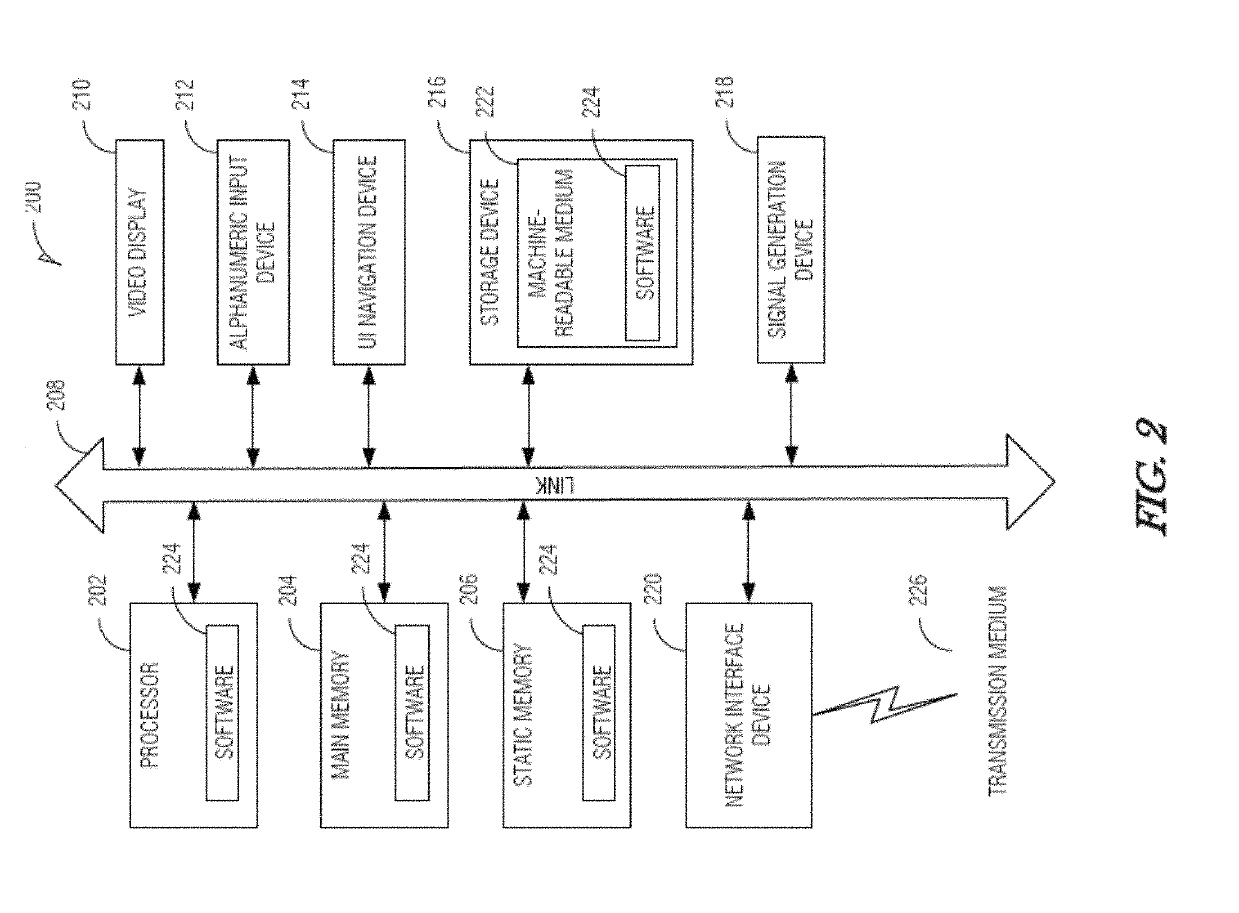
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
119 results about "Security framework" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
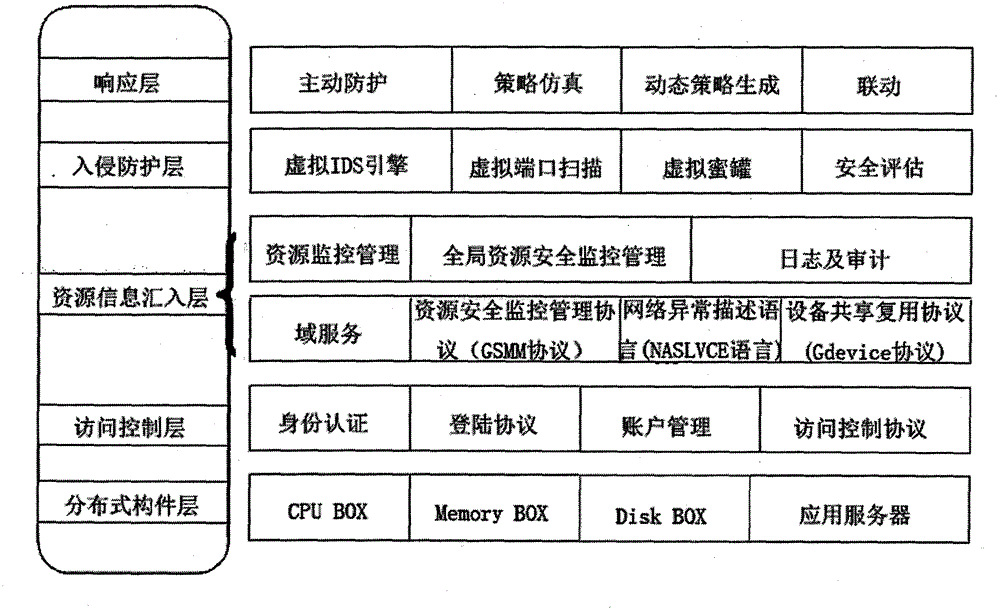
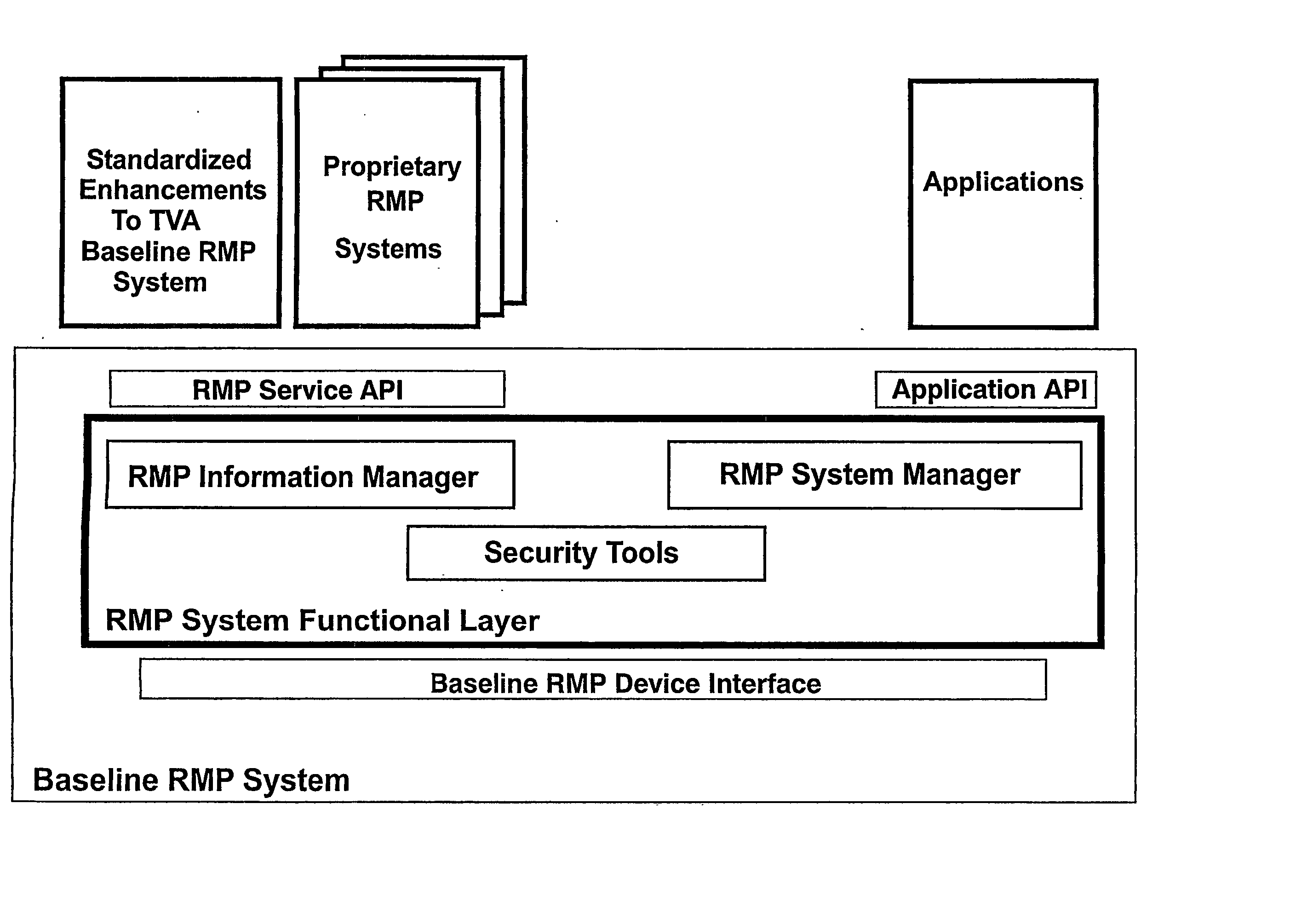
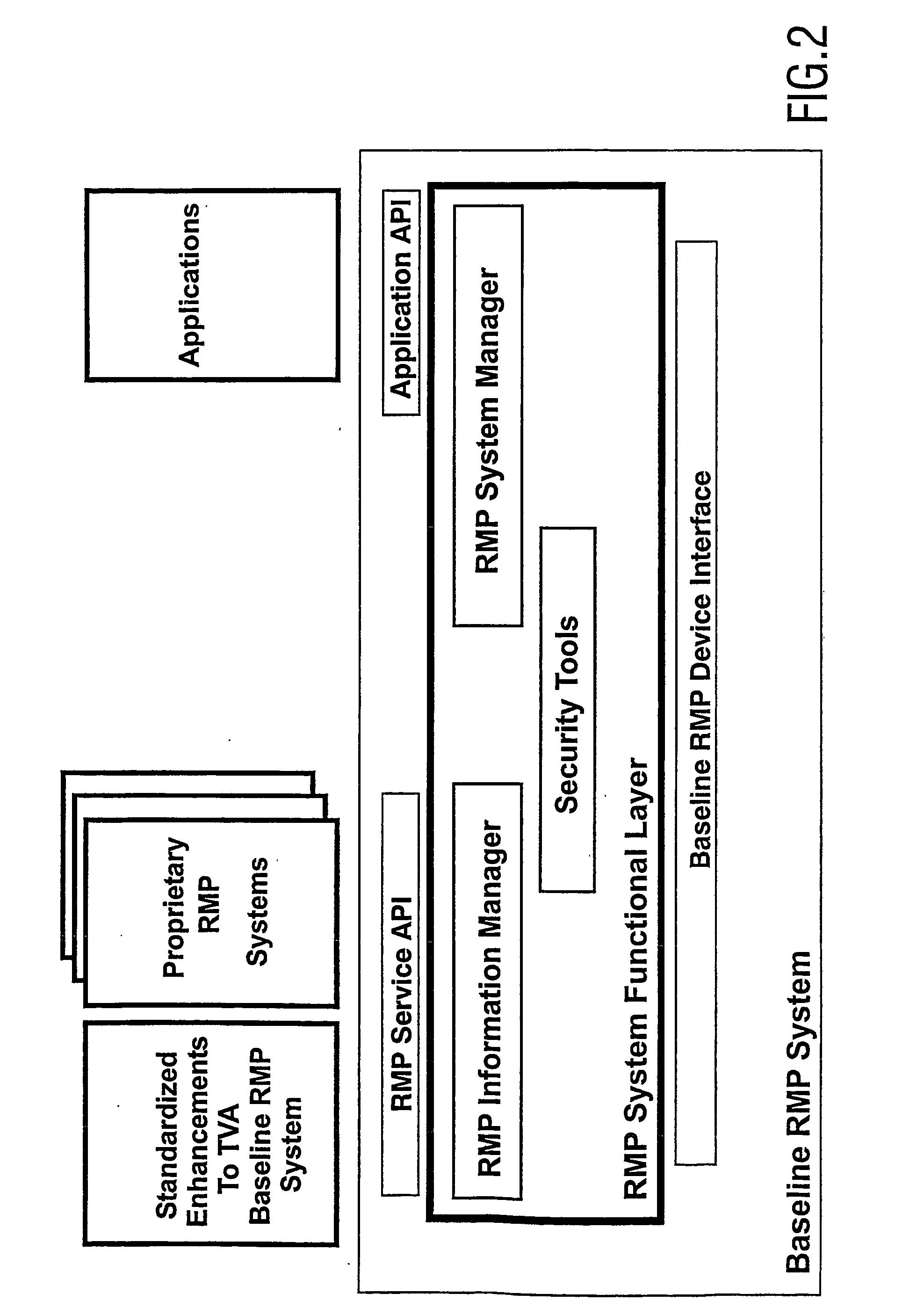
An information security framework is a series of documented processes that are used to define policies and procedures around the implementation and ongoing management of information security controls in an enterprise environment. These frameworks are basically a "blueprint" for building an information security program to manage risk and reduce vulnerabilities.
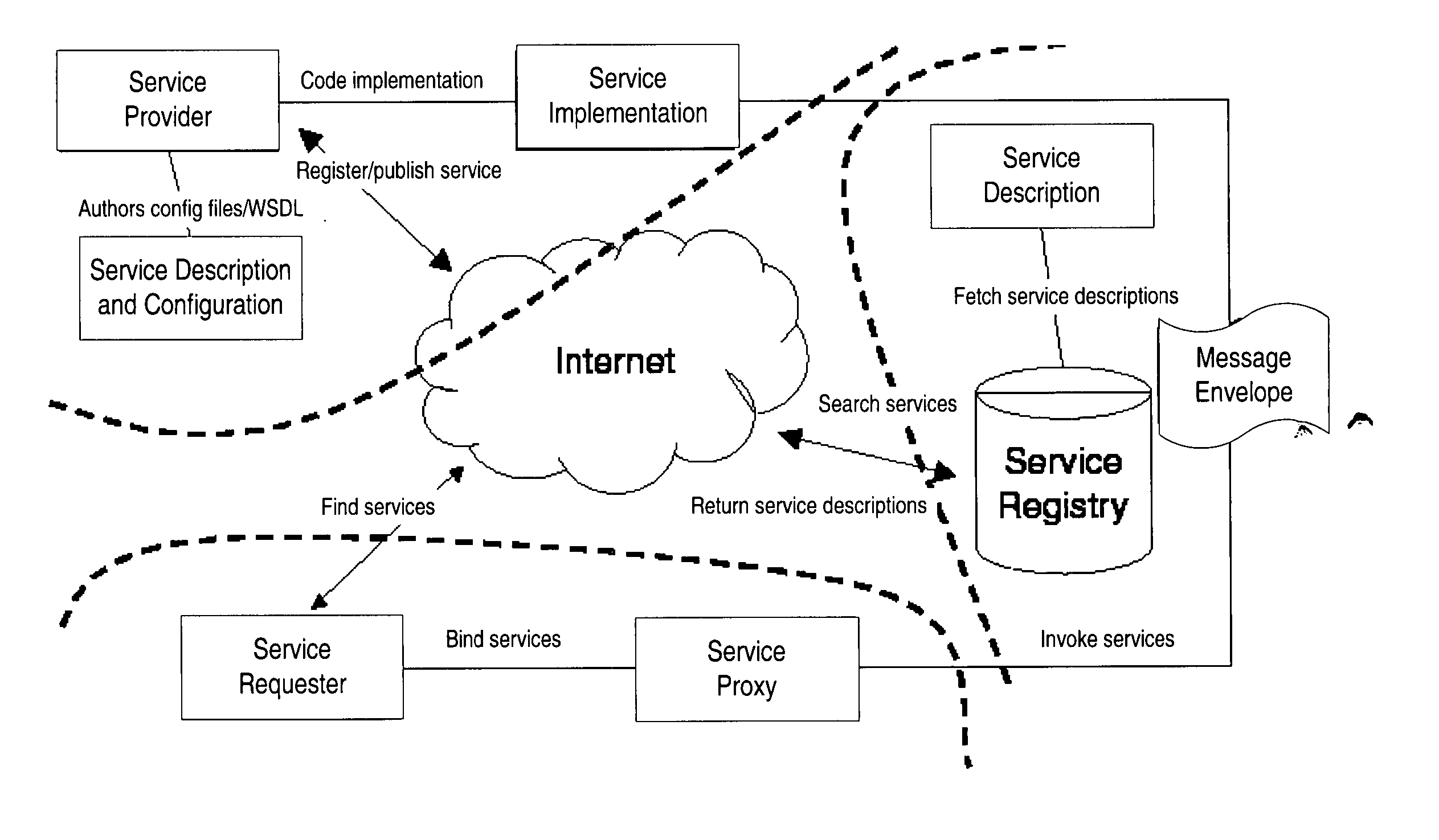
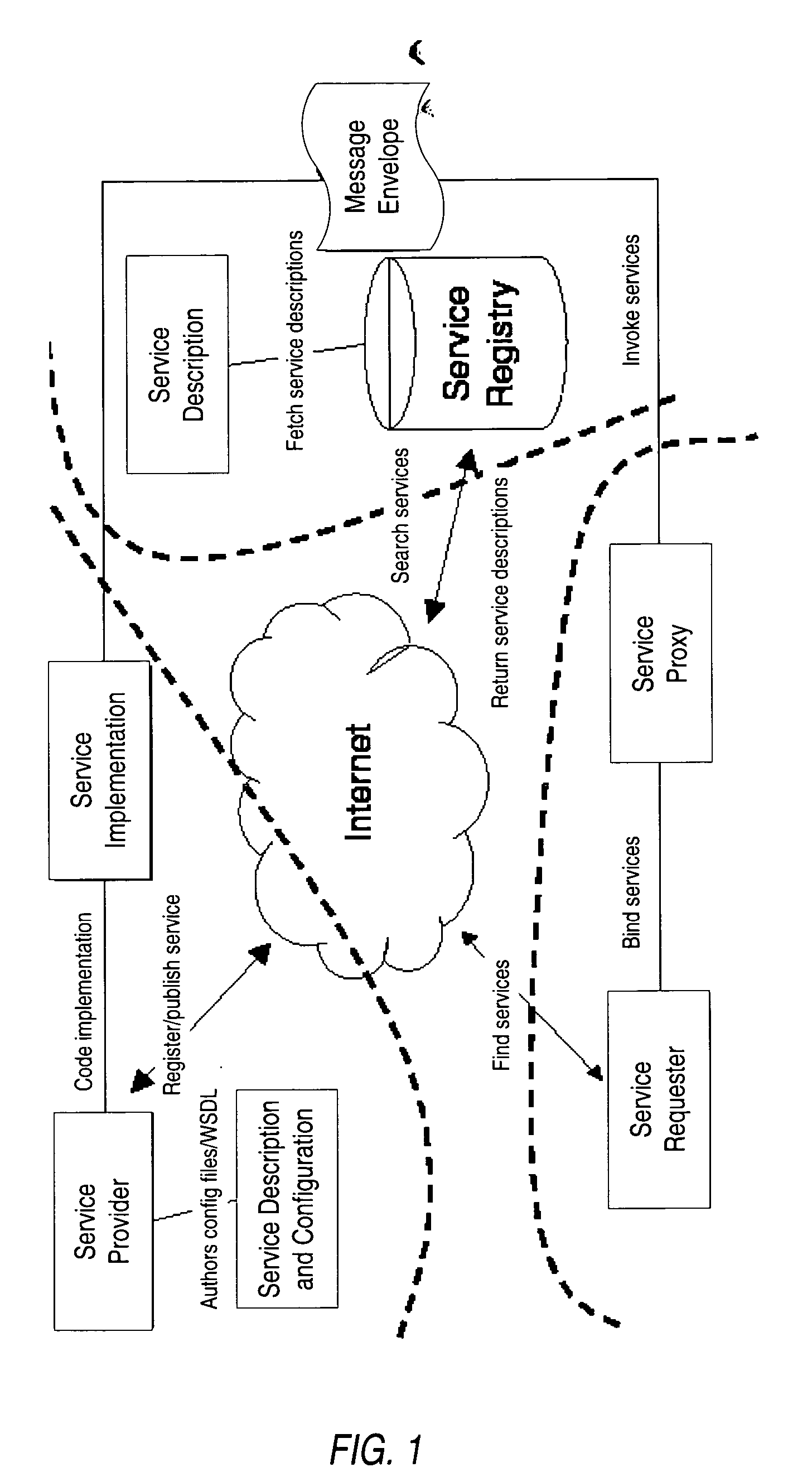
Structured methodology and design patterns for web services
ActiveUS20050044197A1Multiple digital computer combinationsDigital dataQuality of serviceBusiness-to-business
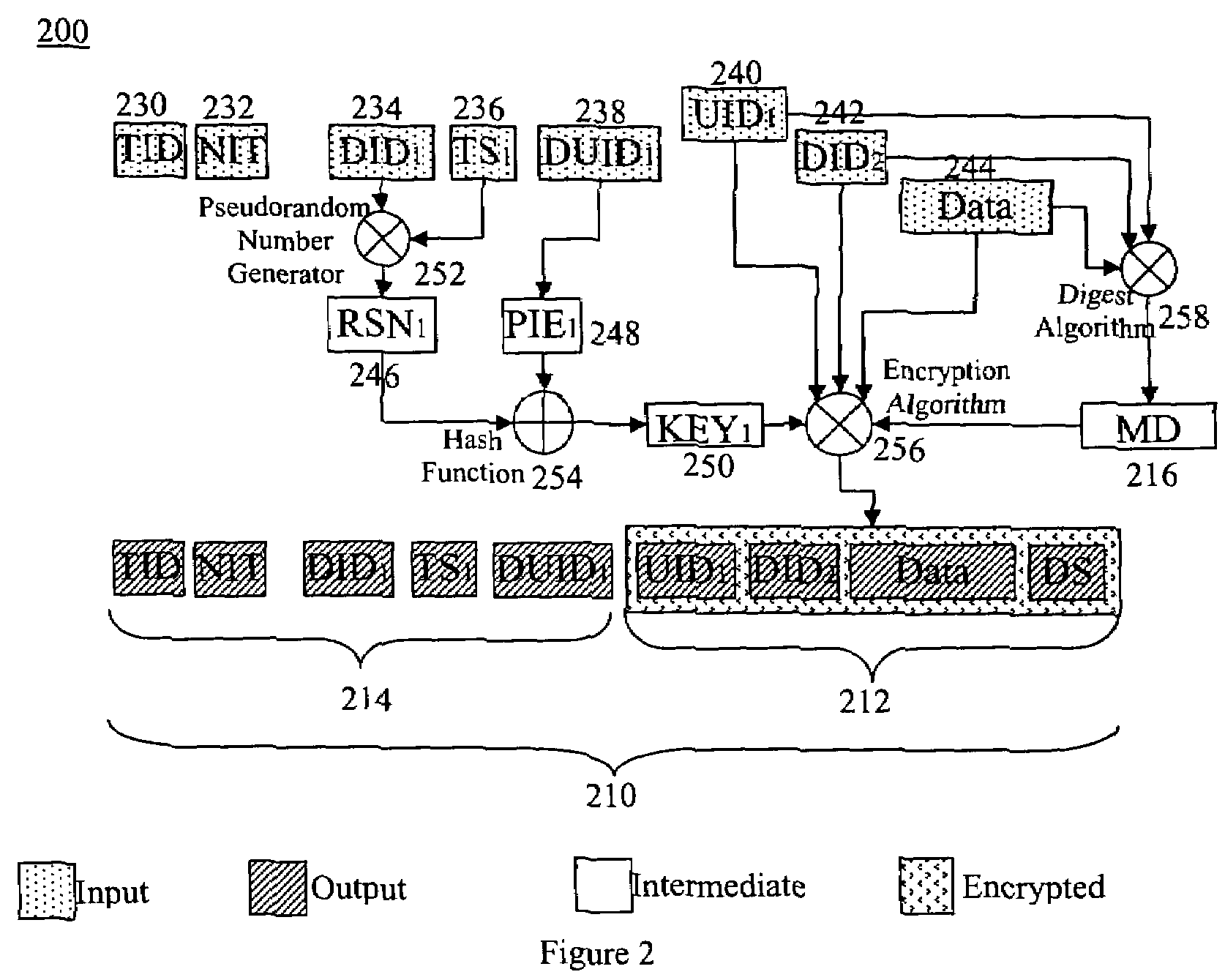
System and method for designing and implementing Web Services according to a structured methodology and design patterns. Embodiments may incorporate a structured methodology, best practices and design patterns that address reliability, availability and scalability of Web Services architecture. Embodiments may provide mechanisms for integrating heterogeneous technology components into Web Services. Embodiments may provide a vendor-independent Web Services architecture framework and reusable Web Services design patterns, which may be used in creating end-to-end solutions based on past experience and best practices. Embodiments may include design patterns and best practices for delivering Web Services solutions with Quality of Services. One embodiment may provide a Business-to-Business Integration (B2Bi) integration framework for Web Services. Embodiments may provide a Web Security framework and design patterns for designing end-to-end Web Services security.
Owner:ORACLE INT CORP
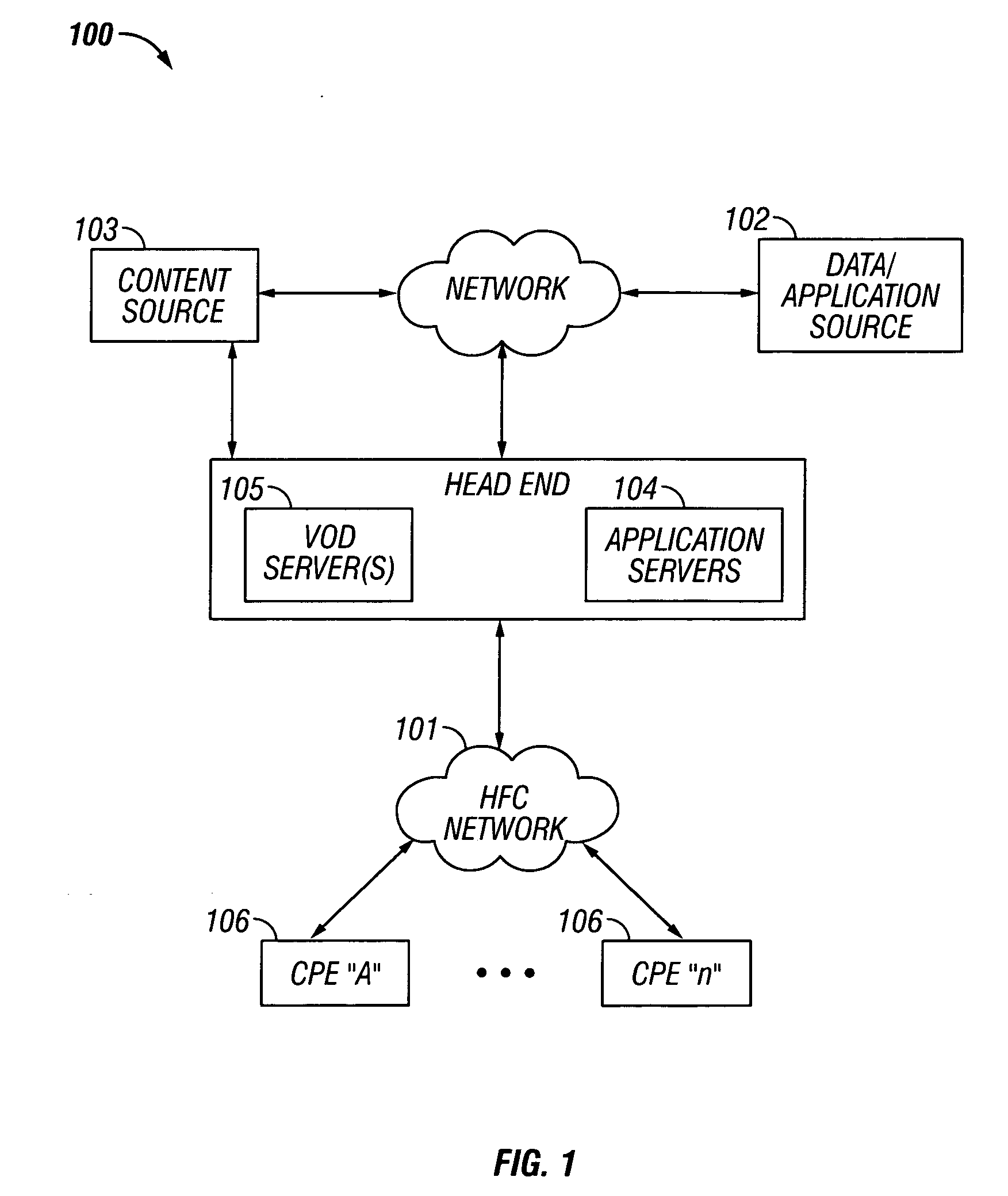
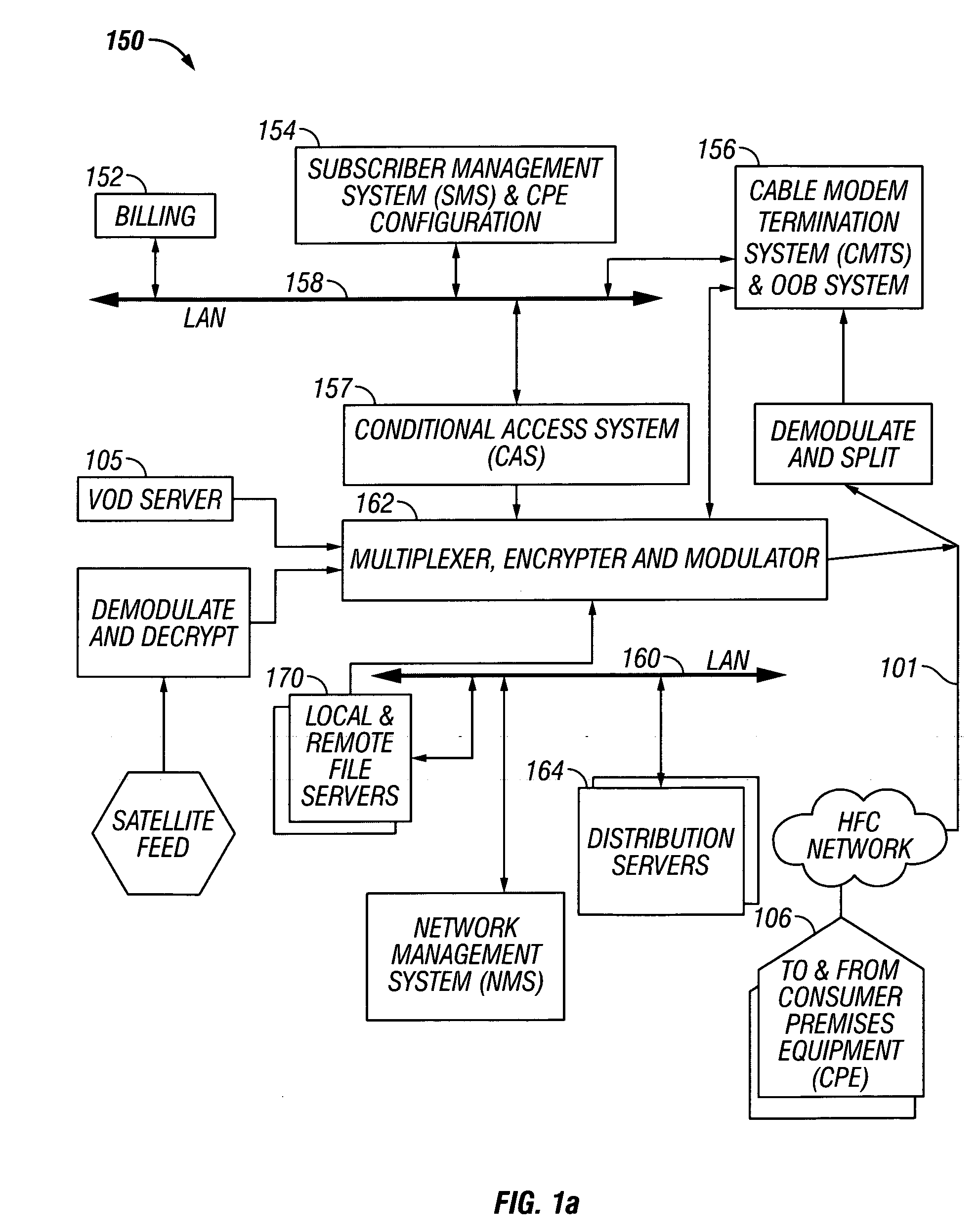
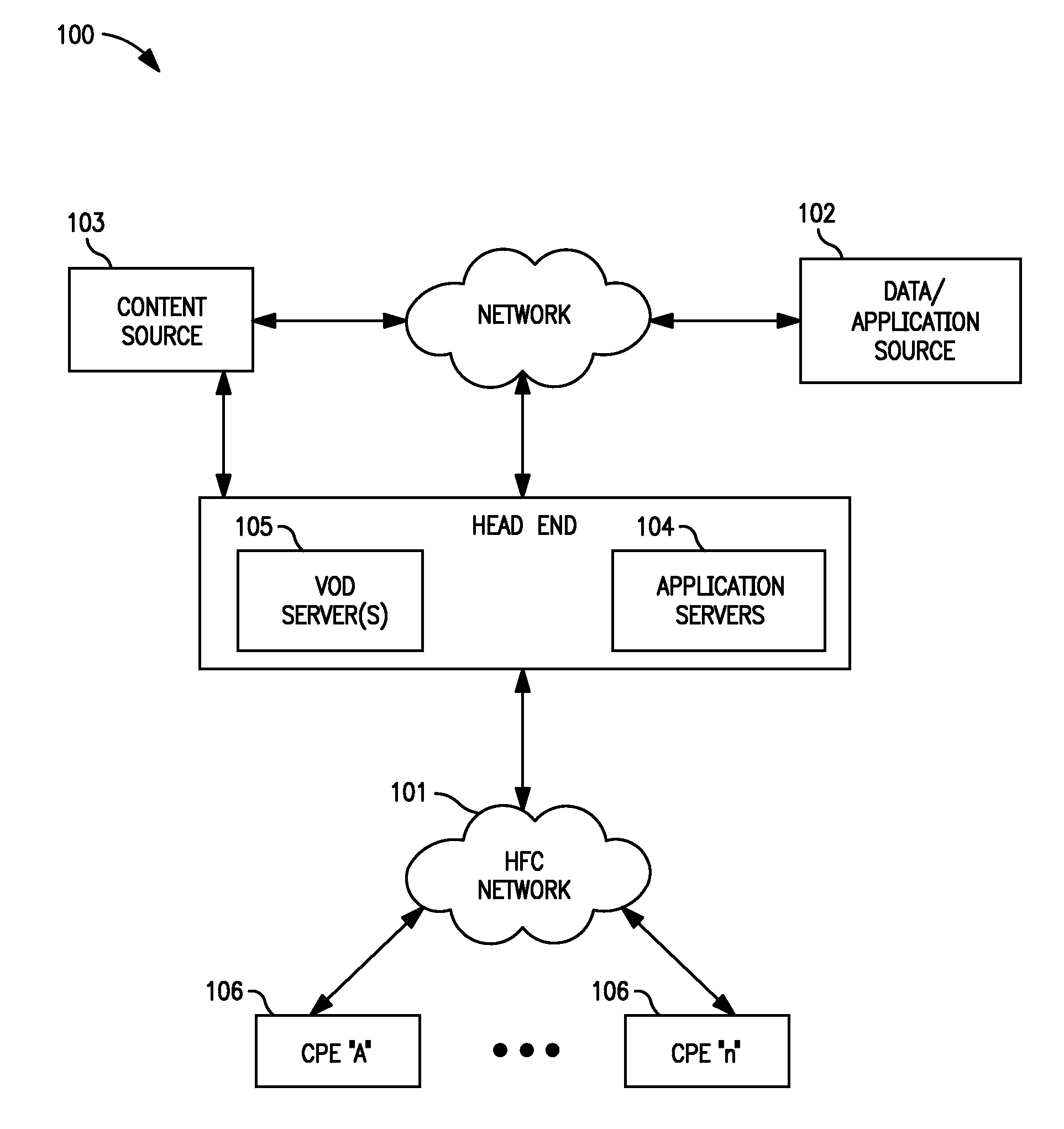
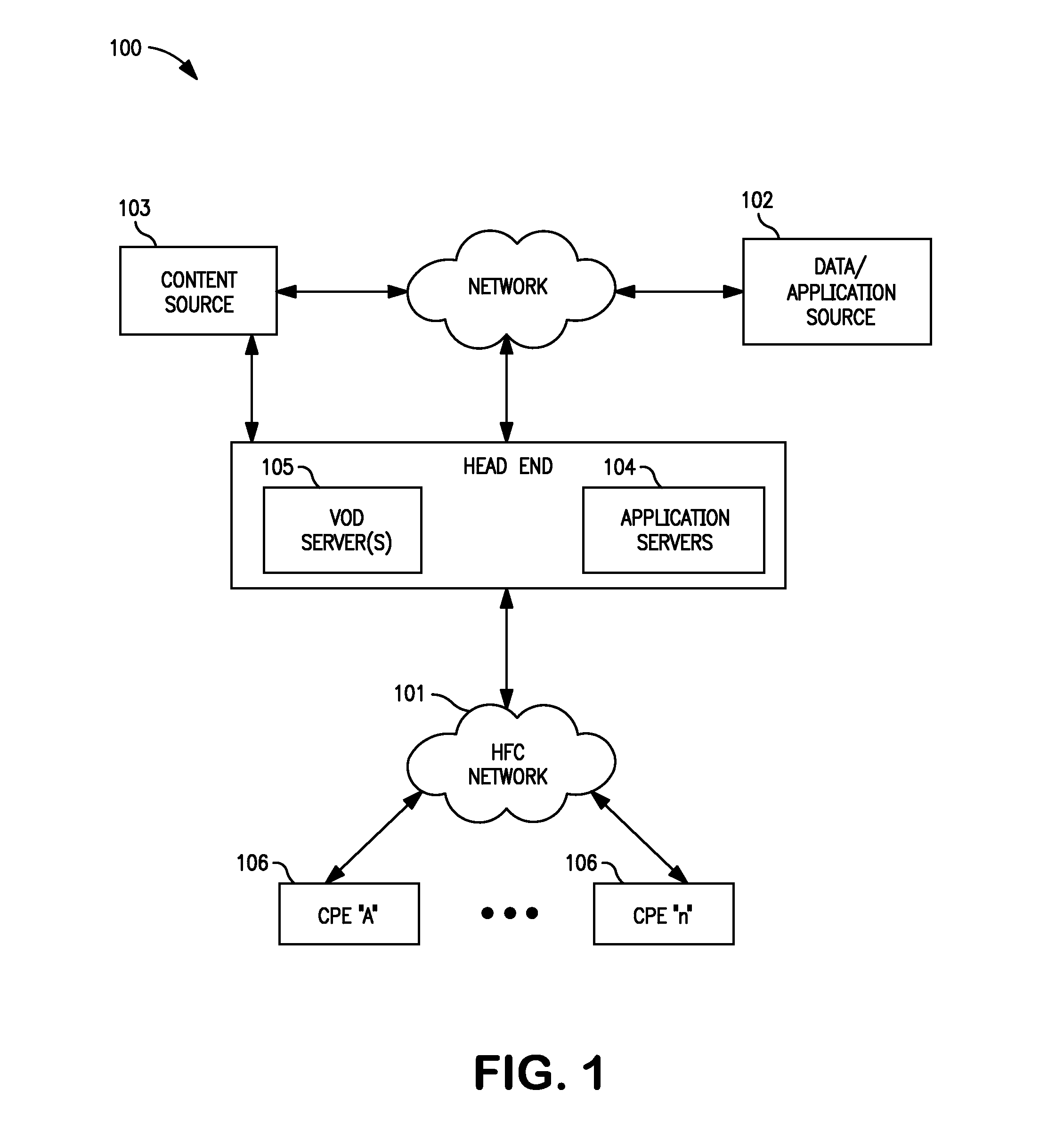
Methods and apparatus for premises content distribution
Apparatus and methods for protected content access, browsing and transfer over a network. In one embodiment, the network comprises a premises (e.g., residential) LAN, and the apparatus comprises a server and renderer consumer premise equipment (CPE). The renderer CPE scans the network to search for a server CPE that implement a compatible security framework. The renderer authenticates itself with the server, and the server allows content browsing and selection access only to an authorized and authenticated renderer. A negotiation and exchange protocol comprises messages exchanged between the renderer and the server that include one or more of device identification, encryption key exchange, digital certificates and information regarding security package used by each CPE.
Owner:TIME WARNER CABLE ENTERPRISES LLC
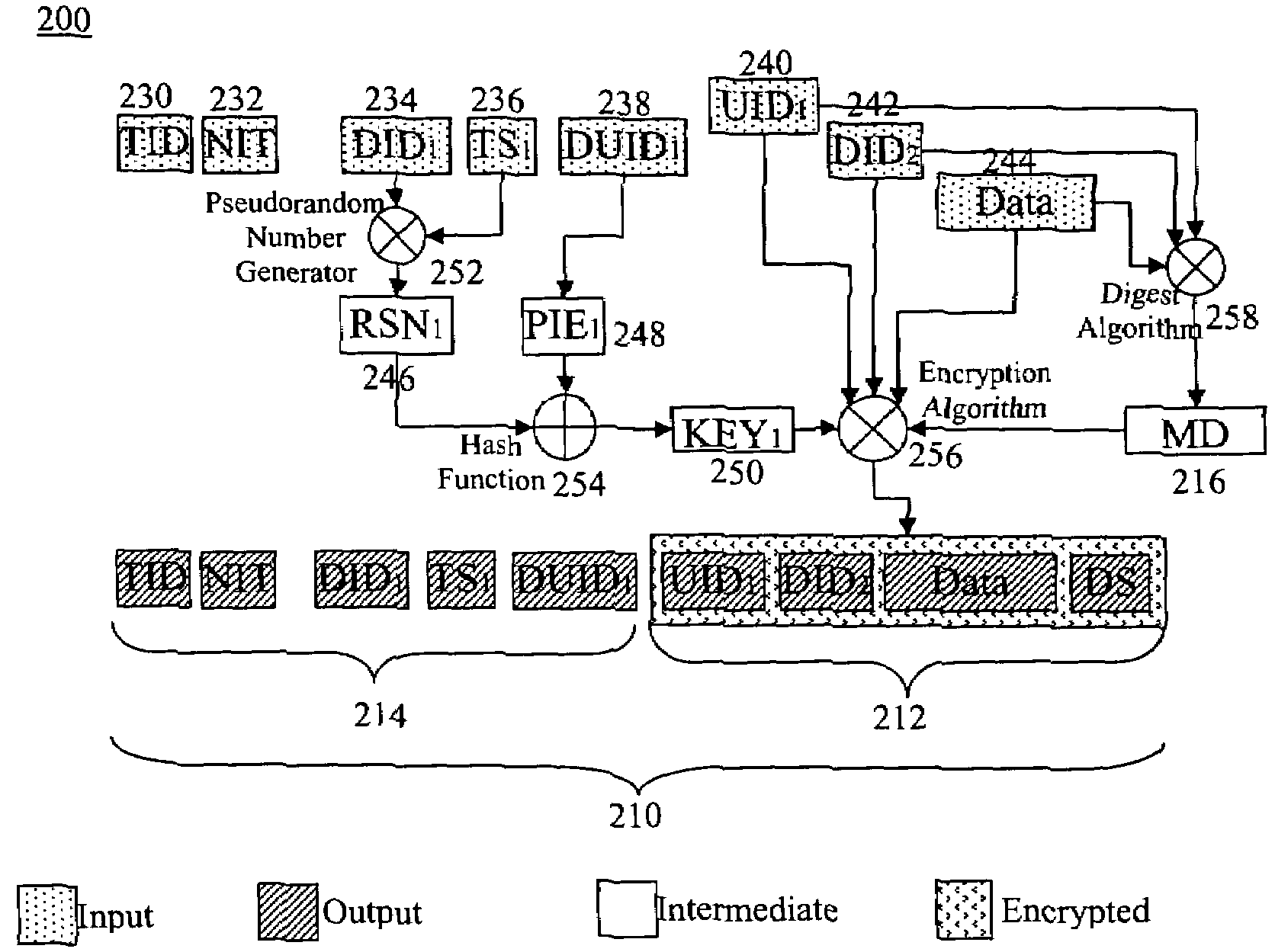
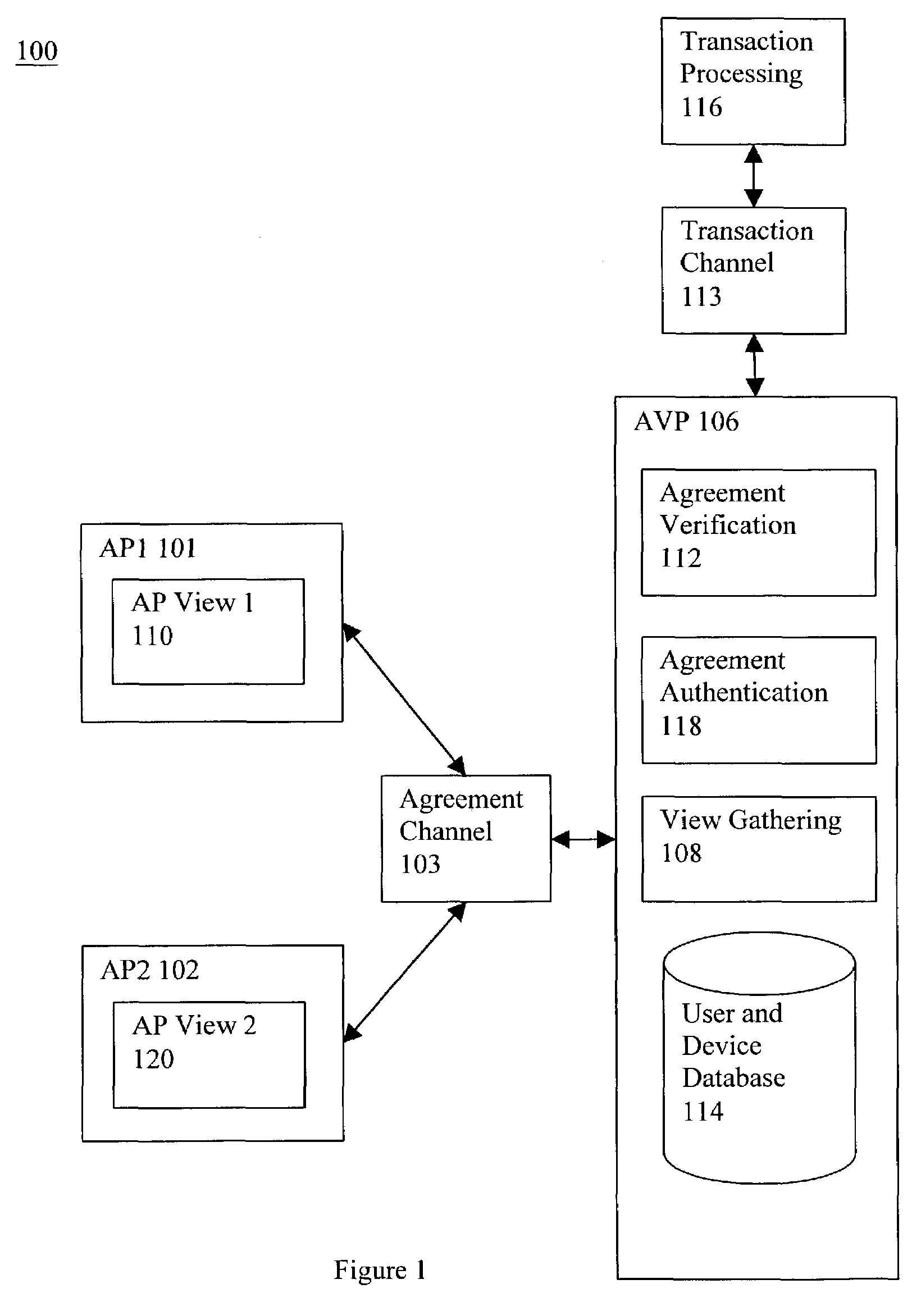
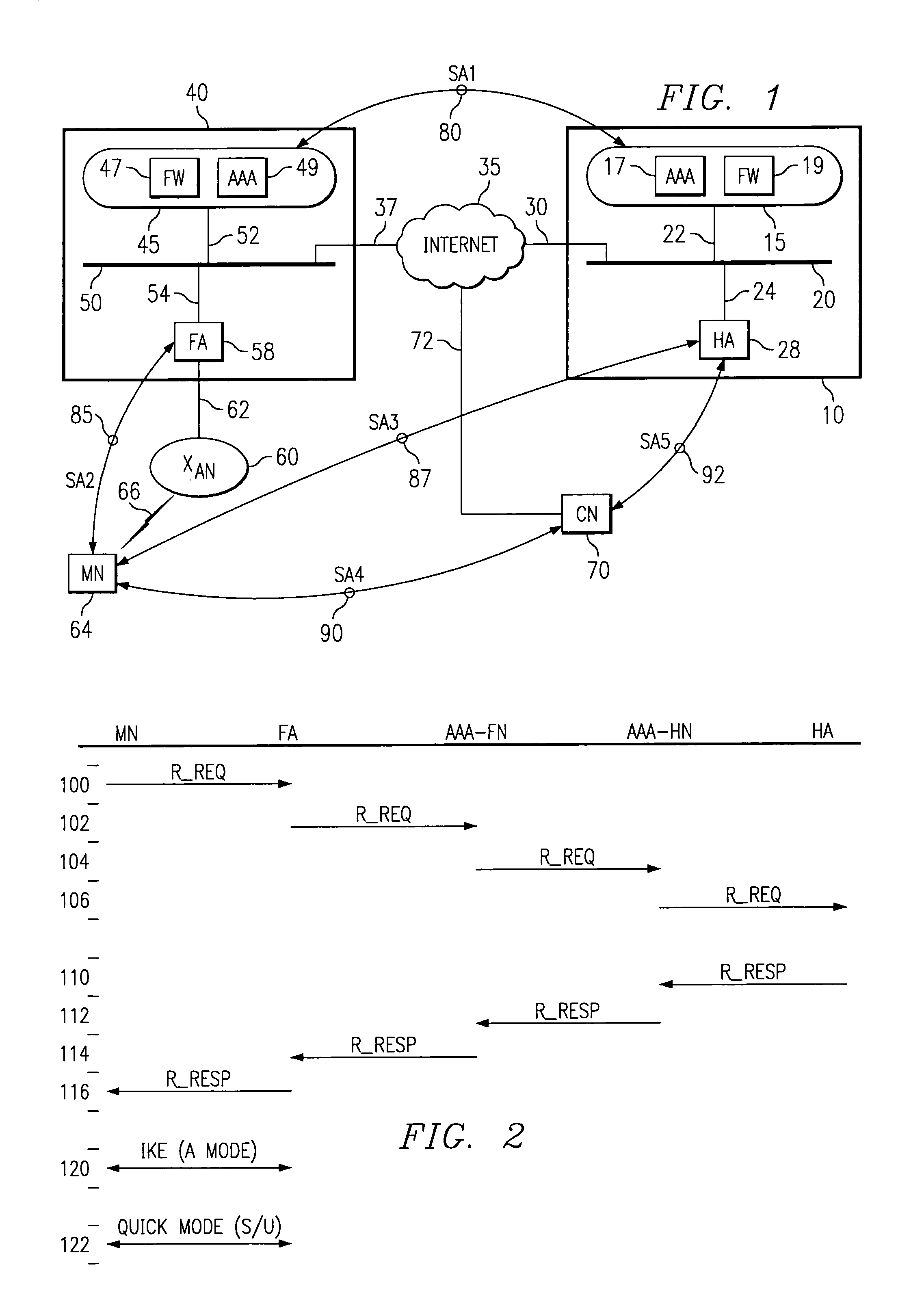
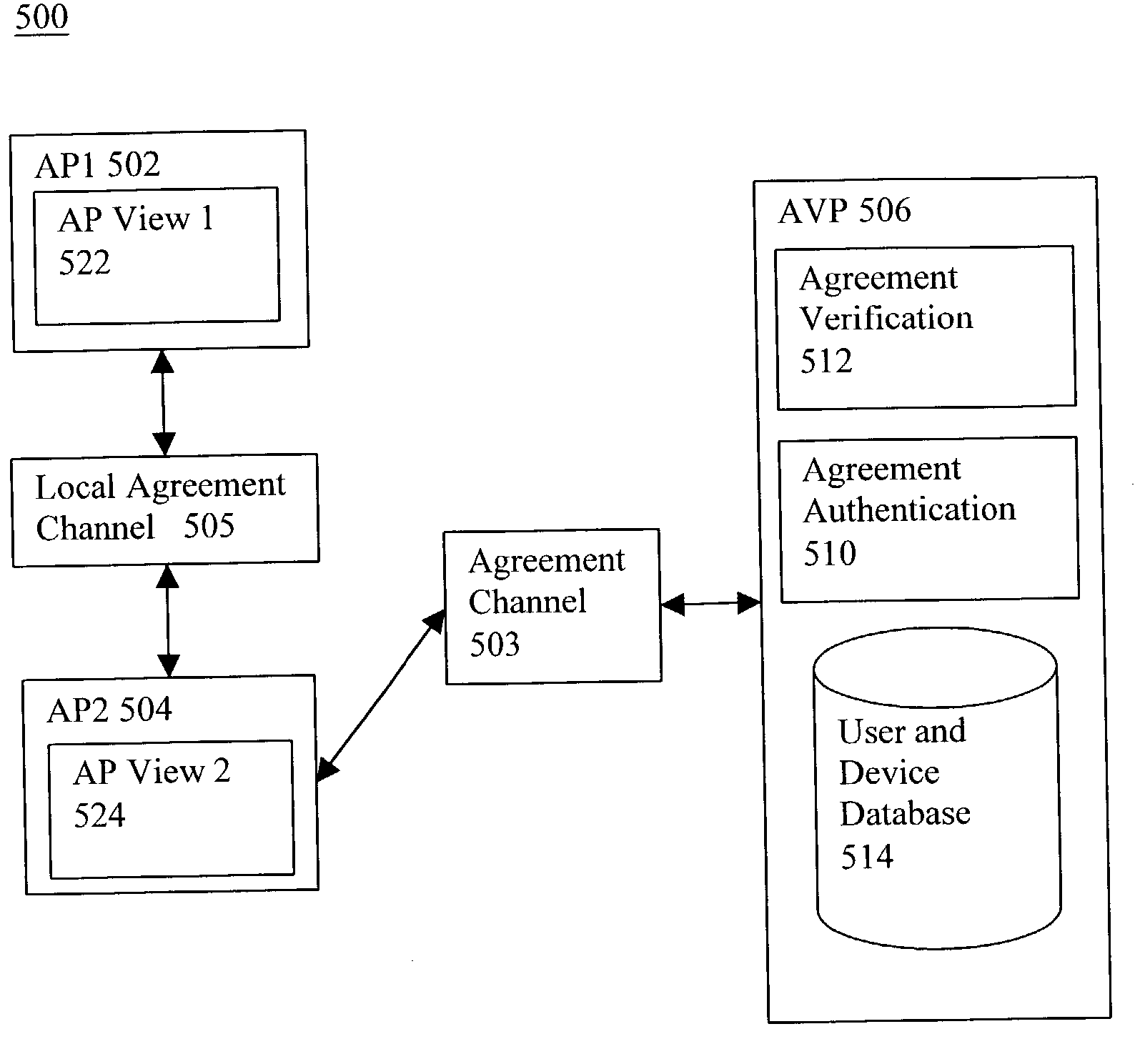
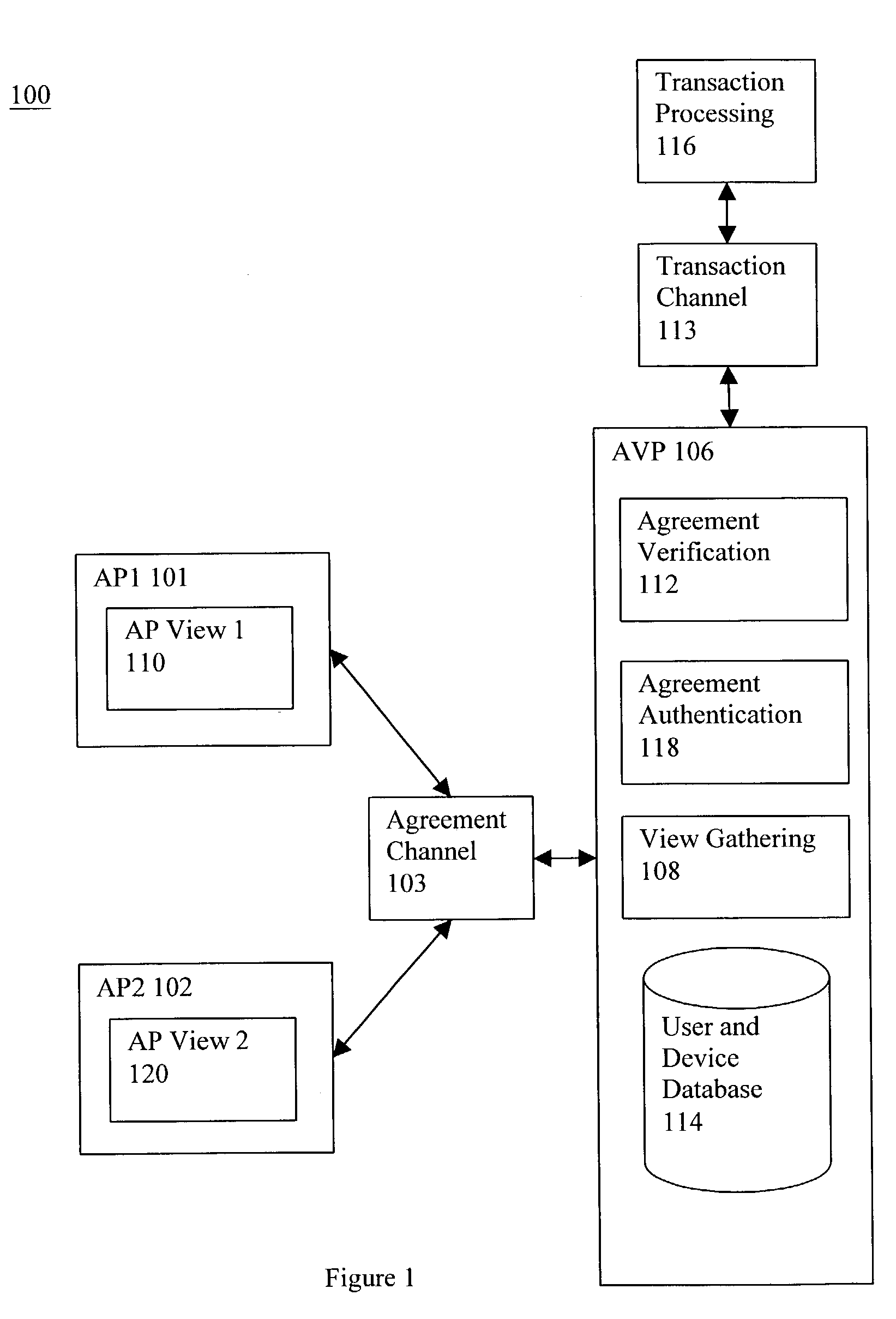
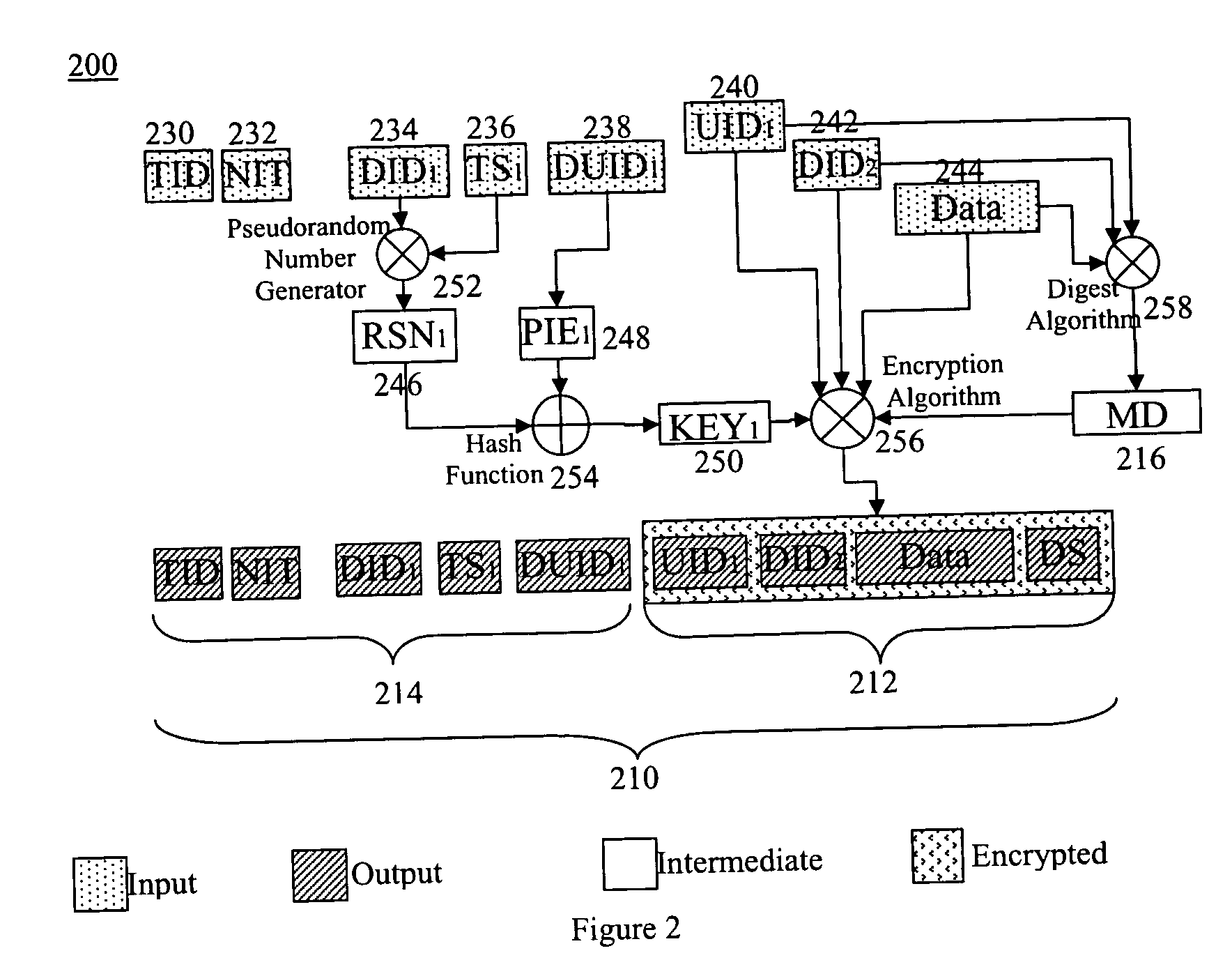
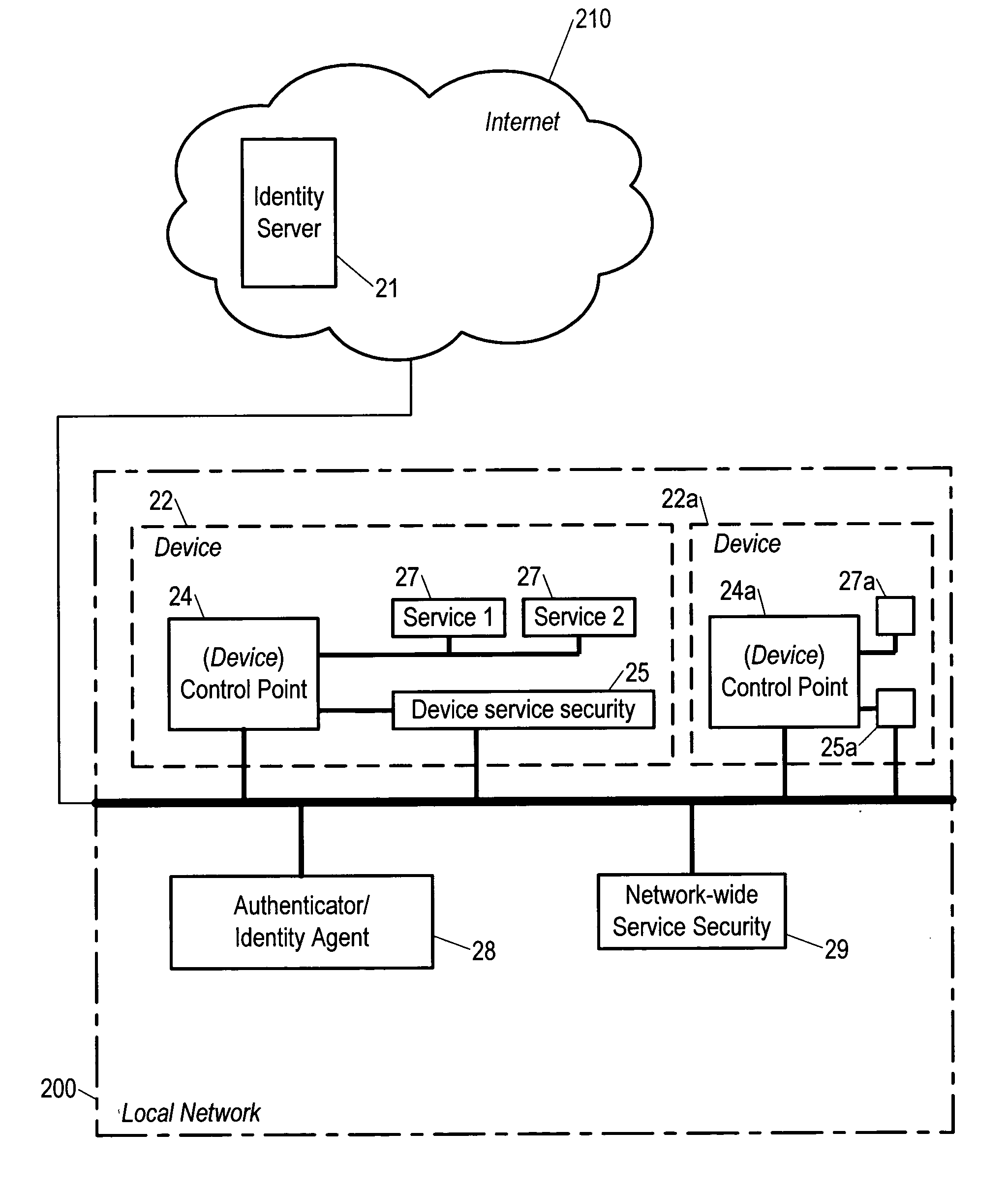
Security framework and protocol for universal pervasive transactions
ActiveUS7353382B2Improve integrityAvoid communicationKey distribution for secure communicationMultiple keys/algorithms usageInternet privacyComputerized system
A computer system, a method of a computer system and a computer-readable medium securely transmit and verify a multiparty agreement. The method, the computer system, and the computer readable medium include developing and transmitting views of the multi-party agreement by each party to a separate verification party. The verification party authenticates the participants and determines whether the views of the agreement are mutually consistent, and notifies the partys of the results of the comparison.
Owner:INTERDIGITAL PATENT HLDG INC
Structured methodology and design patterns for web services
ActiveUS7831693B2Multiple digital computer combinationsDigital dataQuality of serviceBusiness-to-business
System and method for designing and implementing Web Services according to a structured methodology and design patterns. Embodiments may incorporate a structured methodology, best practices and design patterns that address reliability, availability and scalability of Web Services architecture. Embodiments may provide mechanisms for integrating heterogeneous technology components into Web Services. Embodiments may provide a vendor-independent Web Services architecture framework and reusable Web Services design patterns, which may be used in creating end-to-end solutions based on past experience and best practices. Embodiments may include design patterns and best practices for delivering Web Services solutions with Quality of Services. One embodiment may provide a Business-to-Business Integration (B2Bi) integration framework for Web Services. Embodiments may provide a Web Security framework and design patterns for designing end-to-end Web Services security.
Owner:ORACLE INT CORP
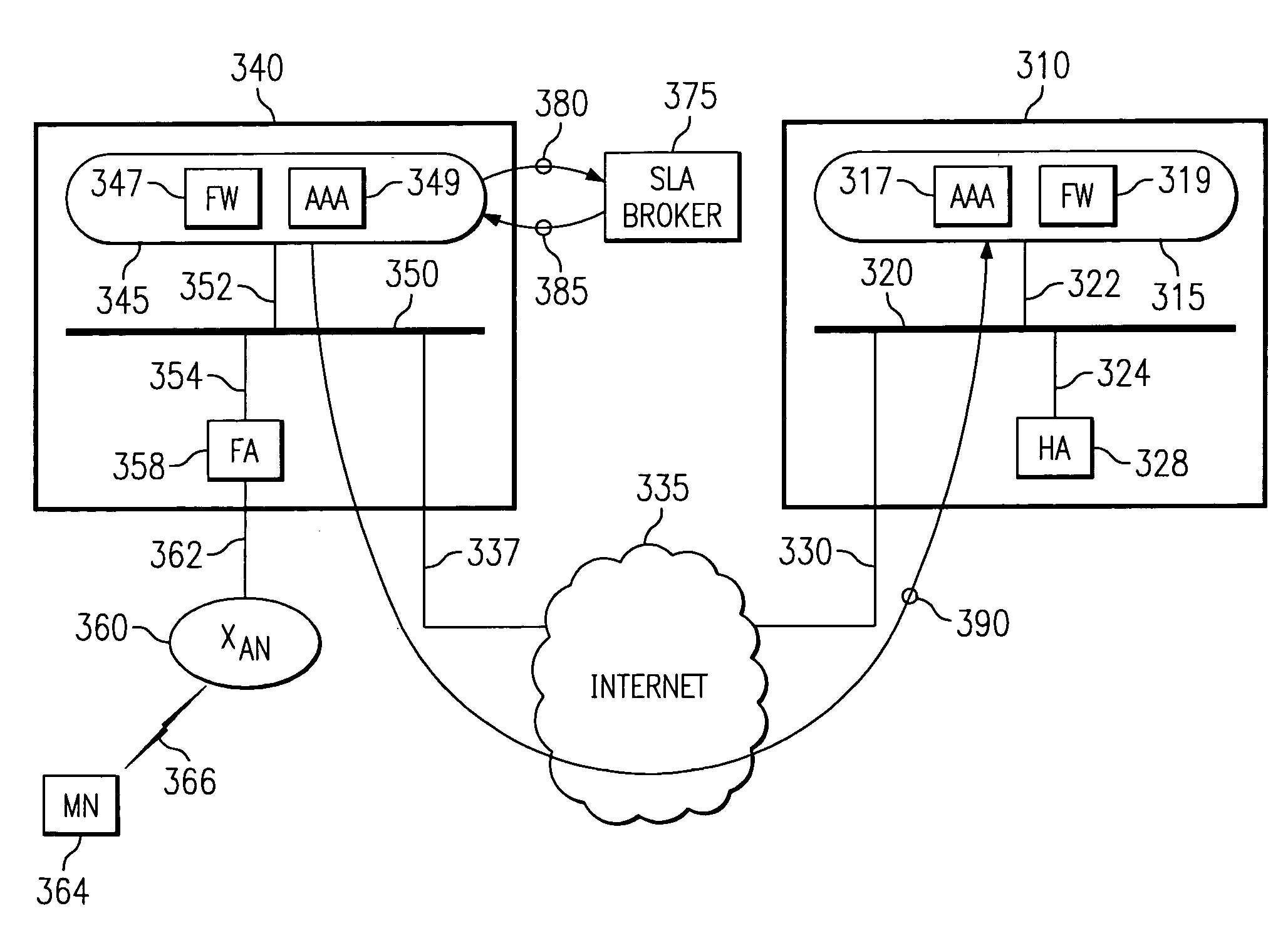
Security framework for an IP mobility system using variable-based security associations and broker redirection
InactiveUS7174018B1Improve securityPromote large-scale roamingWireless network protocolsSecret communicationService-level agreementSecurity association
In an IP-based mobile communications system, the Mobile Node changes its point of attachment to the network while maintaining network connectivity. Security concerns arise in the mobile system because authorized users are subject to the following forms of attack: (1) session stealing where a hostile node hijacks session from mobile node by redirecting packets, (2) spoofing where the identity of an authorized user is utilized in an unauthorized manner to obtain access to the network, and (3) eavesdropping and stealing of data during session with authorized user. No separate secure network exists in the IP-based mobility communications system, and therefore, it is necessary to protect information transmitted in the mobile system from the above-identified security attacks.The present invention improves the security of communications in a IP mobile communications system by creating variable-based Security Associations between various nodes on the system, a Virtual Private Network supported by an Service Level Agreement between various foreign networks and a home network, and an SLA Broker to promote large-scale roaming among different SLAs supported by the SLA Broker or agreements with other SLA Brokers.
Owner:RPX CLEARINGHOUSE
Security framework and protocol for universal pervasive transactions
ActiveUS20040030894A1Improve integrityAvoid communicationKey distribution for secure communicationMultiple keys/algorithms usageInternet privacyComputerized system
A computer system, a method of a computer system and a computer-readable medium securely transmit and verify a multiparty agreement. The method, the computer system, and the computer readable medium include developing and transmitting views of the multi-party agreement by each party to a separate verification party. The verification party authenticates the participants and determines whether the views of the agreement are mutually consistent, and notifies the parties of the results of the comparison.
Owner:INTERDIGITAL PATENT HLDG INC
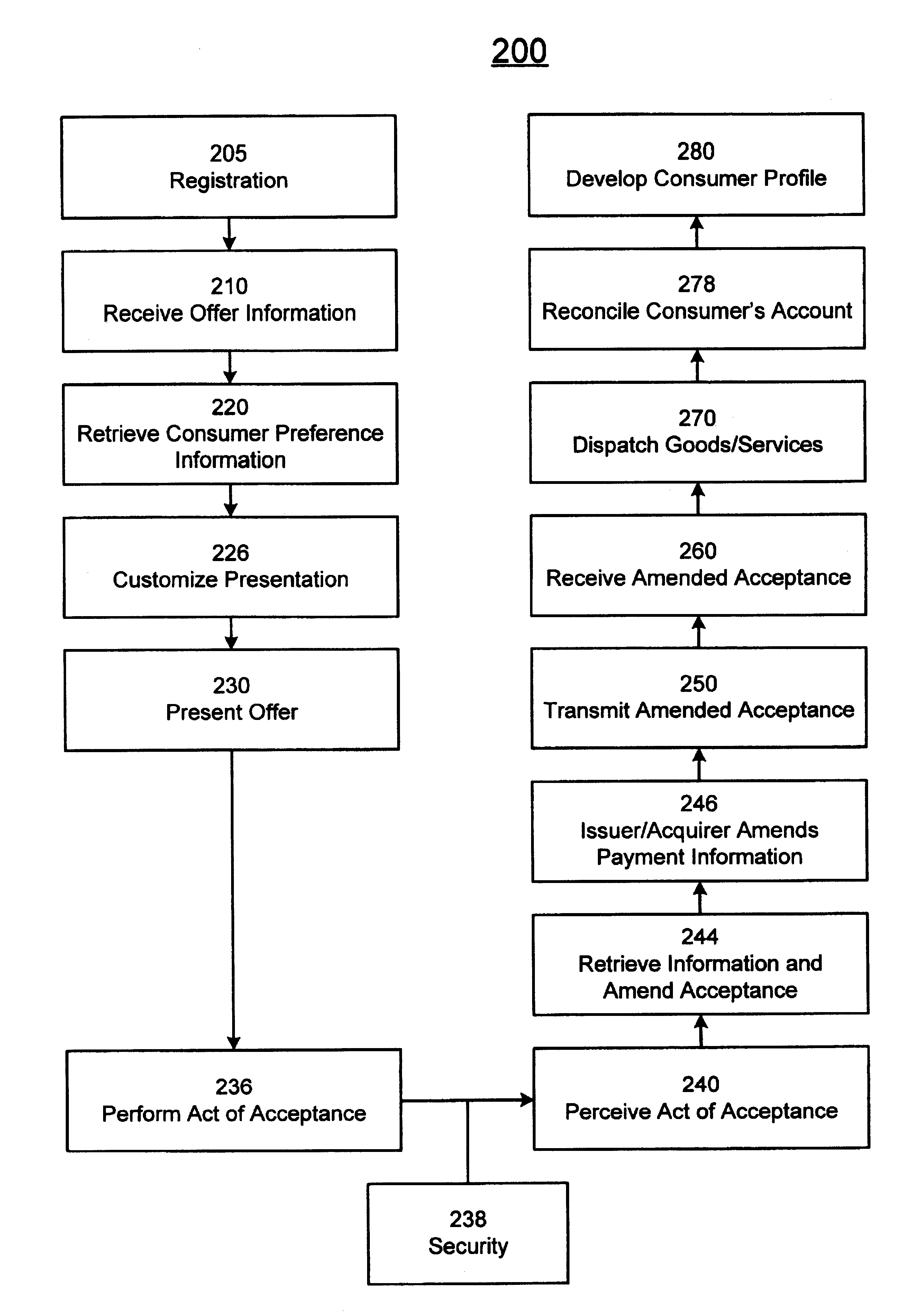
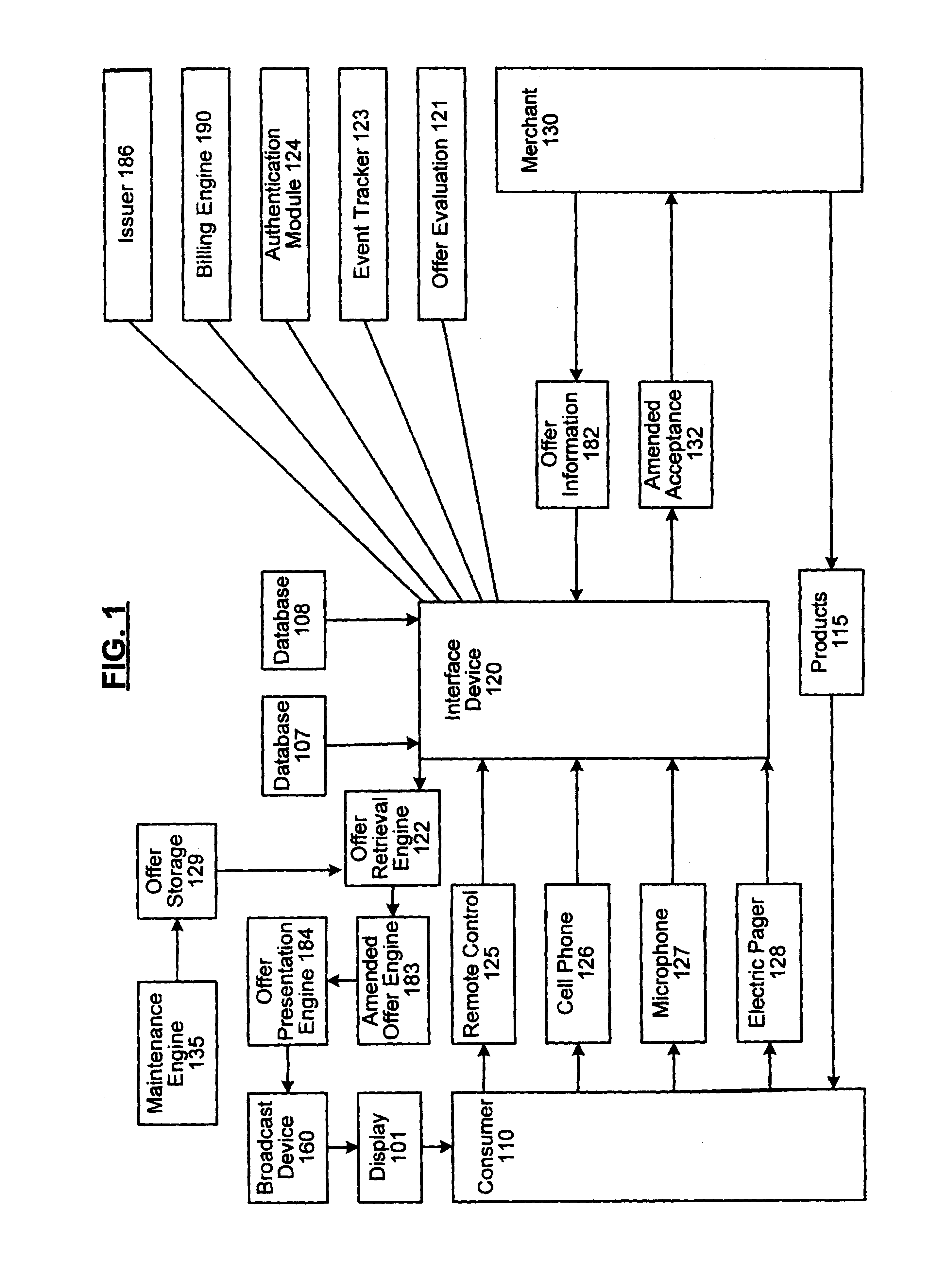
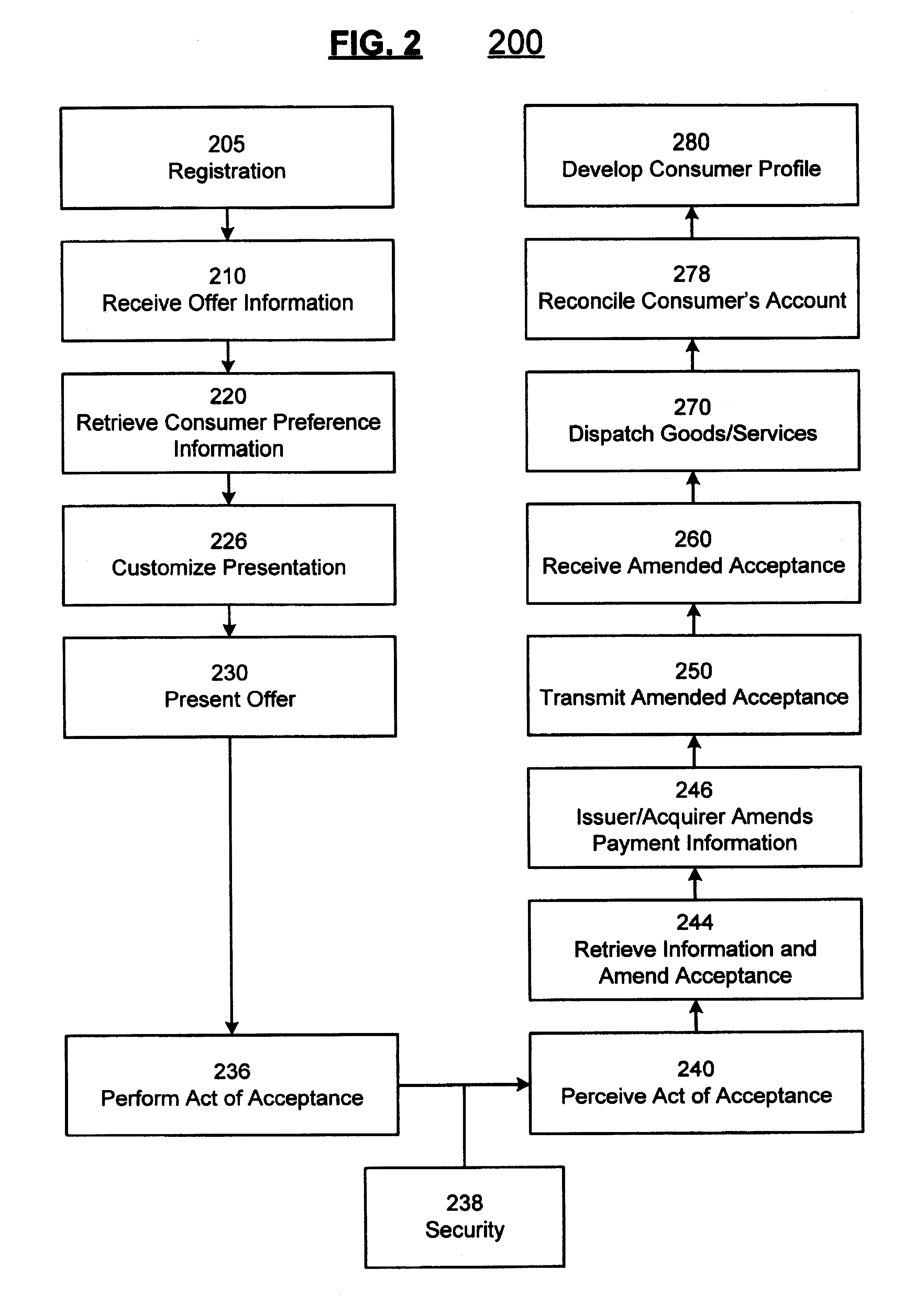
System and method for facilitating interaction between consumer and merchant
InactiveUS7599857B2Enhanced interactionComputer security arrangementsCash registersPaymentRelevant information
An automated method and system is provided for facilitating interaction between a consumer and a merchant using a strong security framework. An offer describing a product and a predetermined means for acceptance is presented via a display. Once the offer has been presented, if the consumer accepts, the system performs various authentications, then facilitates receipt of the acceptance. The system then combines the acceptance data with identification and payment information, and transmits the relevant information to the merchant. Optionally, the system may customize the content or the presentation of the offer based on information about the targeted consumer.
Owner:LIBERTY PEAK VENTURES LLC
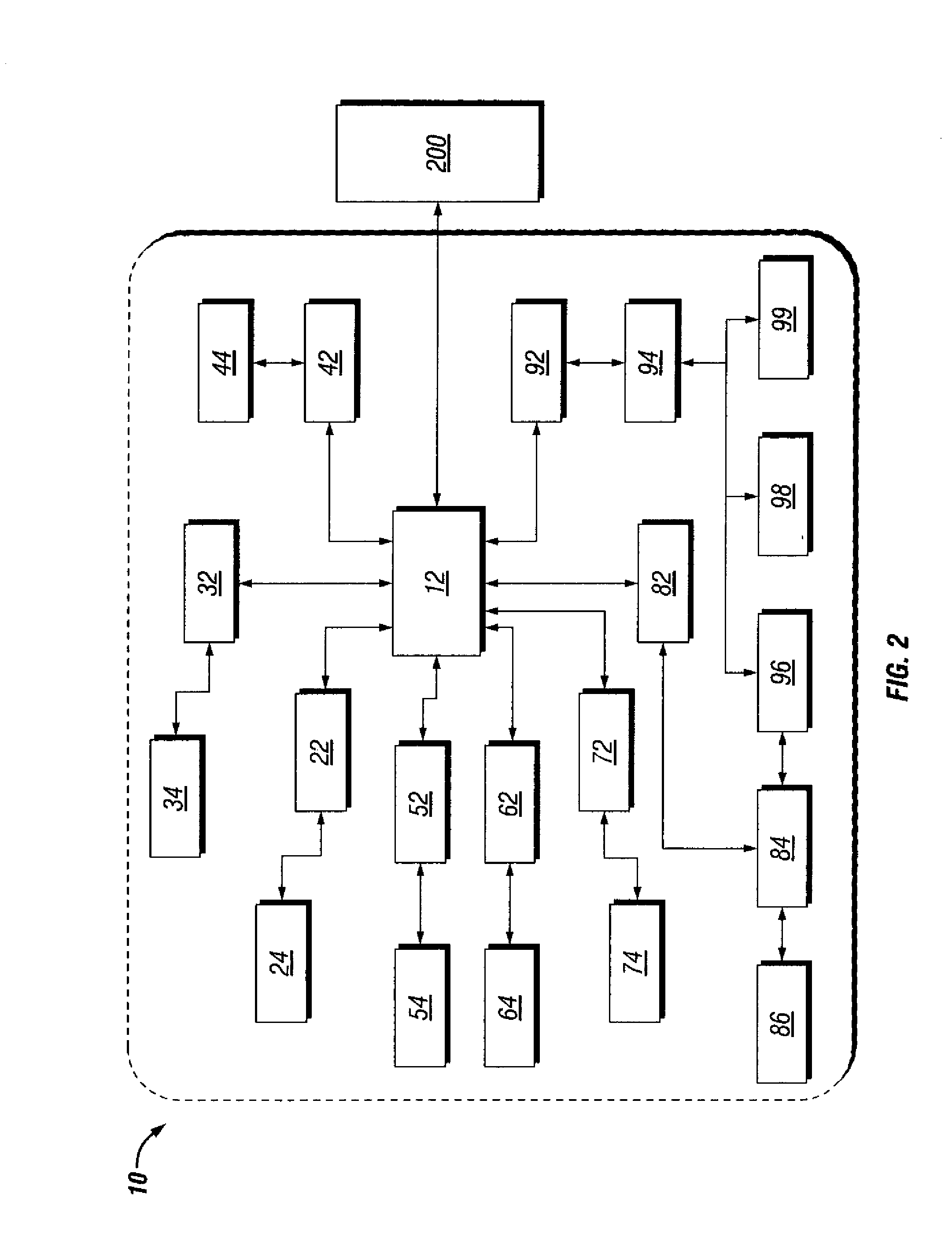
Integrated security framework and privacy database scheme
ActiveUS7263717B1Data processing applicationsDigital data processing detailsIp addressSecurity framework
A system and method for bridging requests for access to resources between requestors in a distributed network and an authenticator servicing the distributed network is provided. The bridging mechanism has security features including a naming service for machine authentication and machine process rules to authorize what process machines can perform. The security proxy bridge intercepts an access request, and checks the IP address for machine authentication as well as the machine process rules and if both verifications are successful, the bridge then forwards the request for access to the authenticator. The security proxy framework utilizes a data structure that provides a method for storing selected security information stored as data records supporting an authentication and authorization system for users to access resources on multiple components of a distributed network supporting multiple business units of an enterprise. Primary authentication information stored herein includes general user information, security, and contact information.
Owner:T MOBILE INNOVATIONS LLC
Information security management improvement system
ActiveUS10860721B1Improving information security management systemWeb data indexingPlatform integrity maintainanceInformation security managementSecurity framework
Systems, methods, and non-transitory mediums for assessing and improving the information security management health of an organization may be used to generate a baseline assessment measuring a level of compliance with proper security framework elements as well as a level of cross-management, interaction, or engagement across four essential information security domains including a benchmark domain, a measurement domain, a decision domain, and an execution domain using a domain-element table with a plurality of measurement types associated with criteria for progressing through an increasing level of difficulty tiered scoring system established by selected frameworks, policies, standards, and guidelines while also providing a path to improve upon a baseline assessment.
Owner:GENTILE MIKE
Method and system for protecting cross-domain interaction of a web application on an unmodified browser
InactiveUS20100186089A1Improve functionalityImprove securityMemory loss protectionDigital data processing detailsWeb applicationSoftware engineering
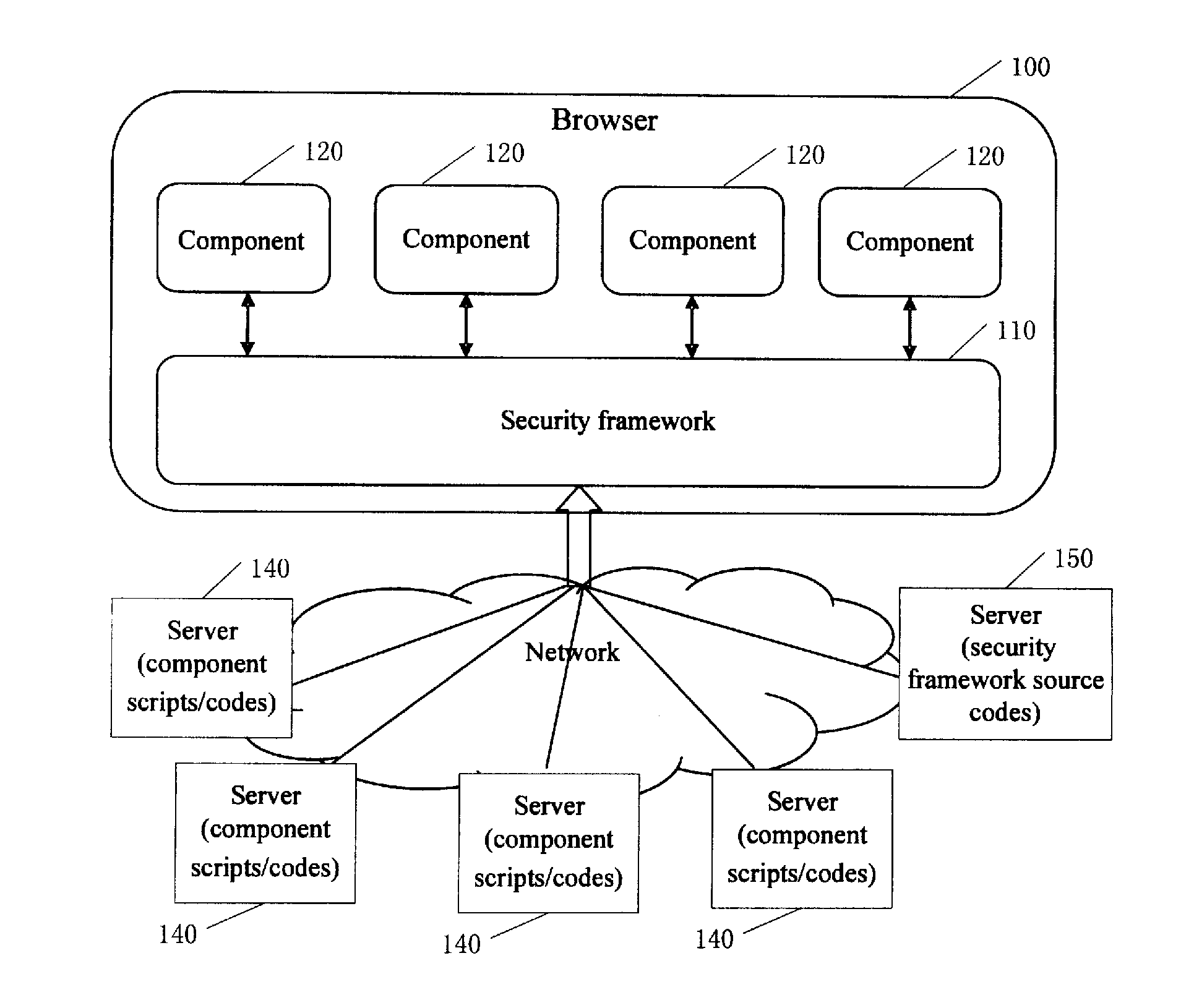
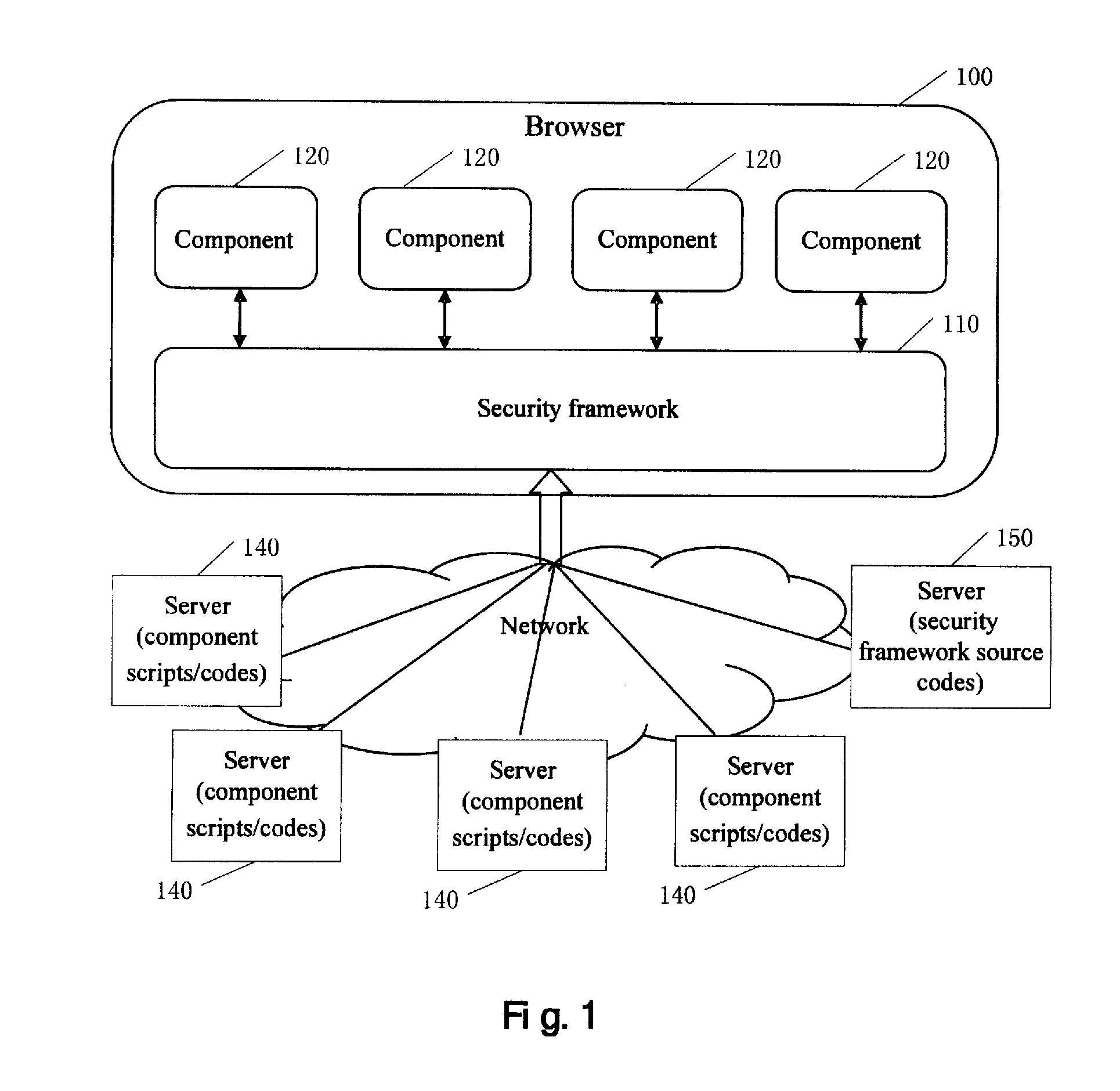
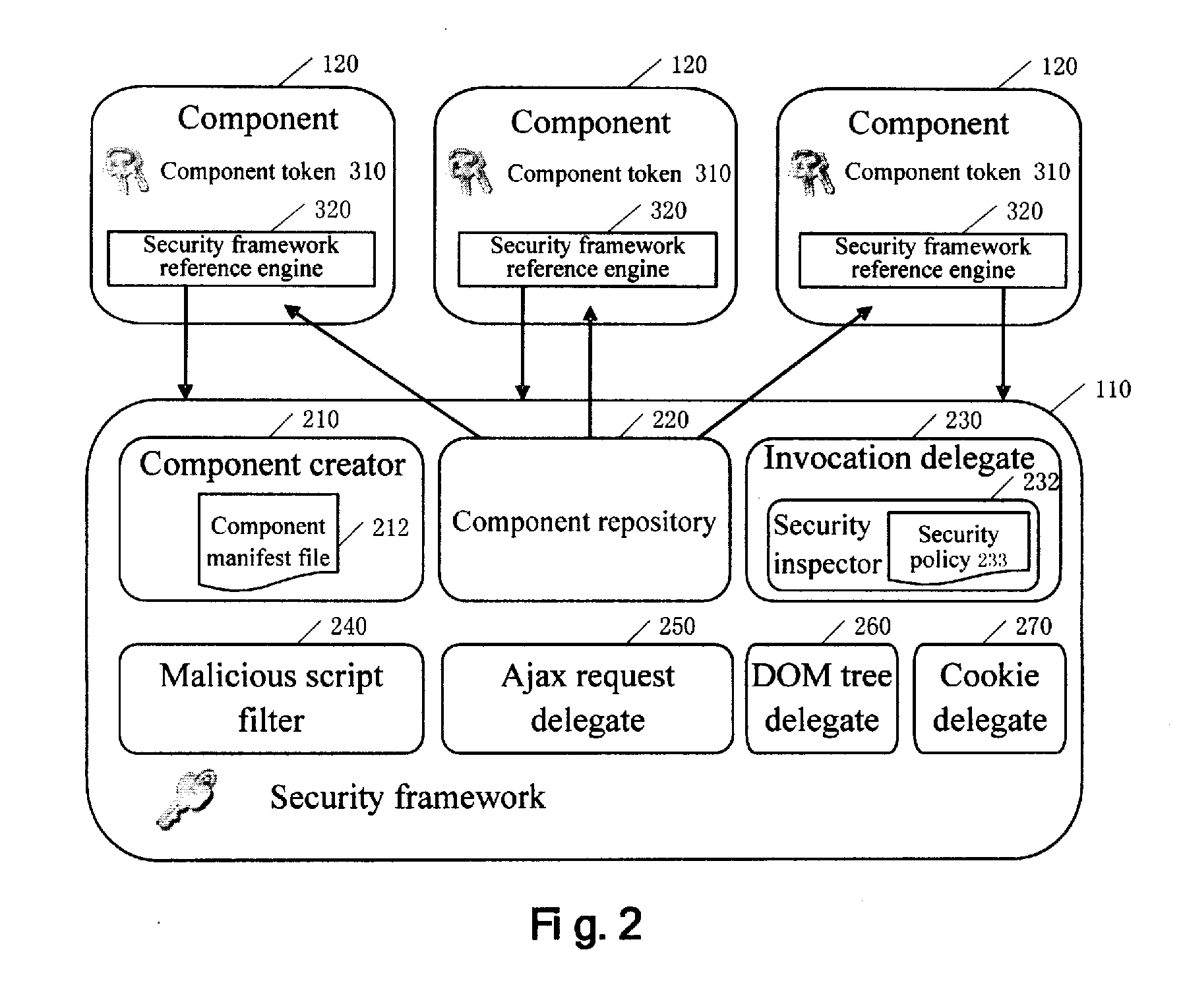
A system and method for protecting cross-domain interaction of a web application on an unmodified browser. The system includes: a security framework, which is created by a browser. The security framework further includes: a component creator for creating components from a plurality of sources; and supervision module for supervising and controlling scripts / codes executed during the creation of components and invocation and interaction operations performed by various components after the creation of components.
Owner:IBM CORP
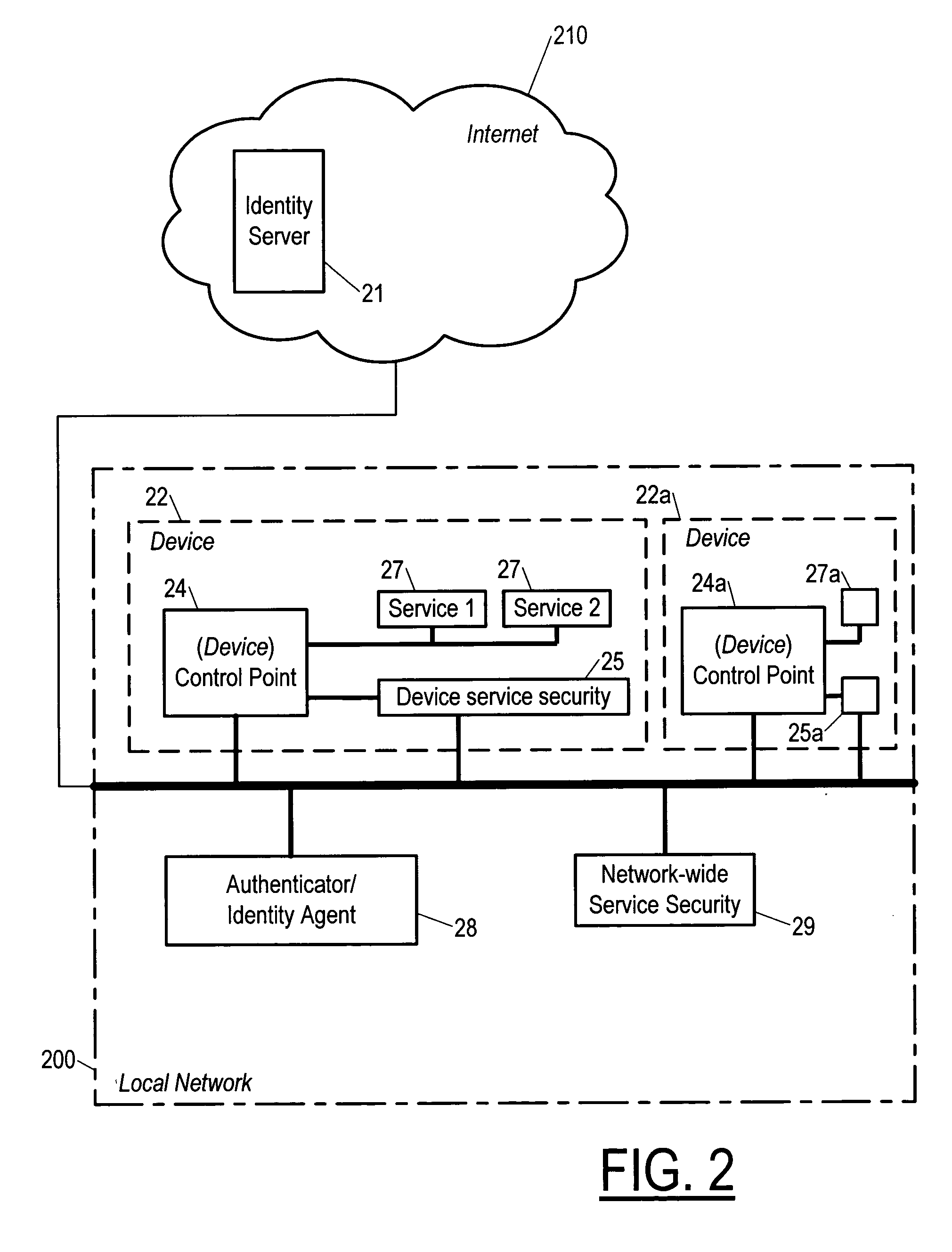
Method and apparatus for a security framework that enables identity and access control services
InactiveUS20060156388A1Provide securityDigital data processing detailsUser identity/authority verificationSecurity frameworkClient-side
A method by which access to services of a network are controlled, including a step in which a client device presents proof of identity to a service security module attached to the network and providing security against unauthorized access to the service.
Owner:NOKIA CORP
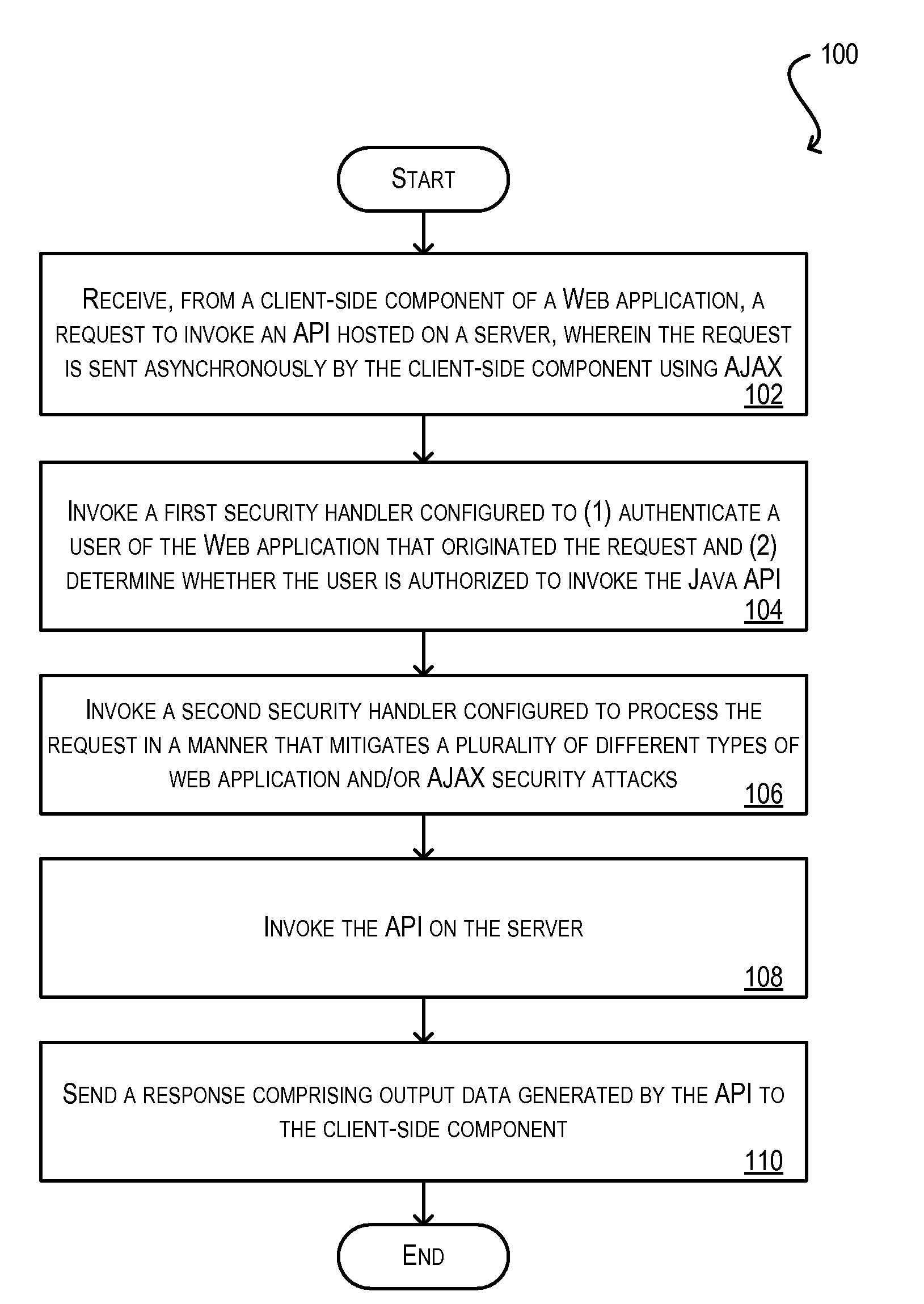
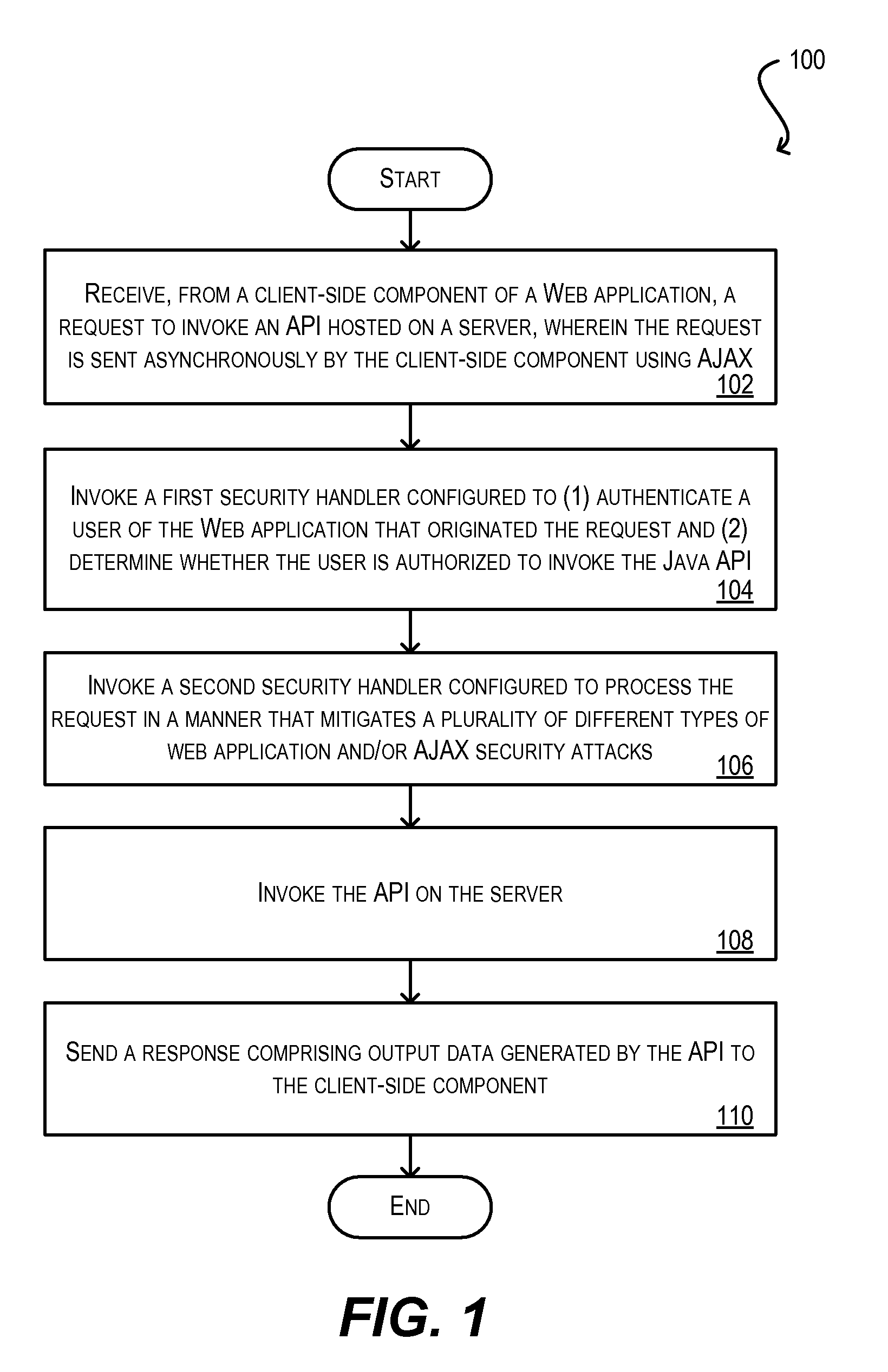
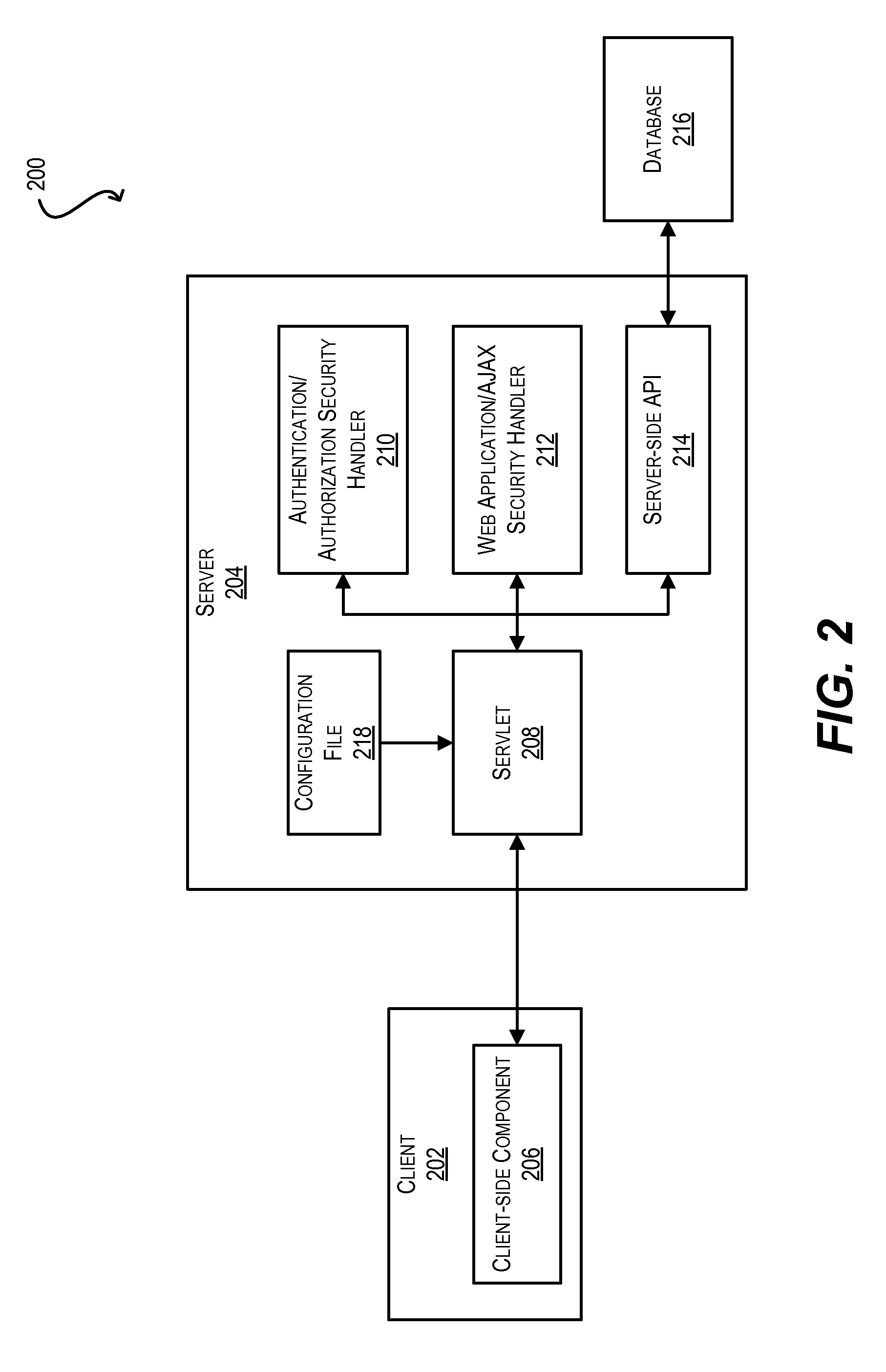
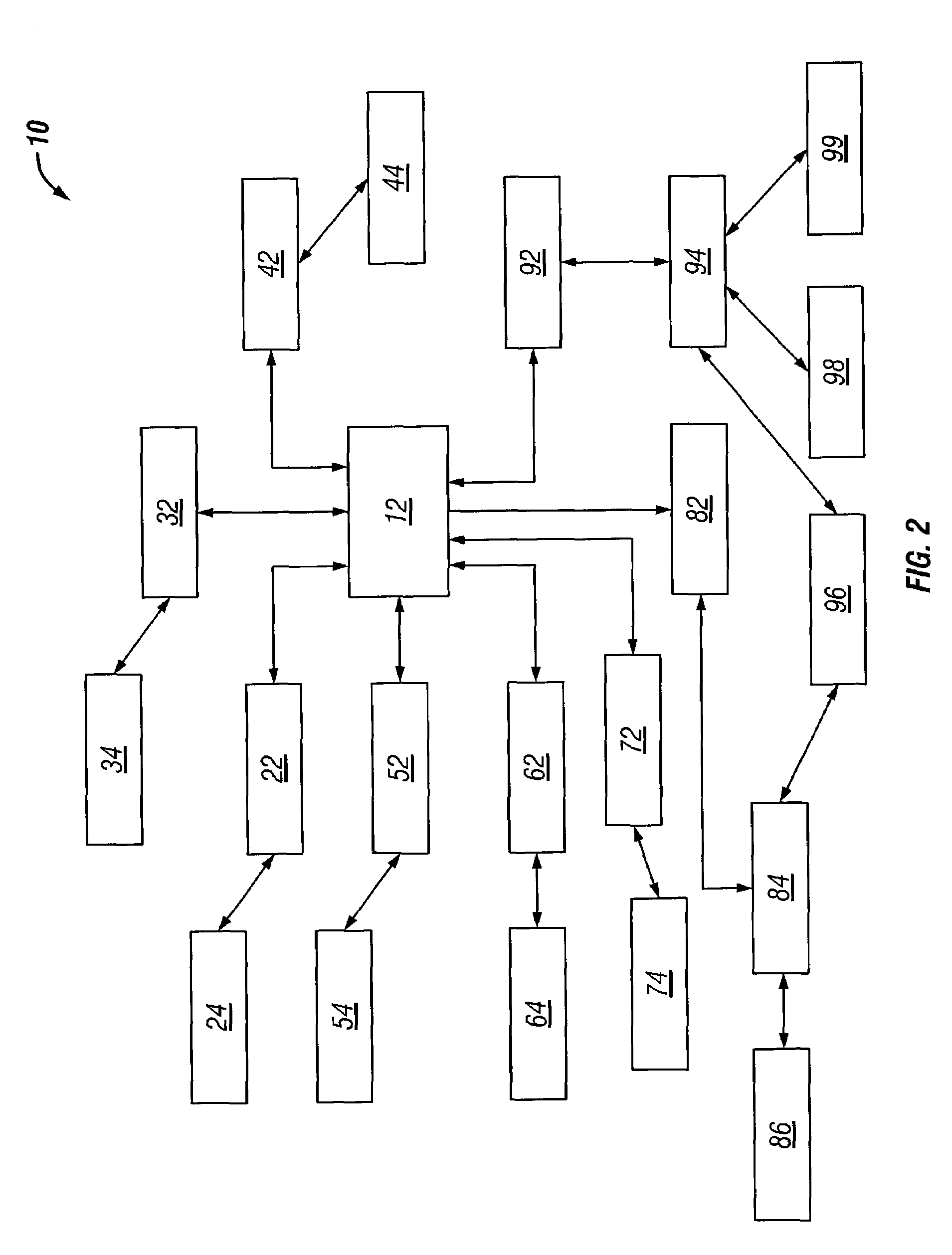
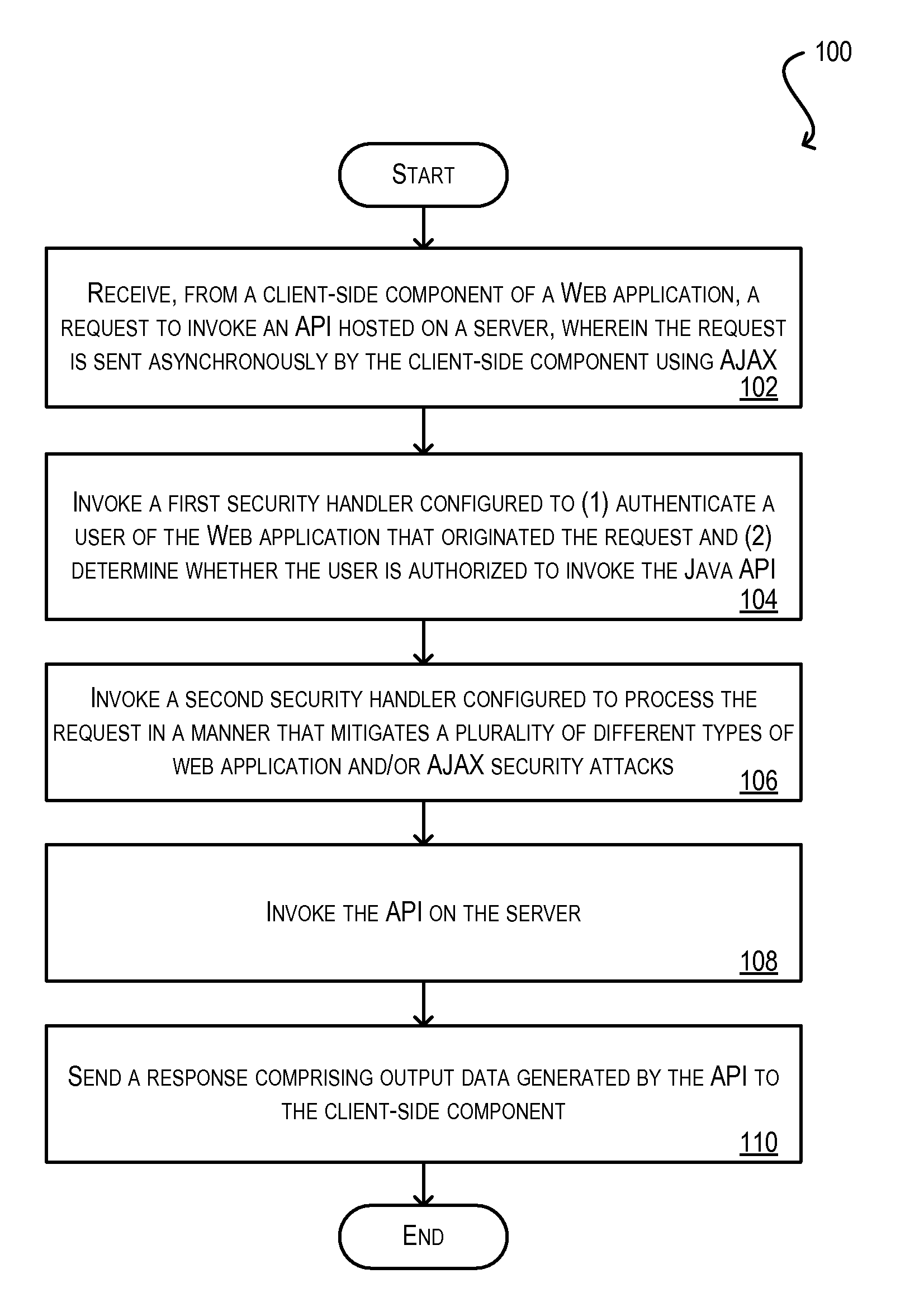
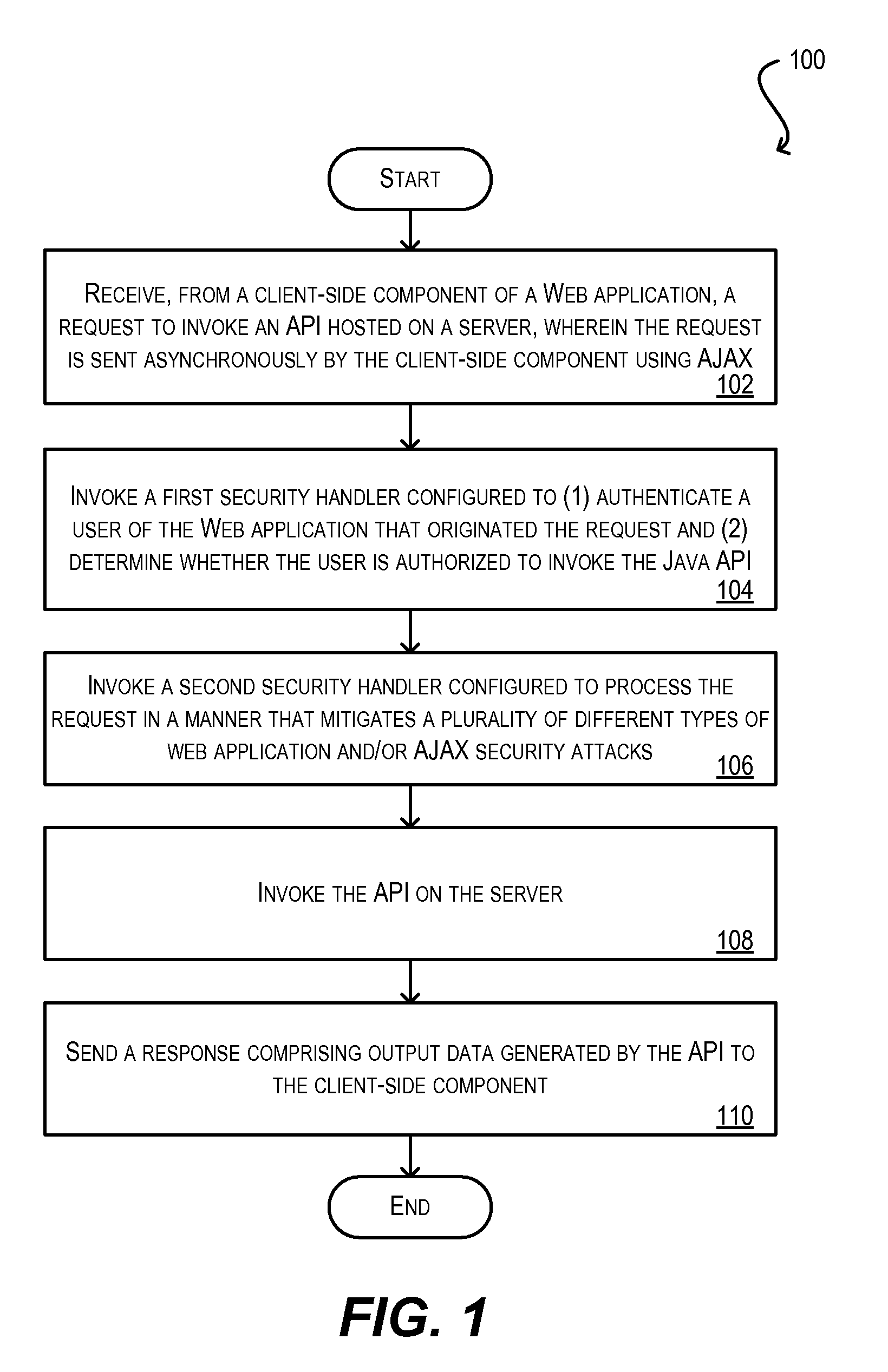
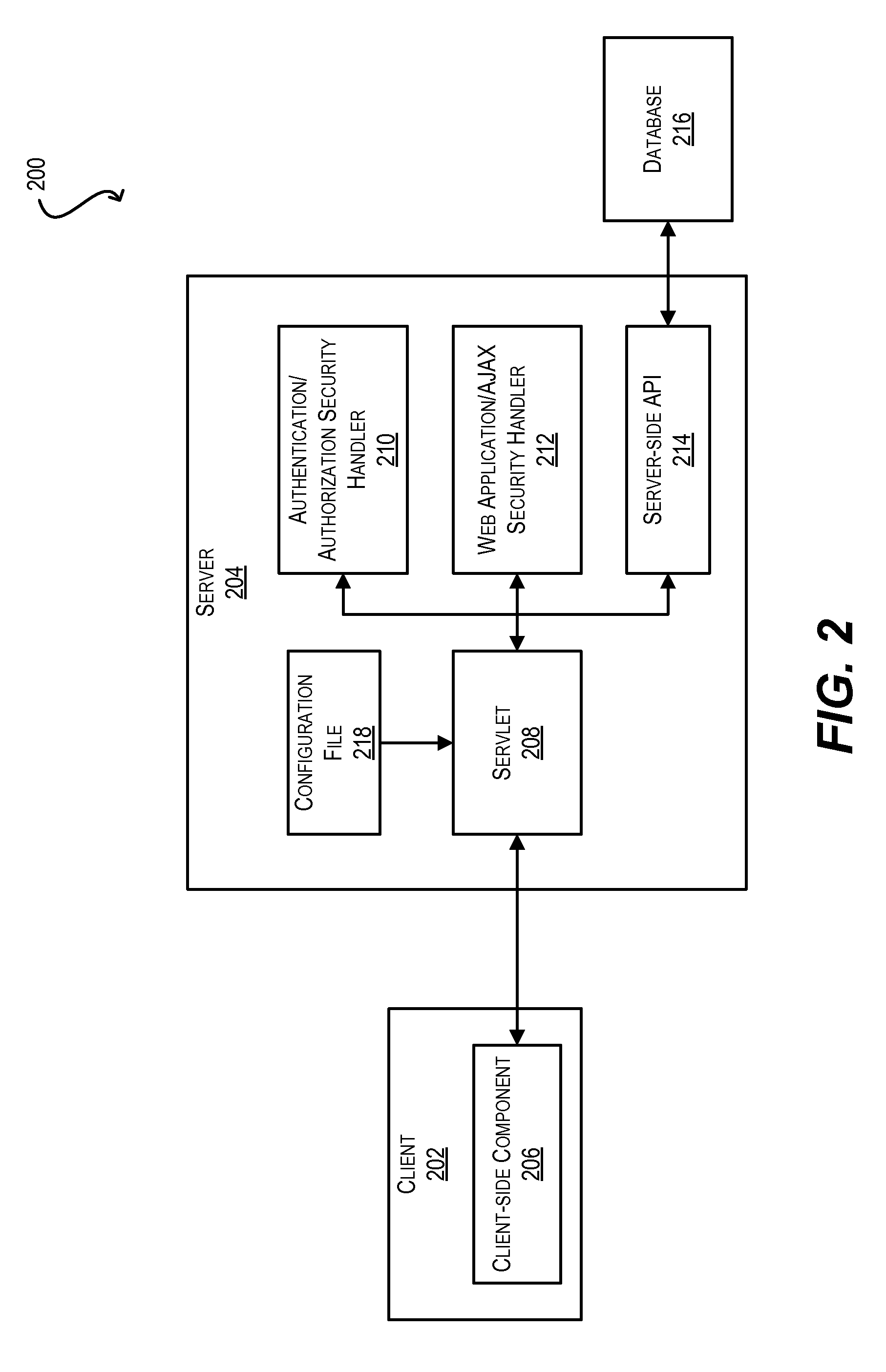
Secure framework for invoking server-side apis using ajax
ActiveUS20100146291A1Mitigates security attackReduce attackMemory loss protectionDigital data processing detailsWeb applicationSecurity framework
Techniques for securely invoking a server-side API from client-side Web application code using AJAX. In one set of embodiments, a request to invoke a server-side API is received from a client-side component of a Web application, where the request is sent asynchronously using AJAX. One or more security handlers are then invoked to process the request in a manner that mitigates various security attacks. In one embodiment, a security handler is invoked to defend against a plurality of different types of Web application / AJAX security attacks. In another embodiment, authentication and authorization security handlers are invoked to authenticate a user of the Web application that originated the request and determine whether the user is authorized to call the server-side API. In yet another embodiment, configuration is implemented at the data storage tier to enforce user-access and data security on data that is retrieved / stored as a result of invoking the server-side API.
Owner:ORACLE INT CORP
Intrusion detection system facing cloud calculating environment
InactiveCN102724176ASolve the large-scale dynamic number of usersEnsure application securityTransmissionCommunications securityService domain
According to the invention, a safety problem based on splitting and under large-scale shared virtual calculating environment is discussed. And the invention provides a safety framework based on a virtual machine and facing the virtual calculating environment and a large-scale distributed extensible intrusion detection system. The system provides resource access monitoring identity authentication inside and outside an ability service domain and an encrypted data transmission channel for a user, provides isolation and protection of a user space and a system space and finally guarantees application safety based on an ability server. By using the system of the invention, many safety problems under the ability server, such as, a large-scale dynamic user quantity, large-scale dynamic virtual resource objects, a calculating load of dynamic increase and reduction, user space isolation, user system isolation and protection, internal and external network attack prevention, equipment safety reuse and sharing, communication safety, uniform authentication, access control and the like, are solved.
Owner:BEIJING COMPUTING CENT
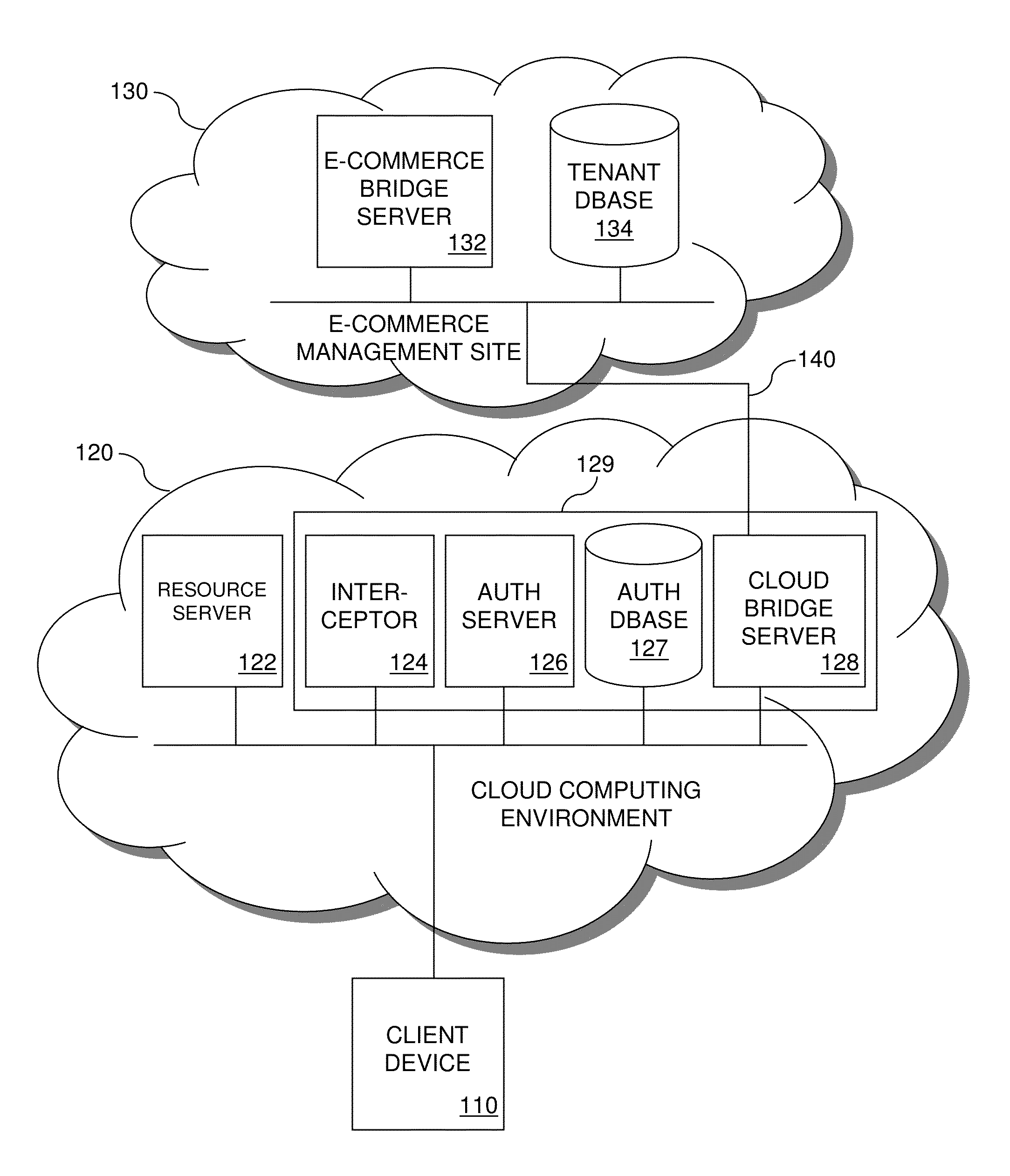
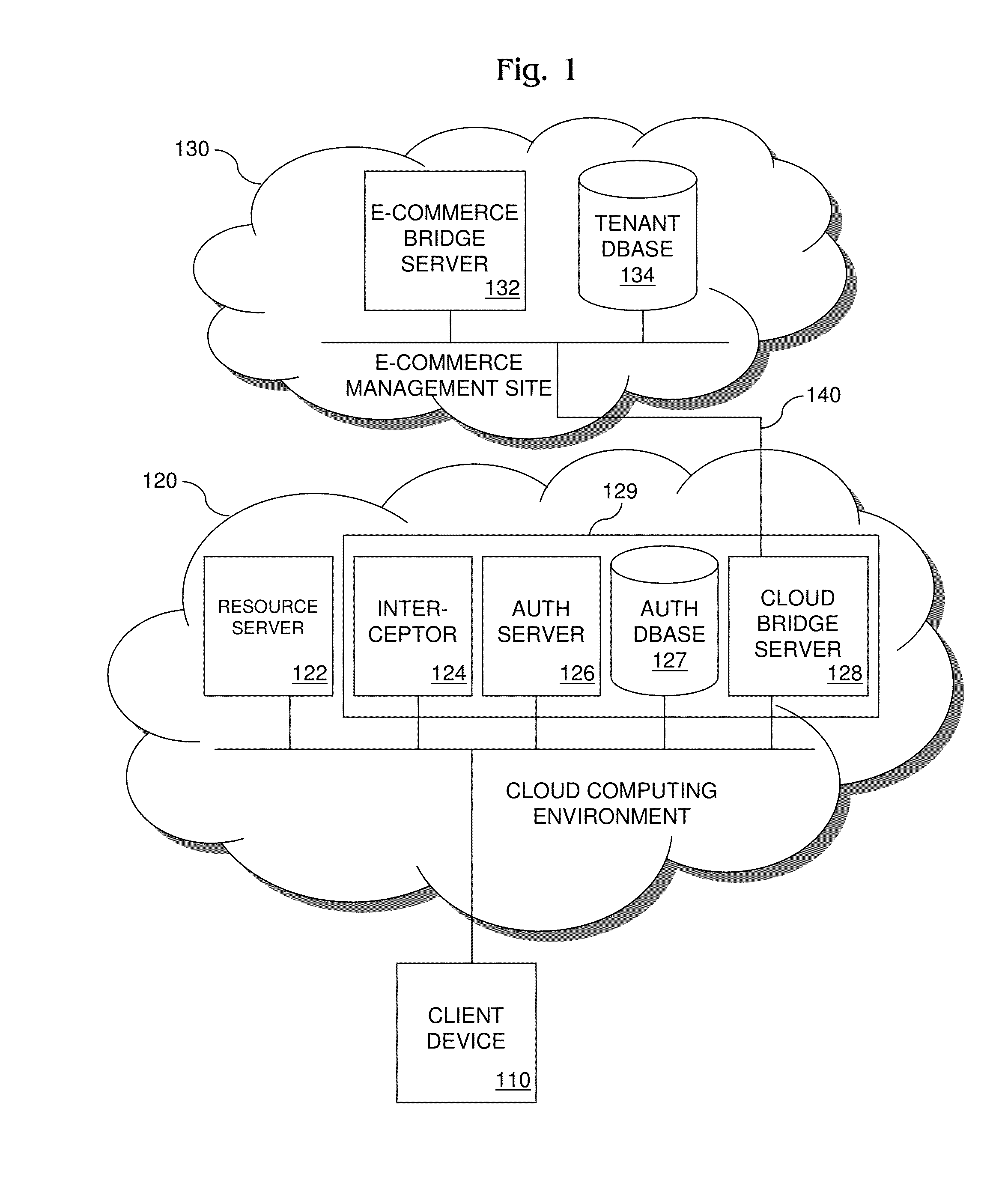
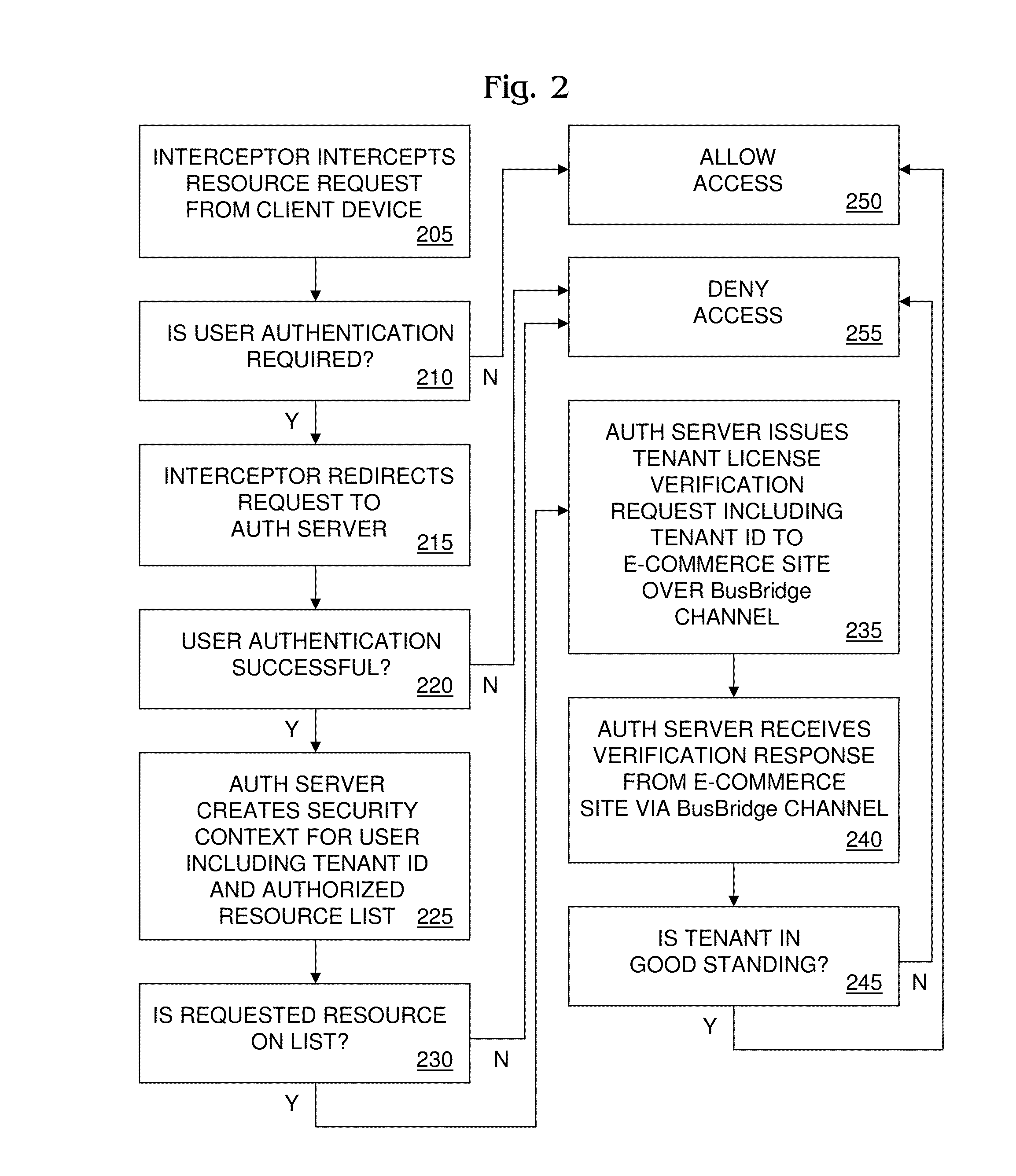
Method and Cloud Security Framework for Implementing Tenant License Verification
ActiveUS20140130142A1Digital data processing detailsComputer security arrangementsWeb serviceSecurity framework
A method and cloud security framework for implementing tenant license verification. The method and framework conduct tenant license verification transparently to cloud resources and users who request them. An exemplary method comprises receiving by the framework from a client device a request for access to a cloud resource and user information; authenticating by the framework a user of the device using the information; obtaining by the framework a security context for the user including a tenant identifier identifying a multi-user enterprise to which the user belongs using the information; transmitting by the framework to an outside entity over a web services interface a tenant license verification request including the identifier; receiving by the framework from the entity a verification that a tenant license associated with the identifier is in good standing; and granting by the framework to the device access to the resource.
Owner:SHARP KK
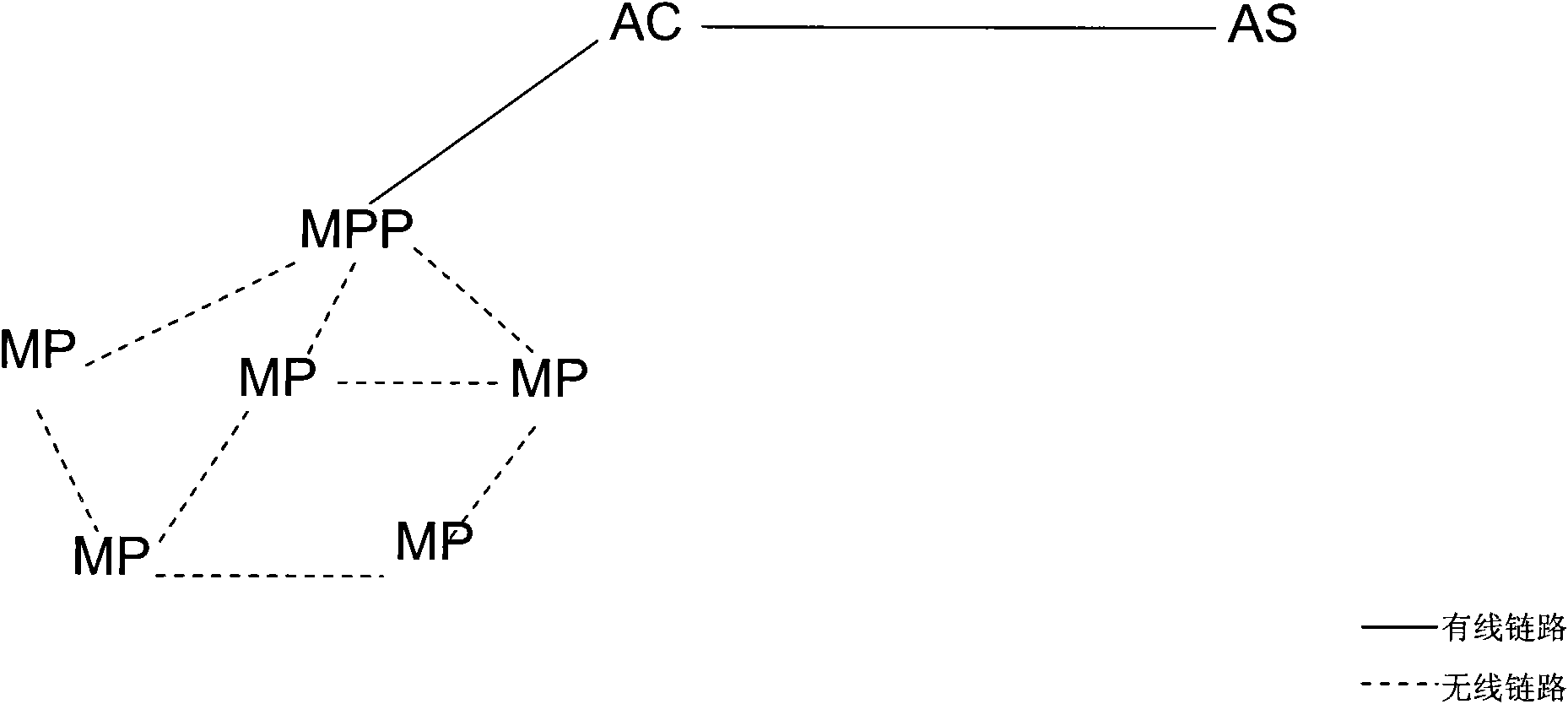
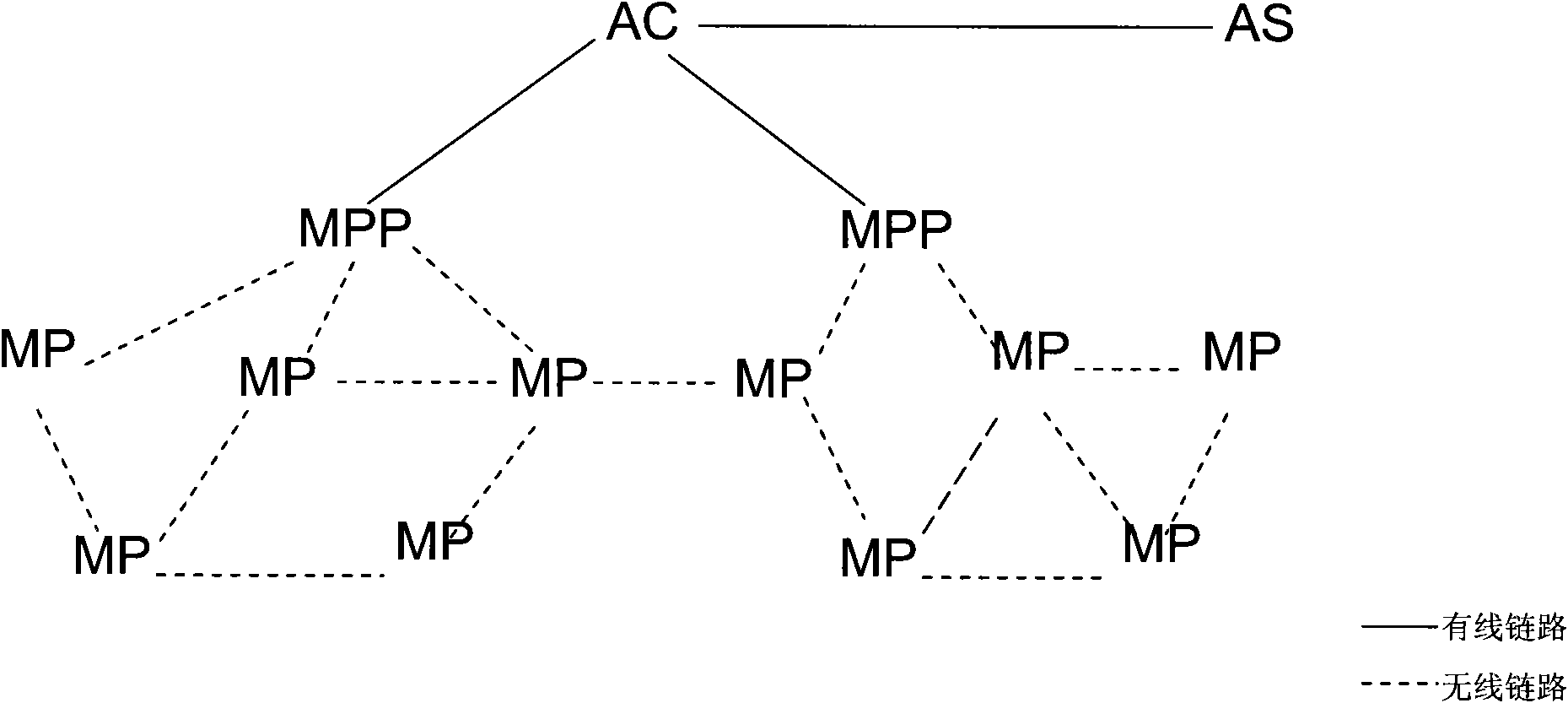
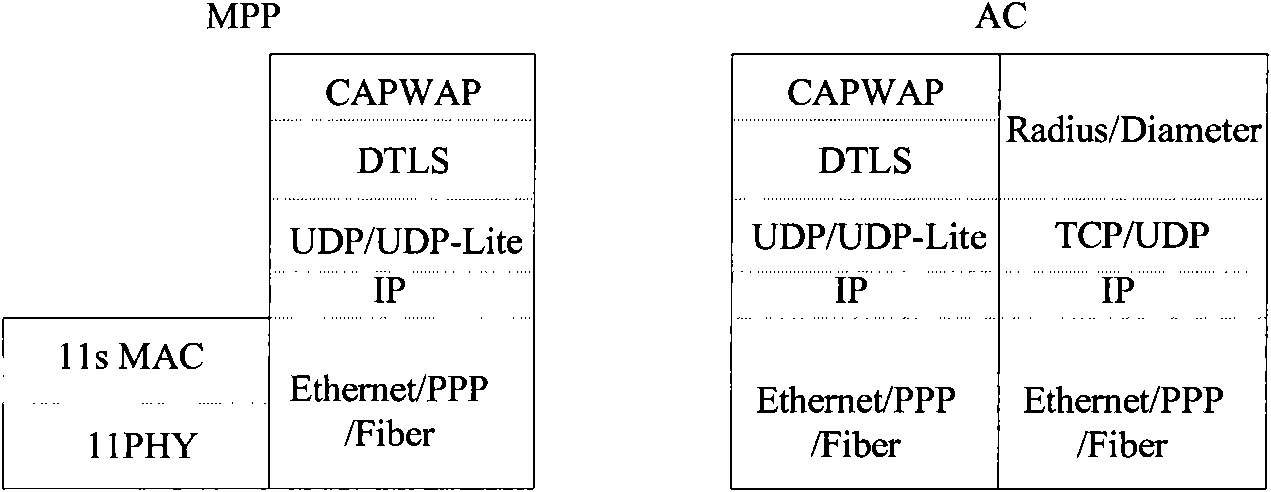
Wireless mesh network system and method for key distribution
The invention discloses a method, a device and a system for the authentication and key distribution of a wireless mesh network. The authentication method mainly comprises the following steps that: MPP (Mesh portal point) equipment receives an authentication request sent by an MP (Mesh point) initially accessing the network; the MPP equipment forwards the authentication request to AC equipment and the AC equipment sends the MP authentication information in the authentication request to an authentication server; and the AC equipment receives MP authentication result fed back by the authentication server and forwards the authentication result to the MPP equipment, and the MPP equipment transmits the authentication result to the MP. The invention provides a manageable and operable safe framework of the Mesh network, and provides an effective authentication and key distribution method to effectively establish associated links between MPs to ensure the safe transmission of link layer data.
Owner:HUAWEI TECH CO LTD
Security framework bridge
ActiveUS7346930B1Digital data processing detailsAnalogue secracy/subscription systemsIp addressSecurity framework
The present disclosure is a method for bridging requests for access to resources between requesters in a distributed network and an authenticator servicing the distributed network. The bridging mechanism has security features including a naming service for machine authentication and machine process rules to authorize what process machines can perform. The security proxy bridge intercepts an access request, and checks the IP address for machine authentication as well as the machine process rules and if both verifications are successful, the bridge then forwards the request for access to the authenticator. The security proxy framework utilizes a data structure that provides a method for storing selected security information stored as data records supporting an authentication and authorization system for users to access resources on multiple components of a distributed network supporting multiple business units of an enterprise. Primary authentication information stored herein includes general user information, security information, and contact information.
Owner:T MOBILE INNOVATIONS LLC
Secure framework for invoking server-side APIs using AJAX
ActiveUS8332654B2Reduce attackMitigates pluralityMemory loss protectionDigital data processing detailsWeb applicationSecurity framework
Techniques for securely invoking a server-side API from client-side Web application code using AJAX. In one set of embodiments, a request to invoke a server-side API is received from a client-side component of a Web application, where the request is sent asynchronously using AJAX. One or more security handlers are then invoked to process the request in a manner that mitigates various security attacks. In one embodiment, a security handler is invoked to defend against a plurality of different types of Web application / AJAX security attacks. In another embodiment, authentication and authorization security handlers are invoked to authenticate a user of the Web application that originated the request and determine whether the user is authorized to call the server-side API. In yet another embodiment, configuration is implemented at the data storage tier to enforce user-access and data security on data that is retrieved / stored as a result of invoking the server-side API.
Owner:ORACLE INT CORP
Security framework data scheme
InactiveUS7257834B1Data processing applicationsDigital data processing detailsIp addressSecurity framework
The present disclosure is a method for bridging requests for access to resources between requestors in a distributed network and an authenticator servicing the distributed network. The bridging mechanism has security features including a naming service for machine authentication and machine process rules to authorize what process machines can perform. The security proxy bridge intercepts an access request, and checks the IP address for machine authentication as well as the machine process rules and if both verifications are successful, the bridge then forwards the request for access to the authenticator. The security proxy framework utilizes a data structure that provides a method for storing selected security information stored as data records supporting an authentication and authorization system for users to access resources on multiple components of a distributed network supporting multiple business units of an enterprise. Primary authentication information stored herein includes general user information, security information, and contact information.
Owner:SPRINT CORPORATION
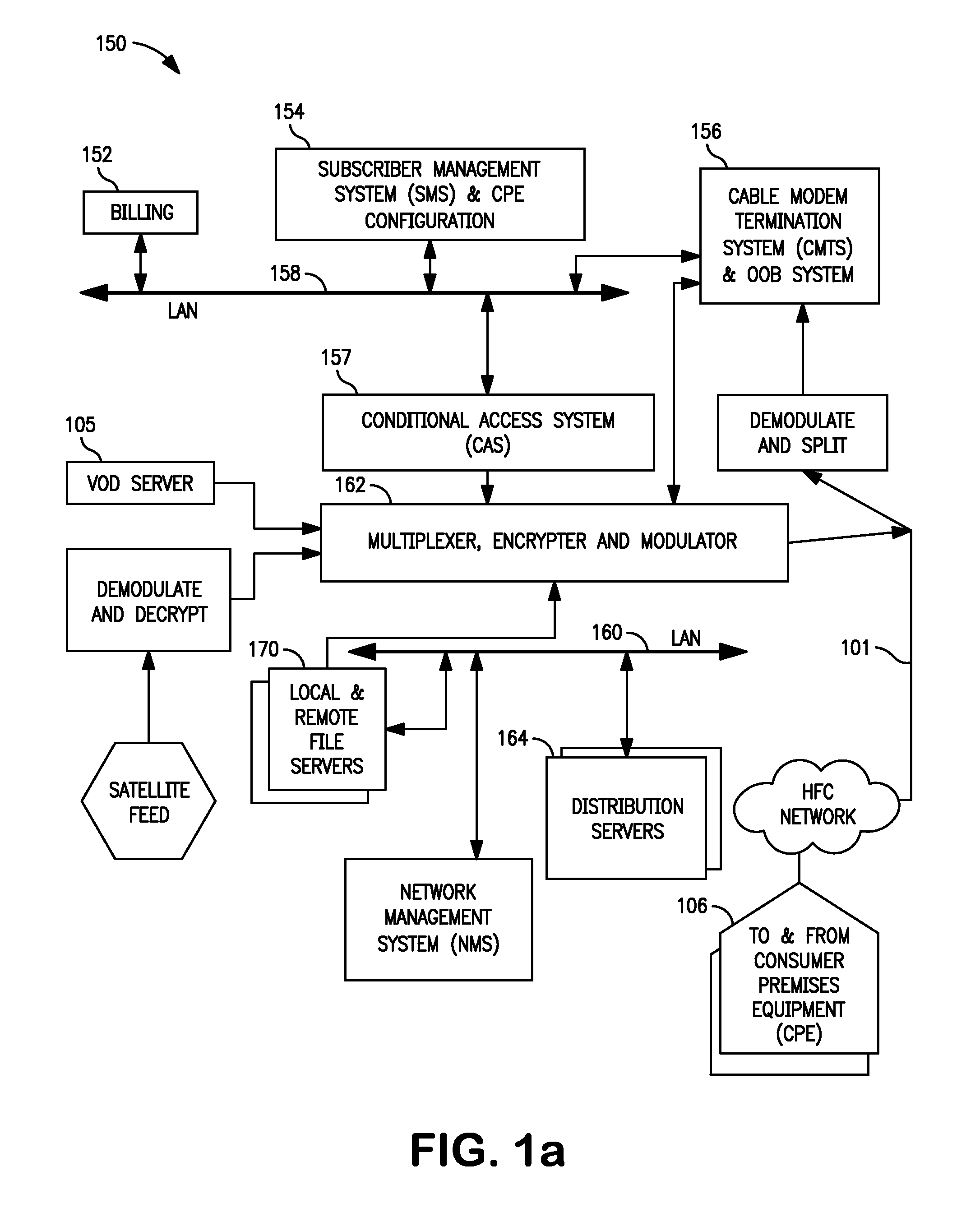
Conditonal access system
InactiveUS20050022015A1Managing accessAvoid layeringError preventionDigital data processing detailsConditional access systemsSecurity framework
A conditional access system comprising a plurality of devices interconnected in a network, the devices being grouped in a first group and a second group, the devices of the first group operating in accordance with a first security framework and the devices of the second group operating in accordance with a second security framework, each device operating using a particular middleware layer, said middleware layer being arranged to authenticate another middleware layer of another device, said middleware layer being authenticated by the security framework in accordance with which the device operates.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
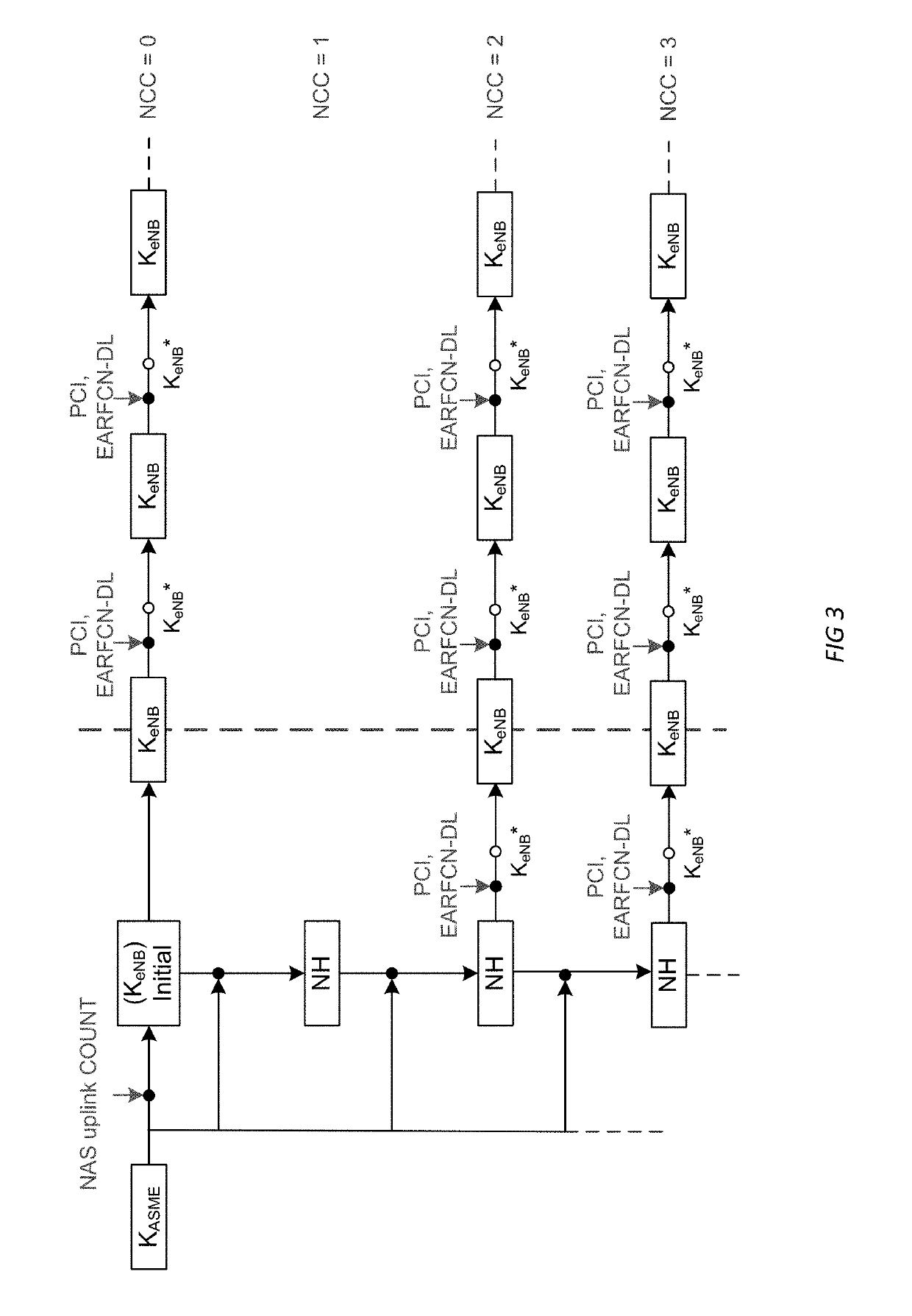
Security framework for msg3 and msg4 in early data transmission
InactiveUS20190208411A1Key distribution for secure communicationNetwork topologiesSecurity frameworkData transmission systems
Systems and methods of a security framework for an RRC connection are described. The UE receives a release message that comprises a current Next Hop Chaining Counter (NCC). The UE derives a new KeNB* using the current NCC and transmits an EDT RA preamble to same or a different base station. After receiving an RAR with an uplink allocation, the UE transmits a RRCConnectionResumeRequest message. The UE transmits uplink data encrypted using KeNB* if the uplink allocation includes a data allocation sufficient for the data, fall backs to a legacy RRC connection procedure in which the stored KeNB* is discarded and then KeNB* is re-derived if the data allocation is insufficient for the data due to a CE level change, and fall backs to a legacy RRC connection procedure in which the stored KeNB* is used instead of discarding KeNB* if the uplink allocation excludes the data allocation.
Owner:APPLE INC
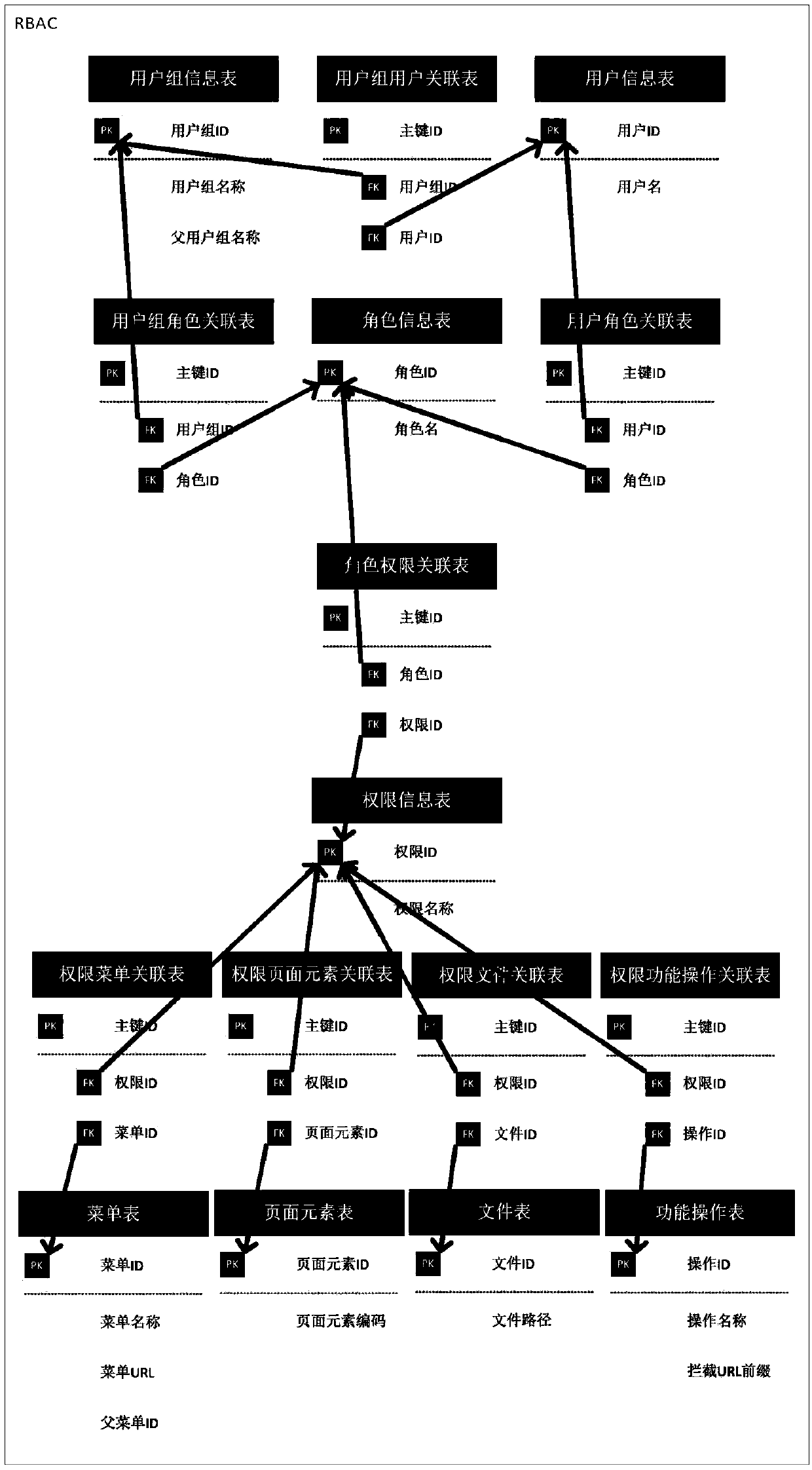
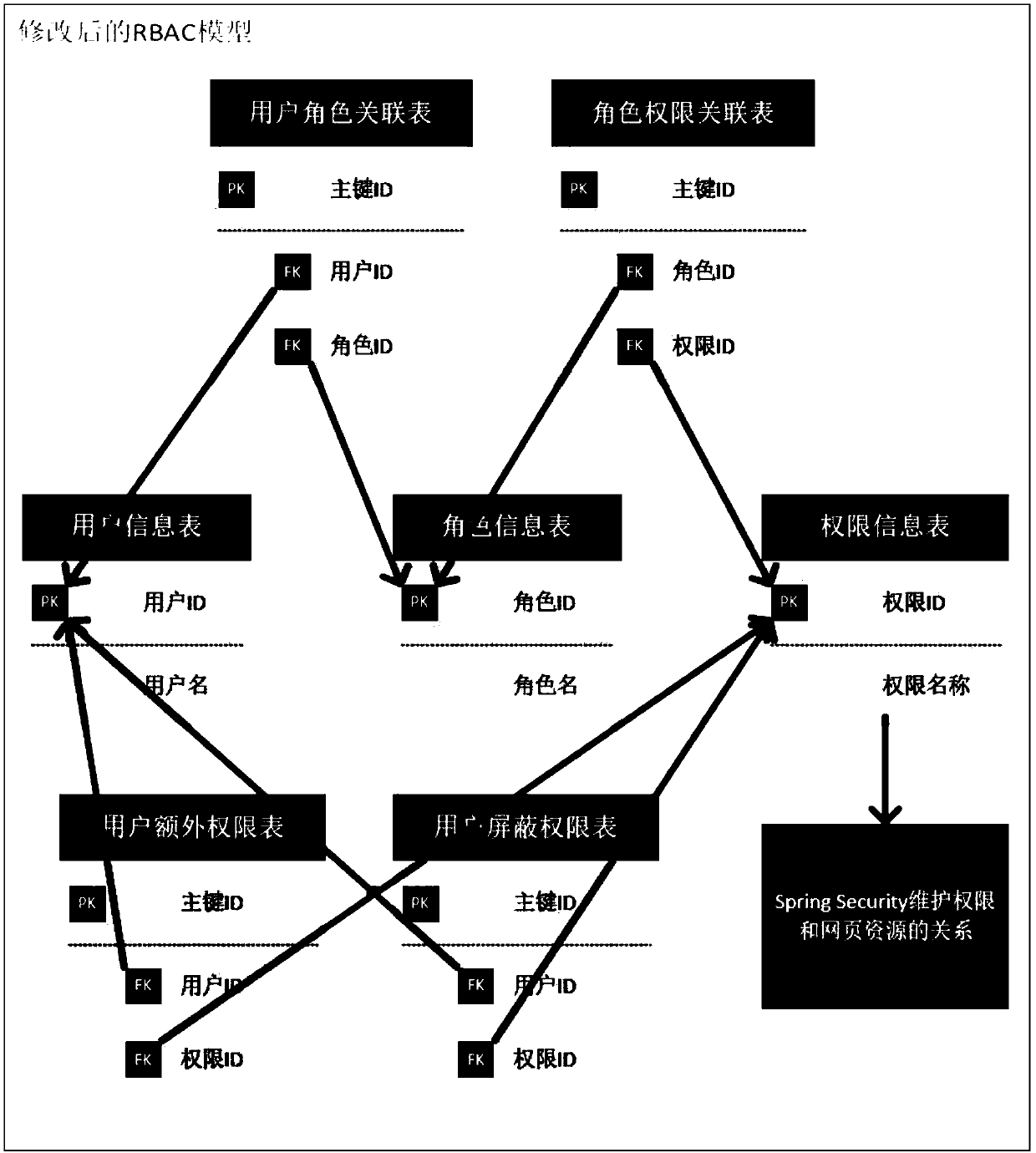
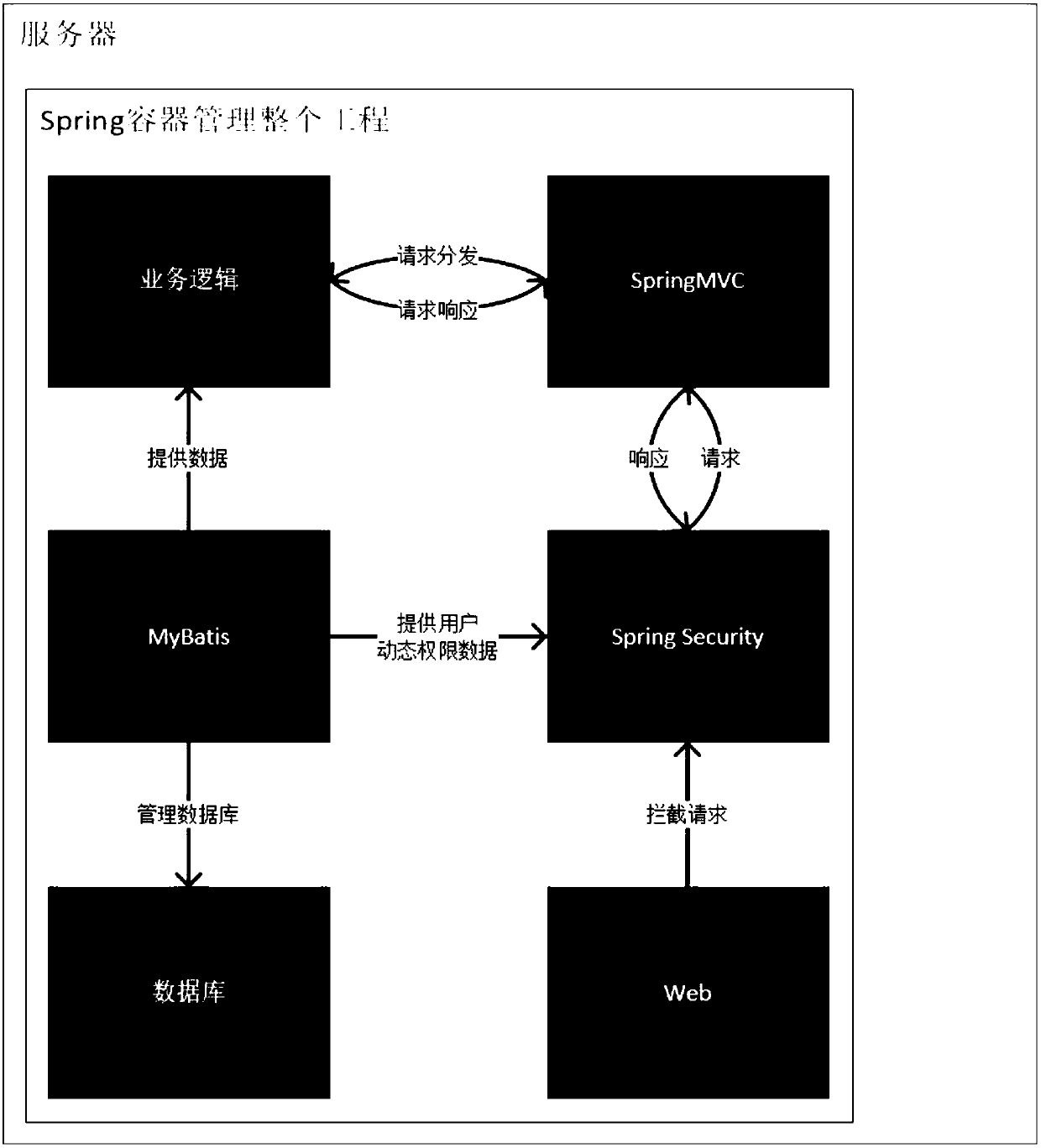
Dynamic rights management system based on improved RBAC model and Spring Security framework
The invention discloses a dynamic rights management system based on an improved RBAC model and a Spring Security framework. The system firstly transfers the concept of "inheritance" on the user groupmodule to the role module, merges the user group module and the role module to some extent, then modifies the definition of website resources in the RBAC model, adopts the control of the method in theweb server controller to satisfy the most application scenarios, and finally adds a user additional permission association table and a user shielding permission association table to increase the flexibility of permission configuration in conjunction with the Spring Security framework. The invention can quickly mark resources of the website through the annotation control method, realize the dynamic rights management scheme based on the improved RBAC model through database management, and can be conveniently integrated into the mainstream Java background server with high flexibility, which greatly reduces the workload of webmasters.
Owner:ZHEJIANG UNIV
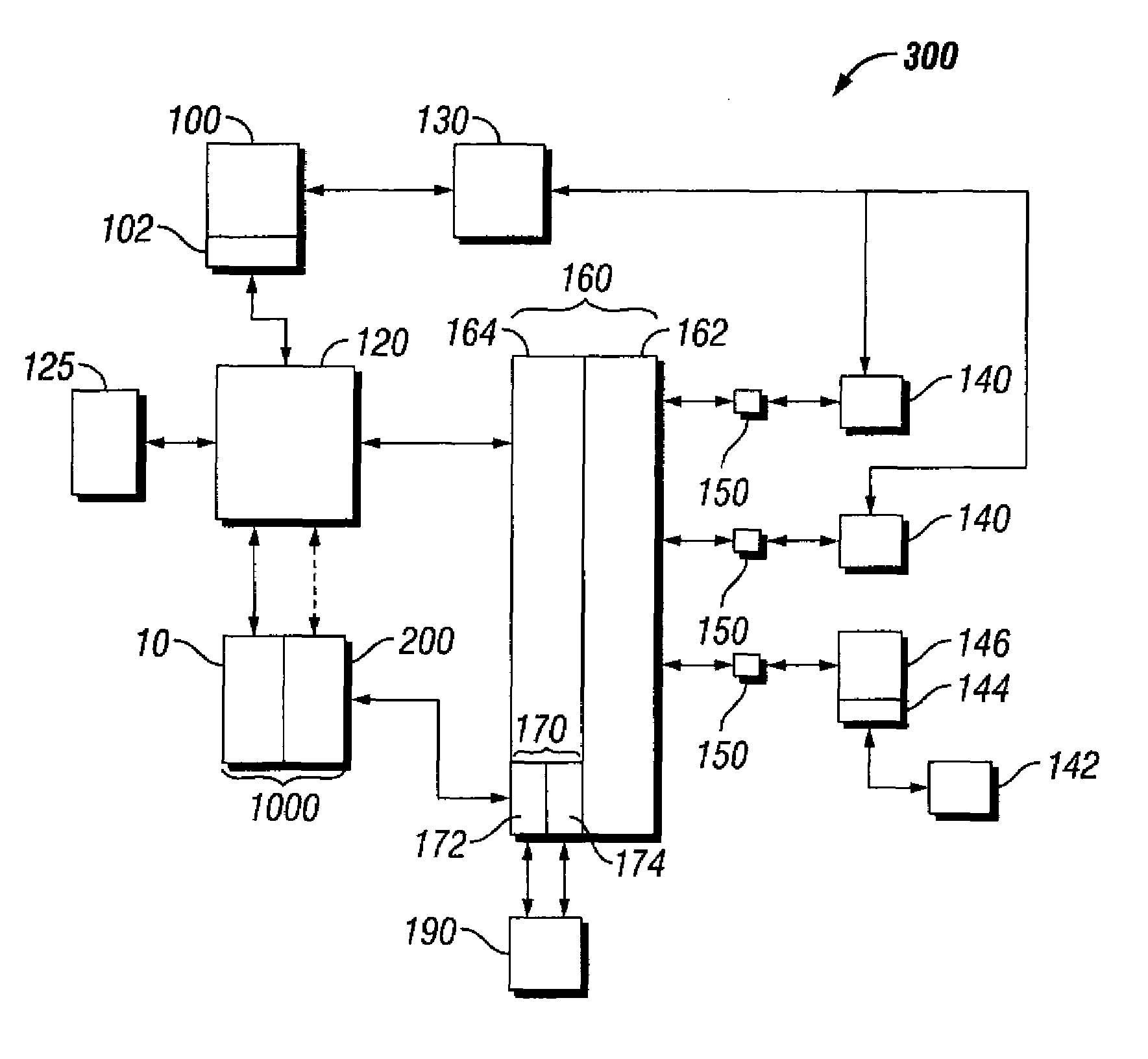
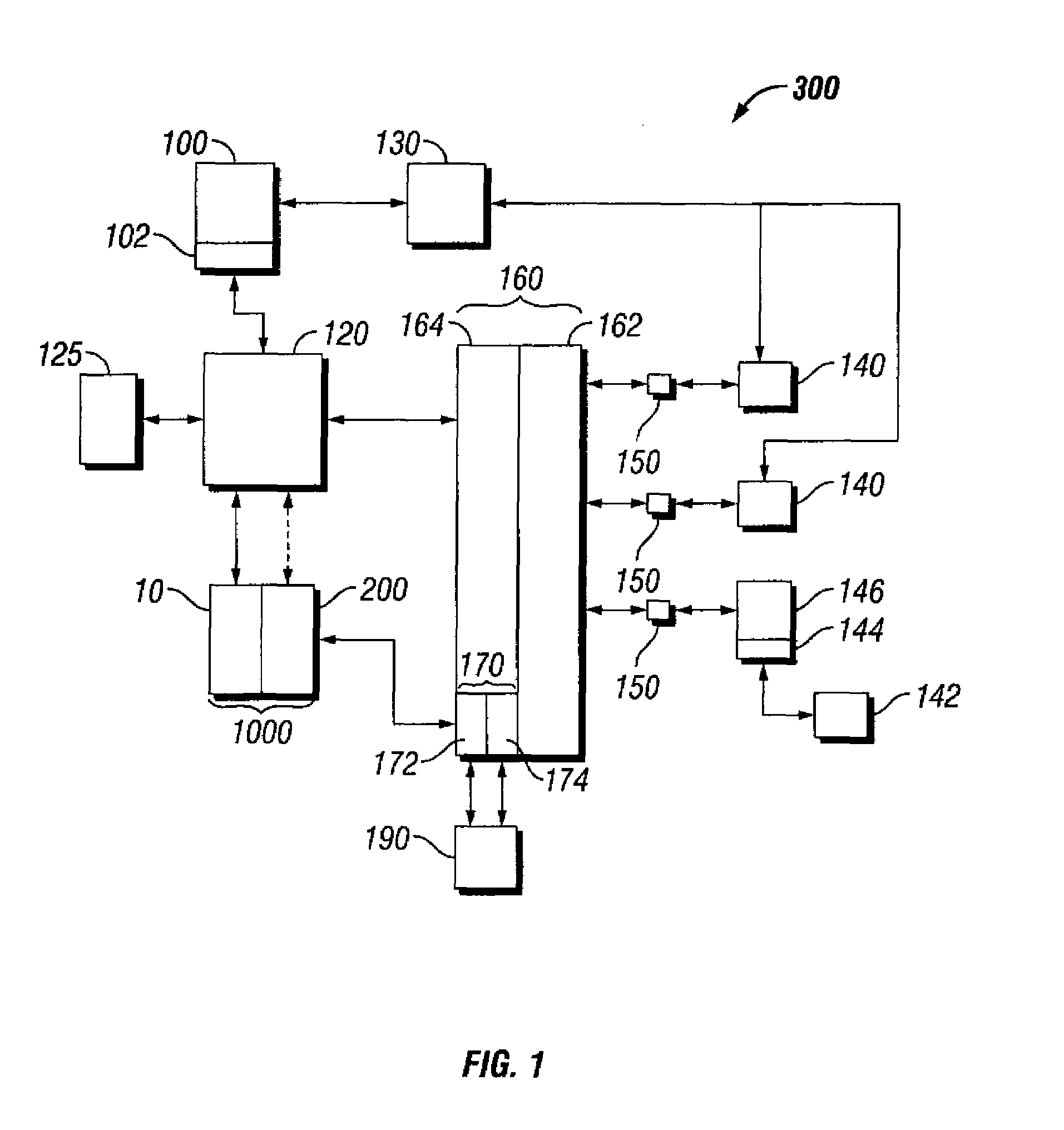
Methods and apparatus for premises content distribution
ActiveUS8732854B2Television system detailsDigital data processing detailsEngineeringExchange protocol
Apparatus and methods for protected content access, browsing and transfer over a network. In one embodiment, the network comprises a premises (e.g., residential) LAN, and the apparatus comprises a server and renderer consumer premise equipment (CPE). The renderer CPE scans the network to search for a server CPE that implement a compatible security framework. The renderer authenticates itself with the server, and the server allows content browsing and selection access only to an authorized and authenticated renderer. A negotiation and exchange protocol comprises messages exchanged between the renderer and the server that include one or more of device identification, encryption key exchange, digital certificates and information regarding security package used by each CPE.
Owner:TIME WARNER CABLE ENTERPRISES LLC
Bonding Contents On Separate Storage Media
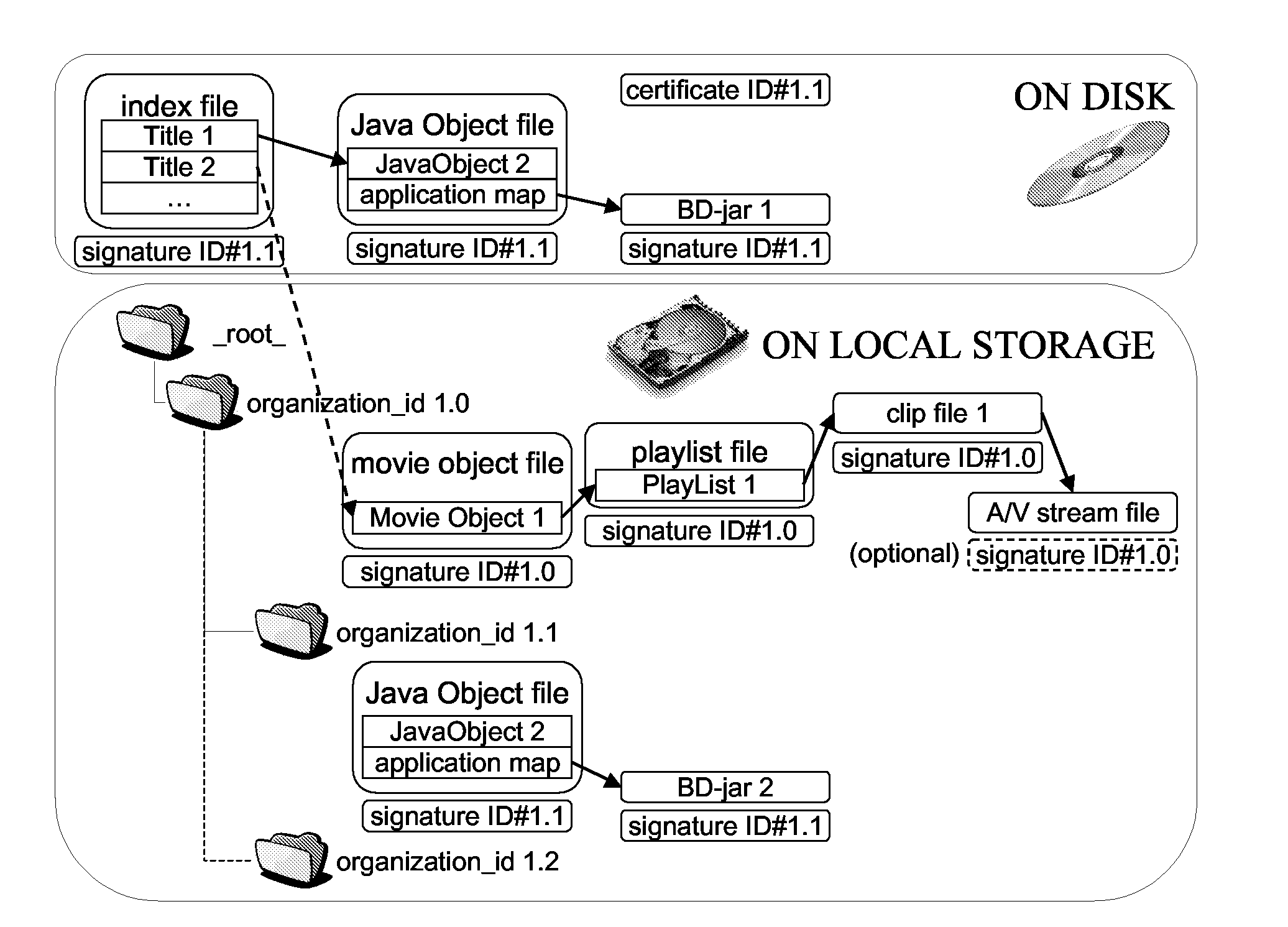
InactiveUS20080133564A1Digital data processing detailsPublic key for secure communicationVirtual file systemSecurity framework
Local storage on player instruments provides the ability for adding further amendments and most recent supplements to the optical disc content. A problem arising with this technically applicable possibility is the protection of copyrights bound to disc and supplement data. The present invention describes a technique to ensure a security framework that is able to handle this, by creating a virtual file system by merging optical disc data and local storage data based upon a common identifier.
Owner:THOMSON LICENSING SA
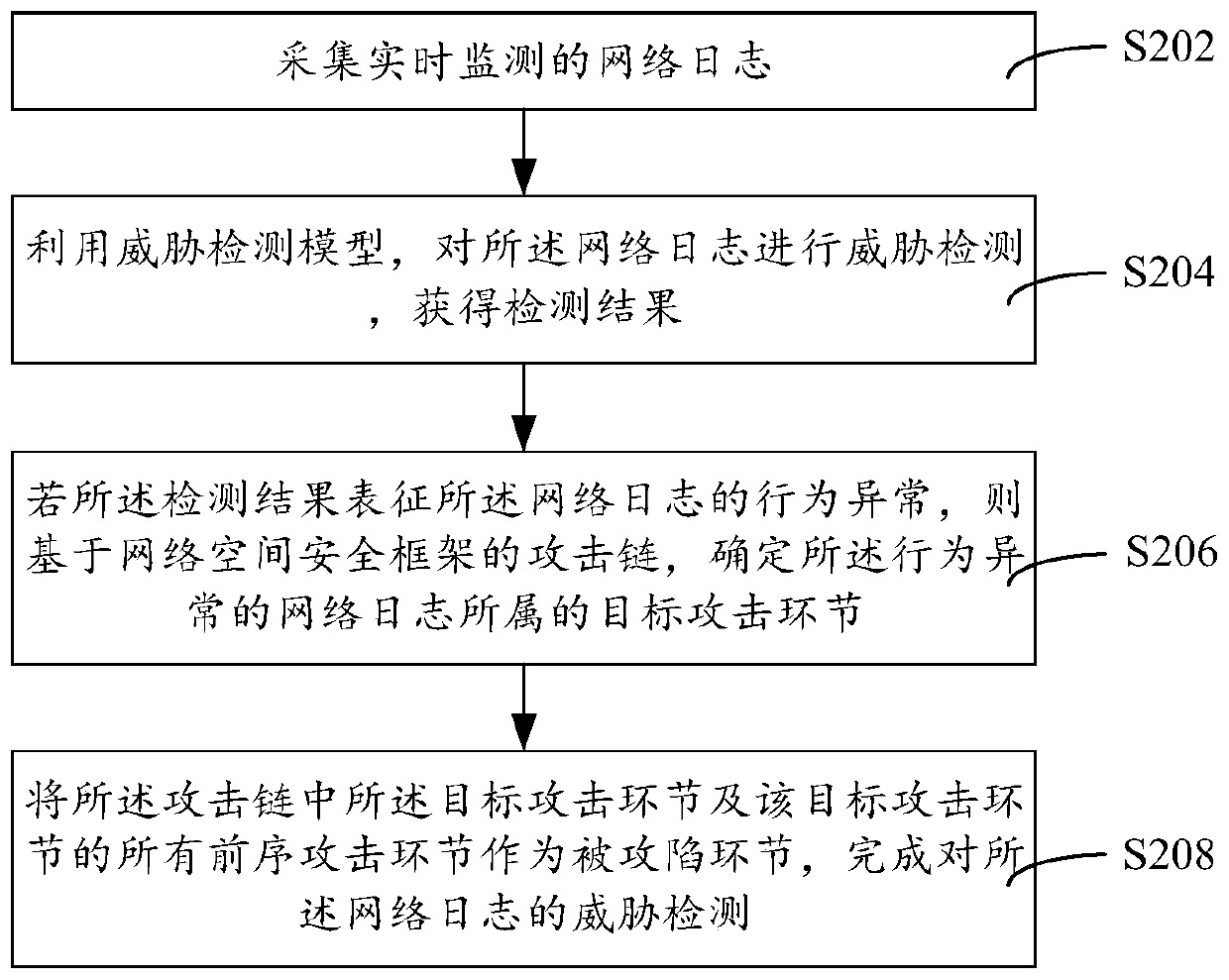
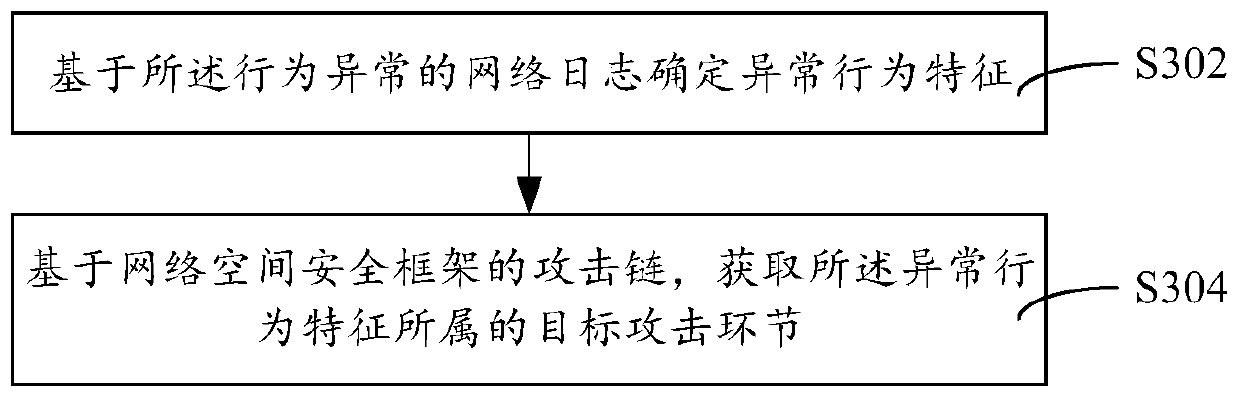
Threat detection method, device and equipment and storage medium
ActiveCN111147504AImprove security defense performanceNeural architecturesTransmissionAttackSecurity framework
The invention discloses a threat detection method. The method comprises the steps of collecting weblog monitored in real time; performing threat detection on the weblog by utilizing a threat detectionmodel to obtain a detection result; if the detection result represents that the behavior of the weblog is abnormal, determining a target attack link to which the weblog with the abnormal behavior belongs based on an attack chain of a network space security framework; and taking the target attack link in the attack chain and all preorder attack links of the target attack link as attacked links tocomplete threat detection of the weblog. The invention further discloses a threat detection device and equipment and a storage medium. Threat capture is carried out from the global perspective of theattack chain, and the security defense capability is improved.
Owner:SANGFOR TECH INC
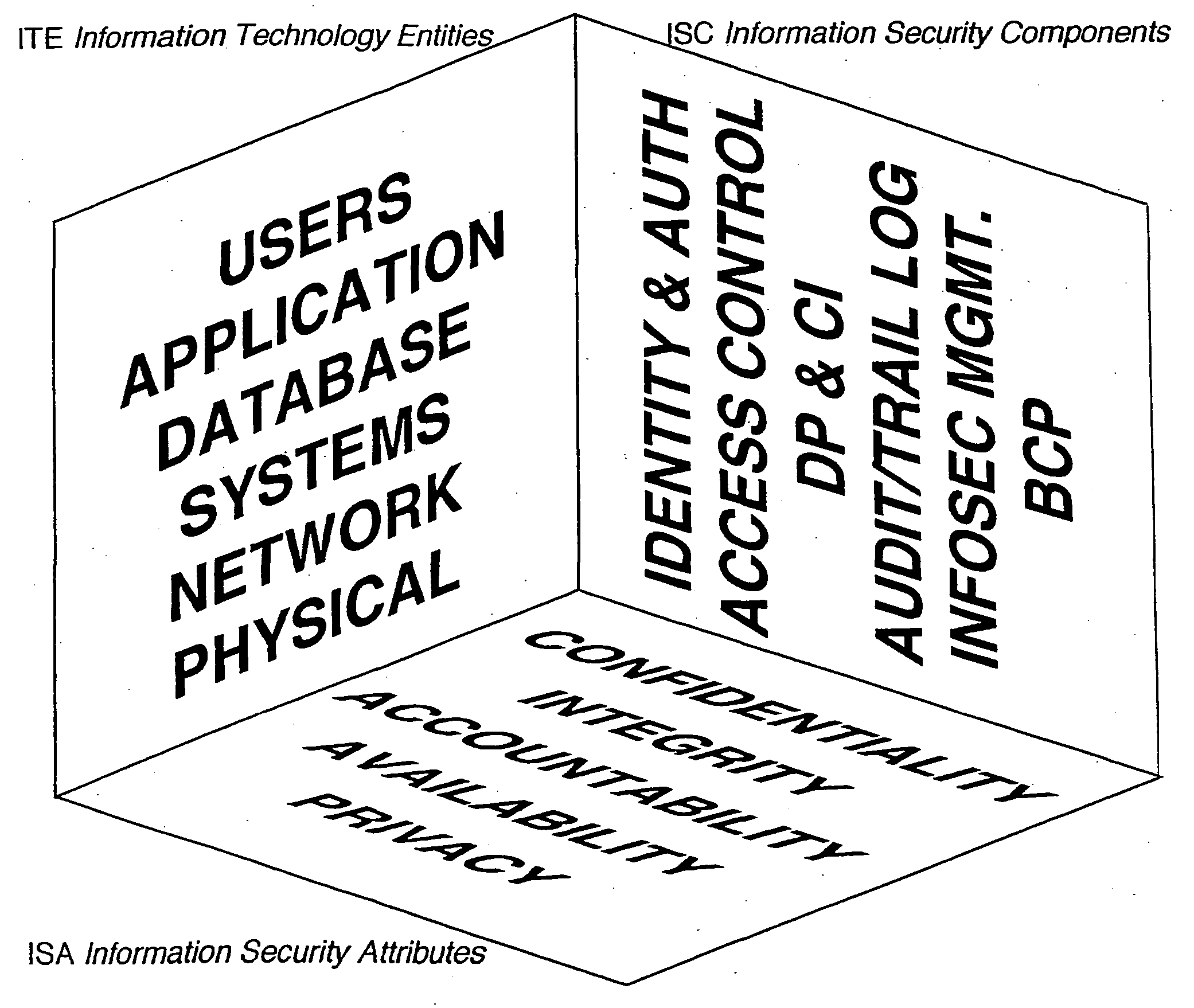
Information security model
InactiveUS20050038993A1Improve securityComputer security arrangementsOffice automationSecurity frameworkInformation security audit
An information security model provides a set of schemas that ensure coverage of all securing components. All points are addressed and evaluated in a net of three-dimensional coorindate knots The model defines the relation between components in the information risk and security space, and provides an information risk and security framework that ensures that all information security components are addressed; enables standardized information security audit; provides information risk compliance numbers; and defines strategic business direction to address information security implementation. The information security model of the present invention standardizes the approach and creates a matrix through which risk compliance factors can be calculated.
Owner:SCIENTON TECH
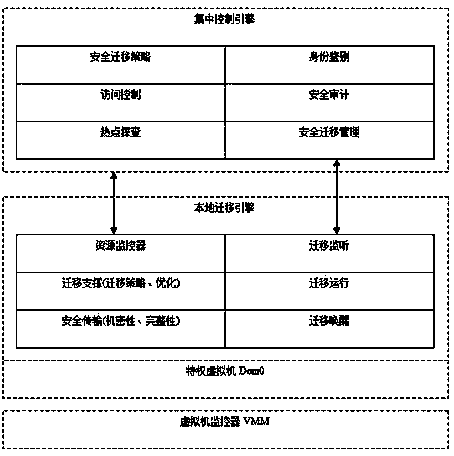
Dynamic migration security framework of virtual machine
InactiveCN103455373AProtection securityDefend against security attacksProgram initiation/switchingDigital data authenticationResource utilizationComputer compatibility
The invention provides a security framework and relates to the technical field of computer information security, in particular to a dynamic migration security framework of a virtual machine. The dynamic migration security framework is composed of a centralized control engine and a local migration engine; the centralized control engine provides functions of two-way authentication, access control and security audit under the control of a security policy, monitors resource utilization of a physical server and the virtual machine in real time, and provides resource basis for dynamic migration of the virtual machine. The local migration engine completes the dynamic migration of the virtual machine in stages according to the established migration strategy and under the control of the security policy. The security framework is supportive of a plurality of security mechanisms and the dynamic migration strategies of the virtual machine, security of sensitive information of the virtual machine can be effectively protected, security attacks upon the dynamic migration of the virtual machine are resisted, and compatibility is high.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
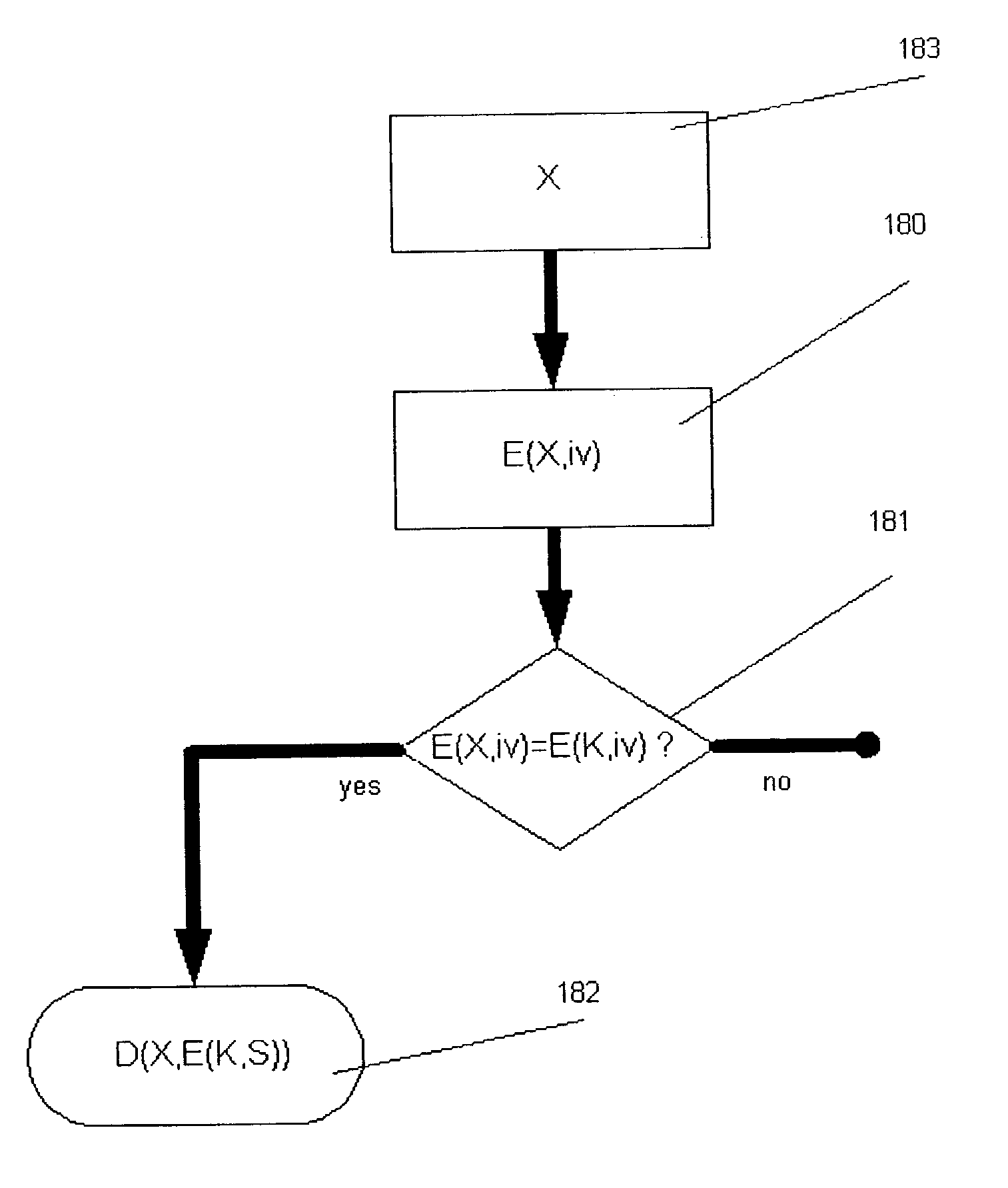
Security framework for protecting rights in computer software
InactiveUS7549147B2Enhance fingerprinting robustnessEnhance license policy enforcementDigital data processing detailsUnauthorized memory use protectionComputer hardwareSecurity framework
A method for protecting software is provided, where source code for the software has a first directive marking an encryption beginning point and a second directive marking an encryption end point. The method contains the steps of: processing the source code to identify a block of code between the first and second directives; compiling the source code to produce a binary file; generating a valid key and a random string; encrypting the random string with the key to obtain a first encrypted value; encrypting a portion of the binary file corresponding to the block of code with the valid key to obtain a second encrypted value; and replacing the portion of the binary file corresponding to the block of code with the second encrypted value and code that can decrypt the second encrypted value during execution of the software.
Owner:HELP SYST LLC
Systems and methods for front-end and back-end data security protocols
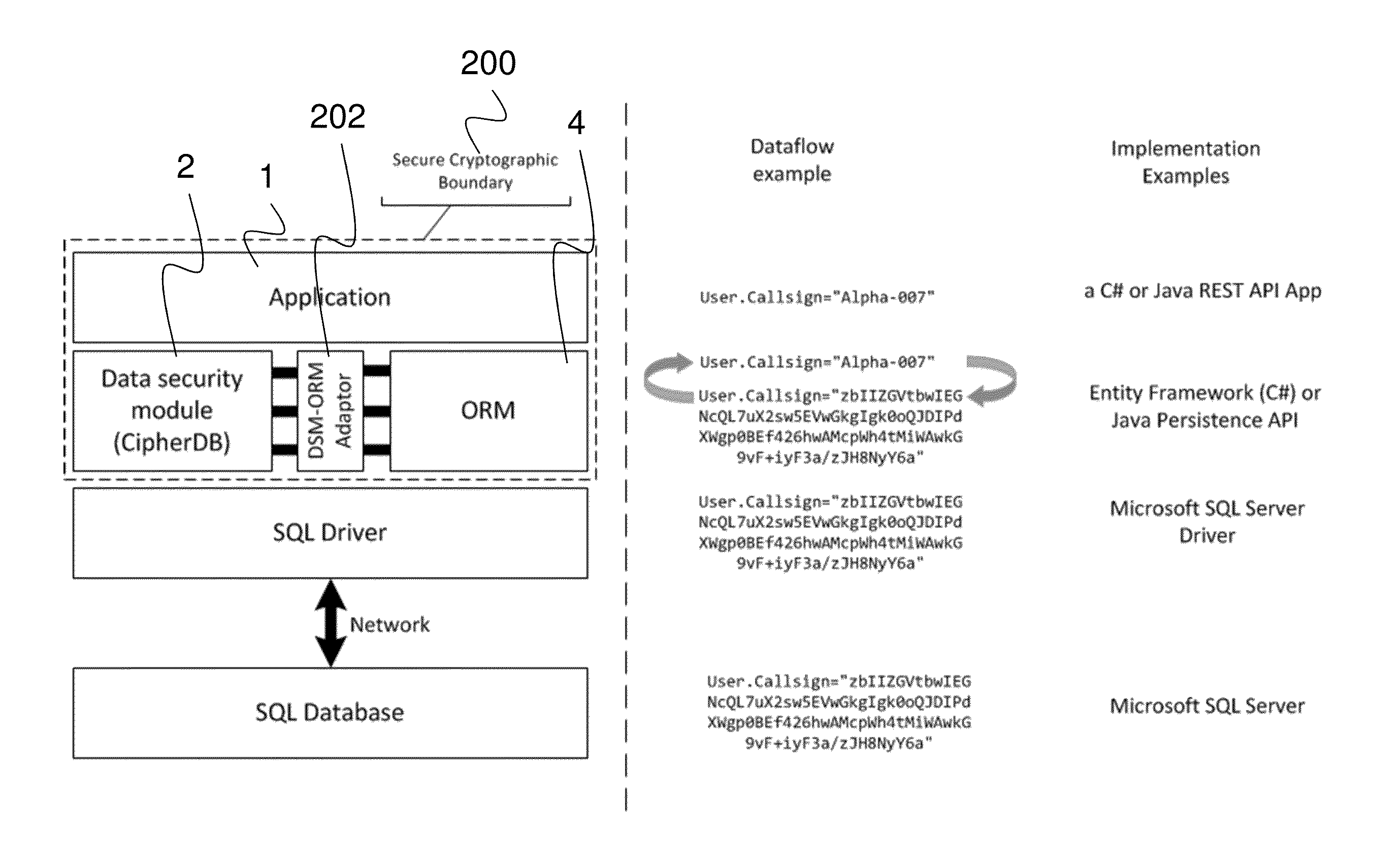
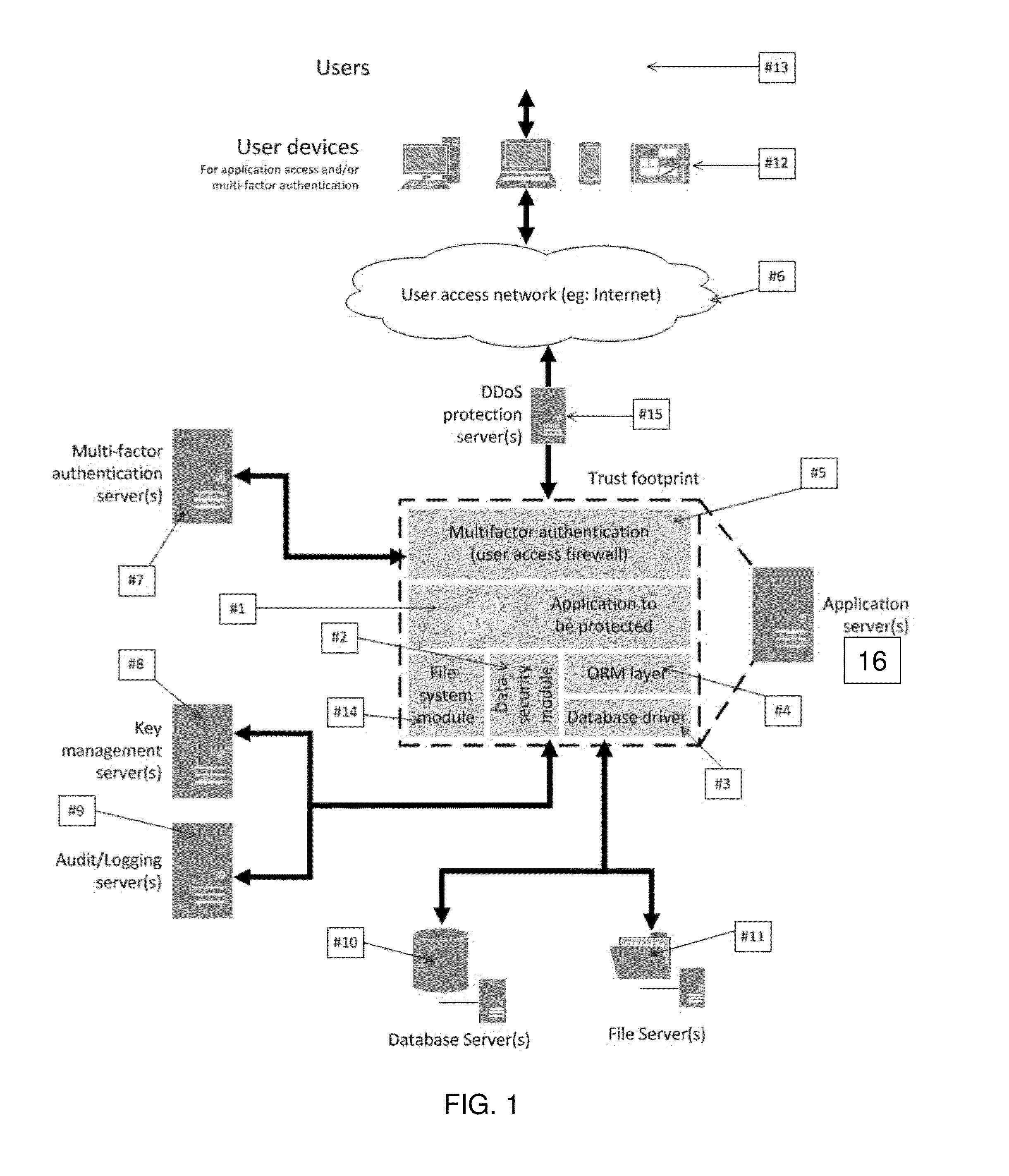
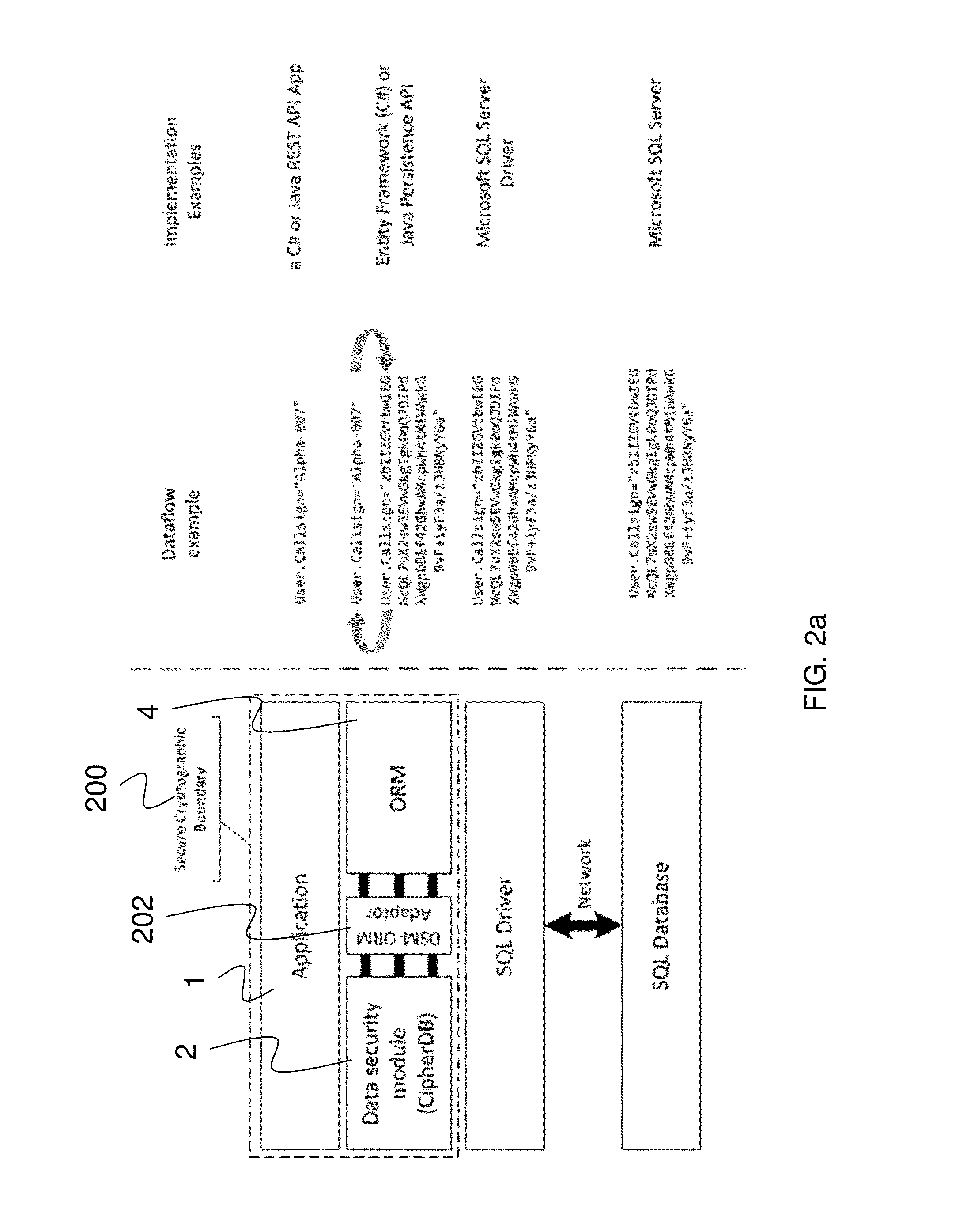
ActiveUS20150339486A1Digital data processing detailsUser identity/authority verificationData integrityCryptographic protocol
A security framework and methodology is provided which provides front-end security through authentication and authorization, and back-end security through a virtual private data-store created within an insecure environment using existing object-relational mapping (ORM) layers or database drivers. The front-end security utilizes numerous multi-factor authentication metrics and a distributed denial of service (DDoS) cryptographic boundary to proactively attack malicious users using a cryptographic puzzle, and the back-end security provides data encryption and decryption, data privacy, data integrity, key management, pattern monitoring, audit trails and security alerts while simultaneously hiding the complexity behind an identical or similar ORM or database drive application programming interface (API).
Owner:CRYPTERON INC
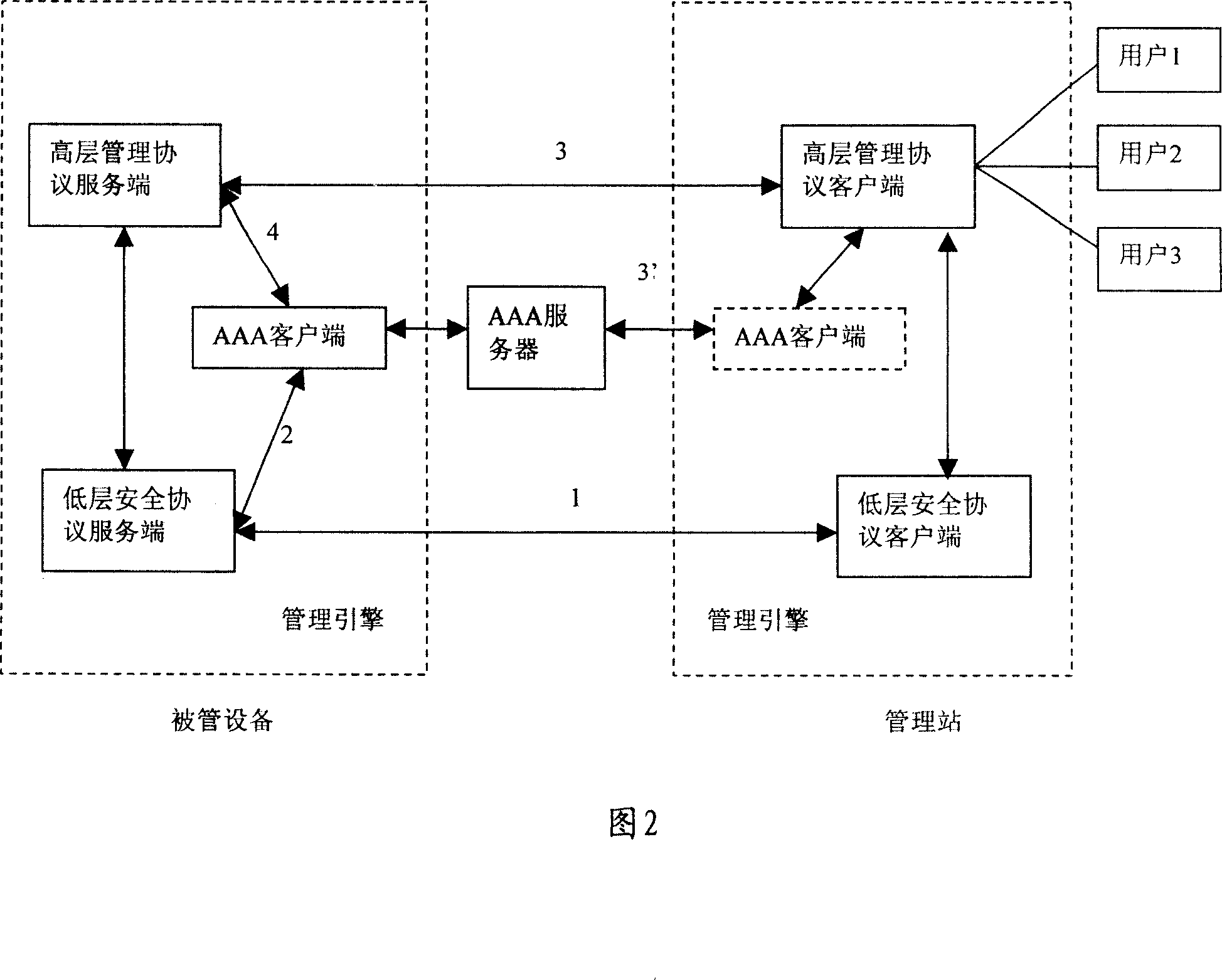
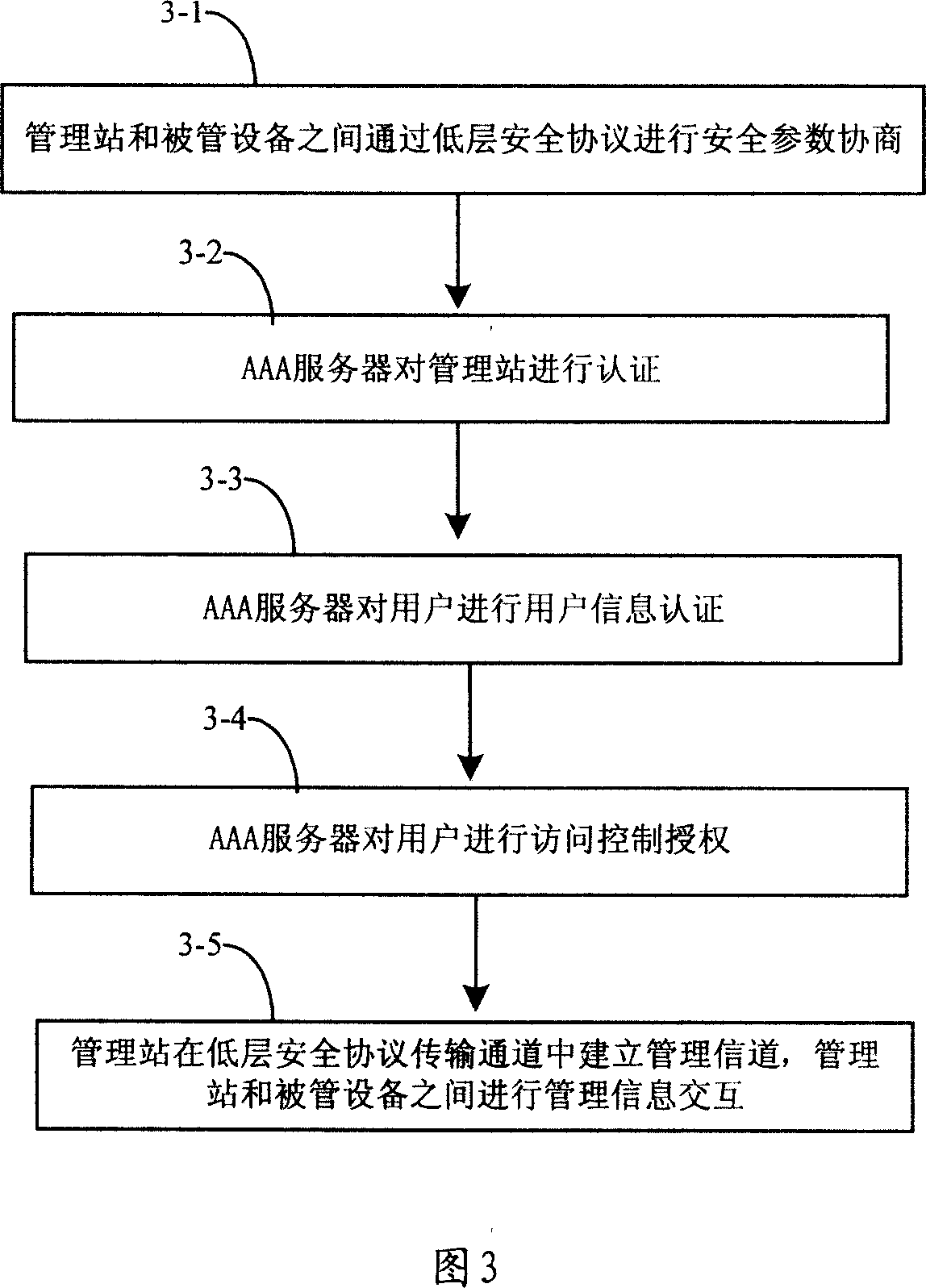
Security framework of managing network, and information processing method
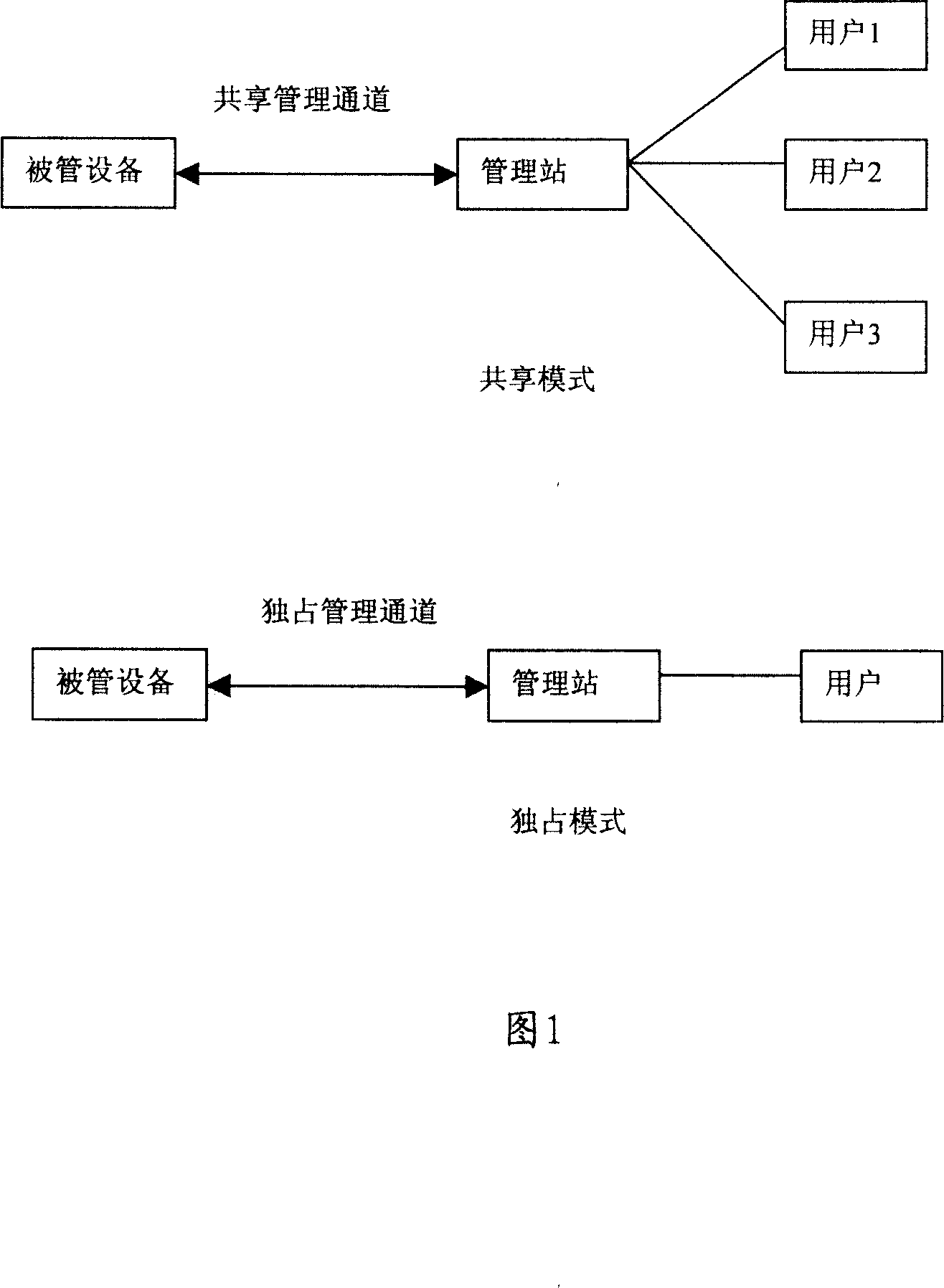
InactiveCN101094226AEasy to integrateReduce overheadTransmissionInformation processingSecure transmission
The management network security architecture comprises: management station and managed device. The method thereof comprises: establishing a security transmission channel between the management station and managed device; making authentication for the management station; using said security transmission channel to make information interaction between said management station and managed device.
Owner:HUAWEI TECH CO LTD
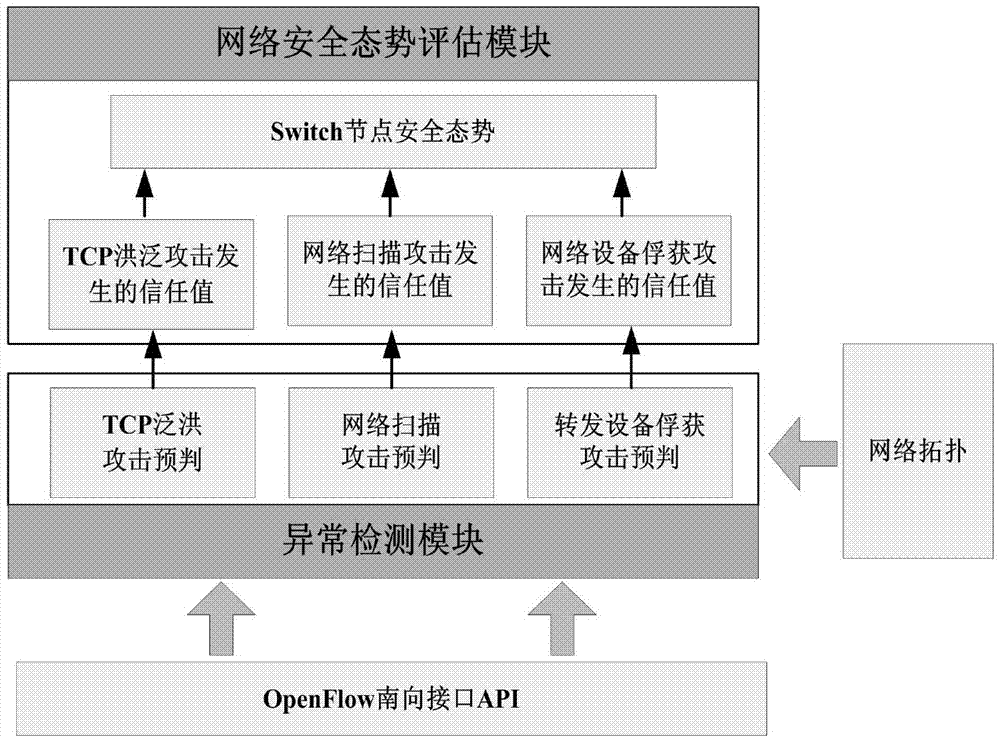
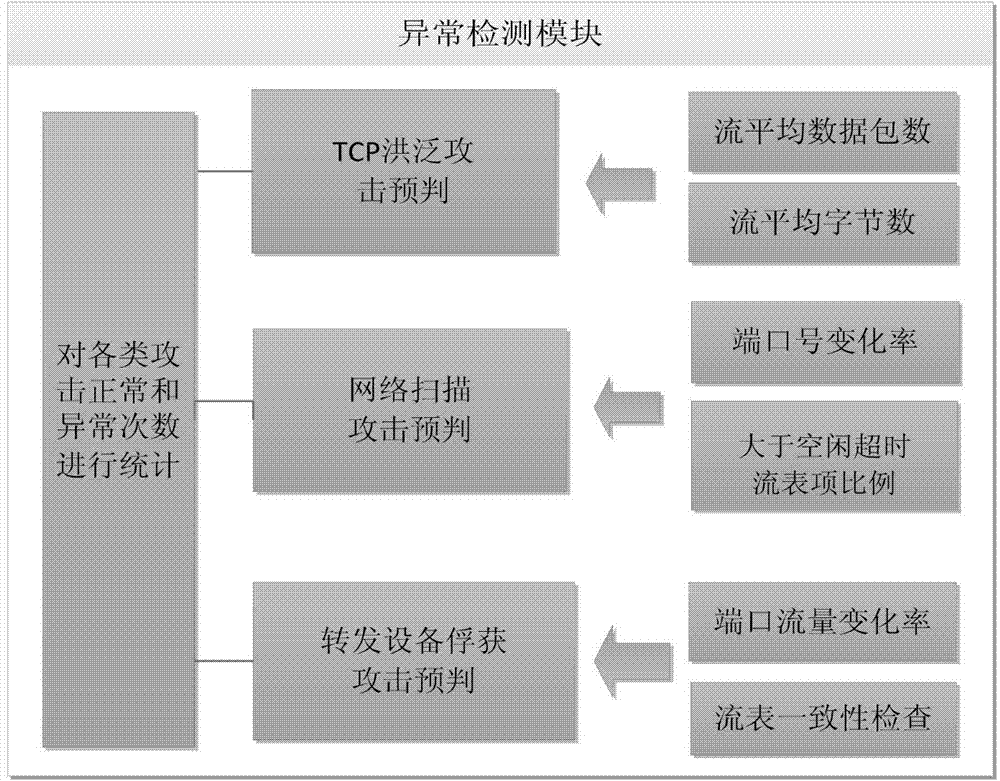
Software defined network security situation assessment method
ActiveCN104506385ASolve the high false positive rateReduce the number of hopsData switching networksSecurity frameworkSafety status
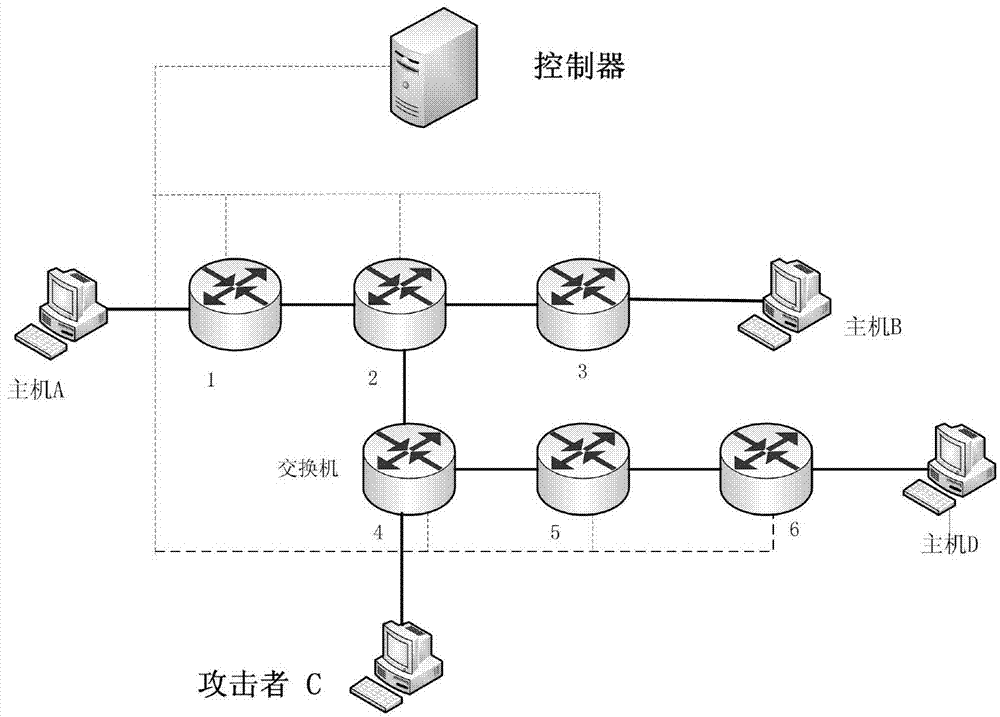
The invention discloses a software defined network security situation assessment method. The advantages of SDN (software defined network) control and direct and quick information collection are combined, an open SDN security situation assessment framework is provided on account of three kinds of attacks of an SDN forwarding surface, the security framework closely fits a framework of an SDN controller, an anomaly detection module extracts characteristic indexes according to the SDN and various attack characteristics, an SVM (support vector machine) classification algorithm is selected for identification, and attack pre-judgment is given. A security situation assessment module performs quantitative assessment on network security situations according to information collected by the anomaly detection module, and attack sensitivity and noise resistance of an assessment system are regulated through setting of a threshold value. Different weights are allocated to different attacks based on an AHP (analytic hierarchy process) so as to fit out a comprehensive security situation of the network. The method is flexible and simple, attach behaviors can be detected accurately, the quantitative assessment of the security situations of the network is given, and monitoring and assessment of the security status of the SDN forwarding surface are realized with lower cost.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com