Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
17461 results about "Network connection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
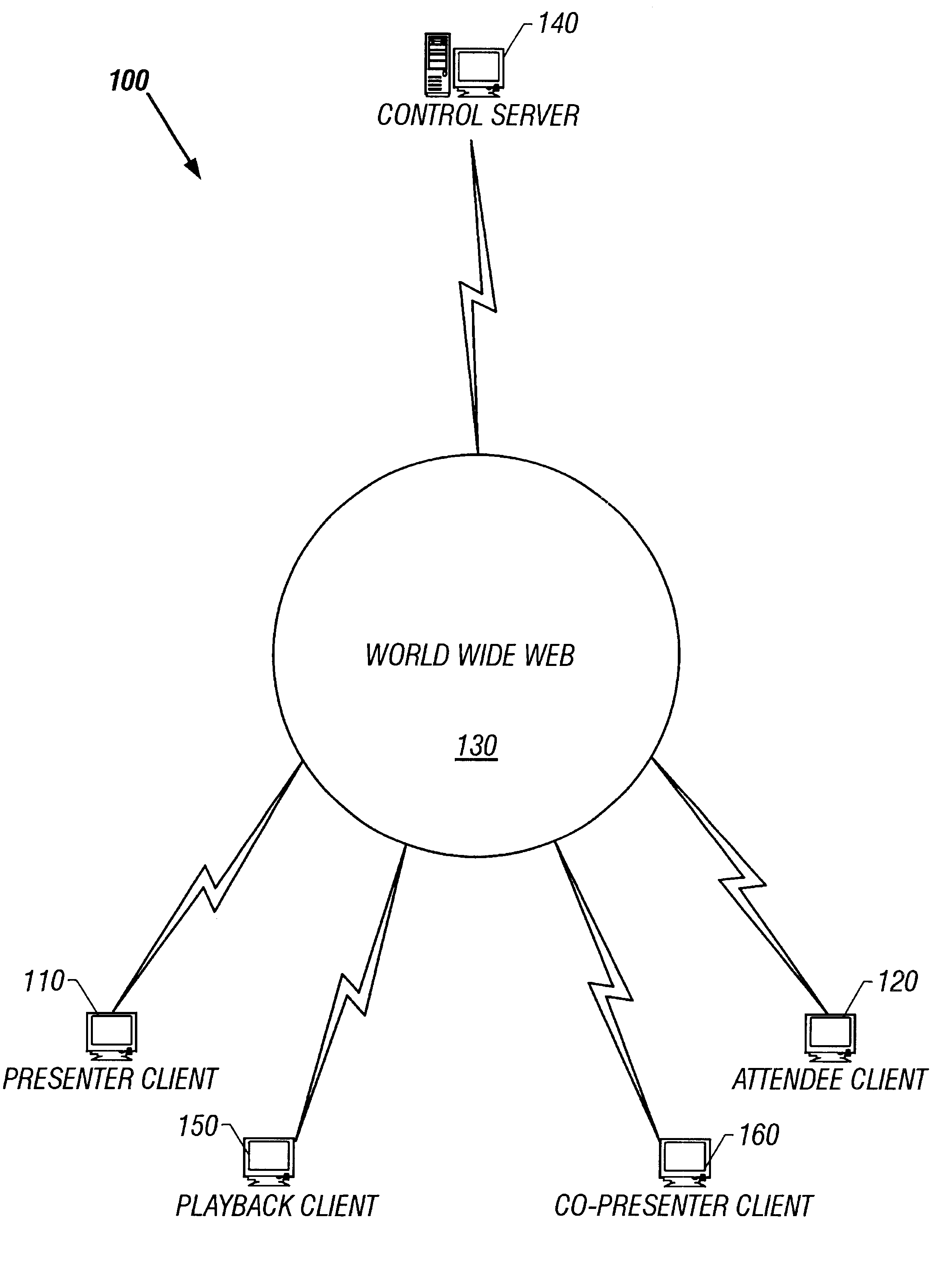
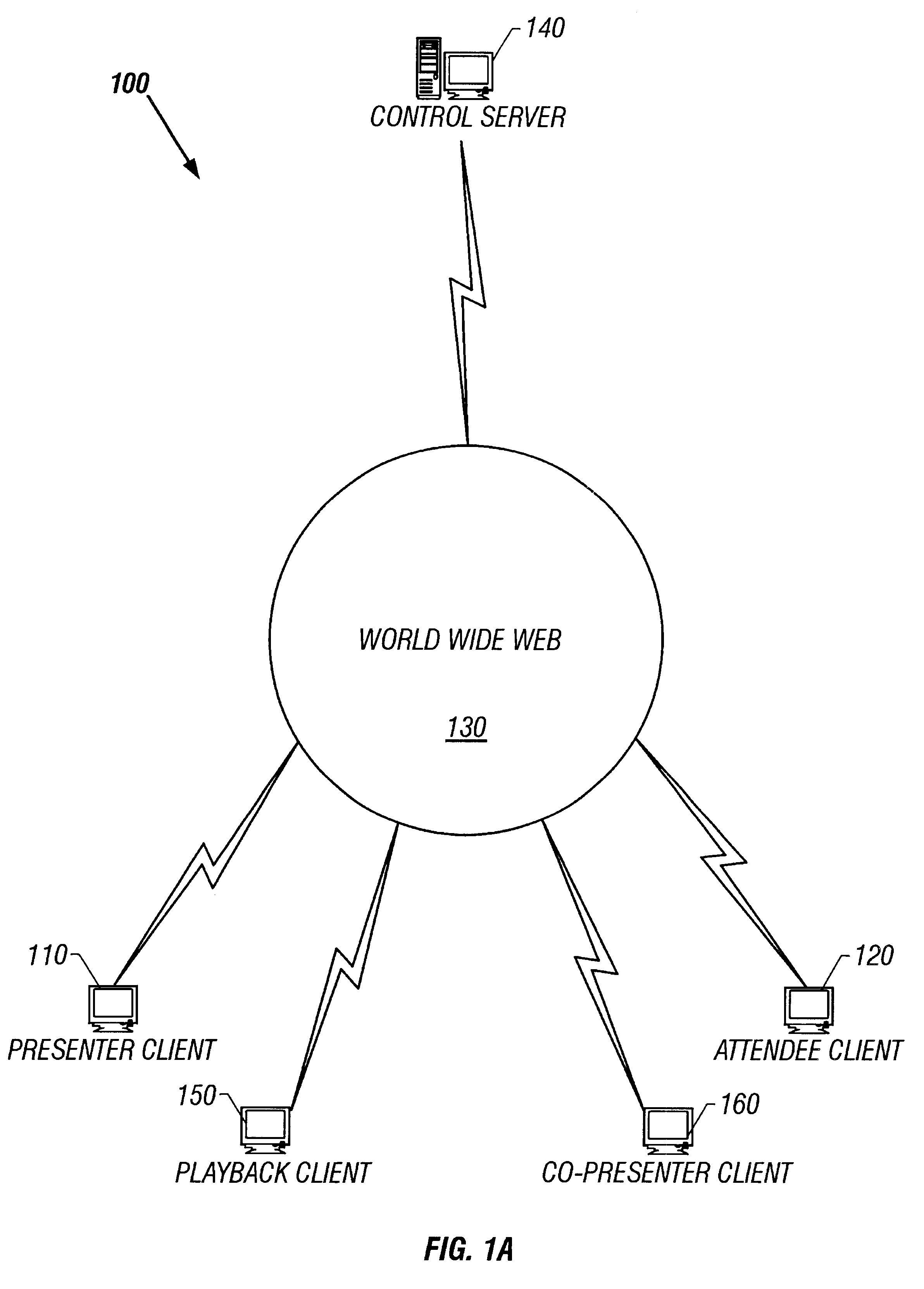
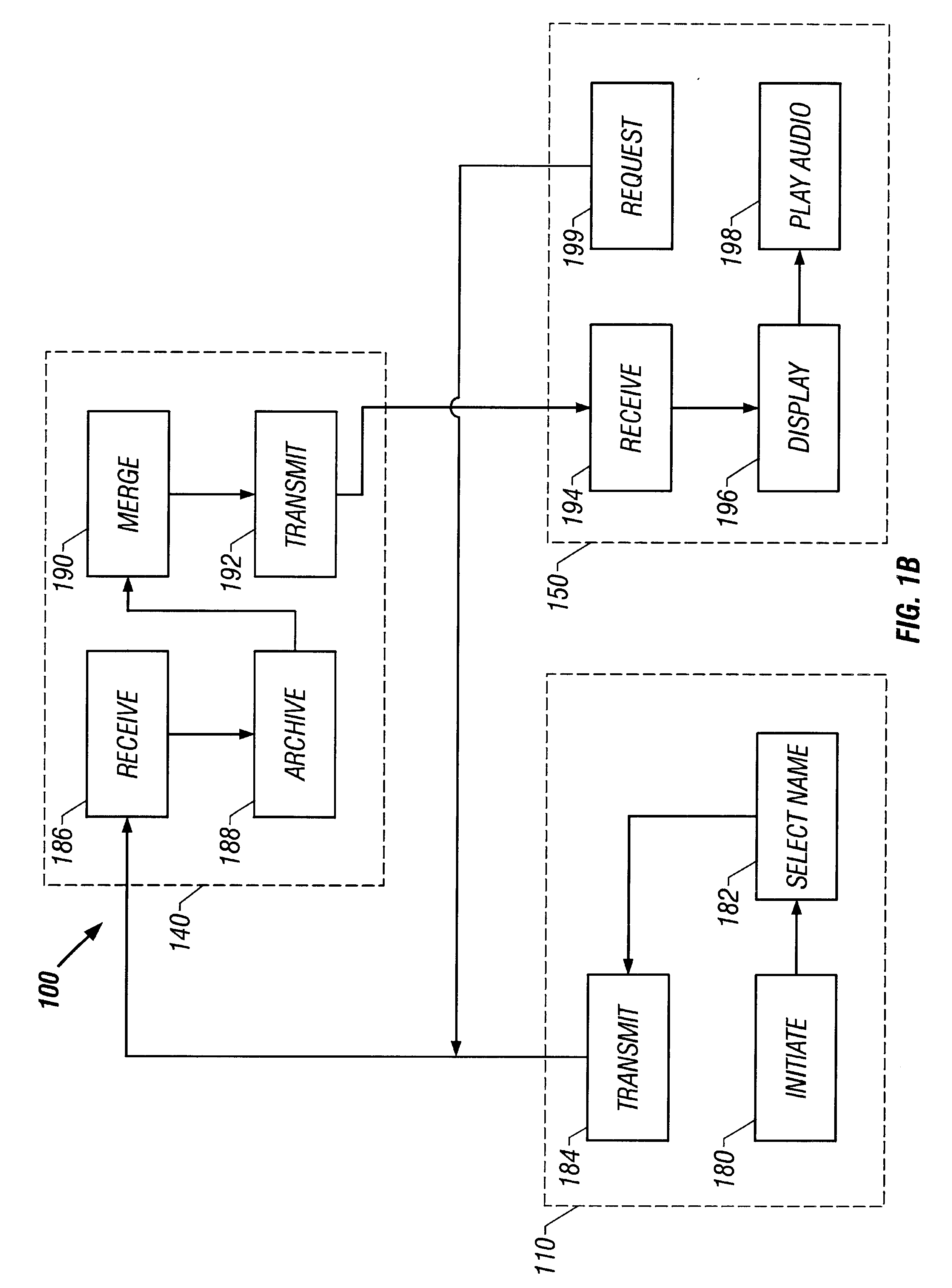
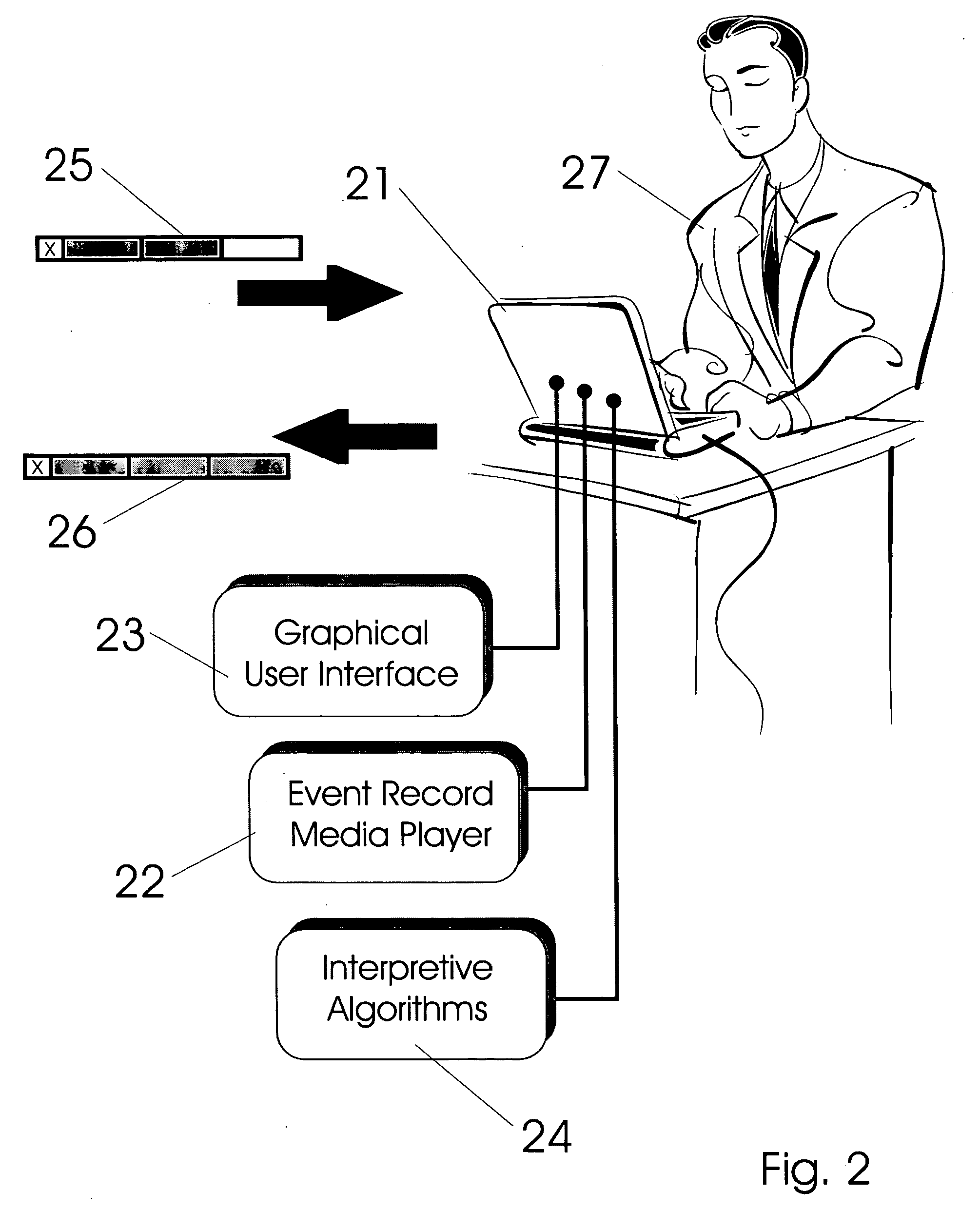
System and method for record and playback of collaborative Web browsing session
InactiveUS6535909B1Cost-effectiveSynchronised browsingWeb data retrievalNetwork connectionWorld Wide Web
A collaborative Web browsing session may take place over a network, allowing the presenter on a first computer to direct the audio and visual components of a browser on one or more second computers. The second computer is instructed to log into a control site that downloads an active control, such as an applet, to the second computer. The present invention allows a collaborative Web browsing session ("session"), as created by the presenter and witnessed by one or more users on second computers, to be recorded and archived by the control site. When a user of a computer is connected to the control site through a communication network such as the World Wide Web, that user may log into the control site and request to view an archived session. The session will then be replayed by the control site on the user's computer, directing the audio and visual components of the browser on the user's computer as if the user was attending the live session. The recorded session replays the events of the live session in real time such that the playback experience contains the same audio and visual events that took place when the session was originally being recorded.
Owner:RED HAT +1
Technology sharing during demand and supply planning in a network-based supply chain environment
The present disclosure provides for supplying collaborative planning by a computerized framework manager. Steps include furnishing network connections and collecting supply and demand information from business entities. Such information is analyzed and used to facilitate planning among the business entites. The network provides data access for multiple data sources and the network is used to store capacity data. The computerized framework manager conducts reverse inventory management of the business entities through the collection of data; analysis of data is then used to predict future demand, and predicted future demand is used to forecast costs to manufacturers, from which suggestions regarding optimization is made.
Owner:ACCENTURE GLOBAL SERVICES LTD
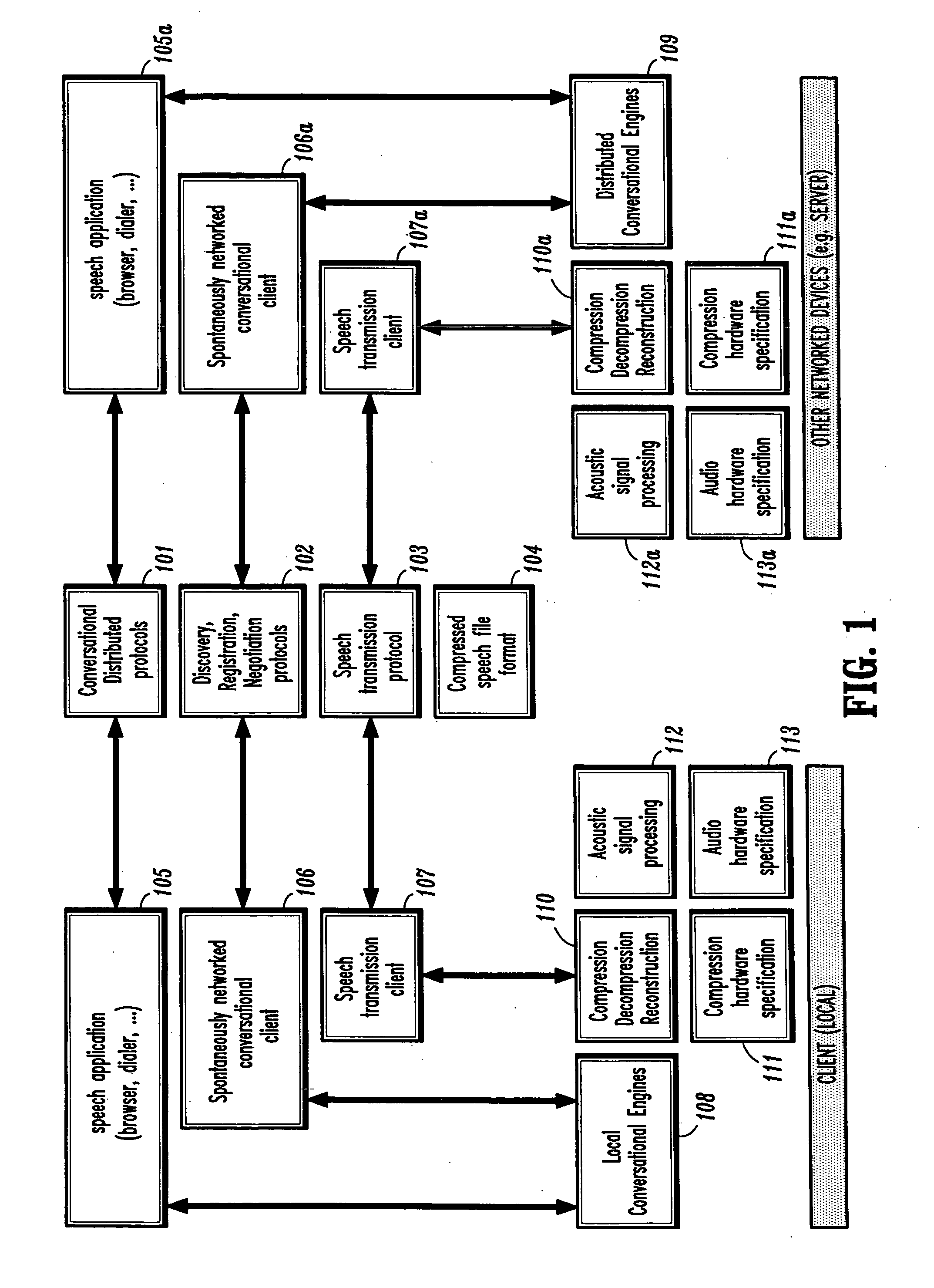
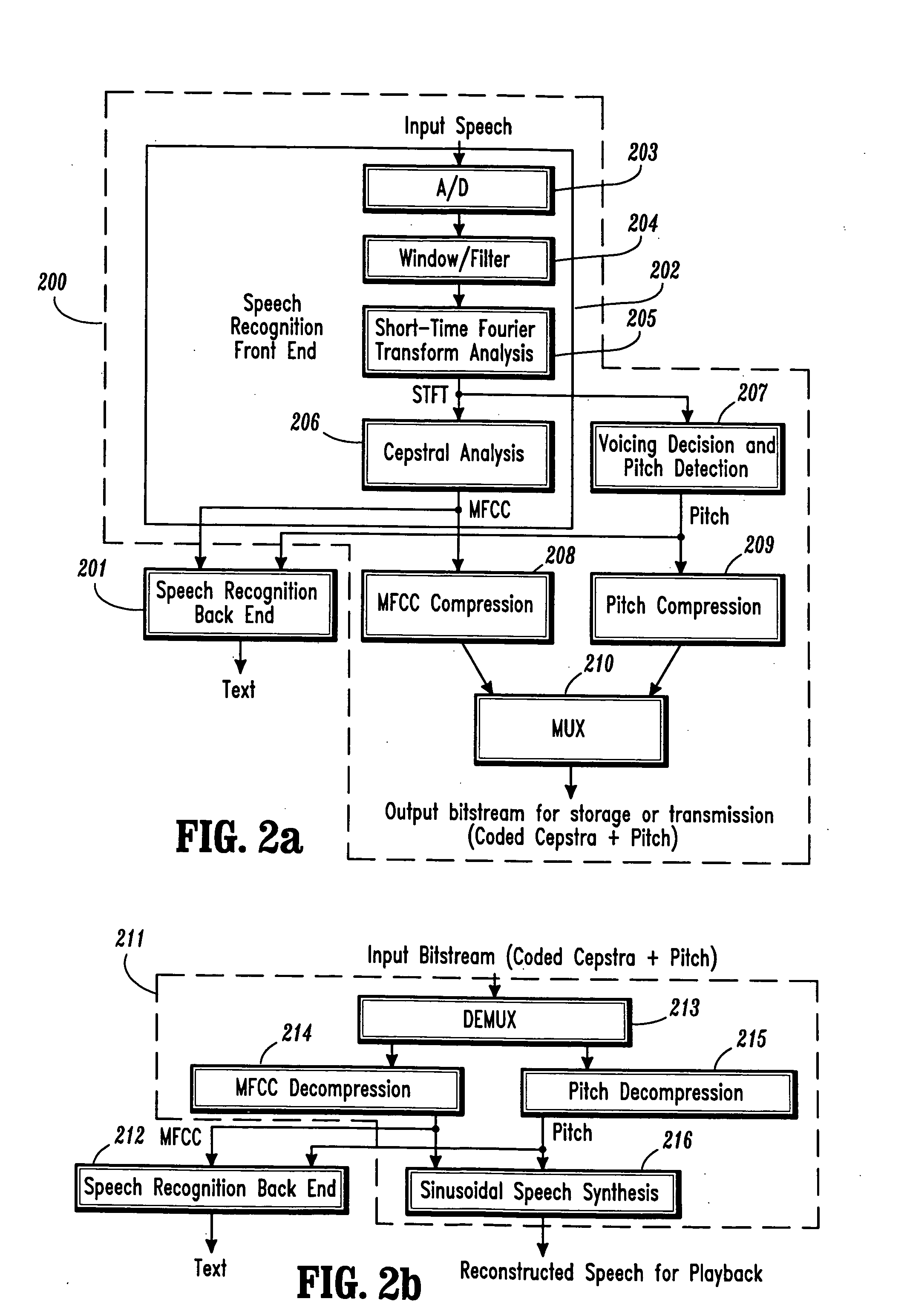
Conversational networking via transport, coding and control conversational protocols
InactiveUS6934756B2Broadcast transmission systemsMultiple digital computer combinationsSession controlRemote control
A system and method for implementing conversational protocols for distributed conversational networking architectures and / or distributed conversational applications, as well as real-time conversational computing between network-connected pervasive computing devices and / or servers over a computer network. The implementation of distributed conversational systems / applications according to the present invention is based, in part, on a suitably defined conversational coding, transport and control protocols. The control protocols include session control protocols, protocols for exchanging of speech meta-information, and speech engine remote control protocols.
Owner:IBM CORP
Event monitoring and management
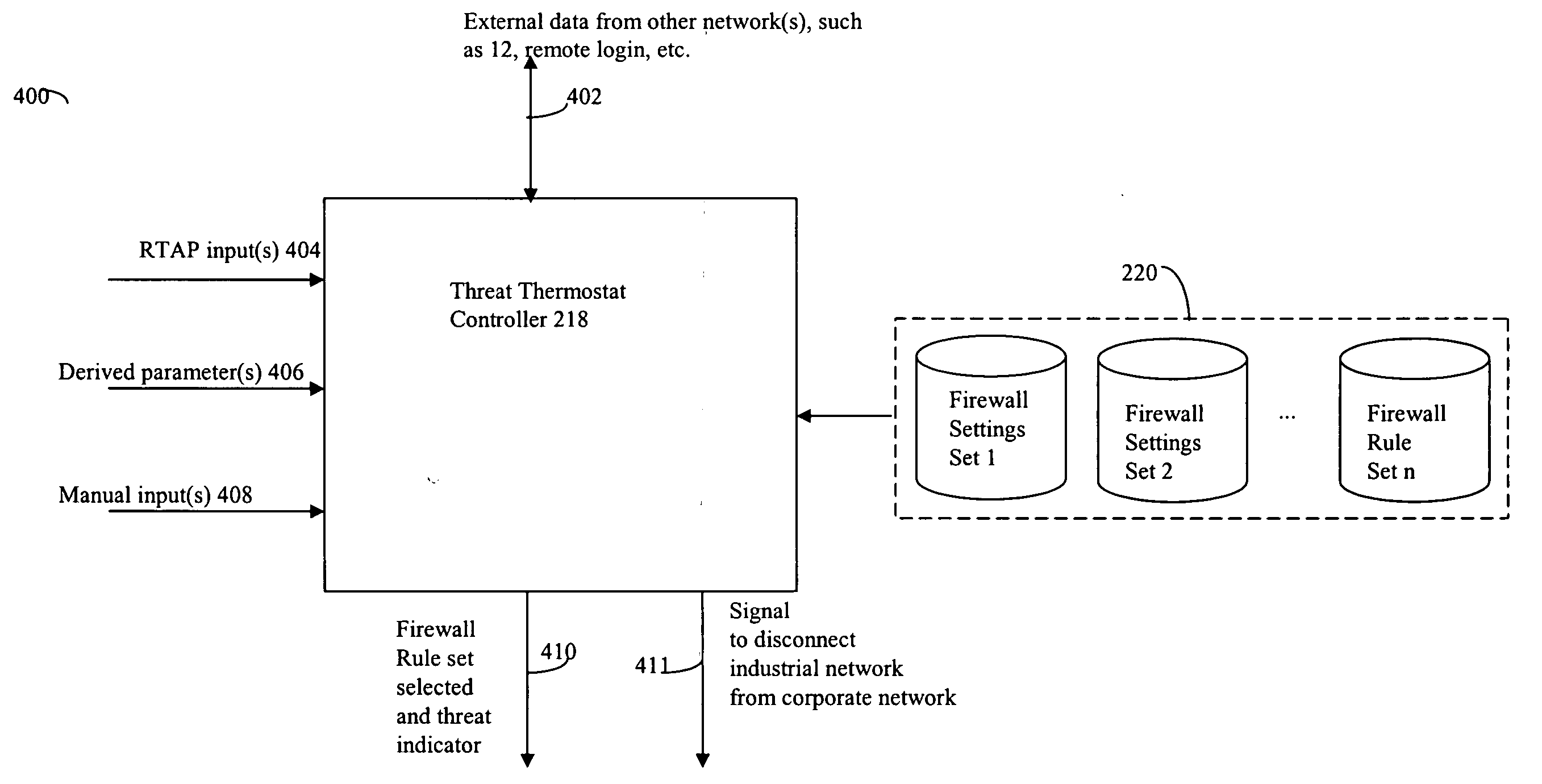
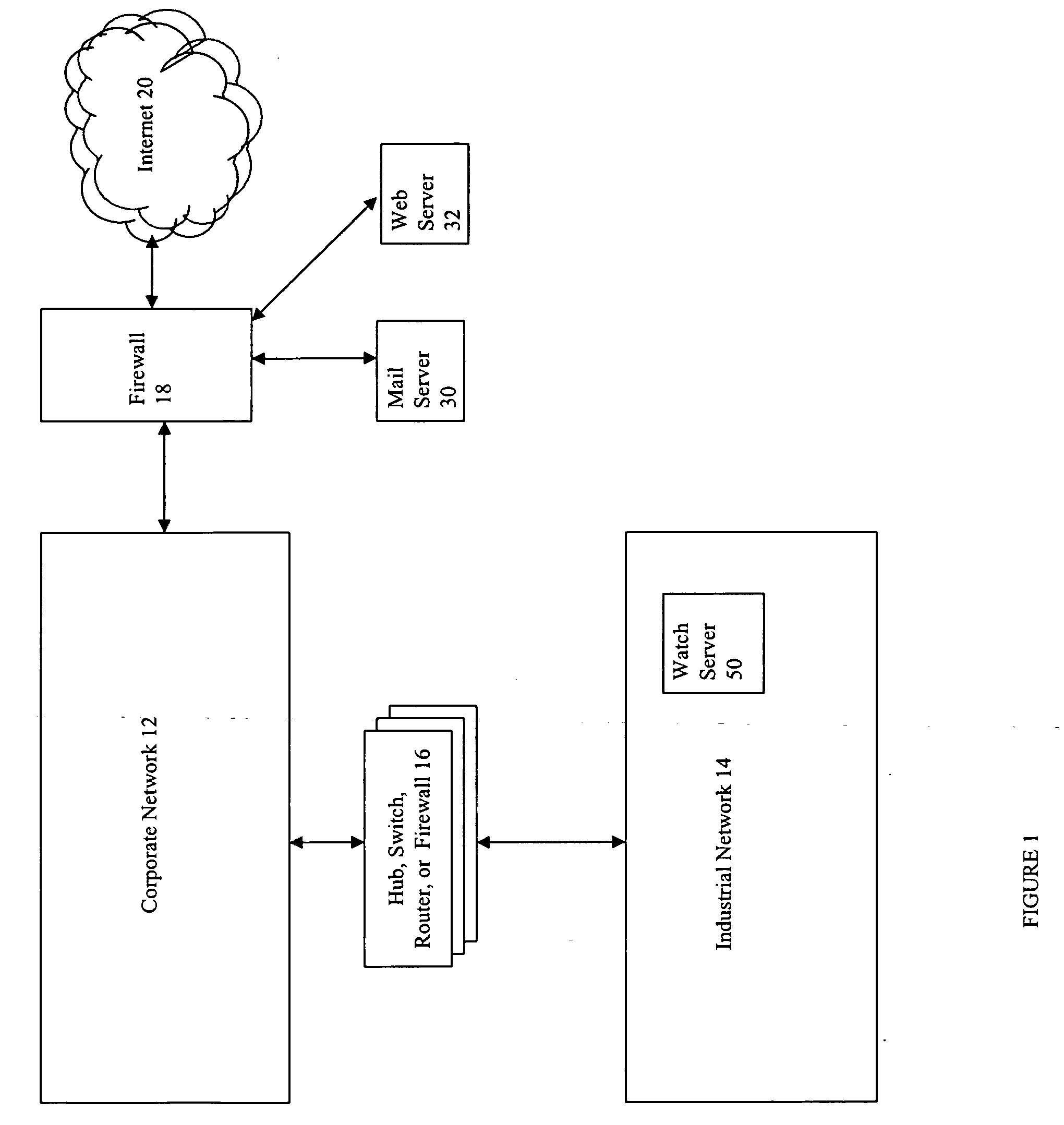
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
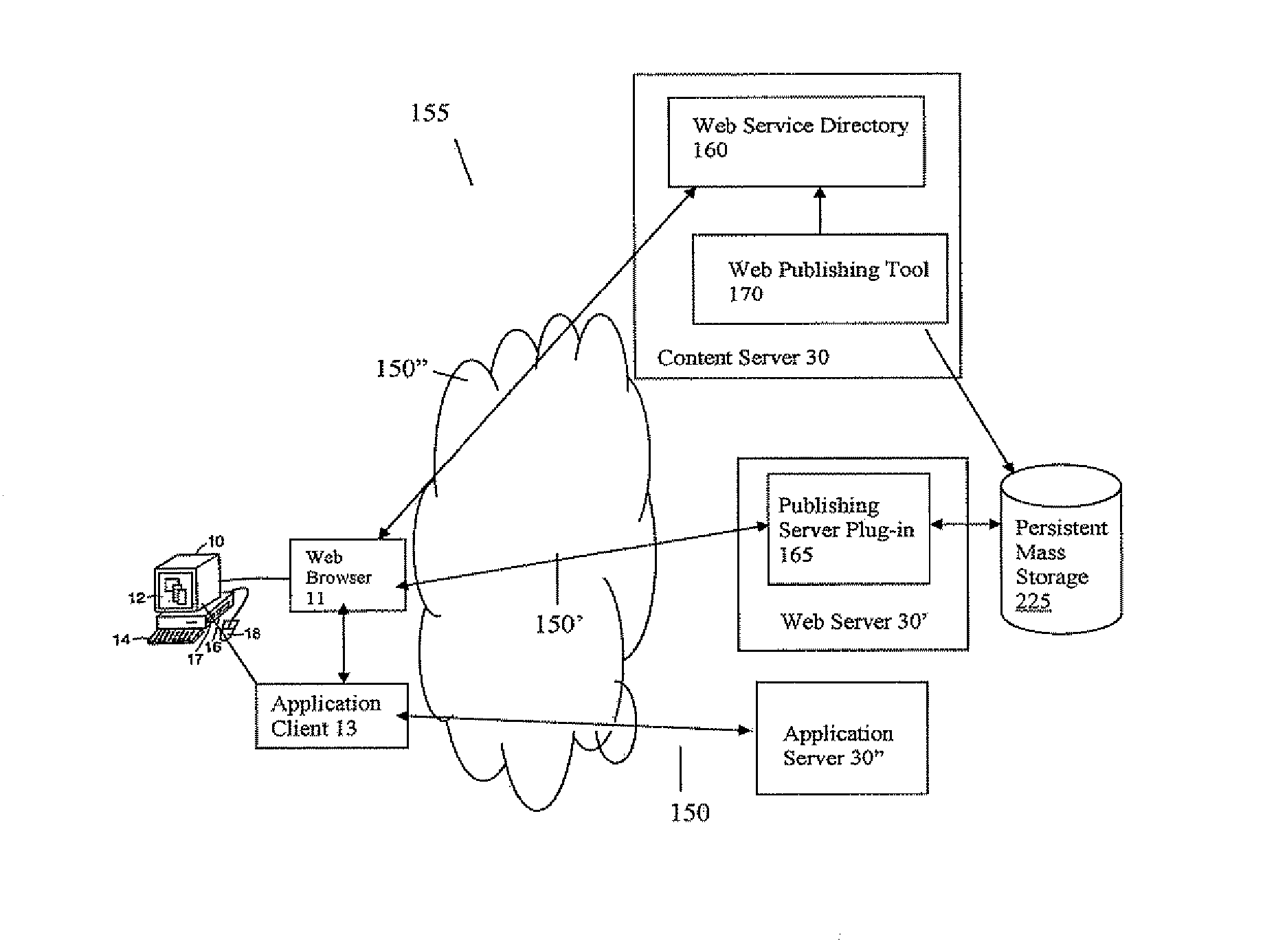
Systems and Methods for Accelerating Delivery of a Computing Environment to a Remote User
ActiveUS20070244987A1Reduce deliveryFacilitate communicationMultiple digital computer combinationsData switching networksNetwork connectionData file
The present invention is directed towards the acceleration of delivery of a computing environment to a remote user of a client at a remote location. The computing environment may include an application and a data file used or processed by the application. The application and data file may be stored or provided via a server remote to the client. The user can request a computing environment from the server that provides for execution of the application by the user via the remote computer. For example, the server may stream the application to the remote client. The client and server may communicate via an appliance that accelerates communications between the client and server. For example, the appliance may accelerate the streaming of the application to the remote user. In some cases, the application or remote user may also request a data file from the server, and the appliance accelerates the delivery of the data file to the remote user. As such, users at remote locations obtain accelerated access via any network connected device to applications and data files located remotely to the user.
Owner:CITRIX SYST INC
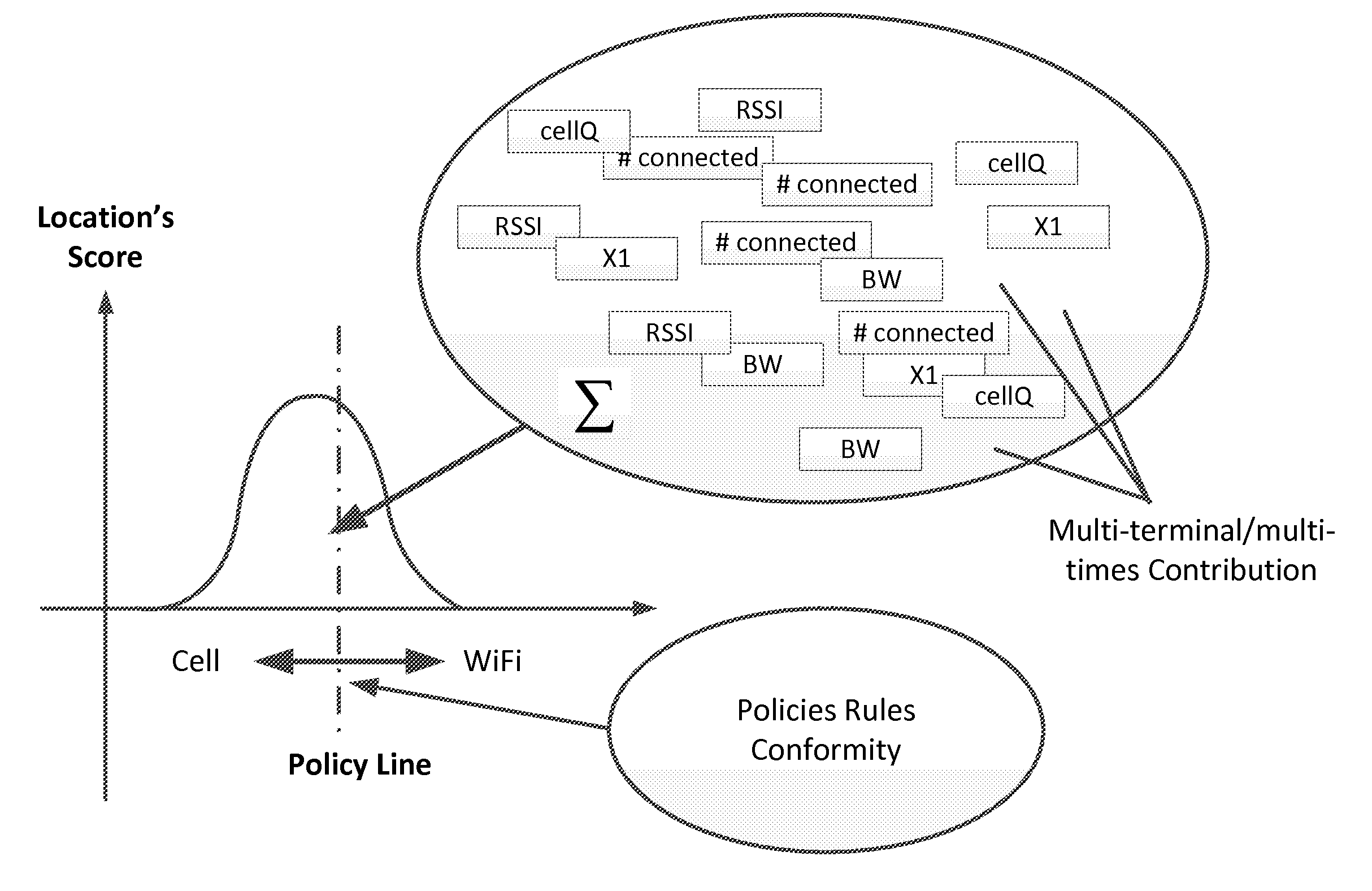
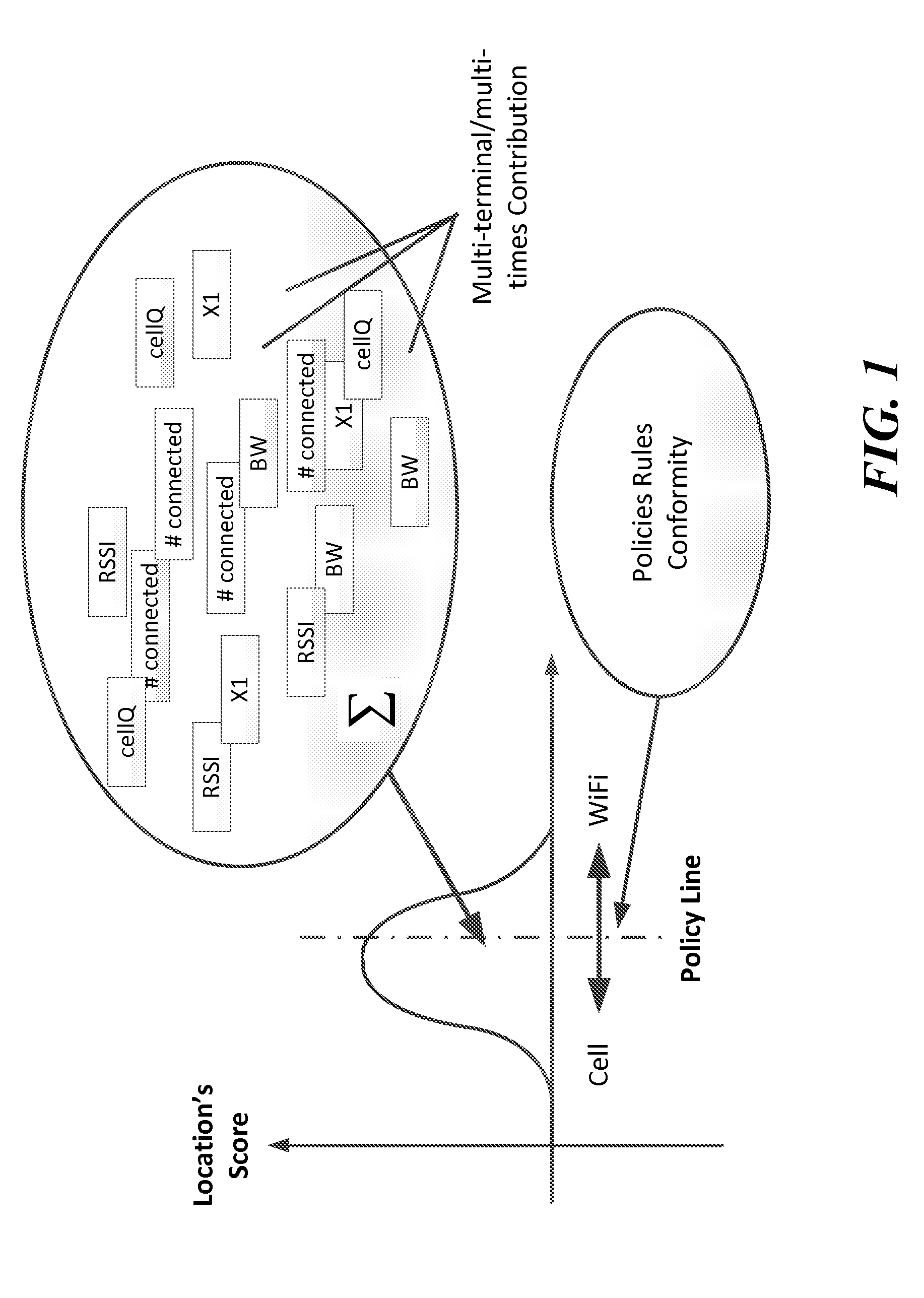
Dynamic Network Connection System and Method
ActiveUS20120196644A1Reduce error rateReduce noiseAssess restrictionRadio transmissionNetwork connectionChoice making
A method and system for selecting a network to establish a connection to from a set of available network includes a network database providing historical information about each of the networks and sends the database information to end user terminals. The end user terminals monitor real-time performance information about each of the available networks and can send this information to the network database. The end user terminals also include network connection policy information which can be used to make the selection decision. The end user terminal determines a network quality score for each available network as a function of the historical information from the network database, the real-time performance information about each available network and the network connection policy information. The end user terminal can select the available network as a function of the network quality score, for example, selecting the available network with the highest network quality score.
Owner:WEFI
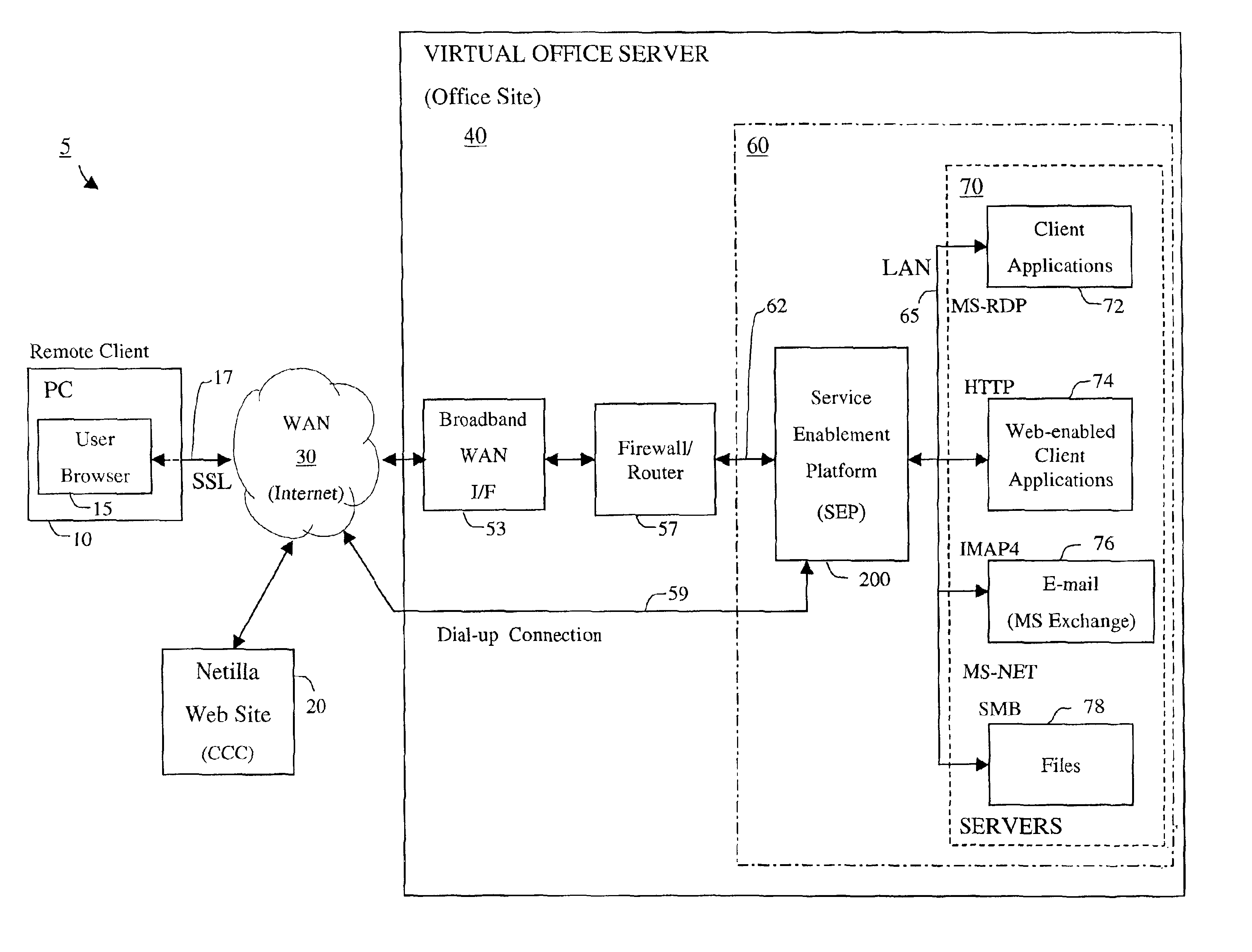
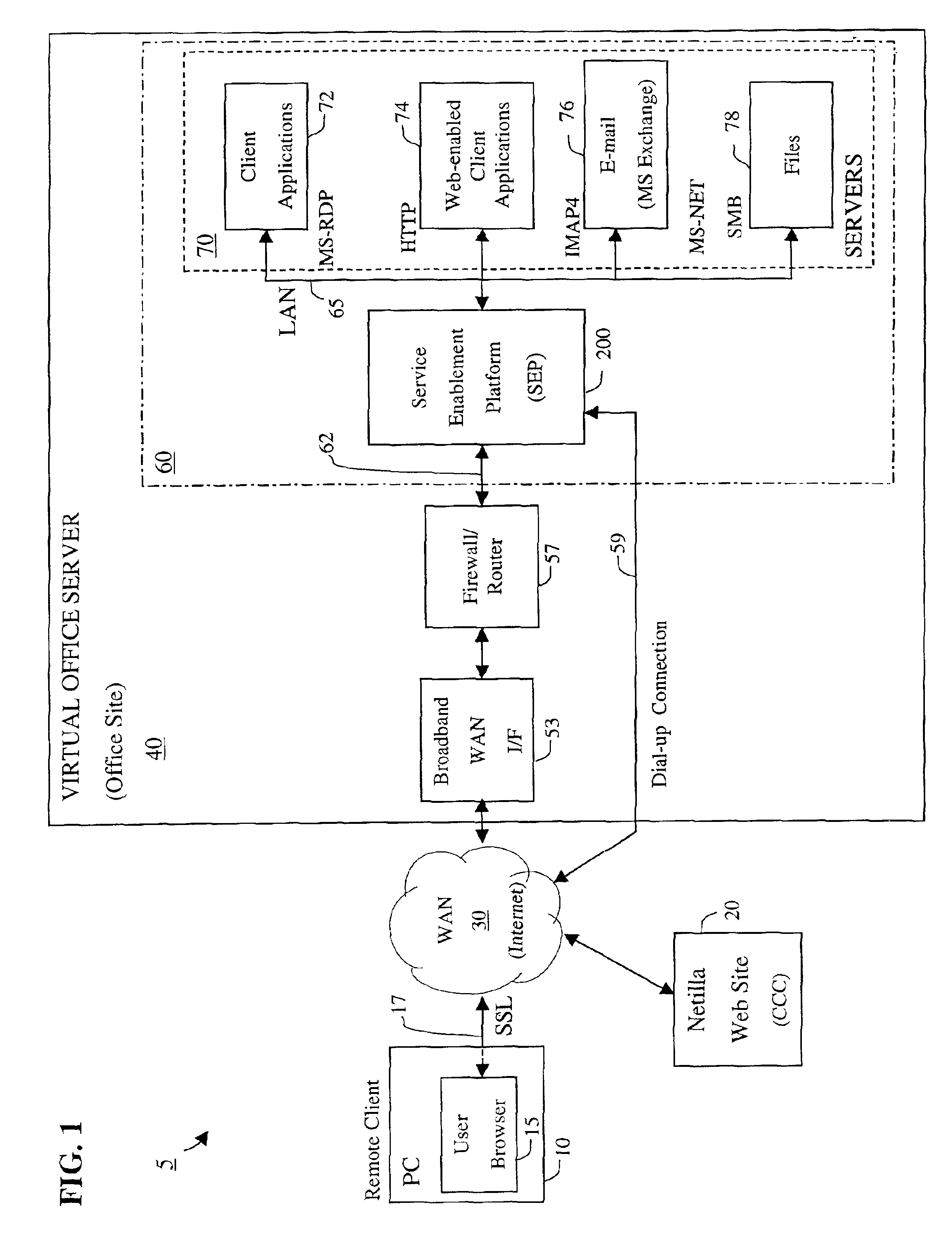
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6920502B2Readily and easily accommodateExpanding processing and storage capacityMultiple digital computer combinationsProgram controlCA protocolNetwork connection
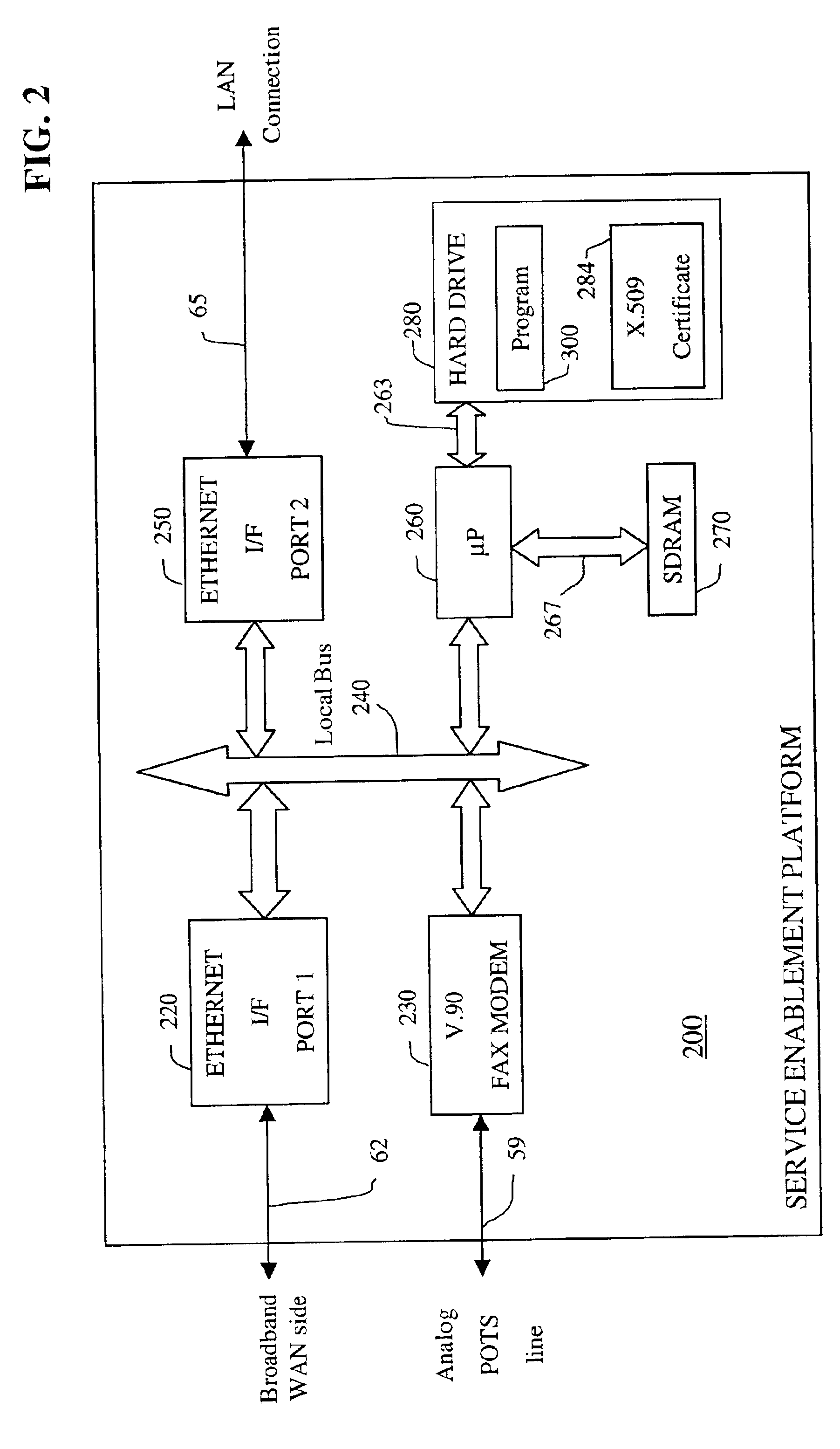
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Movie studio-based network distribution system and method
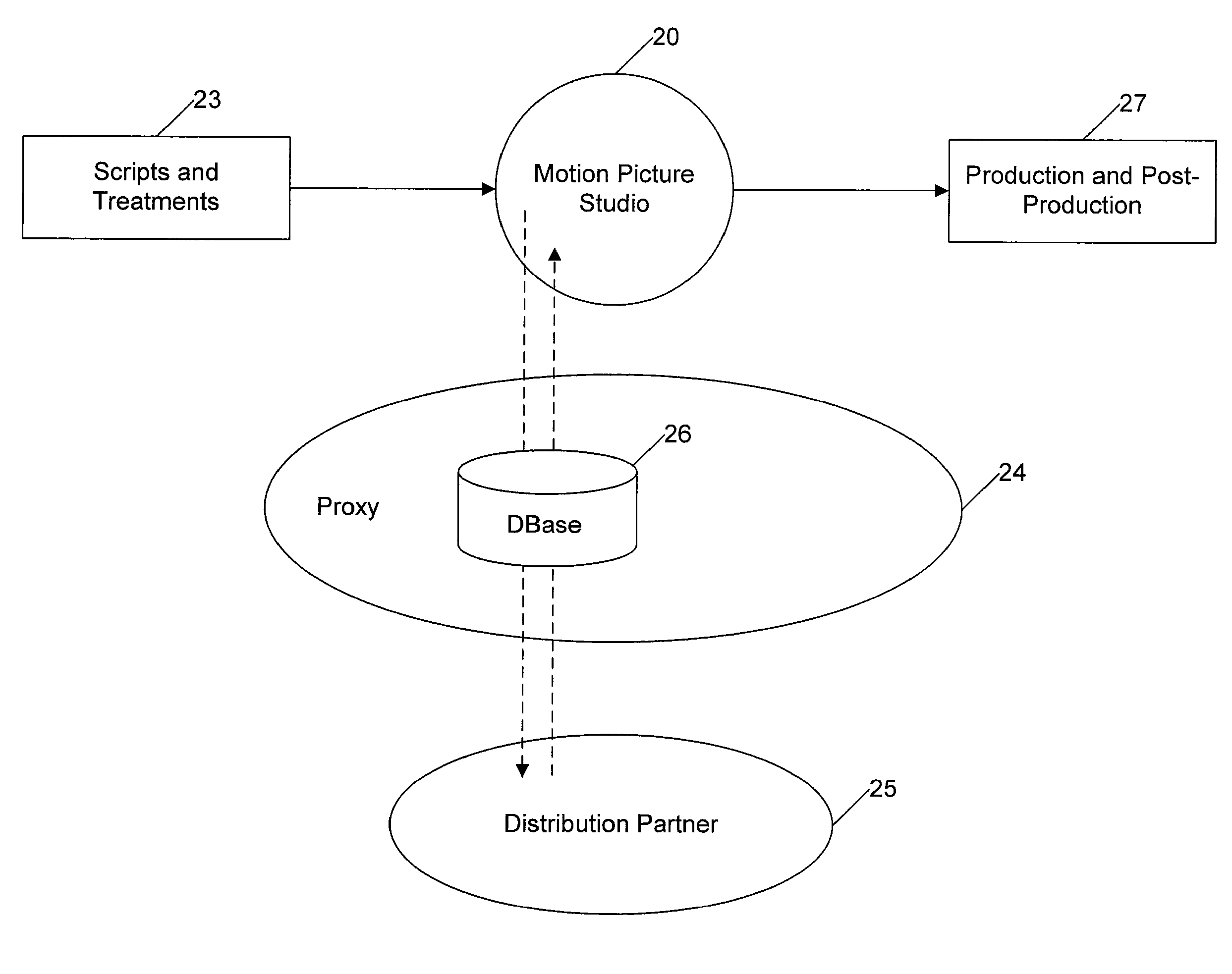
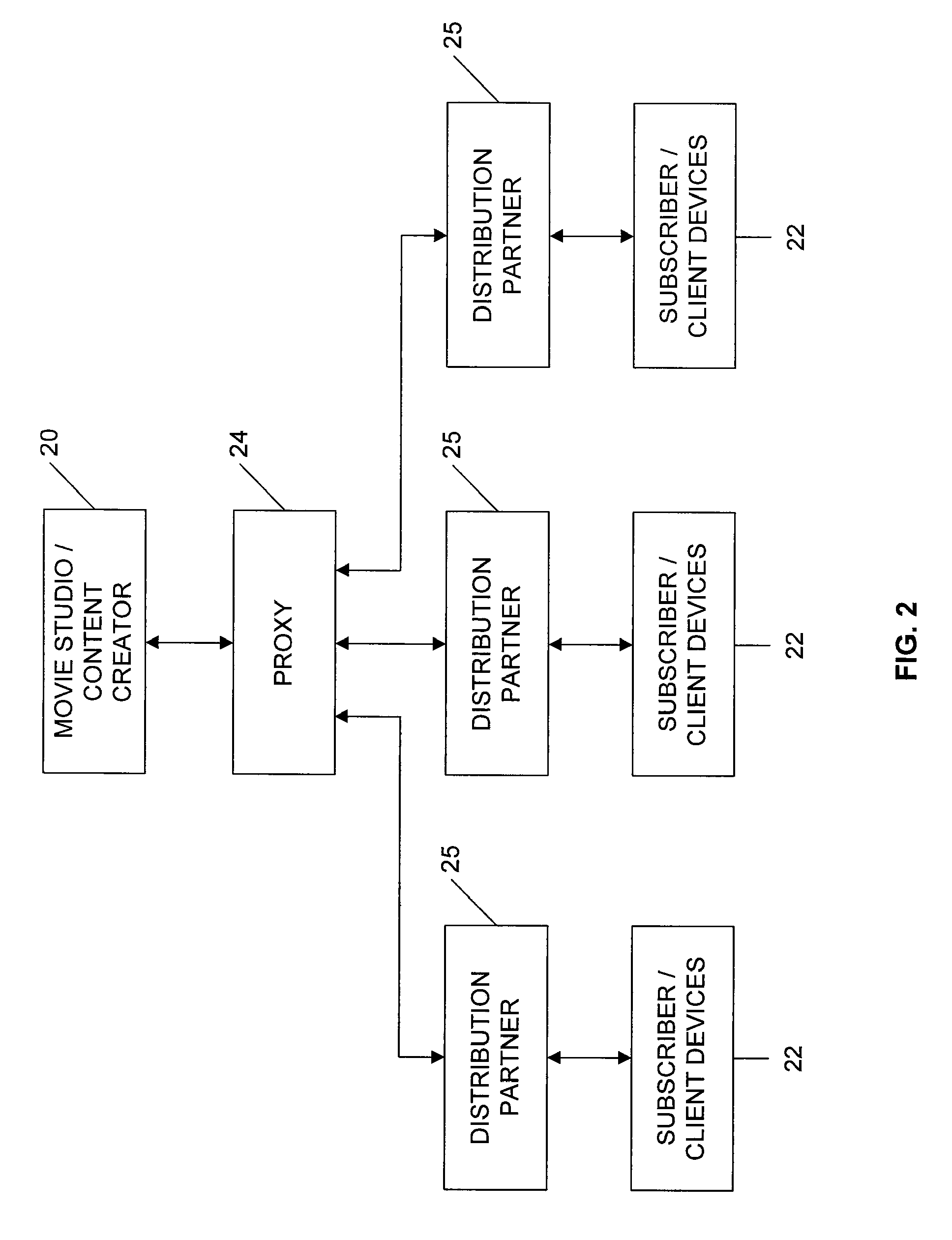
ActiveUS20070220575A1Analogue secracy/subscription systemsTwo-way working systemsAccess networkDigital content
Digital content files containing entertainment media such as movies, TV shows, and the like are distributed from at least one content source primarily responsible for the original creation of the media to subscribers over a network system. The content source is connected over at least one content source network to a plurality of distribution partners, and each distribution partner is connected with a selected group of subscribers over an access network. A requested digital content file is distributed from the content source to a subscriber in a network distribution path comprising at least the content source network, the distribution partner associated with the subscriber, and the second network. A profile information package containing subscriber preferences is transmitted from the subscriber to the content source by way of a proxy over the network distribution path, and the profile information package is stored at the content source.
Owner:VERIMATRIX INC
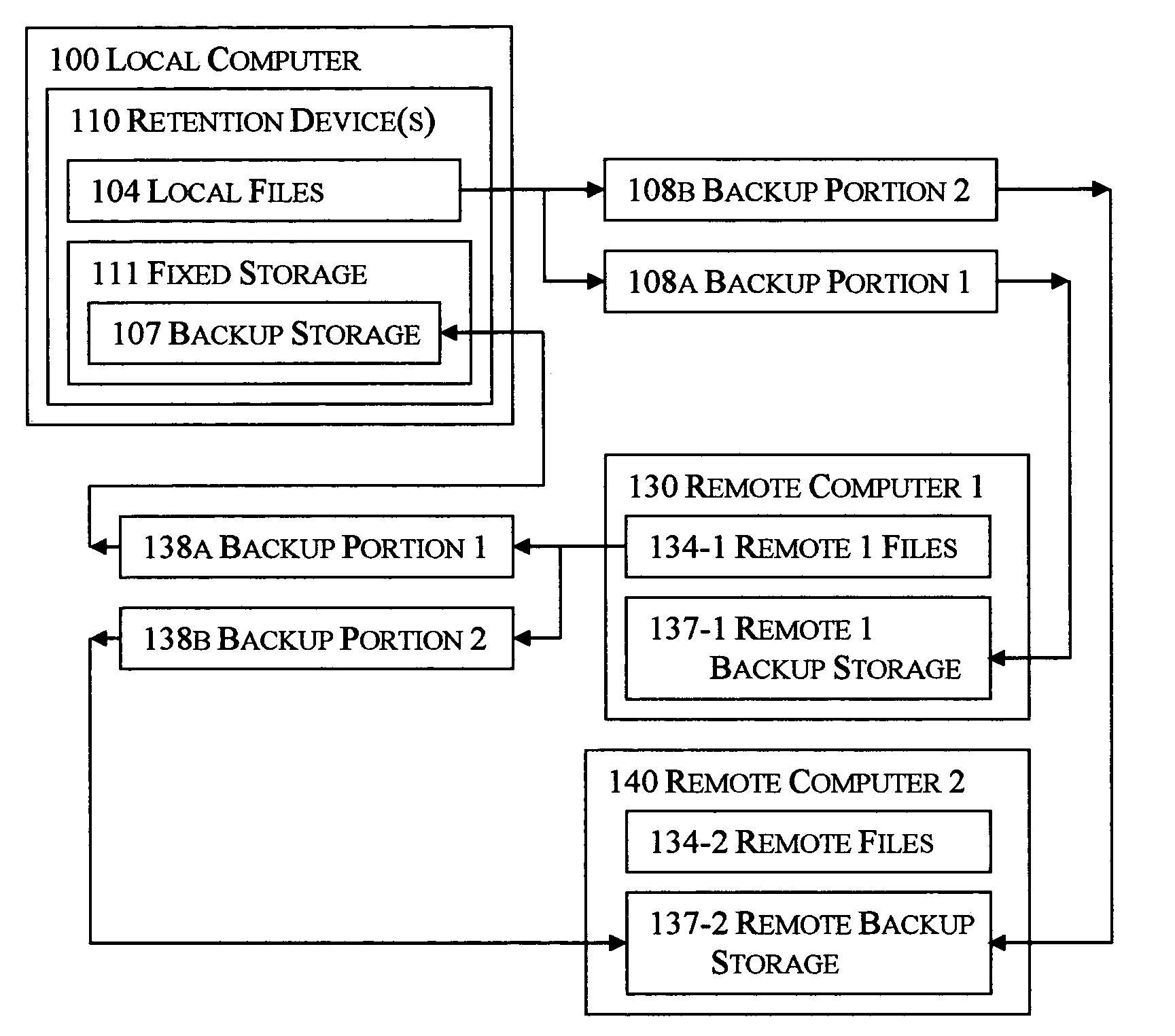
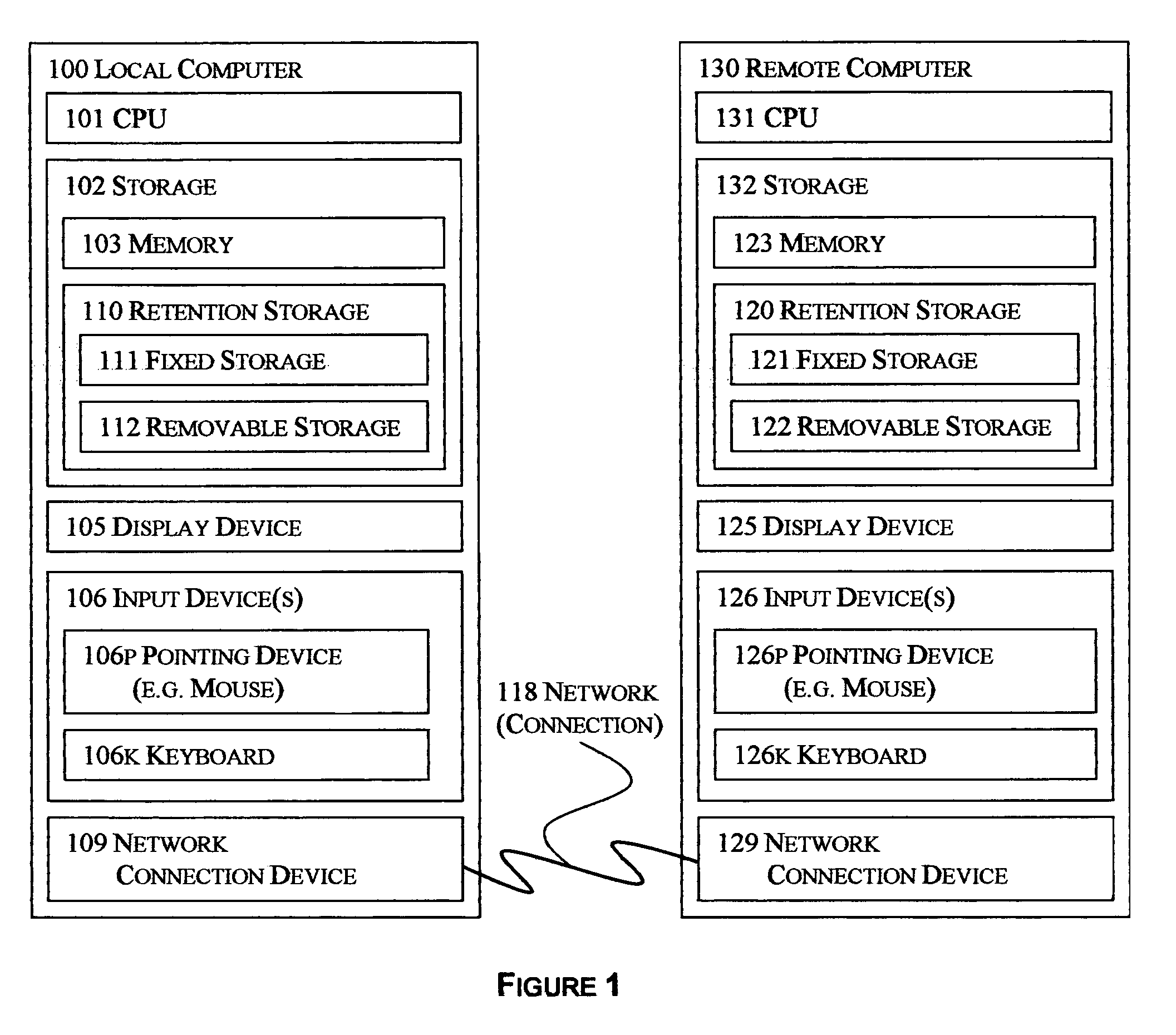
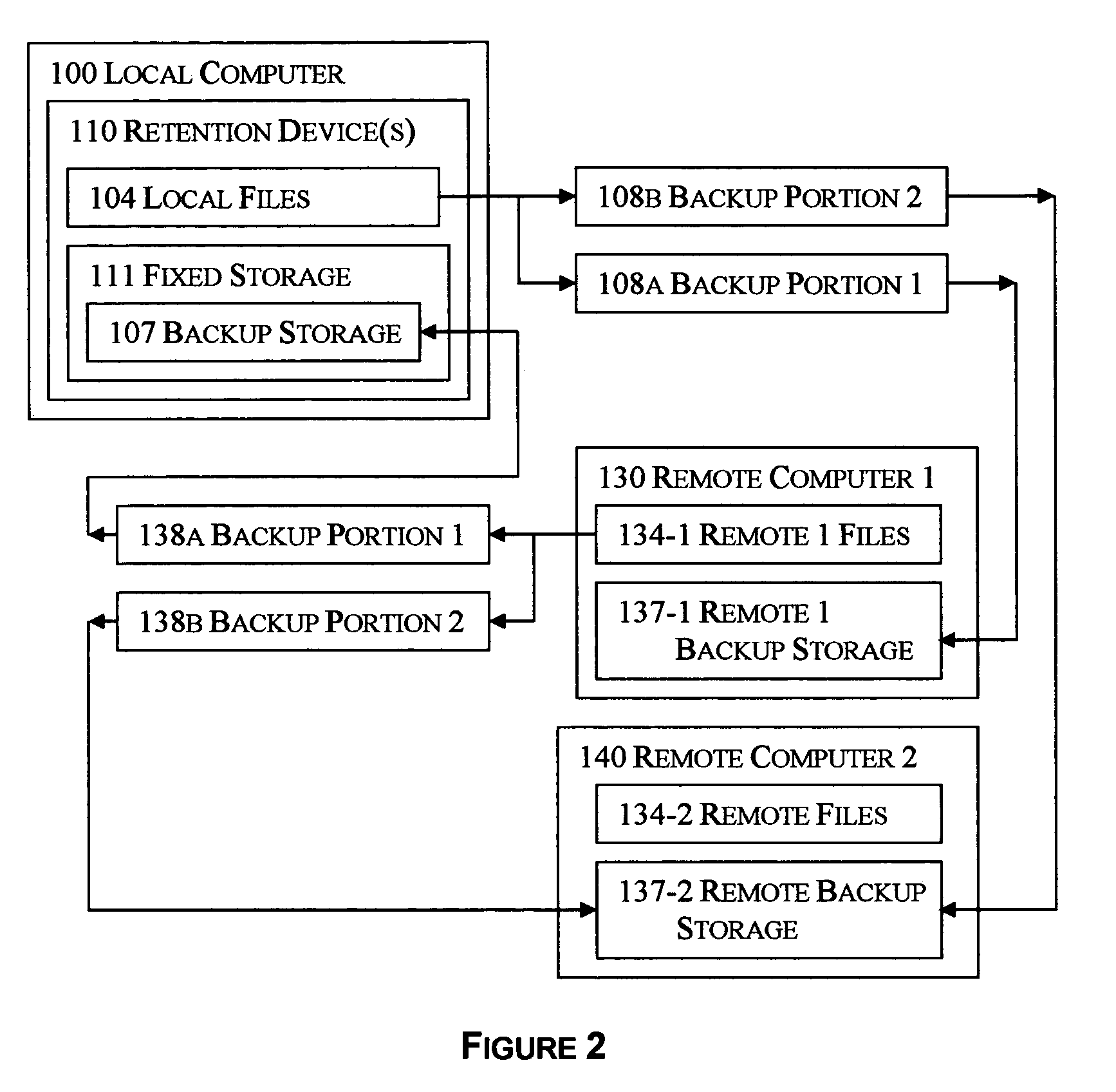
Selective reciprocal backup
InactiveUS7330997B1Risk minimizationIncrease probabilityError detection/correctionMemory systemsNetwork connectionApplication software
The disclosed technology applies the principle of anonymous reciprocity to facilitate remote backups. A local computer stores other computer's backup files, while storing backup copies of local files on other computers connected through a network. Each computer may securely maintain and manage storage for other computers' files. Application may be constrained to a local area network, or work on the Internet. The disclosed technology works in a peer-to-peer environment; no central server is required. The same disclosed technology may also apply to file sharing.
Owner:ODOM GARY
Conversational networking via transport, coding and control conversational protocols
InactiveUS20060041431A1Broadcast transmission systemsAutomatic exchangesSession controlRemote control
Owner:INT BUSINESS MASCH CORP
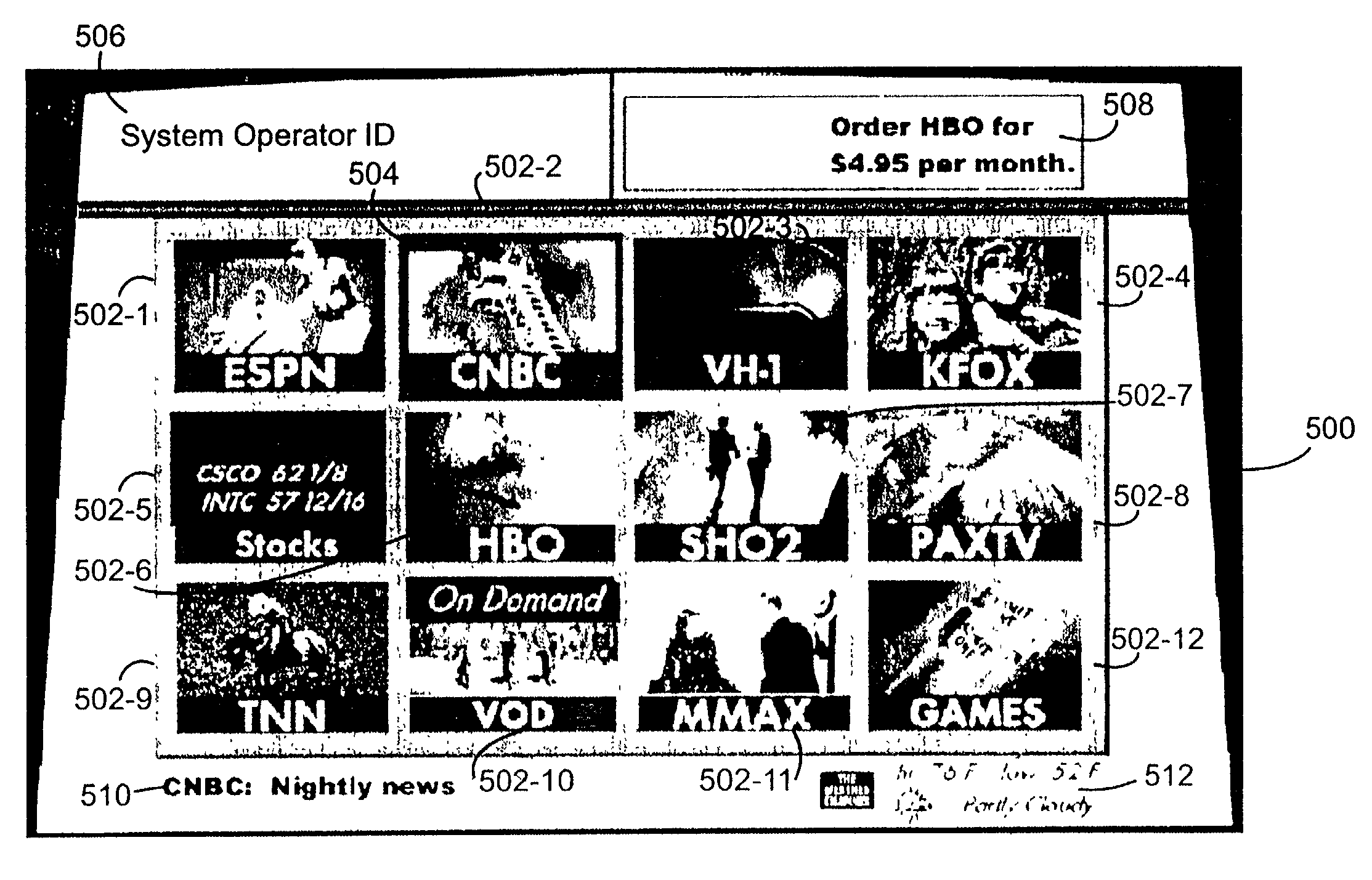
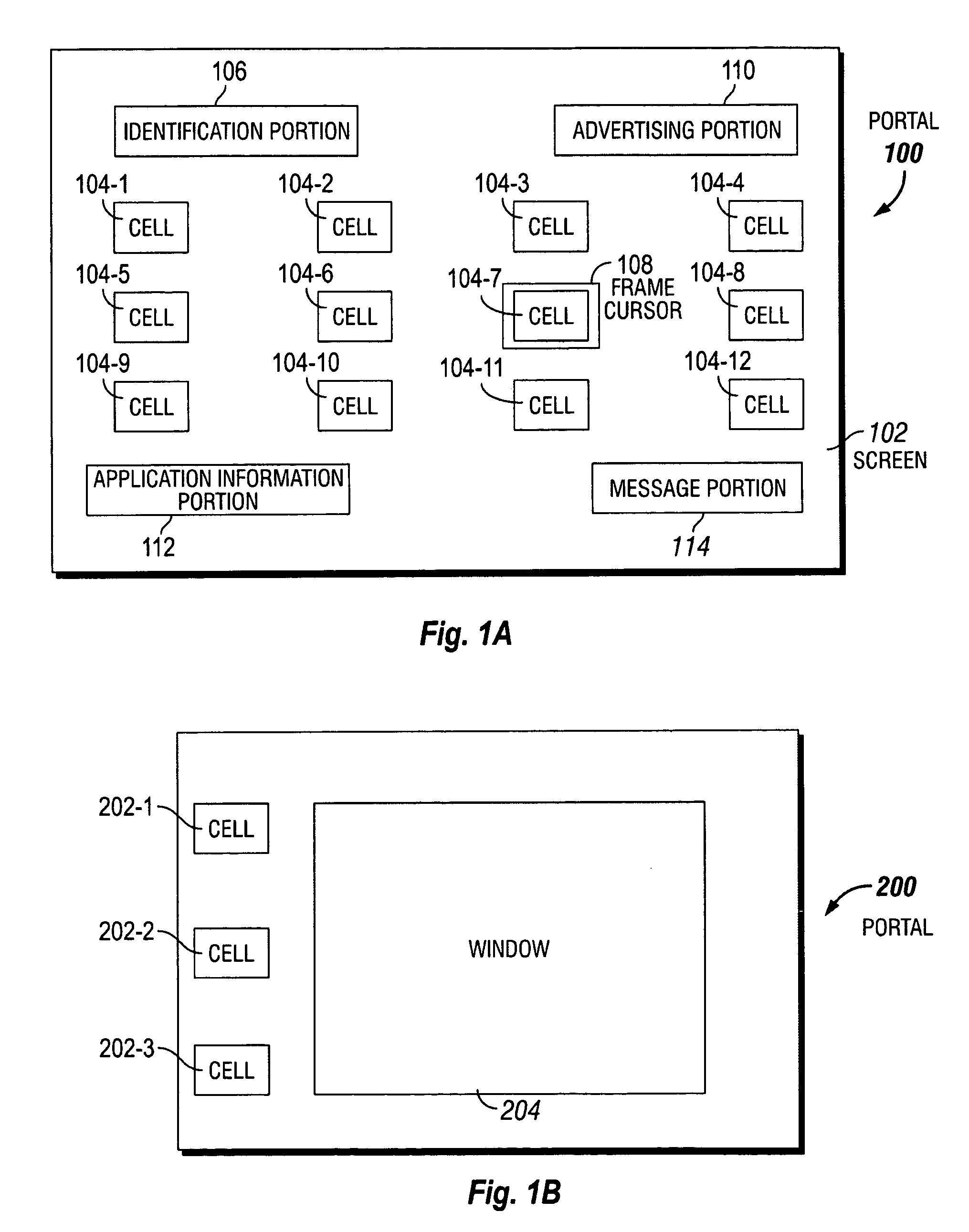
Portal for a communications system
InactiveUS7174512B2Television system detailsRecording carrier detailsCommunications systemUser input
A portal for a communications system that includes a remote terminal connected via a communications network to a broadcast center. The portal includes a display connected to the remote terminal for displaying an arrangement of cells, each cell including a visual object and an underlying application. A user input device enables user inputs to select one of the cells. The portal provides simple and intuitive access to the wide variety of services currently offered, and to be offered in the future, in communications systems.
Owner:INTERDIGITAL MADISON PATENT HLDG
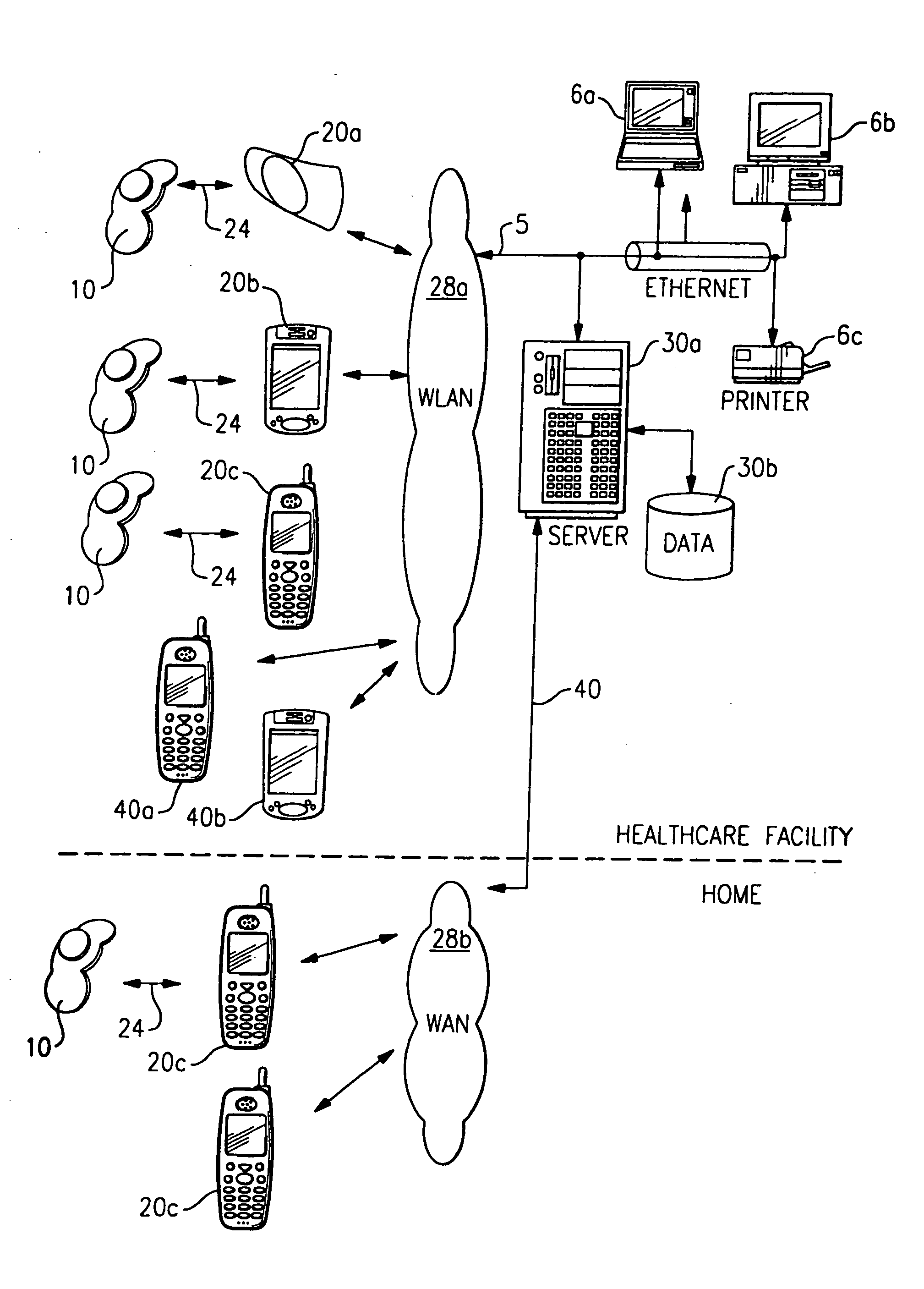
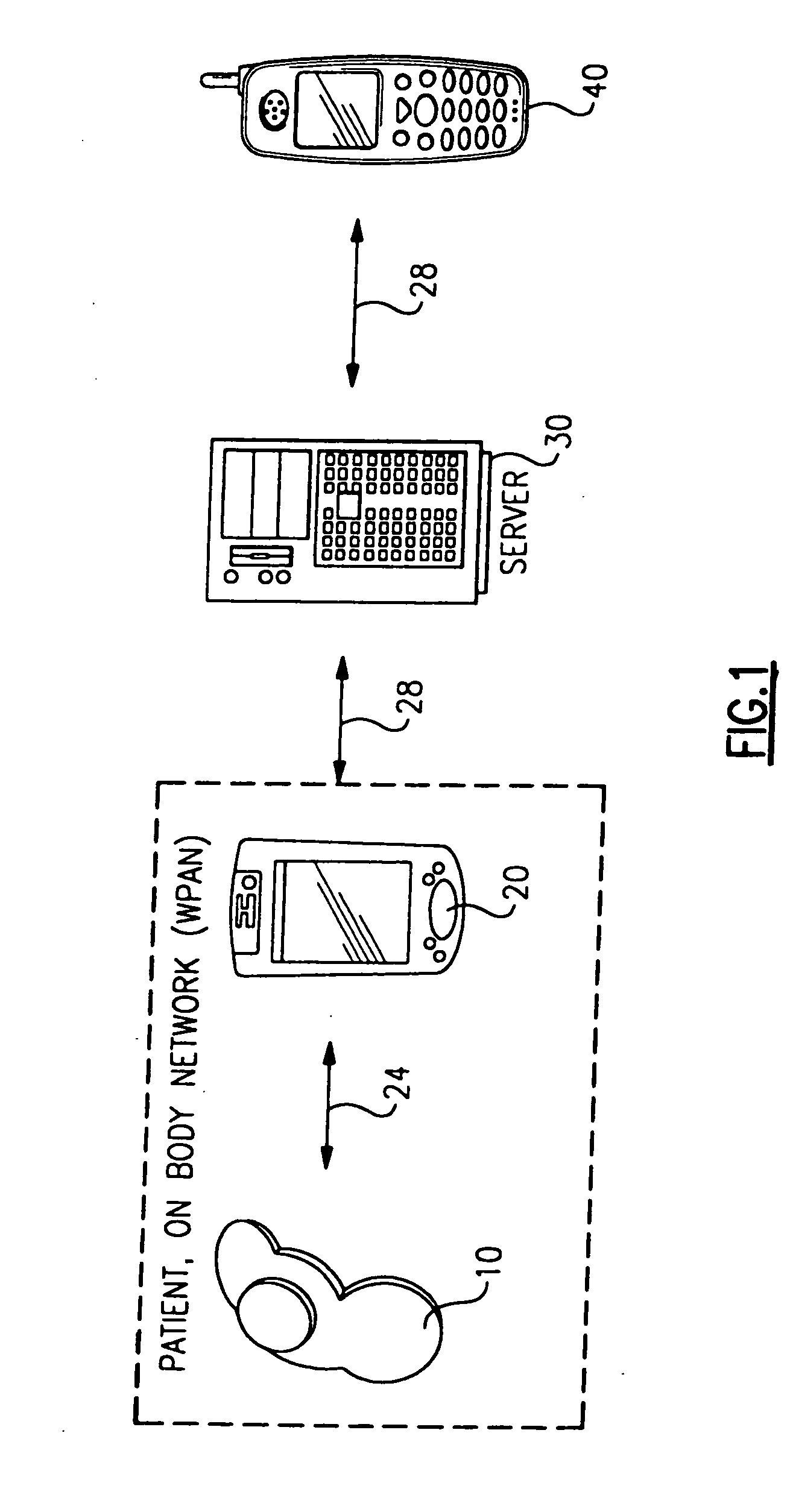
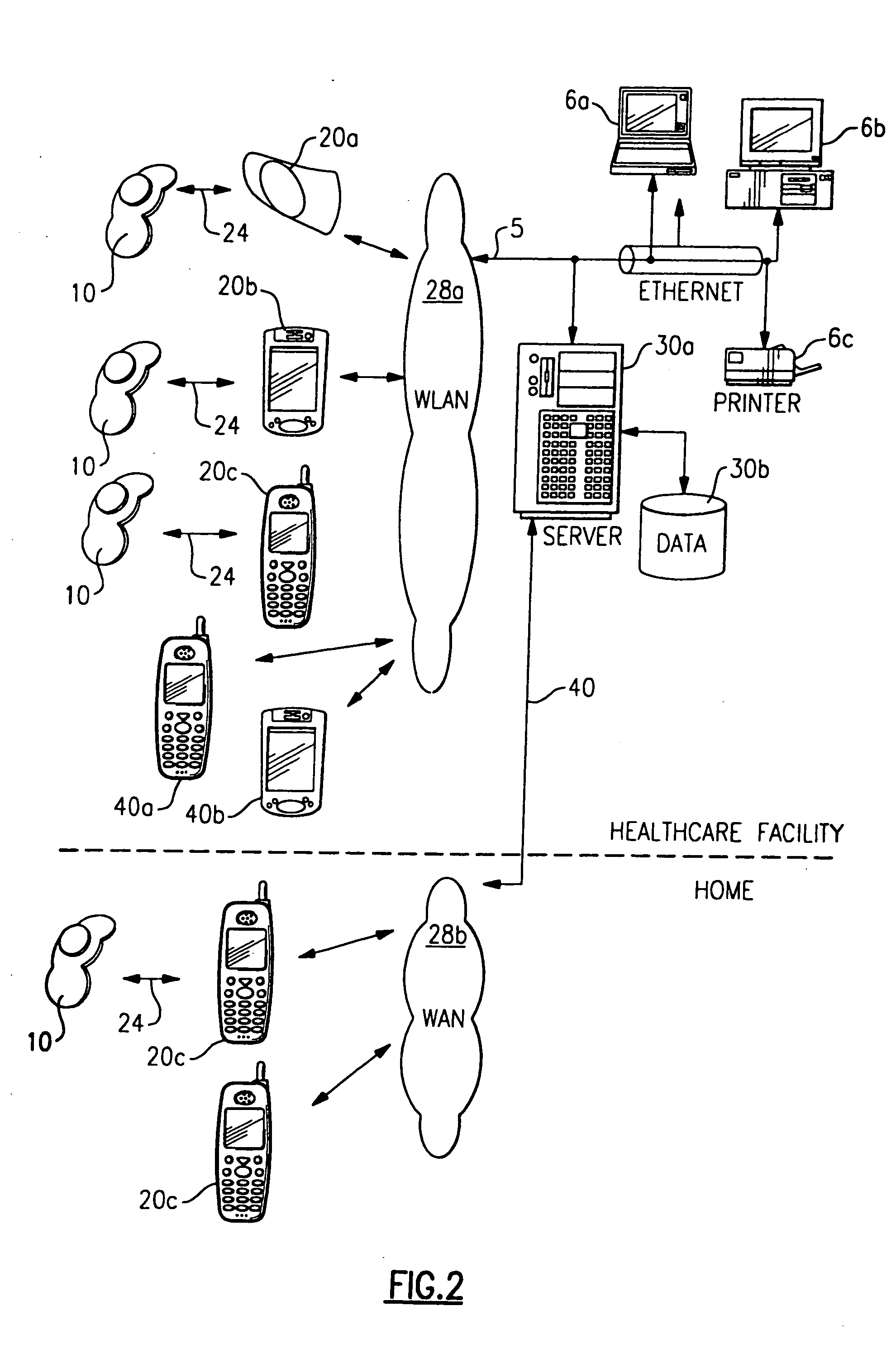
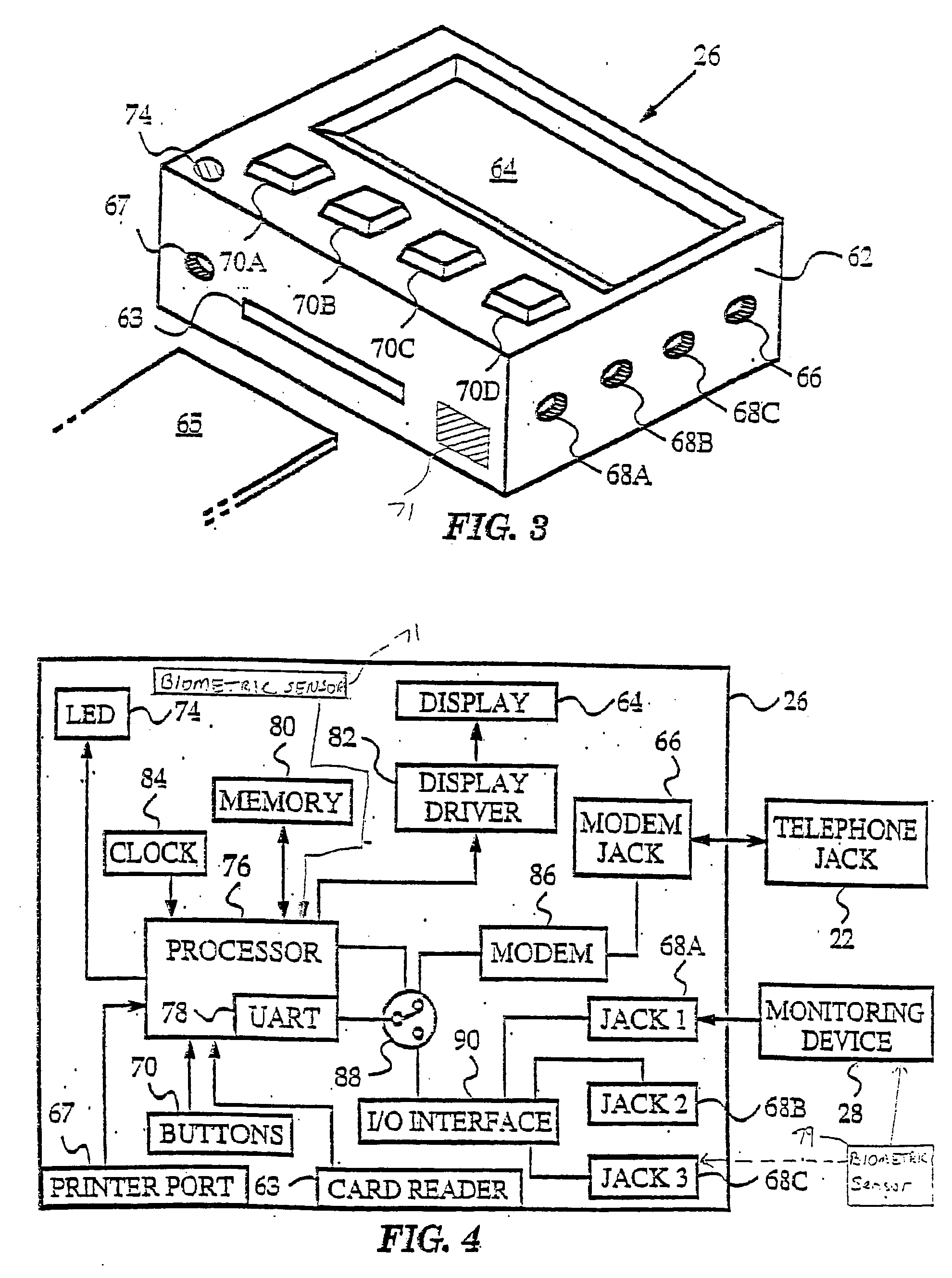
Personal status physiologic monitor system and architecture and related monitoring methods
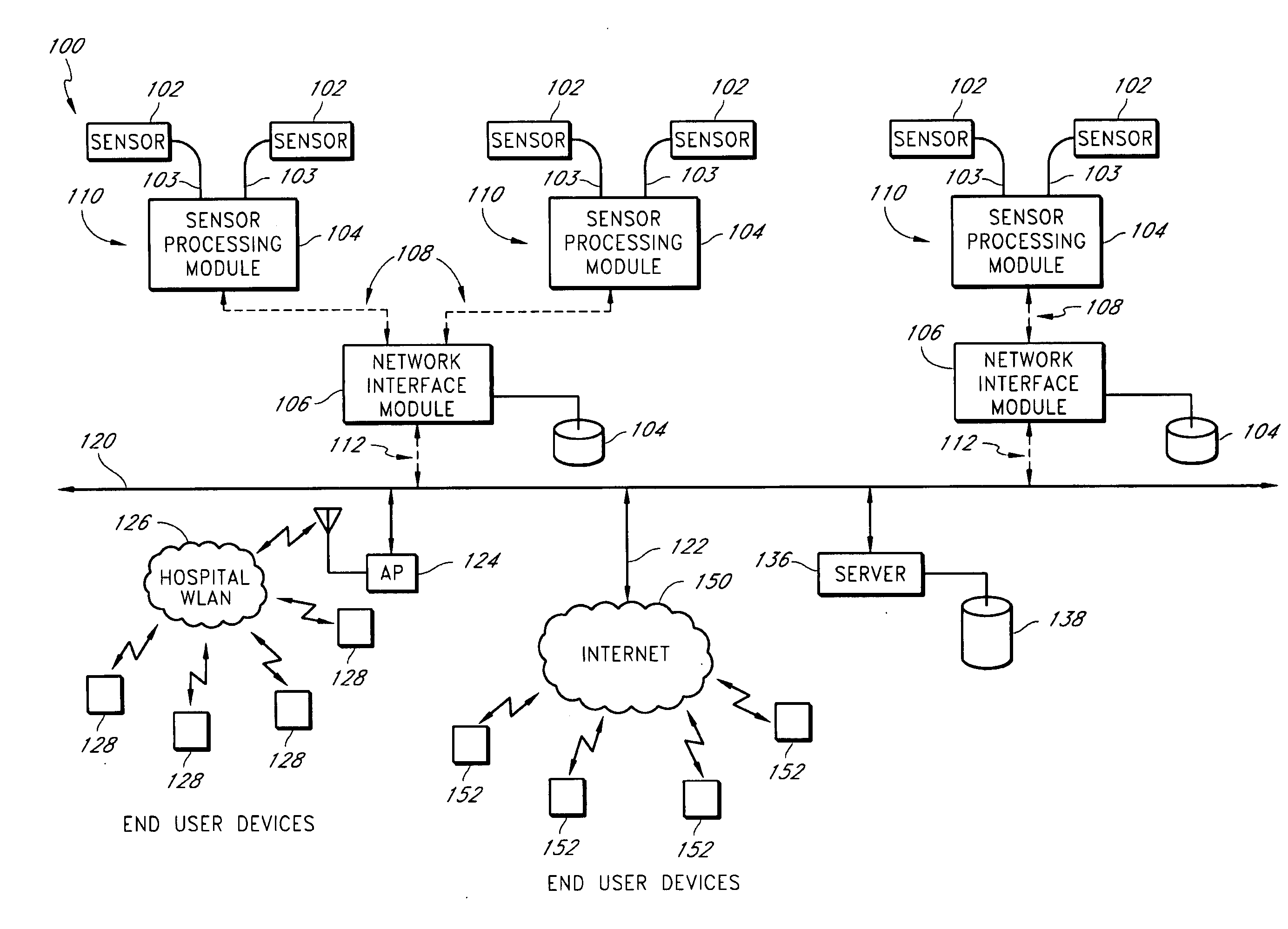
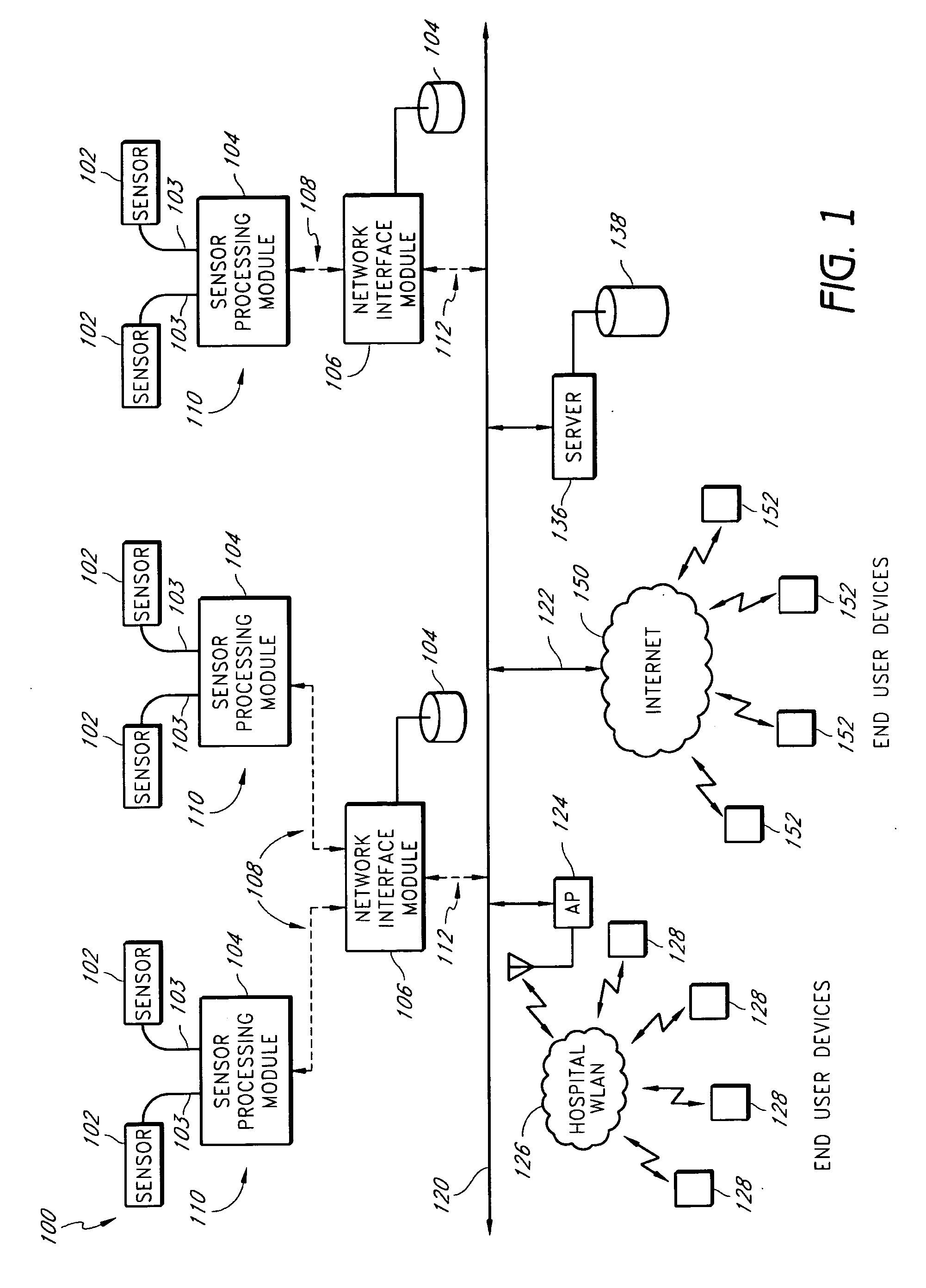
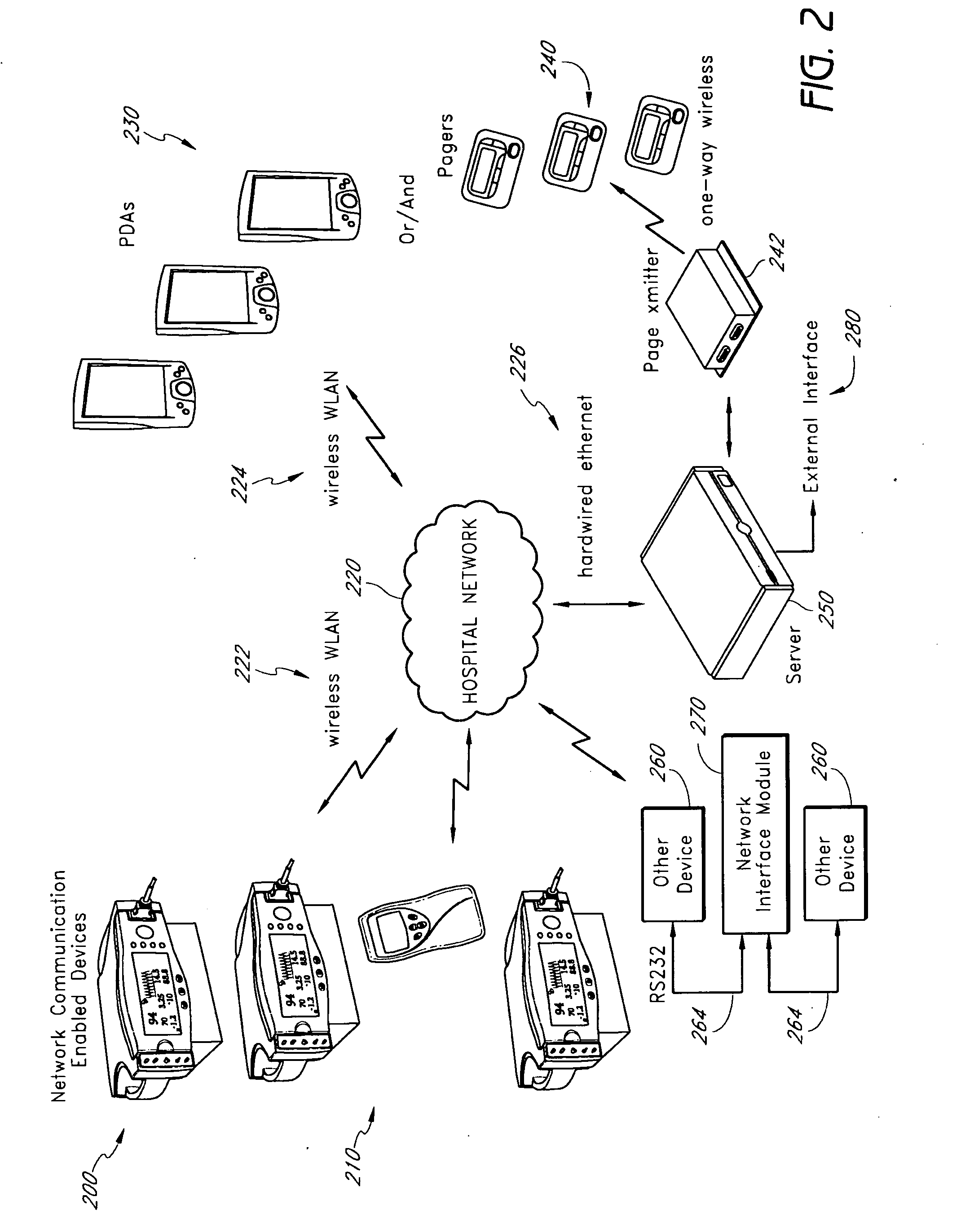
InactiveUS20050206518A1Preserve battery lifeLow costElectrocardiographyLocal control/monitoringNetwork connectionMonitor equipment
A system for actively monitoring a patient includes at least one body-worn monitoring device that has at least one sensor capable of measuring at least one physiologic parameter and detecting at least one predetermined event. At least one intermediary device is, linked to the body-worn monitoring device by means of a first wireless network and at least one respondent device is linked to said at least one intermediary device by a second wireless network wherein the respondent device is programmed to perform a specified function automatically when the at least one predetermined event is realized. The monitoring device operates to periodically transmit patient status data to the intermediary device but the system predominantly operates in a quiet state, providing very low power consumption.
Owner:WELCH ALLYN INC
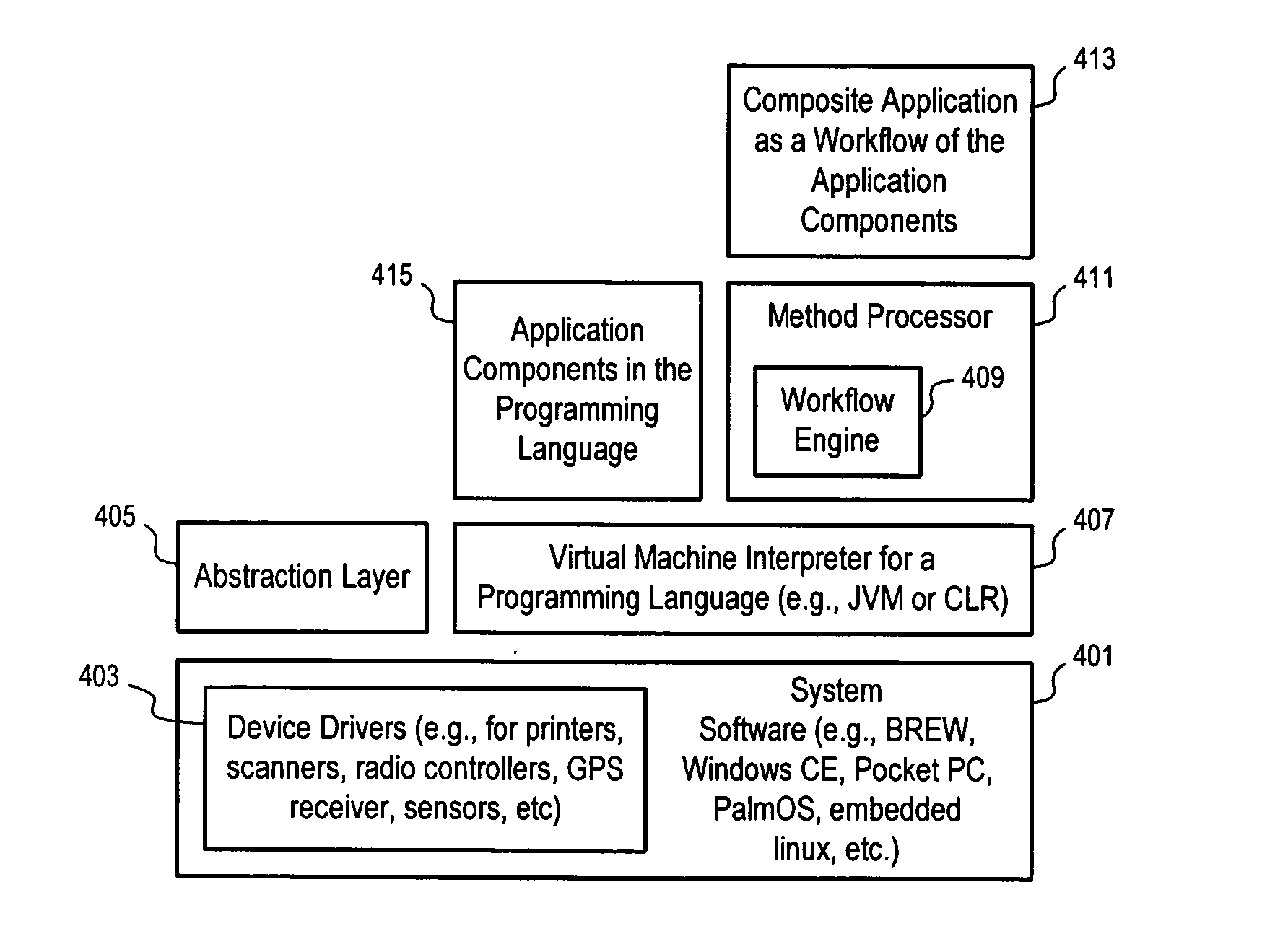
Methods and apparatuses to provide mobile applications
Methods and apparatuses to enable the development, deployment and update of composite applications on mobile devices. In one embodiment, a method processor in a mobile device uses a workflow engine to load modules for execution according to a workflow that specifies the execution flow directions based on the outcomes of the modules. Detached object managers can be used to manage locally data that are checked out from data sources. A object manager can maintain multiple versions of the data locally, receive changes, submit changes, and / or detect conflicts. Conflicts can be resolved over time. Using a check-out check-in model, different devices can work on the same data without having to synchronize with a server sequentially. Data and workflow can be packaged together for transmission over a sometime connected network (e.g., via email) such that a method processor does not have to wait for response if the network connection is not available.
Owner:APACHETA CORP
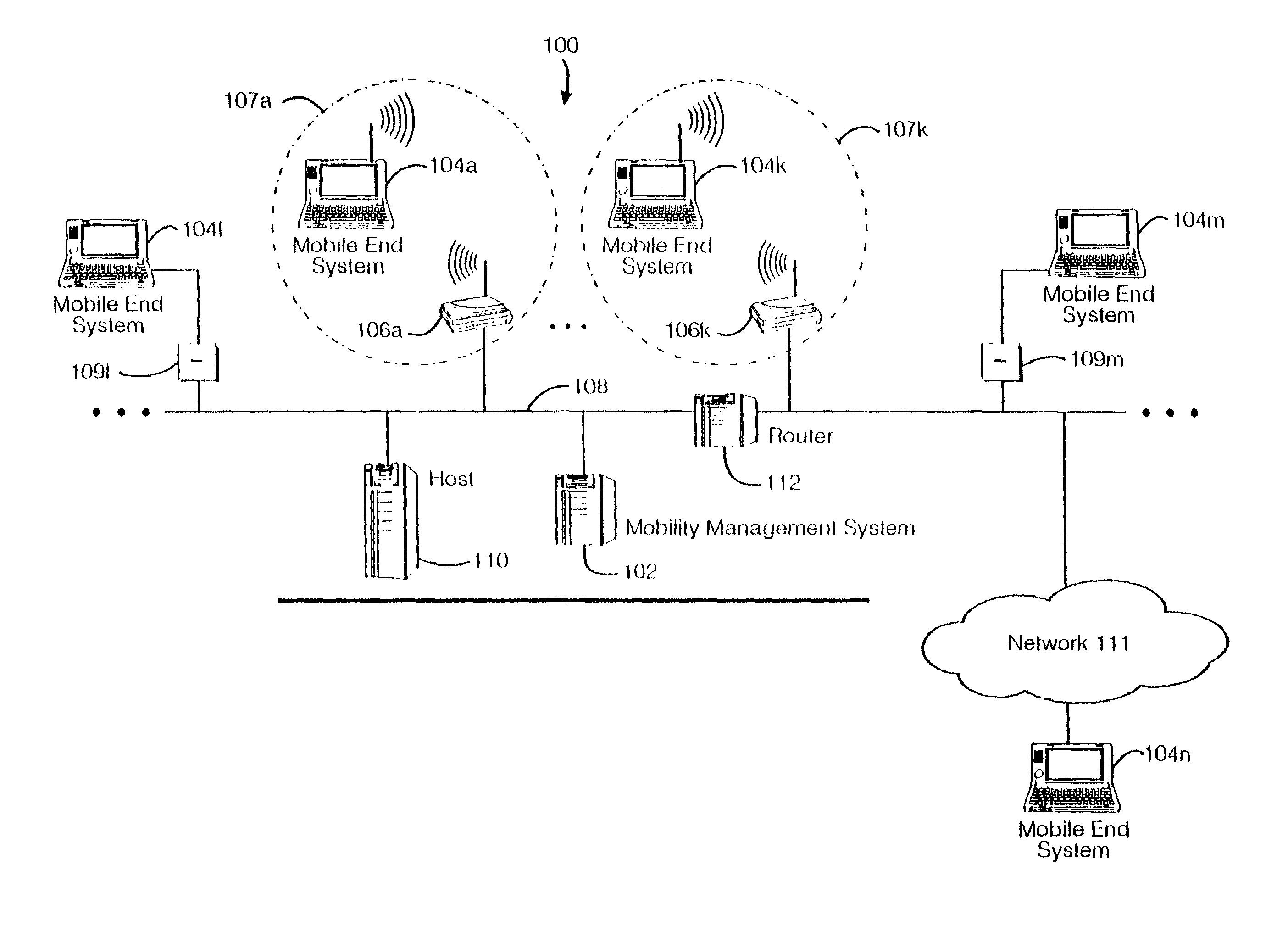
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
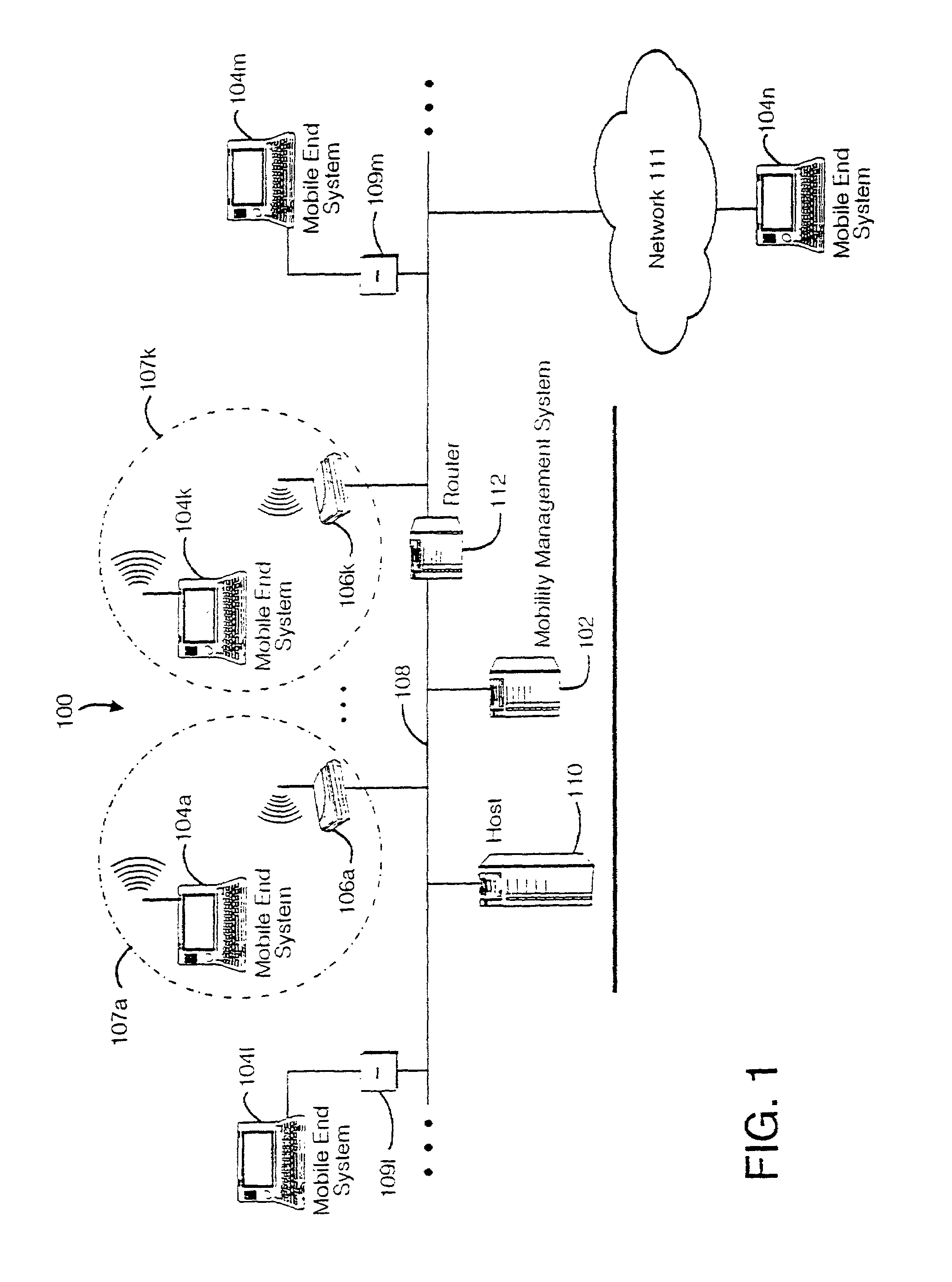
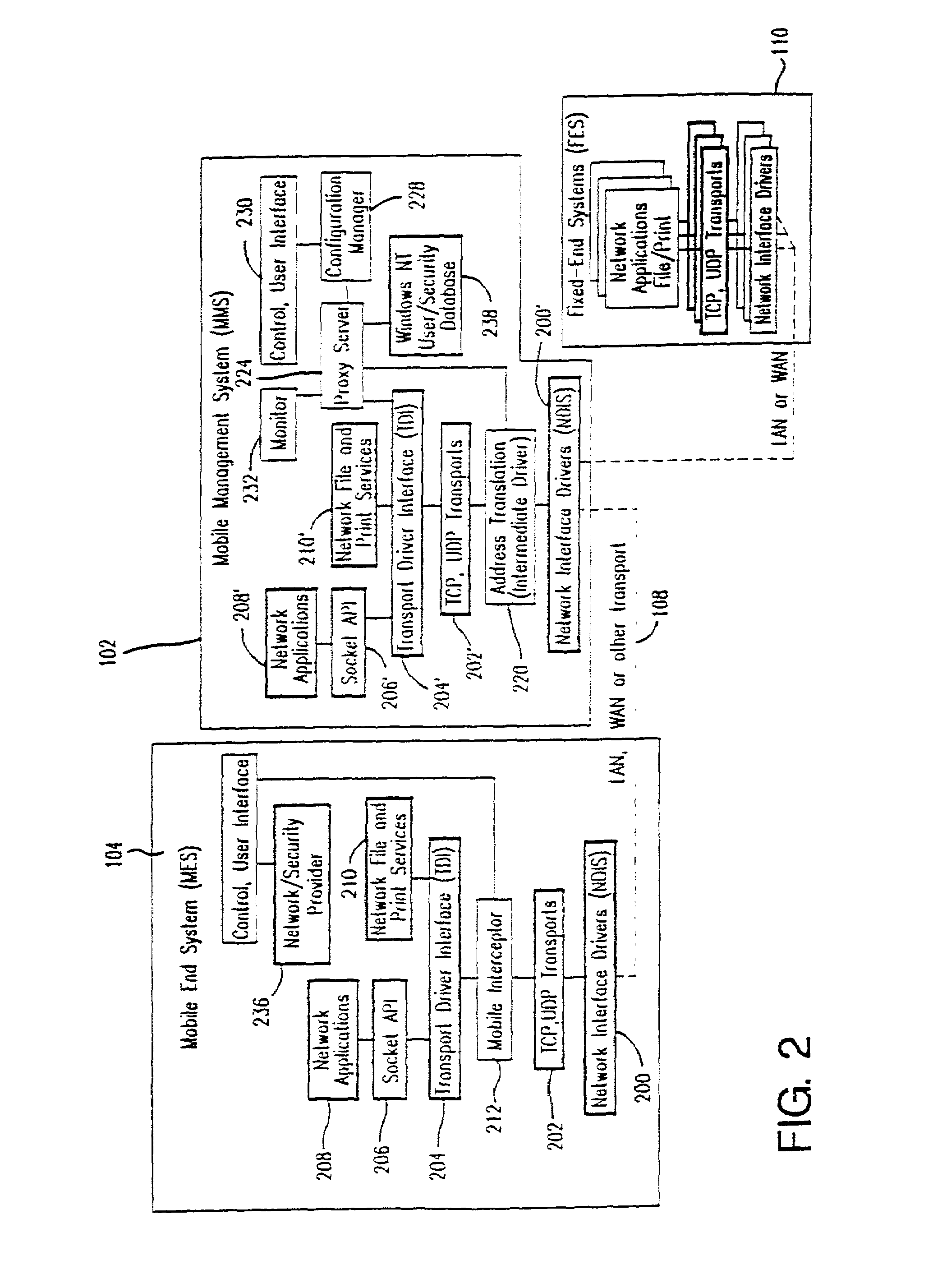
InactiveUS7136645B2Low costEasy accessError prevention/detection by using return channelNetwork traffic/resource managementNetwork connectionMobile end
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
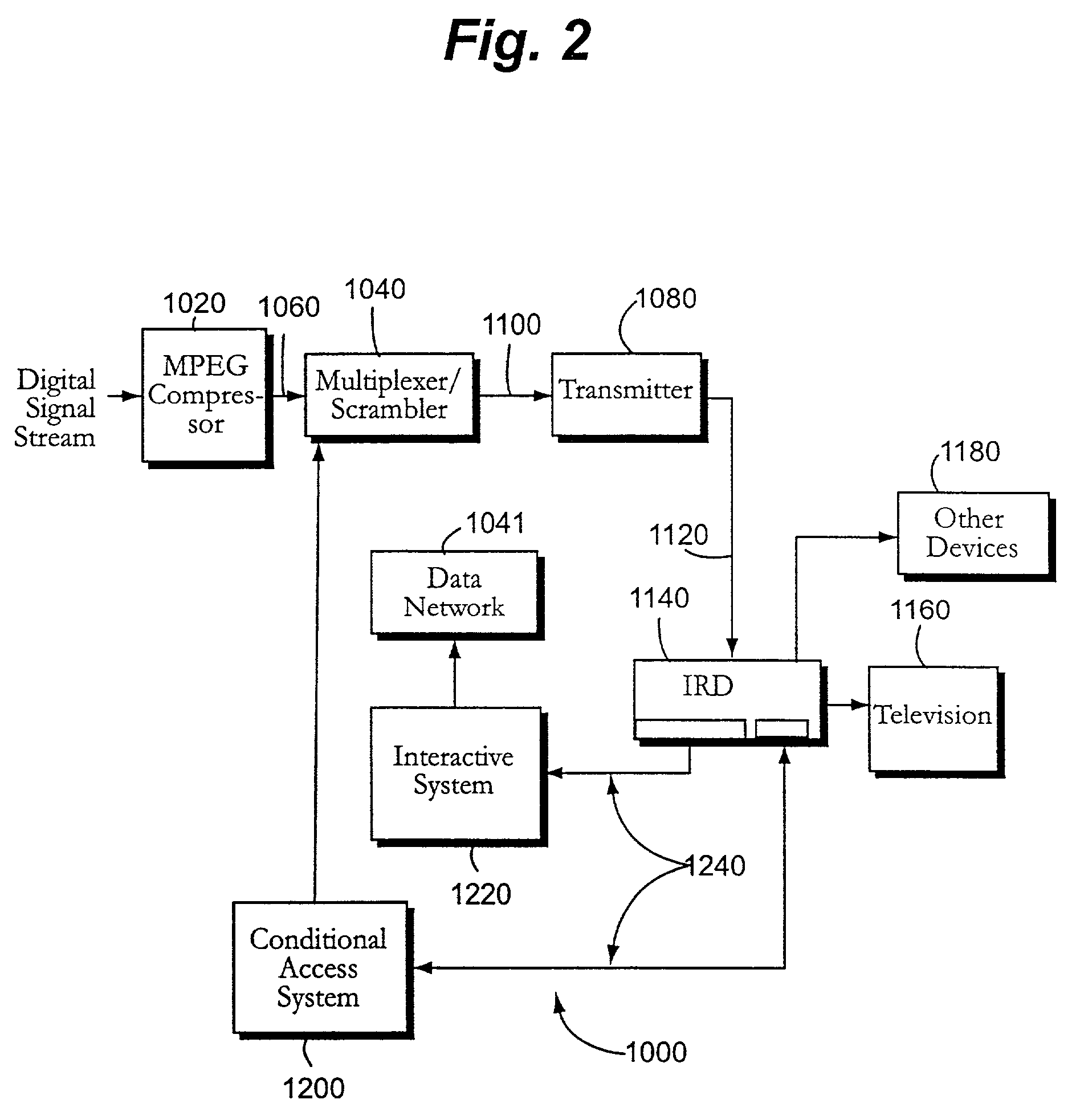
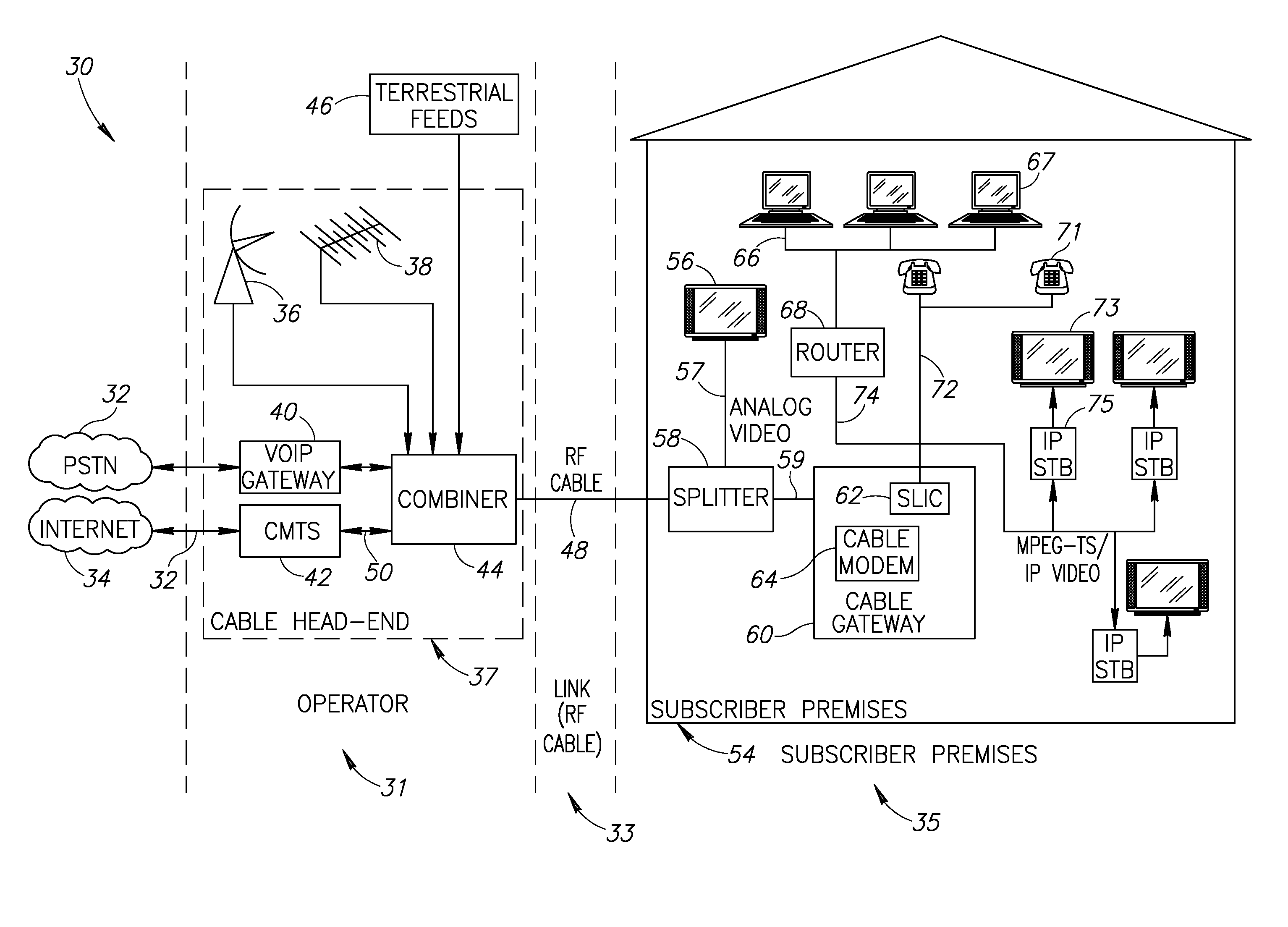
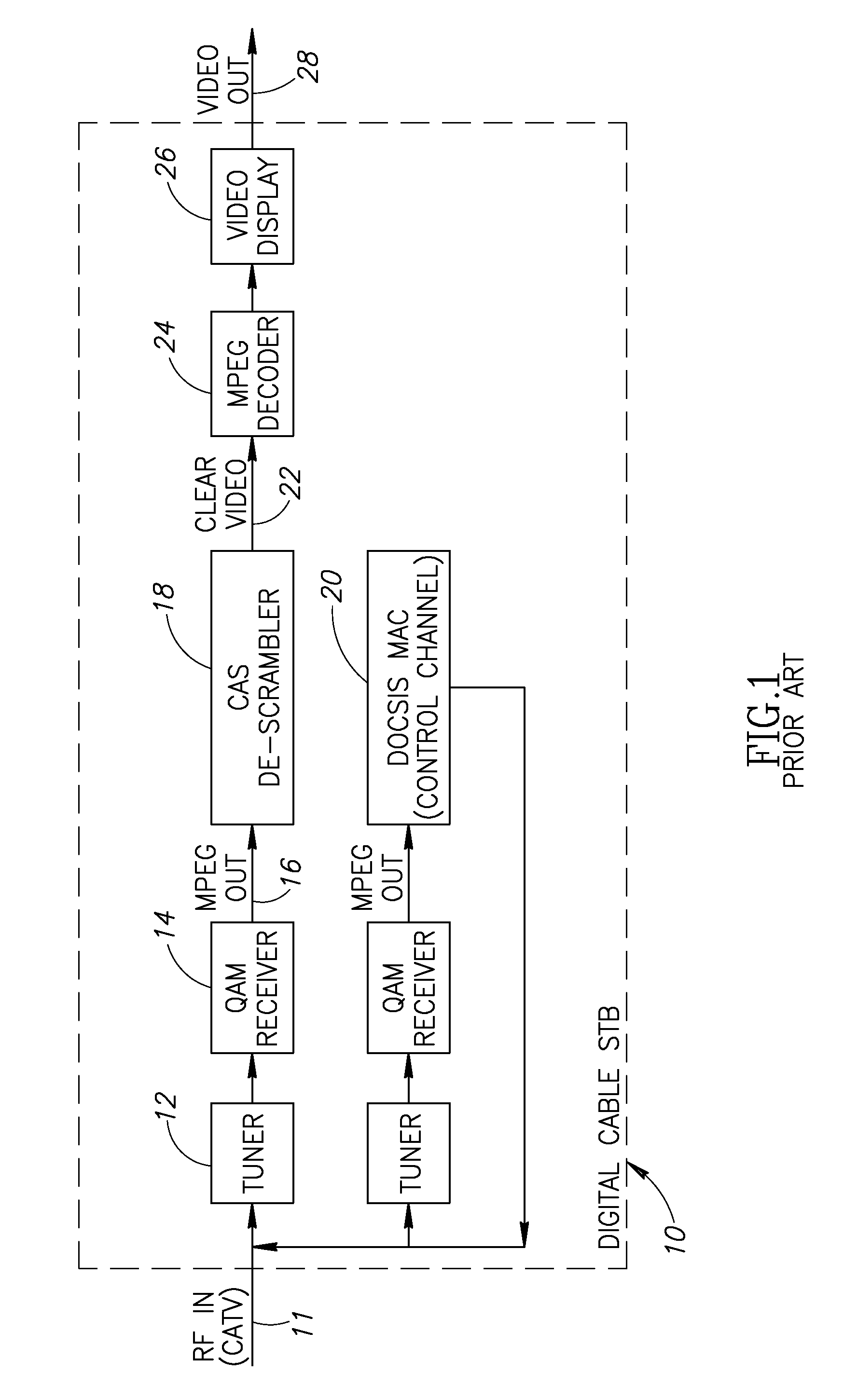
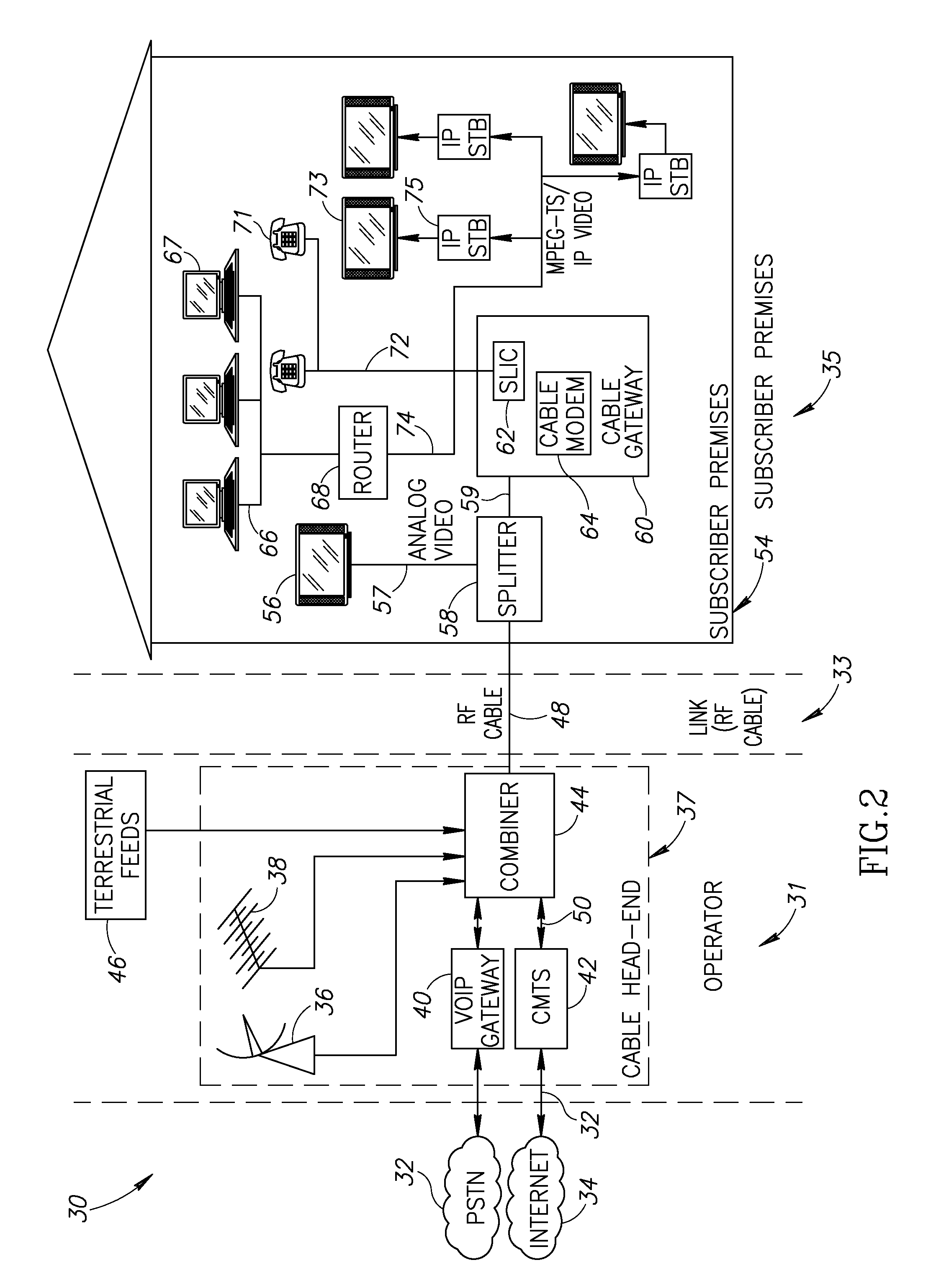
Hybrid mpeg/ip digital cable gateway device and architecture associated therewith
A novel cable gateway system and architecture incorporating a hybrid digital video transceiver. The digital cable system architecture combines reception of legacy video such as MPEG-TS based DVB-C streams with that of original IP video over DOCSIS channels. The system comprises a hybrid DVB / IP cable gateway STB capable of receiving both legacy DVB-C video and original IP video streams. The cable gateway device performs the front-end functionality (including QAM receiver, tuner and broadband connection) while the back-end functionality of video decoding and display is performed by one or more standard IP-STBs connected to the cable gateway device over a network (e.g., home LAN). Legacy MPEG-TS based DVB-C video is captured and encapsulated into packets for distribution over the network to the IP-STBs. The cable gateway distributes the original IP video received over the CATV source and the encapsulated legacy video as video over IP packets over the network.
Owner:INTEL CORP
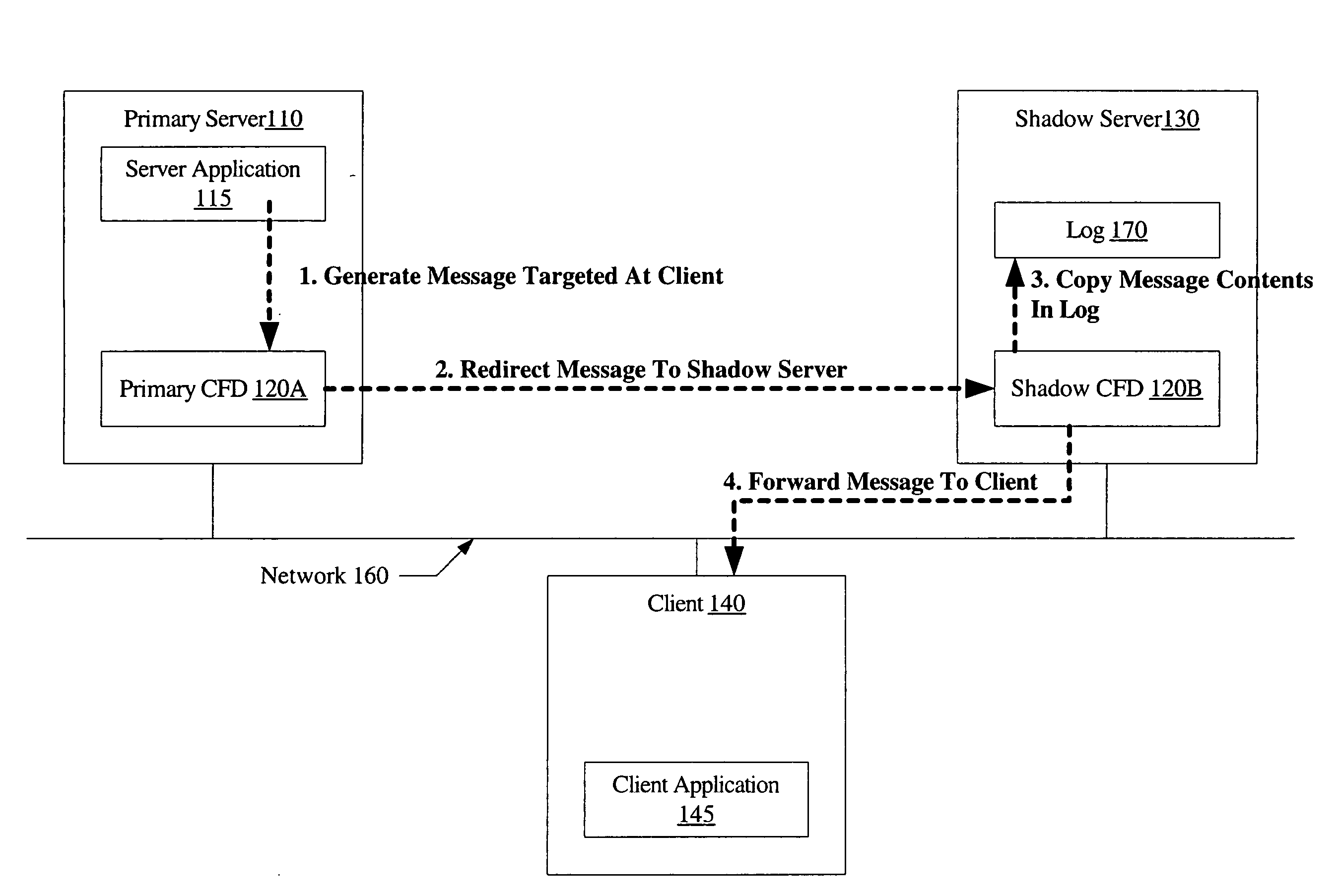
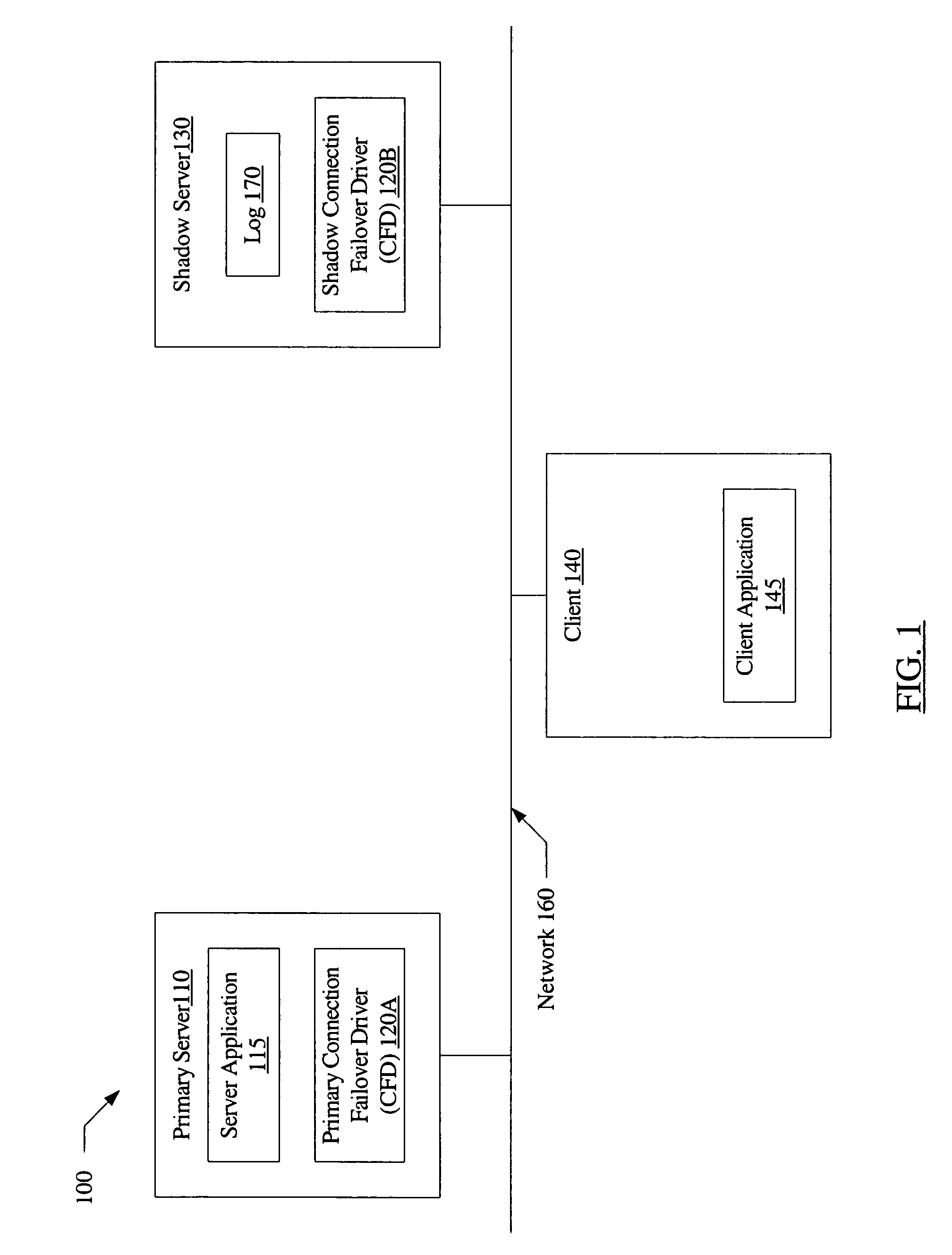
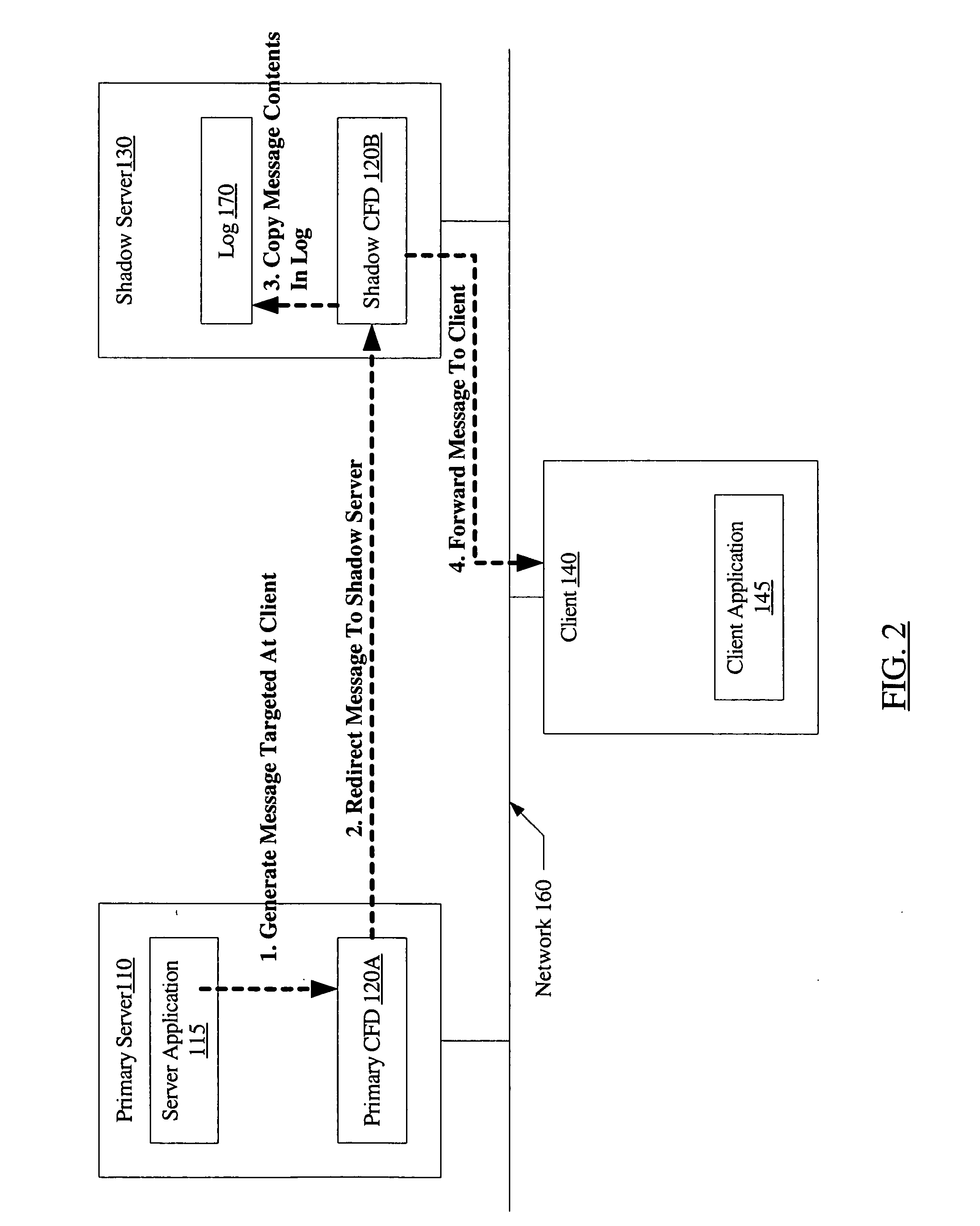
System and method for connection failover using redirection
InactiveUS20060179147A1Multiple digital computer combinationsNetwork connectionsFailoverNetwork connection
A system for connection failover using redirection includes a primary server comprising a primary connection failover driver (CFD), a shadow server comprising a shadow CFD, and a client. The primary and shadow servers and the client are coupled via a network. The primary server and the client are configured to cooperate to establish a network connection. The primary CFD is configured to redirect a first message packet, targeted for transmission to the client over the network connection, to the shadow server. The shadow CFD is configured to copy contents of the first message packet into a log, and forward the first message packet to the client after the contents have been copied.
Owner:SYMANTEC OPERATING CORP
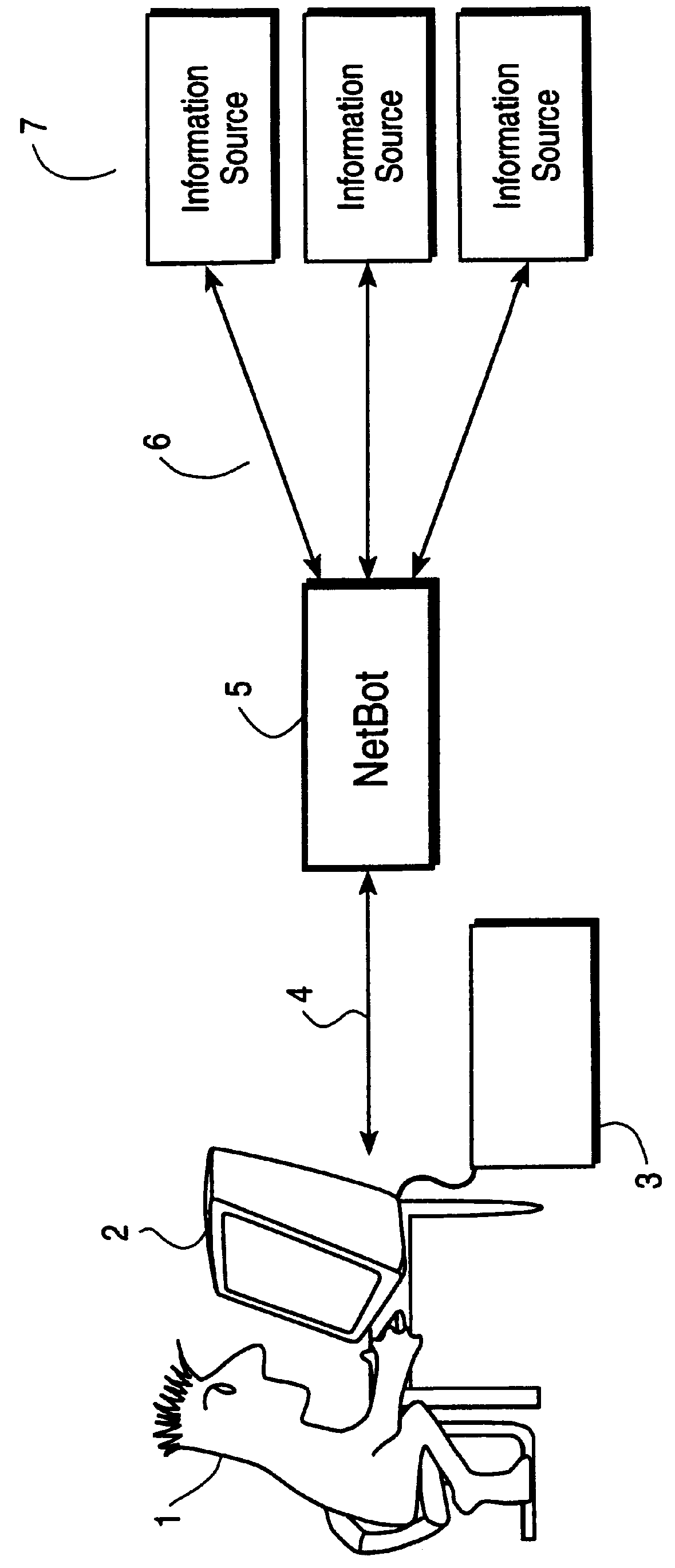
Method and system using information written in a wrapper description language to execute query on a network
InactiveUS6085186AEasy to understandEasy maintenanceData processing applicationsWeb data indexingAccess networkNetwork connection
This invention provides assistance to a user in accessing network attached information sources. In one aspect, the invention is a method for intelligently routing a user query to information sources relevant to that query, extracting relevant data fields from received responses, and intelligently presenting the extracted data in order of estimated relevance. The system of this invention implements one or more steps of the method in a centralized or distributed manner on one or more network attached computers. Further, this invention provides a novel language and implementation that facilitates easily written and maintained descriptions of information source query and response formats.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST
Physiological alarm notification system
A method of context-based communication of physiological information over a network includes receiving physiological information, preparing a contextual data package, establishing a network connection, and communicating the contextual data package. The physiological information is received with a portable network interface module from at least one physiological monitor coupled to a single medical patient. The physiological information is related to a physiological condition of the medical patient, and the portable network interface module is exclusively assigned to the medical patient. The contextual data package is prepared with the portable network interface module. The contextual data package includes context information related to the medical patient and the physiological information. The network connection is established with a user over a network with the portable network interface module, and the portable network interface module manages the network connection with the user. The contextual data package is communicated to the user over the network with the network connection.
Owner:JPMORGAN CHASE BANK NA
Multi-user remote health monitoring system with biometrics support
InactiveUS20030229514A2Easy to identifyData processing applicationsPerson identificationPharmacyPublic place
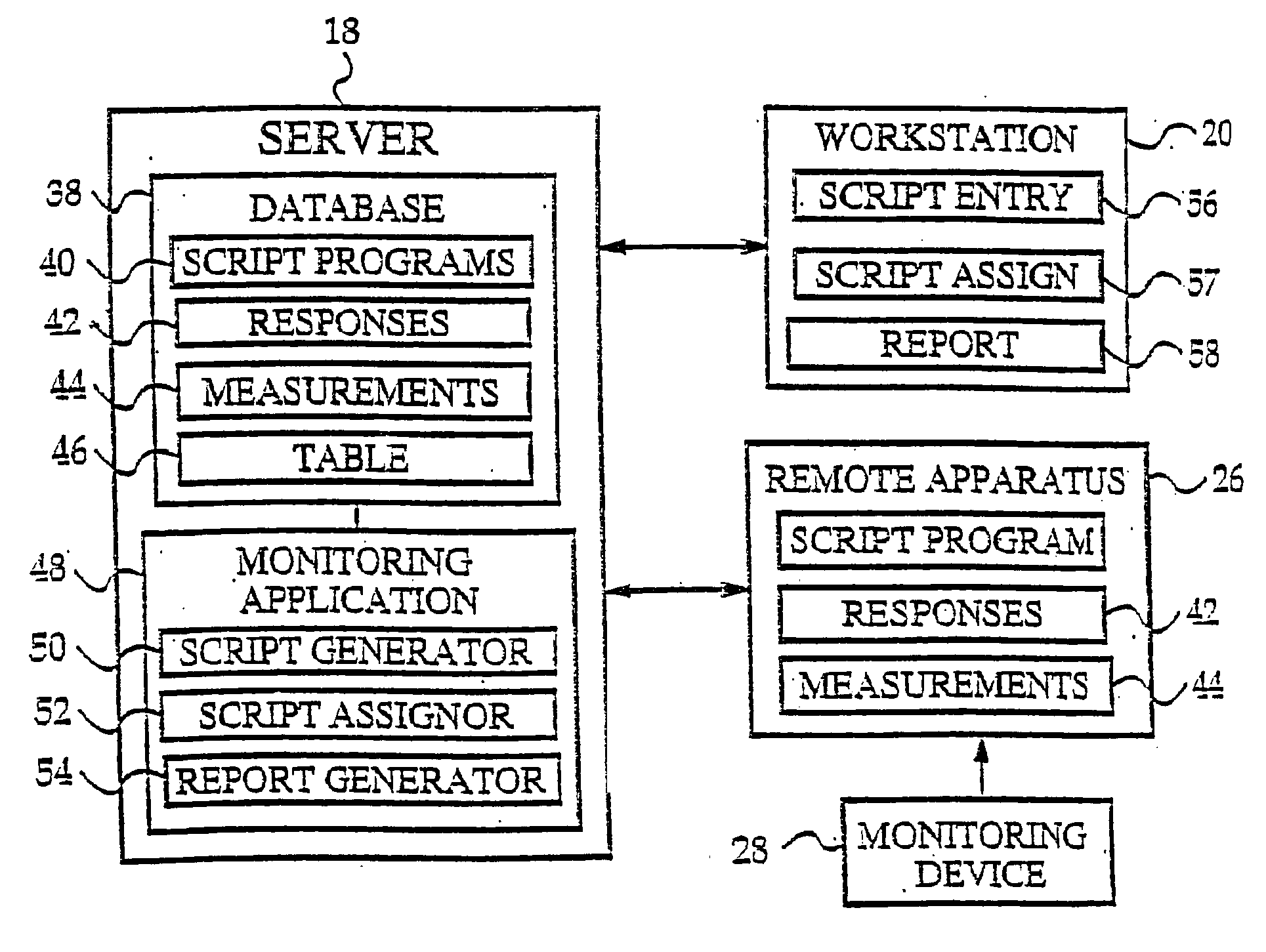
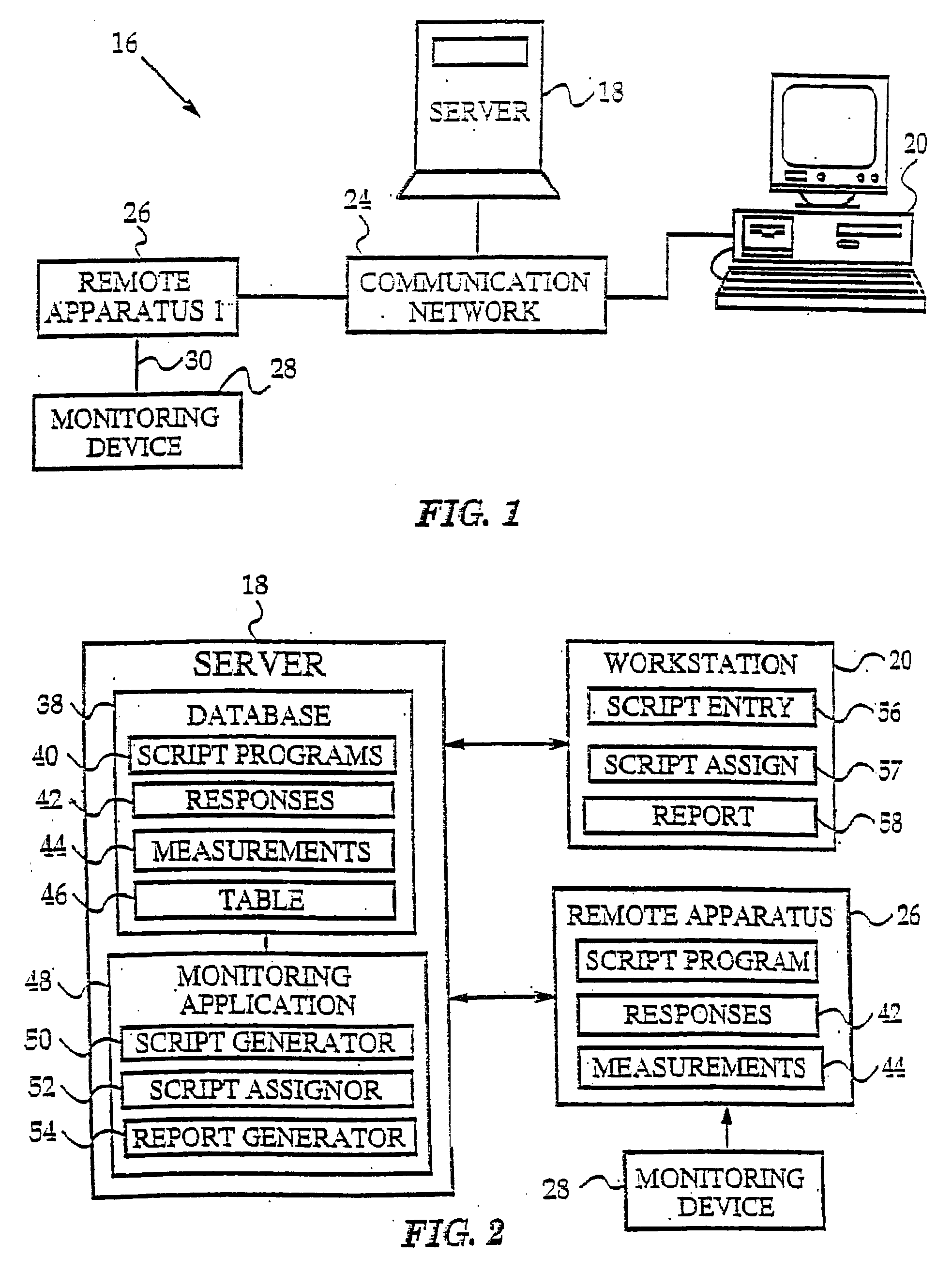
Abstract of the Disclosure The invention presents a networked system for identifying an individual, communicating information to the individual, and remotely monitoring the individual. The system includes a remotely programmable apparatus that occasionally connects to a server via a communication network such as the Internet. The remotely programmable apparatus interacts with the individual in accordance with a script program received from the server Among other capabilities, the script program may instruct the remotely programmable apparatus to identify the individual, to communicate information to the individual, to communicate queries to the individual, to receive responses to the queries, and to transmit information identifying the individual and the responses from the remotely programmable apparatus to the server. Information identifying the individual may be obtained via a biometrics sensor, a data card, a remote monitoring device, or the interception of data from a separate information system. The information identifying the individual may be used by either or both the server system and remotely programmable apparatus for security, customization and other purposes. As the present invention has multi-user capabilities, it can be used in a public place, such as a pharmacy or health care clinic. The multi-user capabilities also allow collection and tracking of user data for the healthcare industry.
Owner:HEALTH HERO NETWORK
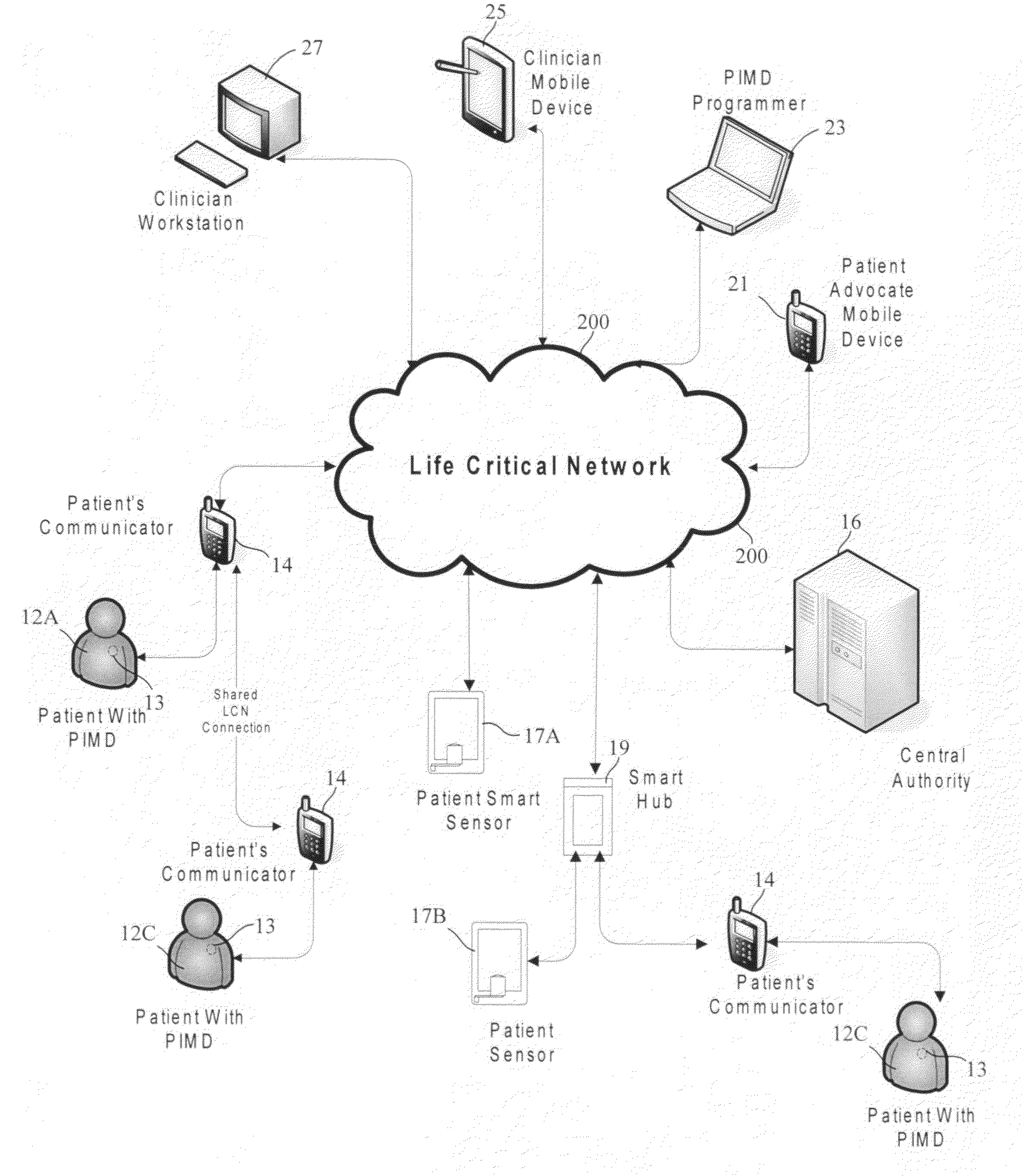
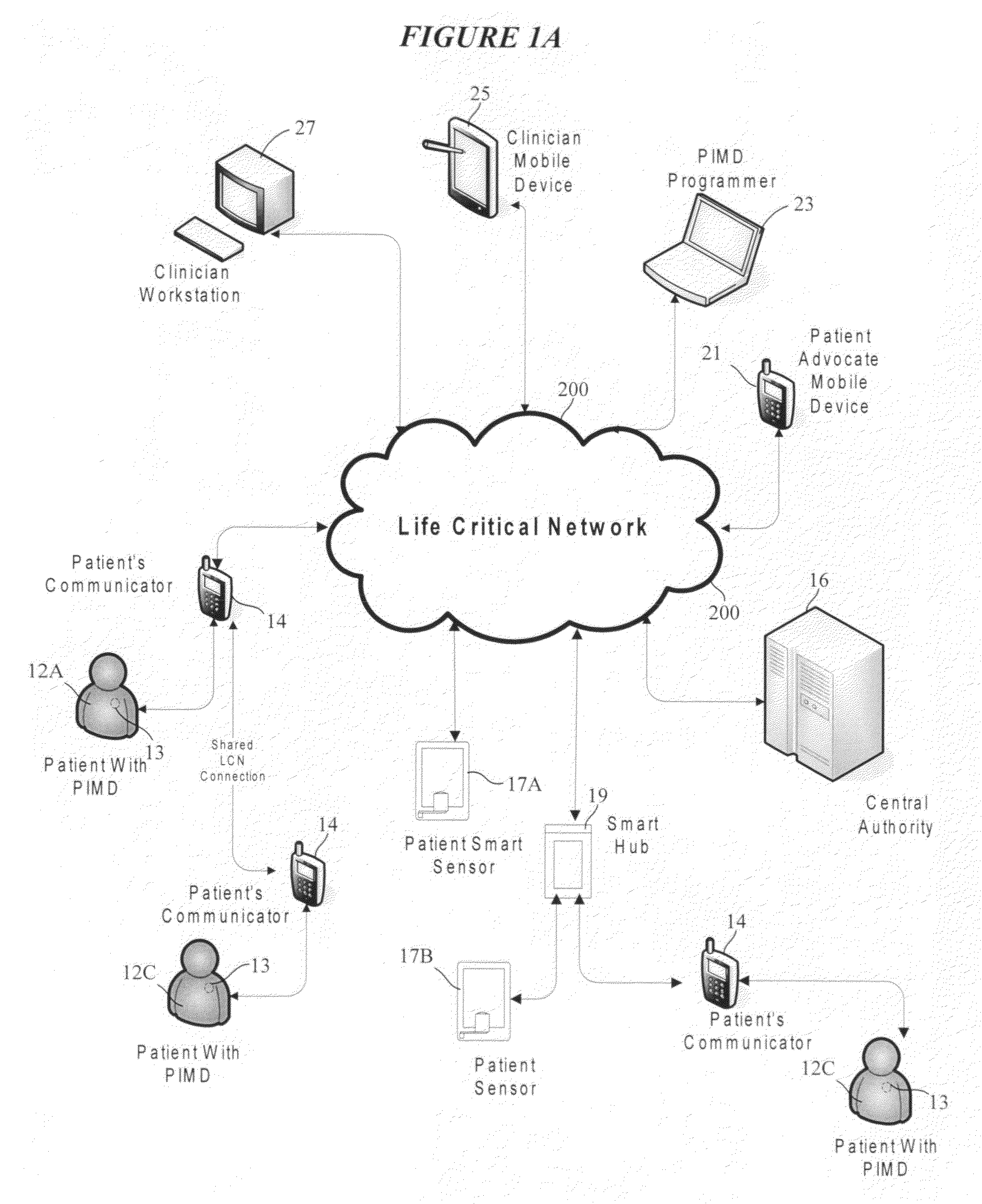
Medical data transport over wireless life critical network employing dynamic communication link mapping
ActiveUS20090063187A1ElectrotherapyMeasuring/recording heart/pulse rateTelecommunications linkNetwork connection
A portable source medical device determines communication links of a network presently available to effect communications with a target component when the source medical device is at each of a multiplicity of geographical locations. A profile is generated comprising information about each available communication link and attributes associated with each available communication link for each geographical location. When the source medical device is at a particular geographical location, a profile associated with the particular geographical location is accessed and a network connection is established between the source medical device and the target component using a communication link associated with the particular profile. Medical information is transferred between the source medical device and the target component via the communication link associated with the particular profile.
Owner:CARDIAC PACEMAKERS INC
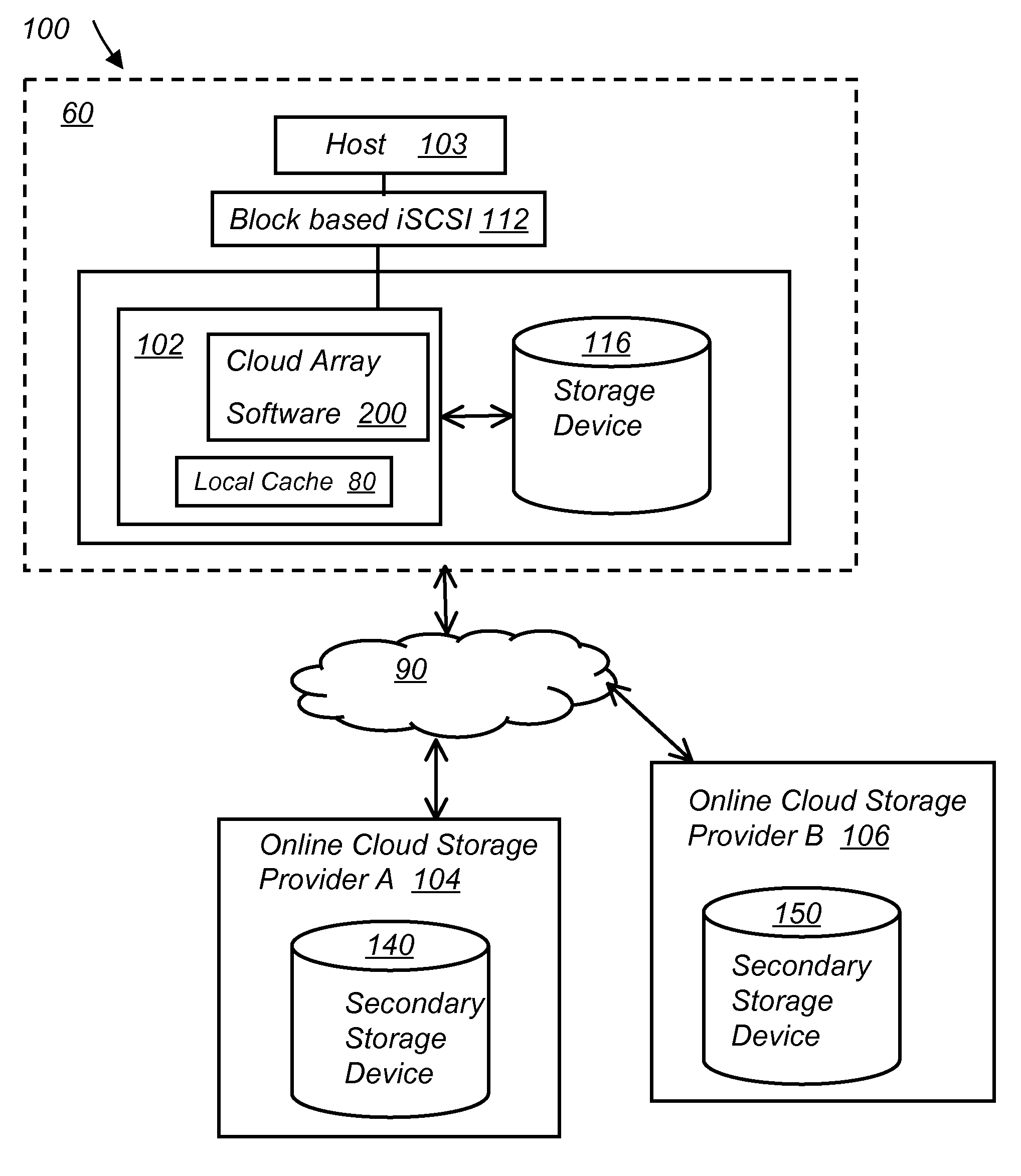
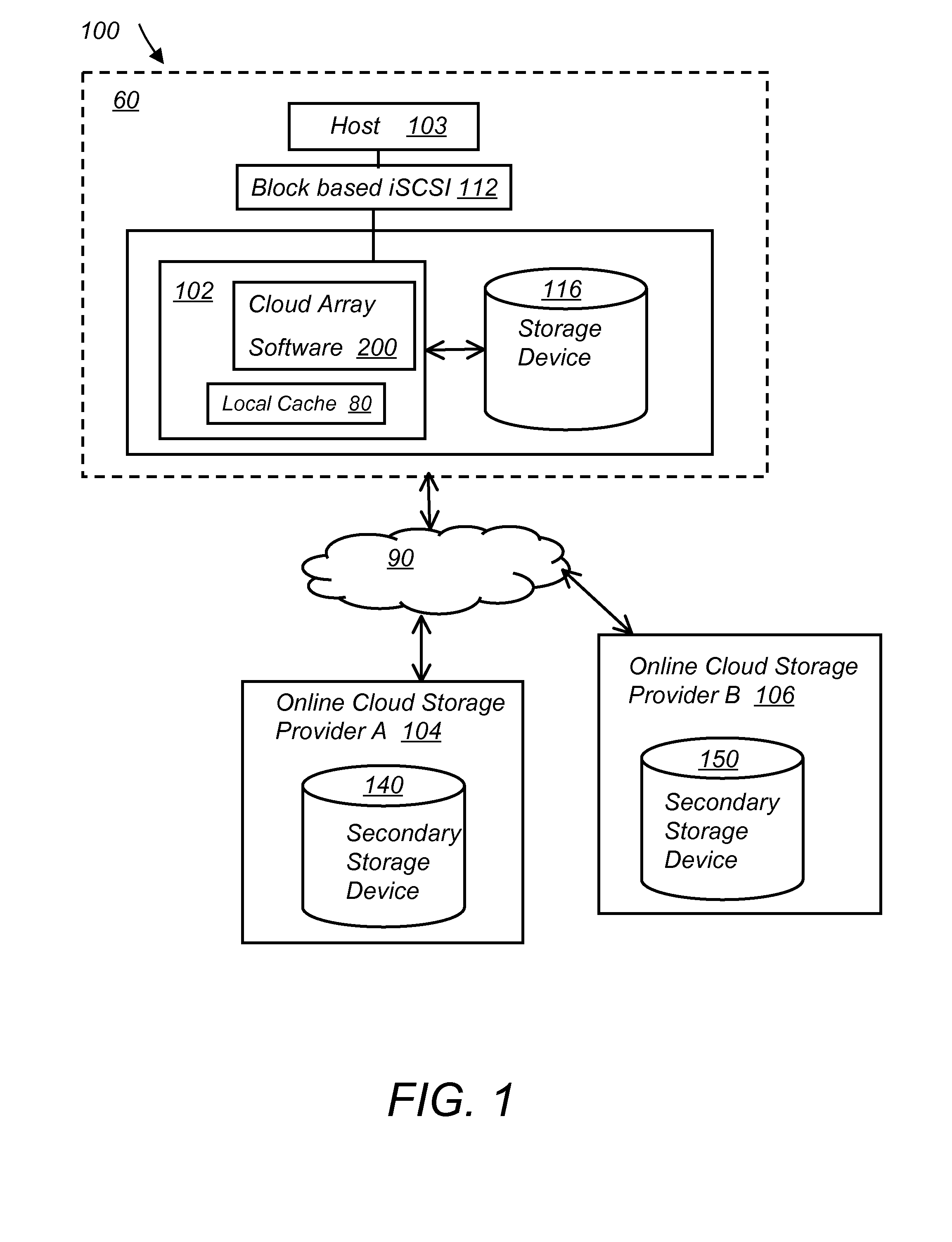
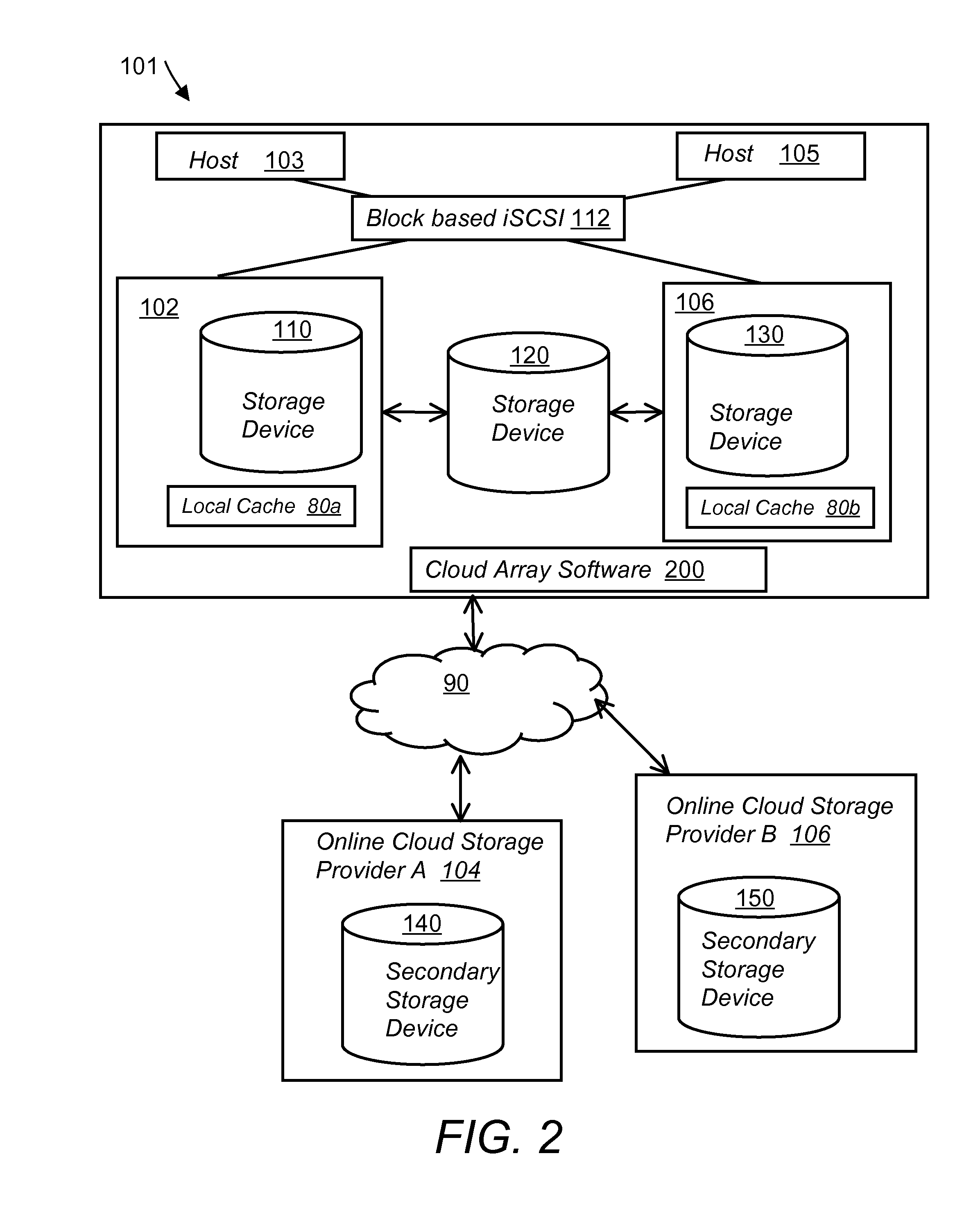
System and method for secure and reliable multi-cloud data replication
ActiveUS8762642B2Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationUnauthorized memory use protectionReliable computingNetwork connection
Owner:EMC IP HLDG CO LLC
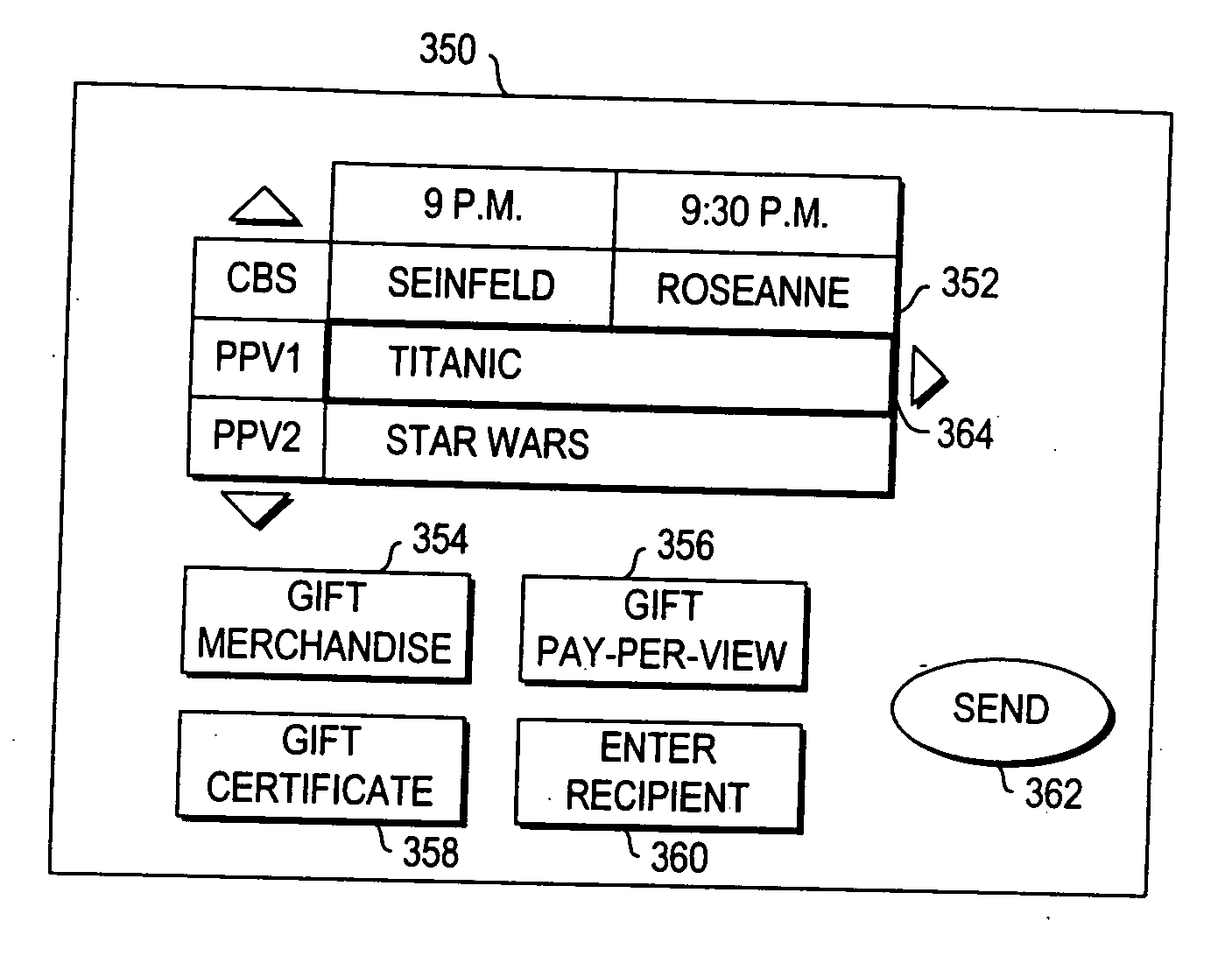
Systems and methods for providing a program as a gift using an interactive application
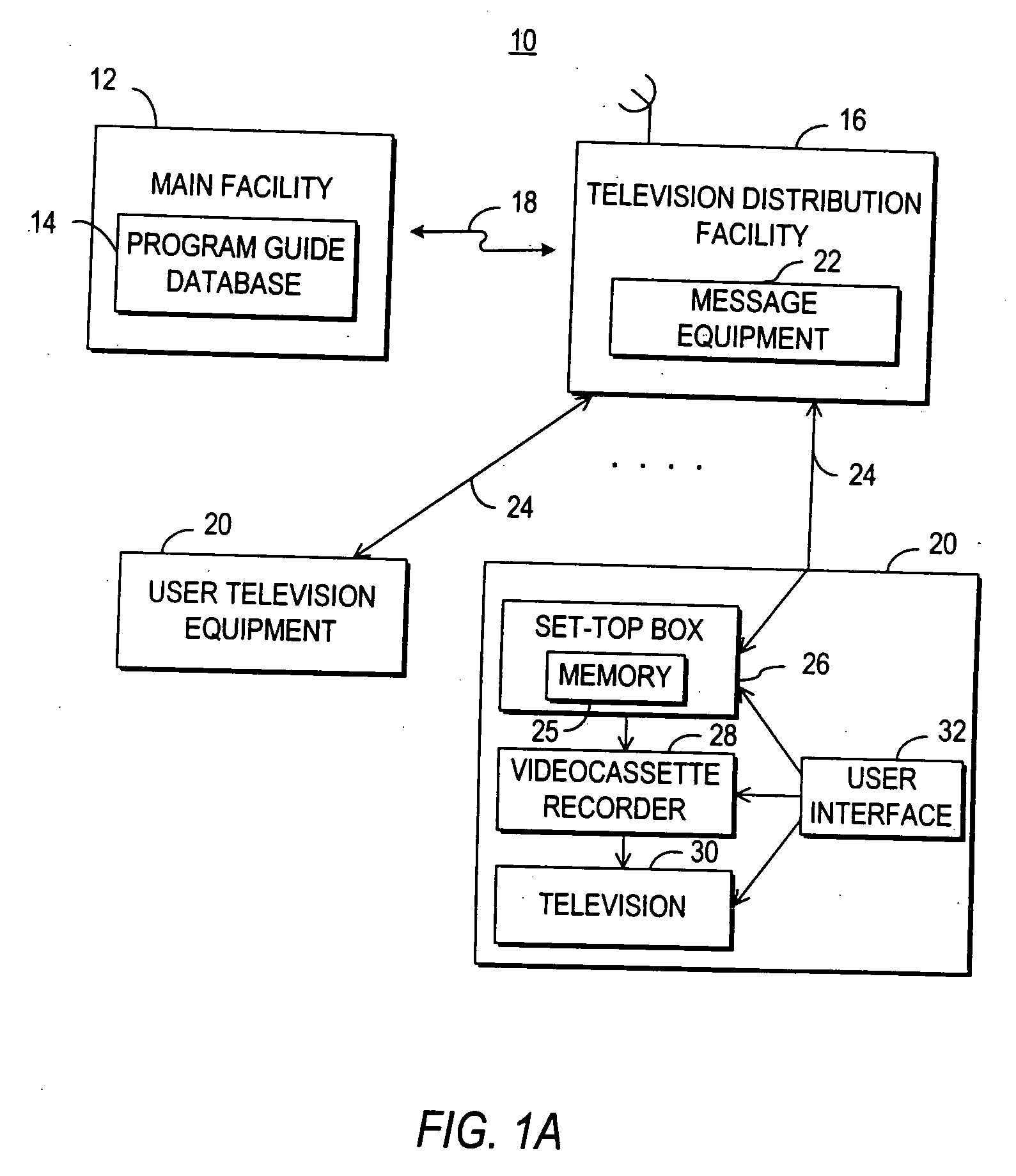
InactiveUS20060190966A1Eliminate needTelevision system detailsAcutation objectsNetwork connectionInteractive television
A television message system is provided that allows users at user television equipment devices that are connected to a television distribution facility to transmit messages to each other relating to a television program or other suitable subject. The television message system permits users to participate in evaluations, contests, promotions, and surveys related to a television program while watching that television program. The television message system also permits users to compose and send a message to a television program entity. Users can send messages through the television message system to users at personal computers who are connected to the user's television distribution facility through a communications network. The television message system also allows a user to purchase a gift related to television programming for a recipient. The gift may be an electronic gift certificate for pay-per-view programming. The television message system may be based on an interactive television program guide or a set-top box application implemented on a set-top box.
Owner:UNITED VIDEO PROPERTIES
Methods of Discretizing data captured at event data recorders
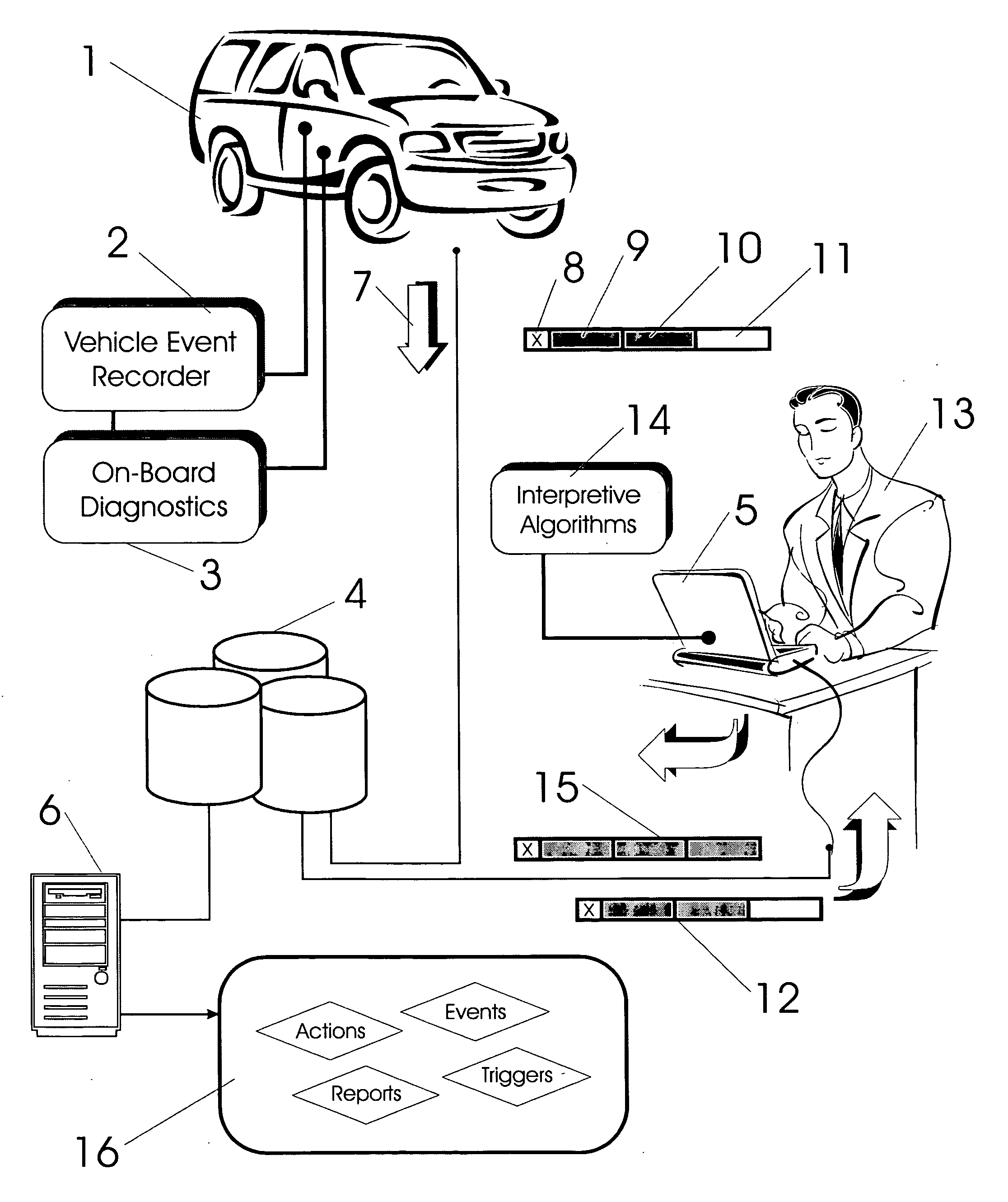
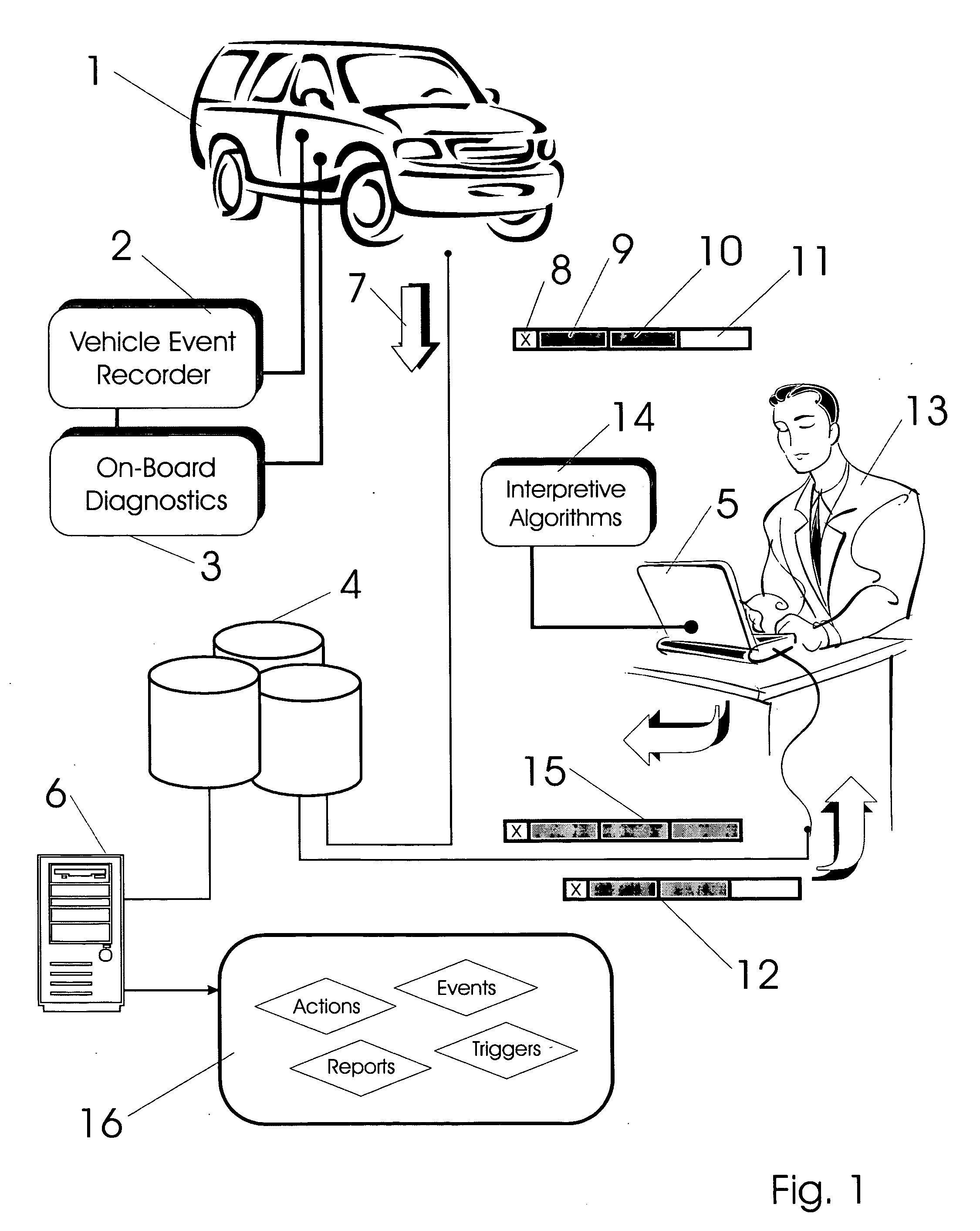
InactiveUS20080147267A1Easy to operateHeat generationVehicle testingRegistering/indicating working of vehiclesMobile vehicleNetwork connection
Exception event recorders and analysis systems include: vehicle mounted sensors arranged as a vehicle event recorder to capture both discrete and non-discrete data; a discretization facility; a database; and an analysis server all coupled together as a computer network. Motor vehicles with video cameras and onboard diagnostic systems capture data when the vehicle is involved in a crash or other anomaly (an ‘event’). In station where interpretation of non-discrete data is rendered, i.e. a discretization facility, captured data is used as a basis for production of supplemental discrete data to further characterize the event. Such interpreted data is joined to captured data and inserted into a database in a structure which is searchable and which supports logical or mathematical analysis by automated machines. A coupled analysis server is arranged to test stored data for prescribed conditions and upon finding such, to initiate further actions appropriate for the detected condition.
Owner:SMARTDRIVE SYSTEMS
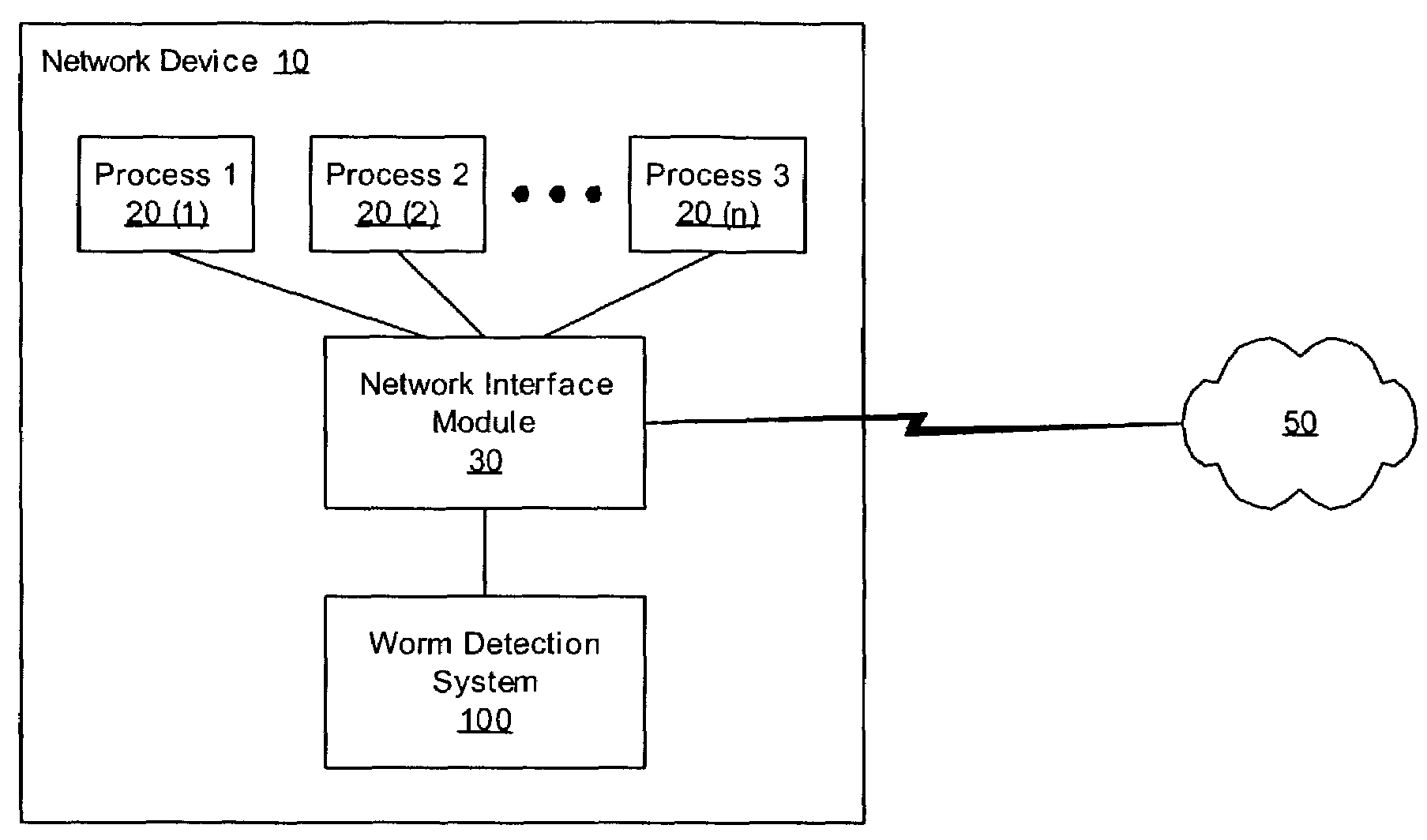
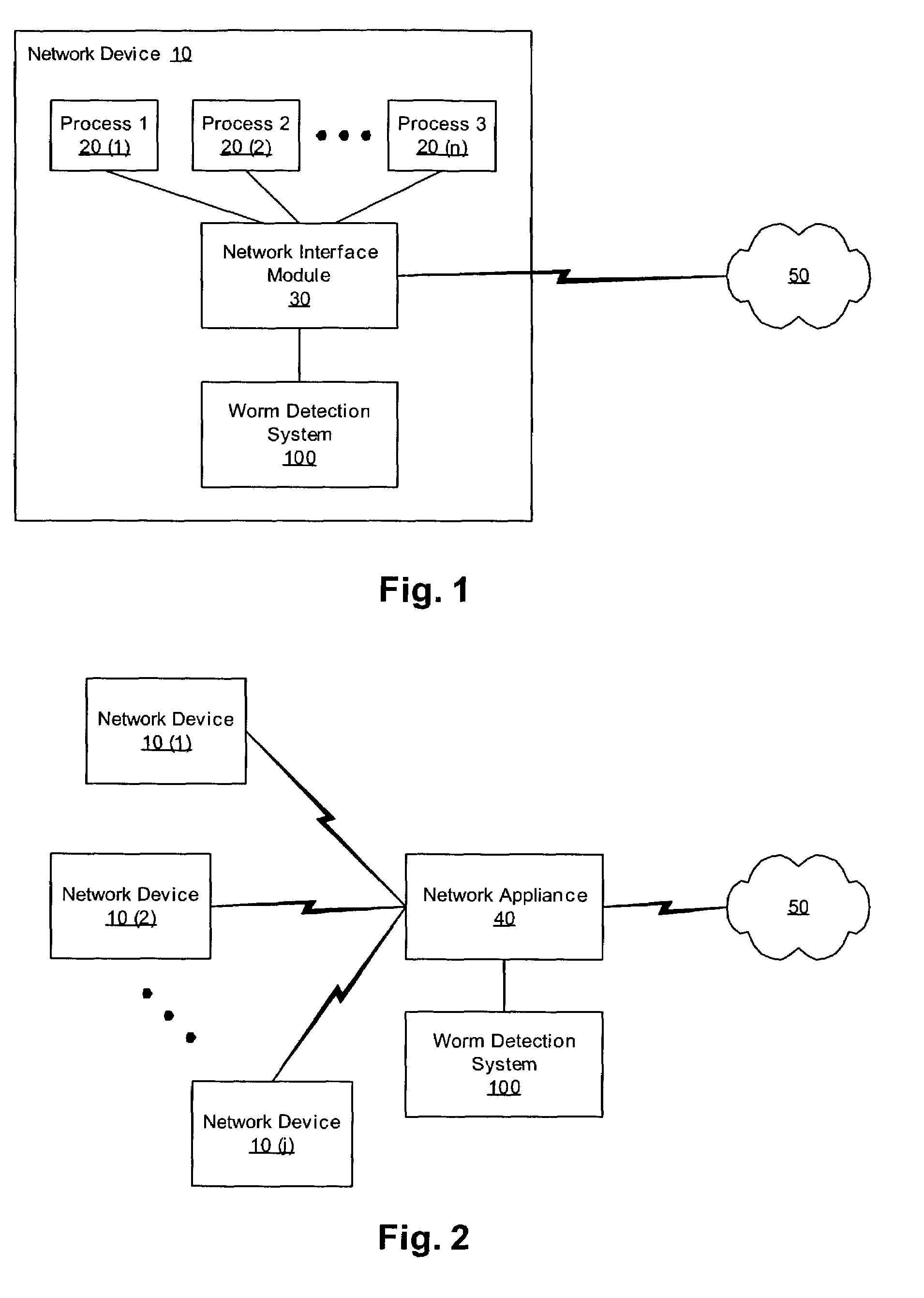
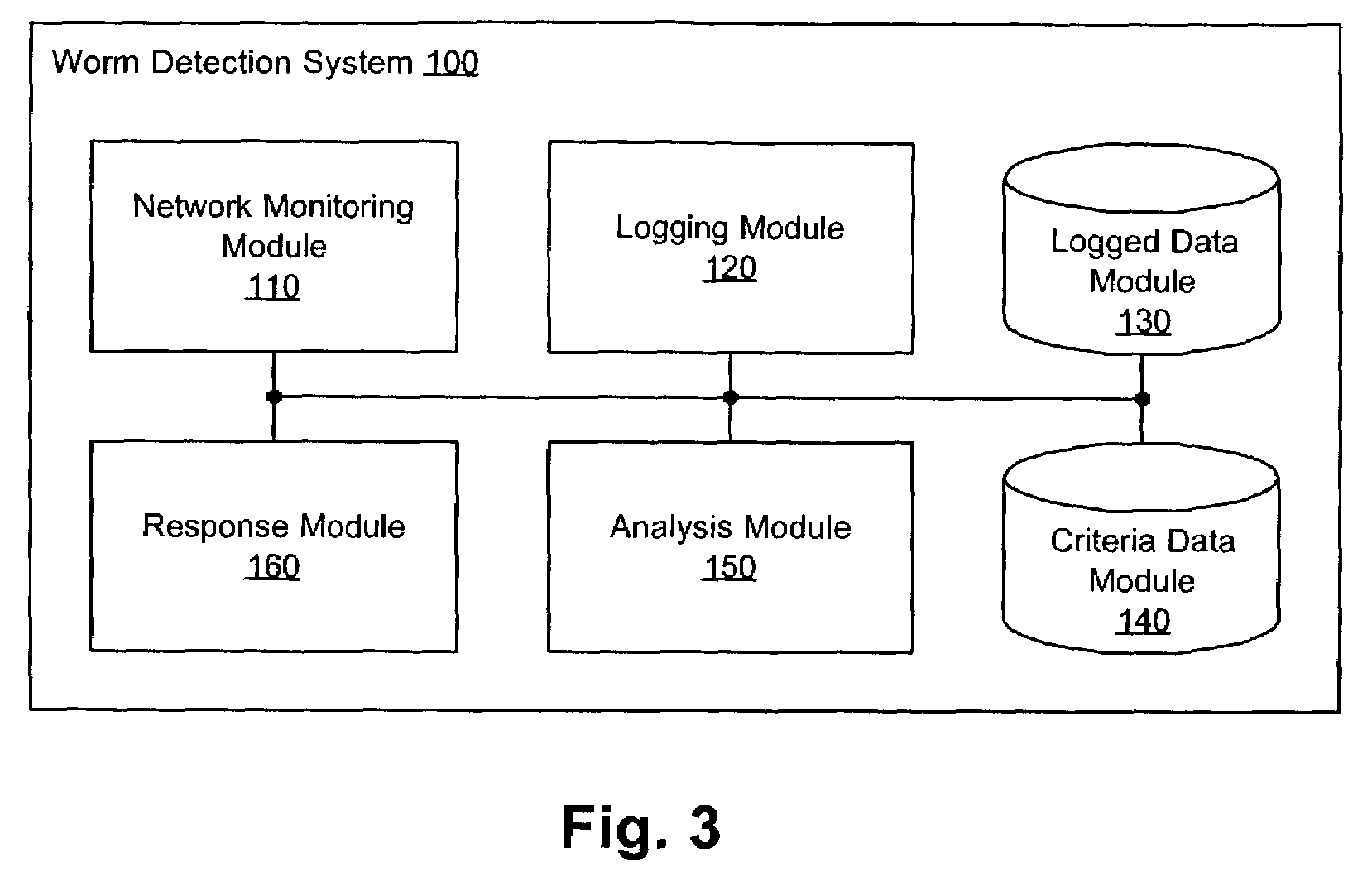
Heuristic detection and termination of fast spreading network worm attacks
Methods, apparati, and computer program products for detecting and responding to fast-spreading network worm attacks include a network monitoring module (110), which observes (205) failed network connection attempts from multiple sources. A logging module (120) logs (220) the failed connection attempts. An analysis module (150) uses the logged data on the failed connection attempts to determine (225) whether a sources is infected with a worm using a set of threshold criteria. The threshold criteria indicate whether a source's failed connection attempts are non-normal. In one embodiment, a response module (160) responds (240) to the computer worm by, e.g., alerting a user or system administrator, terminating an infected process (20), or terminating the infected source's network access.
Owner:CA TECH INC
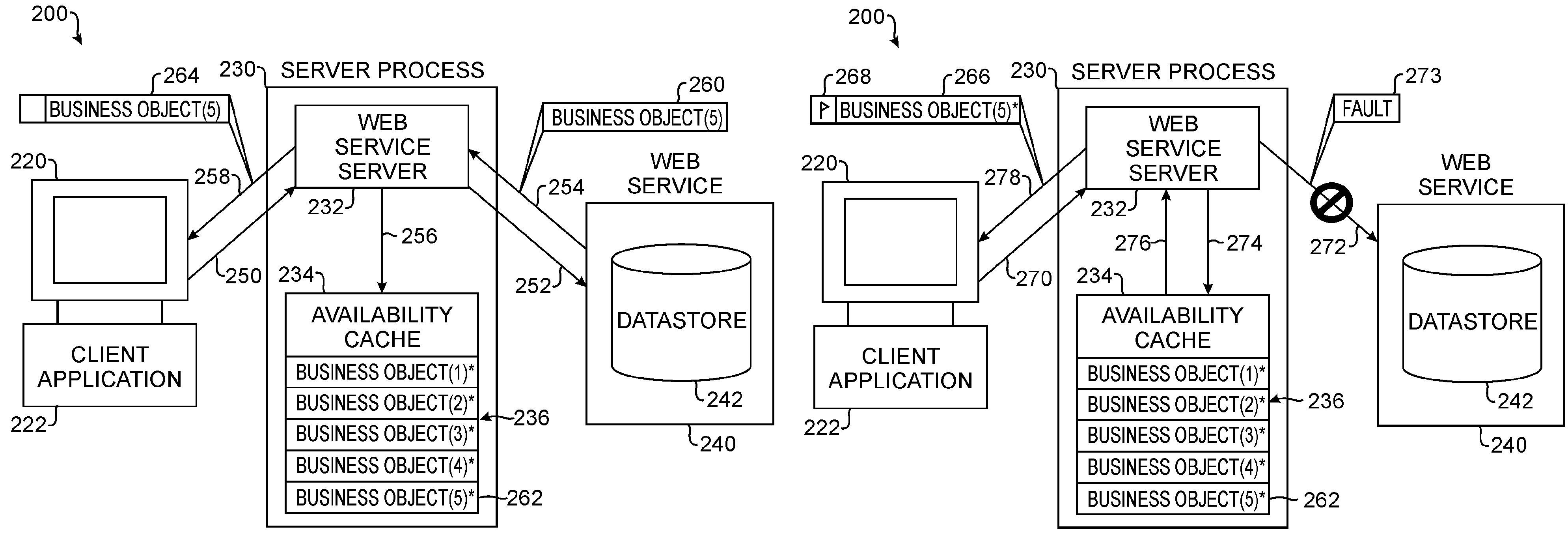
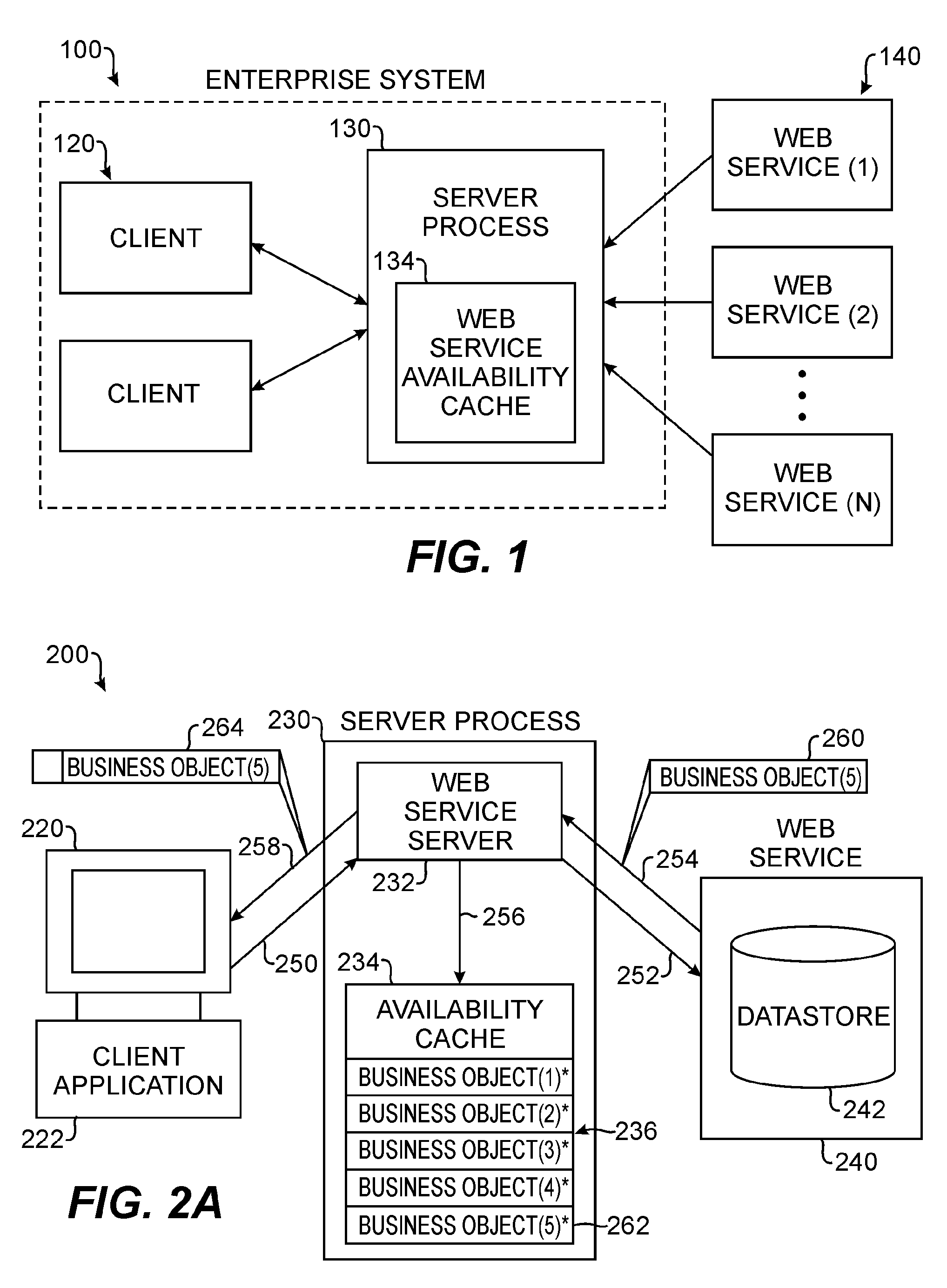
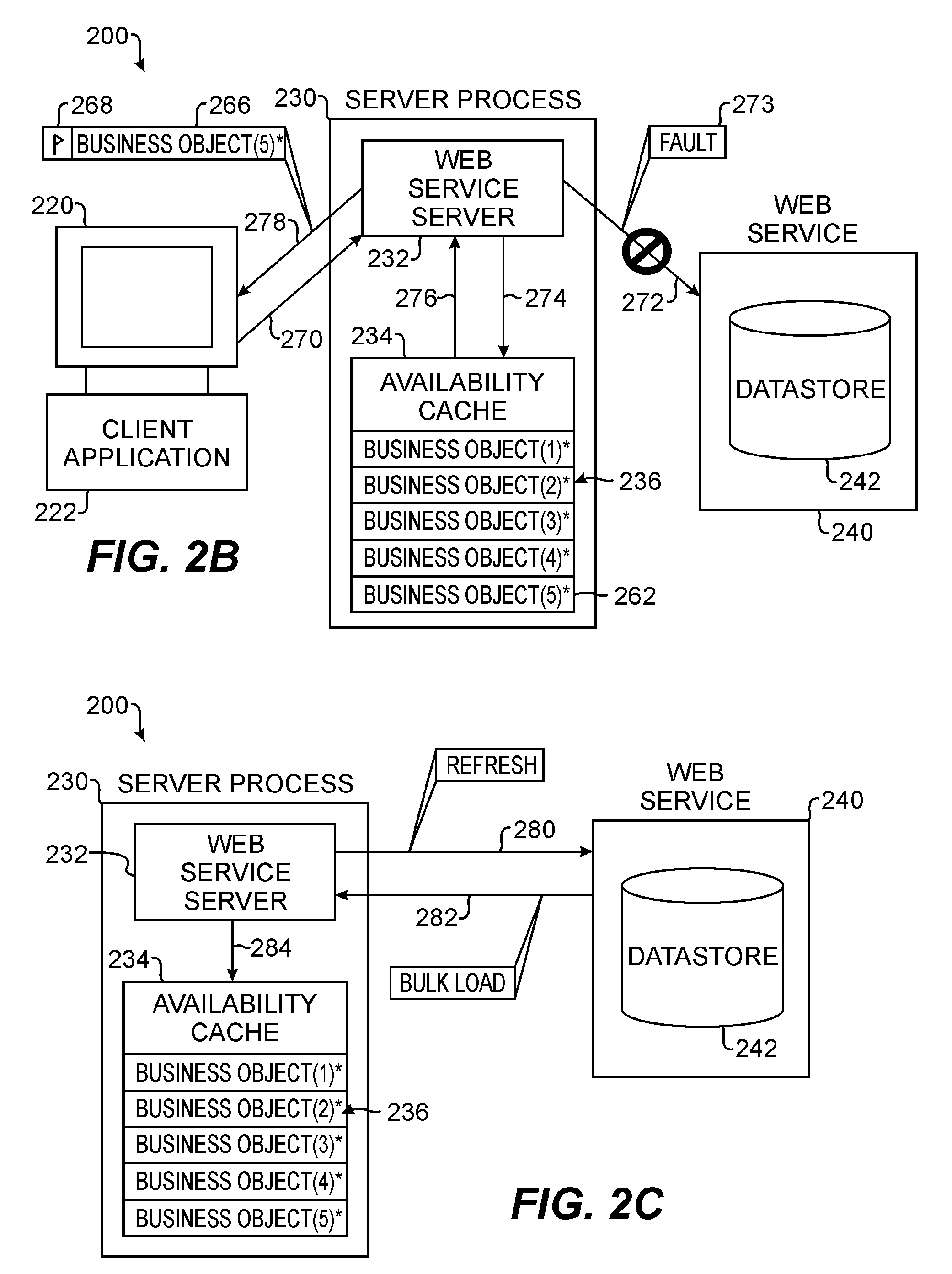
Web services availability cache
ActiveUS7716353B2Multiple digital computer combinationsWebsite content managementNetwork connectionWeb service
A Web Services availability cache is part of a computer system, such as an enterprise system of a business or organization. The availability cache is populated with information from Web Services communicatively connected to the computer system by a network connection. In one embodiment, the availability cache is populated based on each request handled by a server process associated with the availability cache. A server receives a request from a client having an application dependent upon information from the Web Service. The server sends the request to the Web Service and stores returned information in the availability cache. Also, the server sends the returned information to the client, which initiated to request. Once the cache is populated, the server handles subsequent requests for information from the client by using the Web Service if it is available or by using the availability cache if the Web Service is not available.
Owner:BMC SOFTWARE
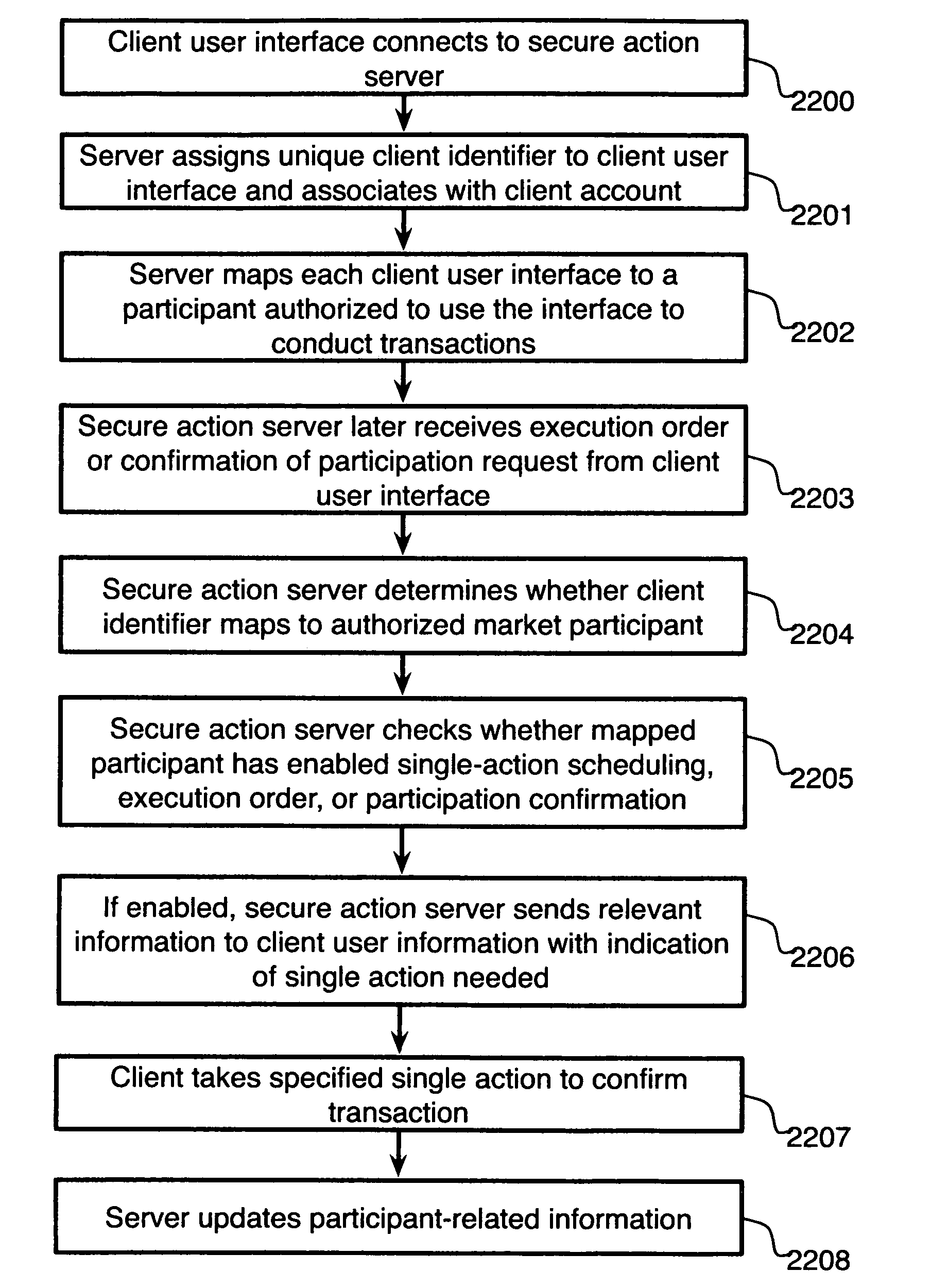
System and method for single-action energy resource scheduling and participation in energy-related securities
InactiveUS20100217642A1Circuit arrangementsDigital data processing detailsCommunication interfaceInformation transmission
A system for single-action energy resource scheduling and participation in energy-related securities, comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of client user interfaces and a secure action server coupled to the communications interface, wherein the secure action server, on receiving a connection from a client user interface, assigns a unique client identifier to the client user interface and associates the unique identifier with a client account, and wherein the secure action server, on receiving a request from a client user interface, determines whether the client user interface is mapped to an authorized market participant who has enabled single-action scheduling, execution order, or participation confirmation functionality for the client user interface, and passes information to the client user interface pertaining at least to a single action needed to confirm scheduling, execution order, or participation and wherein the secure action server, on receiving indication from the communications interface that a required single action has been taken, at least updates information about the market participant who took the action, is disclosed.
Owner:CRUBTREE JASON +4
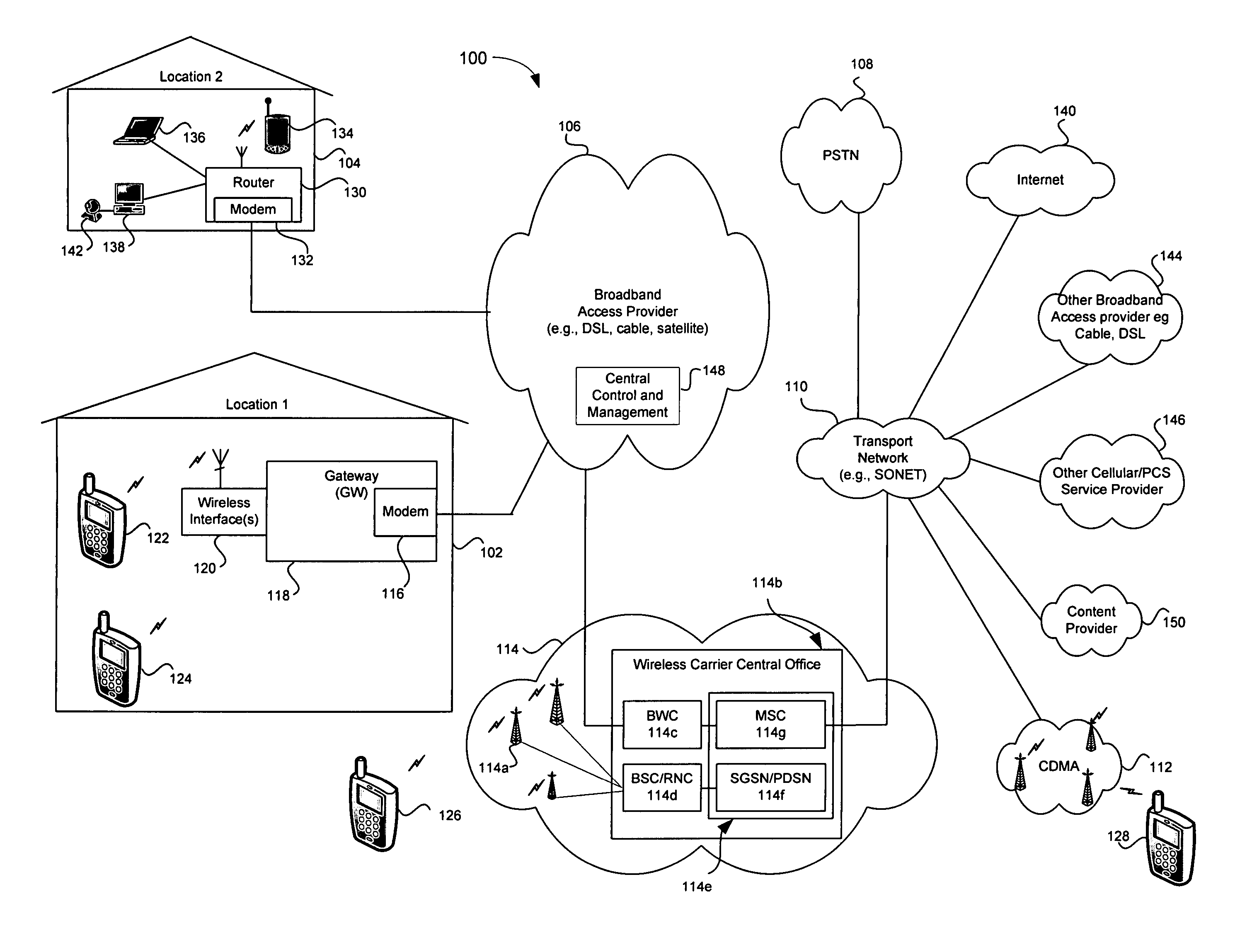
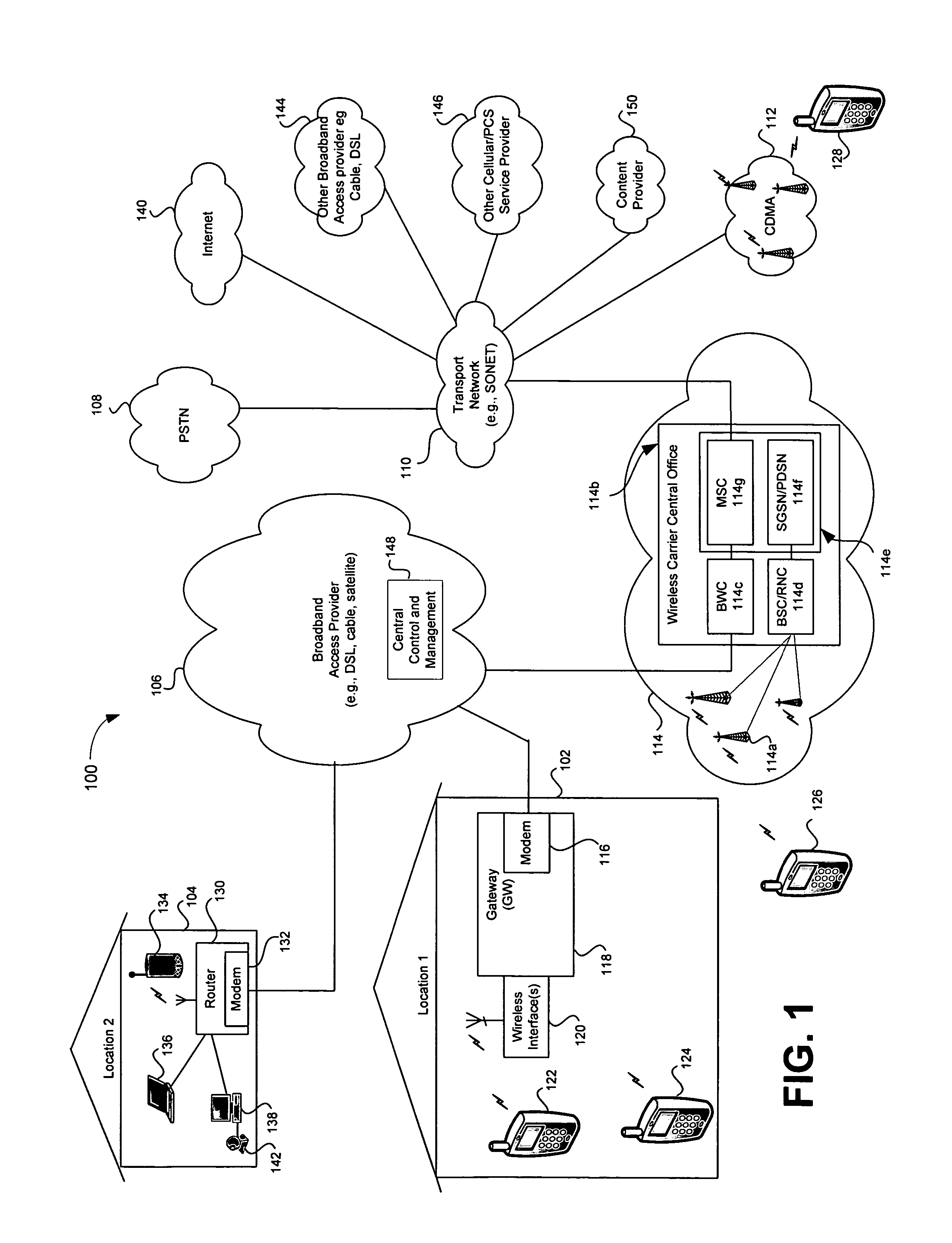
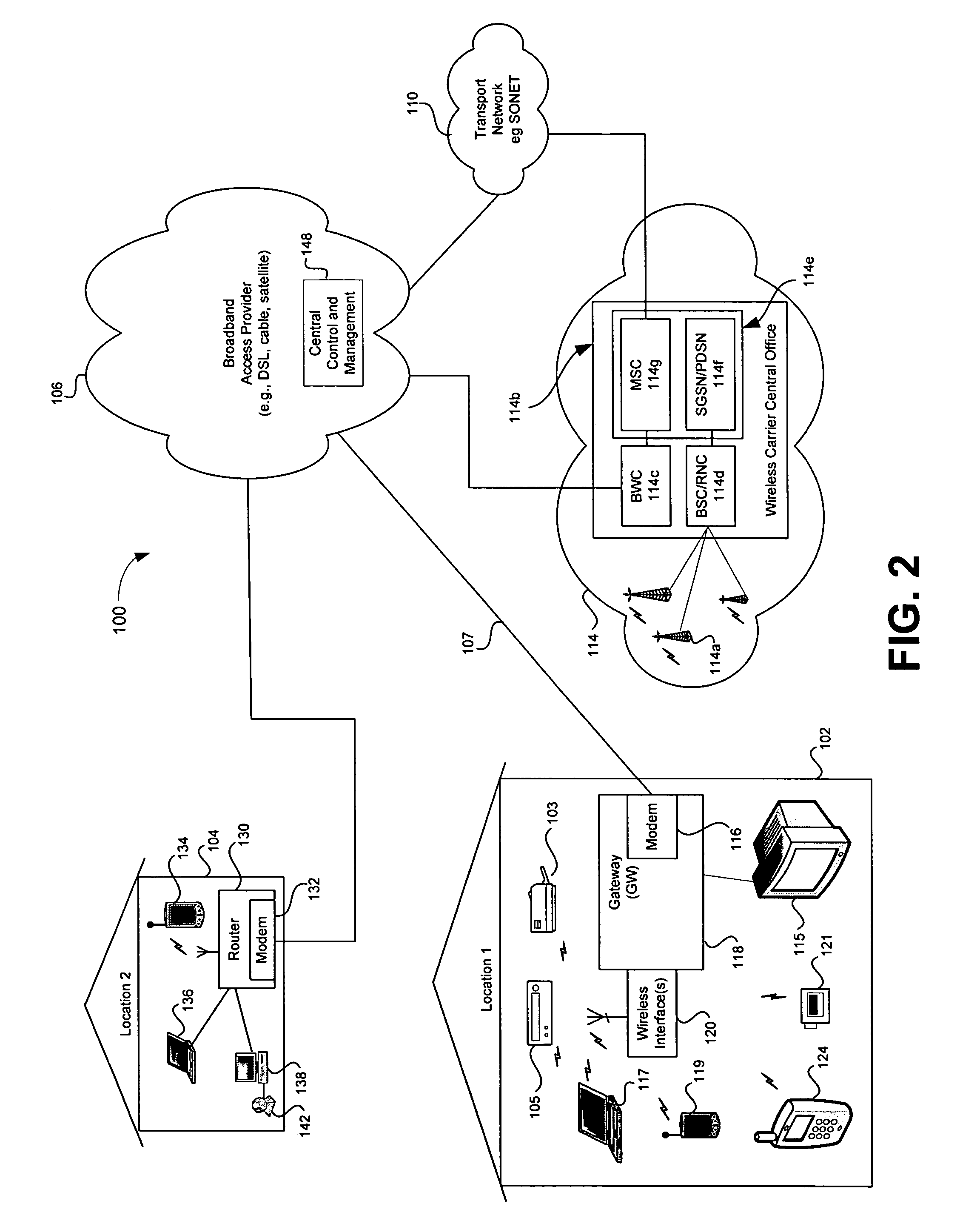
Remote configuration and control of local devices via a broadband access gateway
A system and method for the remote configuration and control of a access devices via a broadband access gateway is disclosed. The broadband access gateway may comprise a wireless interface and a broadband network connection for exchanging information via, for example, a digital subscriber loop, a cable connection, a T1 connection, and T3 network connection. A user using any of a plurality of access devices may communicate with the broadband access gateway via the wireless interface or the broadband network connection to make remote requests of another of the access devices. Such requests may comprise, for example, accessing, recording, playing, exchanging, transmitting, receiving, converting, translating of multimedia information. The remote requests may include enabling, disabling, configuring, monitoring, administering, and scheduling of smart appliances and premise systems such as, for example, security, heating, and cooling systems.
Owner:AVAGO TECH INT SALES PTE LTD
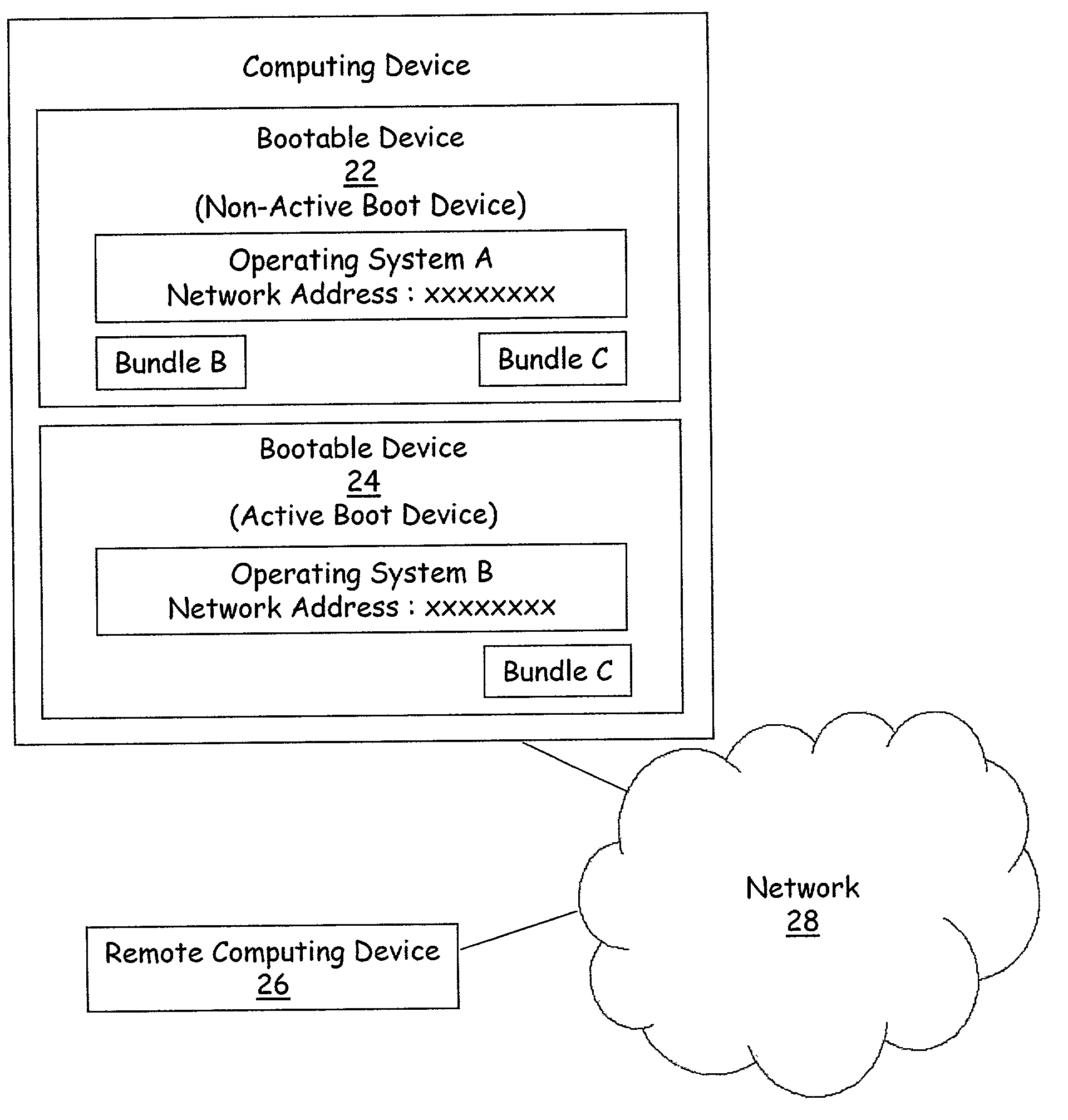
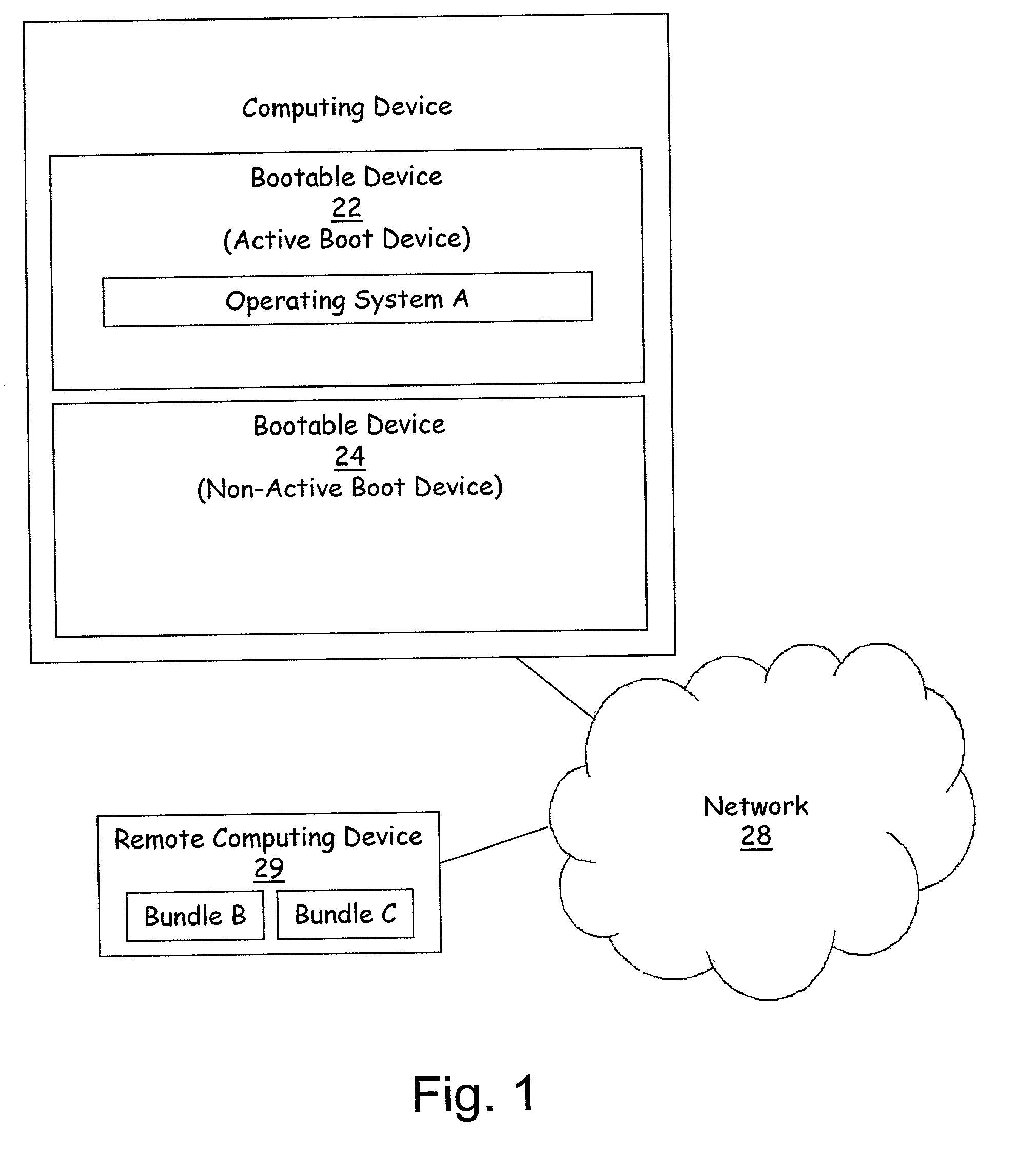
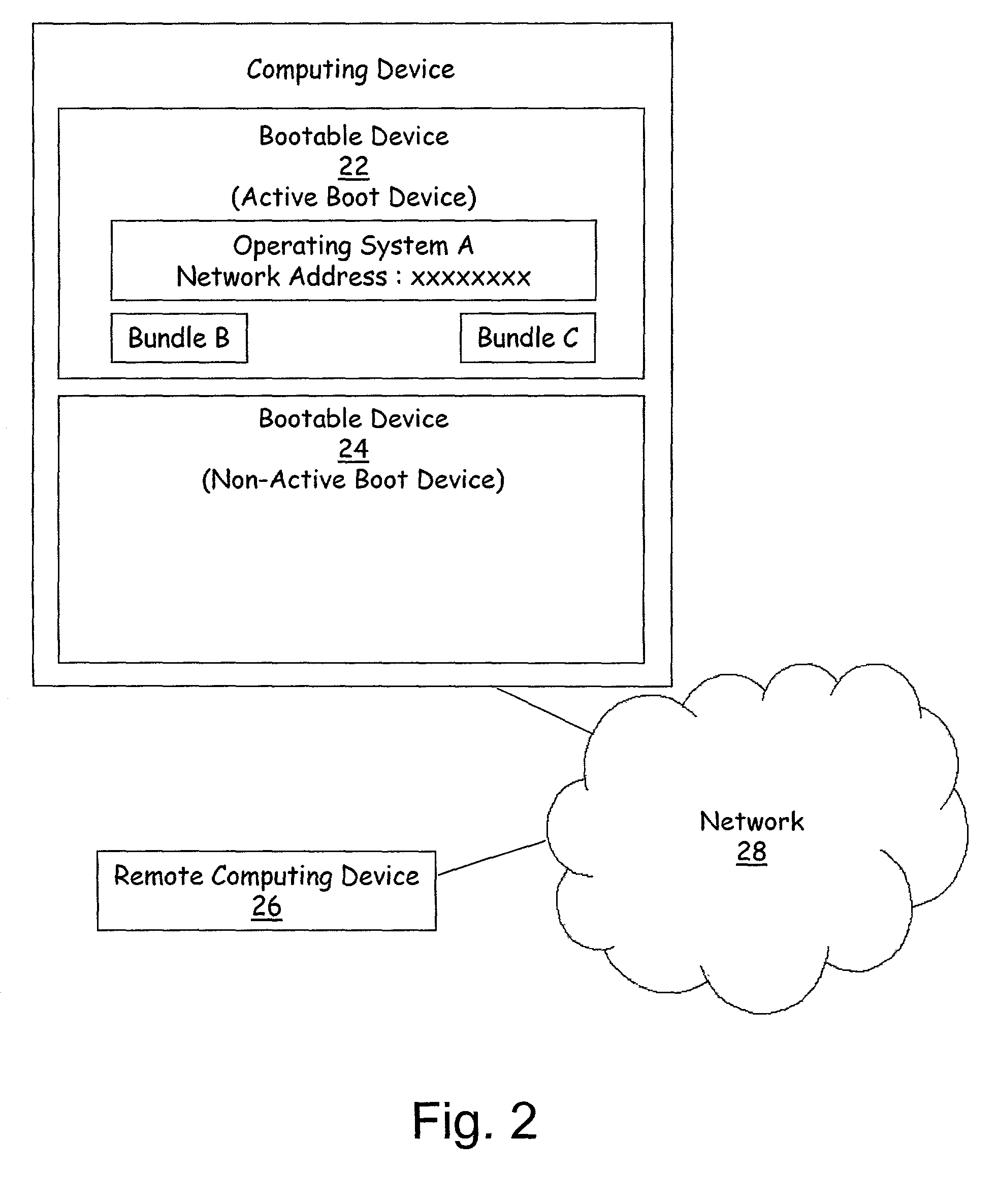
Method and apparatus for remote installation of an operating system over a network connection
InactiveUS6963981B1More securityMemory loss protectionError detection/correctionOperational systemNetwork connection
A method for remote installation of a target operating system is carried out on a machine operating a source operating system. In one embodiment, it is presumed that the source operating system was booted from a first bootable region of a storage associated with the machine. According to the method, a copy of the source operating system together with the target operating system are delivered to the machine and stored in a second bootable region of the storage. The copy of the source operating system may be stored in a first partition of the second bootable region of the storage, and the target operating system may be stored in a second partition of the second bootable region. A boot loader is then configured to boot the copy of the source operating system from the second bootable region of the storage. The machine is then re-booted. At this point, the machine is still running the source operating system, although in this case that operating system was booted from the second bootable region of the storage. The original source operating system (from the first bootable region) is then removed, and the boot loader is re-configured to boot the target operating system from the second bootable region of the storage. The machine is then re-booted again, after which the target operating system is operational. In one embodiment, the first and second bootable regions may be separate hard disks, and the source and target operating systems are Linux and Windows, or vice versa.
Owner:AKAMAI TECH INC
User interface for multi-device control
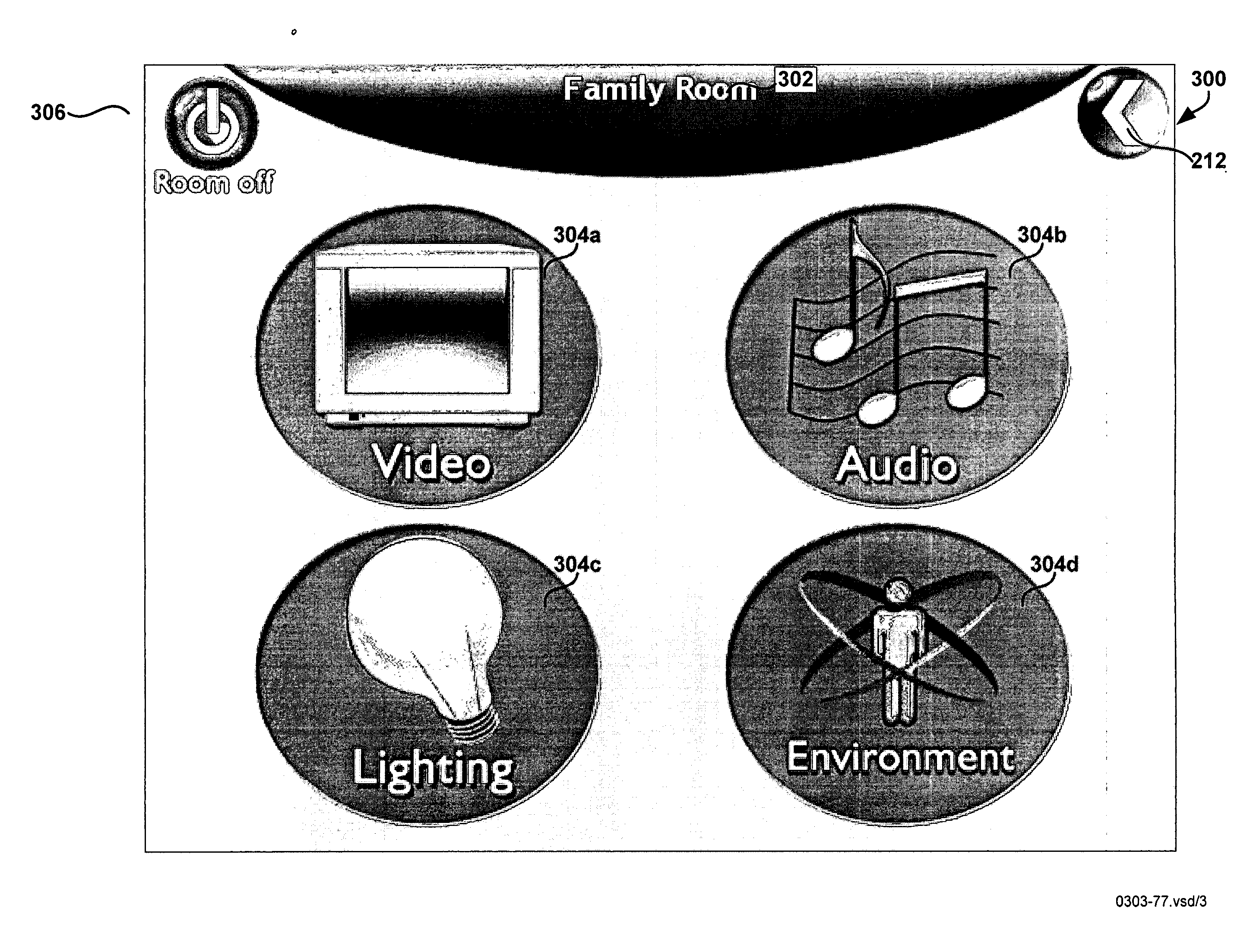
ActiveUS20050097478A1Facilitate control of systemAlter its performanceData processing applicationsComputer controlControl signalNetwork connection
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of system components connected via a wired and / or wireless communications network. The system components include audio / visual components (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). A portable controller allows a user to access and control the system components from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The portable controller includes a user and management interface that contains customized control screens for the system components. The control screens are stored in a hierarchical architecture that is searchable by region or component type.
Owner:MICROSOFT TECH LICENSING LLC
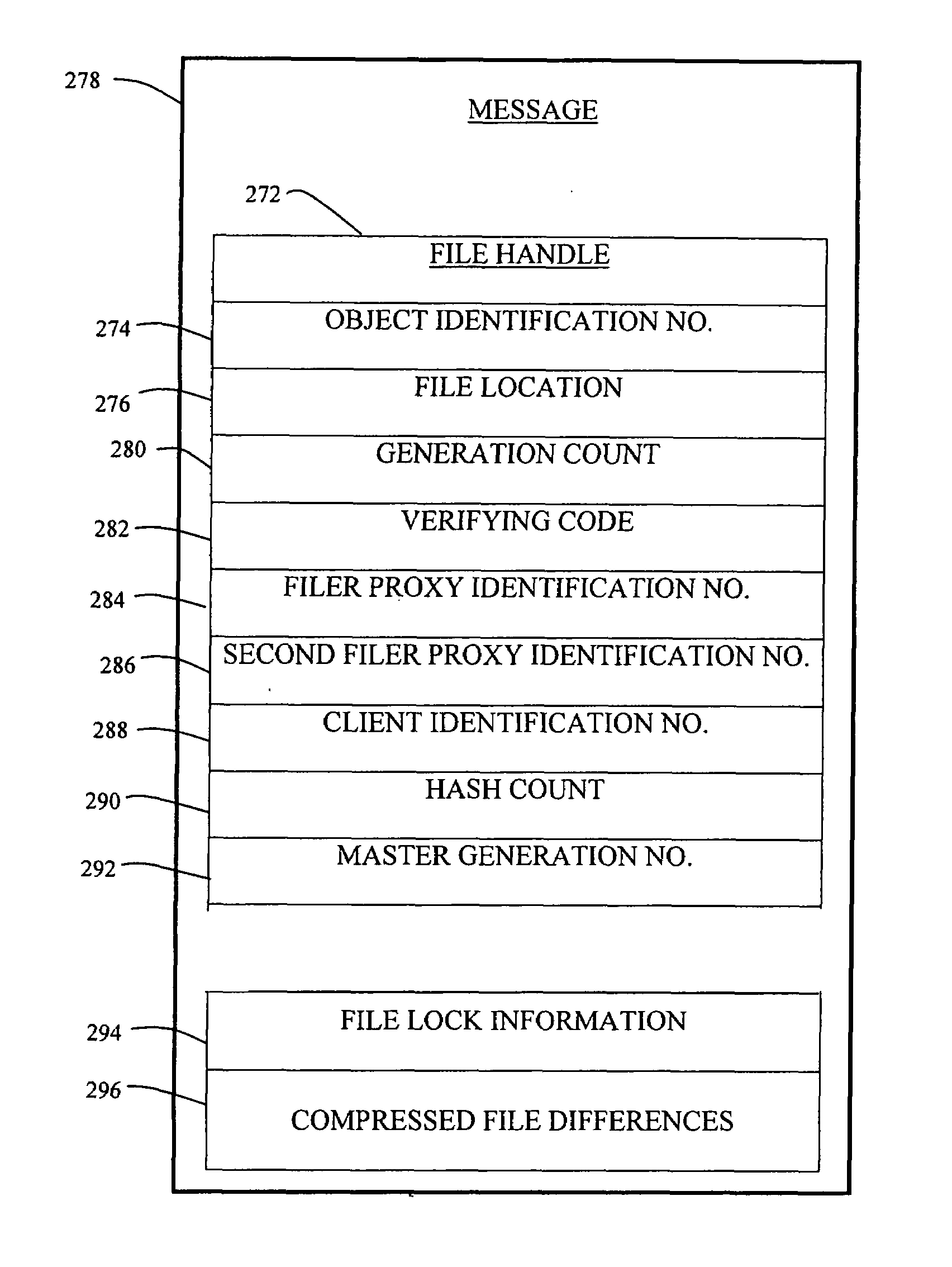
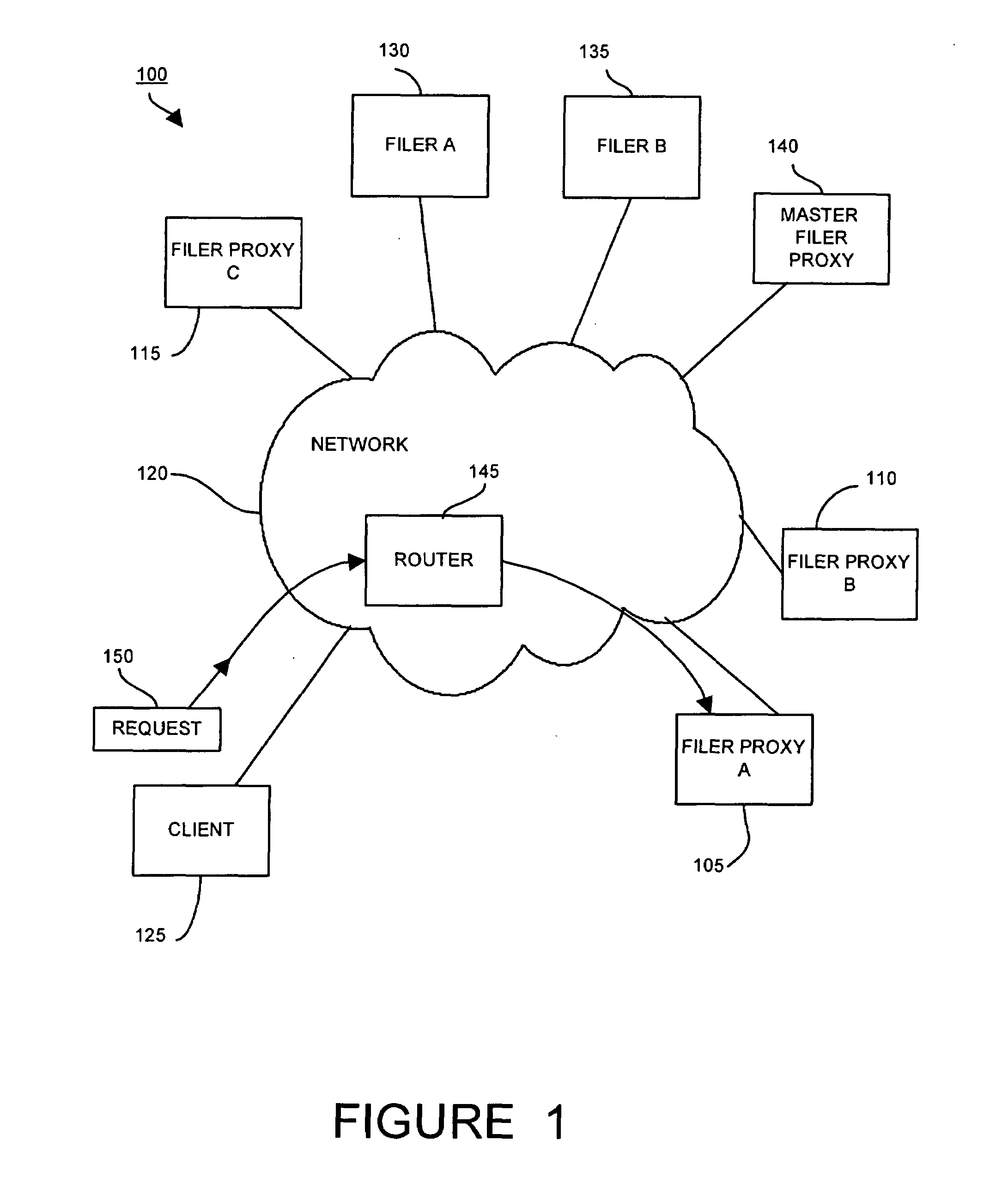
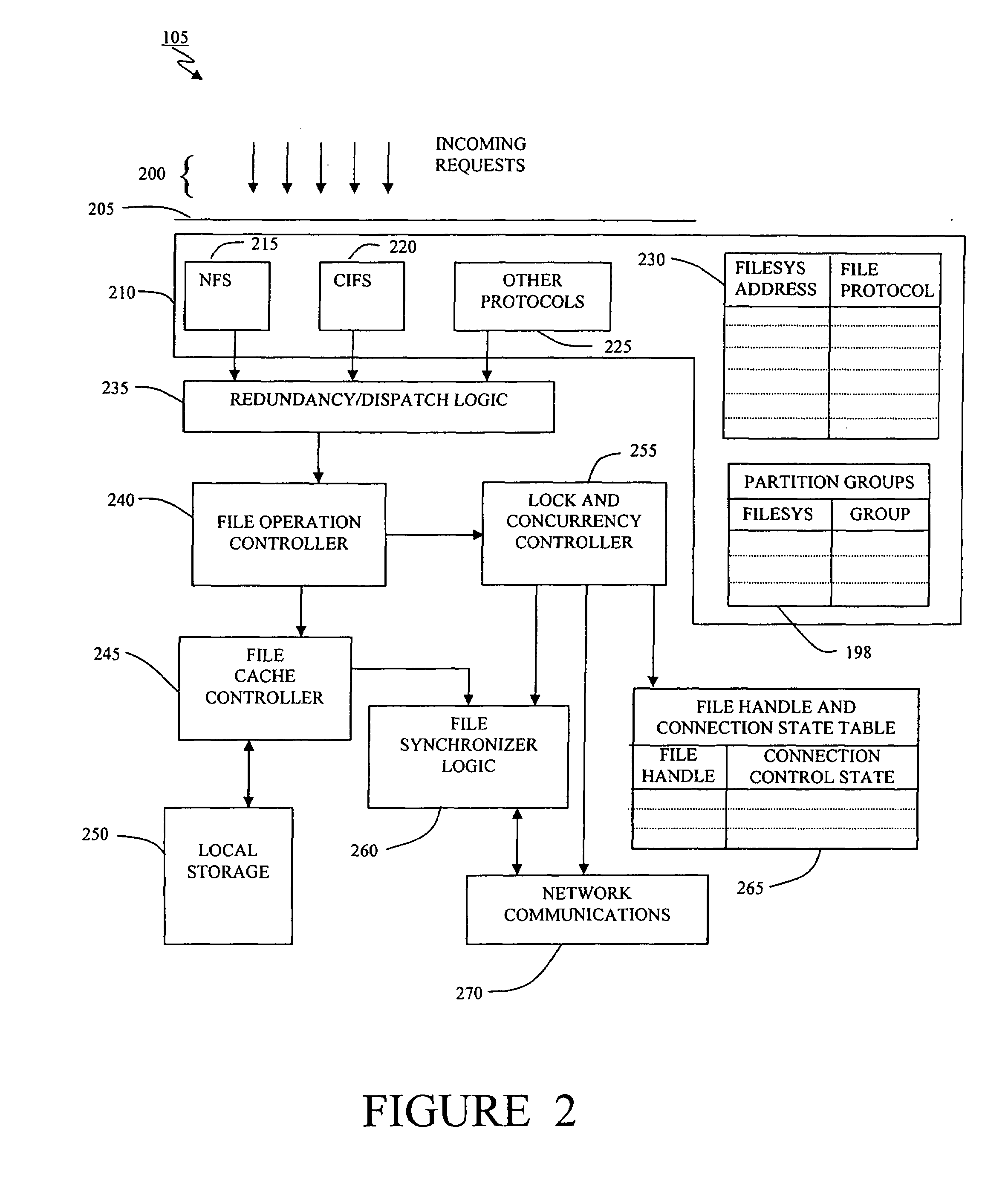
Method and apparatus for transparent distributed network-attached storage with web cache communication protocol/anycast and file handle redundancy
ActiveUS7254636B1Data processing applicationsDigital data processing detailsContent distributionNetwork connection
A distributed network-attached storage network provides content distribution using conventional file transfer protocols such as NFS and CIFS. A filer proxy accepts a client request and translates the client request to a file transfer protocol accepted at the file system having the file requested in the client request. The filer proxy generates a file handle for the file containing redundant filer proxy information to be used for failover to a backup filer proxy in the event of a network error or failure of an original filer proxy. The file handle also contains information for network security purposes such as detection of forged file handles.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com