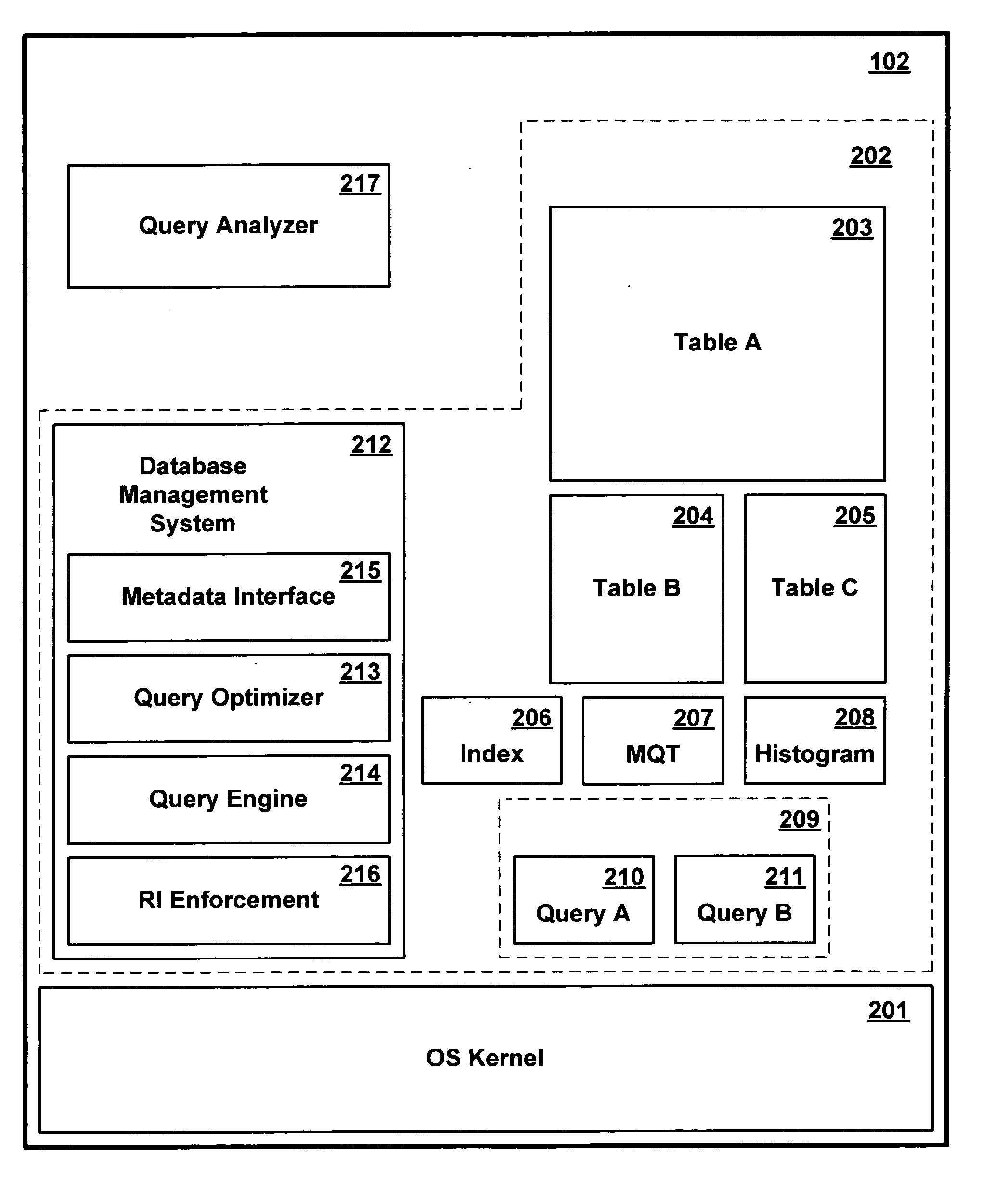
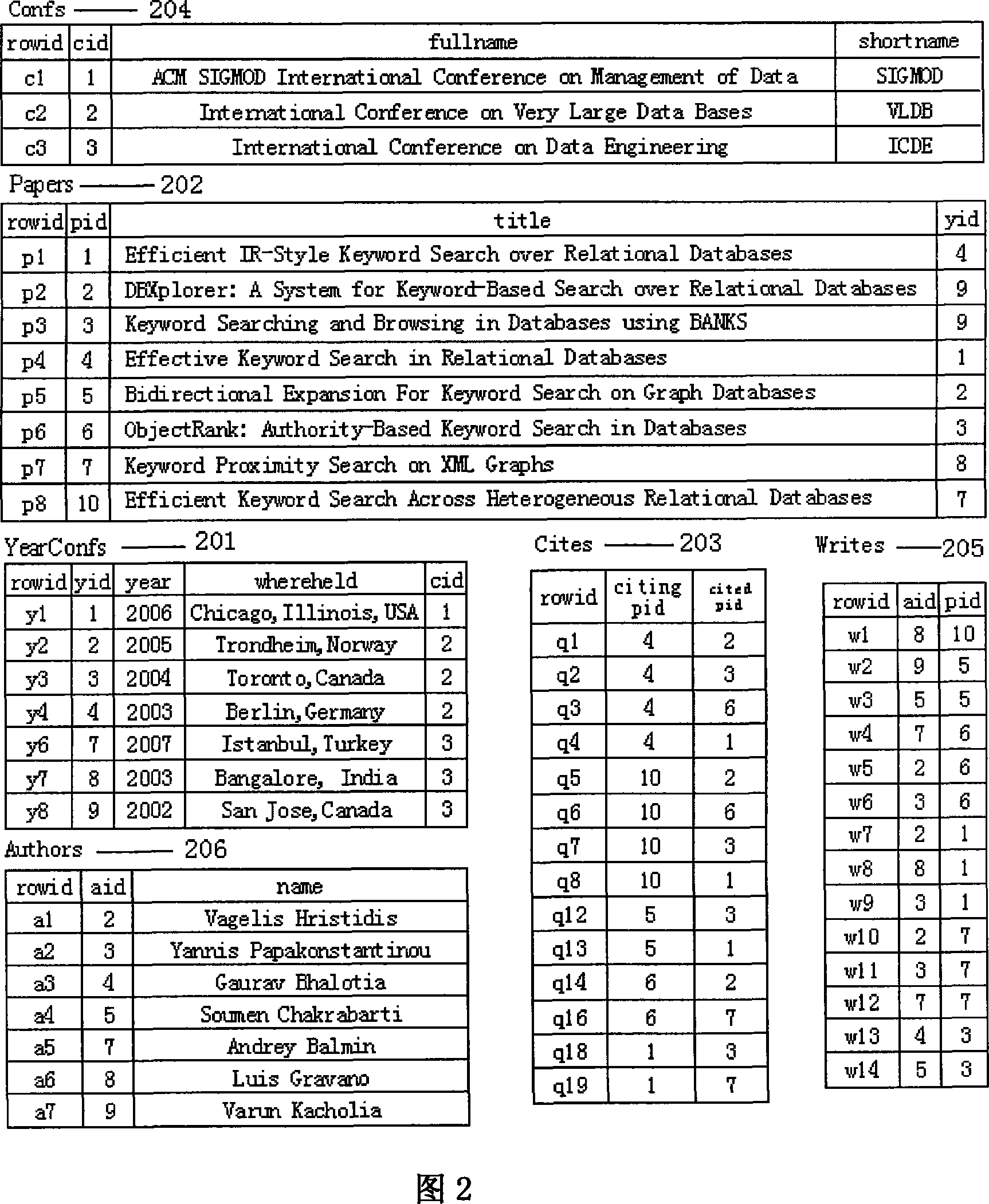
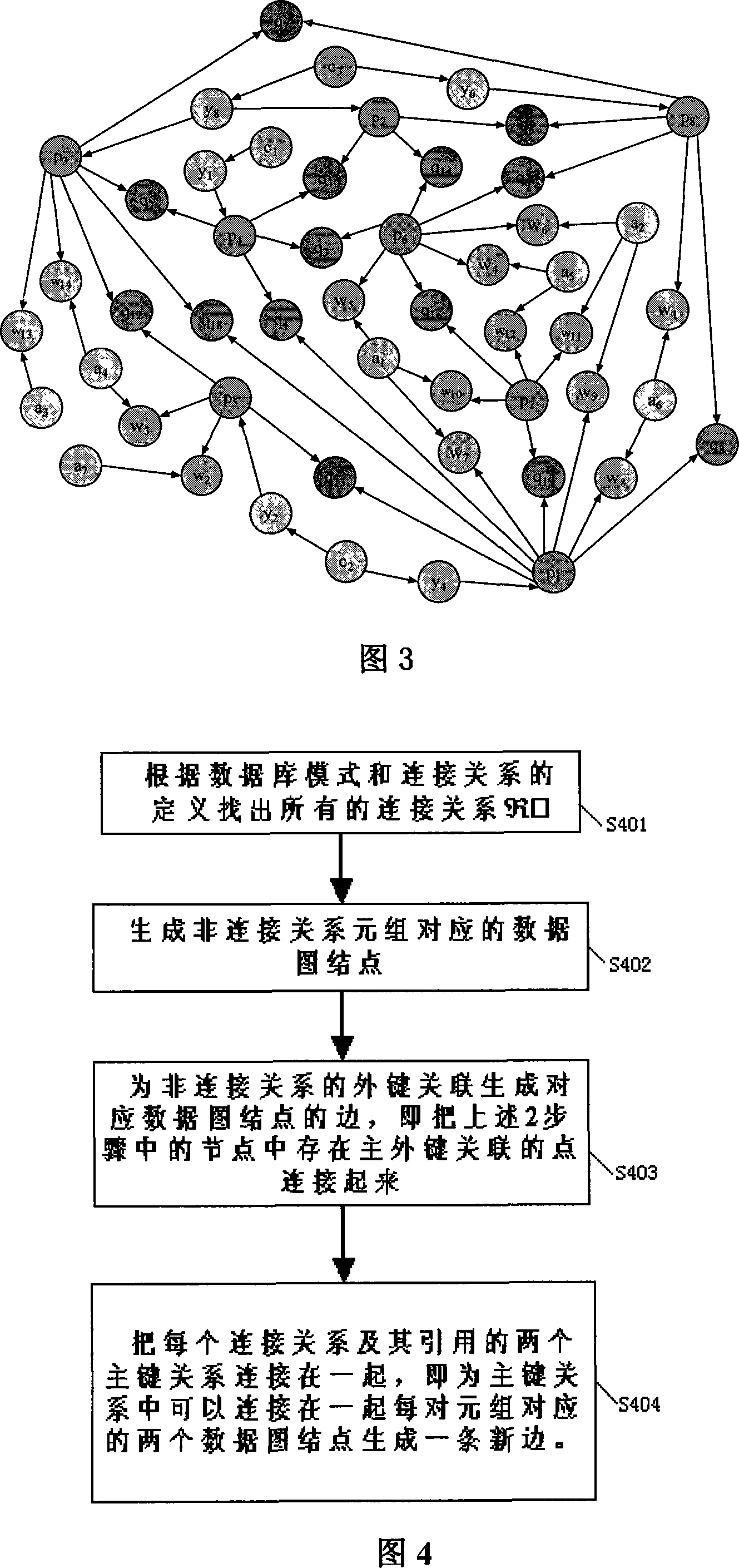
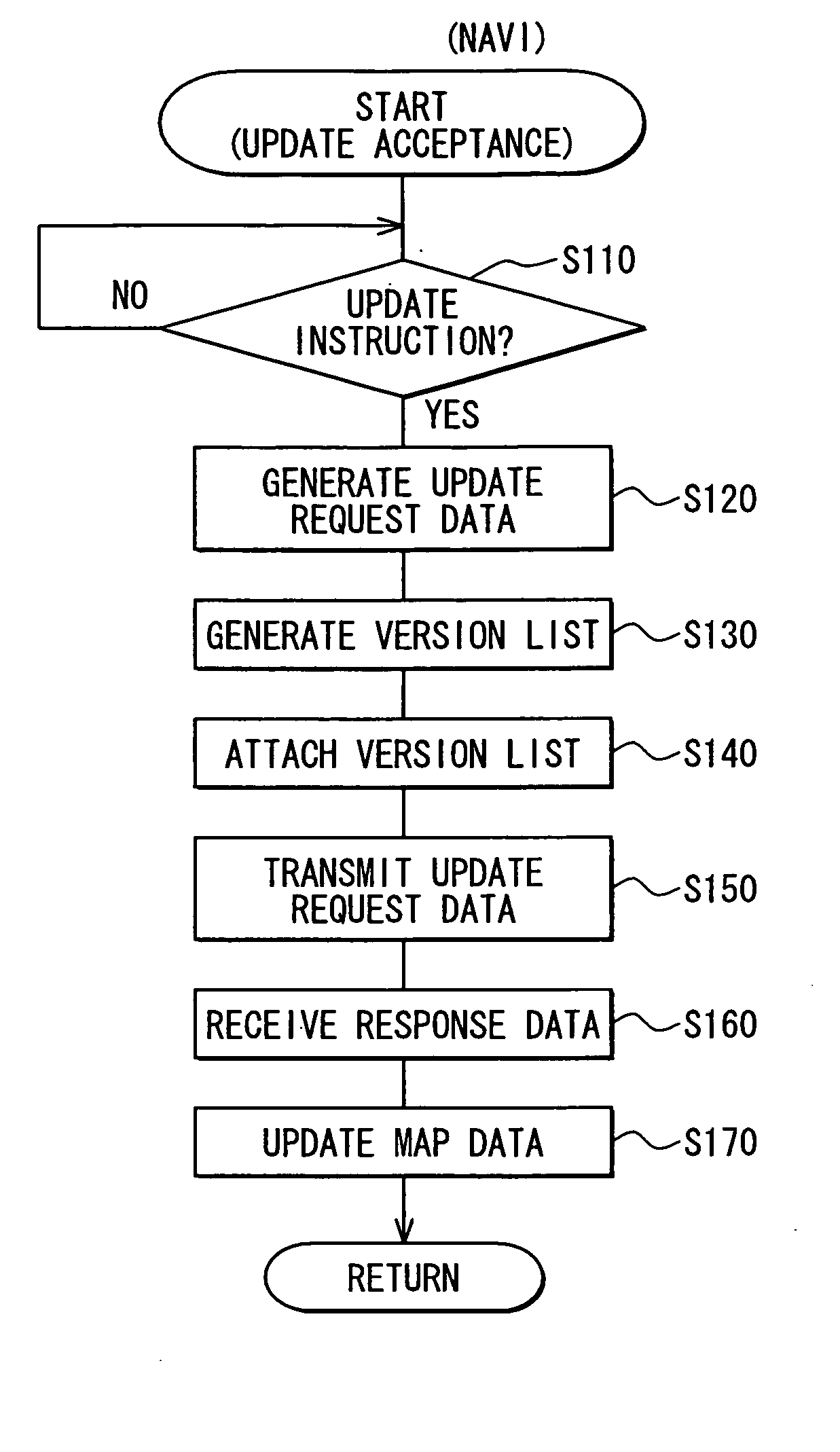
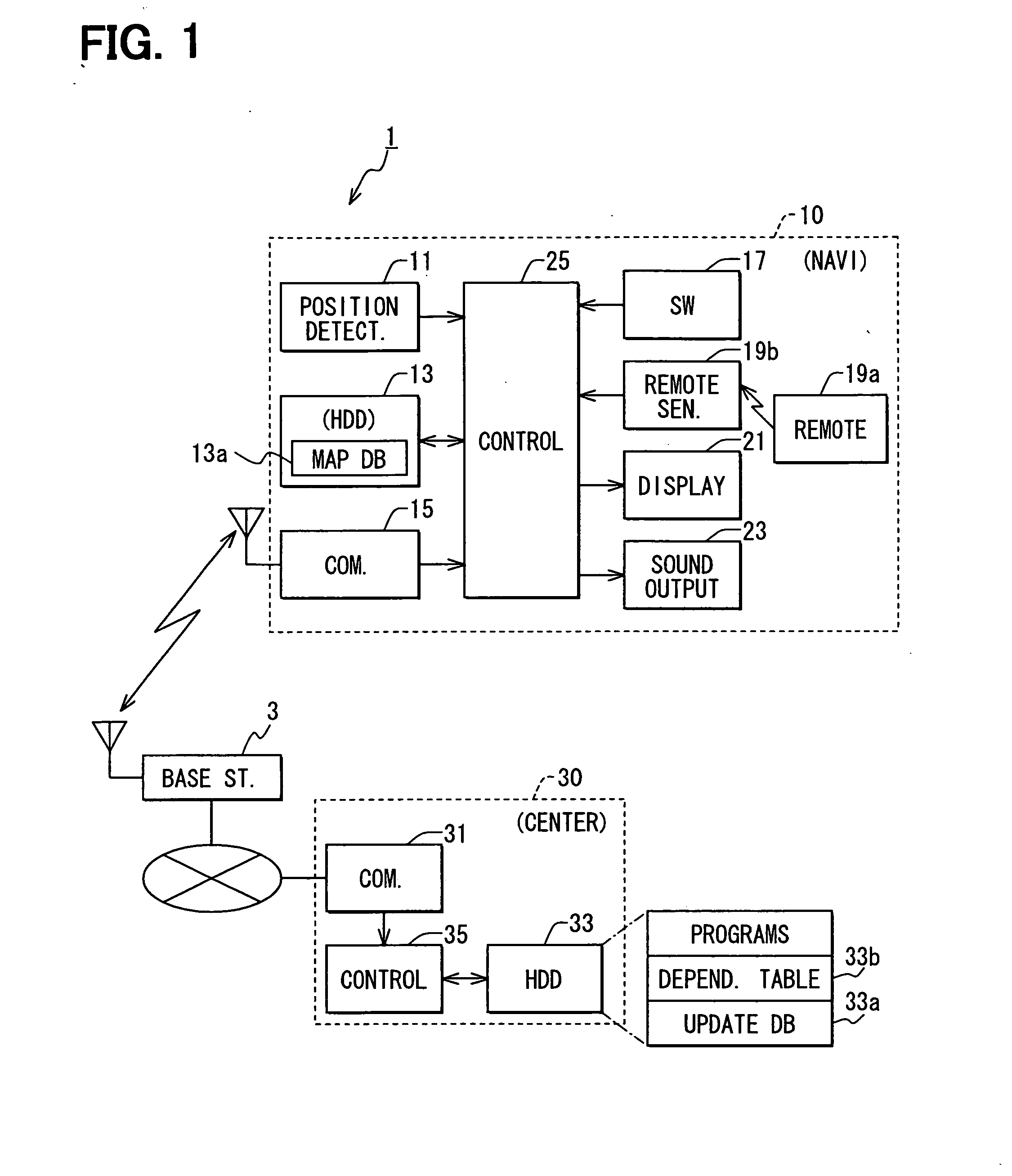
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
464 results about "Connection table" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
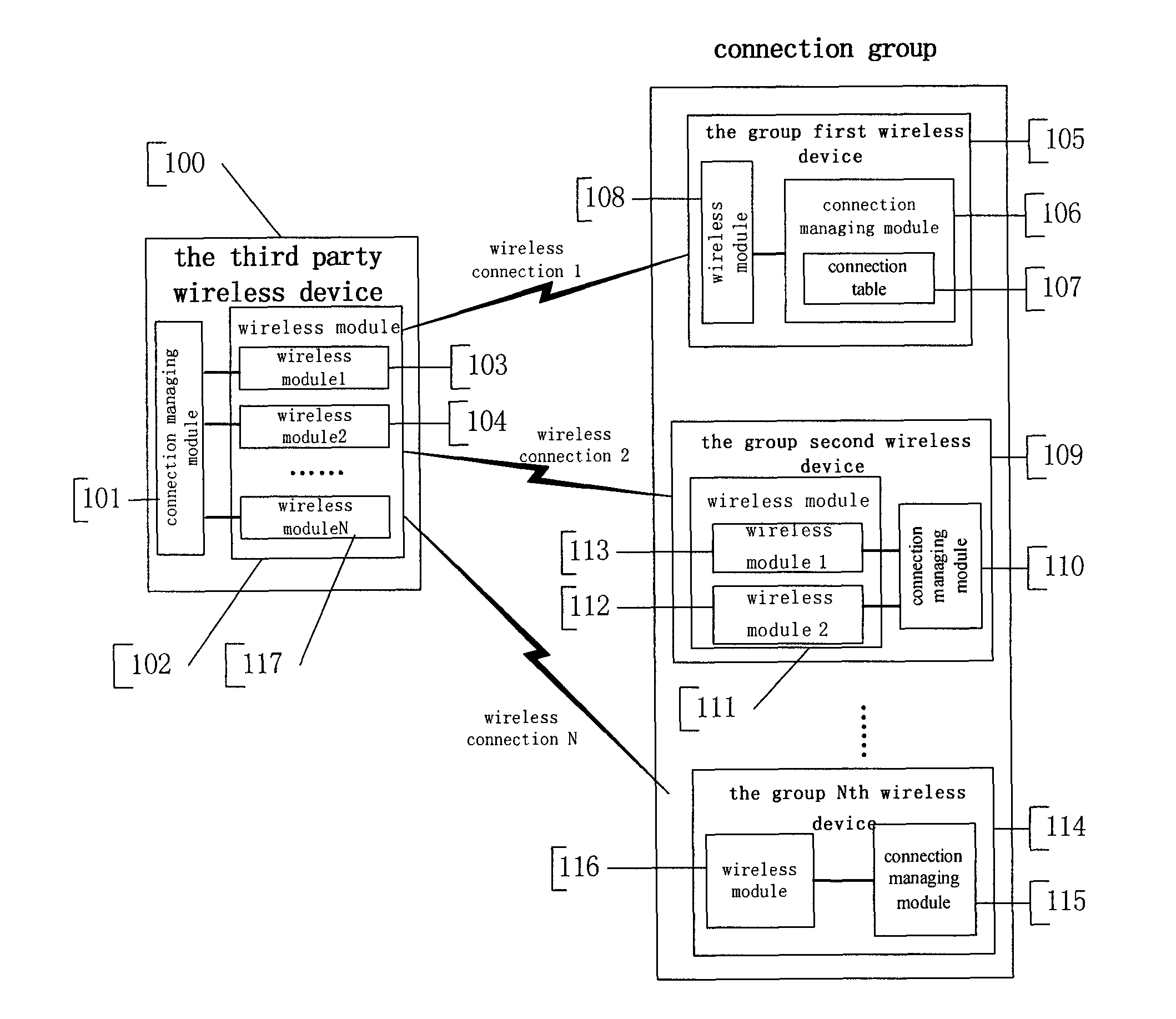
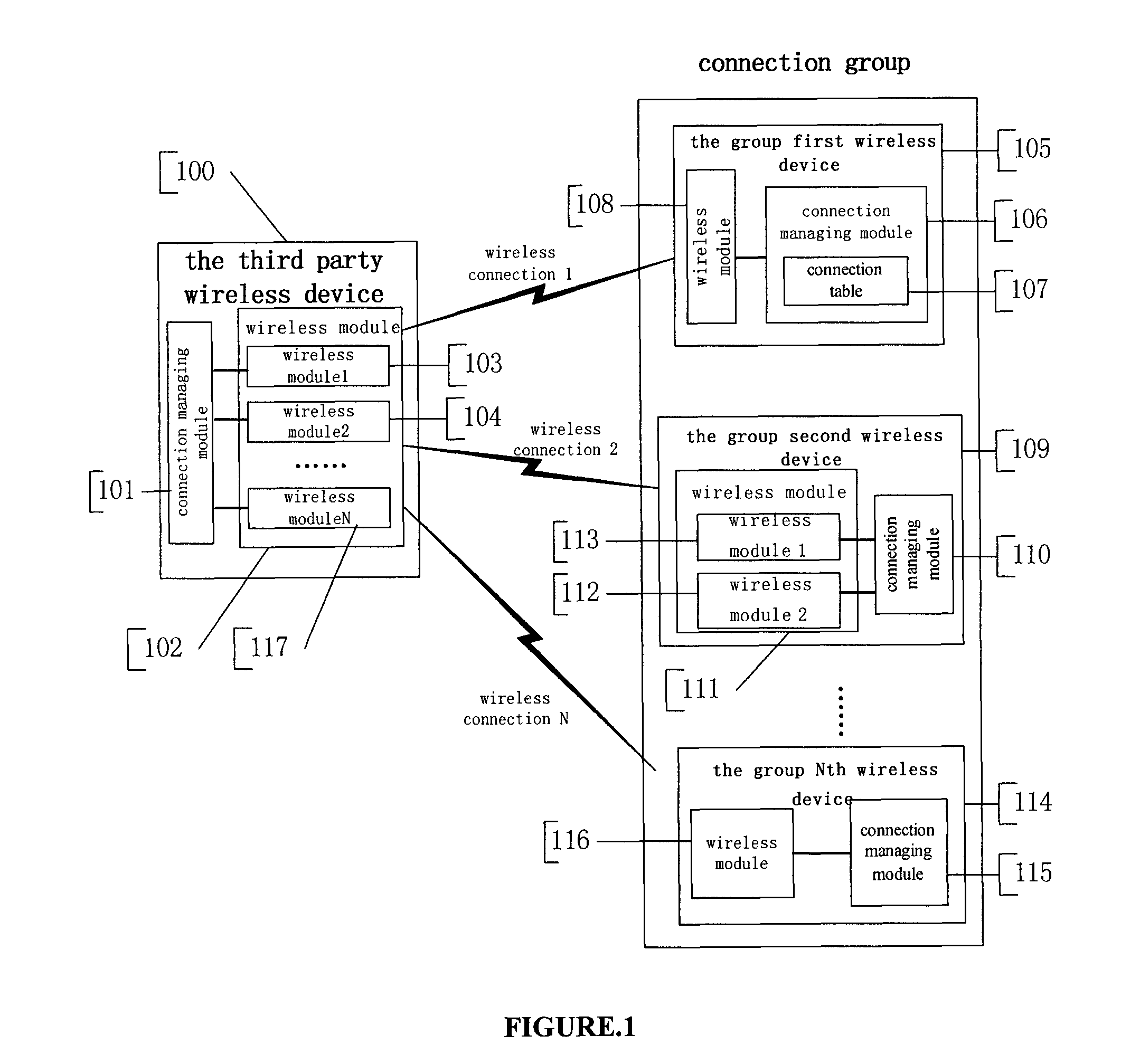
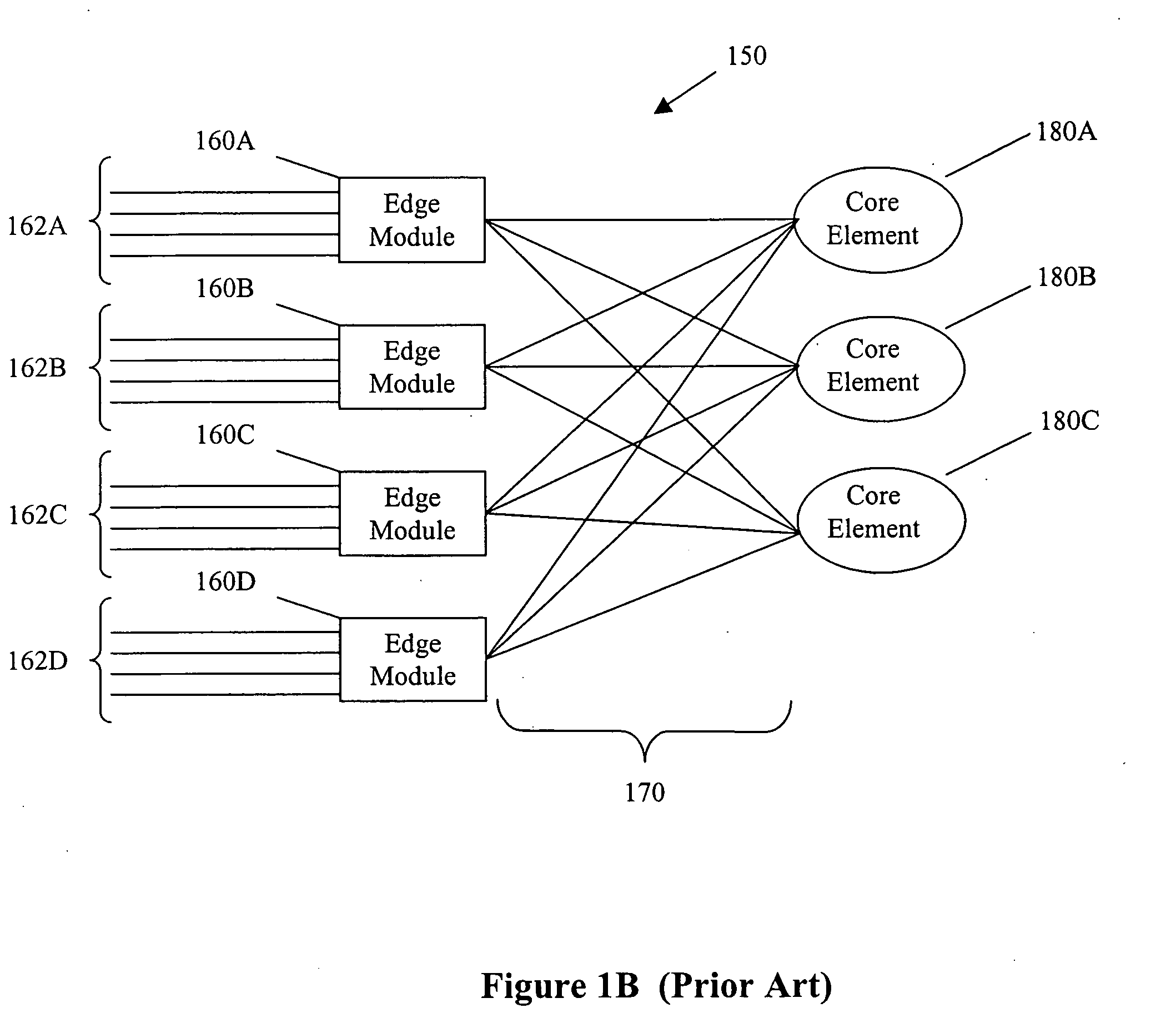
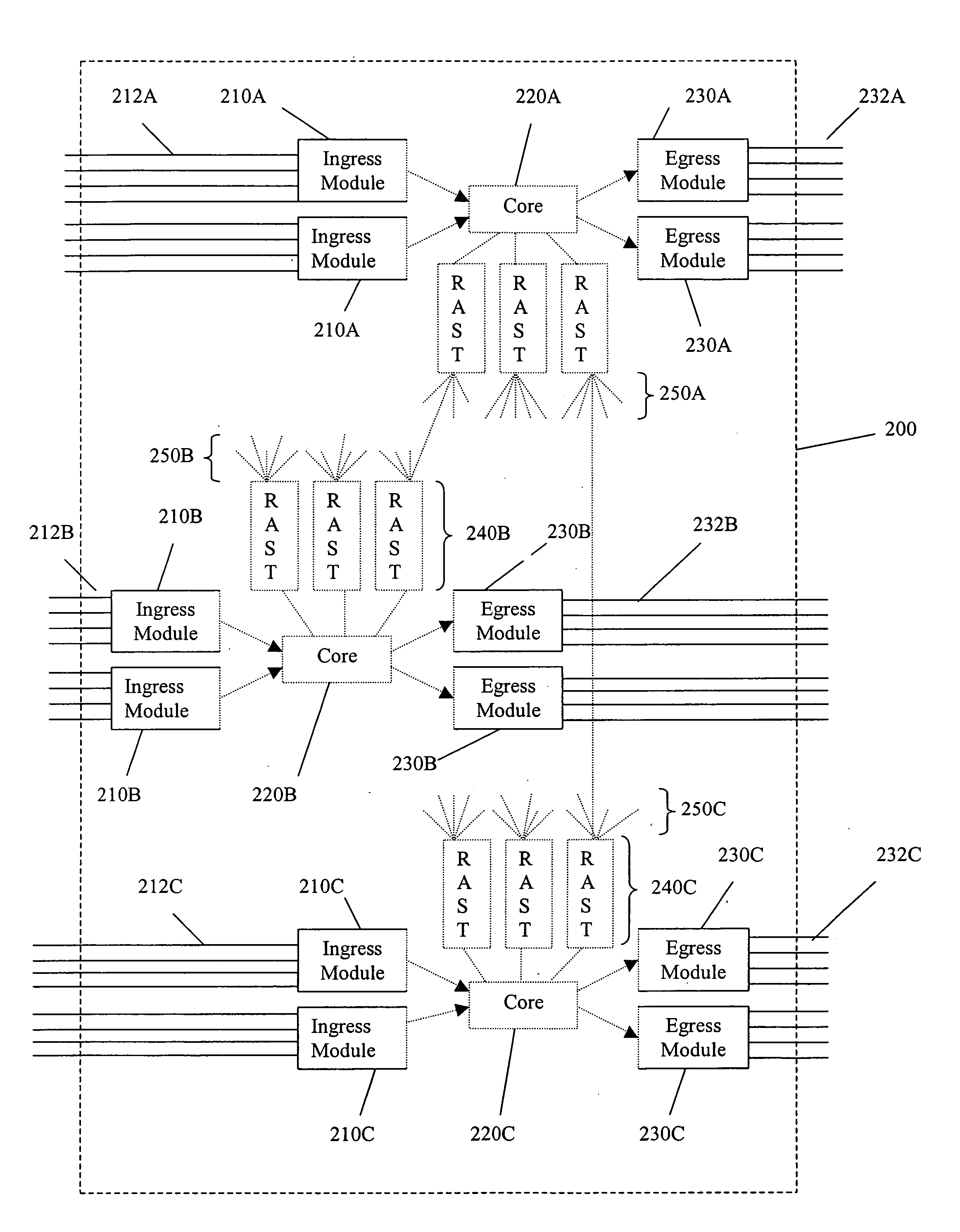
System and method for supporting automatic establishing and disconnecting several wireless connections
InactiveUS8116223B2Improve efficiencyPromote employmentError preventionFrequency-division multiplex detailsThird partyConnection table
A method for automatically establishing wireless connections between a plurality of grouped wireless devices and a third party wireless device, comprising the steps of: forming a connection group having a first wireless device and at least one additional grouped wireless device; configuring a connection table to record connection group attribute parameters for the connection group, the connection group attribute parameters including connection parameters of said first wireless device and other grouped wireless devices; configuring the first wireless device in the connection group such that it is capable of establishing a wireless connection with a third party wireless device; and establishing an additional wireless connection between the third party wireless device and the wireless devices of the group if the additional wireless connection satisfies a connection parameter specified by the connection table in the connection group.
Owner:IVT TECH BEIJING
Virtual machine task management system
InactiveUS20060029056A1Multiplex system selection arrangementsCircuit switching systemsAuto-configurationConnection table
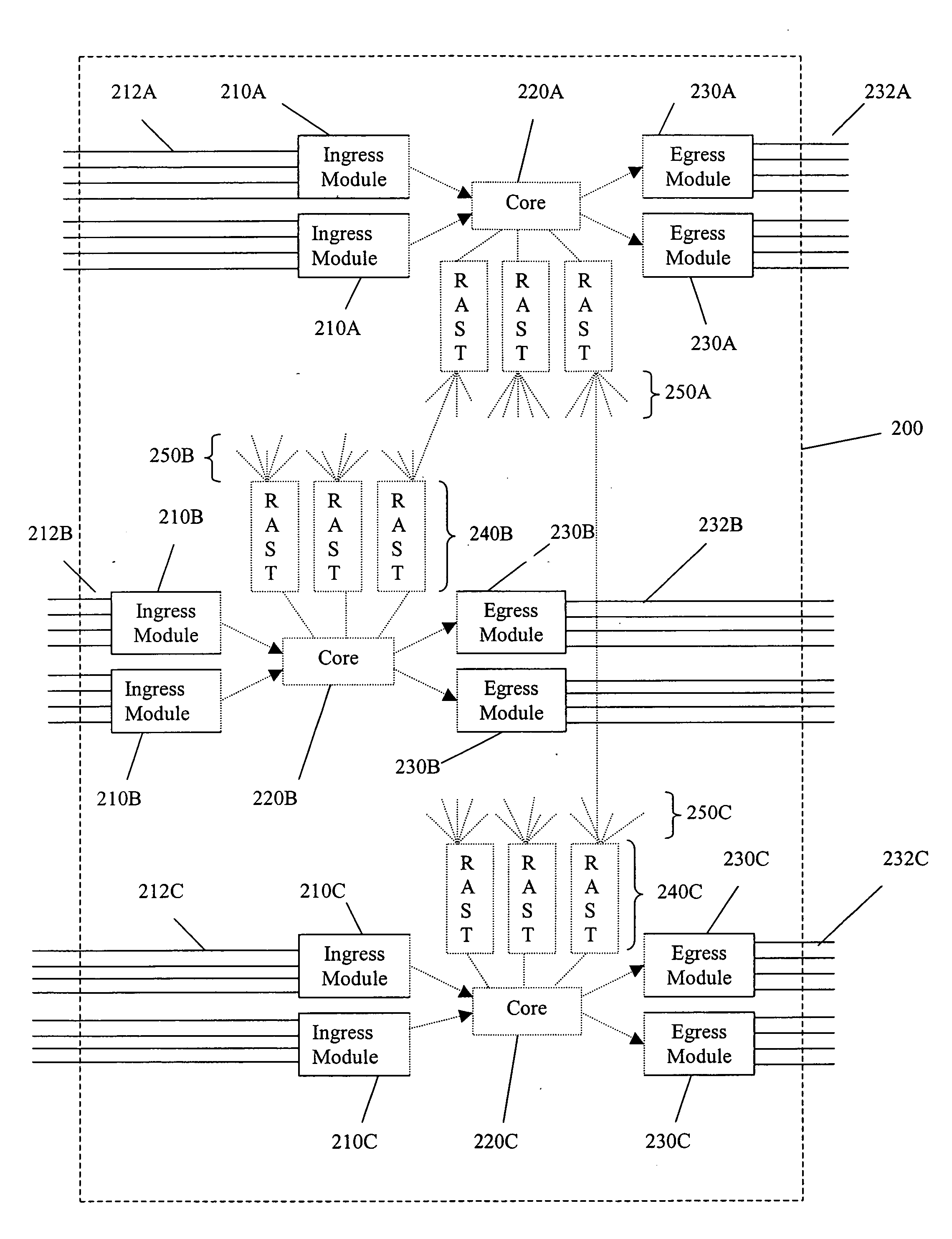
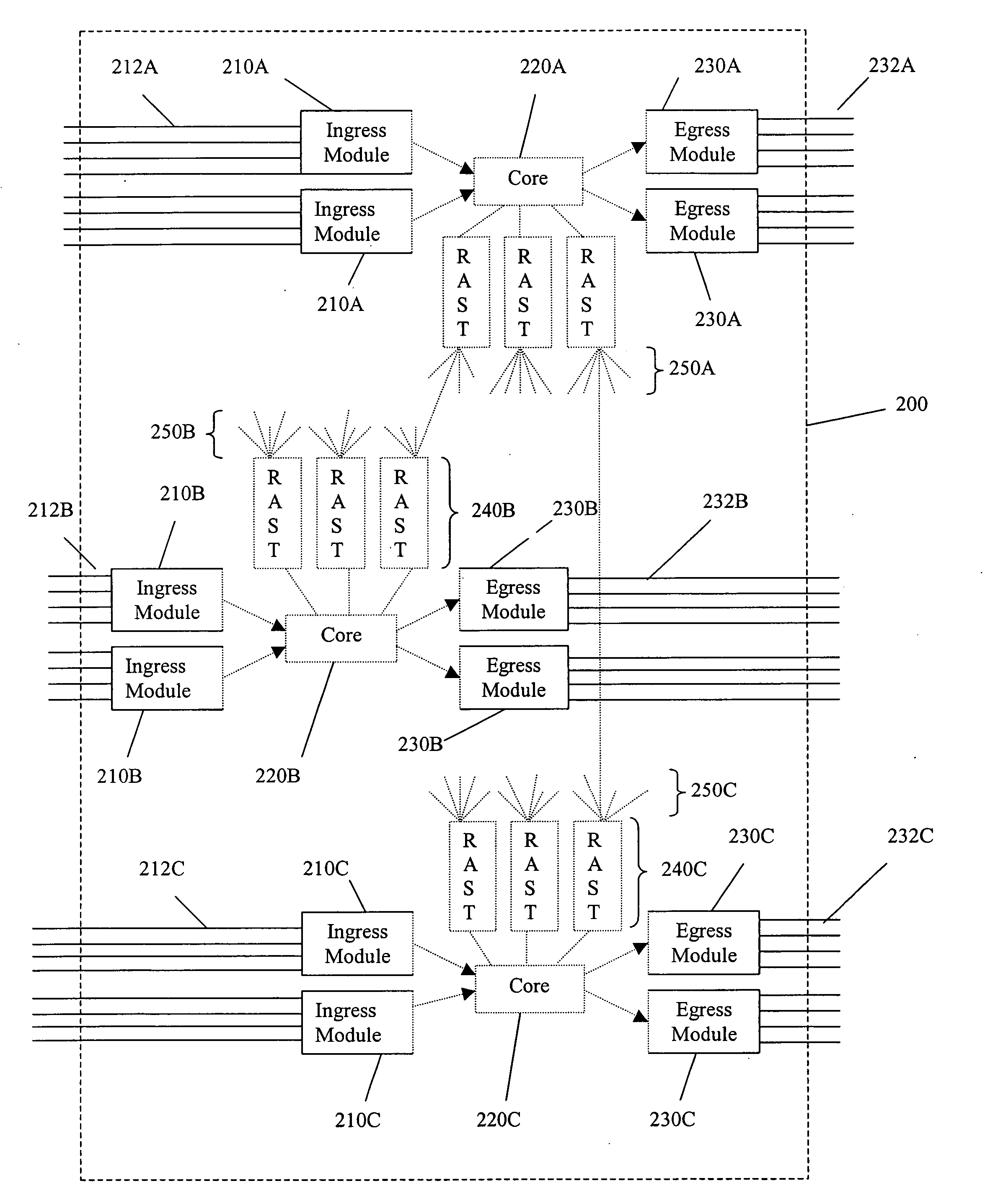
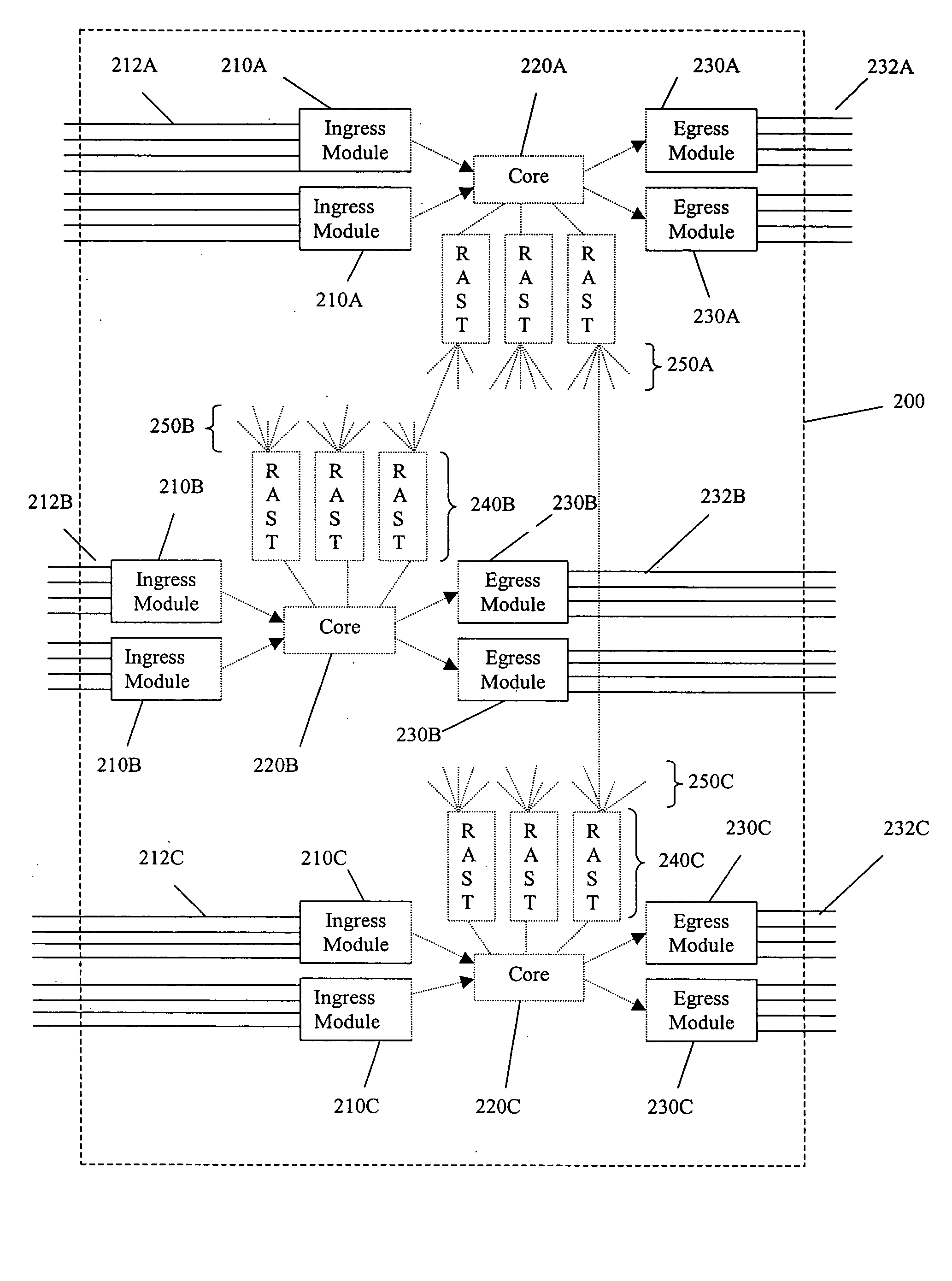
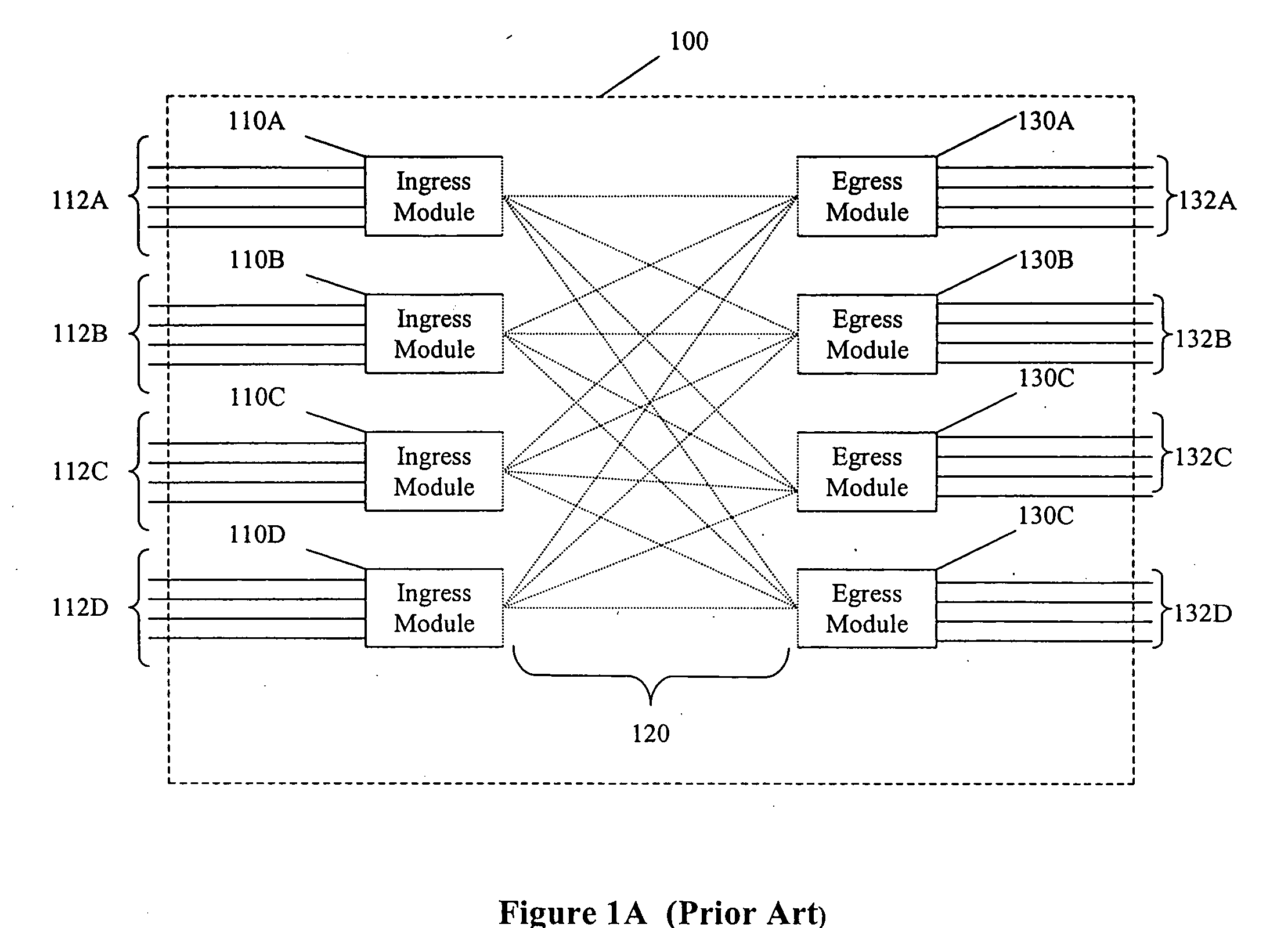
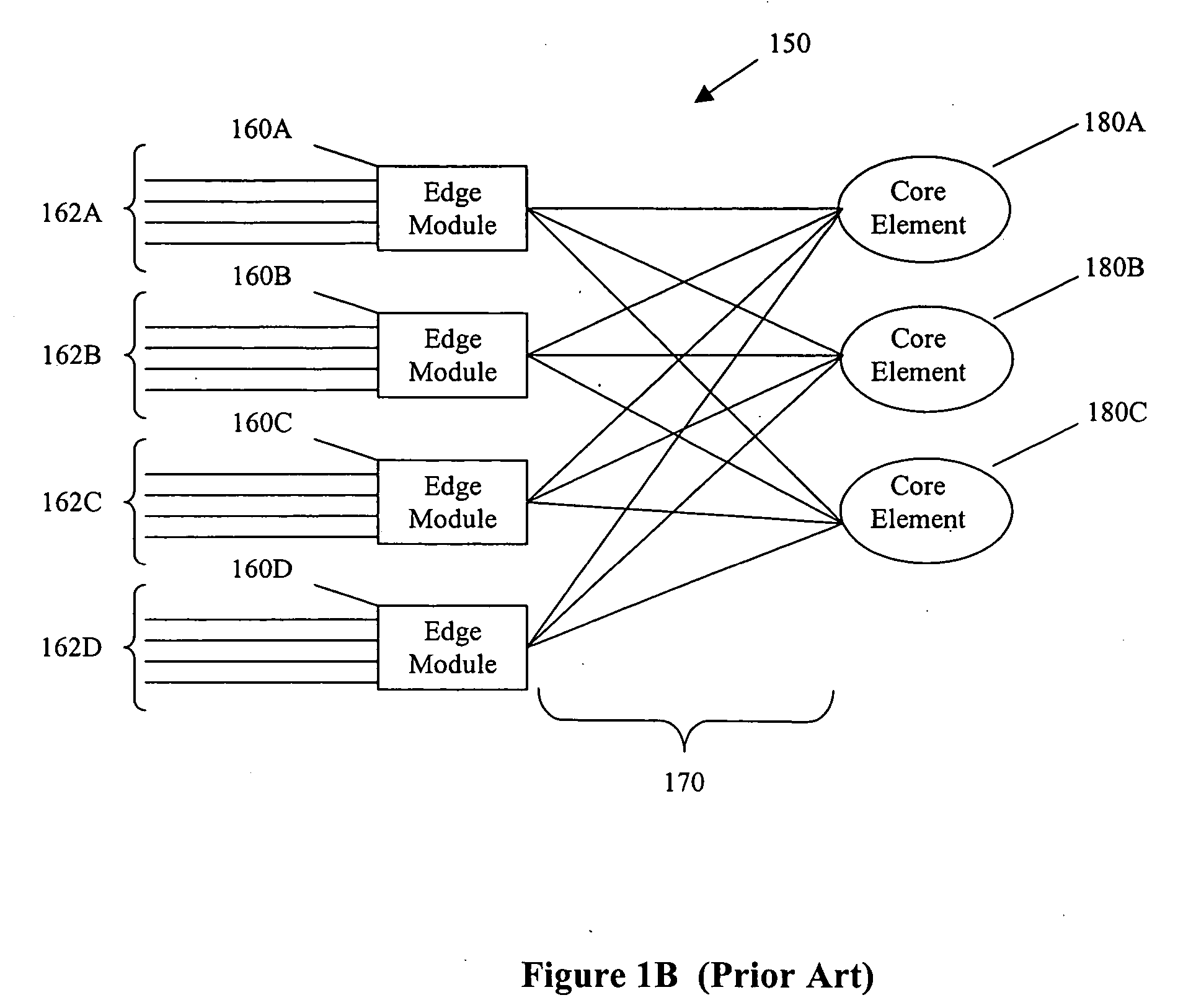
A switch encapsulates incoming information using a header, and removes the header upon egress. The header is used by both distributed ingress nodes and within a distributed core to facilitate switching. The ingress and egress elements preferably support Ethernet or other protocol providing connectionless media with a stateful connection. Preferred switches include management protocols for discovering which elements are connected, for constructing appropriate connection tables, for designating a master element, and for resolving failures and off-line conditions among the switches. Secure data protocol (SDP), port to port (PTP) protocol, and active / active protection service (AAPS) are all preferably implemented. Systems and methods contemplated herein can advantageously use Strict Ring Topology (SRT), and conf configure the topology automatically. Components of a distributed switching fabric can be geographically separated by at least one kilometer, and in some cases by over 150 kilometers.
Owner:RAPTOR NETWORKS TECH
Defining an animation of a virtual object within a virtual world
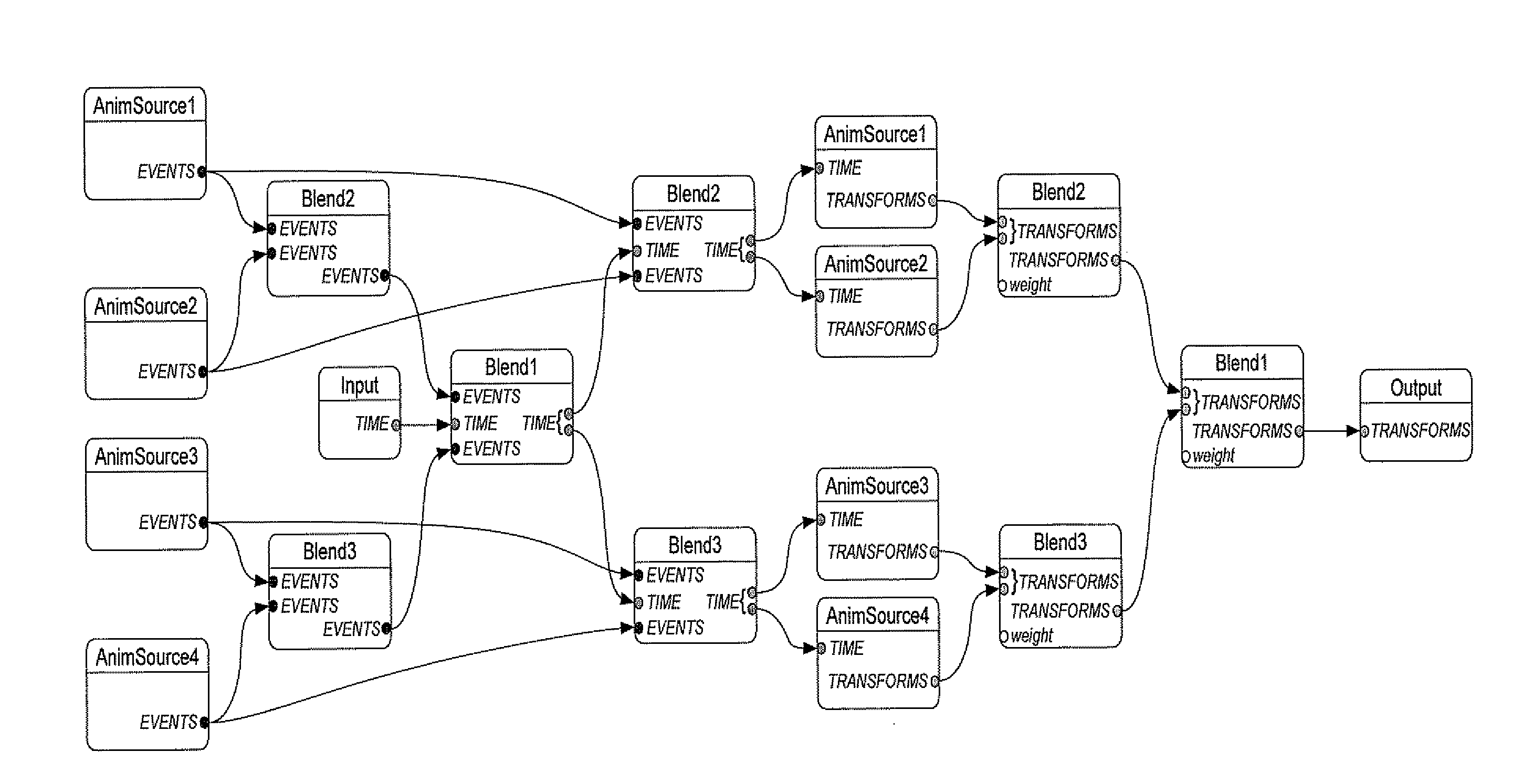
A method of defining an animation of a virtual object within a virtual world, wherein the animation comprises performing, at each of a series of time points, an update that updates values for object attributes of the virtual object, the method comprising: allowing a user to define the update by specifying, on a user interface, a structure representing the update, wherein the structure comprises a plurality of items and one or more connections between respective items, wherein each item represents a respective operation that may be performed when performing the update and wherein a connection between two items represents that data output by the operation represented by one of those two items is input to the operation represented by the other of those two items; allowing the user to specify that the structure comprises one or more items in a predetermined category, the predetermined category being associated with a predetermined process such that an item belongs to the predetermined category if performing the respective operation represented by that item requires execution of the predetermined process, wherein said predetermined process may be executed at most a predetermined number of times at each time point; and applying one or more rules that (a) restrict how the user may specify the structure to ensure that performing the defined update does not require execution of the predetermined process more than the predetermined number of times, (b) do not require the user to specify that an item in the predetermined category is at a particular location within the structure relative to other items and (c) do not require the user to explicitly specify which operations need to be performed before execution of the predetermined process when performing the update nor which operations need to be performed after execution of the predetermined process when performing the update.
Owner:NATURALMOTION
Method and system for optimizing connection set-up operations in a high speed digital network
InactiveUS6246669B1Minimizing overall connection set-up timeError preventionTransmission systemsConnection tableEnd user
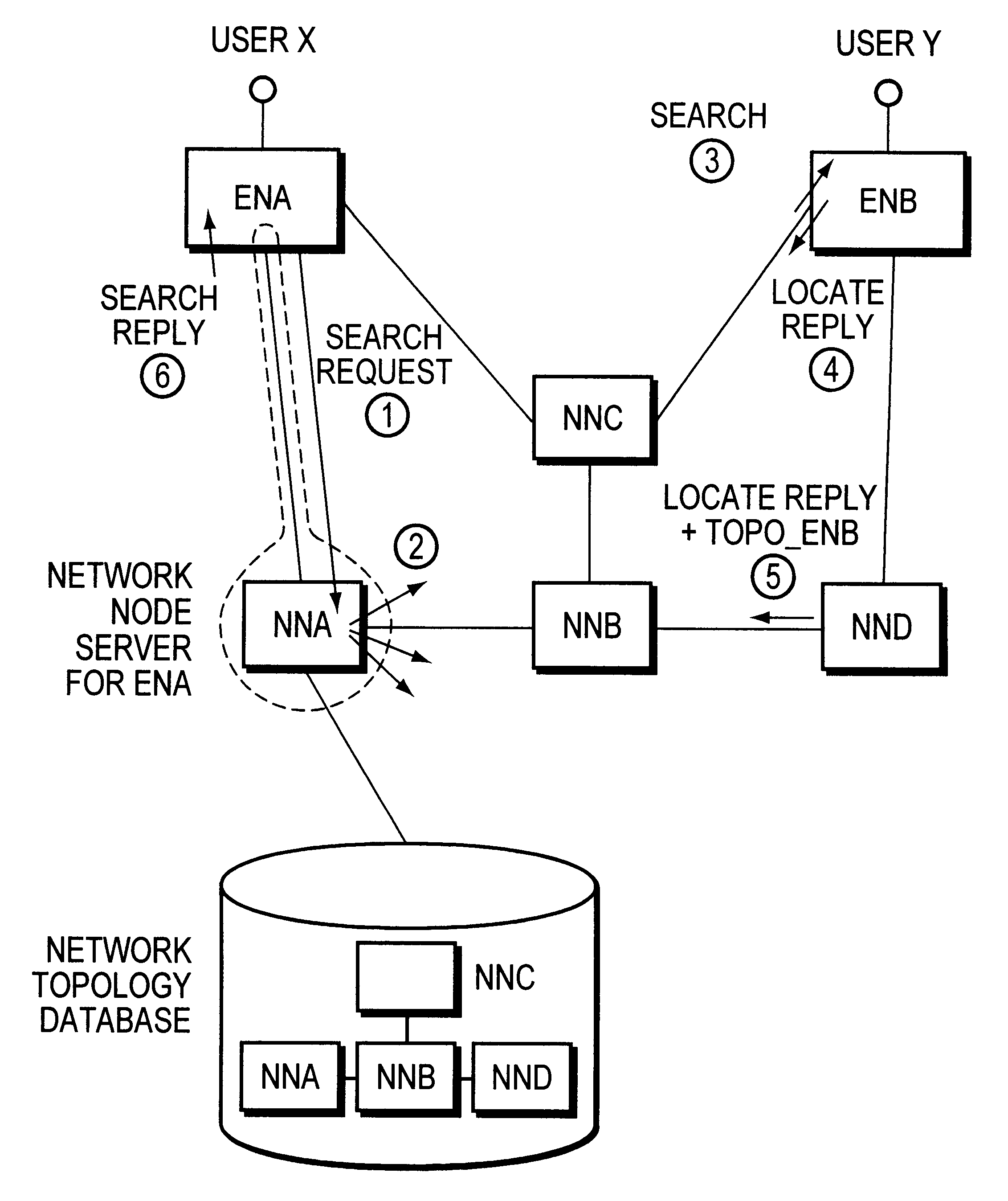
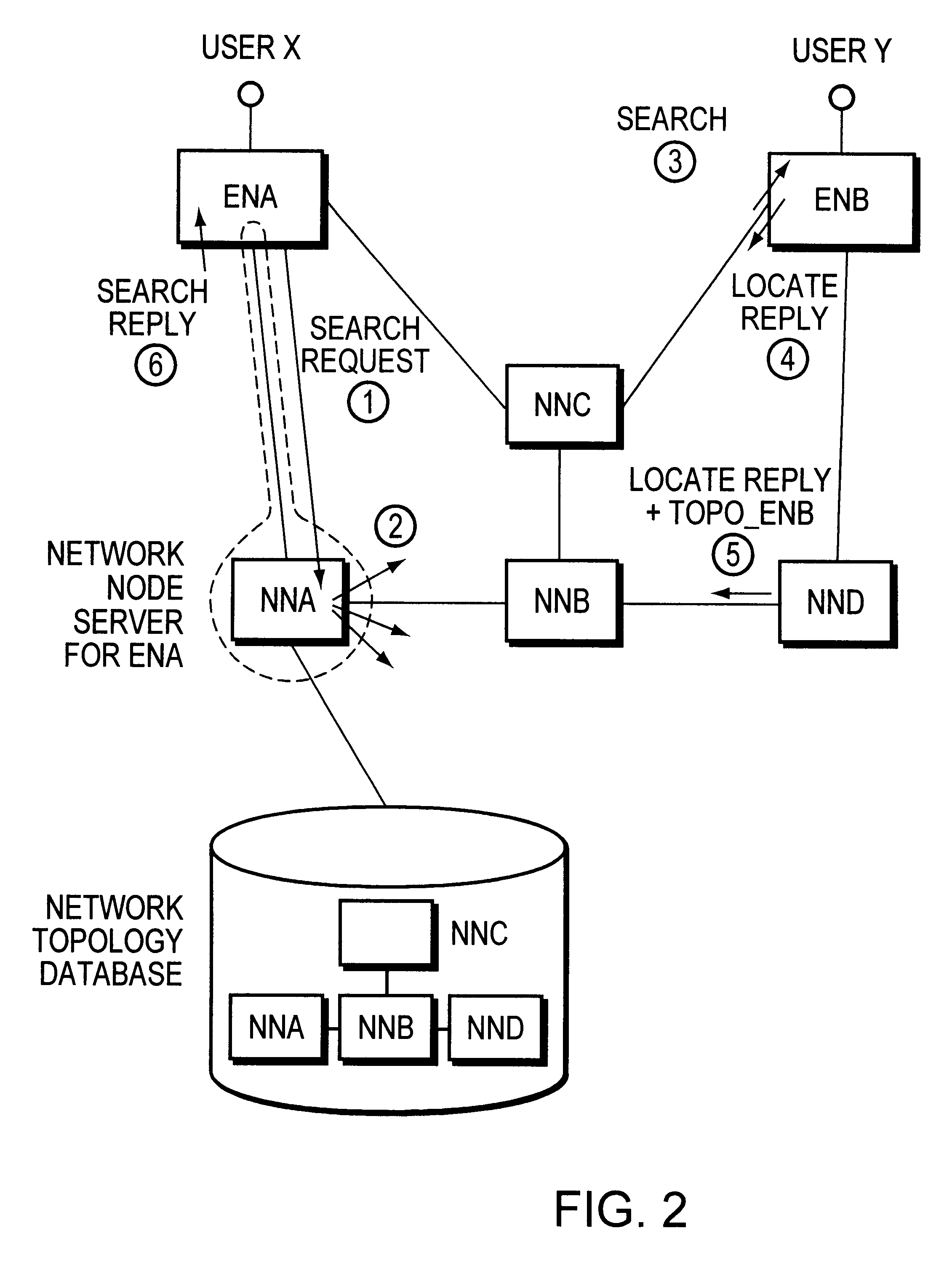
In a high speed digital network including access nodes and network nodes each having topology data bases, a method for optimizing the connection set-up operations required for connecting a calling end-user attached to a local access node to a destination user attached to a remote access node, via a conventional connection set-up operation. An Access Node Connection Table (ANCT) in each access node stores a list of every remote access node for which the local access node has at least one user connection. A field in the locate reply message is defined for the destination remote Access Node Topology Database (ANTDB) and remote ANTDB information is inserted prior to sending the reply message. Locate reply message reception is monitored by the local access node, and upon reception an entry is created for the received remote ANTDB information in the local access node unless the remote access node was already identified in the local access node. An optimal path is then selected and connection set up. The ANCT is then updated accordingly.
Owner:CISCO TECH INC
VLAN fabric network
InactiveUS20060029055A1Multiplex system selection arrangementsCircuit switching systemsAuto-configurationConnection table
Owner:RAPTOR NETWORKS TECH
System and method for supporting automatic establishing and disconnecting several wireless connections
InactiveUS20100195539A1Improve efficiencyPromote employmentError preventionFrequency-division multiplex detailsThird partyConnection table
A method for automatically establishing wireless connections between a plurality of grouped wireless devices and a third party wireless device, comprising the steps of: forming a connection group having a first wireless device and at least one additional grouped wireless device; configuring a connection table to record connection group attribute parameters for the connection group, the connection group attribute parameters including connection parameters of said first wireless device and other grouped wireless devices; configuring the first wireless device in the connection group such that it is capable of establishing a wireless connection with a third party wireless device; and establishing an additional wireless connection between the third party wireless device and the wireless devices of the group if the additional wireless connection satisfies a connection parameter specified by the connection table in the connection group.
Owner:IVT TECH BEIJING
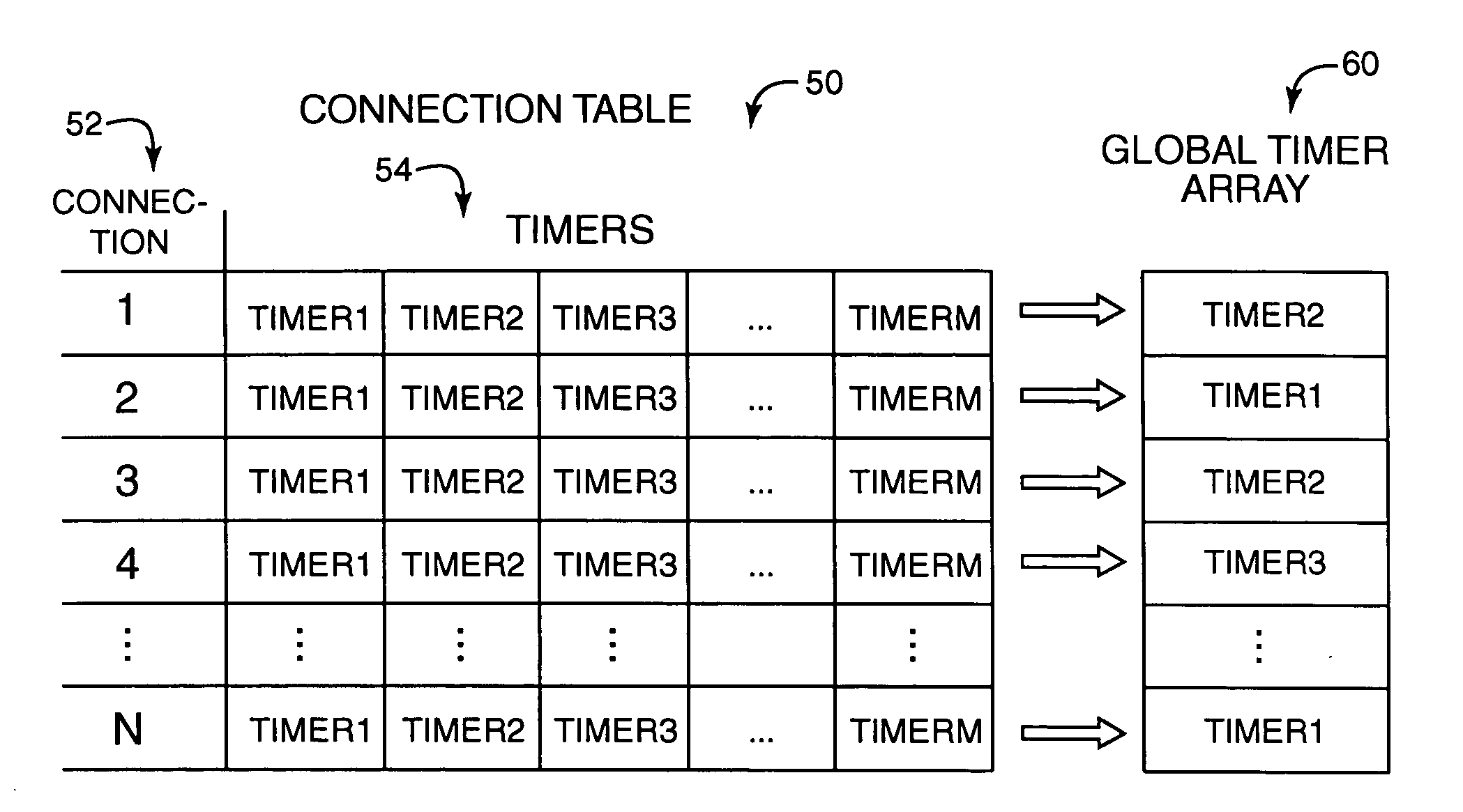
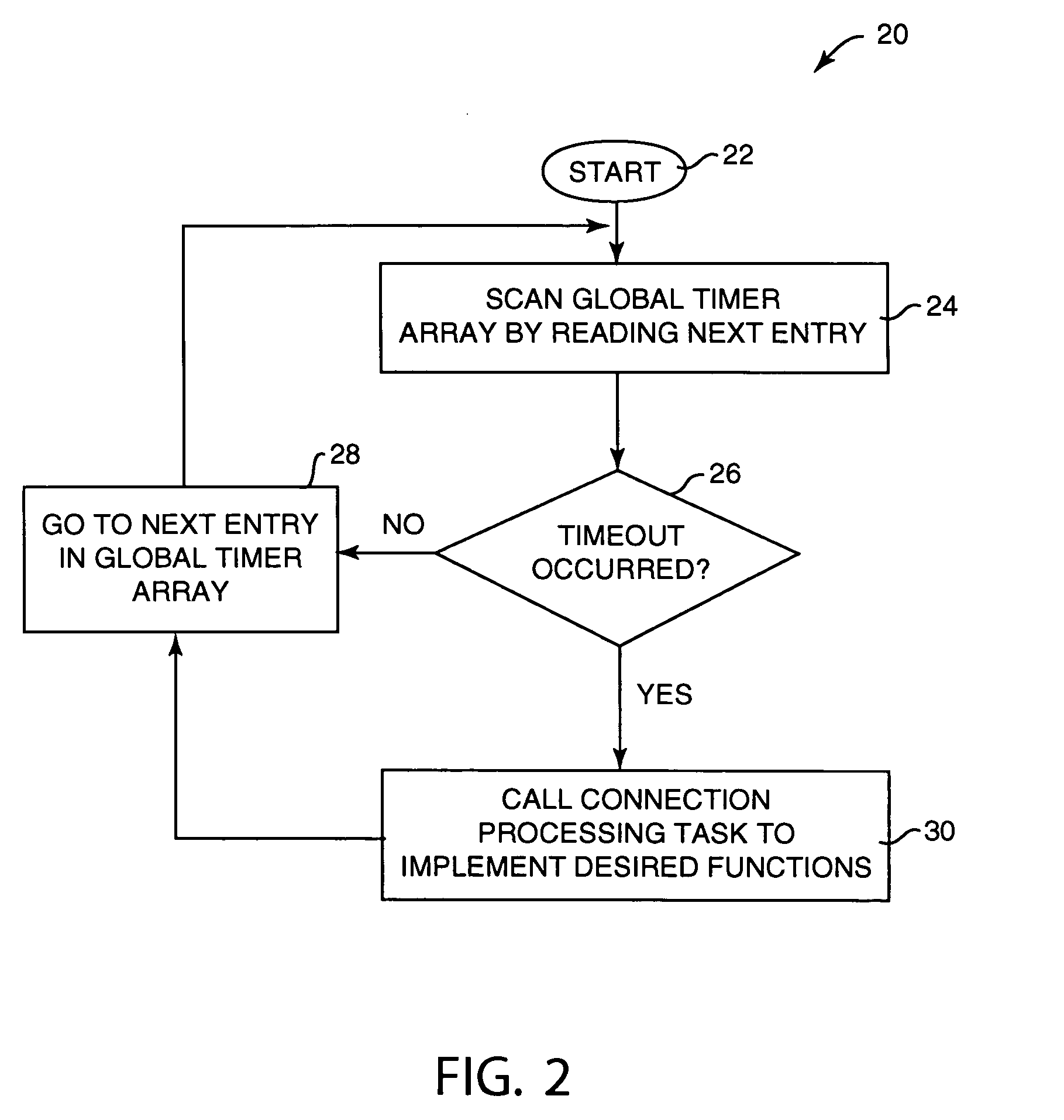
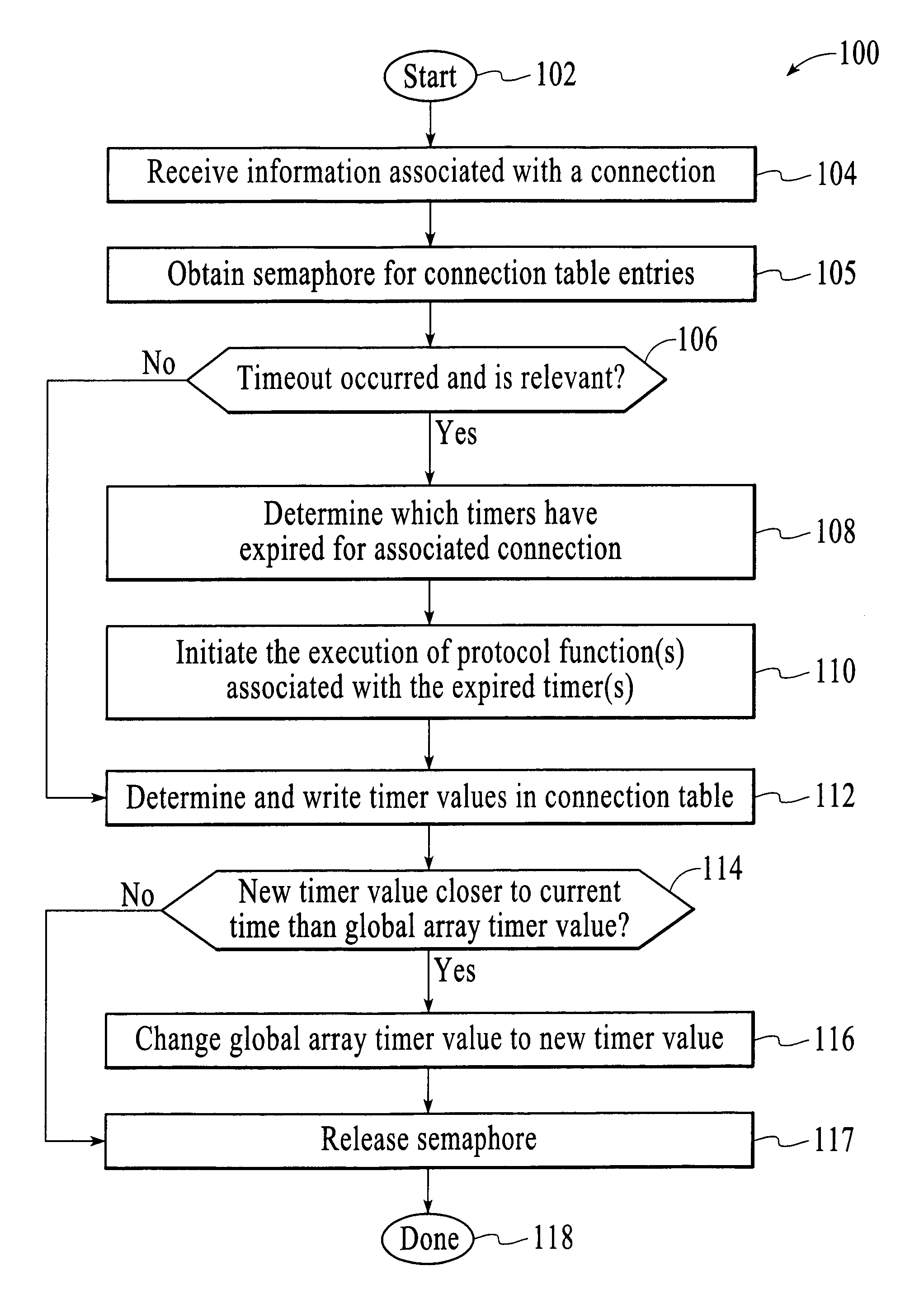
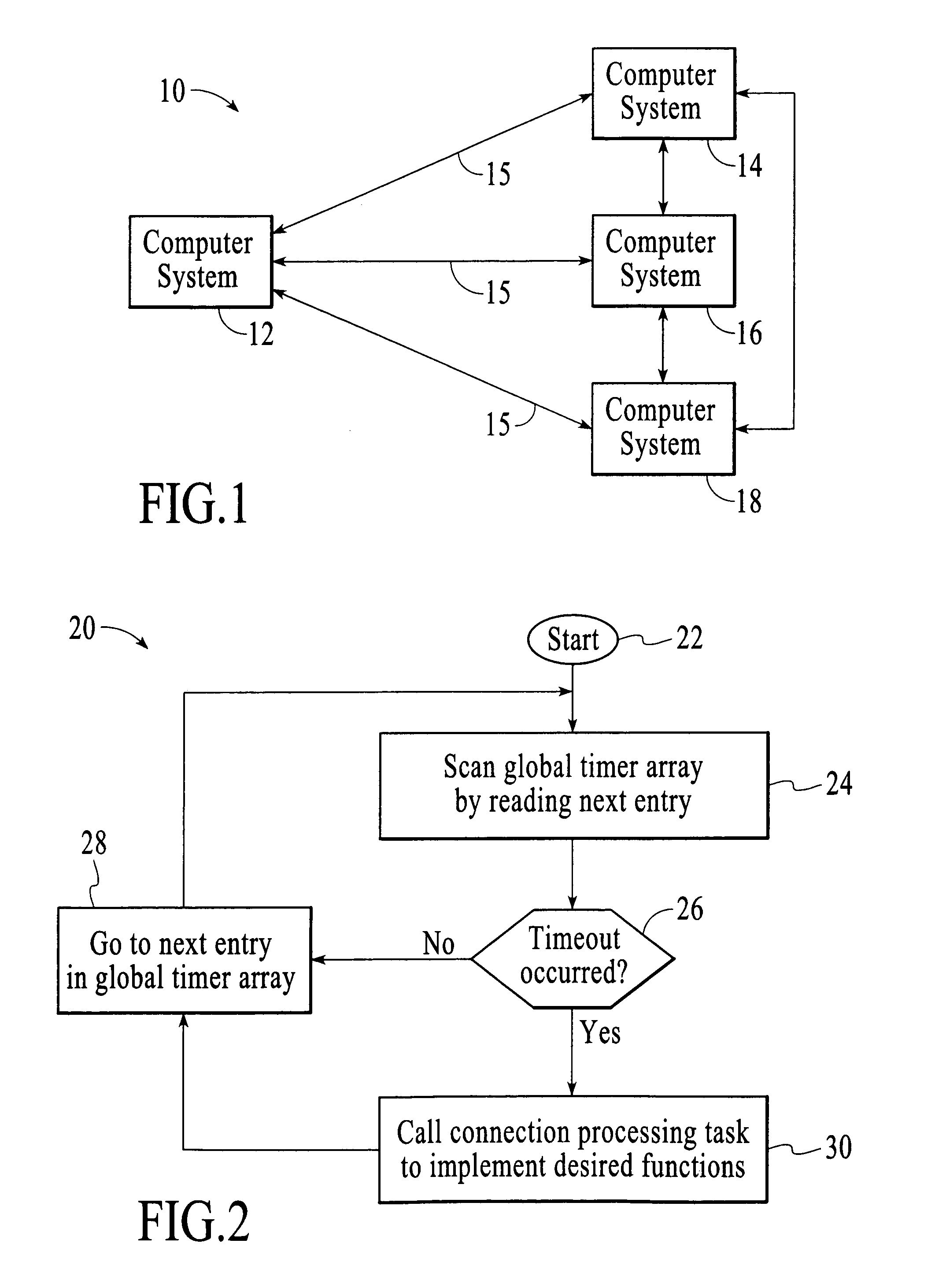
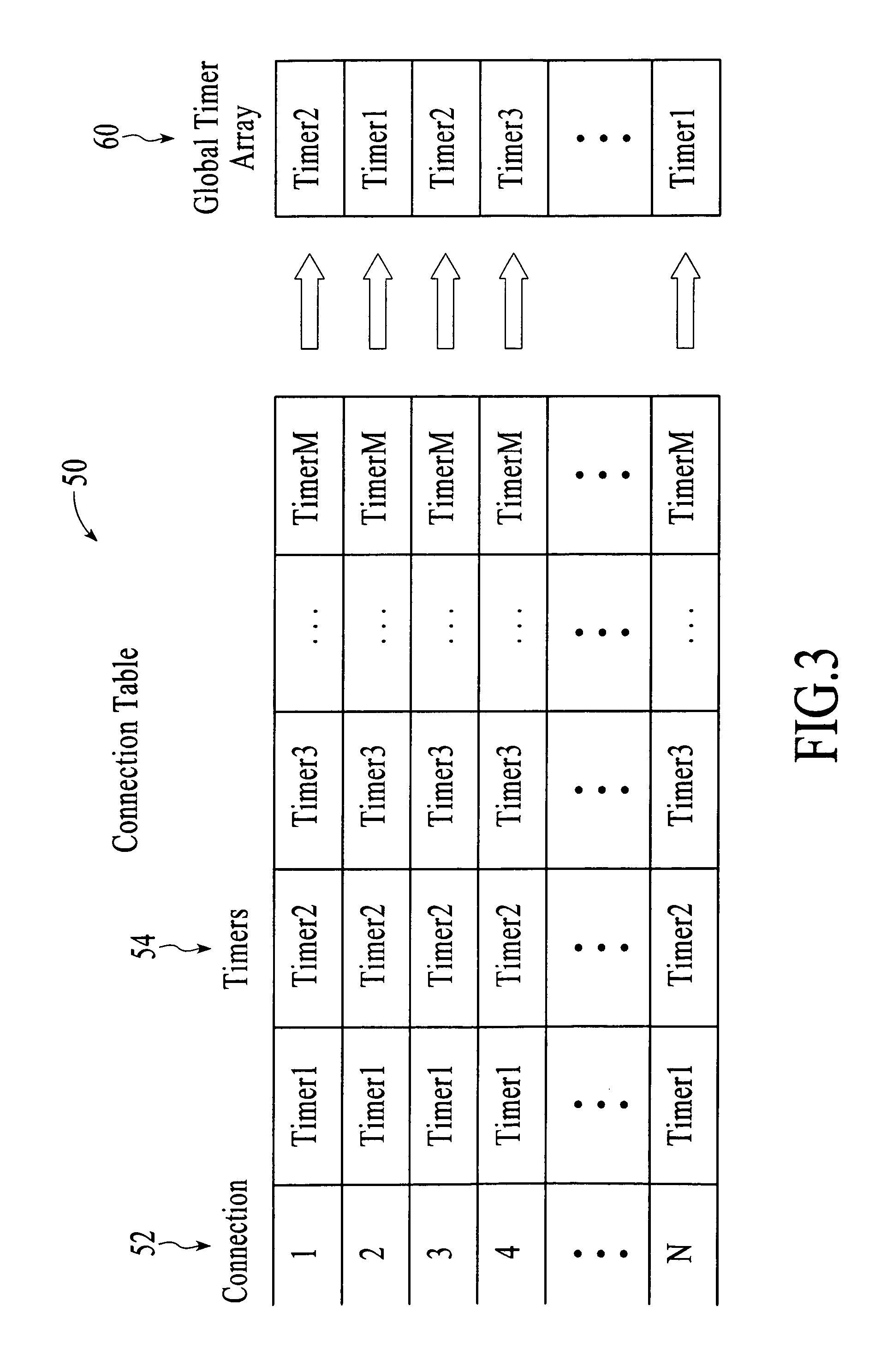
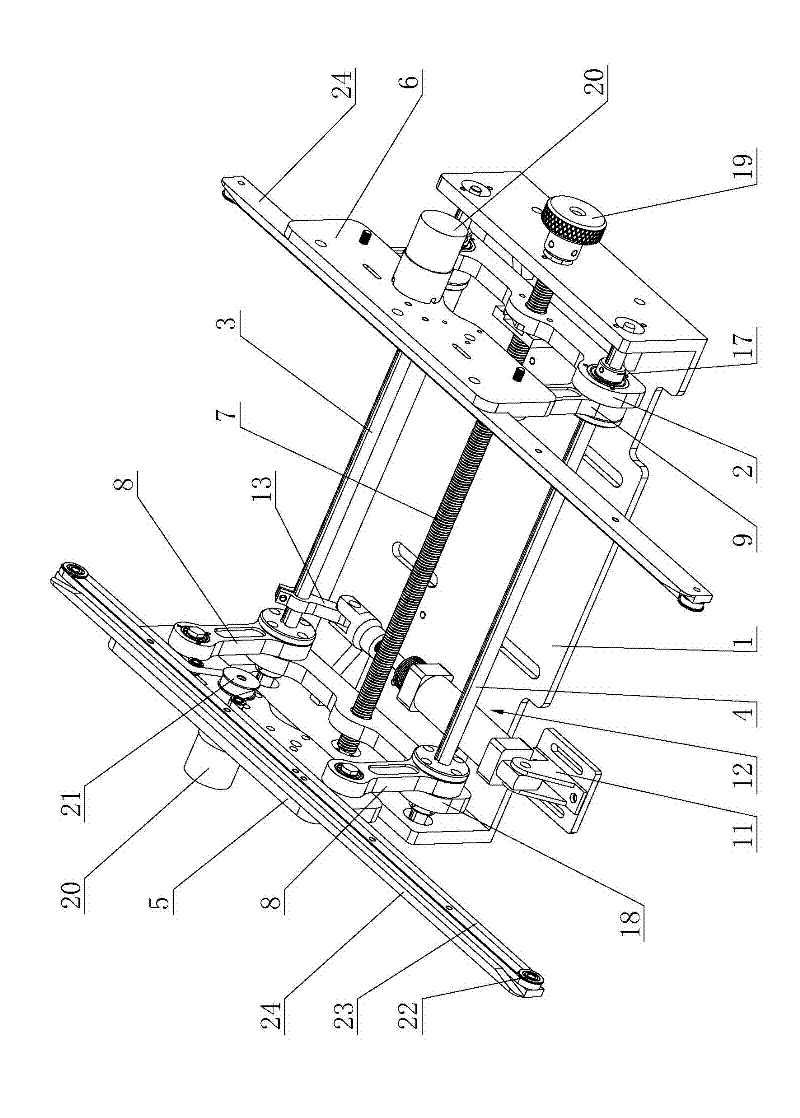
Method and system for maintaining and examining timers for network connections
InactiveUS20050209804A1Shorten the timeReduces processing resourceTime indicationDigital data processing detailsConnection tableNetwork connection
System and method for maintenance and examination of timers for a computer system having connections in a networking system. Timer values in a connection table each indicate a timeout for a timer for a connection, where each connection has multiple timers, and one of the timer values is written to a global timer array for each connection such that the global timer array can be scanned to determine when timeouts occur for active connections. Sparse restart of a timer includes restarting the timer if data is communicated with a connected computer before the timeout occurs and after a predetermined time interval after timer start, and not restarting the timer if data is communicated before the timeout occurs and within the predetermined interval after timer start.
Owner:IBM CORP
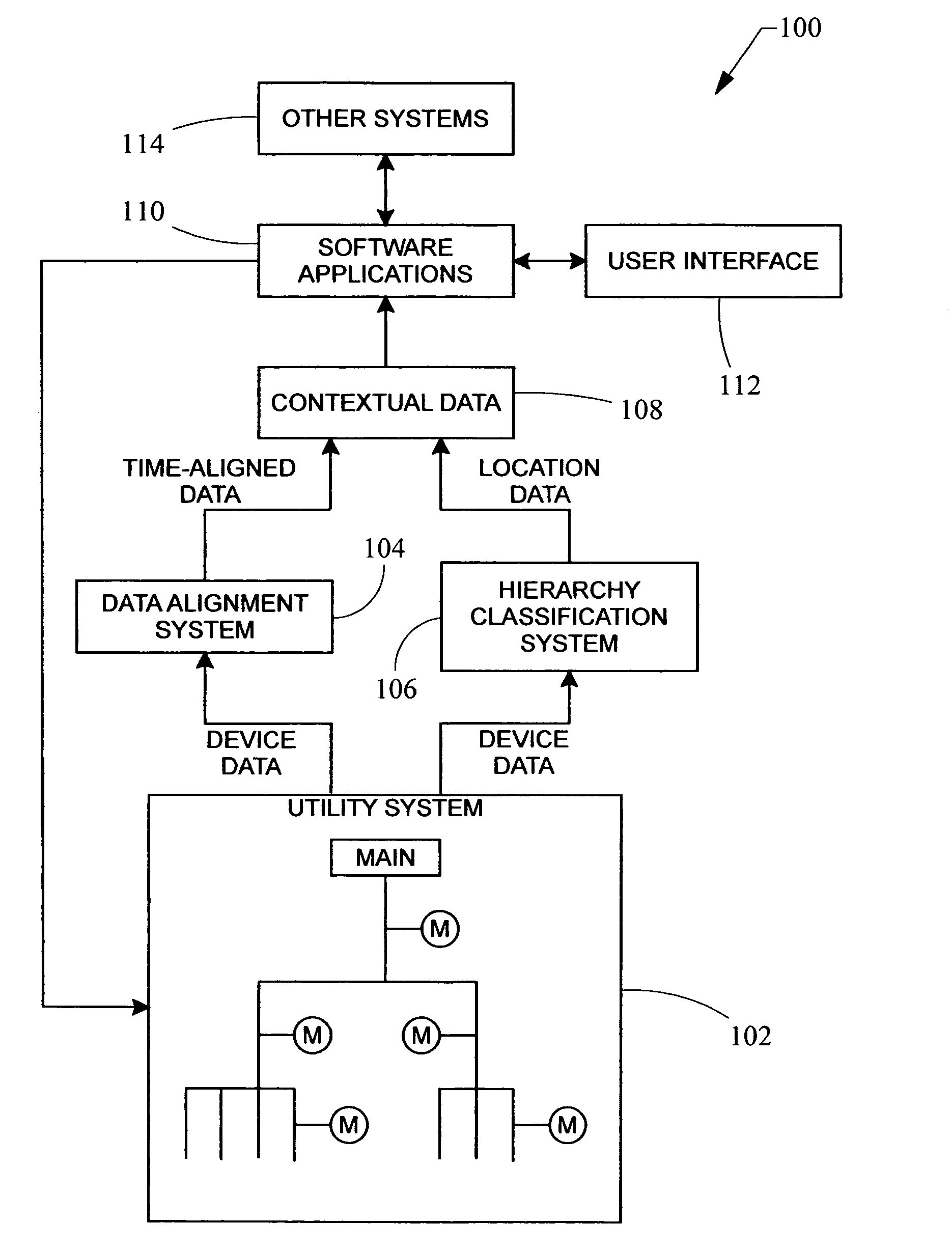
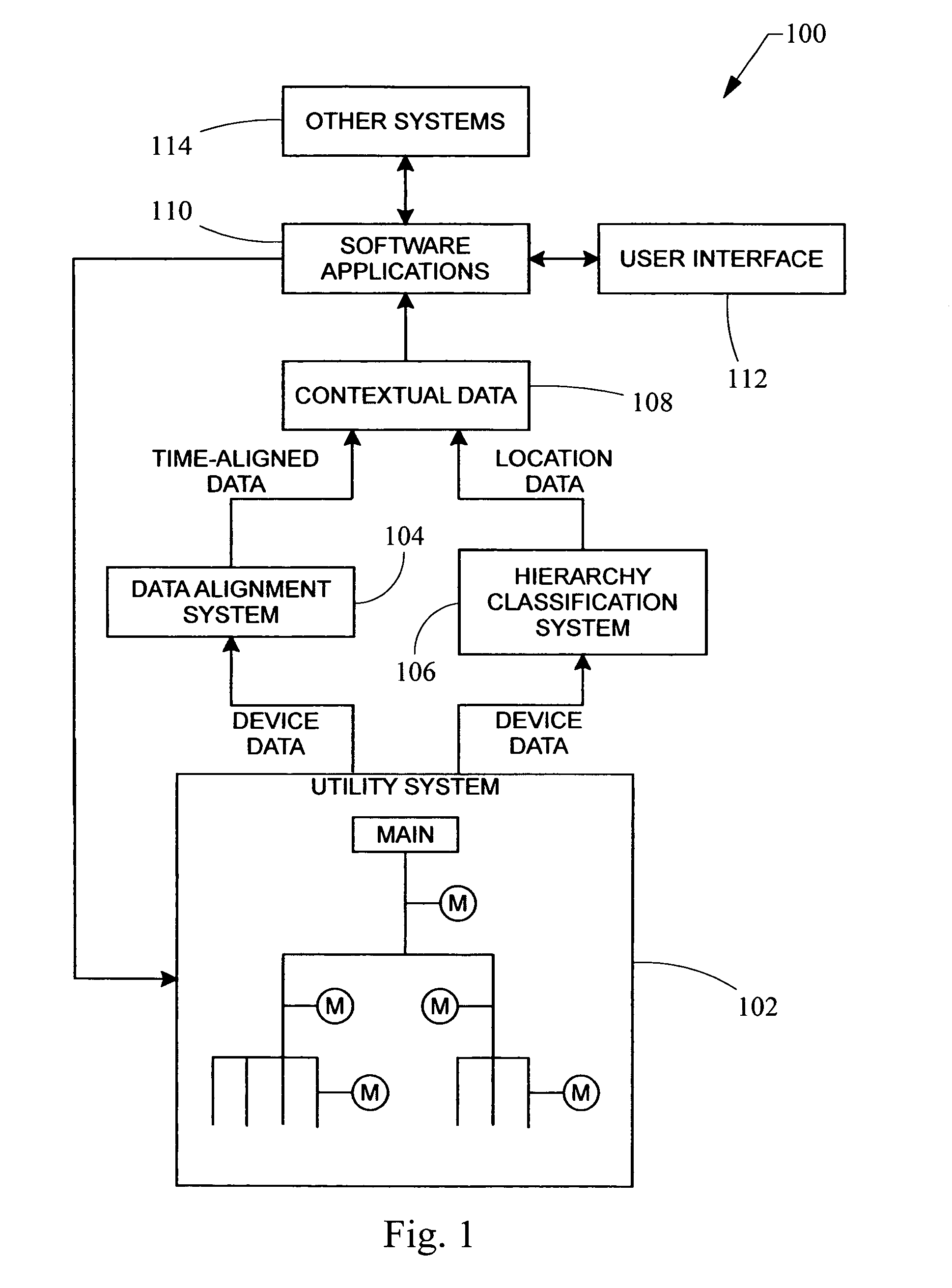
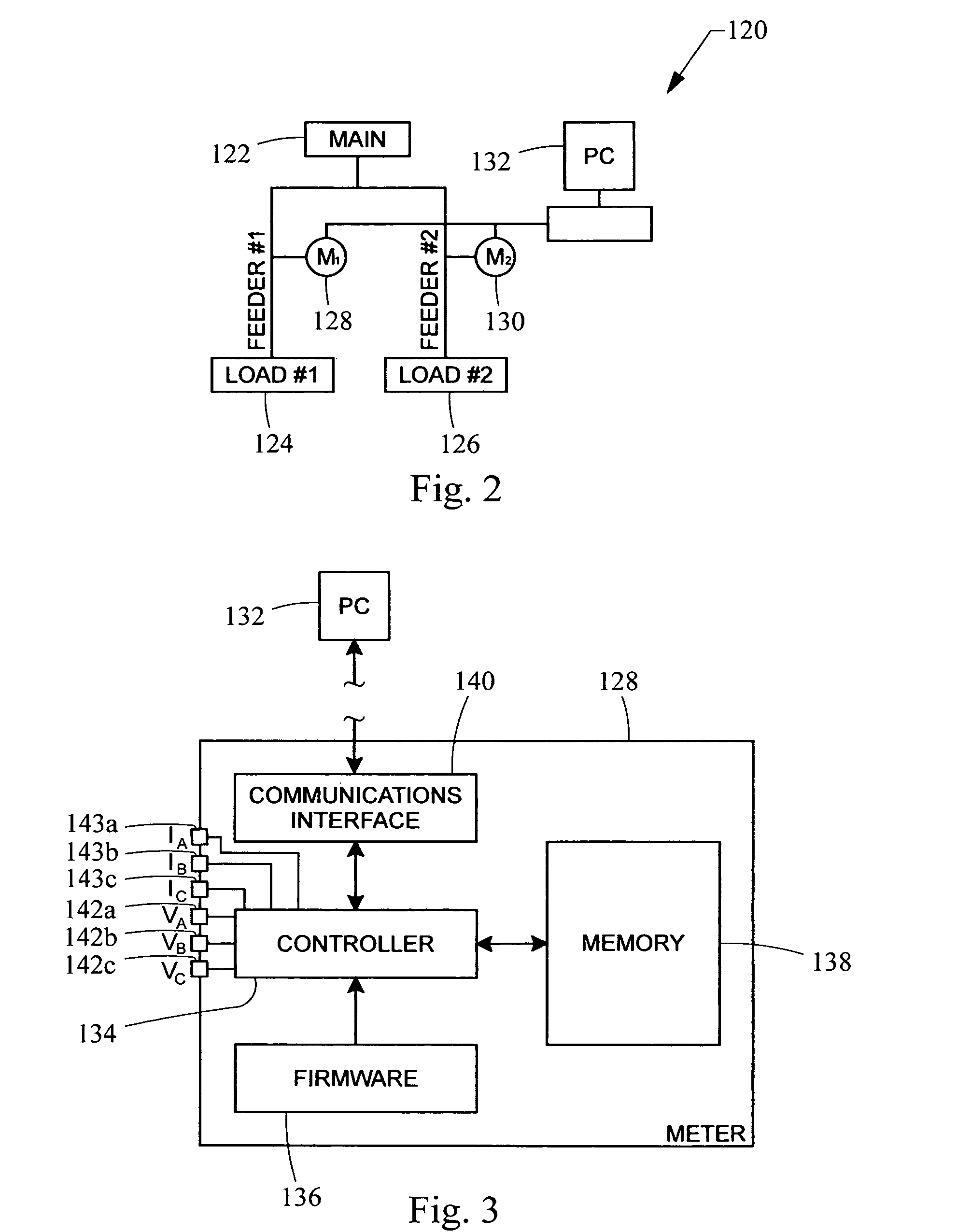
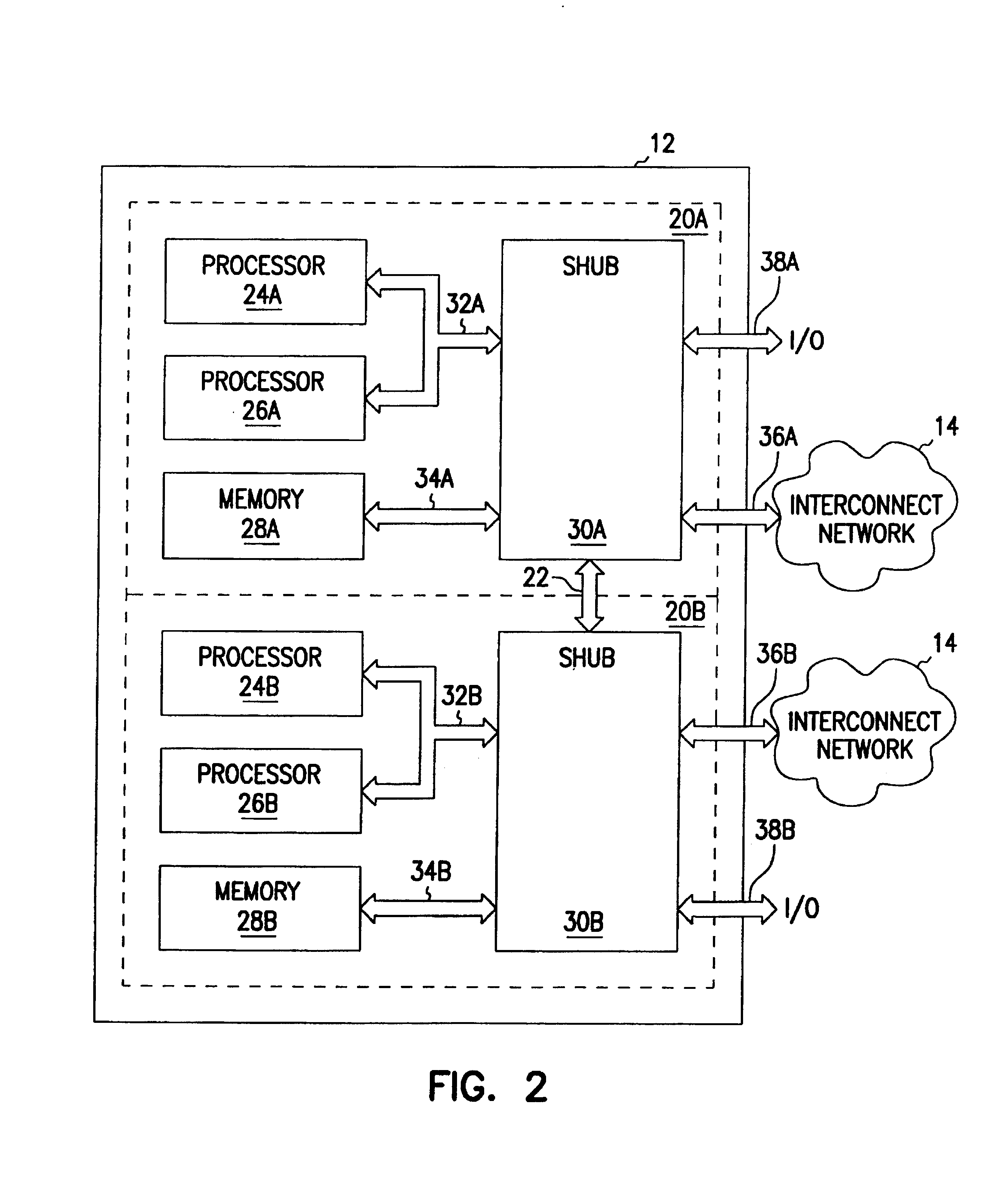
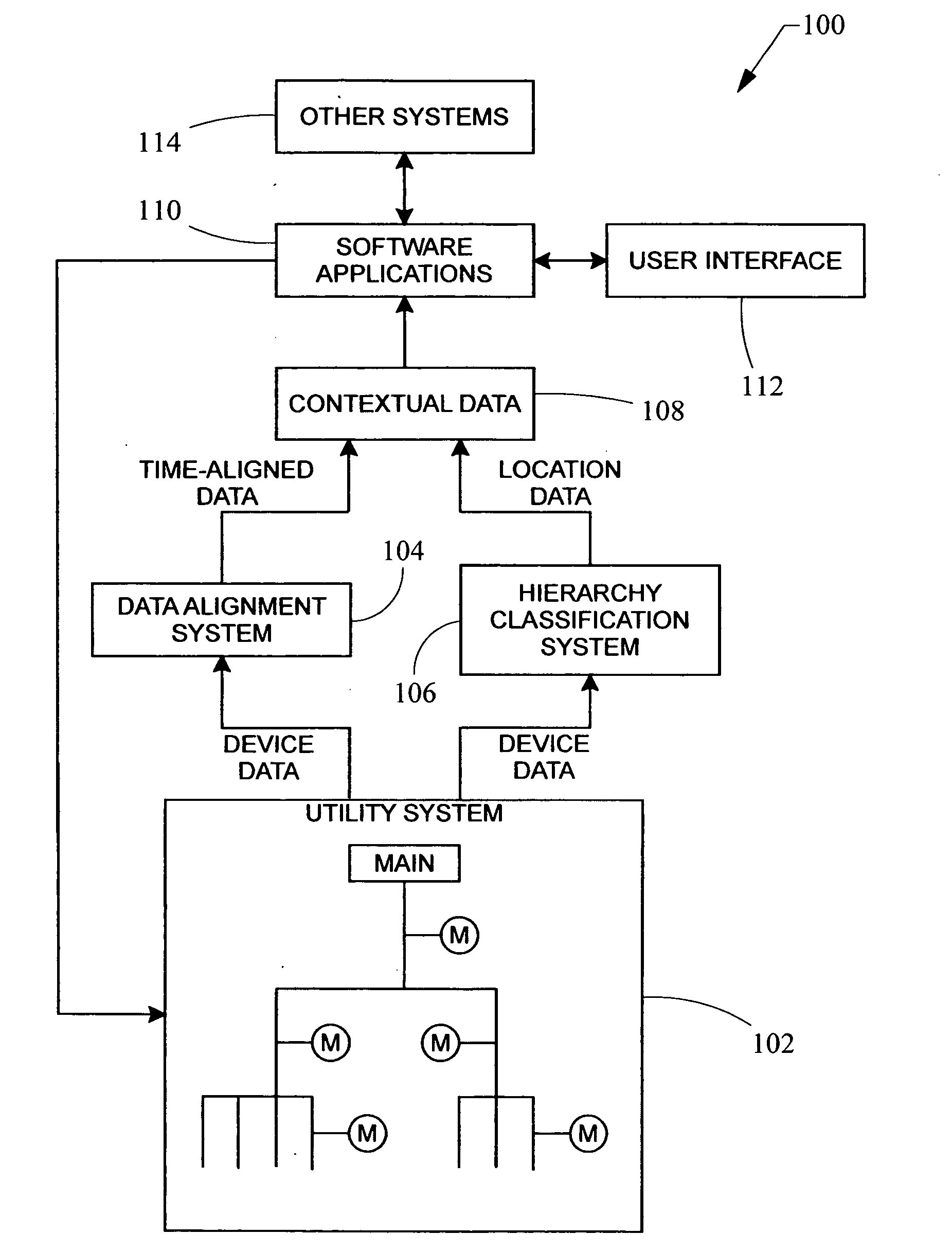
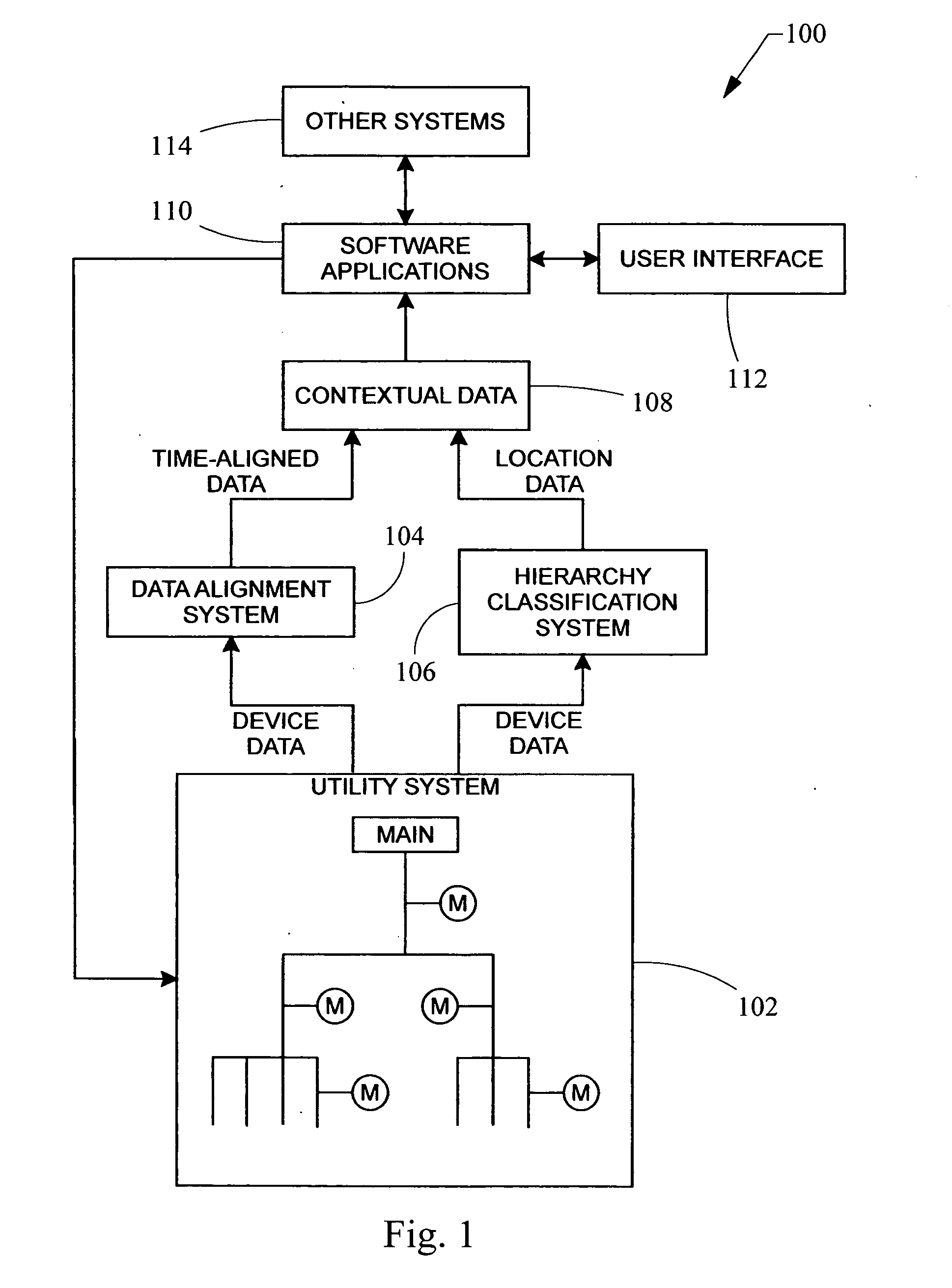
Automated hierarchy classification in utility monitoring systems
An auto-learned hierarchy algorithm that learns the hierarchical layout of a power monitoring system. Historical power data from each meter is received and placed into a data table. The main is assumed to be at the top of the hierarchy and is designated as the reference. A check matrix is developed indicating whether a possible connection exists between each meter pair combination. A correlation coefficient matrix (CCM) is calculated based on the data table, and entries in which no connection is possible are zeroed. The column for the reference meter from the CCM is copied to a correlation reference array (CRA), and the meter having the highest correlation with the reference meter in the CRA is marked as connected to the reference meter in a connection table. That meter's power is subtracted from the data table and the procedure is repeated until all meters have been analyzed.
Owner:SQUARE D CO
Switching system with distributed switching fabric
InactiveUS20050105538A1Data switching by path configurationElectric digital data processingAuto-configurationConnection table
A switch encapsulates incoming information using a header, and removes the header upon egress. The header is used by both distributed ingress nodes and within a distributed core to facilitate switching. The ingress and egress elements preferably support Ethernet or other protocol providing connectionless media with a stateful connection. Preferred switches include management protocols for discovering which elements are connected, for constructing appropriate connection tables, for designating a master element, and for resolving failures and off-line conditions among the switches. Secure data protocol (SDP), port to port (PTP) protocol, and active / active protection service (AAPS) are all preferably implemented. Systems and methods contemplated herein can advantageously use Strict Ring Topology (SRT), and conf configure the topology automatically. Components of a distributed switching fabric can be geographically separated by at least one kilometer, and in some cases by over 150 kilometers.
Owner:RAPTOR NETWORKS TECH
System and method for performing mobile services, in particular push services in a wireless communication
InactiveUS20090300162A1Way fastMultiple digital computer combinationsTransmissionService provisionConnection table
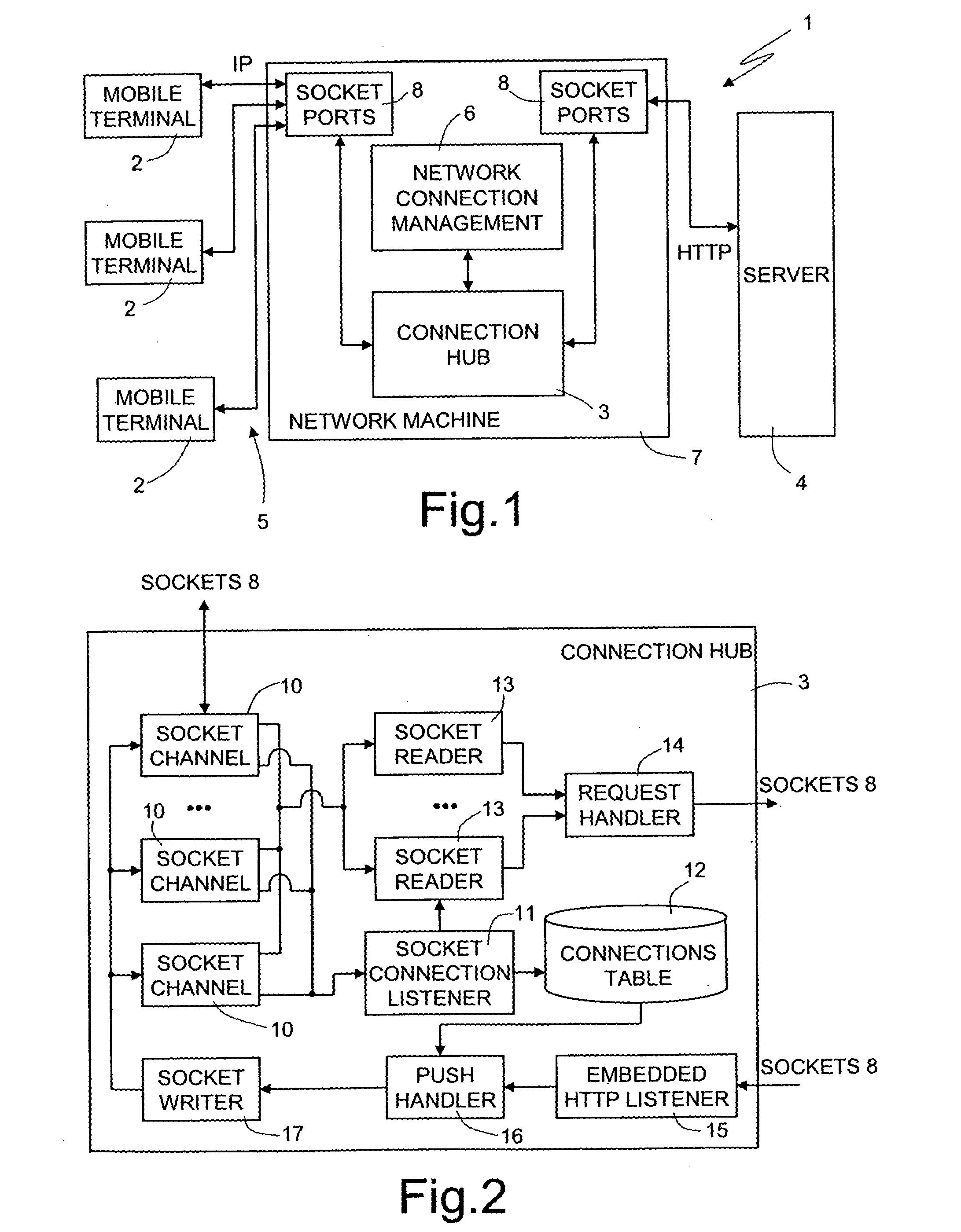
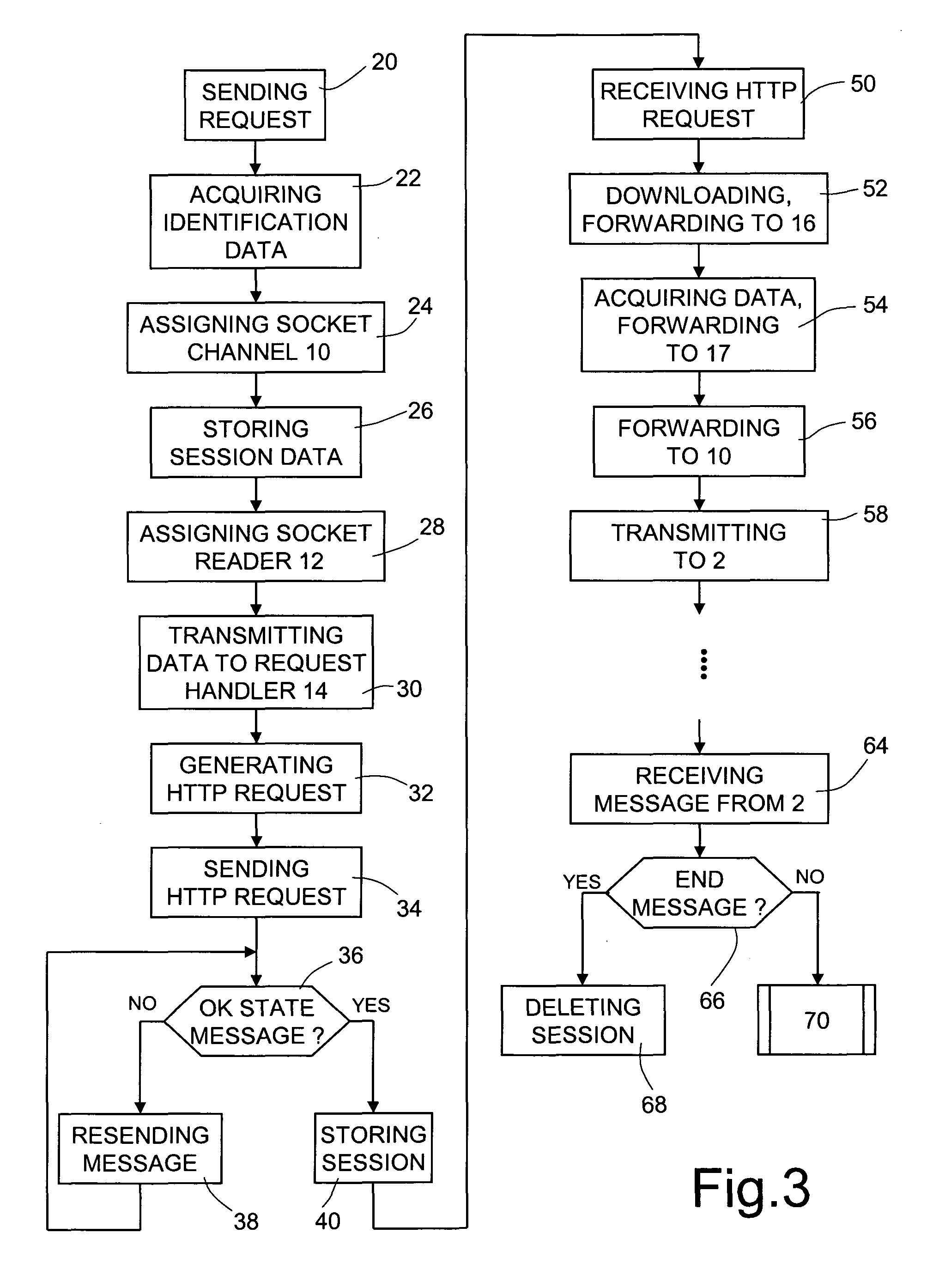
An intermediate component is intermediate between mobile terminals requesting a service, such as a push service, and a service-providing server, such as an HTTP server. The intermediate component is a connection machine or hub that is able to open a session the first time it receives a request from a mobile terminal, by instantiating a communication channel for performing the communications with the mobile terminal and storing the data regarding the open session in a connection table. Then, the connection hub generates a request to a service-providing server, including connection data, and manages the communication with the service-providing server. The connection data are inserted in every communication between the connection hub and the mobile terminal and between the connection hub and the service-providing server. From that moment on, all the data (messages, requests) exchanged between the terminal and the service-providing server are routed on the instantiated channel, thus in a fast and efficient way.
Owner:TELECOM ITALIA SPA
Remote address translation in a multiprocessor system
InactiveUS6925547B2Memory adressing/allocation/relocationData switching by path configurationRemote memory accessConnection table
A method of performing remote address translation in a multiprocessor system includes determining a connection descriptor and a virtual address at a local node, accessing a local connection table at the local node using the connection descriptor to produce a system node identifier for a remote node and a remote address space number, communicating the virtual address and remote address space number to the remote node, and translating the virtual address to a physical address at the remote node (qualified by the remote address space number). A user process running at the local node provides the connection descriptor and virtual address. The translation is performed by matching the virtual address and remote address space number with an entry of a translation-lookaside buffer (TLB) at the remote node. Performing the translation at the remote node reduces the amount of translation information needed at the local node for remote memory accesses. The method supports communication within a scalable multiprocessor, and across the machine boundaries in a cluster.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Automated hierarchy classification in utility monitoring systems
ActiveUS20070005277A1Electric devicesAmplifier modifications to reduce noise influenceCorrelation coefficientConnection table
An auto-learned hierarchy algorithm that learns the hierarchical layout of a power monitoring system. Historical power data from each meter is received and placed into a data table. The main is assumed to be at the top of the hierarchy and is designated as the reference. A check matrix is developed indicating whether a possible connection exists between each meter pair combination. A correlation coefficient matrix (CCM) is calculated based on the data table, and entries in which no connection is possible are zeroed. The column for the reference meter from the CCM is copied to a correlation reference array (CRA), and the meter having the highest correlation with the reference meter in the CRA is marked as connected to the reference meter in a connection table. That meter's power is subtracted from the data table and the procedure is repeated until all meters have been analyzed.
Owner:SQUARE D CO
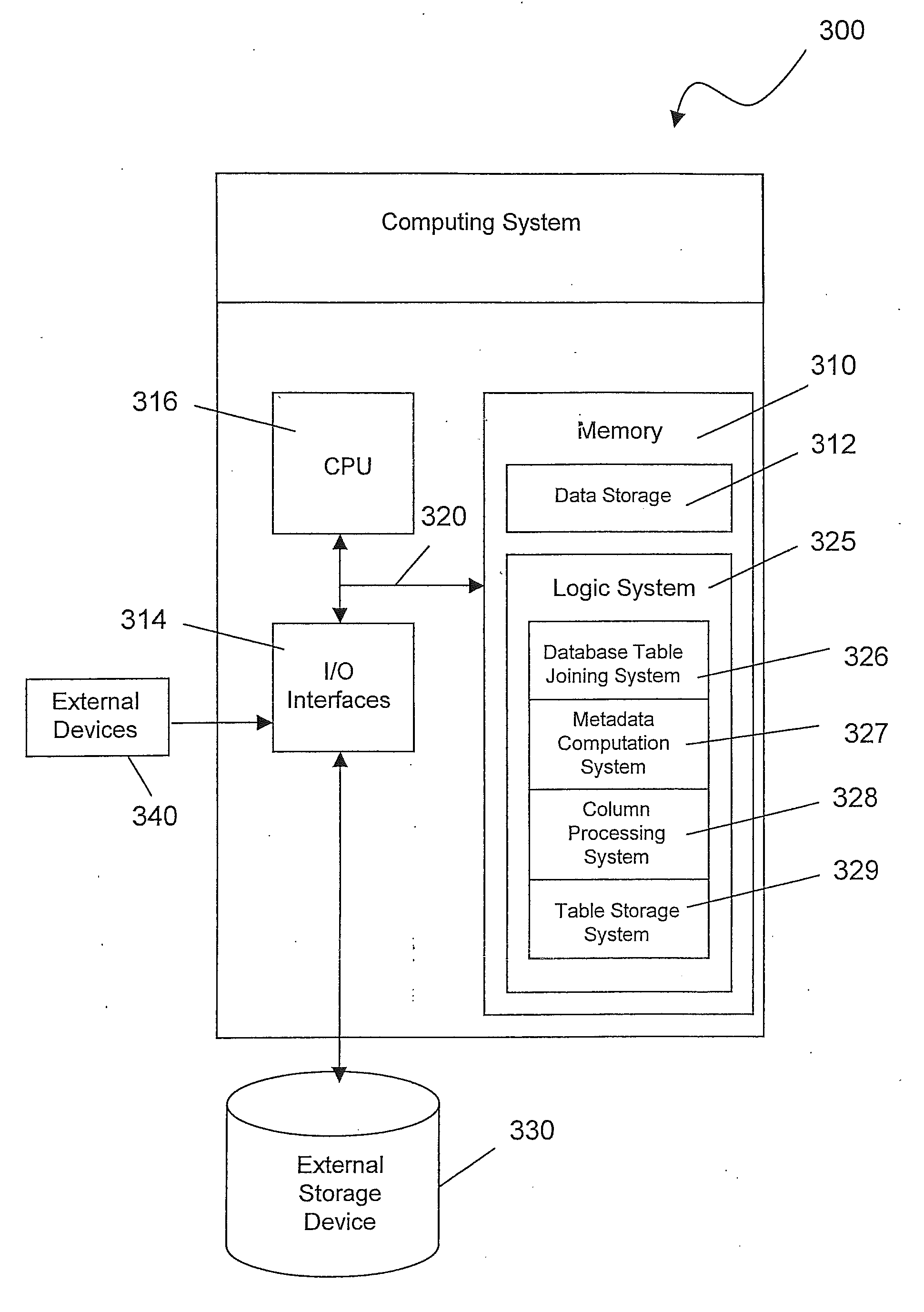
Storing tables in a database system
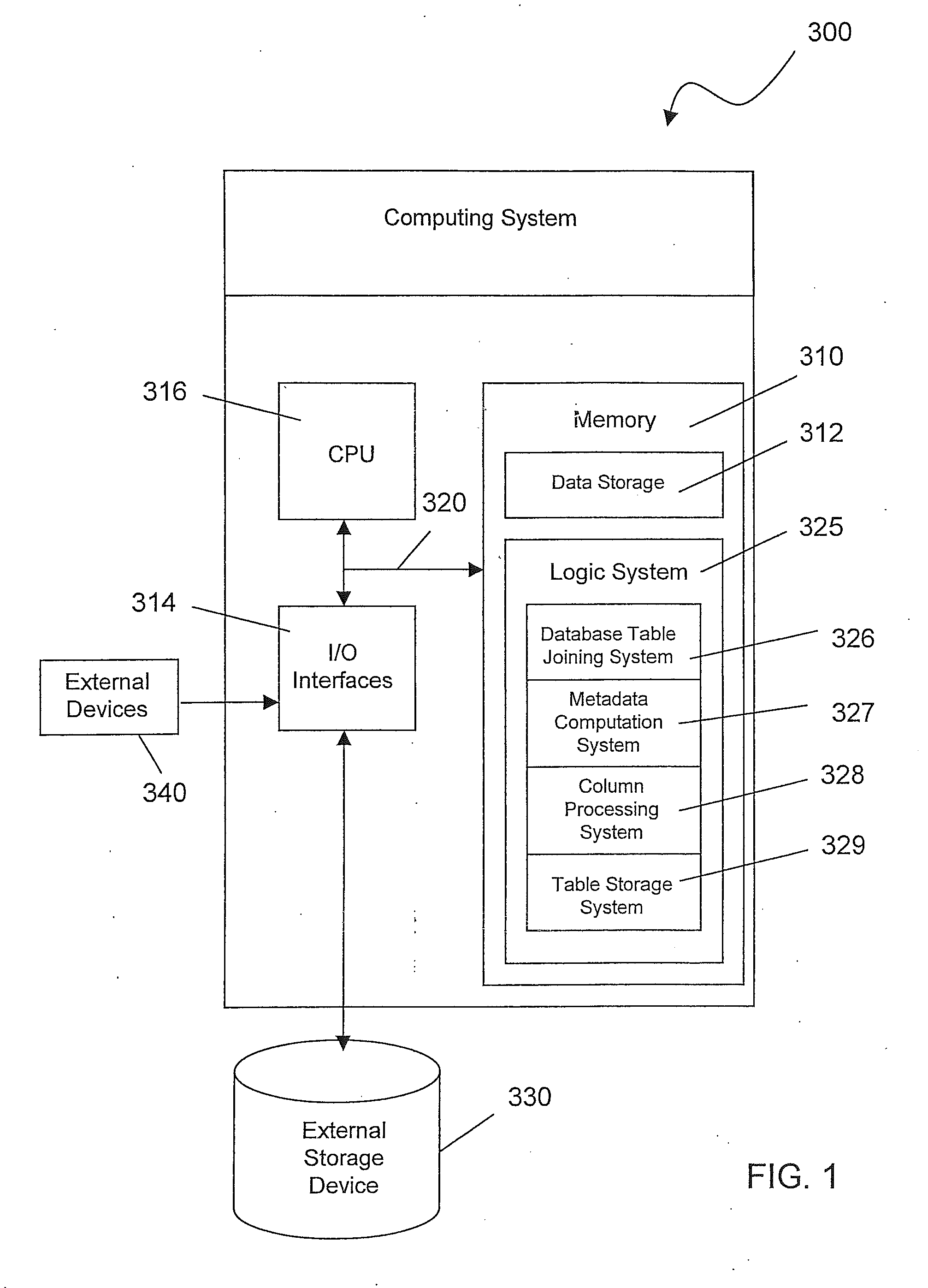
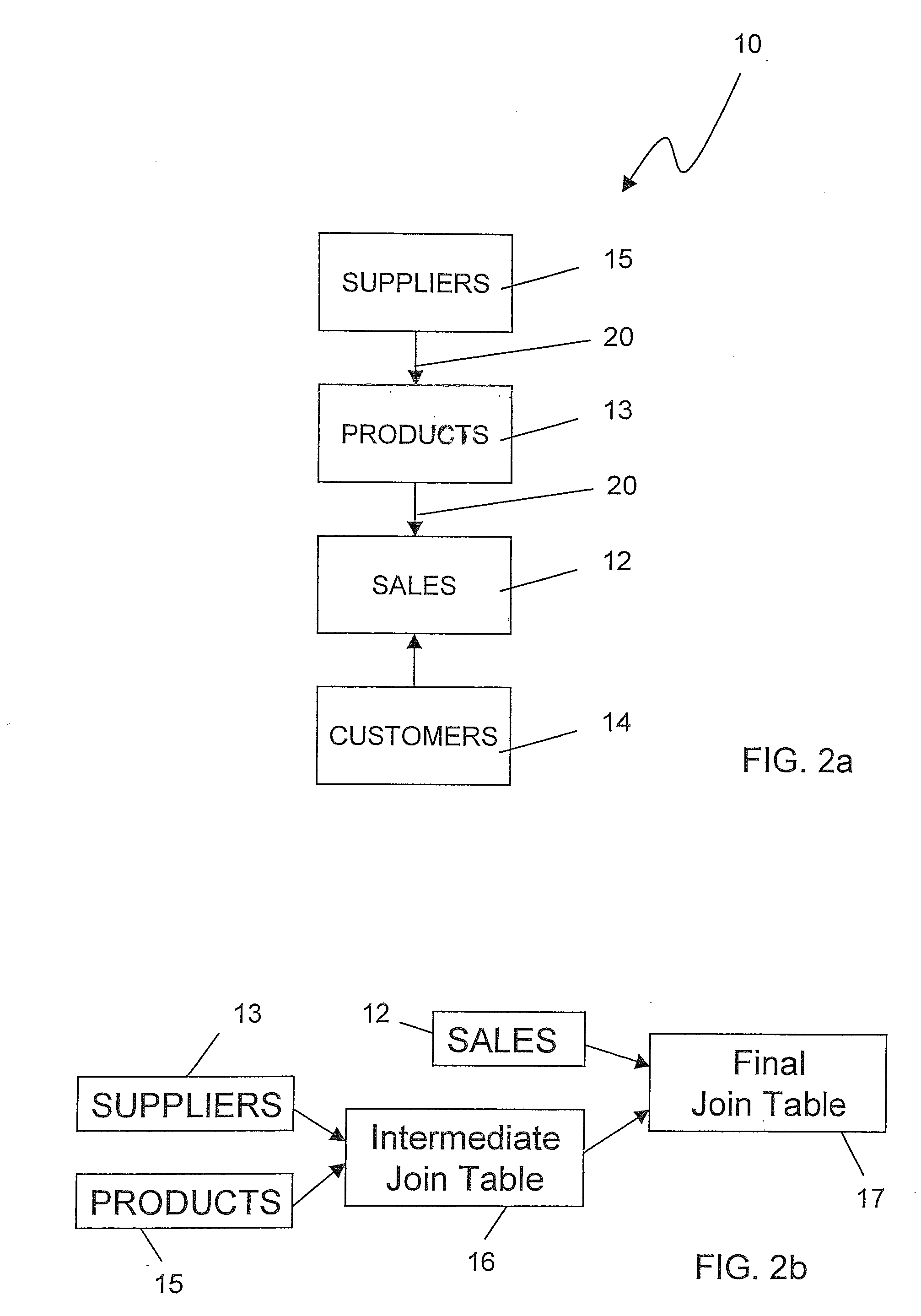
InactiveUS20110173164A1Digital data information retrievalDigital data processing detailsMetadataData library
A method for processing data contained in tables in a relational database includes joining a first table and a second table into a joined table determining metadata for at least one column of a table of the following tables: the first table, the second table, and the joined table. The metadata is used for processing data in the at least one column of the table, and for processing data in at least one column of at least one other table of the following tables: the first table, the second table, and the joined table.
Owner:IBM CORP
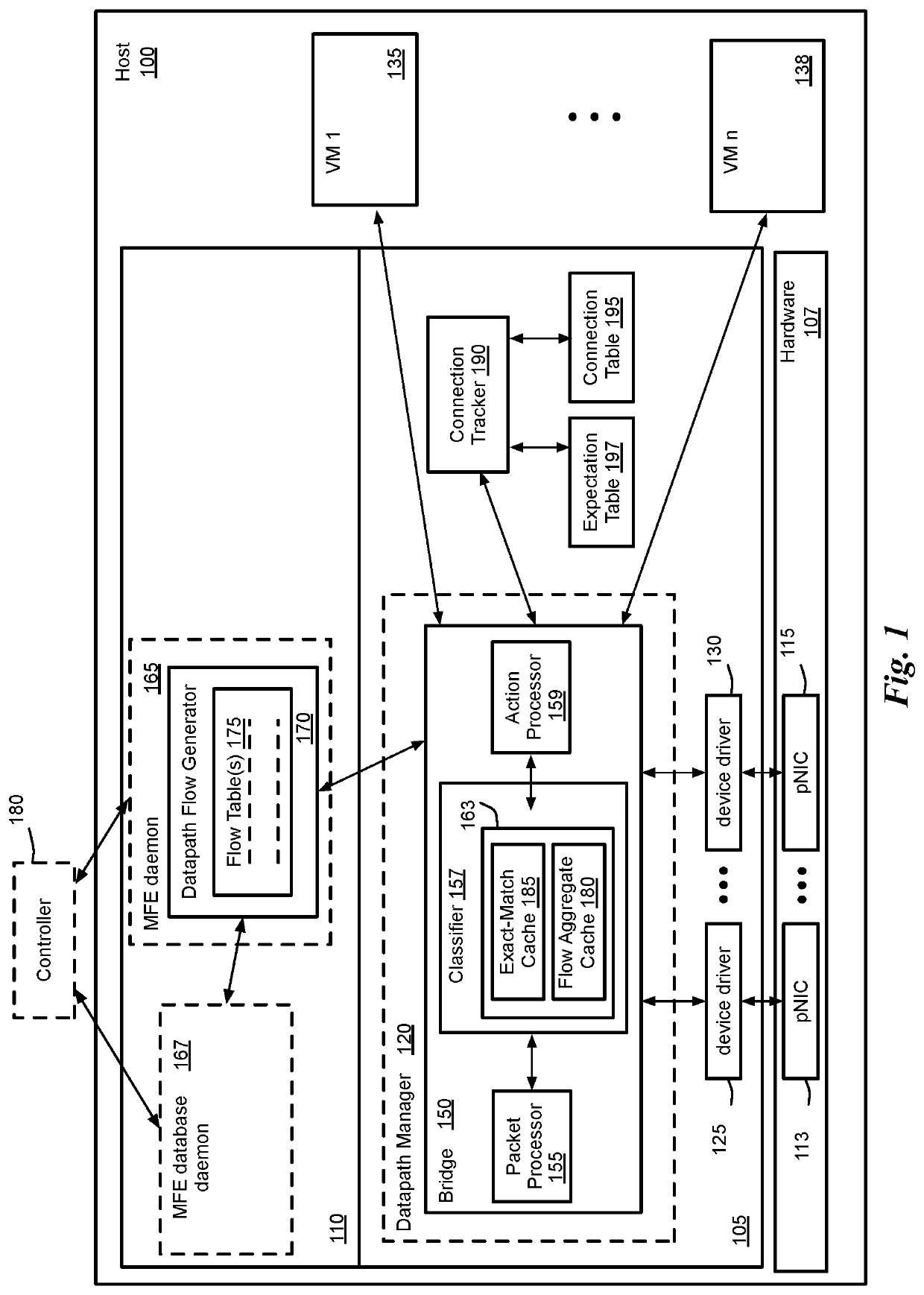
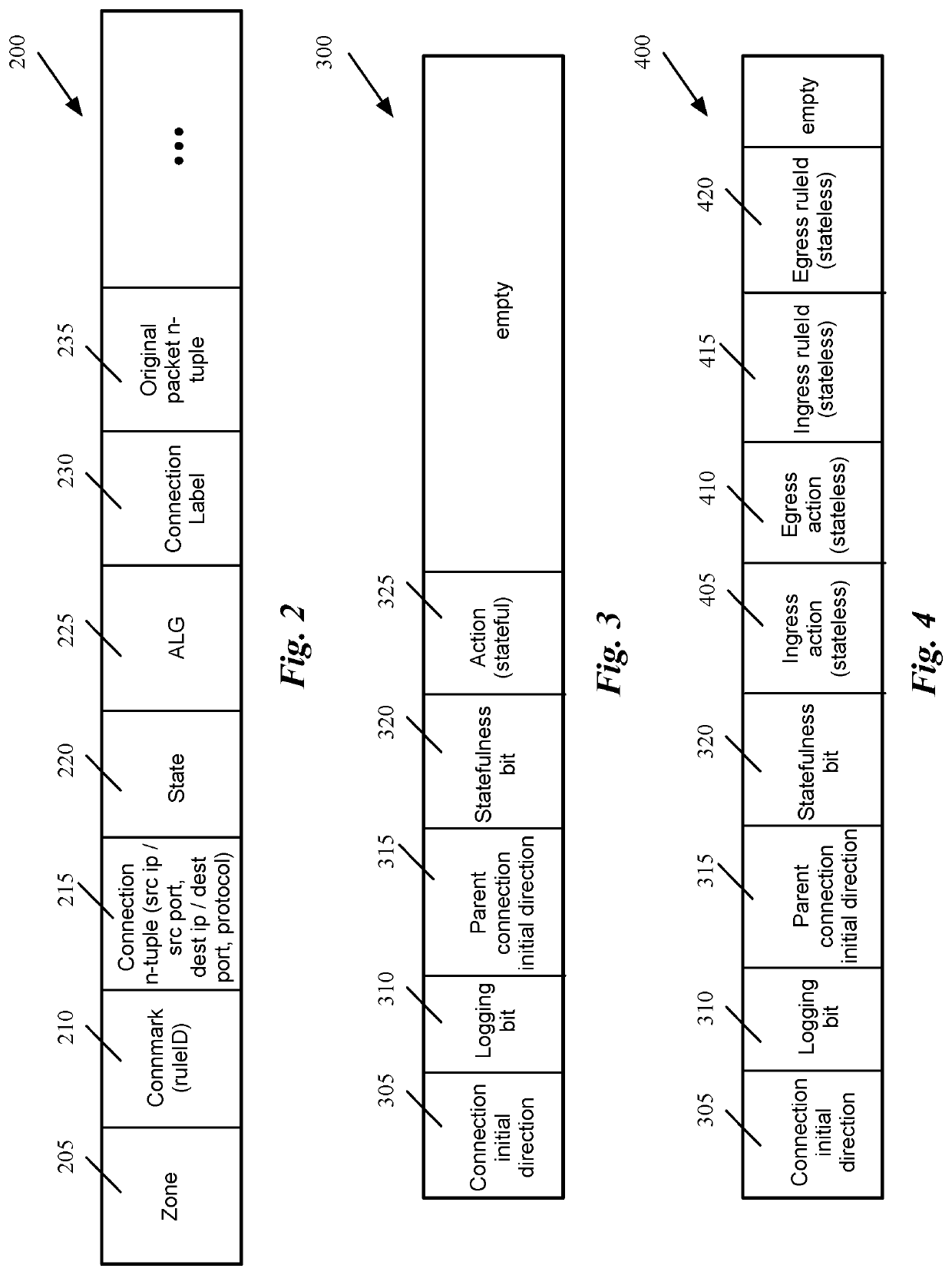
Packet induced revalidation of connection tracker
A method of revalidating a connection tracking table of a flow-based managed forwarding element (MFE) that stores a set of firewall rules associated with each of a set of network connections and a connection table that stores a firewall rule identification and a set of state values associated with each of said network connections. The method receives a change in one or more firewall rules stored at the MFE. The method receives a packet that requires stateful firewall rule check on a particular connection after the change in the firewall rules. When the rule identification retrieved from the connection table is not the same as the new firewall rule associated with the particular connection, the method updates the firewall rule identification and the set of state values associated the particular connection using the new firewall rule identification associated with the particular connection.
Owner:NICIRA
Switching system for virtual LANs
InactiveUS20060029072A1Data switching by path configurationElectric digital data processingVirtual LANAuto-configuration
A switch encapsulates incoming information using a header, and removes the header upon egress. The header is used by both distributed ingress nodes and within a distributed core to facilitate switching. The ingress and egress elements preferably support Ethernet or other protocol providing connectionless media with a stateful connection. Preferred switches include management protocols for discovering which elements are connected, for constructing appropriate connection tables, for designating a master element, and for resolving failures and off-line conditions among the switches. Secure data protocol (SDP), port to port (PTP) protocol, and active / active protection service (AAPS) are all preferably implemented. Systems and methods contemplated herein can advantageously use Strict Ring Topology (SRT), and conf configure the topology automatically. Components of a distributed switching fabric can be geographically separated by at least one kilometer, and in some cases by over 150 kilometers.
Owner:RAPTOR NETWORKS TECH
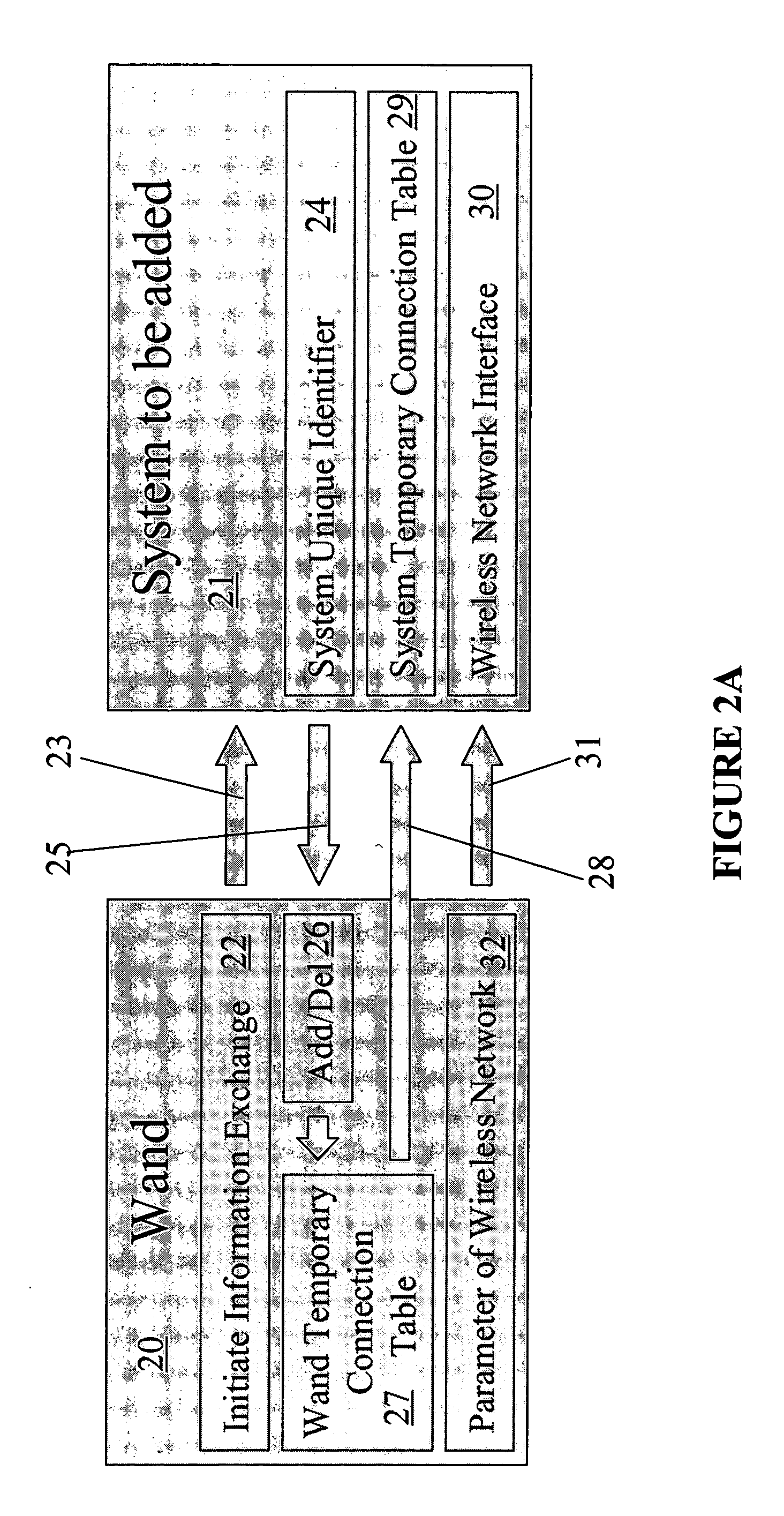
Secure and intuitive method for wireless network set-up and associated device and system
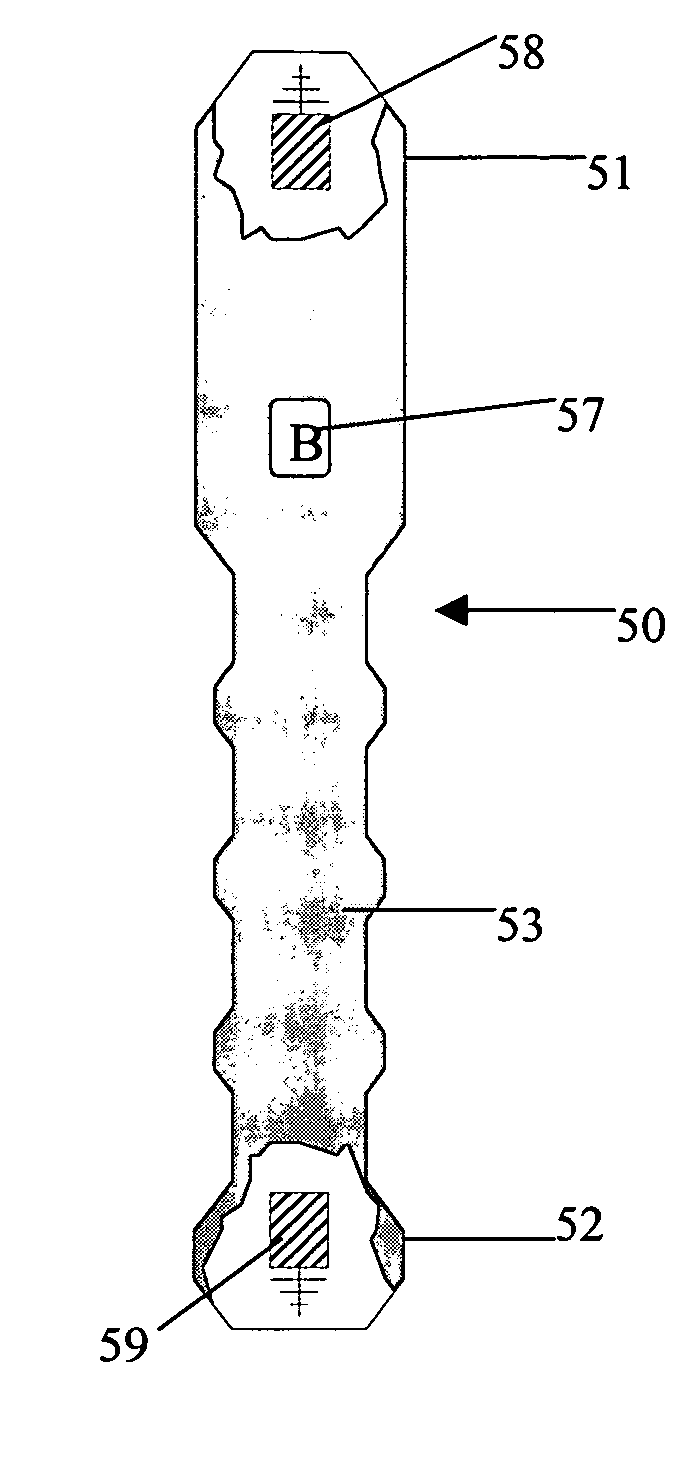
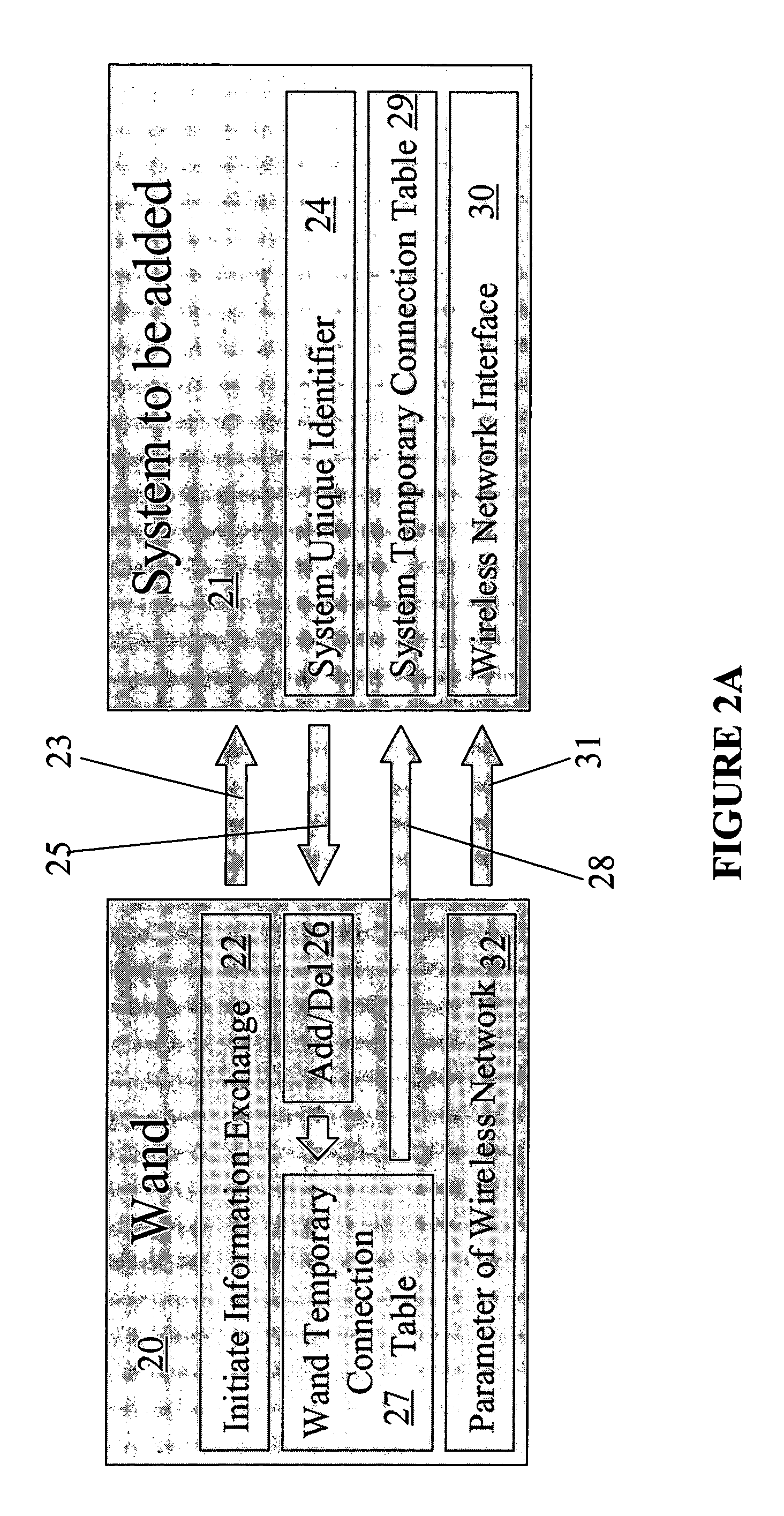
ActiveUS20050143129A1Electric signal transmission systemsEqual length code transmitterElectricityConnection table
A method for configuring a wireless network includes pointing a first end of a network configuration device at a wireless device and actuating the network configuration device to add the wireless device to the wireless network. The method may include positioning the first end in close proximity to the wireless device. A device is provided for configuring wireless networks that includes a transmitter configured to transmit at least one of an initiation signal and a connection table to a wireless device. The initiation signal is sent by the device to the wireless device to add or delete the wireless device from a network that is being configured. The connection table includes information about each wireless device that has previously been added to the network. A receiver is included in the device that is adapted to receive at least one of the connection table and a unique identifier from the wireless device. A memory is included in the device that is configured to store the connection table and electrically coupled to the transmitter and the receiver. The transmitter includes an infrared transmitter or a radio frequency transmitter and the receiver includes an infrared receiver or a radio frequency receiver. A system is provided that includes a pointing device including a connection table and a plurality of wireless network devices wirelessly couplable with the pointing device and with each other.
Owner:ROBERT BOSCH GMBH
Method and apparatus for automatically detecting a latent referential integrity relationship between different tables of a database
InactiveUS20070156736A1Improve performanceDigital data information retrievalDigital data processing detailsTable (database)Query analysis
In one aspect, a database analytical tool or function analyzes join queries to detect queries which could be reduced if a referential integrity relationship were known. In another aspect, a probable latent referential integrity relationship is detected using one or more heuristics. Preferably, a join query is analyzed to detect a joined table which has no other conditions placed on it, and no referential integrity relationship already defined. For any such query, the analysis attempts to verify a probable latent referential integrity relationship using at least one heuristic, such as comparing cardinality of the potential primary key with the size of the table and / or with the cardinality of the foreign key. It is further possible to execute the join for some sample of records, and determine whether any records were found which did not conform to referential integrity constraints.
Owner:IBM CORP
Method and system for maintaining and examining timers for network connections
InactiveUS7050940B2Reducing resourceShorten the timeTime indicationDigital data processing detailsConnection tableNetwork connection
System and method for maintenance and examination of timers for a computer system having connections in a networking system. Timer values in a connection table each indicate a timeout for a timer for a connection, where each connection has multiple timers, and one of the timer values is written to a global timer array for each connection such that the global timer array can be scanned to determine when timeouts occur for active connections. Sparse restart of a timer includes restarting the timer if data is communicated with a connected computer before the timeout occurs and after a predetermined time interval after timer start, and not restarting the timer if data is communicated before the timeout occurs and within the predetermined interval after timer start.
Owner:INT BUSINESS MASCH CORP
Parallelogram type connection table
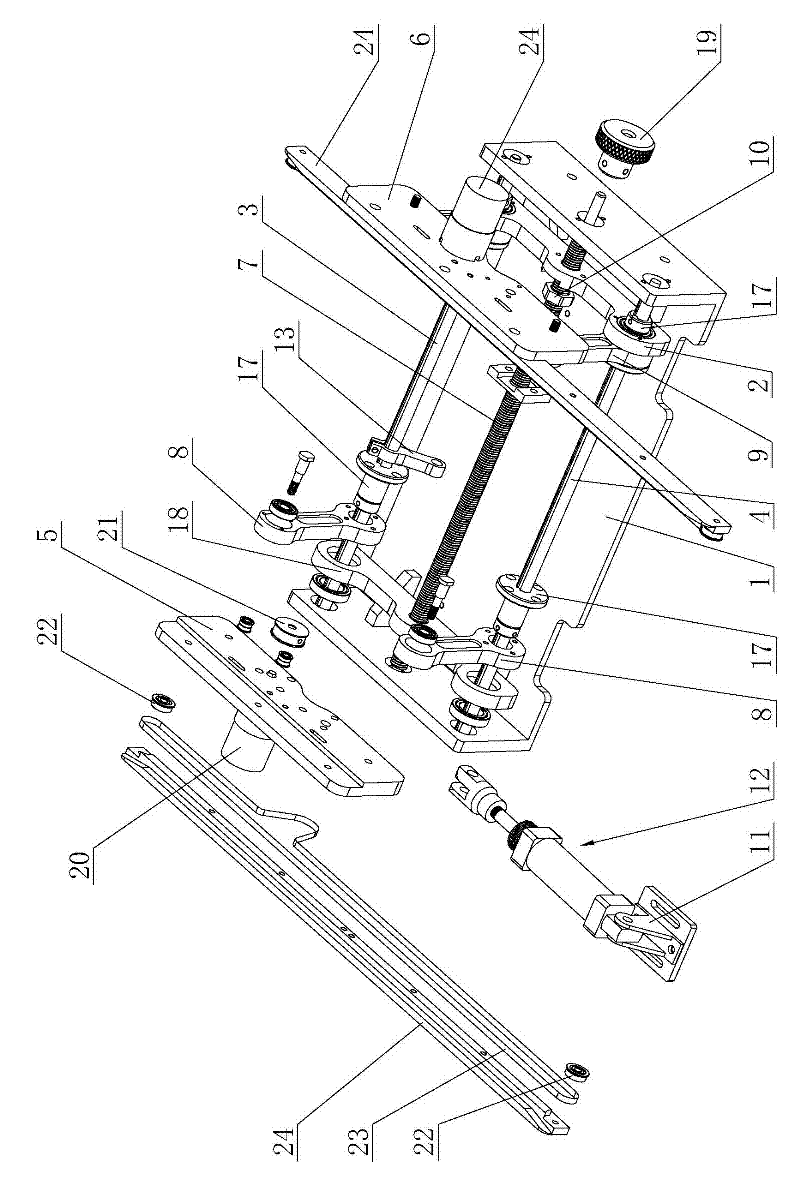
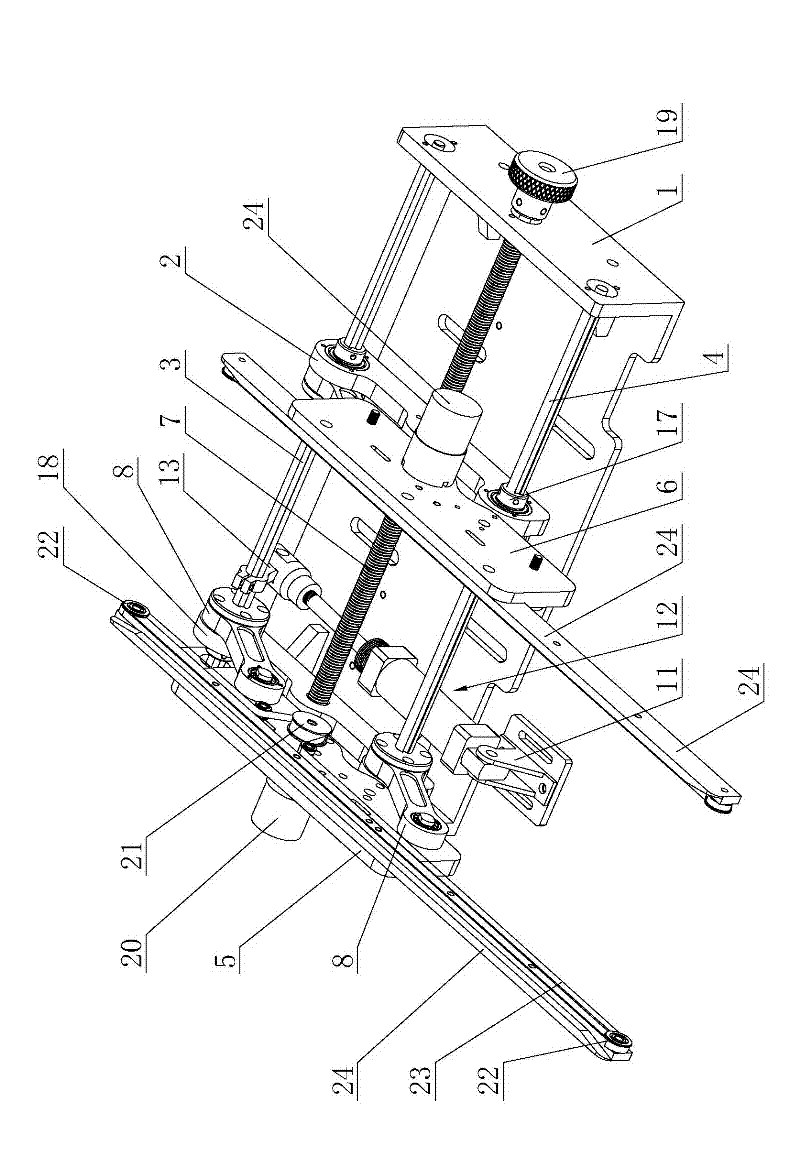
InactiveCN102502241AEasy to assembleReduce working noiseConveyor partsConnection tableMechanical engineering
The invention relates to the technical field of delivery equipment of printed circuit boards (PCBs), in particular to a parallelogram type connection table, which comprises a base, a movable connection block, a rotary main rod, a balancing rod parallel to the rotary main rod, a fixing support board, a movable support board, an adjusting lead screw, two board conveying devices and a driving mechanism for driving the rotary main rod to rotate. The parallelogram type connection table can achieve the aim of adjusting the width of delivered boards by rotating the lead screw and is convenient to adjust, the rotary main rod is driven to rotate under the effect of the driving mechanism and drives a movable rotary arm and a fixed rotary arm to swing, so that the movable support board and the fixed support board translate leftwards or downwards simultaneously, or the movable support board and the fixed support translate rightwards and upwards. Accordingly, transverse conveying and longitudinal conveying functions of the parallelogram type connection table are achieved, and the parallelogram type connection table is small and exquisite in structure, light in weight, convenient to assemble, low in manufacture cost, small in working noise, fast in board conveying speed and high in board delivery efficiency.
Owner:DONGGUAN SCIENCGO MACHINERY MFG
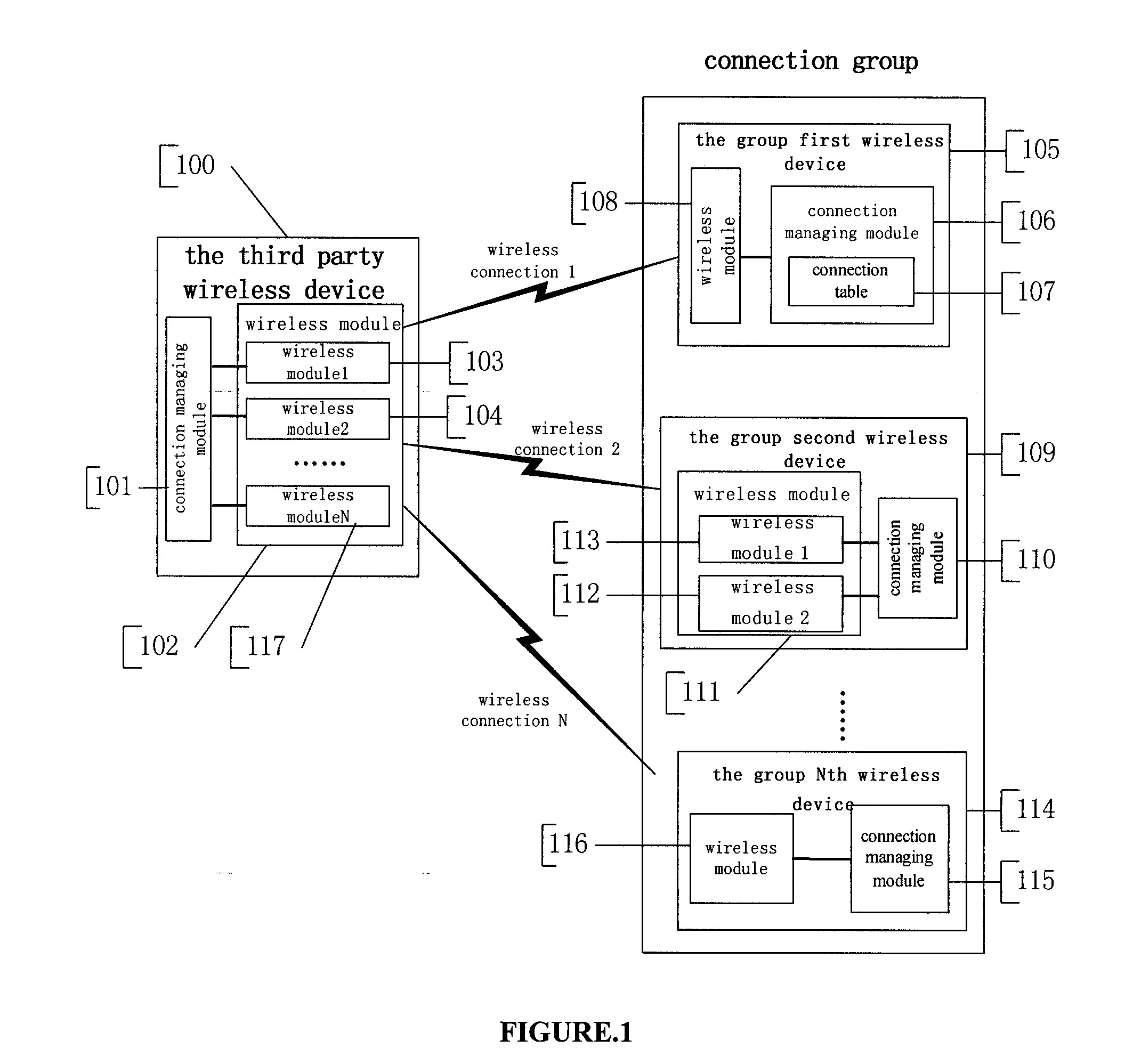
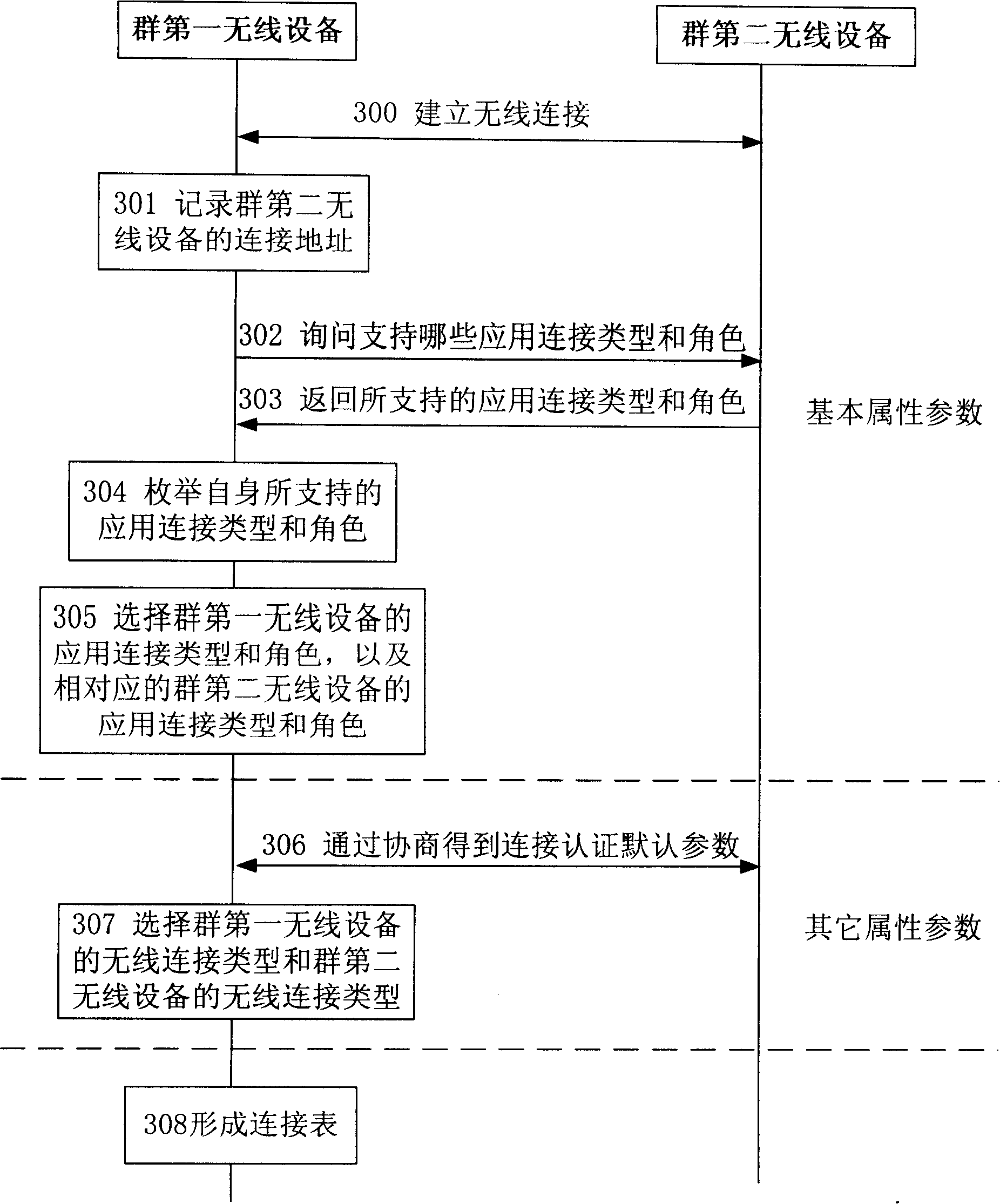
System and method for supporting automatic establishment and disconnection of wireless cluster connection
ActiveCN101179749ASpecial service for subscribersBroadcast service distributionThird partyConnection type
The invention discloses a system and a method for supporting automatically setting up and cutting off the wireless group connection. At least two wireless equipment consisting of a group first wireless equipment and a group second wireless equipment forms a connection group via the connection configuration table, the property parameter of the connection configuration table comprises a connection address, a application type and role of the connection group equipment. If the wireless equipment of the third party is connected with the group first wireless equipment application type and role appointed by the group first wireless equipment automatically setting up connection table, then the wireless equipment of the third party is connected with the group second wireless equipment application type and role appointed by the group first wireless equipment automatically setting up connection table; if the wireless equipment of the third party is connected with the group first wireless equipment application type and role appointed by the group first wireless equipment automatically cutting off connection table, then the wireless equipment of the third party is connected with the group second wireless equipment application type and role appointed by the group first wireless equipment automatically cutting off connection table.
Owner:BEIJING BAIRUI INTERNET TECH CO LTD
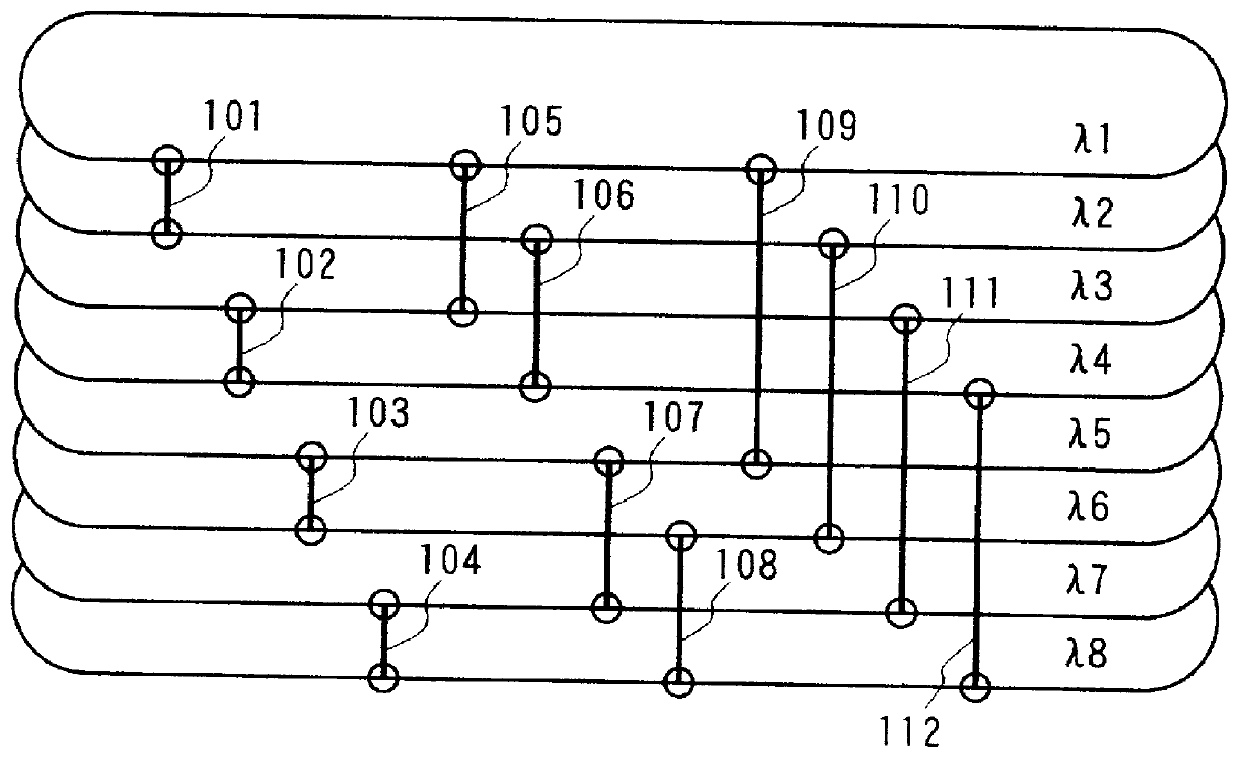
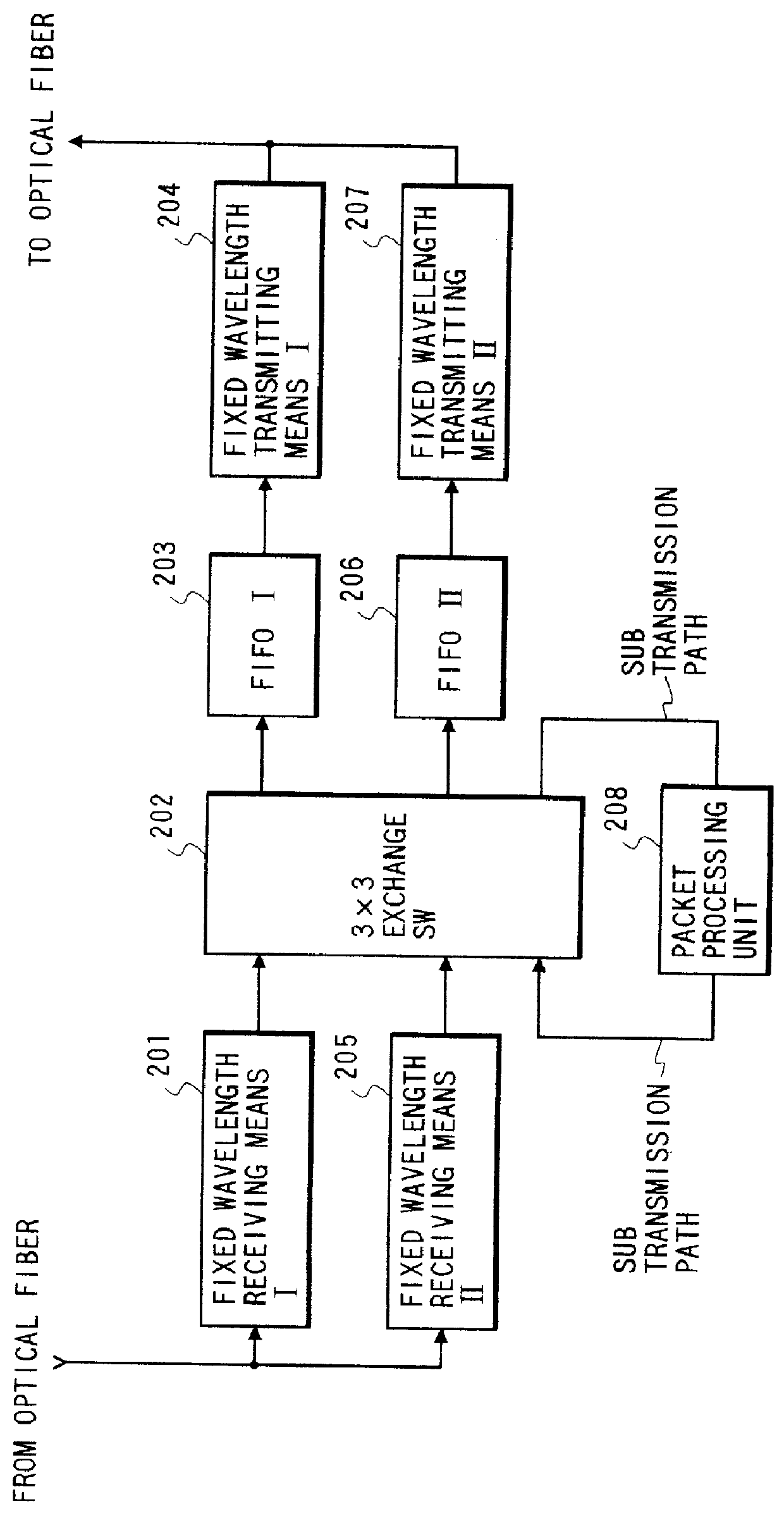
Network system for transmitting a plurality of channels, and node device, packet transmission method, terminal equipment connection table generation method, and connection information registration method used in the system
InactiveUS6044076AEasily discriminatedEfficiently lookingLaser detailsWavelength-division multiplex systemsConnection tableTerminal equipment
A source terminal equipment connected to a node device transmits a packet by appending a section for designating the channel to be used upon relaying the packet by the node device to the packet. The relaying node device determines the channel used upon outputting the packet by looking up the value in the section for designation of the channel. The source terminal equipment transmits the packet by appending relaying number information indicating the number of relayings of the packet to the packet. Each node device looks up the relaying number information upon looking up the value in the section for designation of the channel. When each node device outputs a packet to a terminal equipment using a separation device for separating the packet toward the sub transmission path side, the node devices determines, based on the relaying number information, whether or not it separates the packet. This invention also discloses a method of generating a terminal equipment connection table and a method of registering connection information using the above-mentioned transmission method.
Owner:CANON KK
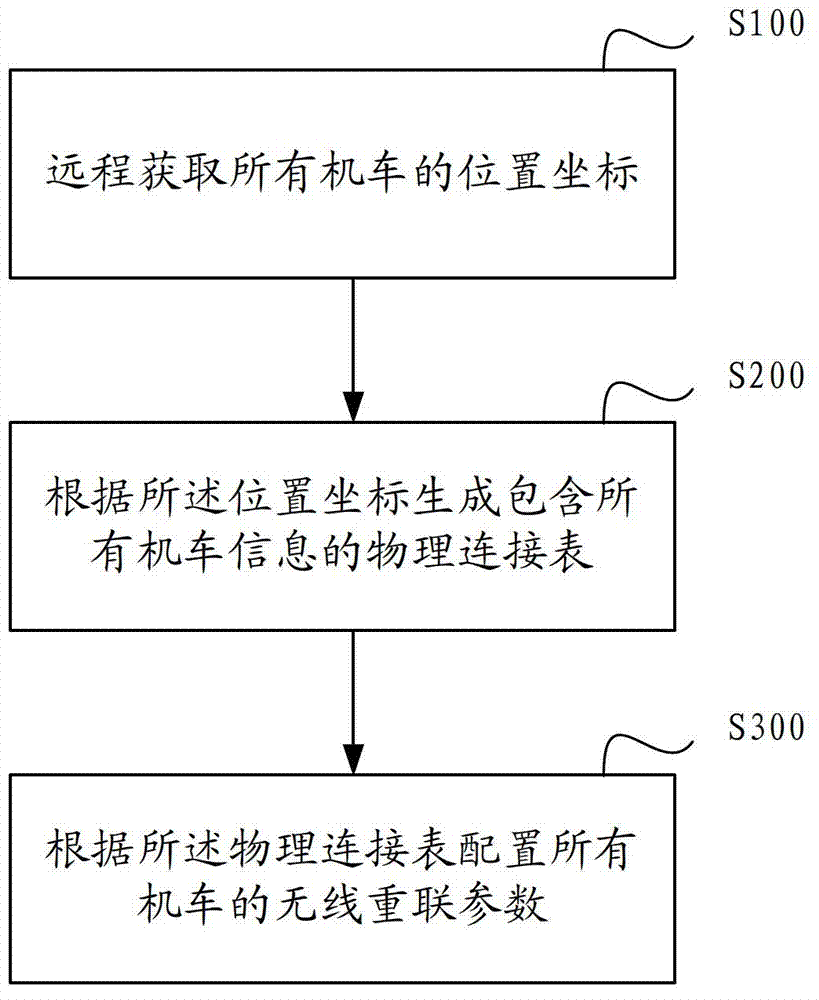
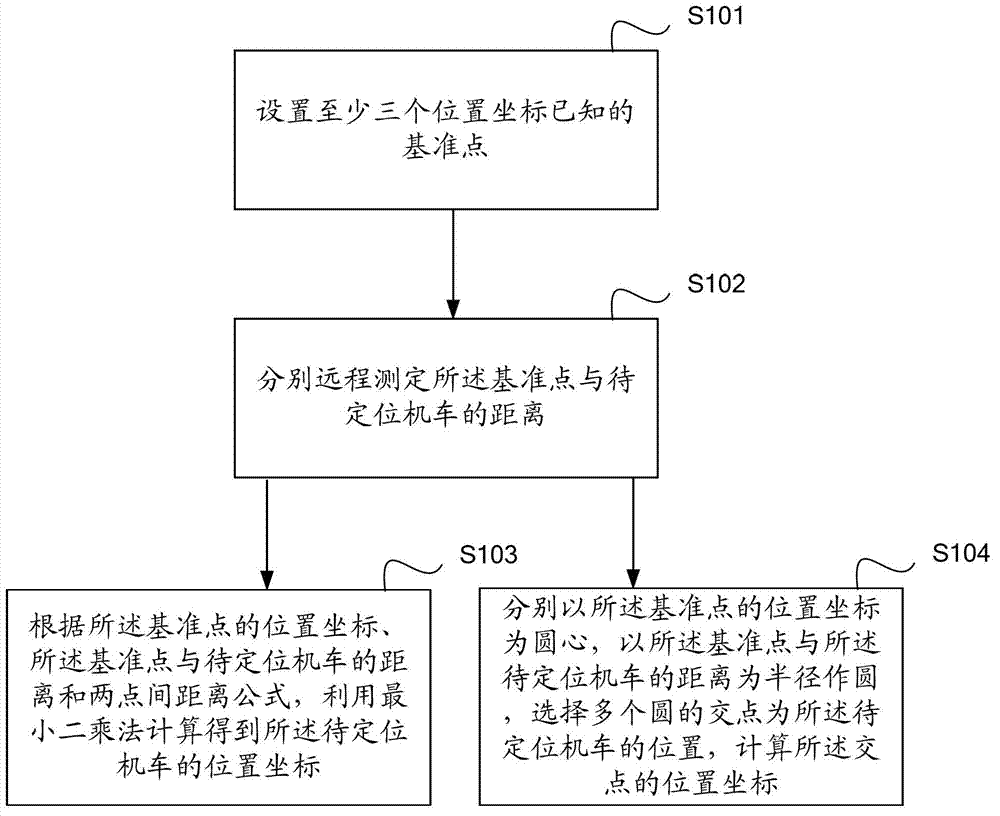
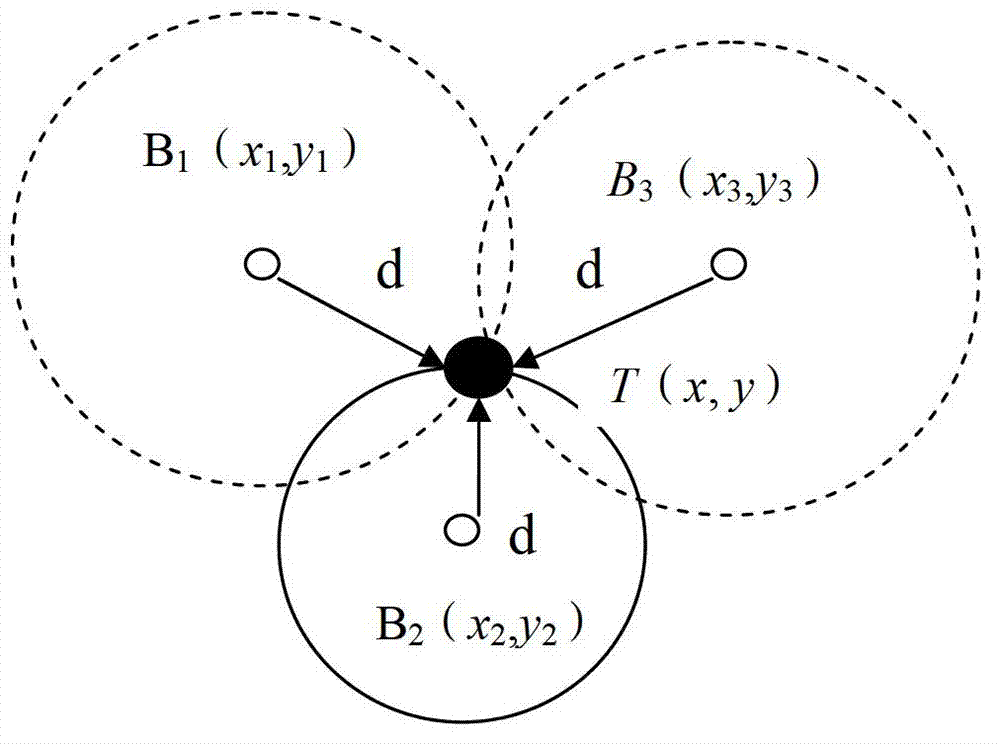
Wireless reconnection automatic parameter configuration method and system for locomotives
ActiveCN103048980AImprove efficiencyImprove securityTotal factory controlLocomotivesConnection tableComputer module
The invention discloses a wireless reconnection automatic parameter configuration method and a wireless reconnection automatic parameter configuration system for locomotives. The method comprises the following steps that position coordinates of all locomotives are remotely obtained; a physical connection table containing information of all locomotives is generated according to the position coordinates; and wireless reconnection parameters of all locomotives are configured according to the physical connection table. The system comprises a position coordinate obtaining module, a physical connection table generating module and a parameter configuration module. The method and the system provided by the invention are based on the remote positioning technology, the wireless reconnection parameter configuration of all locomotives is automatically realized, and the wireless reconnection efficiency and the marshalling safety of the locomotives are greatly improved.
Owner:CSR ZHUZHOU ELECTRIC LOCOMOTIVE RES INST
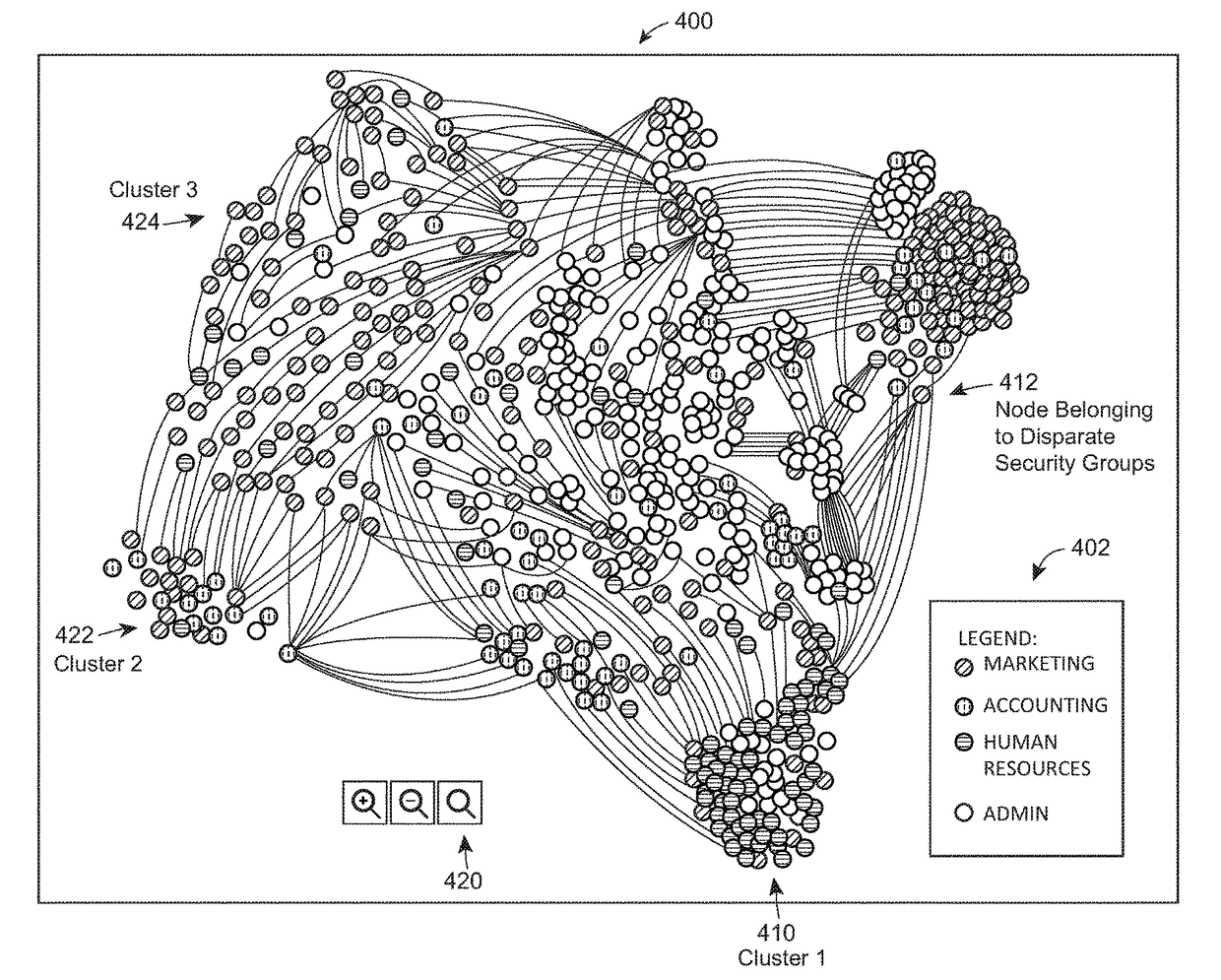
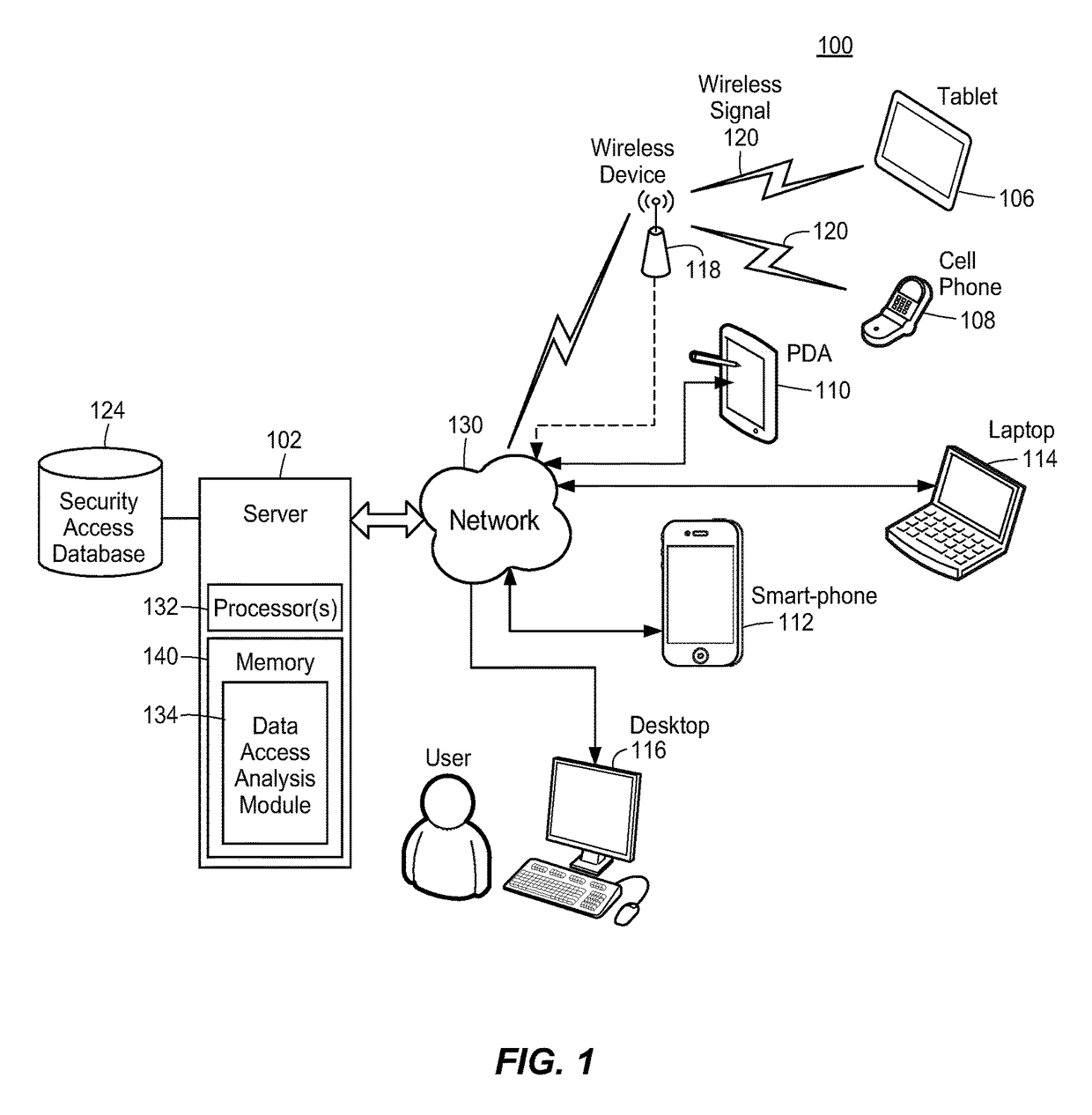
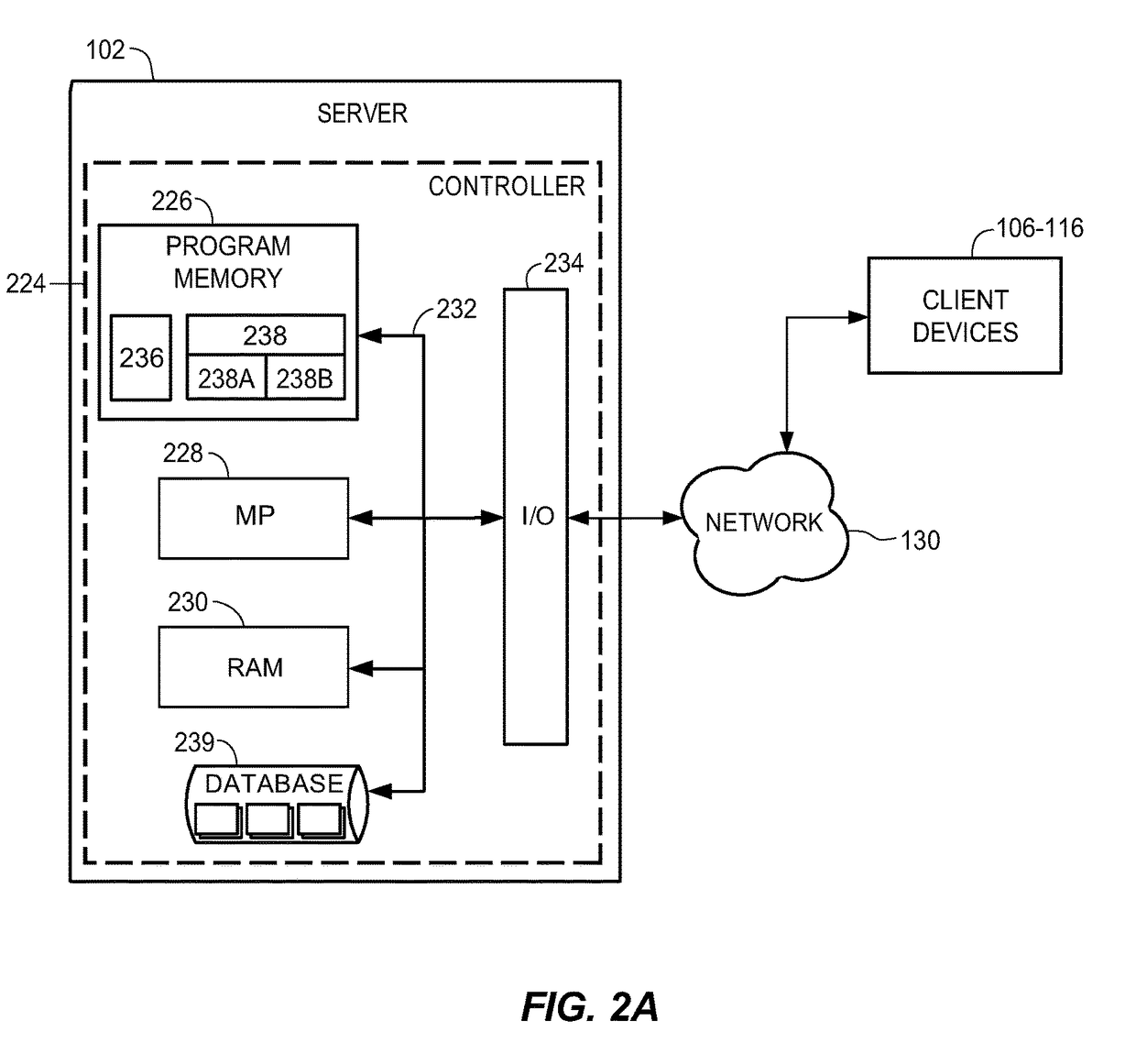
Method and system for identifying security risks using graph analysis
ActiveUS9819685B1Increase in sizeEasy to identifyDigital data processing detailsTransmissionGraphicsInternet privacy
Methods, systems, apparatus, and non-transitory computer readable media are described for identifying users who are likely to have unauthorized access to secure data files in an organizational network. Various aspects may include presenting the identified users on a display for a system administrator and / or security analyst to resolve. For example, the display may include a graph data structure with users represented as nodes and connections between users represented as edges. Each connection may be a pair of users belonging to a same security group. The graph data structure display may be organized and color coded in such a manner, that a system administrator and / or security analyst may quickly and easily view the users who are most likely to have unauthorized access to secure data files. The authorized access may then be remedied or taken away.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
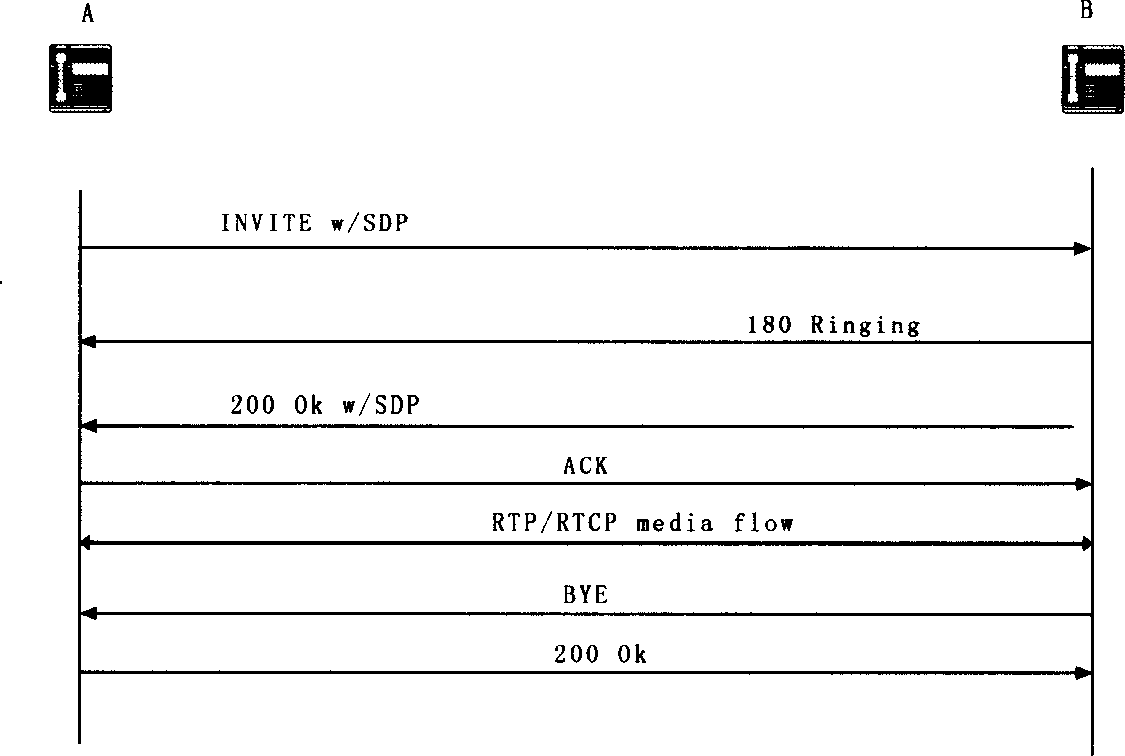
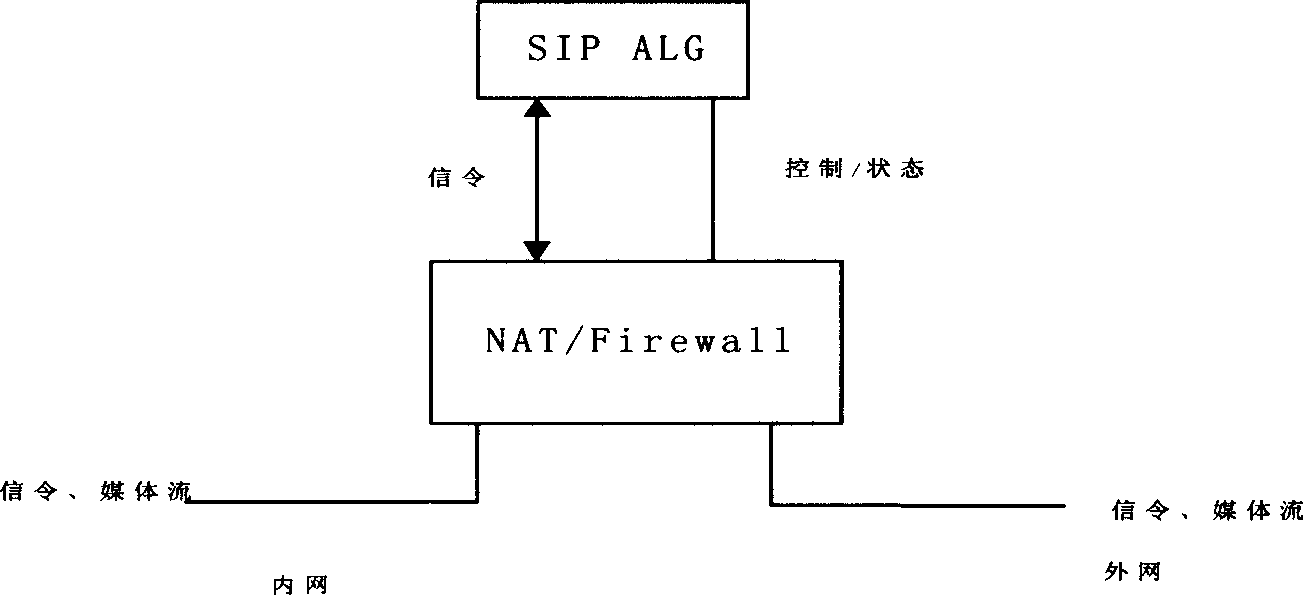
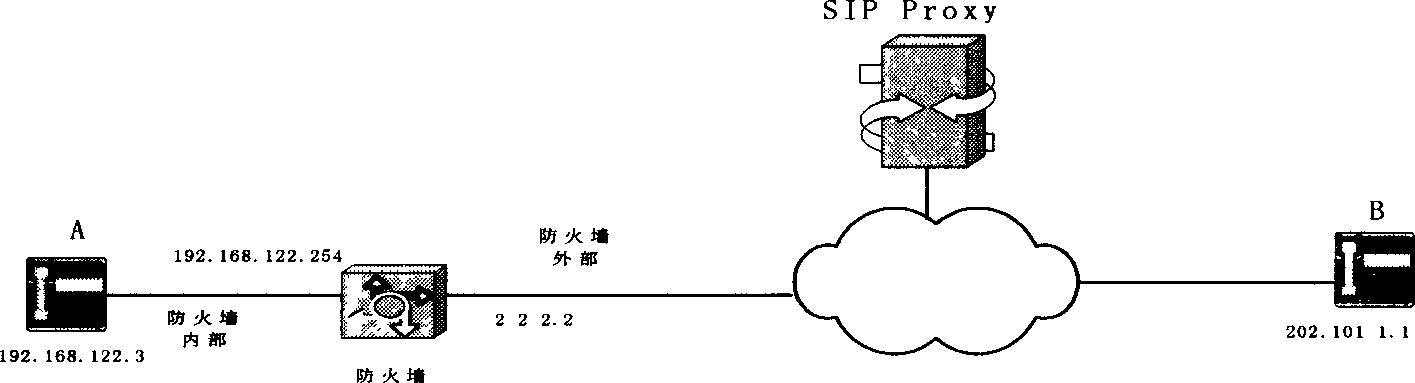
SIP crossing supported firewall implementing method
InactiveCN1604589AExtension limitClear hierarchyData switching networksConnection tableProtocol for Carrying Authentication for Network Access
It is a firewall implementation method that supports the session startup protocol crossover in the field of network security technique. The content is: the firewall analyses the IP division that enters the system. After the IP division enters the system through network interface, the firewall analyses the IP heading information, judges whether the data load is SIP signal information or voice division; the SIP ALG processes the SIP message, SIP ALG analyses SIP message heading to make sure this message belongs to which calling connection. The SIP ALG uses one calling connection state table to track all the calling connection state and modify the content of SIP message heading and / or SDP message according to the information of state table; the firewall processes the down-transferred SIP message from SIP ALG, or performs the instruction issued by SIP ALG, and returns the result to the SIP ALG; according to the result of instruction performing by firewall, the SIP ALG sets or modifies the calling connection table, and sends the SIP message to the firewall, or performs the clearing of calling connection table.
Owner:无锡三通科技有限公司
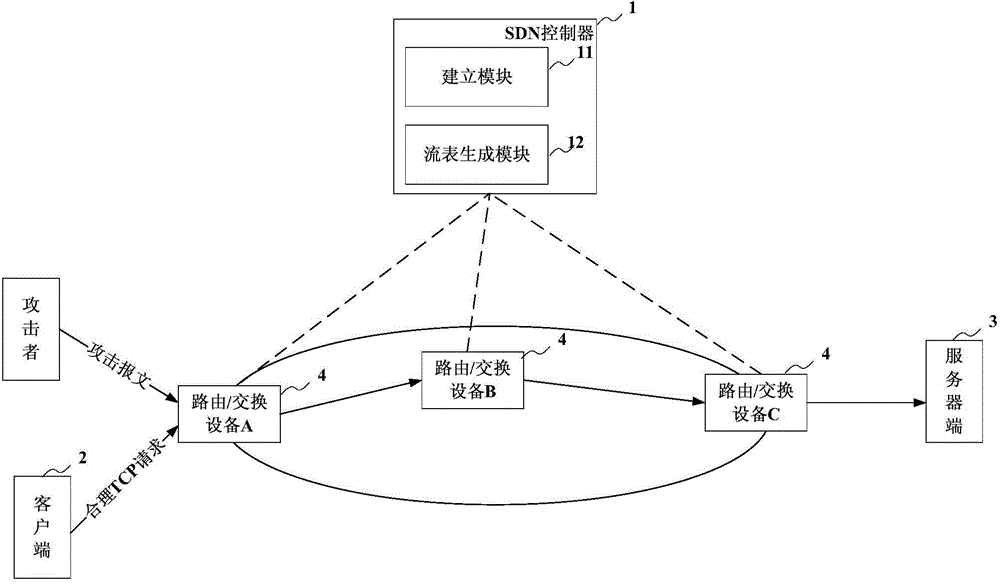
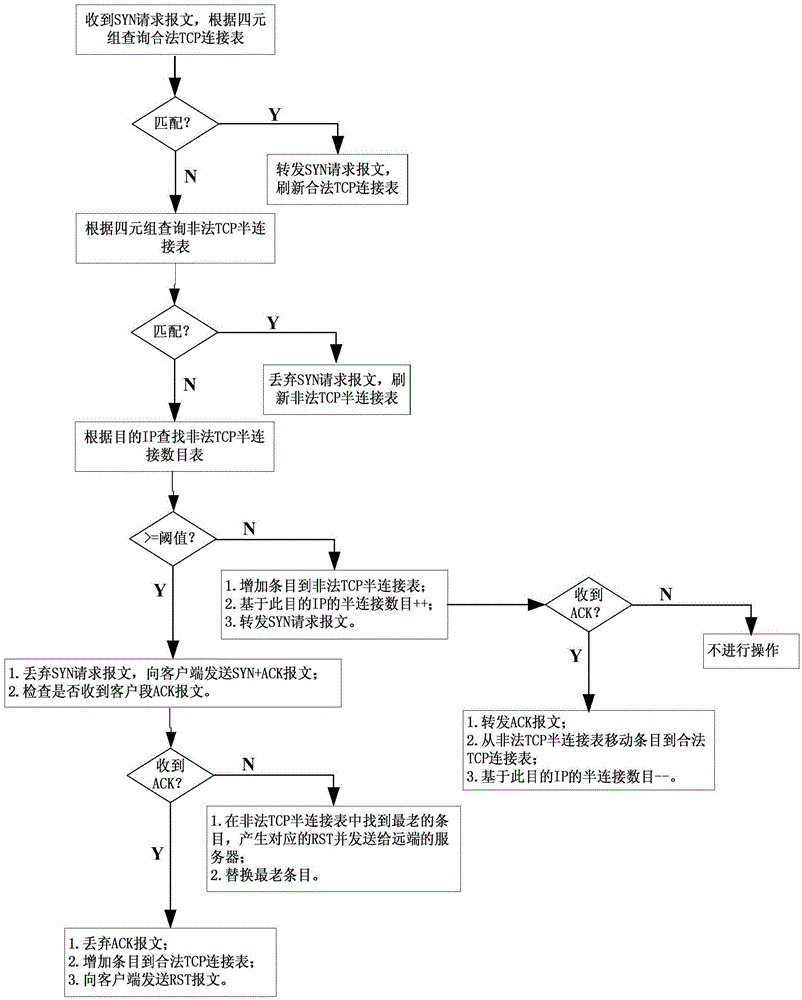
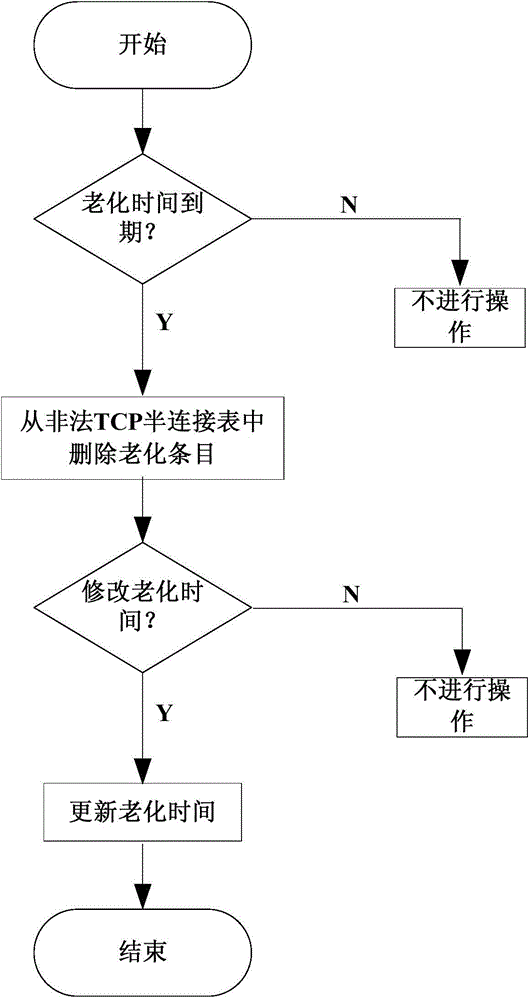
SDN controller, routing/switching device and network defending method
ActiveCN104468624ADoes not affect request processingData switching networksConnection tableConnection number
The invention provides an SDN controller, a routing / switching device and a network defending method applied to a network comprising a client side, a server side and a routing / switching device connected between the client side and the server side. A legal TCP connection table, an illegal TCP half connection table and an illegal TCP half connection number table are established and stored in the SDN controller, and a flow table containing filtering action types is generated and issued to an inlet routing / switching device where an attacker is located to control the routing / switch device to execute corresponding filtering strategies. According to the SDN controller, the routing / switching device and the network defending method, the SDN architecture is adopted, the position of the attacker can be sensed, and attacking messages can be classified accurately.
Owner:湖州帷幄知识产权运营有限公司
Secure and intuitive method for wireless network set-up and associated device and system
ActiveUS7328045B2Electric signal transmission systemsEqual length code transmitterWireless mesh networkConnection table
A method for configuring a wireless network includes pointing a first end of a network configuration device at a wireless device and actuating the network configuration device to add the wireless device to the wireless network. The method may include positioning the first end in close proximity to the wireless device. A device is provided for configuring wireless networks that includes a transmitter configured to transmit at least one of an initiation signal and a connection table to a wireless device. The initiation signal is sent by the device to the wireless device to add or delete the wireless device from a network that is being configured. The connection table includes information about each wireless device that has previously been added to the network. A receiver is included in the device that is adapted to receive at least one of the connection table and a unique identifier from the wireless device. A memory is included in the device that is configured to store the connection table and electrically coupled to the transmitter and the receiver. The transmitter includes an infrared transmitter or a radio frequency transmitter and the receiver includes an infrared receiver or a radio frequency receiver. A system is provided that includes a pointing device including a connection table and a plurality of wireless network devices wirelessly couplable with the pointing device and with each other.
Owner:ROBERT BOSCH GMBH
Method and device for using connection table to compress data diagram
InactiveCN101196933ASave storage spaceImprove execution efficiencySpecial data processing applicationsConnection tableComputer science
The invention relates to a method by adopting a link list to compress a data map and equipment. The method comprises: recognizing the link list; generating data map nodes corresponding to non link list tuples; generating edges corresponding to the data map nodes for external keys not belonging to the link list; connecting two primary key nodes quoted according to the recognized link list and generating a new edge between two data map nodes corresponding to each pair of tuples associated with the link list. The adoption of the invention can delete the nodes in the data map which are from the link list, combine two corresponding edges, reduce the storage space of the data map by reducing the nodes and edges of the data map and at the same time ensure no loss of information in the data map, namely ensure that during retrieving data from the database, the acquired retrieval results are the same as those before compressing the data map, but greatly reduce the retrieval time and improve retrieval efficiency.
Owner:王珊
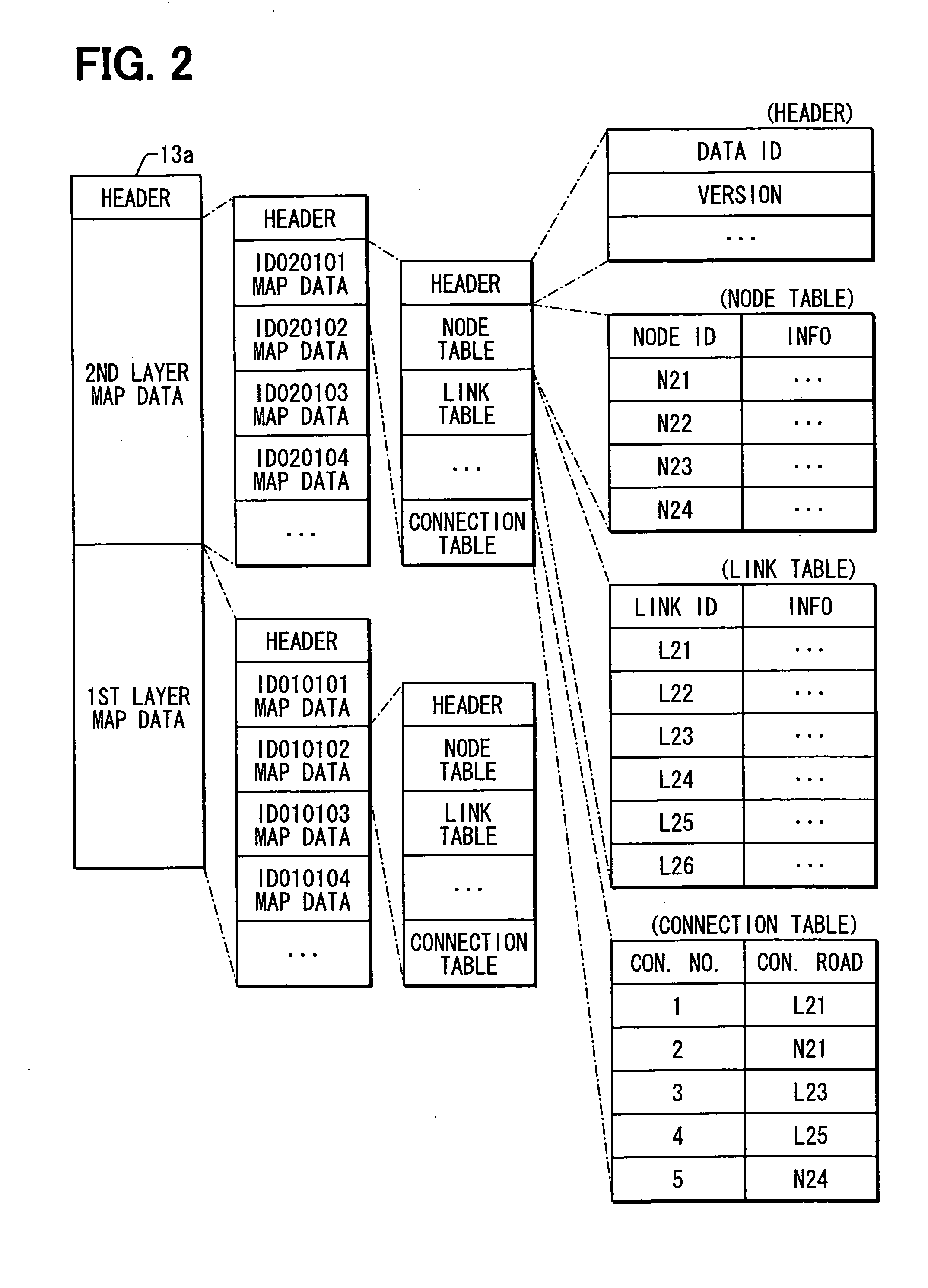
Road map data generation method, road map data update system, and road map data management device
InactiveUS20070093960A1Efficient updateInstruments for road network navigationRoad vehicles traffic controlRoad mapConnection table
A navigation device has a regional map data item for each of multiple regions, into which a nation is divided. A connection table is included in a regional map data item for a certain region and associates (i) a certain ID of a connection road in the certain region with a certain connection number. The connection road is connected with a paired connection road in an adjacent region. A connection table of a regional map data item for the adjacent region associates an ID of the paired connection road with the same connection number as the certain connection number. When the certain ID in the certain region is replaced with a different ID because of a road construction or the like, only the certain ID is replaced in the connection table with the certain connection number unchanged. This eliminates need of amending the connection table for the adjacent region.
Owner:DENSO CORP
Method of providing quality of service (QOS) to voice applications in routed IP networks
InactiveUS7054327B2Simplify methodologyInterconnection arrangementsTime-division multiplexTraffic capacityConnection table
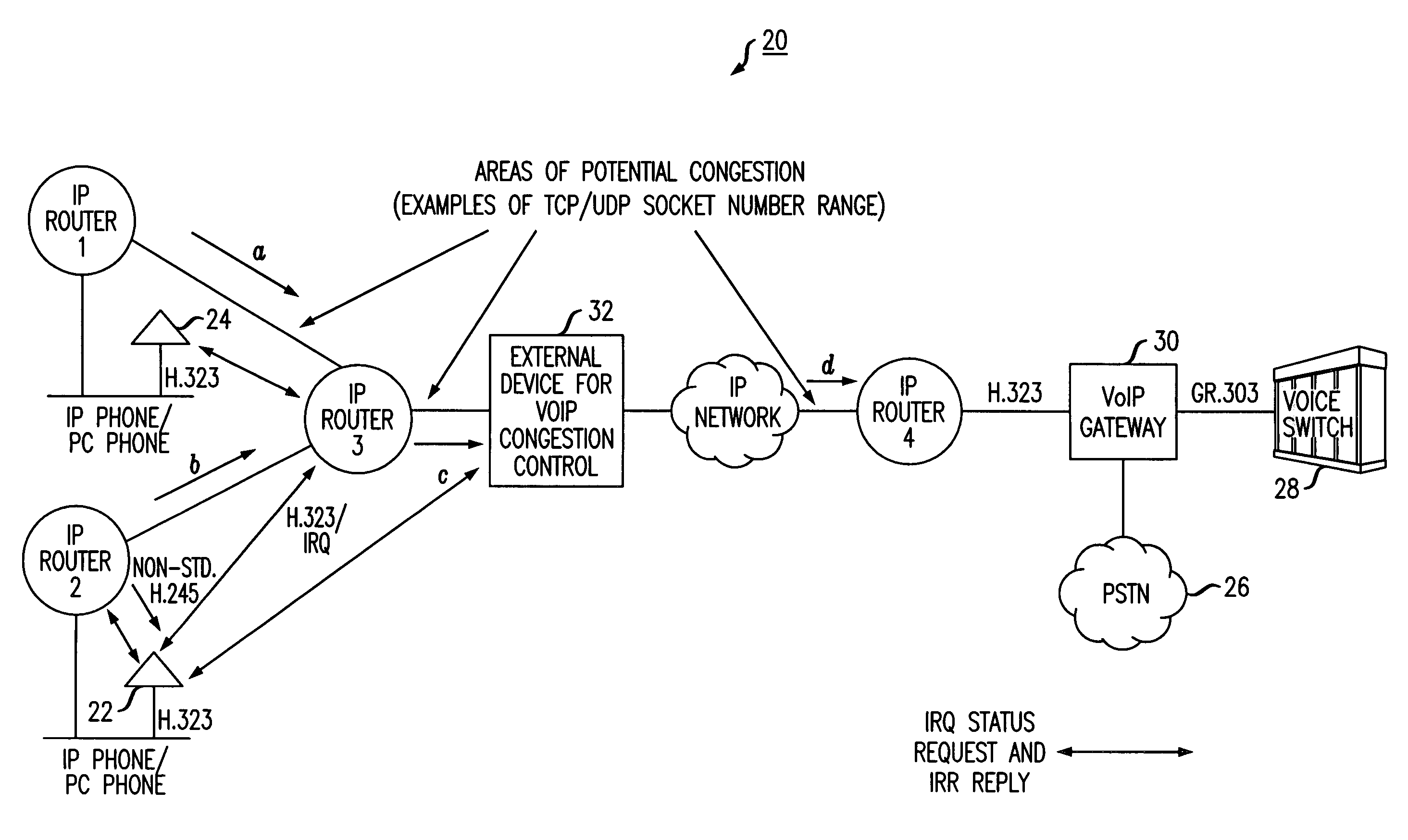
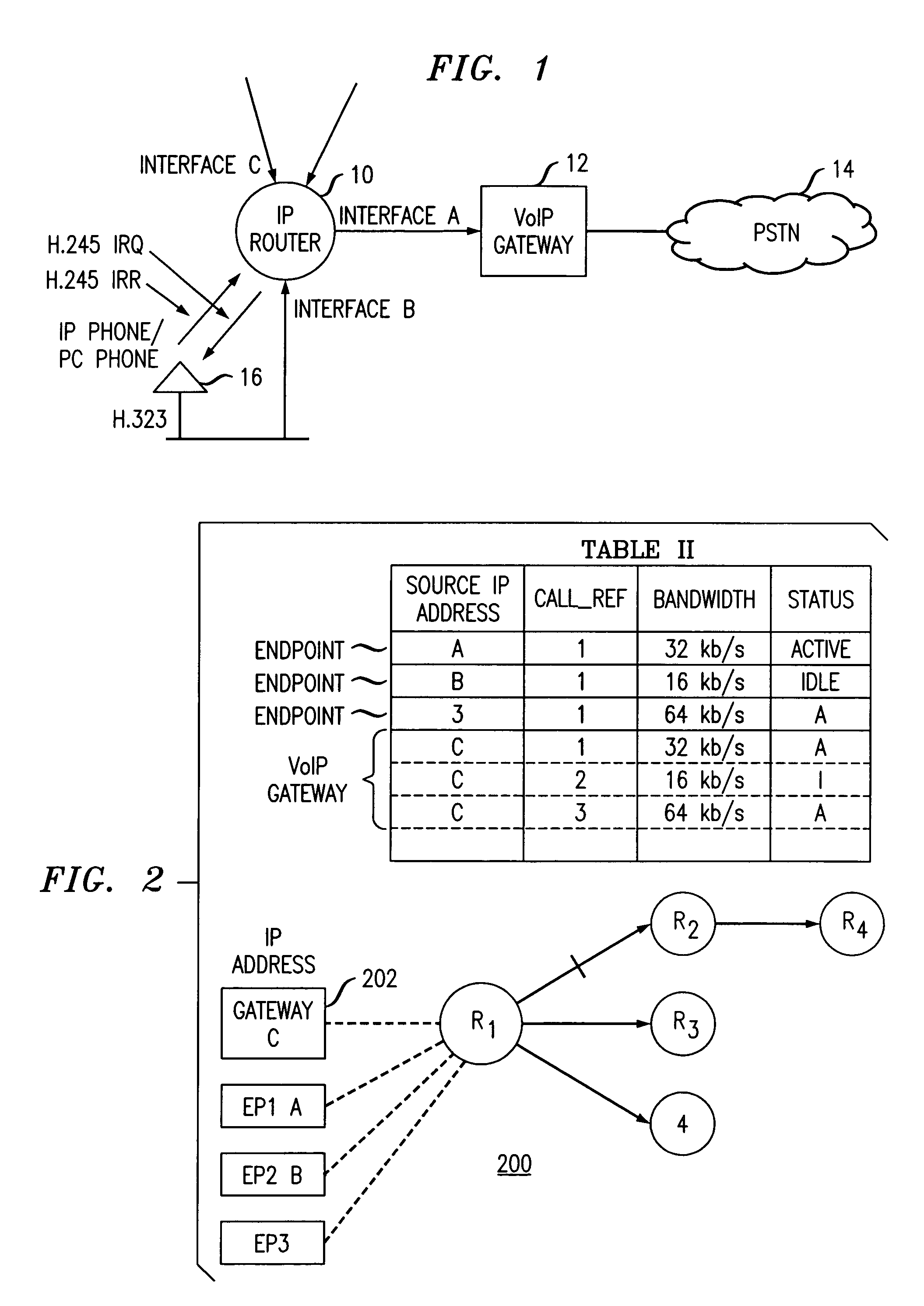
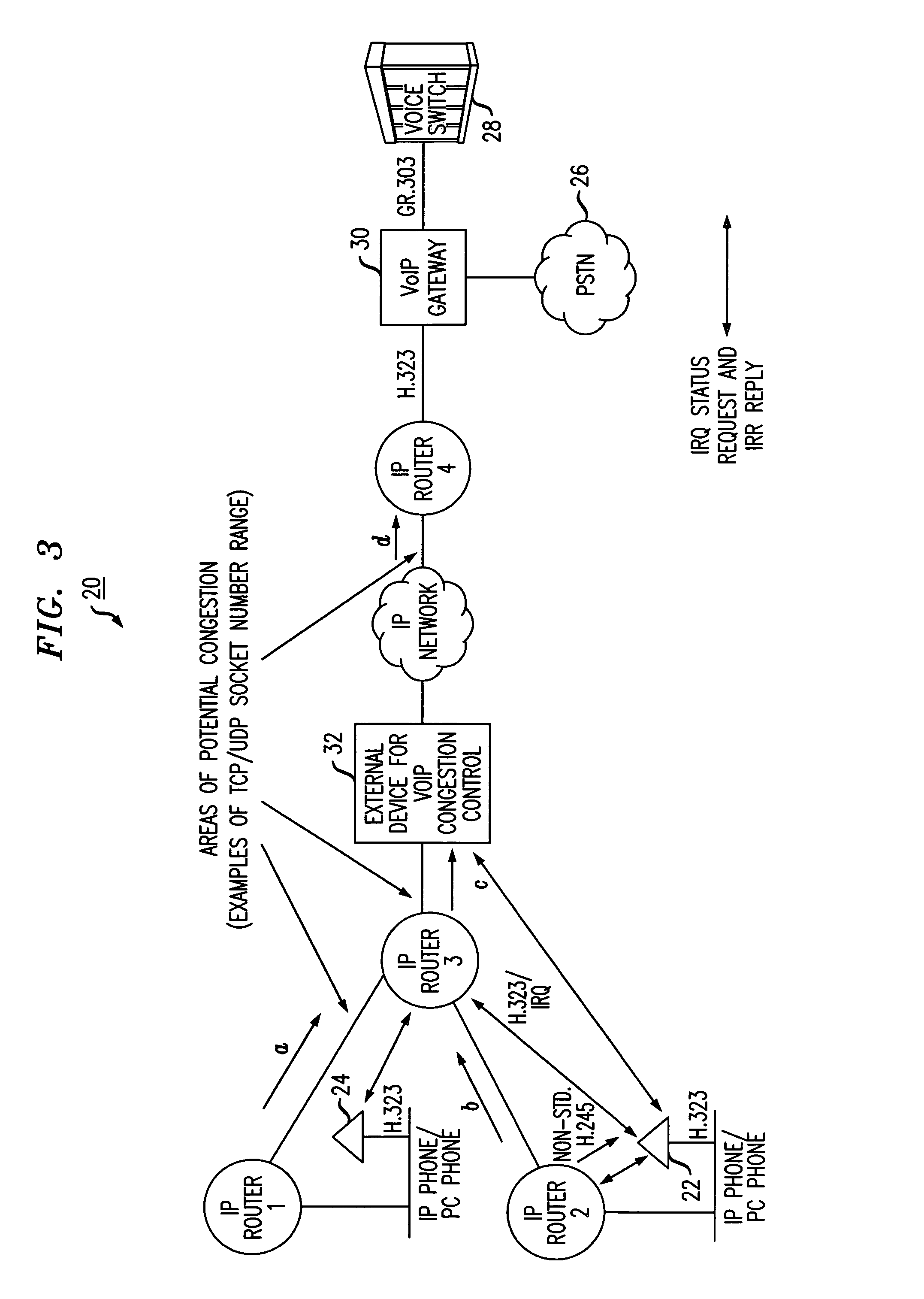
A simplified methodology for accomplishing traffic management in a packet based network is achieved by allowing allocation of bandwidth based on a count of the number of endpoint connections associated with a specific service for a corresponding network device. A network device (e.g., IP router) can be configured to count the number of TCP / IP and UDP / IP connections and bandwidth usage per interface. The counting can be done by identifying the IP Addresses, Type of Service (TOS), and TCP / UDP and / or UDP / IP socket number range in the IP Header of a packet and then querying a specific communication type. When reaching the maximum allowed connections or bandwidth for a specific service, the network device (e.g., IP router) stops forwarding any new calls by means of dropping packets of new calls and informing the given endpoints to disconnect the new calls. In one exemplary embodiment of the invention, a procedure for managing traffic flowing through individual routers of a packet network includes the steps of reserving a given amount of bandwidth on interfaces of the individual routers for specific types of communications traffic, periodically querying endpoint connections based on data from a corresponding router connection table, receiving responses from the periodic querying to determine a current connection status and bandwidth allocation of said endpoints and calculating current bandwidth allocation for a specific type communications service on an interface handled by the router. The router admits additional communications traffic for a specific type of communications service if bandwidth is available.
Owner:LUCENT TECH INC
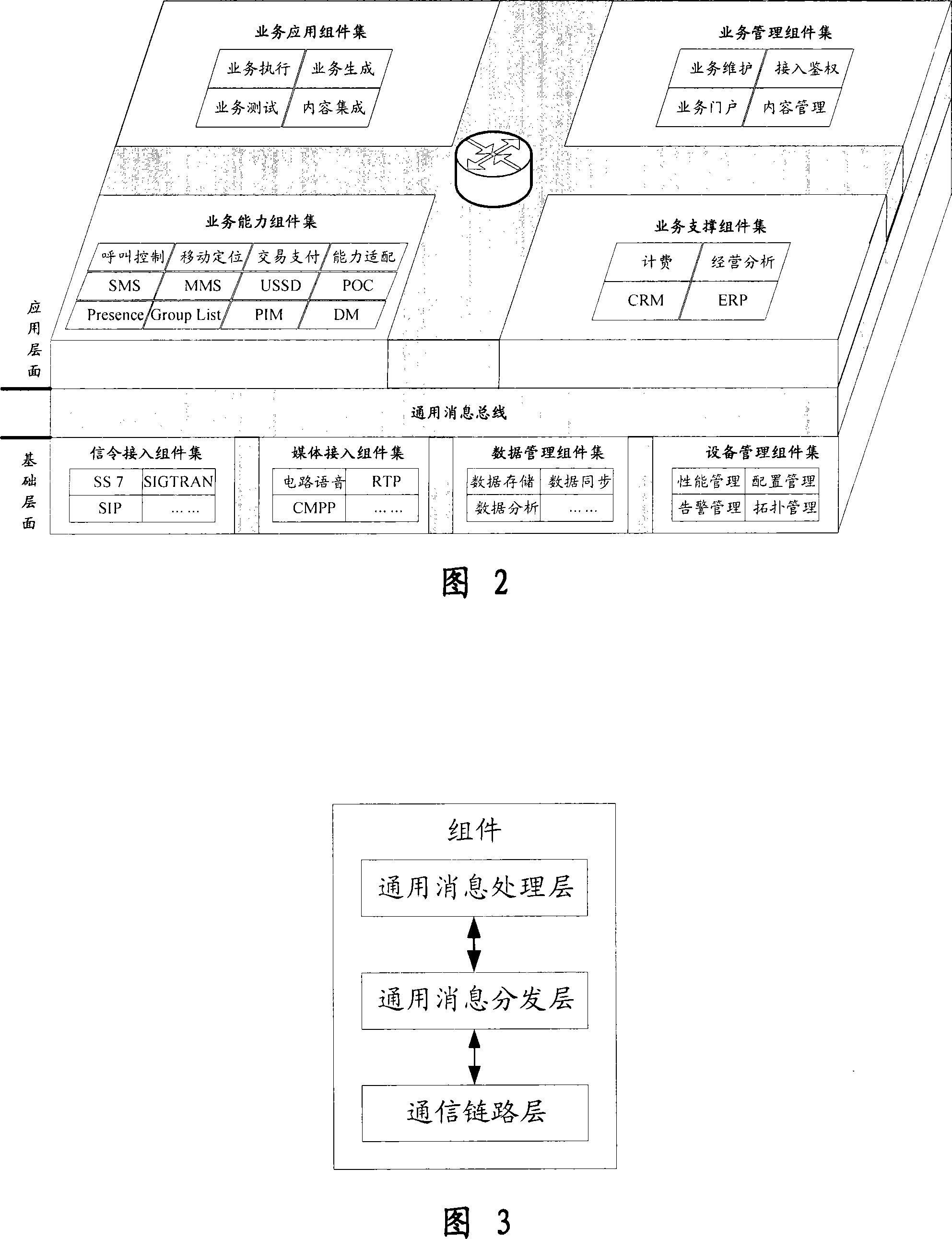
Method for implementing universal message bus based universal service system structure
InactiveCN101119268AMasking complexityGenerate flexibleInterprogram communicationBus networksInformation processingUniversal service
The present invention relates to an implementation method of the common operation system architecture based on common information bus, the operating procedures are as follows: (1) the USSA consists of an application layer component, a common information bus component and a basis layer component, the distribution interaction and the distribution disposing function of each component is realized by the common information bus subassemblies; (2) the components are classified to three layers from the inner functions: a communication link layer, a common information distribution layer and a common information processing layer; the interaction integration between the subassemblies employs the conversation mode of the common information bus format; (3) the global configuration files are composed, the configuration proposal of the USSA system is designed, the components on the operation system are physically deployed, and a function entity table, a subnet table and a link connecting table of the architecture system are hereby constituted; (4) when a new service is added, the arranged subassemblies classifying method and disposing method are used for constituting and disposing the components of the new service. The method can generate a plurality of telecommunication services fast and flexibly and has good reusability, openness and compatibility.
Owner:EB INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com