Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
118826results about "Neural architectures" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
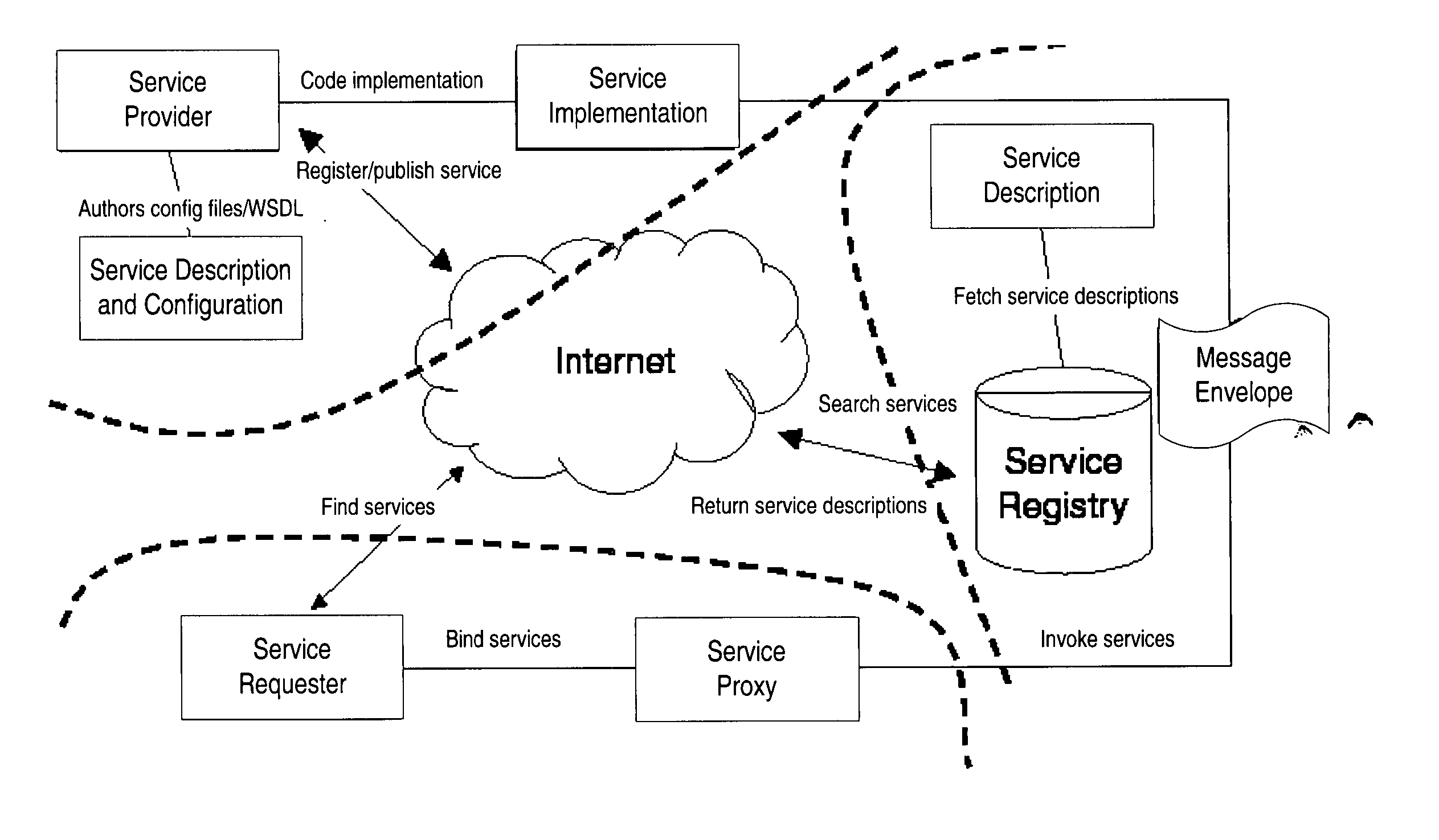
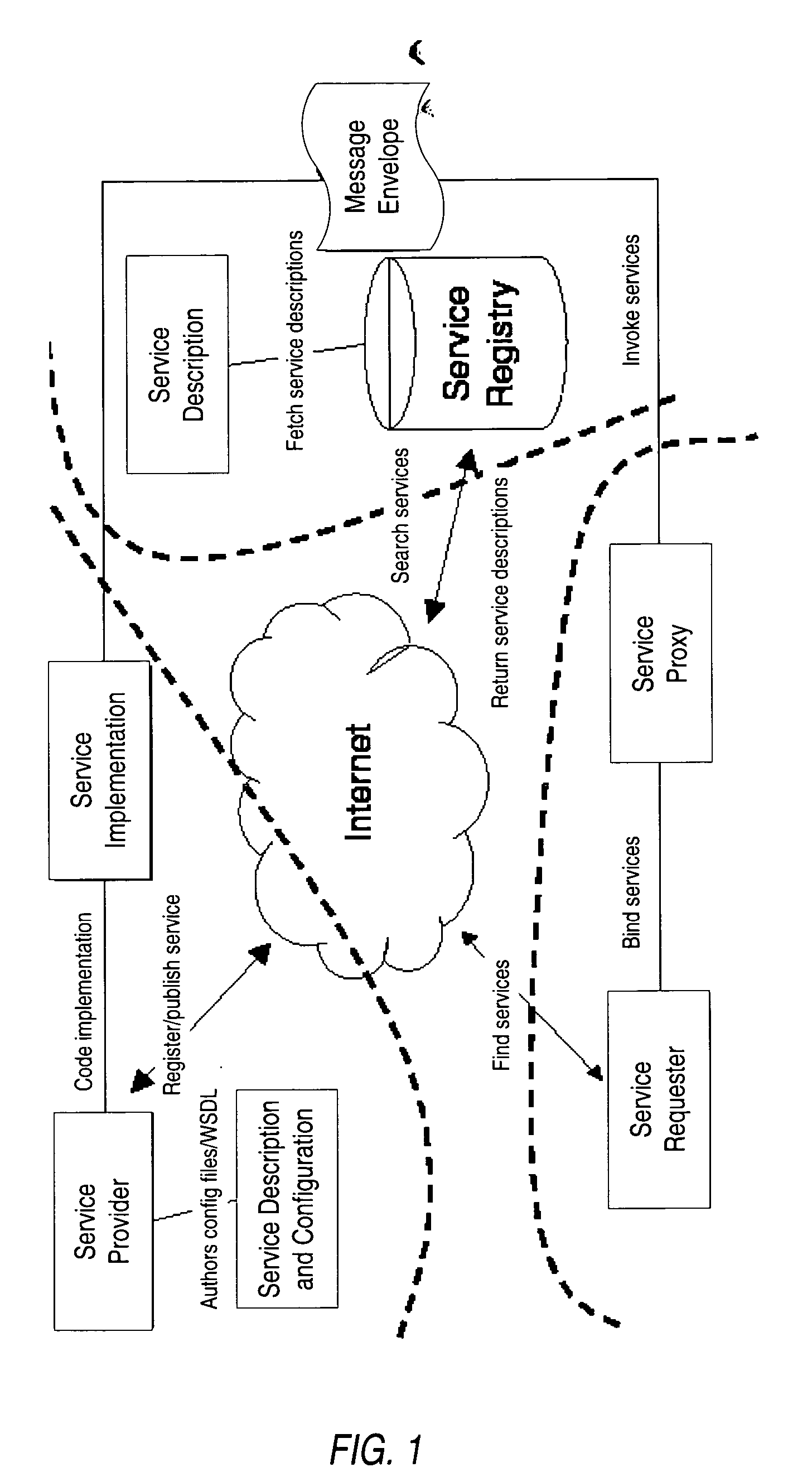
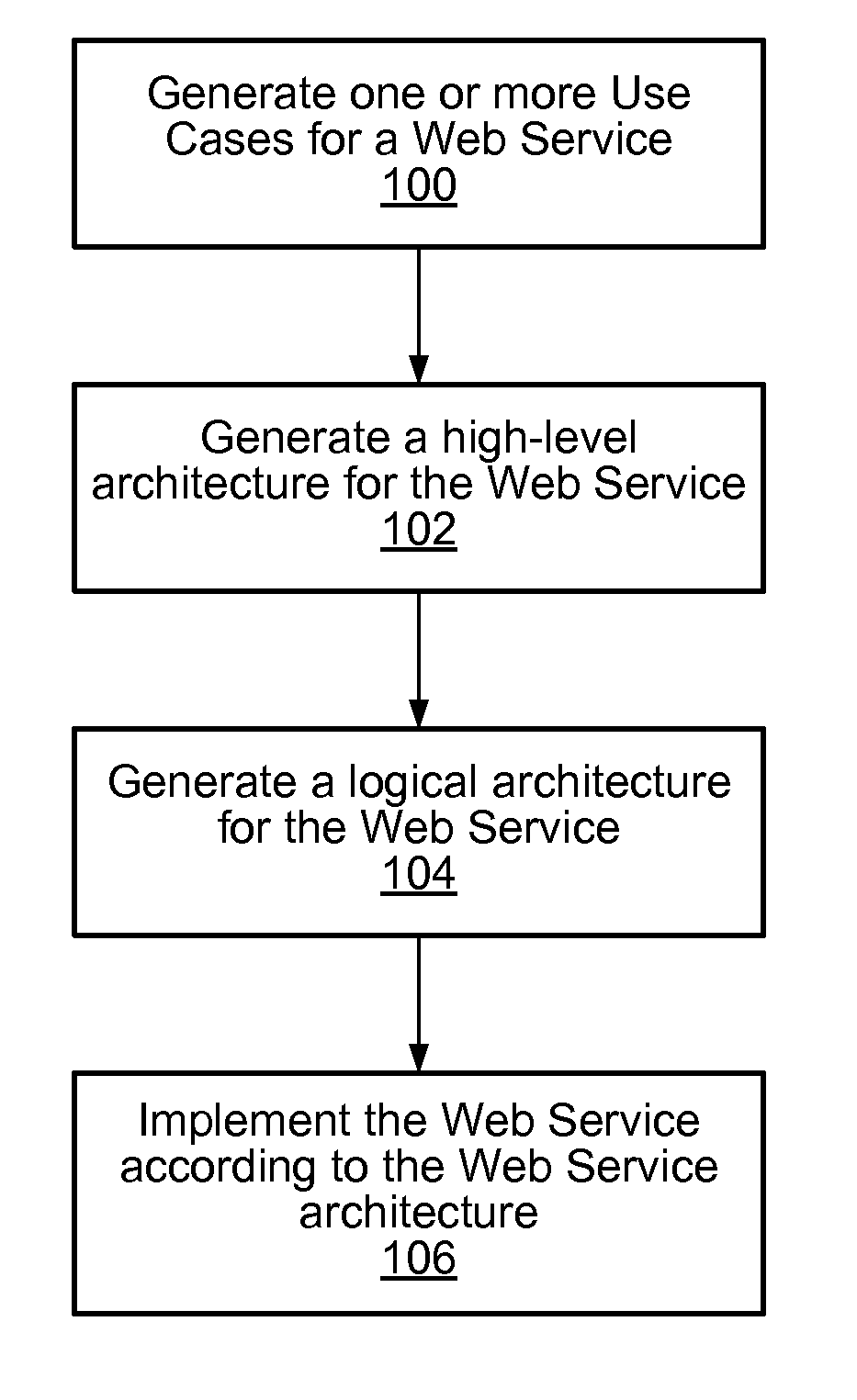
Structured methodology and design patterns for web services
ActiveUS20050044197A1Multiple digital computer combinationsDigital dataQuality of serviceBusiness-to-business
System and method for designing and implementing Web Services according to a structured methodology and design patterns. Embodiments may incorporate a structured methodology, best practices and design patterns that address reliability, availability and scalability of Web Services architecture. Embodiments may provide mechanisms for integrating heterogeneous technology components into Web Services. Embodiments may provide a vendor-independent Web Services architecture framework and reusable Web Services design patterns, which may be used in creating end-to-end solutions based on past experience and best practices. Embodiments may include design patterns and best practices for delivering Web Services solutions with Quality of Services. One embodiment may provide a Business-to-Business Integration (B2Bi) integration framework for Web Services. Embodiments may provide a Web Security framework and design patterns for designing end-to-end Web Services security.
Owner:ORACLE INT CORP
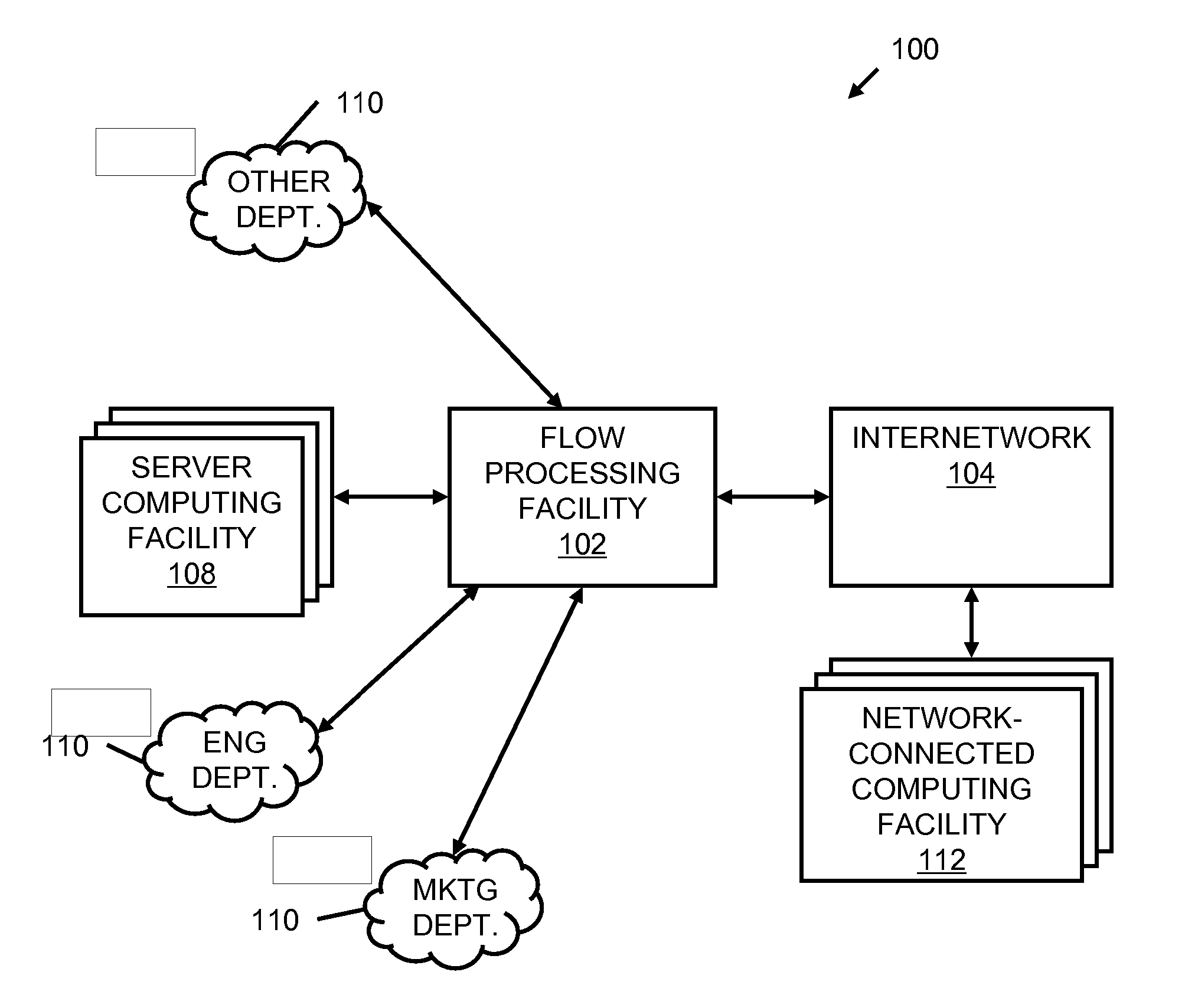
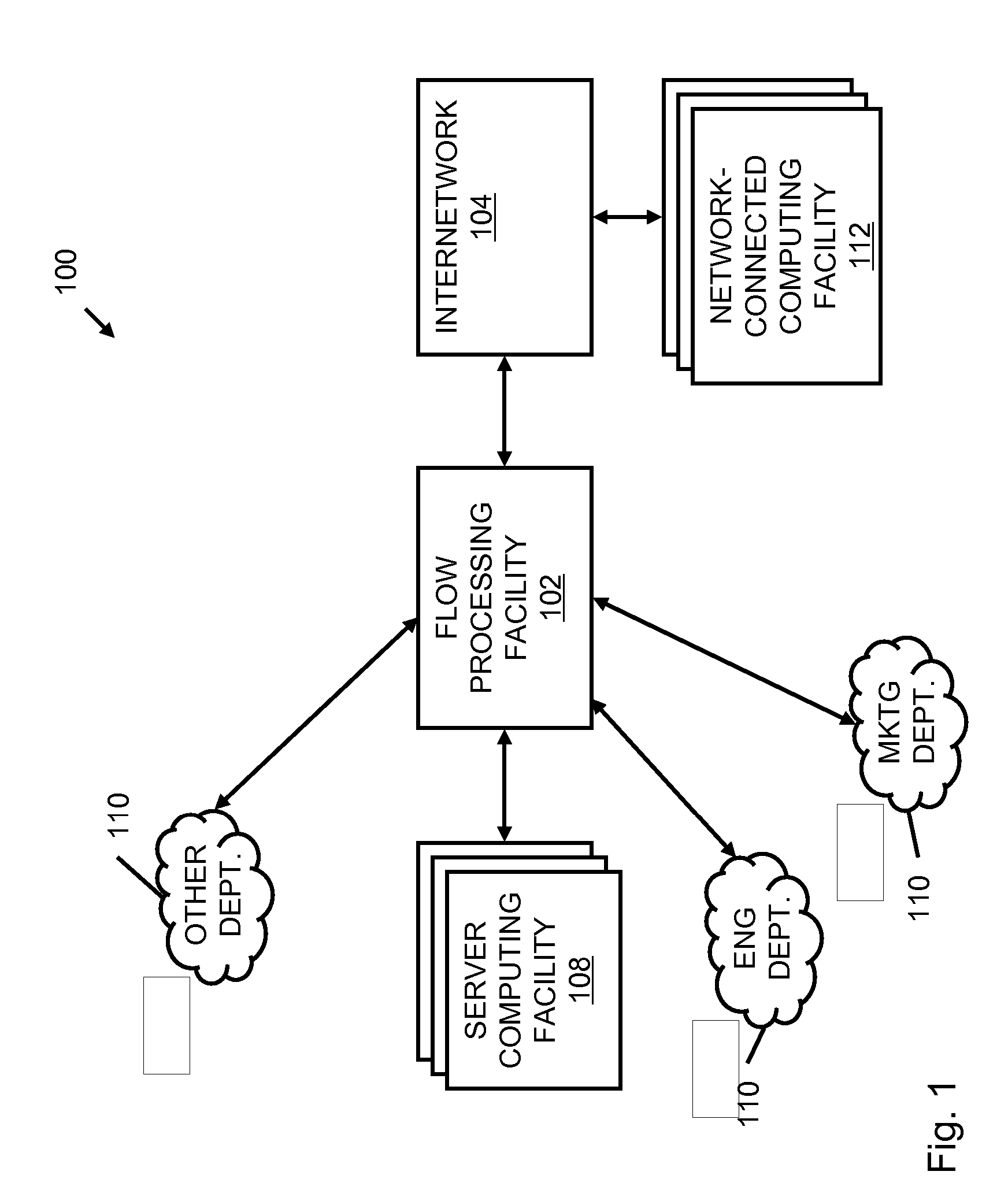
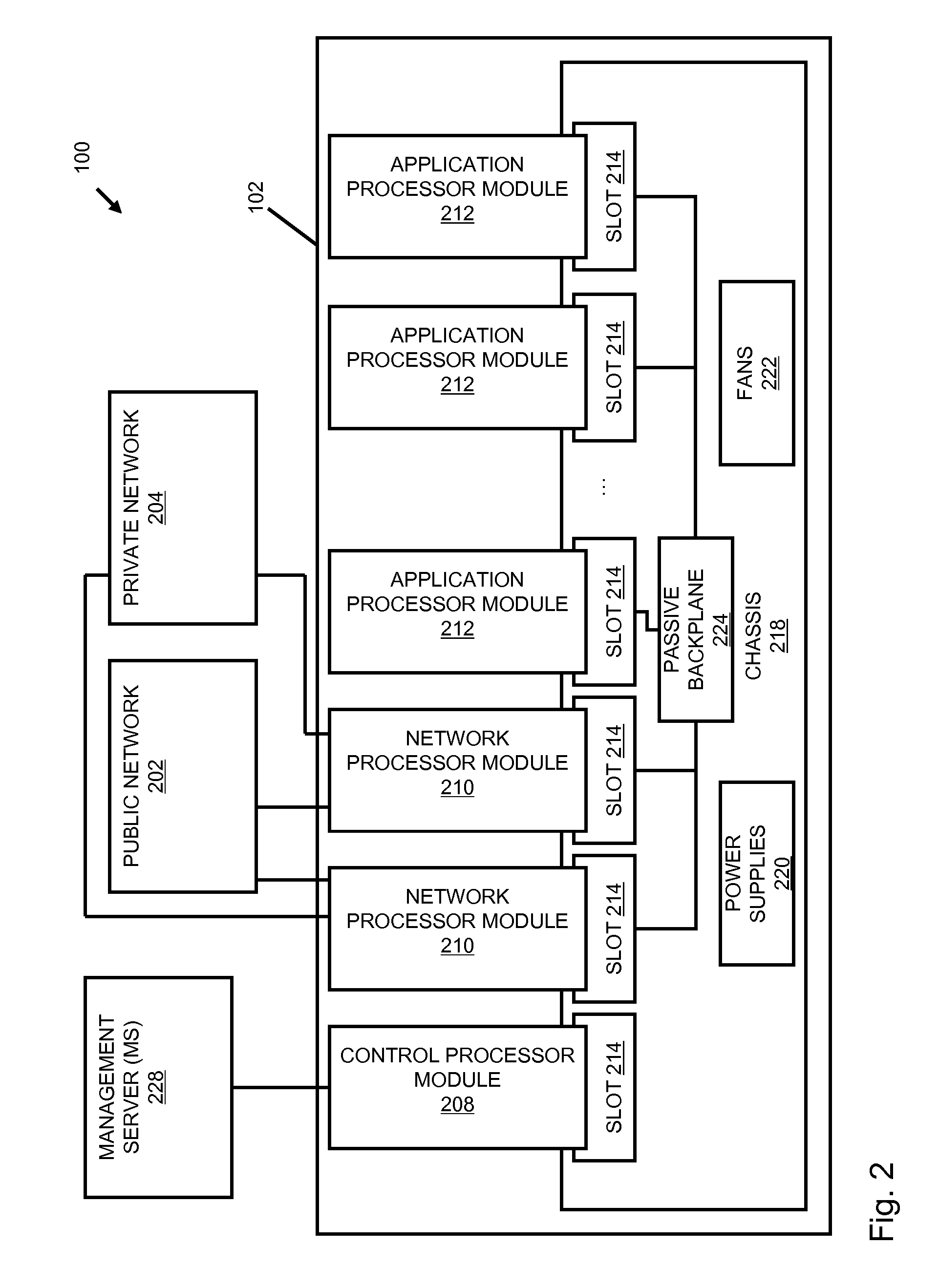
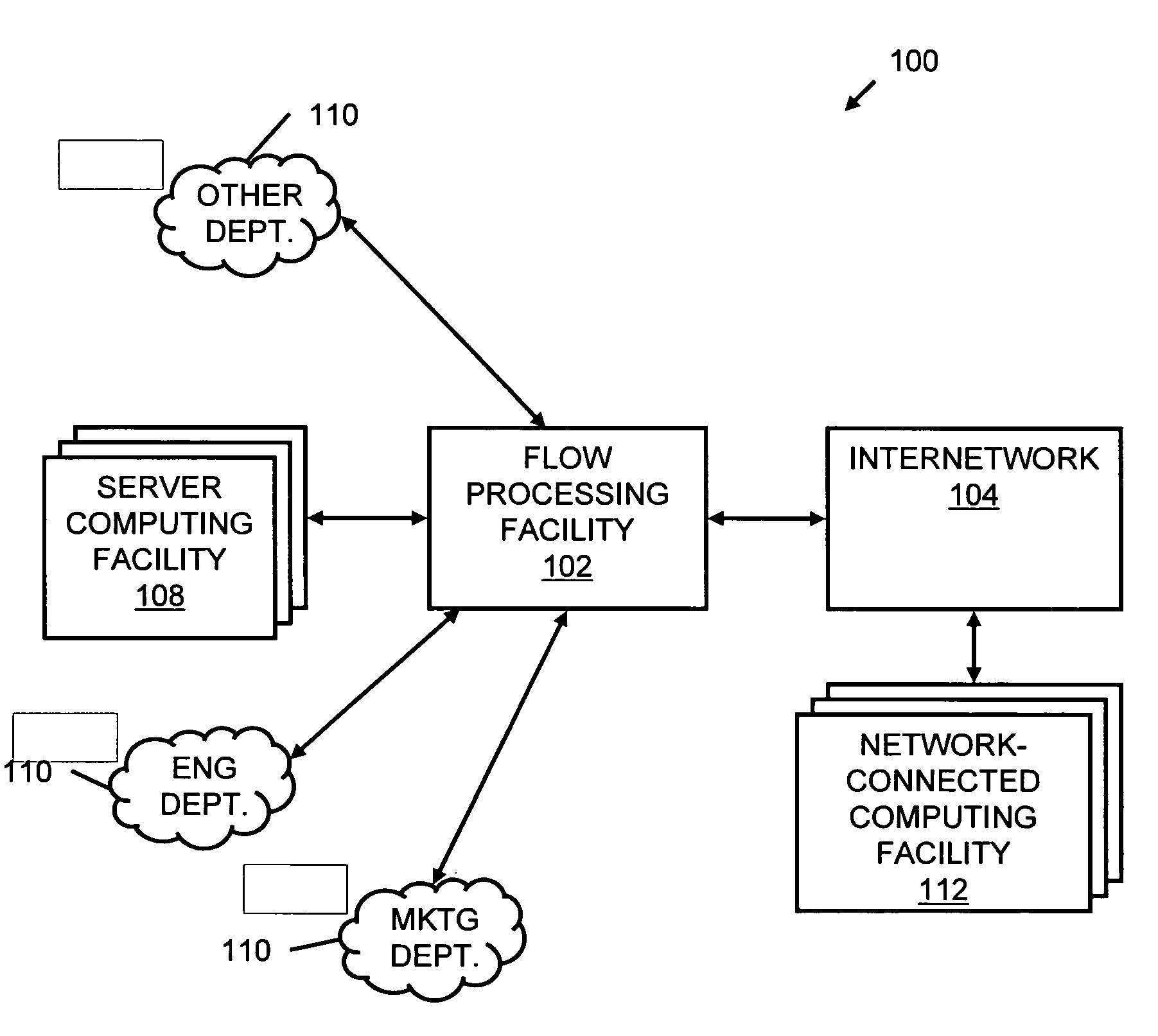
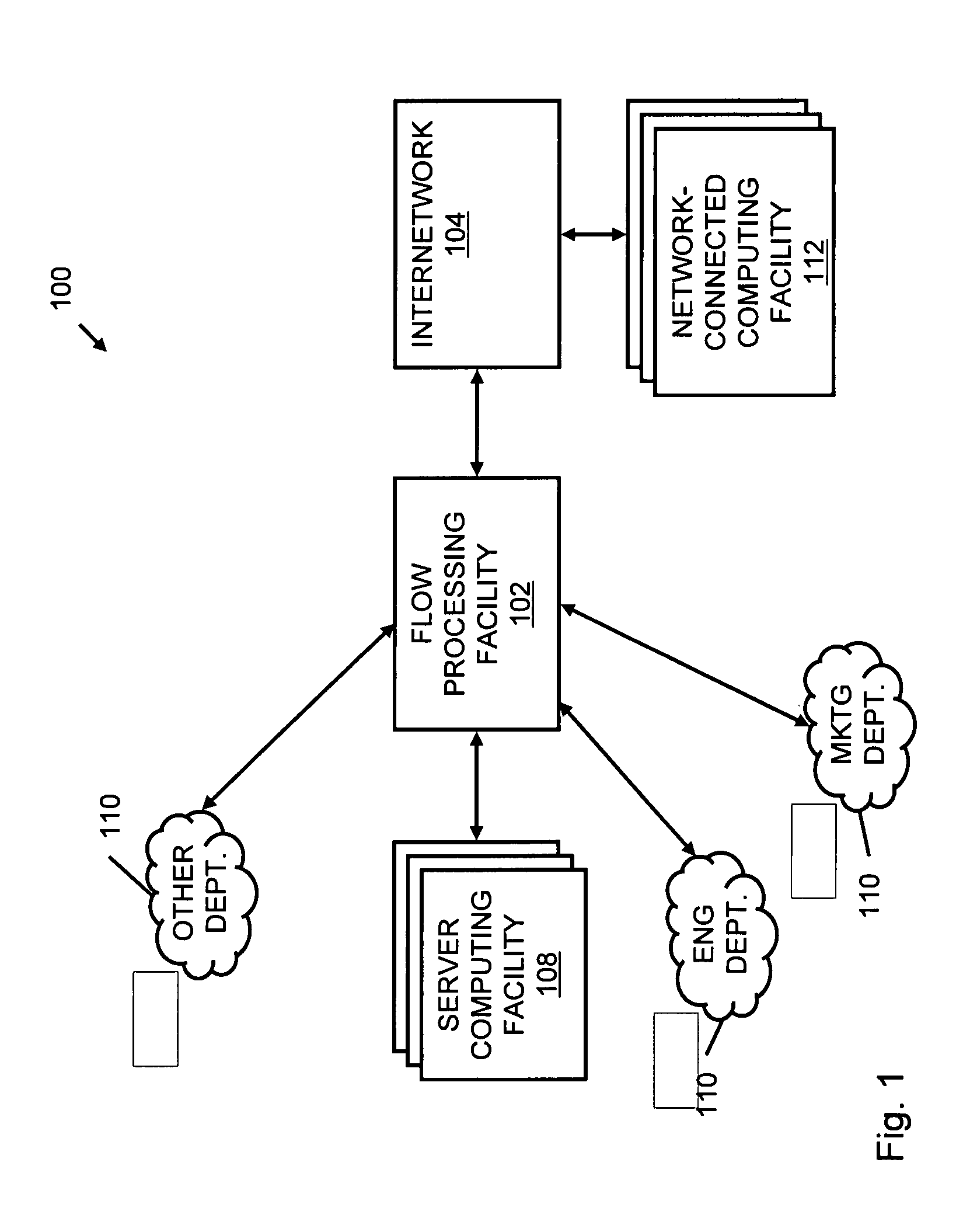
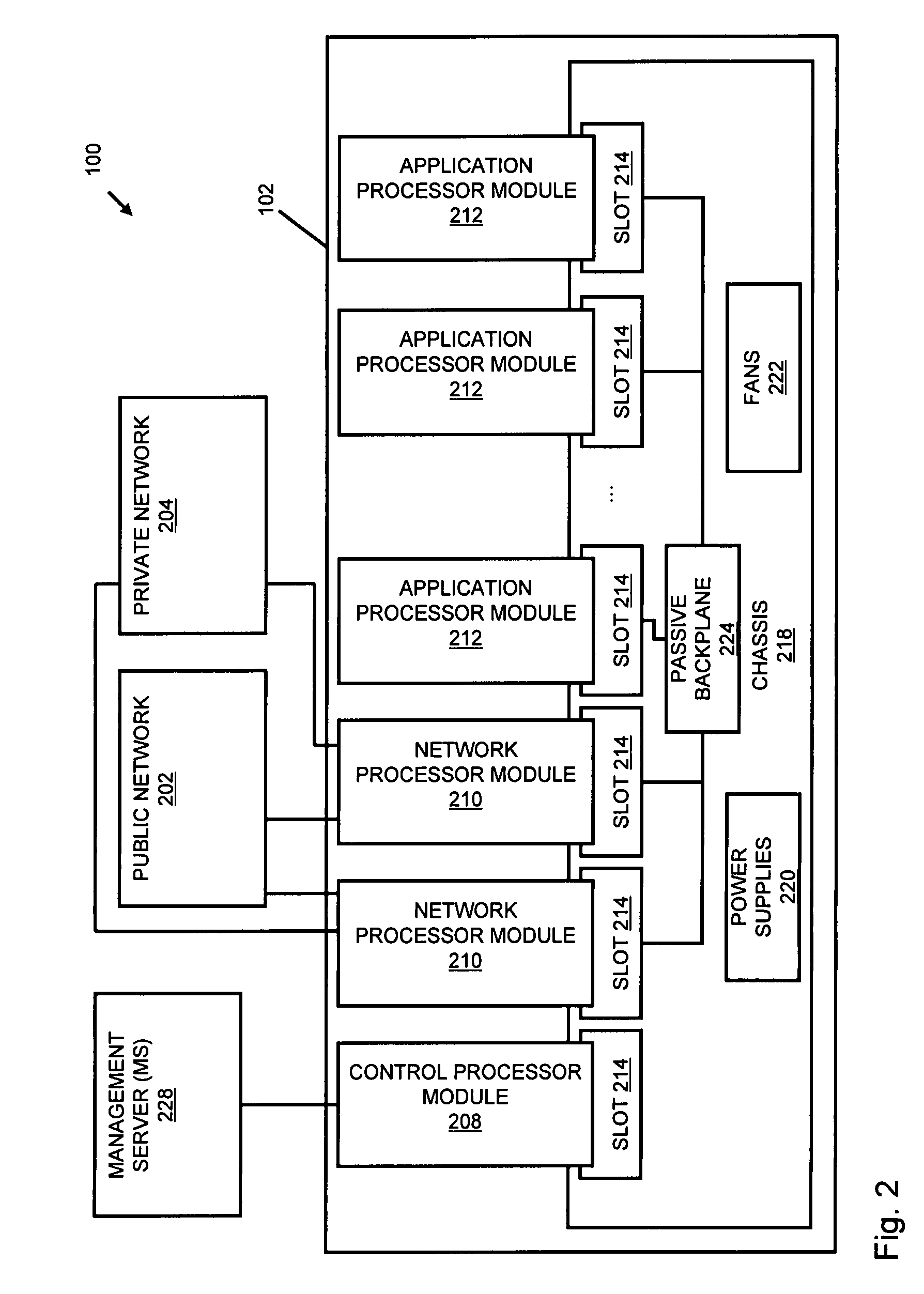
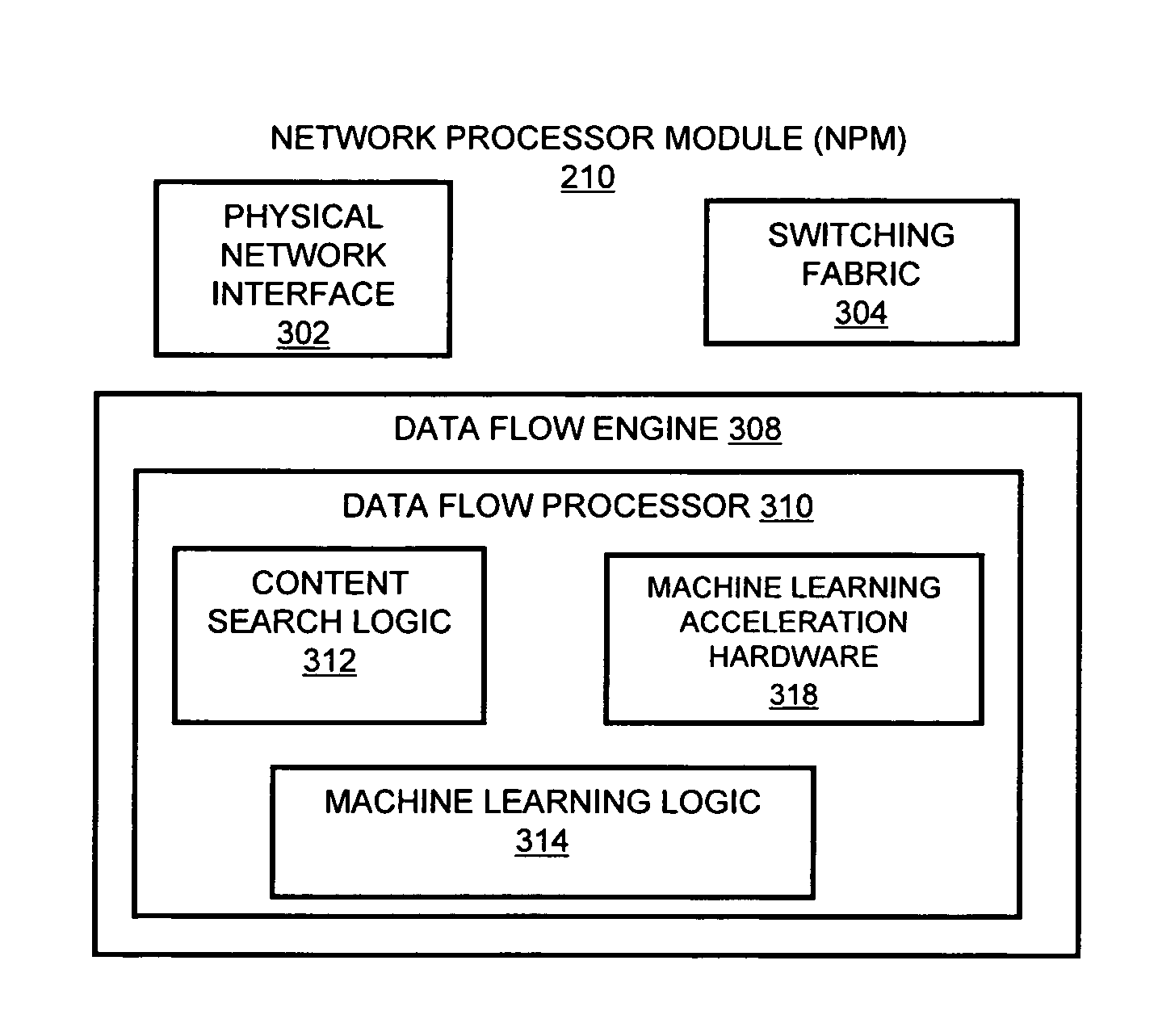
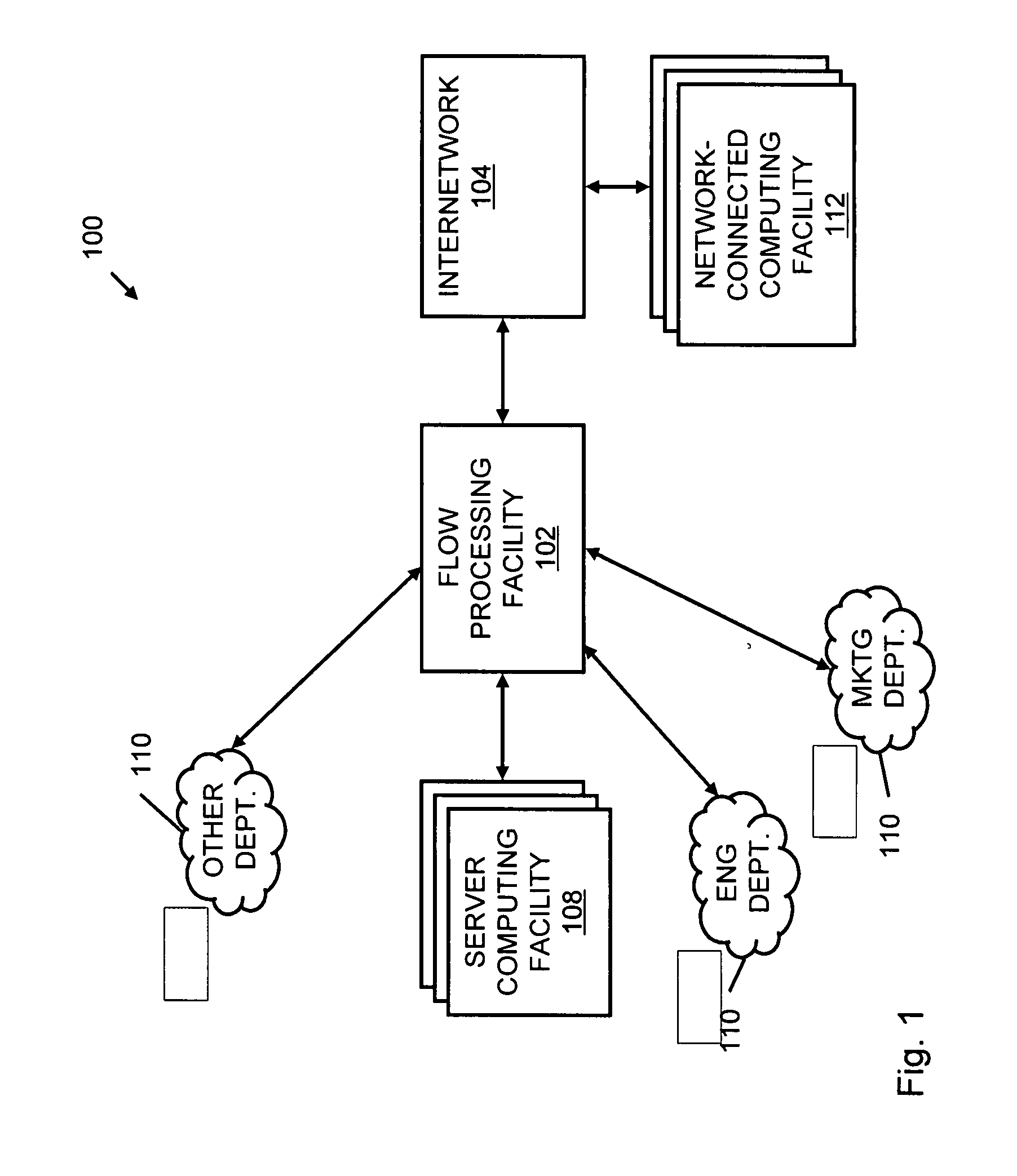
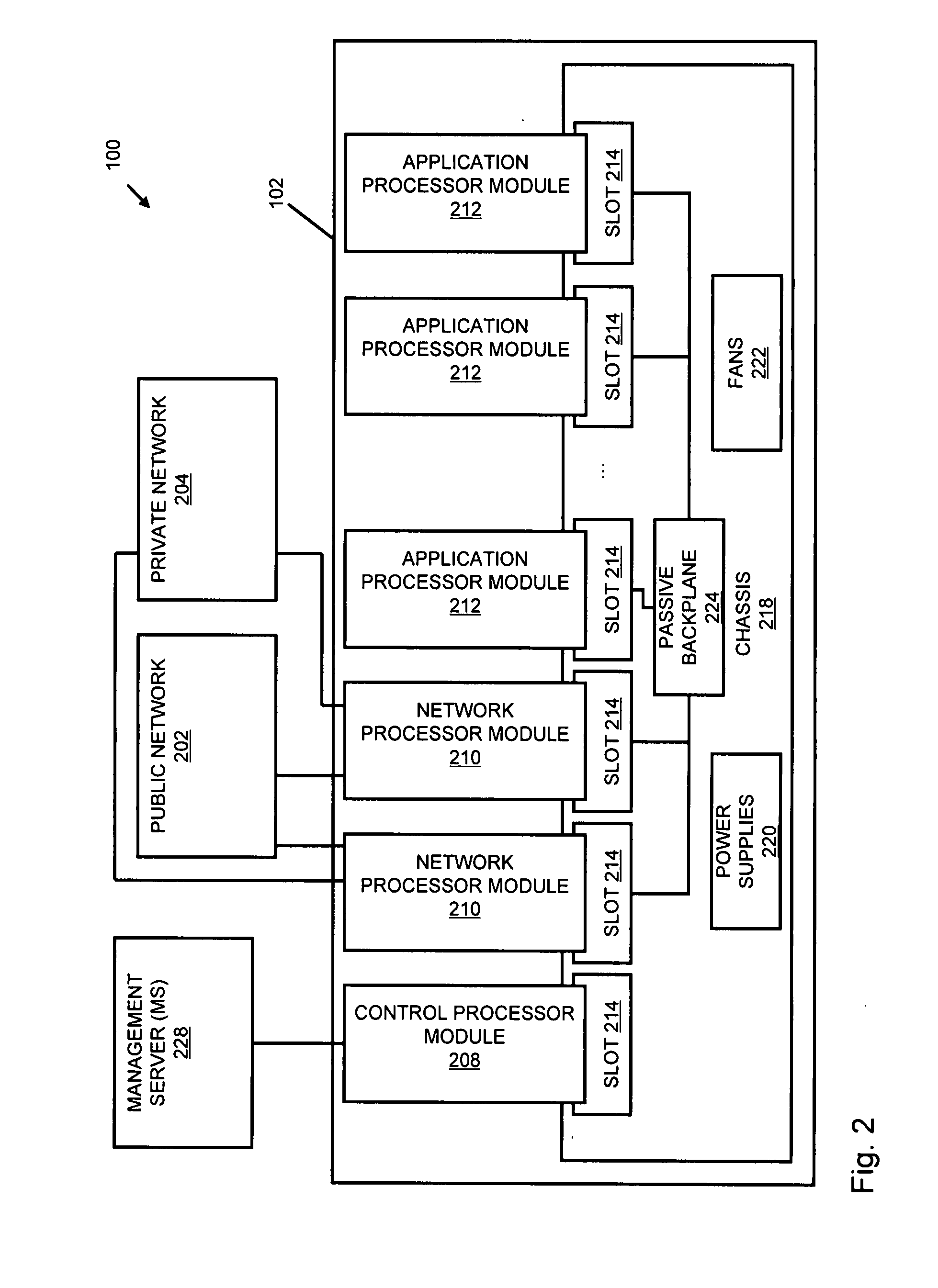
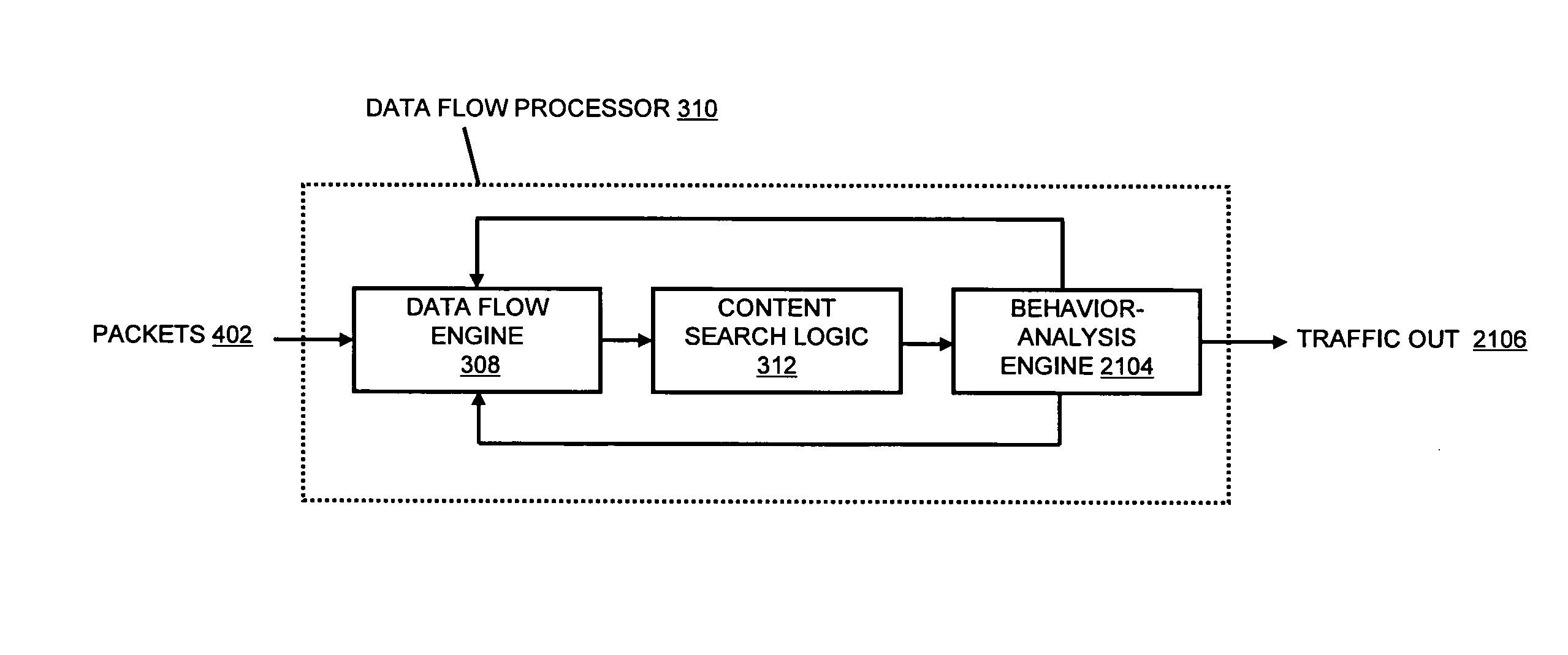
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
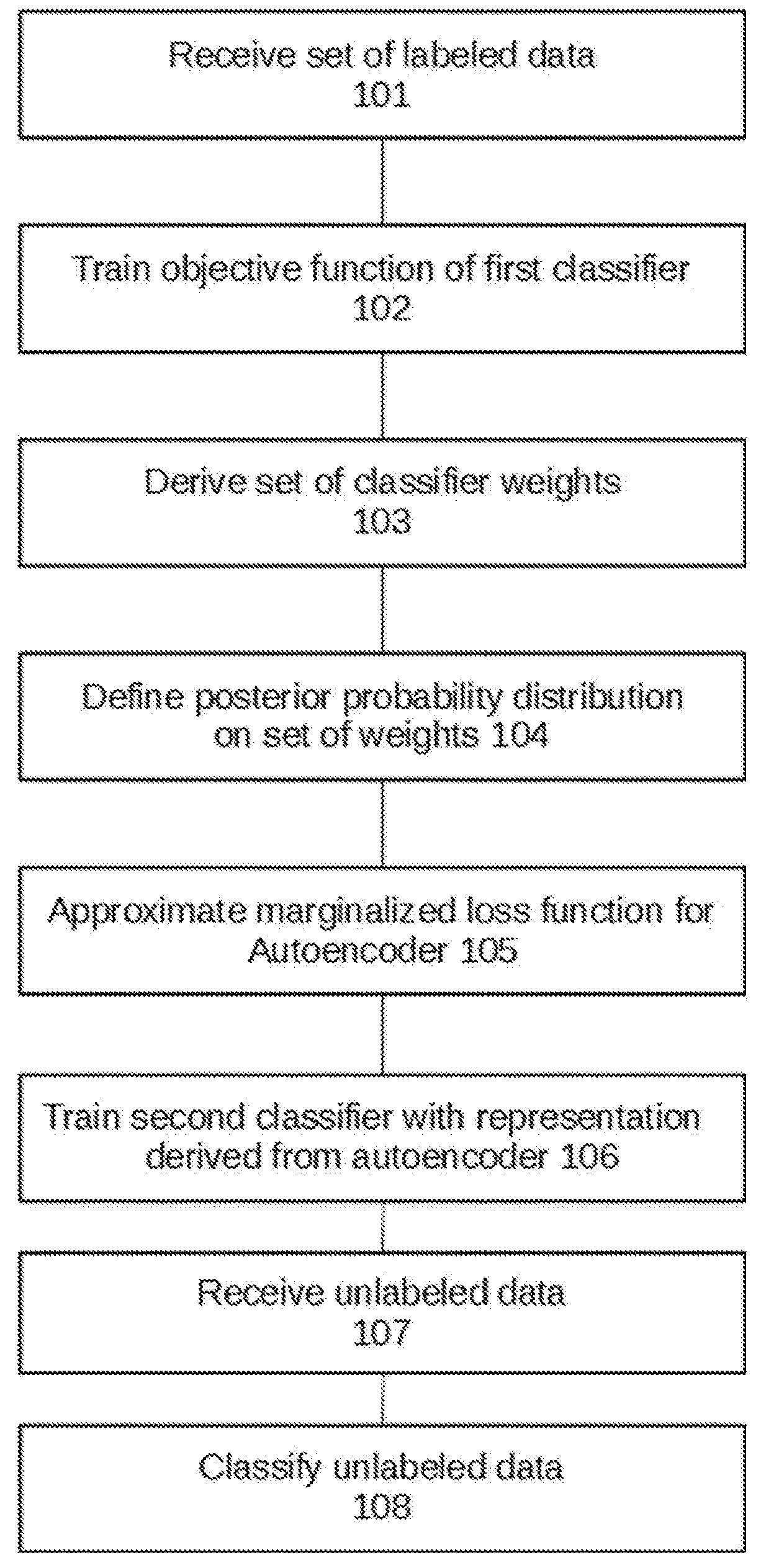
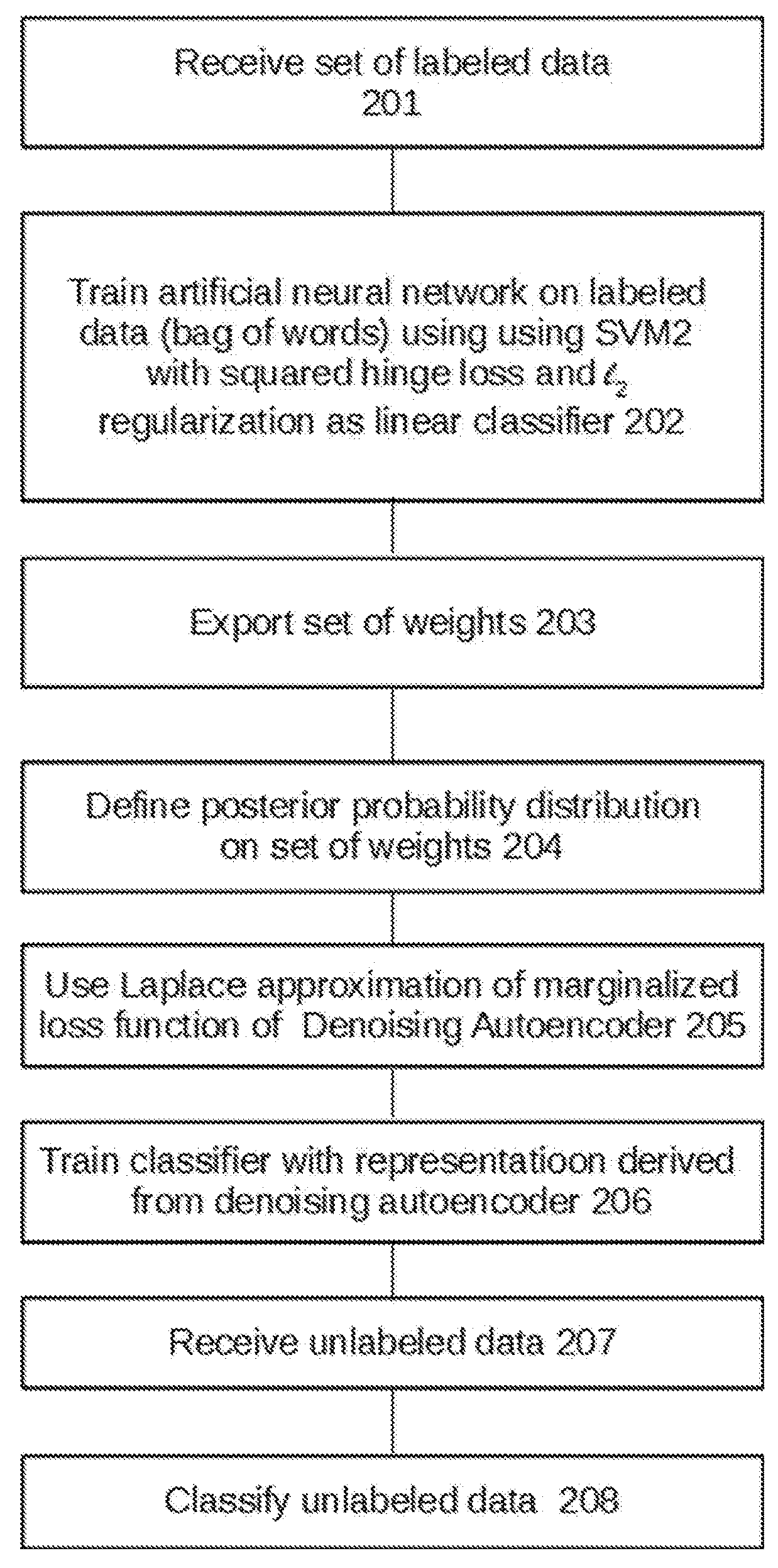
Semisupervised autoencoder for sentiment analysis
ActiveUS20180165554A1Reduce biasImprove performanceMathematical modelsKernel methodsLabeled dataComputer science
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
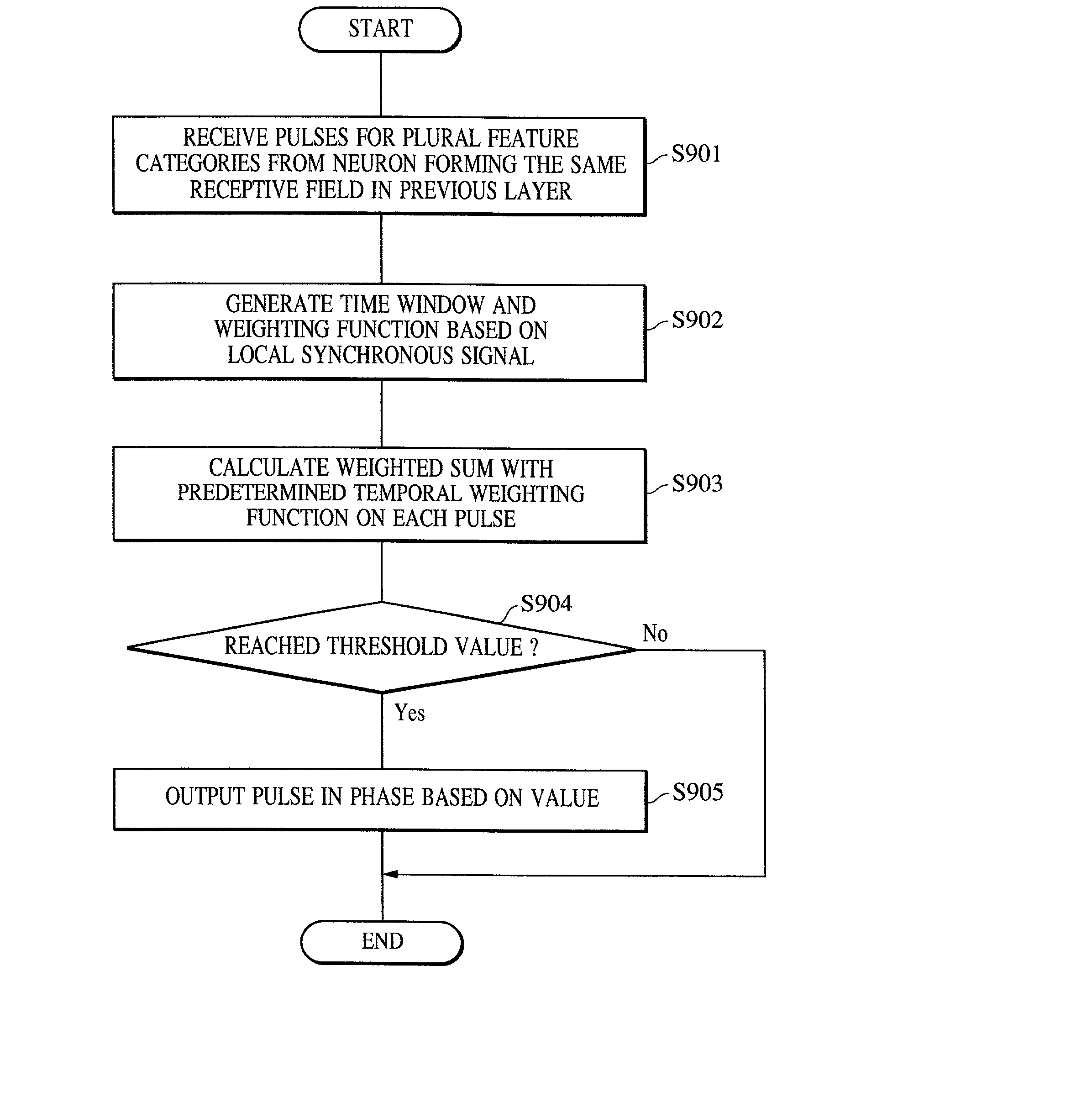
Apparatus and method for detecting or recognizing pattern by employing a plurality of feature detecting elements
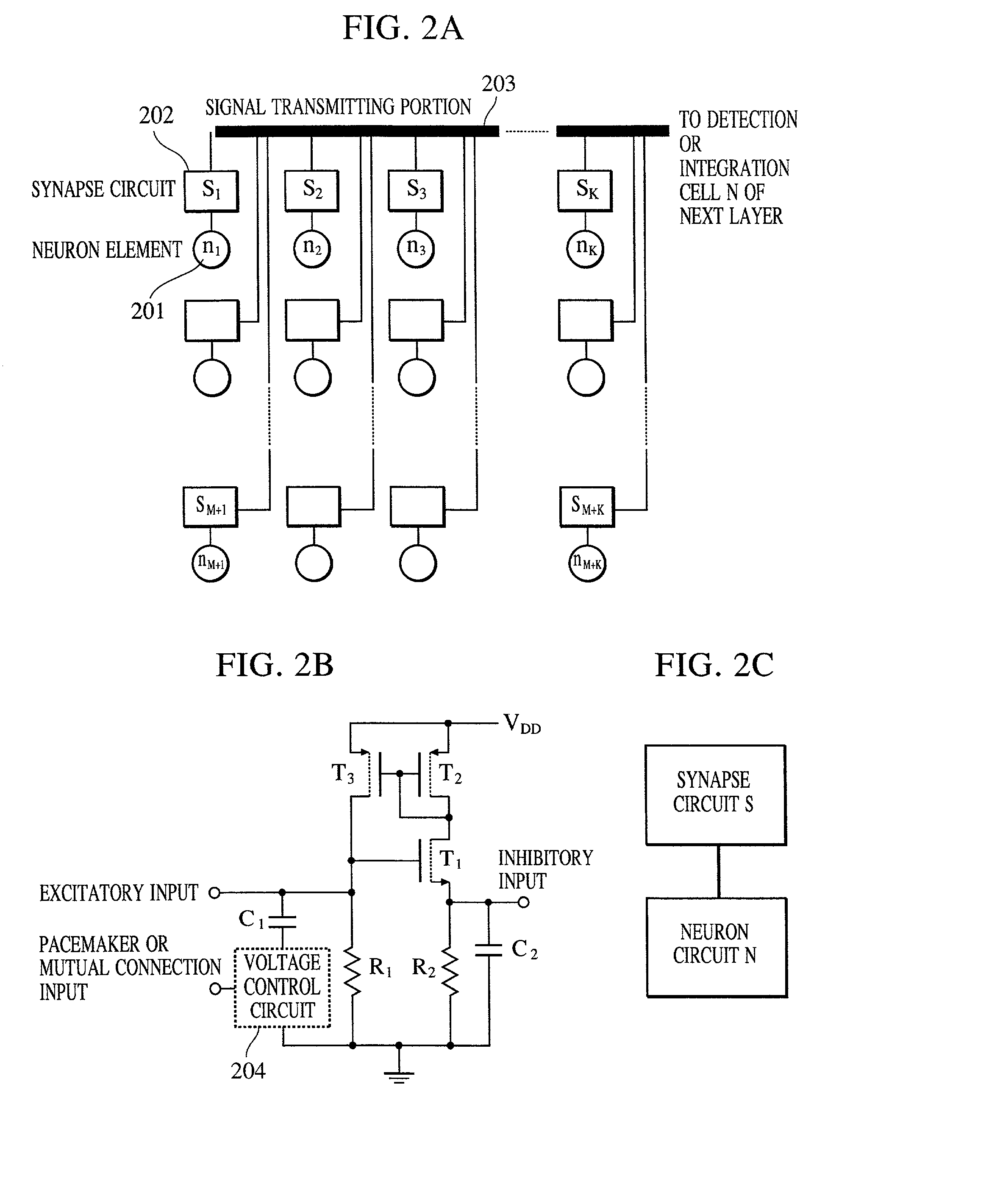
InactiveUS20020038294A1Easy constructionReduce in quantityDigital computer detailsCharacter and pattern recognitionSynapsePattern detection
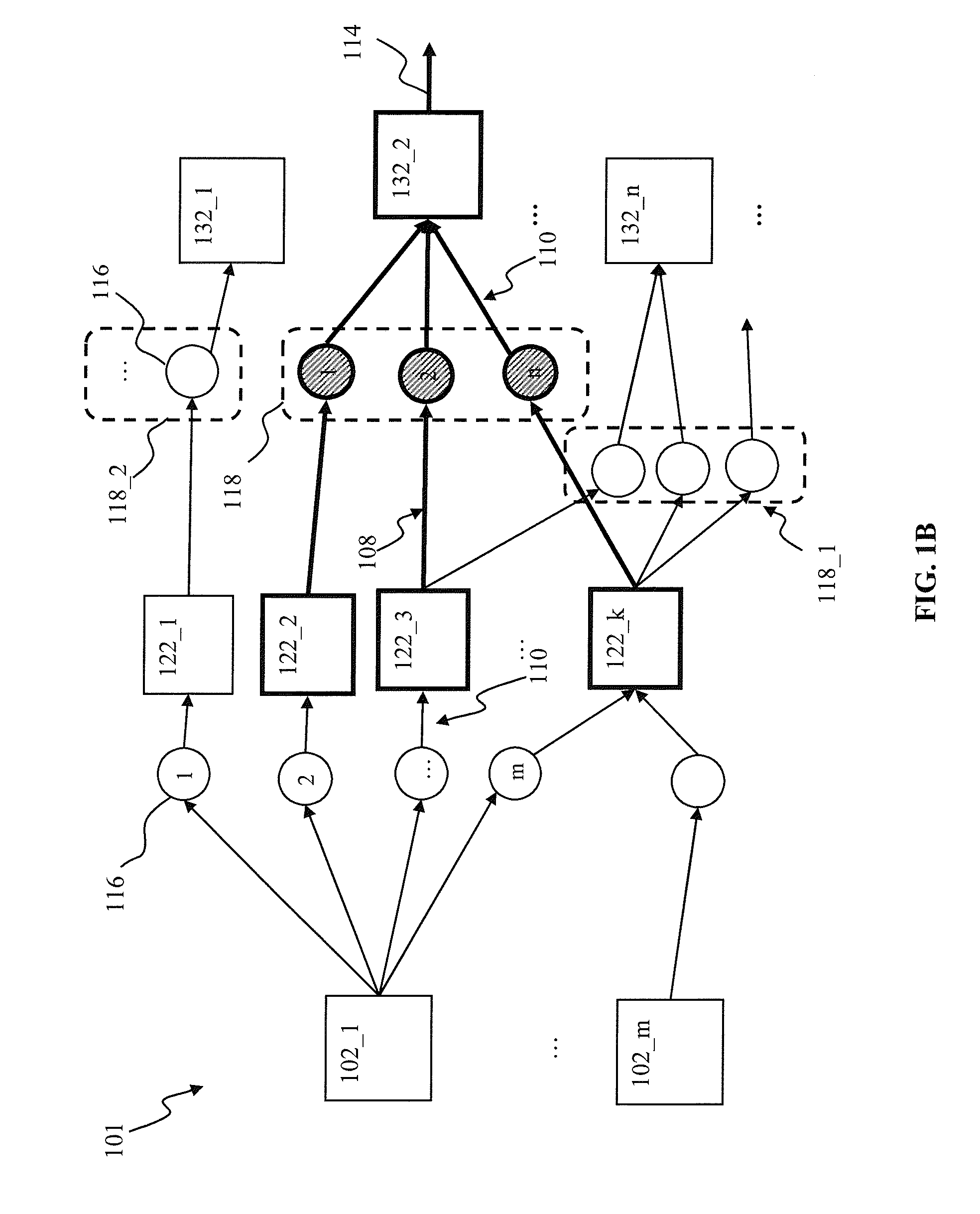
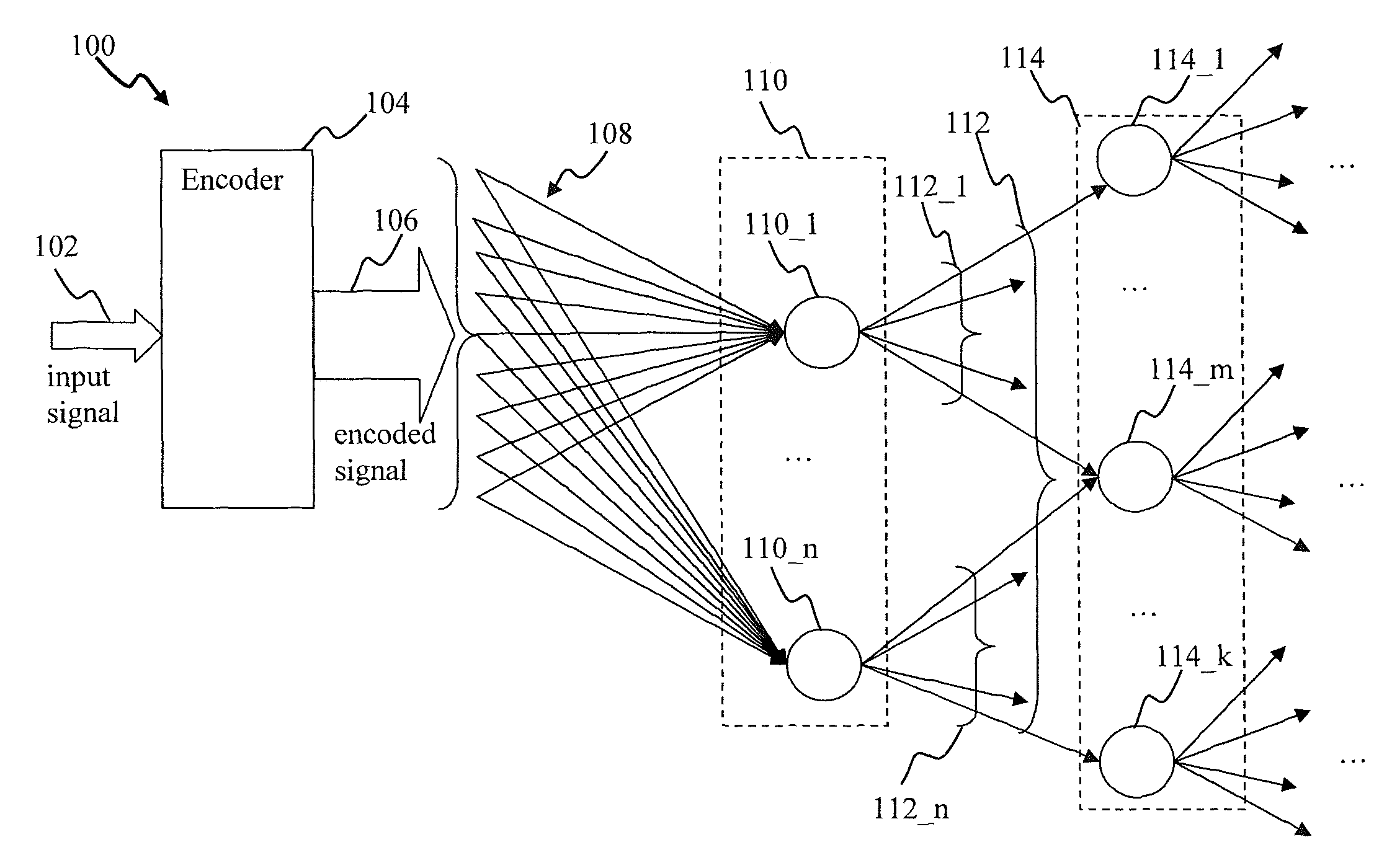
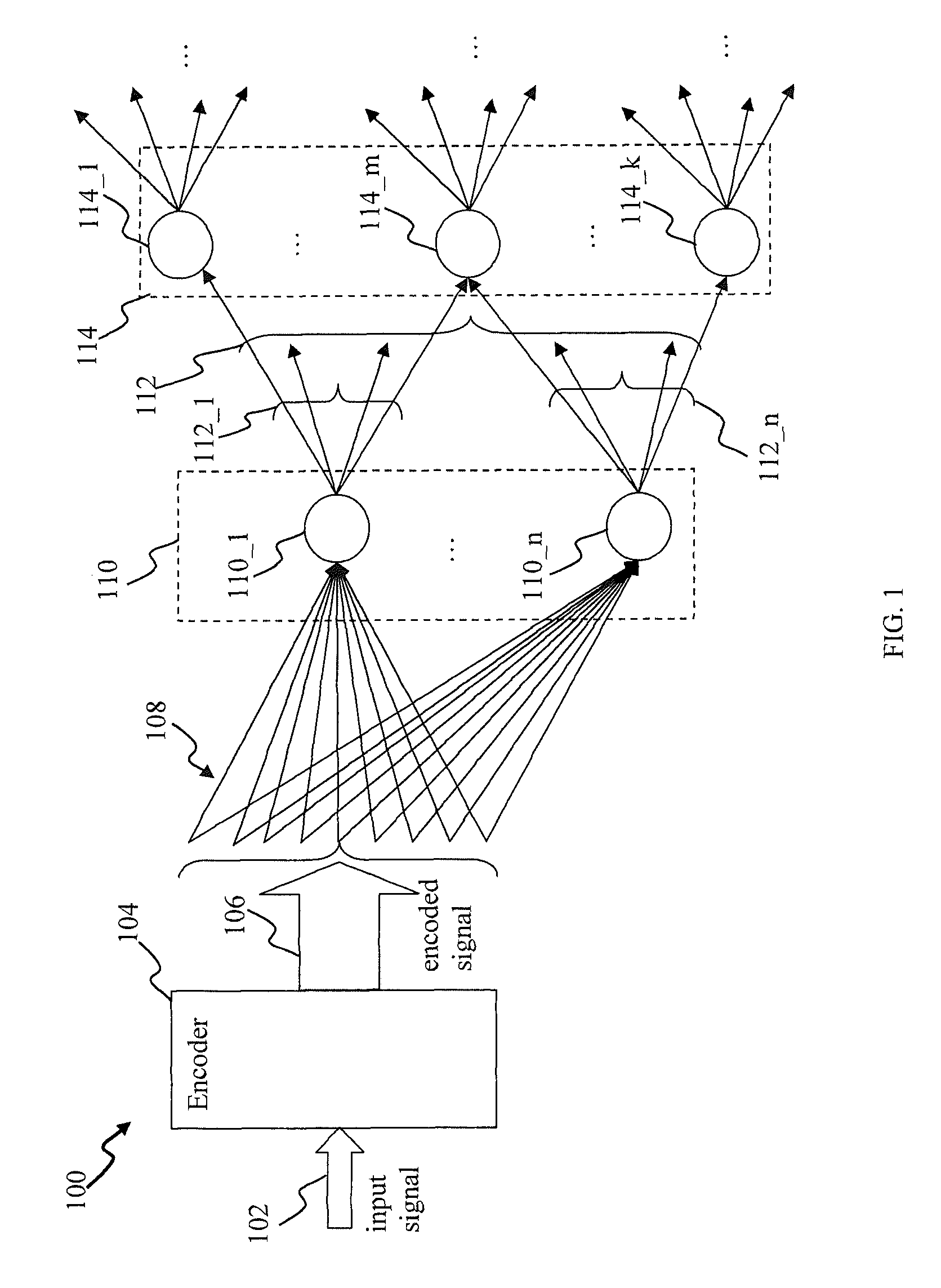
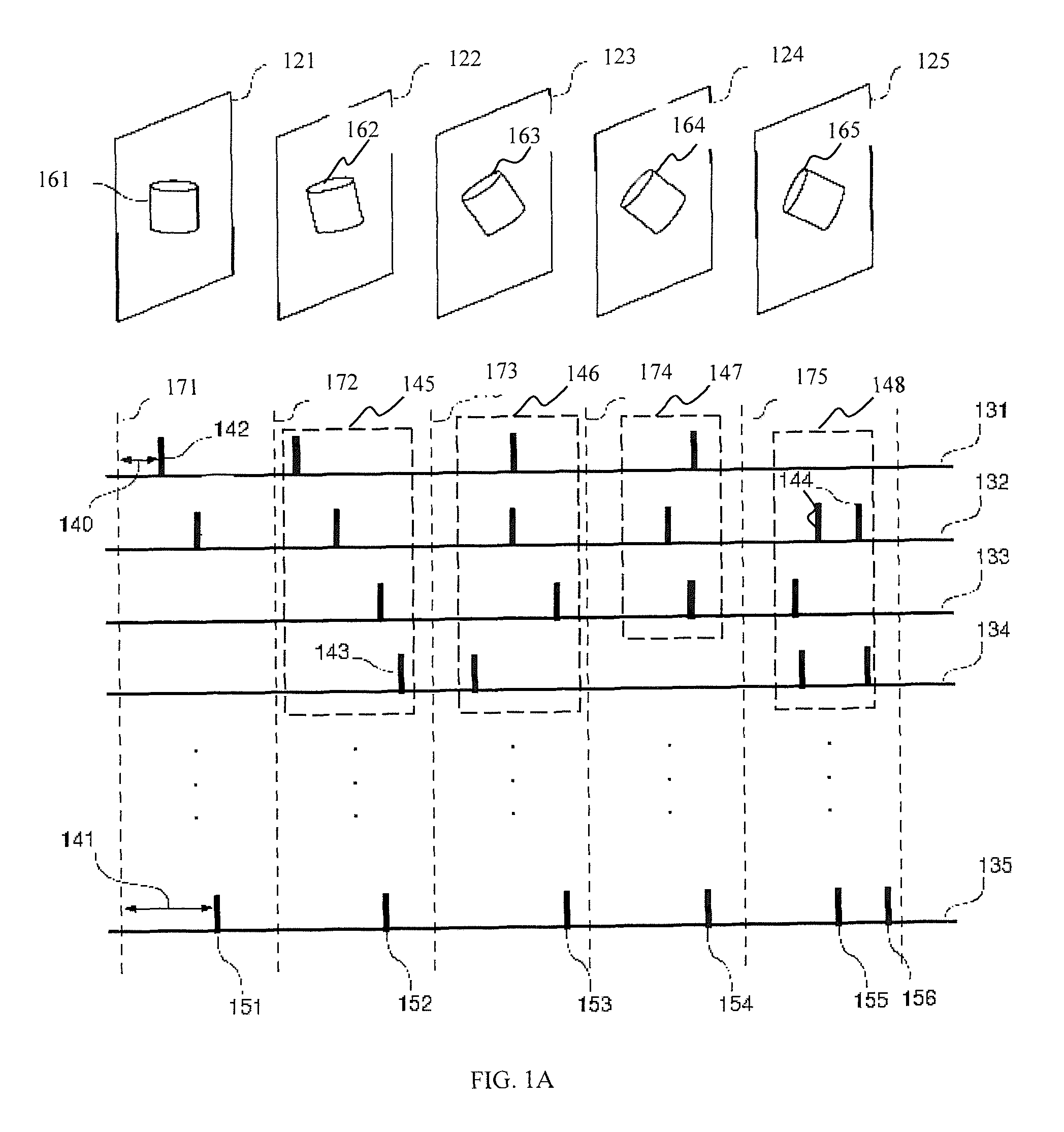
A pattern detecting apparatus has a plurality of hierarchized neuron elements to detect a predetermined pattern included in input patterns. Pulse signals output from the plurality of neuron elements are given specific delays by synapse circuits associated with the individual elements. This makes it possible to transmit the pulse signals to the neuron elements of the succeeding layer through a common bus line so that they can be identified on a time base. The neuron elements of the succeeding layer output the pulse signals at output levels based on a arrival time pattern of the plurality of pulse signals received from the plurality of neuron elements of the preceding layer within a predetermined time window. Thus, the reliability of pattern detection can be improved, and the number of wires interconnecting the elements can be reduced by the use of the common bus line, leading to a small scale of circuit and reduced power consumption.
Owner:CANON KK
Intelligent control with hierarchical stacked neural networks
ActiveUS8775341B1Increased complexityComplex mathematical operationDigital data information retrievalSemantic analysisSemantic propertyNerve network
A system and method of detecting an aberrant message is provided. An ordered set of words within the message is detected. The set of words found within the message is linked to a corresponding set of expected words, the set of expected words having semantic attributes. A set of grammatical structures represented in the message is detected, based on the ordered set of words and the semantic attributes of the corresponding set of expected words. A cognitive noise vector comprising a quantitative measure of a deviation between grammatical structures represented in the message and an expected measure of grammatical structures for a message of the type is then determined. The cognitive noise vector may be processed by higher levels of the neural network and / or an external processor.
Owner:COMMONS MICHAEL LAMPORT
Artificial neural network calculating device and method for sparse connection
ActiveCN105512723ASolve the problem of insufficient computing performance and high front-end decoding overheadAdd supportMemory architecture accessing/allocationDigital data processing detailsActivation functionMemory bandwidth
An artificial neural network calculating device for sparse connection comprises a mapping unit used for converting input data into the storage mode that input nerve cells and weight values correspond one by one, a storage unit used for storing data and instructions, and an operation unit used for executing corresponding operation on the data according to the instructions. The operation unit mainly executes three steps of operation, wherein in the first step, the input nerve cells and weight value data are multiplied; in the second step, addition tree operation is executed, the weighted output nerve cells processed in the first step are added level by level through an addition tree, or the output nerve cells are added with offset to obtain offset-added output nerve cells; in the third step, activation function operation is executed, and the final output nerve cells are obtained. By means of the device, the problems that the operation performance of a CPU and a GPU is insufficient, and the expenditure of front end coding is large are solved, support to a multi-layer artificial neural network operation algorithm is effectively improved, and the problem that memory bandwidth becomes a bottleneck of multi-layer artificial neural network operation and the performance of a training algorithm of the multi-layer artificial neural network operation is solved.
Owner:CAMBRICON TECH CO LTD
Apparatus comprising artificial neuronal assembly
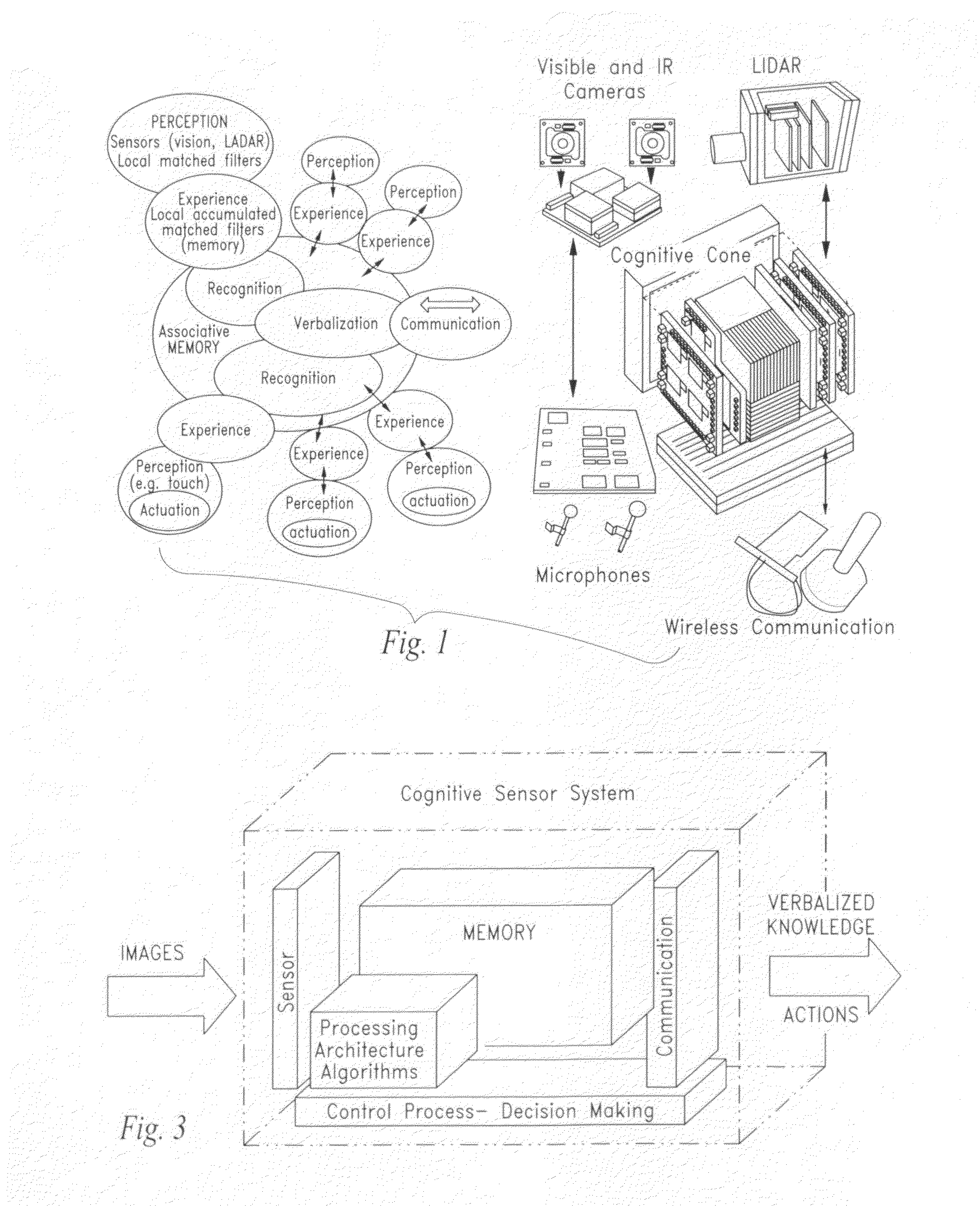
ActiveUS20100241601A1Augment sensory awarenessDigital computer detailsDigital dataVisual cortexRetina
An artificial synapse array and virtual neural space are disclosed.More specifically, a cognitive sensor system and method are disclosed comprising a massively parallel convolution processor capable of, for instance, situationally dependent identification of salient features in a scene of interest by emulating the cortical hierarchy found in the human retina and visual cortex.
Owner:PFG IP +1
Deep Learning Neural Network Classifier Using Non-volatile Memory Array
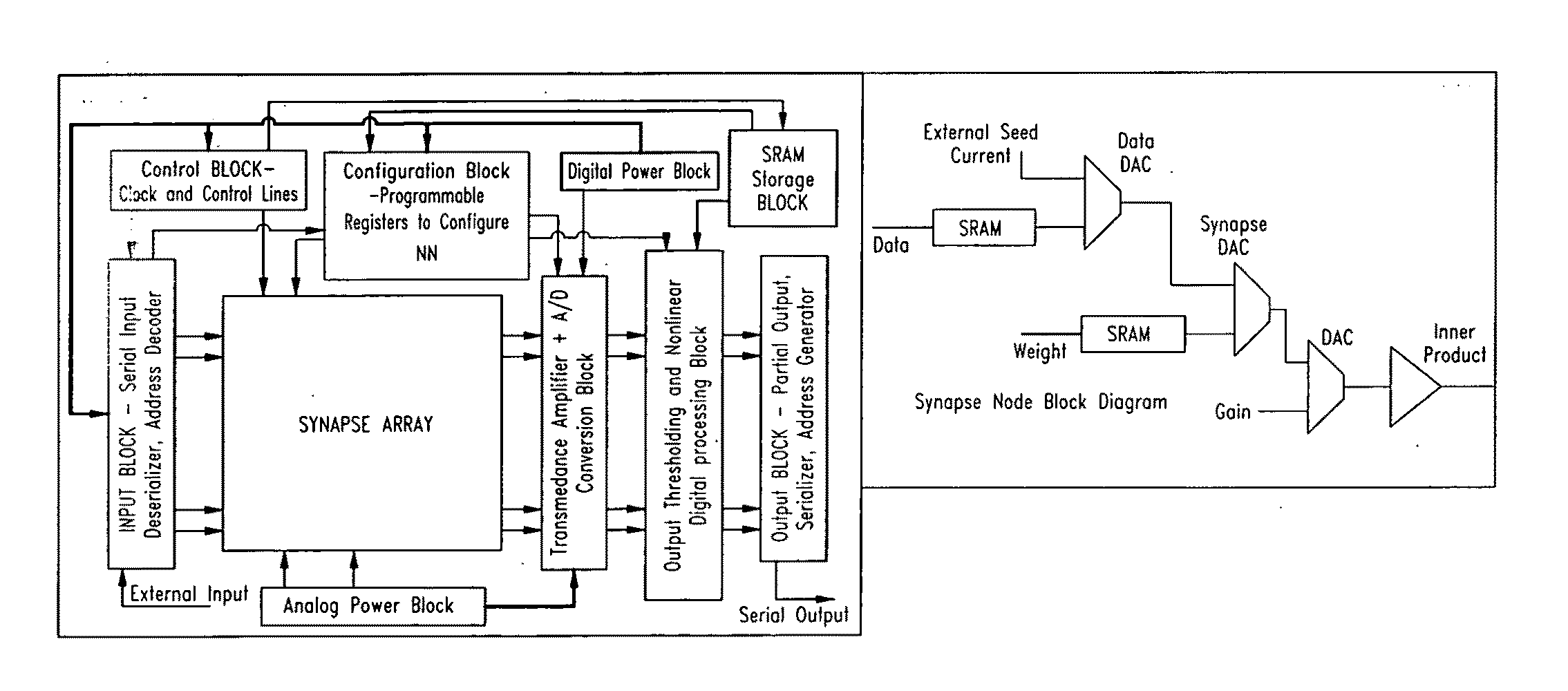
ActiveUS20170337466A1Input/output to record carriersRead-only memoriesSynapseNeural network classifier
An artificial neural network device that utilizes one or more non-volatile memory arrays as the synapses. The synapses are configured to receive inputs and to generate therefrom outputs. Neurons are configured to receive the outputs. The synapses include a plurality of memory cells, wherein each of the memory cells includes spaced apart source and drain regions formed in a semiconductor substrate with a channel region extending there between, a floating gate disposed over and insulated from a first portion of the channel region and a non-floating gate disposed over and insulated from a second portion of the channel region. Each of the plurality of memory cells is configured to store a weight value corresponding to a number of electrons on the floating gate. The plurality of memory cells are configured to multiply the inputs by the stored weight values to generate the outputs.
Owner:RGT UNIV OF CALIFORNIA +1
Methods and systems for neural and cognitive processing
ActiveUS20150339570A1Easily customizedScalable performanceDigital computer detailsDigital dataData miningArtificial intelligence
Provided herein is a system for creating, modifying, deploying and running intelligent systems by combining and customizing the function and operation of reusable component modules arranged into neural processing graphs which direct the flow of signals among the modules, analogous in part to biological brain structure and operation as compositions of variations on functional components and subassemblies.
Owner:SCHEFFLER LEE J
Structured methodology and design patterns for web services
ActiveUS7831693B2Multiple digital computer combinationsDigital dataQuality of serviceBusiness-to-business
System and method for designing and implementing Web Services according to a structured methodology and design patterns. Embodiments may incorporate a structured methodology, best practices and design patterns that address reliability, availability and scalability of Web Services architecture. Embodiments may provide mechanisms for integrating heterogeneous technology components into Web Services. Embodiments may provide a vendor-independent Web Services architecture framework and reusable Web Services design patterns, which may be used in creating end-to-end solutions based on past experience and best practices. Embodiments may include design patterns and best practices for delivering Web Services solutions with Quality of Services. One embodiment may provide a Business-to-Business Integration (B2Bi) integration framework for Web Services. Embodiments may provide a Web Security framework and design patterns for designing end-to-end Web Services security.
Owner:ORACLE INT CORP
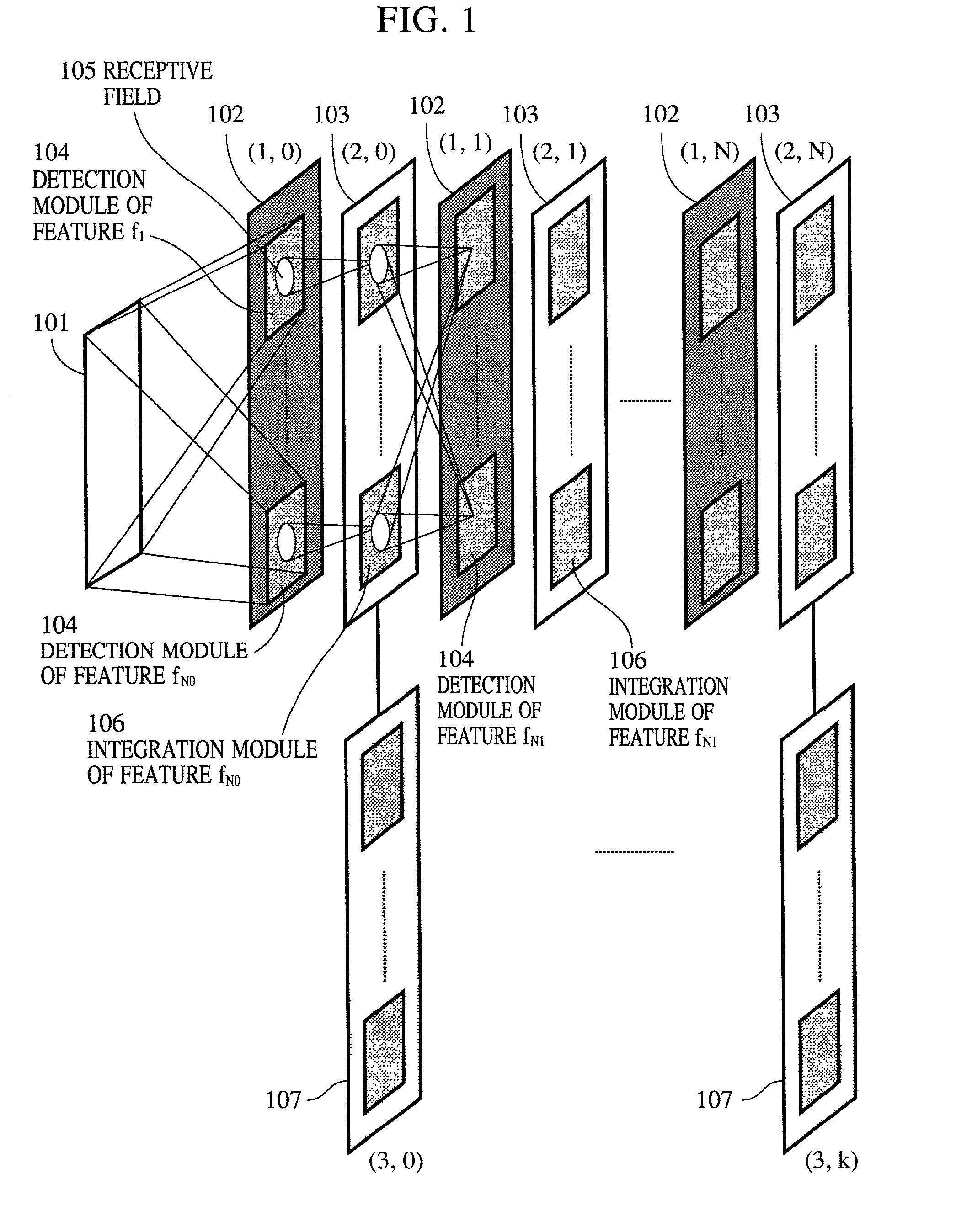
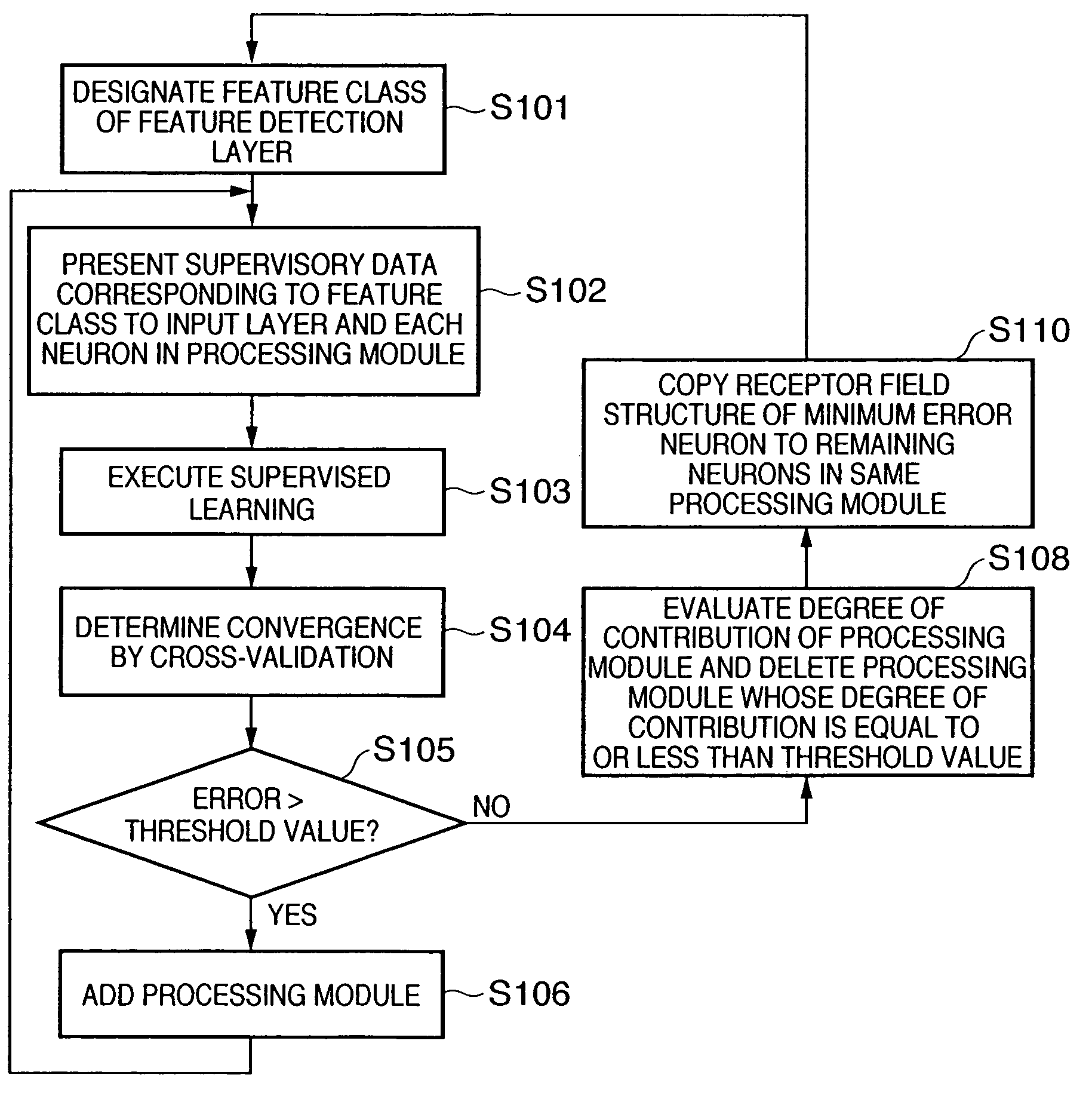
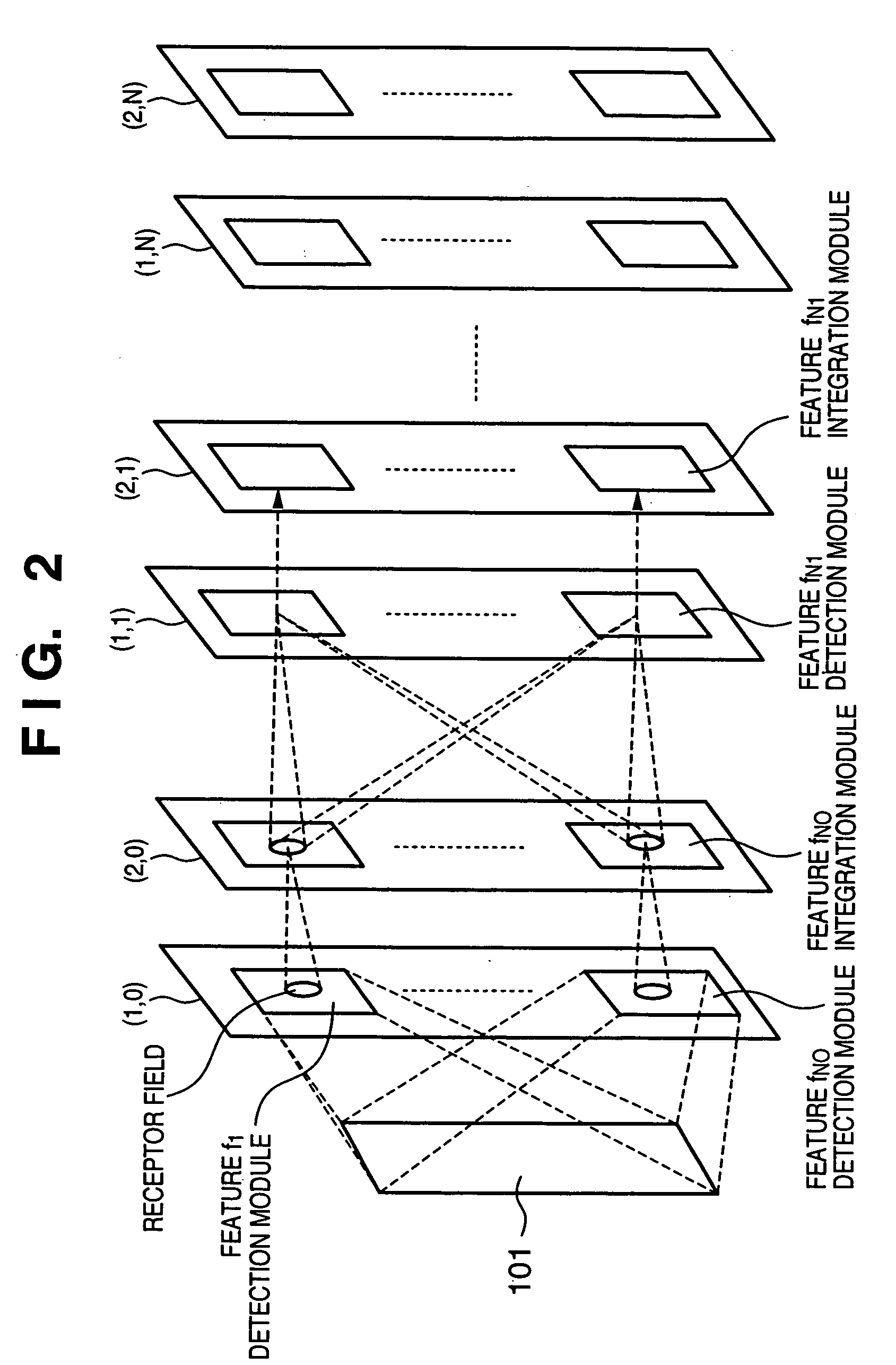
Information processing apparatus, information processing method, pattern recognition apparatus, and pattern recognition method
InactiveUS20050283450A1Image analysisDigital computer detailsPattern recognitionInformation processing
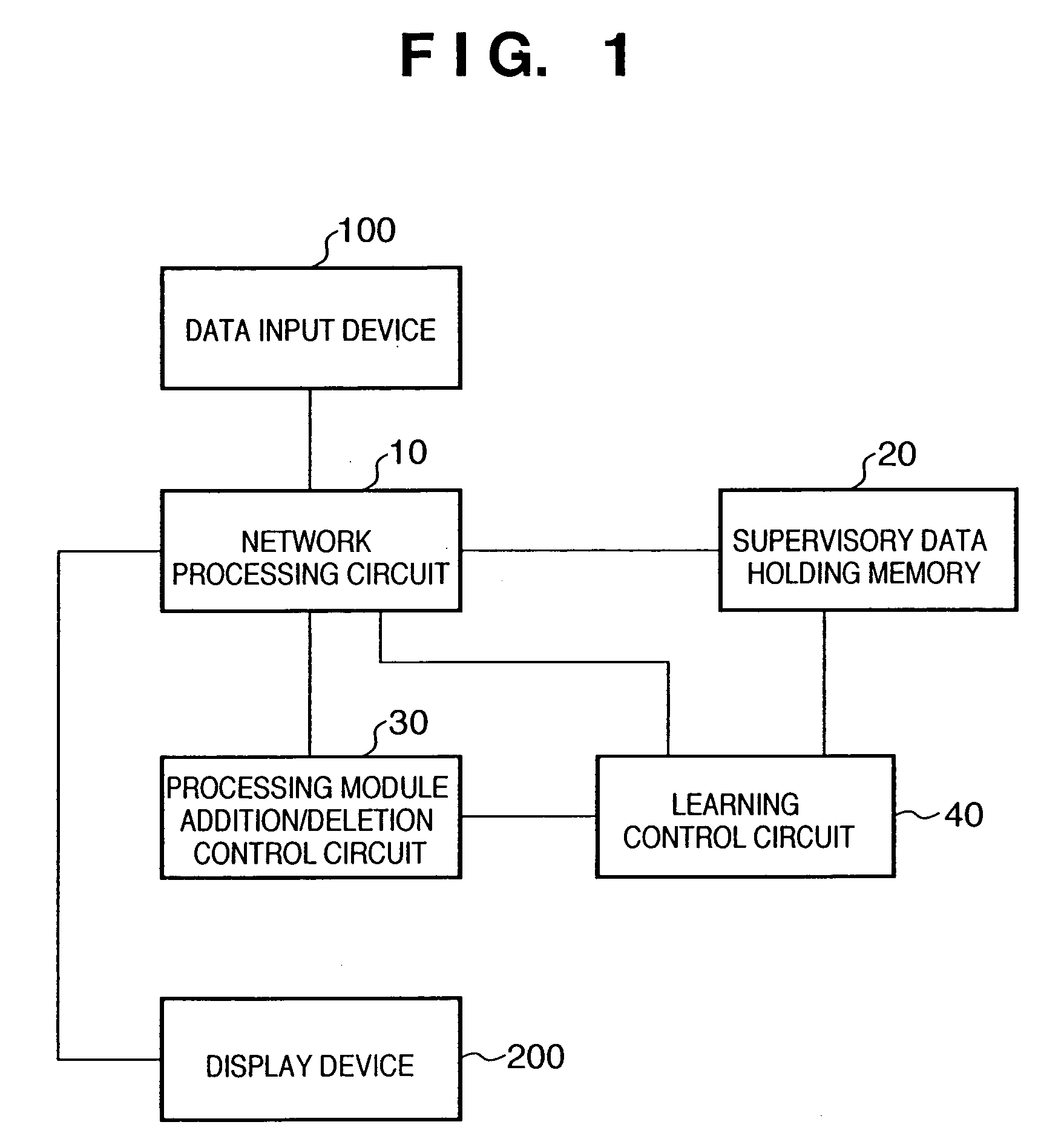
In a hierarchical neural network having a module structure, learning necessary for detection of a new feature class is executed by a processing module which has not finished learning yet and includes a plurality of neurons which should learn an unlearned feature class and have an undetermined receptor field structure by presenting a predetermined pattern to a data input layer. Thus, a feature class necessary for subject recognition can be learned automatically and efficiently.
Owner:CANON KK
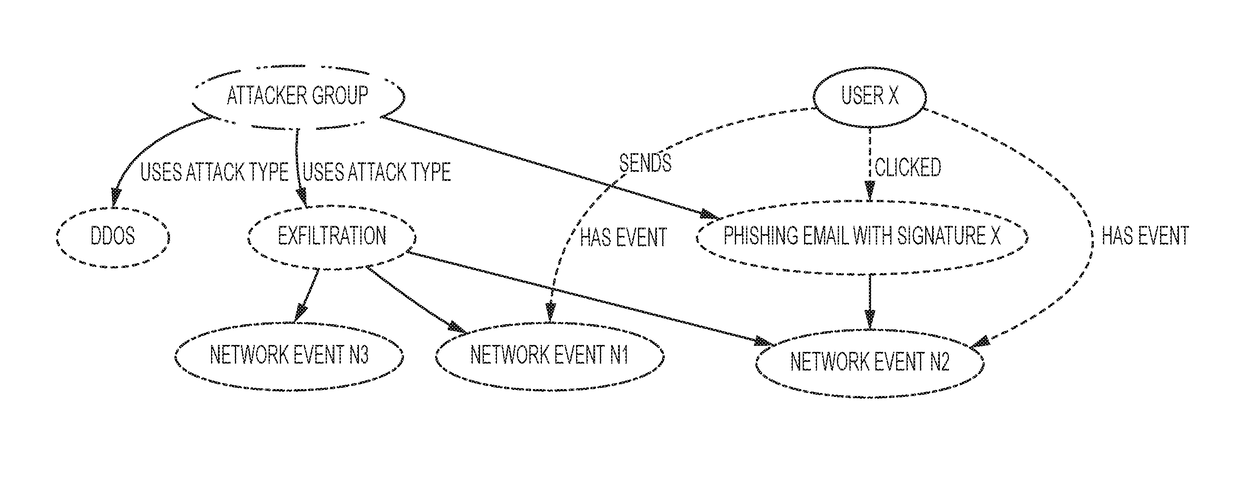
System and methods for automated detection, reasoning and recommendations for resilient cyber systems
ActiveUS20180103052A1Improve applicabilityLarge capacityDigital data information retrievalComputer security arrangementsElastic networkKnowledge extraction
A method for securing an IT (information technology) system using a set of methods for knowledge extraction, event detection, risk estimation and explanation for ranking cyber-alerts which includes a method to explain the relationship (or an attack pathway) from an entity (user or host) and an event context to another entity (a high-value resource) and an event context (attack or service failure).
Owner:BATTELLE MEMORIAL INST
Human face super-resolution reconstruction method based on generative adversarial network and sub-pixel convolution
ActiveCN107154023AImprove recognition accuracyClear outline of the faceGeometric image transformationNeural architecturesData setImage resolution
The invention discloses a human face super-resolution reconstruction method based on a generative adversarial network and sub-pixel convolution, and the method comprises the steps: A, carrying out the preprocessing through a normally used public human face data set, and making a low-resolution human face image and a corresponding high-resolution human face image training set; B, constructing the generative adversarial network for training, adding a sub-pixel convolution to the generative adversarial network to achieve the generation of a super-resolution image and introduce a weighted type loss function comprising feature loss; C, sequentially inputting a training set obtained at step A into a generative adversarial network model for modeling training, adjusting the parameters, and achieving the convergence; D, carrying out the preprocessing of a to-be-processed low-resolution human face image, inputting the image into the generative adversarial network model, and obtaining a high-resolution image after super-resolution reconstruction. The method can achieve the generation of a corresponding high-resolution image which is clearer in human face contour, is more specific in detail and is invariable in features. The method improves the human face recognition accuracy, and is better in human face super-resolution reconstruction effect.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Deep learning medical systems and methods for image reconstruction and quality evaluation
Methods and apparatus to automatically generate an image quality metric for an image are provided. An example method includes automatically processing a first medical image using a deployed learning network model to generate an image quality metric for the first medical image, the deployed learning network model generated from a digital learning and improvement factory including a training network, wherein the training network is tuned using a set of labeled reference medical images of a plurality of image types, and wherein a label associated with each of the labeled reference medical images indicates a central tendency metric associated with image quality of the image. The example method includes computing the image quality metric associated with the first medical image using the deployed learning network model by leveraging labels and associated central tendency metrics to determine the associated image quality metric for the first medical image.
Owner:GENERAL ELECTRIC CO
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Spatio-temporal pattern recognition using a spiking neural network and processing thereof on a portable and/or distributed computer
ActiveUS20090287624A1Digital computer detailsCharacter and pattern recognitionSpiking neural networkNeuron
A system and method for characterizing a pattern, in which a spiking neural network having at least one layer of neurons is provided. The spiking neural network has a plurality of connected neurons for transmitting signals between the connected neurons. A model for inducing spiking in the neurons is specified. Each neuron is connected to a global regulating unit for transmitting signals between the neuron and the global regulating unit. Each neuron is connected to at least one other neuron for transmitting signals from this neuron to the at least one other neuron, this neuron and the at least one other neuron being on the same layer. Spiking of each neuron is synchronized according to a number of active neurons connected to the neuron. At least one pattern is submitted to the spiking neural network for generating sequences of spikes in the spiking neural network, the sequences of spikes (i) being modulated over time by the synchronization of the spiking and (ii) being regulated by the global regulating unit. The at least one pattern is characterized according to the sequences of spikes generated in the spiking neural network.
Owner:ROUAT JEAN +2
Automatic etiology sequencing system
A system and related method for identifying a trigger event to a patient health-related exacerbation. The system includes at least one sensor configured to collect data related to the patient health-related exacerbation, an analyzer configured to validate the collected data, a patient interface device configured to receive patient inputs to at least one question, and an identifier device configured to receive the patient inputs and collected data and identify the trigger event. The system may also include an expert system configured to receive the patient inputs and the validated collected data and identify a primary patient disease, and a reporting device configured to generate reports related to the identified primary patient disease, patient inputs, and sensed patient conditions.
Owner:CARDIAC PACEMAKERS INC
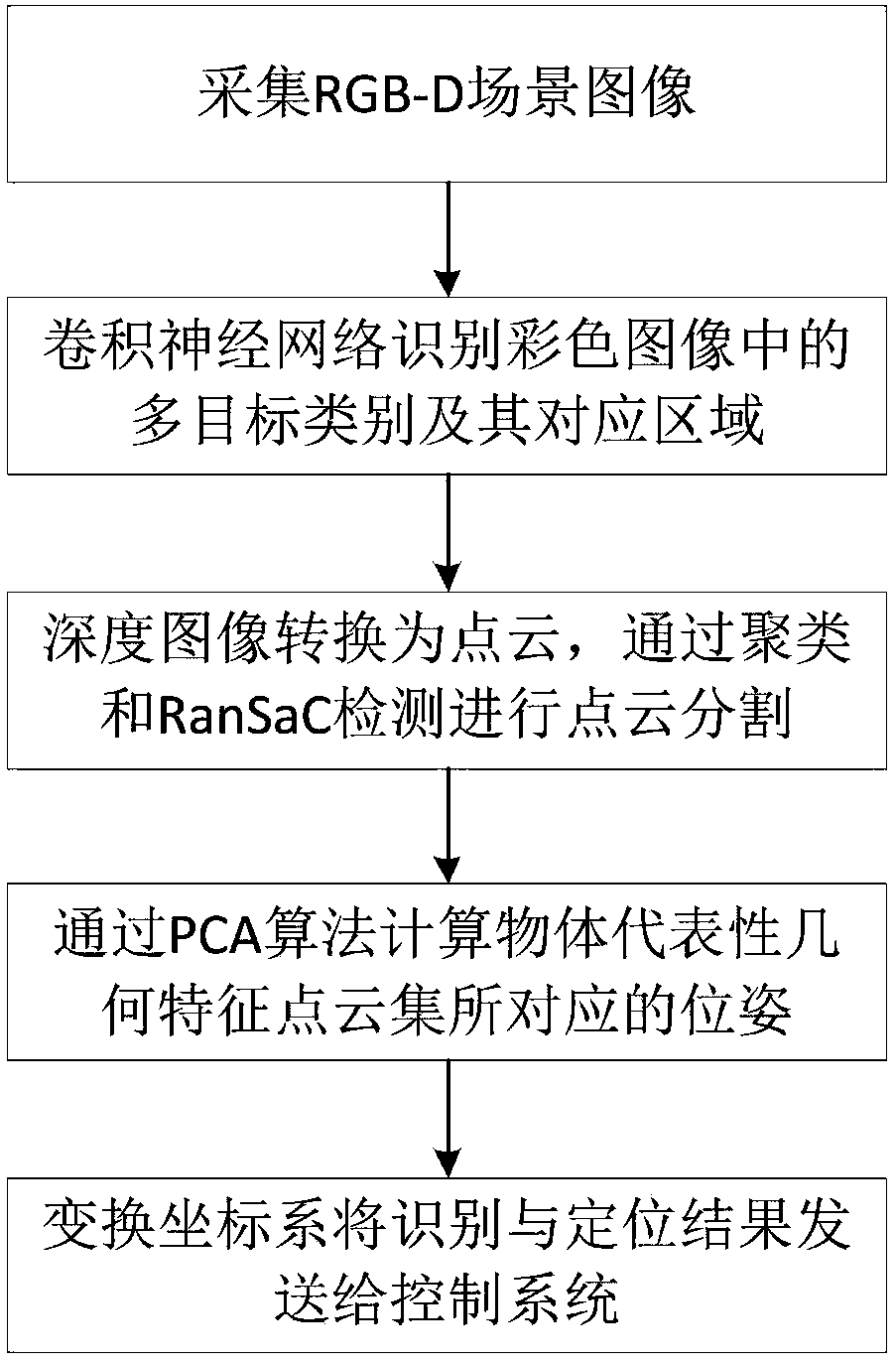
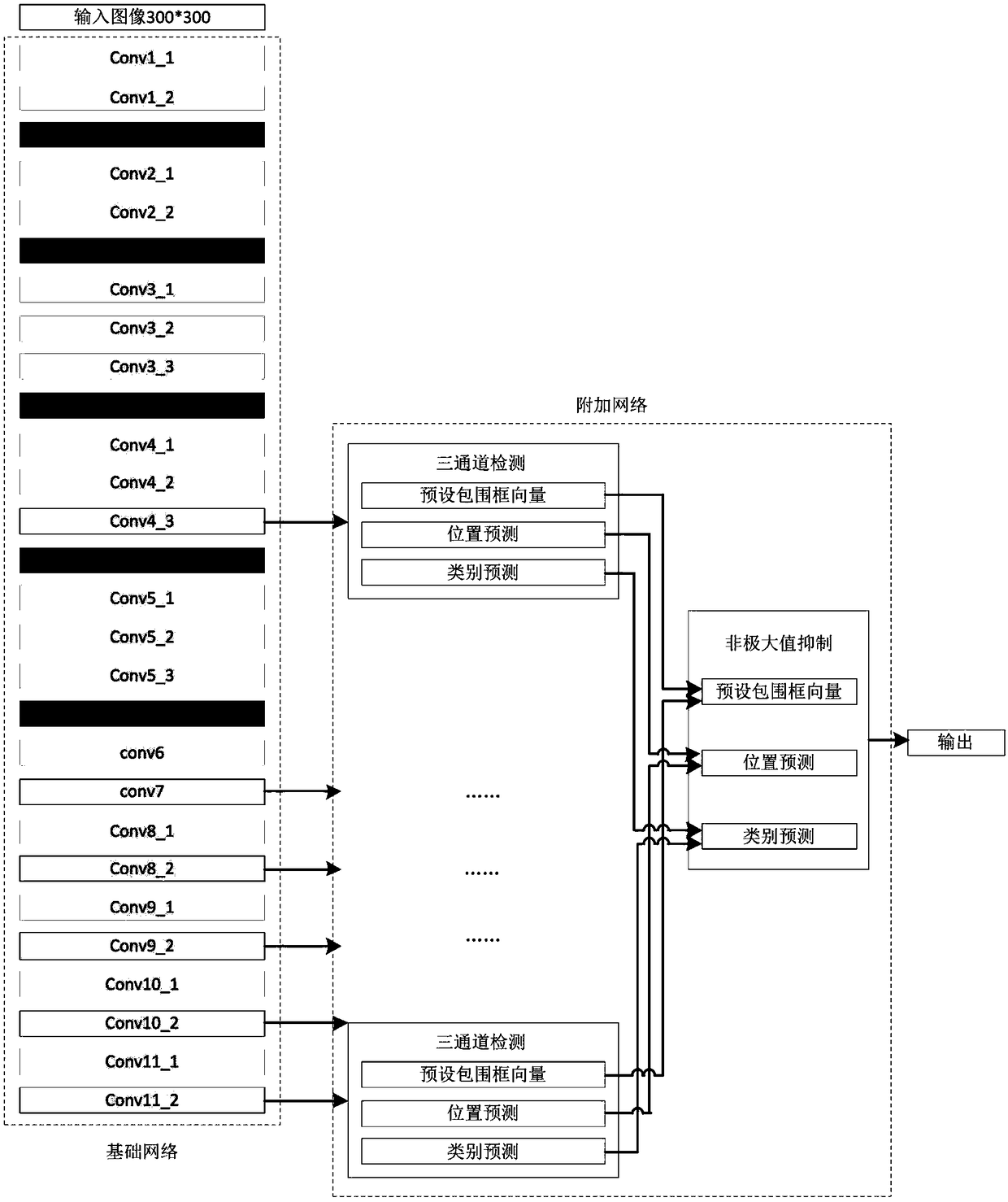
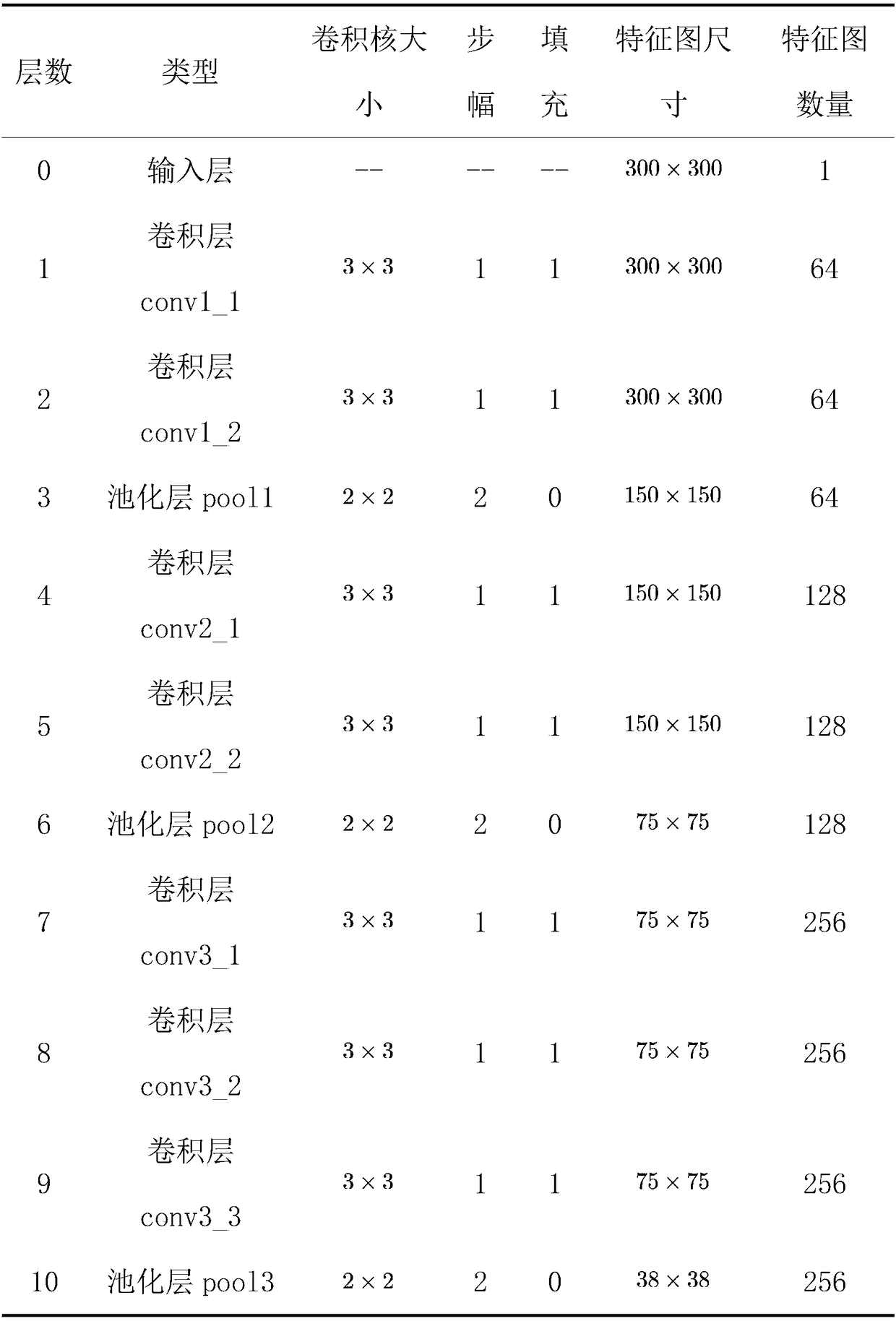
Visual recognition and positioning method for robot intelligent capture application
The invention relates to a visual recognition and positioning method for robot intelligent capture application. According to the method, an RGB-D scene image is collected, a supervised and trained deep convolutional neural network is utilized to recognize the category of a target contained in a color image and a corresponding position region, the pose state of the target is analyzed in combinationwith a deep image, pose information needed by a controller is obtained through coordinate transformation, and visual recognition and positioning are completed. Through the method, the double functions of recognition and positioning can be achieved just through a single visual sensor, the existing target detection process is simplified, and application cost is saved. Meanwhile, a deep convolutional neural network is adopted to obtain image features through learning, the method has high robustness on multiple kinds of environment interference such as target random placement, image viewing anglechanging and illumination background interference, and recognition and positioning accuracy under complicated working conditions is improved. Besides, through the positioning method, exact pose information can be further obtained on the basis of determining object spatial position distribution, and strategy planning of intelligent capture is promoted.
Owner:合肥哈工慧拣智能科技有限公司
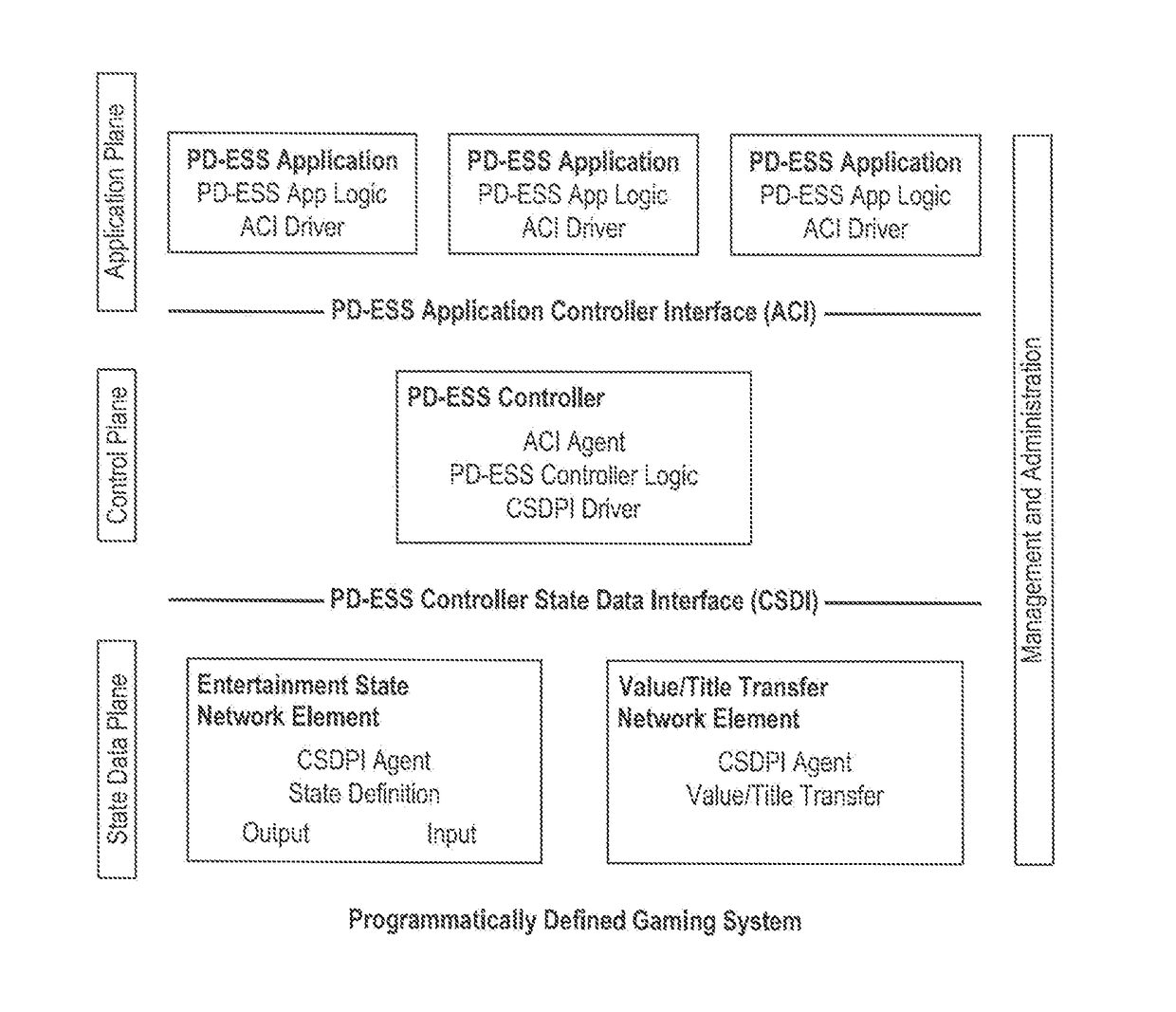
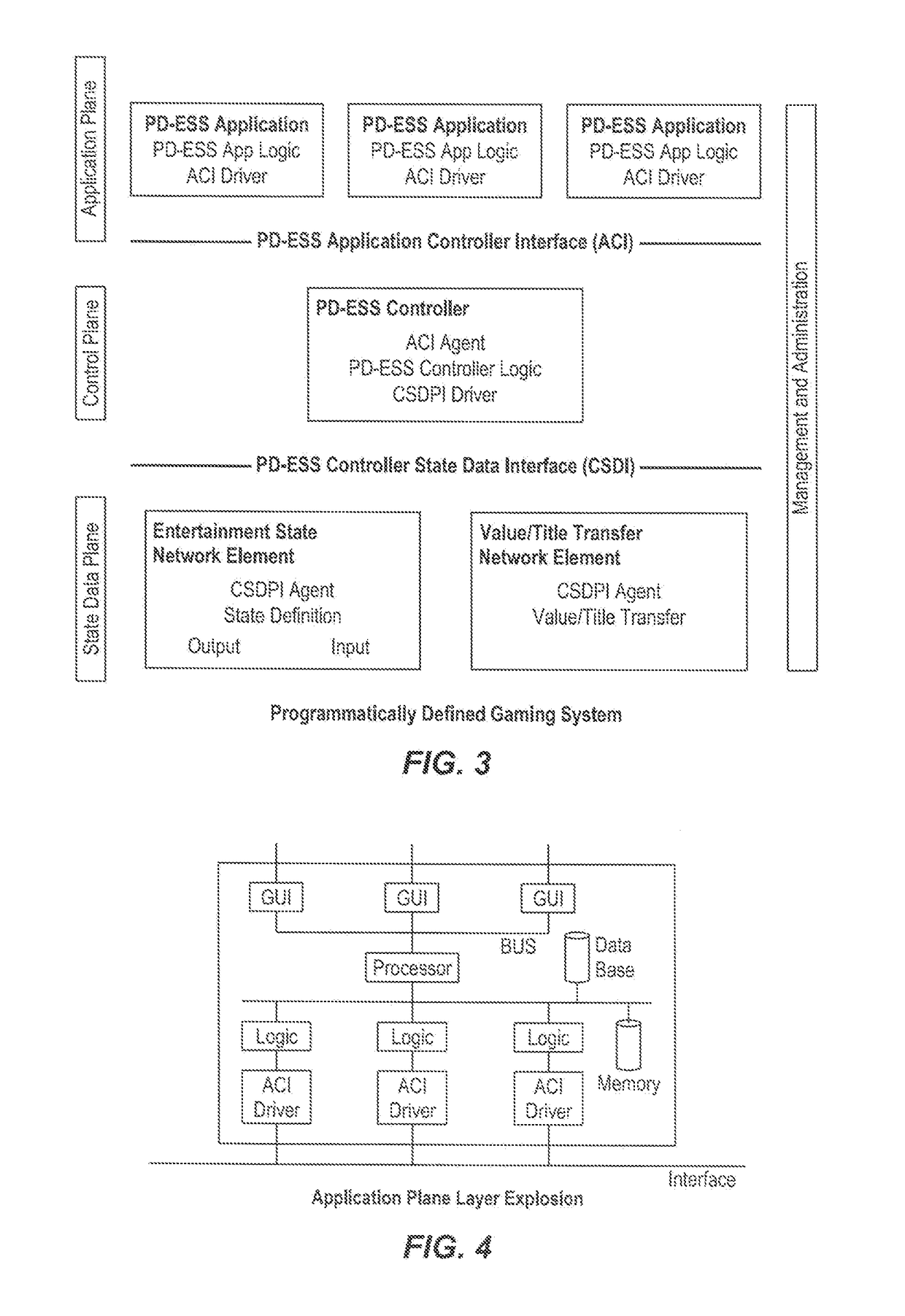
Architectures, systems and methods for program defined entertainment state system, decentralized cryptocurrency system and system with segregated secure functions and public functions
PendingUS20180247191A1Cryptography processingInterprogram communicationMotion detectorDisplay device
Systems and methods are provided for training an artificial intelligence system including the use of one or more human subject responses to stimuli as input to the artificial intelligence system. Displays are oriented to the human subjects to present the stimuli to the human subjects. Detectors monitor the reaction of the human subjects to the stimuli, the detectors including at least motion detectors, the detectors providing an output. An analysis system is coupled to receive the output of the detectors, the analysis system provides an output corresponding to whether the reaction of the human subjects was positive or negative. A neural network utilizes the output of the analysis system, generating a positive weighting for training of the neural network when the output of the analysis system was positive, and a negative weighting for training of the neural network when the output of the analysis system was negative.
Owner:MILESTONE ENTERTAINMENT LLC
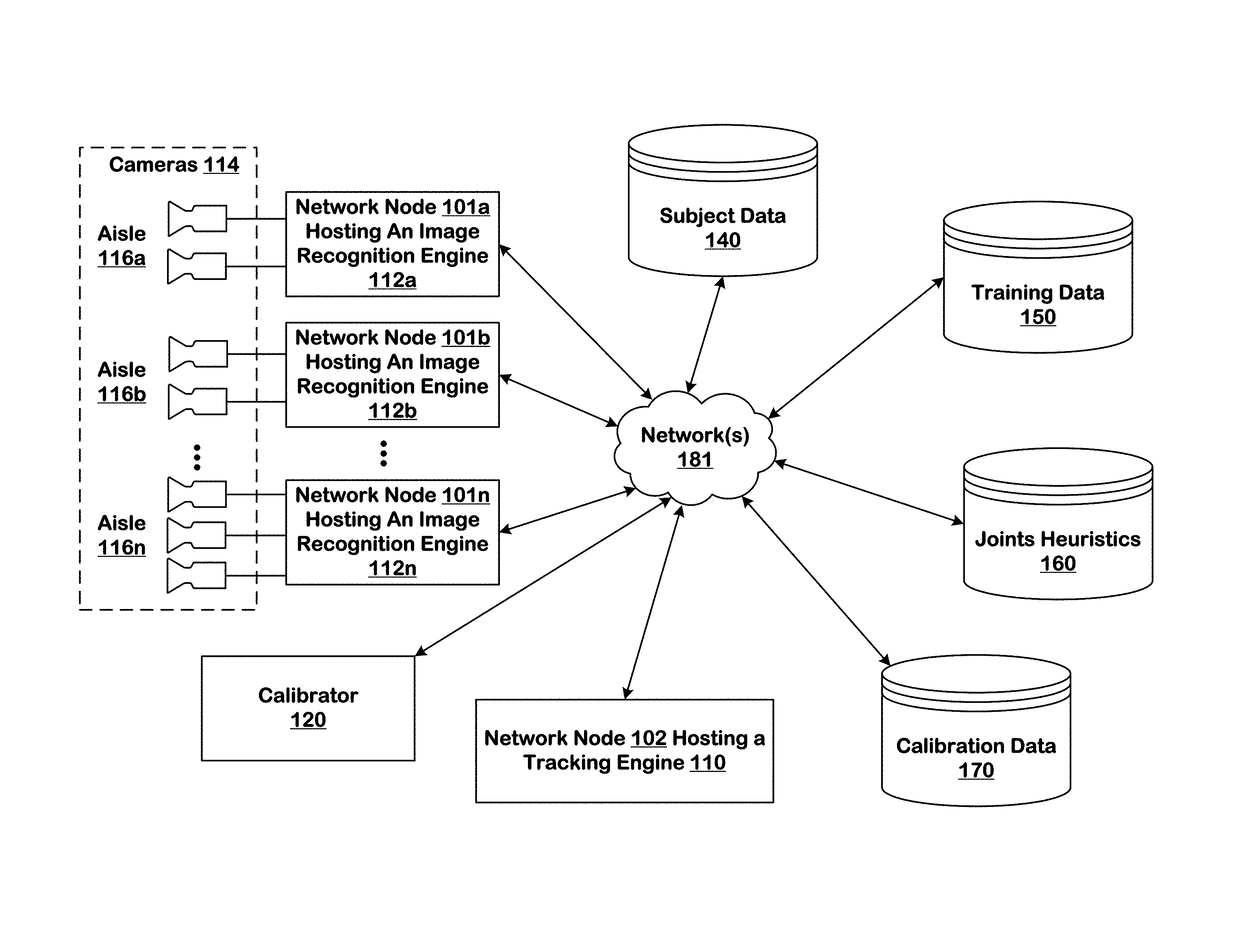
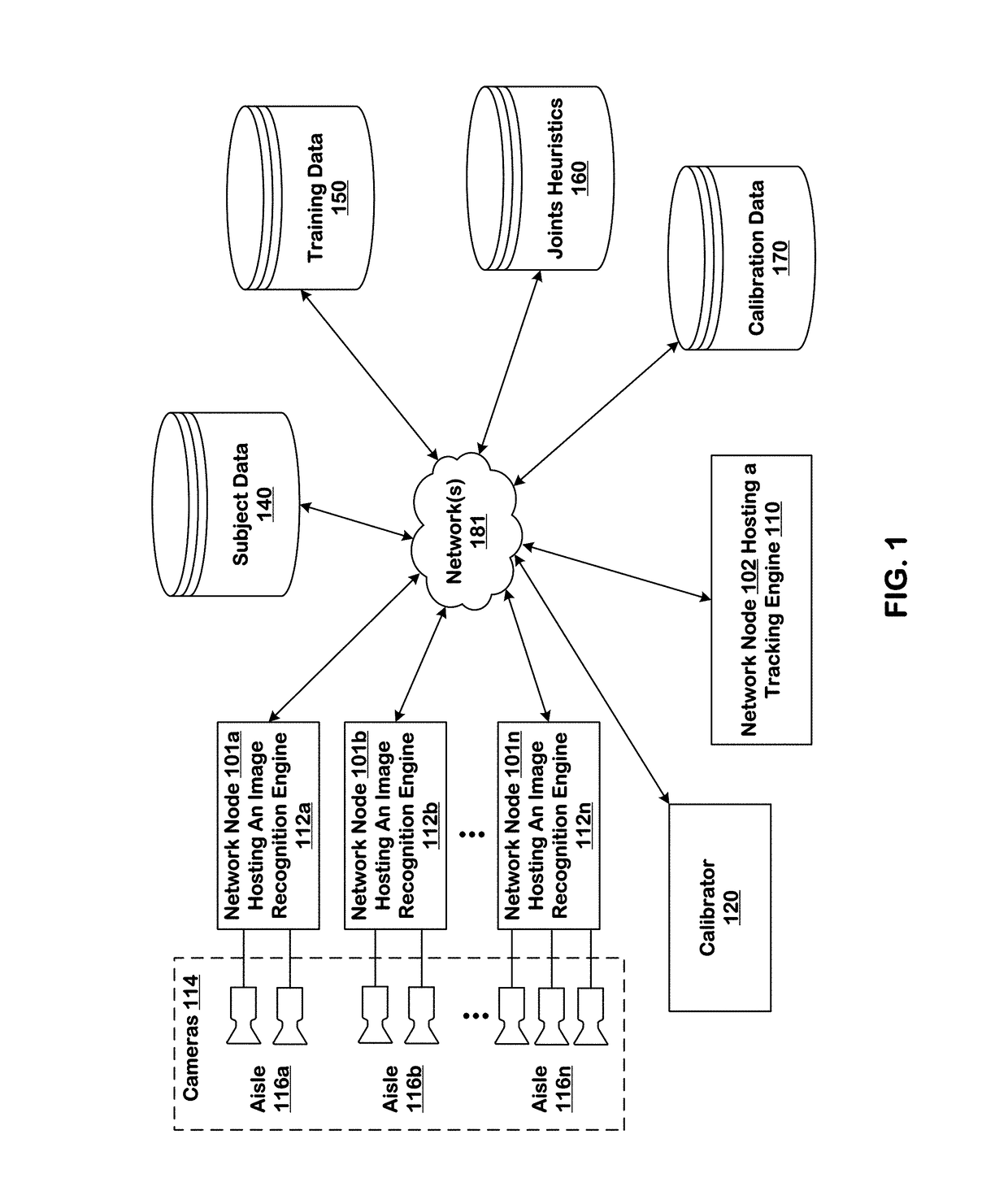
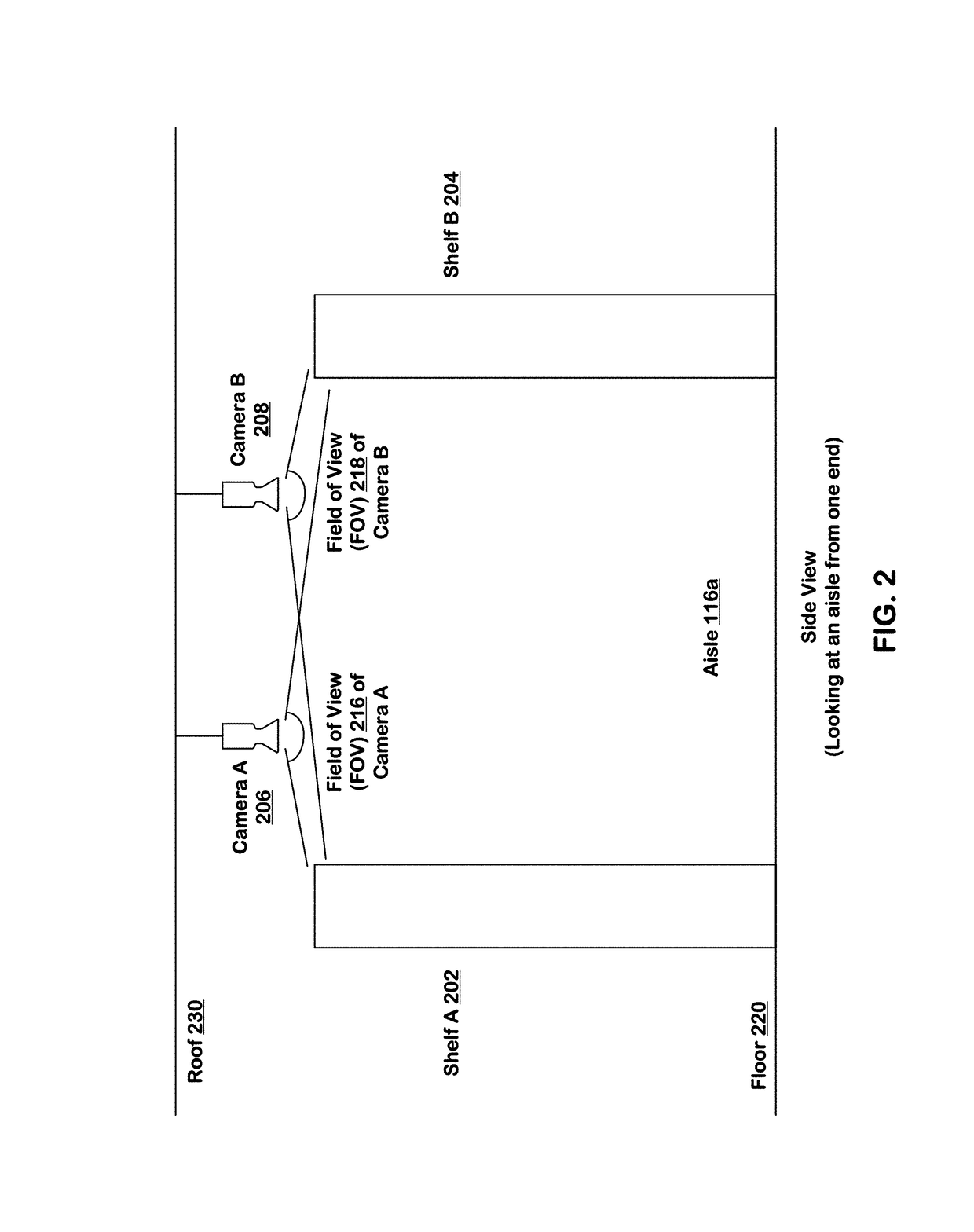
Predicting inventory events using semantic diffing
ActiveUS10127438B1ConfidenceImprove accuracyImage enhancementMathematical modelsInventory managementBackground image
Systems and techniques are provided for tracking puts and takes of inventory items by subjects in an area of real space. A plurality of cameras with overlapping fields of view produce respective sequences of images of corresponding fields of view in the real space. In one embodiment, the system includes first image processors, including subject image recognition engines, receiving corresponding sequences of images from the plurality of cameras. The first image processors process images to identify subjects represented in the images in the corresponding sequences of images. The system includes second image processors, including background image recognition engines, receiving corresponding sequences of images from the plurality of cameras. The second image processors mask the identified subjects to generate masked images. Following this, the second image processors process the masked images to identify and classify background changes represented in the images in the corresponding sequences of images.
Owner:STANDARD COGNITION CORP
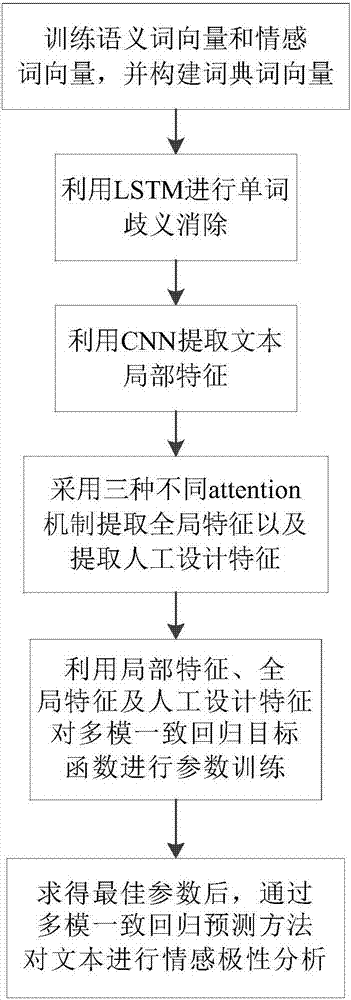
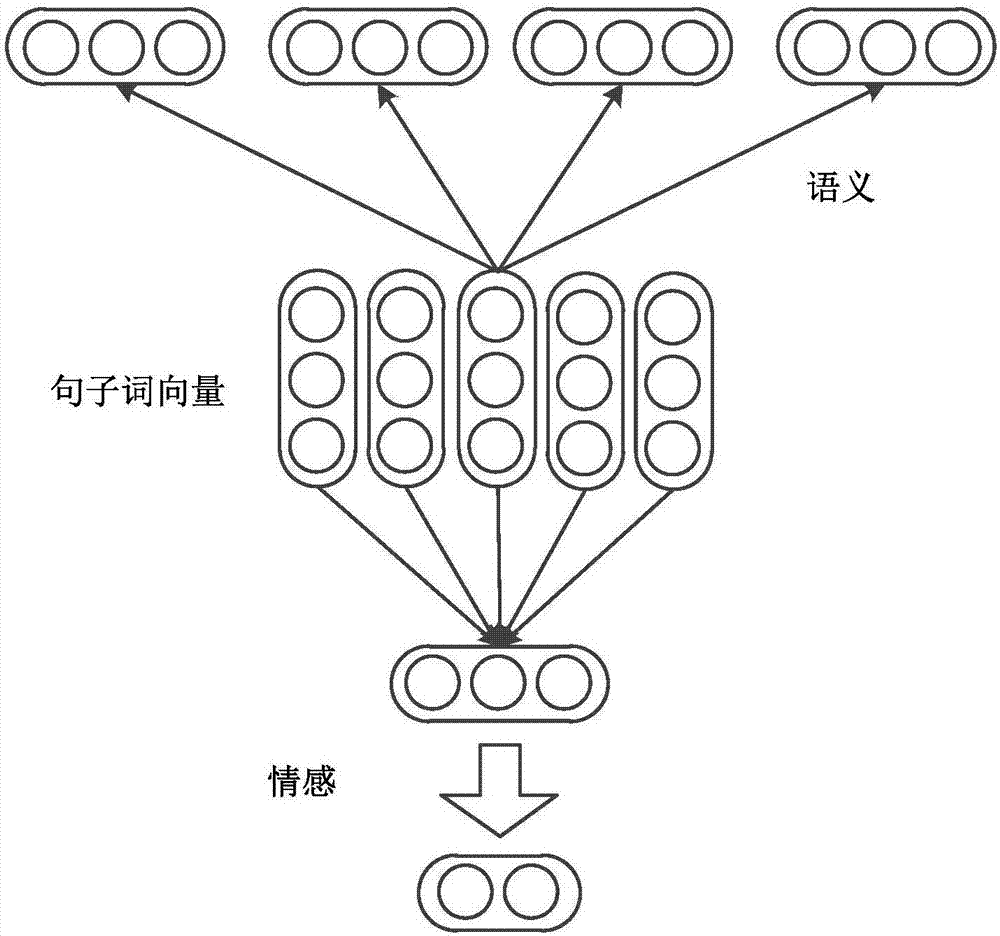
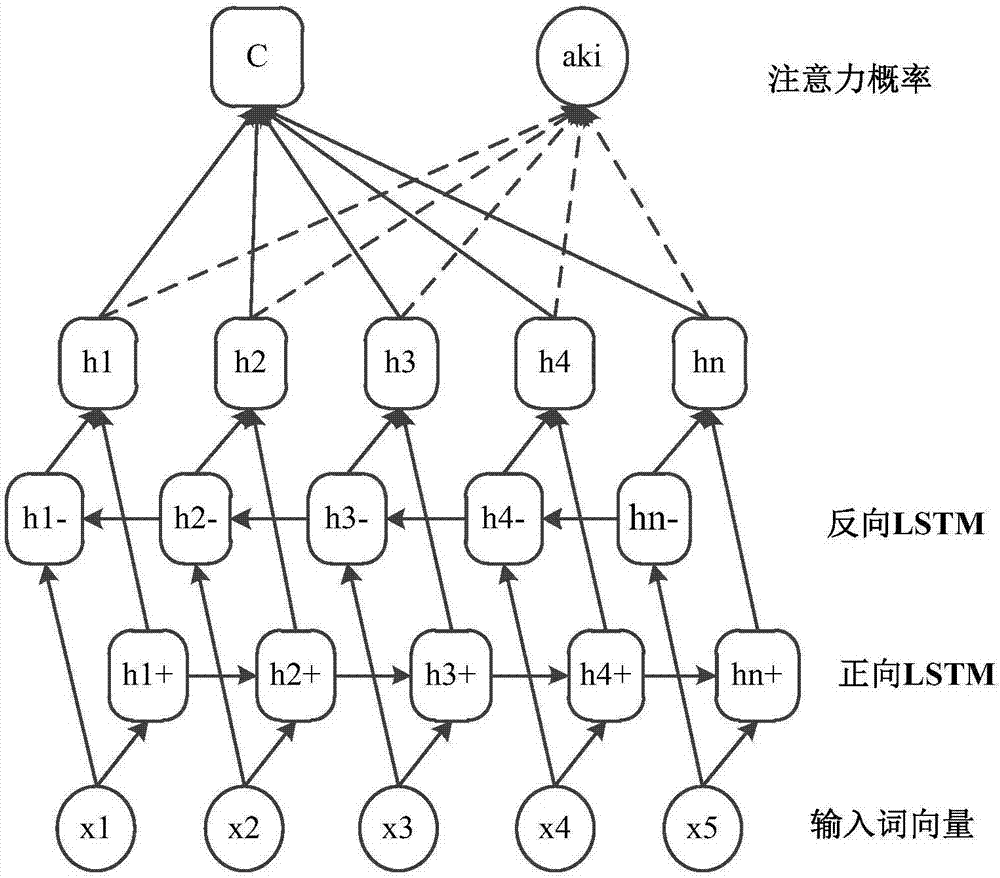
attention CNNs and CCR-based text sentiment analysis method
ActiveCN107092596AHigh precisionImprove classification accuracySemantic analysisNeural architecturesFeature extractionAmbiguity
The invention discloses an attention CNNs and CCR-based text sentiment analysis method and belongs to the field of natural language processing. The method comprises the following steps of 1, training a semantic word vector and a sentiment word vector by utilizing original text data and performing dictionary word vector establishment by utilizing a collected sentiment dictionary; 2, capturing context semantics of words by utilizing a long-short-term memory (LSTM) network to eliminate ambiguity; 3, extracting local features of a text in combination with convolution kernels with different filtering lengths by utilizing a convolutional neural network; 4, extracting global features by utilizing three different attention mechanisms; 5, performing artificial feature extraction on the original text data; 6, training a multimodal uniform regression target function by utilizing the local features, the global features and artificial features; and 7, performing sentiment polarity prediction by utilizing a multimodal uniform regression prediction method. Compared with a method adopting a single word vector, a method only extracting the local features of the text, or the like, the text sentiment analysis method can further improve the sentiment classification precision.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
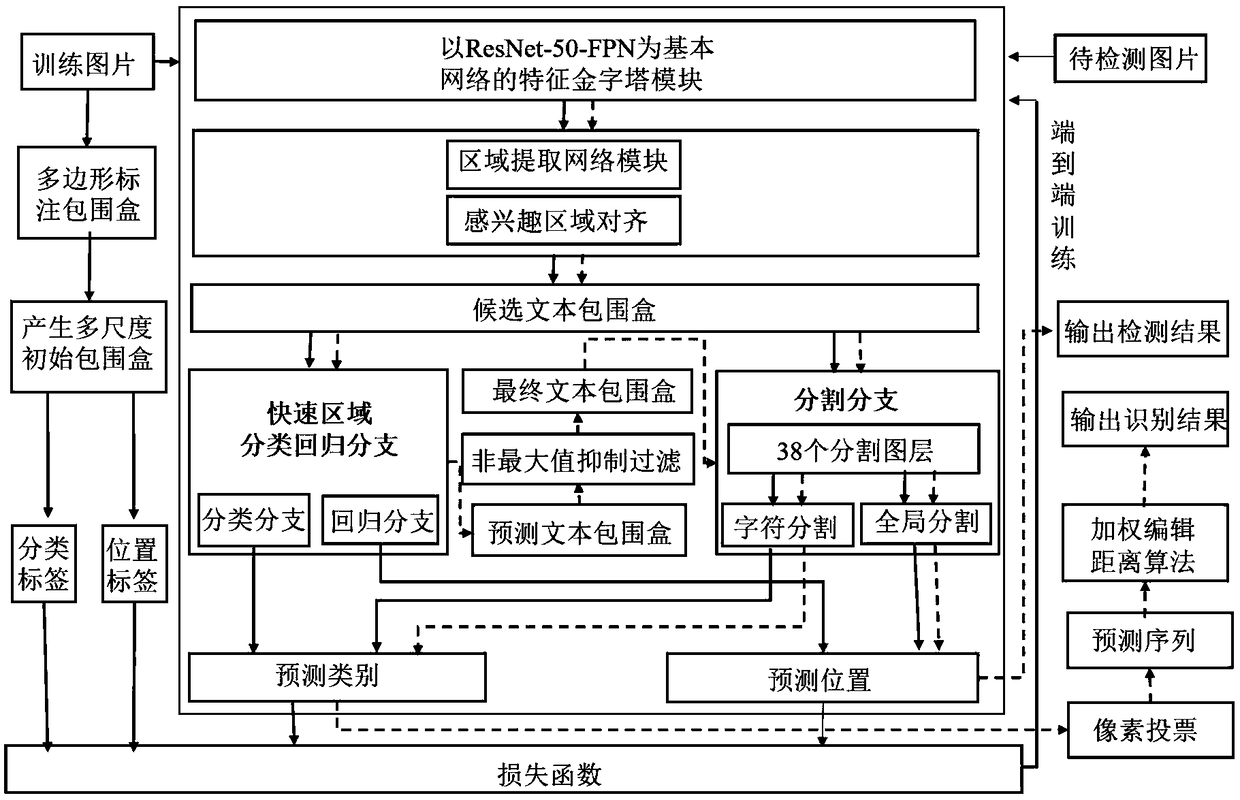
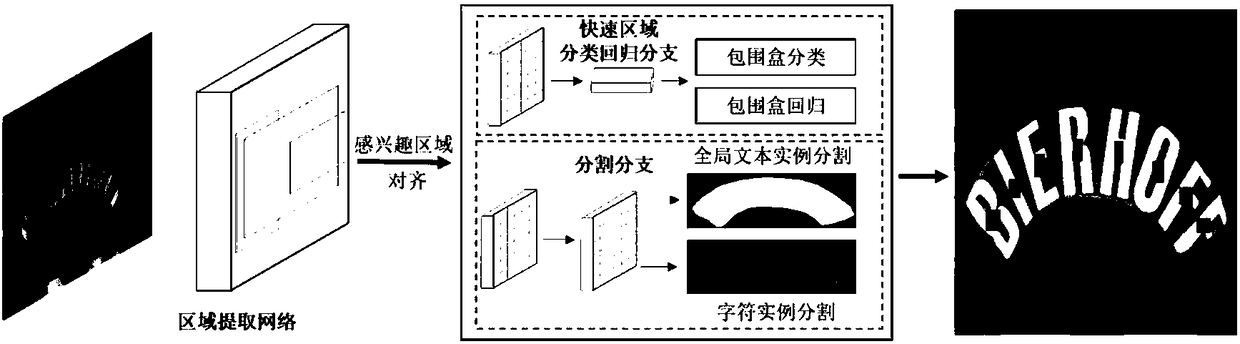
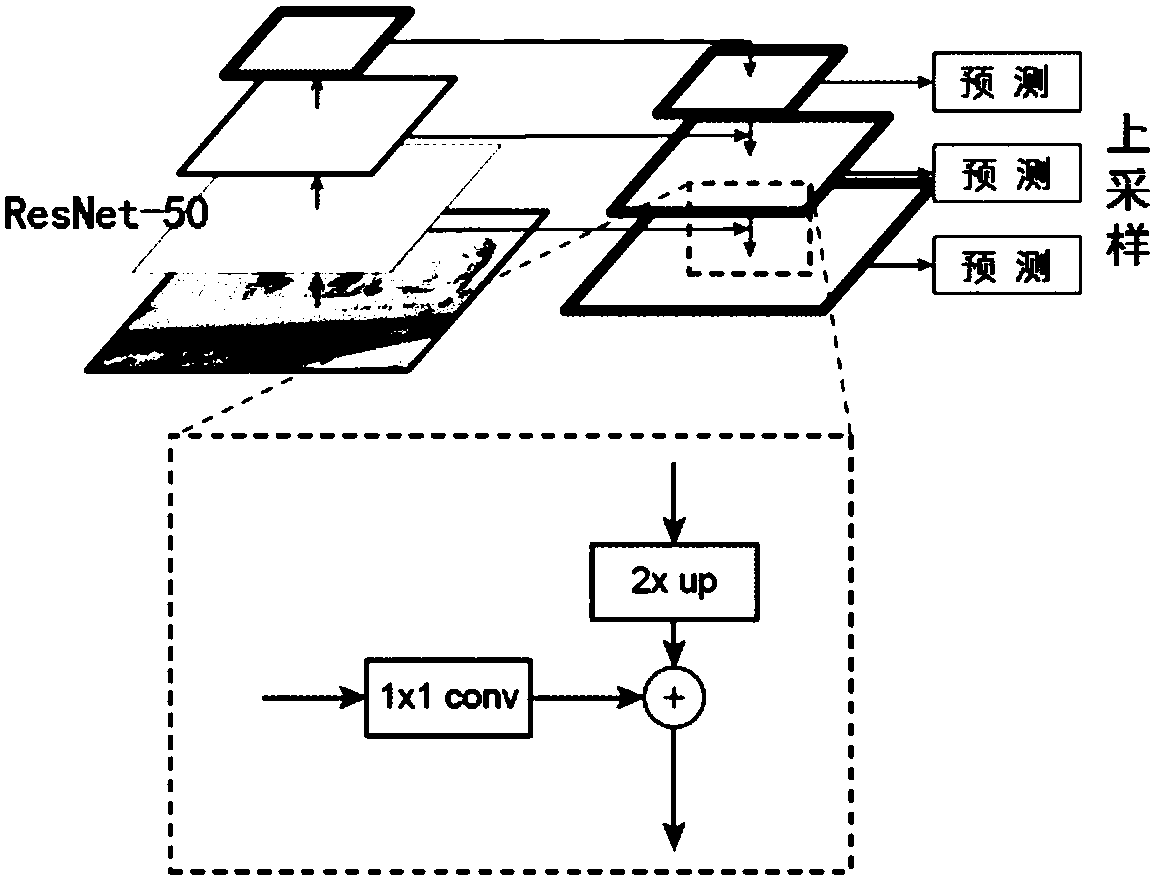
End-to-end identification method for scene text with random shape
ActiveCN108549893AAccurate identificationAccurate detectionCharacter and pattern recognitionNeural architecturesNetwork generationTheoretical computer science
The invention discloses an end-to-end identification method for a scene text with a random shape. The method comprises the steps of extracting a text characteristic through a characteristic pyramid network for generating a candidate text box by an area extracting network; adjusting the position of the candidate text box through quick area classification regression branch for obtaining more accurate position of a text bounding box; inputting the position information of the bounding box into a dividing branch, obtaining a predicated character sequence through a pixel voting algorithm; and finally processing the predicated character sequence through a weighted editing distance algorithm, finding out a most matched word of the predicated character sequence in a given dictionary, thereby obtaining a final text identification result. According to the method of the invention, the scene texts with the random shape can be simultaneously detected and identified, wherein the scene texts comprisehorizontal text, multidirectional text and curved text. Furthermore end-to-end training can be completely performed. Compared with prior art, the identification method according to the invention has advantages of obtaining advantageous effects in accuracy and versatility, and realizing high application value.
Owner:HUAZHONG UNIV OF SCI & TECH
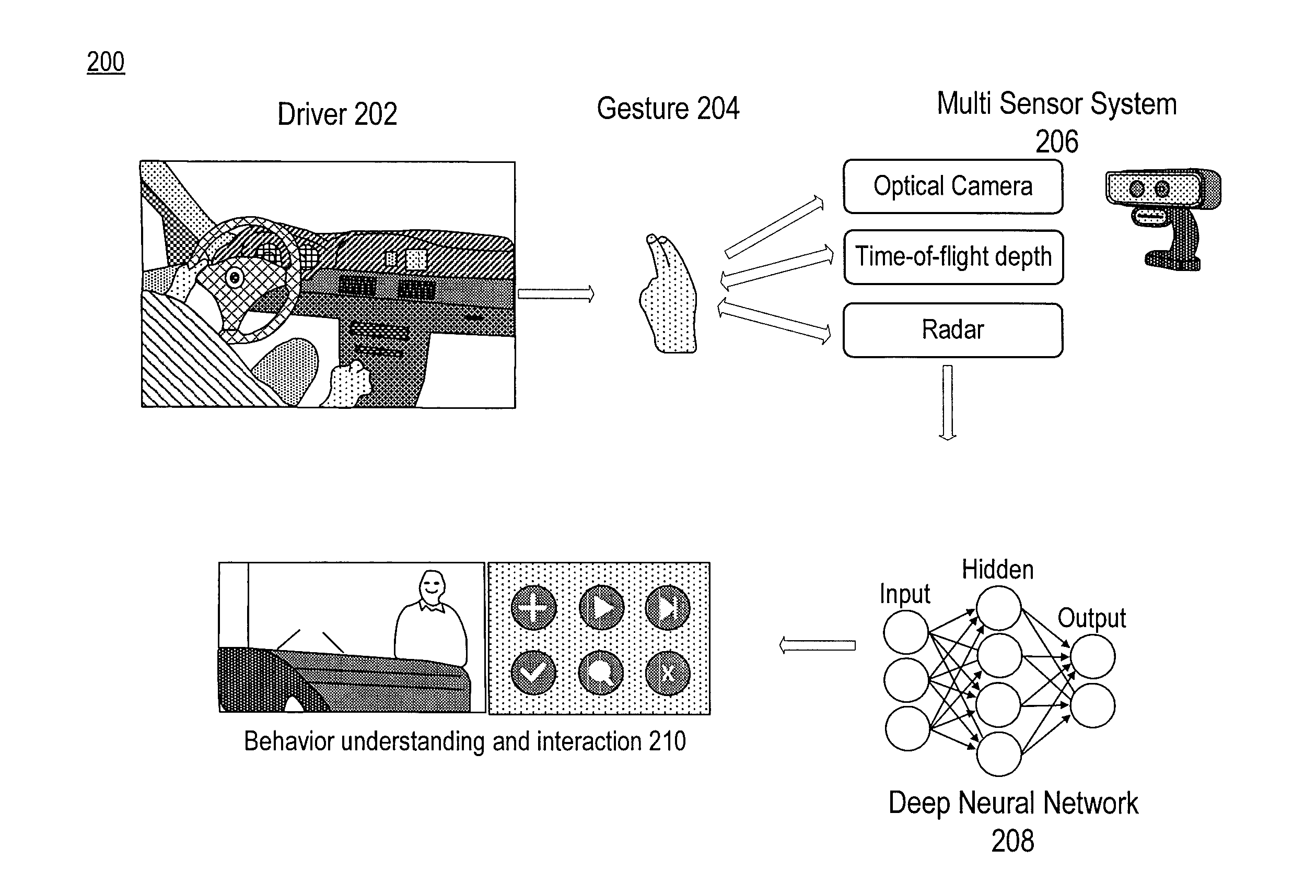
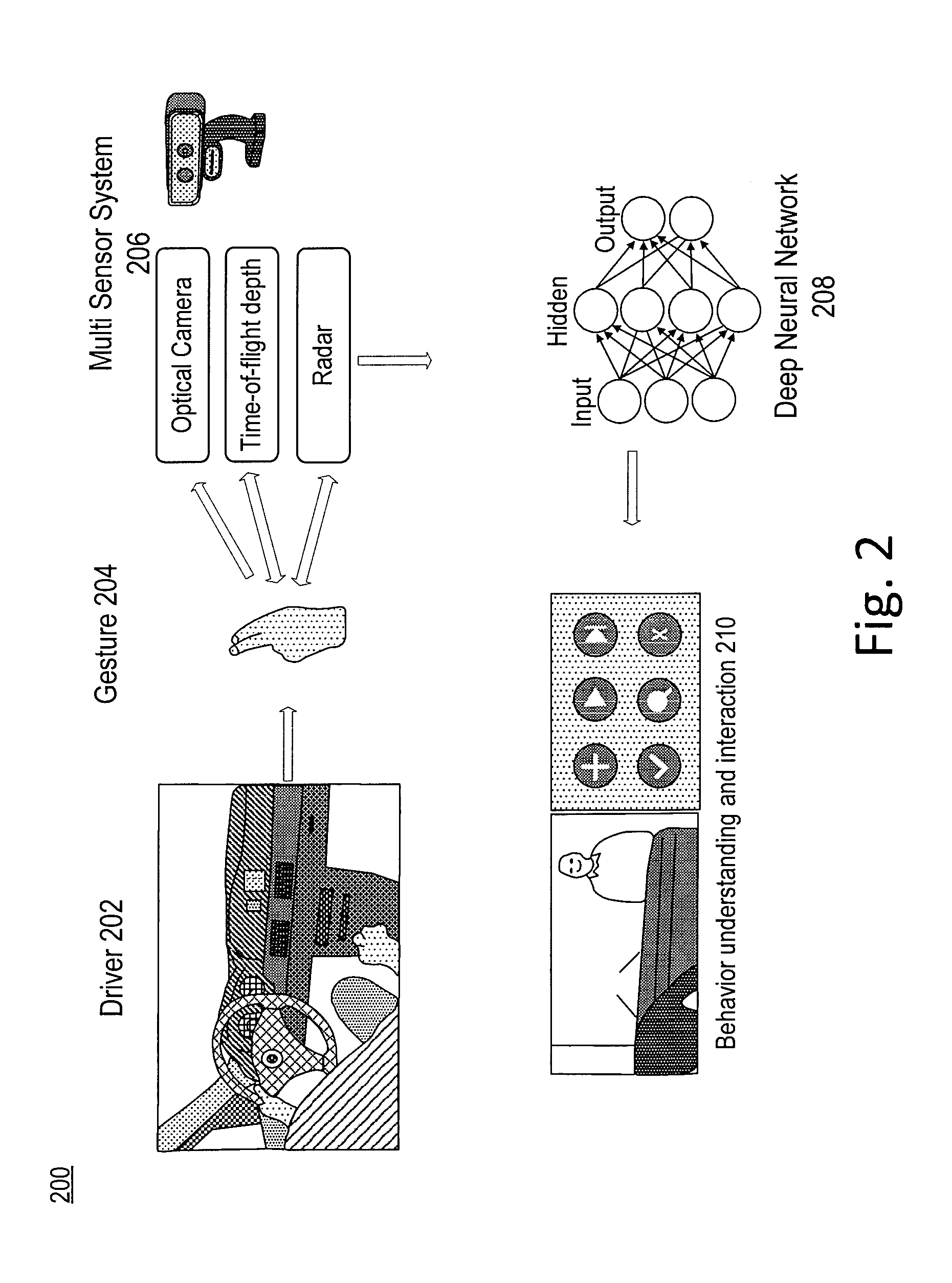
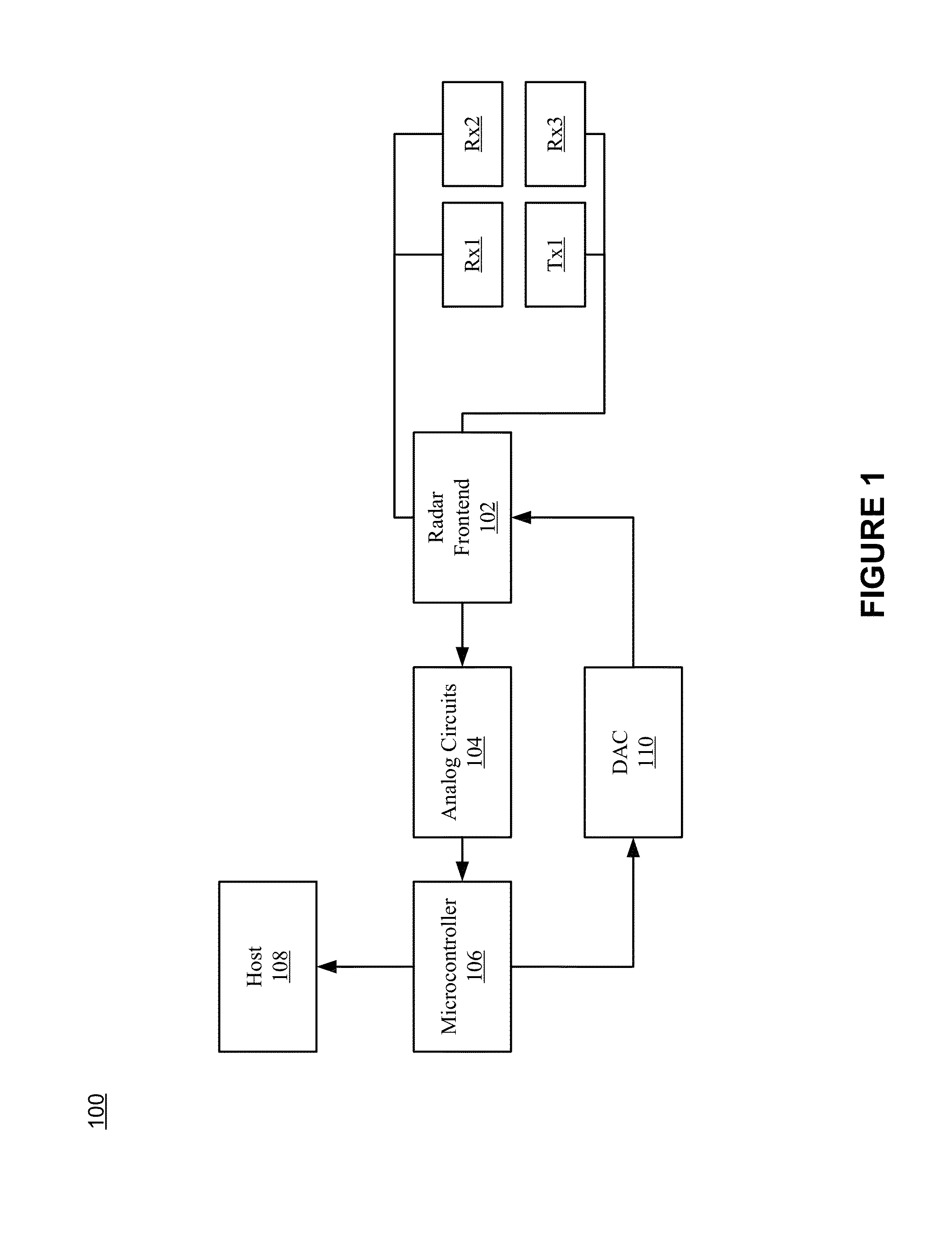
Multi-sensor based user interface
ActiveUS20170060254A1Minimize distractionReduce distractionsInput/output for user-computer interactionCharacter and pattern recognitionRadarProcessing element
An apparatus and method for gesture detection and recognition. The apparatus includes a processing element, a radar sensor, a depth sensor, and an optical sensor. The radar sensor, the depth sensor, and the optical sensor are coupled to the processing element, and the radar sensor, the depth sensor, and the optical sensor are configured for short range gesture detection and recognition. The processing element is further configured to detect and recognize a hand gesture based on data acquired with the radar sensor, the depth sensor, and the optical sensor.
Owner:NVIDIA CORP
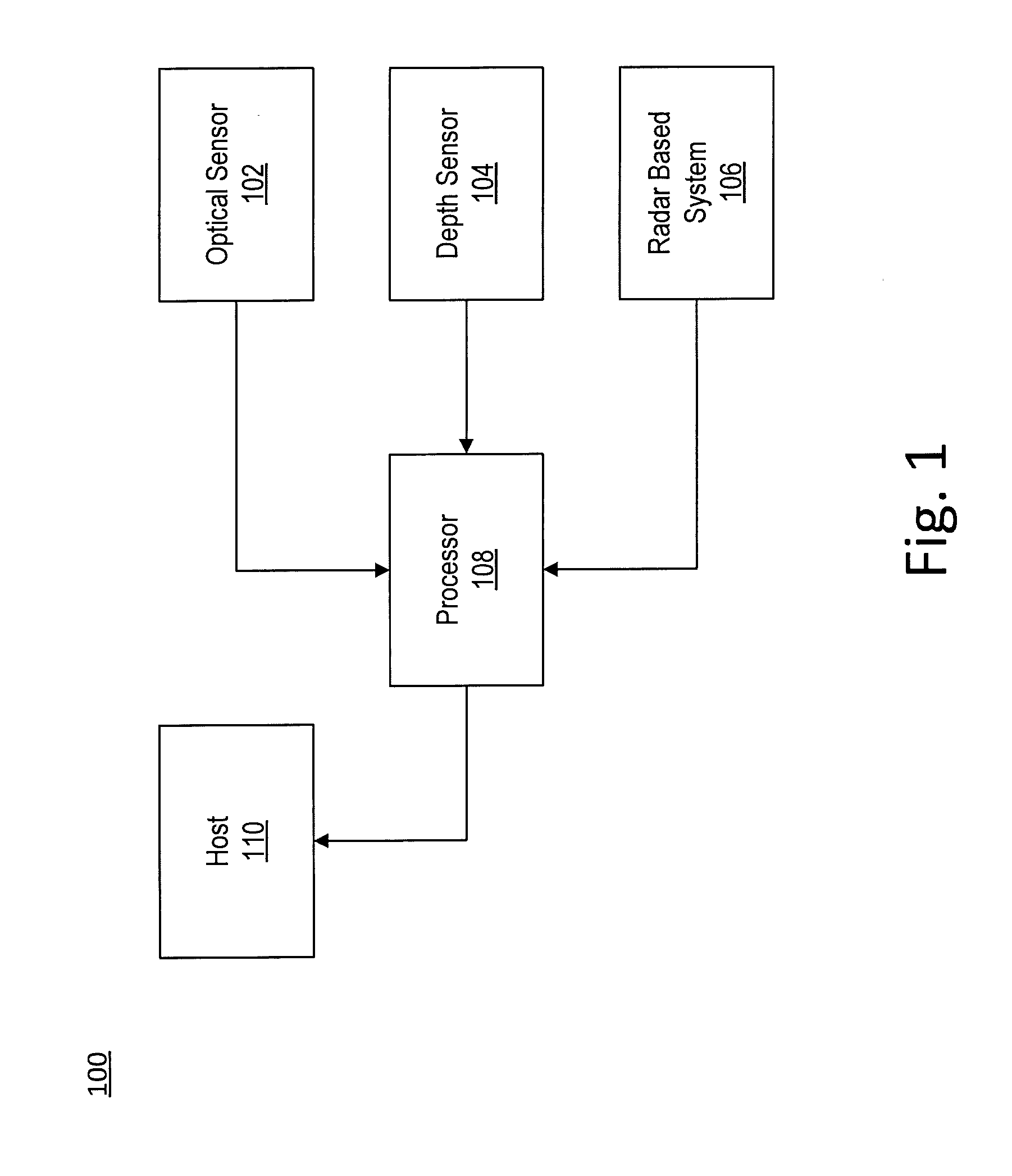
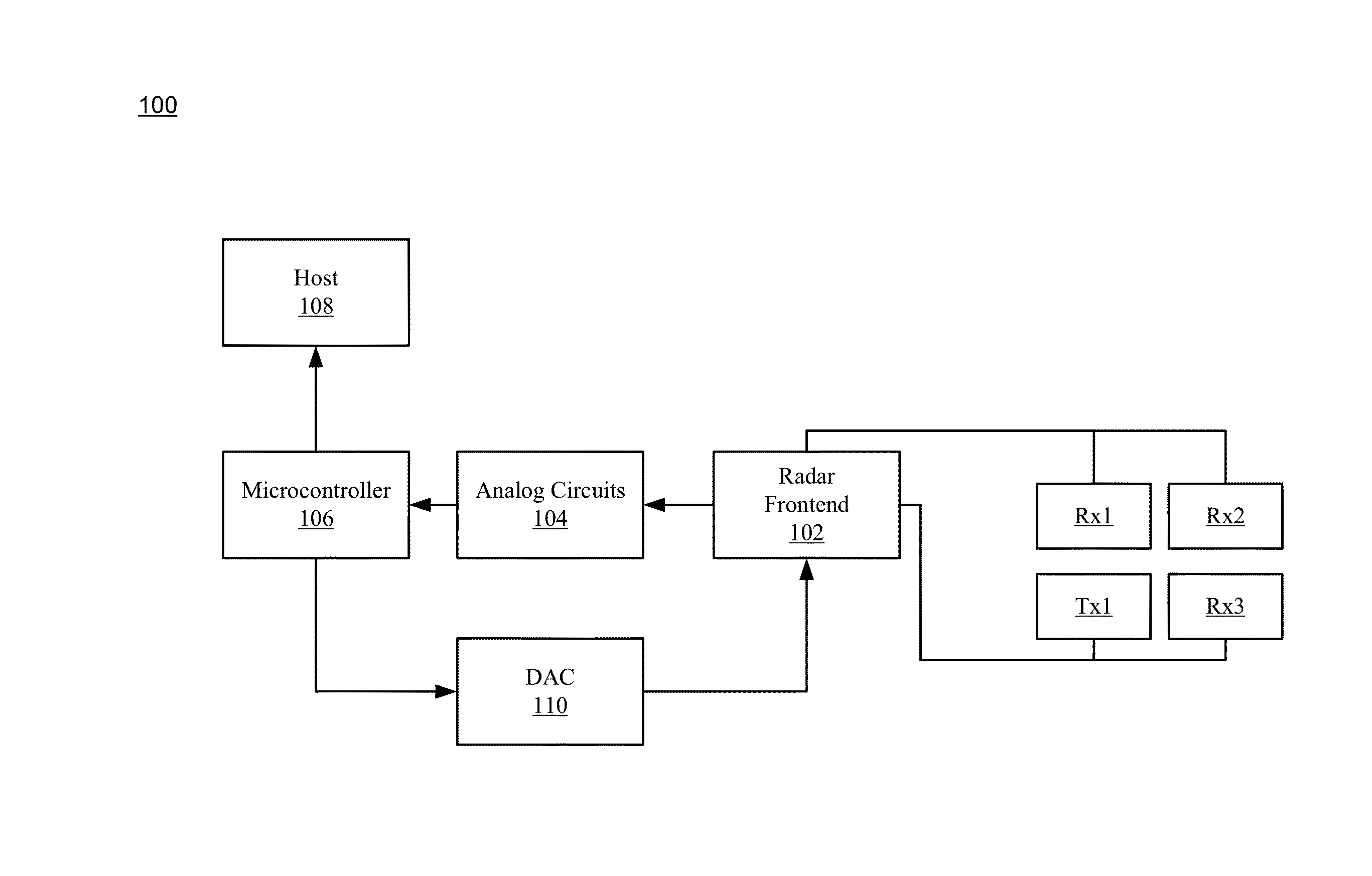
Radar based user interface
ActiveUS20160259037A1Minimize distractionImprove accuracyCharacter and pattern recognitionVehicle componentsProcessing elementUser interface
An apparatus and method for radar based gesture detection. The apparatus includes a processing element and a transmitter configured to transmit radar signals. The transmitter is coupled to the processing element. The apparatus further includes a plurality of receivers configured to receive radar signal reflections, where the plurality of receivers is coupled to the processing element. The transmitter and plurality of receivers are configured for short range radar and the processing element is configured to detect a hand gesture based on the radar signal reflections received by the plurality of receivers.
Owner:NVIDIA CORP
Apparatus and methods for synaptic update in a pulse-coded network
InactiveUS20130073491A1Reducing memory bus overheadReduce overheadDigital computer detailsDigital dataSynapseSpiking neural network
Apparatus and methods for efficient synaptic update in a network such as a spiking neural network. In one embodiment, the post-synaptic updates, in response to generation of a post-synaptic pulse by a post-synaptic unit, are delayed until a subsequent pre-synaptic pulse is received by the unit. Pre-synaptic updates are performed first following by the post-synaptic update, thus ensuring synaptic connection status is up-to-date. The delay update mechanism is used in conjunction with system “flush” events in order to ensure accurate network operation, and prevent loss of information under a variety of pre-synaptic and post-synaptic unit firing rates. A large network partition mechanism is used in one variant with network processing apparatus in order to enable processing of network signals in a limited functionality embedded hardware environment.
Owner:QUALCOMM INC
Apparatus and methods for temporally proximate object recognition
InactiveUS20120308076A1Character and pattern recognitionNeural architecturesTransmission channelObject detection
Object recognition apparatus and methods useful for extracting information from an input signal. In one embodiment, the input signal is representative of an element of an image, and the extracted information is encoded into patterns of pulses. The patterns of pulses are directed via transmission channels to a plurality of detector nodes configured to generate an output pulse upon detecting an object of interest. Upon detecting a particular object, a given detector node elevates its sensitivity to that particular object when processing subsequent inputs. In one implementation, one or more of the detector nodes are also configured to prevent adjacent detector nodes from generating detection signals in response to the same object representation. The object recognition apparatus modulates properties of the transmission channels by promoting contributions from channels carrying information used in object recognition.
Owner:BRAIN CORP
Co-processor IP core of programmable convolutional neural network
ActiveCN106940815AReduce frequencyReduce bandwidth pressureNeural architecturesPhysical realisationHardware structureInstruction set design
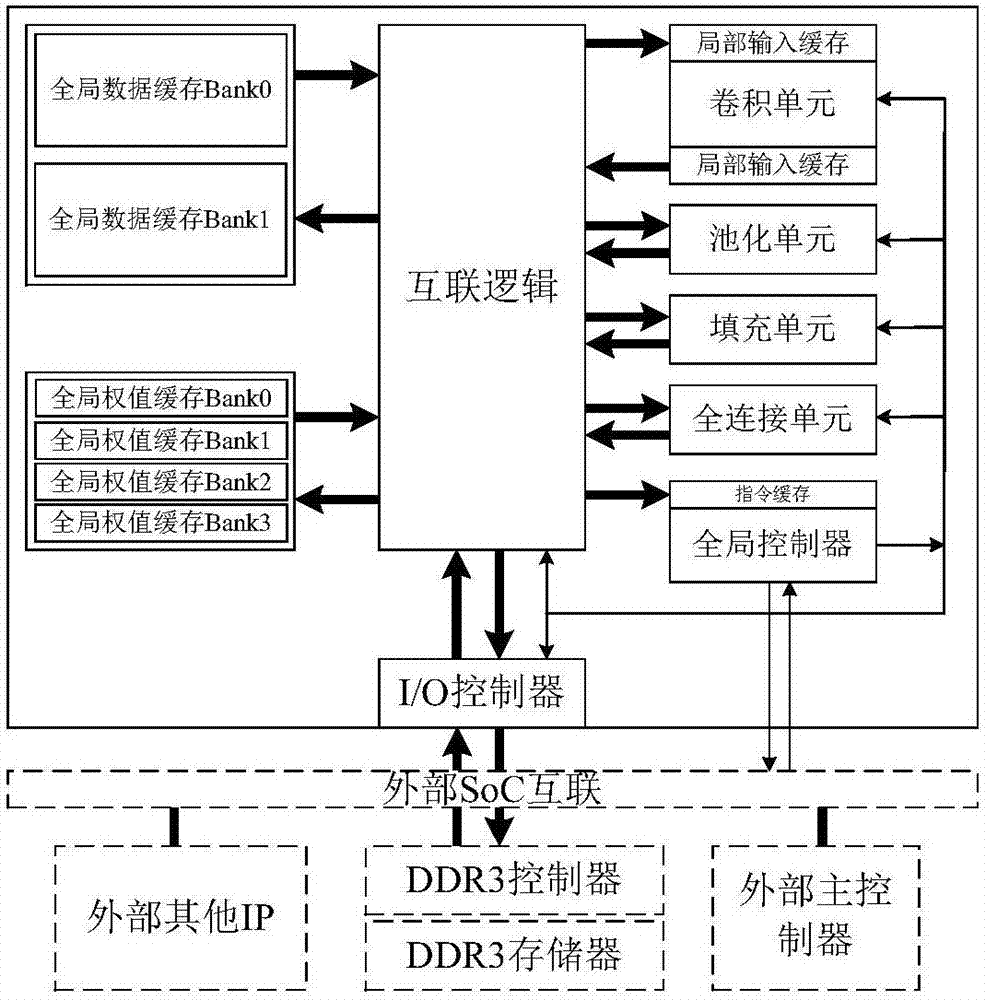
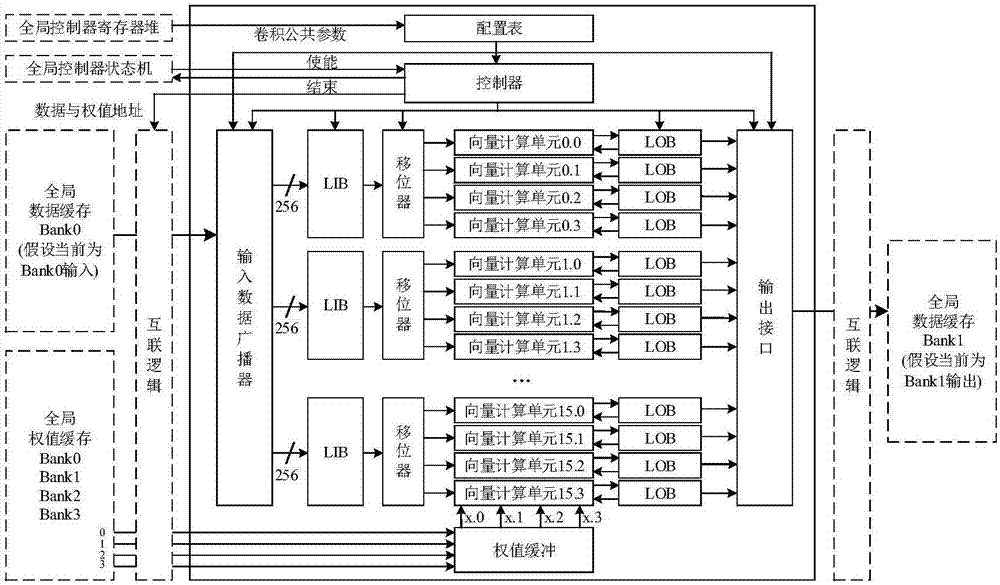
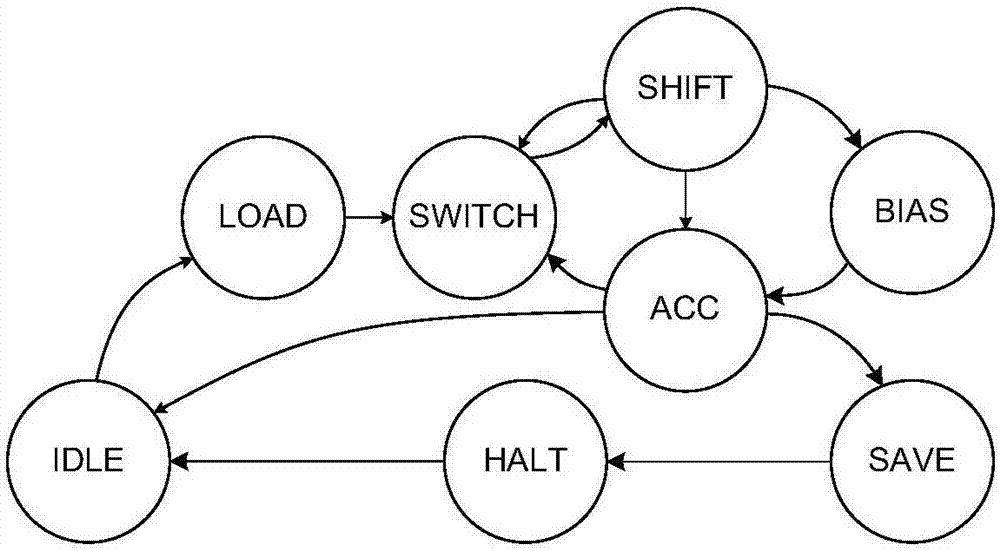
The present invention discloses a co-processor IP core of a programmable convolutional neural network. The invention aims to realize the arithmetic acceleration of the convolutional neural network on a digital chip (FPGA or ASIC). The co-processor IP core specifically comprises a global controller, an I / O controller, a multi-level cache system, a convolution unit, a pooling unit, a filling unit, a full-connection unit, an internal interconnection logical unit, and an instruction set designed for the co-processor IP. The proposed hardware structure supports the complete flows of convolutional neural networks diversified in scale. The hardware-level parallelism is fully utilized and the multi-level cache system is designed. As a result, the characteristics of high performance, low power consumption and the like are realized. The operation flow is controlled through instructions, so that the programmability and the configurability are realized. The co-processor IP core can be easily applied to different application scenes.
Owner:XI AN JIAOTONG UNIV
Intelligent and automatic delineation method for gross tumor volume and organs at risk
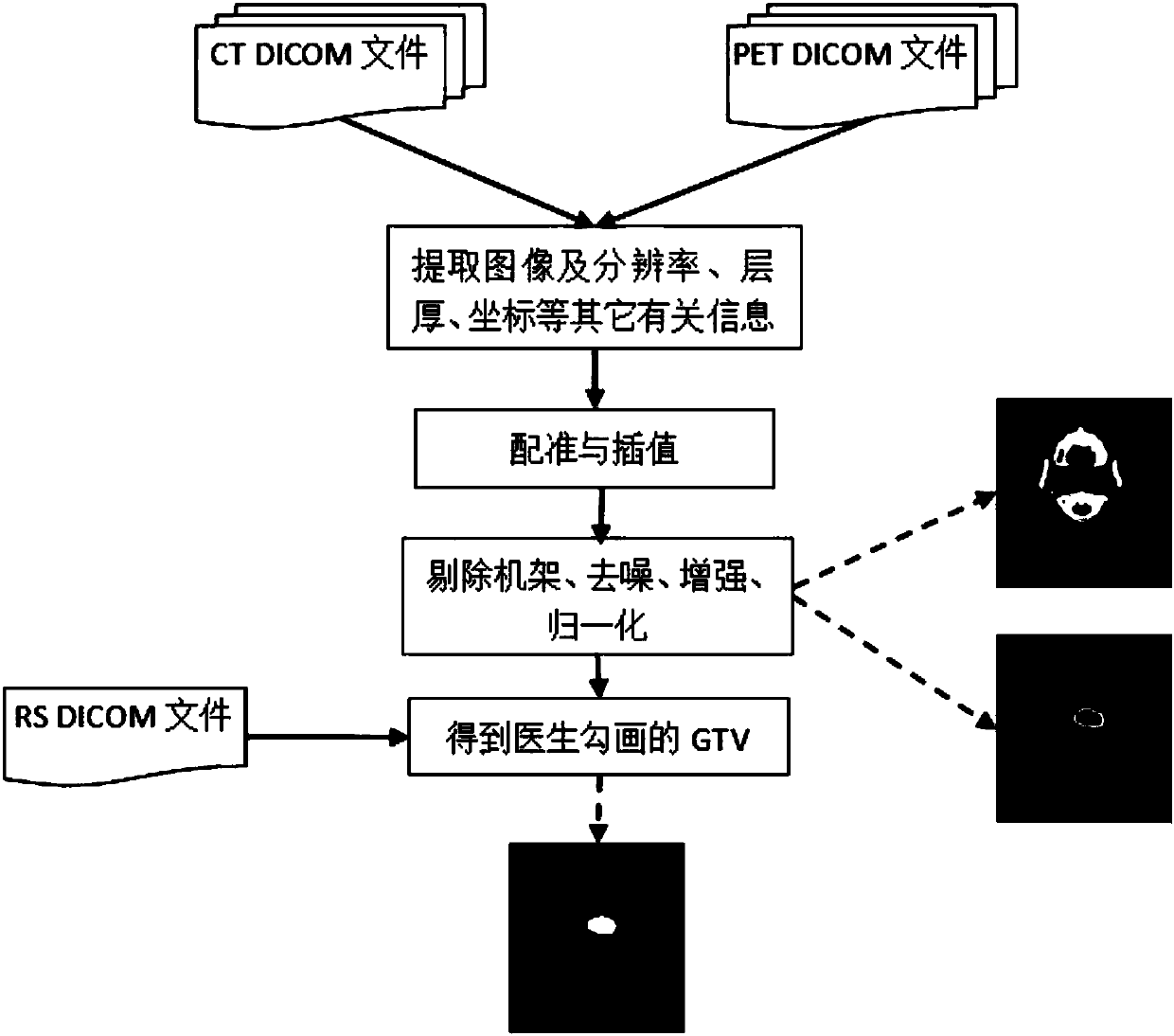
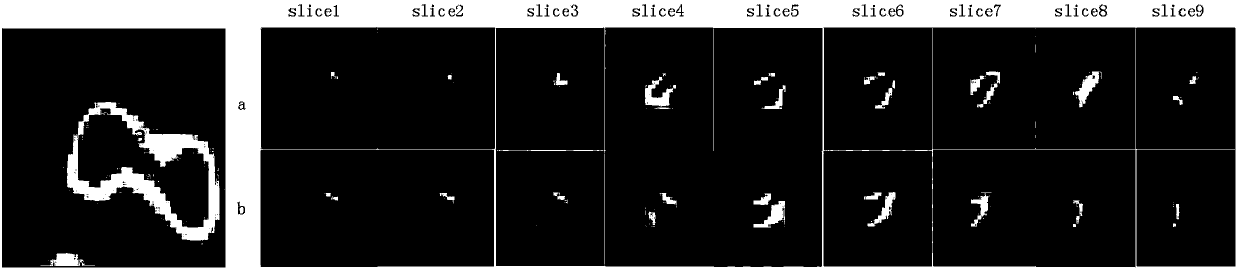
InactiveCN107403201ASmart sketchAutomatically sketchImage enhancementImage analysisSonificationMathematical Graph
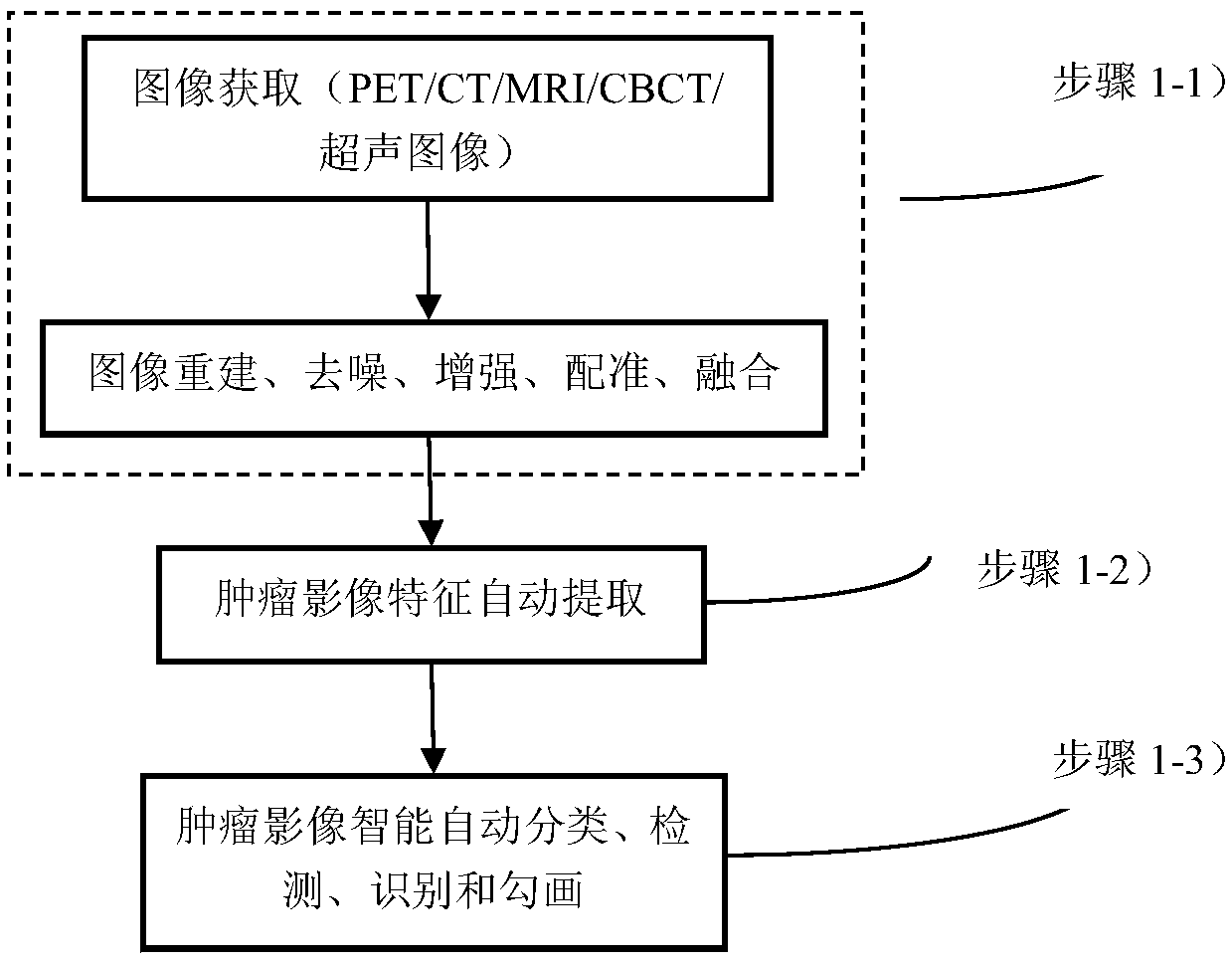
The invention relates to an intelligent and automatic delineation method for a gross tumor volume and organs at risk, which includes the following steps: (1) tumor multi-modal (mode) image reconstruction, de-noising, enhancement, registration, fusion and other preprocessing; (2) automatic extraction of tumor image features: automatically extracting one or more pieces of tumor image group (texture feature spectrum) information from CT, CBCT, MRI, PET and / or ultrasonic multi-modal (mode) tumor medical image data; and (3) intelligently and automatically delineating a gross tumor volume and organs at risk through deep learning, machine learning, artificial intelligence, regional growing, the graph theory (random walk), a geometric level set, and / or a statistical theory method. A gross tumor volume (GTV) and organs at risk (OAR) can be delineated with high precision.
Owner:强深智能医疗科技(昆山)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com