Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5098results about How to "Privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
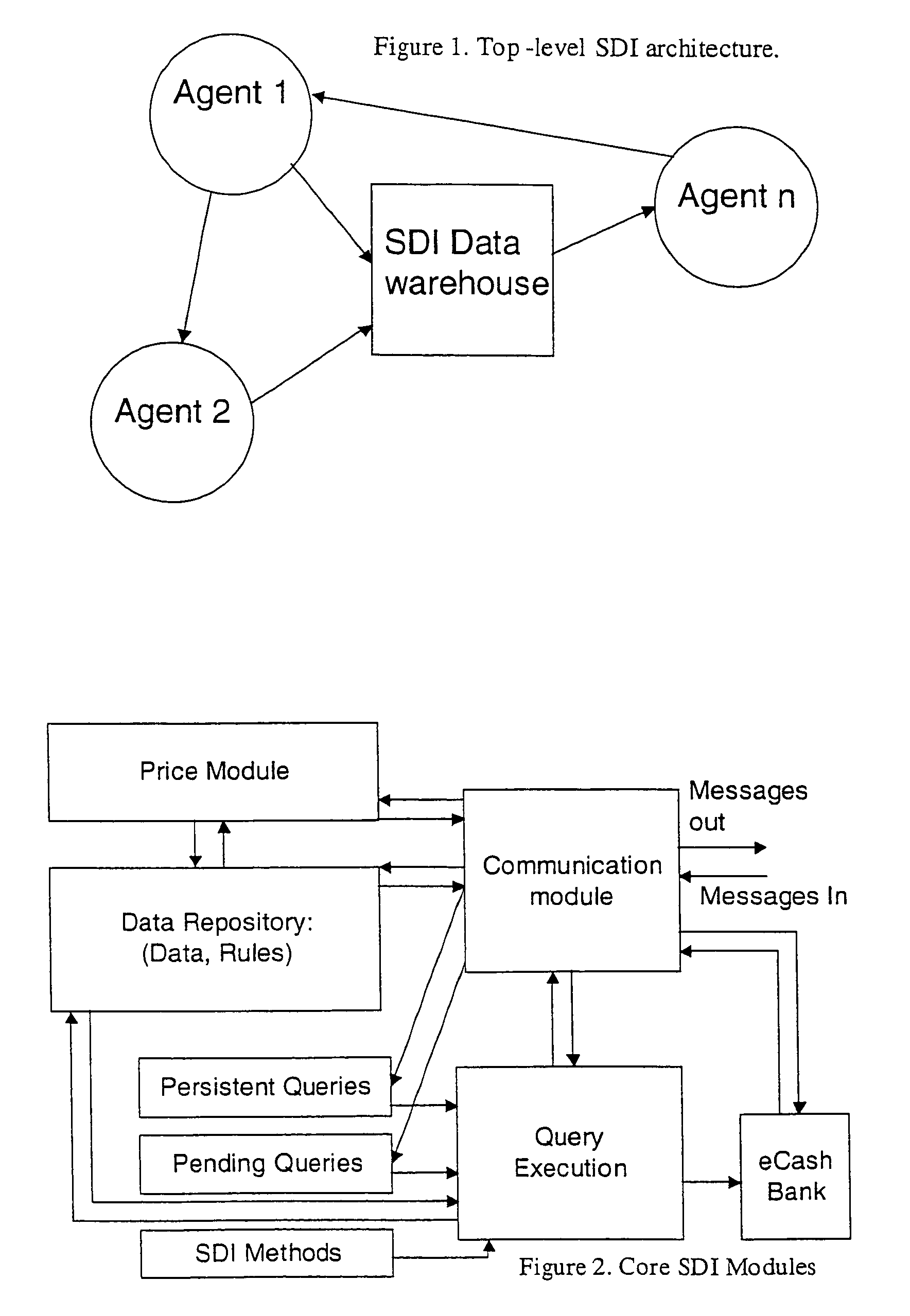
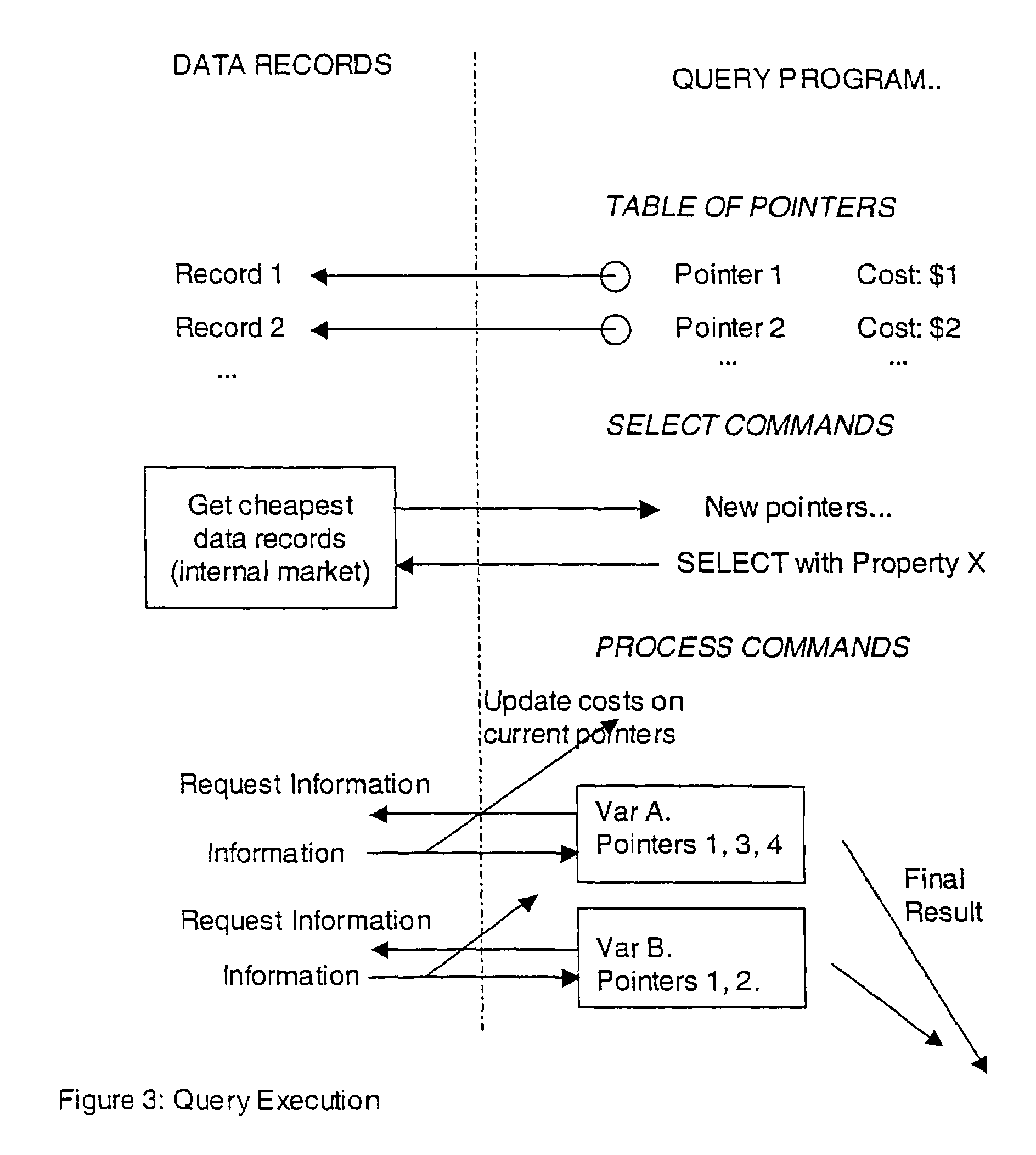
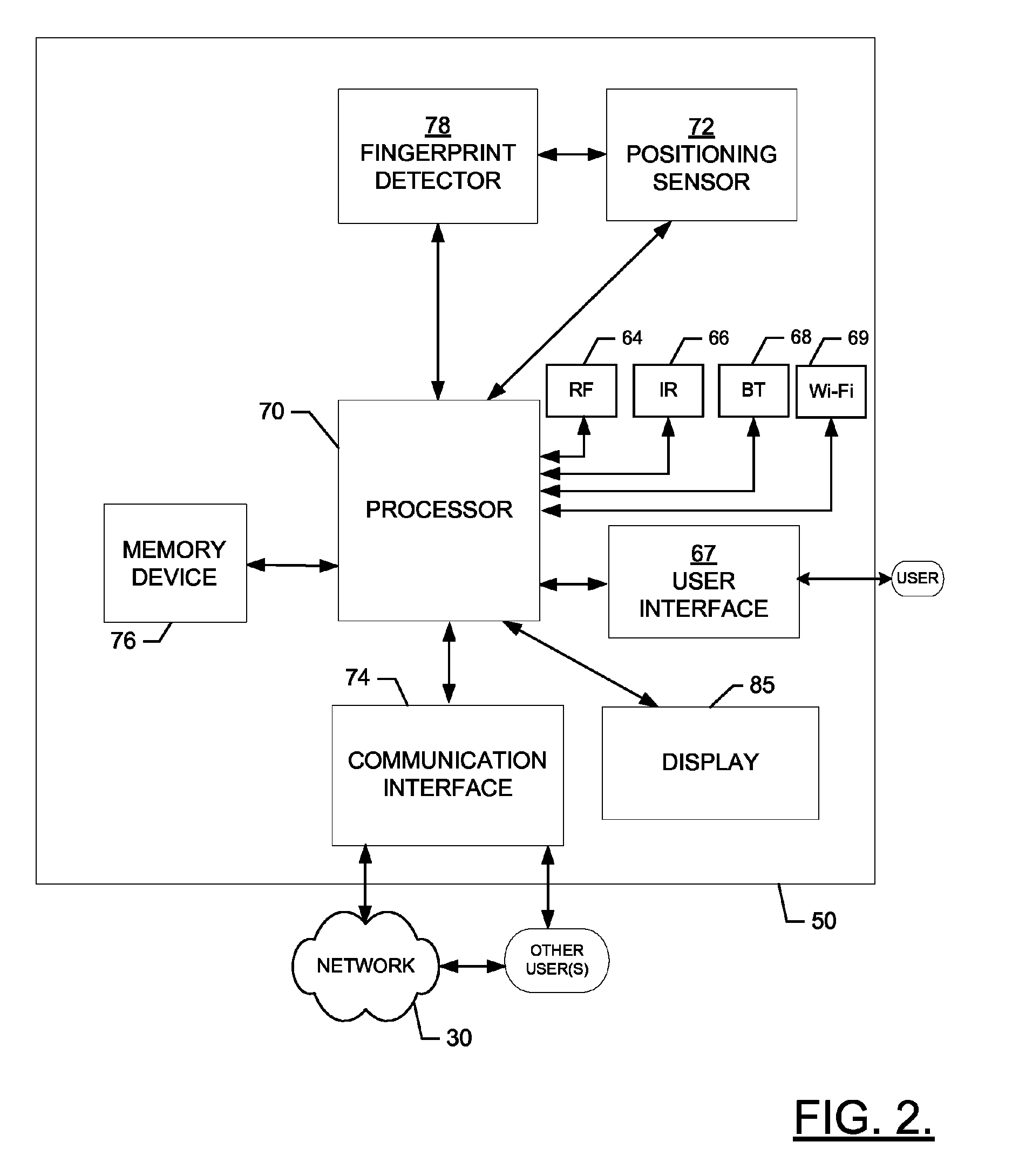
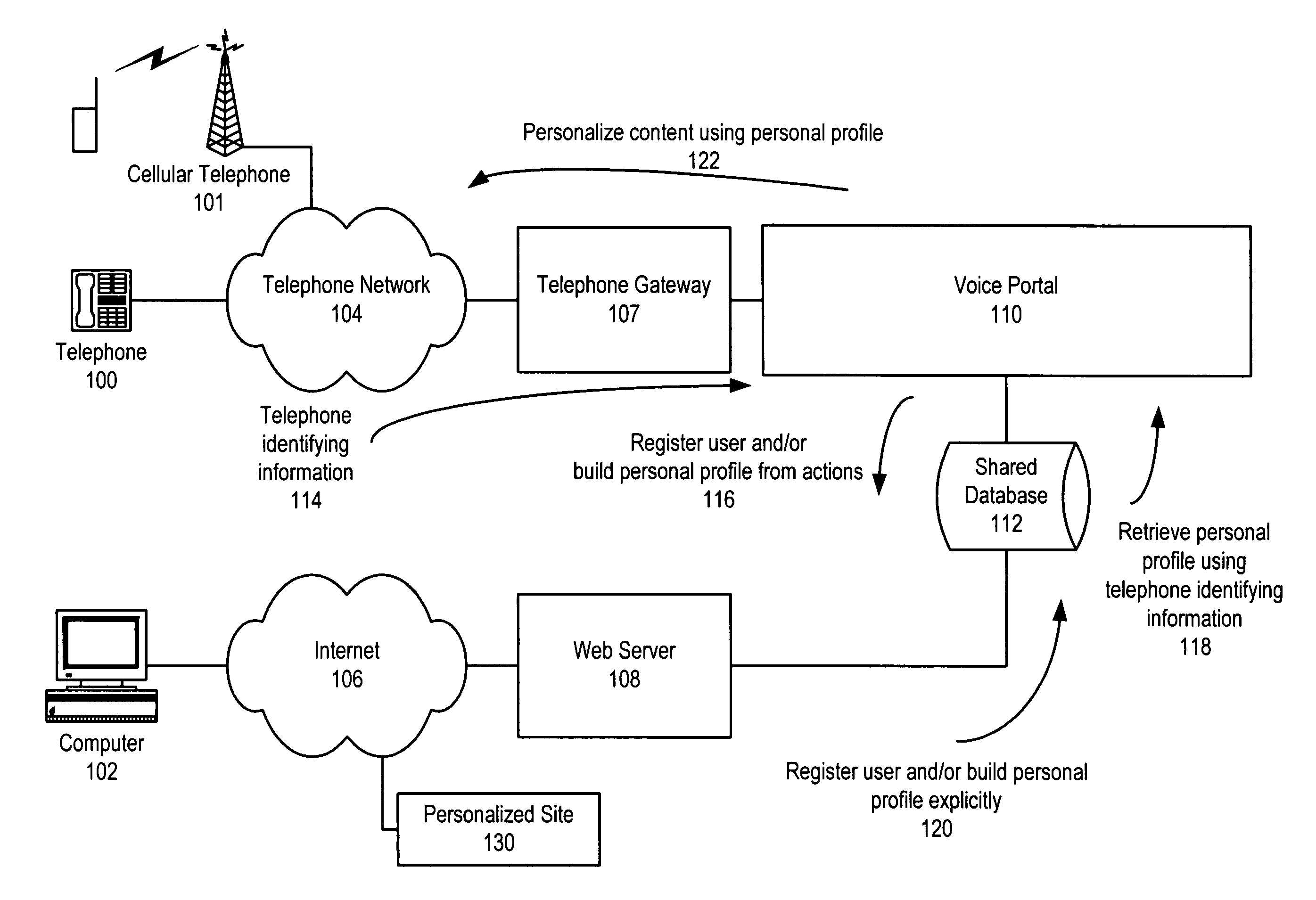
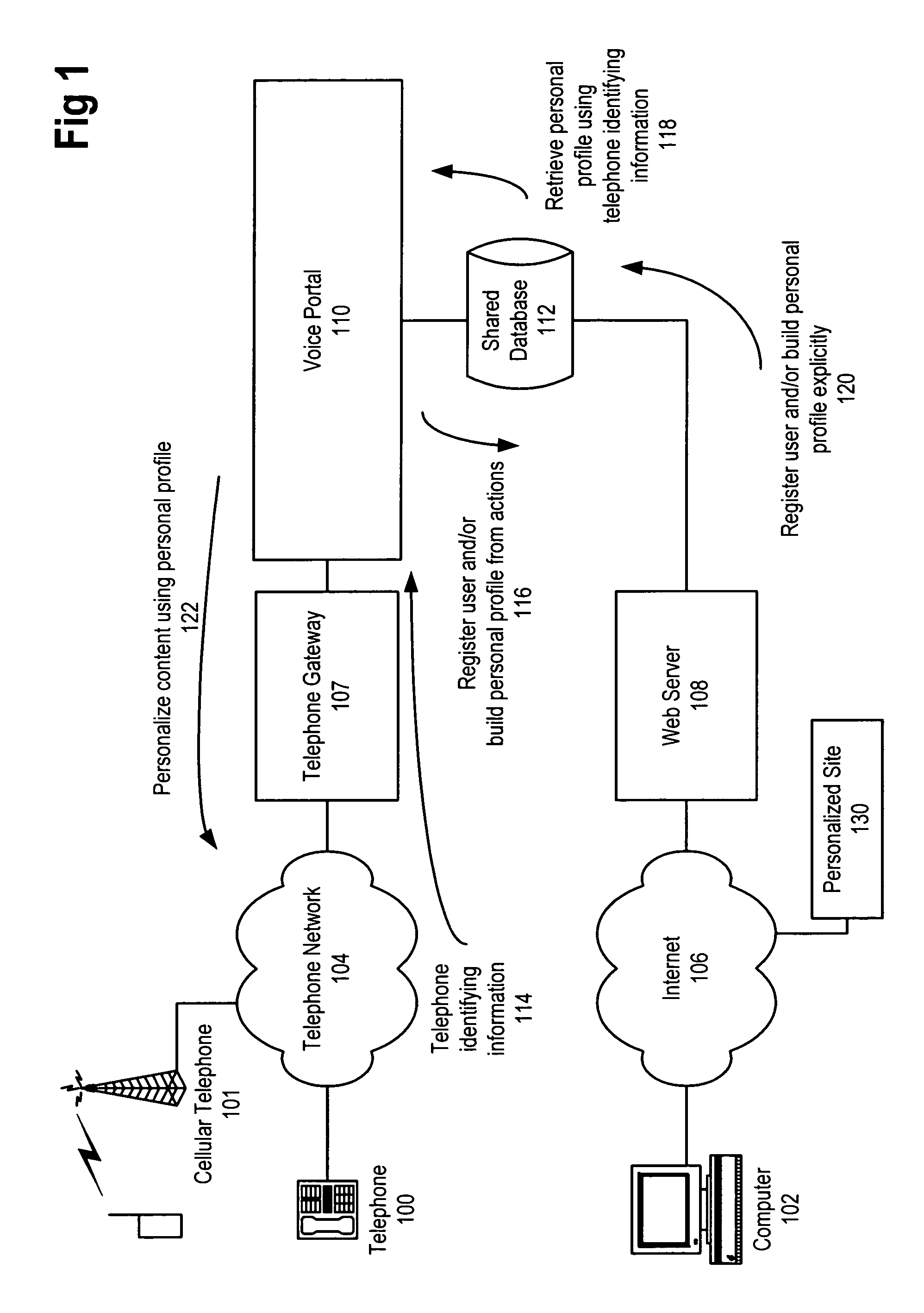
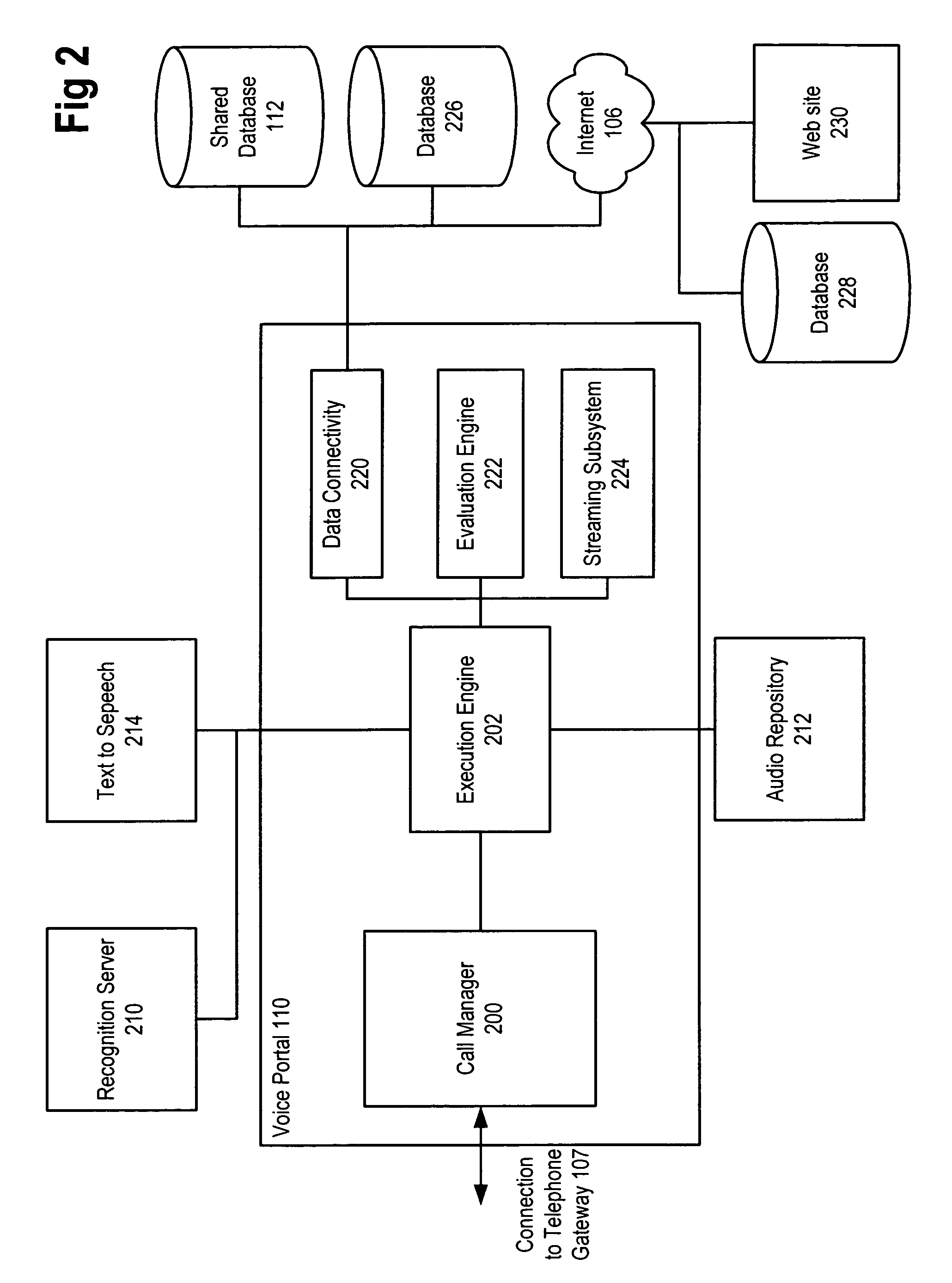
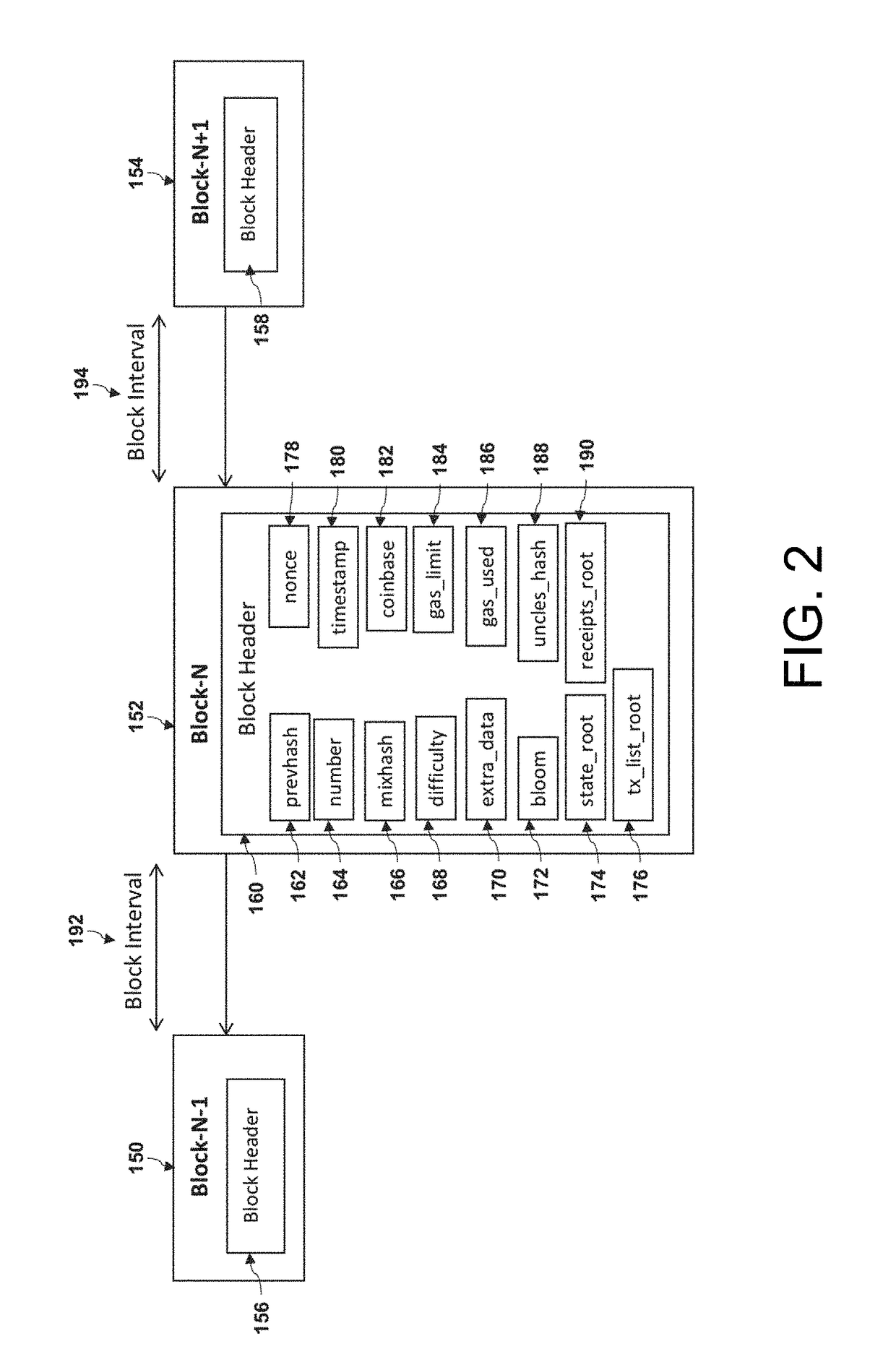
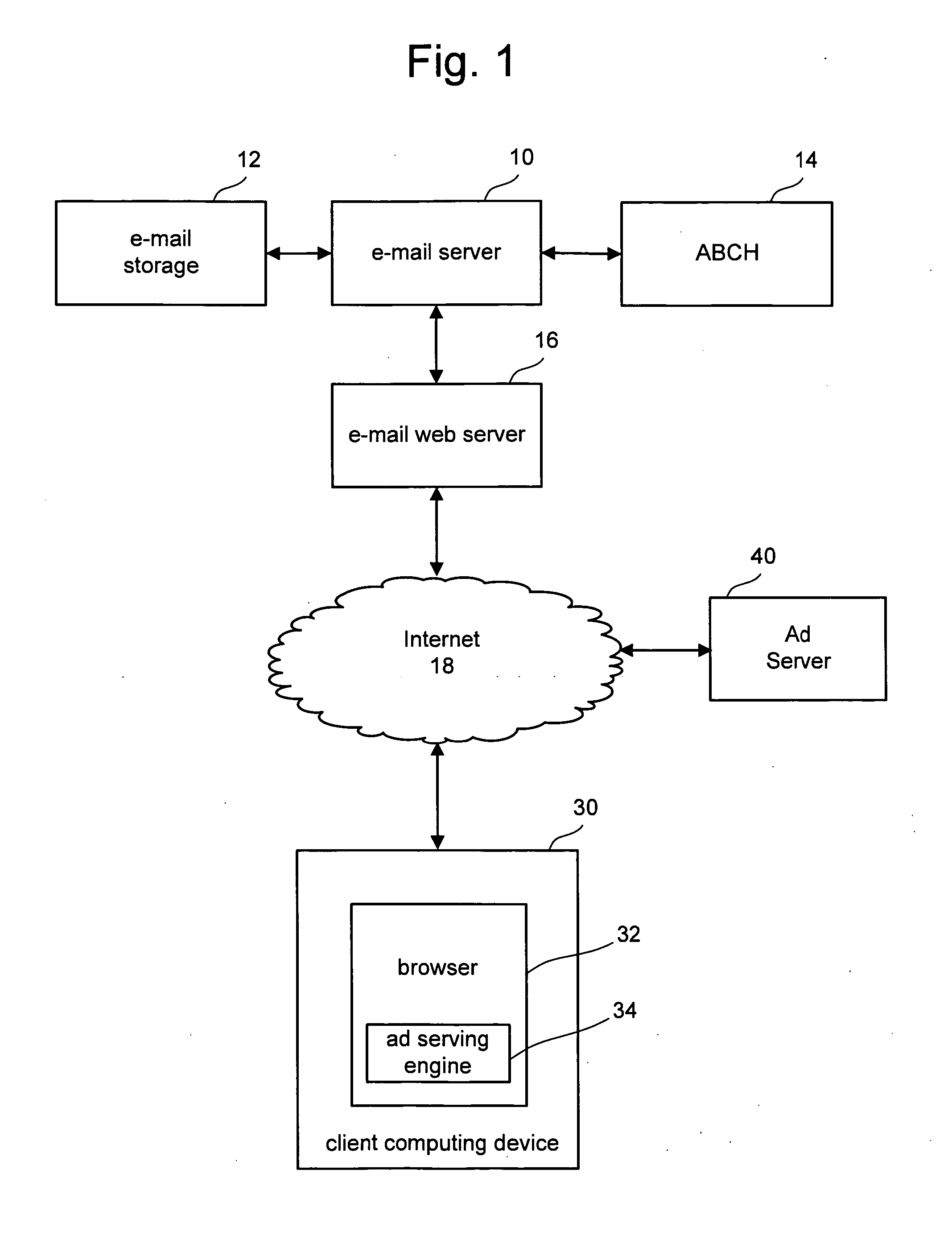
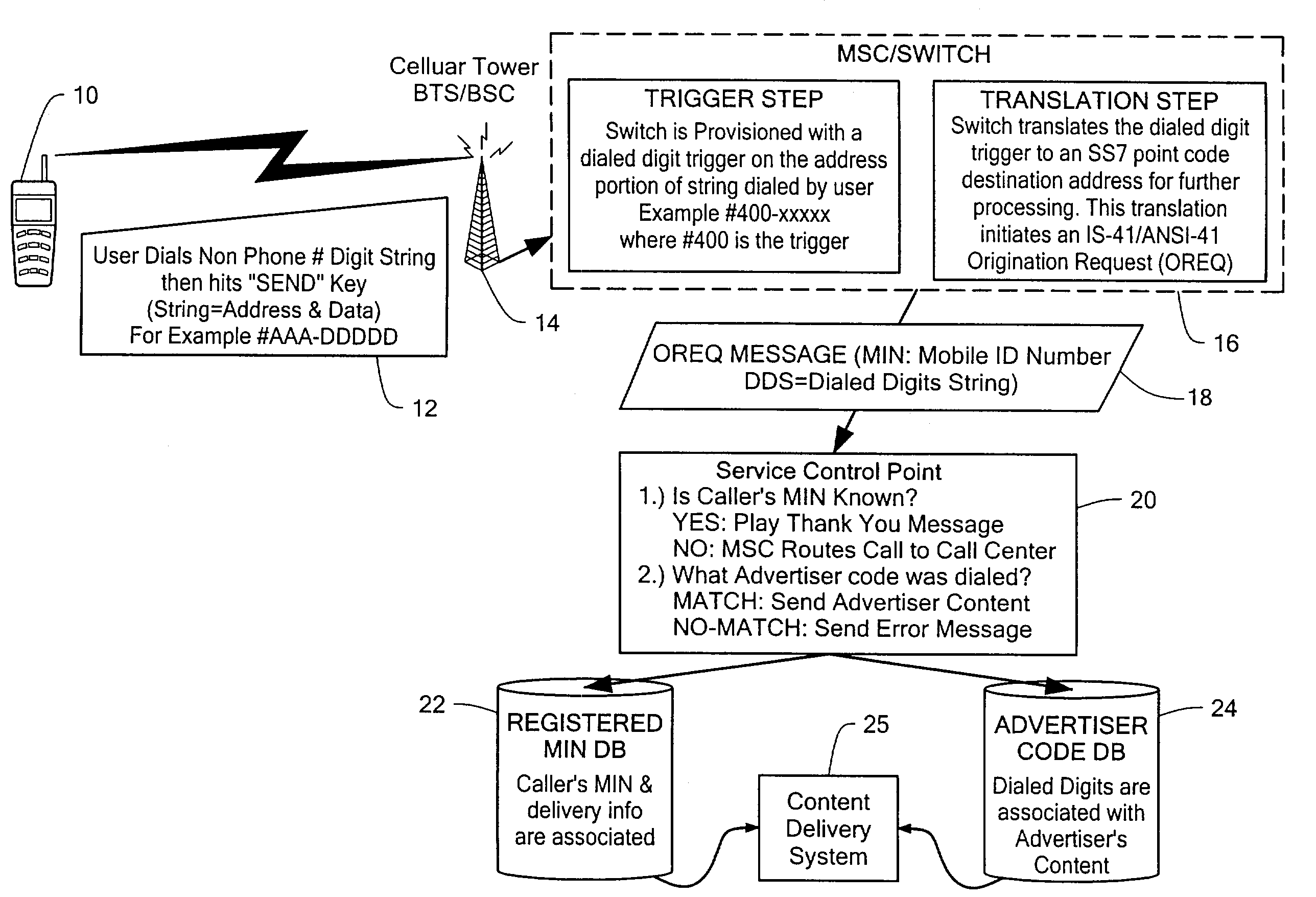
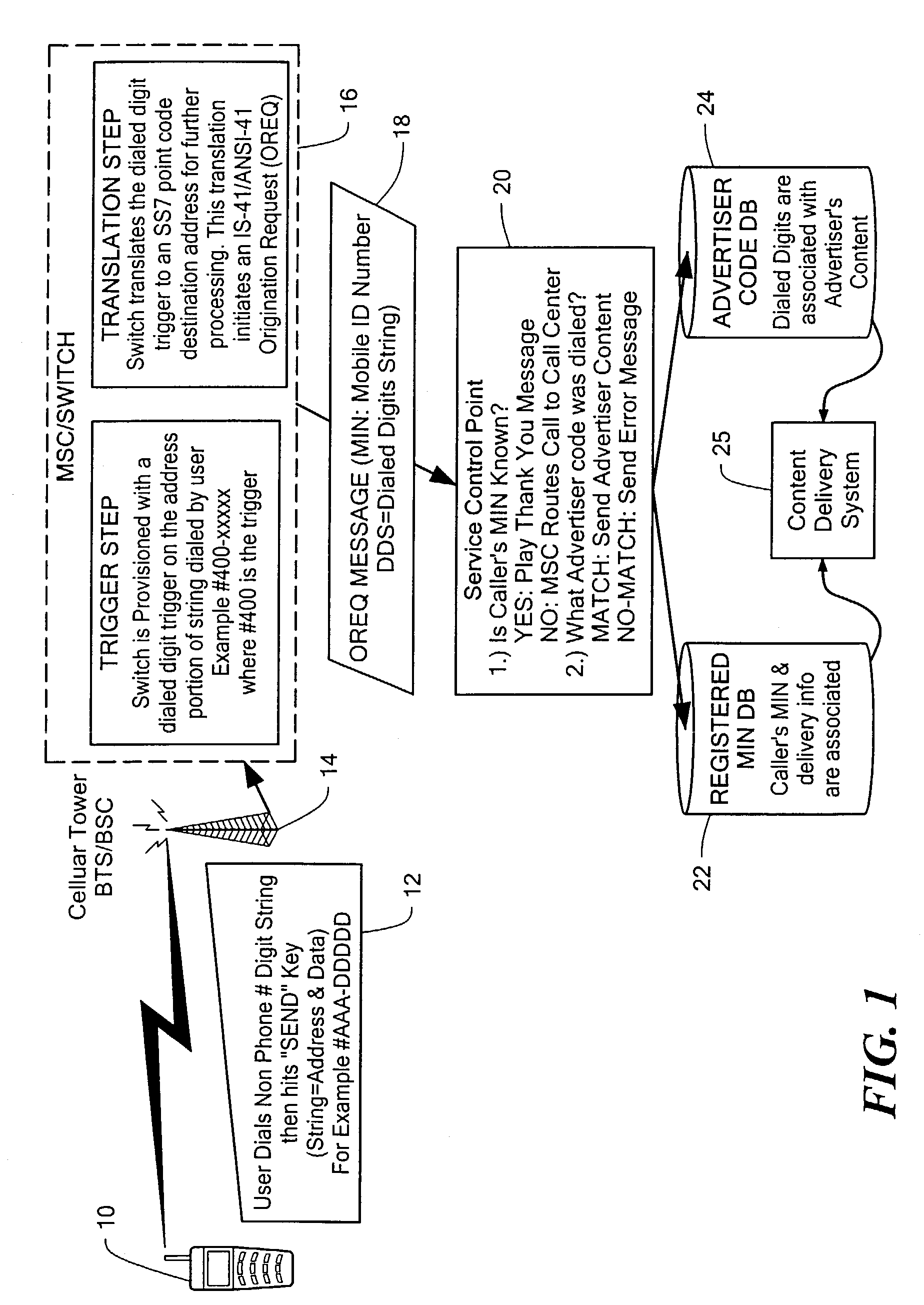
Secure data interchange
InactiveUS20090254971A1Improve privacyLimited accessDigital data processing detailsAnalogue secracy/subscription systemsInformation accessData interchange
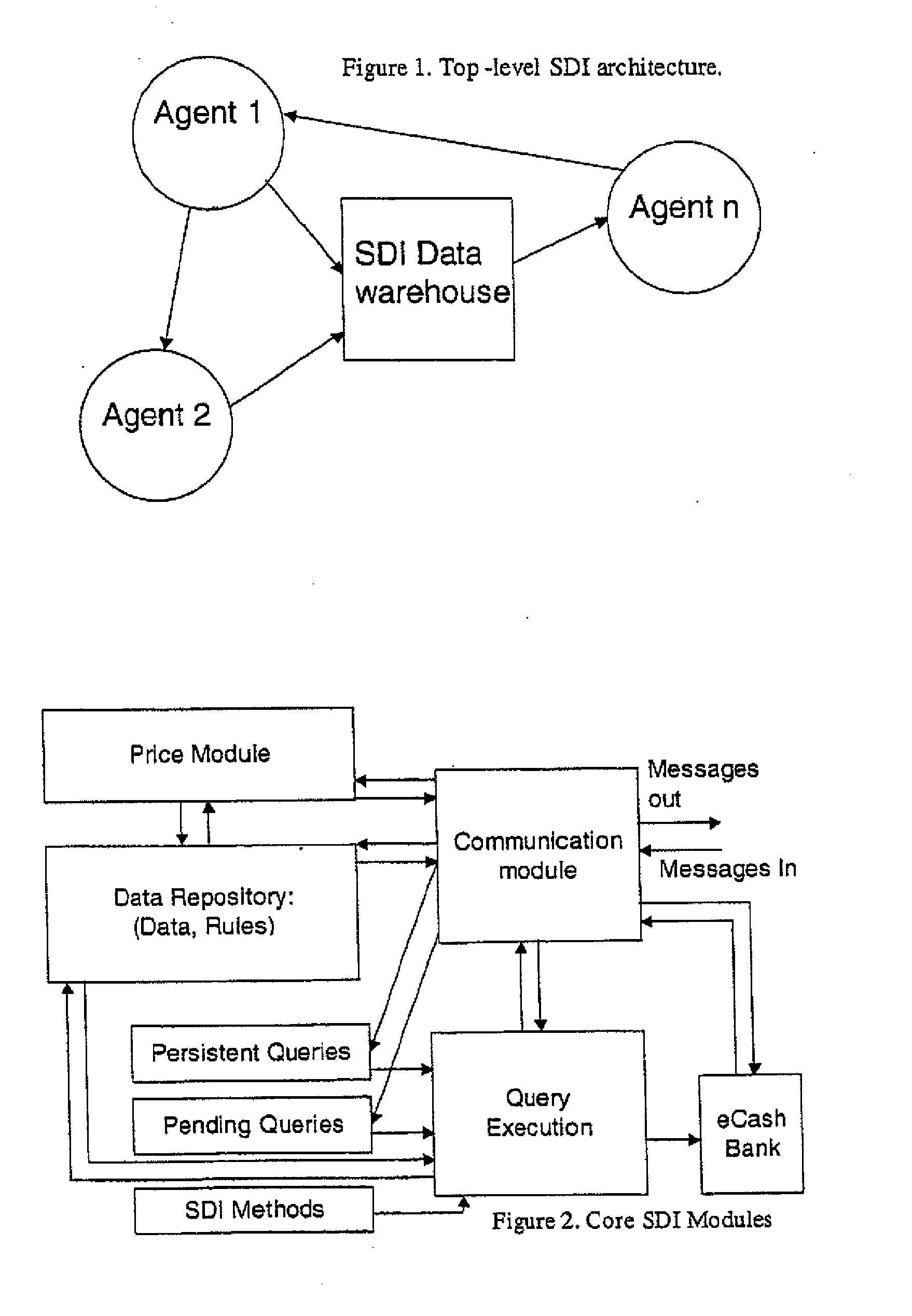
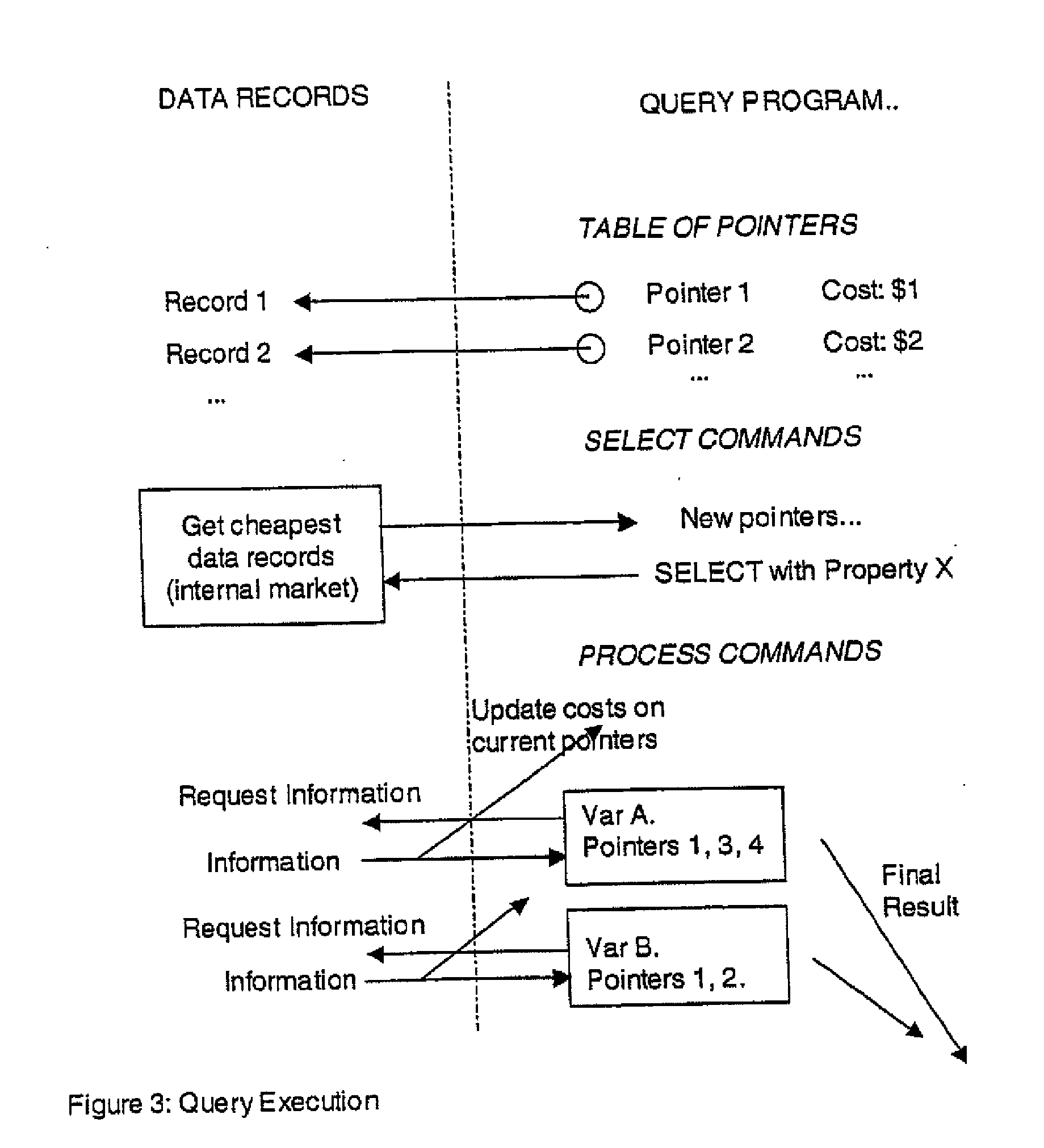
A secure data interchange system enables information about bilateral and multilateral interactions between multiple persistent parties to be exchanged and leveraged within an environment that uses a combination of techniques to control access to information, release of information, and matching of information back to parties. Access to data records can be controlled using an associated price rule. A data owner can specify a price for different types and amounts of information access.
Owner:STRIPE INC
Secure data interchange
InactiveUS7630986B1Low pricePrivacy protectionMultiple digital computer combinationsOffice automationCommunications systemInternet privacy
A system for exchanging data includes a communication system, a first and a second party connected to the communication system, wherein each party has personal data, and each party has a disclosure policy to control dissemination of its data, and a secure intermediate party connected to the communication system, wherein the secure intermediate party exchanges data between the first and second parties in accordance with their respective disclosure policies.
Owner:STRIPE INC
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
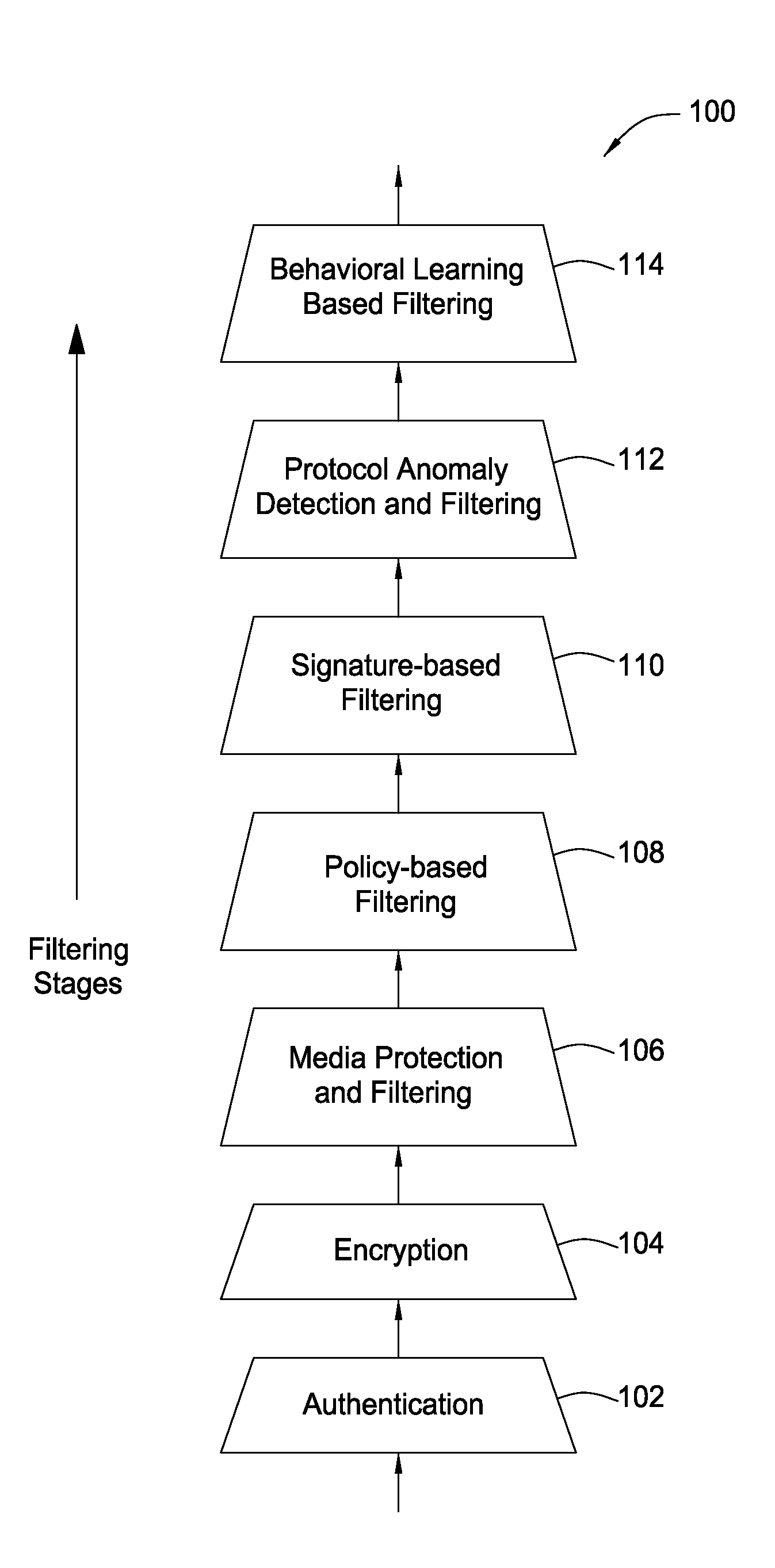
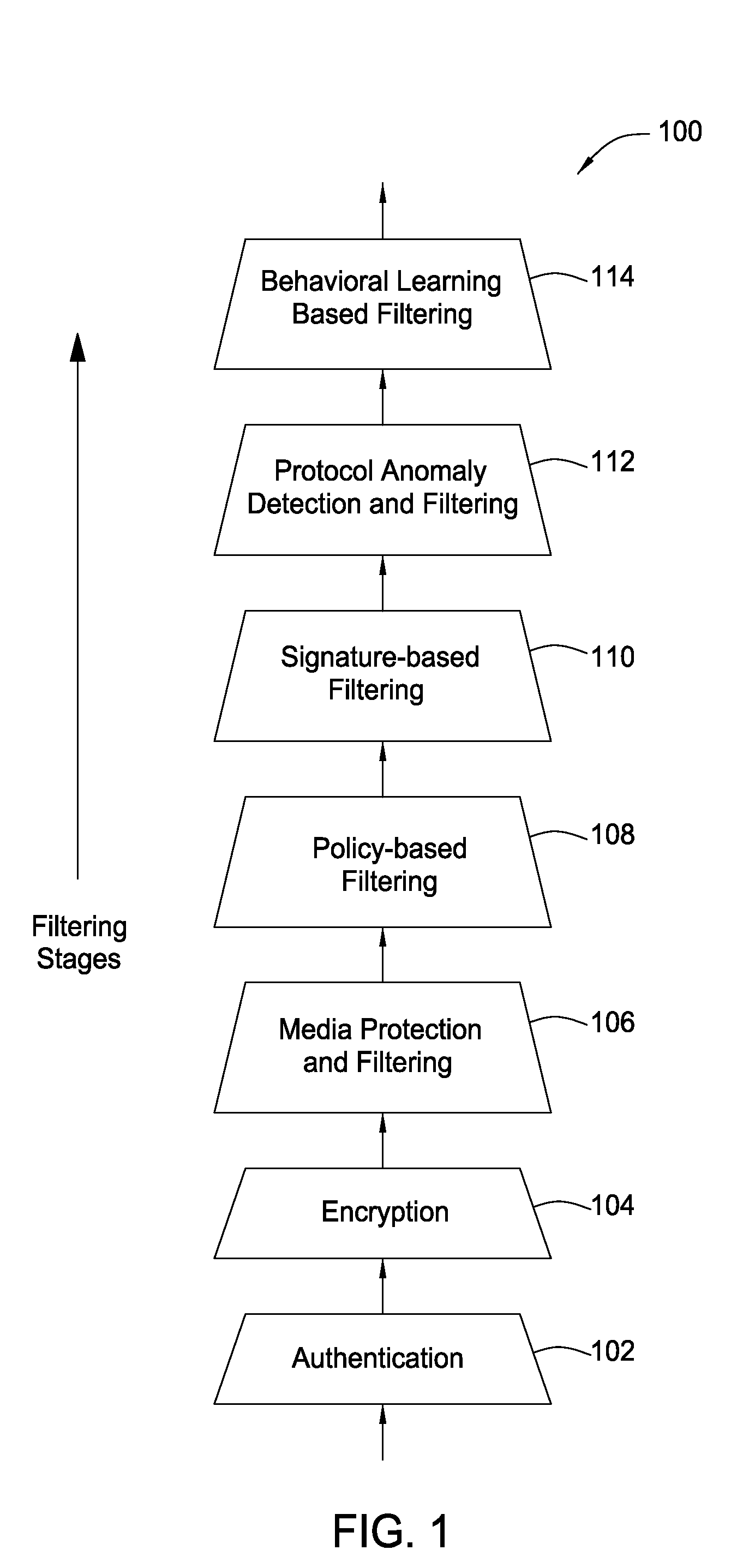
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
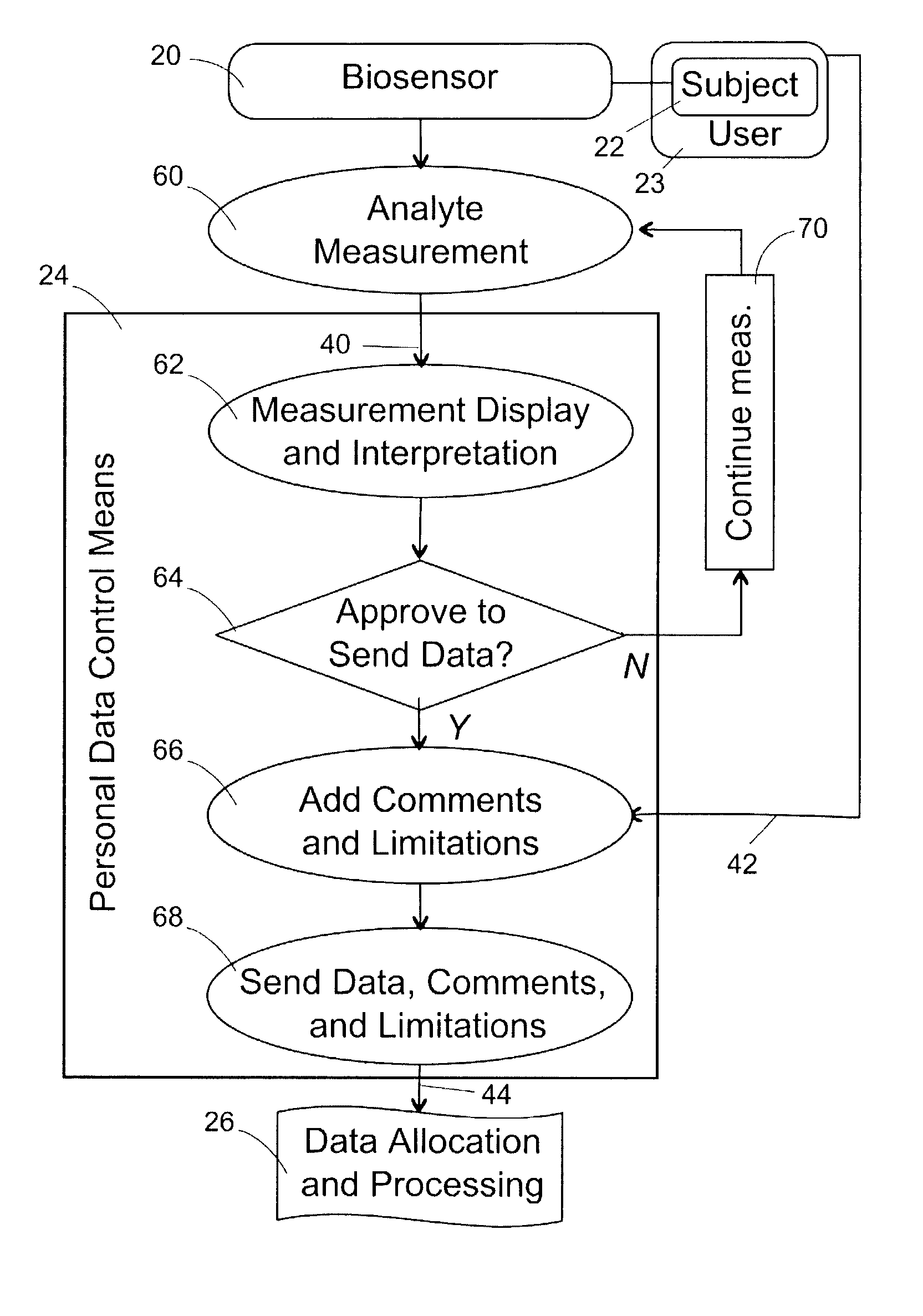
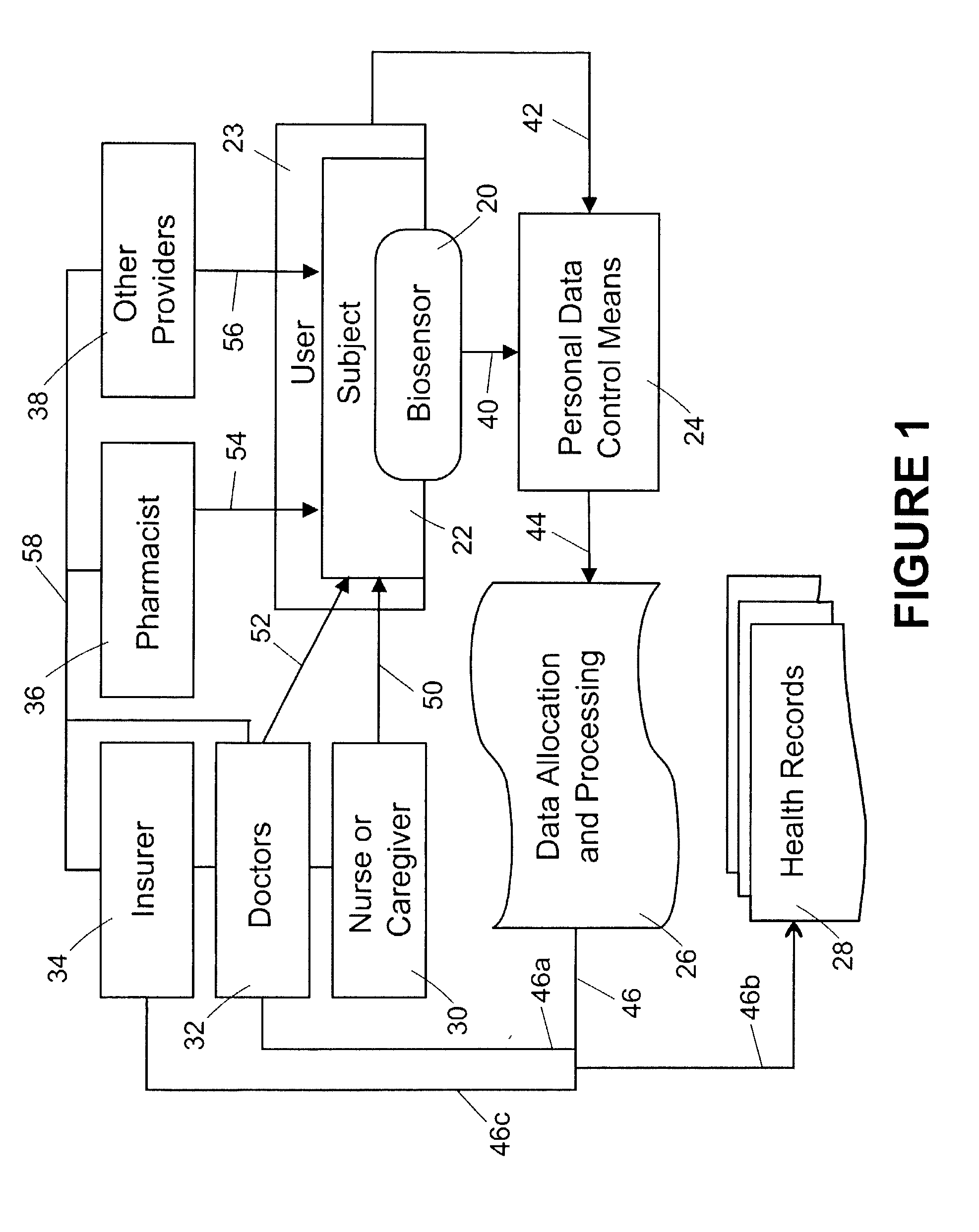
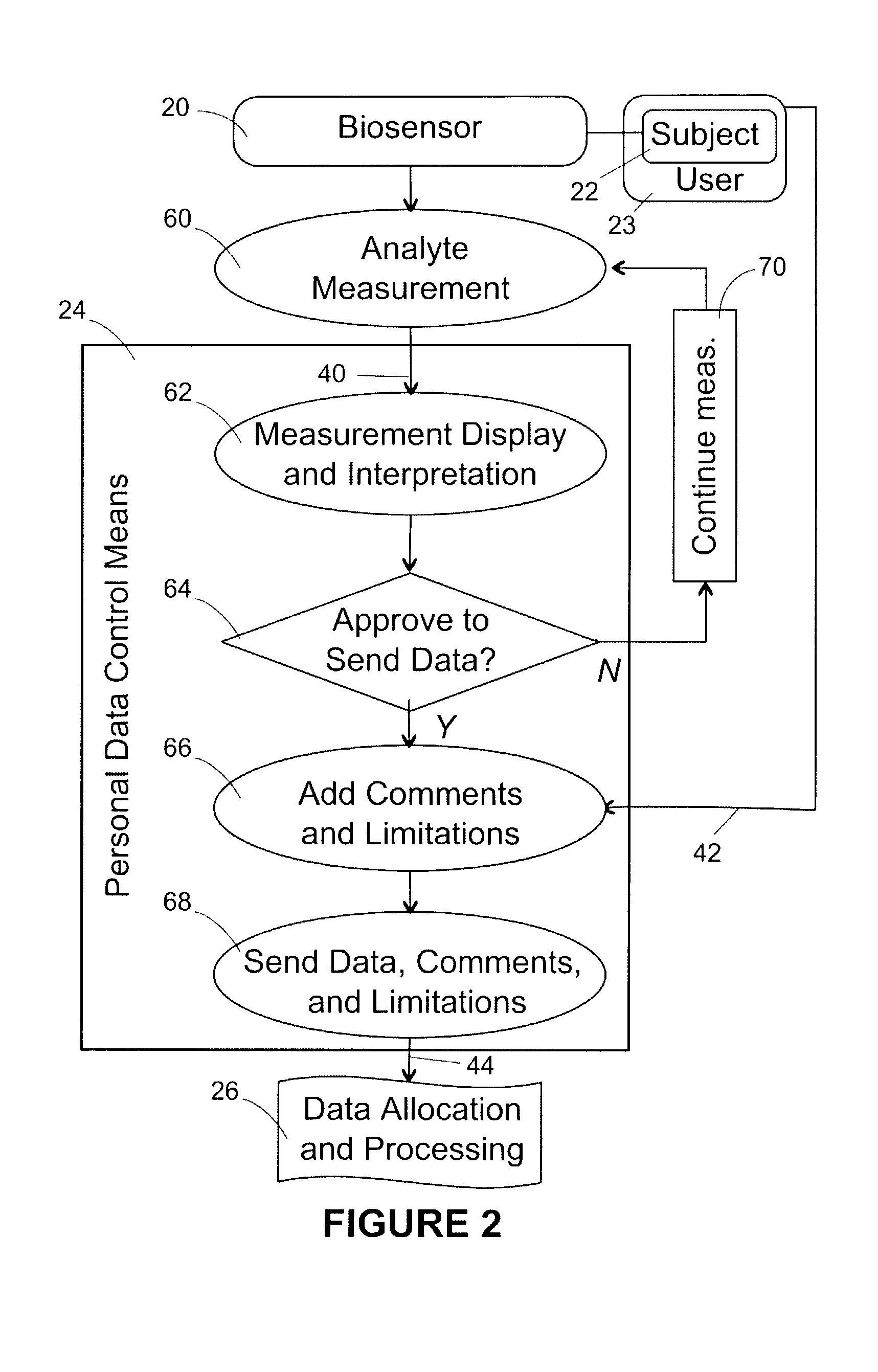
Healthcare networks with biosensors
InactiveUS20050101841A9Privacy protectionElectrotherapyData processing applicationsData controlInternet privacy
A healthcare network is provided for sharing information concerning the health of a user with at least one outside source, the network including a biosensor associated with the user that generates a biosensor signal containing the information; and a personal data control means including receiving means for receiving the biosensor signal, input means for receiving a privacy input from the user, and output means for generating a response signal based on the biosensor signal and privacy input. The network also includes a data allocation and processing module including means for receiving the response signal, and means for generating and directing an output signal to the at least one outside source, wherein the module is responsive to the response signal, and wherein the availability of the information to the at least one outside source is responsive to the privacy input.
Owner:BINFORMA GROUP LIABILITY
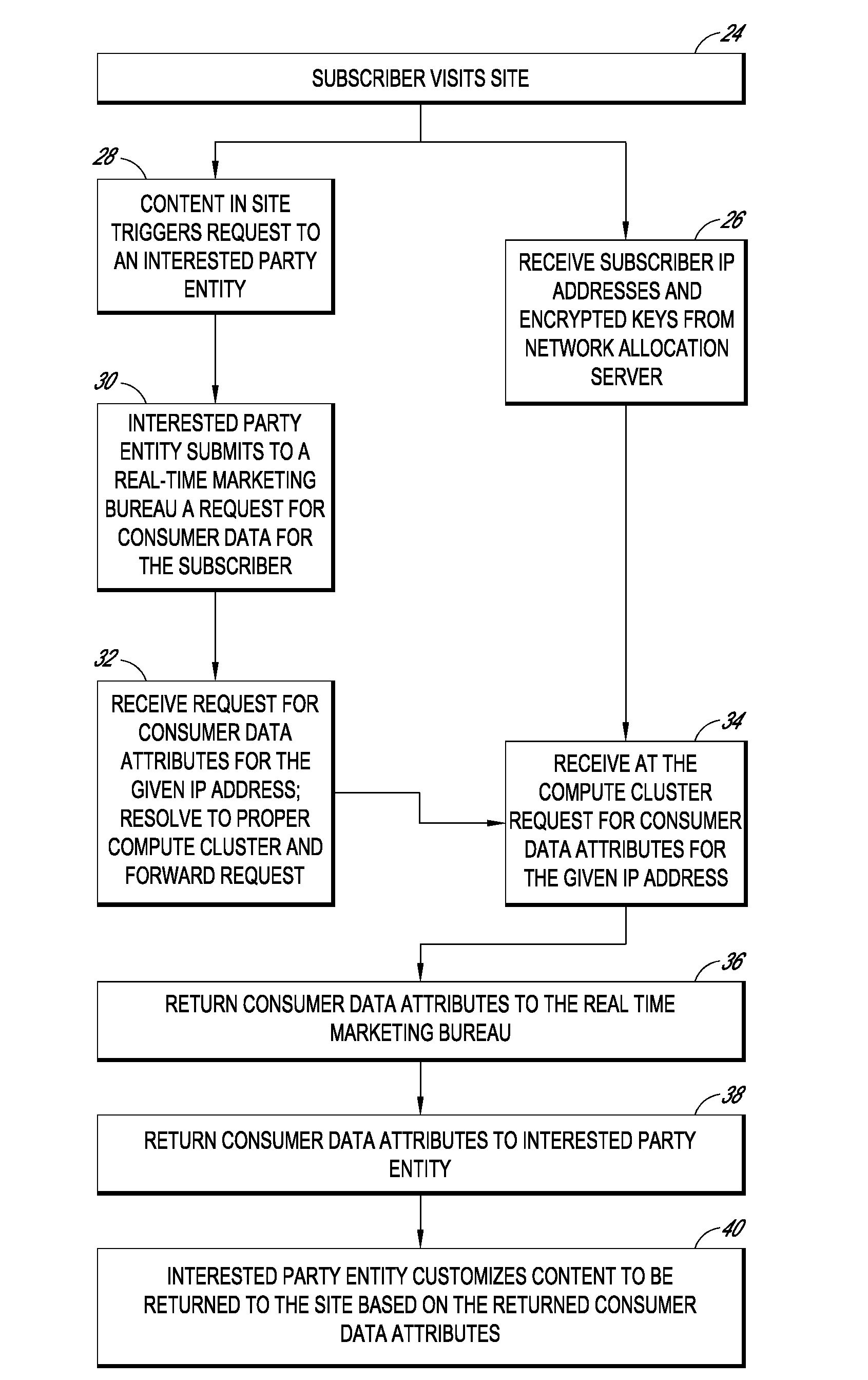
Systems and methods for providing real time anonymized marketing information
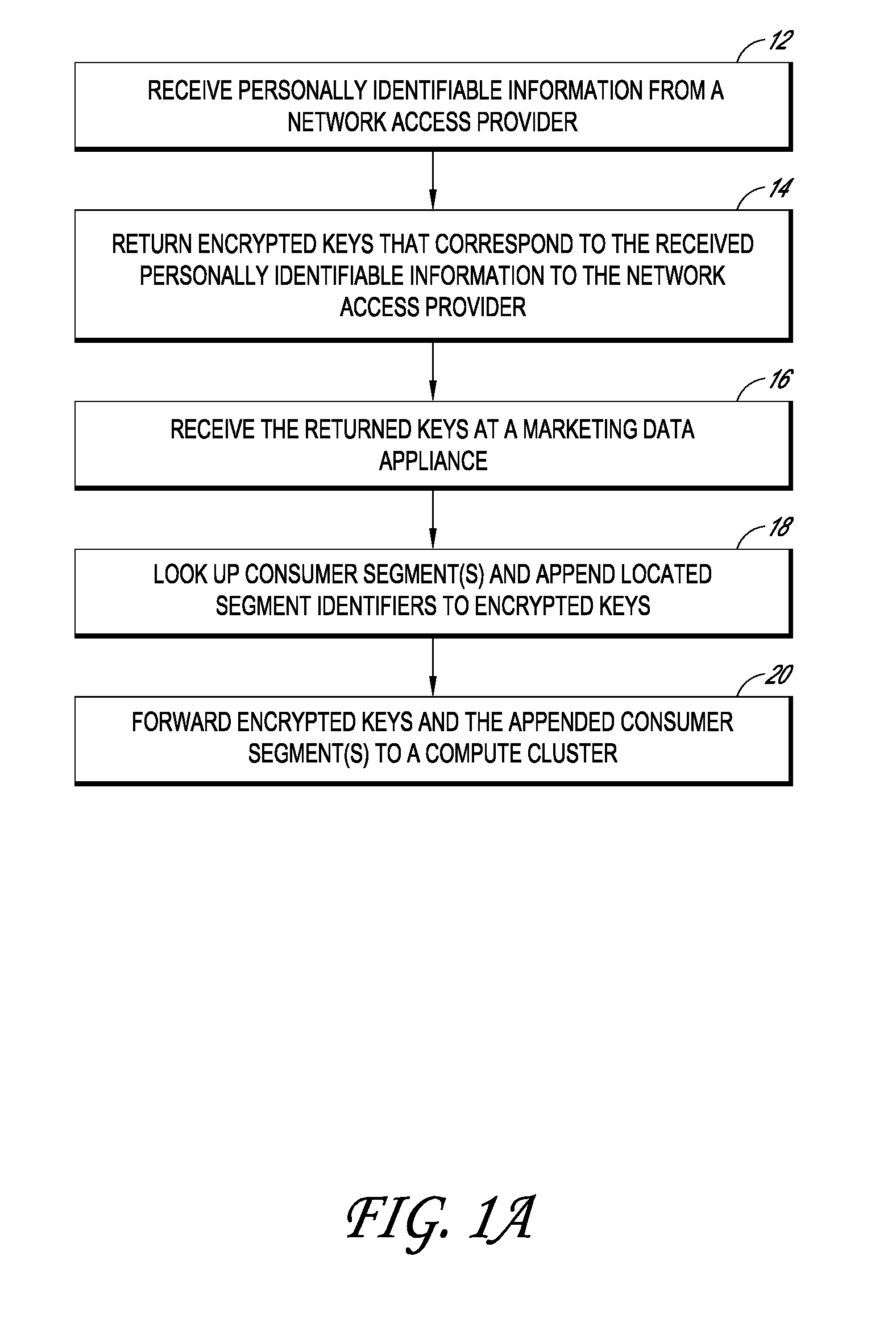
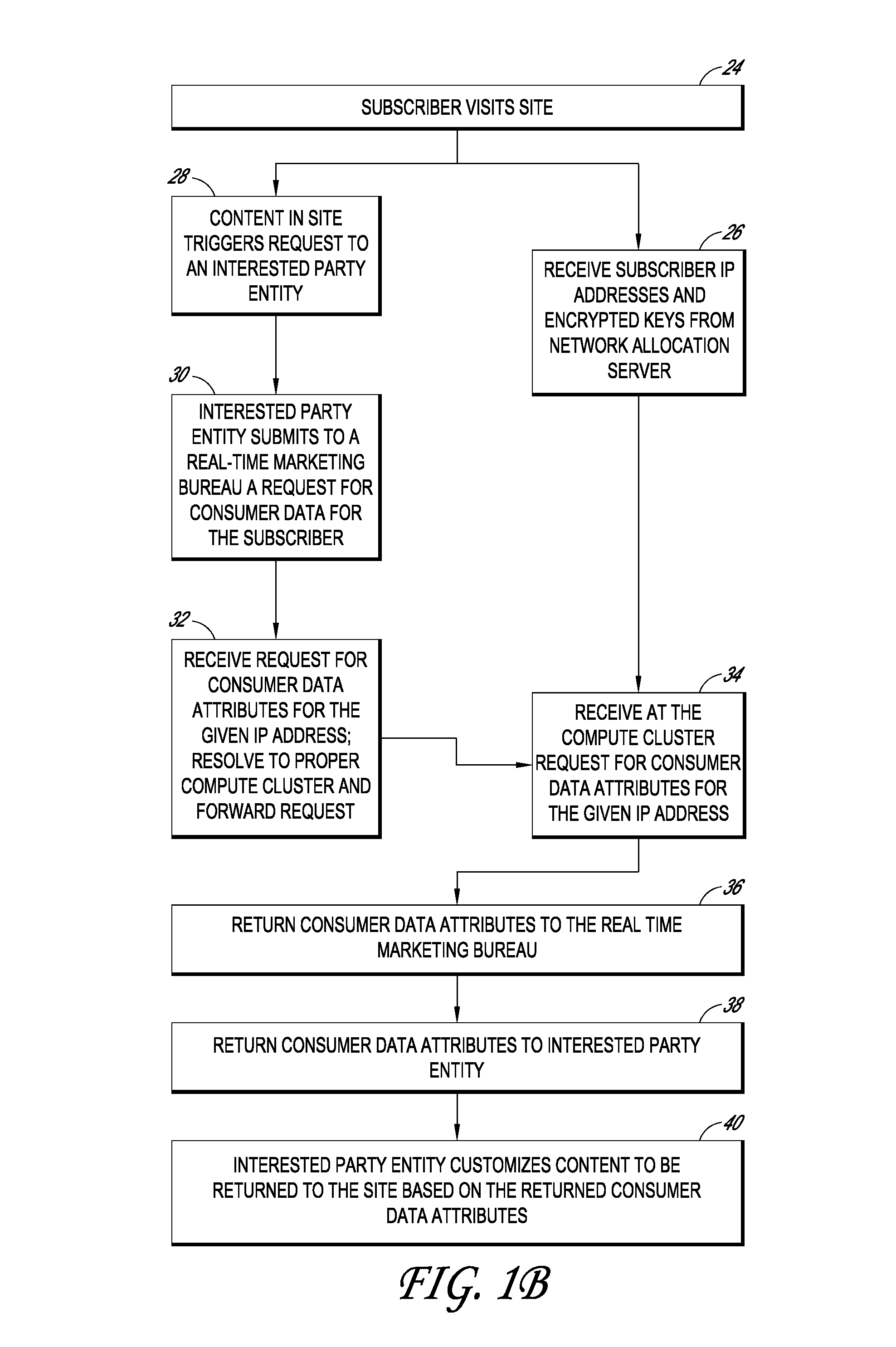
InactiveUS20100094758A1Protects consumer privacyPrivacy protectionMultiple keys/algorithms usageComputer security arrangementsReal-time marketingThird party
Embodiments disclosed herein are directed to systems and methods for enabling the matching of third party data with access providers' subscriber data in a privacy compliant manner, and then connecting an internet user to that third party data for use by marketers, content providers, or other interested parties in a manner that protects consumer privacy at all times. In one embodiment, an access provider such as an ISP sends its subscriber data to a double blind processor that generates an encrypted key for each subscriber. The key is then used to find matching consumer data, for example, consumer segments that represent previously collected or modeled consumer attitudinal, habit, or financial data. The key may be forwarded to a real time marketing bureau, which may use the matched data in subsequent real-time or substantially real-time operations to provide consumer or business data to advertisers, content providers, and other interested parties.
Owner:EXPERIAN MARKETING SOLUTIONS
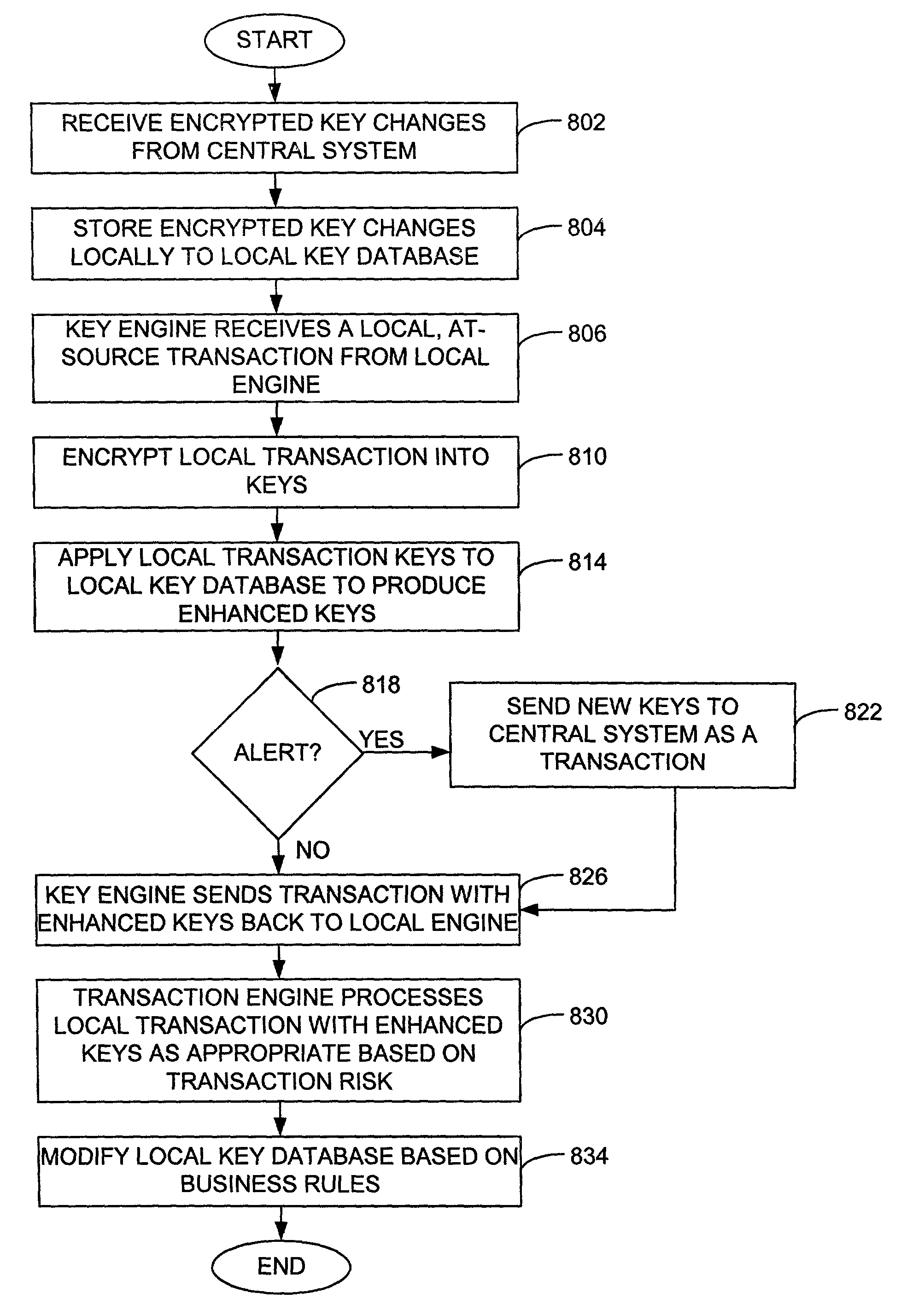
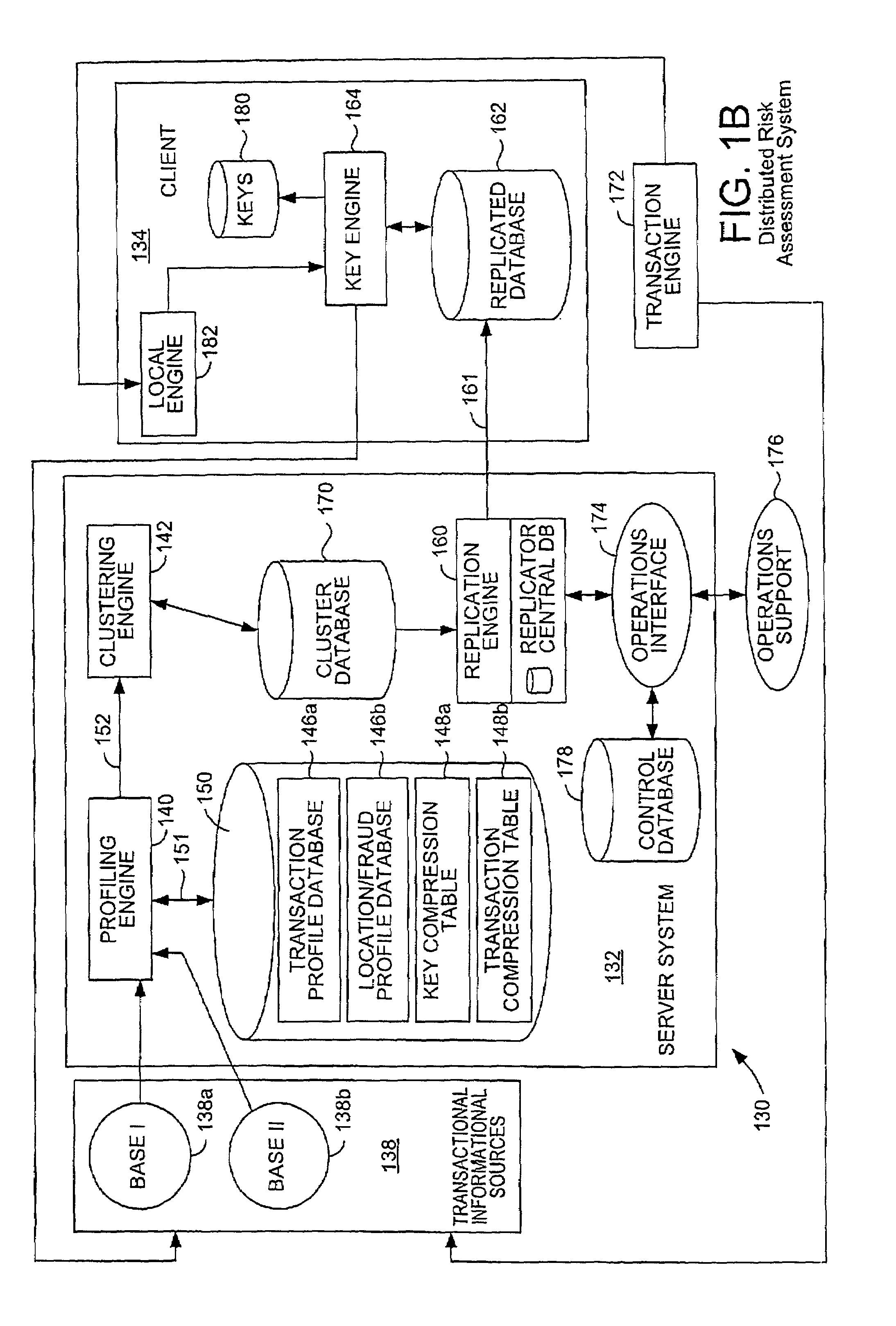
Distributed Quantum Encrypted Pattern Generation And Scoring
InactiveUS20100057622A1Informed decisionPrivacy protectionFinancePublic key for secure communicationPattern generationClient-side
Transaction scoring is performed in a distributed manner across a client-server computing system. A computing system for processing a transaction includes a server system and a client system. The server system is arranged to process information associated with the transaction, while the client system communicates with the server system and includes a key engine which is arranged to generate keys. The client system and the server system are arranged to cooperate to make probabilistic determinations associated with the transaction. The client is arranged to send the keys generated by the key engine as a transaction to the server system.
Owner:VISA USA INC (US)
Proactive Security for Mobile Devices
ActiveUS20110141276A1Improve security levelPrivacy protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsActive safetyPassword
Methods, program products, and systems for proactively securing mobile devices are described. A mobile device can proactively determine whether the mobile device is associated with a security risk and the level of the security risk. Upon determining a security risk, the mobile device can transmit coordinates of its current geographic location to a server. To protect privacy of authorized users, the transmission can be disabled by entering a password. If multiple failed password attempts are detected, the mobile device can proactively increase a security level of the device, and selectively protect files or other content stored on the mobile device. In some implementations, the mobile device can be transitioned into a surveillance mode where the mobile device records or captures information associated with one or more of user actions, ambient sound, images, a trajectory of the device, and transmits the recorded or captured information to the network resource.
Owner:APPLE INC
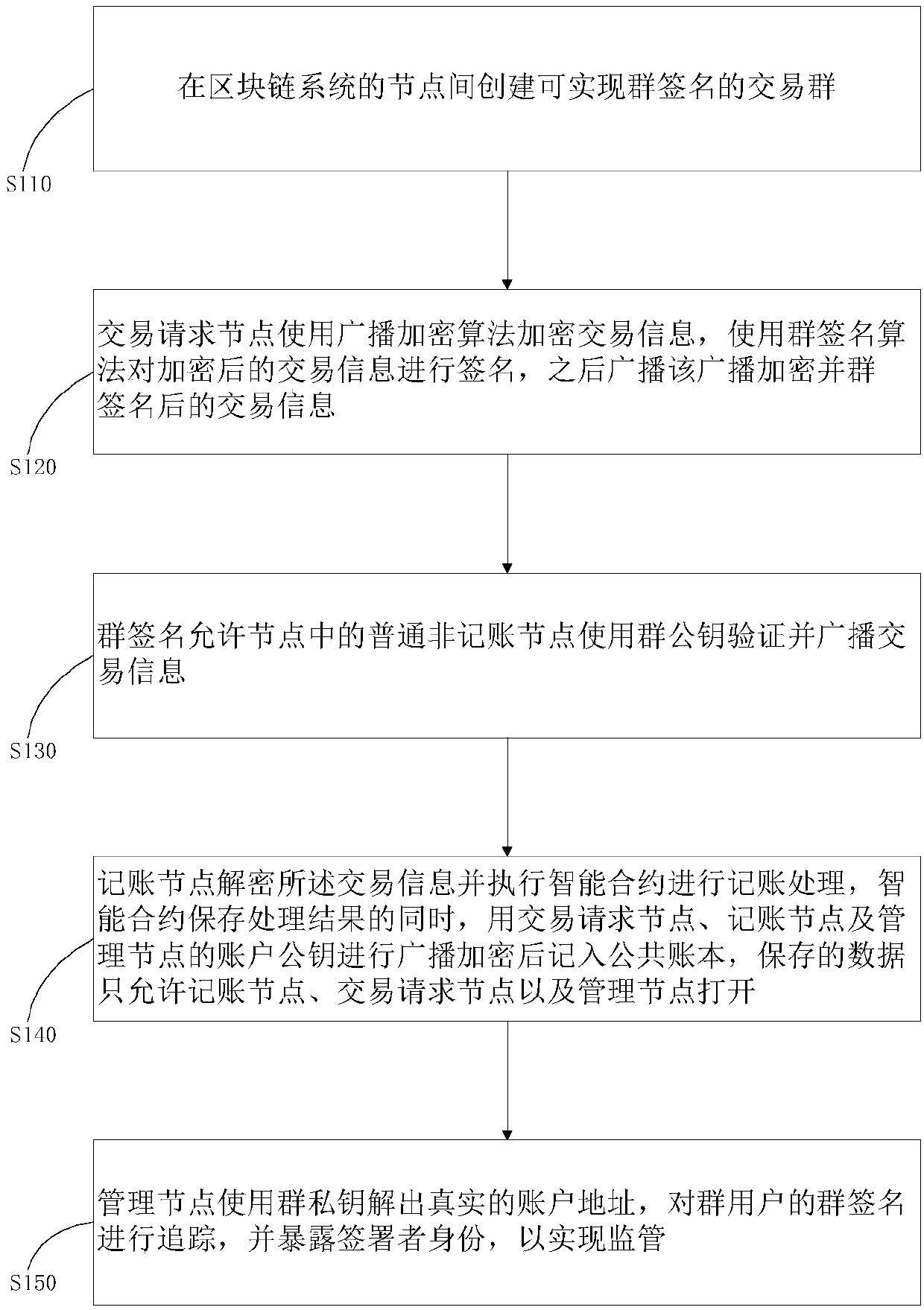
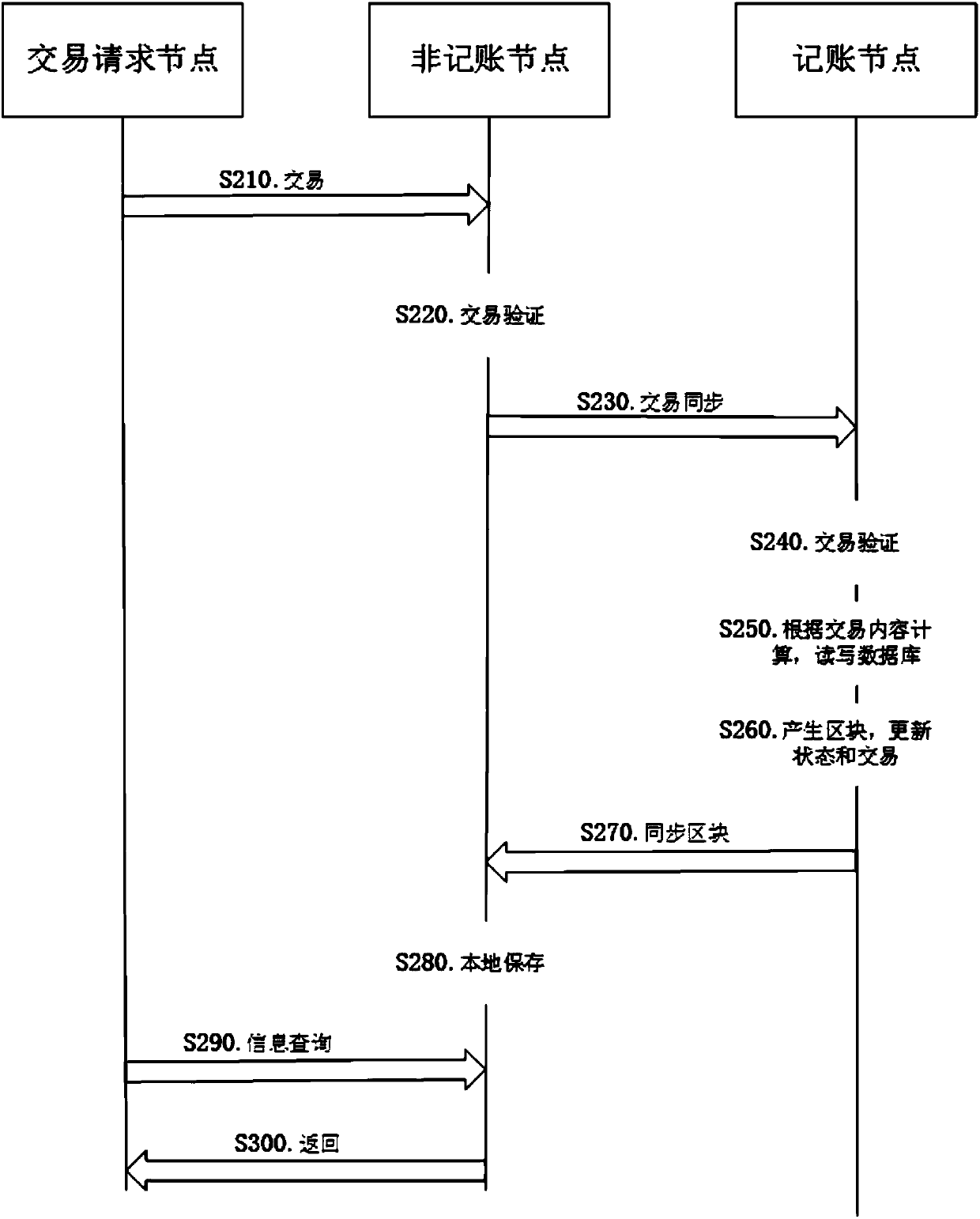
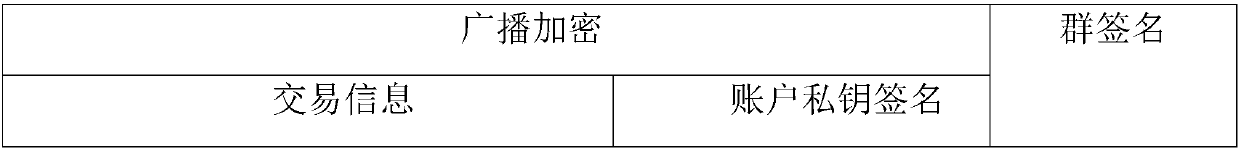
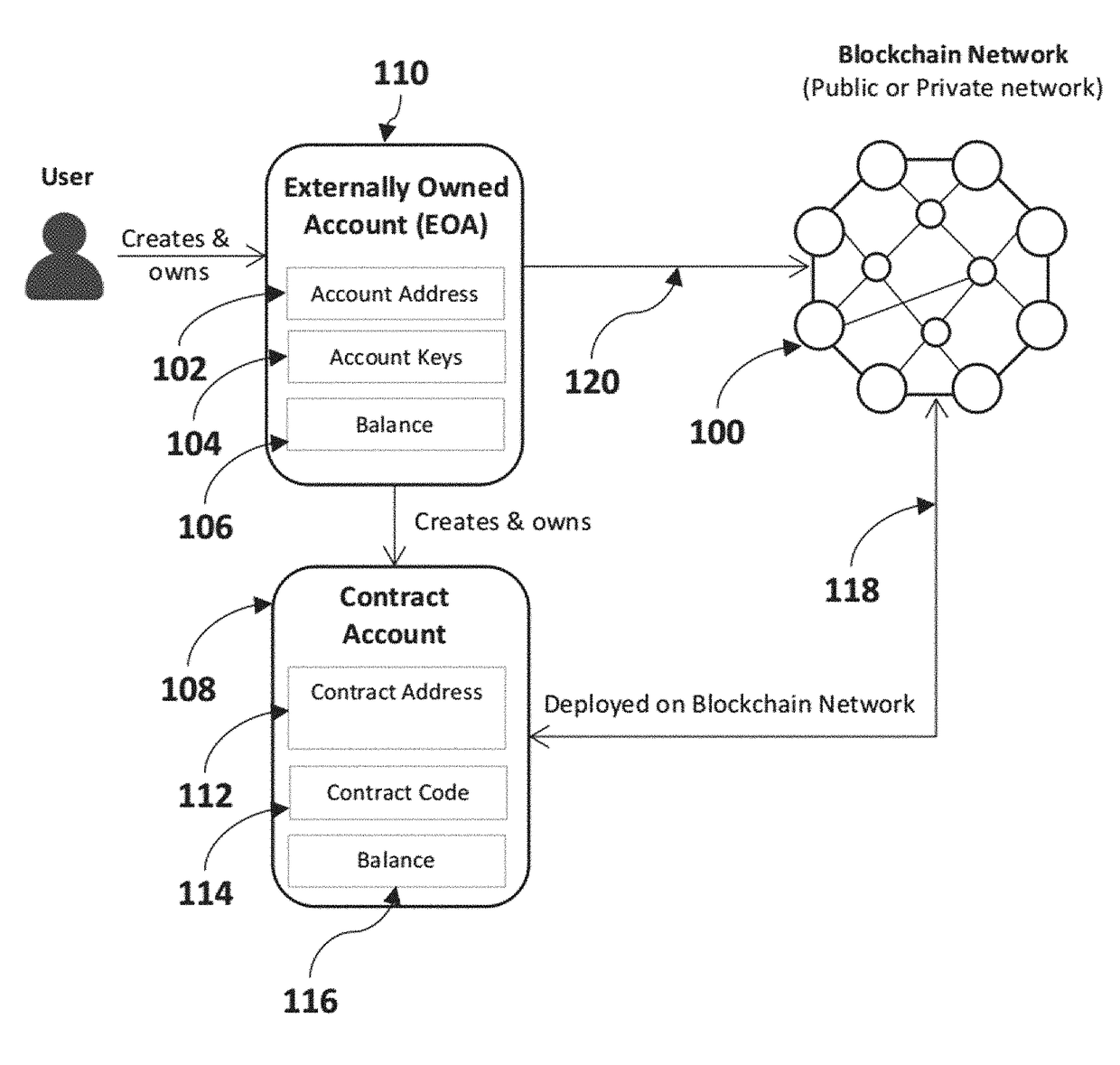
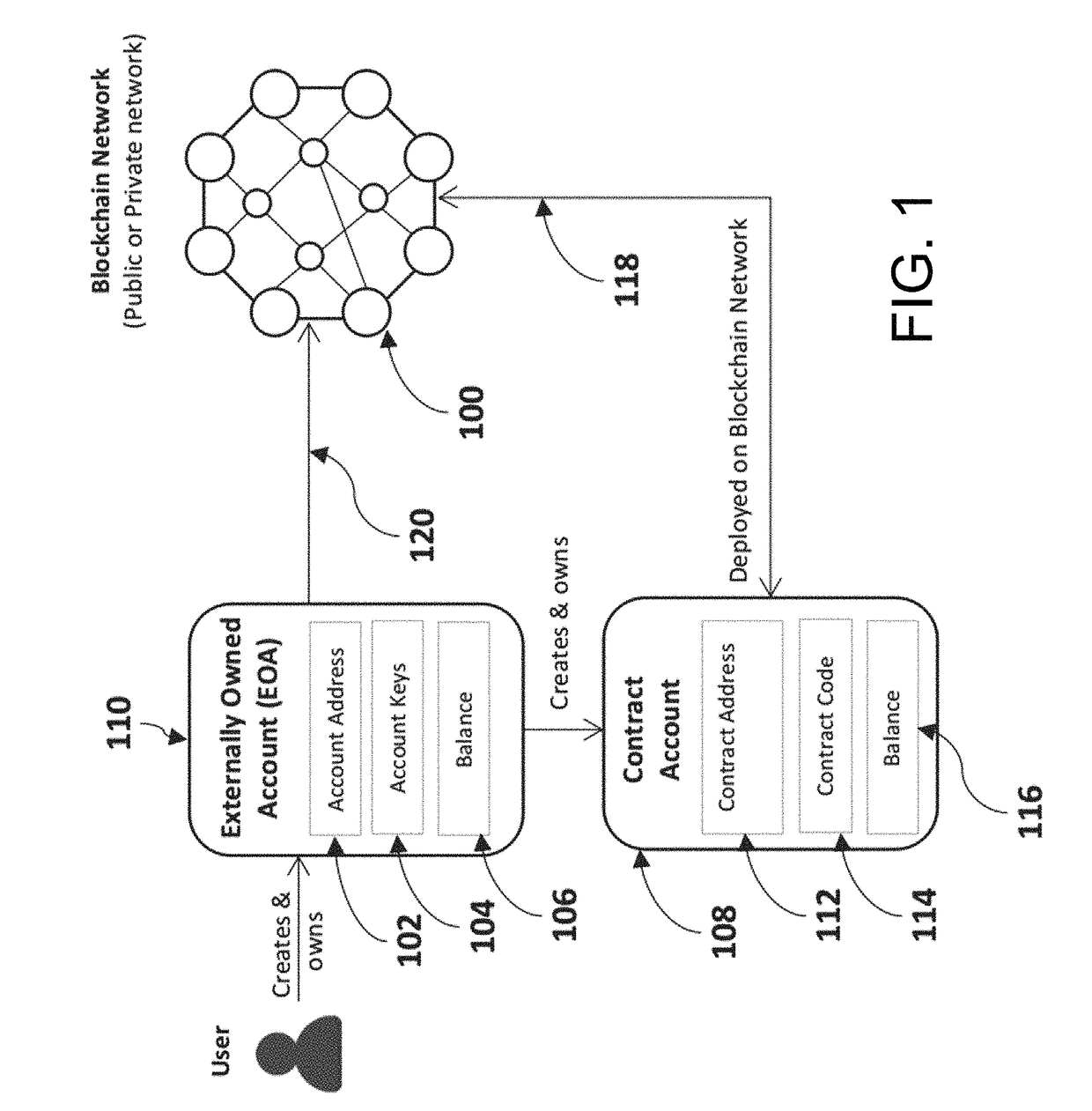
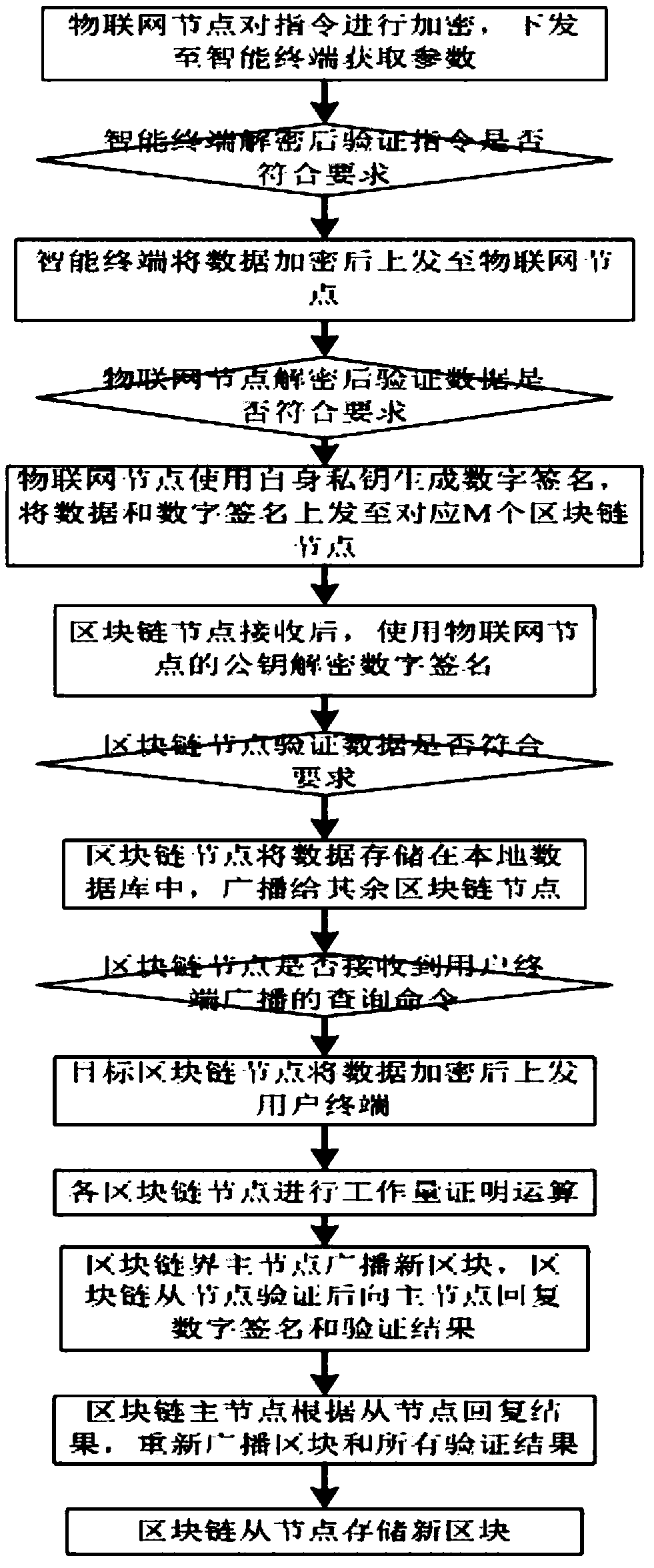
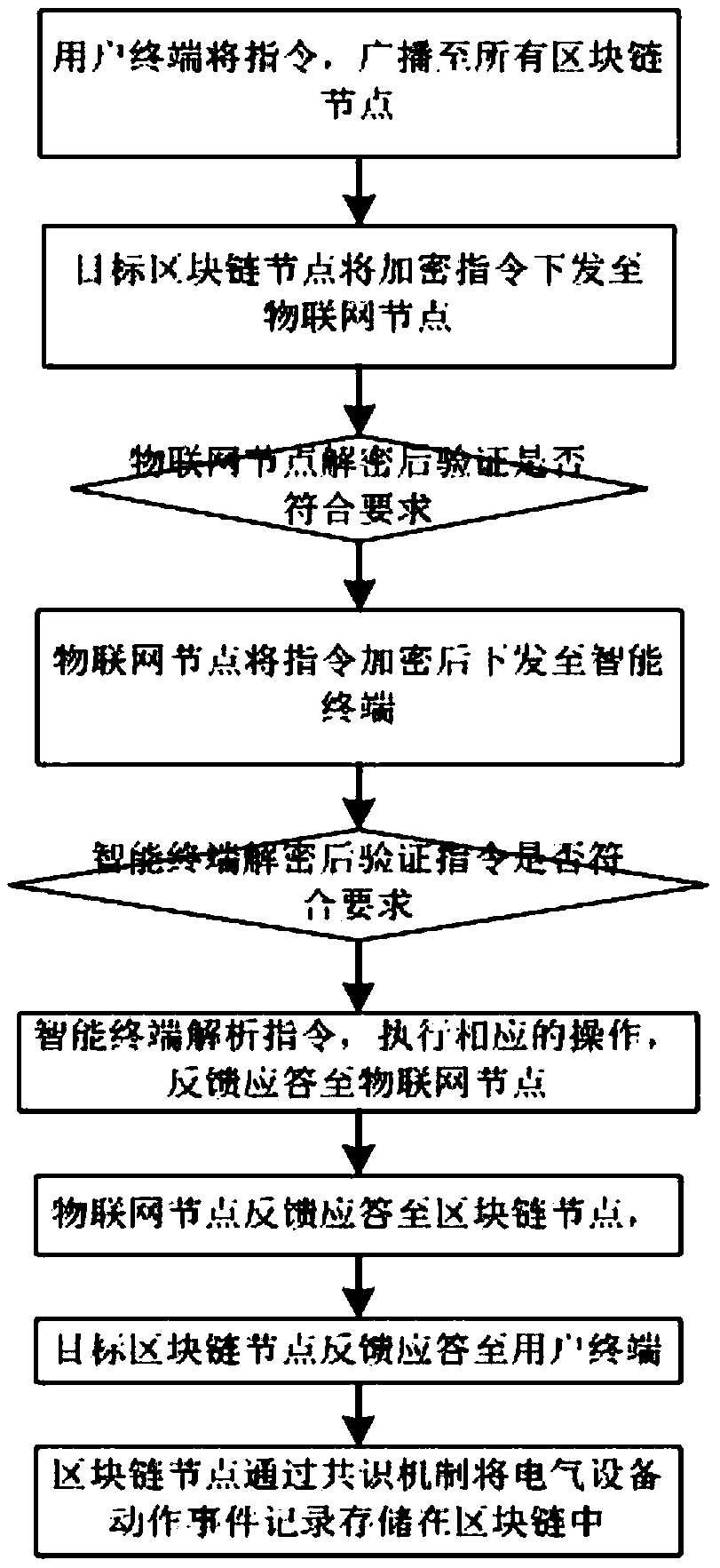
Method and system for privacy protection of block chain transaction
ActiveCN107911216ARealize regulationSupport reviewKey distribution for secure communicationFinancePublic accountPrivacy protection
The invention provides a method and system for privacy protection of block chain transaction. The method comprises: a transaction group is established between nodes of a block chain system, a user establishes an account at a node, and the node generates public and private key information of the account and then joining of a group is carried out; a transaction request node encrypts transaction information by using a broadcast encryption algorithm, carries out group signature processing on the encrypted transaction information, and then broadcasts the transaction information after broadcast encryption and group signature processing; a common non-account-recording node verifies the transaction information and then broadcasts the transaction information, an account-recording node decrypts thetransaction information and performs an intelligent contract to carry out account recording, broadcast encryption is carried out and then the information is recorded into a public account book, wherein the stored data are only allowed to be opened by the account-recording node, the transaction request node and an administration node. With the broadcast encryption algorithm and group signature technology, a privacy protection problem in the block chain system is solved and the traceability of the transaction is ensured.
Owner:JUZIX TECH SHENZHEN CO LTD +1
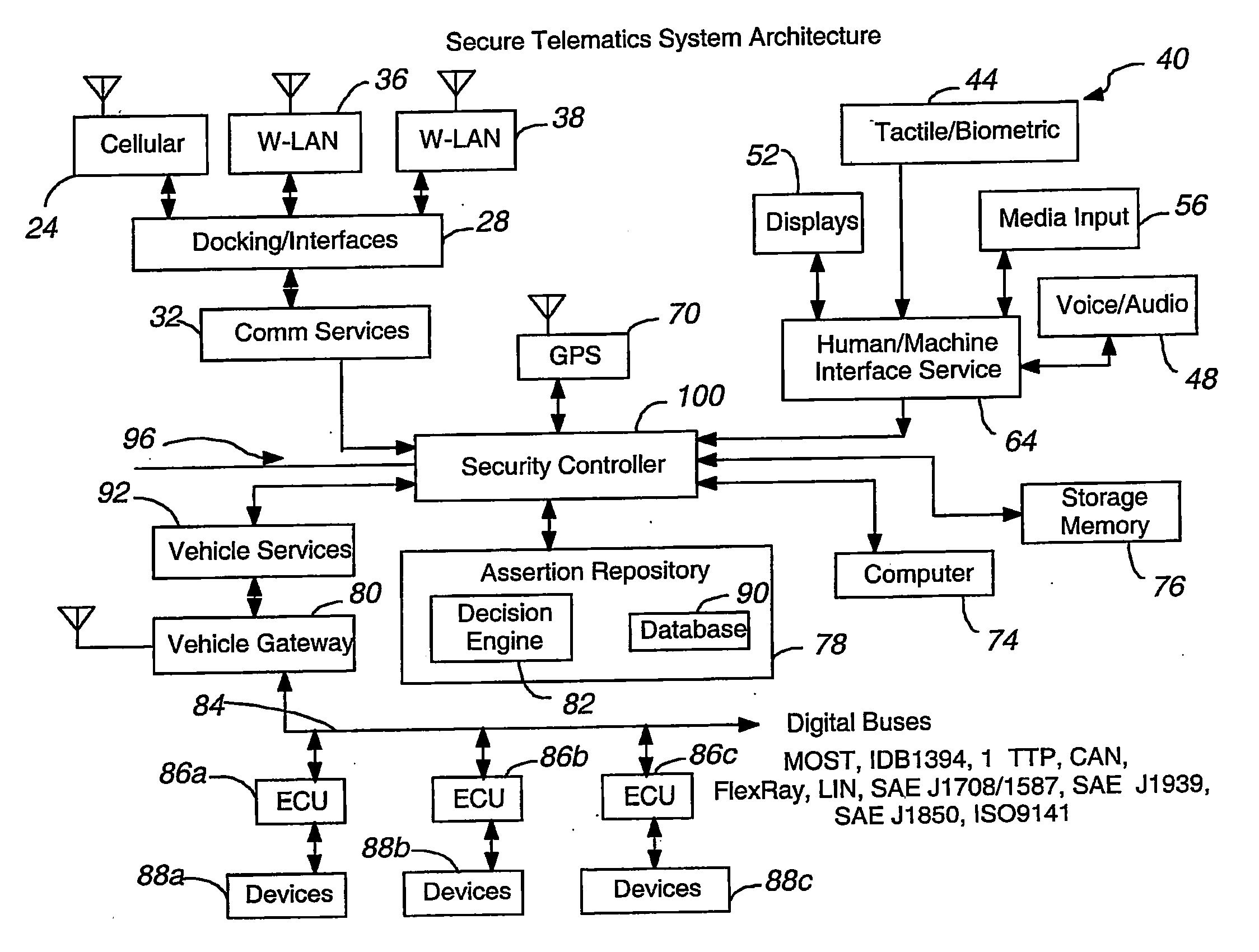
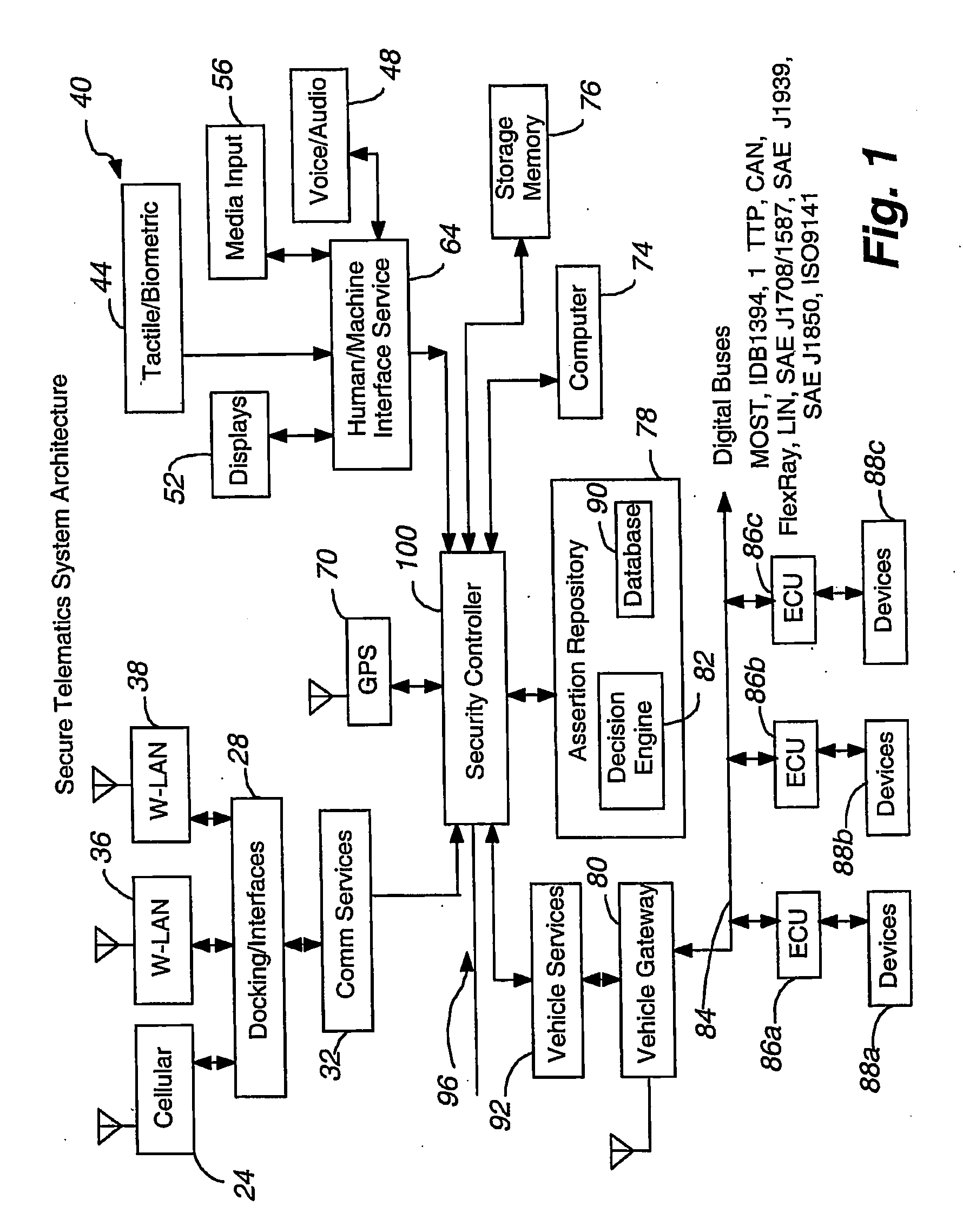
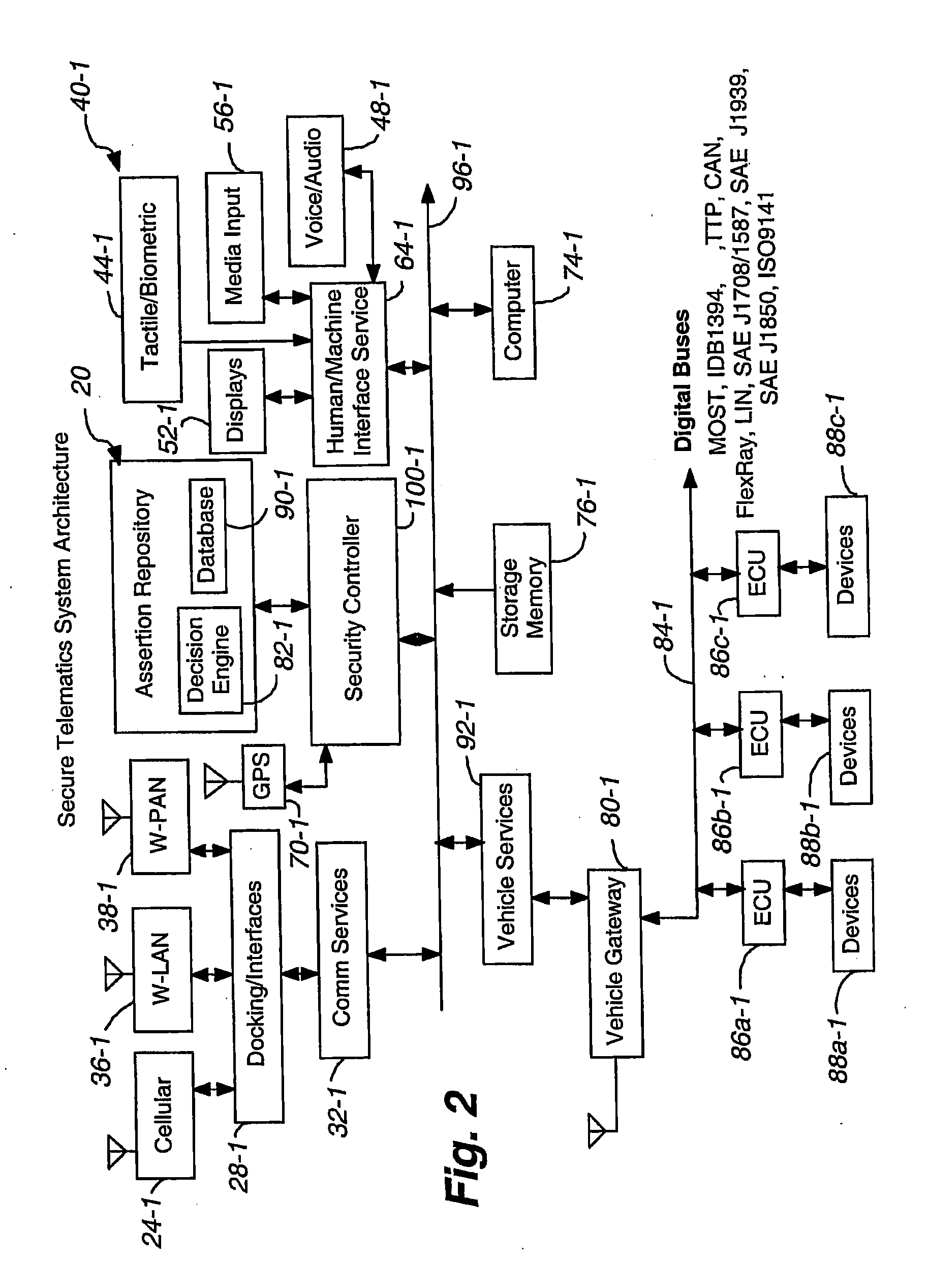
Secure telematics
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Methods, apparatuses and computer program products for providing a private and efficient geolocation system
ActiveUS8594680B2Increase capacityLess attentionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsGeolocationRadio frequency
An apparatus for preserving privacy of a determined location(s) of a device may include a processor and memory storing executable computer code causing the apparatus to at least perform operations including receiving a request for determining a location of a device based on received fingerprint data corresponding to a summary of radio information identifying a physical place, location, area, or region. The summary based on information received from radio frequency (RF) devices. The computer program code may further cause the apparatus to determine whether fingerprint data associated with a geographical location of the RF devices is stored locally for determining whether to request a network device to determine the location of the device based on providing the network device with fingerprint data and false fingerprint data relating to a location(s) that does not correspond to a current location of the device. Corresponding methods and computer program products are also provided.
Owner:NOKIA CORP +1
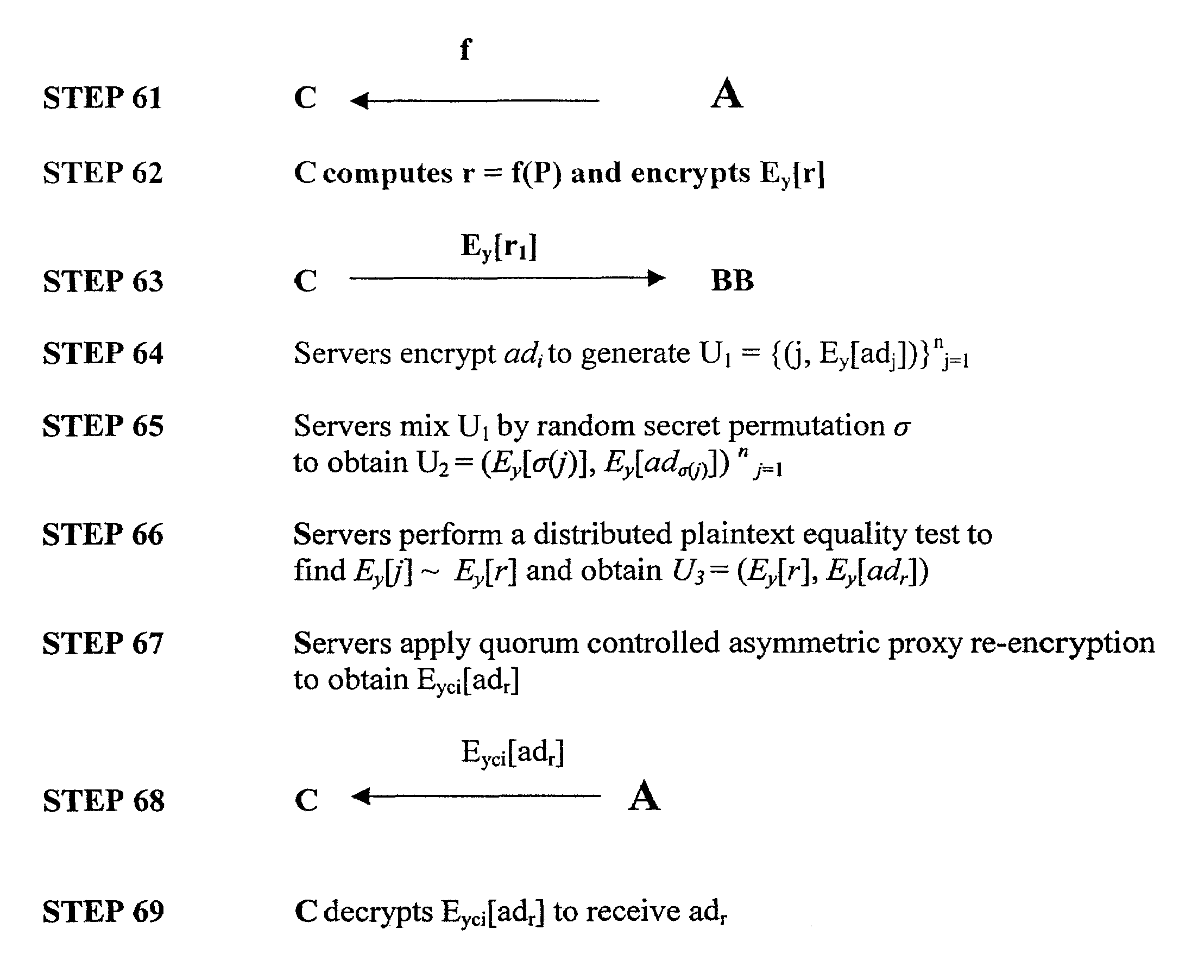
Targeted delivery of informational content with privacy protection
InactiveUS7472093B2Privacy protectionHigh degreeFinanceComputer security arrangementsThird partyObjective information
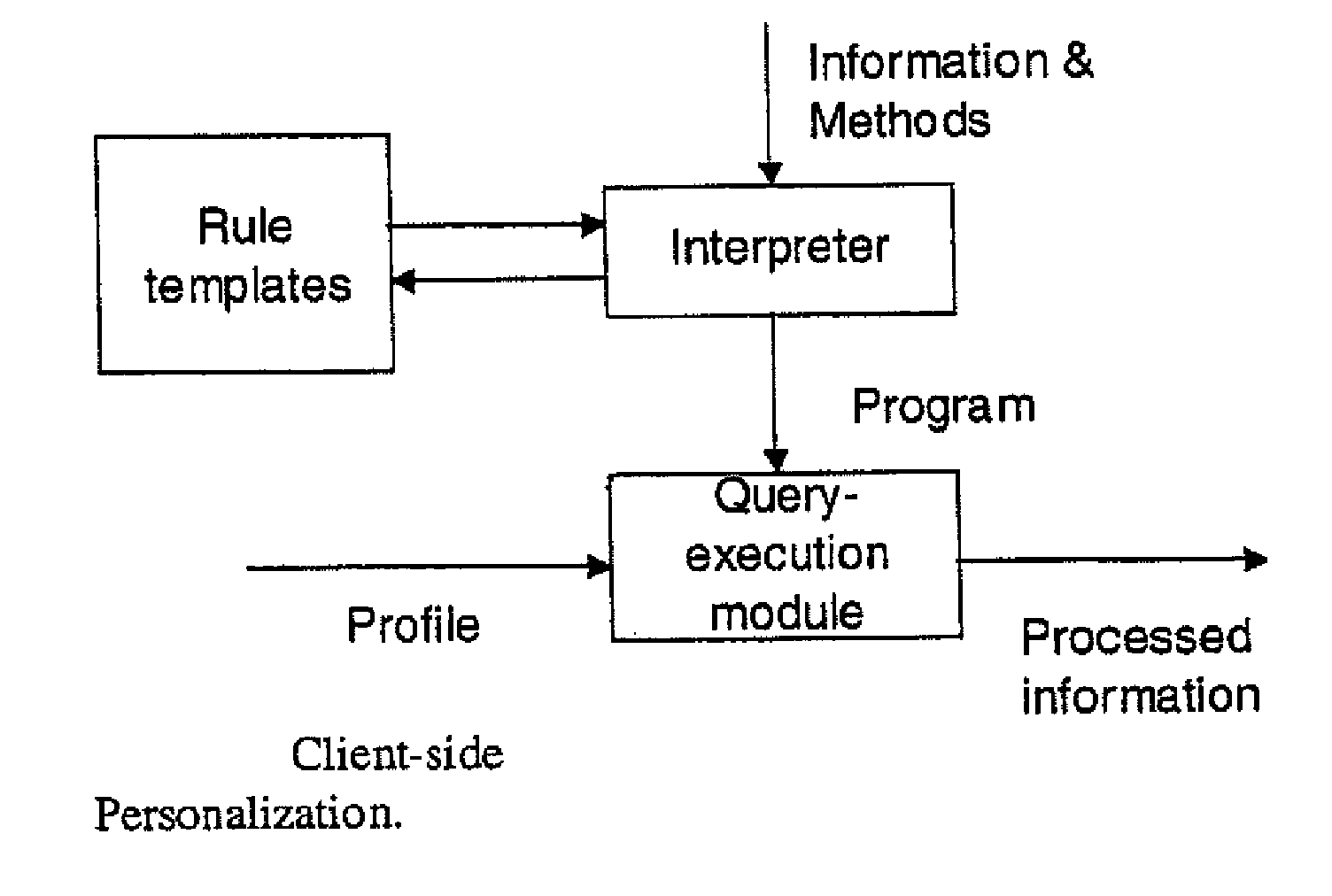
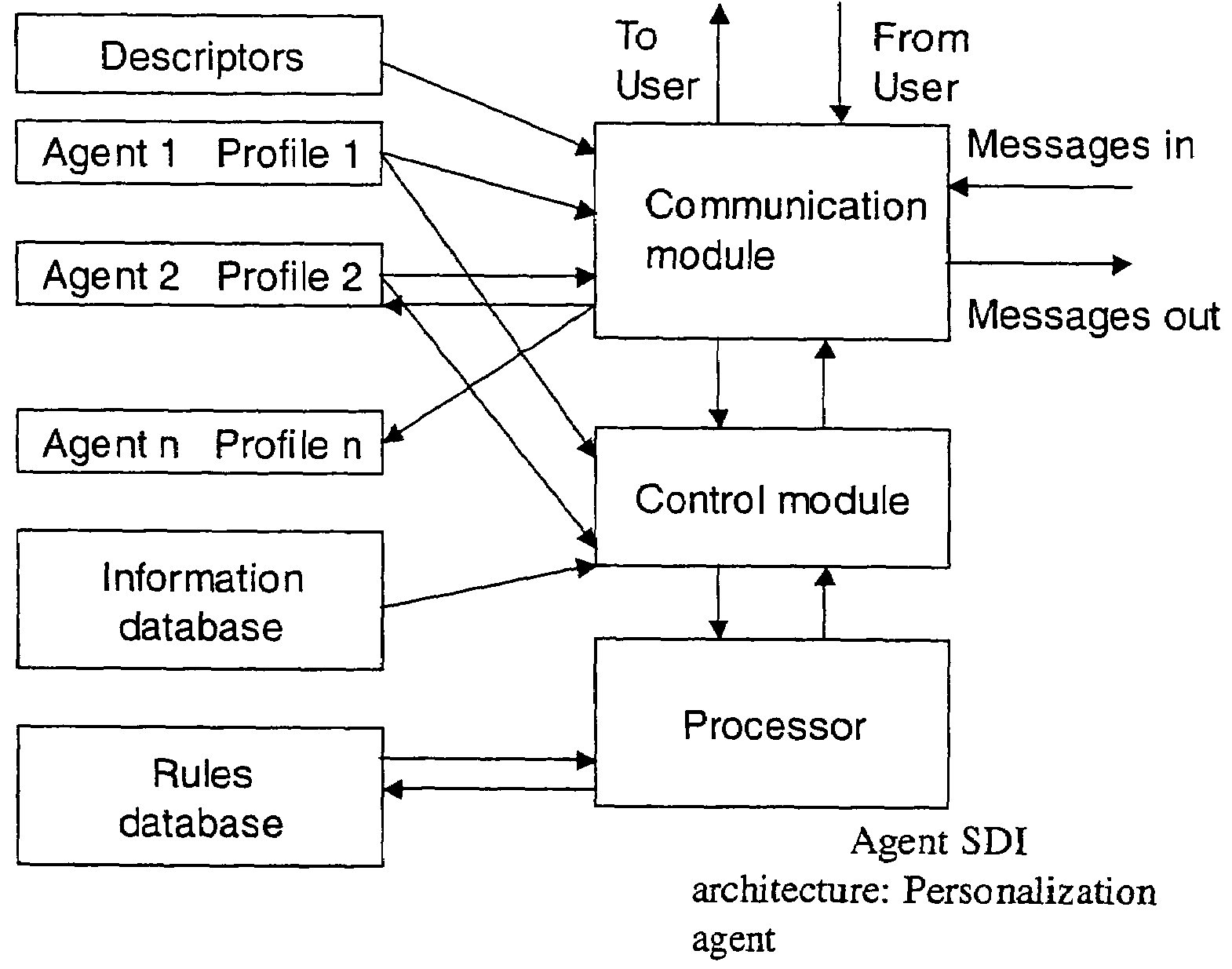
A system and method for enabling use of detailed consumer profiles for the purposes of targeted information delivery while protecting these profiles from disclosure to information providers or hostile third parties are disclosed herein. Rather than gathering data about a consumer in order to decide which information to send her, an information provider makes use of a client-side executable software module called a negotiant function. The negotiant function acts as a client-side proxy to protect consumer data, and it also directs the targeting of information, requesting items of information from the information provider that are tailored to the profile provided by the consumer.
Owner:RSA
Phone application state management mechanism
InactiveUS7376740B1Lowered byMore flexiblyData switching by path configurationMultiple digital computer combinationsApplication procedureState management
Owner:MICROSOFT TECH LICENSING LLC
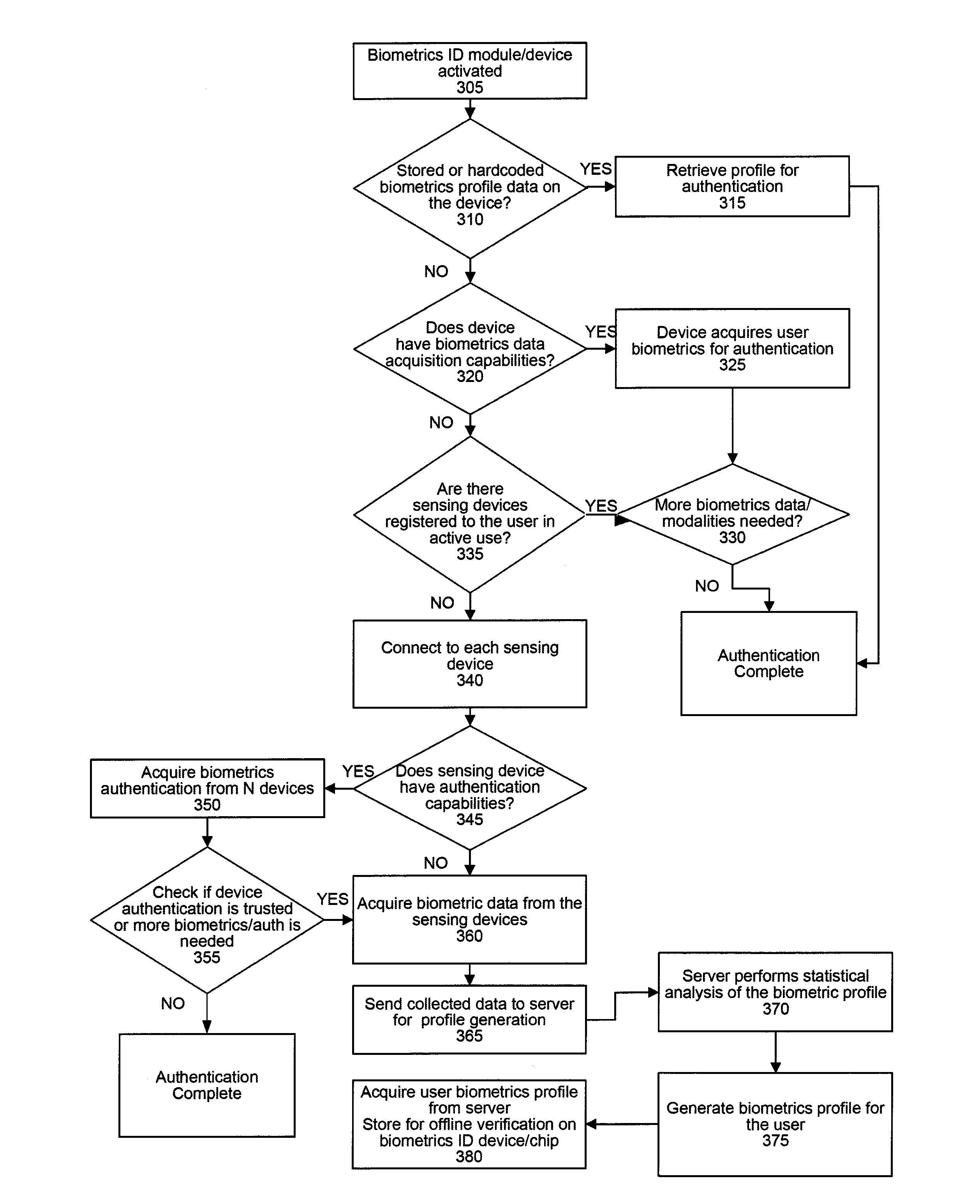
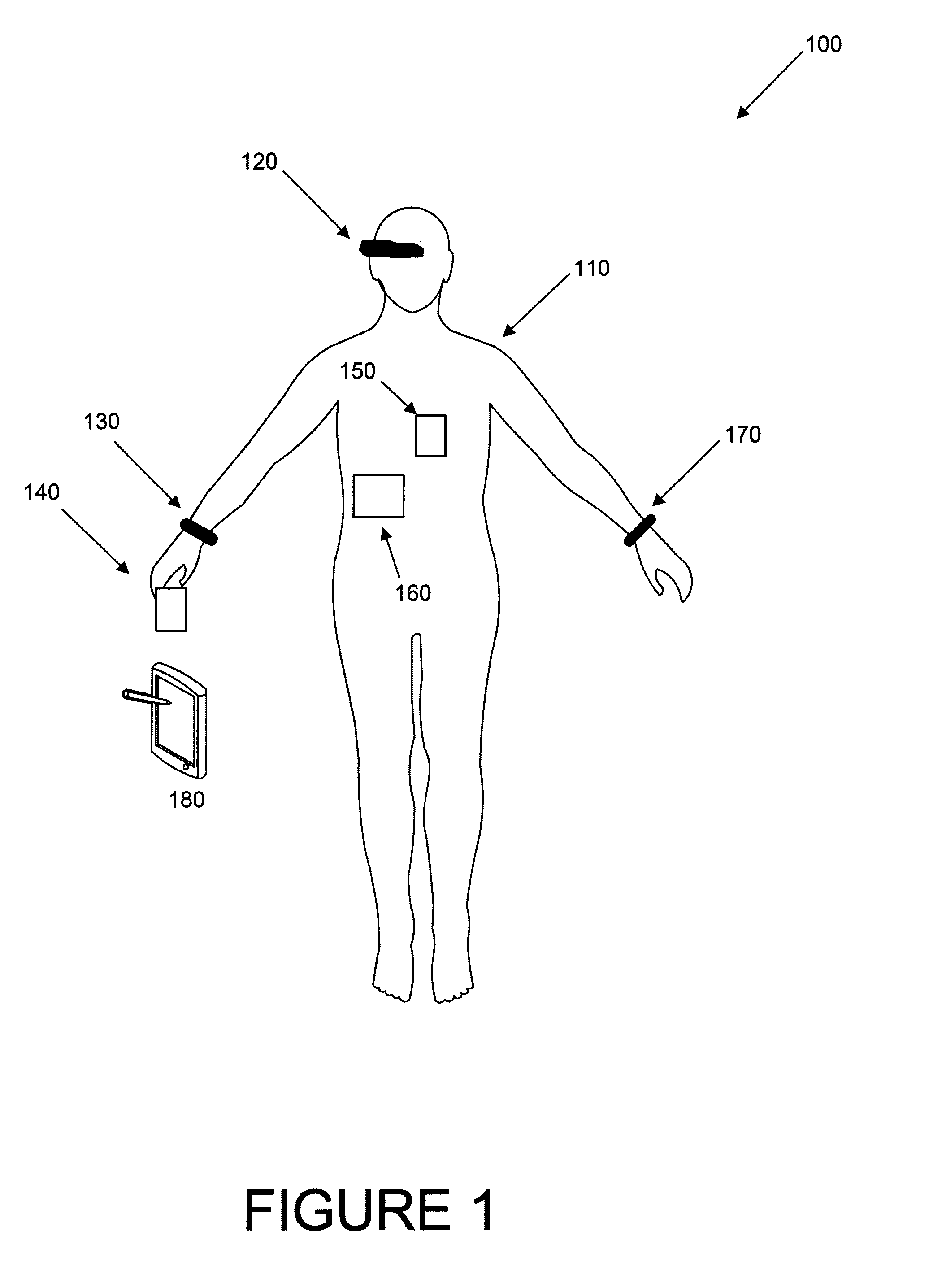
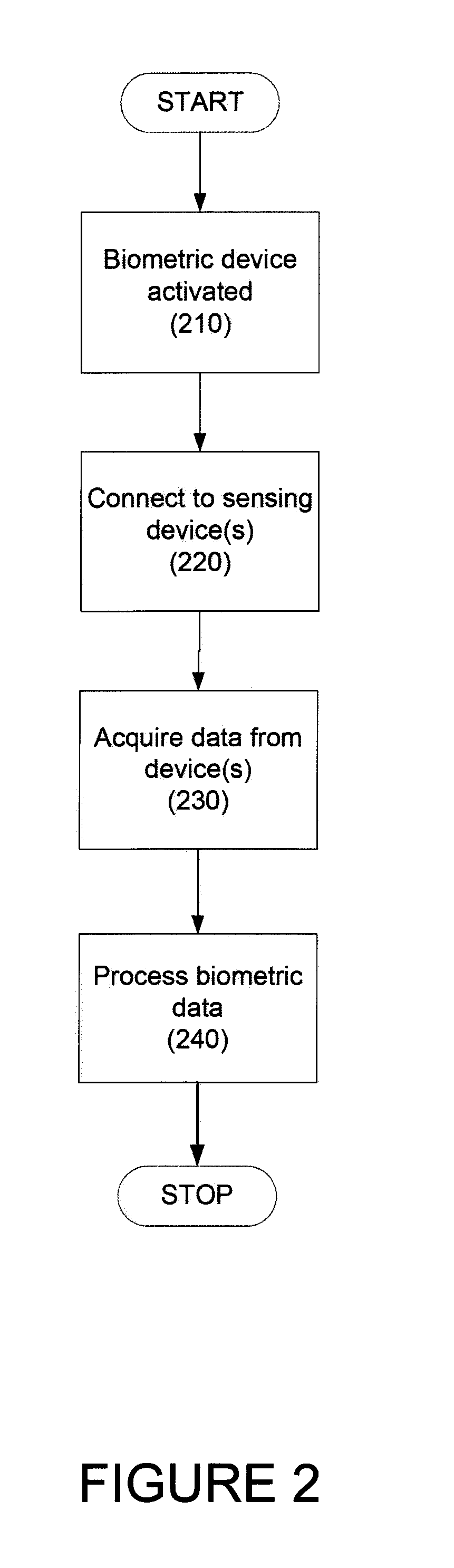
Biometrics identification module and personal wearable electronics network based authentication and transaction processing
ActiveUS20150035643A1Privacy protectionElectric signal transmission systemsDigital data processing detailsElectronicsIdentification device
Biometrics identification module and personal wearable electronics network based authentication and transaction processing are disclosed. According to one embodiment, a method for biometric authentication may include (1) a biometric identification device connecting to a plurality of sensing devices, each of the plurality of sensing devices receiving a user characteristic from a user; (2) the biometric identification device receiving the user characteristics from the sensing devices; (3) the biometric identification device communicating the received user characteristics to a server; (4) the biometric identification device receiving a biometric profile for the user; and (5) the biometric identification device storing the biometric profile.
Owner:JPMORGAN CHASE BANK NA
Method and system for tuning blockchain scalability for fast and low-cost payment and transaction processing
ActiveUS10102265B1Privacy protectionScalability issueEncryption apparatus with shift registers/memoriesCryptography processingPaymentSmart contract
A method of synchronizing transactions between blockchains comprising receiving first and second pluralities of transactions on a first private blockchain network and recording them to first and second private blocks on the first private blockchain network, respectively, generating a first merged block comprising the first private block and the second private block and recording the first merged block to a single block on a second blockchain network, recording each of the first and second private blocks and the first merged block to a first private smart contract linked to the first private blockchain network, performing a synchronization process between the first private smart contract and a second smart contract linked to the second blockchain network, defining a second smart contract, and performing a checkpointing process between the first private smart contract and the second smart contract. The first private blockchain network has a parameter difference from the second blockchain network.
Owner:MADISETTI VIJAY K
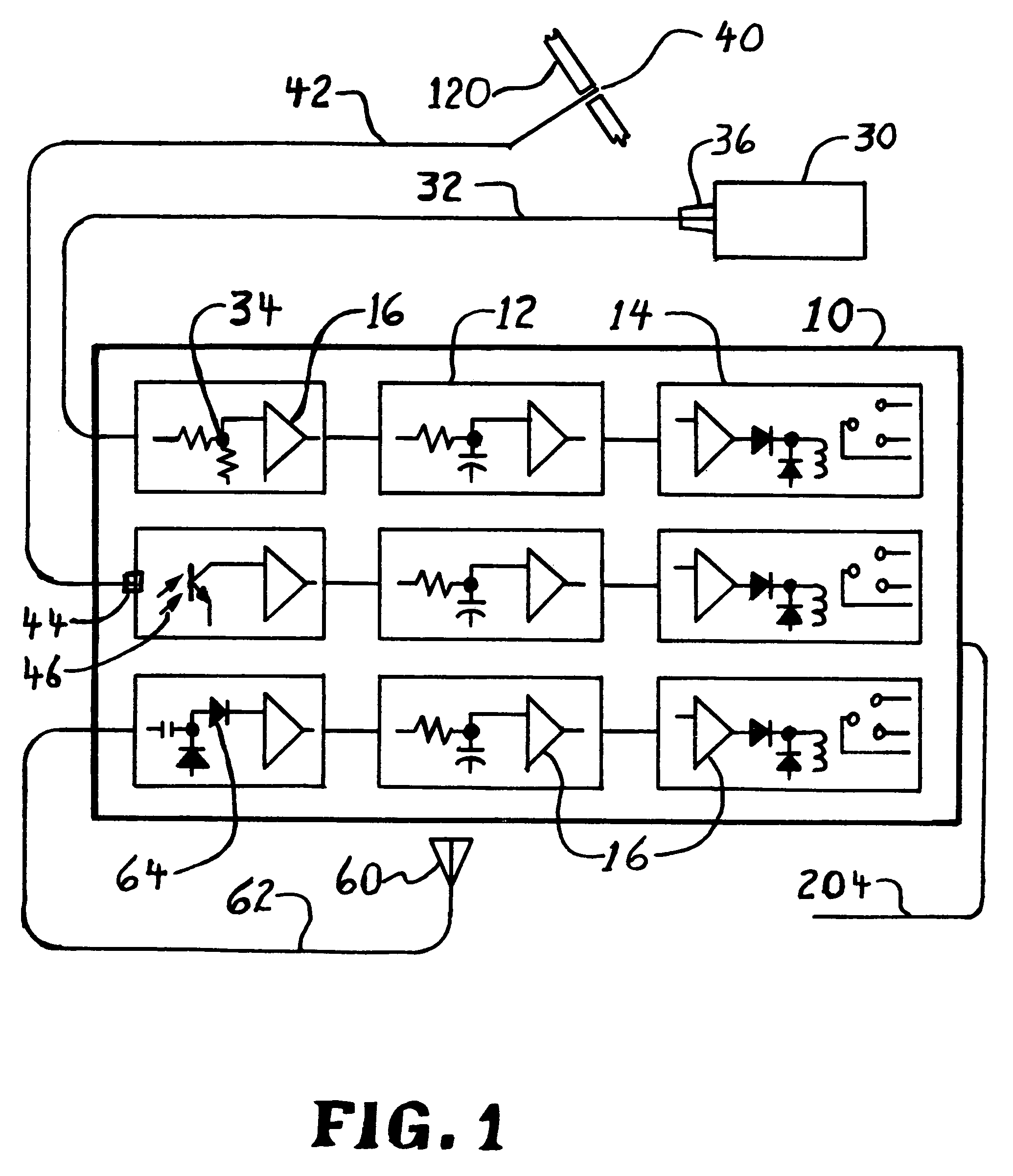
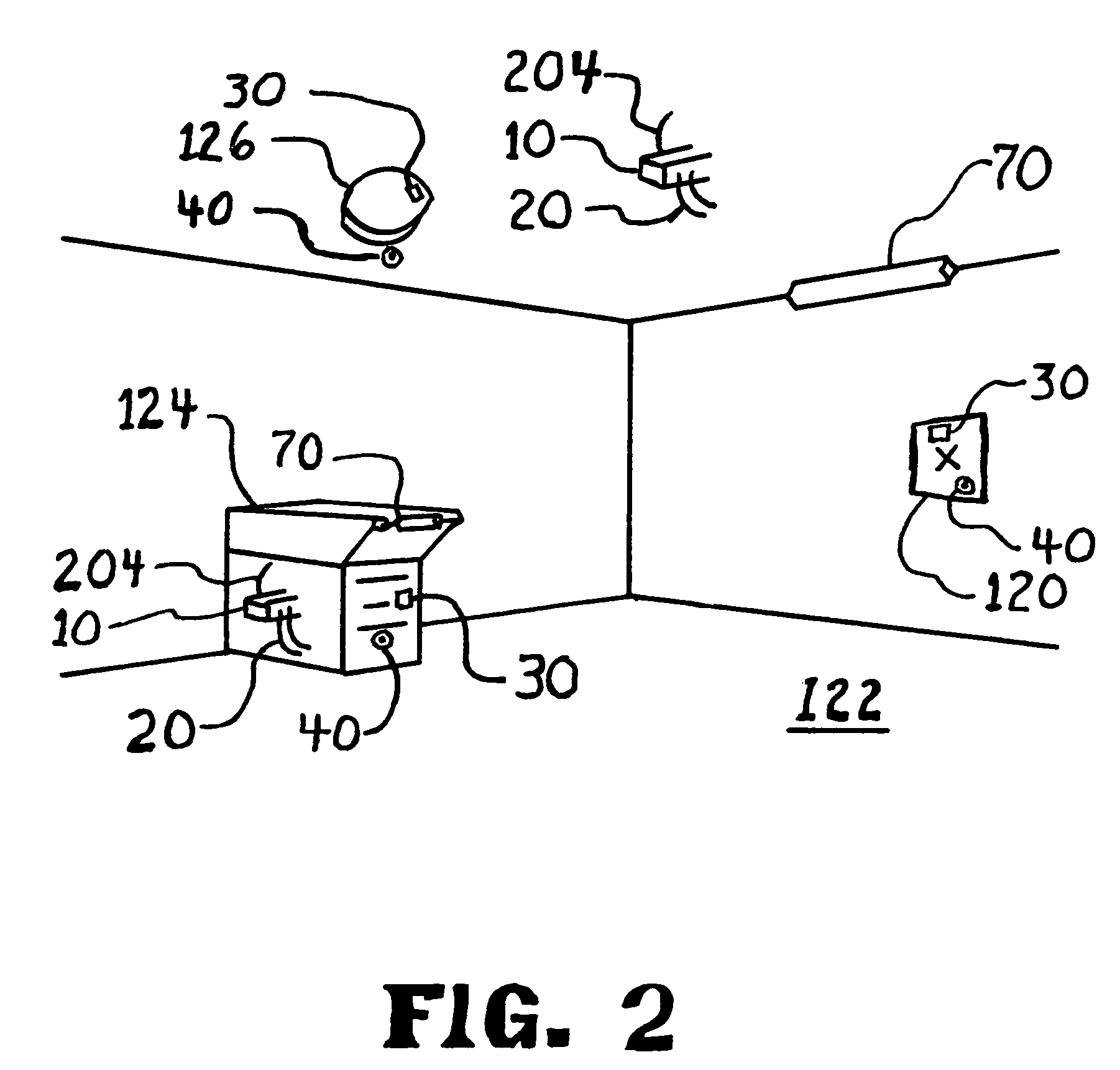
Alarm with remote monitor and delay timer
InactiveUS7075429B2Easy to installEasy maintenanceBurglar alarm by openingATM surveillanceFiberEngineering
An alarm apparatus for detecting an intrusion or compromise situation upon critical equipment or private areas. The apparatus detects an unauthorized radio transmitter (like a wireless camera), or the covering of a critical piece of equipment. Fiber optics, solar cells and special radio antennas are used to detect intrusion remotely and a delay timer will allow normal activity to occur, while reducing false alarms. This alarm apparatus will notify an existing system of the intrusion or compromise when limits are exceeded. This alarm apparatus also addresses privacy concerns of wireless cameras and recording devices in areas like changing rooms, bathrooms, or boardrooms. The apparatus addresses security issues for critical devices like smoke alarms and ATM machines.
Owner:MARSHALL CRANBROOK
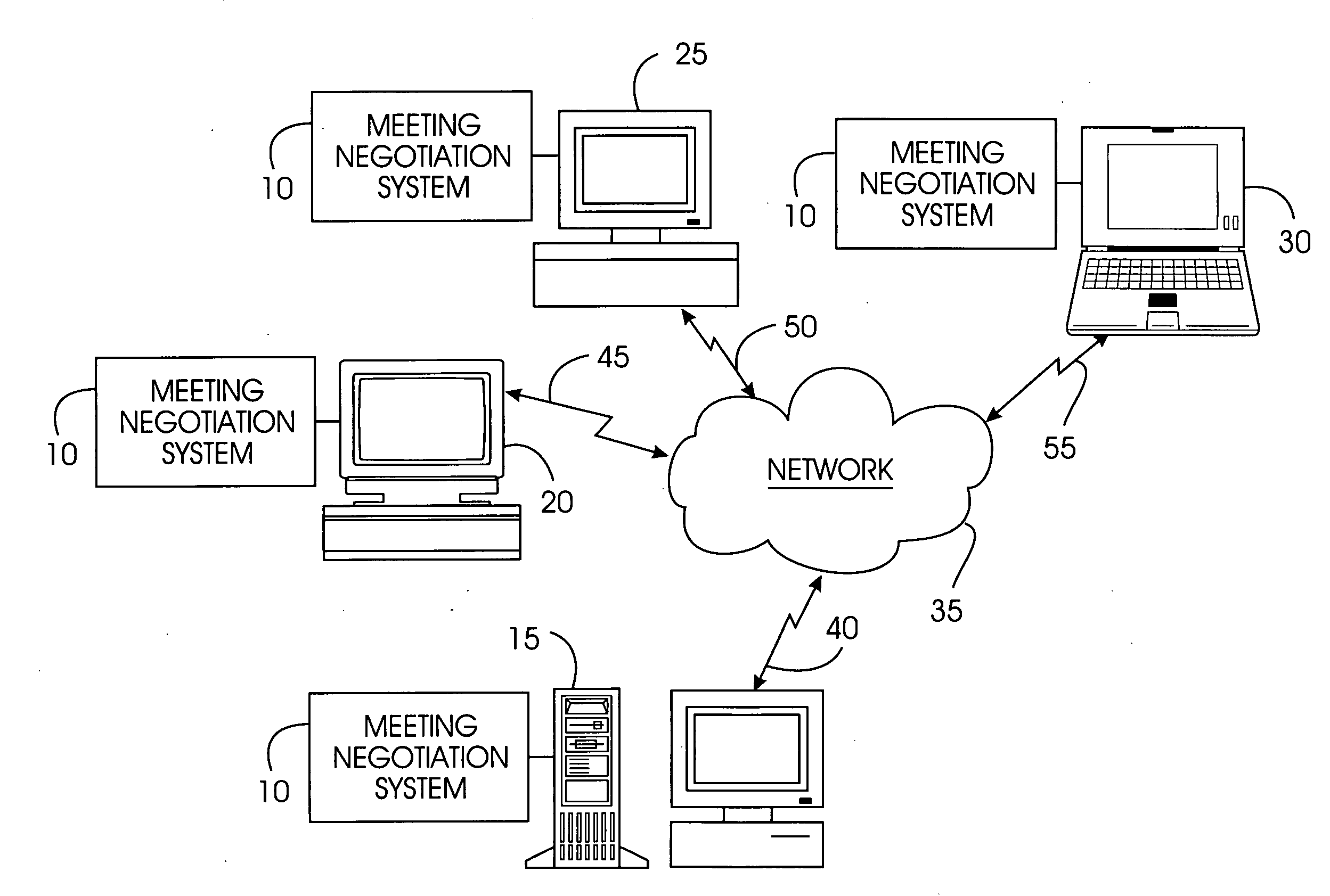
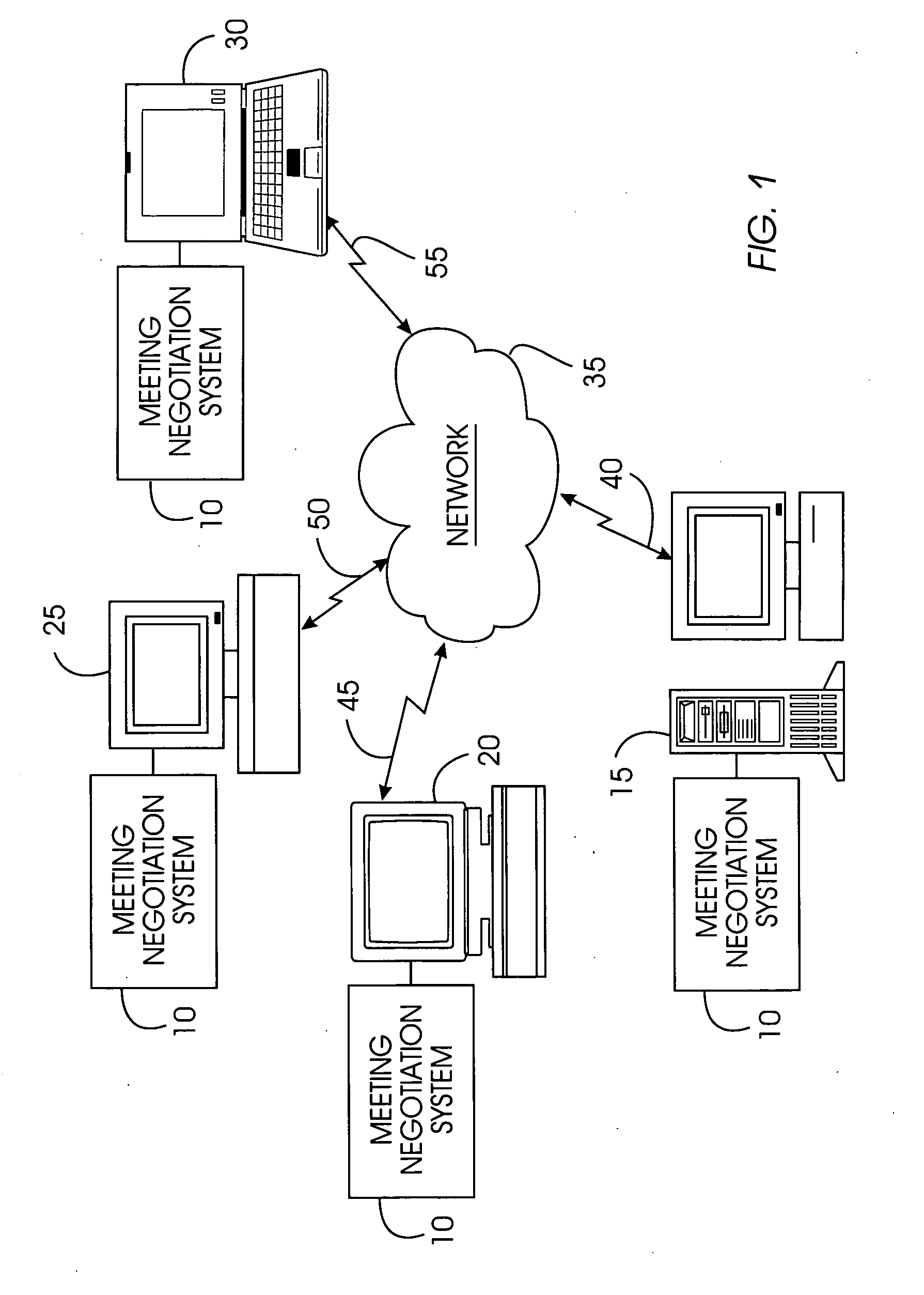
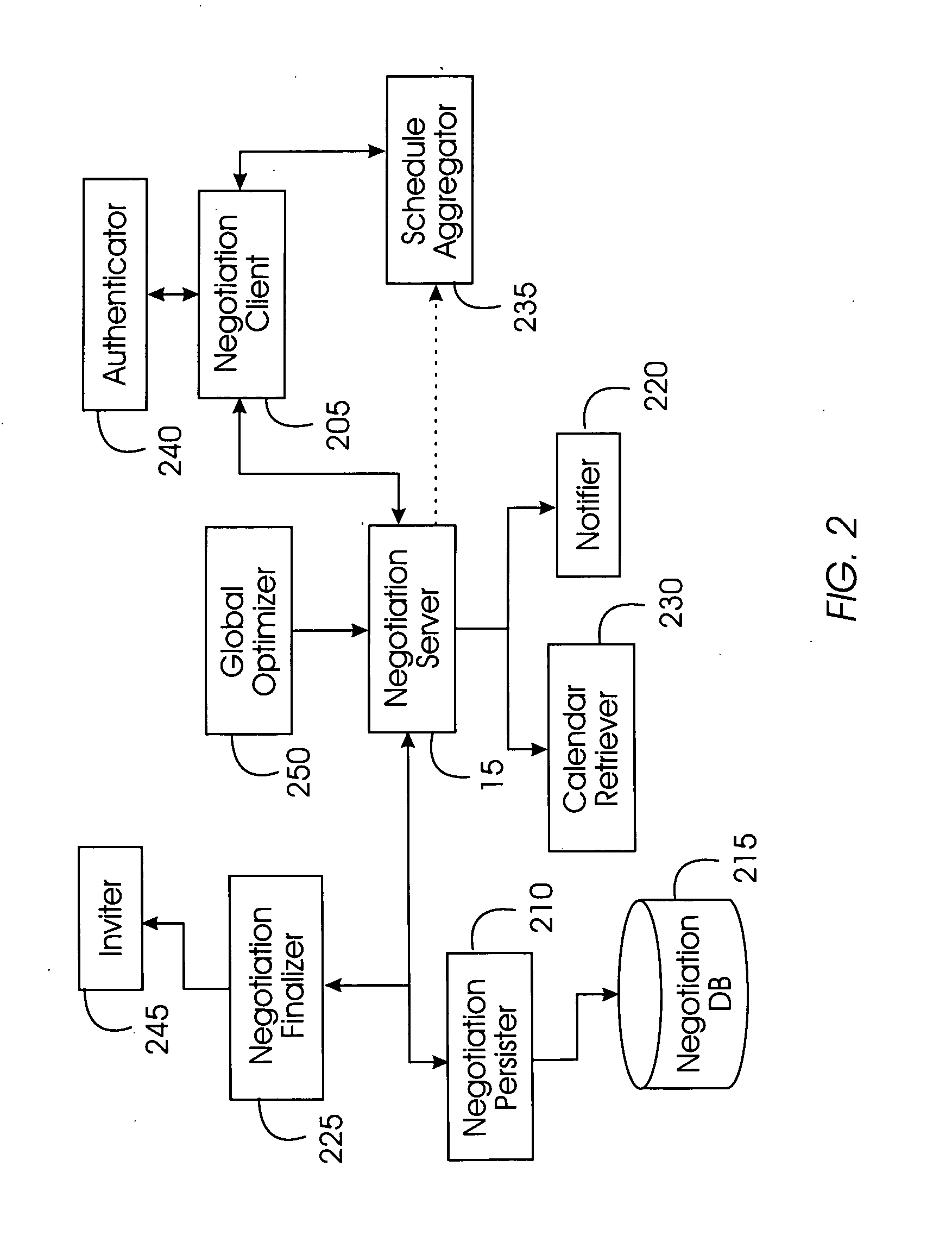
System, method, and service for negotiating schedules while preserving privacy through a shared representation
InactiveUS20050102245A1Large basePrivacy protectionDigital computer detailsPayment architectureTime scheduleBusy time
A meeting negotiation system provides a new approach to scheduling events by negotiating schedules while preserving privacy through a shared representation that separates the meeting negotiation from the meeting invitation. The negotiation system integrates all scheduling-related information such as times users can meet, location, etc. and reduces dependency on designations of time as free or busy by a potential meeting attendee. Consequently, the negotiation system enables time preferences richer than just free or busy, allowing potential meeting attendees to designate preference in addition to time available. The negotiation system supports annotations and comments as a discussion mechanism, giving feedback to the meeting scheduler before the meeting invitation is issued. Possible times provided for the meeting are provided in the form of a bounded negotiation; participants may select the best time for them to attend a meeting from the bounded negotiation. The meeting organizer finalizes the meeting time from the responses provided by participants.
Owner:IBM CORP
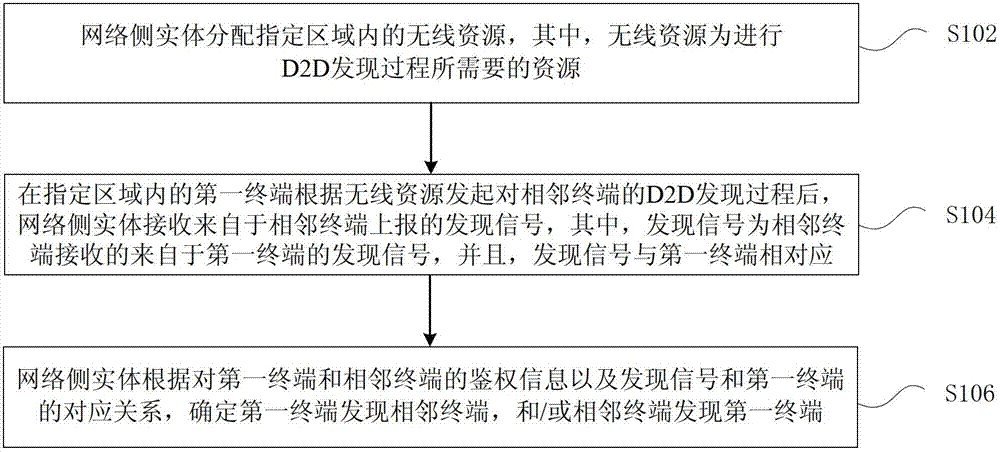
Device discovery method, device discovery processing method and device discovering processing device
InactiveCN102857901APrivacy protectionEasy to controlSecurity arrangementNetwork data managementAuthentication informationWireless resources
The invention provides a device discovery method, a device discovery processing method and a device discovery processing device. The device discovery method includes that a network side entity dispenses wireless resources in a designated area, the wireless resources are required resources in the process of D2D (device to device) discovery; a first device in the designated launches D2D discovery for adjacent devices according to the wireless resources, the network side entity receives discovery signals reported from the adjacent devices, and the discovery signals are received by the adjacent devices, from the first device and correspond to the first device; and the network side entity determines the first device to discover the adjacent devices and / or the adjacent devices to discover the first terminal according to authentication information of the first device and the adjacent devices and the corresponding relation of the discovery signals and the first device. By adopting the above technical scheme, privacy of users in the process of D2D discovery is protected, and meanwhile, control of the network side to the D2D discovery is realized.
Owner:ZTE CORP
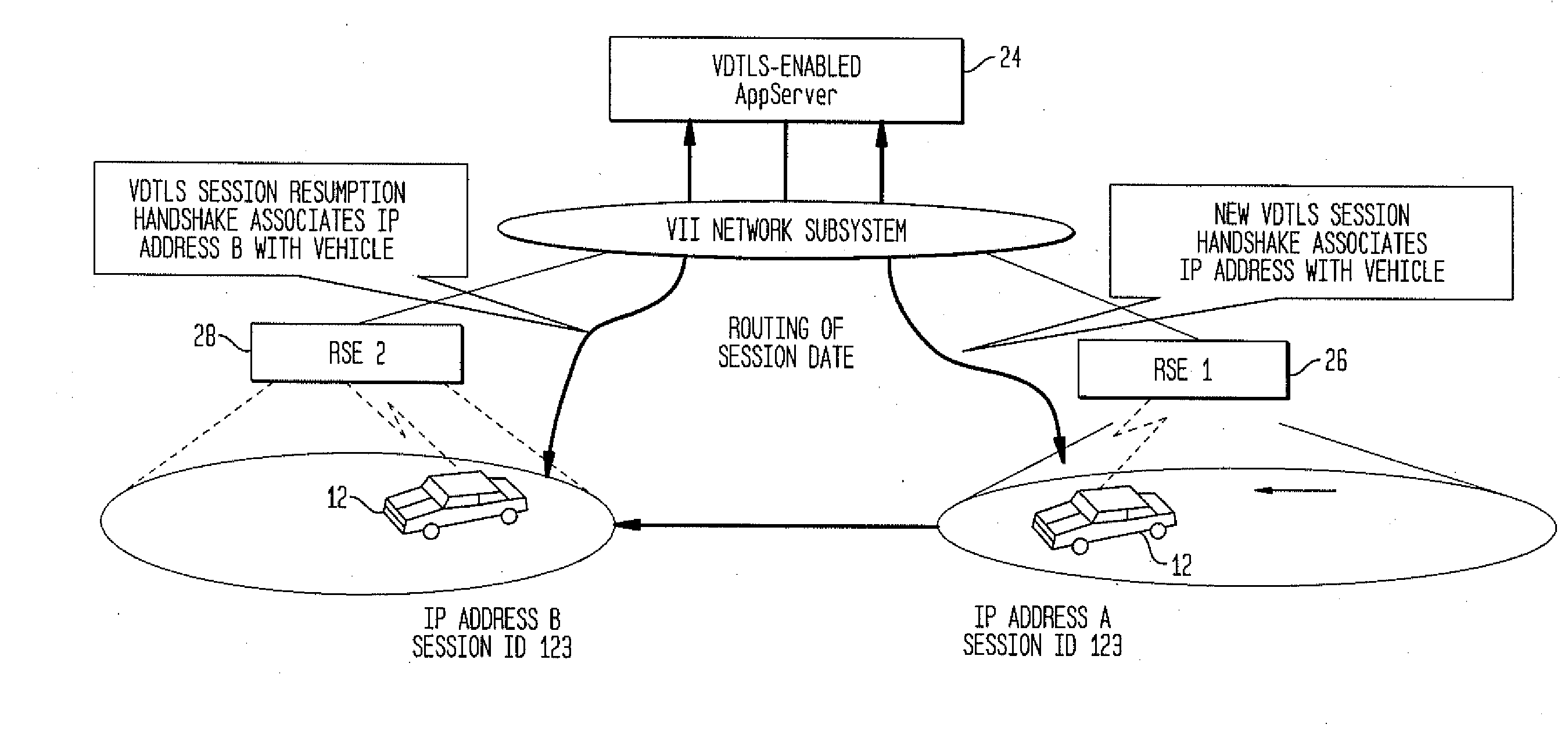
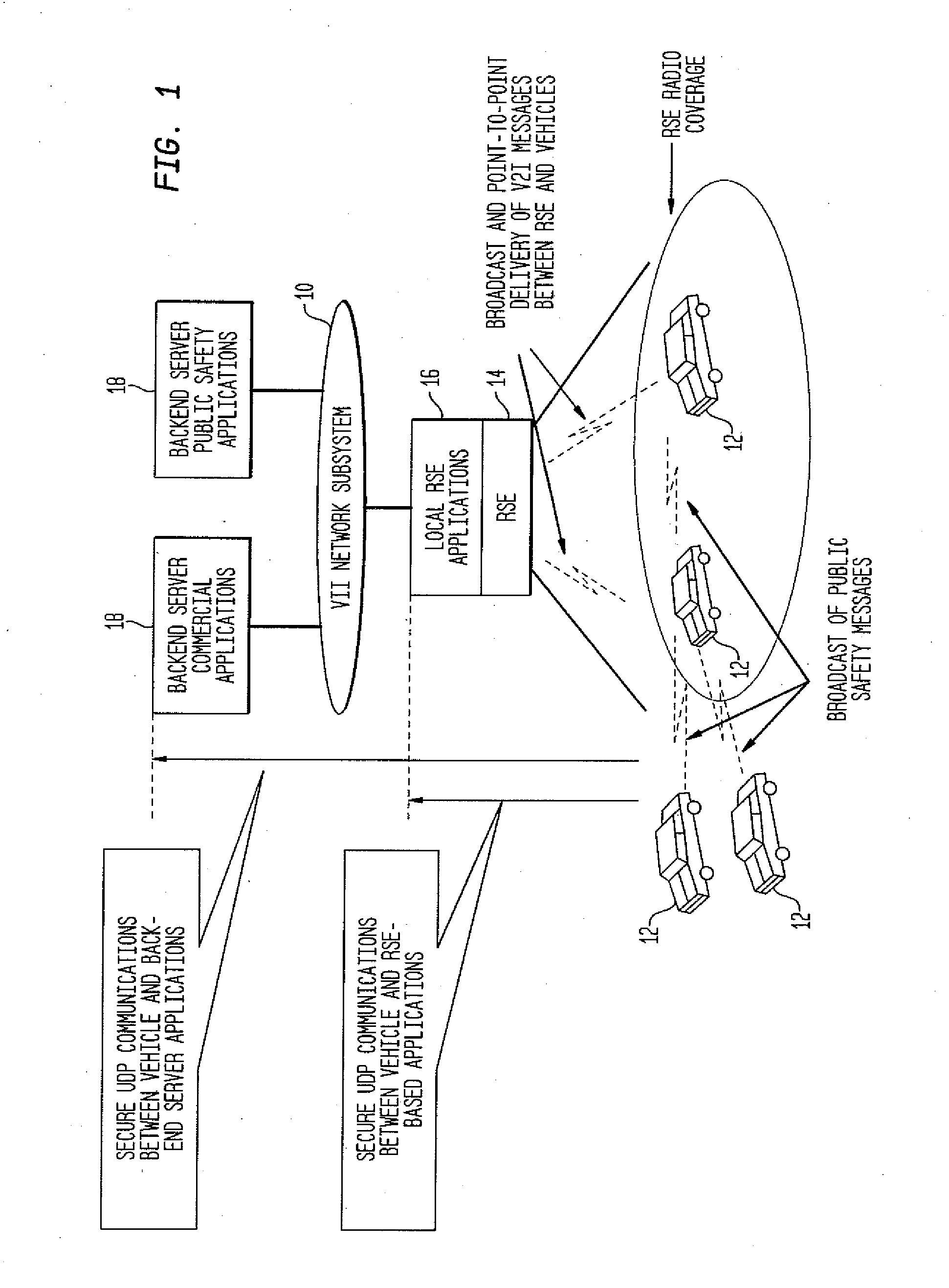
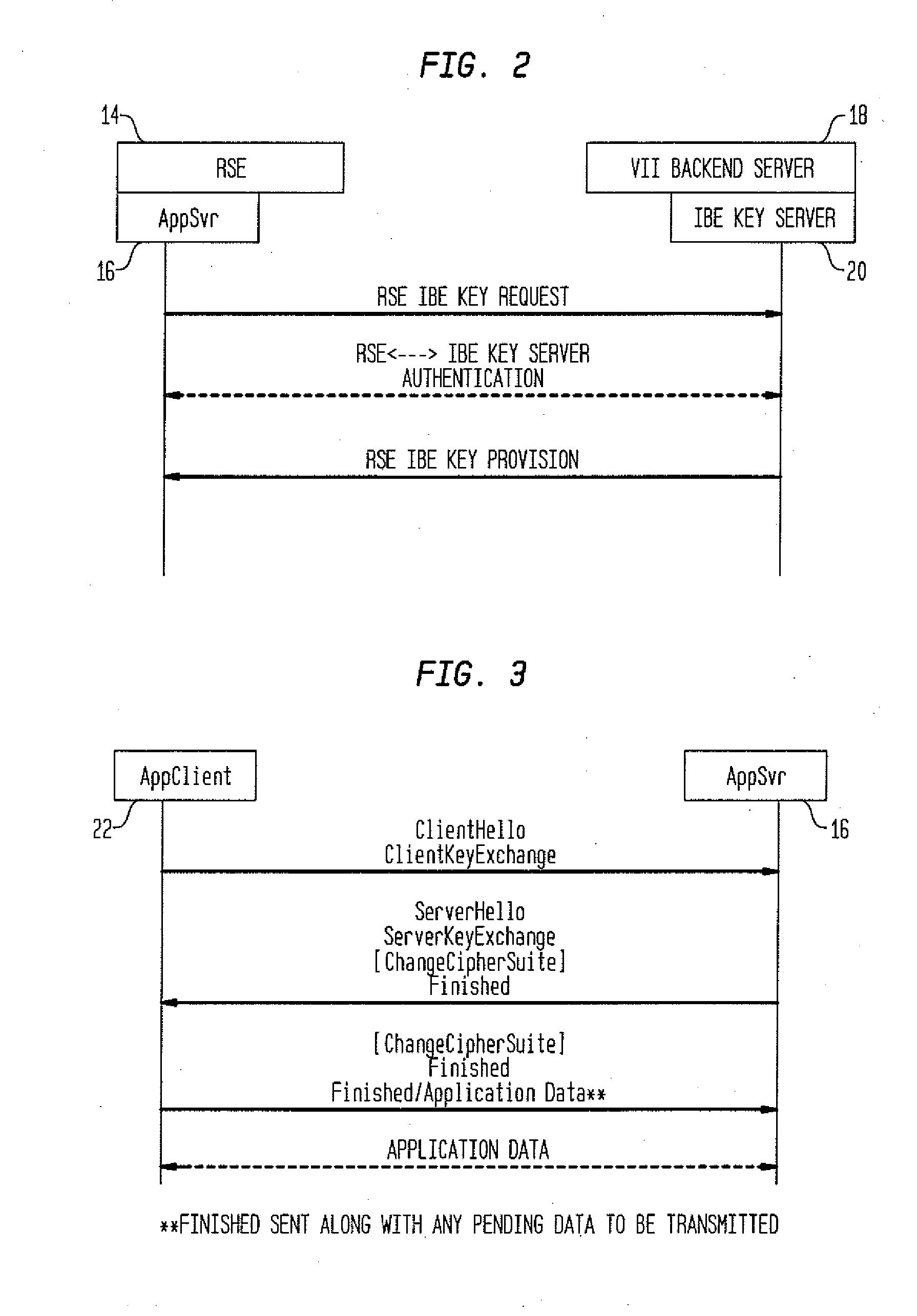
Method and System for Secure Session Establishment Using Identity-Based Encryption (VDTLS)
ActiveUS20100031042A1Communication securityPrivacy protectionUser identity/authority verificationSecurity arrangementID-based encryptionSecure communication
The inventive system for providing strong security for UDP communications in networks comprises a server, a client, and a secure communication protocol wherein authentication of client and server, either unilaterally or mutually, is performed using identity based encryption, the secure communication protocol preserves privacy of the client, achieves significant bandwidth savings, and eliminates overheads associated with certificate management. VDTLS also enables session mobility across multiple IP domains through its session resumption capability.
Owner:TELCORDIA TECHNOLOGIES INC
Social search engine
InactiveUS20110106895A1Privacy protectionMultiple digital computer combinationsOffice automationSocial searchRanking
Methods, systems, and apparatus, including computer programs encoded on a computer storage medium, for a social search engine. In one aspect, a method includes receiving a question from an asker in which the question is associated with one or more topics; selecting candidate answerers based at least partly on each answerer's respective relationship to the asker; sending the question successively to groups of one or more candidate answerers according to the ranking until an answer is received from a particular one of the candidate answerers; and sending to the asker the received answer and information that identifies the particular answerer.
Owner:GOOGLE LLC
Pseudonymous public keys based authentication
InactiveUS20110302412A1High security requirementsImprove securityUser identity/authority verificationAuthentication systemNon-repudiation
Systems and methods for pseudonymous public keys based authentication are described that enable an authentication to achieve pseudonymity and non-repudiation, for example, at the same time. Pseudonymity may provide, for example, that a user can show to different parties different digital identifiers for authentication instead of, for example, always using a single digital identifier everywhere, which may lead to a breach of privacy. Non-repudiation may provide, for example, that the authentication data at the server side can be used, for example, to verify a user's authentication request, but not to generate an authentication request, which might lead to user impersonation. A user may use a physical token to generate the authentication request corresponding to the user's identity to pass the authentication.
Owner:NORTHWESTERN UNIV
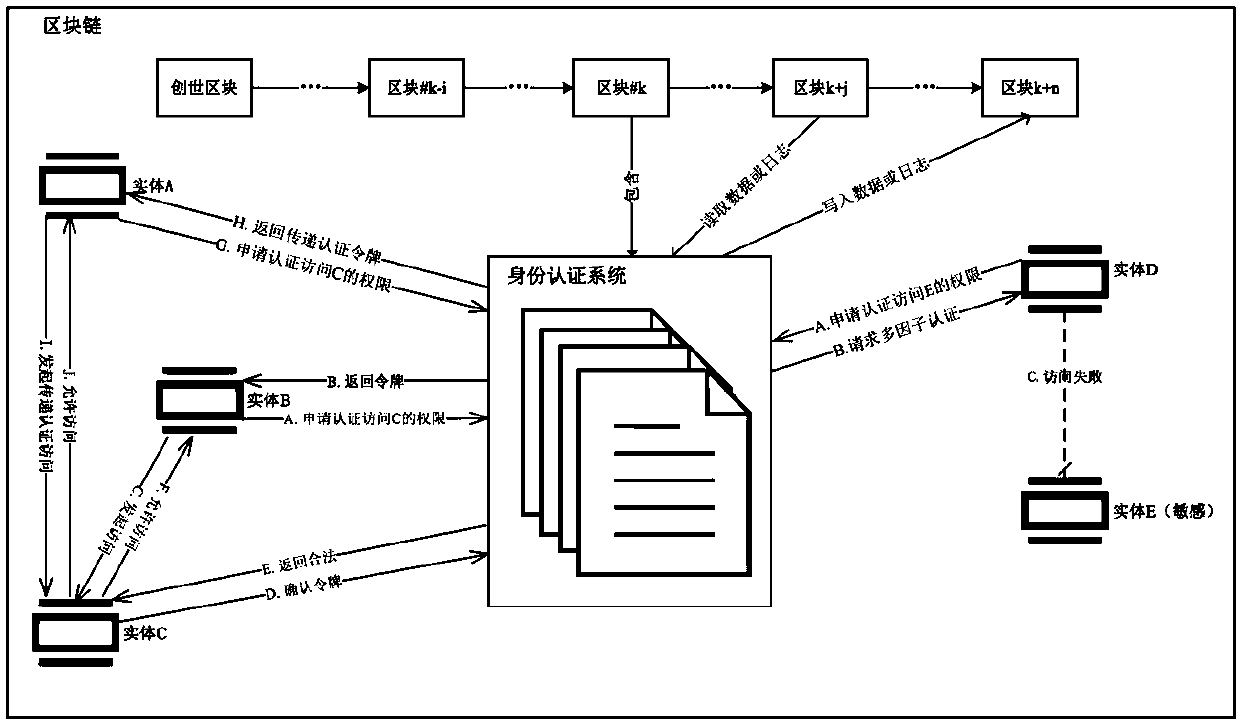
Internet of Things identity authentication method based on blockchain
The invention belongs to the technical field of identity authentication, and specifically provides an Internet of Things identity authentication method based on a blockchain. The basic steps of the Internet of Things identity authentication method provided by the invention are as follows: an entity calls an intelligent contract by means of an own key to accomplish the registration in an identity authentication system; each entity can call the intelligent contract to set an access strategy so as to limit the access of other entities to the entity and to form a trust network of the Internet of Things; when one entity accesses the data of the other entity, the entity needs to apply for a token from the intelligent contract to obtain the access qualification, and the intelligent contract checks whether the entity initiating the access has the access qualification according to the access strategy set by the accessed entity in the trust network between the entities, and if yes, the intelligent contract generates the token and returns the token to the entity initiating the access; or otherwise, the intelligent contract returns token application failure information. By adoption of the method provided by the invention, a centralized authority mechanism in an identity authentication process is removed, malicious tampering of records of identity authentication and data access is prevented, a strategy execution result is not manually manipulated, and a fair, transparent and credible execution environment is provided for the identity authentication of the entities in the Internet of Things.
Owner:FUDAN UNIV
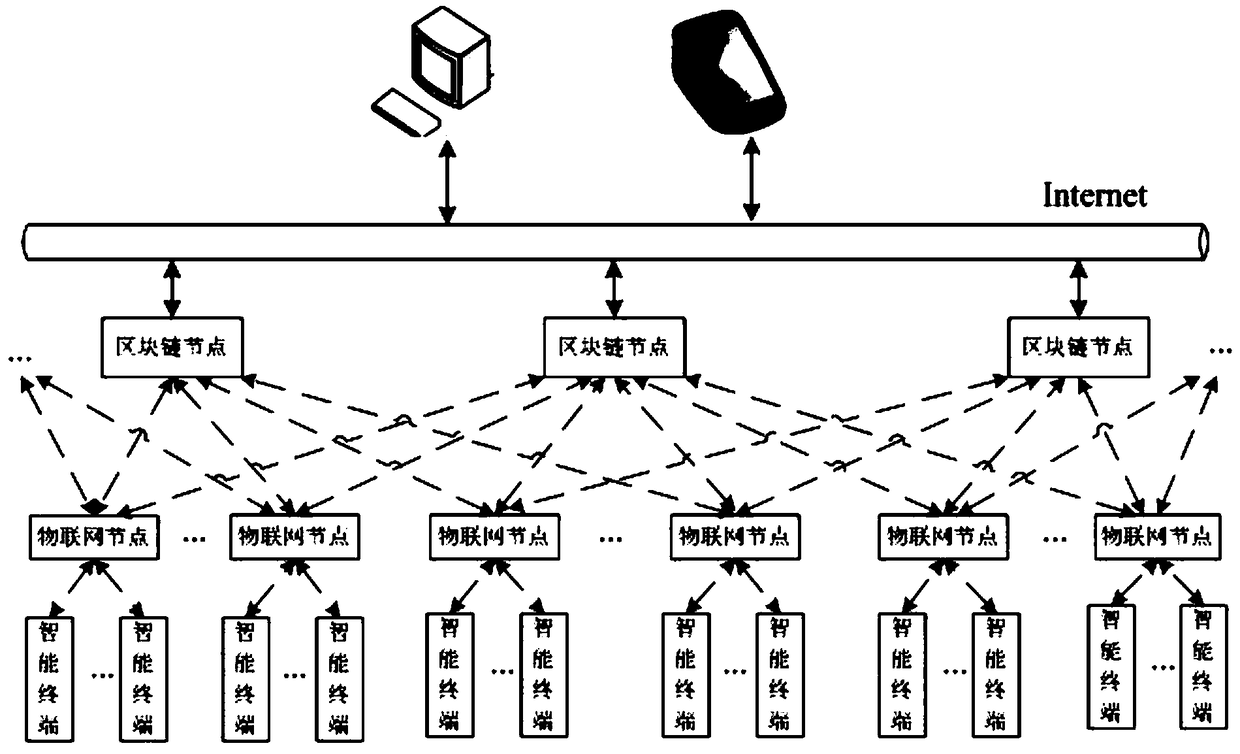
Construction equipment Internet of Things system and method based on blockchain technology
ActiveCN108632293ASolve processing problemsSaving facilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationElectrical devicesThe Internet
The invention discloses a construction equipment Internet of Things system and method based on the blockchain technology. The system comprises a plurality of Internet of Things nodes, a plurality of blockchain nodes, a plurality of intelligent terminals and a plurality of user terminals, the detection of various environmental information in the building and the monitoring of electrical equipment can be achieved, data are stored in the blockchain nodes in a distributed manner, a data transmission process is encrypted by using the asymmetric encryption technology, and data sharing is performed through a smart contract. According to the construction equipment Internet of Things system and method disclosed by the invention, the blockchain technology is combined with the Internet of Things technology, the consensus mechanism, distributed storage, asymmetric encryption and smart contract of the blockchain technology are applied to the Internet of Things, and many problems faced by the current Internet of Things are solved.
Owner:SHANDONG JIANZHU UNIV
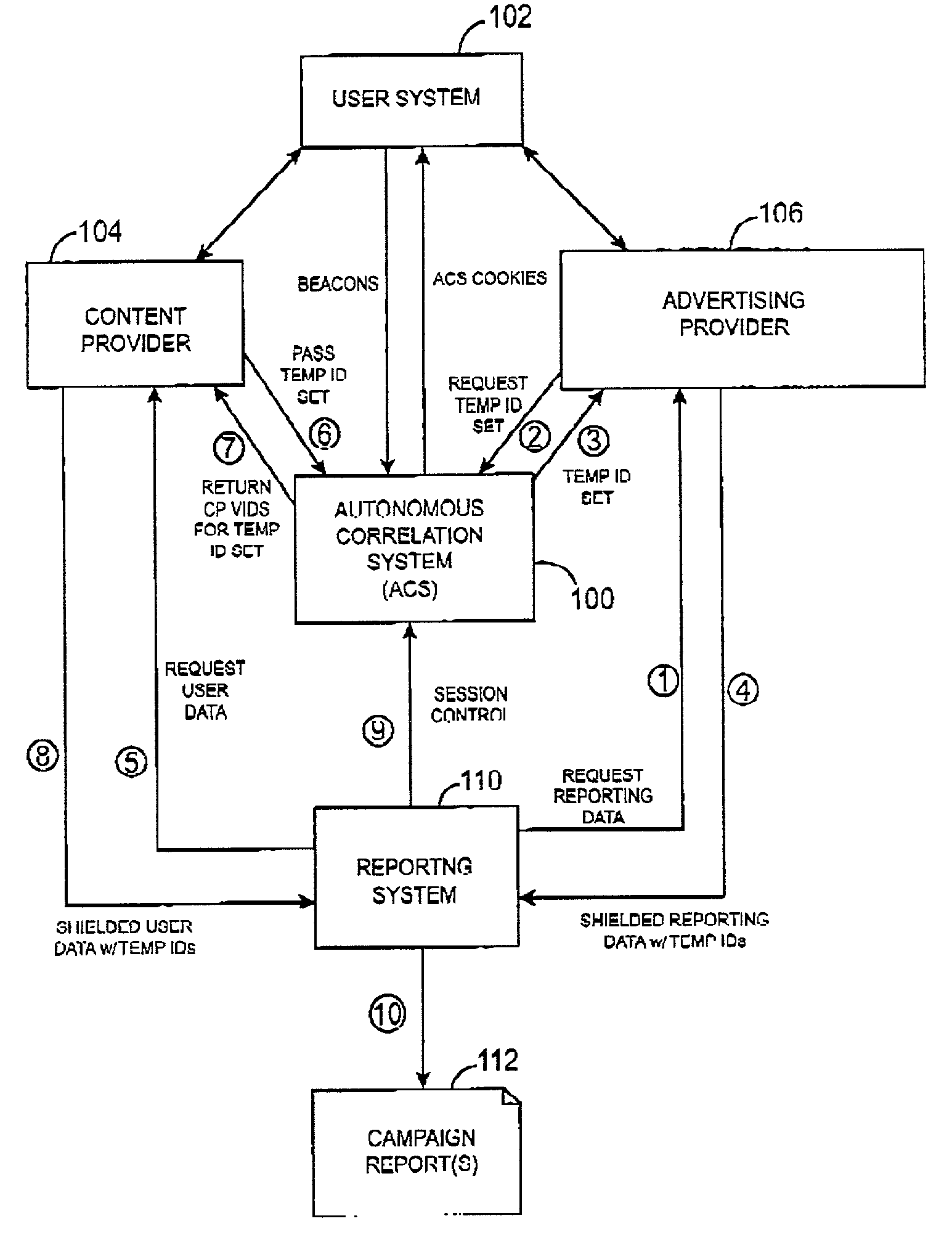
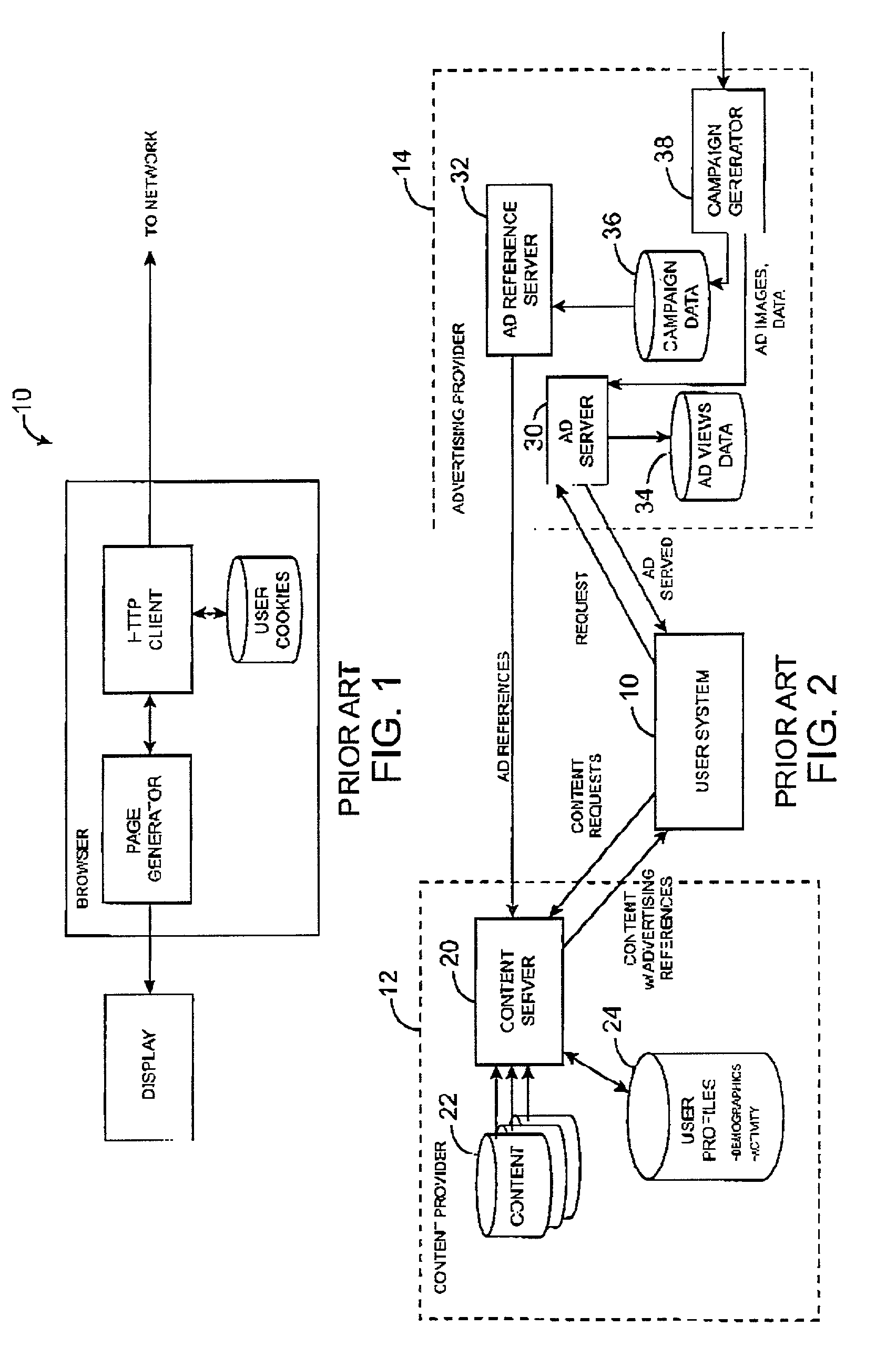
System and method for correlating user data from a content provider and user data from an advertising provider that is stored on autonomous systems
ActiveUS7257546B2Increase valueProtect user privacyAdvertisementsAnalogue secracy/subscription systemsReference databaseUser identifier
An autonomous correlation system correlates user data from a content provider and advertising view data from an advertising provider, wherein the user data is present on one autonomous system and the advertising view data is present on another autonomous system distinct from the one autonomous system, the systems being autonomous in that each is normally secured against unconstrained access by another. The autonomous correlation system comprises logic to accept a first message from a user, wherein the first message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a first user identifier associated with the user by a presenter of the object; a reference database for storing an association between the first user identifier and the user; logic to accept a second message from the user, wherein the second message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a second user identifier associated with the user by a presenter of the object; wherein the reference database stores an association between the second user identifier and the user.
Owner:PINTEREST
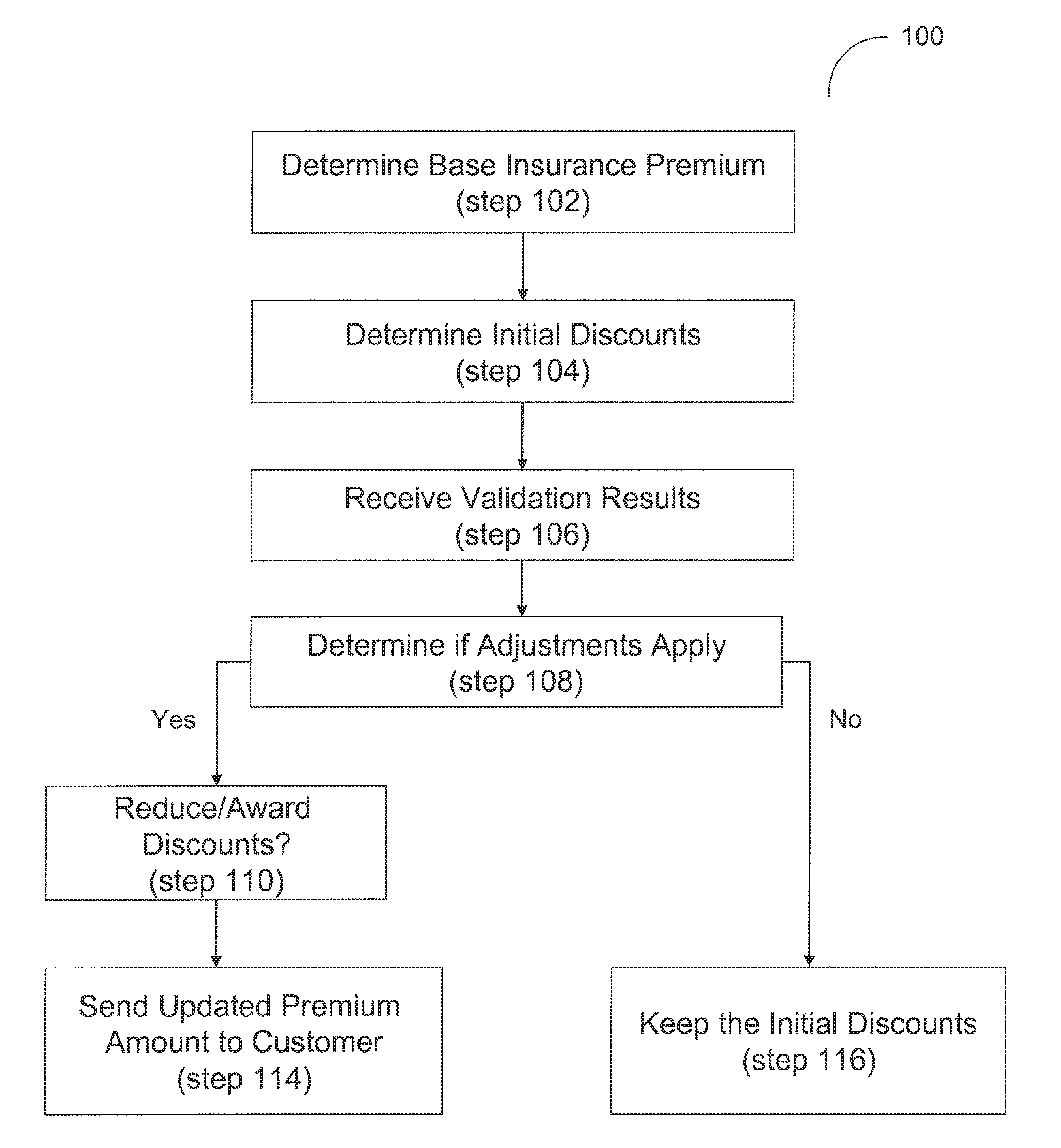
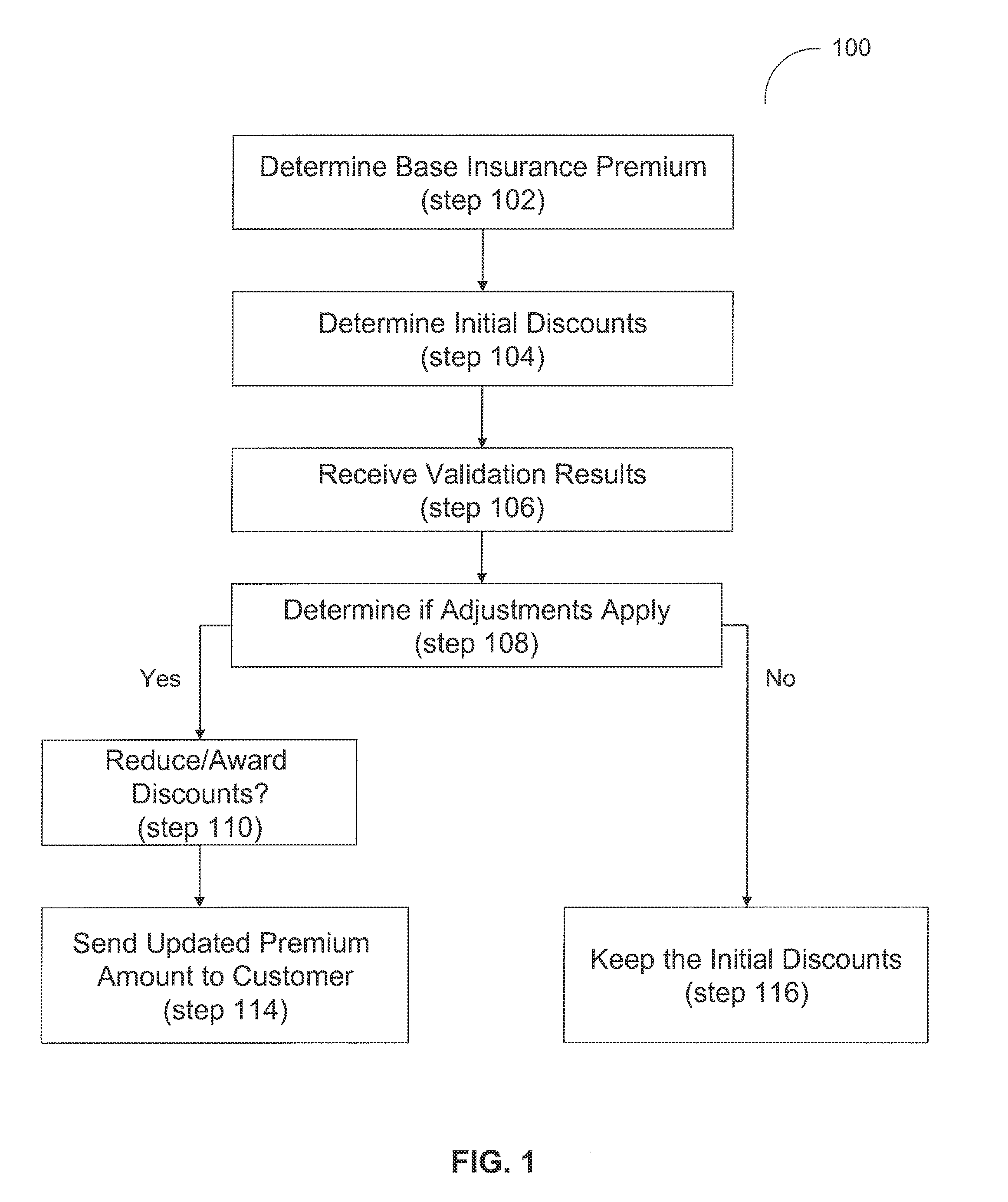
System and method for an automated validation system
System and method are disclosed herein for an automated validation system for validating whether a property of a policyholder receiving at least one insurance benefit is currently receiving remote monitoring services, as claimed by the policyholder. The system comprises an application server, a trusted third party server, and a business logic computer. The application server requests the trusted third party server to validate whether the property of the policyholder is presently receiving remote monitoring services from a service provider. A business logic computer can adjust the policyholder's insurance policy based on the received validation results.
Owner:HARTFORD FIRE INSURANCE
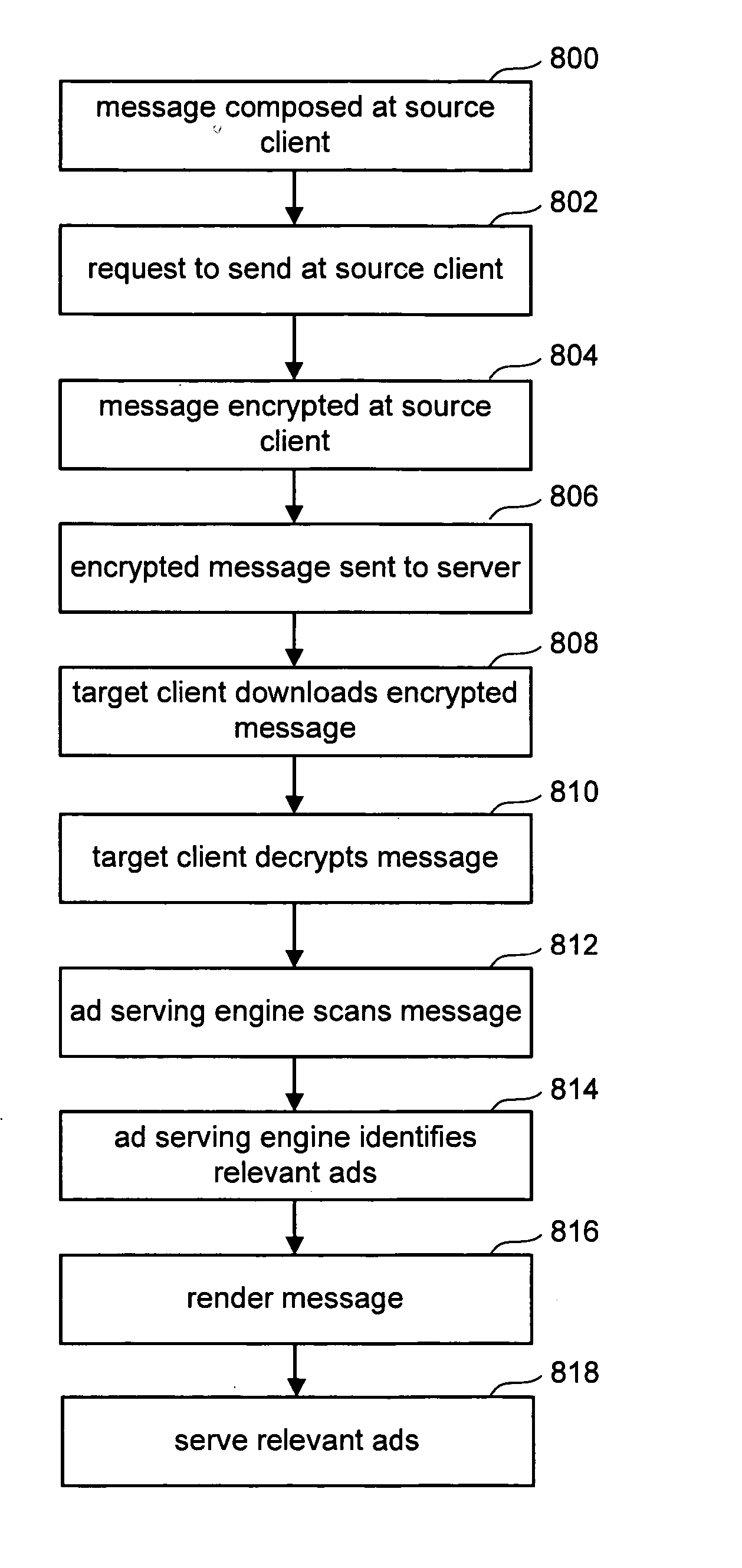
Contextual ad processing on local machine
InactiveUS20060149677A1Privacy protectionMaintain privacyComputer security arrangementsData switching networksClient-sideData storing
A system is disclosed for serving advertisements to a user of a client device. A set of advertisements are downloaded to the client device. Based on data stored on the client device, or action taken on the client device, a subset of the advertisement are chosen for presentation to the user of the client device. In one embodiment, the choice of advertisement to present to the user is based on the content of one or more email messages. The scanning of the email message and the decision as to which advertisement(s) to present are made on the client machine in order to protect the privacy of the user. The chosen advertisements are then displayed with the one or more emails.
Owner:MICROSOFT TECH LICENSING LLC
Distributed quantum encrypted pattern generation and scoring
ActiveUS7227950B2Privacy protectionFinanceDigital data processing detailsPattern generationClient-side
Transaction scoring is performed in a distributed manner across a client-server computing system. A computing system for processing a transaction includes a server system and a client system. The server system is arranged to process information associated with the transaction, while the client system communicates with the server system and includes a key engine which is arranged to generate keys. The client system and the server system are arranged to cooperate to assess risk associated with the transaction. The client is arranged to send the keys generated by the key engine as a transaction to the server system.
Owner:VISA INT SERVICE ASSOC
Wireless data system
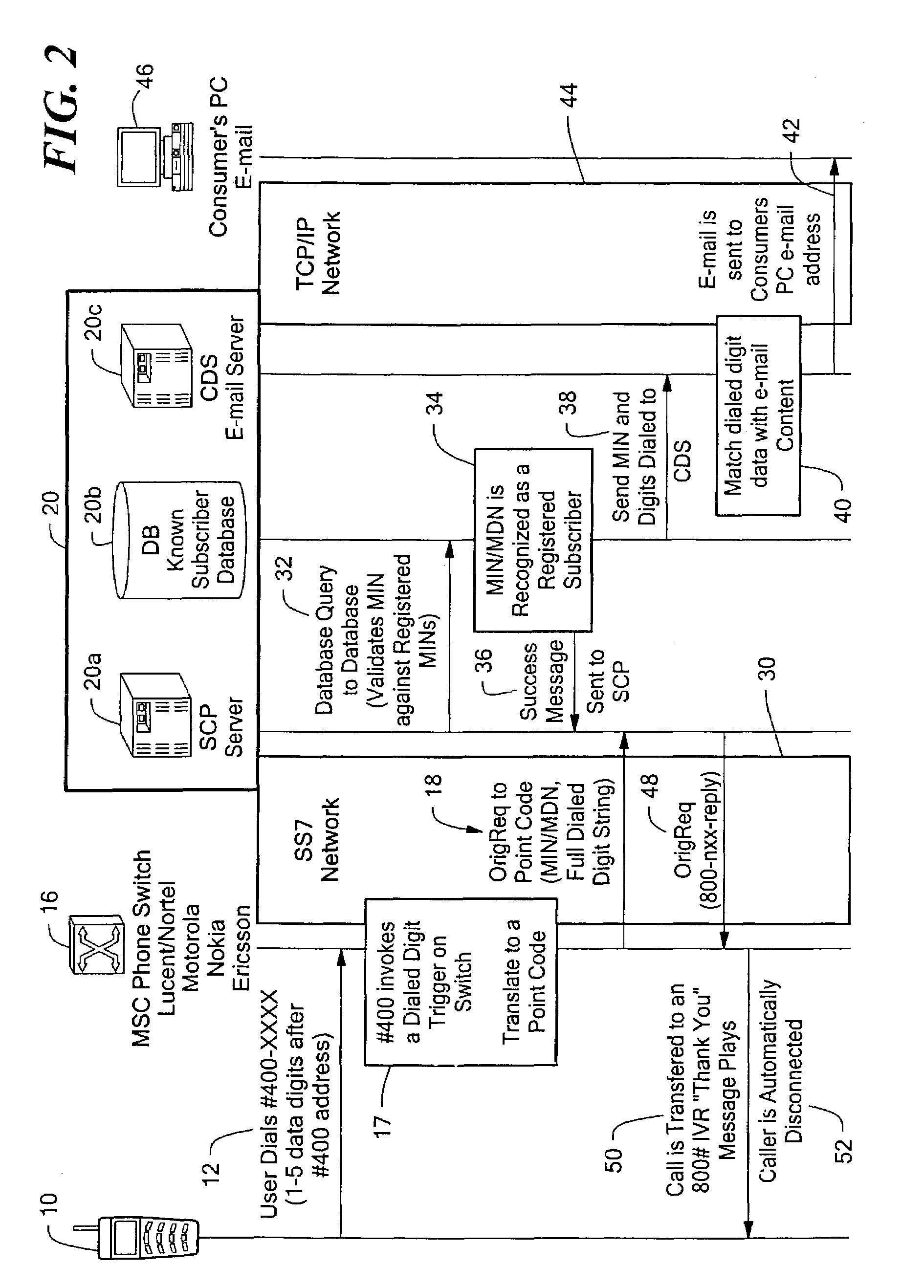
ActiveUS7257391B2Small sizeIncrease contentAdvertisementsSpecial service for subscribersEmail addressUser input
A system and method for enabling a user to request and receive product information, participate in voting or polling activities, reprint an article or other publication, request and authorize a purchase of a magazine subscription, music sound clip, or other product, and / or share personal information with other users. The service request and information delivery may provided over a mobile phone. The user dials a series of digits into their phone and enters them into the disclosed system, for example by pressing the send key on a mobile phone. The digits entered by the user include a prefix or routing code, and a data code. The dialed digits are transferred to a call switching system, which determines, based on the prefix code, a processing system to which a message is sent including the originally dialed digits as well as identification of the user or phone that placed the call. The processing system may then determine, based on the identification of the mobile phone that placed the call, a user account. The processing system further determines, based on the data code of the dialed digits, the product information or other service such as entry of a polling response, vote, or product purchase, that is to be provided. The user account information may then be used to determine a delivery technique, such as electronic mail using an electronic mail address associated with the phone that made the call, SMS / MMS / EMS Text messaging, or WAP push, through which the product information associated with the data code may be forwarded to the requesting user.
Owner:VHT STARSTAR LLC
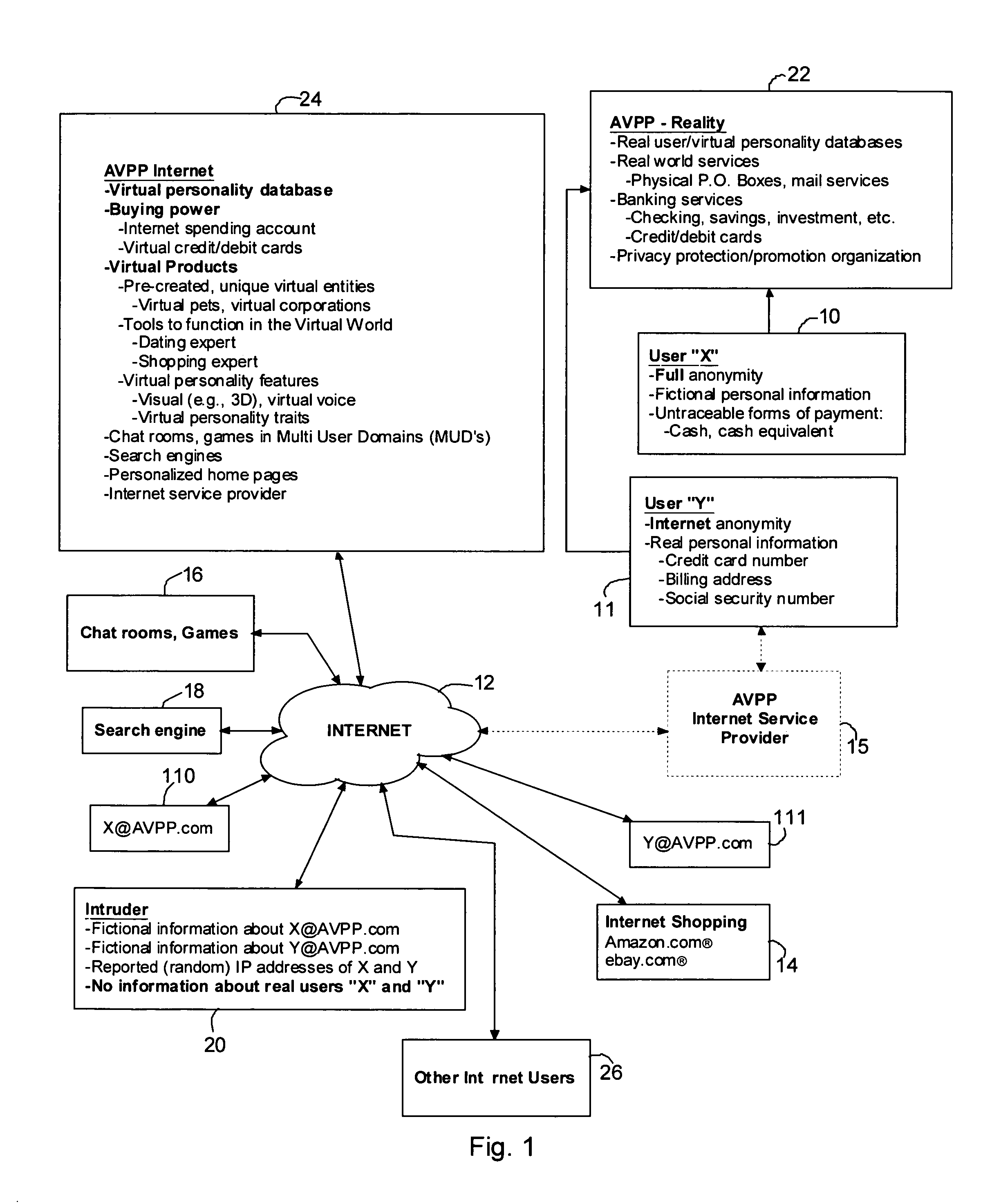
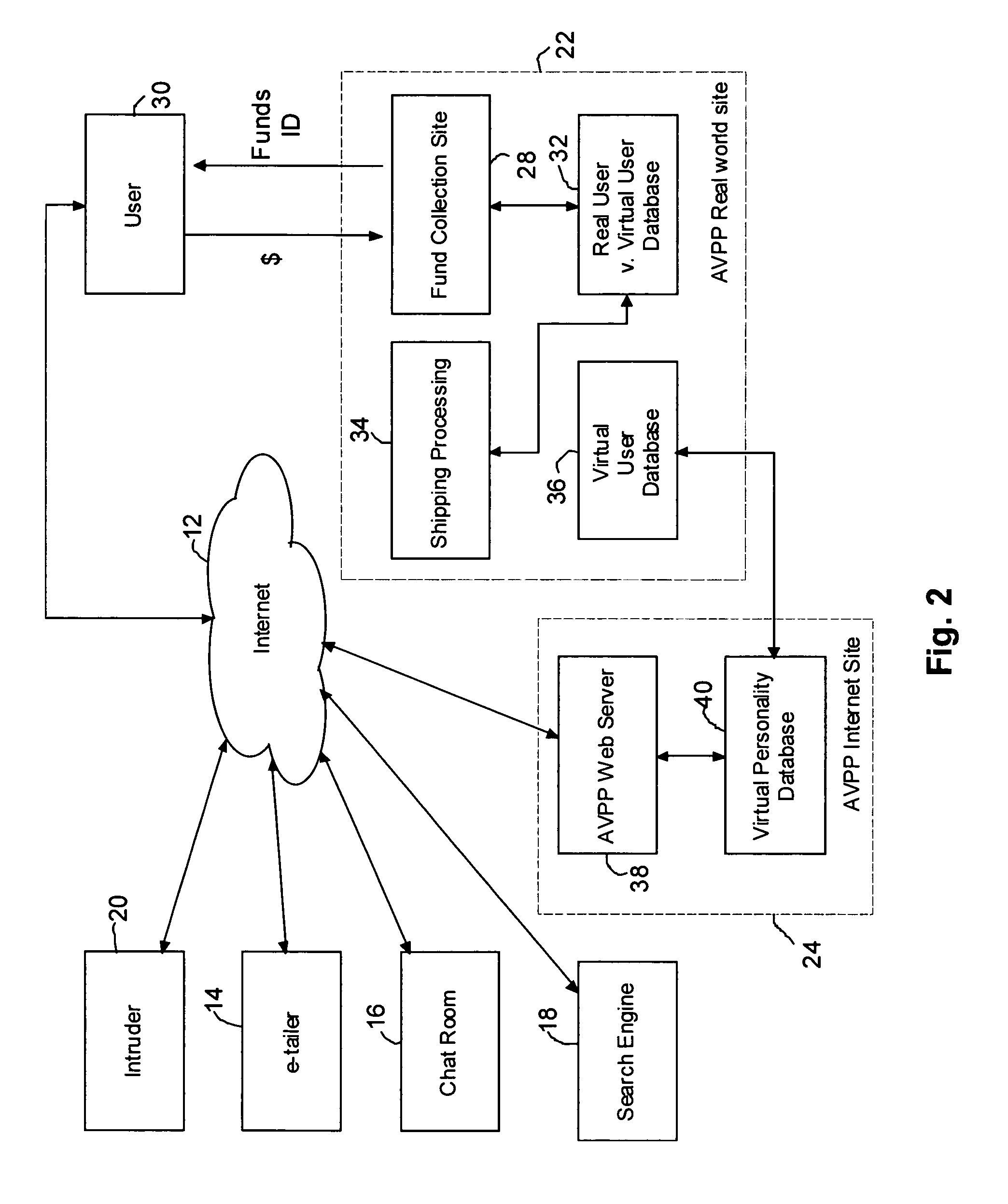
Method and system for securing user identities and creating virtual users to enhance privacy on a communication network
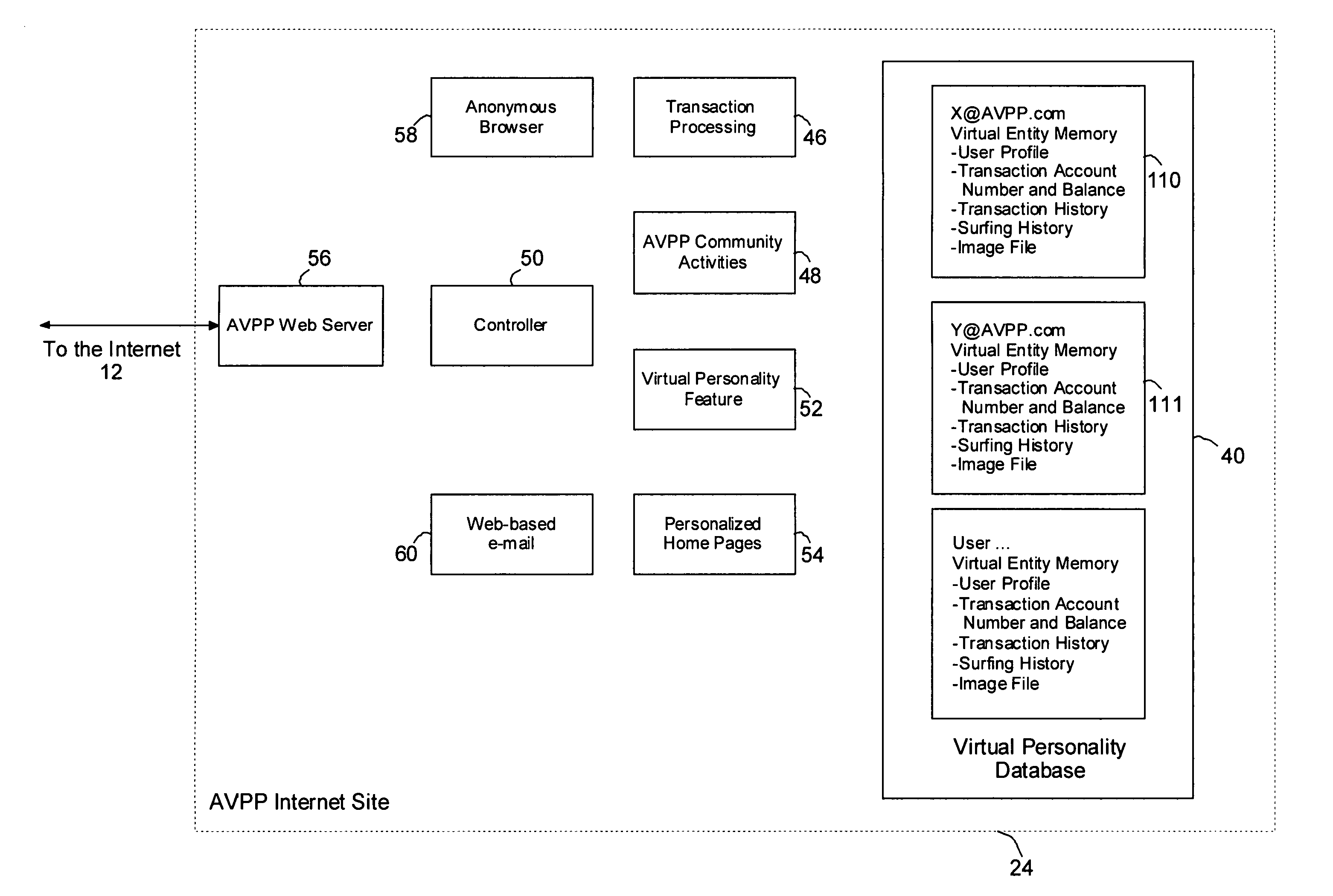
InactiveUS7412422B2Effective distributionMinimize shipping timeComplete banking machinesFinanceVirtual userVirtual entity
A method of enabling a real entity to access a service on a communication network using a virtual entity, the method including the steps of establishing a user account including at least first data corresponding to the identity of the real entity and second data corresponding to the virtual entity and not identifying the real entity, storing the first and second data in a first database, linking between the first and second data in the first database, storing the second data at a second database, associating the second database with a communication network site, connecting the communication network site to the communication network, receiving the second data from an unidentified user on the communication network site, identifying the unidentified user as the virtual entity based on receiving the second data, and allowing the virtual entity to access the service.
Owner:SHILOH DEKEL
Server side mobile audience intelligence creation
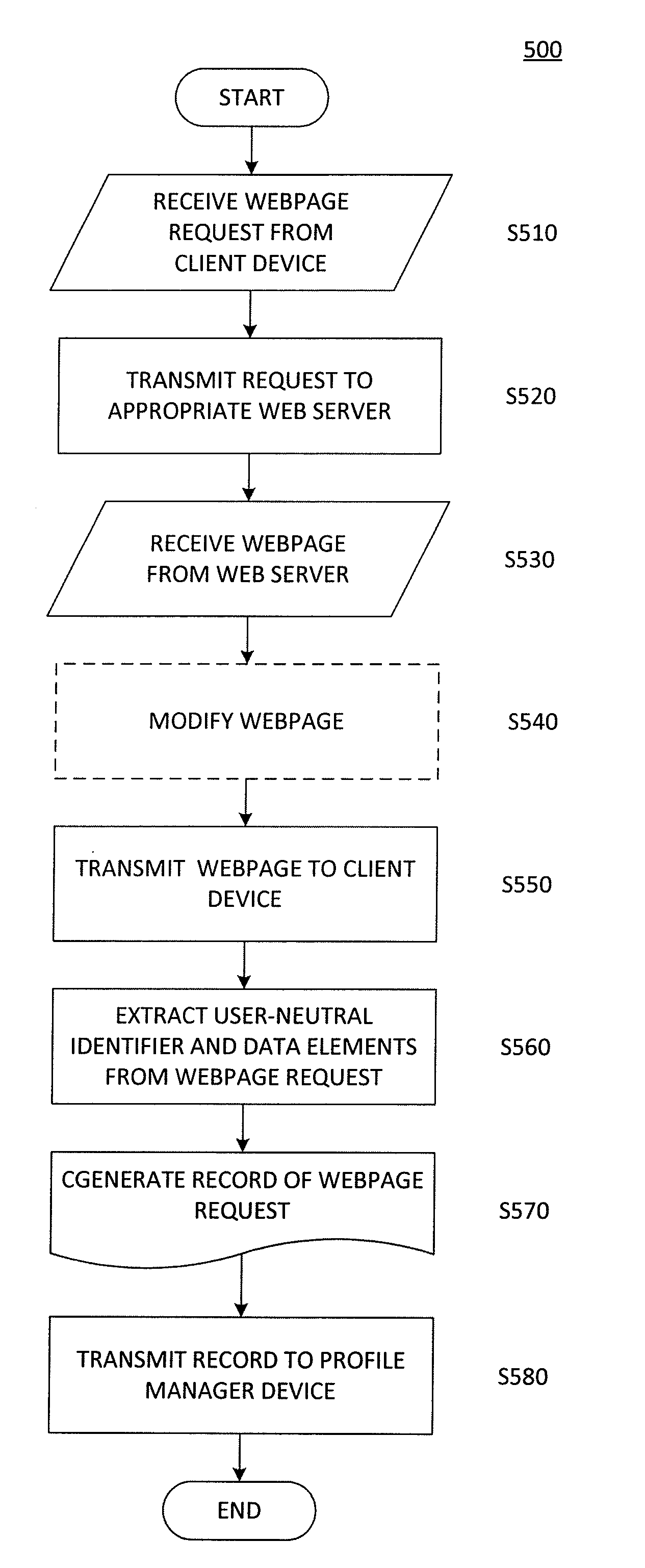
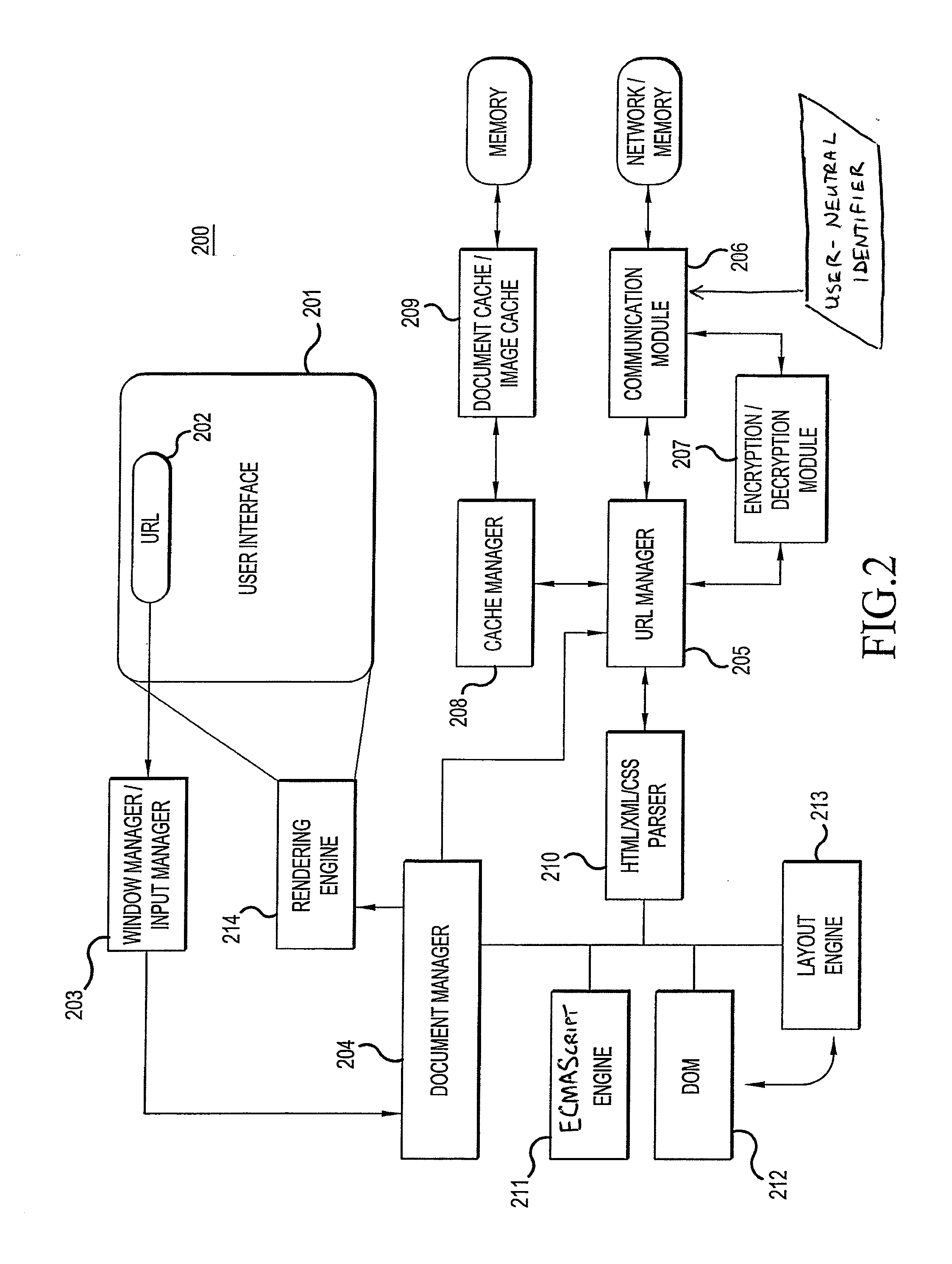
ActiveUS20130080498A1Improve browsing experienceAvoid trackingAdvertisementsMultiple digital computer combinationsWeb siteWeb browser
The present invention is directed toward a method and system for tracking webpage requests from web browsers without invading the privacy of the corresponding users. A server receives the webpage requests, and extracts from each of them a user-neutral identifier and URL. The server creates records of these webpage requests, and these records are used to create and update profiles for the corresponding user-neutral identifiers. Since the user-neutral identifiers are not tied to user-specific information, the profiles are made anonymous and user privacy can be protected. However, since each user-neutral identifier is tied to a particular web browser, useful information regarding individual browsing behavior can be obtained. Furthermore, the requested URL's can be categorized before being used to update the profiles, thus eliminating concerns that a user's browsing activity might be tracked from website to website.
Owner:OPERA SOFTVEAR AS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com