Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58results about "Mosaic printer telegraph system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
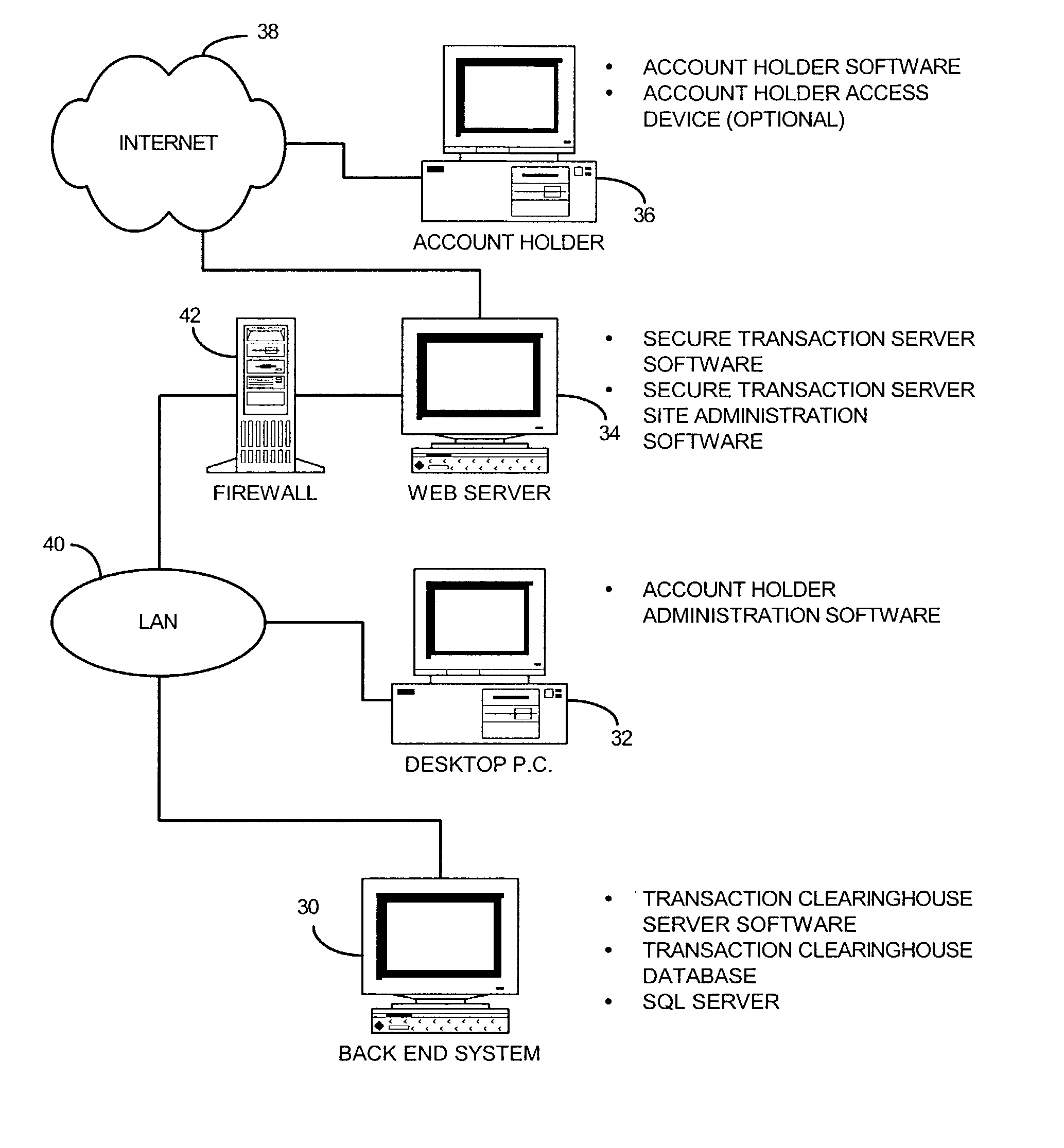
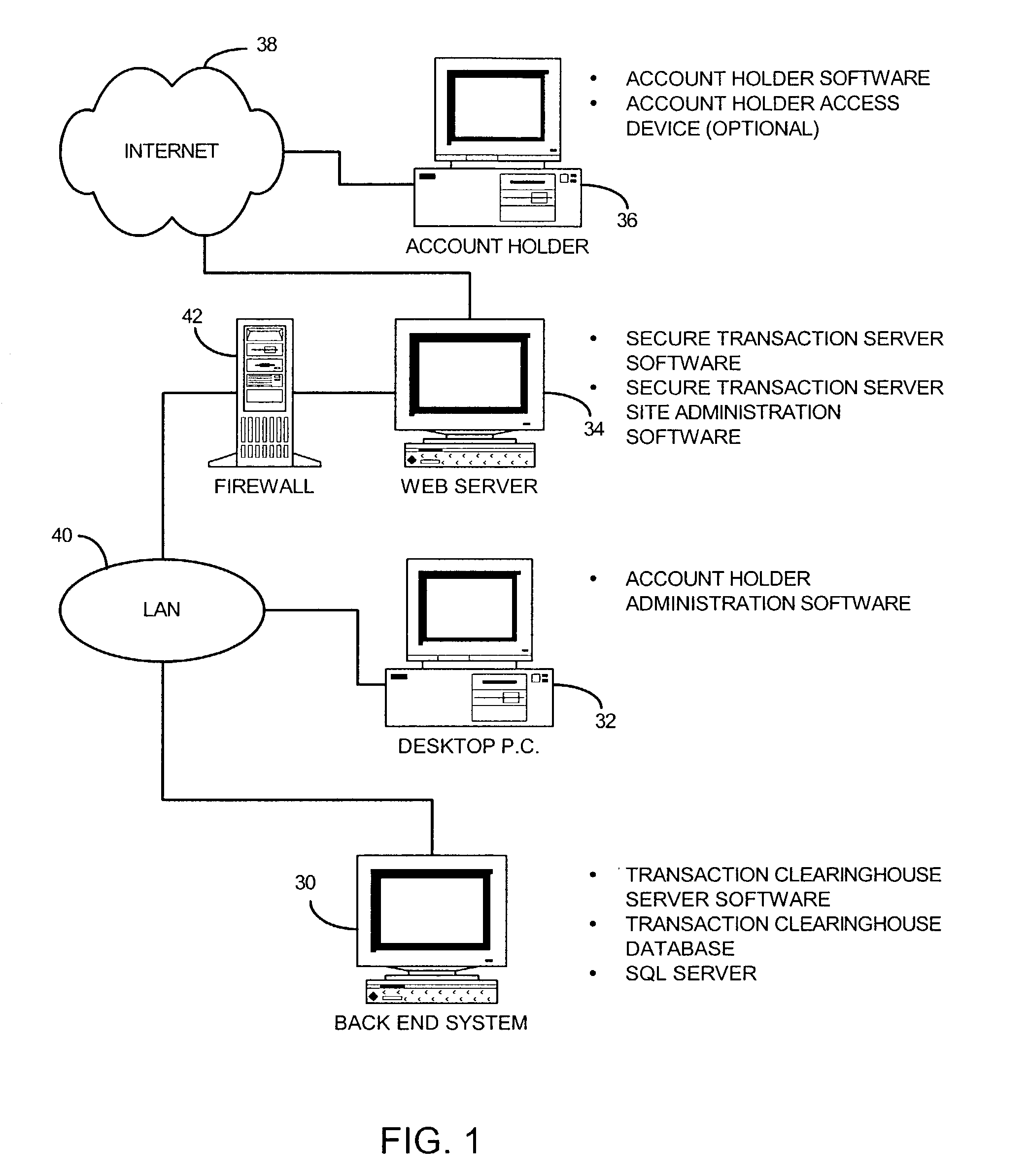
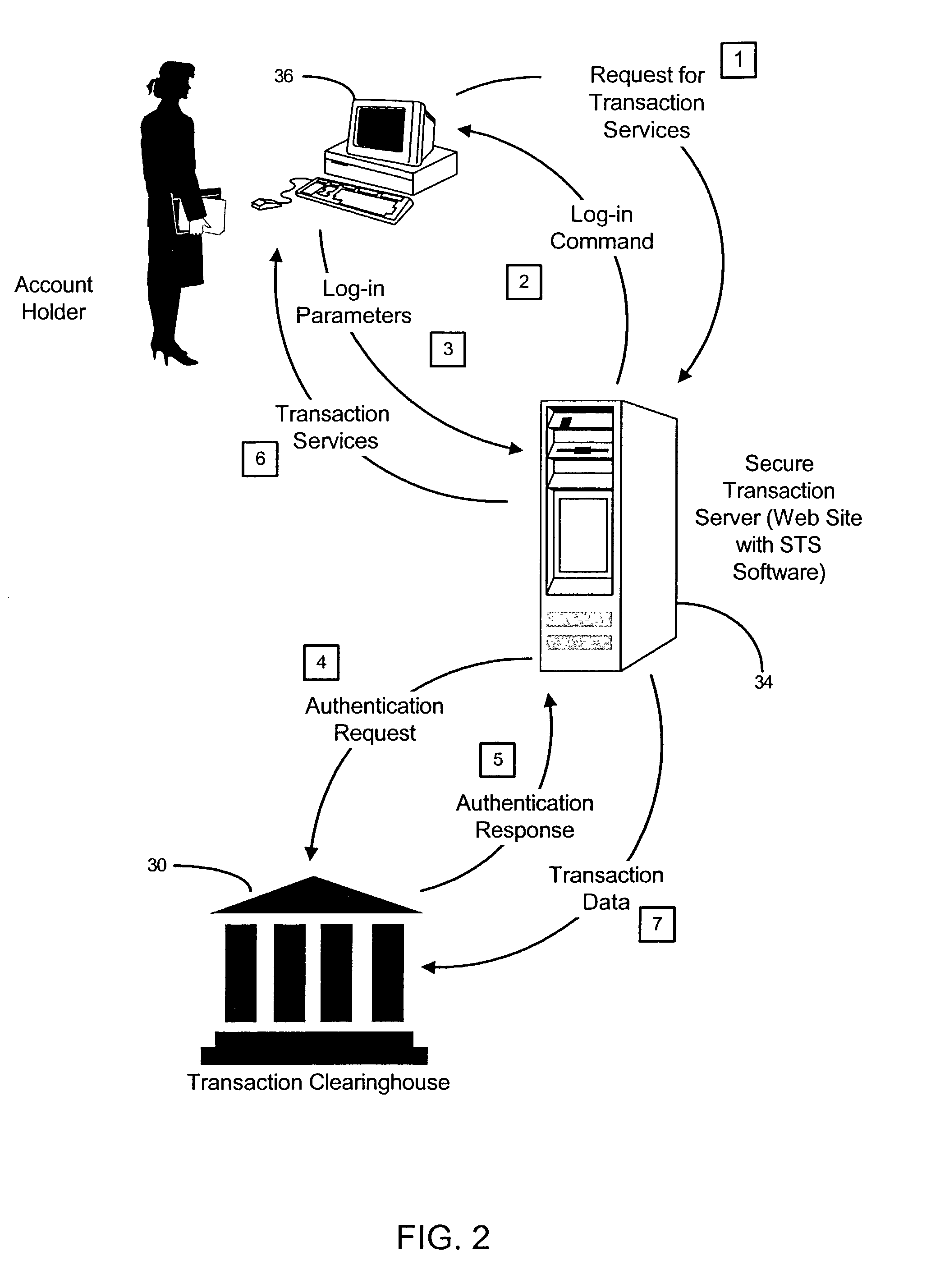
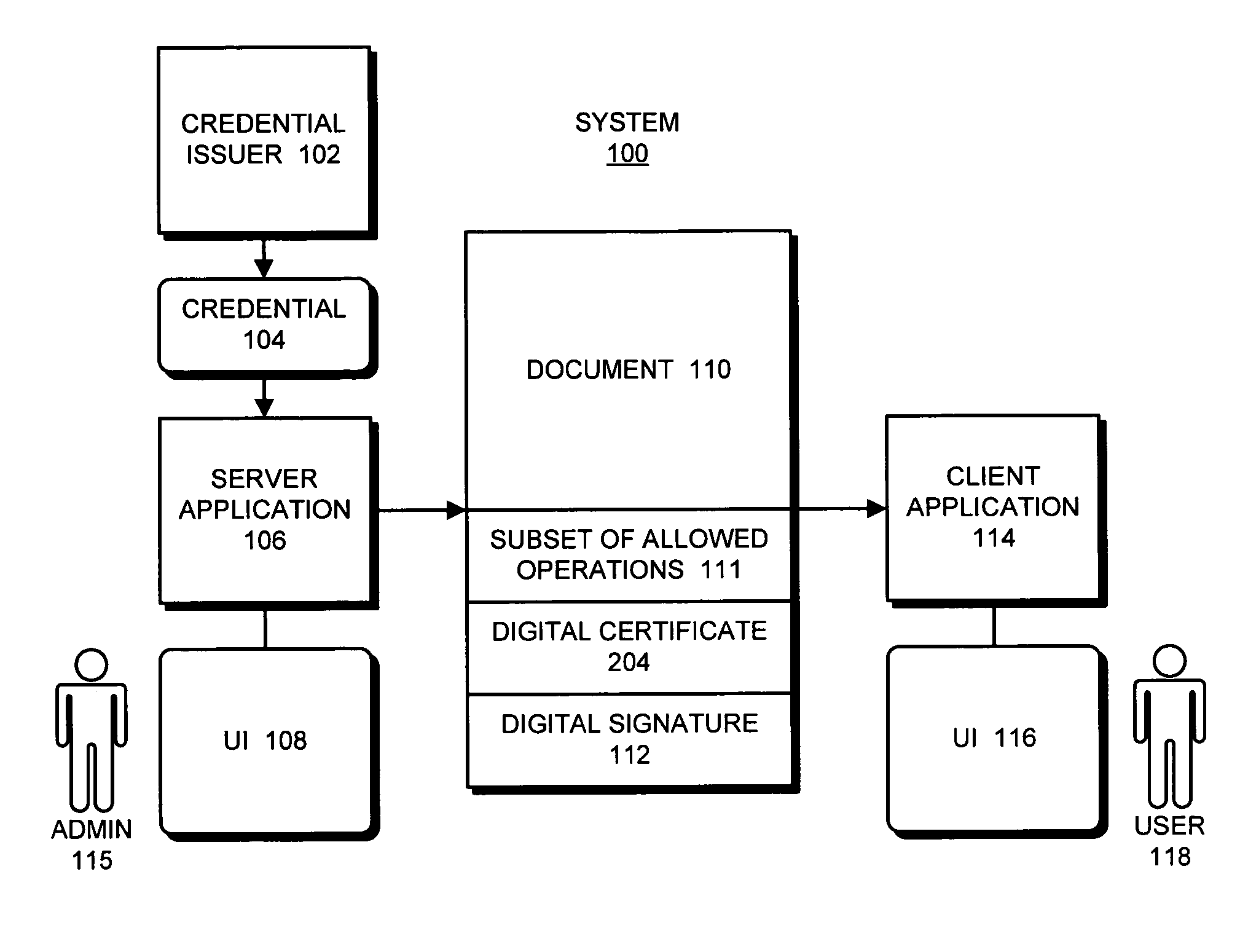
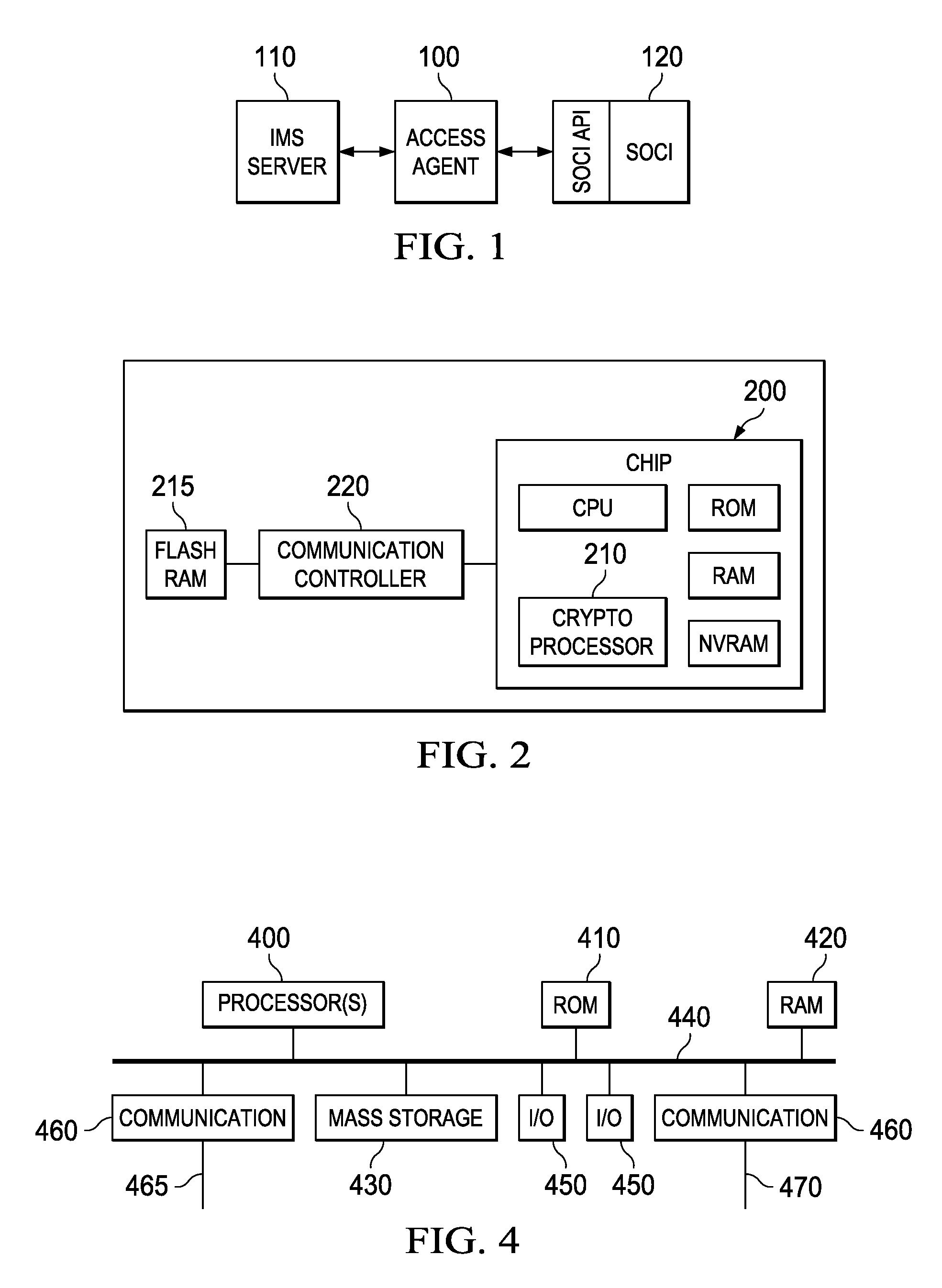
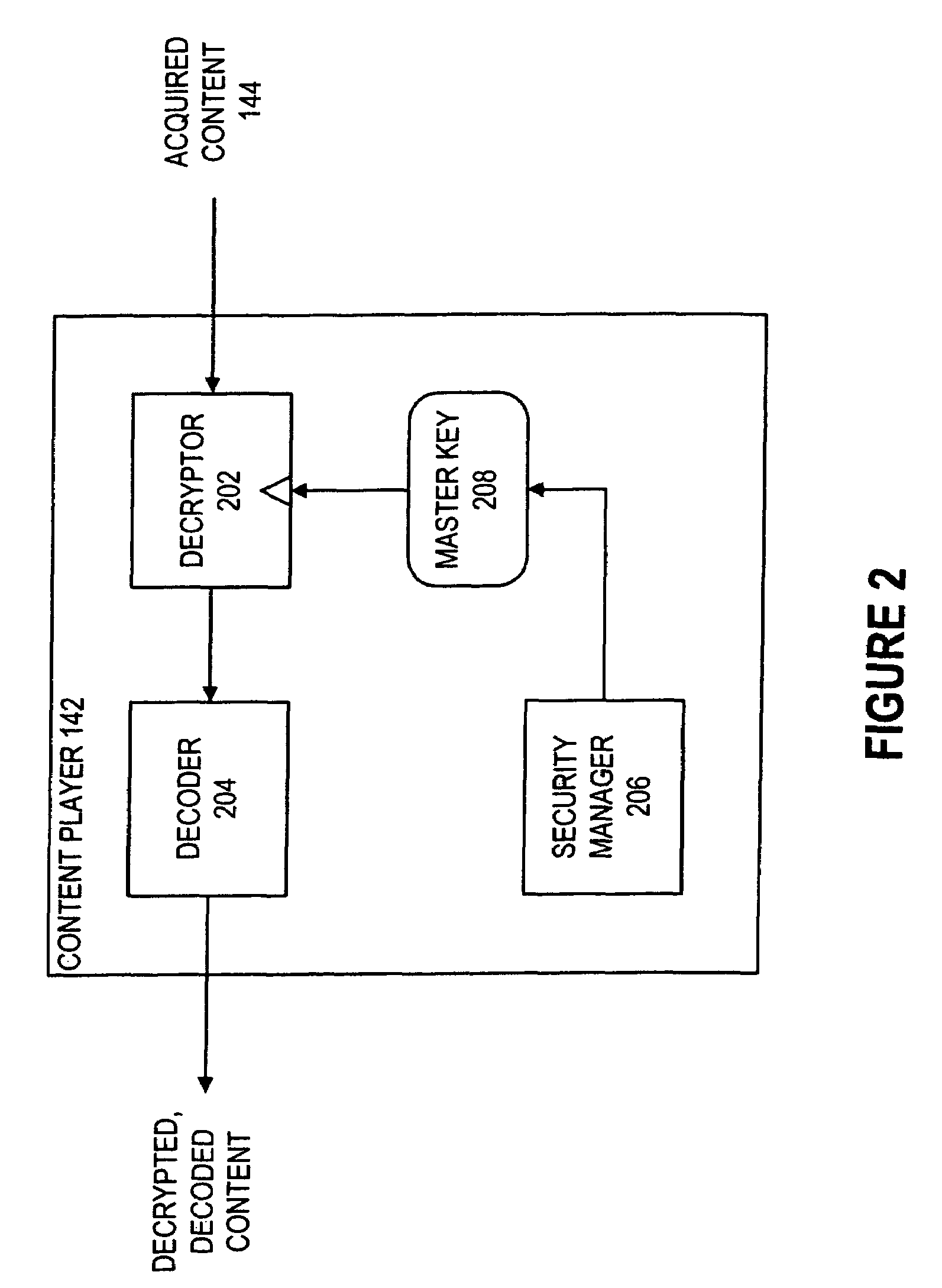
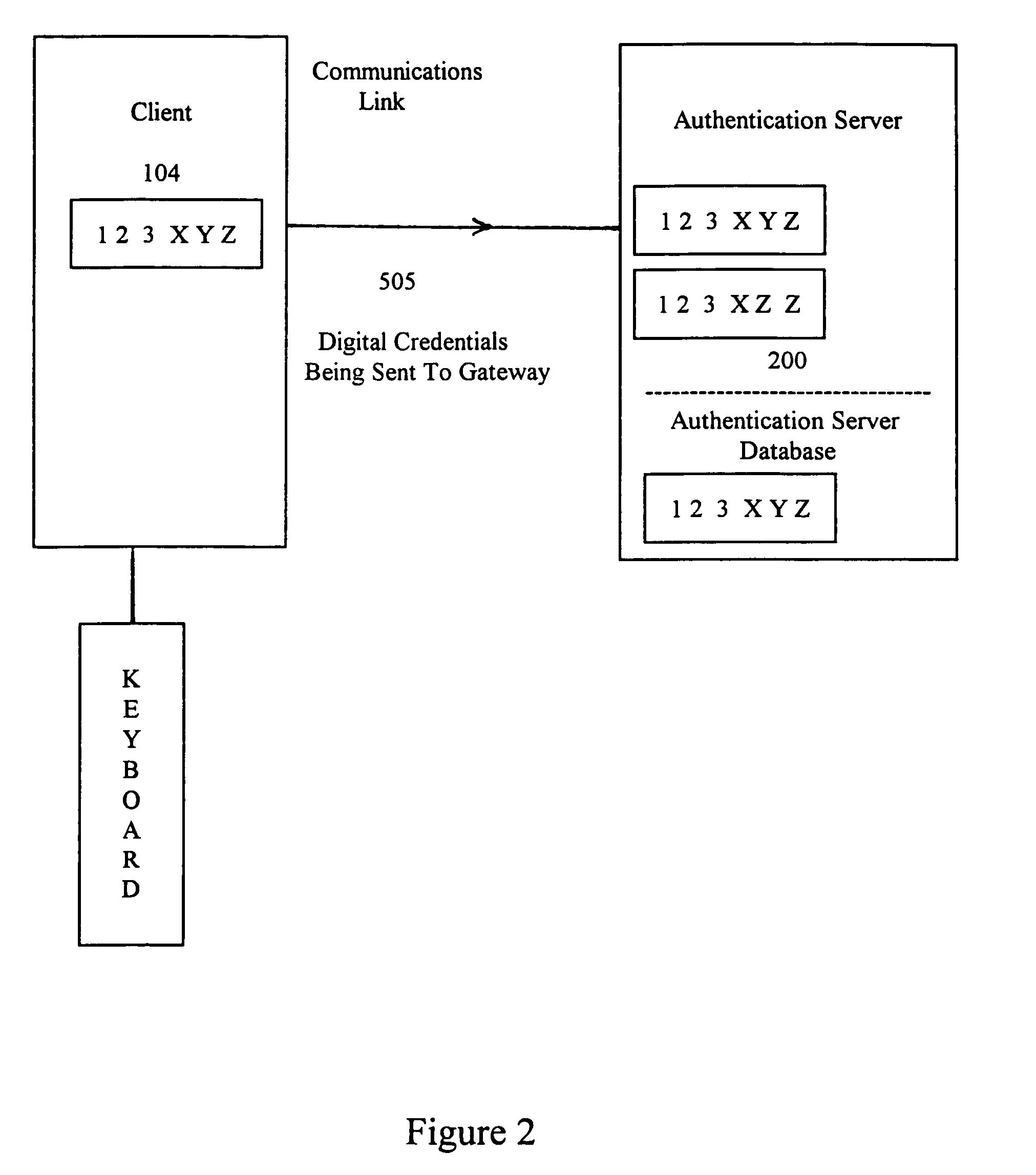
Method and system for controlling access, by an authentication server, to protected computer resources provided via an internet protocol network
InactiveUS7290288B2Mosaic printer telegraph systemDigital data processing detailsComputer resourcesThe Internet
A method and system for controlling access, by an authentication server, to protected computer resources provided via an Internet Protocol network that includes storing (i) a digital identification associated with at least one client computer device, and (ii) data associated with the protected computer resources in at least one database associated with the authentication server; authenticating, by the authentication server, the digital identification forwarded by at least one access server; authorizing, by the authentication server, the at least one client computer device to receive at least a portion of the protected computer resources requested by the at least one client computer device, based on the stored data associated with the requested protected computer resources; and permitting access, by the authentication server, to the at least the portion of the protected computer resources upon successfully authenticating the digital identification and upon successfully authorizing the at least once client computer device.
Owner:PRISM TECH
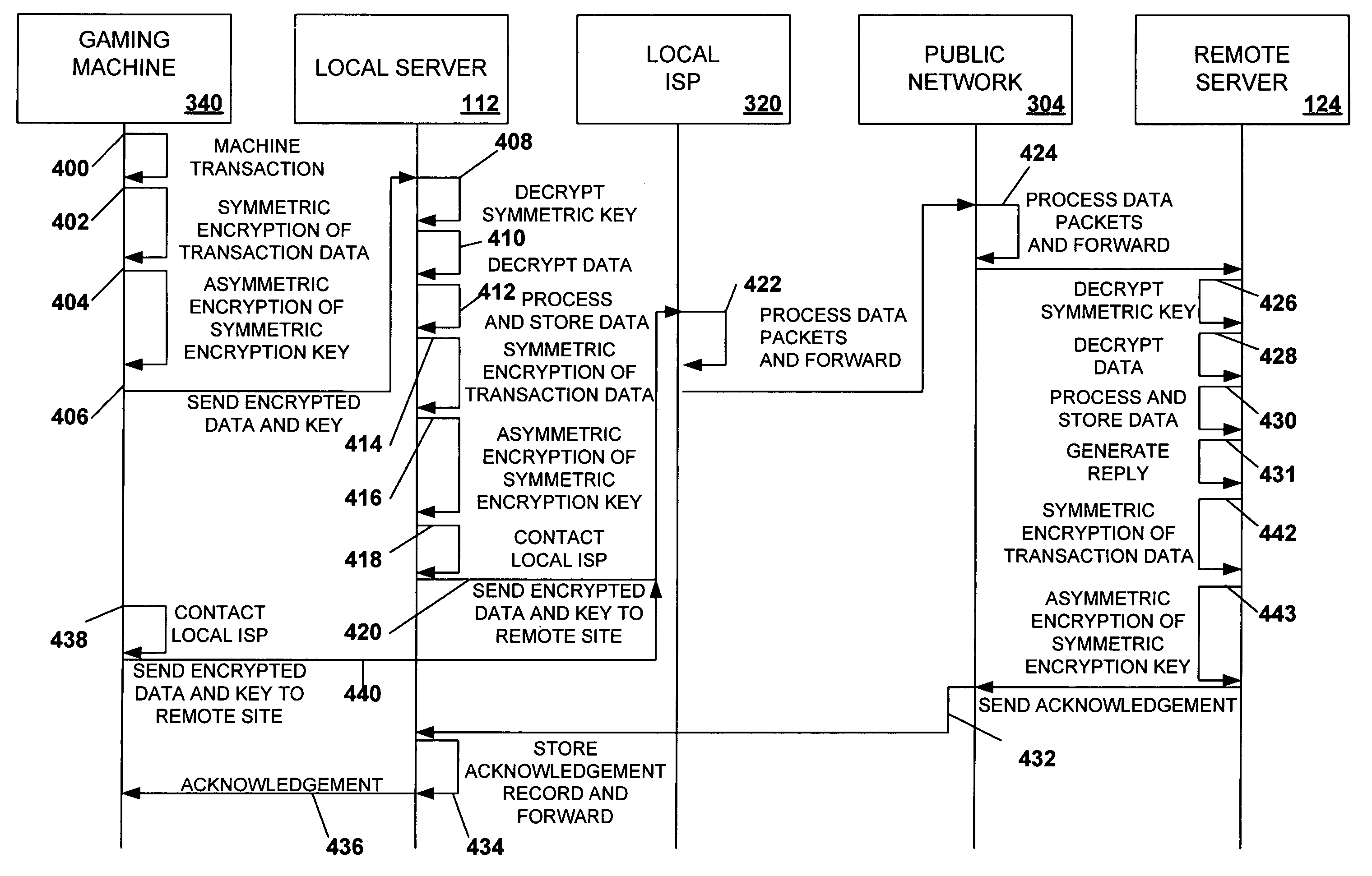
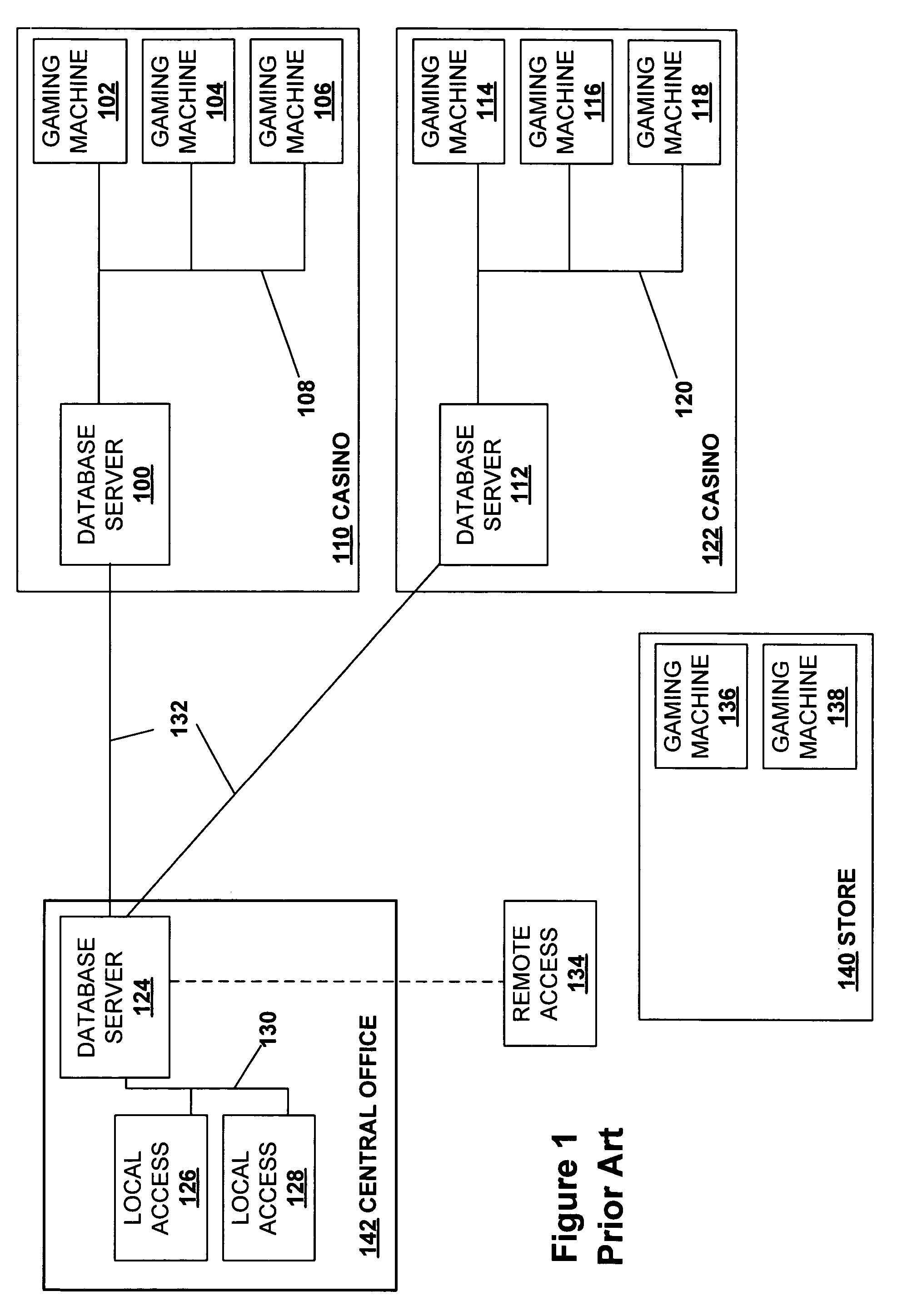
Secured virtual network in a gaming environment
InactiveUS7515718B2Mosaic printer telegraph systemKey distribution for secure communicationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
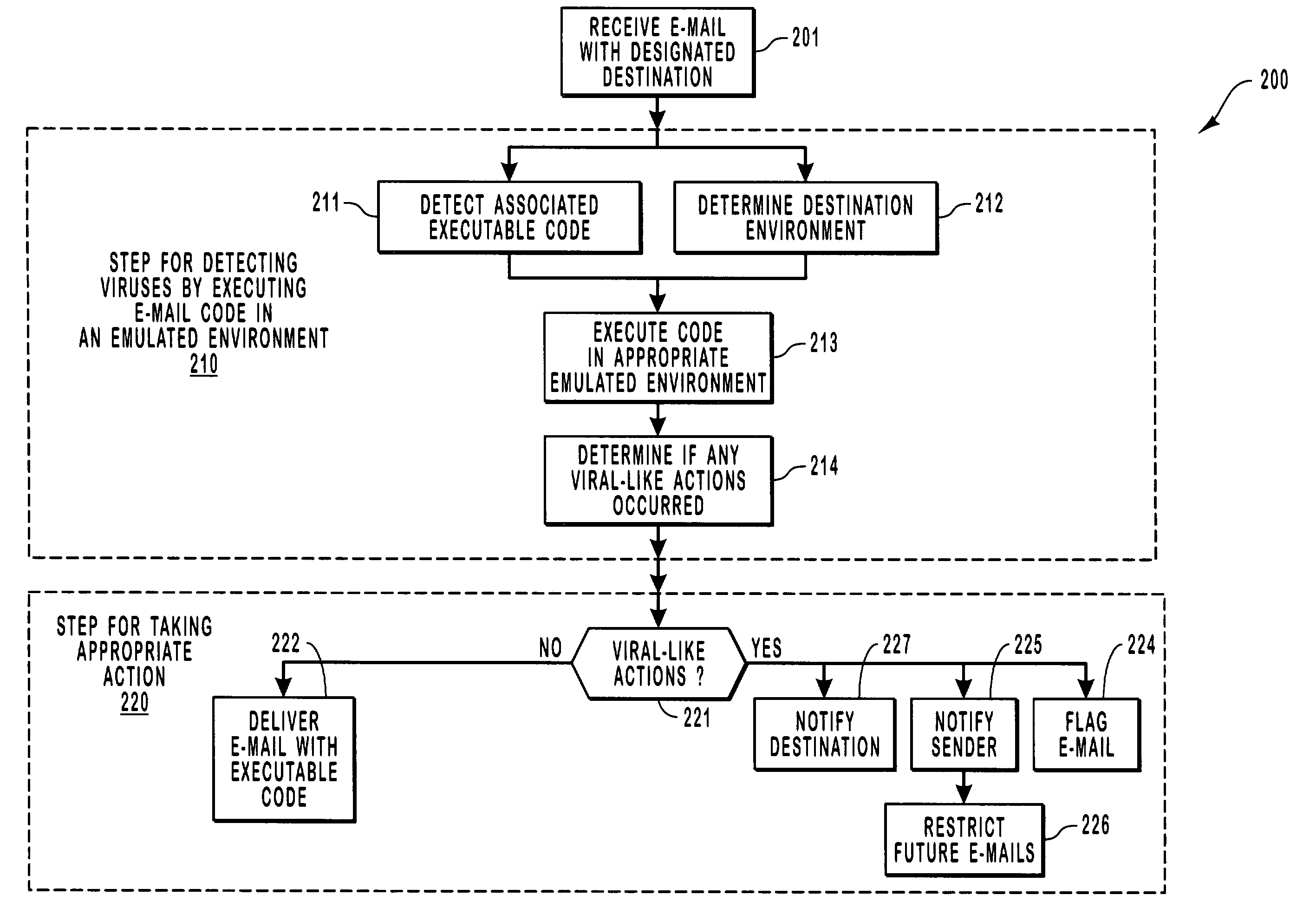
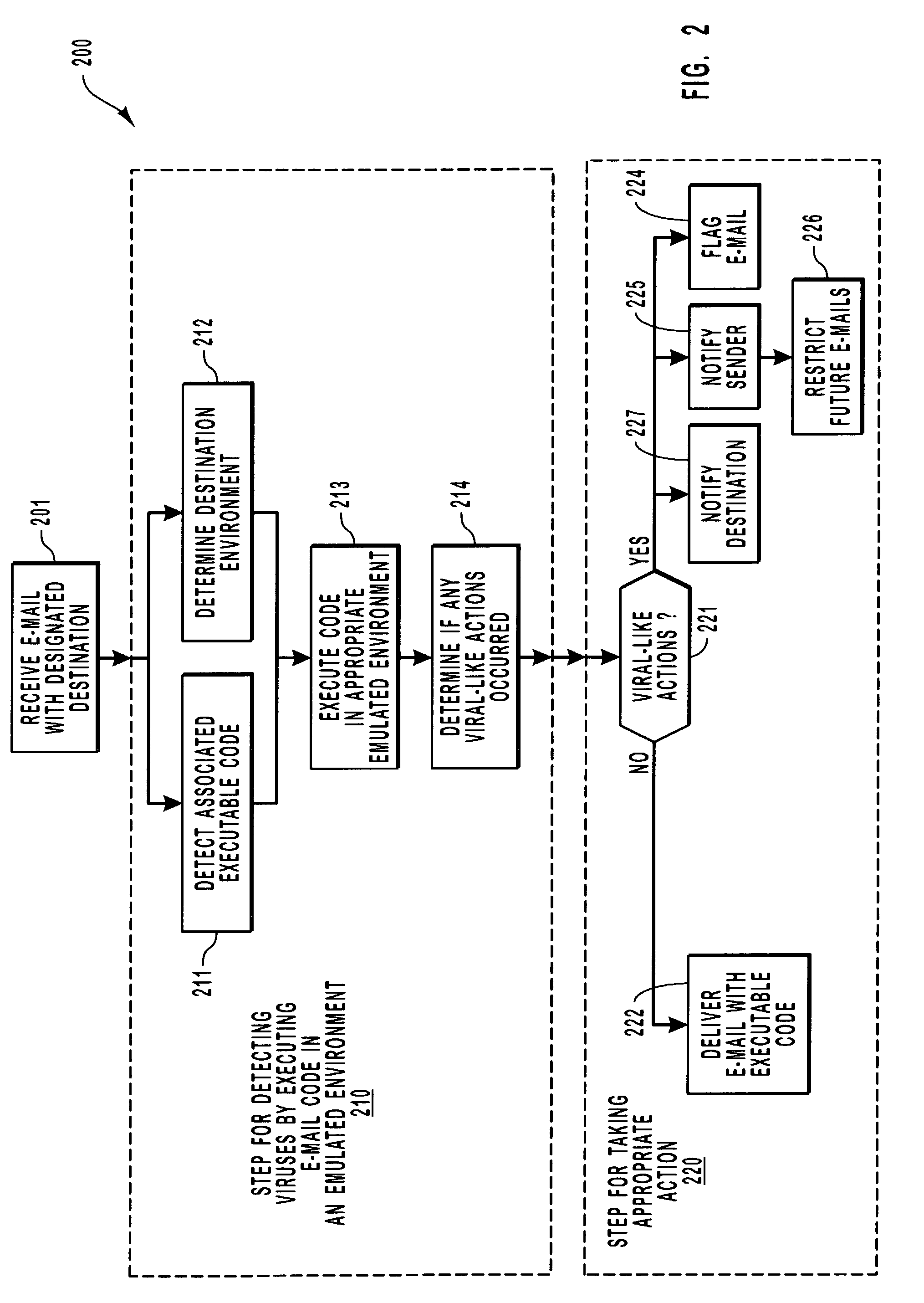
Virus detection by executing e-mail code in a virtual machine
ActiveUS7607171B1Reduce harmAvoid damageMosaic printer telegraph systemMemory loss protectionElectronic mailVirus detection
An intermediary isolation server receives e-mails and isolates any viral behavior from harming its intended destination. After the intermediary receives an e-mail, it determines that the e-mail has associated executable code, and then identifies the environment in which the e-mail code would be executed if delivered. The intermediary then executes the code by emulating how it would be executed in its ultimate environment. If a viral-like behavior is detected, appropriate action is taken to prevent the execution of the code at its intended destination. The attachment is executed in a contained environment that allows for the contained environment to be easily restarted in a clean state.
Owner:AVINTI
Environment integrity assured transactions
InactiveUS7587754B2Suitable for useMosaic printer telegraph systemDigital data processing detailsClient-sideEnvironmental integrity
In a networked computing environment, a server is equipped to assure the integrity of the service components of a service, including the direct service providing component and one or more supporting components as requested, and a client is equipped to request on behalf of an application in need of the service the integrity assurance. The client is further equipped to either request or accept the service, only upon receiving the integrity assurance. In one embodiment, the request for integrity assurance, and the subsequent conditional request or acceptance of the service is performed in real time.
Owner:ORIX VENTURE FINANCE
Systems and methods for dynamic authentication using physical keys
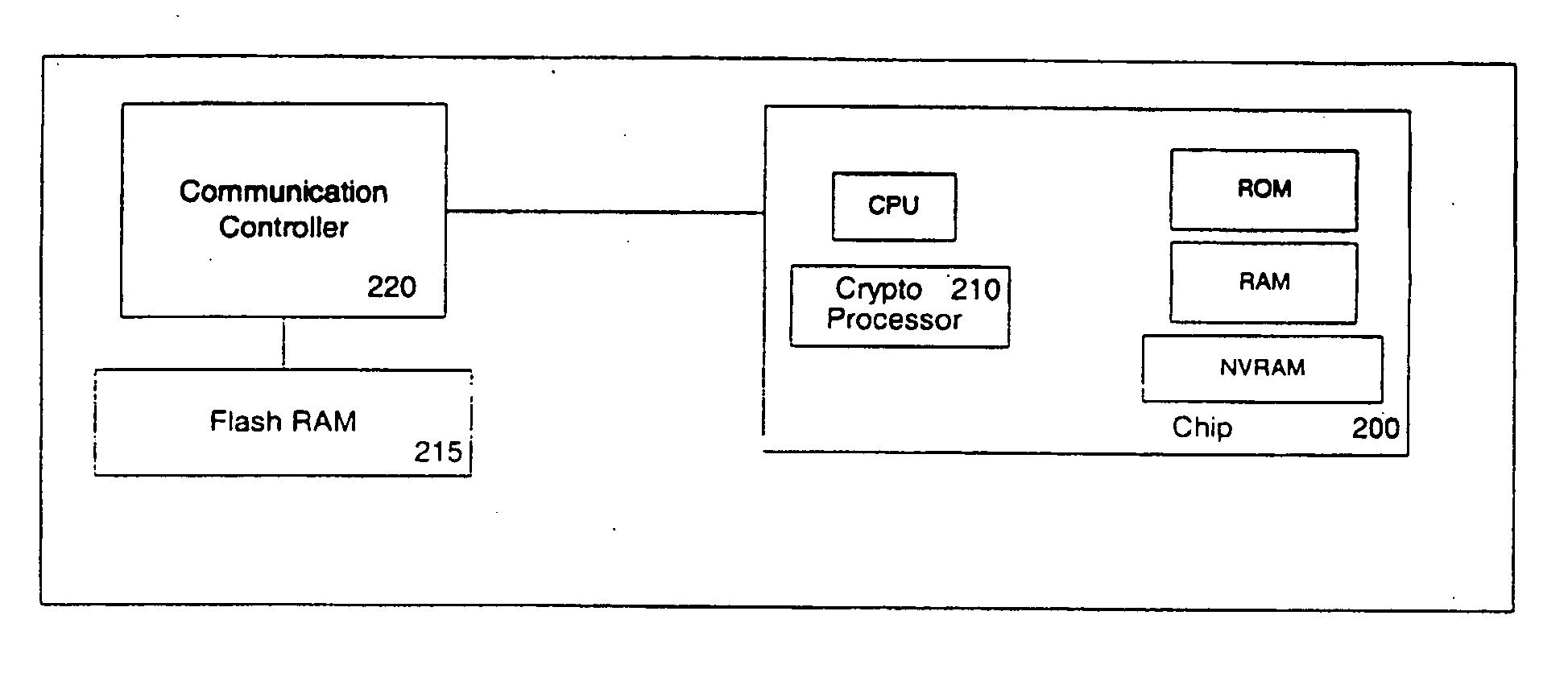
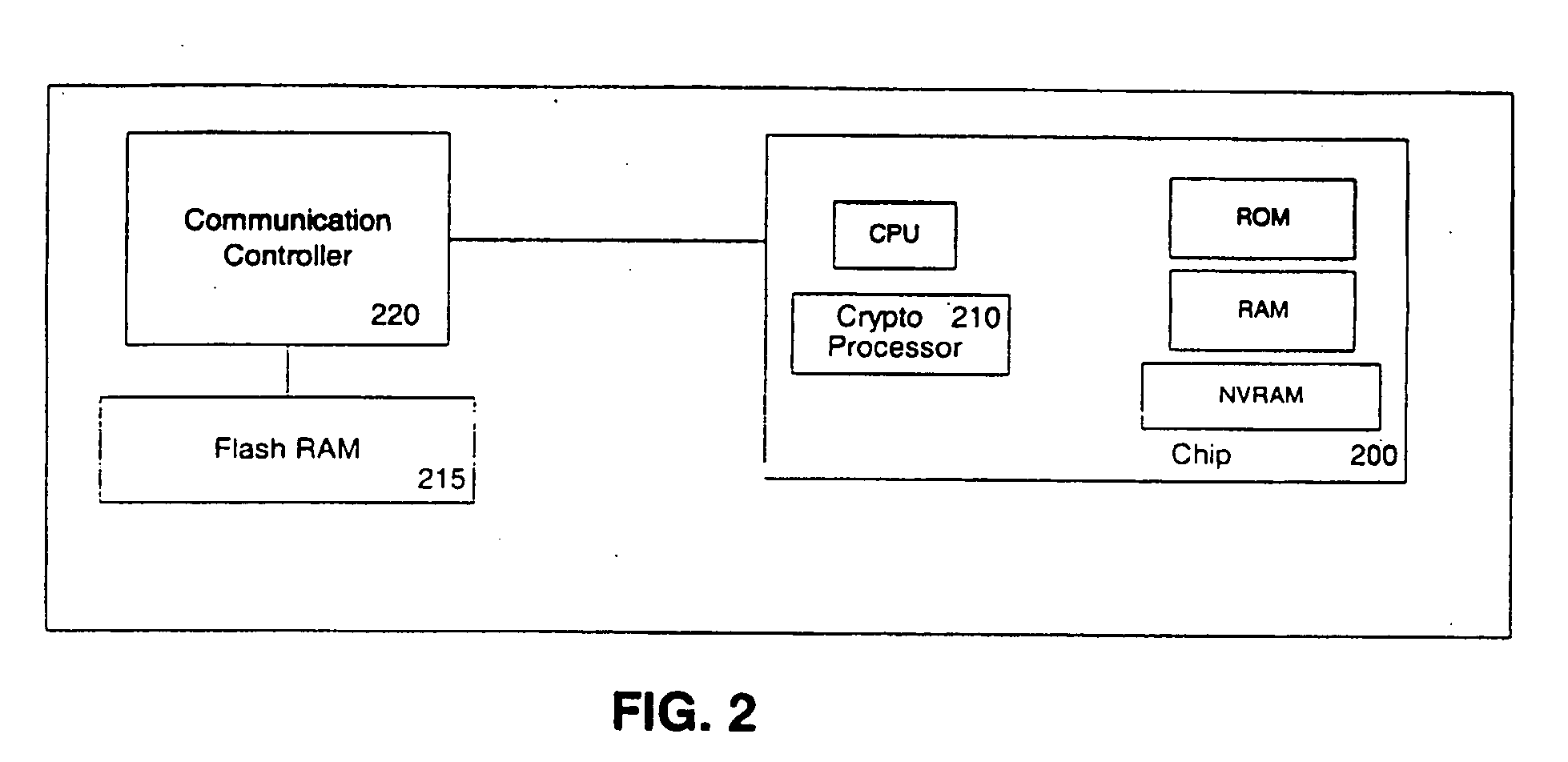
ActiveUS7562385B2Mosaic printer telegraph systemDigital data processing detailsInformation repositoryComputer hardware
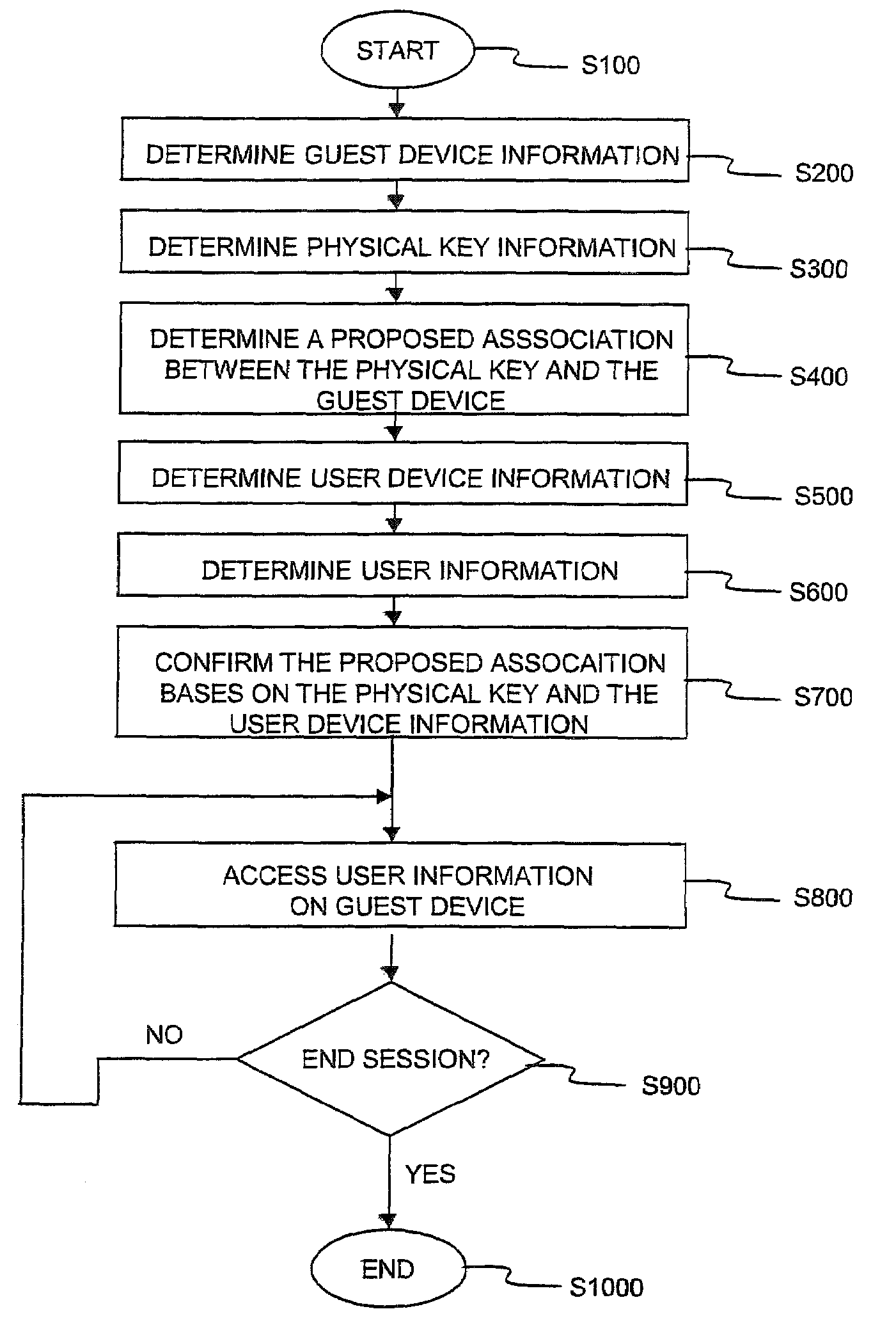
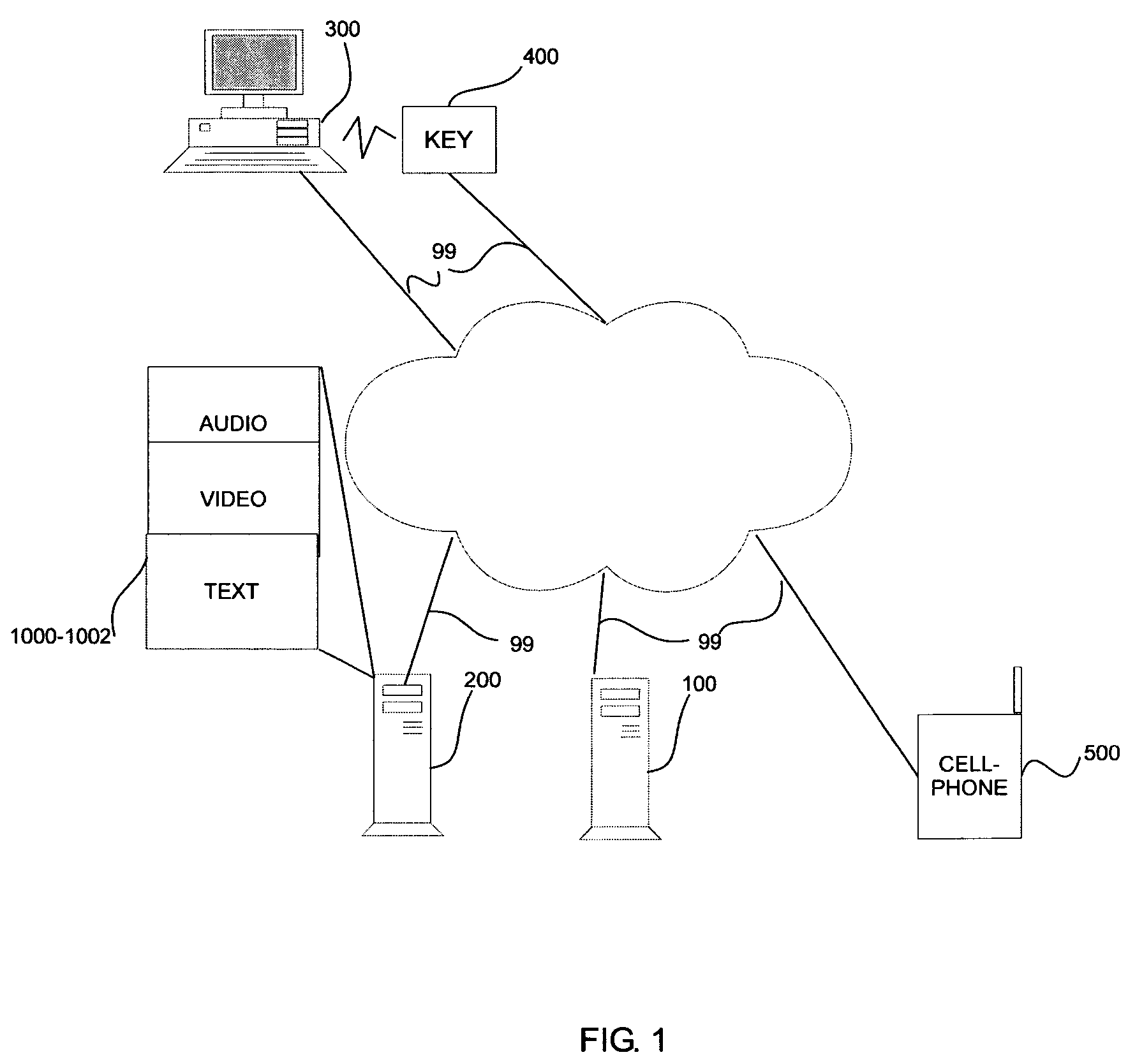
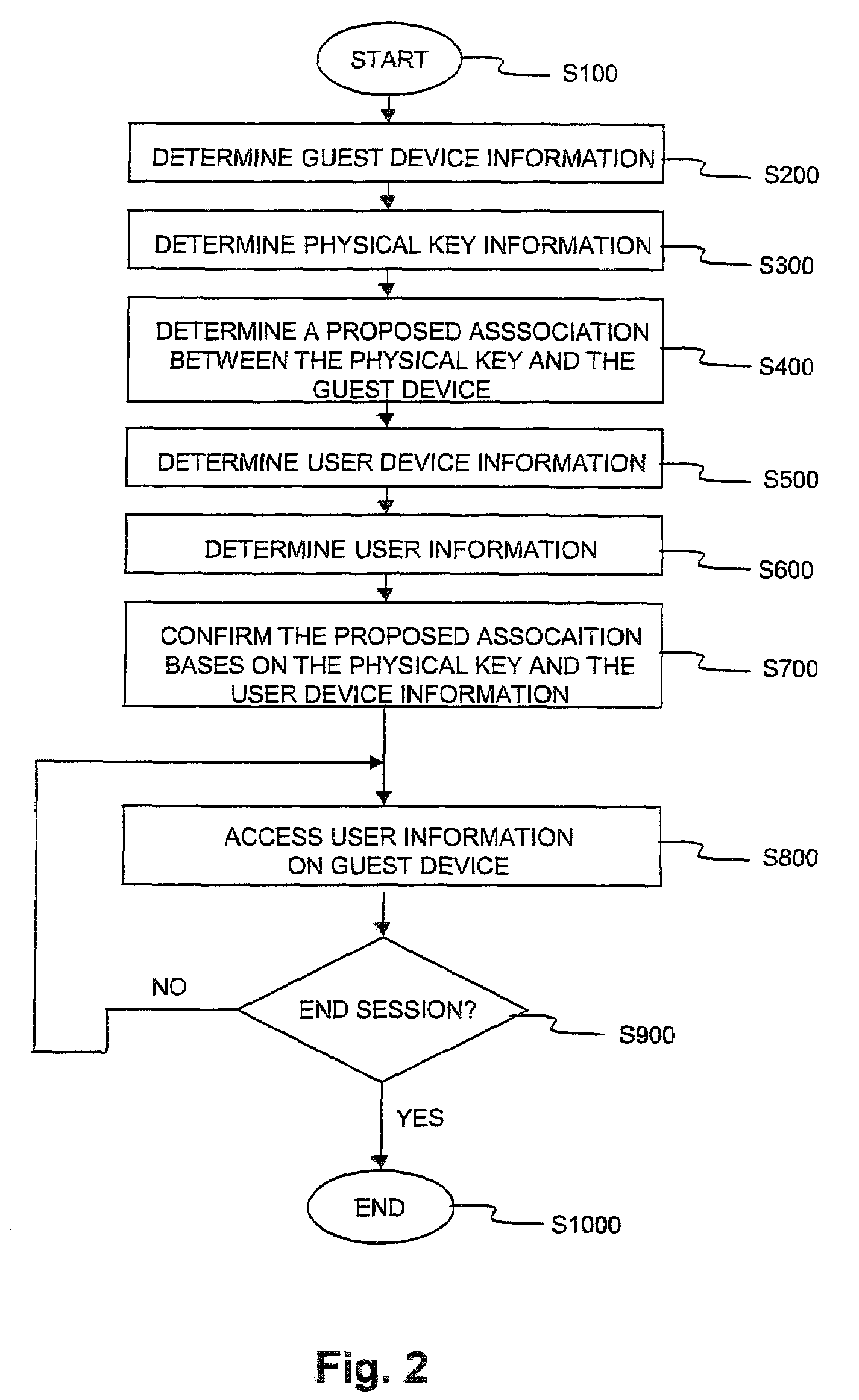
A physical key is used to propose an association between a guest device and user information and services. Contact-based or contact-less connectors are used to establish the proposed association between the physical key and the guest device. The proposed association then communicated to the dynamic authentication system over a first communication channel. The dynamic authentication system determines a user confirmation over a second communications channel based on a user device and previously determined associations between users, user devices and the physical key. The guest device is then authenticated for access to information and / or services associated with the user. The information retrieved from and / or transmitted to the user's personal information repository is optionally protected using various transformations. Optional session identifiers supported on the physical key and / or the user device, ensure the protected information is inaccessible when the physical key is removed and / or the predetermined association with the user device is deleted.
Owner:FUJIFILM BUSINESS INNOVATION CORP
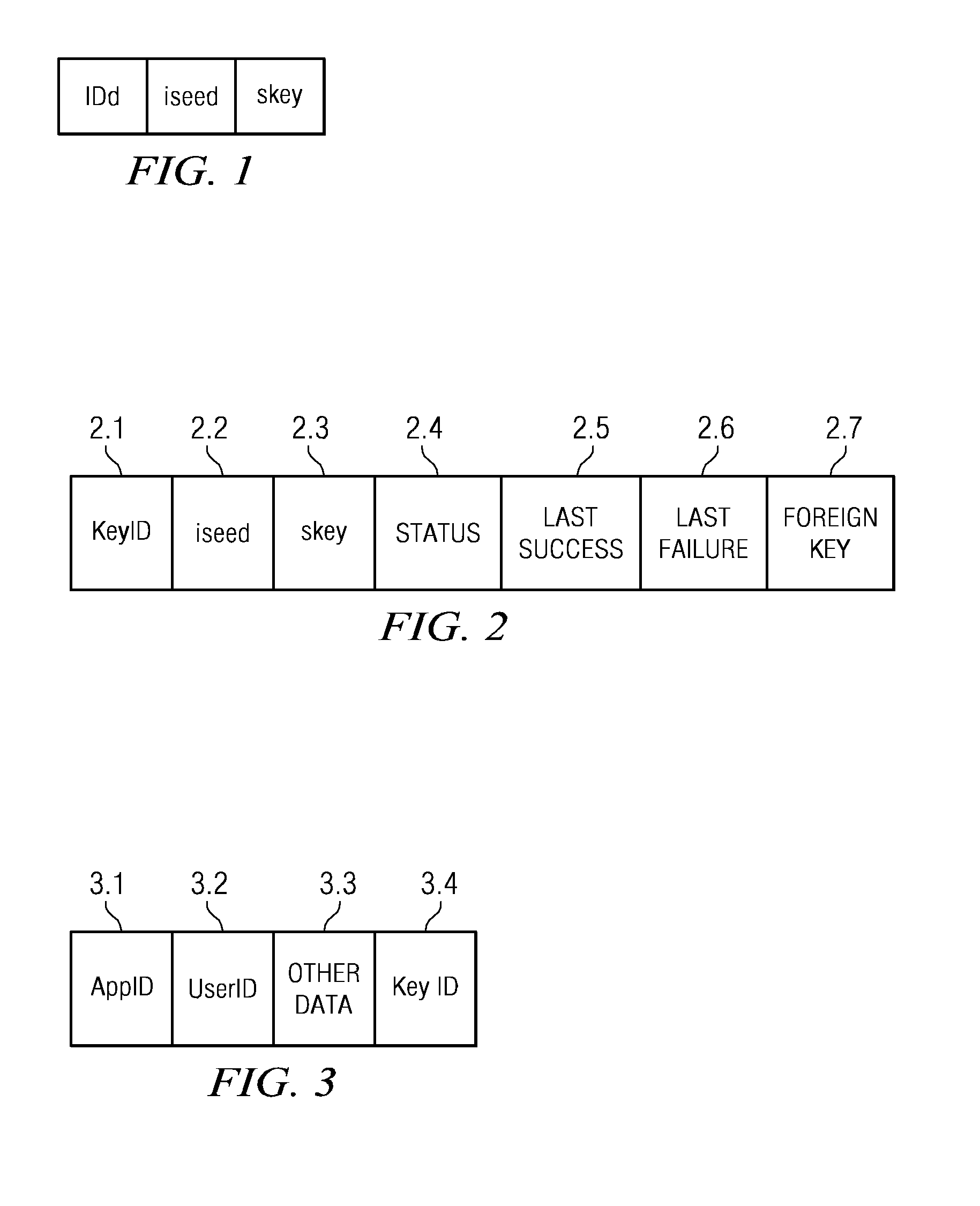
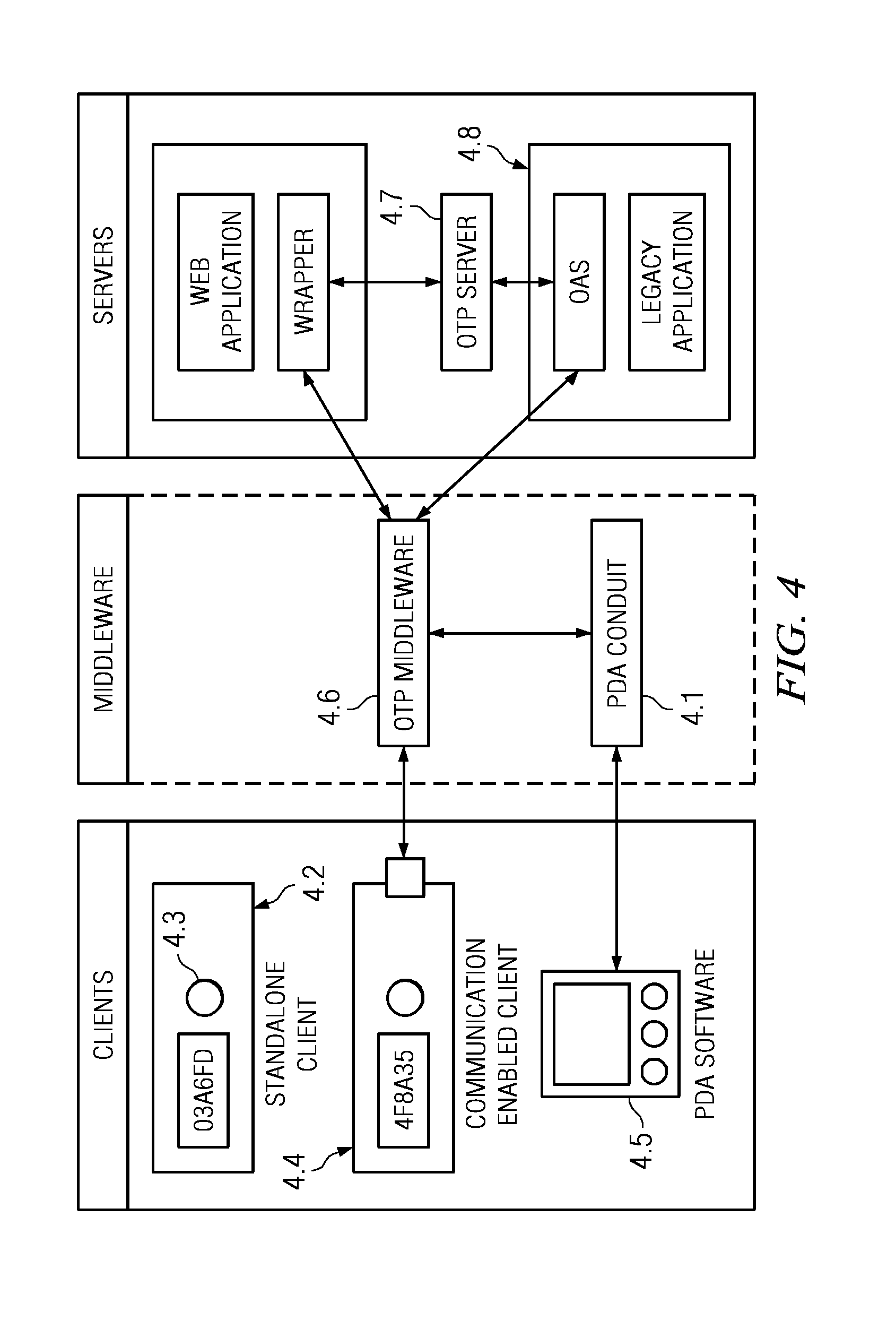
One time passcode system
InactiveUS7571489B2Mosaic printer telegraph systemDigital data processing detailsApplication serverUser input
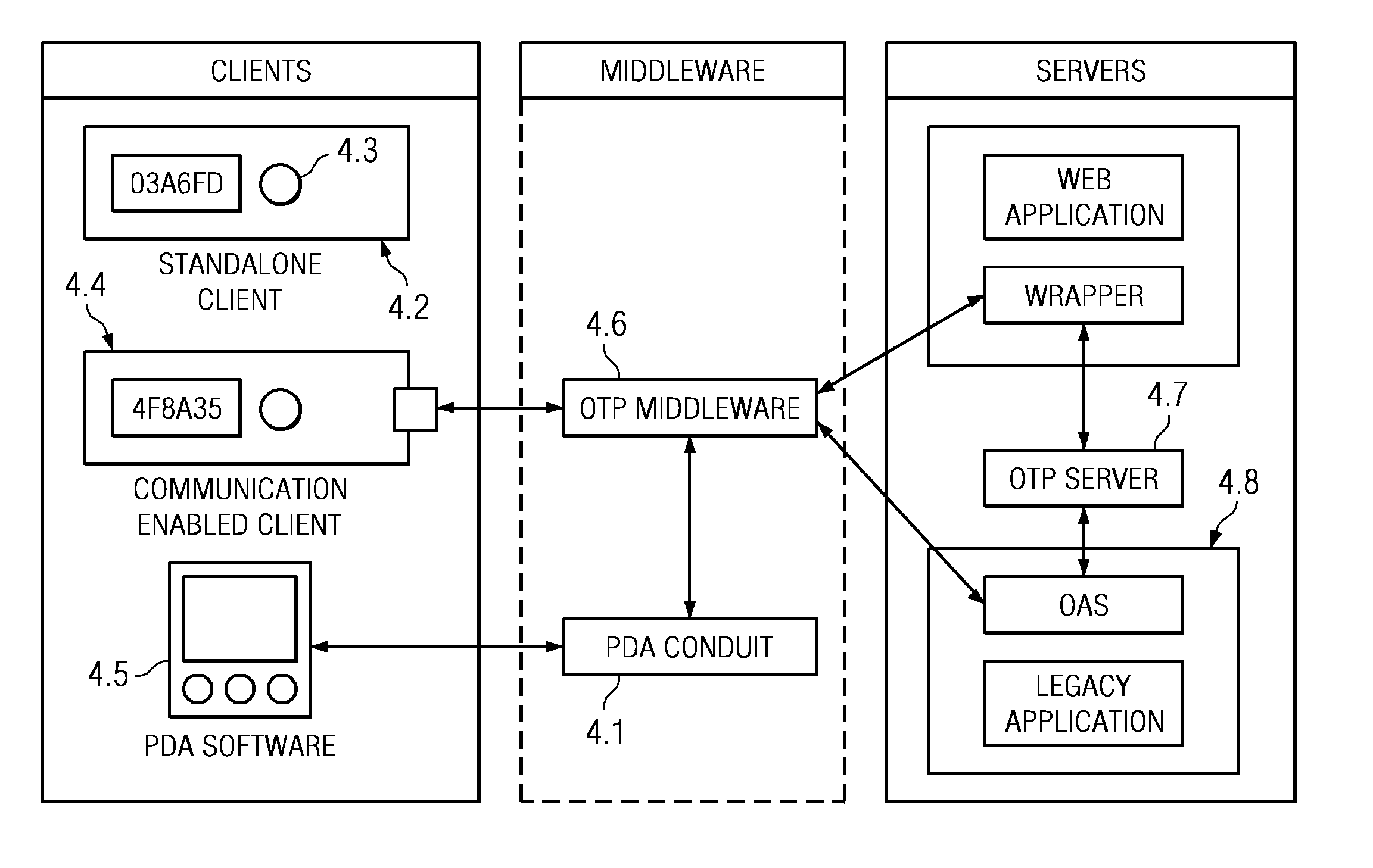
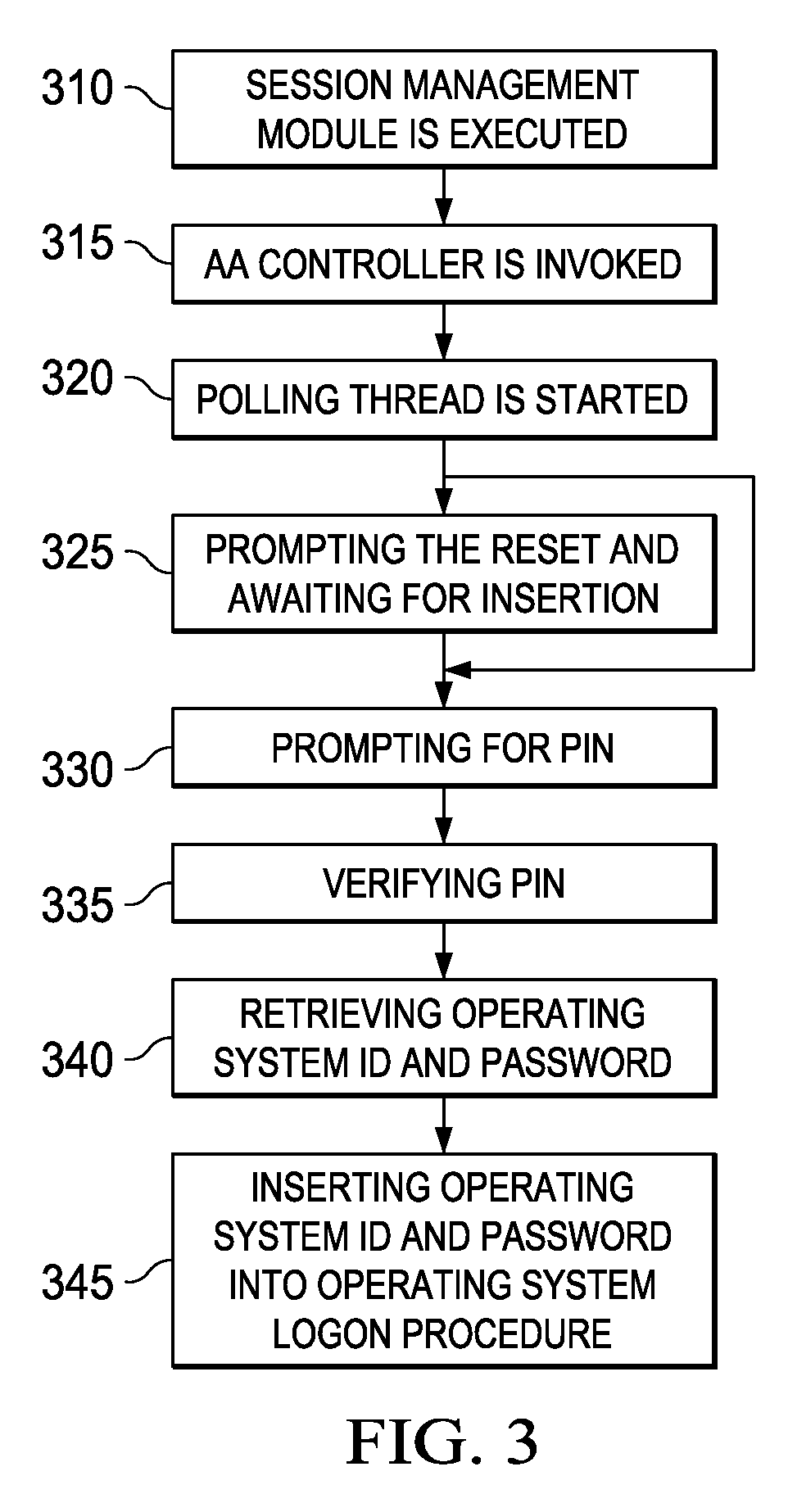
The invention relates to a system for securing access to resources or computer systems by means of a self modifying, single use password that limits access to a system and automatically changes each time it is used. Independent computer systems, or clients, are utilized by users to generate one time passcodes to prove their identity to one or more authentication servers. Servers are used to authenticate user inputted one time passcodes, to maintain and update the status of one time passcode clients, and perform rekeying and reset operations. Middleware, an optional component, allows for the interaction between one time passcode clients and servers. Middleware allows for client rekeying and resets as well as synchronisation between the client and server. The invention facilitates, inter alia, distribution of clients to users, maintaining and administering the status of clients on one or more servers, generation of a one time passcode (OTP), authentication of a one time passcode, rekeying of a one time passcode client, resetting of a one-time passcode client, Resetting of a one time passcode client, requesting for generation of a one time passcode on a communication enabled client through software or hardware interfaces, and authentication of one time passcodes by remote application servers.
Owner:INT BUSINESS MASCH CORP
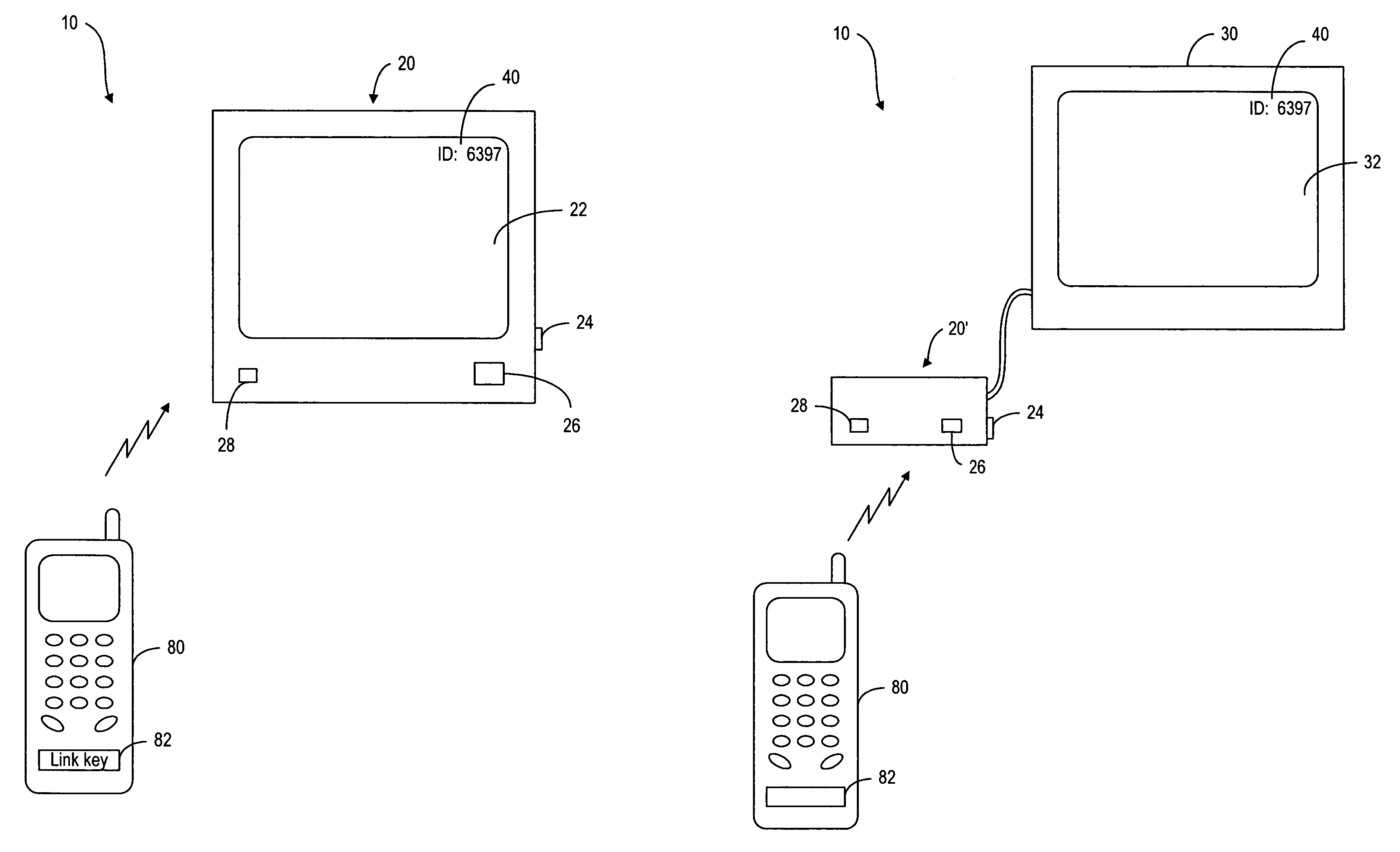
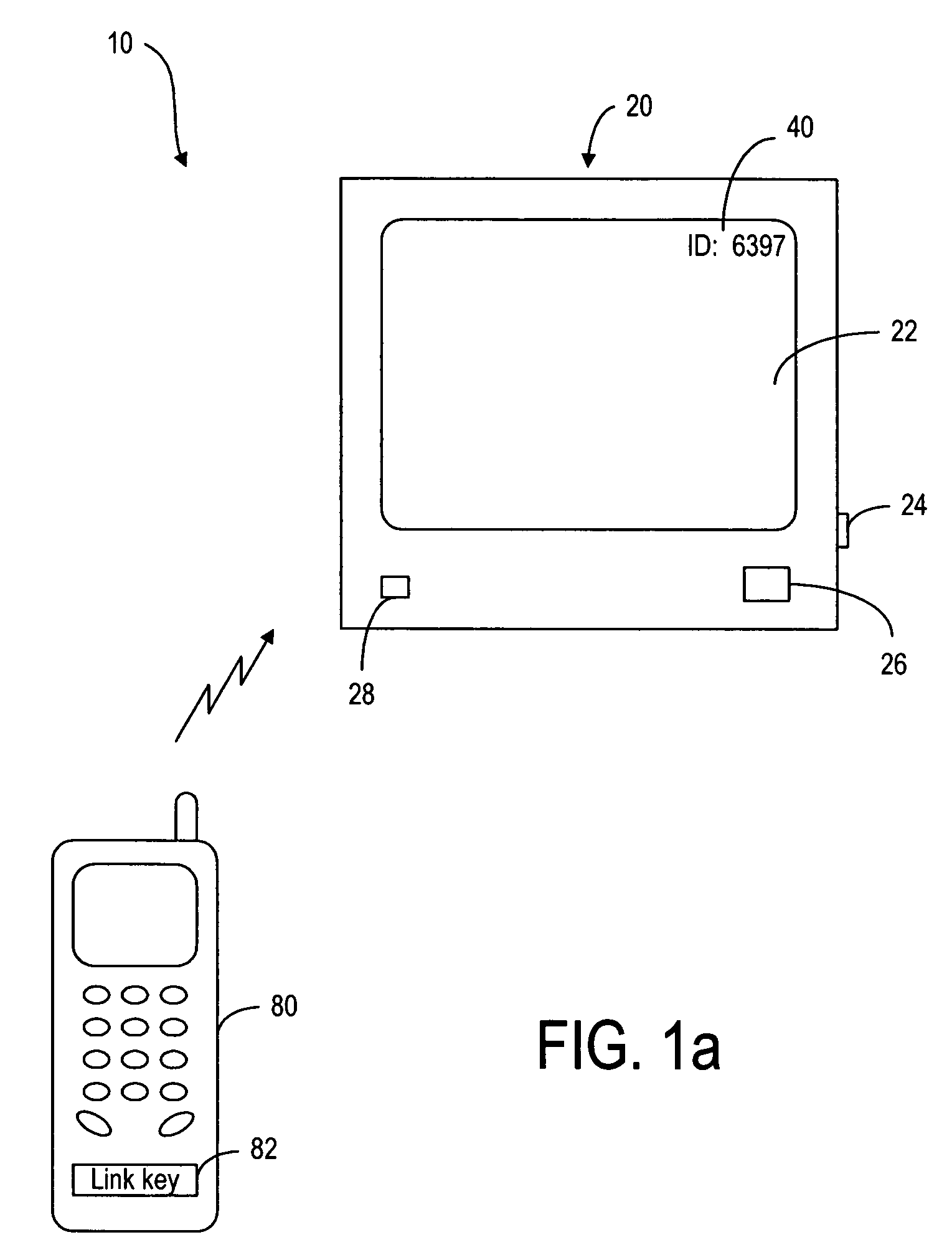
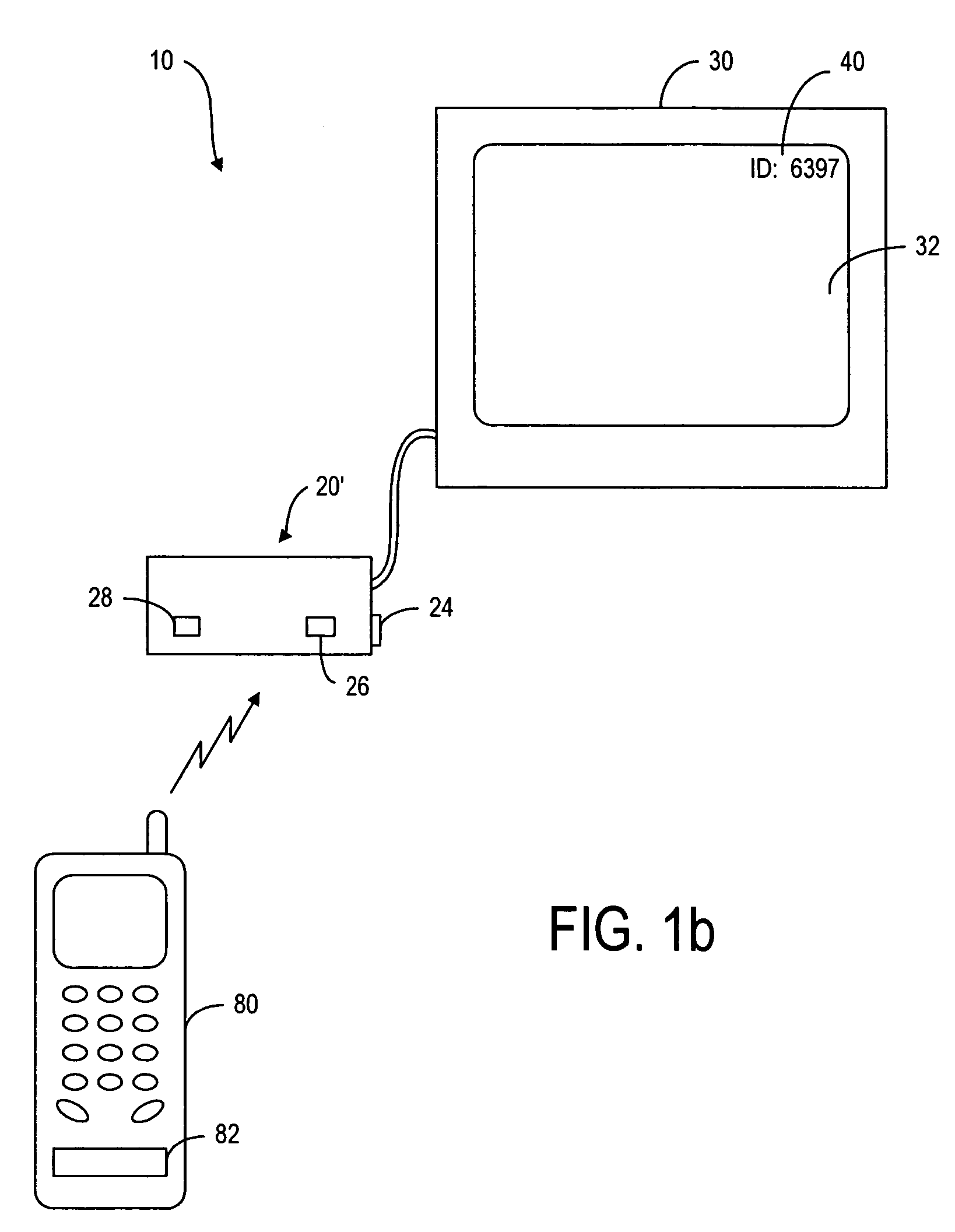
Method and device for identifying and pairing Bluetooth devices
ActiveUS7130584B2Mosaic printer telegraph systemTransmission systemsTelecommunications linkCommunication link
A method of revealing the device identity of a recipient Bluetooth device. When the recipient device is turned on, it displays the device identity. A user enters the device identity of the recipient device into a sending Bluetooth device in order to establish the initial communication link between the sending and recipient devices. Once the initial communication link is established, the devices are paired. It is no longer necessary to enter the device identity of the recipient device into the sending device in order to establish further communication link. Furthermore, if the recipient device has already been turned on when the user wants to establish the initial communication link, the device identity is displayed when the user sends a message or signal from the sending device to the recipient device.
Owner:NOKIA TECHNOLOGLES OY
Mechanism to check the malicious alteration of malware scanner
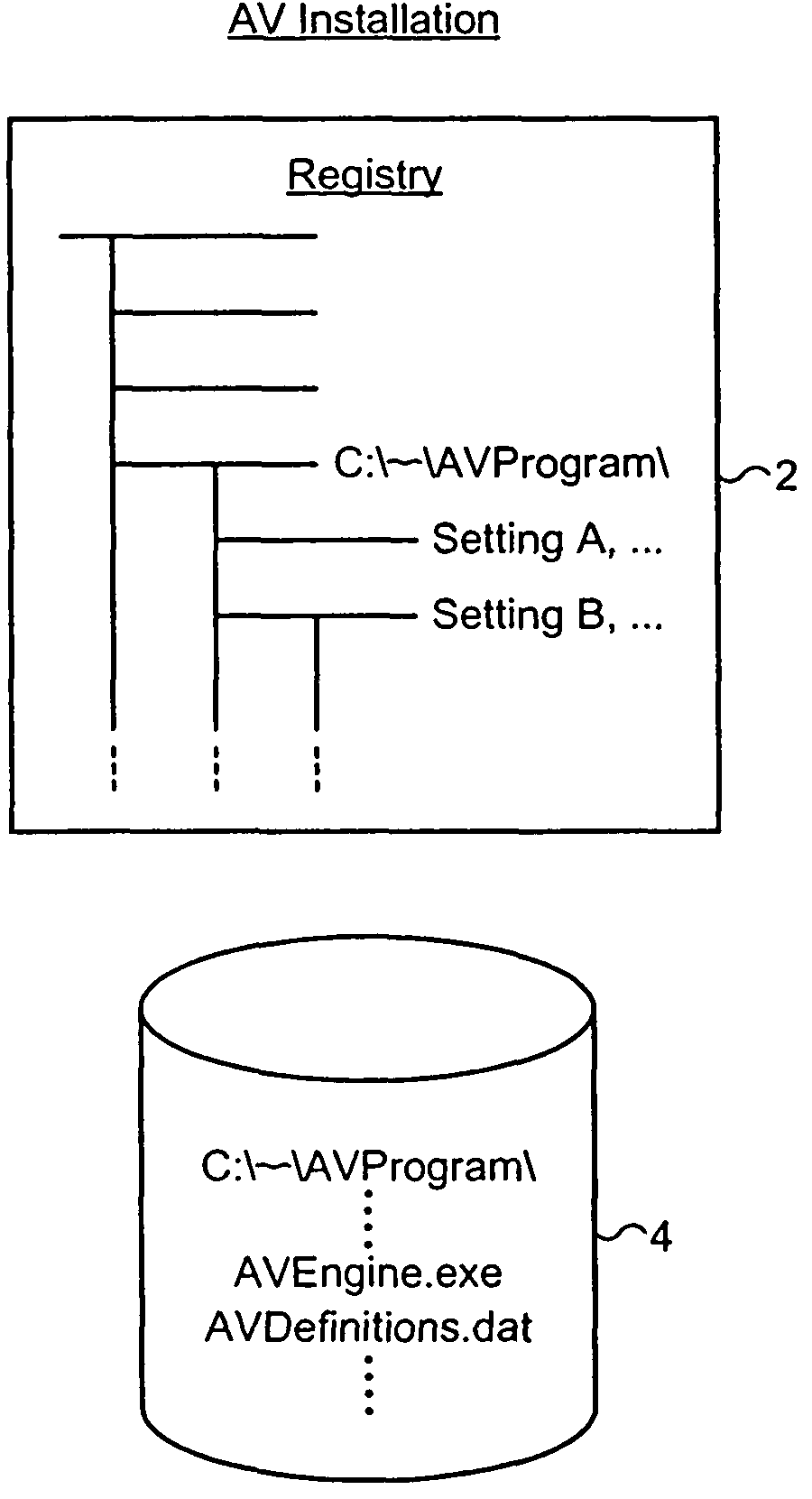
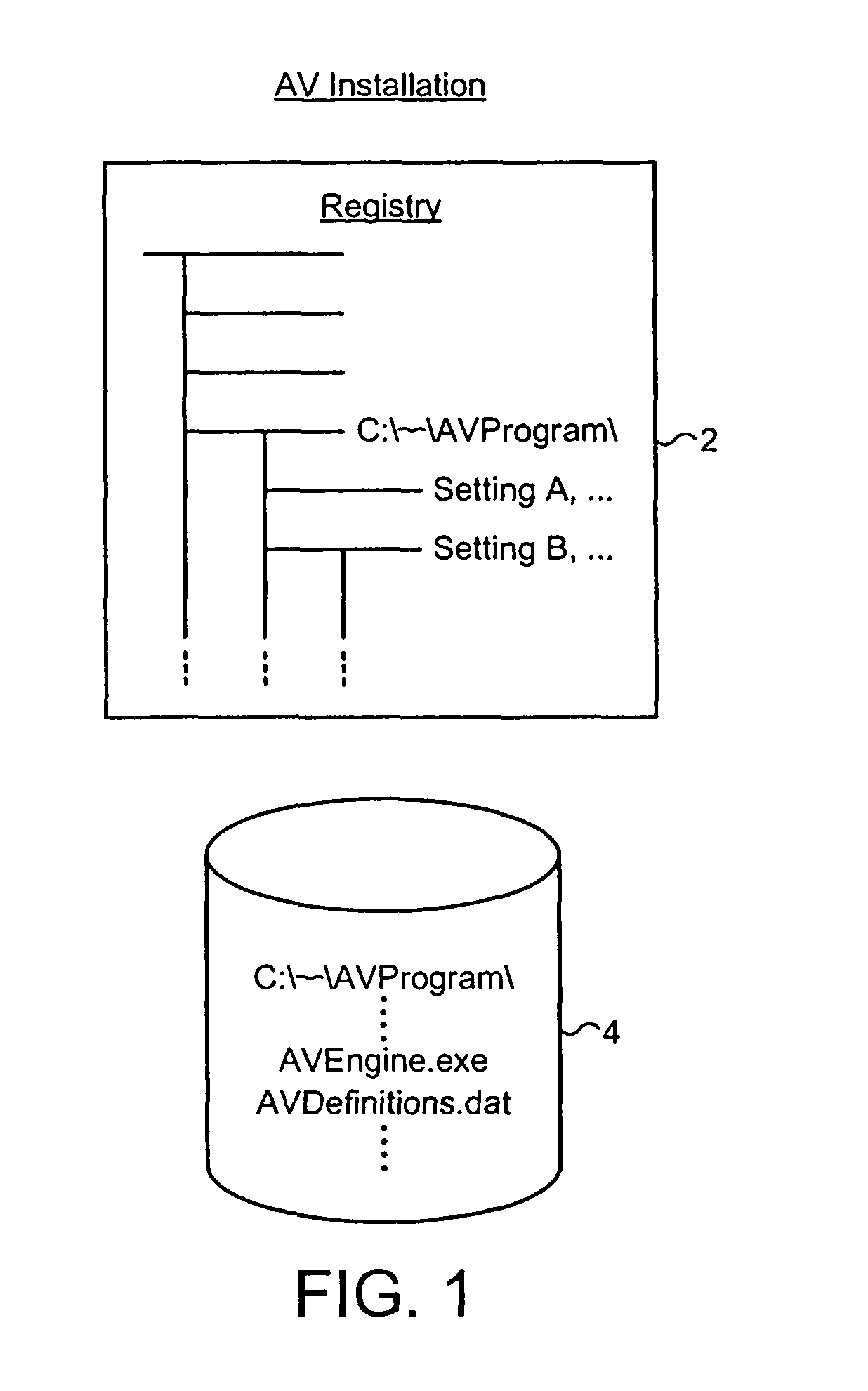
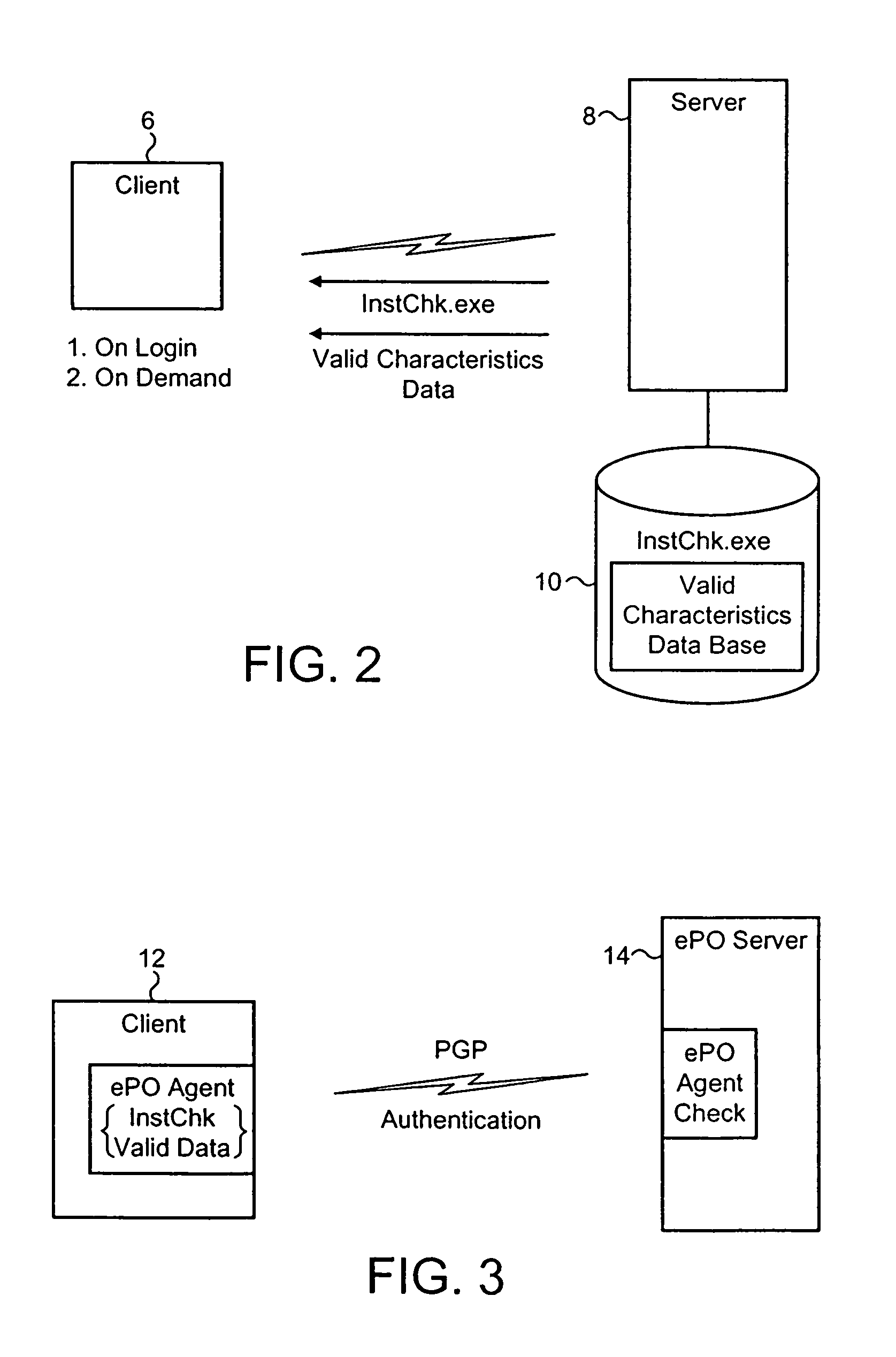
InactiveUS7810091B2Increase flexibilityImprove securityMosaic printer telegraph systemMemory loss protectionOperational systemChecksum
The installation of a computer program, such as a malware scanner, may be checked to determine whether or not it has not been tampered with using an installation checking computer program to gather characteristics of the installation of the target computer program after the installation checking computer program has first been validated by a separate further computer. The installation characteristics may include operating system registry entries, installed files list, file sizes and file checksums.
Owner:MCAFEE LLC
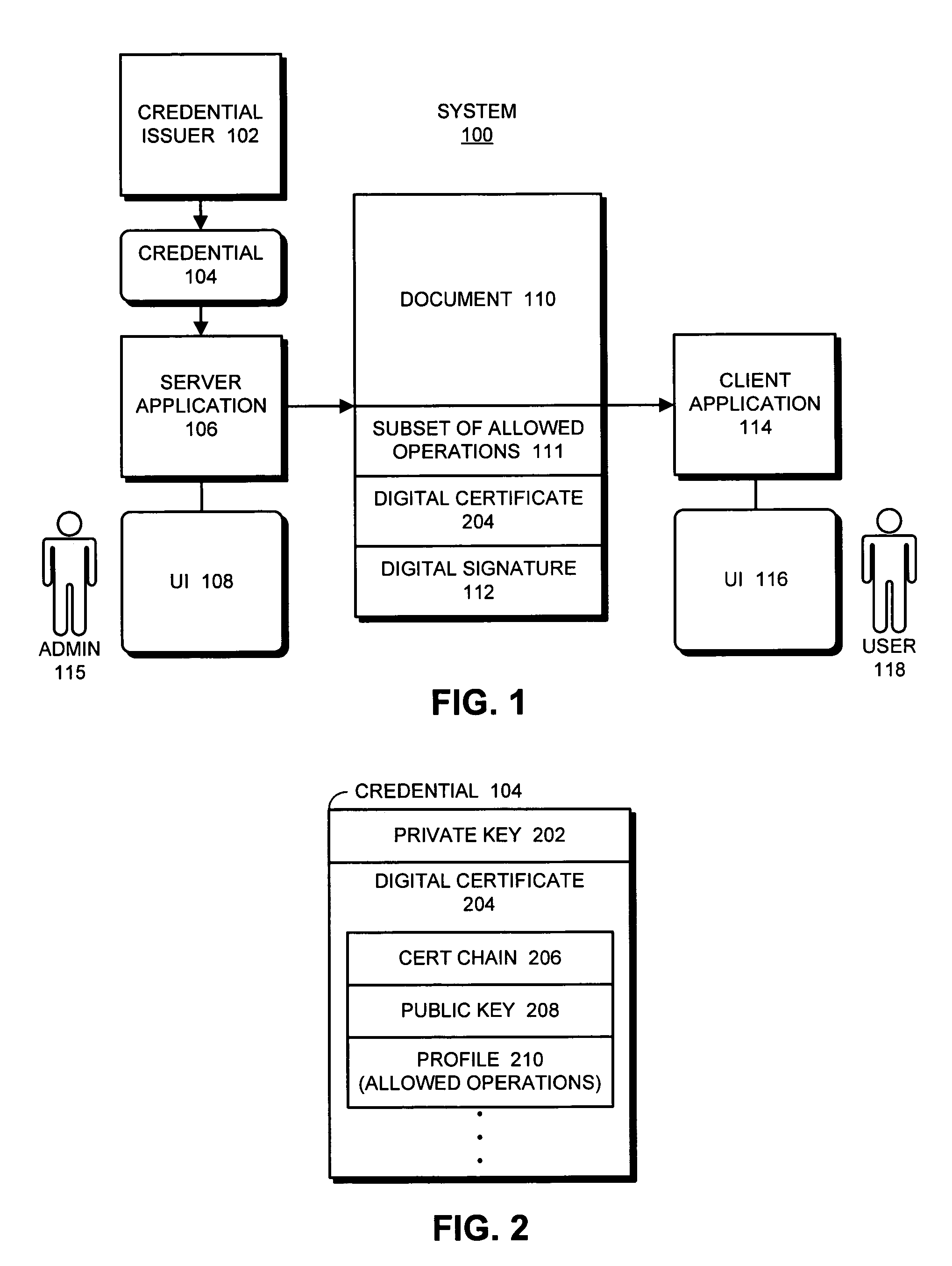
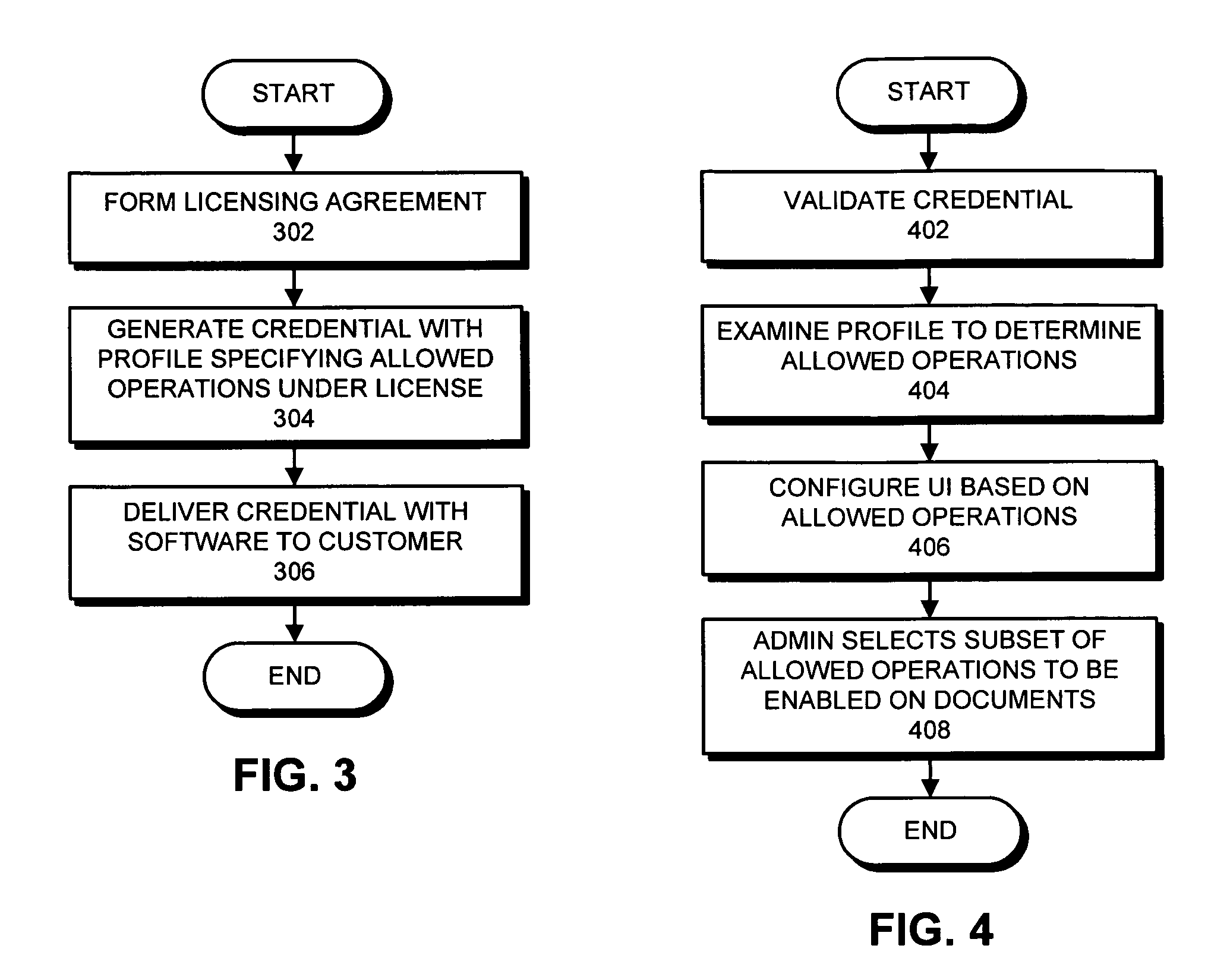
Using digital certificates to facilitate enforcement of product licenses
ActiveUS7581106B1Mosaic printer telegraph systemUser identity/authority verificationDigital signatureDocumentation
One embodiment of the present invention provides a system that uses digital certificates to facilitate enforcing licensing terms for applications that manipulate documents. During operation, the system obtains a credential, wherein the credential includes a private key and a digital certificate containing a corresponding public key. This digital certificate also contains a profile specifying allowed operations which can be performed on documents signed with the credential. Next, the system digitally signs a document using the credential, so that the resulting signed document is signed with the private key and includes a copy of the digital certificate with the profile specifying the allowed operations. The certificate issuer can subsequently revoke the digital certificate (which effectively revokes the license) if terms of a license agreement associated with the digital certificate are violated.
Owner:ADOBE SYST INC
Controlling Access to a Process Using a Separate Hardware Device
InactiveUS20090205030A1Mosaic printer telegraph systemPublic key for secure communicationComputer hardwareUser authentication
A method and apparatus for automatic user authentication are described. The method includes receiving information at a device, the device including a credential container; storing the information at the credential container and performing cryptographic calculations on the received information and providing the encrypted information upon request.
Owner:IBM CORP
Adaptable security mechanism for preventing unauthorized access of digital data
InactiveUS7603563B2Mosaic printer telegraph systemKey distribution for secure communicationDigital dataPlaintext
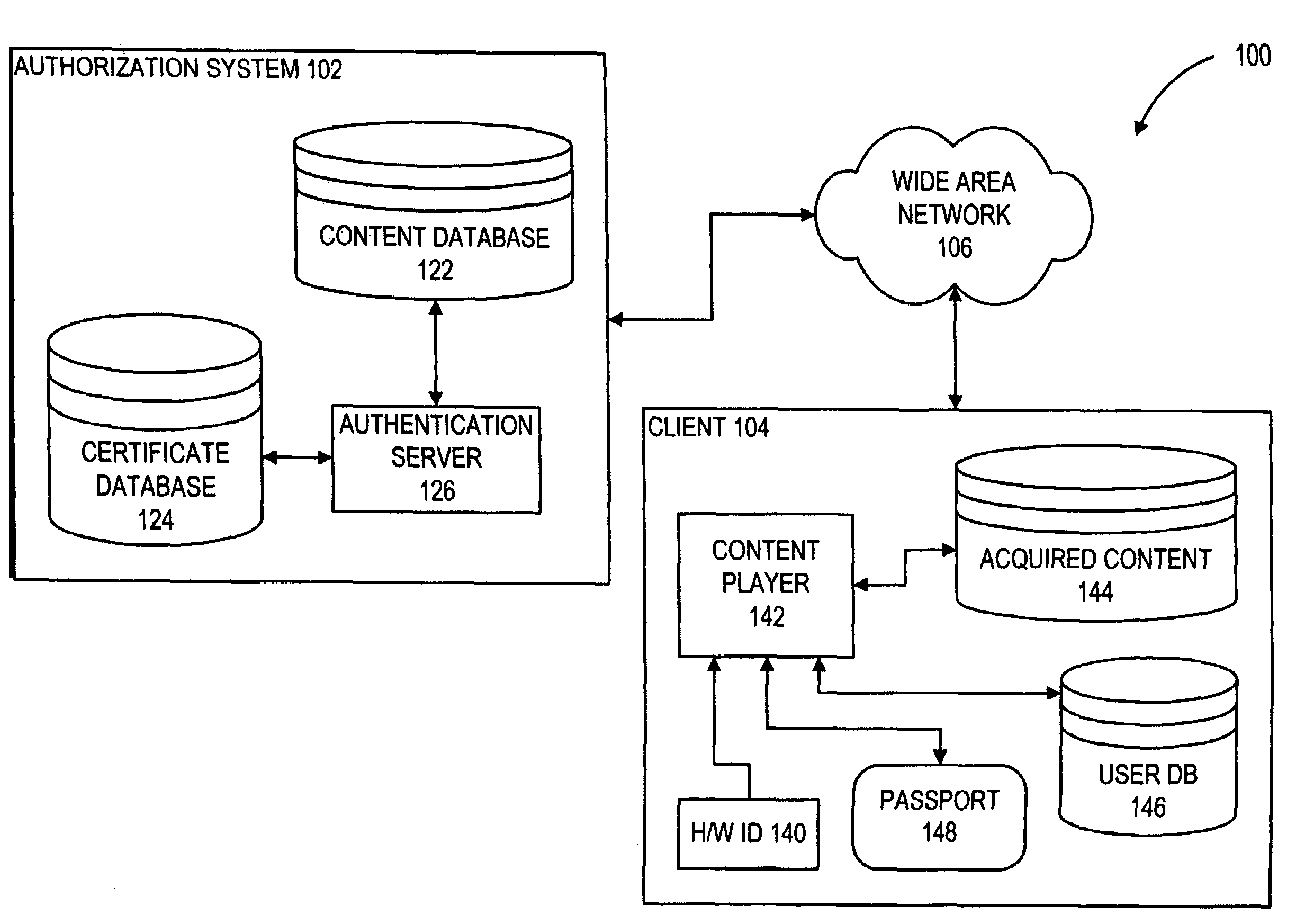
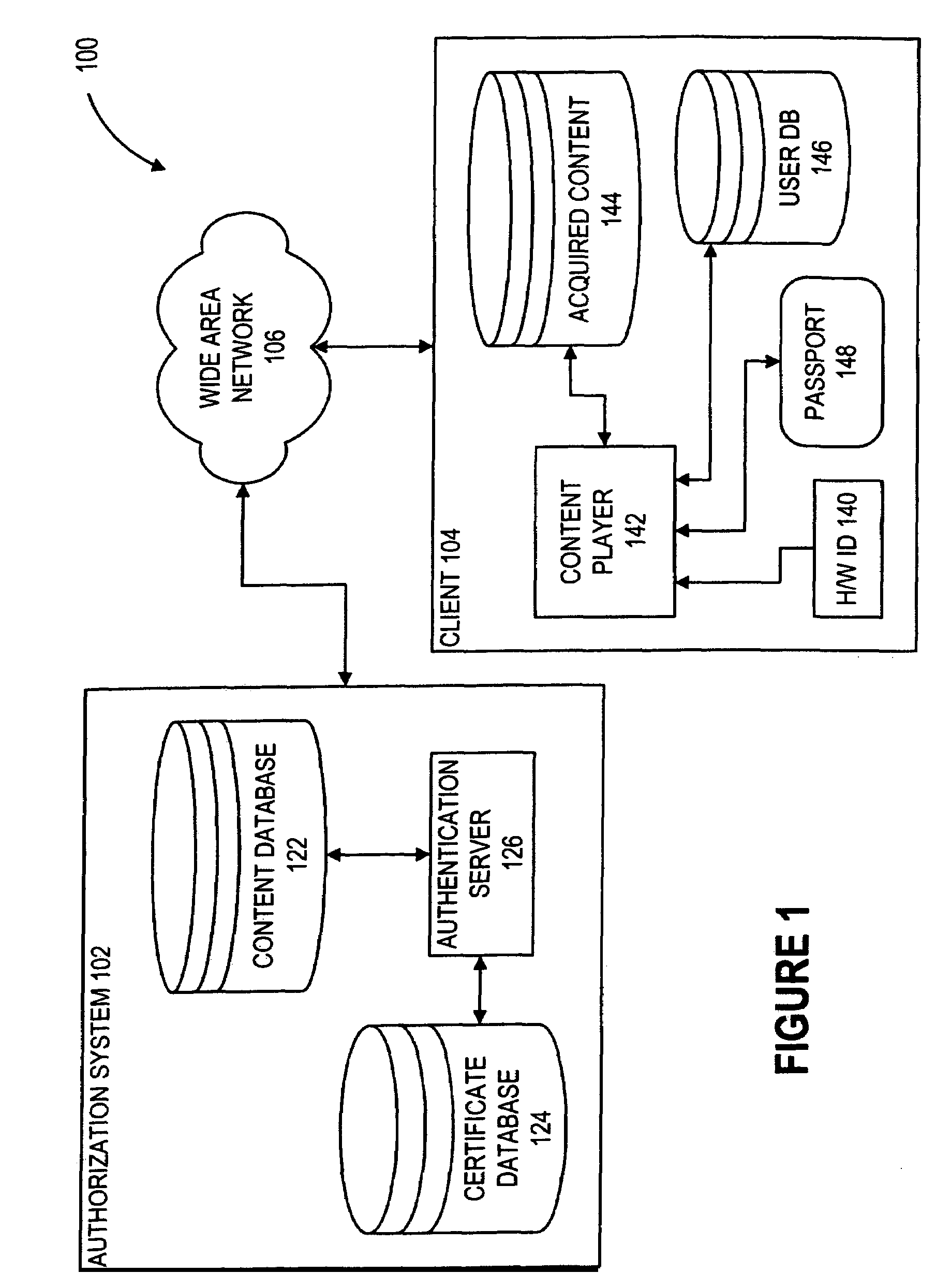
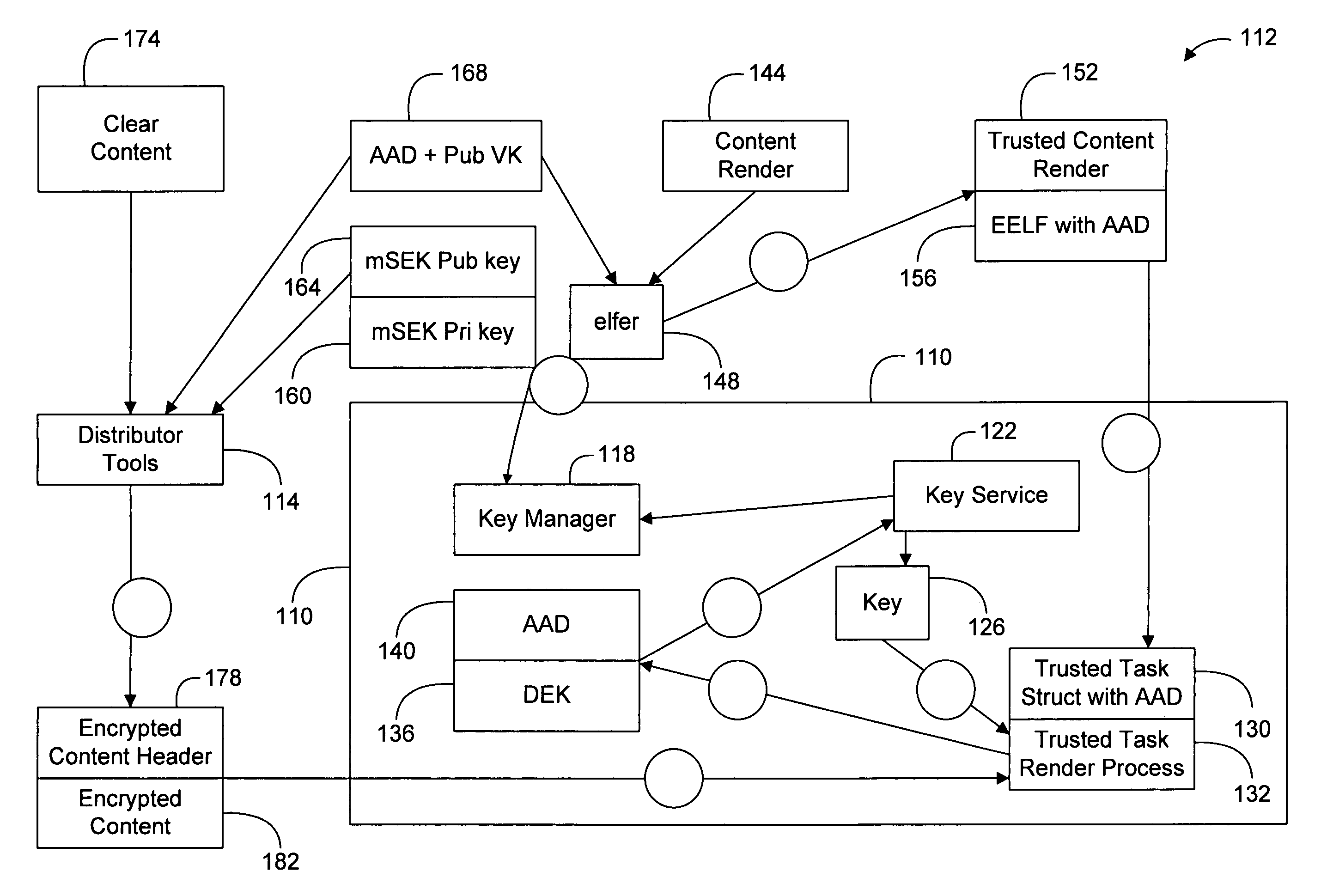
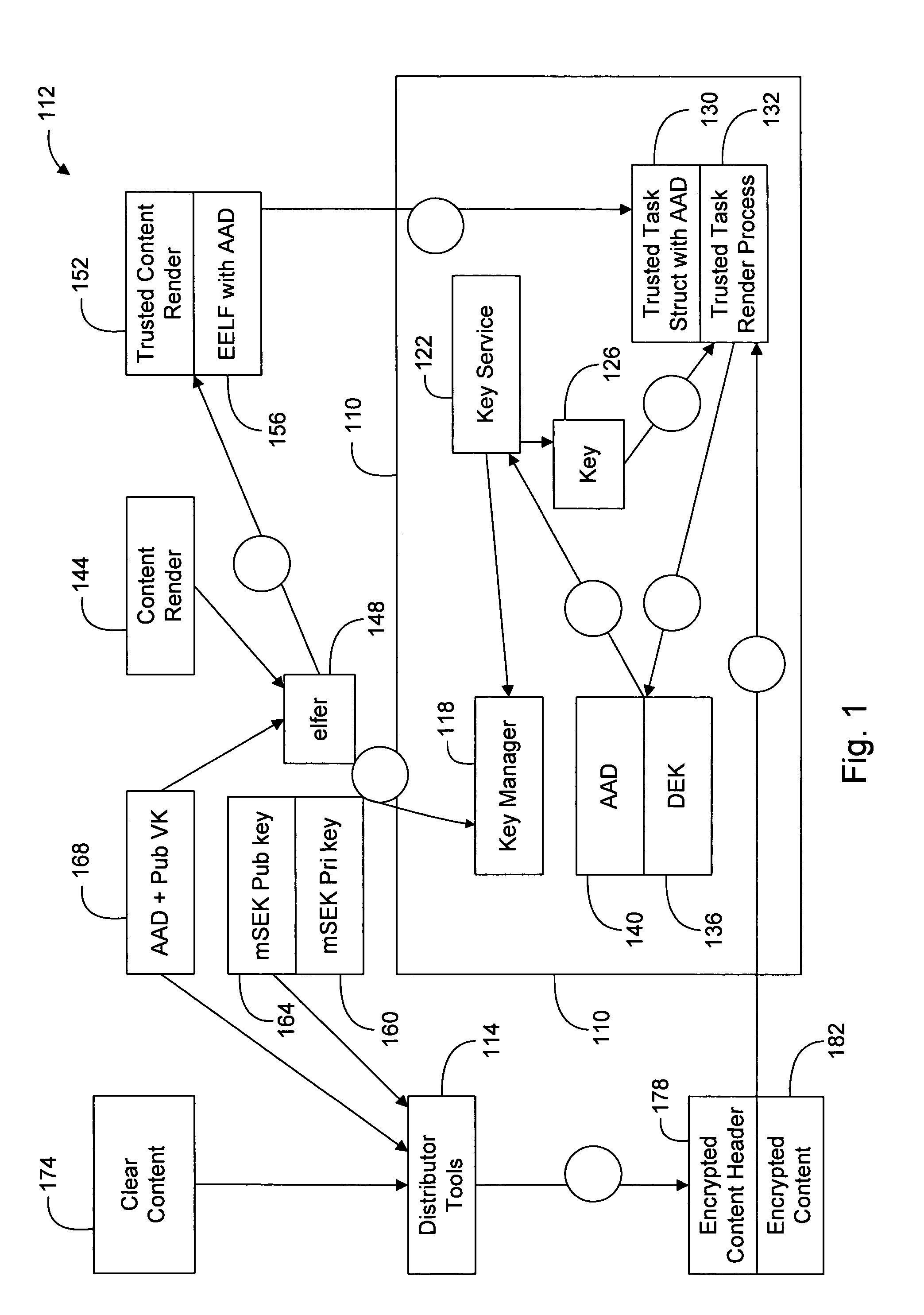
Content such as computer software, data representing audiovisual works, and electronic documents can converted from a machine-bound state to user-bound state without modification to the content data itself. Instead, keys used to access the content are converted from the machine-bound state to the user-bound state. In particular, the keys are kept in a passport data structure which can represent either a machine-binding or a user-binding. A machine-bound passport can be upgraded to a user-bound passport without modifying the bound content. The private key of the machine-bound passport, in cleartext form, is included in the user-bound passport and encrypted using a user-supplied password to bind the private key to the user. In addition, private user information is collected and verified and included in the user-bound passport. Upgrading a machine-bound passport can be initiated automatically upon detection that an attempt is made to play back machine-bound content on a machine other than the one to which the content is bound.
Owner:MICROSOFT TECH LICENSING LLC
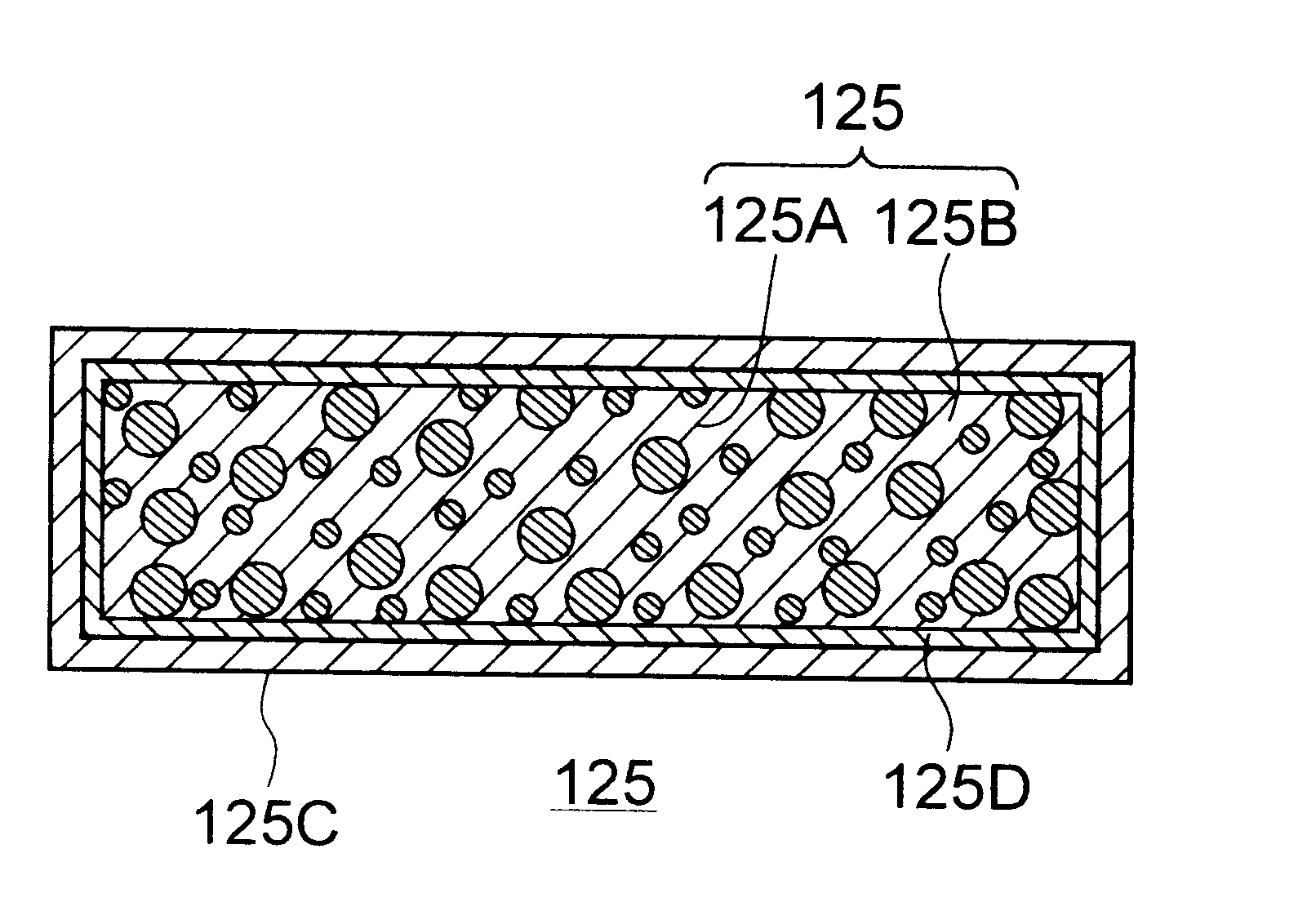
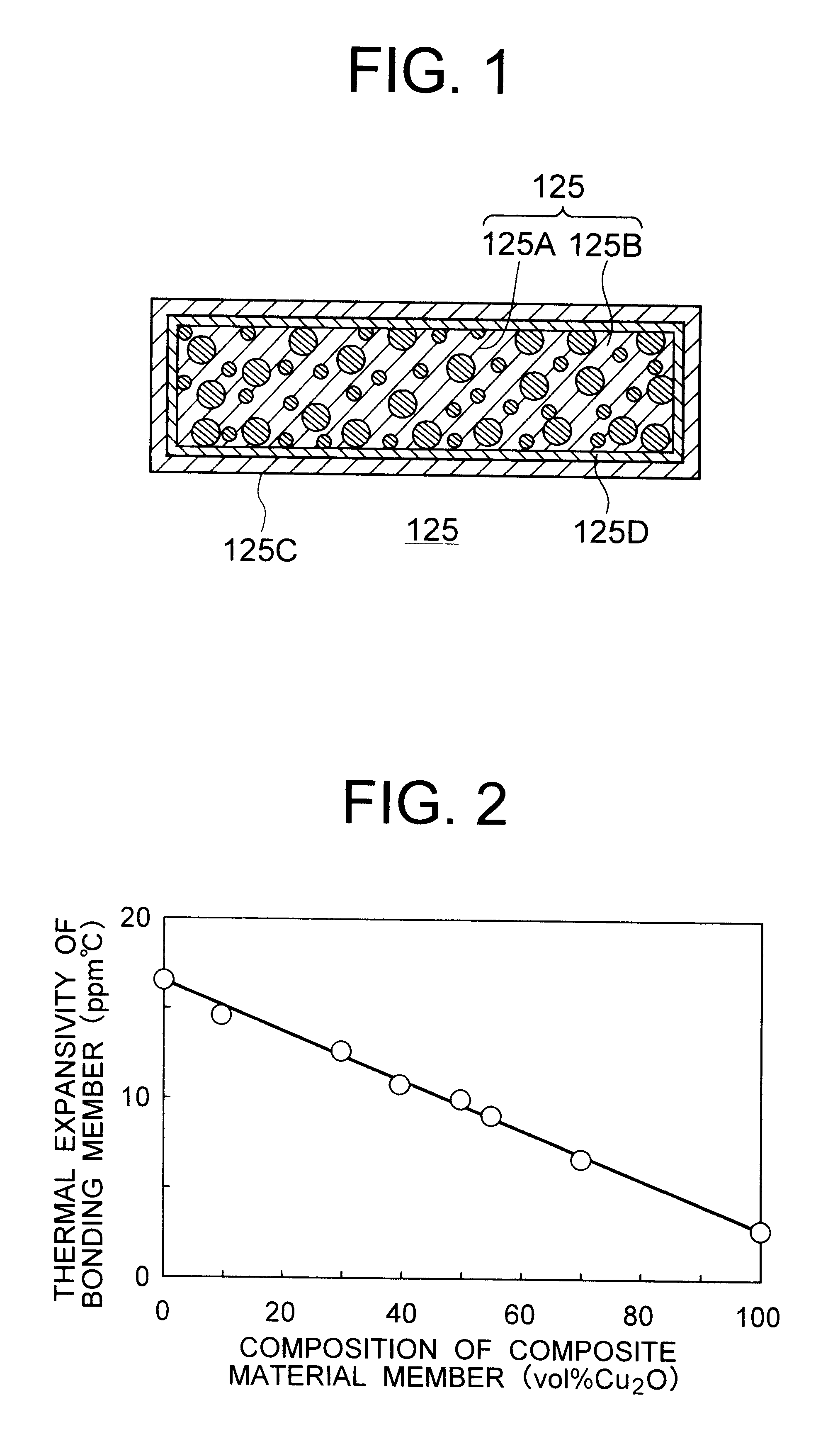
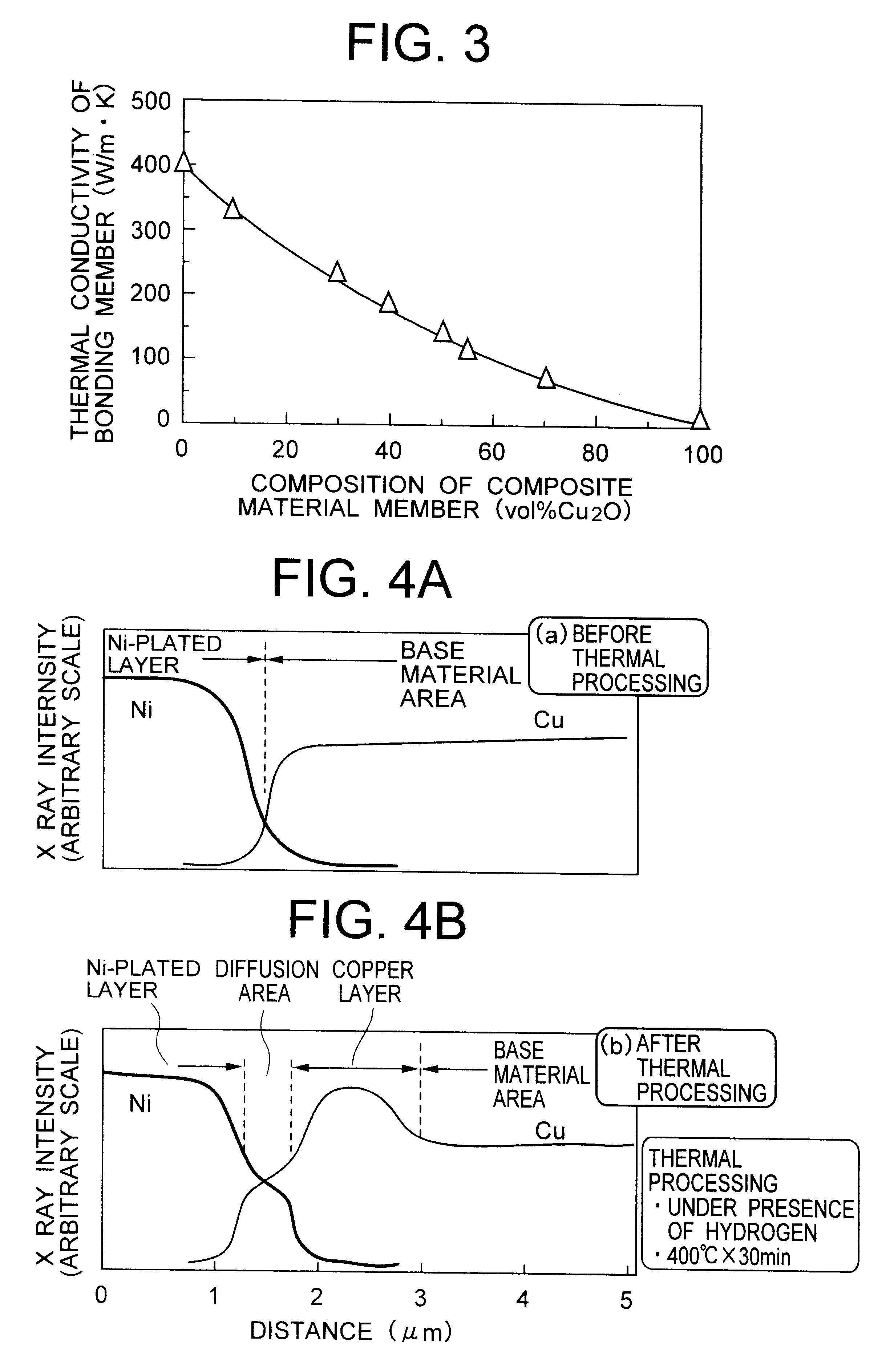
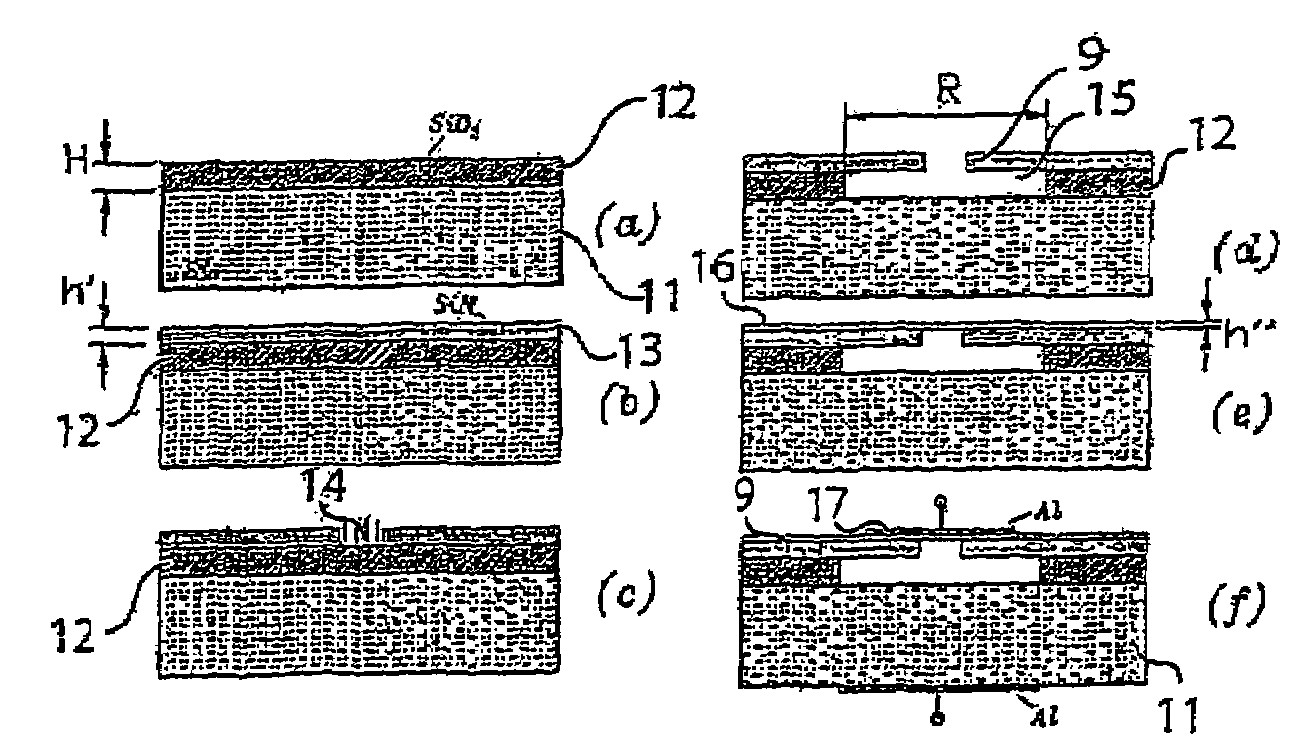
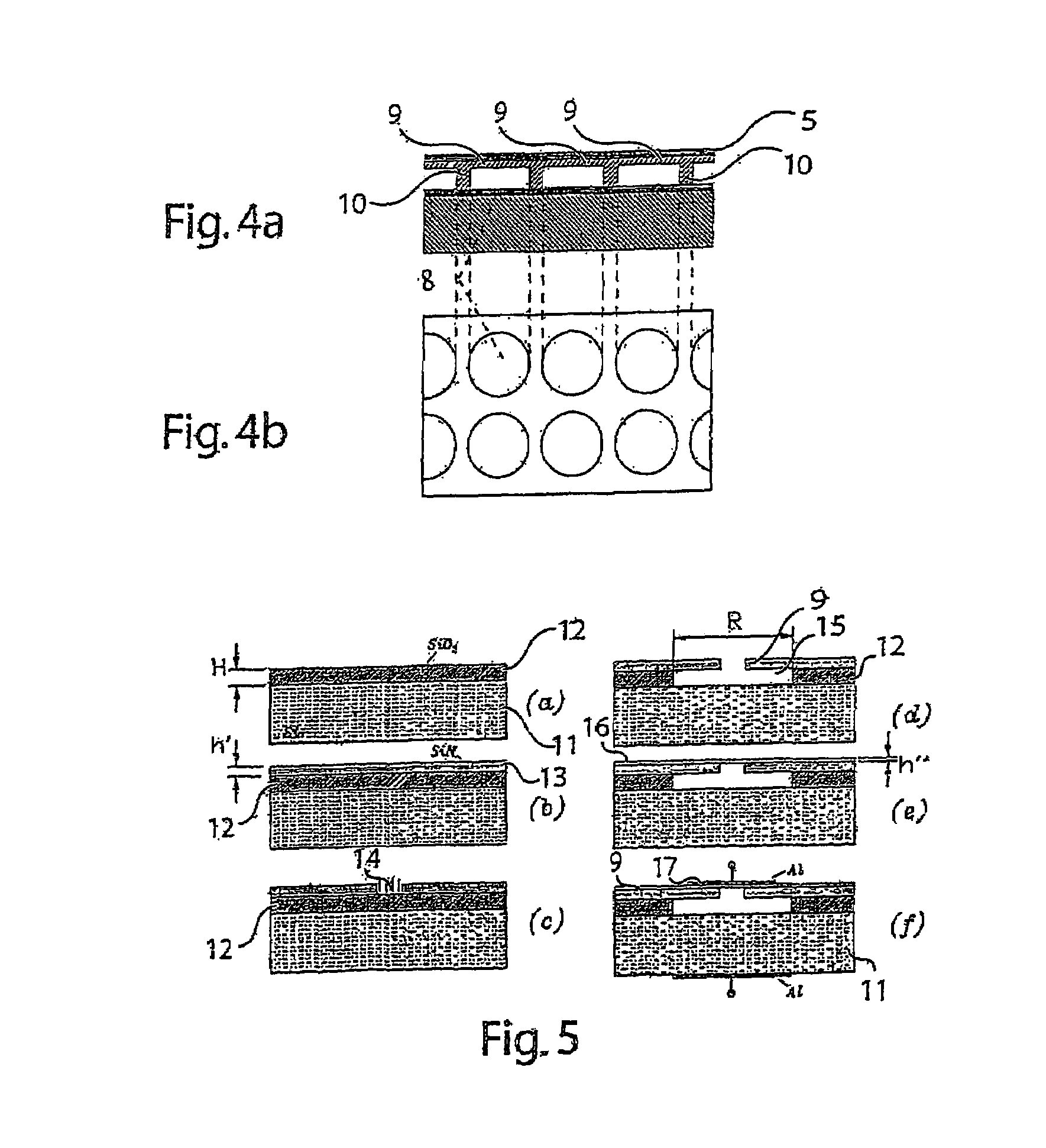
Composite material member for semiconductor device and insulated and non-insulated semiconductor devices using composite material member
InactiveUS6579623B2Mosaic printer telegraph systemSemiconductor/solid-state device detailsSemiconductorMetal
To provide a composite material member for semiconductor device, an insulated semiconductor device and non-insulated semiconductor device using the composite material member, which are effective for obtaining a semiconductor device that alleviates thermal stress or thermal strain occurring during production or operation, has no possibilities of deformation, degeneration and rupture of each member, and is highly reliably and inexpensive. The composite material member for semiconductor device is characterized by being a composite metal plate with particles composed of cuprous oxide dispersed in a copper matrix, in which a surface of the composite metal plate is covered with a metal layer, and a copper layer with thickness of 0.5 mum or larger exists in an interface formed by the composite metal plate and the metal layer.
Owner:HITACHI LTD +1
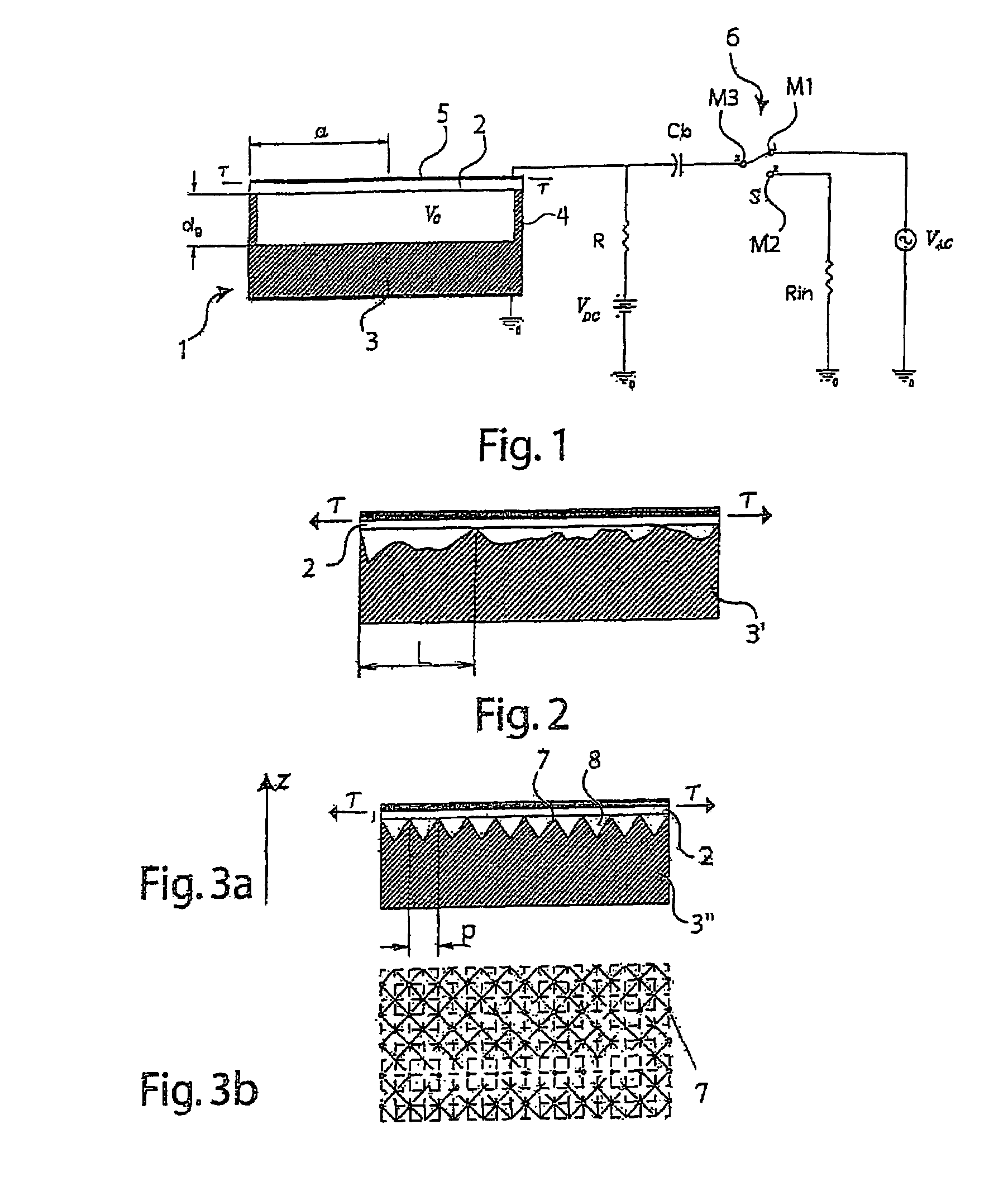
Microfabricated capacitive ultrasonic transducer for high frequency applications
ActiveUS7477572B2Mosaic printer telegraph systemMechanical vibrations separationUltrasonic sensorTransducer
The invention relates to an electro-acoustic transducer, particularly an ultrasonic transducer, comprising a plurality of electrostatic micro-cells of the cMUT type. The electrostatic micro-cells are arranged in homogeneous groups of micro-cells having the same geometrical characteristics. The micro-cells of each group have geometries different from the geometry of the micro-cells of the other group or groups.
Owner:ESAOTE
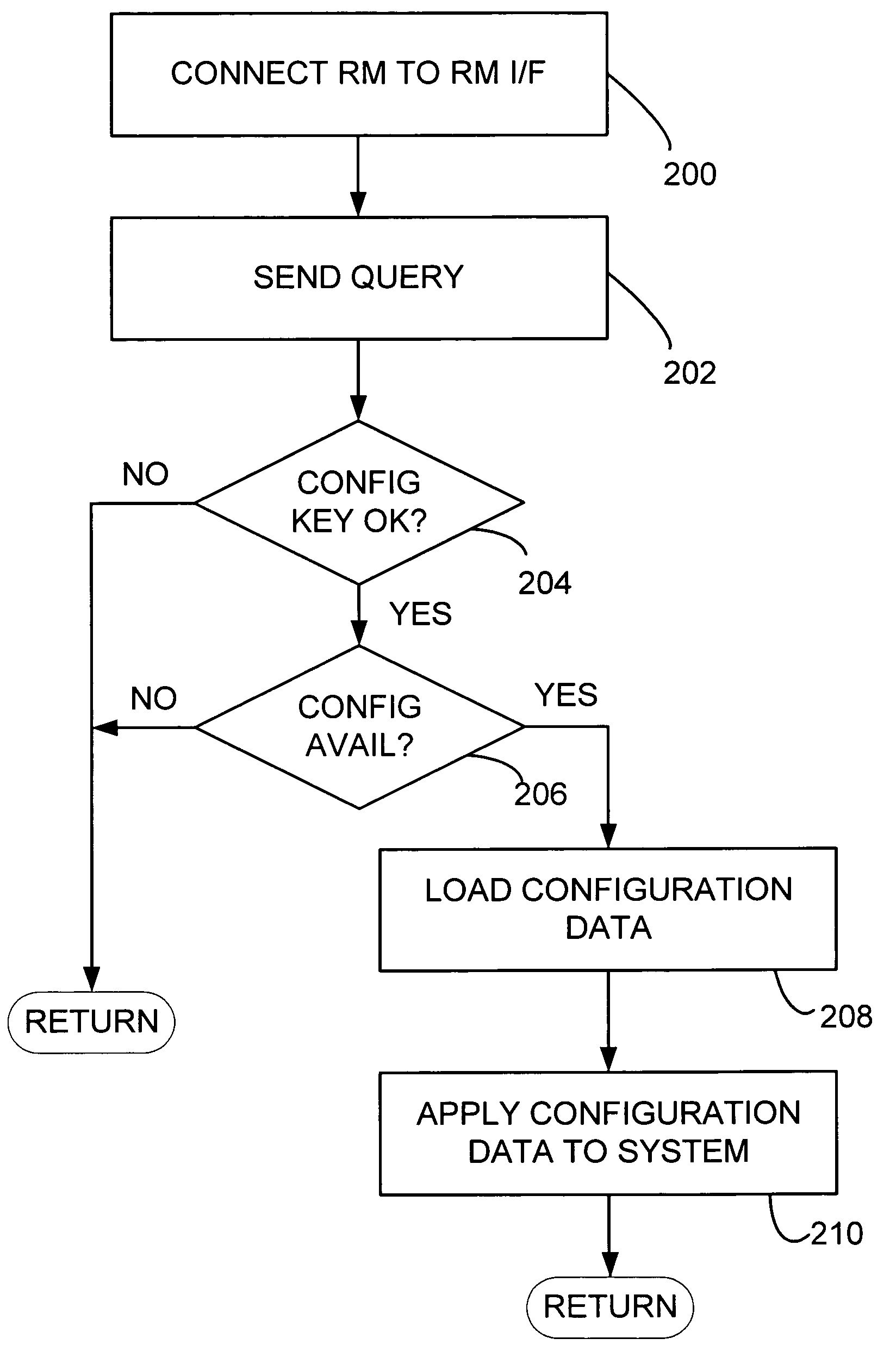
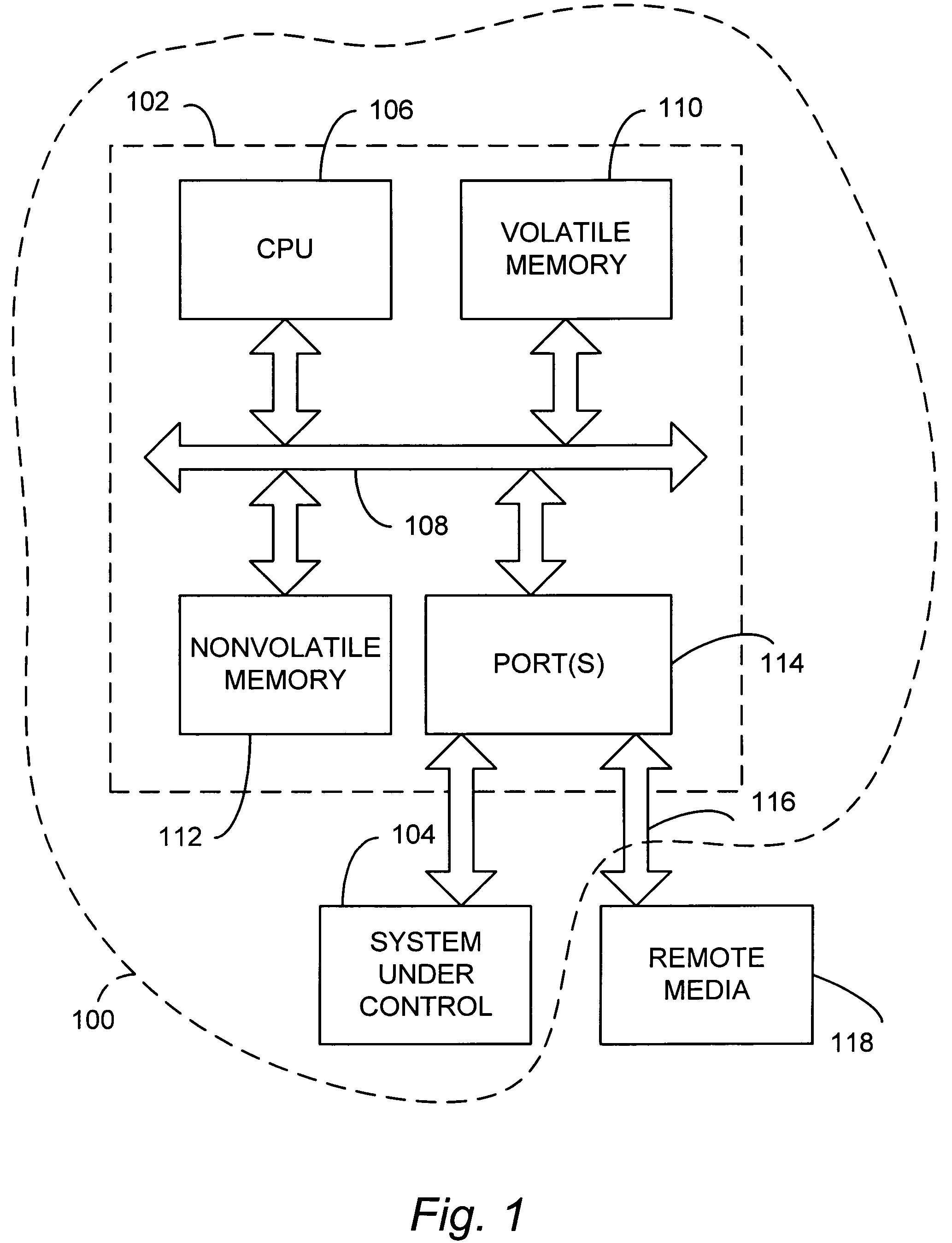
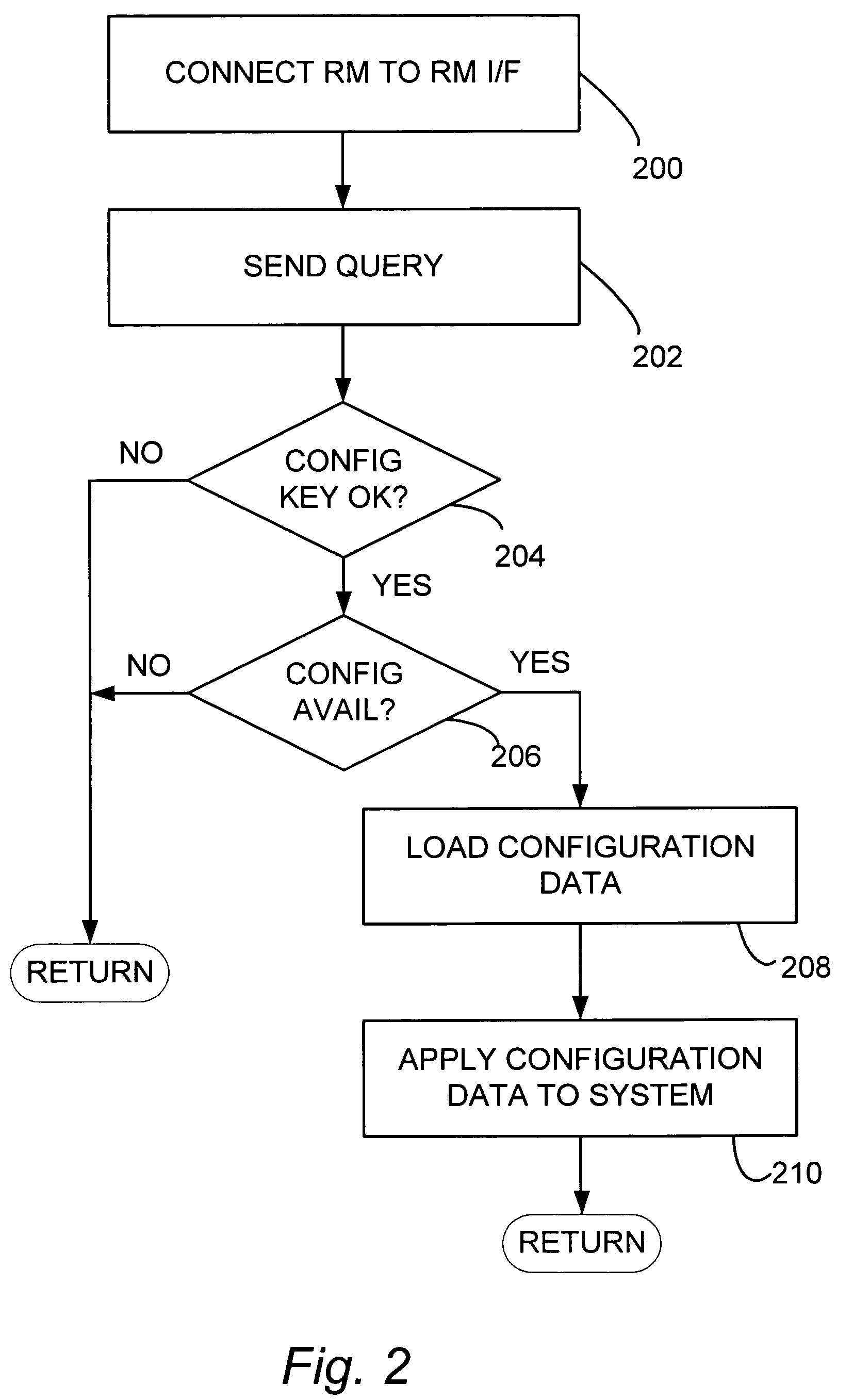
Automatic device configuration using removable storage
ActiveUS7624452B2Mosaic printer telegraph systemAnalogue secracy/subscription systemsRemovable mediaData application
A system and method of configuring an embedded system from removable media. The removable media is connected to the embedded system and the embedded system determines if the removable media includes a configuration key. If the removable media includes a configuration key, the embedded system determines if the configuration key includes configuration data applicable to the embedded system and, if the removable media includes a configuration key and the configuration key includes configuration data applicable to the embedded system, the embedded system applies the configuration data to the embedded system.
Owner:DIGI INTERNATIONAL
Location based service
InactiveUS8806653B2Digital data processing detailsRoad vehicles traffic controlWeb authenticationClient-side
Owner:DI RIENZO ANDREW L
Device and method for detecting command and control channel
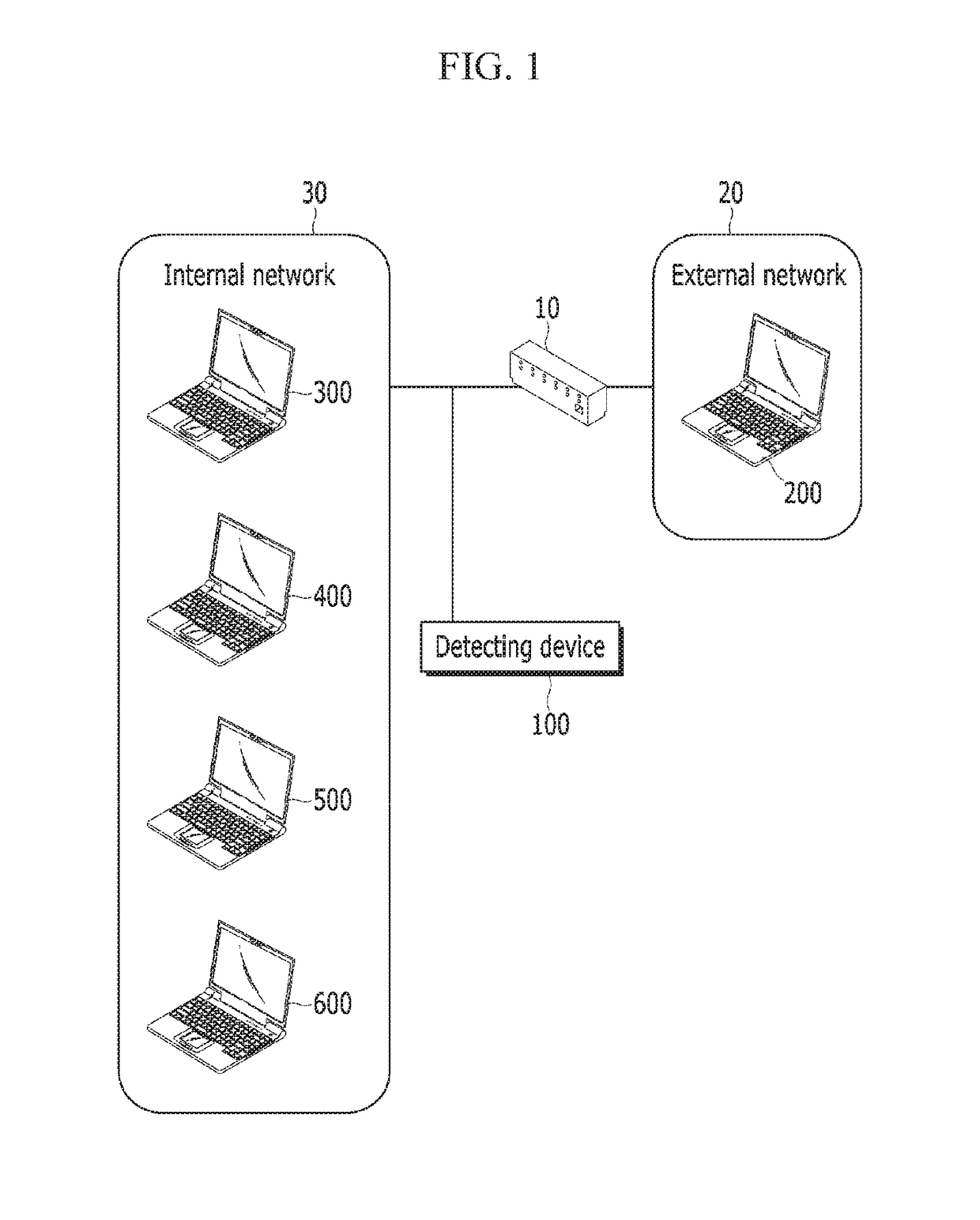
ActiveUS10218725B2Efficient processingMosaic printer telegraph systemAbnormal distributionCommand and control
A device for detecting a command and control channel includes: a session log collector for collecting log information of sessions generated between at least one communication device of the first network and at least one communication device of the second network; an analyzer for generating test data for respective sessions based on the log information, and calculating a test data distribution based on test data of the sessions; and a determiner for extracting a test data value corresponding to an abnormal distribution from the test data distribution based on an abnormal distribution determination standard, and estimating sessions relating to the extracted test data value as a command and control channel.
Owner:NARU SECURITY
Secure object for convenient identification
InactiveUS20070208950A1Mosaic printer telegraph systemPublic key for secure communicationUser authenticationInformation storage
A method and apparatus for automatic user authentication are described. The method includes receiving information at a device, the device including a credential container; storing the information at the credential container and performing cryptographic calculations on the received information and providing the encrypted information upon request.
Owner:IBM CORP
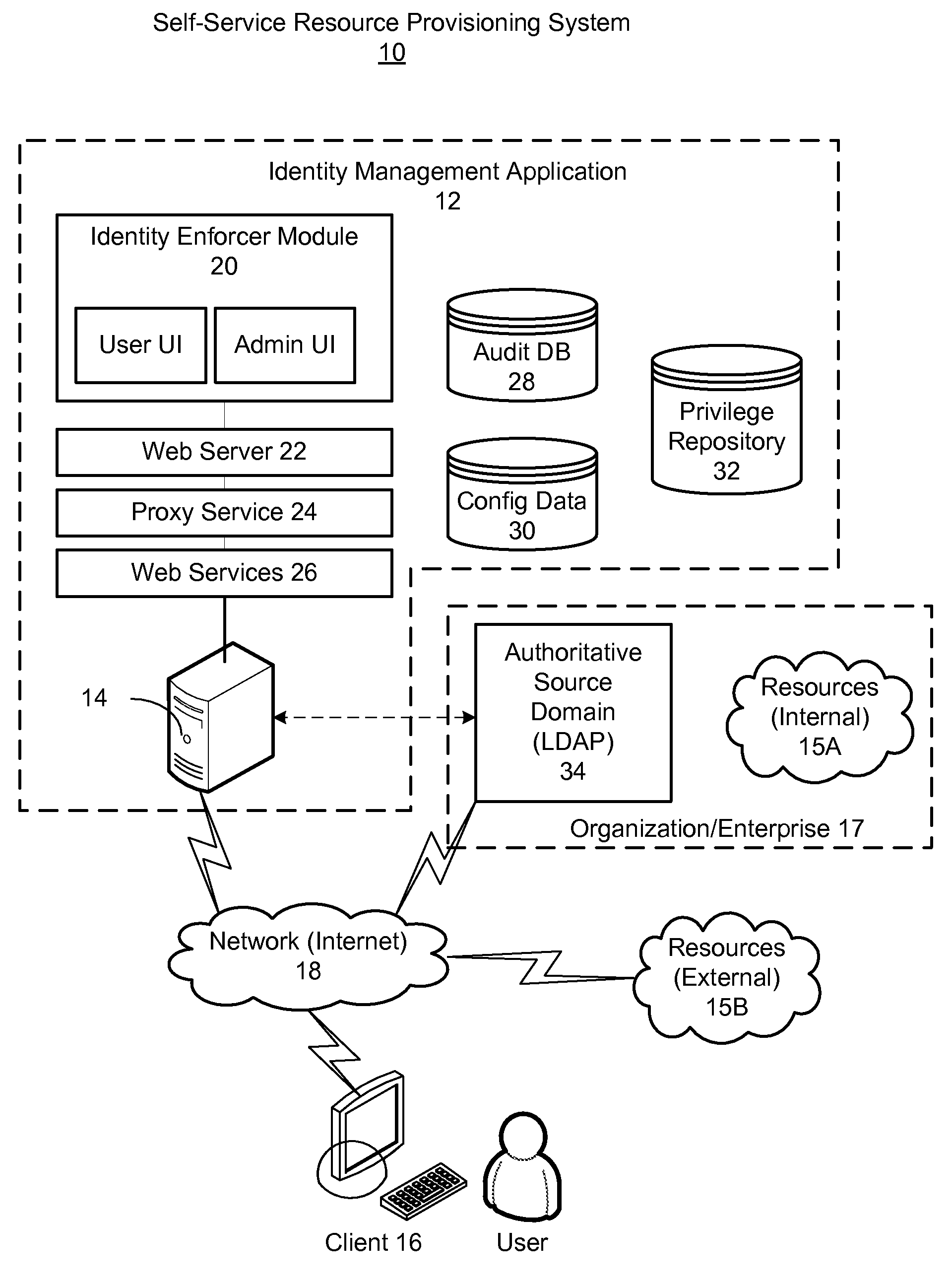
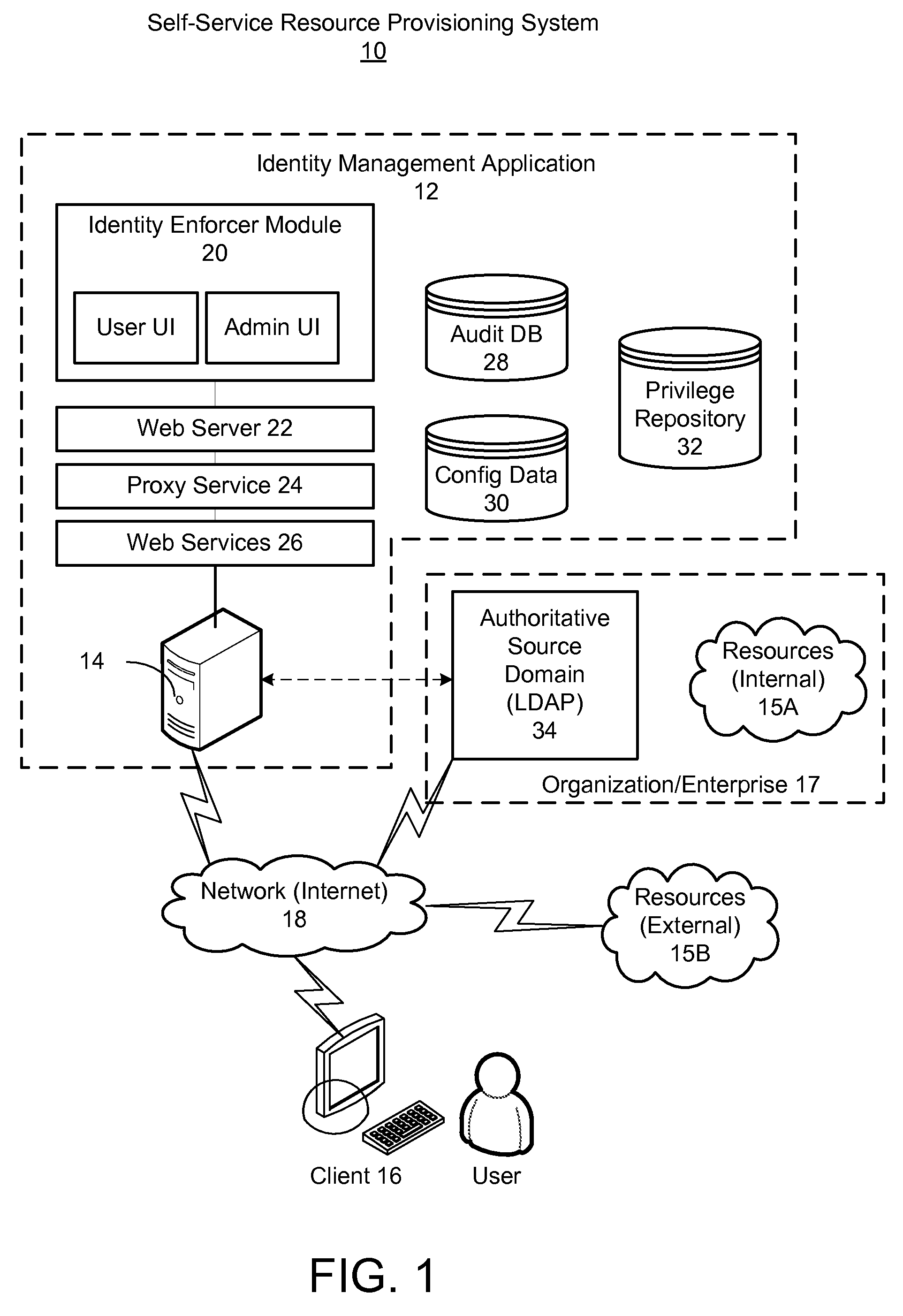
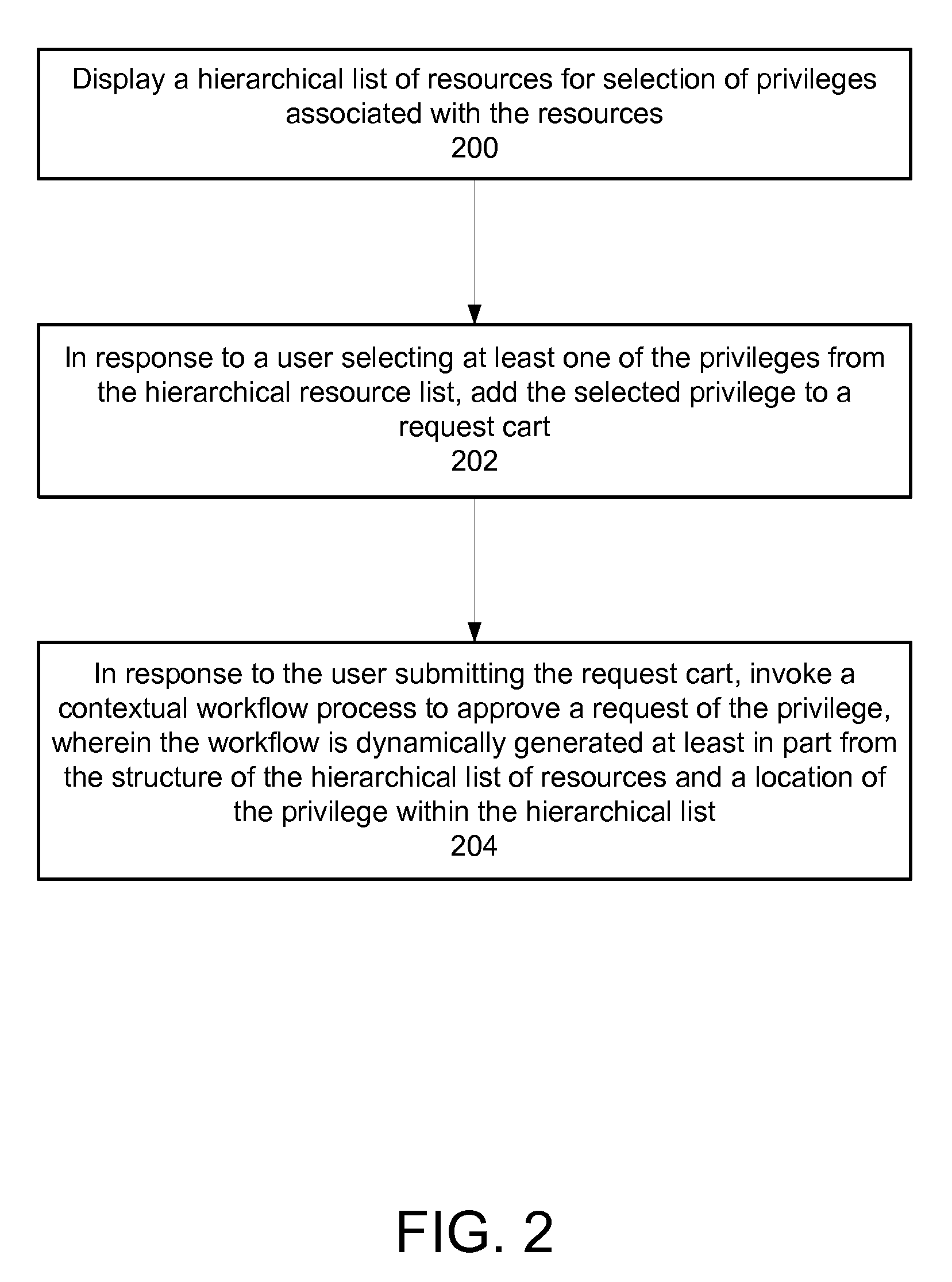
Self-service resource provisioning having collaborative compliance enforcement
ActiveUS7707623B2Mosaic printer telegraph systemDigital data processing detailsSelf-serviceWorld Wide Web
Exemplary embodiments provide a method and system for self-service resource provisioning having collaborative compliance enforcement. Method and system aspects of the exemplary embodiments include displaying a hierarchical list of resources for selection of at least one privilege associated with the resources; in response to a user selecting least one of the privileges from the hierarchical list, adding the selected privilege to a request cart to enable the user to initiate a request for the privilege; and in response to a user submitting the request cart, automatically invoking a workflow process to approve a request for the privilege, wherein the workflow is dynamically generated at least in part from the structure of the hierarchical list of resources and a location of the privilege within the hierarchical list.
Owner:AVATIER CORP
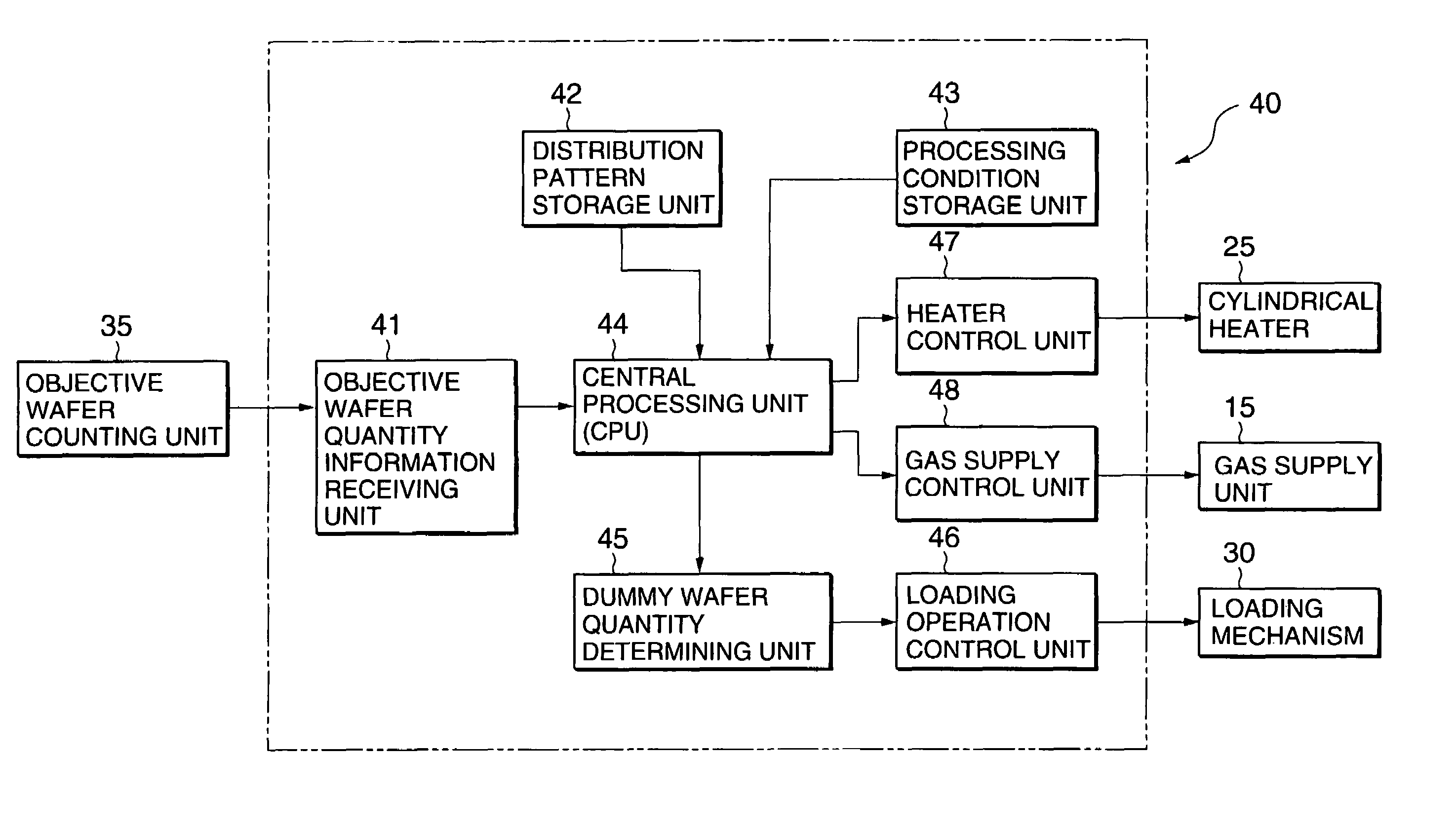
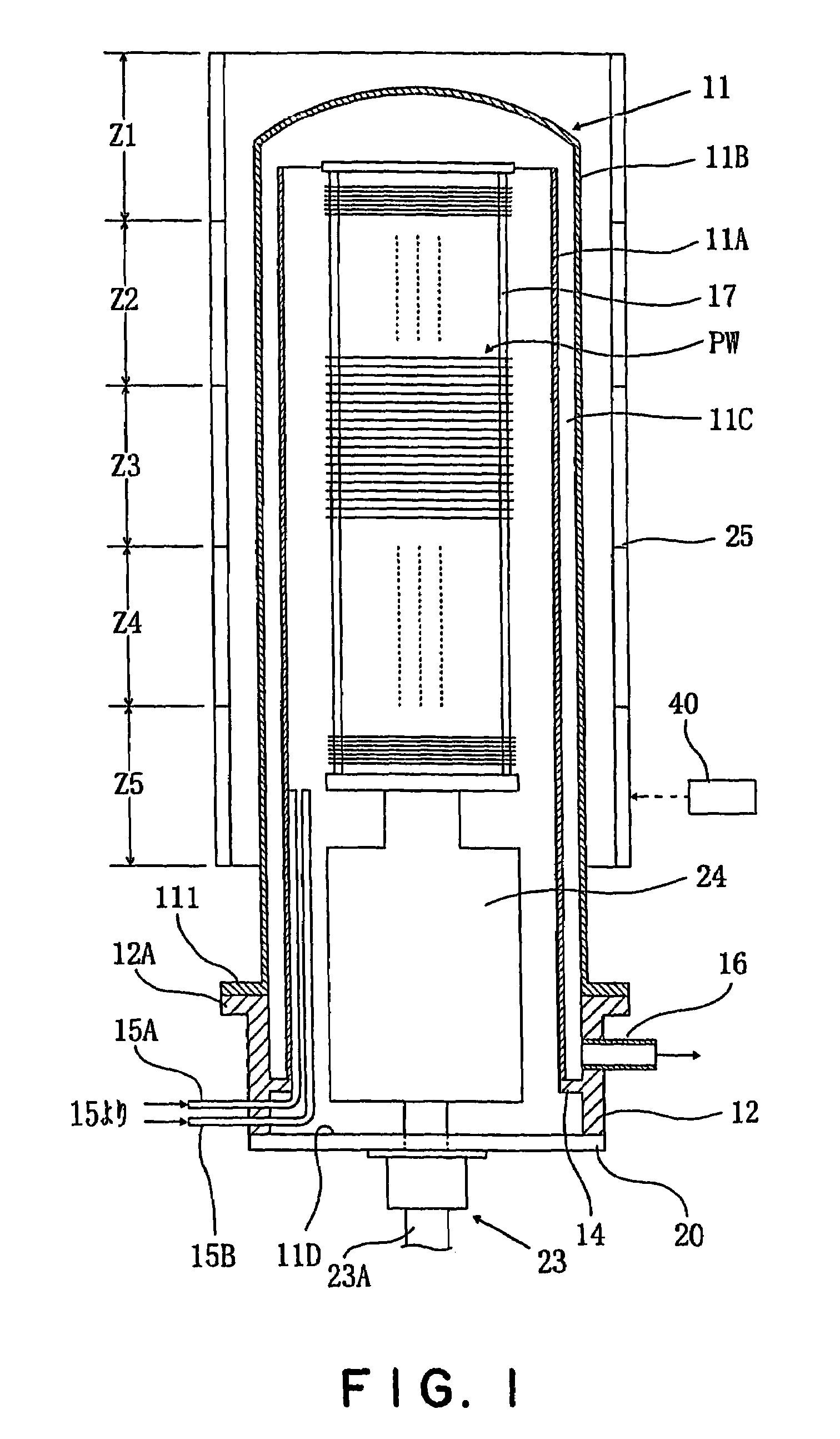
Heat treatment method and heat treatment device
InactiveUS6975917B2Reduce in quantitySatisfactory uniformityMosaic printer telegraph systemMuffle furnacesDistribution patternThermal treatment
A thermal processing method selects a batch size range including the number of workpieces to be processed from a plurality of batch size ranges including batch size ranges in which reference numbers smaller than the holding capacity of a workpiece holder are maximums. The workpieces are distributed in the workpiece holder on the basis of the workpiece distribution pattern determined corresponding to the specified batch size range. Processing conditions of the thermal process are determined according to the workpiece distribution pattern. A thermal processing apparatus comprises a controller capable of carrying out the thermal processing method.
Owner:TOKYO ELECTRON LTD
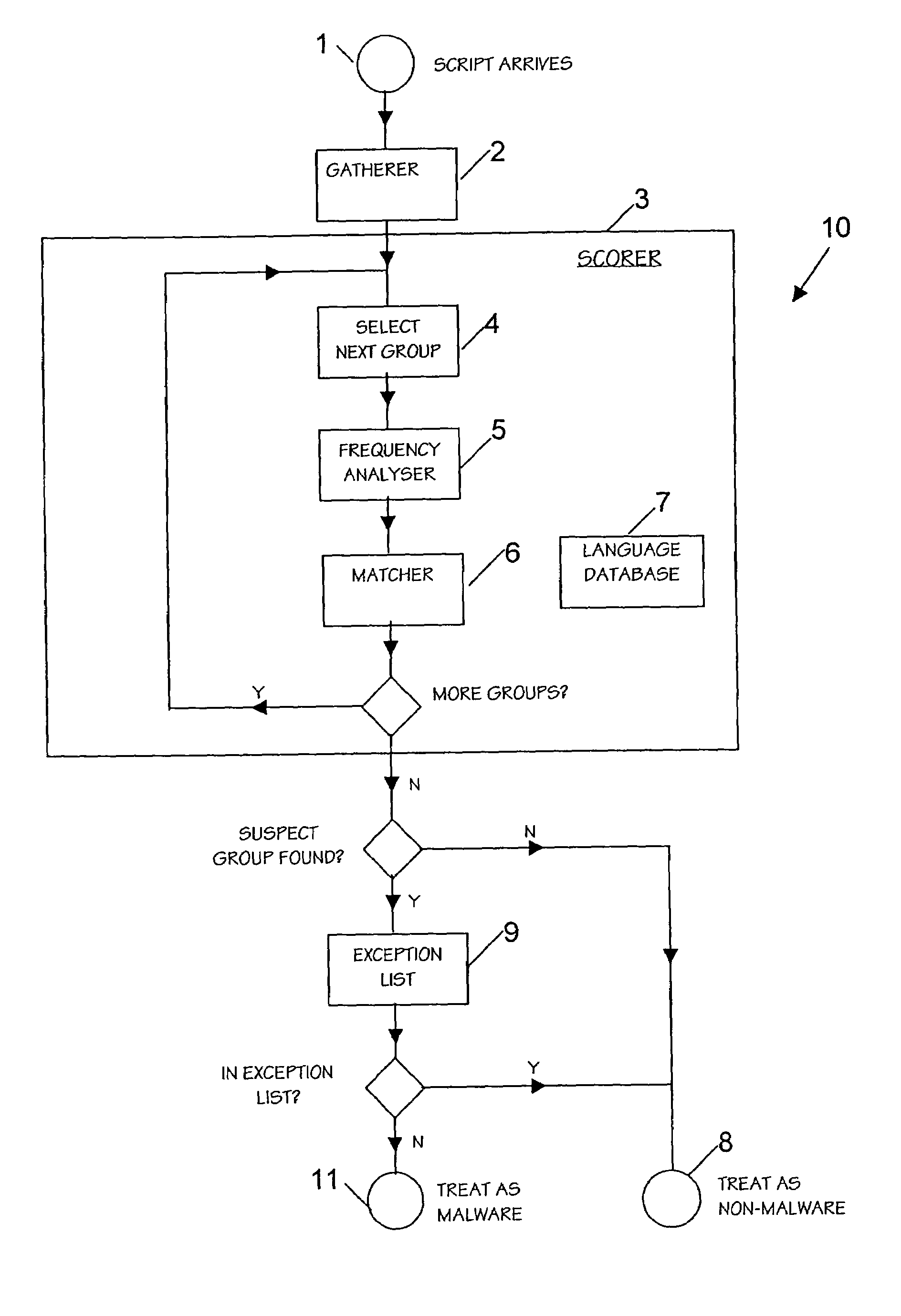
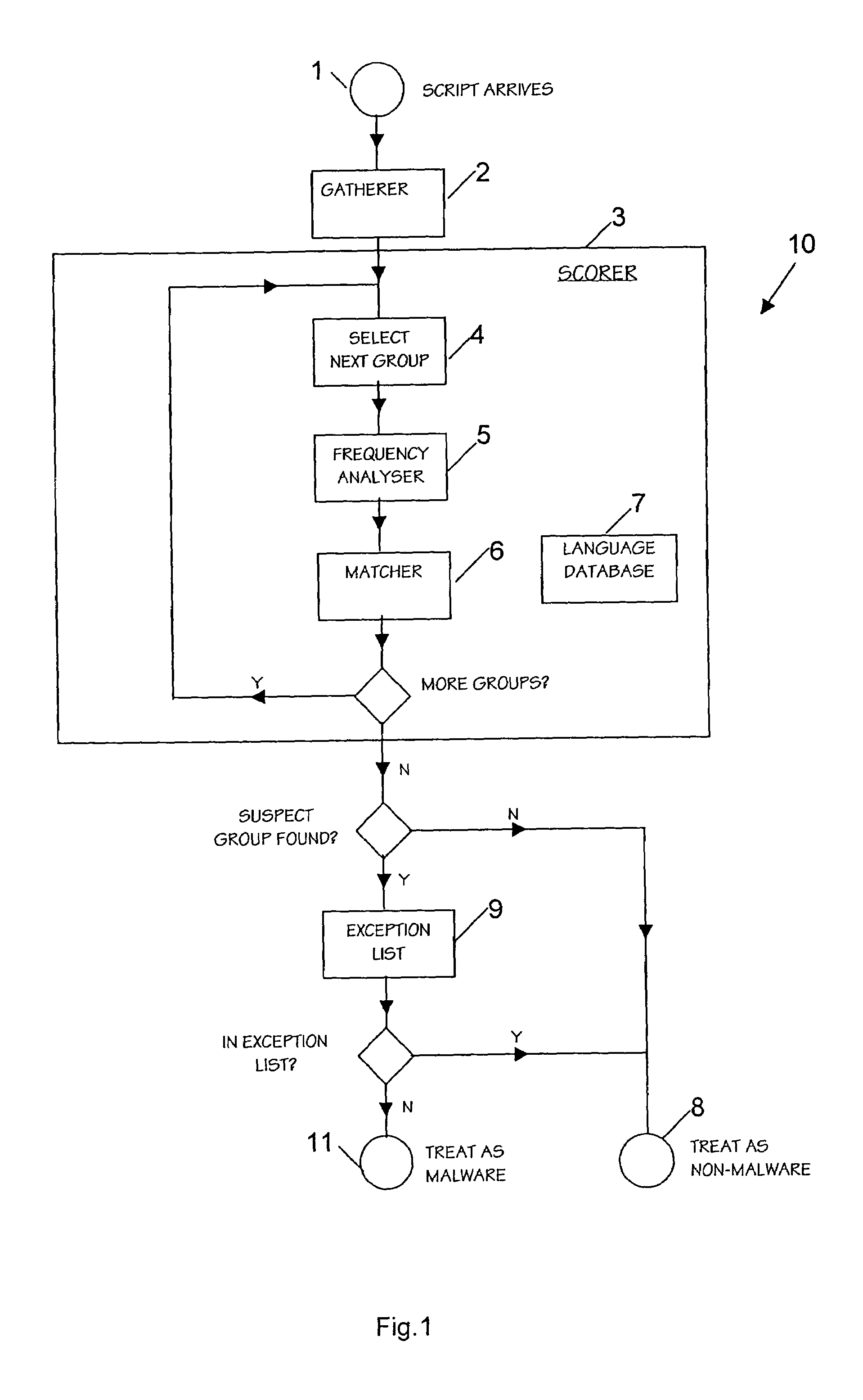
System for and method of detecting malware in macros and executable scripts
ActiveUS7493658B2Improve usabilityMosaic printer telegraph systemMemory loss protectionMalwareSource code
An anti malware scanner for files is provided with means for processing script and macro files and flagging them as suspect or not based upon an automated analysis of source code in the file. This analysis involves separating the program source into groups of parts such as comment, variable names and routine names, eliminating duplicates and performing a character frequency distribution analysis of the resulting strings. The system may include an exception list to omit flagging a file as suspect if it is on the exception list.
Owner:CA TECH INC
System and method for authorizing the use of stored information in an operating system
InactiveUS7568102B2Mosaic printer telegraph systemUser identity/authority verificationOperational systemApplication software
A method and apparatus for authorizing a file to use stored information for executing a process in a Linux operating system. The file includes an executable linking format, an application authorization data, and other attributes for the application.
Owner:SONY CORP +1
Self aligned metal interconnection and method of making the same
InactiveUS6887784B1Mosaic printer telegraph systemSemiconductor/solid-state device detailsConductive materialsInterconnection
A method of making a structure, includes filling a via hole with a conductive material, to form a via. The via hole passes through an etch-stop opening. In both directions along a first axis dielectric material is present between the via hole and edges of the etch-stop layer, and in both directions along a second axis, perpendicular to said first axis, dielectric material is not present between the via hole and edges of the etch-stop layer.
Owner:MONTEREY RES LLC
System Independent Remote Storing of Digital Content
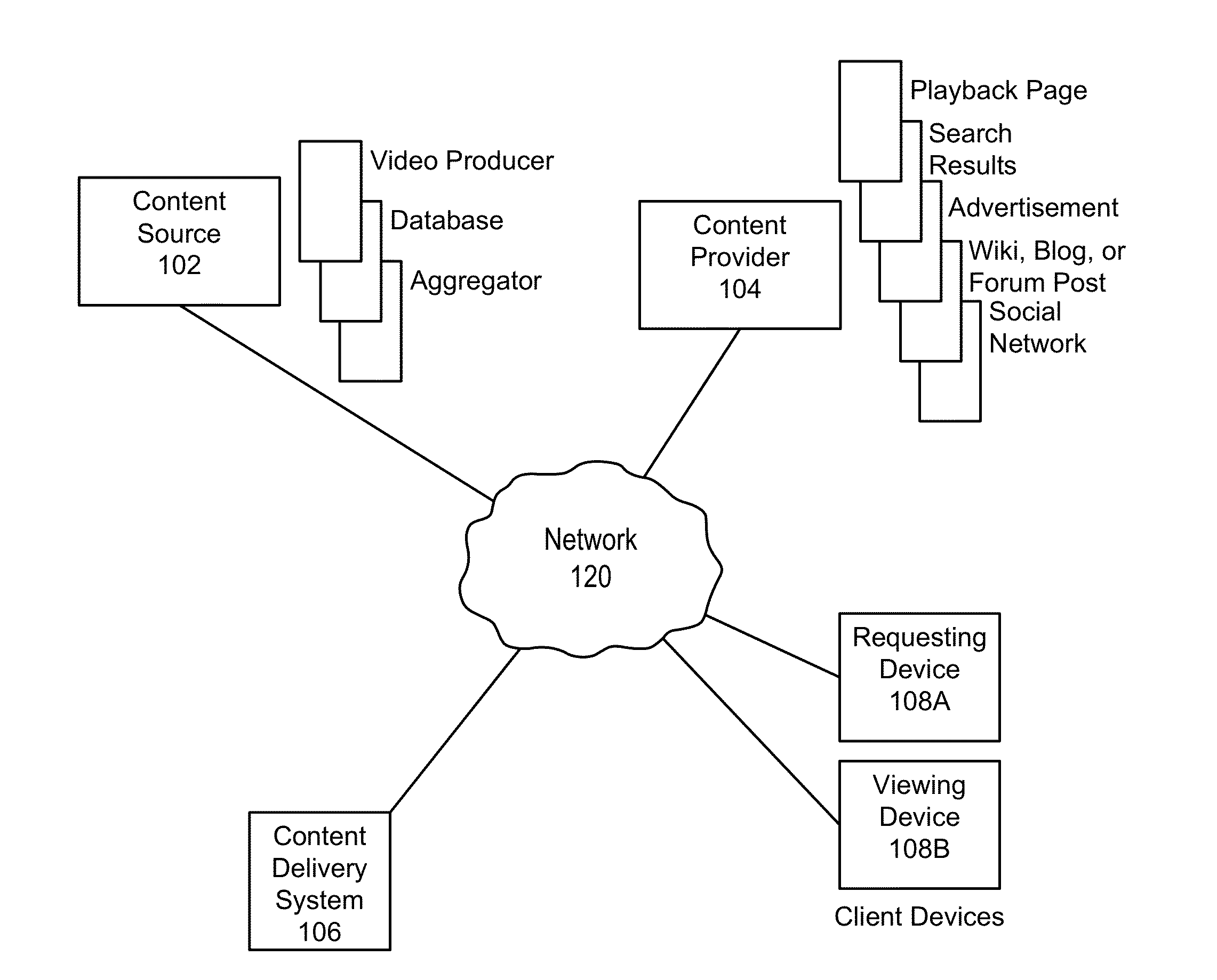
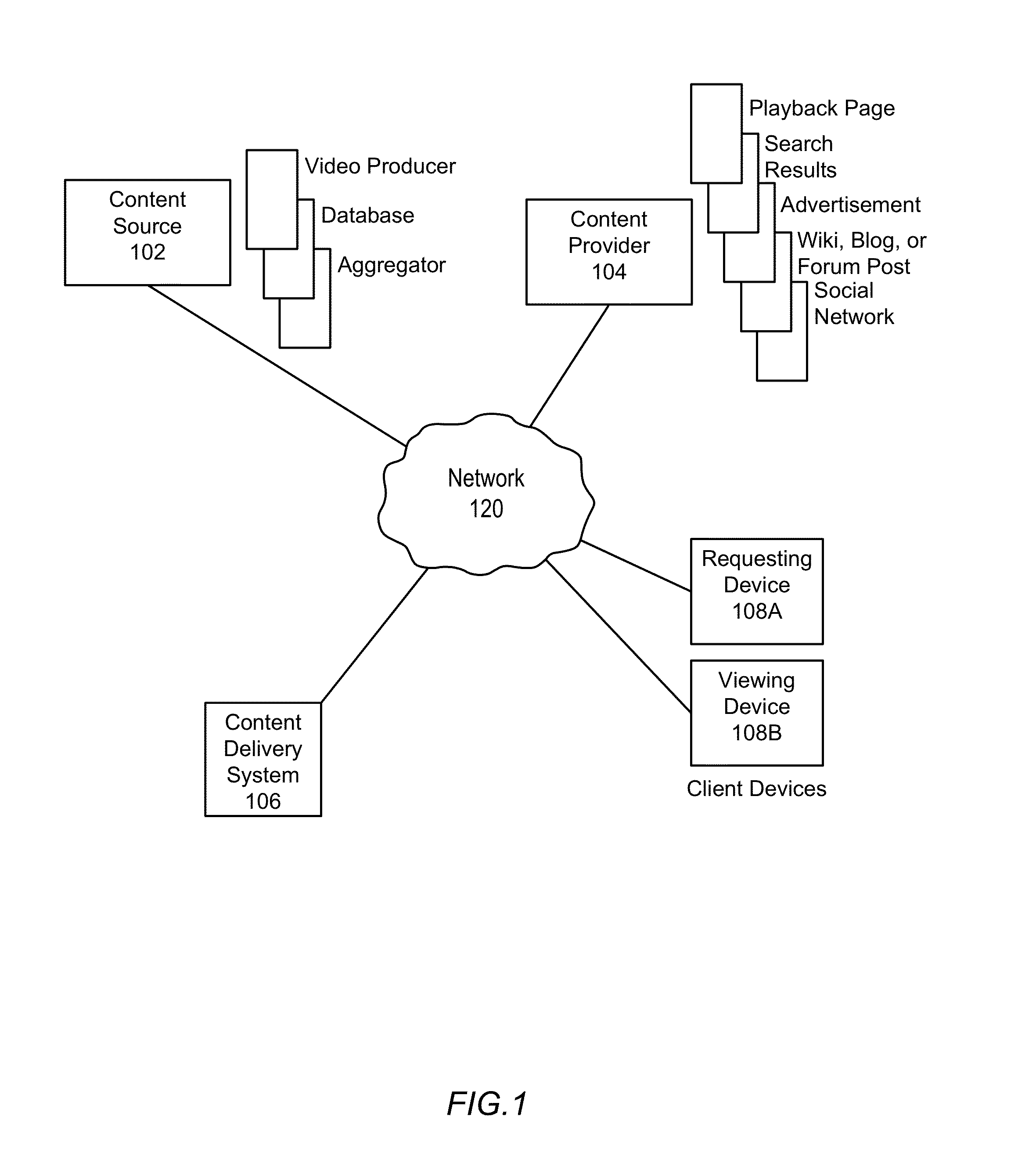
ActiveUS20130227076A1Mosaic printer telegraph systemMultiple digital computer combinationsDigital contentWeb page
A system and a method are disclosed for a content delivery system that enable system-independent, remote storing of digital content on any number of a user's devices. The system and method enable a user to designate a digital content item appearing in a web page for storage, as well as a specific, separate device on which to store the content item. The digital content item is not restricted to being viewed or accessed within the content delivery system, but rather the content delivery system enables remote storing of digital content across multiple different systems, from multiple different content sources, for viewing on multiple different devices for any given user.
Owner:GOOGLE LLC
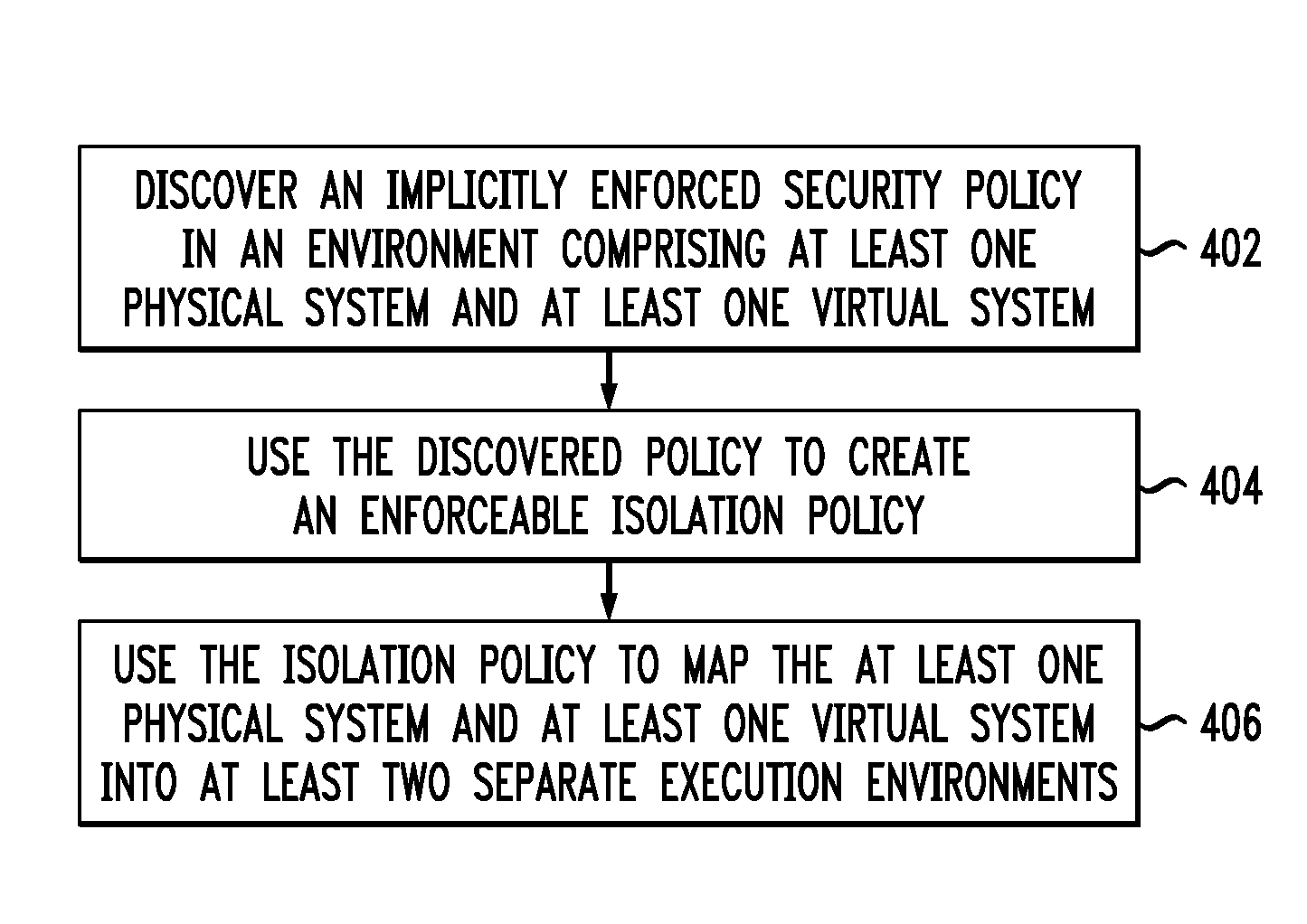
Method for discovering a security policy
ActiveUS8839345B2Mosaic printer telegraph systemDigital computer detailsInternet privacyPhysical system
Techniques for mapping at least one physical system and at least one virtual system into at least two separate execution environments are provided. The techniques include discovering an implicitly enforced security policy in an environment comprising at least one physical system and at least one virtual system, using the discovered policy to create an enforceable isolation policy, and using the isolation policy to map the at least one physical system and at least one virtual system into at least two separate execution environments. Techniques are also provided for generating a database of one or more isolation policies.
Owner:INT BUSINESS MASCH CORP
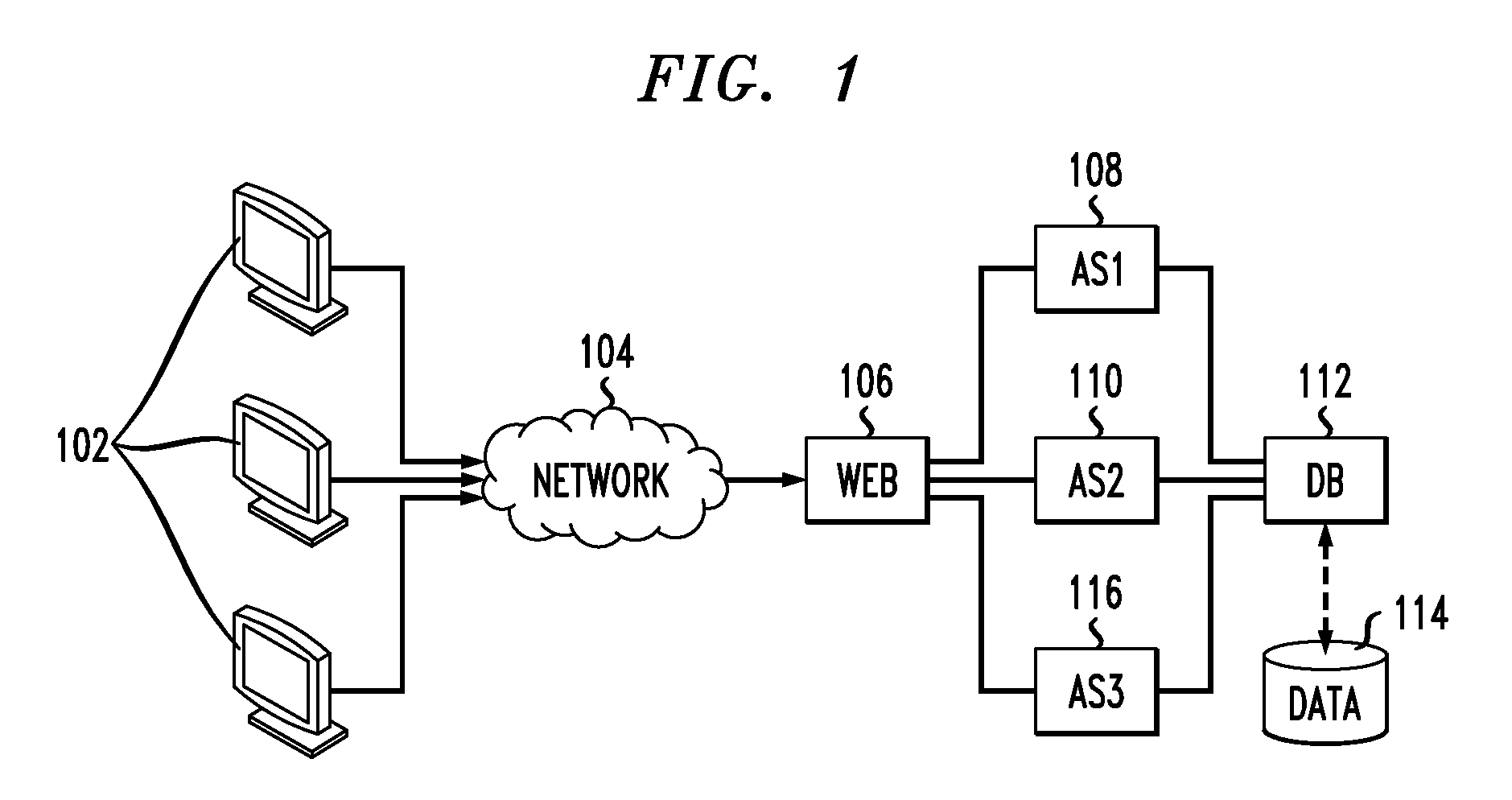
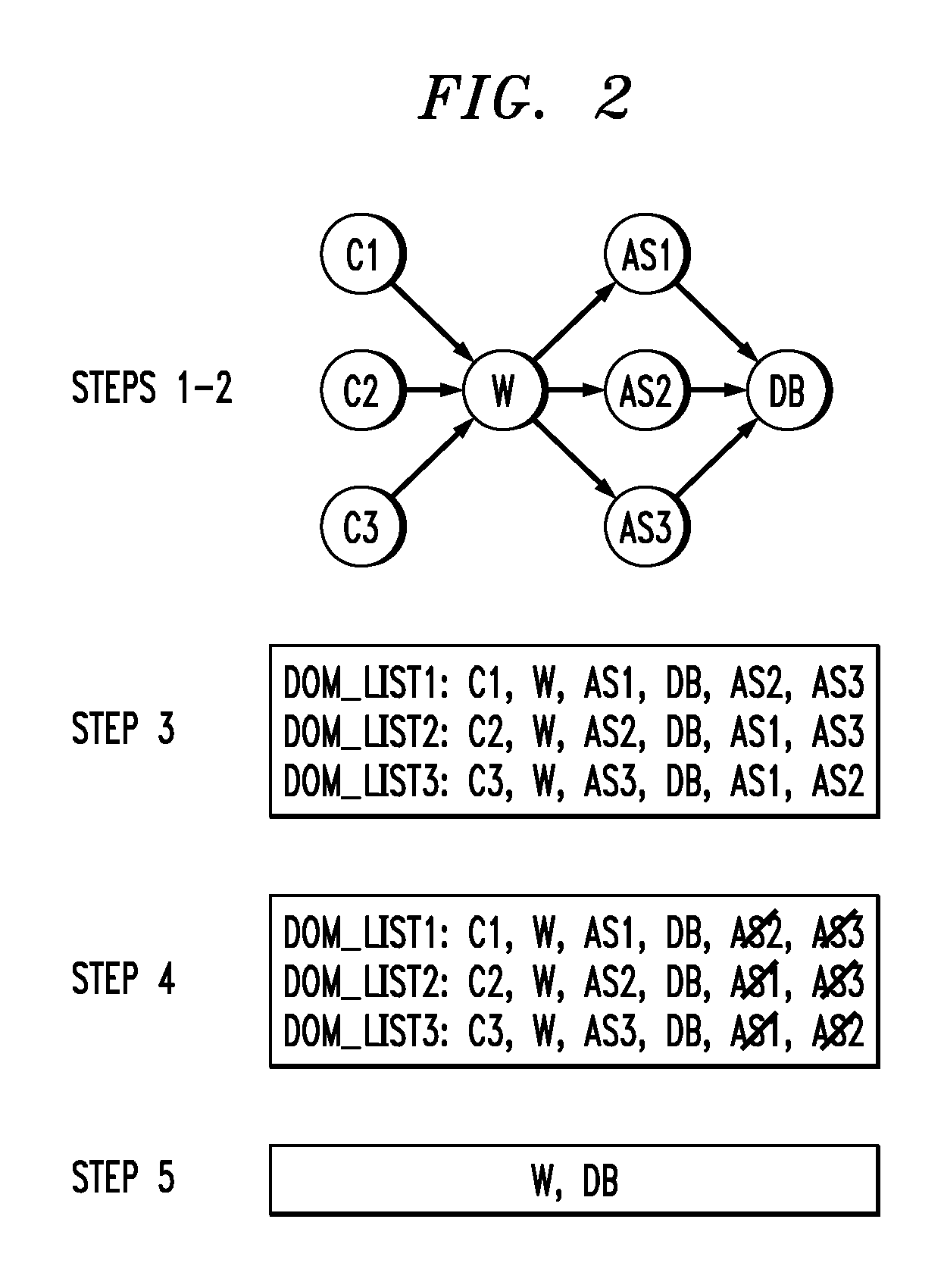
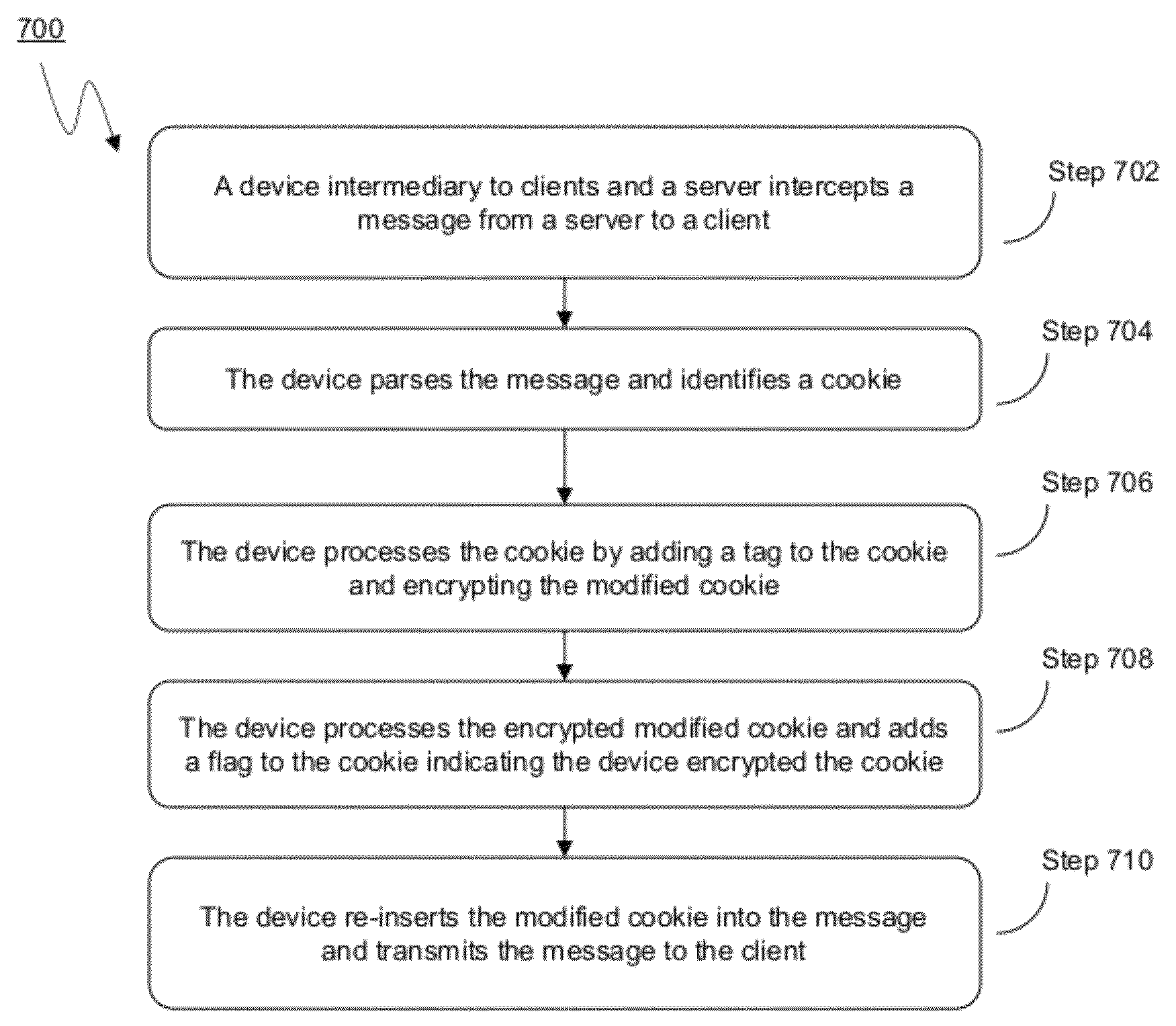
Systems and methods for multi-level tagging of encrypted items for additional security and efficient encrypted item determination
ActiveUS8862870B2Effective judgmentFine grained controlMosaic printer telegraph systemUser identity/authority verificationClient-sideComputer science
The present disclosure is directed towards systems and methods for performing multi-level tagging of encrypted items for additional security and efficient encrypted item determination. A device intercepts a message from a server to a client, parses the message and identifies a cookie. The device processes and encrypts the cookie. The device adds a flag to the cookie indicating the device encrypted the cookie. The device re-inserts the modified cookie into the message and transmits the message. The device intercepts a message from a client and determines whether the cookie in the message was encrypted by the device. If the message was not encrypted by the device, the device transmits the message to its destination. If the message was encrypted by the device, the device removes the flag, decrypts the cookie, removes the tag from the cookie, re-inserts the cookie into the message and transmits the message to its final destination.
Owner:CITRIX SYST INC
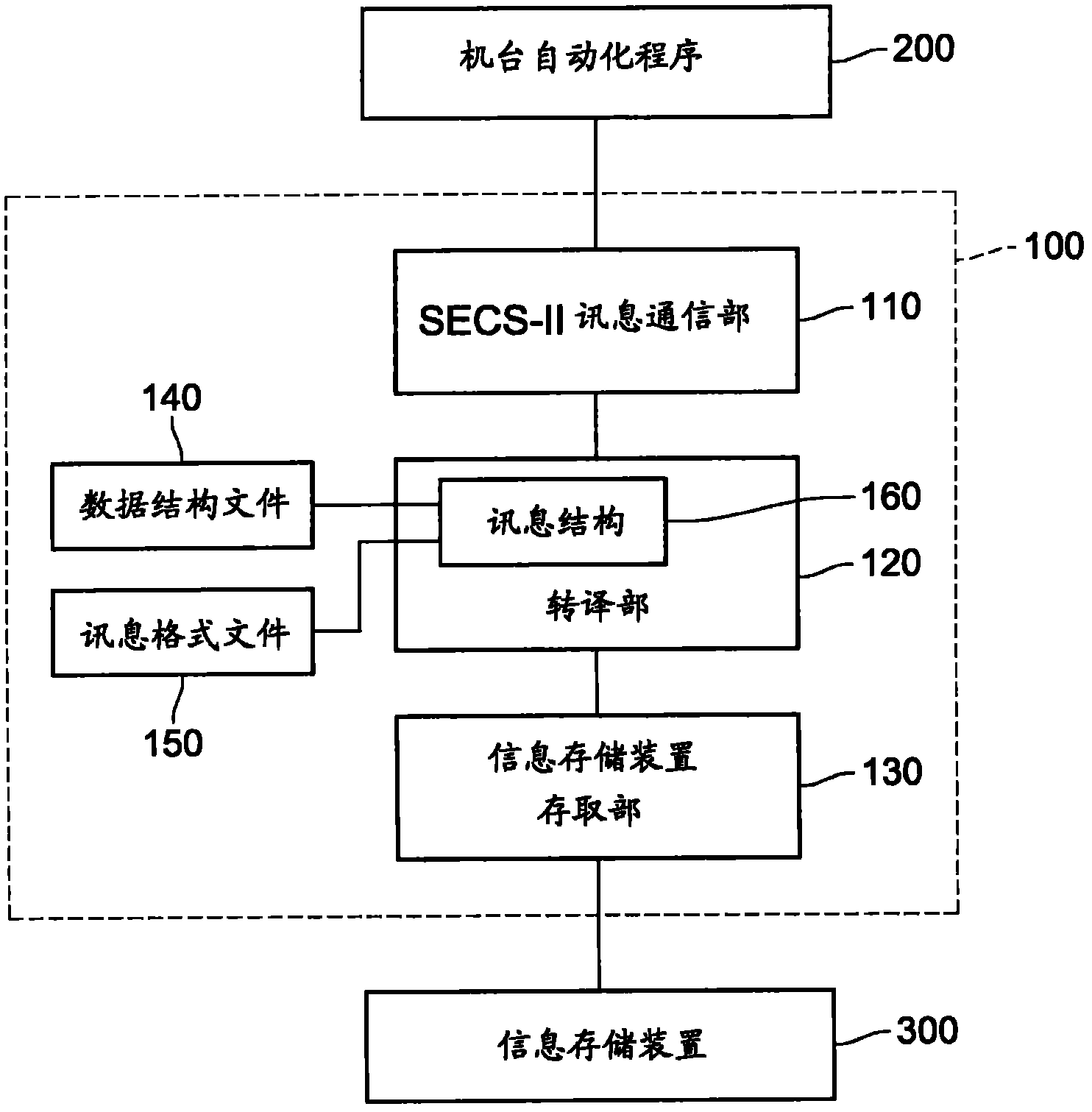
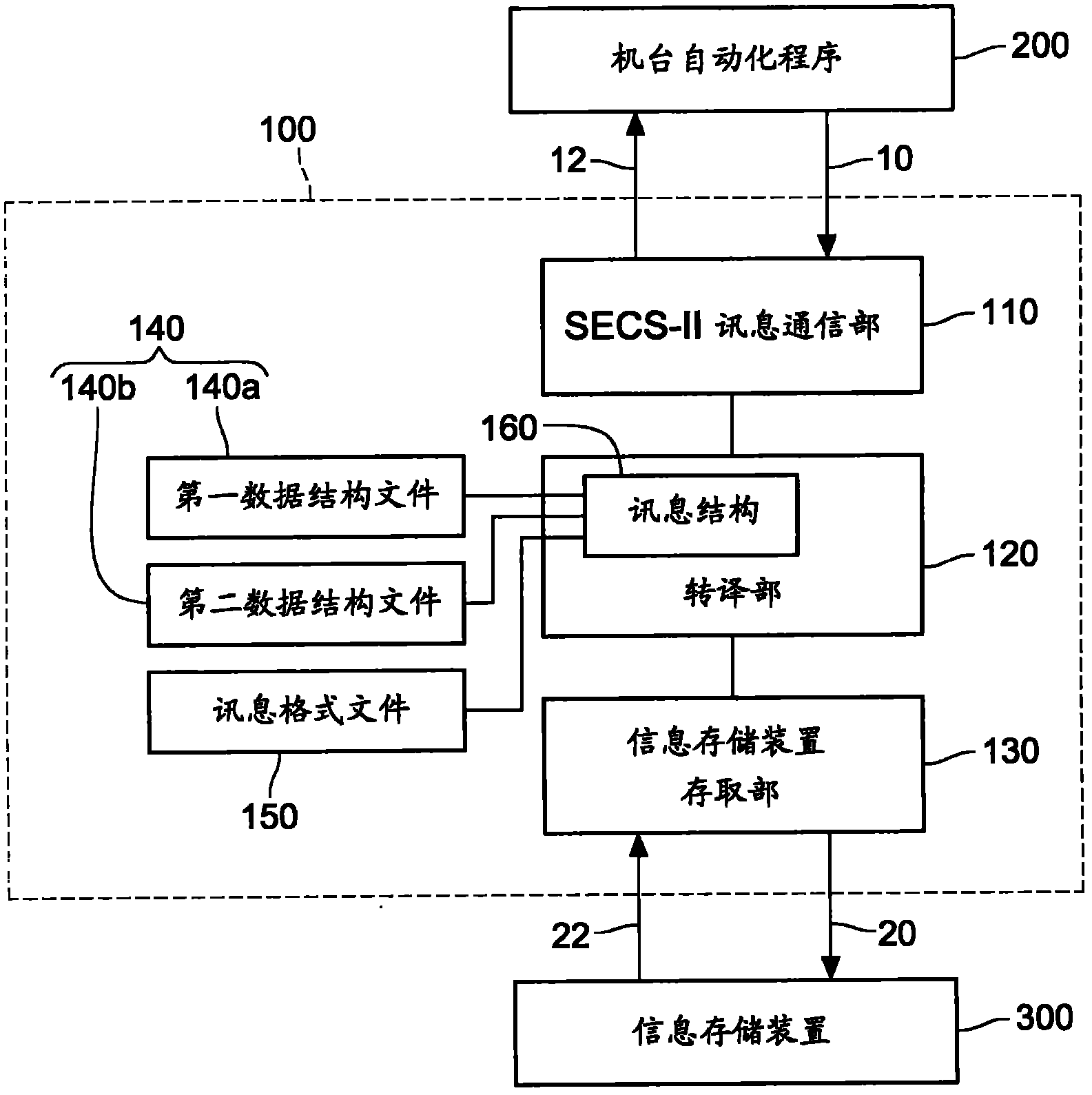
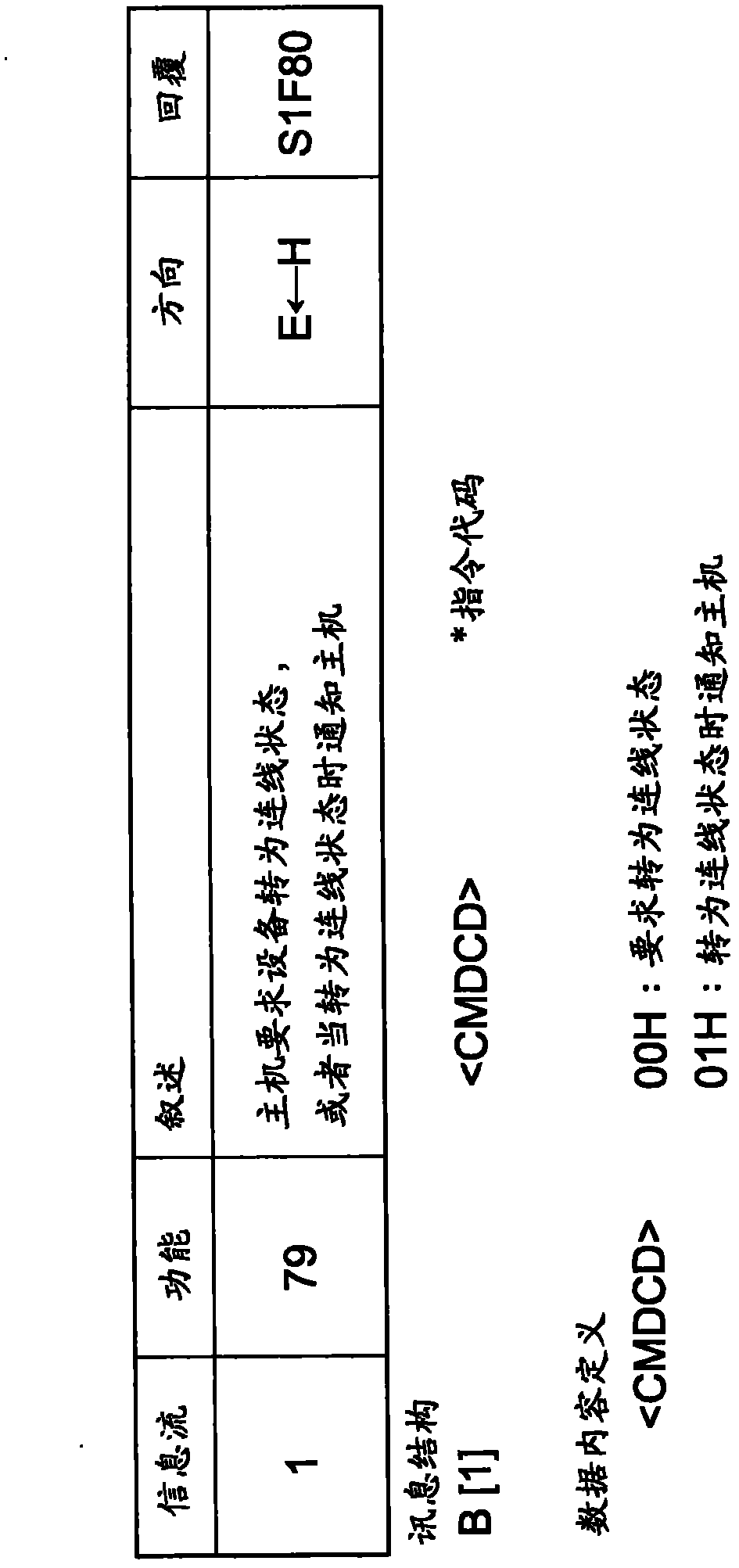
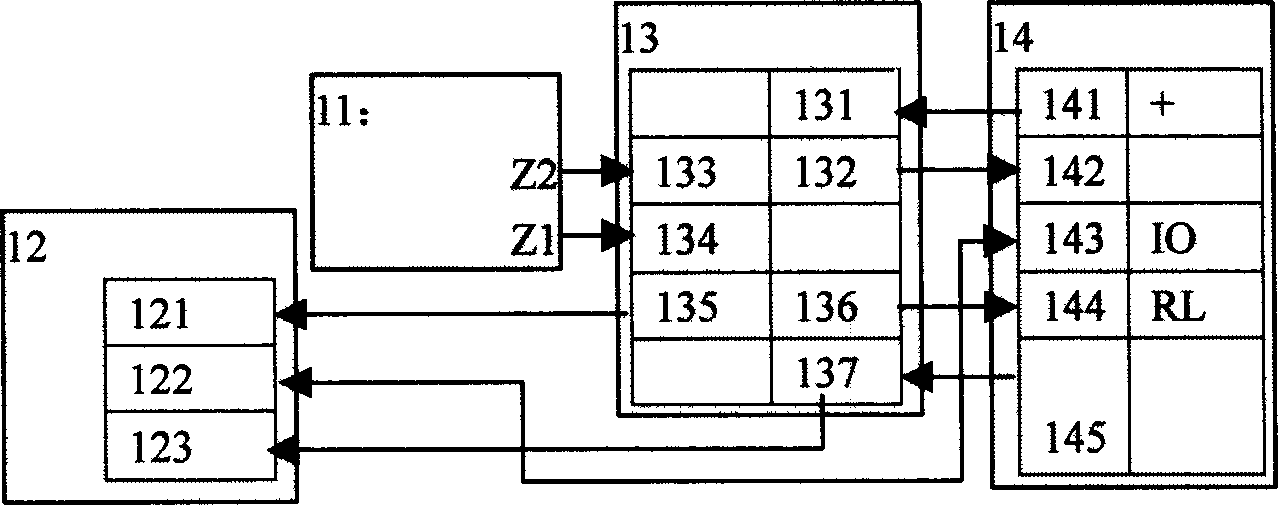
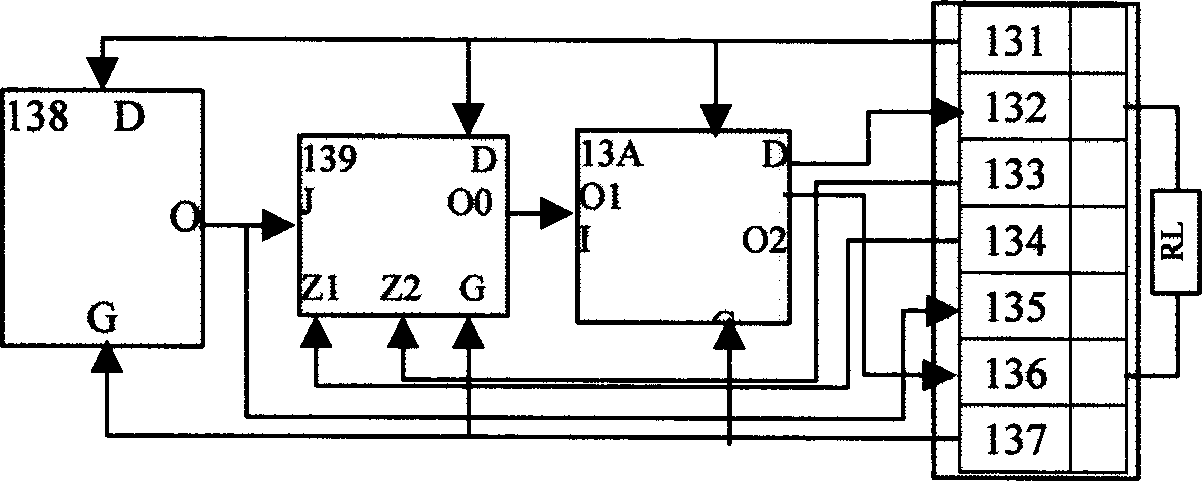
SECS communication device and SECS communication method thereof
InactiveCN102467467AMeets requirementsCompliant with SECS communication functionMosaic printer telegraph systemElectric digital data processingComputer hardwareTechnical standard
An SECS communication device and an SECS communication method thereof are presented. The SECS communication device includes an SECS-II message communication part, a translation part, and an information storage device access part, and further includes at least one set of data structure files and a message format file for defining a message content and a message format of an SECS-II message. The translation part decodes the SECS-II message into data in various information storage formats of an information storage device according to the data structure file and the message format file, and encodes the data in various information storage formats of the information storage device into the SECS-II message, so as to enable message exchange between an EAP and the information storage device through the SECS communication device. By applying the SECS communication method, cost of program development is reduced, and meanwhile, high system stability and industrial efficiency are achieved.
Owner:IND TECH RES INST
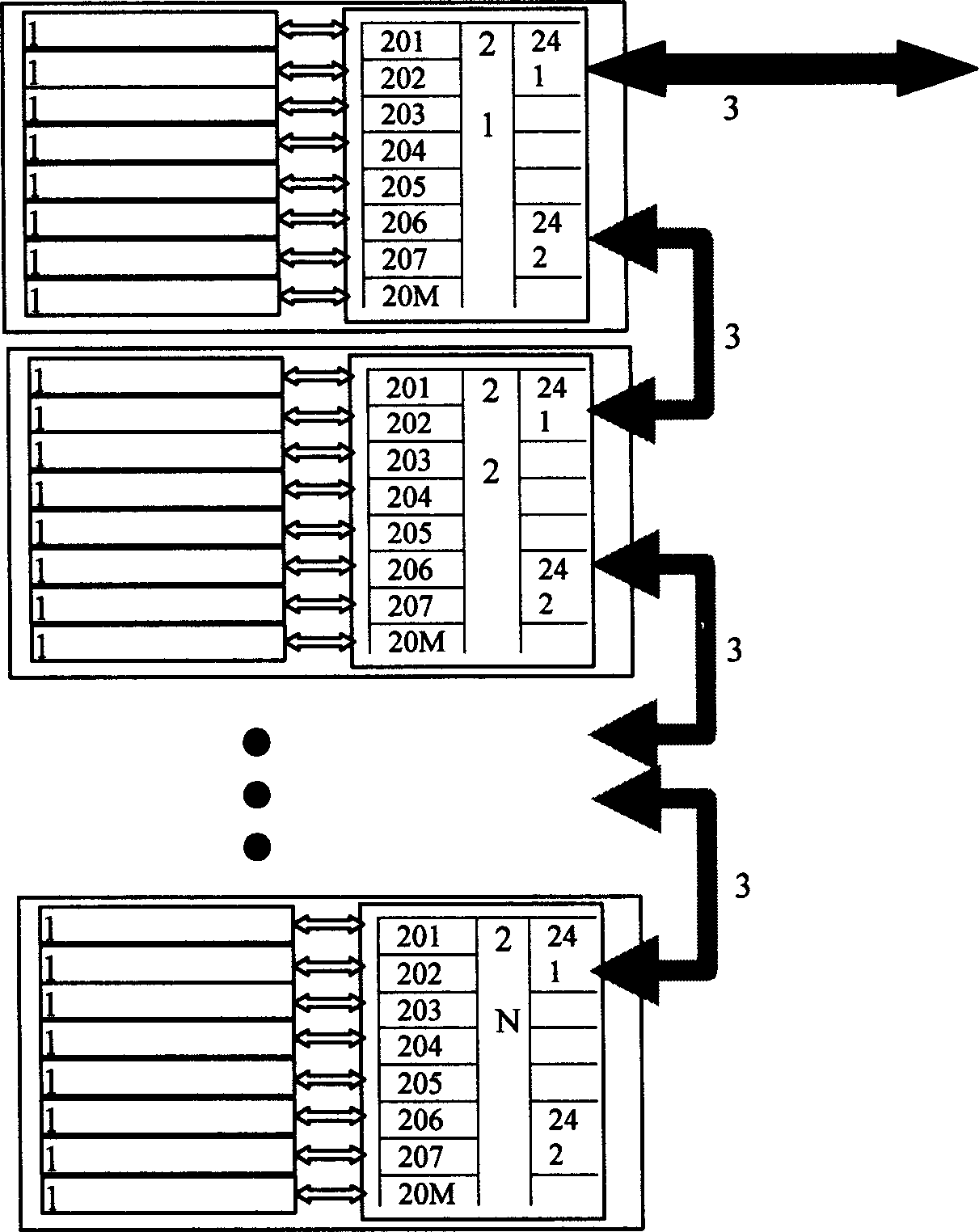
Several multiple physical quantity sensor dignal bus transmission system
InactiveCN1460838ASolve the problem of using a large number of cablesSolve the real problemMosaic printer telegraph systemMagnetic/electric field switchesDiagnostic systemPollution
The present invention utilizes single composite bus and several active joint-boxes to detect lots of signals of composite sensor containing several physical quantities sensing devices and internal-mounted modulator. It can obtain rich information, and can make voltage and current conversion in the active joint-boxes so as to can raise transmission distance, improve frequency response, resist interference and make treatment for resisting pollution in the joint-box. It has excellent effect in the tests of vehicle fault diagnosis system.
Owner:北京唐智科技发展有限公司
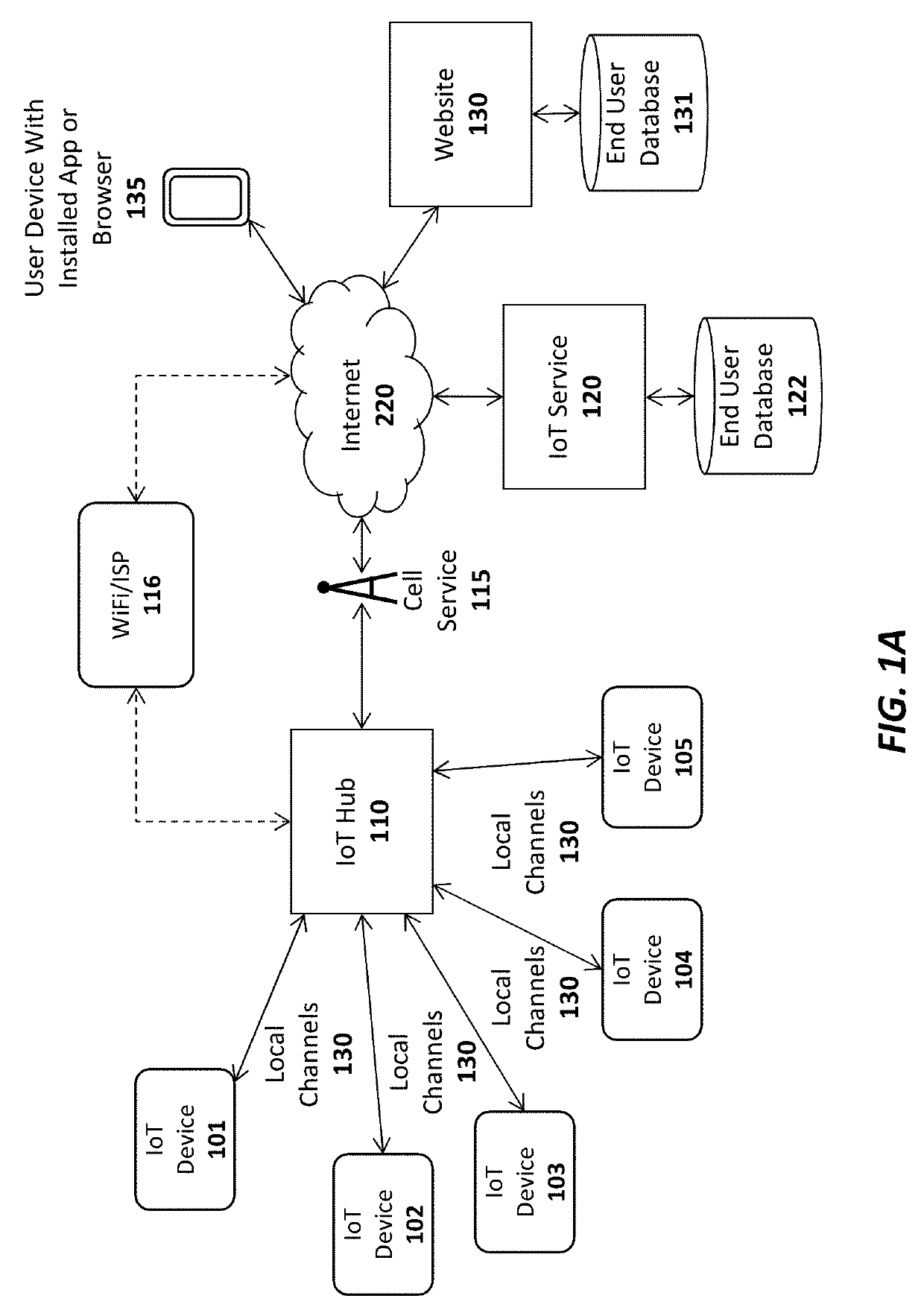
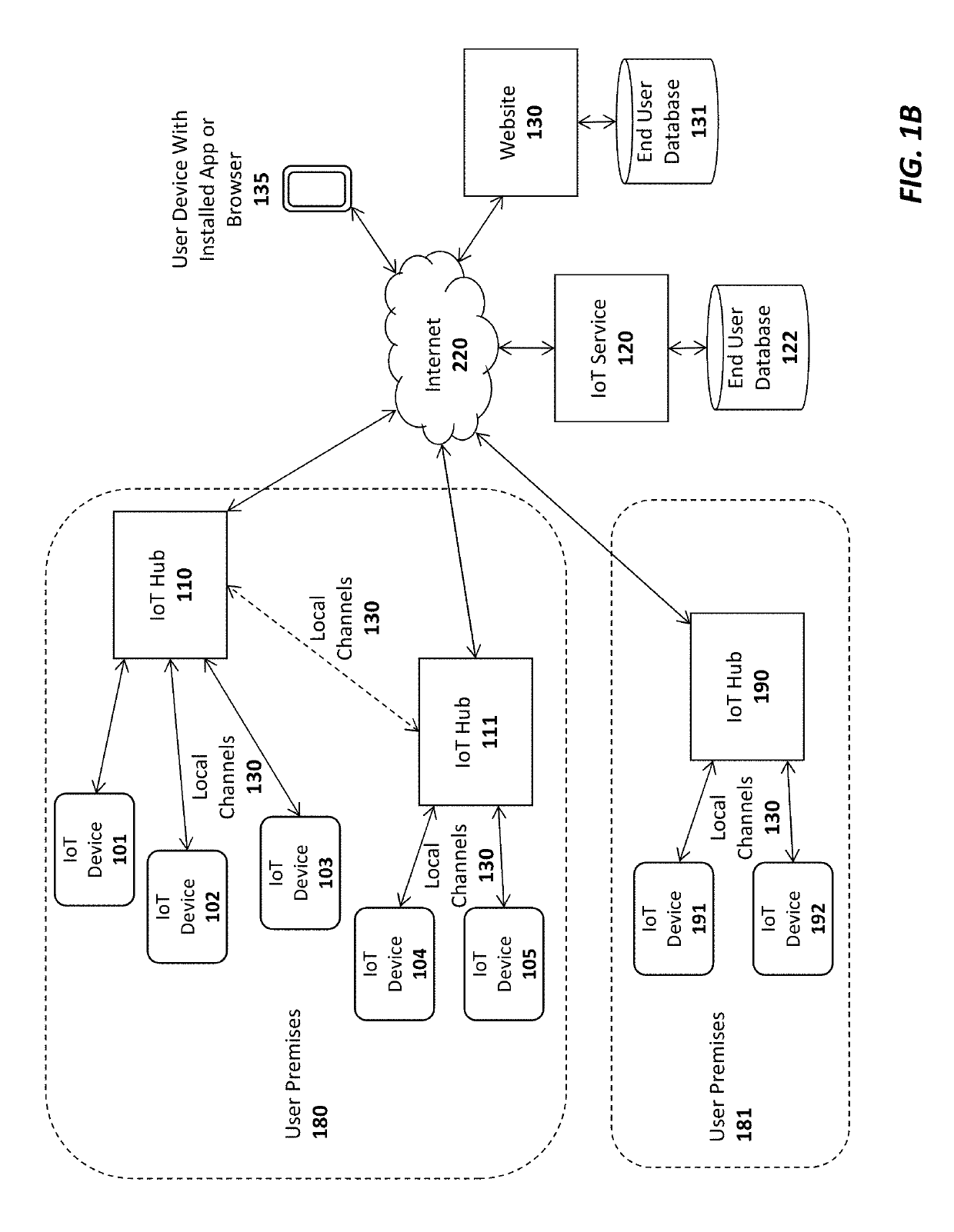
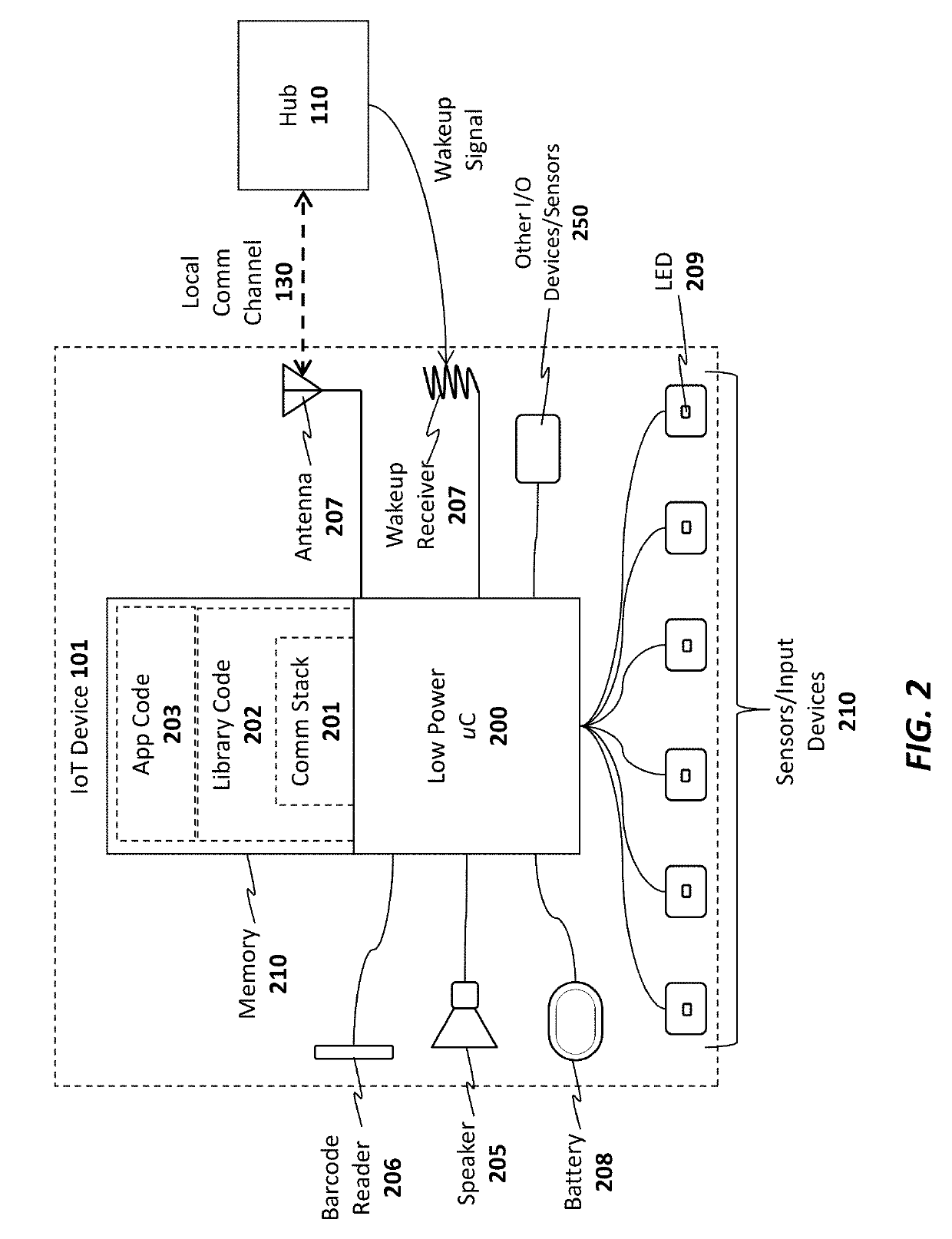
Apparatus and method for internet of things (IOT) security lock and notification device
ActiveUS10275962B2Mosaic printer telegraph systemInternal/peripheral component protectionComputer networkInternet of Things
An apparatus and method are for providing security to a computing device using an Internet of Things (IoT) device. For example, one embodiment of a system comprises: an Internet of Things (IoT) security device to be communicatively coupled to a computing device; an IoT service to establish a communication channel with the IoT device, the IoT service; and the IoT service to generate and transmit a notification to a client device of a user when the IoT service can no longer communicate with the IoT device over the communication channel.
Owner:AFERO
Systems and methods for a dynamic user interface proxy using physical keys
ActiveUS7562383B2Mosaic printer telegraph systemDigital data processing detailsUser deviceSmart card
Owner:FUJIFILM BUSINESS INNOVATION CORP
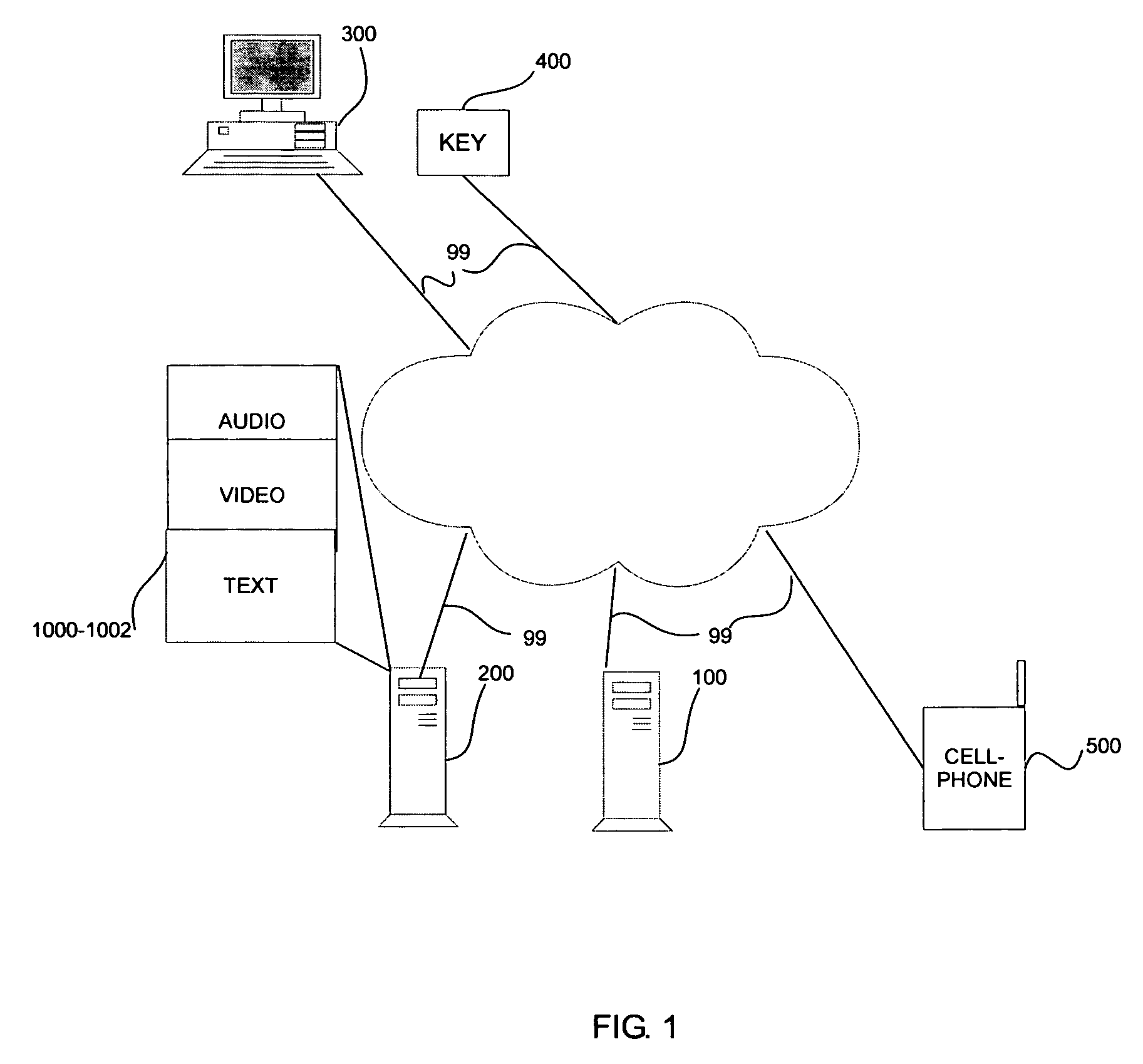
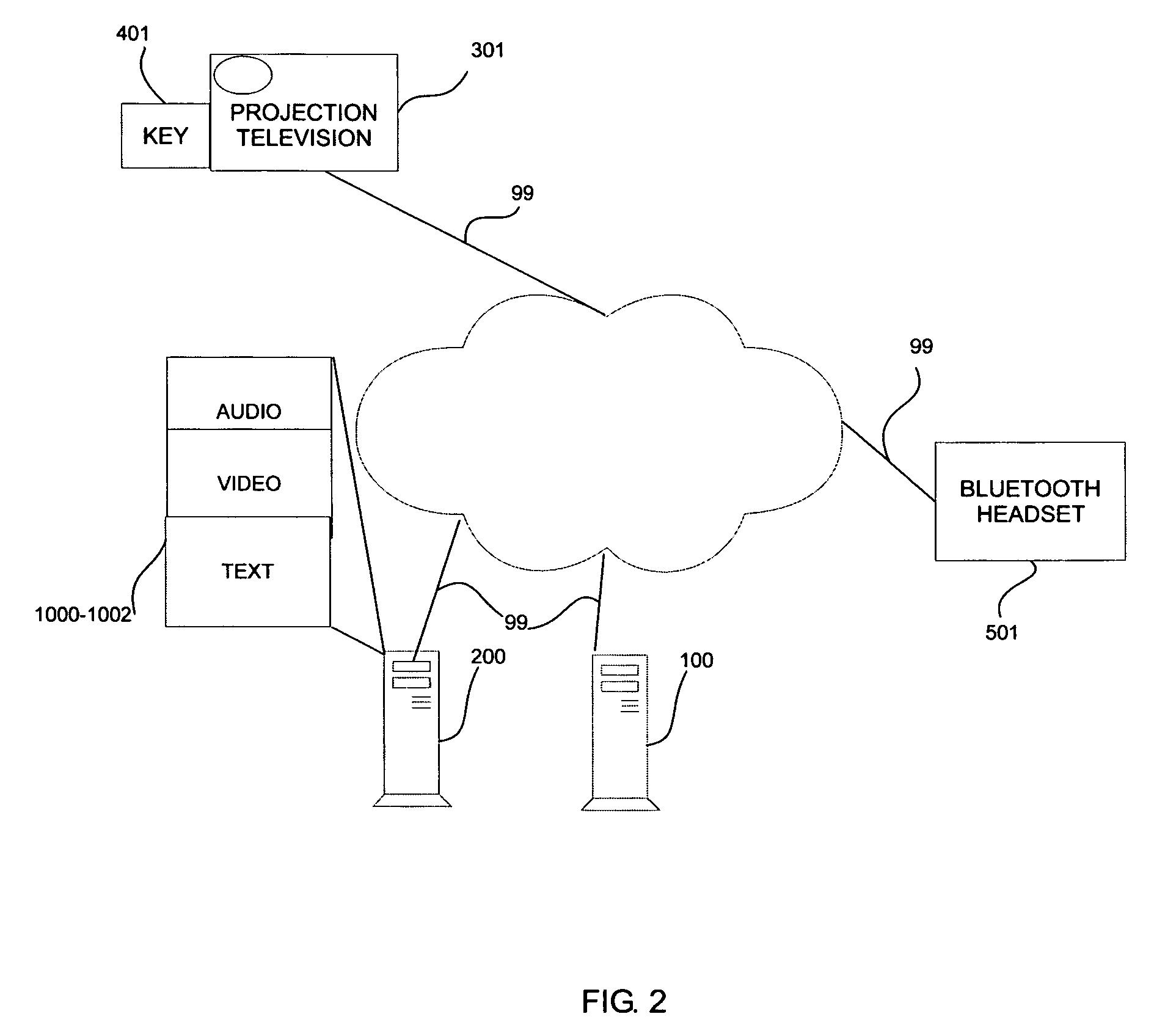
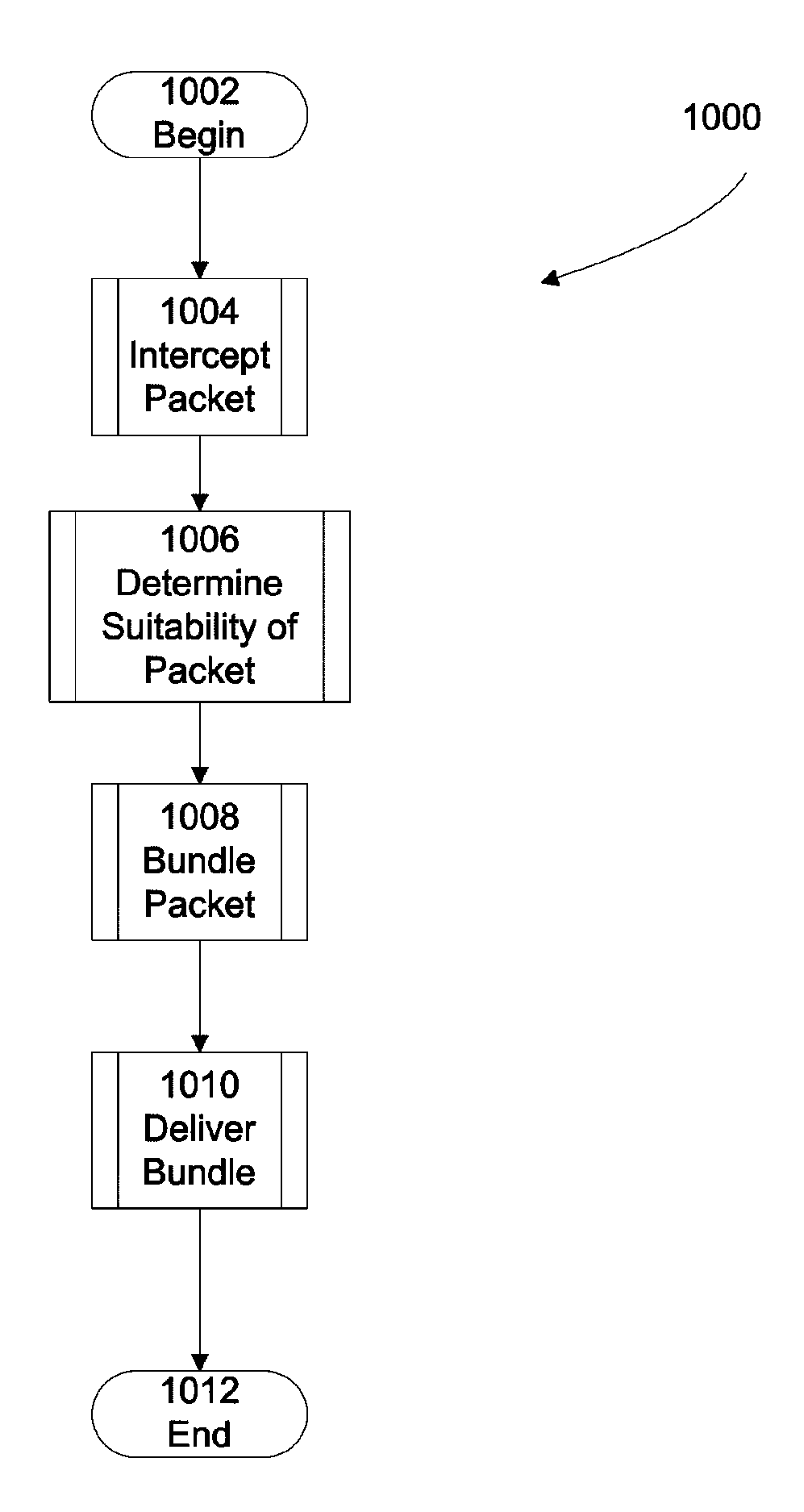
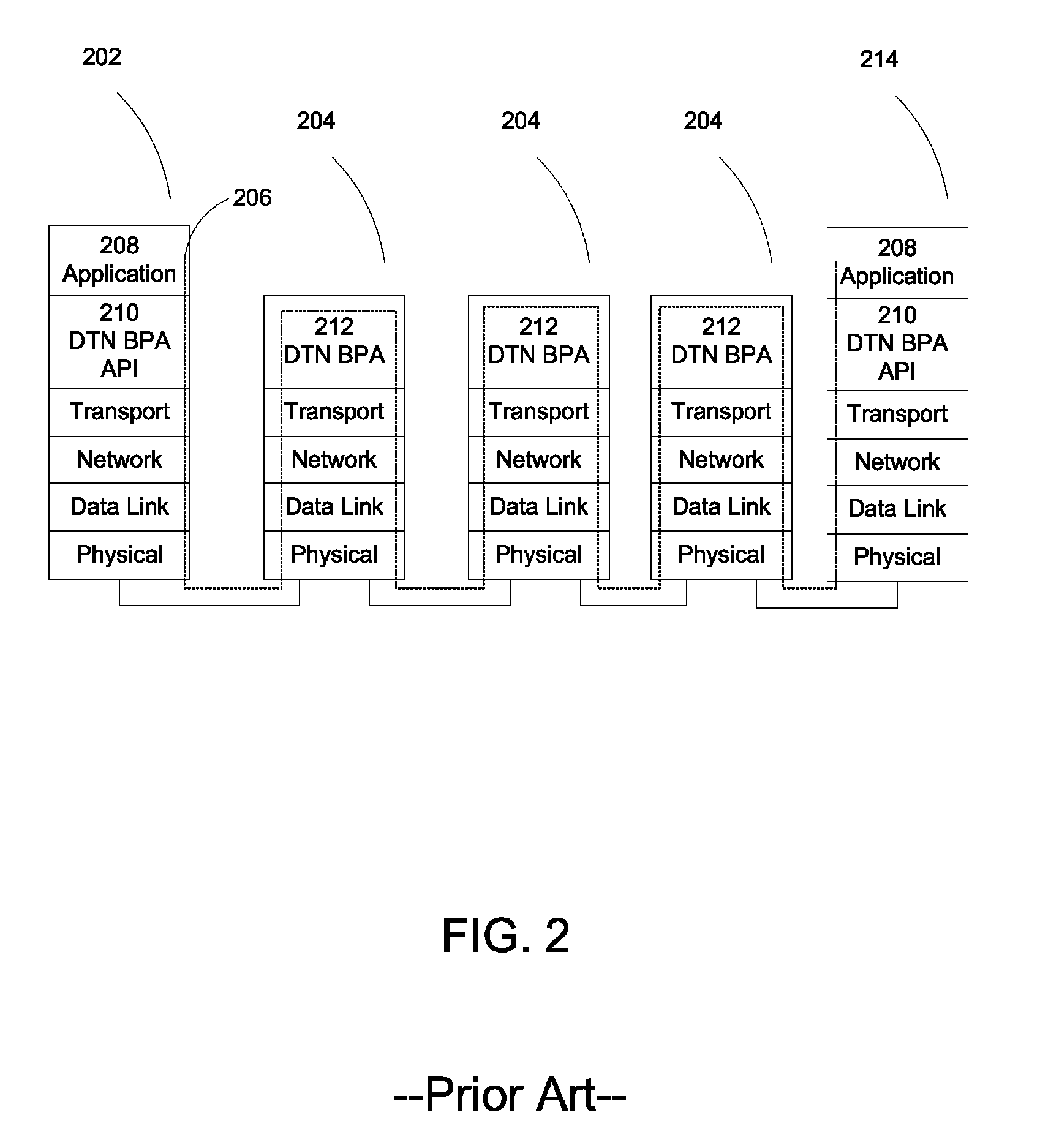
Automatic invocation of DTN bundle protocol
ActiveUS9015822B2Stable deliveryReduce bandwidth consumptionMosaic printer telegraph systemMultiple digital computer combinationsBundle protocolNetwork packet
A system and method for providing DTN services to legacy applications is provided. According to one example, a method for providing delay tolerant networking (DTN) services to legacy applications includes acts of intercepting a packet addressed to a software application, the packet including a payload, the software application being resident on a first computer, determining suitability of the packet for DTN processing and encoding the payload into a DTN bundle. According to another example, a system for providing delay tolerant networking (DTN) services to legacy applications includes a network interface, a memory anda controller coupled to the network interface and the memory. In this example, the controller is configured to intercept a packet addressed to a software application, the packet including a payload, the software application being resident on a computer, determine suitability of the packet for DTN processing and encode the payload into a DTN bundle.
Owner:RAYTHEON CO
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com