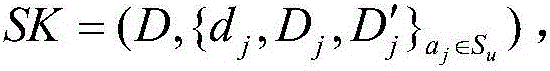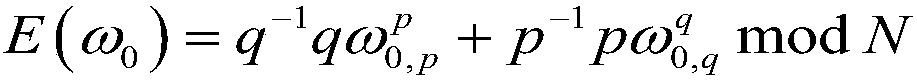Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5133 results about "Privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
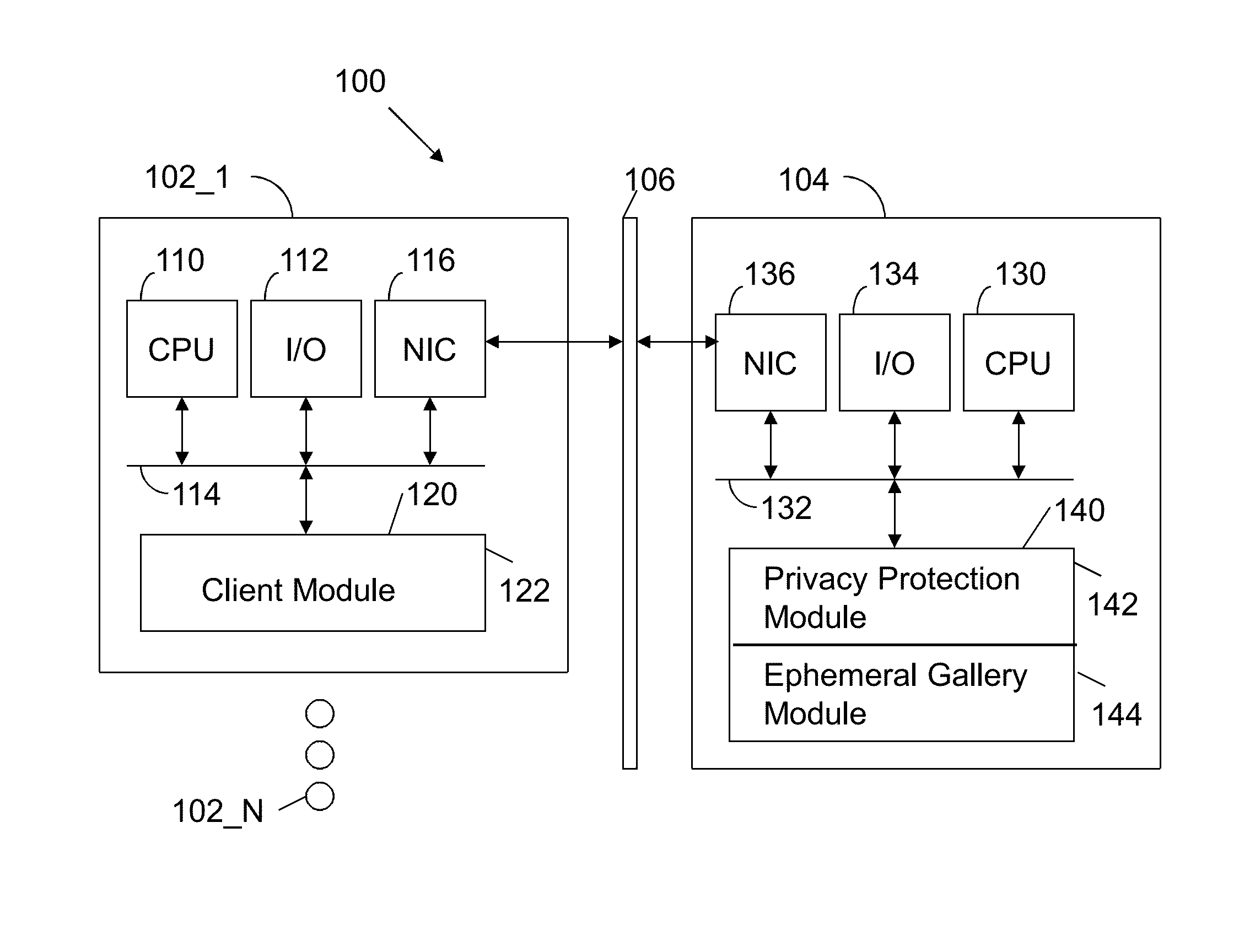
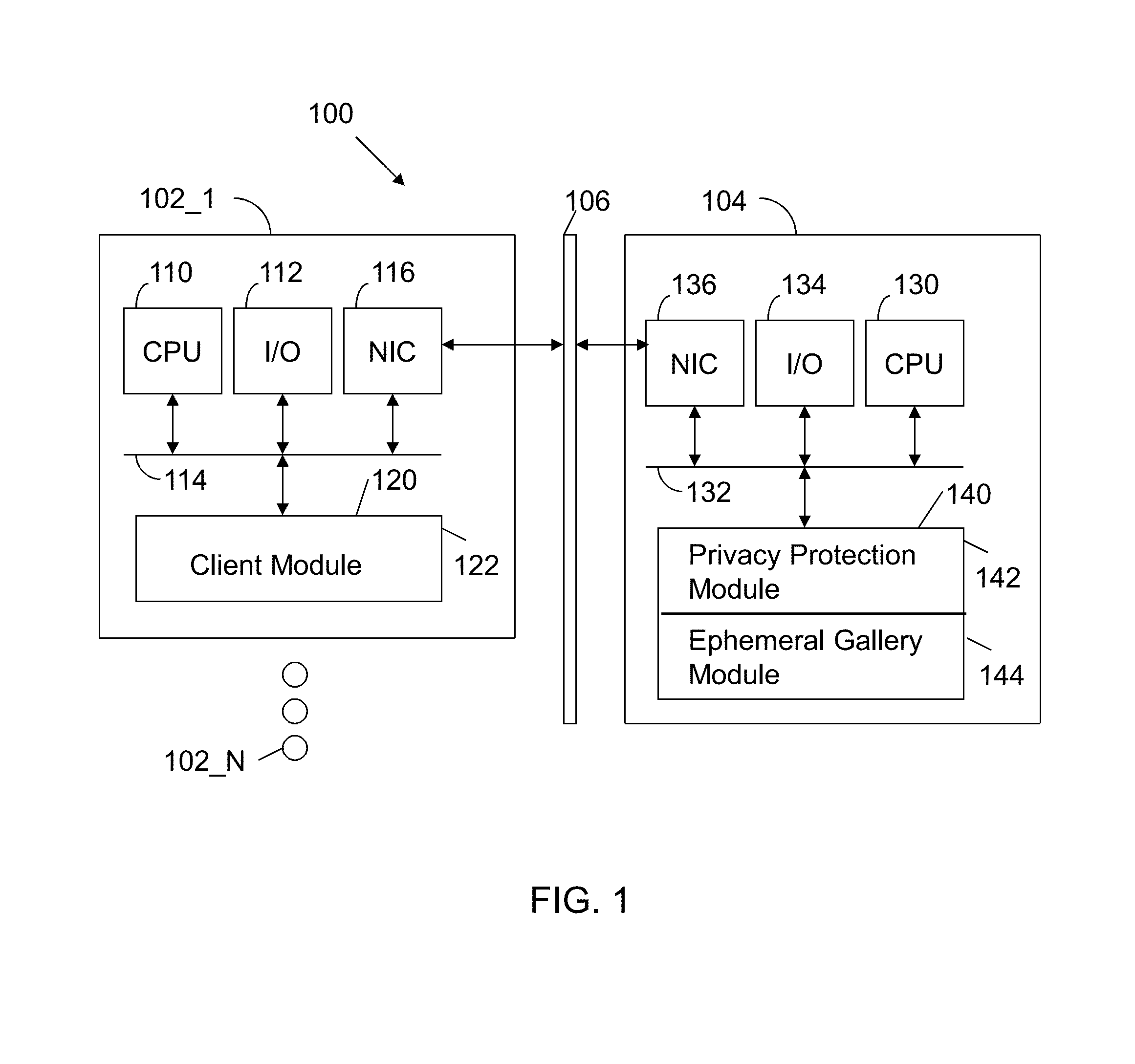
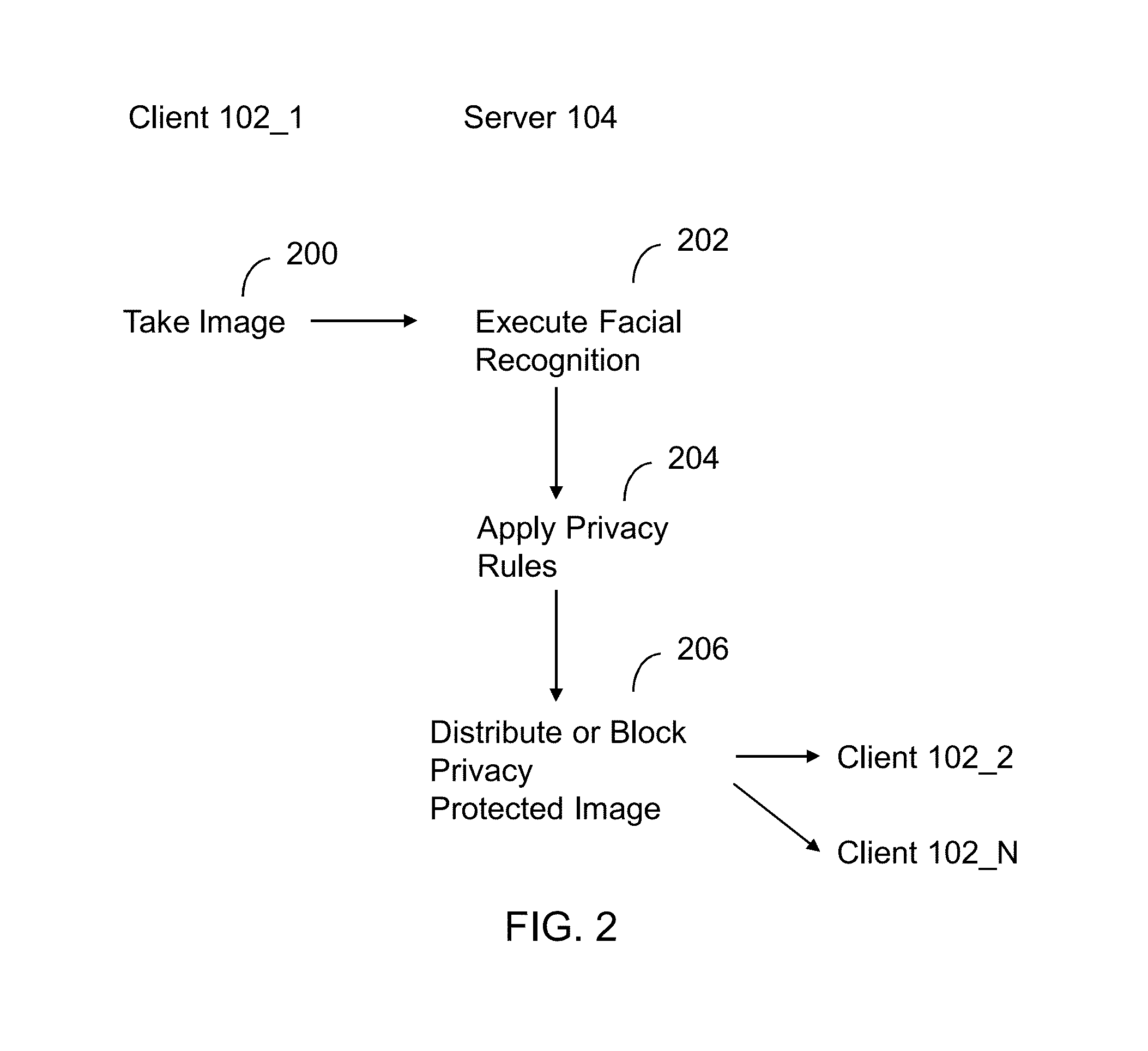
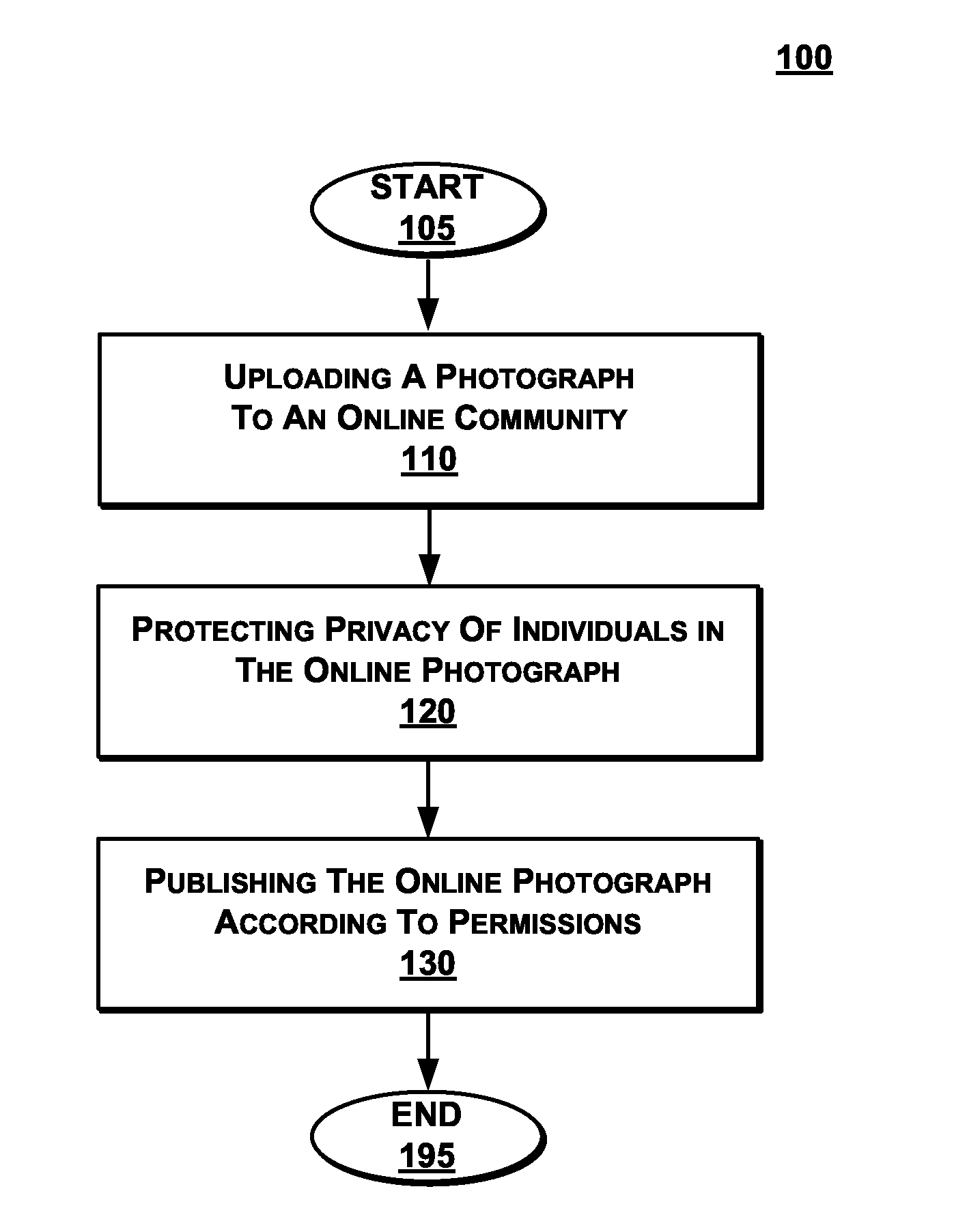
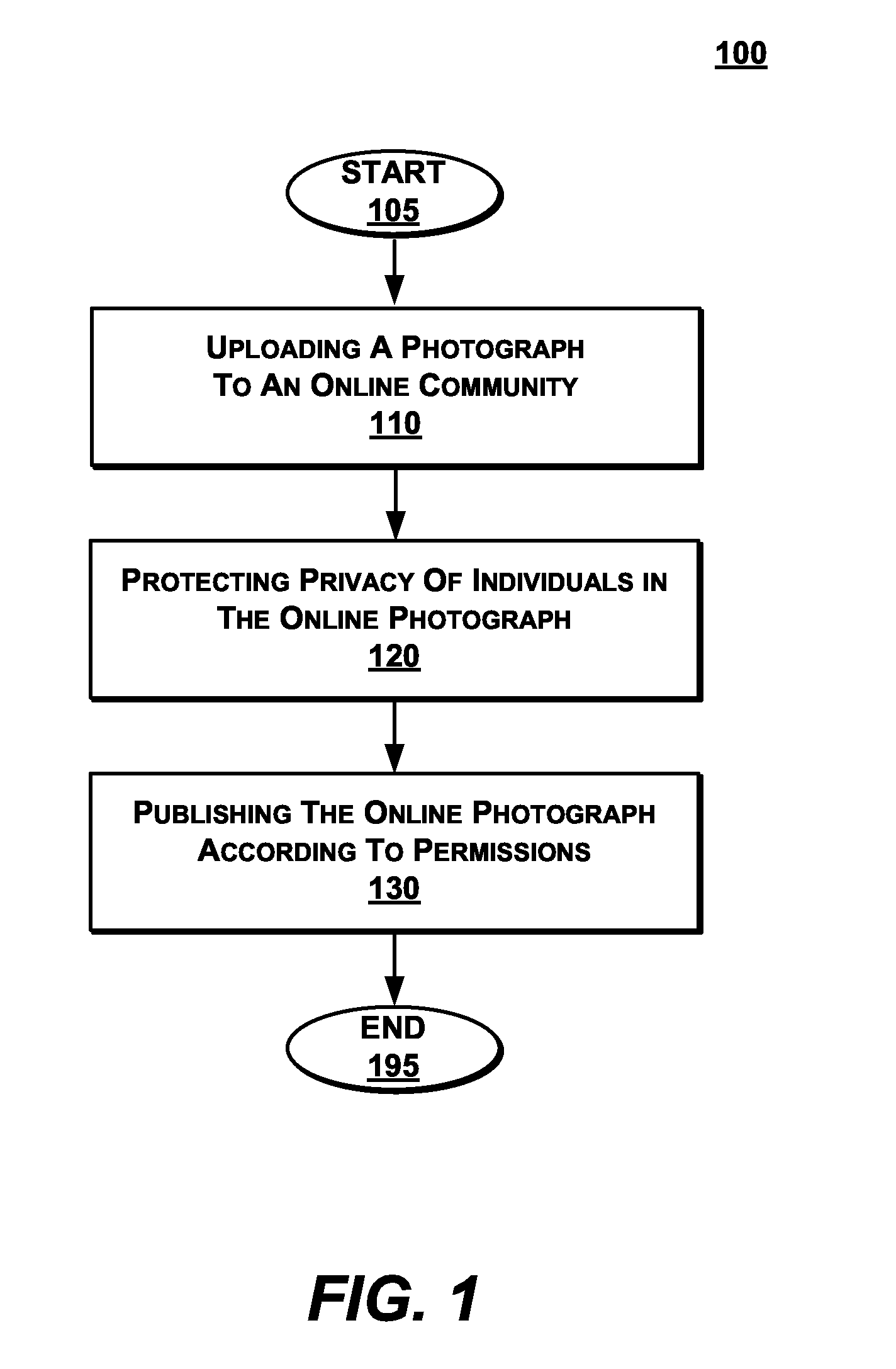
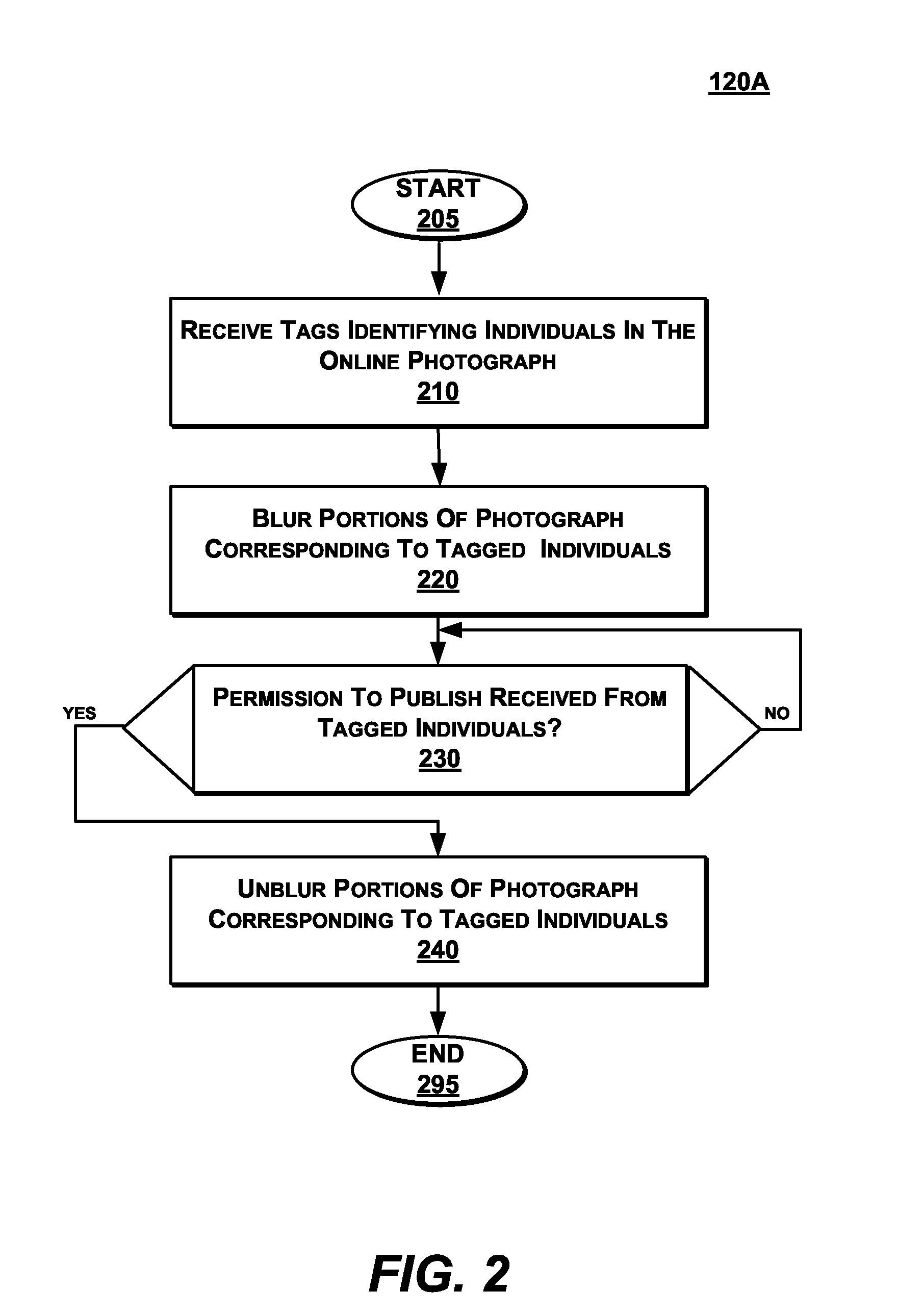
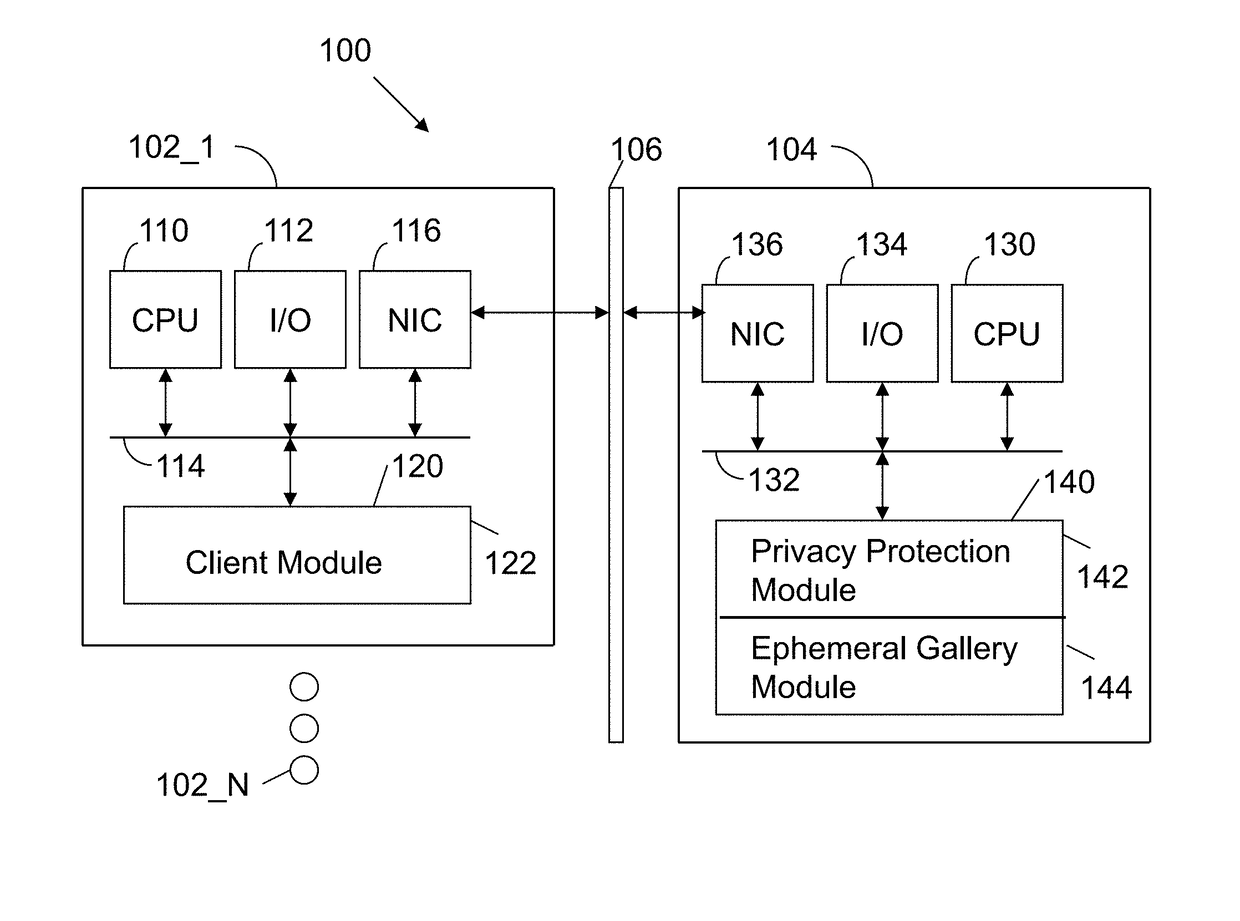
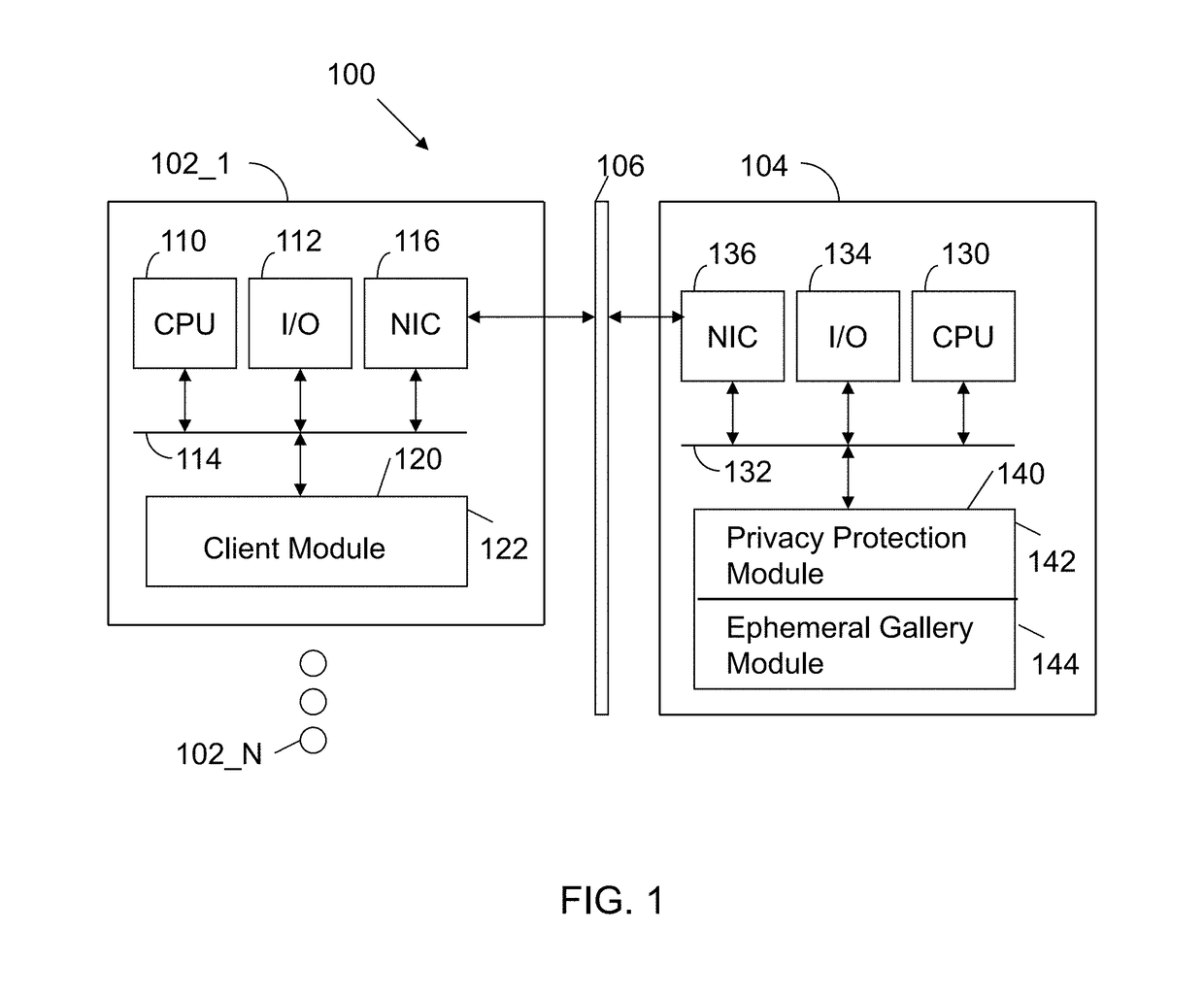
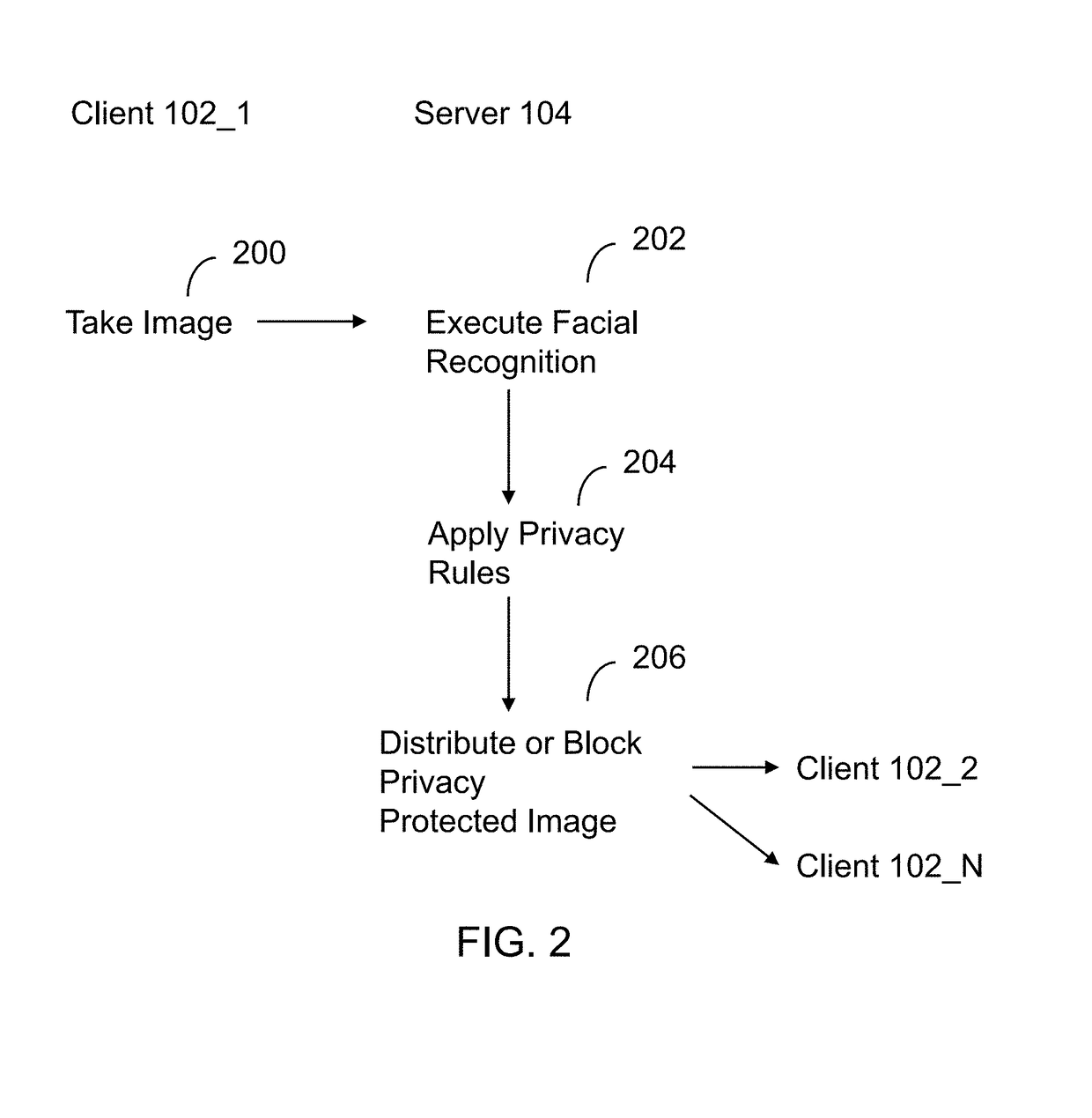
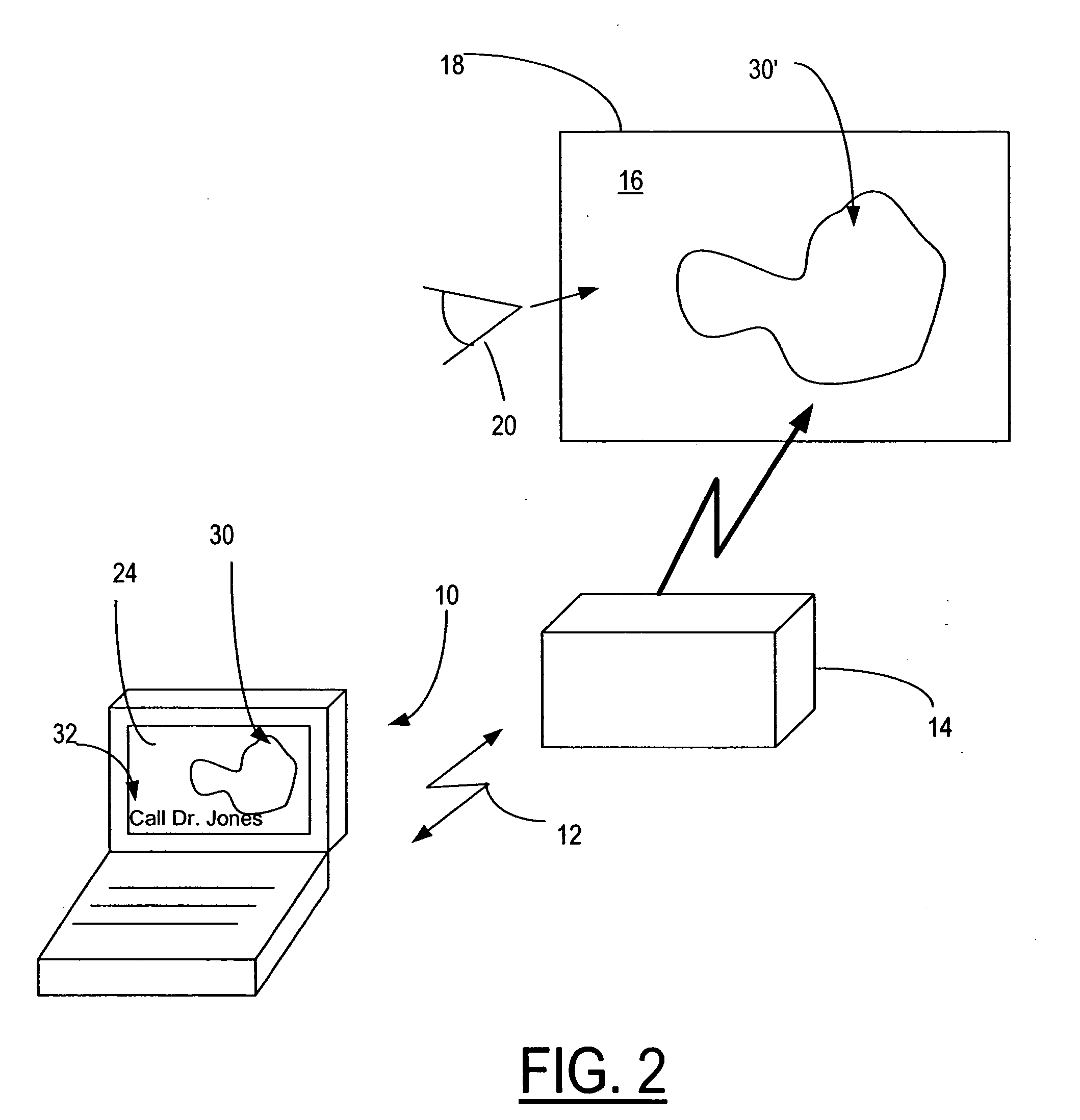
Apparatus and method for automated privacy protection in distributed images
ActiveUS9396354B1Data processing applicationsCharacter and pattern recognitionPrivacy rulePrivacy protection
A method executed by a computer includes receiving an image from a client device. A facial recognition technique is executed against an individual face within the image to obtain a recognized face. Privacy rules are applied to the image, where the privacy rules are associated with privacy settings for a user associated with the recognized face. A privacy protected version of the image is distributed, where the privacy protected version of the image has an altered image feature.
Owner:SNAP INC
Adding privacy protection to photo uploading/ tagging in social networks
ActiveUS20120250951A1Data processing applicationsCharacter and pattern recognitionPrivacy protectionSocial web
Owner:VERIZON PATENT & LICENSING INC
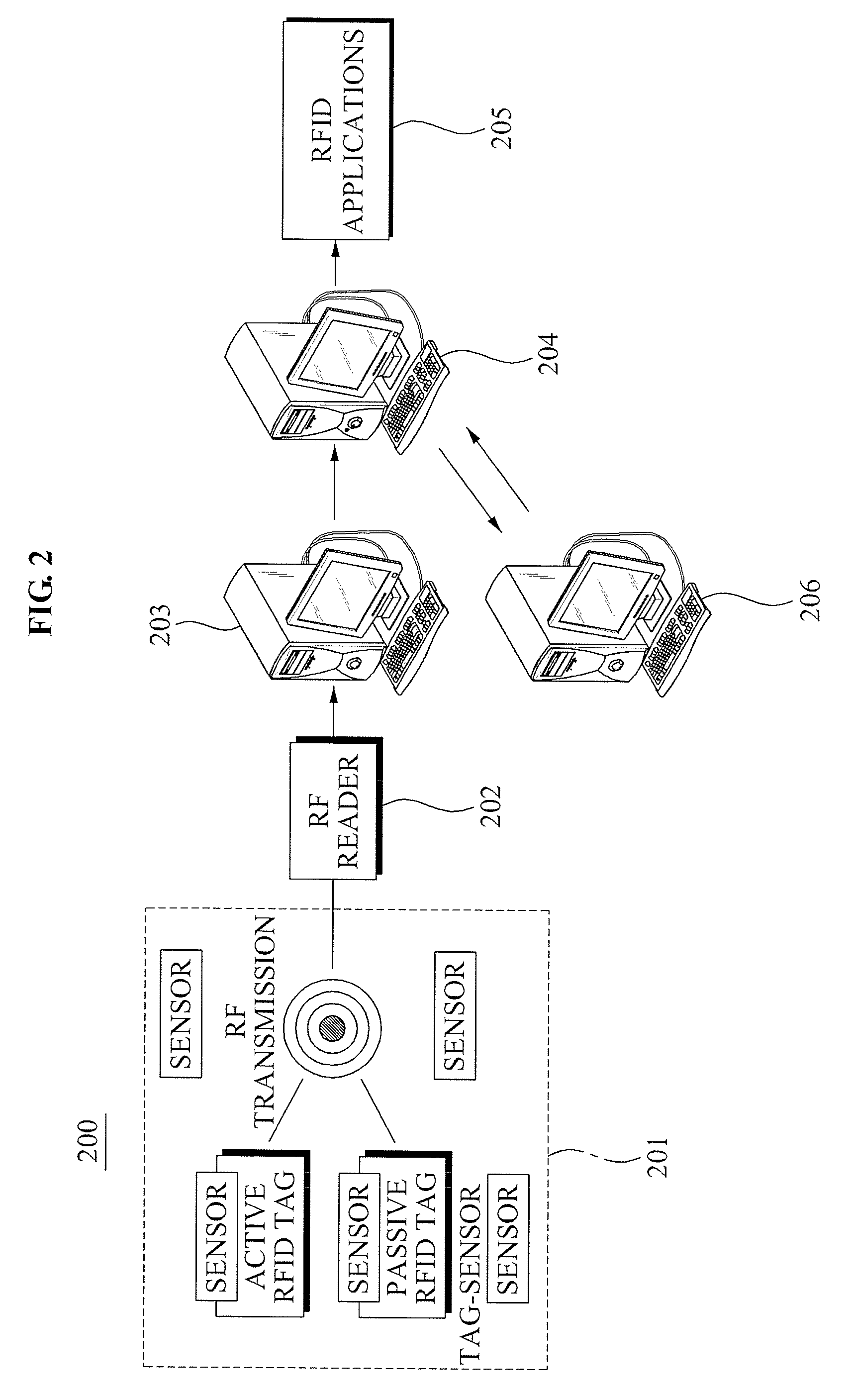
Context-aware based RFID privacy control system and personal privacy protection method using the same
InactiveUS8681984B2Avoid contactImprove securityDigital data processing detailsUnauthorized memory use protectionControl systemPrivacy protection
Owner:ELECTRONICS & TELECOMM RES INST
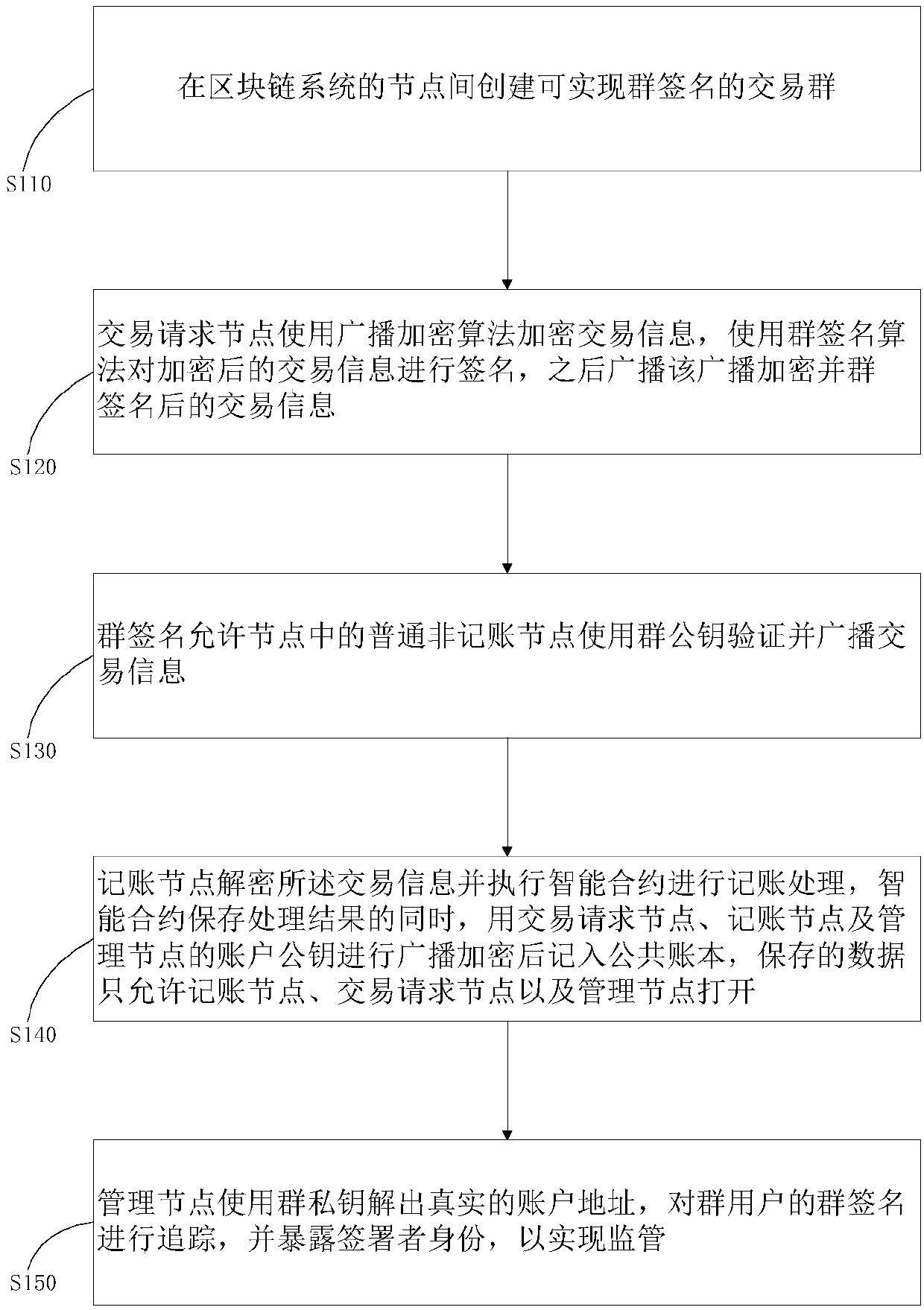
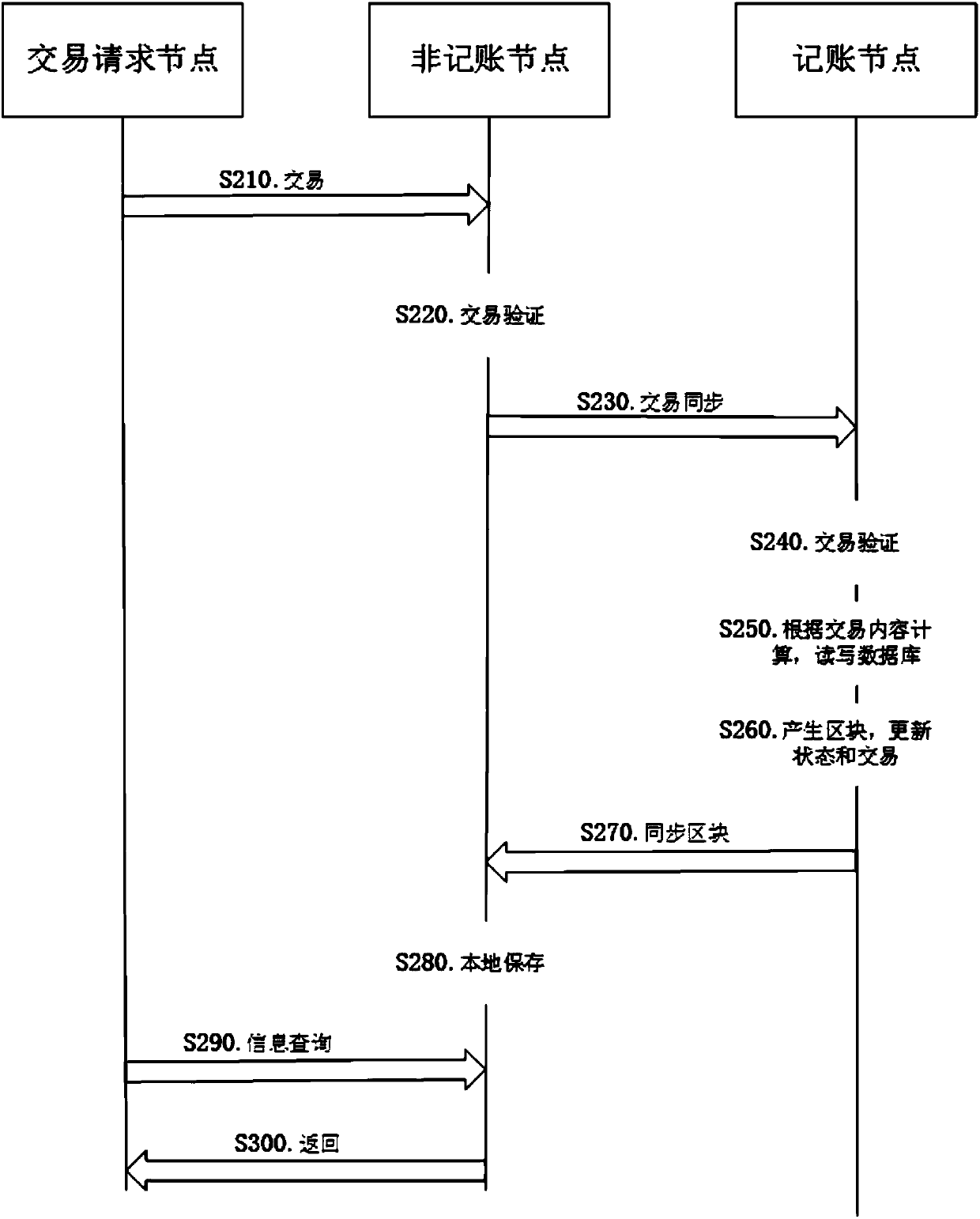
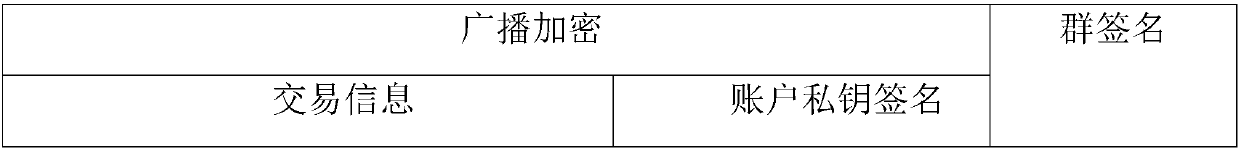
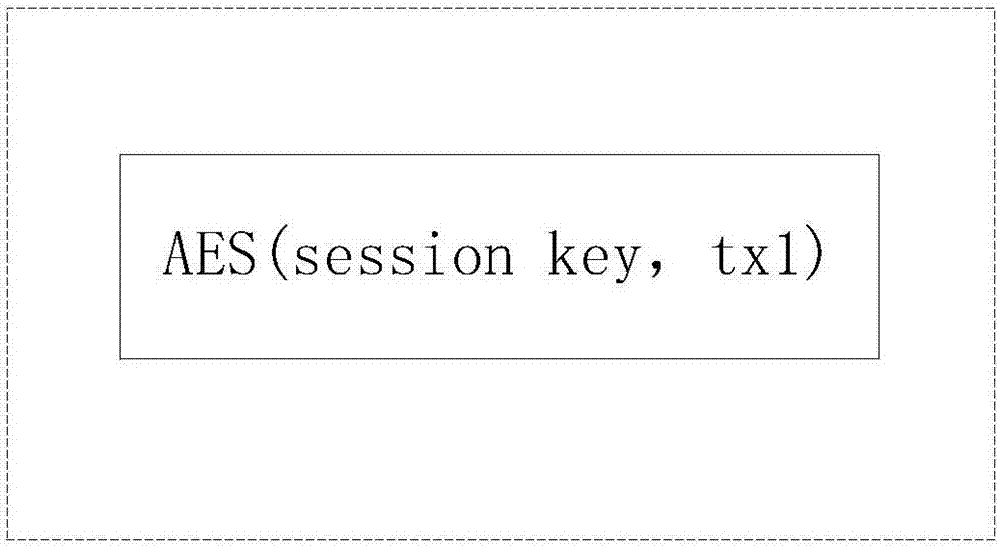
Method and system for privacy protection of block chain transaction
ActiveCN107911216ARealize regulationSupport reviewKey distribution for secure communicationFinancePublic accountPrivacy protection
The invention provides a method and system for privacy protection of block chain transaction. The method comprises: a transaction group is established between nodes of a block chain system, a user establishes an account at a node, and the node generates public and private key information of the account and then joining of a group is carried out; a transaction request node encrypts transaction information by using a broadcast encryption algorithm, carries out group signature processing on the encrypted transaction information, and then broadcasts the transaction information after broadcast encryption and group signature processing; a common non-account-recording node verifies the transaction information and then broadcasts the transaction information, an account-recording node decrypts thetransaction information and performs an intelligent contract to carry out account recording, broadcast encryption is carried out and then the information is recorded into a public account book, wherein the stored data are only allowed to be opened by the account-recording node, the transaction request node and an administration node. With the broadcast encryption algorithm and group signature technology, a privacy protection problem in the block chain system is solved and the traceability of the transaction is ensured.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Targeted delivery of informational content with privacy protection
InactiveUS7472093B2Privacy protectionHigh degreeFinanceComputer security arrangementsThird partyObjective information
A system and method for enabling use of detailed consumer profiles for the purposes of targeted information delivery while protecting these profiles from disclosure to information providers or hostile third parties are disclosed herein. Rather than gathering data about a consumer in order to decide which information to send her, an information provider makes use of a client-side executable software module called a negotiant function. The negotiant function acts as a client-side proxy to protect consumer data, and it also directs the targeting of information, requesting items of information from the information provider that are tailored to the profile provided by the consumer.
Owner:RSA
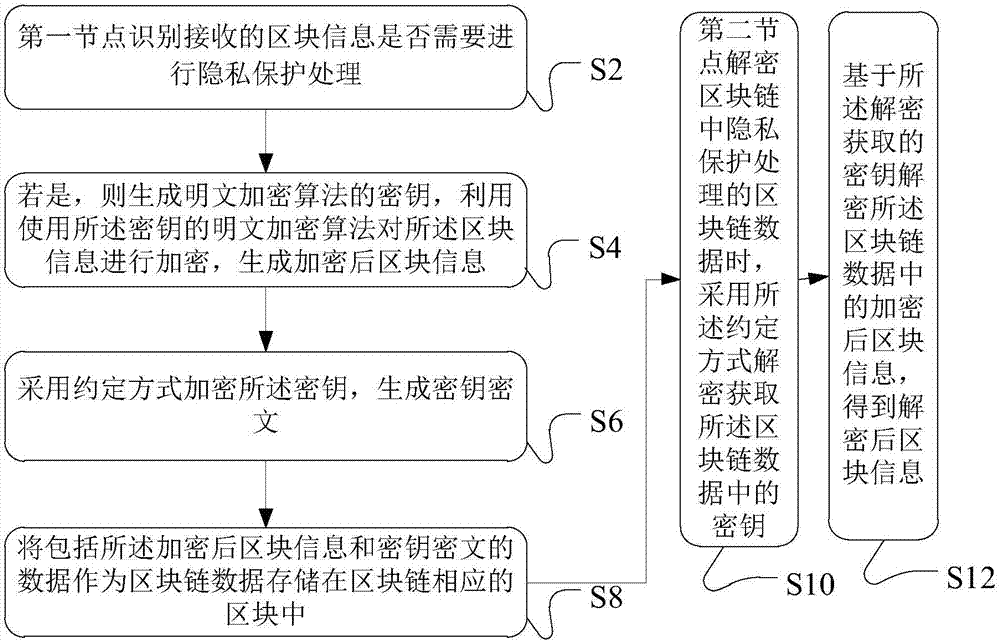
Blockchain data processing method, device and system
InactiveCN107294709ATo achieve the purpose of privacy protectionPrivacy protection is safe and reliableKey distribution for secure communicationCiphertextPrivacy protection
The invention discloses a blockchain data processing method, device and system. The blockchain data processing method comprises that a first node identifies whether received block information needs privacy protection processing; if the received block information needs privacy protection processing, a secret key of a plaintext encryption algorithm is generated, the block information is encrypted by means of the plaintext encryption algorithm employing the secret key, and encrypted block information is generated; the secret key is encrypted in a stipulated way, a secret key ciphertext is generated, the stipulated way comprises an algorithm through which a second node associated with the first node in the first node and the blockchain encrypts and decrypts the secret key ciphertext according to a preset mode; and data including the encrypted block information and the secret key ciphertext is stored a corresponding block of the blockchain as blockchain data. According to each embodiment of the invention, information data stored in the blockchain can be encrypted, so that only specific members can decrypt and check the information data, and the aim of carrying out privacy protection on special transaction information is achieved.
Owner:ADVANCED NEW TECH CO LTD
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
Apparatus and method for automated privacy protection in distributed images
ActiveUS9785796B1Data processing applicationsCharacter and pattern recognitionPrivacy rulePrivacy protection
A method executed by a computer includes receiving an image from a client device. A facial recognition technique is executed against an individual face within the image to obtain a recognized face. Privacy rules are applied to the image, where the privacy rules are associated with privacy settings for a user associated with the recognized face. A privacy protected version of the image is distributed, where the privacy protected version of the image has an altered image feature.
Owner:SNAP INC
Privacy-protected advertising system
InactiveUS7949565B1Easy to usePermit targetingBroadcast-related systemsBroadcast information switching/replacementPrivacy protectionDemographic data
A database of consumer profiles is generated from multiple sources of information including demographic databases identifying demographic attributes of the consumers and transaction records for the consumers. The transaction records are processed to generate transaction attributes and interests of the consumer. The consumer profiles identify deterministic and probabilistic attributes about the consumer, but do not contain privacy violating information such as raw transaction records. The consumer profiles may be maintained in a plurality of distributed databases. Advertisers generate profiles that identify attributes of an intended target market of the advertisement. The advertisement profiles are in the form of operators that can be applied to the database of consumer profiles to determine applicability of advertisements to the subscribers. The operators may only be applied to or make measurements on certain “observables”. The operators will not be able to obtain private information from the database of consumer profiles.
Owner:PRIME RES ALLIANCE E LLC
Building management system with privacy-guarded assistance mechanism and method of operation thereof
ActiveUS20130257626A1Signalling system detailsVisible signalling systemsPrivacy protectionBehaviour pattern
A method for operating a building management system includes: identifying a movement-pattern from a sensed attribute at a first sensor; determining a behavior-pattern at the first sensor when the movement-pattern matches a template-pattern; transmitting the behavior-pattern and the sensed attribute from the first sensor to a second sensor; and tracking the sensed attribute at the second sensor for displaying on a device.
Owner:SONY CORP
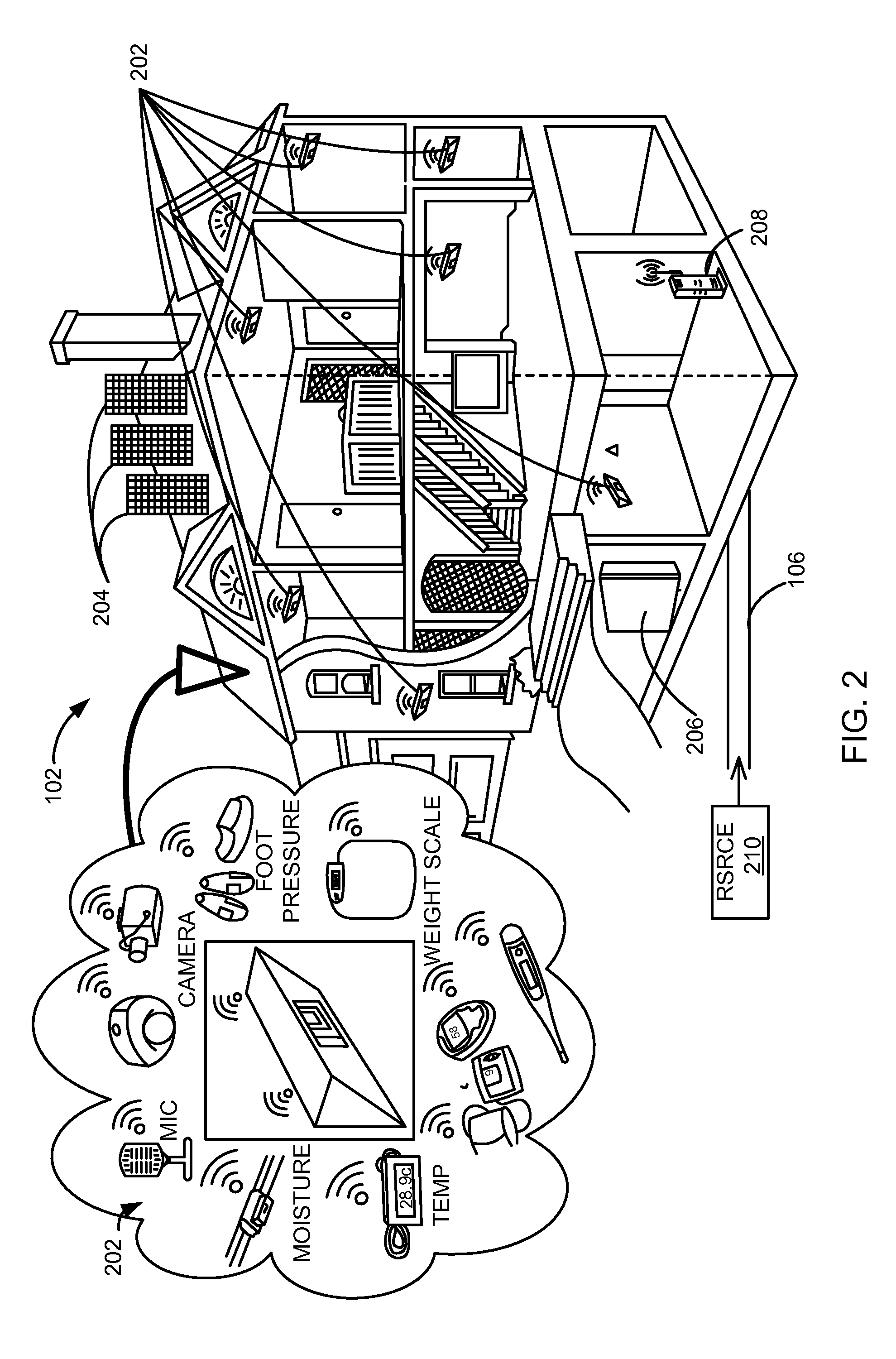
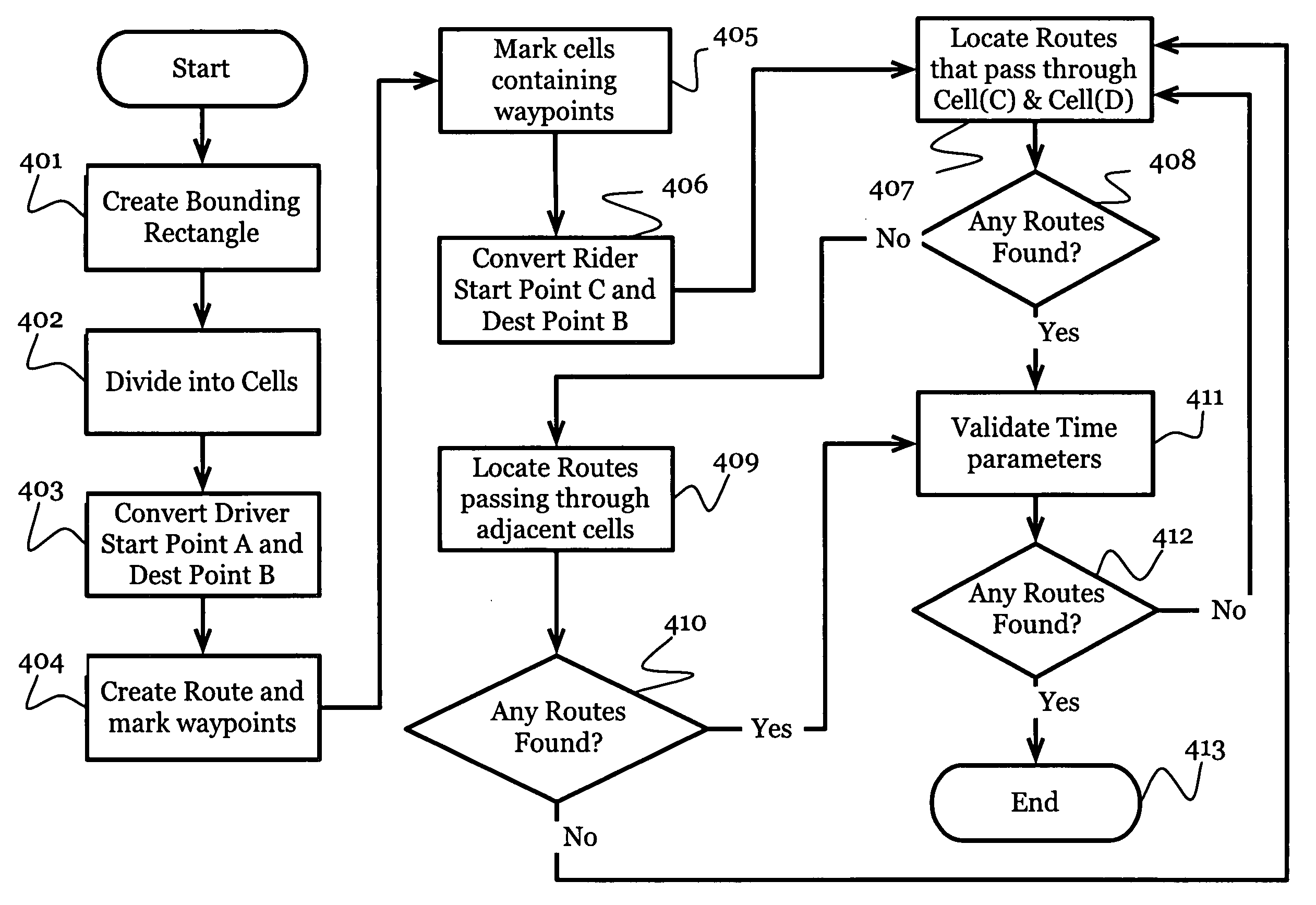
Systems and methods for enhancing private transportation
InactiveUS20080270019A1Good choiceEnhance and streamline and improve flexibility and efficiency and functionality of systemInstruments for road network navigationRoad vehicles traffic controlPrivacy protectionRouting algorithm
Systems and methods are disclosed for enhancing the convenience, security, and efficiency of ridesharing through the incorporation of trusted communities, geotemporal routing algorithms, and by providing monetary incentives and privacy safeguards to encourage system growth.
Owner:HIGH REGARD SOFTWARE
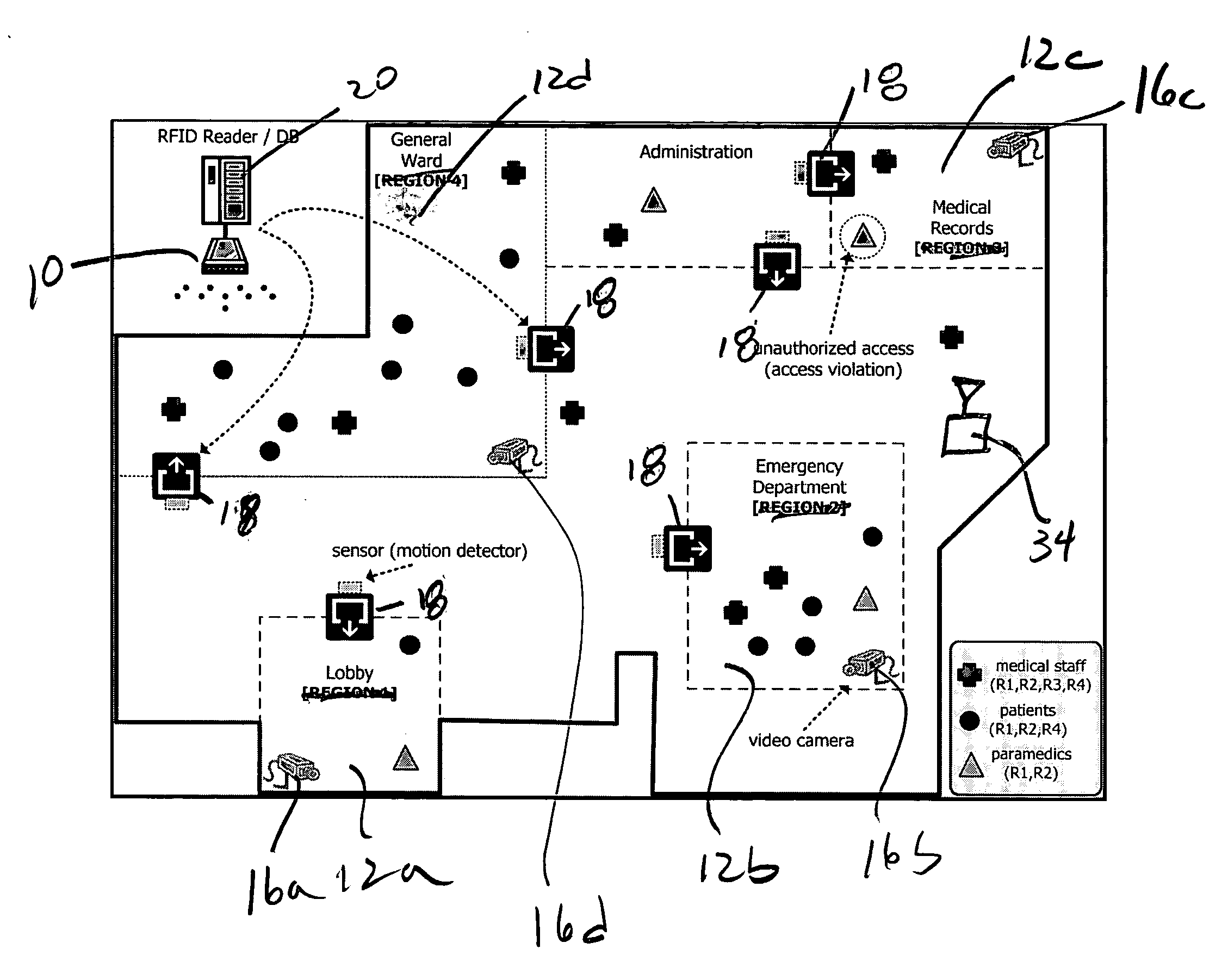
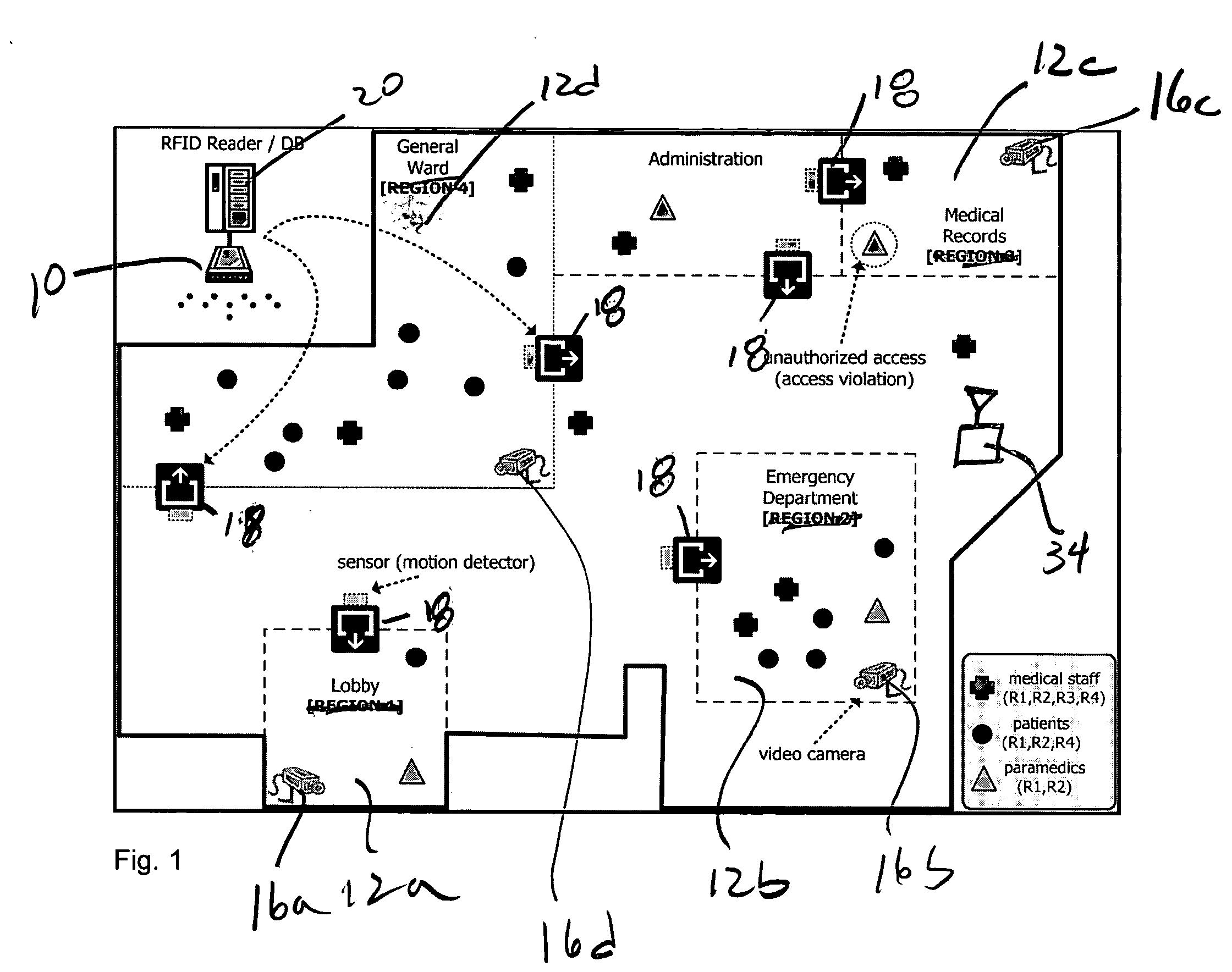
Apparatus and method for privacy protection of data collection in pervasive environments
ActiveUS20060064384A1Improve emergency responseImprove securityElectric signal transmission systemsDigital data processing detailsVideo monitoringPrivacy protection
A security system which is nonintrusive of personal privacy of a person in a space comprises at least a first localization sensor subsystem, if any, in the possession of the person; a video surveillance subsystem arranged and configured to collect visual data related to the person in the space; and a computer subsystem coupled to the localization sensor subsystem and video surveillance subsystem to associate a predetermined privacy level with the localization sensor subsystem, and to provide an access control privilege with the localization sensor subsystem, the computer subsystem determining how to present, store and / or retrieve the visual data while meeting predetermined the privacy level associated with the person.
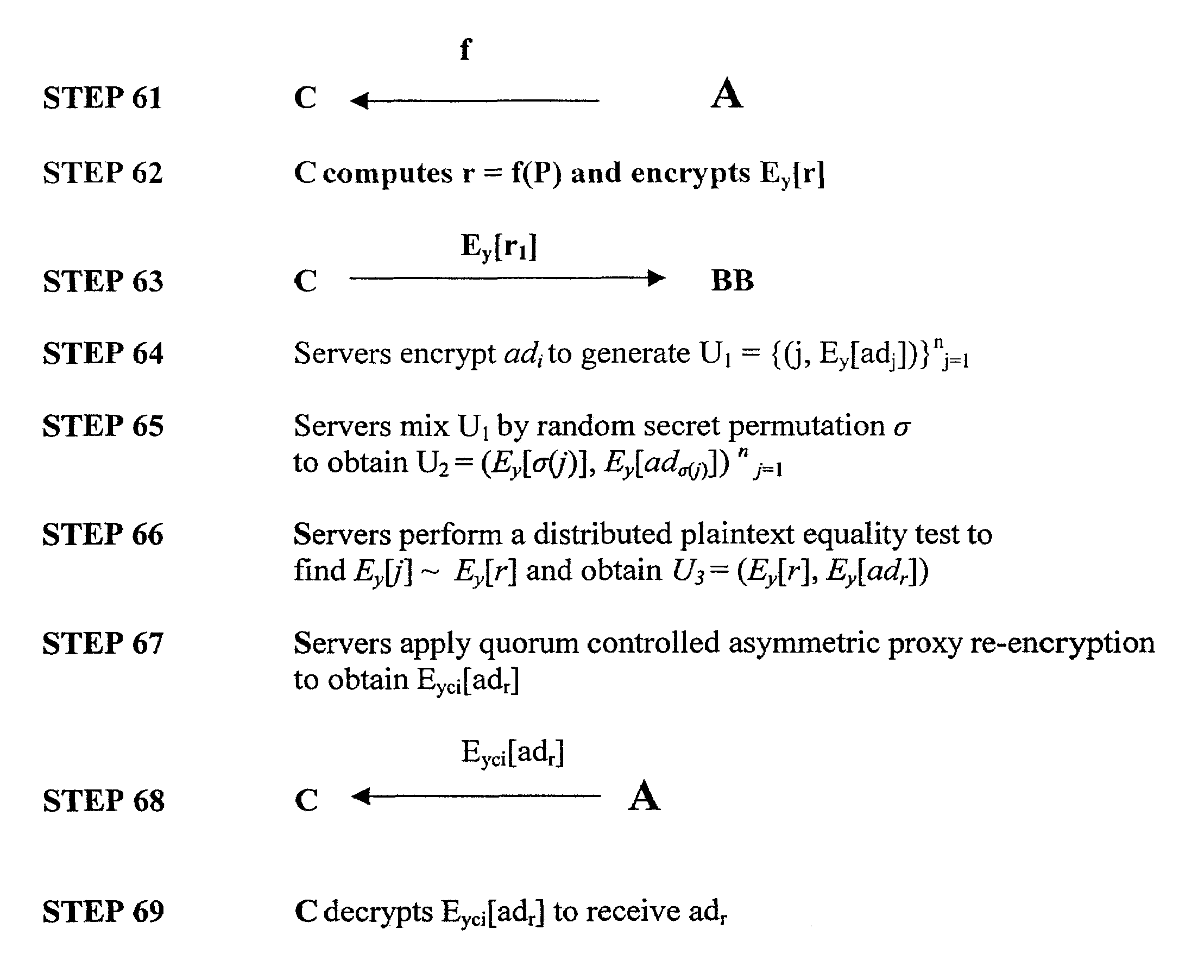
Owner:RGT UNIV OF CALIFORNIA
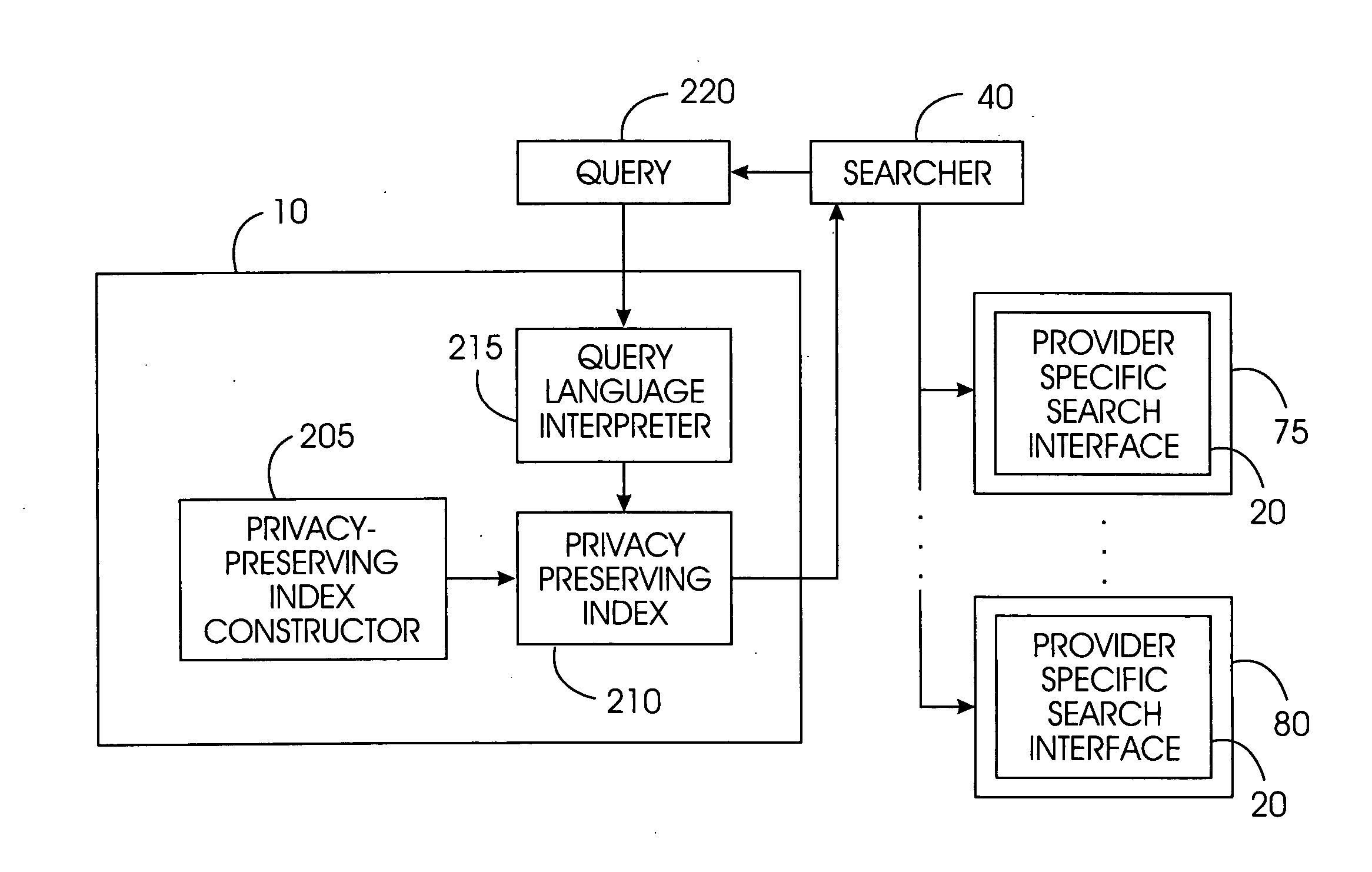
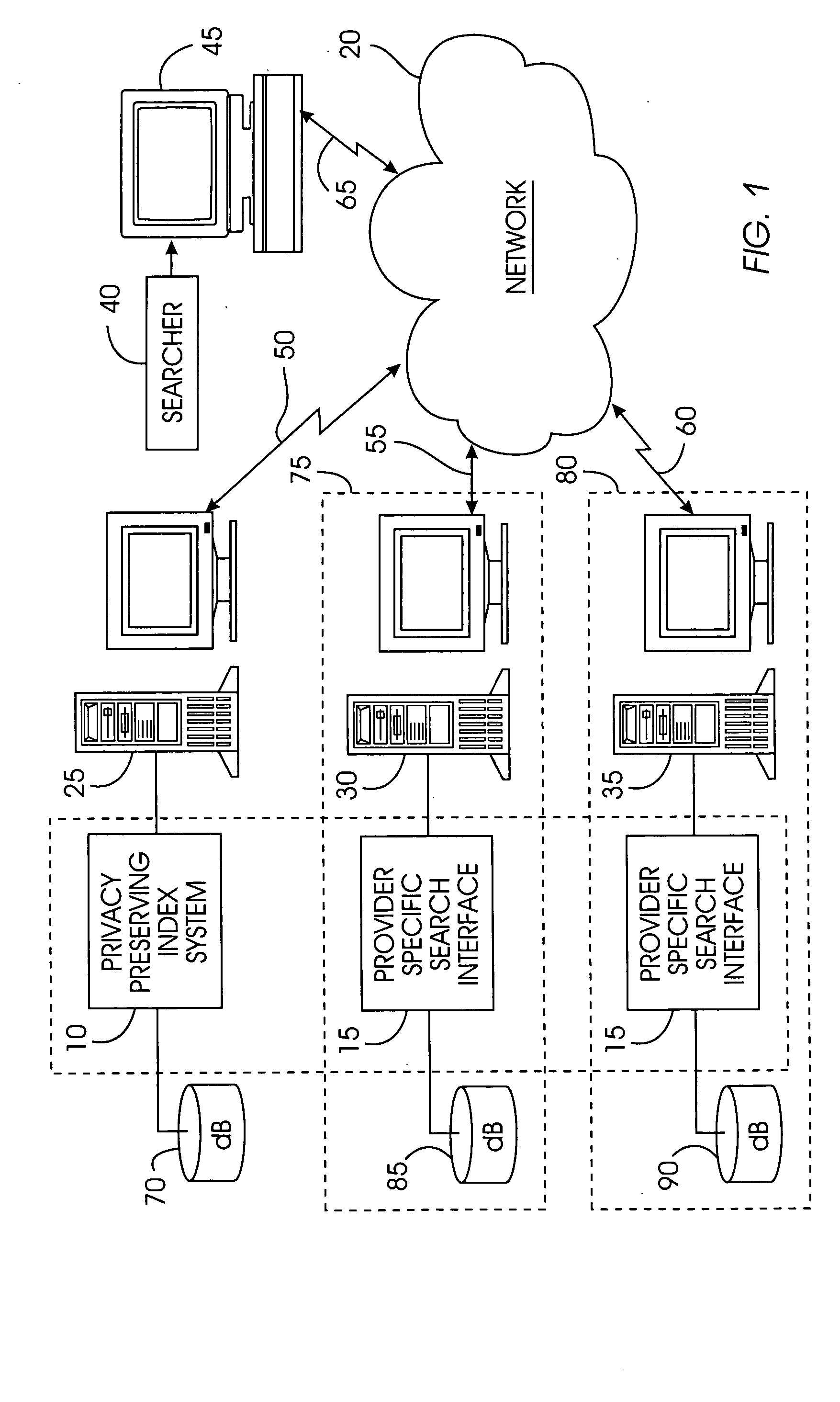
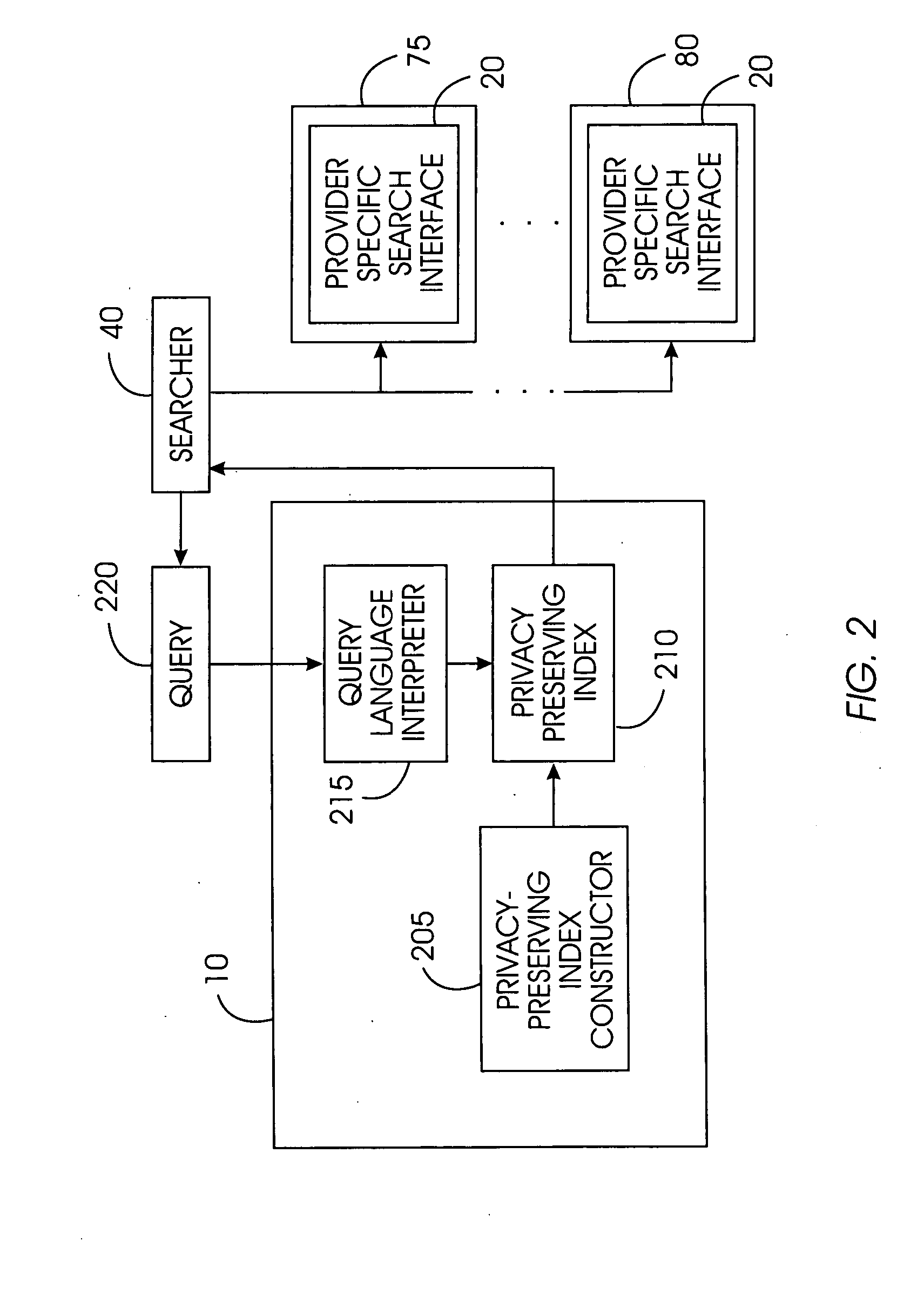
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS20050055327A1Keep full controlNot allowData processing applicationsWeb data indexingRandomized algorithmPrivacy protection
A privacy-preserving index system addresses the problem of providing a privacy-preserving search over distributed access-controlled content. Indexed documents can be readily reconstructed from inverted indexes used in the search. The privacy-preserving index system builds a centralized privacy-preserving index in conjunction with a distributed access-control enforcing search protocol. The privacy-preserving index utilizes a randomized algorithm for constructing a privacy-preserving index. The privacy-preserving index is strongly resilient to privacy breaches. The privacy-preserving index system allows content providers to maintain complete control in defining access groups and ensuring its compliance, and further allows system implementors to retain tunable knobs to balance privacy and efficiency concerns for their particular domains.
Owner:IBM CORP
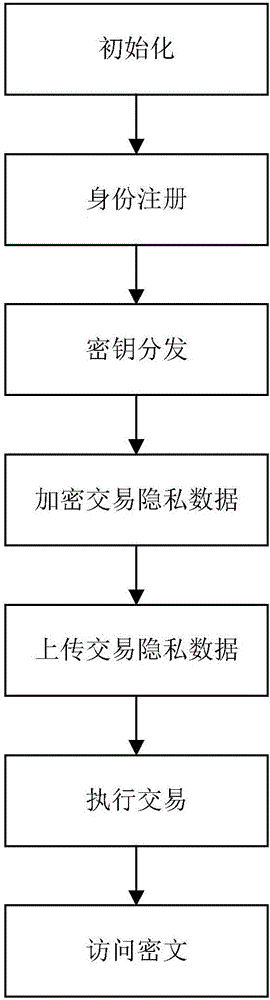
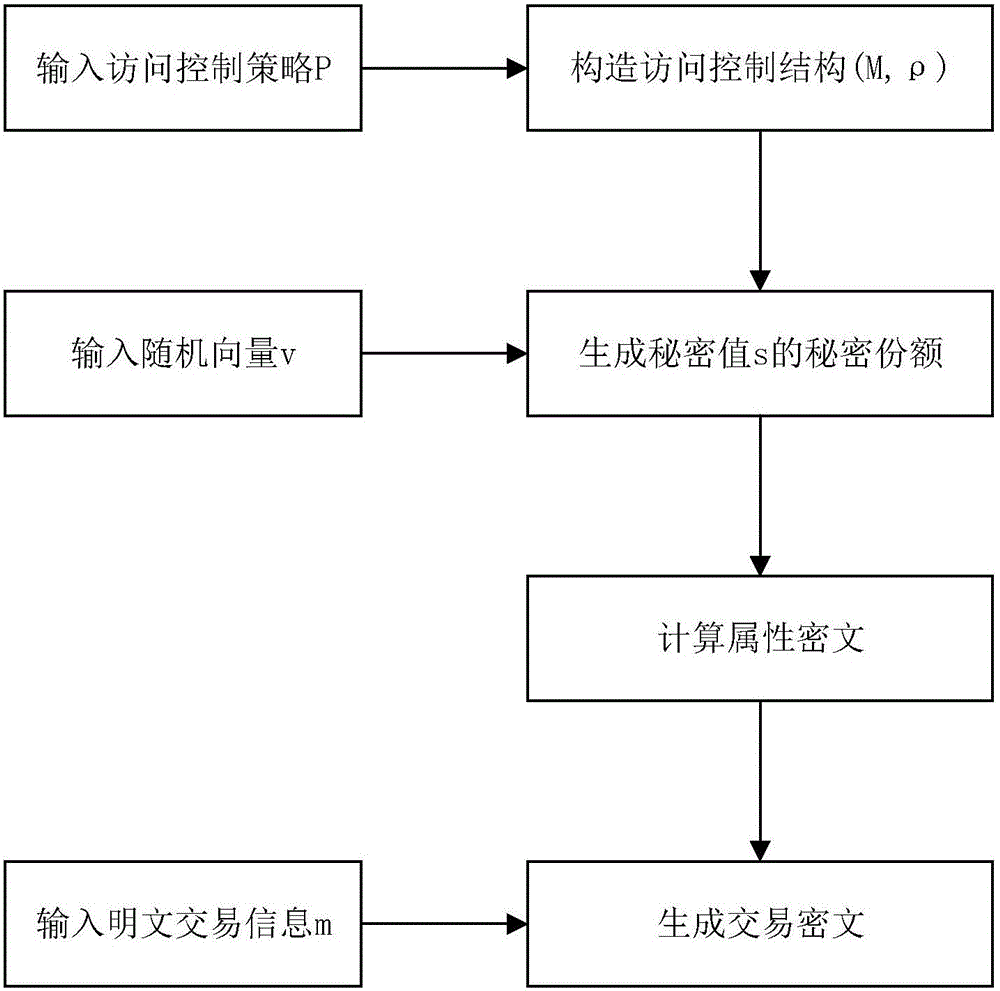
Block chain privacy data access control method based on attribute encryption
ActiveCN106503994AAddress privacy breachesRealize privacy protectionKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
The invention discloses a block chain privacy data access control method based on attribute encryption, which mainly solves a problem in the prior art that the real identity of a user in the block chain is anonymously protected but the and transaction privacy information is not encrypted so as to cause privacy leakage. The method comprises the steps that 1. a system is initialized; 1, a user registers to obtain attribute information; 3, an authoritative center, according to the user attribute information, distributes a user private key; 4 a transaction party encrypts transaction privacy data and uploads the transaction privacy data to a block chain; 5, an accountant verifies the transaction information and performs the transaction; 6, a supervisory center is authorized to use the authorized private key to decrypt and check the transaction ciphertext. The method encrypts the transaction privacy information, avoids the leakage of data privacy and can be used for privacy protection of the virtual asset transaction data in the block chain.
Owner:XIDIAN UNIV
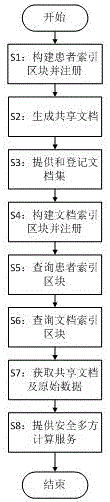
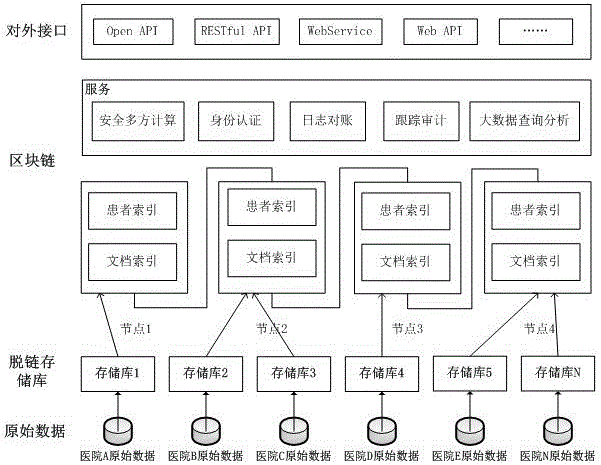
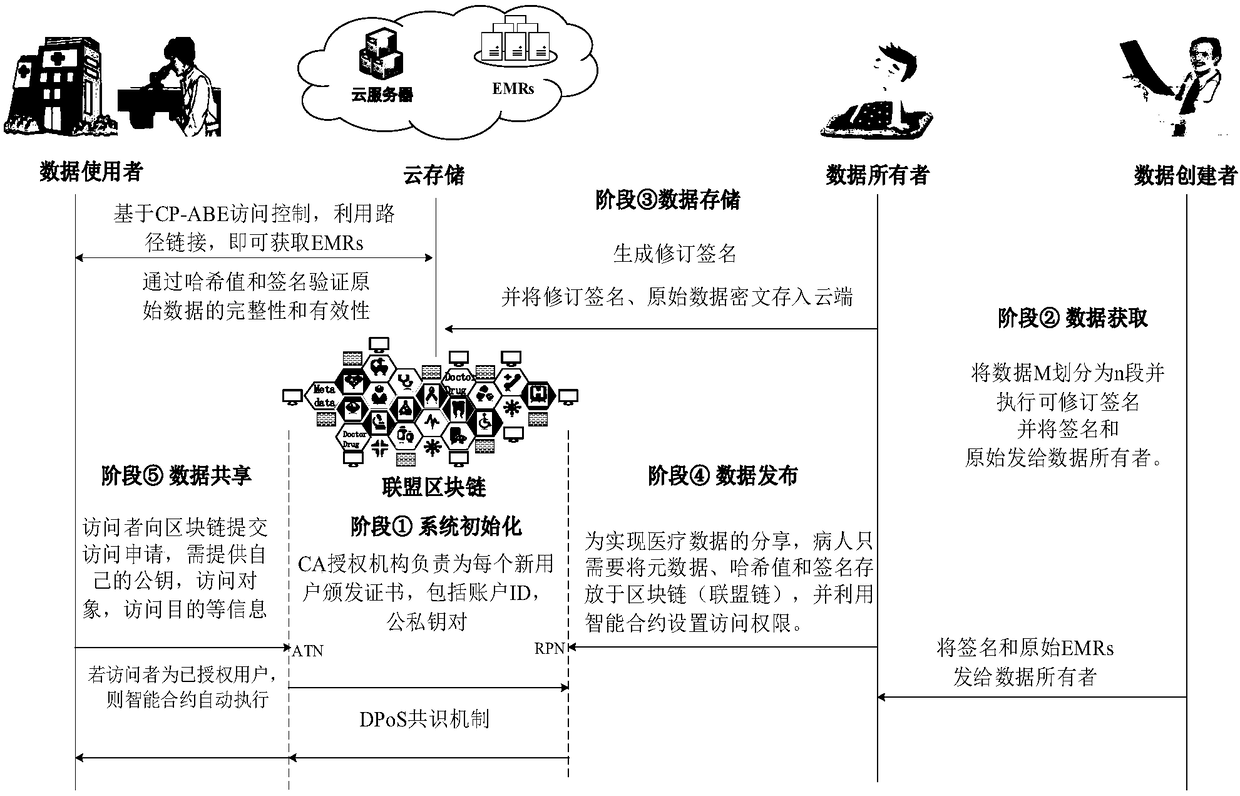
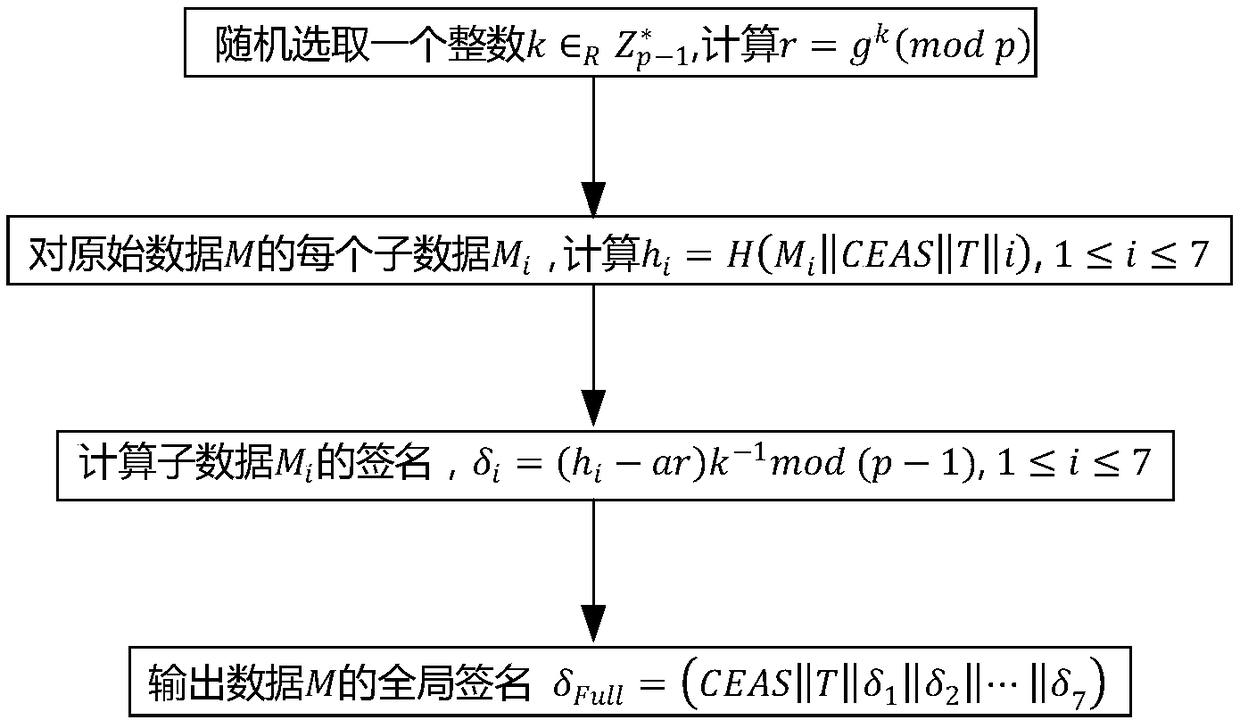
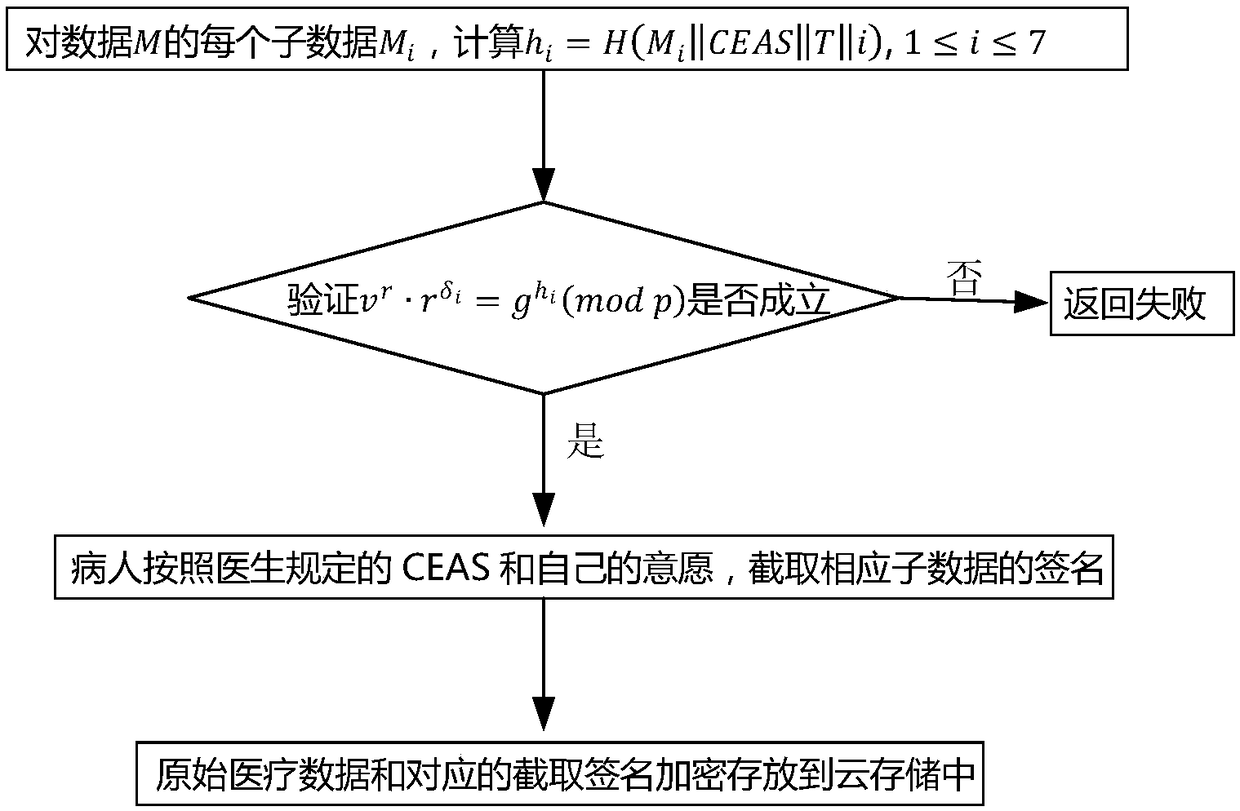
Electronic medical record storage and sharing model and method based on blockchains
ActiveCN109326337AEasy to controlImplement storage securityDigital data protectionPatient-specific dataPrivacy protectionData access
The invention discloses an electronic medical record storage and sharing model and method based on the blockchains and solves problems of patient's rights of access to personal medical data and insecure storage and sharing of sensitive medical data in the prior art. The model is characterized by comprising data creators, data owners, cloud storage, federated blockchains and data consumers, whereinthe blockchain is a control center. The method comprises steps that system initialization is performed; medical data are acquired, and data storage with intercepted signatures is employed; data publishing with the improved DPOS consensus mechanism is employed; data sharing based on smart contracts is performed. The method is advantaged in that security, reliability, privacy protection and securestorage are achieved, in combination with the cloud storage technology and the interceptable signature technology, in the federated blockchains, users can set sharing conditions through the smart contracts, safe and effective data sharing and access can be realized, and strong practicality is achieved.
Owner:XIDIAN UNIV
Block chain information archiving and privacy protection method
ActiveCN105610578APrevent tamperingEasy retrievalKey distribution for secure communicationThird partyPrivacy protection
The invention discloses a block chain information archiving and privacy protection method. The block chain information archiving and privacy protection method comprises the steps of adding random number generation Hash values to information needing archiving; then signing by an interest-related person or a eyewitness and generating Hash values; and finally recording at a block chain. Some information needing archiving is formatting and separable formatting information and self-filling information respectively stored and subjected to Hash verification, such as gap-filling information, selection information, postscript information, random number information (for preventing brute force attack). Data which are encrypted by using a public key only can be decrypted by a relevant person who knows the original information by using a private key; a third party verifies true and false of the information; and the encrypted information can be disclosed for a judicial institution if judiciary involvement is needed.
Owner:苏州交链科技有限公司 +1
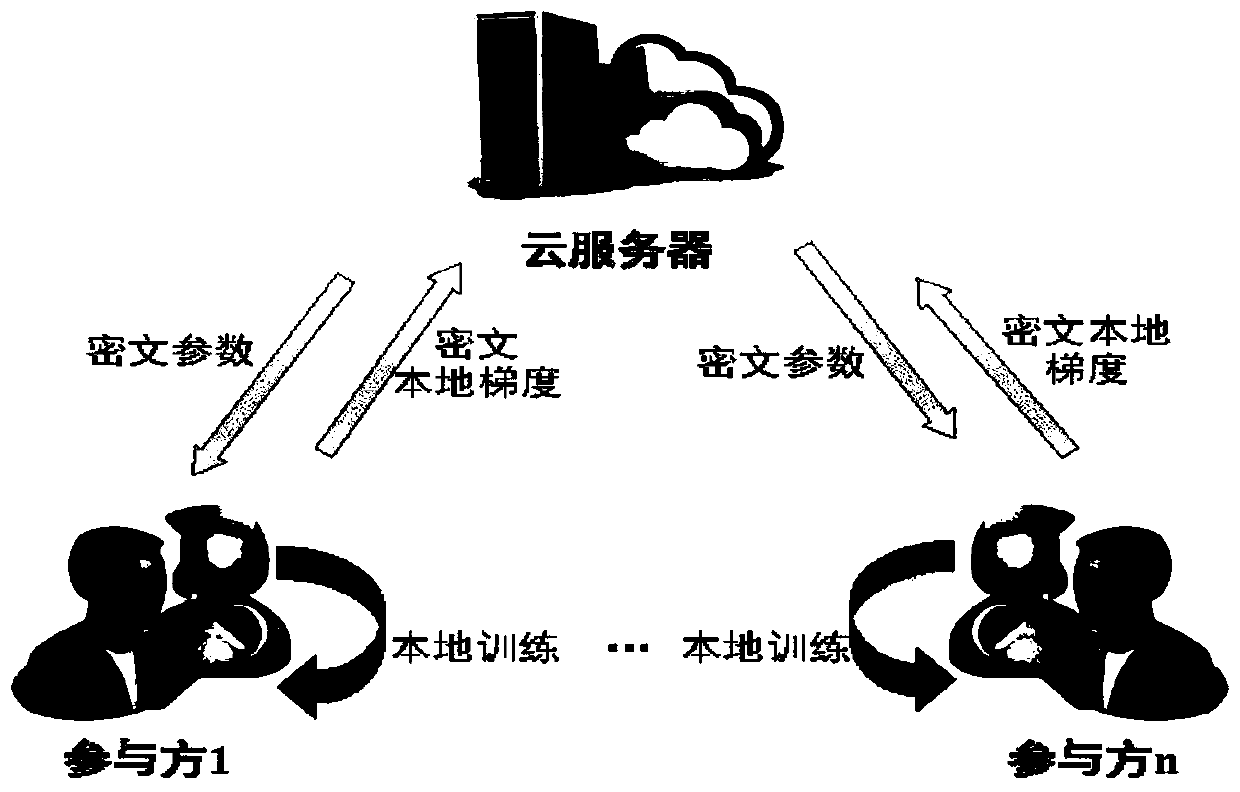
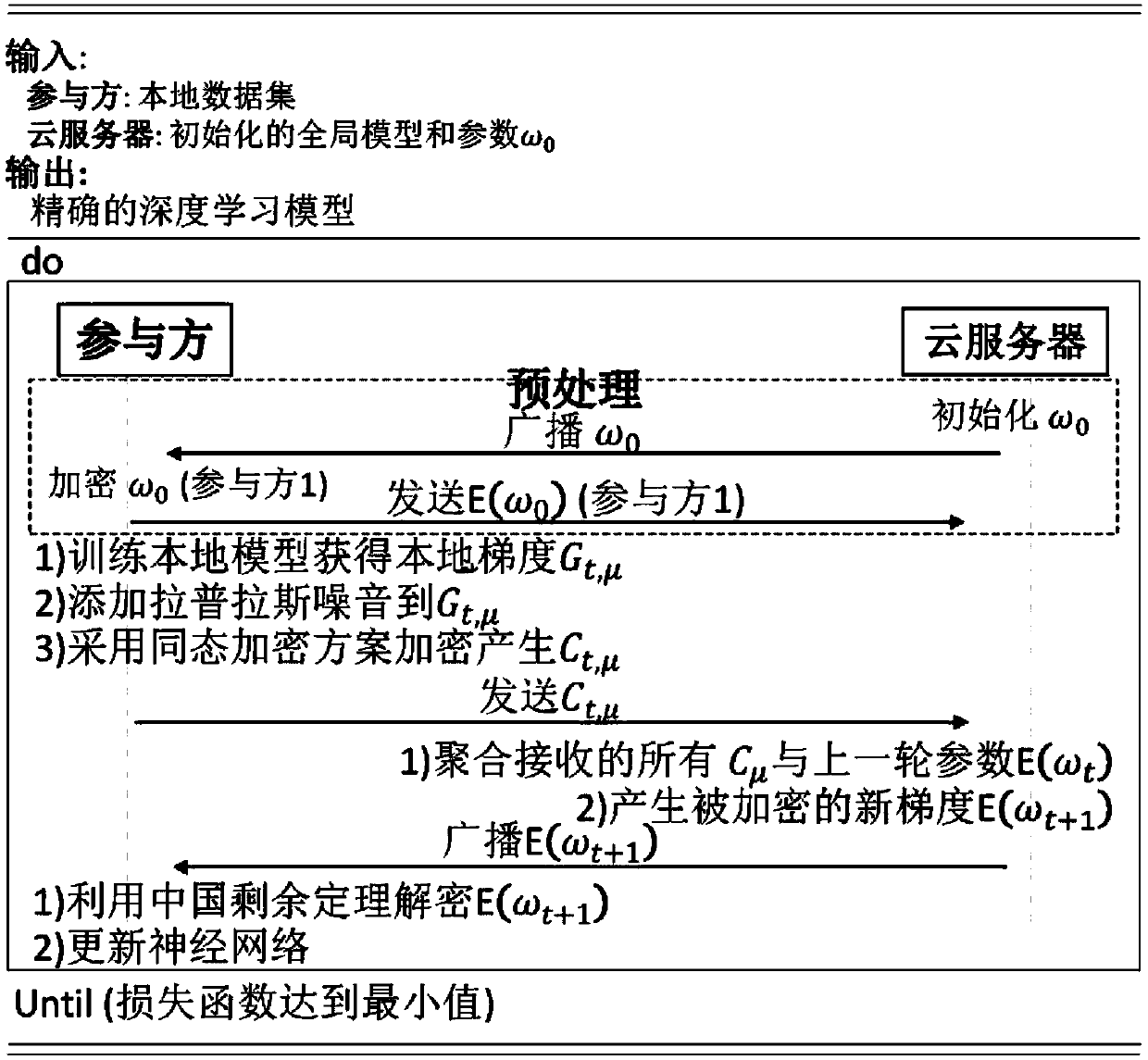
A combined deep learning training method based on a privacy protection technology
ActiveCN109684855AAvoid gettingSafe and efficient deep learning training methodDigital data protectionCommunication with homomorphic encryptionPattern recognitionData set
The invention belongs to the technical field of artificial intelligence, and relates to a combined deep learning training method based on a privacy protection technology. The efficient combined deep learning training method based on the privacy protection technology is achieved. In the invention, each participant first trains a local model on a private data set to obtain a local gradient, then performs Laplace noise disturbance on the local gradient, encrypts the local gradient and sends the encrypted local gradient to a cloud server; The cloud server performs aggregation operation on all thereceived local gradients and the ciphertext parameters of the last round, and broadcasts the generated ciphertext parameters; And finally, the participant decrypts the received ciphertext parameters and updates the local model so as to carry out subsequent training. According to the method, a homomorphic encryption scheme and a differential privacy technology are combined, a safe and efficient deep learning training method is provided, the accuracy of a training model is guaranteed, and meanwhile a server is prevented from inferring model parameters, training data privacy and internal attacksto obtain private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
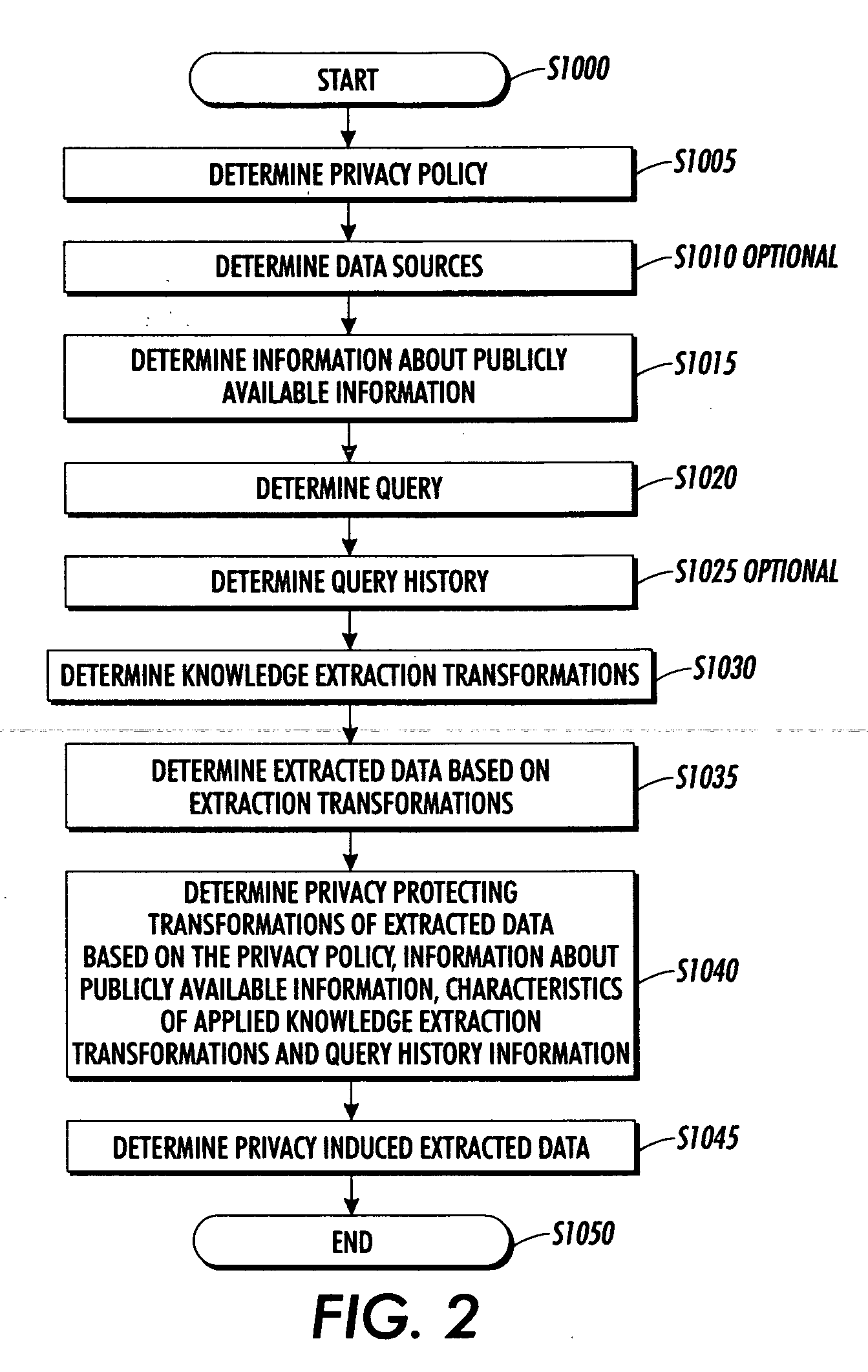
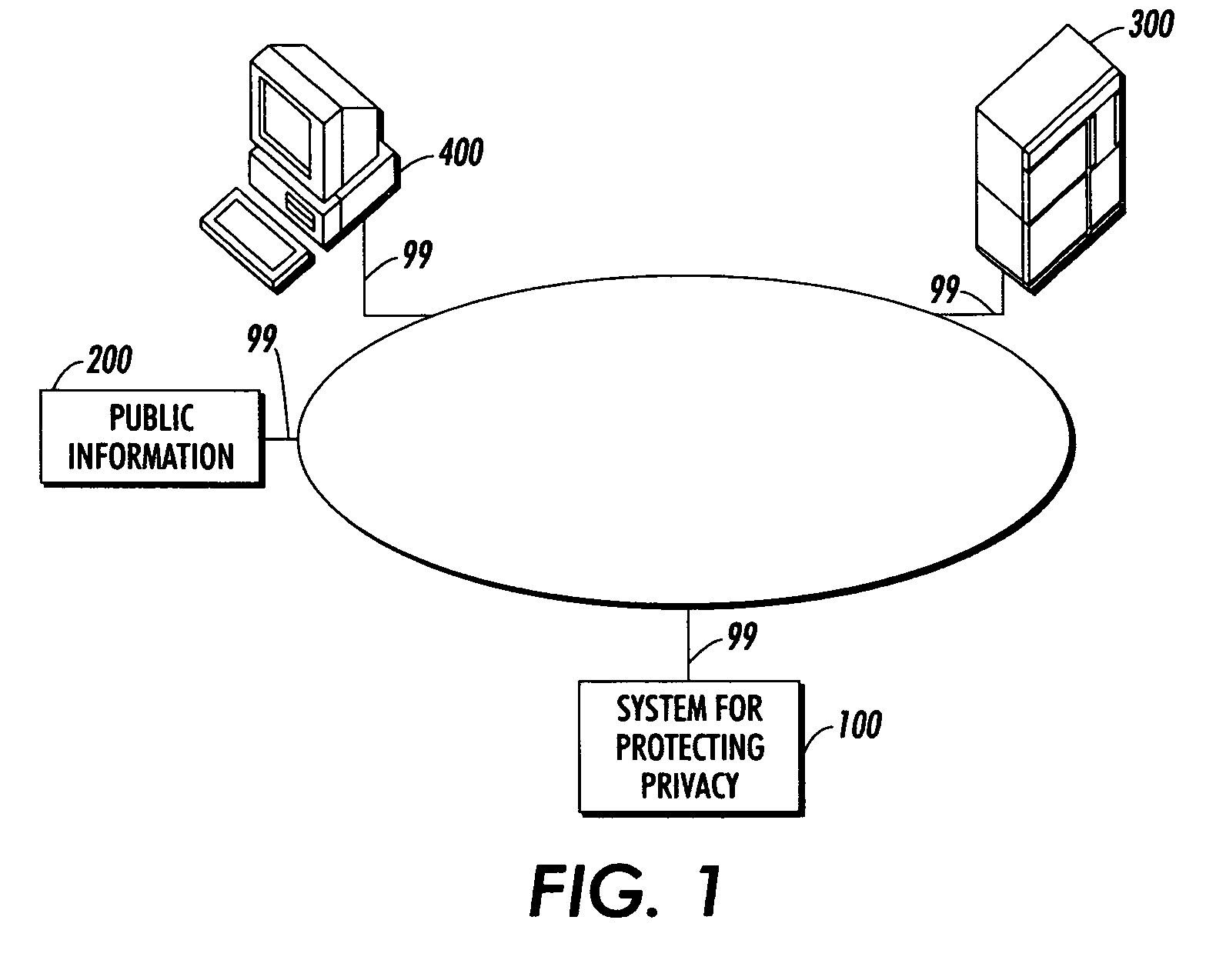
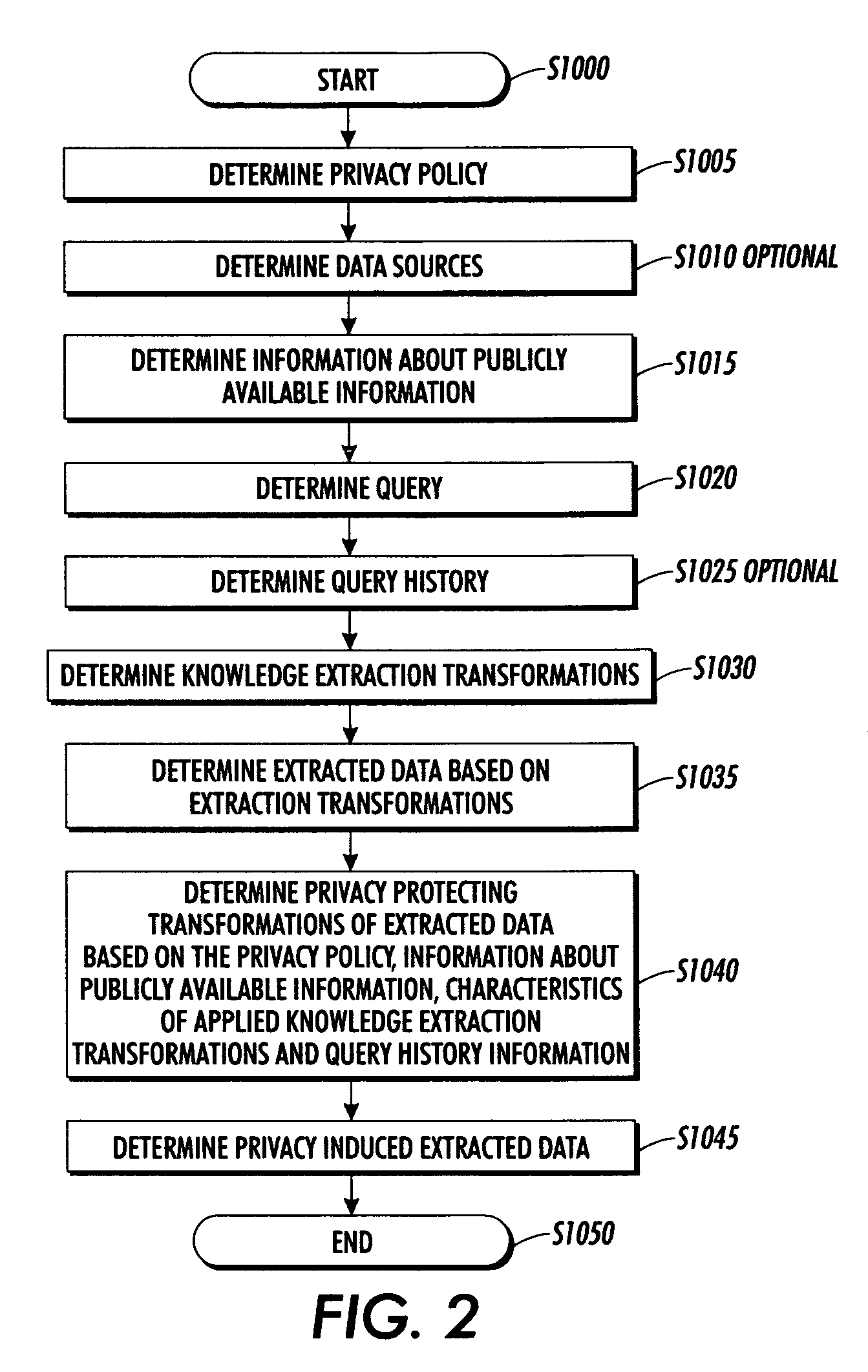
Systems and methods for protecting privacy
InactiveUS20060123461A1Digital data processing detailsComputer security arrangementsPrivacy protectionKnowledge extraction
Techniques for providing privacy protection are provided. A query is received. Privacy policy information, extracted knowledge and optional information about available public information are determined. Information about the knowledge extraction transformations applied to create the extracted knowledge and the source data is determined. Privacy protecting transformations are determined and applied to transform the extracted knowledge based on the selected privacy policy, optional information about available public information, the characteristics of the applied knowledge extractions transformations, the source data and optional previous user queries.
Owner:PALO ALTO RES CENT INC
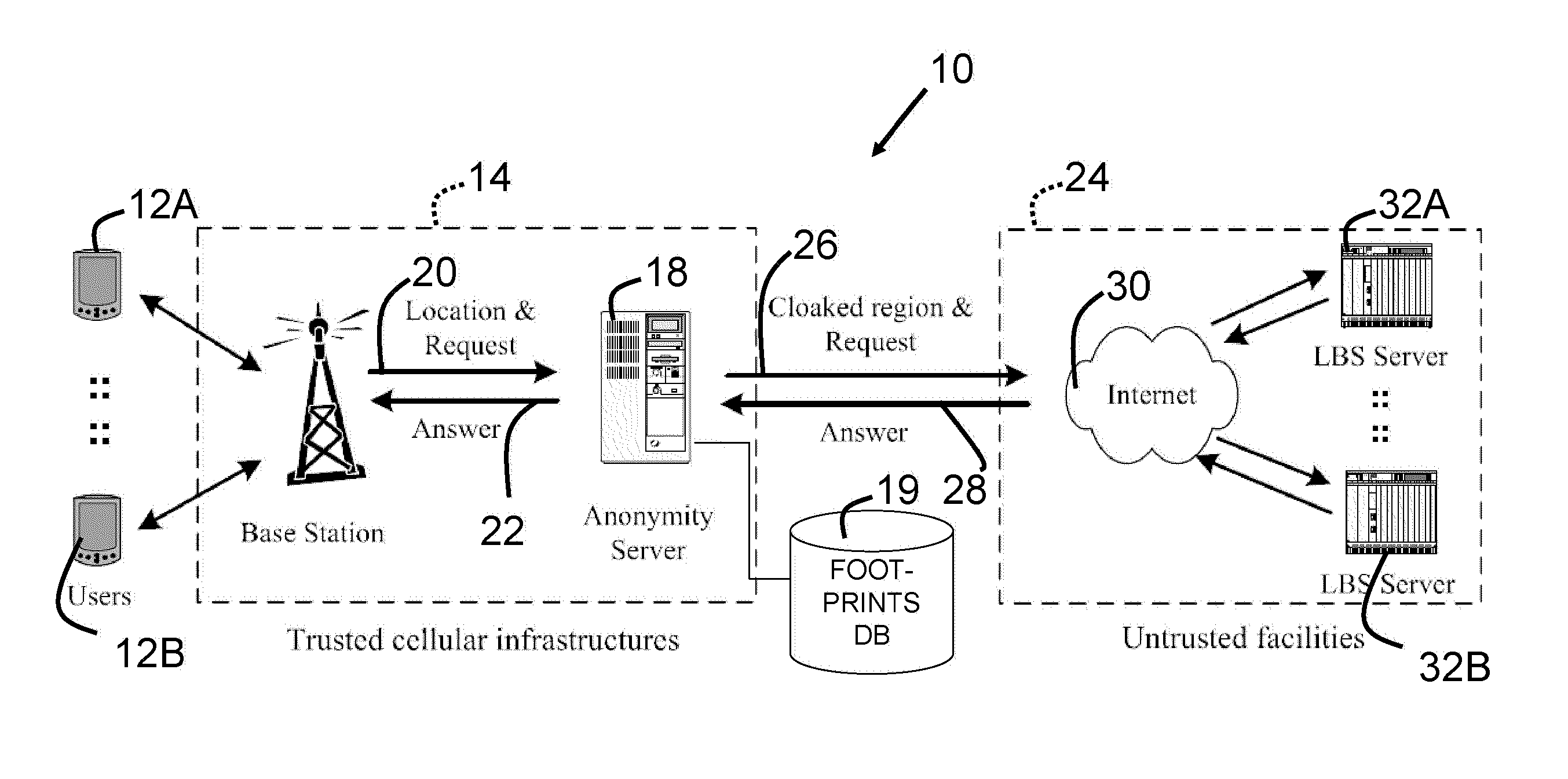
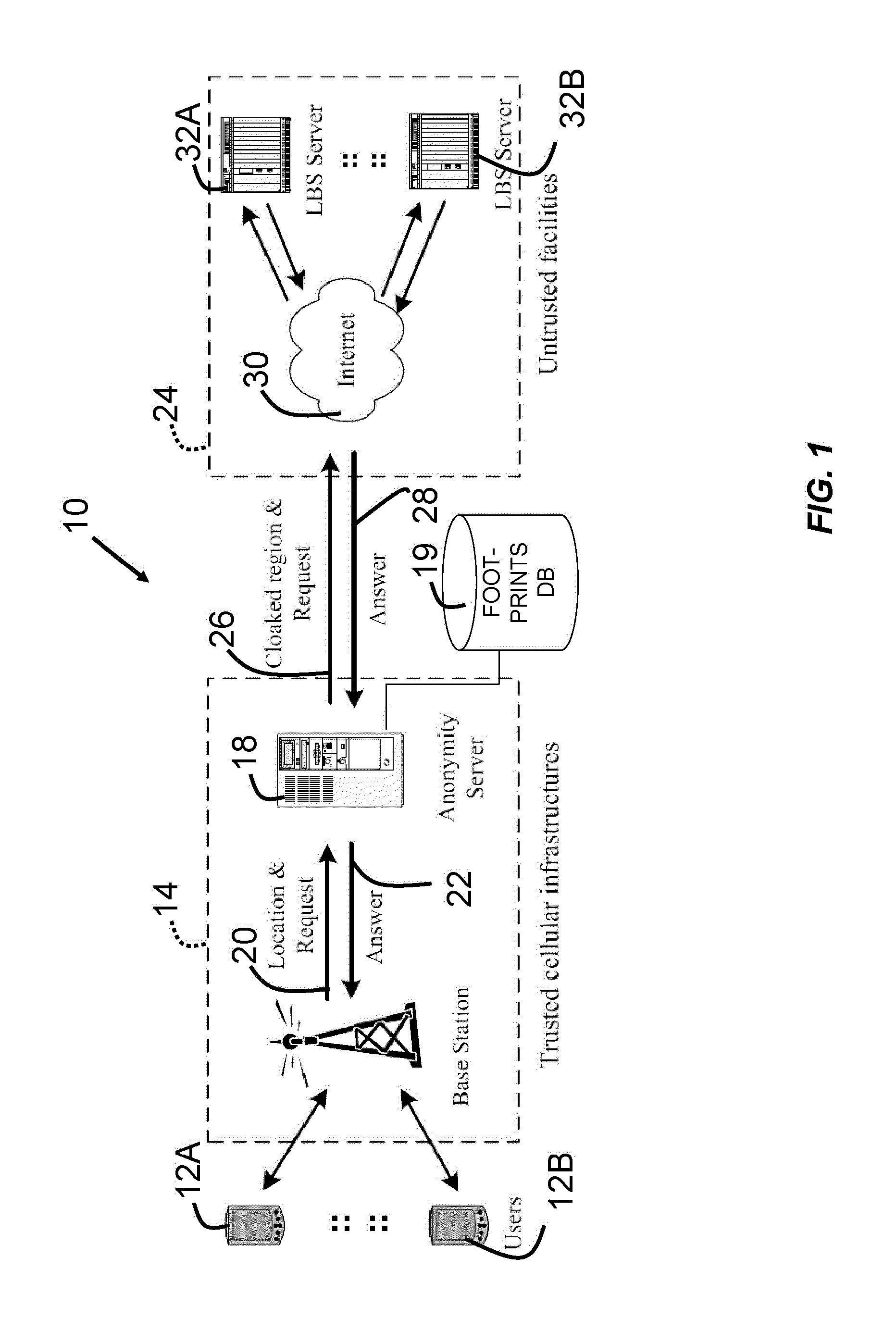
Cloaking with footprints to provide location privacy protection in location-based services
InactiveUS20100064373A1Improve cloaking resolutionMinimal impactDigital data processing detailsAnalogue secracy/subscription systemsPrivacy protectionMobile device
A method for using a location-based service while preserving anonymity includes receiving a location associated with a mobile node, receiving an anonymity level associated with the mobile node, computing a region containing the location of the mobile node and a number of footprints based on the anonymity level, wherein each of the footprints from a different user, and providing the region to a location-based service to thereby preserve anonymity of the mobile node. A method also allow a mobile device or its user to specify the anonymity level by selecting a public region consistent with a user's feelings towards desired privacy.
Owner:IOWA STATE UNIV RES FOUND
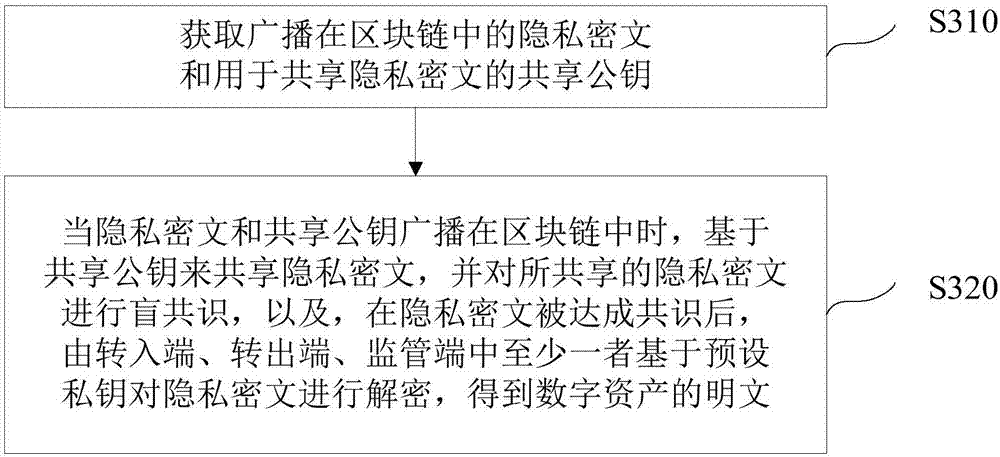
Blockchain-based digital asset processing method and device
ActiveCN106982205AProtection of privacySmooth circulationKey distribution for secure communicationDigital data protectionPlaintextCiphertext
The invention discloses a blockchain-based digital asset processing method and device. The method comprises the following steps: receiving private ciphertext for a digital asset circulated from a sending end to a receiving end through a blockchain, and a preset public key; and obtaining a sharing public key for sharing the private ciphertext based on the preset public key, so that when the private ciphertext and the sharing public key are broadcast in the blockchain, blockchain nodes on the blockchain can share the private ciphertext based on the sharing public key and reach a blind consensus on the shared private ciphertext, and after the consensus on the private ciphertext is reached, the private ciphertext can be decrypted by at least one of three parties, i.e., the sending end, the receiving end and a monitoring end, based on a preset private key to obtain plaintext of the digital asset. The method and device provided by the embodiment of the invention has the advantages that the privacy right of a user is protected; under the premise of privacy protection, the single general digital asset can be smoothly circulated within one blockchain or among multiple blockchains, and a total currency amount remains unchanged; and a monitoring party other than the transaction parties can monitor transaction information at any time.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院 +1
Preserving privacy when statistically analyzing a large database
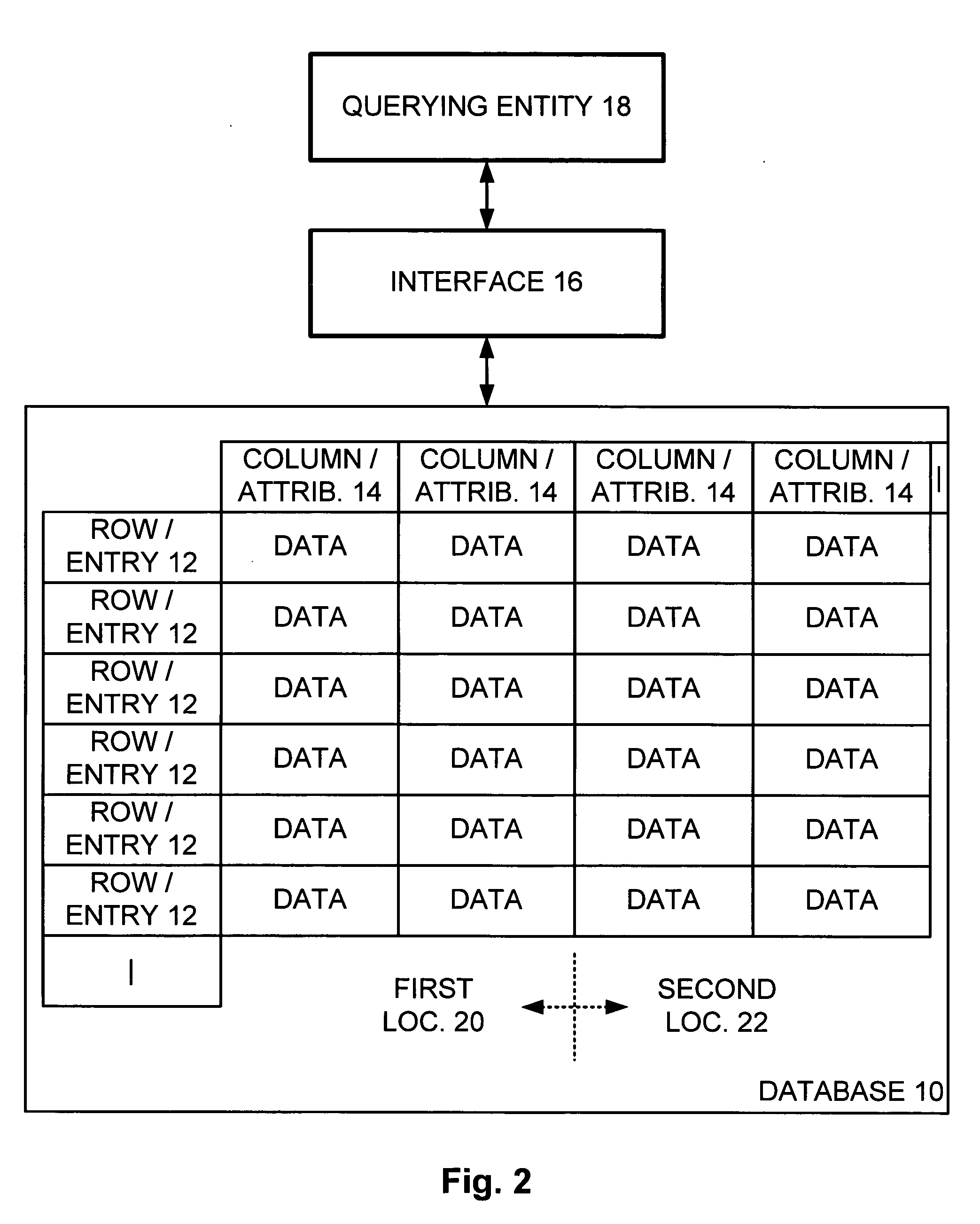
InactiveUS20060161527A1Level of protectionComputer security arrangementsSpecial data processing applicationsStatistical analysisPrivacy protection
A database has a plurality of entries and a plurality of attributes common to each entry, where each entry corresponds to an individual. A query q is received from a querying entity query q and is passed to the database, and an answer a is received in response. An amount of noise e is generated and added to the answer a to result in an obscured answer o, and the obscured answer o is returned to the querying entity. Thus, a level of protection of privacy is provided to each individual represented within the database.
Owner:MICROSOFT TECH LICENSING LLC
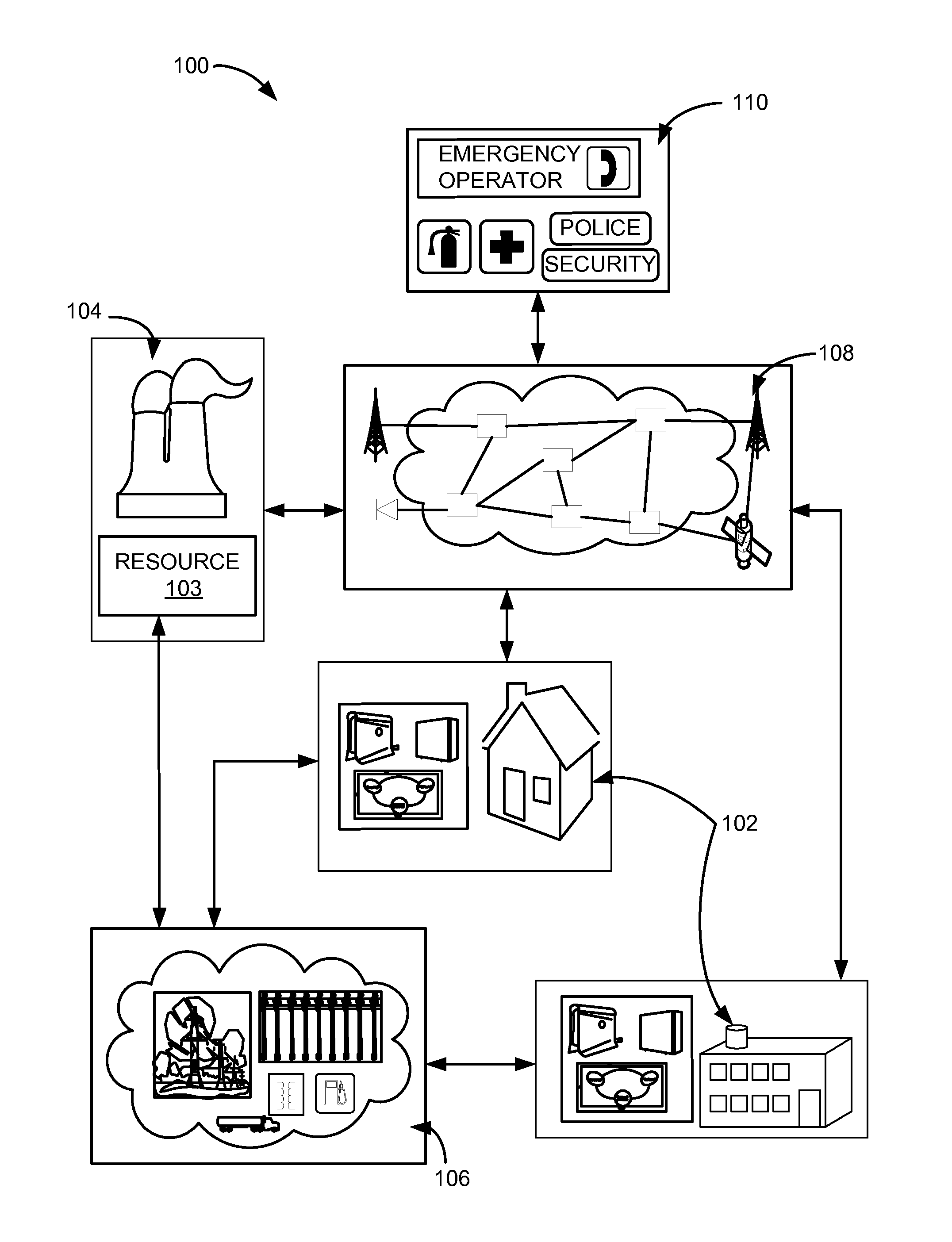
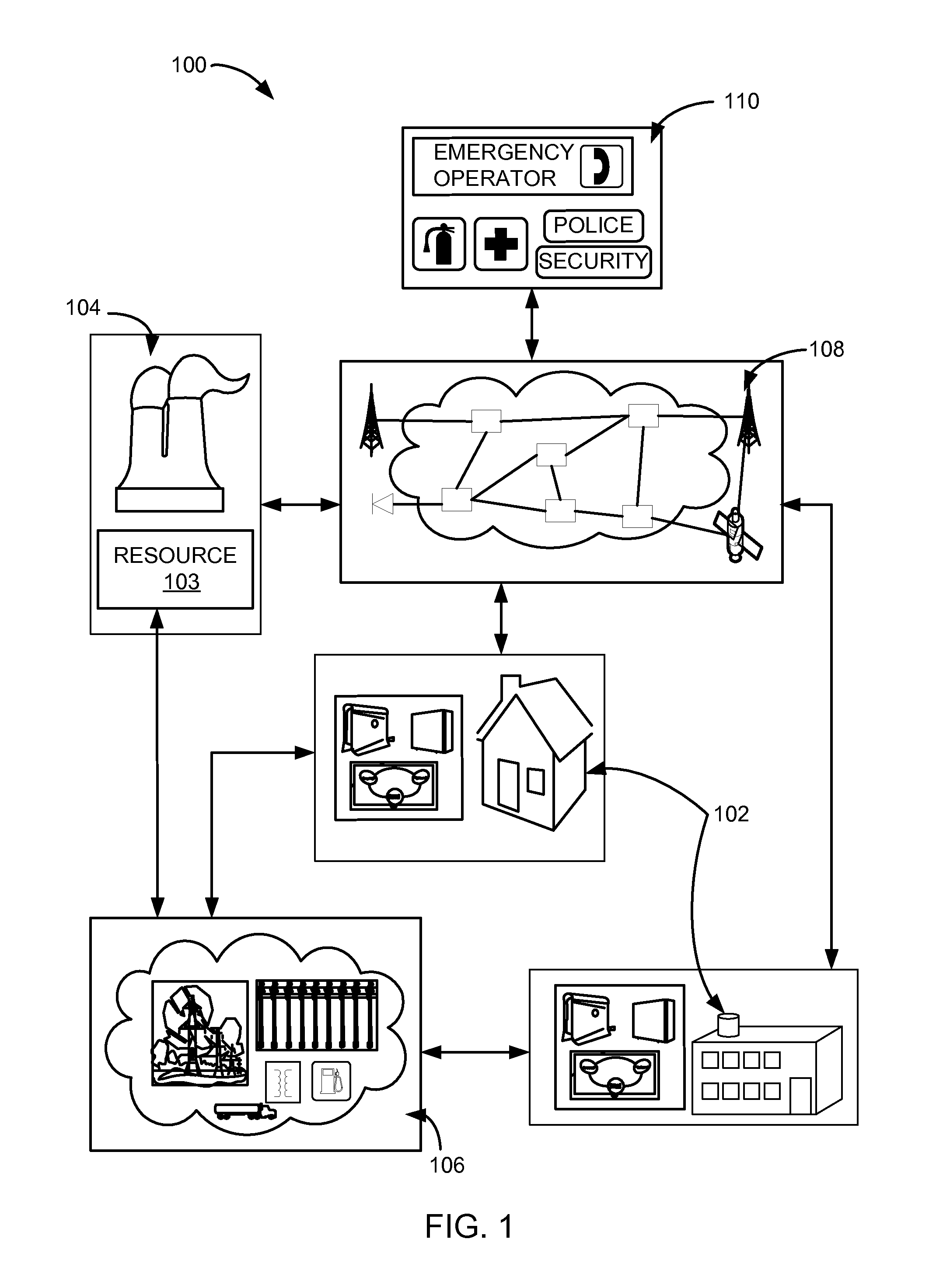
System and method for E911 location privacy protection
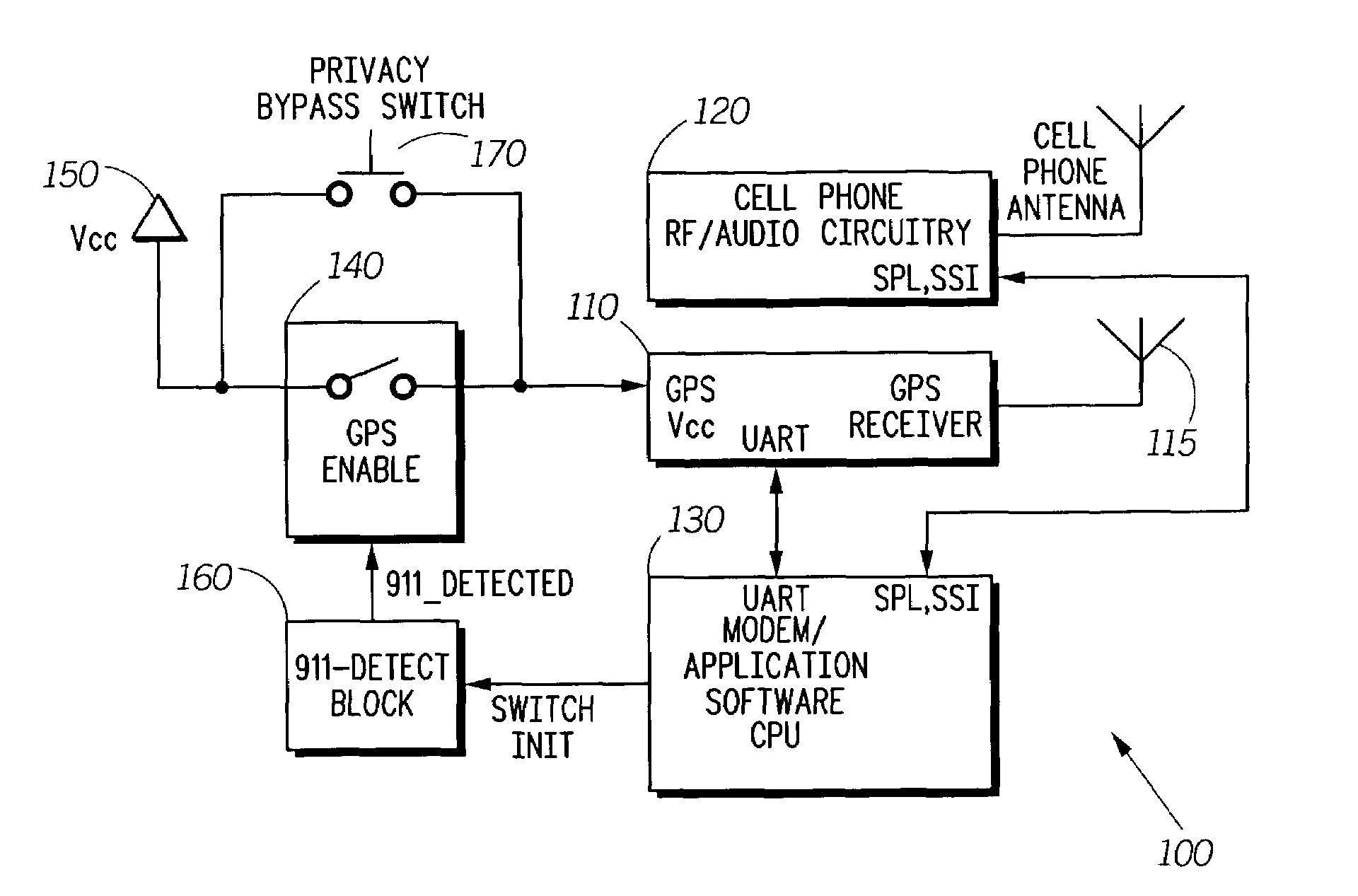
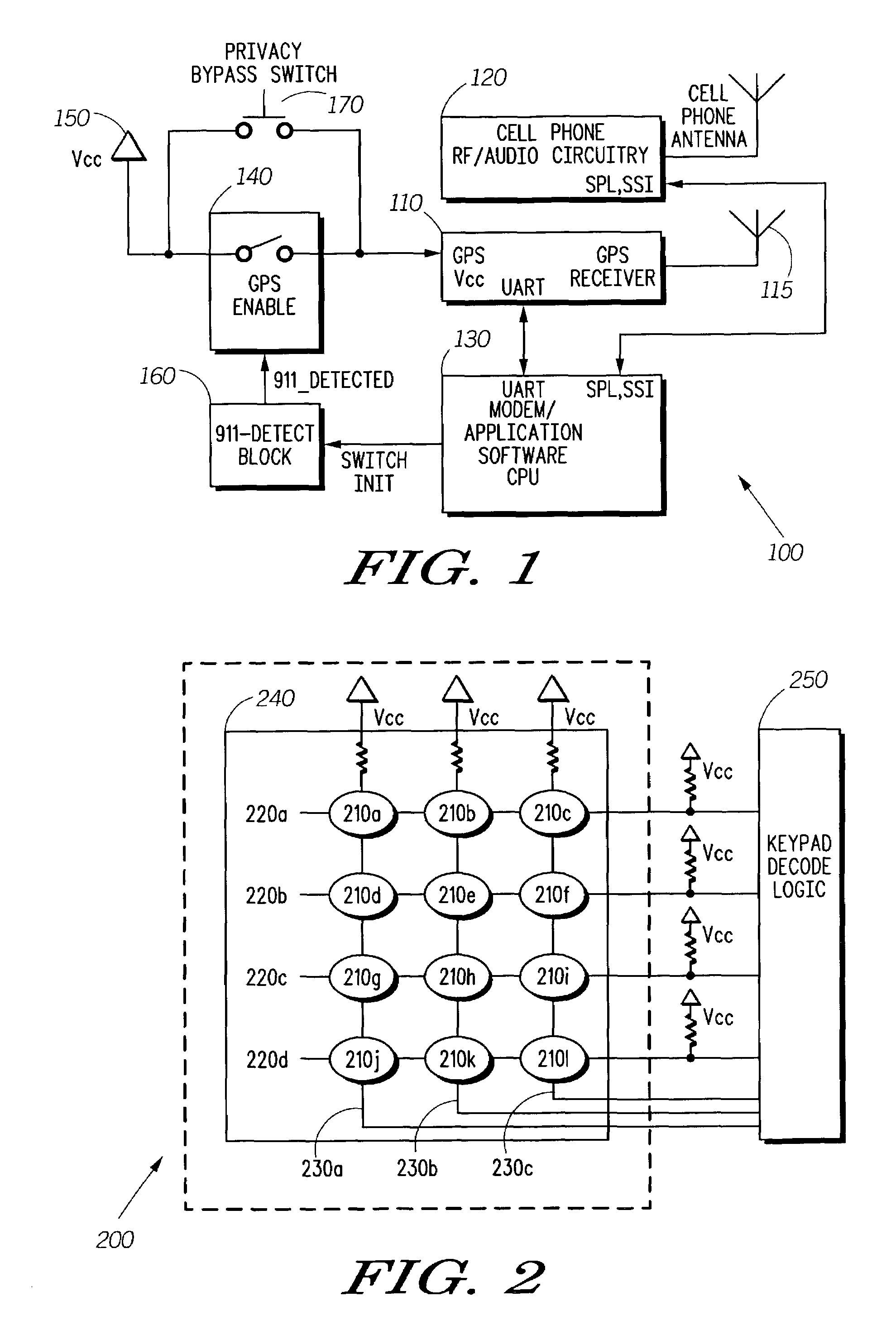
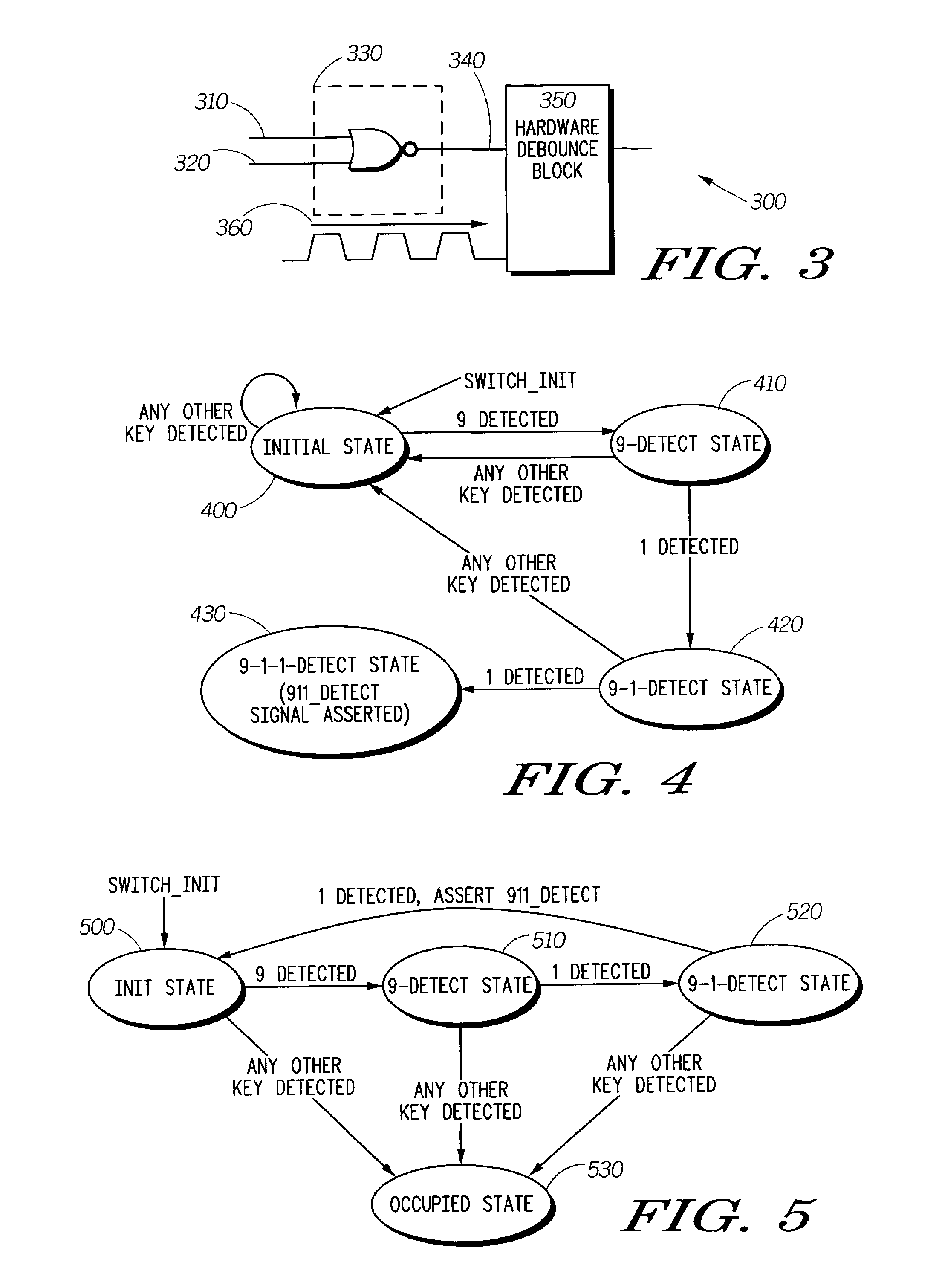
ActiveUS7751826B2Emergency connection handlingSpecial service for subscribersUser inputPrivacy protection
The invention relates to a system that enables power to be selectively applied to GPS circuitry in a cellular telephone or other mobile device only when a specific user input is detected. In one embodiment, power to the GPS circuitry may be enabled only when the user strikes the keys “9-1-l.” In other embodiments, other types of GPS enablement or disablement may be employed, such as selectively decoupling the GPS antenna. In another embodiment, the user may depress a privacy bypass button, which alternately enables and disables power to the GPS circuitry. Cellular telephones or other communication devices may therefore activate GPS location service during an emergency call, or when a user wishes to allow their location to be determined, but protect the privacy of that user's location and movement at other times.
Owner:GOOGLE TECH HLDG LLC
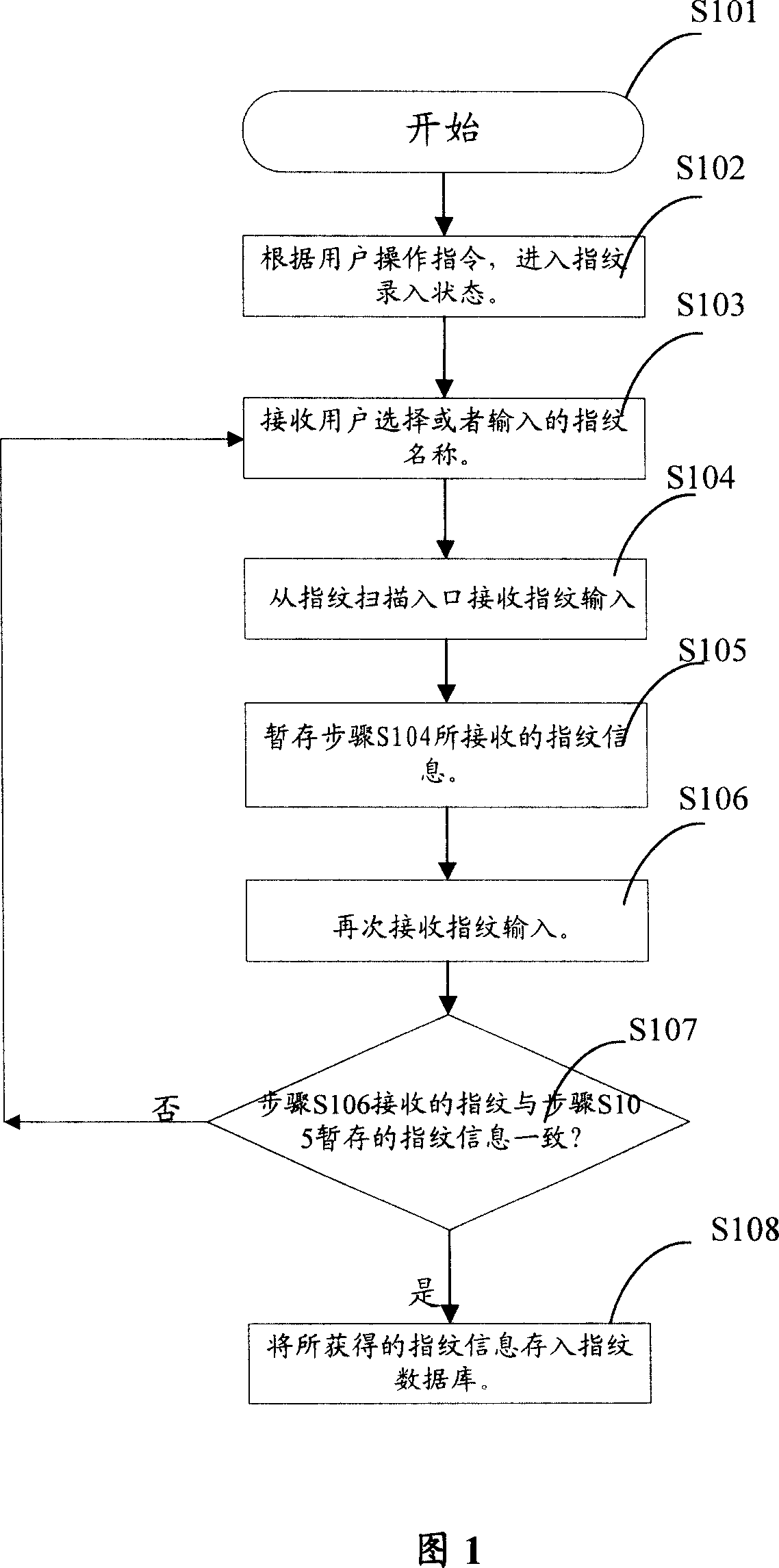
Mobile phone privacy protection method
InactiveCN101035335AImprove confidentialityCharacter and pattern recognitionDigital data authenticationRelevant informationPrivacy protection
The present invention relates to a method of private and secret information protection on the mobile telephone. It includes: 11) checking consumer's fingerprint information; 12) checking if the information judging the given fingerprint are authorized; If it come into existence, then going to step 13); If it does not , then the telephone comes into private and private protection state; 13) unlock the private and secret protection state. The fingerprint information can be saved as following steps: 21) The telephone turns into fingerprint record state according to consumer operation; 22) Receiving a fingerprint from the fingerprint scanning entrance; 23)The fingerprint information is saved into the fingerprint data base. Compared with present available technology, the invention has provided the physiology characteristics distinguishing the human body. It has realized that private and secret information protecting in the mobile telephone.
Owner:CECT
Systems and methods for protecting privacy
InactiveUS7797725B2Digital data processing detailsComputer security arrangementsApplying knowledgePrivacy protection
Techniques for providing privacy protection are provided. A query is received. Privacy policy information, extracted knowledge and optional information about available public information are determined. Information about the knowledge extraction transformations applied to create the extracted knowledge and the source data is determined. Privacy protecting transformations are determined and applied to transform the extracted knowledge based on the selected privacy policy, optional information about available public information, the characteristics of the applied knowledge extractions transformations, the source data and optional previous user queries.
Owner:PALO ALTO RES CENT INC
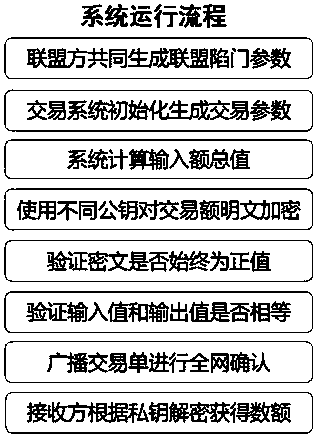
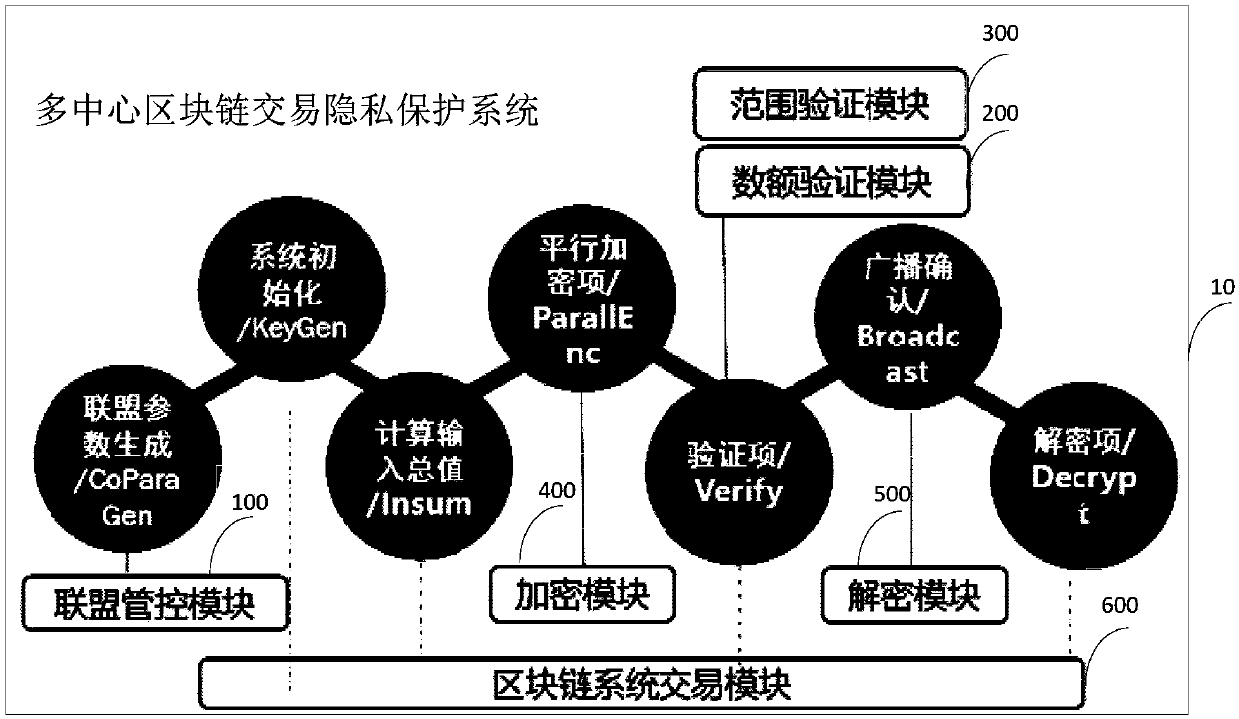
Multi-center block chain transaction privacy protection system and method
InactiveCN108021821ARealize privacy protectionEnhance the security of plaintext amountDigital data protectionCommunication with homomorphic encryptionDigital currencyCiphertext
The invention discloses a multi-center block chain transaction privacy protection system and method. The system comprises an alliance control module, an amount verification module, a range verification module, an encryption module, a decryption module and a block chain system transaction module, wherein the alliance control module is used for generating alliance parameters by multiple participants; the amount verification module is used for verifying that input and output of an encrypted ciphertext amount in a transaction are equal; the range verification module is used for verifying that theencrypted ciphertext amount in the transaction is in a specific interval and is constantly positive; the encryption module and the decryption module are used for carrying out homomorphic encryption and decryption on the amount in transmission and reception processes; and the block chain system transaction module is used for complete bitcoin-like digital currency transaction systems, and has a complete transaction process which comprises transmission, reception, broadcasting and block confirmation. The system is capable of enhancing general structures through block chain transaction privacies under a multi-center supervision mode, so as to realize privacy protection for trapdoor parameters under joint control of multiple parties and transaction metadata in transaction process, and effectively strengthen the safety of plaintext amounts in multi-center block chain system transaction process.
Owner:BEIHANG UNIV
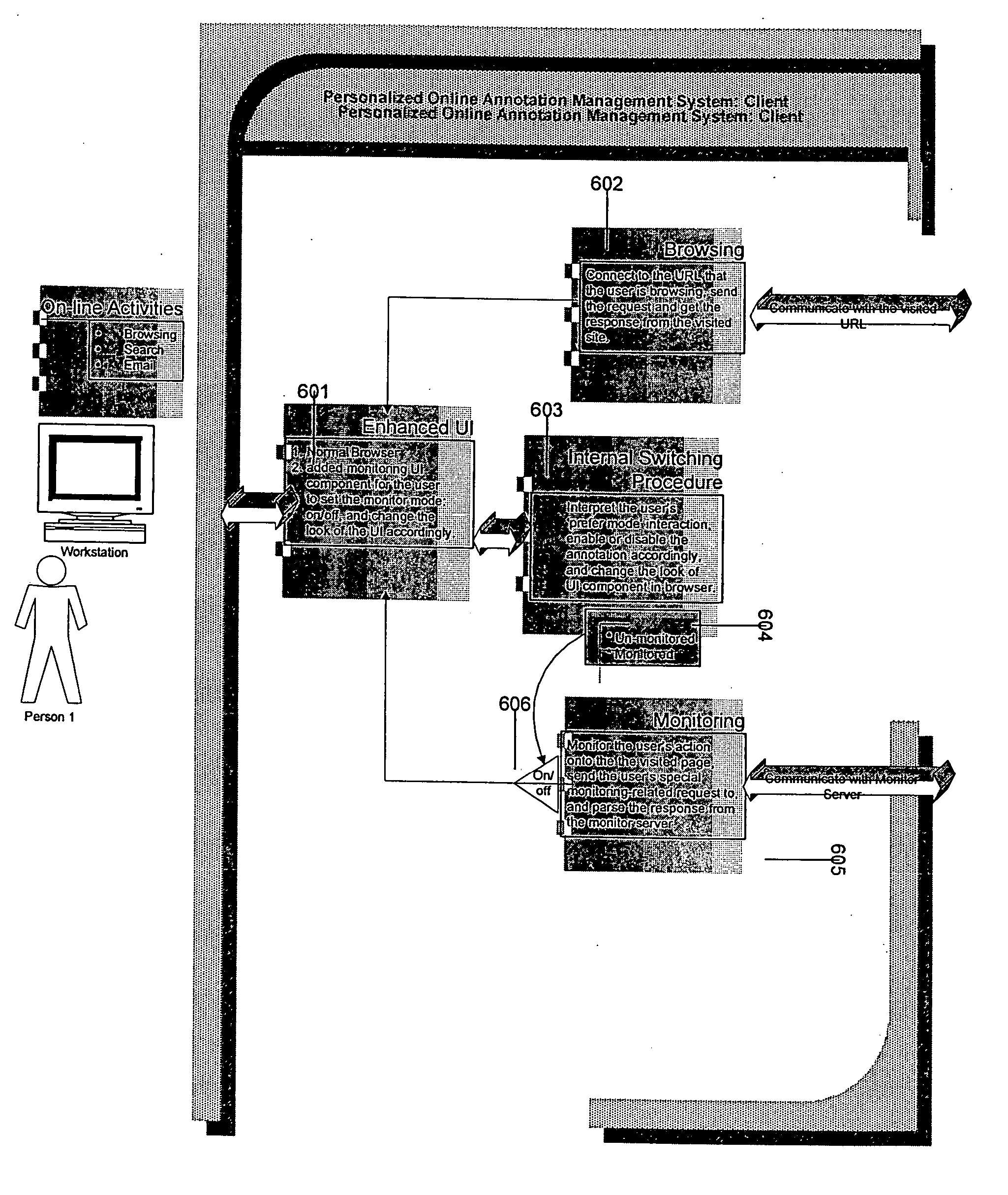
Personal online information management system
InactiveUS20060155764A1Easy to controlEnsuring privacyDigital data processing detailsComputer security arrangementsMonitor modePrivacy protection
A personal online information management system allows users to monitor, manage, retrieve, and utilize their personal online behaviors such as browsing, searching, editing / commenting, discussion, shopping, and peer to peer communications. The system provides personalized service with explicitly self-controlled privacy protection. The system enables an anonymous or identified user to easily switch between a monitored mode and an un-monitored mode.
Owner:NAVIPAL
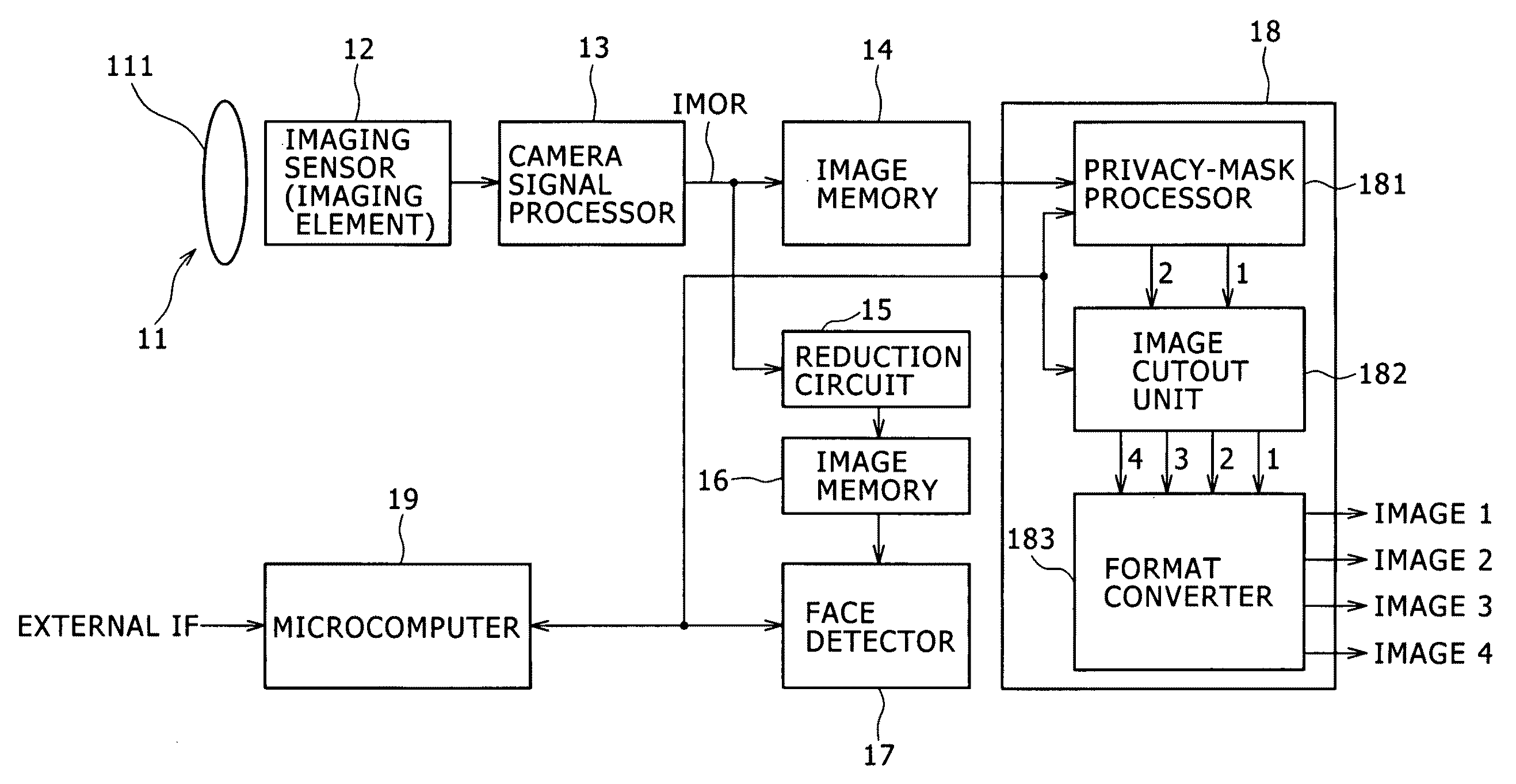
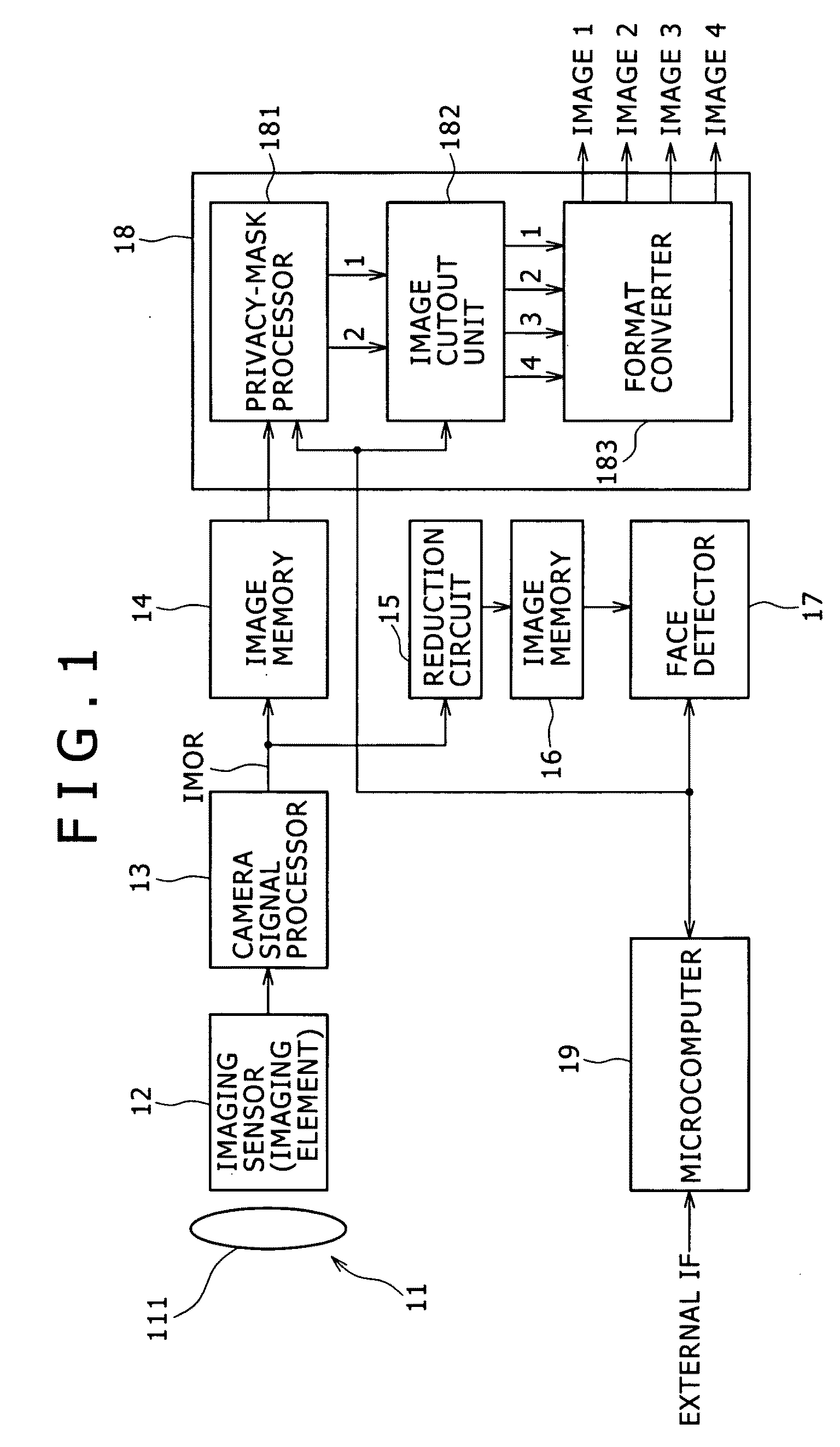
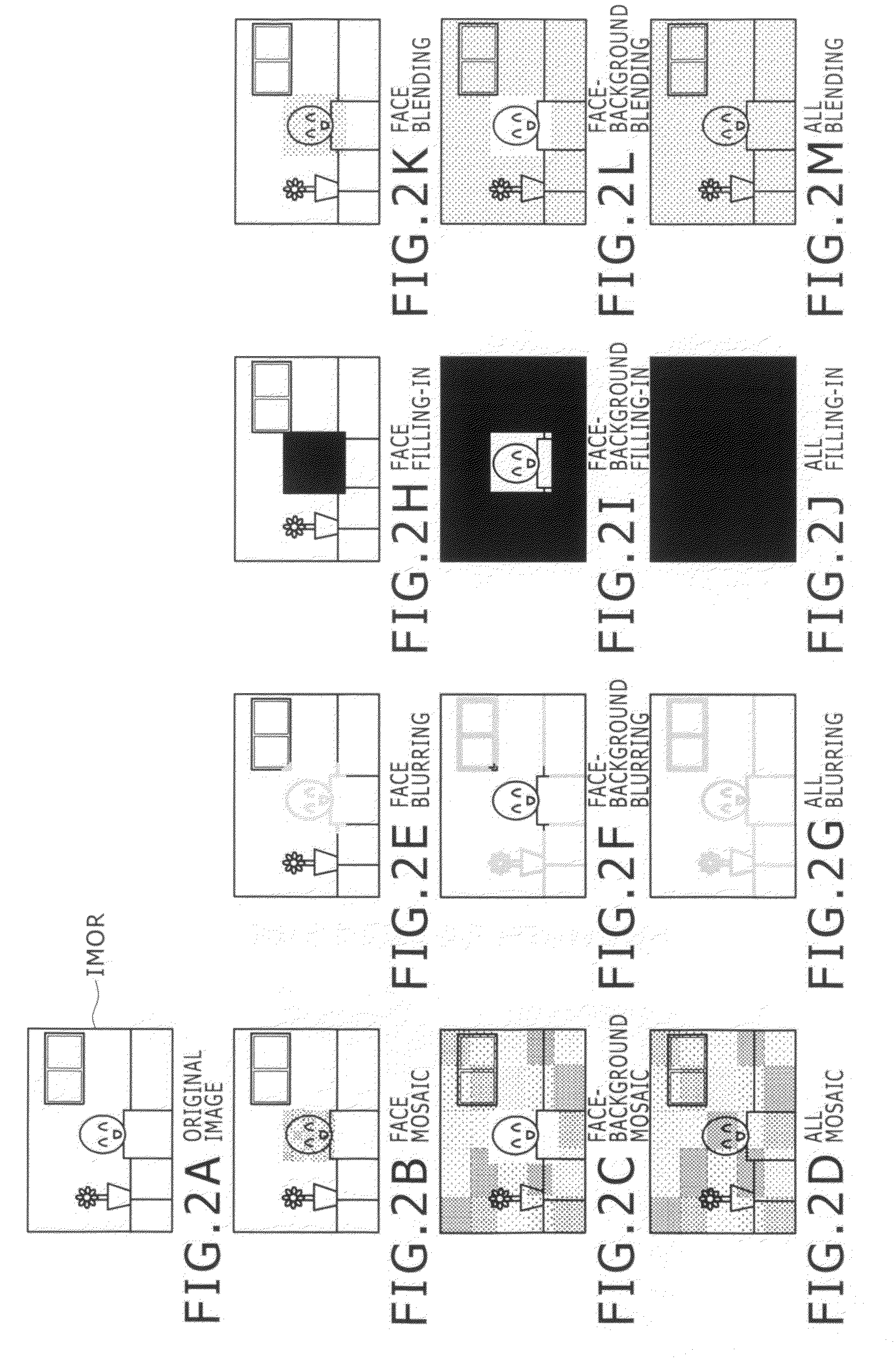
Image processing device, camera device, communication system, image processing method, and program
ActiveUS20090207269A1Reduce latencyReduce loadTelevision system detailsCharacter and pattern recognitionPattern recognitionCommunications system
An image processing device includes a face detector configured to detect a face based on a taken image, and an output processor configured to have a function to execute privacy-mask processing for privacy protection for an image of a face detected by the face detector or an image of a background of the face. The output processor includes a function to separately output an image of a face detected by the face detector and an image of a background of the face which are each subjected to or not subjected to the privacy-mask processing.
Owner:SONY SEMICON SOLUTIONS CORP
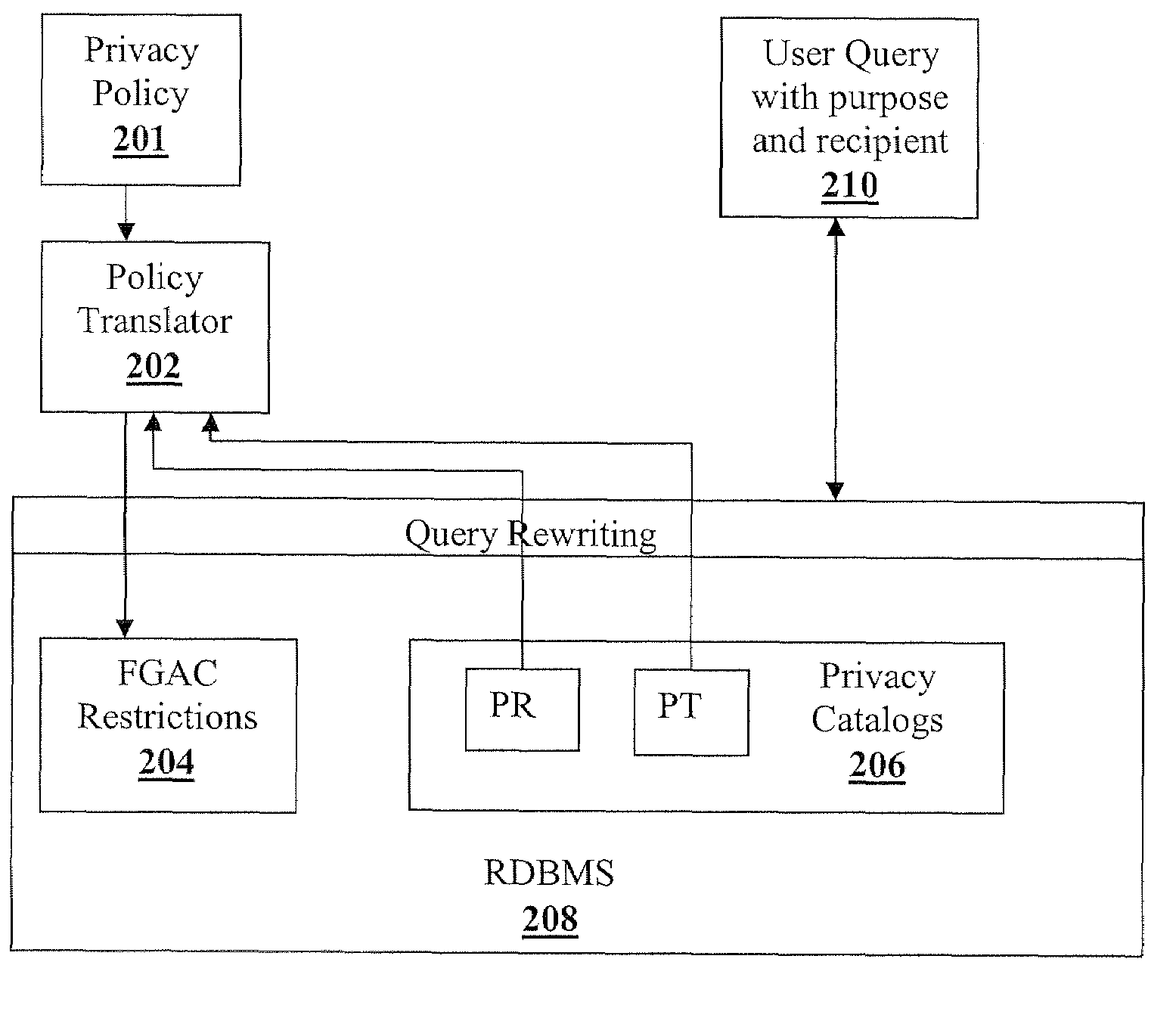
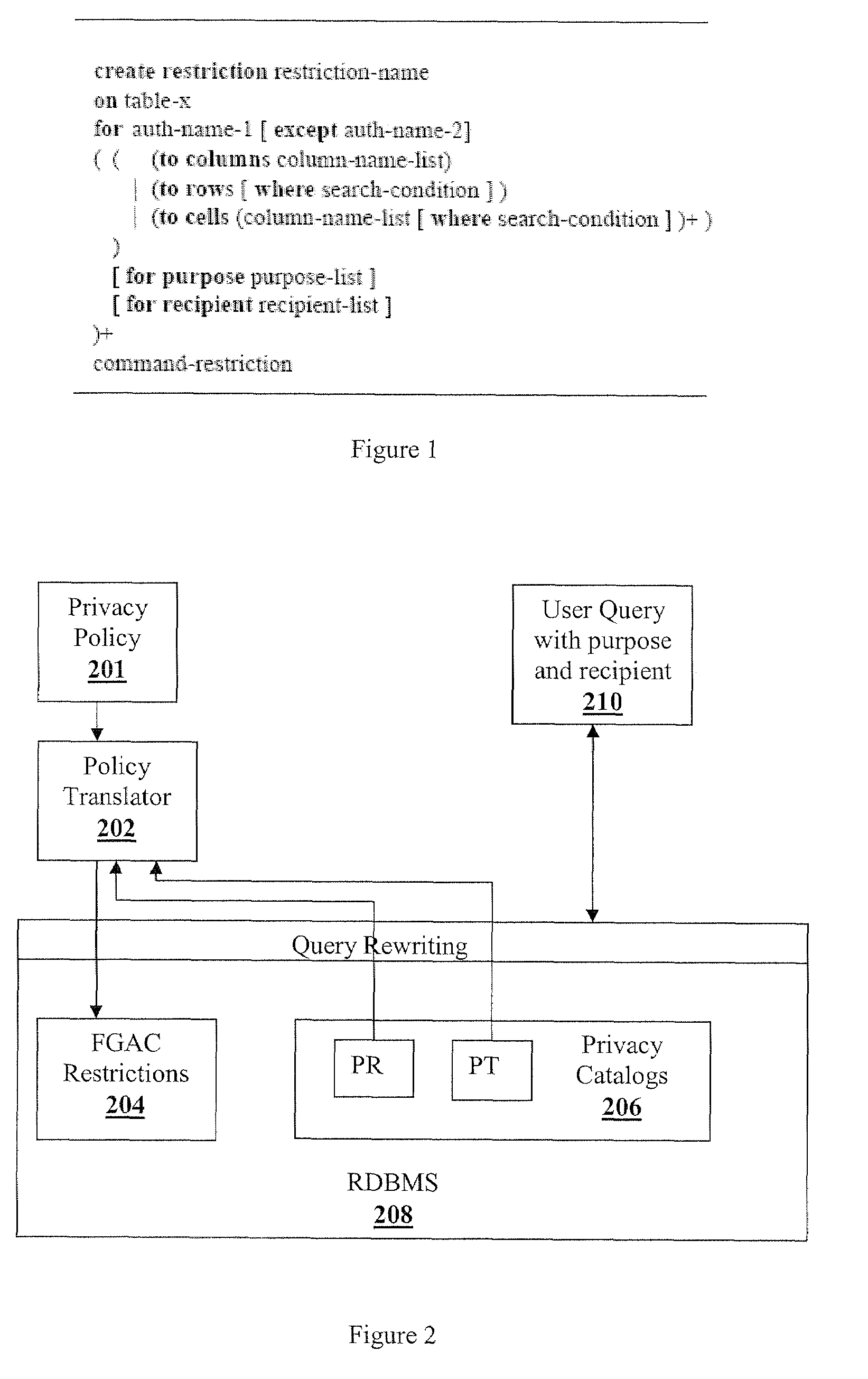
Extending relational database systems to automatically enforce privacy policies
ActiveUS7243097B1Data processing applicationsDigital data information retrievalLanguage constructPrivacy protection
A method of transforming relational database management systems into their privacy-preserving equivalents is provided. Language constructs allow fine grained access control (FGAC) restrictions to be specified on the access to data in a table at the level of a row, a column or a cell. Fine grained restrictions are a combination of access control and privacy policy restrictions, which ensure compliance with current privacy legislation mandates.
Owner:IBM CORP
User data reconstruction attack method oriented to deep federal learning
PendingCN110008696AIncrease authenticityImprove concealmentDigital data protectionPlatform integrity maintainancePrivacy protectionData mining
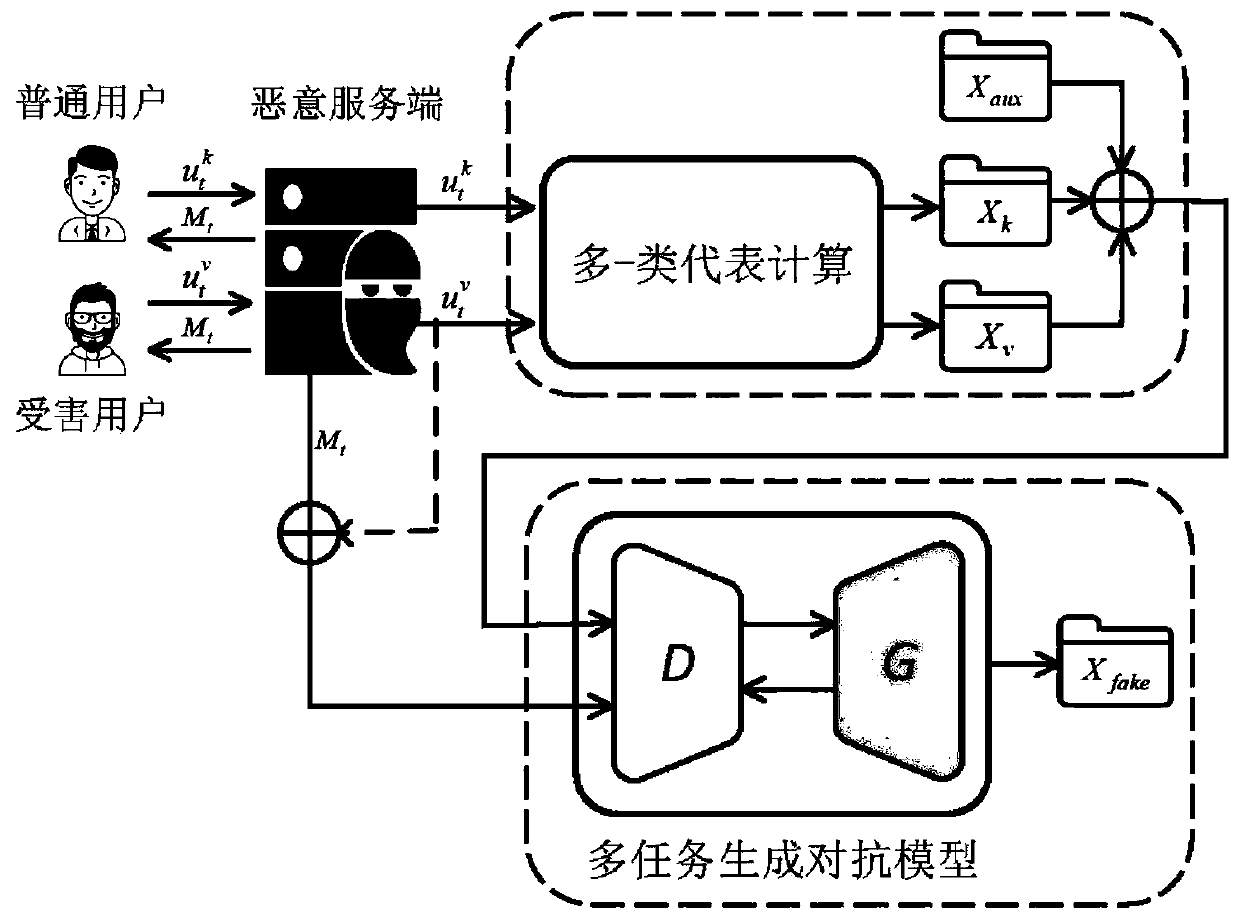
The invention discloses a user data reconstruction attack method oriented to deep federal learning, which can reconstruct private data of a specific user and consider that attacks are implemented by amalicious server, so that negative effects are prevented from being introduced into an original shared model compared with a conventional attack method which can only reconstruct category representation data. Furthermore, the method introduces a multi-task generative adversarial model to simulate the distribution of user data, and the model is used for training the authenticity and category of aninput sample and the identification of the user identity to which the model belongs, so that the quality of the generated sample is improved. In order to better distinguish different users, the method introduces an optimized user data representative calculation method to describe user characteristics participating in federal learning, and the method is used for supervising training of a generative adversarial model. For an existing federal learning architecture concerning privacy protection, privacy leakage can be caused by a data reconstruction attack based on a multi-task generative adversarial model provided by the invention.
Owner:WUHAN UNIV
Privacy protection on application sharing and data projector connectivity
ActiveUS20070136466A1Digital computer detailsInternal/peripheral component protectionPrivacy protectionTerminal equipment
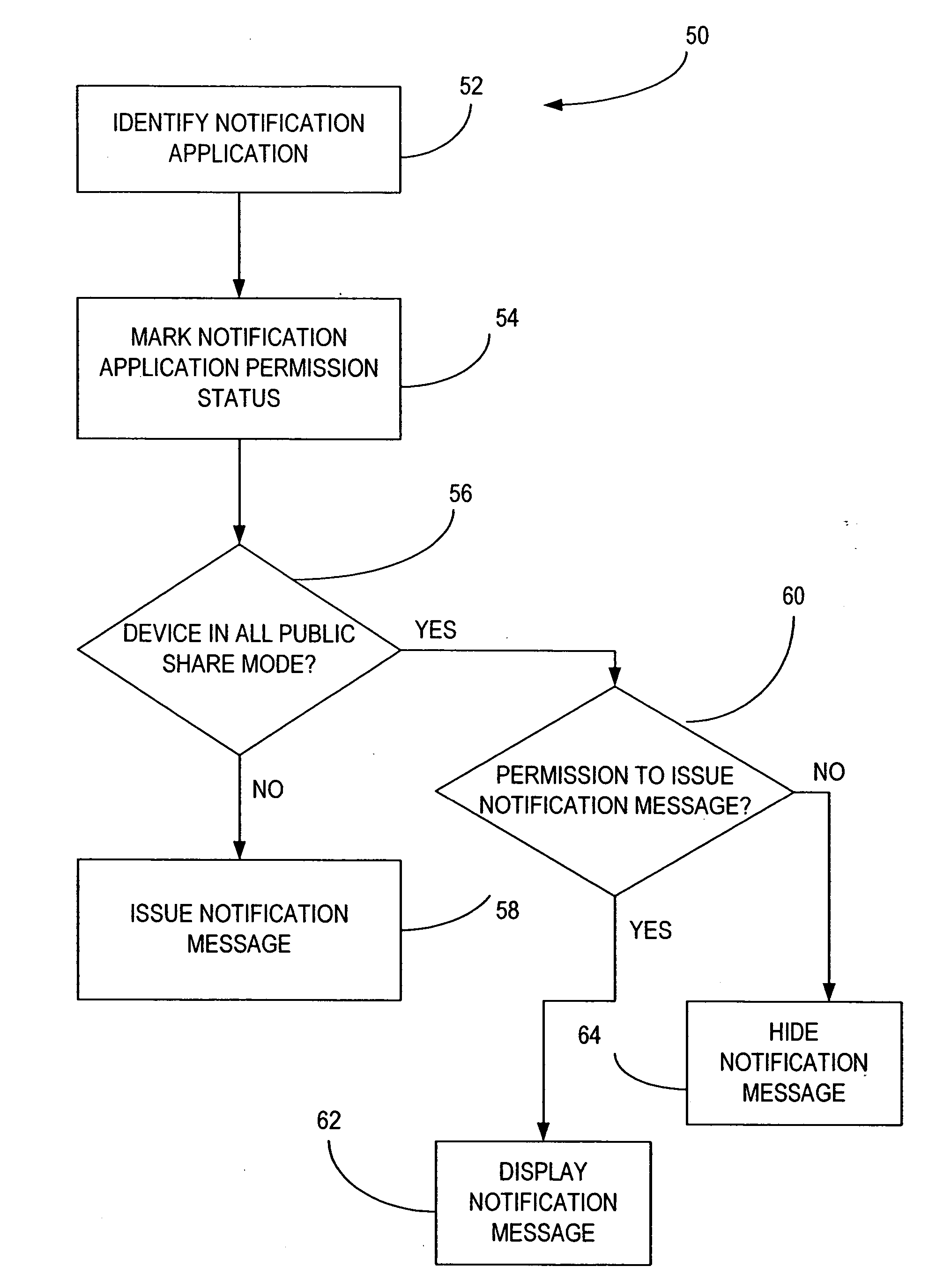
Privacy protection of data content is provided by identifying one or more applications running on a suitably configured device, and marking each of the applications to indicate that a respective one of the applications is permitted or not permitted to issue messages in an all share public mode. The data content of such messages is hidden from public view in response to the application not having the requisite permission to issue messages in the all share public mode. A computer program and mobile terminal device for providing privacy protection of data content are also presented.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com