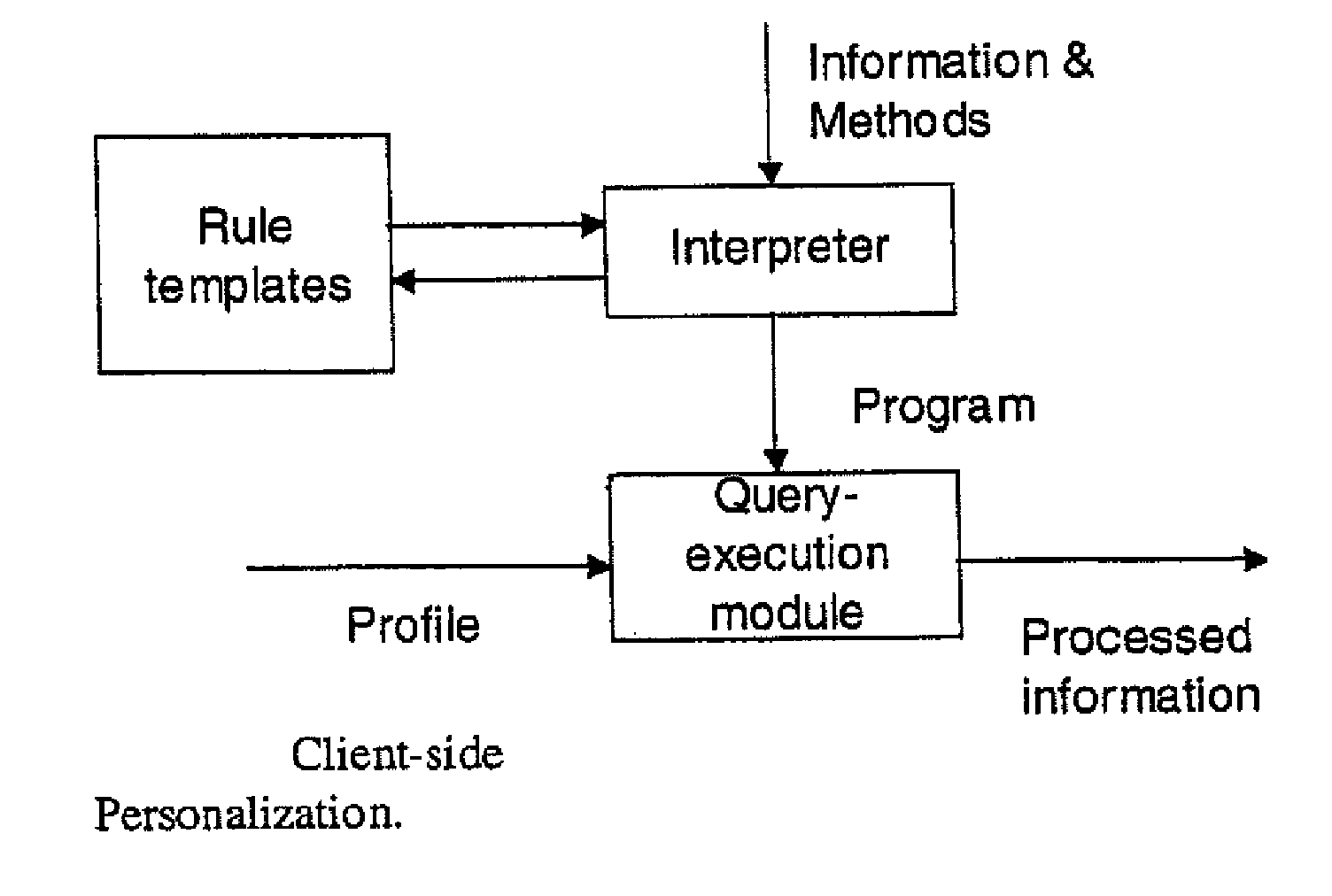
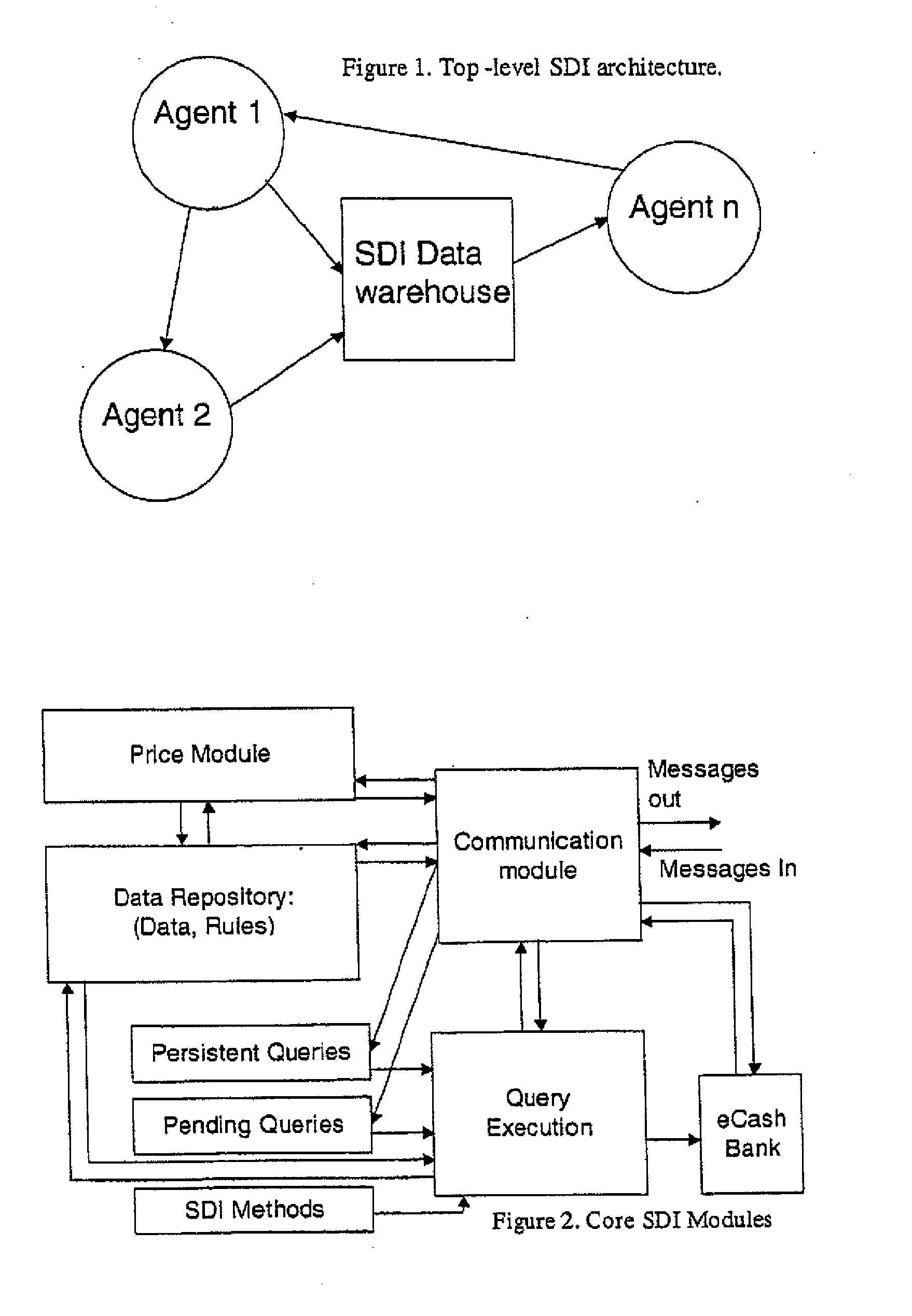
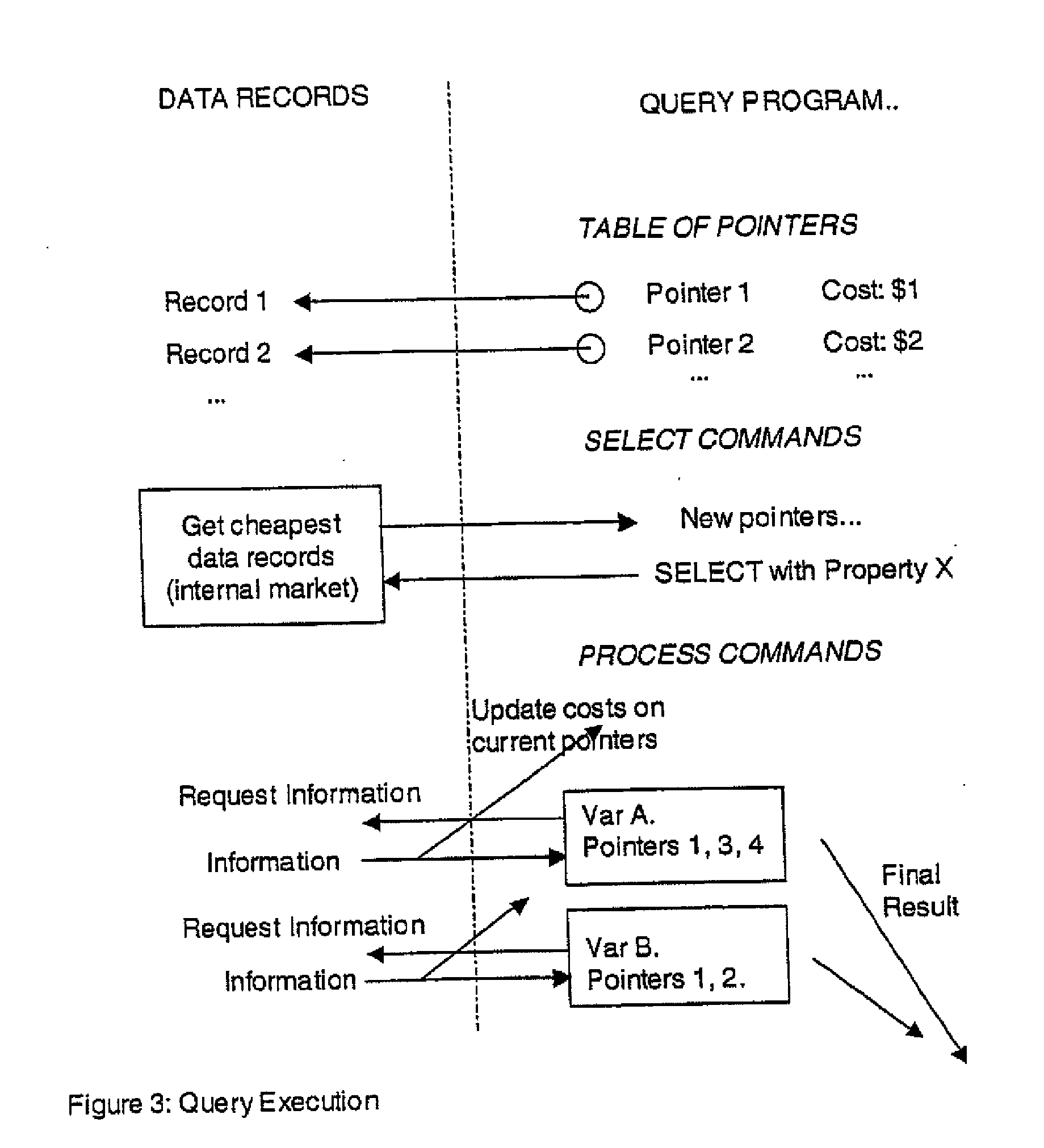
Secure data interchange
a data exchange and data technology, applied in the field of secure data exchange, can solve the problems of user's desire for controlled personalization, large corpus of data extrapolation, and inability to be desirable, and achieve the effect of avoiding loss of privacy, facilitating bilateral exchange of profiles/preferences, and facilitating the exchange of information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
case 1
[0628] All Customers Use a Single Pseudonym, and Appear in all Databases Considered.[0629]This is the simplest situation to handle. Since all customers appear in all the databases, the customer vectors' fields are essentially scattered across several locations, but can be easily reconstructed. For each customer, we define a new data vector that concatenates that customer's representation from across the different databases.
[0630]Hence, if we are considering databases A, B, . . . , Z, and customer i appears in each one, we define a new vector ci=(cAi, cBi, . . . , cZi), where cAi is customer i's vector in database A. We then proceed as usual, making inferences with these augmented customer vectors.
case 2
[0631] Most Customers Use a Unique Pseudonym, and Frequently Appear in Different Databases.[0632]In this situation, although we see some connections between the databases, many pseudonyms appear in only a single location. Using Bayesian techniques, however, we can still make predictions for customer vectors across databases.[0633]Suppose we have a set of databases, A, B, . . . , Z. Taking each database in turn, we cluster it using all available data. Thus, using every record in database A, we group A's customers into clusters A1, A2, . . . , An. Taking database B, we create clusters using all of B's information, creating customer clusters B1, B2, . . . , Bm, and so forth.[0634]Now, scan both databases for common pseudonyms (representing those customers who have interacted with both vendors under the same pseudonym) and create count variables wij to represent the number of pseudonyms that appear jointly in Ai and Bj.[0635]We can now produce the probability that a pseudonym appearing ...
case 3
[0640] All Customers Use Several Pseudonyms, and None Appear in Different Databases[0641]In this situation, there are no common customer codes that can be used to create links across the databases. However, the mere fact that several databases have been brought together for analysis should imply that there are semantic commonalties in the data.[0642]Although each database contains different fields, it may be the case that those fields deal with related subjects. A human expert, knowledgeable in the content of the databases, the subtleties of the domain, and the overall goal of the analysis (e.g. the creation of recommendations), will be in a position to create a “common-information profile” that spans the databases. In essence, the common-information profile defines a format that allows vectors from different databases to share a common coordinate space.[0643]The idea is this: the expert designs a high-level vector format that embodies the content deemed important for the project go...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com