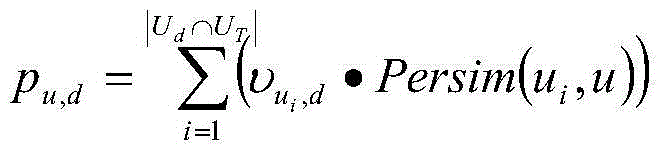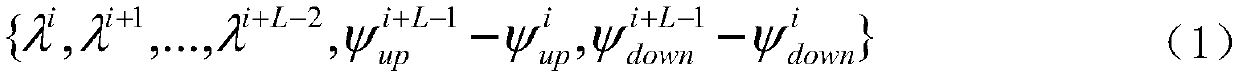Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
113results about How to "Avoid privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
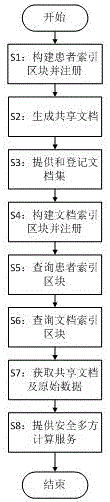
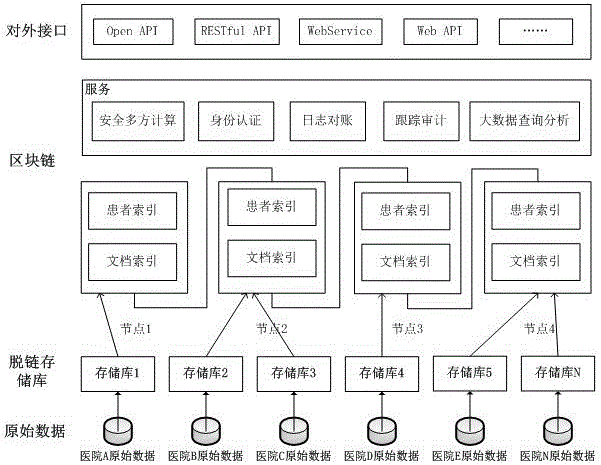
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
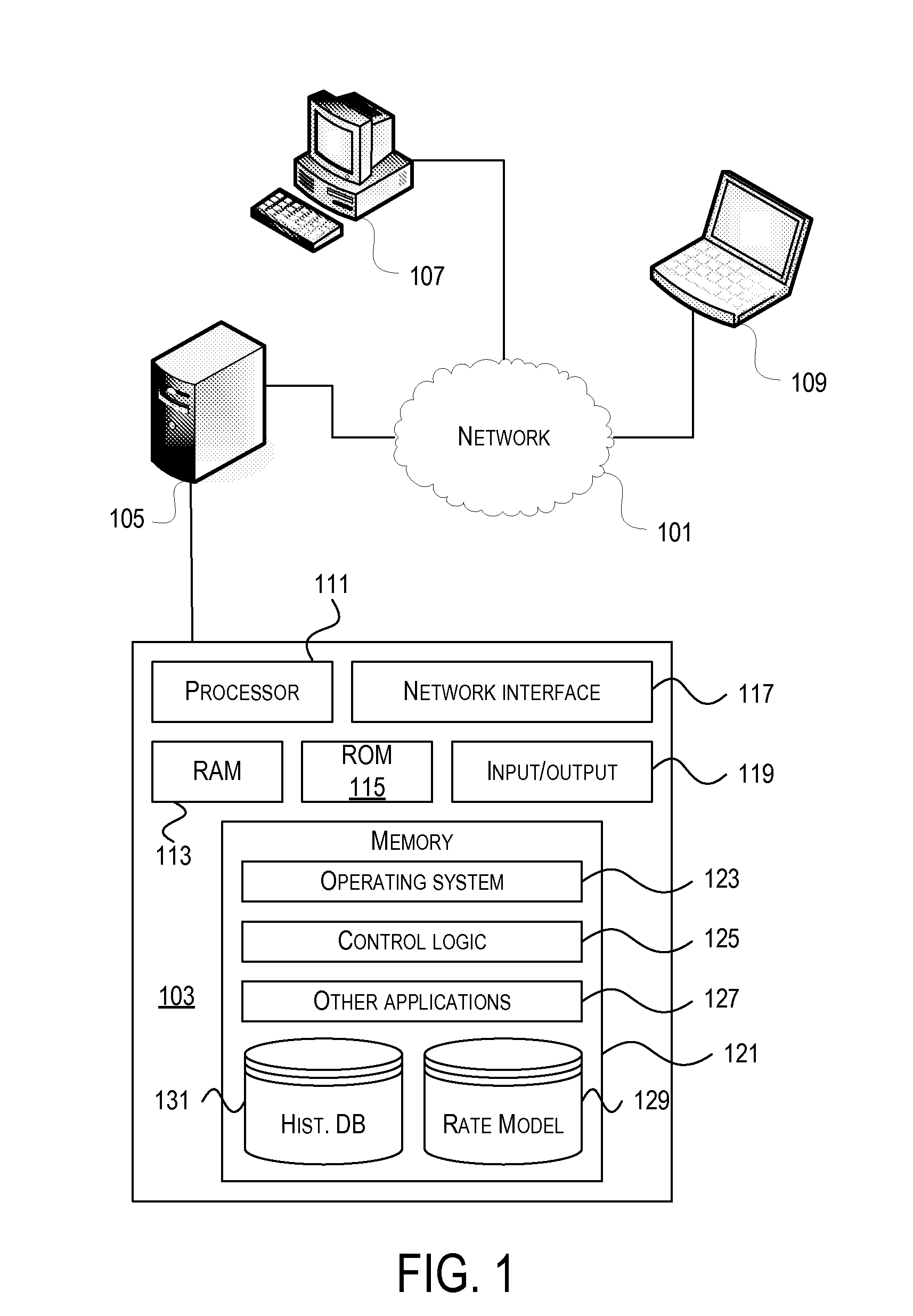
Real-time insurance estimate based on non-personal identifying information
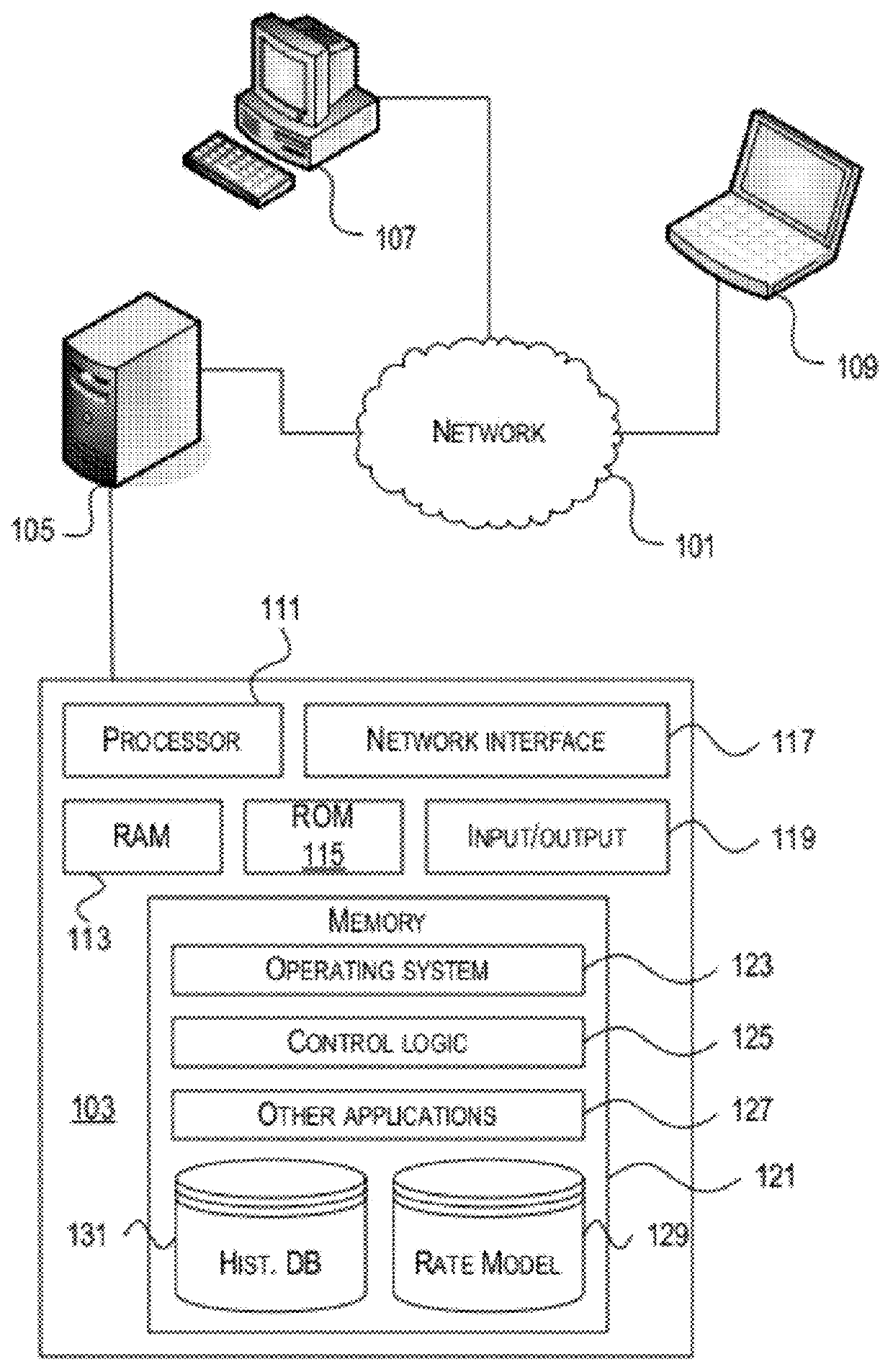
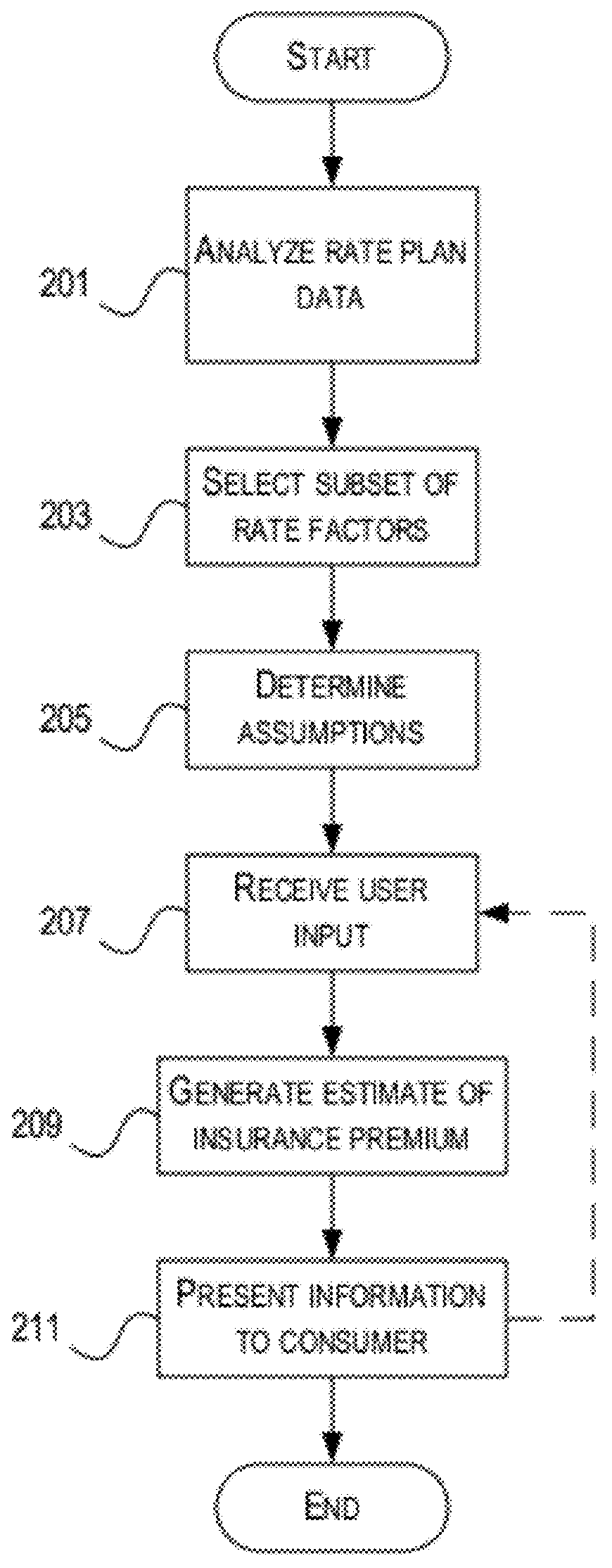
Methods and systems for providing estimated insurance quotes / premiums are described herein. After analyzing rate factors, a subset of rate factors are selected that yield a fairly accurate estimated insurance premium from a minimum amount of information easily obtainable from a user. The user inputs a value from a predetermined set of allowable inputs (value input filter). After receiving and analyzing the user inputs, the system generates one or more estimates and displays the one or more estimates to the user, e.g., via a web page. When multiple estimates are provided, the multiple estimates may differ based on the level of coverage, add-on features, or both. Readily known non-personal identifying information is preferably requested and used, thereby alleviating privacy concerns while still being able to provide an estimate to the user very quickly, e.g., under 30 seconds, once all the requested information is obtained.
Owner:ALLSTATE INSURANCE
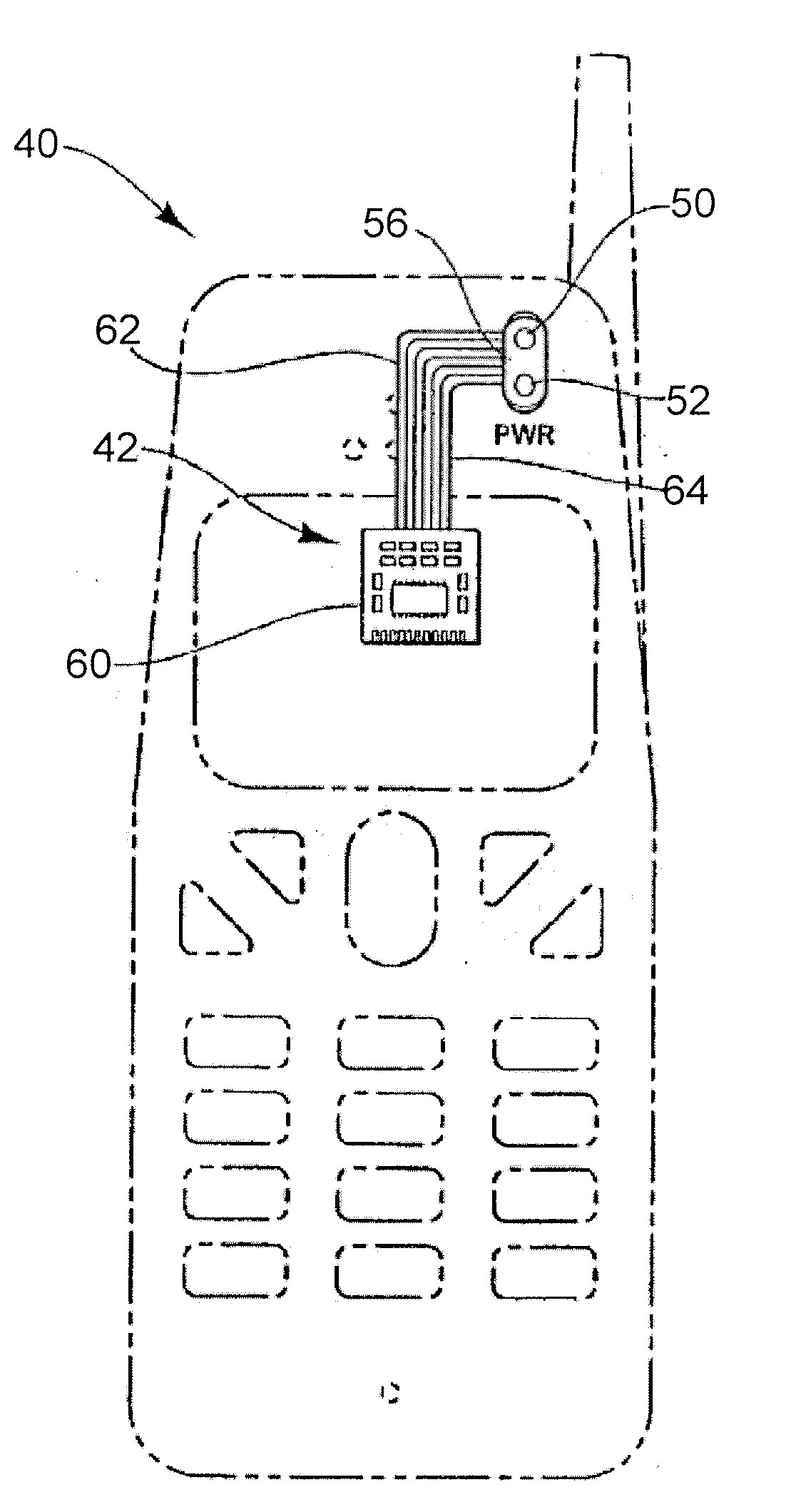
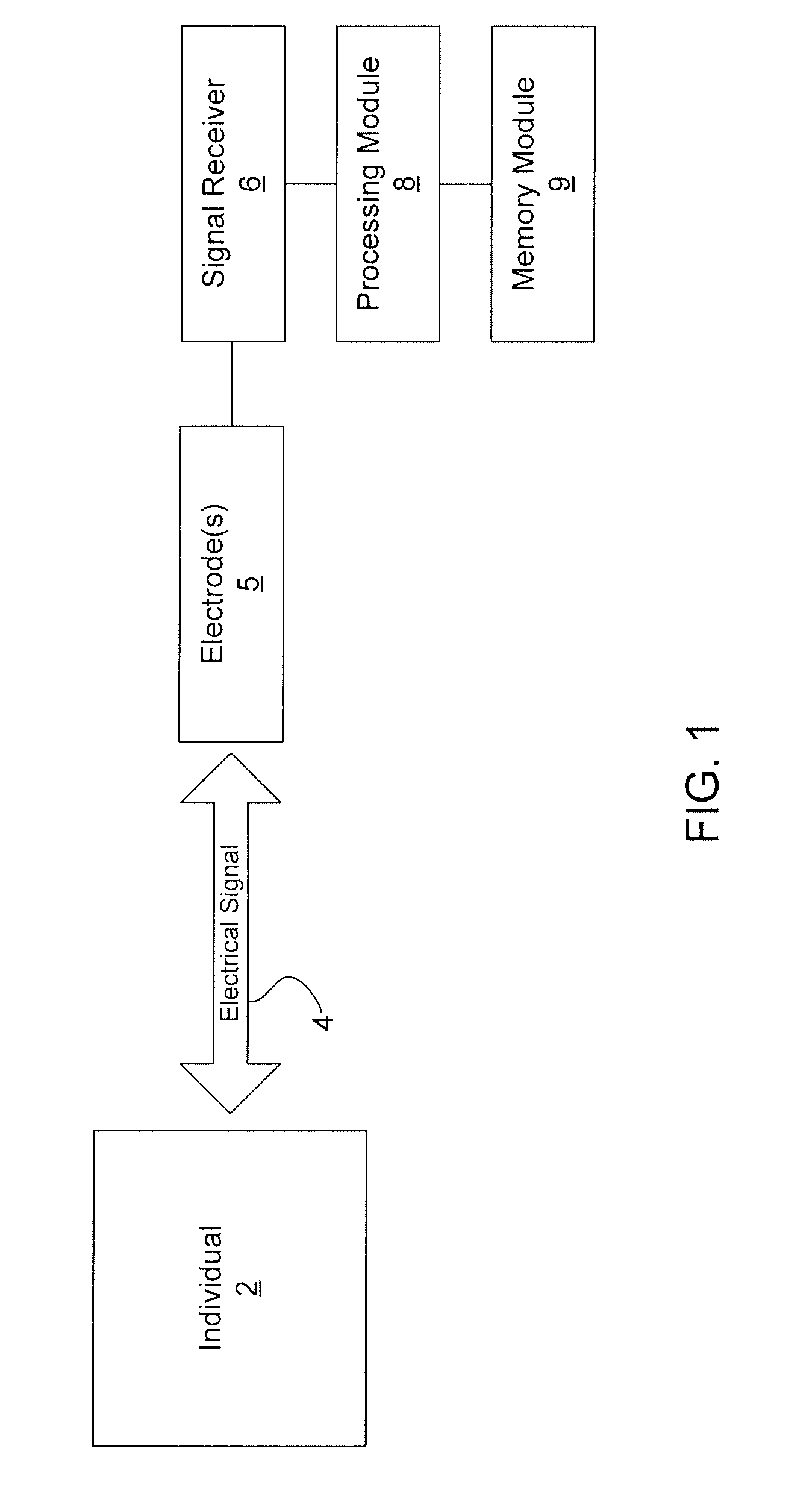
Systems and methods for authenticating an individual
InactiveUS20080260211A1Improve securityImprove application diversityProgramme controlElectric signal transmission systemsElectricitySkin surface
Systems and methods for employing histological and physiological biometric markers that are substantially unique to an individual in order to activate a device, participate in a transaction, or identify himself or herself, wherein at least one biometric marker is obtained by one or more electrical contacts on the surface of the skin. A biometric identification of an individual is obtained by a heartbeat waveform, which is acquired by one or more direct electrical contacts. A mechanism for biometric authentication is used that includes one or more electrodes, an electrical signal receiver, a memory module, and a processing module.
Owner:CONVERGENCE BIOMETRICS
Real-Time Insurance Estimate Based on Limited Identification
Methods and systems for providing estimated insurance quotes / premiums are described herein. After analyzing rate factors, a subset of rate factors are selected that yield a fairly accurate estimated insurance premium from a minimum amount of information easily obtainable from a user. The user inputs a value from a predetermined set of allowable inputs (value input filter), or provides identifying information from which the minimum information may be readily obtained from private and / or vended databases. After receiving and analyzing the user inputs, the system generates one or more estimates and provides the one or more estimates to the user, e.g., via a display screen, printed receipt, SMS messages, etc. Multiple estimates may differ based on the level of insurance coverage, add-on features, or both. The methods and systems provide an insurance estimate to the user very quickly, e.g., under 30 seconds, during a goods or services transaction unrelated to insurance.
Owner:ALLSTATE INSURANCE
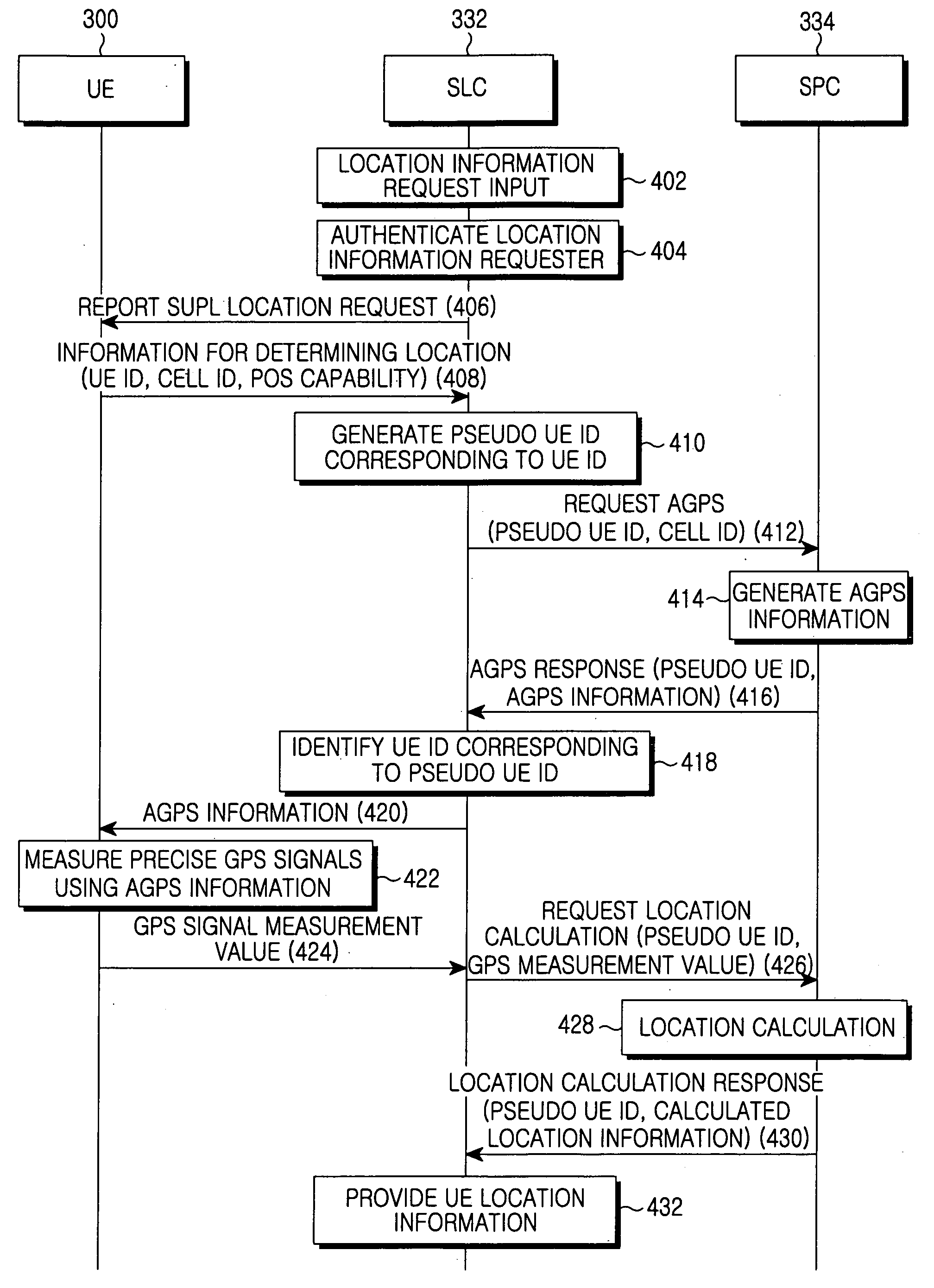
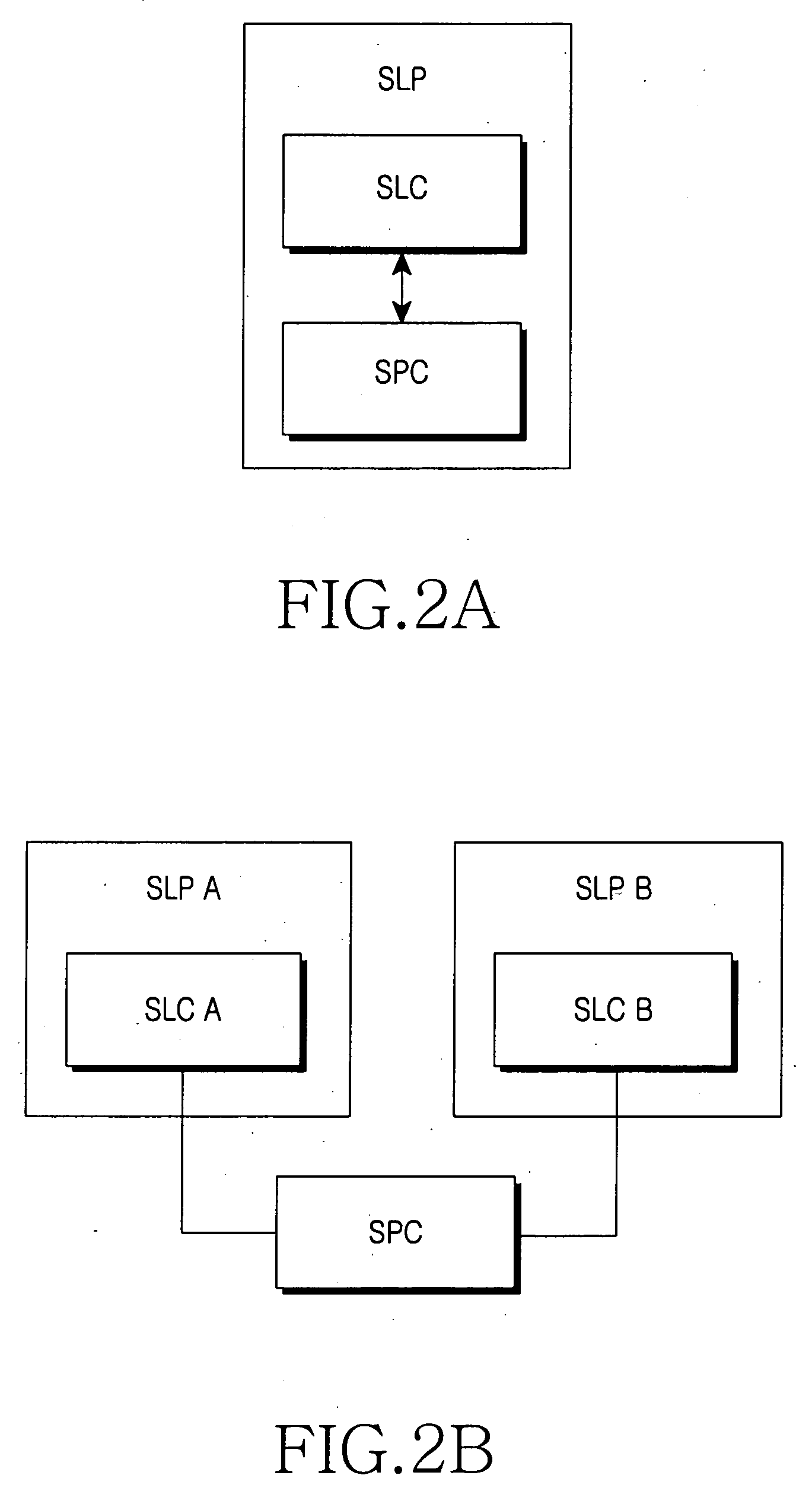
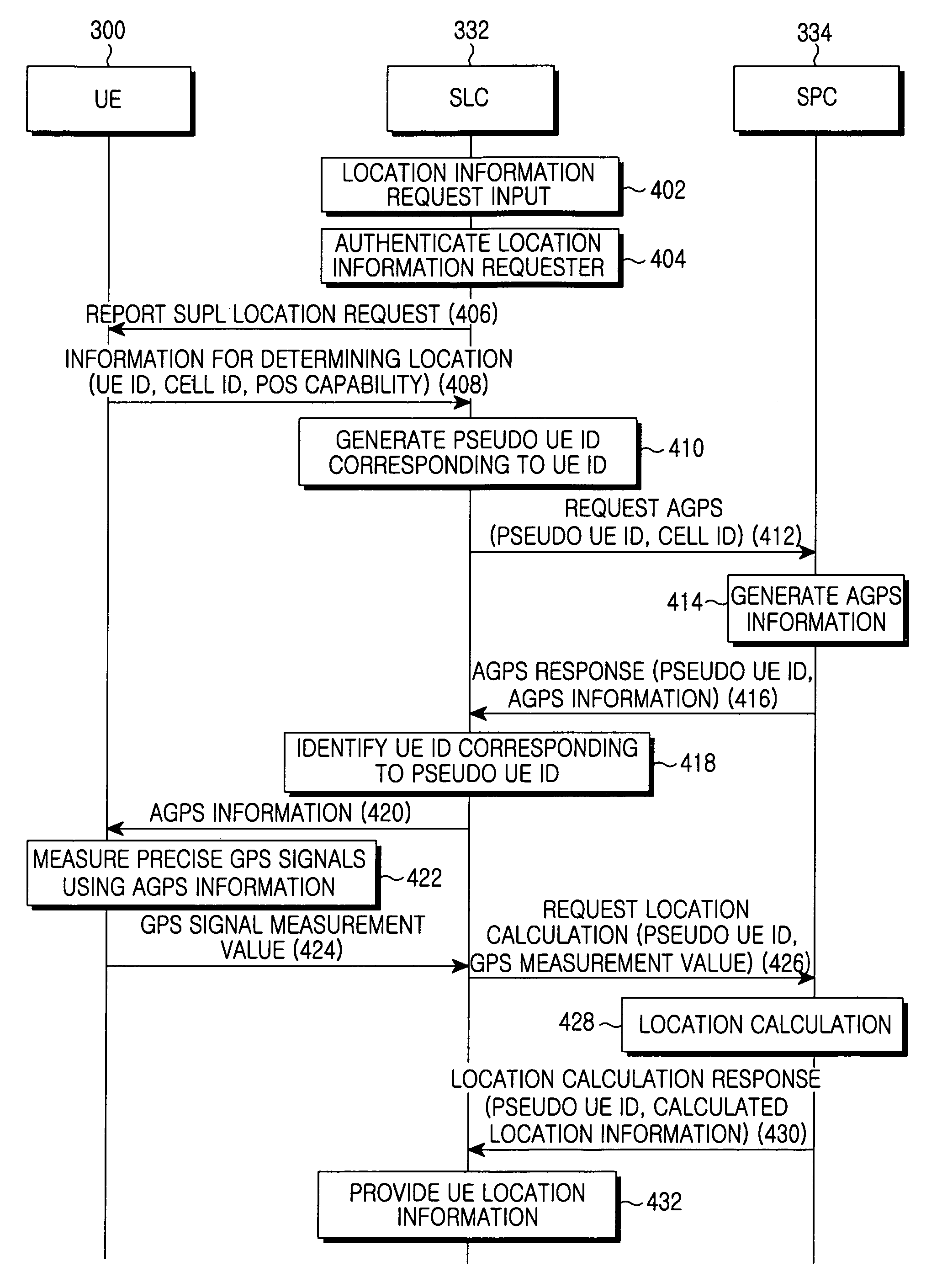
Method for determining location of UE by using AGPS information
ActiveUS20060063536A1Avoid privacyImprove securityPosition fixationRadio/inductive link selection arrangementsTelecommunicationsComputer science
Disclosed is a method for determining a location of a UE by means of AGPS information. The method includes generating by an SLC a pseudo UE ID according to a request for location information of the UE, the pseudo UE ID being used for maintaining security in communication with an SPC, requesting AGPS information for the UE, the location information of which has been requested, to the SPC by means of the pseudo UE ID, and receiving the AGPS information, transferring the received AGPS information to the UE, and receiving GPS signal measurement values using the AGPS information from the UE, requesting a location calculation of the UE for the GPS signal measurement values to the SPC by means of the pseudo UE ID, and receiving calculated location values, and providing the location information of the UE by means of the received location values of the UE.
Owner:SAMSUNG ELECTRONICS CO LTD
Certified email messages and attachments
ActiveUS20110276638A1Avoid privacyAvoid security issuesMultiple digital computer combinationsData switching networksEmail managementBiometrics
The current Invention is a method to combine into a complete solution the following: Biometrics (initially a registered fingerprint scan), a separate and secure network and infrastructure, an email management system and additional email message format options. The solution provides improvements to: 1) sender and recipient identity verification, 2) security and privacy, 3) proof of delivery and 4) effectiveness in communications during the exchange of certified email messages and attachments. Improved effectiveness is communication occurs based on the ability to use any combination of text, audio and visual (video) email message formats in an integrated, coordinated process of communication with another email recipient.
Owner:PRIVACYDATASYST
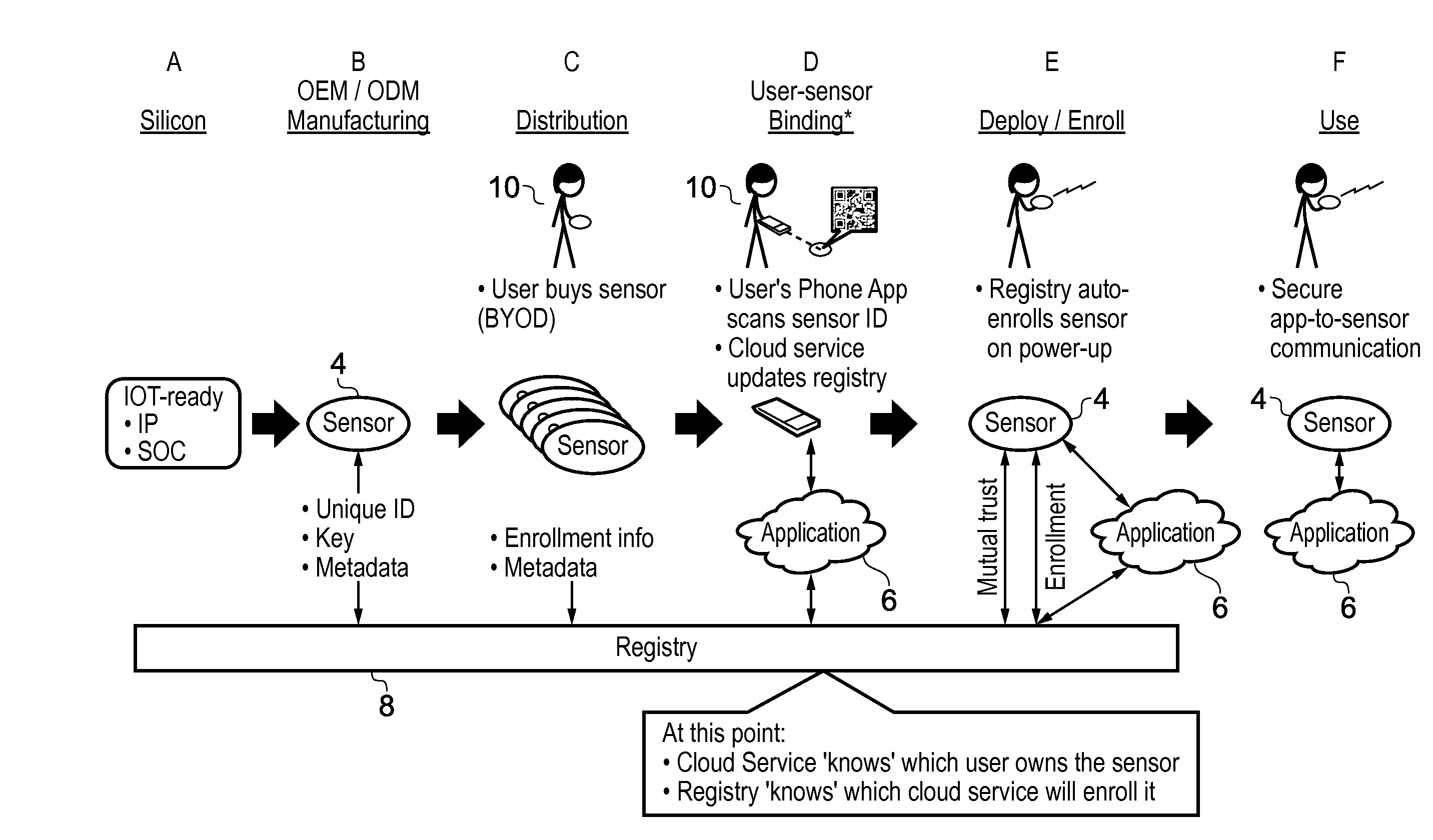
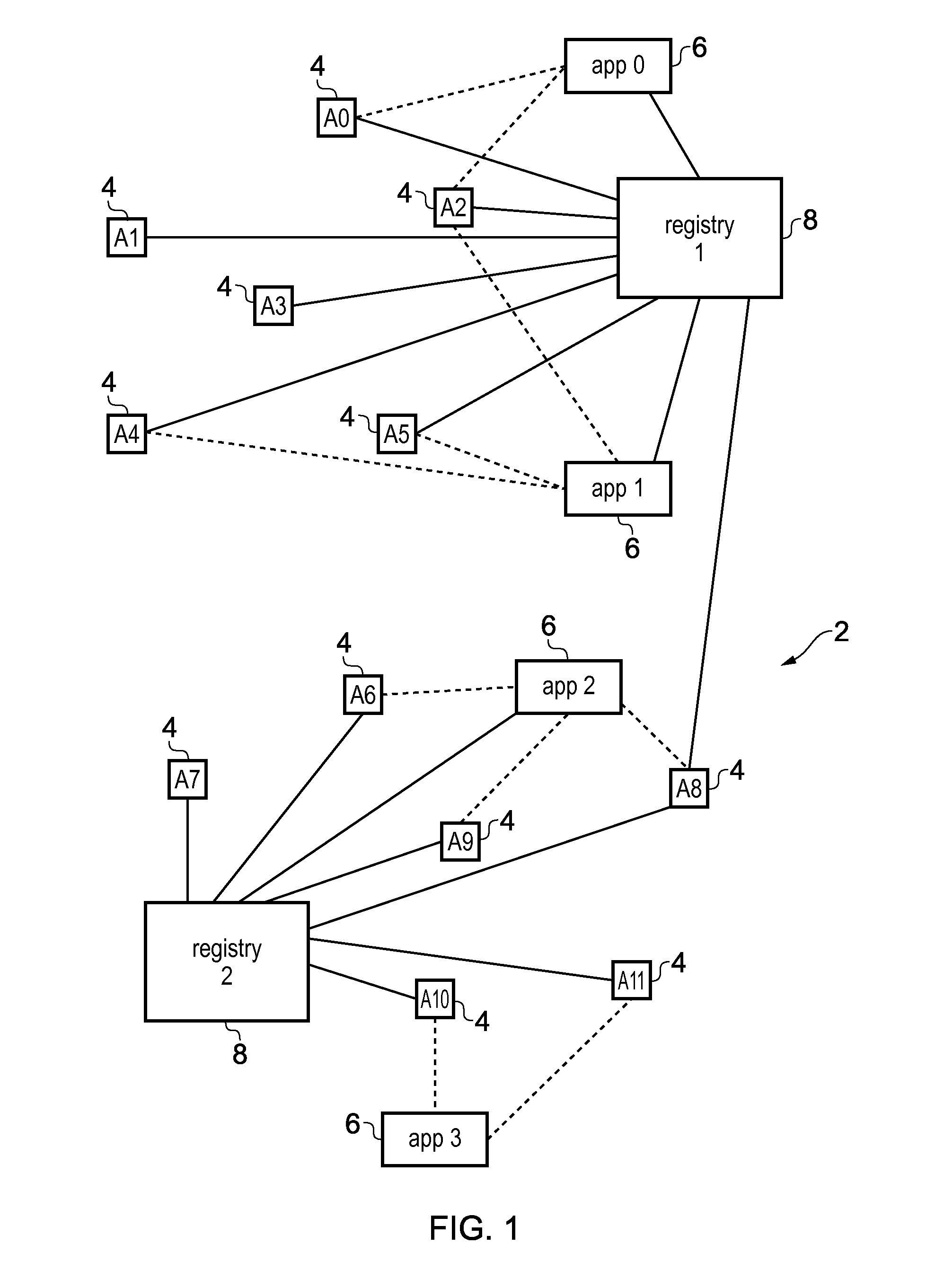
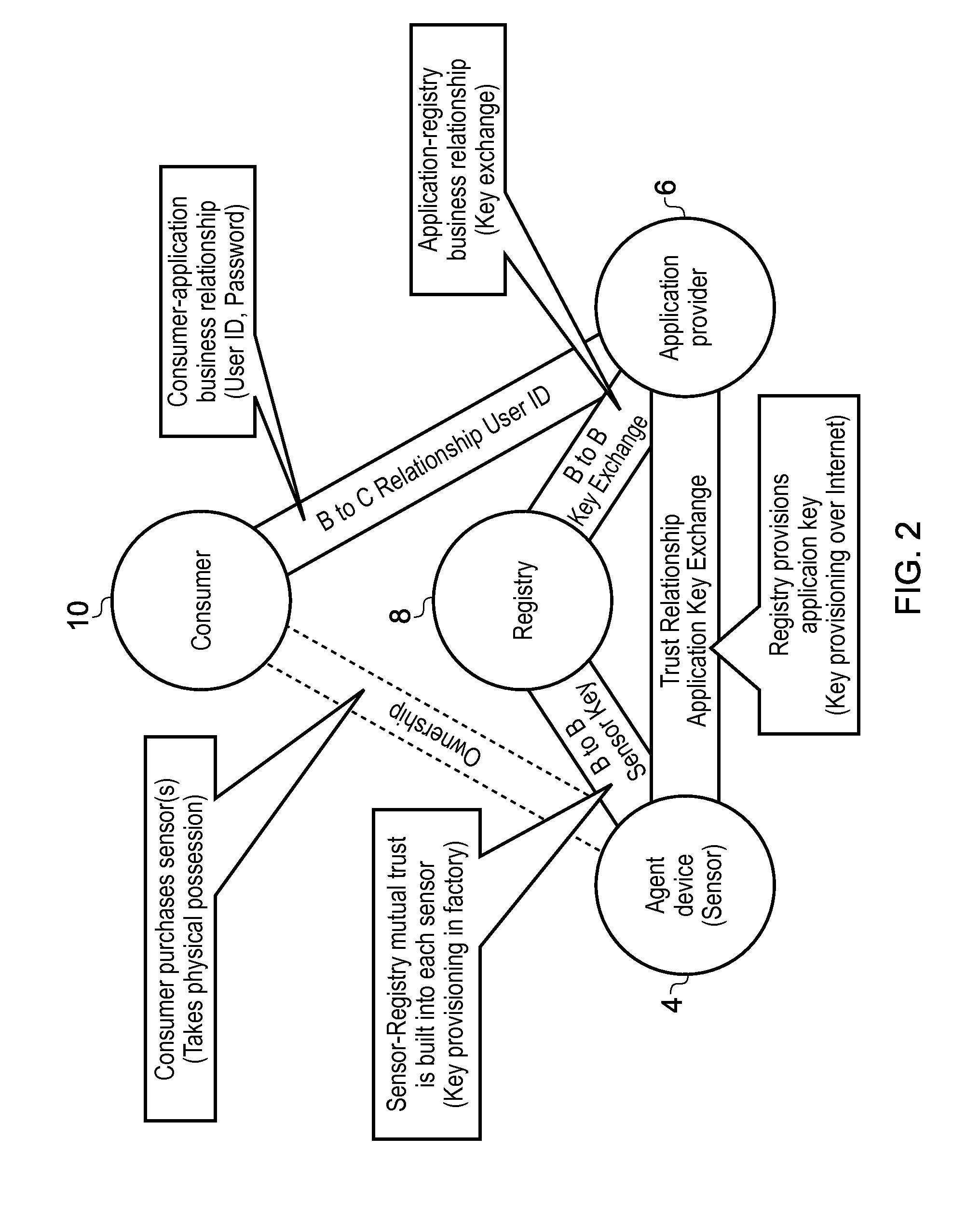
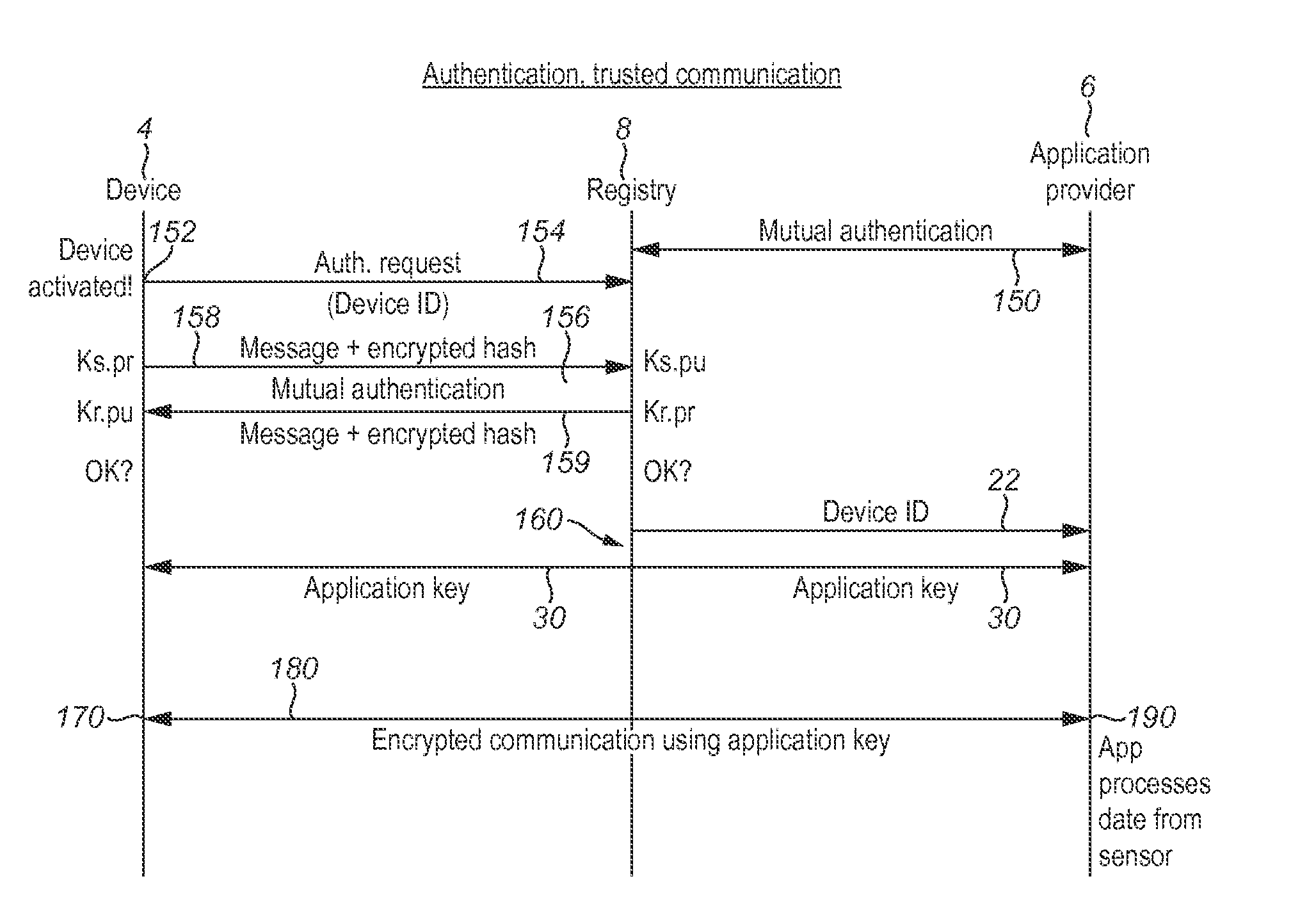
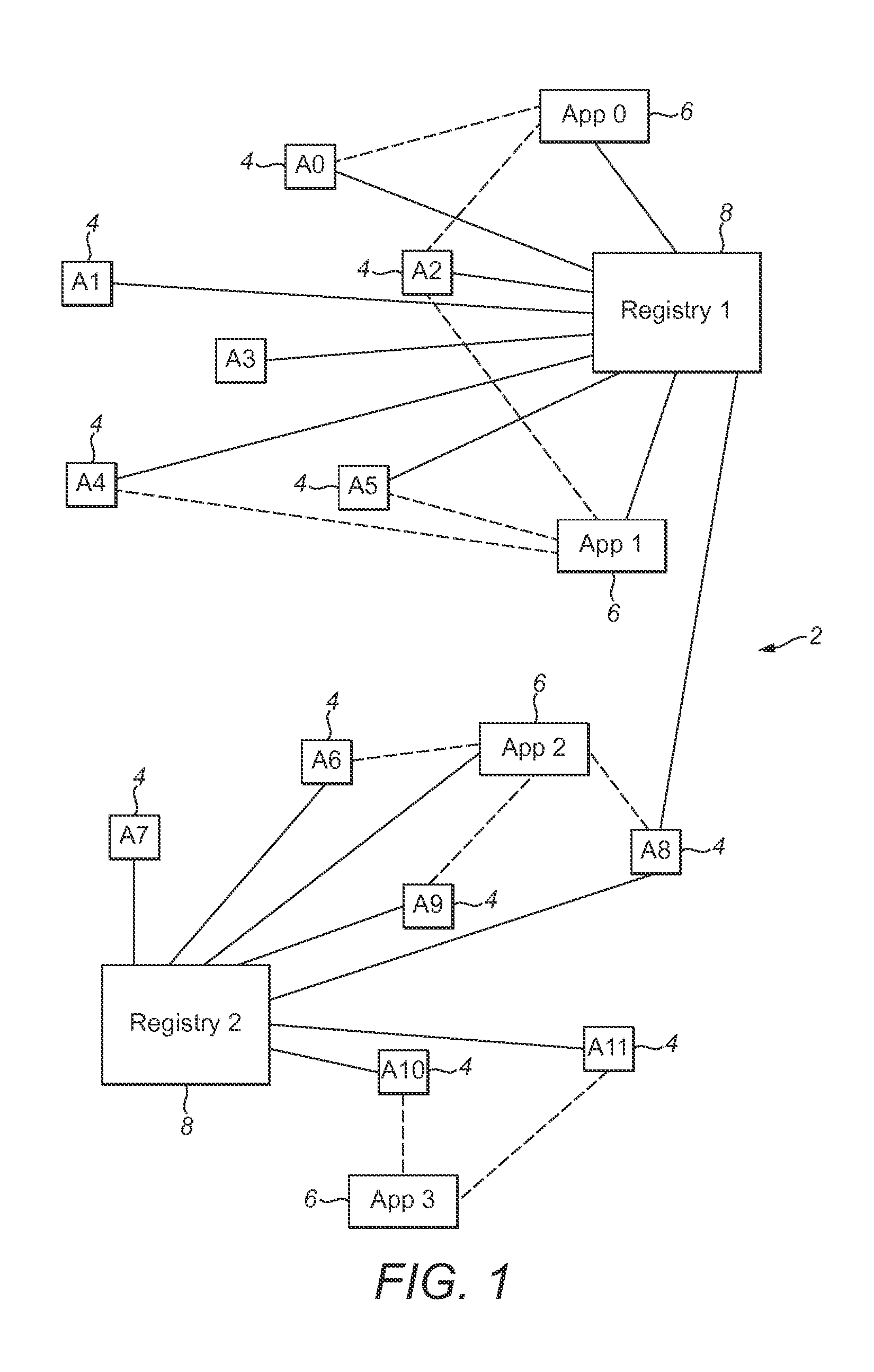
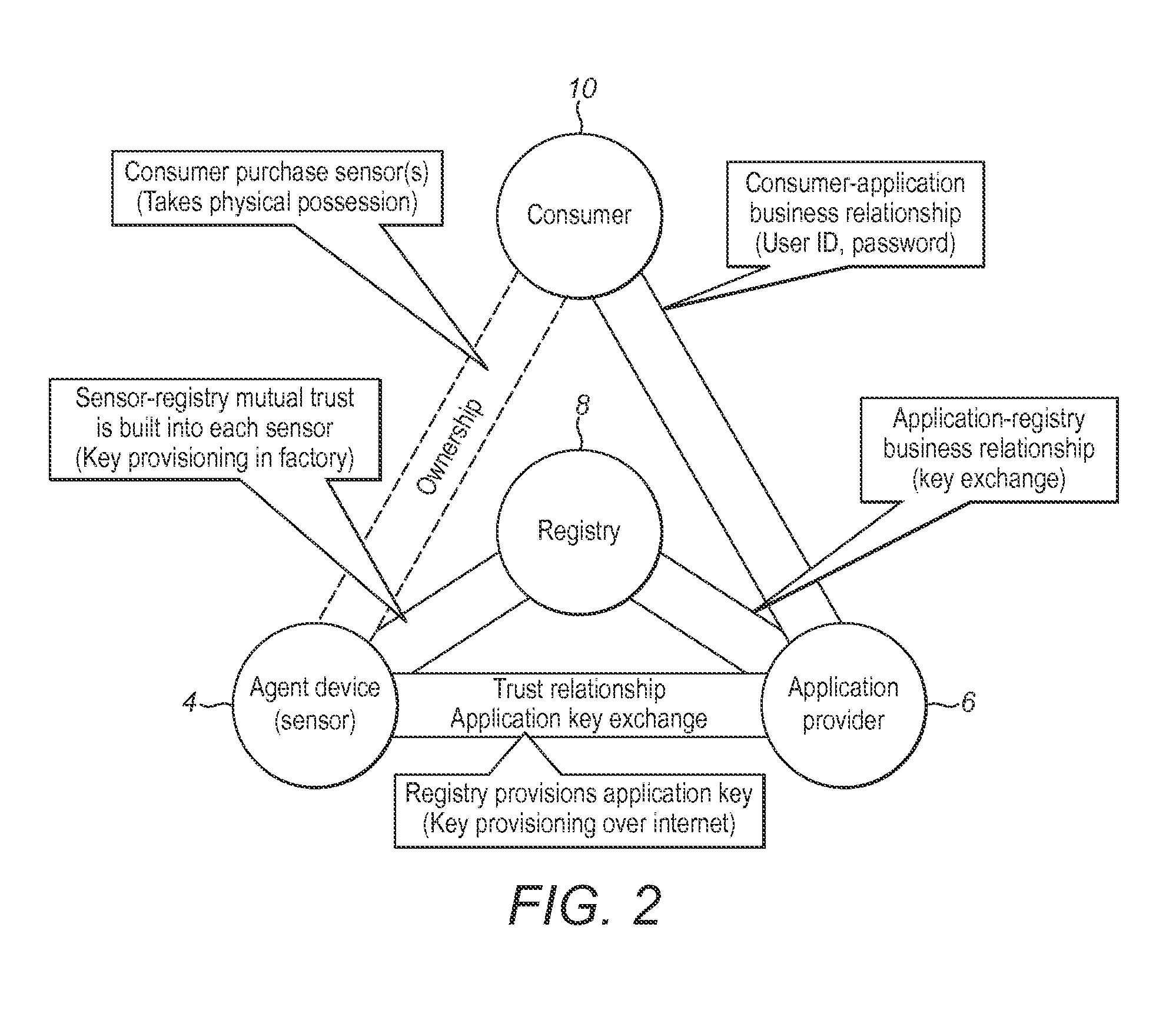
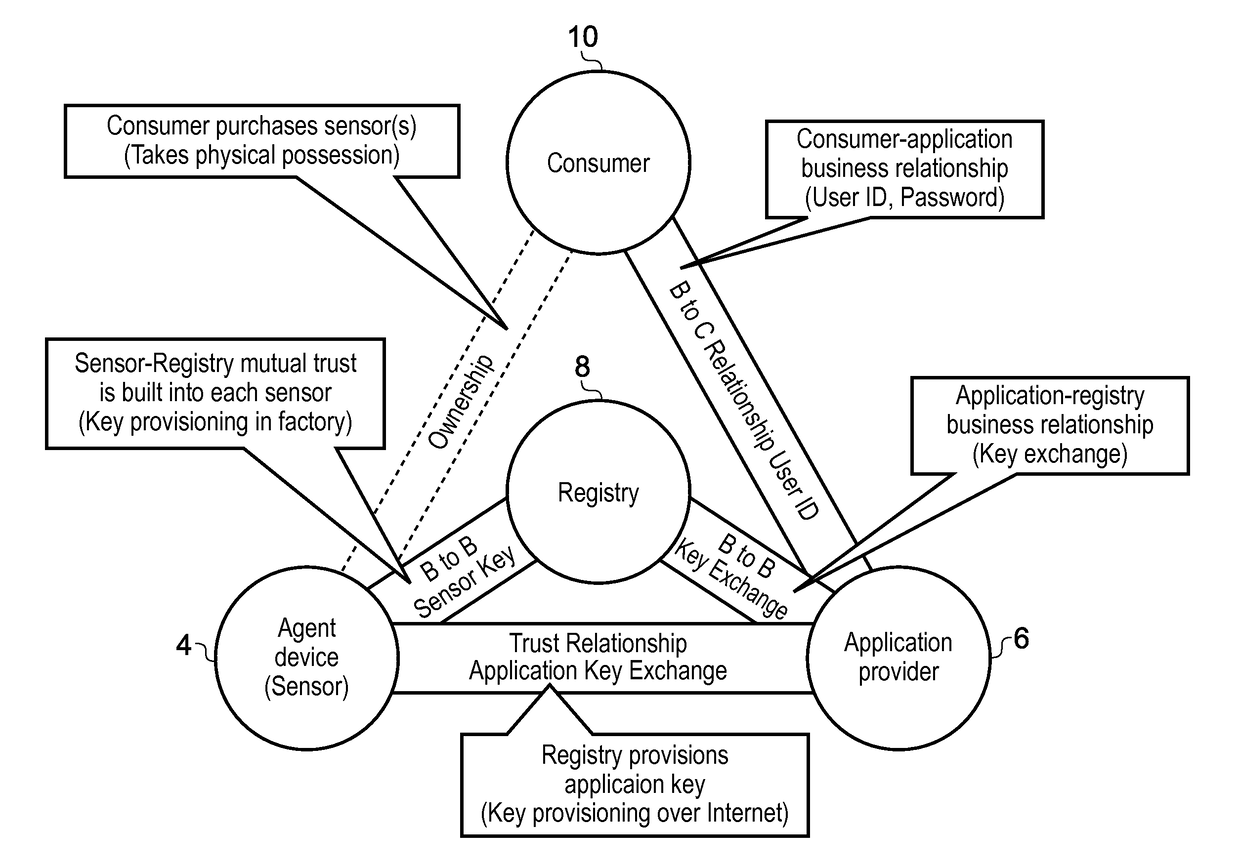
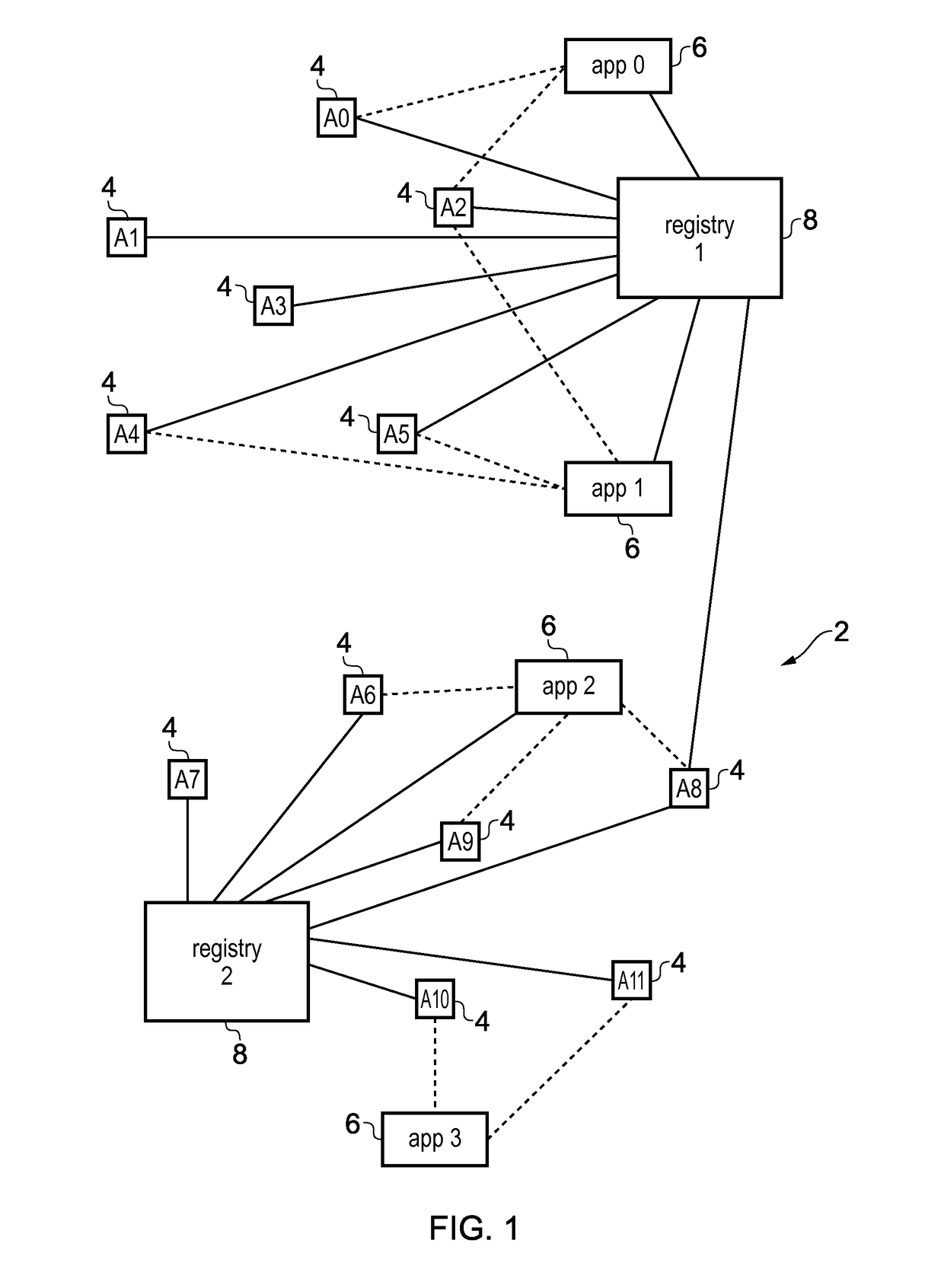
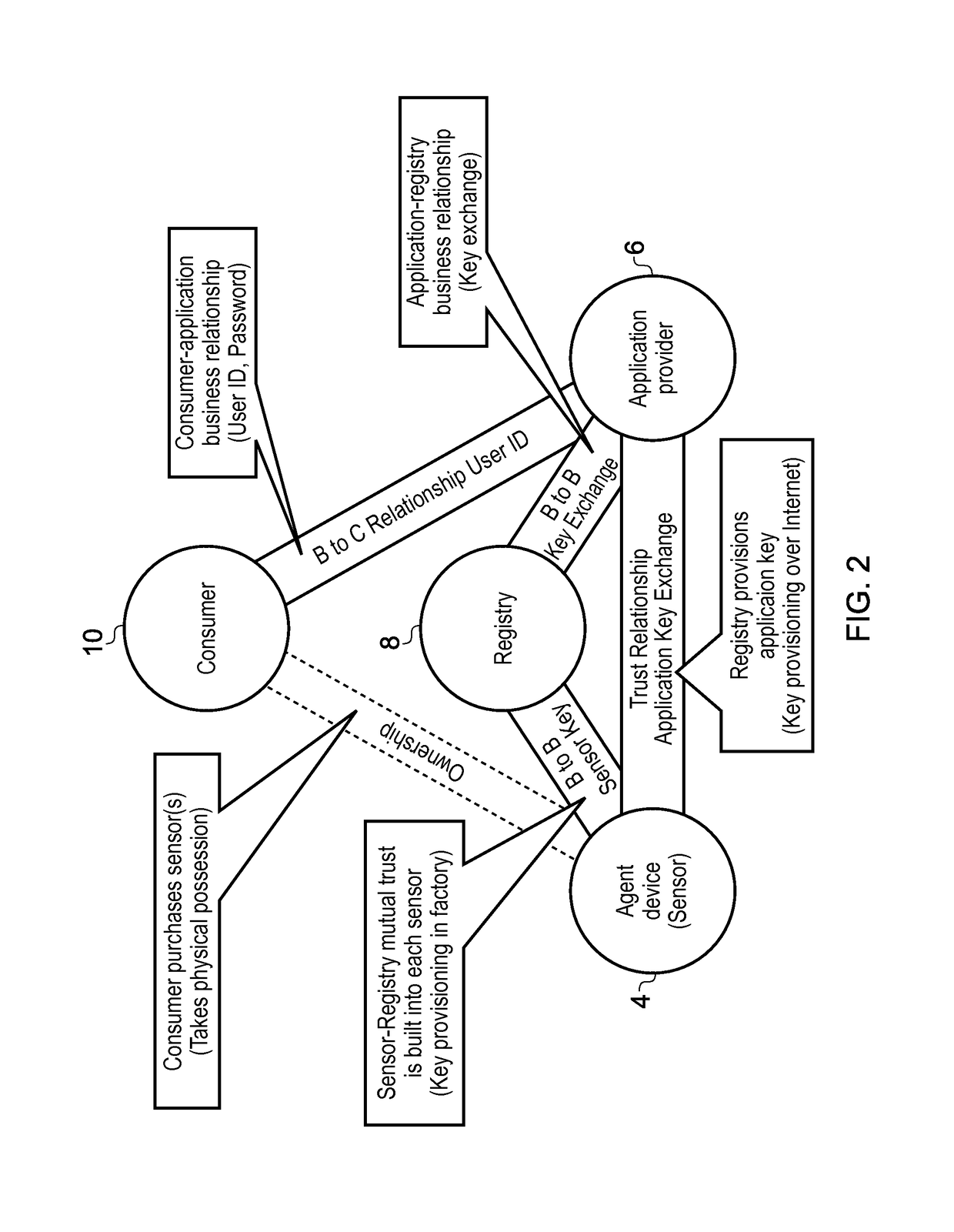
Registry apparatus, agent device, application providing apparatus and corresponding methods
ActiveUS20150113599A1Avoid user privacyIncrease flexibilityDigital data processing detailsMultiple digital computer combinationsComputer hardwareAuthentication information
A registry apparatus is provided for maintaining a device registry of agent devices for communicating with application providing apparatus. The registry comprises authentication information for uniquely authenticating at least one trusted agent device. In response to an authentication request from an agent device, the authentication information for that device is obtained from the registry, and authentication of the agent device is performed. If the authentication is successful, then application key information is transmitted to at least one of the agent device and the application providing apparatus.
Owner:ARM IP
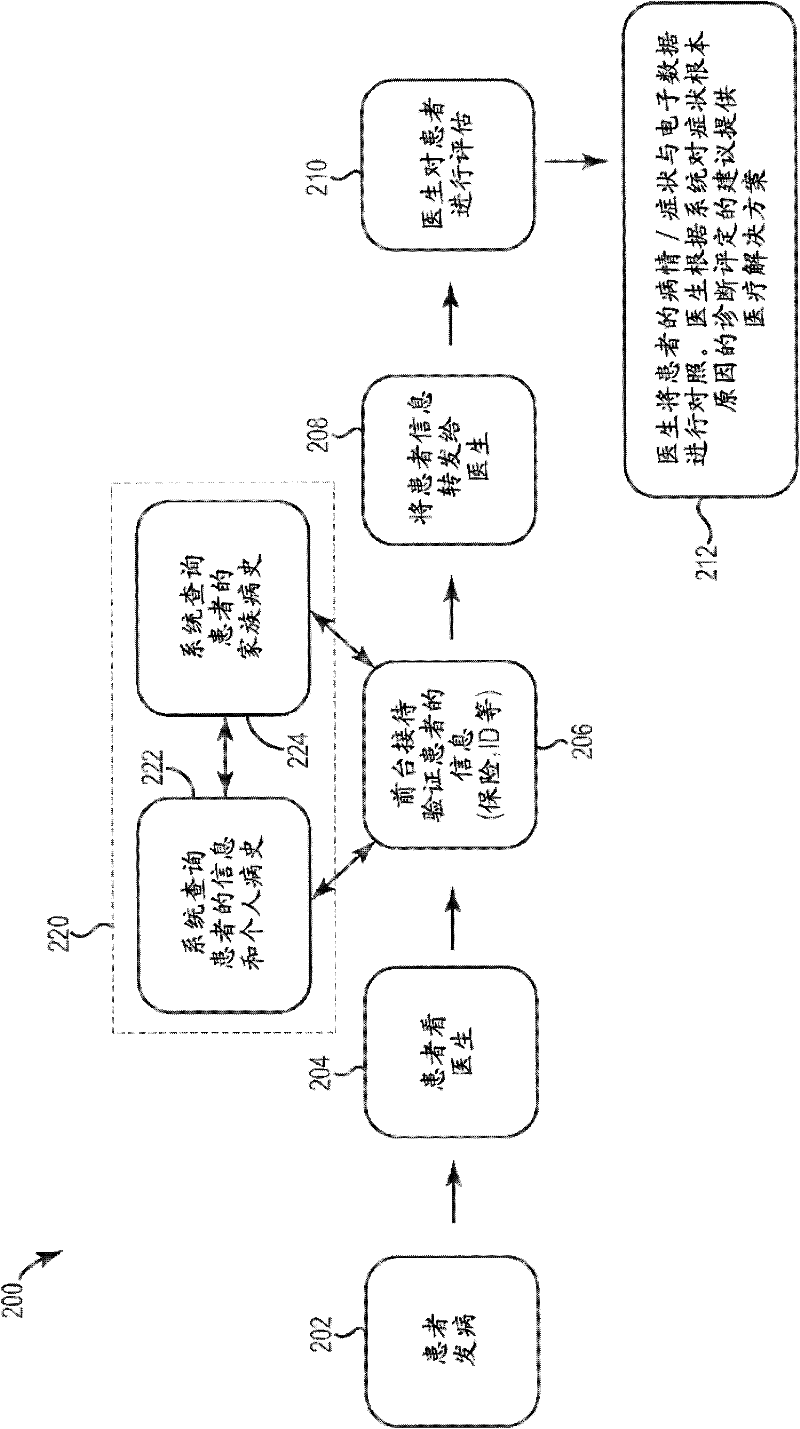
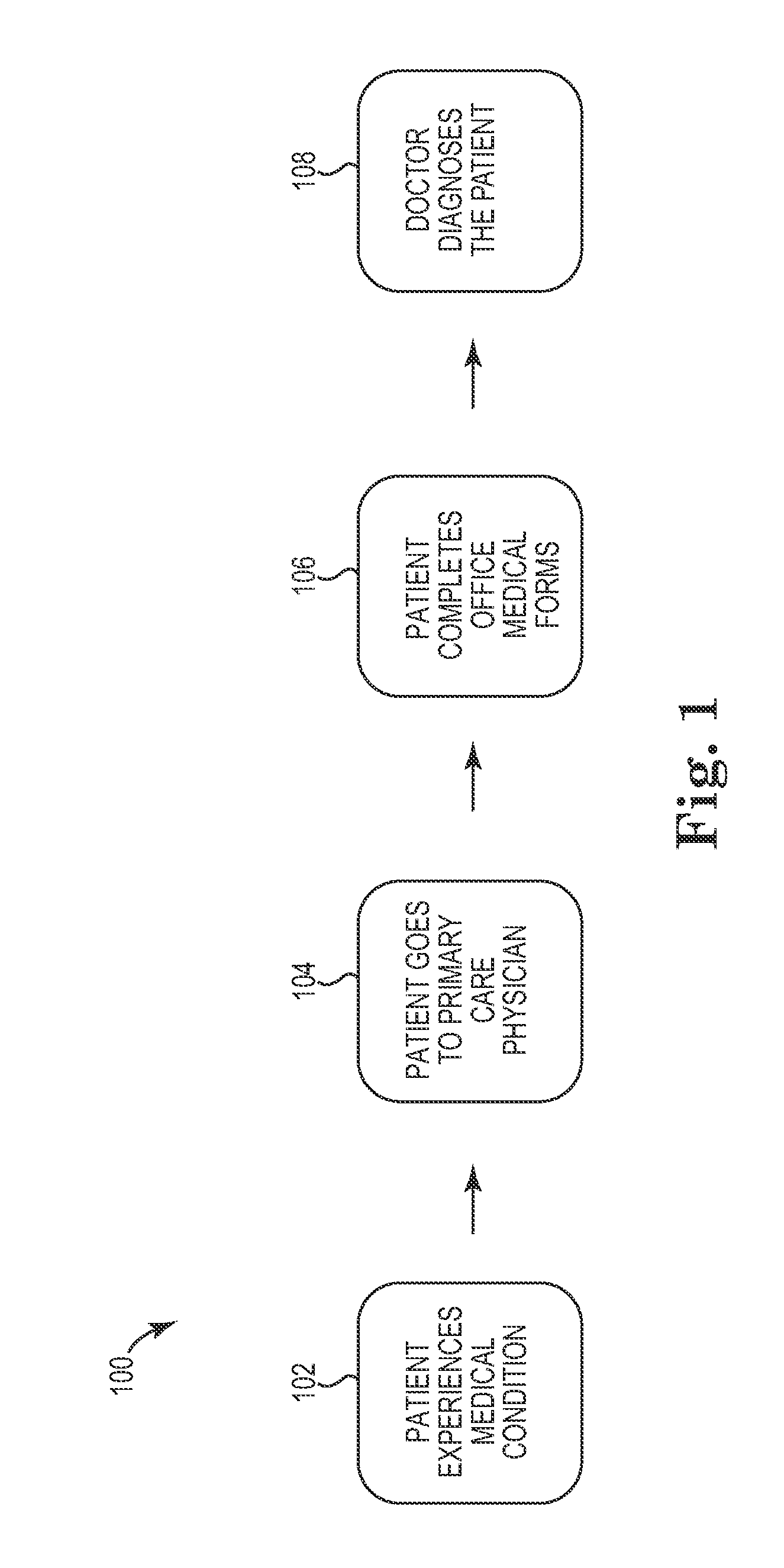
Medical history diagnosis system and method
InactiveCN102270274AAvoid privacyAvoid carryingMedical data miningData processing applicationsDiseaseHealth condition
Owner:INT BUSINESS MASCH CORP
Registry apparatus, agent device, application providing apparatus and corresponding methods
ActiveUS20160072808A1Increase flexibilityReduce manufacturing costUser identity/authority verificationDigital data authenticationDevice IdentifiersAuthentication information
A method for verifying trusted communication between an agent device and an application providing apparatus using a registry apparatus. The registry apparatus maintains a device registry comprising authentication information for uniquely authenticating at least one agent device. The method includes the steps of obtaining from the device registry the authentication information for the agent device identified by a device identifier specified in an the authentication request from the agent device, performing verification of the agent device using the authentication information obtained from the device registry, and if the verification is not successful, transmitting to at least one of the agent device and the application providing apparatus revocation information for denying the trusted communication between the agent device and the application providing apparatus.
Owner:ARM LTD
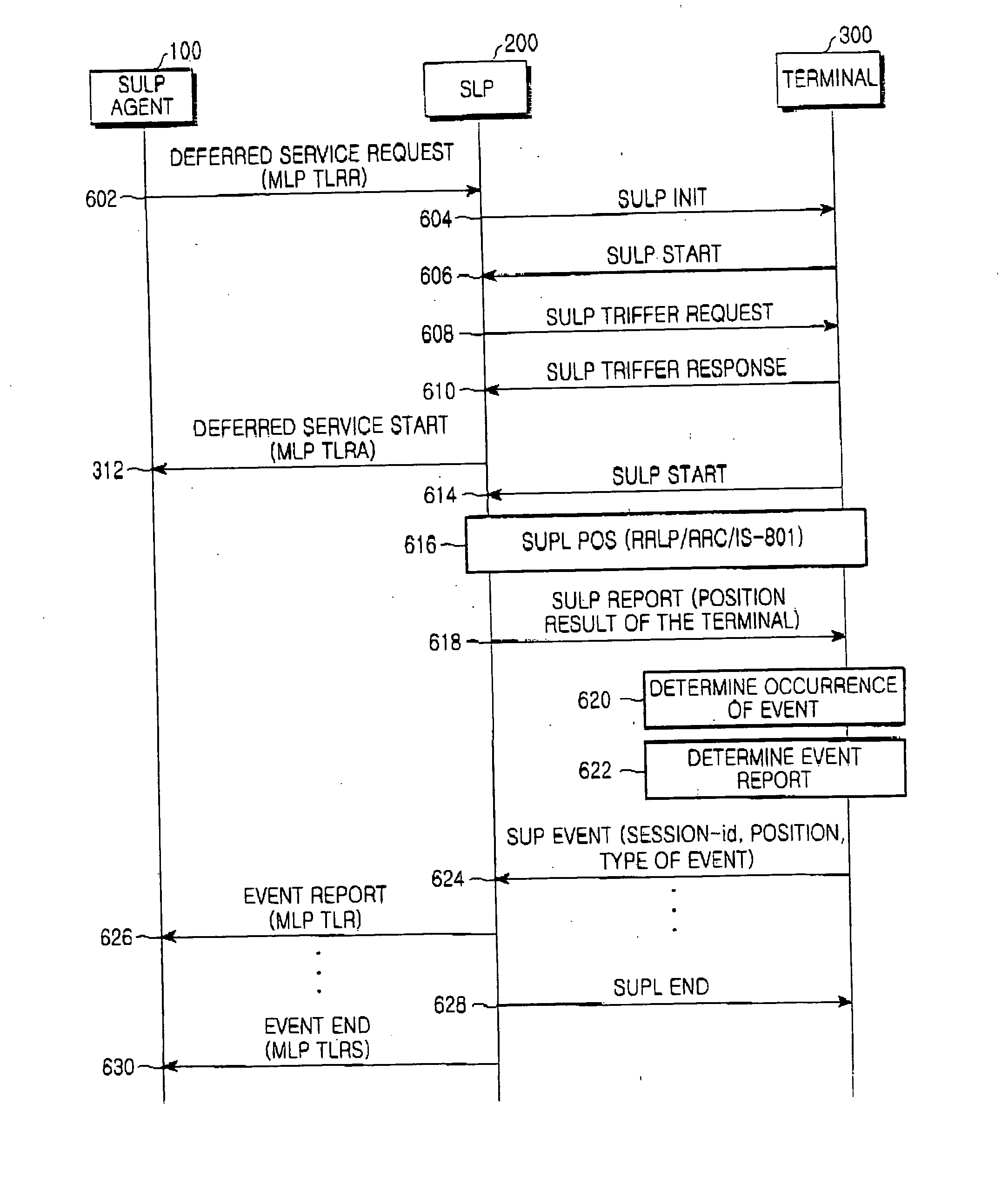
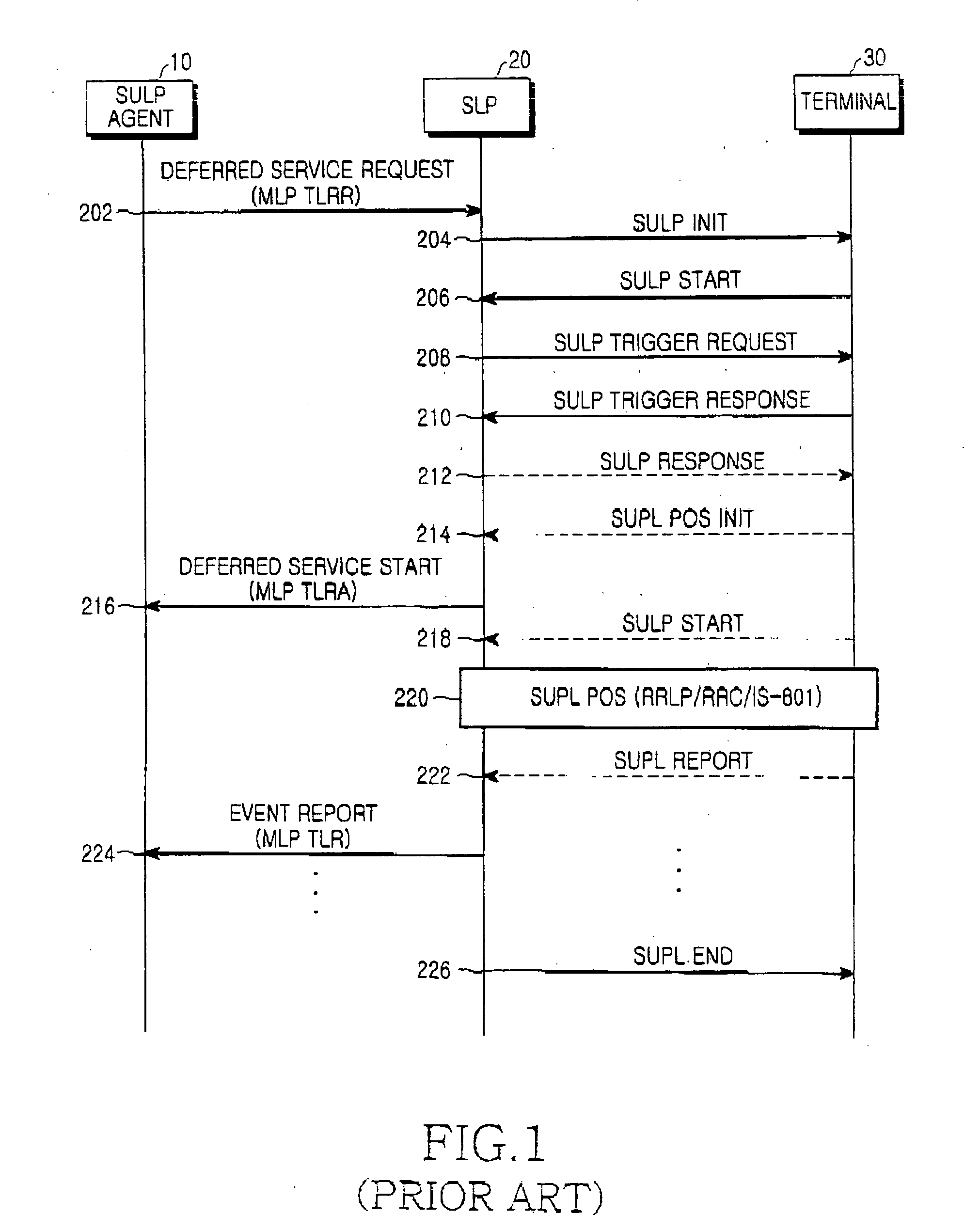
System and method for providing deferred service
InactiveUS20060223490A1Prevent privacy of userAvoid privacyTelephonic communicationRadio/inductive link selection arrangementsClient-sideSecure User Plane Location
Disclosed is a system for providing a deferred service, the system including a Secure User Plane Location (SUPL) agent for requesting the deferred service according to a requirement of a client; and a SUPL Location Platform (SLP) for checking for allowance or denial of an event report for an event when the event occurs during the deferred service according to the request. In the system, allowance or denial of a user for a deferred service is reflected during the deferred service, and as a result, it is possible to prevent the violation of a user's privacy.
Owner:SAMSUNG ELECTRONICS CO LTD
Radio frequency identification (RFID) safety communication method established according to ultra-lightweight RFID bidirectional authentication protocol
InactiveCN102880891ATroubleshoot key synchronization issuesSolve the forward security problemCo-operative working arrangementsExclusive orNumber generator
The invention discloses a radio frequency identification (RFID) safety communication method established according to an ultra-lightweight RFID bidirectional authentication protocol. By adoption of the method, the security problems of a low-grade tag RFID system can be effectively solved. The method has the main characteristics of security, high efficiency, simplicity and practicability. A tag is only required to provide simple operation such as random number generator operation, exclusive-OR operation, modular operation (MOD) and displacement. Resources required by the simple operation are extremely limited, so the scheme is in complete accordance with an EPCglobal C1G2 tag specification, has the characteristics of low storage cost, low operation cost, low communication cost, novel and simple algorithm and the like, and is easy to implement. The method has the advantages that the problems about synchronization of the tag and a rear-end database key, forward security and security privacy (privacy leak, flow analysis and positioning tracking) can be effectively solved, and the common security problems of an RFID system about imitation attack, cloning attack, monitoring attack, replay attack and denial-of-service attack are solved. The method is quite applicable to solving the security problems of an EPCglobal C1G2 RFID tag.
Owner:SUN YAT SEN UNIV
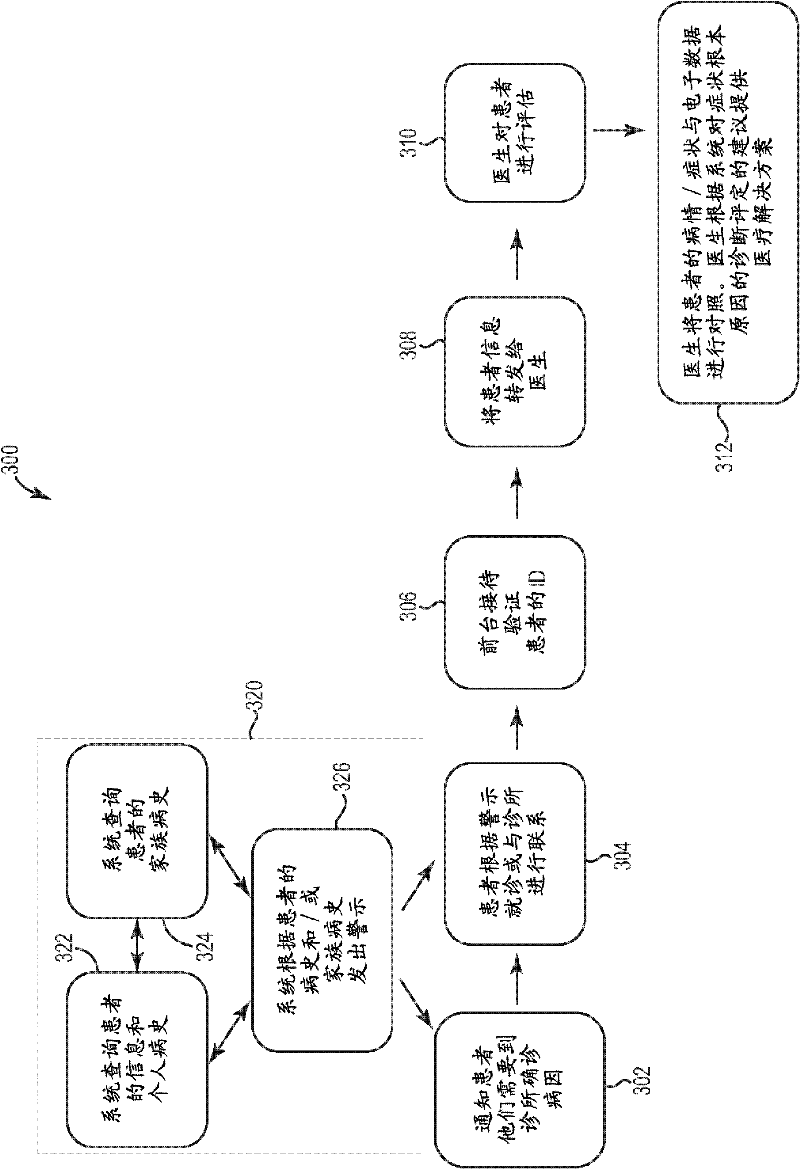
Medical history diagnosis system and method
InactiveUS20110301976A1Reduce costs and risksAvoid portabilityMedical data miningData processing applicationsMedical diagnosisHealth condition
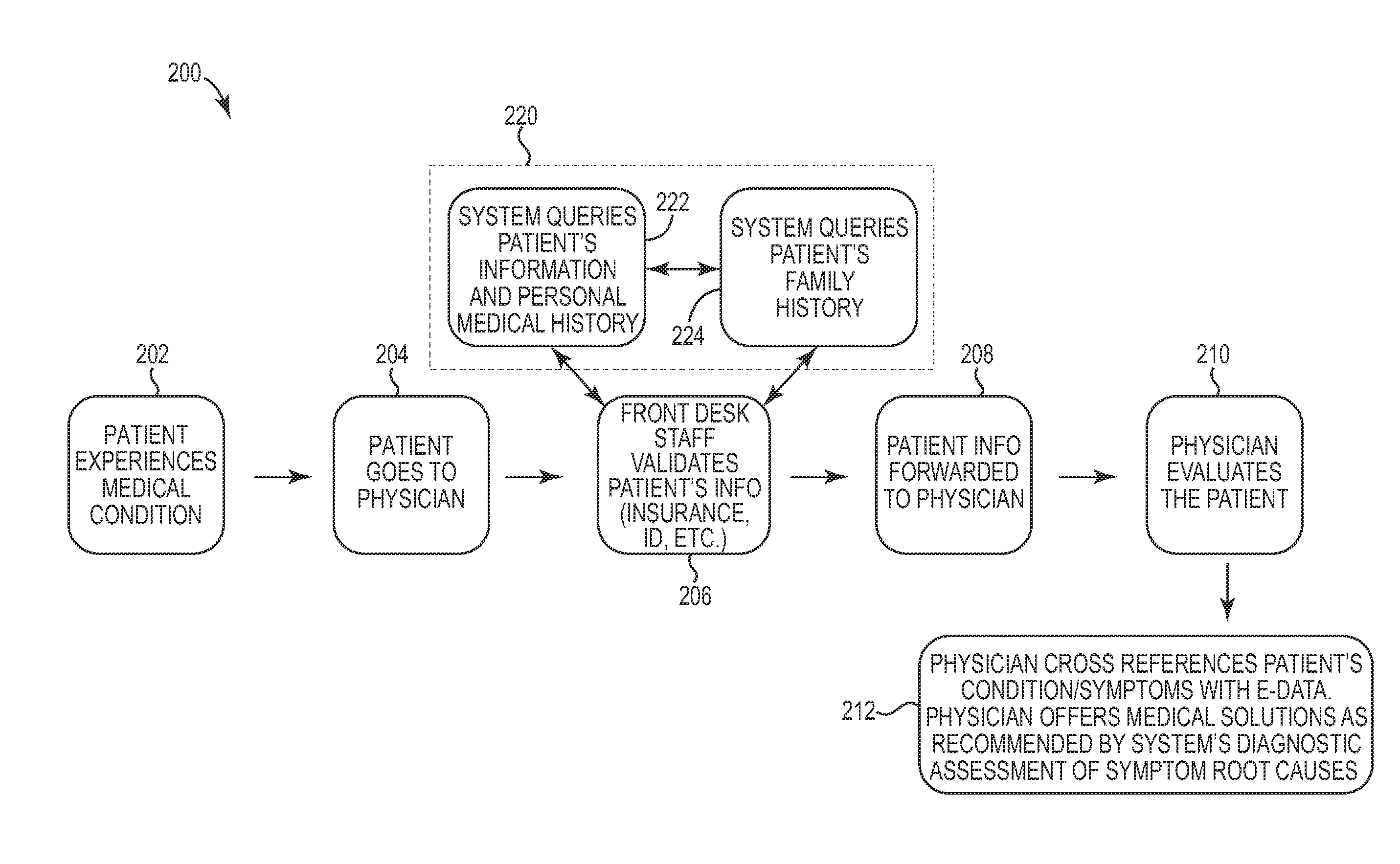
An intelligent system for collecting, storing, processing, and analyzing a patient's relevant medical history data is disclosed. In one embodiment, a patient's medical history, including the patient's personal medical history and the patient's family medical history, may be accessed within the system. The system may be queried by doctors and other medical professionals to compare symptoms, diagnoses, prescriptions, and medical issues against the known medical history. Further, the intelligent system may query the medical history of family members, providing an accurate yet discreet evaluation of related health conditions that may have genetic or hereditary implications. A further embodiment utilizes the intelligent system to generate alerts on the basis of the patient's personal or family medical history. These alerts may be issued separately or in conjunction with the patient's current medical issues, in order to help patients and medical professionals recognize potential health conditions and obtain enhanced medical evaluation.
Owner:IBM CORP
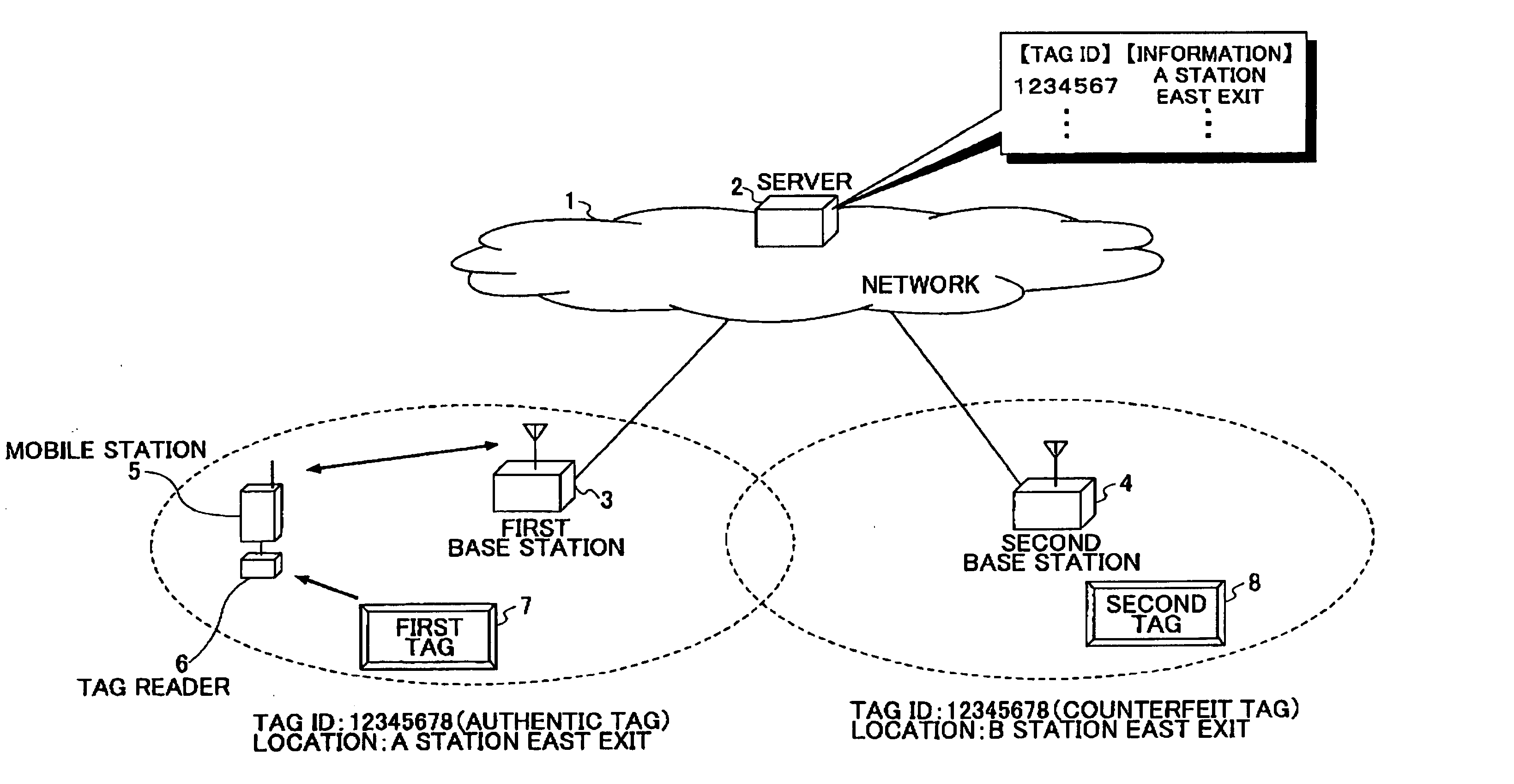
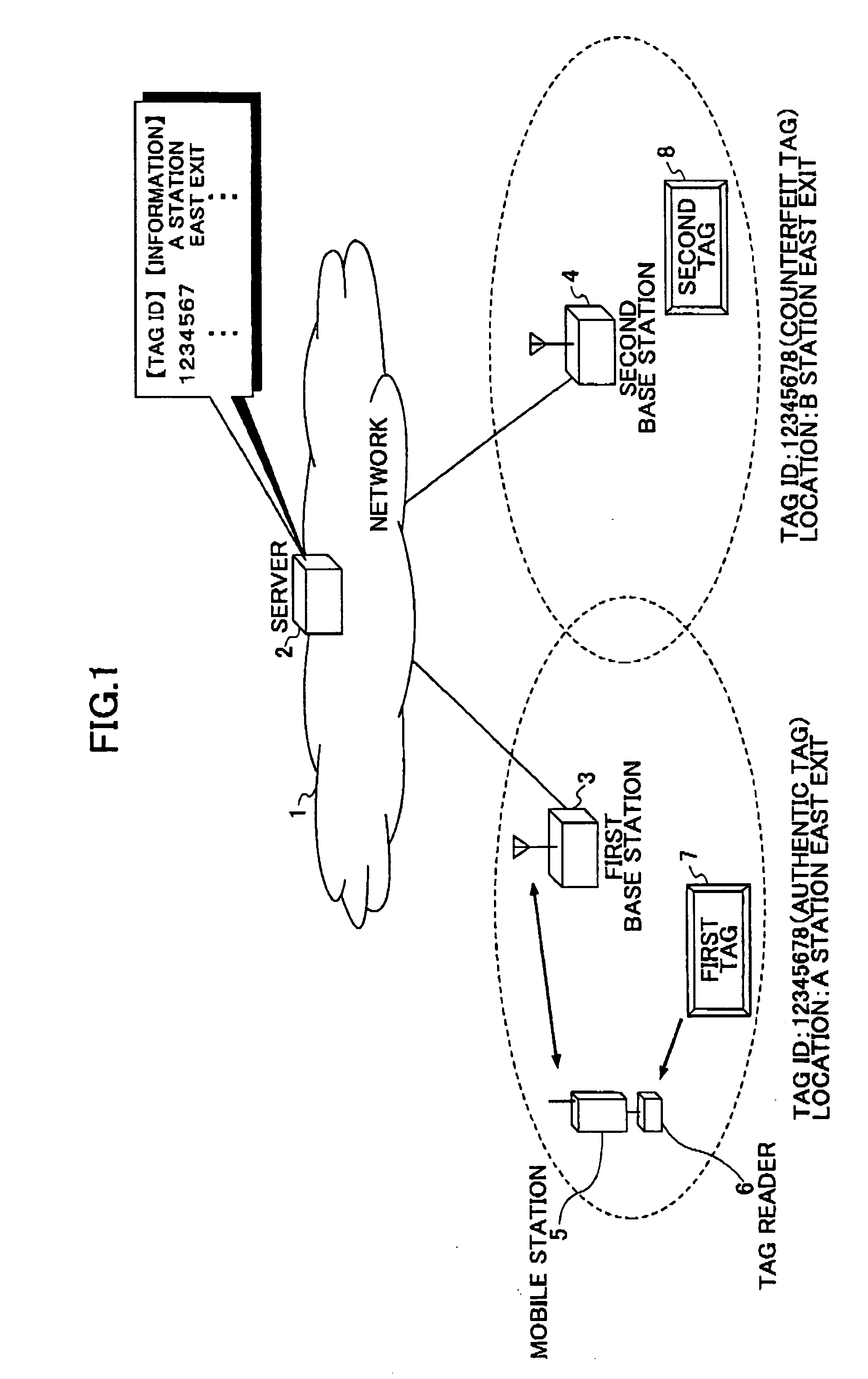
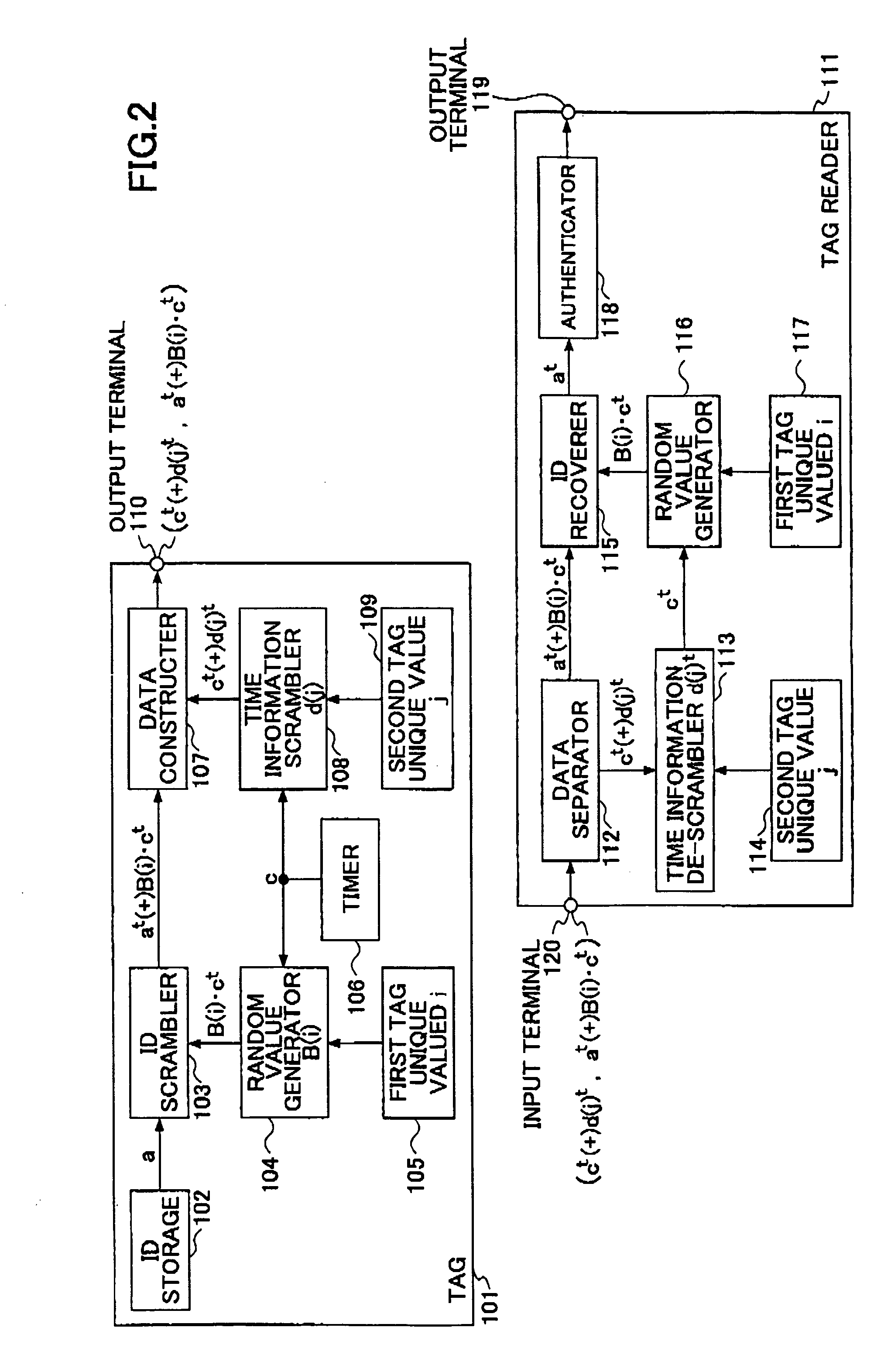
ID tag, a tag reader, ID tag transmitting and recovering methods, and a tag manager
InactiveUS20050247779A1Avoid service degradationAvoid privacy invasionUser identity/authority verificationCo-operative working arrangementsTime informationRadio frequency
An ID tag for RF transmitting its own tag ID information is disclosed. The ID tag comprises an ID storage for outputting the tag ID information stored therein; an ID concealing unit that conceals the tag ID information based on a certain value relating to time and outputs a concealed ID; a time information concealing unit that conceals the certain value based on a stored tag unique value and outputs concealed information; and a data outputting unit that receives and combines the concealed ID and the concealed information, and outputs combined data.
Owner:NTT DOCOMO INC
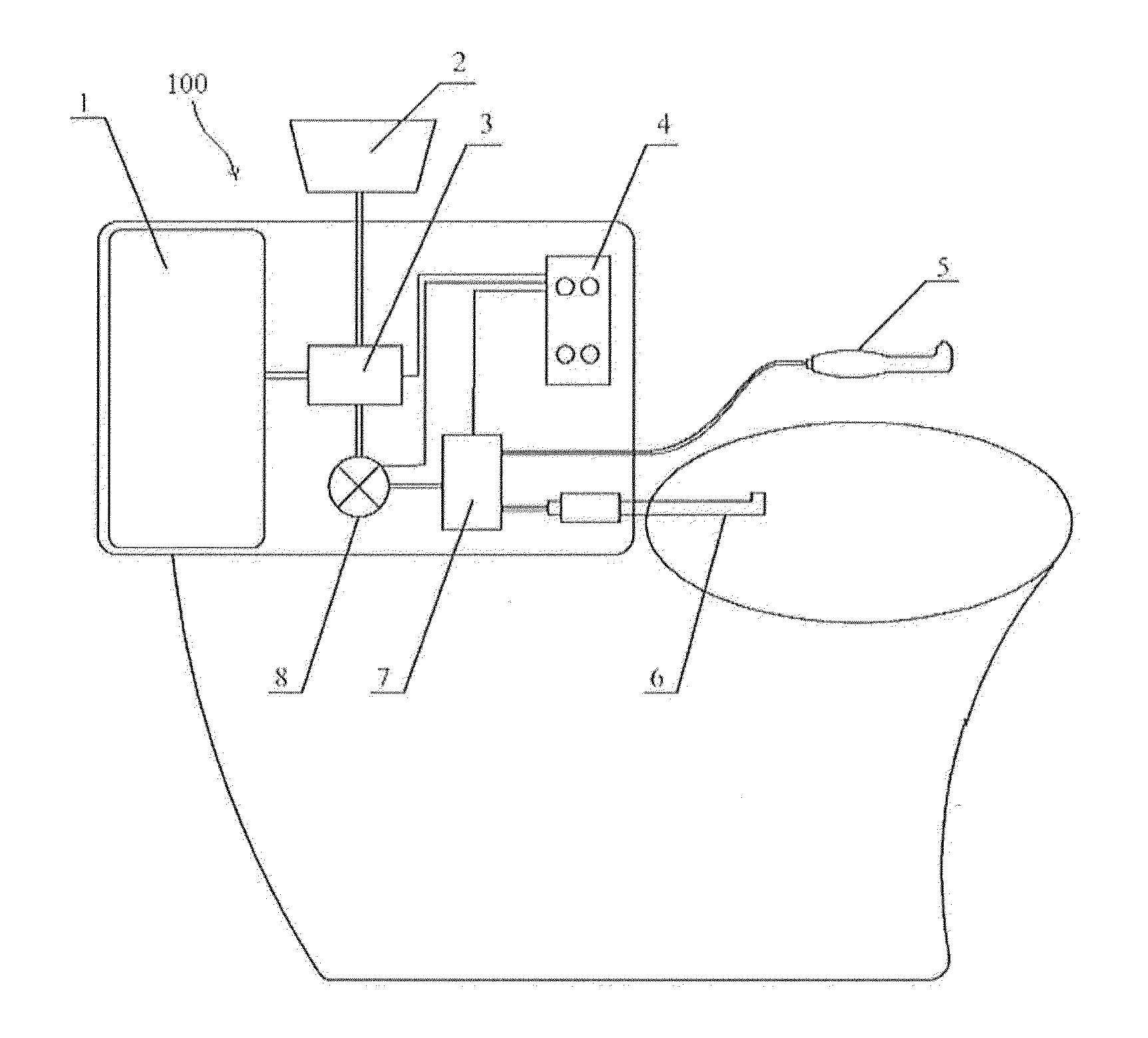
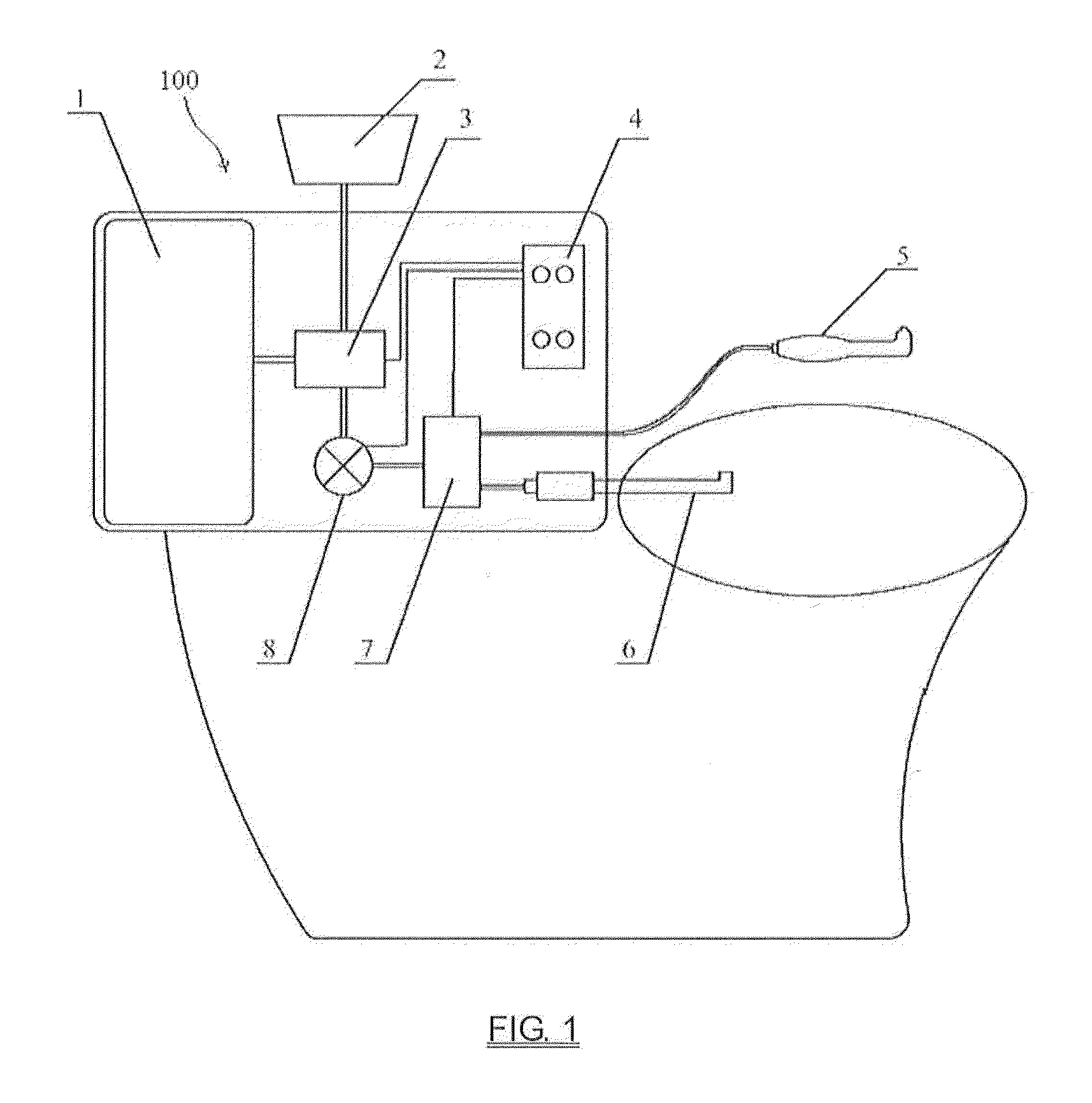
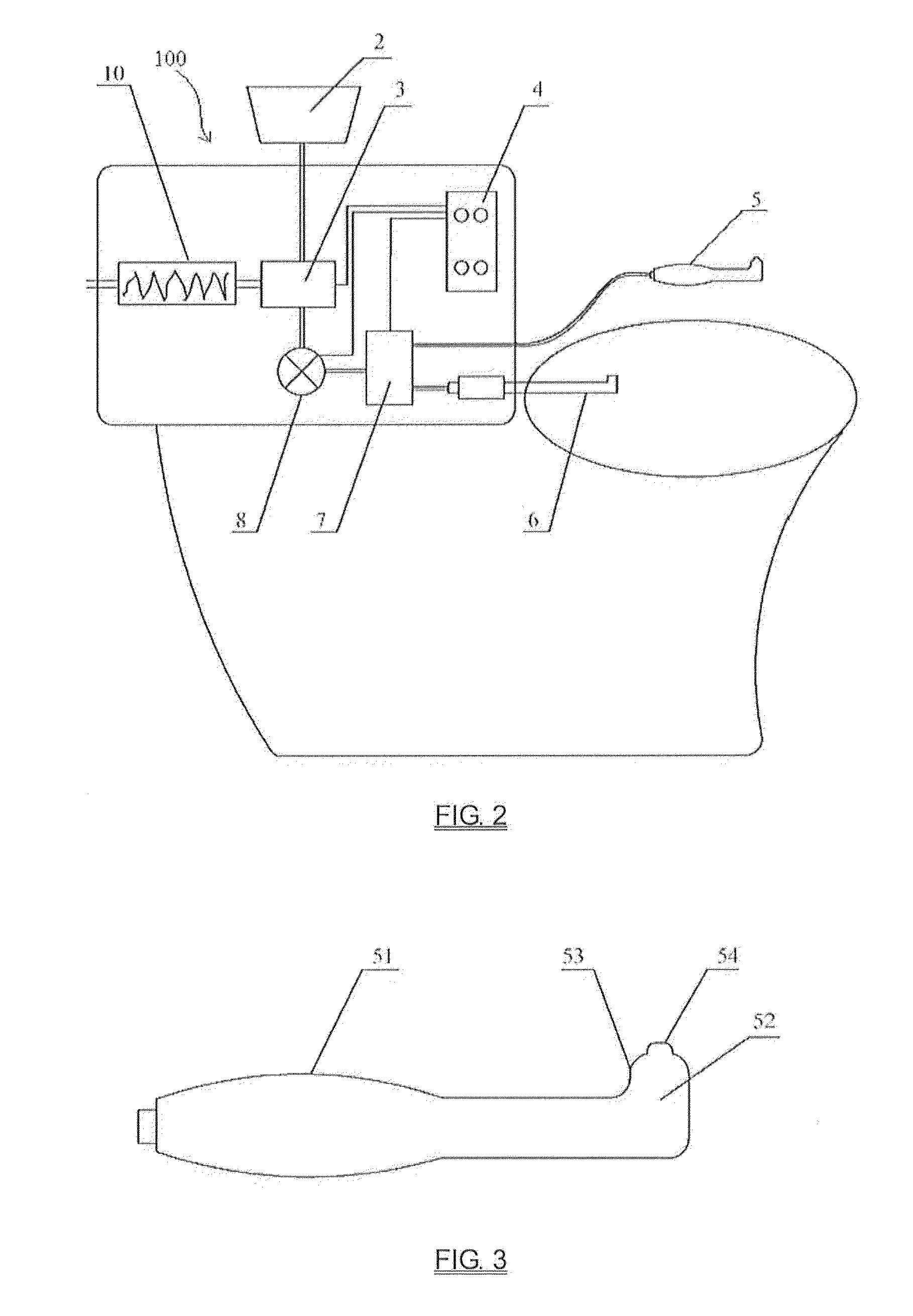
Automatic bidet
InactiveUS20130180041A1Easy to washAvoid inconvenienceLavatory sanitoryBathing devicesSprayerWater storage tank
An automatic bidet has a toilet seat fixedly mounted to a toilet, a bottom sprayer disposed in the toilet seat that can stretch out freely from the toilet seat, and a handheld sprayer that is separated from the toilet seat. A water storage tank, a booster pump, a liquid valve are disposed in the toilet seat and are connected in sequence. The water in the water storage tank flows respectively to the bottom sprayer and the handheld sprayer from the liquid valve under the pressure of the booster pump. The handheld sprayer comprises a hollow handle portion and a curved head portion having a bulge. The top of the bulge is provided with a mammilliform water outlet. The automatic bidet is capable of cleaning anus and private parts of a male or a female, and the handheld spray device can be used to carry out enema by a user and the wastes can be let off completely. The whole process can be done under the condition that a user sits on the toilet. The wastes directly enter the toilet and the user's clothes are kept clean. The user can independently operate the present invention without help from other people so as to avoid the embarrassment of exposure of privacy.
Owner:NANJING LANGSAI SANITARY WARE
Method for determining location of UE by using AGPS information
ActiveUS8150415B2Avoid privacyImprove securitySpecial service for subscribersPosition fixationTelecommunicationsGPS signals
Disclosed is a method for determining a location of a UE by means of AGPS information. The method includes generating by an SLC a pseudo UE ID according to a request for location information of the UE, the pseudo UE ID being used for maintaining security in communication with an SPC, requesting AGPS information for the UE, the location information of which has been requested, to the SPC by means of the pseudo UE ID, and receiving the AGPS information, transferring the received AGPS information to the UE, and receiving GPS signal measurement values using the AGPS information from the UE, requesting a location calculation of the UE for the GPS signal measurement values to the SPC by means of the pseudo UE ID, and receiving calculated location values, and providing the location information of the UE by means of the received location values of the UE.
Owner:SAMSUNG ELECTRONICS CO LTD
Intelligent household monitoring method and system based on vibration detection
InactiveCN106251572AAvoid privacyEasy to useComputer controlBurglar alarmData acquisitionVibration detection
The invention relates to the technical field of intelligent homes, and discloses an intelligent household monitoring method based on vibration detection. The monitoring method comprises following steps of that a data acquisition module acquires structure vibration information generated by behavior activities of people; and by analyzing and processing signals, the behavior activities of people in a home are intelligently monitored and an alarm is made for the abnormity. The beneficial effects are that a privacy problem of the monitoring in a camera chamber is solved; a user's live will not be affected; and easy use by the user is achieved.
Owner:SHENZHEN UNIV +1
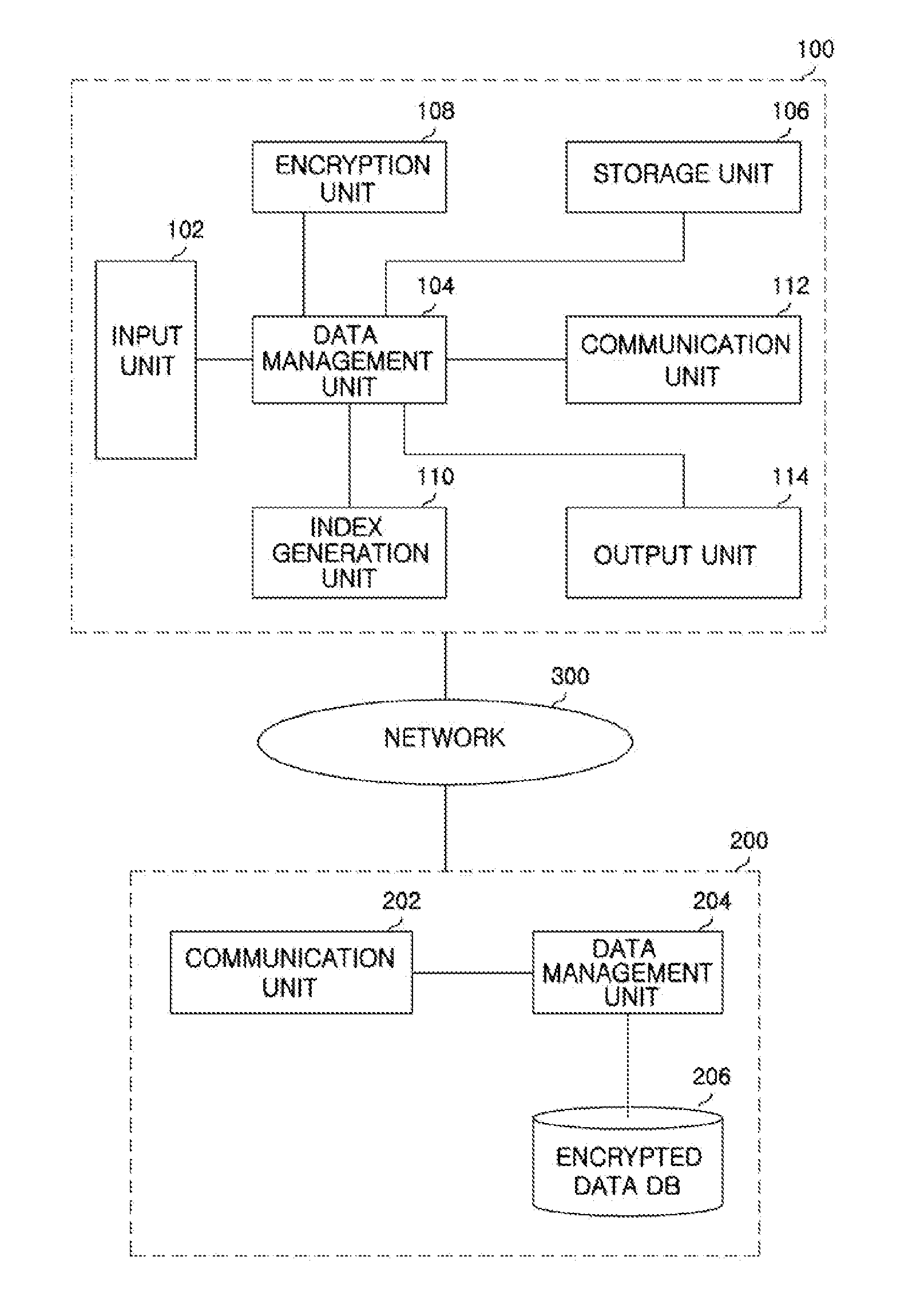
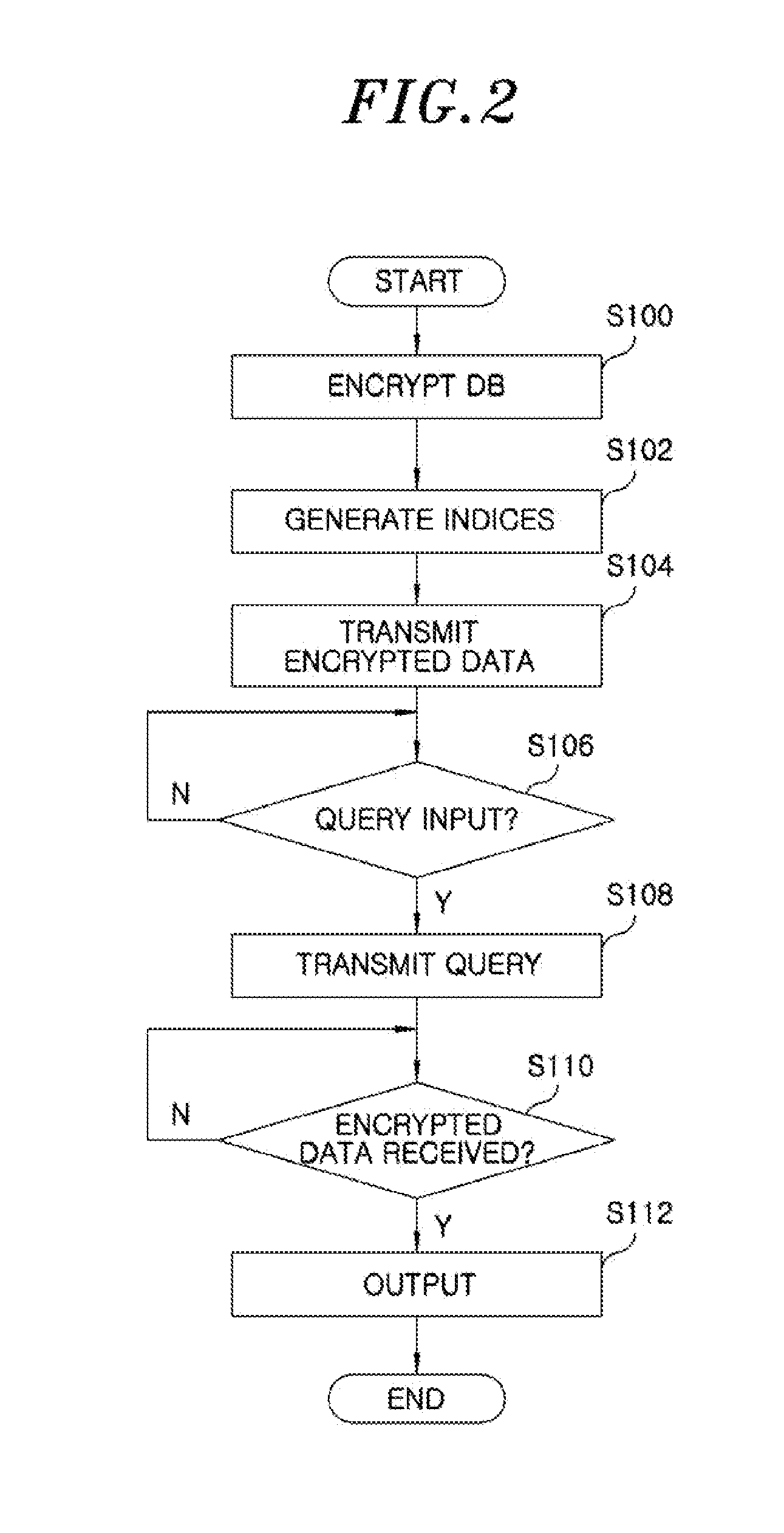
Data management system and method
InactiveUS20120158734A1Improve securityEfficient searchDigital data processing detailsDigital data protectionManagement unitData management
A data management apparatus includes an index generation unit configured to subdivide an entire interval of data into bucket intervals, allocate indices for the respective bucket intervals, transform the bucket intervals having the allocated indices into bucket intervals of specific lengths, and generate bucket-based indices for pieces of data included in the bucket intervals of the specific lengths. The data management apparatus further includes a data management unit configured to transmit the encrypted data and the bucket-based indices to a server-side data management apparatus in order to store the encrypted data, transmit a user query to the server-side data management apparatus in order to search for a desired encrypted data, and decrypt encrypted data corresponding to the user query from the server-side data management apparatus. The user query includes the index of first bucket interval and the index of second bucket interval neighboring to the first bucket interval.
Owner:ELECTRONICS & TELECOMM RES INST
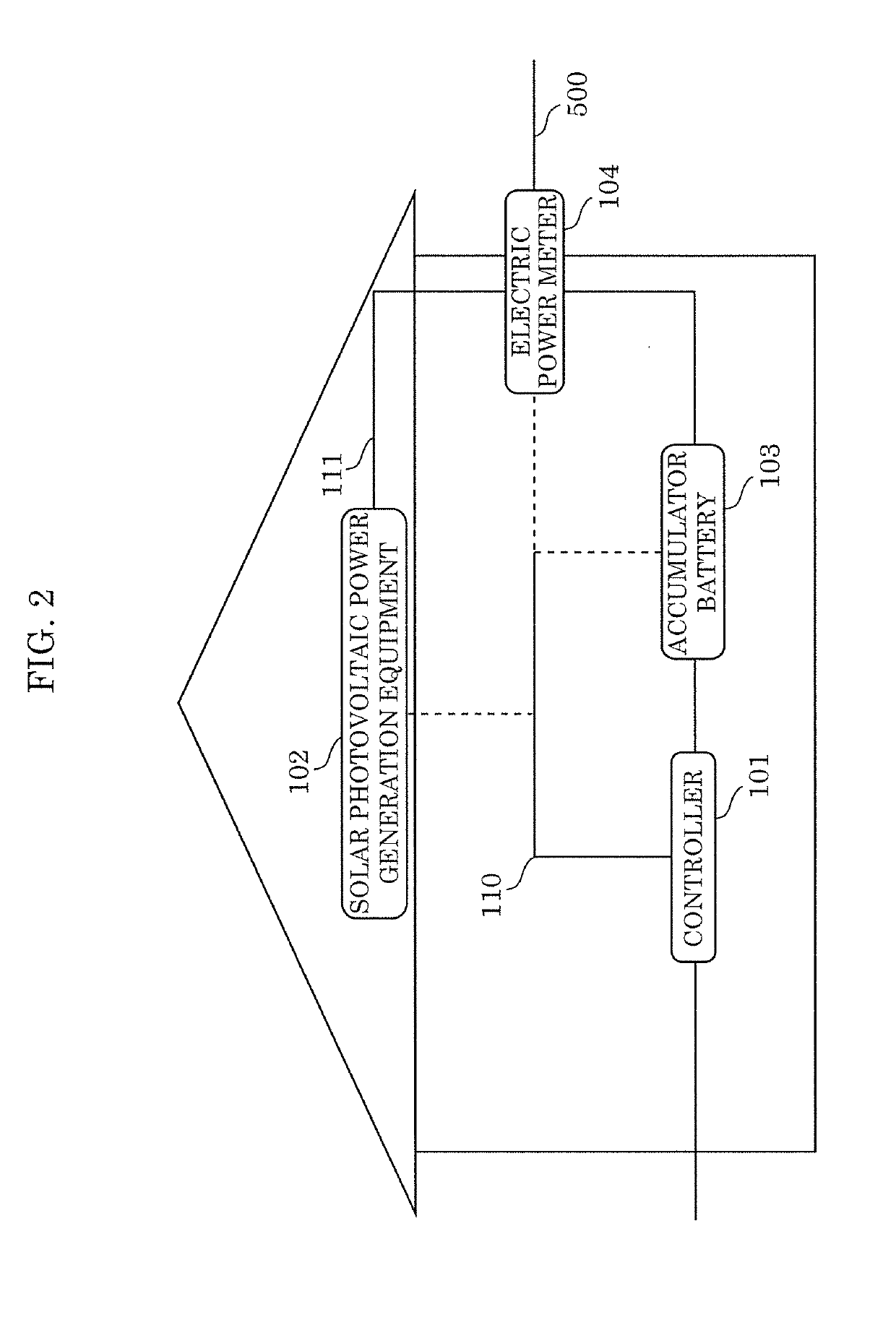
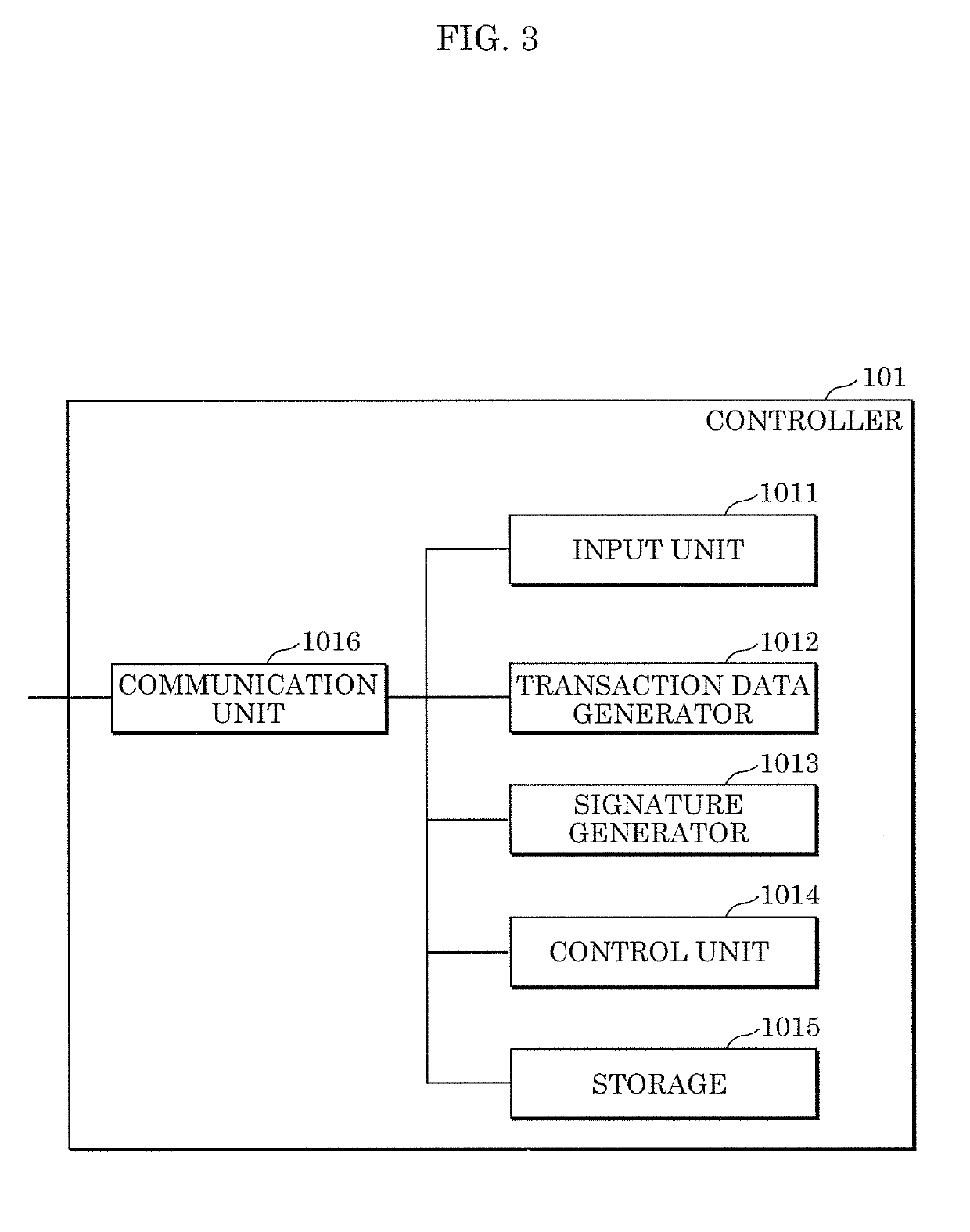
Control method, controller, data structure, and electric power transaction system
ActiveUS20190236726A1Prevent leakageAvoid privacyDiscounts/incentivesFinanceElectric power transmissionTransaction data
A control method including: receiving first transaction data including a first electronic signature from the a home of a first user; verifying whether the received first electronic signature included in the first transaction data is valid; verifying validity of the received first transaction data; when the first electronic signature and the validity of the first transaction data are verified successfully, executing a first consensus algorithm for the first transaction data; and when the validity of the first transaction data is verified according to the first consensus algorithm, recording a block including the first transaction data in a distributed ledger. The first electronic signature is a group signature assigned to a group to which the first user belongs.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
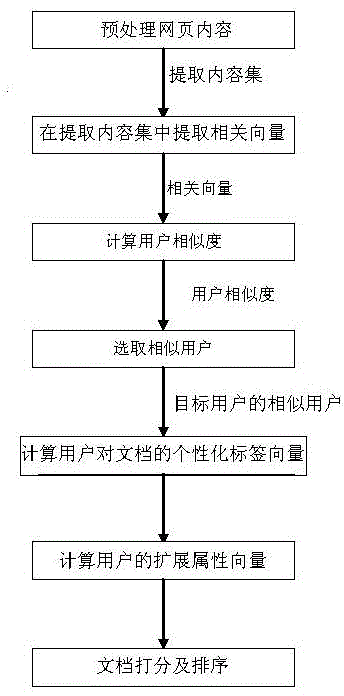
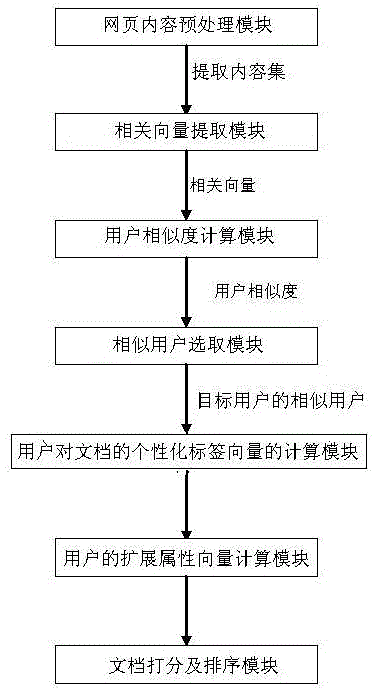
Personalized searching method and system on basis of social annotation
ActiveCN104866554AAvoid privacyImprove accuracySpecial data processing applicationsPersonalized searchData mining
A personalized searching method and a personalized searching system on the basis of social annotation are provided. The method comprises the following steps of: A: preprocessing webpage contents; B: extracting related vectors from a set of extracted contents; C: computing user similarity; D: selecting similar users; E: computing personalized label vectors of the users to files; F: computing extended attribute vectors of the users; and G, carrying out scoring and ranking on the files. According to the searching method and the searching system which are provided by the present invention, preferences and interests of the users are deeply mined by labels given by the users, i.e. starting from annotated information of the webpage users, information actively disclosed by the users are used for carrying out personalized optimization; privacy and cold start problems are avoided; consideration is carried out completely on the basis of the users; and searching accuracy is well promoted.
Owner:DALIAN UNIV OF TECH
Method and system for time series anomaly detection based on secure multi-party
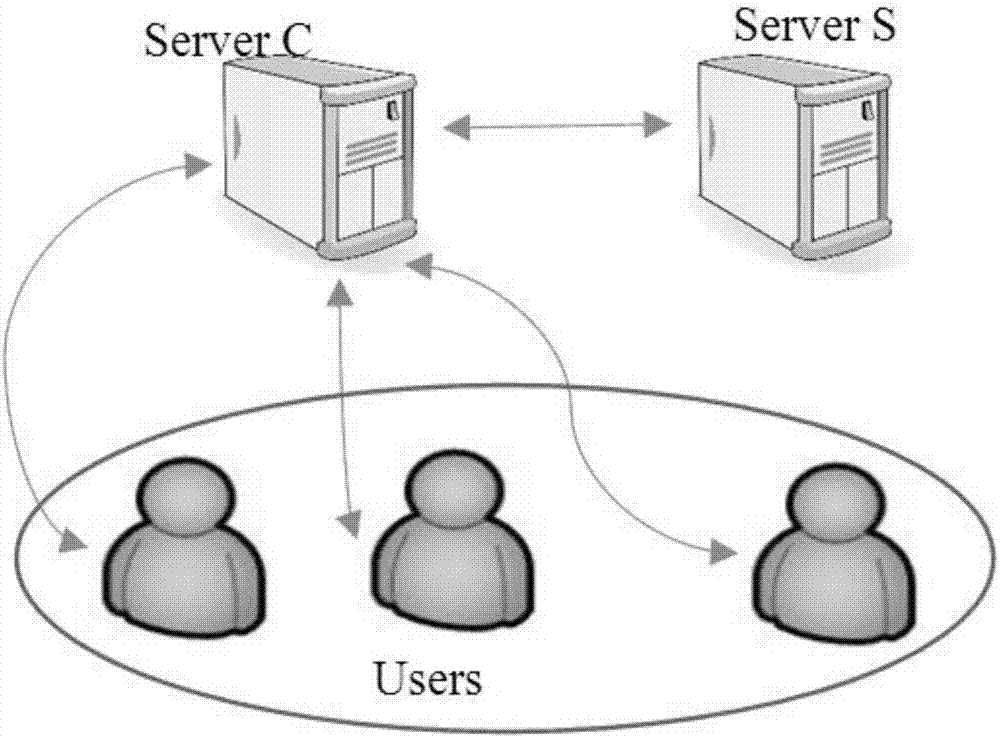
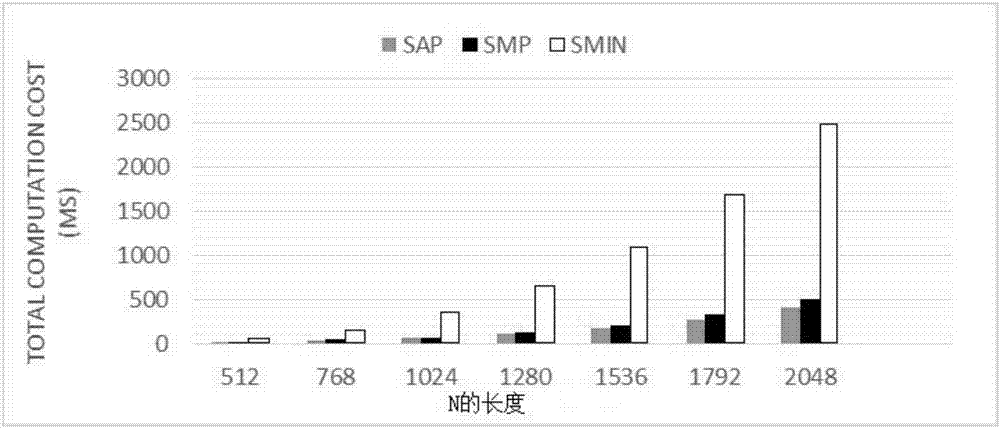
The invention provides a system and a method for time series anomaly detection based on secure multi-party. The system includes a server side and a user side. The server side includes at least two servers: a server C and a server S. Time series constituting a complete data set are stored in the server side in a distributed manner. The server C is a server providing service for the user side. Multi-party time series sharing is carried out between the server S and the server C based on a BCP encryption system. The server S is semi-honest, and has a master key mk for decryption. Disturbance is added to all operations in which S participates, in order to prevent S from getting relevant information about users. The server C and the server S initialize the BCP encryption system. The server C encrypts the time series stored therein, and then supplies the time series to the server S. The server S detects whether the time series are abnormal under a security protocol. The time series anomaly detection based on secure multi-party presented by the invention is of great practical value.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
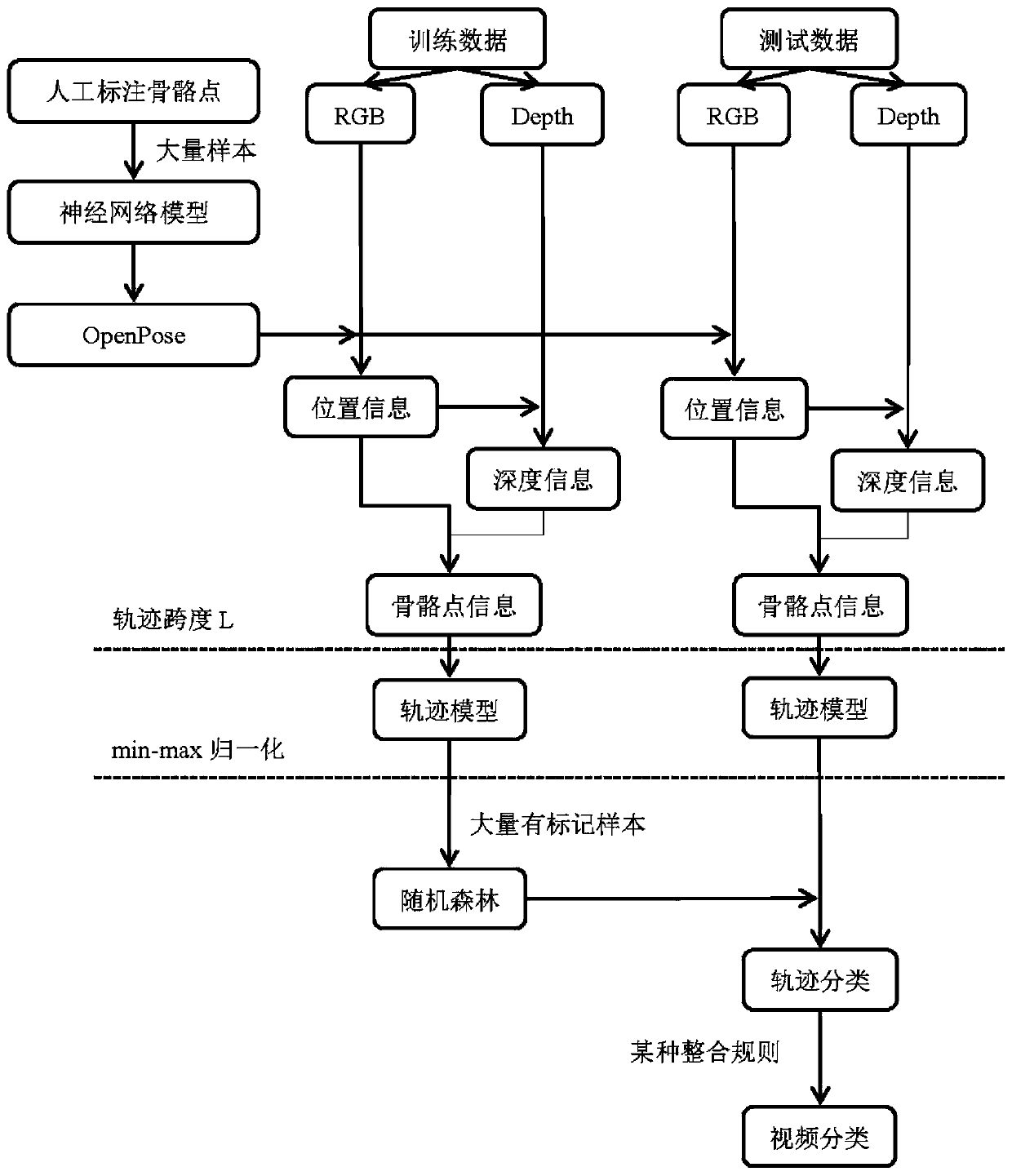
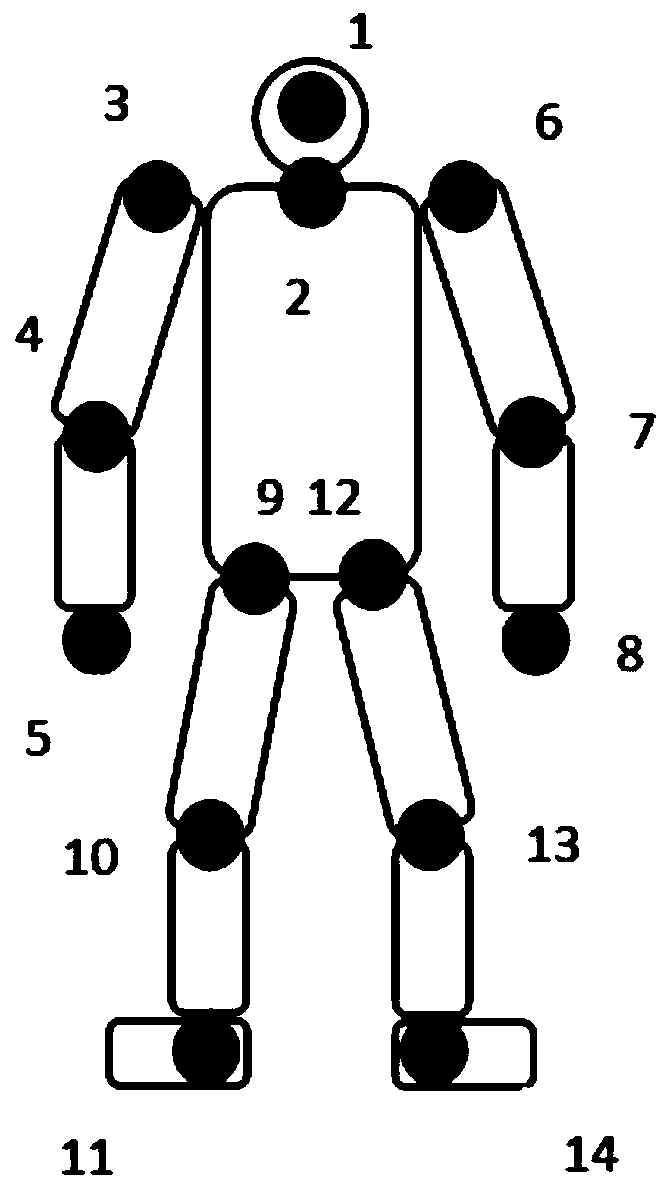
Falling action detection method based on key skeleton point track analysis
ActiveCN110287825AAddress unacceptable privacy concernsAvoid privacyCharacter and pattern recognitionHuman bodyRelevant information
The invention provides a falling action detection method based on key skeleton point track analysis. The falling action detection method comprises the following steps of 1, firstly, collecting a plurality of groups of image sequences including the falling actions and a plurality of groups of image sequences including other actions except the falling actions; 2, extracting the key skeleton points, extracting the related information of the key skeleton points of the human body from the positive and negative samples, wherein the related information comprises the position information and the depth information of each skeleton point in the RGB image; 3, constructing a feature model, and generating a feature descriptor based on a key skeleton point track; and 4, constructing a classifier, classifying the track feature descriptors, and detecting a falling action. According to the present invention, the human skeleton position information is extracted by utilizing the OpenPose human skeleton detection algorithm based on the neural network, the most persuasive human skeleton points can be directly obtained, the method is not limited to the specific conditions and special environments, a user does not need to wear anything, the complex installation is not needed, and the cost is very low.
Owner:SHENYANG AEROSPACE UNIVERSITY
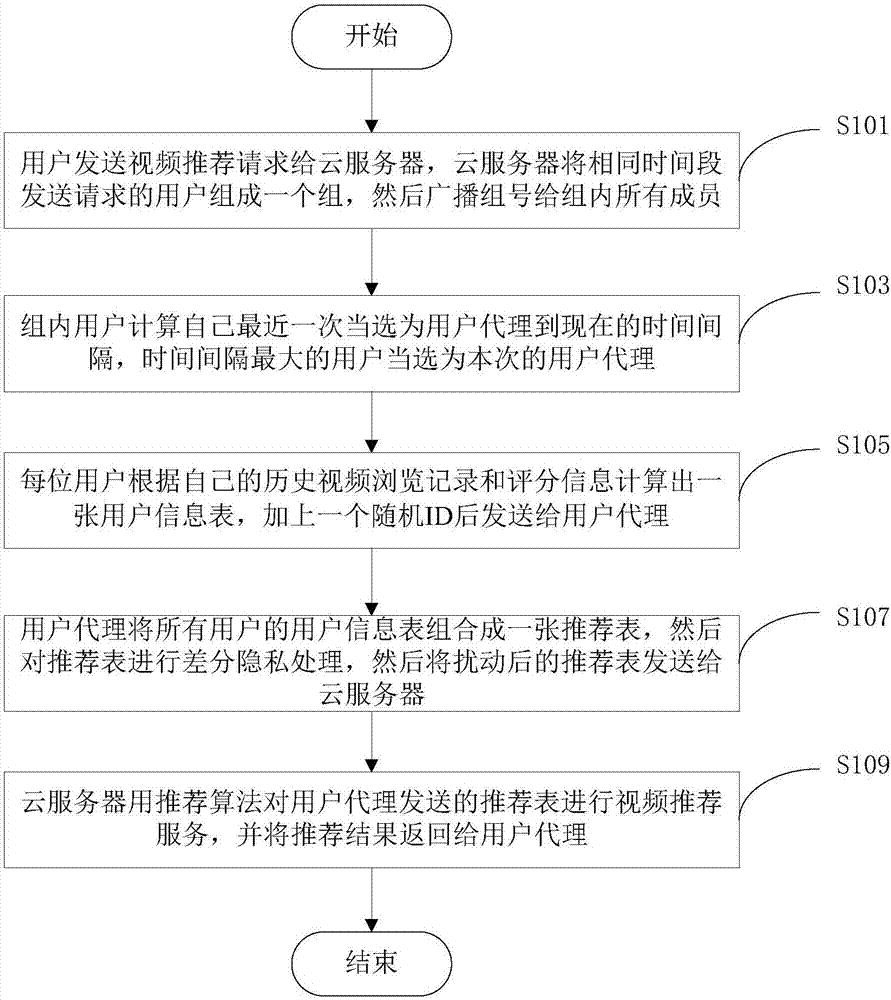
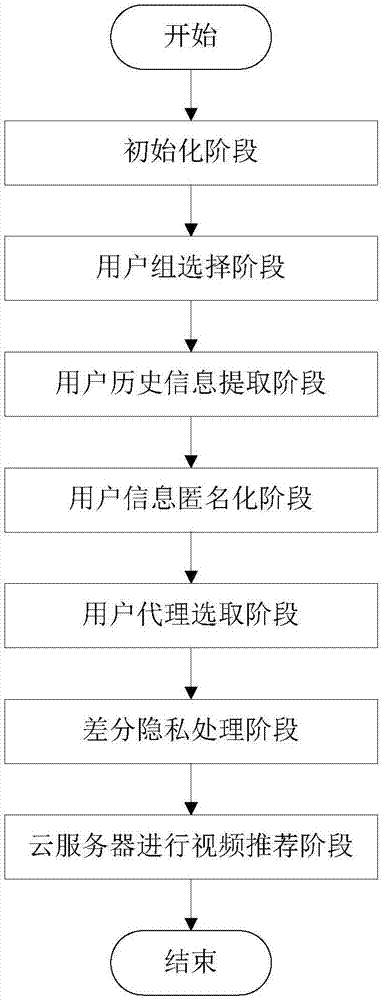
Privacy protection method for video recommendation system and video recommendation method
ActiveCN107257499APrivacy protectionMake up for problems that reduce the quality of referral servicesSelective content distributionPrivacy protectionDifferential privacy
The invention discloses a privacy protection method for a video recommendation system and a video recommendation method. In the privacy protection method, protection of personal privacy of a user is realized in a video recommendation process based on information anonymization and differential privacy. The method comprises the following steps that: each user requesting for video recommendation needs to generate a user information table, and meanwhile a user is randomly selected from a plurality of users to serve as a user agent; the user agent combines collected anonymized information tables of the users into a recommendation table; the user agent performs differential privacy processing on the recommendation table, and transmits the processed recommendation table to a server side; the server side performs video recommendation by a recommendation algorithm, and returns a recommendation result to the user agent; and lastly, the user agent transmits the recommendation result to the users. Through adoption of the method, the problem that the personal privacies of the users cannot be protected effectively in a conventional recommendation algorithm is solved on the premise of not changing a cloud recommendation algorithm, and meanwhile a high-quality video recommendation service is provided.
Owner:ANHUI UNIVERSITY
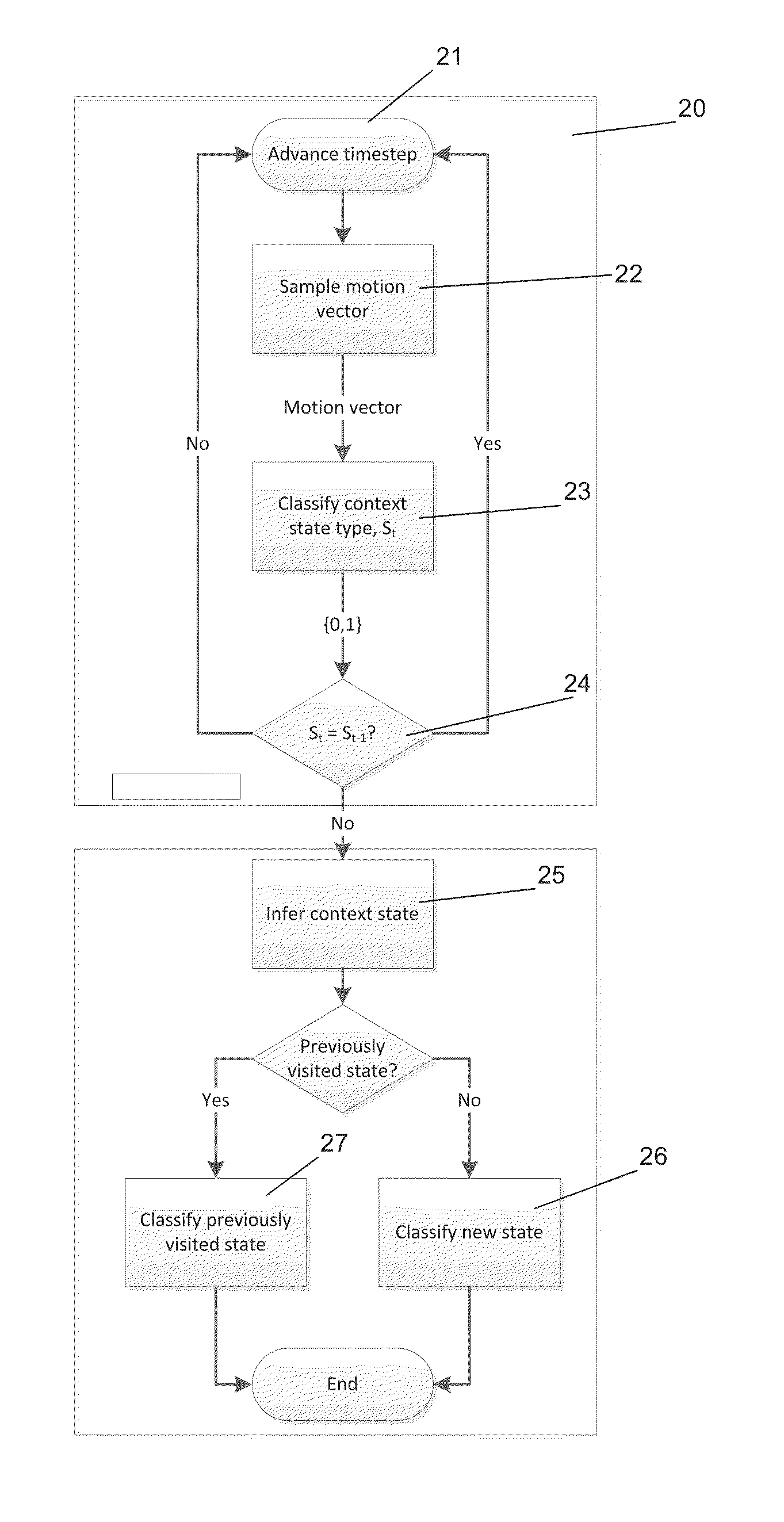
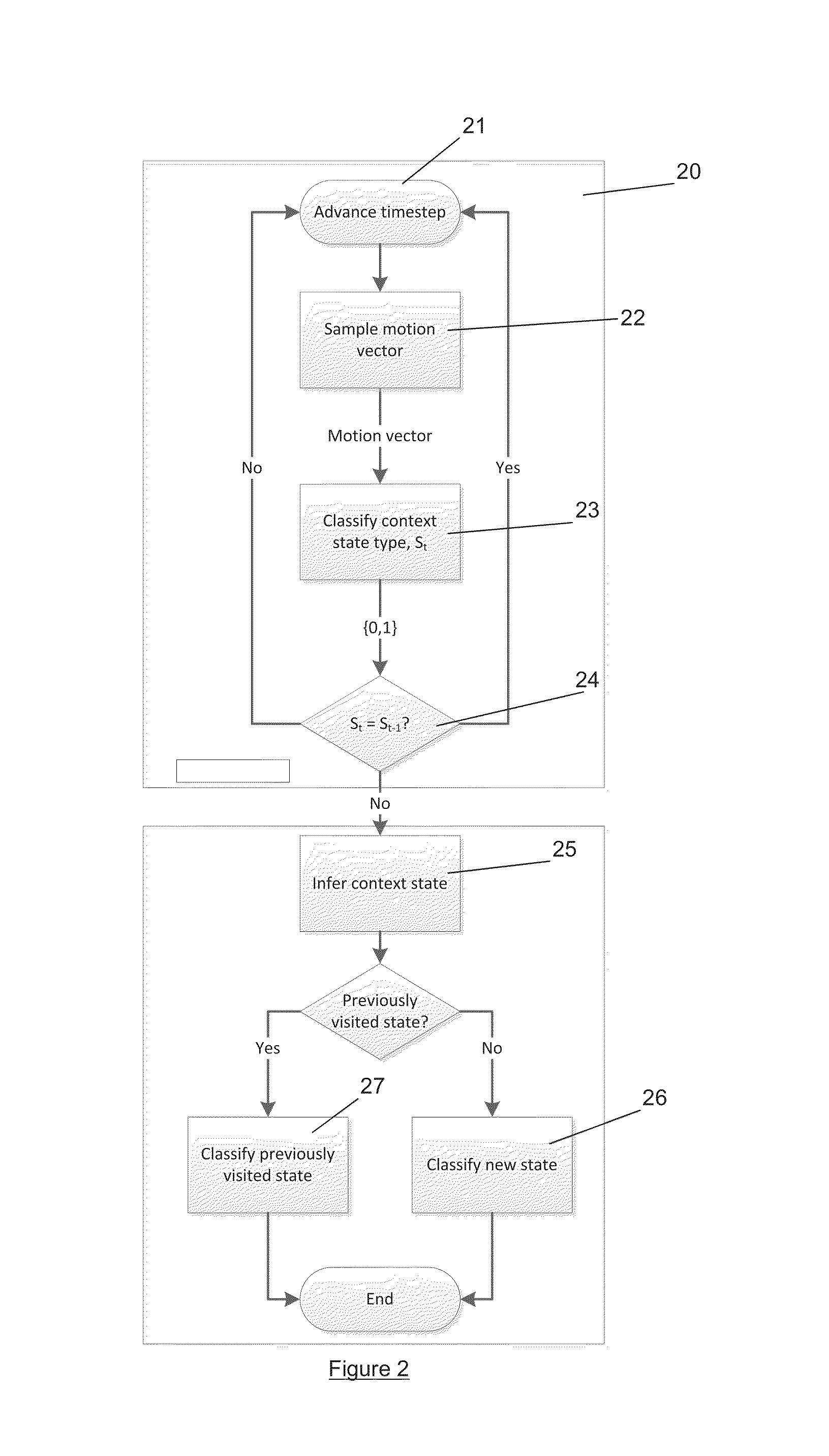
State detection
InactiveUS20130210480A1Avoid privacyAvoid connectionDevices with sensorSubstation equipmentMobile deviceComputer science
Method of determining a state of a mobile device, the mobile device having a one or more sensors, the method comprising the steps of: obtaining sensor data from the one or more sensors of the mobile device in an initial state. Determining if the initial state matches a previous state by comparing the obtained sensor data to previous sensor data acquired with the mobile device in the previous state. A mobile device includes logic to carry out this method.
Owner:VODAFONE IP LICENSING
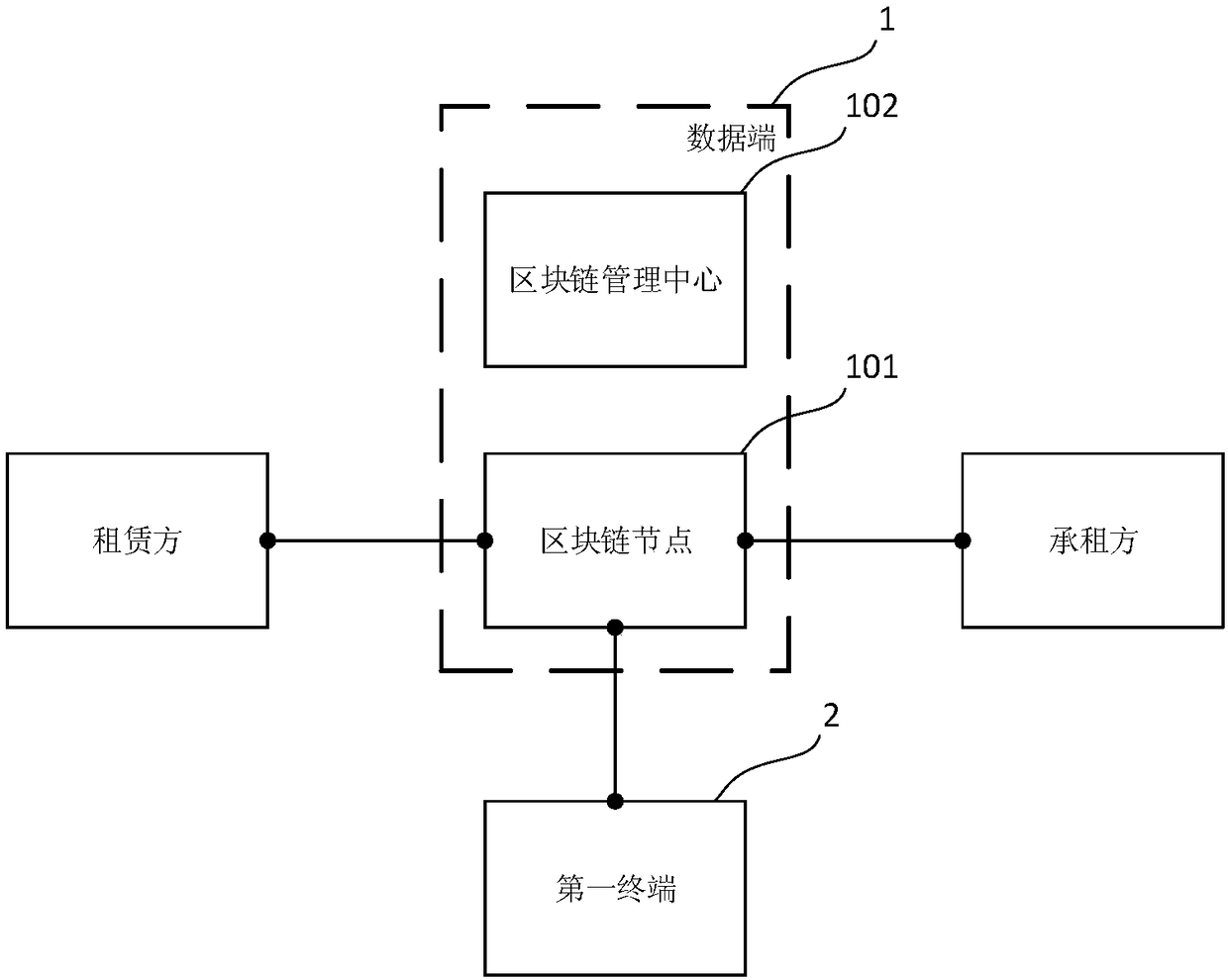
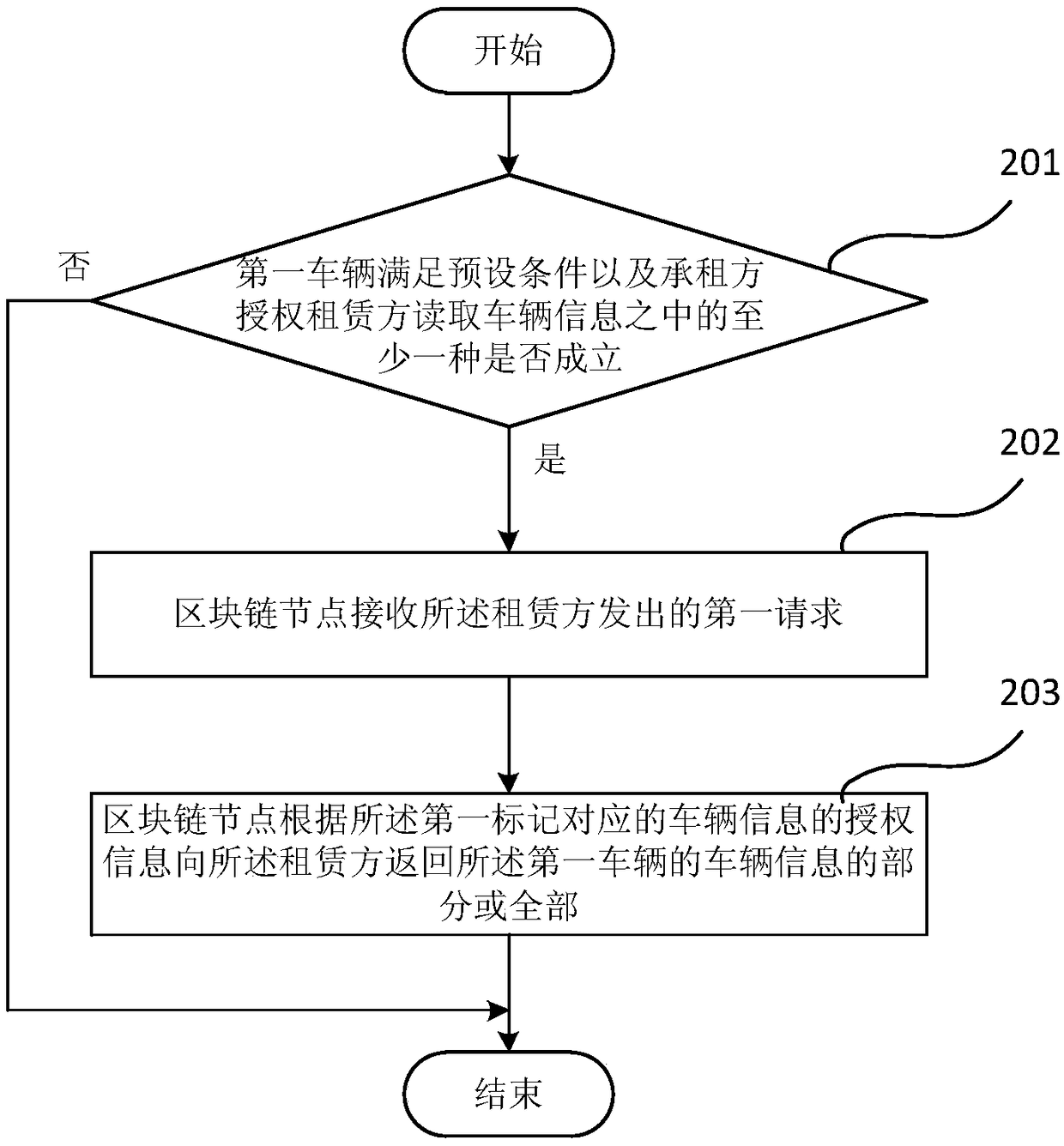
Blockchain based vehicle information processing method and server
InactiveCN108335425ASolve regulationAvoid privacyPayment protocolsApparatus for meter-controlled dispensingInformation processingComputer science
The invention relates to the technical field of terminals, in particular to a blockchain based vehicle information processing method and a server. The method comprises the following steps: when a first vehicle meets preset conditions and / or a lessor is authorized by a lessee to read vehicle information, blockchain nodes receive a first request sent by the lessor, the first request carries a firstmarker which corresponds to the first vehicle, and part or all information of the first vehicle is stored in the blockchain nodes; the blockchain nodes return information of the first vehicle to the lessor according to the authorization information of the vehicle information corresponding to the first marker. In the embodiment of the invention, the blockchain nodes for storing the information of the first vehicle open access to vehicle information reading for the lessor only when the first vehicle meets the preset conditions and / or the lessor is authorized by the lessee to the read vehicle information, so that not only is the problem about privacy of the lessee solved, but also effective supervision of the vehicle by the lessor is realized.
Owner:GOLO IOV DATA TECH CO LTD
Registry apparatus, agent device, application providing apparatus and corresponding methods
ActiveUS10069811B2Increase flexibilityReduce manufacturing costTransmissionComputer hardwareWindows Registry
A registry apparatus is provided for maintaining a device registry of agent devices for communicating with application providing apparatus. The registry comprises authentication information for uniquely authenticating at least one trusted agent device. In response to an authentication request from an agent device, the authentication information for that device is obtained from the registry, and authentication of the agent device is performed. If the authentication is successful, then application key information is transmitted to at least one of the agent device and the application providing apparatus.
Owner:ARM IP
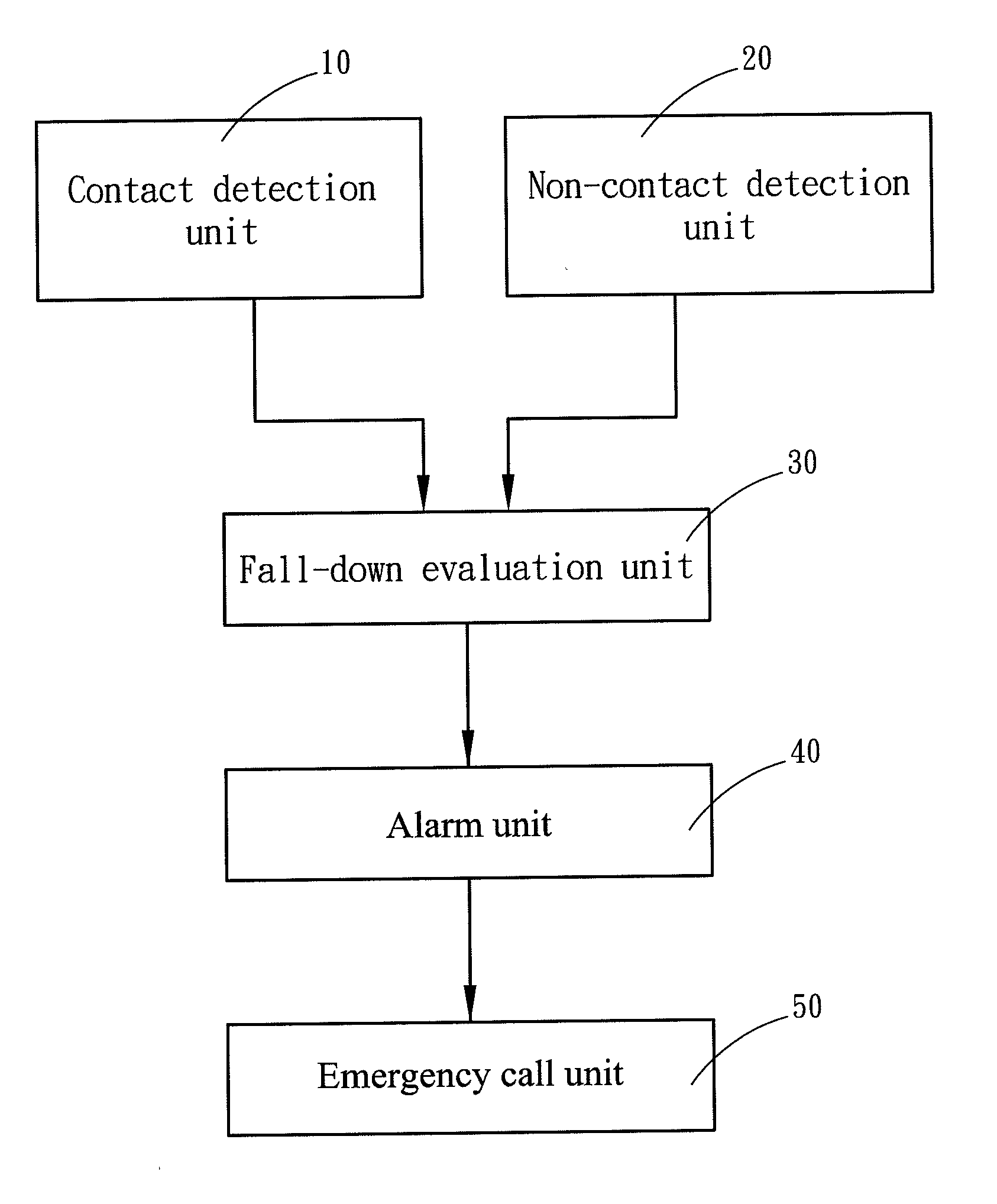
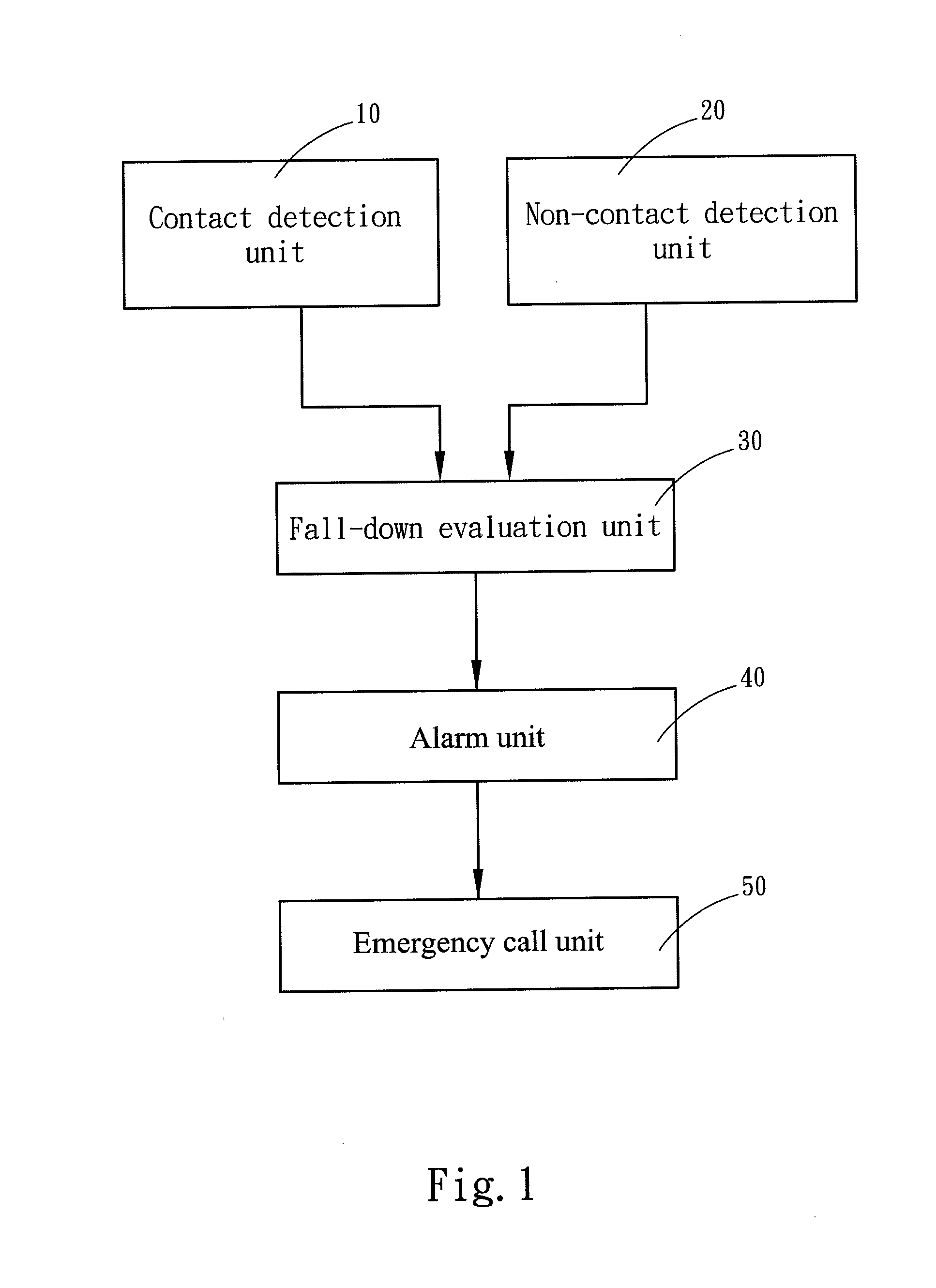
Fall-down alarm system
ActiveUS20120019387A1Erroneous fall-down judgmentAvoid privacyBurglar alarm by hand-portable articles removalAnomaly detectionEngineering
A fall-down alarm system includes a contact detection unit, a non-contact detection unit and a fall-down evaluation unit connecting respectively to the contact detection unit and non-contact detection unit. The contact detection unit and non-contact detection unit respectively detect an abnormal detected shape of an object and abnormal life symptoms of the object, and then the fall-down evaluation unit determines a fall-down condition and sends a trigger signal to request assistance. Through the contact detection unit and non-contact detection unit respectively detecting the shape and life symptoms of the object, the erroneous fall-down judgment can be reduced.
Owner:CHINA MEDICAL UNIVERSITY(TW)
Human body sitting posture detection method based on depth camera
ActiveCN110309787AAccurate analysis of sitting postureAvoid privacyImage enhancementTelevision system detailsHuman bodyColor image
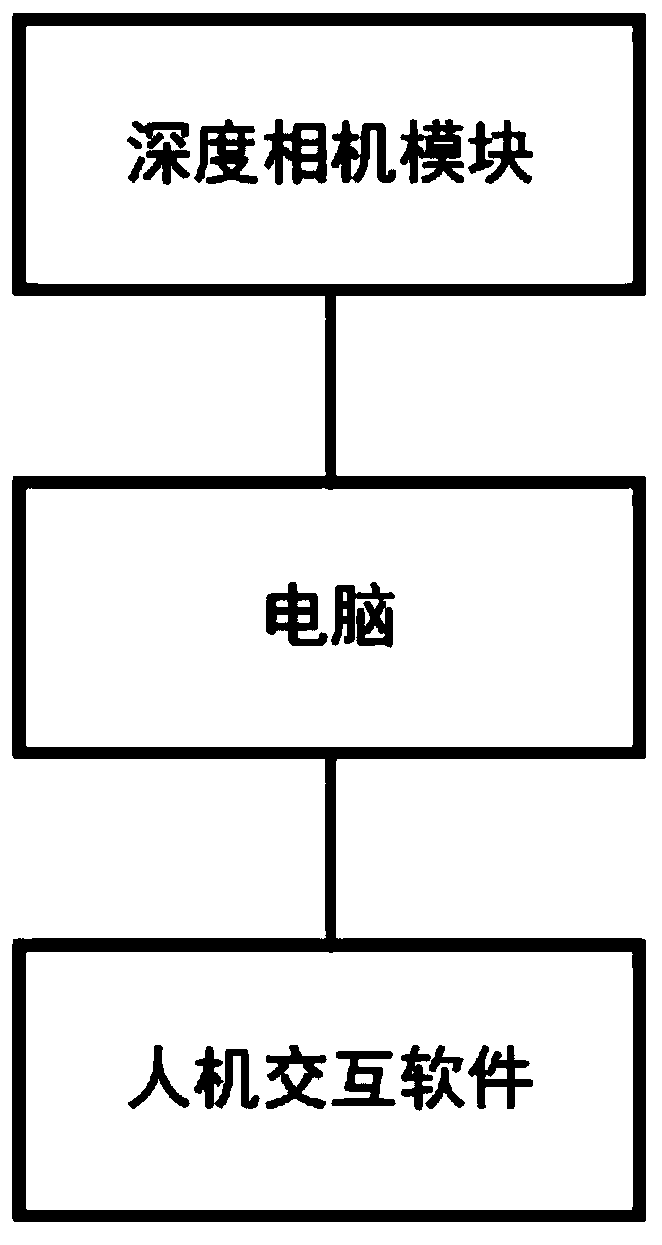
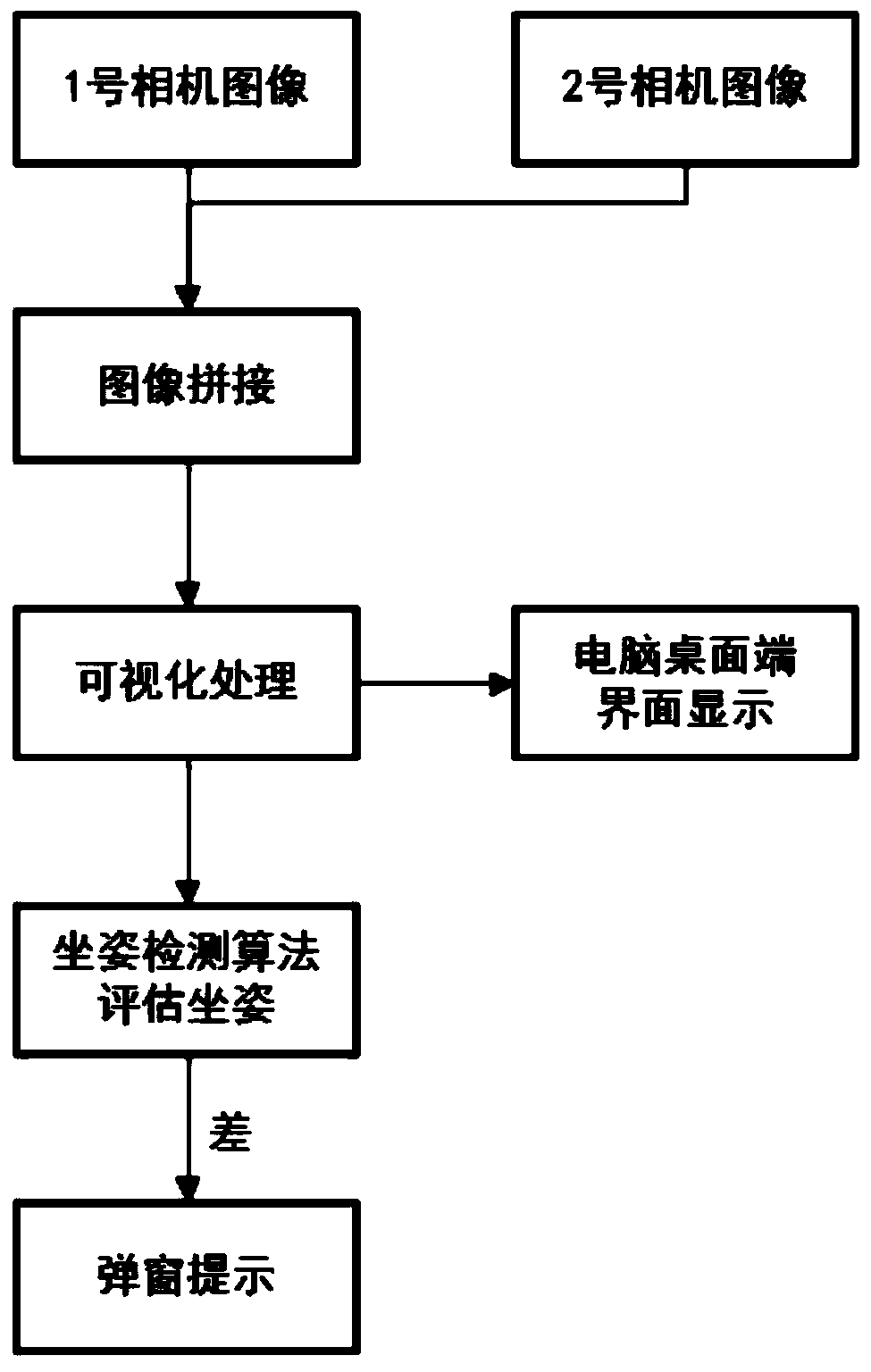
The invention discloses a human body sitting posture detection method based on a depth camera, and relates to the field of image processing. The method comprises the following steps that a depth imageand a color image of a back area of a human body are acquired, a foreground area of an image is acquired by combining the depth image and the color image, and whether the sitting posture of the humanbody is correct or not is calculated by the partial area of the foreground area, so that the purpose of the invention is achieved. According to the non-contact type sitting posture monitoring methodbased on the machine vision, human back data is collected by means of the depth camera, images can be obtained in real time through a sitting posture monitoring algorithm, sitting posture monitoring is completed in a full-automatic mode, and when the sitting posture is abnormal, computer-side human-computer interaction software reminds a user to correct the sitting posture in time. A sitting posture of the person is closely related to the spine state, so that the collected back data is most accurate to analyze the sitting posture, and meanwhile, the privacy problem caused by the collection ofhuman face information can be avoided.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
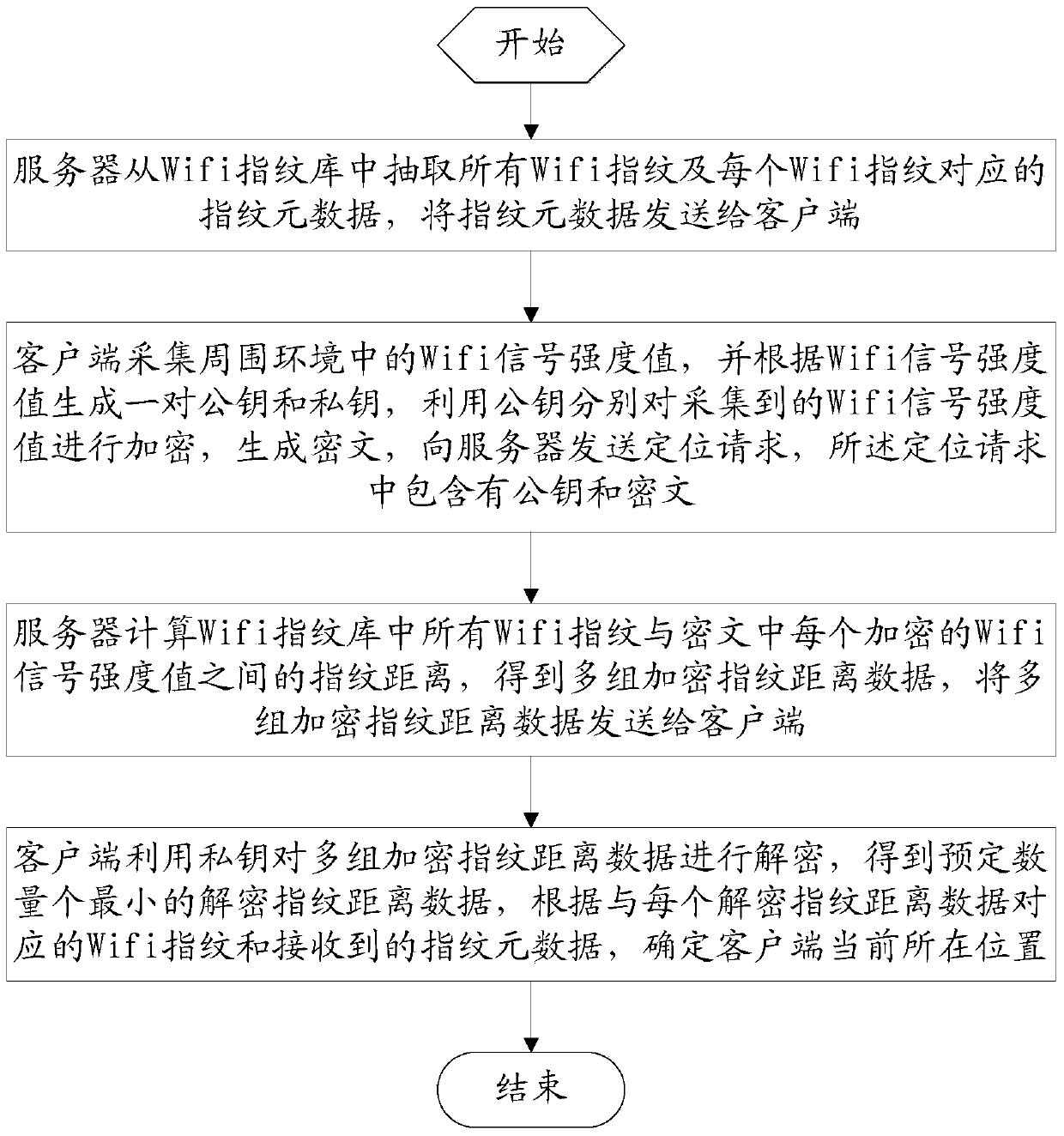
Privacy protection method and device for Wifi fingerprint positioning
InactiveCN103442335AAvoid privacyGuaranteed positionWireless commuication servicesSecurity arrangementPrivacy protectionEngineering
The invention relates to a privacy protection method and device for Wifi fingerprint positioning. The privacy protection method for Wifi fingerprint positioning comprises the following steps that a server extracts all the Wifi fingerprints and fingerprint metadata; a client terminal collects Wifi signal intensity values in the peripheral environment and generates a public key and a private key according to the asymmetrical encryption algorithm, encryption is respectively conducted on the collected Wifi signal intensity values by the public key and a positioning request is sent to the server; the server calculates the fingerprint distance between all the Wifi fingerprints and each encrypted Wifi signal intensity value and transmits multiple sets of encrypted fingerprint distance data to the client terminal; the client terminal uses the private key to decrypt the multiple sets of the encrypted fingerprint distance data, and determines the current location of the client terminal according to the Wifi fingerprint corresponding to each decrypted fingerprint distance datum and the received fingerprint metadata. The privacy protection method and device for Wifi fingerprint positioning solves the privacy problem in an existing WiFi fingerprint positioning technology, and can protect the location privacy of a user and the data privacy of a service provider.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
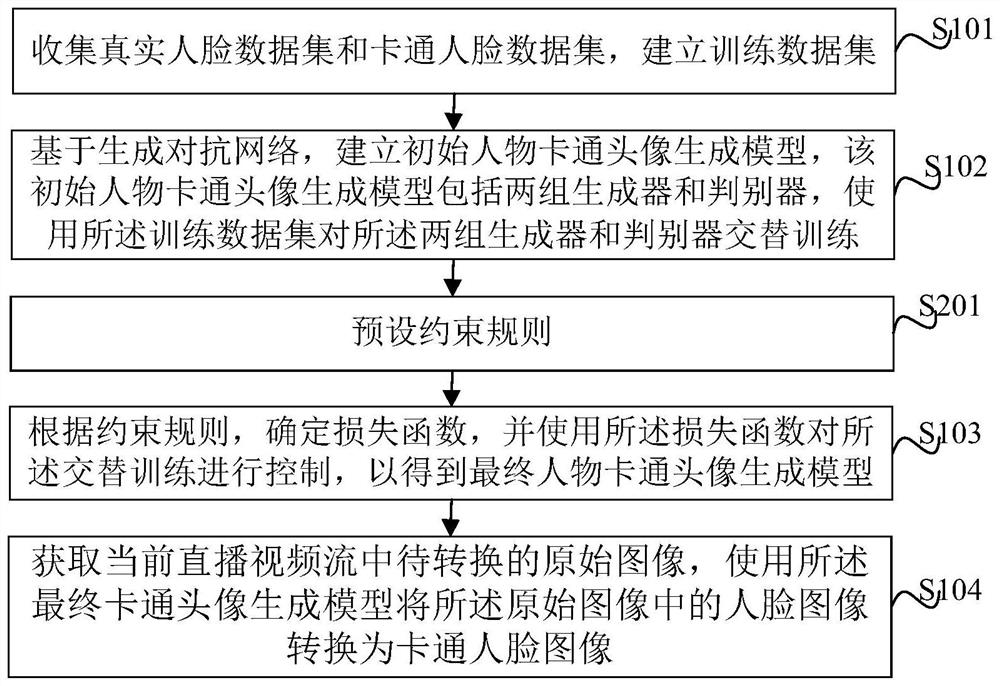
Online live broadcast method and device based on image cartoonization and electronic equipment
PendingCN112561786AEnsure consistencyAvoid privacyGeometric image transformationCharacter and pattern recognitionPattern recognitionData set
The invention belongs to the field of education, and provides an online live broadcast method and device based on image cartoonization, and electronic equipment, the method is used for identifying anoriginal image in a live broadcast video stream in real time and cartoonizing a face image in the original image, and the method further comprises the steps of collecting a real face data set and a cartoon face data set, establishing a training data set; based on the generative adversarial network, establishing an initial figure cartoon head portrait generation model, and performing alternate training by using the training data set; determining a loss function according to a constraint rule, and controlling the alternate training by using the loss function to obtain a final figure cartoon headportrait generation model; and obtaining a to-be-converted original image in the current live video stream, and converting a face image in the original image into a cartoon face image by using the final cartoon head portrait generation model. According to the invention, the consistency of images before and after the figure cartoon image is generated in multiple dimensions such as color, position,edge, texture, head portrait attribute and the like can be ensured.
Owner:作业帮教育科技(北京)有限公司
Digital location-based data methods and product
ActiveUS20150213055A1Good flexibilityAvoid the needRoad vehicles traffic controlDigital data processing detailsData miningLocation data
Owner:TOMTOM GLOBAL CONTENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com