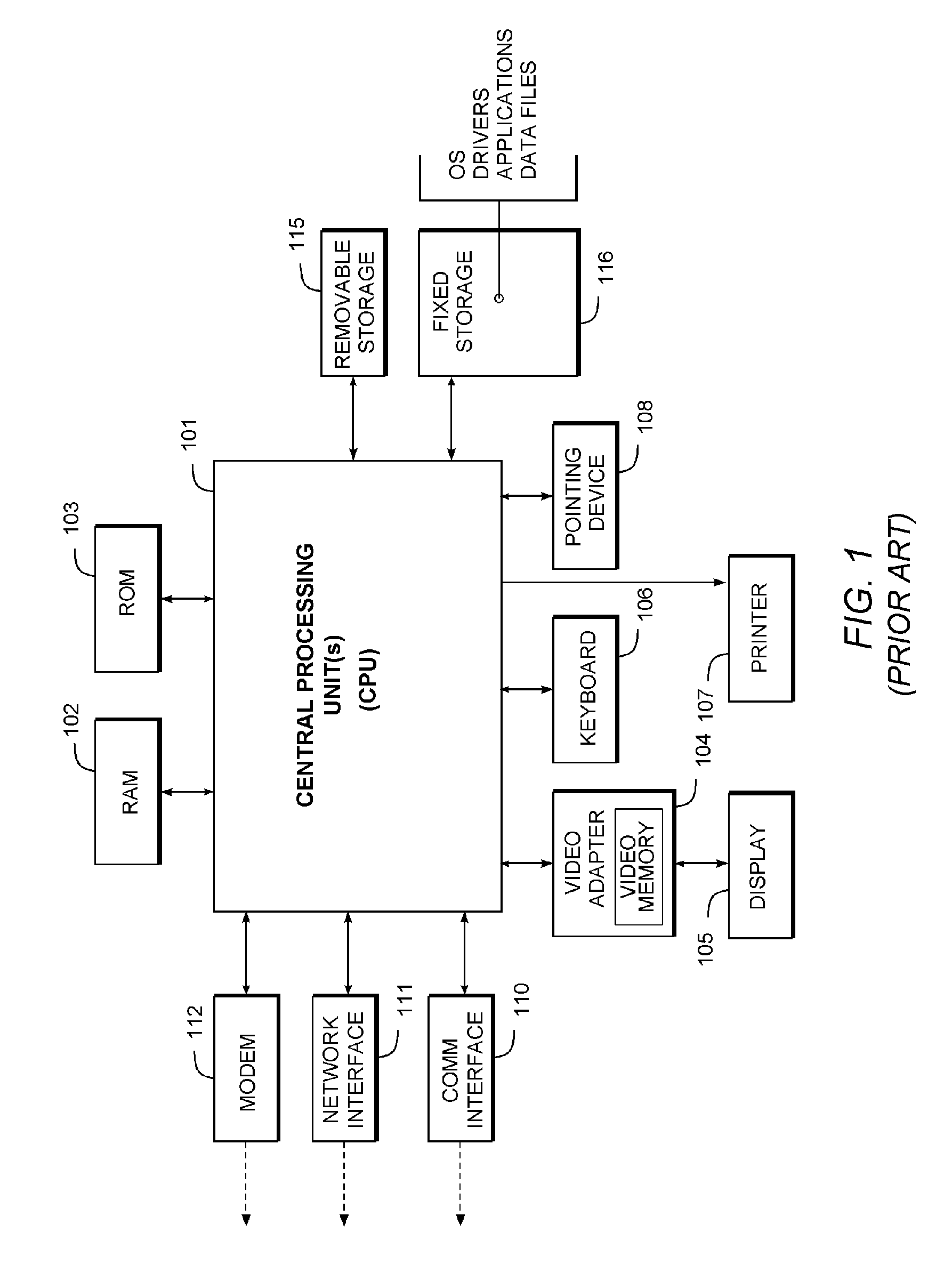
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33164results about "Platform integrity maintainance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
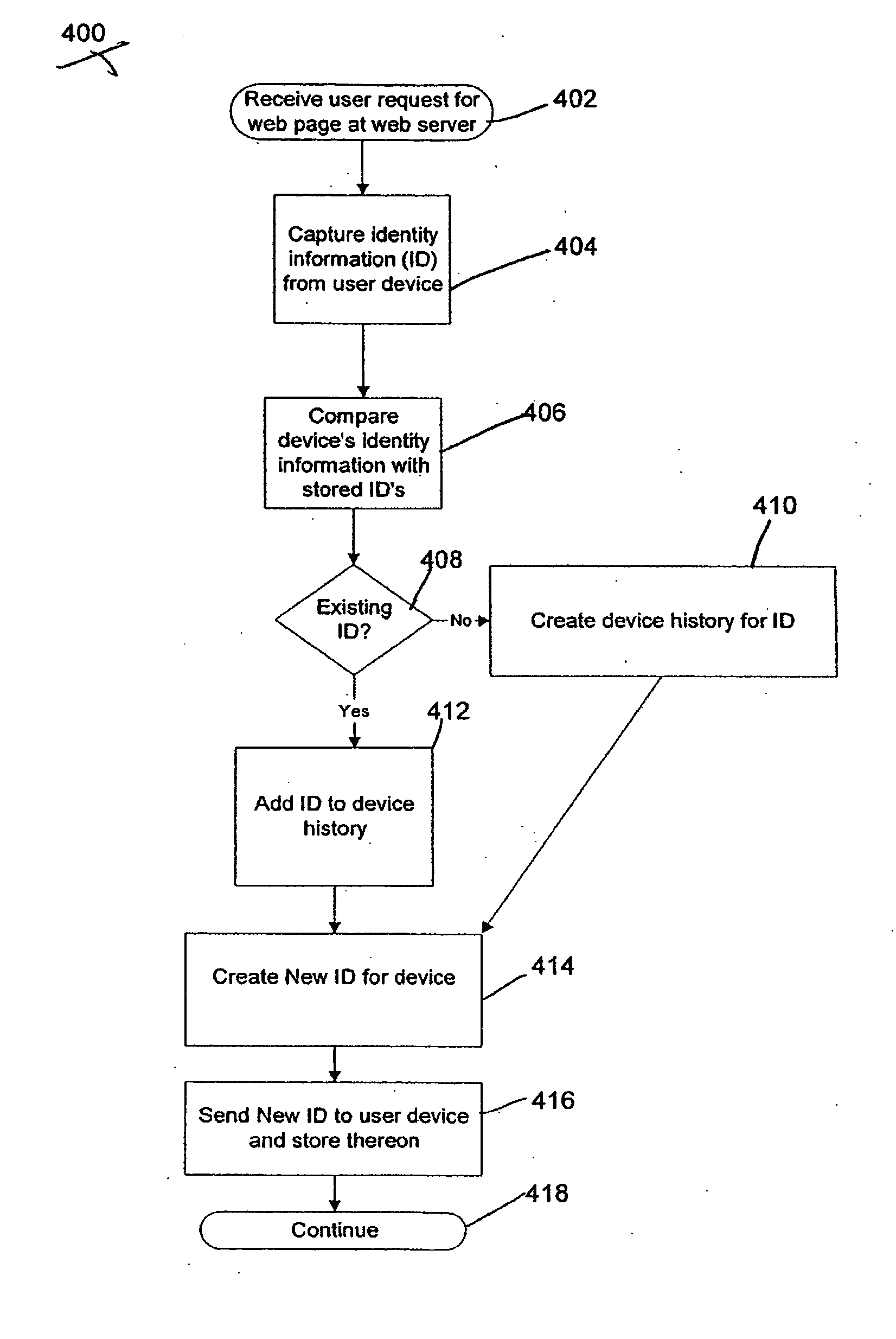
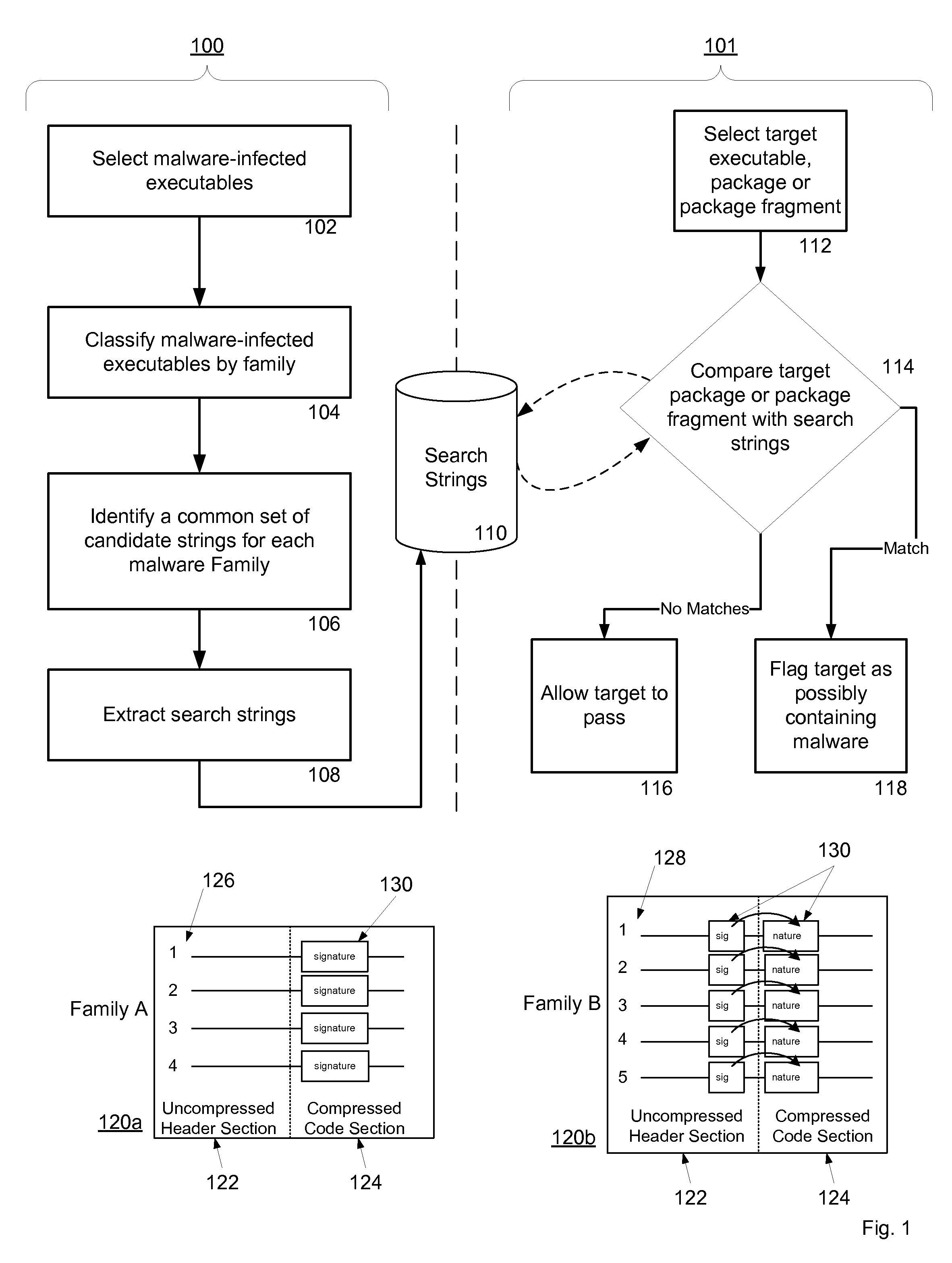
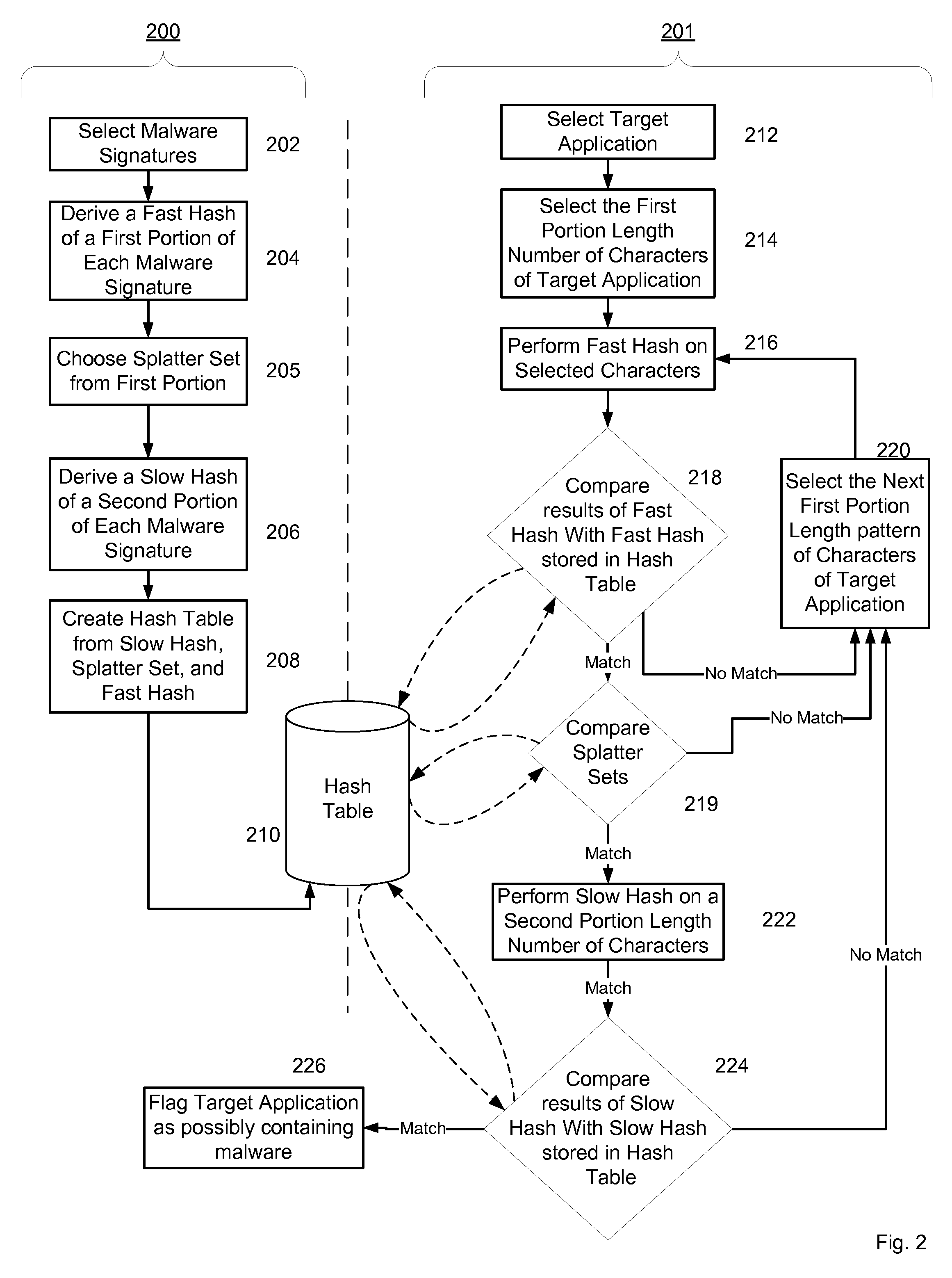
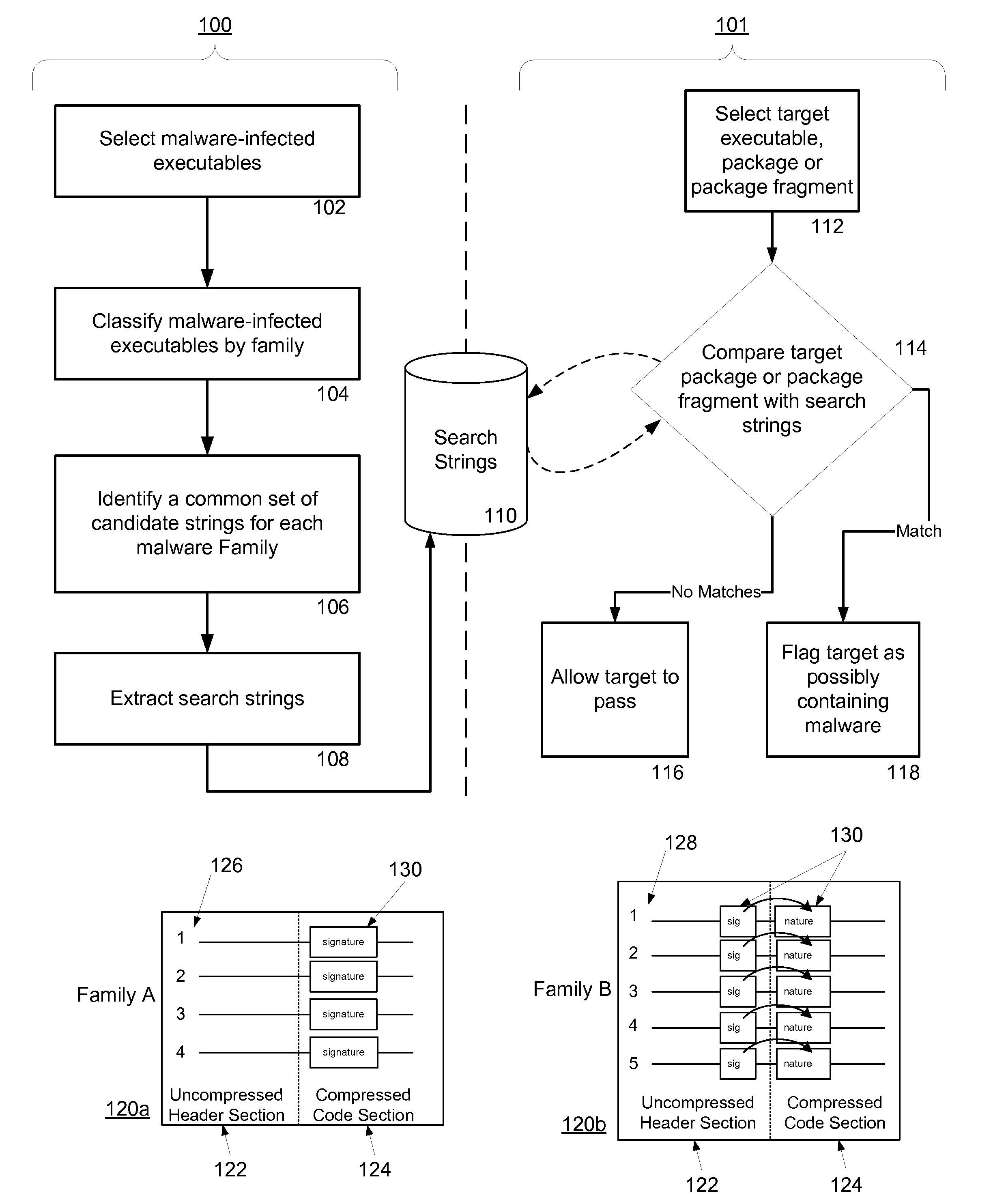
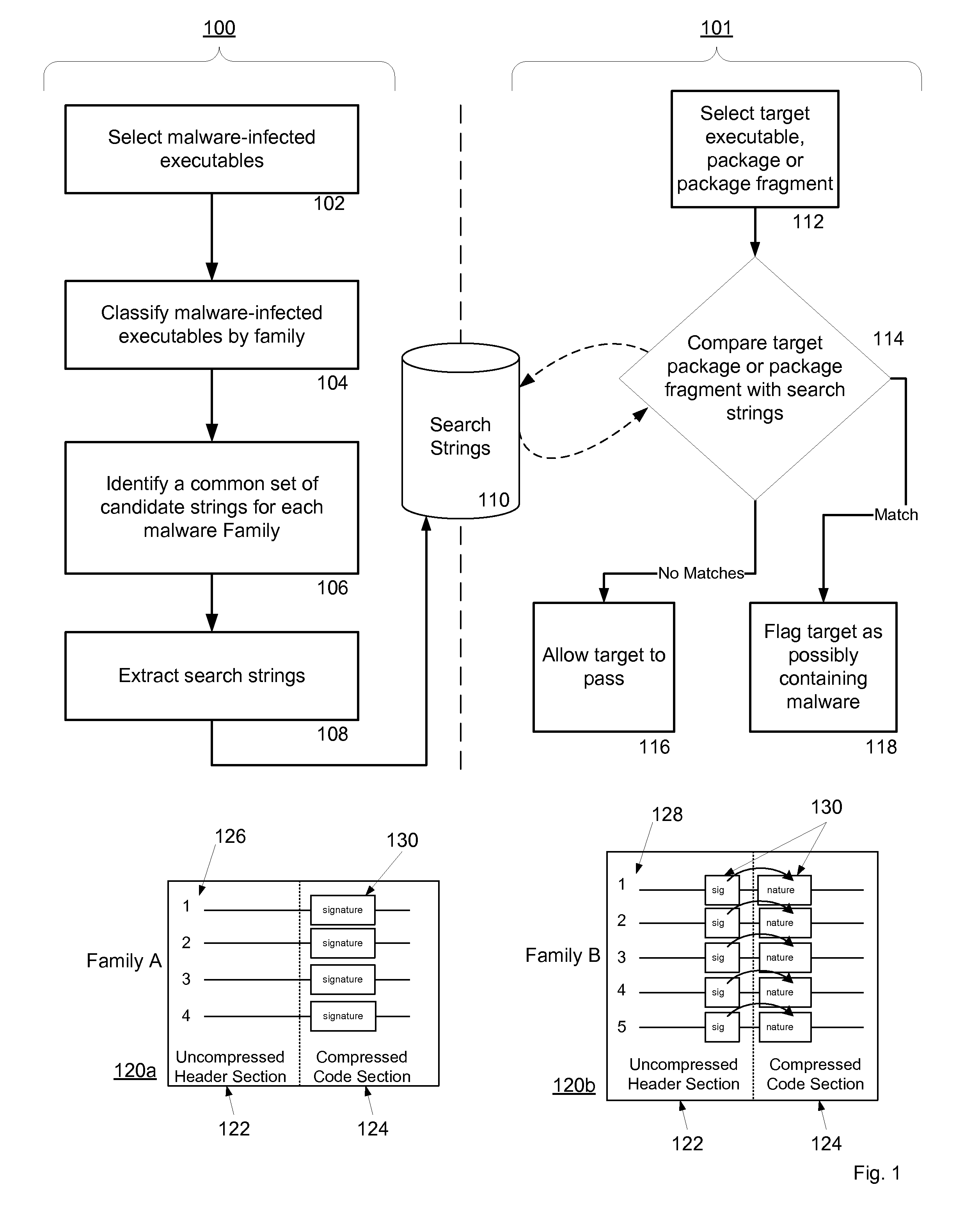
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
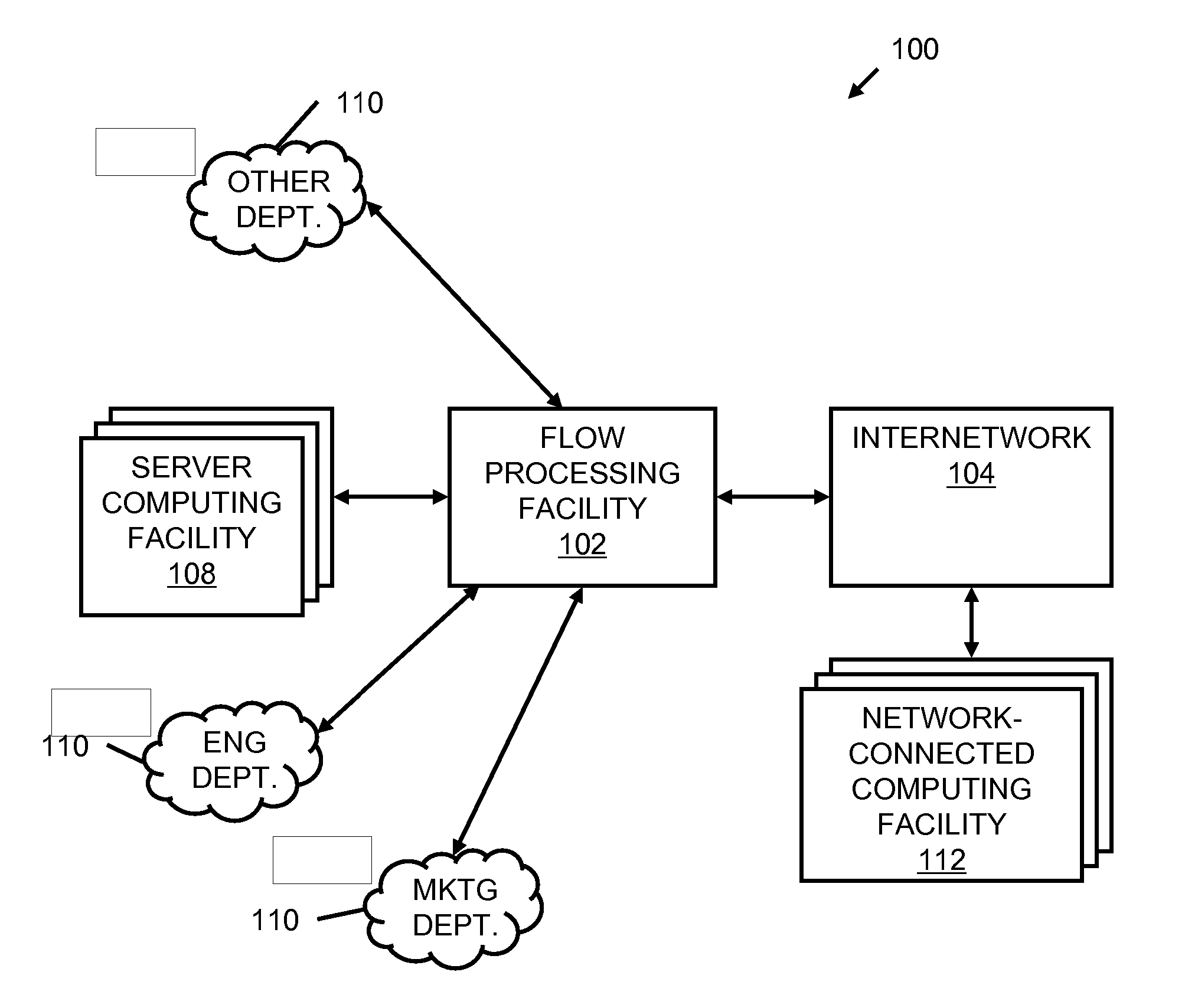
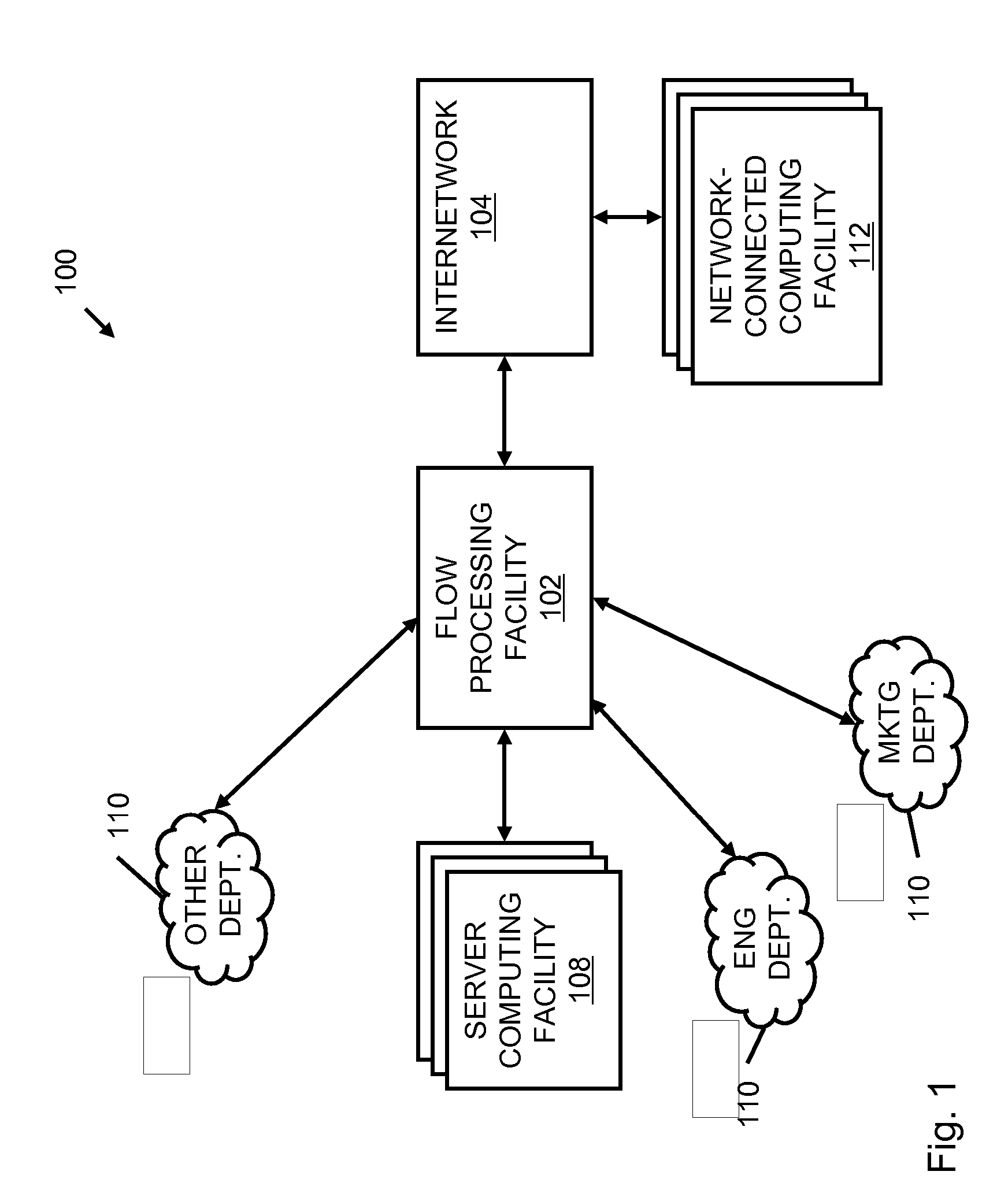
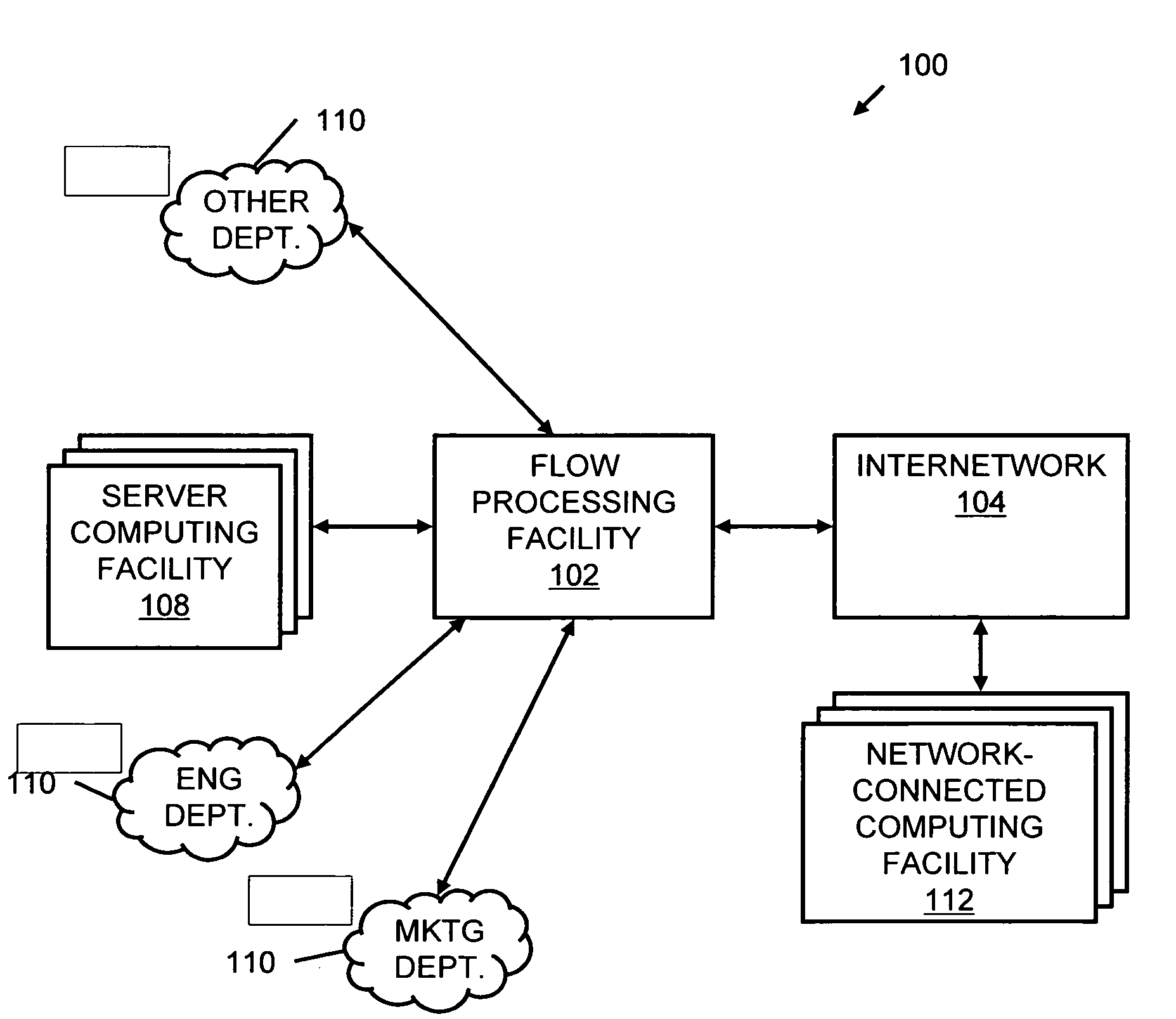
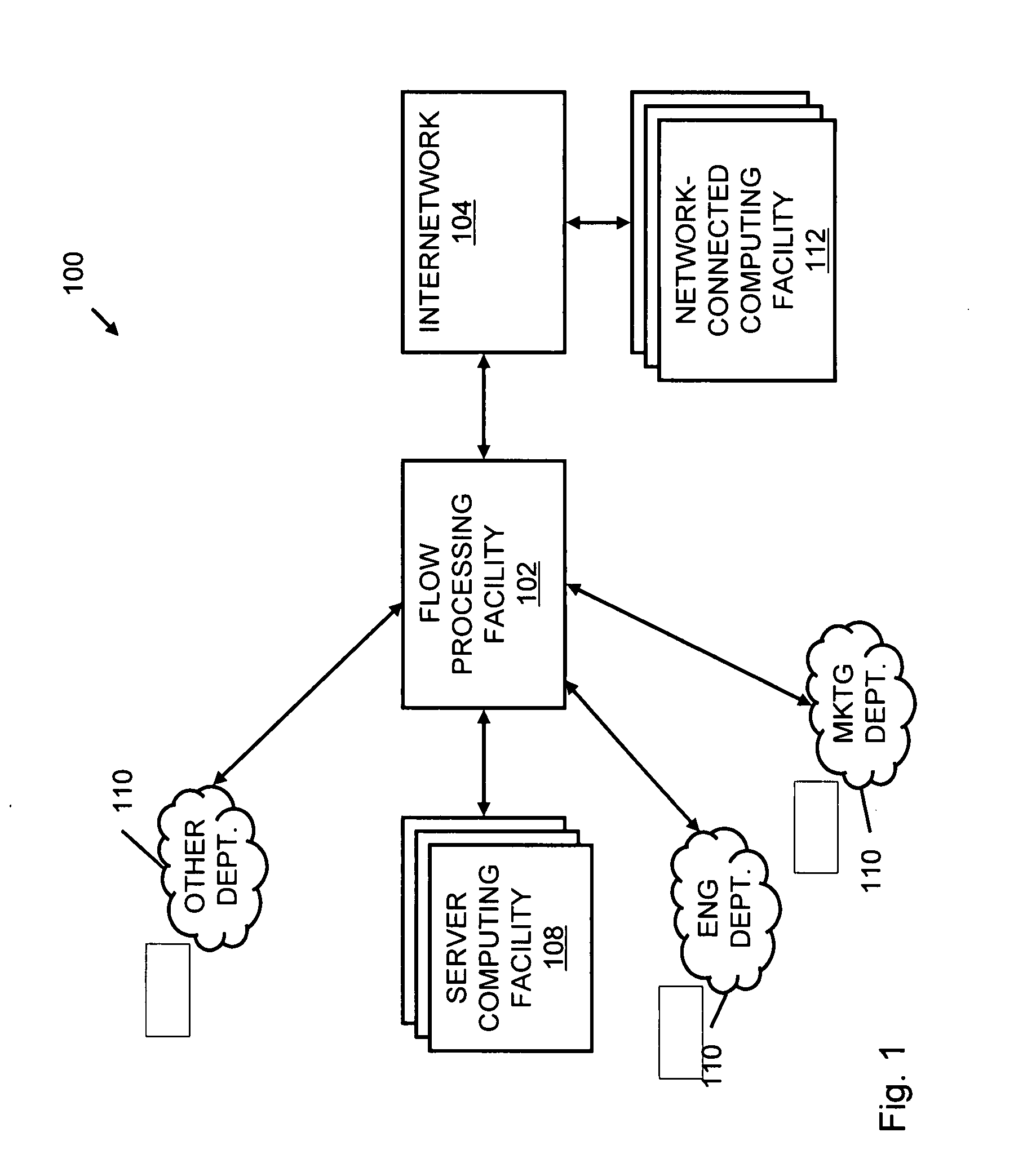
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
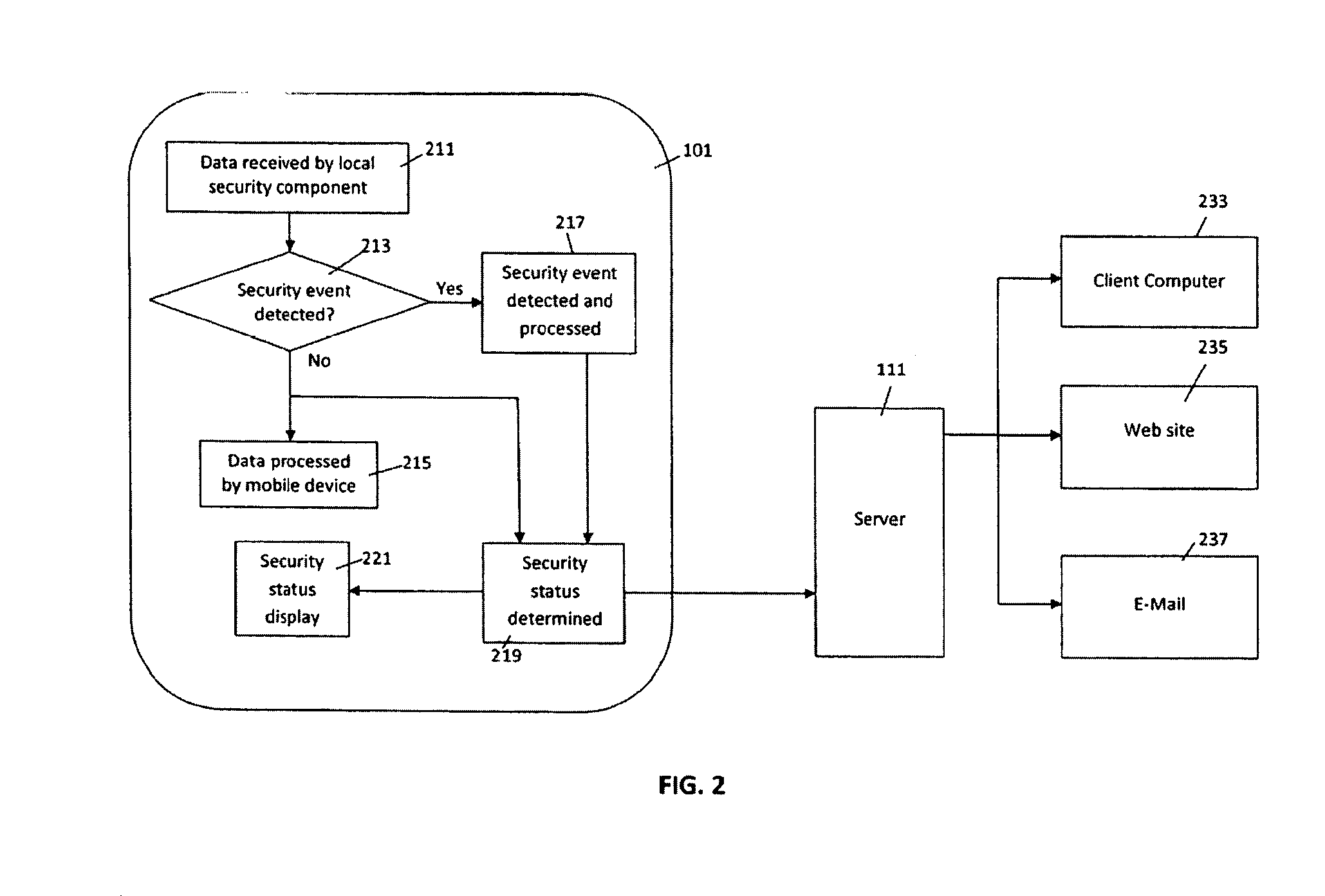
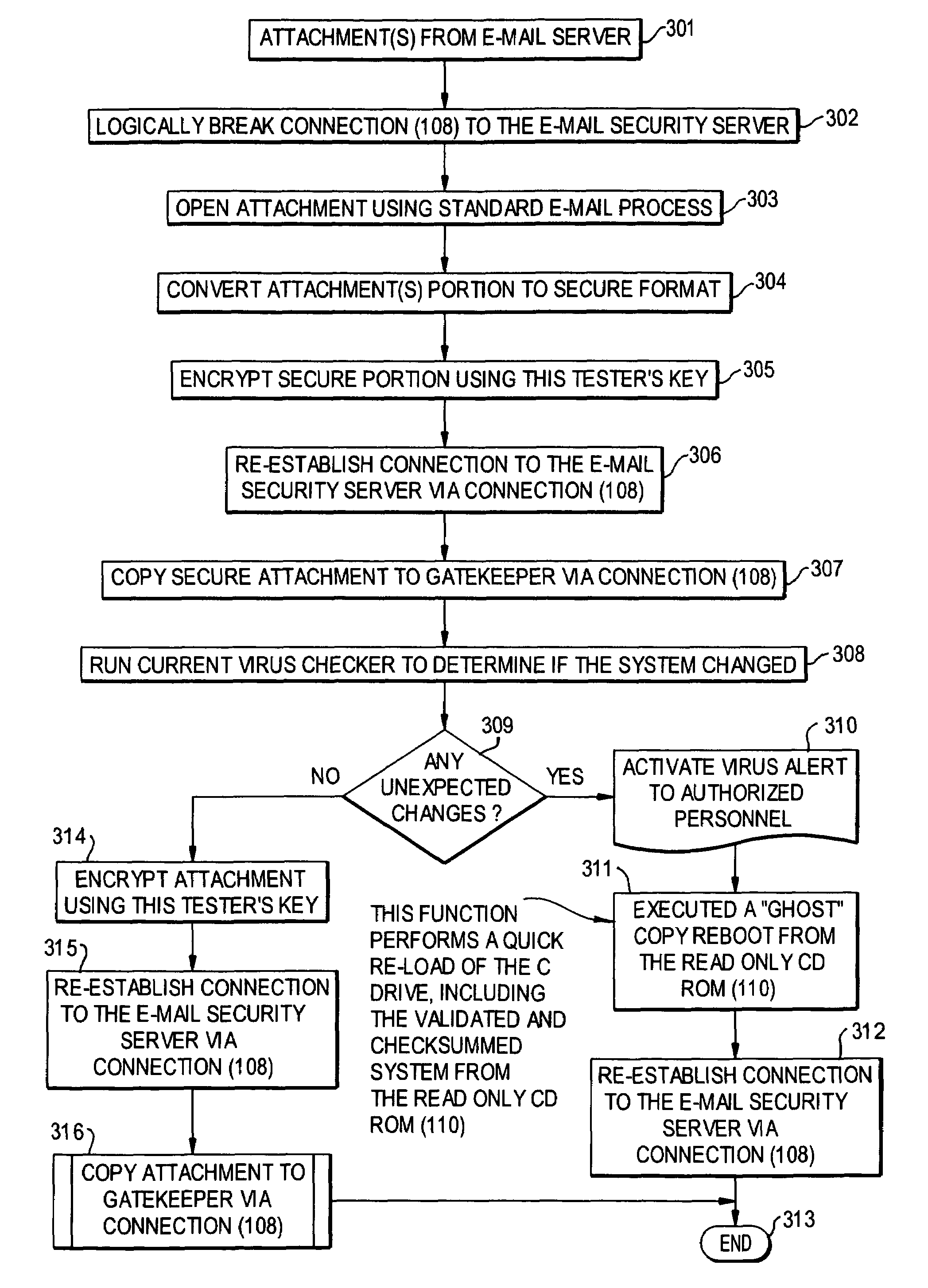
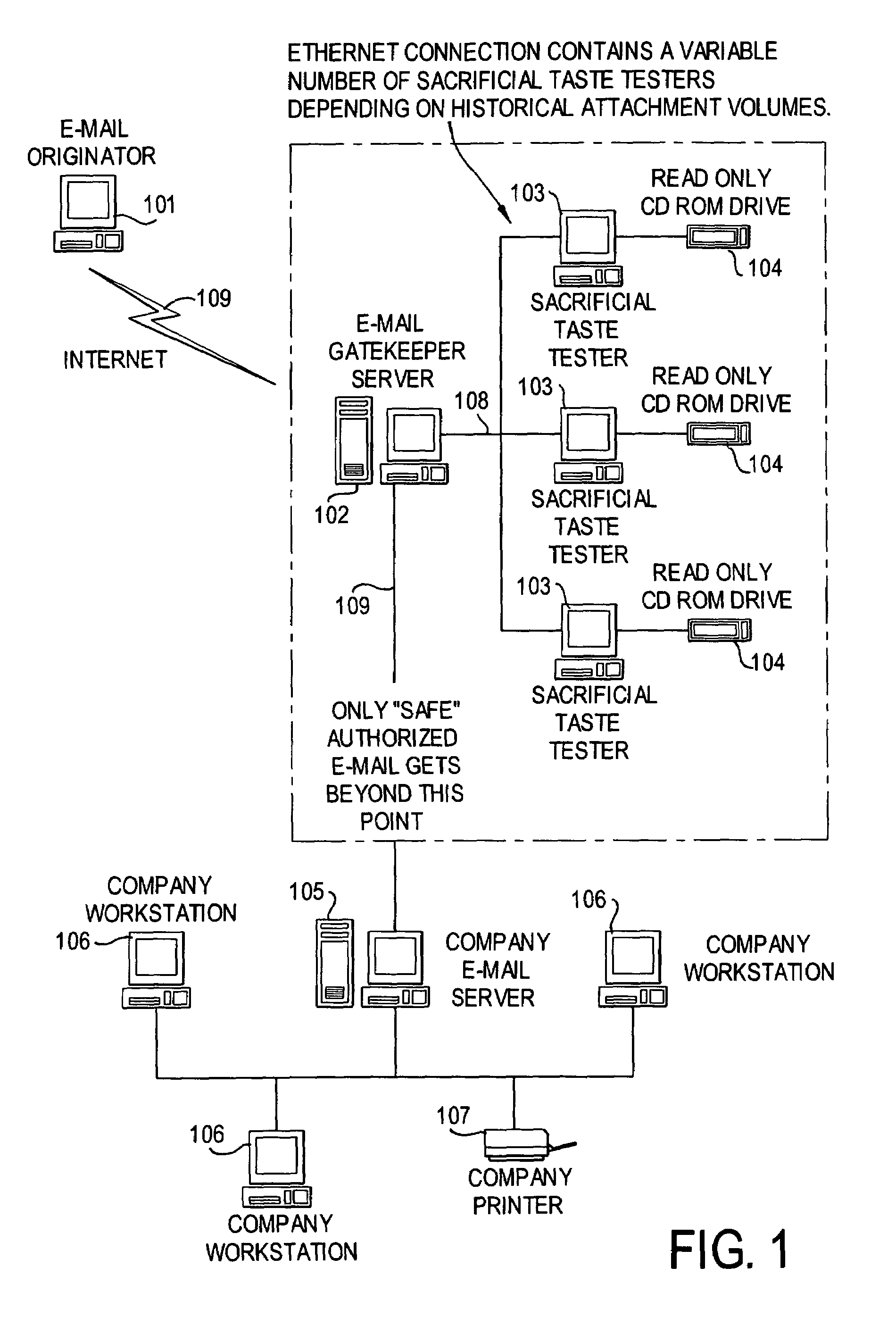
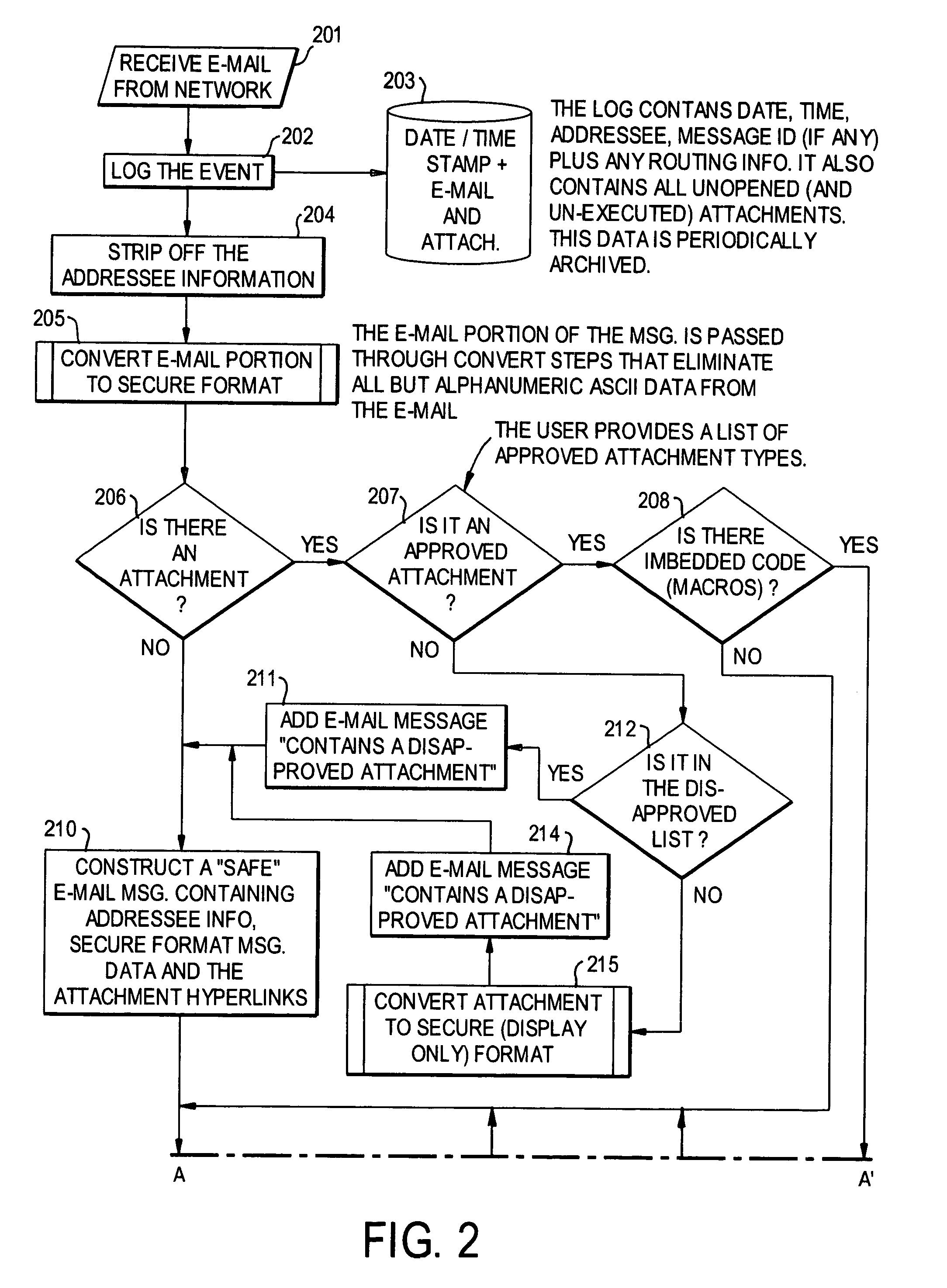
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
Methods and systems for interacting, via a hypermedium page, with a virtual machine executing in a terminal services session
ActiveUS20070171921A1Low costReduce difficultyDigital data information retrievalInterprogram communicationHyperlinkClient agent
A method for making a hypermedium page interactive, the hypermedium page displayed by a network browser, includes the step of selecting a hyperlink on the hypermedium page displayed on a client machine, the hyperlink identifying a desired computing resource. A hyperlink configuration file is retrieved, the hyperlink configuration file corresponding to the hyperlink and identifying a server machine. A client agent is started on the client machine. The client agent creates, via a terminal services session, a communication link to a virtual machine executing on the server identified by the hyperlink configuration file, the virtual machine executed by a hypervisor executing in the terminal services session provided by an operating system executing on the server. The client agent receives data from the virtual machine and displays, on the client machine, the received data without intervention by the network browser.
Owner:CITRIX SYST INC
Distributed trusted virtualization platform
InactiveUS20090204964A1Key distribution for secure communicationMultiple digital computer combinationsVirtualizationEnd to end security
A platform architecture shifts the networked computing paradigm from PC+Network to a system using trusted mobile internet end-point (MIEP) devices and cooperative agents hosted on a trusted server. The MIEP device can participate in data flows, arbitrate authentication, and / or participate in implementing security mechanisms, all within the context of assured end-to-end security. The MIEP architecture improves platform-level capabilities by suitably (and even dynamically) partitioning what is done at the MIEP nodes, the network, and the server based infrastructure for delivering services.
Owner:MOTEGRITY +1
Techniques for fraud monitoring and detection using application fingerprinting
ActiveUS20090089869A1Acutation objectsDigital data processing detailsMultiple contextApplication software
Techniques for fraud monitoring and detection using application fingerprinting. As used herein, an “application fingerprint” is a signature that uniquely identifies data submitted to a software application. In an embodiment, a plurality of historical application fingerprints are stored for data previously submitted to a software application. Each historical application fingerprint is associated with one or more contexts in which its corresponding data was submitted. When new (i.e., additional) data is subsequently submitted to the application, a new application fingerprint is generated based on the new data, and the new application fingerprint is associated with one or more contexts in which the new data was submitted. The new application fingerprint is then compared with one or more historical application fingerprints that share the same, or substantially similar, context(s). Based on this comparison, a risk score is generated indicating a likelihood that the new data was submitted for a fraudulent / malicious purpose.
Owner:ORACLE INT CORP
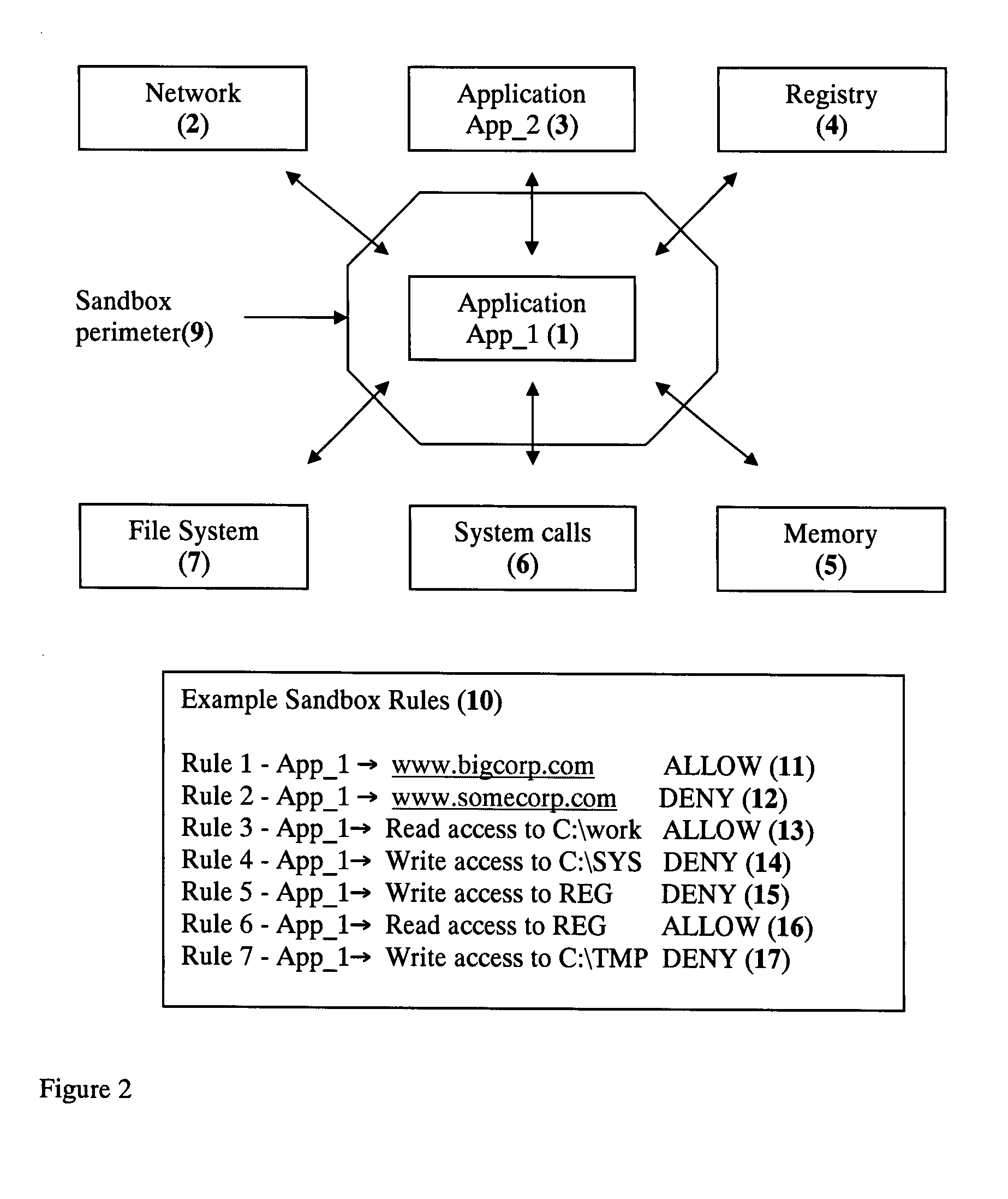
Application Sandbox to Detect, Remove, and Prevent Malware
InactiveUS20080016339A1Limit and eliminate attackRemove or neutralized malware on disk and in memoryPlatform integrity maintainanceSecuring communicationNetwork attackMalware
The disclosed invention is a new method and apparatus for protecting applications from local and network attacks. This method also detects and removes malware and is based on creating a sandbox at application and kernel layer. By monitoring and controlling the behavior and access privileges of the application and only selectively granting access, any attacks that try to take advantage of the application vulnerabilities are thwarted.
Owner:SHUKLA JAYANT
Virtual machine with dynamic data flow analysis
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
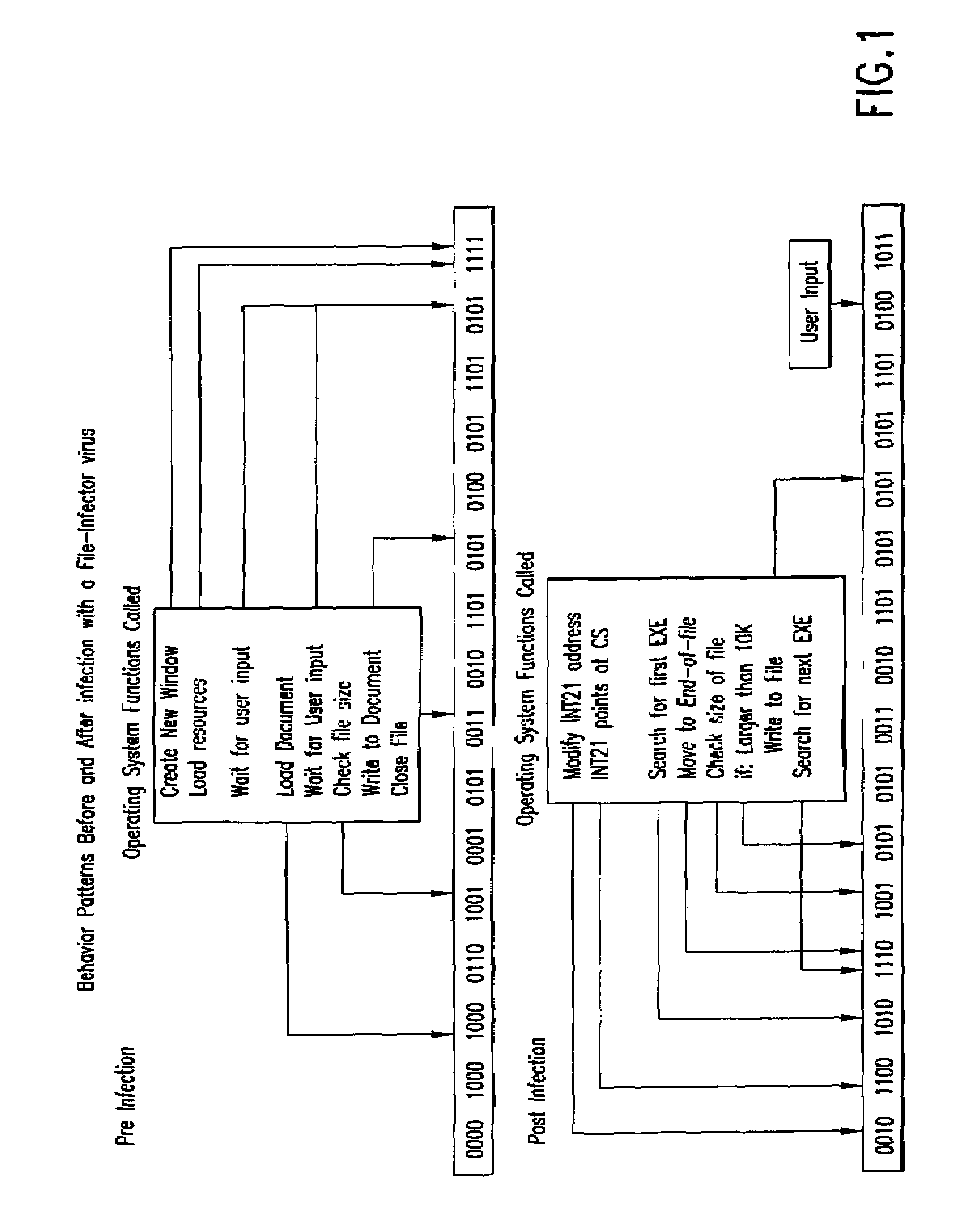
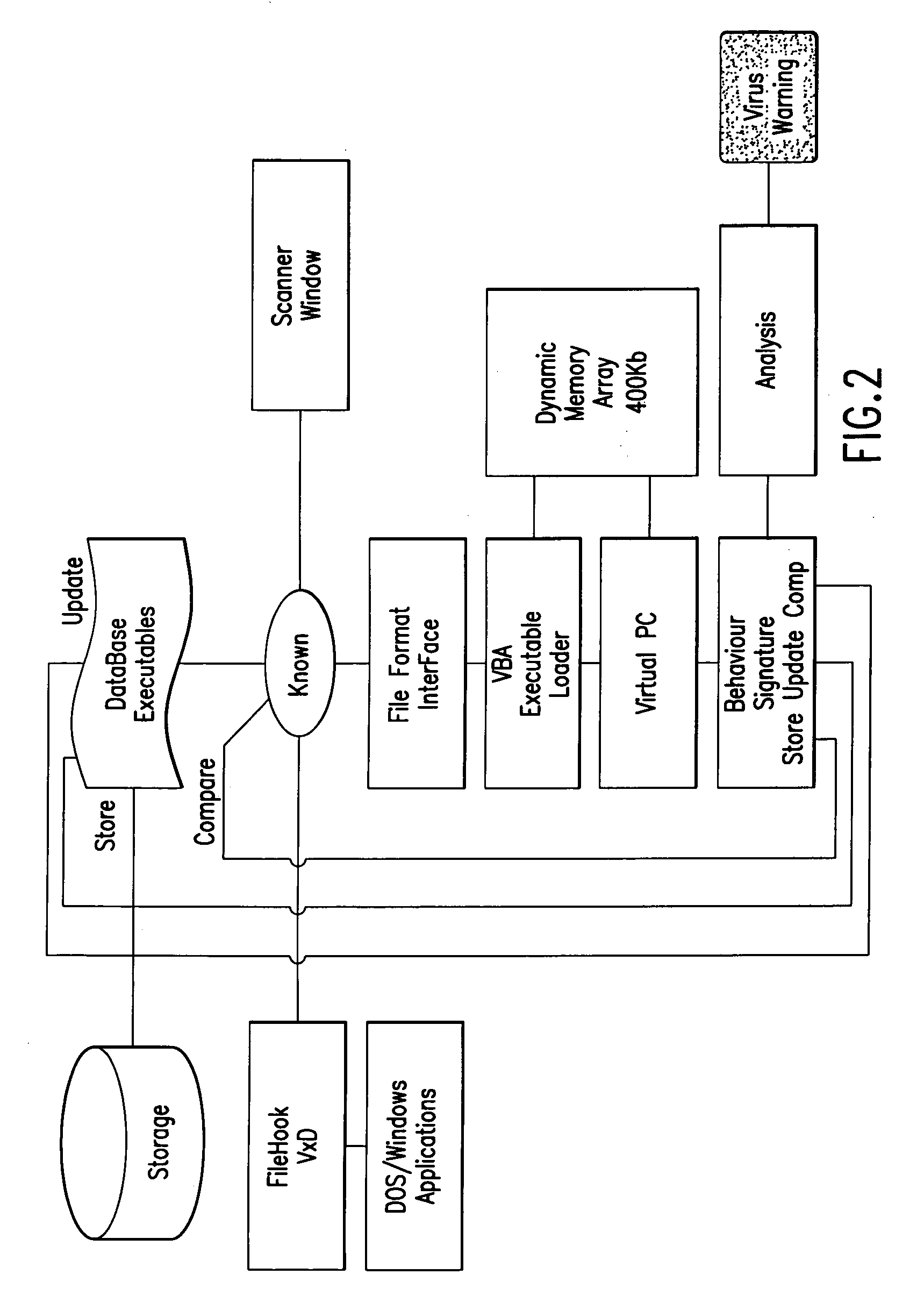
Computer immune system and method for detecting unwanted code in a computer system
InactiveUS7093239B1Memory loss protectionDigital data processing detailsTheoretical computer scienceComputerized system
An automated analysis system detects malicious code within a computer system by generating and subsequently analyzing a behavior pattern for each computer program introduced to the computer system. Generation of the behavior pattern is accomplished by a virtual machine invoked within the computer system. An initial analysis may be performed on the behavior pattern to identify infected programs on initial presentation of the program to the computer system. The analysis system also stores behavior patterns and sequences with their corresponding analysis results in a database. Newly infected programs can be detected by analyzing a newly generated behavior pattern for the program with reference to a stored behavior pattern to identify presence of an infection or payload pattern.
Owner:PALO ALTO NETWORKS INC
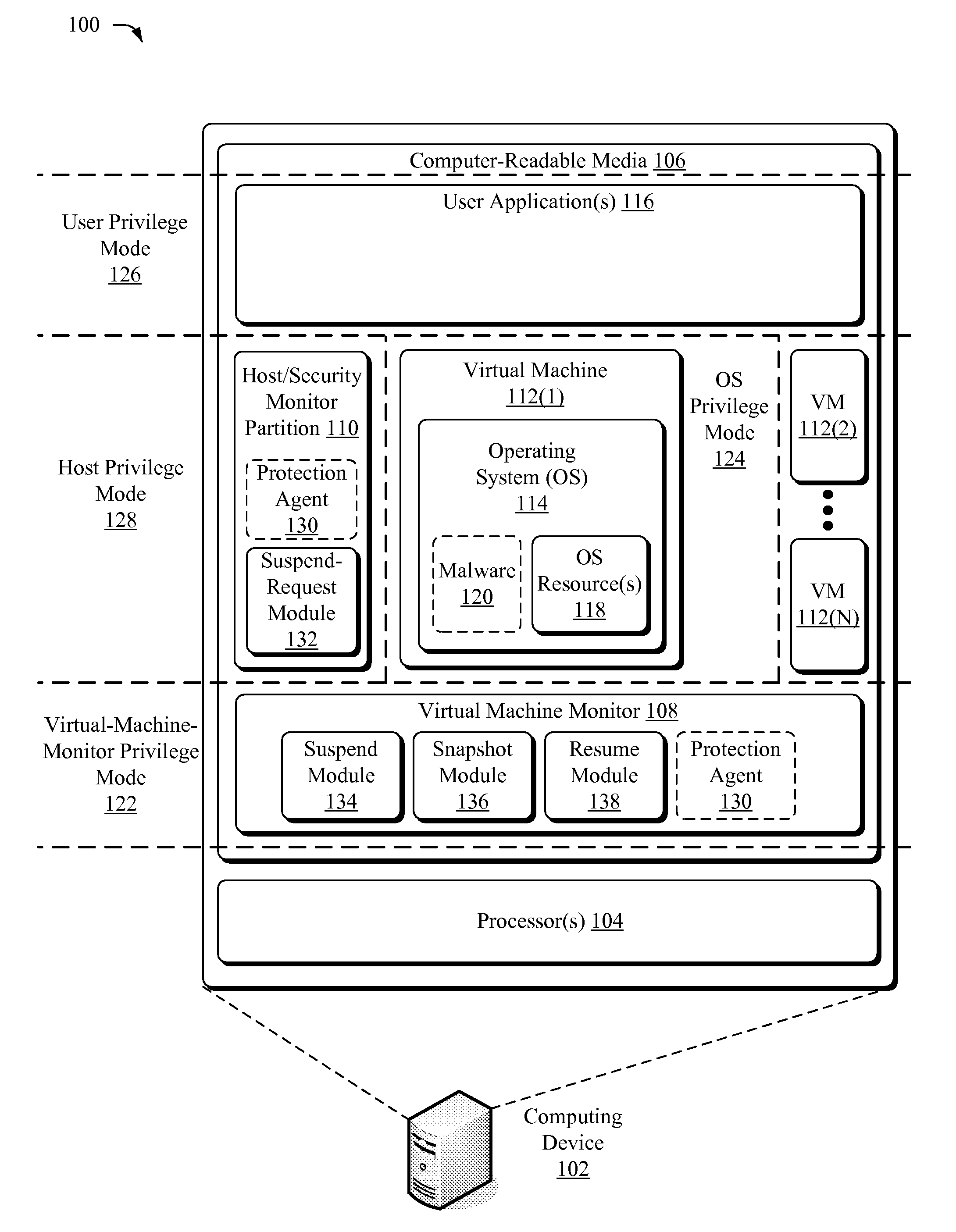
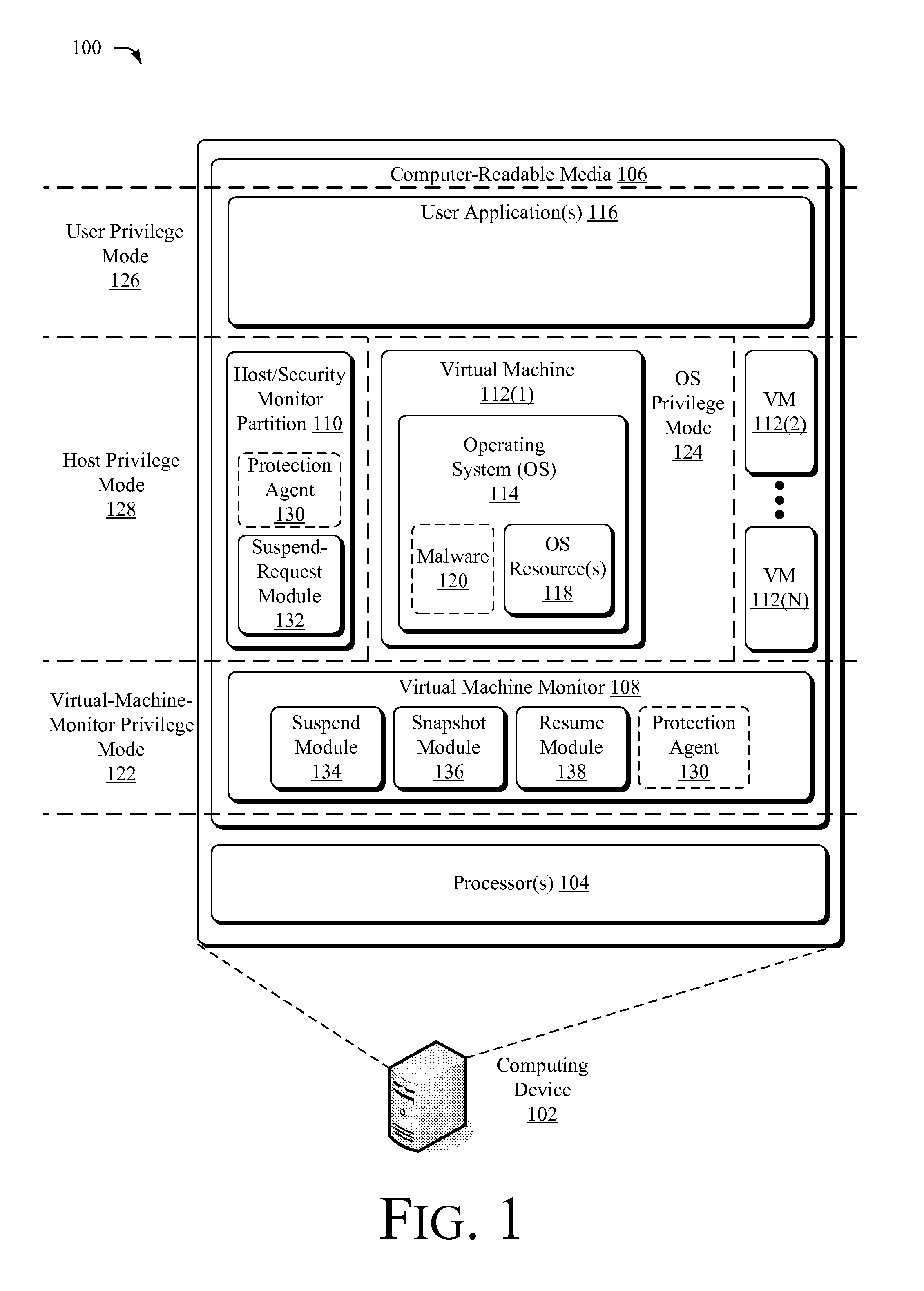
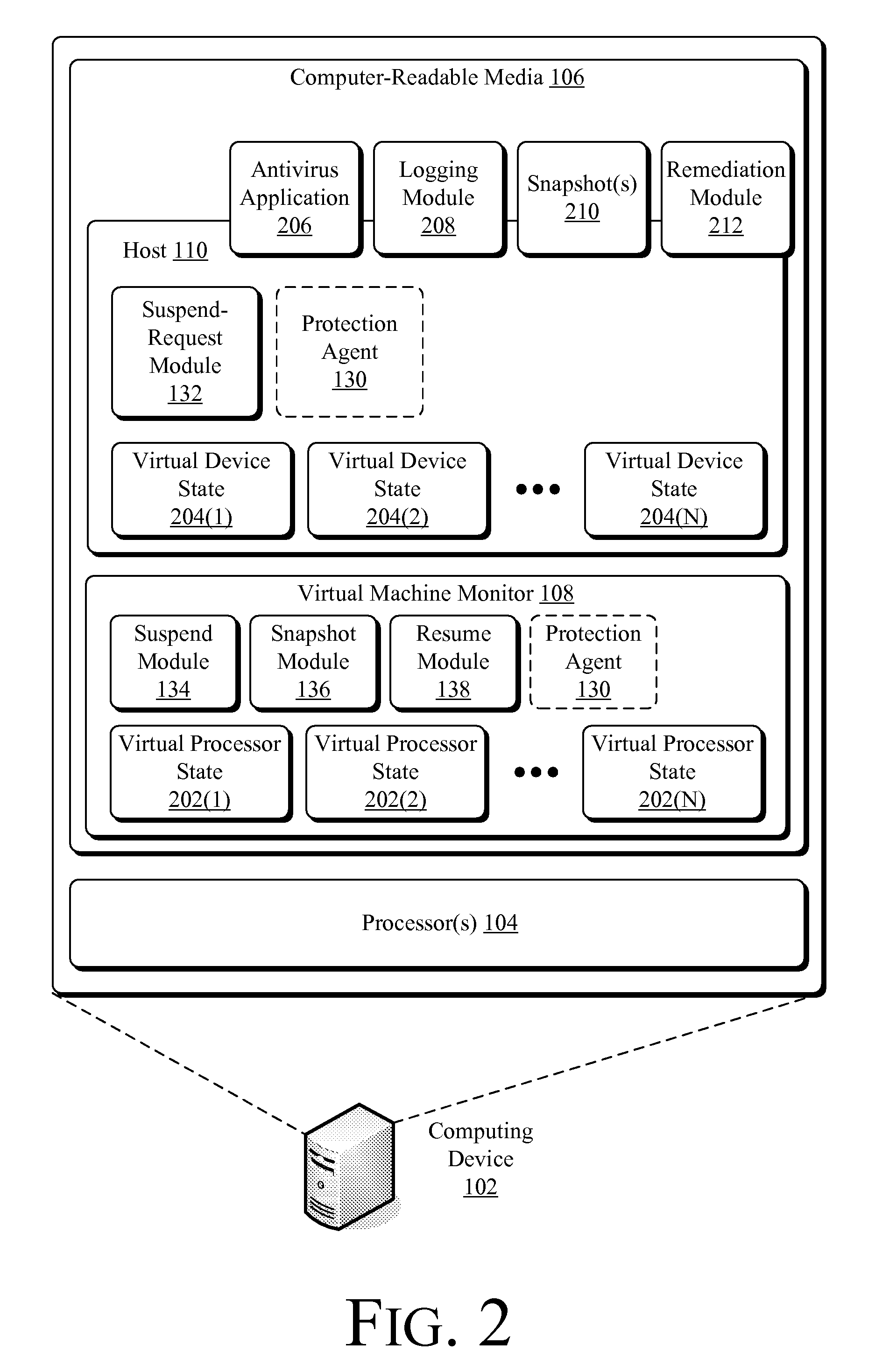
Suspending a Running Operating System to Enable Security Scanning
InactiveUS20090007100A1Well formedUser identity/authority verificationPlatform integrity maintainanceOperational systemRemedial action
Techniques described herein enable virtualizing a processor into one or more virtual machines and suspending an operating system of one of the virtual machines from outside of the operating system environment. Once suspended, these techniques capture a snapshot of the virtual machine to determine a presence of malware. This snapshot may also be used to determine whether an unauthorized change has occurred within contents of the virtual machine. Remedial action may occur responsive to determining a presence of malware or an unauthorized change.
Owner:MICROSOFT TECH LICENSING LLC
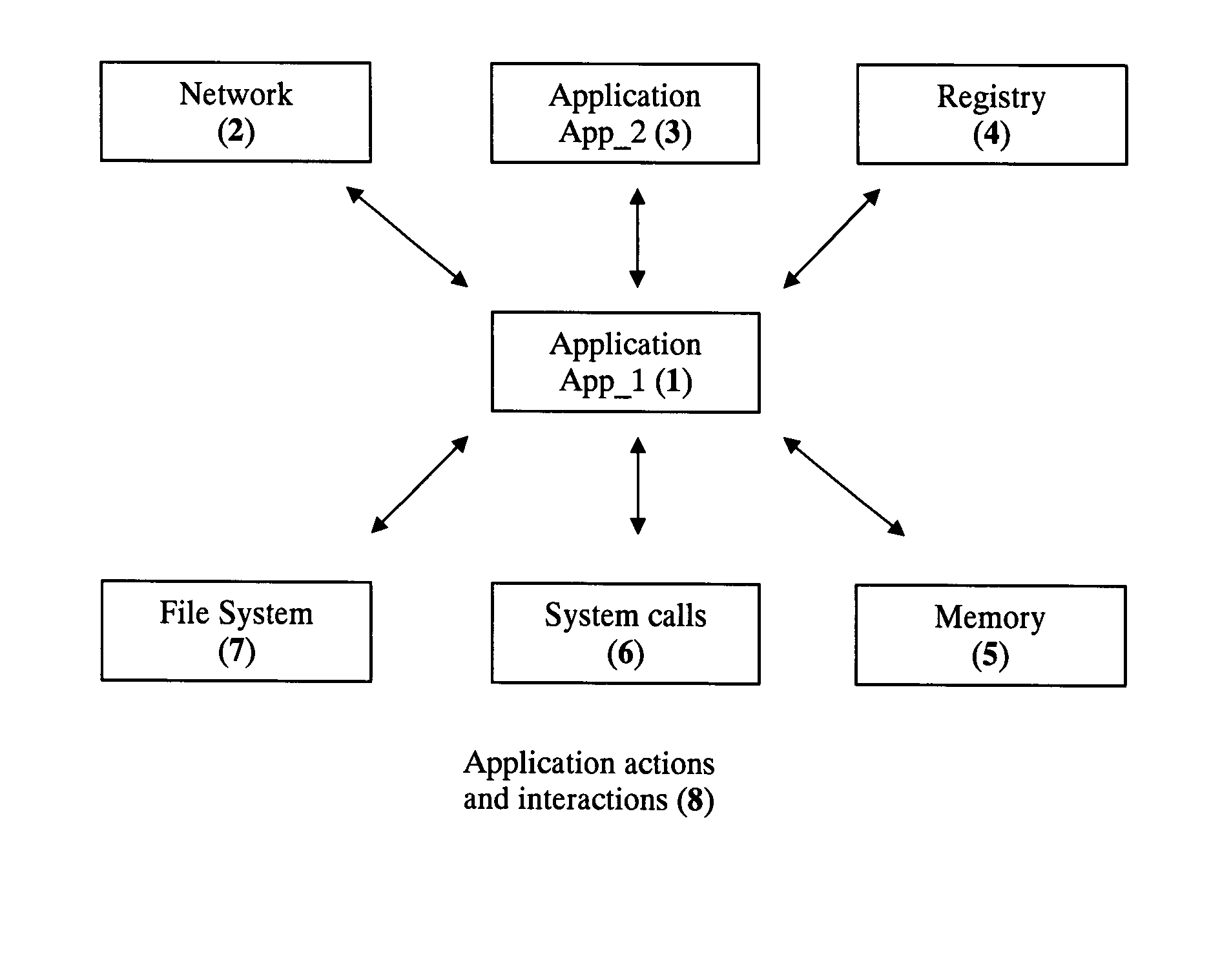
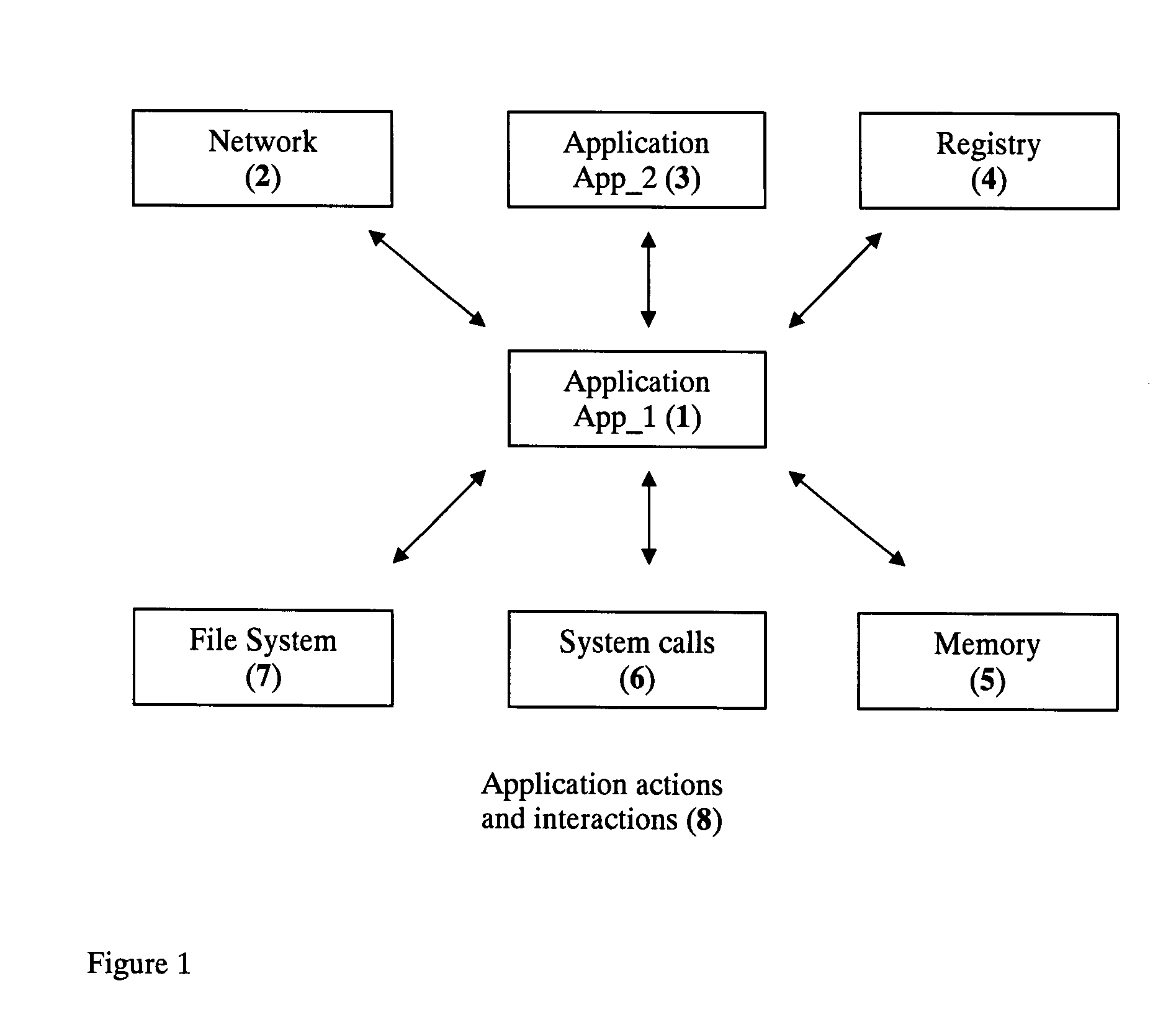
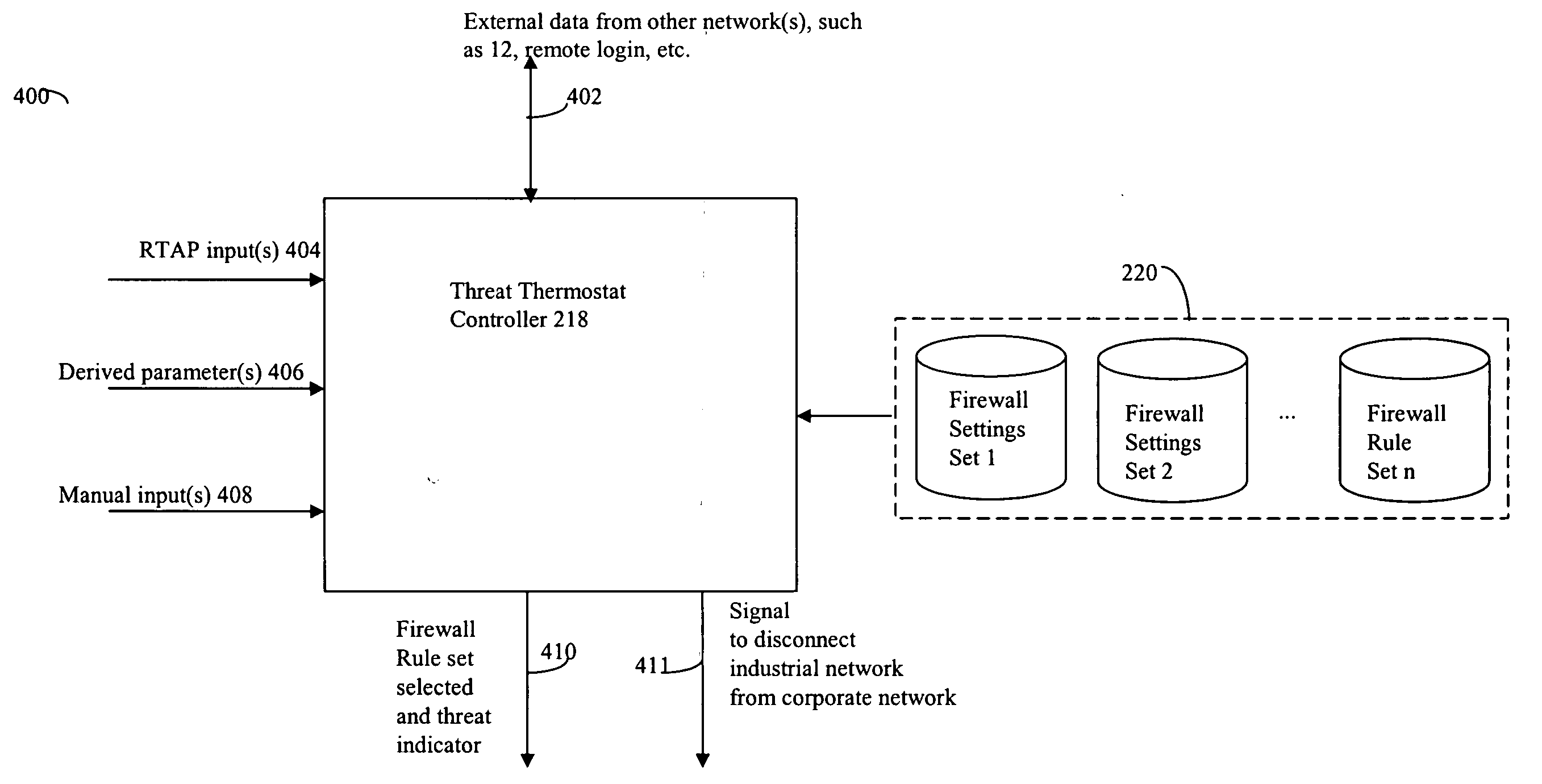
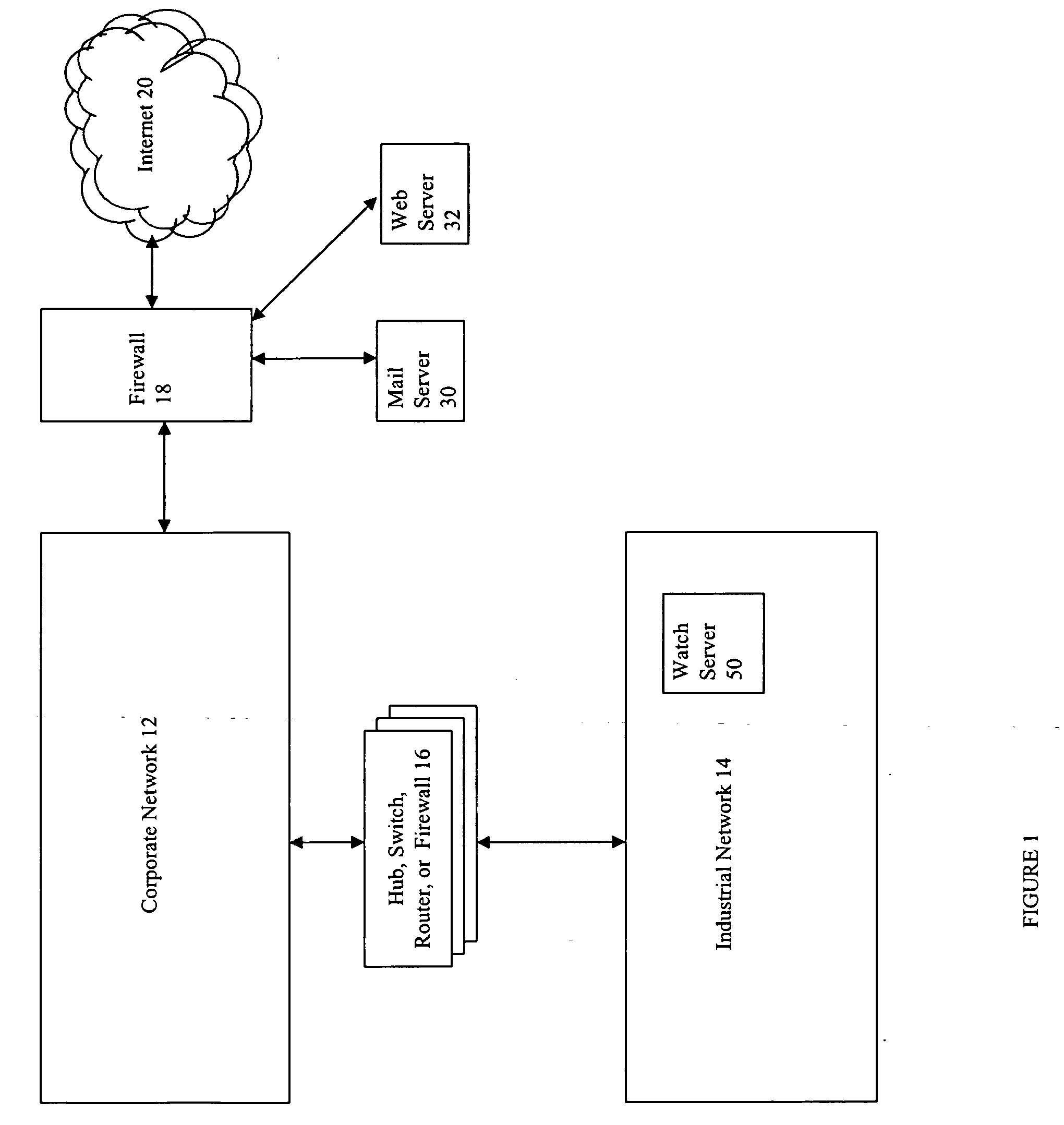
Event monitoring and management
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
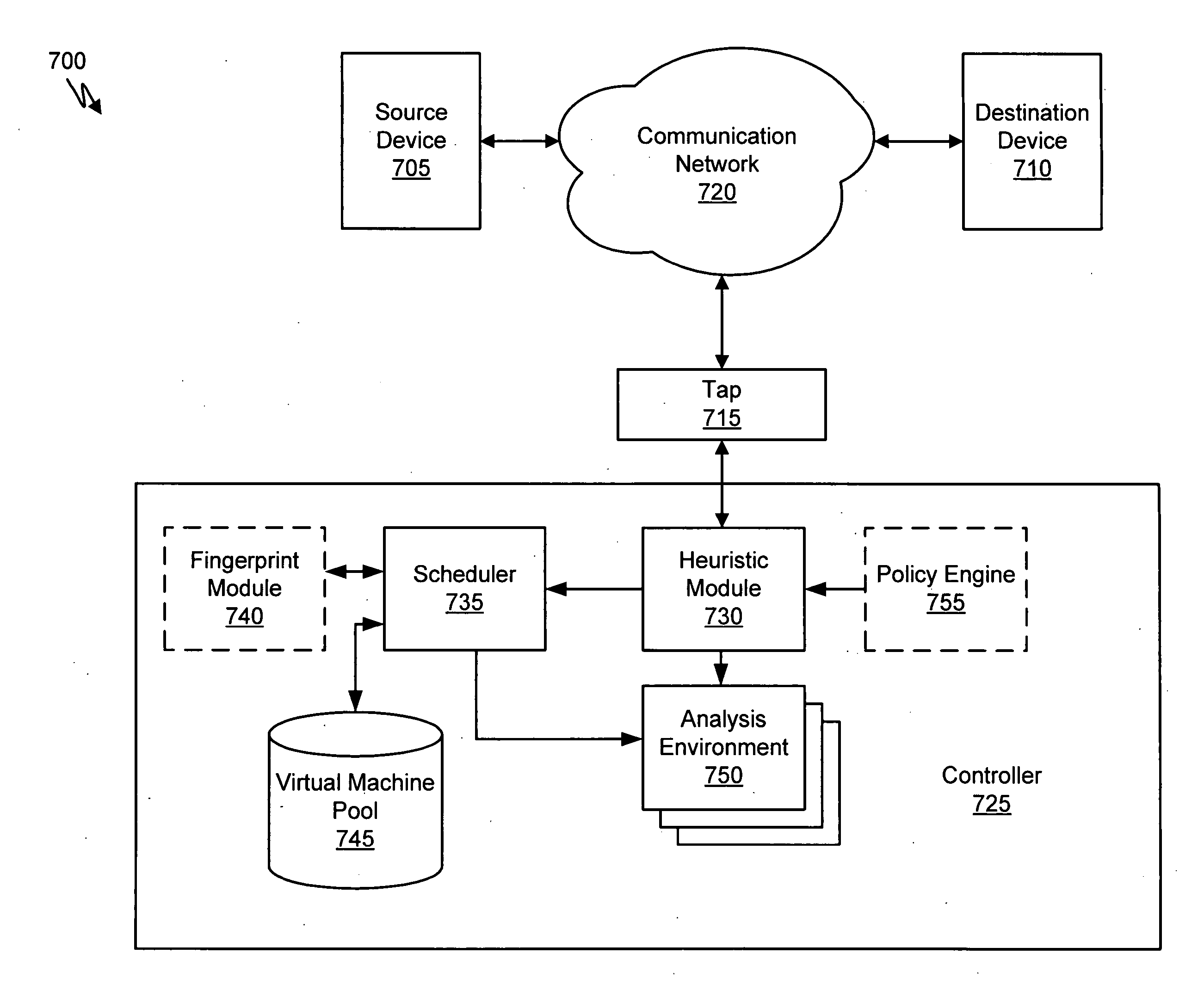
Heuristic based capture with replay to virtual machine
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
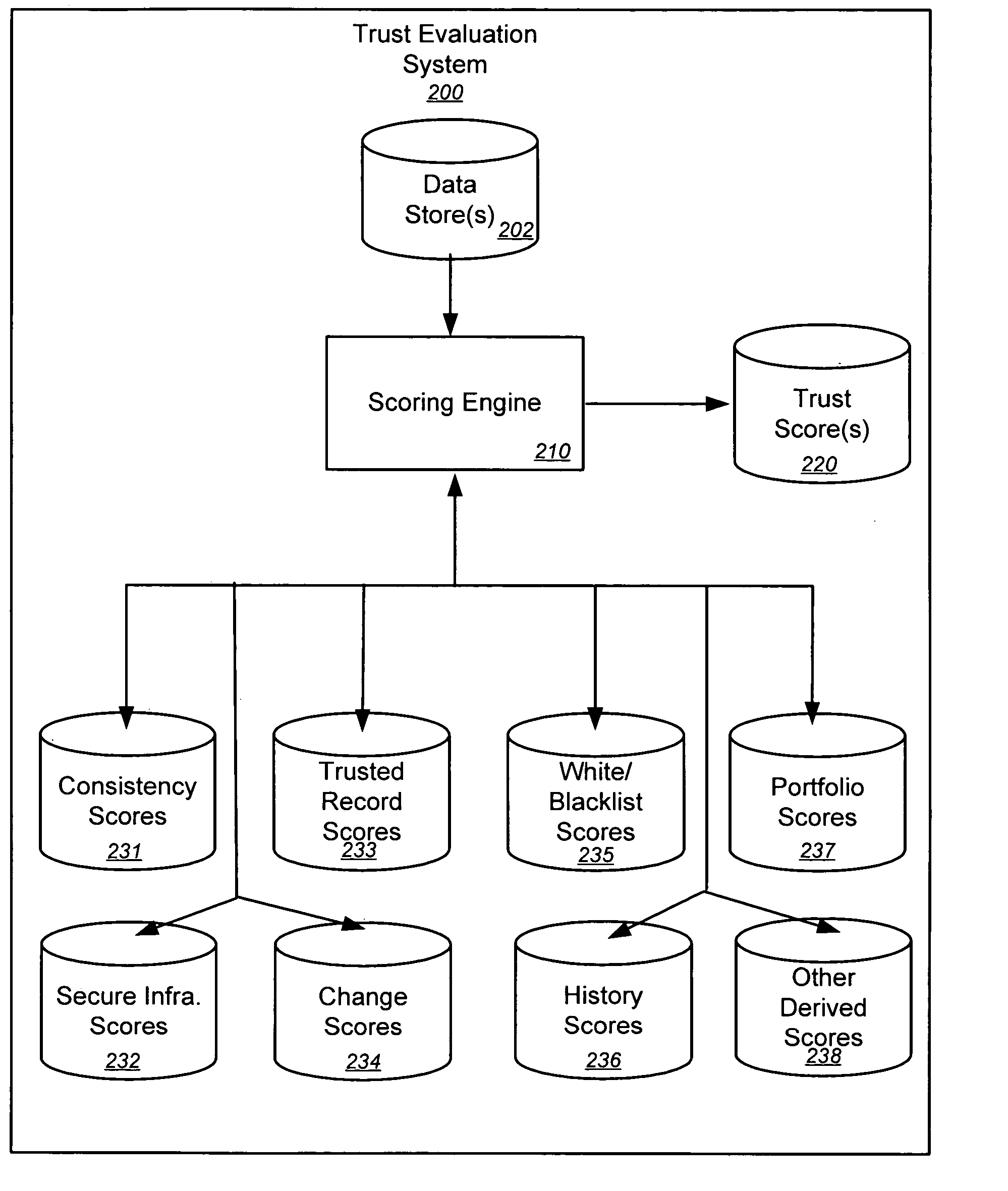
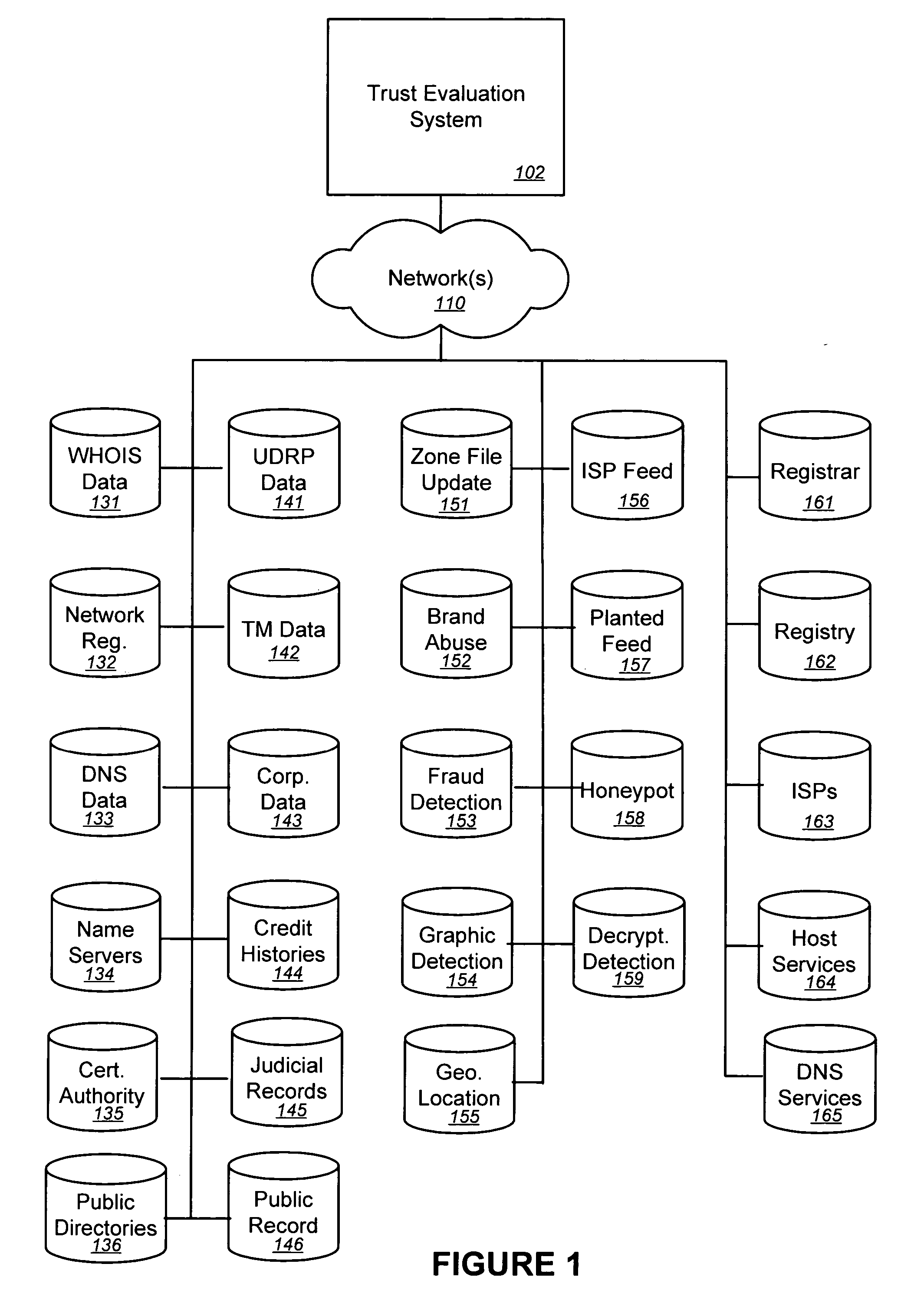
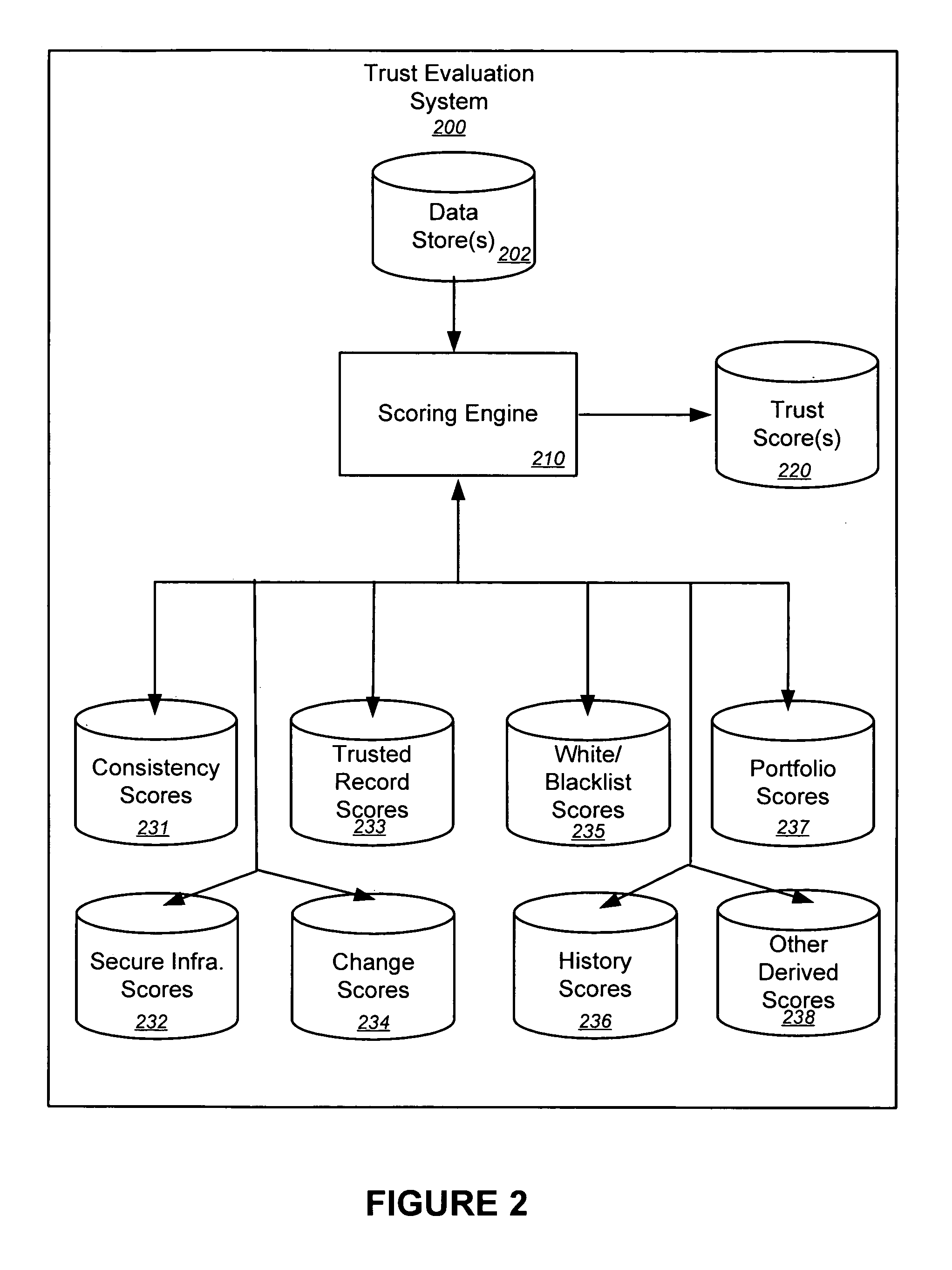
Trust evaluation systems and methods
InactiveUS20060212931A1Digital data processing detailsUser identity/authority verificationData storingEvaluation system
Embodiments of the present invention provide methods, systems, and software for implementing evaluating online entities and / or for providing a trust score for such entities. The trust score may provide an indication of the trustworthiness of the online entity. In some cases, data may be obtained from a variety of sources, and such data may be used to evaluate an online entity and / or to provide a score for the entity. In an aspect of the invention, a plurality of trust scores, each of which related to a behavioral characteristic and / or a category of activity, may be assigned to a particular entity. Such scores may be stored in one or more data stores and / or may be provided to others.
Owner:MARKMONITOR
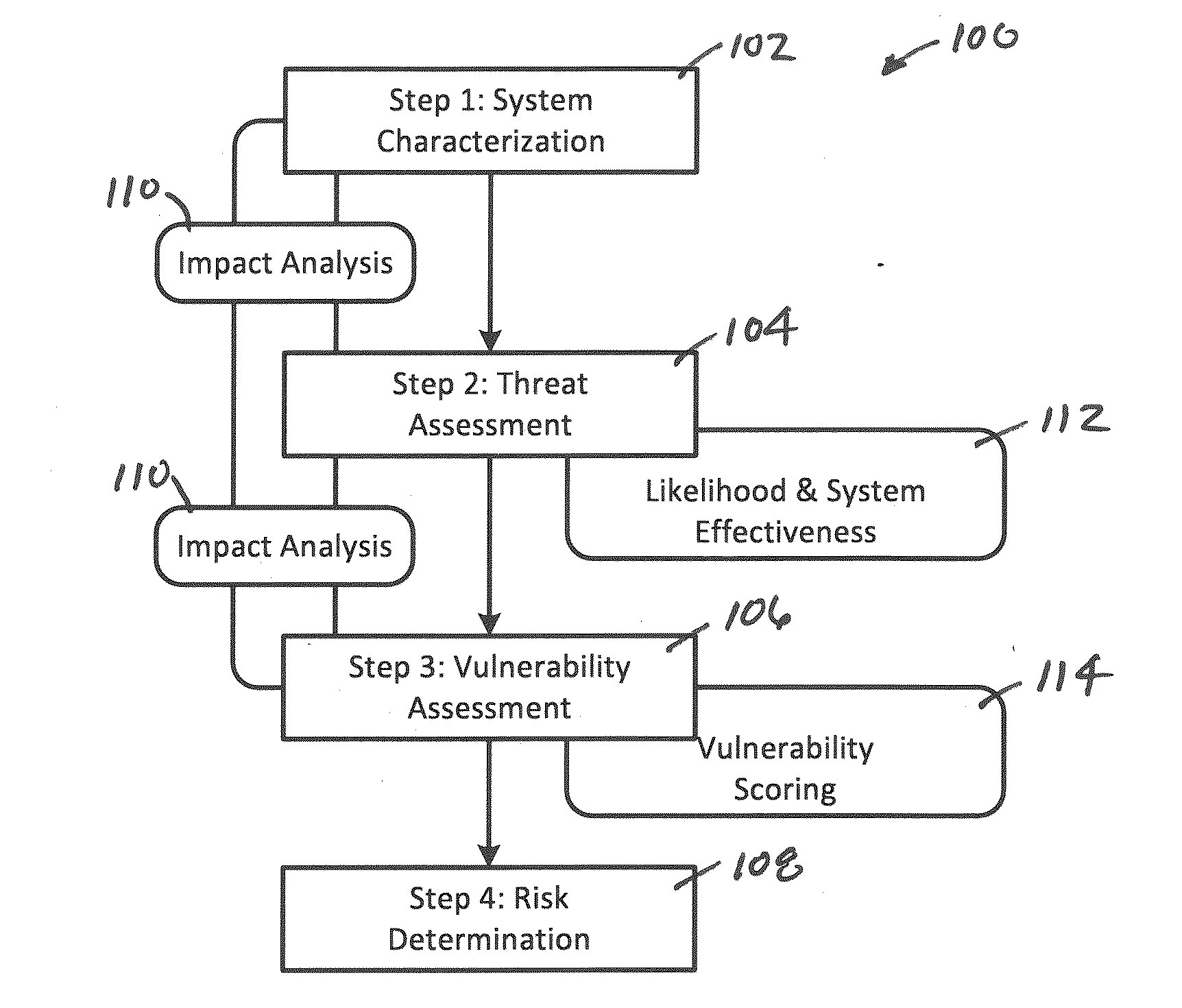
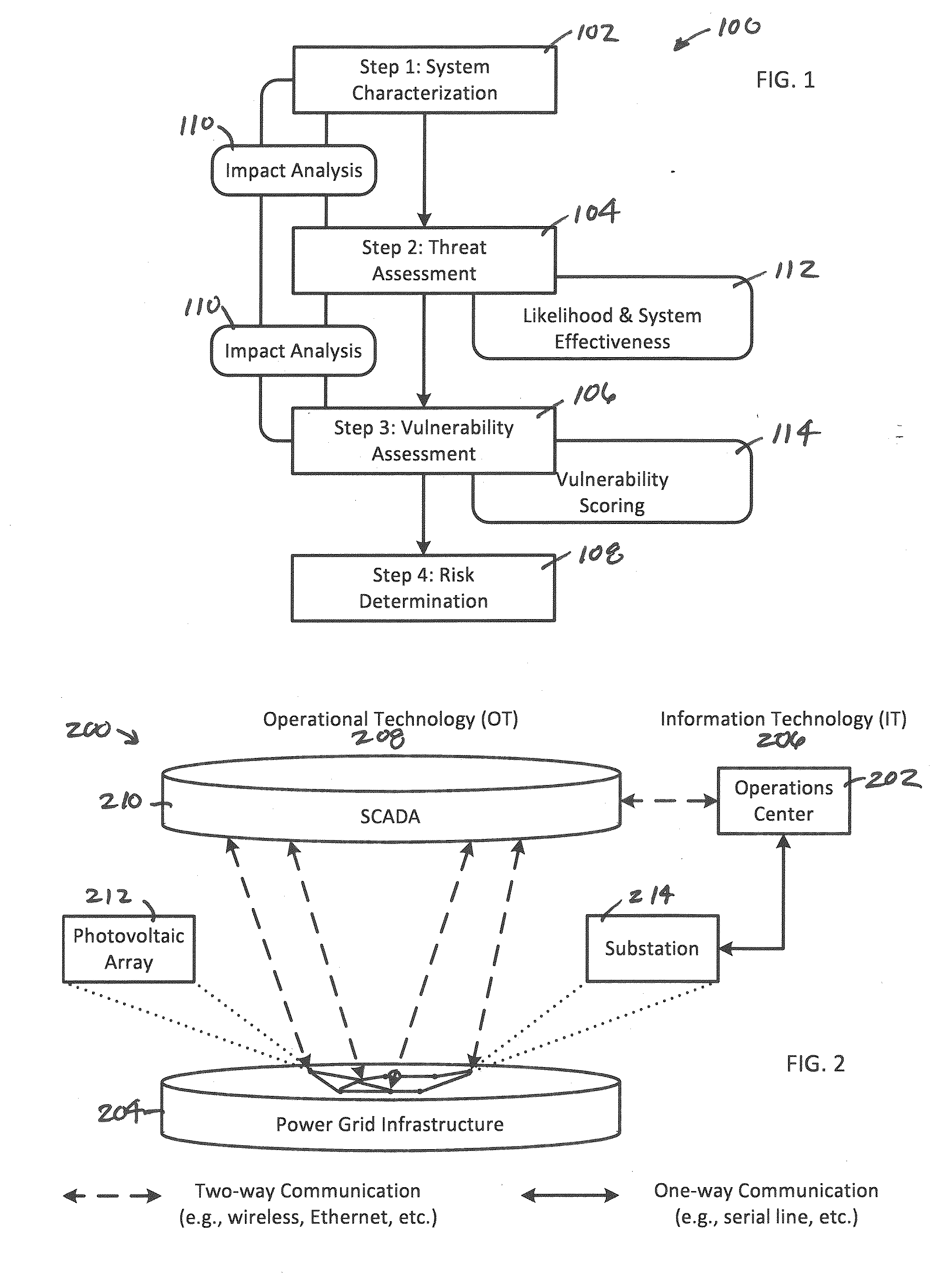
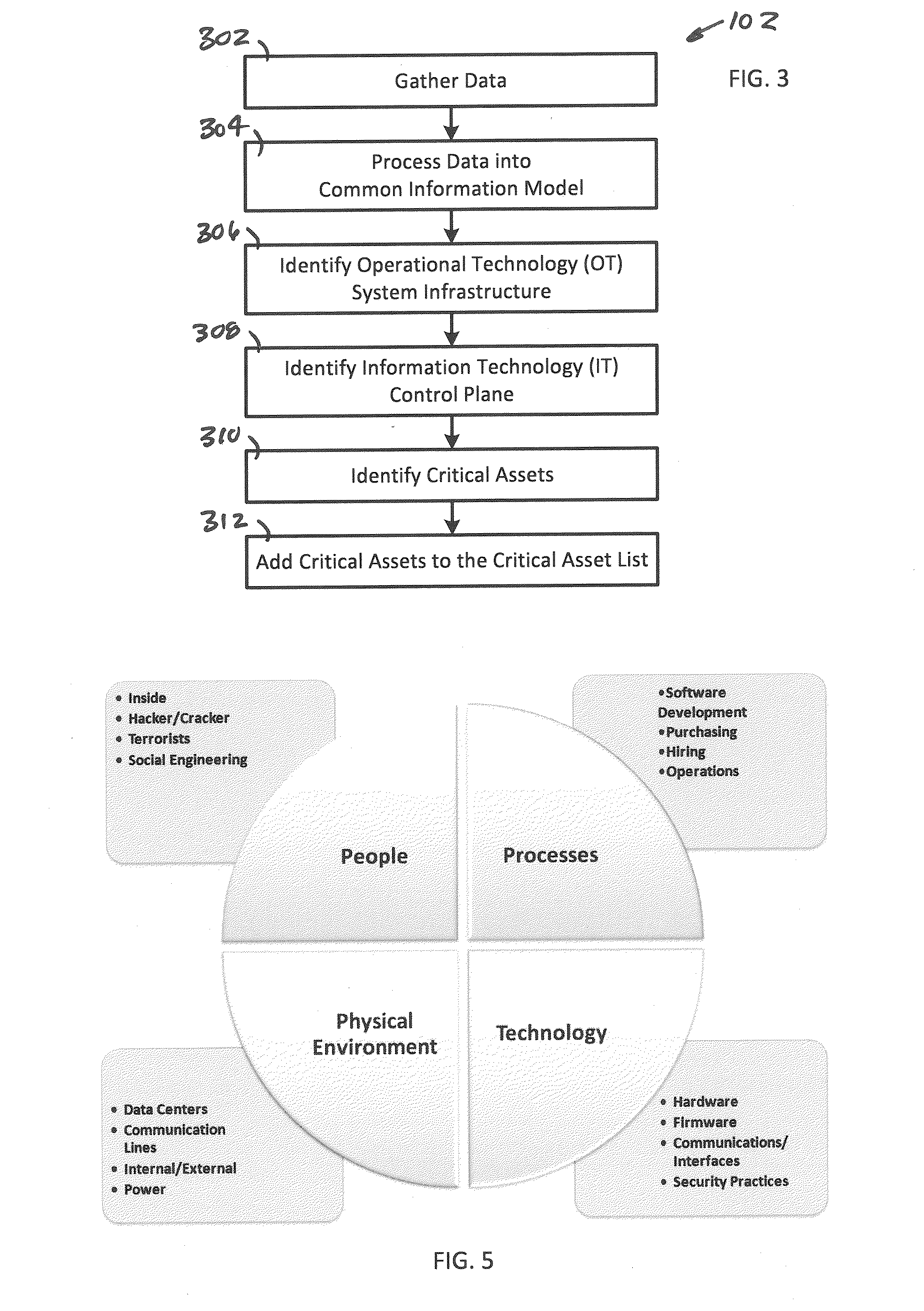
System, Method and Apparatus for Assessing a Risk of One or More Assets Within an Operational Technology Infrastructure
A system, method and apparatus assesses a risk of one or more assets within an operational technology infrastructure by providing a database containing data relating to the one or more assets, calculating a threat score for the one or more assets using one or more processors communicably coupled to the database, calculating a vulnerability score for the one or more assets using the one or more processors, calculating an impact score for the one or more assets using the one or more processors, and determining the risk of the one or more assets based on the threat score, the vulnerability score and the impact score using the one or more processors.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
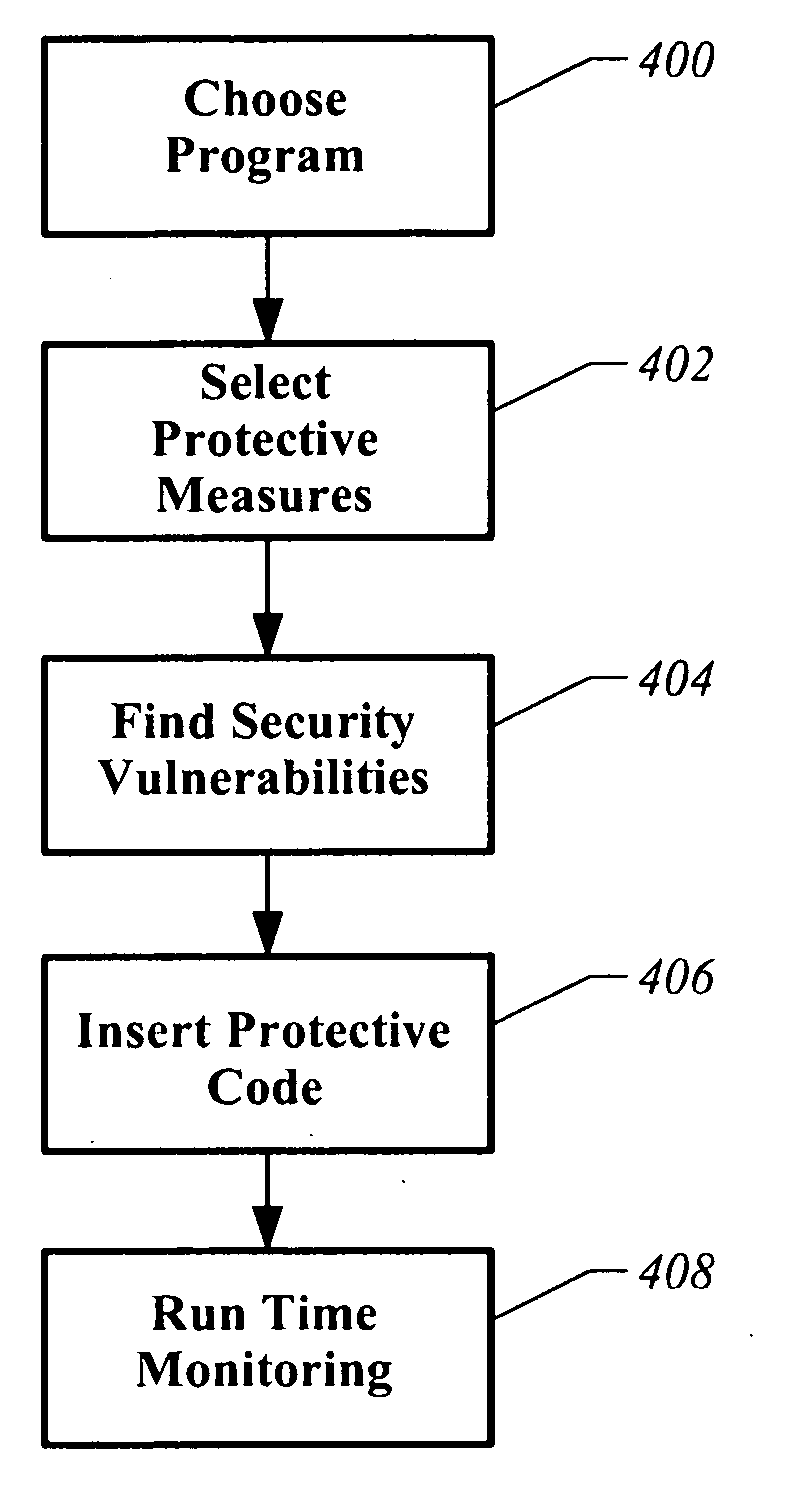
Apparatus and method for analyzing and supplementing a program to provide security
ActiveUS20070074169A1Memory loss protectionError detection/correctionProgramming languageProgram instruction
A computer readable storage medium has executable instructions to perform an automated analysis of program instructions. The automated analysis includes at least two analyses selected from an automated analysis of injection vulnerabilities, an automated analysis of potential repetitive attacks, an automated analysis of sensitive information, and an automated analysis of specific HTTP attributes. Protective instructions are inserted into the program instructions. The protective instructions are utilized to detect and respond to attacks during execution of the program instructions.
Owner:MICRO FOCUS LLC
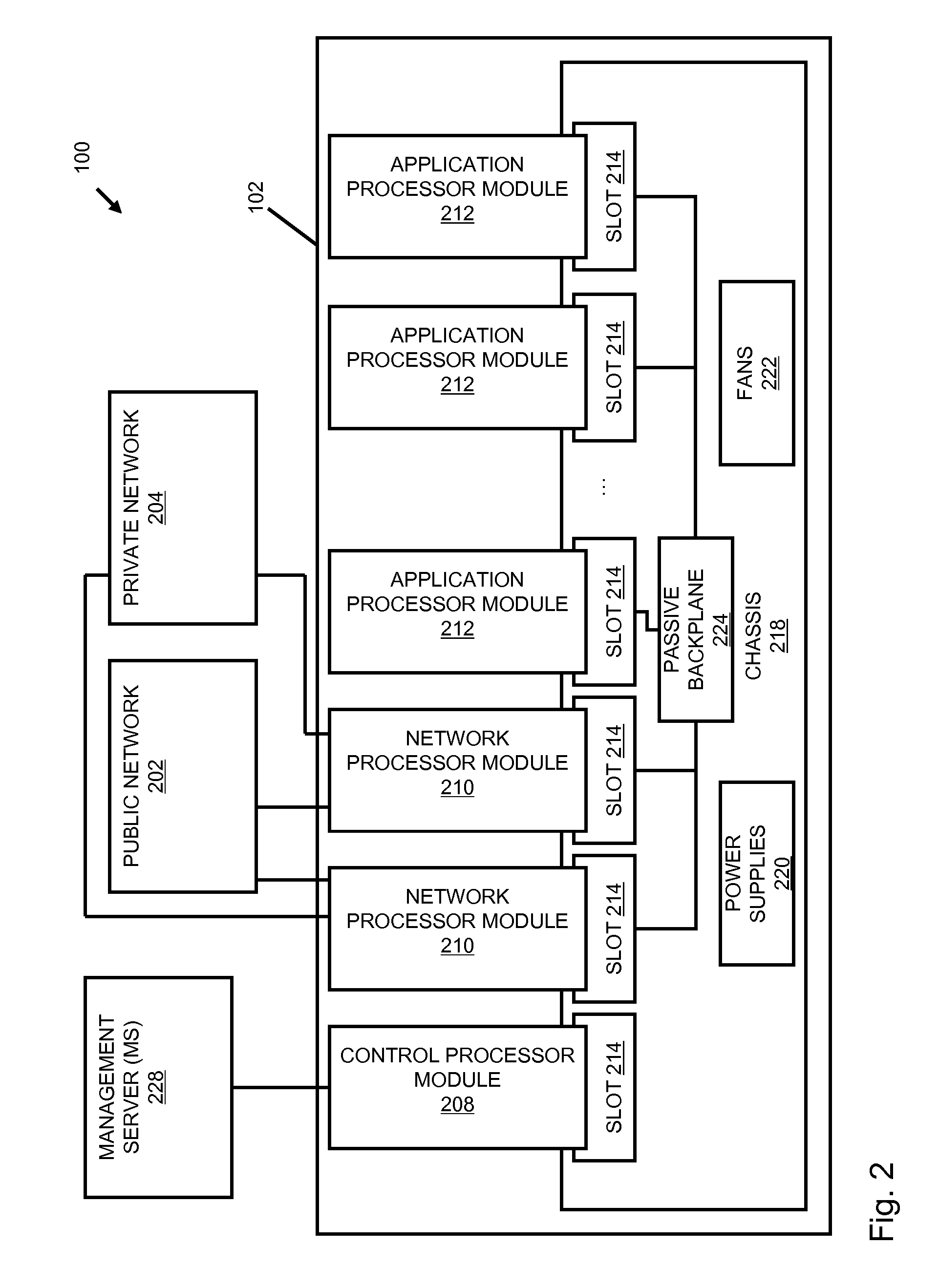
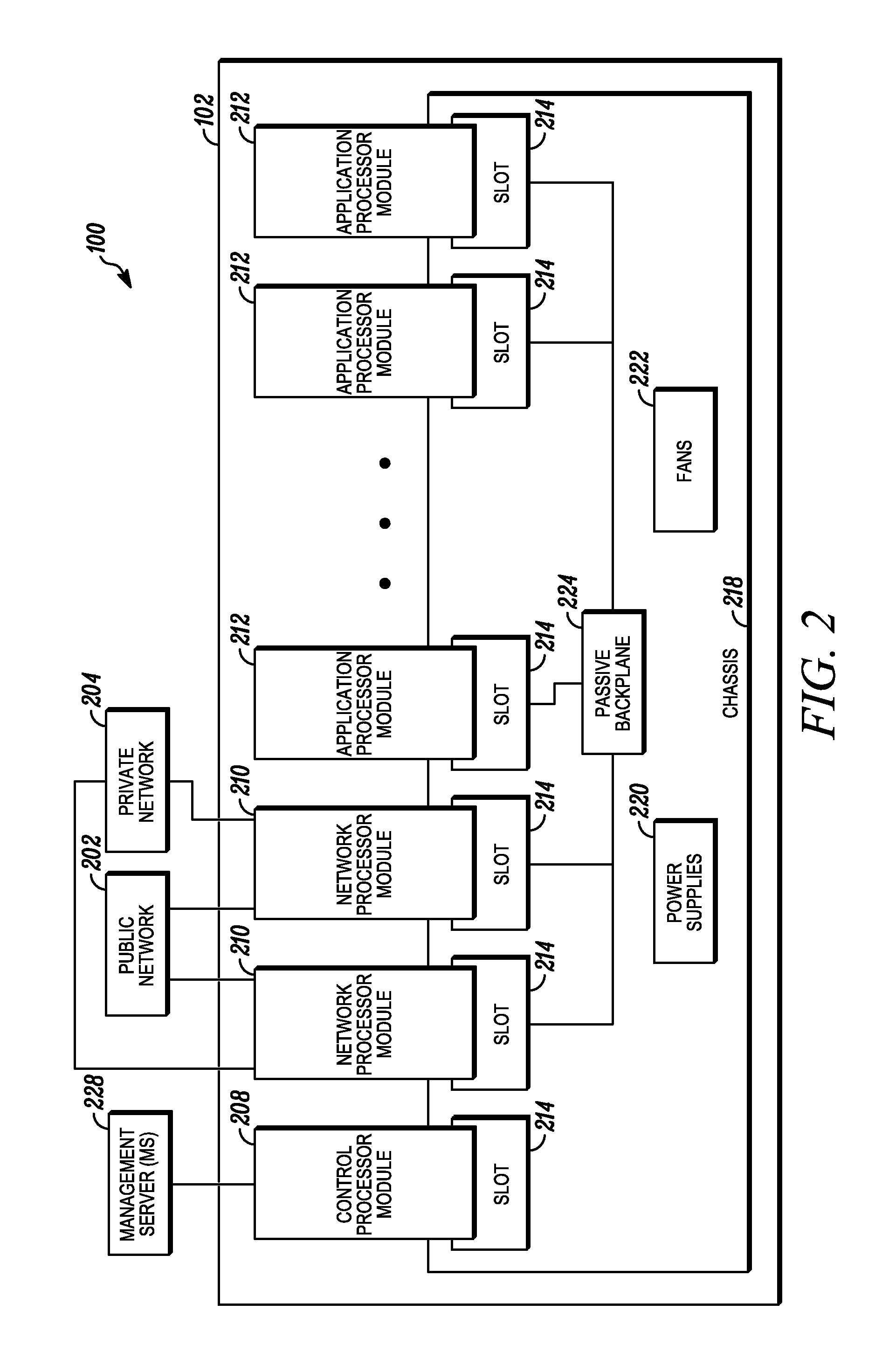
Processing data flows with a data flow processor
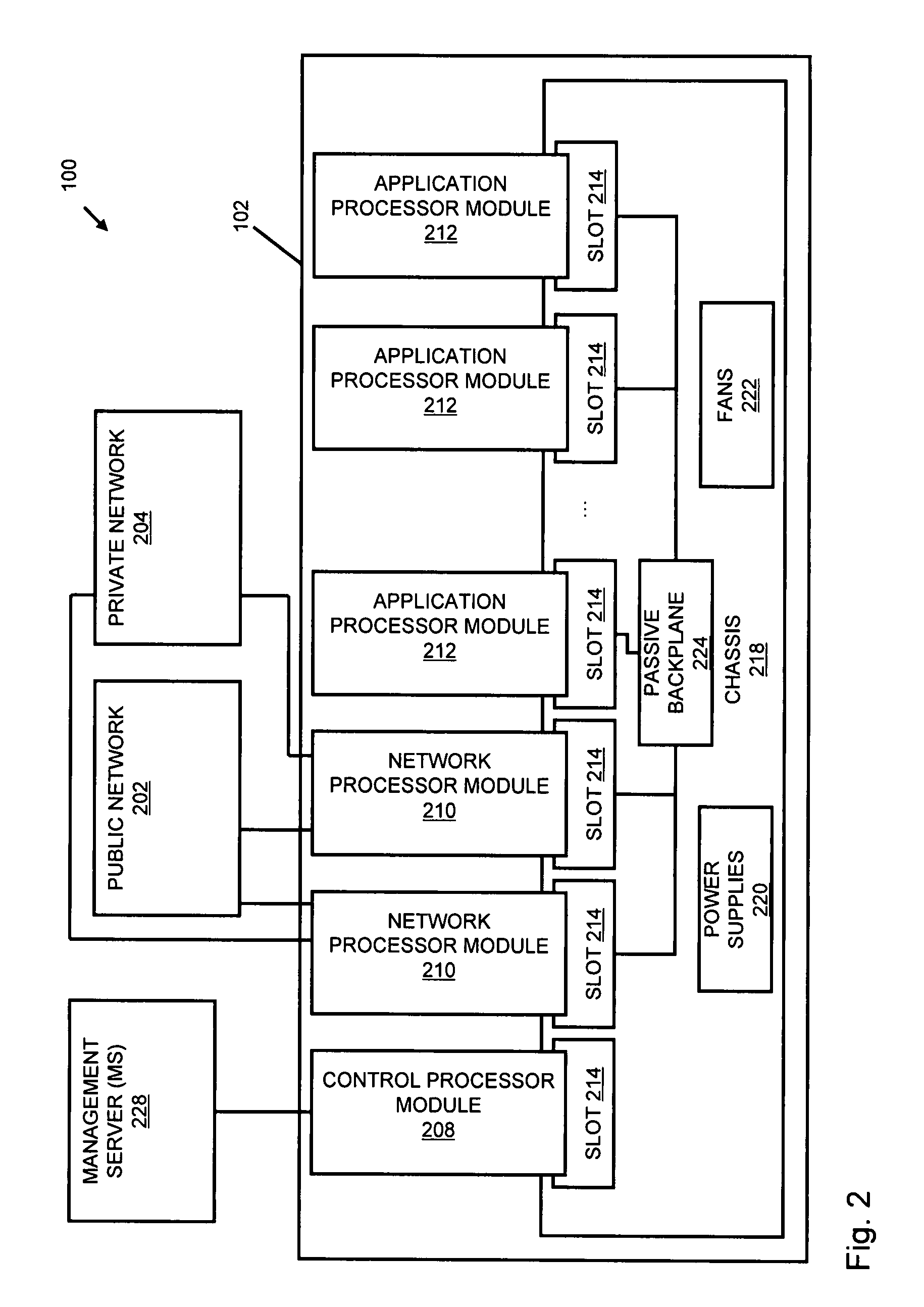
InactiveUS20110238855A1Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData controlConfigfs
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
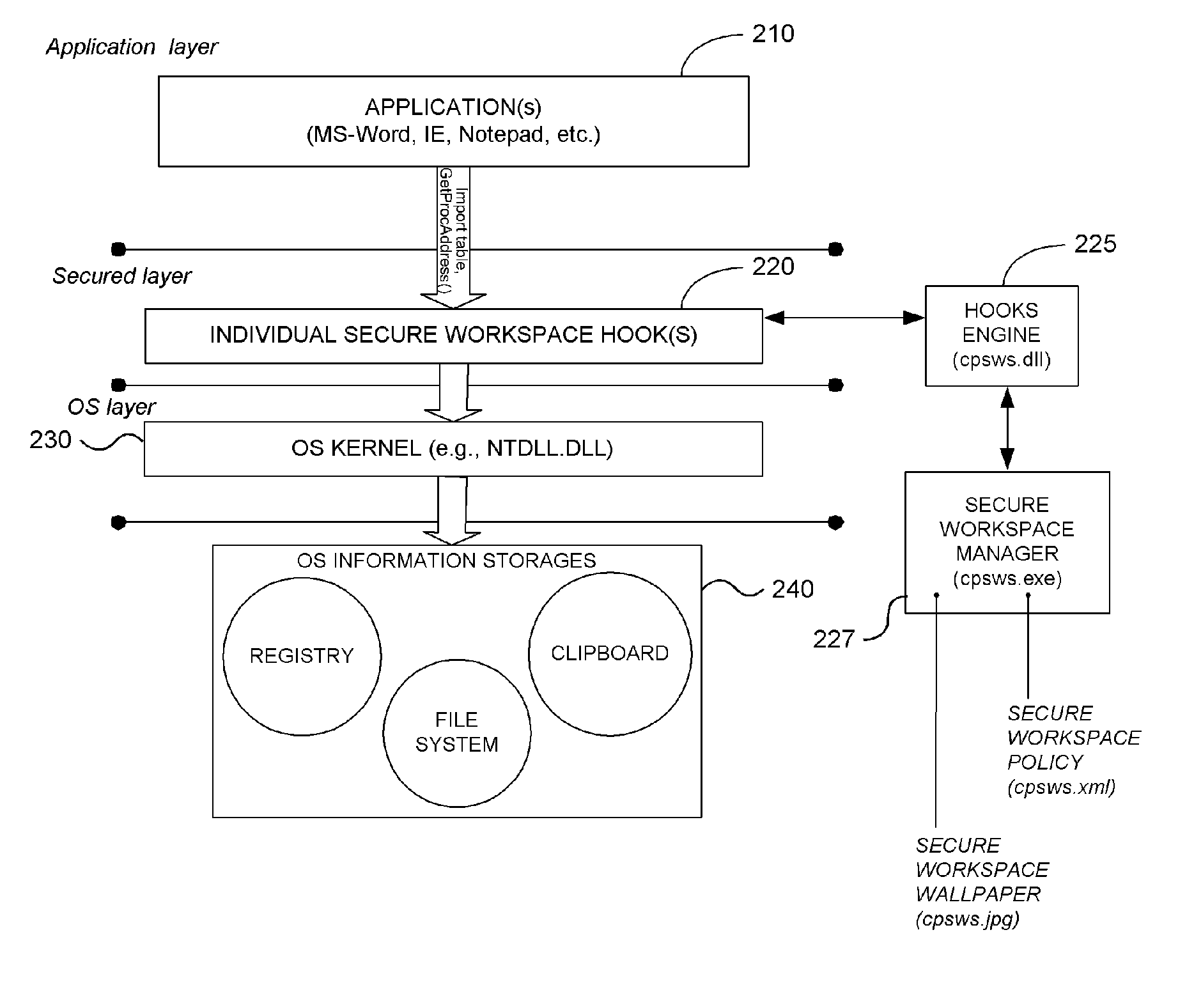
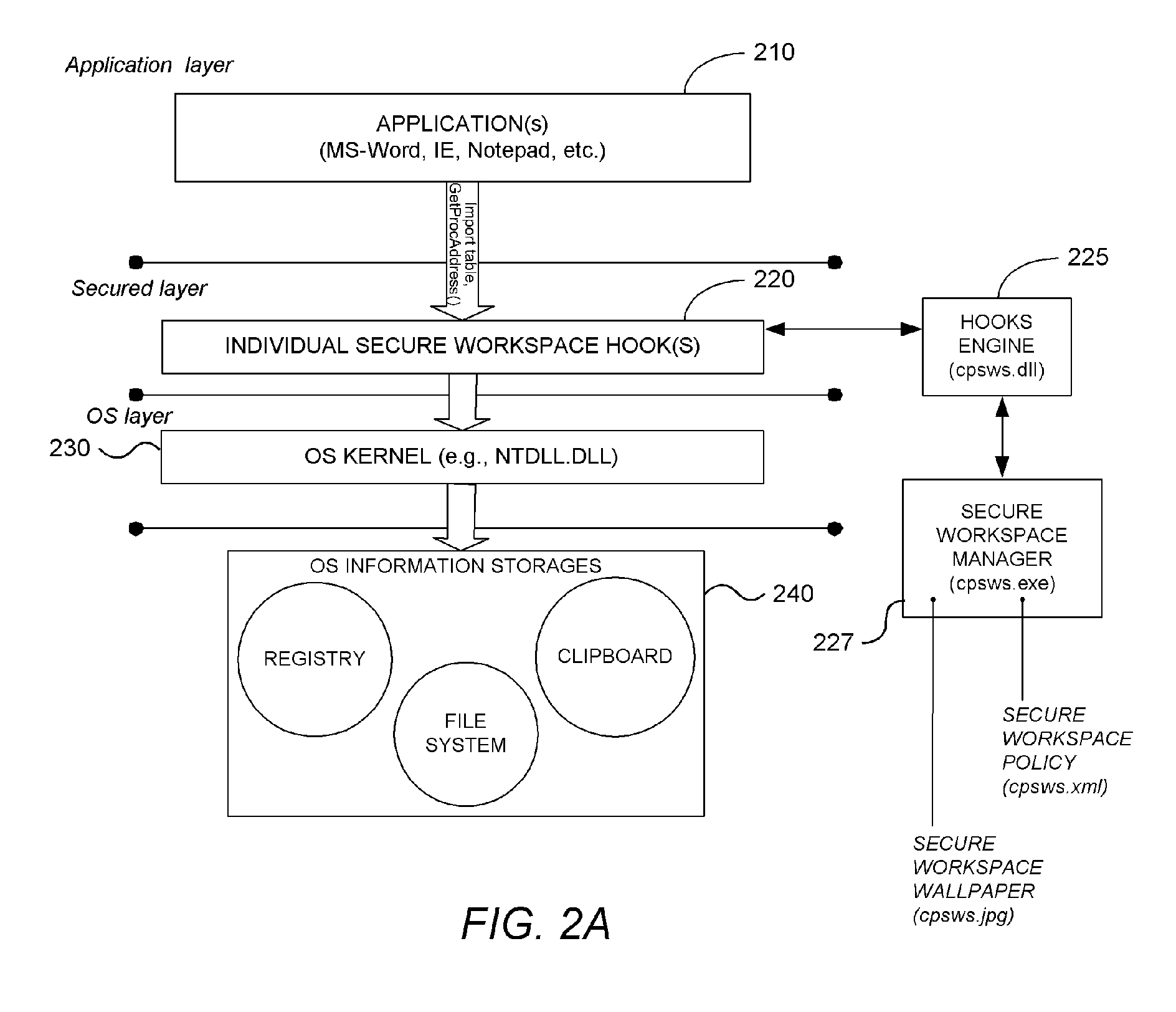
System and Methodology Providing Secure Workspace Environment
ActiveUS20070101435A1Avoid violationsUser identity/authority verificationAnalogue secracy/subscription systemsOperational systemWorkspace
System and methodology providing a secure workspace environment is described. In one embodiment, for example, in a computer system, a method is described for creating a secured workspace within an existing operating system for allowing users to run applications in a secured manner, the method comprises steps of: creating a policy for configuring the secured workspace, the policy specifying how information created during operation of the applications may be accessed; hooking particular functions of the operating system in order to obtain control over the information created during operation of the applications; during operation of the applications, encrypting the information to prevent unauthorized access; in response to a request for access to the information, determining whether the request complies with the policy; and if the request complies with the policy, satisfying the request by providing access to a decrypted copy of the information.
Owner:CHECK POINT SOFTWARE TECH INC
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
Methods, systems, and media for detecting covert malware
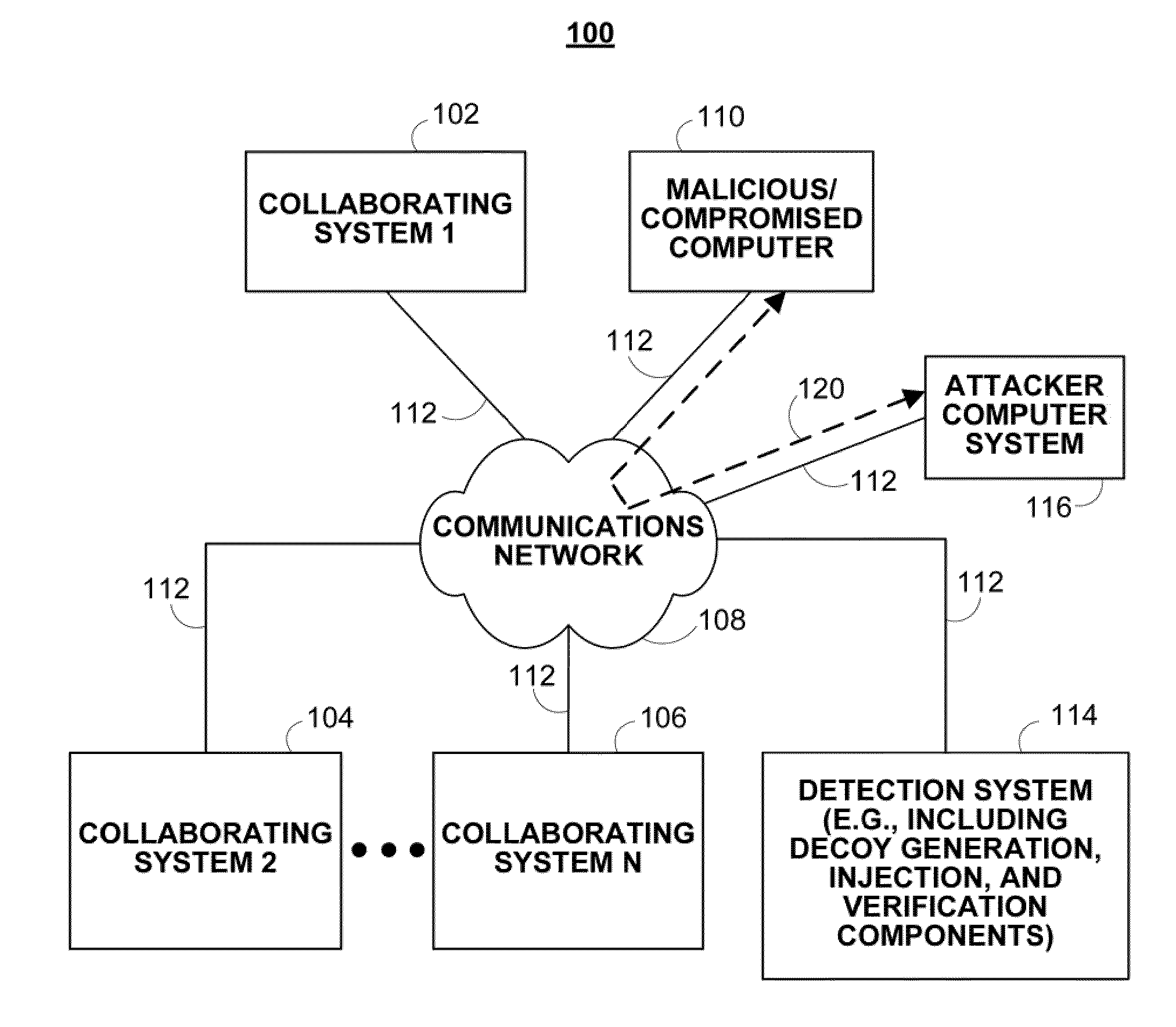
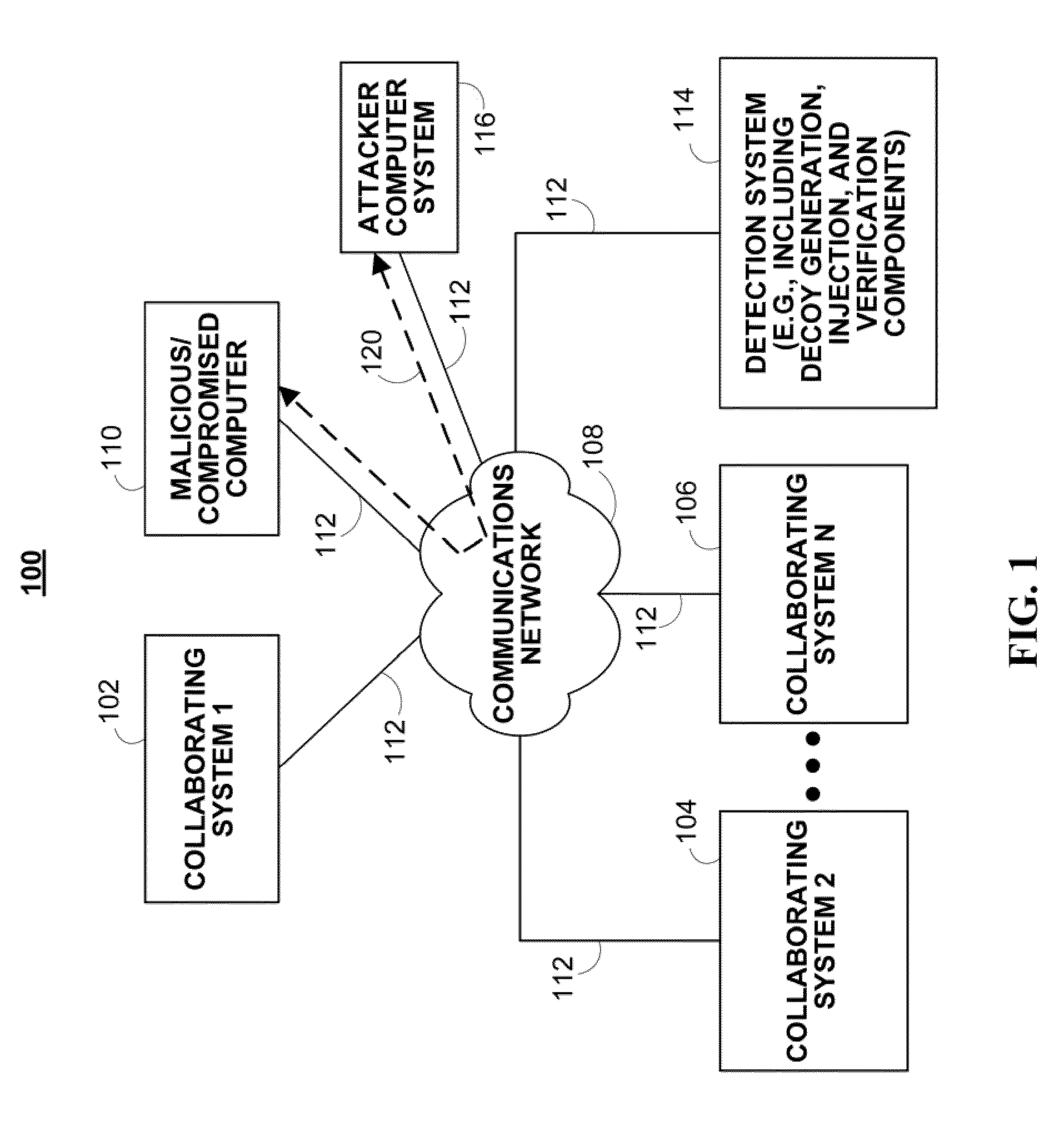
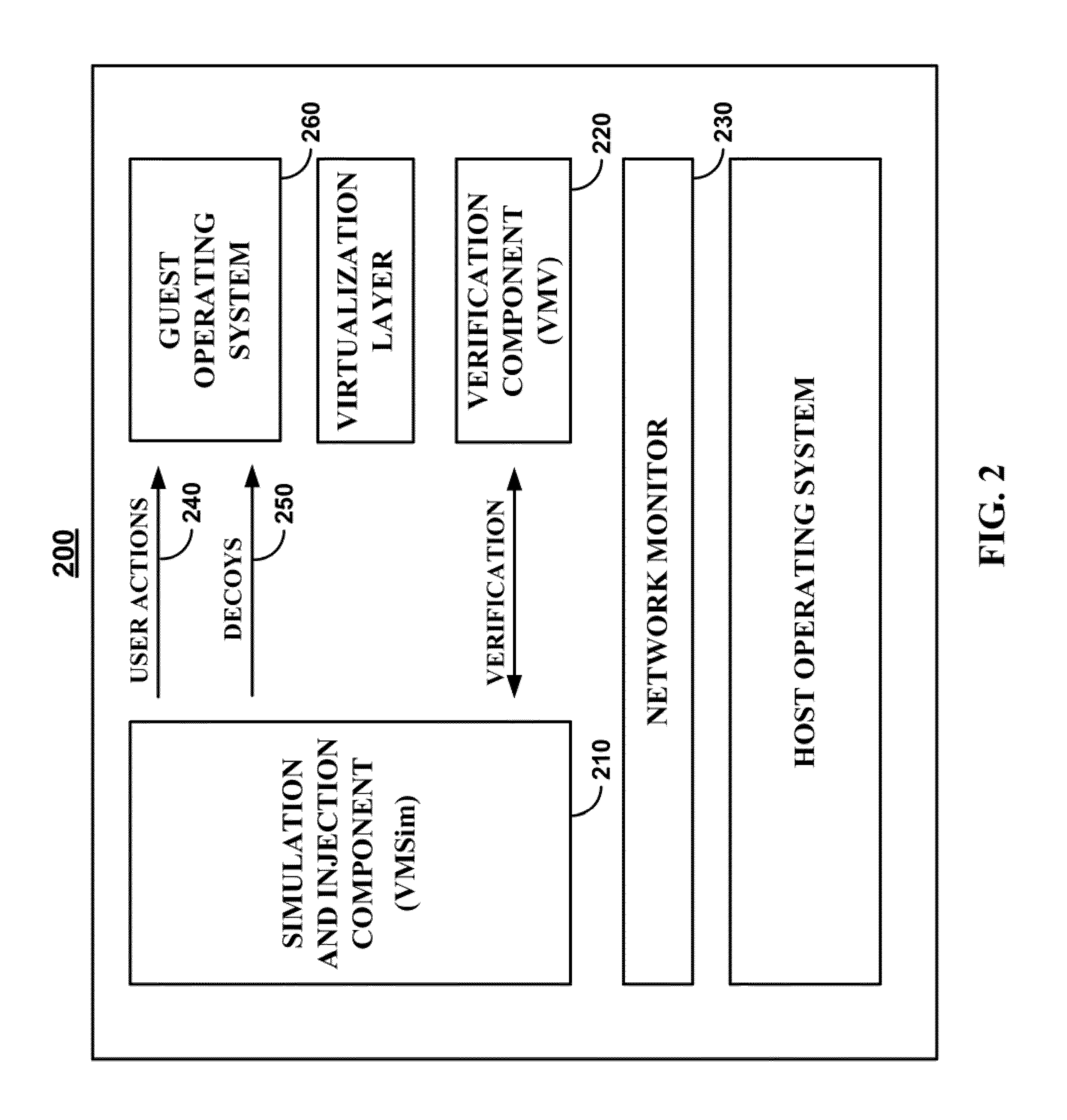
ActiveUS20110167494A1Reduce level of system knowledgeMemory loss protectionError detection/correctionDecoyApplication software
Methods, systems, and media for detecting covert malware are provided. In accordance with some embodiments, a method for detecting covert malware in a computing environment is provided, the method comprising: generating simulated user activity outside of the computing environment; conveying the simulated user activity to an application inside the computing environment; and determining whether a decoy corresponding to the simulated user activity has been accessed by an unauthorized entity.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
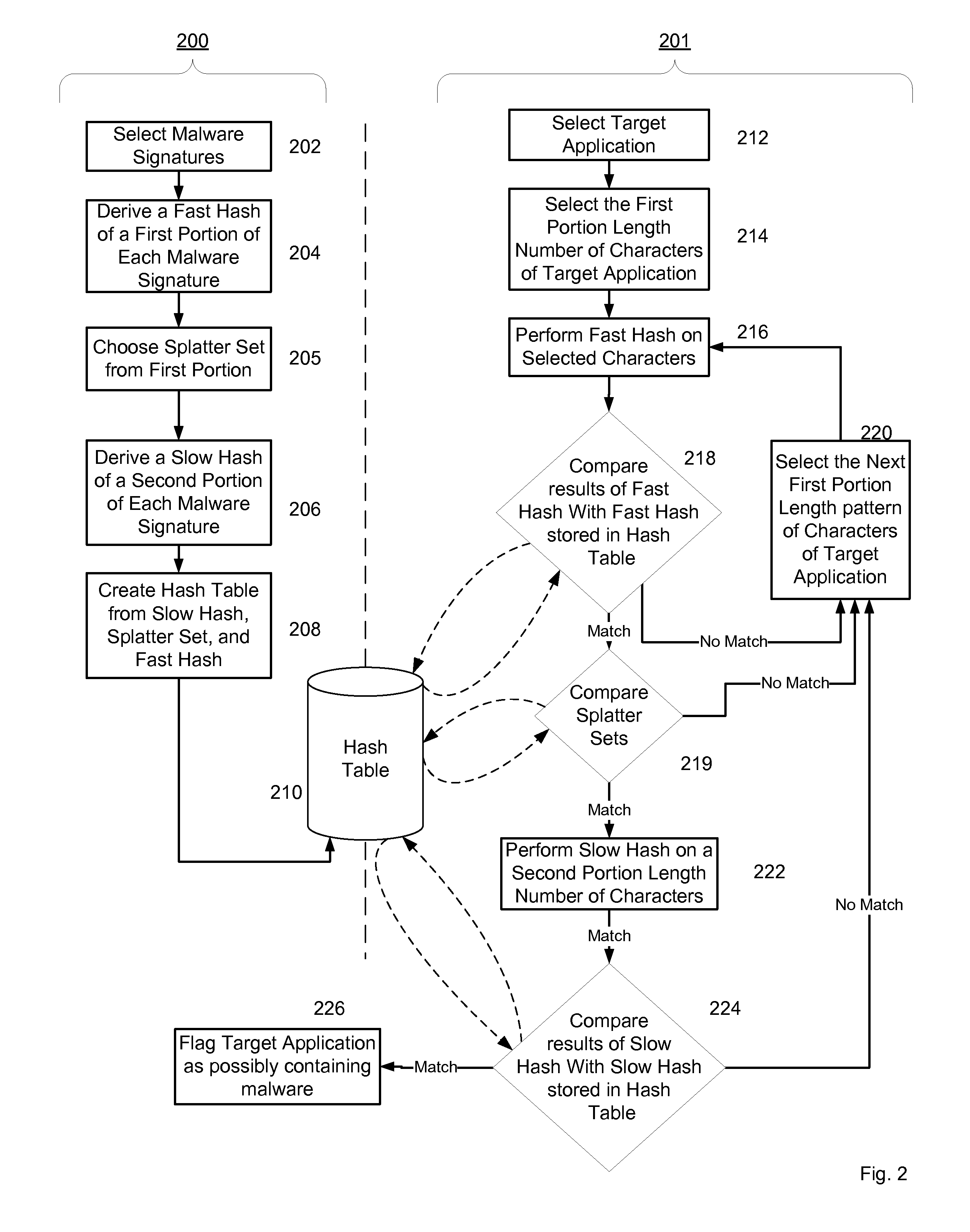
Malware Modeling Detection System And Method for Mobile Platforms
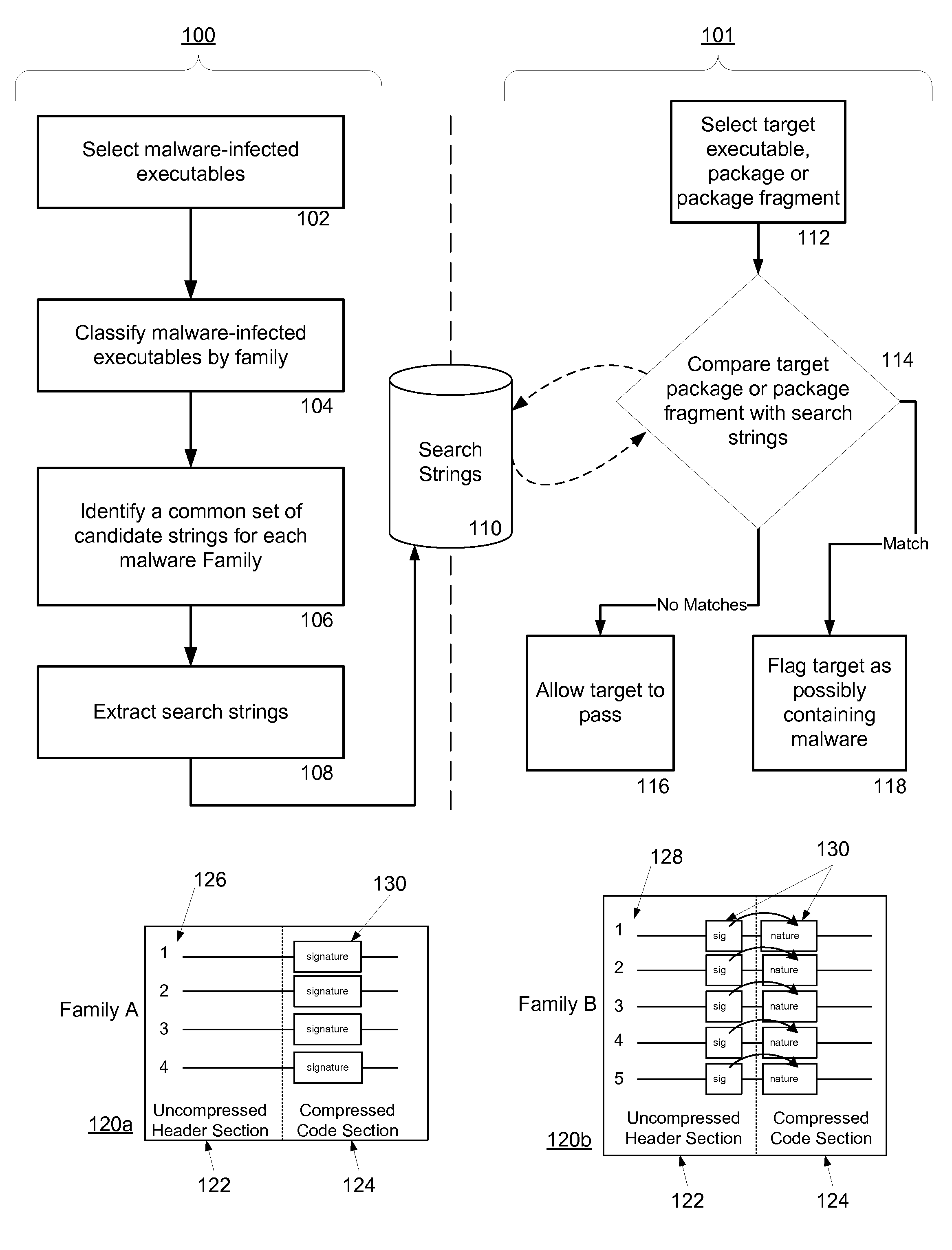
ActiveUS20070240217A1Suitable for useReliable detectionMemory loss protectionUser identity/authority verificationFeature setAlgorithm
A system and method for detecting malware by modeling the behavior of malware and comparing a suspect executable with the model. The system and method extracts feature elements from malware-infected applications, groups the feature elements into feature sets, and develops rules describing a malicious probability relationship between the feature elements. Using malware-free and malware-infected applications as training data, the system and method heuristically trains the rules and creates a probability model for identifying malware. To detect malware, the system and method scans the suspect executable for feature sets and applies the results to the probability model to determine the probability that the suspect executable is malware-infected.
Owner:PULSE SECURE
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
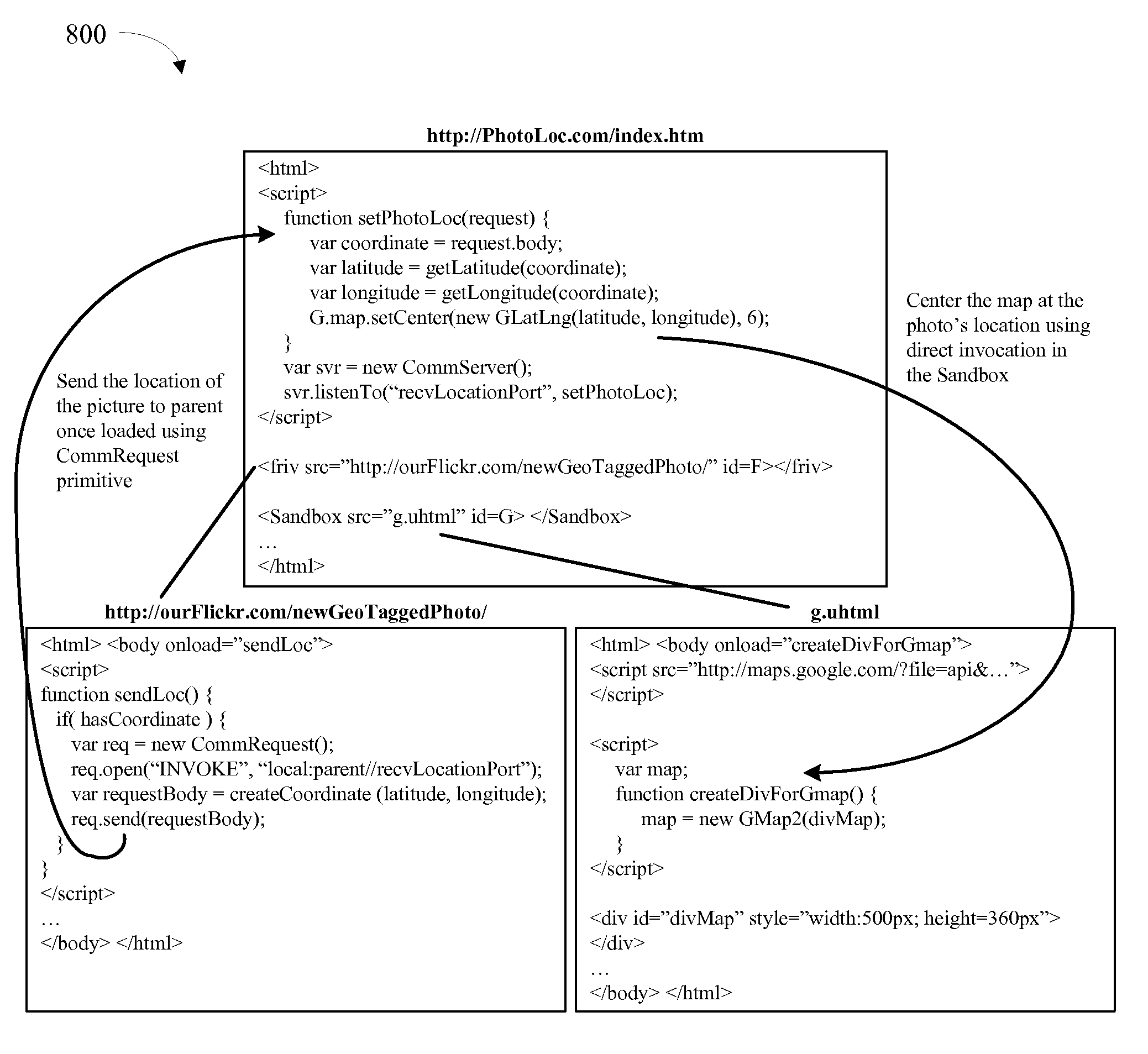
Protection and communication abstractions for web browsers
ActiveUS20080313648A1Facilitate asymmetric level of trustAvoid attackPlatform integrity maintainanceTransmissionWeb browserResource management
Systems and methodologies for accessing resources associated with a Web-based application in accordance with one or more embodiments disclosed herein may include a browser that obtains at least first resources from a first domain and second resources from a second domain and a resource management component that facilitates controlled communication between the first resources and the second resources and prevents the first resources and the second resources from accessing other resources that the first resources and the second resources are not permitted to access. The resource management component may be further operable to contain restricted services in a sandbox containment structure and / or to isolate access-controlled resources in a service instance. In addition, the resource management component may be operable to facilitate the flexible display of resources from disparate domains and / or controlled communication therebetween.
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for assigning access control levels in providing access to resources via virtual machines
ActiveUS20070180493A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
Owner:CITRIX SYST INC
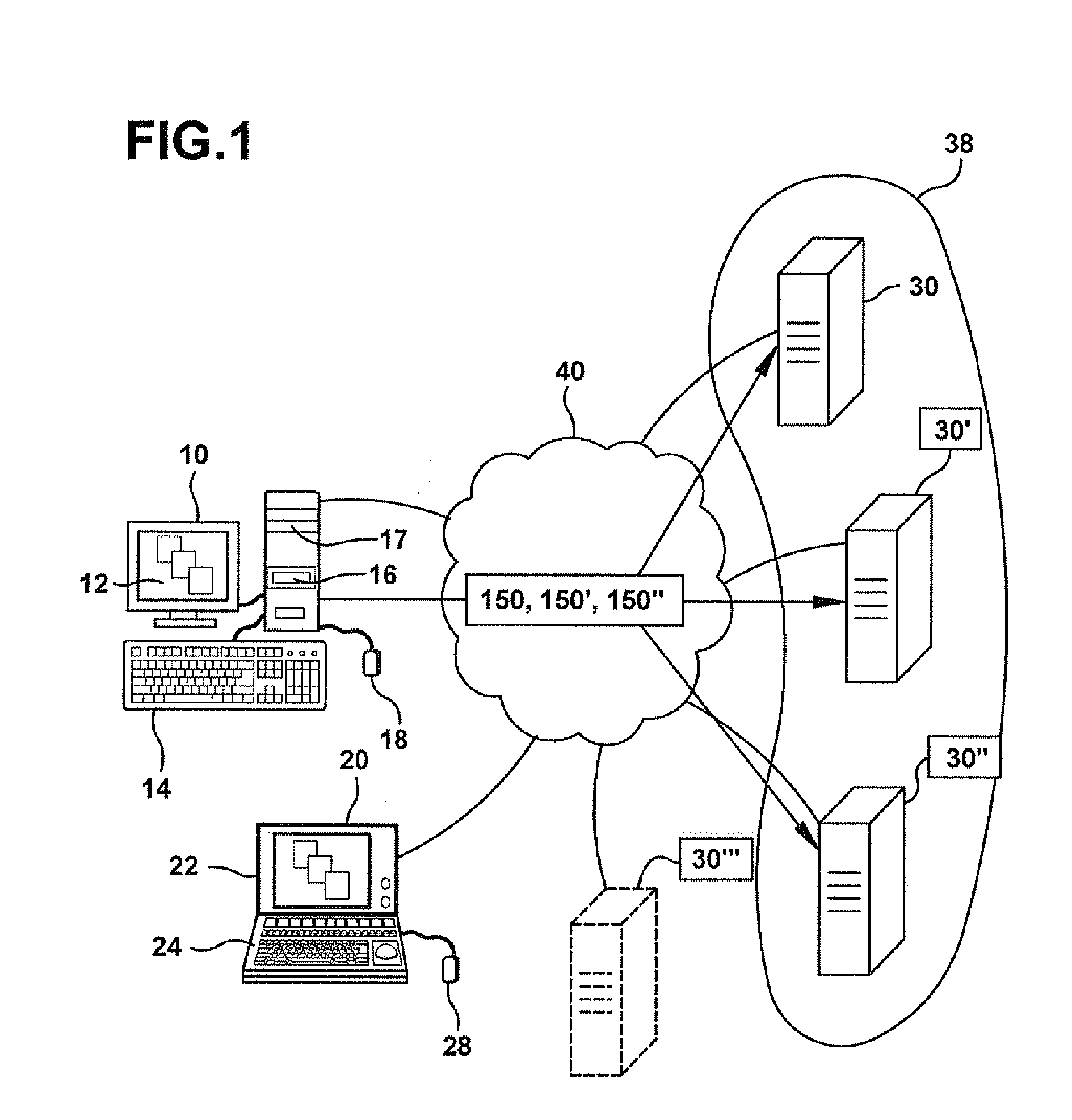
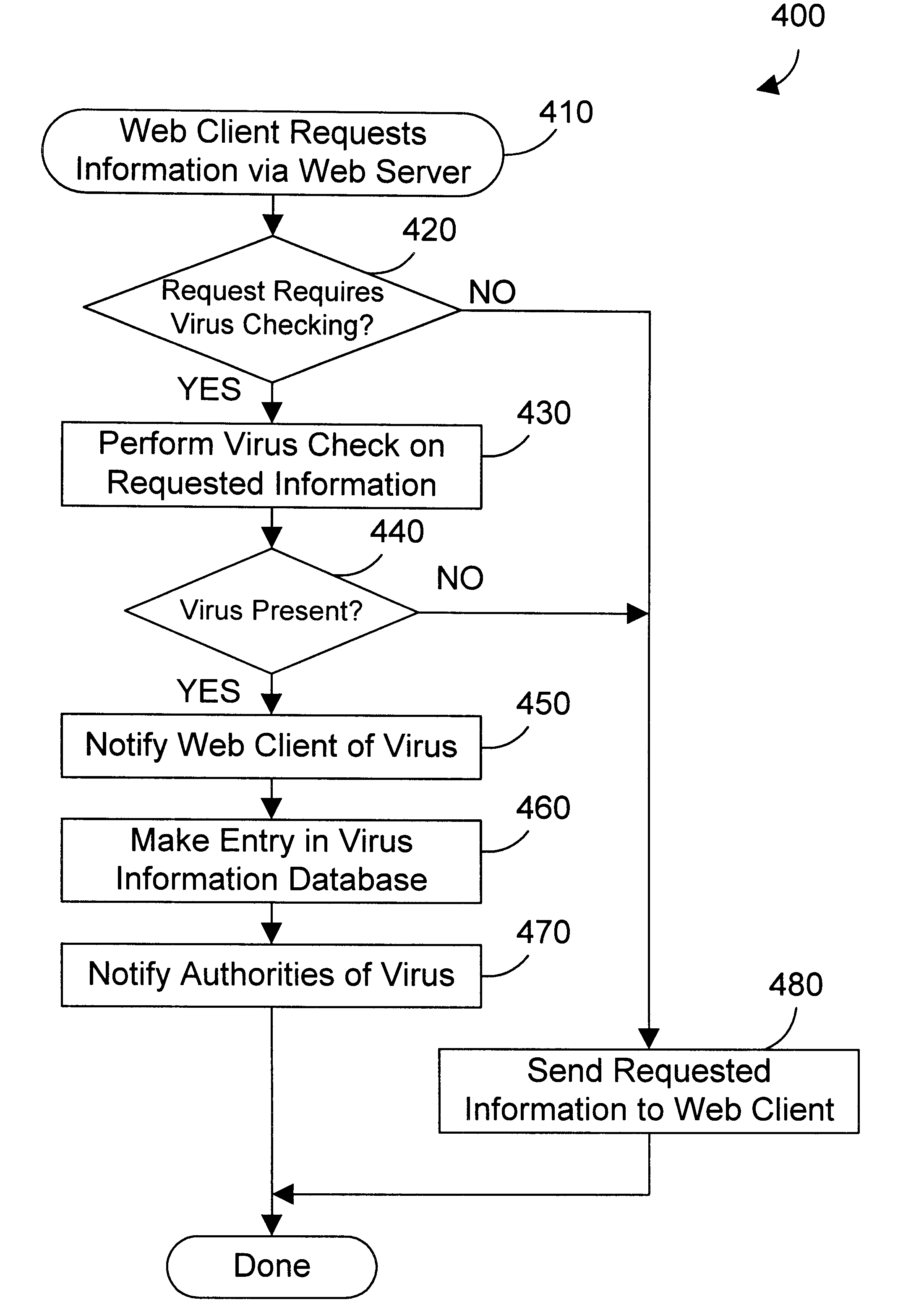
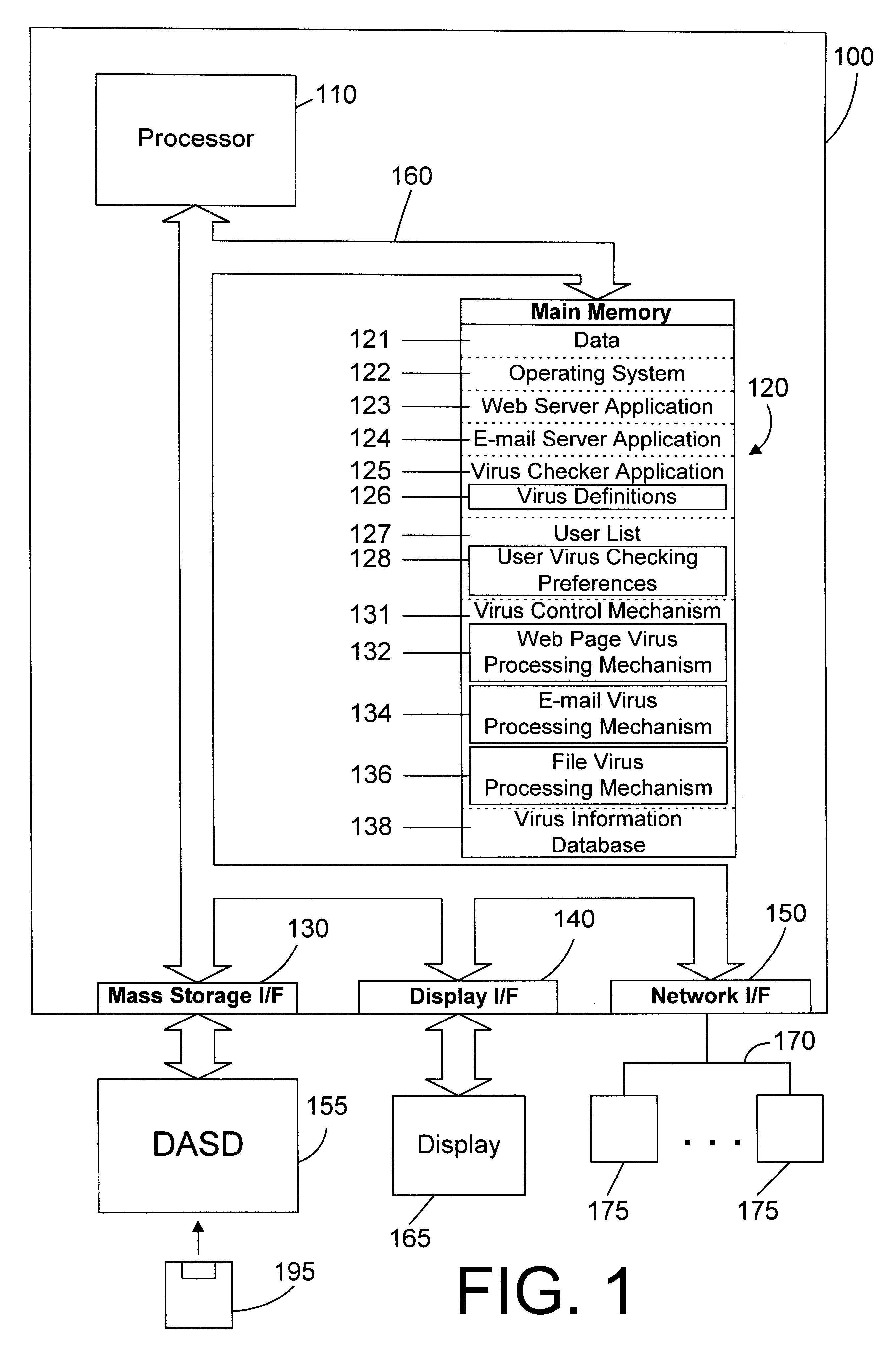
Web server apparatus and method for virus checking
InactiveUS6785732B1Eliminate needPrevent proliferationMemory loss protectionDigital data processing detailsWeb serviceUniform resource locator
A web server computer system includes a virus checker and mechanisms for checking e-mails and their attachments, downloaded files, and web sites for possible viruses. When an e-mail message contains a detected virus, the message is discarded, and both the sender and recipient are informed via e-mail that the message contained a virus. When an e-mail attachment contains a detected virus, the attachment is deleted, and the e-mail message without the attachment is sent to the web client, along with a message explaining that the e-mail message had an attachment that was automatically deleted because it had a virus. When a downloaded file contains a virus, the downloaded file is deleted, and an error message is sent to the web client to inform the web client that the requested file had a virus. When a requested web site (i.e., Uniform Resource Locator (or URL)) has been labeled as a source for a known virus, a message is sent to the web client stating that a virus may have been downloaded from that URL. In addition, if the requested URL has not been labeled as a source for a known virus, but it contains links that have been so labeled, the web page is processed before being sent to the user to identify those potentially dangerous links. In this manner a web server can perform virus checking of different types of information real-time as the information is requested by a web client. In addition, a web client may also request that the server perform virus checking on a particular drive on the web client. If this case, the web server may receive information from the web client drive, scan the information for viruses, and inform the web client whether any viruses were found. In the alternative, the web server may download a client virus checker to the web client and cause the client virus checker to be run on the web client. The preferred embodiments thus allow a virus checker on a web server to dynamically scan incoming data, and to scan web clients coupled to the web server, thereby eliminating the need for virus checking software to be installed on each web client.
Owner:FINJAN BLUE INC
System and method of securing web applications across an enterprise
ActiveUS20080034425A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
A system and method for protection of Web based applications are described. The techniques described provide an enterprise wide approach to preventing attacks of Web based applications. Individual computer networks within the enterprise monitor network traffic to identify anomalous traffic. The anomalous traffic can be identified by comparing the traffic to a profile of acceptable user traffic when interacting with the application. The anomalous traffic, or security events, identified at the individual computer networks are communicated to a central security manager. The central security manager correlates the security events at the individual computer networks to determine if there is an enterprise wide security threat. The central security manager can then communicate instructions to the individual computer networks so as to provide an enterprise wide solution to the threat
Owner:TRUSTWAVE HOLDINGS
System and method for managing malware protection on mobile devices
ActiveUS20070240220A1Suitable for useReliable detectionMemory loss protectionError detection/correctionLimited accessFeature set
A system and method for detecting malware on a limited access mobile platform in a mobile network. The system and method uses one or more feature sets that describe various non-executable portions of malware-infected and malware-free applications, and compares a application on the limited access mobile platform to the features sets. A match of the features in a suspect application to one of the feature sets provides an indication as to whether the suspect application is malware-infected or malware-free.
Owner:PULSE SECURE
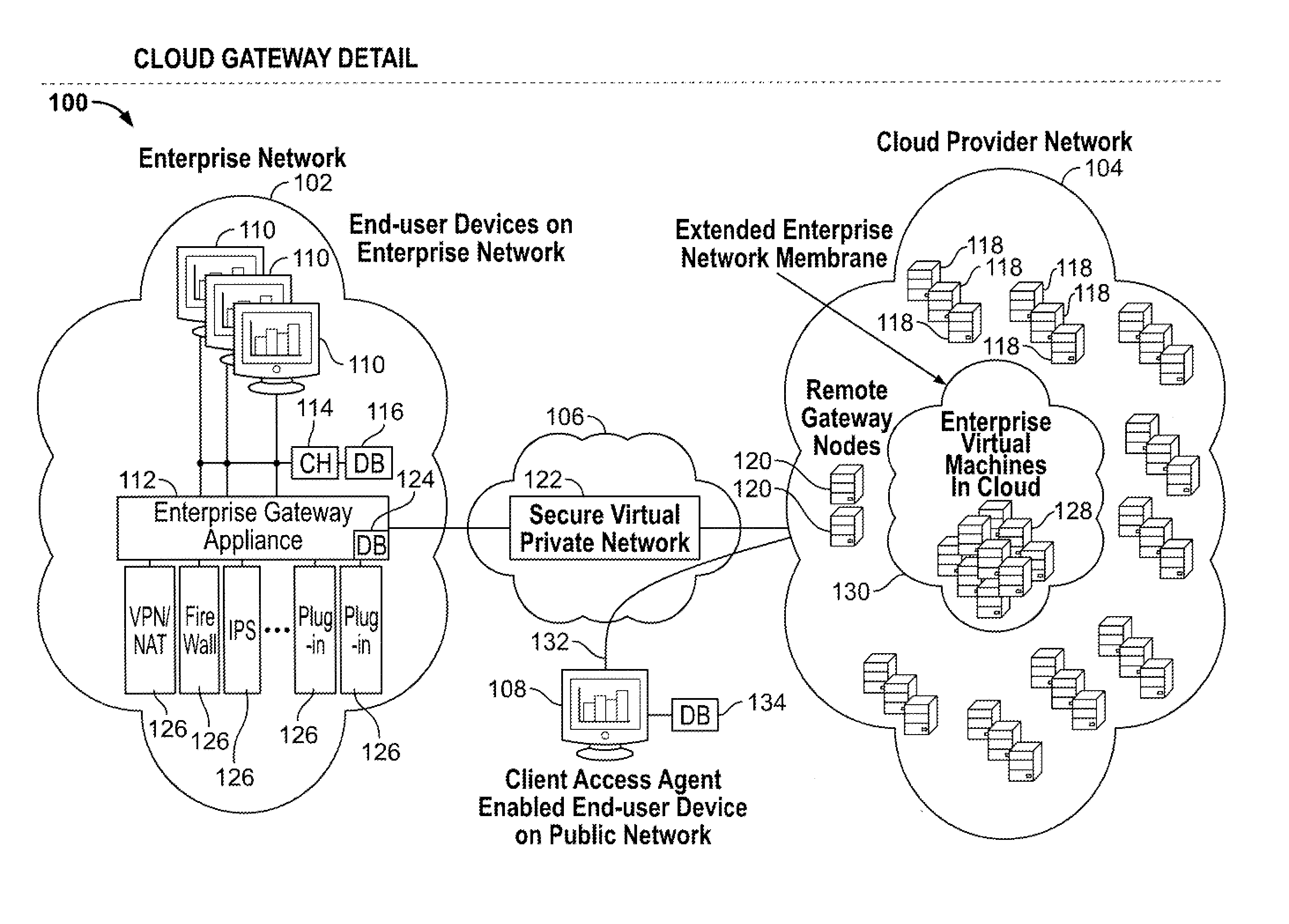
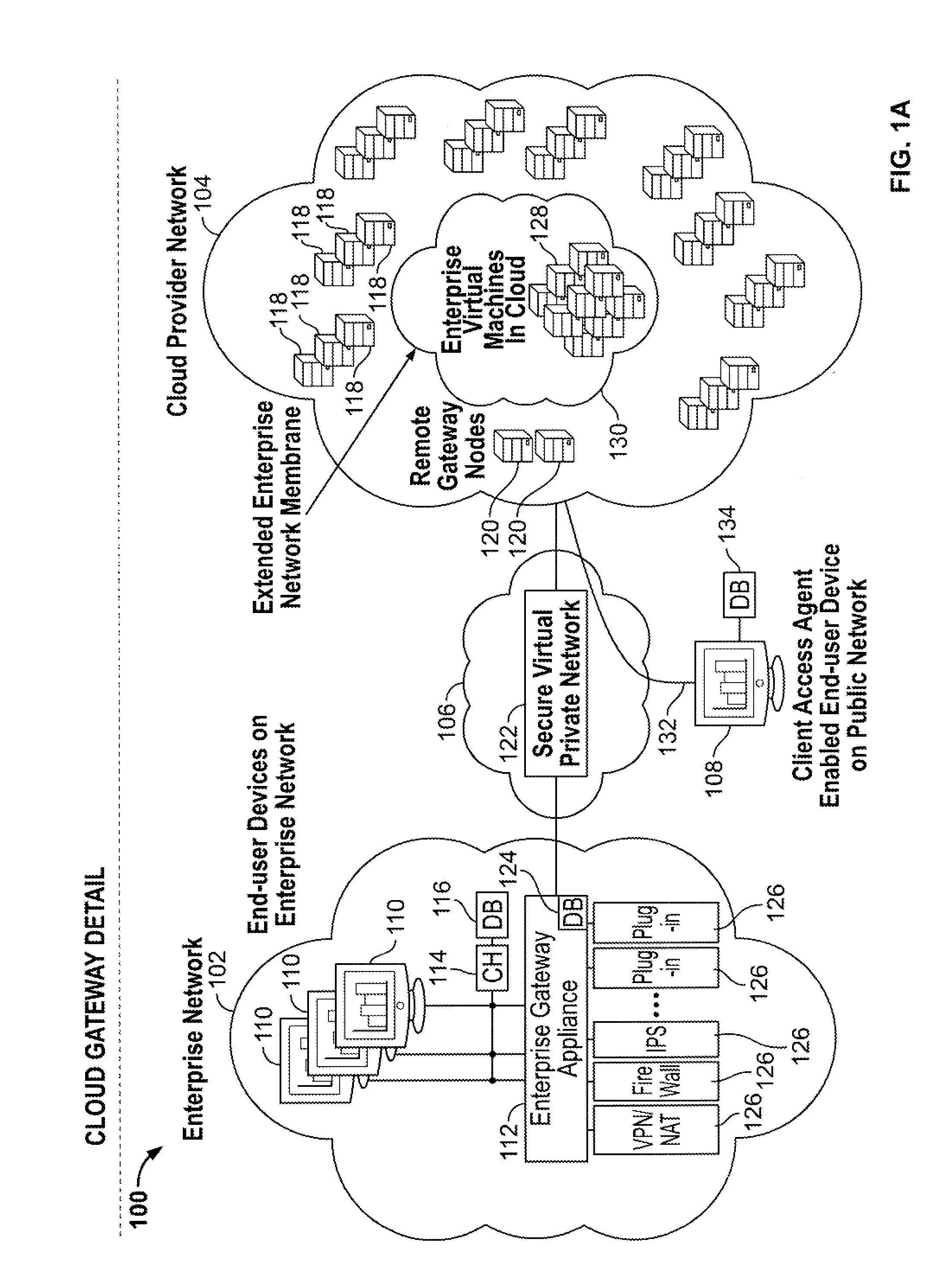
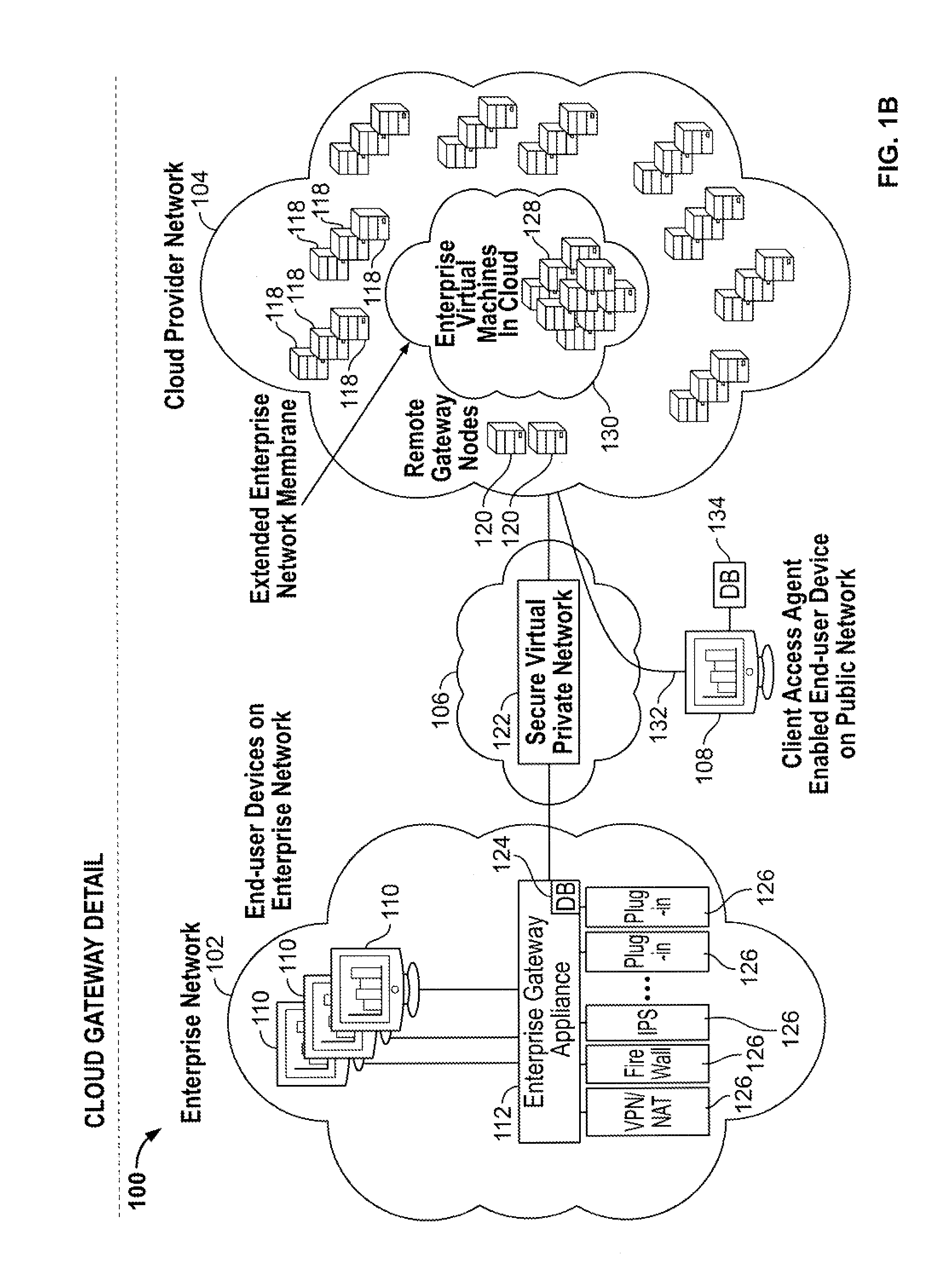
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS20100027552A1Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com