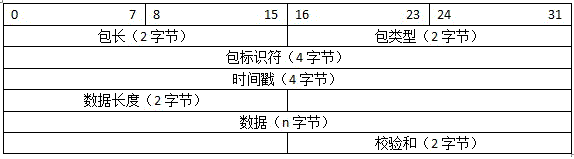
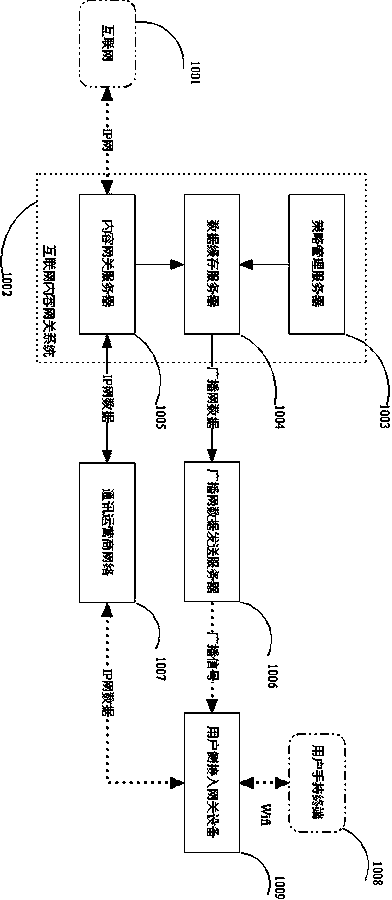
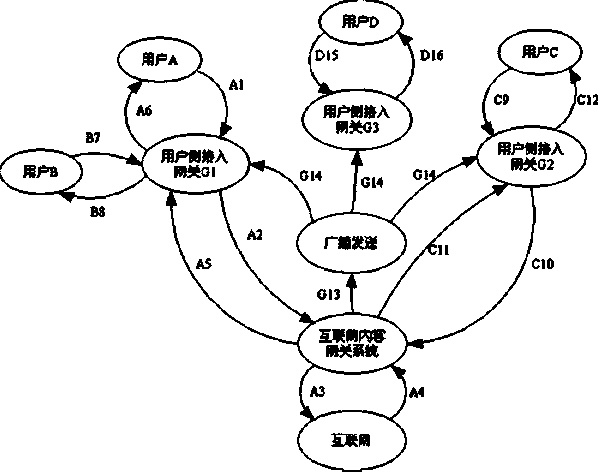
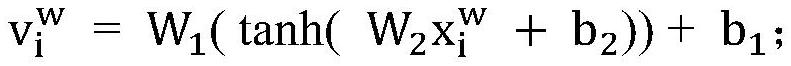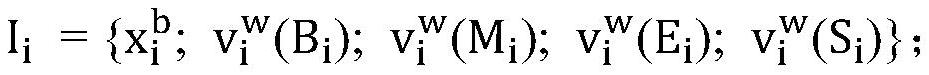Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
109 results about "Network completion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
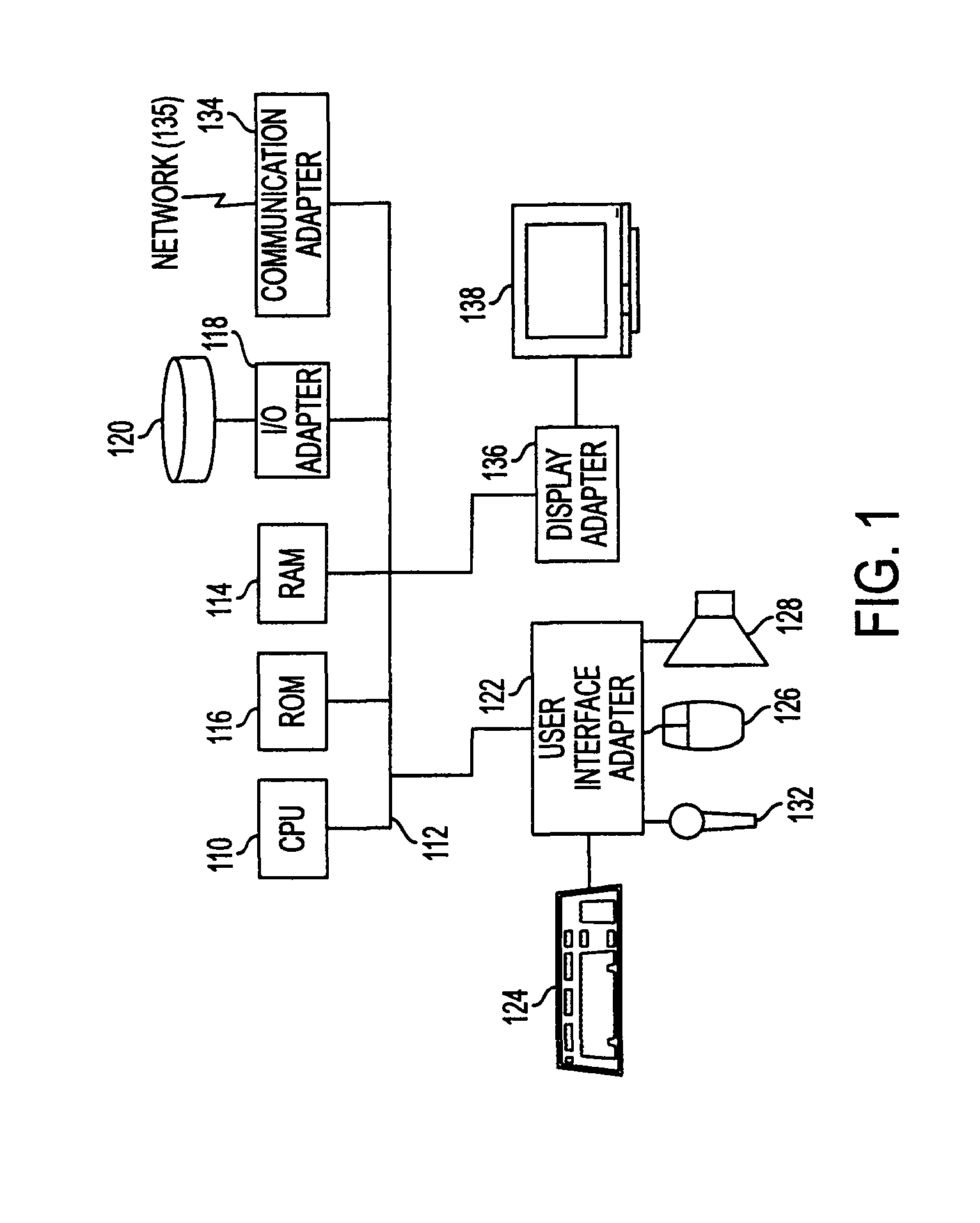
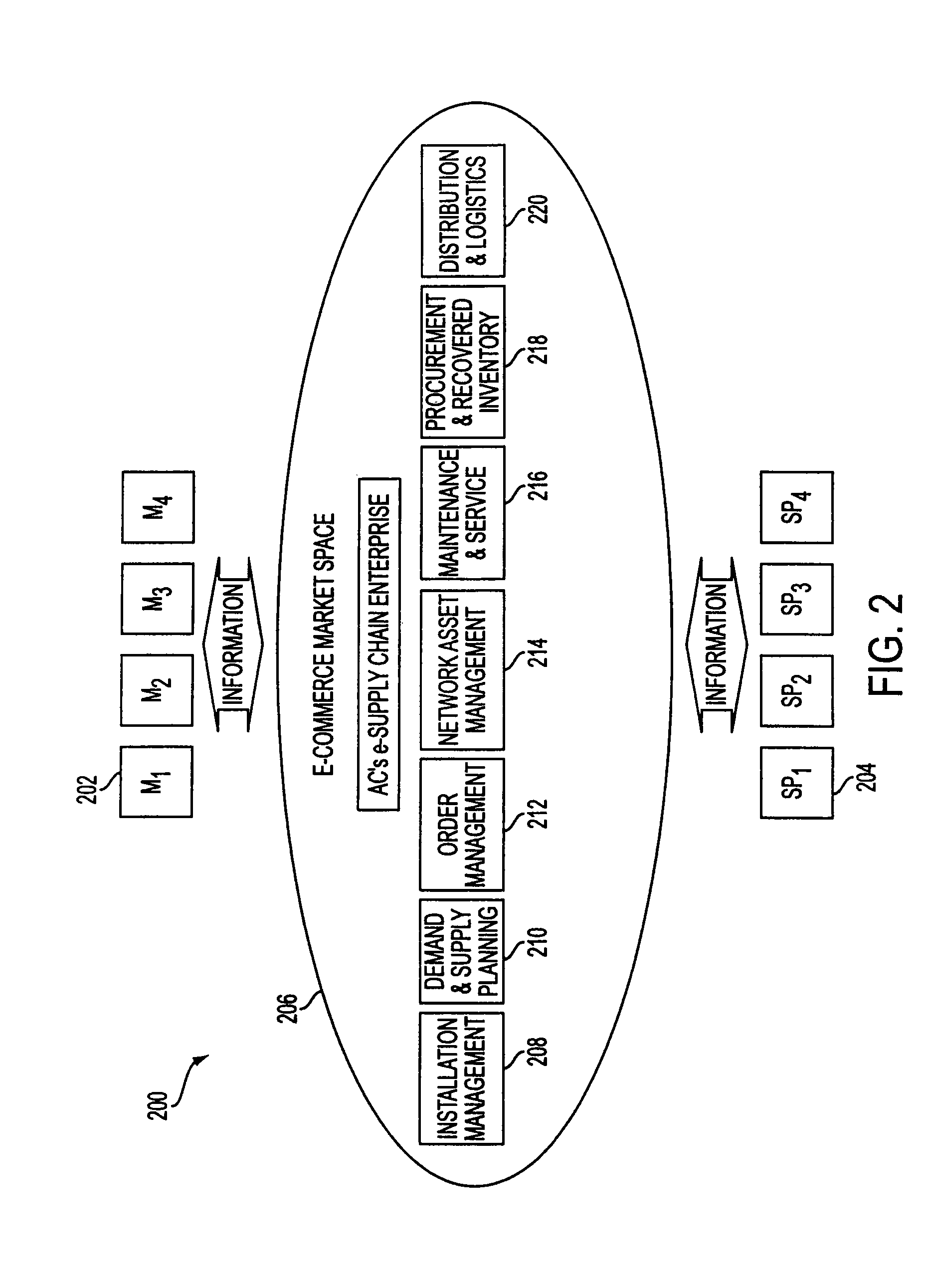
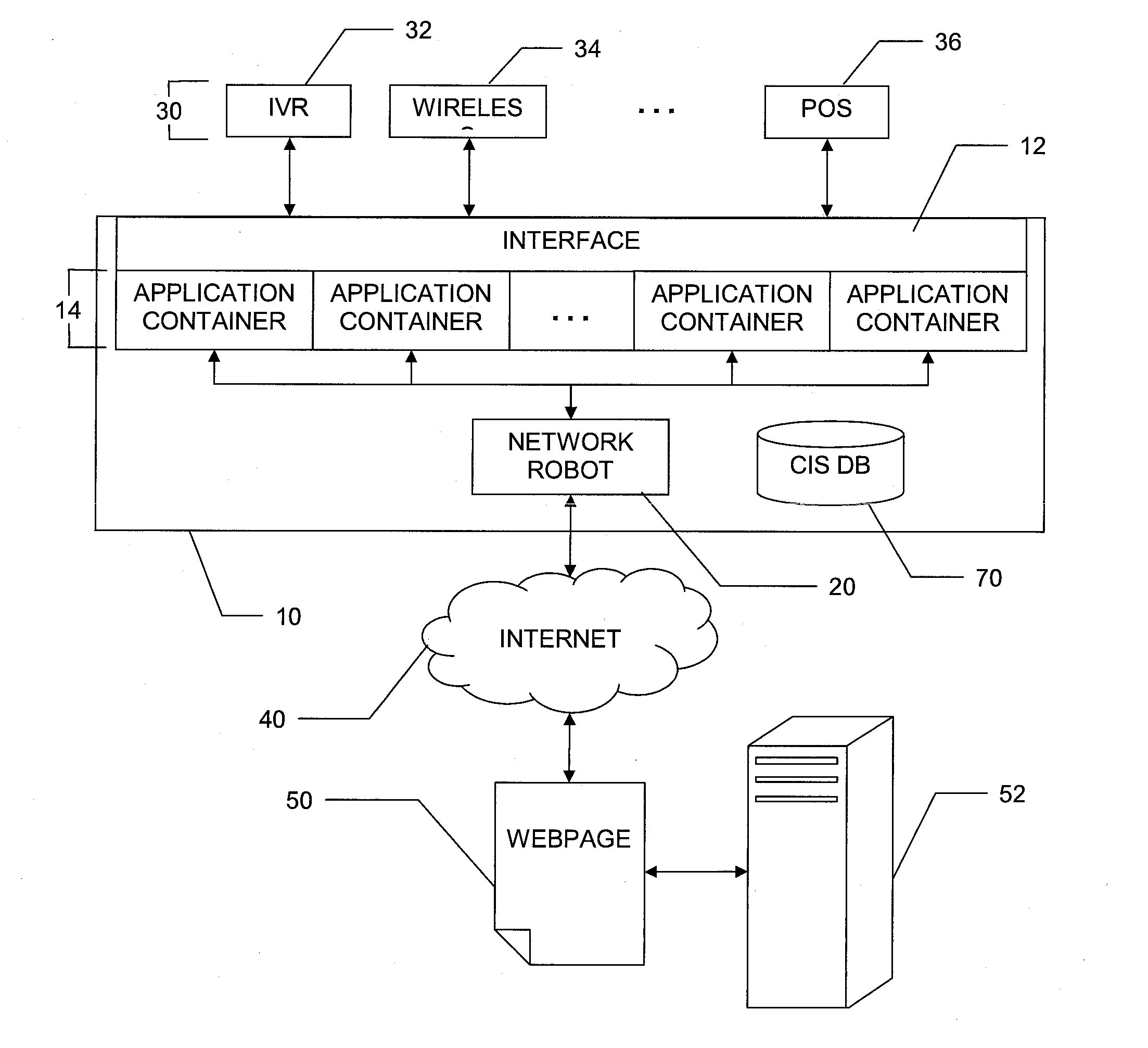
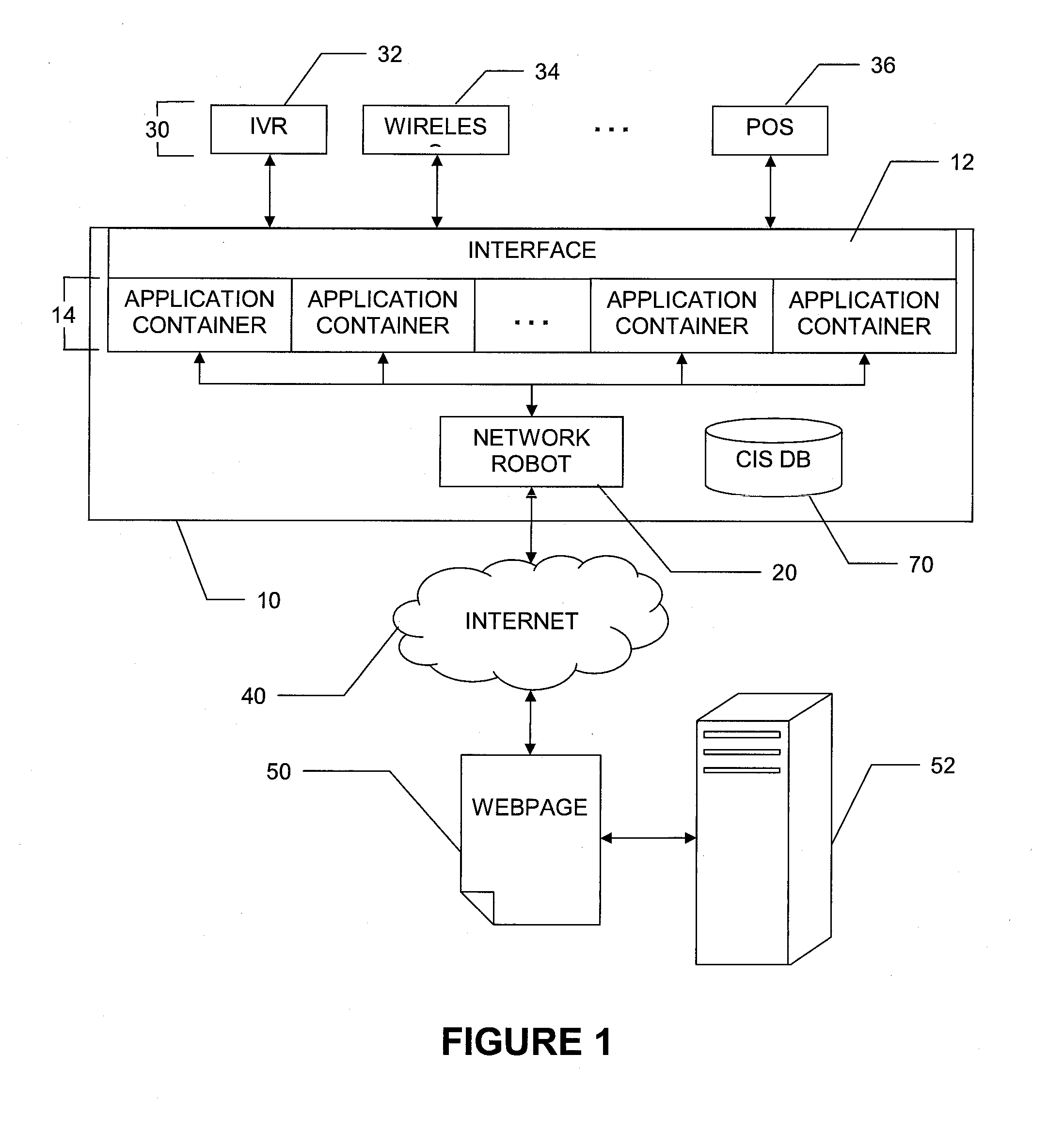
Increased visibility during order management in a network-based supply chain environment
ActiveUS8271336B2Simple personalization processHand manipulated computer devicesNon-fuel substance addition to fuelVisibilityNetwork completion
A system, method and article of manufacture are provided for a first business entity to provide a network-based supply chain framework for collaborative order management between at least a second and a third independent business entity, such as a service provider, vendor, reseller, manufacturer and the like. A request for an order is received over a network with an automated system, from at least a second business entity. The order is transmitted over a network, with an automated system, to at least the third business entity. Information is received from the third business entity relating to a status of completion of the order by the third business entity using a network. The progress in completing the order is tracked based on the information received from the third business entity. Progress reports from the tracking are generated periodically; and transmitted to the second business entity using the network.
Owner:ACCENTURE GLOBAL SERVICES LTD
Increased visibility during order management in a network-based supply chain environment
InactiveUS8732023B2Hand manipulated computer devicesNon-fuel substance addition to fuelVisibilityKnowledge management
A system, method and article of manufacture are provided for a first business entity to provide a network-based supply chain framework for collaborative order management between at least a second and a third independent business entity, such as a service provider, vendor, reseller, manufacturer and the like. A request for an order is received over a network with an automated system, from at least a second business entity. The order is transmitted over a network, with an automated system, to at least the third business entity. Information is received from the third business entity relating to a status of completion of the order by the third business entity using a network. The progress in completing the order is tracked based on the information received from the third business entity. Progress reports from the tracking are generated periodically; and transmitted to the second business entity using the network.
Owner:ACCENTURE GLOBAL SERVICES LTD
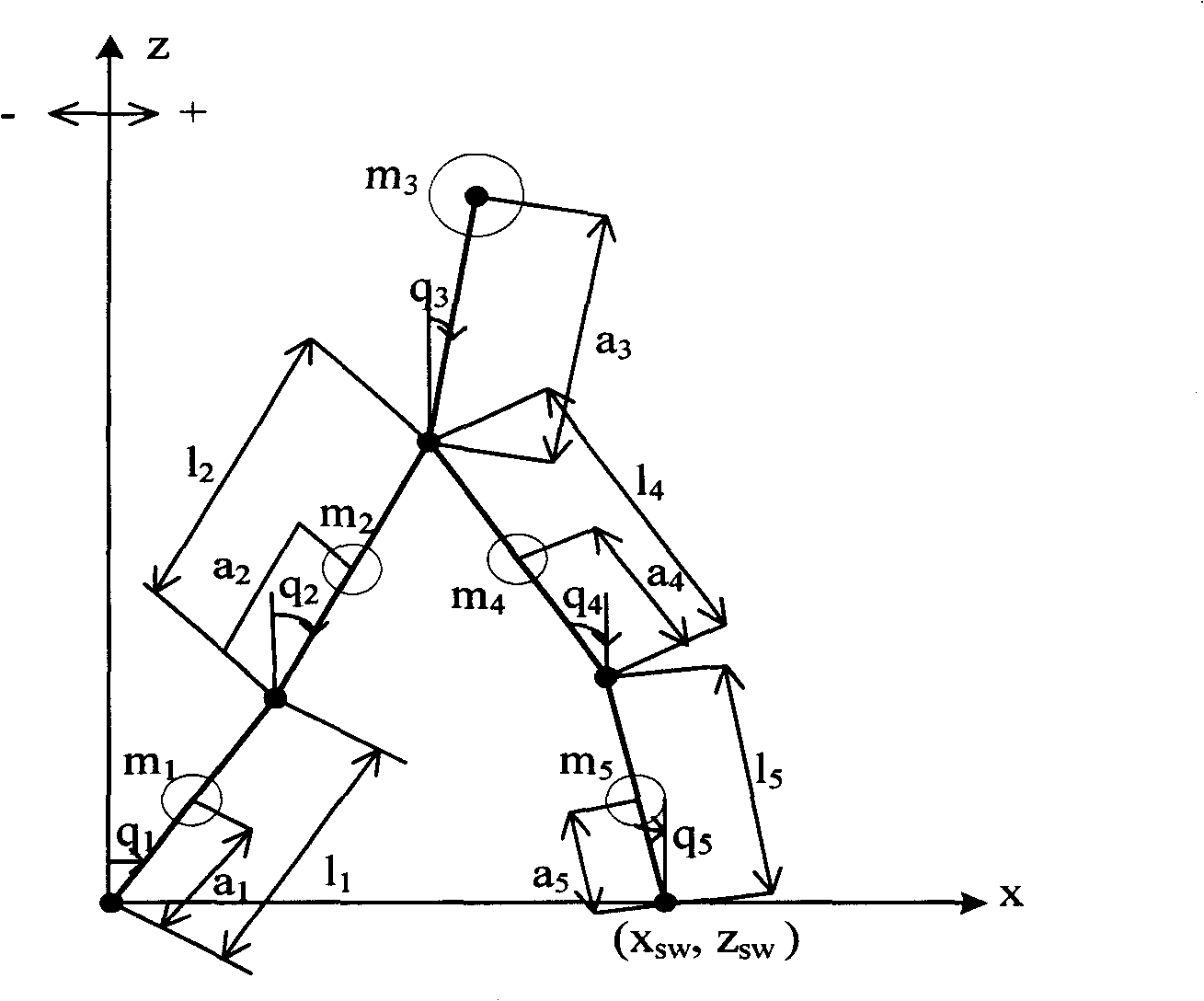
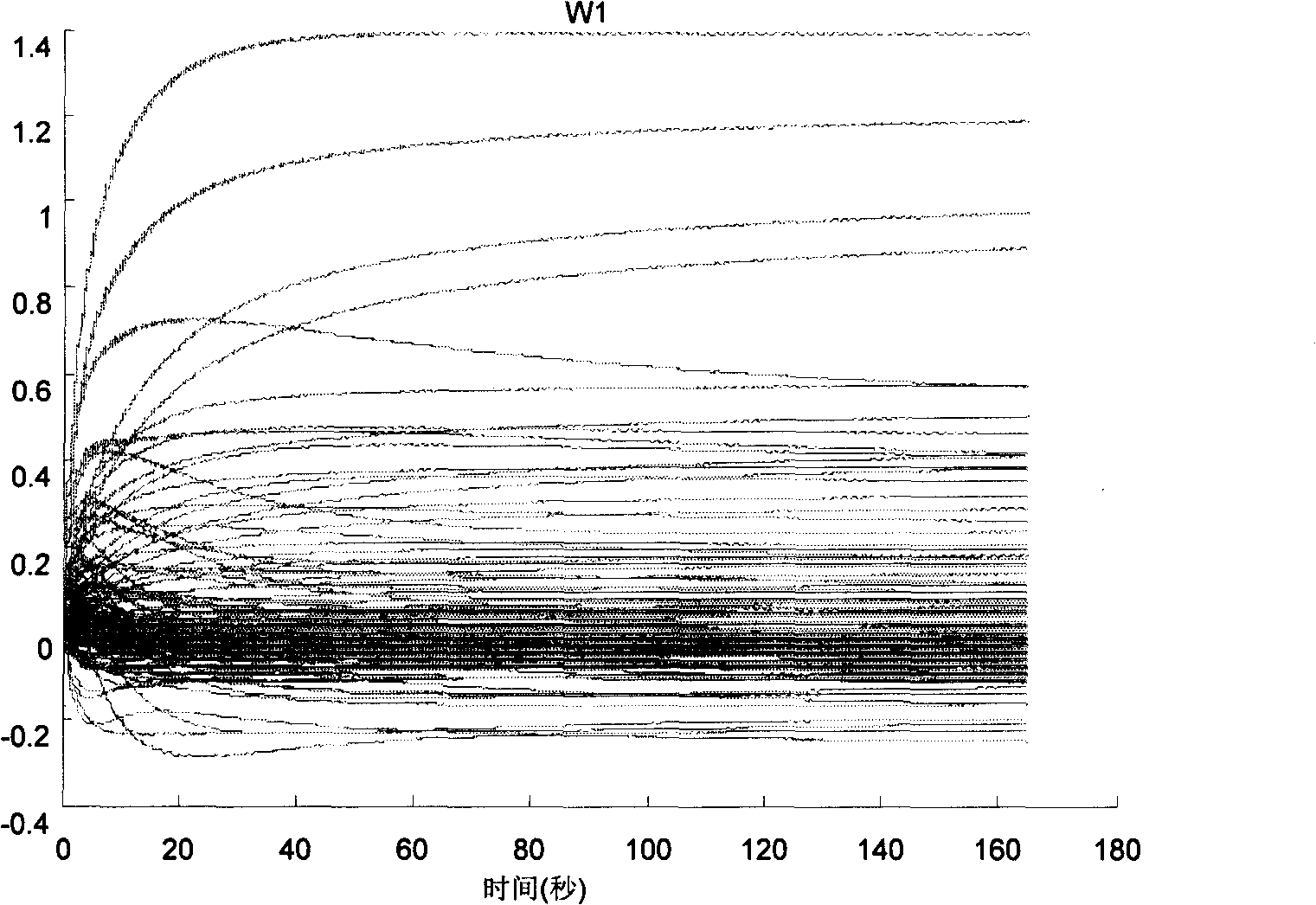
Robot ambulation control method based on confirmation learning theory
InactiveCN101320251AReal learningShorten the timeAdaptive controlPosition/course control in two dimensionsDynamic modelsClosed loop
The invention relates to a robot walking control method based on the determined study theory. The method comprises the processes such as the establishment of robot walking model, the establishment of referenced gait model, the study on the neural network, the establishment of constant neural network, the completion of walking task by utilizing the constant RBF neural network, etc. The invention overcomes the disadvantages of learning ability in the current neural network study and the control method and realizes the accurate study of the unknown dynamic model of a robot closed-loop control system along the periodic gait track of the robot within a local area, and can study the effective knowledge of the system dynamics during the stable dynamic control process and apply the knowledge to the subsequent same or similar tasks successfully. The method not only can realize the rapid walking on the basis of energy saving, but also provides the powerful support for the development of the humanoid robots.
Owner:SOUTH CHINA UNIV OF TECH
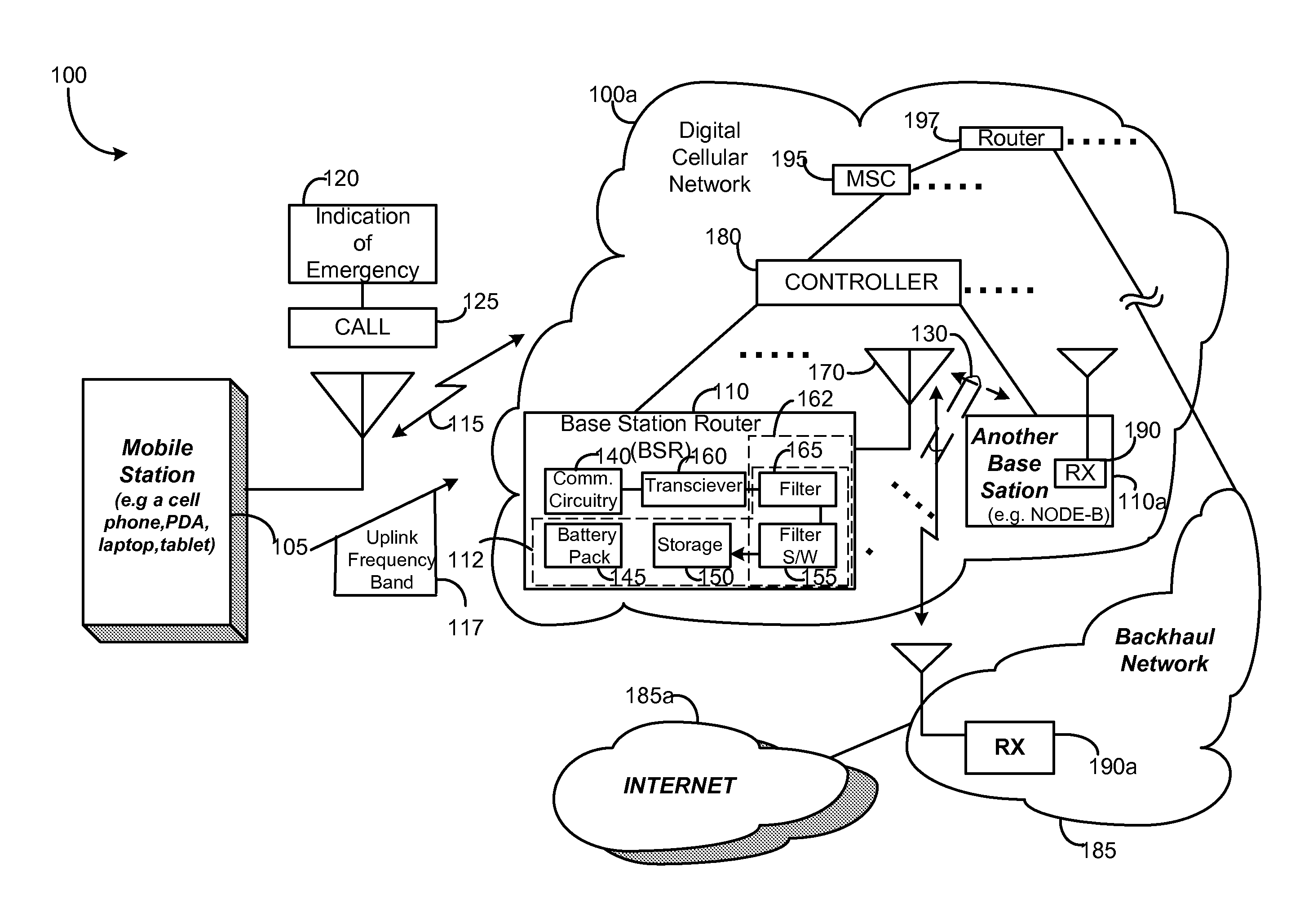
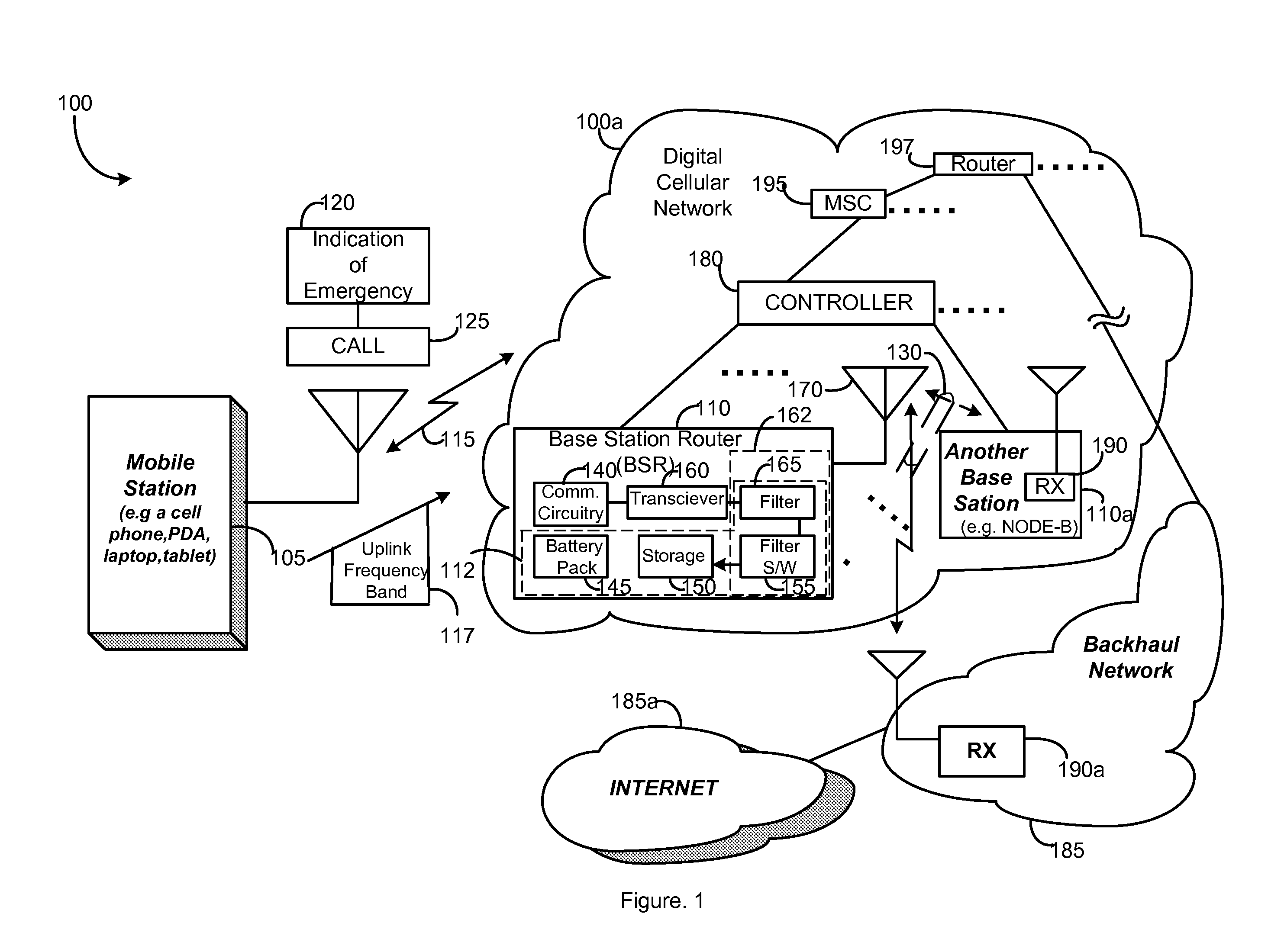
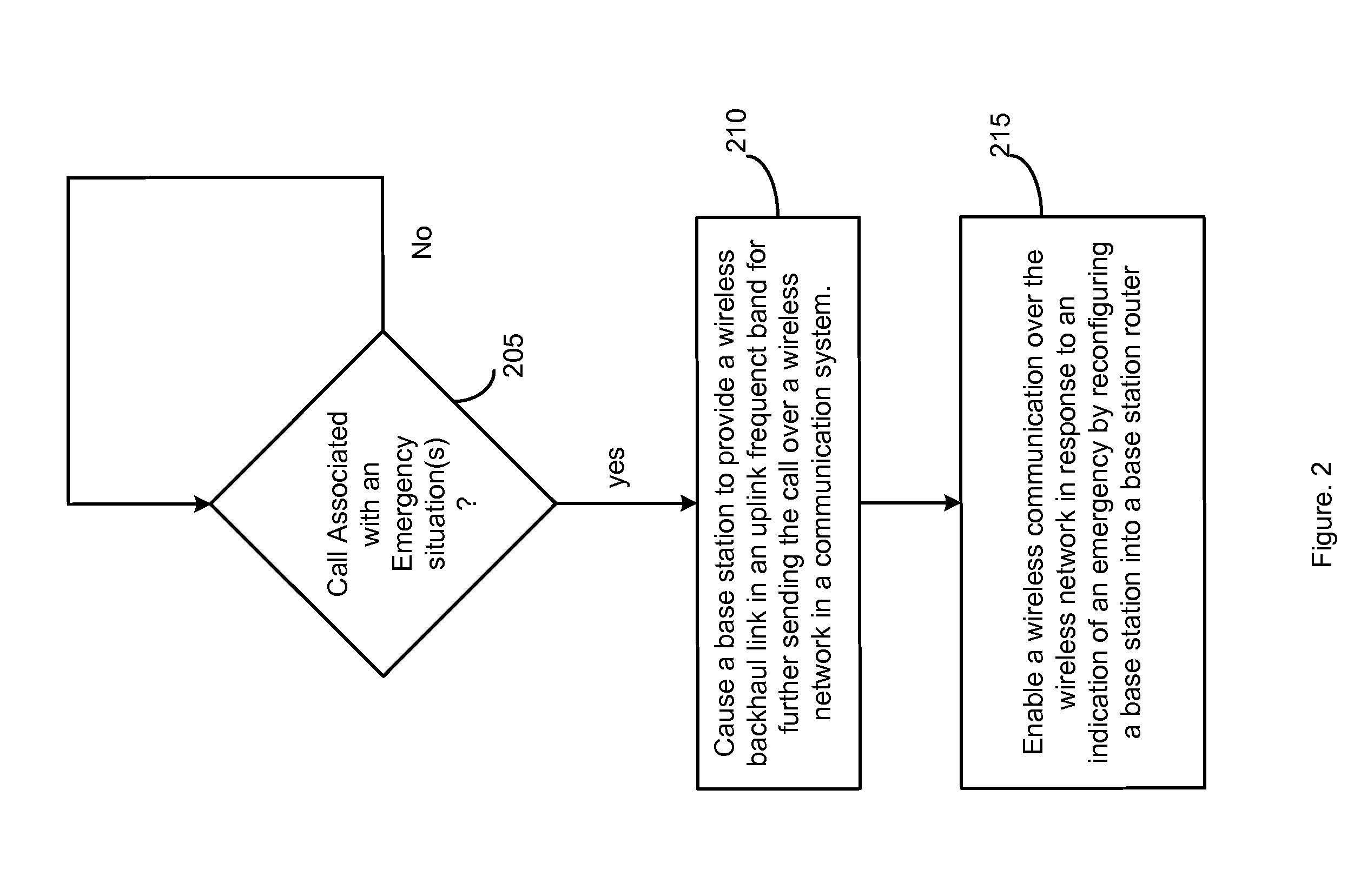
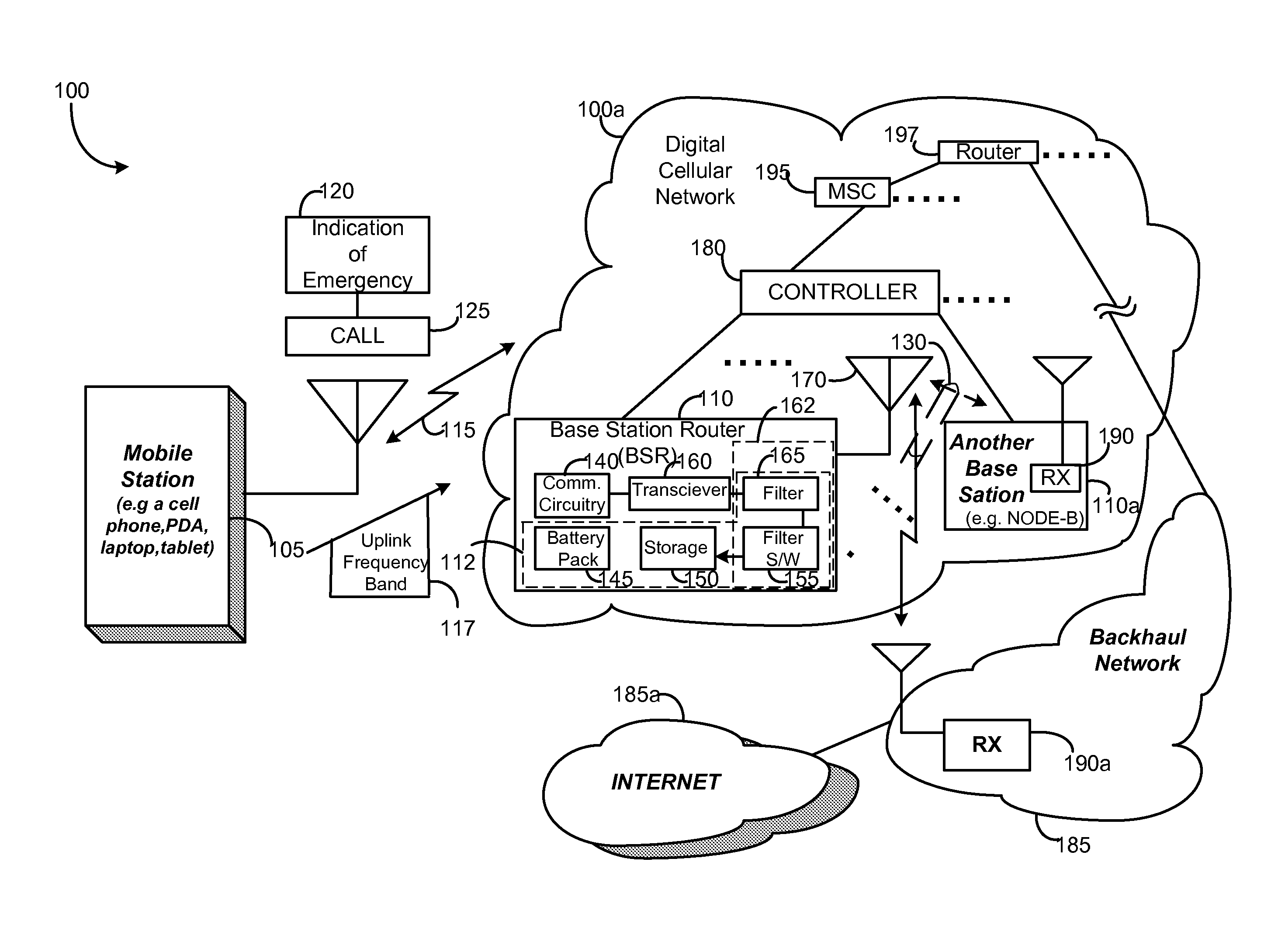
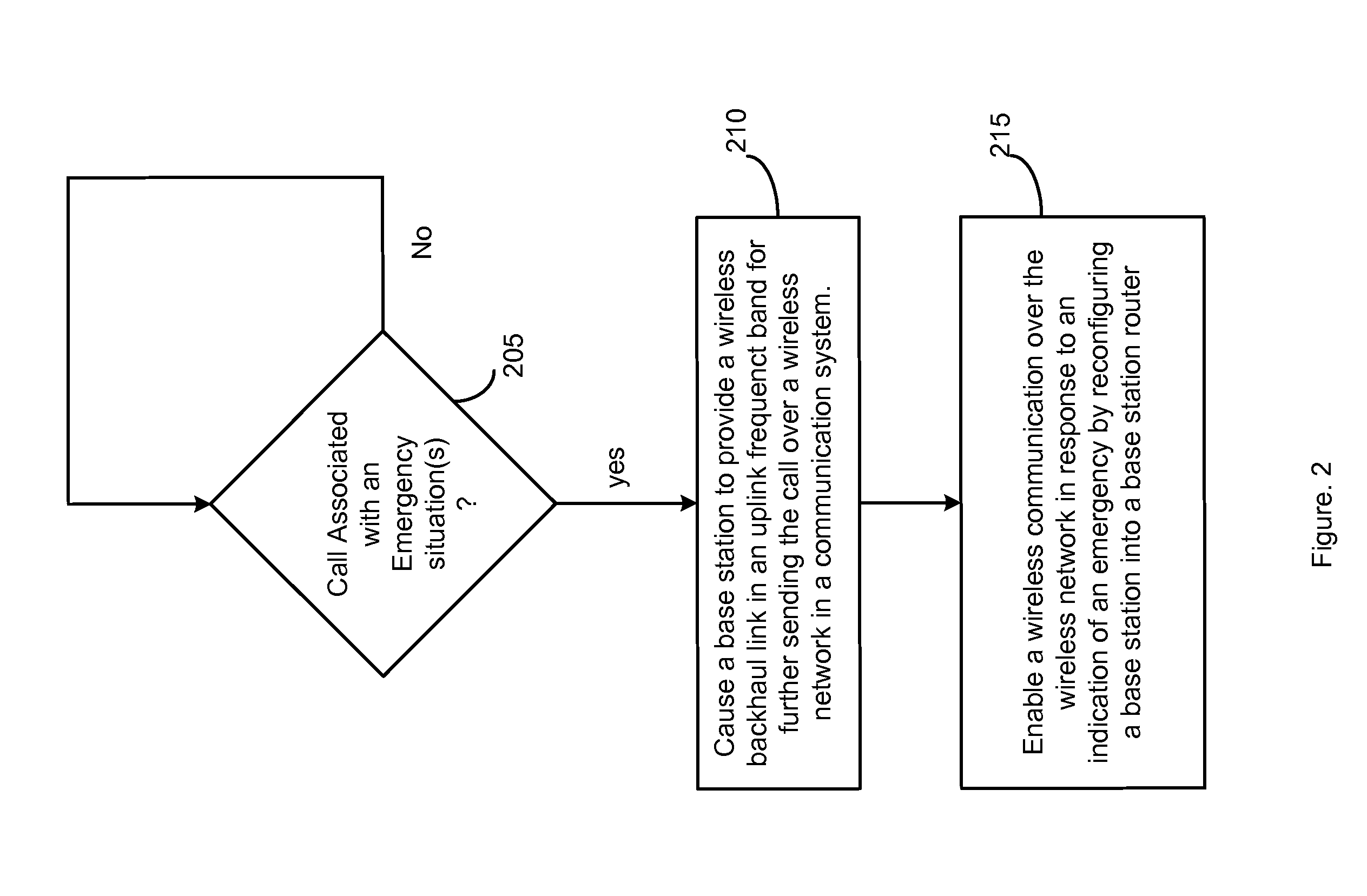
Completing emergency calls over a network with a malfunctioning backhaul communications link
InactiveUS20070218868A1Well formedEmergency connection handlingNetwork topologiesTelecommunications linkCommunication link
A method and an apparatus are provided for enabling a wireless communication over a network in response to an indication of an emergency. The method comprises causing a base station to provide a wireless backhaul link in an uplink frequency band for further sending a call over the network in response to the call associated with the emergency. Reconfiguration enables turning a base station or base station router into a high power terminal. In this way, emergency calls may be completed over a network having at least one malfunctioning backhaul communications link in a network backbone.
Owner:ALCATEL-LUCENT USA INC
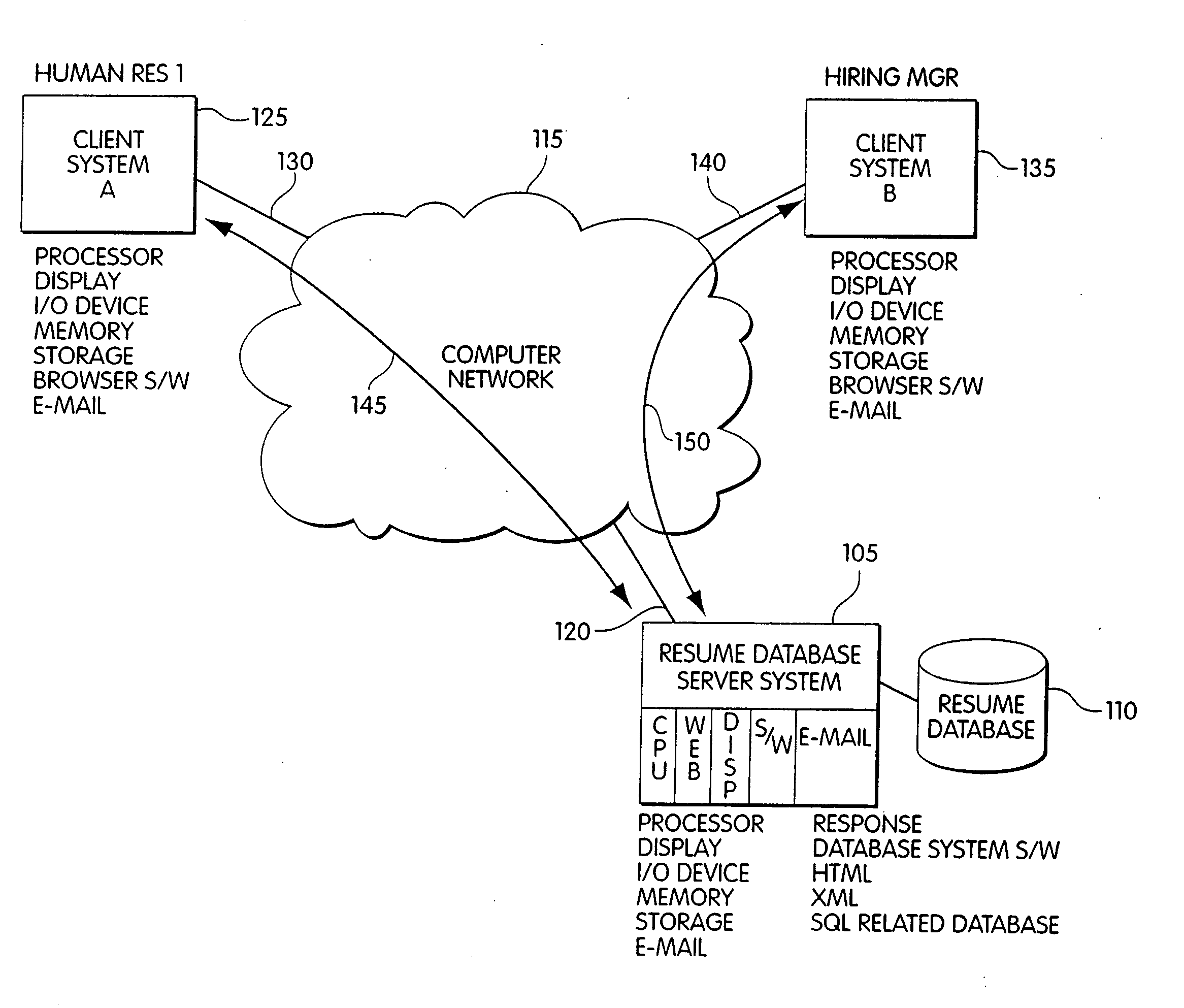
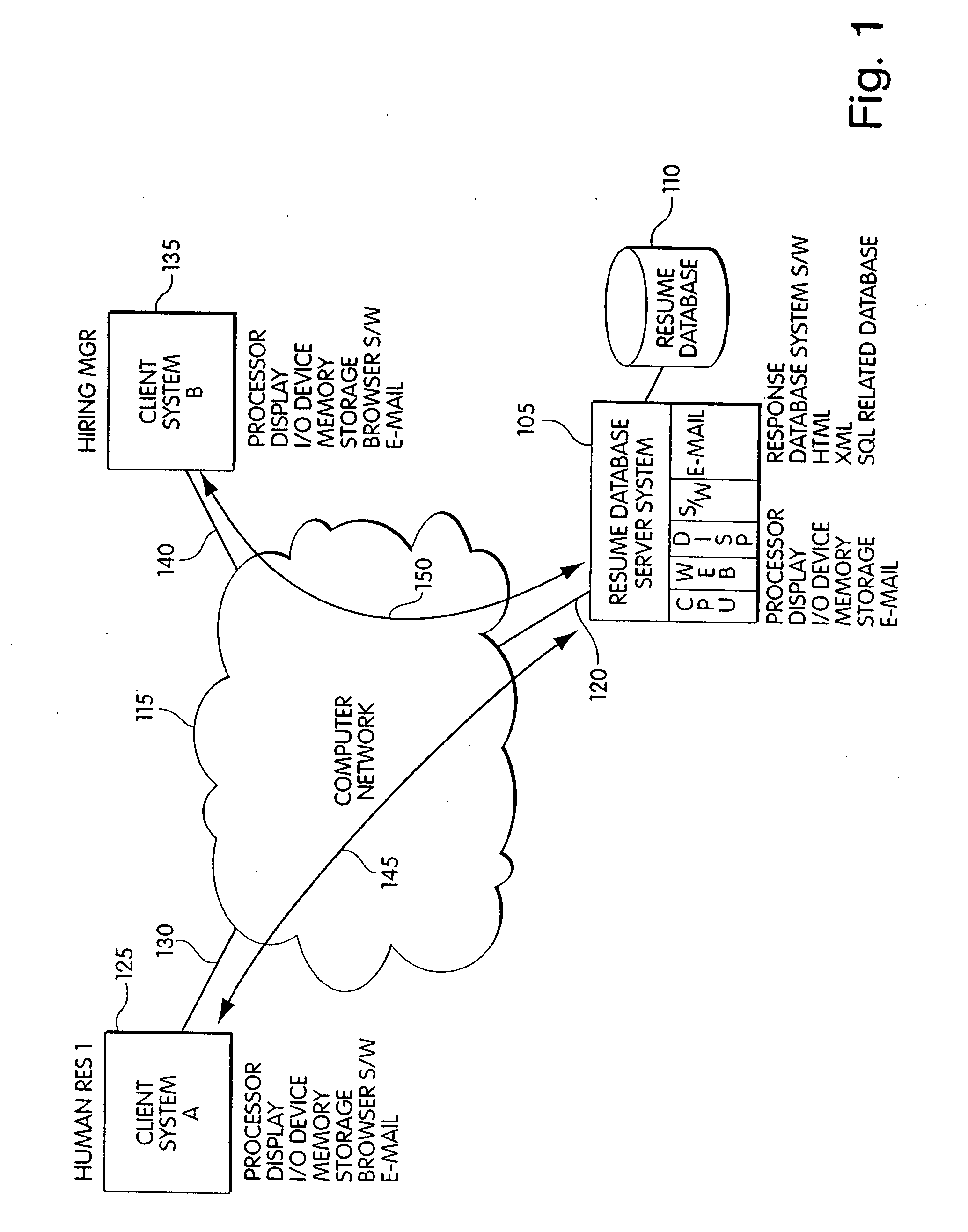
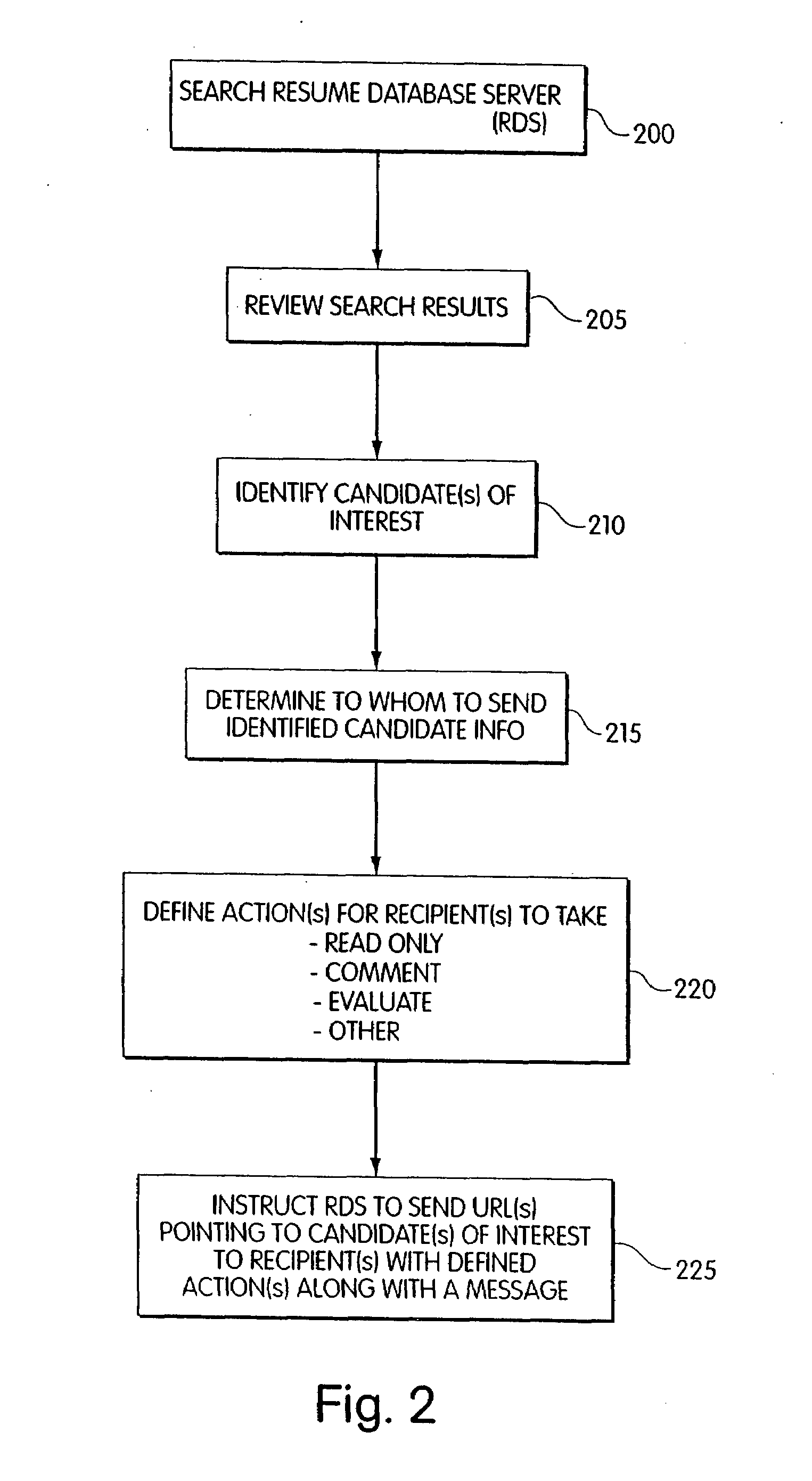
Method and apparatus for sending and tracking resume data sent via URL
InactiveUS20080147736A1Digital data processing detailsComputer security arrangementsWeb browserDatabase server
A resume database system allows for resume records on the resume database system to be viewed by others via a Uniform Resource Locator, URL. In addition, in response to instructions from an authorized user of the resume database system, input from an unauthorized, but otherwise verified, source can be added to the database by the resume database system. The verified user accesses the resume database and completes any necessary forms via a web browser and submits the information. The authorized user defines the actions that the verified user is allowed to take. These actions include, for example, only being able to review resume information, or being able to add information to the resume database without needing training on the operation of the database. A resume database server system coordinates the activity of the authorized and verified users. Communications between all three users is accomplished via a computer network.
Owner:INFINITE COMP SOLUTIONS INC
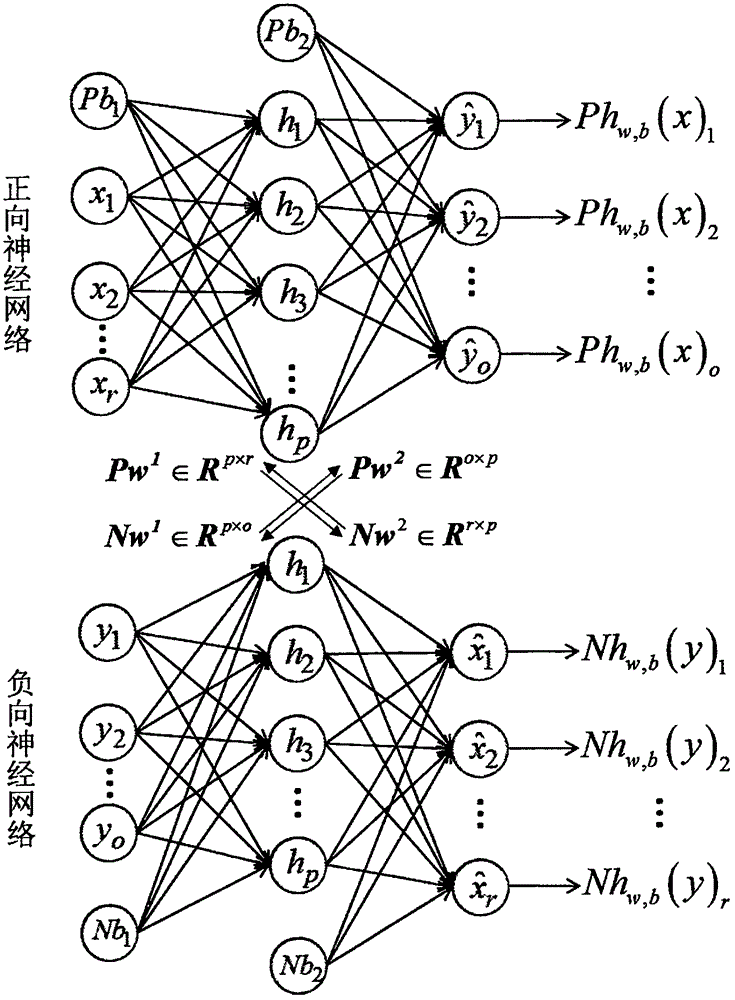
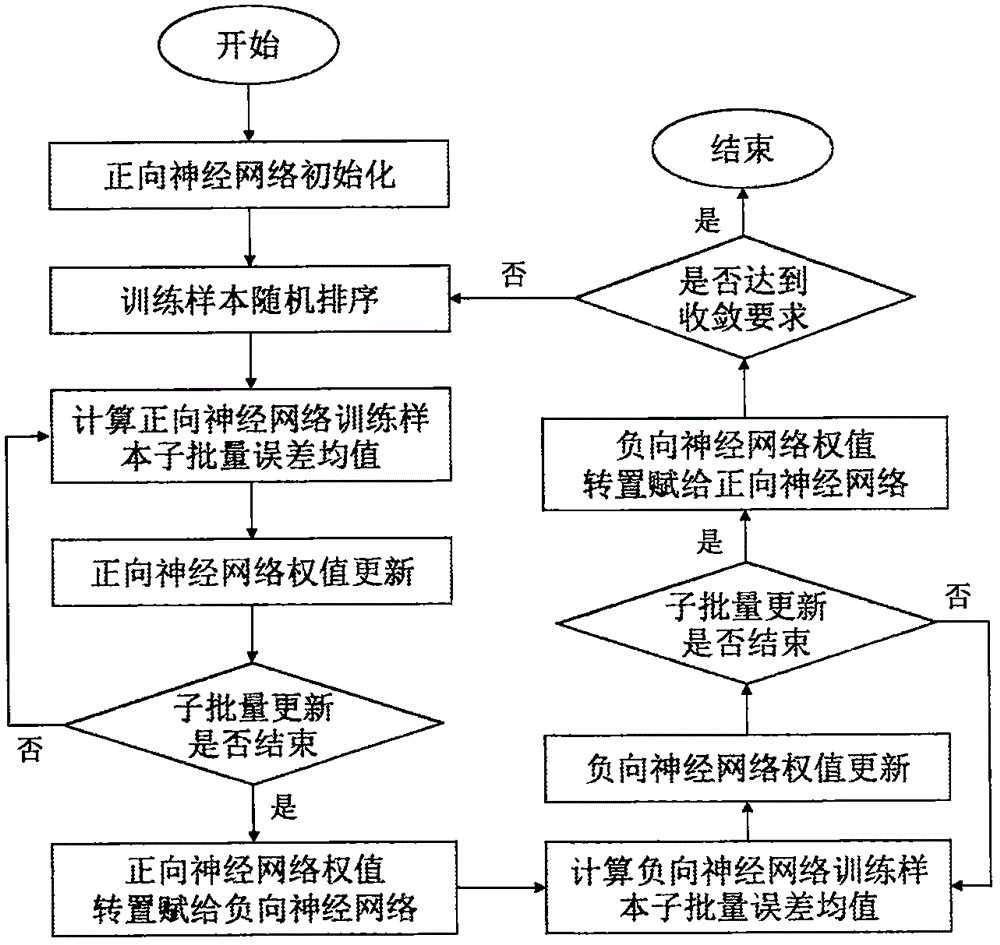
Novel neural network model for simulating biological bidirectional cognition capability, and training method
ActiveCN106560848AProof of validityQuick searchPhysical realisationNeural learning methodsNerve networkCognition
The invention discloses a novel neural network model for simulating biological bidirectional cognition capability, and a training method. The model consists of a positive neural network and a negative neural network. The positive neural network completes the simulation of a positive cognition process from the input to the output, and the negative neural network completes the simulation of a positive cognition process from the output to the input, wherein the two neural network structures are symmetric, and share a weight. The corresponding connection weight matrixes of the positive and negative neural networks are in a transposition relation. According to the invention, a coordinative structure of the positive and negative neural networks which are symmetric in structure and shares the weight is built, thereby achieving the simulation of the biological bidirectional cognition capability. A mode of negative learning process is introduced into a process of a standard BP algorithm, and a novel neural network training method is proposed.
Owner:LIAONING TECHNICAL UNIVERSITY
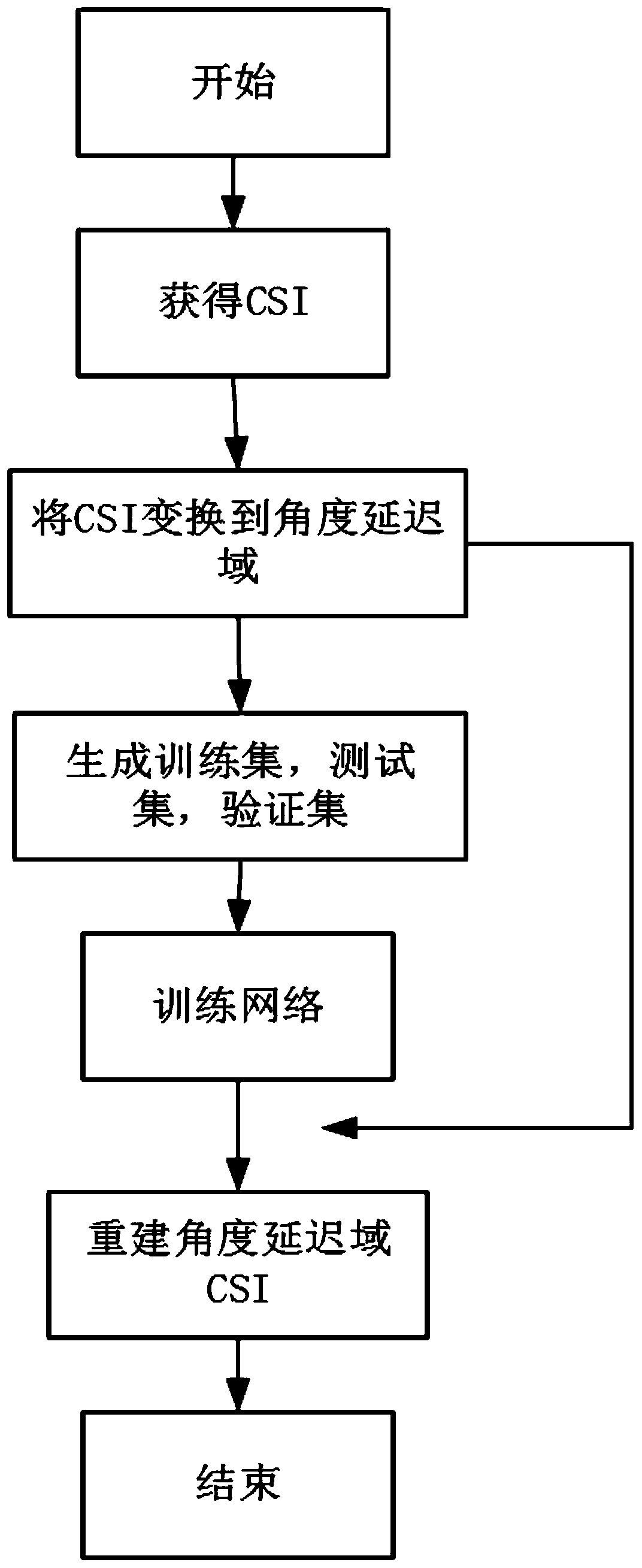
Channel state information reconstruction method based on deep learning
ActiveCN111464220AReduce overfittingEasy to compressSpatial transmit diversityChannel estimationOriginal dataInformation networks
The invention discloses a channel state information reconstruction method based on deep learning. The method comprises the following steps: obtaining an NBS * Nc-dimensional channel matrix H on a frequency domain at a user side; converting the obtained channel matrix H into an angle delay domain channel matrix Ha with only non-zero elements; in the angle time delay domain, acquiring a new dimension matrix by advancing in the intercepted channel matrix Ha, converting the new matrix into a non-sparse vector X with the dimension of 2N * 1, wherein the non-sparse vector X serves as to-be-compressed data, and carrying out compression through the compressed sensing technology to obtain to-be-fed back channel state information Y; reconstructing and training a channel state information network; and according to the trained ReNet network model, recovering Y as input data of the network and as output data of the network from the obtained channel state information Y to be fed back, and performinginverse Fourier transform to obtain original CSI after obtaining. The original CSI data obtained by the user side is processed, subsequent compression and feedback are facilitated, and recovery ofthe compressed data is completed through the network trained by the known samples.
Owner:XI AN JIAOTONG UNIV
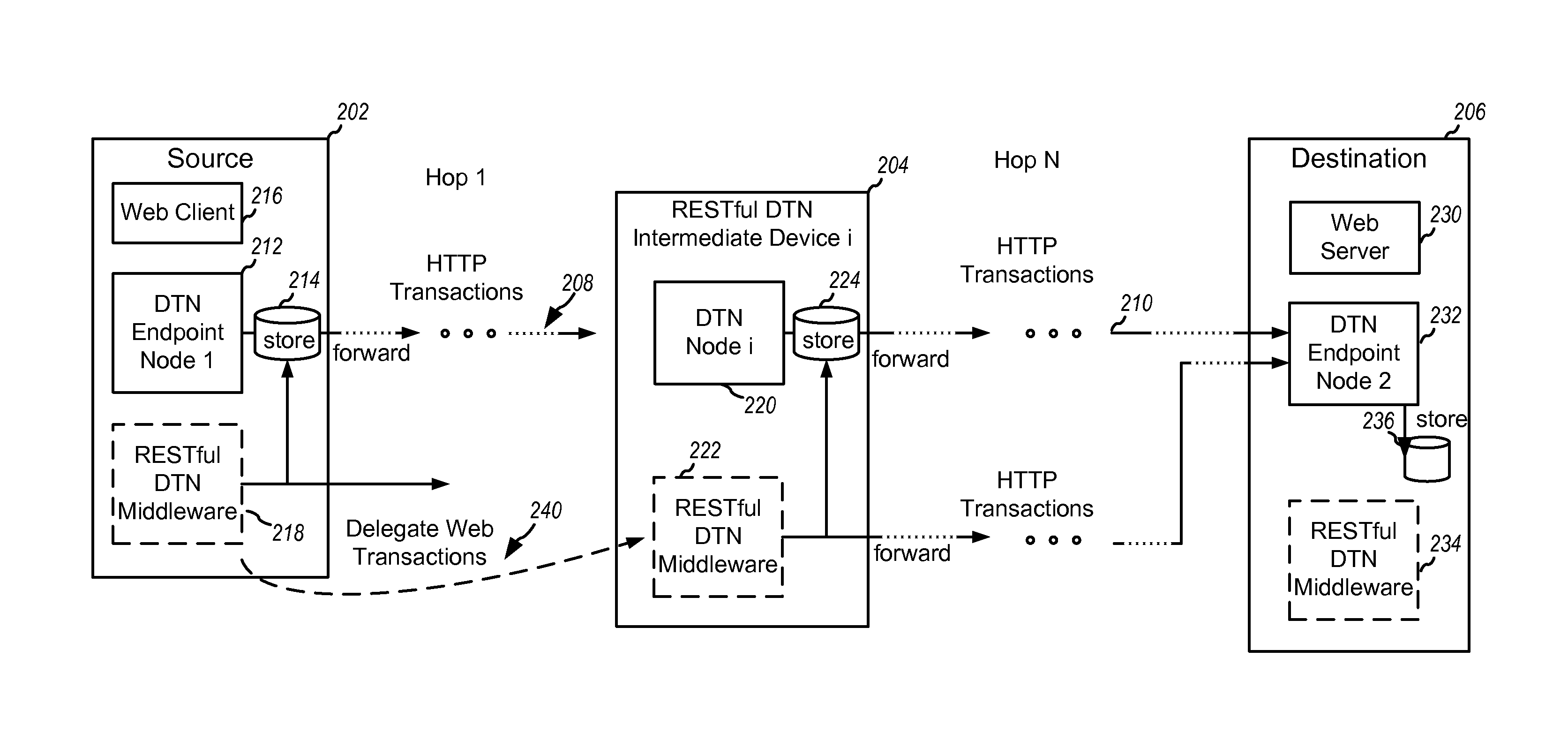
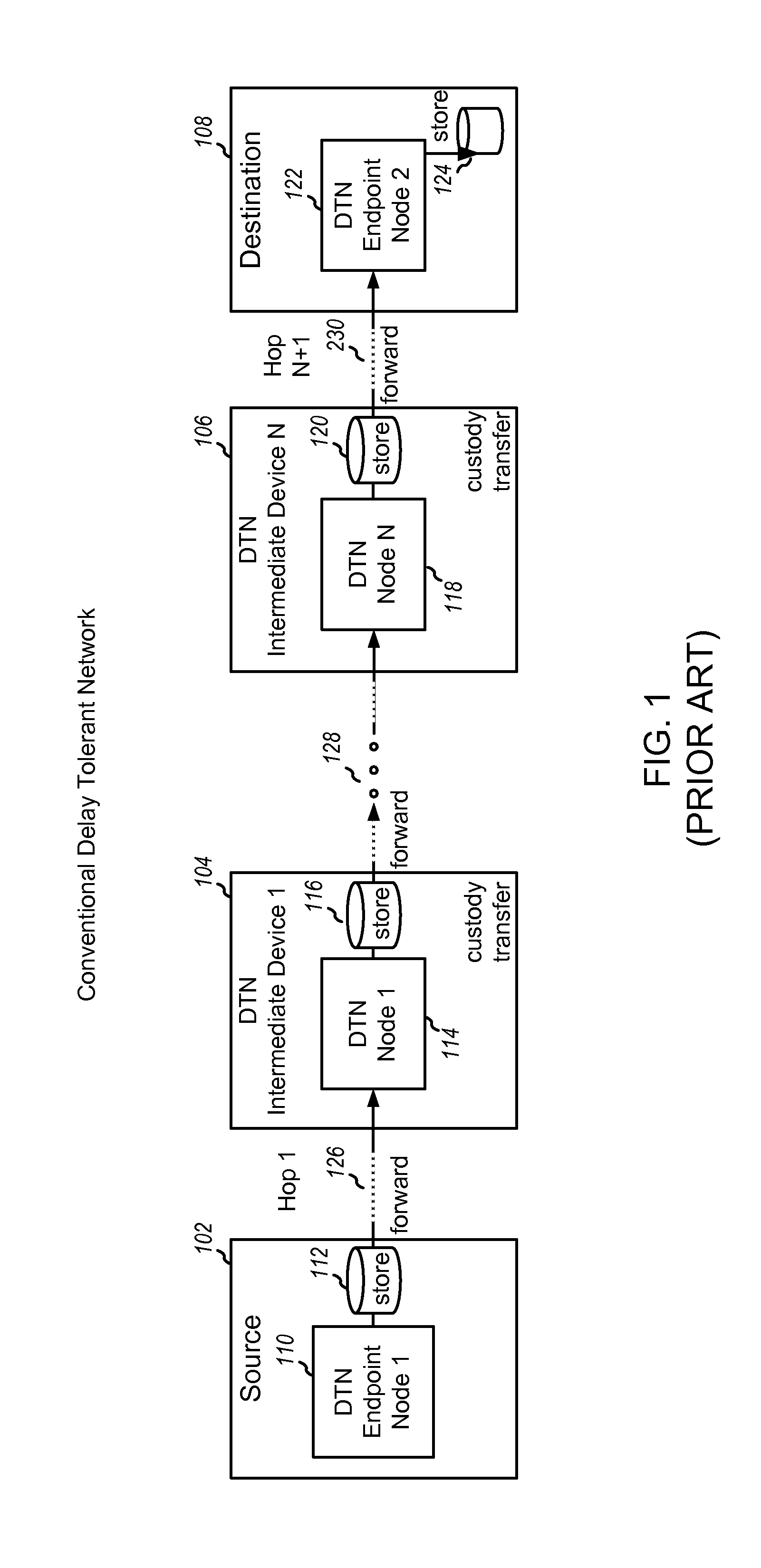
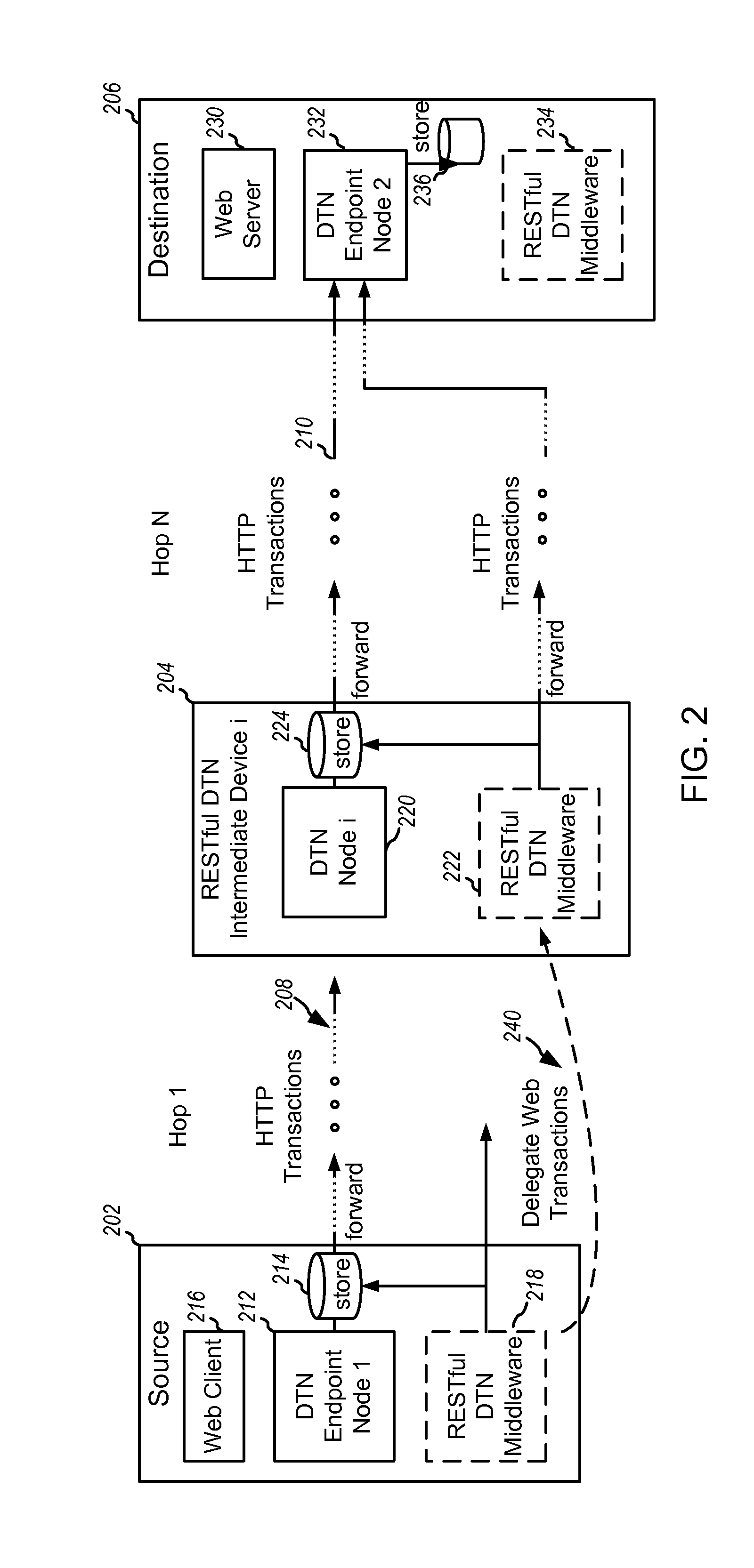
Delay-tolerant web transaction delegations
InactiveUS20140032730A1Good flexibilityGreat temporal flexibilityDigital computer detailsTransmissionFinancial transactionNetwork completion
Embodiment methods and systems enable completing online transactions when there is insufficiently reliable connectivity between the initiating computing device and the remote server to enable completing the transaction directly. Transactions in such situations are accomplished using a RESTful Delay Tolerant Network. A set of messages constituting the web transaction are bundled, together with instructions and other metadata, in a manner that enables intermediate nodes in the network to complete the transactions on behalf of the source computing device. The source computing device then delegates the web transaction to an intermediate node. If the intermediate node can complete the transaction with the destination device, it does so on behalf of the source computing device. If not, the intermediate node delegates the web transaction to another intermediate node, which may be repeated until an intermediate node is able to complete the transaction with the destination.
Owner:QUALCOMM INC
Method for realizing STA cross-domain roaming through cloud AC
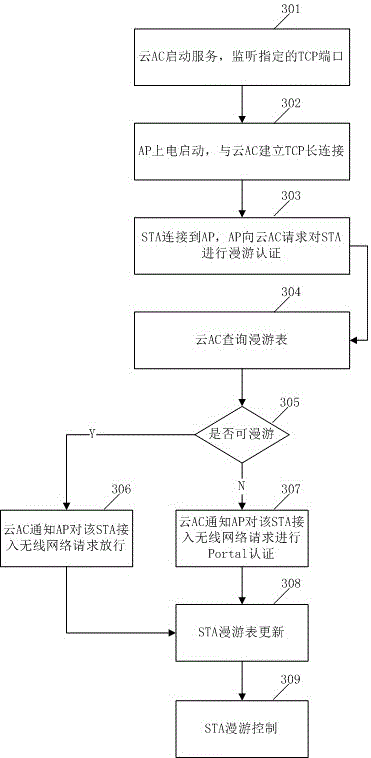
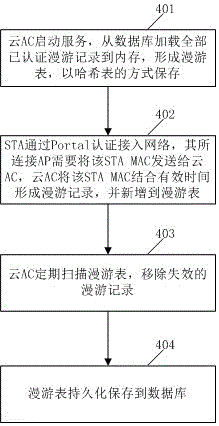
PendingCN105848131AEfficient managementLow costNetwork traffic/resource managementTransmissionRoamingEngineering
The invention provides a method for realizing STA cross-domain roaming through a cloud AC. The method comprises the steps that an AP uses a private protocol to keep communication with the cloud AC through TCP long connection, and the MAC address of an STA accessed to the AP is transmitted to the cloud AC according to a defined message format; the cloud AC receives the message transmitted by the AP, and the message is analyzed and then the MAC address of the STA is saved in a cloud AC roaming table; and when the AP receives an STA authentication request, the MAC address of the STA is transmitted to the cloud AC to perform roaming judgment, if the cloud AC inquires the roaming table and then determines that the MAC address of the STA is authenticated and in the period of validity, the cloud AC responds an STA access authentication roaming success message to the AP, and the AP enables the STA connected with the AP to be successfully authenticated and accessed to the network and thus roaming is completed. The problem of STA cross-domain roaming can be effectively realized at low cost without dependence on a hardware AC so that deployment and operation are facilitated.
Owner:XIAMEN FOUR FAITH COMM TECH
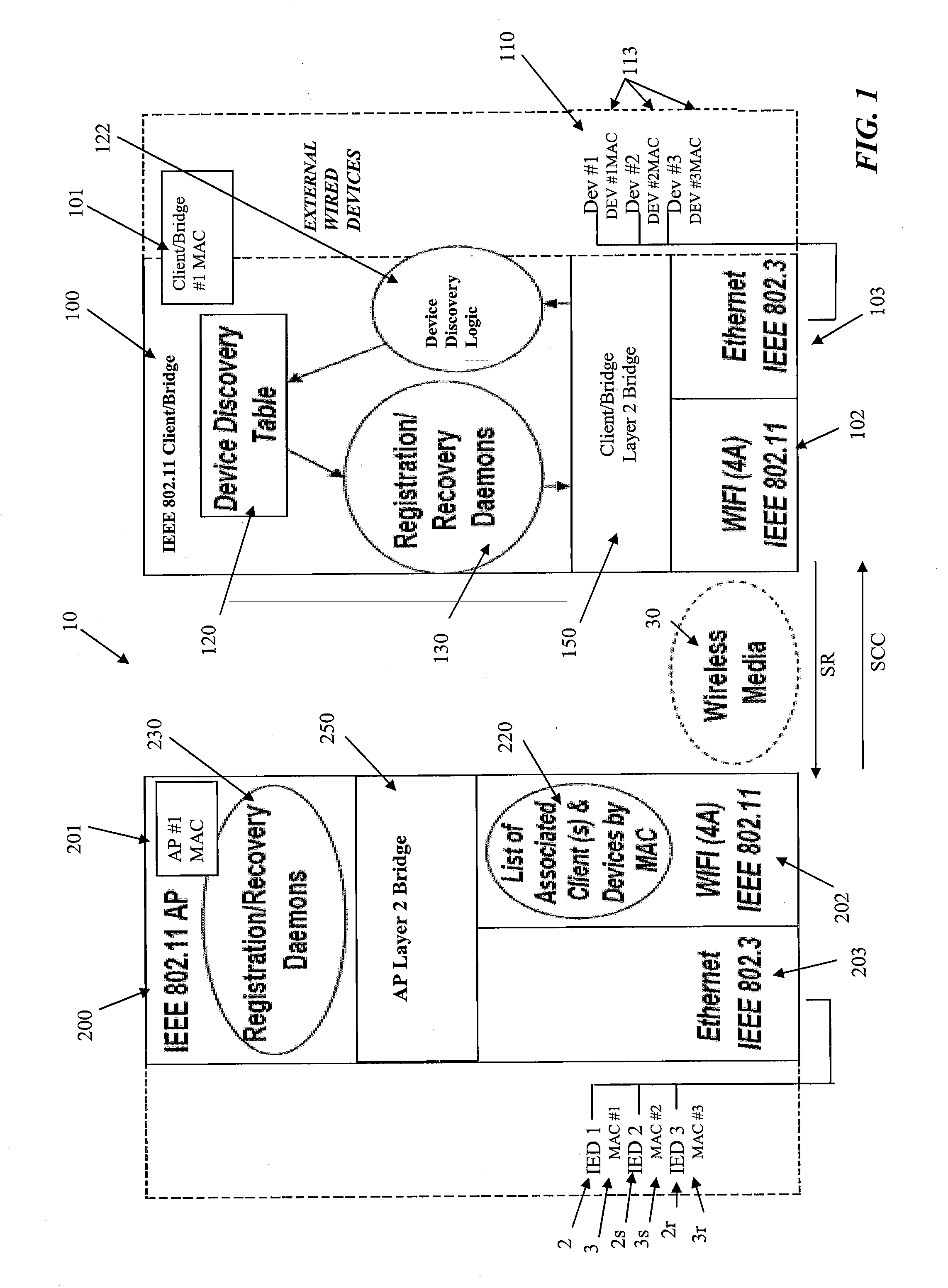
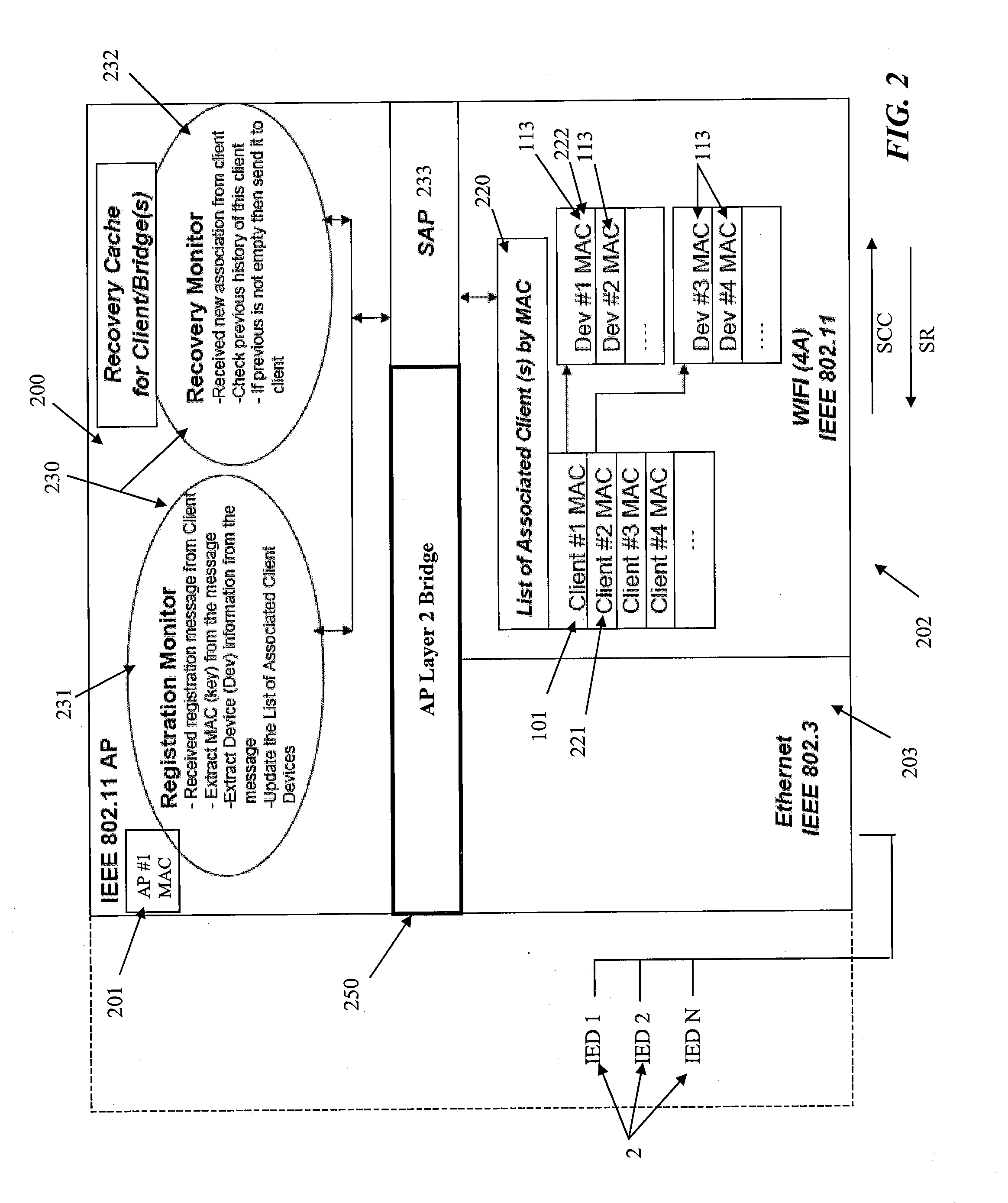
Client/Bridge and Method and System for Using Same
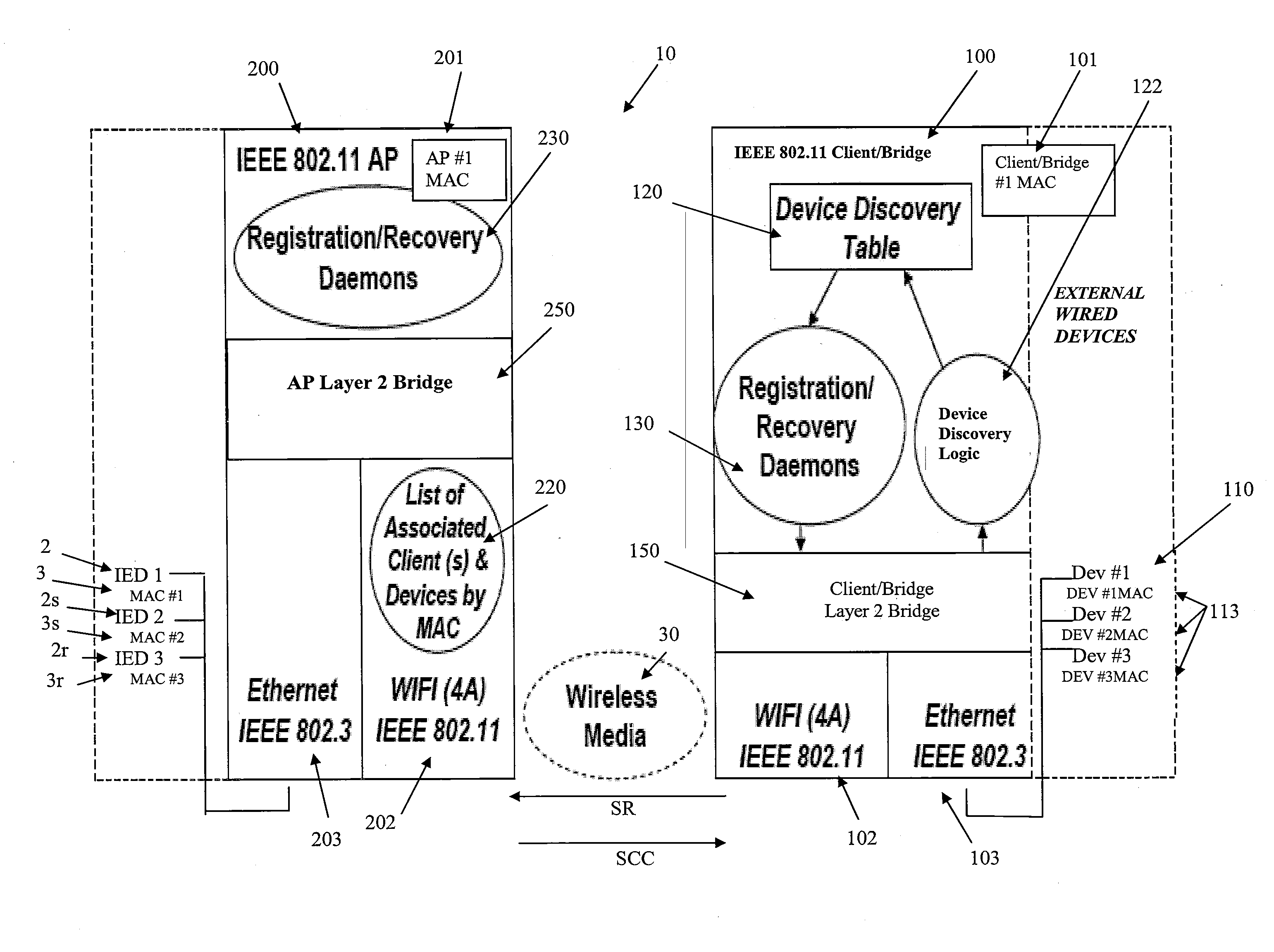
ActiveUS20100220701A1Facilitate Layer bridgingGood synchronizationNetwork topologiesWireless commuication servicesMedia access controlClient-side
The transmission of data is accomplished across a network having wireless and wired interfaces. Data is transferred through a wireless interface from an Access Point to a Client / Bridge and then to one of a Intelligent Electrical Device (IED) connected to the Client / Bridge through a wired connection. Data is transferred from the Access Point to the Client / Bridge through a 4 address mode wireless interface having originator, transmitter, receiver and destination address fields. The originator address uniquely identifies an IED in the overall network, the transmitter address identifies the AP transmitting the data, the receiver address identifies the Client / Bridge receiving the data through the wireless interface while the destination address refers to one of the IEDs connected to the Client / Bridge through the wired interface. Communication can also be performed in reverse from one of the IEDs connected to the Client / Bridge through the wired interface to an IED in the overall network. The Client / Bridge determines context cache information representing the media access control numbers of each of the IEDs connected to the Client / Bridge through the wired interface and transfers this context cache information to the AP. In the event of a failure of the Client / Bridge, the context cache information stored at the AP can be transferred to the Client / Bridge using the wireless interface to facilitate recovery of the Client / Bridge.
Owner:SIEMENS CANADA LTD
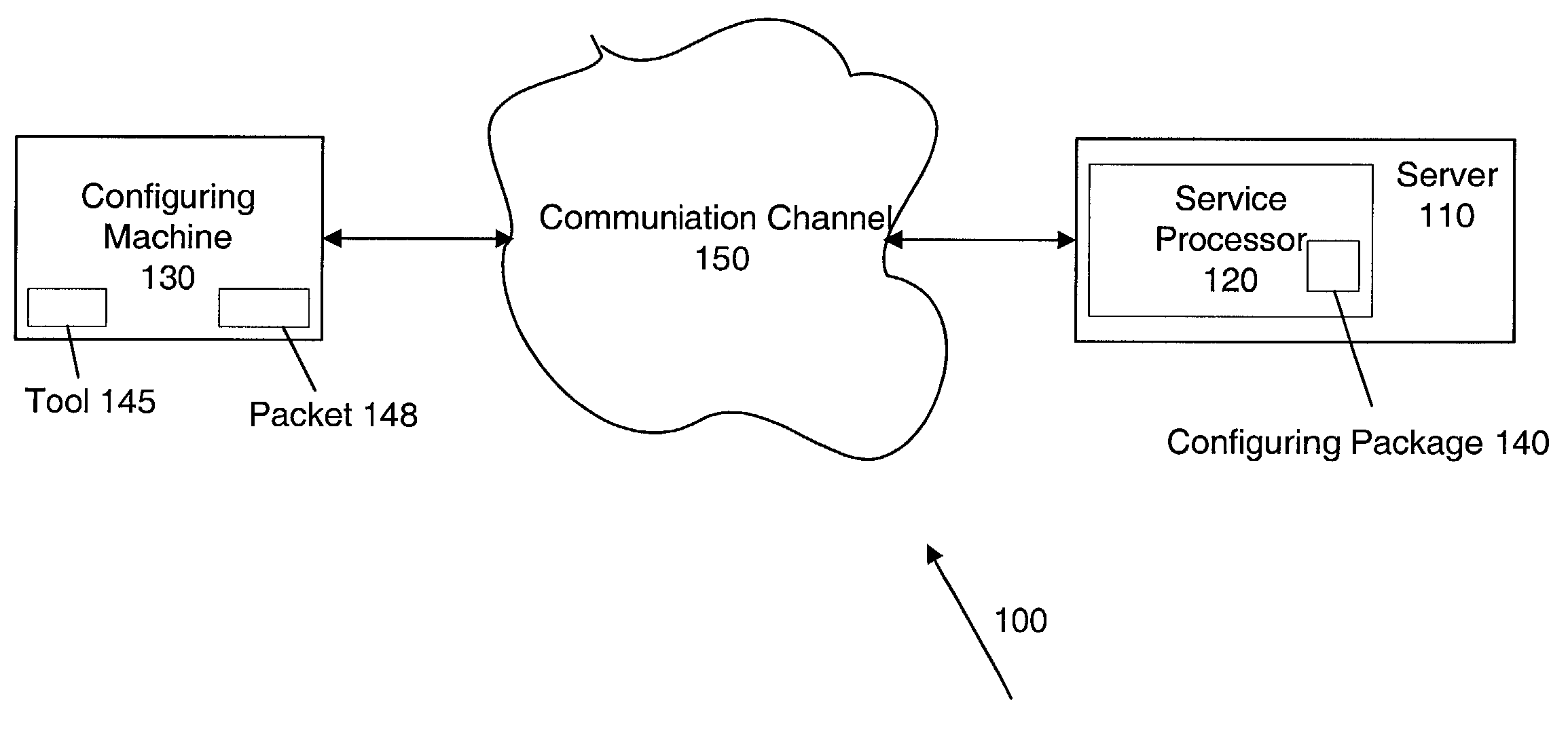
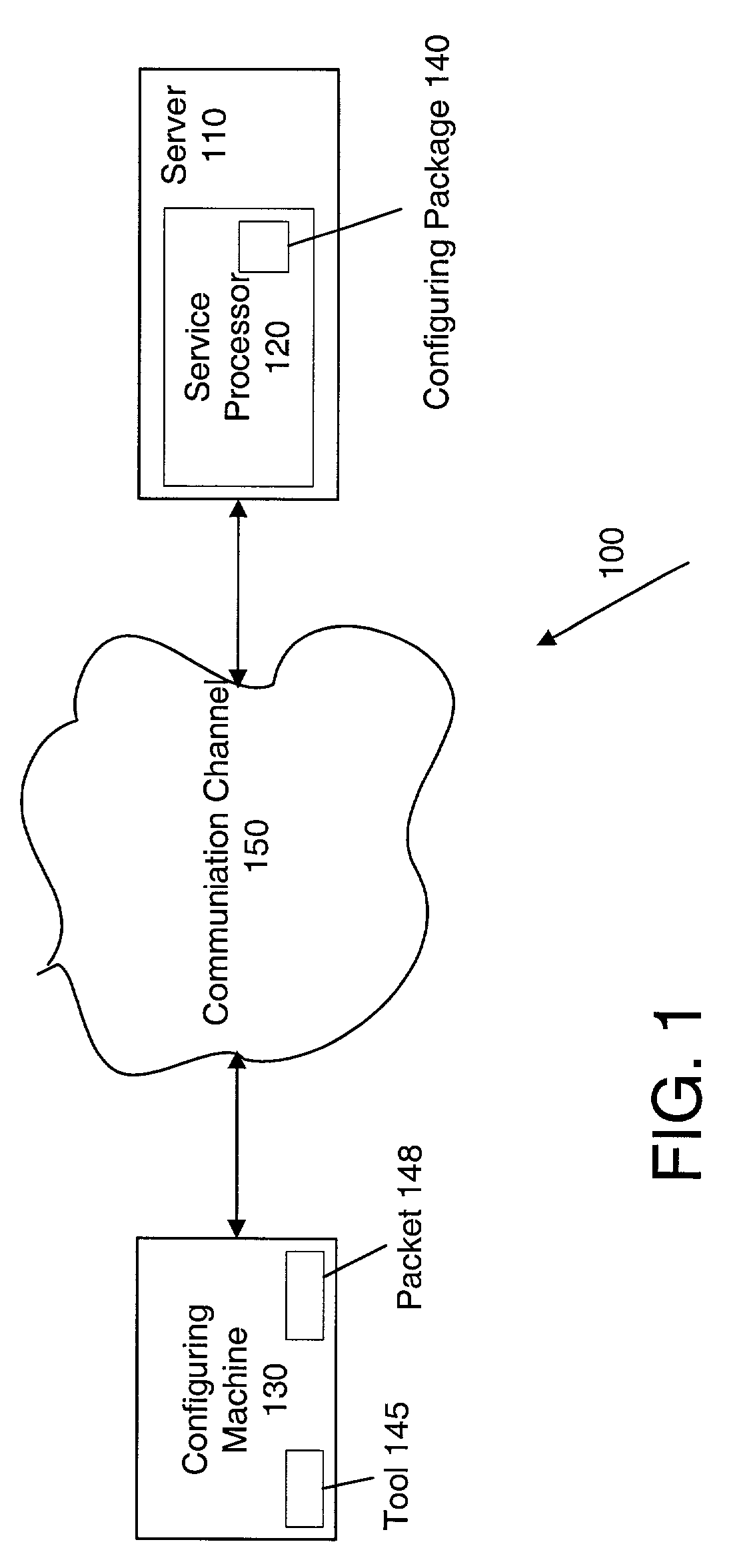
Configuring a network parameter to a device
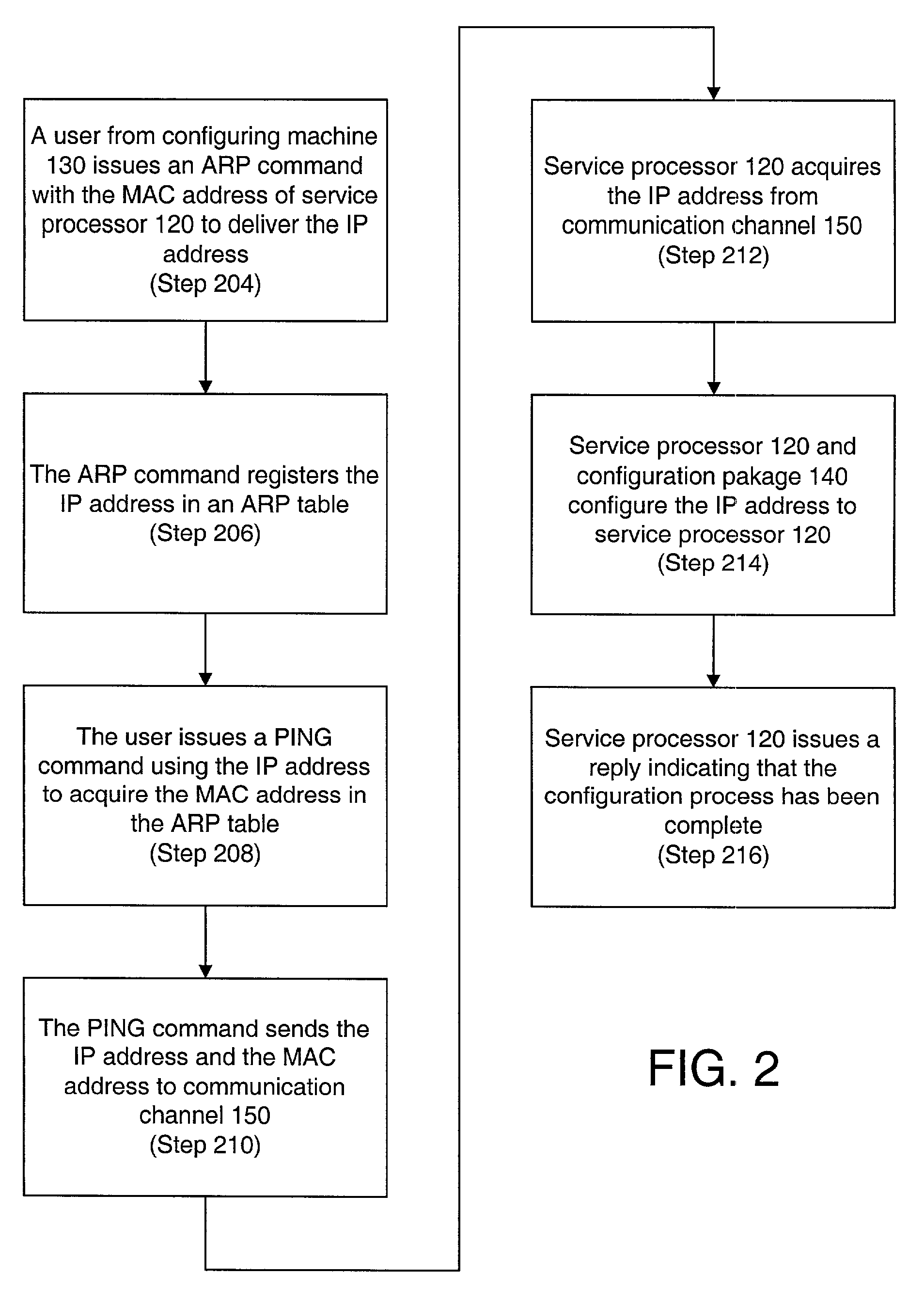
InactiveUS7155497B2Eliminate requirementsMultiple digital computer combinationsTransmissionAuto-configurationNetwork addressing
Techniques for configuring network parameters to a device are disclosed. In an embodiment, the device is a service processor that provides administrative capabilities to another device and that does not include a terminal. The network parameters include a network address, and configuring is done over a network. A user, from a configuring machine, sends a packet including the to-be-assigned address and the identifier of the configured device to the network. To acquire the packet and thus the address, the configured device regularly checks the network for the packet having the device's identifier. Having acquired the address, the device configures itself, and, to confirm that the address has been configured, the device generates a response to the configuring machine. Once the device is configured with the address, the device disables the automatic configuration feature until the device is in an un-configured state.
Owner:HEWLETT PACKARD DEV CO LP
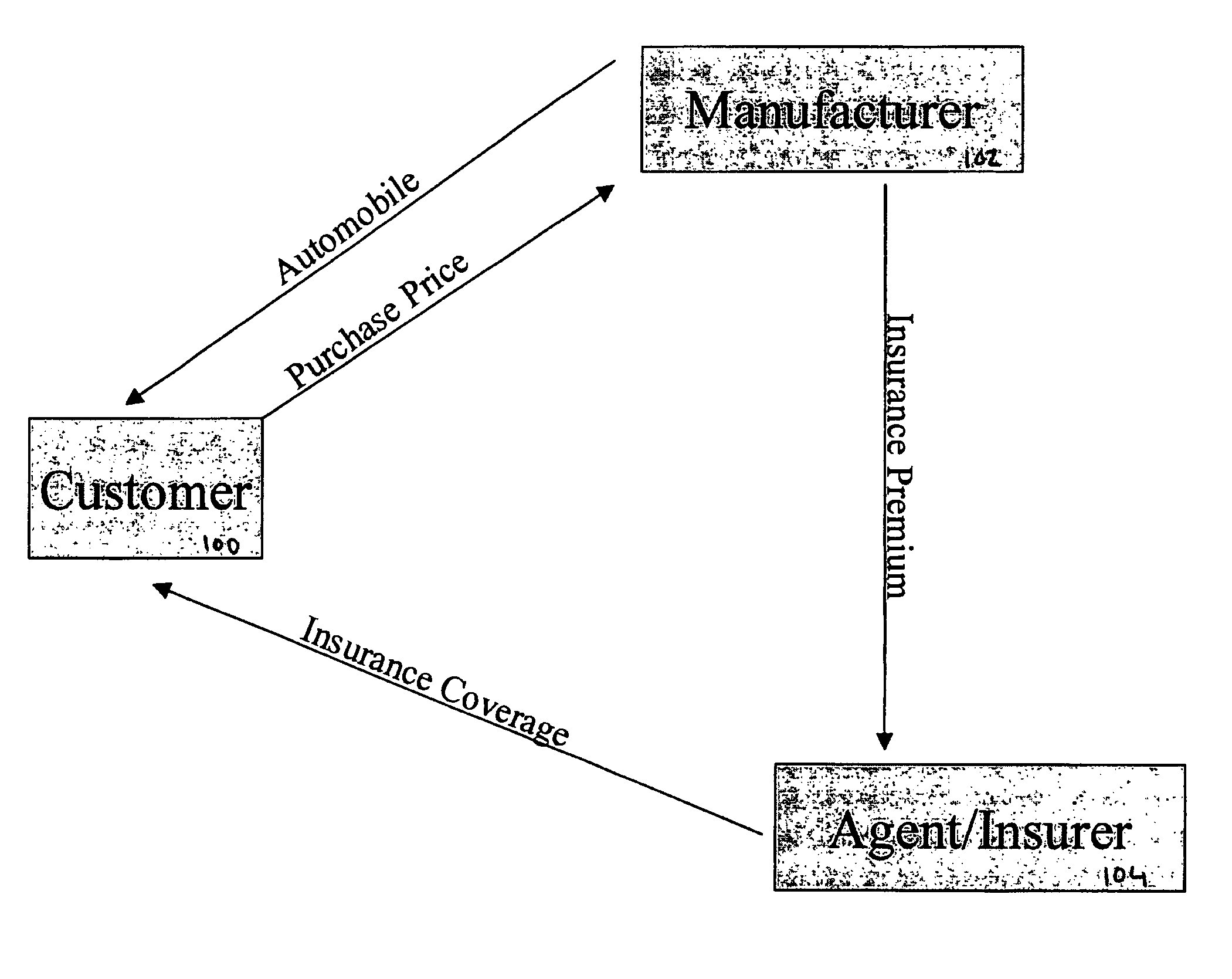
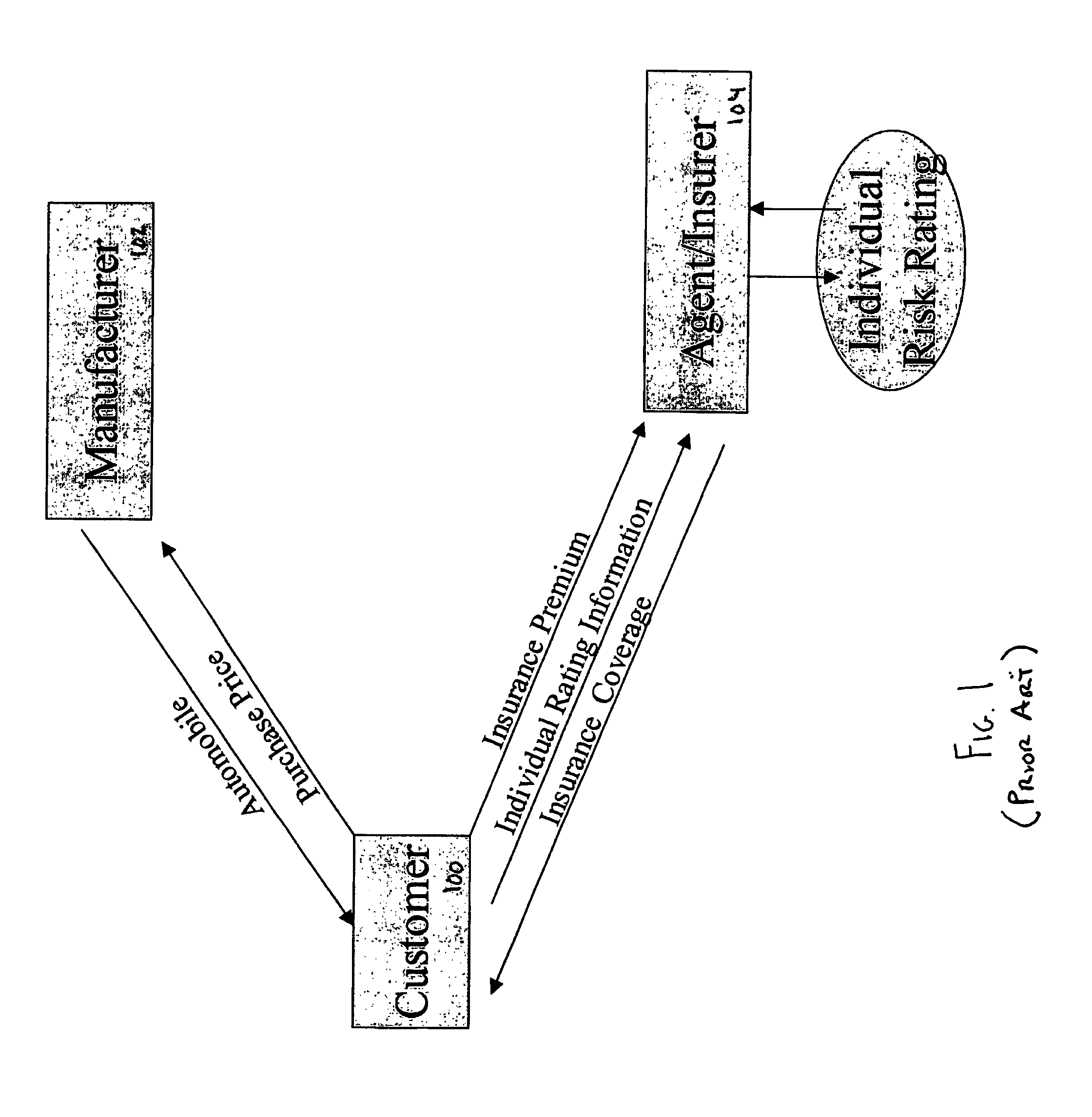
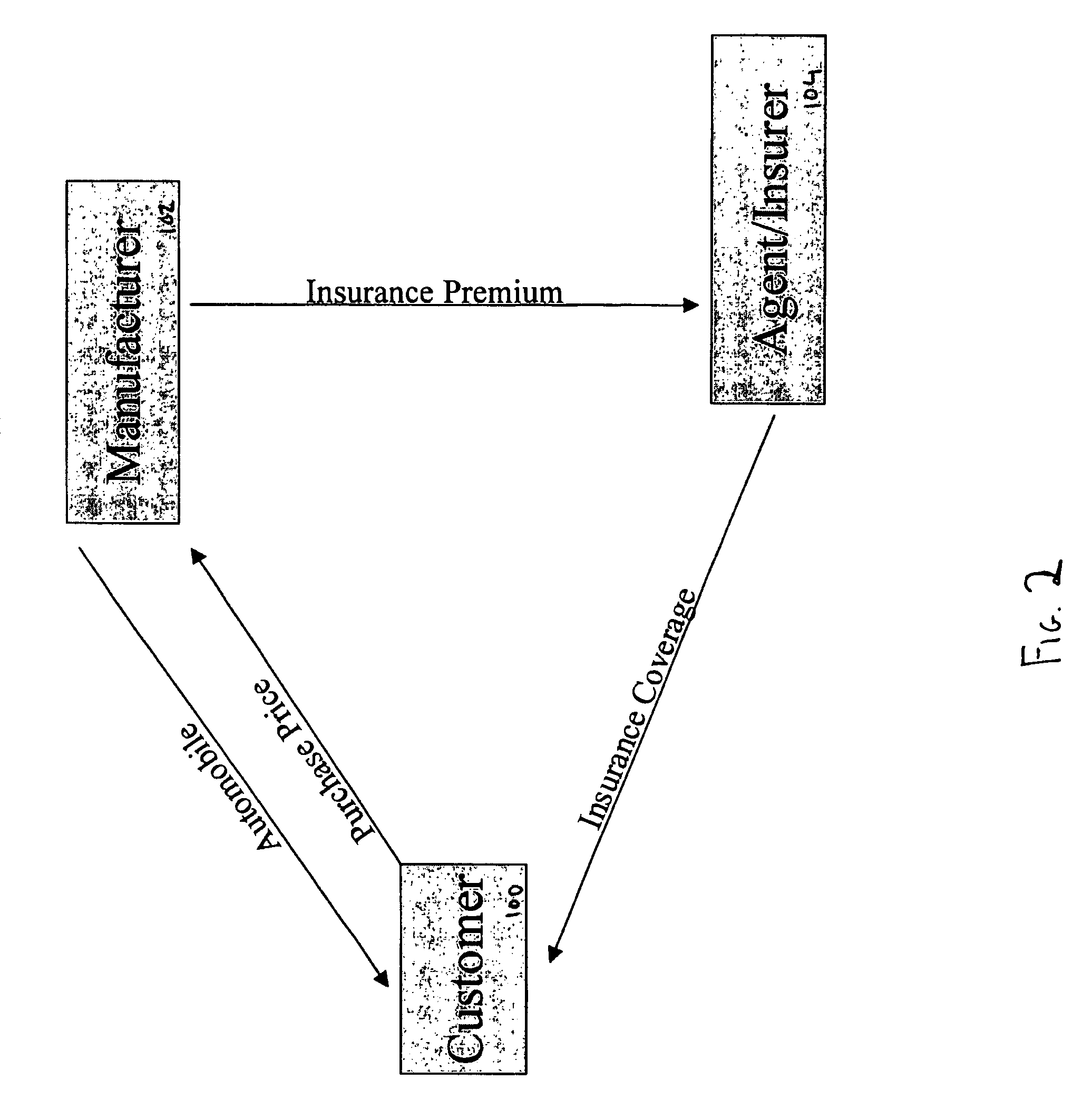
Insurance incentive program for promoting the purchase or lease of an automobile
Included in the terms of a purchase or lease agreement, particularly pertaining to automobiles, a party having a business relationship with the seller or lessor, or the seller or lessor itself, agrees to provide a policy, including at least collision and / or comprehensive coverage, to a qualified buyer. The insurance coverage protects against losses related to the item being purchased or leased for a predetermined period of time. To be qualified, the purchaser or lessor must reside in a particular geographic region and purchase or lease, for example, a particular make and model of automobile. No further characteristics of the purchaser or lessor are considered in obtaining the insurance policy. The sale or lease of the item and provision of the insurance policy may be completed over a computer network, such as the Internet.
Owner:IN THE CAR LLC
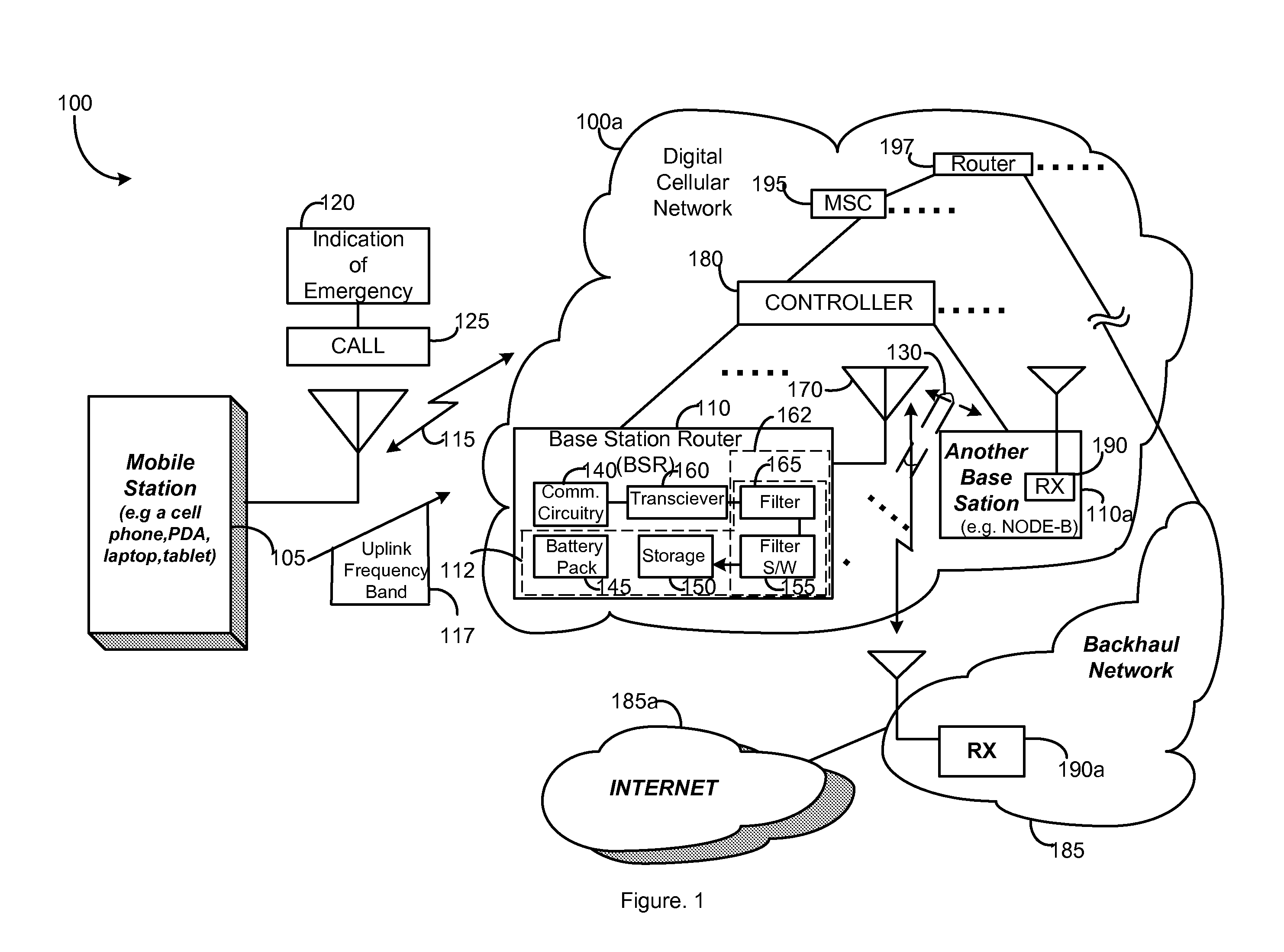
Completing emergency calls over a network with a malfunctioning backhaul communications link
InactiveUS7929942B2Emergency connection handlingNetwork topologiesTelecommunications linkCommunication link
A method and an apparatus are provided for enabling a wireless communication over a network in response to an indication of an emergency. The method comprises causing a base station to provide a wireless backhaul link in an uplink frequency band for further sending a call over the network in response to the call associated with the emergency. Reconfiguration enables turning a base station or base station router into a high power terminal. In this way, emergency calls may be completed over a network having at least one malfunctioning backhaul communications link in a network backbone.
Owner:ALCATEL-LUCENT USA INC
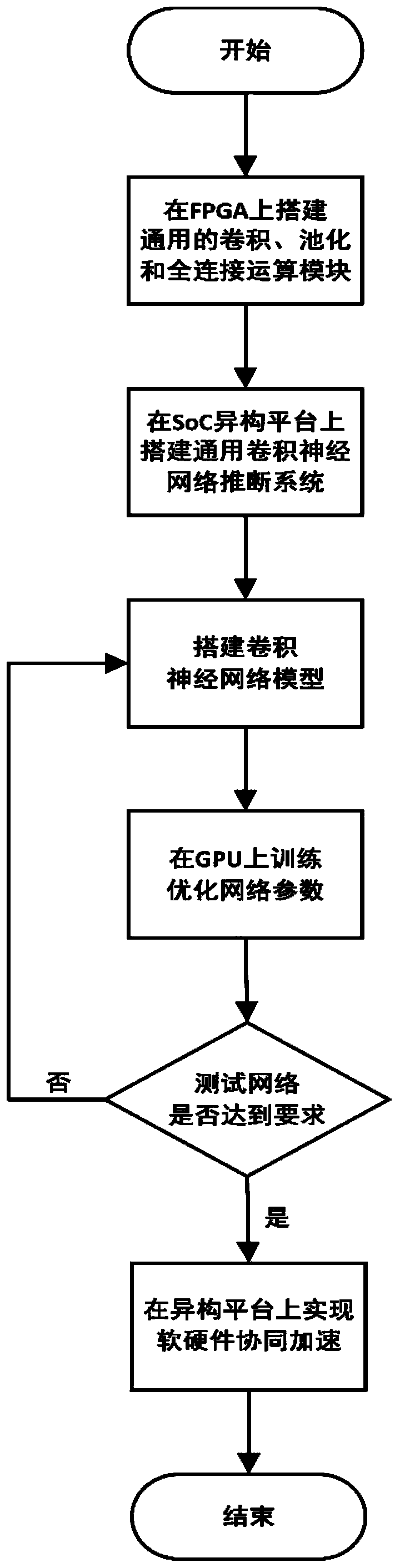
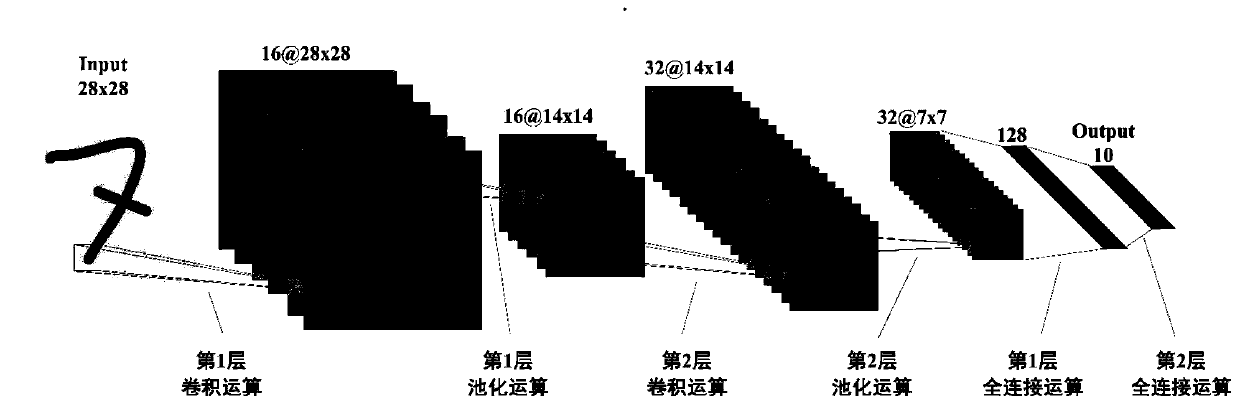
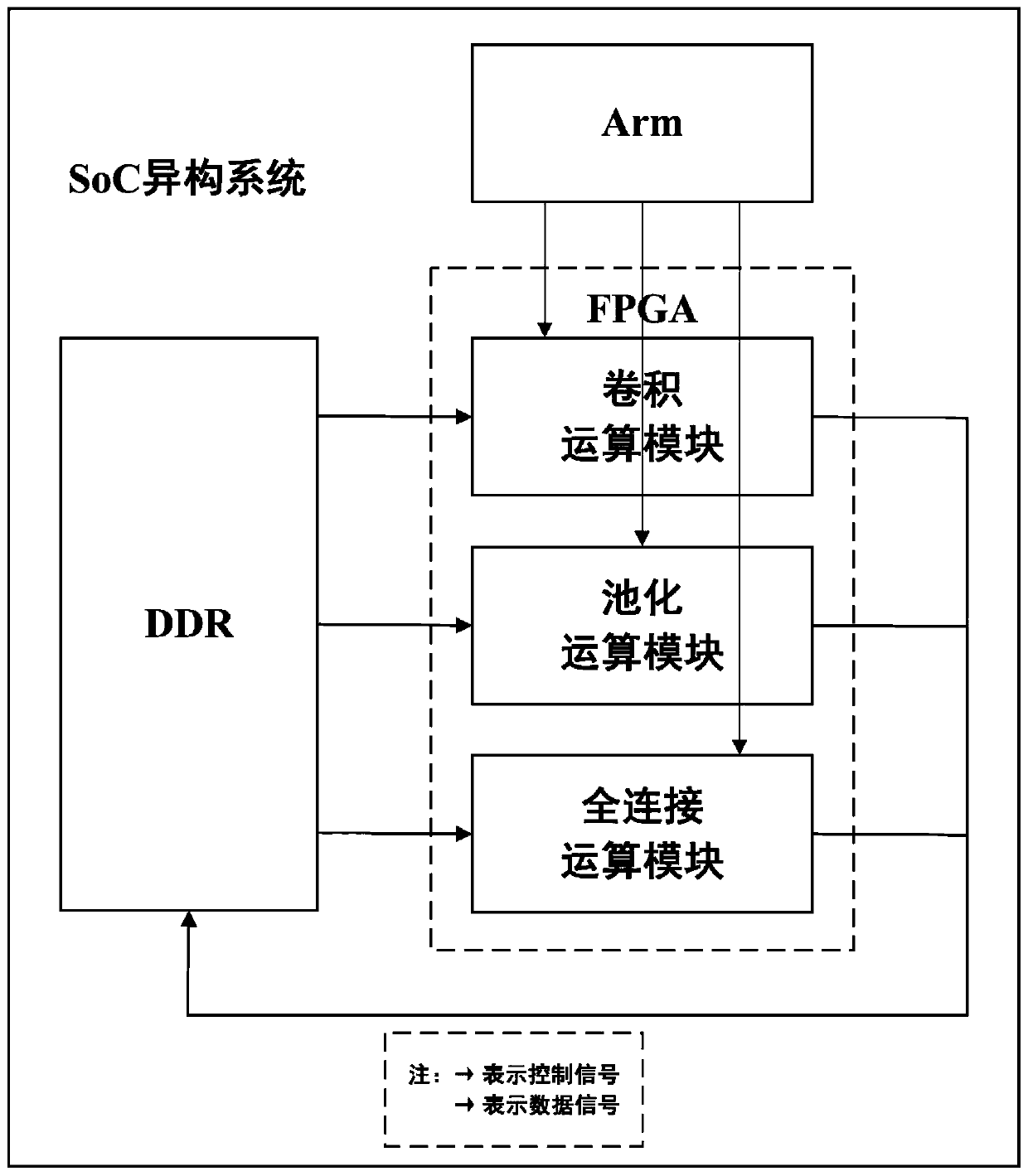
Neural network inference method based on software and hardware cooperative acceleration
ActiveCN111210019AIncrease profitAchieving Collaborative AccelerationNeural architecturesPhysical realisationAlgorithmInference system
A neural network inference method based on software and hardware cooperative acceleration comprises the steps that firstly, a convolution operation module, a pooling operation module and a full connection operation module are built and configured, then, the configured modules are used for building a neural network inference system, and a neural network comprises convolution layers and pooling layers which are alternately connected and a full connection layer which is in pipeline connection; the trained parameters and input data of the neural network are stored into a neural network inference system; and finally, the neural network inference system starts to work. A first input signal is input into the first convolution layer in a first small work period of each large work period, a secondinput signal is input into the first convolution layer in a second small work period of each large work period, one layer of operation is complted by each small work period neural network, and an operation result is input into the next layer; and the first input signal and the second input signal are sequentially subjected to each layer of operation of the neural network to obtain inference results of the first input signal and the second input signal.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
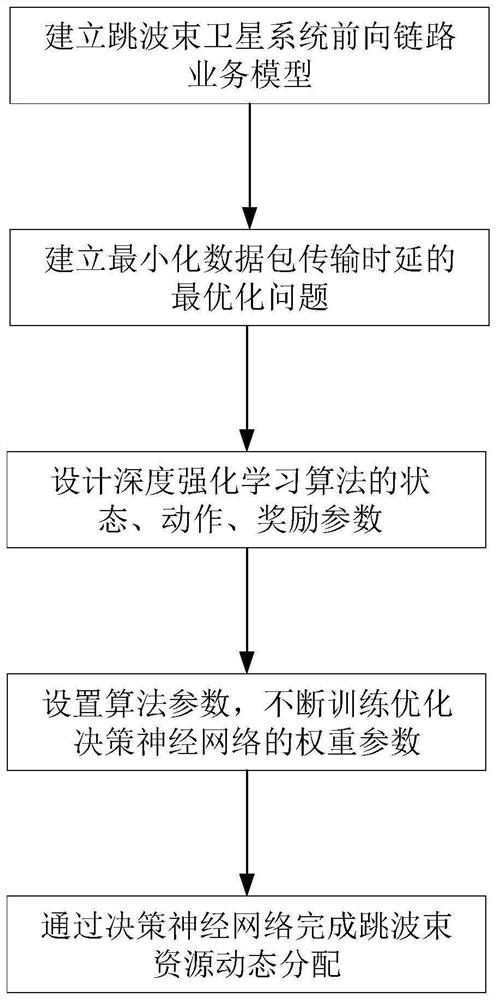
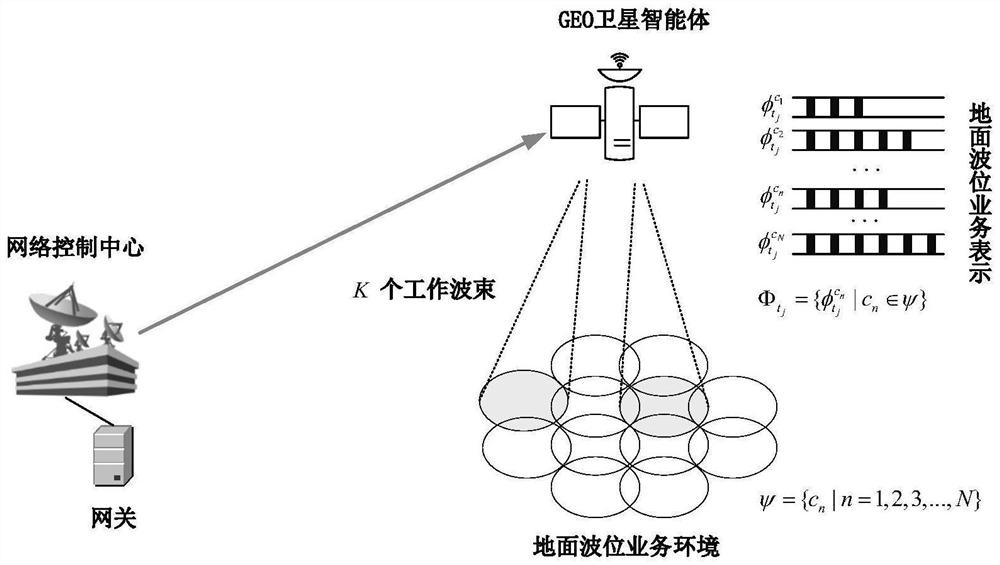
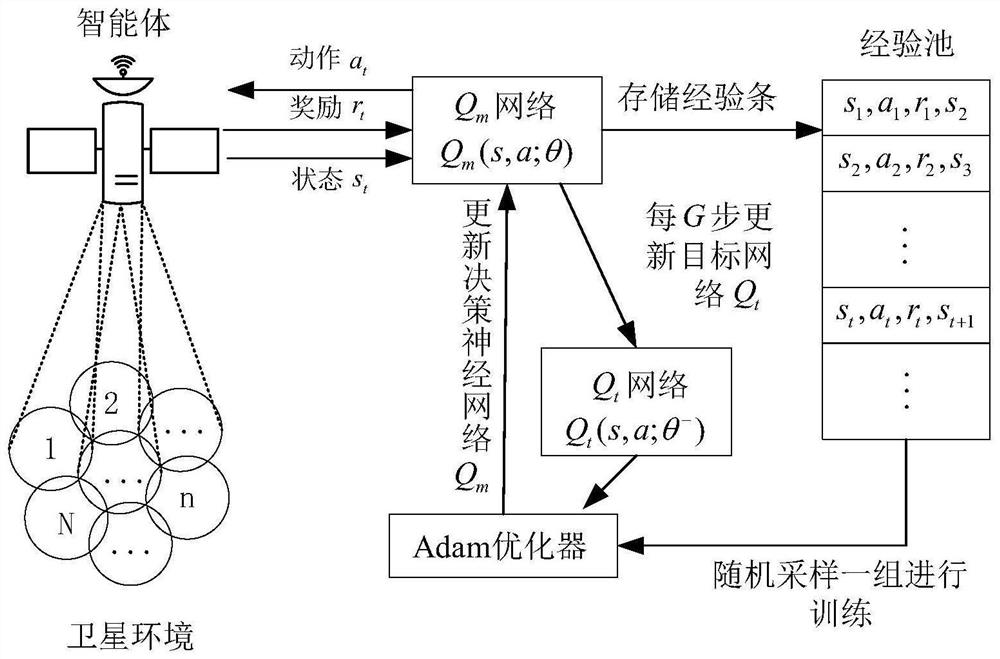
Dynamic resource allocation method for beam hopping satellite system based on deep reinforcement learning
PendingCN114499629AImprove throughputReduce transmission delayRadio transmissionNeural learning methodsData packDynamic resource
The invention discloses a dynamic resource allocation method for a beam-hopping satellite system based on deep reinforcement learning. The method comprises the following steps: step 1, establishing a service model of a forward link of a beam-hopping GEO satellite system; step 2, storing a data packet of a service arriving at a ground wave position in each time slot in a data packet buffer queue; step 3, utilizing a degree reinforcement learning algorithm to model a resource allocation module of the satellite into an intelligent agent, and designing state input of the intelligent agent, an output decision action of the intelligent agent and an award of an evaluation action; 4, simulating the deep reinforcement learning algorithm in the step 3, and continuously training decision neural network weight parameters of the deep reinforcement learning algorithm; and step 5, completing dynamic allocation of the resources of the beam-hopping satellite system by using the decision neural network obtained by training in the step 4, and solving an optimal scheme of resource allocation of the beam-hopping satellite system. According to the invention, the transmission delay of the data packet is reduced, and the throughput of the beam-hopping satellite system is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
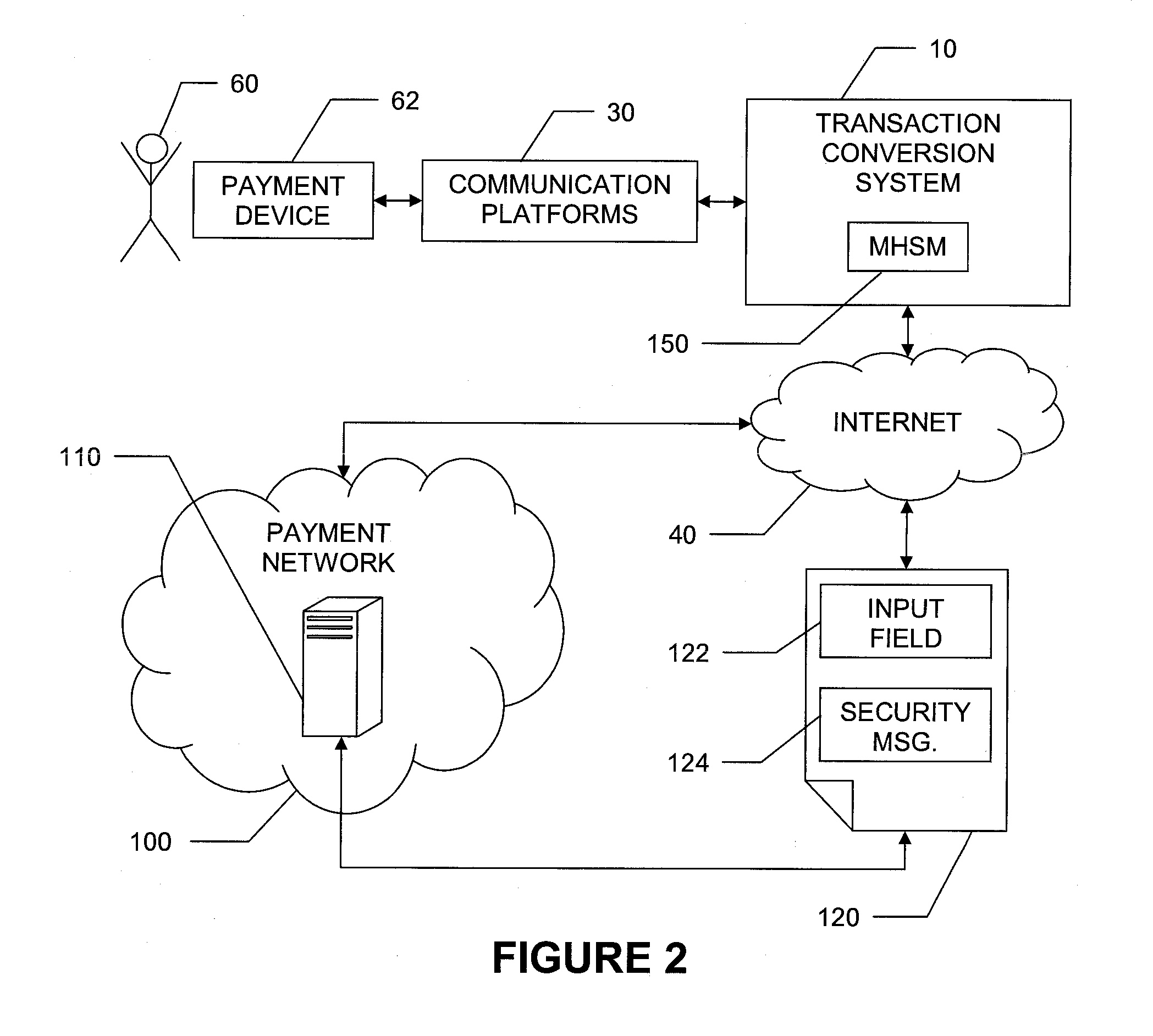
System and method for conversion between internet and non-internet based transactions
Owner:CARDINALCOMMERCE CORP
Method of implementing updating of web cache through broadcast network
InactiveCN104348856AIncrease access rateQuick responseSpecial service provision for substationStatistical analysisCache server
The invention discloses a method of implementing updating of a web cache through a broadcast network. The method comprises the following steps that a user handheld device visits user side gateway equipment with data cache capacity through a network link, when cache data is searched, a user request is immediately answered; when the cache data is not searched, network service is completed through requesting an operator network; the operator network is provided with a unified content gateway server, through a user access content, a data cache is stored in a data cache server as a file, after multiple users request for many times, hot content data is determined through algorithms, such as statistical analysis, of a strategy management server, and the hot content data is transmitted to the user side access gateway equipment through the broadcast network, so that updating of the network data cache is implemented. In comparison with the prior art, the network cache data of the user side access gateway equipment is updated according to a principle that hot spot data is transmitted at one point and is received at multiple points through the broadcast network according to the strategy algorithms, such as the request times and the probability, so that the request for the operator network by a user is reduced, and the method of improving the network access rate and the network response speed is achieved.
Owner:HANGZHOU MICORUNIT TECH
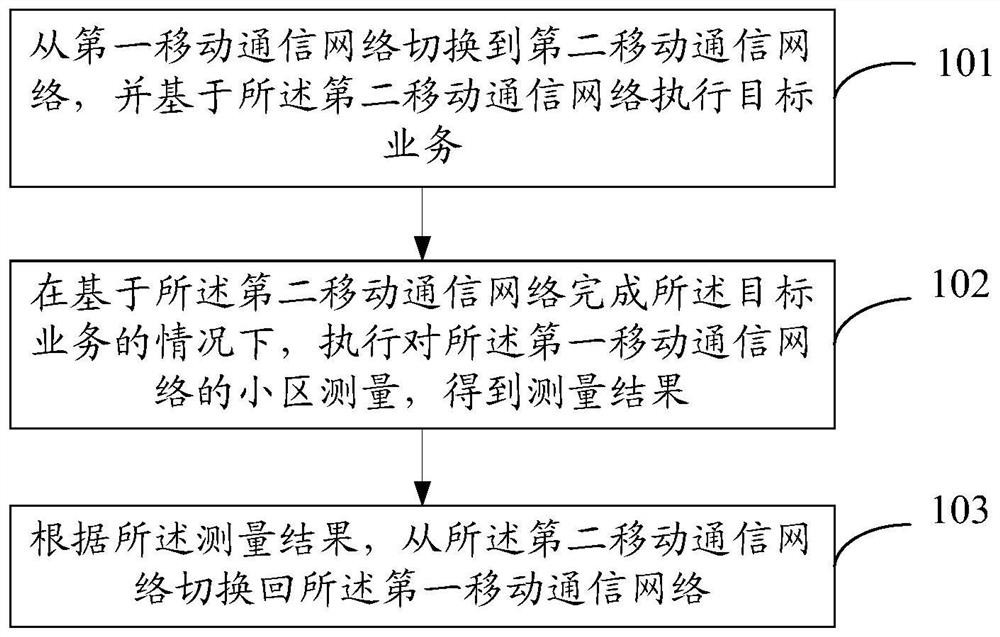
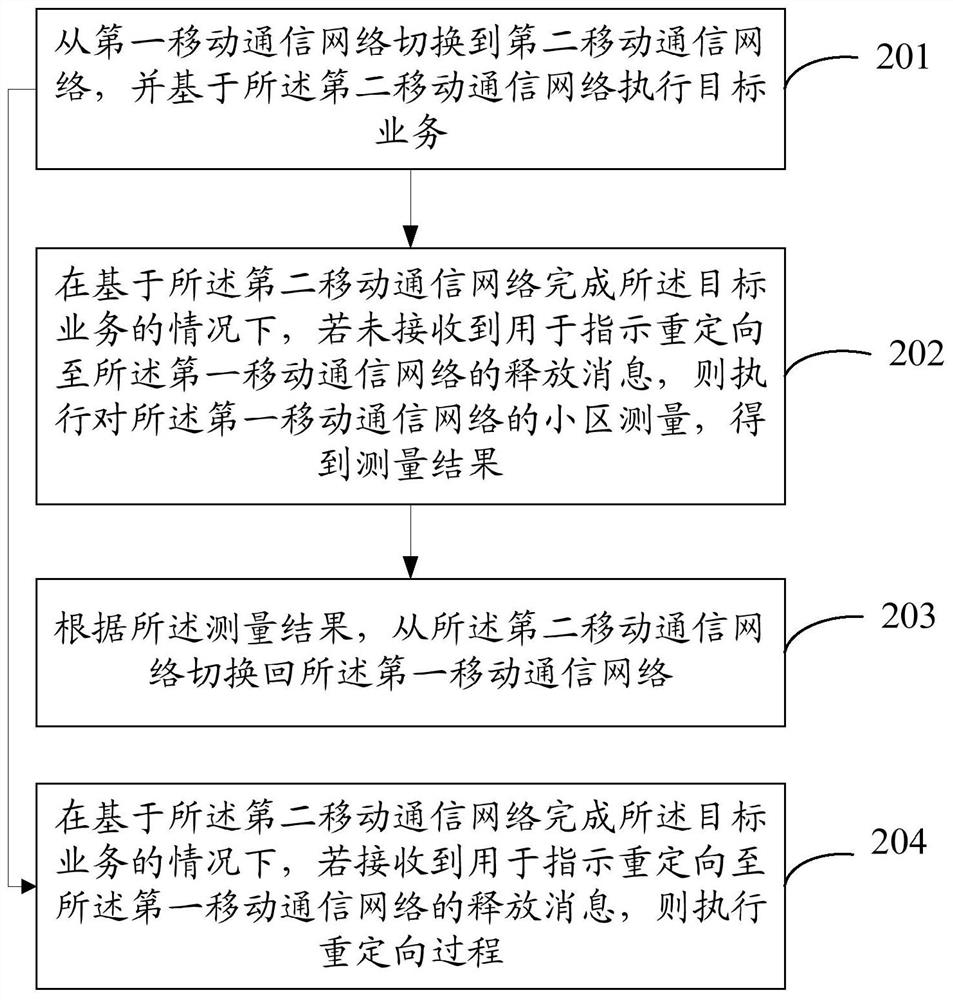
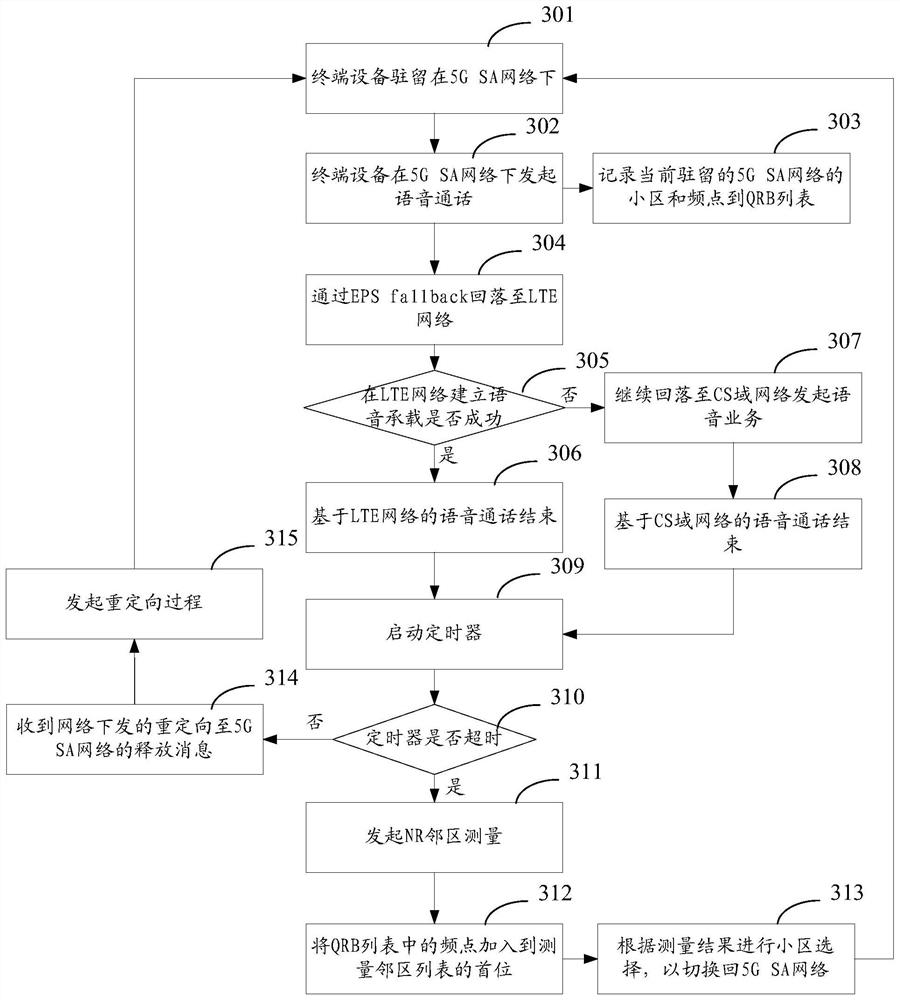
Network switching method and device and electronic equipment
PendingCN112533261AQuick switchImprove communication service qualityWireless communicationQuality of serviceEngineering
The invention discloses a network switching method and device and electronic equipment, and belongs to the technical field of communication. The method comprises: switching from a first mobile communication network to a second mobile communication network; executing a target service based on the second mobile communication network, the first mobile communication network being an Nth generation mobile communication network, the second mobile communication network being an Mth generation mobile communication network, M being less than N, and both M and N being positive integers; under the condition that the target service is completed based on the second mobile communication network, executing cell measurement on the first mobile communication network to obtain a measurement result; and switching back to the first mobile communication network from the second mobile communication network according to the measurement result. According to the network switching method provided by the invention, the second mobile communication network can be quickly switched back to the first mobile communication network, so that the second mobile communication network is prevented from staying for a longtime, and the network communication service quality can be further improved.
Owner:VIVO MOBILE COMM CO LTD
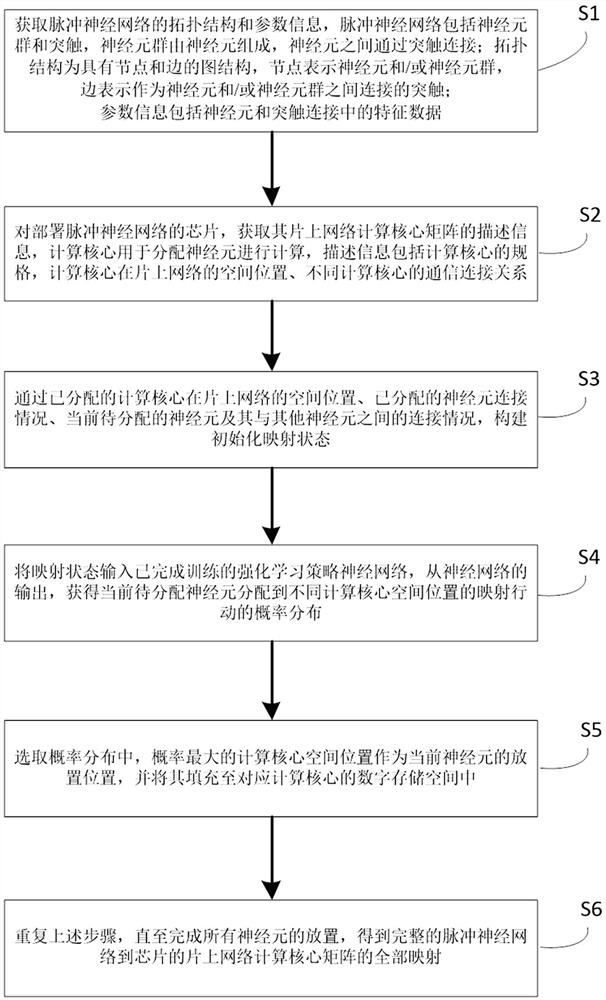
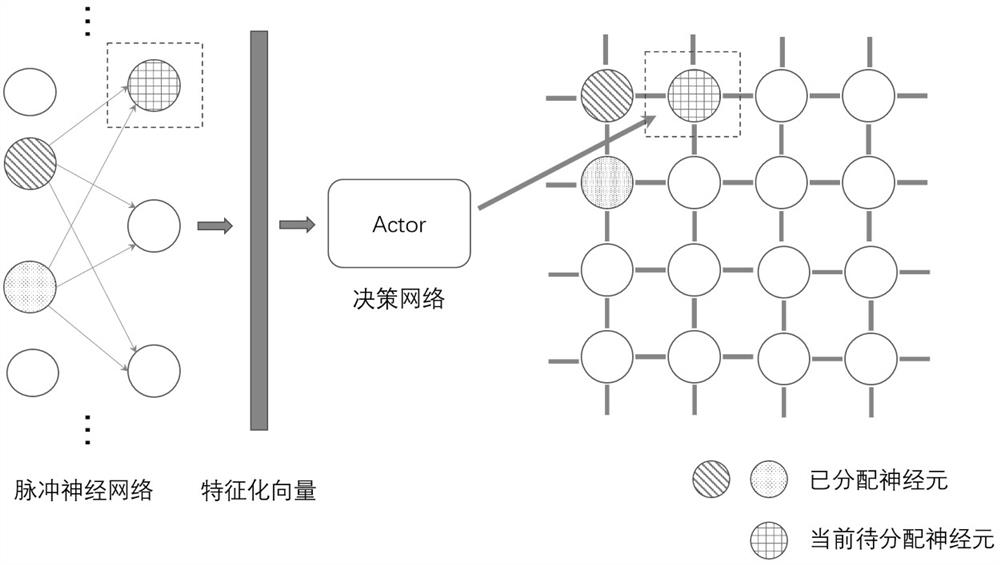
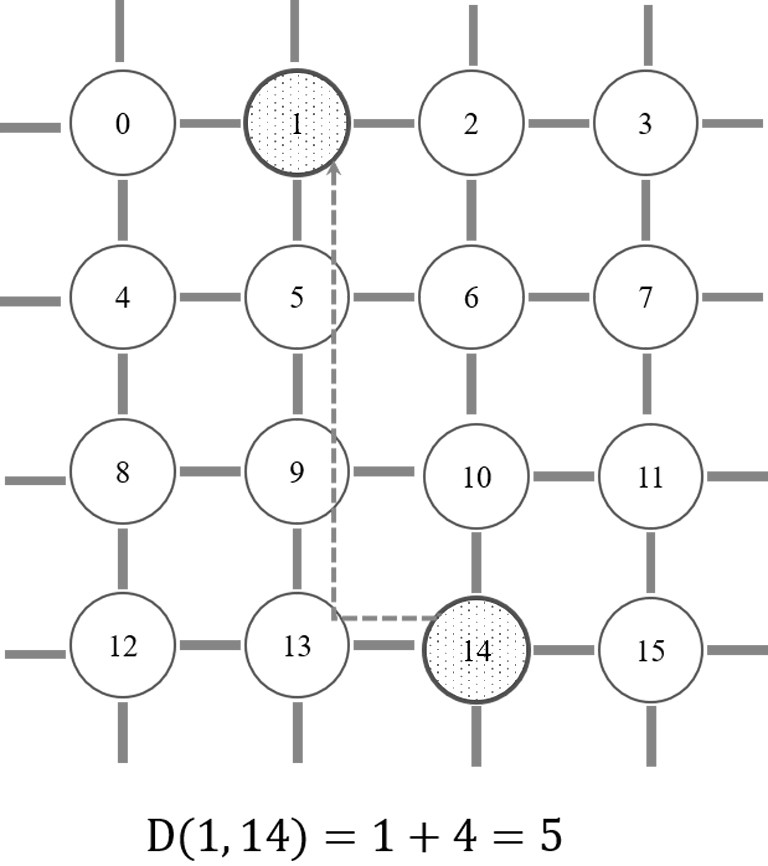
On-chip core compiling and mapping method and device of neural network based on reinforcement learning
ActiveCN114492782AShorten the transmission distanceImprove Mapping YieldNeural architecturesArchitecture with single central processing unitAlgorithmEngineering
The invention discloses an on-chip core compilation mapping method and device for a neural network based on reinforcement learning, and the method comprises the steps: putting a conventional mapping planning problem into a reinforcement learning framework, constructing a state description, a reward function and an action space, and obtaining a strategy deep network through reinforcement learning training. Neurons are sequentially placed within a plurality of cores of a network-on-chip. The mapping income is constructed by communication cost, mapping area and core internal utilization rate, the strategy network is trained by using an Actor-Critic algorithm to obtain higher mapping income, and the reinforcement learning strategy network is trained to learn the optimal mapping position of any pulse neural network neurons. And finally, finishing from the neural network needing to be deployed to the on-chip core array by using the trained strategy network, thereby reducing the on-chip communication distance cost of the interconnected neurons, effectively improving the chip calculation efficiency and reducing the overall power consumption.
Owner:ZHEJIANG LAB +1
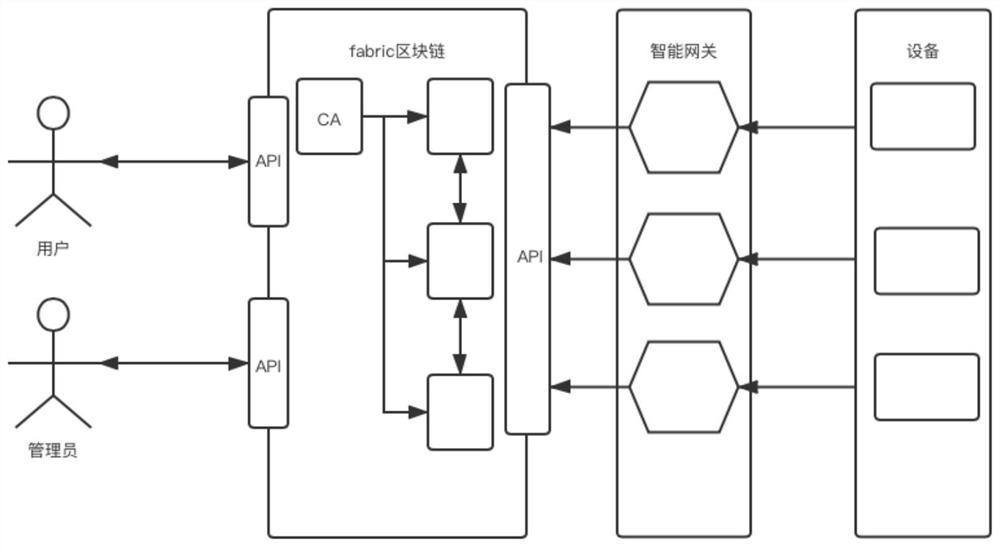
Internet of Things access control system and method based on block chain
PendingCN111950019ATroubleshoot access control issuesDigital data protectionTransmissionThe InternetEngineering
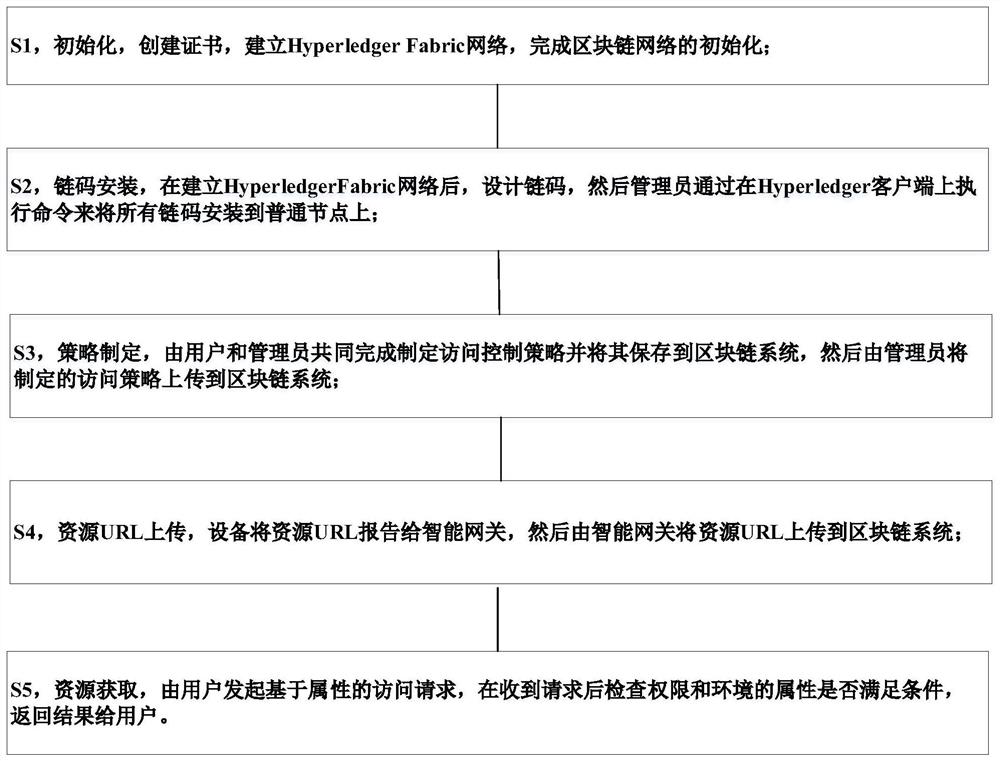
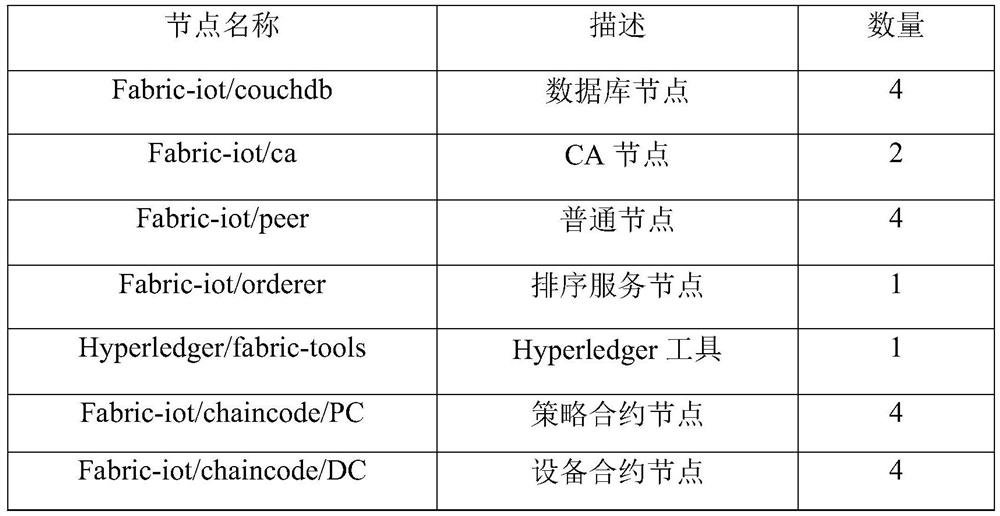
The invention discloses an Internet of Things access control system and method based on a block chain, and the method comprises the steps: S1, carrying out the initialization, building a certificate,building a HyperledgerFabric network, and completing the initialization of a block chain network; s2, chain code installation: after a HyperledgerFabric network is established, designing chain codes,and then enabling an administrator to install all the chain codes on a common node by executing a command on a Hyperledger client; s3, strategy making: enabling the user and the administrator to complete making of an access control strategy together and store the access control strategy in the blockchain system, and then enabling the administrator to upload the made access strategy to the blockchain system; s4, uploading the resource URLs, reporting the resource URLs to an intelligent gateway by the equipment, and then uploading the resource URLs to a block chain system and the like by the intelligent gateway; according to the invention, the security and throughput of the Internet of Things control system are improved, and the data consistency and the like can be ensured.
Owner:四川链向科技集团有限公司
Network transaction platform and method
InactiveCN104376404AShorten the timeReduce workloadFinanceResourcesBusiness enterpriseFinancial transaction
The invention discloses a network transaction platform. The network transaction platform comprises a recommended listing system, a directional financing system, a share transaction system and an information disclosure system; the recommended listing system, the directional financing system, the share transaction system and the information disclosure system are arranged in parallel. Material submitting and checking between enterprises, recommendation institutions and exchanges are finished through the network, an objection is raised on files which have a problem in submitting or are submitted unqualifiedly in time, enterprise staff and the recommendation institutions can effectively correct the files in time through the network, the staff can finish related operations only by sitting in front of a computer, it is not needed that staff of the enterprises and the recommendation institutions go to the exchanges and back many times, the time of the enterprise staff is shortened greatly, a large number of materials do not need to be collated by the staff and workloads of the staff are relieved greatly to a certain extent. The whole structure is simple, operation is easy, transactions can be achieved effectively, efficiently, rapidly and conveniently, and the requirements of modern rapidly developed commercial transactions are met.
Owner:TSINGHUA SWIFT SHANGHAI INVESTMENT MANAGEMENT CO LTD
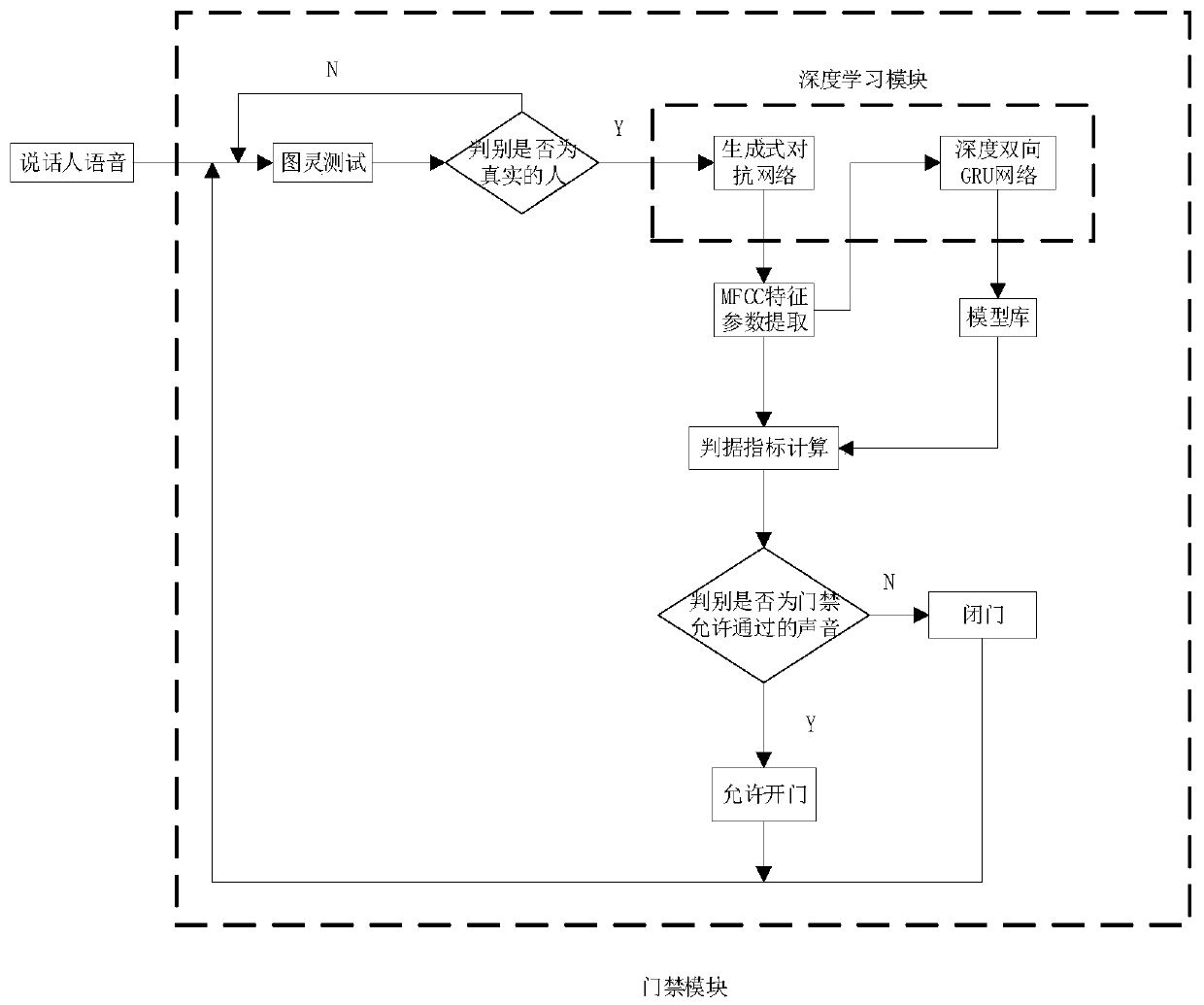
Voice access control system
InactiveCN110223429AImprove experienceImprove speech recognition accuracySpeech analysisIndividual entry/exit registersFeature extractionGenerative adversarial network
The invention provides a voice access control system, and aims at using voice anti-fake Turing test and deep learning to carry out immortal voice recognition so as to realize an access control function. The system comprises a processor loaded with a Turing test module, a generative adversarial network and a bidirectional GRU neural network, wherein the processor is communicable connected with an access control driving mechanism and is used for starting or closing the access control according to voice characteristics. The voice access control system is suitable for carrying out Turing test on the obtained voices under specific environments that the speakers are not on the spots, carrying out voice enhancement processing through the generative adversarial network after determining the voicesas real voices, carrying out feature extraction on the enhanced voices by adoption of parameters such as Mel cepstrum (MFCC) and the like, and completing speaker recognition through a deep bidirectional gated recurrent unit) network.
Owner:SHANGHAI INST OF TECH
Power plant safety behavior information automatic detection method based on deep learning
PendingCN112364778AImprove the problem of inability to accurately identify small targetsEasy to detectCharacter and pattern recognitionNeural architecturesVideo monitoringAlgorithm
The invention relates to a power plant safety behavior information automatic detection method based on deep learning, and the method comprises the steps: firstly constructing a deep convolutional neural network, and positioning each safety helmet in a monitoring video image through the deep convolutional neural network; completing detection, feature extraction, accurate segmentation and target identification of a safety helmet target by using FPN and RPN networks; then, making a learning data set, and training a computer to complete safety helmet identification and complete network parameter optimization; and finally, applying the trained optimization network to streaming video monitoring to realize correct helmet wearing behavior identification and alarm of the personnel. Compared with the prior art, the invention has the advantage that the problem that whether a target wears a safety helmet or not cannot be accurately recognized due to dense people, body image shielding and overlapping conditions is solved.
Owner:SHANGHAI MINGHUA ELECTRIC POWER TECH & ENG
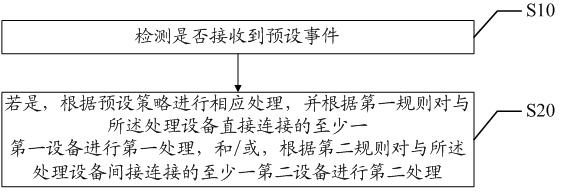
Information processing method and device and storage medium
InactiveCN111935849ASmart experienceIntelligent, convenient and flexible experienceConnection managementComputer hardwareInformation processing
The invention discloses an information processing method and device and a storage medium. The method comprises the steps of: detecting whether a preset event is received or not; and if so, carrying out corresponding processing according to a preset strategy, and carrying out first processing on at least one first device directly connected with the processing device according to a first rule, and / or carrying out second processing on at least one second device indirectly connected with the processing device according to a second rule. According to the invention, after the preset event is received, corresponding processing is carried out through the preset strategy, first processing is carried out on the first device, and / or second processing is carried out on the second device, so that the situation that only simple information processing can be carried out among the devices after connection establishment of the connection network is avoided, and information processing after mutual connection establishment of the device is more intelligent, convenient and flexible.
Owner:SHENZHEN TRANSSION HLDG CO LTD
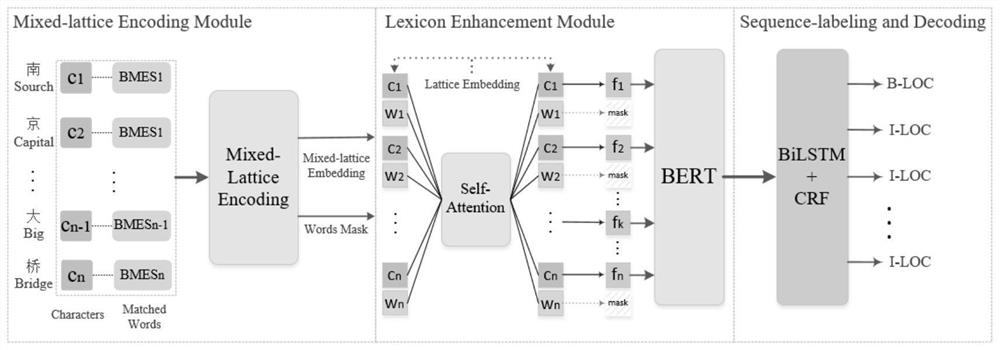
Named entity recognition method and device based on hybrid lattice self-attention network
PendingCN114429132AHigh precisionNatural language data processingNeural architecturesData setNamed-entity recognition
The invention discloses a named entity recognition method based on a mixed lattice self-attention network, and the method comprises the steps: S1, encoding a sentence feature vector represented by a word pair into a matrix with a fixed dimension, and obtaining a word vector representation of a mixed lattice structure; constructing a self-attention network to capture the influence of a word vector on a word vector in the vector, and enhancing the feature representation of each word vector; word features are fused in an Embedding layer of BERT, and better word vector representation is obtained through learning by fine tuning of a learning process; an entity sequence labeling task and a decoding process in entity recognition are realized according to a BiLSTM-CRF network, modeling of fused character features is completed through the network, and an entity recognition model based on the hybrid lattice self-attention network is constructed. According to the method, global vocabulary information can be captured, semantic-rich word vector representation is generated, and the Chinese named entity recognition precision is improved on multiple data sets.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
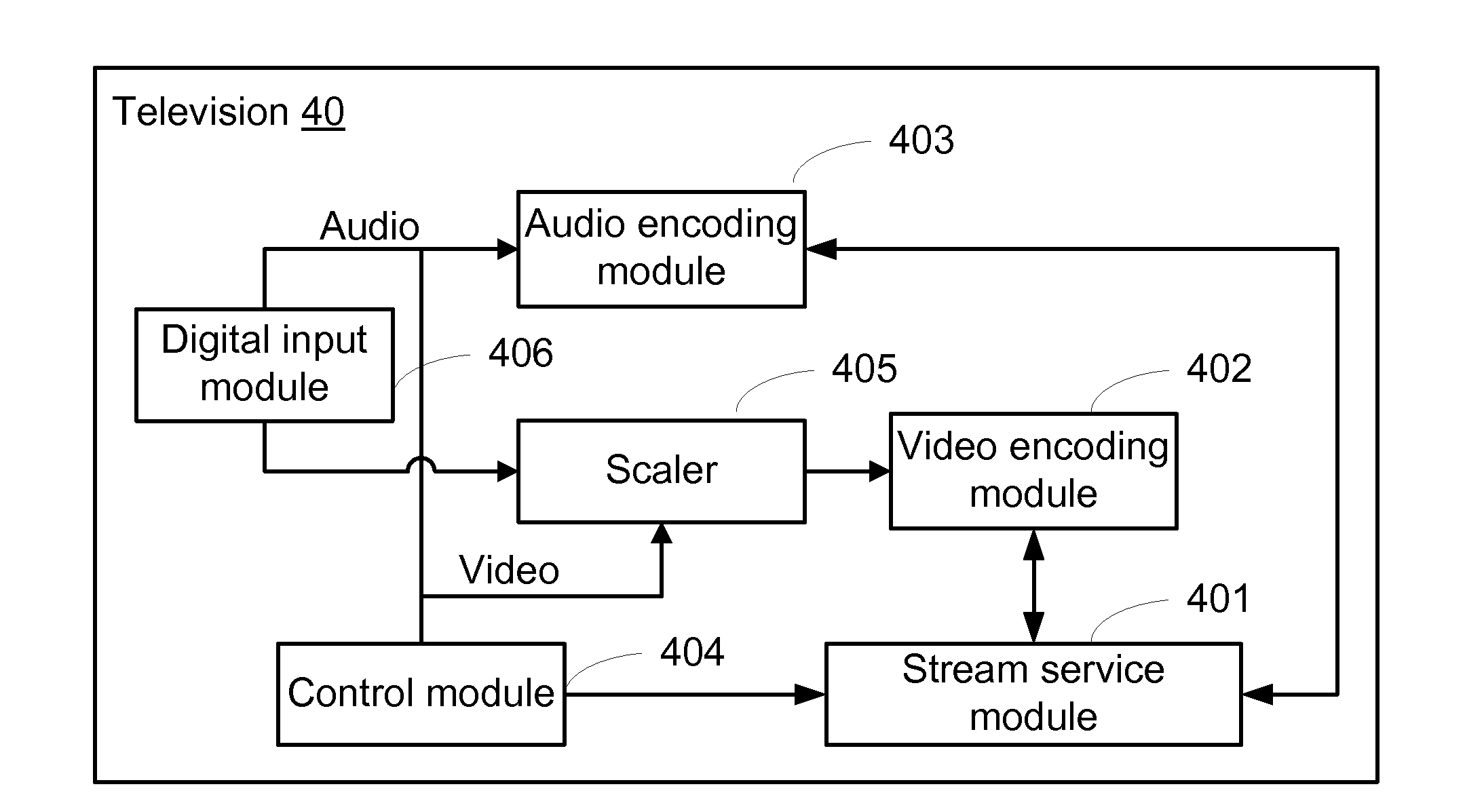
Method, system and television for picture reproduction
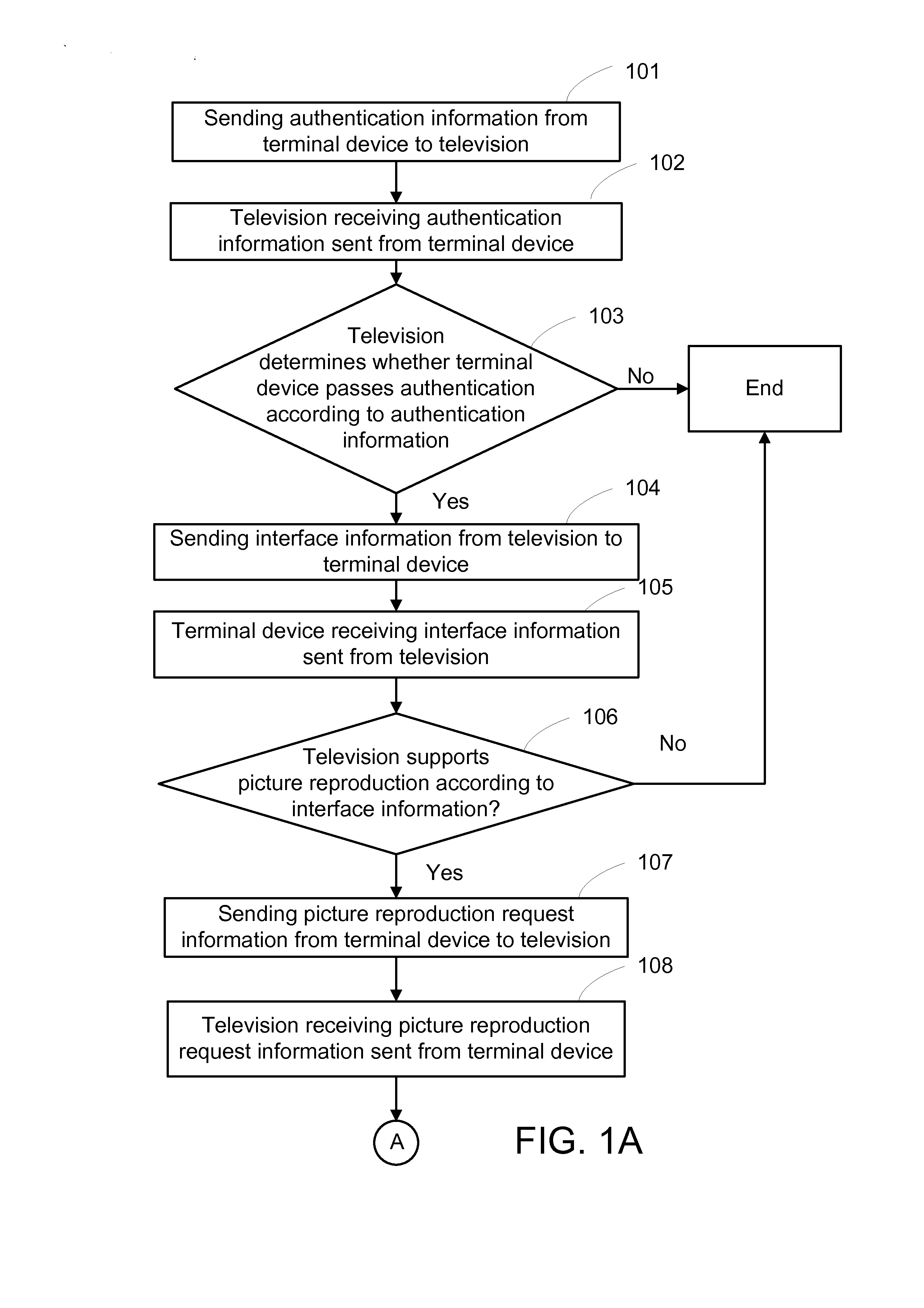
InactiveUS20130185745A1Analogue secracy/subscription systemsClosed circuit television systemsComputer hardwareShortest distance
A method, system, and television for television picture reproduction via a network is provided. The television receives picture reproduction request information sent from a terminal device, real-time encodes video and audio data inputted from a multimedia server, respectively packs the encoded video and audio data into video data packets and audio data packets, and sends the video data packets and the audio data packets to the terminal device. The terminal device performs playback according to the video data packets and the audio data packets. Thus, the method accomplishes television picture reproduction through a network to fulfill short-distance picture reproduction requirements without occupying resources and network bandwidth of the multimedia server.
Owner:MSTAR SEMICON INC
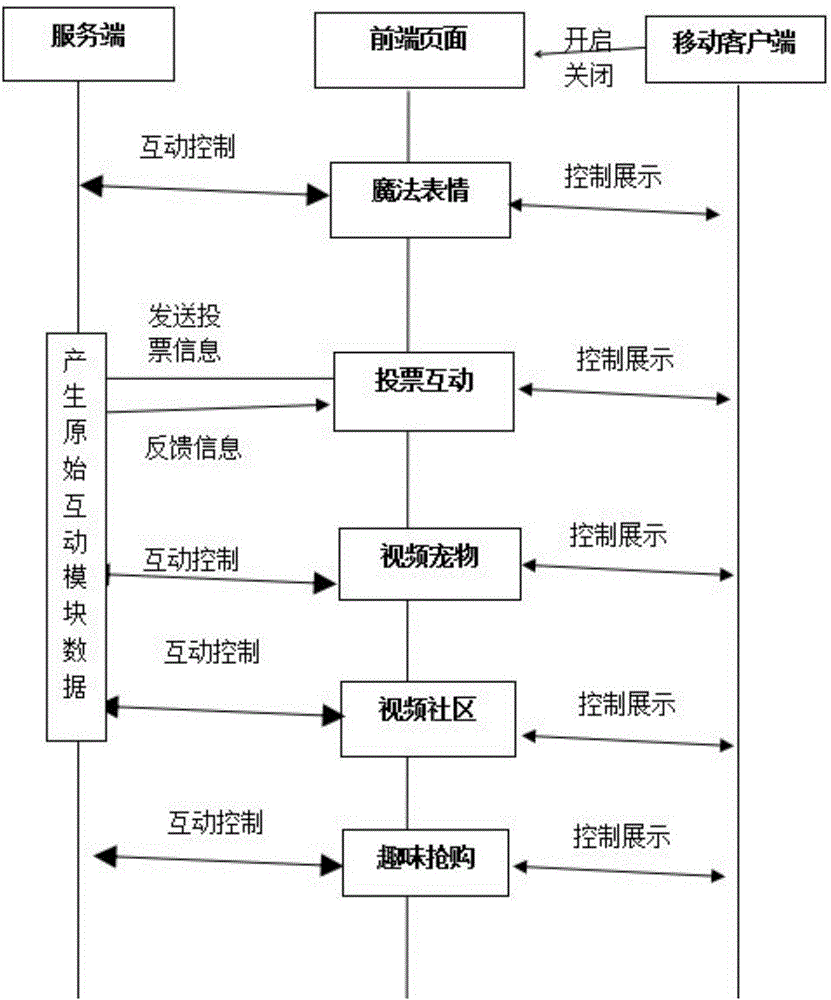
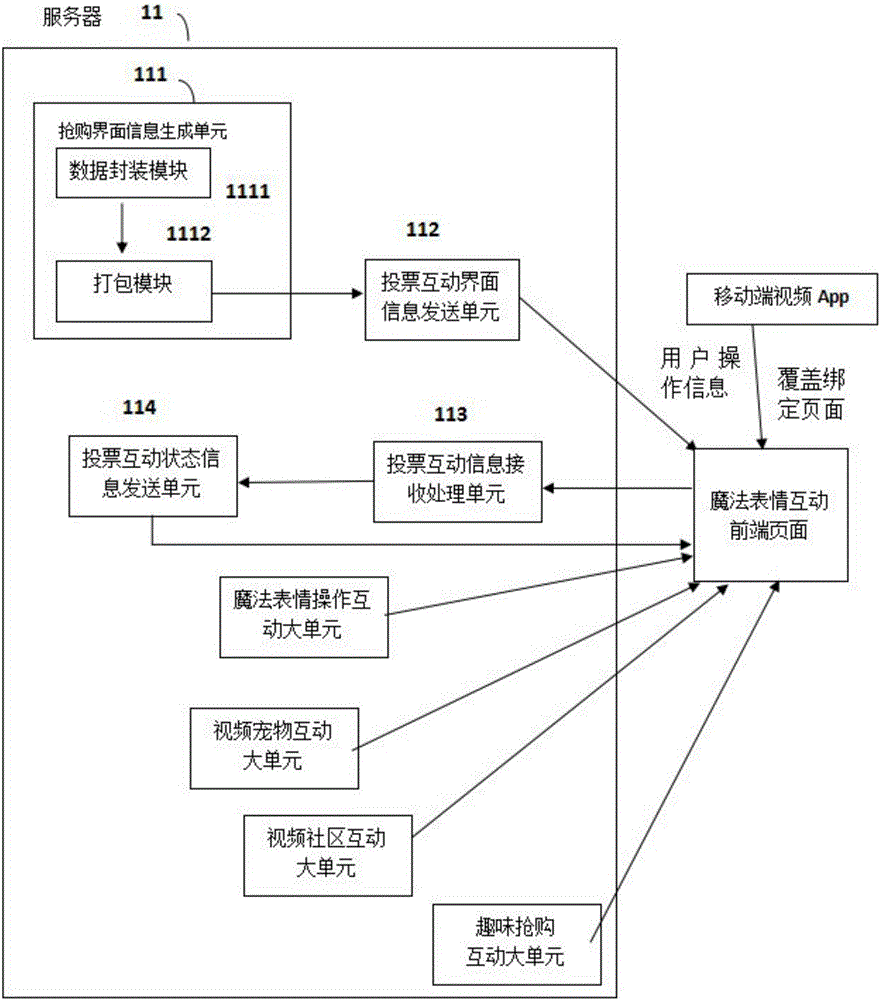
Interactive entertainment server and system for video application
InactiveCN106028164AInteractive funMore interactiveSelective content distributionInput/output processes for data processingInteraction systemsInteractive content
The invention provides an interactive entertainment server and system for a mobile terminal to watch a video. A service side generates interactive voting interface information, kind management information of magic expressions and interface parameter information of a video pet; an interface is made on an internet page; an application of the mobile terminal is associated with the page and covers the video picture with the page floating on the video picture; an interactive content is displayed on the page; the page can request the server for obtaining data information, such as voting; and information spreading is completed through an external network. The invention provides a network magic expression interaction method for the mobile terminal to play a video; therefore, it is more interested and interactive for users to watch the video; the system can customize topics and embed multiple different virtual props for the users to use; and thus, the users can have better entertainment and operability while watching a television.
Owner:安徽省谷威天地传媒科技有限公司
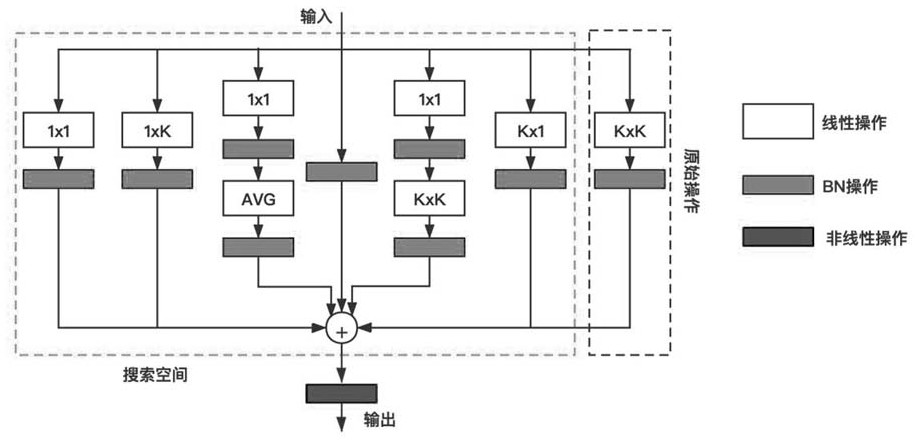
Edge calculation-oriented reparametric neural network architecture search method
ActiveCN113435590AImprove accuracyReduce the amount of calculationNeural architecturesNeural learning methodsNetwork structureEngineering
The invention discloses an edge calculation-oriented reparametric neural network architecture search method. The method comprises the following steps of 1, designing a linear operator and multiple branch block structures; 2, constructing a super network by stacking the multiple branch block structures; 3, training the super network through a gradient-based first-stage search algorithm; 4, deleting redundant branches in the super network to construct an optimal sub-network; 5, converting the multi-branch optimal sub-network into a single-branch network; and 6, completing task reasoning by using the single-branch network. The method is used for searching the neural network structure capable of performing re-parameterization, and ensures the reasoning real-time performance and the high efficiency of model operation while ensuring the reasoning precision.
Owner:ZHEJIANG LAB
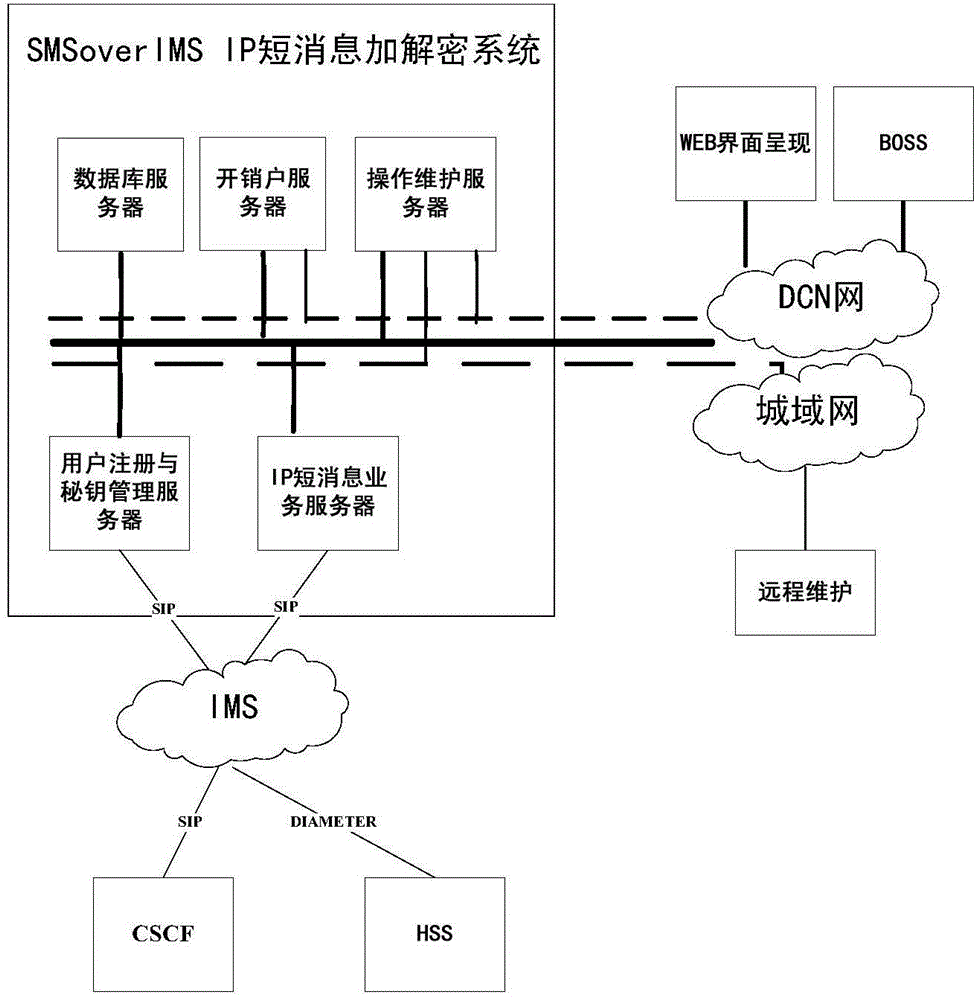
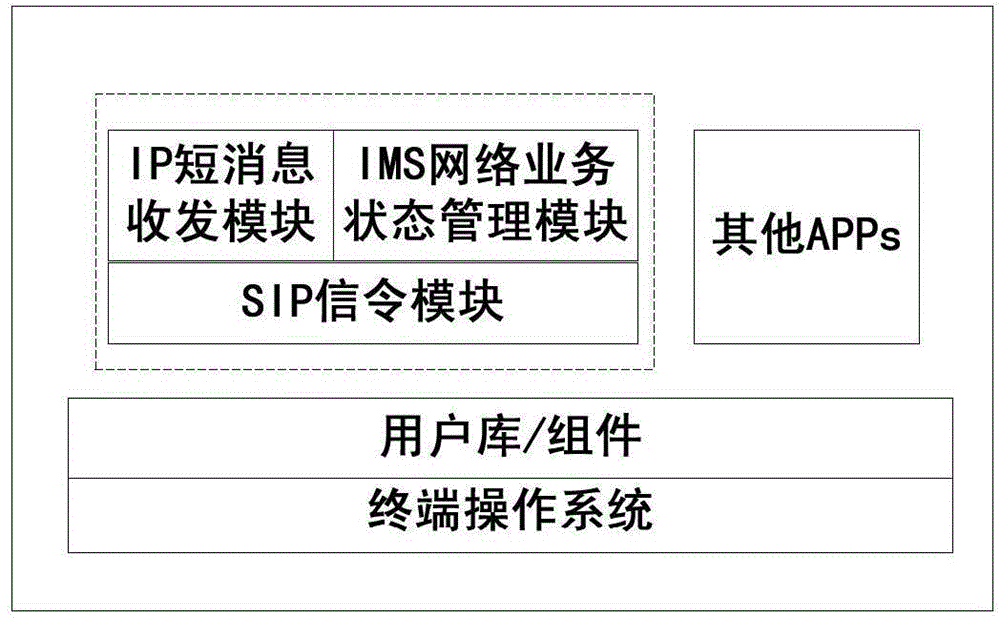
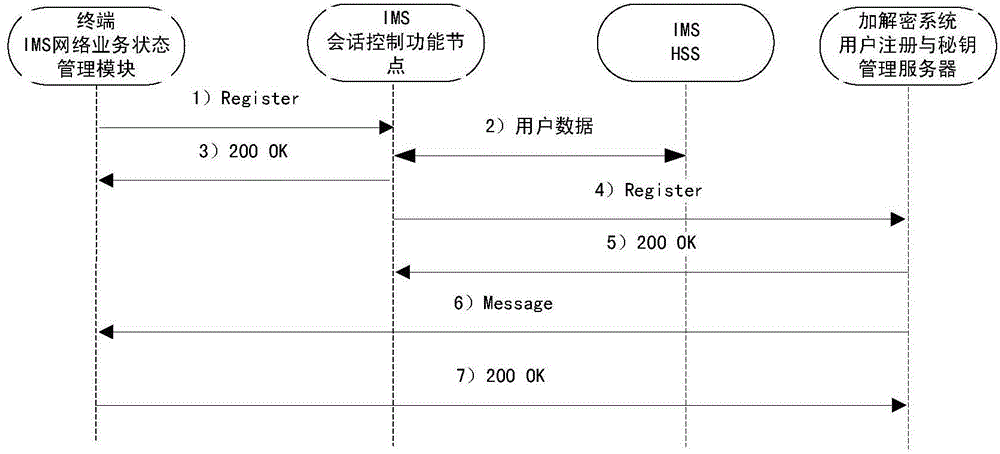
Method and system for encrypting/ decrypting IP (Internet Protocol) short messages based on SMS (Short Messaging Service) over IMS (IP Multimedia Subsystem)
ActiveCN104618898AImplement encryption and decryption functionsLow running costSecurity arrangementComputer hardwareCiphertext
The invention provides a method for encrypting / decrypting IP short messages based on SMS over IMS; the method comprises the steps: when LTE (Long Term Evolution) users send and receive IP short messages in the IMS region in an SMS over IMS manner, the short messages are encrypted short messages, the content parts of which are ciphertexts; an IP short message encrypting and decrypting centre of the users finishes the encryption and decryption at the network side and then returns the IMS core network to finish the follow-up route at the end of the encryption and decryption. The corresponding technical solution is provided by analyzing the technical feature of the SMS over IMS and deeply analyzing key problems; the coordination of user registration management and user's secret key in the registration process is realized by the iFC (Initial Filter Criteria) triggering mechanism of the IMS and the encrypting and decryption functions of the short message contents in the IP short messaging service process are realized; the coordination of the terminal side to the encrypted and decrypted secret key is realized and the function of the short message content from encryption / decryption to representation on user's interface is realized by developing new terminal application software; the scheme can be implemented without modifying the present network equipment and the cost of operation and maintenance is lower.
Owner:EASTERN COMM
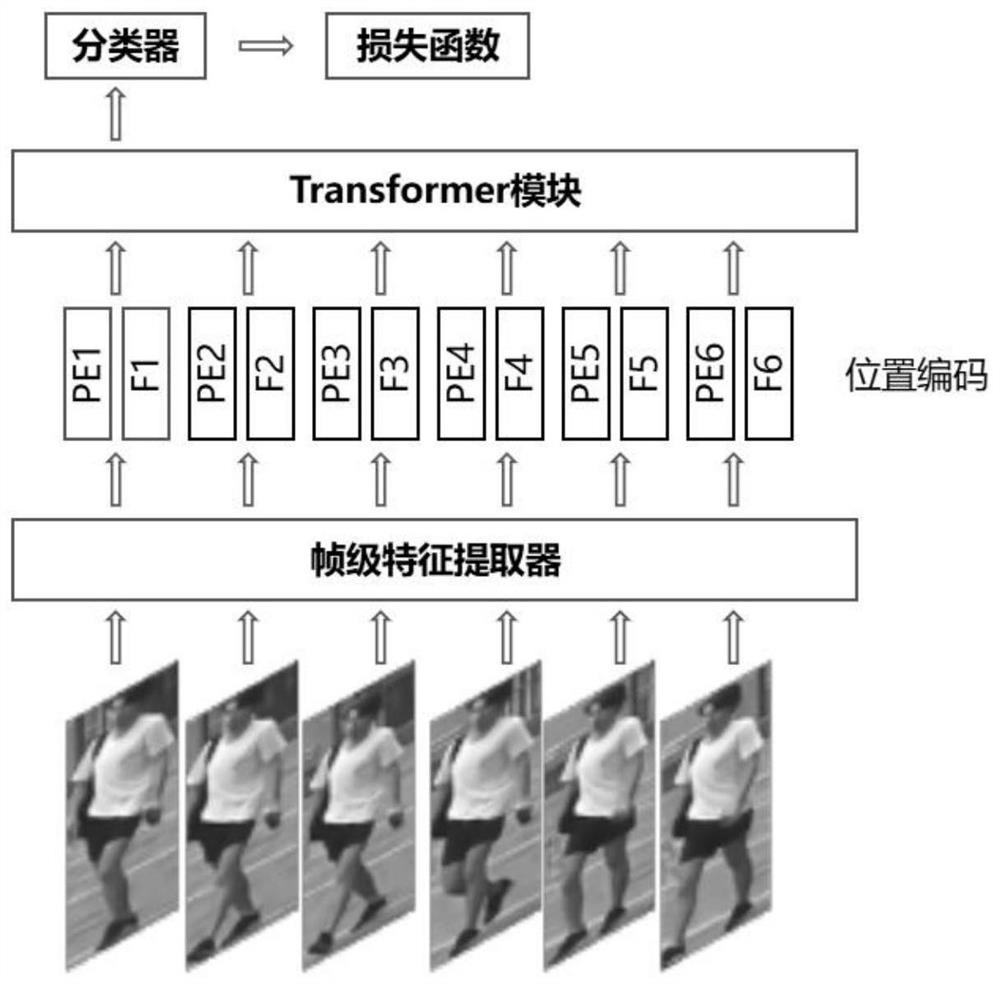
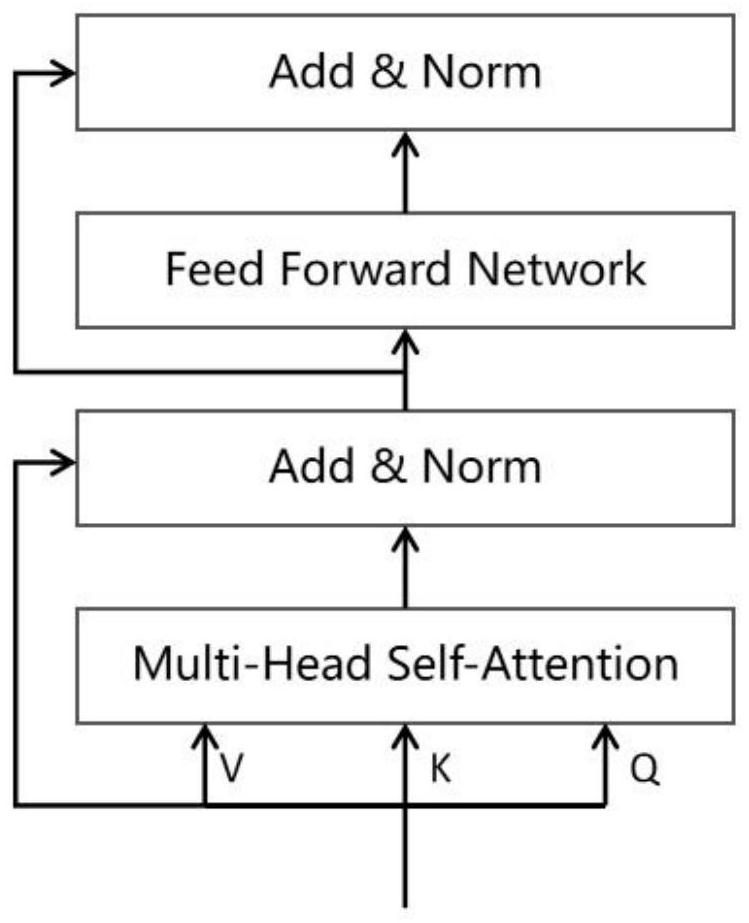
Video pedestrian re-recognition method based on Transform space-time modeling
ActiveCN113627266APreserve timing informationImprove performanceCharacter and pattern recognitionNeural architecturesEngineeringNetwork model
The invention relates to a video pedestrian re-recognition method based on Transform space-time modeling. The method comprises the following steps: firstly, extracting frame-level features by using an image-level feature network ResNet50, then adding position information to the frame-level features through a position coding layer to ensure sequence information of video frames to the greatest extent, then completing space-time modeling on recoded features through a Transform network, and further extracting space-time features with higher discrimination performance. According to the method, position codes are added to frame-level features, so that time sequence information of video clips can be fully utilized; a Transform structure is utilized to map input features to three spaces for feature fusion, so that more robust spatial-temporal features are extracted, and the performance of the network is improved; an end-to-end network model is provided, the application process from input to model to output is realized, and the training difficulty of the pedestrian re-recognition network model based on the video is reduced.
Owner:WUHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com