Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1393 results about "Computer resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
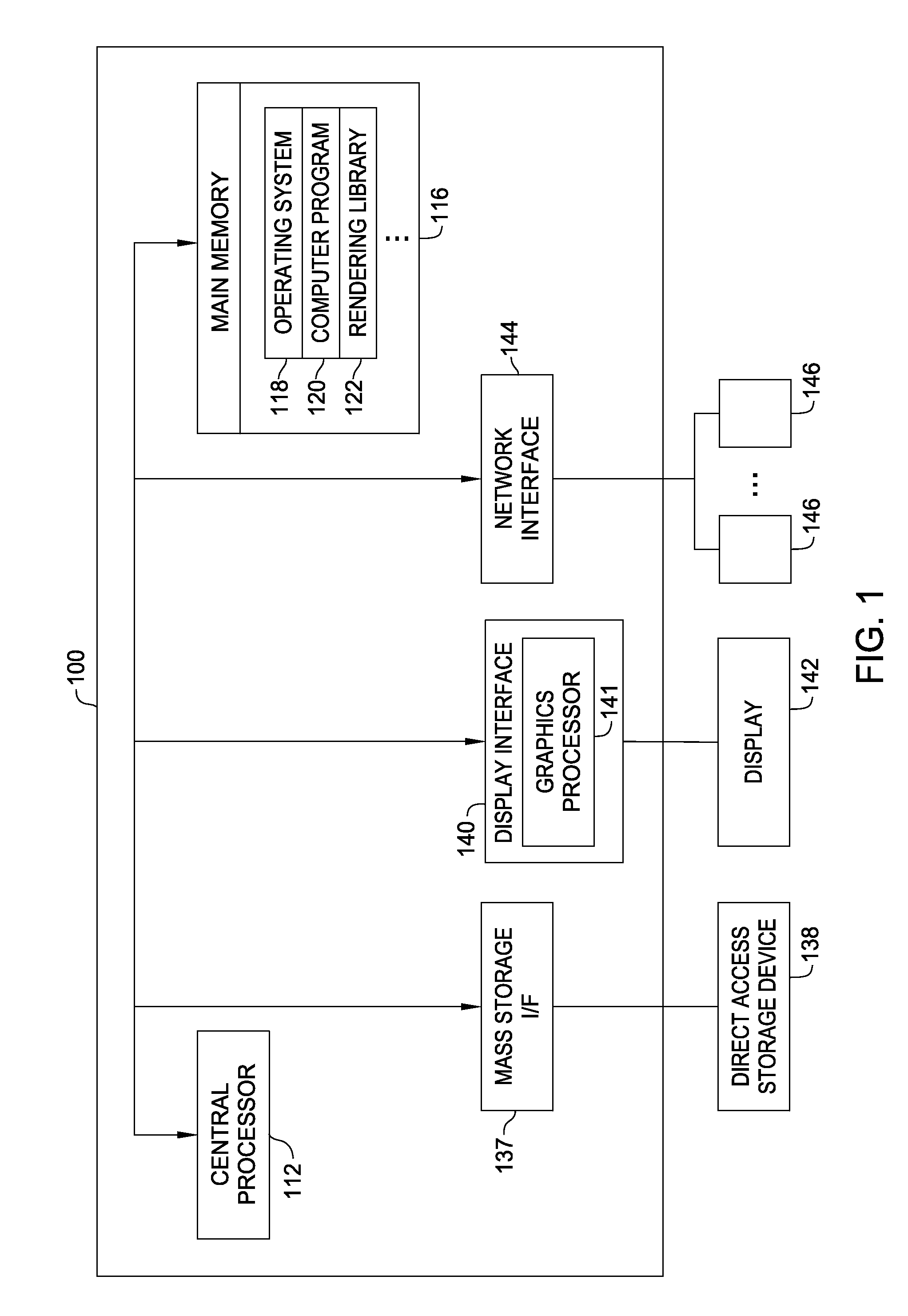
A computer resource is any physical or virtual component of limited availability within a computer or information management system. Computer resources include means for input, processing, output, communication, and storage.
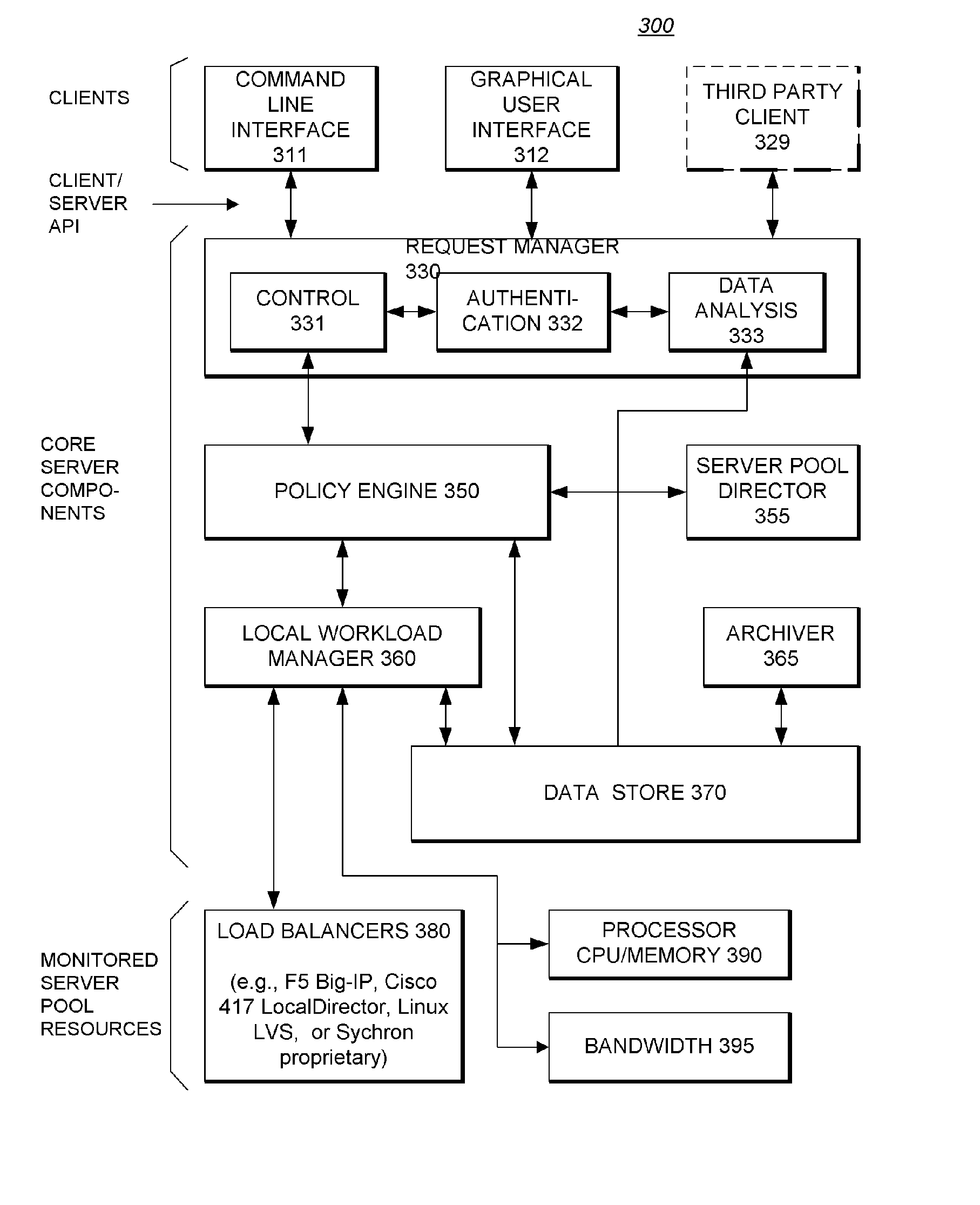
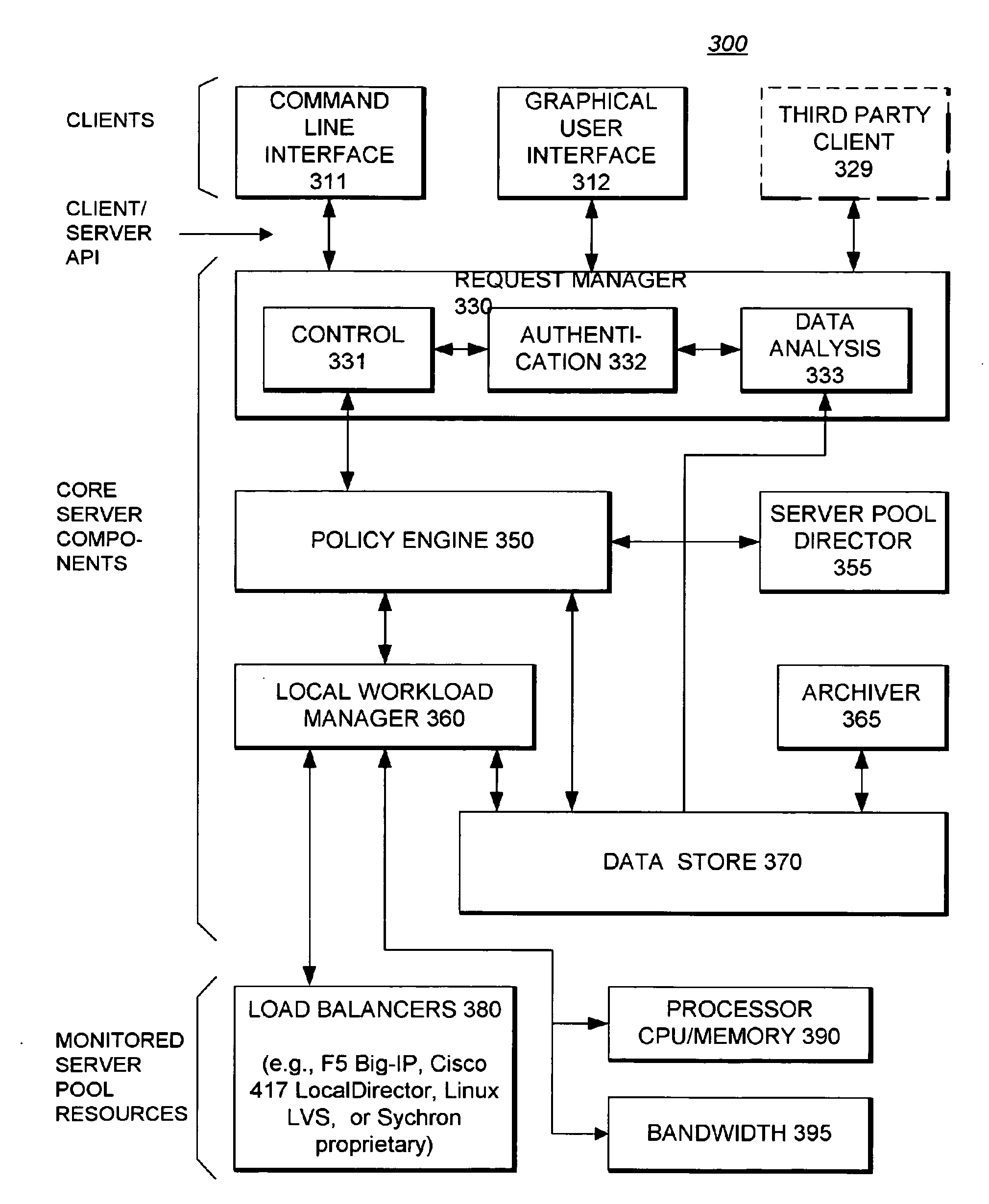
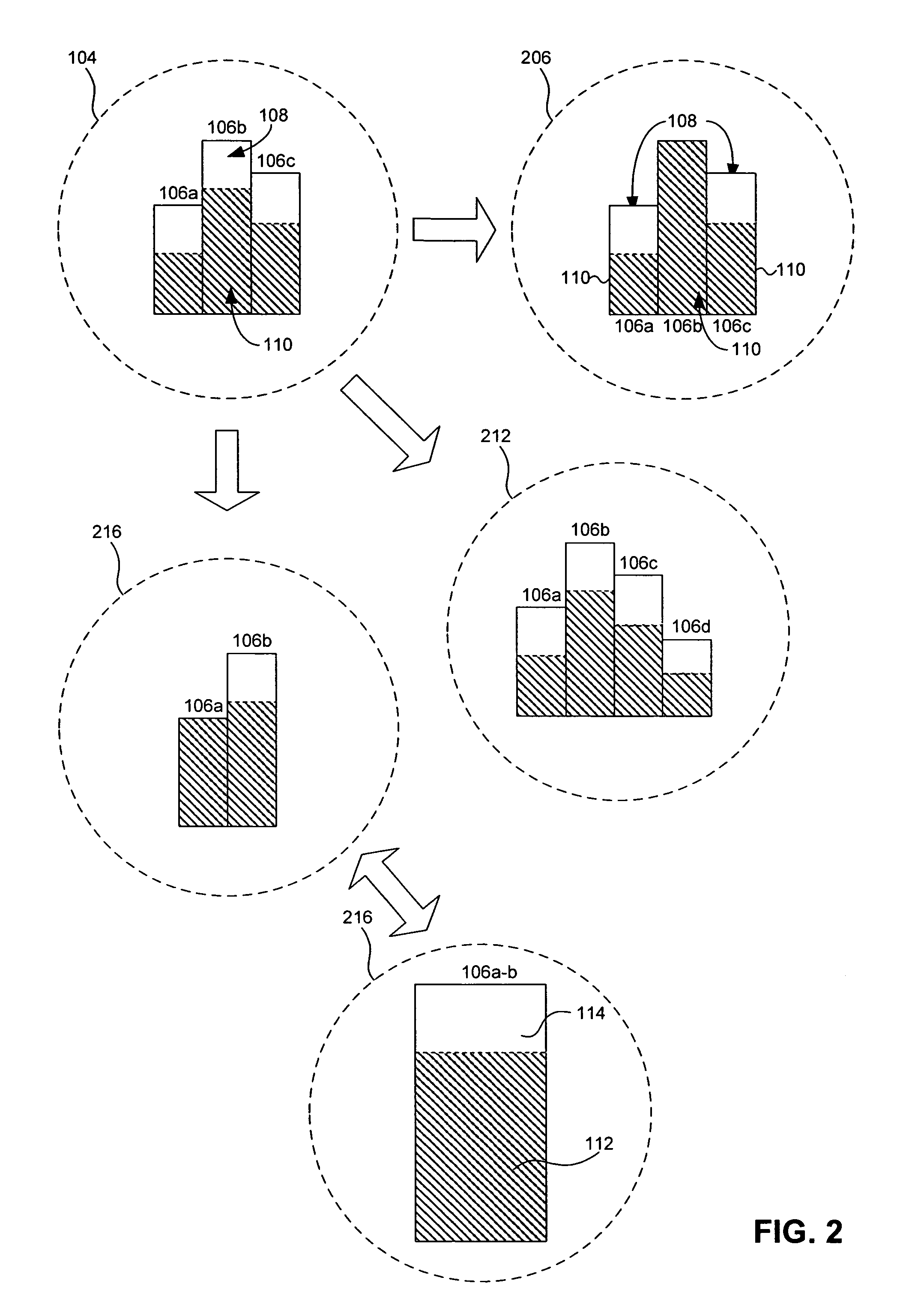
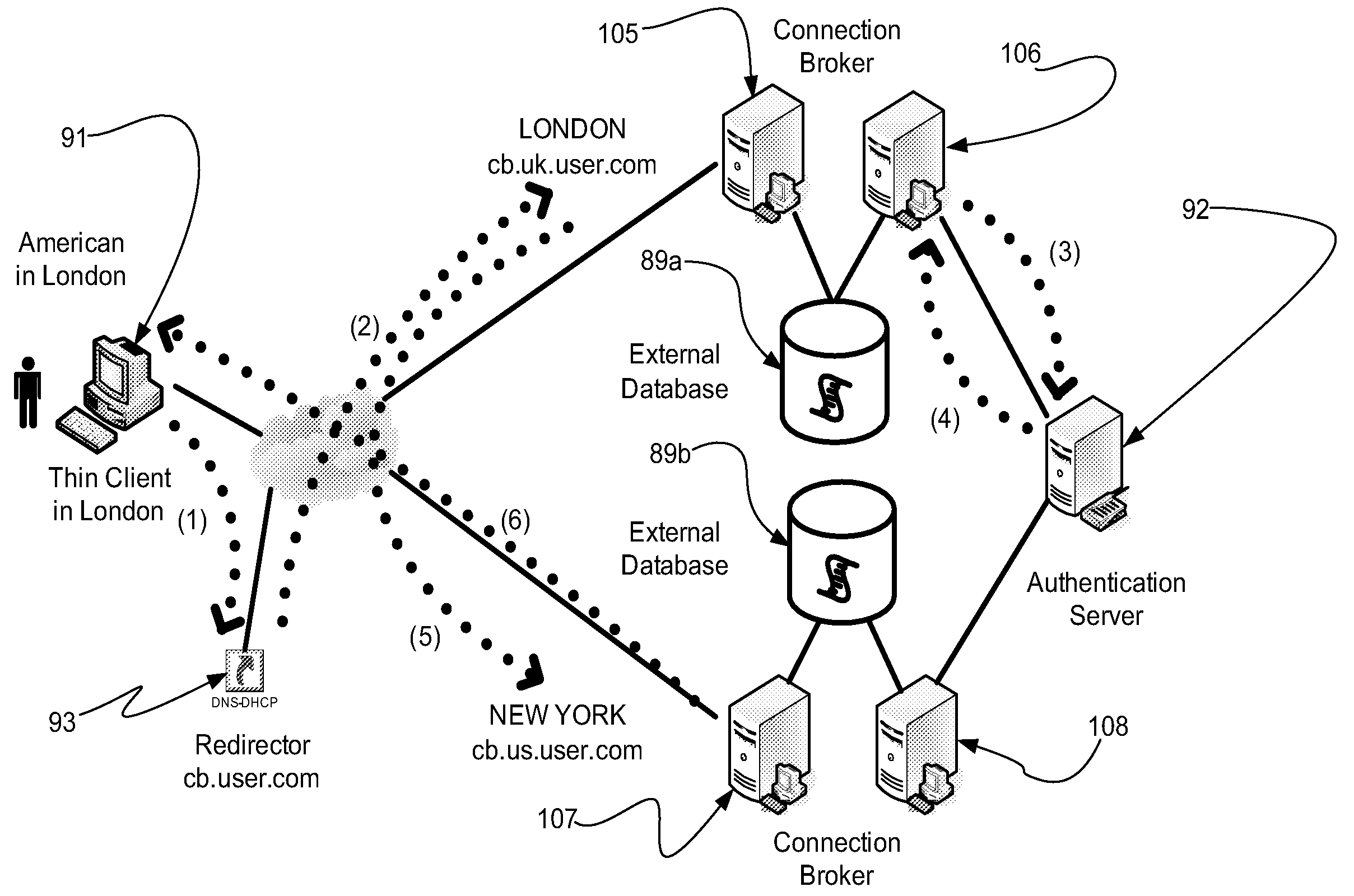
System Providing Methodology for Policy-Based Resource Allocation
A system providing methodology for policy-based resource allocation is described. In one embodiment, for example, a system for allocating computer resources amongst a plurality of applications based on a policy is described that comprises: a plurality of computers connected to one another through a network; a policy engine for specifying a policy for allocation of resources of the plurality of computers amongst a plurality of applications having access to the resources; a monitoring module at each computer for detecting demands for the resources and exchanging information regarding demands for the resources at the plurality of computers; and an enforcement module at each computer for allocating the resources amongst the plurality of applications based on the policy and information regarding demands for the resources.
Owner:CAVALIER NEWCO +1
Method and system for controlling access, by an authentication server, to protected computer resources provided via an internet protocol network
InactiveUS7290288B2Mosaic printer telegraph systemDigital data processing detailsComputer resourcesThe Internet
A method and system for controlling access, by an authentication server, to protected computer resources provided via an Internet Protocol network that includes storing (i) a digital identification associated with at least one client computer device, and (ii) data associated with the protected computer resources in at least one database associated with the authentication server; authenticating, by the authentication server, the digital identification forwarded by at least one access server; authorizing, by the authentication server, the at least one client computer device to receive at least a portion of the protected computer resources requested by the at least one client computer device, based on the stored data associated with the requested protected computer resources; and permitting access, by the authentication server, to the at least the portion of the protected computer resources upon successfully authenticating the digital identification and upon successfully authorizing the at least once client computer device.
Owner:PRISM TECH
Deviation detection of usage patterns of computer resources
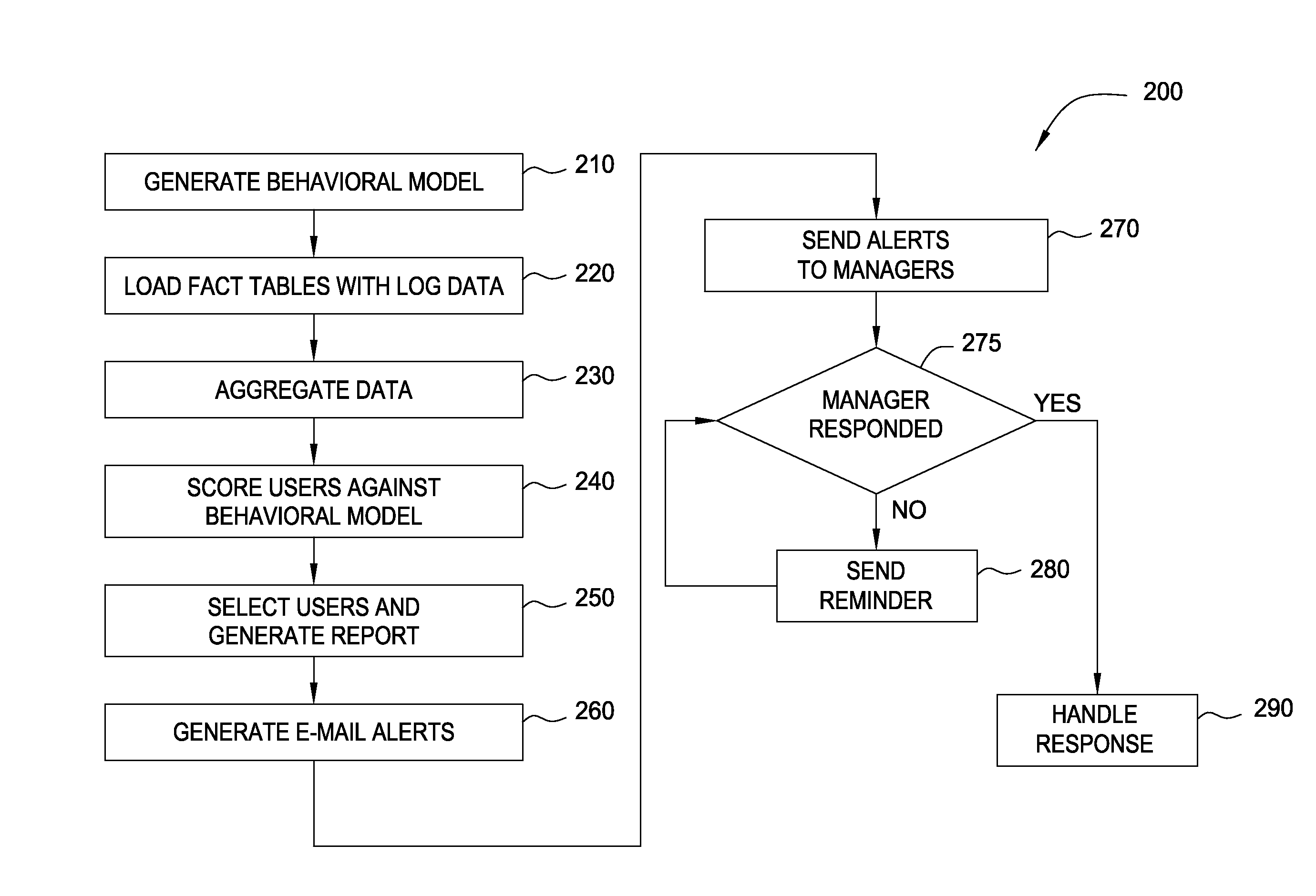
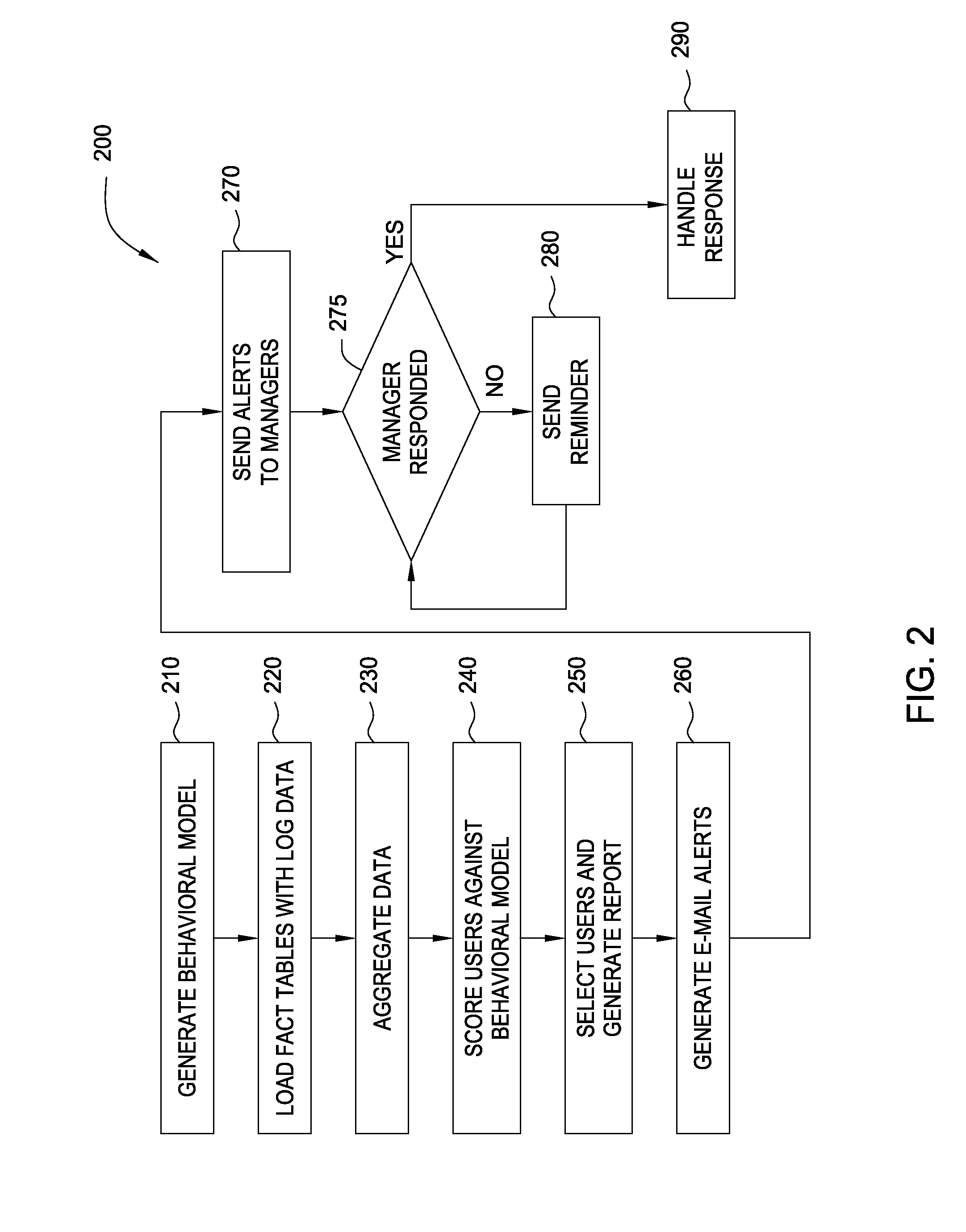
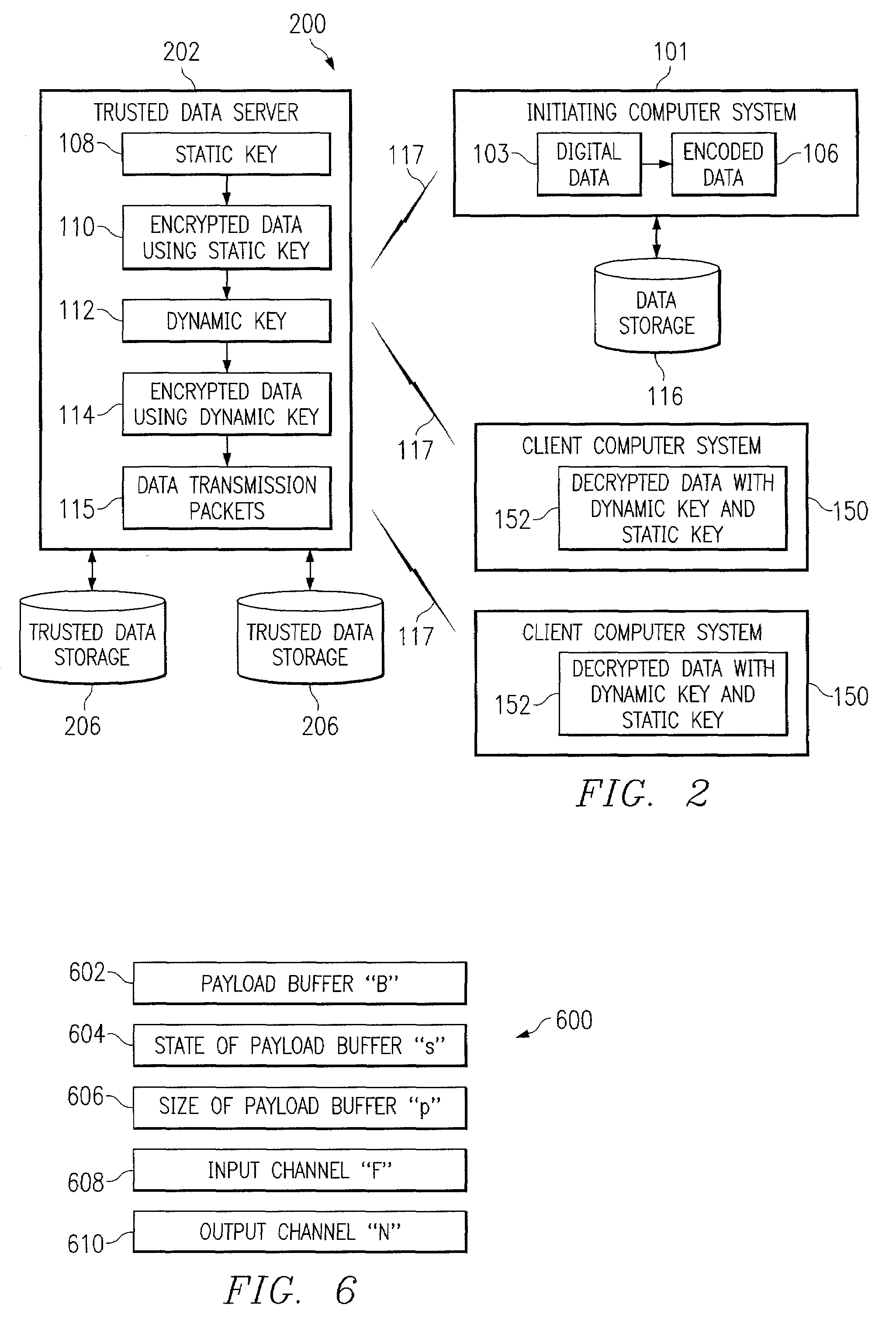
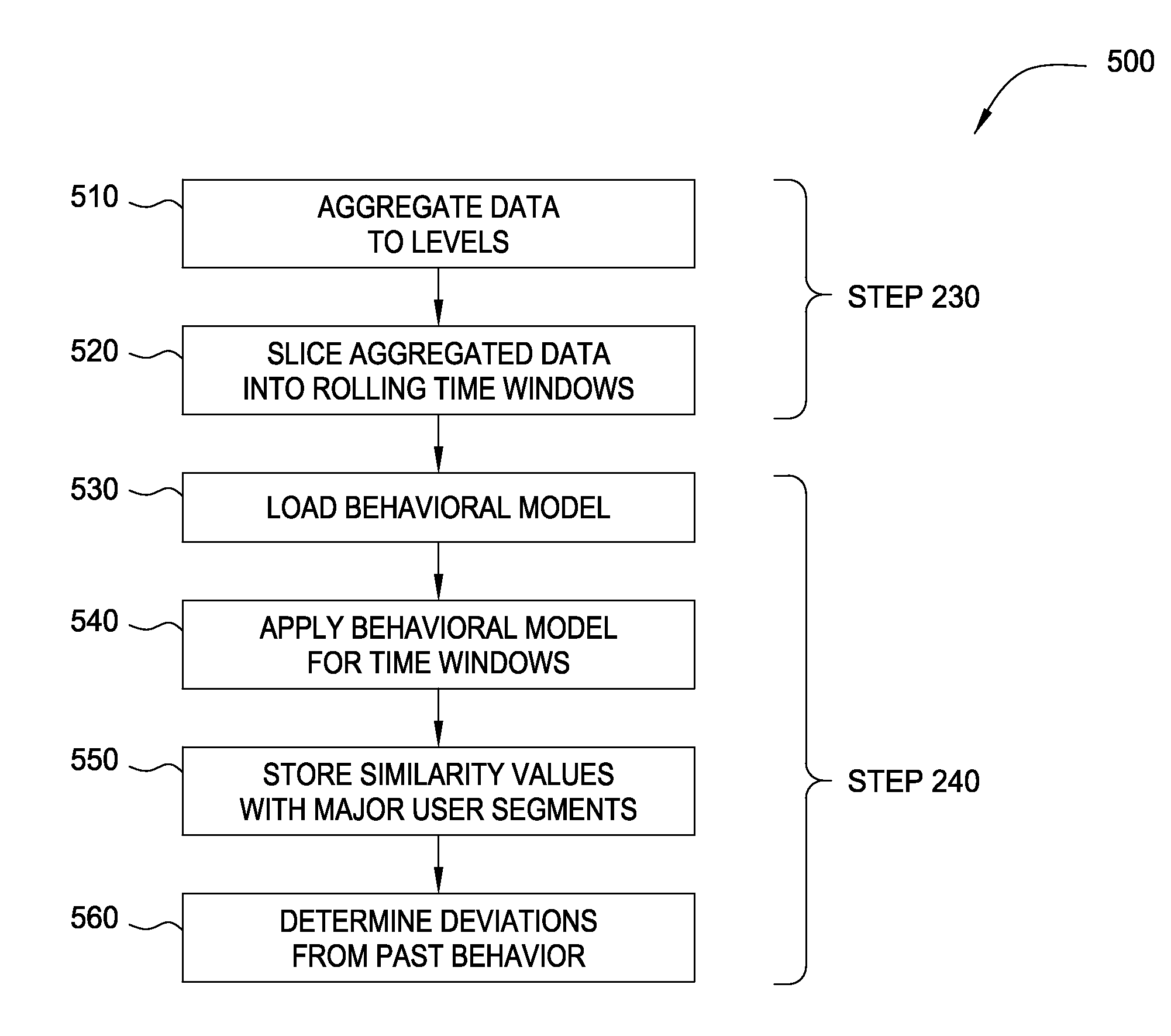
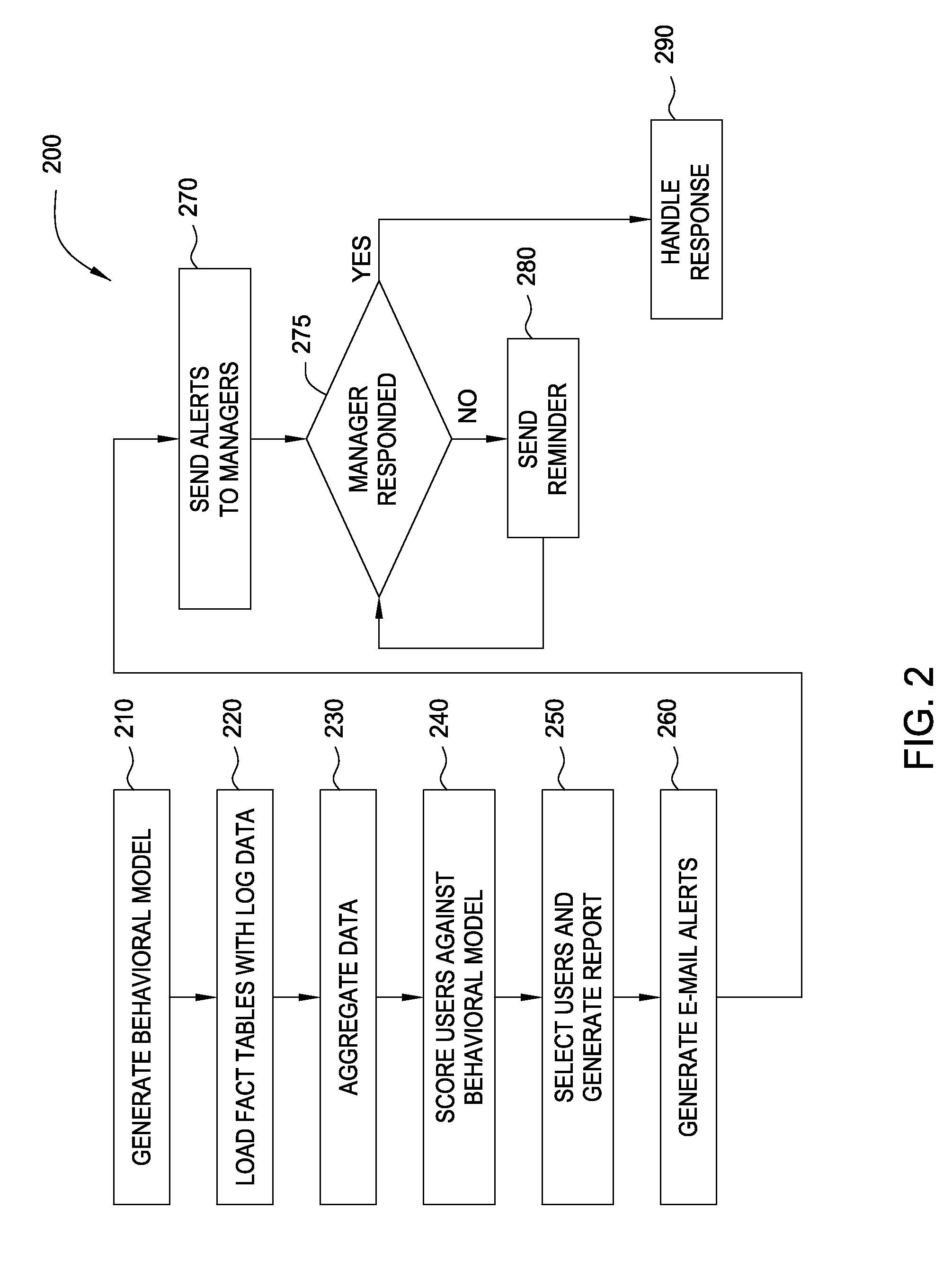
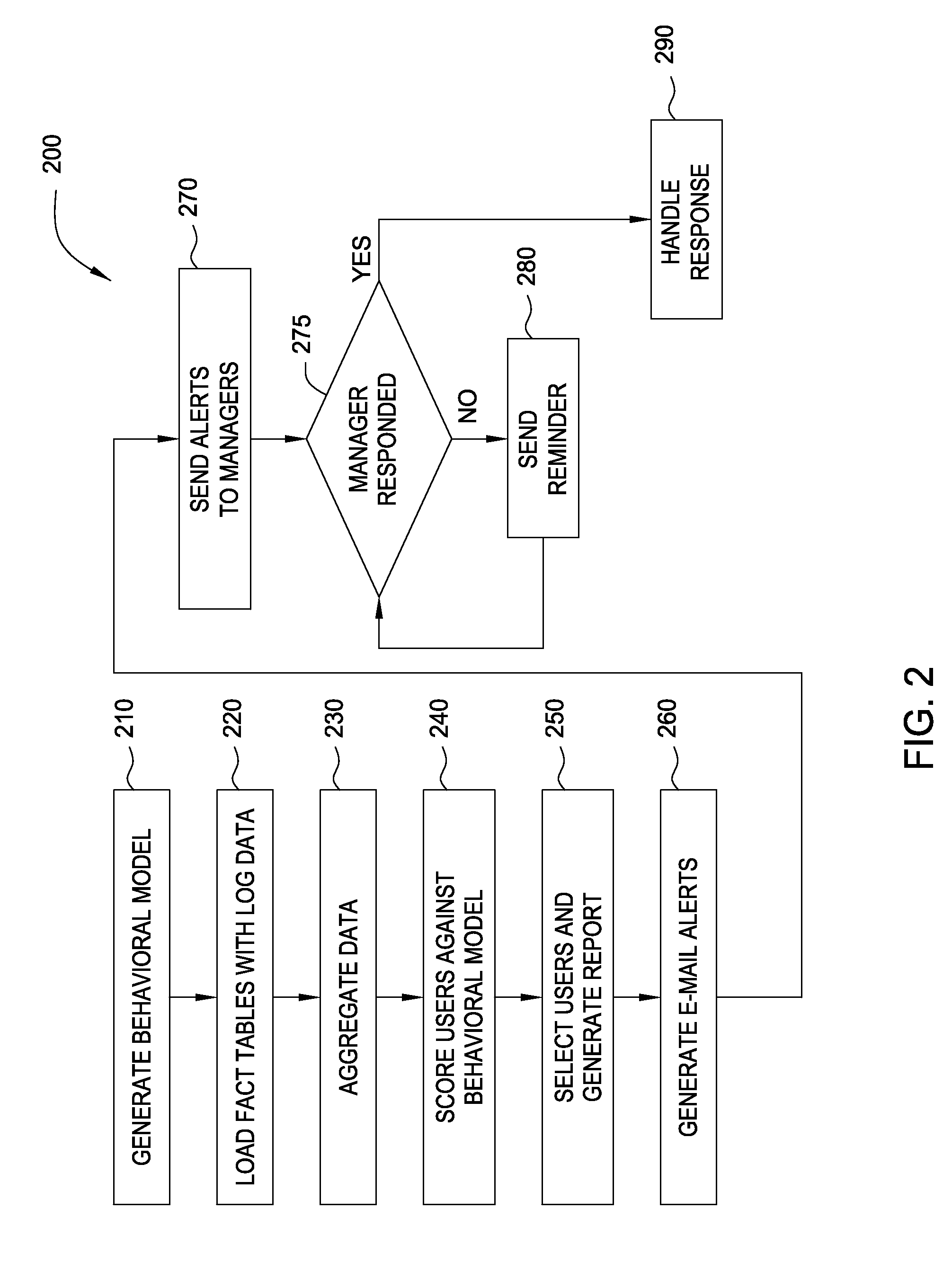
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:IBM CORP
Method and apparatus providing optimistic locking of shared computer resources
InactiveUS6850938B1Digital data information retrievalData processing applicationsComputer resourcesLock manager
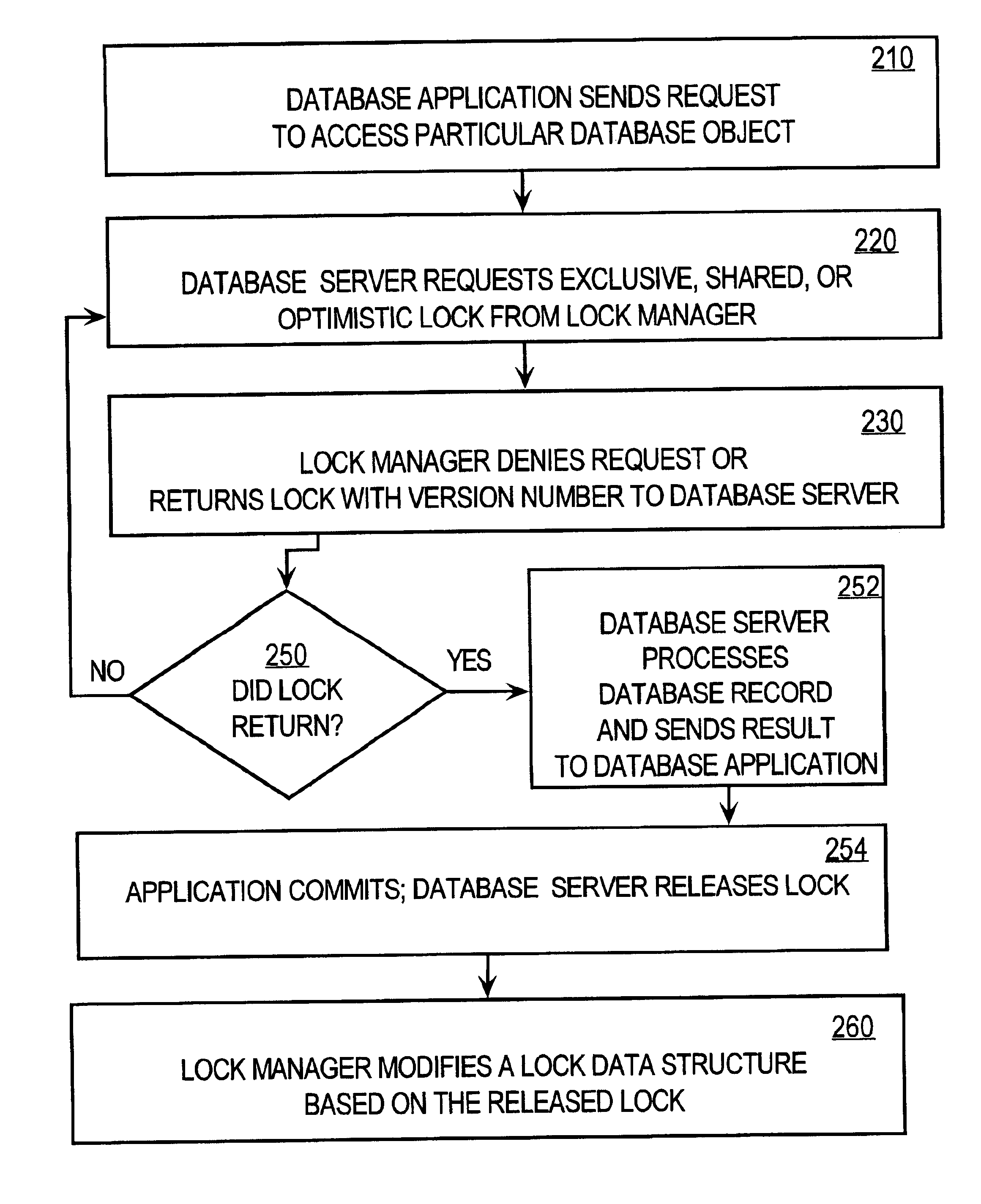
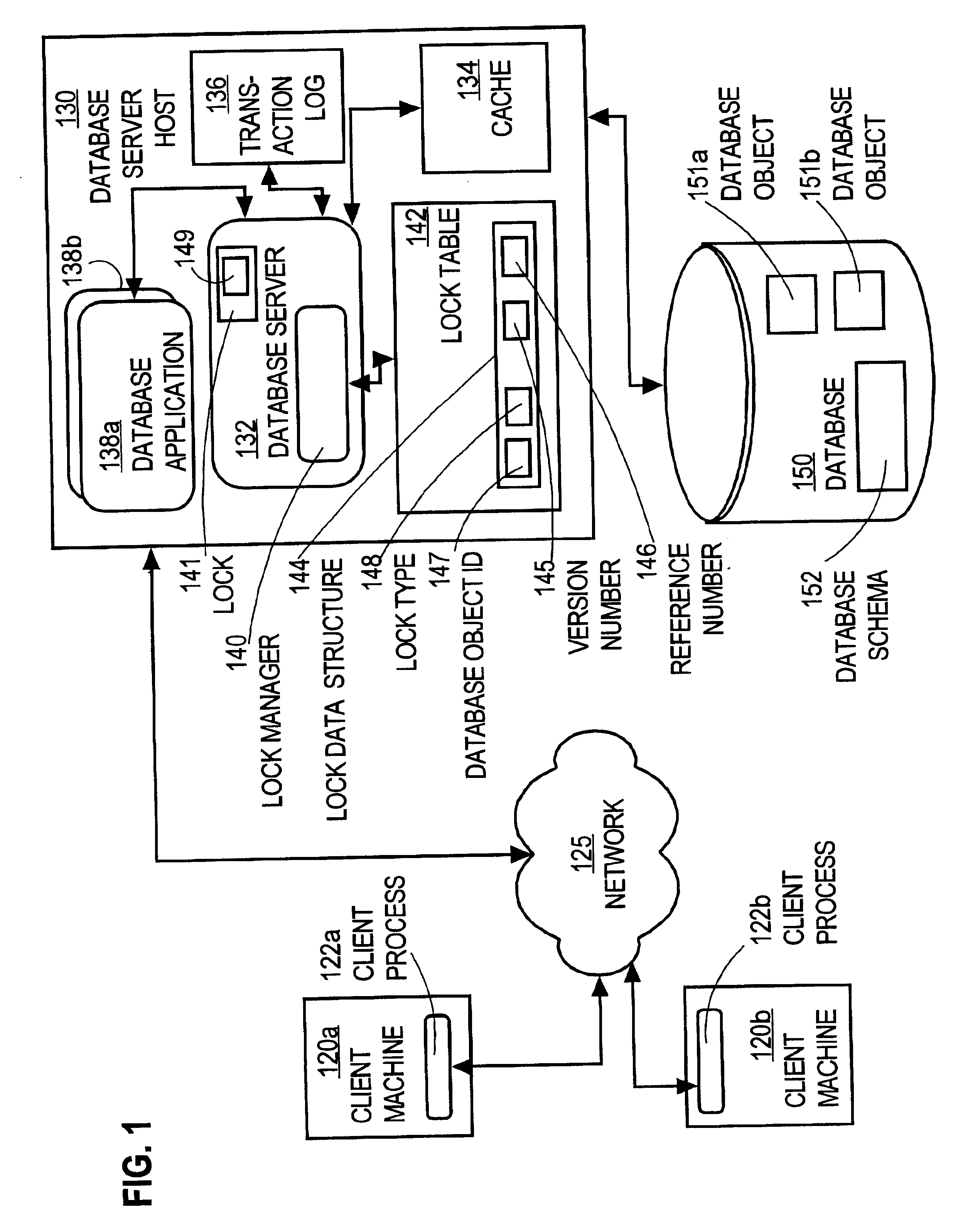
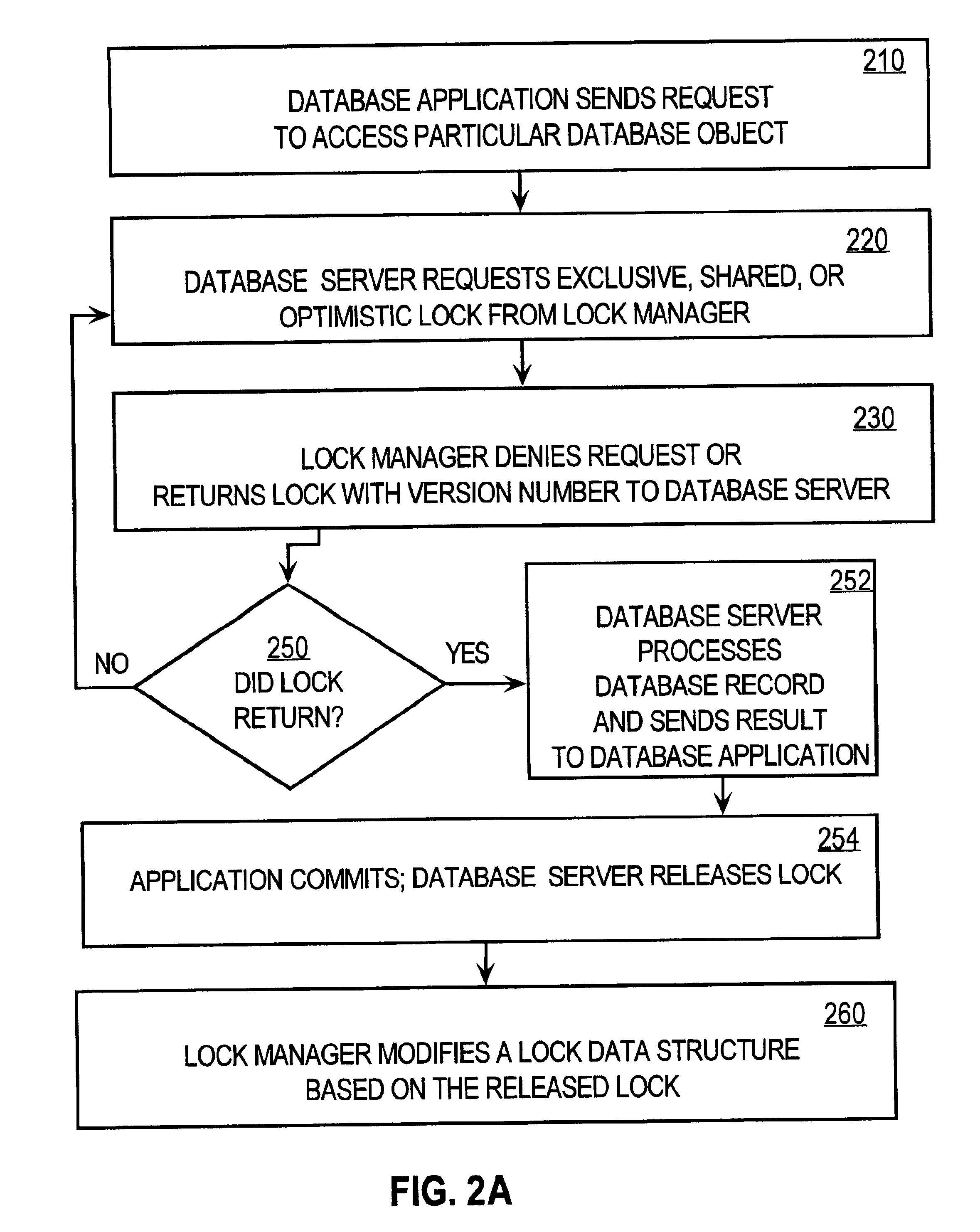
Techniques for concurrent access to a resource object, such as a database, include generating a lock data structure for a particular resource object. The lock data structure includes data values for a resource object identification, a lock type, and a version number. The version number is related to a number of changes to the resource object since the lock data structure was generated. A request is received from a requesting process. The request is for a requested lock type for access to the particular resource object. It is determined whether to grant the request based on the requested lock type and the lock type in the lock data structure. By carrying a lock version number in a lock data structure managed by a lock manager, improved optimistic locking is provided in a database. In particular, the approach enables introduction of optimistic locking to a legacy database without requiring burdensome changes to a database table schema.
Owner:CISCO TECH INC
System and method for application performance management
InactiveUS7350209B2General purpose stored program computerHardware monitoringComputer resourcesUser interface
Owner:BMC SOFTWARE
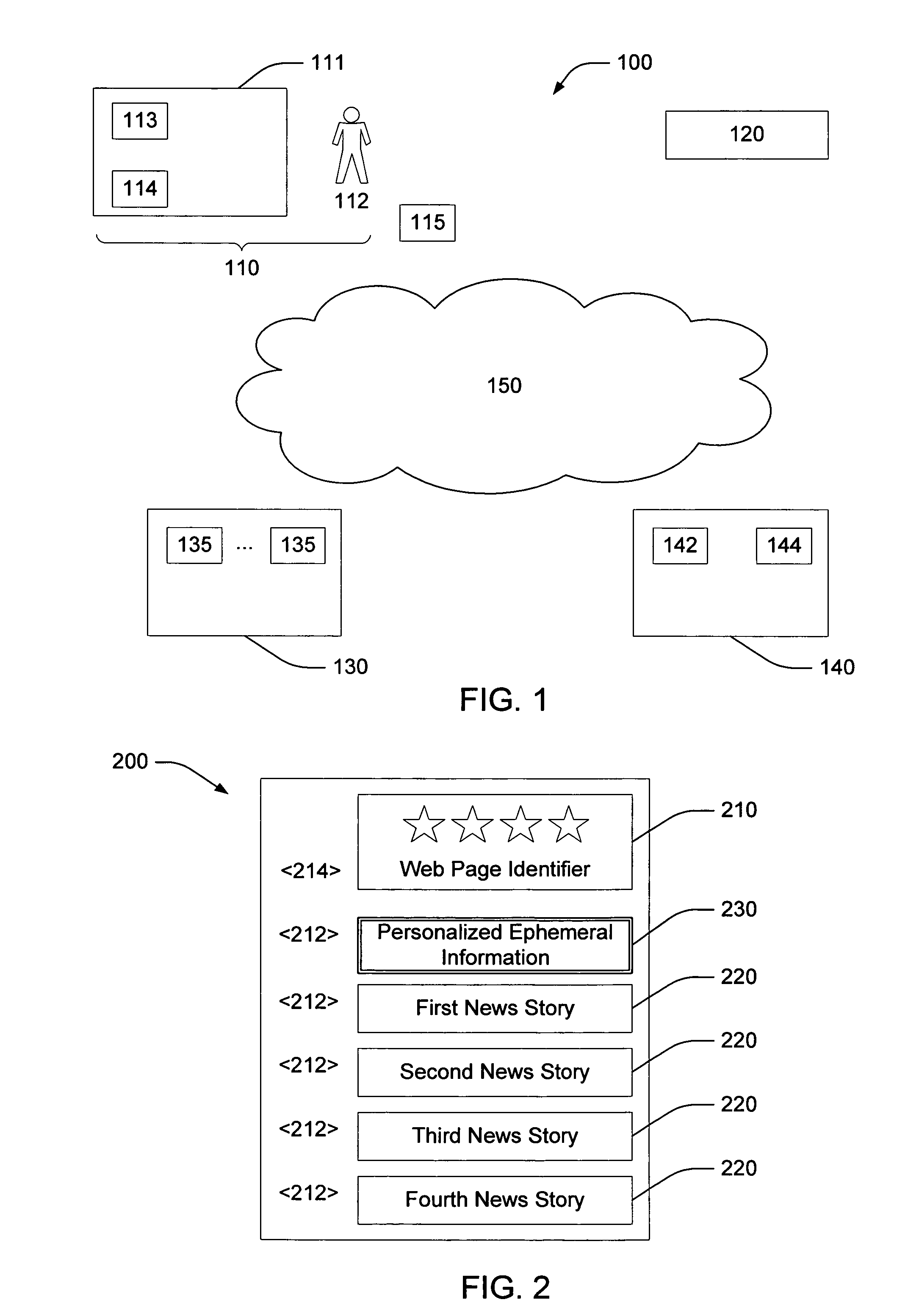
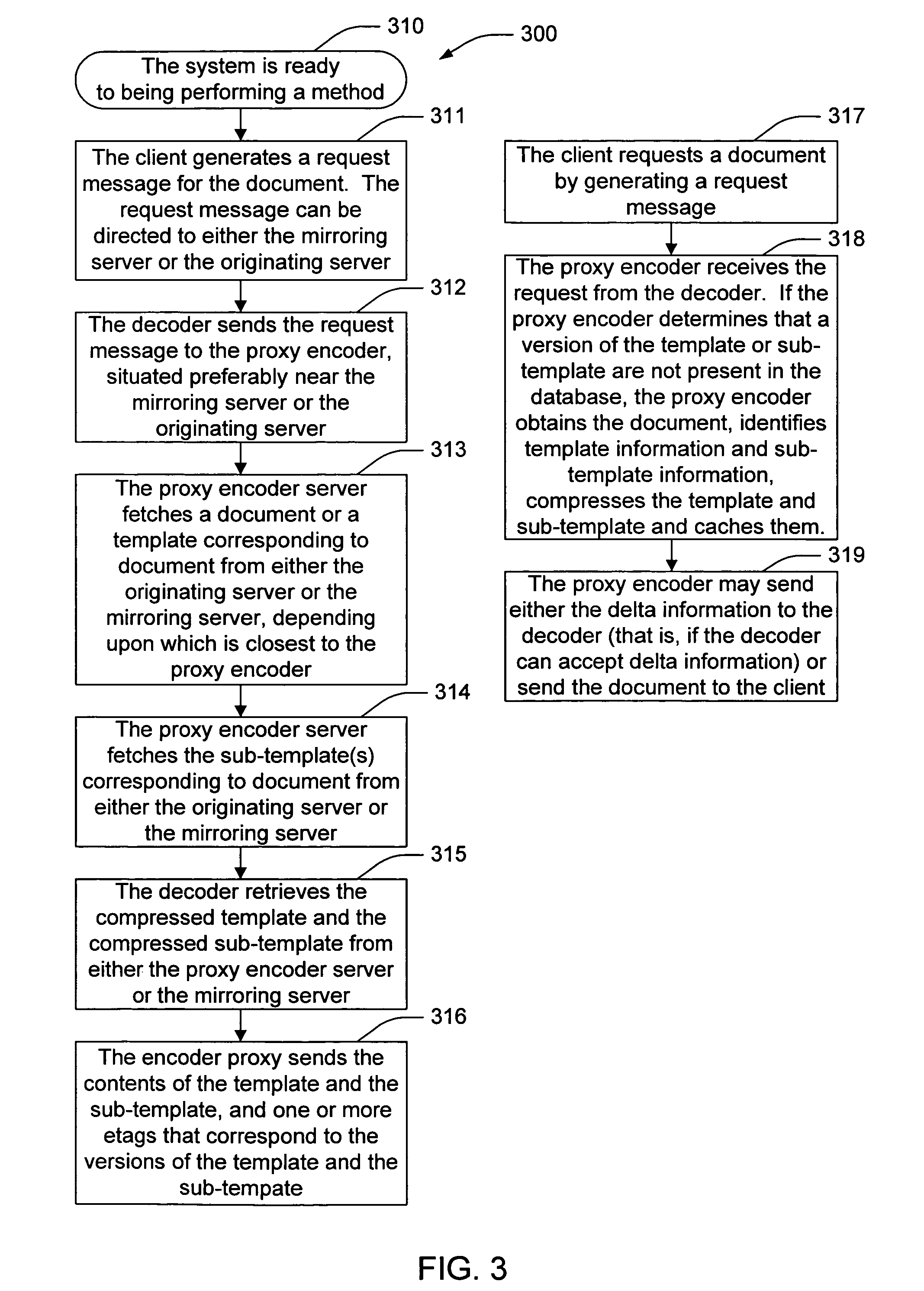
Template identification with differential caching
ActiveUS7092997B1Save bandwidthSave resourcesMultiple digital computer combinationsTransmissionComputer resourcesDocumentation procedure
It is desirable to send documents to a user in such a way as to minimize the bandwidth and other computer resources required. To this end, a document may be categorized as (1) delta information (information that changes rapidly), (2) sub-template information (information that changes less frequently) and (3) template information, which changes very seldom. The template information and sub-template information are compressed and cached at a site remote from the requesting party. Compressing and caching both sub-template information and template information results in a significant savings of bandwidth and computing resources, such as would be required if the sub-template information were treated as delta information and were not stored in a cache as is the case in the prior art. This savings is enhanced when the compressed template and sub-template information are sent to a large number of users.
Owner:DIGITAL RIVER INC
Systems, methods, and computer program products for accelerated dynamic protection of data
InactiveUS7280658B2Sufficient protectionKey distribution for secure communicationSecret communicationComputer resourcesEnd to end security
Owner:SNAP INC
Modeling user access to computer resources
ActiveUS20090292743A1Memory loss protectionDigital data processing detailsComputer resourcesData loss
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:DAEDALUS BLUE LLC
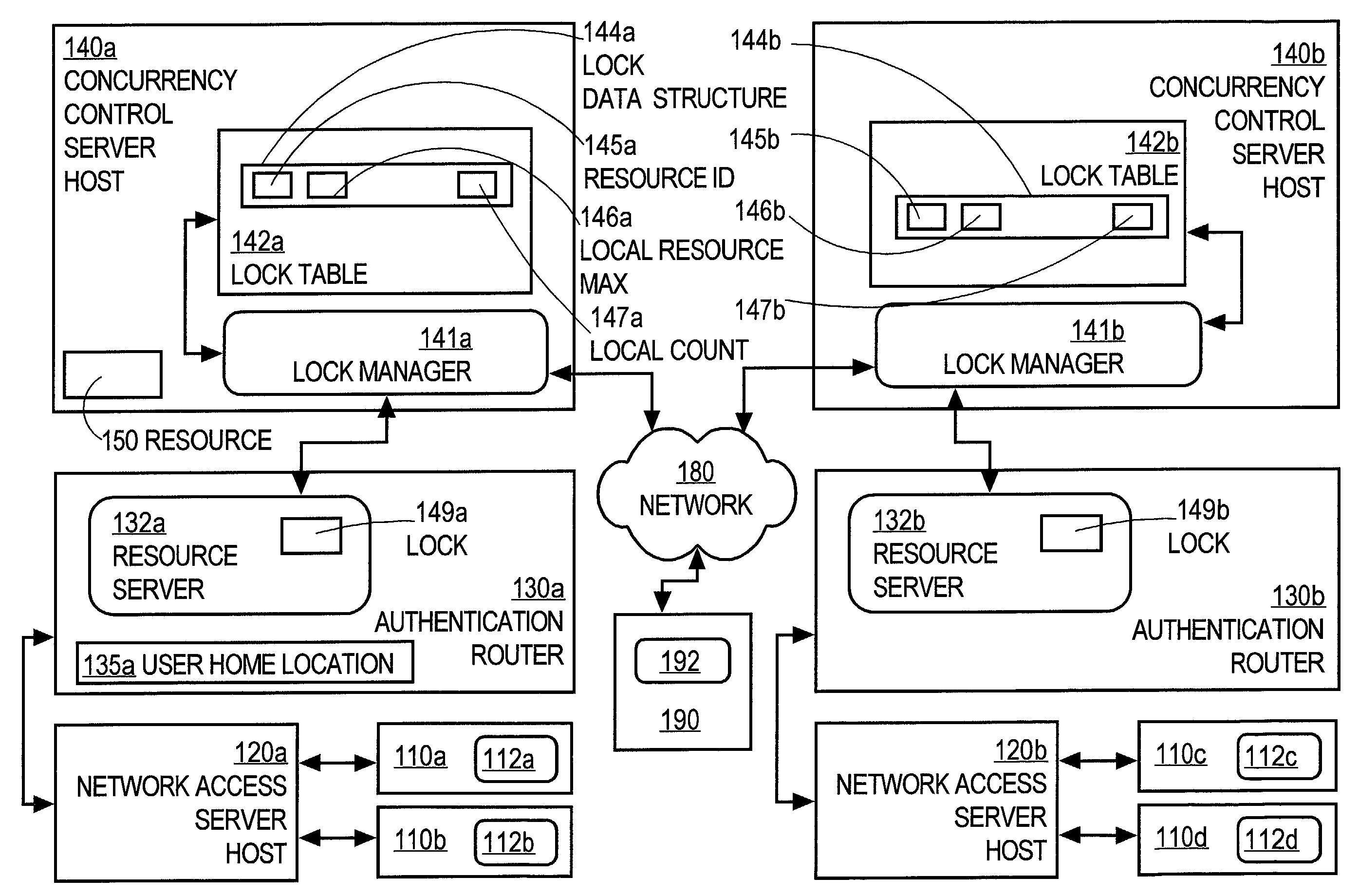
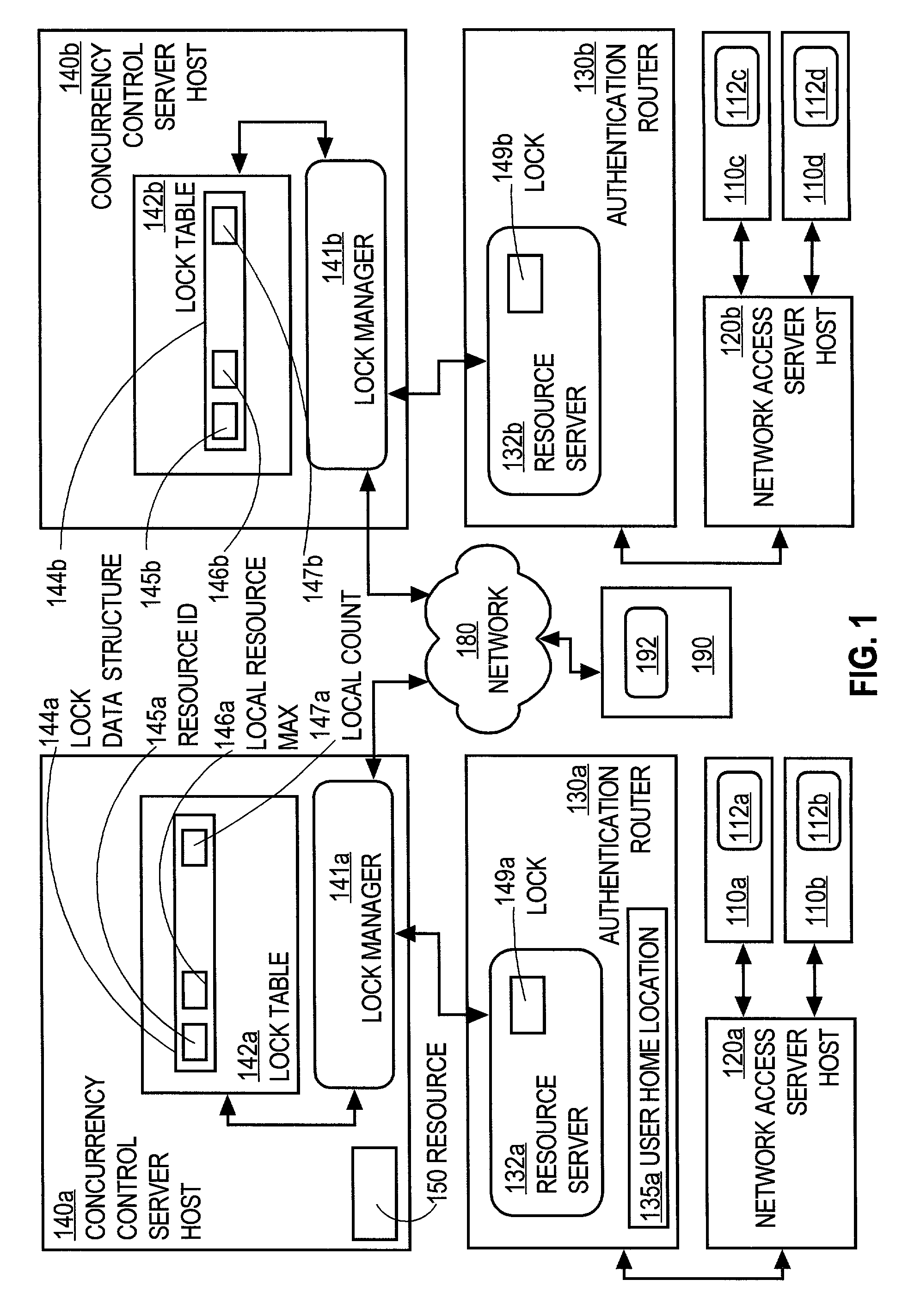
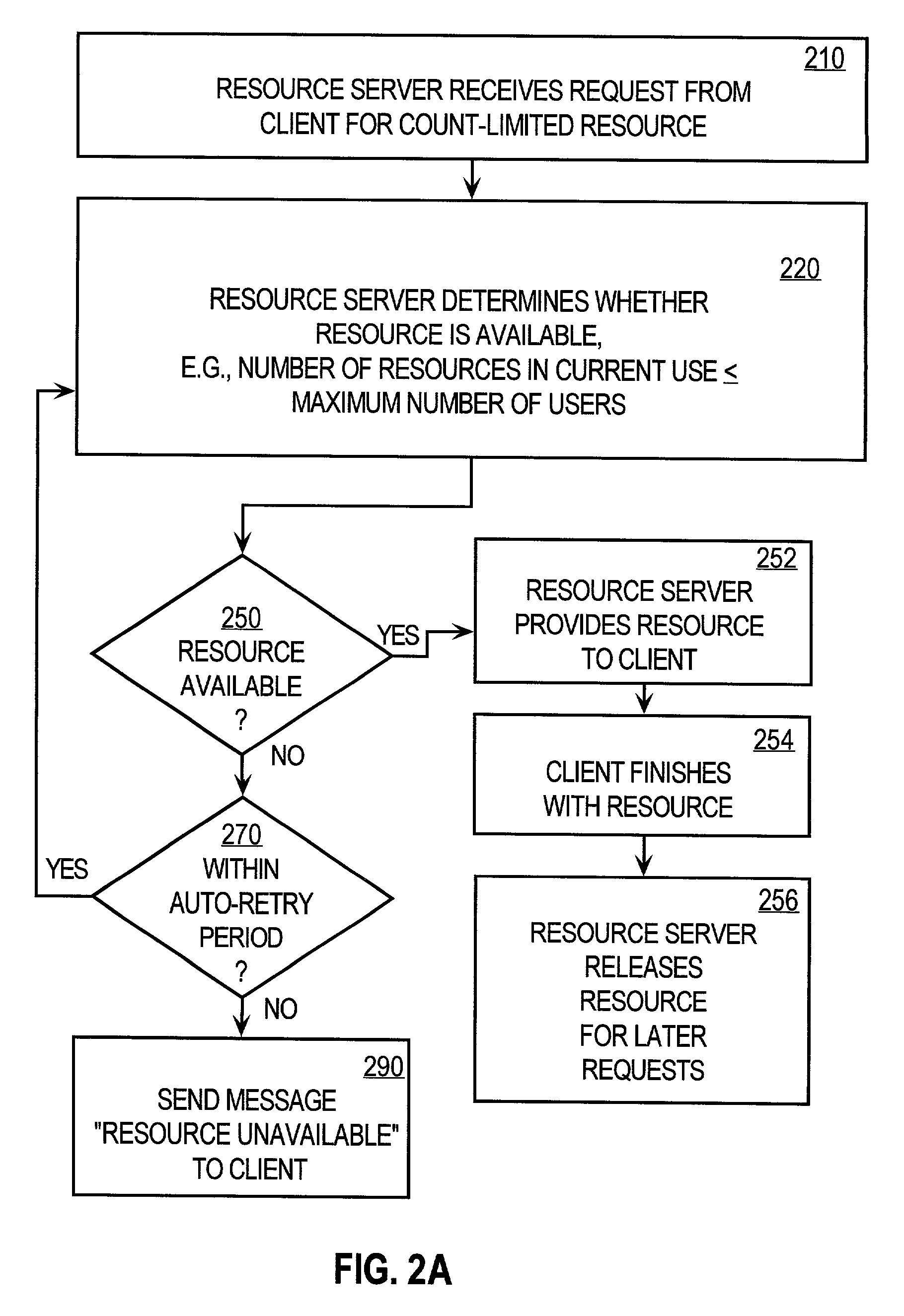
Controlling access of concurrent users of computer resources in a distributed system using an improved semaphore counting approach
ActiveUS7328263B1Data processing applicationsUnauthorized memory use protectionLimited resourcesComputer resources
A method of controlling concurrent users of a distributed resource on a network is disclosed. In one aspect, there are one or more local lock managers executing on corresponding hosts and cooperating as a distributed lock manager. The resource is limited to a maximum number of concurrent users. A user identification for each user is associated with one host. In response to a request associated with a particular user associated with a first host, a lock is requested from a first local lock manager process executing on the first host. A related method of handling a request for a count-limited resource includes receiving a request from a client process for the computer resource. If it is determined that the request exceeds a maximum count for the resource, then it is determined whether a current time is within a retry time period of the client's first request. If it is determined the current time is within the retry time period, then it is automatically determined again whether the request exceeds the maximum count for the resource. If it is determined that the request does not exceed the maximum count, then the resource is provided to the client process.
Owner:CISCO TECH INC
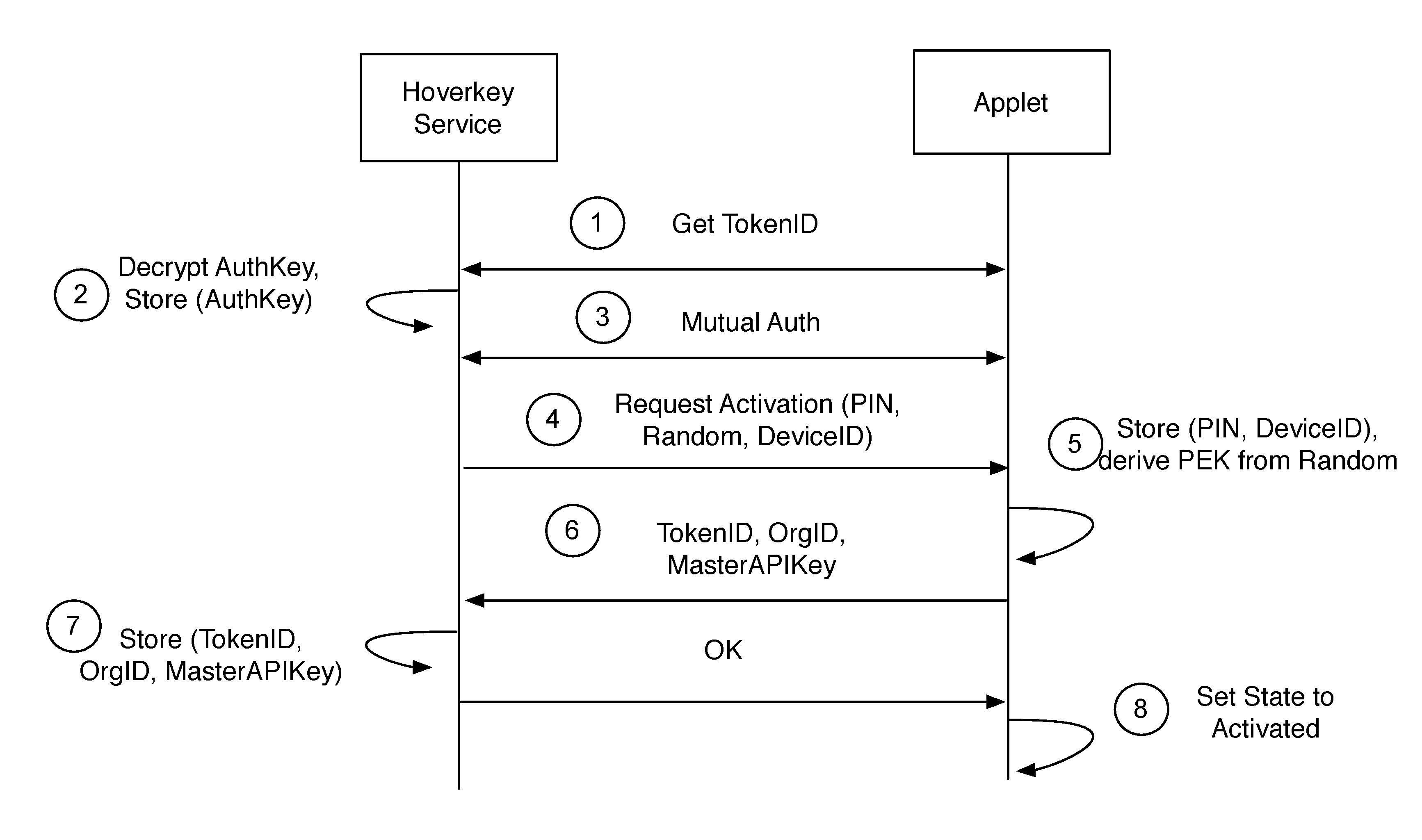
Method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors
ActiveUS20160261411A1Easy to rememberPromote cloningKey distribution for secure communicationCryptography processingComputer resourcesPassword
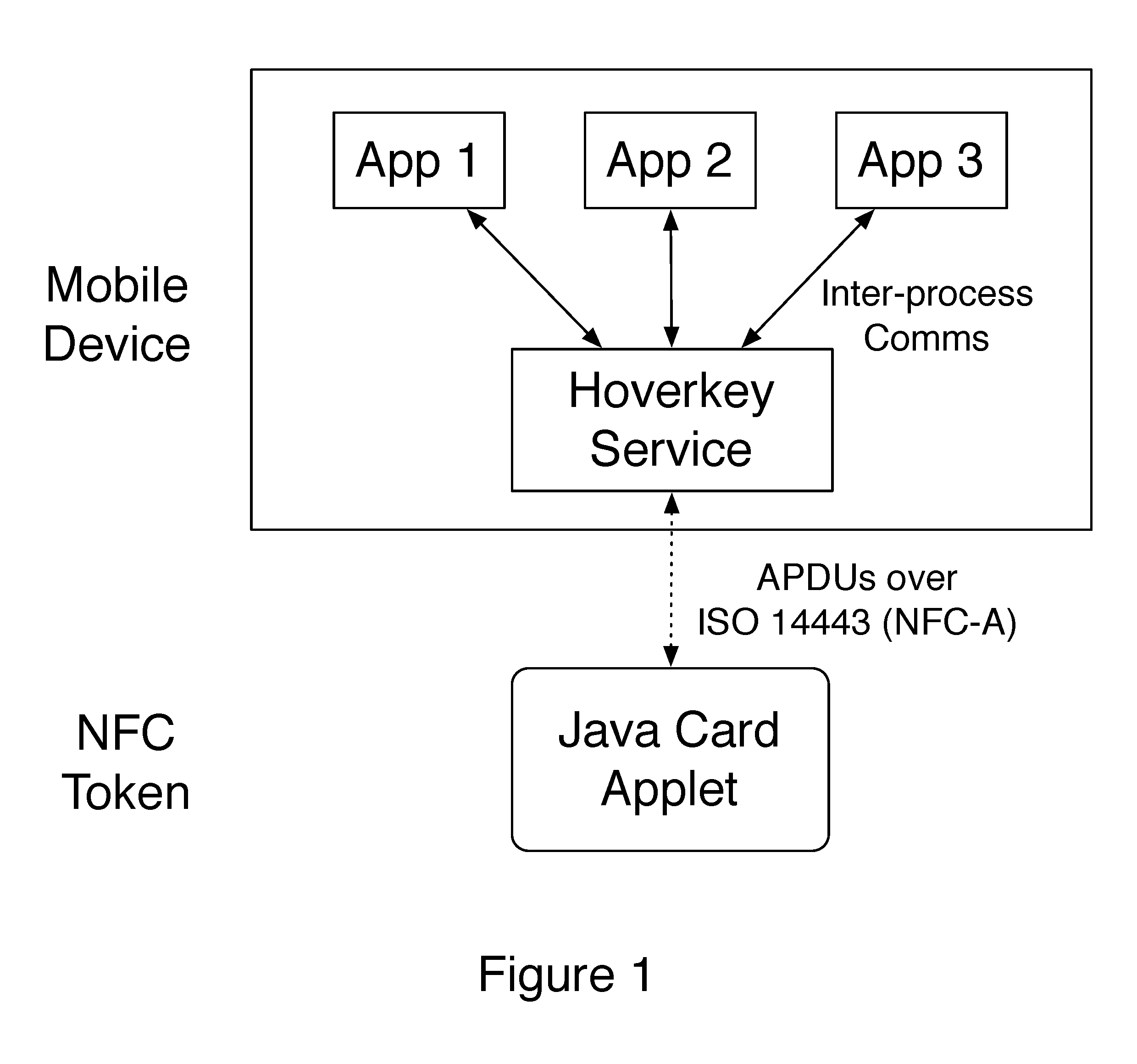
A method and system of authenticating a computer resource such as an application or data on a mobile device uses a contactless token to provide multi-factor user authentication. User credentials are stored on the token in the form of private keys, and encrypted data and passwords are stored on the device. When an application user requires access to the resource an encrypted password is transmitted to and decrypted on the token using a stored key. An unencrypted data encryption key or password is then transmitted back to the device under the protection of a cryptographic session key which is generated as a result of strong mutual authentication between the device and the token.
Owner:HOVERKEY
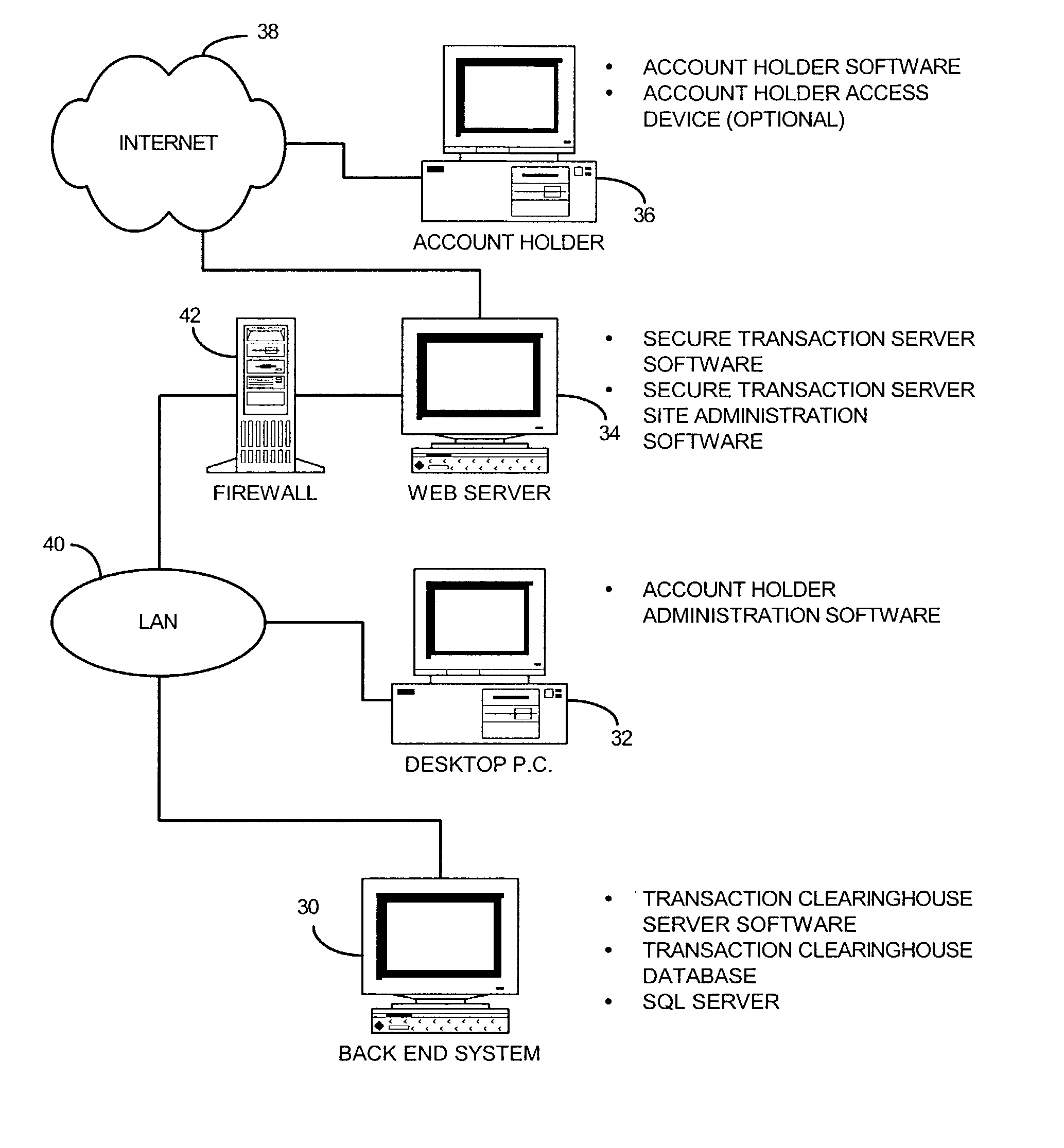
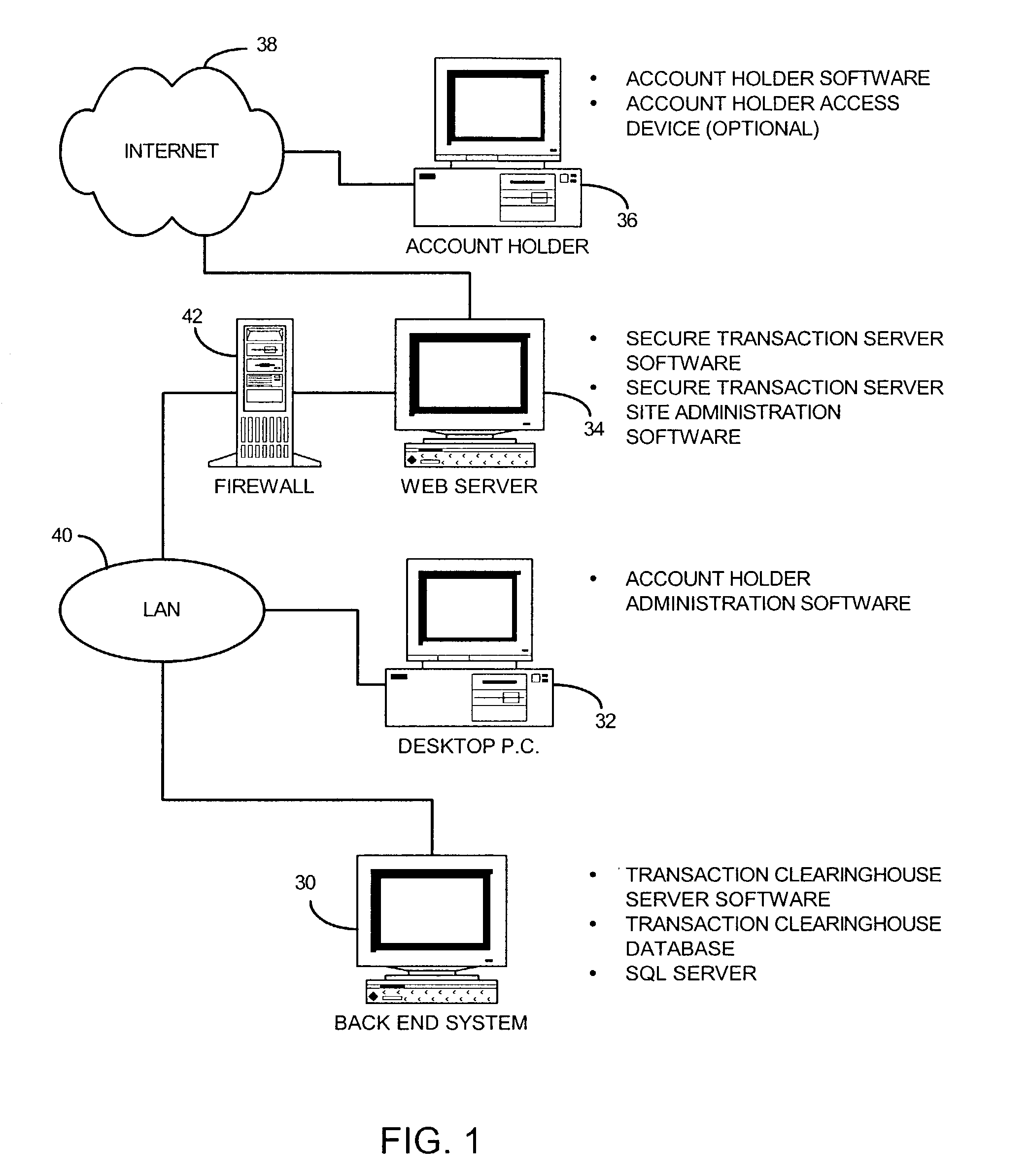
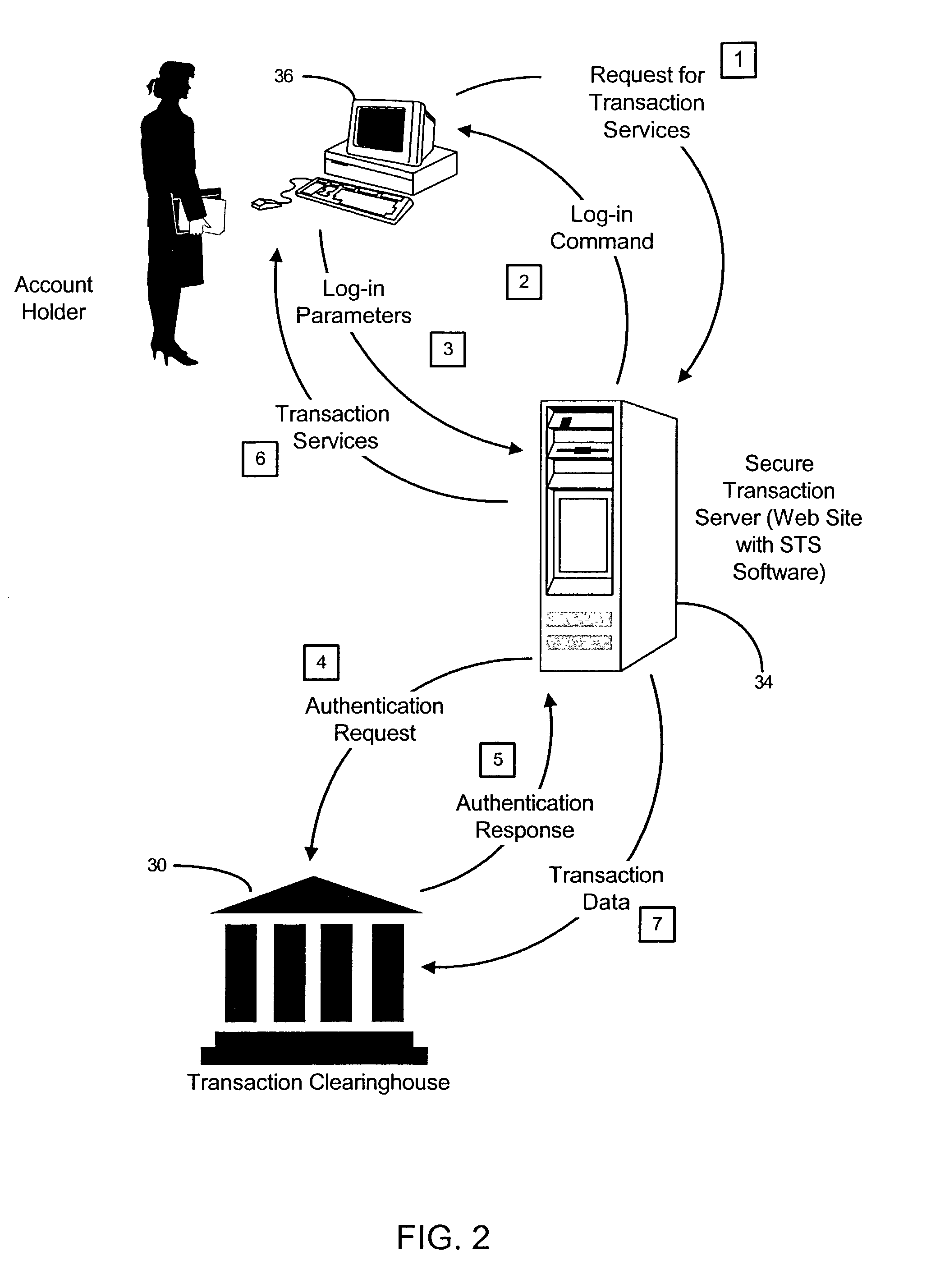
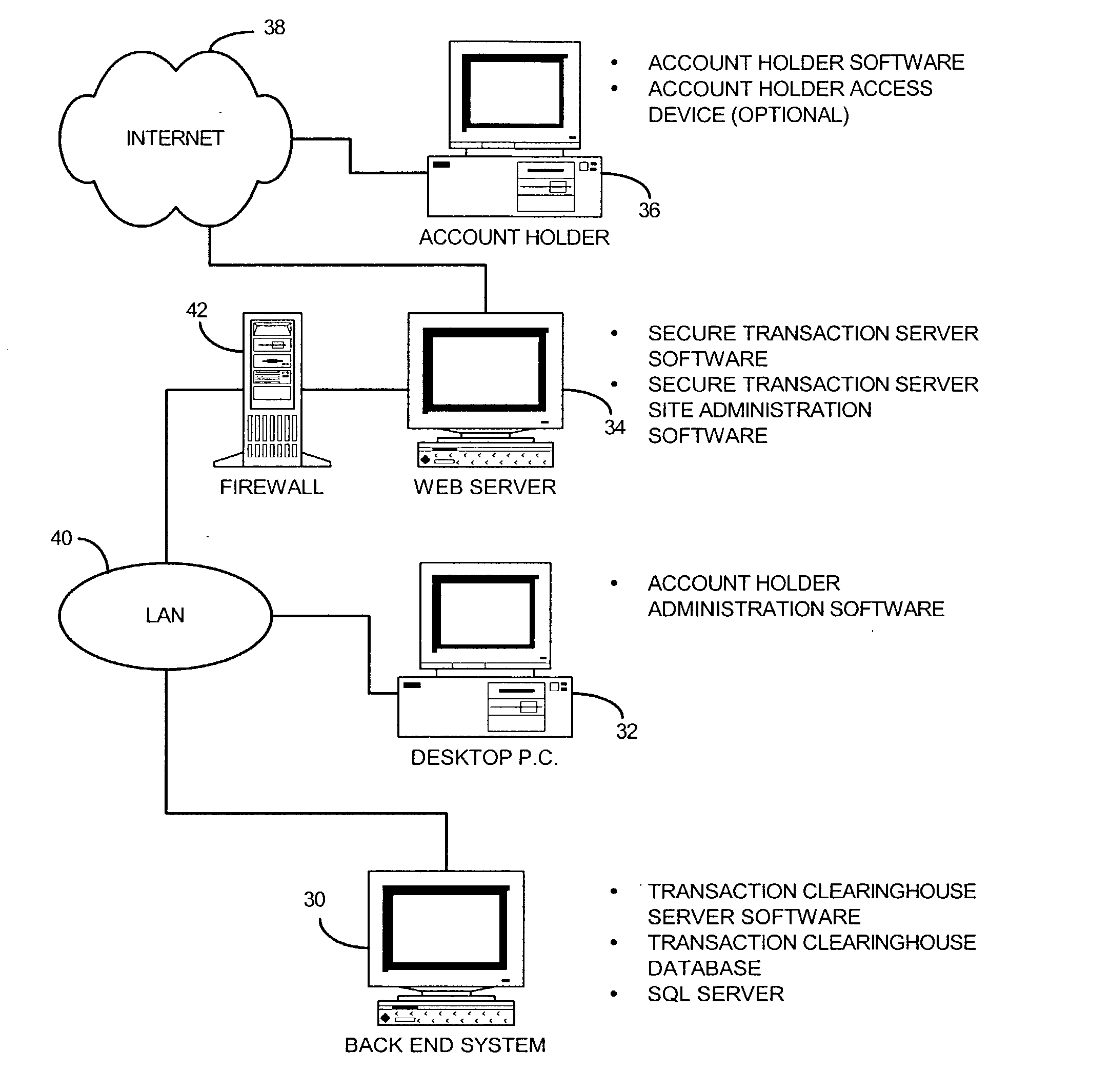
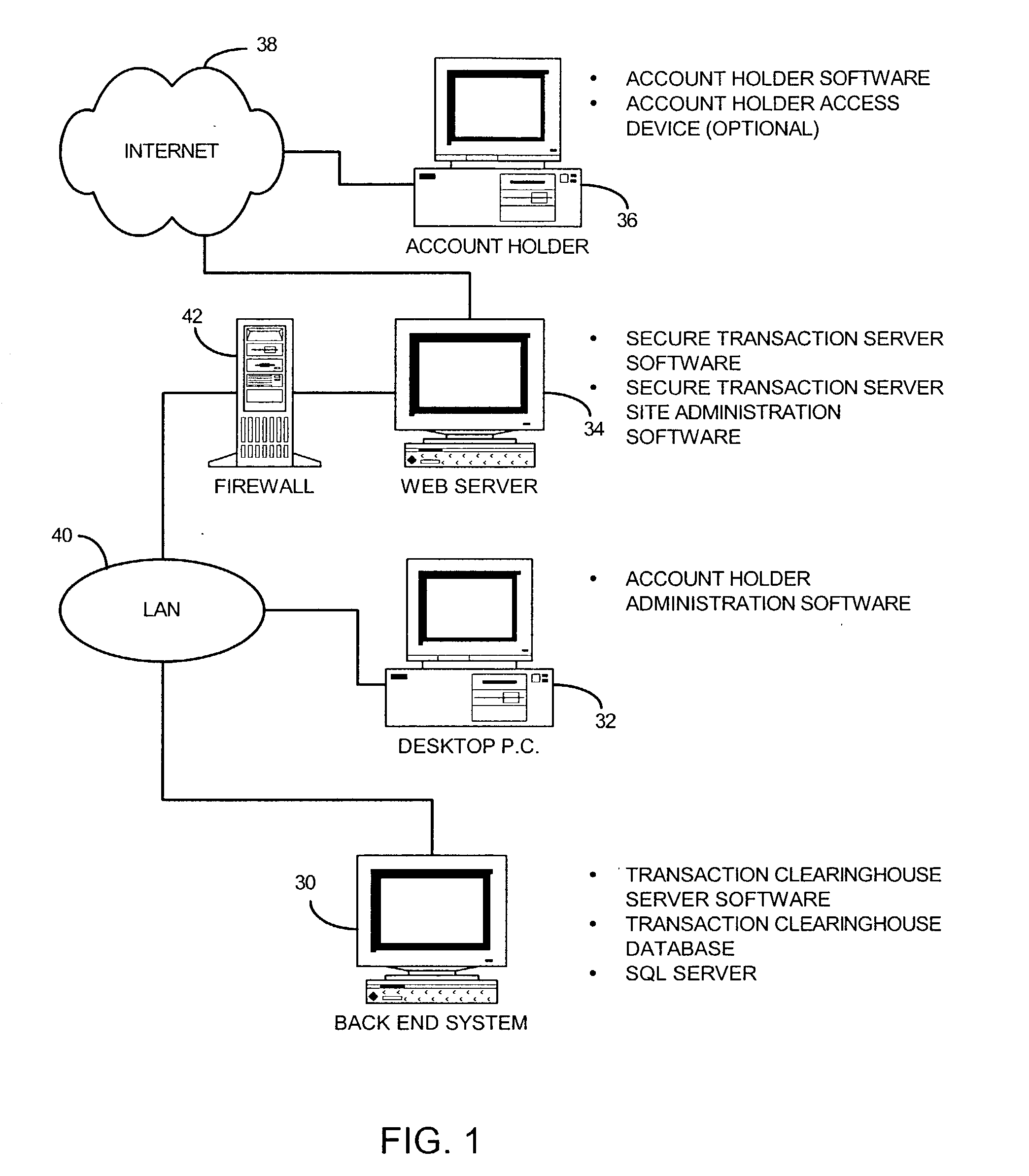
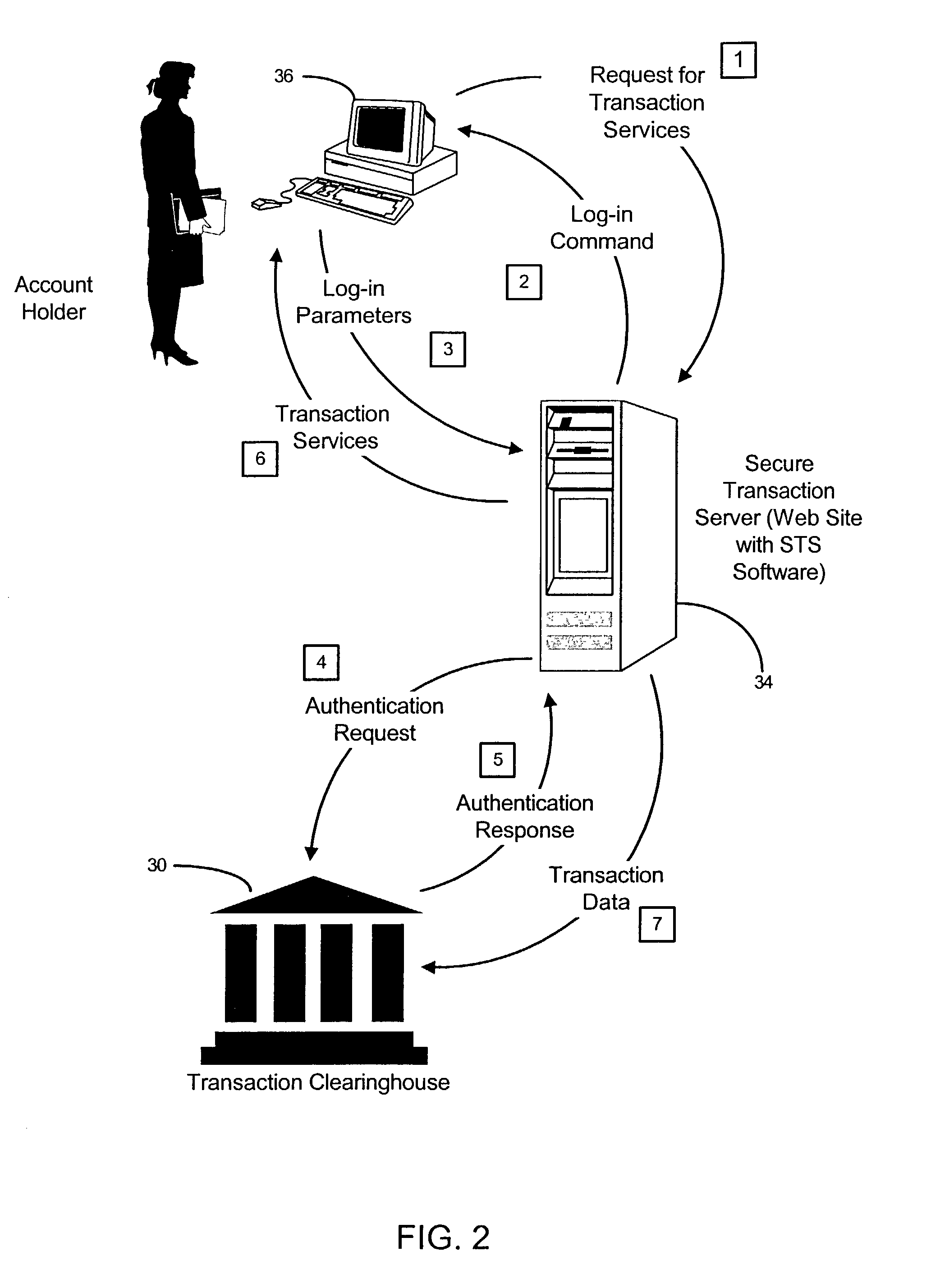
System and method for securing transactions and computer resources with an untrusted network
InactiveUS20030046589A1Digital data processing detailsCryptography processingComputer resourcesTransaction service
A system for securing and tracking usage of transaction services or computer resources by a client computer from a first server computer, which includes clearinghouse means for storing identity data of the first server computer and the client computer(s); server software means and client software means adapted to forward its identity data and identity data of the client computer(s) to the clearinghouse means at the beginning of an operating session; and a hardware key connected to the client computer, the key being adapted to generate a digital identification as part of the identity data; wherein the hardware key is implemented using a hardware token access system, a magnetic card access system, a smart card access system, a biometric identification access system or a central processing unit with a unique embedded digital identification.
Owner:PRISM TECH
System providing methodology for policy-based resource allocation
InactiveUS20100107172A1Resource allocationDigital computer detailsComputer resourcesApplication software
A system providing methodology for policy-based resource allocation is described. In one embodiment, for example, a system for allocating computer resources amongst a plurality of applications based on a policy is described that comprises: a plurality of computers connected to one another through a network; a policy engine for. specifying a policy for allocation of resources of the plurality of computers amongst a plurality of applications having access to the resources; a monitoring module at each computer for detecting demands for the resources and exchanging information regarding demands for the resources at the plurality of computers; and an enforcement module at each computer for allocating the resources amongst the plurality of applications based on the policy and information regarding demands for the resources.
Owner:SYCHRON
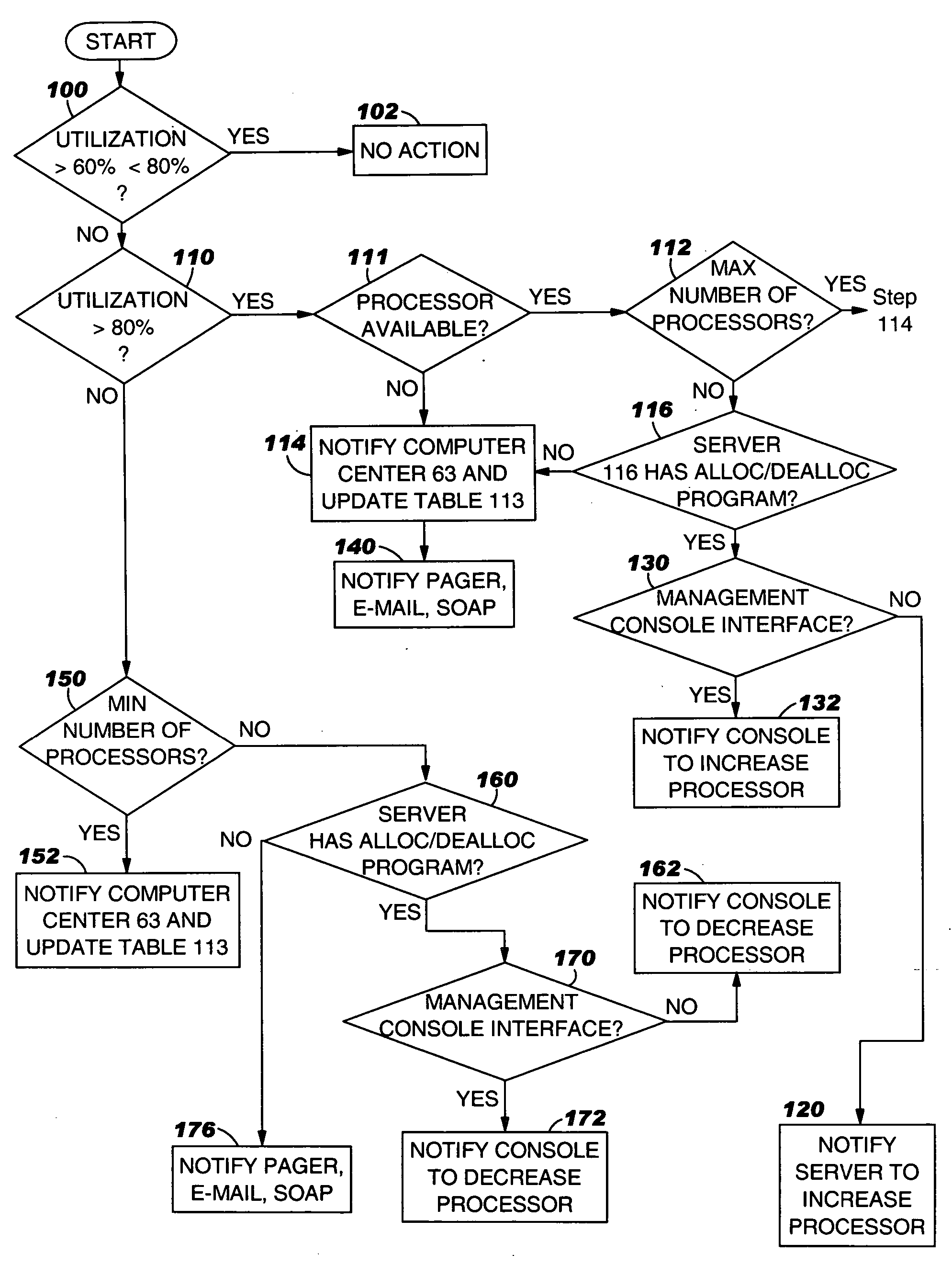
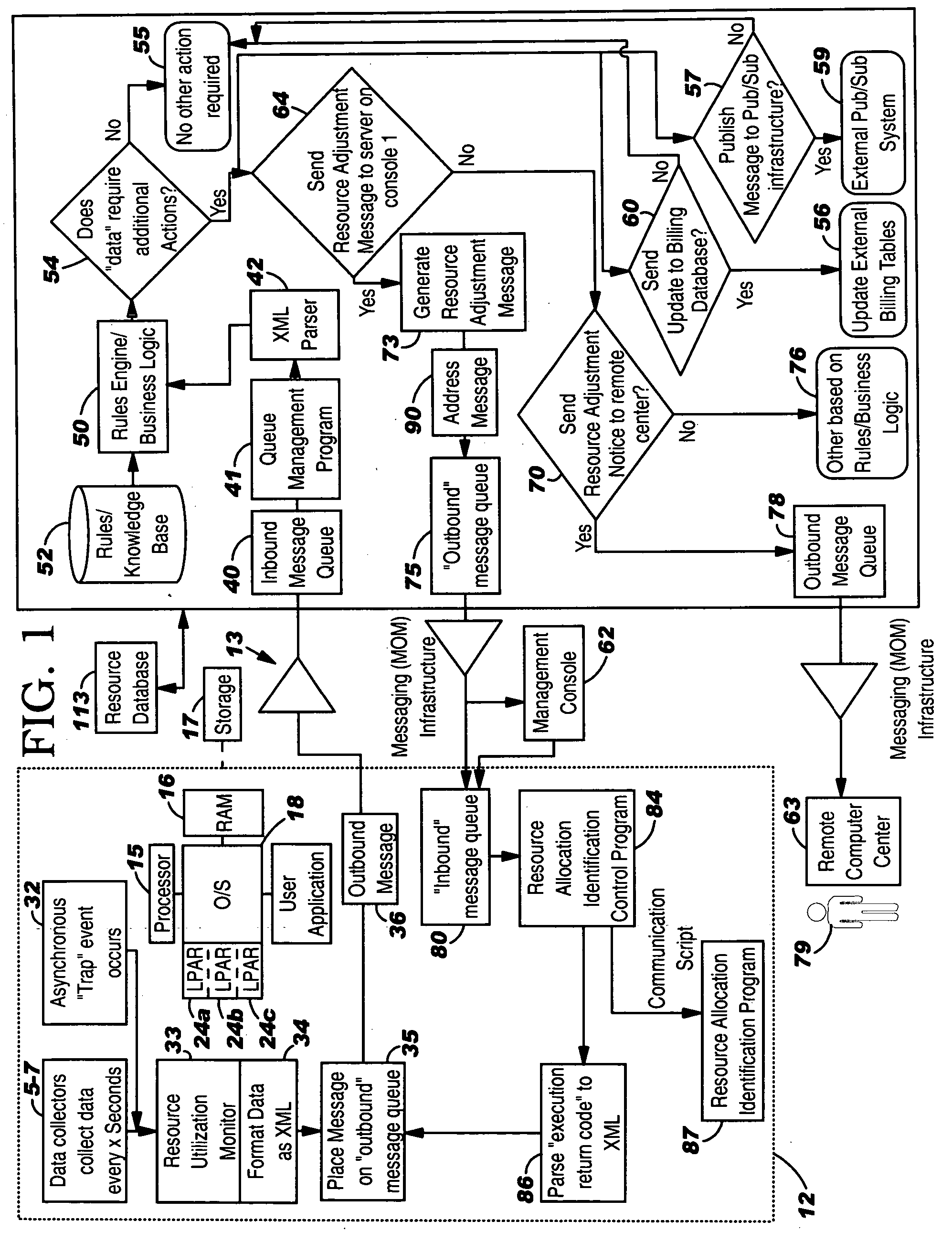
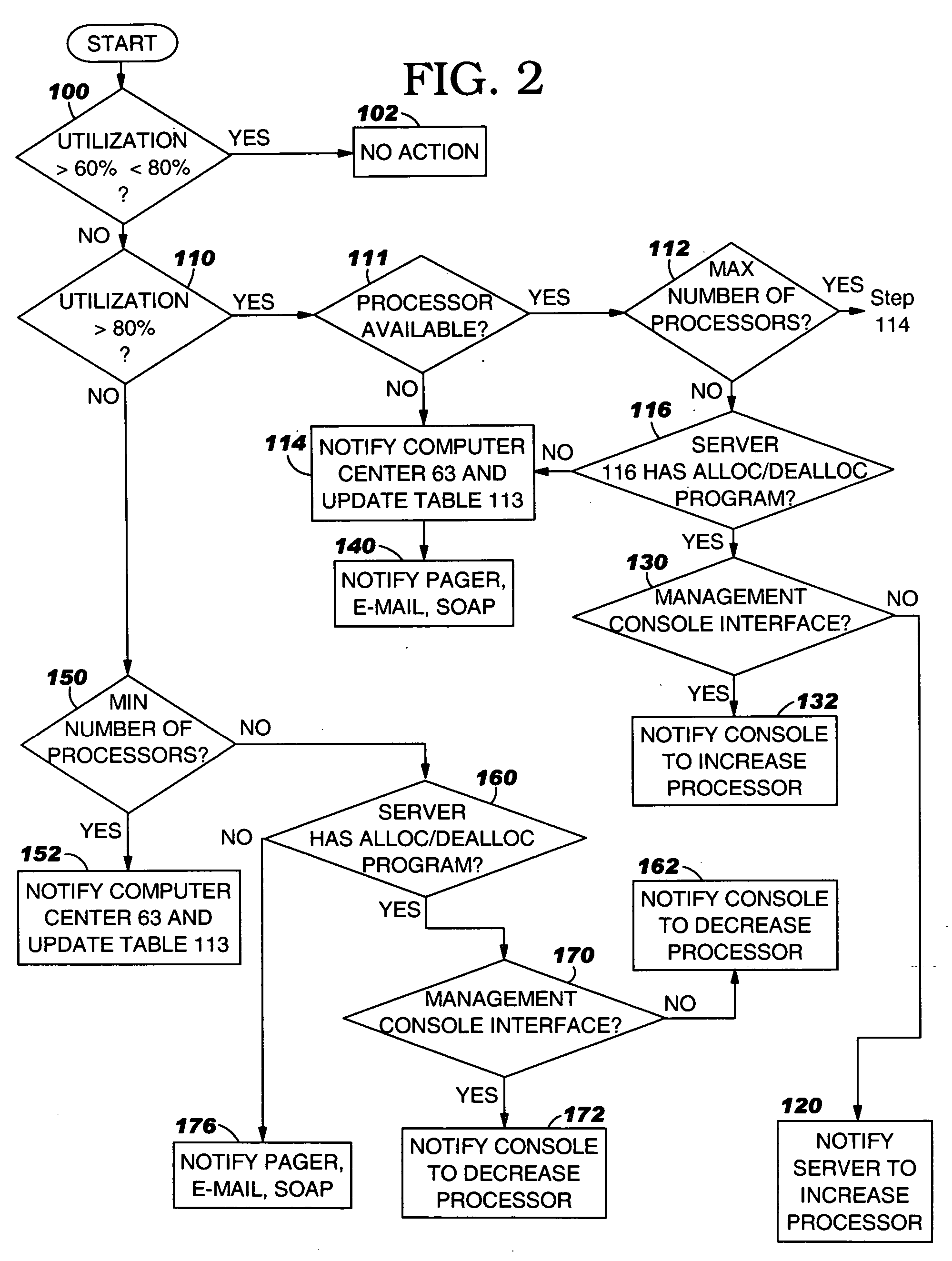
System, method and program to automatically adjust allocation of computer resources
InactiveUS20060136761A1Volume/mass flow measurementDigital computer detailsComputer resourcesProgram instruction
System and computer program product for automatically adjusting allocation of processing power in a server. The server includes means for monitoring utilization of the processing power in the server and reporting the utilization of the processing power to the system, or means for monitoring availability of the processing power in the server and reporting the availability of the processing power to the system. The system comprises means or program instructions, responsive to a report that the processor utilization is above a first predetermined upper threshold or the processor availability is below a first predetermined lower threshold, for determining if the server can accommodate allocation of additional processing power, and if so, generating a request to allocate additional processing power to the server. The system also comprises other means or program instructions, responsive to a report that the processor utilization is below a second predetermined lower threshold or the processor availability is above a second predetermined upper threshold, for determining if the server can accommodate a de allocation of processing power, and if so, generating a request to de allocate some of the currently allocated processing power from the server. The system and program product also automatically adjust allocation of memory in the server.
Owner:IBM CORP
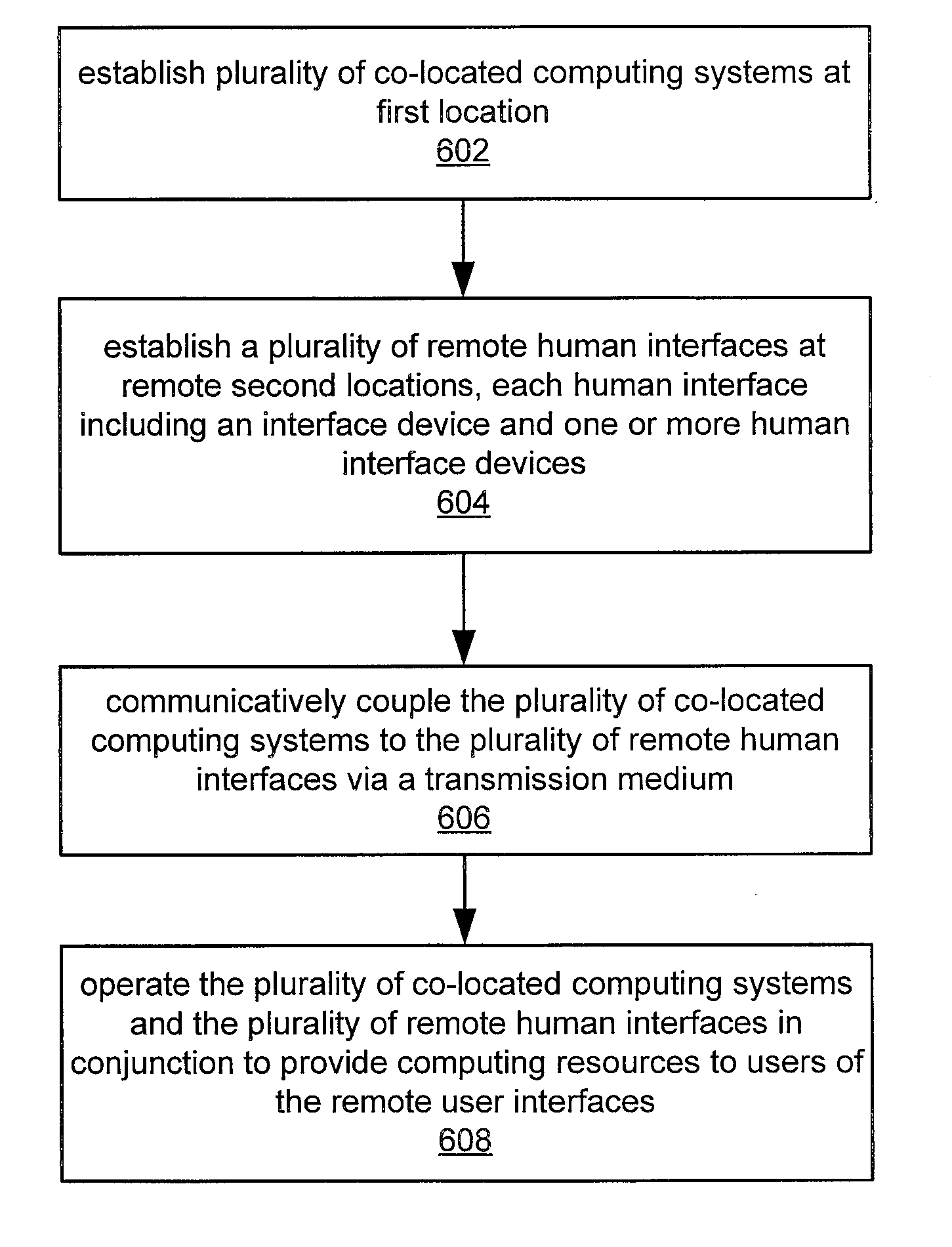
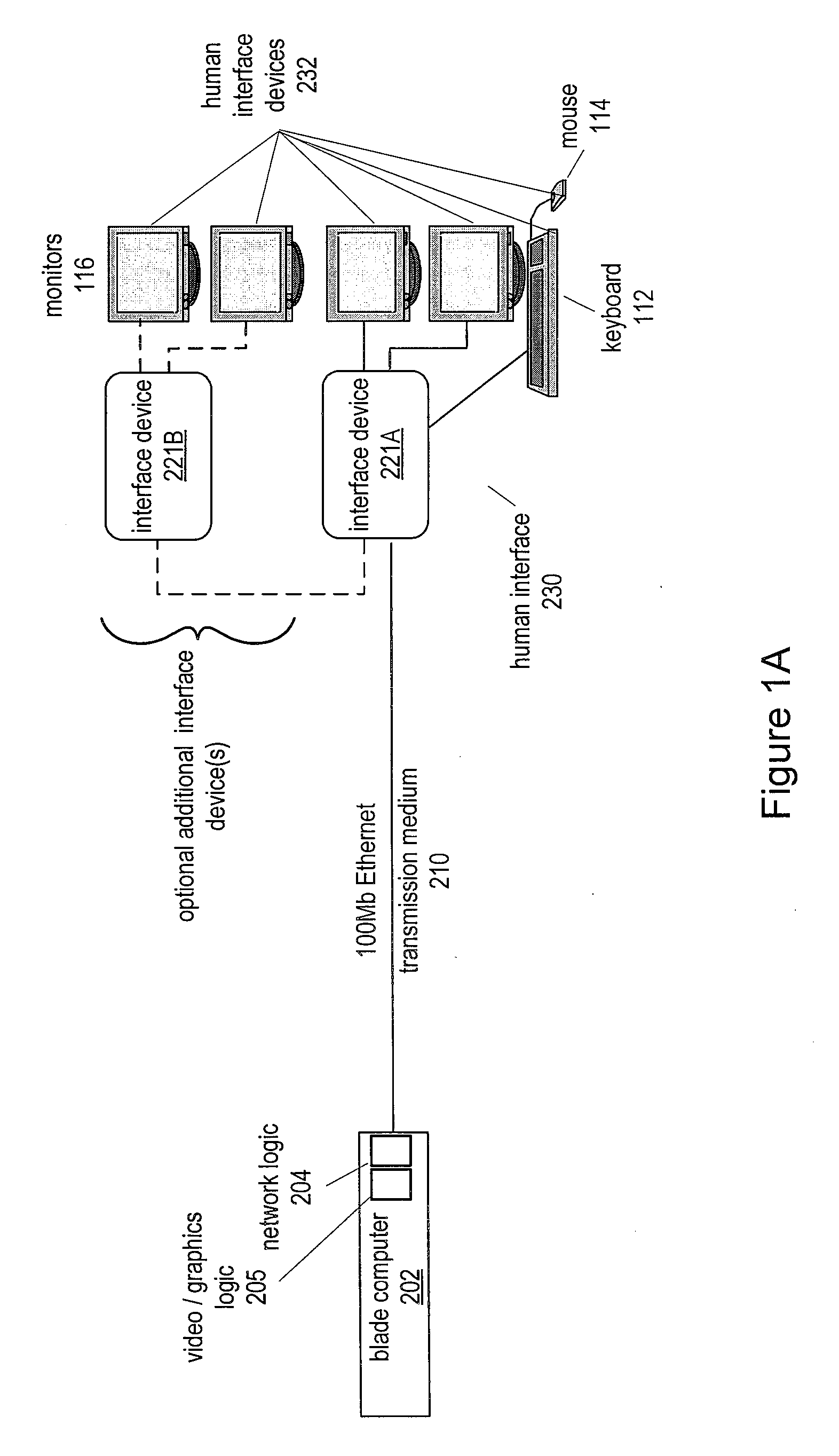
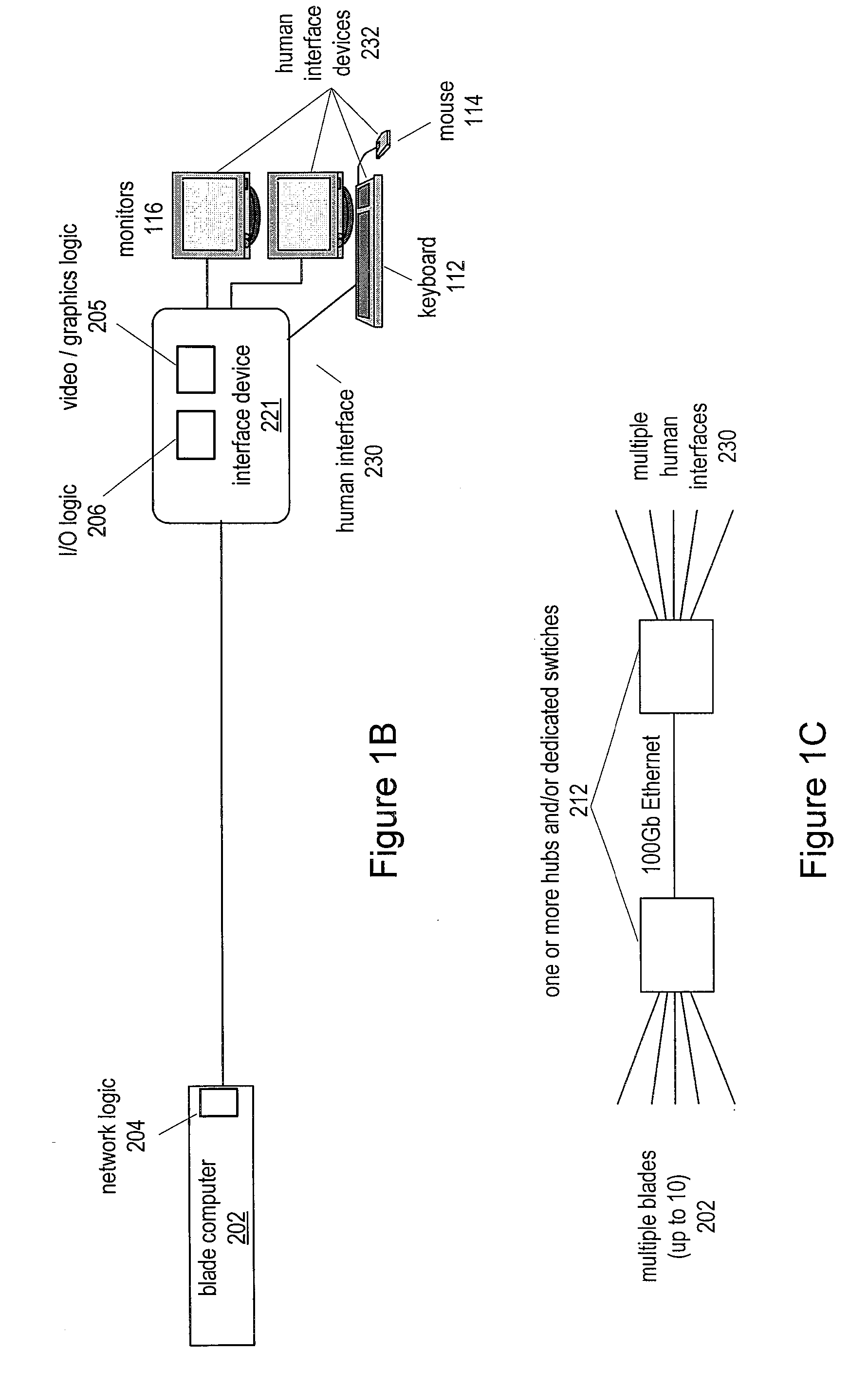
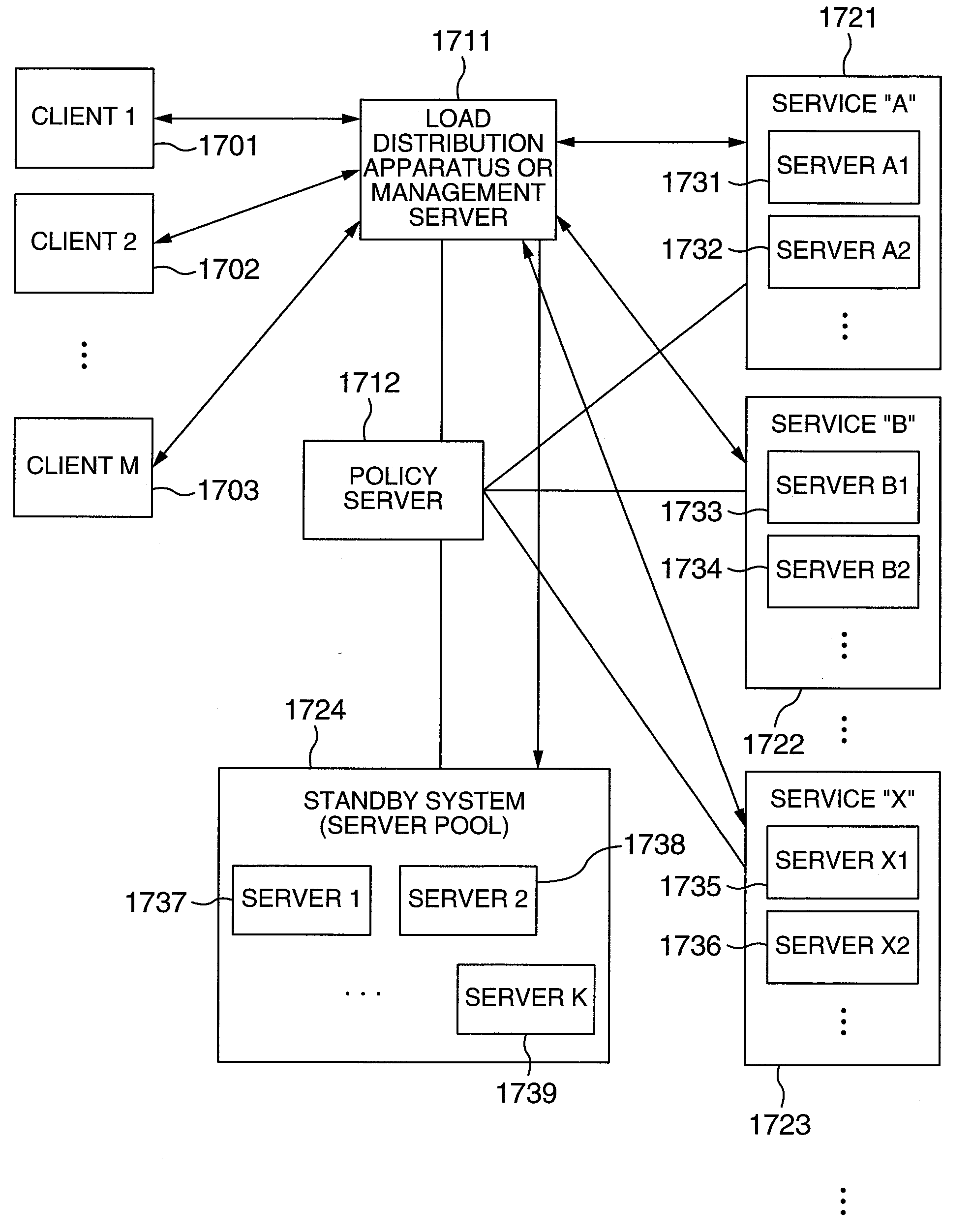
Utility Computing System Having Co-located Computer Systems for Provision of Computing Resources
System and method for providing computer resources to users. The system includes a plurality of co-located computing systems, e.g., blade computers, comprising a hierarchy of computer resources based on performance, and located at a first location, each computing system including a processor, a memory medium coupled to the processor, and a plurality of human interface systems, each located at a second location remote from the first location, and each including an interface device, and one or more human interface devices coupled to the interface device, where each human interface system is coupled to the co-located computing systems over a network, such as a LAN or a WAN, via the interface device. Computer resources are provided to users of the plurality of remote human interface systems over the network in accordance with the computer resource performance needs of the users. Charges may be assessed for usage of the computer resources.
Owner:CLEARCUBE TECHNOLOGY INC
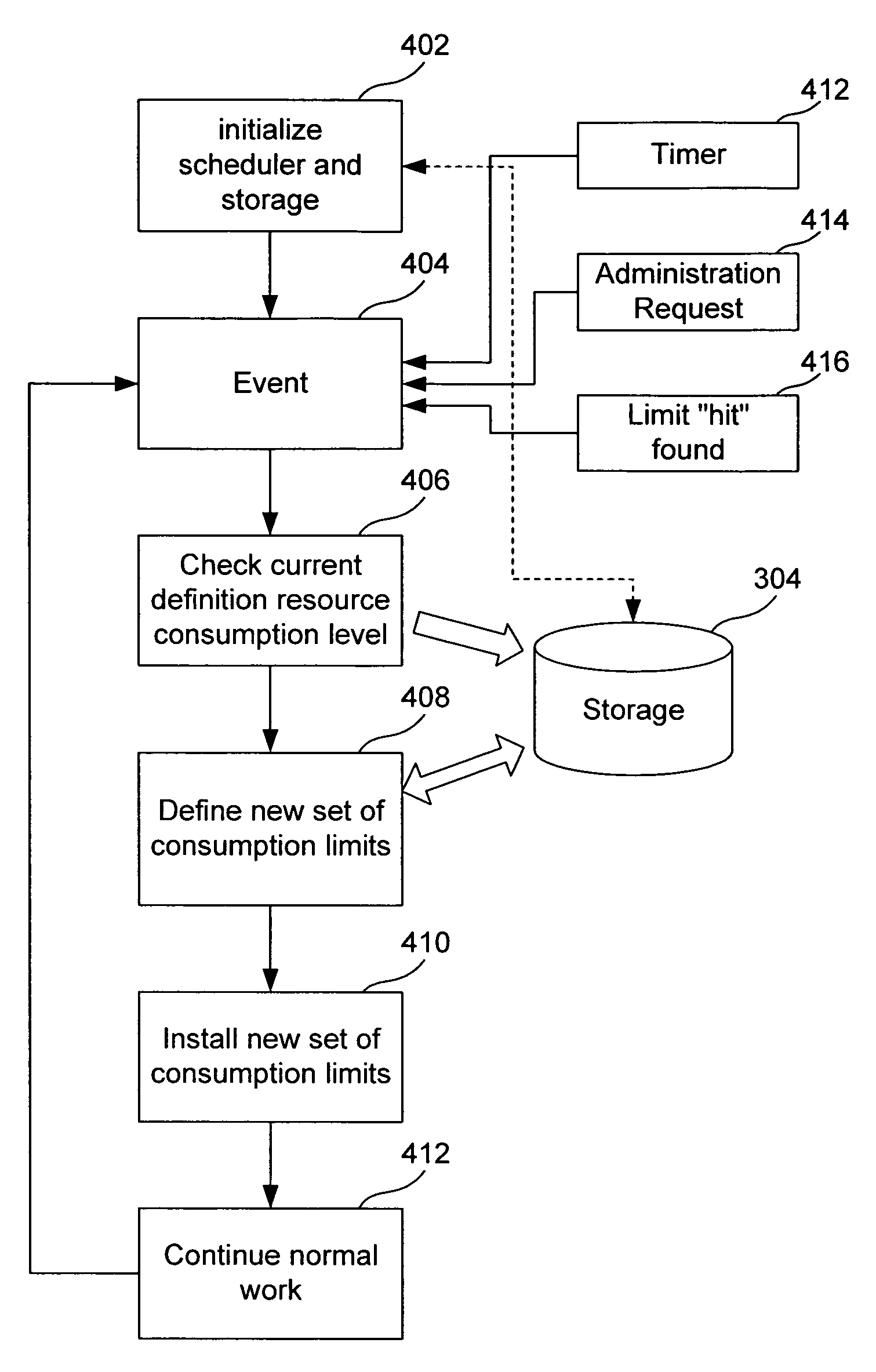
System, method, and computer program product for group scheduling of computer resources
A system, method and computer program product for managing computer resources in a computer system running an operating system and a plurality of processes grouped into at least two groups. A set of resource limits corresponds to the processes. A scheduler of resource allocation allocates resources to each process such that total resource allocation to a group to which that process belongs remains constant. The resources comprise, e.g., network bandwidth, number of network connections, I / O bandwidth for peripheral devices, number of operations in a period of time for service operation with countable requests for service, number of operations in a period of time for a daemon with countable requests for service, permission for execution of operation, number of security descriptors, and number of terminals. The scheduler reallocates the resources based on a predictive algorithm, or based on process priority, or based on relative weighting of the processes. The scheduler can adjust an increase and a decrease of the resources available to a particular process. The scheduler is capable of increasing a resource allocation restriction to one process by and by waiting for that resource to become available. The scheduler is capable of increasing a resource allocation to one process by reducing allocation restriction to other processes in the same group on a basis proportional to their current use of that resource. The scheduler can reduce a resource allocation to a particular process based on a history of consumption of the resource by that process and a history of consumption of other resources by that process.
Owner:VIRTUOZZO INT GMBH
Computer resource distribution method based on prediciton
InactiveUS20090113056A1Reduce in quantityReduce maintenance costsResource allocationDigital computer detailsComputer resourcesDistribution method
Owner:HITACHI LTD
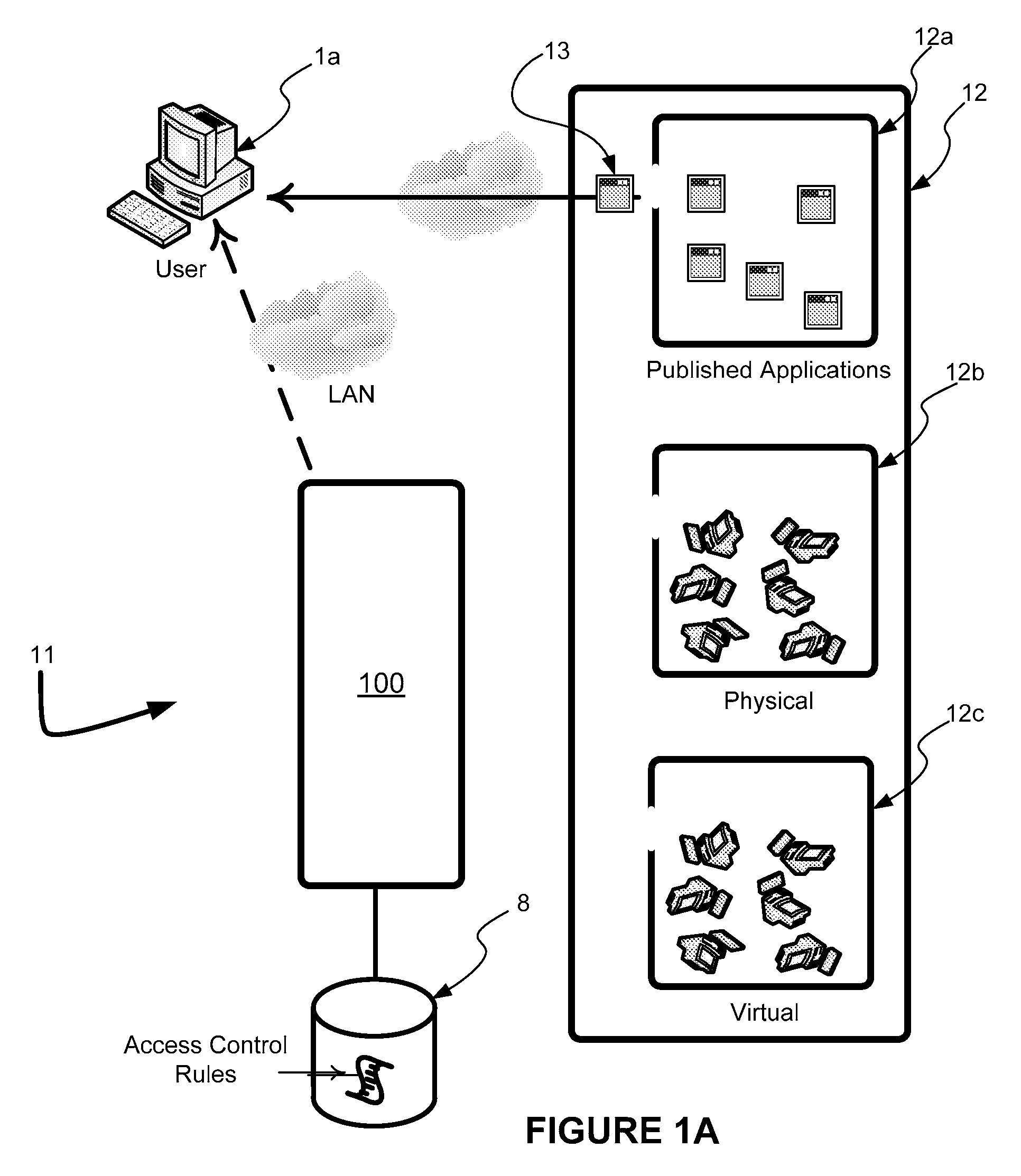
Management layer method and apparatus for dynamic assignment of users to computer resources
InactiveUS20080235361A1Increasing mobile contemporary workforceDigital computer detailsProgram controlComputer resourcesComputer users
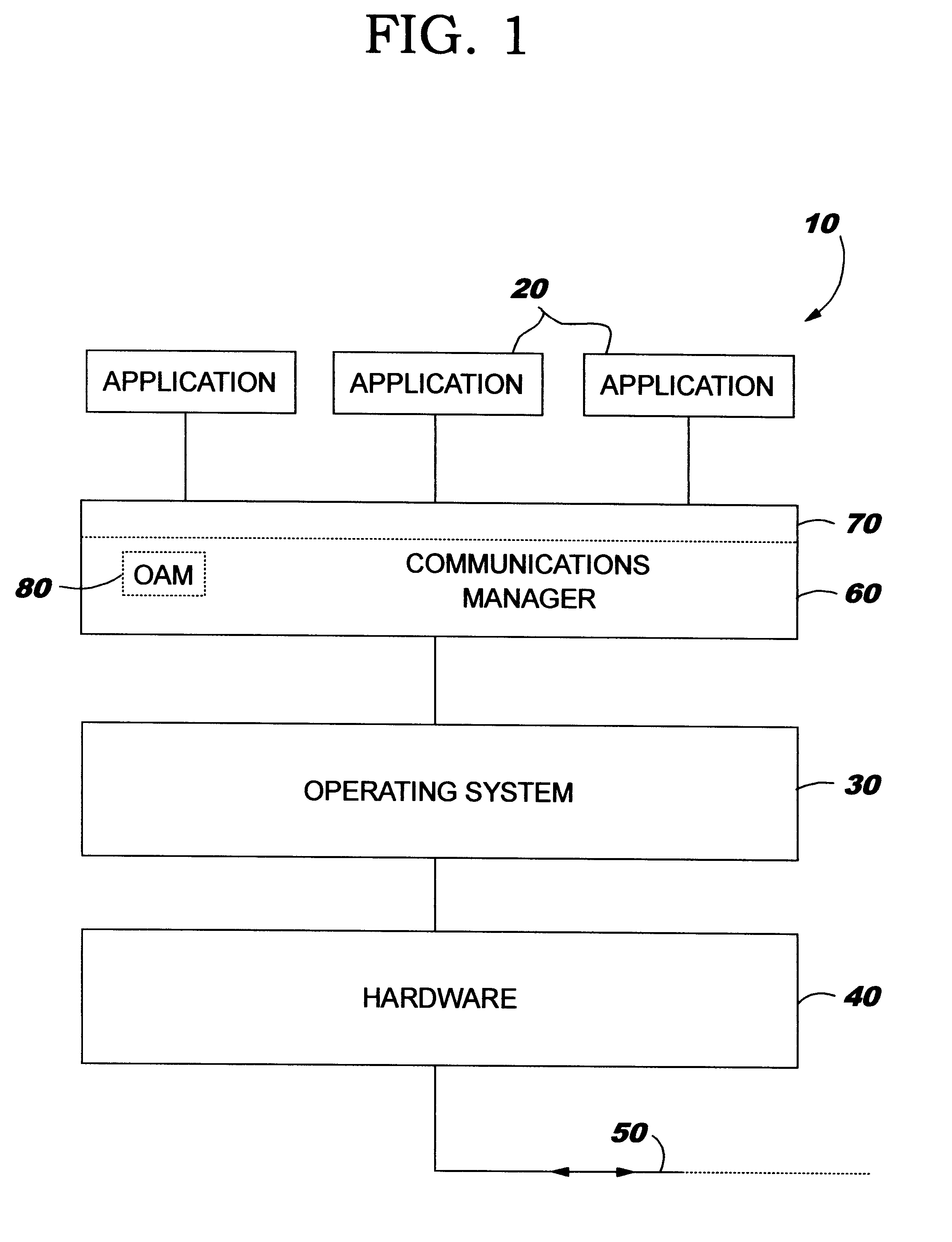
A management layer method and apparatus for dynamically assigning computer users to remote computer resources according to predetermined rules and irrespective of remote viewer protocol utilized by the user. The method and apparatus is capable of managing hundreds of thousands of users across multiple physical sites and is operable with a wide variety of network, Internet, and application solutions. The method and apparatus is useful for an increasing mobile contemporary workforce in a world where the need for around the clock coverage coexists with the ever present possibility of catastrophic network failure.
Owner:LEOSTREAM
Modeling user access to computer resources
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:DAEDALUS BLUE LLC
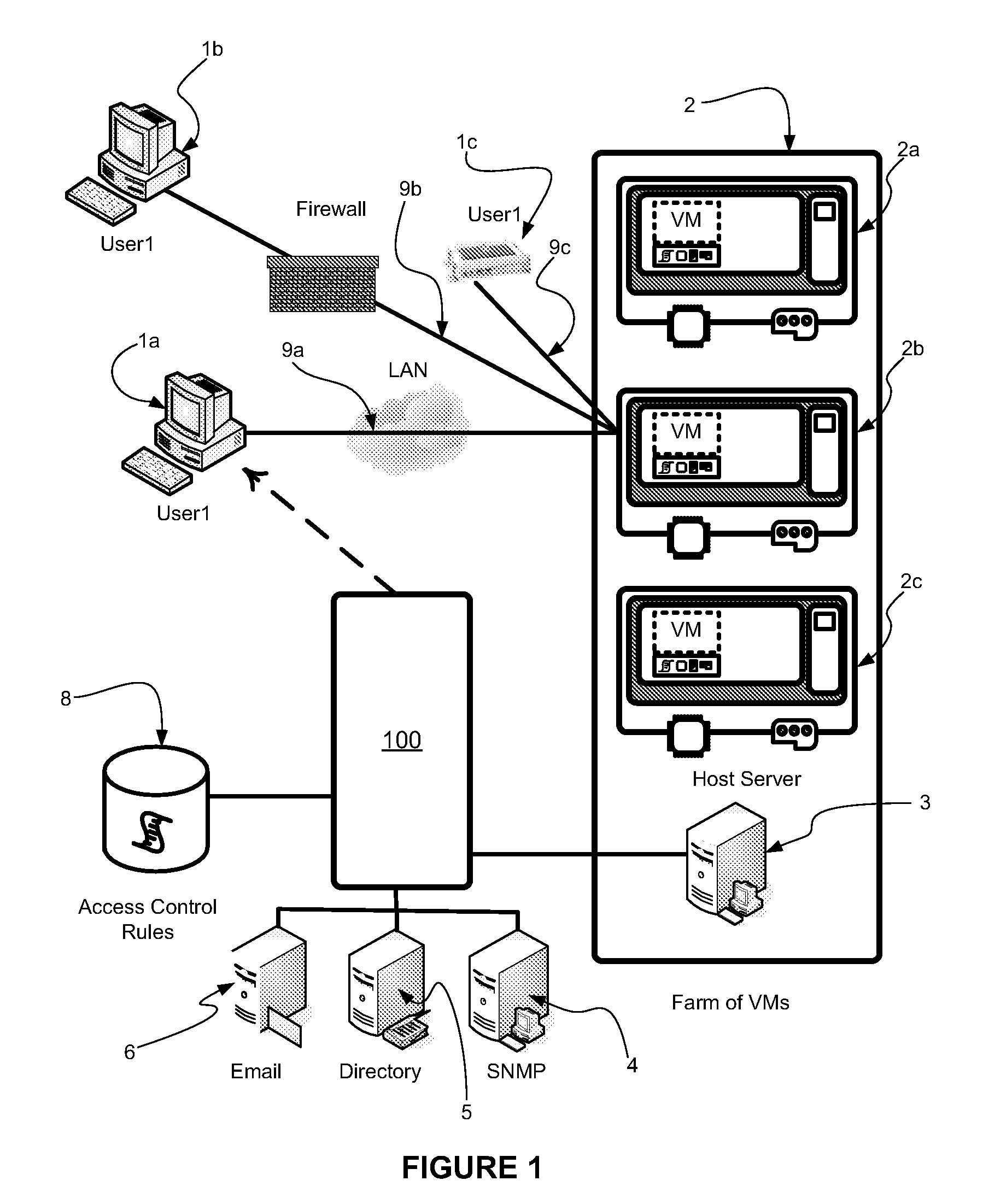
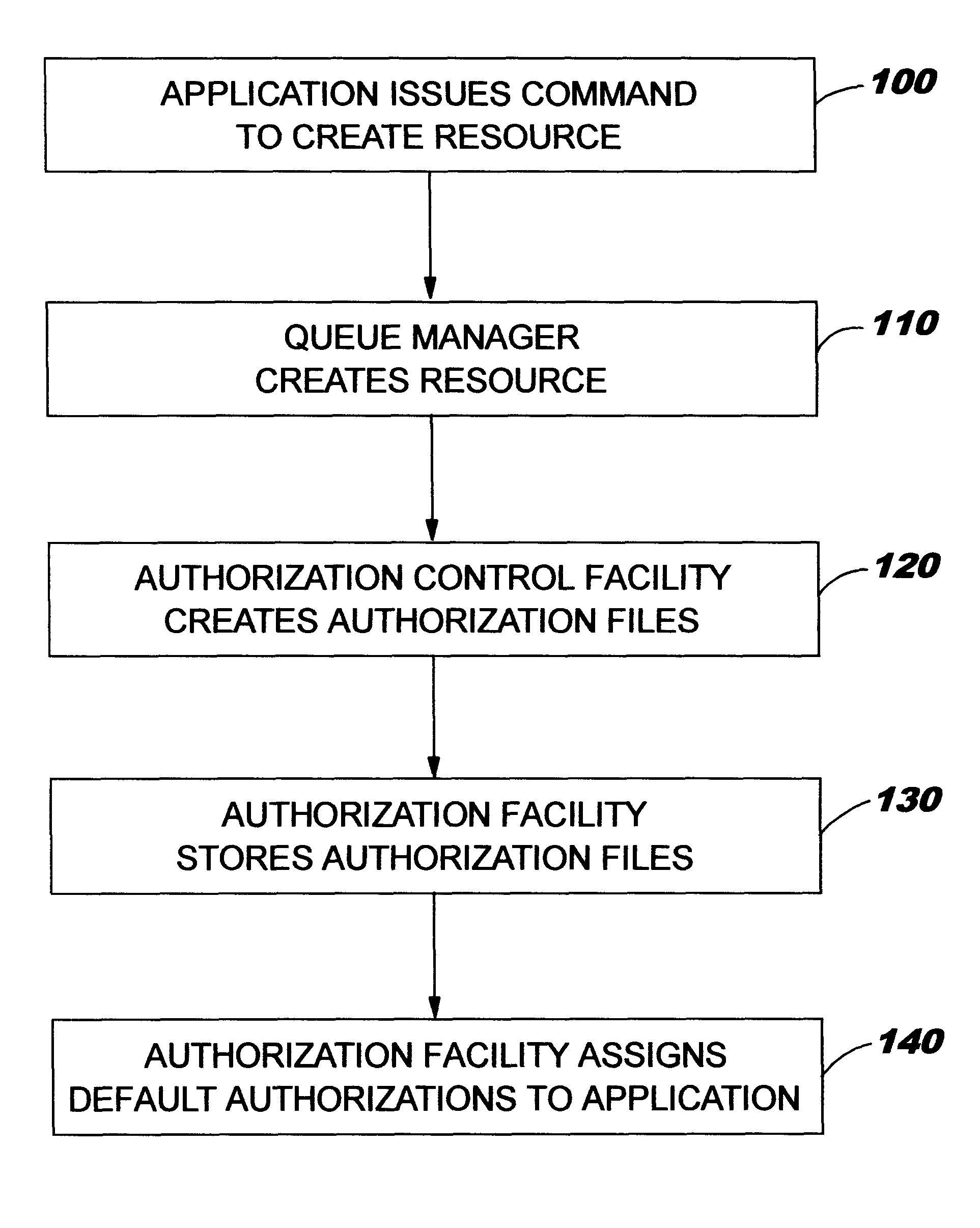
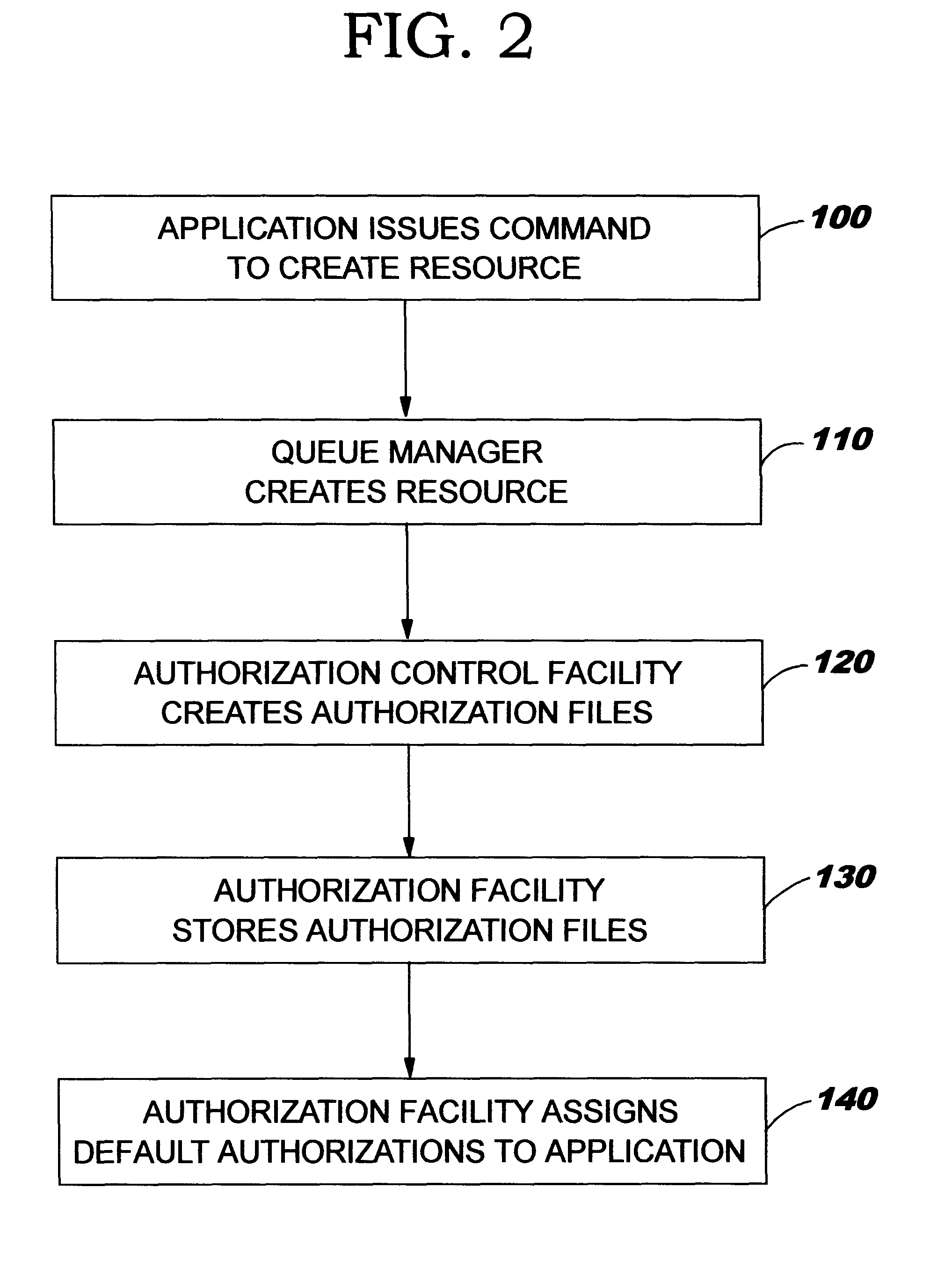
Enhanced security for computer system resources with a resource access authorization control facility that creates files and provides increased granularity of resource permission
InactiveUS6233576B1Provide flexibilitySpecific access rightsData processing applicationsComputer resourcesOperational system
Provided is a scheme for implementing flexible control of subject authorizations (i.e. the authorizations which users or processes have) to perform operations in relation to computer resources. The methods, computer systems and authorization facilities which are provided by the invention enhance the security provisions of operating systems which have only very limited authorization facilities, by mapping the available operating system permissions to specified resource authorities for each of a set of aspects or characteristics of a computer system resource. Thus, the standard operating system permissions (e.g. read, write, execute) can have different meanings for different resource aspects, and an individual subject can have separate authorization levels set for the different resource aspects. The mappings between authorities and the available permissions may be different for different types of resources. The invention provides great flexibility in setting the authorizations that a subject may have in relation to particular resources.
Owner:TREND MICRO INC
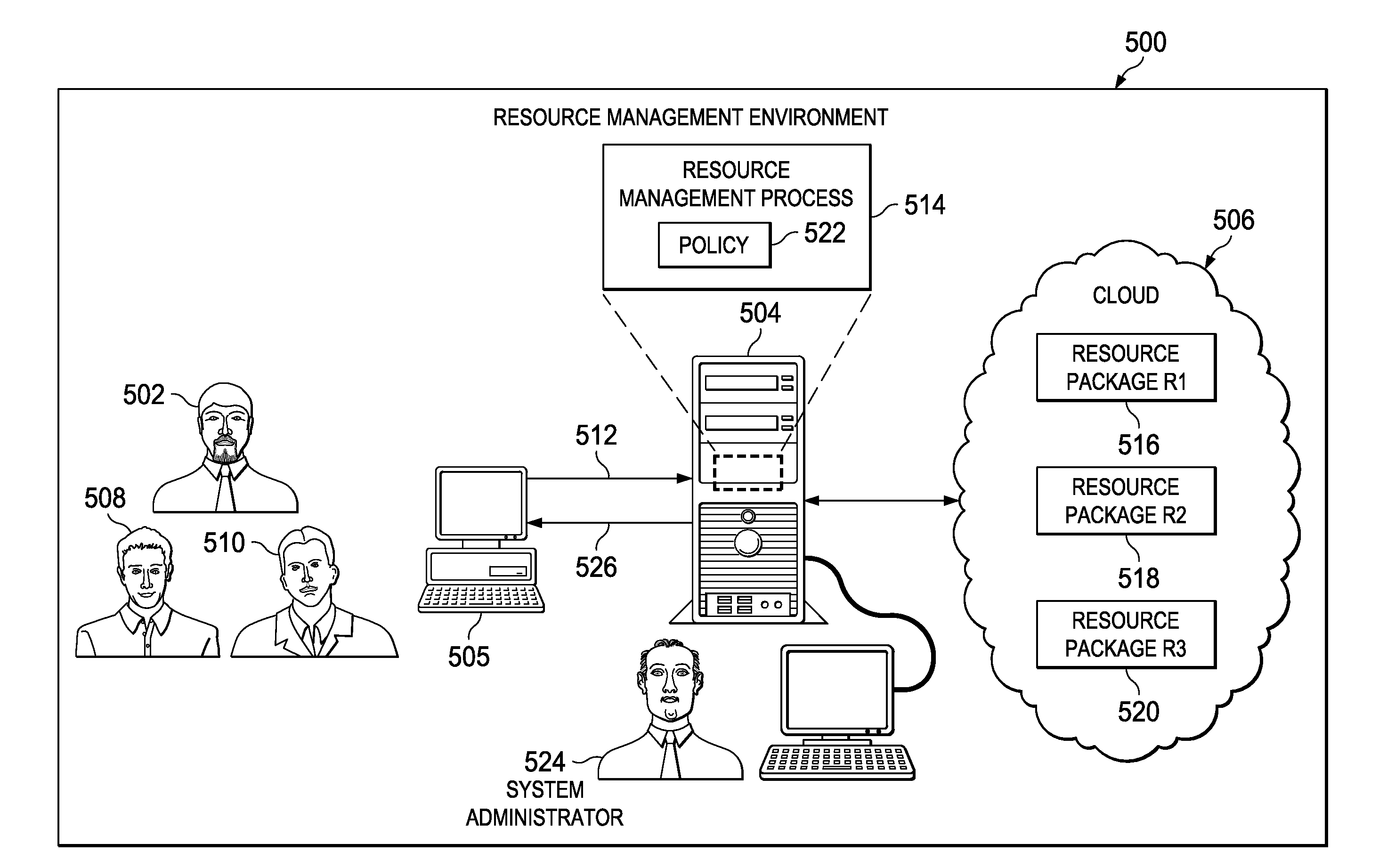
Allocating Computer Resources in a Cloud Environment
ActiveUS20110320606A1Data processing applicationsUser identity/authority verificationComputer resourcesData processing system
A method, data processing system, and computer program product for managing resources. A request for resources in the network data processing system is received. The request comprises requested values for a plurality of attributes for the resources in the network data processing system. In response to receiving the request, potential resources in the network data processing system are identified. The request is evaluated using a function configured to generate identified values for the plurality of attributes from the requested values in the request based on proximity scores for the plurality of attributes in the potential resources relative to an ideal allocation of the potential resources and resource weights for the plurality of attributes in the potential resources.
Owner:IBM CORP
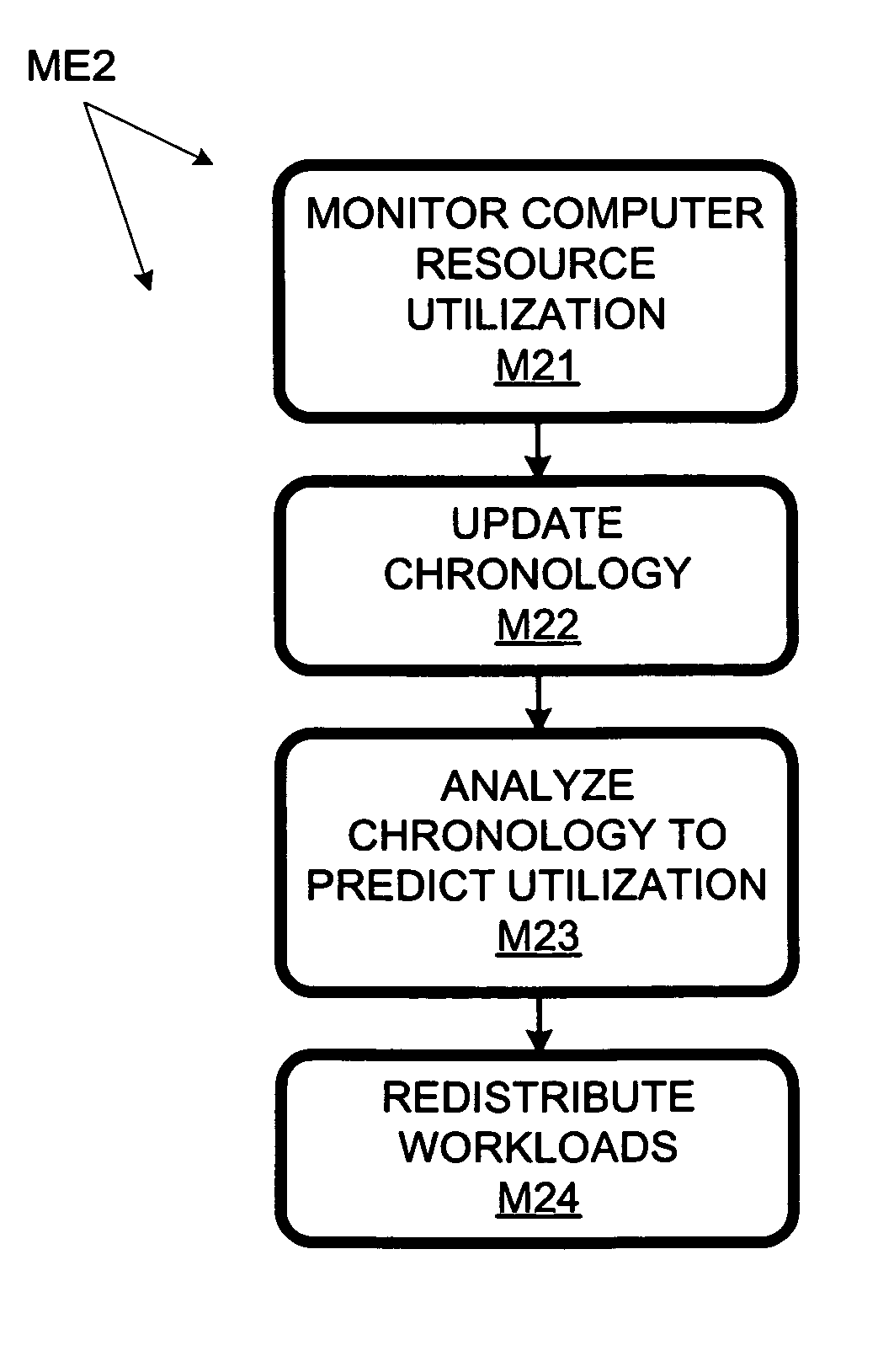
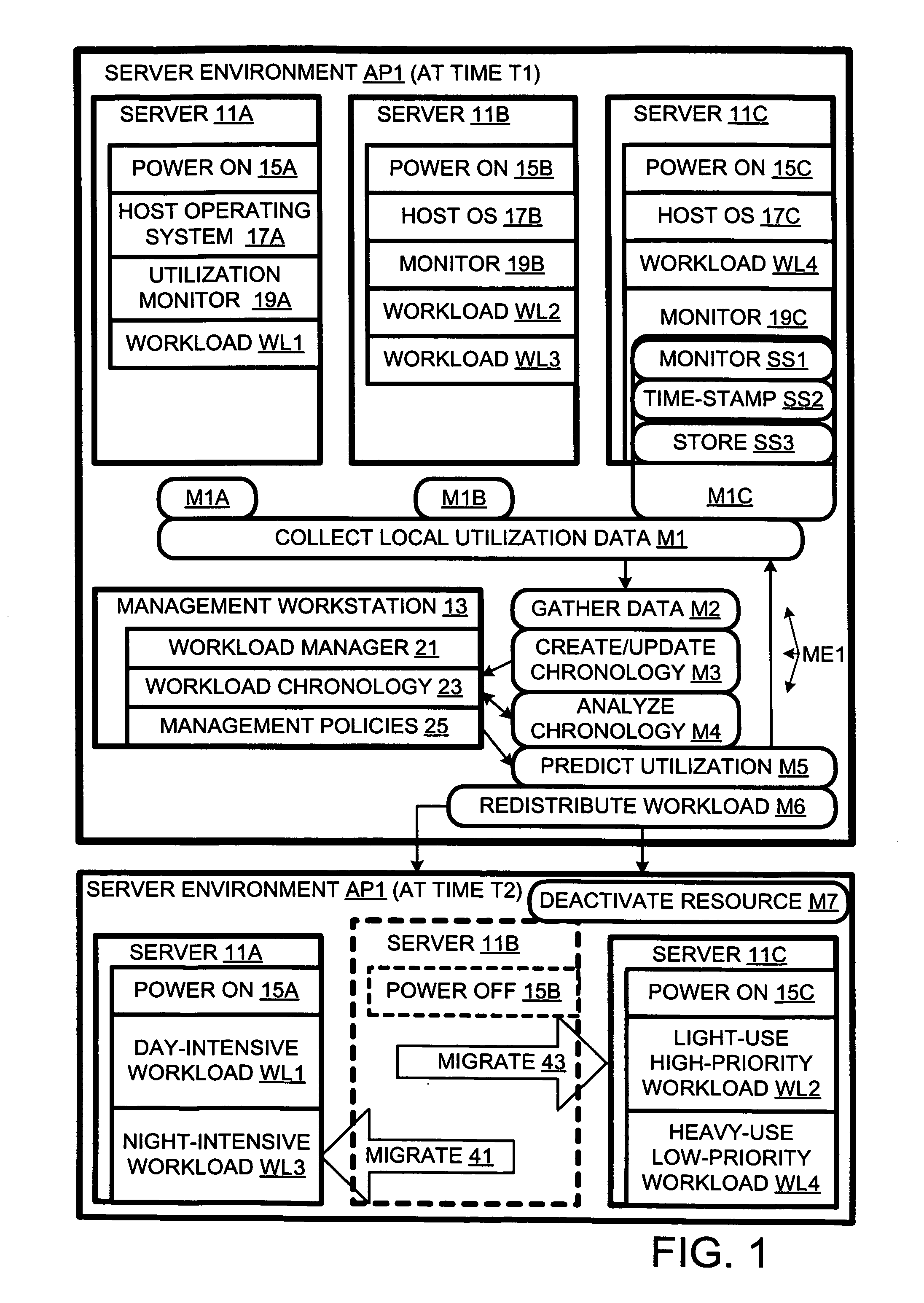
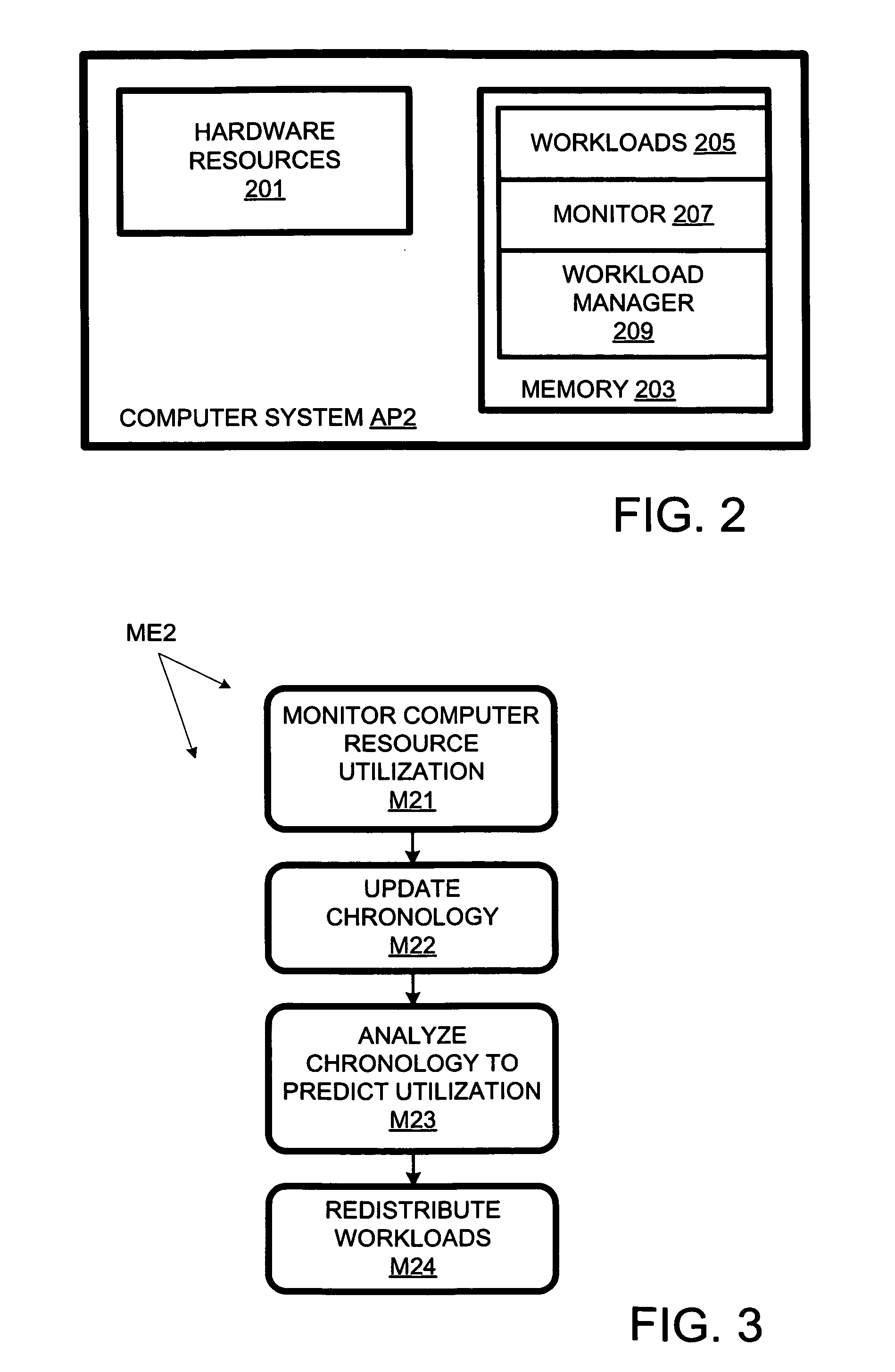
Computer workload redistribution
ActiveUS20070250838A1Error detection/correctionVolume/mass flow measurementComputer resourcesResource utilization
The present invention provides for redistributing workloads among computers to optimize resource utilization. Utilization by software workloads of computer resources is monitored to yield utilization data. A utilization chronology is updated using the utilization data. The chronology is analyzed to yield resource utilization predictions. The workloads are redistributed among the resources at least in part as function of said predictions.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
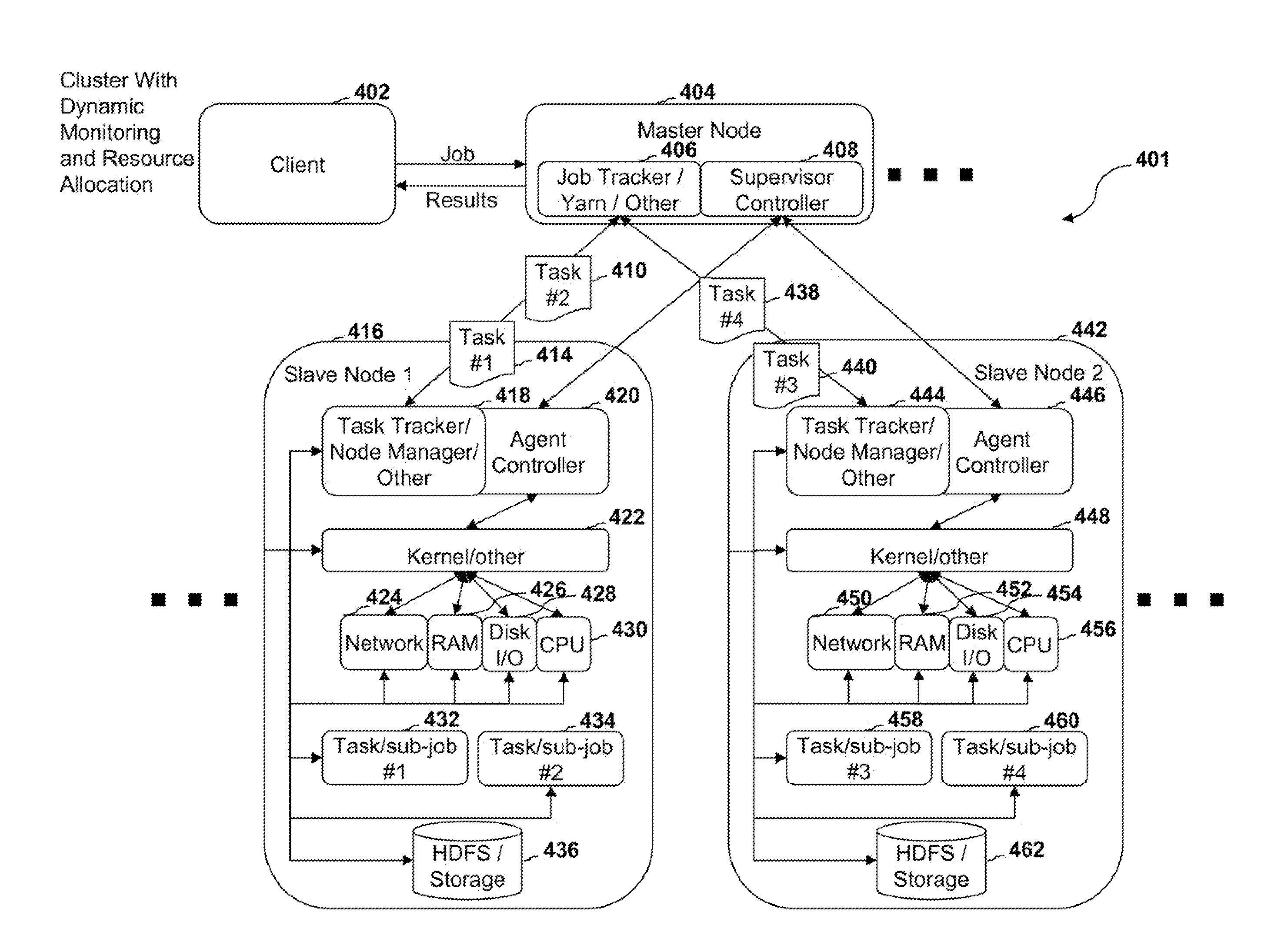
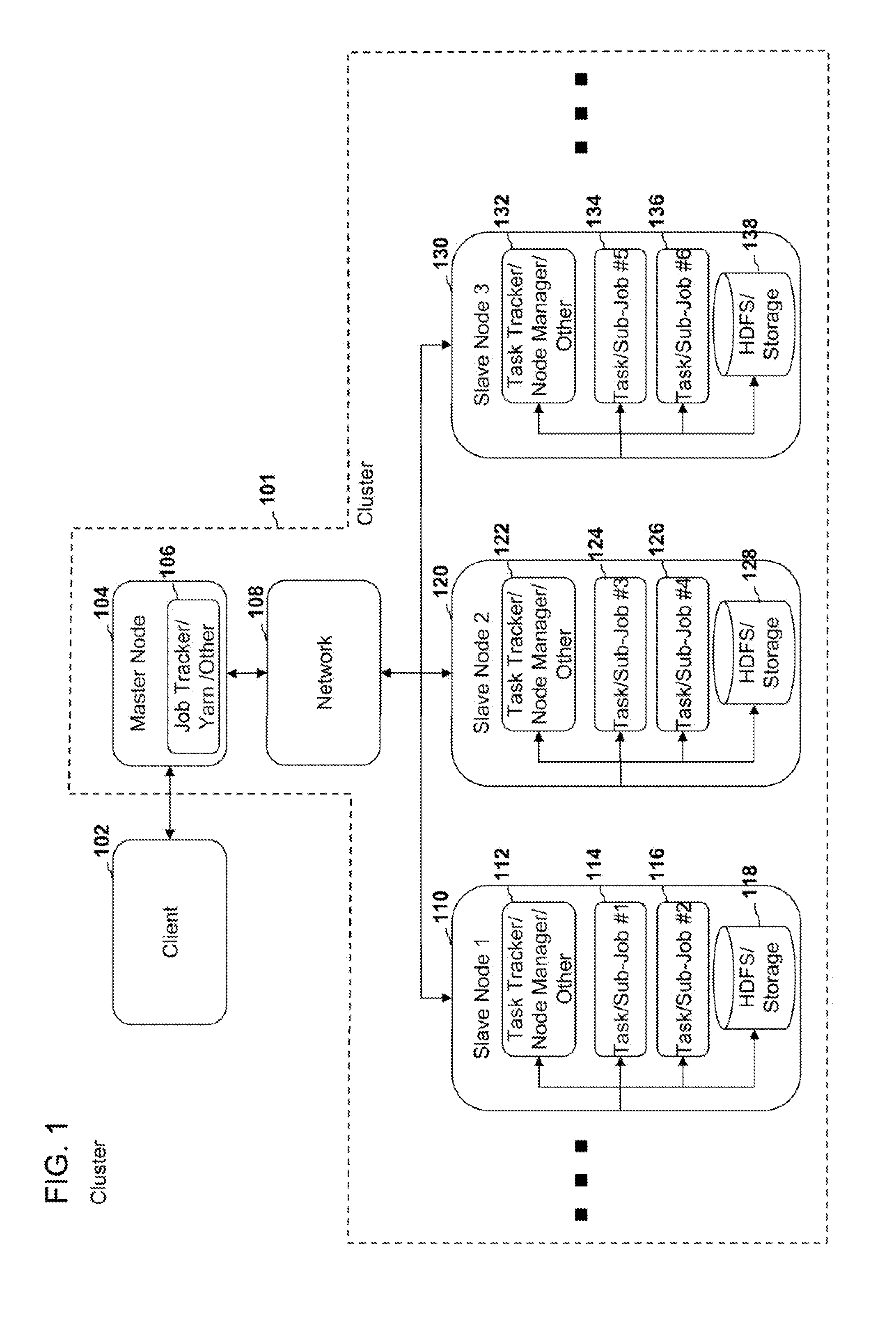
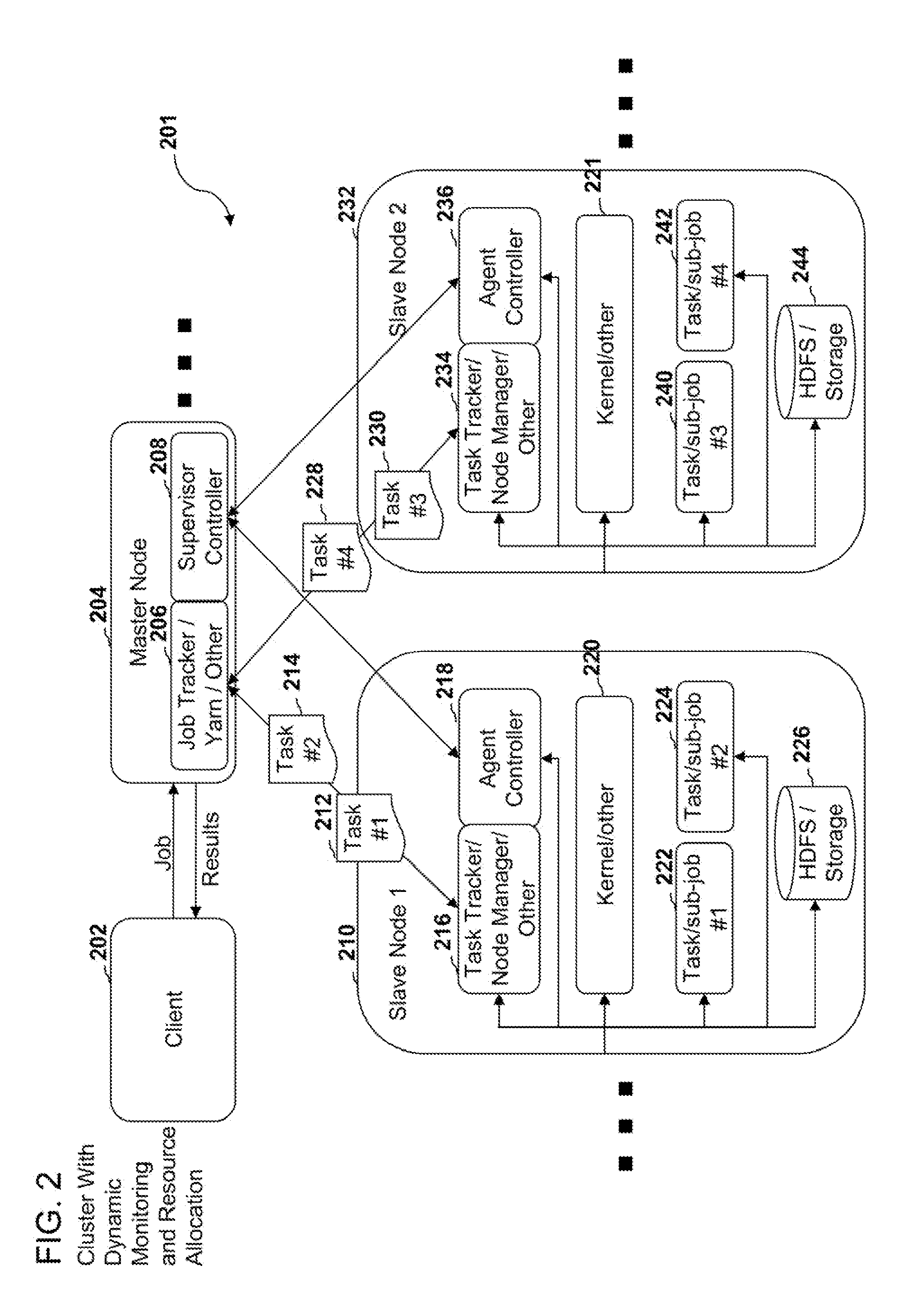
Systems, methods, and devices for dynamic resource monitoring and allocation in a cluster system
ActiveUS8706798B1Easy to operateMultiple digital computer combinationsProgram controlComputer resourcesCluster systems
In an embodiment, the systems, methods, and devices disclosed herein comprise a computer resource monitoring and allocation system. In an embodiment, the resource monitoring and allocation system can be configured to allocate computer resources that are available on various nodes of a cluster to specific jobs and / or sub-jobs and / or tasks and / or processes.
Owner:PEPPERDATA
Intelligent pre-caching on a network
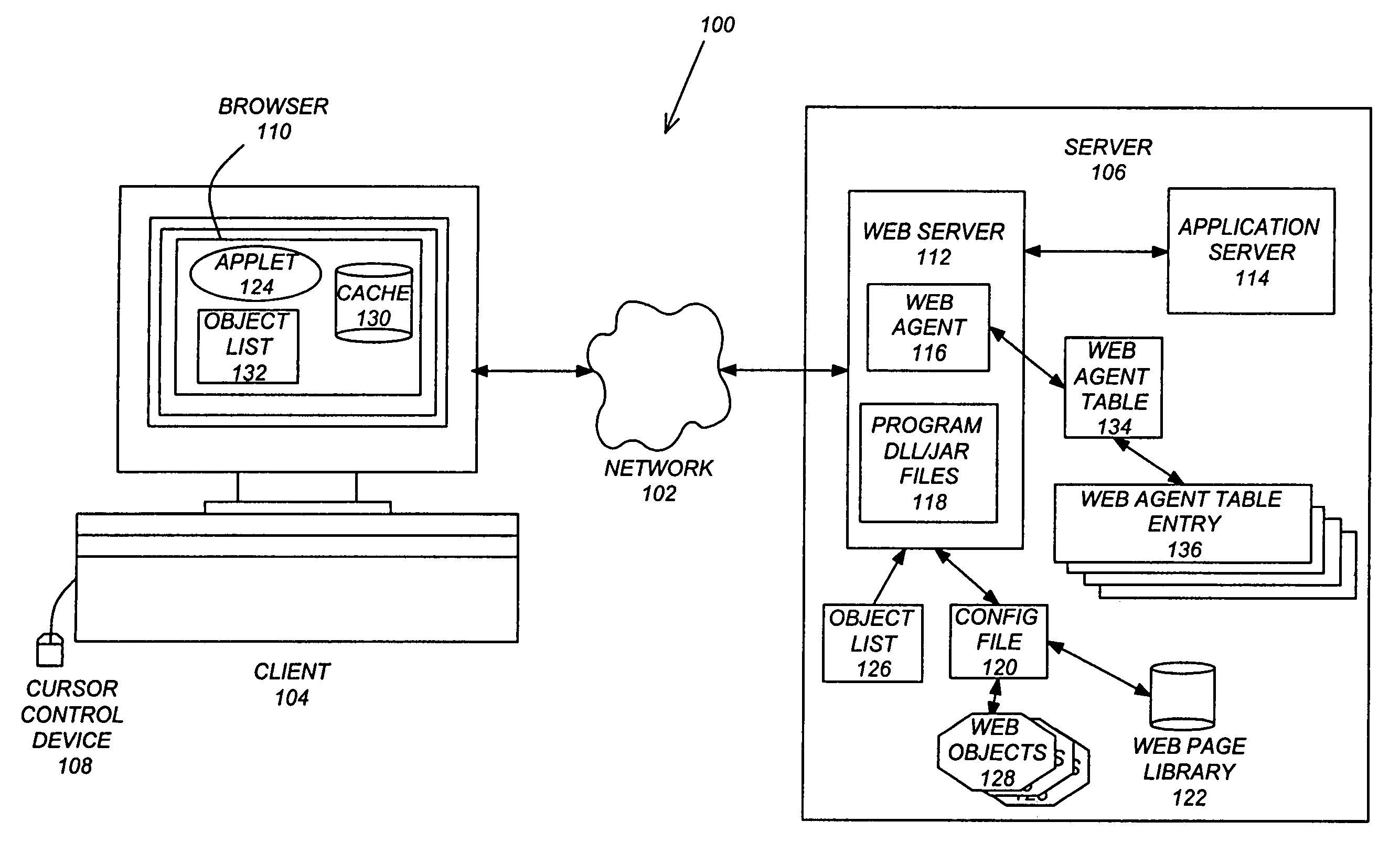
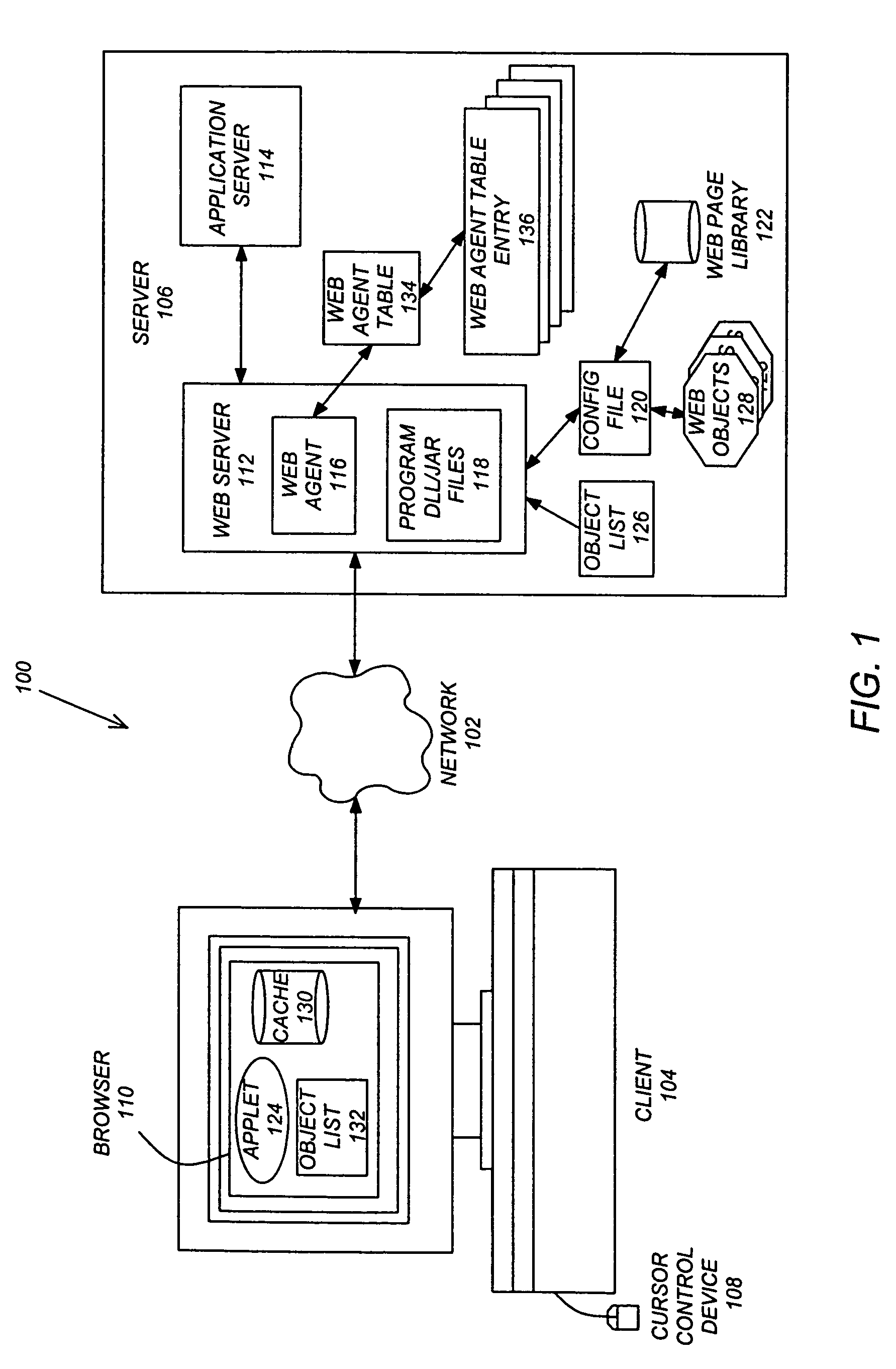
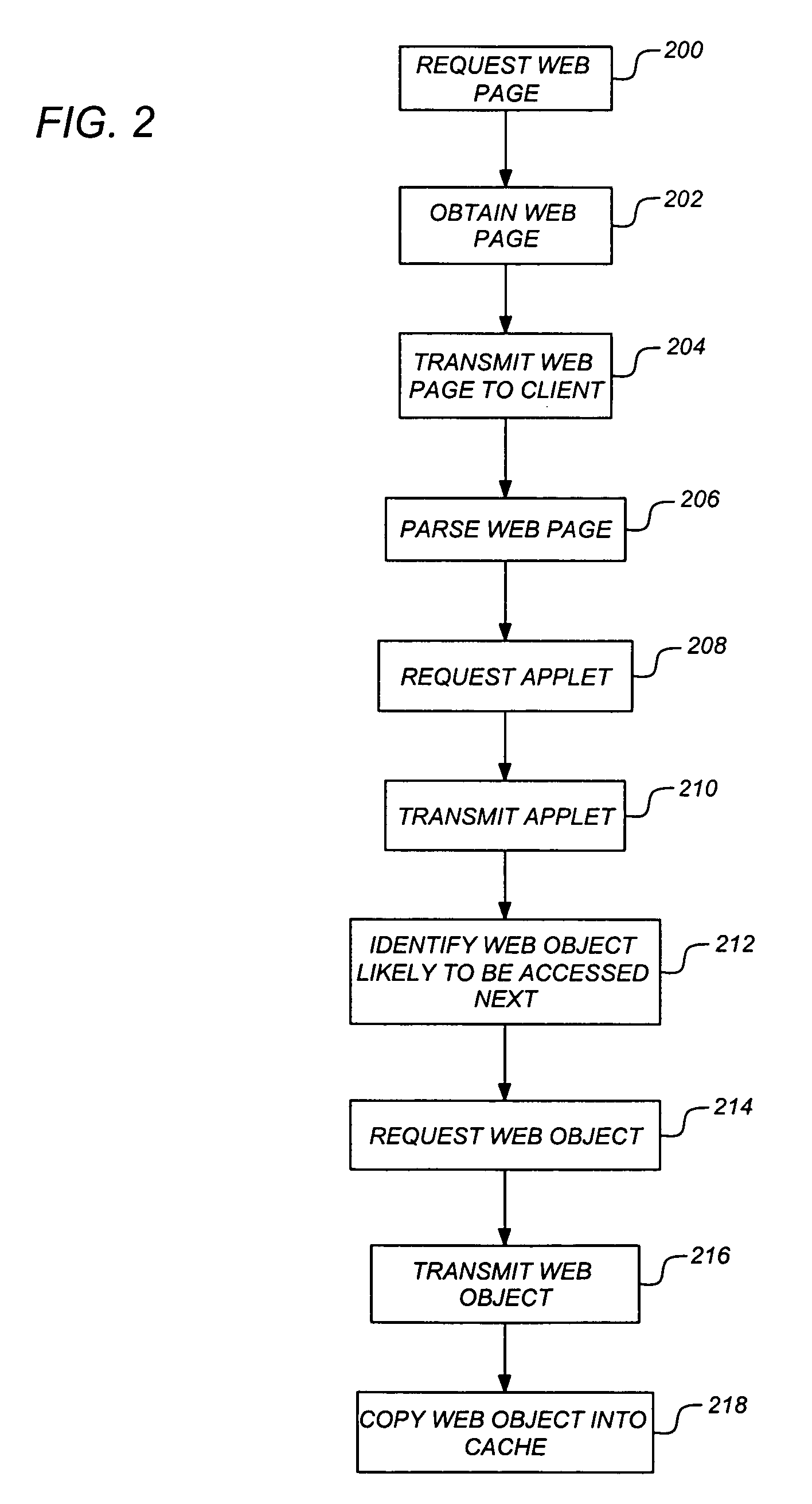
InactiveUS7047485B1Easy accessAmount of computer being consumedDigital data information retrievalSpecial data processing applicationsComputer resourcesWeb browser
A Fast method of retrieving Internet web pages based on pre-caching of web pages and their objects. Access by web browsers to these objects are faster since the objects are available in the web browser's local memory cache in advance of actually needing them. Thus, when the web browser needs these objects, no network delays are experienced due to having to get them from the web server located some distance away over the Internet. In addition, a computer efficient method is provided that allows for the statistical selection of which objects to pre-cache. This pre-caching method avoids excessive pre-caching of objects that are statistically insignificant but costly in their use of computer resources. Thus, with pre-caching only the objects most likely to be used in subsequent web browser interactions will take up the computer resources in the pre-caching process. A partial-intelligent method is also provided that allows for fast retrieval of complete web pages and their objects when statistical selection of objects can not be provided. In this method, all web page objects that makeup the web pages are pre-cached without consequence of their significance to subsequent web browser interactions. With partial-intelligent pre-caching, all web page objects have equal significance and all objects are pre-cached. Thus, making access to subsequent web pages very fast at the expense of not optimizing computer resource utilization.
Owner:IBM CORP
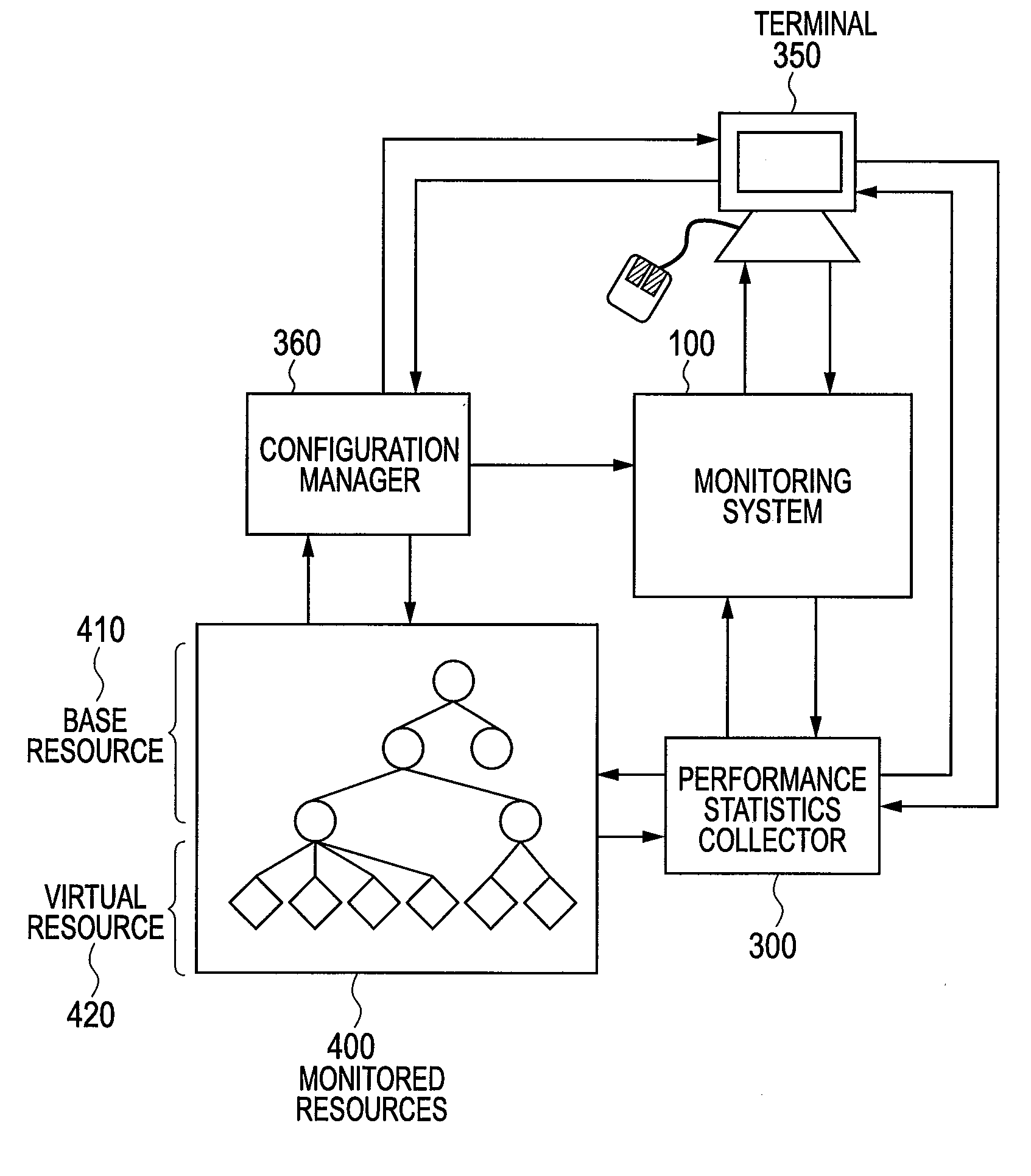
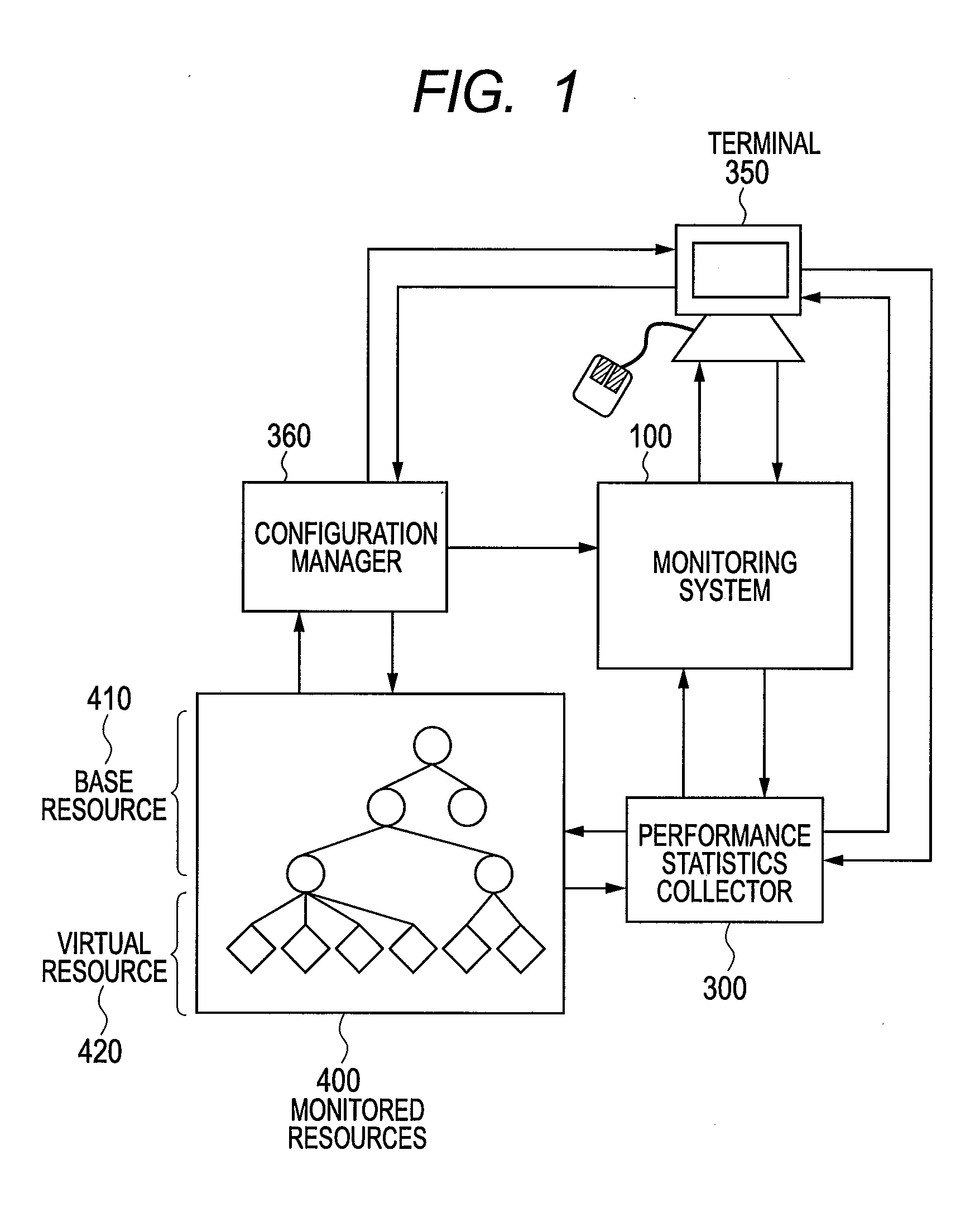
Monitoring system of computer and monitoring method
InactiveUS20120117226A1Low costEasy to analyzeDigital computer detailsProgram controlVirtualizationComputer resources
There is provided a monitoring system capable of representing relationships of computer resources that virtual servers use in a tree structure and aggregating the performance statistics of the virtual resources sharing physical resources. The monitoring system has: a virtualization module that makes virtual computers operate; and a monitoring module for monitoring the physical computers and components of the virtual computers. The monitoring module designates the physical computer and the components of the virtualizing module as base resources, manages the components of the virtual computers as virtual resources, generates a platform tree by extracting a tree structure from the virtual resources and the components of the base resources for predetermined platforms, generates a service provision tree by extracting a tree structure having the base or virtual resources as starting points, and establishes a reference relationship for the components contained in the platform tree and also contained in the service provision tree.
Owner:HITACHI LTD
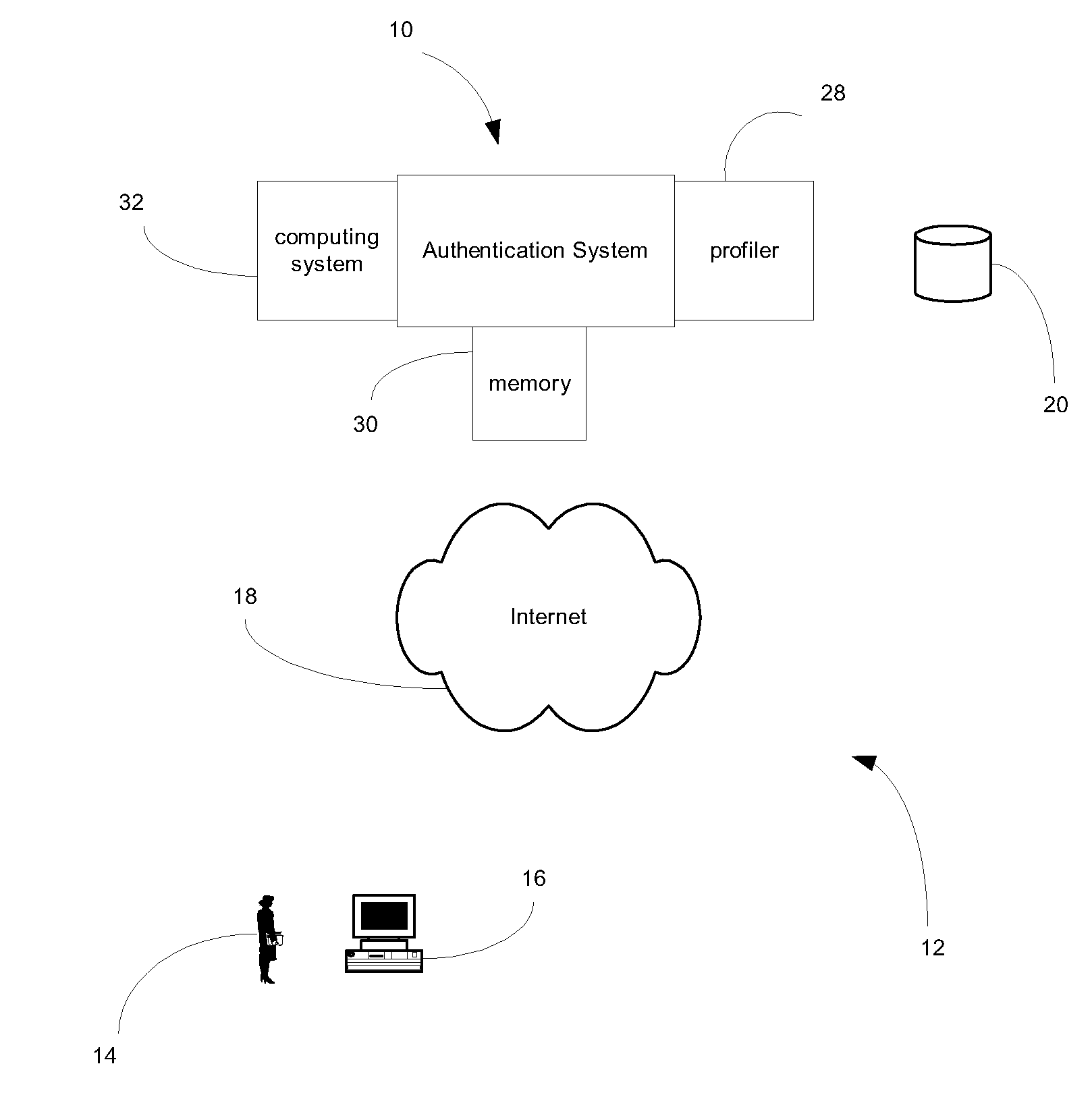
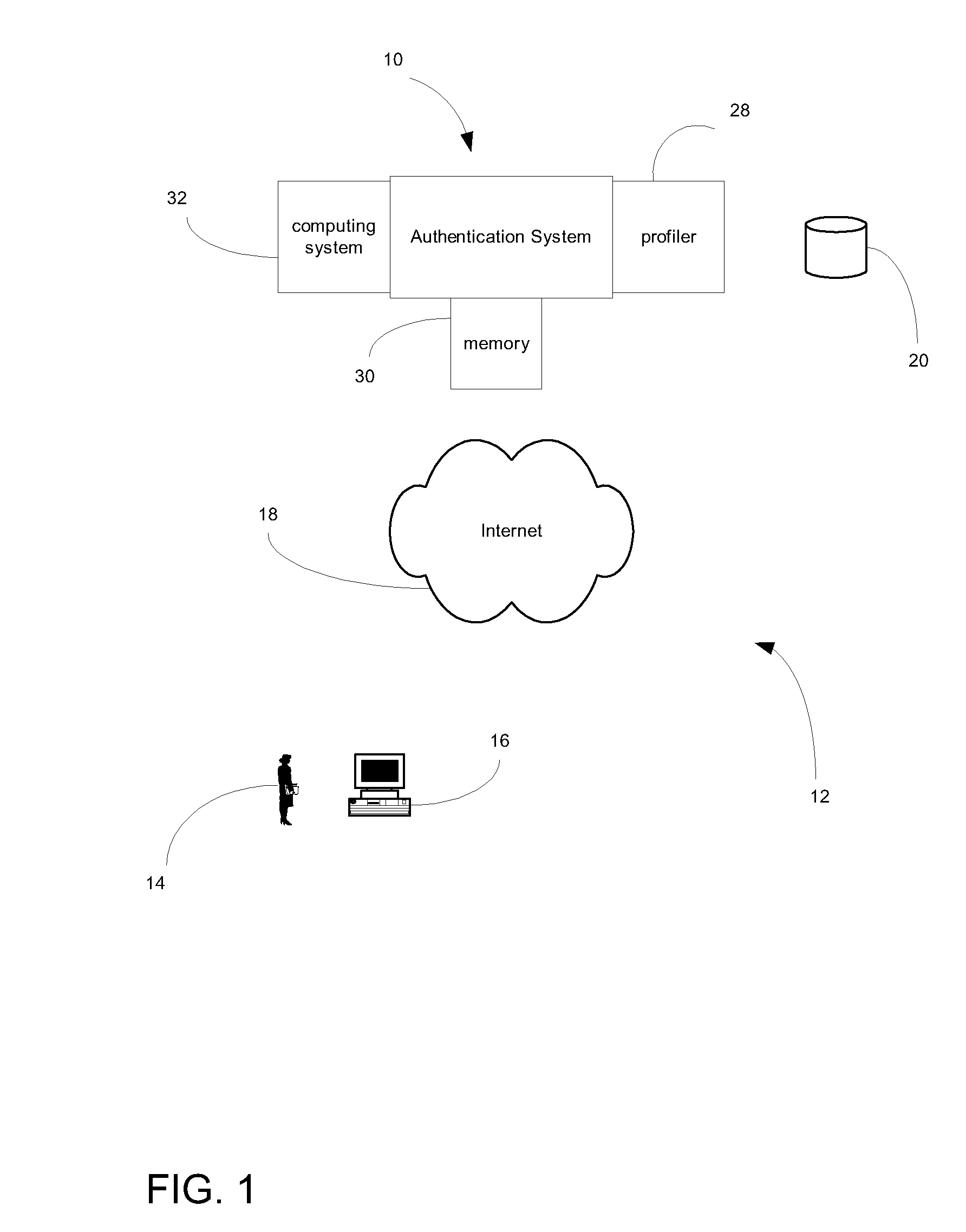
User-centric authentication system and method
ActiveUS20090037983A1Difficult to answerGood degreeDigital data processing detailsAnalogue secracy/subscription systemsComputer resourcesCorrect response
A system for authenticating a user in a network. The authentication system includes a computer resource having secure data, an authentication computing system providing dynamic authentication of a user accessing the computer resource, and a user communication device for communicating between the user and the computer resource. The computing system presents a challenge for which a specified response is required based upon a pre-determined function. Access is then granted by the computing system upon providing the correct response to the presented challenge by the user.
Owner:CHIRUVOLU GIRISH
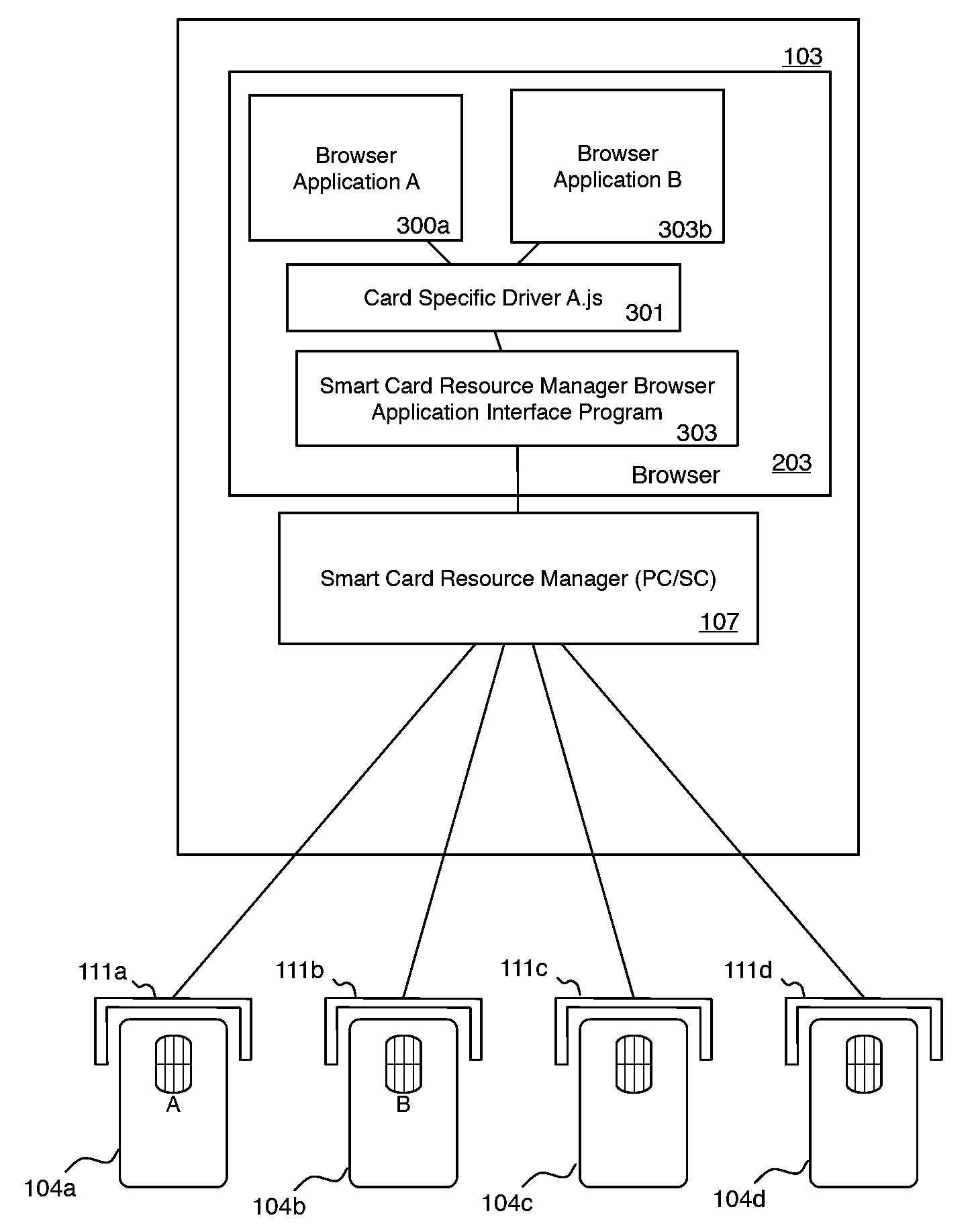
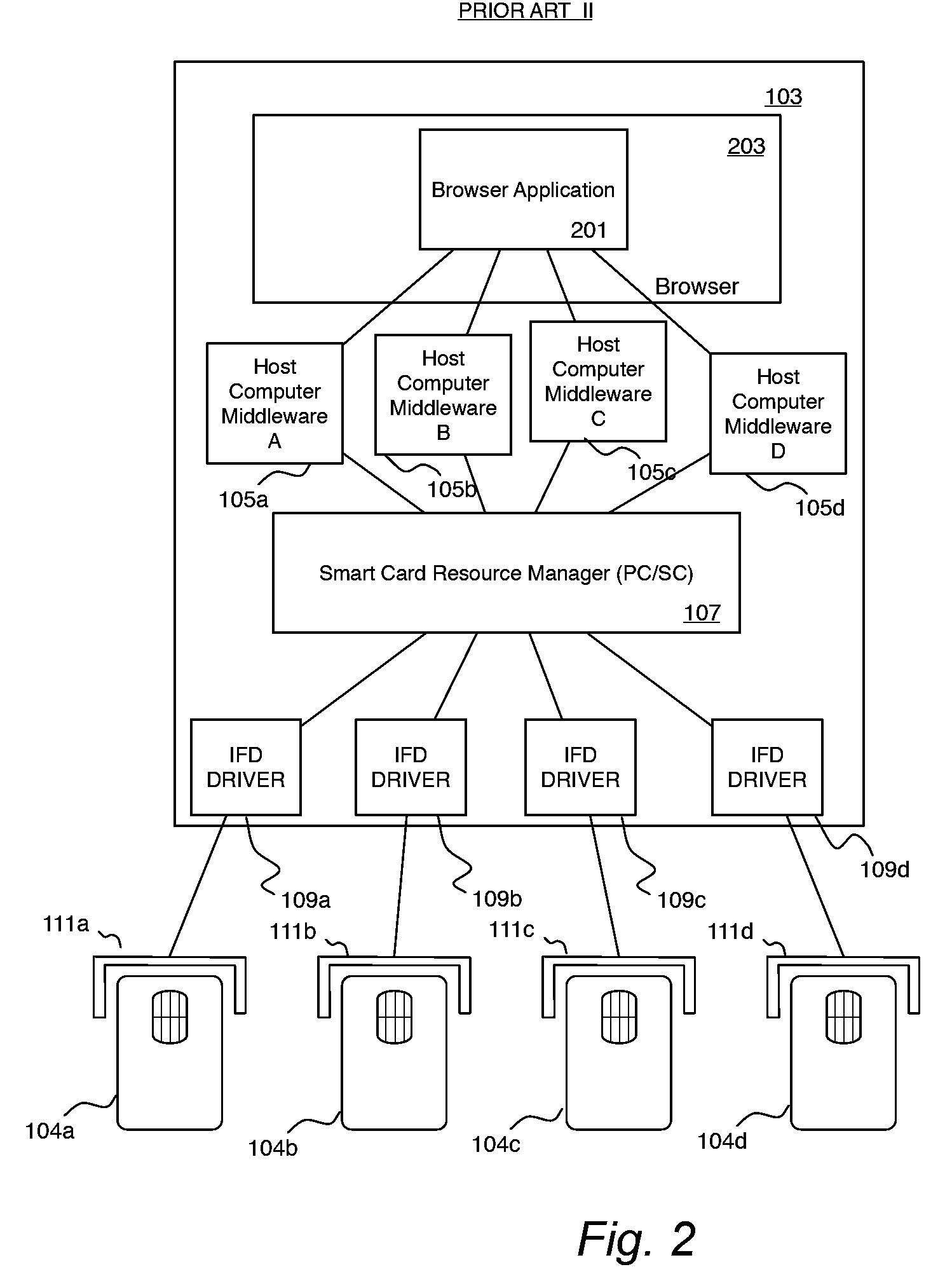
System and method for browser based access to smart cards
A client-side application extension executable on a host computer from within a web-browser having the capability of executing at least one web-browser add-on to provide a user access to a smart card, connected to the host computer having a smart card resource manager, via the web-browser. The web-browser extension has instructions to direct the central processing unit to access data on the smart card via a web-browser and platform independent interface module and a web-browser and platform dependent wrapper module connected to the web-browser and platform independent interface module and to the smart card resource manager having a function processing module operable to receive a call to the at least one function for accessing data on the smart card and for transforming the function call into a corresponding call to the smart card resource manager.
Owner:THALES DIS USA INC
Method of providing secure access to computer resources
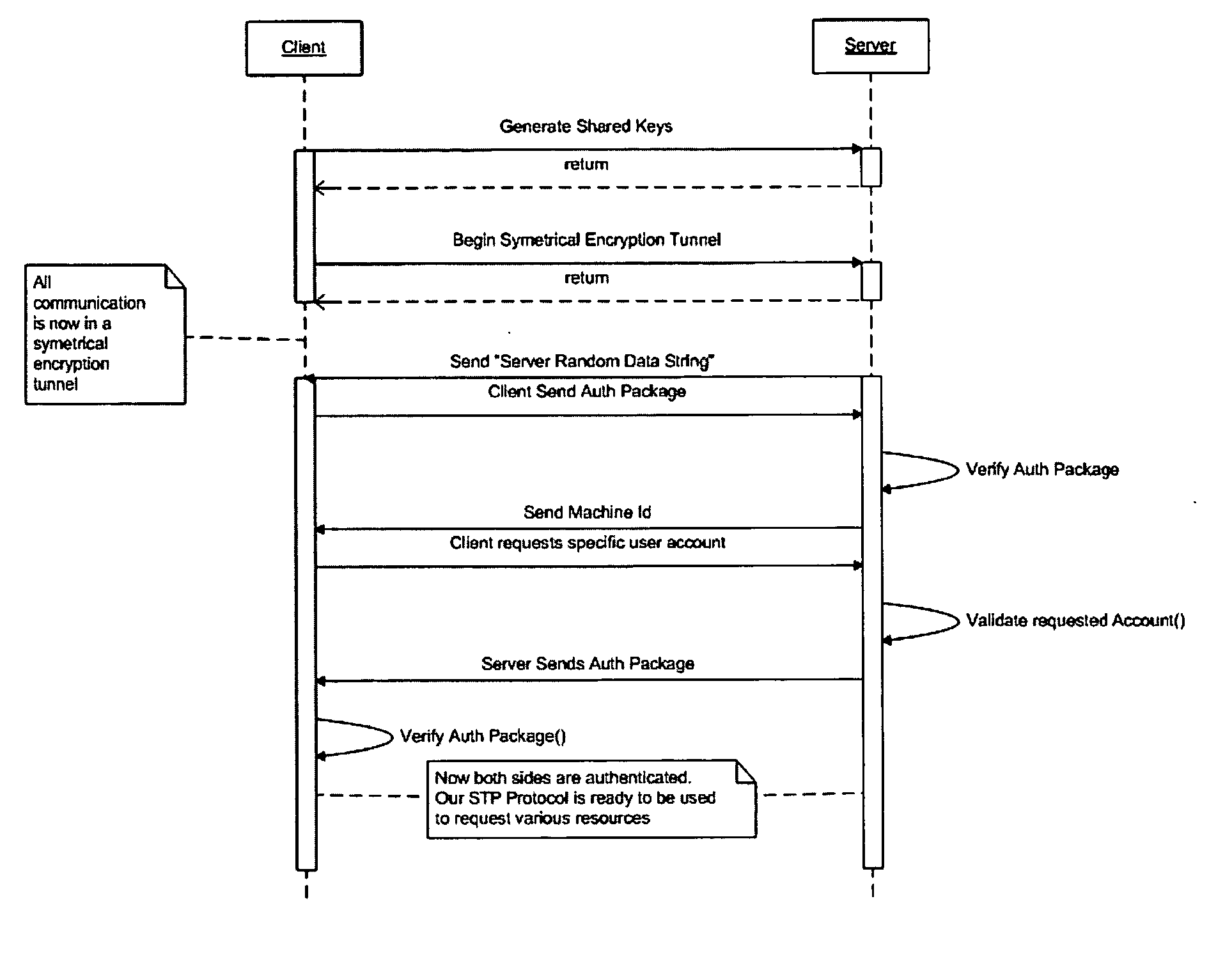
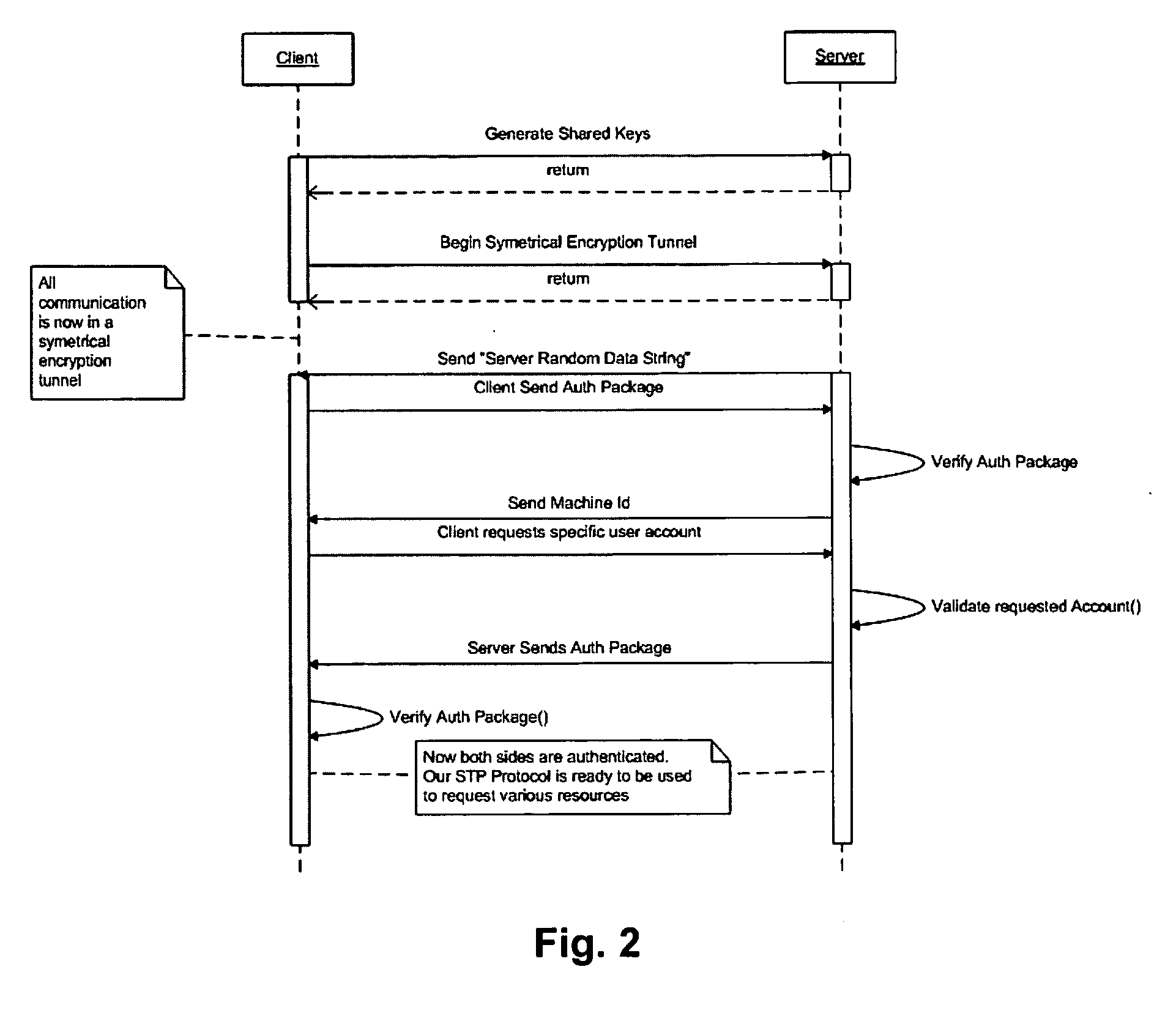
InactiveUS20070101400A1Easy accessLow level of trustDigital data processing detailsUser identity/authority verificationComputer resourcesTrusted authority
A method of providing varying levels of secure access to computer resources. A certificate is used to identify a particular data requester and the certificate is authenticated using asymmetrical encryption techniques, such as public-private key pairs. One or more trust authorities may be consulted to ascribe a trust level to the certificate, which is an indication of the veracity of the identity of the data requester. Individual system users may set differing levels of access to a number of shared system resources for a particular data requester. The authenticated and verified data requester is then provided with the pre-set level of access to the desired shared resource. The level of access to a particular shared system resource therefore depends upon the user the data is being accessed through, the authenticated identity of the data requester, and their ascribed trust level. The shared resource may comprise data and / or an application module that is accessed or executed through a secure symmetric encryption tunnel.
Owner:OVERCOW CORP
System and method for application performance management
ActiveUS20030009507A1General purpose stored program computerHardware monitoringComputer resourcesApplication software
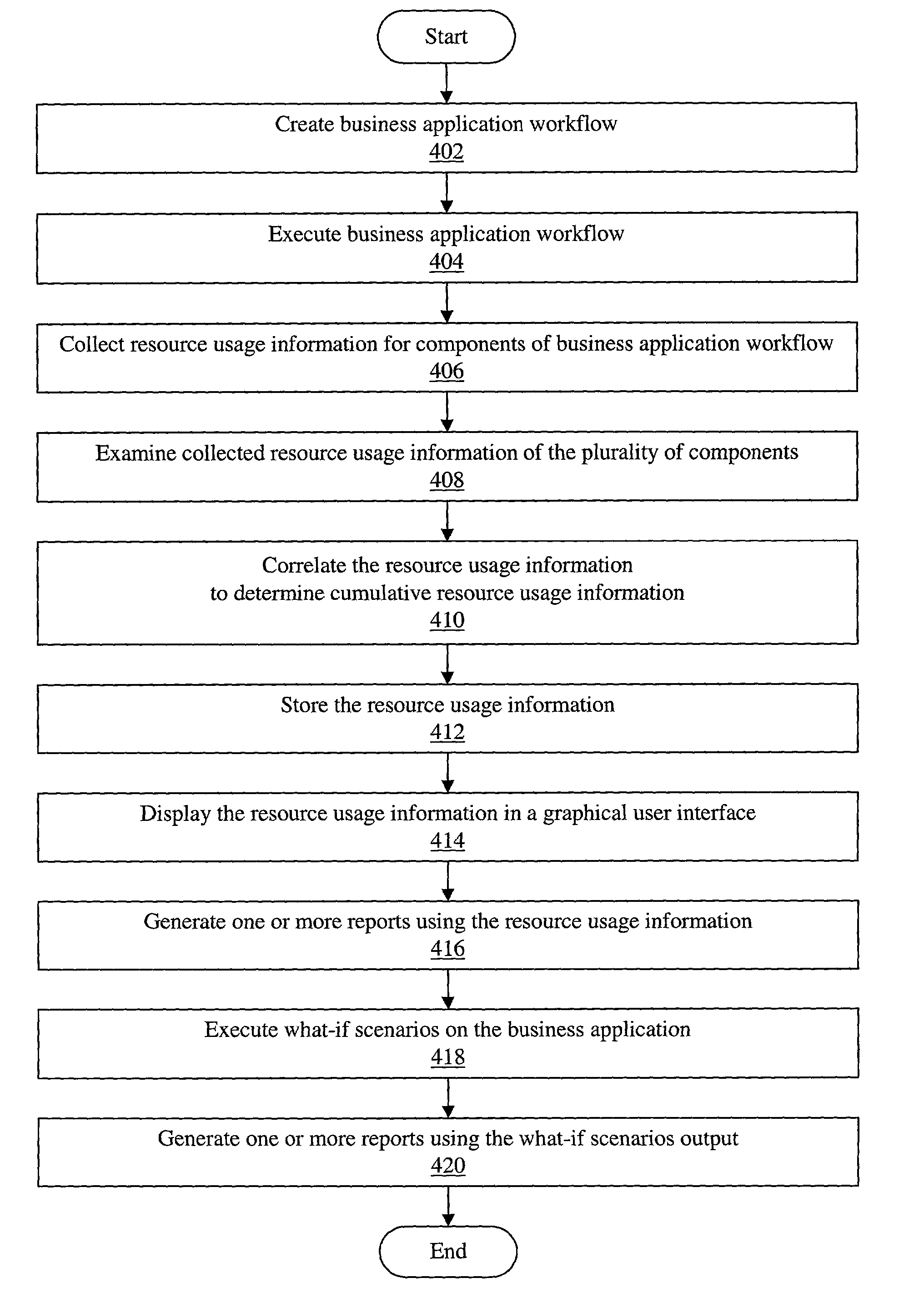
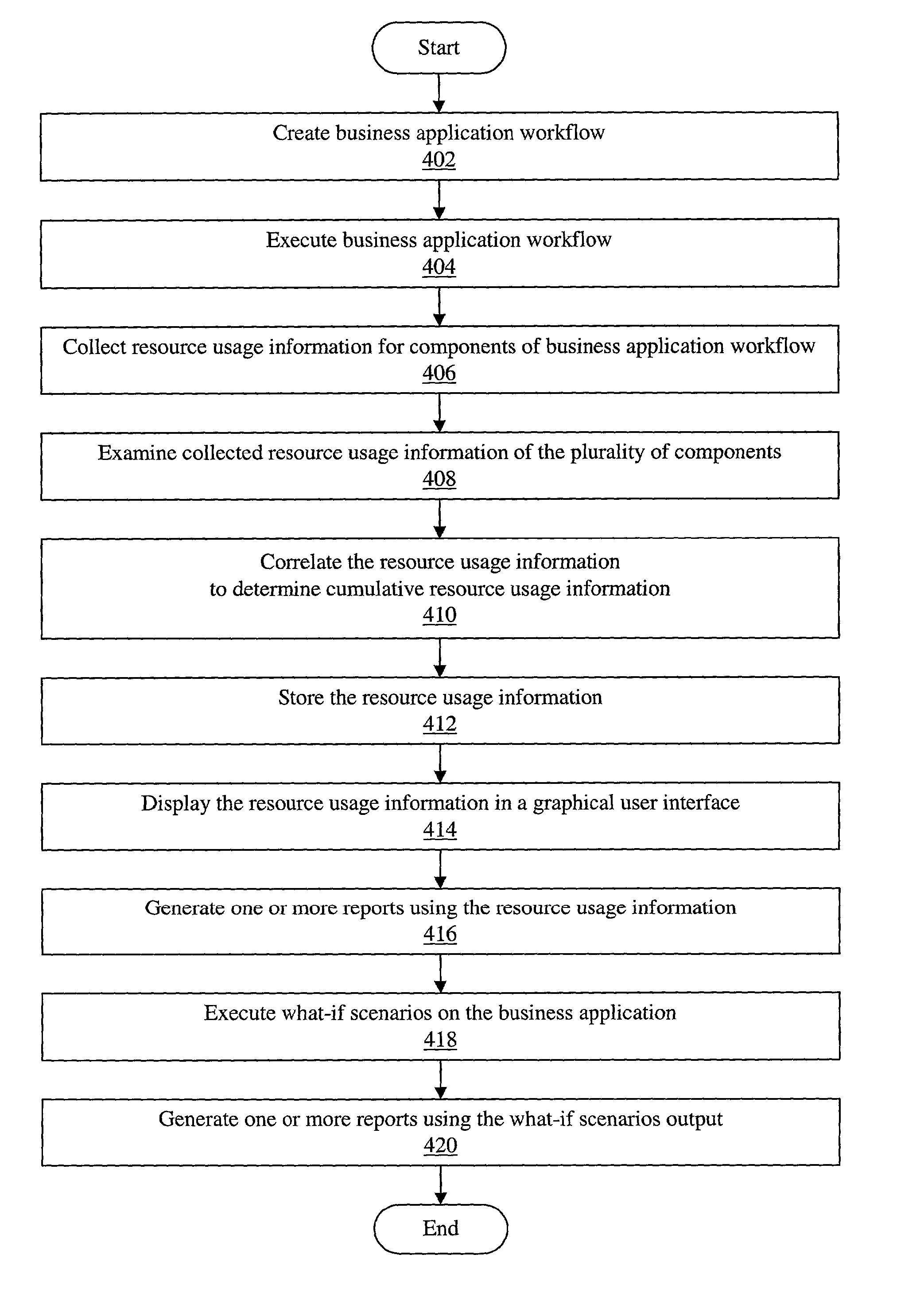
An improved method and system for complex and integrated application performance management which tracks end-to-end computer resource consumption of a first business application workflow in an enterprise system. The first business application workflow may include a plurality of components. The plurality of components may further include one or more component types. A second or subsequent business application workflow may be embedded or linked as a component of the first business application workflow. Resource usage information of the plurality of components (including resource usage information of underlying units of work of the plurality of components) may be correlated to determine cumulative resource usage information for the first business application workflow. The resource usage information may be displayed in a graphical user interface. User input may be received indicating one or more of the following for the first business application workflow: an application name, a natural business unit, and a mission-critical ranking.
Owner:BMC SOFTWARE
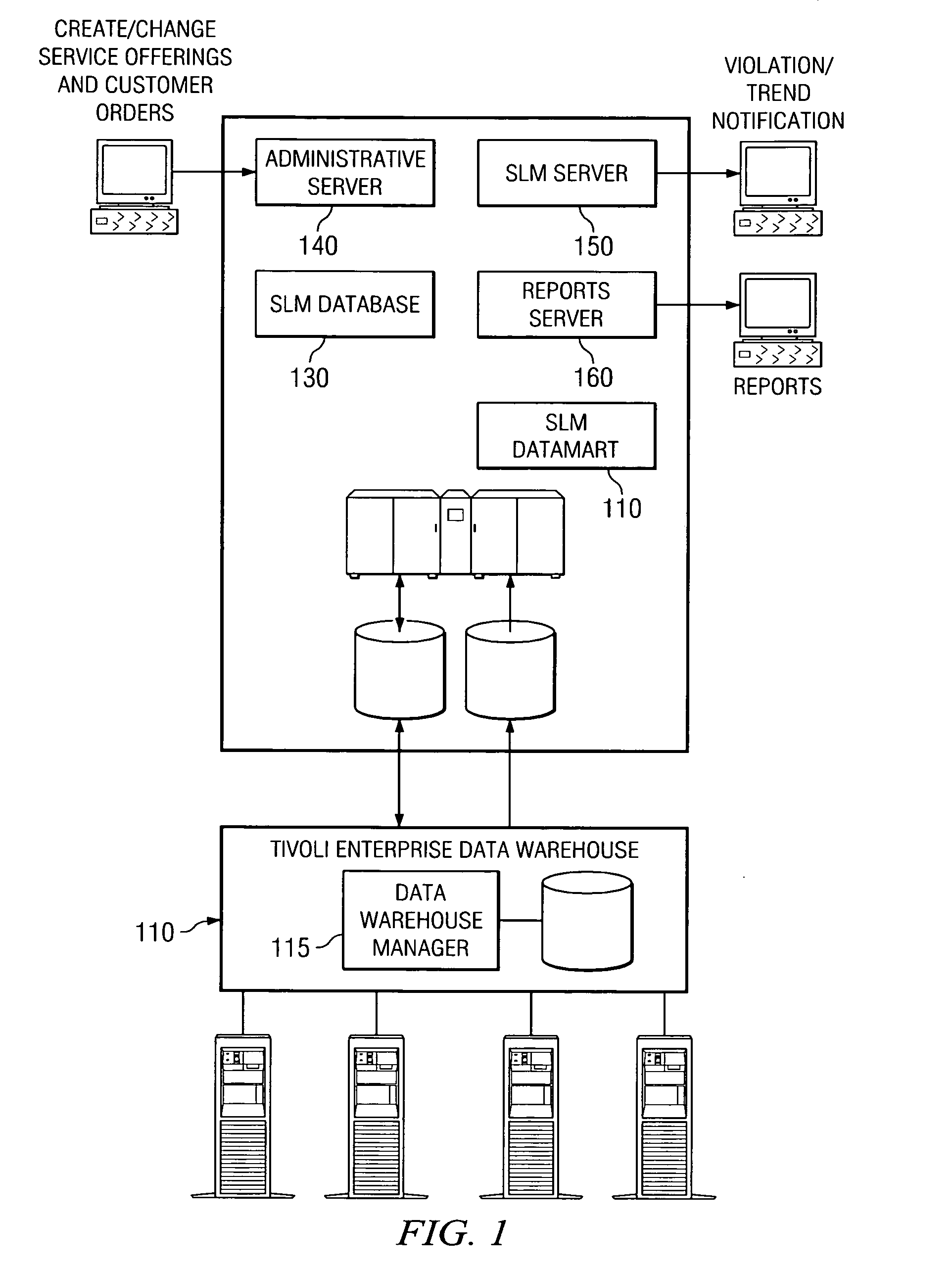
Apparatus and method for allocating resources based on service level agreement predictions and associated costs
ActiveUS20050256946A1Low costEasy maintenanceSpecial service provision for substationDigital computer detailsService-level agreementComputer resources
A method, apparatus, and computer instructions for allocating resources based on predictions of service level agreement (SLA) breaches in order to minimize costs are provided. With the method, apparatus, and computer instructions, a prediction that an SLA will be breached is received from a prediction engine associated with the SLM system. Based on a prediction that an SLA will be breached, a minimum cost analysis is performed to determine if computer resources may be shifted from another service consumer under another SLA to facilitate the service consumer of the potentially breached SLA in order to reduce the cost of the penalty associated with breaching SLAs. If so, resources are reallocated in order to minimize penalties associated with SLA breaches.
Owner:SERVICENOW INC
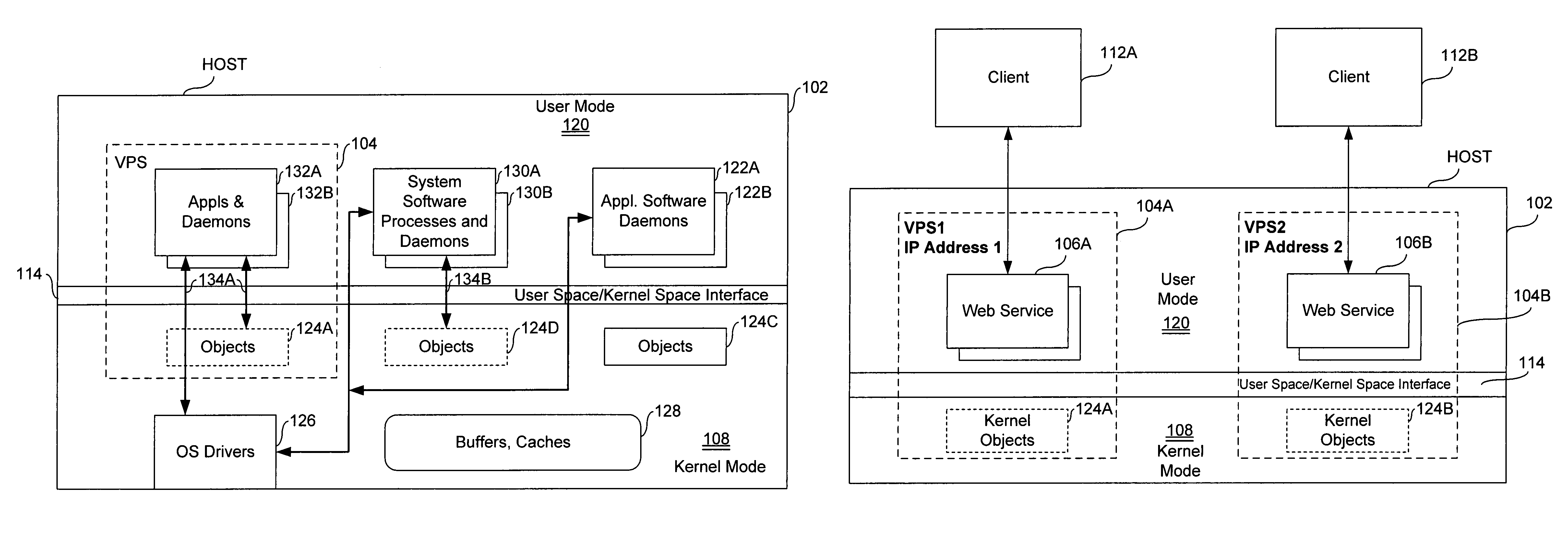
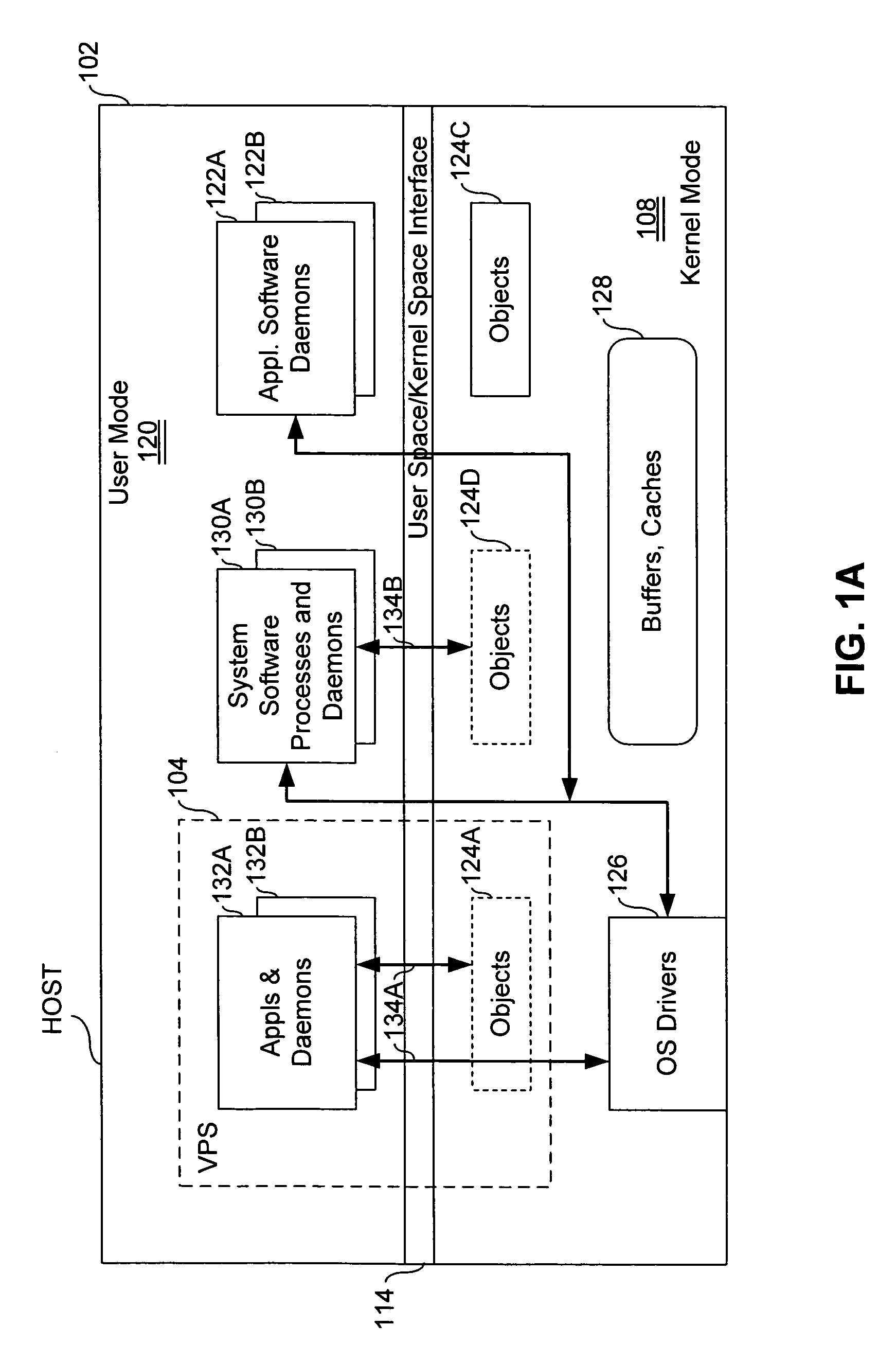
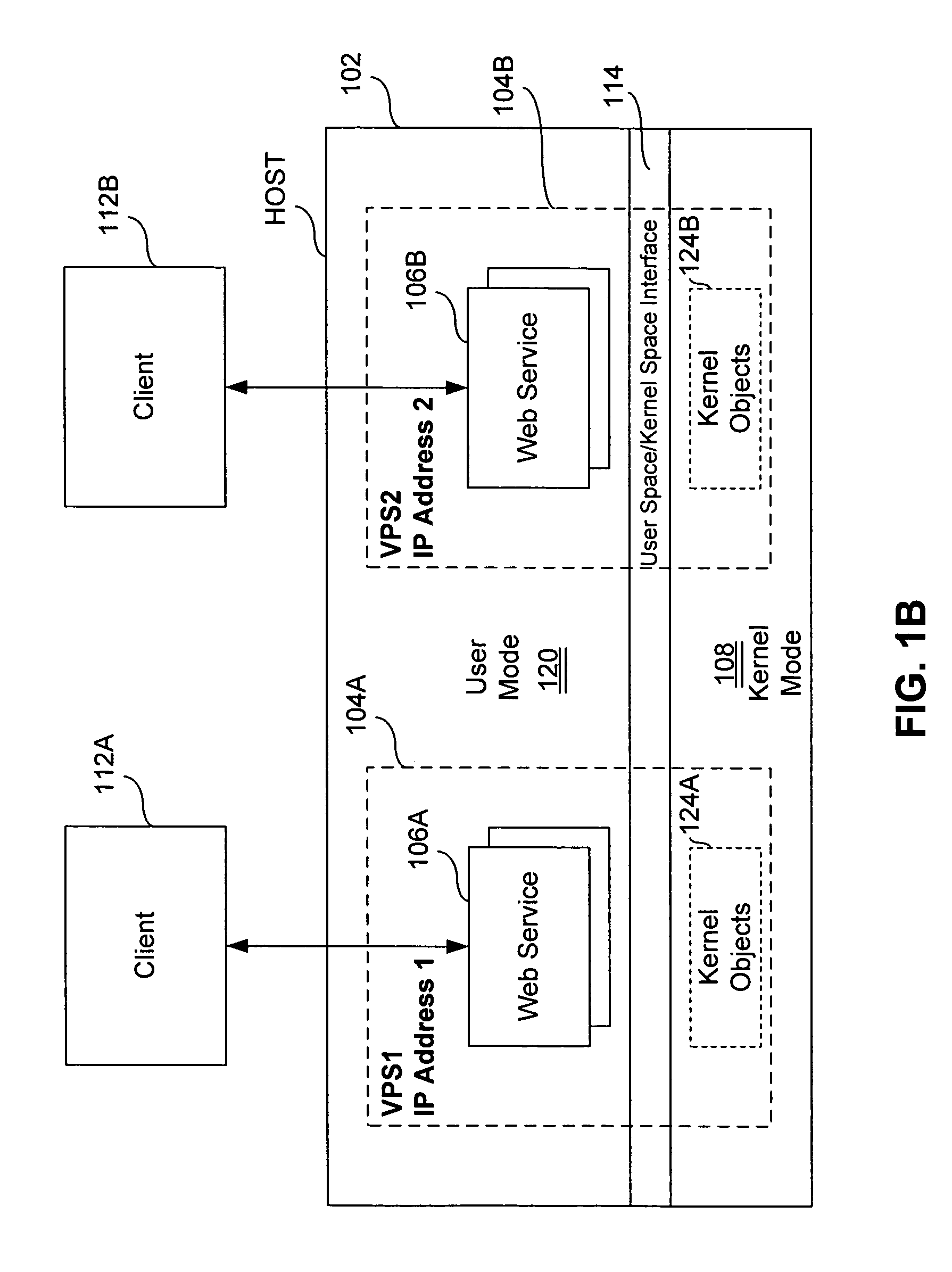
Virtual private server with enhanced security
ActiveUS7461144B1Improve securityData processing applicationsDigital computer detailsComputer resourcesOperational system
An end user computer includes a processor running an operating system. A plurality of virtual private servers (VPSs) are supported within the operating system. A plurality of applications are available to a user of the end user computer. The applications are launched within different VPSs. At least one of the VPSs has multiple applications launched within it. At least two of the applications are launched within different VPSs, and communicate with each other using secure communications means, such as firewalls, proxies, dedicated clipboards, named pipes, shared memory, dedicated inter-process communications, Local Procedure Calls / Remote Procedure Calls, API, network sockets, TCP / IP communications, network protocol communications and memory mapped files. The VPSs can be dynamically created and terminated. VPS control means are available to the user and include means for creation / termination of VPSs, a file system and registry backup, control information for backup / restore of data on a VPS level, placement of applications / processes rules for creation / support of corresponding VPSs, granulation of isolation for VPS / applications / processes, computer resource control, definition of permissible operations for inter-VPS communication, means for definition of permissible operations for inter-process communications.
Owner:VIRTUOZZO INT GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com