Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3535 results about "Web transport" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
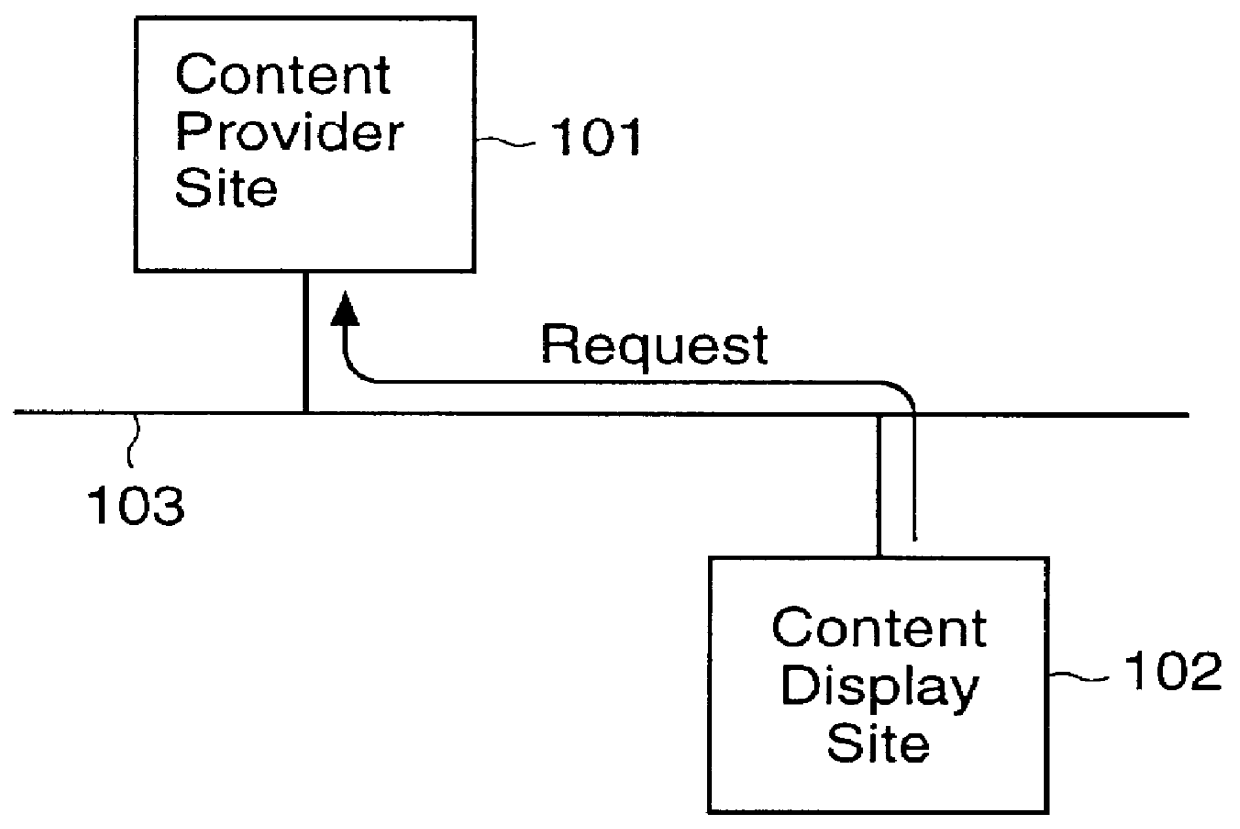
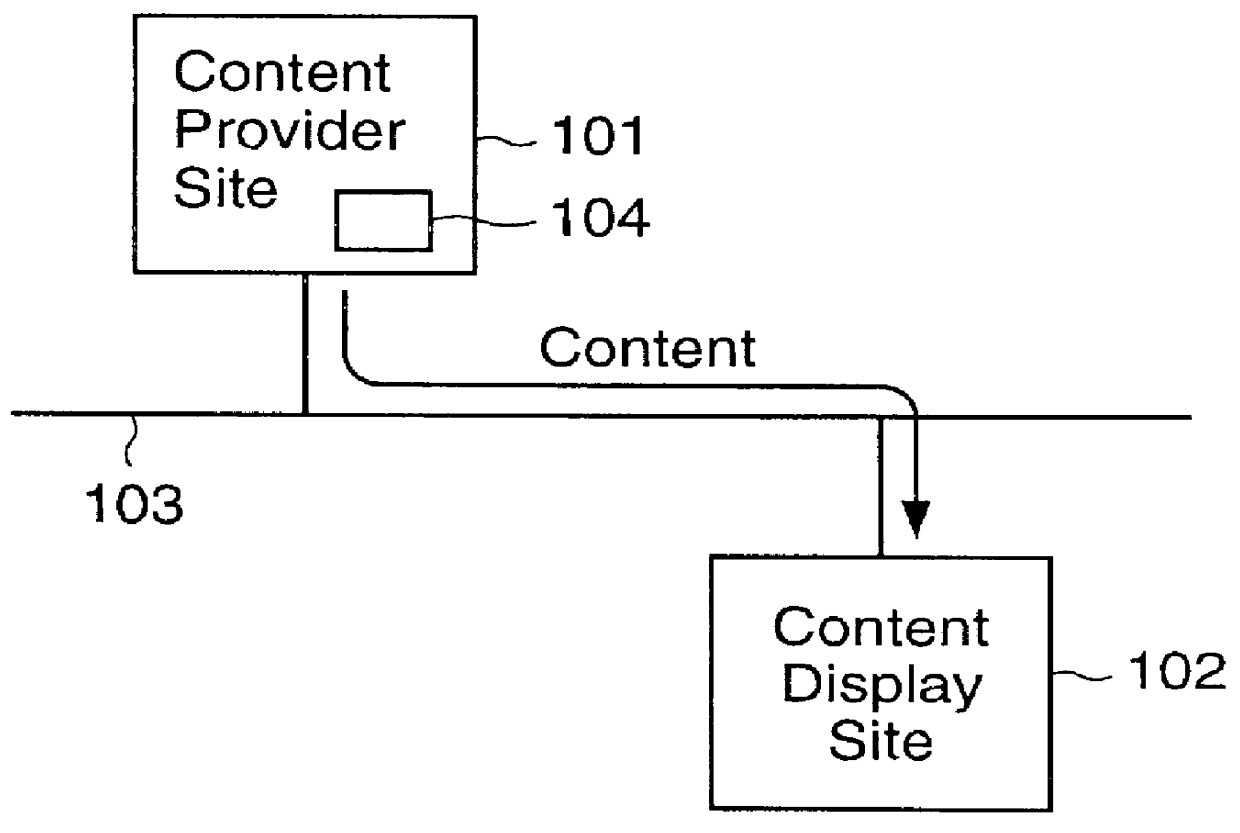
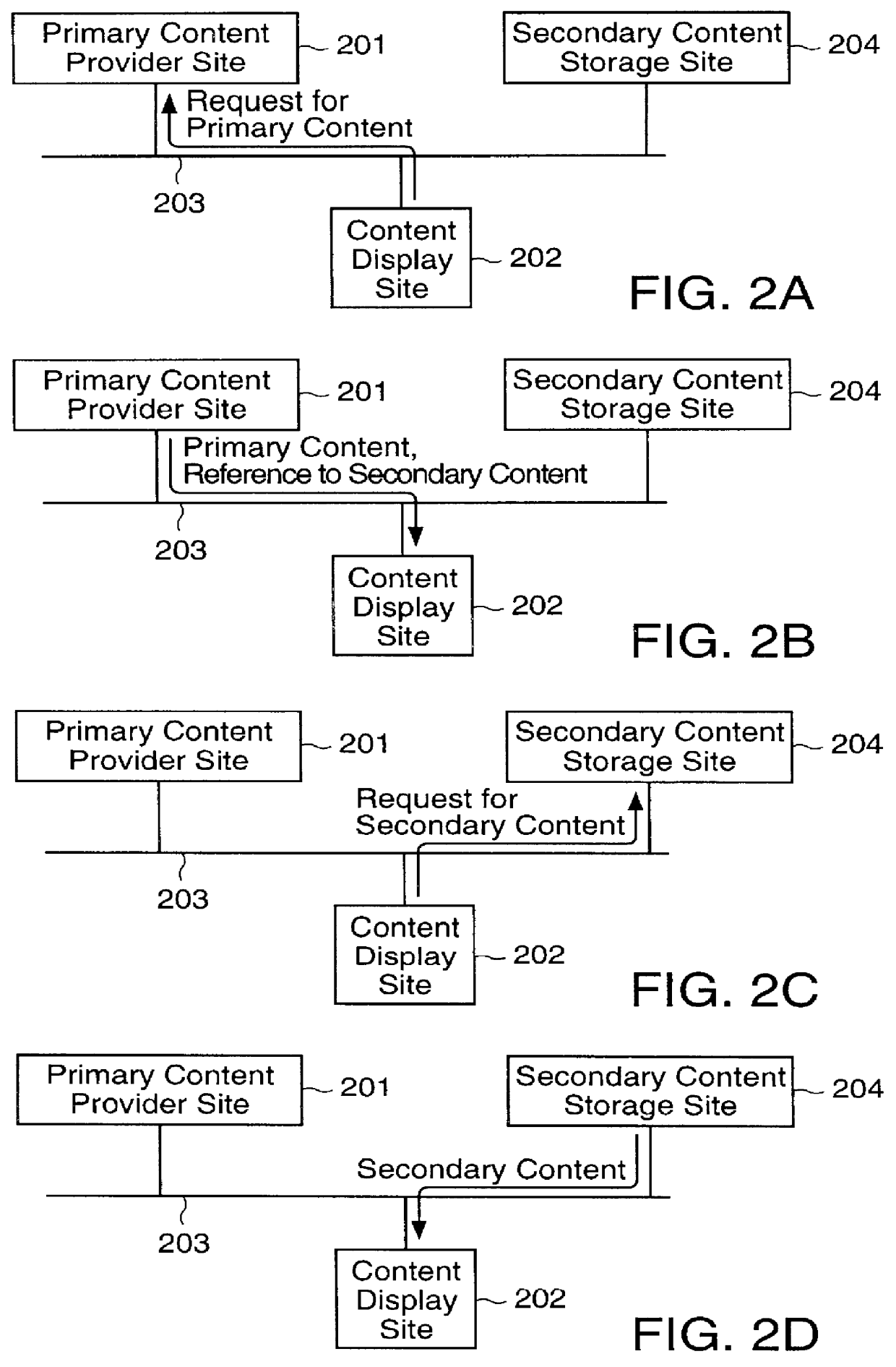
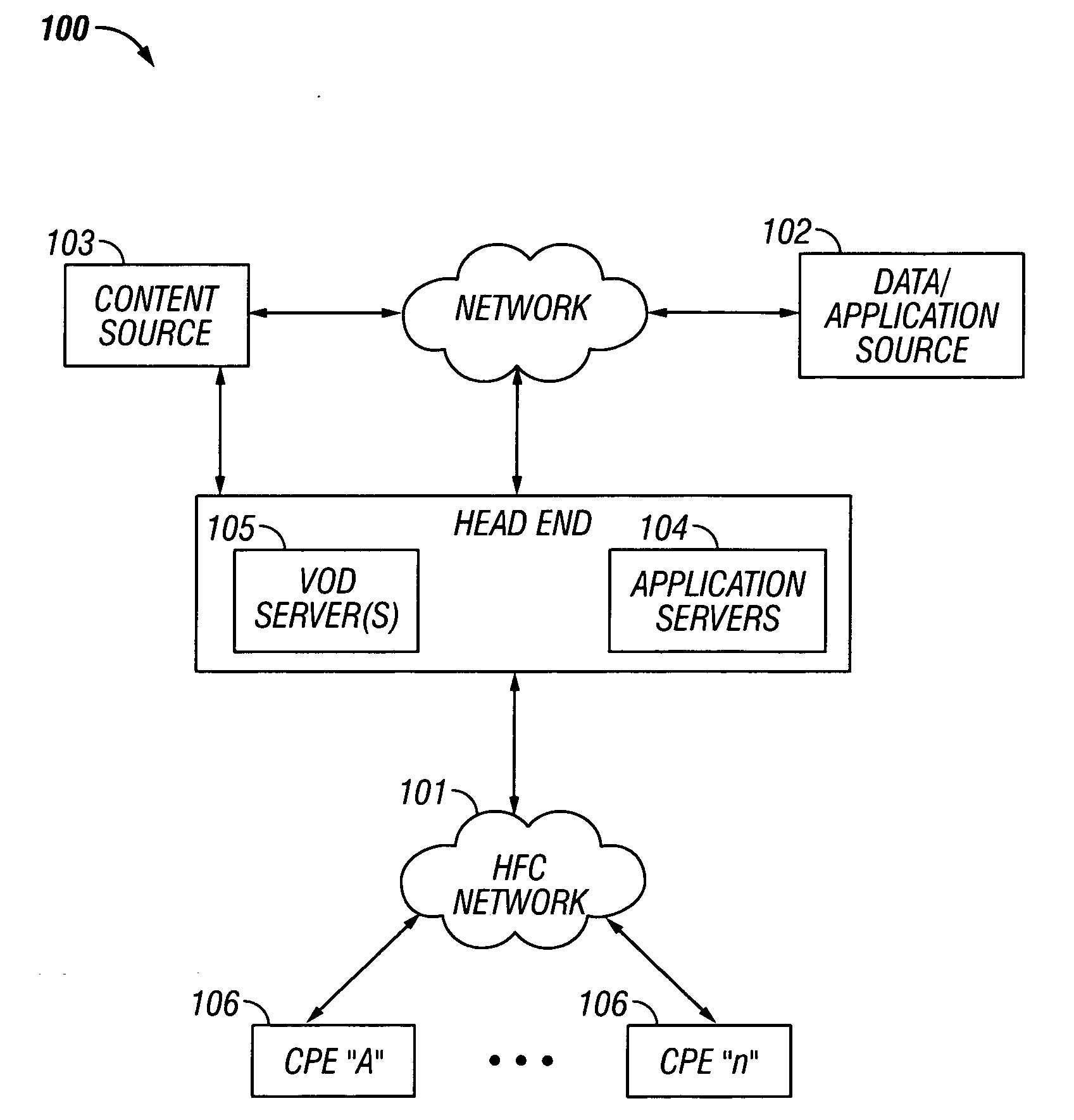
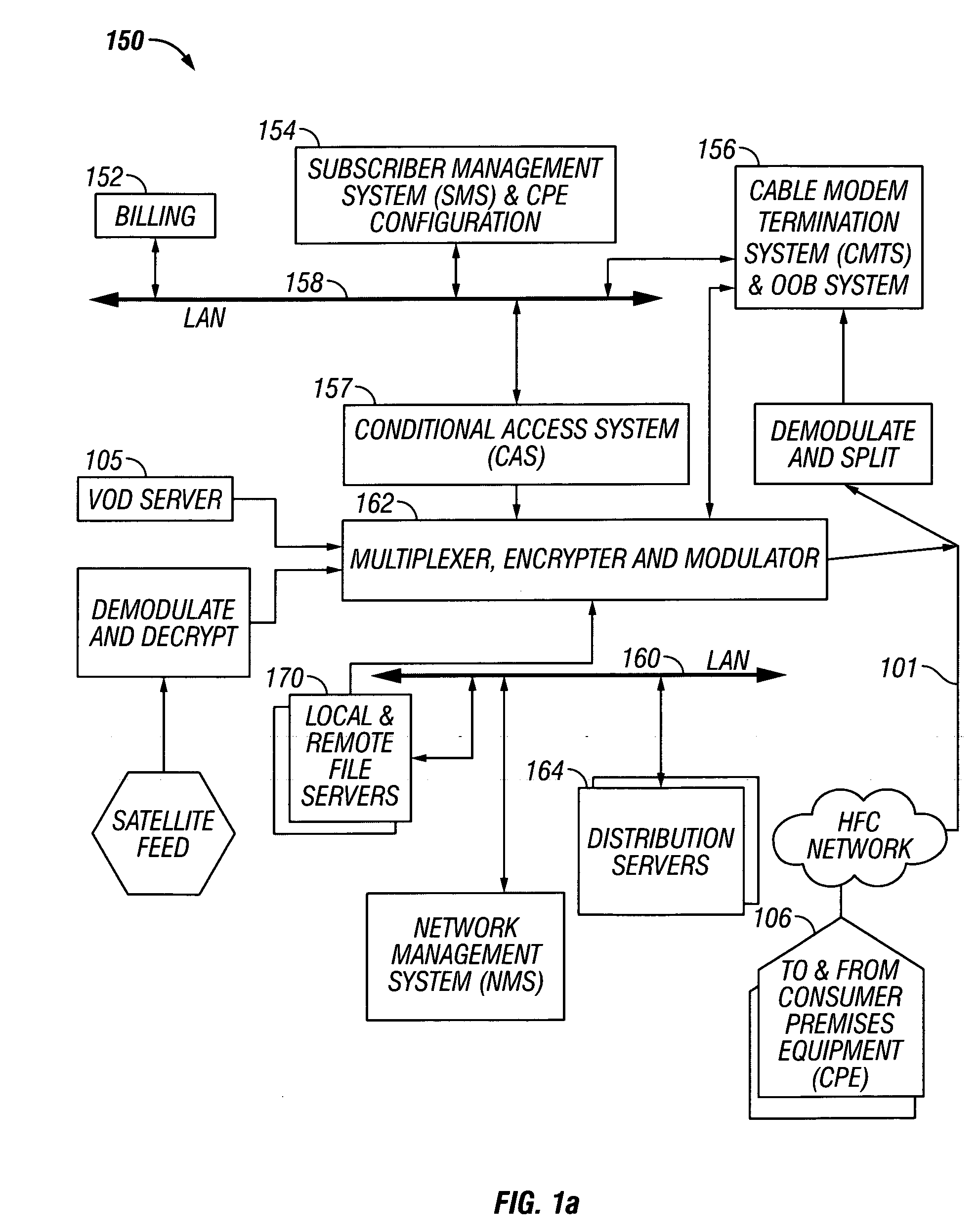
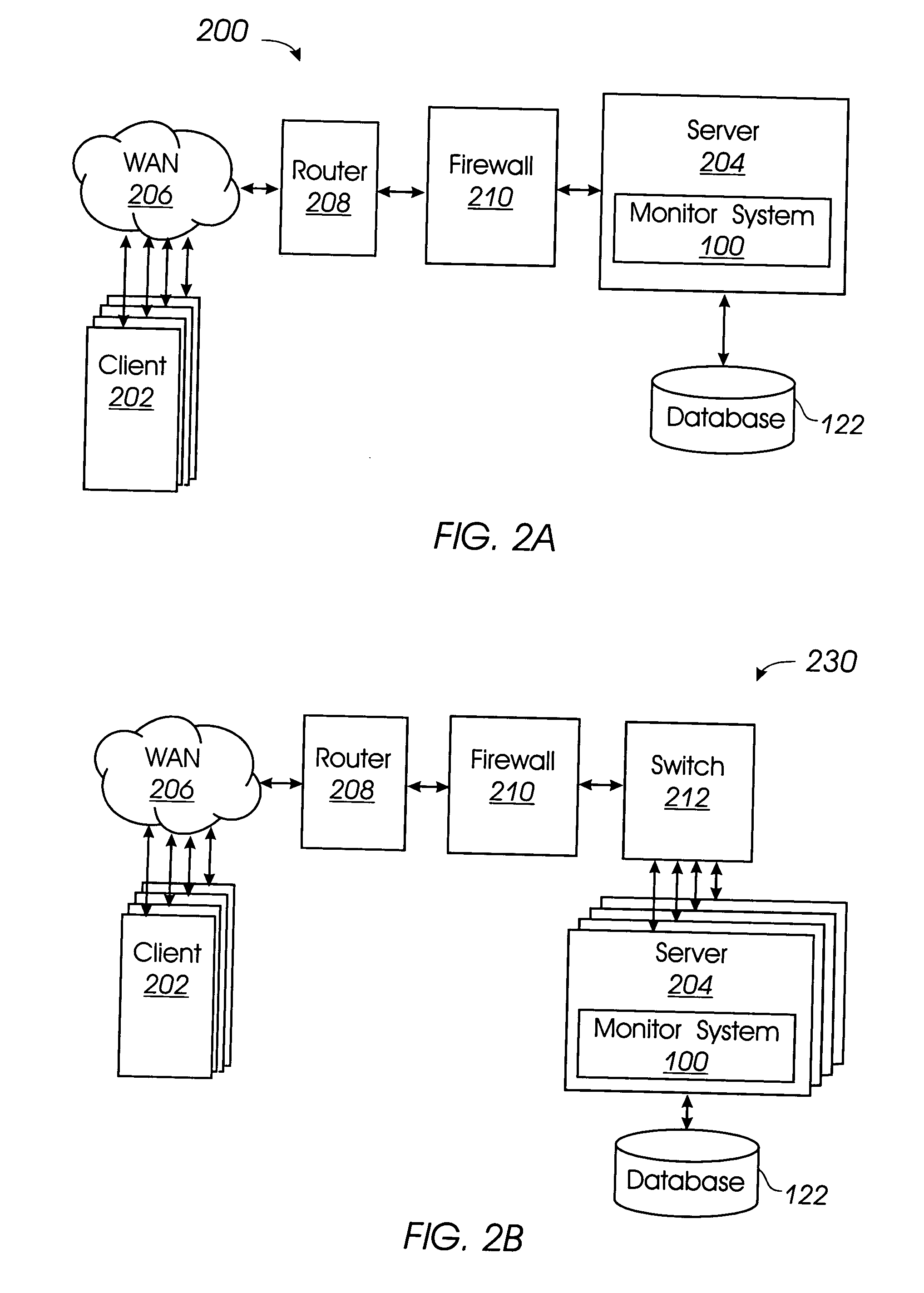
Content display monitor
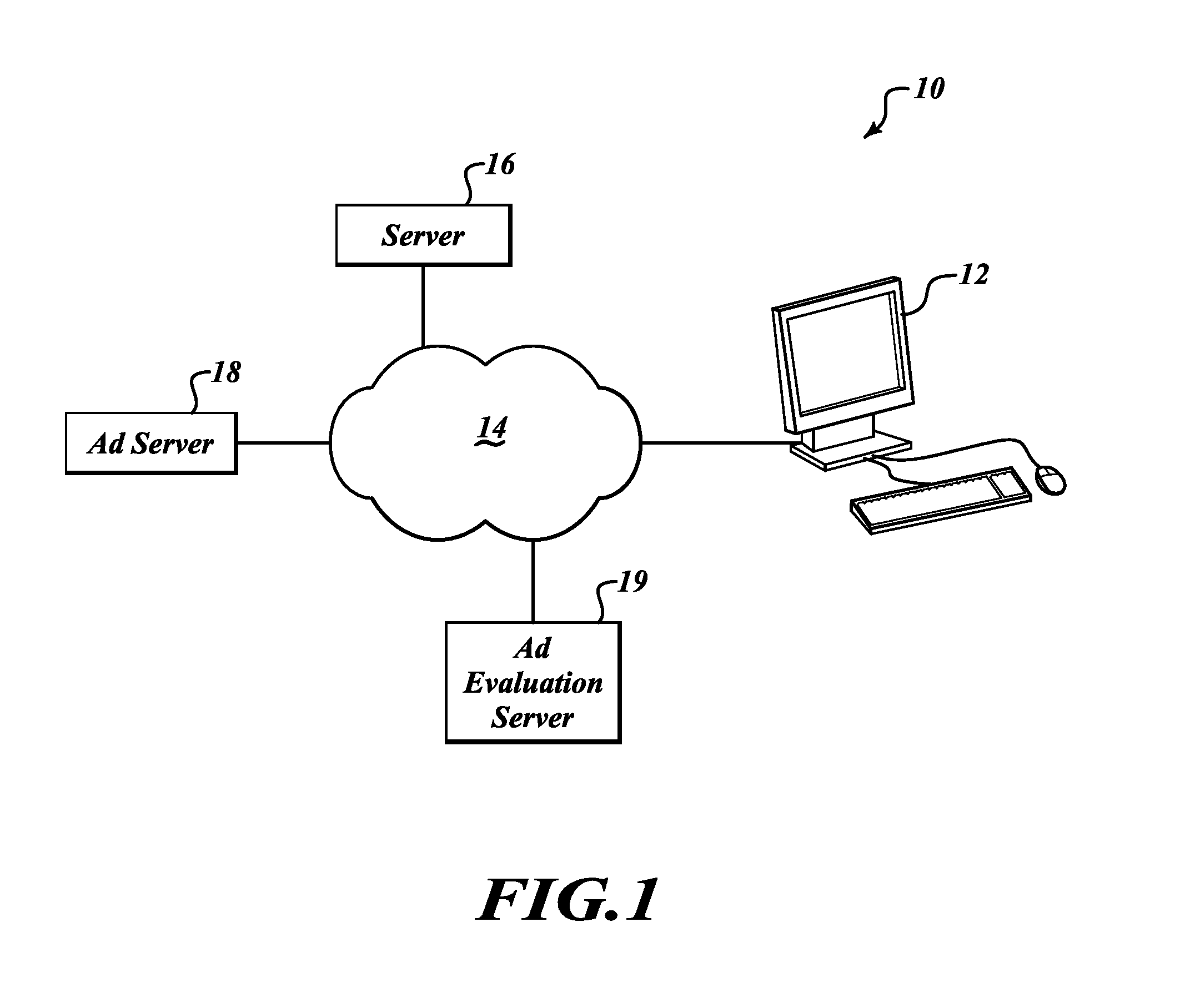
InactiveUS6108637AComplete banking machinesDigital data information retrievalWeb siteComputerized system
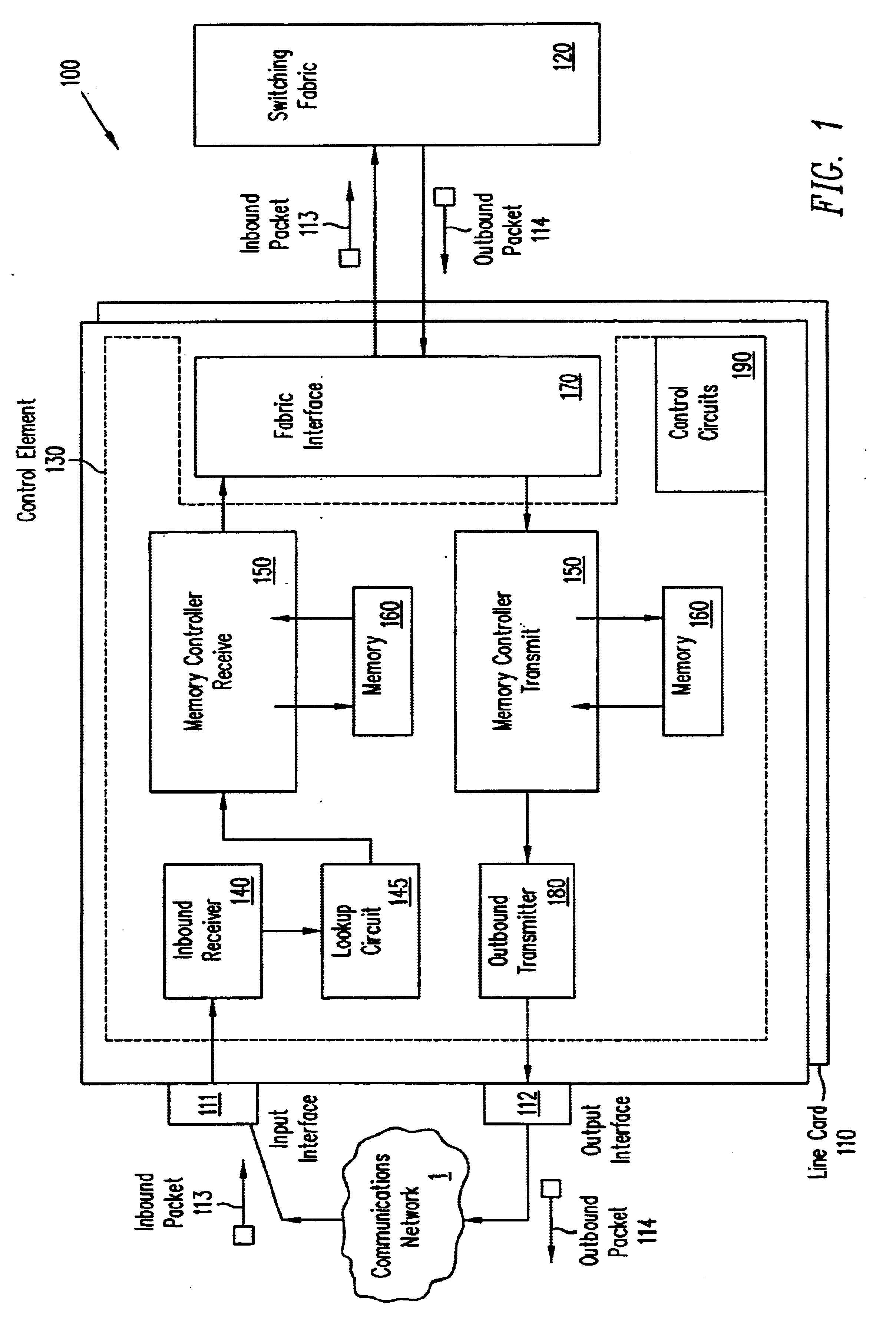
The invention can enable monitoring of the display of content by a computer system. Moreover, the invention can enable monitoring of the displayed content to produce monitoring information from which conclusions may be deduced regarding the observation of the displayed content by an observer. The invention can also enable monitoring of the display at a content display site of content that is provided by a content provider site over a network to the content display site. Additionally, the invention can enable the expeditious provision of updated and / or tailored content over a network from a content provider site to a content display site so that the content provider's current and appropriately tailored content is always displayed at the content display site. Aspects of the invention related to transfer of content over a network are generally applicable to any type of network. However, it is contemplated that the invention can be particularly useful with a computer network, including private computer networks (e.g., America Online TM ) and public computer networks (e.g., the Internet). In particular, the invention can be advantageously used with computer networks or portions of computer networks over which video and / or audio content are transferred from one network site to another network site for observation, such as the World Wide Web portion of the Internet.
Owner:NIELSEN COMPANY US LLC THE A DELAWARE LIMITED LIABILITY
Software control plane for switches and routers
ActiveUS20080219268A1Bridging the gapImprove convenienceError preventionTransmission systemsQuality of serviceAbstraction layer
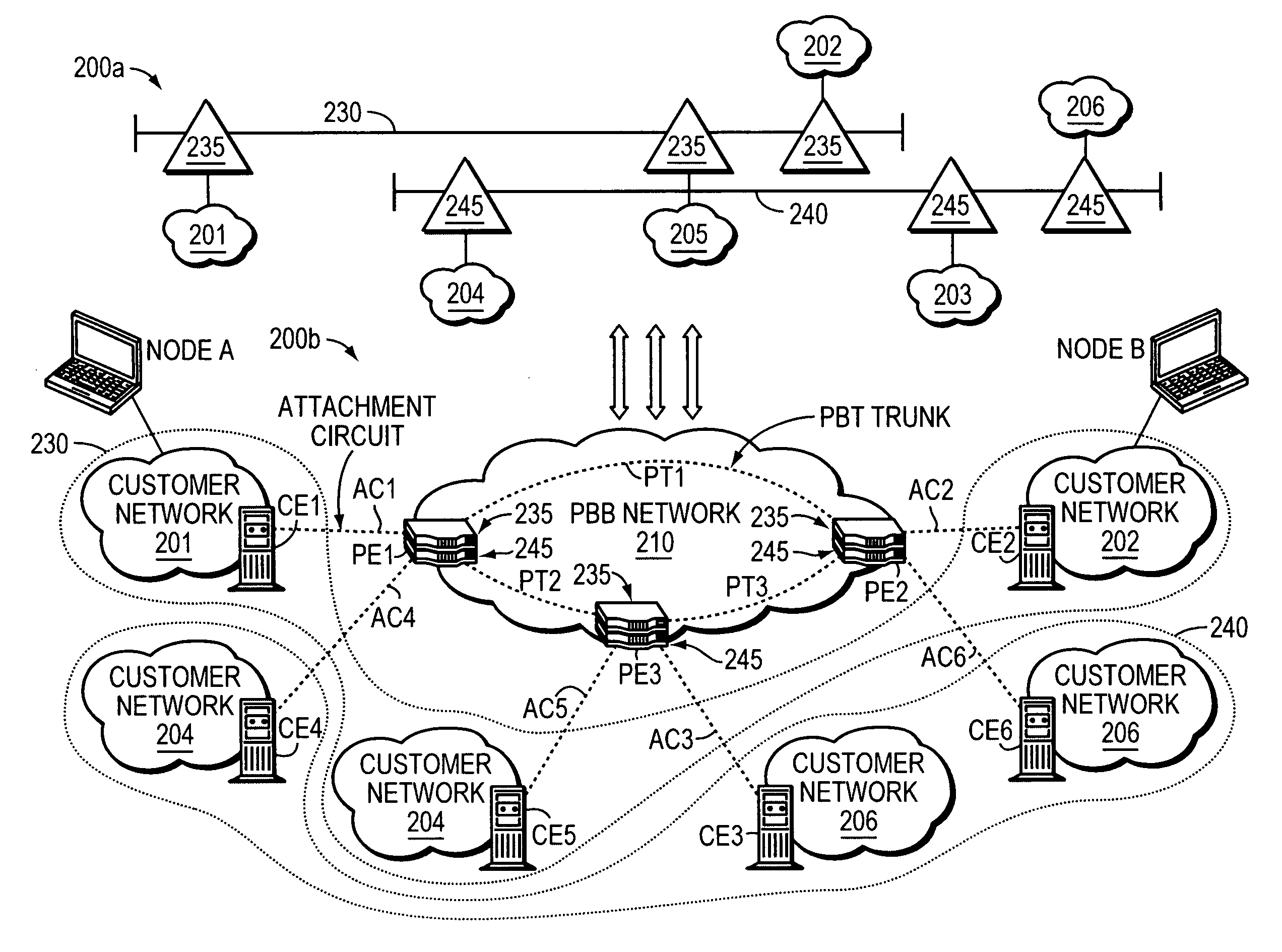
A Provider Network Controller (PNC) addresses the challenges in building services across Next Generation Network (NGN) architectures and creates an abstraction layer as a bridge, or glue, between the network transport and applications running over it. The PNC is a multi-layer, multi-vendor dynamic control plane that implements service activation and Layer 0-2 management tools for multiple transport technologies including Carrier Ethernet, Provider Backbone Transport (PBT), Multi-protocol Label Switching (MPLS), Transport MPLS (T-MPLS), optical and integrated networking platforms. Decoupling transport controls and services from the network equipment simplifies service creation and provides options for carriers to choose best-in-class equipment that leverages the PNC to enable rapid creation and management of transports and services. The PNC provides Service-Oriented Architecture (SOA) interfaces to abstract transport objects expressly designed to support both wholesale and retail services, and supports service offerings with varied bandwidth and Quality of Service (QoS) requirements, thus achieving enterprise Ethernet economics.
Owner:EXTREME NETWORKS INC
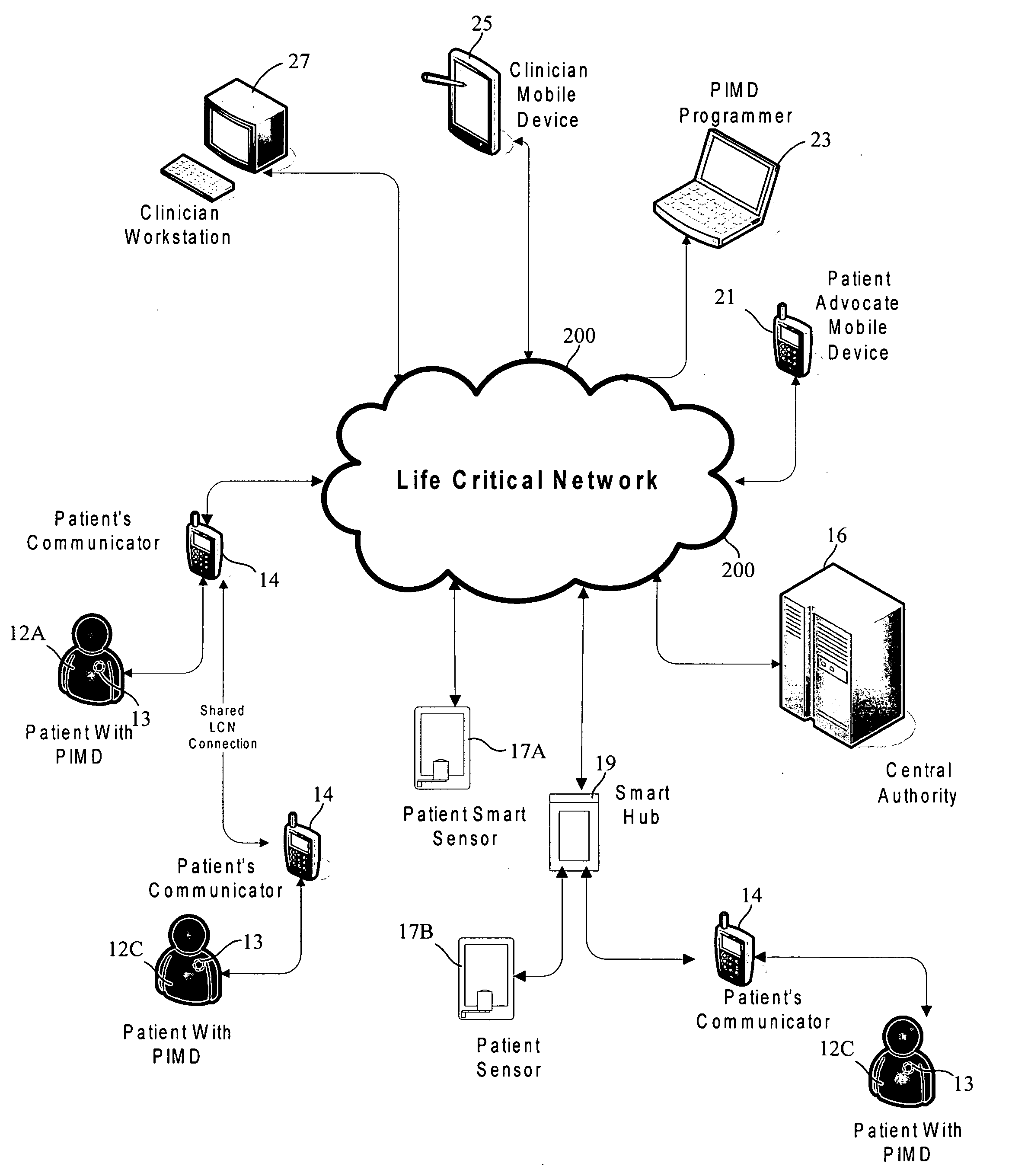
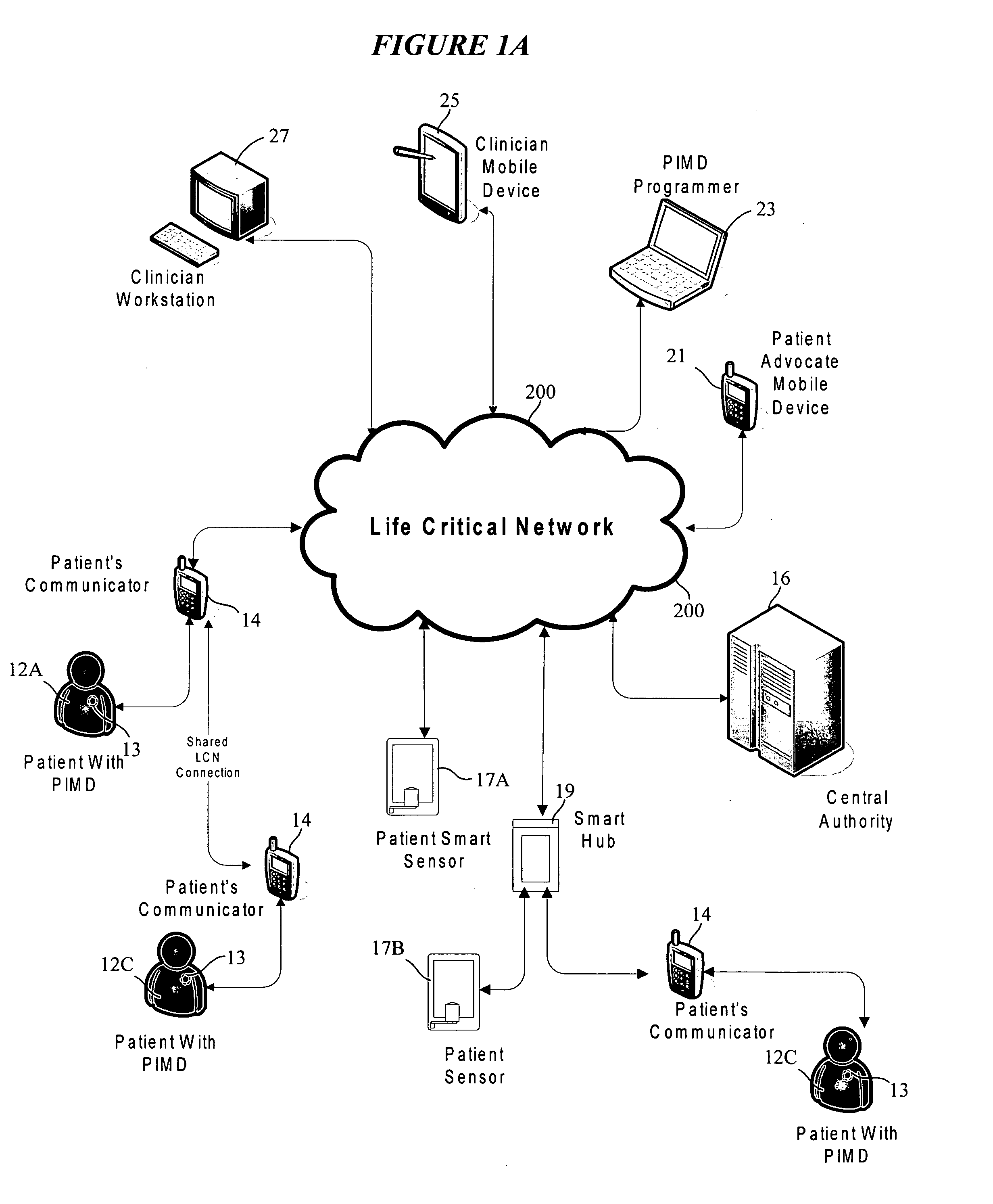
Medical data transport over wireless life critical network
ActiveUS20090058635A1Facilitate communicationElectrotherapyDiagnostic recording/measuringMedical equipmentProgram instruction
A portable patient communicator (PPC) includes a portable housing that supports a processor coupled to memory for storing medical firmware and wireless radio firmware, first and second radios, a processor, and a power source. Communications between a patient implantable medical device (PIMD) and the first radio of the PPC are effected in accordance with program instructions of the medical firmware, and communications between the second radio of the PPC and the wireless network are effected in accordance with program instructions of the wireless radio firmware. Data from the PIMD is received via the first radio to which a priority level is assigned, such as in a tiered manner. A data transport mechanism is selected among disparate data transport mechanisms based at least in part on the priority level. PIMD data is transmitted to the wireless network using the selected transport mechanism via the second radio.
Owner:CARDIAC PACEMAKERS INC
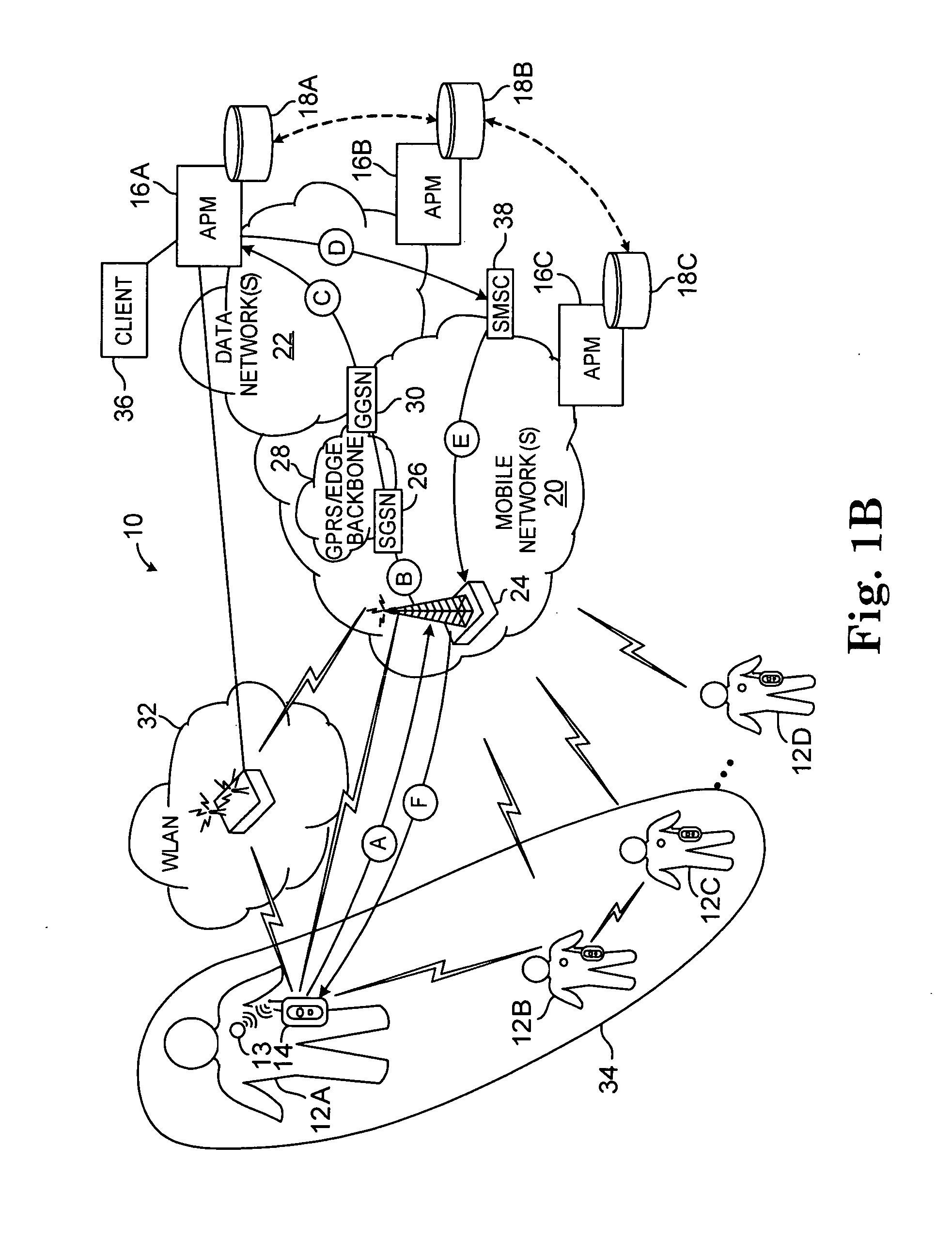
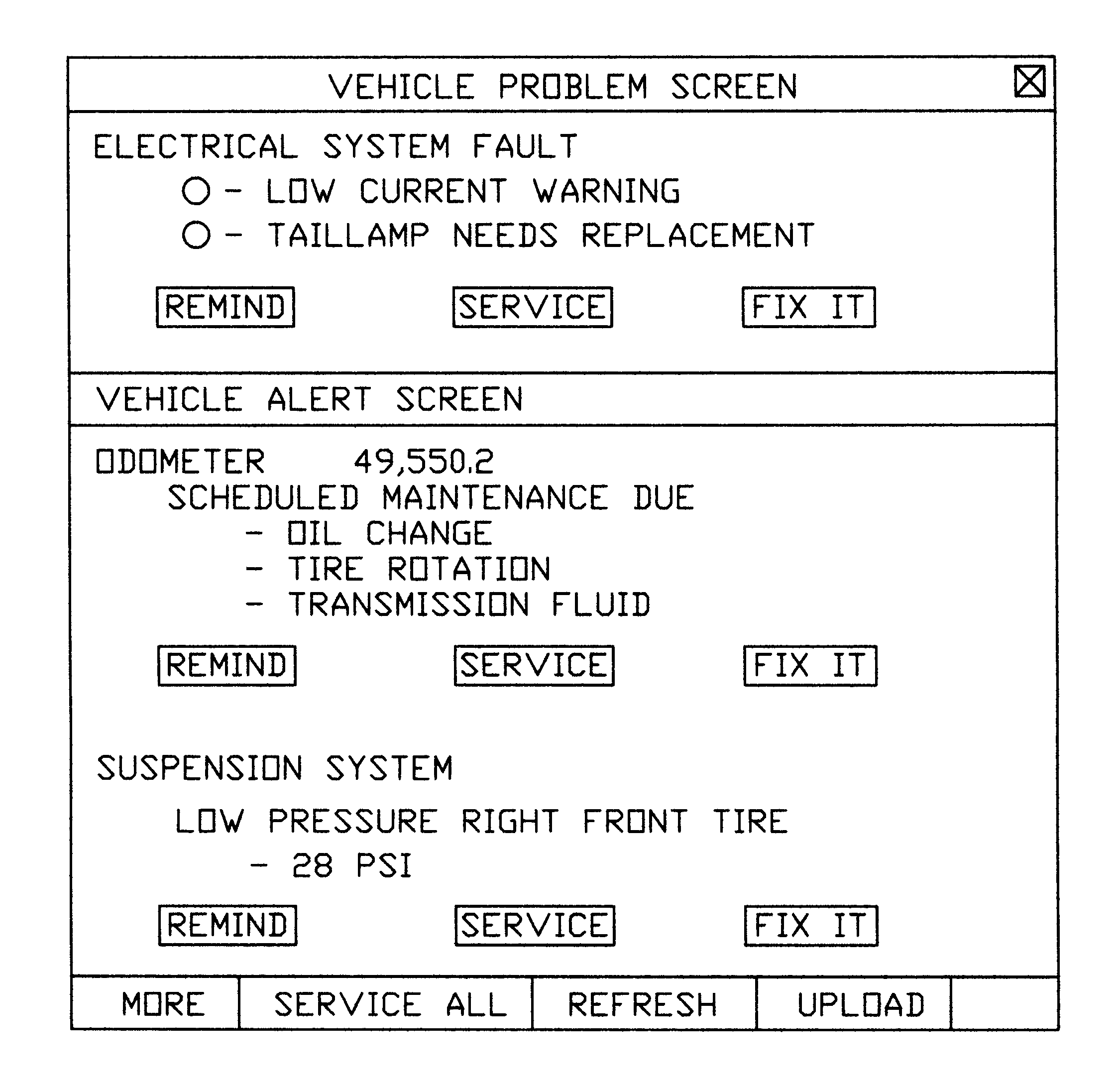
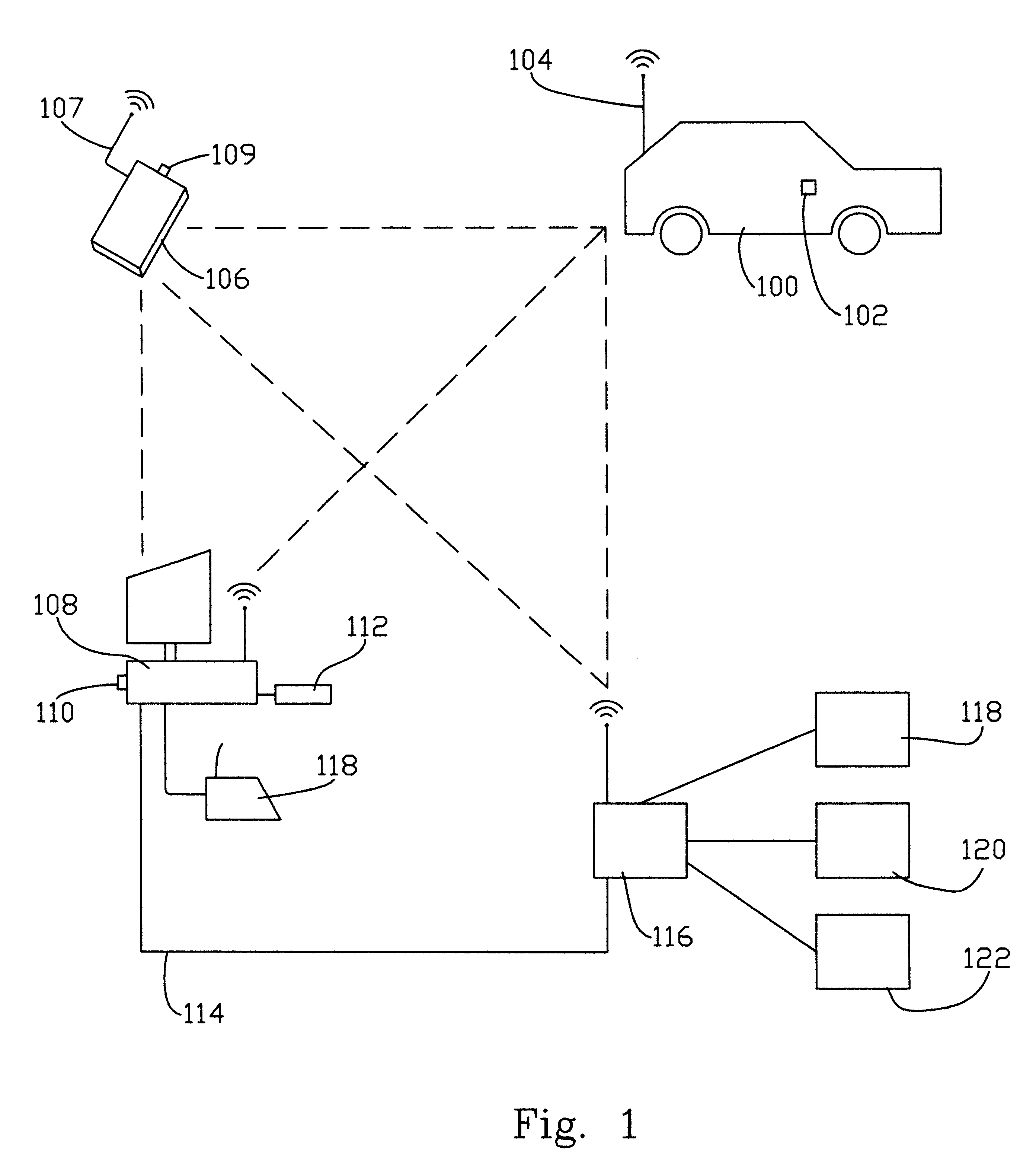
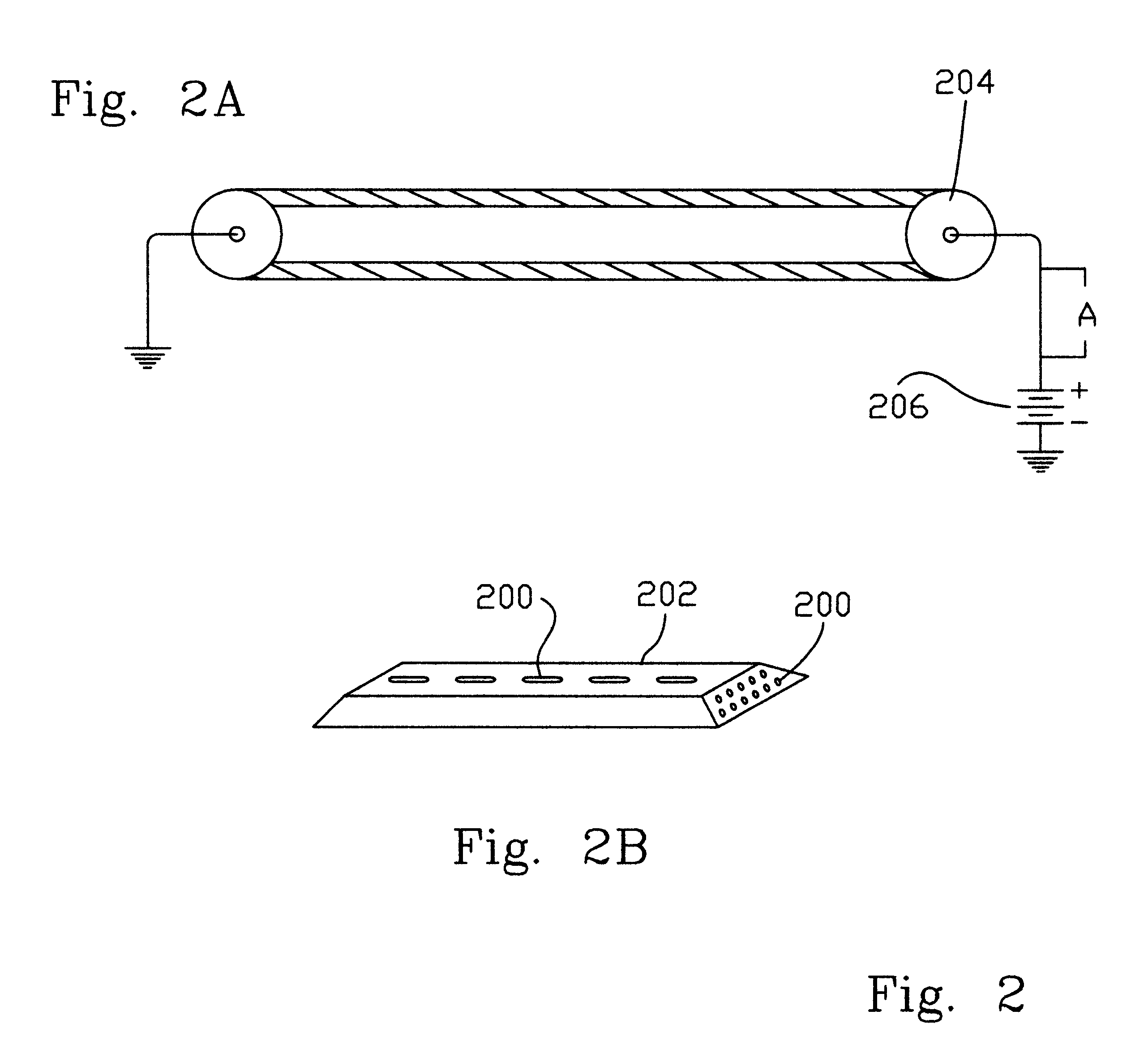
Apparatus and method for monitoring and maintaining mechanized equipment
InactiveUS6370454B1Convenient cost analysisConvenient scheduleVehicle testingRegistering/indicating working of vehiclesOn boardThe Internet
A method and apparatus for the maintenance of mechanized equipment such as an automobile is disclosed. Various sensors located within the automobile provide information to an on-board computing device, a personal digital assistant, or a local computing device which are networkable to a network such as the Internet. The information may be transferred across the network, and service obtained appropriately. Information located in various remote servers relating to the performance and service of the vehicle may be downloaded across the network and easily used in servicing and maintaining the vehicle. Optionally, the apparatus includes a notification system, such as an email system, for notifying of, scheduling, and / or paying for services.
Owner:EDWIN S MOORE III +1
Methods and apparatus for premises content distribution
Apparatus and methods for protected content access, browsing and transfer over a network. In one embodiment, the network comprises a premises (e.g., residential) LAN, and the apparatus comprises a server and renderer consumer premise equipment (CPE). The renderer CPE scans the network to search for a server CPE that implement a compatible security framework. The renderer authenticates itself with the server, and the server allows content browsing and selection access only to an authorized and authenticated renderer. A negotiation and exchange protocol comprises messages exchanged between the renderer and the server that include one or more of device identification, encryption key exchange, digital certificates and information regarding security package used by each CPE.
Owner:TIME WARNER CABLE ENTERPRISES LLC
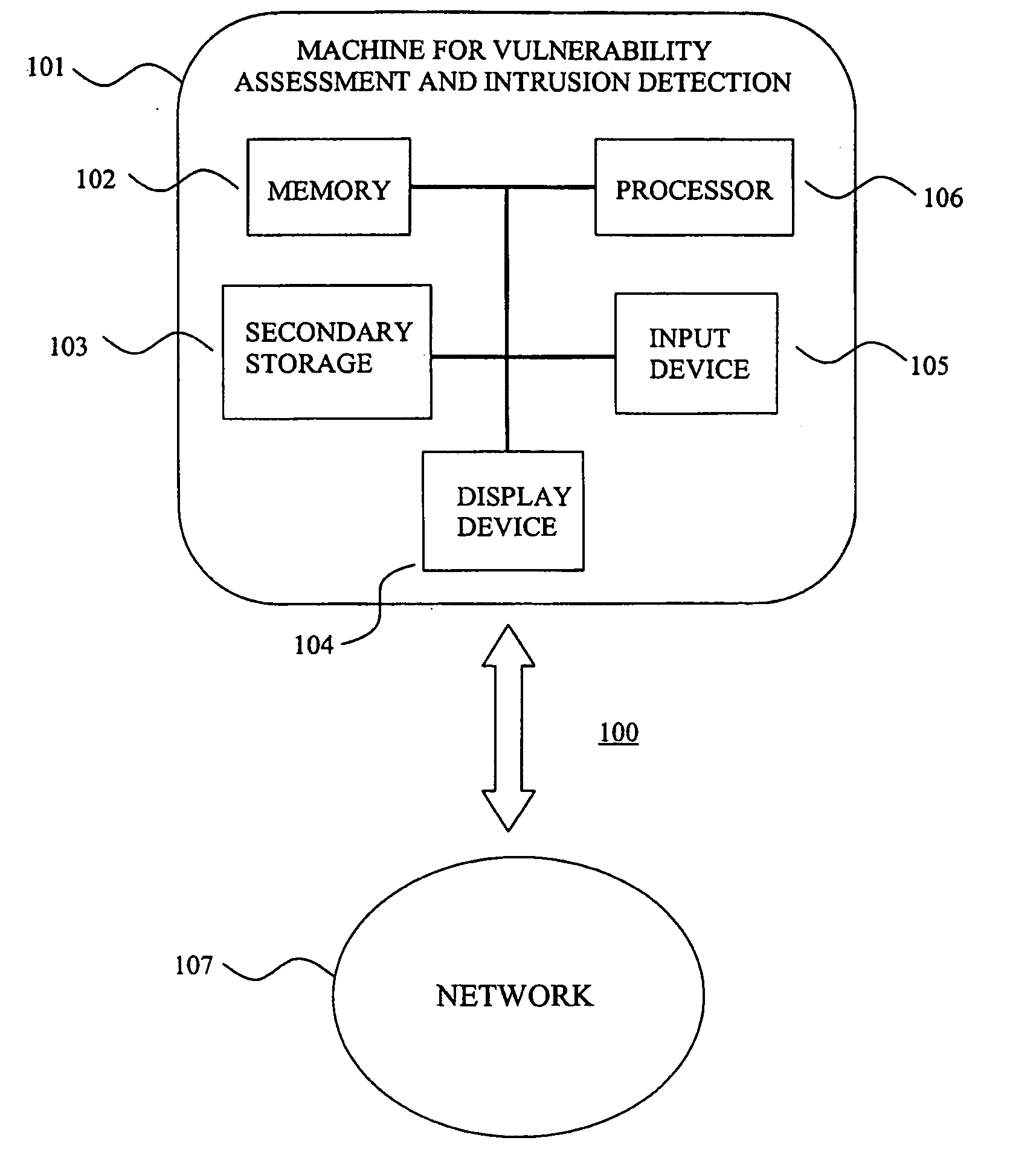
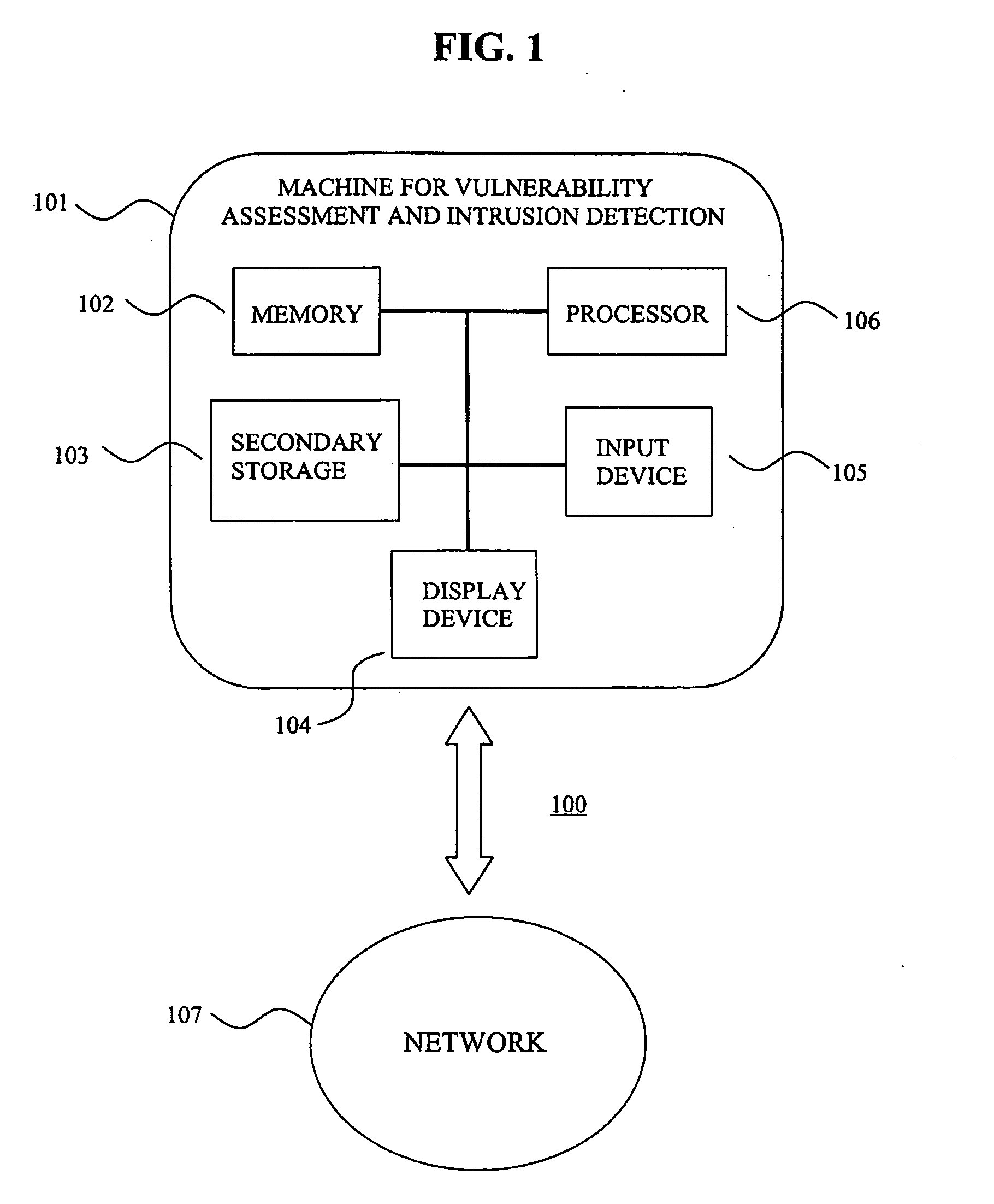
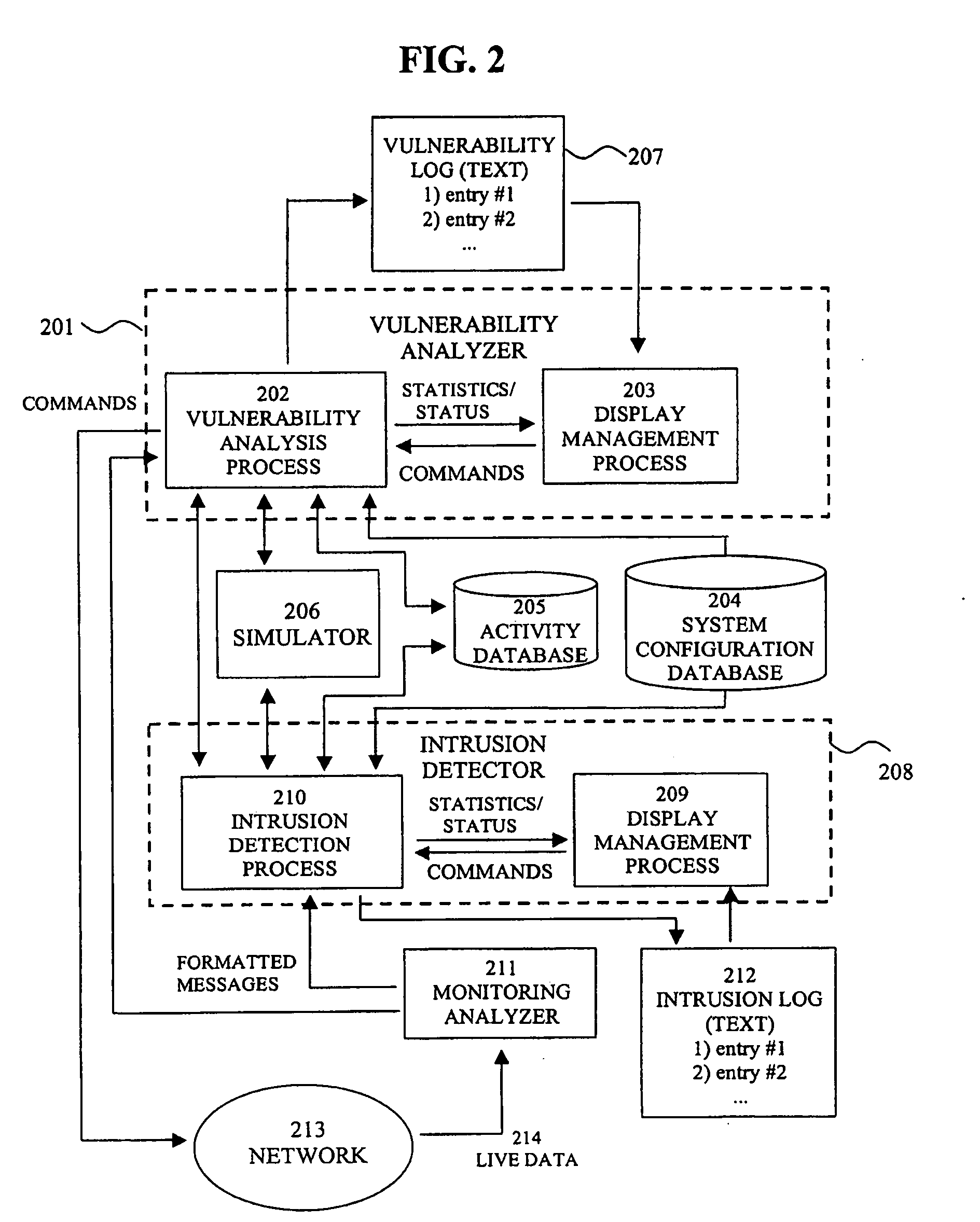
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS20060191010A1Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
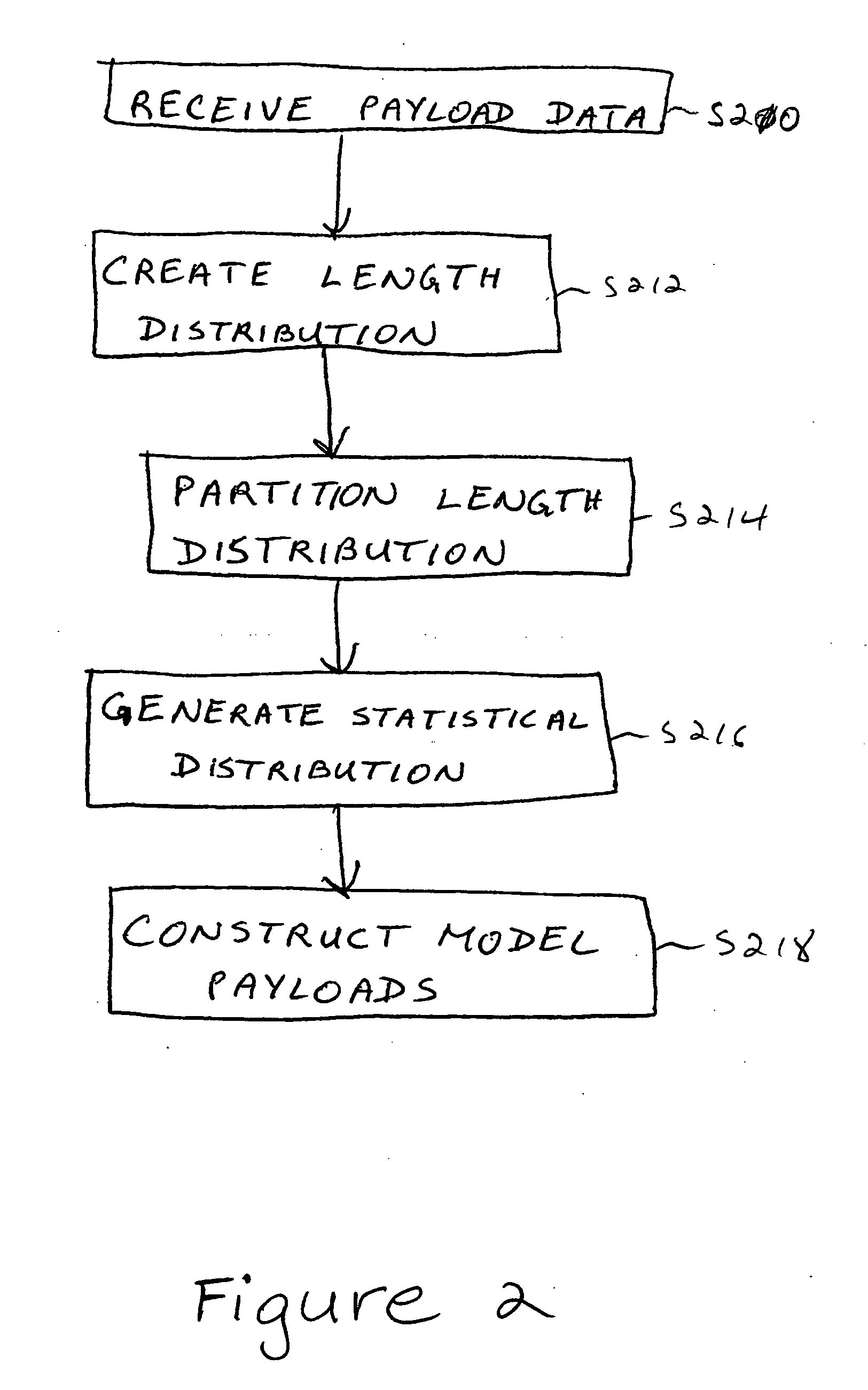
Apparatus method and medium for tracing the origin of network transmissions using n-gram distribution of data
ActiveUS20050265331A1Unauthorized memory use protectionTime-division multiplexWeb transportReal-time computing
A method, apparatus, and medium are provided for tracing the origin of network transmissions. Connection records are maintained at computer system for storing source and destination addresses. The connection records also maintain a statistical distribution of data corresponding to the data payload being transmitted. The statistical distribution can be compared to that of the connection records in order to identify the sender. The location of the sender can subsequently be determined from the source address stored in the connection record. The process can be repeated multiple times until the location of the original sender has been traced.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
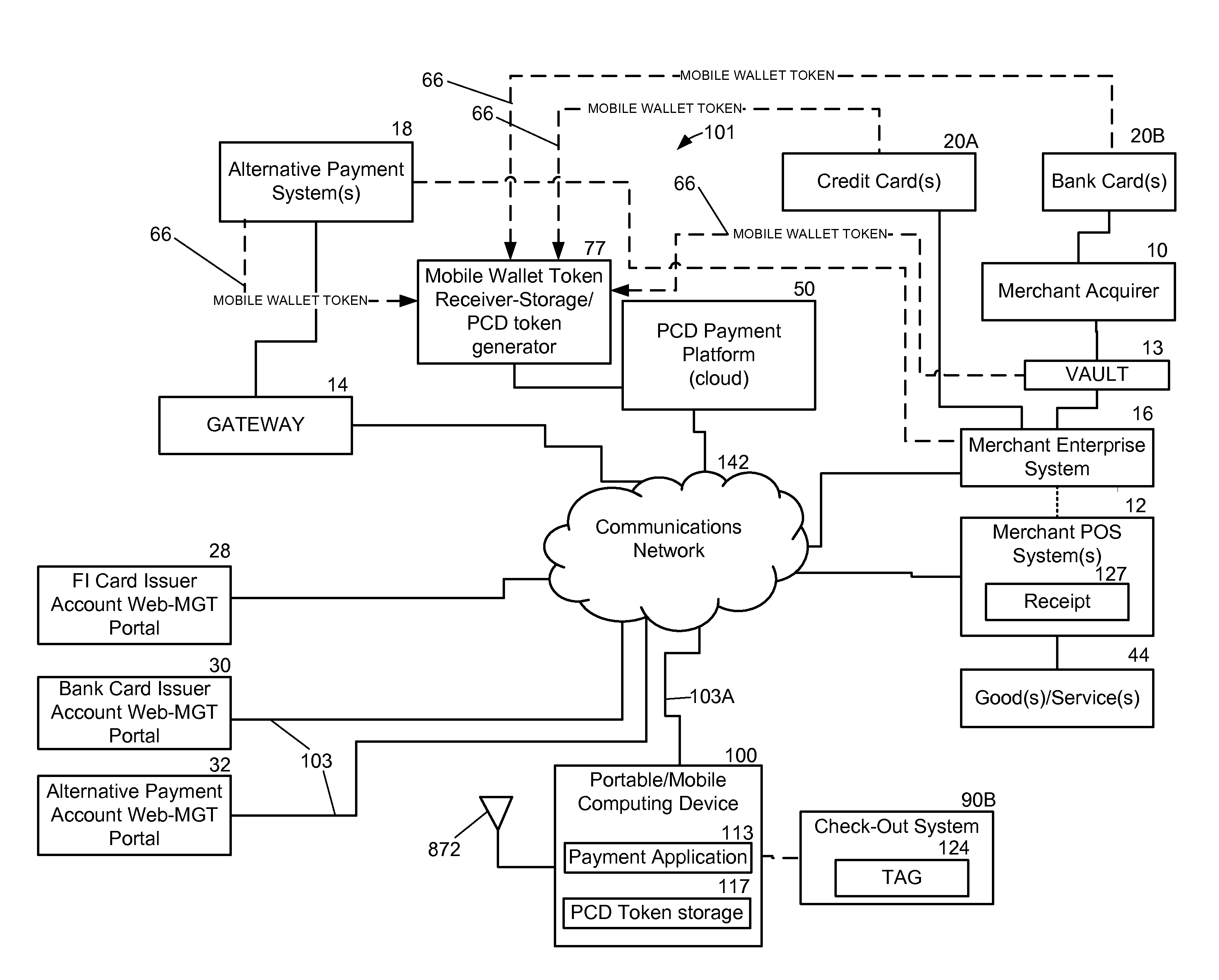
System and method for managing payment in transactions with a pcd
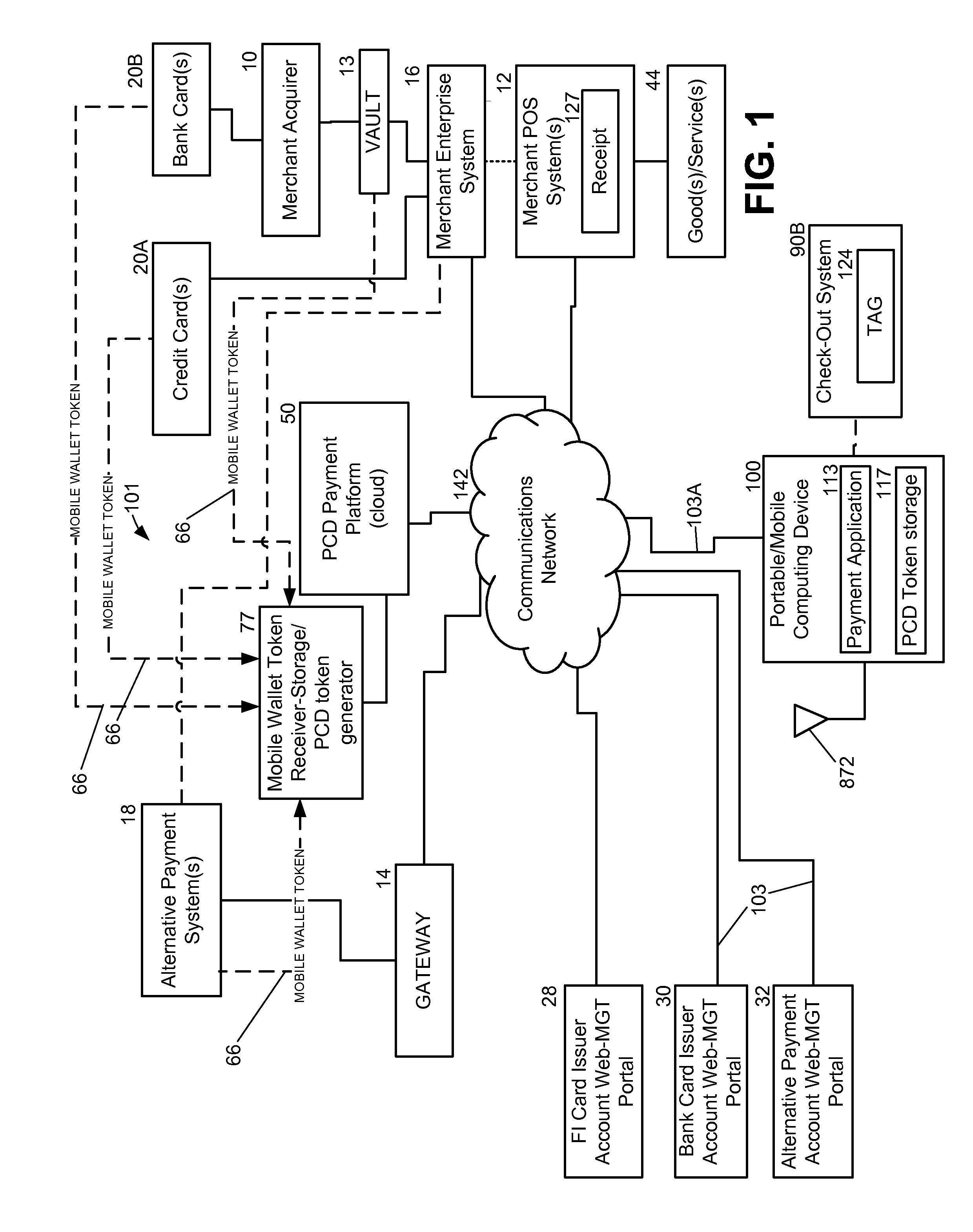
A system and method for managing payment in a transaction using a portable computing device (“PCD”) includes a mobile wallet token being received from an account issuing entity. Next, the mobile wallet token is stored in memory within a PCD payment platform (i.e., a cloud payment solution). A PCD token that corresponds with the mobile wallet token is generated by the PCD payment platform. The PCD token is transmitted over a communications network to a PCD. The mobile wallet token corresponds to at least one of: a credit card account, an alternative or non-traditional payment account, a stored value account, an account from a financial institution, and a merchant based card account. A mobile wallet token may be generated in response to receiving input from an on-line portal that future use of a payment account with a PCD is desired or in response to input received from a point-of-sale terminal.
Owner:QUALCOMM INC
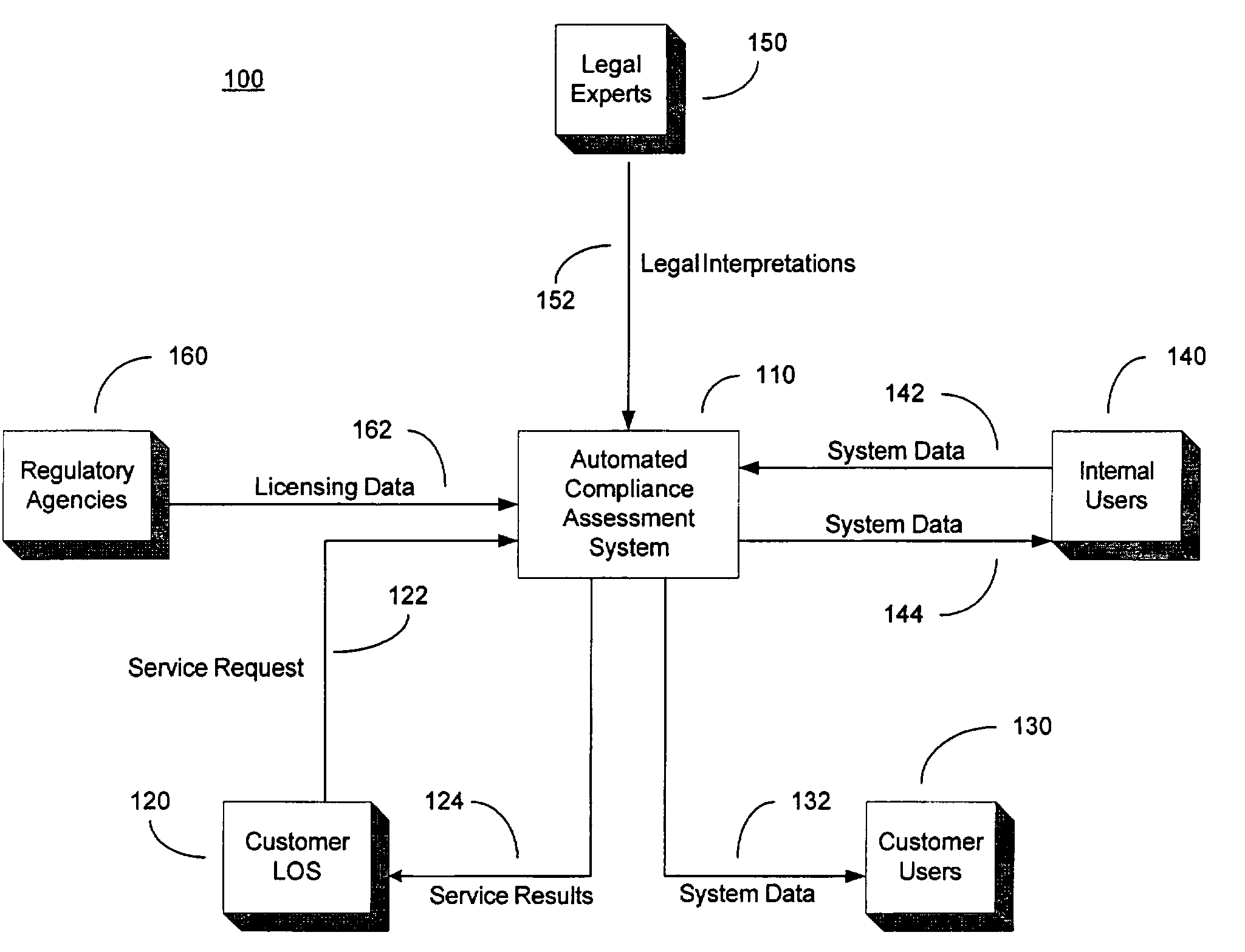
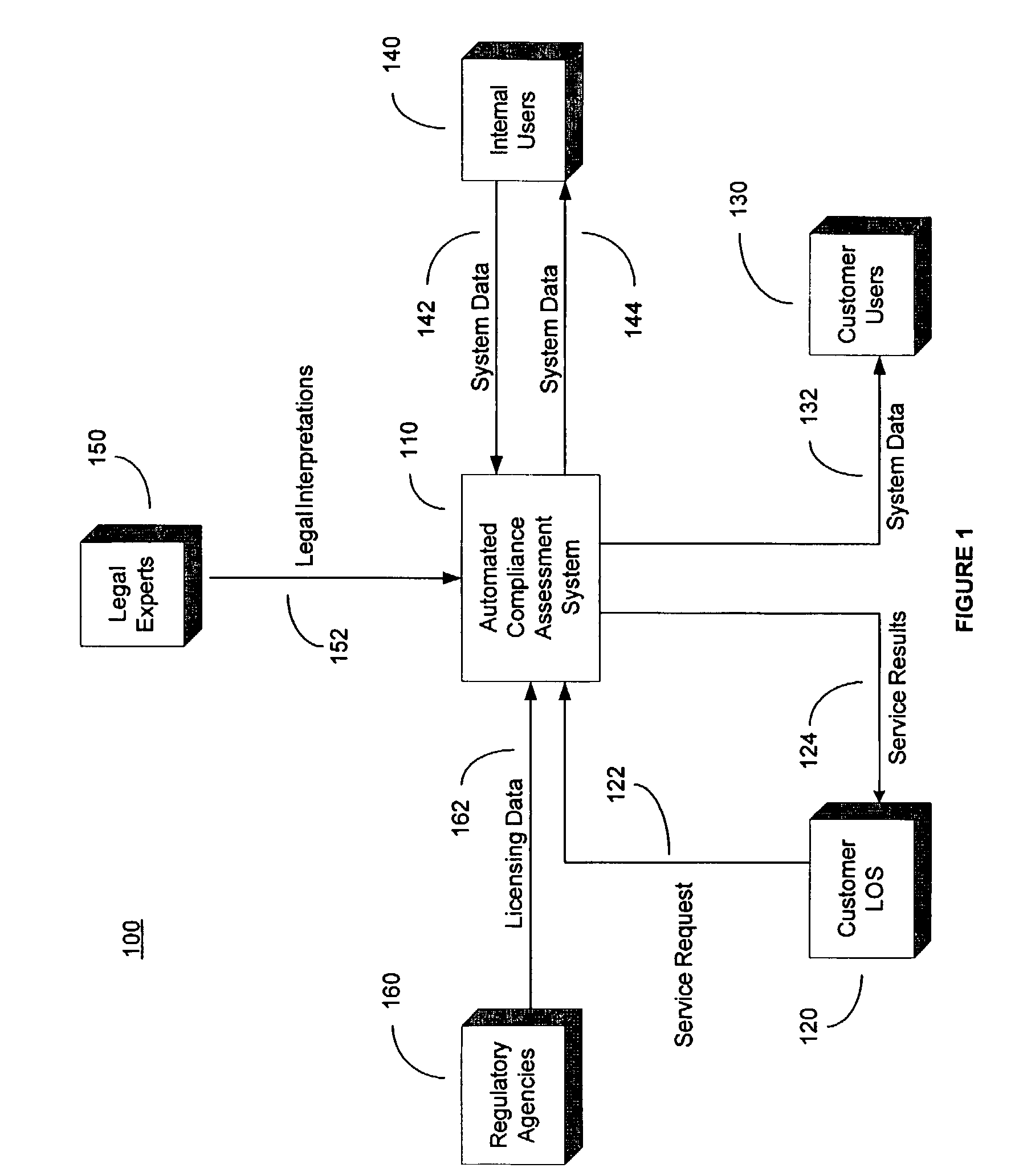
System and method for automated loan compliance assessment
An automated system and method for reviewing and assessing compliance with legal compliance requirements for loan applications. Loan application data is extracted from client loan origination systems and transmitted as a loan information file over a secure communication network to an automated compliance assessment system server where the loan information file is audited for compliance with Federal, state, and local legal compliance requirements. The loan information file is reviewed for legal compliance requirements imposed by Federal, State, and local jurisdictions, as well as licensing requirements that the client loan company and related personnel must satisfy. The results of the audit process are transmitted over a secure communication network to the client loan company, with areas of noncompliance indicated. The automated compliance assessment system server also stores rules data derived from legal compliance requirements, license data derived from regulatory requirements, system setup data and supplemental system application data.
Owner:ICE MORTGAGE TECH INC
Portable devices and methods employing digital watermarking
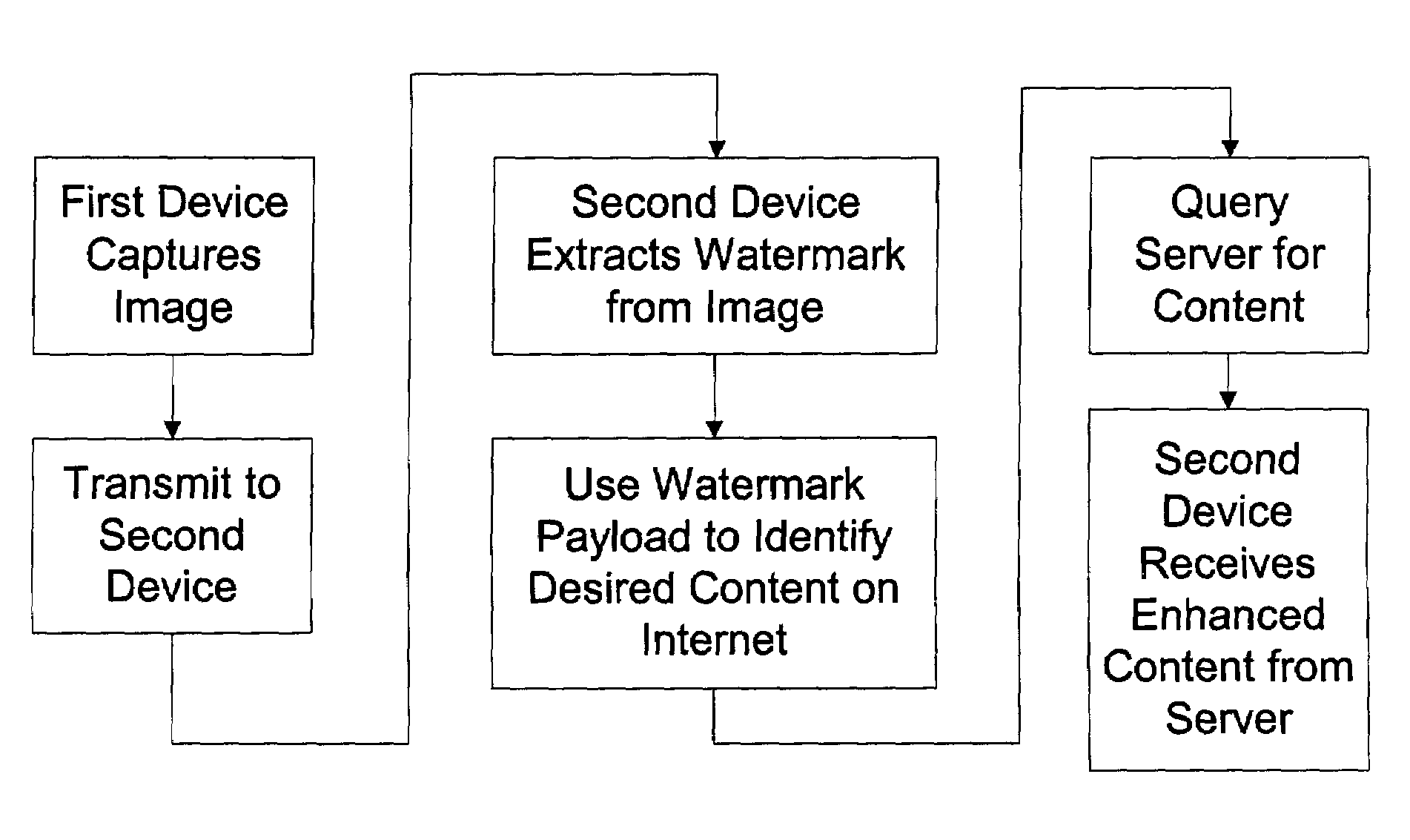
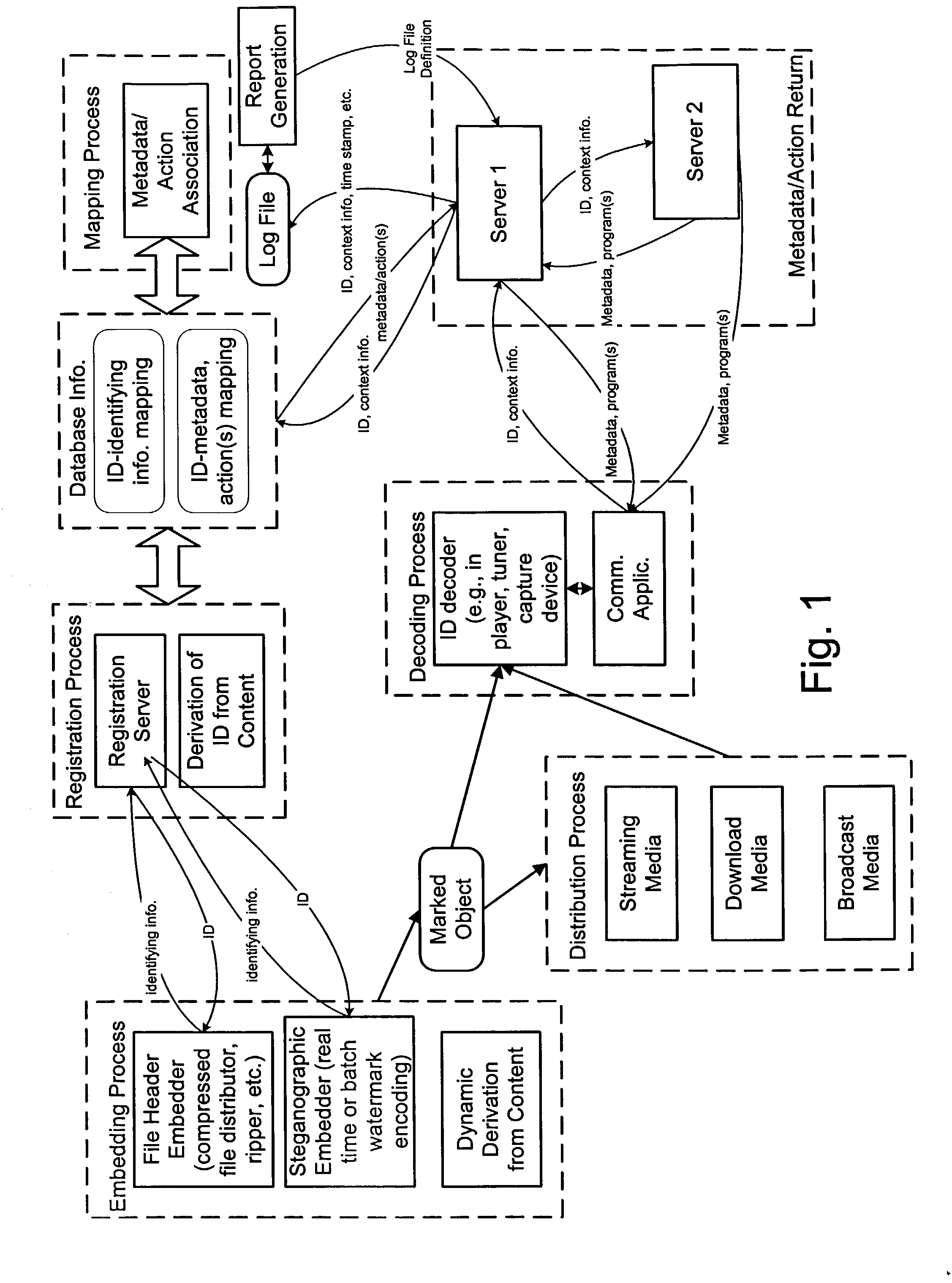
Media objects are transformed into active, connected objects via identifiers embedded into them or their containers. In the context of a user's playback experience, a decoding process extracts the identifier from a media object and possibly additional context information and forwards it to a server. The server, in turn, maps the identifier to an action, such as returning metadata, re-directing the request to one or more other servers, requesting information from another server to identify the media object, etc. The server may return a higher fidelity version of content from which the identifier was extracted. In some applications, the higher fidelity version may be substituted for the original media object and rendered to provide higher quality output. The linking process applies to broadcast objects as well as objects transmitted over networks in streaming and compressed file formats.
Owner:DIGIMARC CORP
Integrated system for network layer security and fine-grained identity-based access control
ActiveUS6986061B1Simple technologyUser identity/authority verificationDigital computer detailsKey exchangeMedia access control
Owner:TREND MICRO INC
System and method for socially aware identity manager
InactiveUS20100063993A1Multiple digital computer combinationsOffice automationWeb siteSelection criterion
A system and method for a Socially Aware Identity Manager. A request is received over a network from a first user for data relating to a second user, wherein the request comprises an identification of the second user. Spatial, temporal, topical, and social data available to the network relating to the second user is retrieved using a global index of data available to the network, wherein such data comprises at least one website comprising data relating to the second user, which can include social networking sites. The data relating to the second user is filtered using at least one filter criteria. A subset of the filtered data relating to the second user is selected using at least one selection criteria. The filtered subset of data relating to the second user is transmitted over the network to the first user.
Owner:YAHOO INC
Authentication arrangement and method for use with financial transactions
ActiveUS20050119978A1User identity/authority verificationCo-operative working arrangementsIntegrated circuit cardClient-side
An authentication arrangement for use in a network payment system for transacting a sale of merchandise over a network using an Integrated Circuit Card is described, the arrangement comprising: a merchant server in communication with said network, said merchant server having at least a first item of merchandise for sale; a client terminal in communication with said network, said client terminal having an output device for reviewing said first item for sale, and an input device for initiating a purchase transaction to purchase said first item for sale, said client terminal being arranged to build a purchase message using information relating to a merchant identifier and financial transaction information obtained from said merchant server; a card reader for communicating with said Integrated Circuit Card, said client terminal having means to generate a challenge message, said challenge message being generated from the information relating to the merchant identifier and an account number, means for receiving the challenge message at the card reader and for generating a value from the challenge message; said Integrated Circuit Card having means for generating a cryptographic message from at least a part of said value, the card reader having means to generate an authentication token from at least a part of the cryptographic message, and said client terminal having means for transmitting at least part of the authentication token in a message for transmission via the network.
Owner:MASTERCARD INT INC
Method and apparatus for transmitting data over a network using a docking device
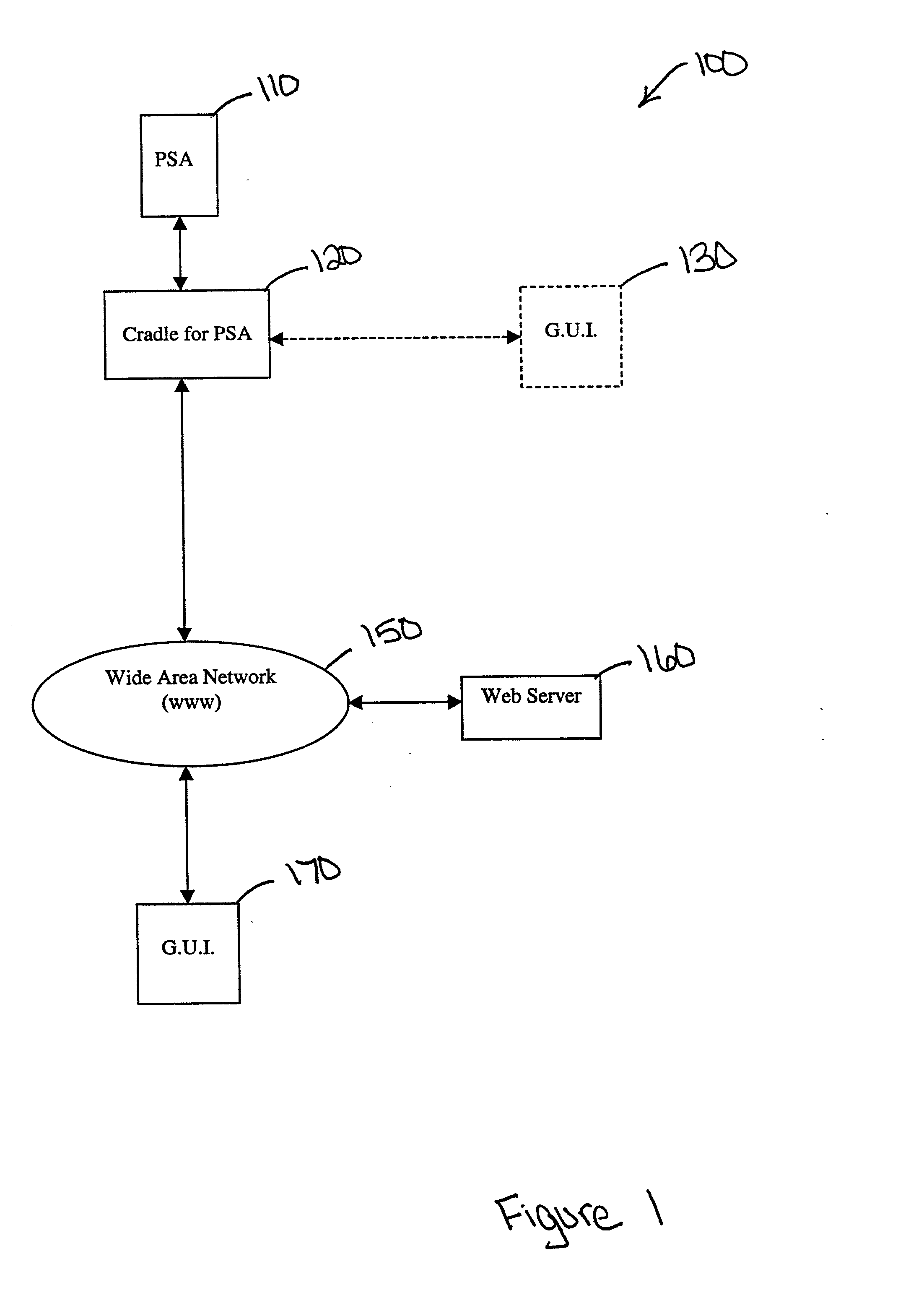
InactiveUS20020091796A1Telephonic communicationMultiple digital computer combinationsData connectionNetworked Transport of RTCM via Internet Protocol
A method and system for transmitting data over a network are described. In one embodiment, the system comprises a cradle to transmit data to a network server and an electronic device coupled to the cradle. The electronic device includes a sensor to trigger a data connection between the electronic device and the cradle. The electronic device also includes a transmitter to download the data to the cradle.
Owner:SPORTBRAIN
Methods, systems, and products for intrusion detection
InactiveUS7971053B2Reduce rogue accessReduce intrusionMemory loss protectionError detection/correctionComputer networkComputerized system
Methods, systems, and products are disclosed for detecting an intrusion to a communications network. One embodiment describes a system for detecting intrusions. The system has a peripheral card coupled to a host computer system. The peripheral card has a communications portion and a processor managing the communications portion. The communications portion has only a capability for receiving data packets via a communications network. The communications portion lacks capability of transmitting the data packets via the communications network. The communications portion of the peripheral card reduces intrusion of the communications network.
Owner:BELLSOUTH INTPROP COR
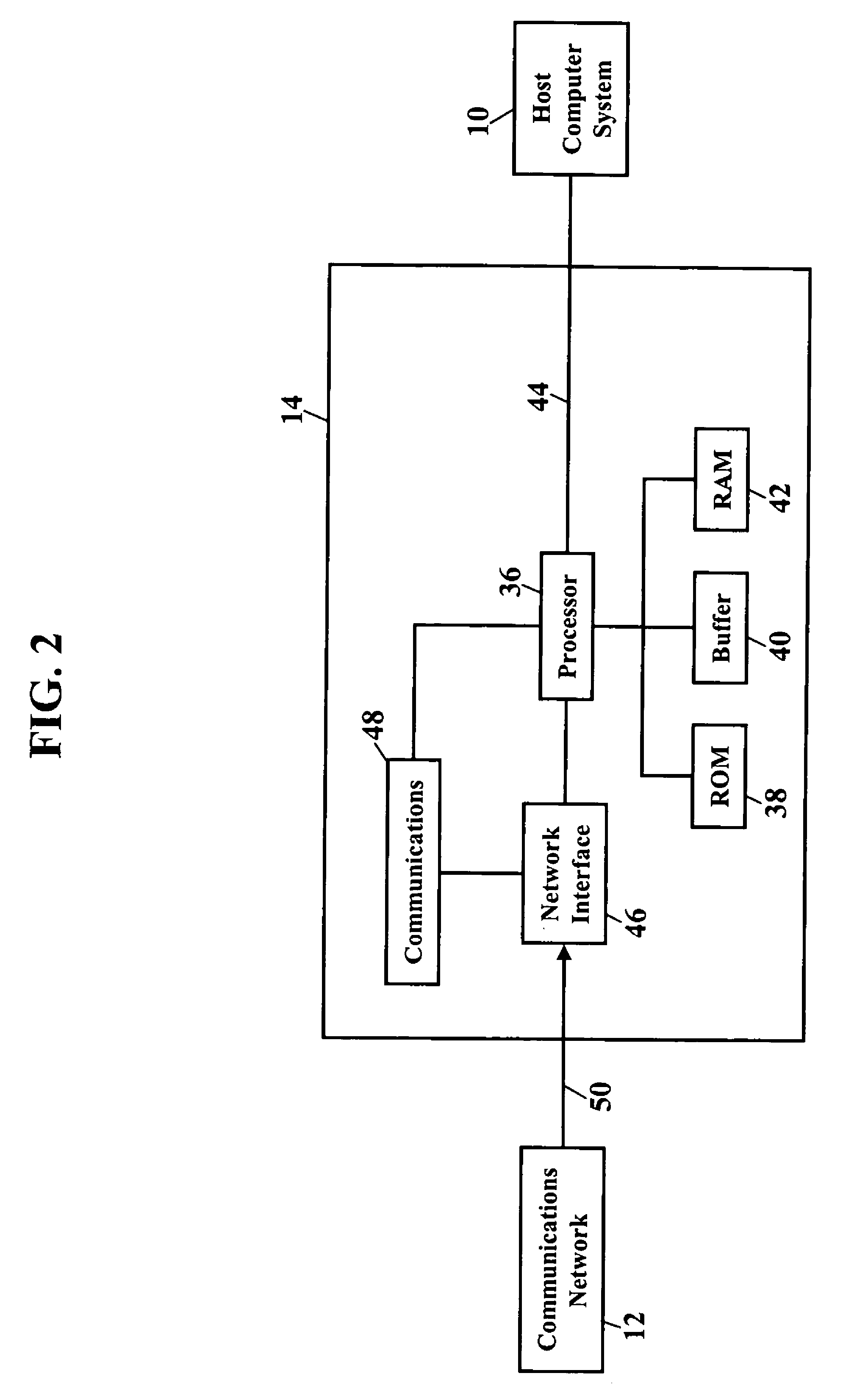
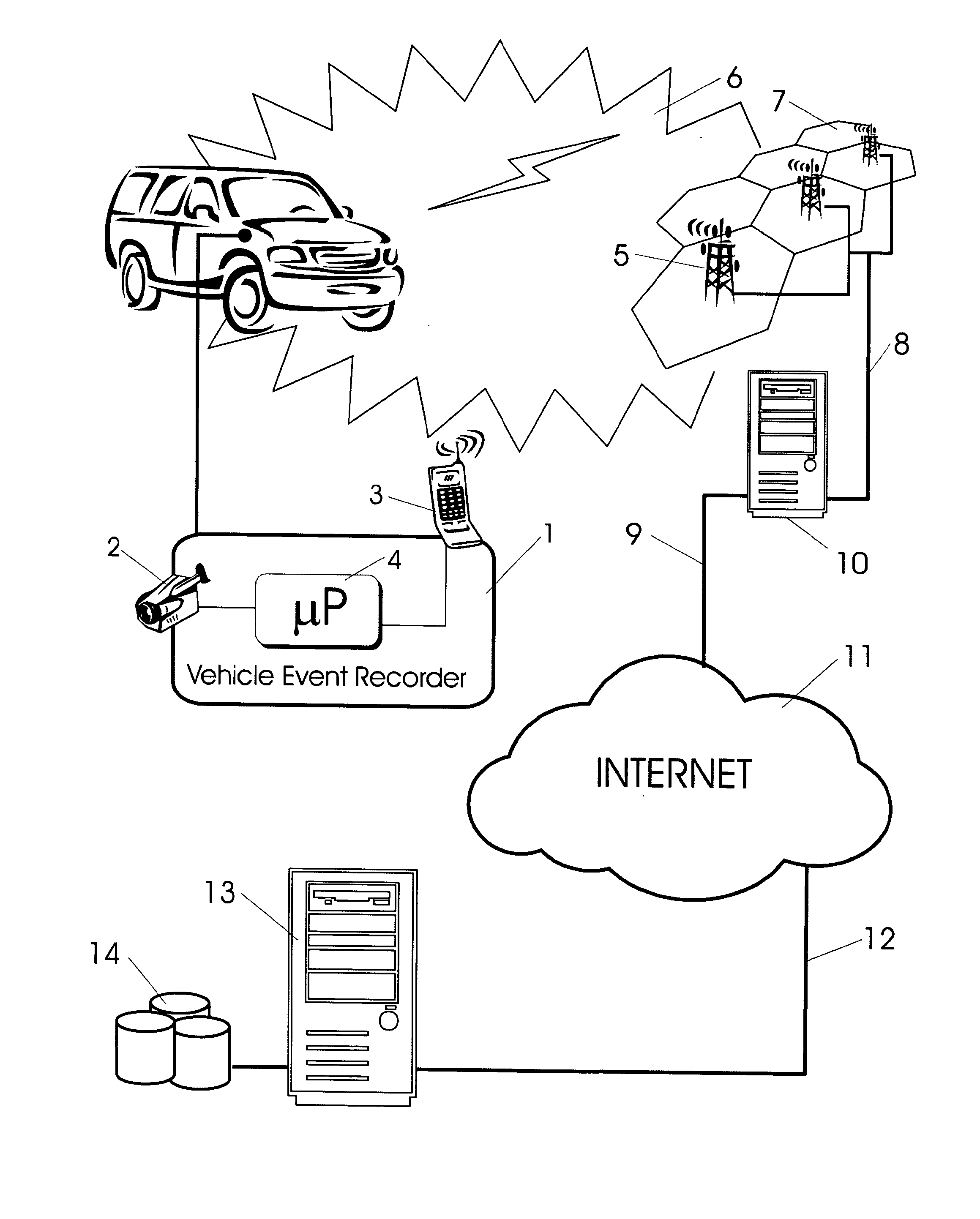
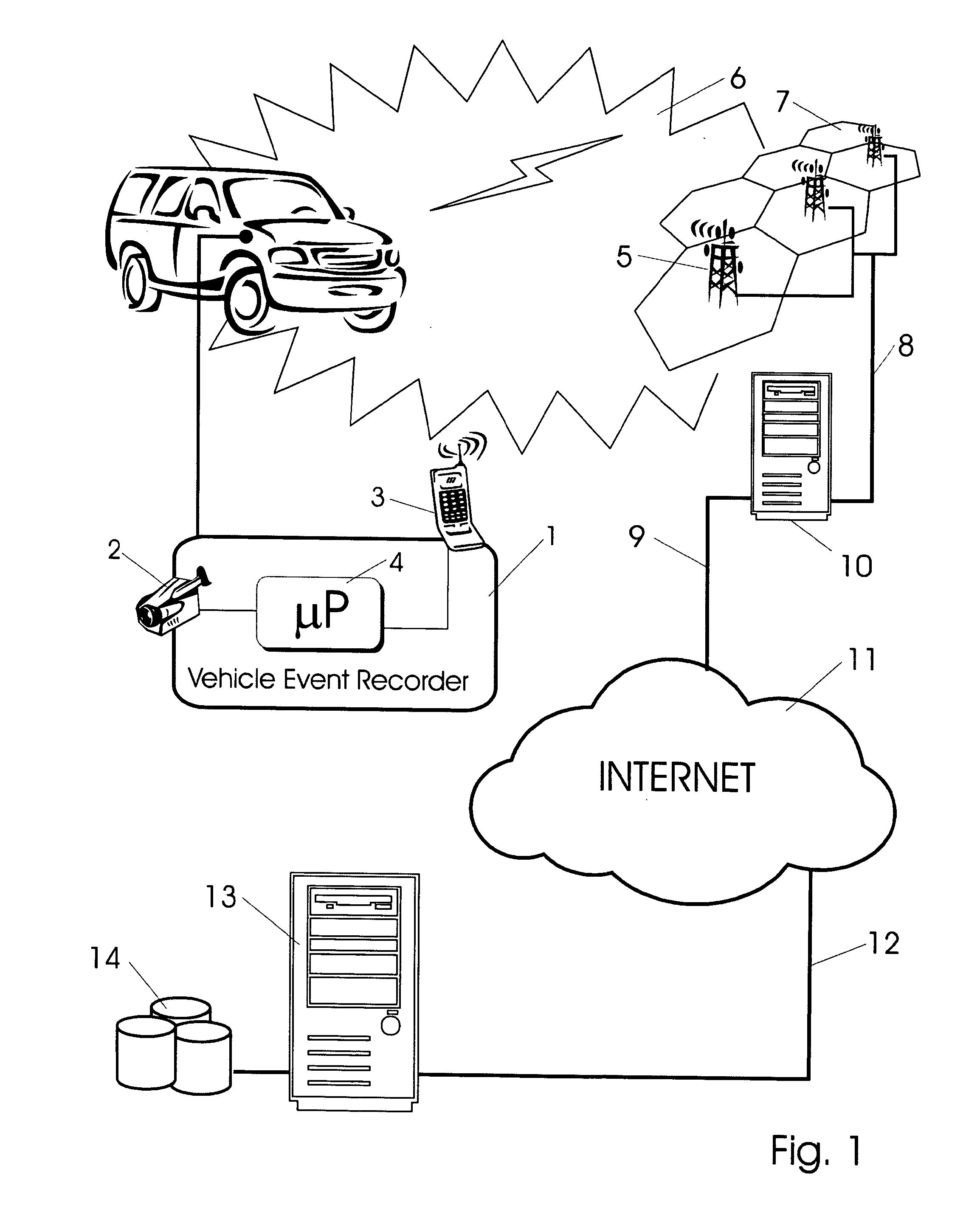
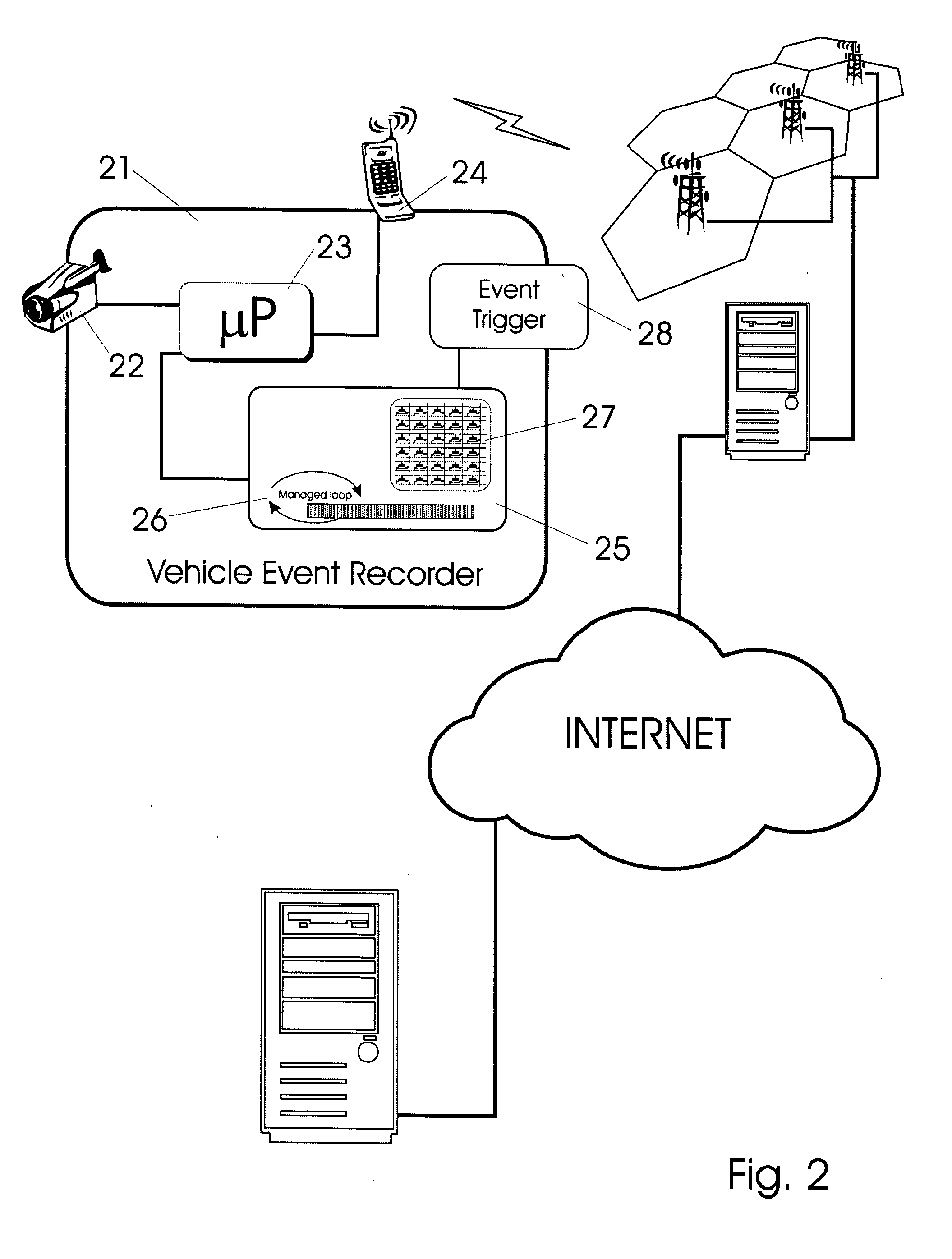
Vehicle Event Recorder Systems and Networks Having Integrated Cellular Wireless Communications Systems
ActiveUS20130317711A1Analogue computers for vehiclesRegistering/indicating working of vehiclesTransceiverEvent trigger
Vehicle event recorder systems are arranged to be in constant communication with remote servers and administrators via mobile wireless cellular networks. Vehicle event recorders equipped with video cameras capture video and other data records of important events relating to vehicle use. These data are then transmitted over special communications networks having very high coverage space but limited bandwidth. A vehicle may be operated over very large region while maintaining continuous communications connections with a remote fixed server. As such, systems of these inventions may be characterized as including a mobile unit having: a video camera; a microprocessor; memory; an event trigger; and mobile wireless transceivers, and a fixed network portion including: mobile wireless cellular network, a protocol translation gateway, the Internet and an application-specific server.
Owner:SMARTDRIVE SYSTEMS
Flexible engine and data structure for packet header processing
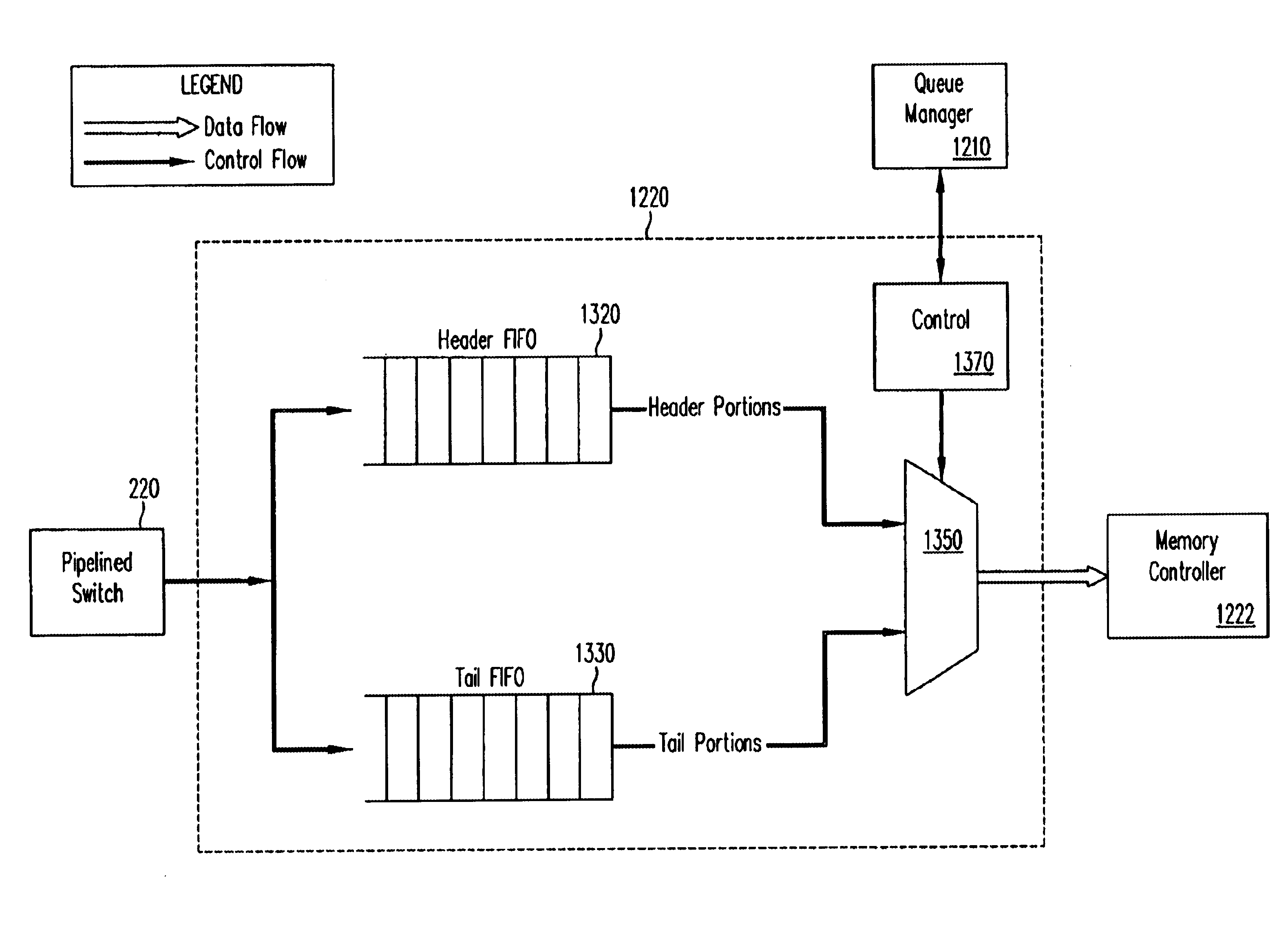
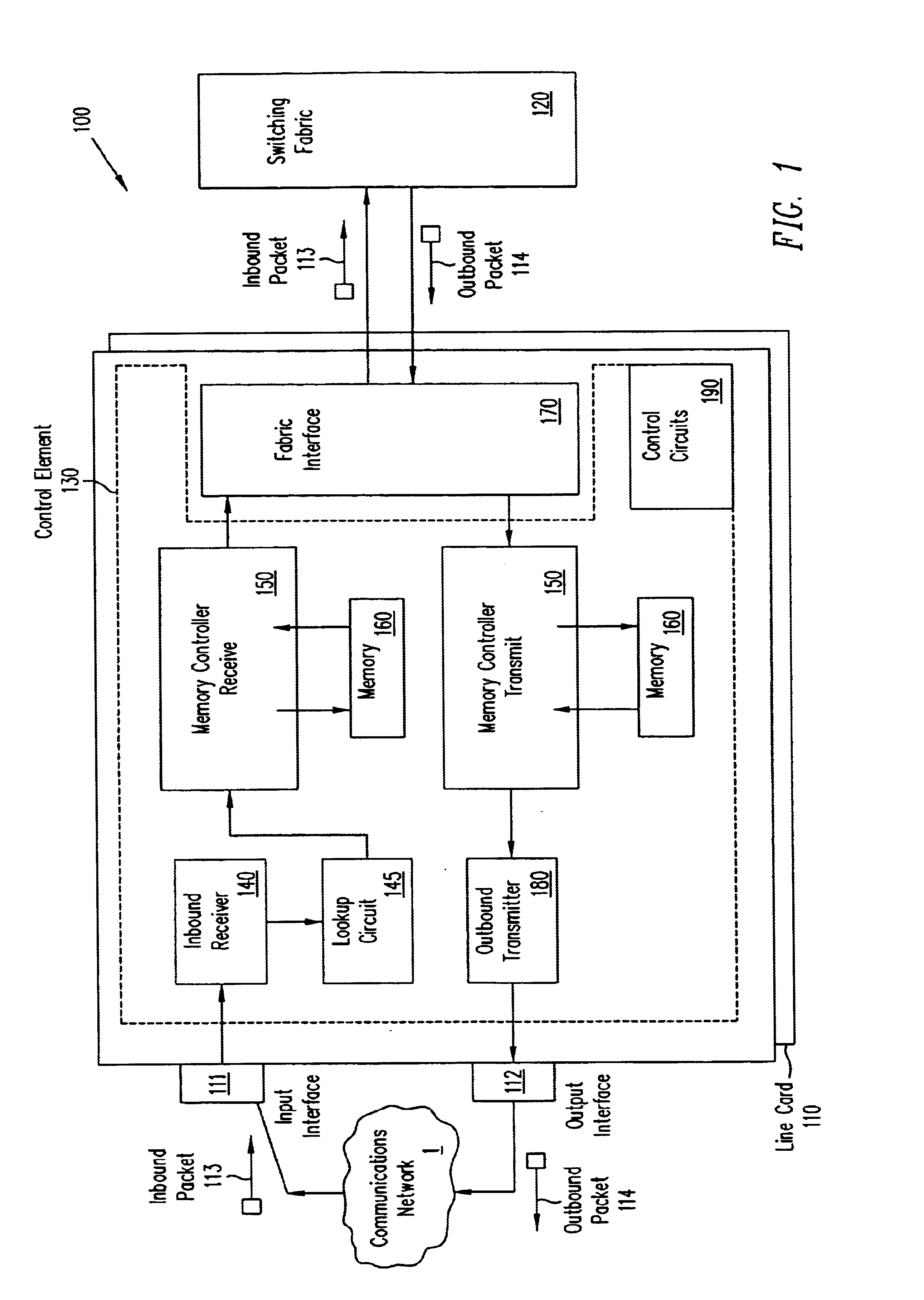
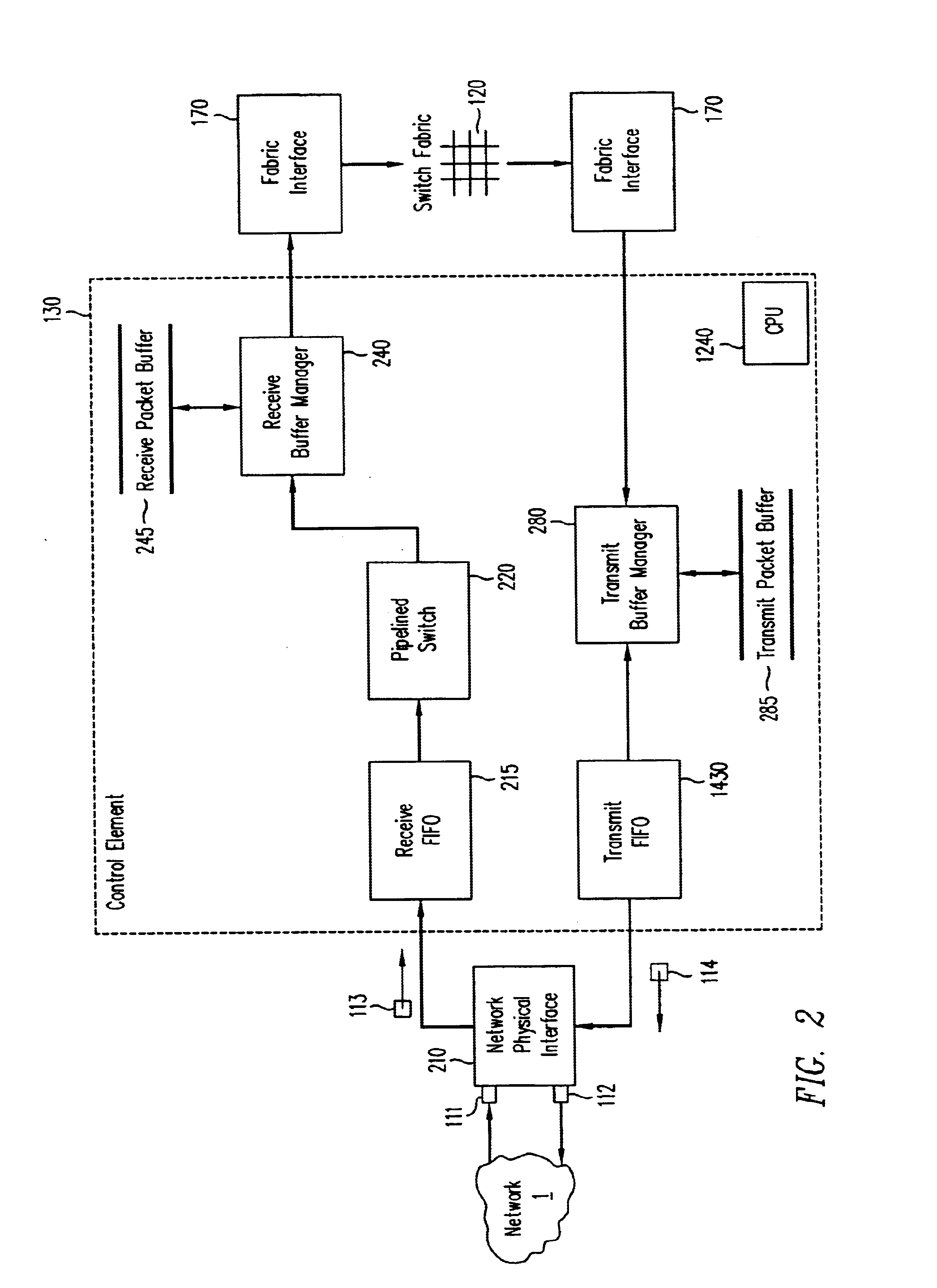
InactiveUS6721316B1Multiplex system selection arrangementsData switching by path configurationWeb transportLinked list
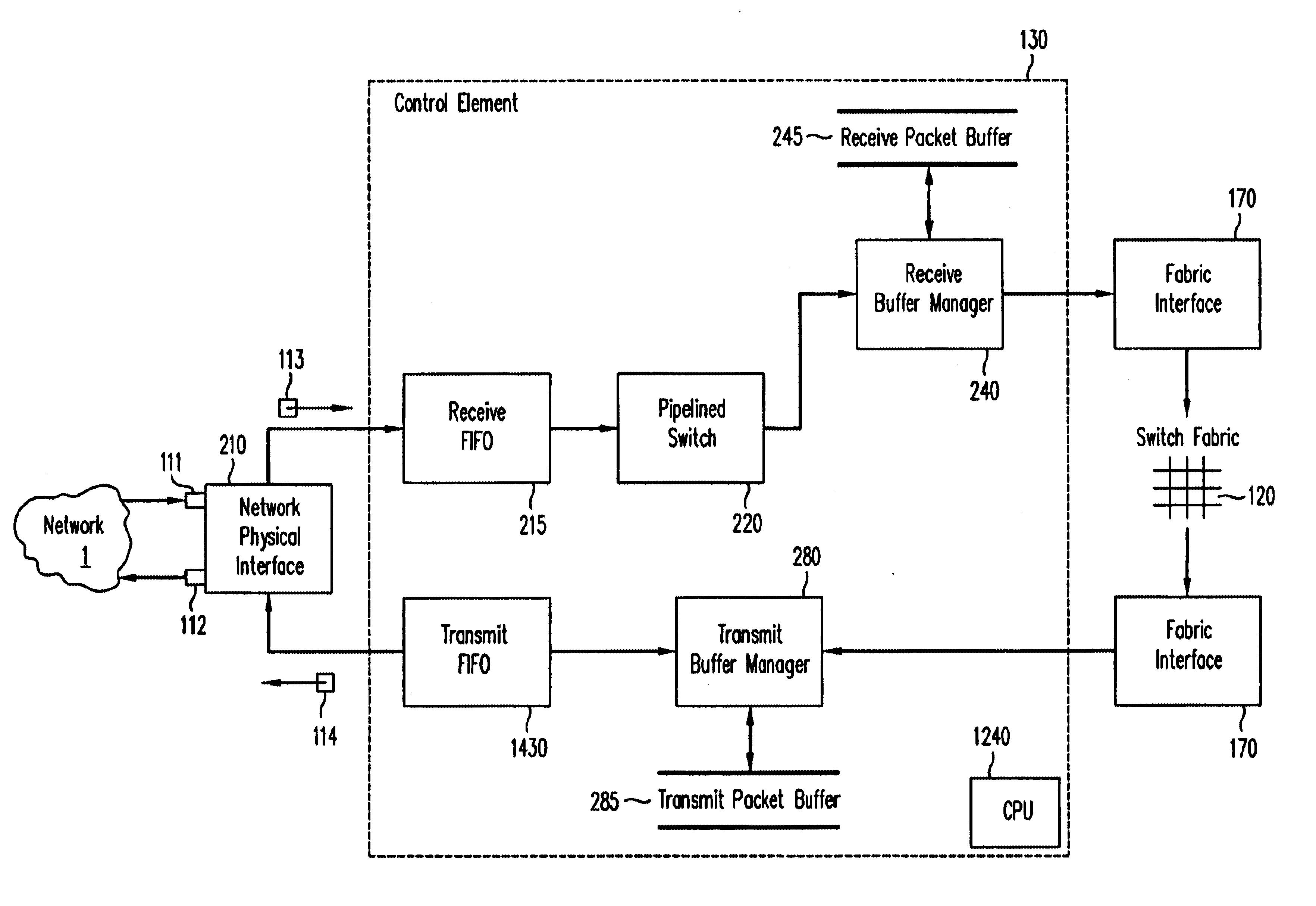
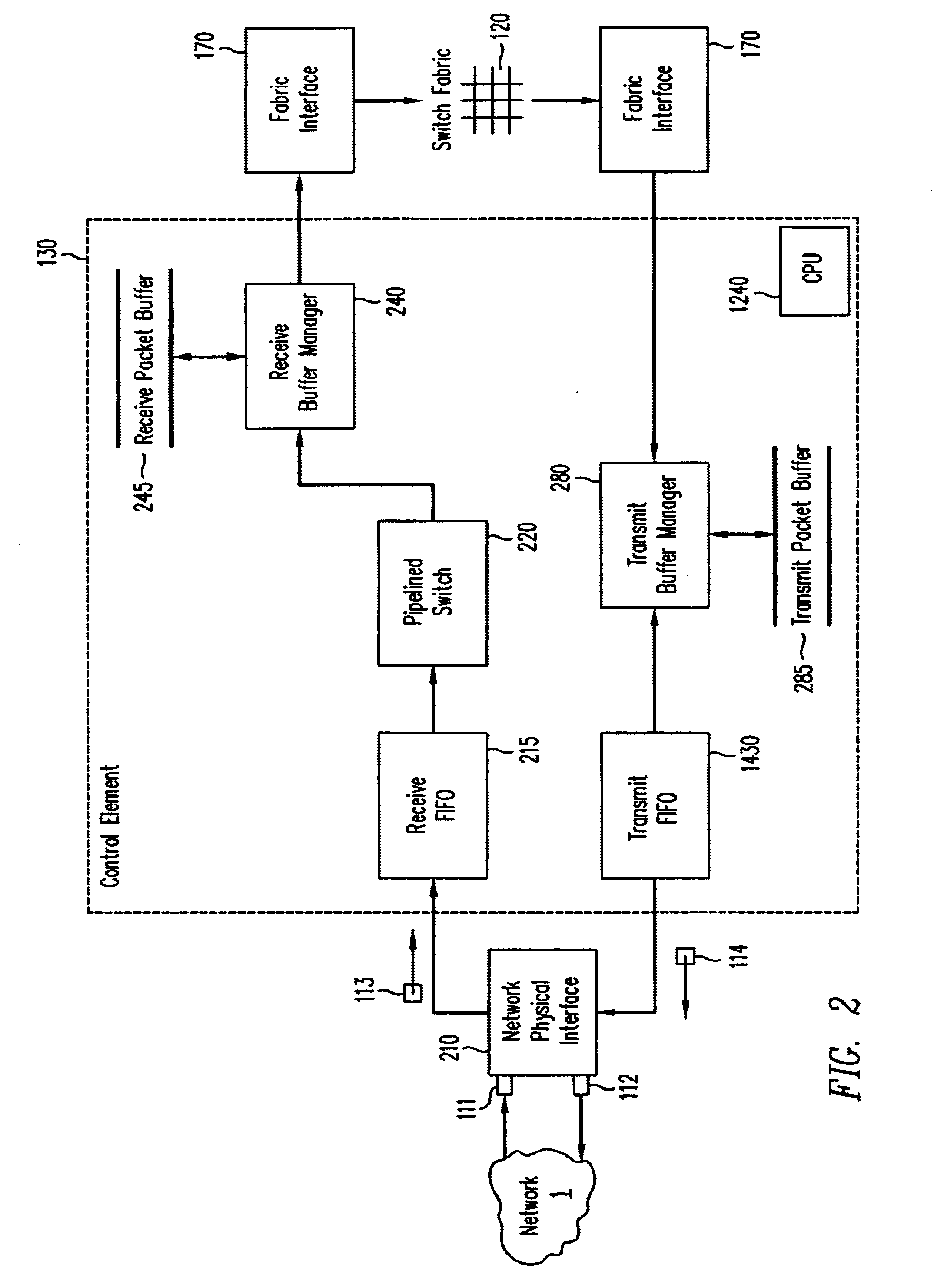
A pipelined linecard architecture for receiving, modifying, switching, buffering, queuing and dequeuing packets for transmission in a communications network. The linecard has two paths: the receive path, which carries packets into the switch device from the network, and the transmit path, which carries packets from the switch to the network. In the receive path, received packets are processed and switched in an asynchronous, multi-stage pipeline utilizing programmable data structures for fast table lookup and linked list traversal. The pipelined switch operates on several packets in parallel while determining each packet's routing destination. Once that determination is made, each packet is modified to contain new routing information as well as additional header data to help speed it through the switch. Each packet is then buffered and enqueued for transmission over the switching fabric to the linecard attached to the proper destination port. The destination linecard may be the same physical linecard as that receiving the inbound packet or a different physical linecard. The transmit path consists of a buffer / queuing circuit similar to that used in the receive path. Both enqueuing and dequeuing of packets is accomplished using CoS-based decision making apparatus and congestion avoidance and dequeue management hardware. The architecture of the present invention has the advantages of high throughput and the ability to rapidly implement new features and capabilities.
Owner:CISCO TECH INC
On-line image processing and communication system
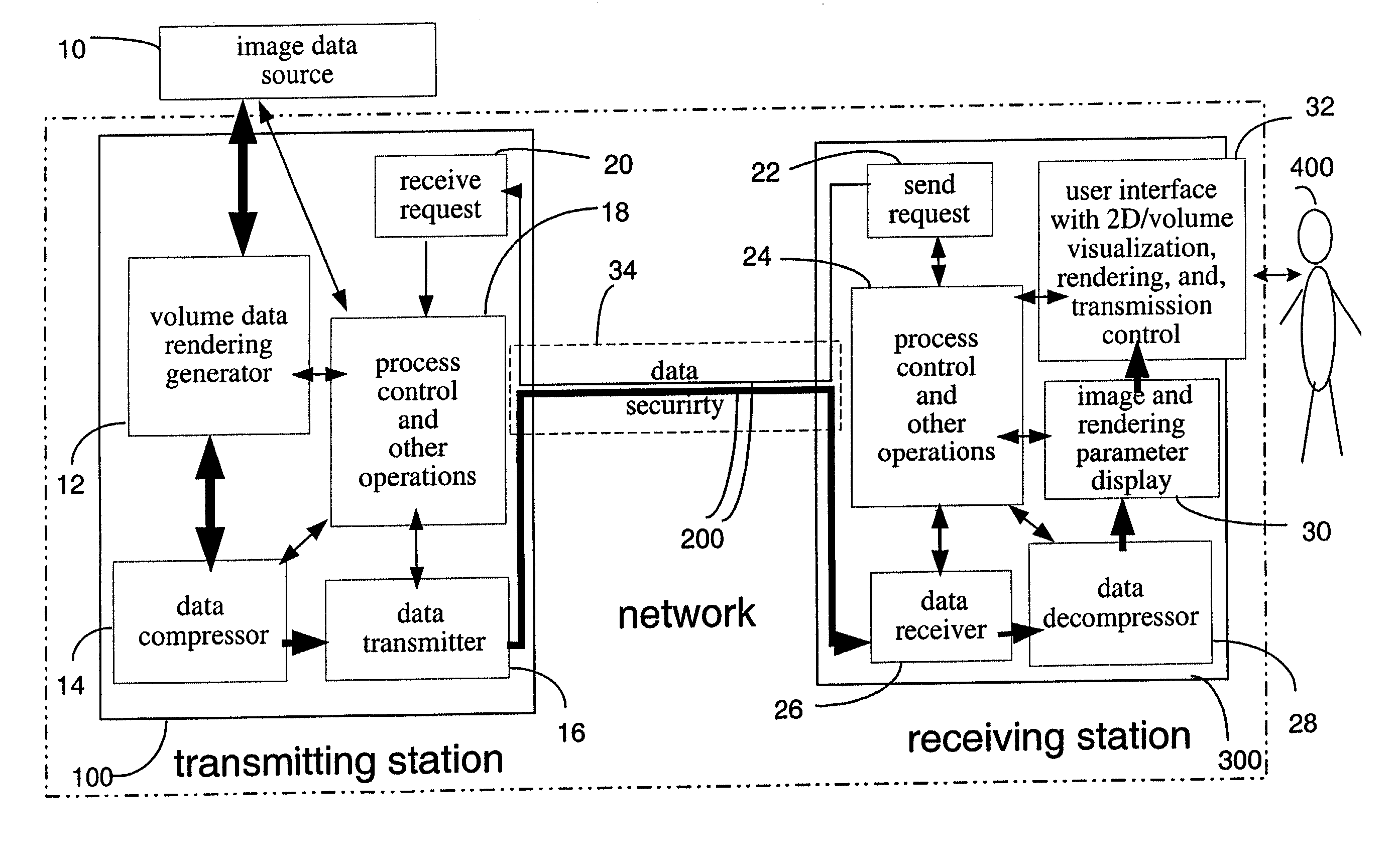
An image data manipulation system is described in which users located remotely from an image data storage library may participate in a collaborative image data rendering and evaluation session. The system includes the exchange of state parameters between the client computer of a user controlling the image rendering, the session driver, and a server computer which relays updated state parameters to other client computers participating in a session. The state parameters are used to update the view on each users computer to keep all the displays of the participants in synch with that of the session driver. The server processes extensive image rendering task for which the remote clients are not equipped and transmits newly-processed image data to the clients as appropriate. One embodiment for educational applications utilizes pre-stored image data sets which eliminates the need to transmit large blocks of image data over a network during a collaborative session.
Owner:CANON MEDICAL SYST COPRPORATION
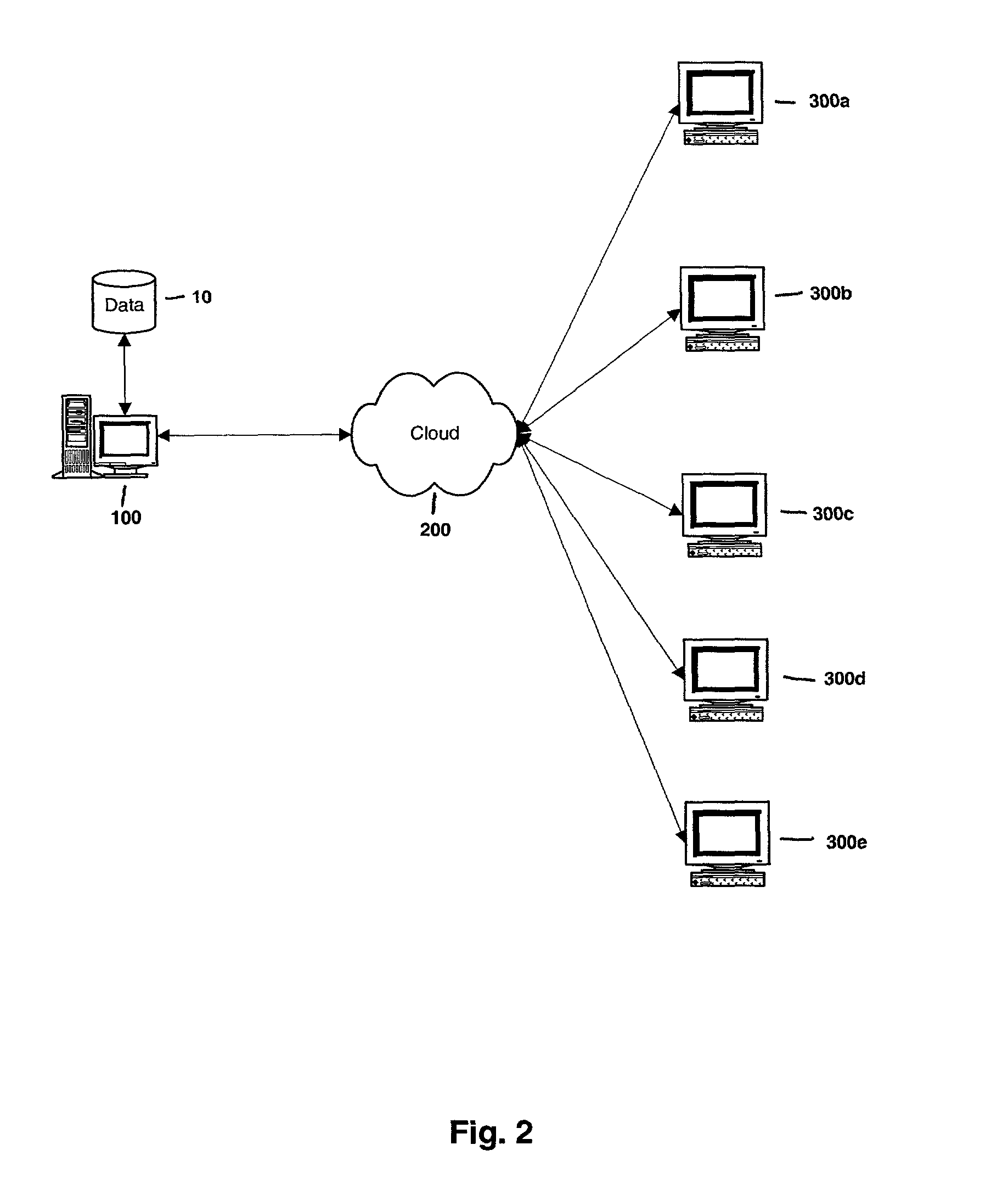
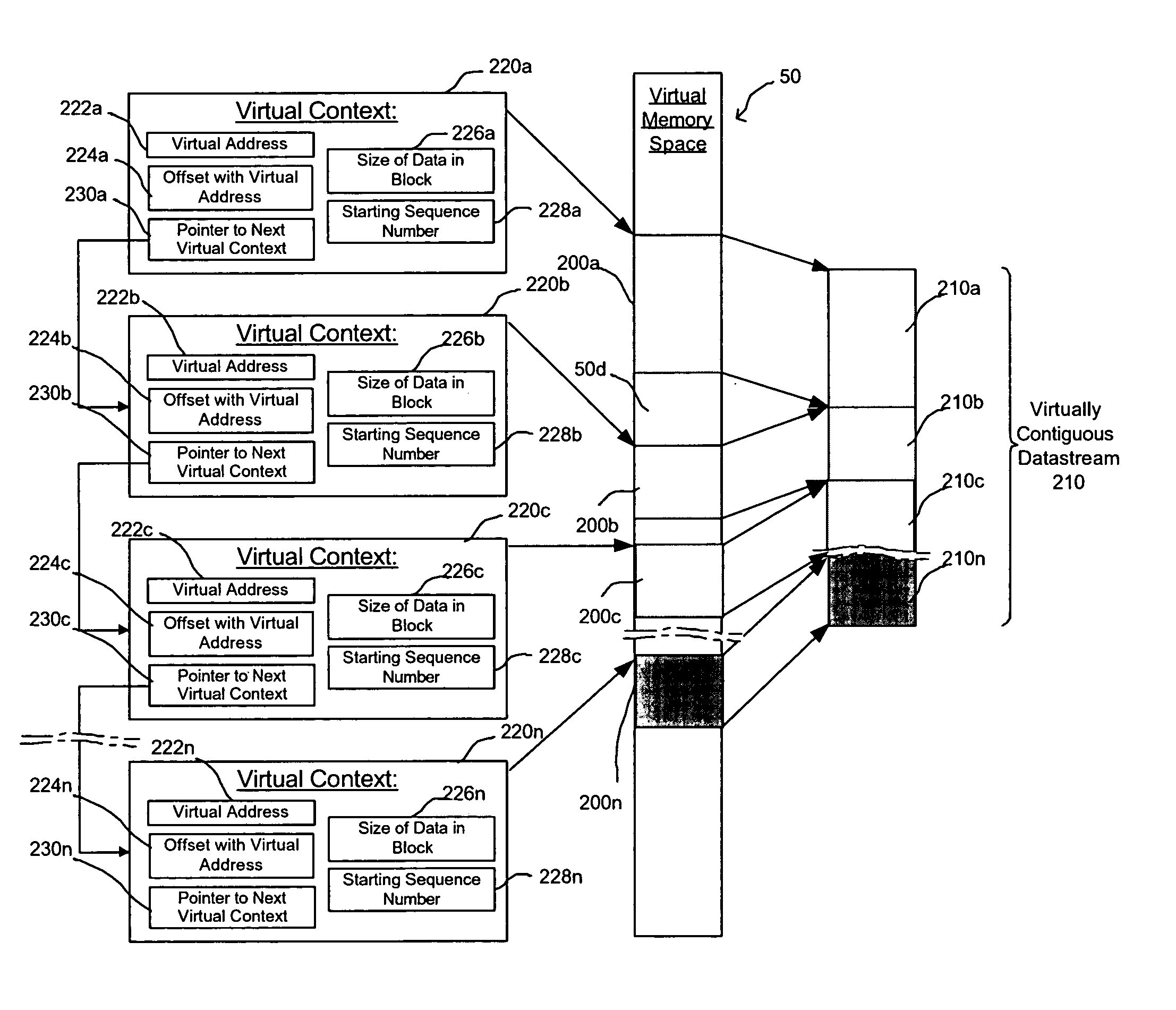
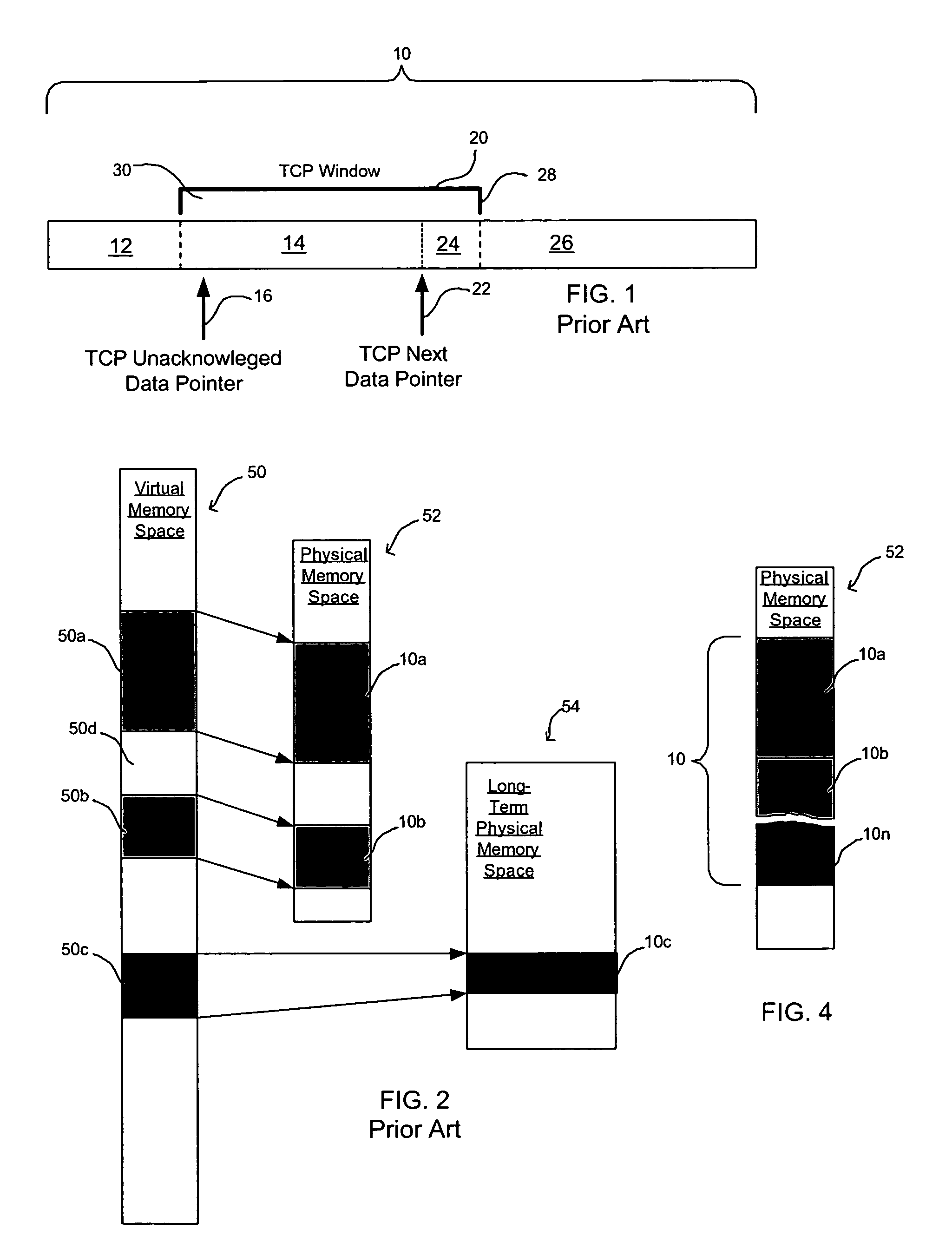
Method, system, and program for managing memory for data transmission through a network
InactiveUS20050080928A1Memory adressing/allocation/relocationMultiple digital computer combinationsVirtual memoryData transmission
Provided are a method, system, and program for managing memory for data transmission through a network. Virtual memory addresses of the data to be sent are provided to a sending agent. The sending agent provides to a host the virtual addresses of requested data. In response, the requested data addressed by the virtual addresses or the physical memory locations of the requested data are provided to the sending agent for sending to a destination.
Owner:INTEL CORP
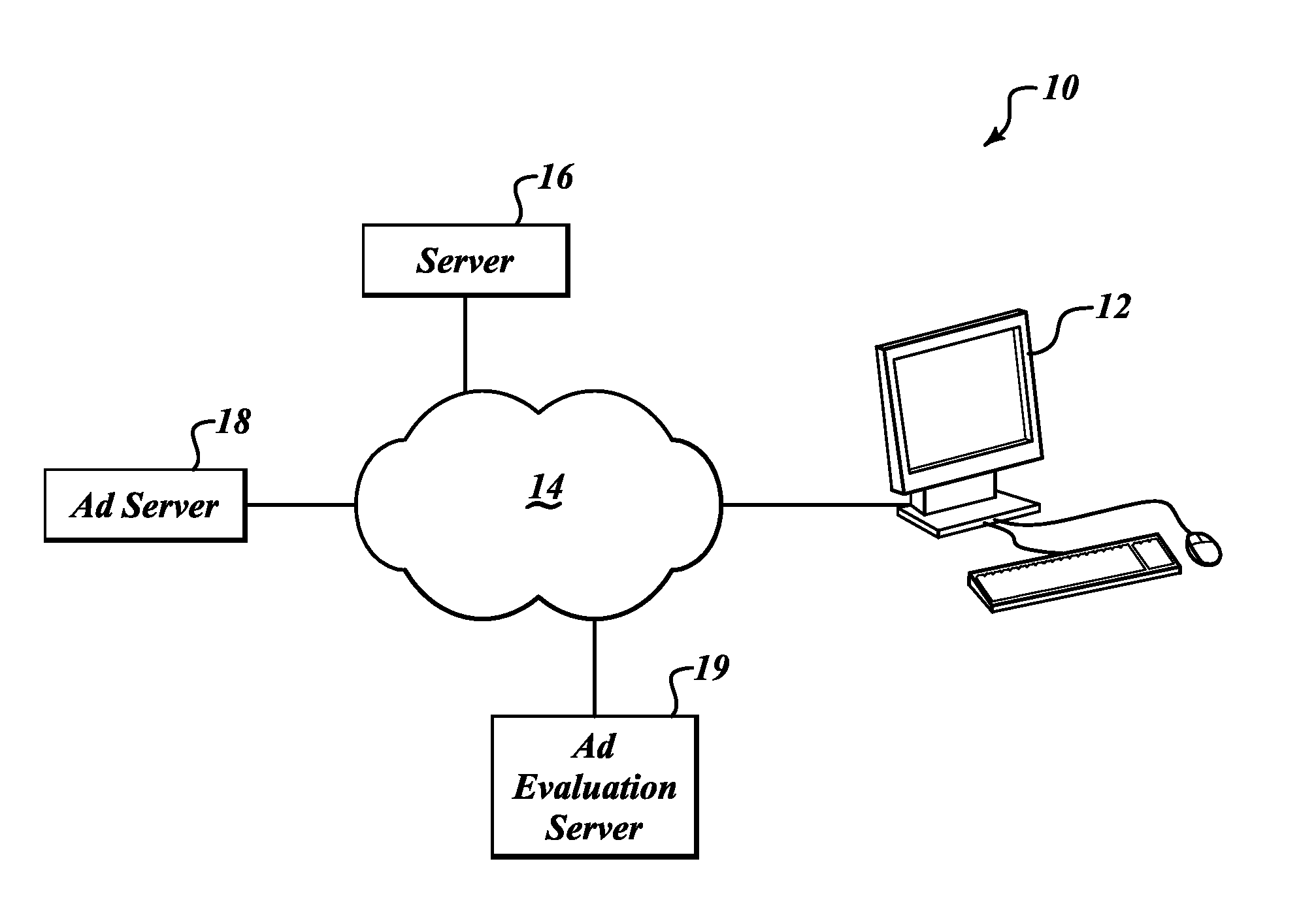
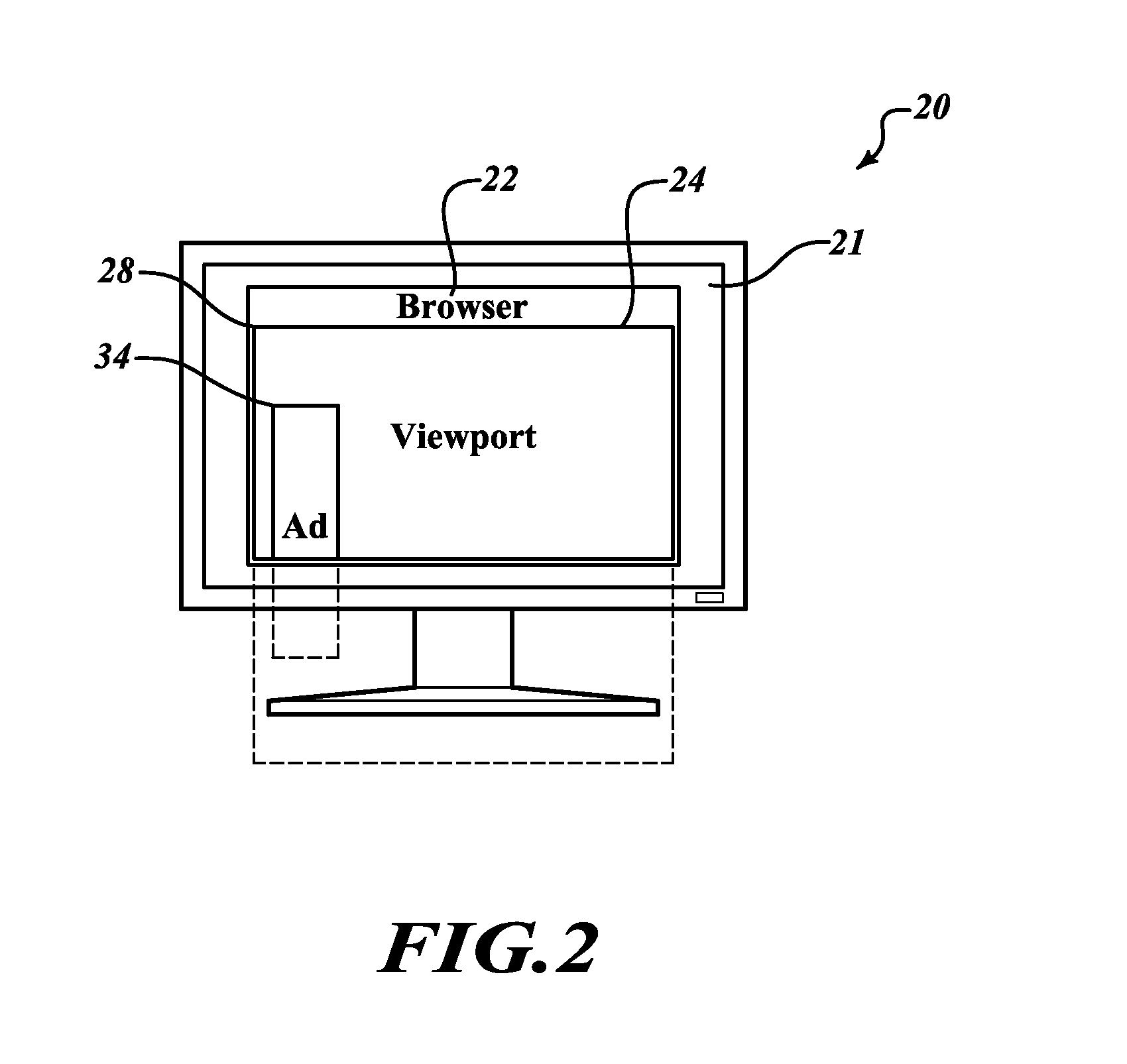
Methods for capturing and reporting metrics regarding ad placement
Systems and methods for recording impression events of Ad content on a webpage. An example method renders on a display of a computer device a webpage accessible over a network. The webpage includes at least one Ad unit. Then Ad tag information associated with the at least one Ad unit and browser viewport information (display location and size information) is retrieved. The occurrence of an Ad Placement event is determined if based on the comparison a predefined percentage of the Ad unit is within the browser viewport. An Ad Placement event timer is begun upon the determination of occurrence of the Ad Placement event. The Ad Placement event timer is stopped if an out-of-view event has occurred based on the Ad tag information and the browser viewport information. An Ad Placement event is then recorded. The recorded Ad Placement event is transmitted to a previously designated server over the network.
Owner:COMSCORE
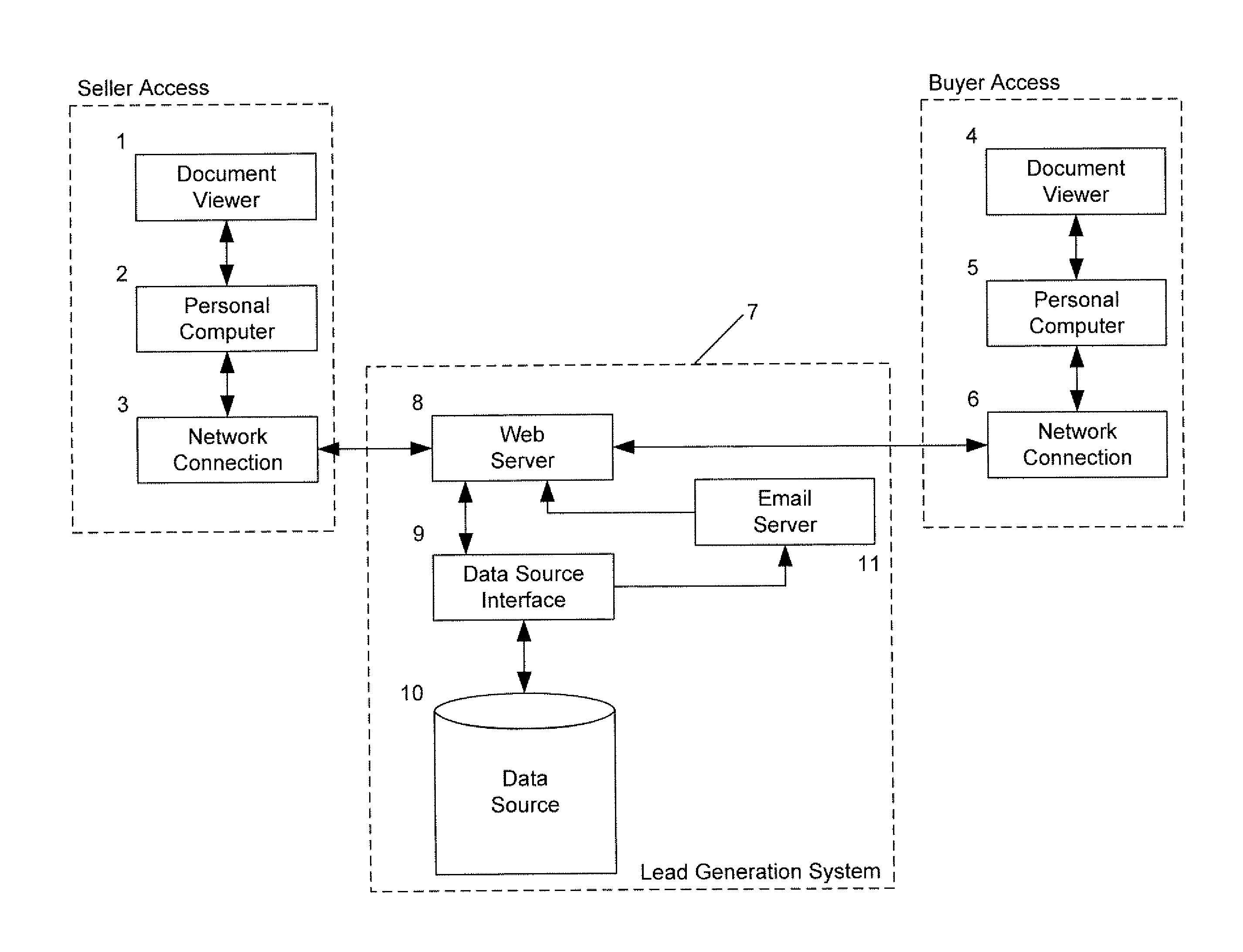
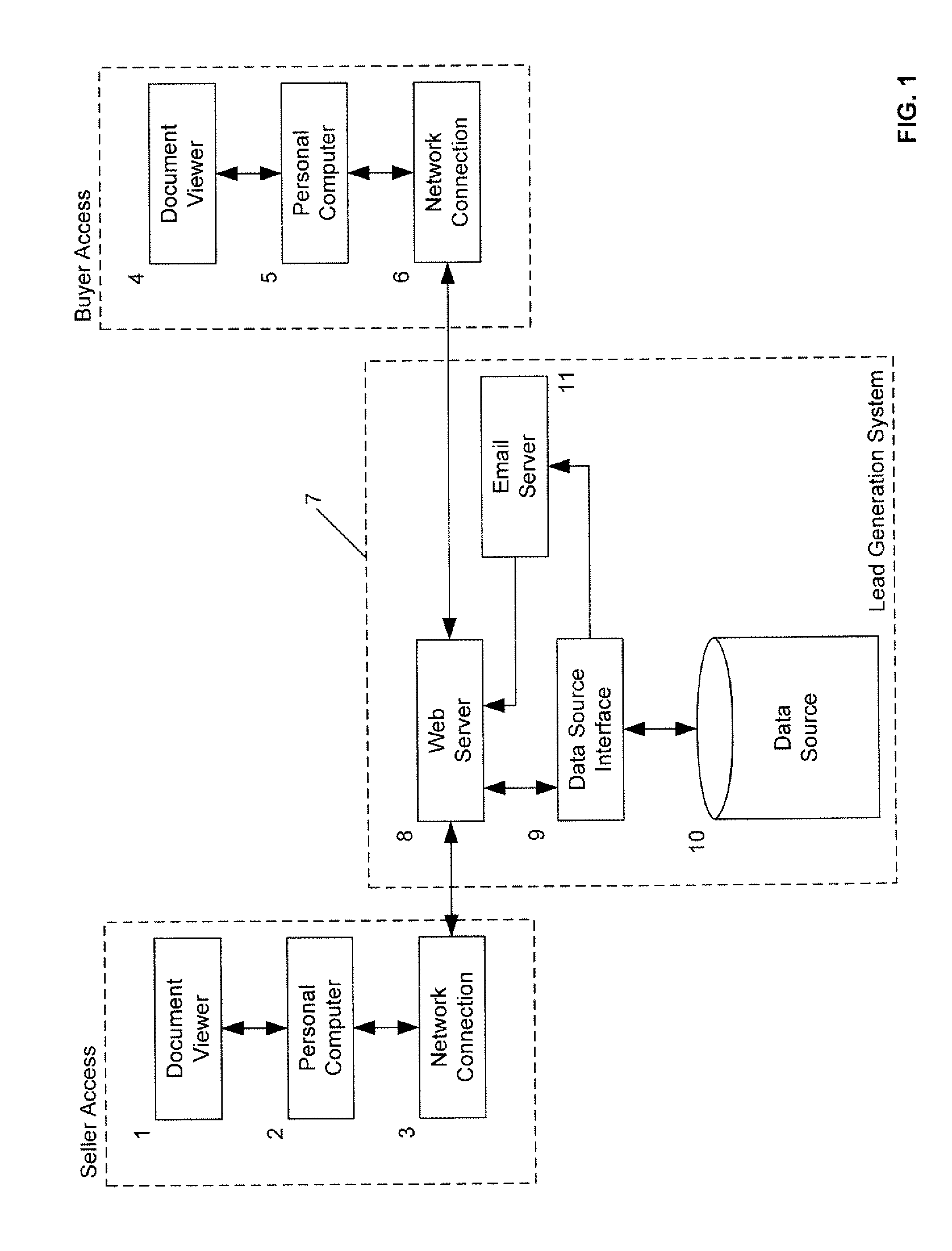
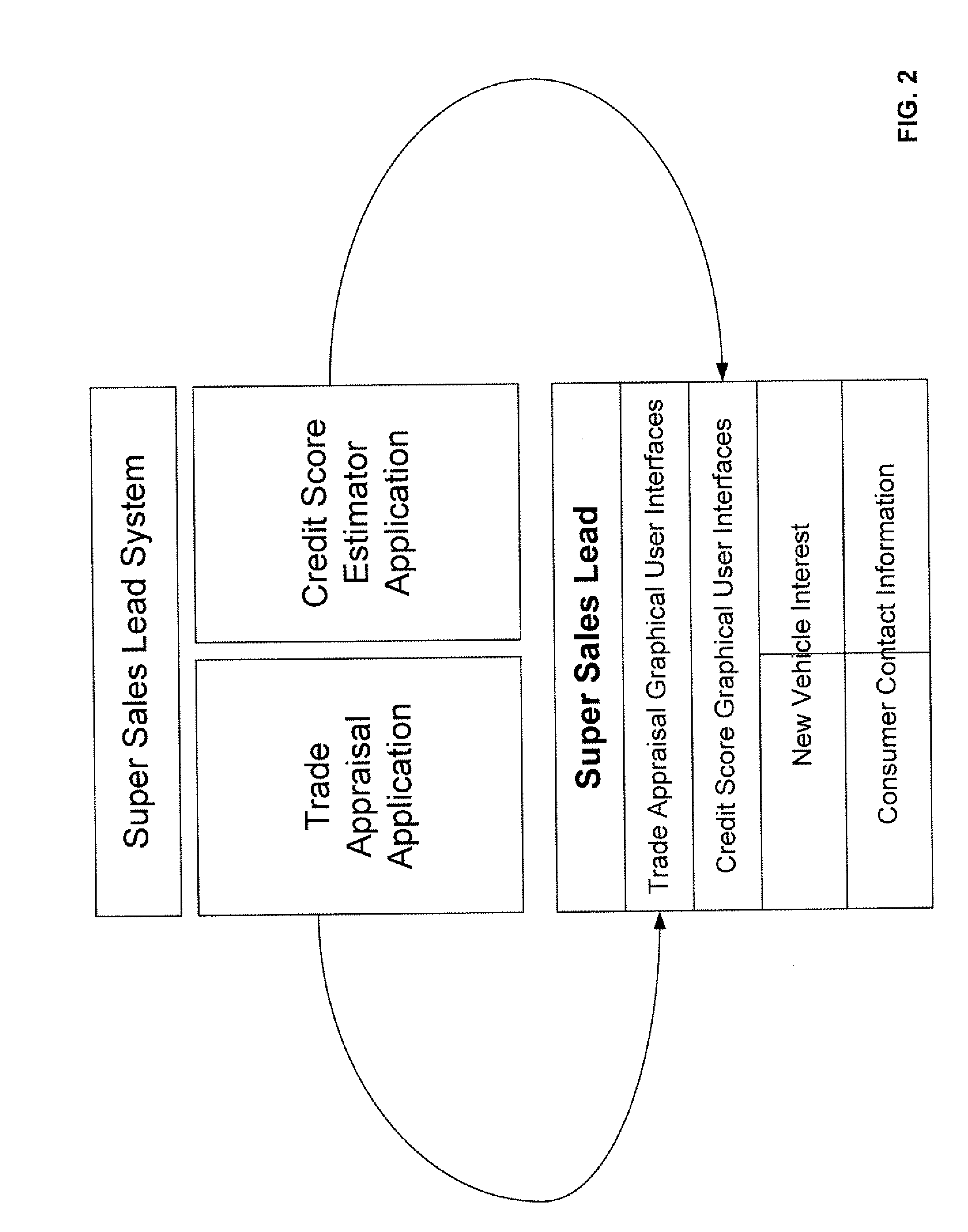
Sales lead generation system using a credit score survey
The invention is directed to a system for and a method of generating sales leads as a service for one or more vehicle dealerships that are not otherwise affiliated with the service. The invention may include maintaining a web site independently of the one or more vehicle dealerships that is accessible over a computer network by a consumer who is considering purchasing a vehicle, offering to the consumer while the consumer is accessing the web site to provide the consumer with an estimated credit score, wherein the consumer provides the consumer's contact information before the estimated credit score is provided, outputting a credit score survey to the consumer over the computer network, receiving one or more answers to the credit score survey from the consumer over the computer network, receiving information indicative of the vehicle transmitted from the consumer over the computer network, the information indicative of the vehicle comprising one or more selected from the group consisting of year, make, model, style, and color of the vehicle, receiving contact information of the consumer transmitted from the consumer over the computer network, determining, independently of the one or more vehicle dealerships, the estimated credit score by applying at least one scoring algorithm to the one or more answers to the credit score survey, providing the estimated credit score over the computer network to the consumer, and transmitting the contact information of the consumer, the estimated credit score, and the information indicative of the vehicle to the one or more vehicle dealerships as a sales lead.
Owner:VERETECH HLDG
Increased visibility during order management in a network-based supply chain environment
ActiveUS8271336B2Simple personalization processHand manipulated computer devicesNon-fuel substance addition to fuelVisibilityNetwork completion
A system, method and article of manufacture are provided for a first business entity to provide a network-based supply chain framework for collaborative order management between at least a second and a third independent business entity, such as a service provider, vendor, reseller, manufacturer and the like. A request for an order is received over a network with an automated system, from at least a second business entity. The order is transmitted over a network, with an automated system, to at least the third business entity. Information is received from the third business entity relating to a status of completion of the order by the third business entity using a network. The progress in completing the order is tracked based on the information received from the third business entity. Progress reports from the tracking are generated periodically; and transmitted to the second business entity using the network.
Owner:ACCENTURE GLOBAL SERVICES LTD
System and method for monitoring network traffic
ActiveUS20050063377A1Error preventionFrequency-division multiplex detailsInternet trafficComputer science
A system includes a packet reader configured to scan packets transmitted through a network for pre-specified criteria. The packets include endpoint information and data. A request / response matcher determines whether each packet meets pre-specified criteria, and matches request packets with corresponding response packets when the packets meet the pre-specified criteria. A message analyzer determines the format, or structure, of the data of the matched packets, and analyzes the data of the matched packets to generate at least a portion of a model of the data.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
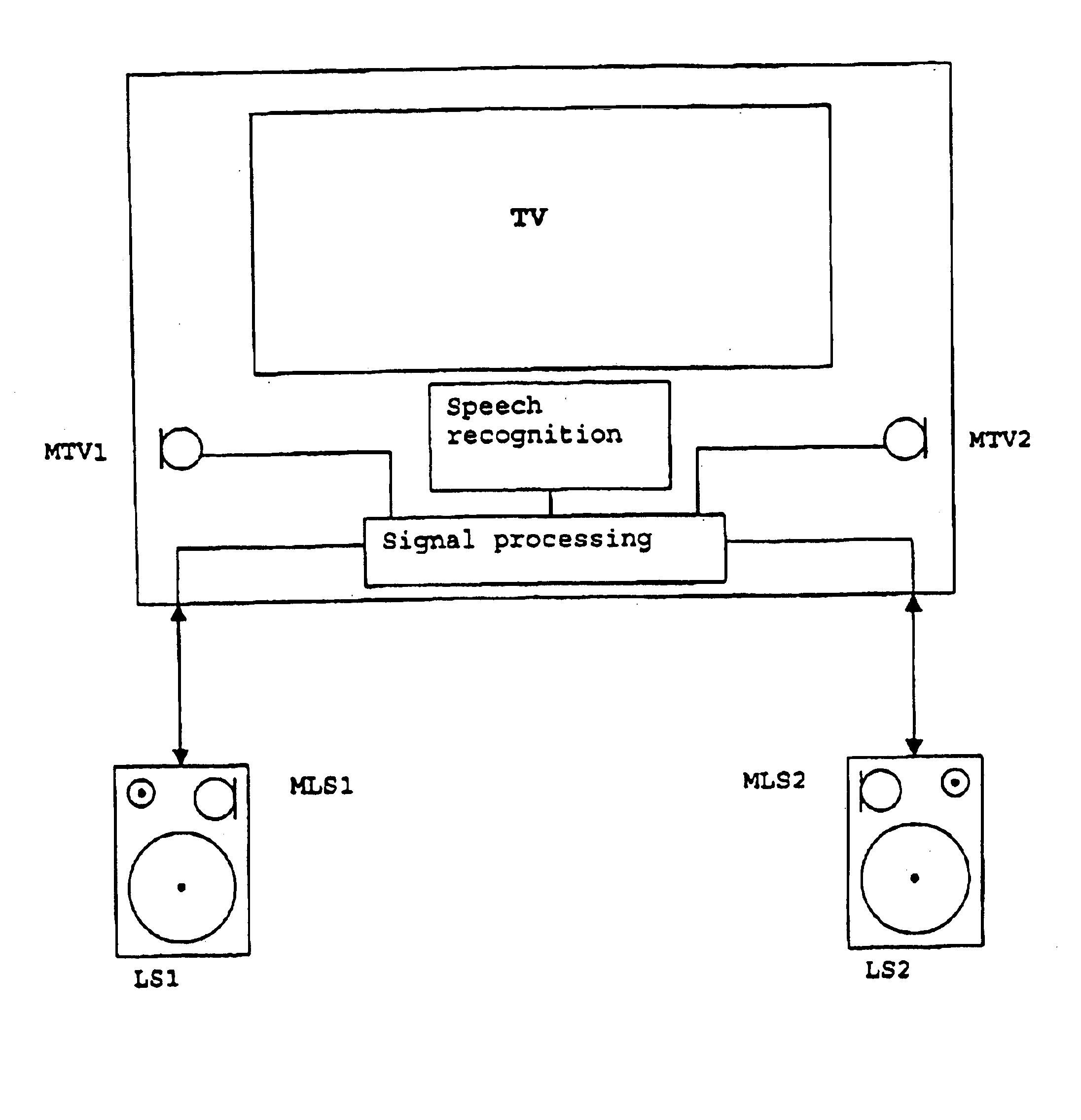
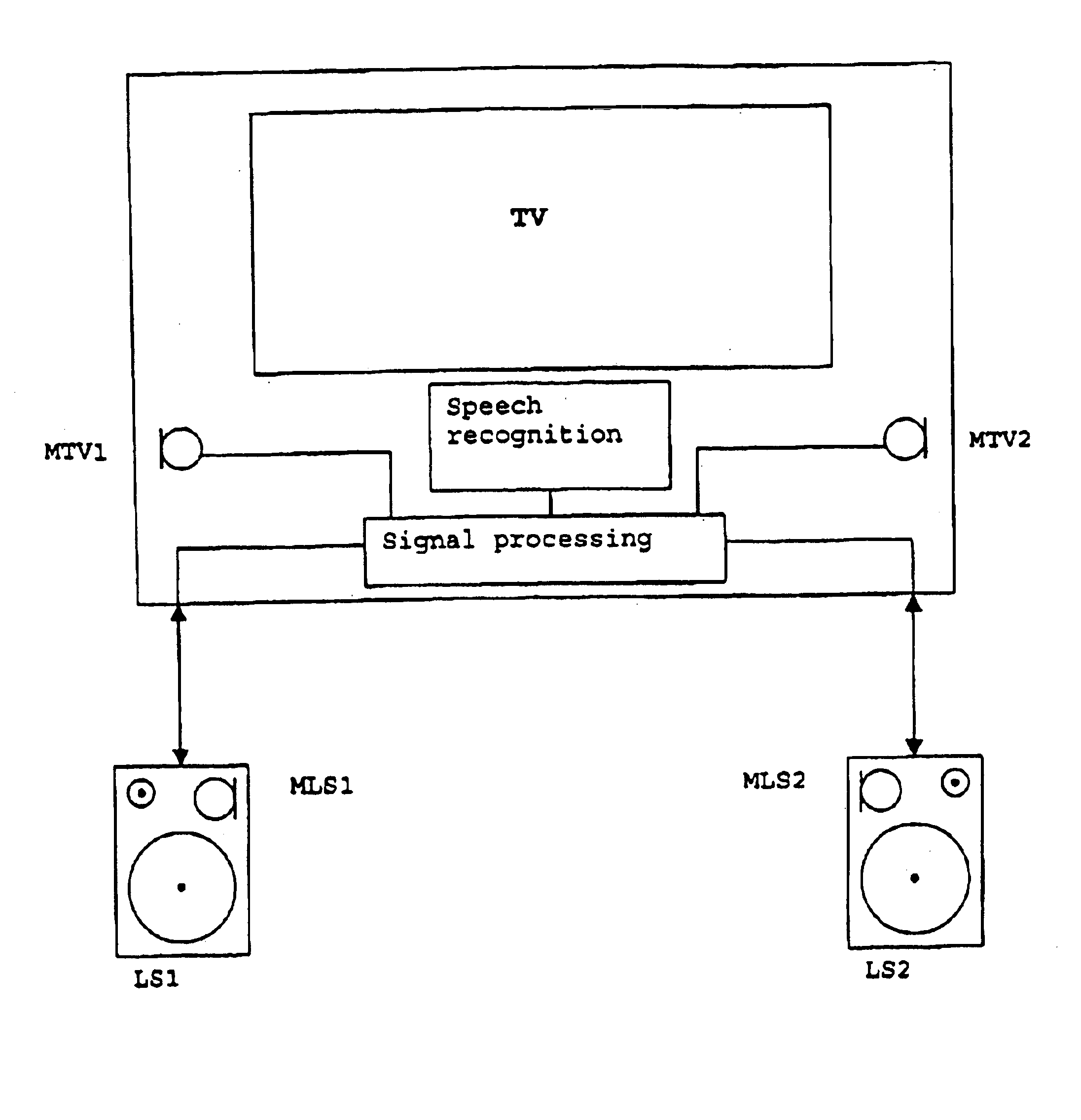
Voice control system with a microphone array
InactiveUS6868045B1Sufficient interference immunityBeacon systems using ultrasonic/sonic/infrasonic wavesElectric signal transmission systemsIEEE 1394VIT signals
Voice control systems are used in diverse technical fields. In this case, the spoken words are detected by one or more microphones and then fed to a speech recognition system. In order to enable voice control even from a relatively great distance, the voice signal must be separated from interfering background signals. This can be effected by spatial separation using microphone arrays comprising two or more microphones. In this case, it is advantageous for the individual microphones of the microphone array to be distributed spatially over the greatest possible distance. In an individual consumer electronics appliance, however, the distances between the individual microphones are limited on account of the dimensions of the appliance. Therefore, the voice control system according to the invention comprises a microphone array having a plurality of microphones which are distributed between different appliances, in which case the signals generated by the microphones can be transmitted to the central speech recognition unit, advantageously via a bidirectional network based on an IEEE 1394 bus.
Owner:INTERDIGITAL CE PATENT HLDG
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050144195A1Permit useDigital data processing detailsMultiple digital computer combinationsNetwork connectionData access
Applications, systems and methods for permitting simultaneous use of a file by two or more computers over a network may include storing the file locally in a local storage device associated with a local computer; providing access to the file by at least one remote computer which is connectable to the local computer via the network, and wherein at least one of the computers is connectable to the network through a firewall element. The file may be stored in at least one remote storage device associated with the at least one remote computer, respectively, and versions of the file contained on the one or more remote storage devices are synchronized with that on the local device by transmitting over the network connecting the one or more remote storage devices with the local device, at least one of Delta files and Inverse Delta files between the remote storage devices and the local storage device. A method of remotely observing computer activity on a second computer remote with respect to a first computer is also provided. Further, file sharing systems and methods are provided for sharing files among computers.
Owner:WESTERN DIGITAL TECH INC
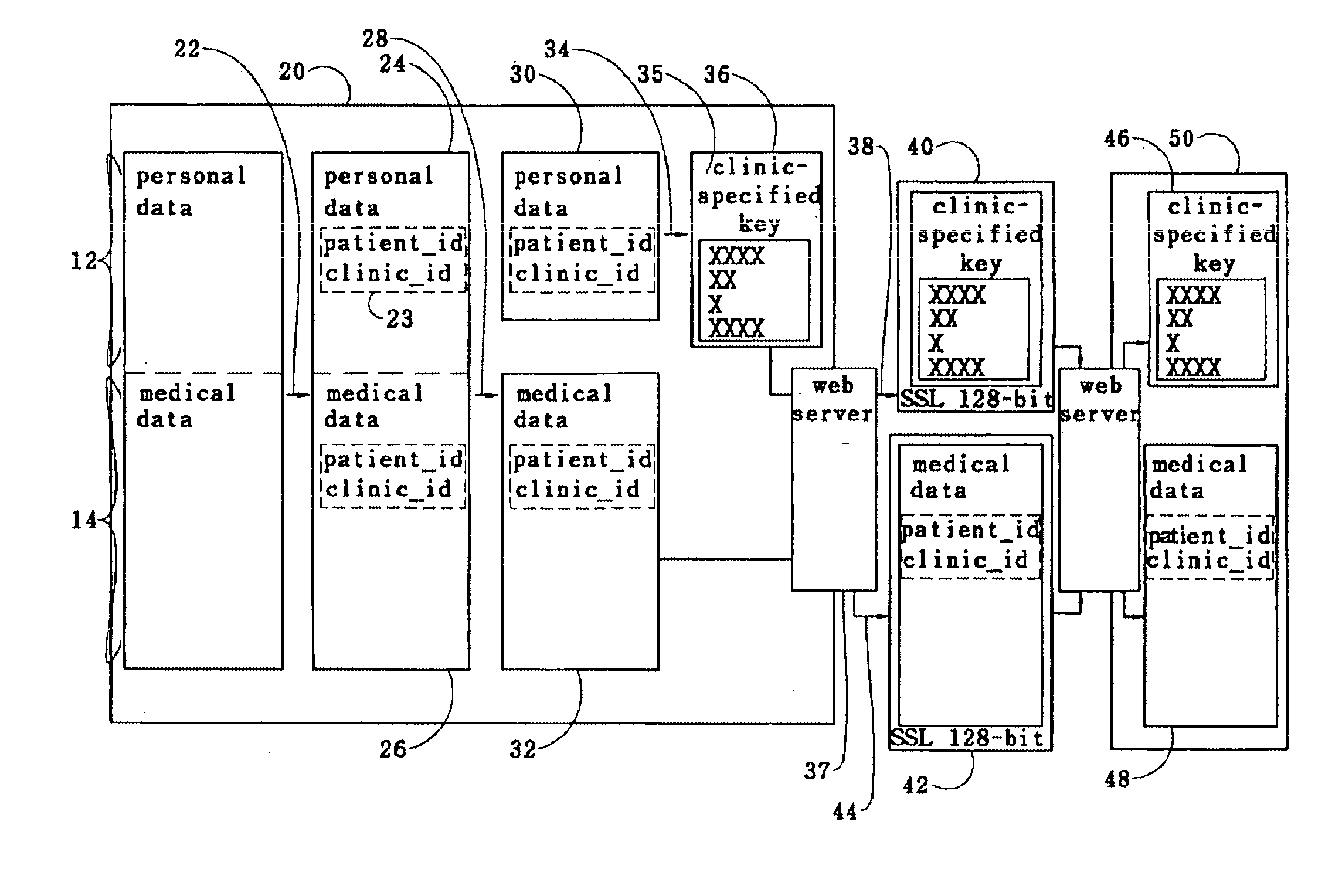
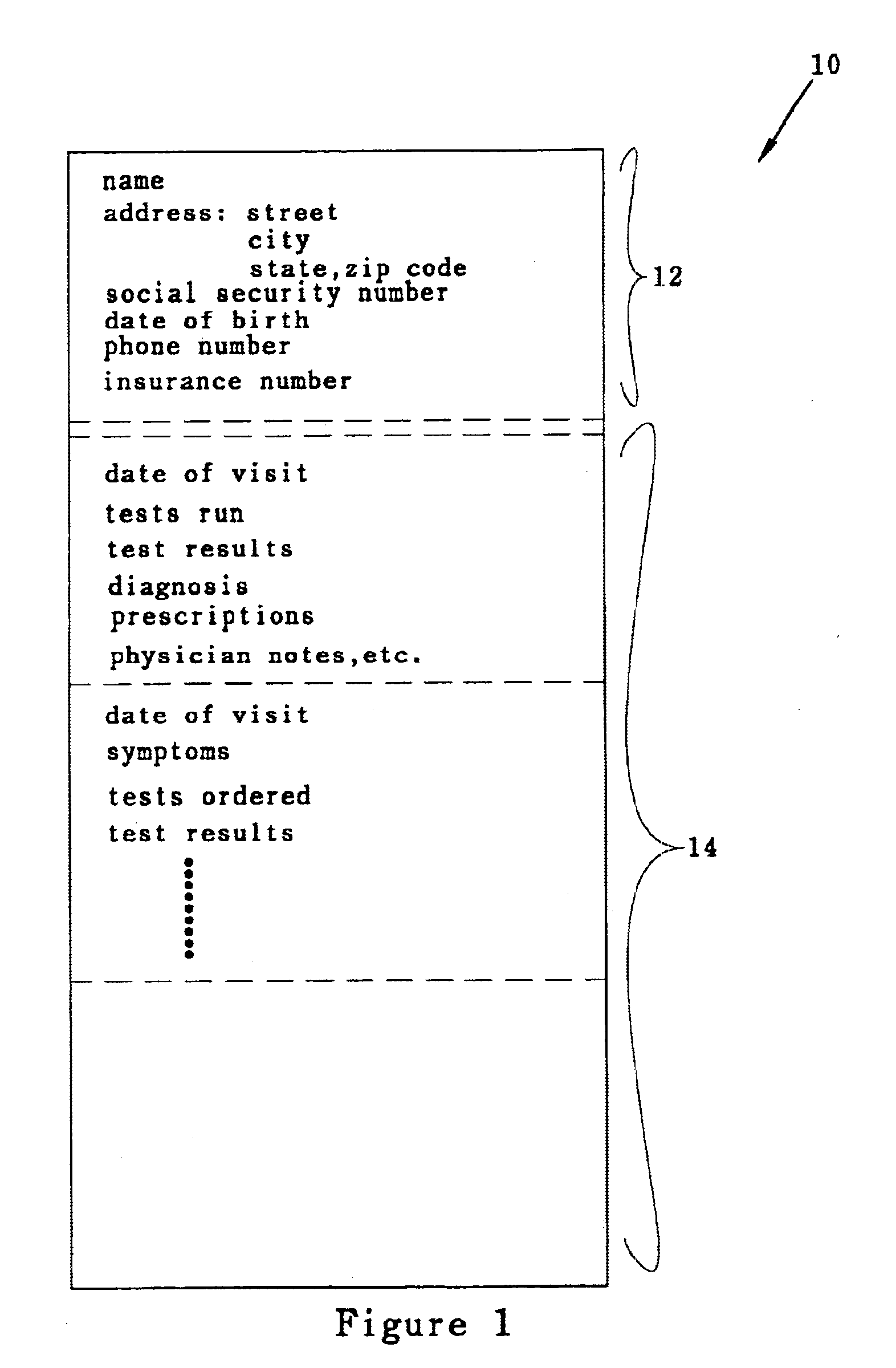
Medical records data security system
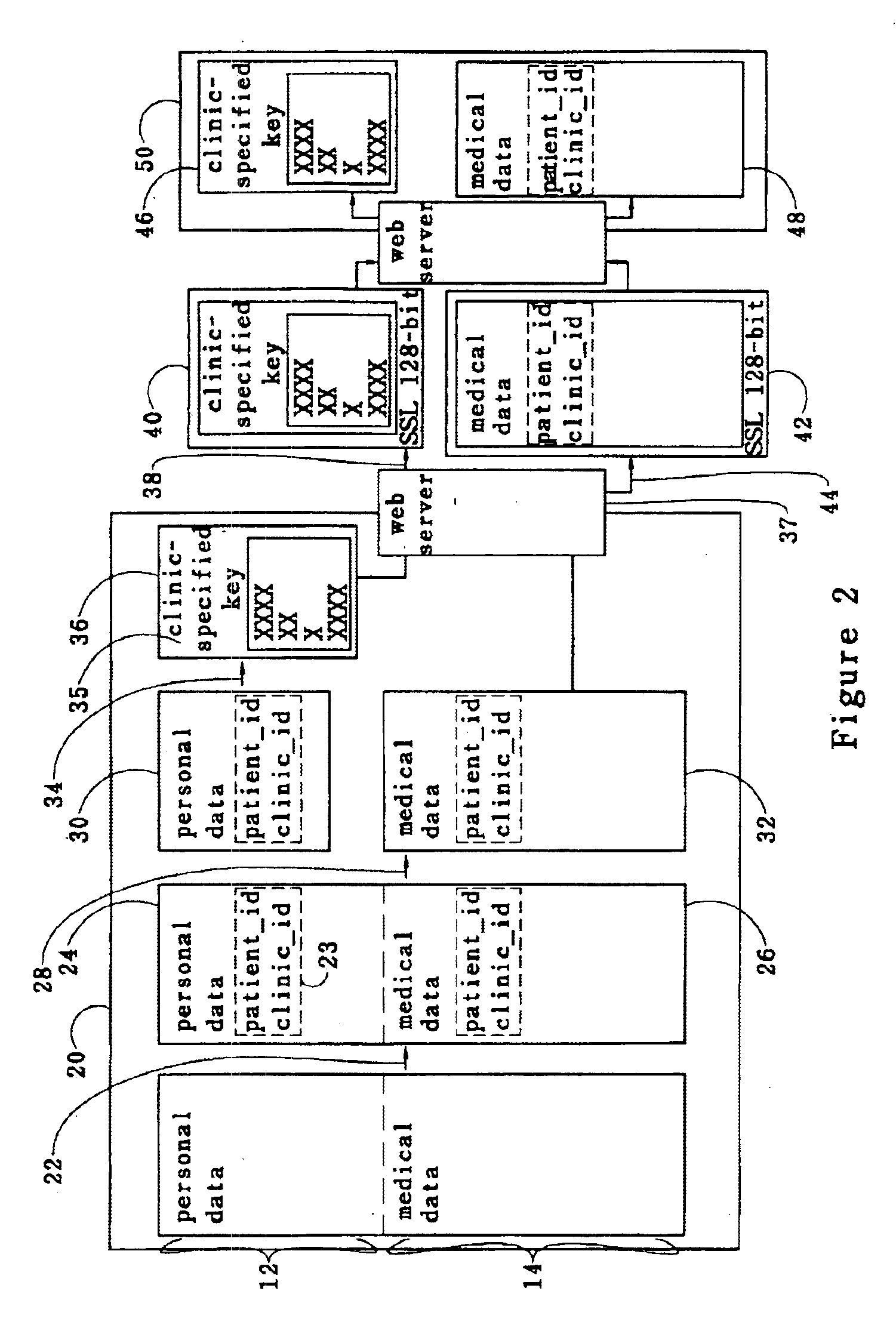
InactiveUS6874085B1Secure identityComputer security arrangementsSecuring communicationMedical recordThe Internet
A medical record is partitioned into personal and medical data portions, and an identification code is concatenated into each portion. The personal data portion is encrypted so a patient's identity cannot be linked to the patient's medical data except by authorized viewers. Each portion of the secure medical record can be transferred over a network as separate files, and stored in a data storage system separately. Access to the entire medical record is thereby provided only to those who know the key for the personal data portion of the medical record. The system and method can be used to help ensure patient confidentiality while allowing patient medical records to be accessed over a network such as the Internet, providing physicians and patients quick access to their medical records. The system and method can be used to create a database of anonymous medical records useful for medical research.
Owner:APRIMA MEDICAL SOFTWARE
High-speed hardware implementation of MDRR algorithm over a large number of queues
InactiveUS6778546B1Data switching by path configurationStore-and-forward switching systemsHardware implementationsComputer science
A pipelined linecard architecture for receiving, modifying, switching, buffering, queuing and dequeuing packets for transmission in a communications network. The linecard has two paths: the receive path, which carries packets into the switch device from the network, and the transmit path, which carries packets from the switch to the network. In the receive path, received packets are processed and switched in an asynchronous, multi-stage pipeline utilizing programmable data structures for fast table lookup and linked list traversal. The pipelined switch operates on several packets in parallel while determining each packet's routing destination. Once that determination is made, each packet is modified to contain new routing information as well as additional header data to help speed it through the switch. Each packet is then buffered and enqueued for transmission over the switching fabric to the linecard attached to the proper destination port. The destination linecard may be the same physical linecard as that receiving the inbound packet or a different physical linecard. The transmit path consists of a buffer / queuing circuit similar to that used in the receive path. Both enqueuing and dequeuing of packets is accomplished using CoS-based decision making apparatus and congestion avoidance and dequeue management hardware. The architecture of the present invention has the advantages of high throughput and the ability to rapidly implement new features and capabilities.
Owner:CISCO TECH INC
Multi-camera residential communication system
InactiveUS20080297587A1Television conference systemsCharacter and pattern recognitionMulti cameraCommunications system
Video communication devices and methods are provided. The device has an image display device; a first image capture device that acquires video images depicting a wide field of view within the local environment; a second image capture device that acquires video images depicting a narrow field of view within the wide field of view; a communication system that is adapted to use a communication network to transmit outgoing video images; and a computer causing the capture of video images during a communication event, and further being adapted to identify a video context for the communication event; wherein said computer uses a scene analysis algorithm to examine concurrent video images from the image capture device based upon the identified video context to determine the extent to which video images from the first image capture device and the second image capture device are to be incorporated into the outgoing video images.
Owner:MONUMENT PEAK VENTURES LLC
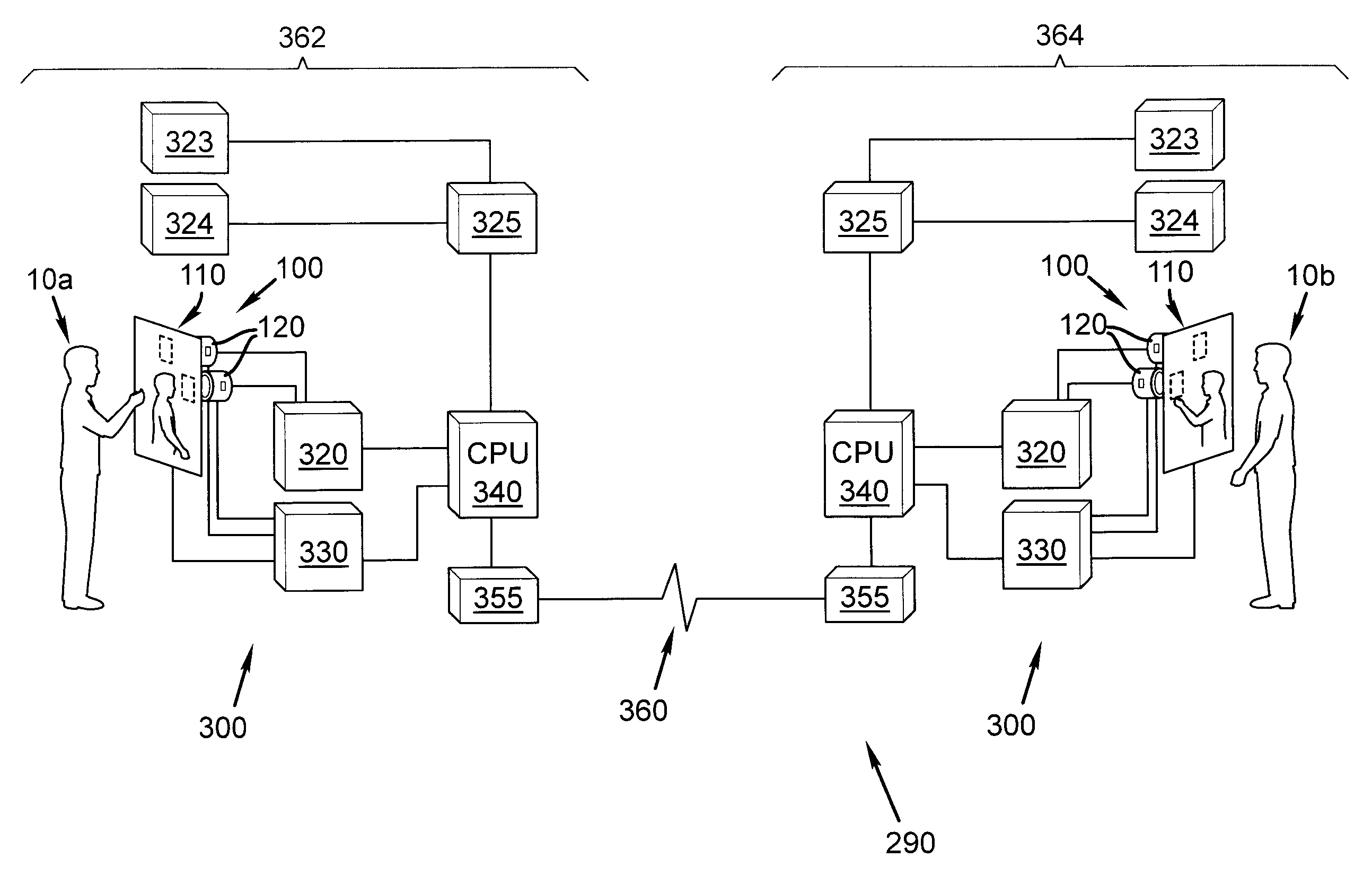
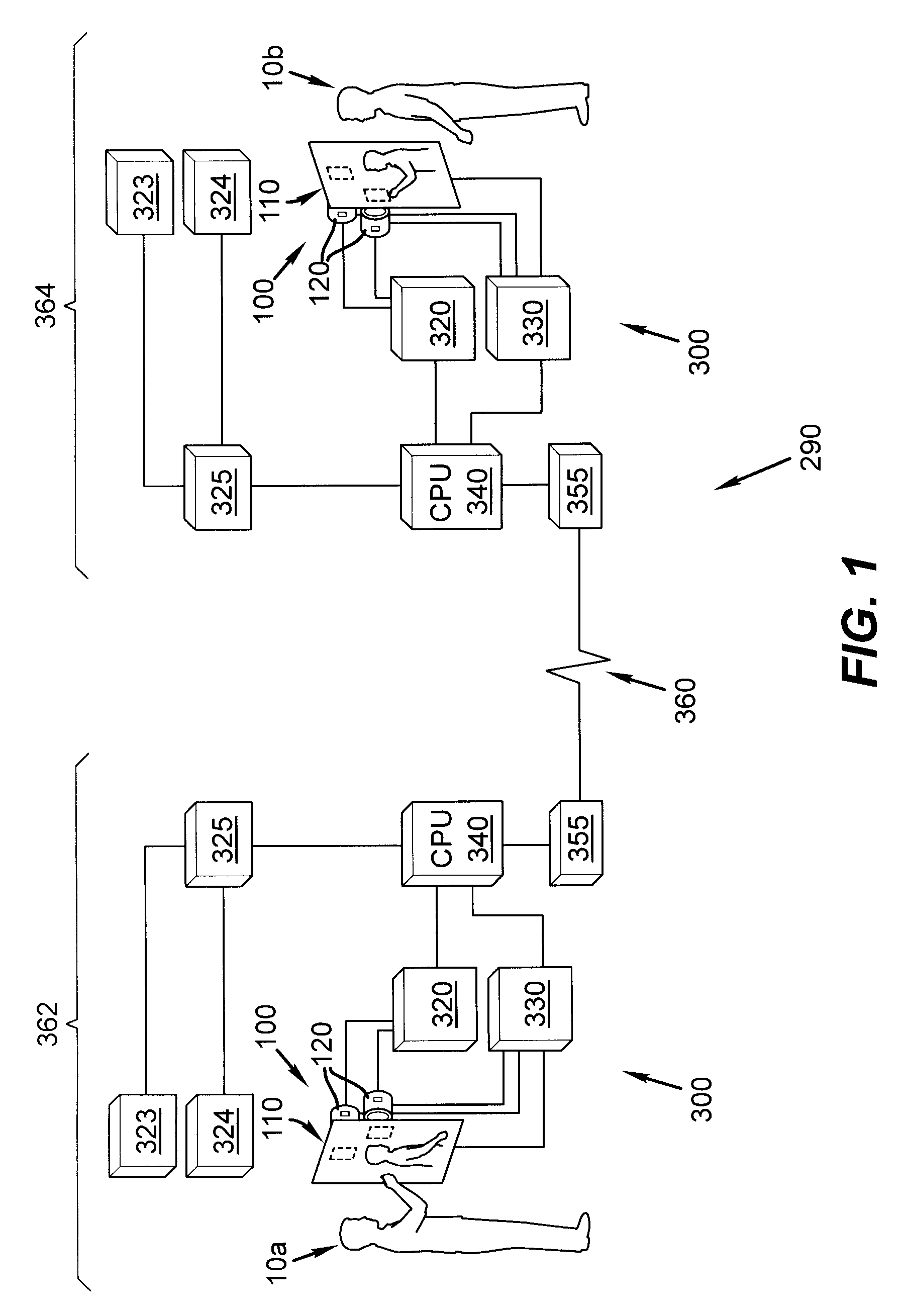
Database system and method for industrial automation services
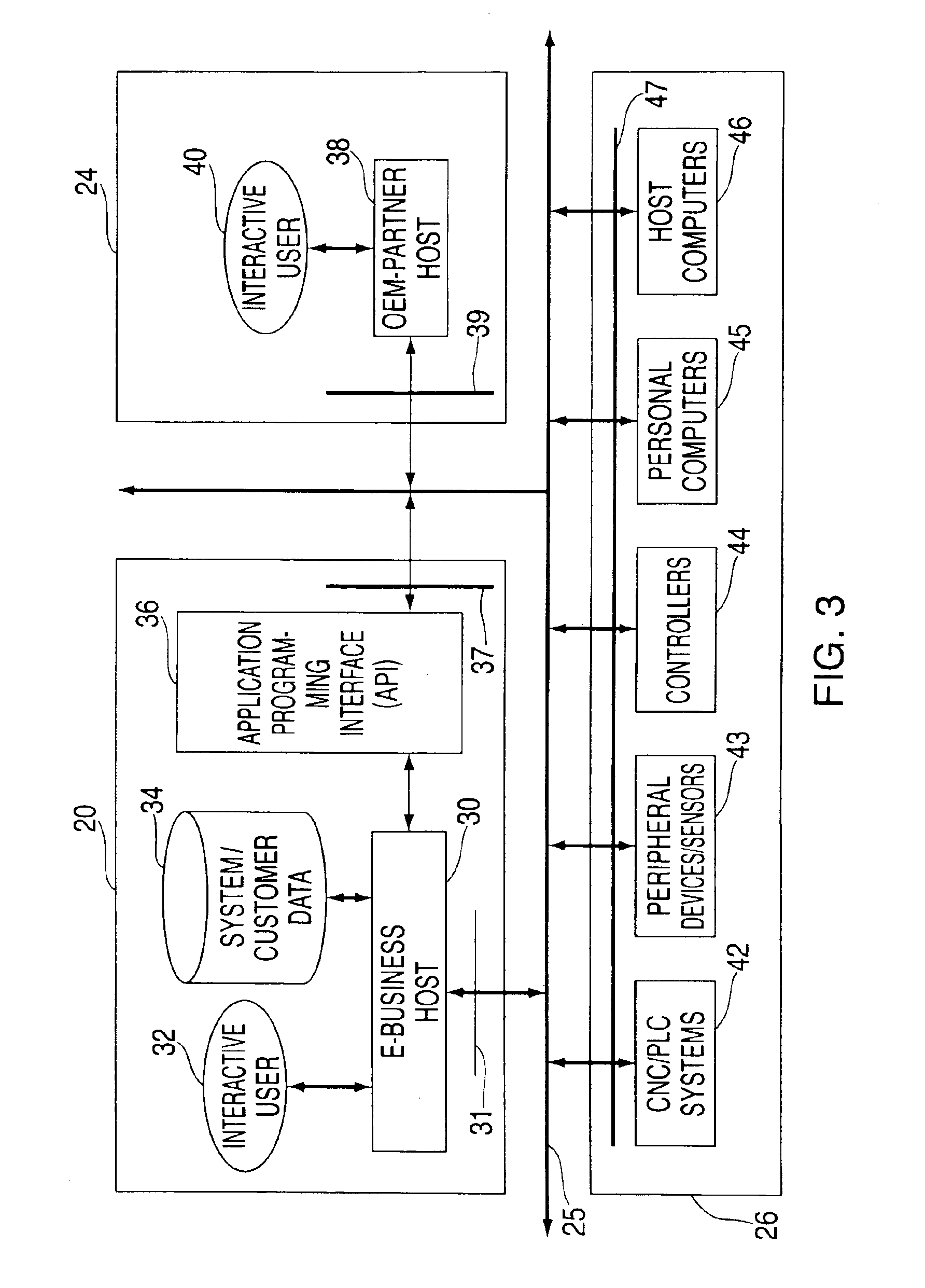
InactiveUS6975913B2Improve data securityProvide informationComputer controlSimulator controlReal-time dataOriginal equipment manufacturer
A host system generates and manages databases incorporating data gathered from a plurality of client automation systems, such as CNC machine tools. The data may include real-time data, and is captured from the client systems under supervision of software downloaded over a network from the host system to the client systems. The captured data is transmitted over the network to the host, which creates the databases. The databases preferably include a commercial database comprising data associated with customer owners or operators of the client automation system, as well as a technical database, comprising captured data, administrative and other data, organized by customer and client system. Captured data is preferably associated with the date of capture, providing for the creation of a historical database for given client equipment. With customer authorization, others, such as original equipment manufacturers, may access the captured data, for which they may be charged a fee.
Owner:SIEMENS AG
Methods and apparatus for network communications via a transparent security proxy
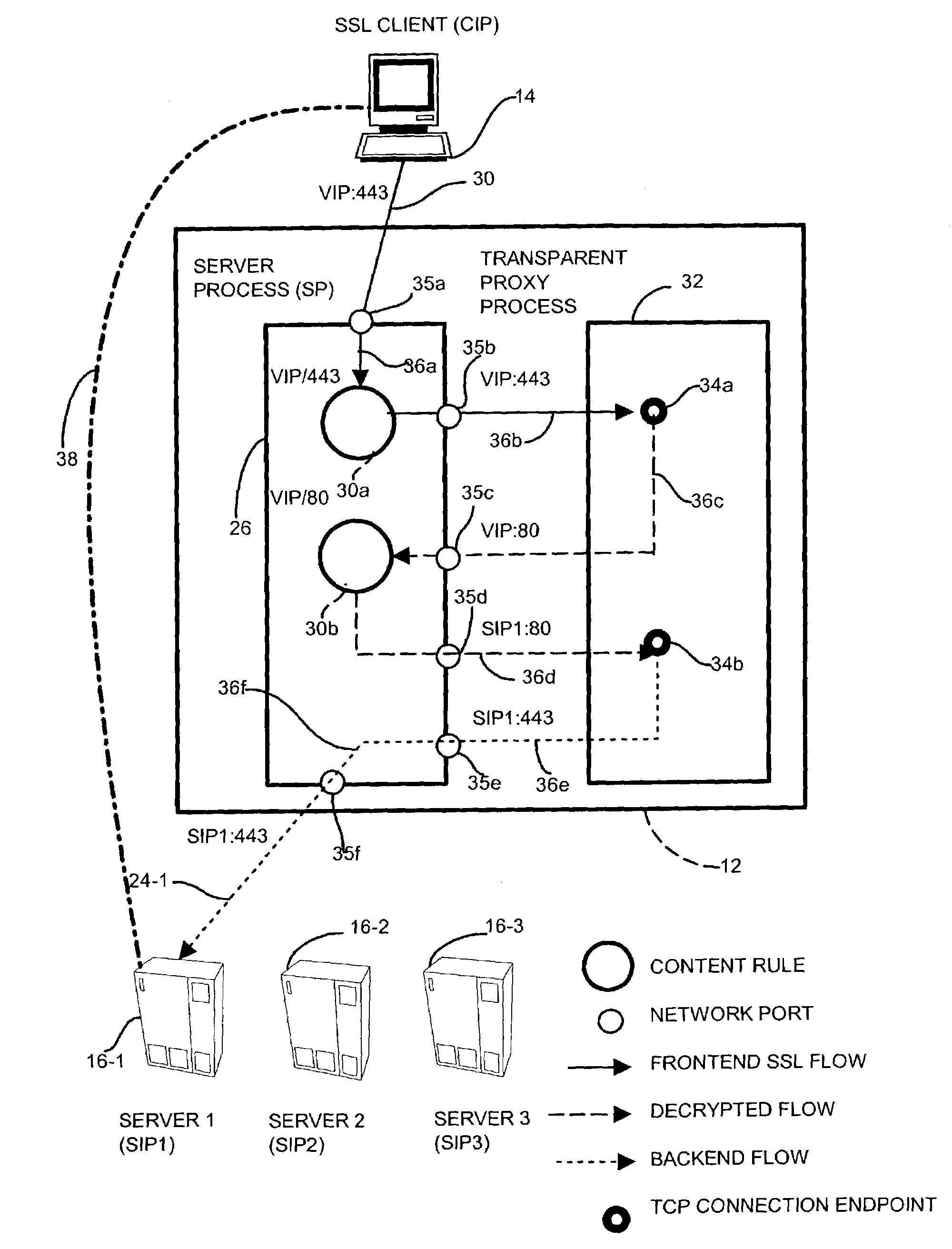
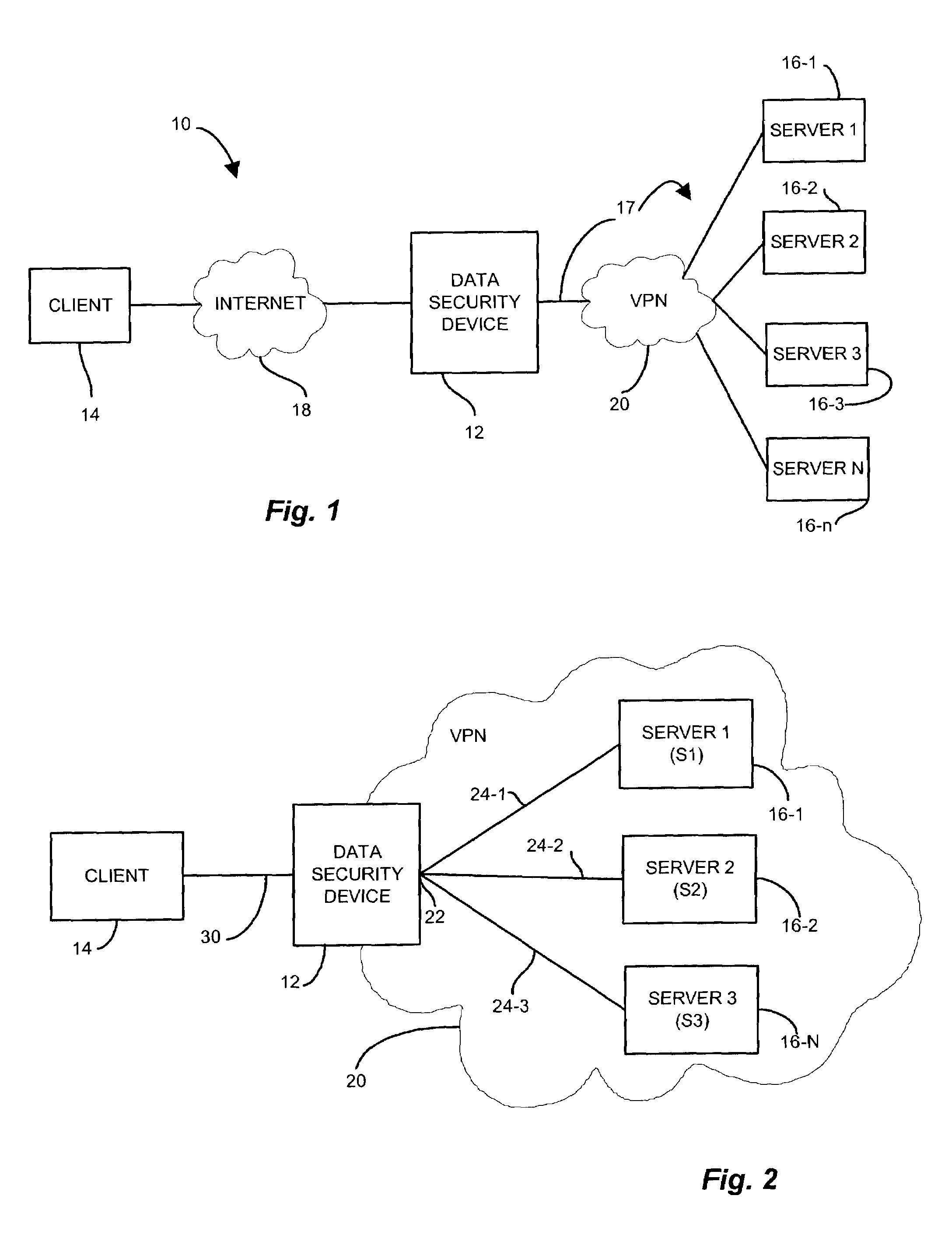
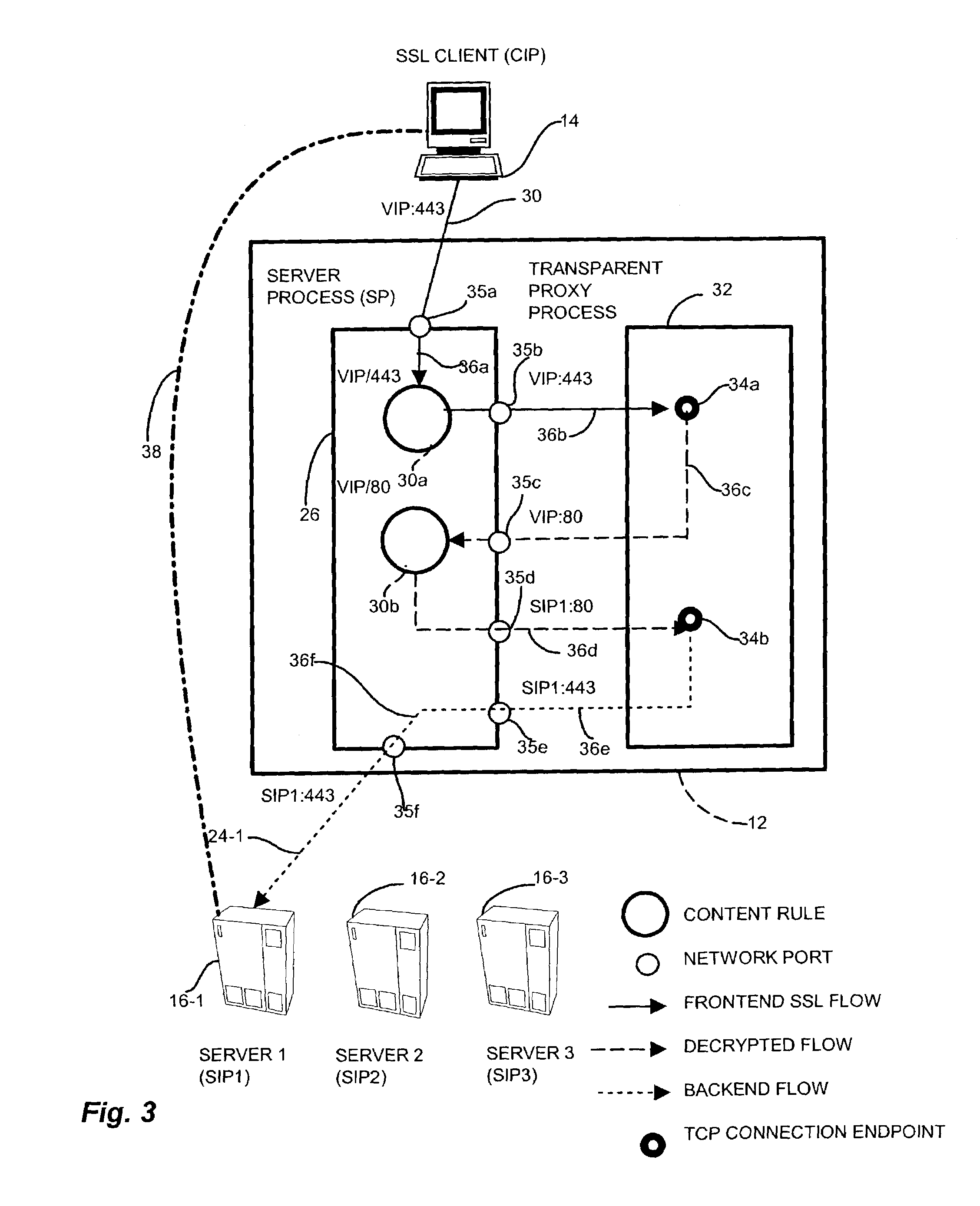
InactiveUS7506368B1Reduce encryption overheadPerformance degradation can be preventedMultiple keys/algorithms usageUser identity/authority verificationSecure communicationNetwork communication
A data security device for providing a network transport connection via a transparent network proxy that employs different encryption security mediums along a communications session between two endpoints by emulating one of the endpoints at an intermediate node such that the communication session appears as an atomic, secure connection to the endpoints yet provides appropriate security over the end-to-end connection. A sender node sends a connection request to establish a secure communication session with an intended receiver node. A transparent proxy on an intermediate node receives the request and establishes the link employing an encryption mechanism. The transparent proxy establishes a second link with the intended receiver, and applies a second, less expensive encryption mechanism. The transparent proxy combines the two links to form the trusted, secure connection but incurring only the mitigated expense over the second link.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com