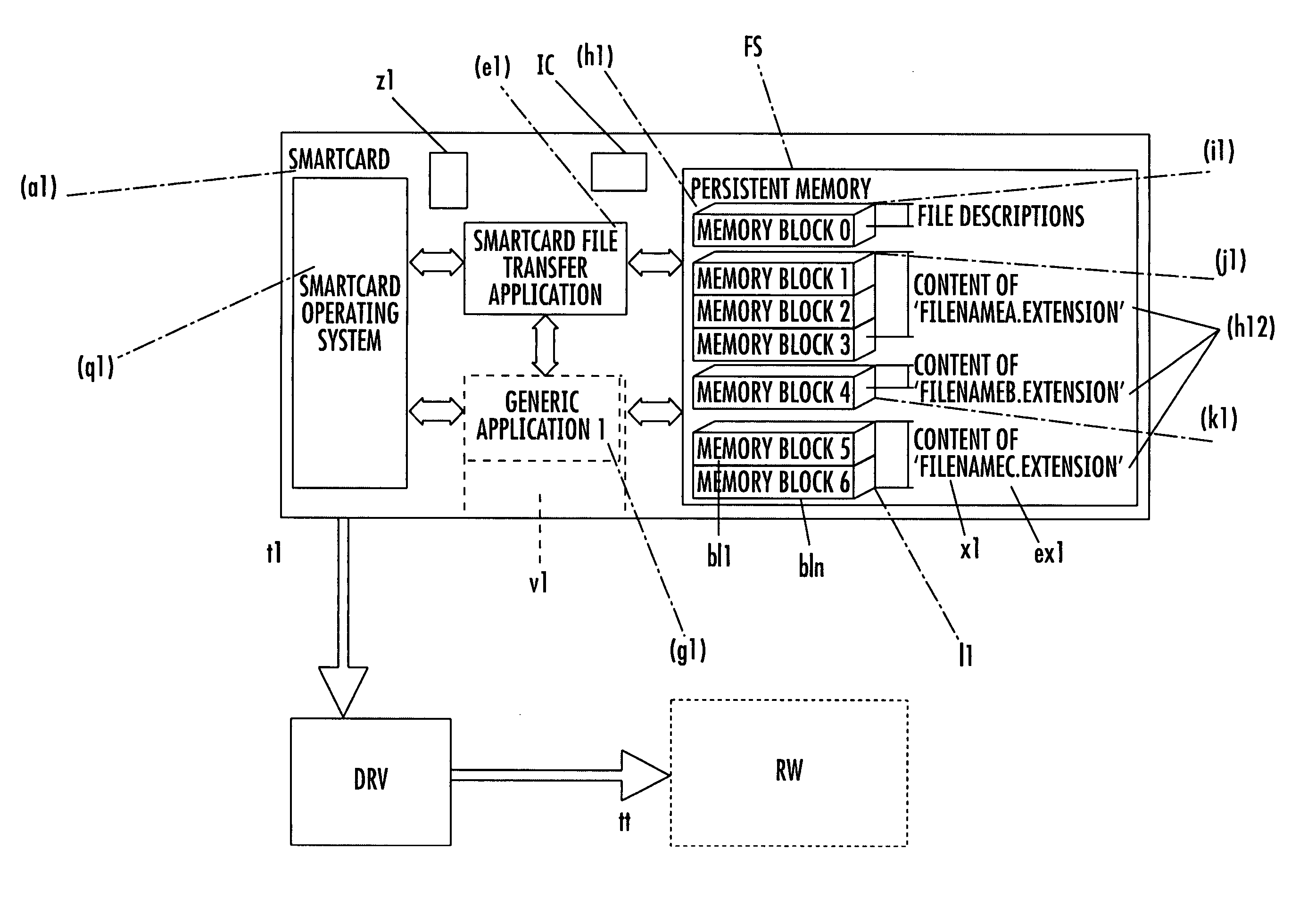
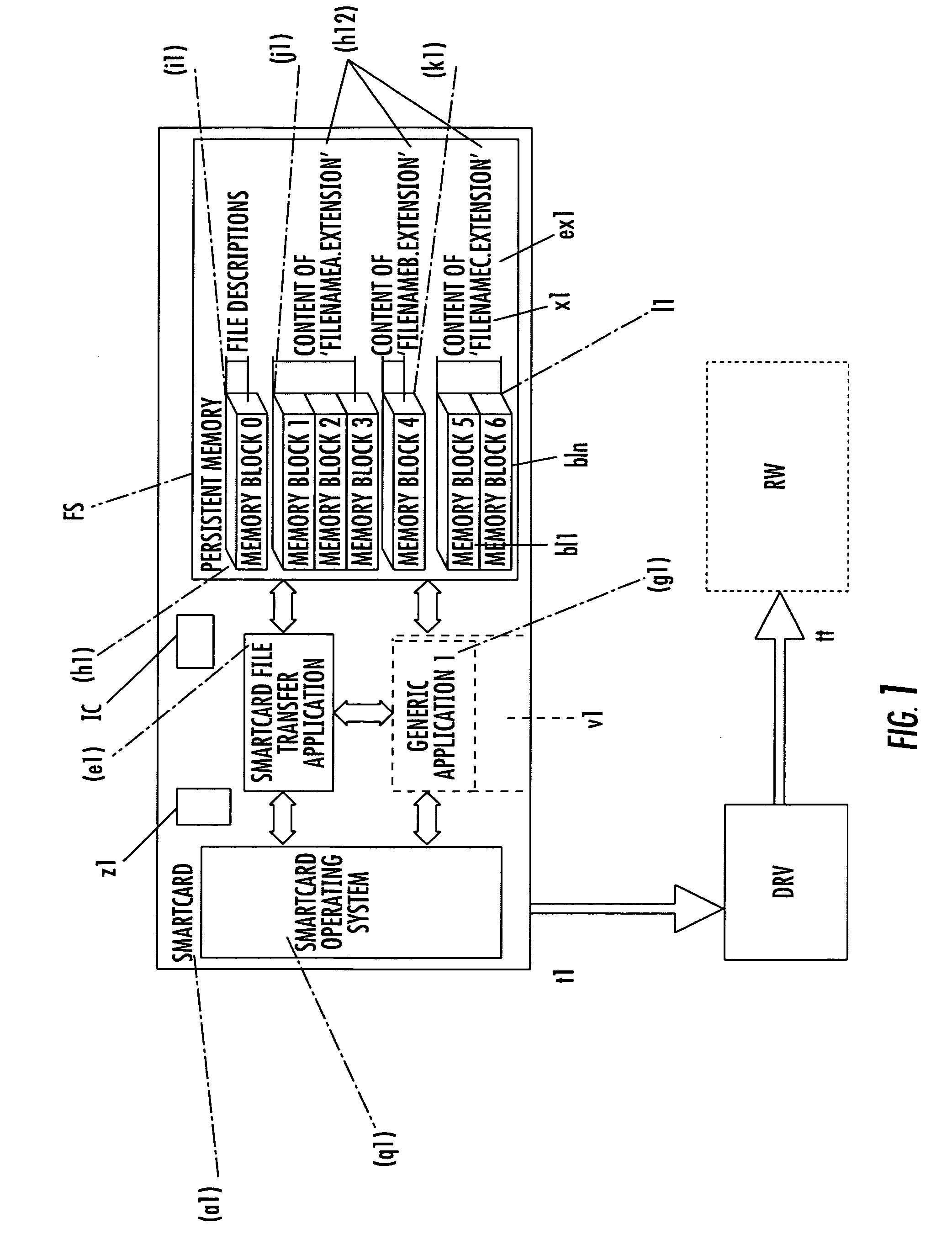
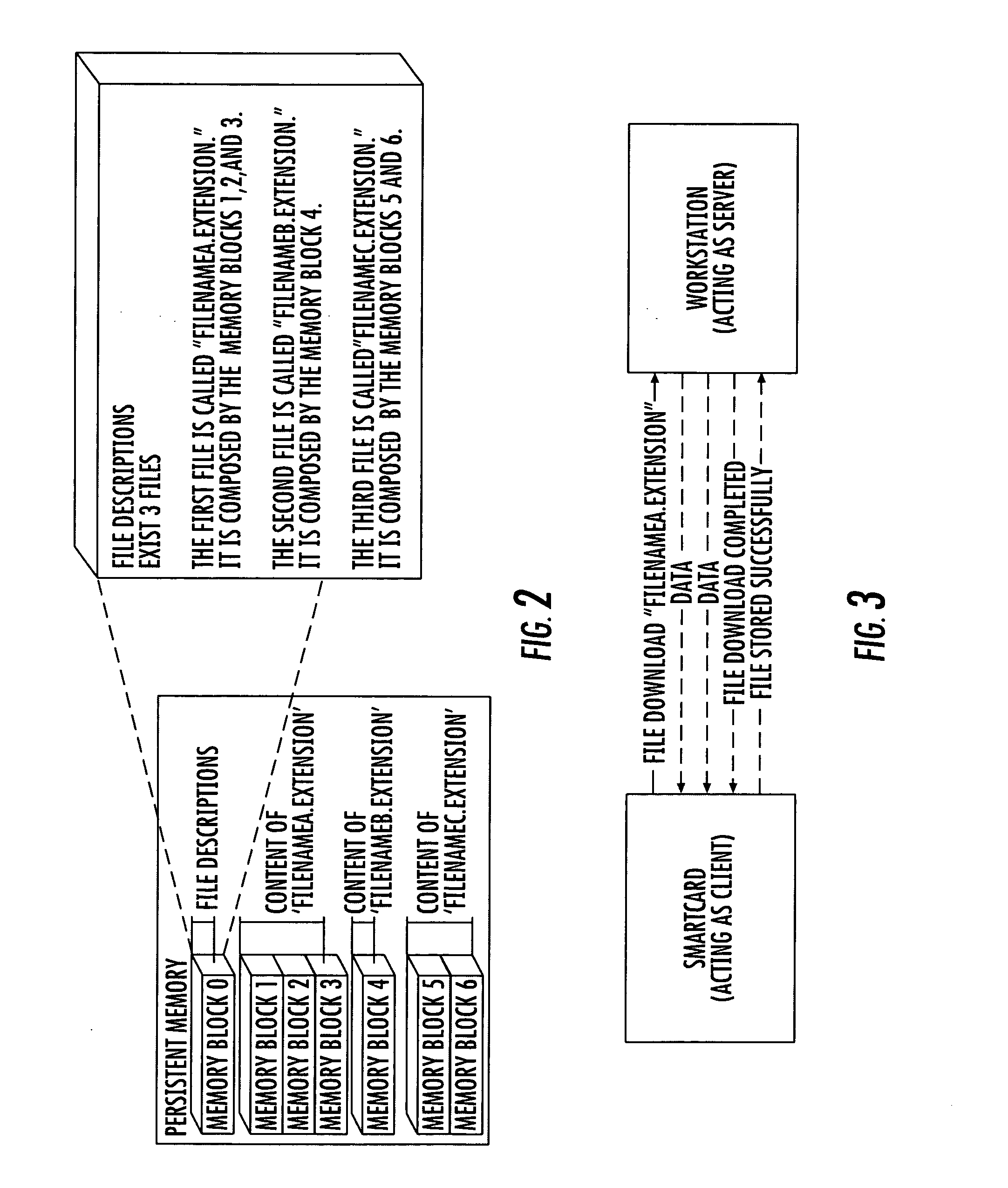
InactiveUS20070152070A1AccessibilityAcutation objectsDigital data information retrievalIntel HEXApplication software
File system for IC CARD comprising an integrated circuit IC, non volatile memories ROM and / or E2PROM and at least a volatile memory RAM, for organizing files storage inside the non volatile memories and defining, through a logical structure, their accessibility by an IC Card application, stored inside one of said non volatile memories or IC or loaded in the volatile memory and in communication with an external read-write device; an interchange application, stored inside one of said non volatile memories, drives the organization of files in an additional tag-length logic structures of arbitrary length, allowing the identification of files through alphanumeric identifiers of arbitrary length and extension, and their accessibility by an external read-write device, eventually non IC card purpose, like a workstation a personal computer or a PDA interconnected to the IC Card by means of standard communication interface. The file system organizes said tag-length logic structure as individually memory blocks, each identified by an hexadecimal identification number and a block size and one of these memory blocks, more particularly one per non volatile memory, describes the content of the non volatile memory, comprising the number of files stored, their file name and extension and, for each file, the location of memory blocks composing its content.
Owner:STMICROELECTRONICS INT NV
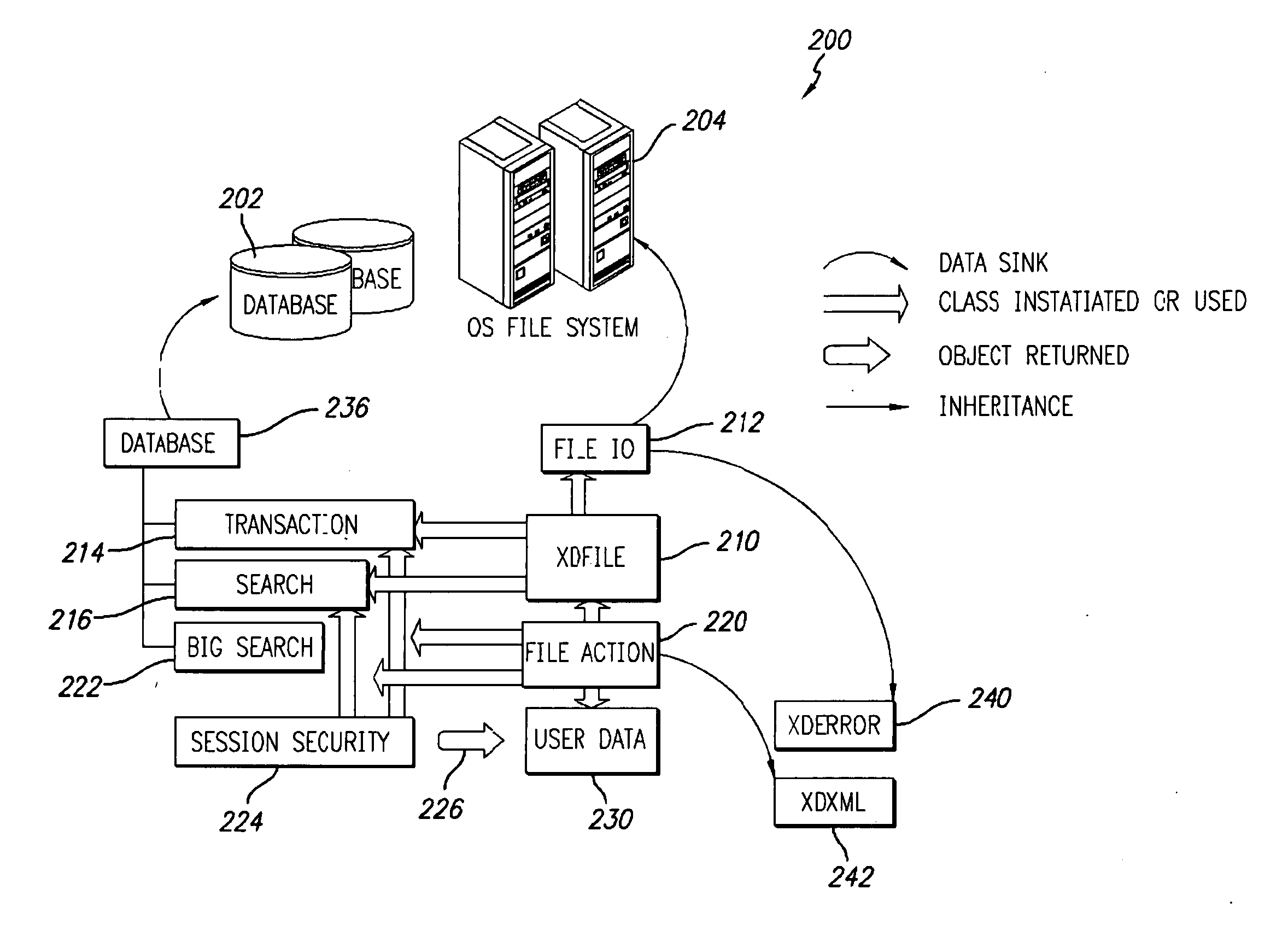
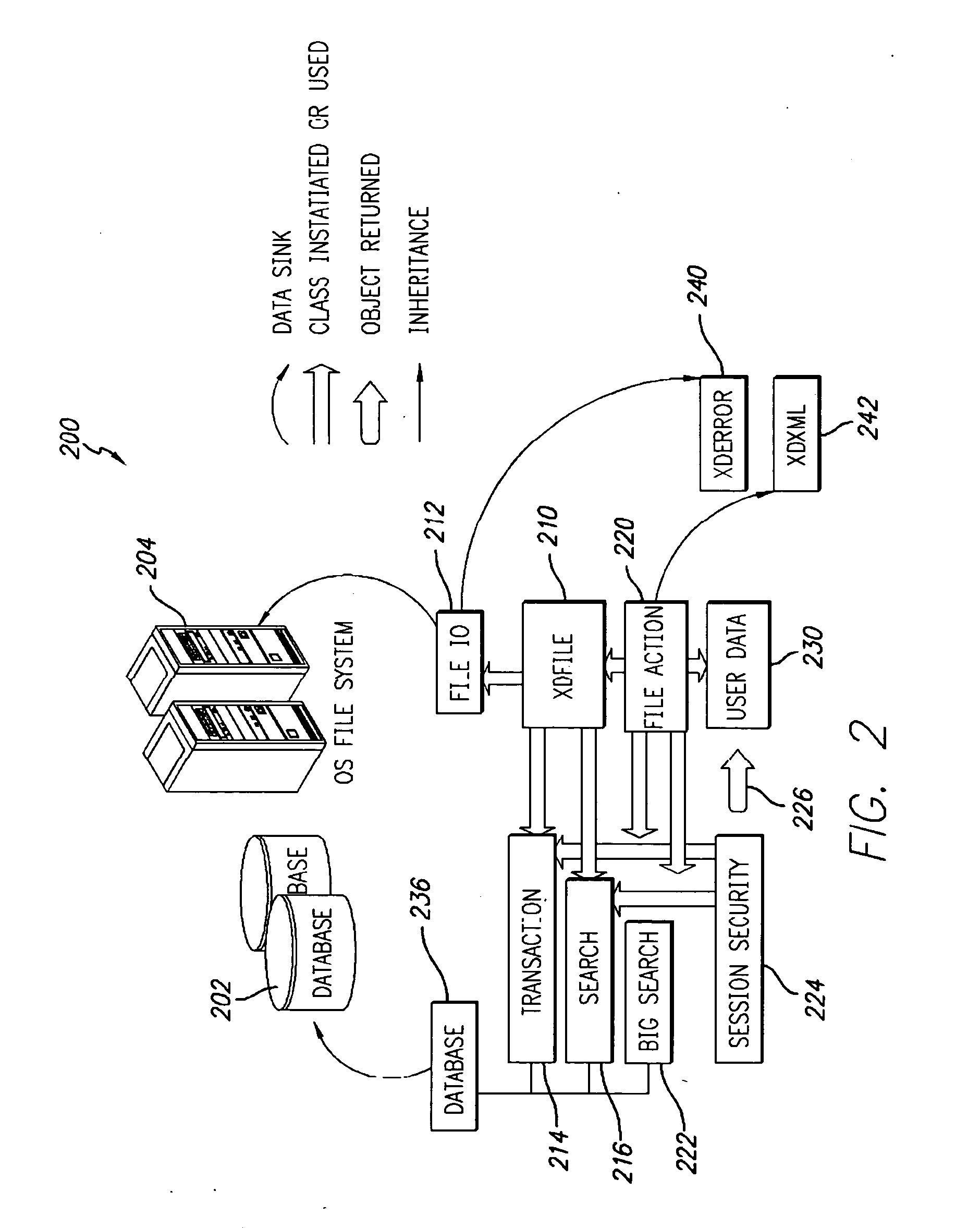
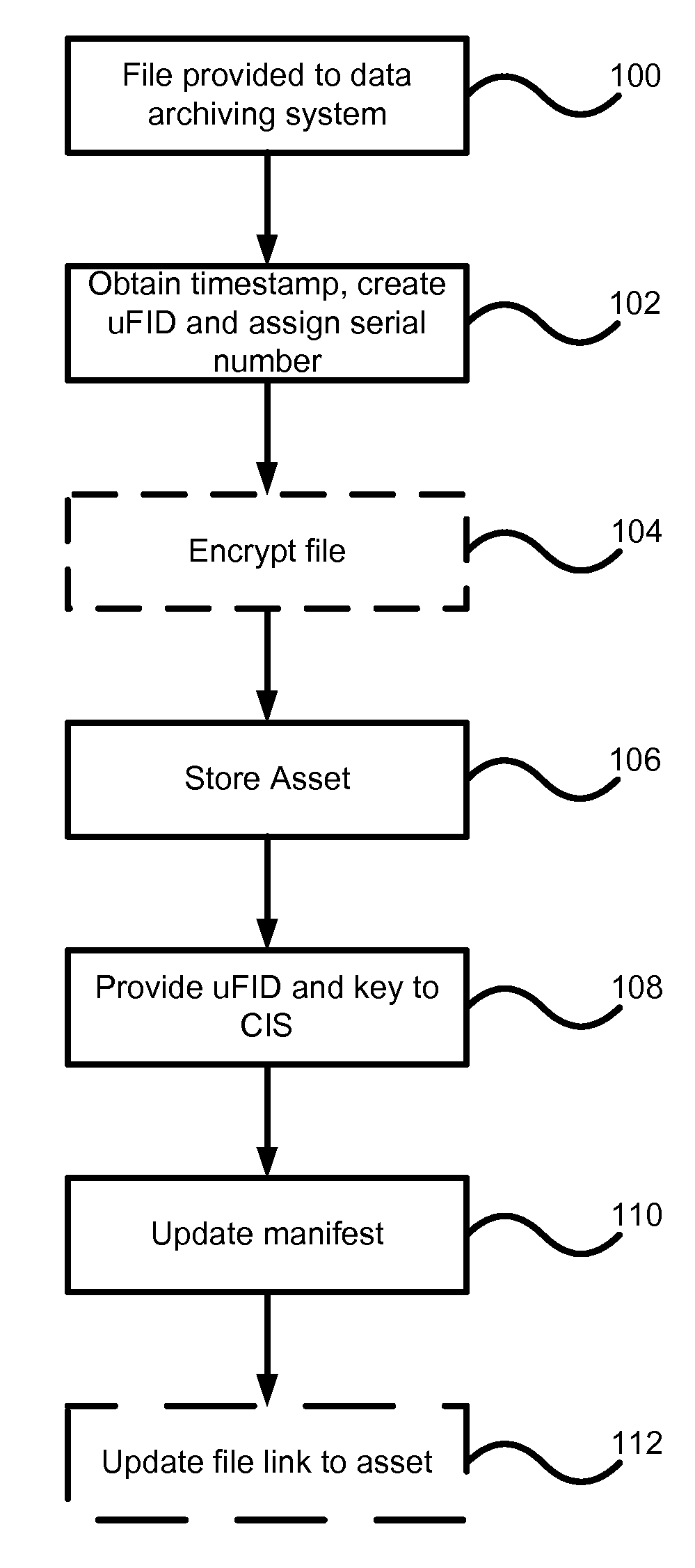
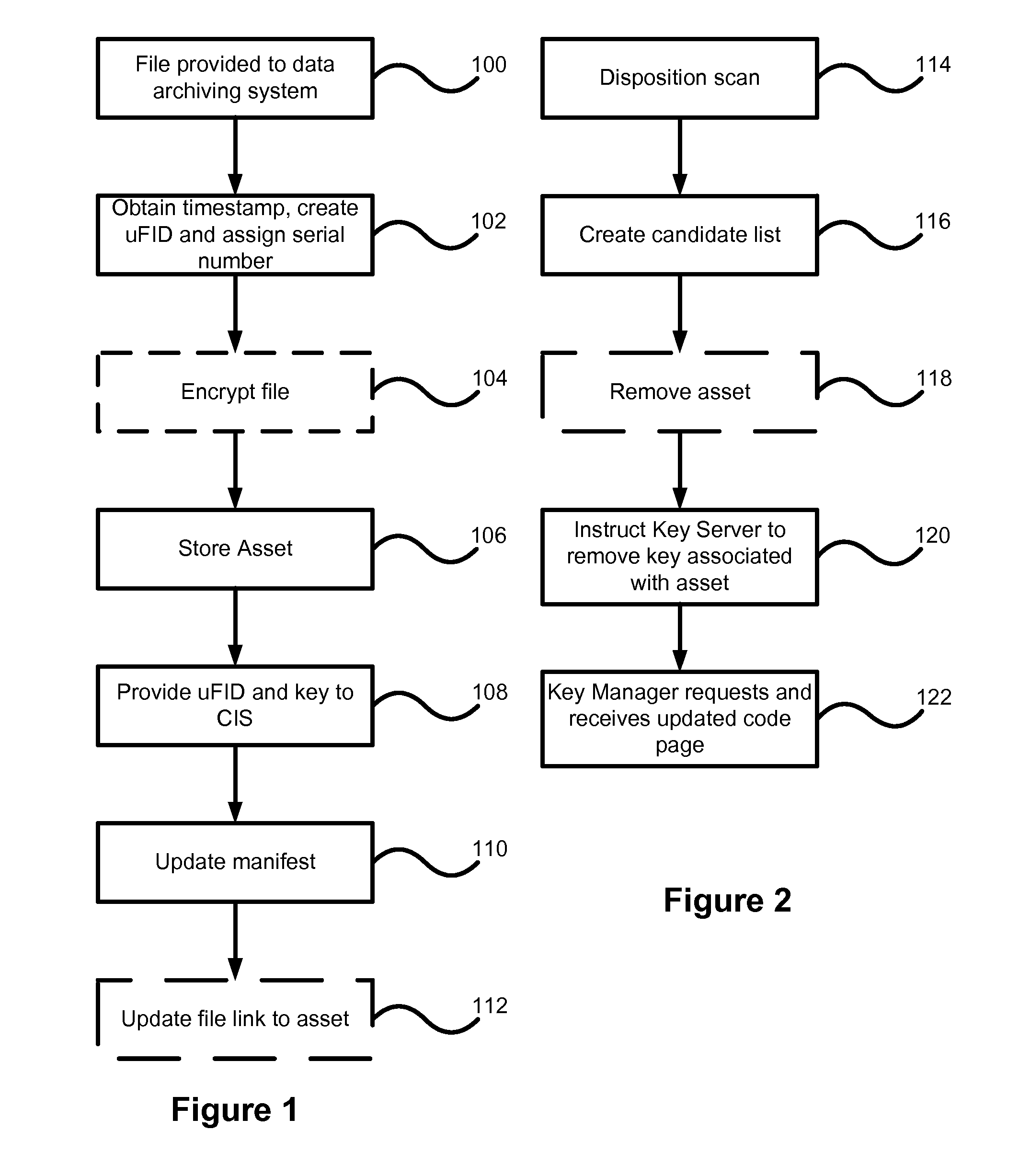
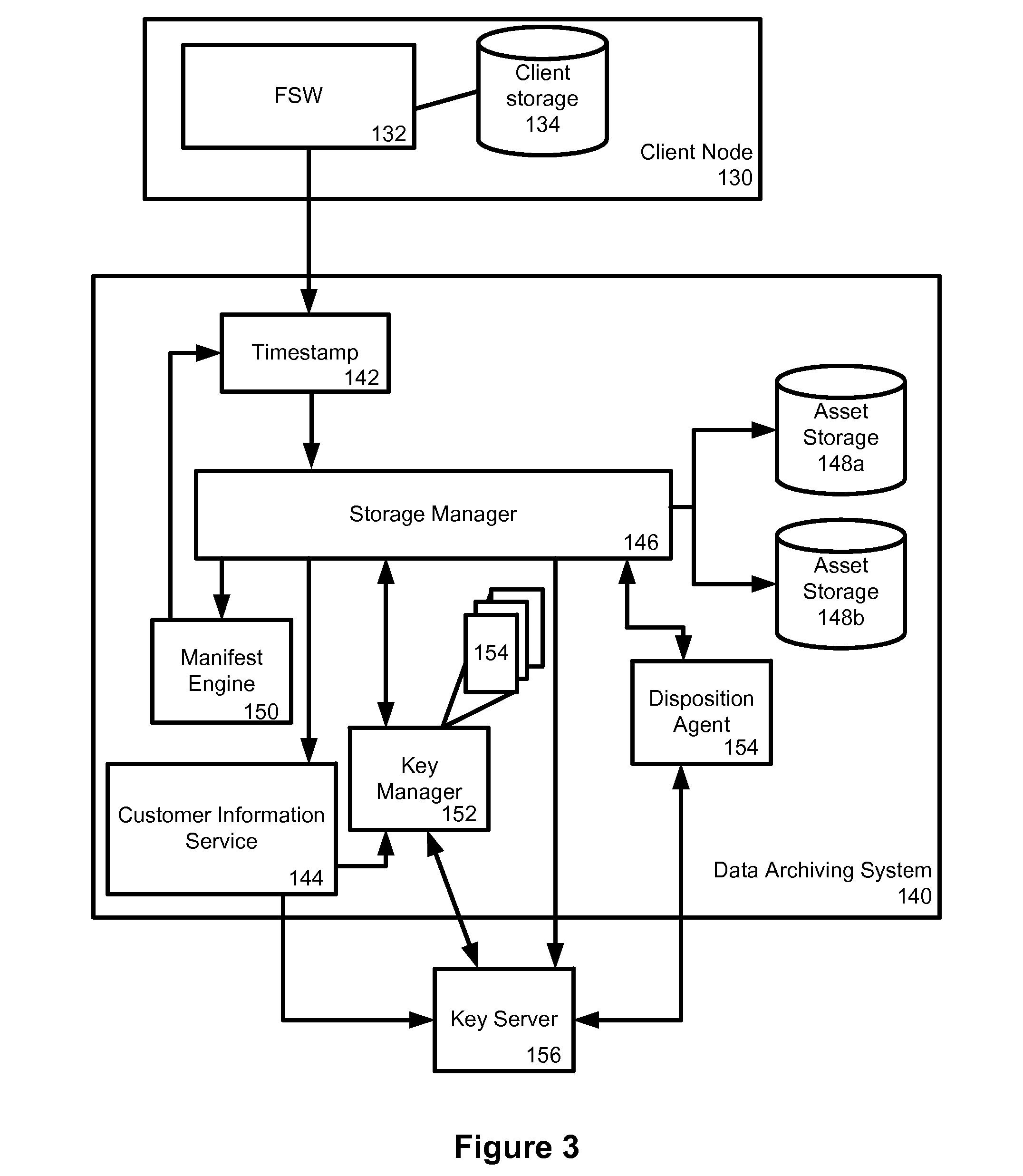
Data archiving system
ActiveUS7801871B2Digital data processing detailsComputer security arrangementsFault toleranceApplication server
An encrypted file storage solution consists of a cluster of processing nodes, external data storage, and a software agent (the “File System Watcher”), which is installed on the application servers. Cluster sizes of one node up to many hundreds of nodes are possible. There are also remote “Key Servers” which provide various services to one or more clusters. The preceding describes a preferred embodiment, though in some cases it may be desirable to “collapse” some of the functionality into a smaller number of hardware devices, typically trading off cost versus security and fault-tolerance.
Owner:STORCENTRIC DIP LENDER LLC +1
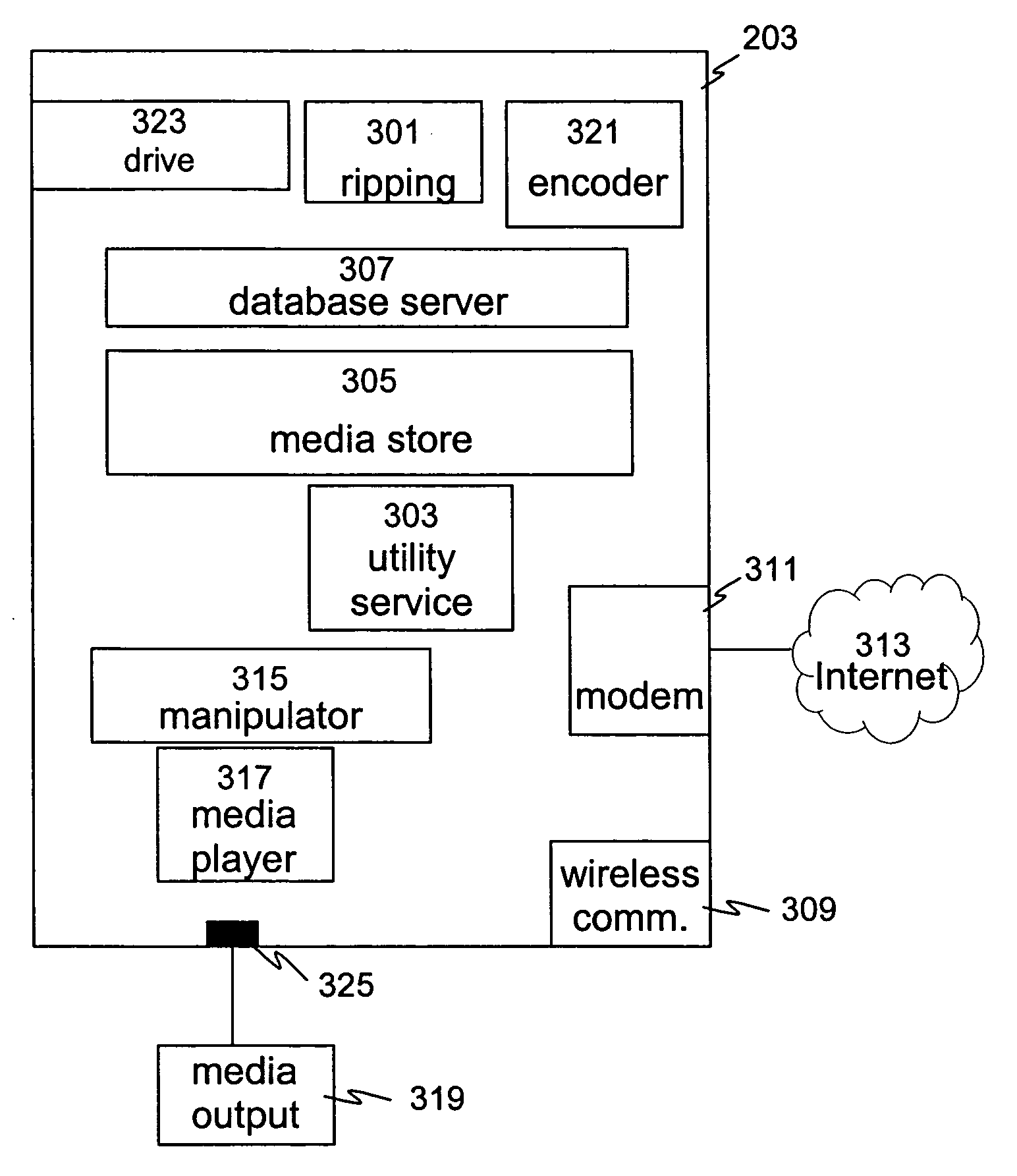
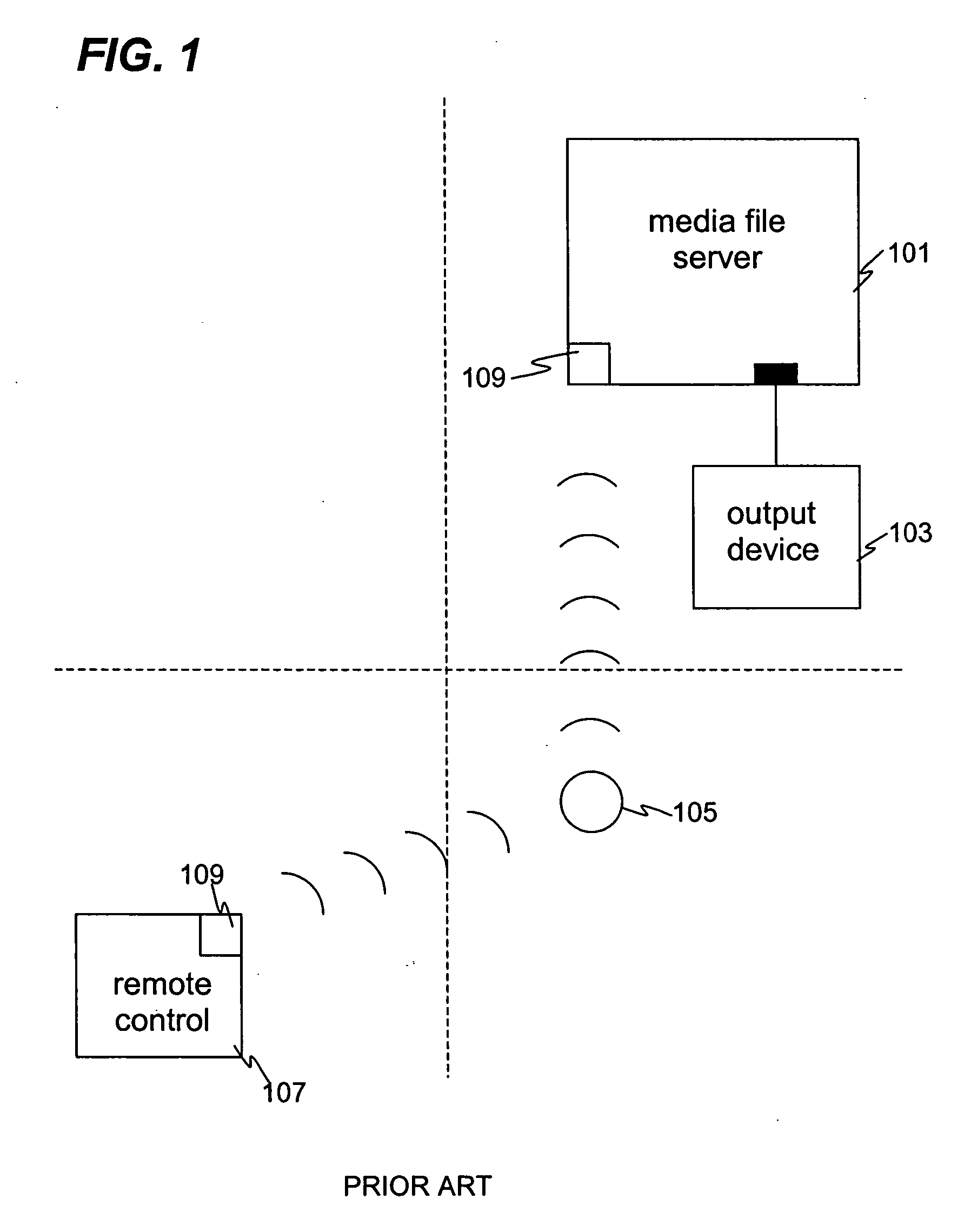
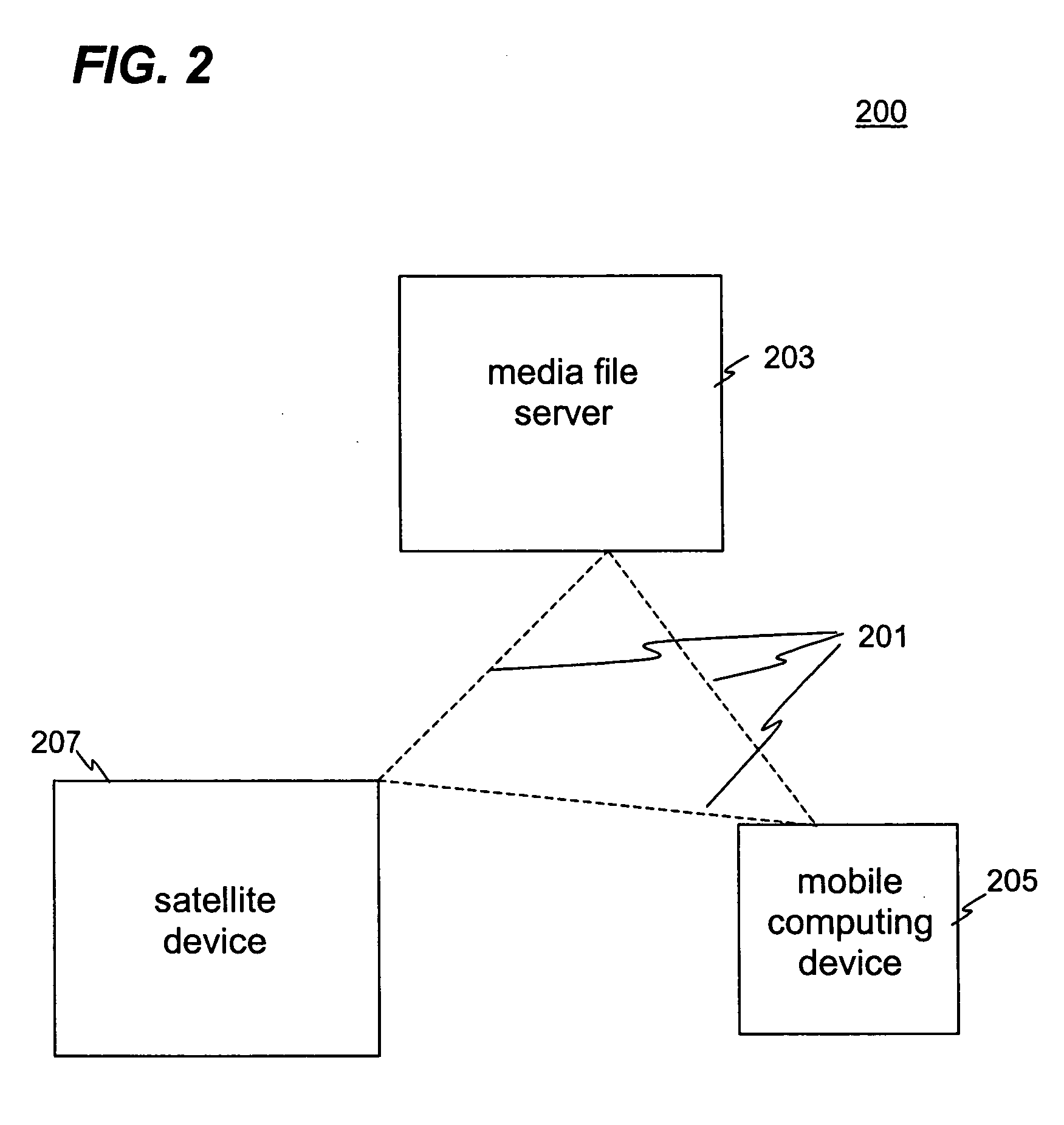
Media file distribution system and method
InactiveUS20040225746A1Quality improvementDigital data processing detailsData switching by path configurationDistribution systemOutput device
A media file distribution system comprising a media server and one or more satellite units, wherein the media server comprises a media file store for storing one or more media files and a first wireless communicator. The one or more satellite units comprise a second wireless communication means and a first output device for playing the one or more media files stored on the media server.
Owner:DIGIFI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com