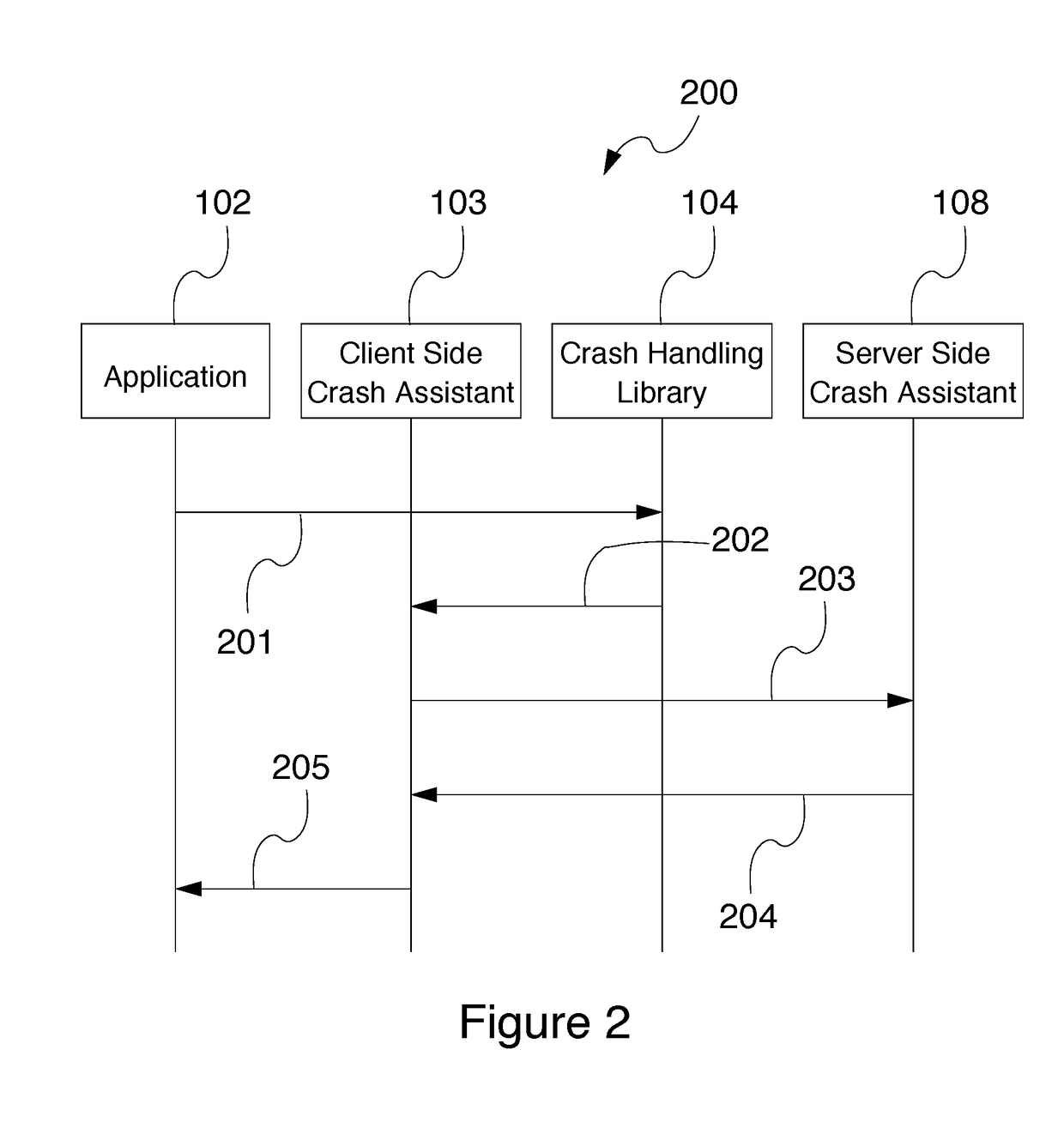
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
238 results about "Crash" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
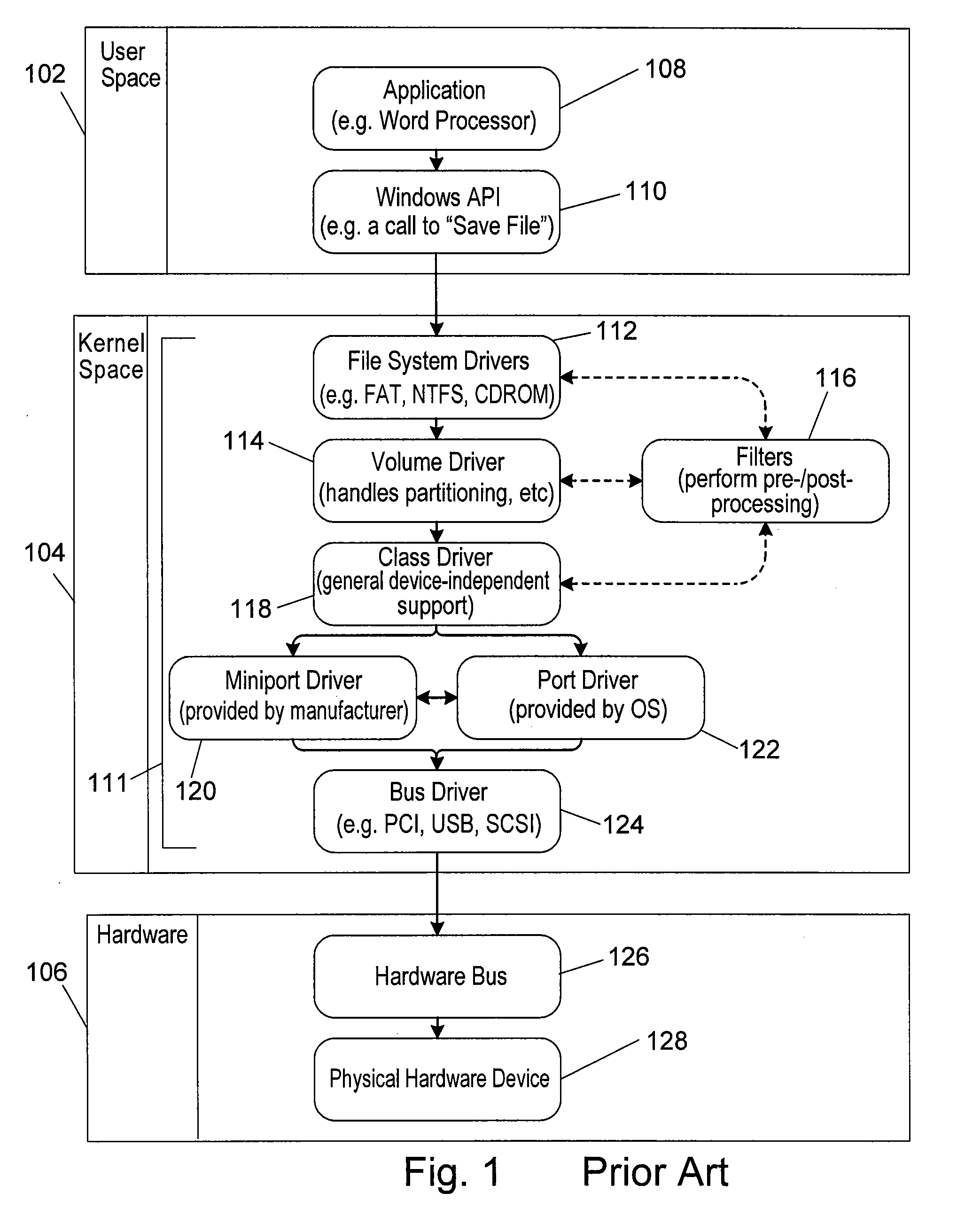
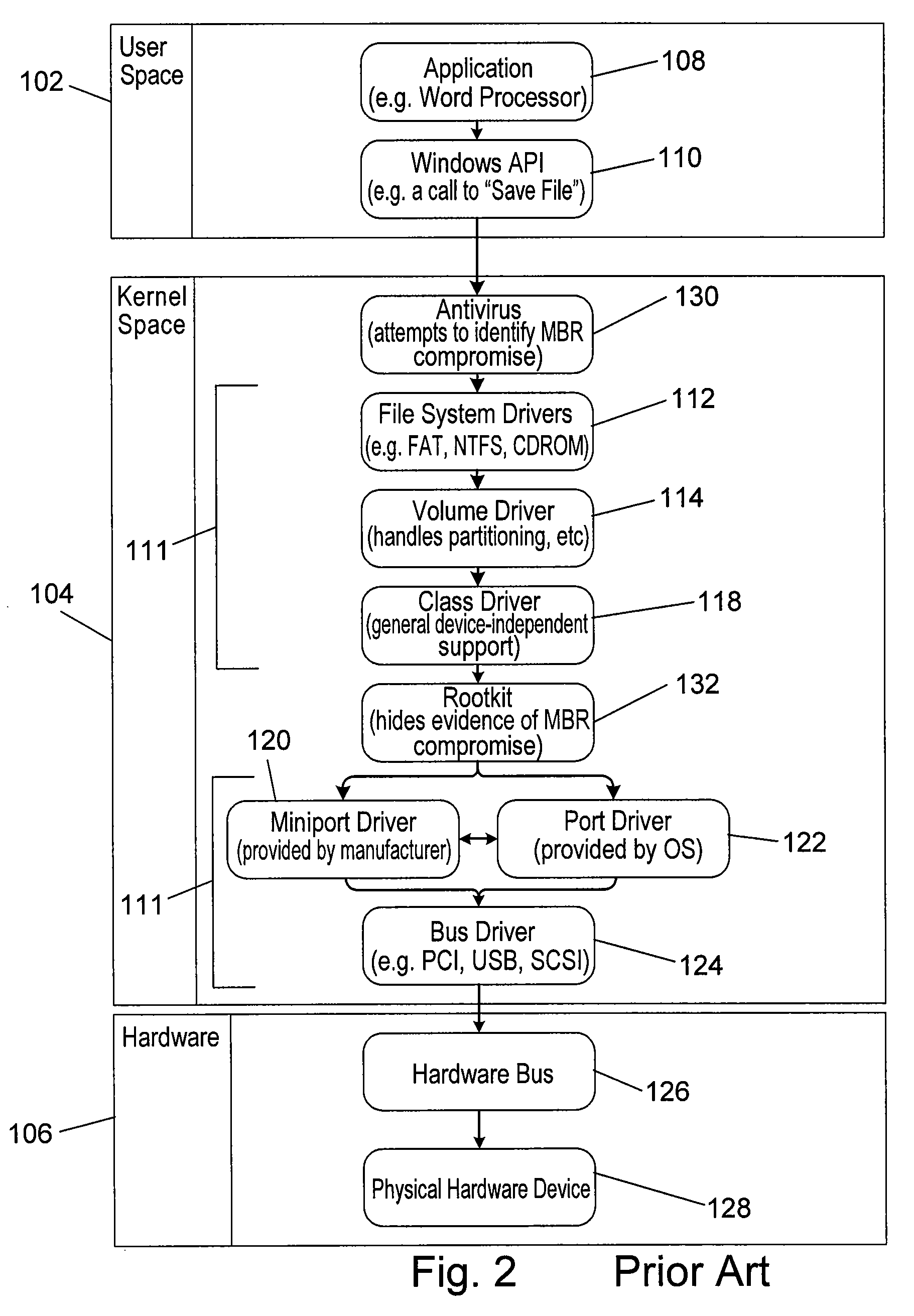
In computing, a crash, or system crash, occurs when a computer program such as a software application or an operating system stops functioning properly and exits. The program responsible may appear to hang until a crash reporting service reports the crash and any details relating to it. If the program is a critical part of the operating system, the entire system may crash or hang, often resulting in a kernel panic or fatal system error.
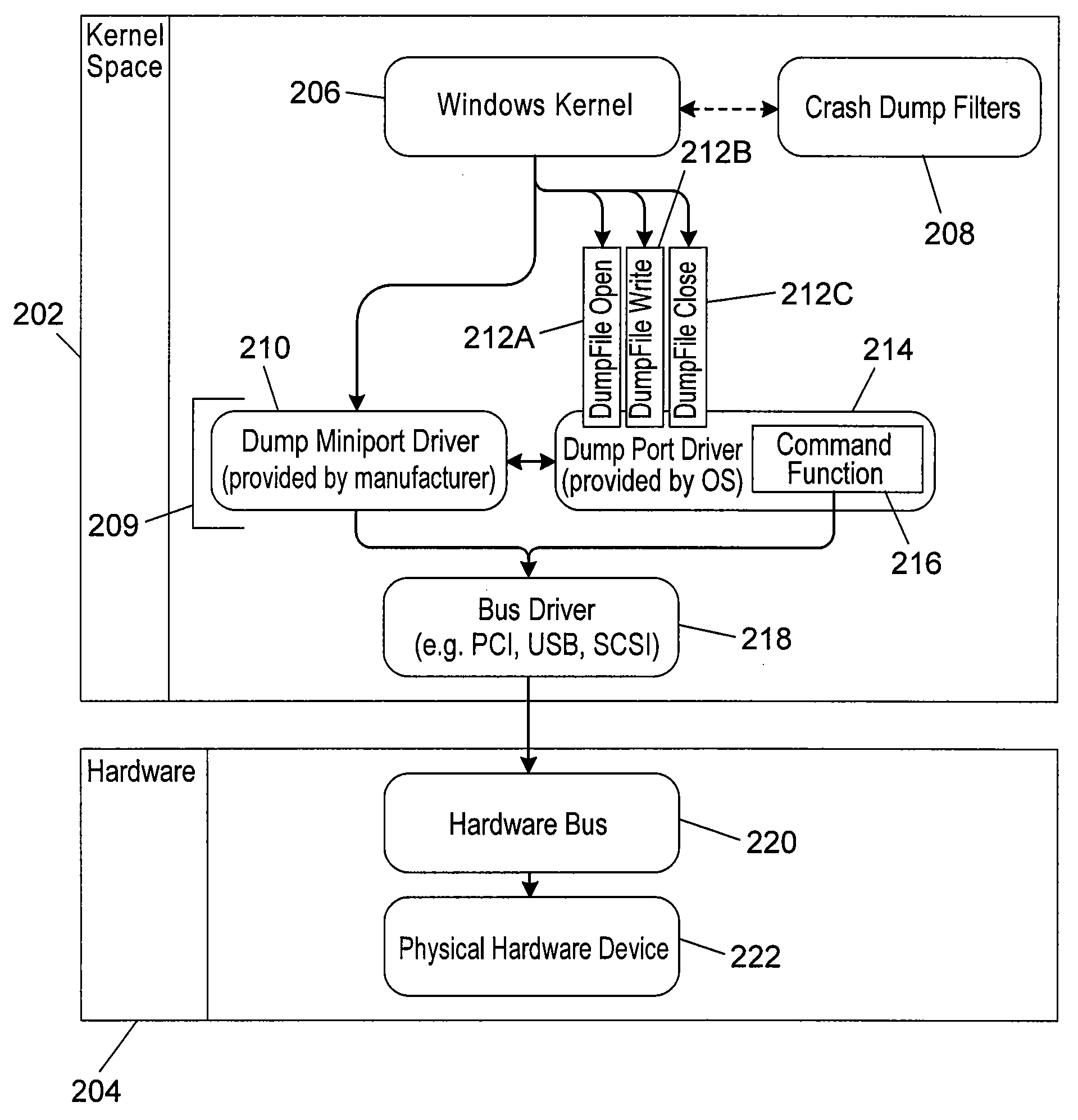
System to Bypass a Compromised Mass Storage Device Driver Stack and Method Thereof
ActiveUS20130247186A1Less susceptible to malicious software compromiseFunction increaseMemory loss protectionError detection/correctionMass storageMalware
A method to circumvent malicious software via a system configured to bypass a device driver stack and, consequently, also bypass the malicious software that may be adversely affecting the device driver stack by using an alternative stack such as a crash dump I / O stack. The crash dump I / O stack is poorly documented relative to the device driver stack and functions independently from the device driver stack.
Owner:FIREEYE SECURITY HLDG US LLC
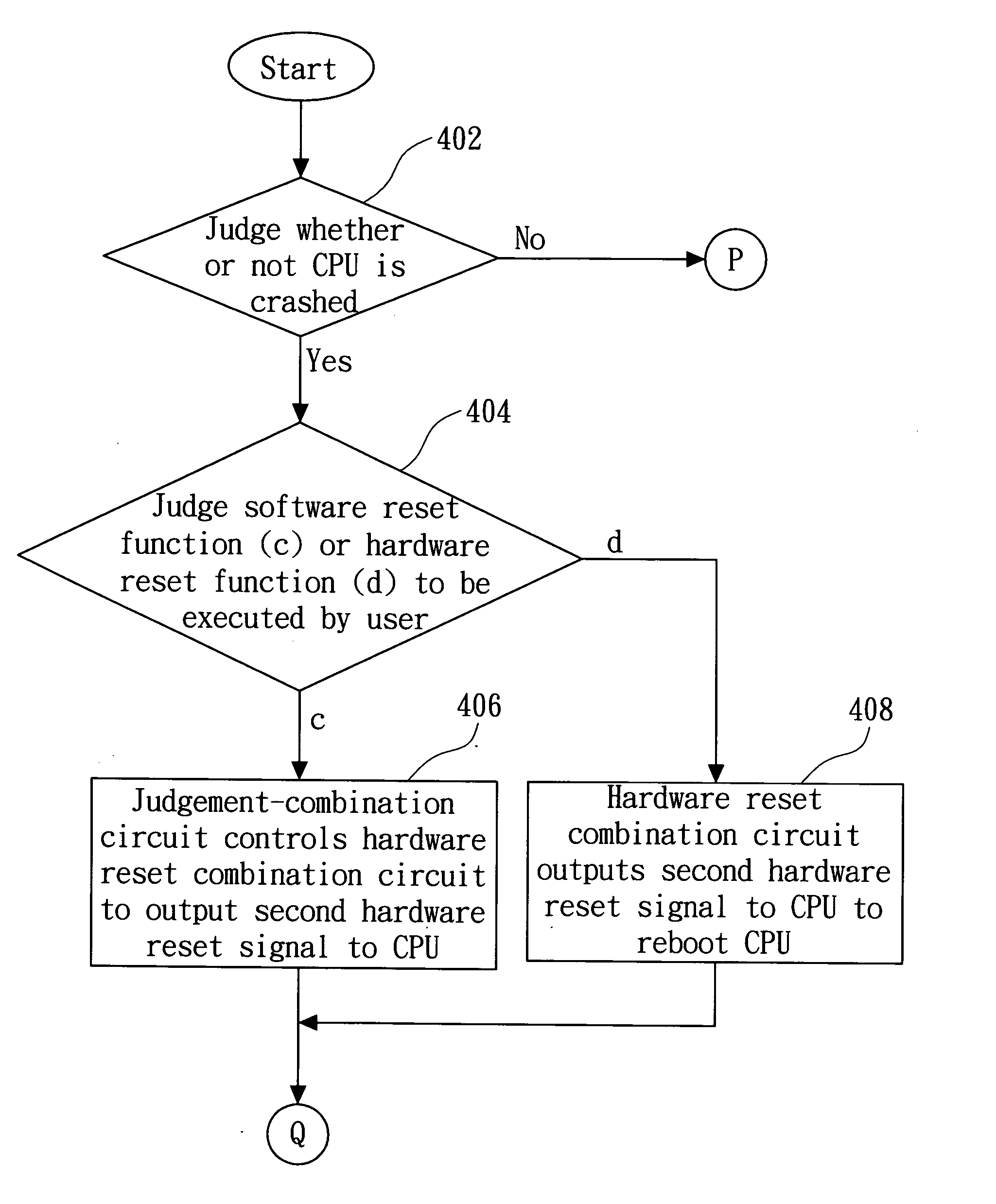
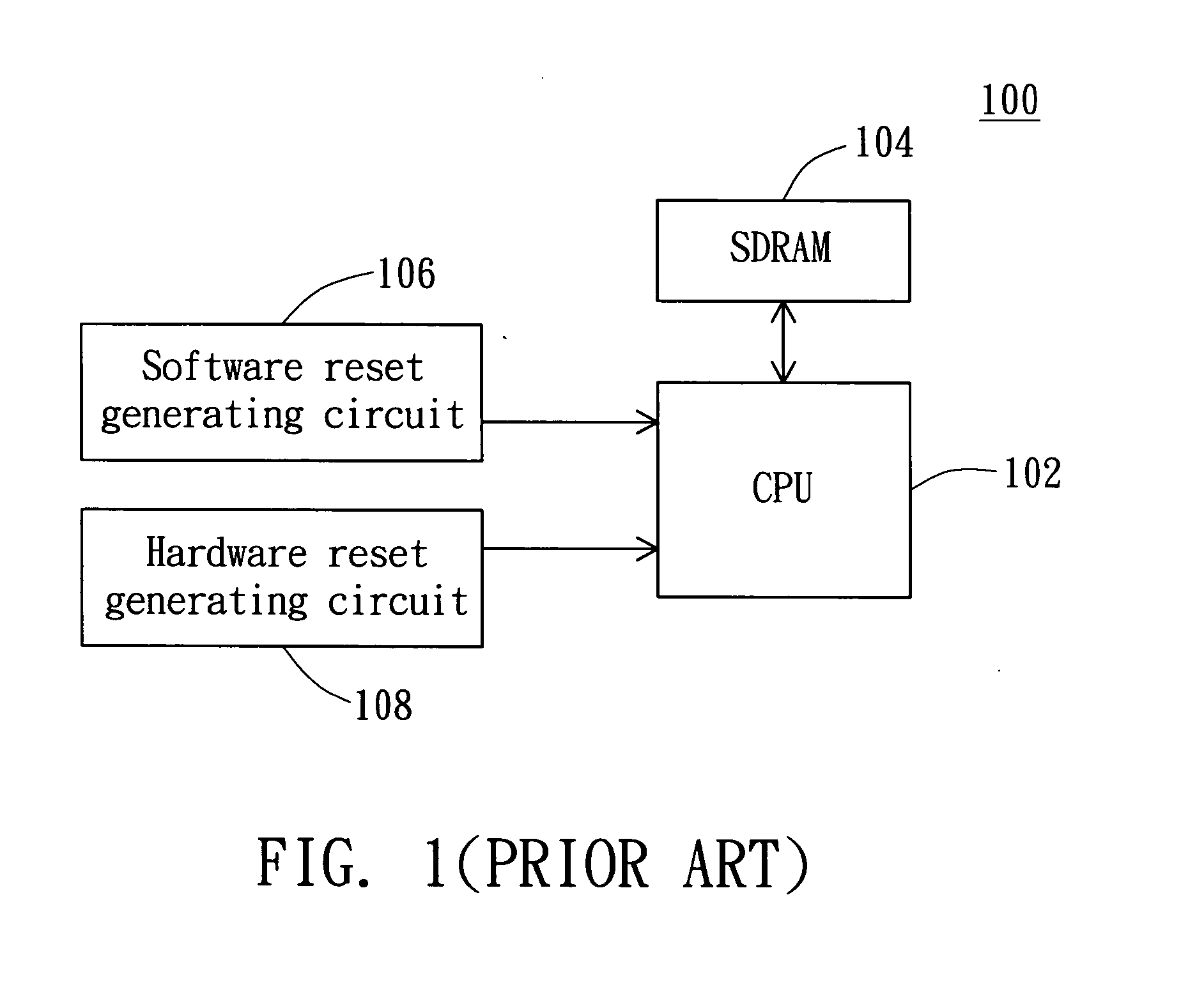
Booting method capable of executing a warm boot or a cold boot when a CPU crash occurs and computer system therefor
ActiveUS20050055598A1Eliminate timeData can be lostDigital computer detailsData resettingSystem recoveryBooting
A booting method capable of executing a warm boot or a cold boot when a CPU crash occurs in a computer system having a CPU and a memory. First, when the CPU is in a crash state, it is detected that a user wants to execute a hardware reset function or a software reset function. Next, a hardware reset operation is executed to reboot the CPU. Then, when the user chooses to execute the hardware reset function, data and predefined values of the memory are deleted to make the computer system return to a default state. Thereafter, when the user chooses to execute the software reset function, the hardware reset operation is regarded as an operation to replace a software reset operation, and the computer system holds the data and predefined values to make the computer system return to a setting state before the computer system is crashed.
Owner:HTC CORP
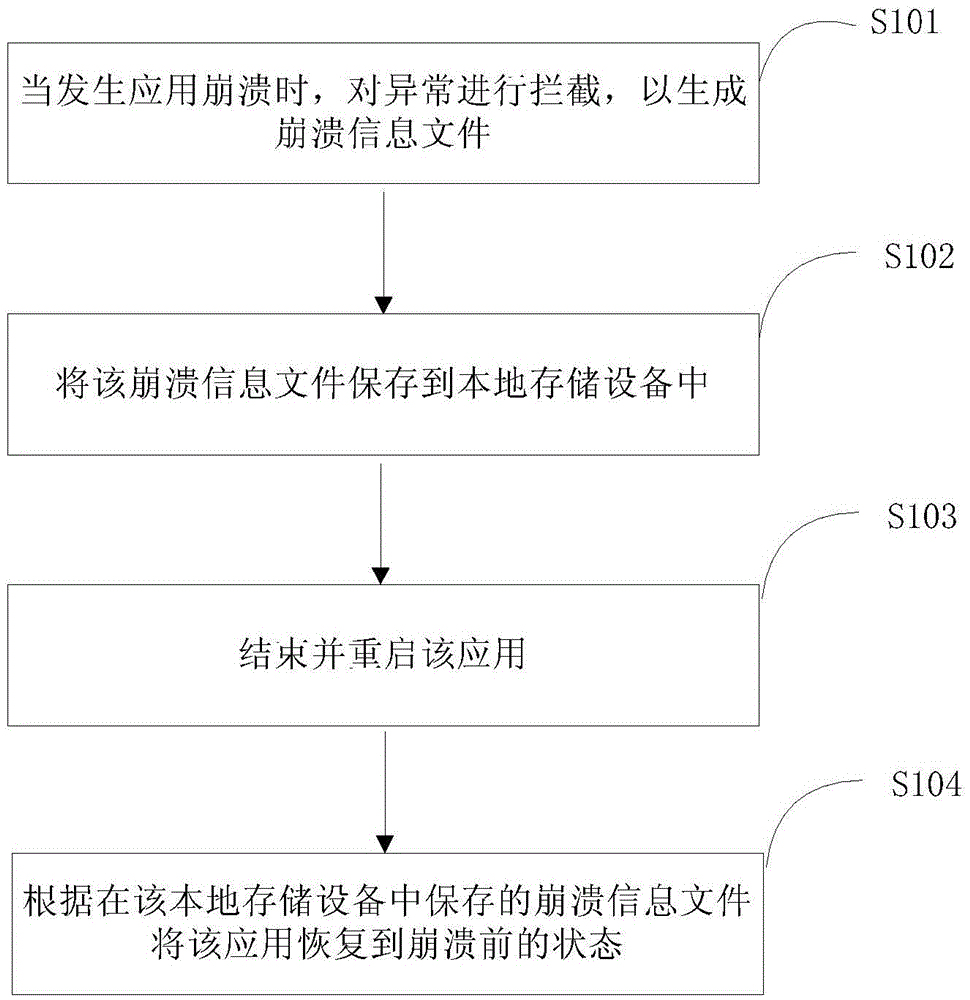
Recovery method and apparatus for business data after application crash
ActiveCN105468478ARecover in timeNo interruption of business operation flowRedundant operation error correctionRecovery methodBusiness data
The invention provides a recovery method and apparatus for business data after application crash. The method comprises: when application crash occurs, intercepting an exception to generate a crash information file; storing the crash information file in a local storage device; ending and restarting the application; and according to the crash information file stored in the local storage device, recovering the application to be in a state before crash. Through the recovery method and apparatus for the business data after the application crash, provided by the invention, when the application crash occurs, user data can be effectively and timely recovered, so that an original business operation process is not interrupted and the data loss caused by crash is reduced.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
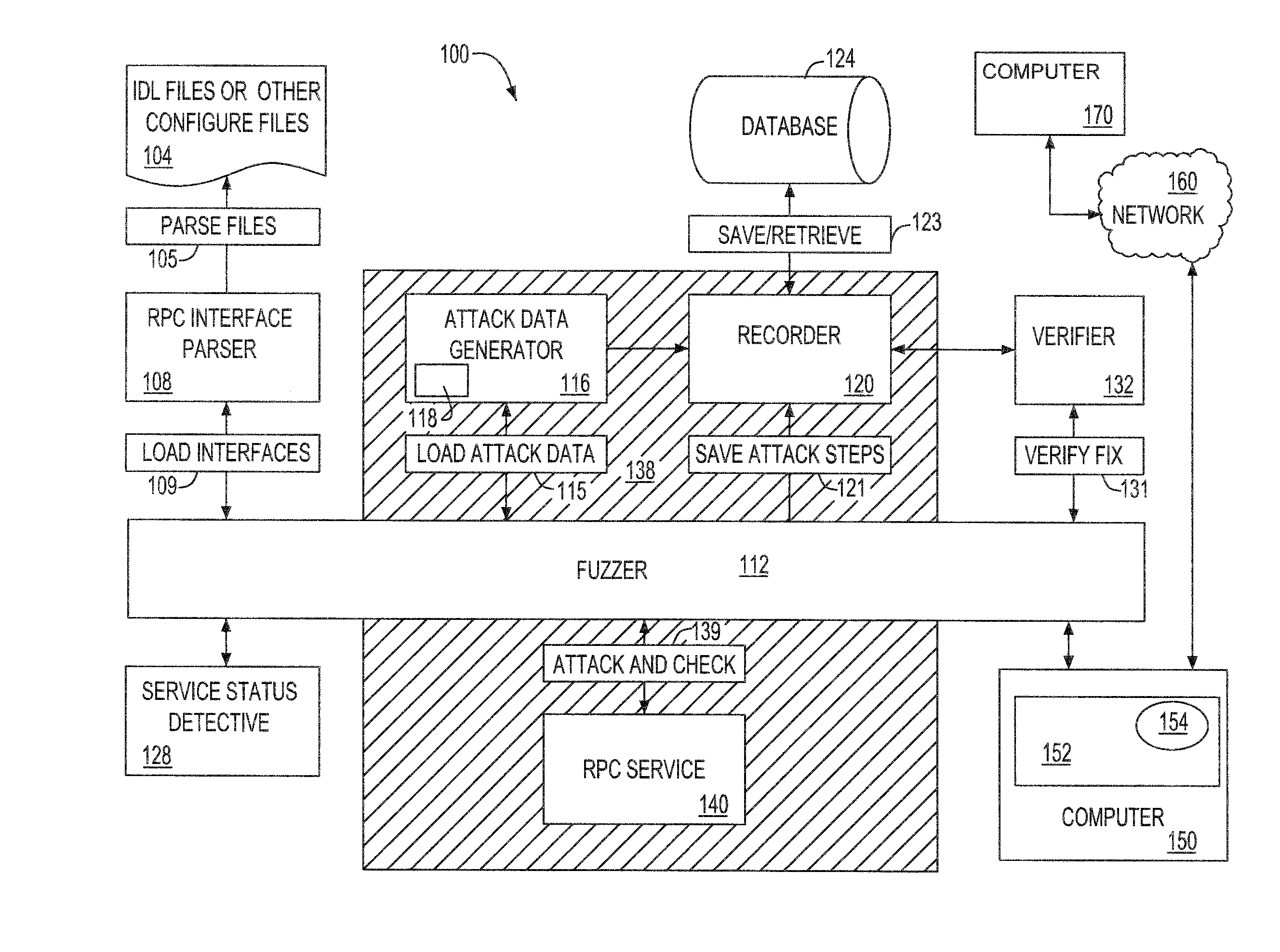
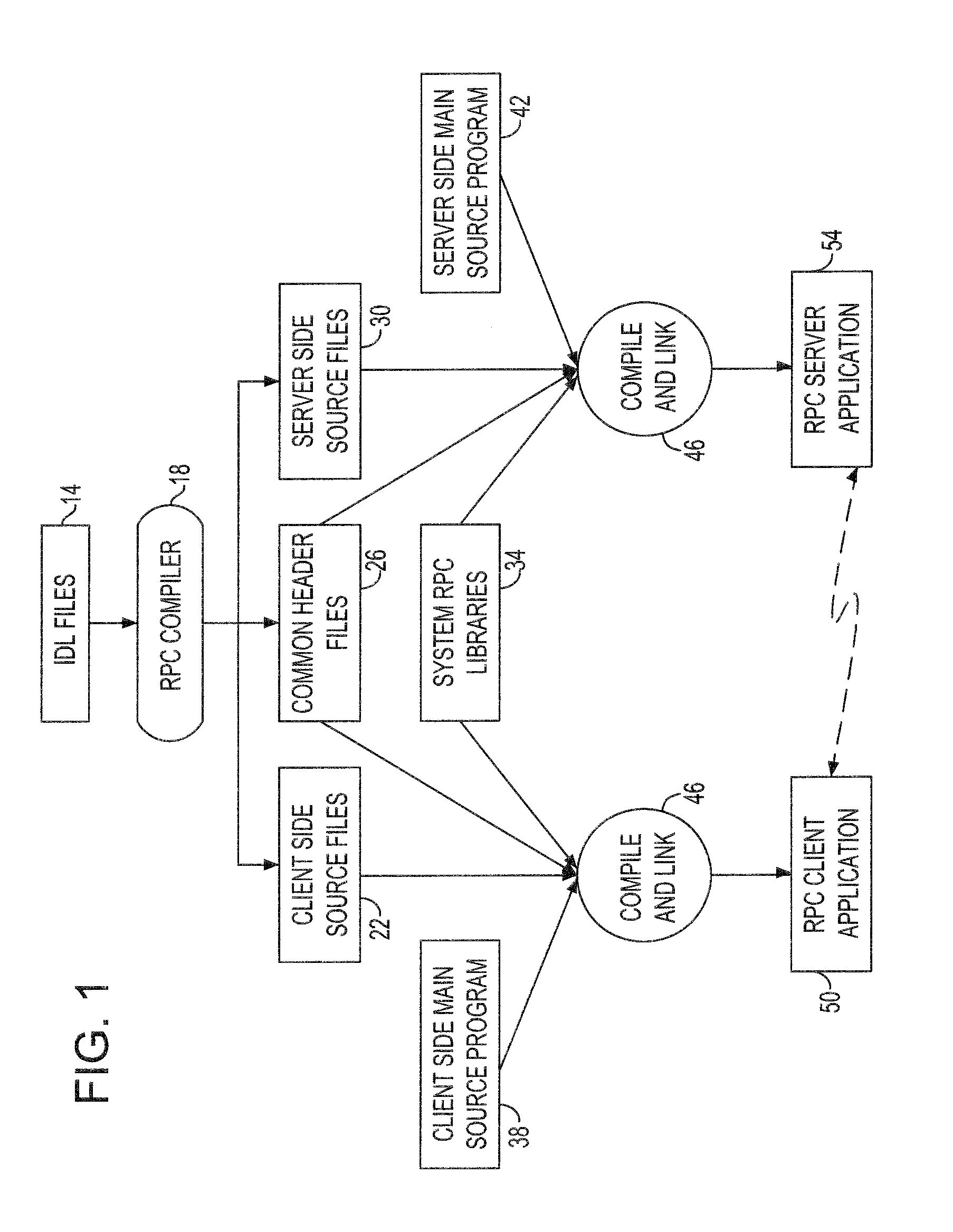
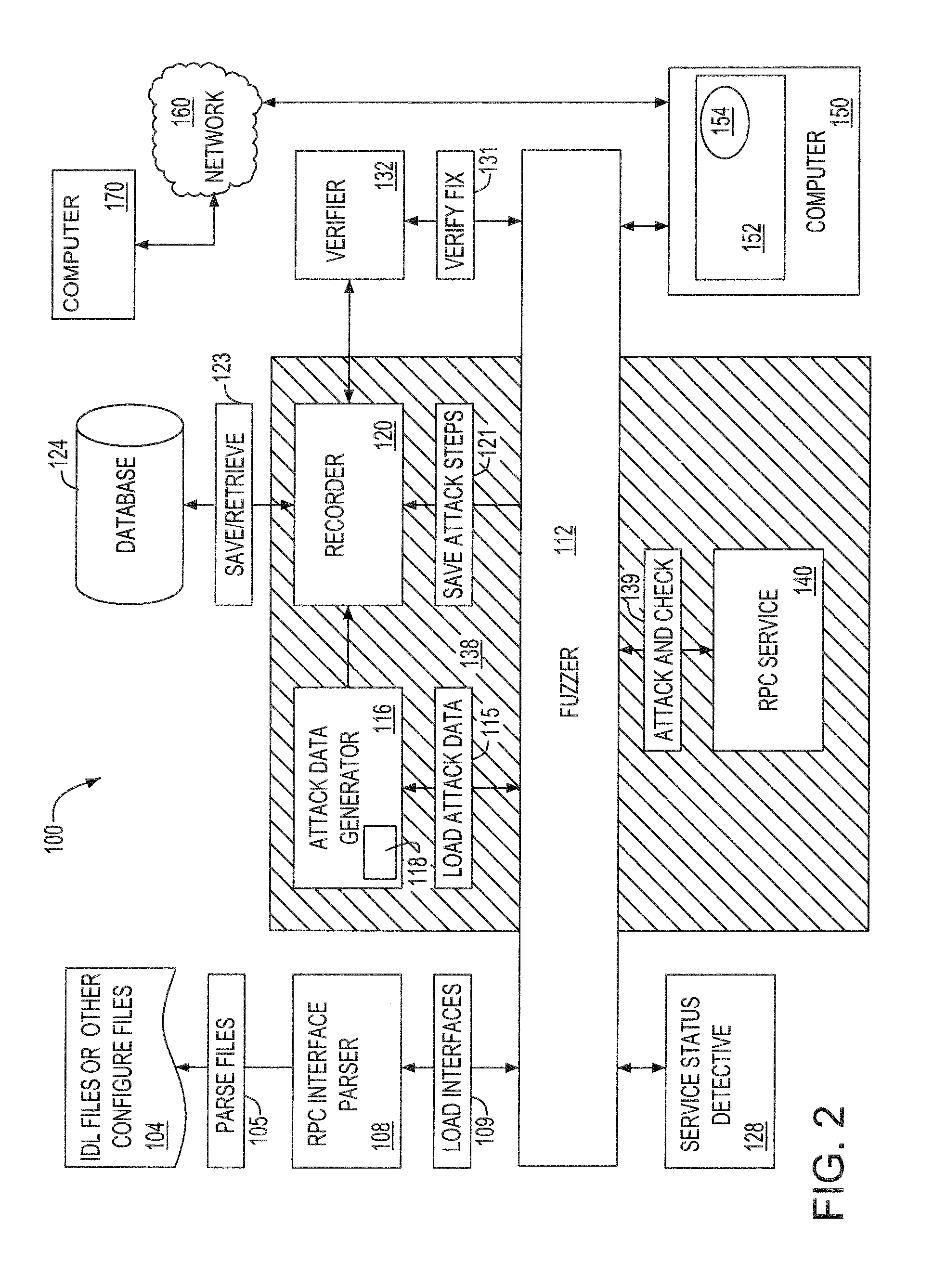
Remote procedure call (RPC) services fuzz attacking tool
A system and method for testing a computer program using a computer system includes a plurality of computer systems communicating using a network. An interface parser module defines at least one program interface in a program file of a specified program. A fuzzer module reads the program file and identifies the program interfaces. An attack data generator module attacks the program interfaces and communicates with the fuzzer, and the fuzzer determines vulnerabilities in the specified program. A recorder records the attacking procedure. A verifier verifies remedies for vulnerabilities by replaying the attacking procedure of the program interface and determining vulnerabilities. A service status detective module restarts the specified program when the specified program ceases to operate or crashes.
Owner:CA TECH INC
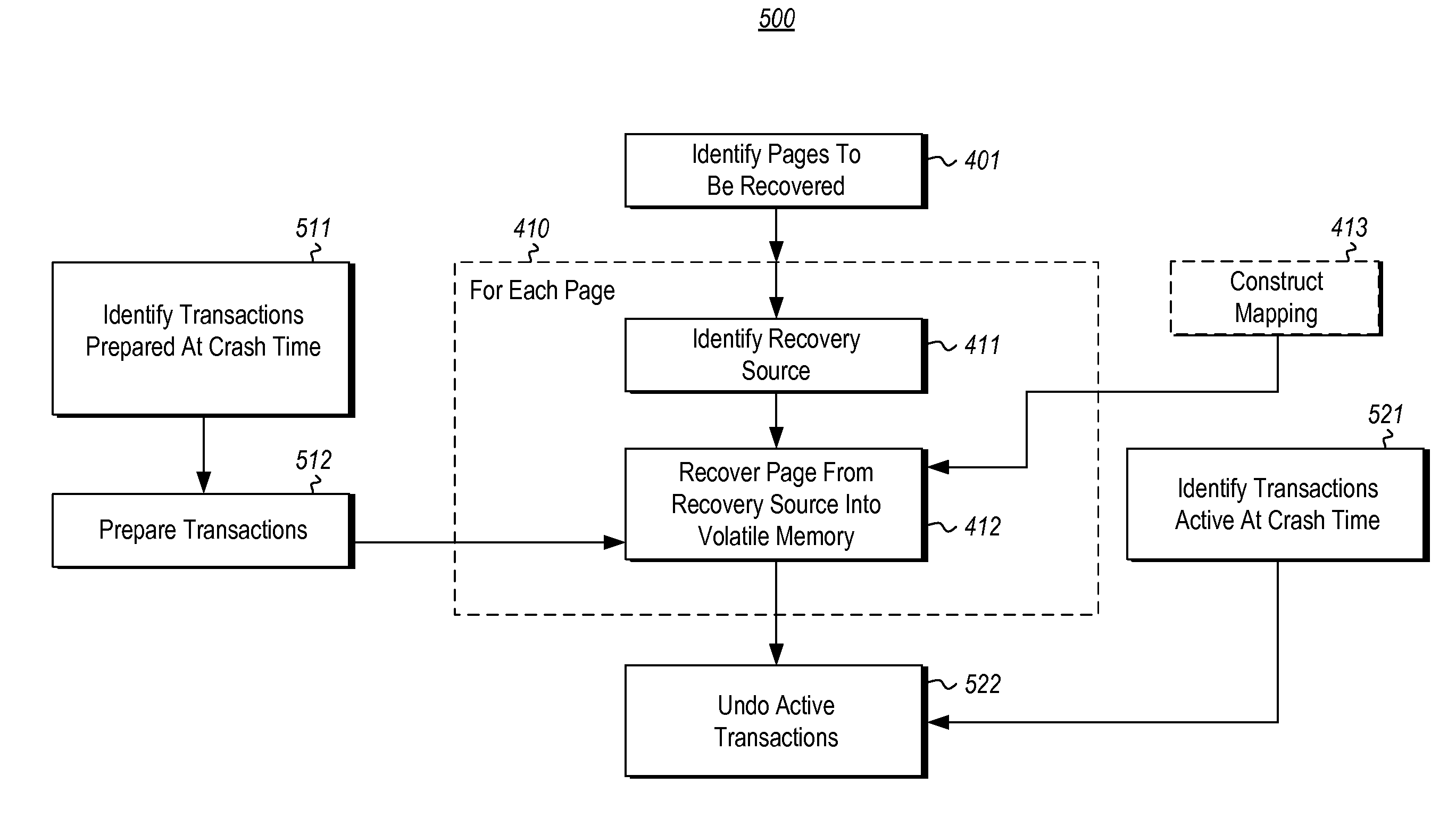
Crash recovery using non-volatile memory
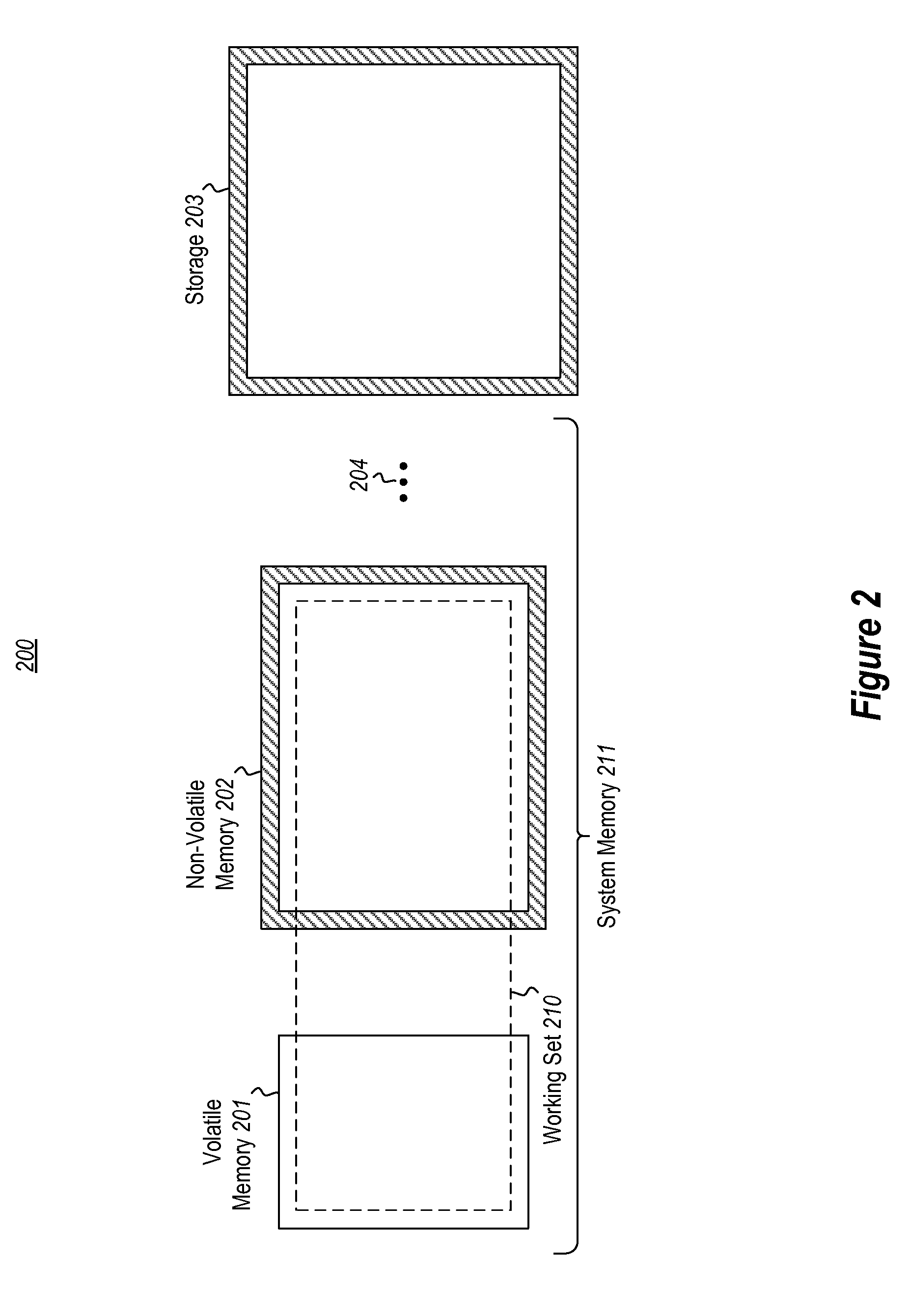
ActiveUS20150121126A1Access speedShorten recovery timeNon-redundant fault processingRedundant operation error correctionActive memoryComputing systems
Crash recovery of a computing system in the context in which the computing system includes a volatile memory which has contents lost due to the crash, an intermediate non-volatile memory that (together with the volatile memory) contributes to the active memory of the computing system, and non-volatile storage. The recovery occurs by identifying pages that were in the volatile memory at the time of the crash. For each of these pages, the recovery determines whether to recover the page into the volatile memory from either the intermediate non-volatile memory or the storage, and then performs the recovery. In embodiments in which access speeds for the intermediate non-volatile memory may be much faster than for the storage, and in which much of the pages to be recovered are recovered from the intermediate non-volatile memory, the recovery time may be reduced.
Owner:MICROSOFT TECH LICENSING LLC
Efficient cloud-based annotation of crash reports
ActiveUS9104797B1Software testing/debuggingNon-redundant fault processingApplication softwareDatabase
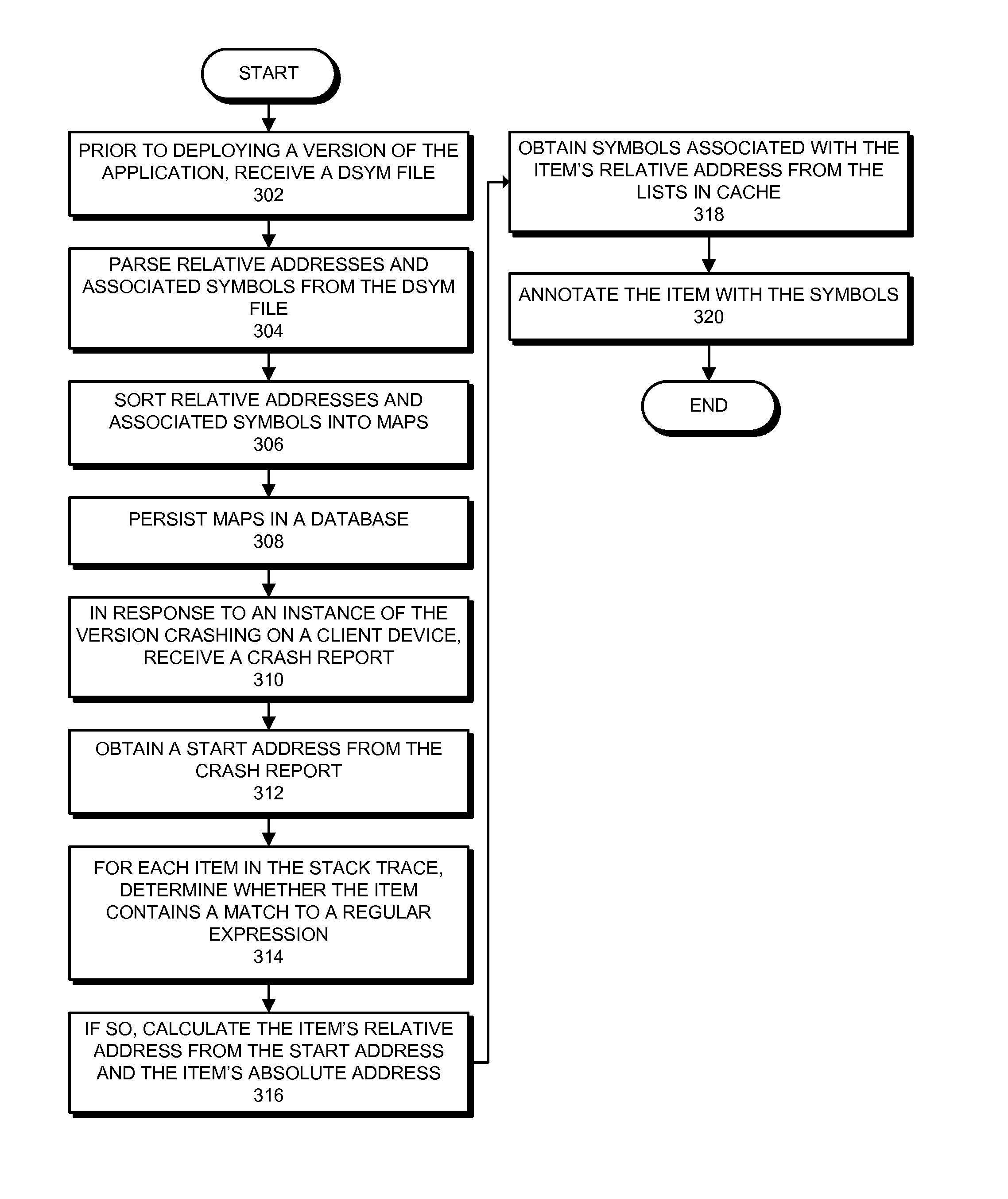
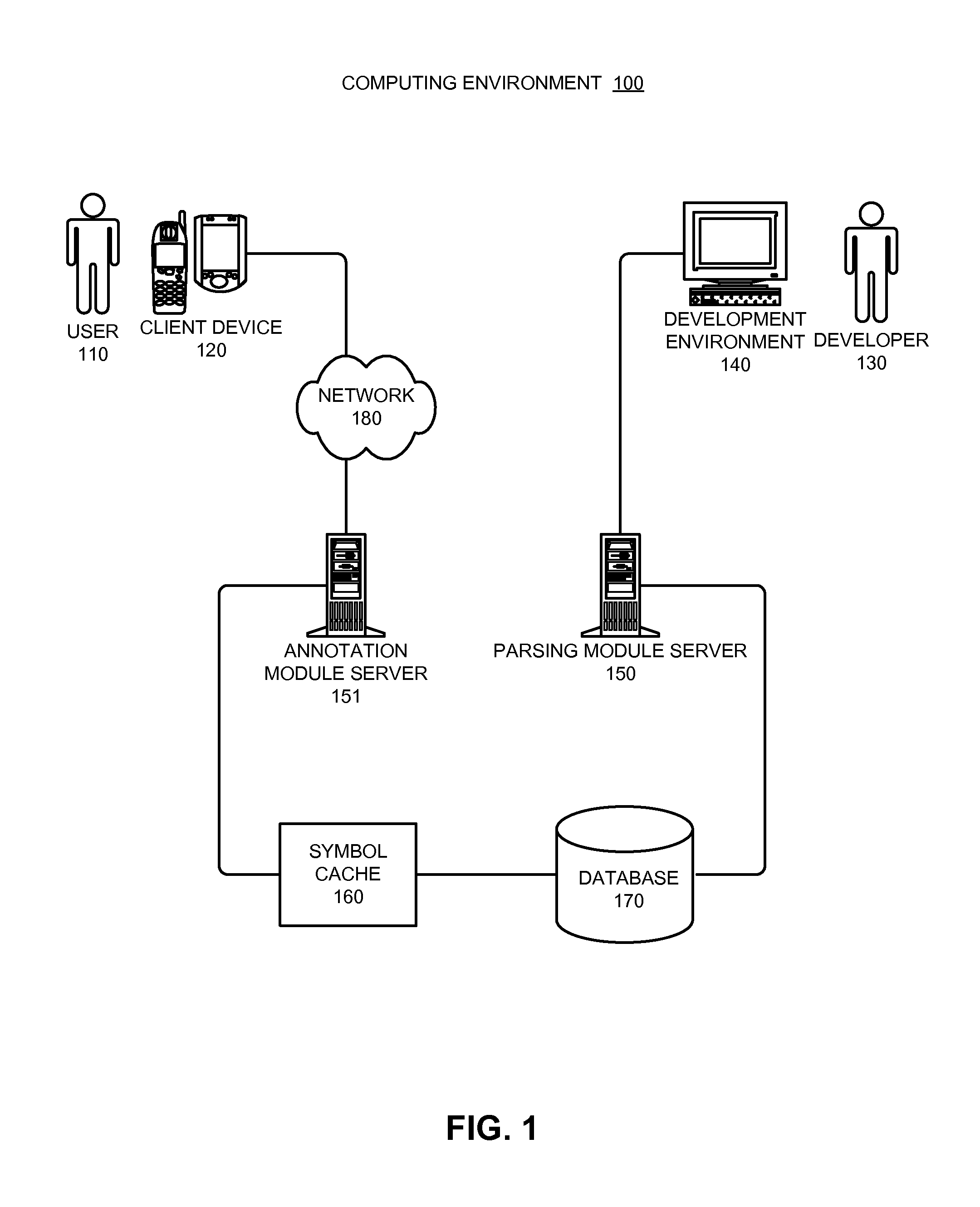
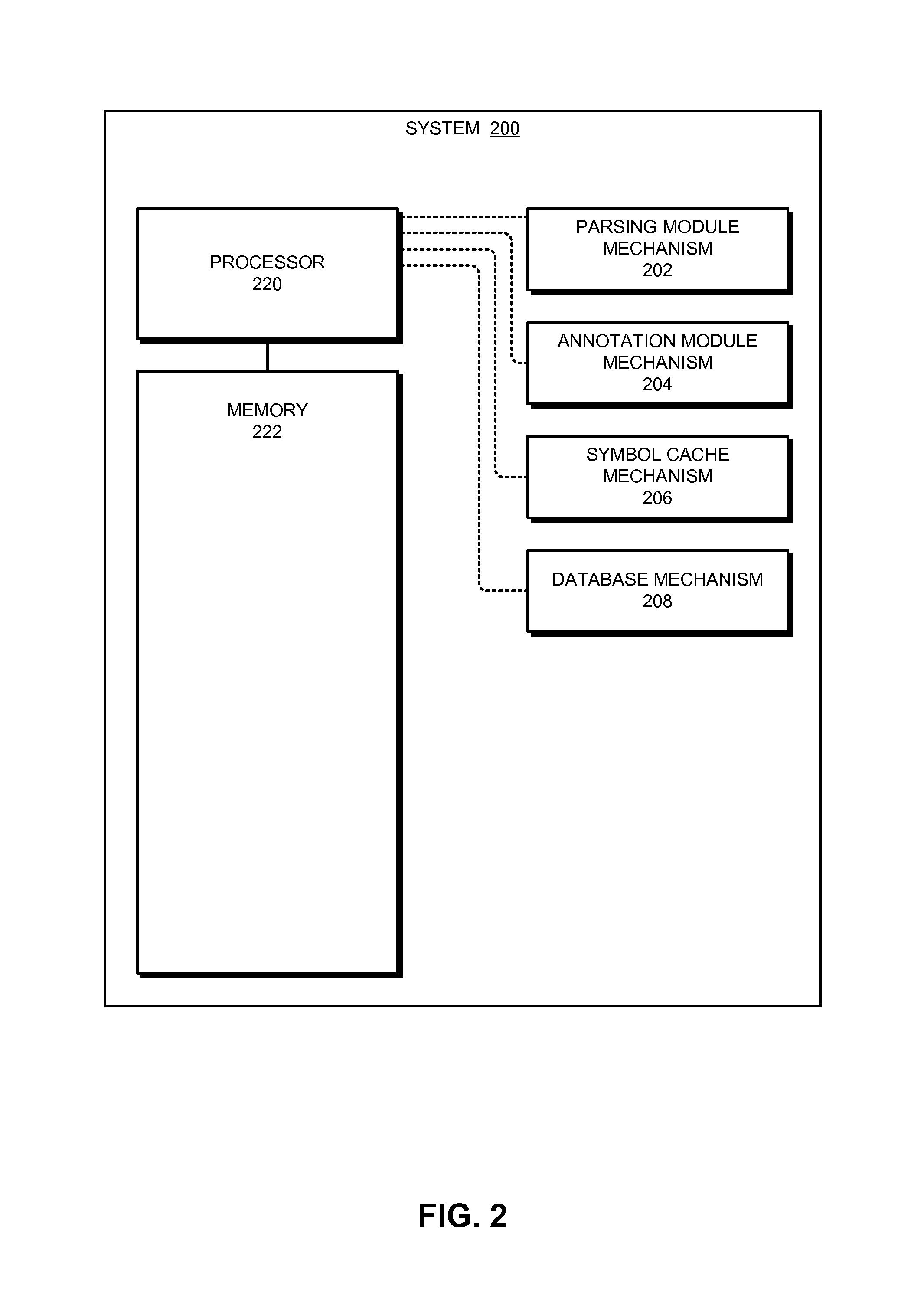
One embodiment of the present invention relates to a system for efficiently annotating numerous crash reports originating from multiple instances of an application. Prior to deploying a version of the application, a service receives a file that stores debugging information associated with the version. Next, the service parses the debugging information from the file. The service then converts the debugging information into an object representation in memory and stores the object representation in a database. Next, in response to an instance of the version crashing on a client device, the service receives a crash report from the client device. Then, for each item in the crash report, the service determines whether that item needs to be annotated and, if so, annotates the item.
Owner:INTUIT INC
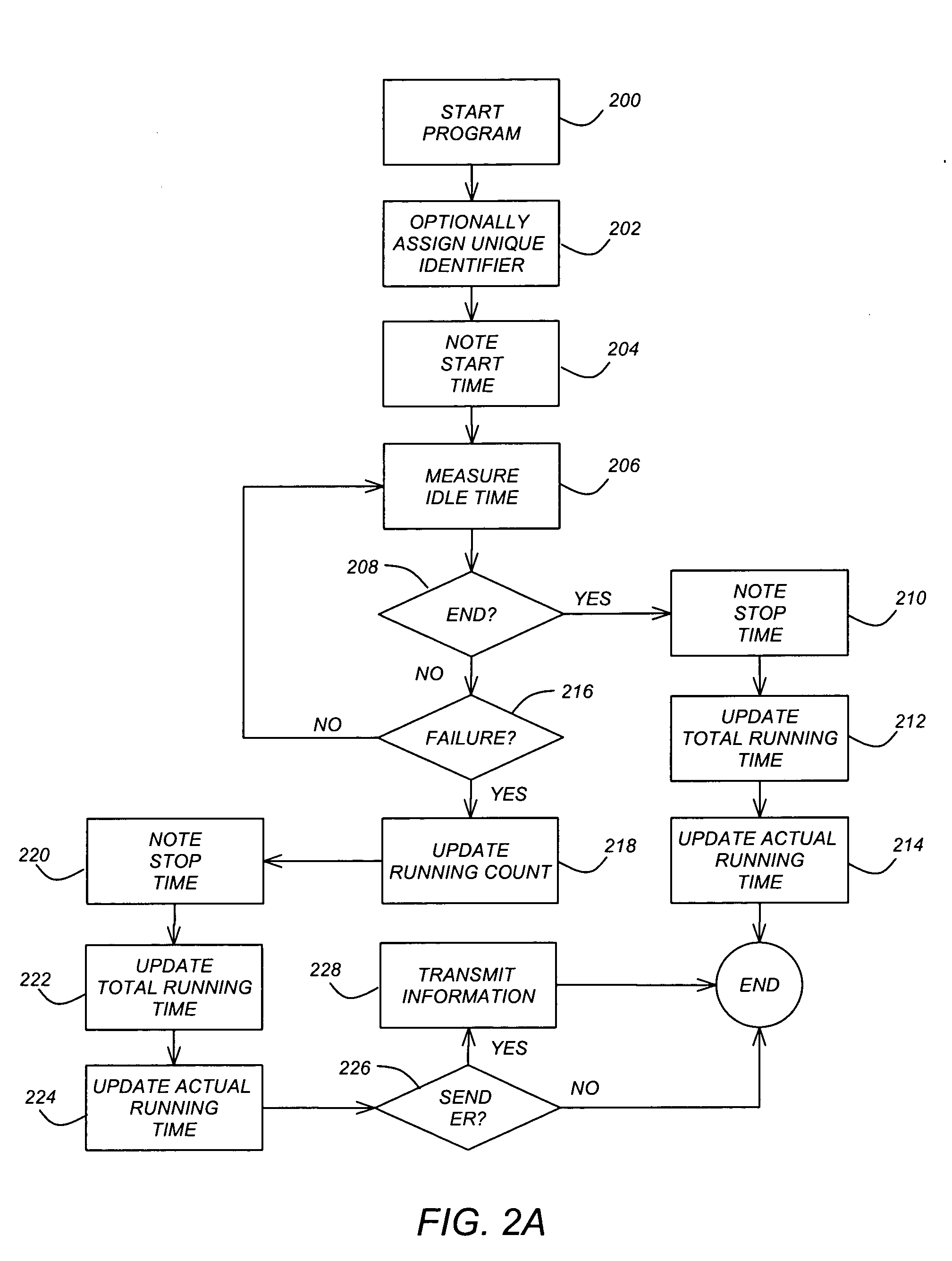
Measuring mean time between software failures using customer error reporting
ActiveUS20050204200A1Reliability/availability analysisSpecific program execution arrangementsReal-time computingTime average
A method, apparatus, and article of manufacture for measuring a mean time between program failures by maintaining a running count of program crashes per user per product version on a customer computer, and transmitting this information to a server computer when customers send error reports.
Owner:AUTODESK INC
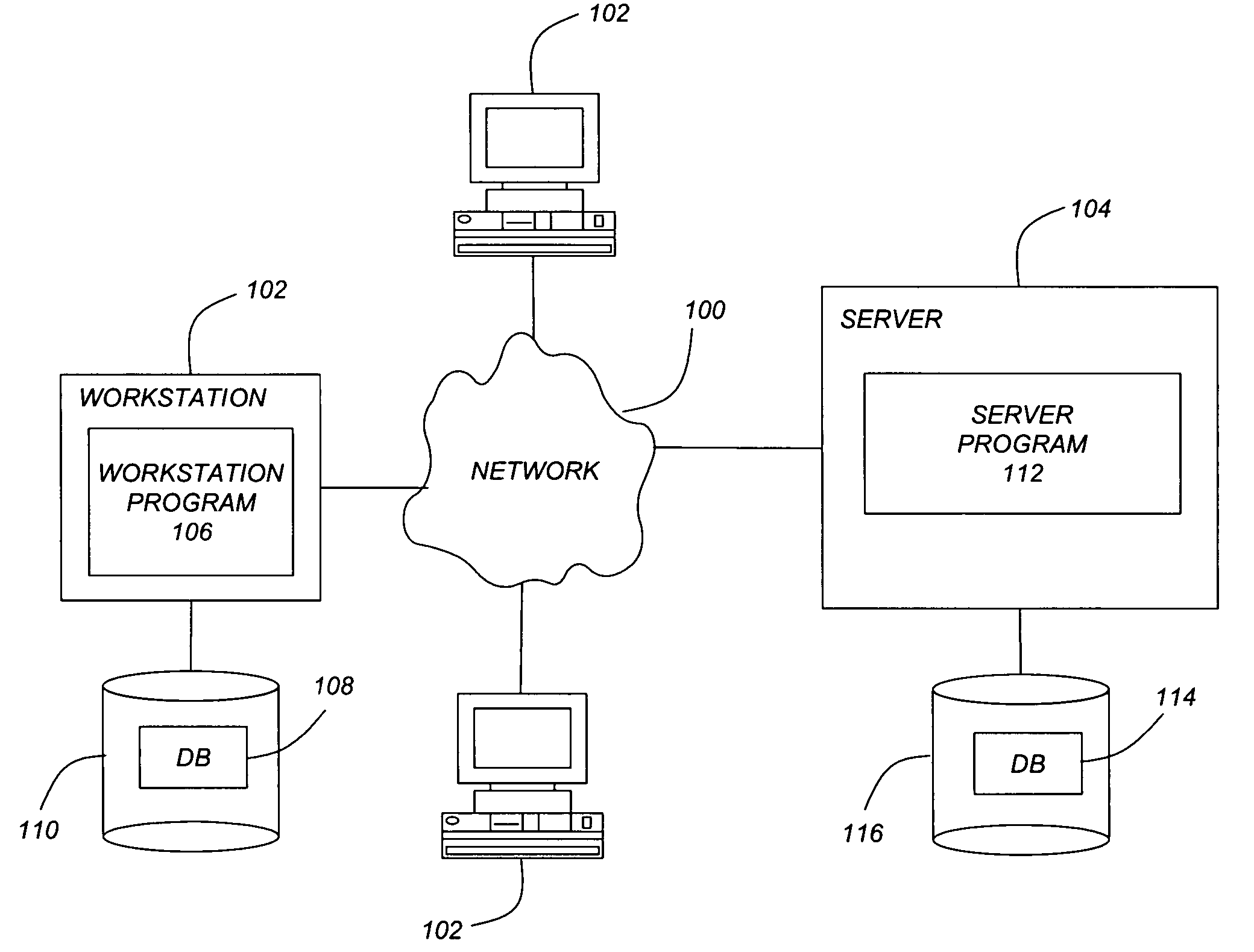
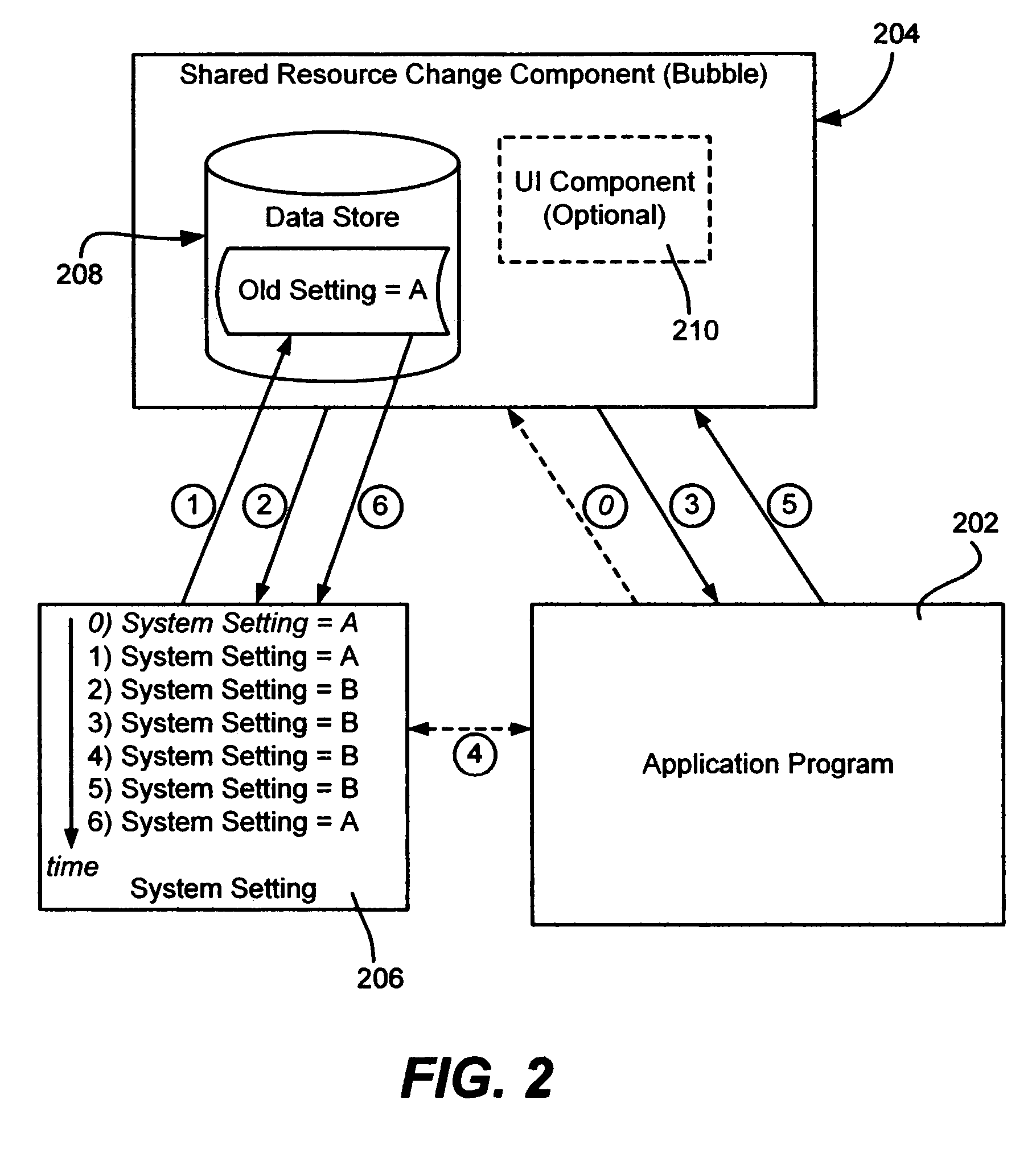
Transient shared computer resource and settings change bubble for computer programs
Owner:MICROSOFT TECH LICENSING LLC
Software process monitor
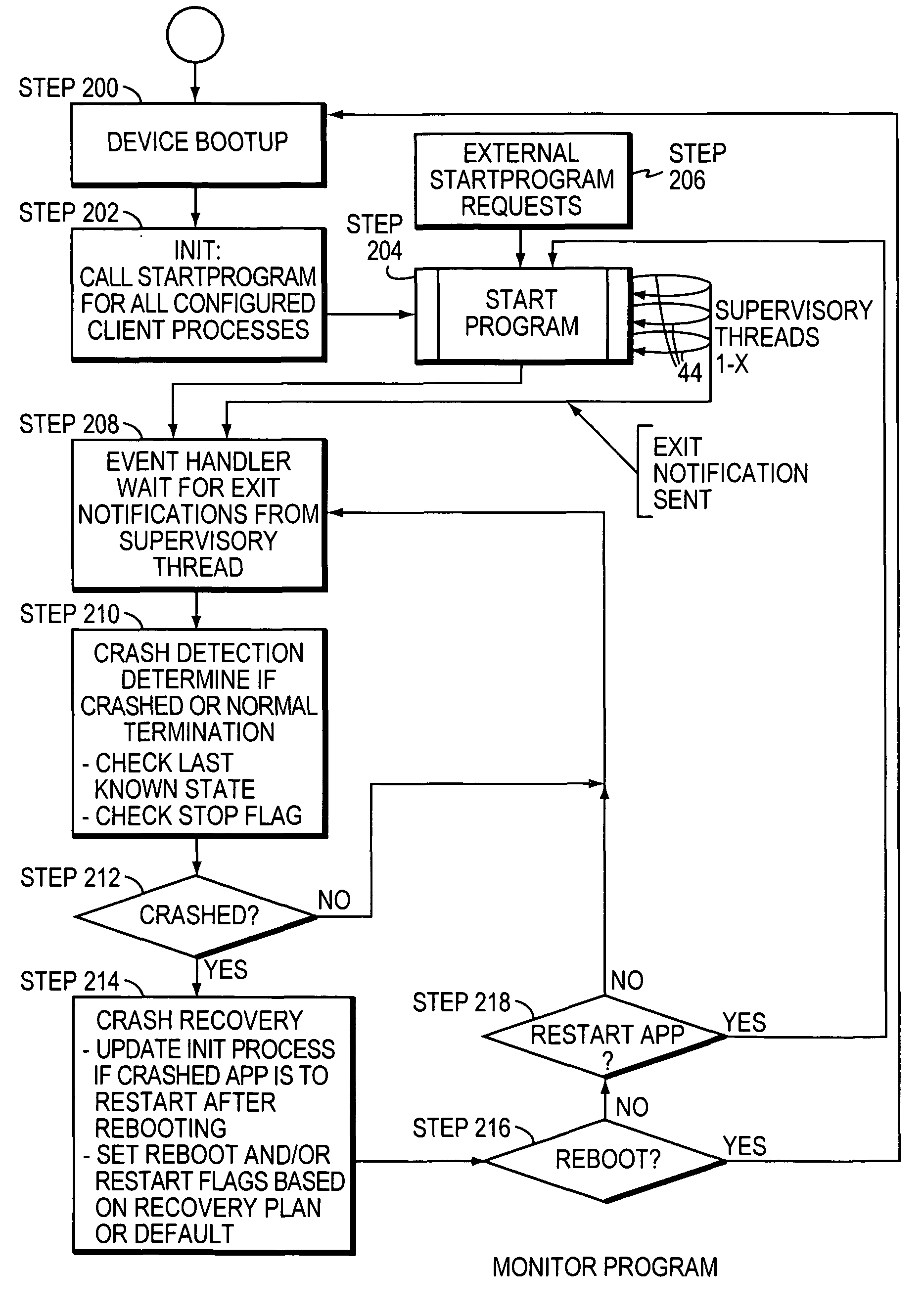
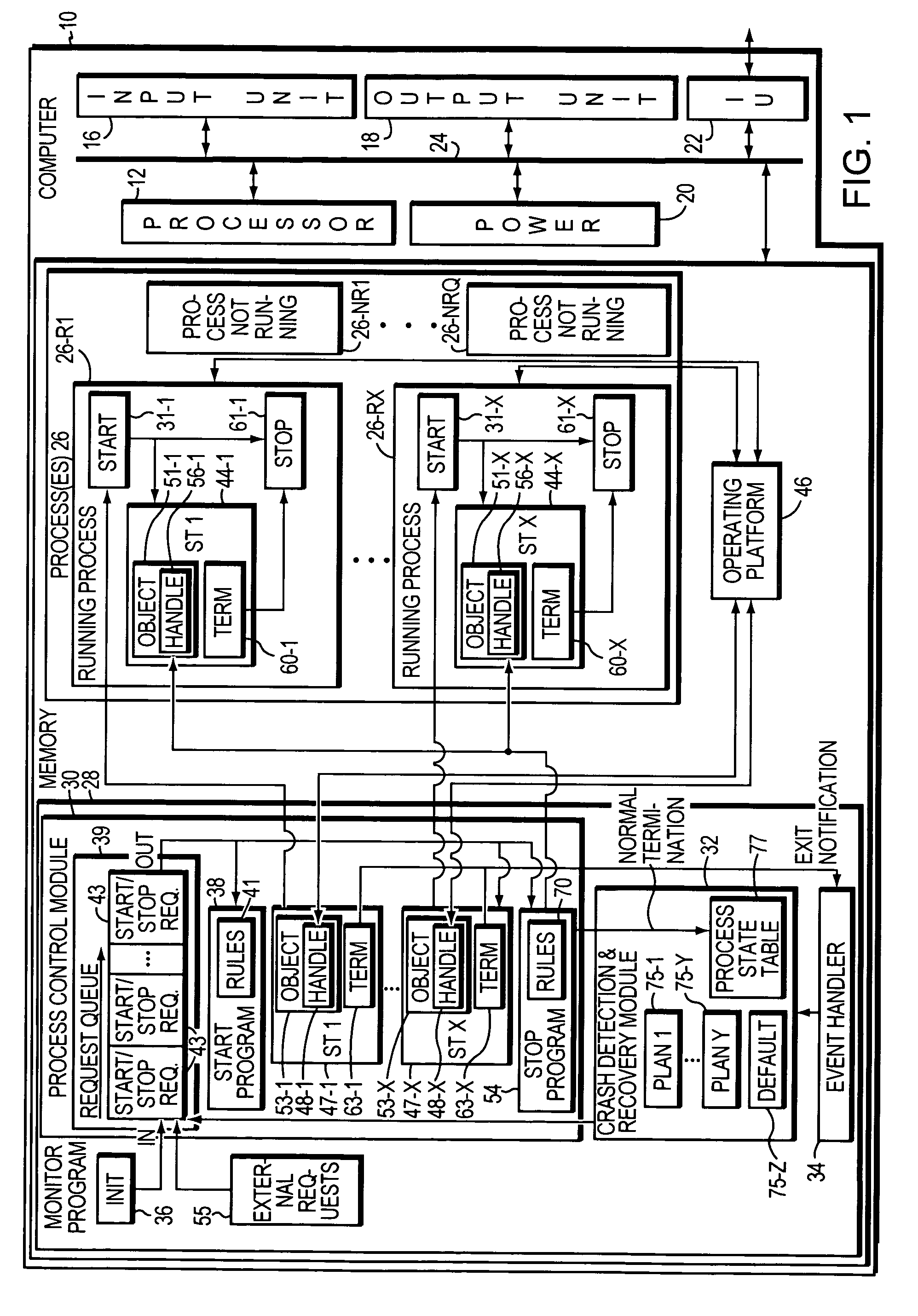
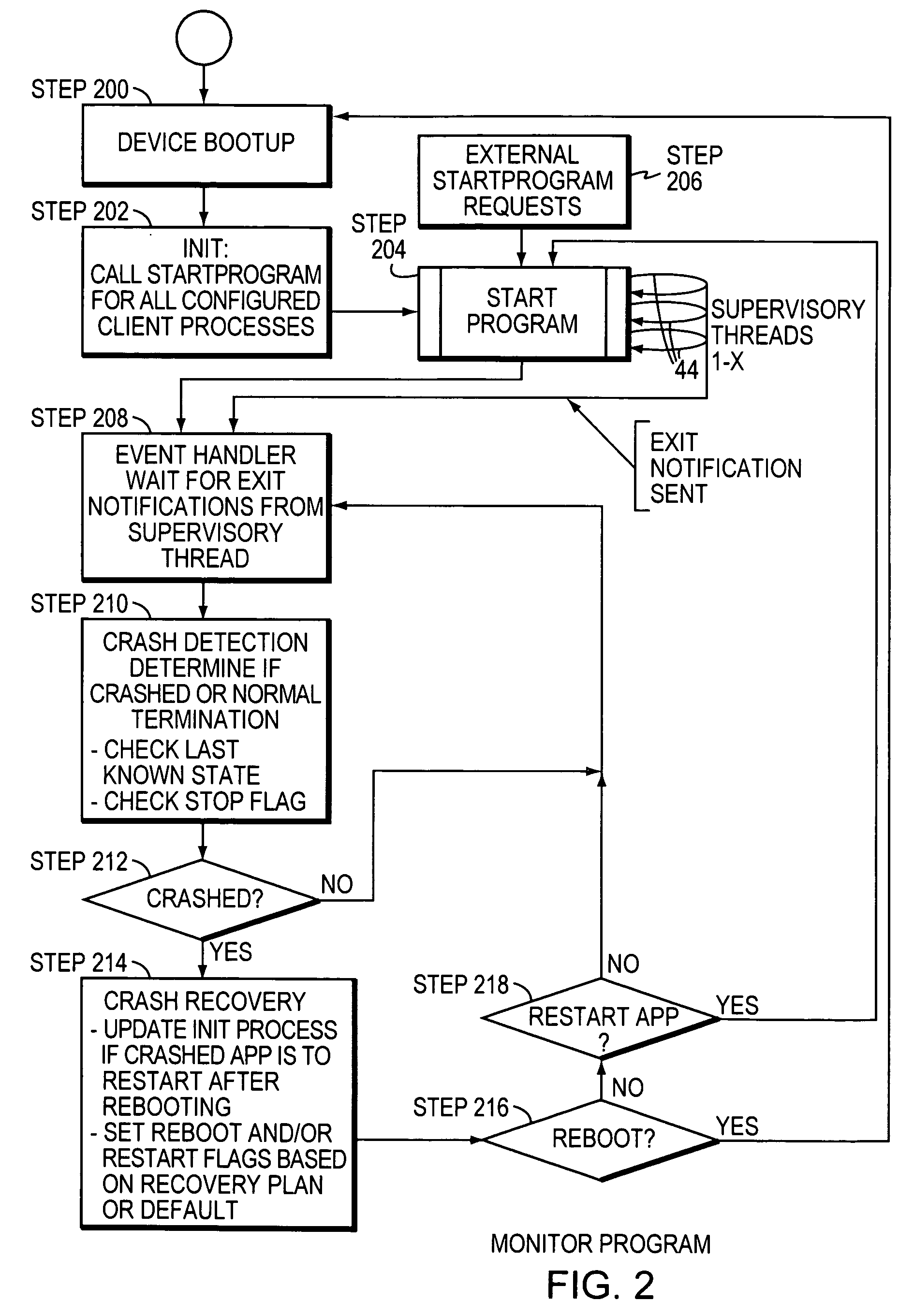
ActiveUS7823021B2Saved time and effort and troubleHardware monitoringNon-redundant fault processingSoftware engineeringCrash
A monitor program executes a set of client processes upon reboot of a computer, starts, stops and monitors client processes running on the computer, and / or detects and recovers automatically from process crashes. The program monitors a client process using a supervisory thread it creates when the client process is started, and uses the process's handle to detect its termination. When process termination is detected, the state table within the monitor program is checked to determine if the client process crashed or was exited normally. If the exit was the result of a crash, the program can automatically execute crash recovery using a preconfigured plan.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
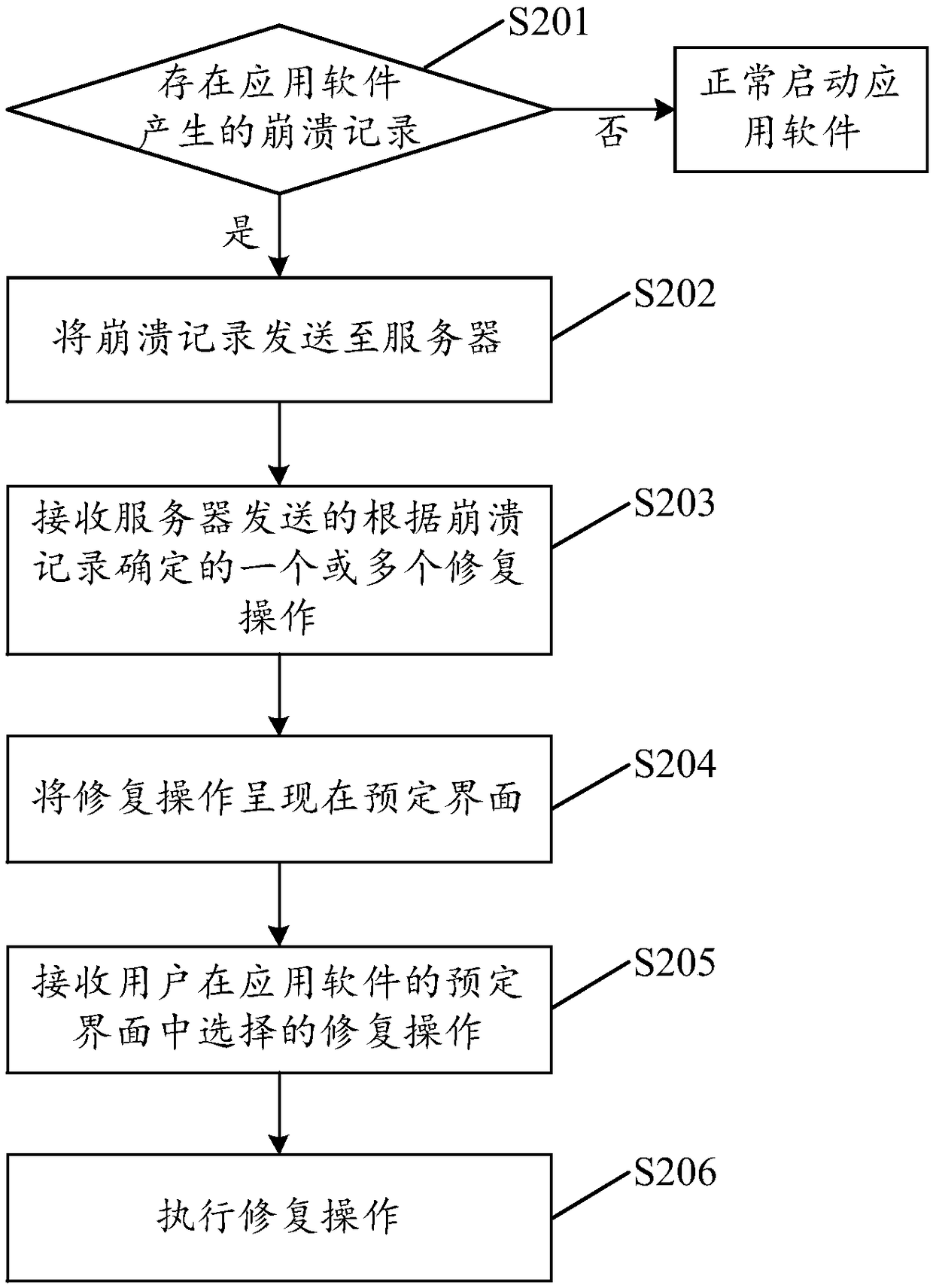
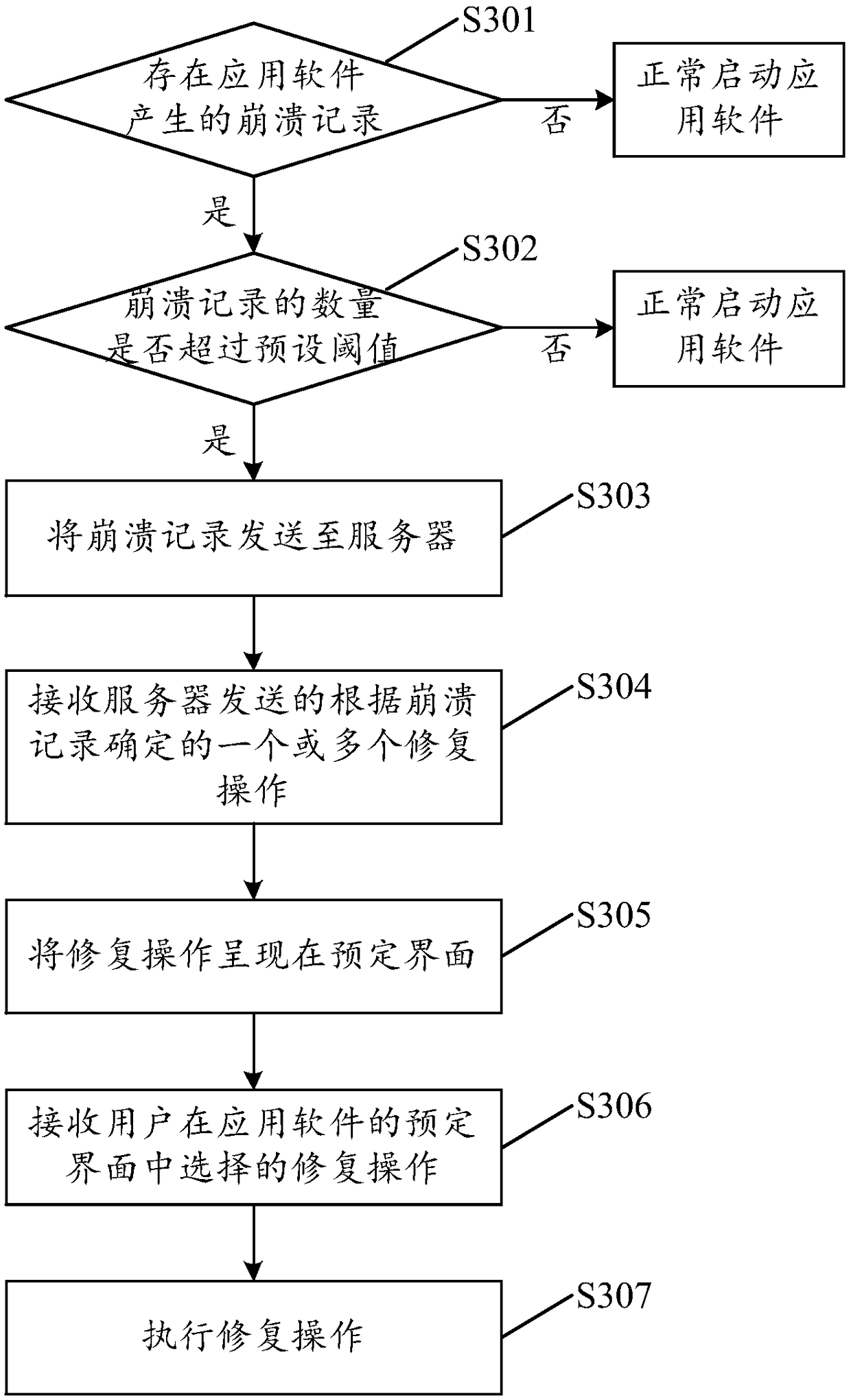
Systems and methods for assisting user in software application crashes
InactiveUS20170083399A1Eliminate the problemNon-redundant fault processingRemedial actionComputerized system
A method for handling a crash of an application, the computer-implemented method being performed in connection with a distributed computer system comprising a client system directly accessible by a user and a server system, the client system including a CPU and a memory, the method involving: upon occurrence of the crash of the application on the client system, locally storing an application crash information; and upon a subsequent launch of the application: suspending execution of at least a portion of a code of the application; retrieving from the memory the stored application crash information; generating a signature of the crash of the application based on the retrieved application crash information; sending the generated signature of the crash of the application to the server system; receiving remedial action information from the server system; and performing a remedial action in connection with the application based on the received remedial action information.
Owner:LIMITED LIABILITY COMPANY MAIL RU
Robust event prediction
A system and method predicts events in a computer system. The system and method includes a controller that receives a crash profile. The controller generates granular information that identifies data indicative of a potential server cluster failure in an enterprise system without needing to identify an originating cause of the potential server cluster failure. The system and method trains a model by sampling portions of a profile that may include directives and data indicative of a normal operating state and a conditioned preamble operating state. The system and method provides a trained model to a prediction engine. The system and method modifies an allocation of computing resources in response to the prediction of the potential server cluster failure by the prediction engine monitoring one or more servers of a server cluster.
Owner:PROGRESSIVE CASUALTY INSURANCE
Dynamic computer system reset architecture
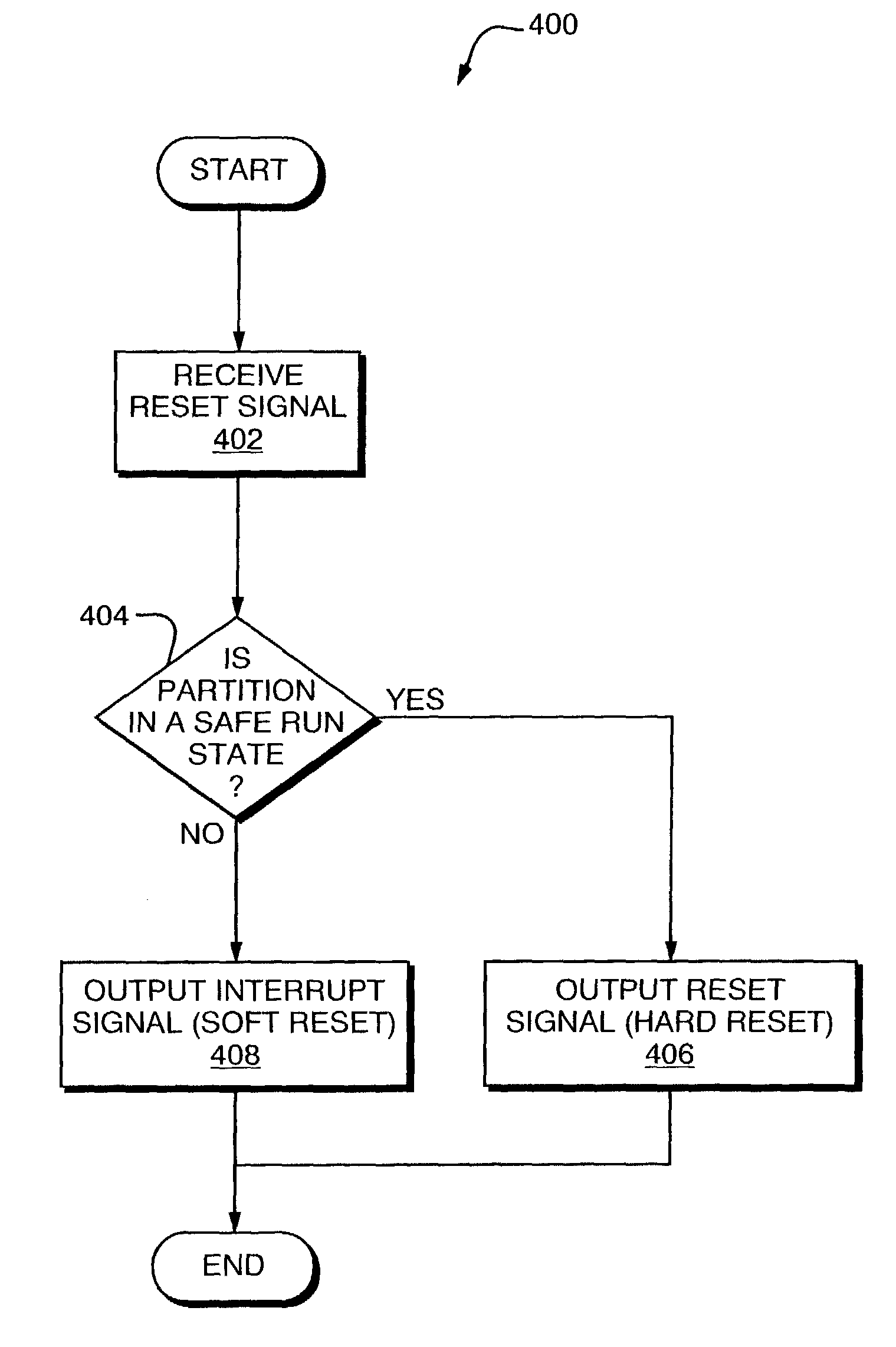
Techniques are disclosed for resetting agents in a computer system without requiring the computer system, or partitions thereof, to be reset. In one embodiment, each agent in the system is associated with a corresponding partition. A reset signal directed to an agent is redirected to a reset type selector which determines whether the partition associated with the agent is in a run state (an “unsafe run state”) in which resetting the agent will cause the partition to crash. If the partition is in an unsafe run state, a soft reset is performed on the agent. Otherwise, a hard reset is performed on the agent. If performing a soft reset does not solve the problem that was the impetus for the reset signal, the partition may be brought into a safe run state before performing a hard reset on it.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
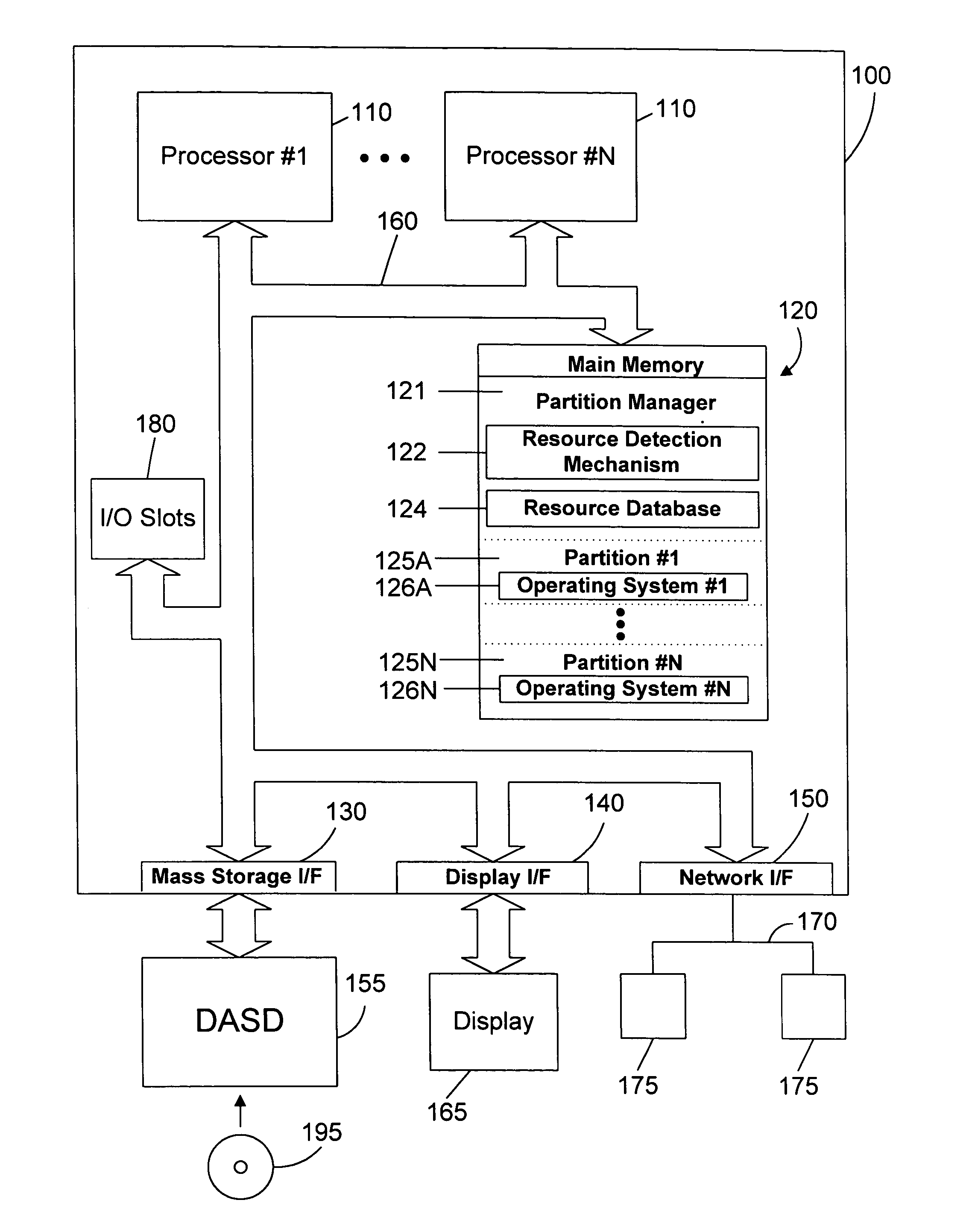
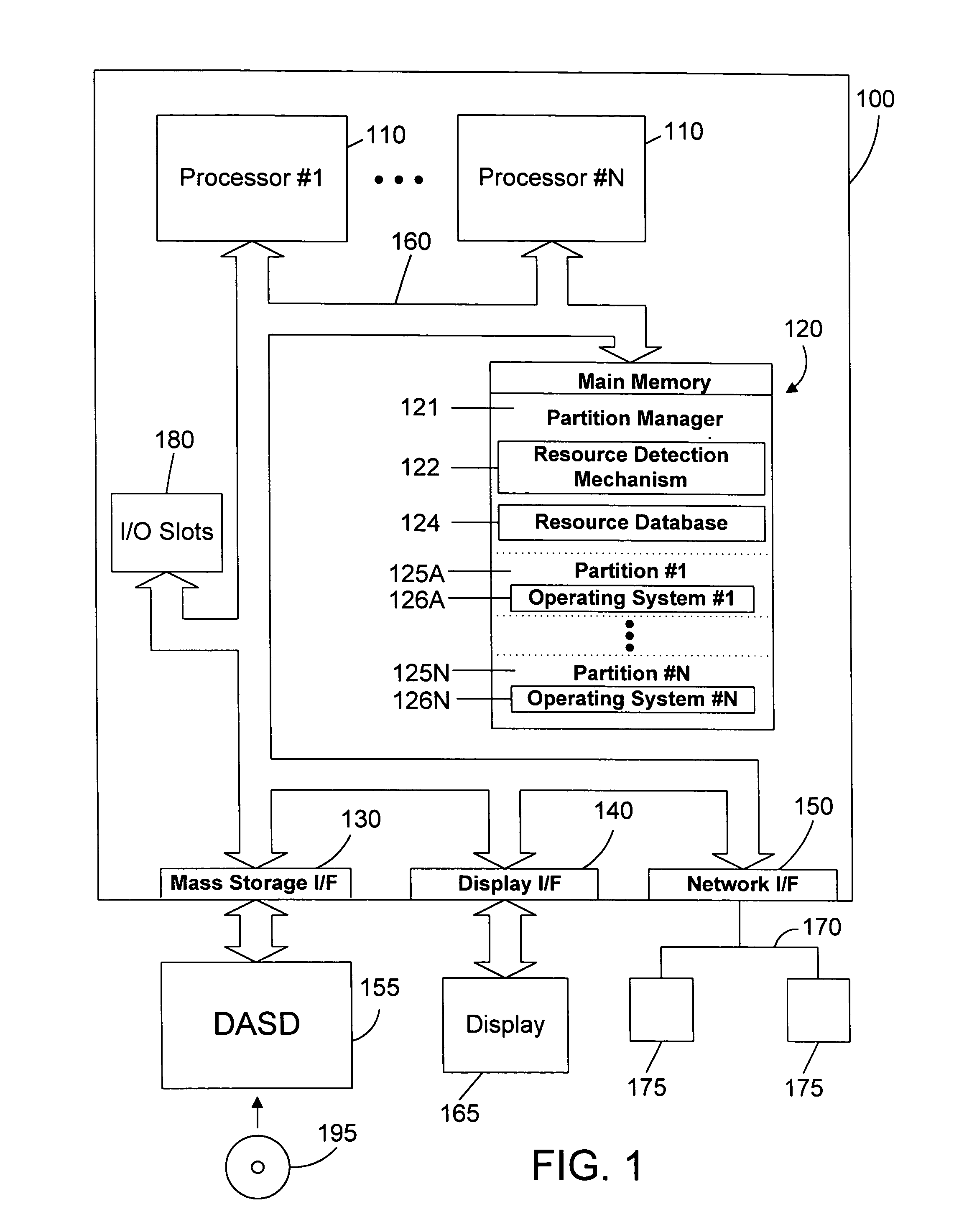
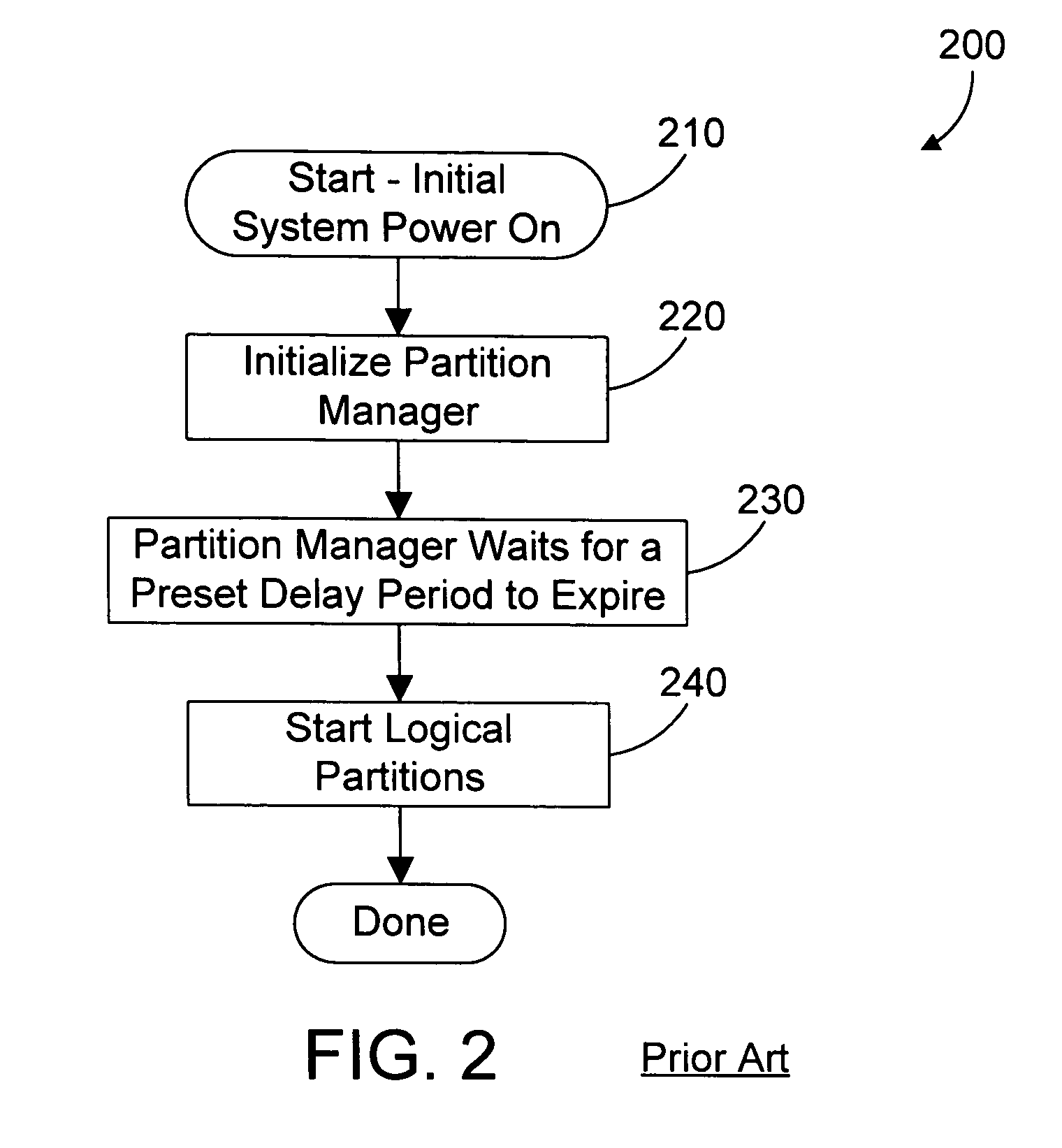
Apparatus and method for autonomically detecting resources in a logically partitioned computer system
ActiveUS20050022200A1Prevent crashAvoid startingSpecific access rightsResource allocationLogical partitionZoning
A partition manager includes a resource detection mechanism that uses a persistent resource database to determine which resources were seen previously, and to determine which resources are required for a logical partition to start. Once all required resources for a logical partition are detected, the logical partition is started. In this manner, a logical partition may be started as soon as all of its resources are available, without waiting on the resources of other logical partitions. In addition, a missing required resource will prevent a logical partition from starting, thus avoiding the crash of a logical partition due to missing resources.
Owner:IBM CORP
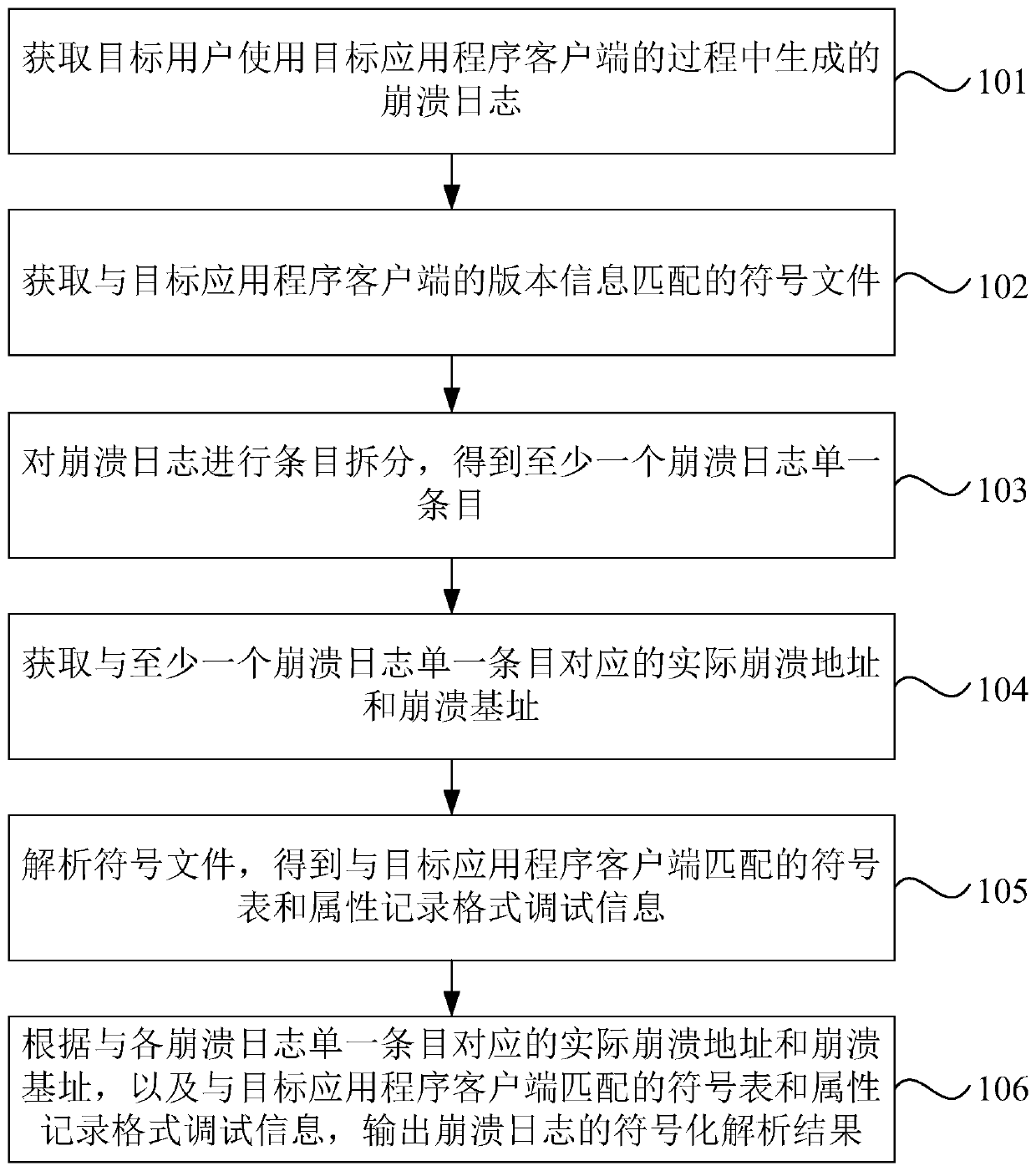
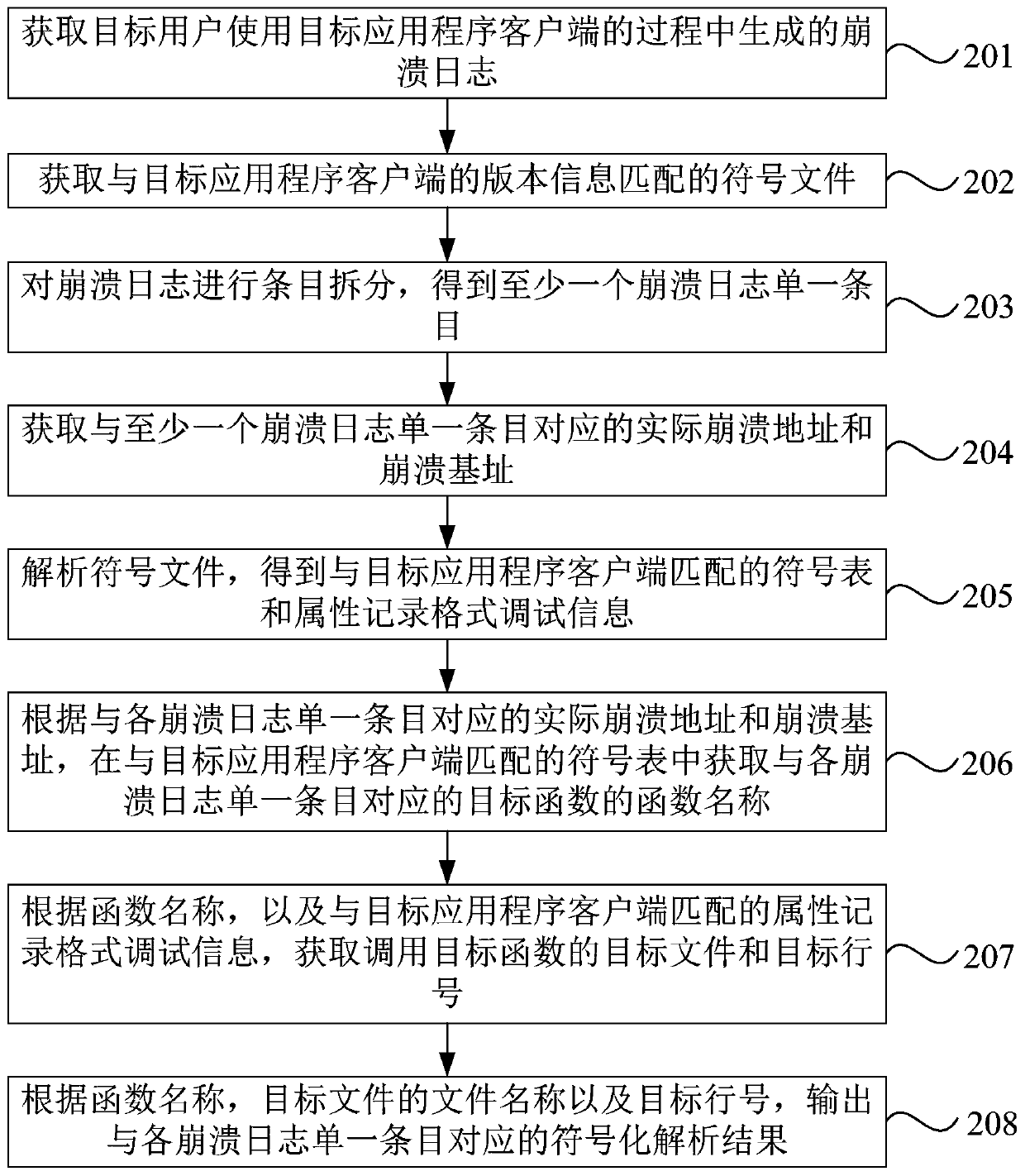
Crash log processing method and device, equipment and storage medium
ActiveCN110764945AAccurate Function Symbol ResolutionFault responseEnergy efficient computingApplication procedureCrash
The invention discloses a crash log processing method and device, equipment and a storage medium. The method comprises the steps of obtaining a crash log generated in a process that a target user usesa target application client; obtaining a symbol file matched with the version information of the target application program client; performing entry splitting on the crash log to obtain at least onecrash log single entry; obtaining an actual crash address and a crash base address corresponding to the at least one crash log single entry; analyzing the symbol file to obtain a symbol table matchedwith the target application program client and attribute record format debugging information; and outputting a symbolization analysis result of the crash log according to the actual crash address andthe crash base address corresponding to the single entry of each crash log, and the symbol table and the attribute record format debugging information matched with the target application client. According to the embodiment of the invention, the function symbol analysis can be accurately carried out on the crash log on the server of the Linux system.
Owner:北京博睿宏远数据科技股份有限公司
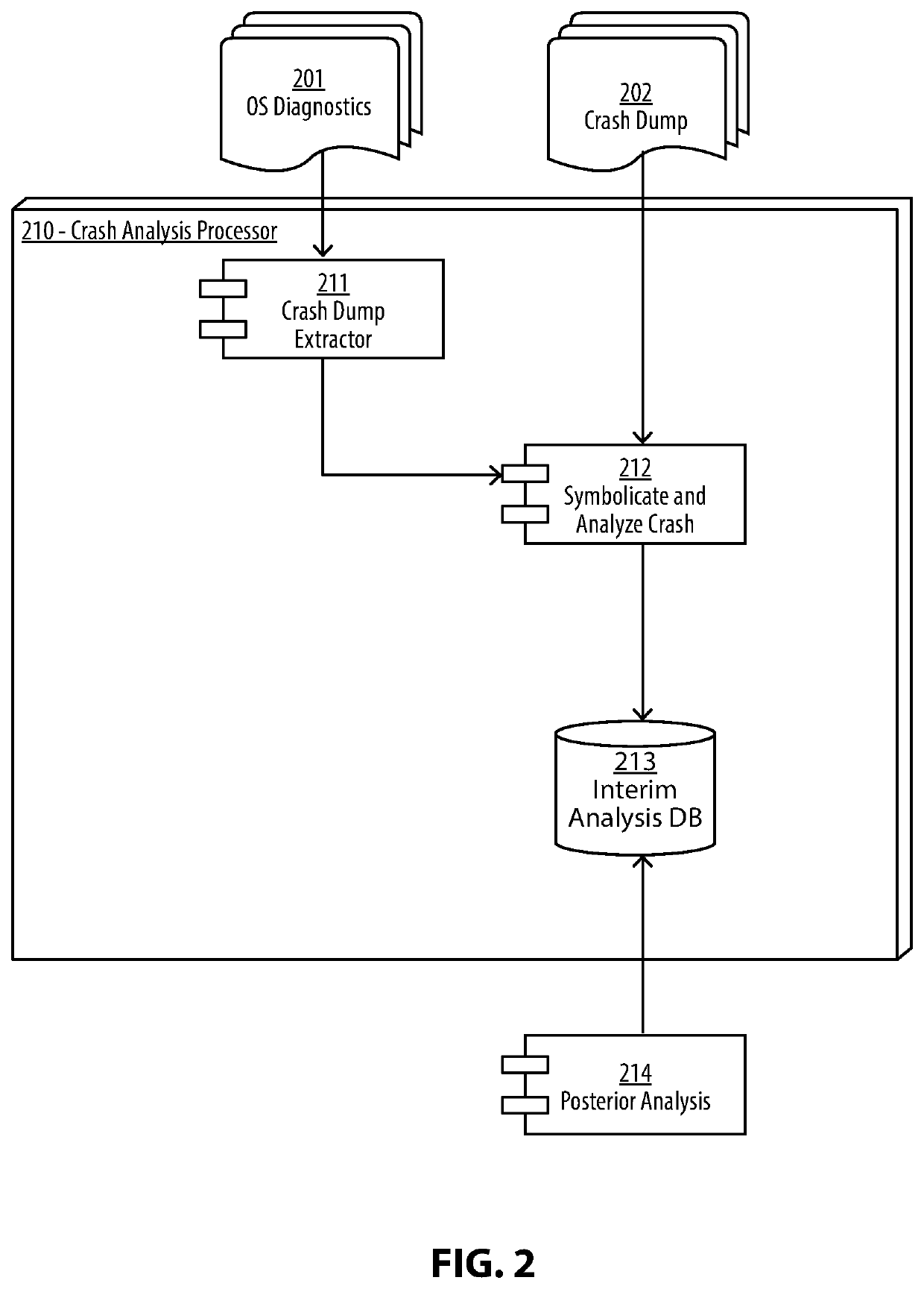
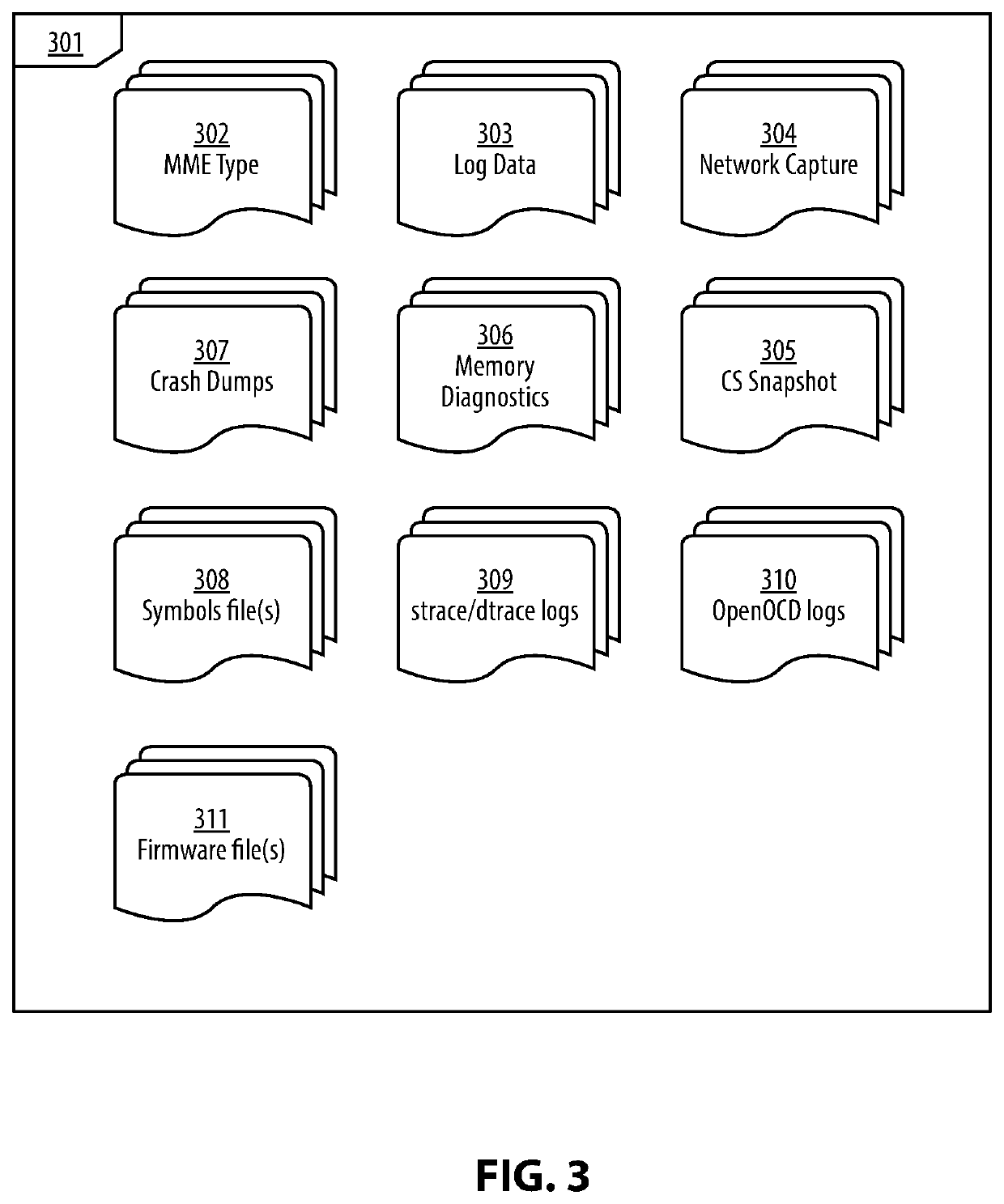
System and Method for an Automated Analysis of Operating System Samples, Crashes and Vulnerability Reproduction
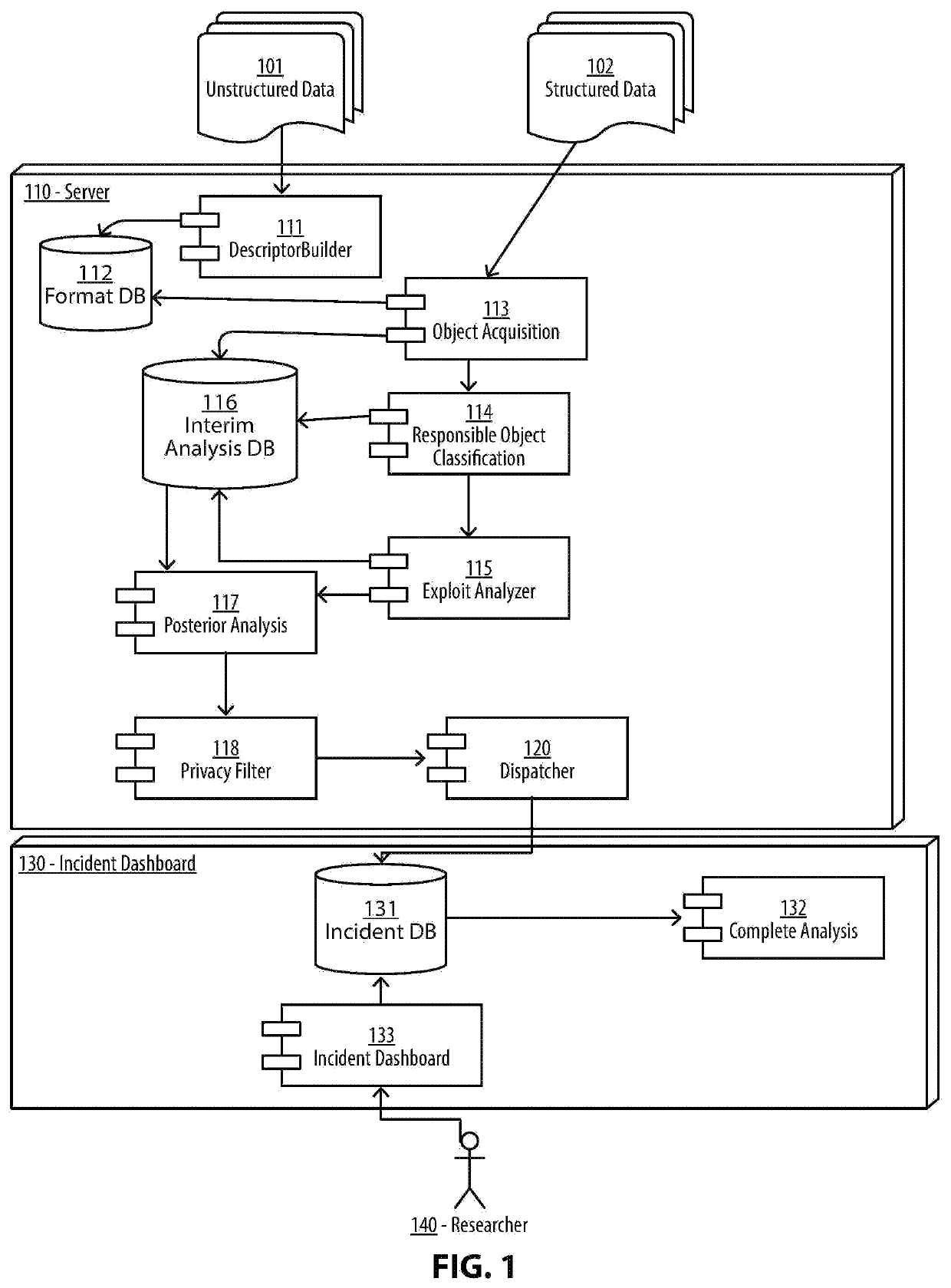
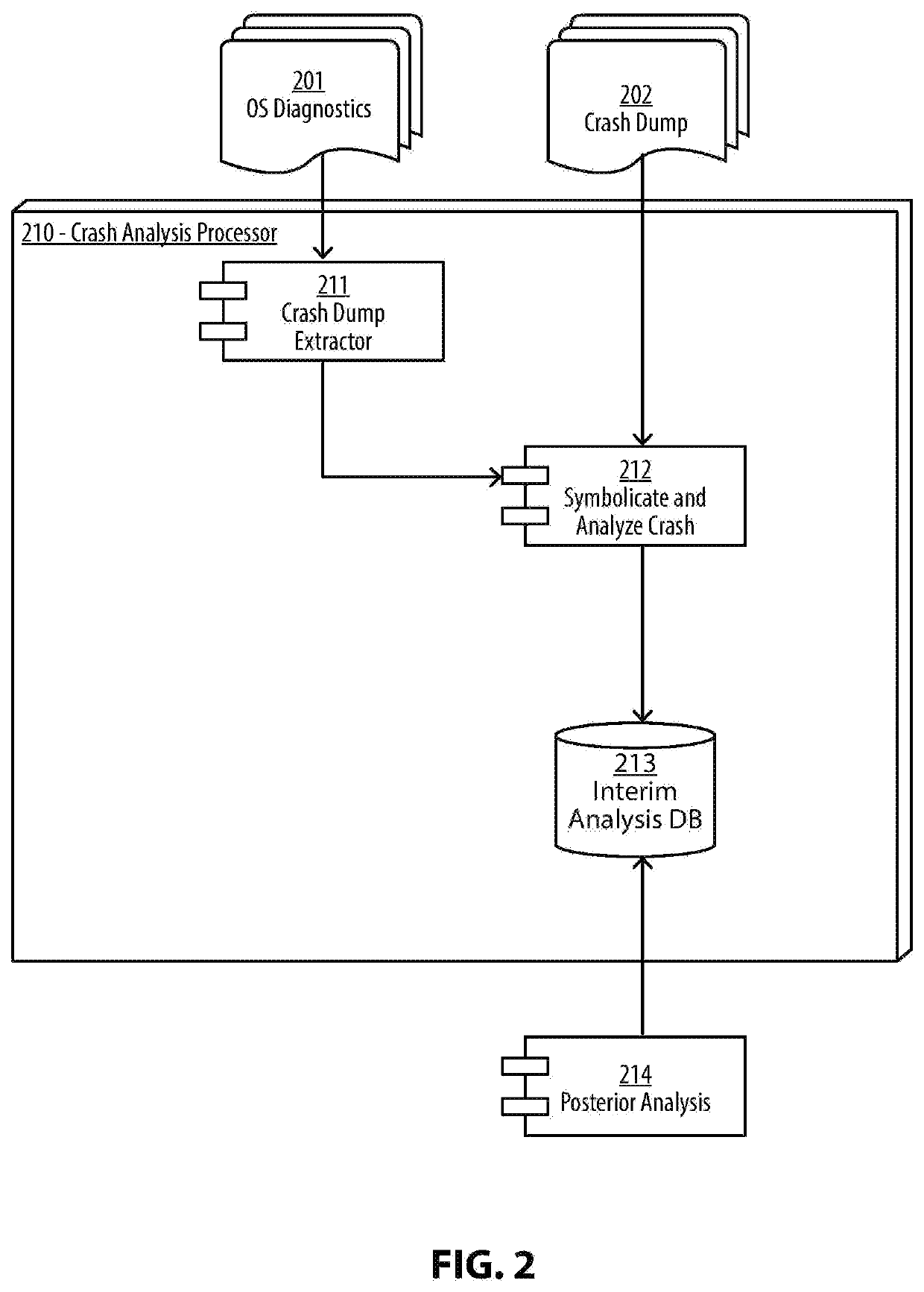
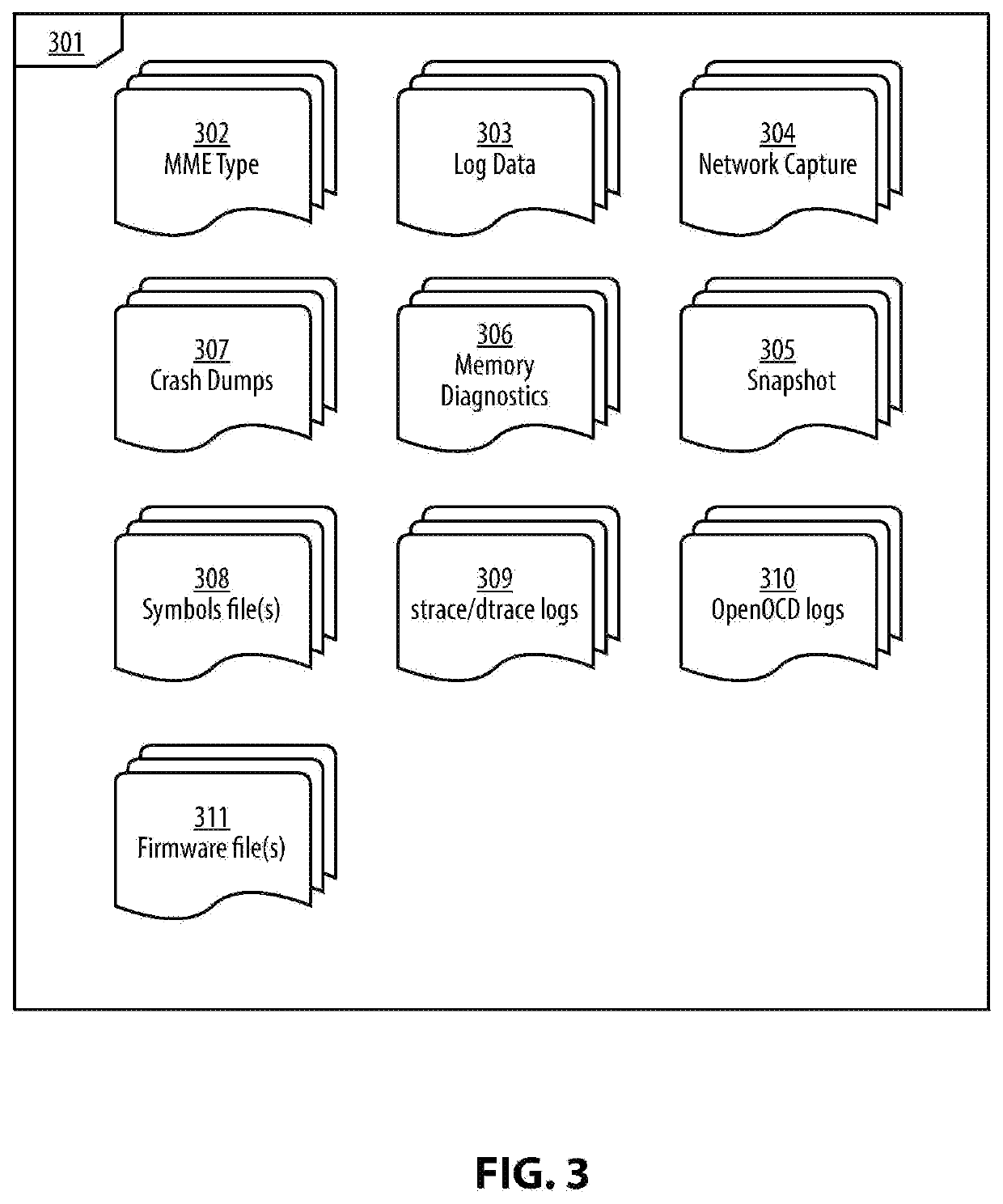
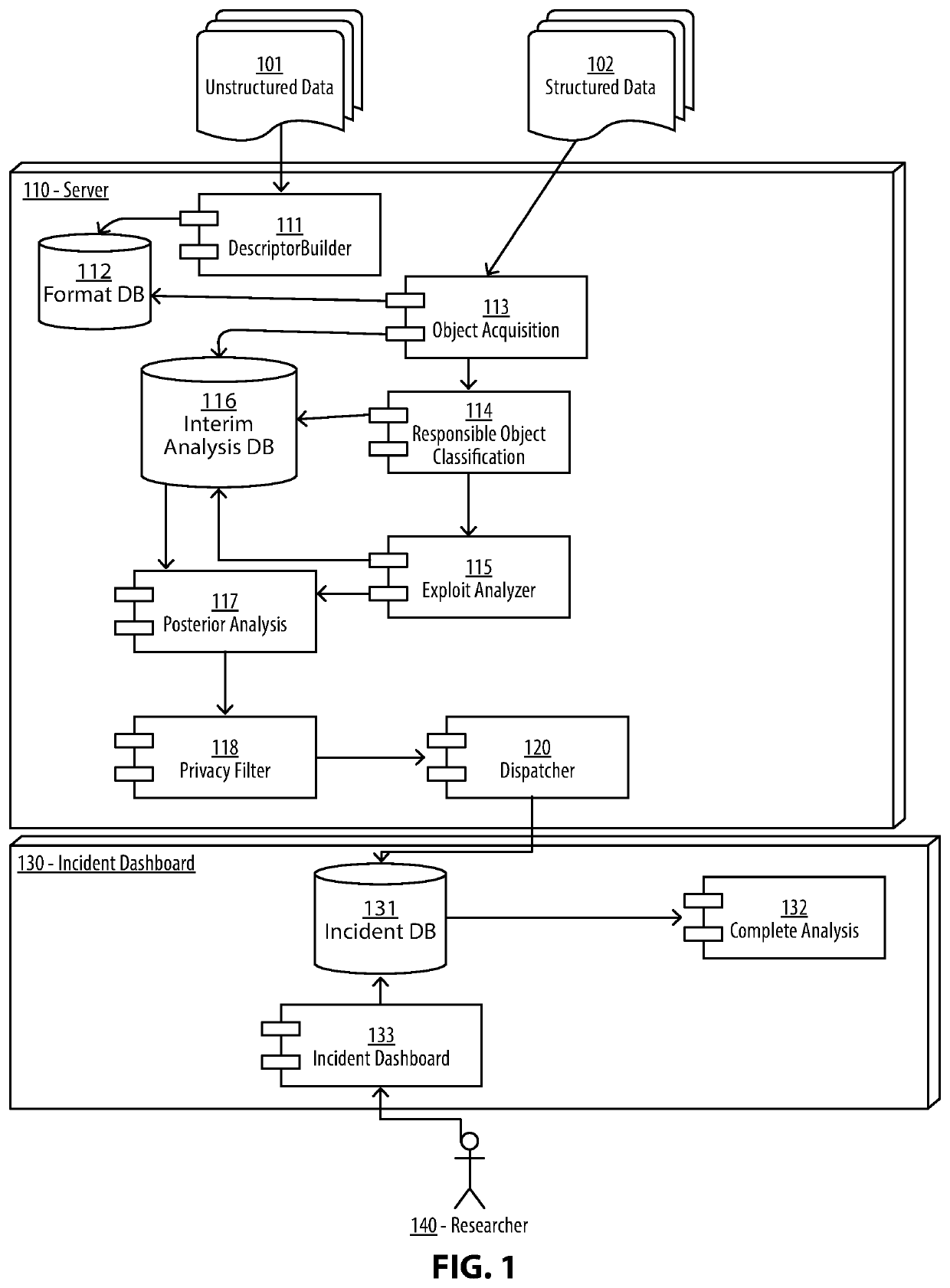
Malware analysis and root-cause analysis, and information security insights based on Operating System sampled data. Sampled data includes structured logs, Operating System Snapshots, programs and / or processes and / or kernel crashes, crash dumps, memory dumps, stackshots, simulated crashes or samples. The sampled data contains payload for extraction for the purpose of detection, evaluation and reproduction of threats, infection vector, threat actors and persistence methods in the form of backdoors or Trojans or exploitable vulnerabilities used for initial infiltration or lateral movement.
Owner:ZECOPS
System and Method for An Automated Analysis of Operating System Samples
InactiveUS20200012793A1Digital data protectionPlatform integrity maintainanceMalware analysisOperational system
Methods and apparatuses for malware analysis and root-cause analysis, and information security insights based on Operating System sampled data such as structured logs, Operating System Snapshots, programs and / or processes and / or kernel crash dumps or samples containing payload for extraction for the purpose of detection and evaluation of threats, infection vector, threat actors and persistence methods in the form of backdoors or Trojans or unknown exploitable vulnerabilities used.
Owner:ZECOPS
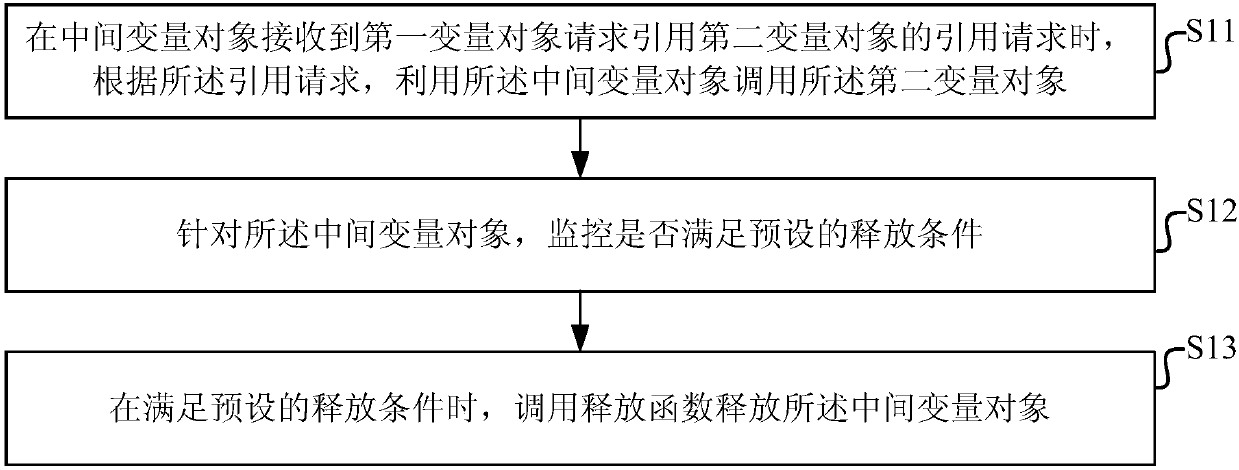
Java object reference method, Java object reference devices and medium
The invention discloses a Java object reference method, Java object reference devices and a medium, which are used for solving the program crash problem due to that strong references cannot be automatically released and cause excessive occupied memories. The Java object reference method includes: when an intermediate variable object receives a reference request of requesting a reference of a second variable object by a first variable object, utilizing the intermediate variable object to invoke the second variable object according to the reference request, wherein the intermediate variable object is defined for the first variable object and the second variable object of which a strong-reference relationship exists; for the intermediate variable object, monitoring whether a preset releasingcondition is met; and invoking a releasing function to release the intermediate variable object when the preset releasing condition is met.
Owner:TENCENT TECH (SHENZHEN) CO LTD
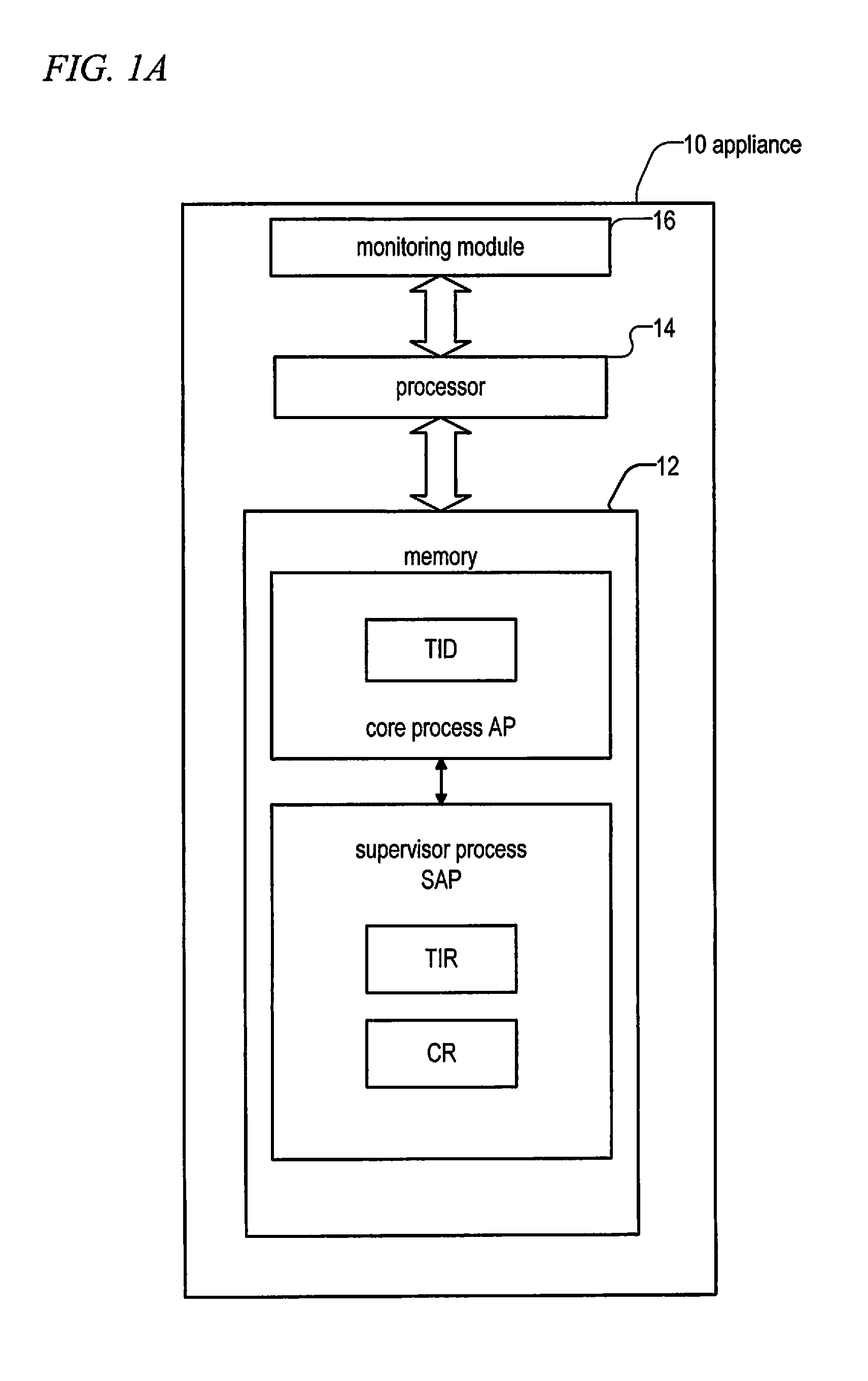
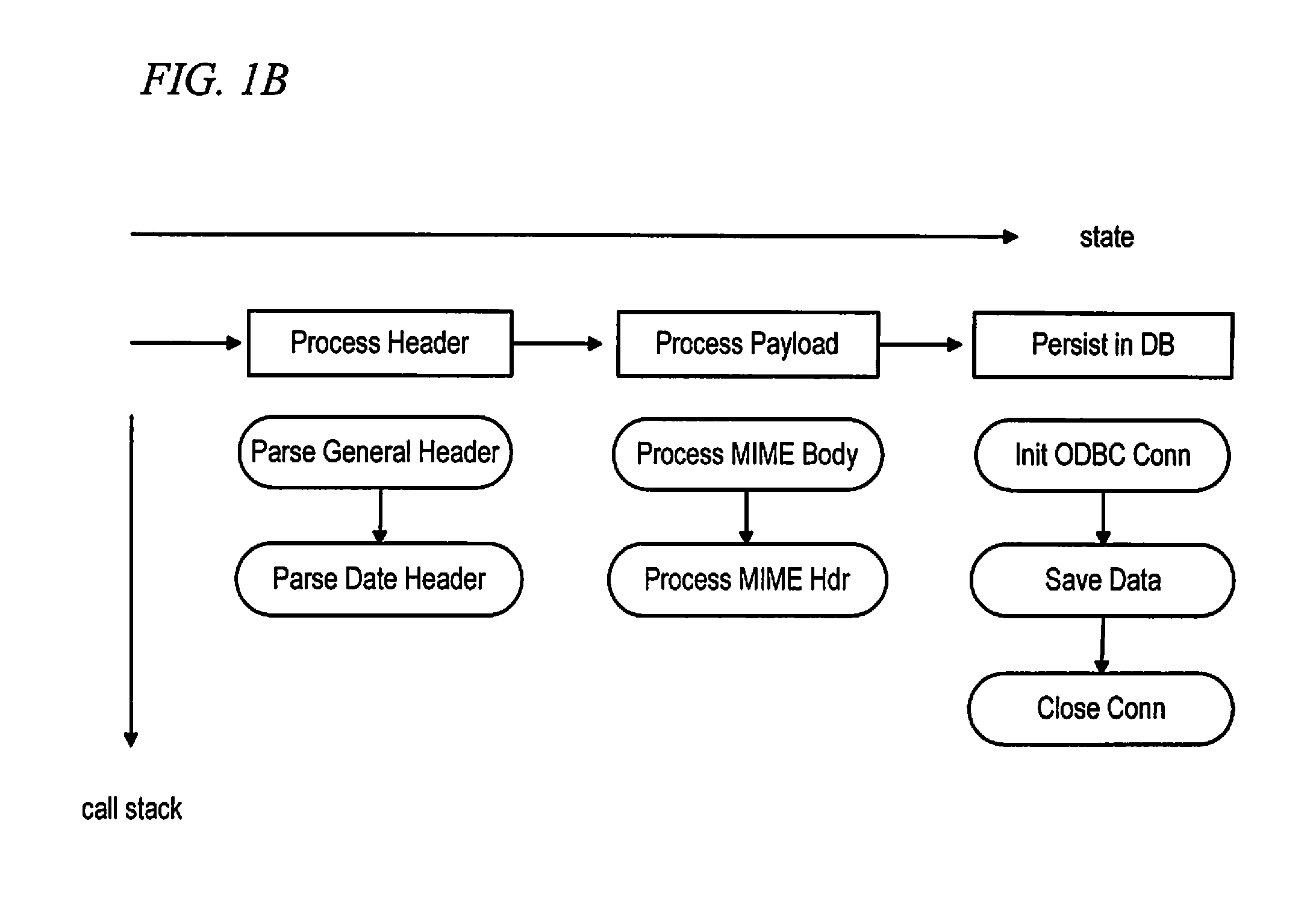
Recording and Preventing Crash in an Appliance
A computer implemented method for recording a crash in an appliance is provided. The method includes the following steps: running a core process to perform a transaction, which will make the core process undergo at least one state sequentially, wherein each state includes at least one call stack; executing a supervisor process to generate a state record, to sequentially record all undergone states of the core process in the transaction; in response to a crash of the core process in the transaction, generating a fault record to record all call stacks in a latest state of the core process; generating a crash report according to the state record and the fault record.
Owner:IBM CORP
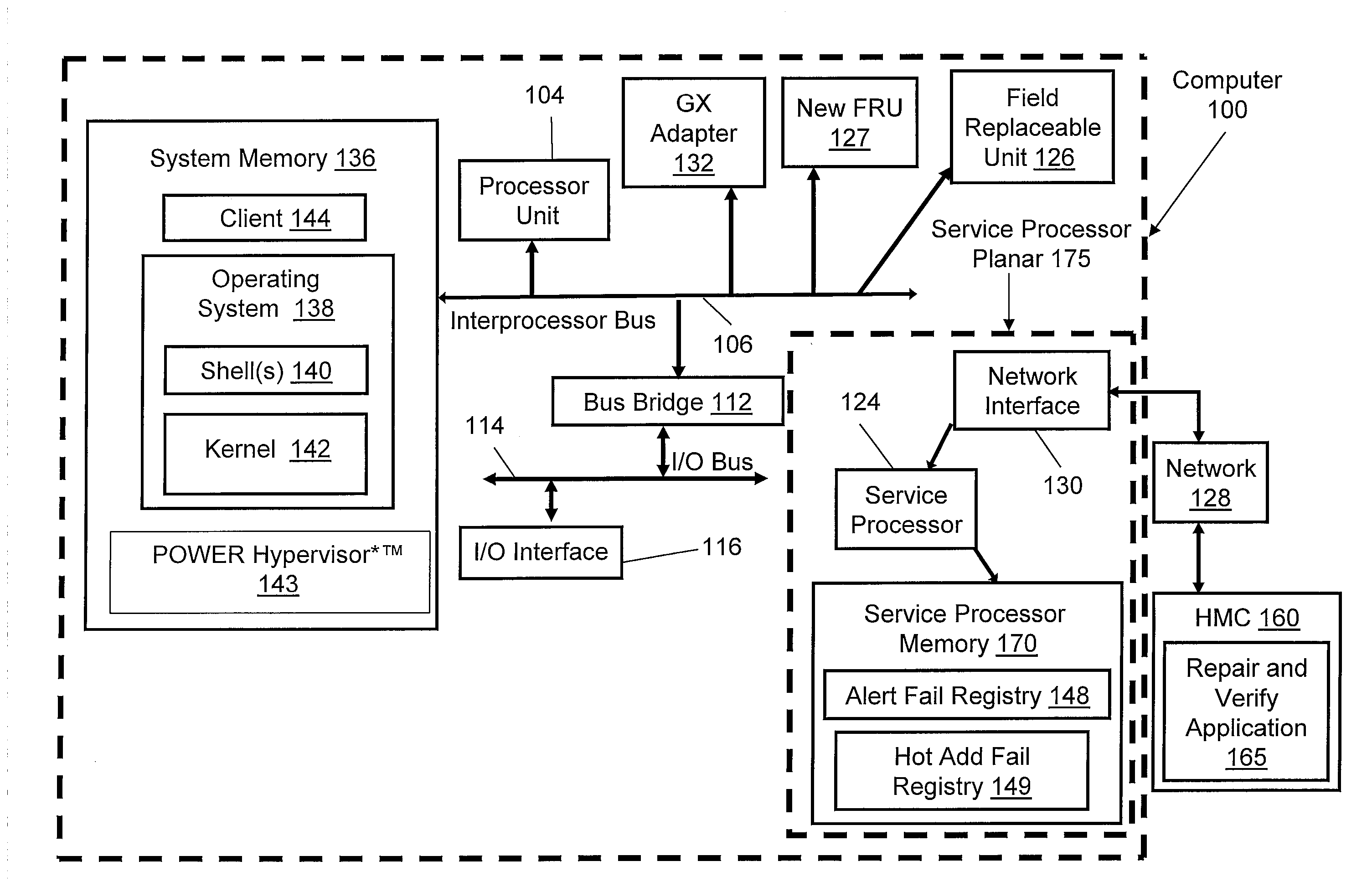
Method and system to handle hardware failures in critical system communication pathways via concurrent maintenance
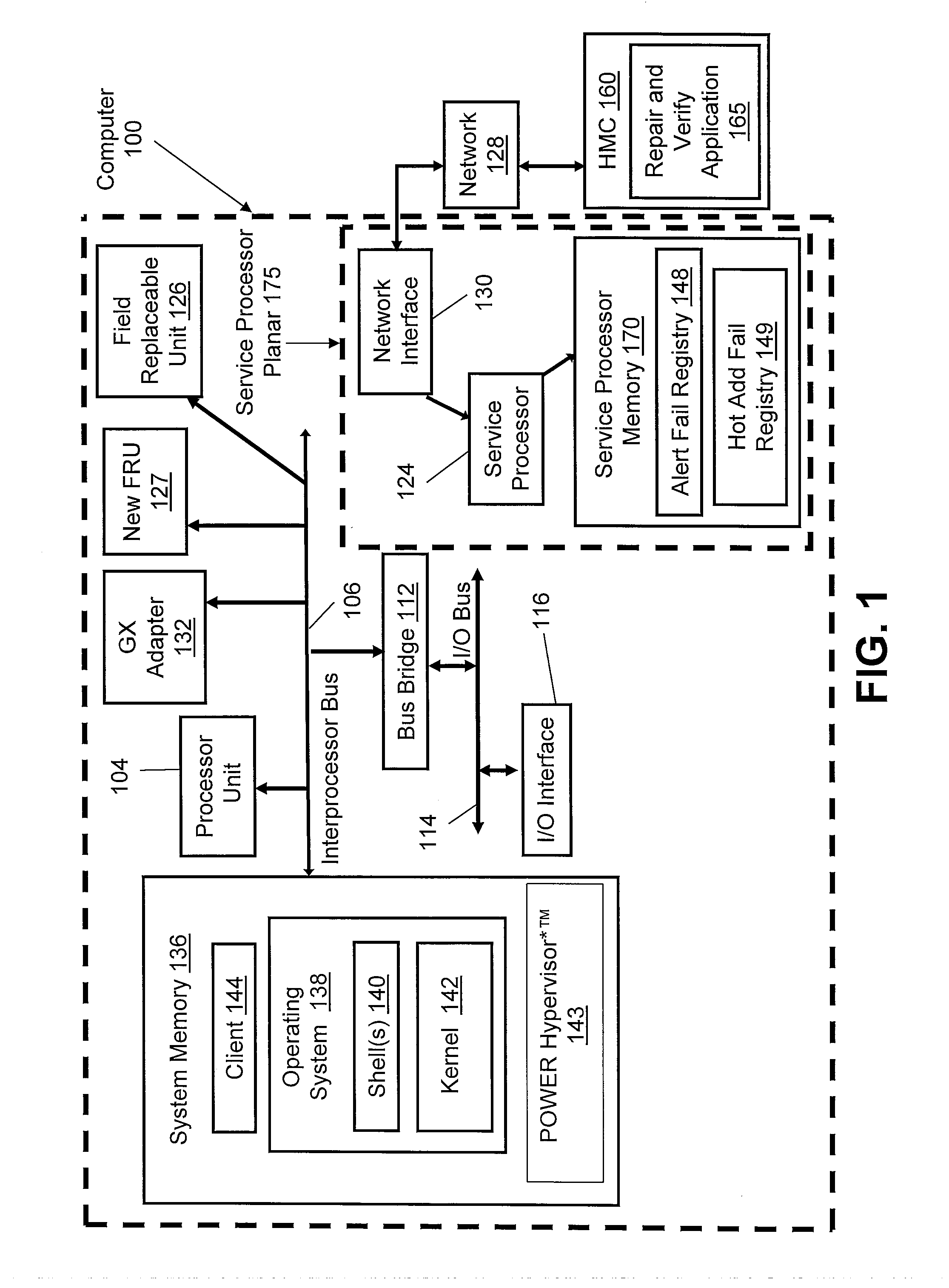
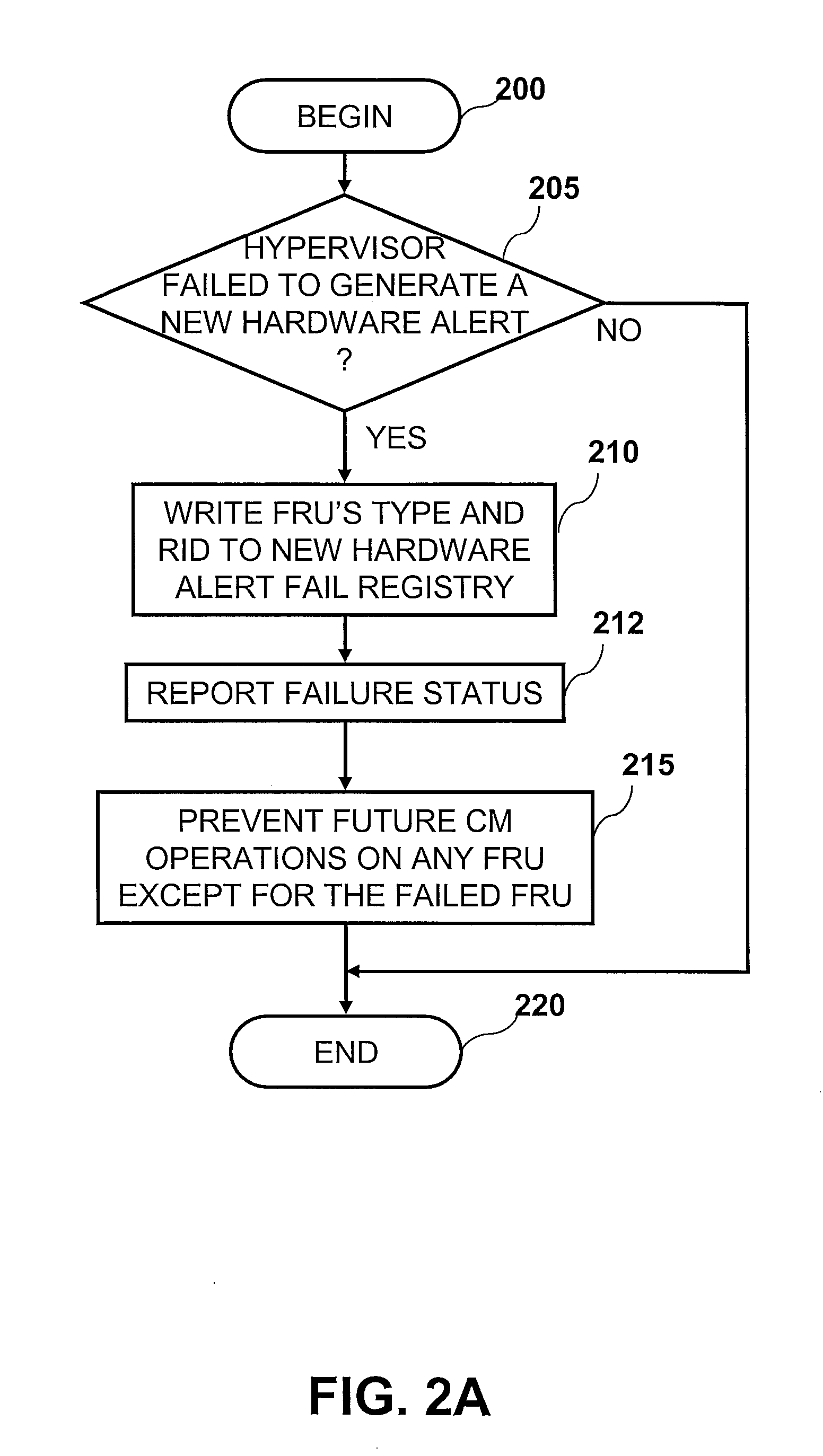
InactiveUS20080133962A1Error avoidanceRedundant hardware error correctionField replaceable unitApplication software
A method of preventing failed field replaceable units (FRUs) directly connected to an interprocessor bus or fabric from interfering with the operation of a computer system during concurrent maintenance operations. When a FRU fails a concurrent maintenance operation, the service processor stores identification information corresponding to the failed FRU in an alert fail registry or a hot add fail registry and reports the failure status to a user. When a user attempts to perform a new concurrent maintenance operation on a FRU, the service processor compares that FRU to the alert fail registry or the hot add fail registry. If a concurrent maintenance operation on the requested FRU would cause a system crash due to interference with the failed FRU, the service processor notifies the repair and verify application (which notifies the user) and prevents concurrent maintenance operations from occurring on the new FRU.
Owner:IBM CORP
Systems and methods for memory failure prevention, management, and mitigation
ActiveUS20200210272A1Memory architecture accessing/allocationMemory adressing/allocation/relocationRandom access memoryTerm memory
Some embodiments described herein are directed to memory page or bad block monitoring and retirement algorithms, systems and methods for random access memory (RAM). Reliability issues or errors can be detected for multiple memory pages using one or more retirement criterion. In some embodiments, when reliability errors are detected, it may be desired to remove such pages from operation before they create a more serious problem, such as a computer crash. Thus, bad block retirement and replacement mechanisms are described herein.
Owner:FORMULUS BLACK CORP
Method and system for handling an unexpected exception generated by an application
InactiveUS7089455B2Improve securitySimple methodProgram initiation/switchingError detection/correctionGraphicsGraphical user interface
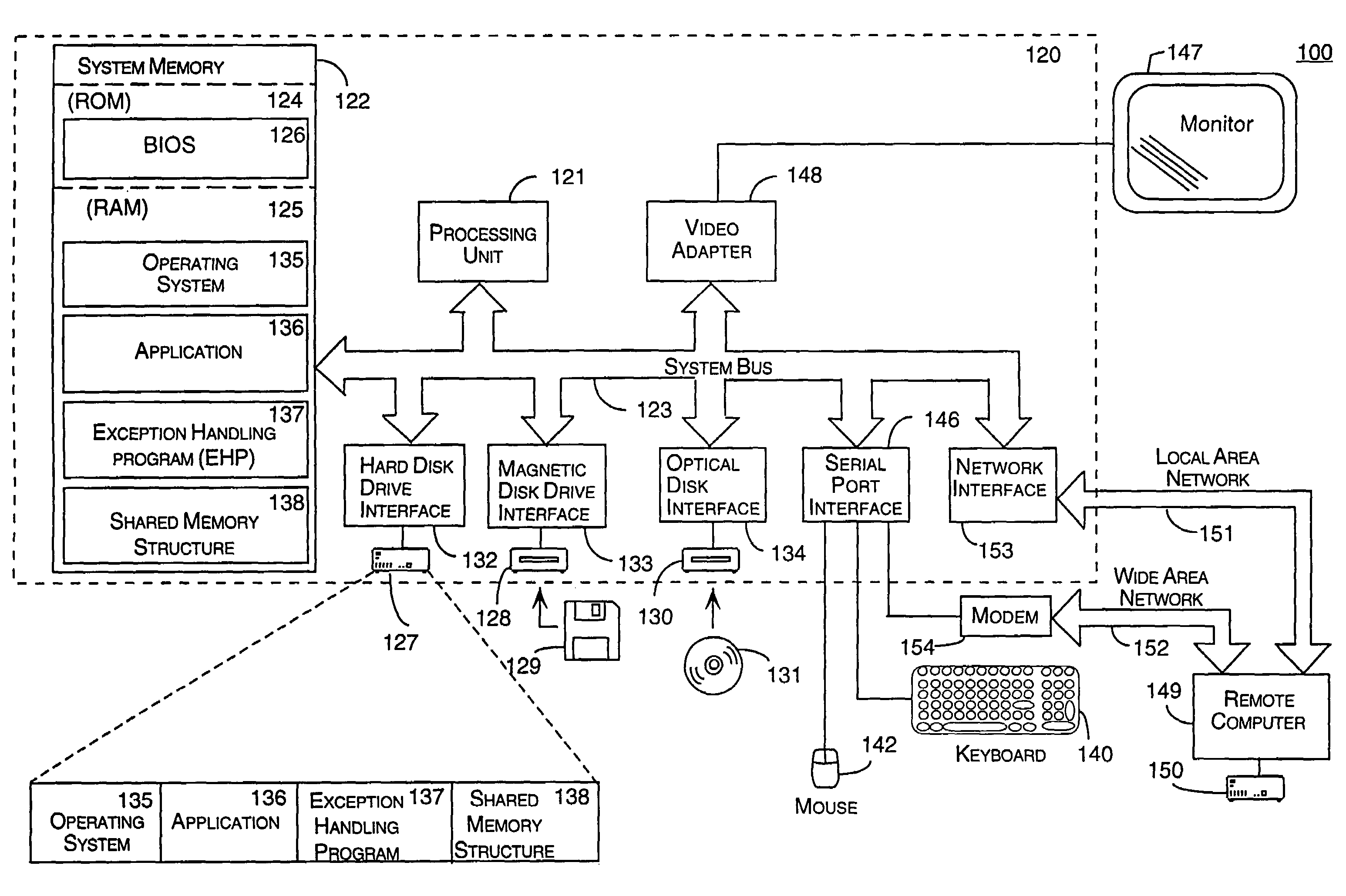
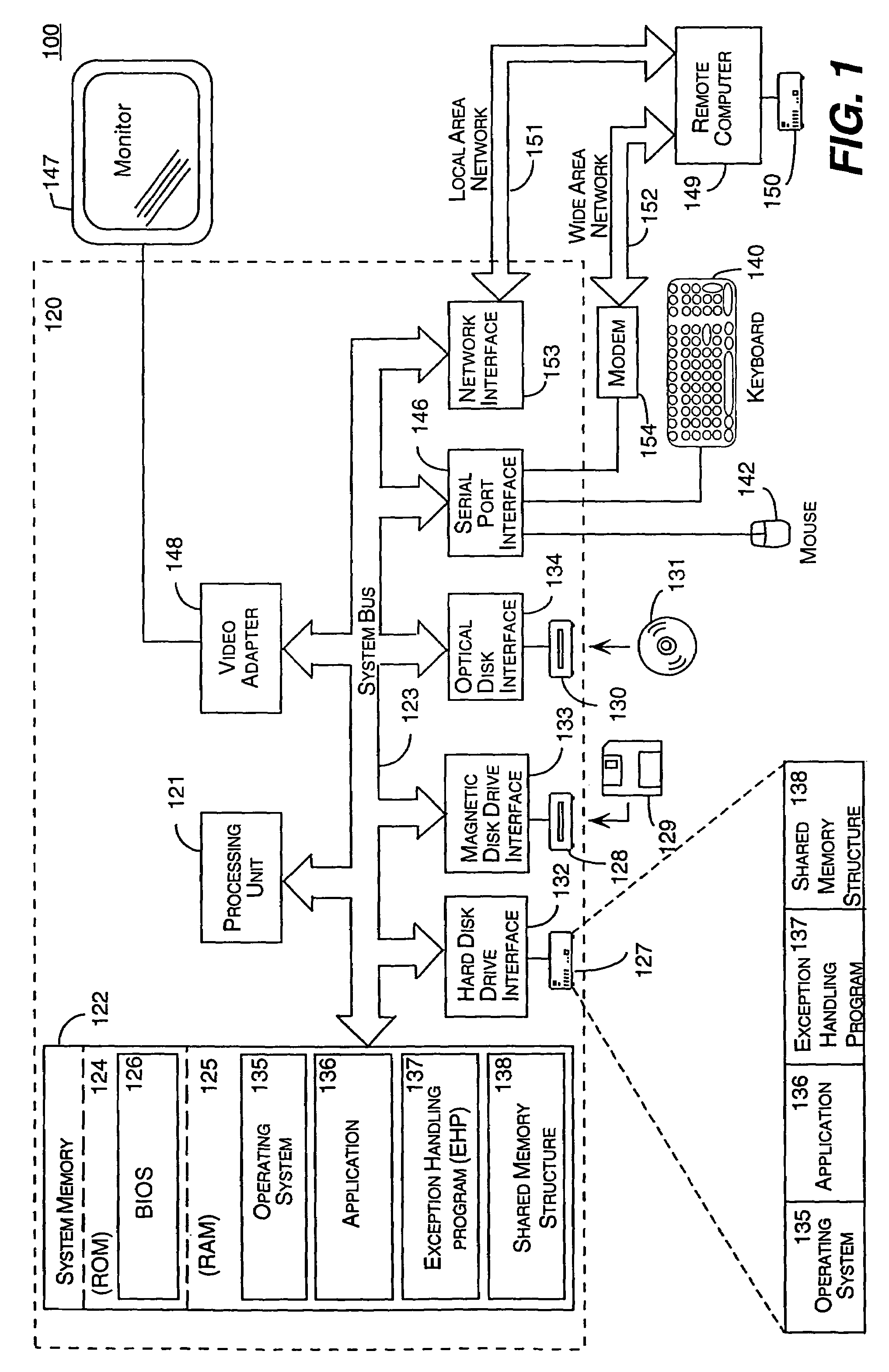
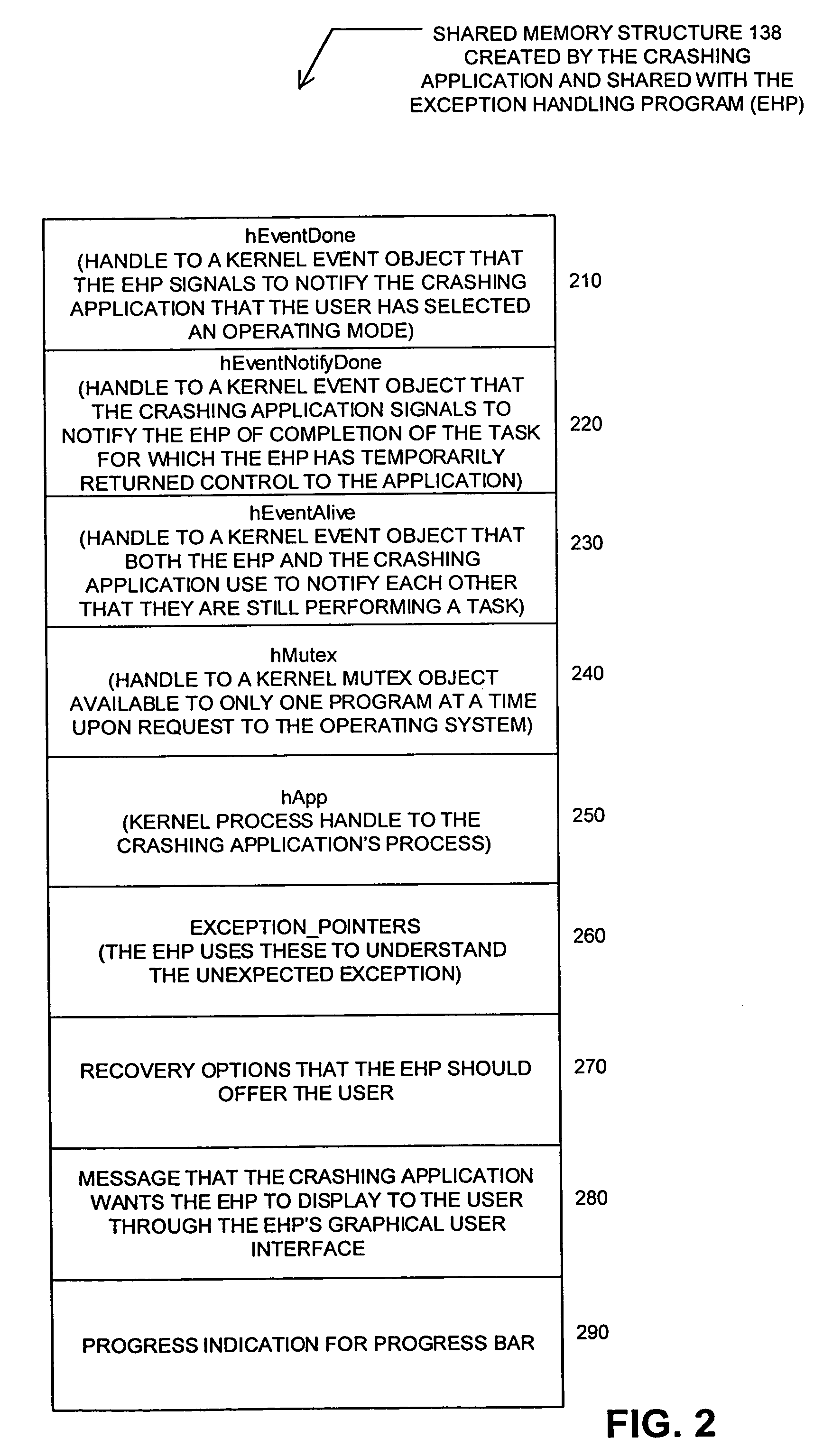
A system and method for handling the generation of an unexpected exception by an application. When the application generates an unexpected exception (i.e., crashes), the application's exception filter launches an outside exception handling program (EHP) that is separate and distinct from the application. Through a special protocol, the application and the EHP collaborate in responding to the unexpected exception. In this protocol, the application and the EHP communicate through kernel objects accessible by handles in a shared memory structure that the application creates before launching of the exception handling program and then shares with the EHP. Through this shared memory, the application also provides the EHP with information about the types of recovery options to offer the user. Through a graphical user interface, the EHP is then responsible for notifying the user of the application that an unexpected exception has occurred. Through the graphical user interface, the EHP also provides the user with the ability to specify various courses of action in response to the unexpected exception.
Owner:ZHIGU HLDG
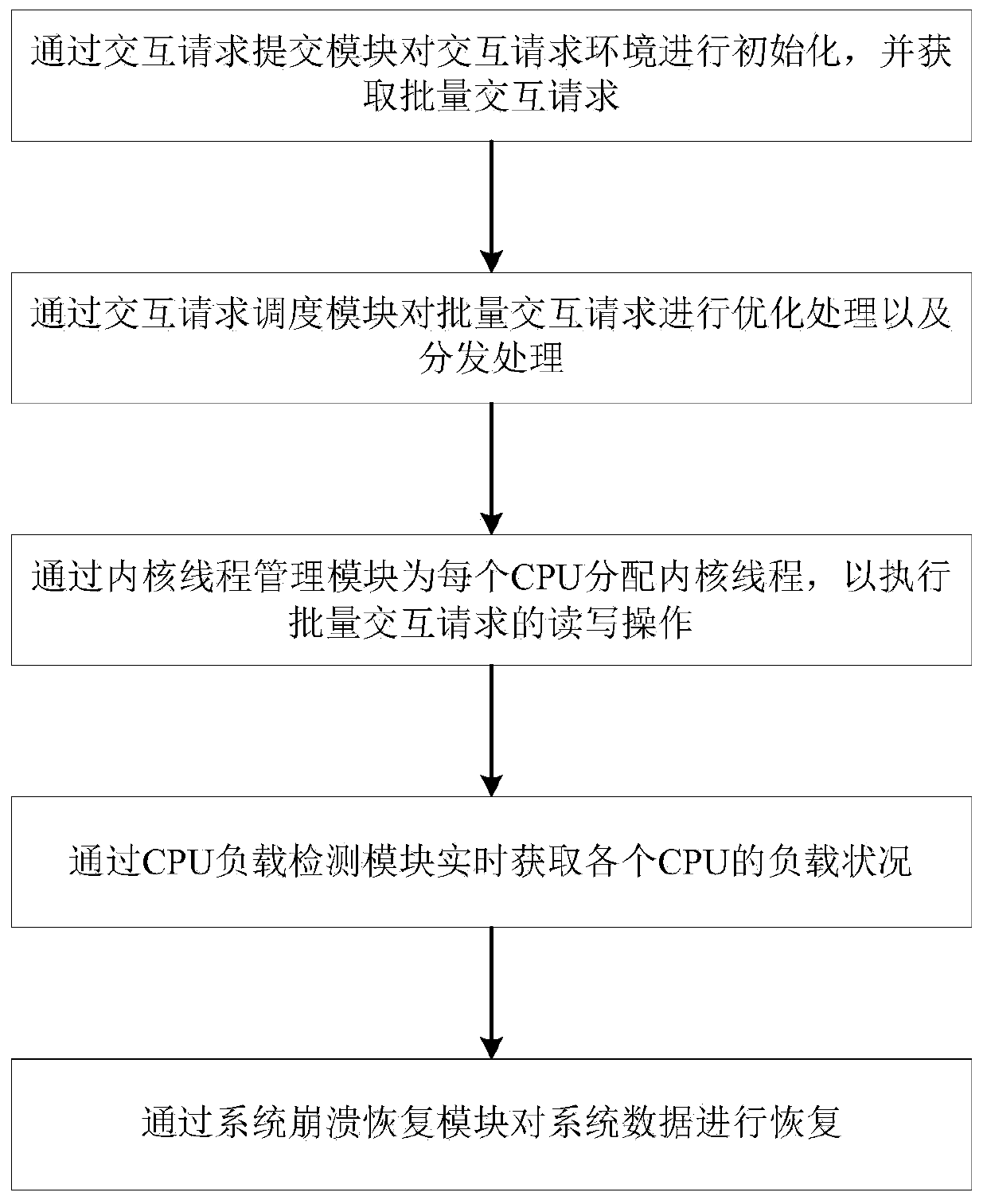
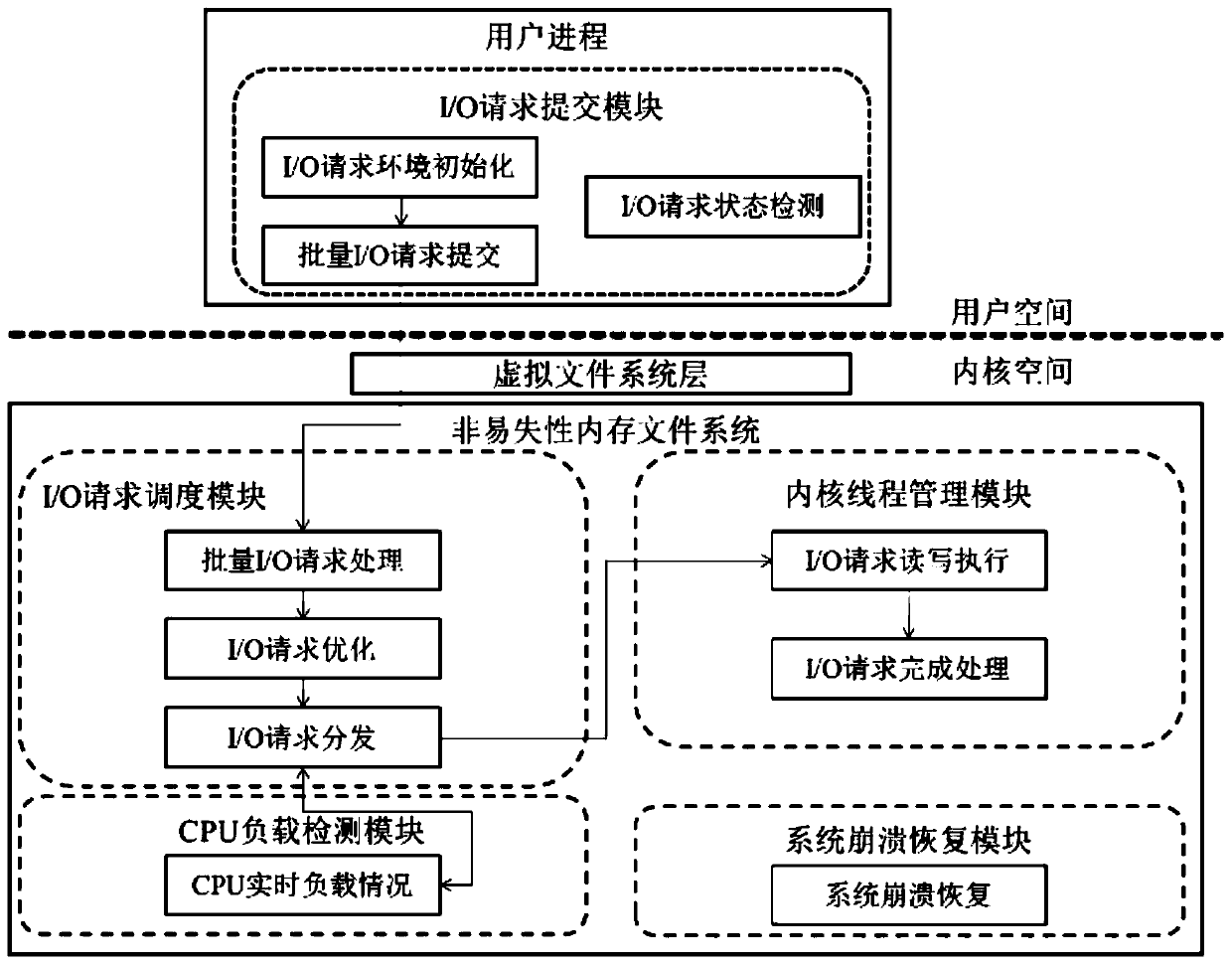
Multi-core interaction method and system suitable for nonvolatile memory and storage medium
ActiveCN110750356AImprove efficiencyImprove concurrencyResource allocationProgram synchronisationComputer architectureInit
The invention discloses a multi-core interaction method and system suitable for a nonvolatile memory and a storage medium. The system comprises an interaction request submitting module, an interactionrequest scheduling module, a kernel thread management module, a CPU load detection module and a system crash recovery module. According to the method, an interaction request environment is initialized through an interaction request submitting module, then batch interaction requests are optimized and distributed through an interaction request scheduling module, and then kernel threads are distributed to each CPU through a kernel thread management module. According to the method, batch interaction requests are processed, the advantages of multi-core asynchronous concurrent processing can be brought into full play, the efficiency is high, and the concurrency is high; besides, the load condition of each CPU can be acquired in real time through the CPU load detection module, and the system data can be recovered through the system crash recovery module, so that the stability of the system is improved, and the method and system can be widely applied to the technical field of computers.
Owner:SOUTH CHINA NORMAL UNIVERSITY
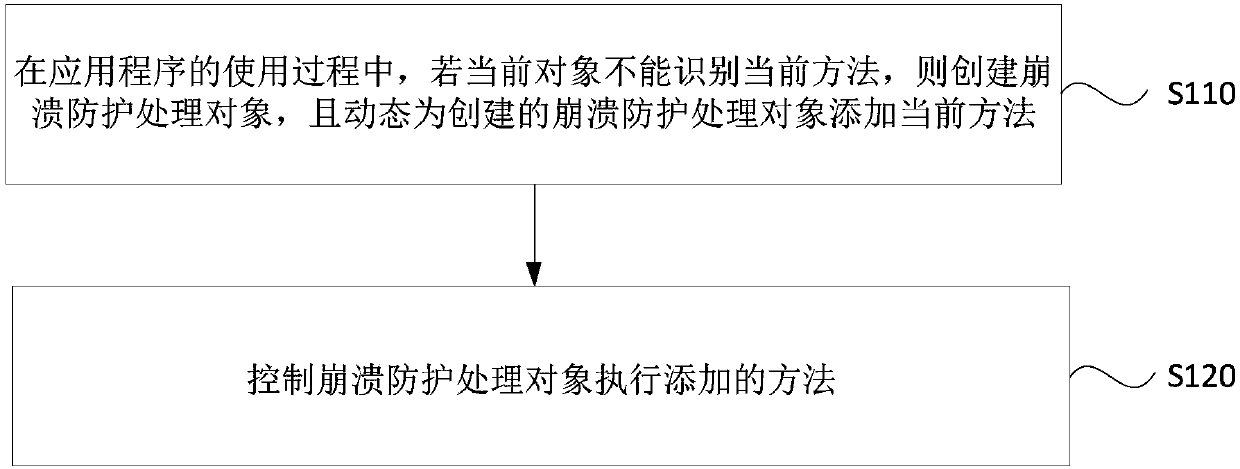
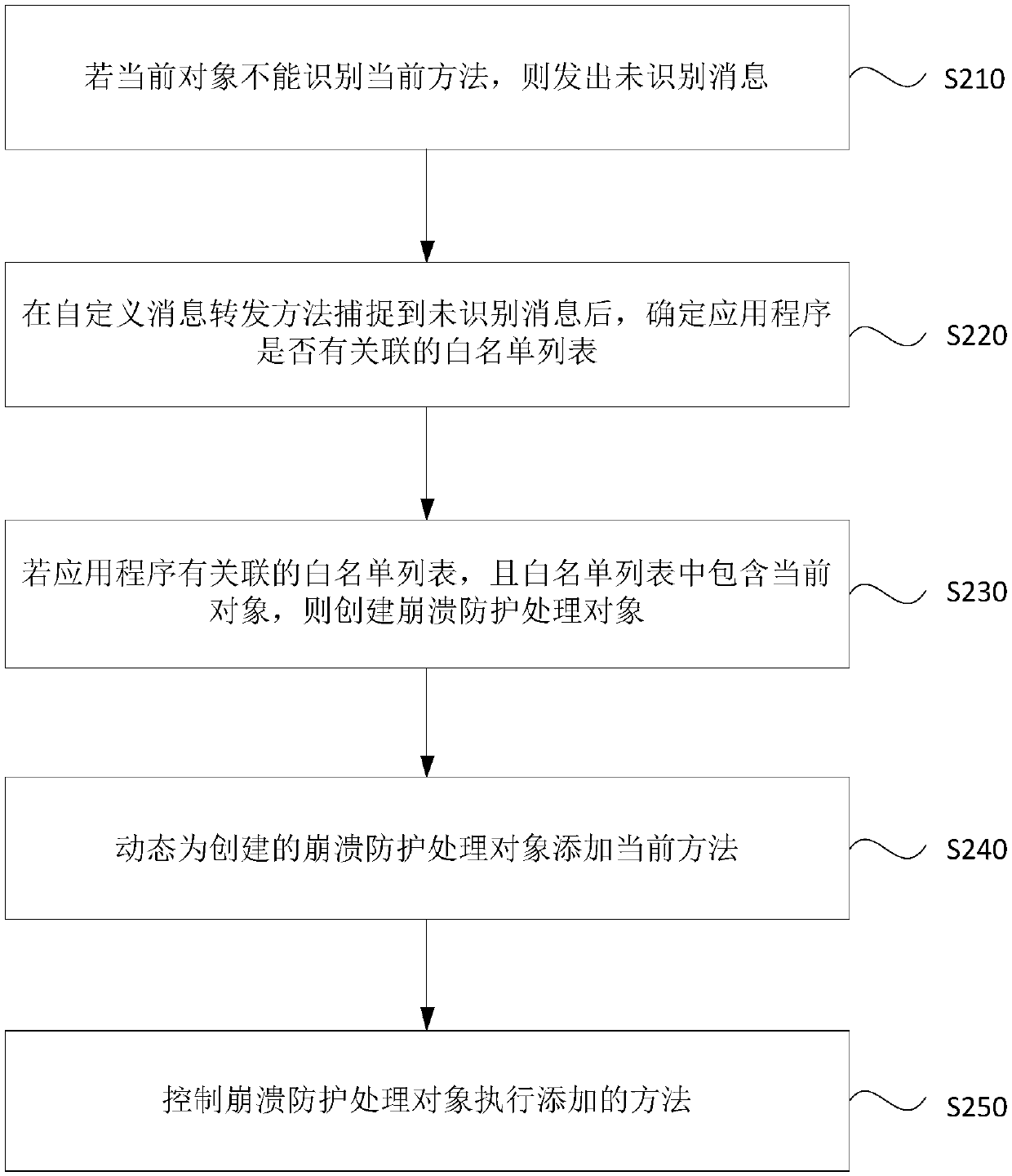
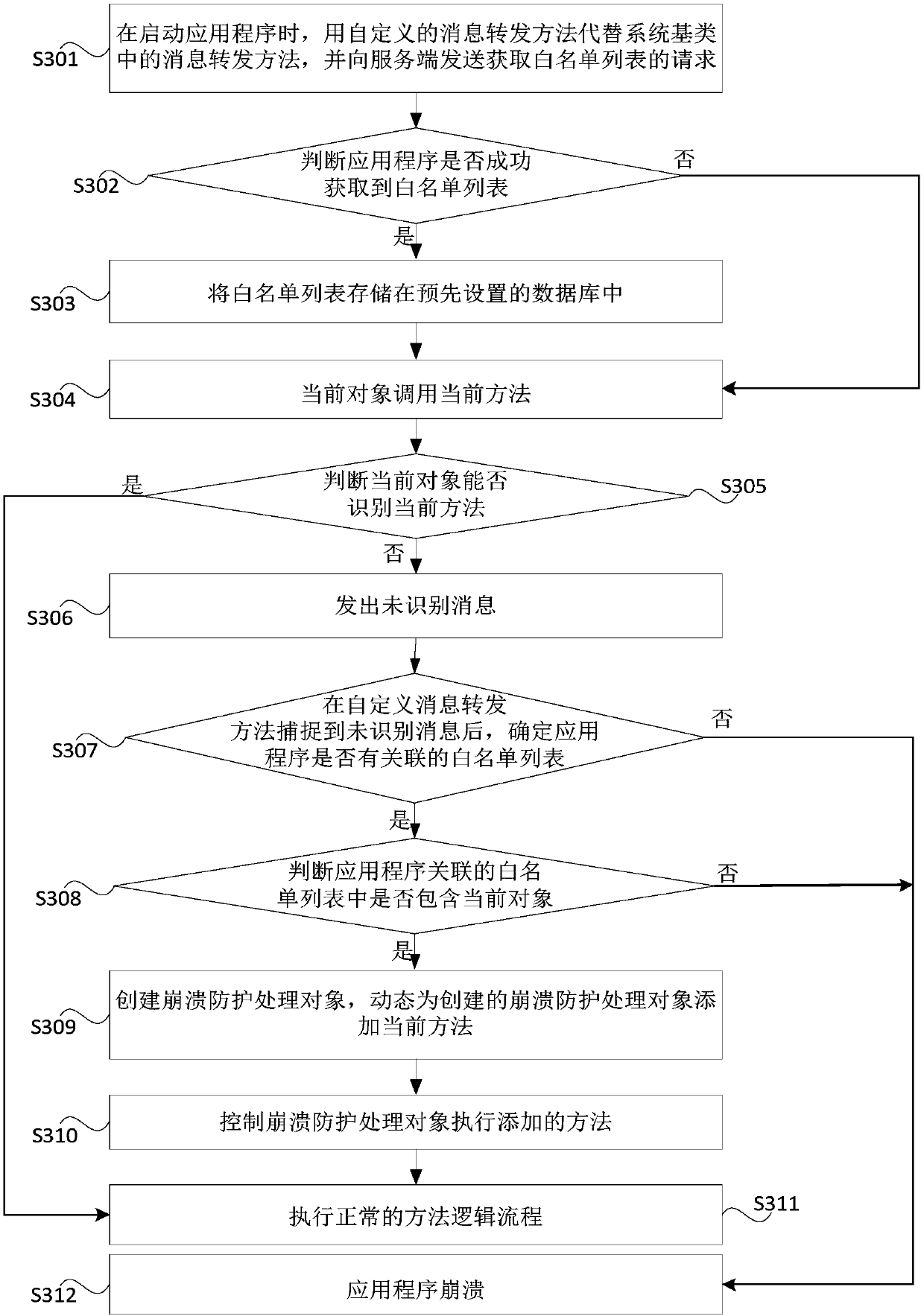
Application crash protection method and apparatus, device and storage medium
InactiveCN108052407APrevent crashImprove experienceNon-redundant fault processingOperating systemApplication procedure
Embodiments of the invention disclose an application crash protection method and apparatus, a device and a storage medium. The method comprises the steps of in a using process of an application, if acurrent object cannot identify the current method, creating a crash protection processing object, and dynamically adding the current method for the created crash protection processing object; and controlling the crash protection processing object to execute the added method. According to the technical scheme provided by the method and the apparatus, when the current object cannot identify the current method, the crash protection object executes the method by dynamically adding the current method to the crash protection object, so that the phenomenon of application crash caused by the fact thatthe current object cannot identify the current method can be avoided, the product robustness and stability and the user experience are improved, and the code conciseness is kept.
Owner:SHENZHEN LEXIN SOFTWARE TECH CO LTD
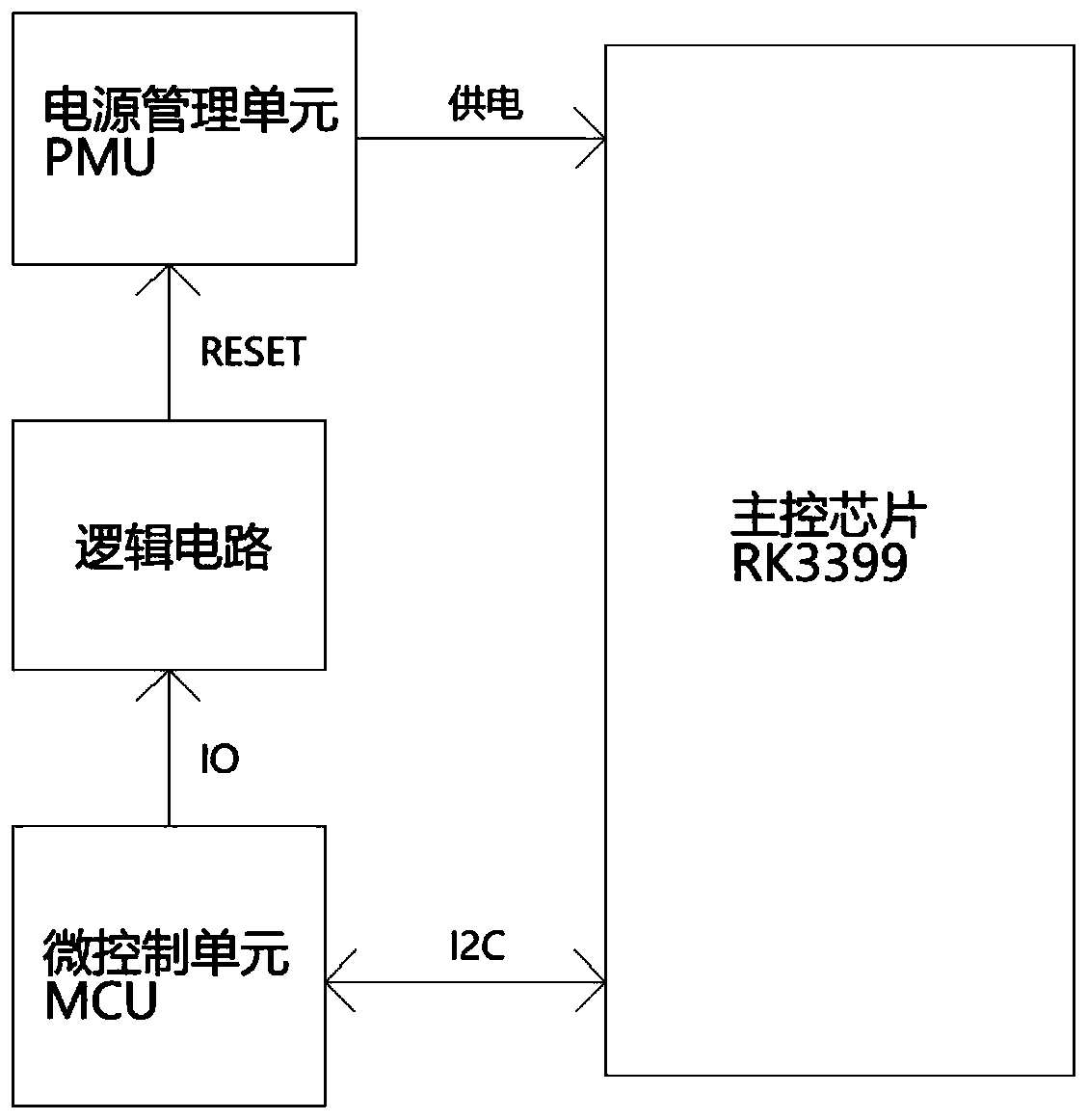
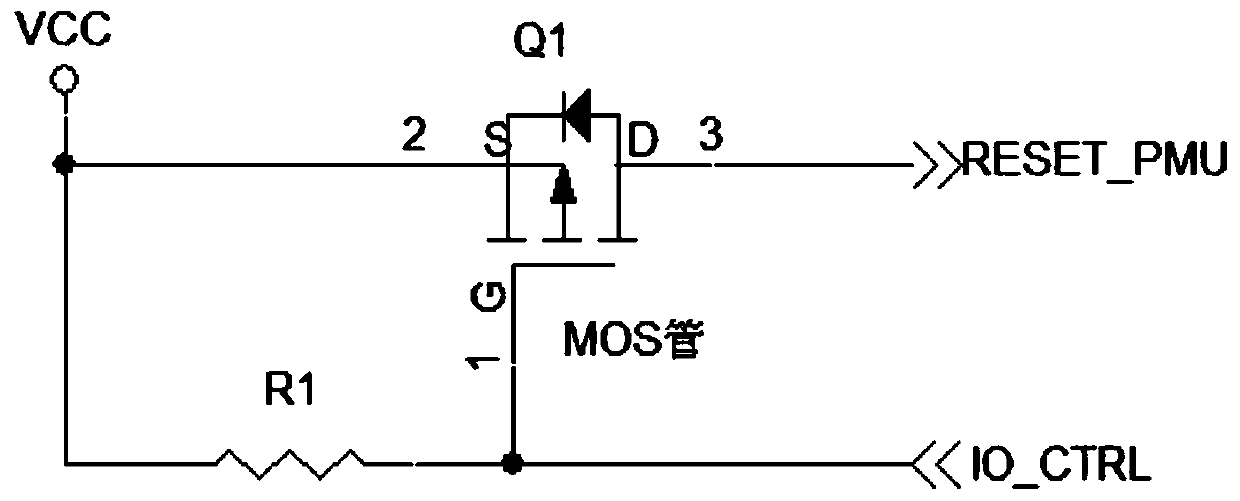
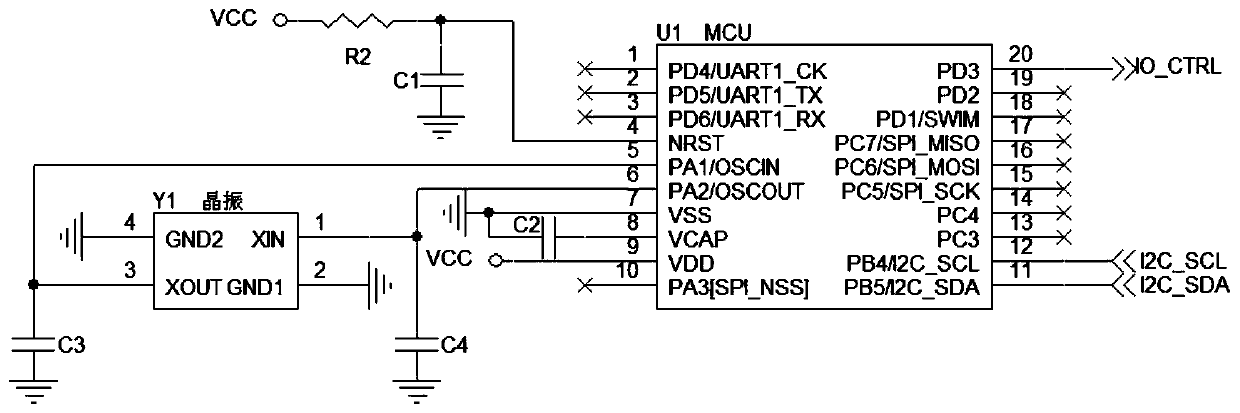
System and method for realizing automatic restart and recovery of crash of RK3399 mainboard
InactiveCN110569148AImprove reliabilityNo human intervention requiredRedundant operation error correctionControl signalPower Management Unit
The invention discloses a system and a method for realizing automatic restart recovery of crash of an RK3399 mainboard which belongs to the technical field of electronics. The technical problem to besolved by the invention is how to enable a main control chip RK3399 to be automatically restarted to recover normal work when crash occurs without manual intervention. According to the technical scheme, the system comprises the main control chip RK3399, a micro control unit MCU, a power management unit PMU and a logic circuit; the main control chip RK3399 is used for communicating with the micro control unit MCU; the micro control unit MCU is used for communicating with the main control chip RK3399, judging the running state of the main control chip RK3399 and selecting whether to send a control signal to the logic circuit or not; the power management unit PMU is used for providing power for the main control chip RK3399, so that the main control chip RK3399 works normally; and the logic circuit is used for converting a control signal sent by the MCU into an RESET reset signal of the PMU to reset the PMU, so that the main control chip RK3399 is restarted. The invention also discloses amethod for realizing the automatic restart recovery of the crash of the RK3399 mainboard.
Owner:INSPUR FINANCIAL INFORMATION TECH CO LTD
Application restoration method and device, terminal and storage medium
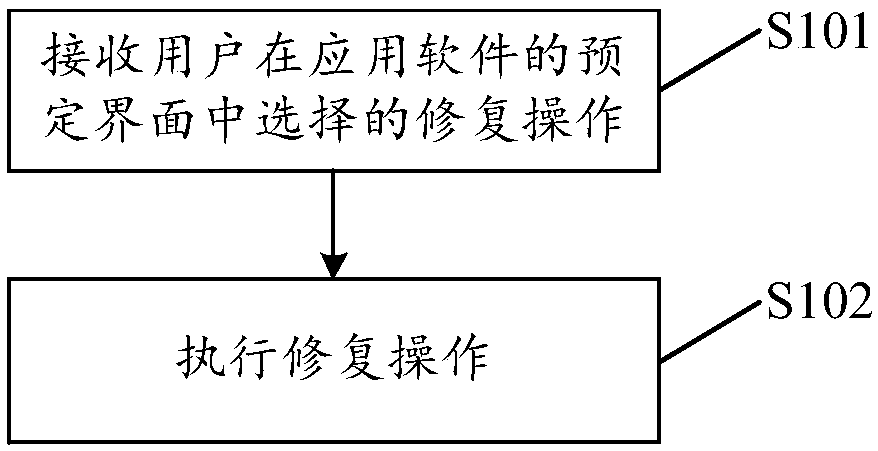
InactiveCN108196972AGood repair experienceNon-redundant fault processingRestoration methodComputer terminal
The invention discloses an application restoration method and device, a terminal and a storage medium. The method comprises the steps that restoration operation selected by a user in a predetermined interface of an application is received, wherein the restoration operation comprises at least one of file saving, program restoration and restoration operation execution. The application is provided with the predetermined interface, and the predetermined interface can be displayed when the application is rebooted after crash; and after the predetermined interface receives the restoration operationselected by the user, the corresponding restoration operation can be executed. In this way, the user autonomously selects a restoration process which the user hopes to execute, the user obtains betterrestoration experience, and the problems that in the prior art, crash only can be processed by rebooting the application or reinstalling the application, and restoration cannot be performed accordingto the actual demand of the user are solved.
Owner:BEIJING 58 INFORMATION TTECH CO LTD
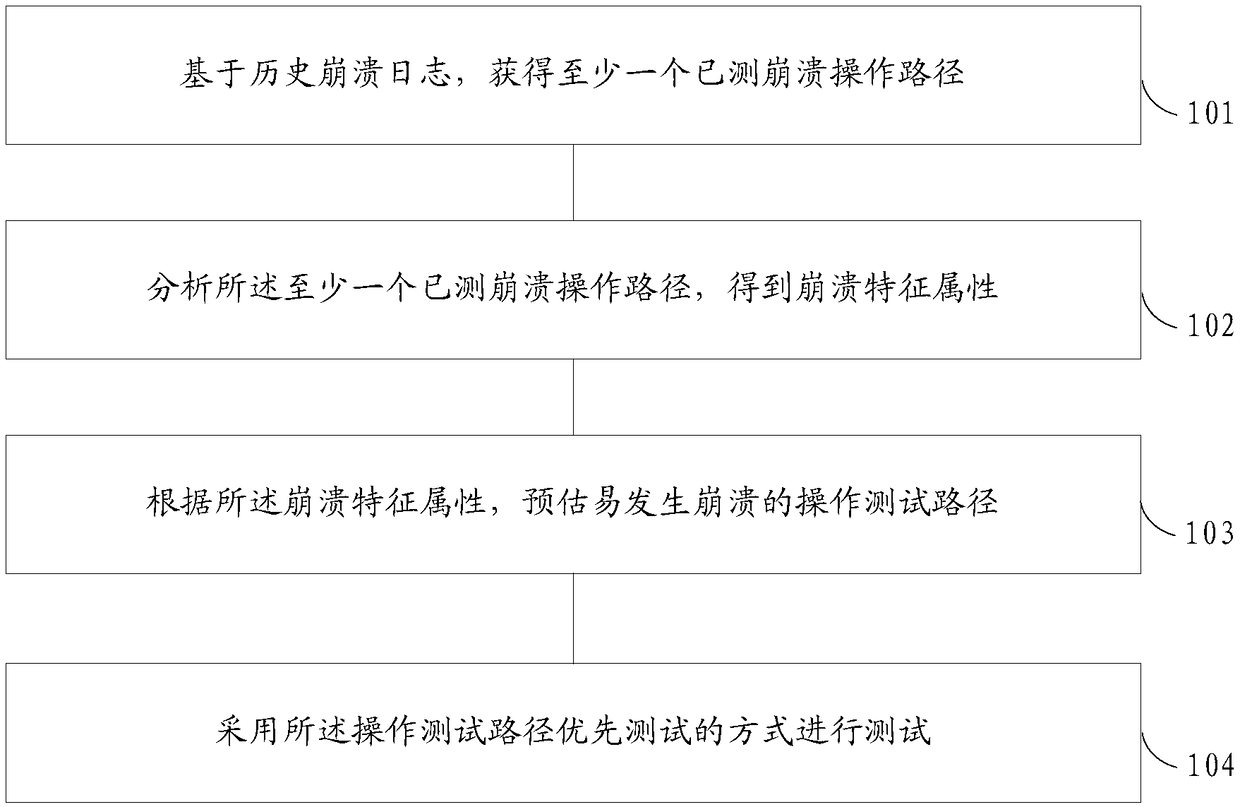
Application test method and device
InactiveCN108595330AIncreased crash rateHigh recurrence rateSoftware testing/debuggingExecution for user interfacesAutomatic testingComputer science
The embodiment of the invention provides an application test method and device. The method comprises the following steps: based on a historical crash log, obtaining at least one tested crash operationpath; analyzing at least one tested crash operation path, and obtaining crash characteristic attributes; according to the crash characteristic attributes, predicting an operation test path easy to becrashed; and testing by adopting a way that the operation test path is tested preferentially. The technical scheme provided by the embodiment of the invention can enable application crashes to be more easily caused during automated testing, and recurrence rate of a crash scene is also improved.
Owner:北京龙之心科技有限公司
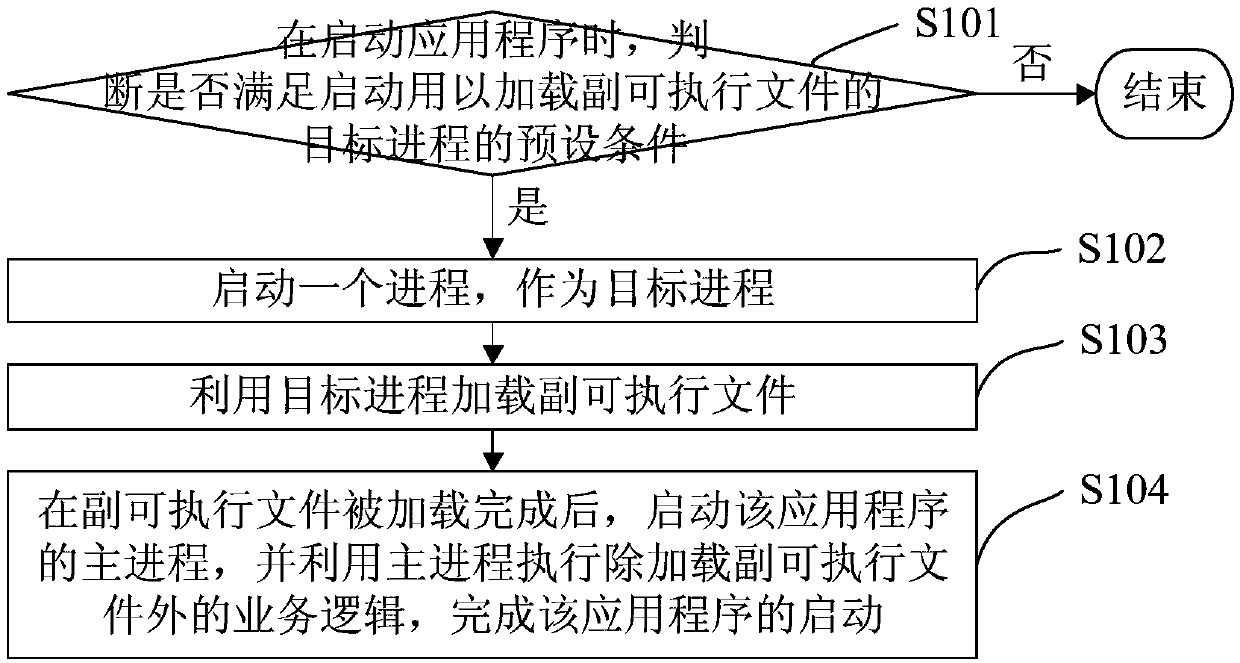
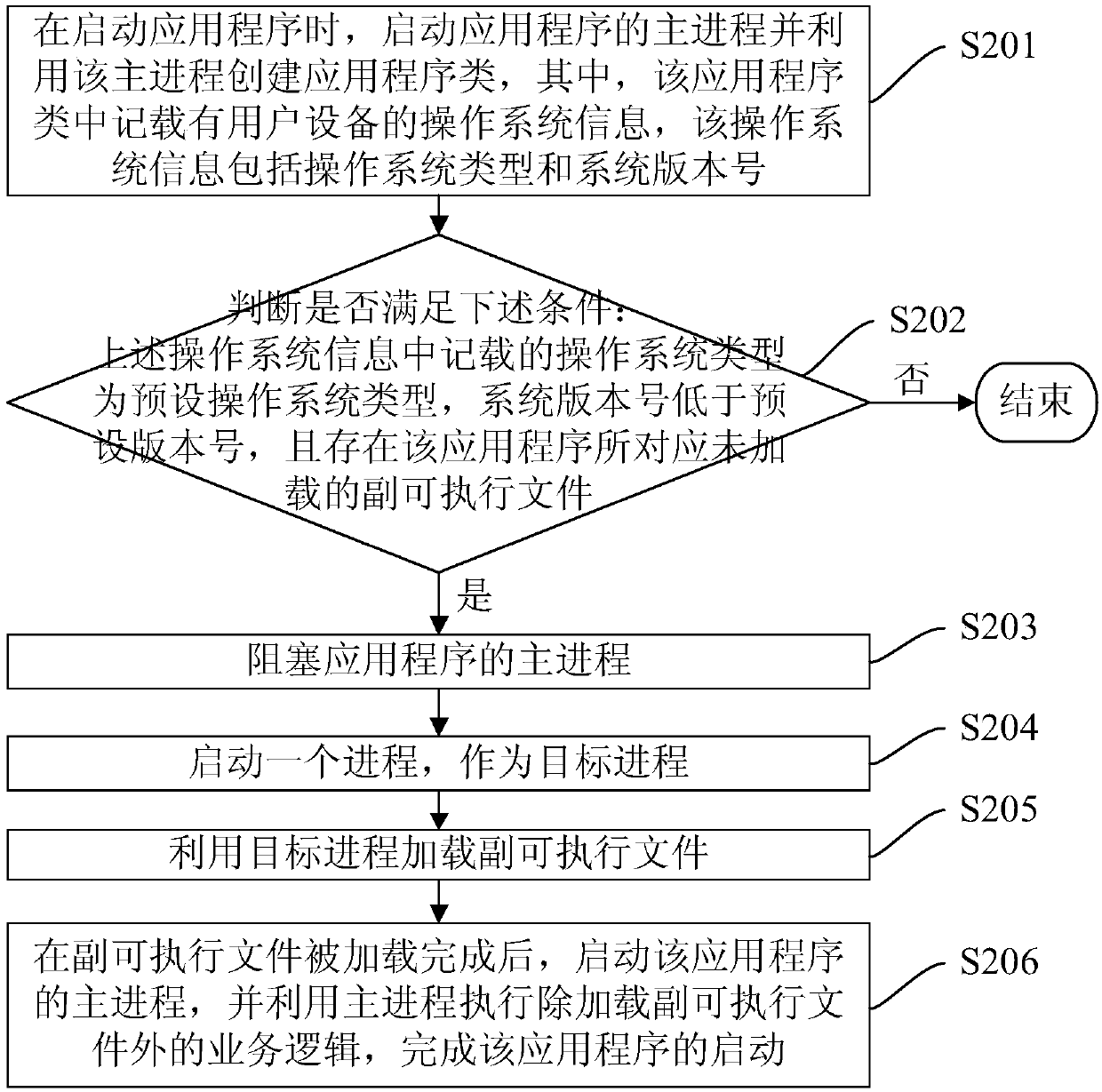
Application program starting method and device, electronic equipment and storage medium
The embodiment of the invention provides an application program starting method and device, electronic equipment and a storage medium, and the method comprises the steps: firstly judging whether a preset condition for starting a target process for loading an auxiliary executable file is met or not in the application program starting process; If yes, starting a process as a target process; Loadingan auxiliary executable file of the application program by utilizing the target process; And finally, after the auxiliary executable file is loaded, starting a main process of the application program,and executing service logic except for loading the auxiliary executable file by utilizing the main process to complete the starting of the application program. Wherein the auxiliary executable filesare executable files except the main executable file in all the executable files corresponding to the application program. Compared with the prior art, the scheme provided by the embodiment of the invention has the advantage that the phenomenon of system crash caused by the fact that data and resources required when a main process executes other service logics except for loading an auxiliary executable file are not loaded can be avoided.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
A method and a device for avoiding application crash
PendingCN109901950APrevent crashImprove user experienceRedundant operation error correctionSoftware engineeringApplication software
The invention provides a method and device for avoiding application crash. The method comprises the steps of starting an application; When the application program crashes in the running process, obtaining function calling information generated when the application program crashes; Determining a target service component causing the application program to crash according to the function calling information, the target service component being a value-added service component included in the application program; Recording the identification information of the target service component in a running configuration file of the application program, so that the target service component is not executed according to the identification information recorded in the running configuration file after the application program is restarted; And restarting the application program. According to the scheme, the user experience can be improved.
Owner:SHANDONG INSPUR COMML SYST CO LTD
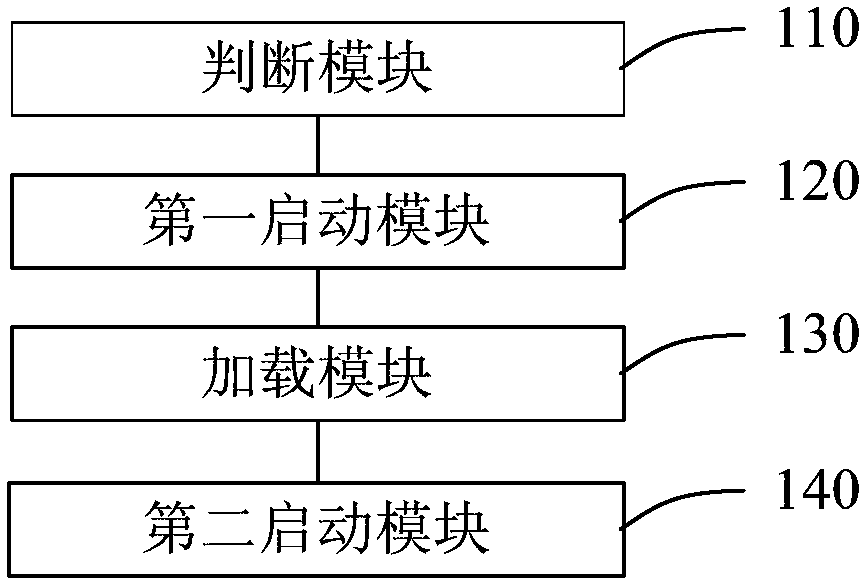
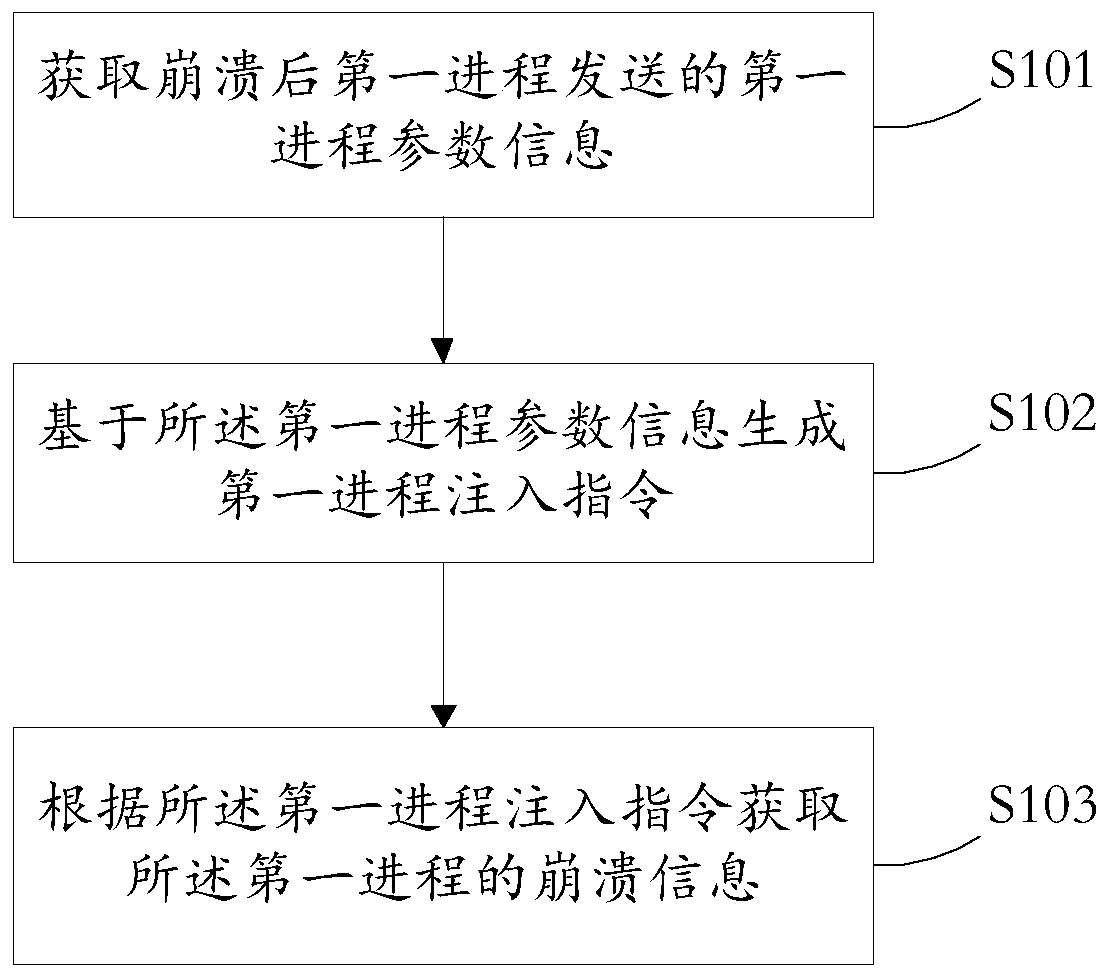
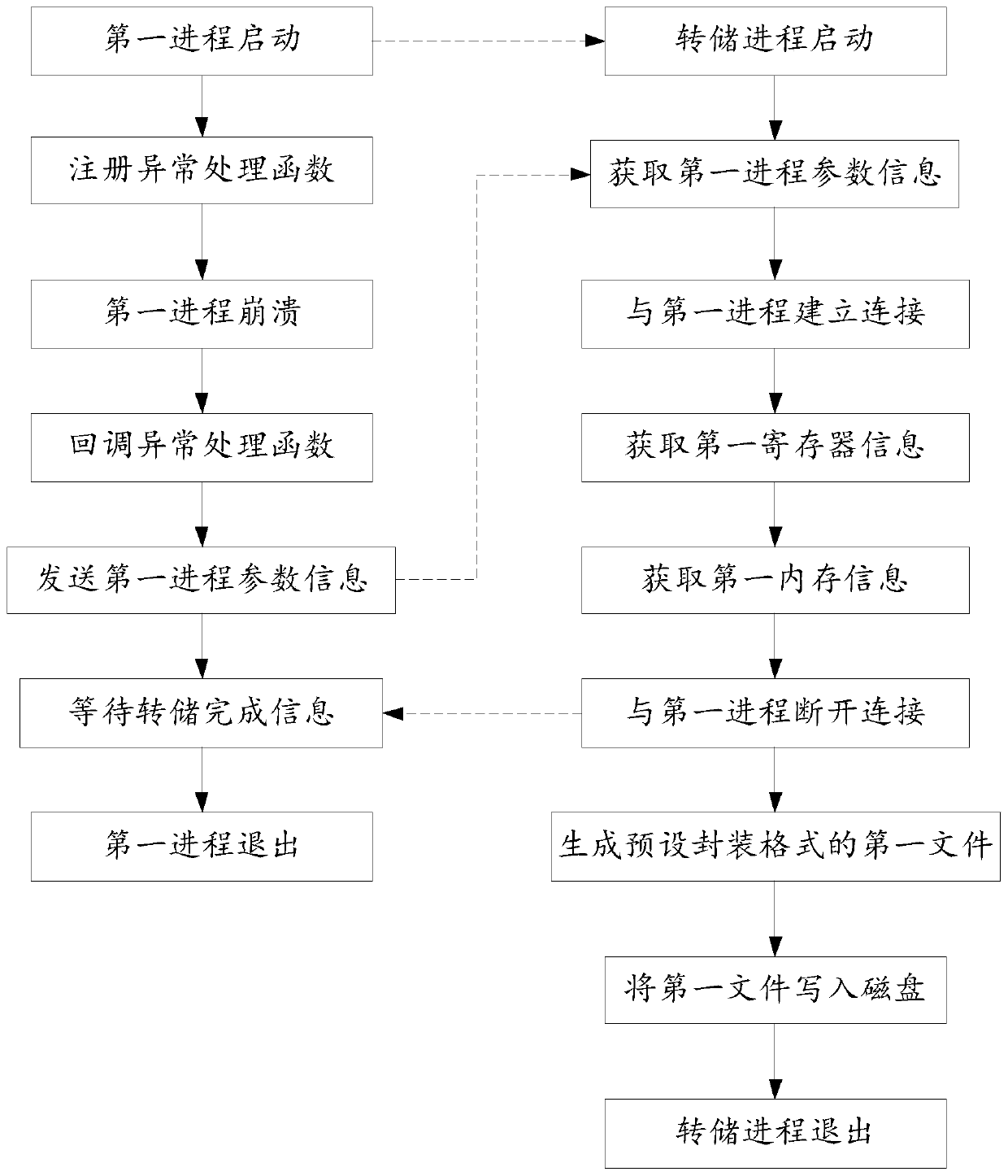
Method and device for obtaining process crash information, medium and electronic equipment
ActiveCN110727566APrecise positioningFix crashHardware monitoringEnergy efficient computingCore dumpSimulation
The invention provides a method and device for obtaining process crash information, a medium and electronic equipment. The method comprises the steps of obtaining first process parameter information sent by a first process after crash; generating a first process injection instruction based on the first process parameter information; and obtaining crash information of the first process according tothe first process injection instruction. According to the method, instruction injection is carried out on the first process through the dump process, and the crash information is obtained, and information before and after process operation when the first process crashes can be obtained from the crash information, and the crash problem is conveniently positioned. By comprehensively analyzing the crash information of the first process, the crash reason of the crash of the first process can be obtained. The problem that process crash cannot be analyzed due to the fact that a core dump mechanismdoes not exist is solved, and the problem of system crash is further solved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
High-reliability embedded software upgrading method and system
PendingCN111562932ASimple structureImprove performanceSoftware deploymentEmbedded softwareData interface
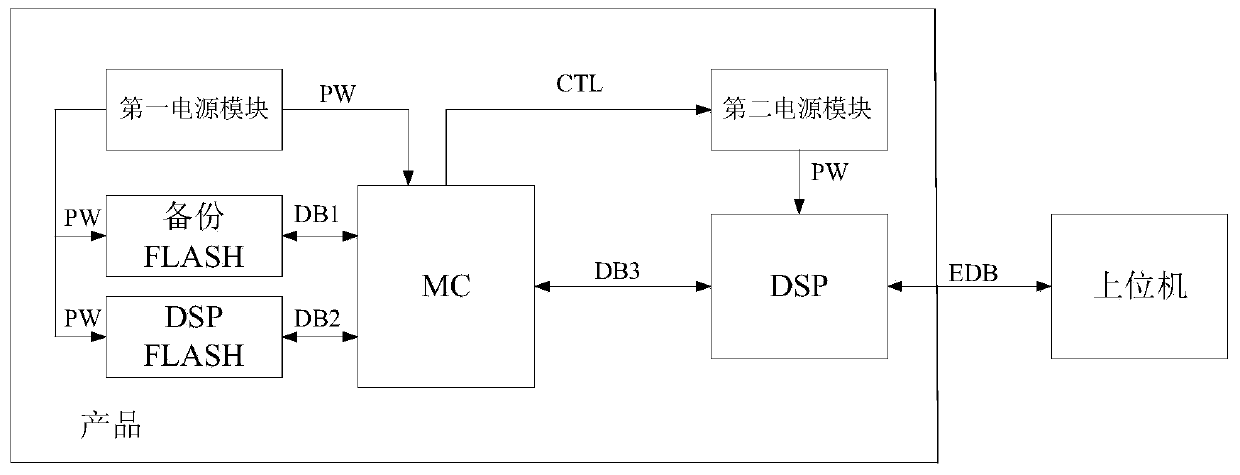
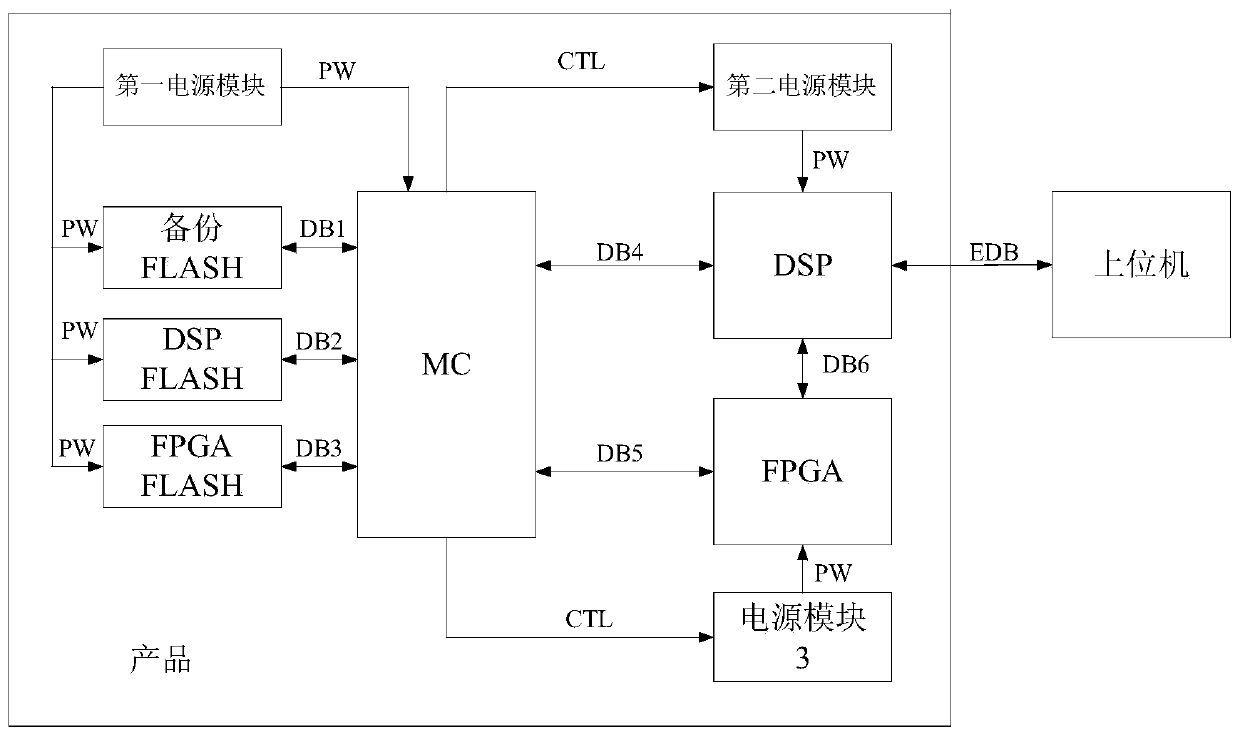
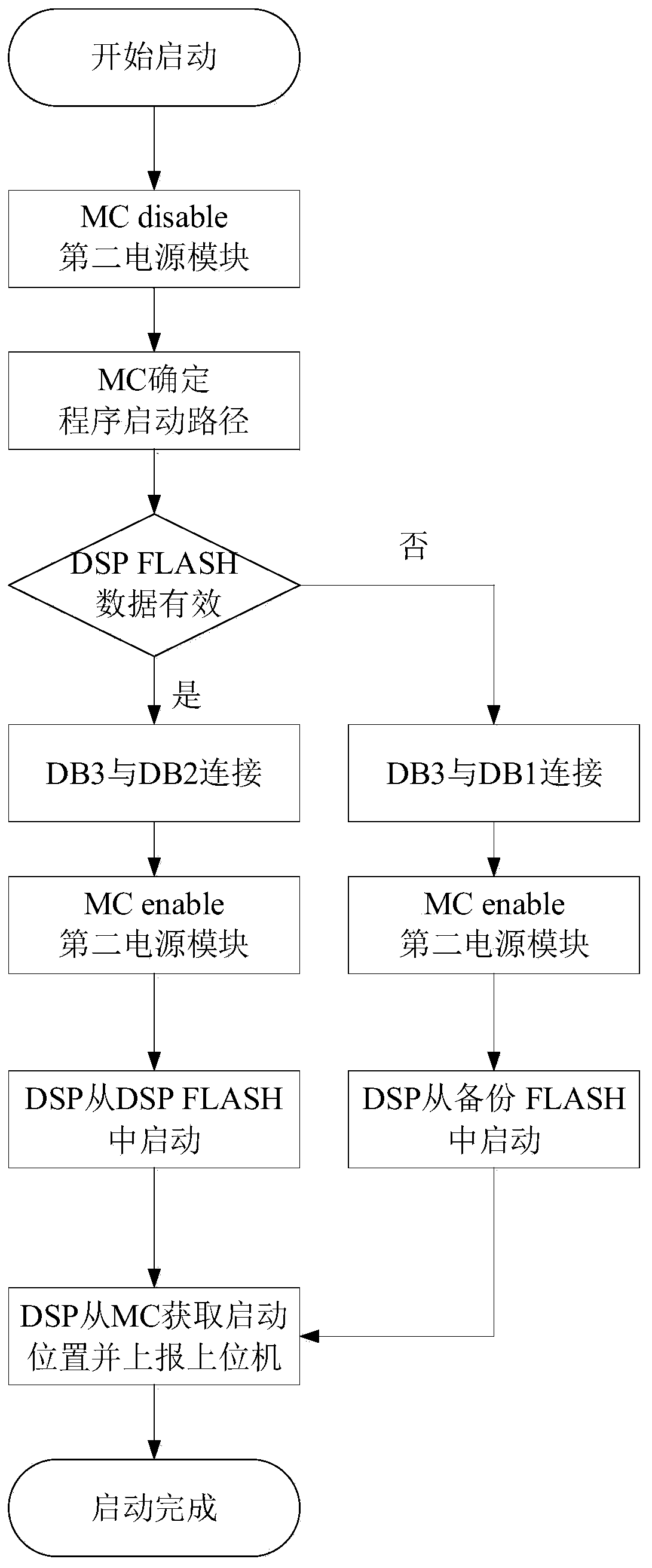
The invention relates to a high-reliability embedded software upgrading method and system, and the system comprises: a management controller which is used for configuring an internal data path; a DSPwhich is used for storing an application program and automatically loading and running the application program from the program memory through a data interface; an FPGA which is matched with the DSP to carry out interface control; a DSP FLASH which is used for storing an application program used by the DSP, wherein the backup FLASH is used for storing an application program of the DSP when a product leaves a factory; an FPGA FLASH which is used for storing a configuration program used by the FPGA, wherein the backup FLASH is used for storing a DSP application program and an FPGA configurationprogram when a product leaves a factory; in the DSP FLASH and the FPGA FLASH, a program effective mark in the current FLASH is stored in a user specified address behind a program storage space. According to the invention, when abnormal conditions such as power failure, crash, misoperation and the like occur in a program updating process, system crash caused by destroying an original version program can be avoided.
Owner:BEIJING INST OF COMP TECH & APPL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com