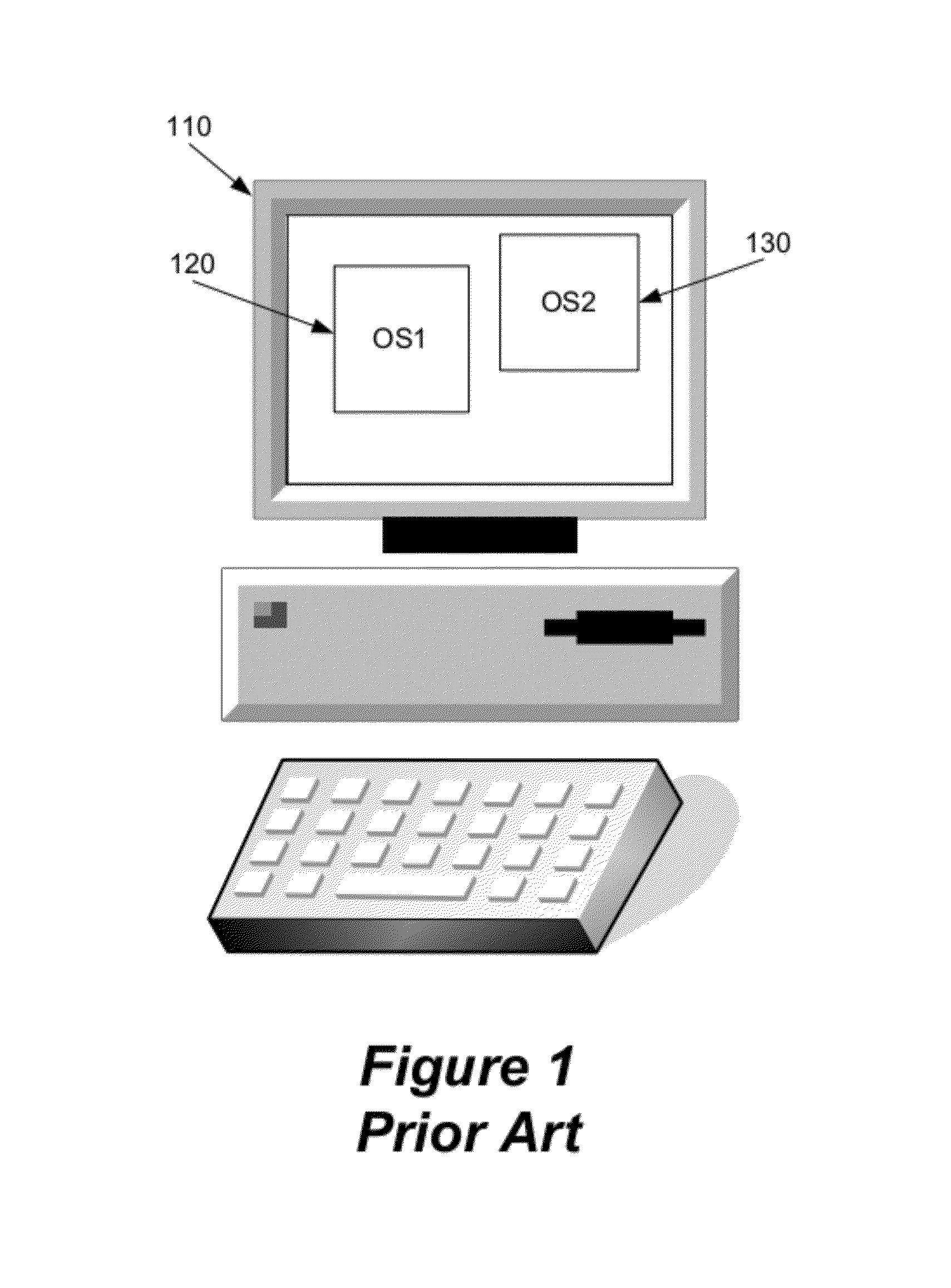
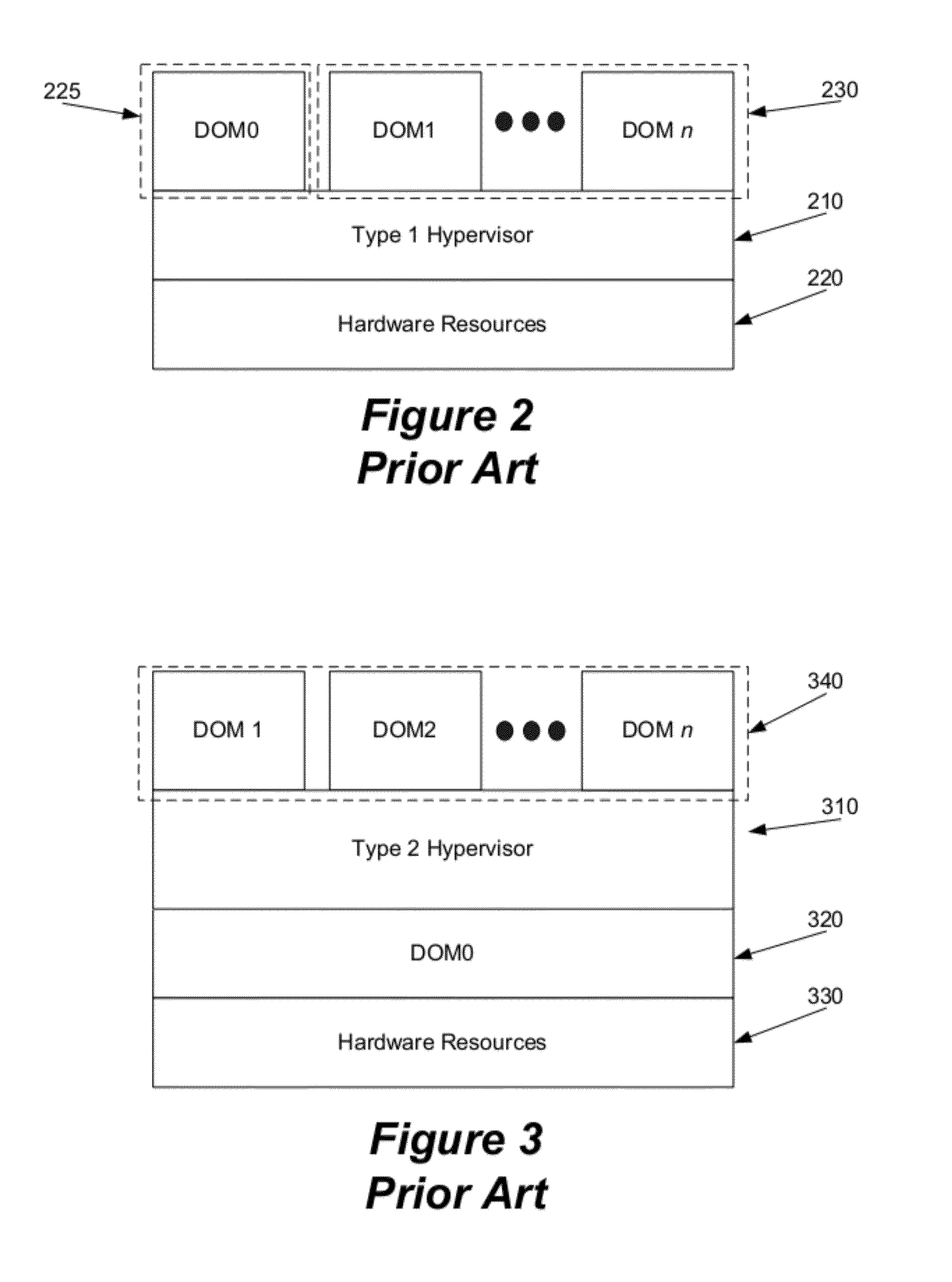
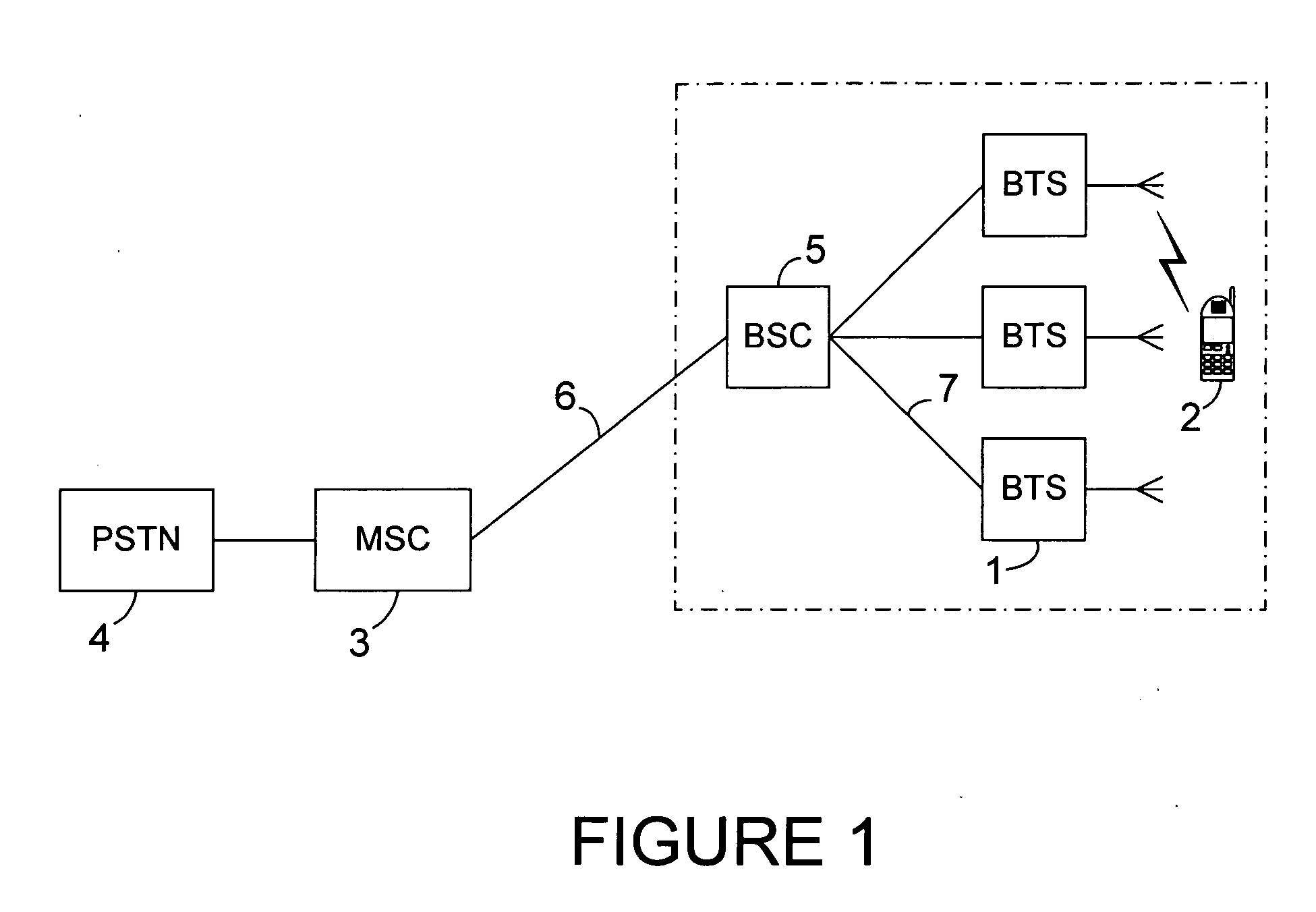
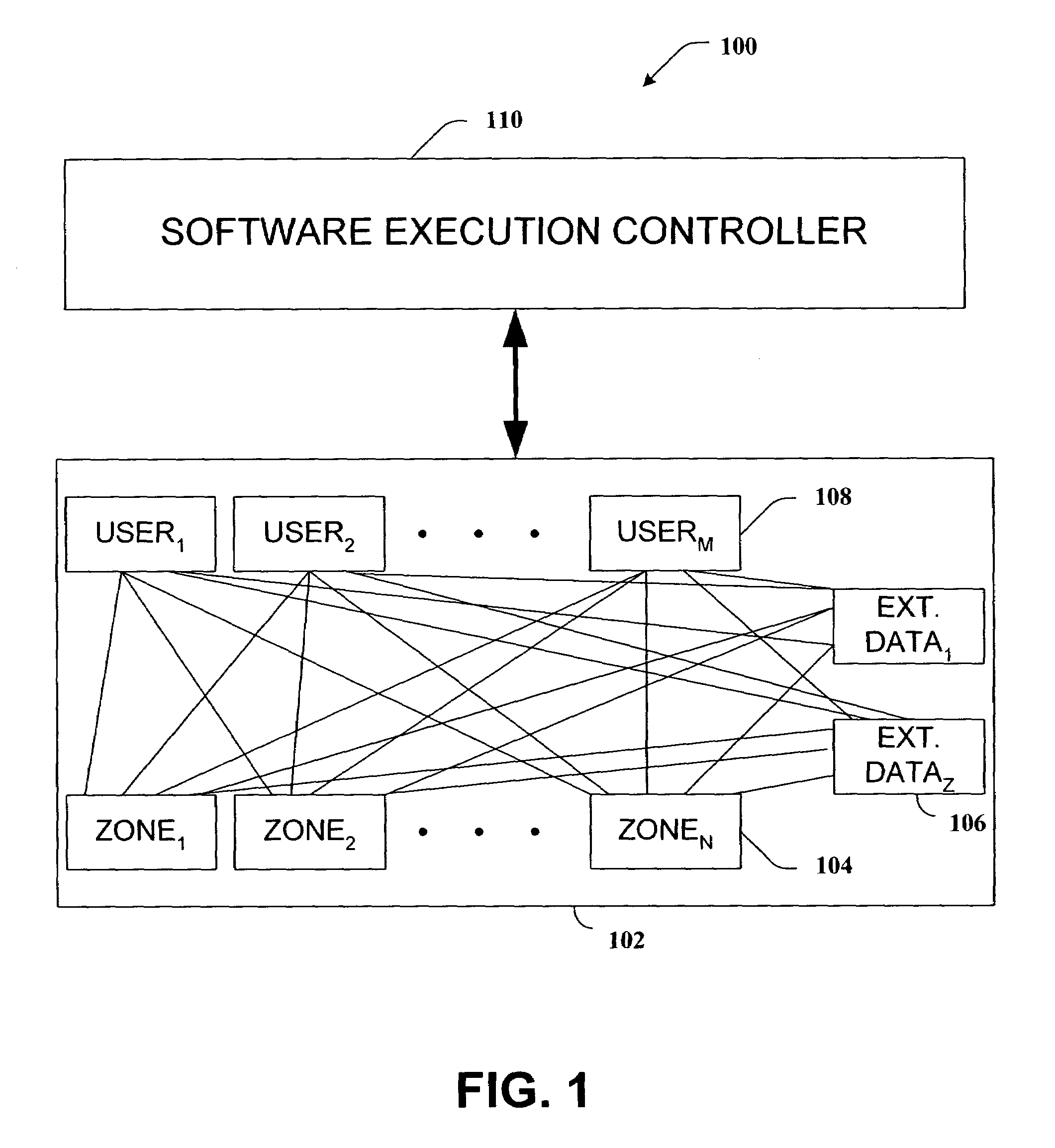
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2190 results about "Auto-configuration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Auto-configuration is the automatic configuration of devices without manual intervention, without any need for software configuration programs or jumpers. Ideally, auto-configuring devices should just "plug and play". Auto-configuration has been made common because of the low cost of microprocessors and other embedded controller devices.
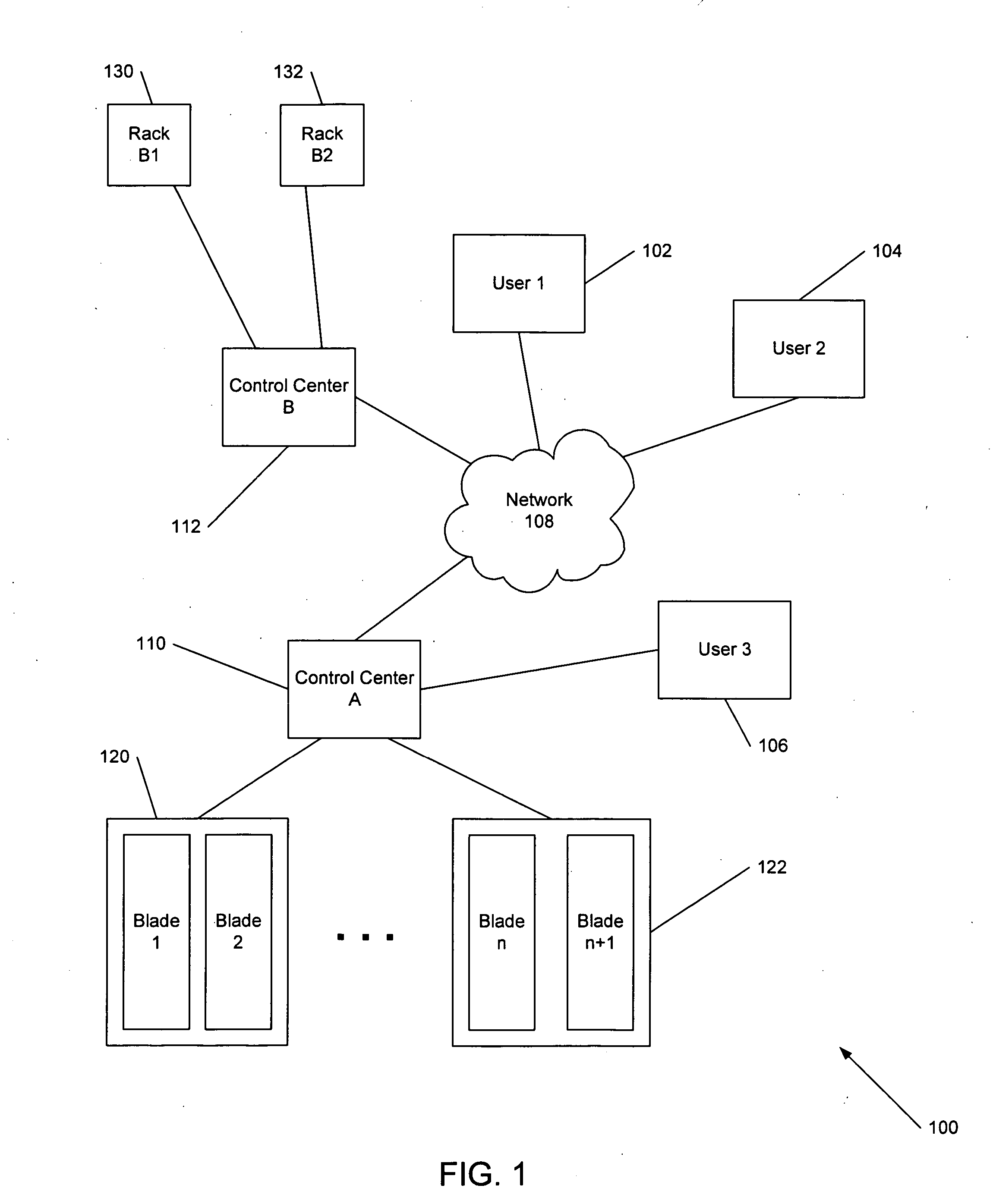
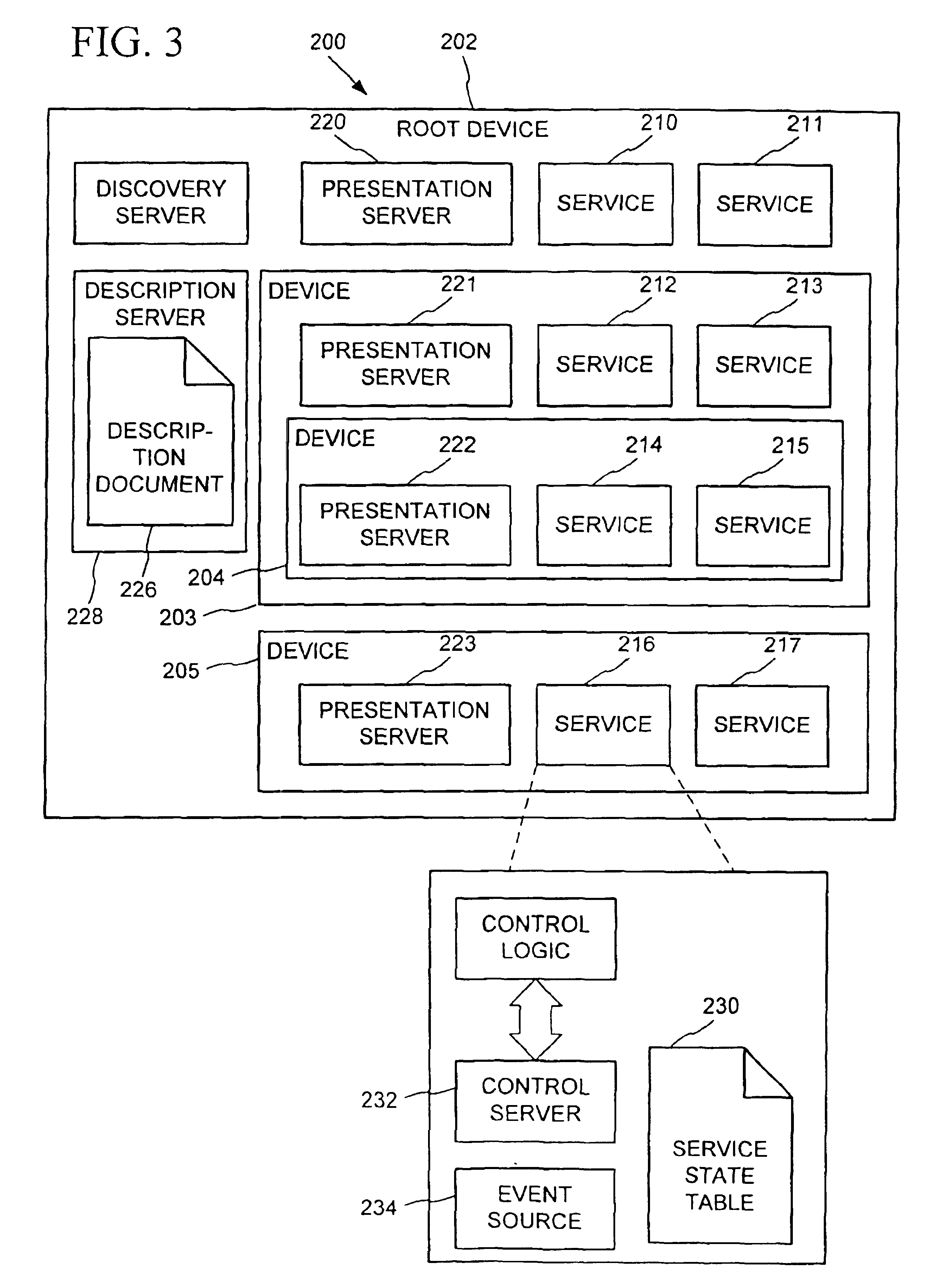
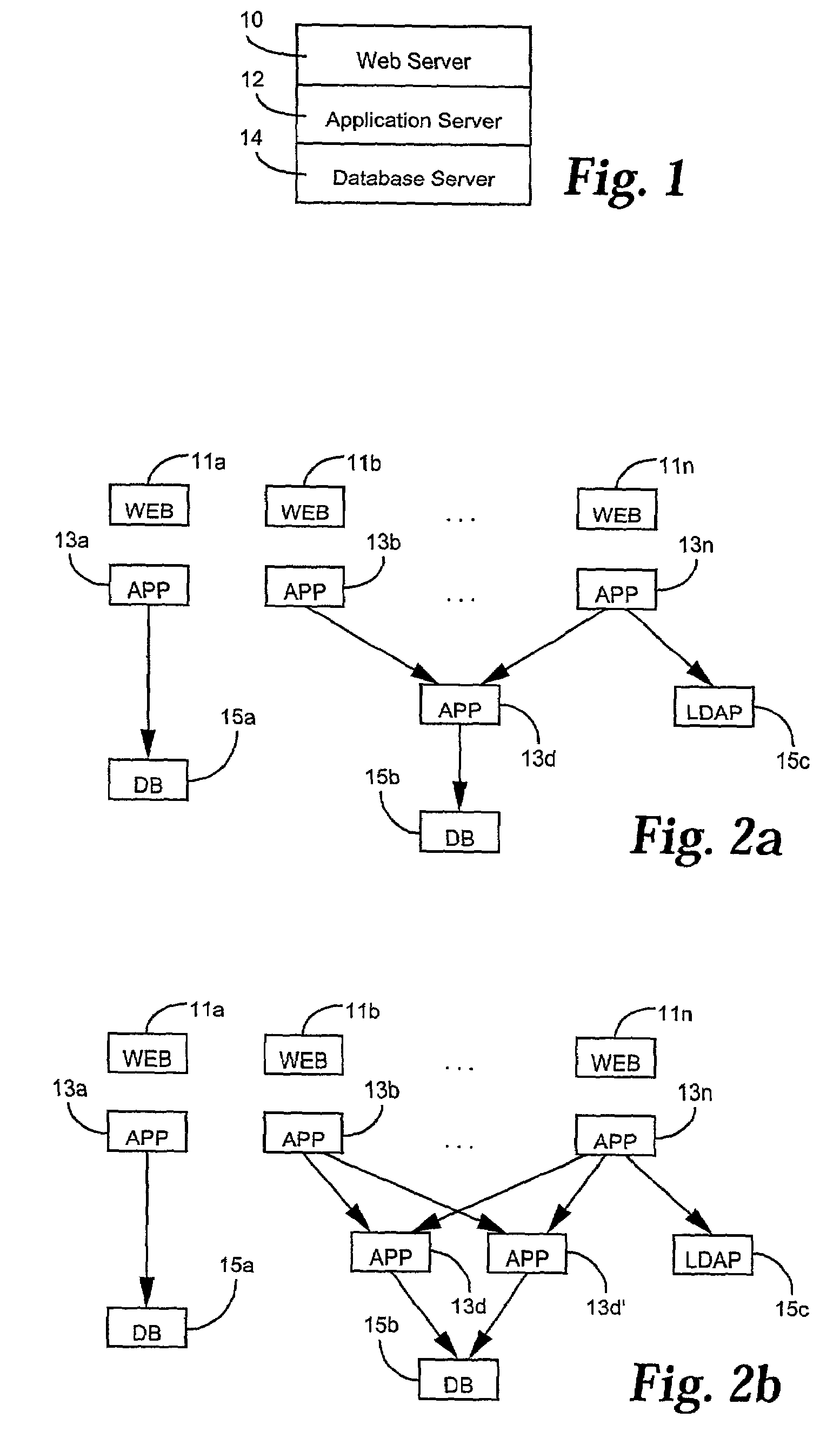
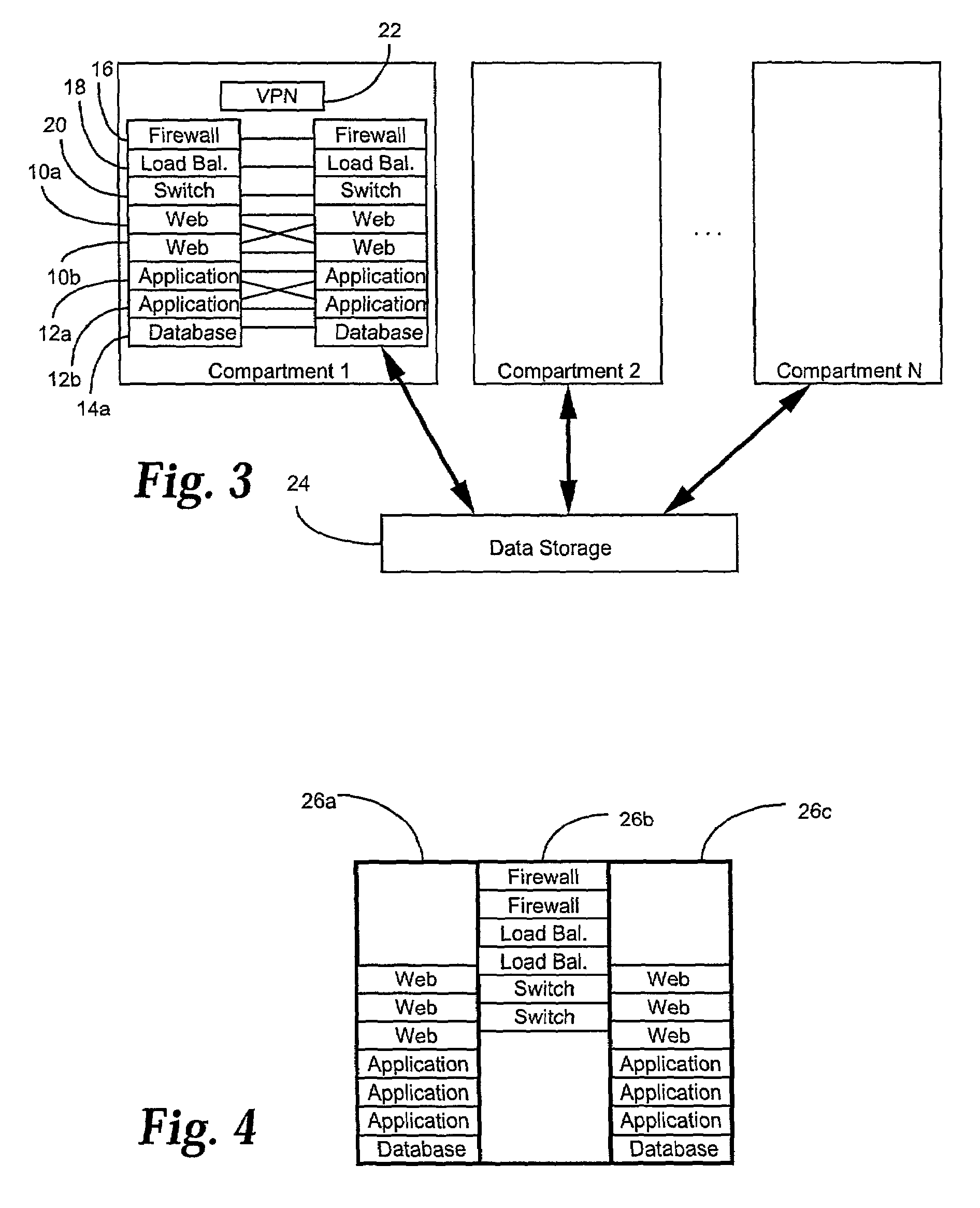
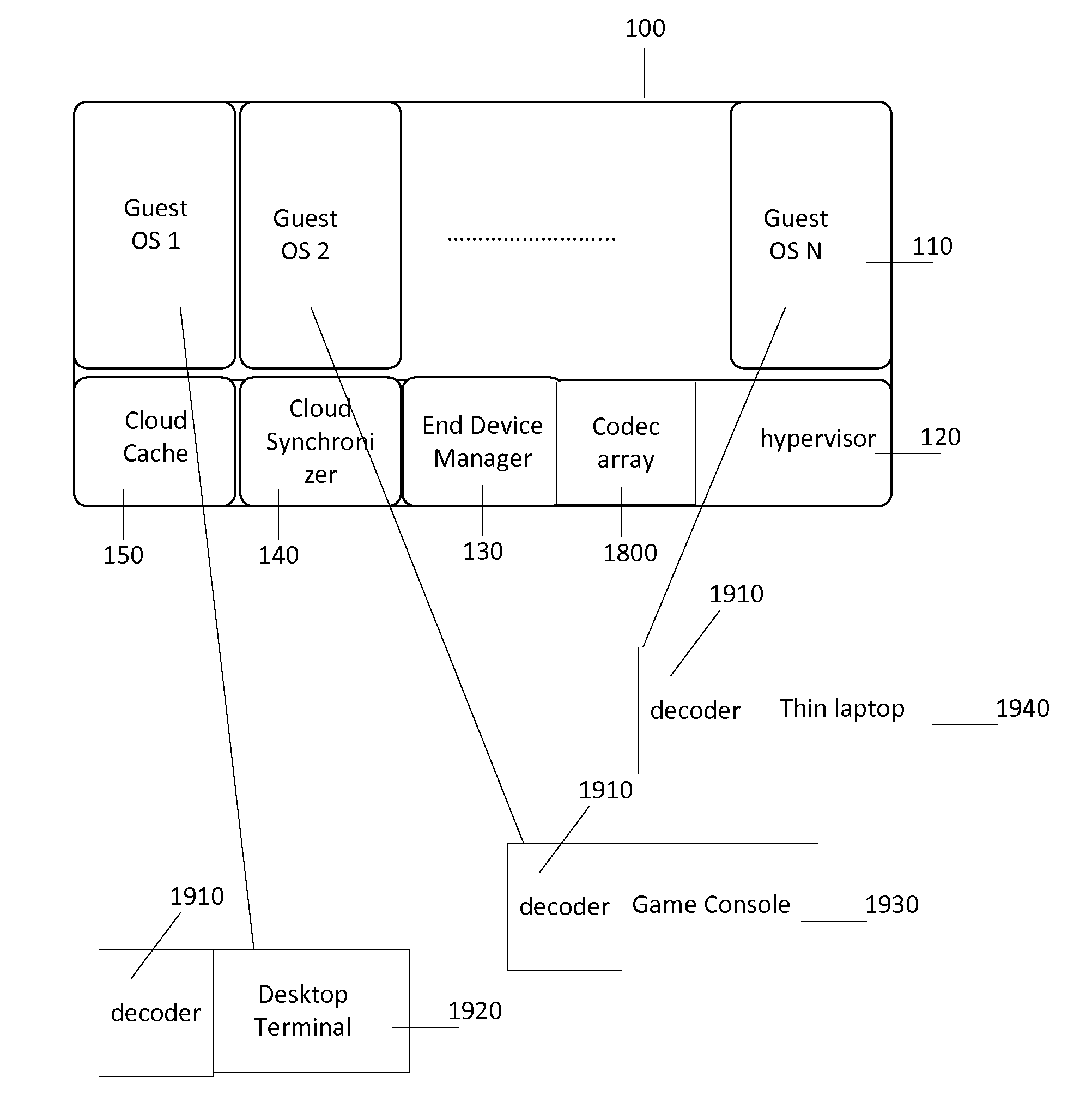
Methods and systems for automatic configuration of peripherals
ActiveUS20080140868A1Service provisioningDigital data processing detailsData processing systemAuto-configuration
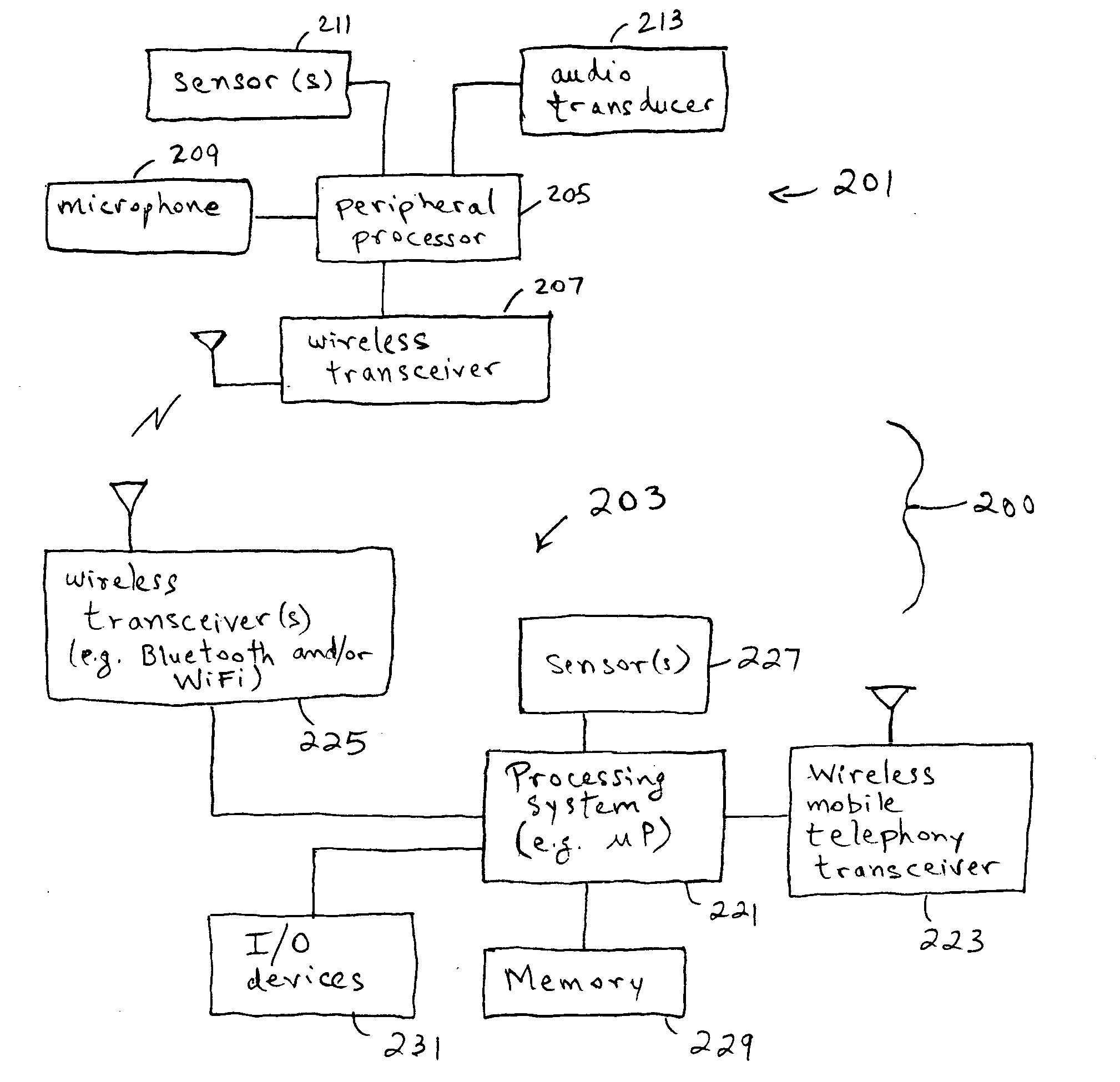
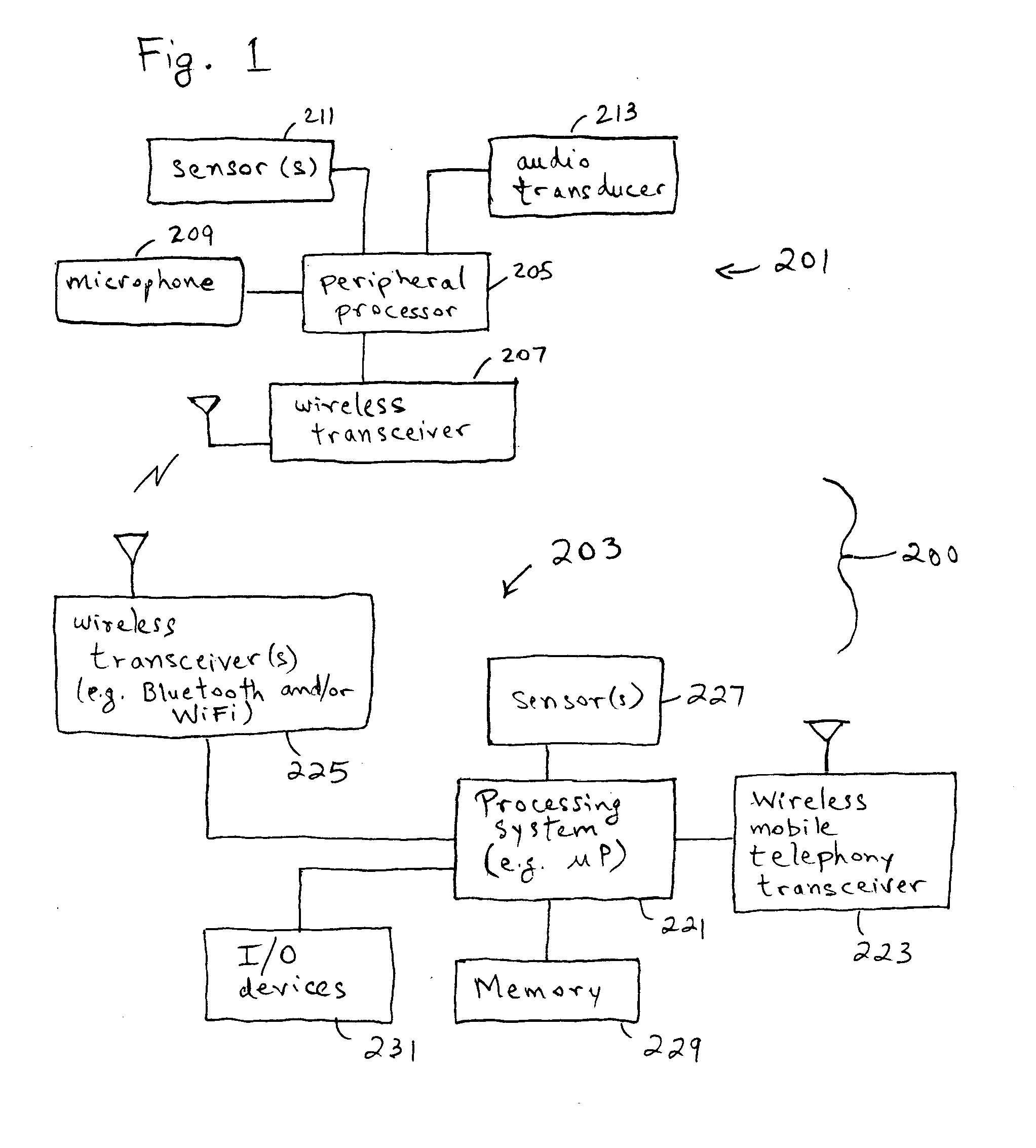
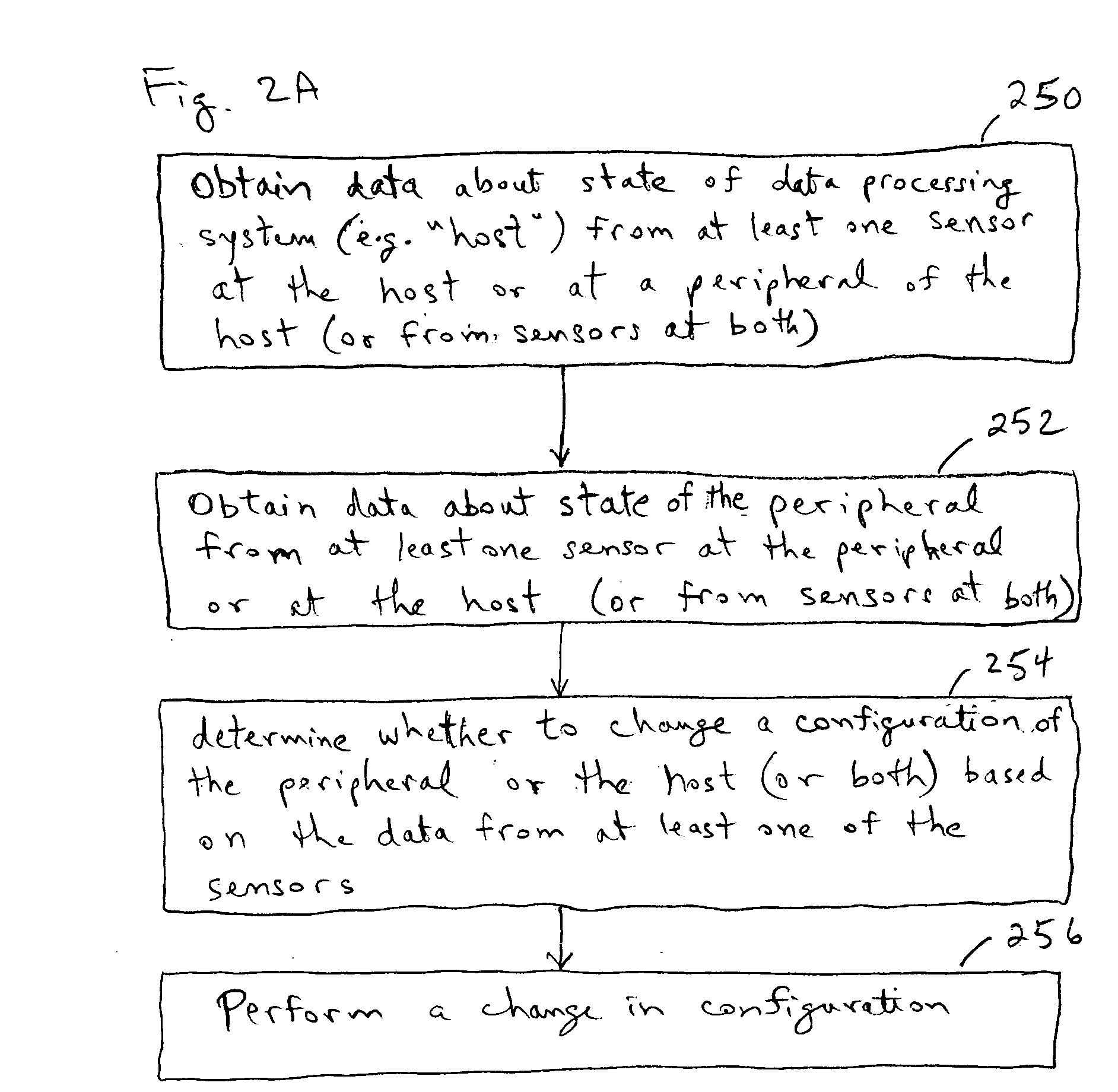
Peripherals and data processing systems are disclosed which can be configured to interact based upon sensor data. In one embodiment, a peripheral, which is configured to be used with a data processing system, includes an interface to couple the peripheral to the data processing system, and at least one sensor, such as a proximity sensor, to sense a user of the peripheral, and a processor coupled to the interface and to the at least one sensor, wherein the processor configures the peripheral in response to data from the at least one sensor. The peripheral may communicate sensor data from its sensors to the data processing system, which may be a wireless PDA, and the data processing system analyzes the sensor data from its sensors and from the peripheral's sensors to decide how to configure the peripheral and / or the data processing system based on the sensor.
Owner:APPLE INC
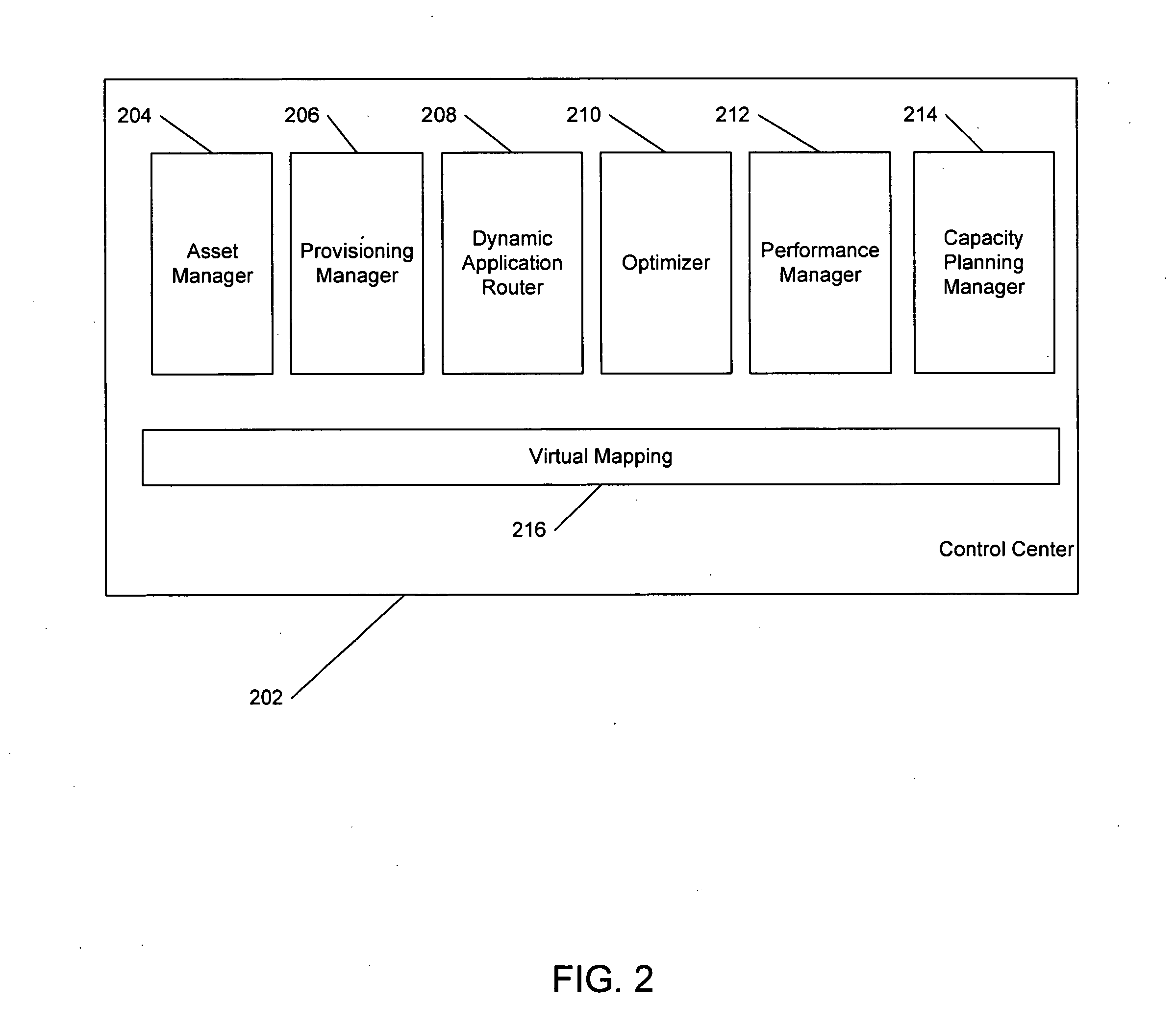
Virtual systems management
Automatic configuration management of a network is provided by determining an inventory of resources at a virtualization layer of a node of the network, assigning prioritization to members of a set of network configuration elements, allocating virtual resources among the set of network configuration elements, establishing a network configuration. The configuration is managed by determining real time performance metrics for the configuration, producing a reallocation of the virtual resources based on the performance metrics that are estimated to change the established configuration, change the performance metrics, and initiating the reallocation of the virtual resources. This Abstract is provided for the sole purpose of complying with the Abstract requirement that allows a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:TOUTVIRTUAL
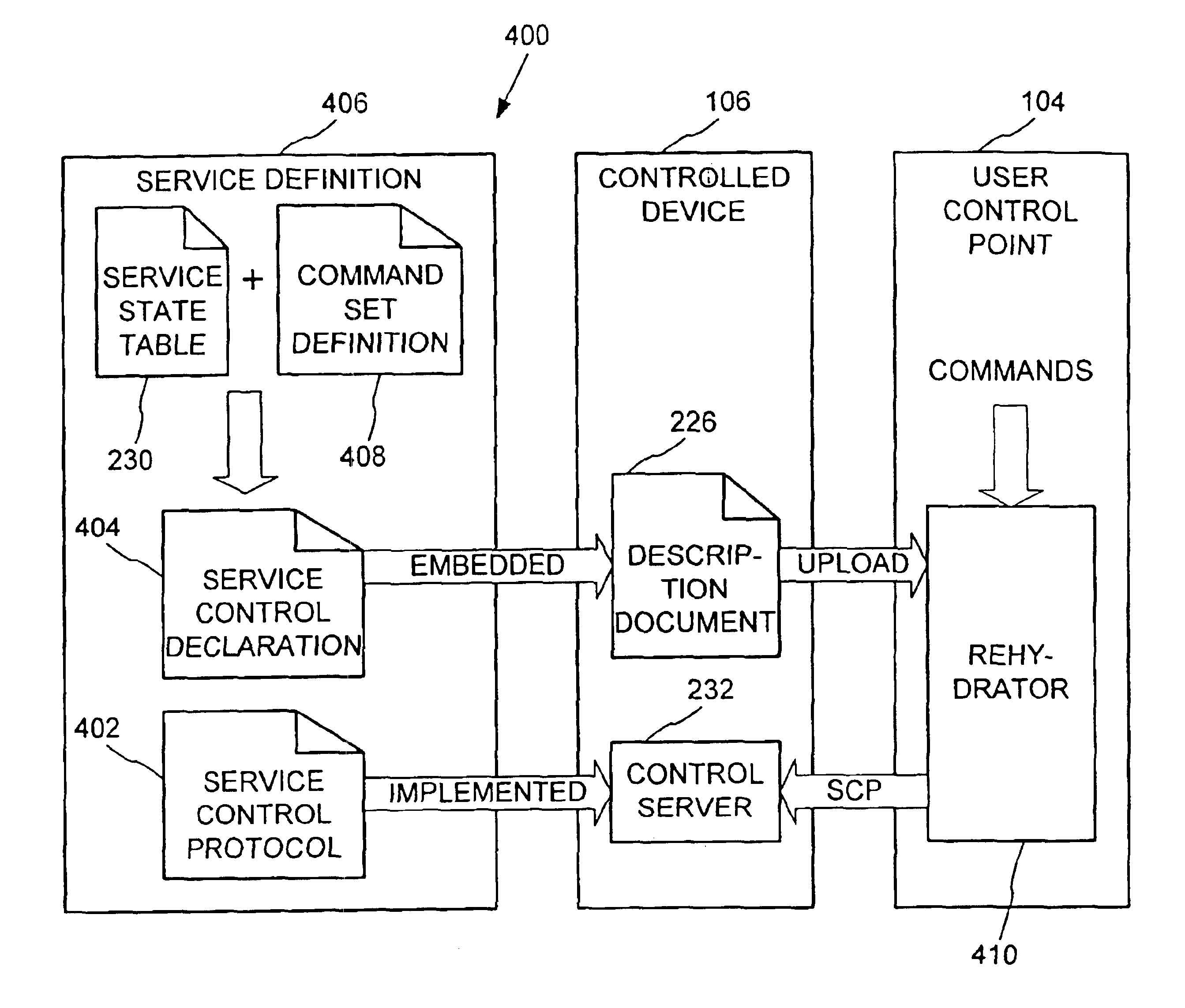
Dynamic self-configuration for ad hoc peer networking using mark-up language formated description messages
InactiveUS6892230B1CostConnectivity solutionDigital computer detailsNetworks interconnectionAuto-configurationHuman language
A device control model provides an integrated set of addressing, naming, discovery and description processes that enables automatic, dynamic and ad-hoc self-setup by devices to interoperate with other devices on a network. This permits a computing device when introduced into a network to automatically configure so as to connect and interact with other computing devices available on the network, without a user installation experience and without downloading driver software or persisting a configuration setup for connecting and interacting with such other computing devices. Upon completing interaction with such other devices, the computing device automatically releases the setup for such other devices so as to avoid persistent device configurations that might create a configuration maintenance and management burden.
Owner:ROVI TECH CORP
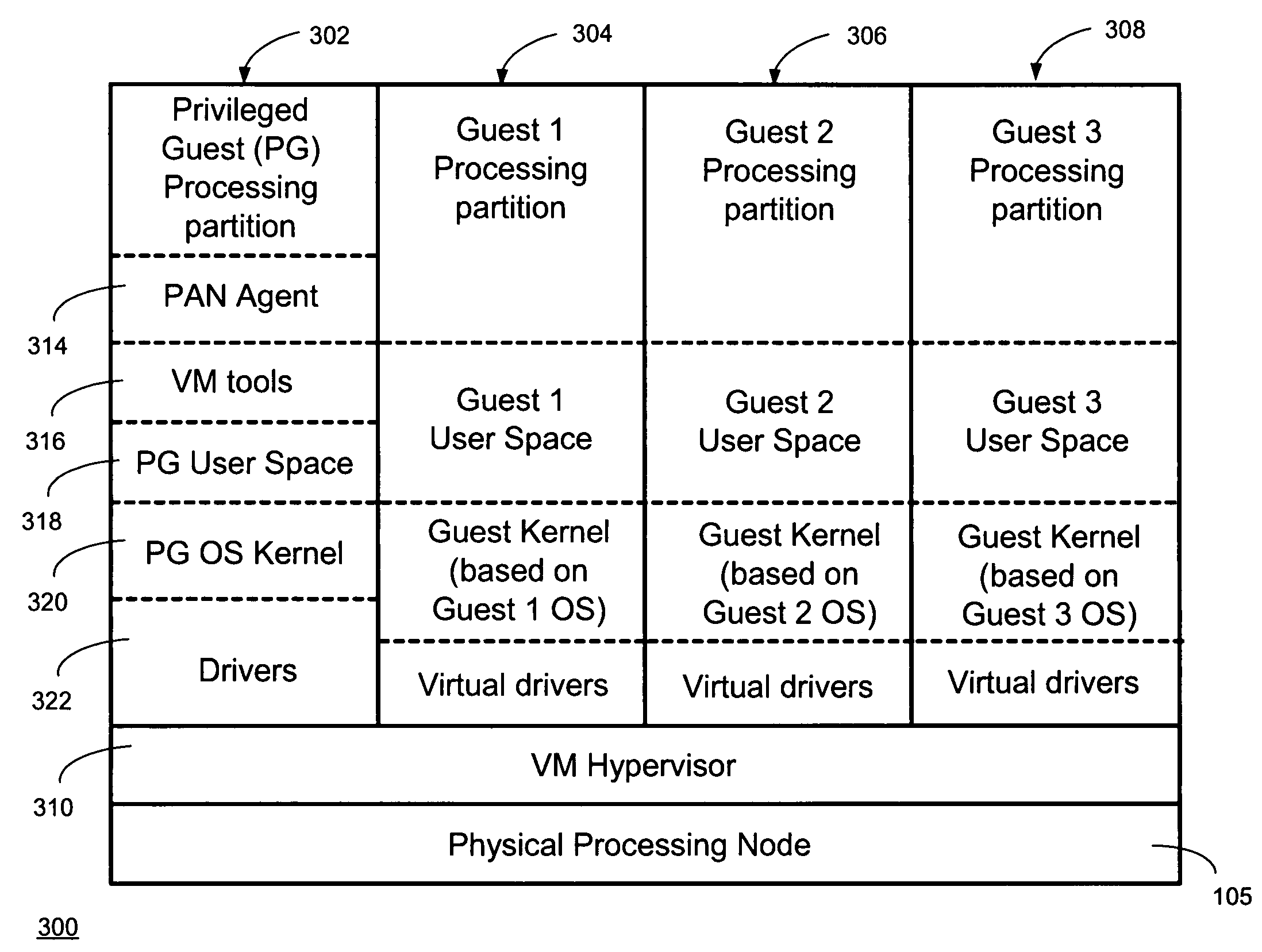
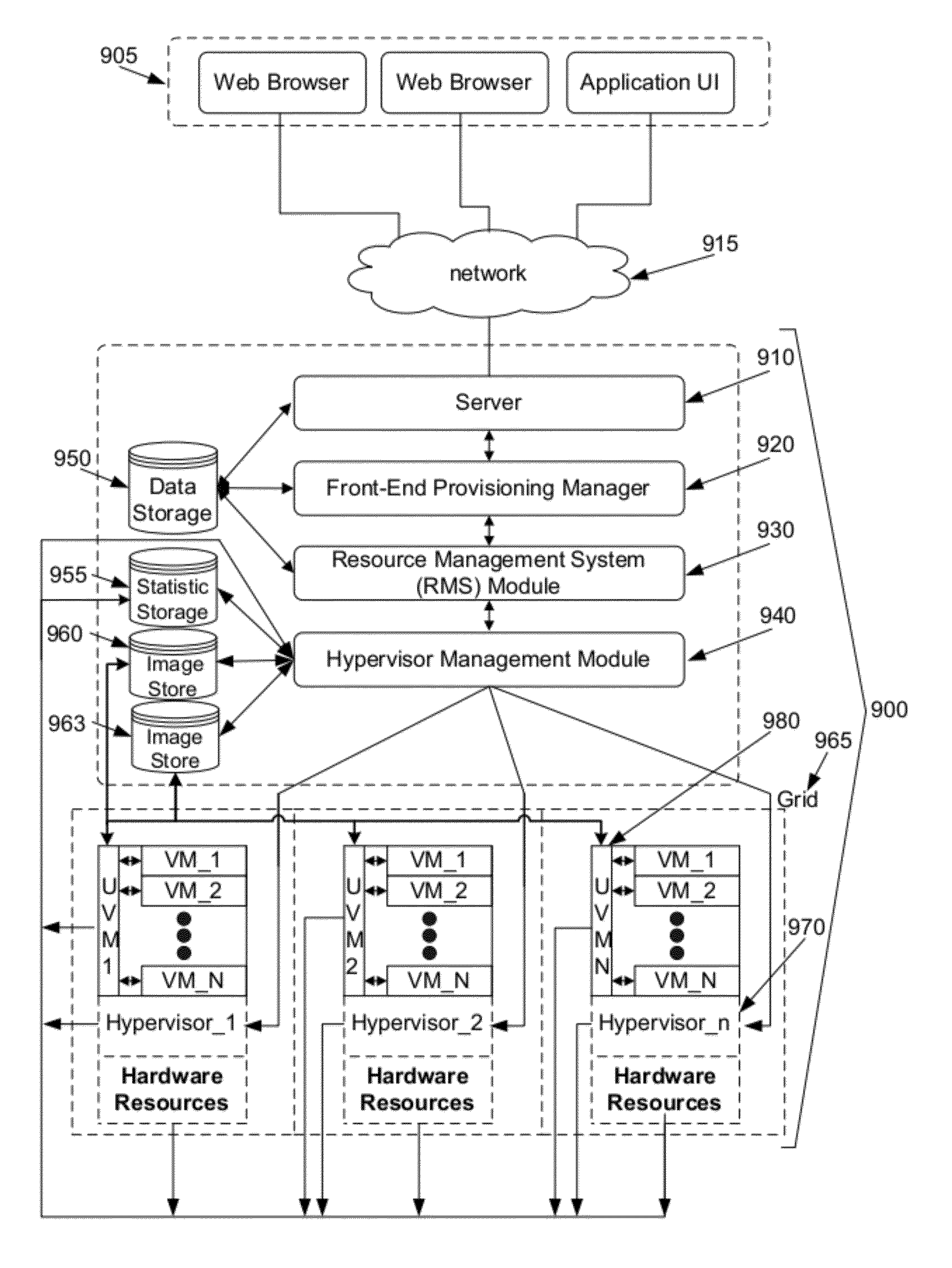
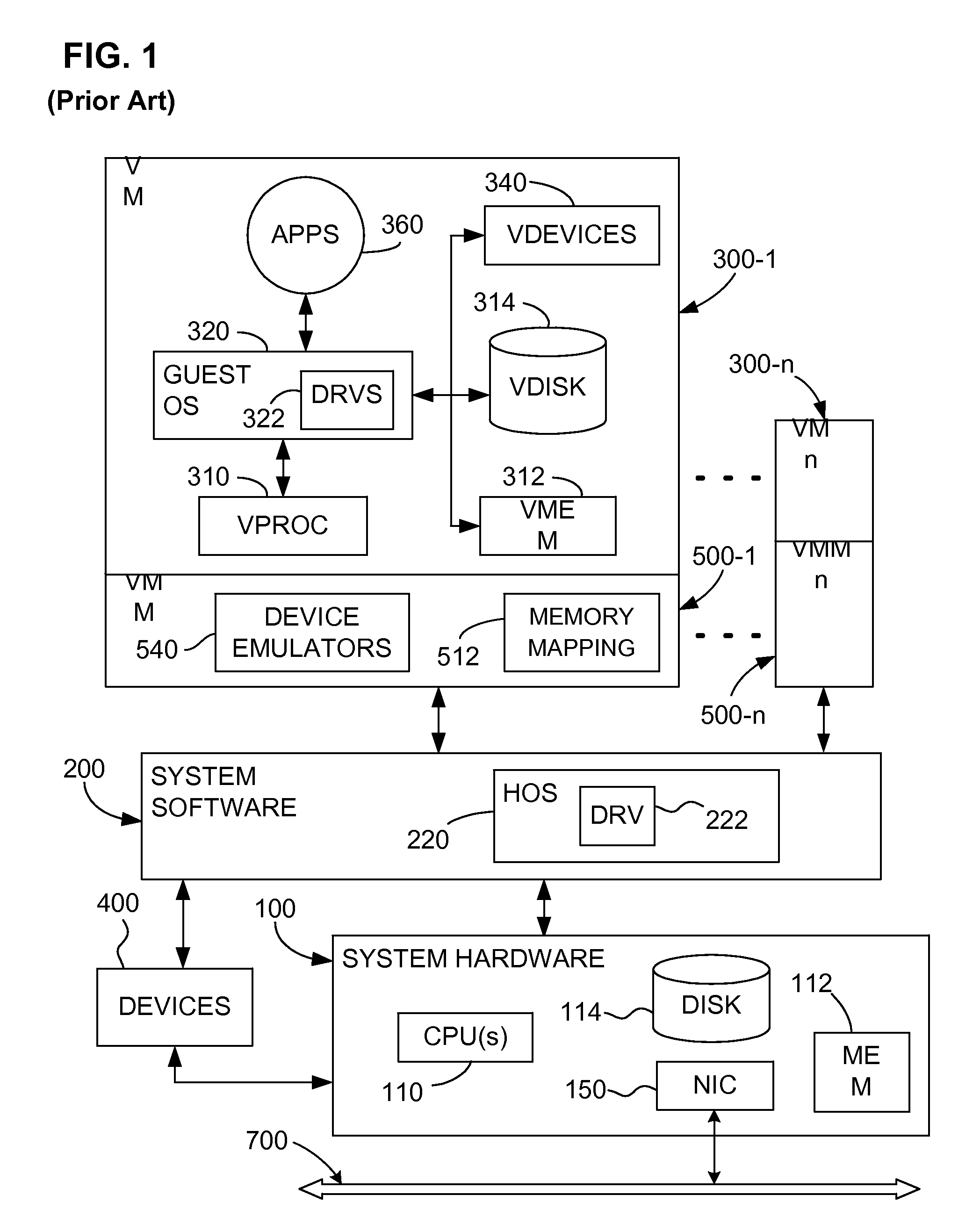
Providing virtual machine technology as an embedded layer within a processing platform
InactiveUS20080059556A1Satisfies specificationMultiple digital computer combinationsProgram controlAuto-configurationProcessor node
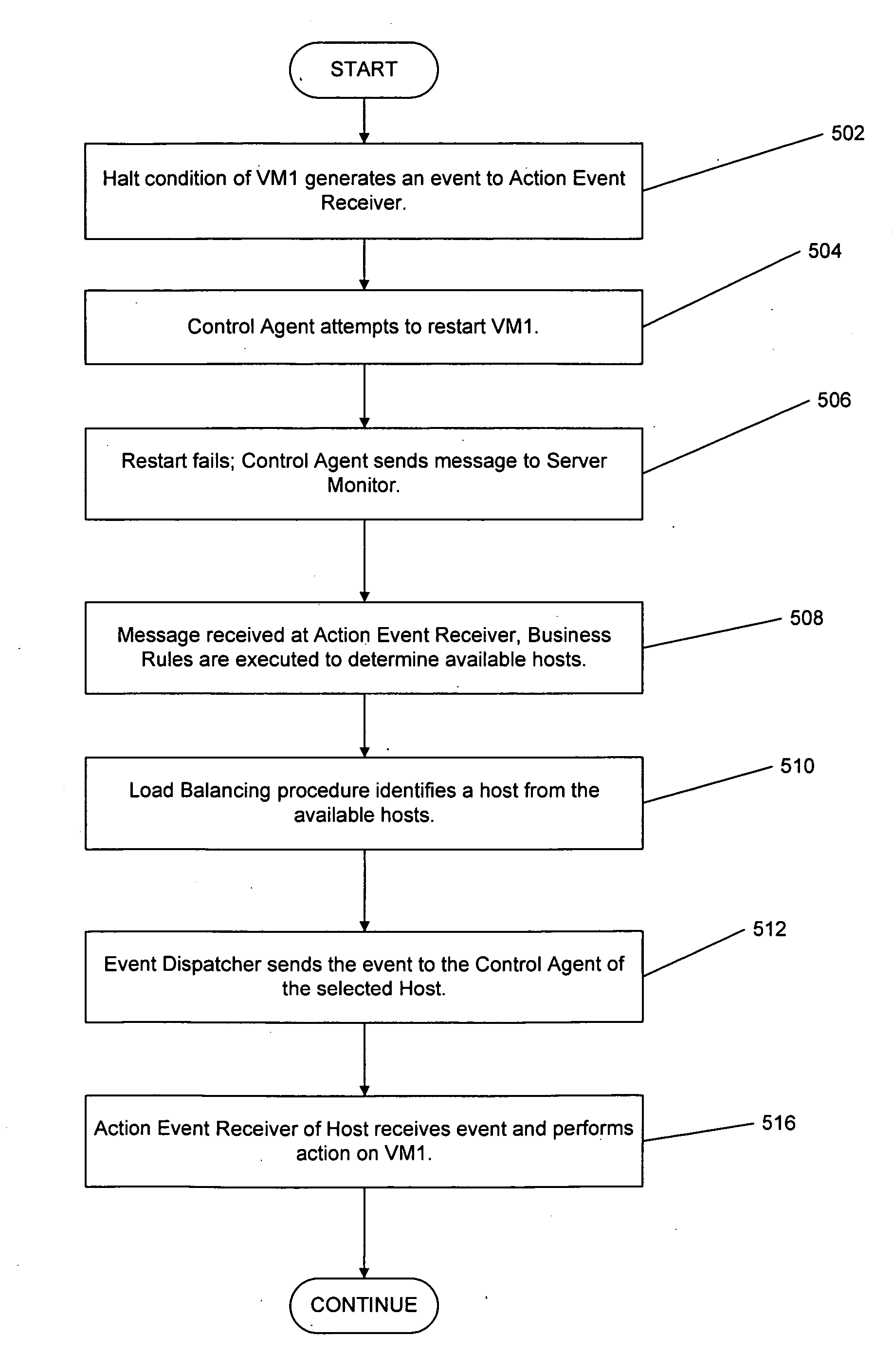
A platform, method, and computer program product, provides virtual machine technology within a processing platform. A computing platform automatically deploys one or more servers in response to receiving corresponding server specifications. Each server specification identifies a server application that a corresponding server should execute and defines communication network and storage network connectivity for the server. The platform includes a plurality of processor nodes and virtual machine hypervisor. The virtual machine hypervisor logic has logic for instantiating and controlling the execution of one or more guest virtual machines on a computer processor. In response to interpreting the server specification, control software deploys computer processors or guest virtual machines to execute the identified server application and automatically configures the defined communication network and storage network connectivity to the selected computer processors or guest virtual machines to thereby deploy the server defined in the server specification.
Owner:EGENERA
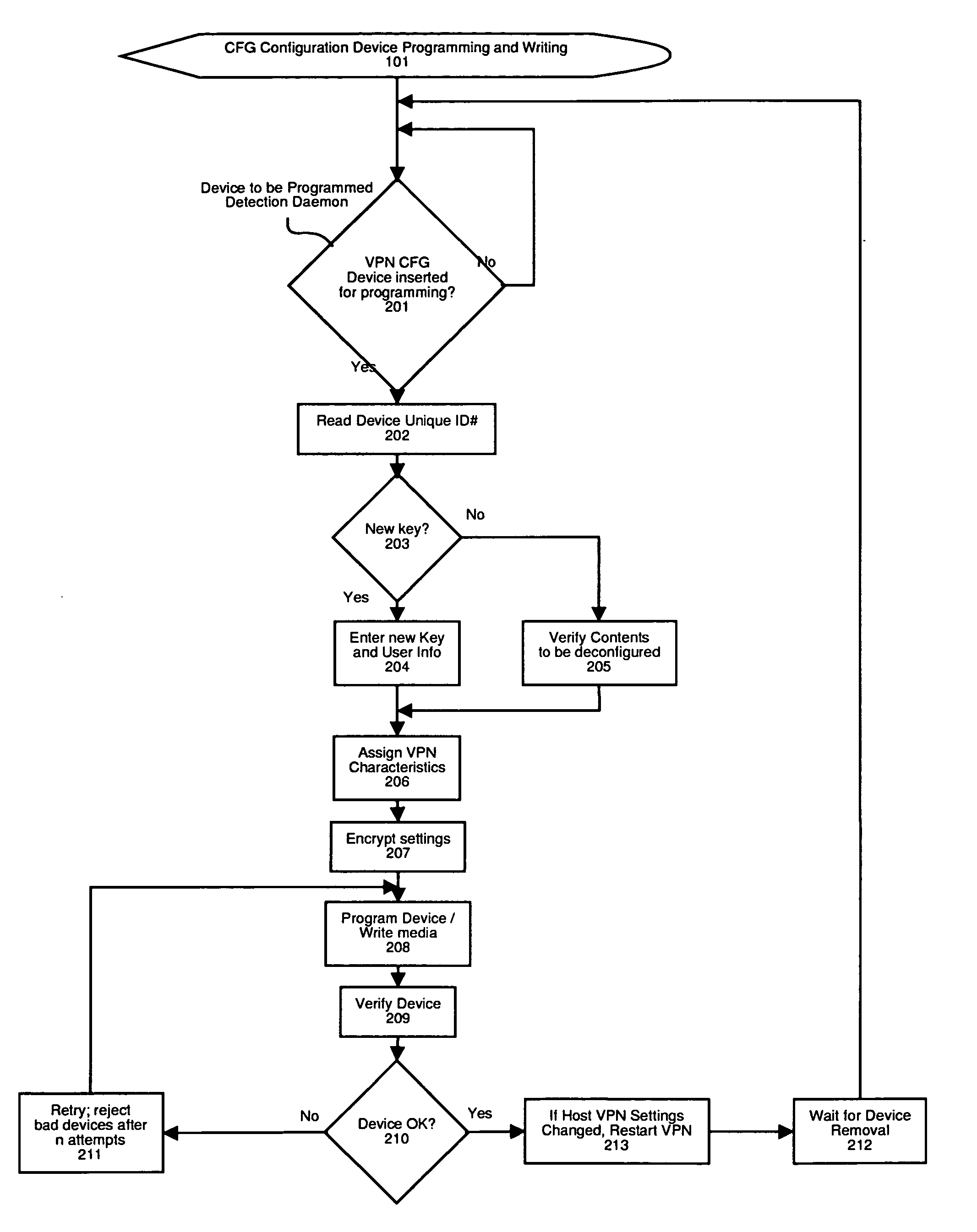
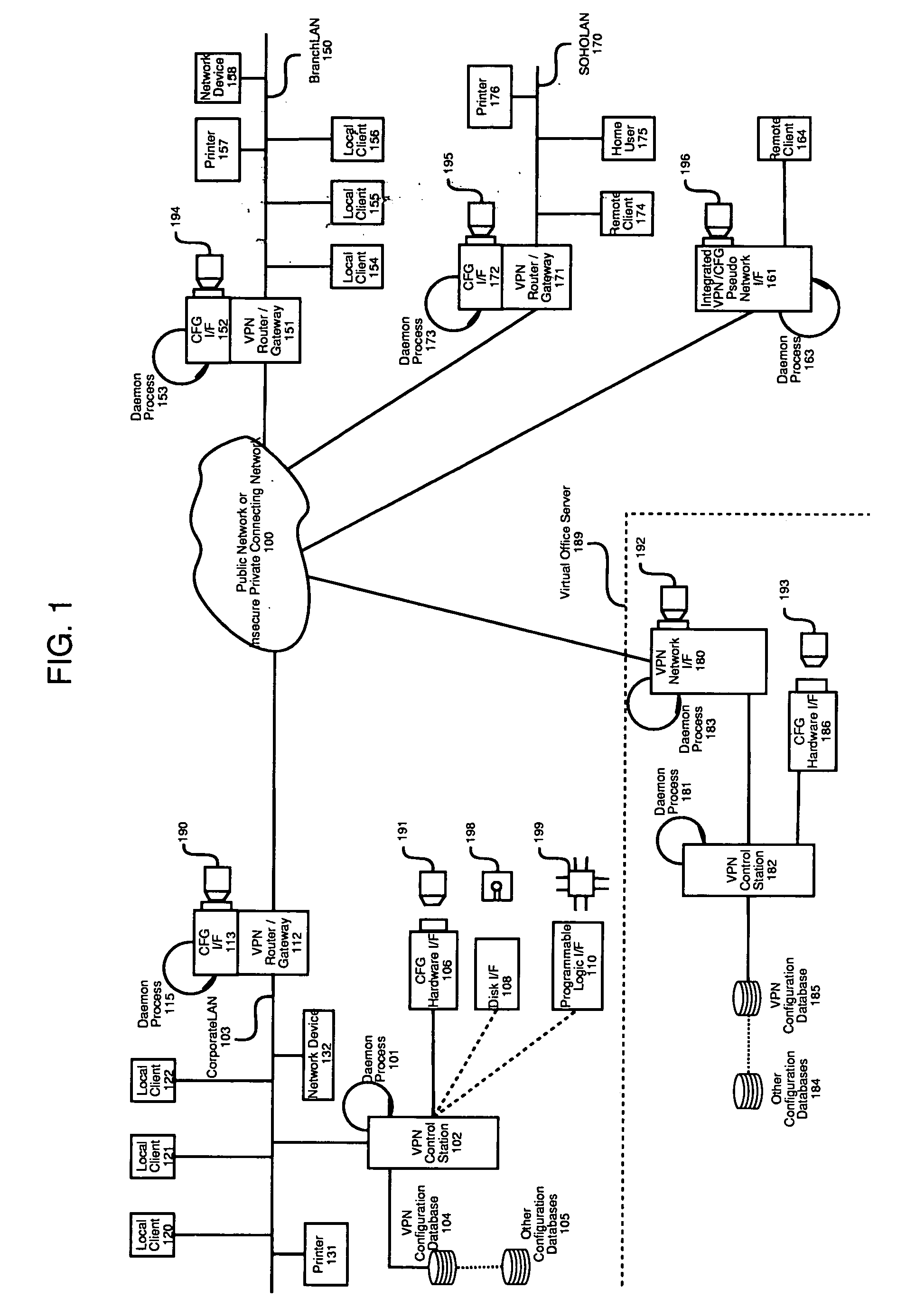
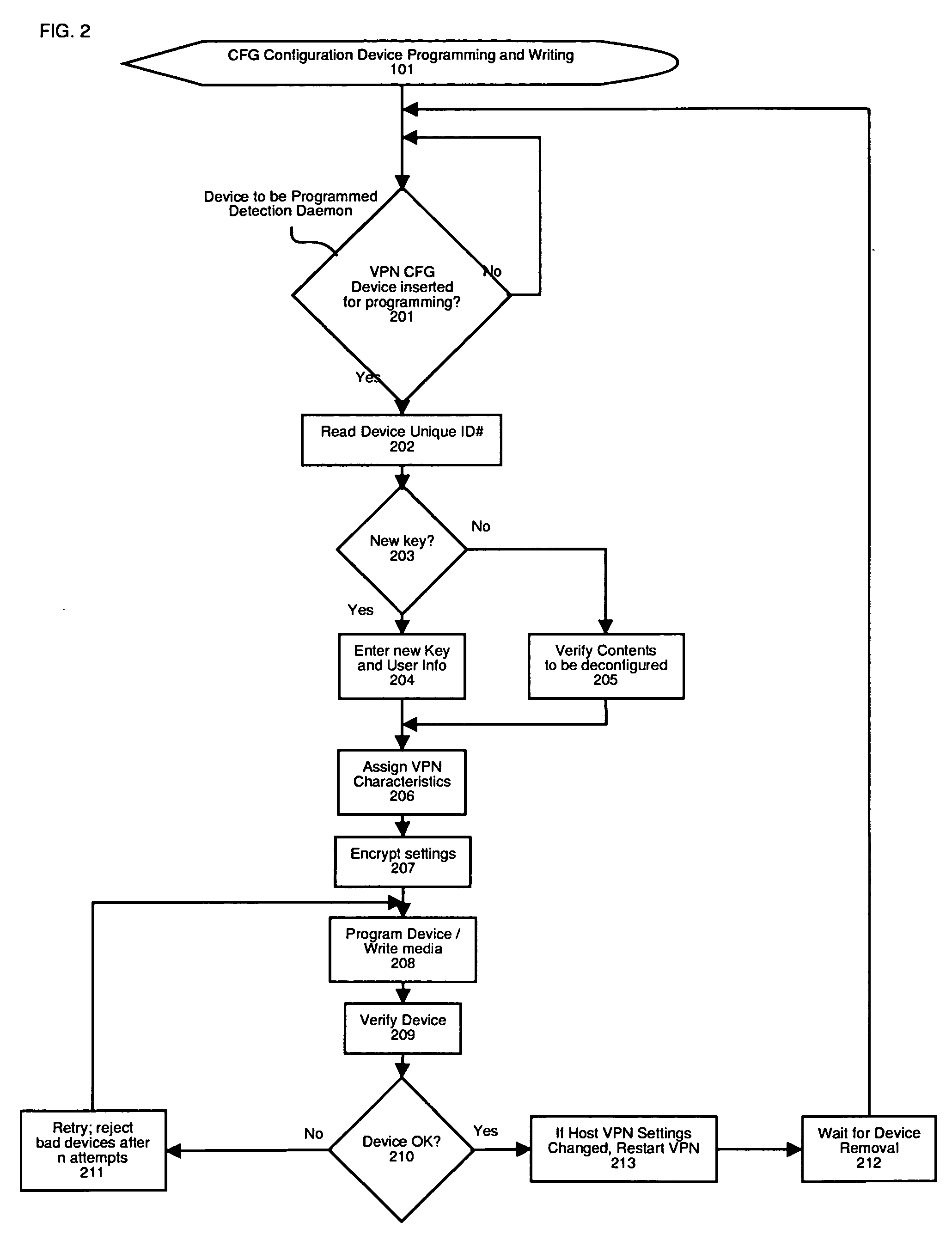
Method and apparatus for automatic configuration and management of a virtual private network
InactiveUS20050193103A1Reduce chanceDigital computer detailsTransmissionAuto-configurationPrivate network
The present invention provides a method and apparatus for automatic configuration and management of a virtual private network operating over a public data network, and a method and apparatus for delivery of the configuration parameters to client interface equipment participating in the virtual private network. The system defines allowed connections between client and server gateway devices, and the parameters associated with the virtual private network. The system defines methods and apparatus for automatic startup, configuration, and shutdown of nodes of the resulting virtual private network based on factors such as the presence of a configuration carrier device. The present invention also describes a class of pseudo-interface mechanism that can hide the complexity of the underlying system from client devices incorporating the present invention, via a conventional network device interface.
Owner:DRABIK JOHN
System and method for automated configuration of hosting resources
ActiveUS8352608B1Facilitate efficient deploymentMaximize useDigital computer detailsProgram controlAuto-configurationFile system
Some embodiments provide a method for automated configuration of a set of resources for hosting a virtual machine at a particular node in a hosting system. The hosting system includes several nodes for hosting several virtual machines. The method, at a first virtual machine operating using a first set of resources of the particular node, receives a configuration for a second virtual machine to be hosted on a second set of resources of the particular node. The method, from the first virtual machine, accesses the second set of resources to partition a file system for storing the second virtual machine. The method modifies the file system to configure the second virtual machine as specified by the configuration.
Owner:GOOGLE LLC
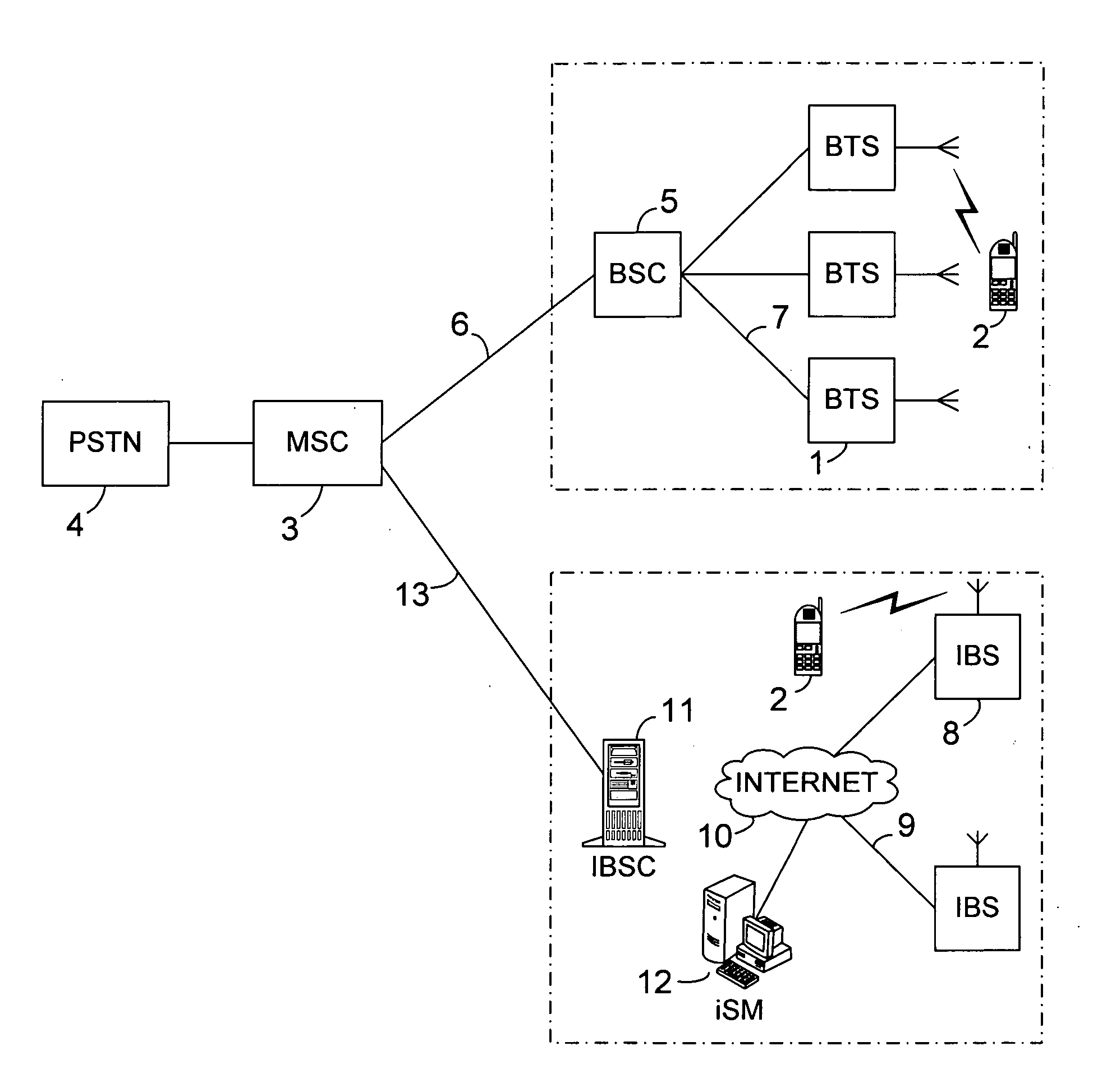
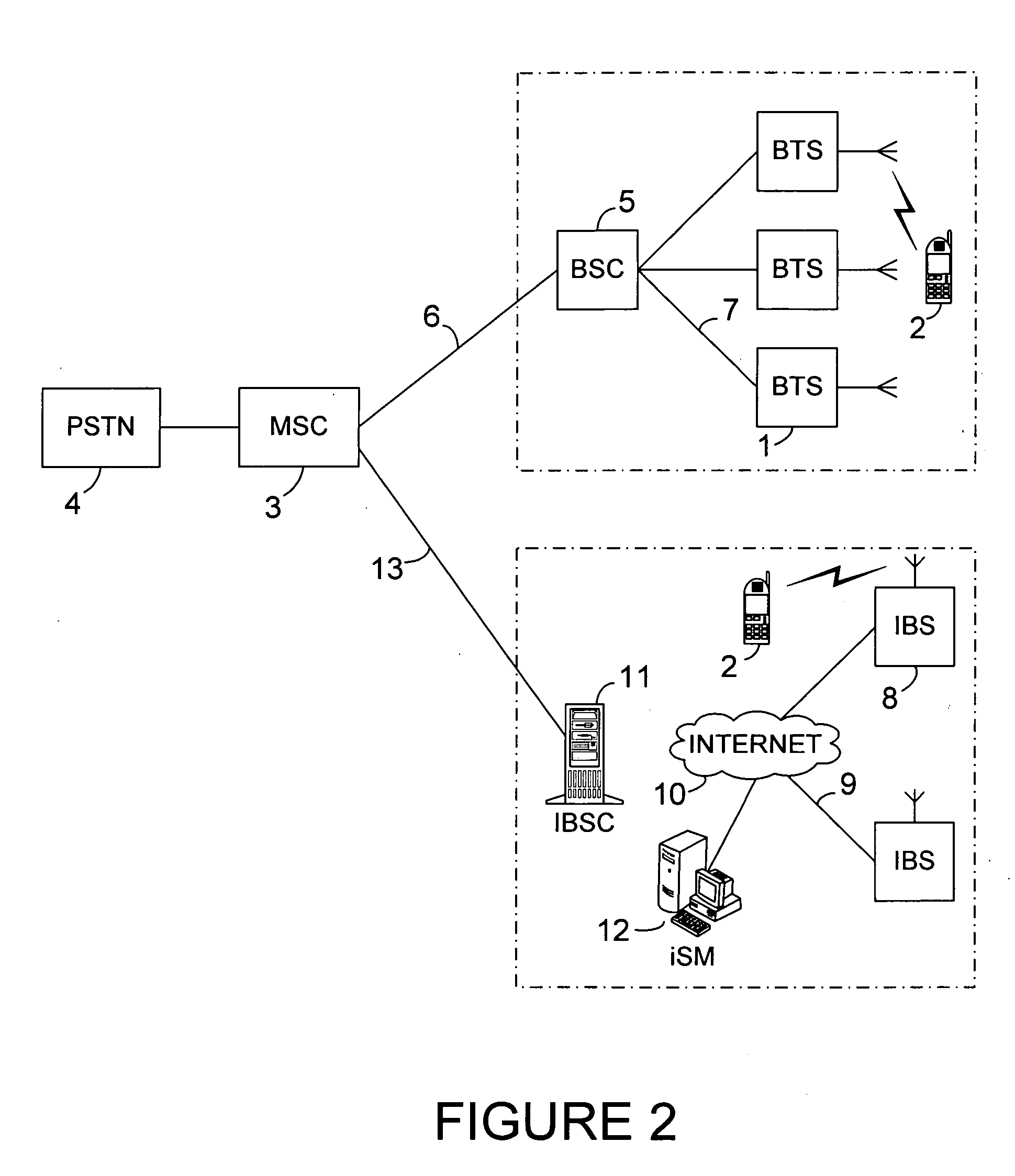
System and method for automatically configuring and integrating a radio base station into an existing wireless cellular communication network with full bi-directional roaming and handover capability
ActiveUS20050148368A1High densityAvoid the needNetwork traffic/resource managementNetwork topologiesAuto-configurationRoaming
A radio base station in a mobile communication network collects information about the network and exchanges data with a configuration device, the Internet System Manager (iSM). The iSM automatically configures and integrates the base station into the network by defining configuration parameter settings that allow fill interoperation of the base station with the network, with regards to roaming and handover in particular, without the need to add or modify parameter settings in other existing network elements. A very large number and high geographical density of such base stations is supported with full interoperation between them, allowing to overcome limitations of conventional mobile communication networks in this regard, by utilizing a certain combination of parameter settings and a new method to address the different base stations in the network.
Owner:APPLE INC
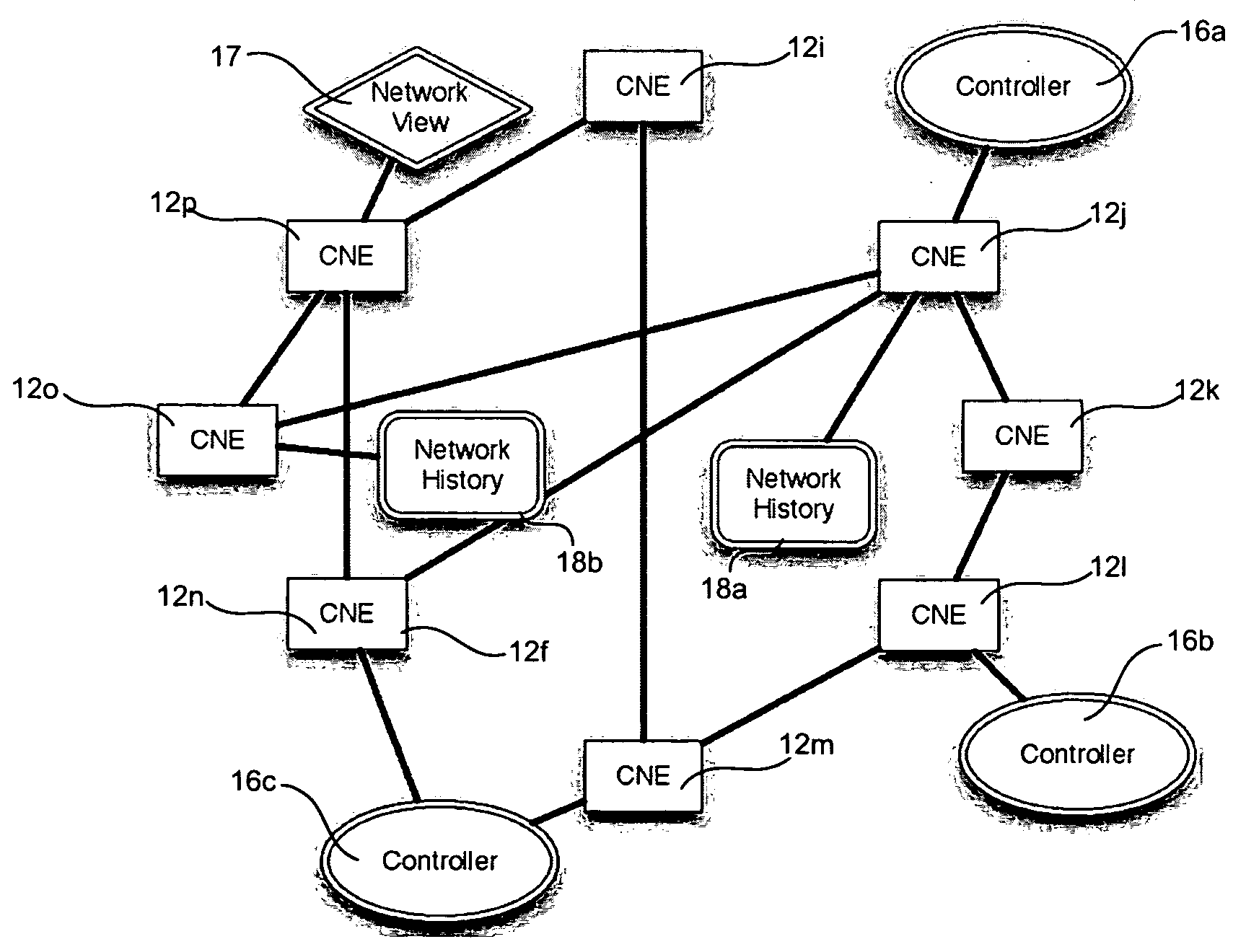
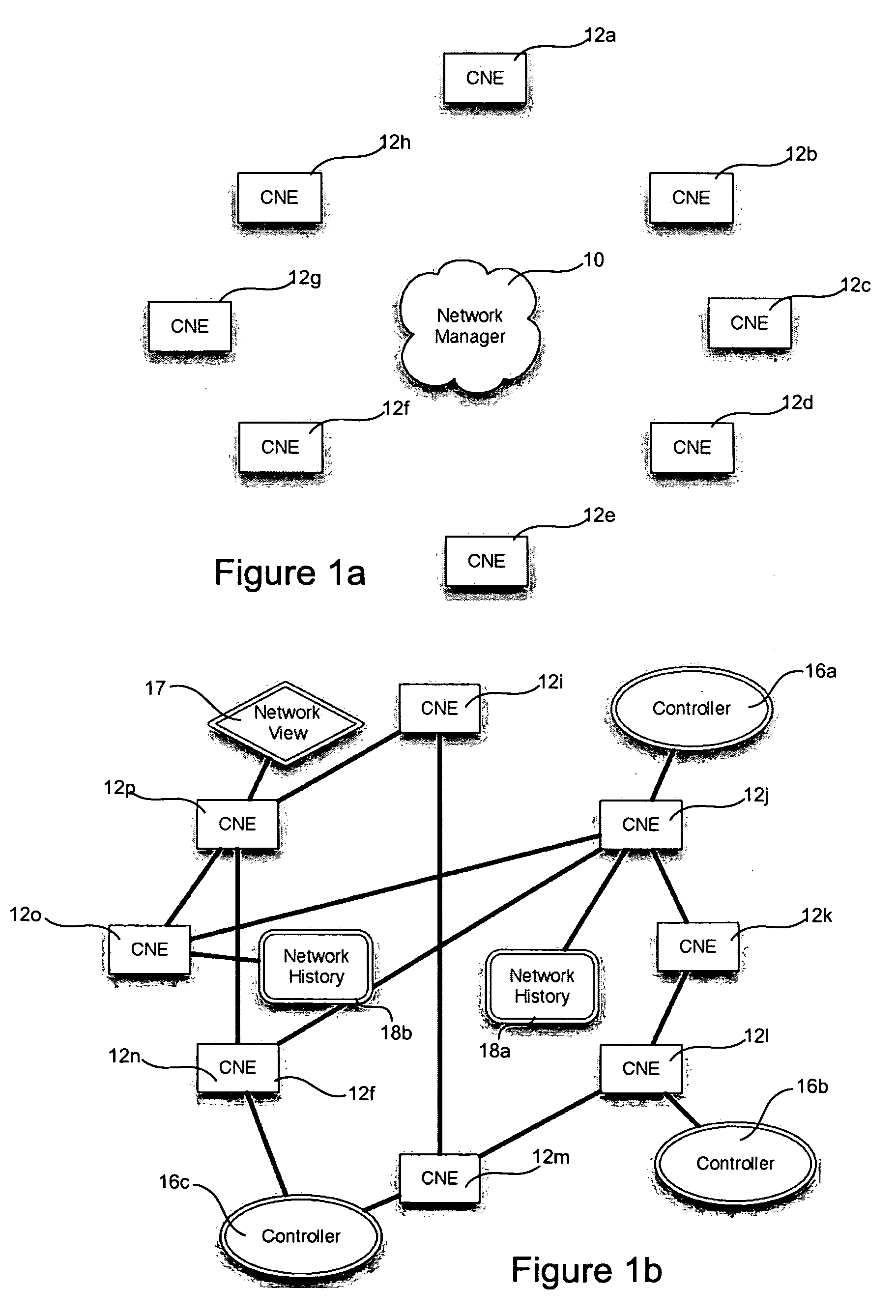
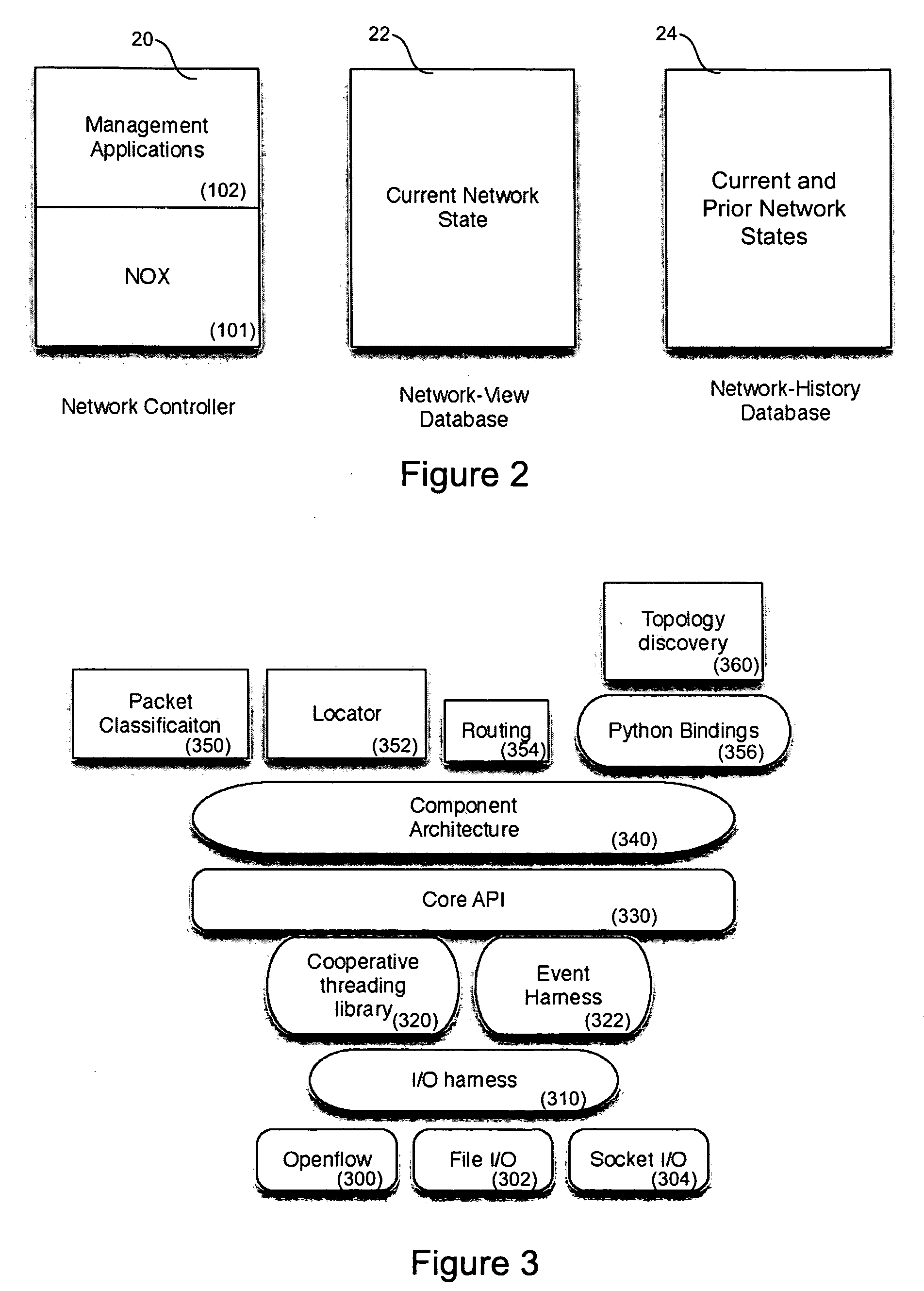
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
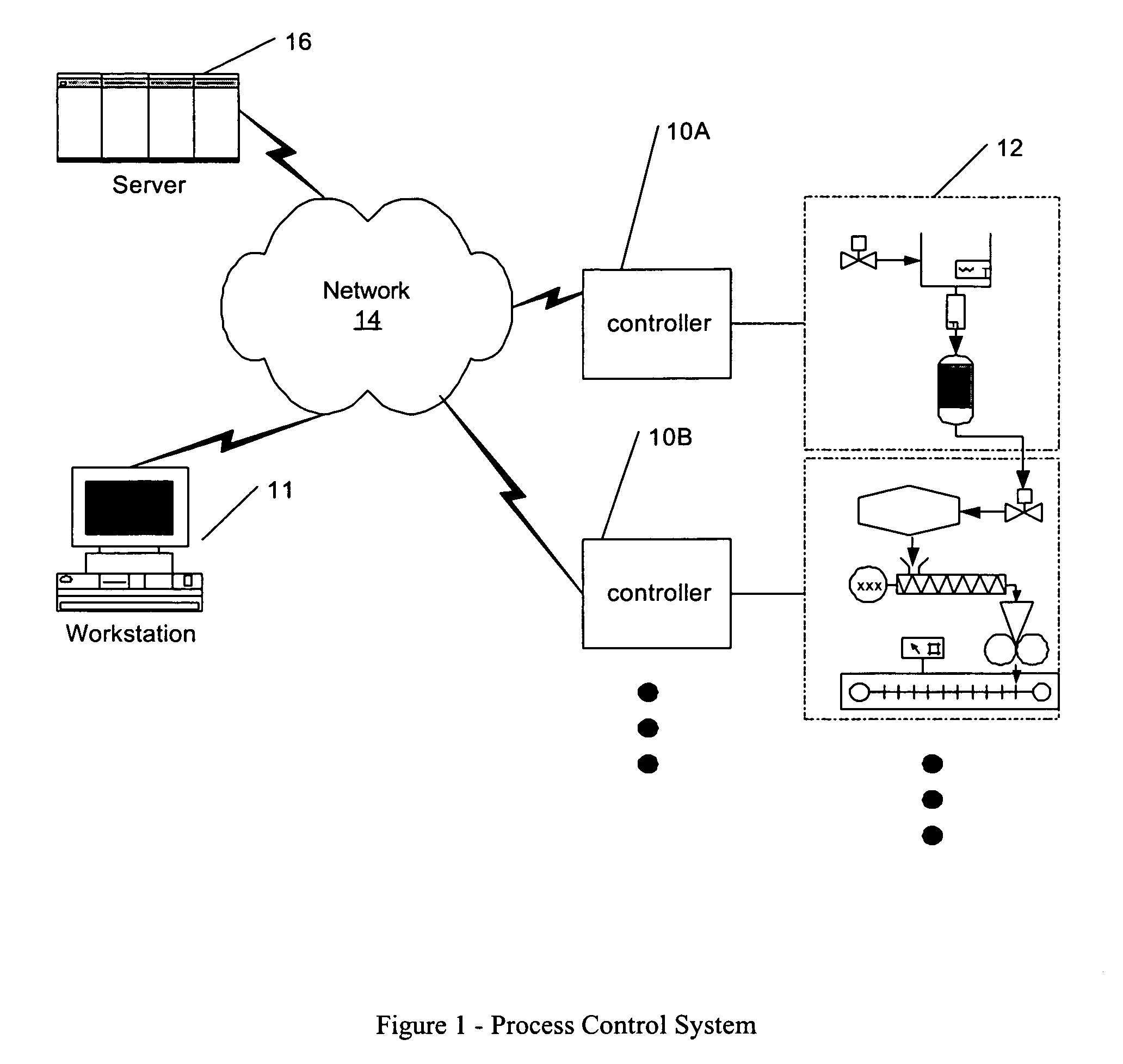
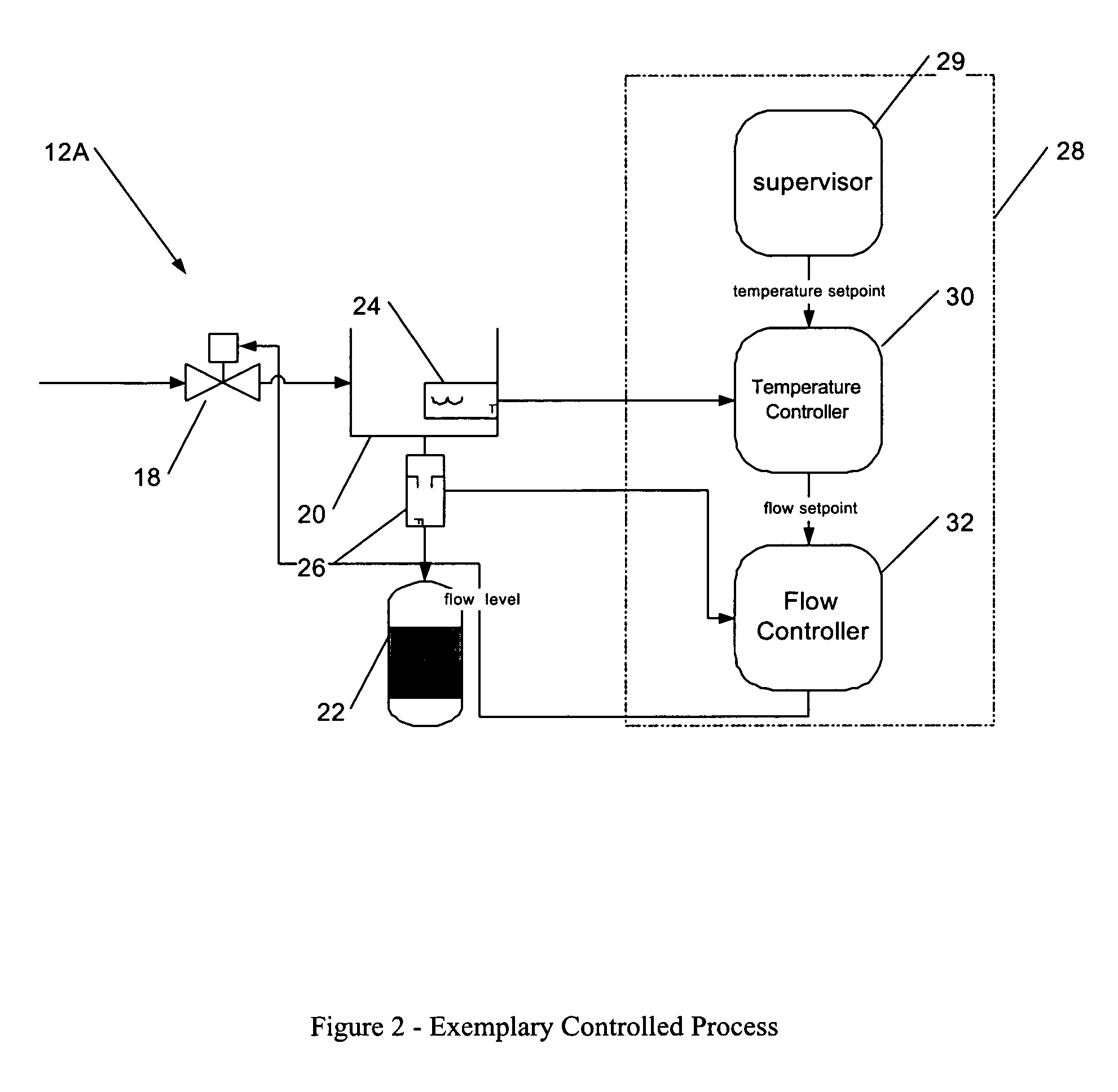
Process control configuration system with connection validation and configuration
Connection objects or other such data structures facilitate establishing and configuring connections between objects that model components in a process control system. A first set of data structures (e.g. the object connection type structures) identify valid types for component-to-component pairings and the respective roles of each component in the pairing (e.g., parent or child, source or sink). A second set of data structures (e.g., the parameter connection type structures) supply similar information for parameter-to-parameter connections. Together, these data structures can be used, for example, to validate component-to-component connections suggested by the user and to automatically configure parameter-to-parameter connections. Actual connections, both at the component or parameter level, are reflected using parameter overrides within the parameterized object model—with which the connection objects are constructed.
Owner:SCHNEIDER ELECTRIC SYST USA INC
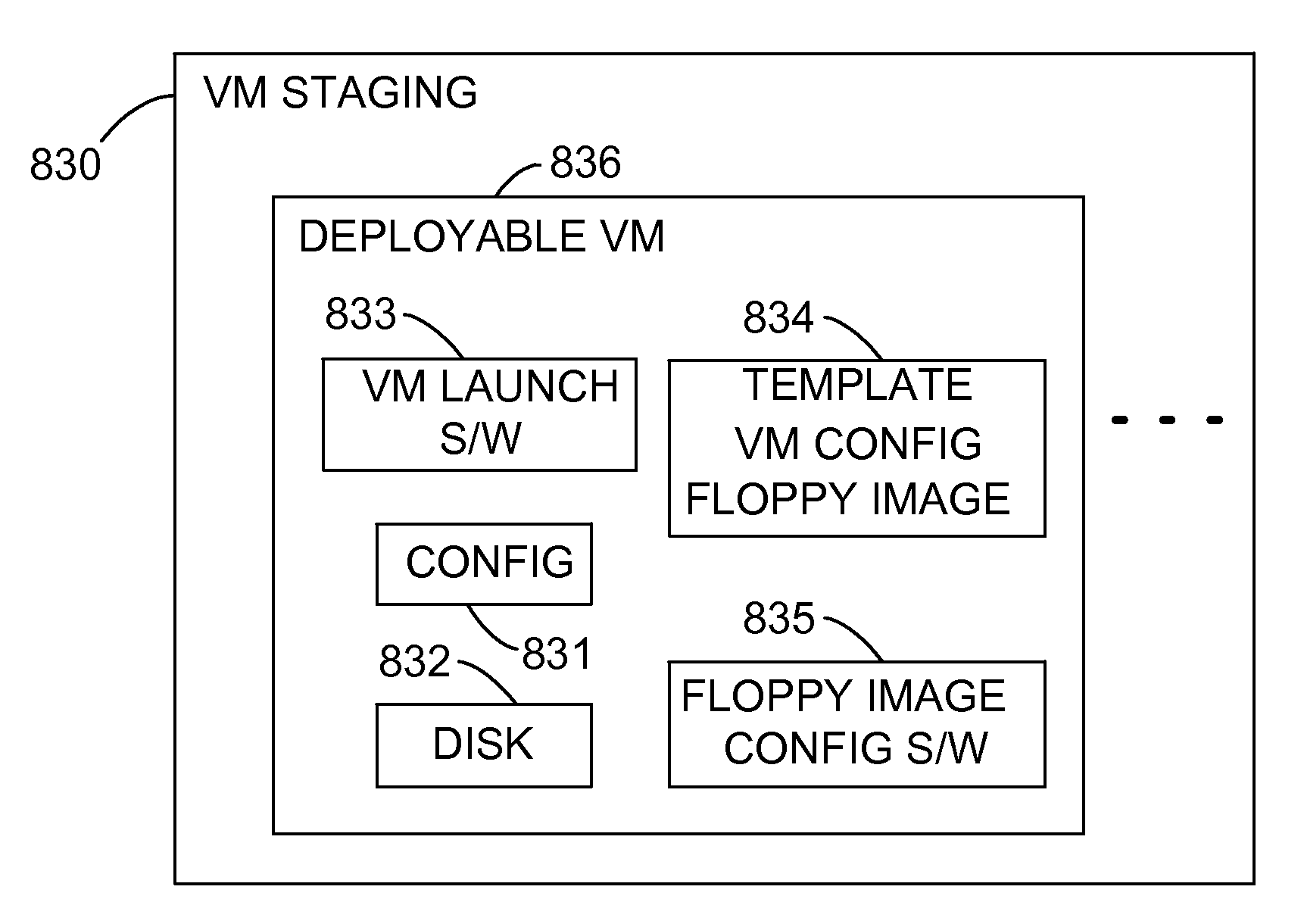
Provisioning of Computer Systems Using Virtual Machines
InactiveUS20090282404A1Multiple digital computer combinationsSoftware simulation/interpretation/emulationOperational systemAuto-configuration
Owner:VMWARE INC
Systems and methods for automatically configuring and managing network devices and virtual private networks
ActiveUS20060236095A1Multiple digital computer combinationsSpecial data processing applicationsComputer hardwareGraphics
Systems and methods are disclosed for automatically configuring, managing, and maintaining a network device or VPN using a public network such as the Internet. Initial configuration of a network device or VPN occurs upon a user entering minimal information via a simple HTML page. After receipt of this minimal information, the present invention automatically configures the network device or VPN without user intervention. Thereafter, a user may modify the network device or VPN configuration via an easy-to-use and easy-to-understand graphical user interface. Parameters are presented such that a user simply checks and unchecks boxes, or clicks on radio buttons, to configure network device parameters. Upon completion of the selection, the user clicks on save, and the configuration is automatically modified. In addition, upon a significant change to any network device, the changed network device automatically initiates reconfiguration of the network device or VPN with zero input from a user.
Owner:ANXEBUSINESS
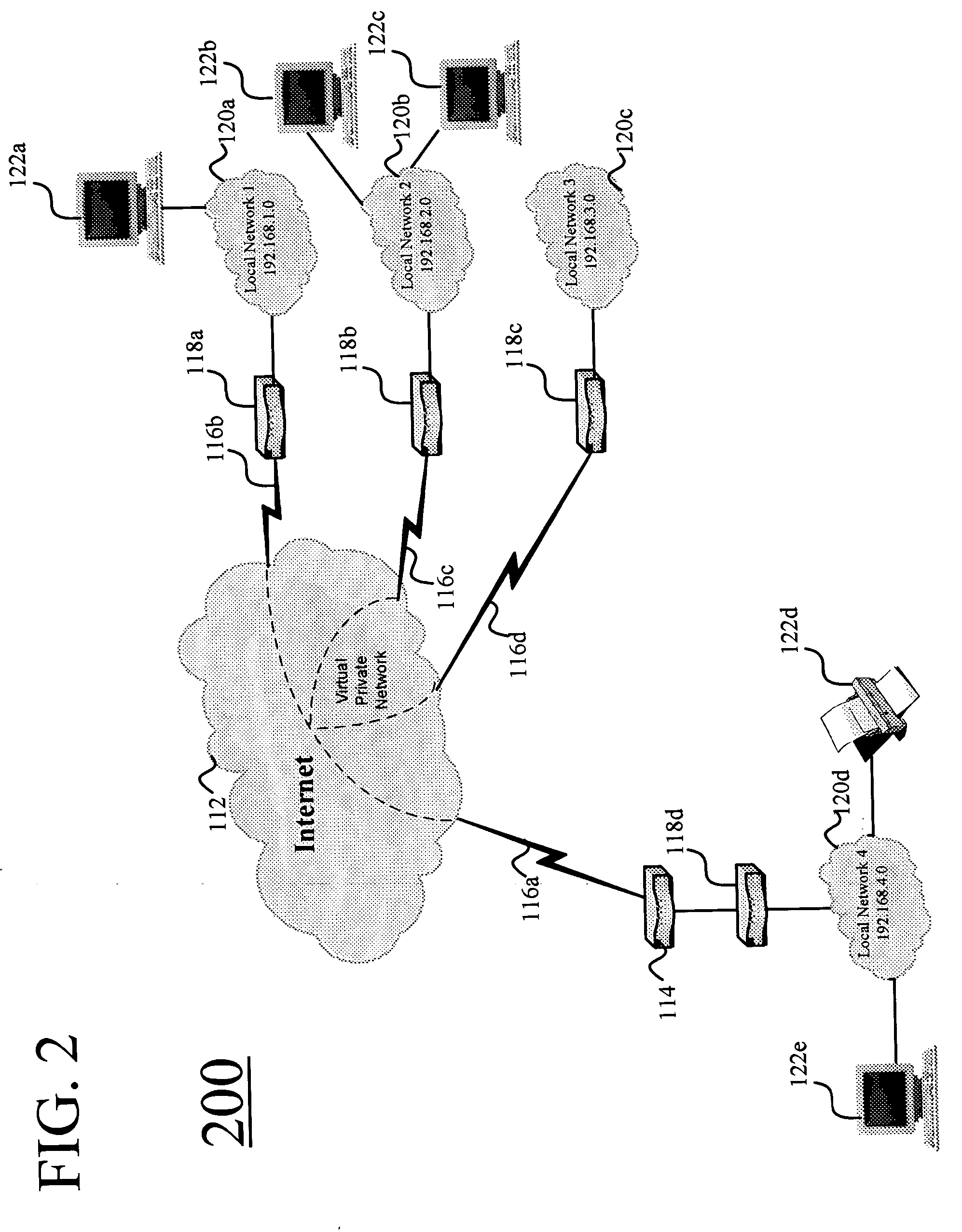
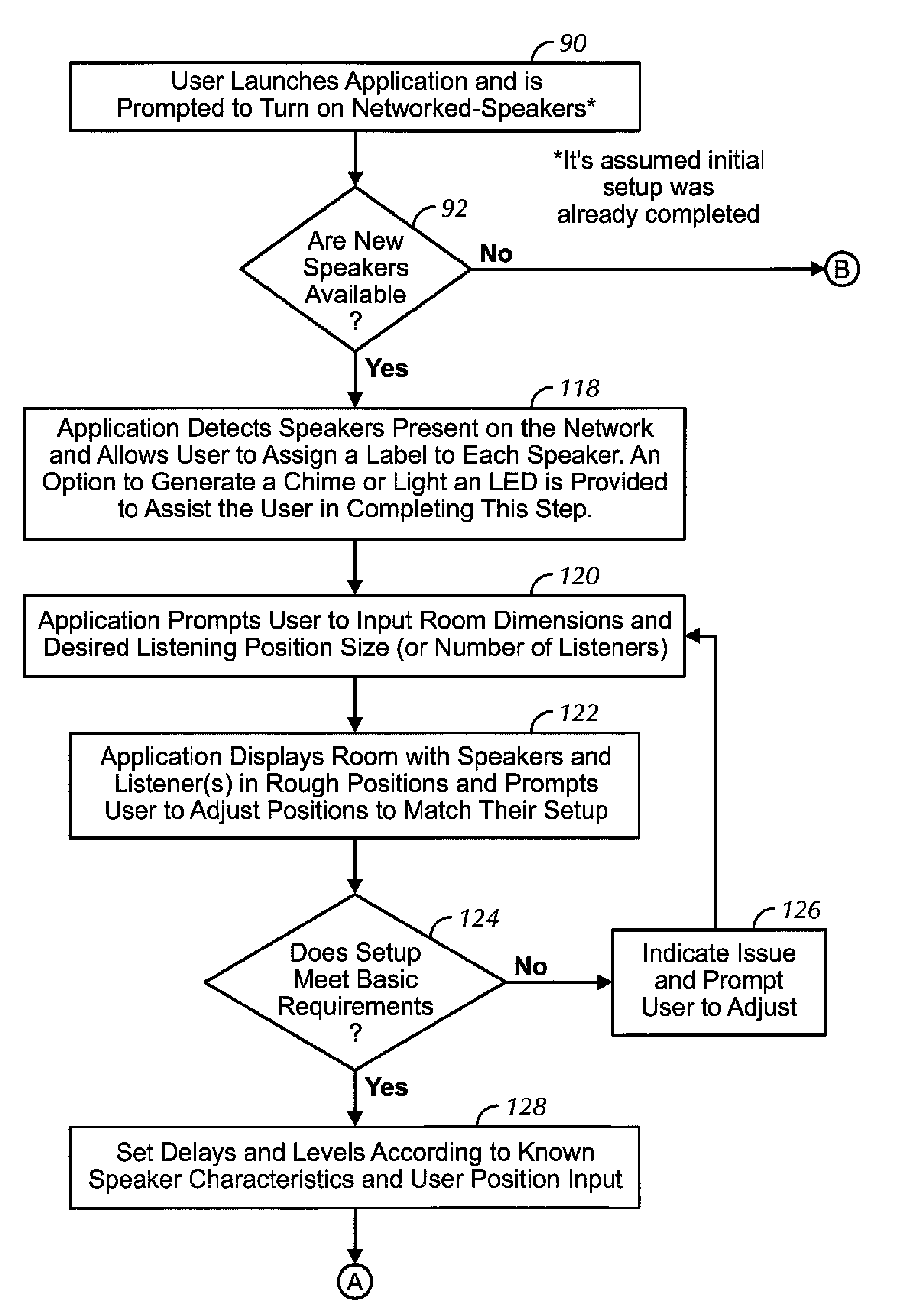
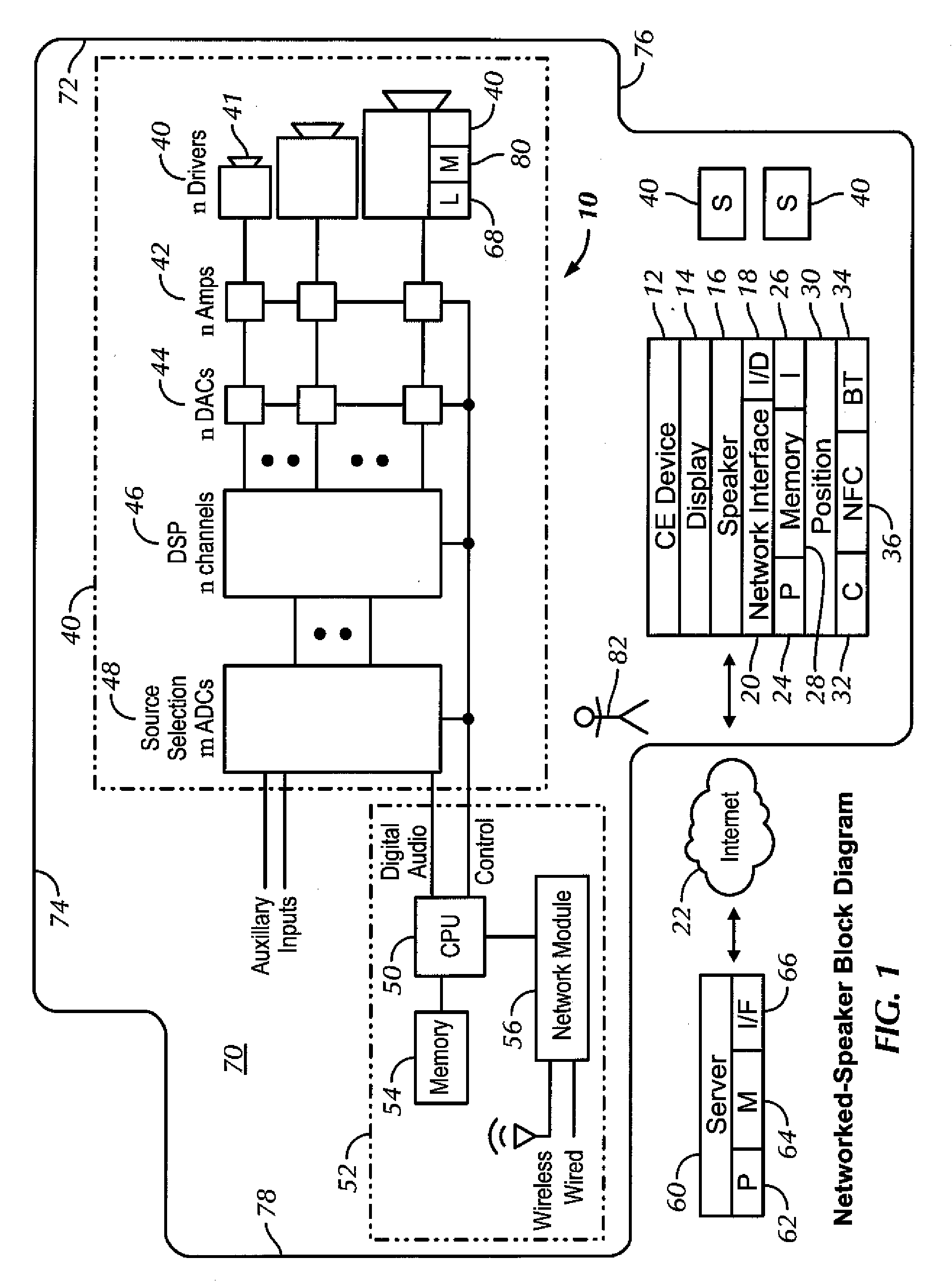
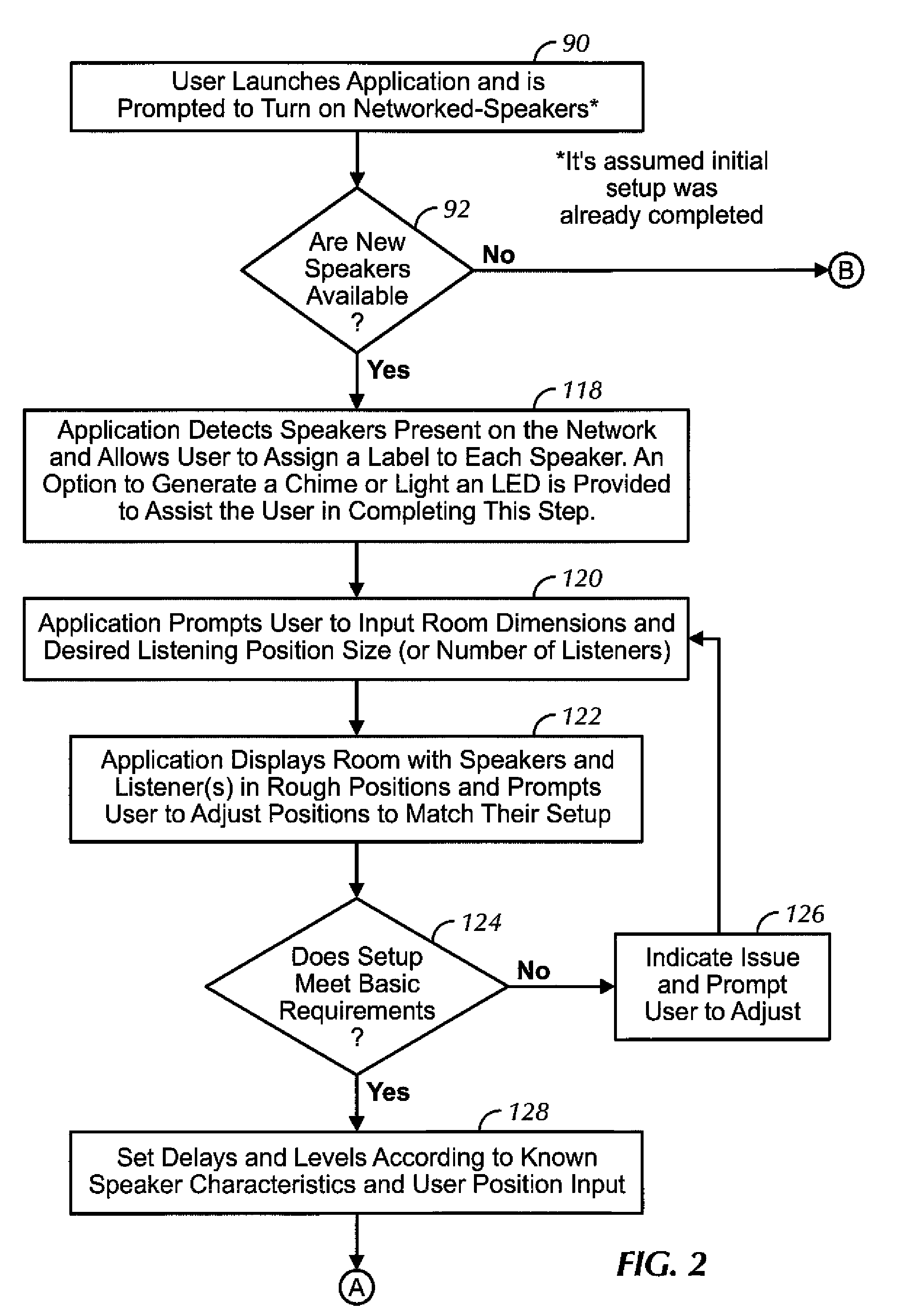
Distributed wireless speaker system with automatic configuration determination when new speakers are added
ActiveUS9288597B2Facilitate easier setupIncrease experienceTransducer detailsPublic address systemsAuto-configurationUser input
Owner:SONY CORP
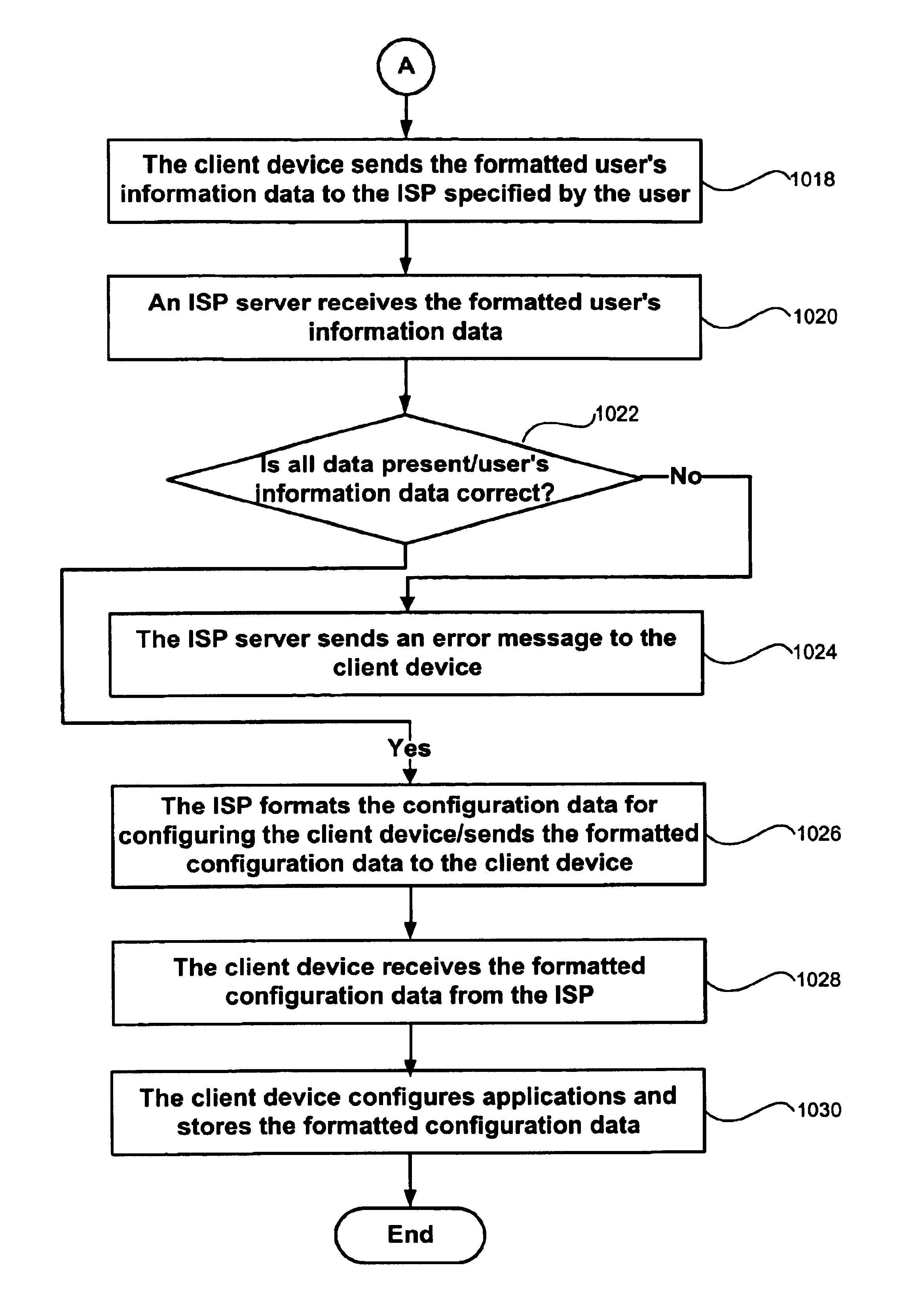
System and method for automatically configuring a client device
InactiveUS6938079B1Multiple digital computer combinationsProgram loading/initiatingAuto-configurationService provision
A user of a client device selects a service provider from a plurality of available service providers. The client device then queries the user for the user's information and formats the user's information into a predetermined data structure and format. The client device connects to the service provider and sends the formatted user's information to the service provider. The service provider responsively creates configuration data and provides it to the client device. The configuration data is used to configure a plurality of applications on the client device, allowing the user to establish future communication sessions with the service provider.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
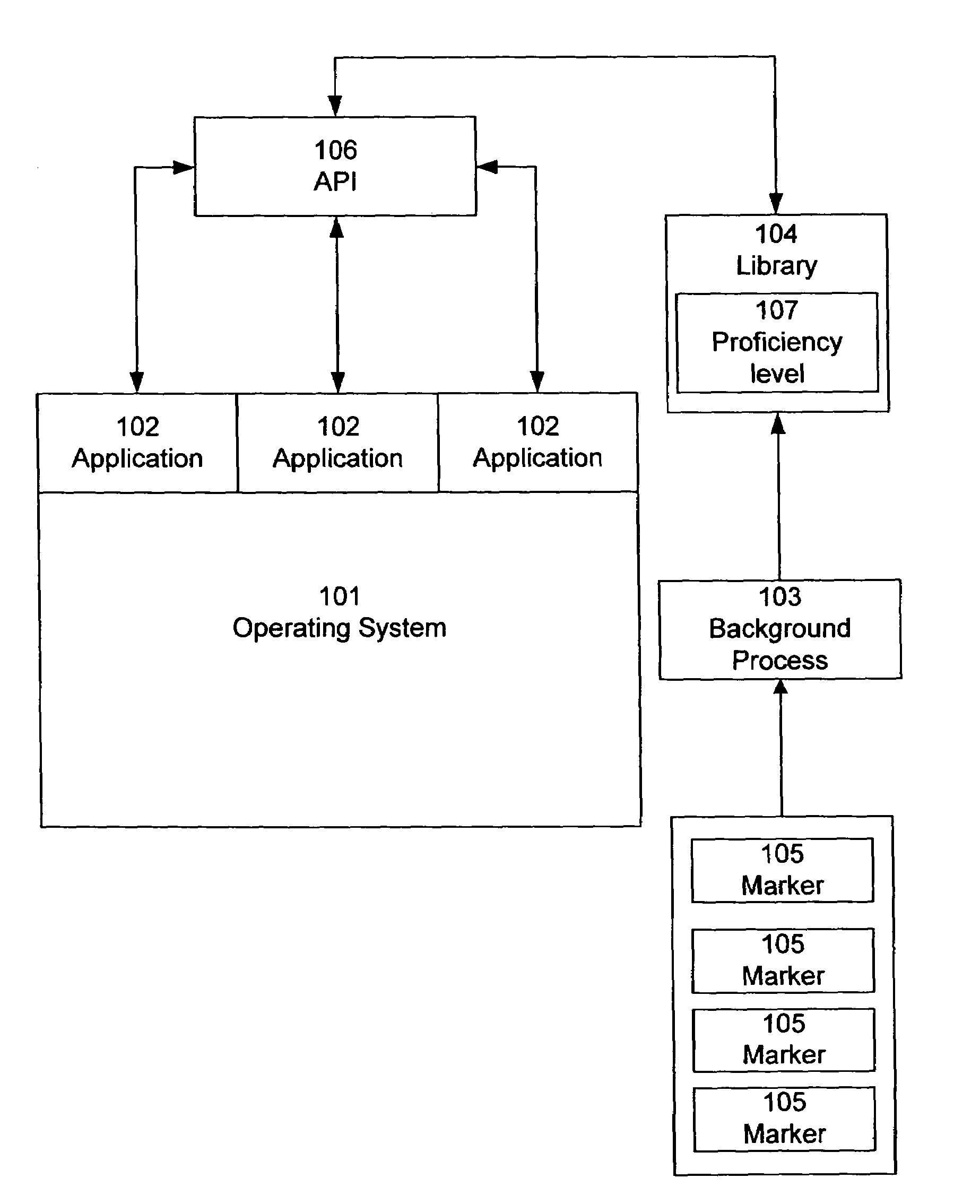
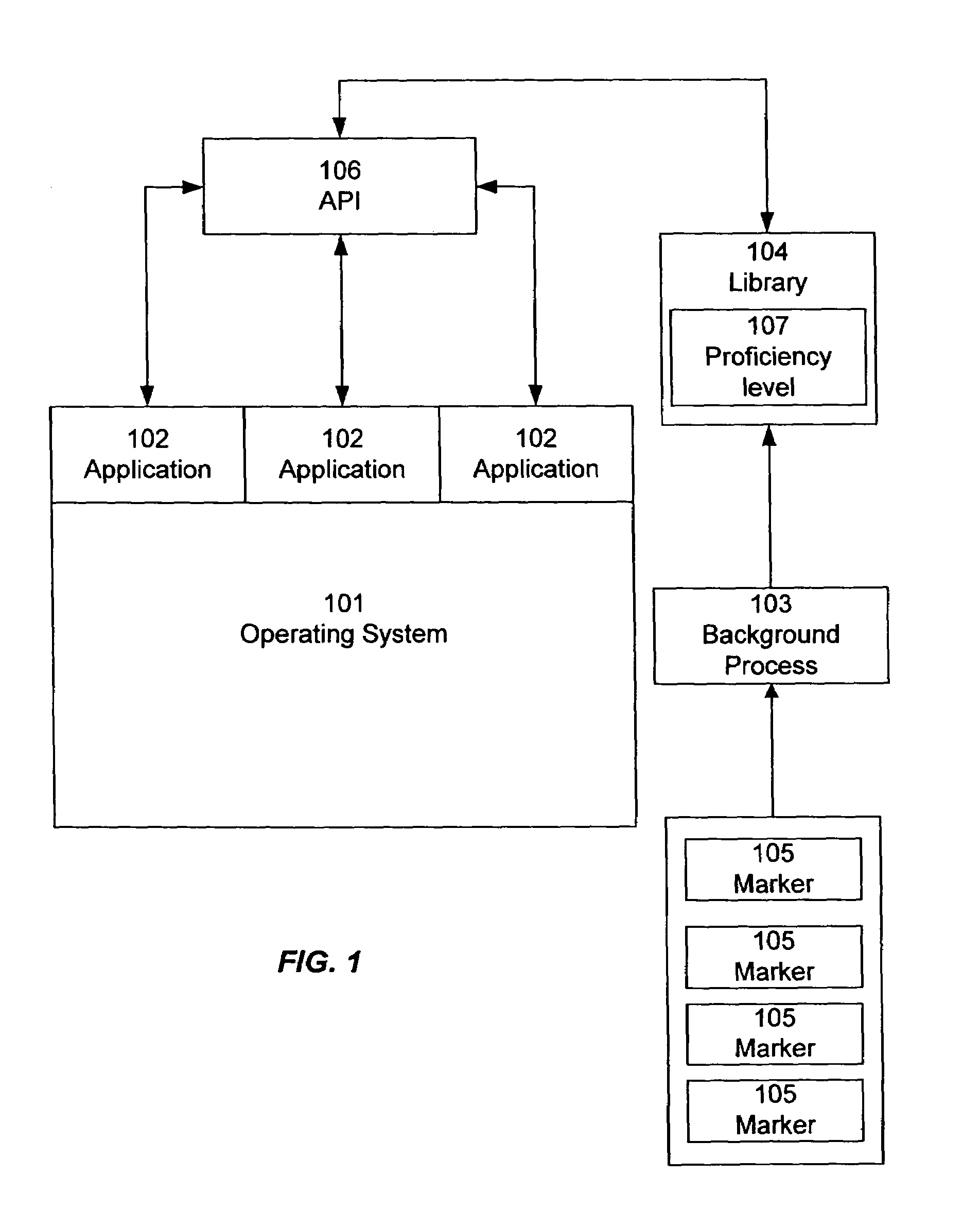
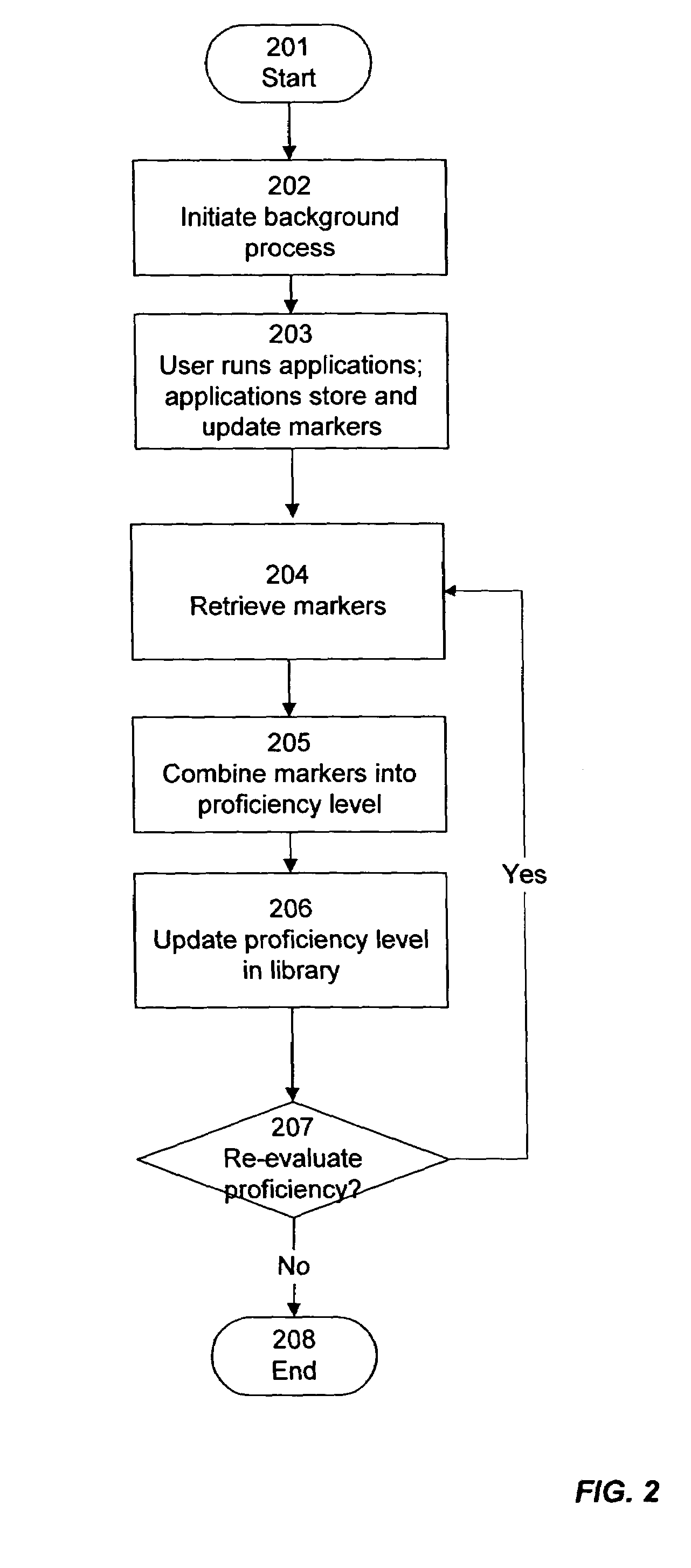
Automatic, dynamic user interface configuration
InactiveUS7620894B1Increased complexityDetect changeExecution for user interfacesInput/output processes for data processingAuto-configurationHuman–computer interaction
Markers that describe a user's actions are monitored in order to determine his or her level of proficiency with a user interface. A proficiency level is determined based on the markers. The proficiency level is adjusted periodically or in response to trigger events, to provide updated proficiency level information as the user becomes more experienced. One or more user interface features are automatically configured according to the detected proficiency level, so that the user is presented with an interface that is appropriate for his or her level of proficiency.
Owner:APPLE INC
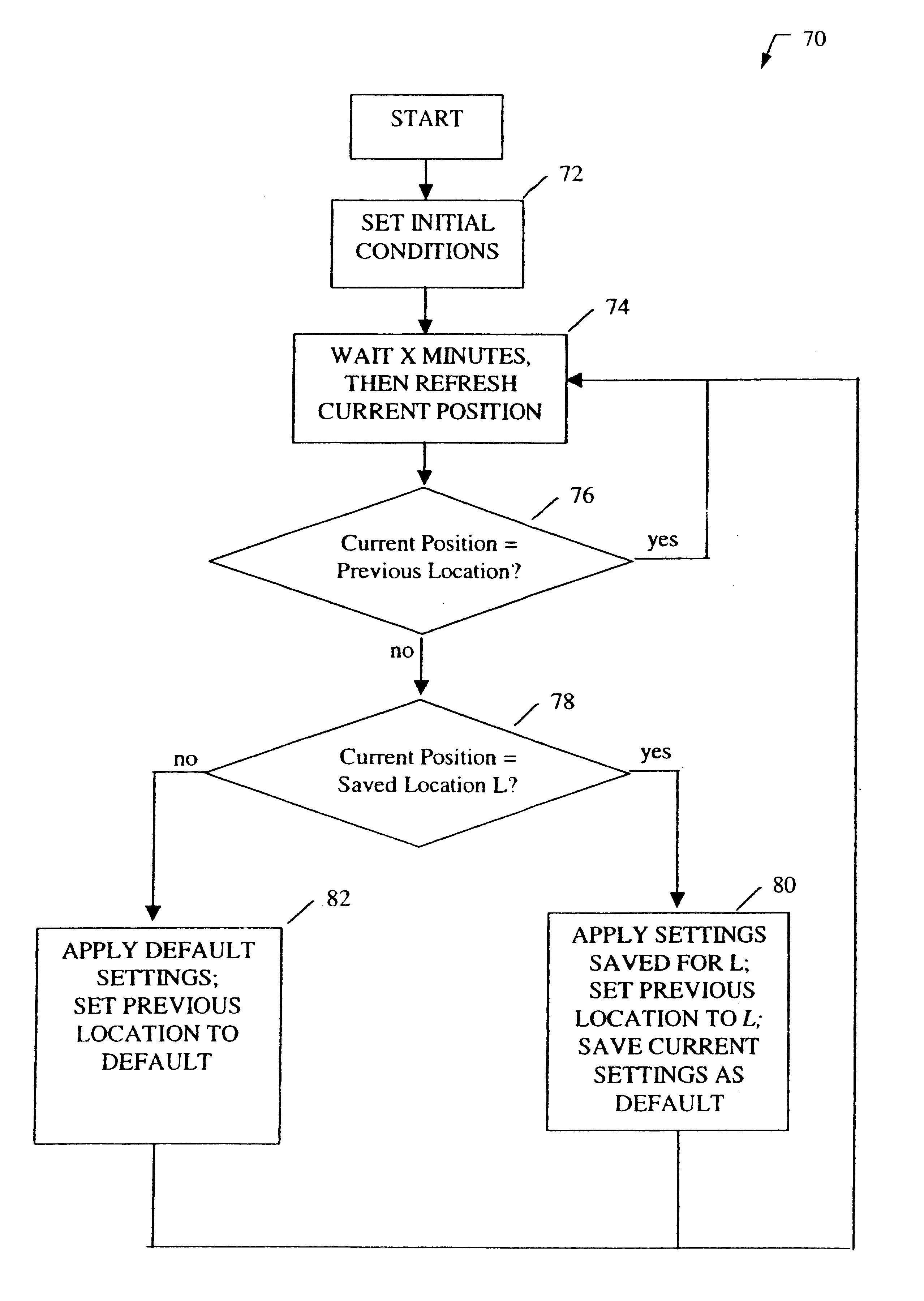
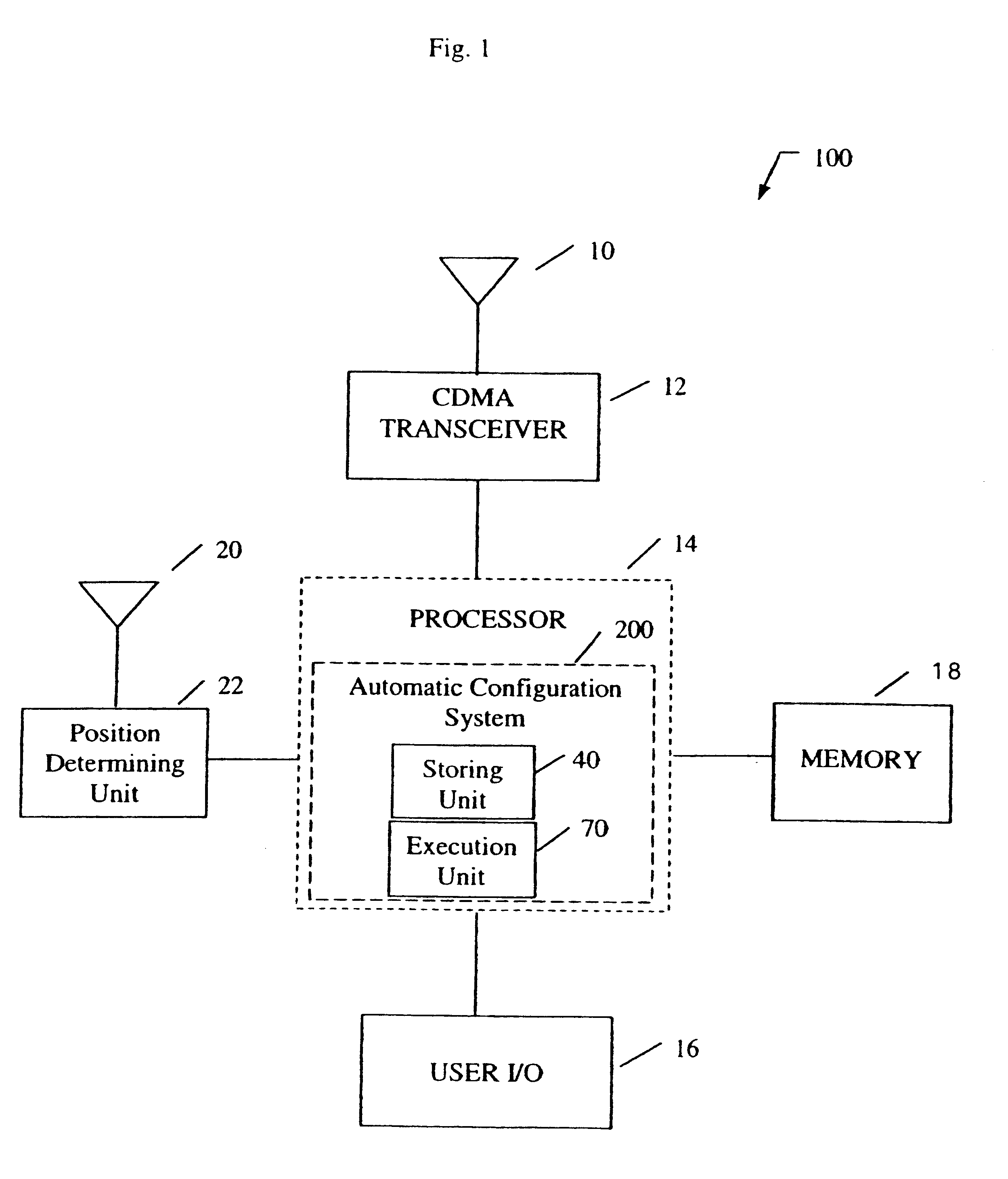
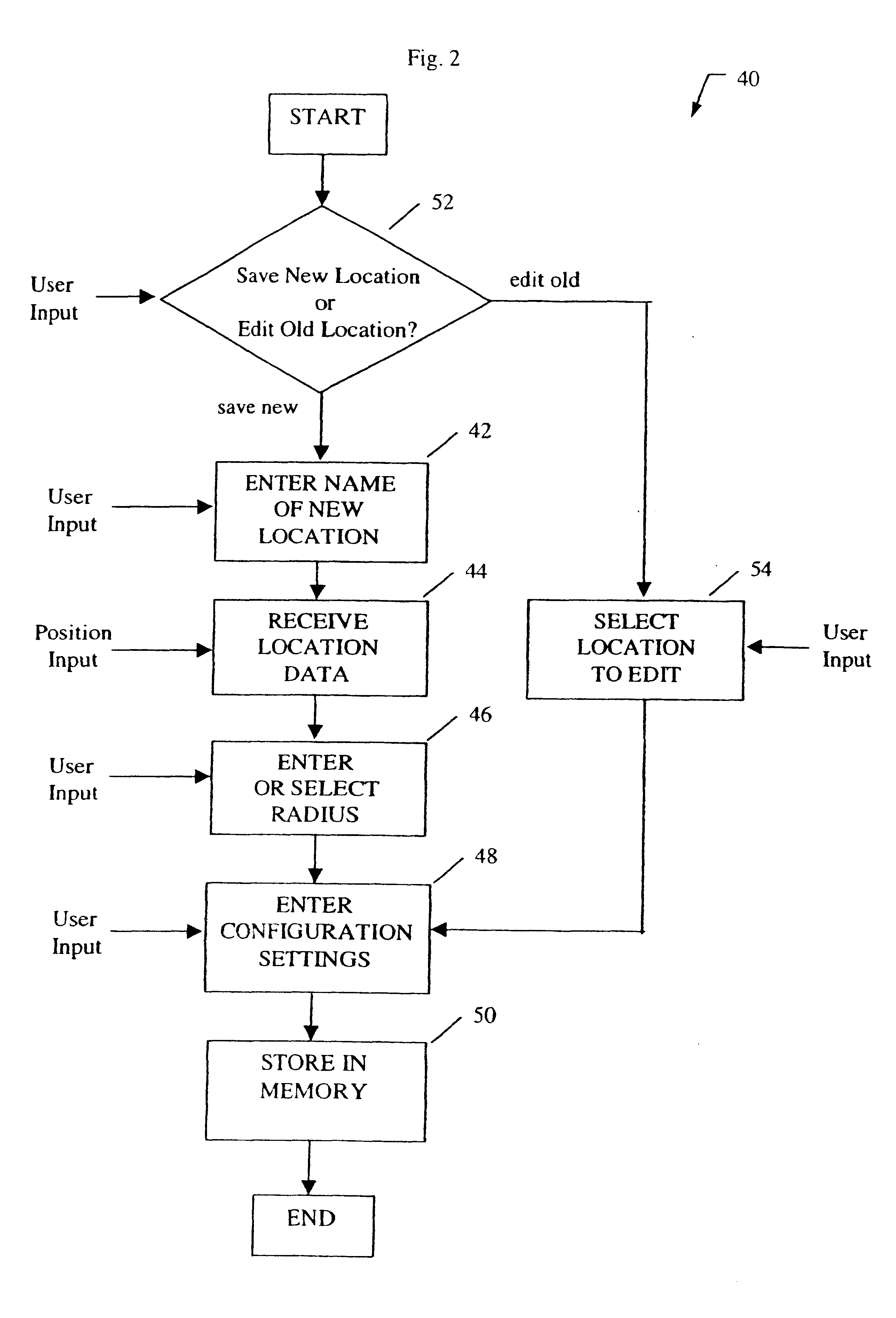
System for automatically configuring features on a mobile telephone based on geographic location
A system for automatically reconfiguring a mobile telephone based on geographic location. In the illustrative embodiment, the invention includes a storing unit (40) and an execution unit (70). The storing unit (40) allows the user to save a particular location and the desired configurations corresponding to that location. The execution unit (70) monitors the position of the telephone and, upon entering a saved location, executes the configurations corresponding to that location. The execution unit (70) also returns the configurations to their previous settings after the telephone has exited from the saved location.
Owner:QUALCOMM INC
Method and apparatus for establishing ad hoc communications pathways between source and destination nodes in a communications network
InactiveUS7463890B2Error preventionFrequency-division multiplex detailsAuto-configurationClient-side
Autoband's distributed networking intelligence provides a novel architecture capable of dynamically reconfiguring communications pathways consisting of links whose transmission media are opportunistically and dynamically selectable. At least one constituent node in such automatically configurable transient pathways is mobile, for example, information (source) server, intervening router node(s), gateway server and / or client device. Additionally, Autoband's ad hoc communications pathways may seamlessly and dynamically integrate (i.e., “graft”) into standard fixed node networks such as terrestrial networks, other wireless networks or combinations thereof. These communications may consist of point-to-point or multicast links. An economic market-based approach further assures allocation of available network resources (i.e., bandwidth and processing) needed to achieve the most optimally resource efficient communications pathway configurations for the totality of communications. Consequently, optimal network resource allocation and efficiency at a system-wide level is continuously achieved.
Owner:GULA CONSULTING LLC
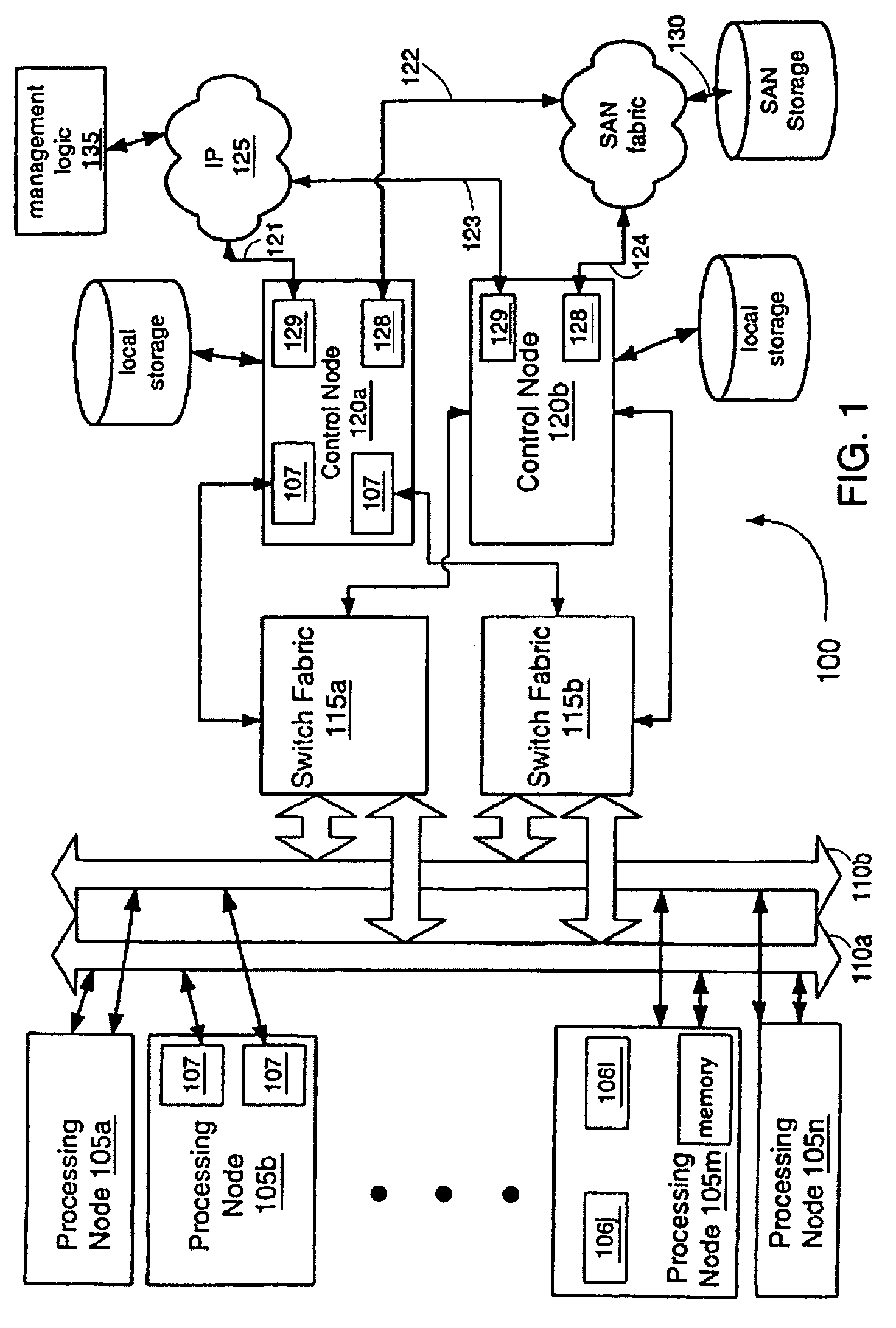
Virtual machine task management system
InactiveUS20060029056A1Multiplex system selection arrangementsCircuit switching systemsAuto-configurationConnection table
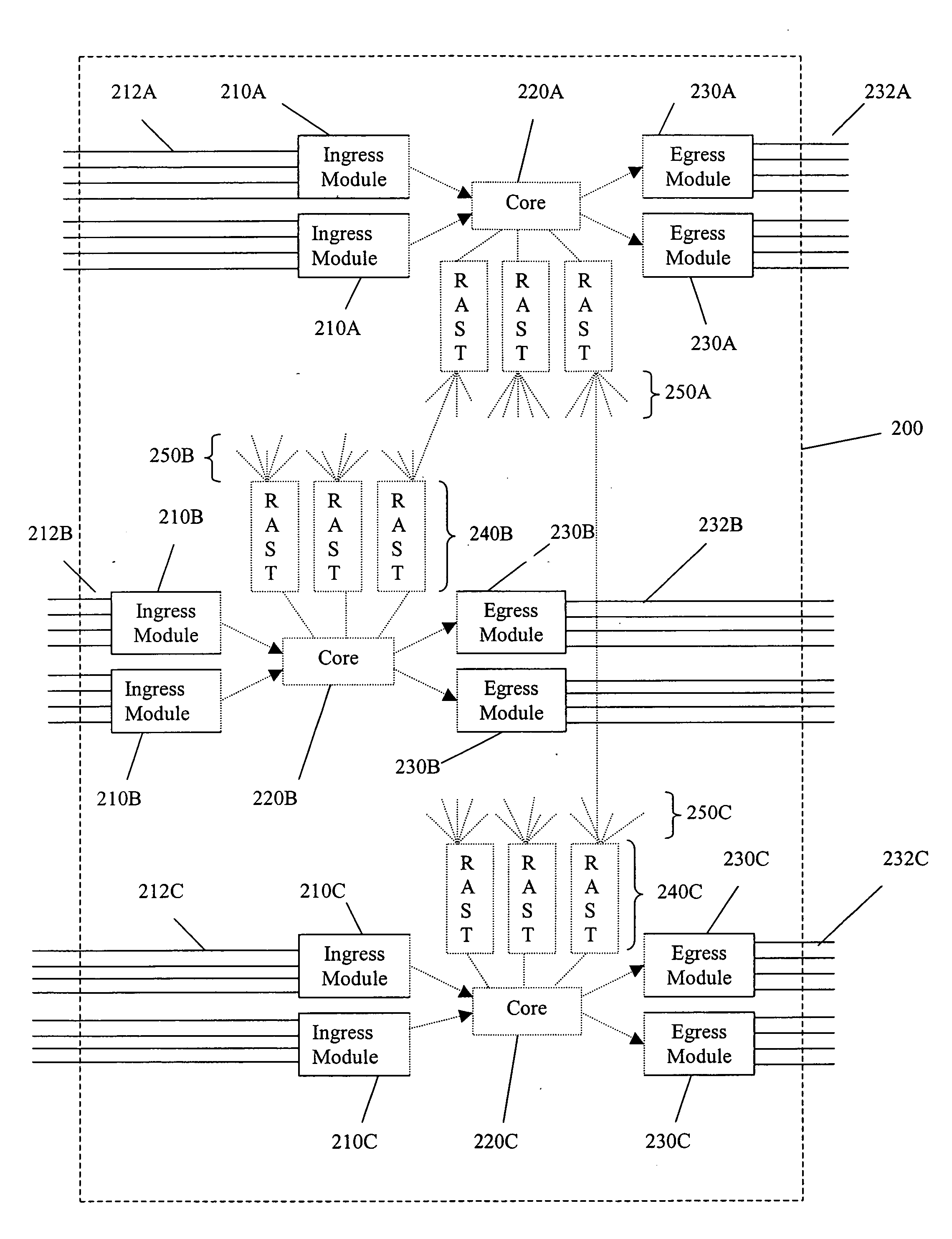
A switch encapsulates incoming information using a header, and removes the header upon egress. The header is used by both distributed ingress nodes and within a distributed core to facilitate switching. The ingress and egress elements preferably support Ethernet or other protocol providing connectionless media with a stateful connection. Preferred switches include management protocols for discovering which elements are connected, for constructing appropriate connection tables, for designating a master element, and for resolving failures and off-line conditions among the switches. Secure data protocol (SDP), port to port (PTP) protocol, and active / active protection service (AAPS) are all preferably implemented. Systems and methods contemplated herein can advantageously use Strict Ring Topology (SRT), and conf configure the topology automatically. Components of a distributed switching fabric can be geographically separated by at least one kilometer, and in some cases by over 150 kilometers.
Owner:RAPTOR NETWORKS TECH
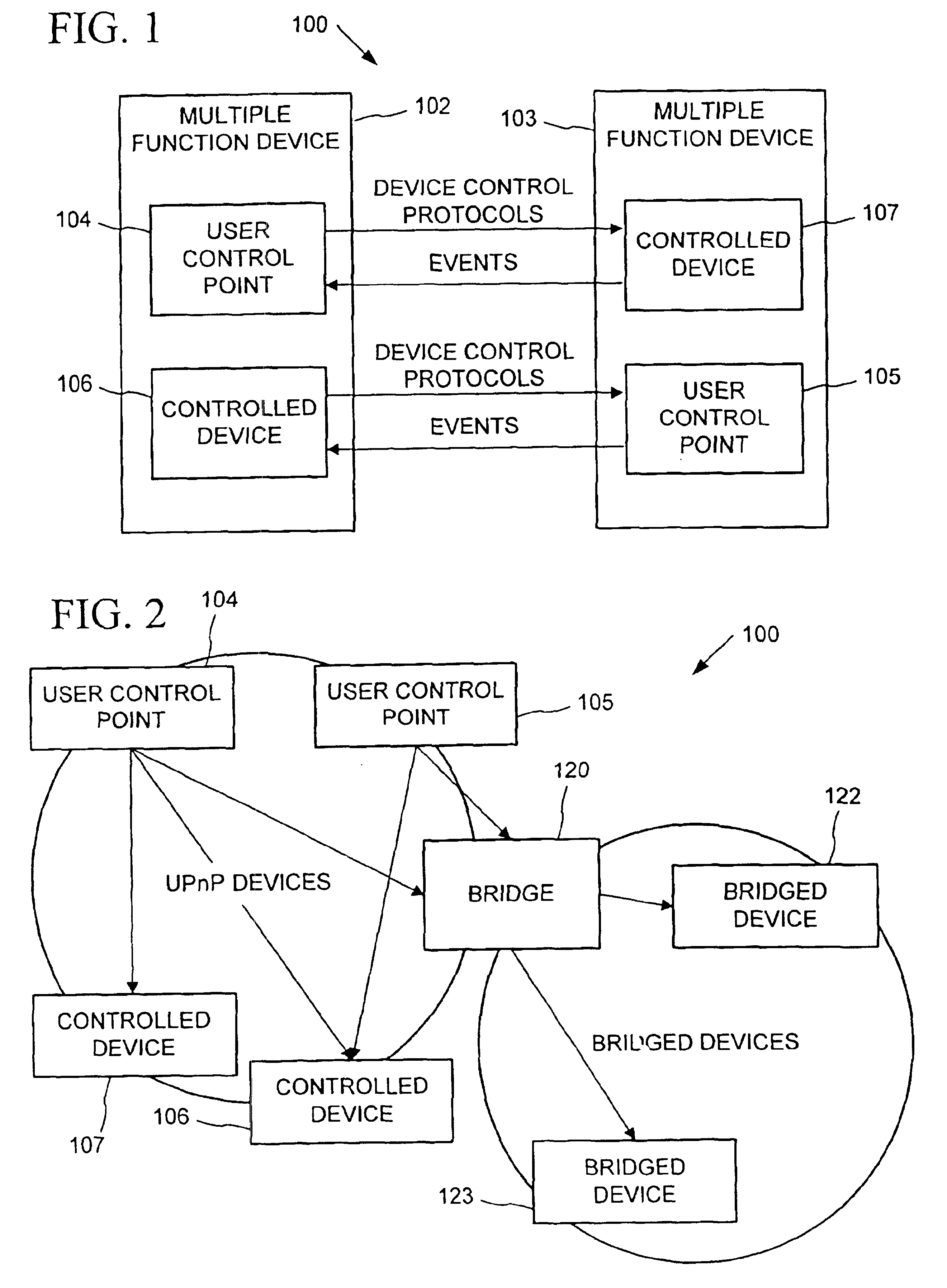
Dynamic self-configuration for ad hoc peer networking
InactiveUS20050240665A1CostConnectivity solutionDigital computer detailsNetworks interconnectionAuto-configurationSoftware
A device control model provides an integrated set of addressing, naming, discovery and description processes that enables automatic, dynamic and ad-hoc self-setup by devices to interoperate with other devices on a network. This permits a computing device when introduced into a network to automatically configure so as to connect and interact with other computing devices available on the network, without a user installation experience and without downloading driver software or persisting a configuration setup for connecting and interacting with such other computing devices. Upon completing interaction with such other devices, the computing device automatically releases the setup for such other devices so as to avoid persistent device configurations that might create a configuration maintenance and management burden.
Owner:ROVI TECH CORP
Interactive mobile messaging system
InactiveUS20070155411A1Interconnection arrangementsInformation formatAuto-configurationNetwork Communication Protocols
An interactive mobile messaging system (IMMS) for mobile telephone marketing and promotional campaigns integrates interactive voice response (IVR), SMS, fast analysis of shared multidimensional information, and online analytical processing. Online interactive message communication protocols are managed through mobile-originated, short code-based message platforms which are interfaced with an IVR query system. Automatic configuration of multiformat messages can be performed directly into multiple telecommunications carrier networks to all supported mobile handsets.
Owner:MORRISON
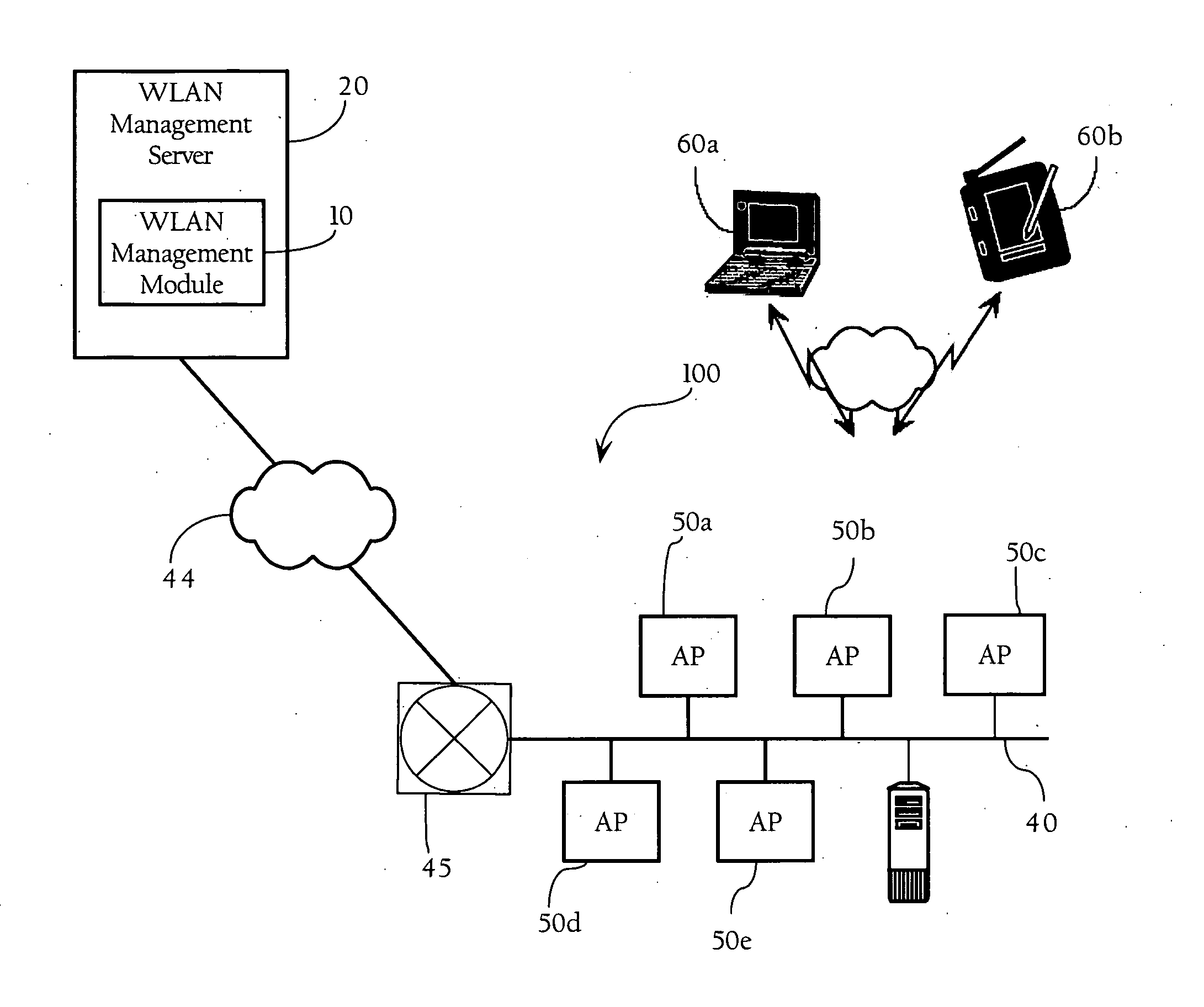
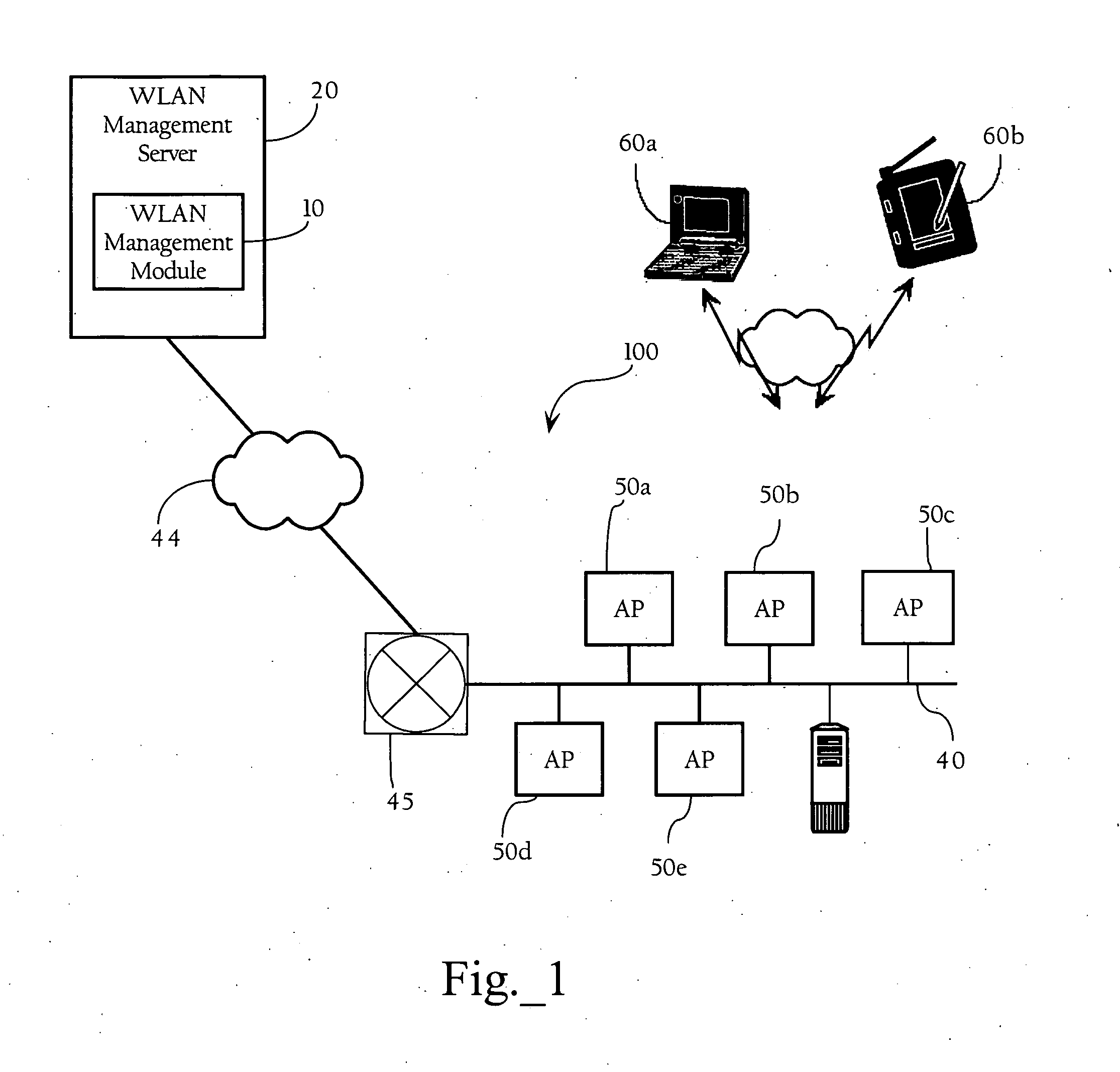
Automated configuration of RF WLANs via selected sensors
ActiveUS20070082677A1Substation equipmentRadio/inductive link selection arrangementsAuto-configurationCoverage map
In a wireless LAN (WLAN), methods, apparatuses and systems directed to facilitating configuration of a wireless network is provided. According to one implementation of the present invention, sensors are used to collect data associated with locations and other properties of access points of the wireless network. The collected data can then be used to assist in automatically configuring one or more aspects of the wireless network. In some implementations, the collected data can be used to dynamically re-configure the wireless network in real time. According to another implementation of the present invention, location computation mechanisms are used to collect data associated with the location of one or more wireless clients, and the data is used to dynamically adjust one or more radio frequency (RF) coverage maps in real time. The revised RF coverage maps can then be used to re-configure one or more operational parameters of the wireless network. Implementations of the present invention provide many advantages, such as automating the configuration of the wireless network in real time and facilitating network management decisions.
Owner:CISCO TECH INC
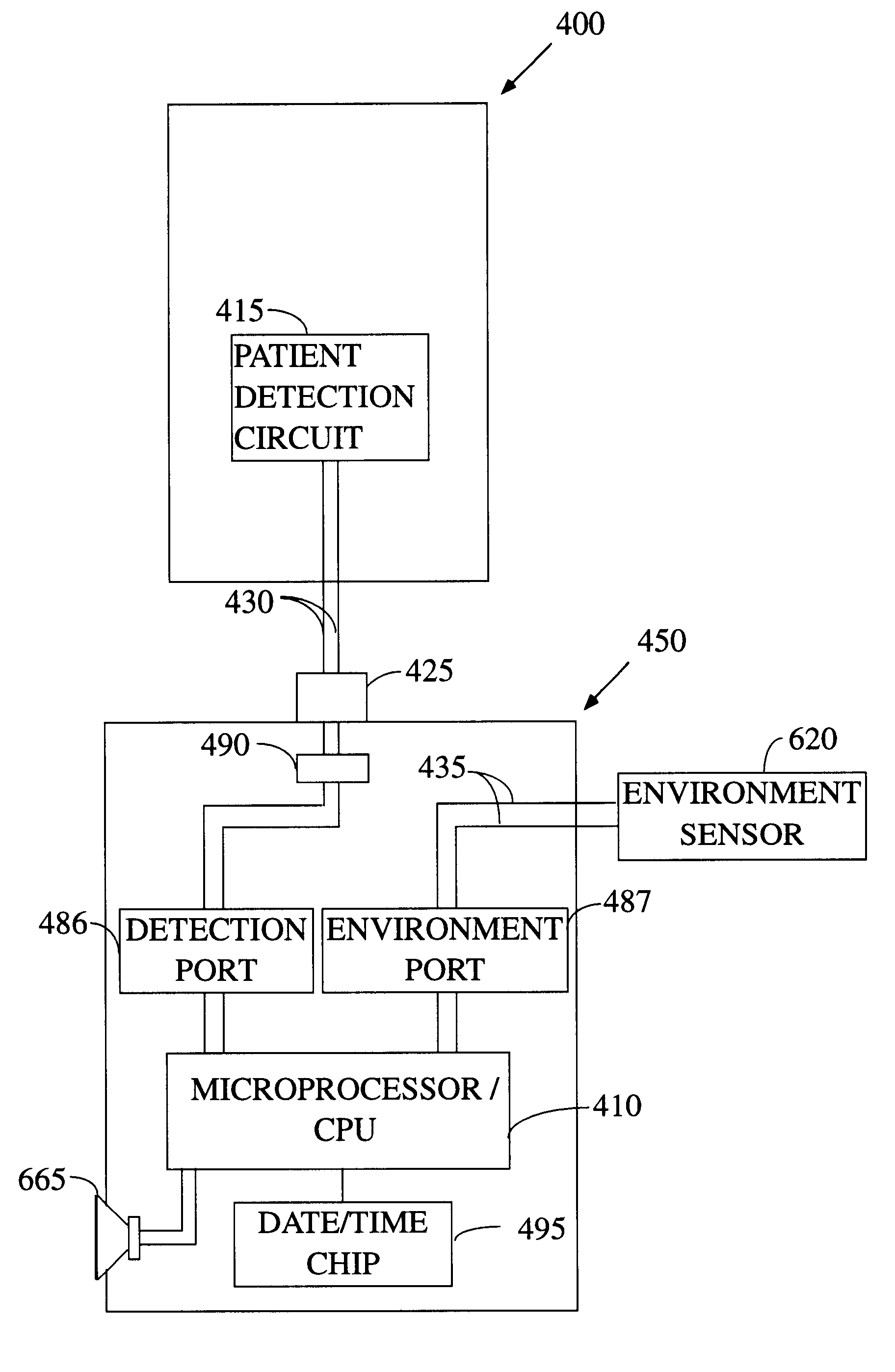
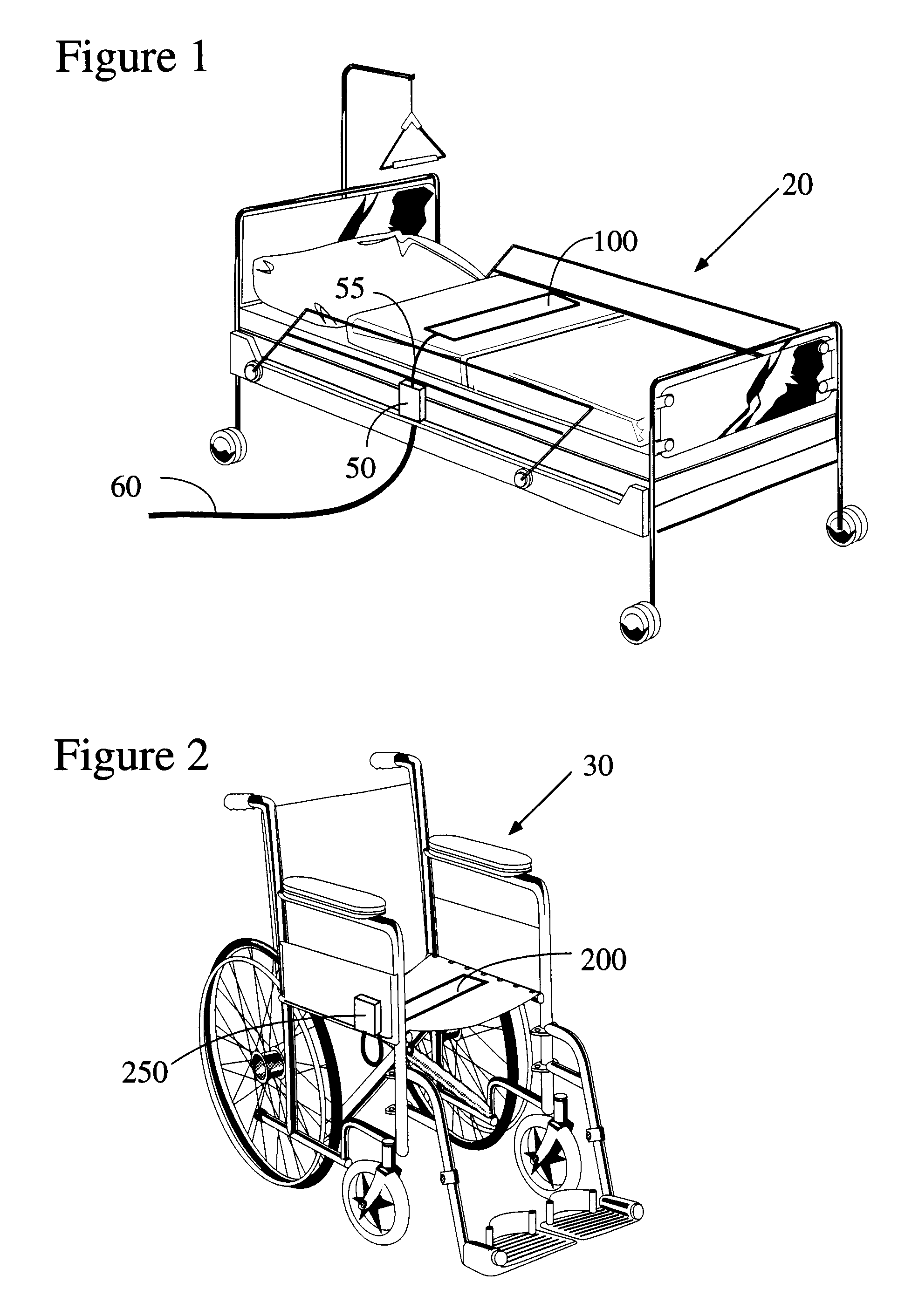
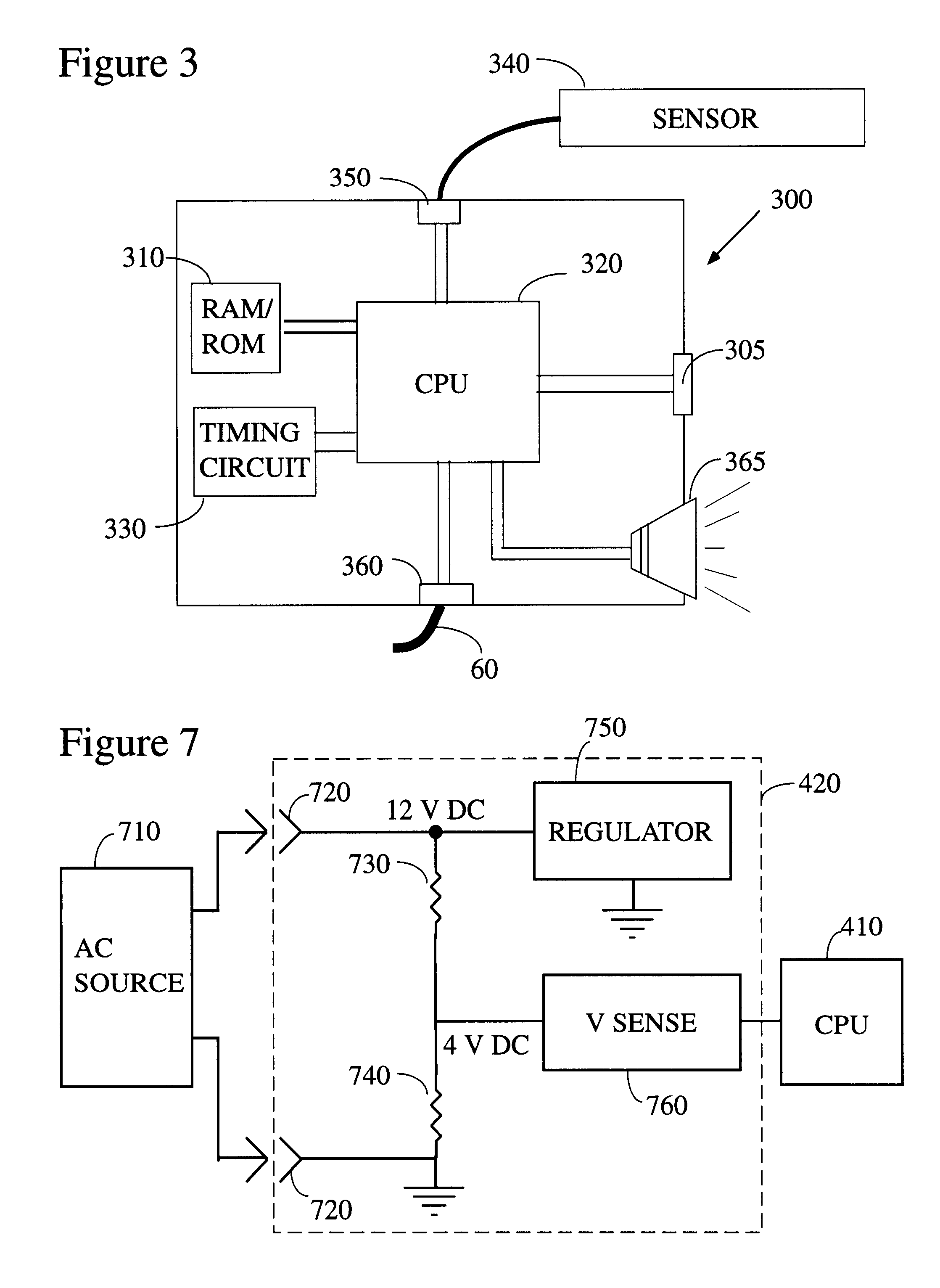
Electronic patient monitor with automatically configured alarm parameters
There is provided herein an electronic patient monitor that is suitable for use with a variety of different sensors and which automatically configures itself depending on the sensor that is used and / or the environment in which the electronic monitor is placed. In a first preferred embodiment, the electronic monitor determines whether it is being used on a bed or a chair by sensing whether or not a nurse call connector is present. If such a connector is plugged into the monitor, the unit will assume that it is being used with a sensor that has been placed on a bed and will configure its internal parameters appropriately. Such configuration would include changing a delay time to provide for longer delays before sounding an alarm than would be used with a chair monitor.
Owner:BED CHECK
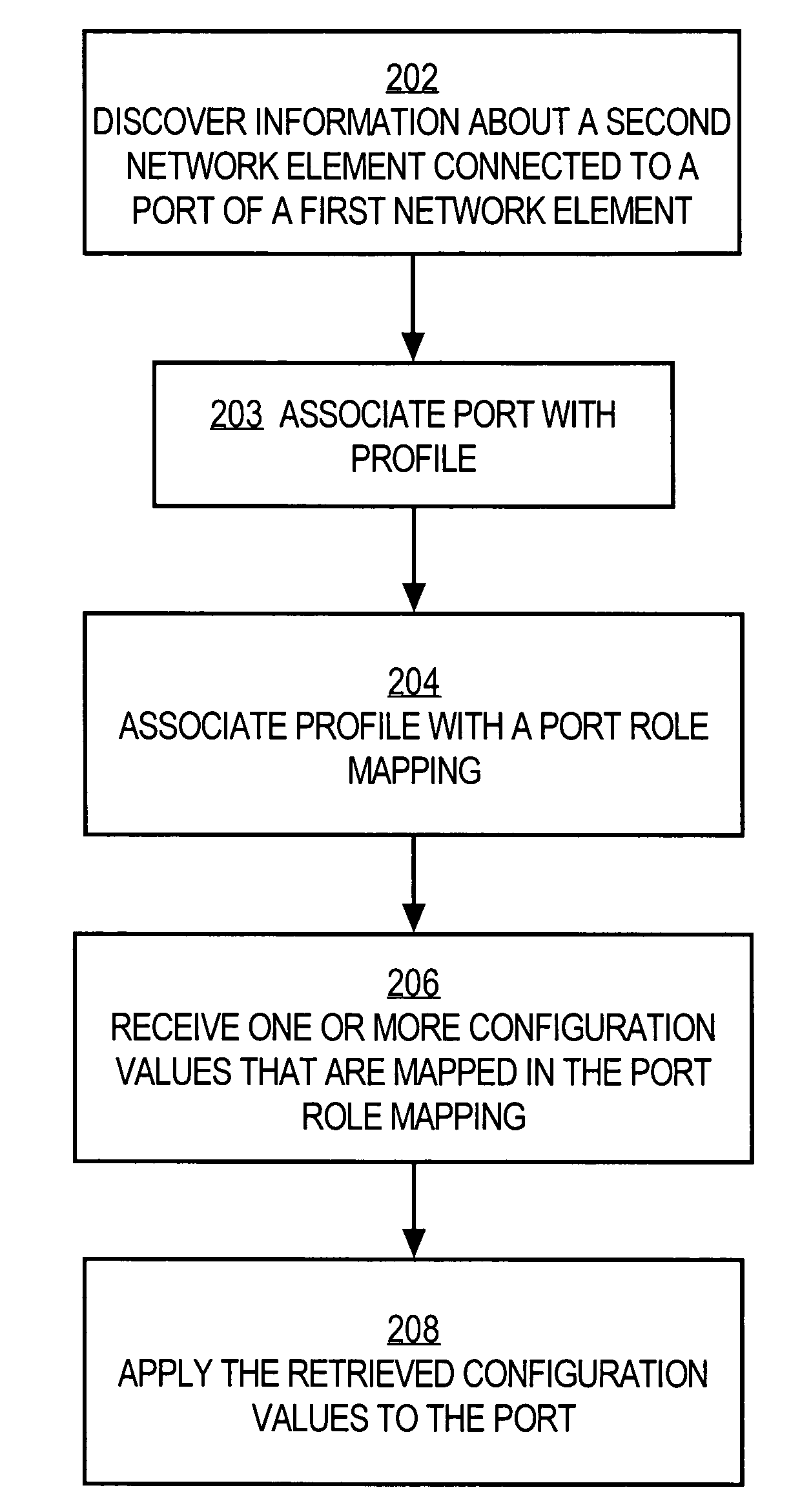
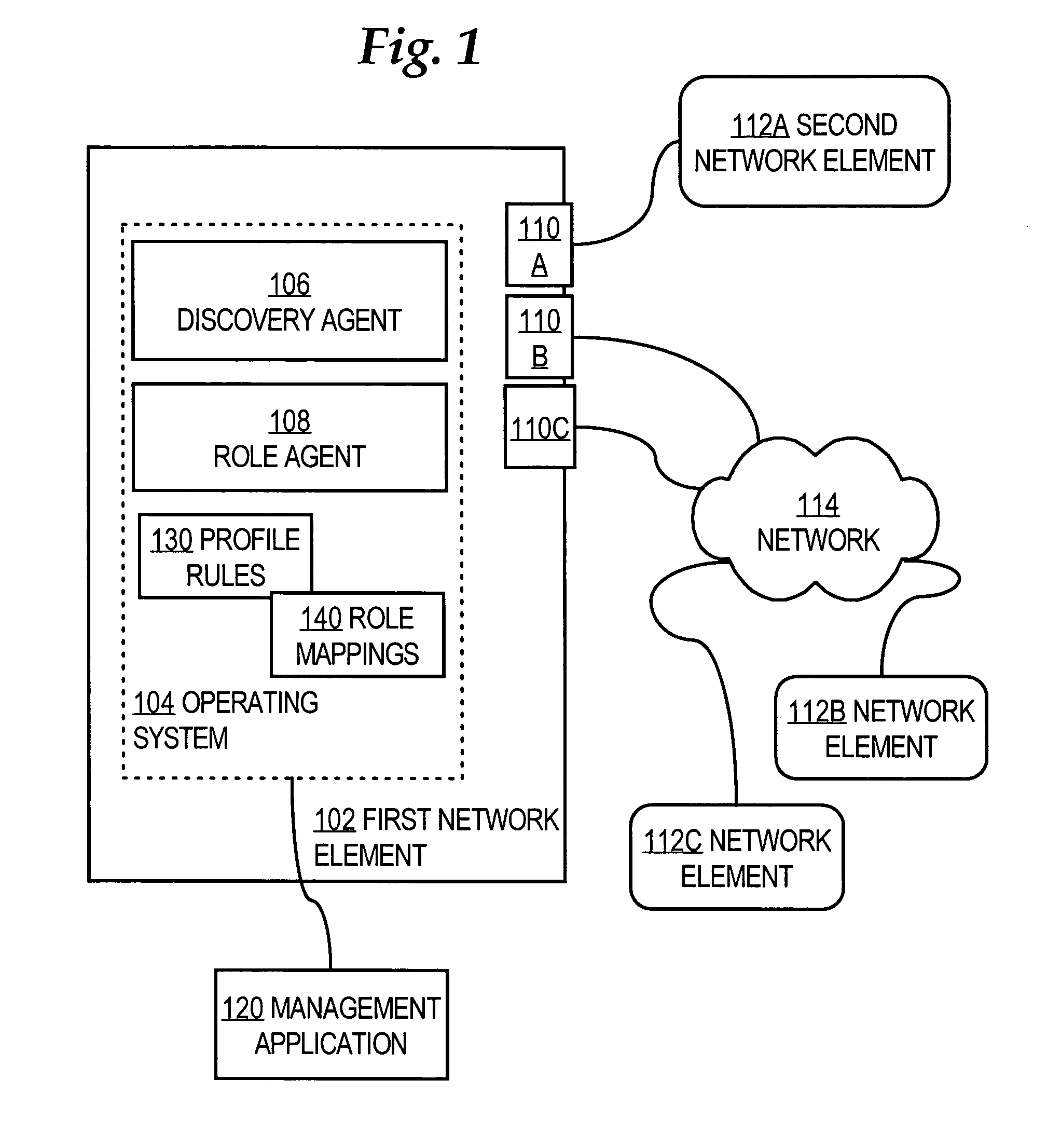
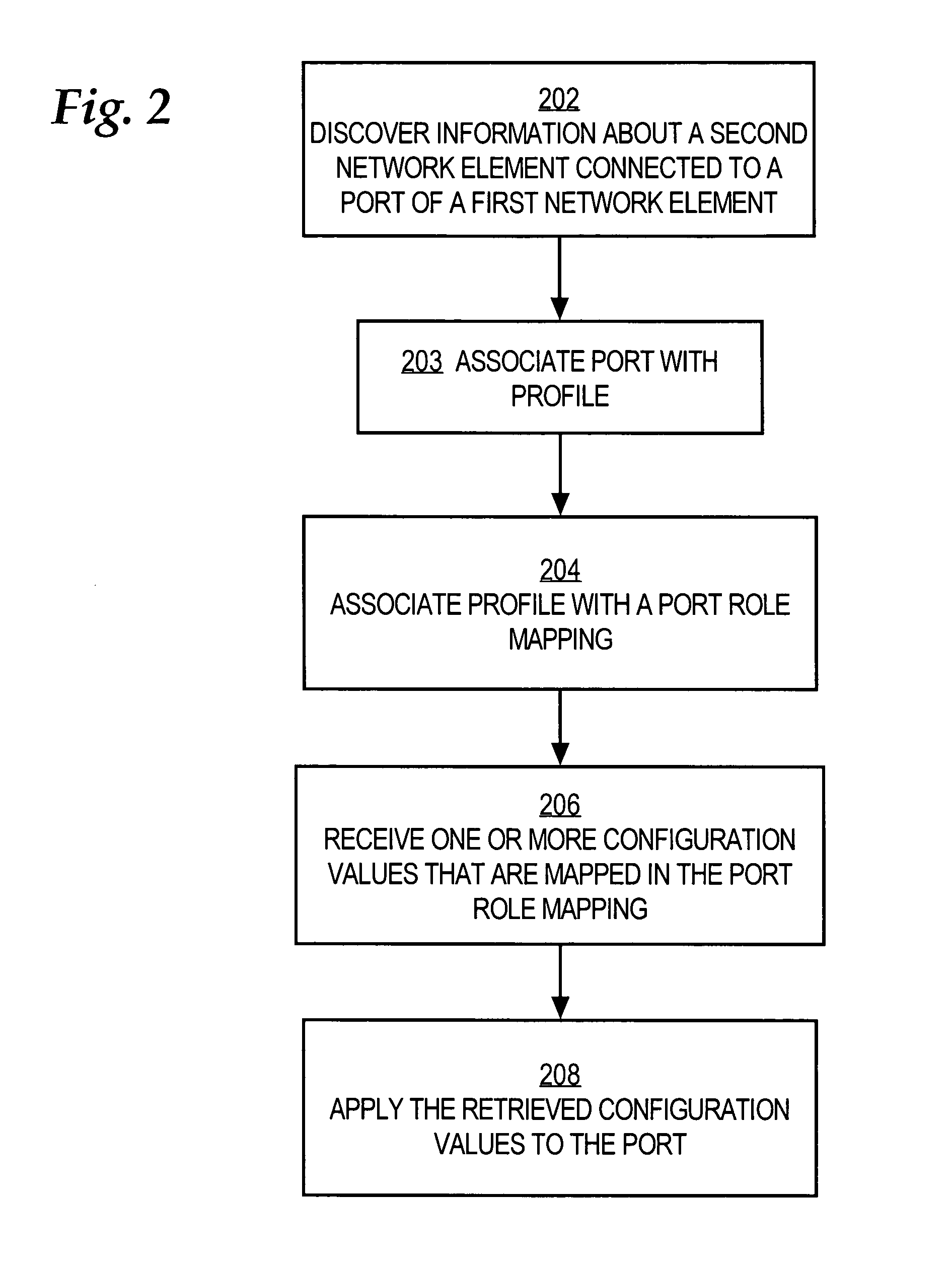
Method and apparatus providing role-based configuration of a port of a network element
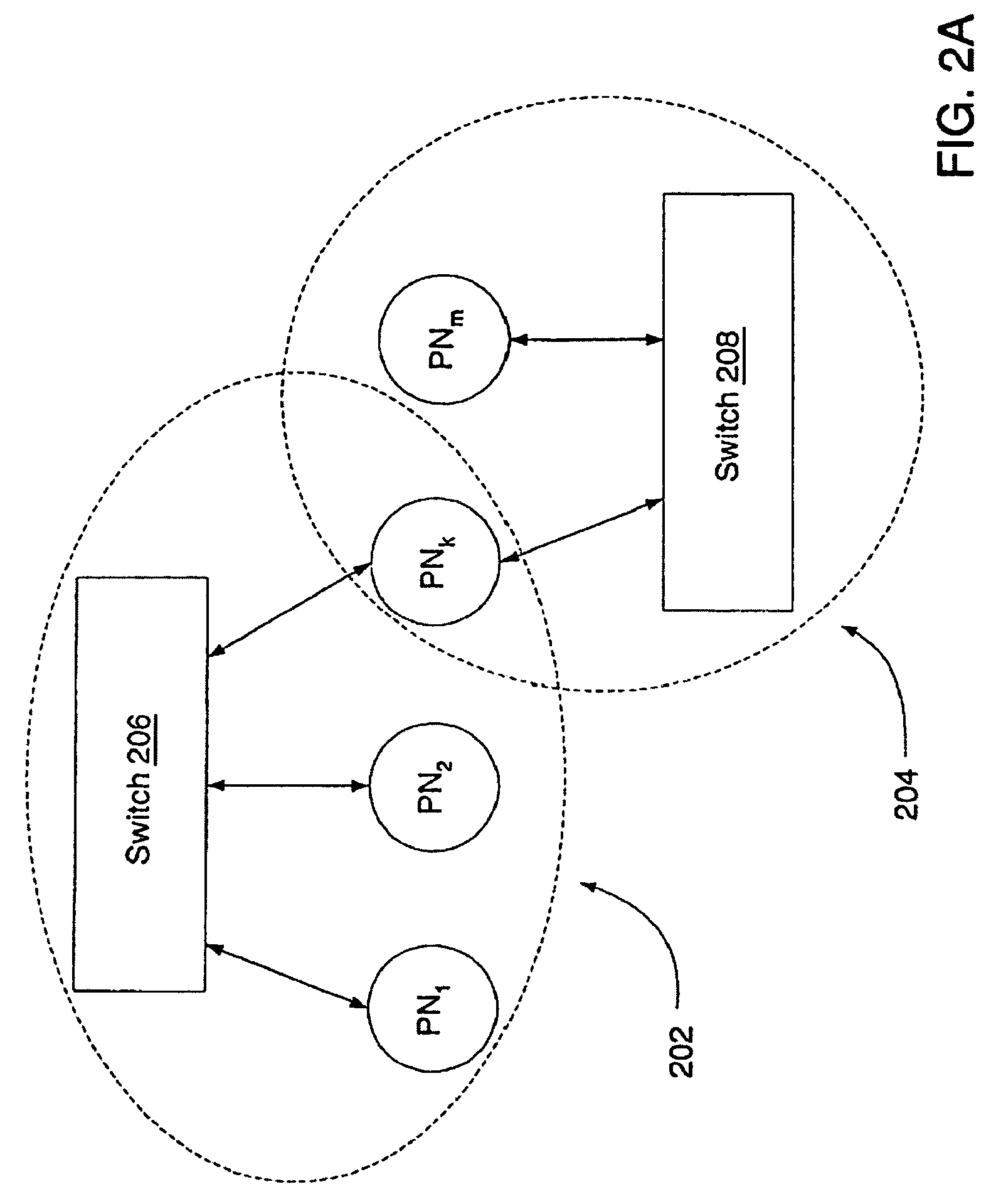
ActiveUS7380025B1TransmissionInput/output processes for data processingAuto-configurationNetwork element
A method of automatically configuring a port of a network element comprises the steps of discovering information that identifies or describes a second network element that is coupled to a port of a first network element; associating the port with a port role definition selected from a plurality of port role definitions based on the discovered information; retrieving one or more configuration settings that are associated with the selected port role definition; and applying the one or more configuration settings to the port.
Owner:CISCO TECH INC
Network architecture for remote robot with interchangeable tools
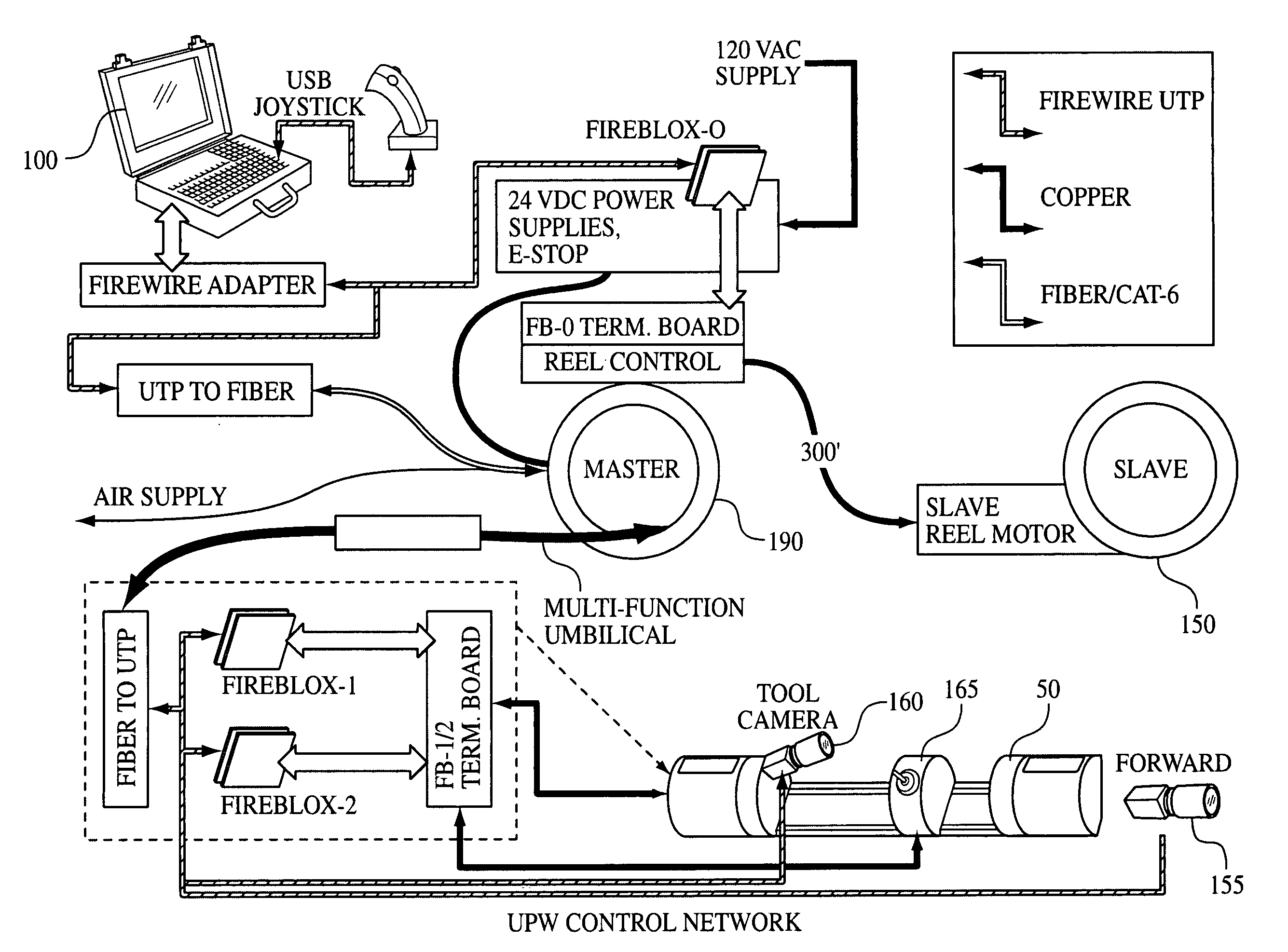
ActiveUS20060074525A1Slow feedback loopLess time-critical decisionProgramme controlProgramme-controlled manipulatorDigital feedbackAuto-configuration
Systems, methods and devices for the remote control of a robot which incorporates interchangeable tool heads. Although applicable to many different industries, the core structure of the system includes a robot with a tool head interface for mechanically, electrically and operatively interconnecting a plurality of interchangeable tool heads to perform various work functions. The robot and tool head may include several levels of digital feedback (local, remote and wide area) depending on the application. The systems include a single umbilical cord to send power, air, and communications signals between the robot and a remote computer. Additionally, all communication (including video) is preferably sent in a digital format. Finally, a GUI running on the remote computer automatically queries and identifies all of the various devices on the network and automatically configures its user options to parallel the installed devices. Systems according to the preferred embodiments find particular application in the pipeline arts. For example, interchangeable tool heads may be designed to facilitate inspection, debris clearing, cleaning, relining, lateral cutting after relining, mapping, and various other common pipeline-related tasks.
Owner:REDZONE ROBOTICS
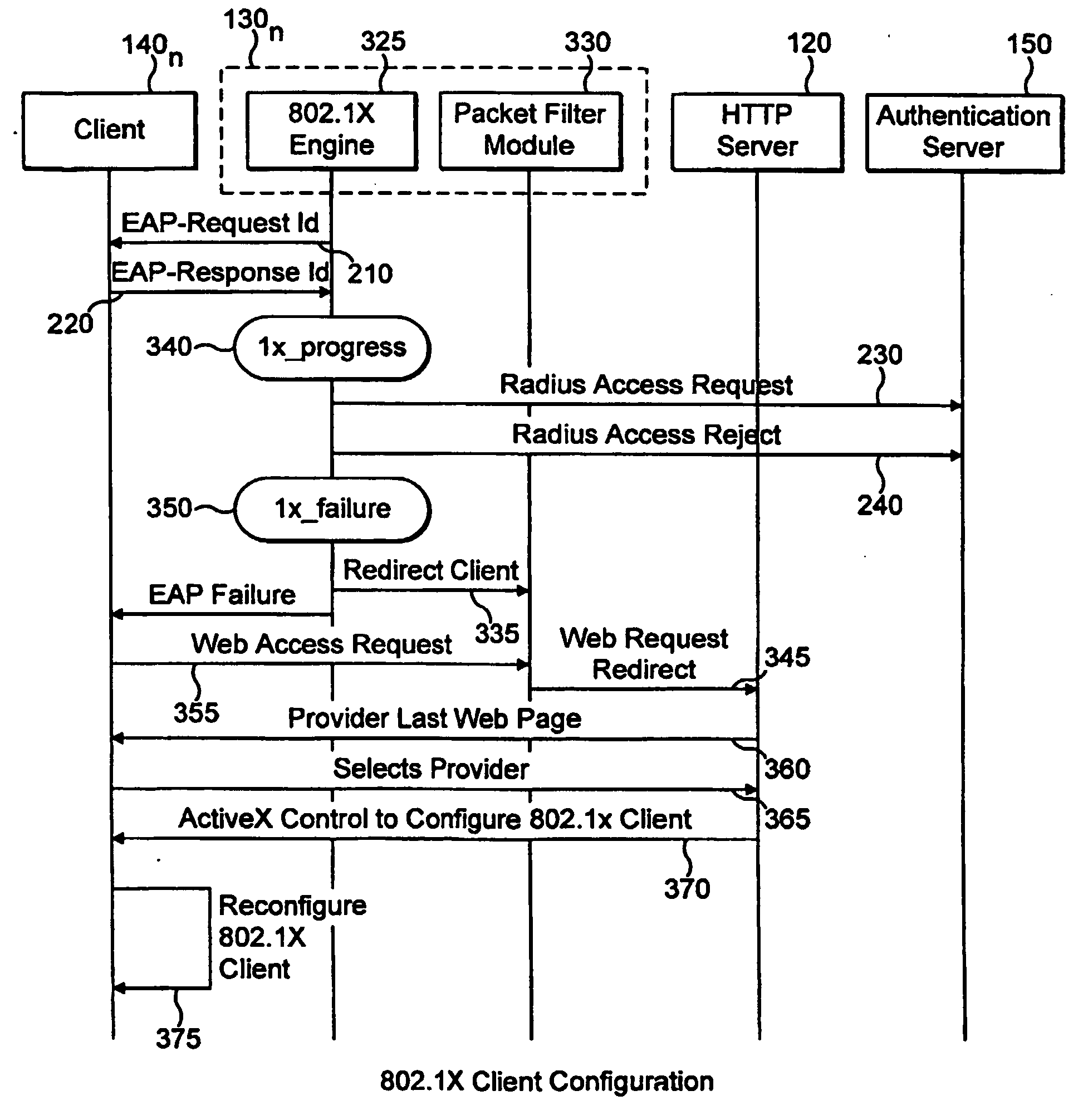
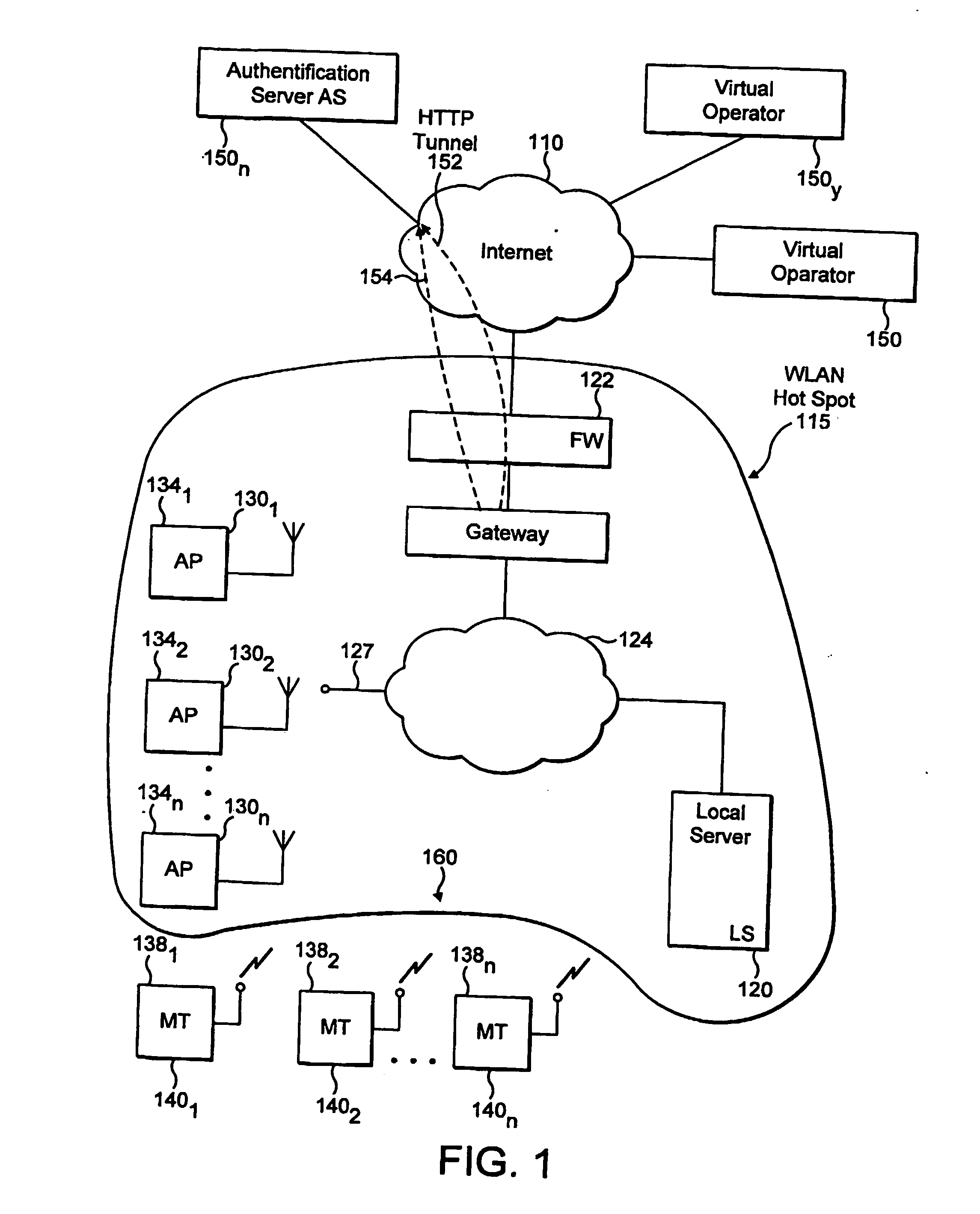
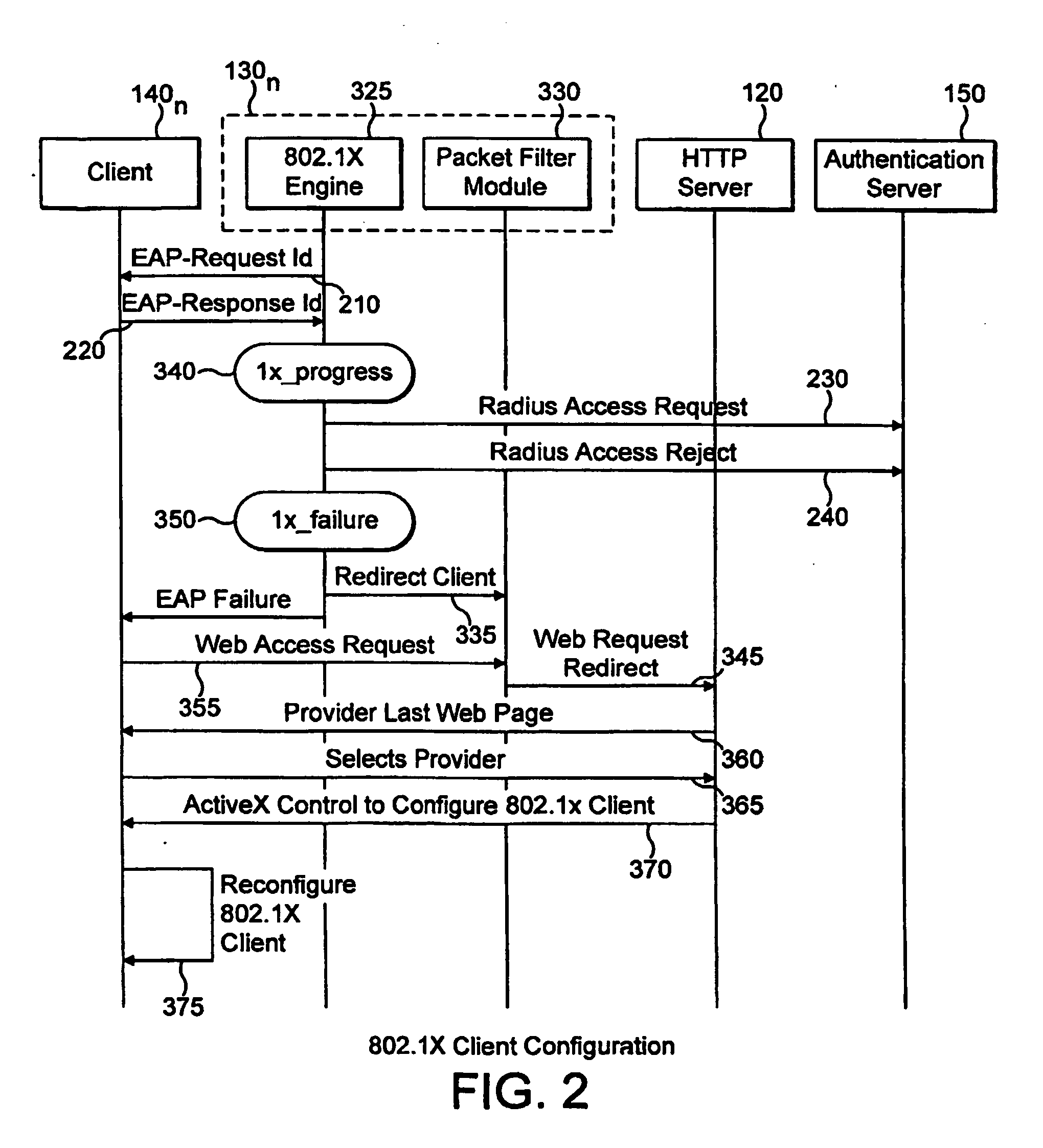
Automatic configuration of client terminal in public hot spot
ActiveUS20060173844A1Easy accessDigital data processing detailsUser identity/authority verificationLimited accessAuto-configuration
The invention herein provides an apparatus and a method for automatically configuring an IEEE 802.1x client terminal to provide limited access in a WLAN environment, specifically utilizing the access point to filter traffic associated with the limited access so as to redirect the client terminal's HTTP request to a designated local web server. The web server responds to the client terminal by requesting information required to establish an authorized communication. Thereafter the client terminal provides information required to establish an authorized communication. In the course of the communication the web server sends information such as transmission rates, new user account creation information, authentication method selection, and access user terms and conditions of acceptance, all typically required to establish an authorized access. The client responds with information, required to establish an authorized communication.
Owner:BOSTON MEDICAL CENTER INC +1
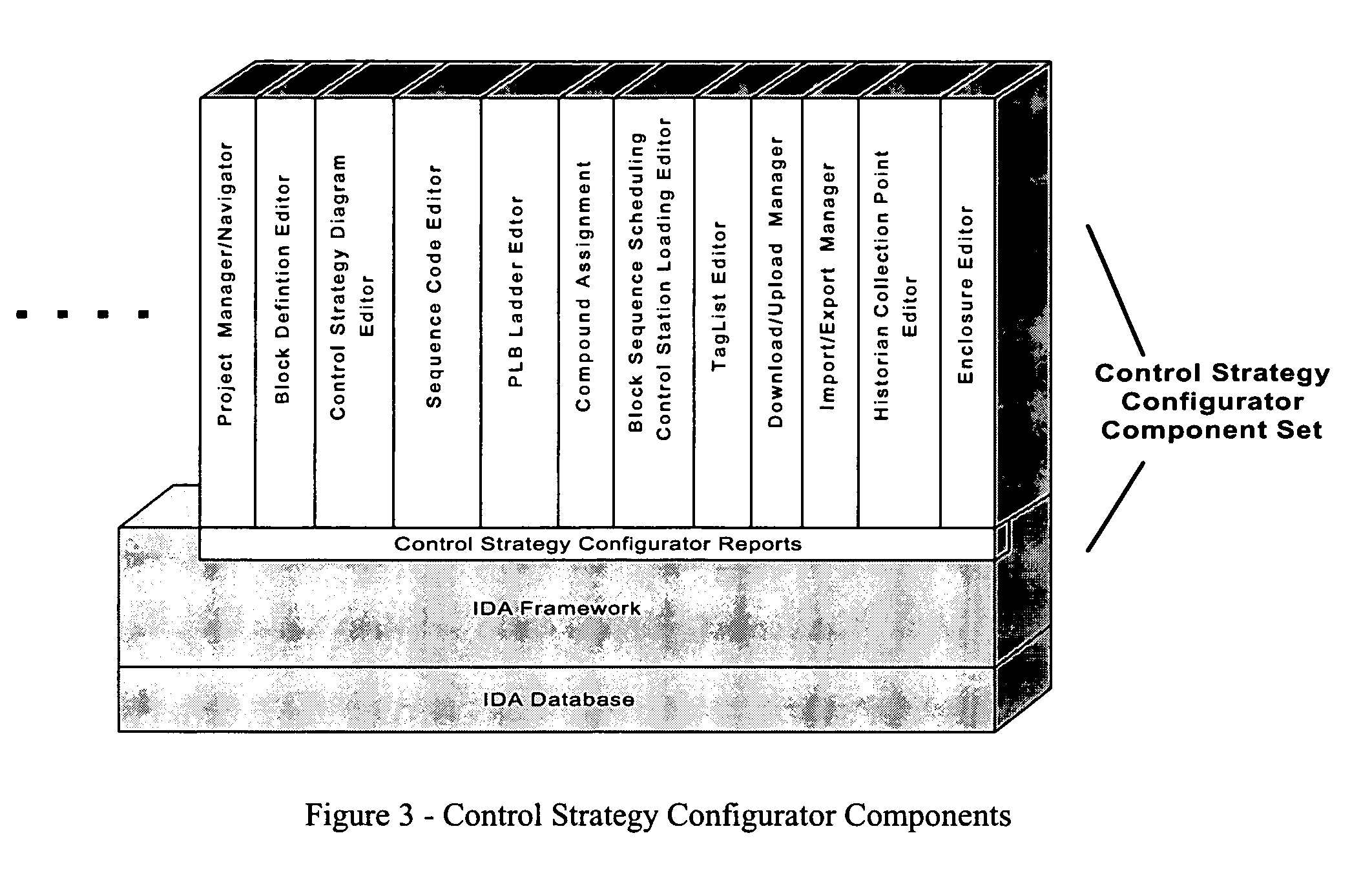
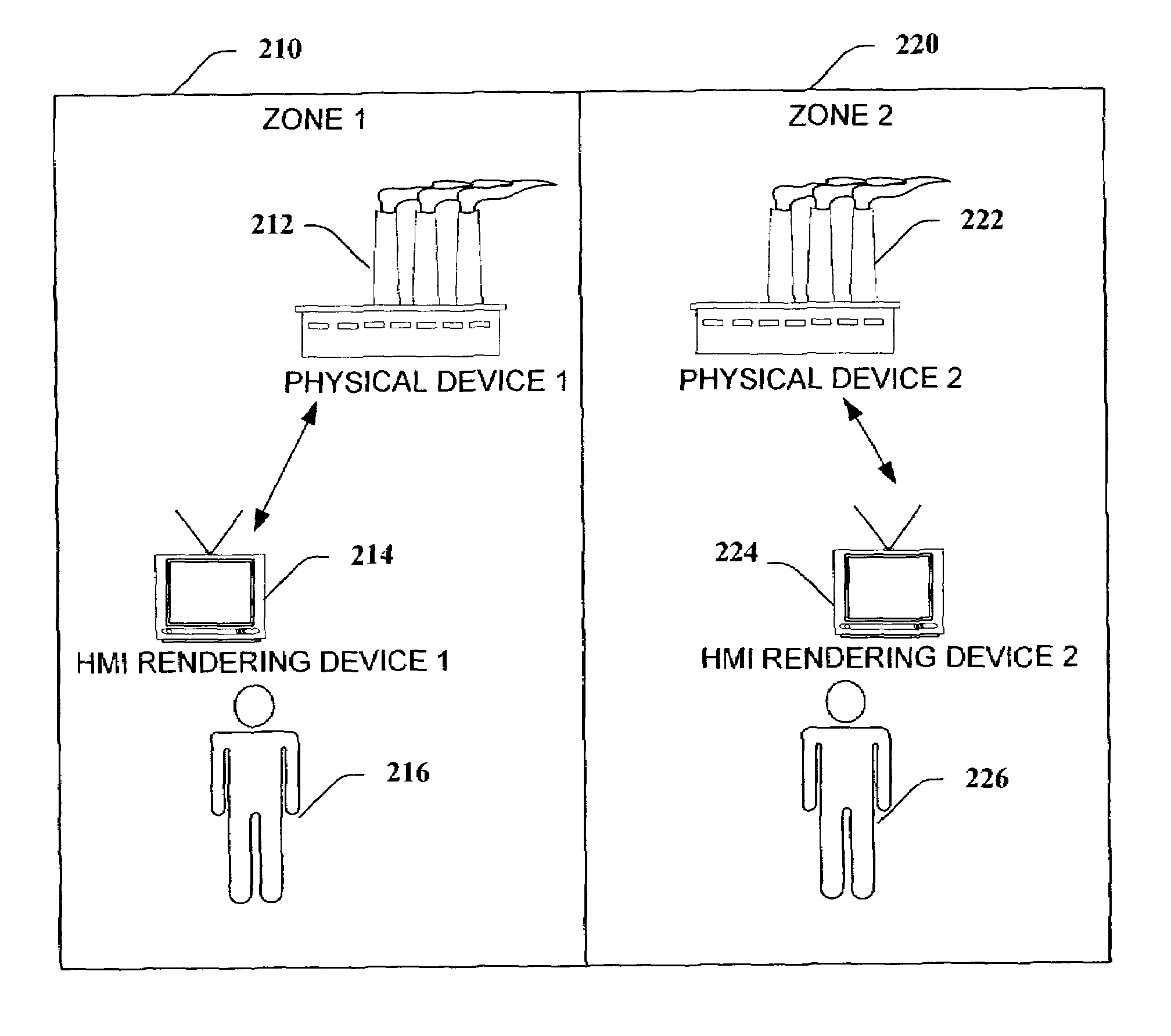
Location-based execution of software/HMI
ActiveUS7194446B1Consistent and reliableFacilitate HMI renderingProgramme controlDigital computer detailsHuman–machine interfaceAutomation
A system and / or method that configures a HMI based at least upon a current state of parameters and a predefined protocol. A processing component queries an industrial automation environment receiving a current state of parameters relating to a human machine interface (HMI). A rendering component automatically configures the HMI to function in accordance with a predefined protocol.
Owner:ROCKWELL SOFTWARE
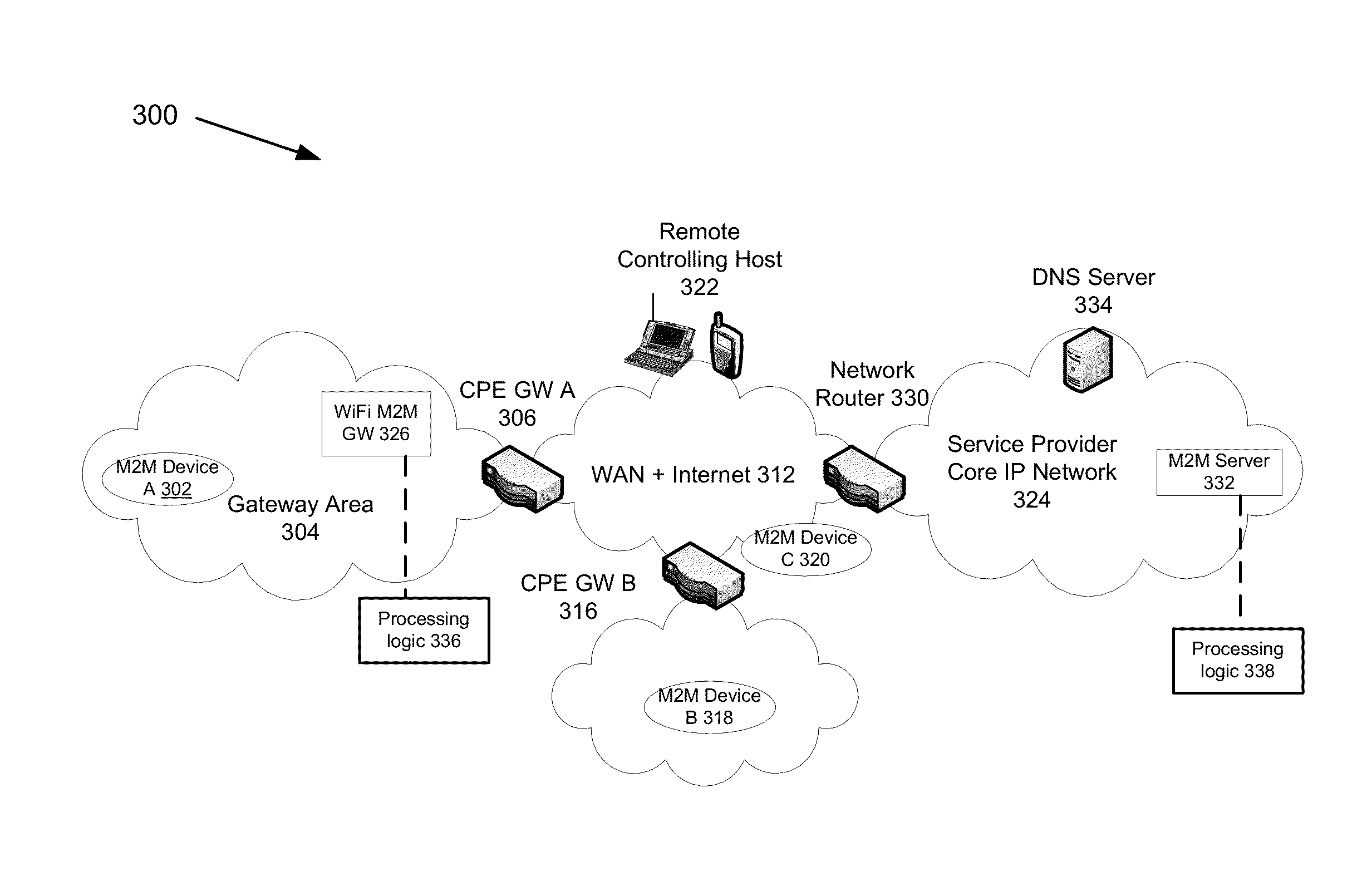
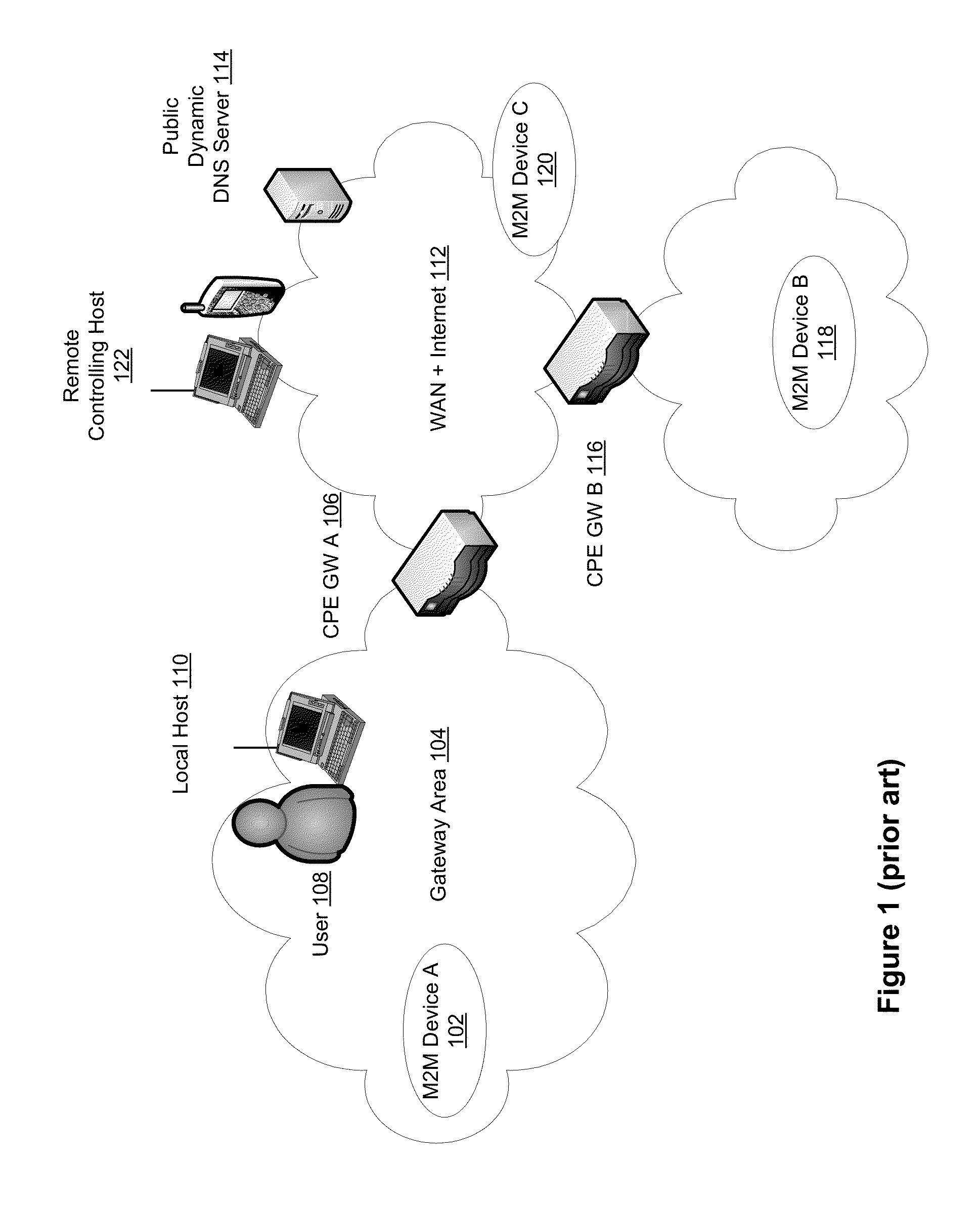
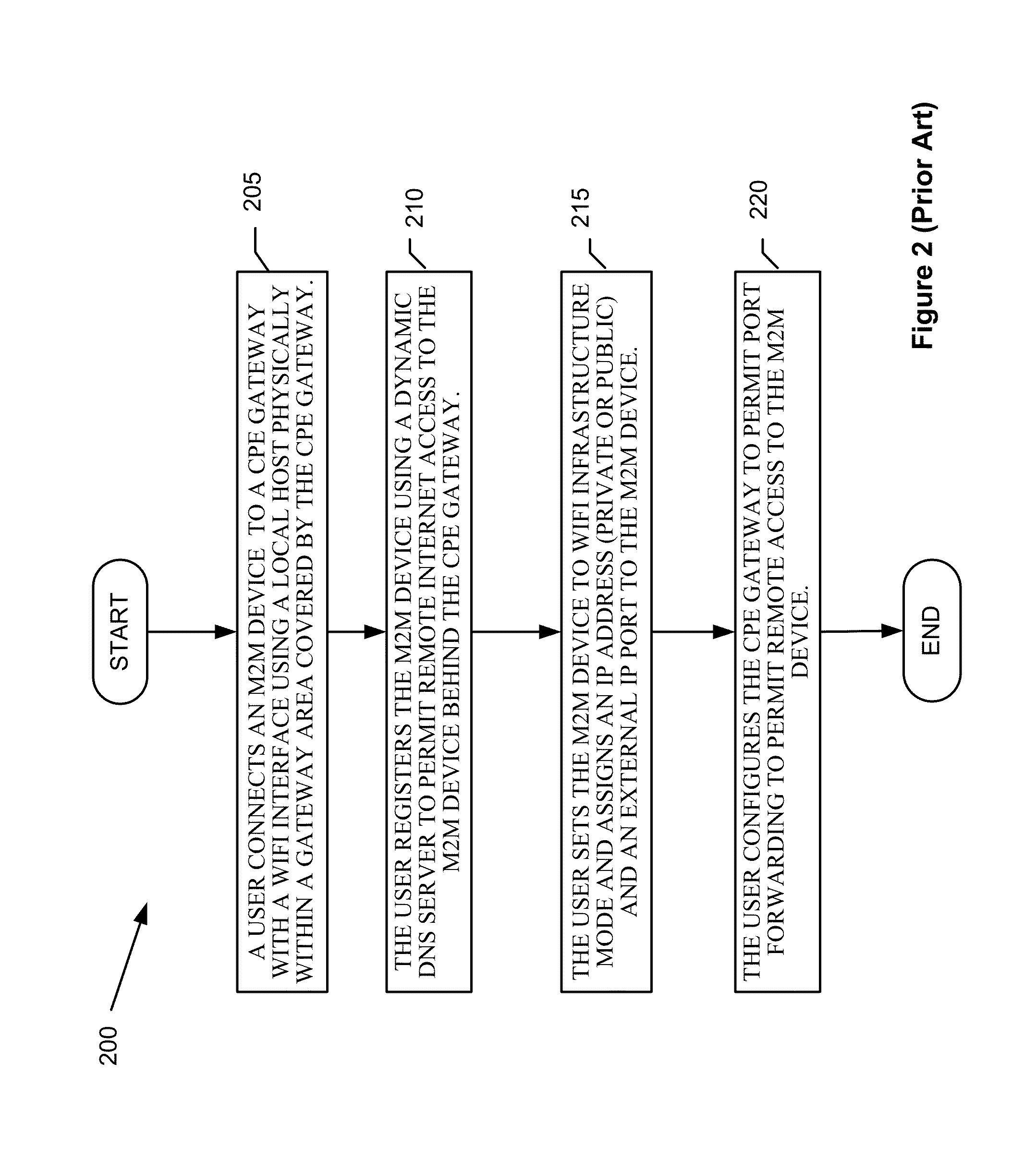
Automatic provisioning of an m2m device having a WIFI interface
InactiveUS20130094444A1Facilitate fast responseService provisioningNetwork topologiesDomain nameFully qualified domain name
A method for automatically provisioning a WiFi-equipped machine-to-machine (M2M) device is disclosed. A WiFi M2M gateway identifies a WiFi network identifier broadcast by a powered-on M2M device in WiFi ad hoc mode through a scanning procedure and joins the ad hoc network defined by the M2M device. The WiFi M2M gateway obtains device information (e.g., MAC address) of the M2M device. The WiFi M2M gateway transmits a command to the M2M device to switch from ad hoc mode to infrastructure mode. The WiFi M2M gateway registers the M2M device with an M2M server associated with a service provider based on the device information of the M2M device. The WiFi M2M gateway receives a fully qualified domain name (FQDN) associated with the M2M device from the M2M server.
Owner:APPLIED COMMUNICATION SCIENCES
Automatic configuration of the network devices via connection to specific switch ports
InactiveUS20050114474A1Optimize networkDigital computer detailsLocation information based serviceAuto-configurationNetwork management application
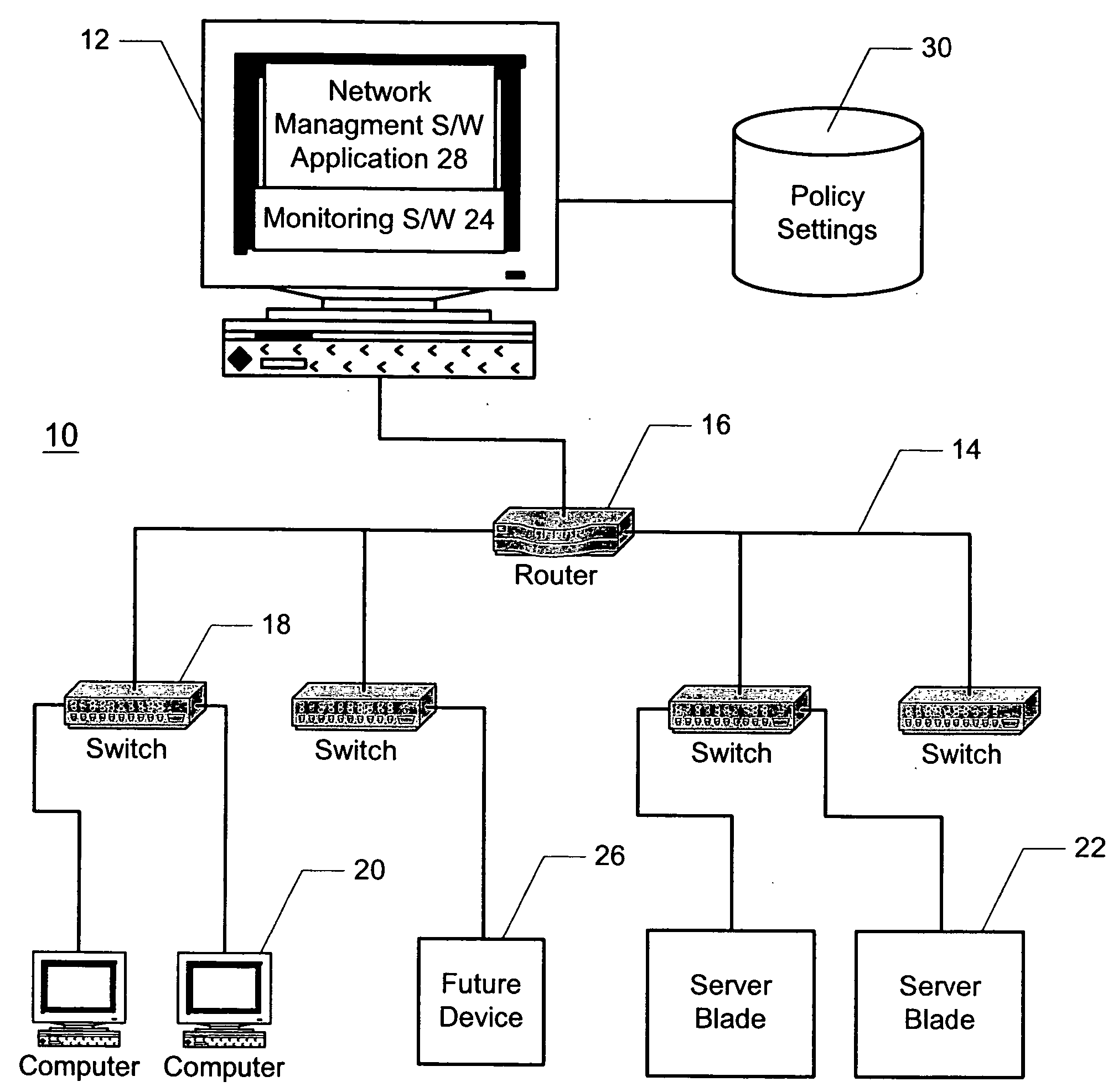
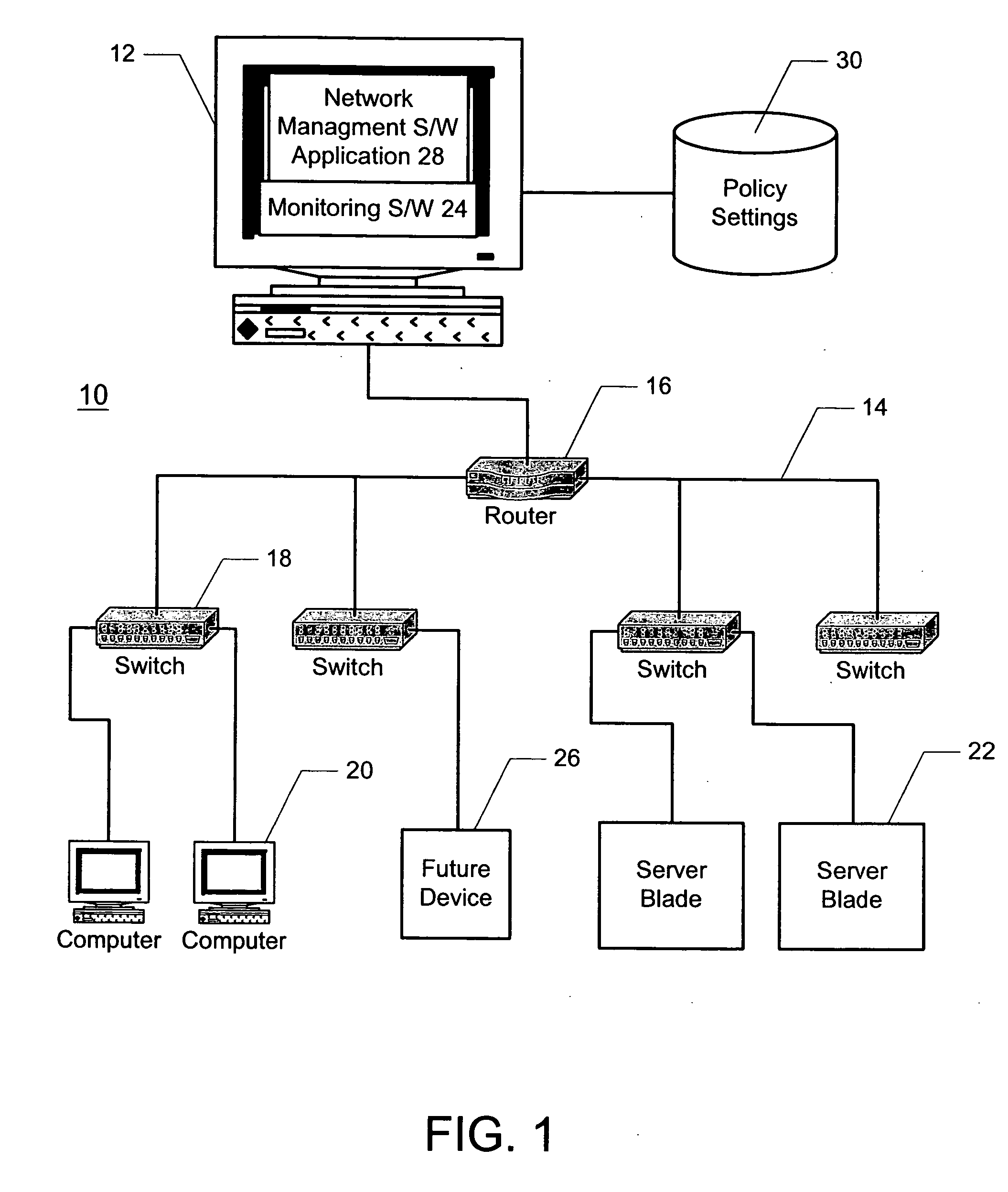
A method and system for automatically configuring devices in a network is disclosed. A network management software application is provided that enables a user to associate policy settings with physical locations in the network. During an operational mode of the network management application, the application automatically detects when a network device is plugged into the network, and determines a location of the device in the network. The device is then automatically configured based on the policy settings associated with the corresponding location.
Owner:IBM CORP
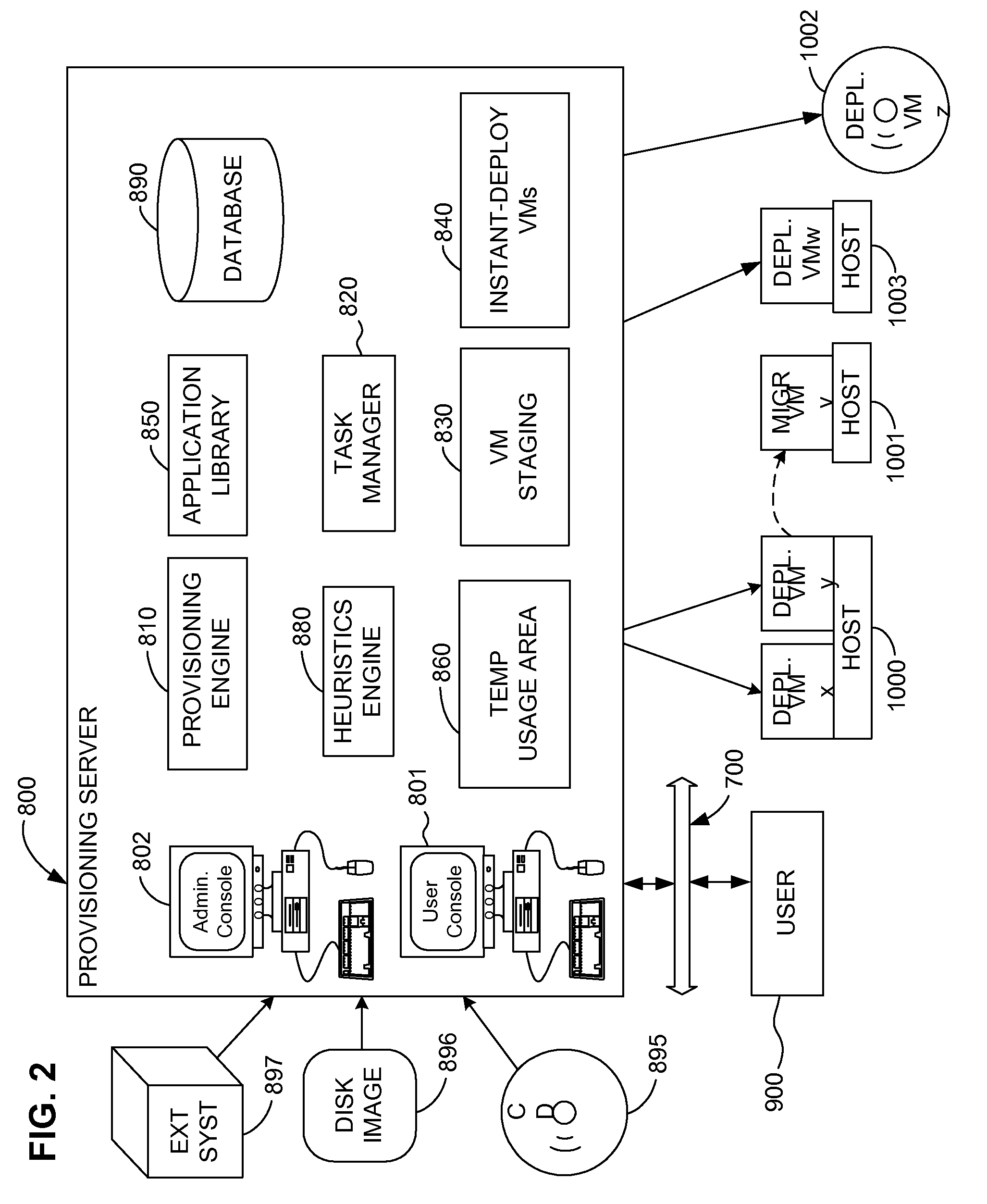
Automated provisioning of computing networks according to customer accounts using a network database data model
InactiveUS7152109B2Minimize security riskRepeatability is assuredMultiple digital computer combinationsProgram loading/initiatingComputer hardwareAuto-configuration
A framework for automatically provisioning computing devices includes a central database system and a central file system. Information stored in the database comprises a model of the individual devices, as well as the interconnections of the devices. The central file system stores the software components to be installed on the devices. When provisioning is carried out, the database sends commands to agents located on each device which cause them to retrieve and install the software components from the file system, and to configure the components according to the stored model.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
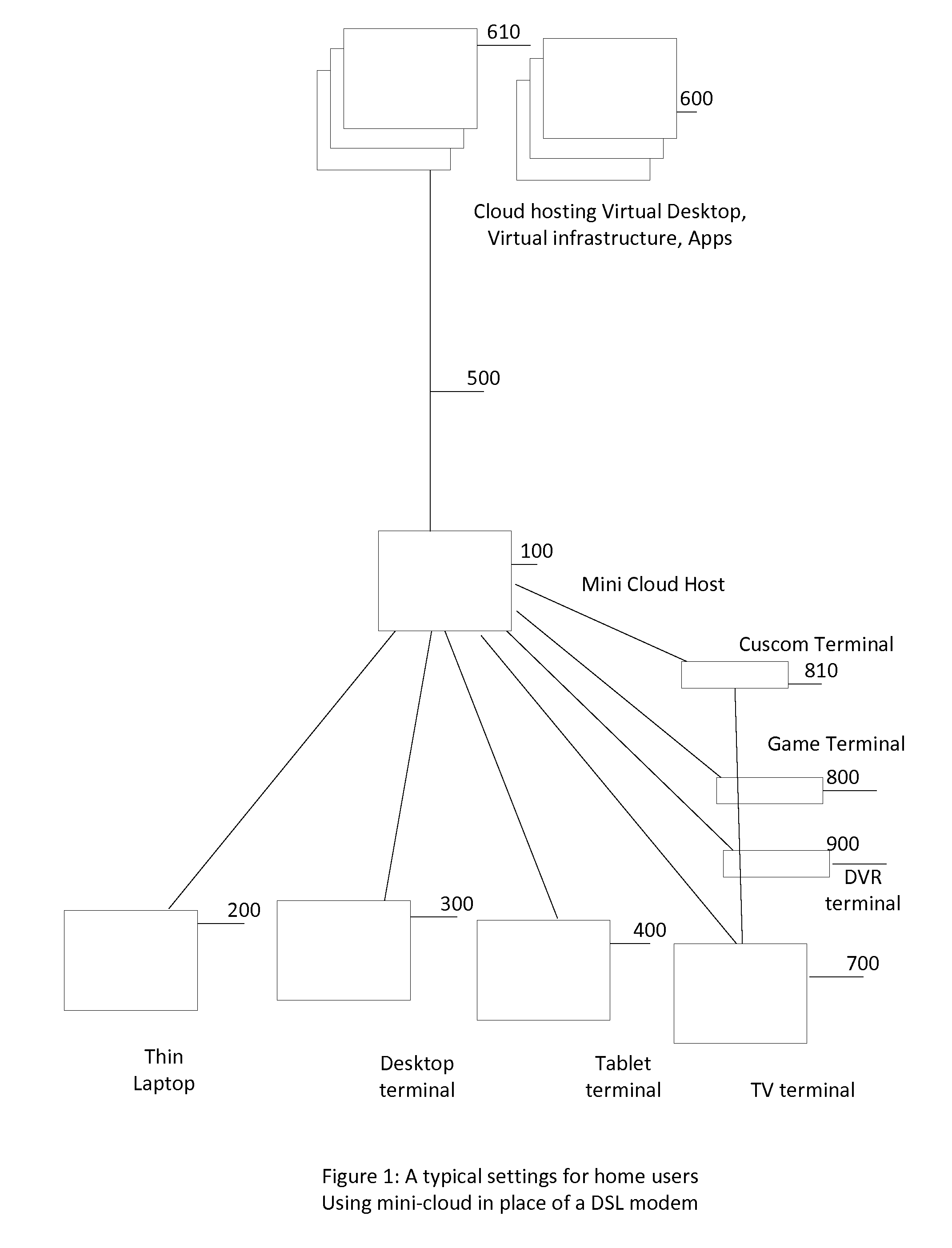
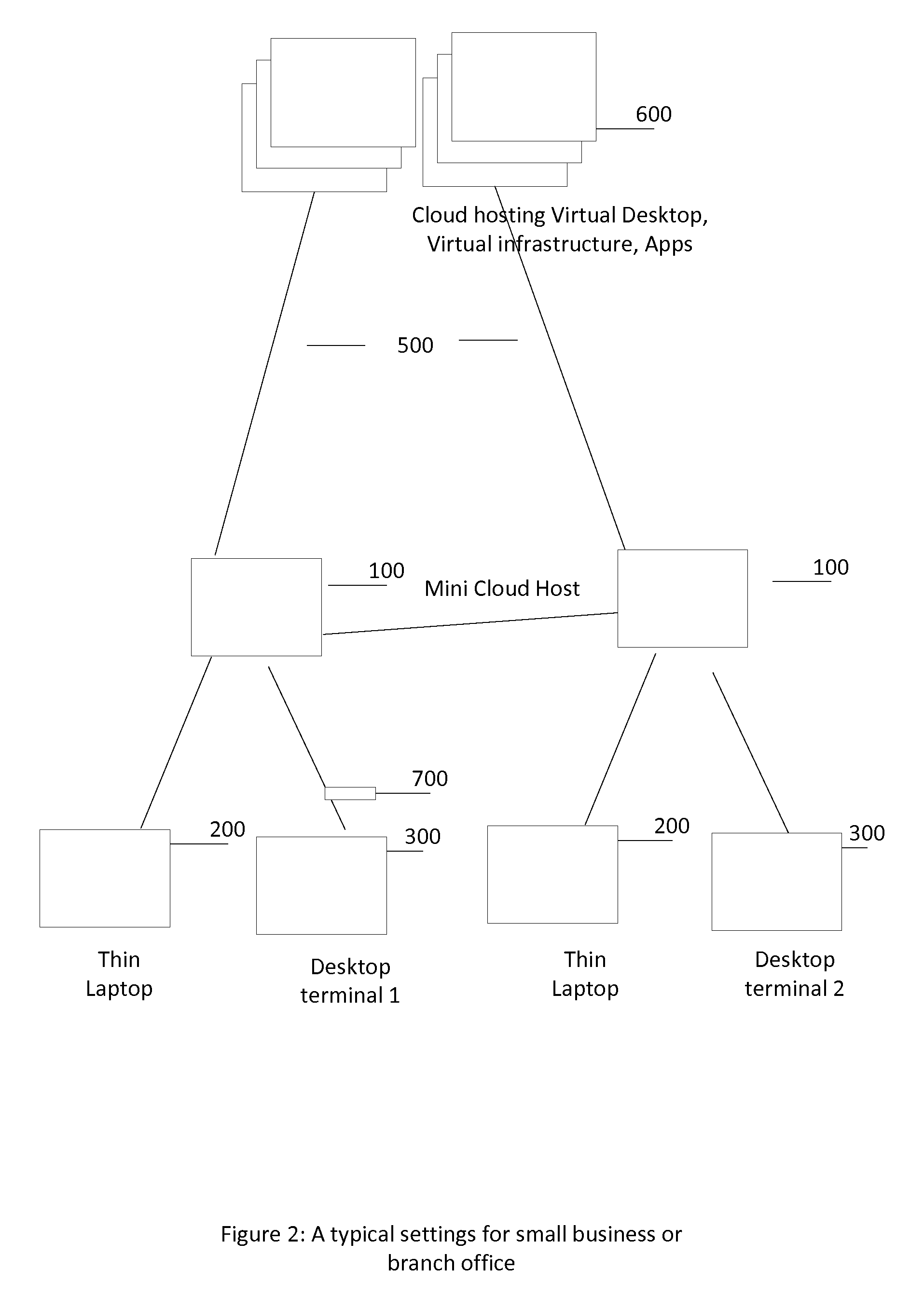
System and method to support subscription based Infrastructure and software as a service
A mini-cloud system has been described to enable subscription or service model for computing infrastructure, software and Digital content. The mini-cloud system work as a pipe line for information delivery connecting end user, infrastructure provider, content provider, and retailer offering automatic provisioning of infrastructure, content lifecycle management, automatic upgrade, servicing, license managements based on subscription model. Mini-cloud system uses a subscription management component, virtualization host to back computing environment, then add routing component to connect to backend cloud infrastructure along with a digital content delivery framework. The system allow a user to subscribe a computing environment, preferred software applications, and digital content like move and pay a monthly utility bill.
Owner:XENCARE SOFTWARE
Methods and devices for providing scalable RFID networks
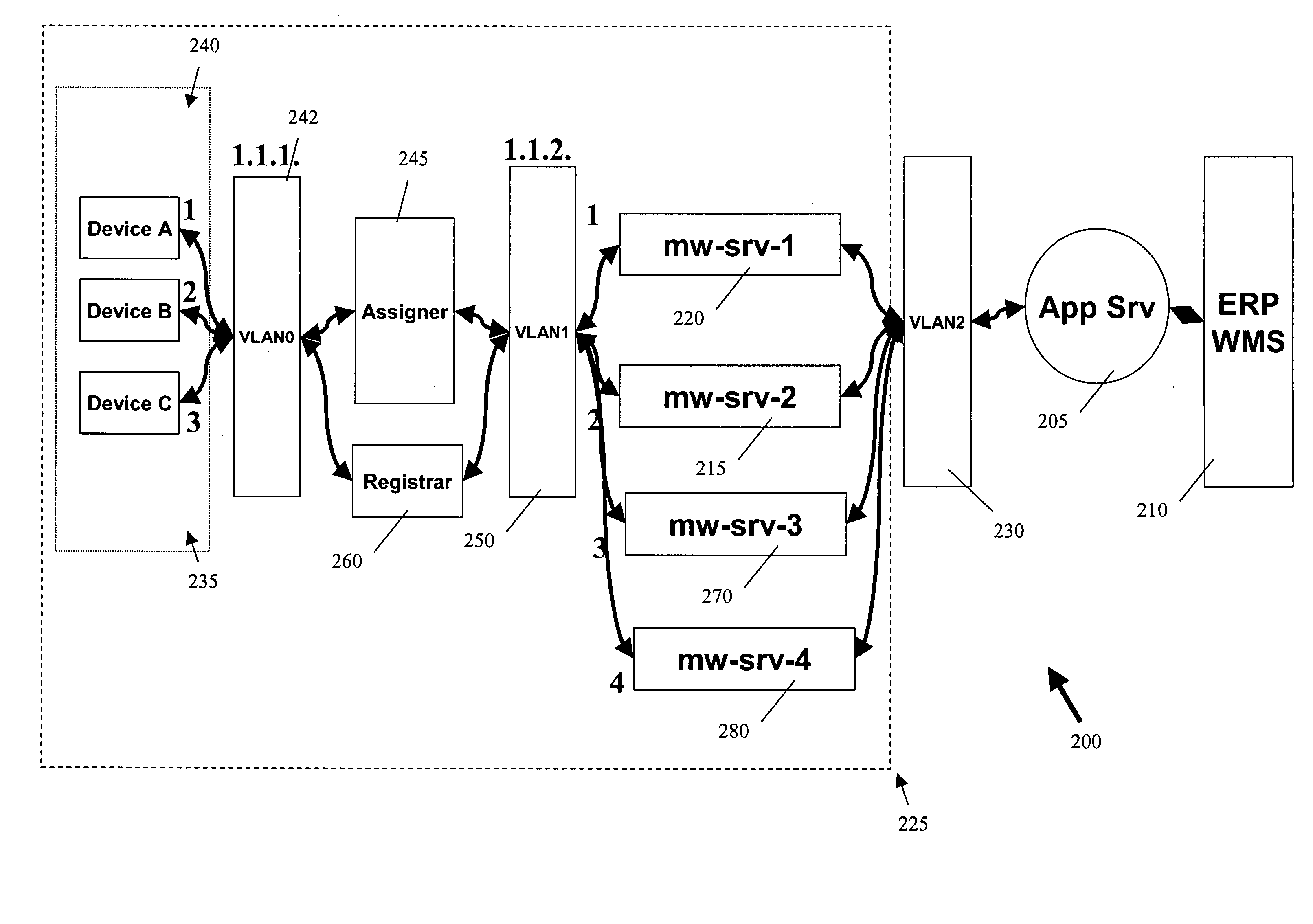
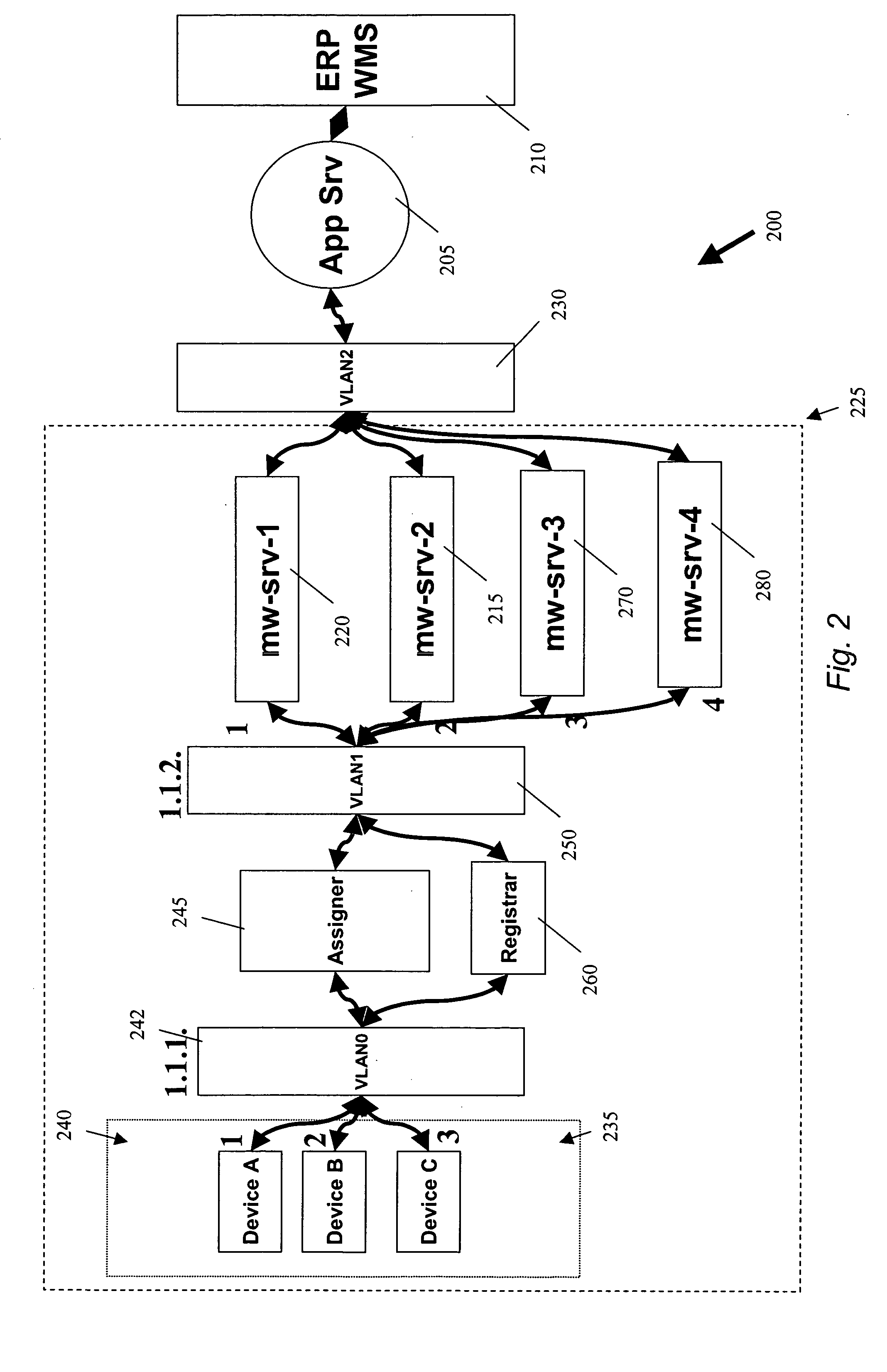
ActiveUS20050252971A1Network traffic/resource managementSensing record carriersAuto-configurationNetwork addressing
According to some implementations of the present invention, RFID devices and middleware servers are automatically provisioned with a network address and with instructions for sending a request for a middleware server to a middleware server assigner. In some implementations, the middleware server assigner is a load balancer. In some implementations, a middleware server is associated with a plurality of RFID devices by associating a middleware server network address or names with the network addresses of the RFID devices. Preferred methods also provide for redundancy of middleware servers and dynamic re-assignment of RFID devices from an unavailable middleware server to an available middleware server.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com