Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
71results about How to "Fine grained control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
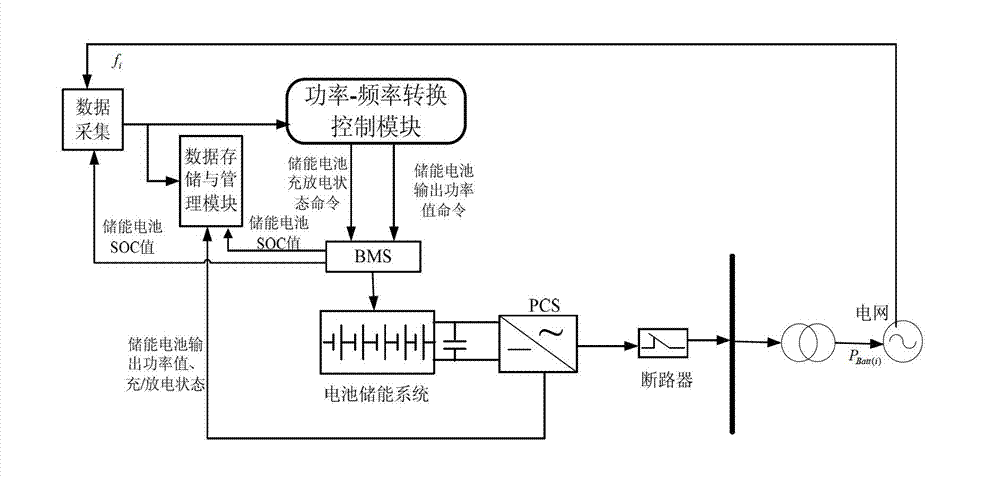
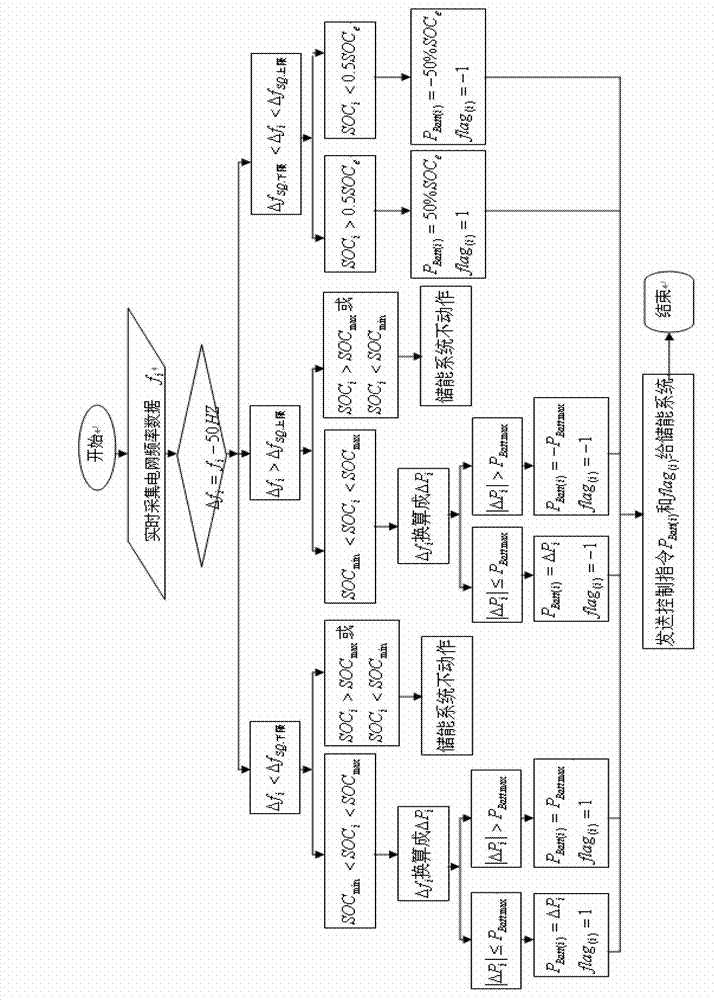
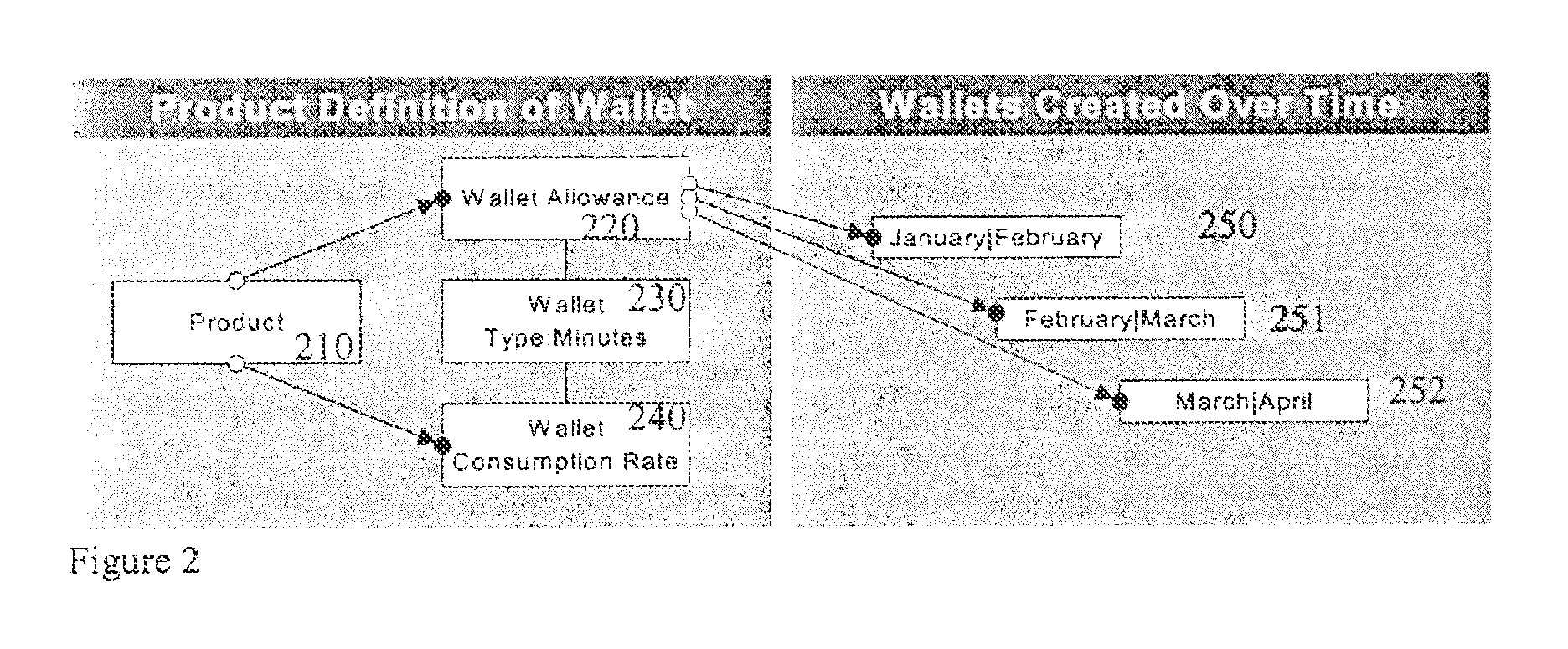
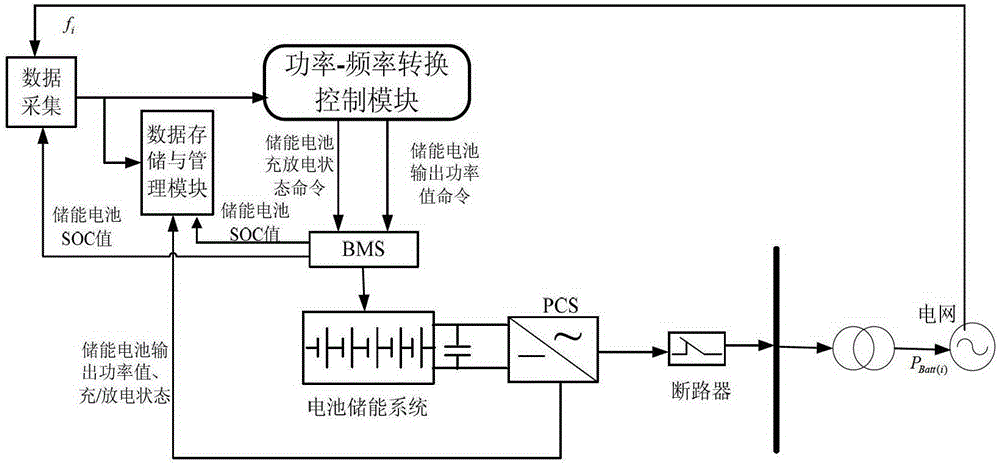
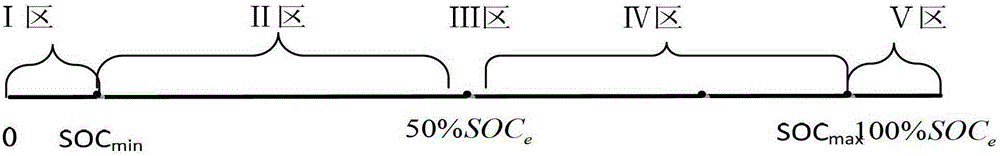
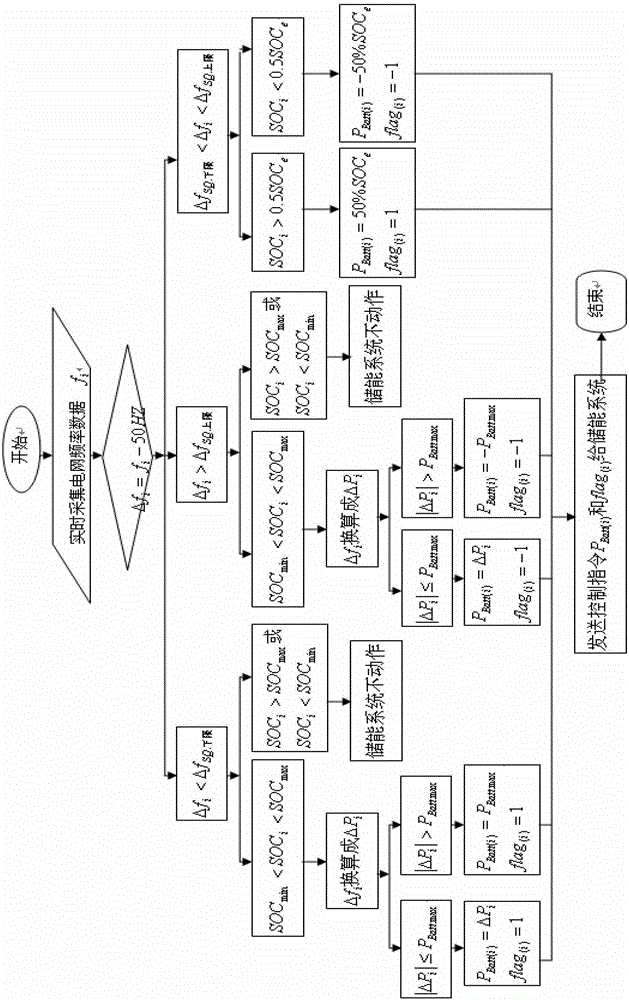
Method used for controlling participation of battery energy storing system in primary frequency modulation and optimization of power gird
ActiveCN102891495AImprove charge/discharge performanceFine-grained controlFlexible AC transmissionAc network load balancingControl principleElectrical network frequency
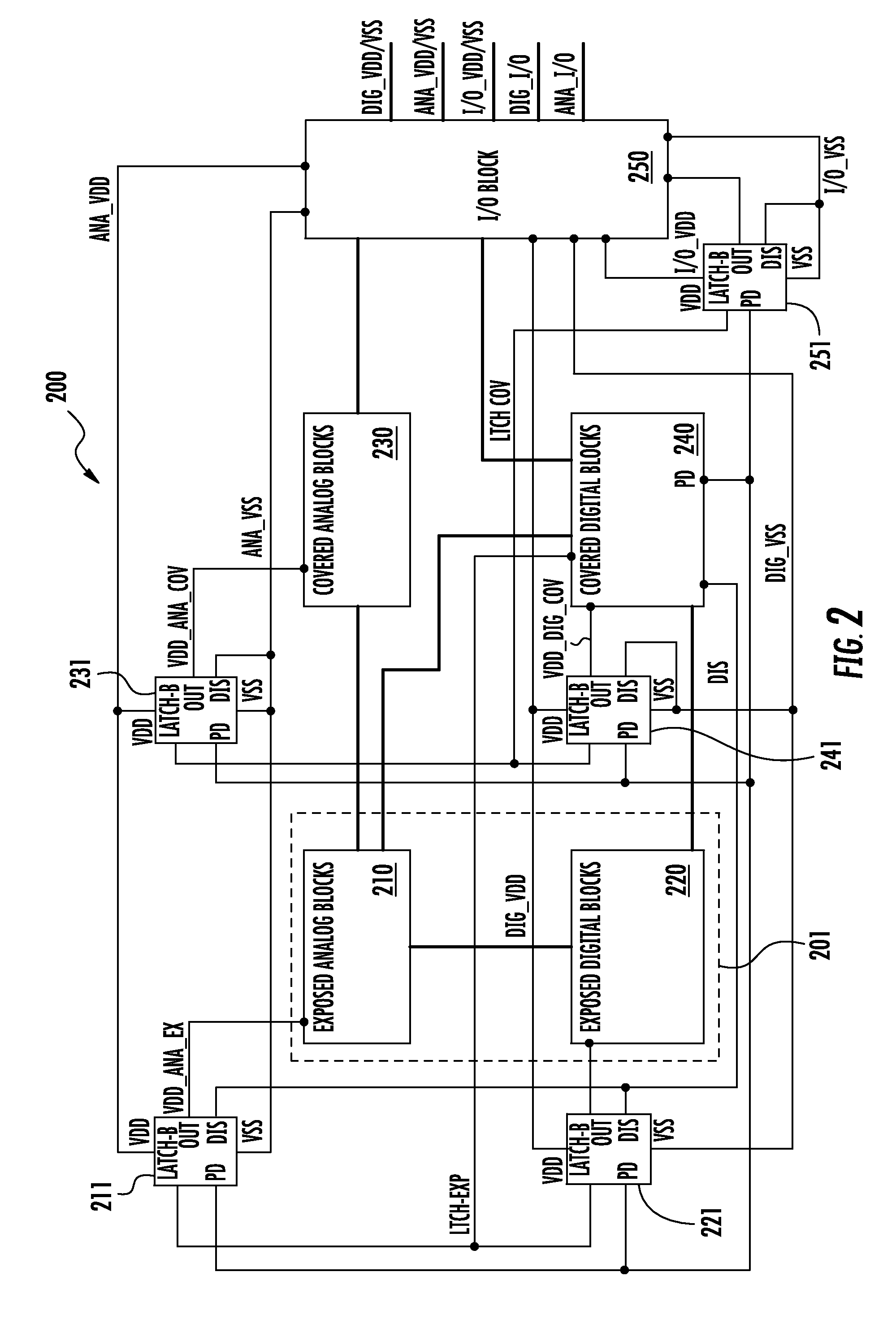
The invention discloses a method used for controlling participation of a battery energy storing system in primary frequency modulation and optimization of a power gird. The method comprises the following steps: collecting a power grid frequency through a data collecting module and inputting the power grid frequency to a power-frequency conversion control module; taking the lower limit of frequency bias fSQ and upper limit as the control goal in the power-frequency conversion control module, wherein delta fi is more than the lower limit and less than fSQ; and taking meeting the control goal and keeping relatively good charging / discharging ability and excellent system on chip (SOC) level of the battery energy storing system as the control principle, conducting operation treatment on the input data according to a power-frequency conversion control strategy; judging whether the real-time grid frequency bias delta fi exceeds the frequency dead zone; if so, transforming the frequency bias delta fi to a corresponding power bias delta Pi, comparing the obtained power balance delta Pi of the power grid at the moment i with the maximum output limit value PBatt.Max of the battery energy storing system; judging the degree of the battery energy storing system participating in the primary frequency regulation of the power grid; controlling the output of the battery energy storing system by a battery management system (BMS), correcting the balance between supply and demand of the power gird, preventing the aggravation of the frequency fluctuation, and maintaining the stability of the power grid frequency.
Owner:CHINA ELECTRIC POWER RES INST +1
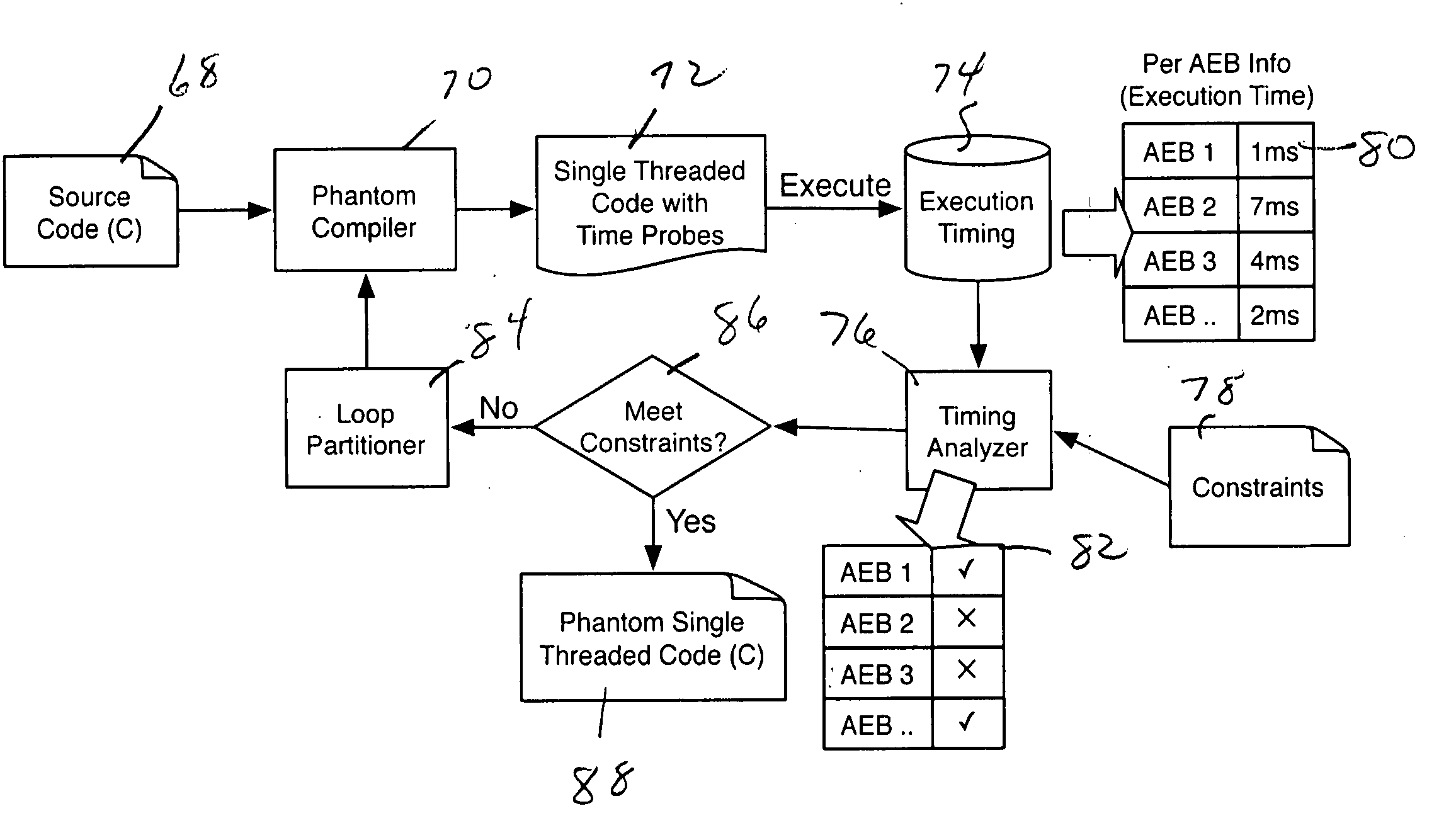
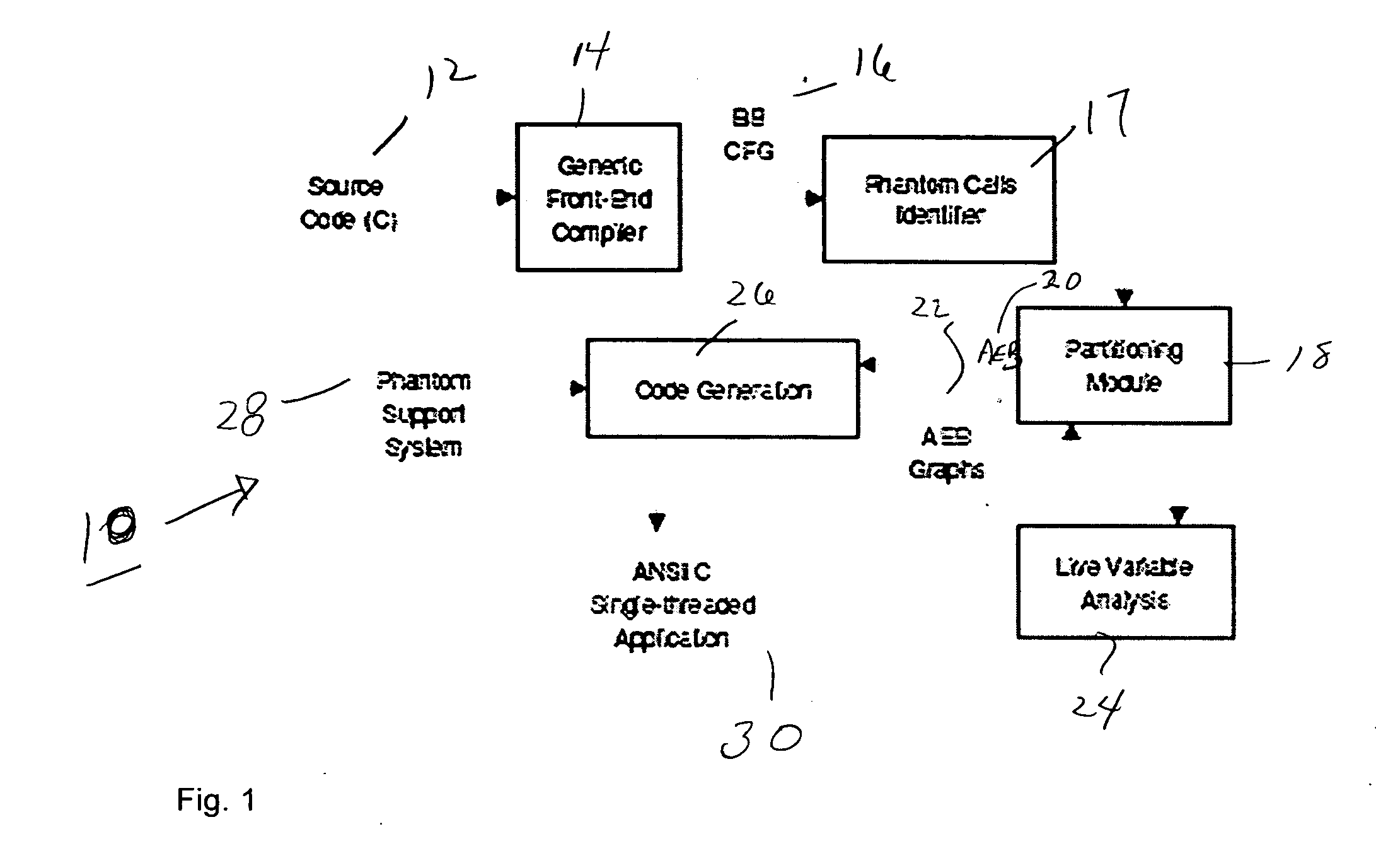
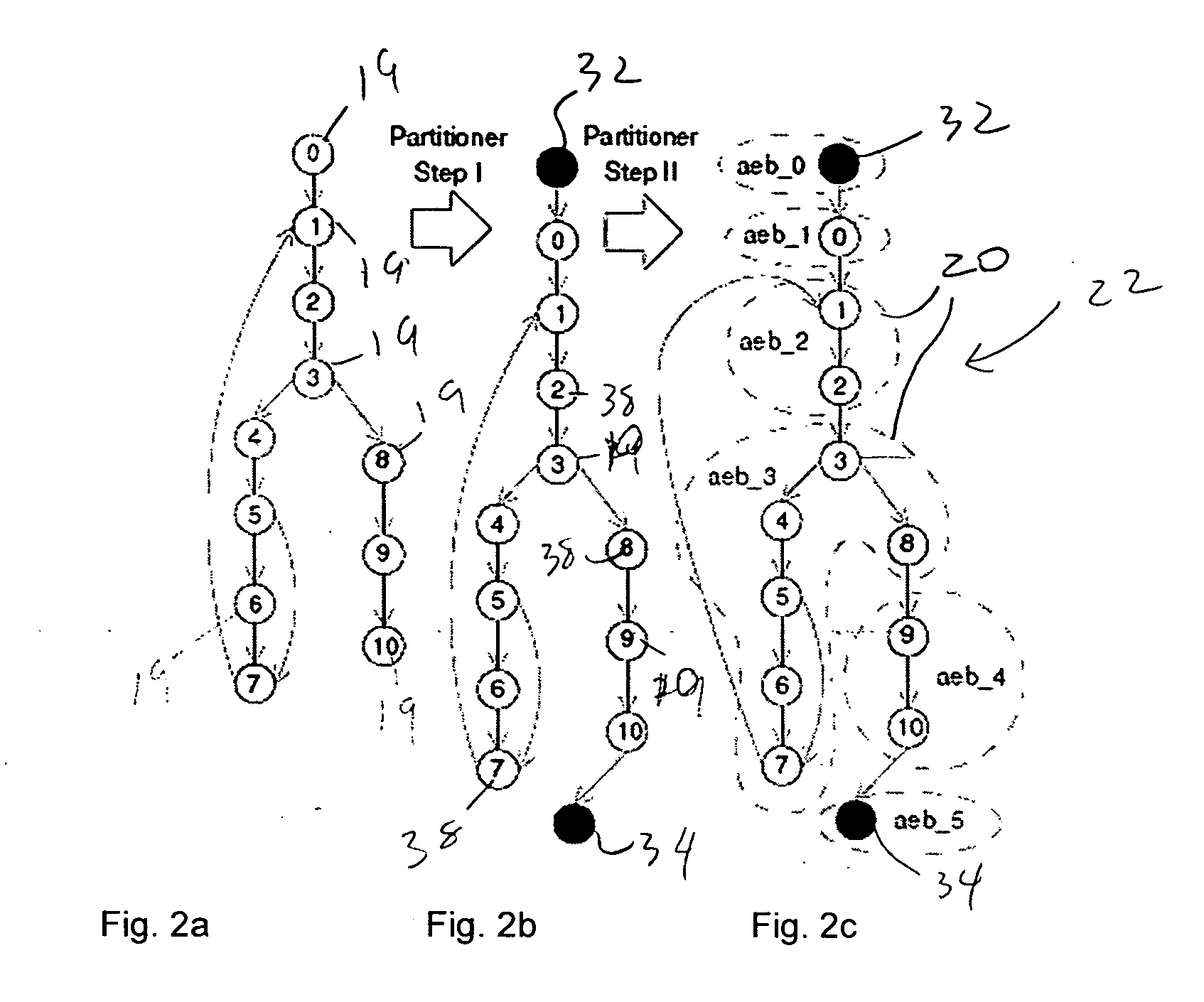
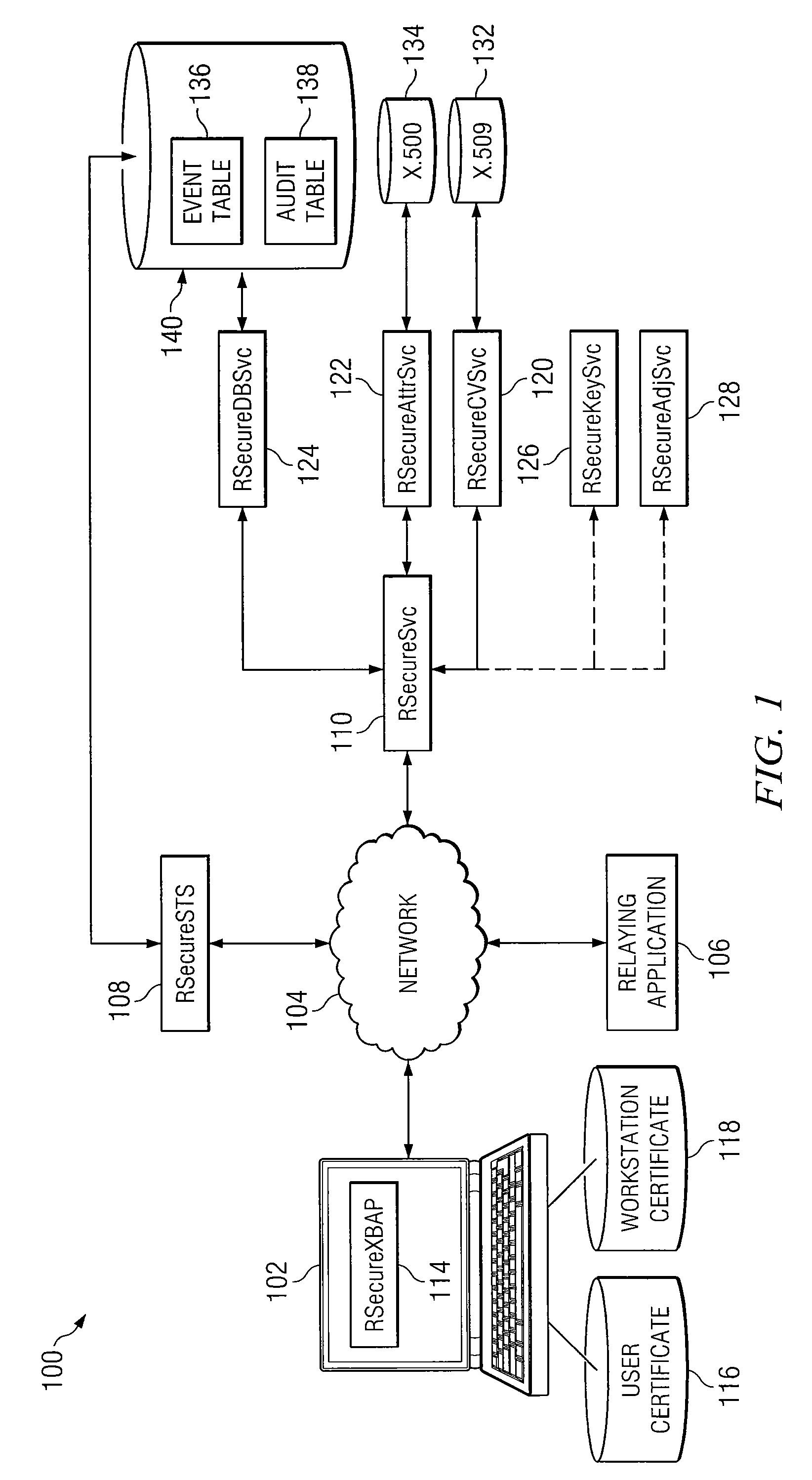
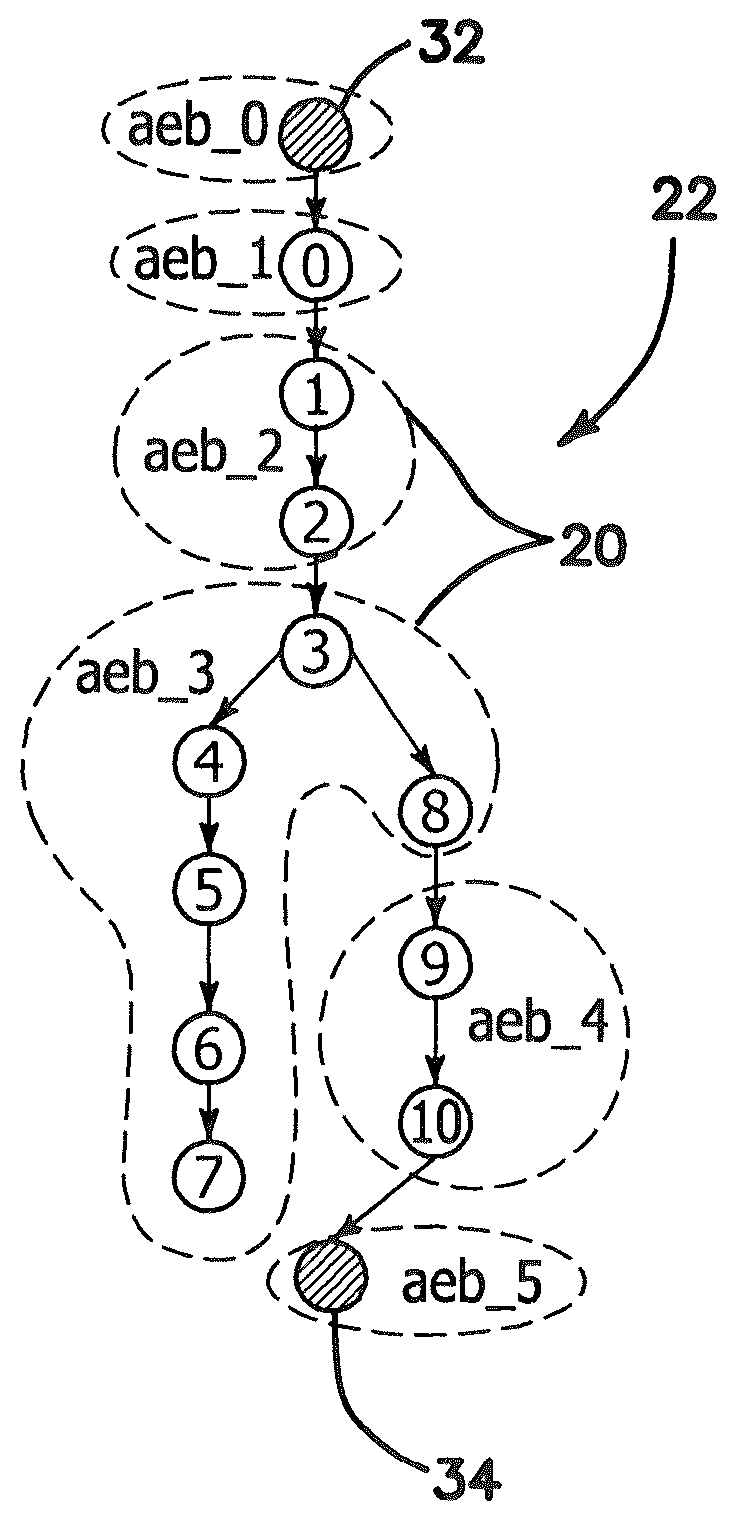
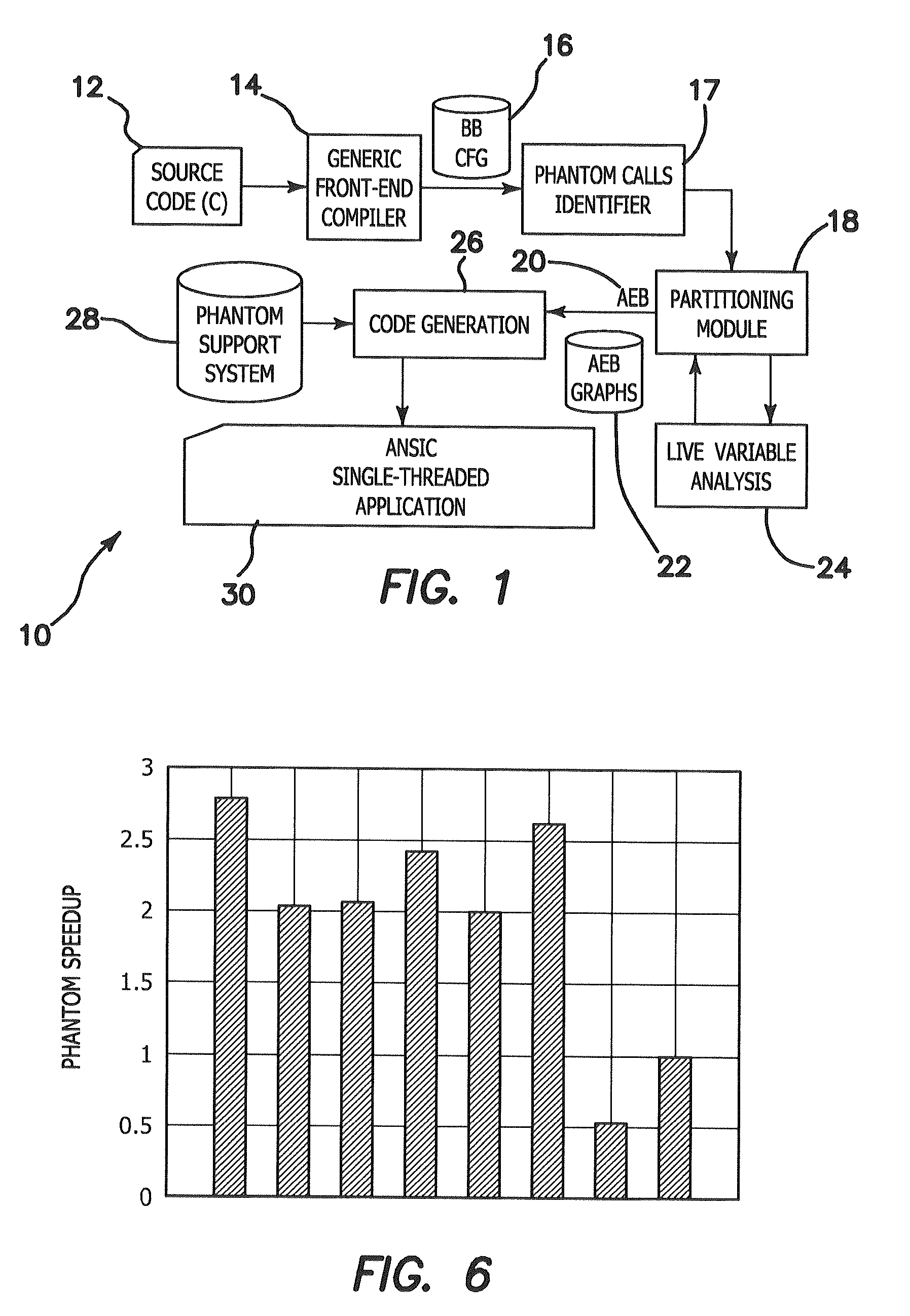
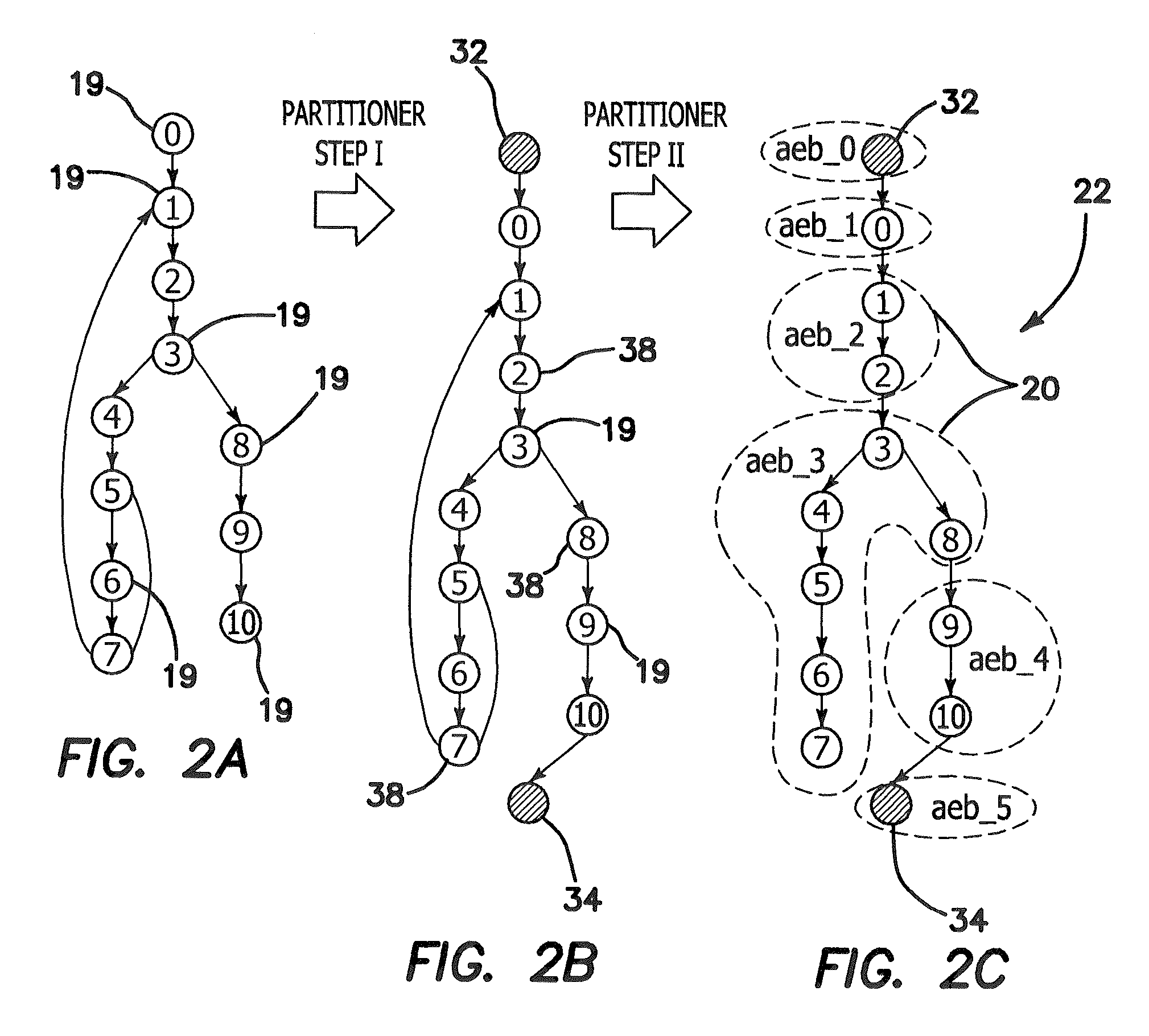
Phantom serializing compiler and method of operation of same
ActiveUS20060112377A1Fine grained controlImprove performanceSoftware engineeringProgram controlLive variable analysisSerialization
The invention includes a computer and a method of operating a computer to generate a program for an embedded processor comprising the steps of compiling a multitask application with a generic front-end compiler to generate a basic block (BB) control flow graph (CFG) of the multitask application; generating non-preemptive blocks of code from the control flow graph (CFG) with a partitioning module, which blocks of code are defined as AEBs (atomic execution blocks); performing a live variable analysis on the AEB graphs to generate a live variable result; feeding back to the live variable result to the partitioning module to refine the partitions until acceptable preemption, timing, and latency are achieved, the AEB graphs having determined AEB nodes; and generating a corresponding executable code for each AEB node in a code generator.
Owner:RGT UNIV OF CALIFORNIA
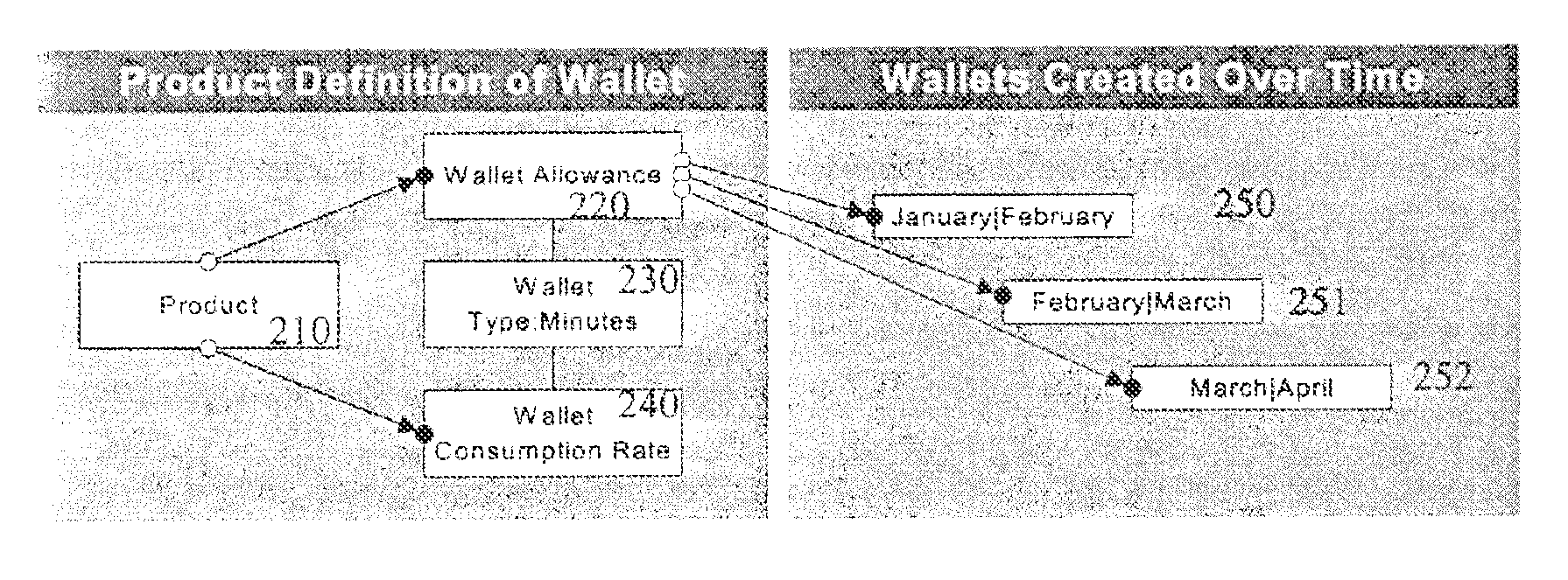
System and method for revenue and authorization management
ActiveUS8577795B2Improve functionalityImprove availabilityFinancePayment architectureAuthorizationManagement system
A system is disclosed for facilitating relationship-centric authorization of transactions in a manner which provides optimum scalability and availability by logically partitioning wallets in conjunction with partitioning a resource associated with a group of consumers.
Owner:NETCRACKER TECH SOLUTIONS
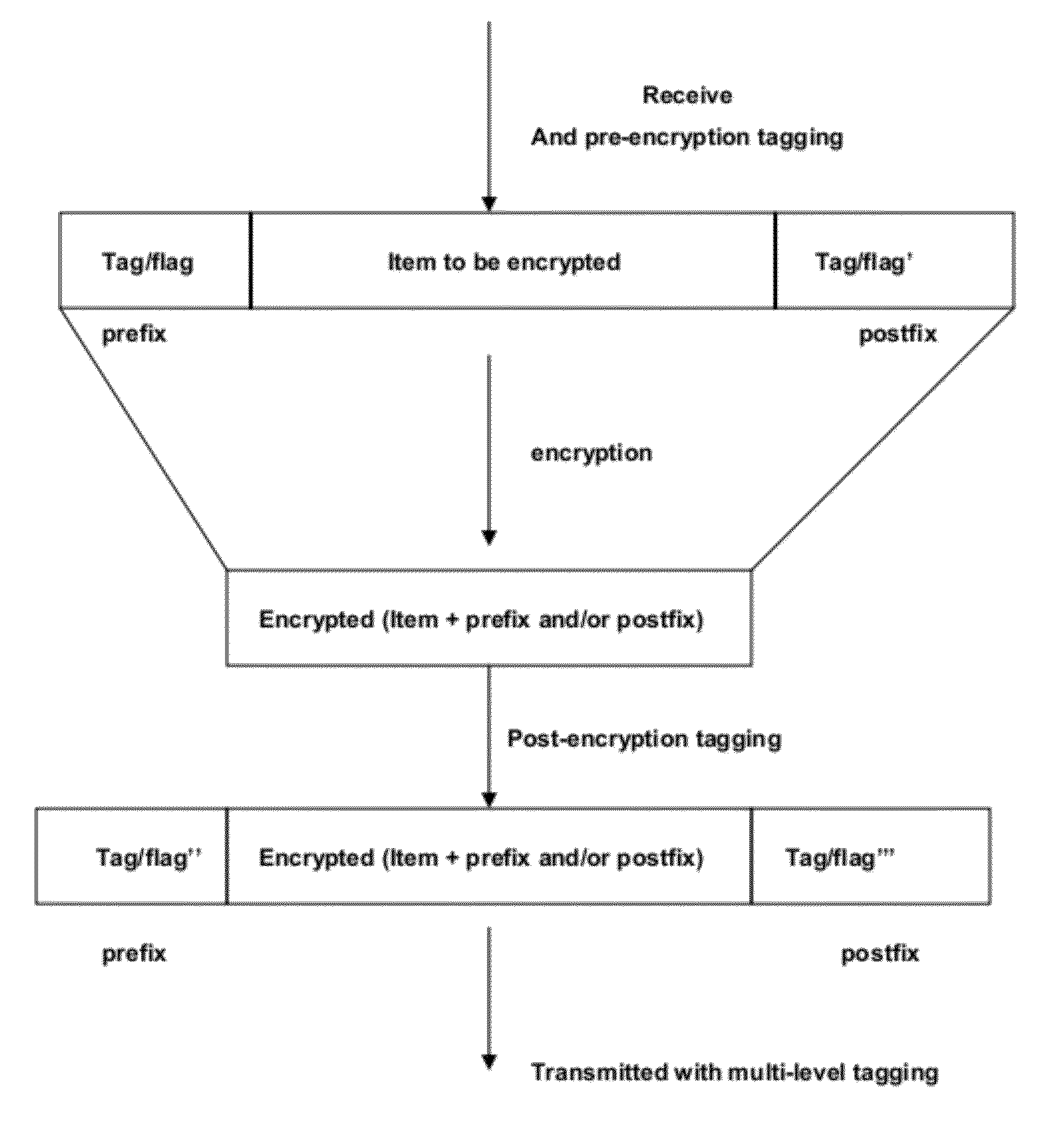
Systems and Methods for Multi-Level Tagging of Encrypted Items for Additional Security and Efficient Encrypted Item Determination
ActiveUS20120173870A1Efficient encrypted item determinationImprove securityComputer security arrangementsTransmissionClient-sideComputer security
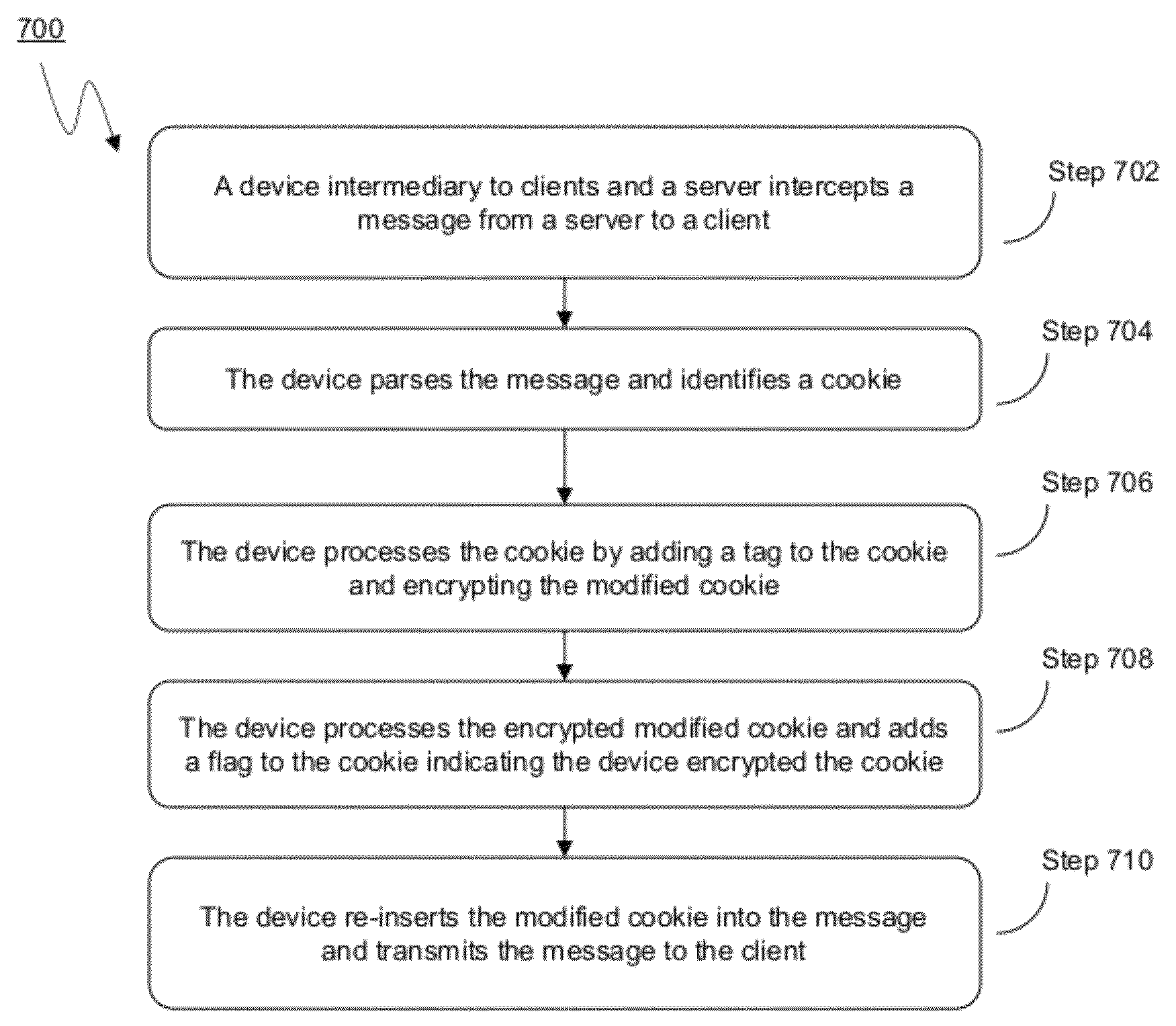
The present disclosure is directed towards systems and methods for performing multi-level tagging of encrypted items for additional security and efficient encrypted item determination. A device intercepts a message from a server to a client, parses the message and identifies a cookie. The device processes and encrypts the cookie. The device adds a flag to the cookie indicating the device encrypted the cookie. The device re-inserts the modified cookie into the message and transmits the message. The device intercepts a message from a client and determines whether the cookie in the message was encrypted by the device. If the message was not encrypted by the device, the device transmits the message to its destination. If the message was encrypted by the device, the device removes the flag, decrypts the cookie, removes the tag from the cookie, re-inserts the cookie into the message and transmits the message to its final destination.
Owner:CITRIX SYST INC
System and method for trusted storage of data
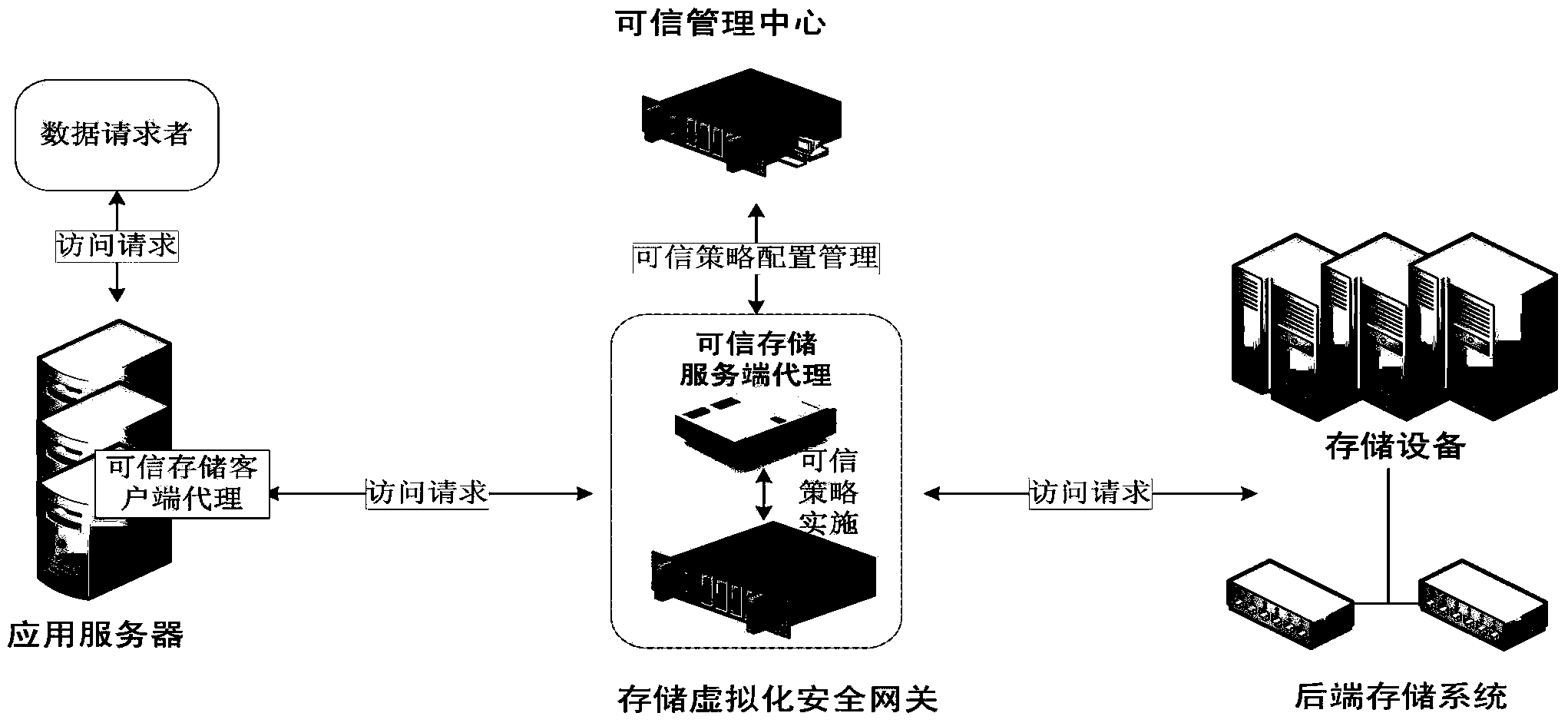
InactiveCN103927489AHigh strengthIllegal access reductionDigital data protectionPlatform integrity maintainanceControl flowApplication server
The invention discloses a system and method for trusted storage of data. The system mainly comprises four logical entities, namely, a trusted management center, an application server, a storage virtualization security gateway and a rear-end storage system. The trusted management center serves as a configuration and management entity for a trusted strategy. The application server serves as an entity sending a data access request. The storage virtualization security gateway serves as an entity receiving the data request of an application layer and achieving mapping of a virtual port, converting of a virtual storage device address and a physical storage device address and encapsulating of an IO request through the virtualization technology. The rear-end storage system provides a physical medium for data storage and operation. On the basis of the storage virtualization technology, a data access control flow in the trusted technology is provided for the storage virtualization security gateway or an agent layer so that strict security check and control can be carried out on an access request for a storage system, and illegal access or vicious data access operation can be prevented.
Owner:娄绍钢 +1
Three dimension mode compression coding/decoding method based on octree
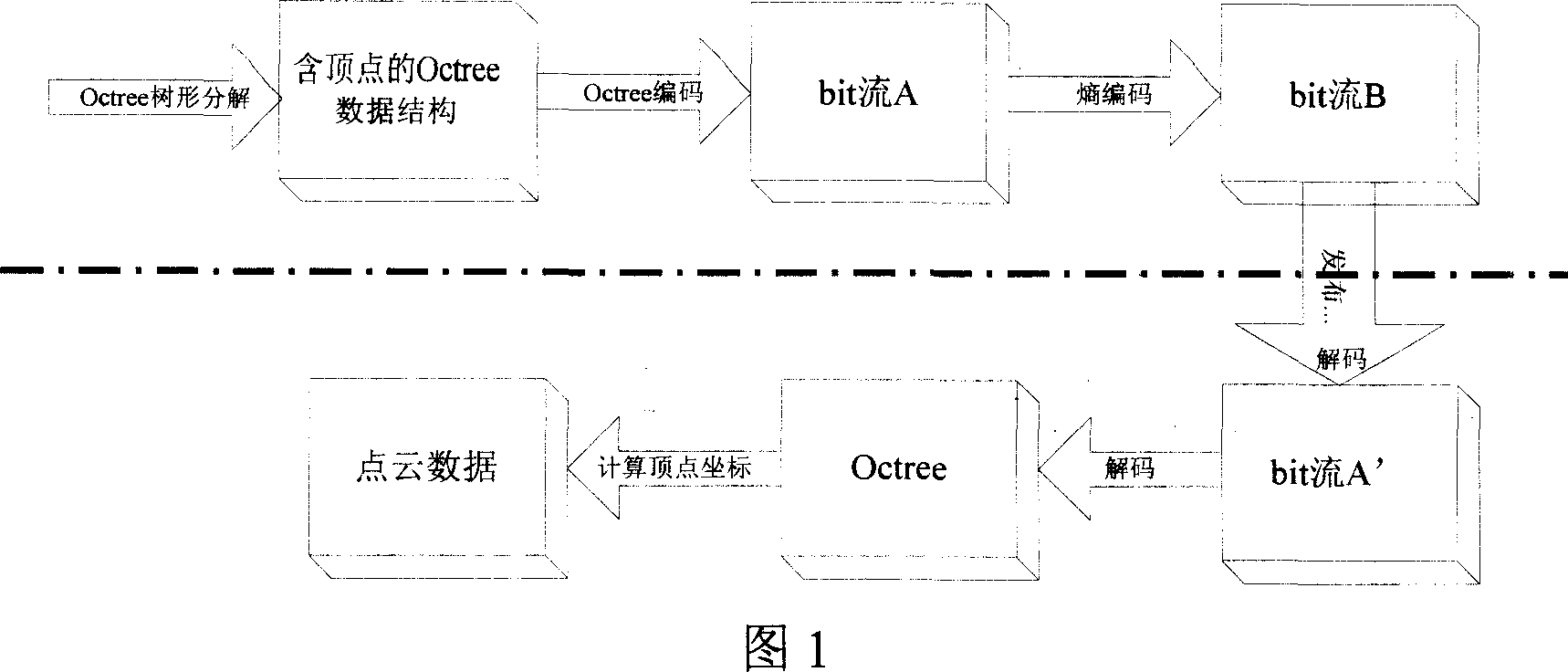
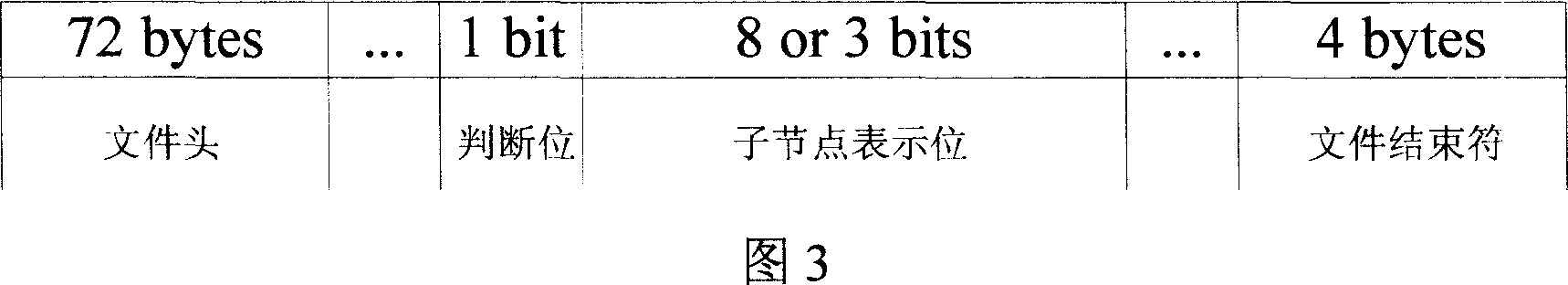
InactiveCN1946180AShort response timeFine-grained controlImage codingTelevision systemsStatistical analysisTheoretical computer science
This invention relates to a compression code / decode method for three-dimension models based on Octree, which redivides the Octree space of the peak information of a three-dimension lattice model to calculate and analyze different kinds of nodes in them to find out one or several with the maximum number of total nodes and carries out less bit coding, re-arranging the topological information and attribute information and code based on the transmission sequence of geometrical information separately and sets separate ascending files to control transmission and display of geometrical information and the synchronous mapping of the topological and attribute information.
Owner:BEIHANG UNIV
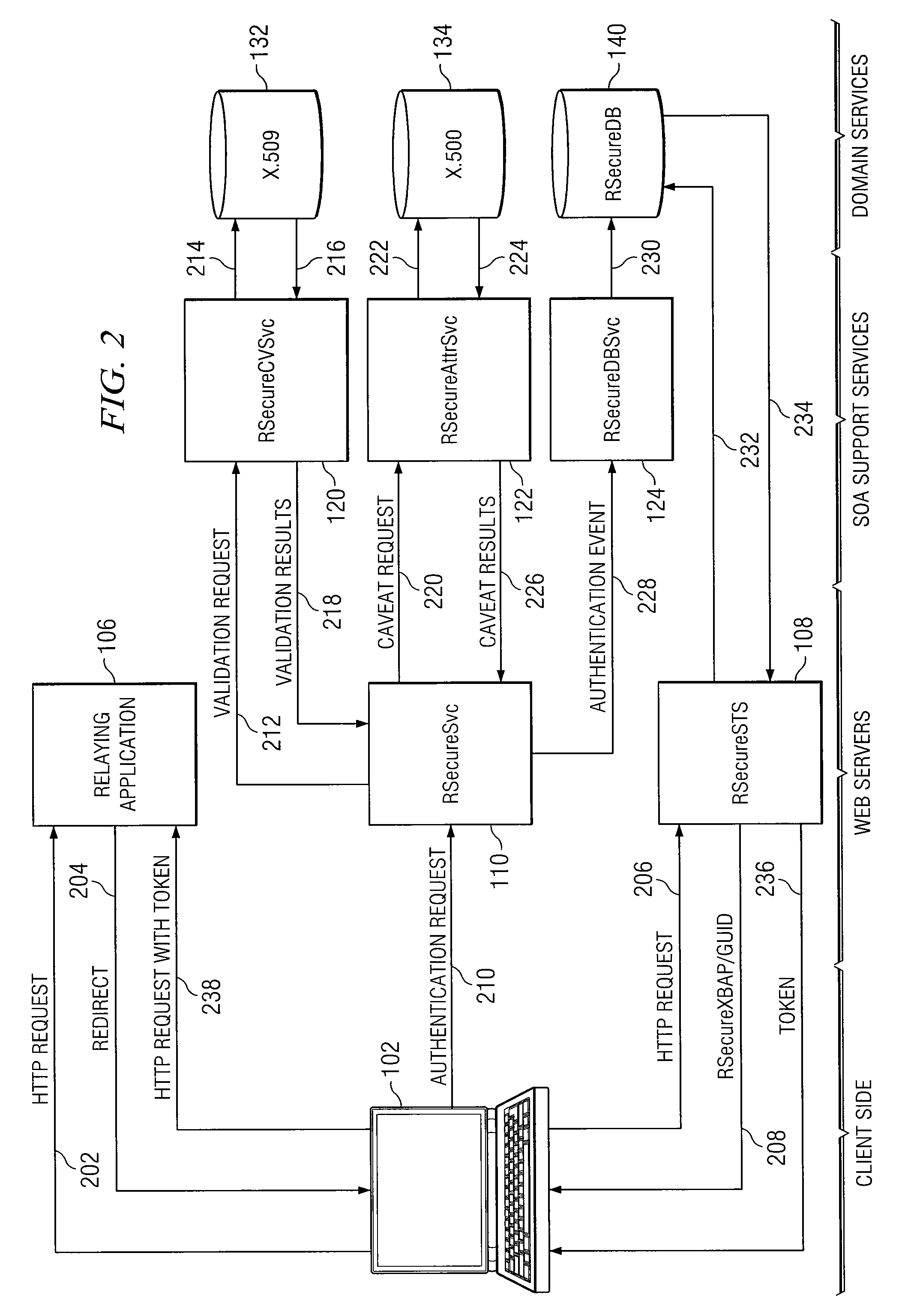
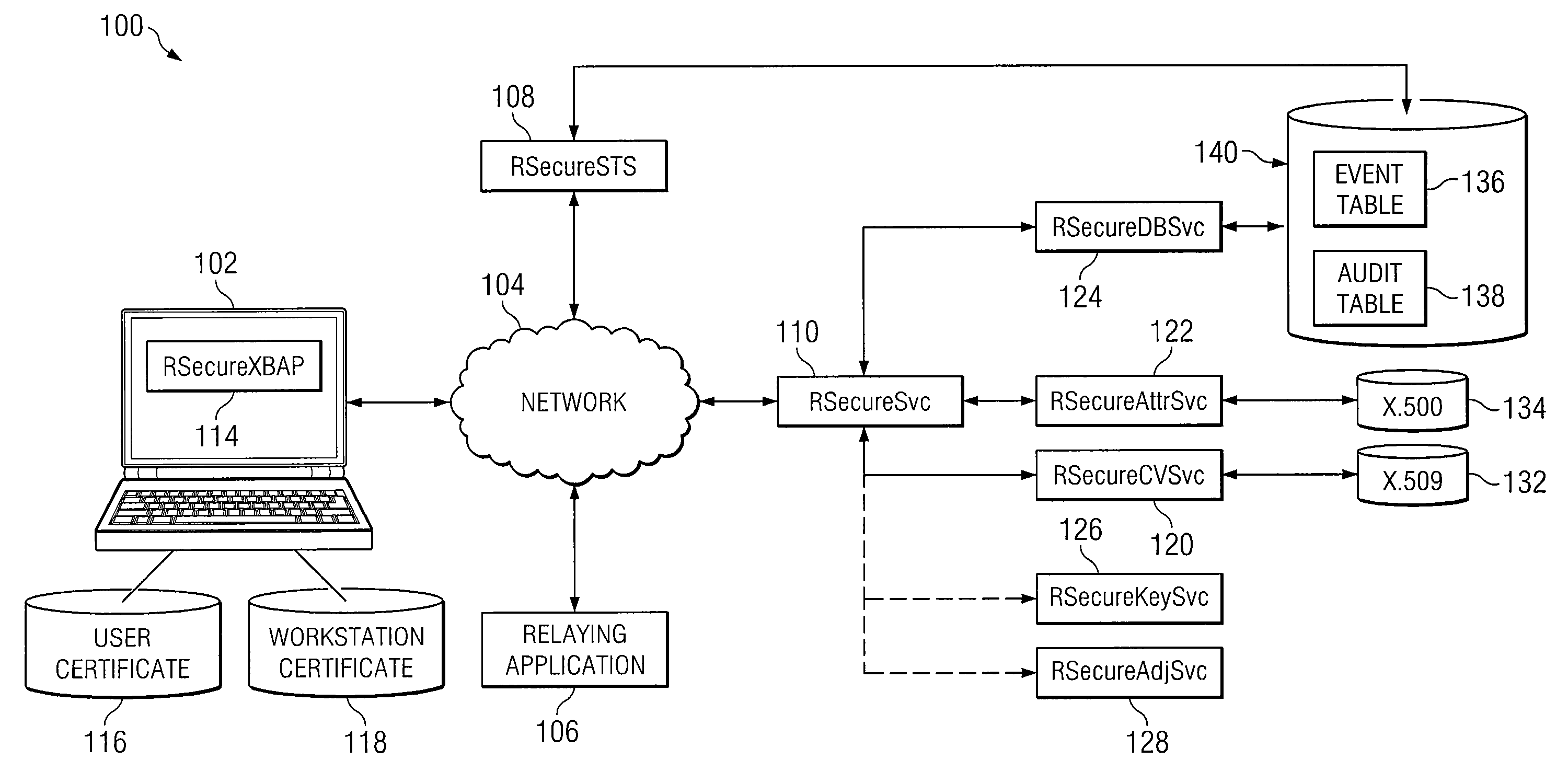
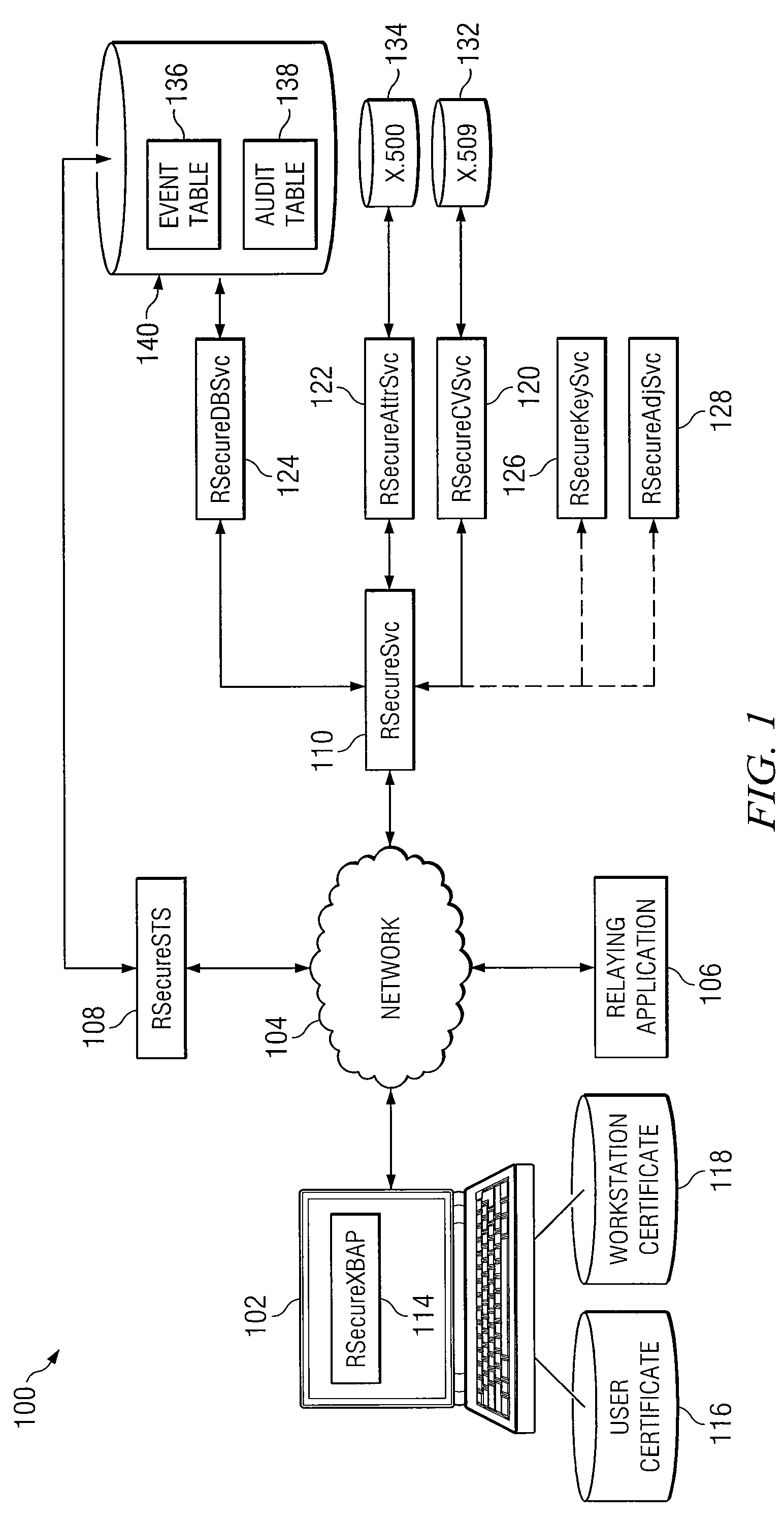
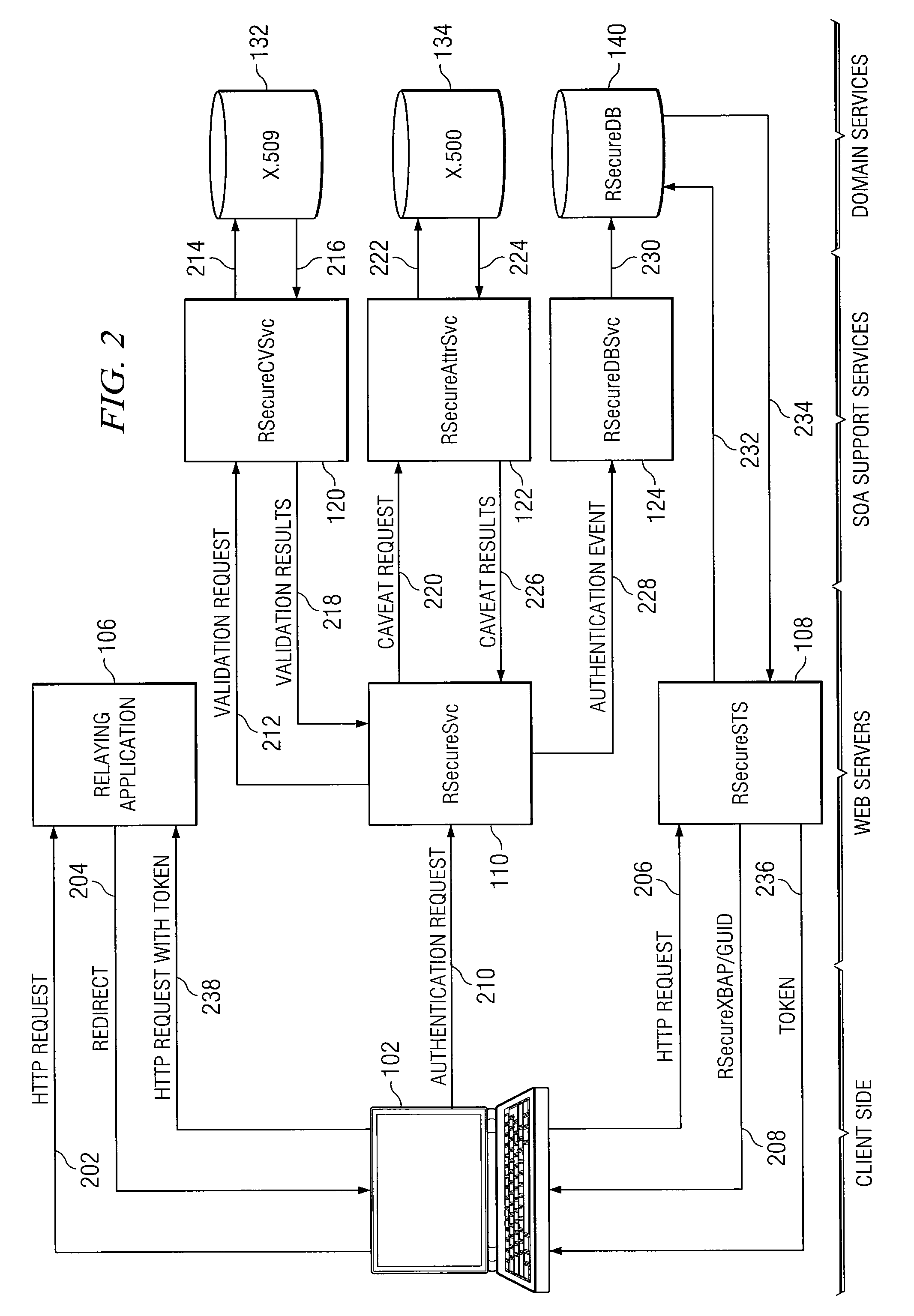
System and Method for Dynamic Multi-Attribute Authentication
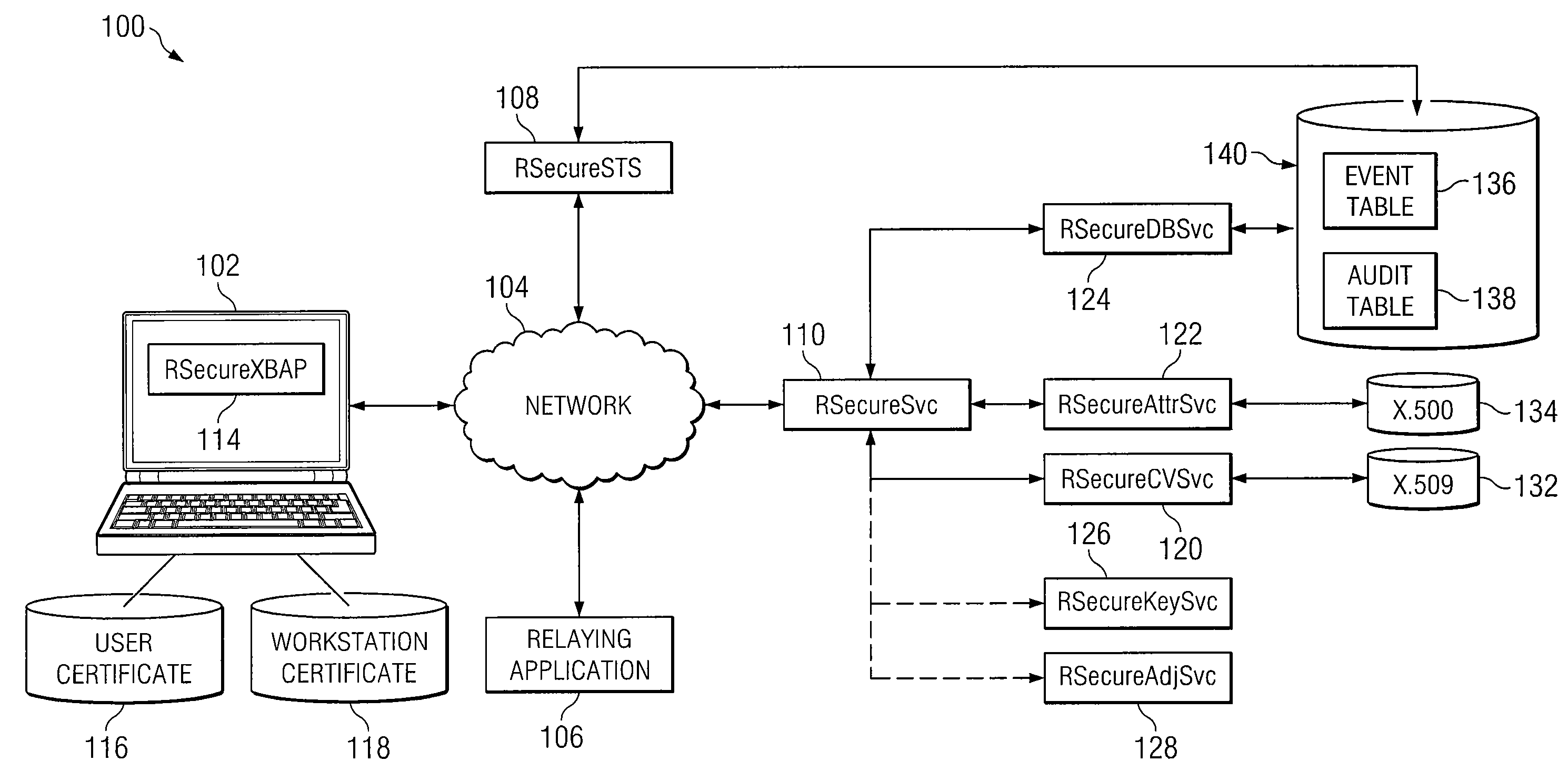
ActiveUS20100332825A1Reduce workstation signature substitution workstationReduce workstation workstation spoofingDigital data processing detailsUser identity/authority verificationInternet privacyWeb service
In accordance with the teachings of the present invention, a system and method for dynamic, multi-attribute authentication are provided. In a particular embodiment, a method for authentication includes receiving, at an authentication web server, an authentication request comprising a workstation message and a user message, wherein the workstation message comprises a workstation object and a workstation signature, the workstation object comprises a workstation certificate associated with a workstation, the user message comprises a user object and a user signature, and the user object comprises a copy of the workstation message and a user certificate associated with a user of the workstation. The method further includes verifying the workstation signature and user signature, validating the workstation certificate and the user certificate, retrieving one or more caveats associated with the workstation and one or more caveats associated with the user, and determining one or more caveats associated with both the workstation and the user.
Owner:FORCEPOINT FEDERAL
Phantom serializing compiler and method of operation of same
ActiveUS7886283B2Fine grained controlImprove performanceSoftware engineeringProgram controlOperational systemApplication software
An alternative to a real time operating system (RTOS) is provided based on serializing compilers. A serializing compiler can transform a multitasking application into an equivalent and optimized monolithic sequential code, to be compiled with the embedded processor's native optimizing compiler, effectively filling the RTOS gap. The serializing compiler can analyze the tasks at compile time and generate a fine-tuned, application specific infrastructure to support multitasking, resulting in a more efficient executable than one that is intended to run on top of a generic RTOS. By having control over the application execution and context switches, the serializing compiler enables the fine grain control of task timing while enhancing overall performance. The serializing compiler technology strengthens existing compilers, making them timing and task-aware. The Phantom compiler provides a fully automated mechanism to synthesize a single threaded, ANSI C / C++ program from a multithreaded C / C++ (extended with POSIX) program.
Owner:RGT UNIV OF CALIFORNIA
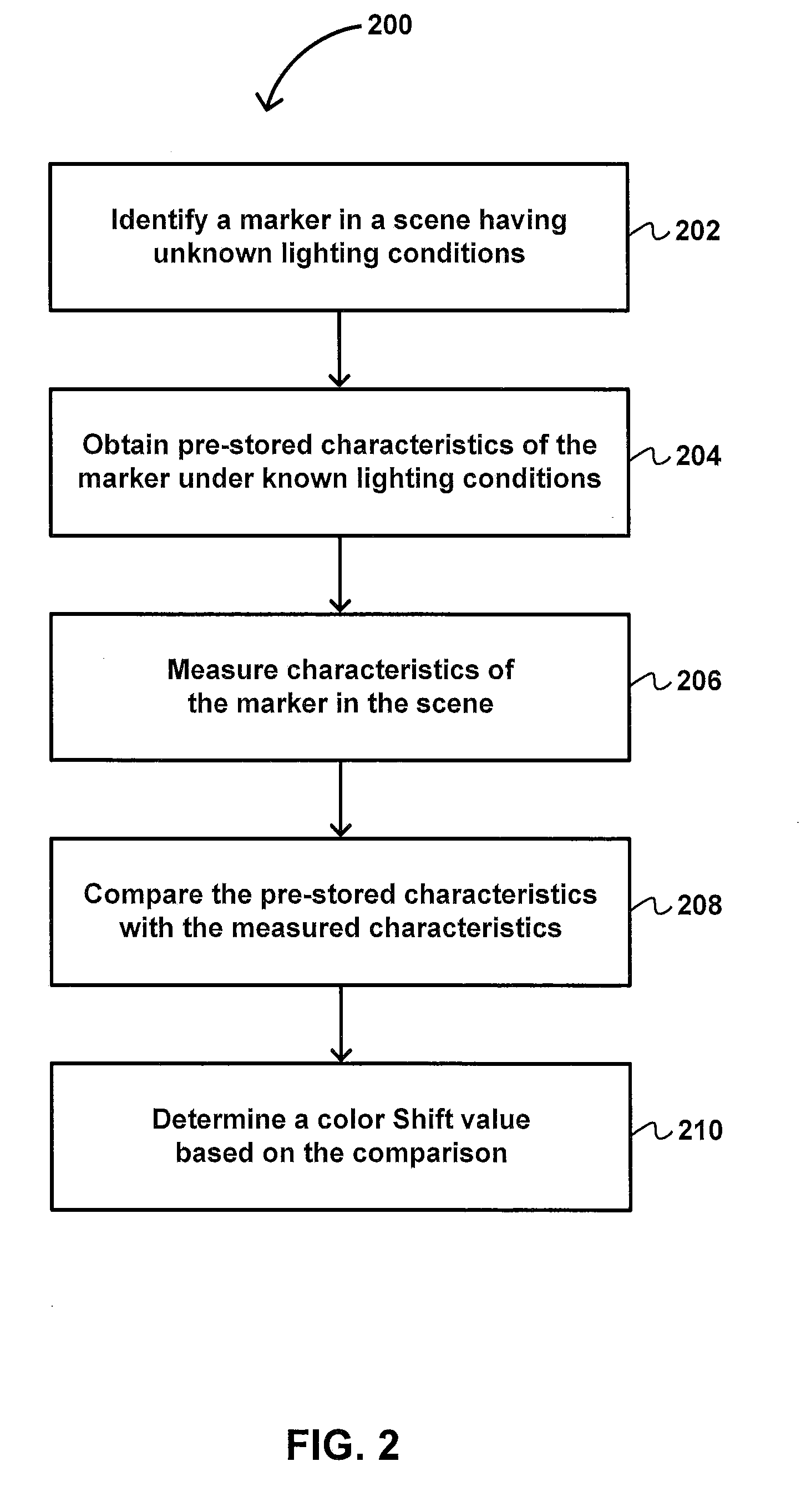
System and Method of Adjusting the Color of Image Objects Based on Chained Reference Points, Gradient Characterization, and Pre-stored Indicators of Environmental Lighting Conditions
ActiveUS20150207960A1Eliminate the effects ofColor shiftImage enhancementImage analysisColor shiftEffect light
The invention relates to a system and method for adjusting the color of image objects based on chained reference points and / or light gradients to account for the effects of lighting conditions that can vary across different environments, according to an implementation of the invention. To chain reference points and / or characterize light gradients, the system may determine a color shift value, which represents the effects of lighting conditions of a target environment (in which the lighting conditions may be unknown) relative to a reference environment (in which the lighting conditions may be known). The chained reference points, gradient characterization, color shift values, and / or other information may be used to store a delta map that characterizes the lighting conditions of an environment so that it may be reused for subsequent color shifts without re-characterizing the environment.
Owner:CARBON OBJECTS
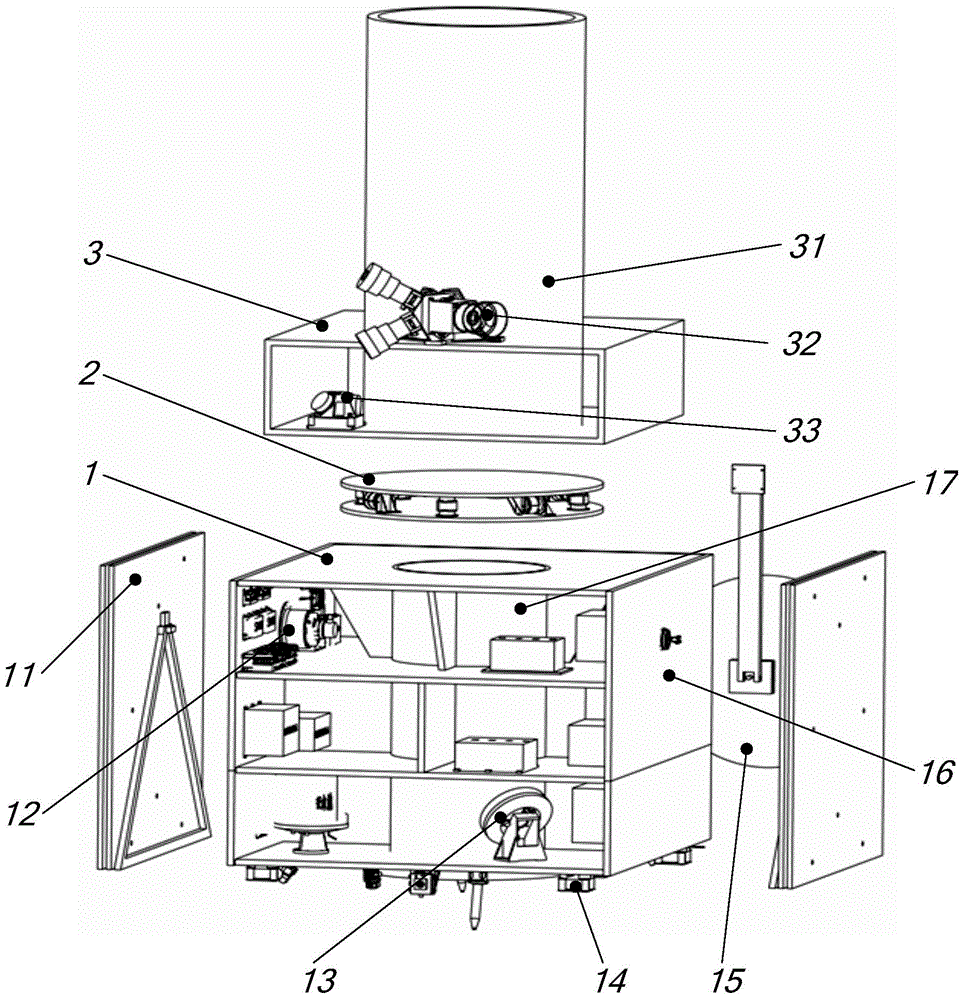
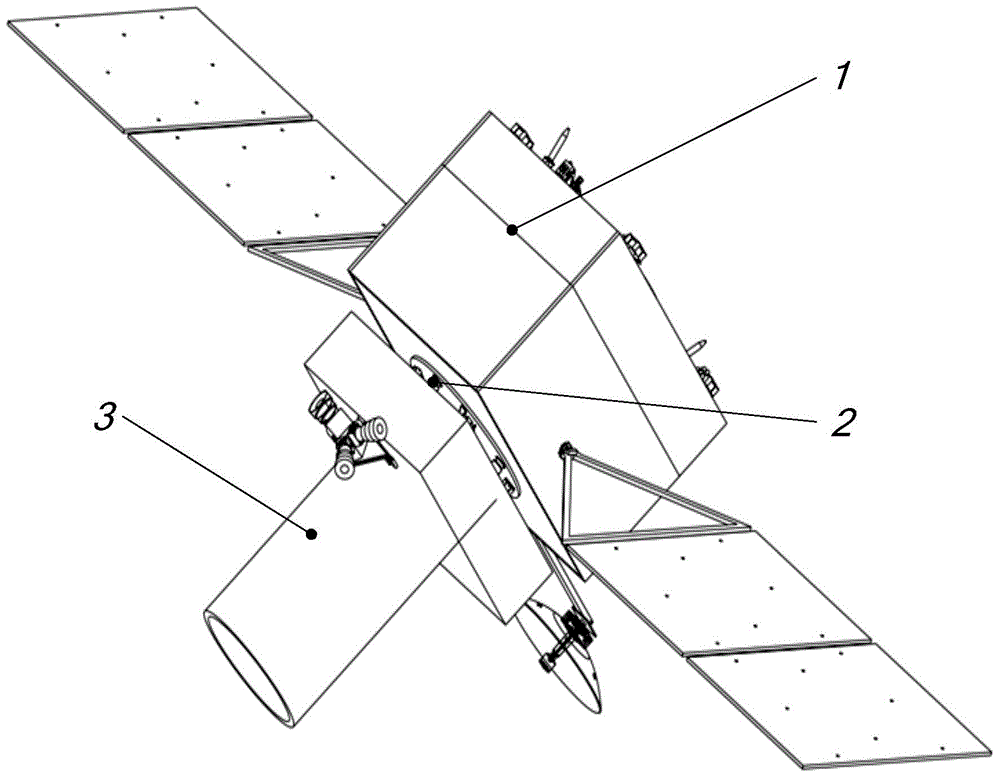
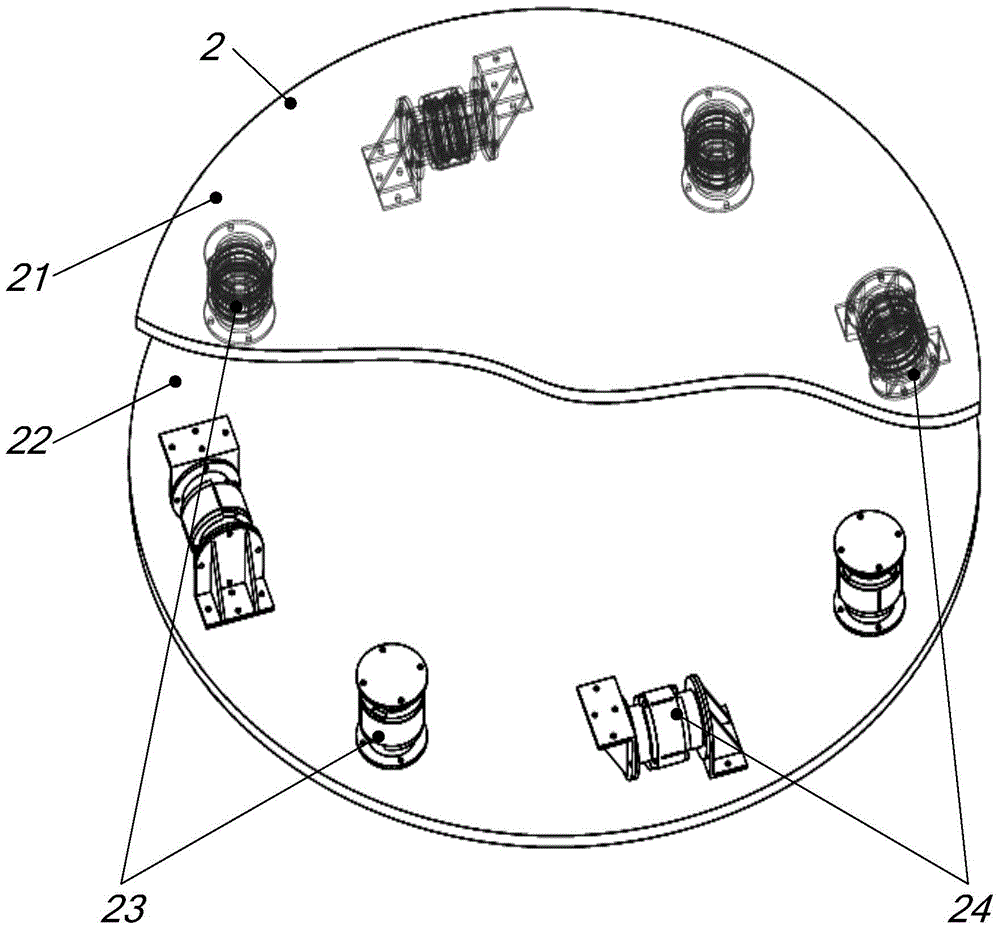
Eight-rod-connecting type non-contact satellite platform configuration and assembling method
ActiveCN104058102AFocus on ultra-precise and ultra-stable tasksFine-grained controlCosmonautic partsArtificial satellitesDeep space explorationAstronomical telescopes
The invention provides an eight-rod-connecting type non-contact satellite platform configuration and an assembling method. The eight-rod-connecting type non-contact satellite platform configuration comprises an upper connecting plate, a lower connecting plate, four same vertical mounting force actuators and four same horizontal mounting force actuators; both the vertical mounting force actuators and the horizontal mounting force actuators are connected between the upper connecting plate and the lower connecting plate and are arranged in a circumference manner; the vertical mounting force actuators and the horizontal mounting force actuators are arranged along the same circumference in a staggered and orthorhombic manner; the vertical mounting force actuators are vertical to the horizontal mounting force actuators. The eight-rod-connecting type non-contact satellite platform configuration implements complete isolation of an effective load on platform vibration and interference response, can be applied to spacecrafts with high-resolution sensitive effective load, such as a very-high accuracy remote sensing satellite, a deep space exploration astronomical telescope and the like, and can greatly improve exploration performance of spacecrafts.
Owner:SHANGHAI SATELLITE ENG INST
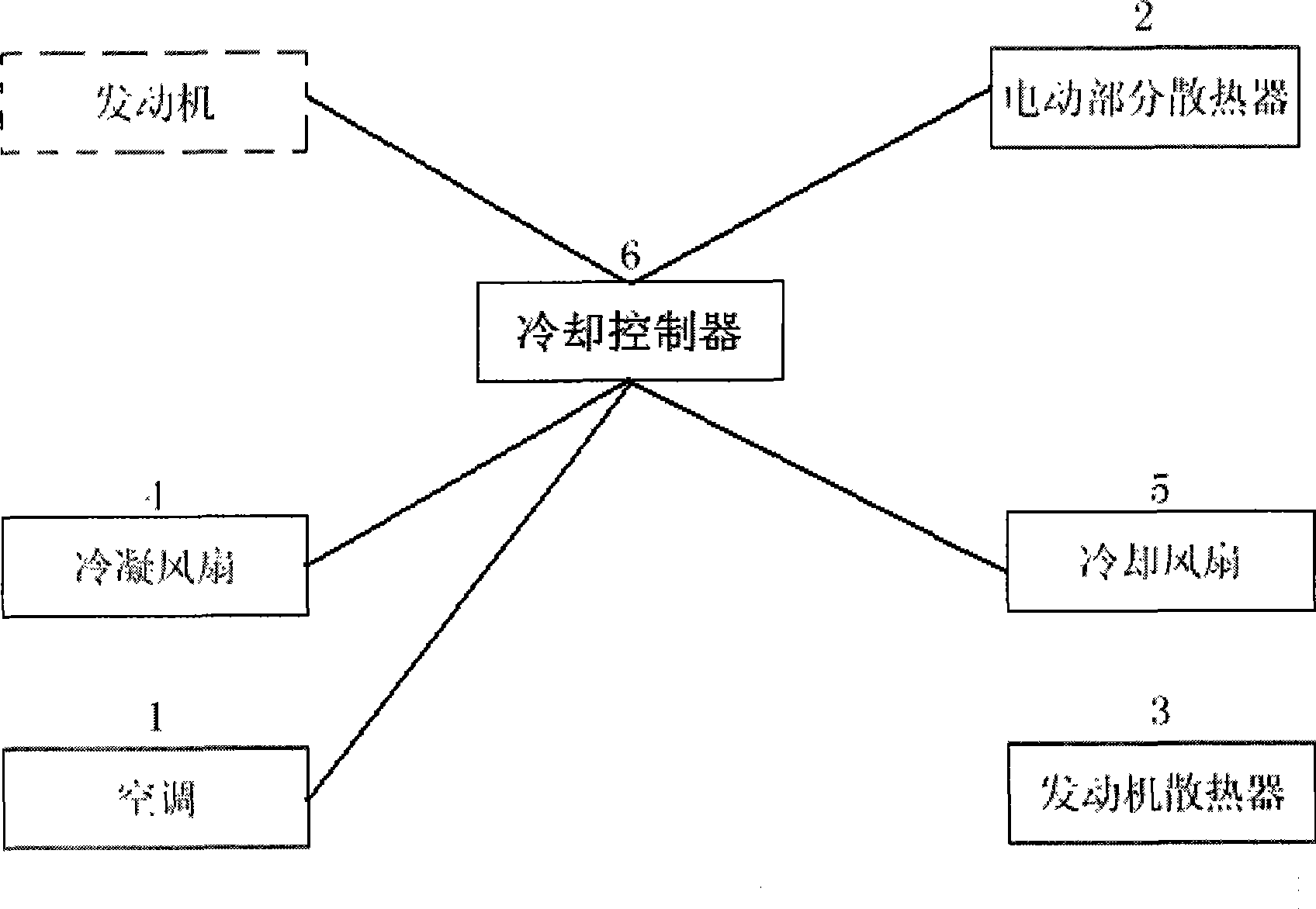
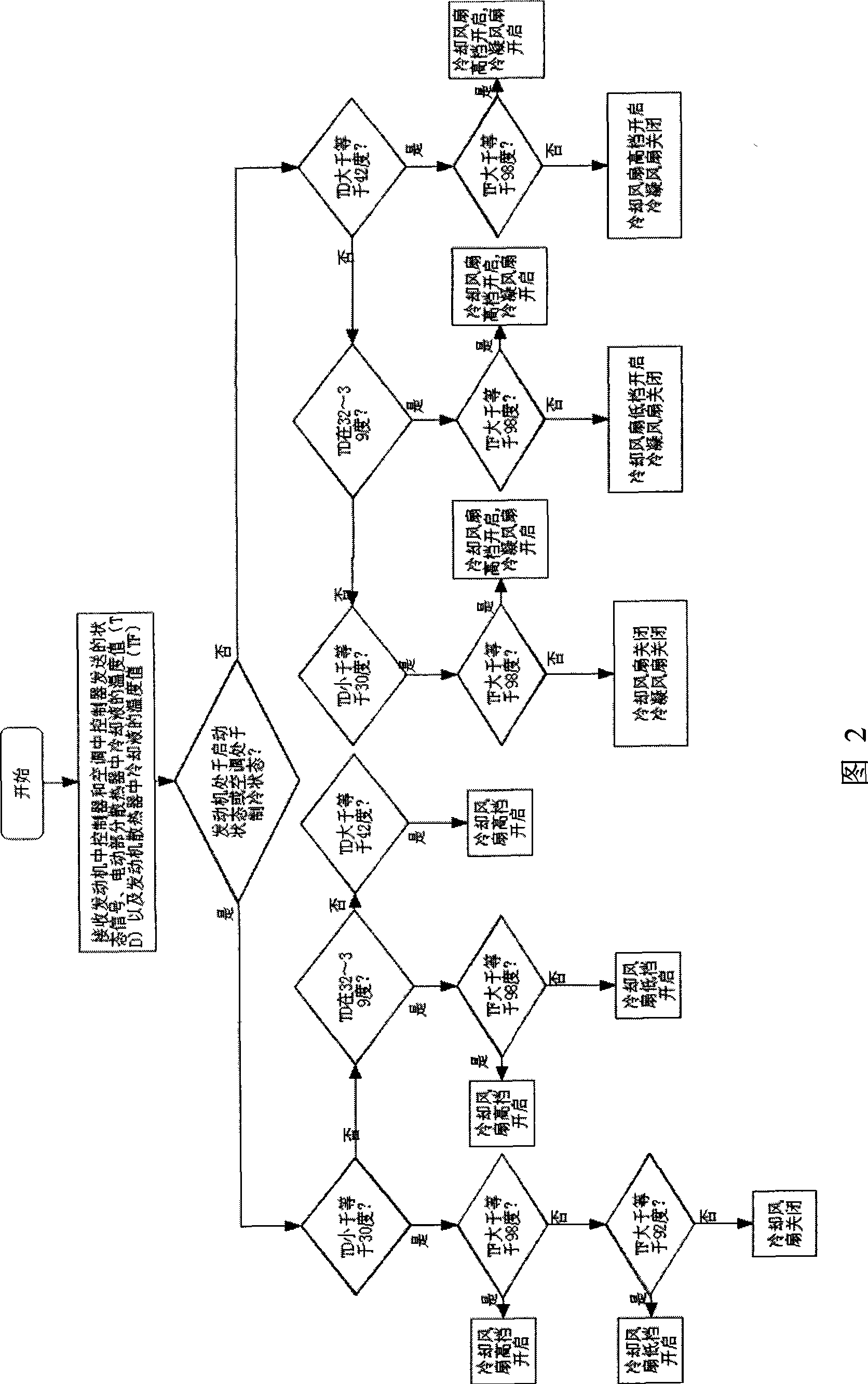
Cooling system for hybrid power automobile and control method thereof
ActiveCN101376337ARealize heat dissipationFine-grained controlPropulsion coolingAerospace engineeringCooling fluid
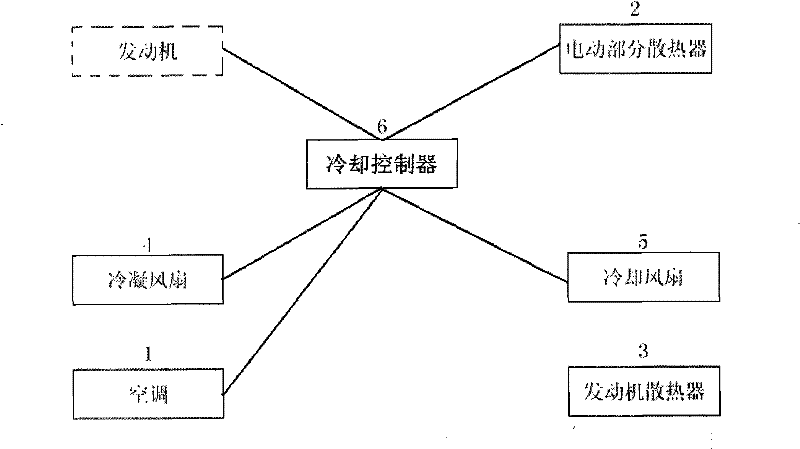
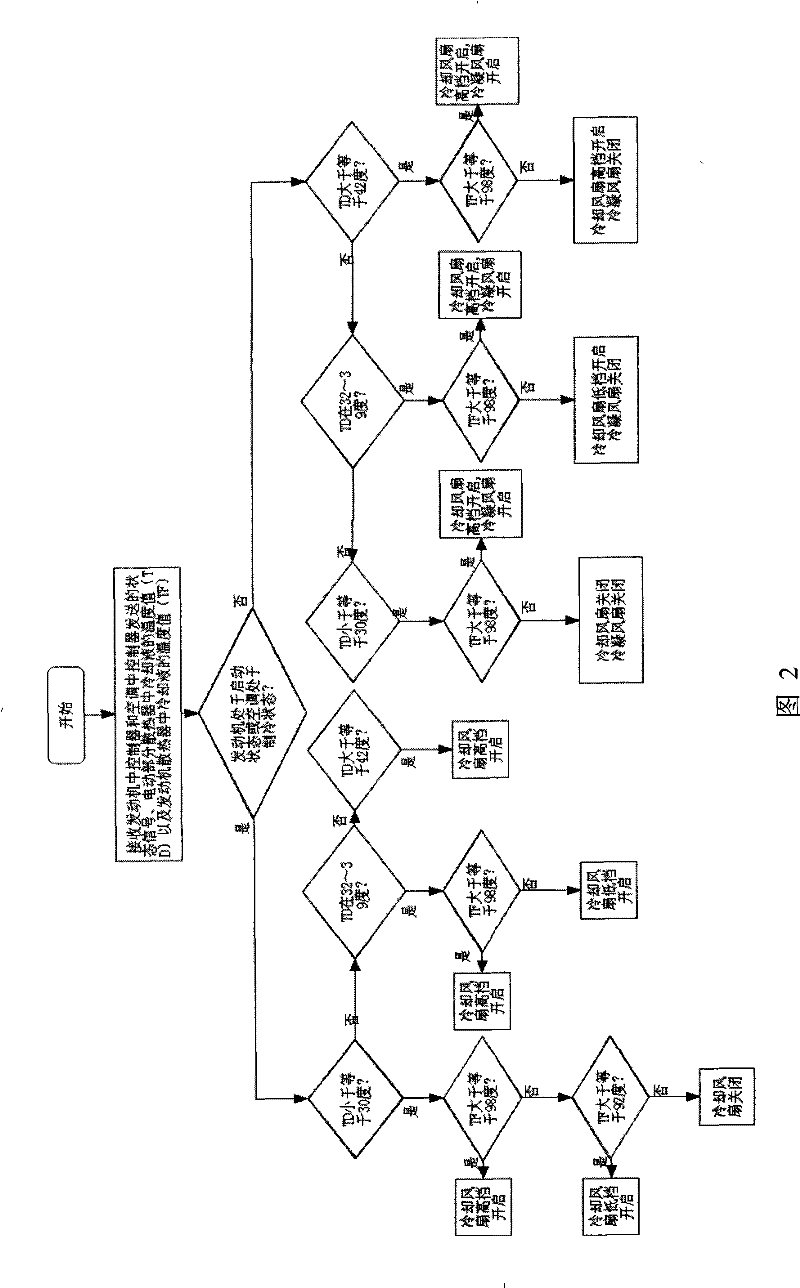
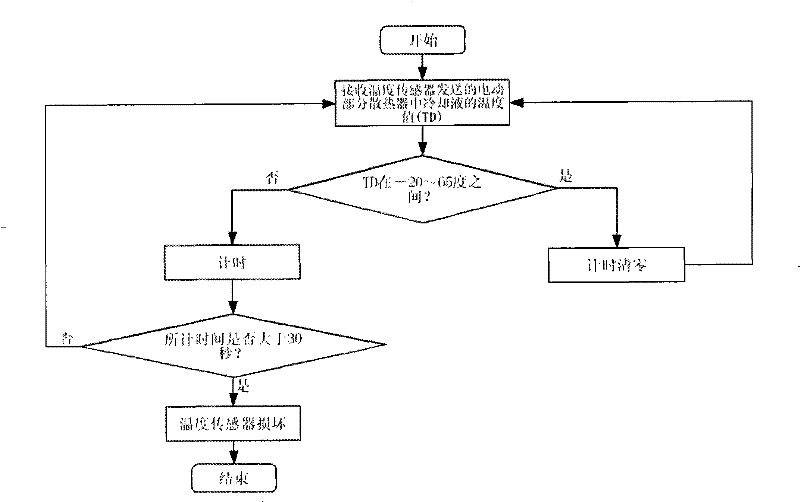
The invention provides a cooling system of a hybrid power automobile, which comprises an air-conditioner with an air-conditioner controller, a radiator of electrical parts with a temperature sensor, an engine radiator, a condensating fan and a cooling fan. The condensating fan and the cooling fan are used for reducing the temperatures at the inlet parts of a condensator and the engine radiator in the air-conditioner respectively; wherein the cooling system further comprises a cooling controller which is connected with the air-conditioner controller in the air-conditioner, the temperature sensor in the radiator of the electrical part, the cooling fan and the condensating fan respectively; The cooling controller can control the operation of the condensating fan and the cooling fan based on the operation mode of the air-conditioner, which is transmitted from the air-conditioner controller, the temperature value of the cooling liquid in the radiator of the electrical part, which is sensed by the temperature sensor, or the external temperature value which is transmitted by the air-conditioner controller, the temperature value of the cooling liquid in the engine radiator, and the operating condition of the engine. The cooling system can minimize the power consumption on the premise that the requirements for the cooling system are met.
Owner:BYD CO LTD
System for and method of protecting an integrated circuit from over currents
InactiveUS20070207681A1Protection from damageElectrostatic discharge damageElectric signal transmission systemsImage analysisControl powerEngineering
Owner:APPLE INC
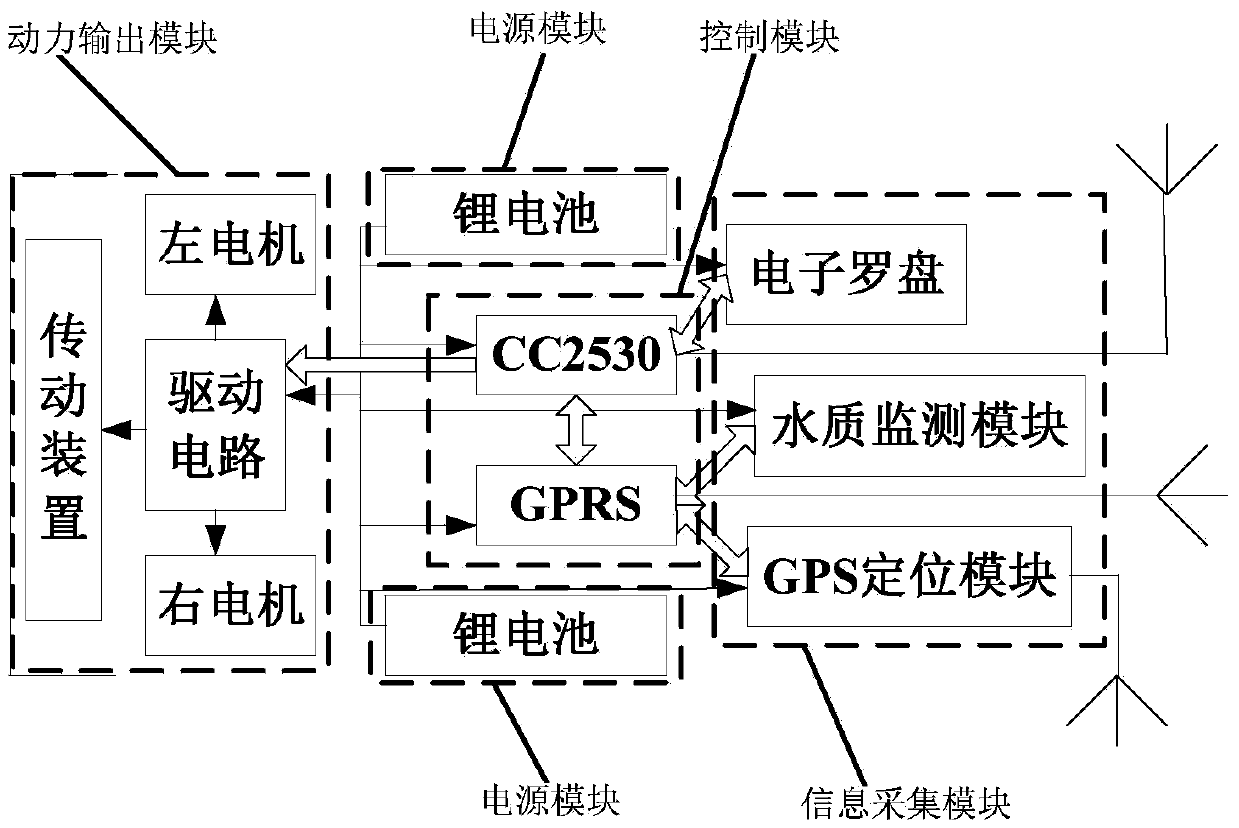
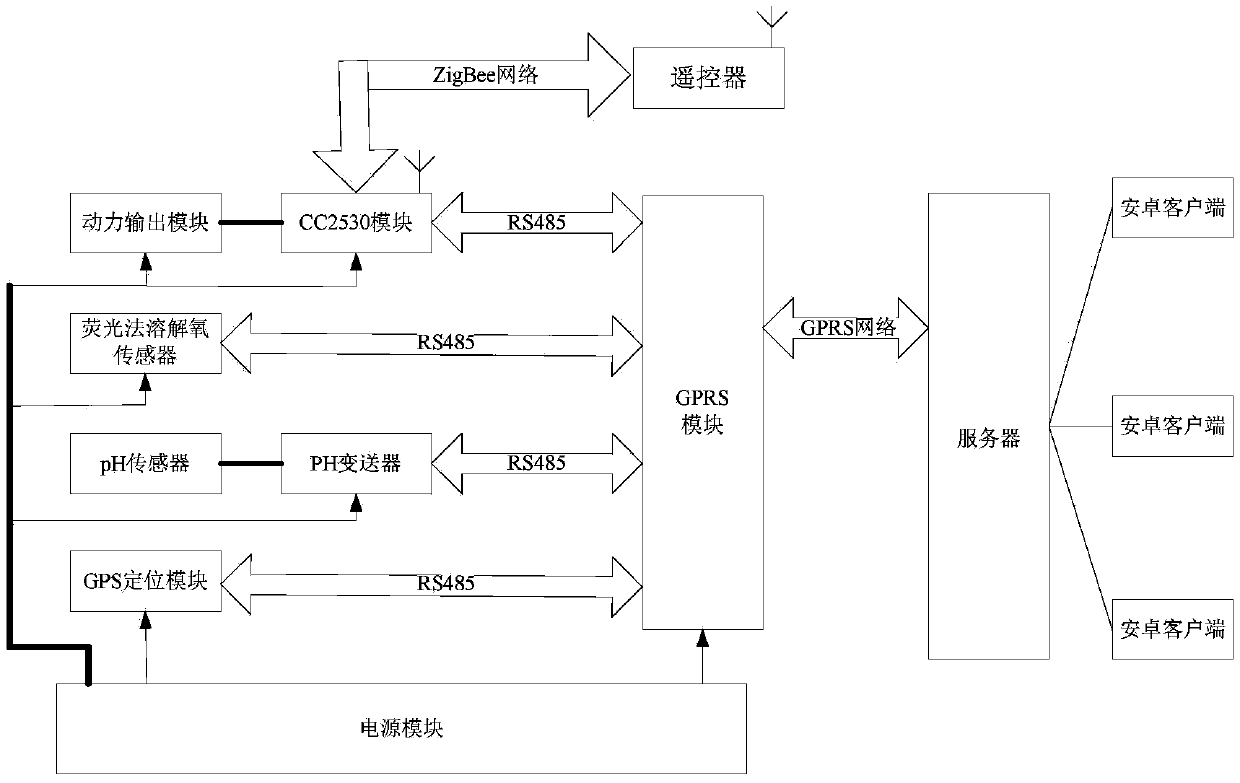
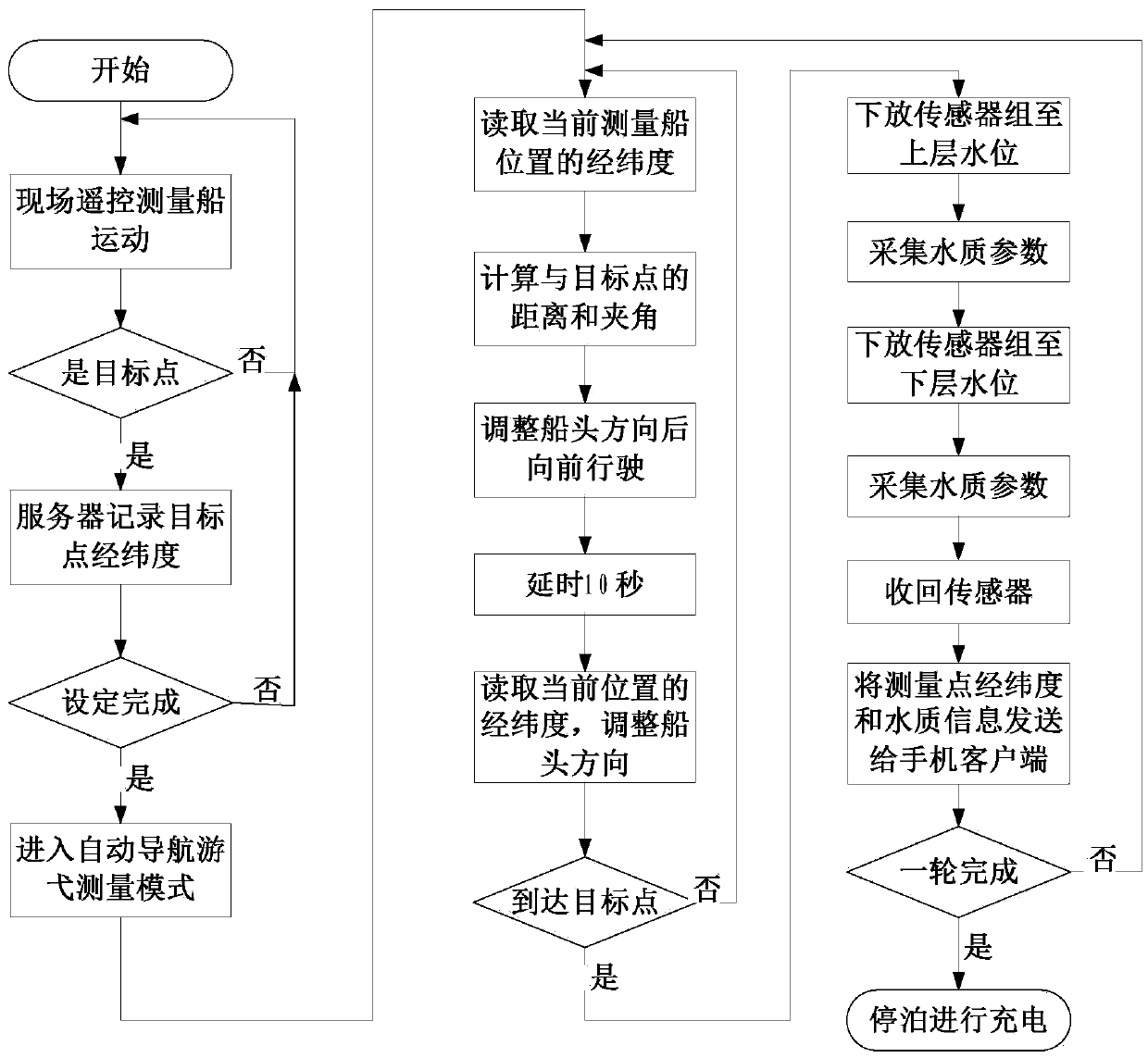
Cruising water quality multi-parameter remote monitoring system and method capable of self-learning locus navigation
ActiveCN105371896AHelps monitor and analyzeFine-grained controlMeasurement devicesMeasurement deviceEnvironmental geology
The present invention discloses a cruising water quality multi-parameter remote monitoring system and method capable of self-learning locus navigation, belonging to the field of aquaculture technology. The cruising water quality multi-parameter remote monitoring system comprises a boat body, a measurement device, an executive device and a server, wherein the measurement device, the executive device and the server are located on the boat body. A GPS positioning module is adopted to accurately measure the position information of the boat body; the server is configured to record the motion locus of the boat body and measurement target points; the boat body is able to learn the route and perform automatic navigation according to the route after the on-site remote manual control is performed to demonstrate the route, and is able to stop at the target points to carry out measurement and perform remote wireless transmission of water quality parameters such as water temperature, dissolved oxygen value, pH value, water level and the like; the server is configured to control the executive device to regulate the water quality according to the measured parameters, and at the same time, users may monitor the date of the operation position and water quality parameters of the measured boat in real time through a mobile phone client, may send control instructions to control the motions of control nodes near the measured boat and may correct the motion locus of the measured boat. The cruising water quality multi-parameter remote monitoring system is low in cost, high in mobility and wide in measurement range.
Owner:JIANGSU UNIV
Compressing encode/decode method for three-dimensional model texture based on Quardtree
ActiveCN101447084AImprove division efficiencyFast convergenceImage codingTelevision systemsENCODEThree dimensional model
A compressing encode method for a three-dimensional model texture based on Quardtree comprises the following steps: (1) dividing texture images according to Quardtree, resolving the texture images into a series of base textures with different resolutions, and coding the base textures; (2) arranging texture coordinates, and coding the texture coordinates successively. A decoding method corresponding to the coding method comprises the following steps: synchronously transferring texture data stream and geometric grid data, and decoding and recovering the texture data stream and the geometric grid data; and matching the texture data stream and the geometric grid data with geometrical model of the corresponding resolutions according to the textures with different resolutions. The compressing encode / decode method f of the invention has the advantages of high division efficiency, fast convergence rate as well as short client terminal responding and waiting time, and can control precision of model texture decode.
Owner:SHENZHEN FUTURE 3D EDU TECH CO LTD
Security enhancement system and method for software
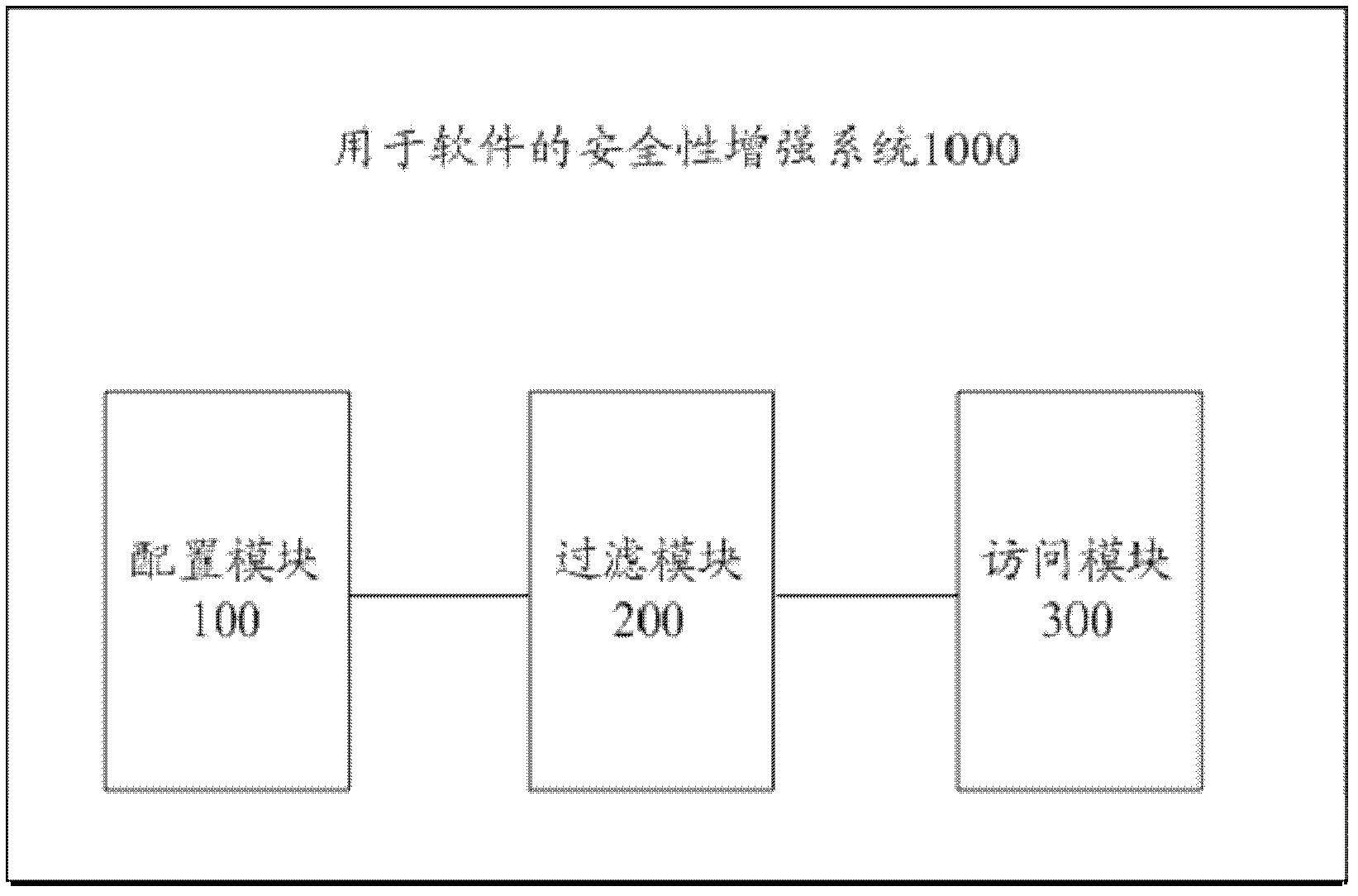
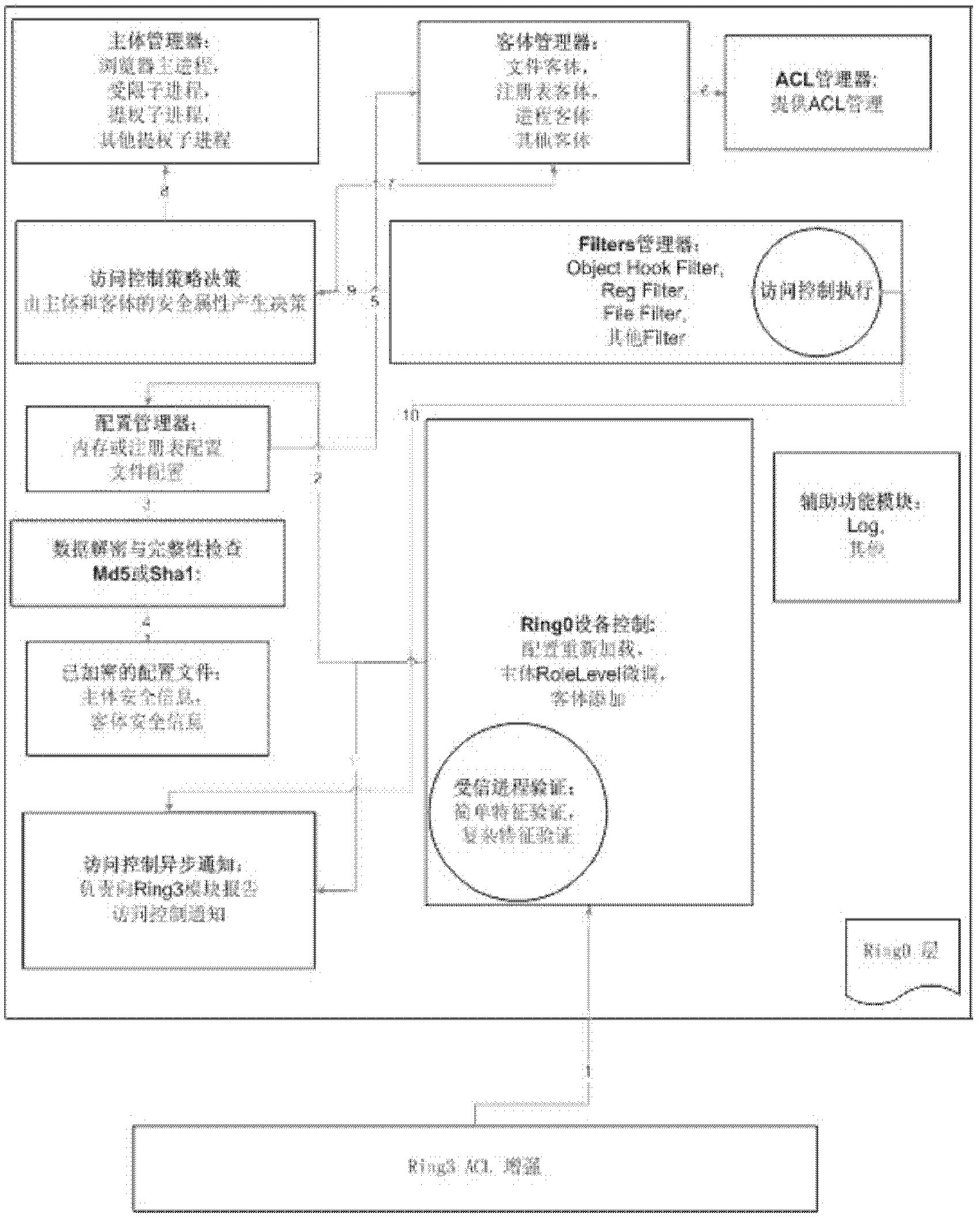
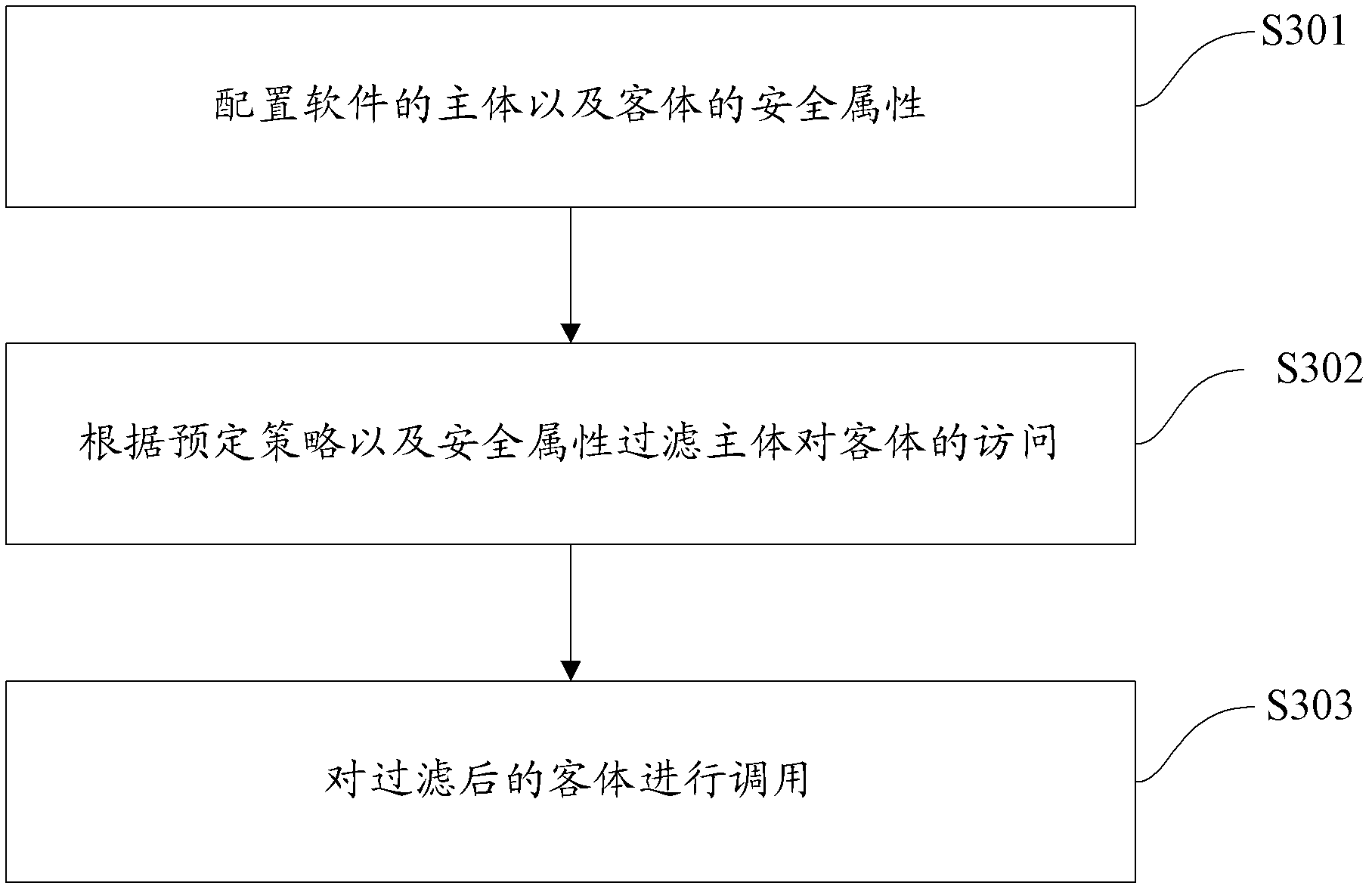
ActiveCN102663321AFine grained controlGuaranteed feasibility and safetyComputer security arrangementsSecurity propertiesSecurity enhancement
The invention discloses a security enhancement system for software. The security enhancement system for software comprises a configuration module for configuring the security properties of a main body and an object of the software, a filter module for filtering access of the main body to the object according to a preset strategy and the security properties and an access module for calling the object processed by the filter module. The system meets the minimized authority rule, so that the probability of enhancing the security of the software can be guaranteed, and relatively high generality is realized. The invention also discloses a security enhancement method for the software.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
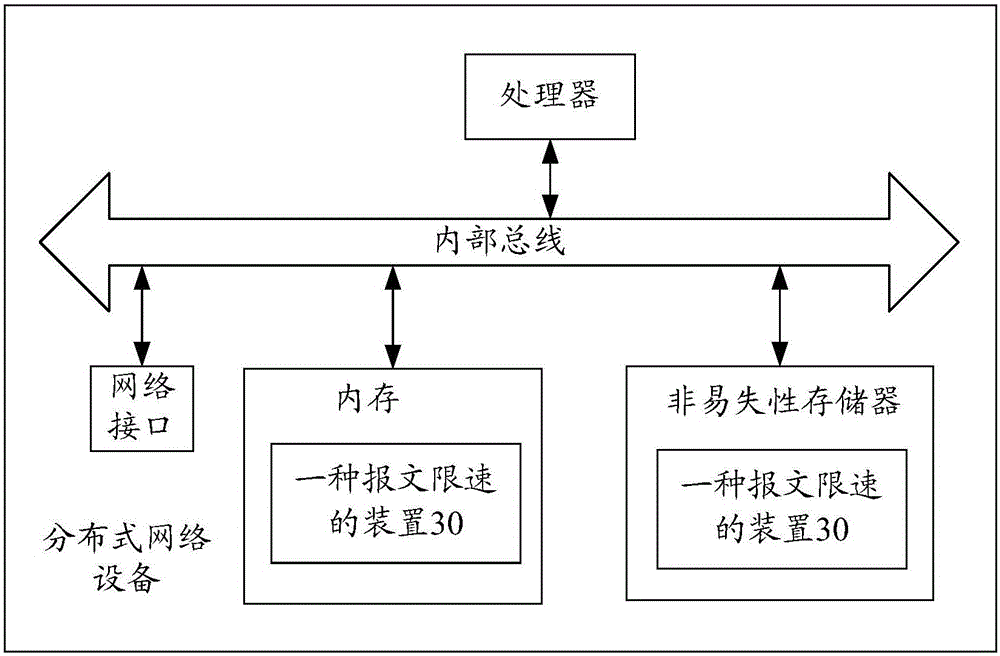
Message speed limiting method and device
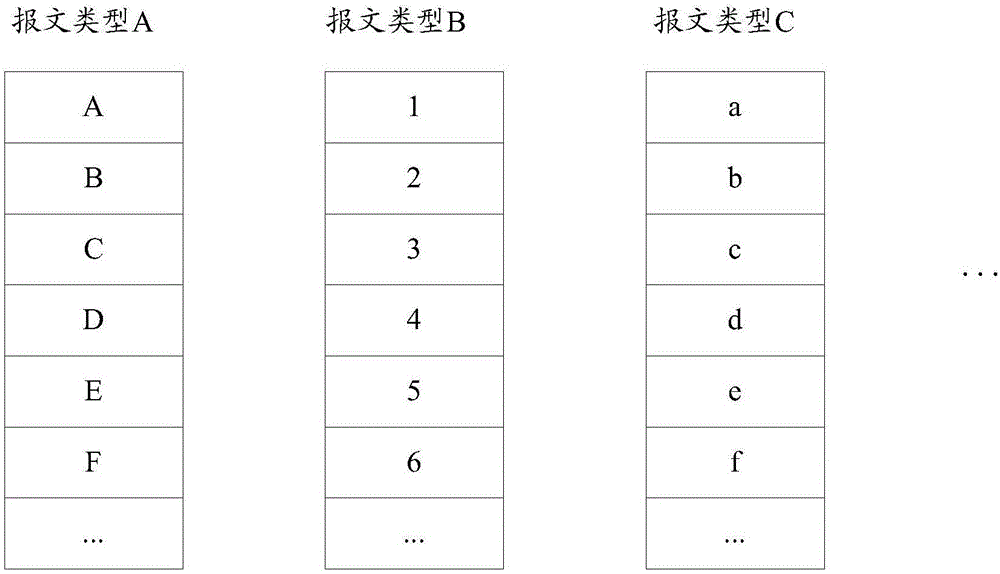
ActiveCN106656857AImprove stabilityFine-grained controlData switching networksComputer hardwareMessage type
The invention provides a message speed limiting method and device applied to a distributed network device. The message speed limiting method comprises the steps of judging whether the protocol type of a protocol message supports multiple message types when a service board sends the received protocol message to a main control board; if the protocol type of the protocol message supports multiple message types, determining the message type of the protocol message and adding the protocol message to a speed limiting queue corresponding to the message type; and when the number of the protocol message in the speed limiting queue is not beyond a preset speed limiting threshold, sending the protocol message to the main control board, wherein different message types respectively correspond to different speed limiting queues. By adoption of the technical scheme provided by the invention, the stability of network operation can be improved.
Owner:HANGZHOU DPTECH TECH
An optimal control method for battery energy storage system to participate in power grid primary frequency regulation
ActiveCN102891495BImprove charge/discharge performanceFine-grained controlFlexible AC transmissionAc network load balancingElectrical batteryPower Balance
The invention discloses a method used for controlling participation of a battery energy storing system in primary frequency modulation and optimization of a power gird. The method comprises the following steps: collecting a power grid frequency through a data collecting module and inputting the power grid frequency to a power-frequency conversion control module; taking the lower limit of frequency bias fSQ and upper limit as the control goal in the power-frequency conversion control module, wherein delta fi is more than the lower limit and less than fSQ; and taking meeting the control goal and keeping relatively good charging / discharging ability and excellent system on chip (SOC) level of the battery energy storing system as the control principle, conducting operation treatment on the input data according to a power-frequency conversion control strategy; judging whether the real-time grid frequency bias delta fi exceeds the frequency dead zone; if so, transforming the frequency bias delta fi to a corresponding power bias delta Pi, comparing the obtained power balance delta Pi of the power grid at the moment i with the maximum output limit value PBatt.Max of the battery energy storing system; judging the degree of the battery energy storing system participating in the primary frequency regulation of the power grid; controlling the output of the battery energy storing system by a battery management system (BMS), correcting the balance between supply and demand of the power gird, preventing the aggravation of the frequency fluctuation, and maintaining the stability of the power grid frequency.
Owner:CHINA ELECTRIC POWER RES INST +1
Method and system for preventing robot attack
InactiveCN107592300ABlocker attackFine grained controlDigital data protectionPlatform integrity maintainanceSingle sessionGranularity
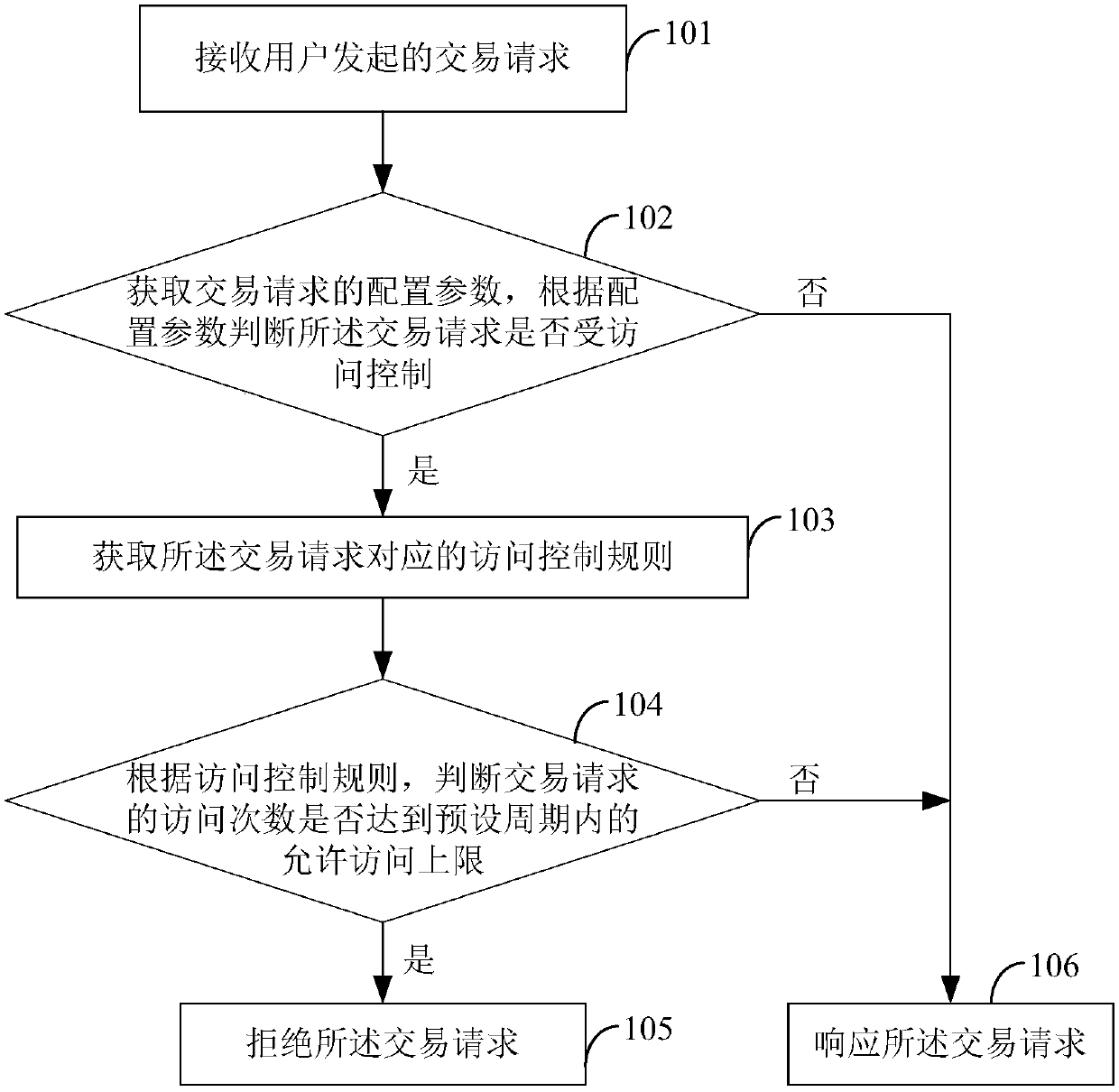
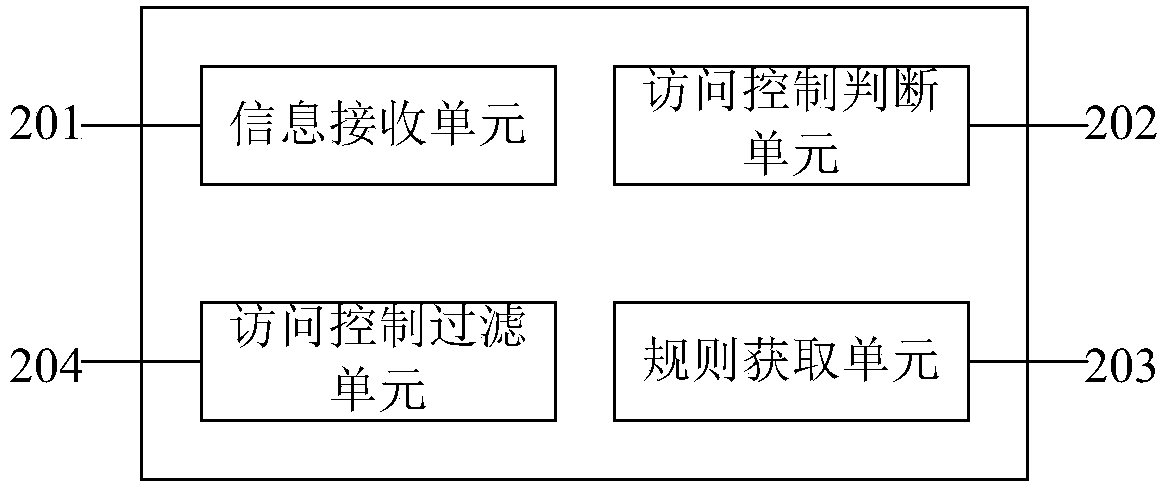
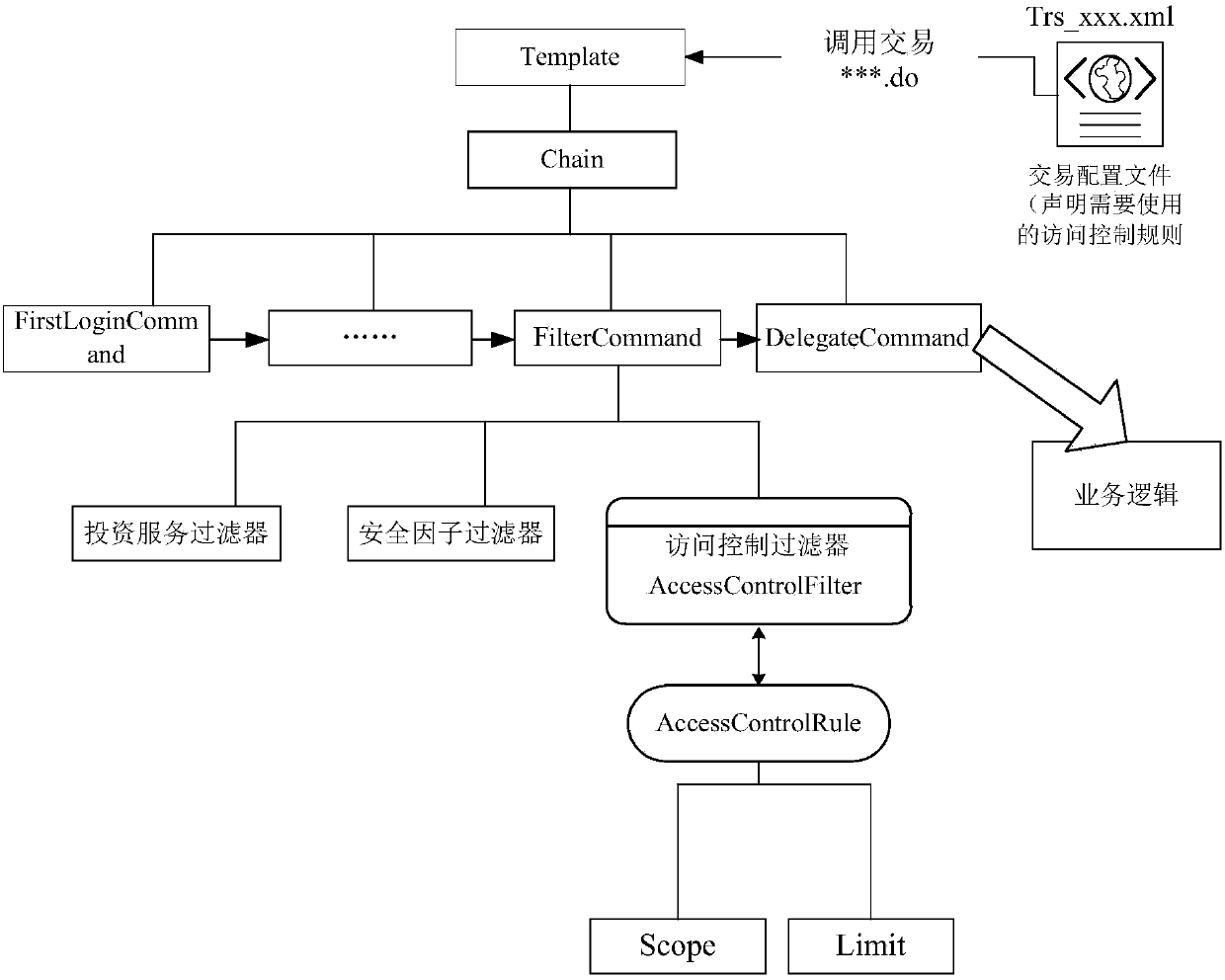
The invention provides a method and system for preventing a robot attack. The method comprises: receiving a transaction request initiated by a user; acquiring a configuration parameter of the transaction request and determining whether the transaction request is subjected to access control according to the configuration parameter; if so, acquiring an access control rule corresponding to the transaction request; on the basis of the access control rule, determining whether the number of times of access of the transaction request reaches an allowable access upper limit within a preset period; andif so, the transaction request is refused. Therefore, control for a single client or a single session is realized; the control granularity becomes fine and accurate; and thus the program attack froma robot can be prevented completely.
Owner:BANK OF CHINA
Operation control method and device
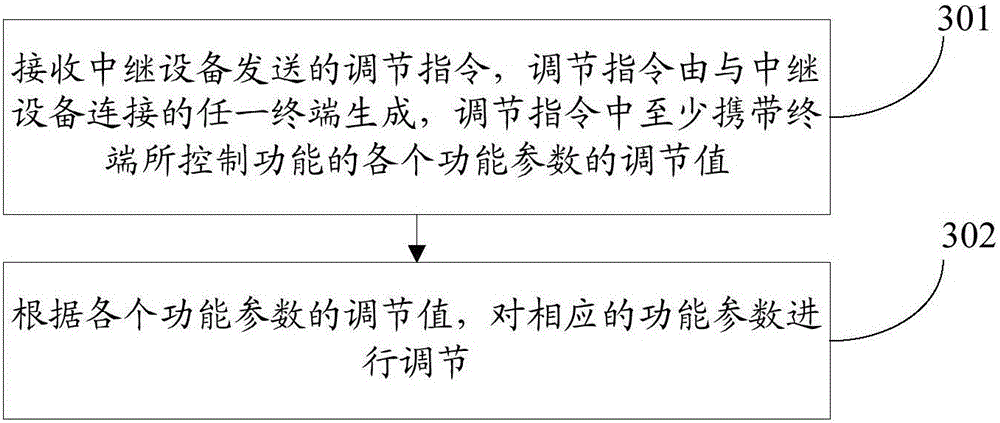
PendingCN105100439AFine-grained controlReduce difficultyConnection managementSubstation equipmentGranularityComputer engineering
The invention provides an operation control method and device, and belongs to the technical field of terminals. The method is applied to relay equipment and comprises the following steps: establishing connection with a plurality of terminals, wherein each terminal is used for controlling one function of target equipment, and each function comprises at least one function parameter; receiving a regulation instruction sent by any terminal, wherein the regulation instruction at least carries regulation values of various function parameters of the functions controlled by the terminal; and sending the regulation instruction to the target equipment, and the target equipment regulates the corresponding function parameters according to the regulation values of the function parameters. According to the operation control method and device provided by the invention, since the connection is established with the plurality of terminals, and each terminal respectively controls one function of the target equipment, thereby thinning the control granularity of the target equipment; and moreover, each terminal is responsible for one specific relatively simple operation, and the target equipment is controlled on different terminals, so that the control difficulty and complexity are effectively reduced.
Owner:GUANGZHOU FEIMI ELECTRONICS SCI & TECH +1
Method for controlling pocket data transmission rate in mobile communication network and system thereof
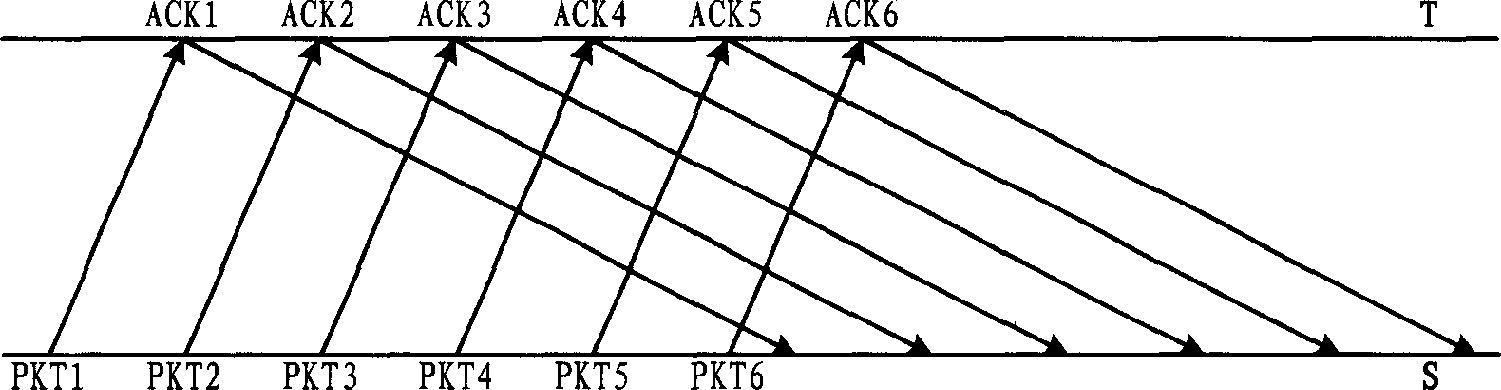
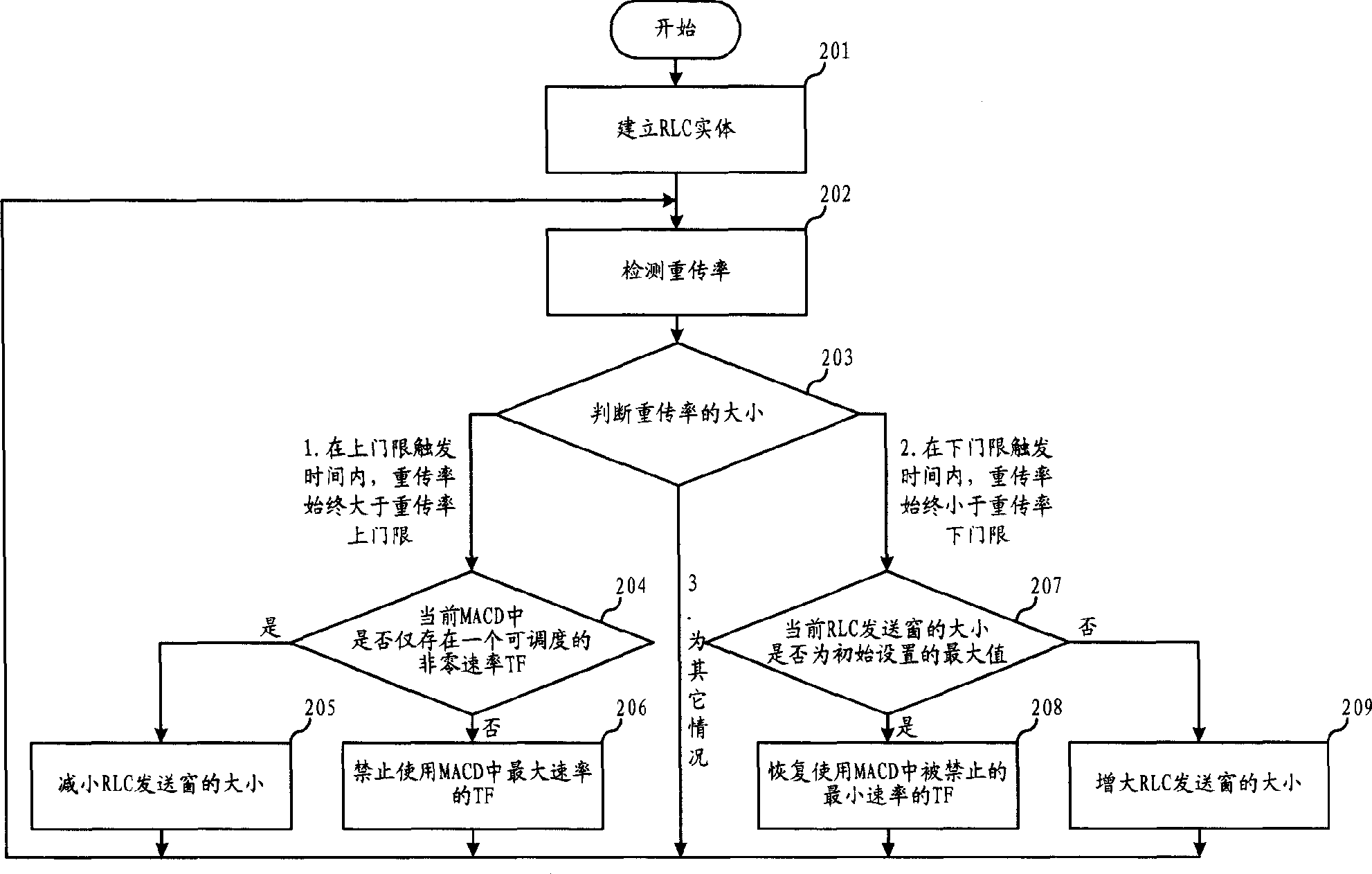
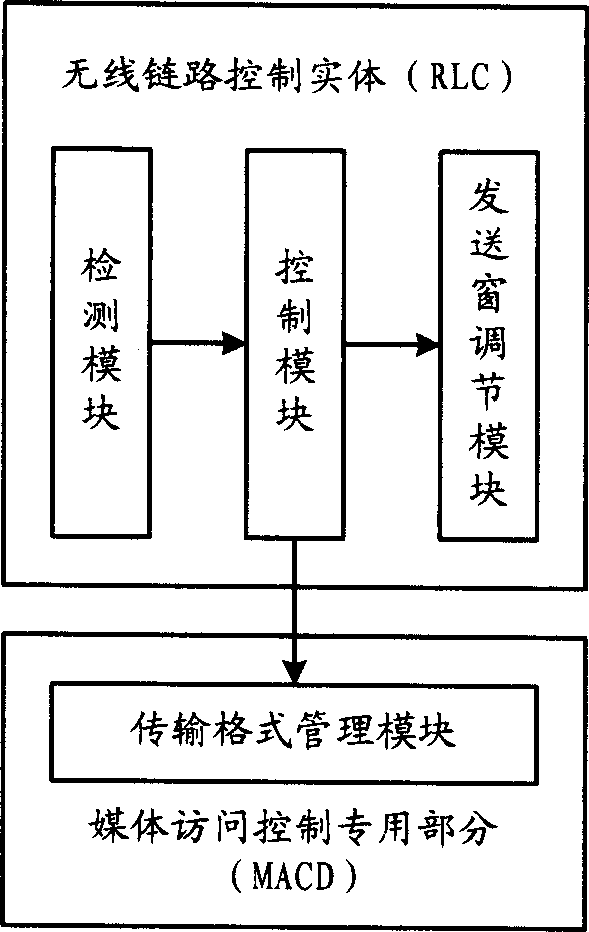
InactiveCN1863030ATrack congestionFast Track CongestionCorrect operation testingMACDPacket data transmission
The invention discloses a grouped data transferring speed controlling method and the system in mobile communication network that could improve the transmission layer bandwidth utilization and application layer speed under congestion situation. The RLC identity could take testing for retransmission ratio of data block to trace the congestion situation. By the method of adjusting the size of sending window and the combination of restricting or restoring operation schedulable TF in MACD by RLC identity, the data transmission speed would be controlled.
Owner:HUAWEI TECH CO LTD
System and method for dynamic multi-attribute authentication
ActiveUS8332647B2Reduce workstation signature substitution and/or workstation spoofingFine grained controlDigital data processing detailsUser identity/authority verificationInternet privacyWeb service
In accordance with the teachings of the present invention, a system and method for dynamic, multi-attribute authentication are provided. In a particular embodiment, a method for authentication includes receiving, at an authentication web server, an authentication request comprising a workstation message and a user message, wherein the workstation message comprises a workstation object and a workstation signature, the workstation object comprises a workstation certificate associated with a workstation, the user message comprises a user object and a user signature, and the user object comprises a copy of the workstation message and a user certificate associated with a user of the workstation. The method further includes verifying the workstation signature and user signature, validating the workstation certificate and the user certificate, retrieving one or more caveats associated with the workstation and one or more caveats associated with the user, and determining one or more caveats associated with both the workstation and the user.
Owner:FORCEPOINT FEDERAL
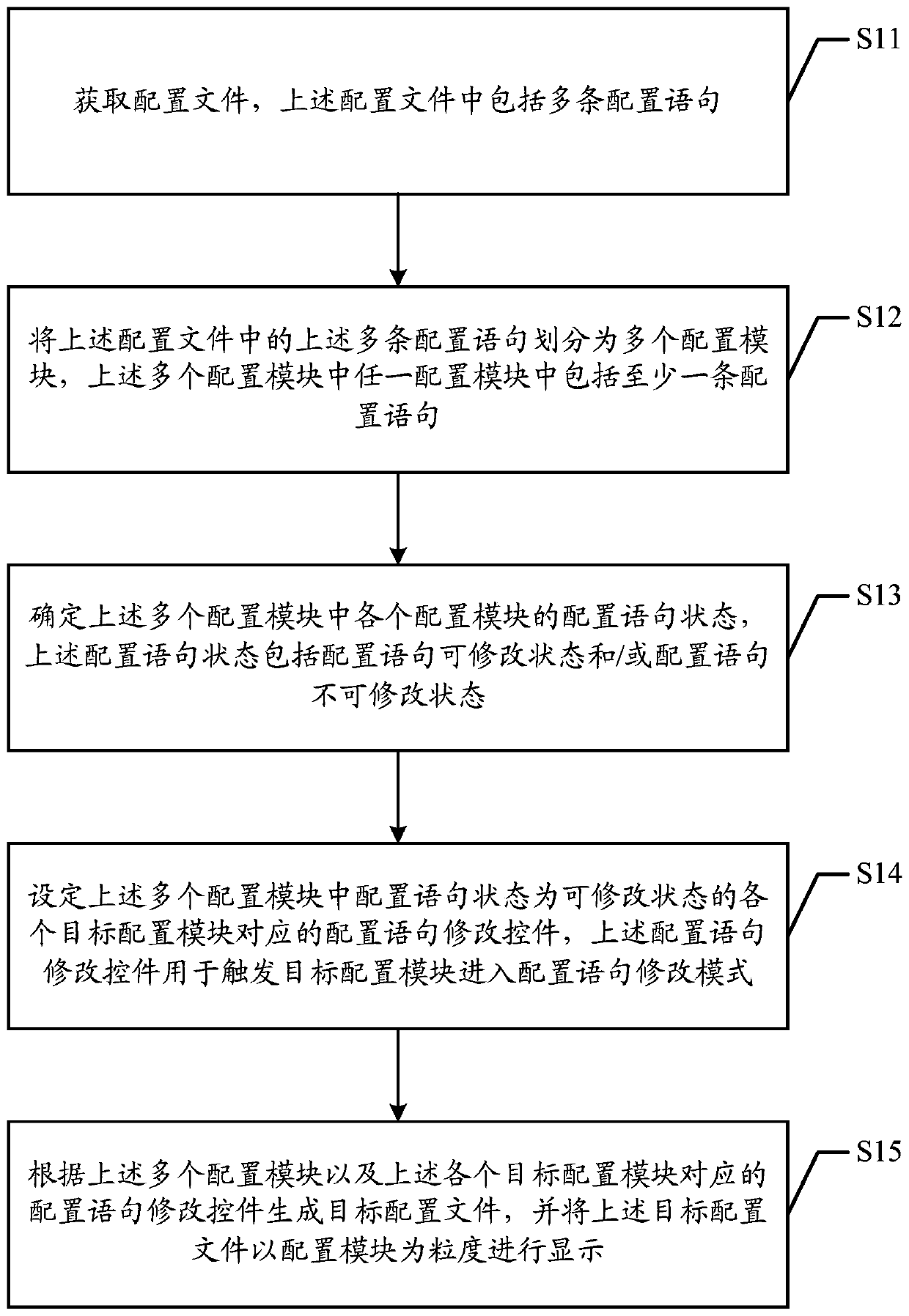
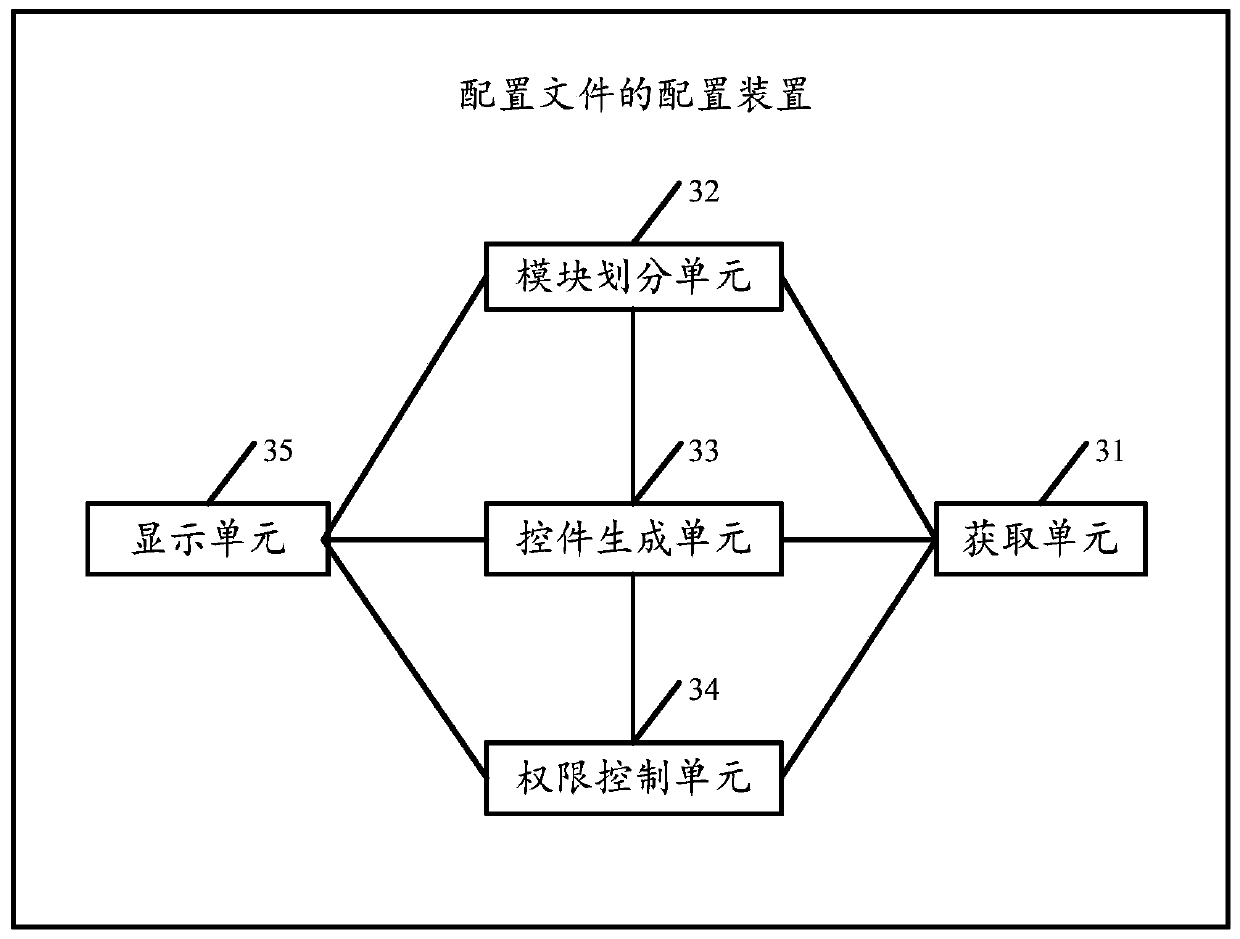
A configuration file configuration method and device
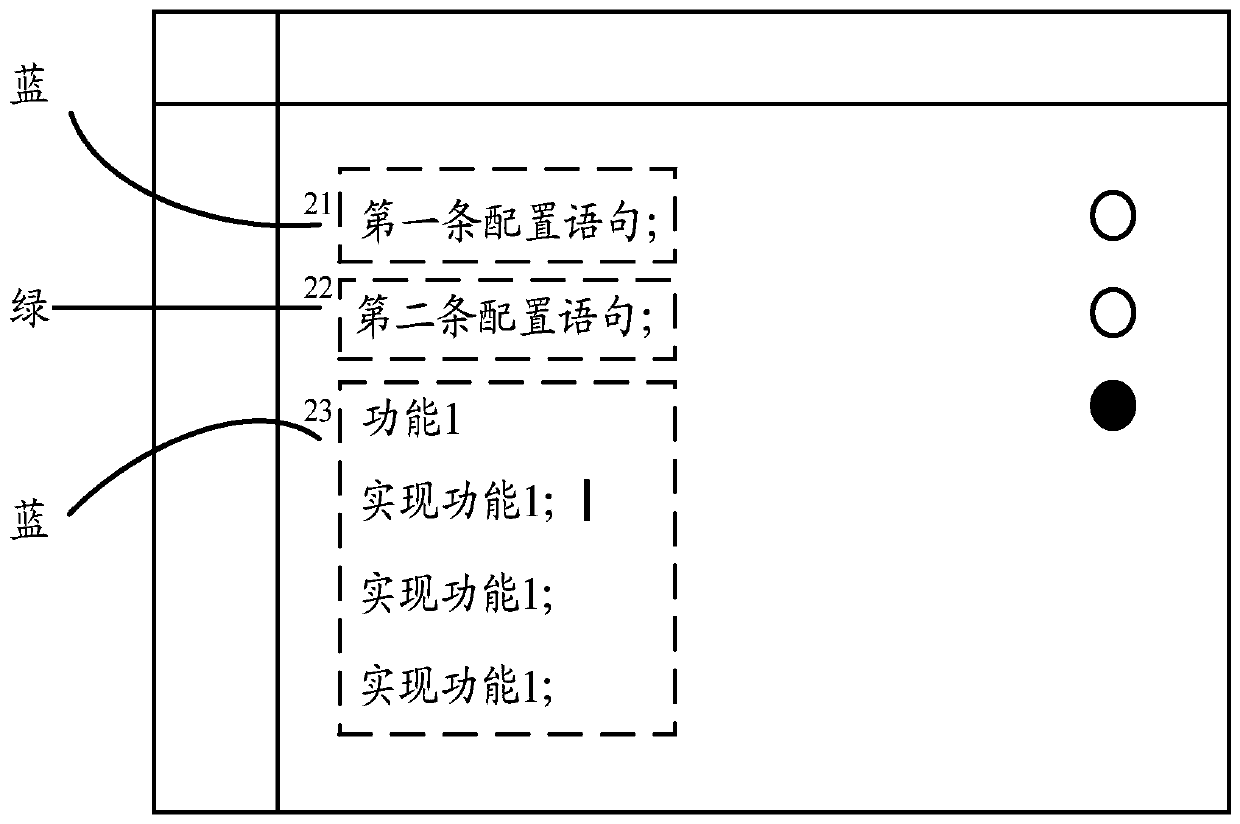
The embodiment of the invention discloses a configuration file configuration method and device suitable for developing an auxiliary tool. The method comprises the steps of obtaining a configuration file which comprises a plurality of configuration statements; dividing a plurality of configuration statements in the configuration file into a plurality of configuration modules; determining a configuration statement state of each configuration module in the plurality of configuration modules, wherein the configuration statement state comprises a configuration statement modifiable state and / or a configuration statement unmodifiable state; setting a configuration statement modification control corresponding to each target configuration module of which the configuration statement state is a modifiable state in the plurality of configuration modules; and modifying the control according to the configuration modules and the configuration statements corresponding to the target configuration modules to generate a target configuration file, and displaying the target configuration file by taking the configuration modules as granularity. By adopting the embodiment of the invention, the configuration flexibility of the configuration file can be enhanced, the configuration accuracy and the configuration efficiency of configuration personnel on the configuration file are improved, and the applicability is stronger.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
A configuration file configuration method and a related device
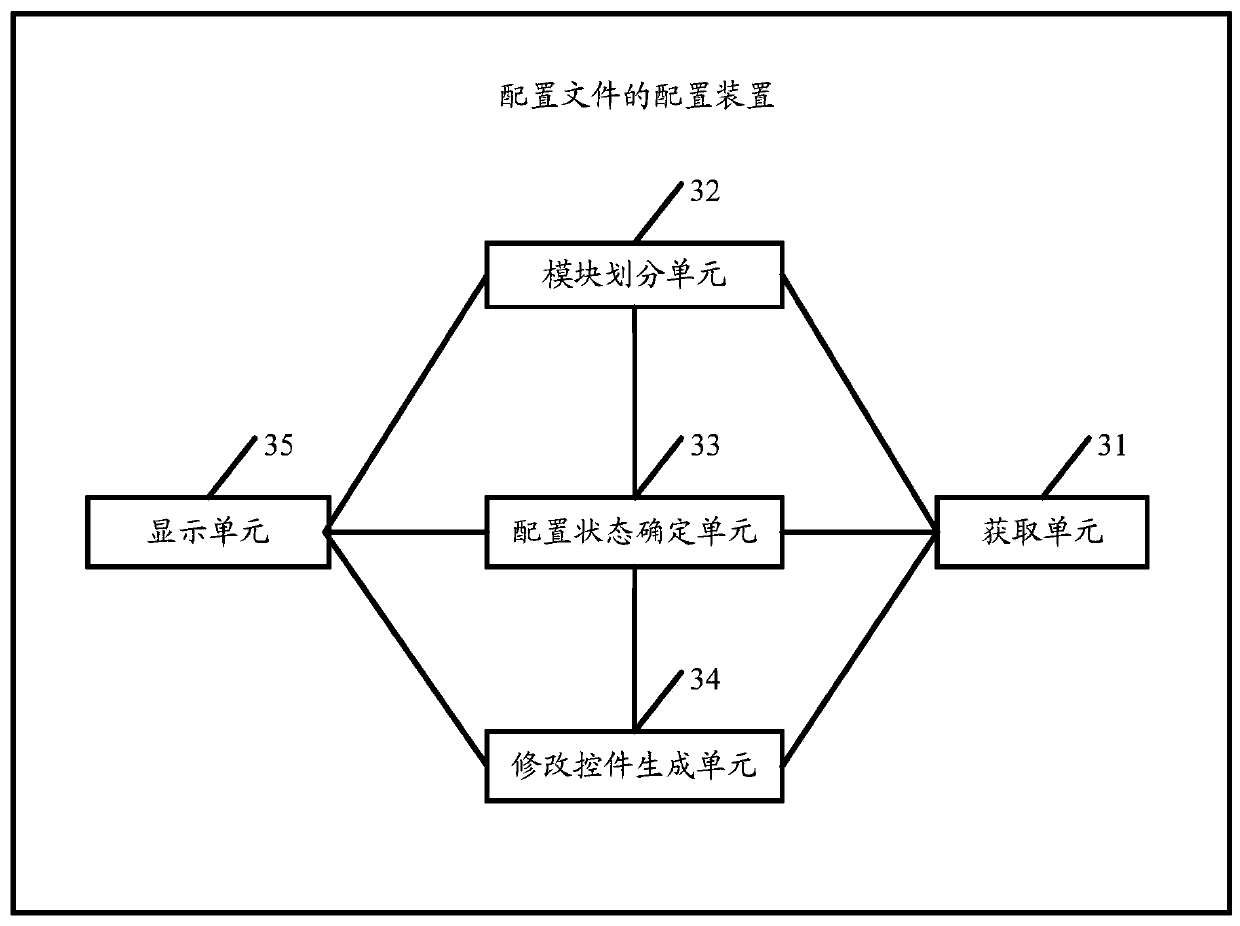
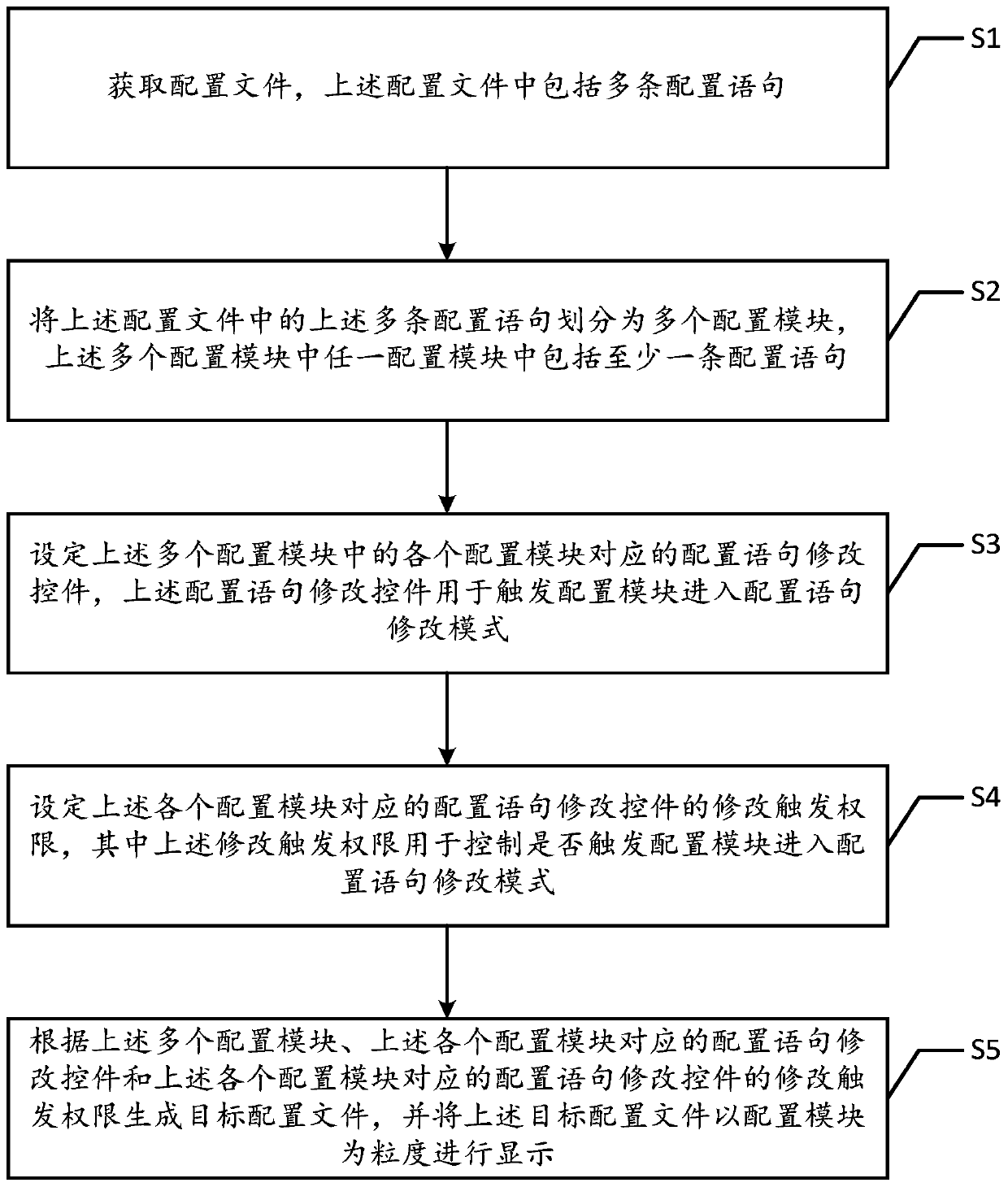
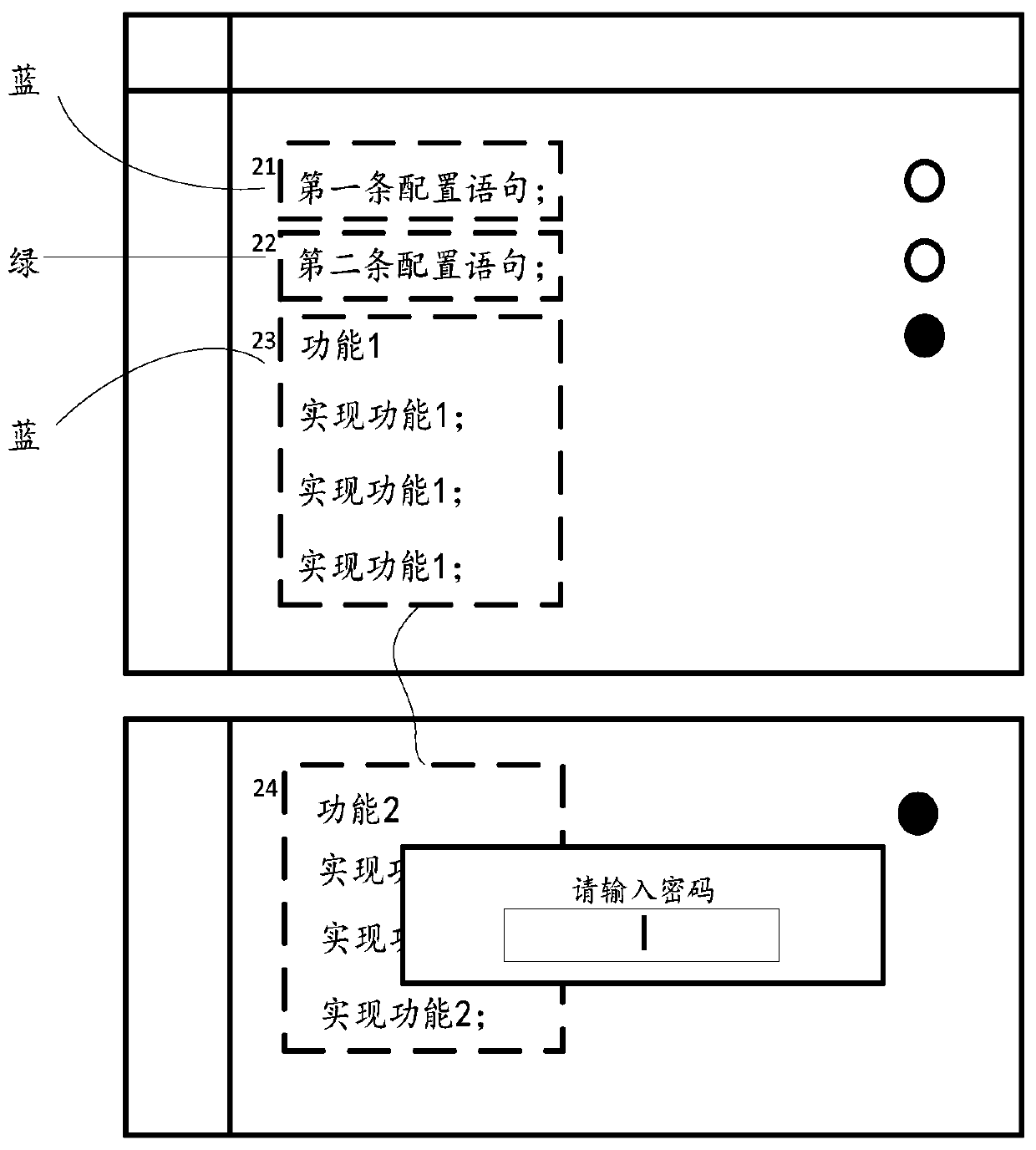
ActiveCN109787957ARapid positioningImprove configuration efficiencyProgram loading/initiatingTransmissionGranularityComputer module
The embodiment of the invention discloses a configuration method and a configuration device of a configuration file, which are suitable for developing an auxiliary tool, and the configuration method comprises the following steps: obtaining the configuration file which comprises a plurality of configuration statements; Dividing a plurality of configuration statements in the configuration file intoa plurality of configuration modules; Setting a configuration statement modification control corresponding to each configuration module in the plurality of configuration modules, wherein the configuration statement modification control is used for triggering the configuration modules to enter a configuration statement modification mode; Setting a modification trigger permission of a configurationstatement modification control corresponding to each configuration module; And generating a target configuration file according to the configuration modules, the configuration statement modification controls corresponding to the configuration modules and the modification trigger authority of the configuration statement modification controls corresponding to the configuration modules, and displaying the target configuration file by taking the configuration modules as granularity. By adopting the embodiment of the invention, the configuration flexibility of the configuration file can be enhanced, meanwhile, the configuration security of the configuration file is enhanced, and the applicability is stronger.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Systems and methods for multi-level tagging of encrypted items for additional security and efficient encrypted item determination
ActiveUS8862870B2Effective judgmentFine grained controlMosaic printer telegraph systemUser identity/authority verificationClient-sideComputer science
The present disclosure is directed towards systems and methods for performing multi-level tagging of encrypted items for additional security and efficient encrypted item determination. A device intercepts a message from a server to a client, parses the message and identifies a cookie. The device processes and encrypts the cookie. The device adds a flag to the cookie indicating the device encrypted the cookie. The device re-inserts the modified cookie into the message and transmits the message. The device intercepts a message from a client and determines whether the cookie in the message was encrypted by the device. If the message was not encrypted by the device, the device transmits the message to its destination. If the message was encrypted by the device, the device removes the flag, decrypts the cookie, removes the tag from the cookie, re-inserts the cookie into the message and transmits the message to its final destination.
Owner:CITRIX SYST INC
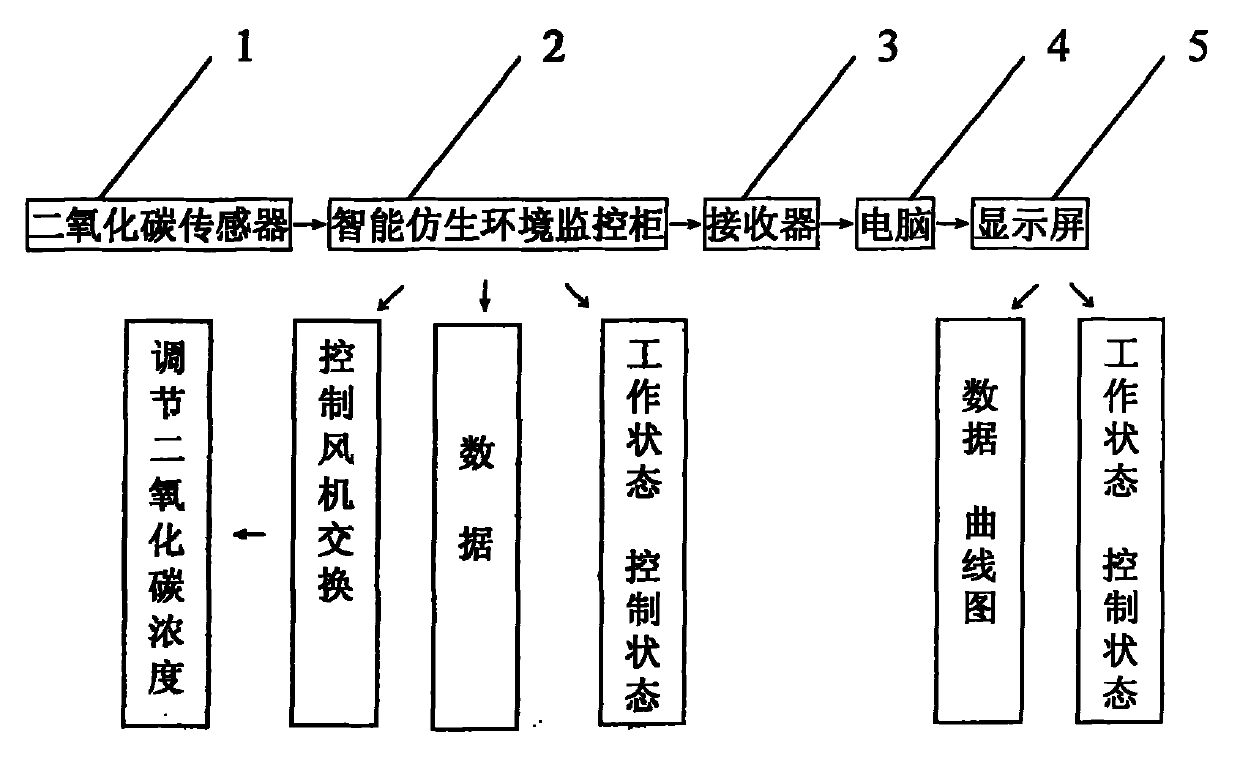
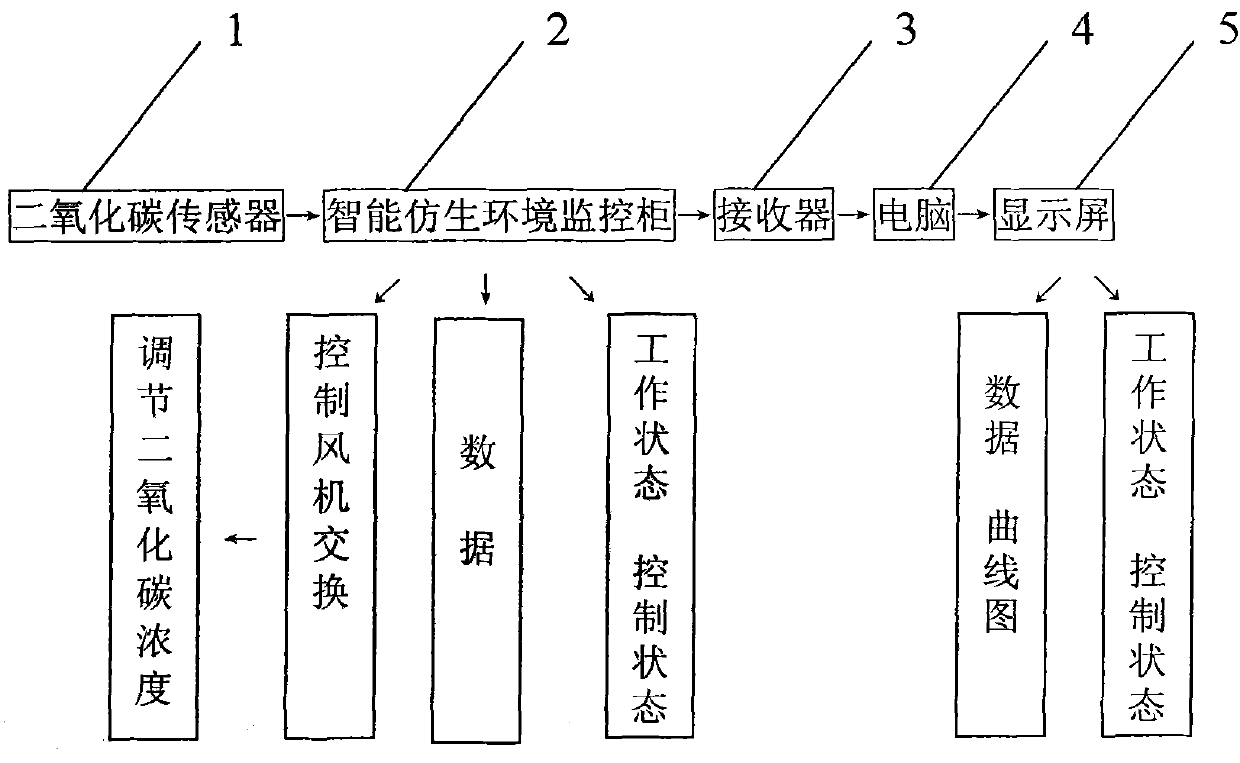
Device for automatically controlling carbon dioxide in factory cultivation of pleurotus eryngii
InactiveCN101950183AIncrease productionImprove qualityControlling ratio of multiple fluid flowsHorticulturePleurotus eryngiiAutomatic control
The invention discloses a device for automatically controlling carbon dioxide in the factory cultivation of pleurotus eryngii, which consists of carbon dioxide sensors, intelligent bionic environment monitoring cabinets, a receiving converter, a computer, a video transmitting device and a liquid display screen, and is characterized in that: a carbon dioxide sensor is arranged in each fruiting room in a cultivation workshop; an intelligent bionic environment monitoring cabinet is arranged outside each fruiting room; the carbon dioxide sensor and the intelligent bionic environment monitoring cabinet are connected to the receiving converter by wires; the receiving converter is connected to a computer, so that the computer can control the device; videos are transmitted to the display screen through a video transmitting device, so that the concentration values of the carbon dioxide and the working states in all fruiting rooms can be seen directly for convenient remote direct observation and control; the whole-process control and management of the fruiting stage can be performed through data observation; the indoor carbon dioxide concentration can be quantized, and control and management is more detailed; and thus, the product yield and quality can be improved.
Owner:李文生
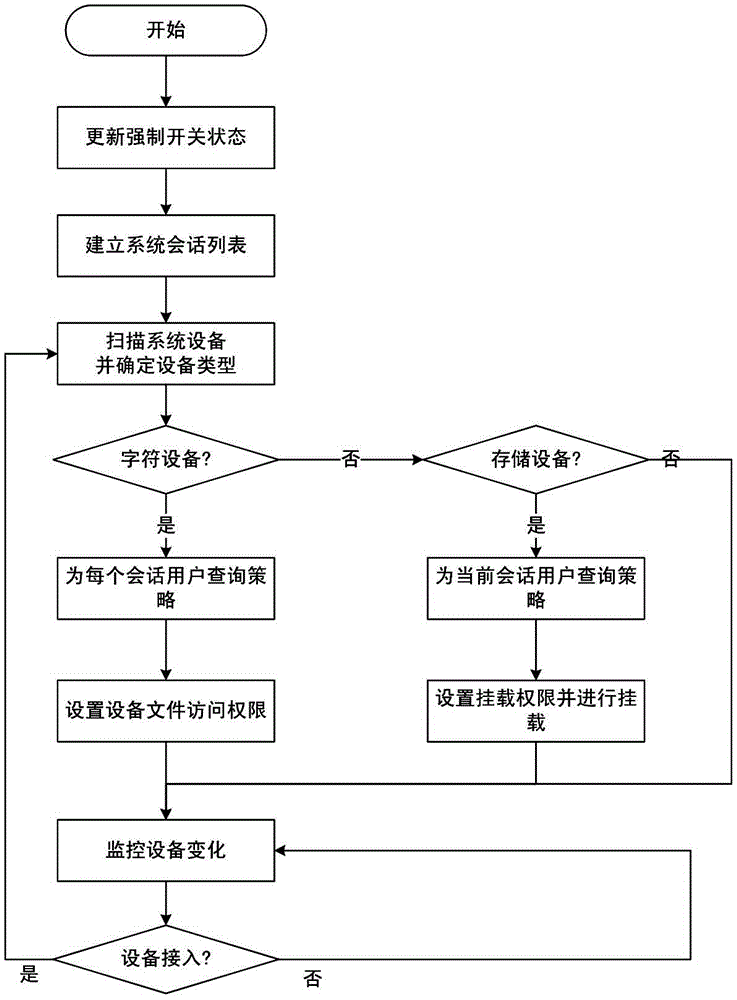
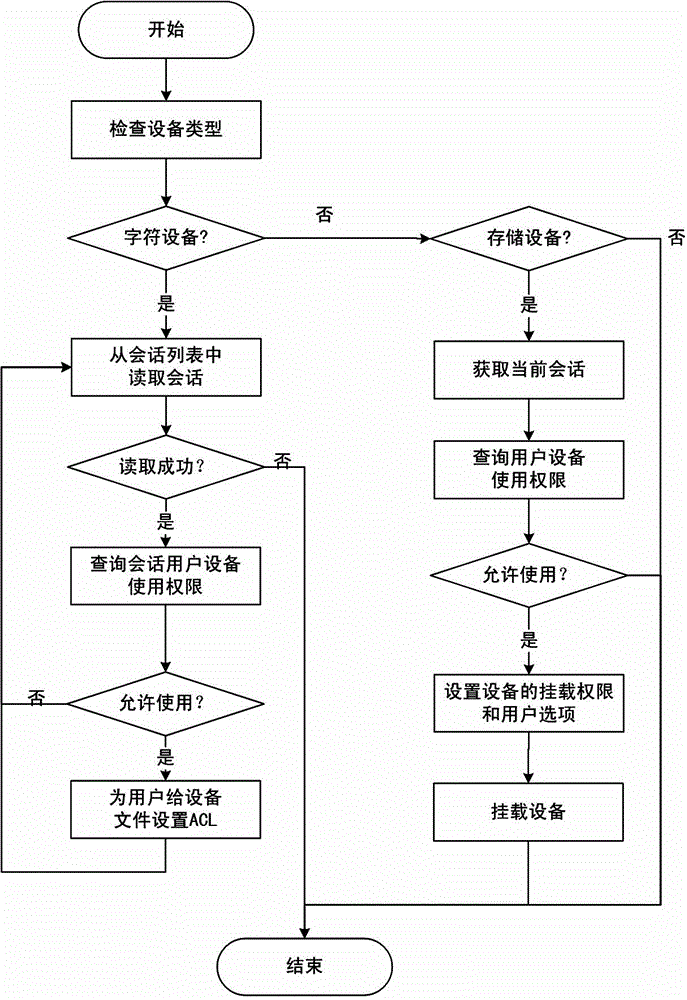
Operating system peripheral access permission control method based on users
ActiveCN104462937AStrong ability to identify peripheralsImprove general performanceDigital data authenticationOperational systemEquipment use
The invention discloses an operating system peripheral access permission control method based on users. The method includes the steps of firstly, building an equipment feature database, classifying the users into different user roles, building equipment application strategies and mandatory access control switches, and respectively building a user access control list, a user group access control list, and a user role access control list; updating the states of all the mandatory access control switches; secondly building and maintaining a system dialogue list; thirdly, monitoring equipment change in an operating system; fourthly, determining final access permission information according to peripheral equipment types, and controlling users' peripheral application in the operating system according to the mandatory access control switches and the final access permission information. The method is high in peripheral identification capability, safe and reliable, good in stability, good in universality, high in expandability, high in malware destroying preventing capability, fine in control granularity, and high in overall flexibility.
Owner:NAT UNIV OF DEFENSE TECH
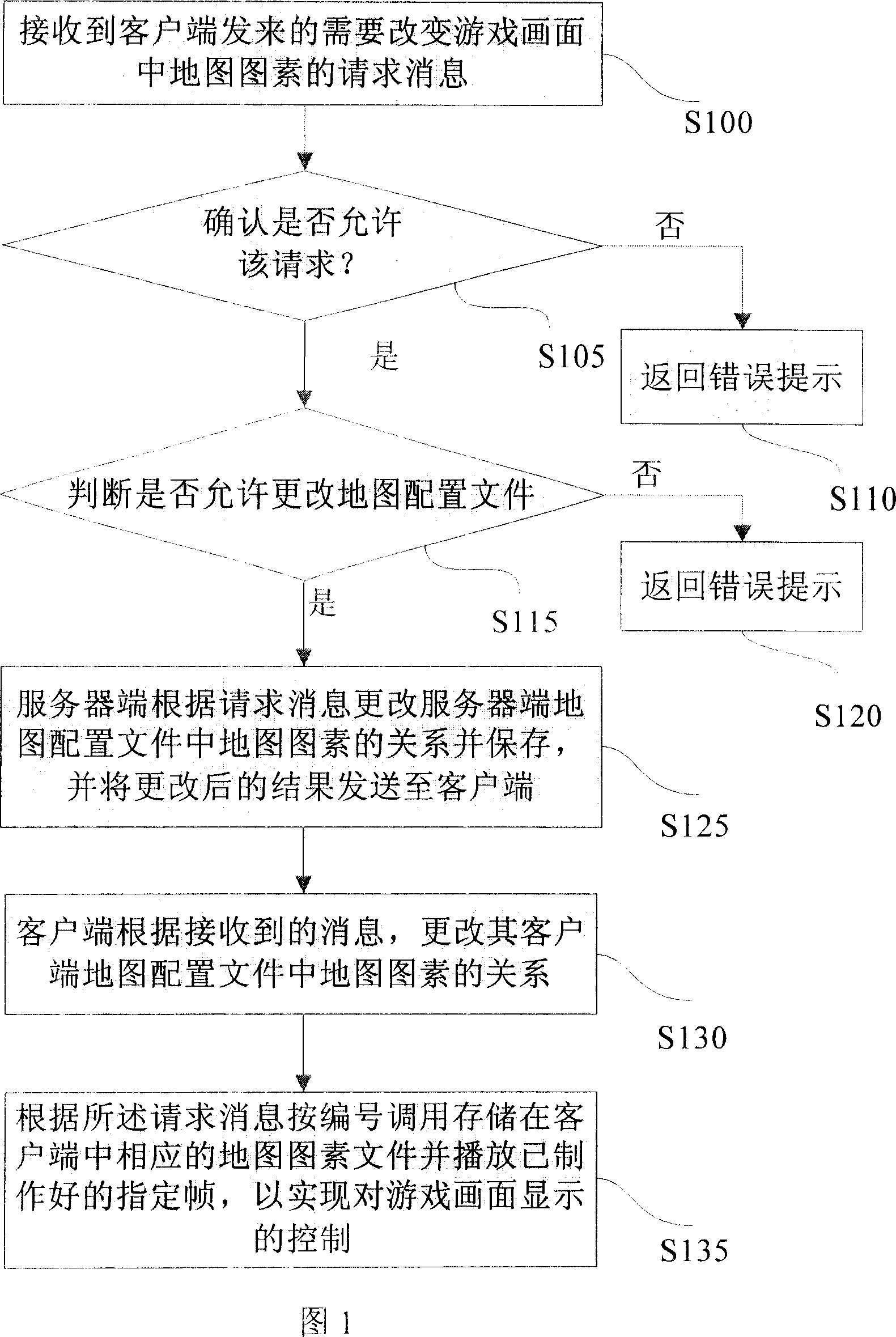
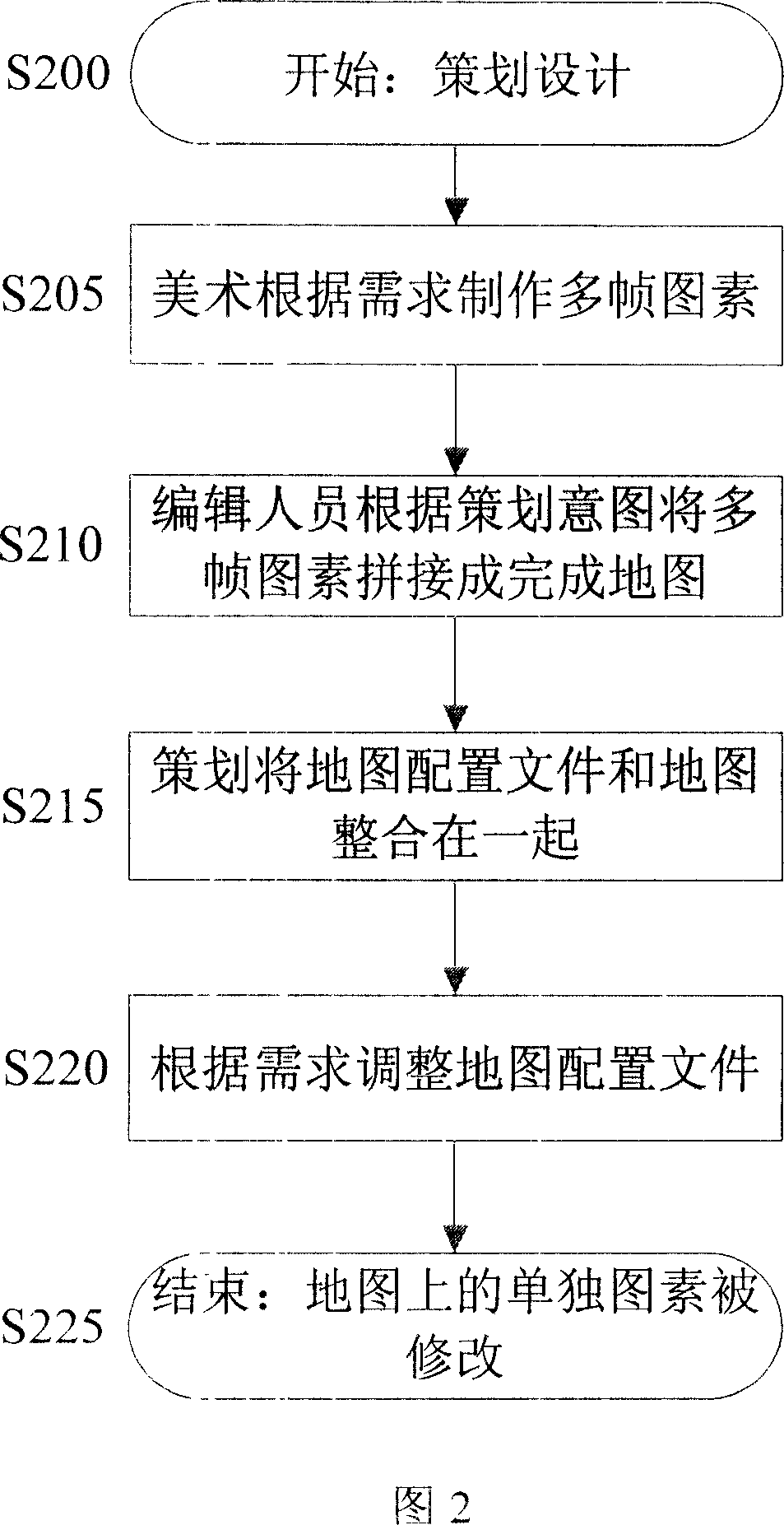
Control method for game picture display and system thereof
ActiveCN101034422AVarietyFine-grained controlVideo gamesSpecial data processing applicationsComputer graphics (images)Computer science
The invention relates to a game picture display control method, comprising the steps of: S1. server end receives a map element change request message; S2. according to the request information, calling map element files to redraw the specified frame of corresponding elements in the corresponding map files and playing the specified frame. And the invention makes the game picture change richer, saving element quantity and fining the control of the follow-up maintenance for the management of the whole map.
Owner:TENCENT TECH CHENGDU
System for and method of protecting an integrated circuit from over currents
InactiveUS8231056B2Electrostatic discharge damageMinimize occurrenceImage analysisDigital data processing detailsControl powerPower switching
A contact detector having power switches for disconnecting power to portions of the contact sensor when an over current is detected is disclosed. The power switches thus protect the contact sensor from over-current as the result of latch-up or other current-generating conditions. These current-generating conditions are often the result of ESD events on a surface of the contact detector. A contact detector comprises an exposed surface for detecting the presence of an object, an insulating surface, and a protection element disposed under the insulating surface for controlling power to the contact detector. The protection element is configured to disconnect power to the contact detector when a current to the contact detector is detected above a threshold. Preferably, the contact detector is a finger swipe sensor, but it can be a finger placement sensor or any other type of device that functions on contact with a finger or other patterned object.
Owner:APPLE INC
Cooling system for hybrid power automobile and control method thereof
ActiveCN101376337BRealize heat dissipationFine-grained controlPropulsion coolingOperation modeCooling fluid
The invention provides a cooling system of a hybrid power automobile, which comprises an air-conditioner with an air-conditioner controller, a radiator of electrical parts with a temperature sensor, an engine radiator, a condensating fan and a cooling fan. The condensating fan and the cooling fan are used for reducing the temperatures at the inlet parts of a condensator and the engine radiator inthe air-conditioner respectively; wherein the cooling system further comprises a cooling controller which is connected with the air-conditioner controller in the air-conditioner, the temperature sensor in the radiator of the electrical part, the cooling fan and the condensating fan respectively; The cooling controller can control the operation of the condensating fan and the cooling fan based on the operation mode of the air-conditioner, which is transmitted from the air-conditioner controller, the temperature value of the cooling liquid in the radiator of the electrical part, which is sensedby the temperature sensor, or the external temperature value which is transmitted by the air-conditioner controller, the temperature value of the cooling liquid in the engine radiator, and the operating condition of the engine. The cooling system can minimize the power consumption on the premise that the requirements for the cooling system are met.
Owner:BYD CO LTD
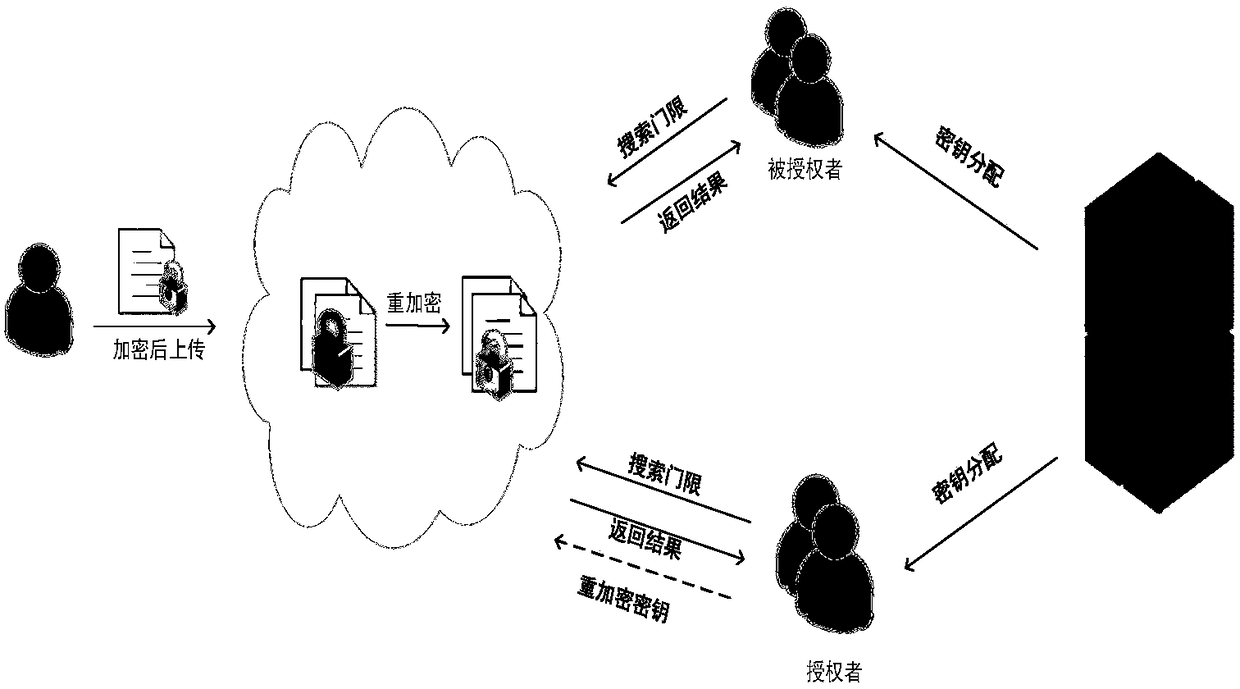
Permission sharing model by medical cloud search
InactiveCN109451077AEnsure safetyEnable controllable searchKey distribution for secure communicationDigital data information retrievalAuthorizationEncryption
A permission sharing model by medical cloud search belongs to the field of searchable encryption, and solves the problem that the search permission cannot be shared. The model includes four entities,namely an authorization center, a cloud server, a data owner and a search user, and the data owner uploads personal medical data and data keywords to the cloud after encryption, thereby separating thesearch and decryption to make the design be more flexible and easy to operate.
Owner:DALIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com