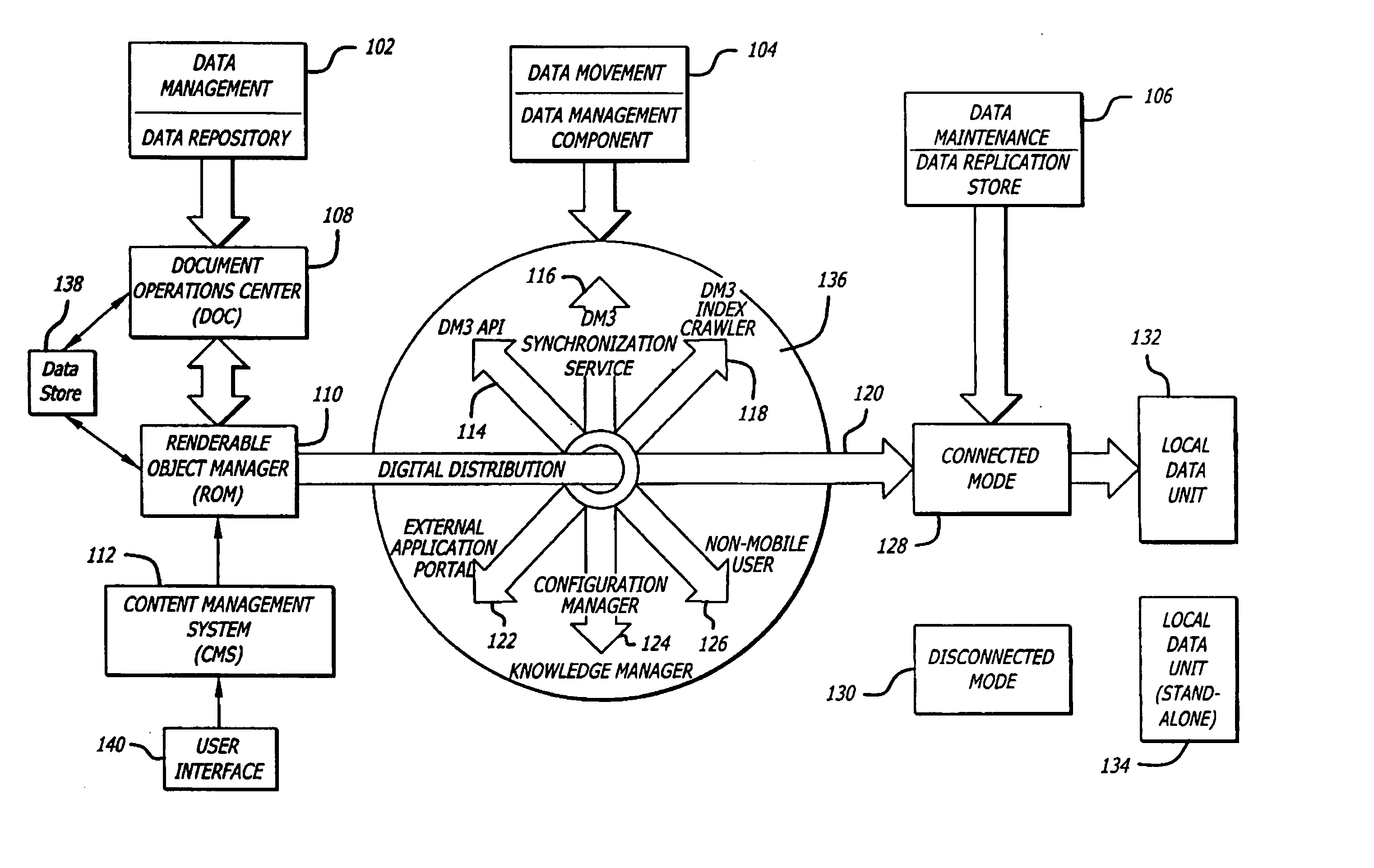
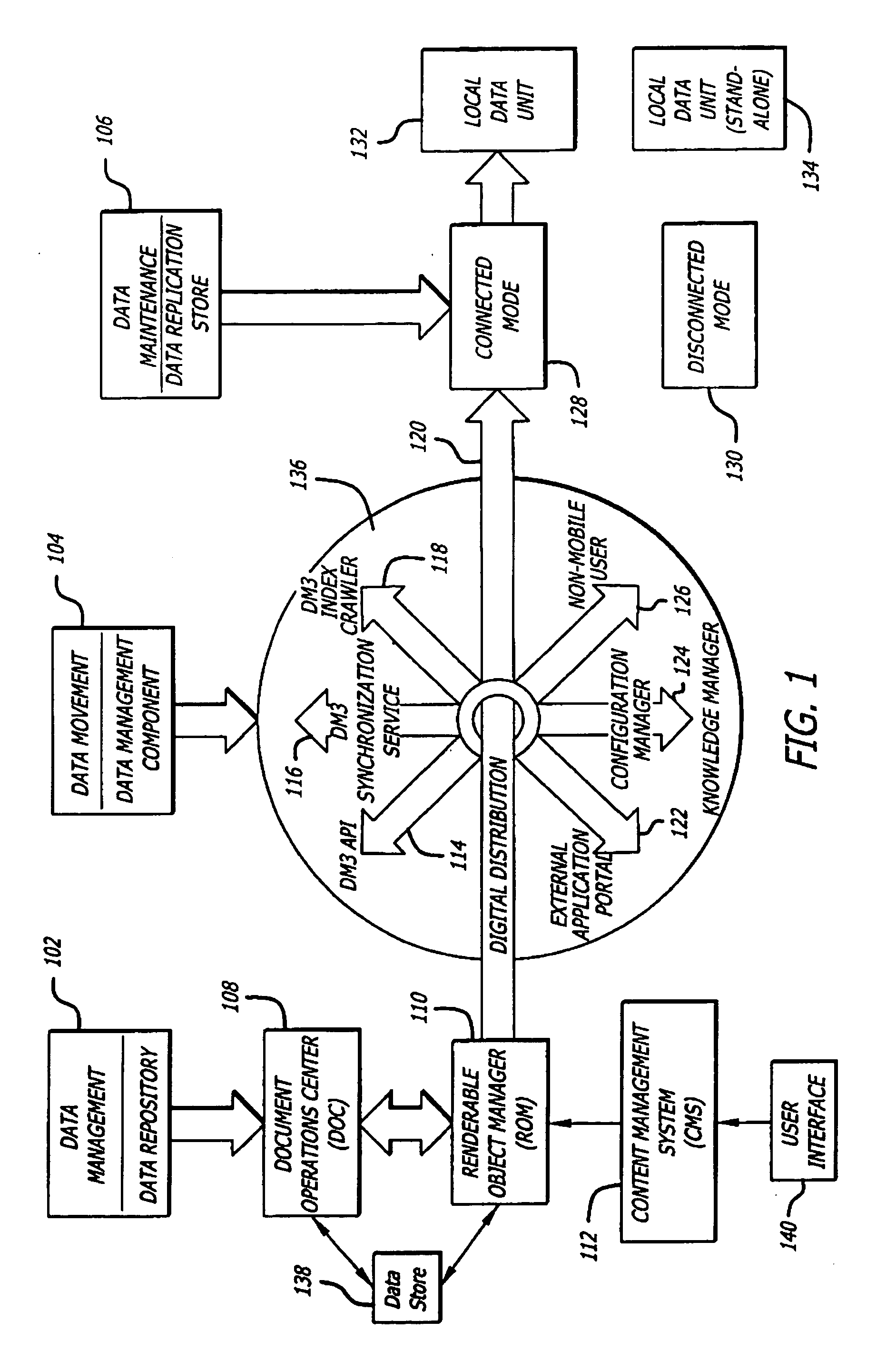
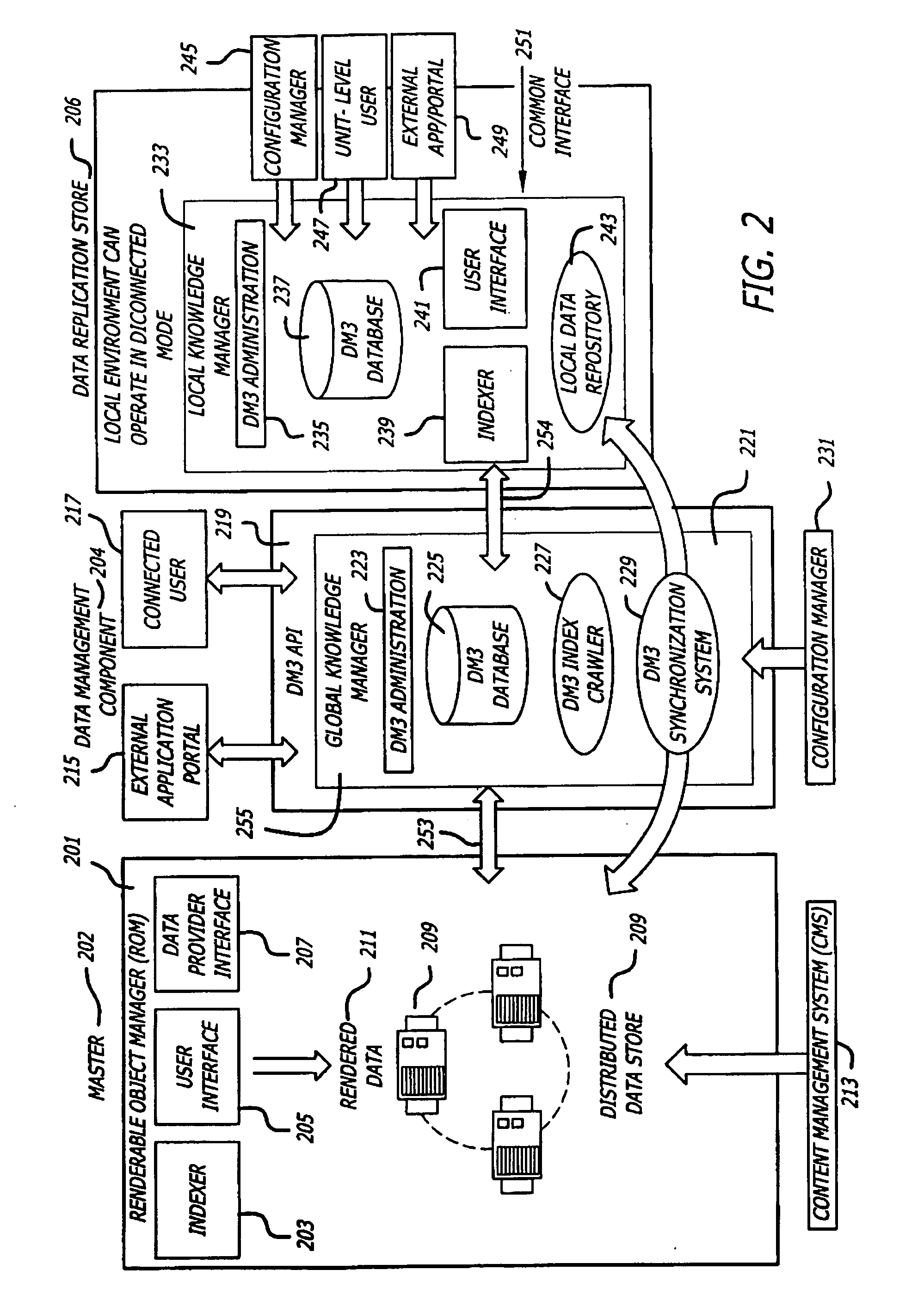
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4556 results about "Network parameter" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
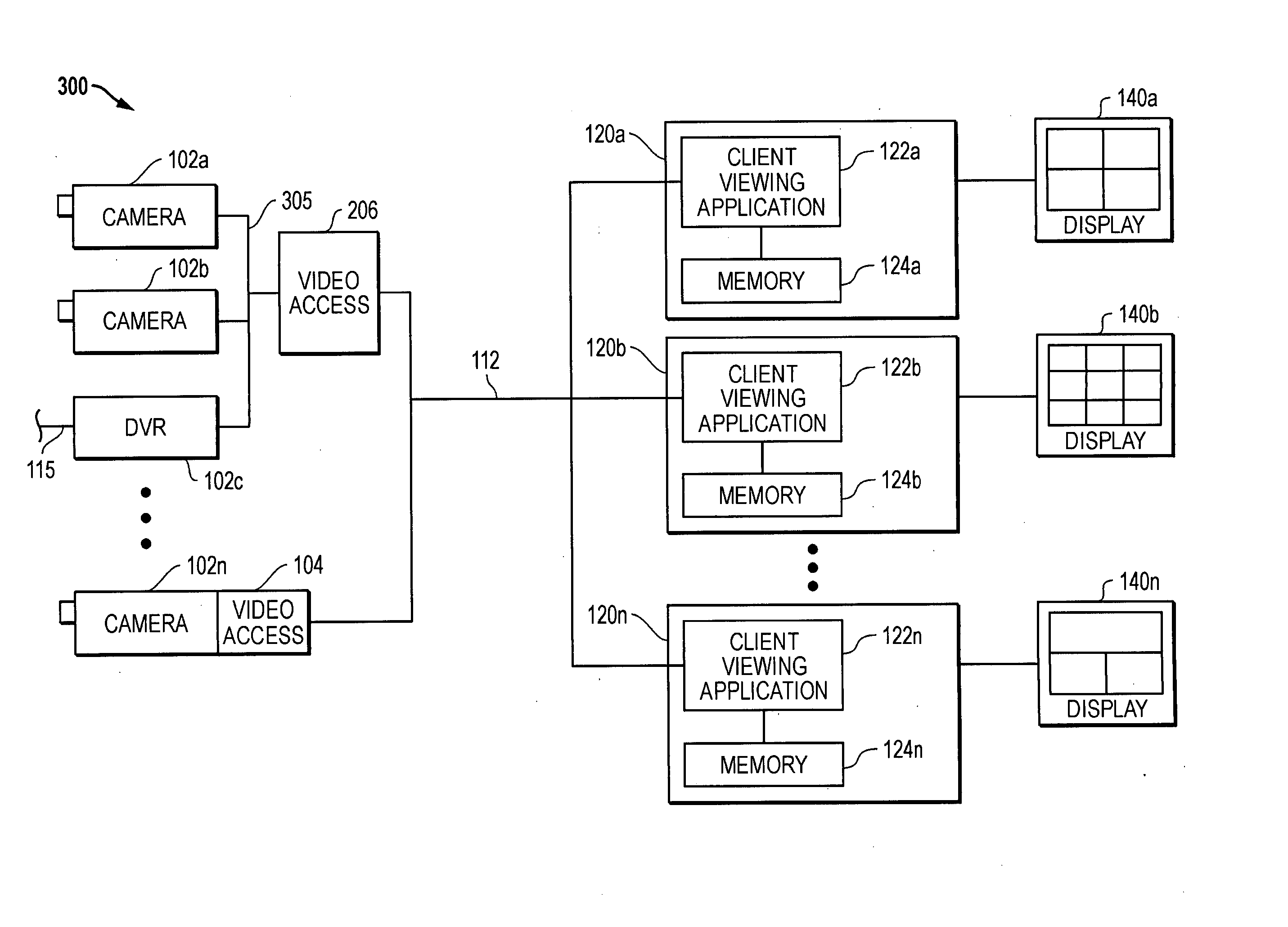
The Network Parameter Utility (NPU) is a light-weight, OEM-customizable application that reads and writes Network Configuration Parameters stored in a device's internal database via a USB connection. It provides configuration of all applicable network settings, automatically manages device firmware, and allows updating devices in the field.
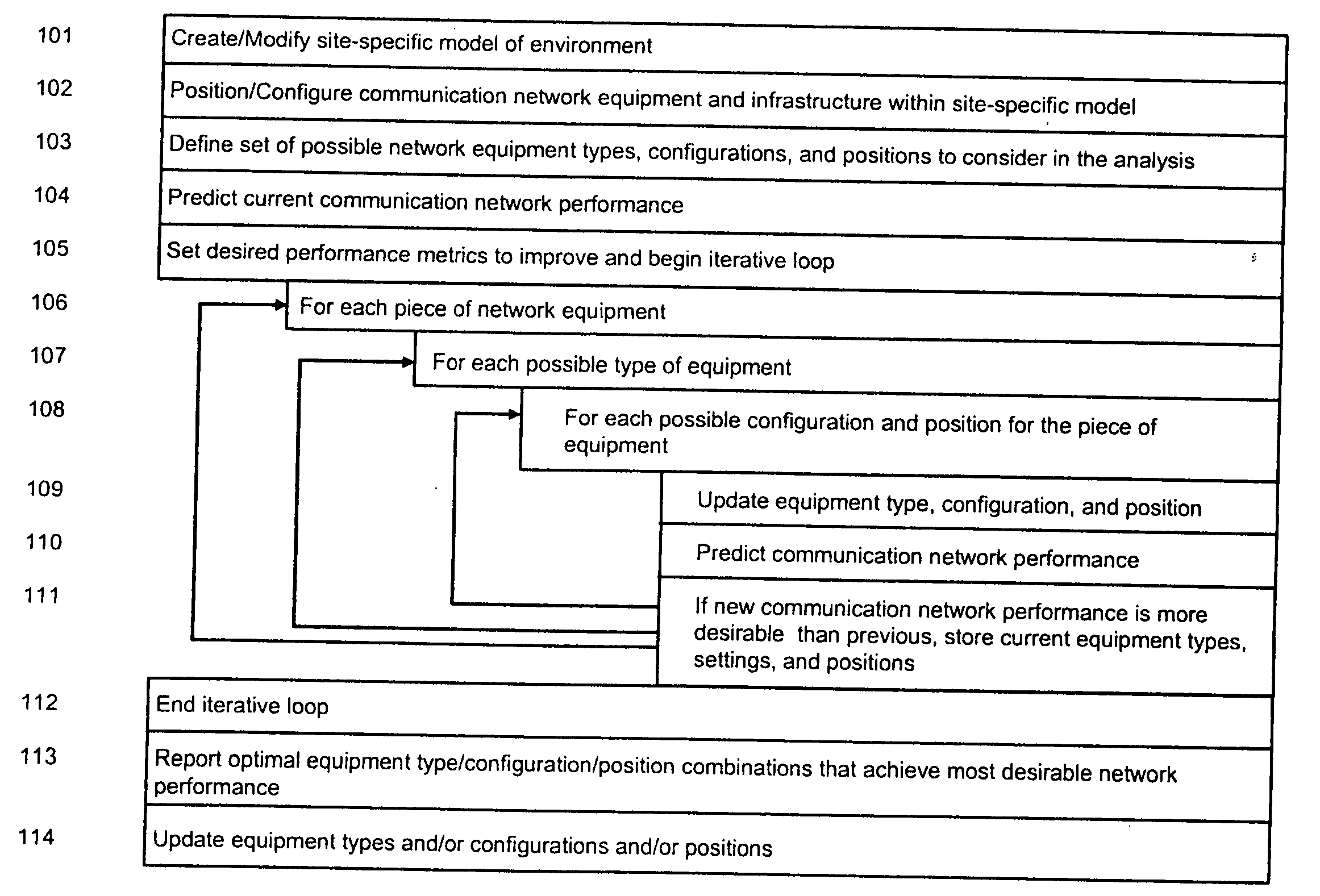
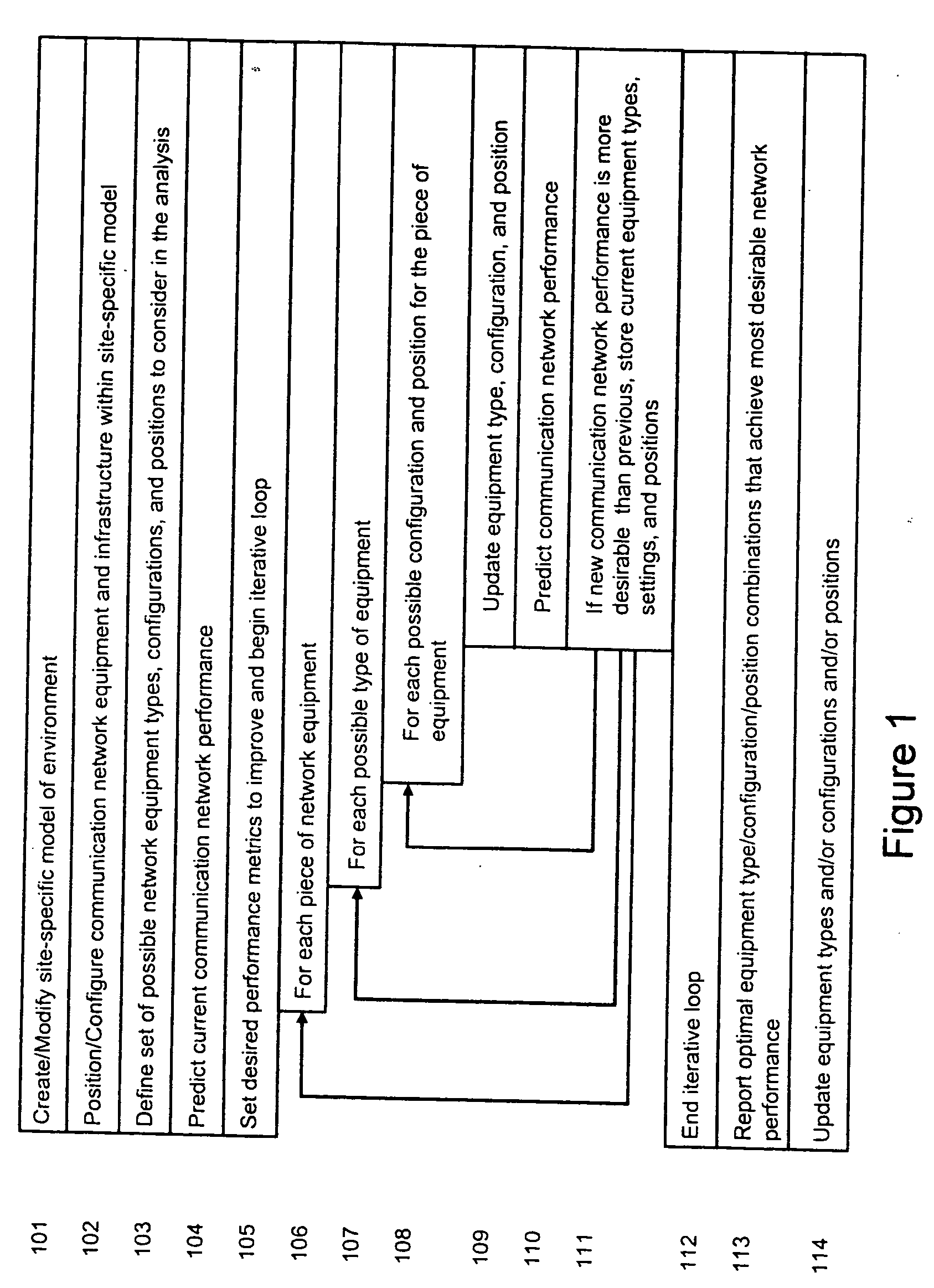
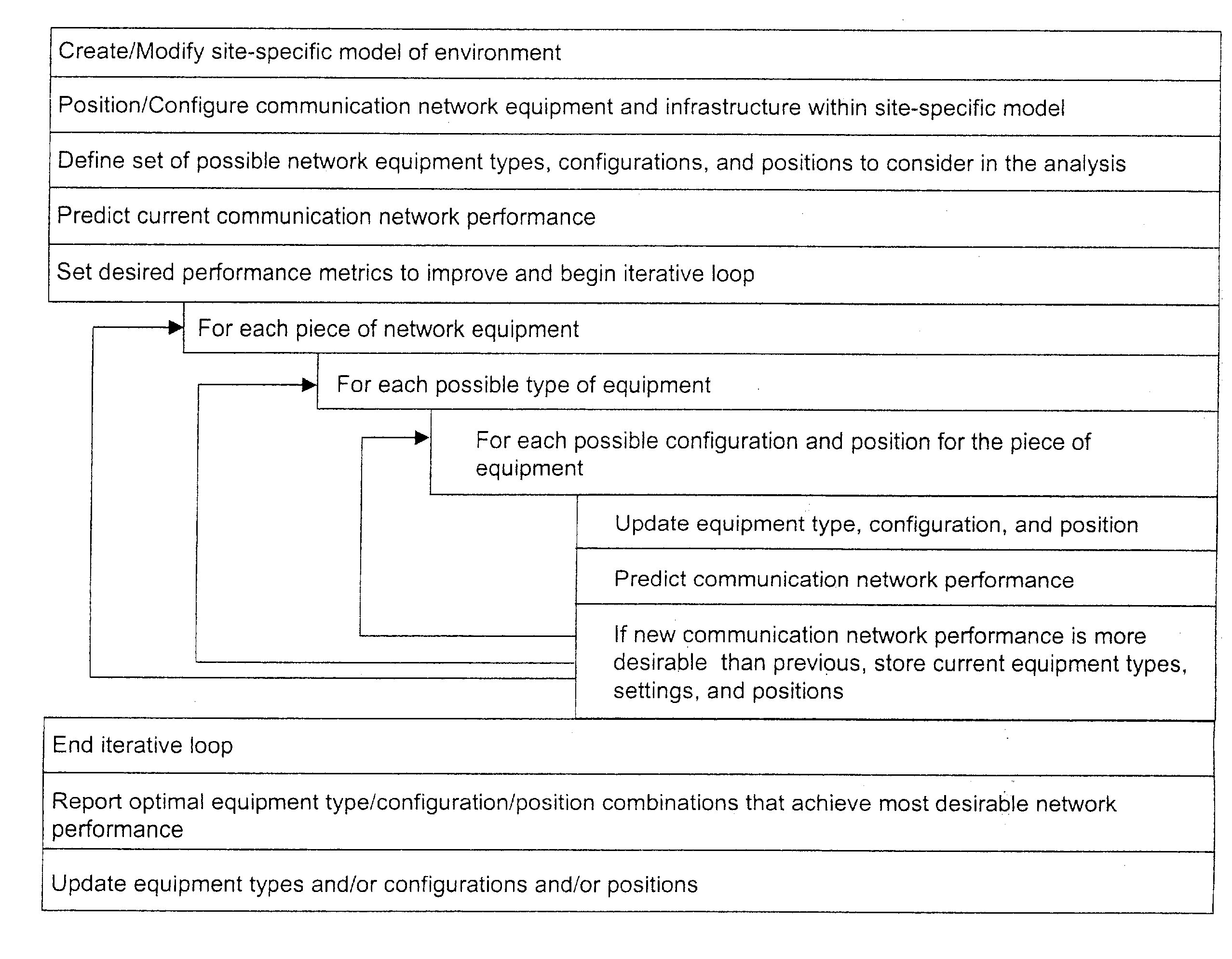
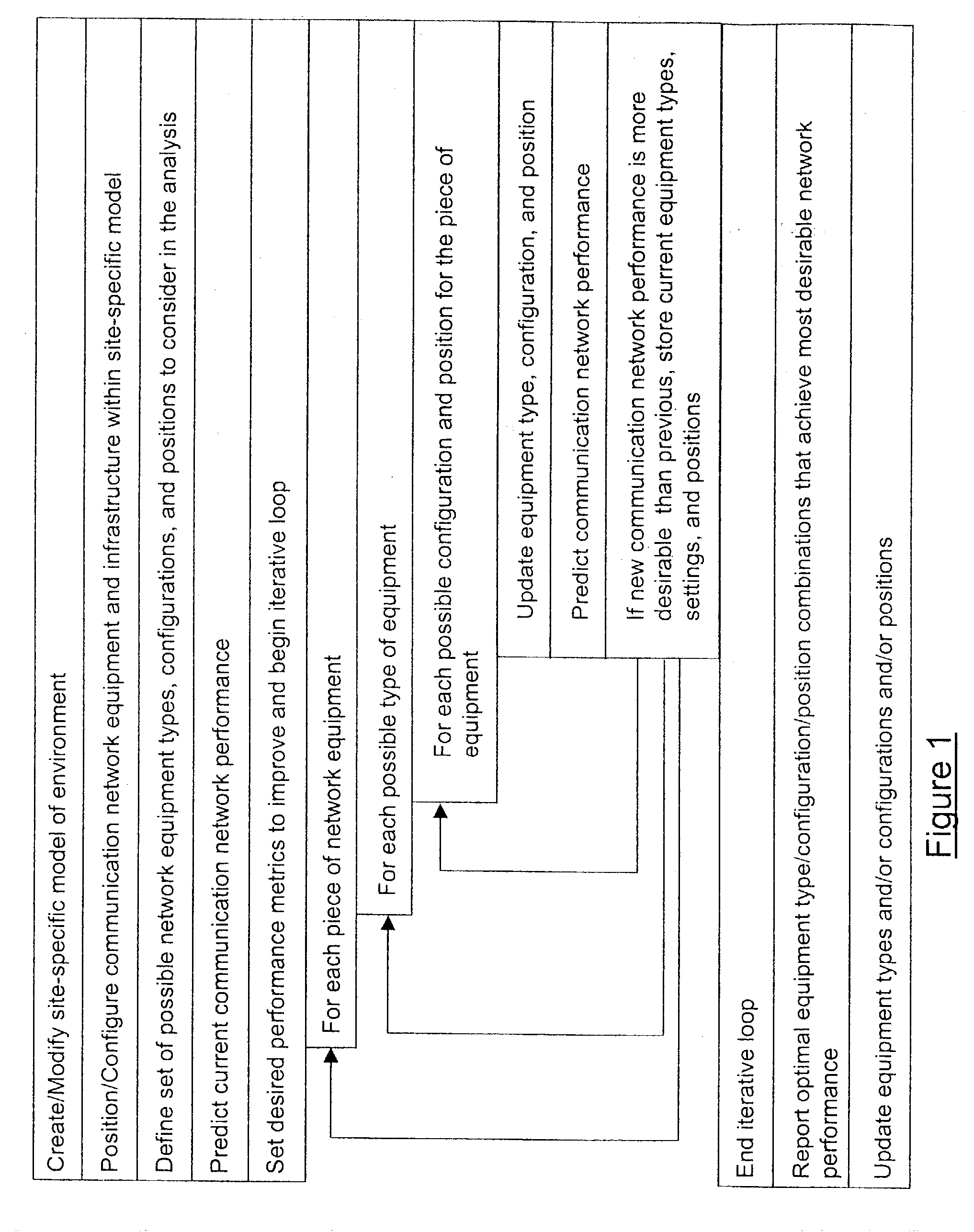
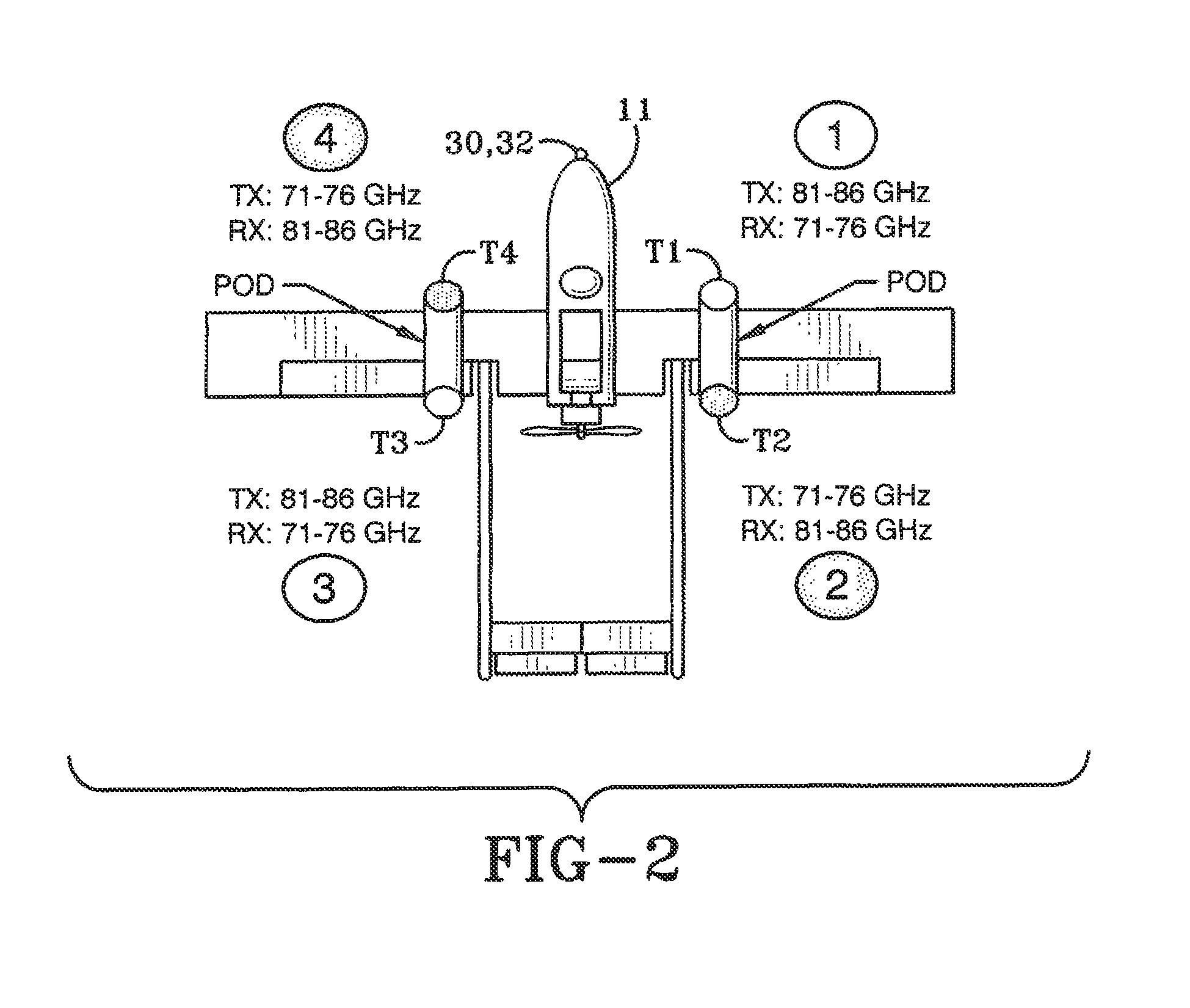
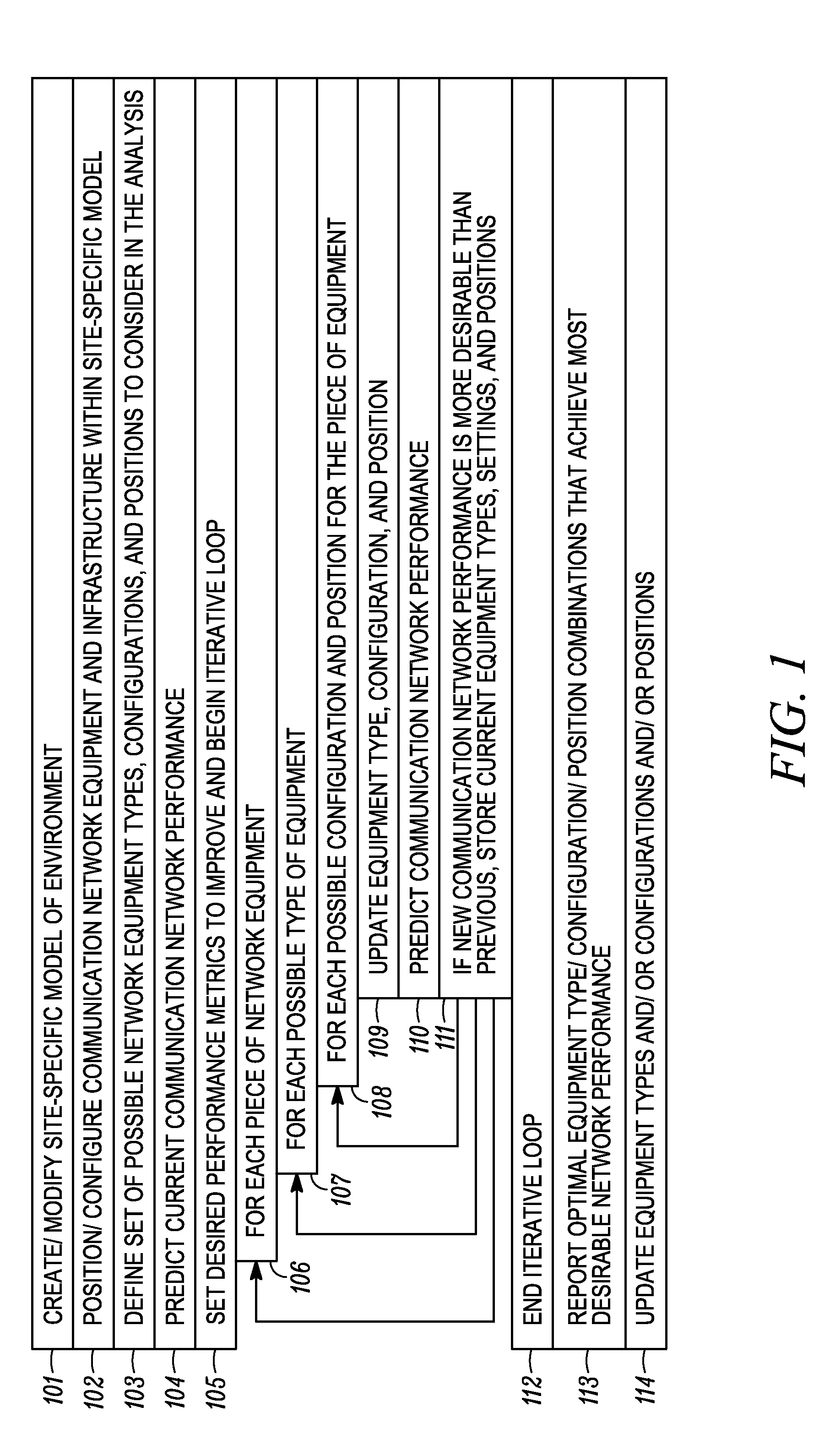
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
ActiveUS20040143428A1Significant valueEasy to explainGeometric CADProgram controlHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
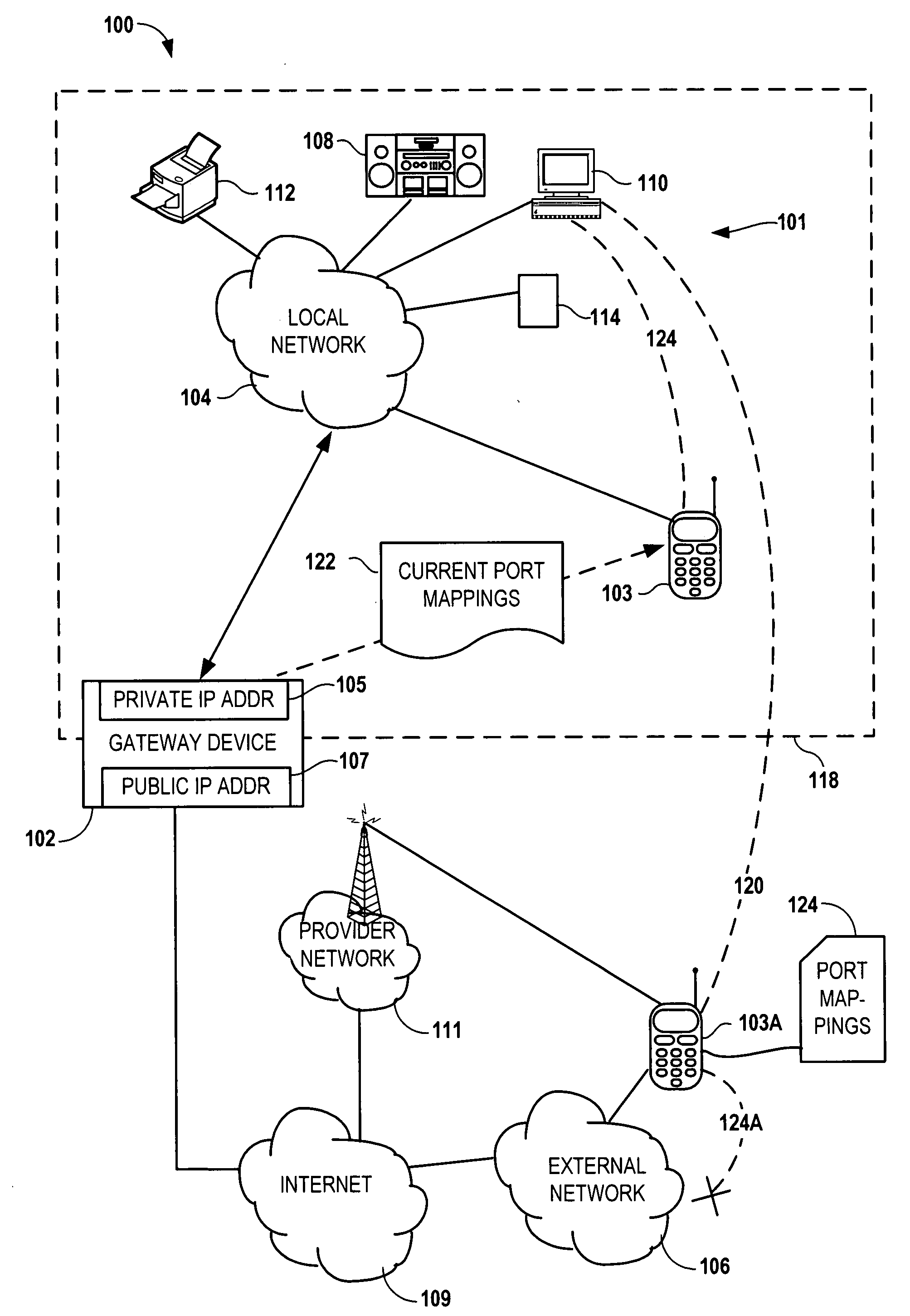
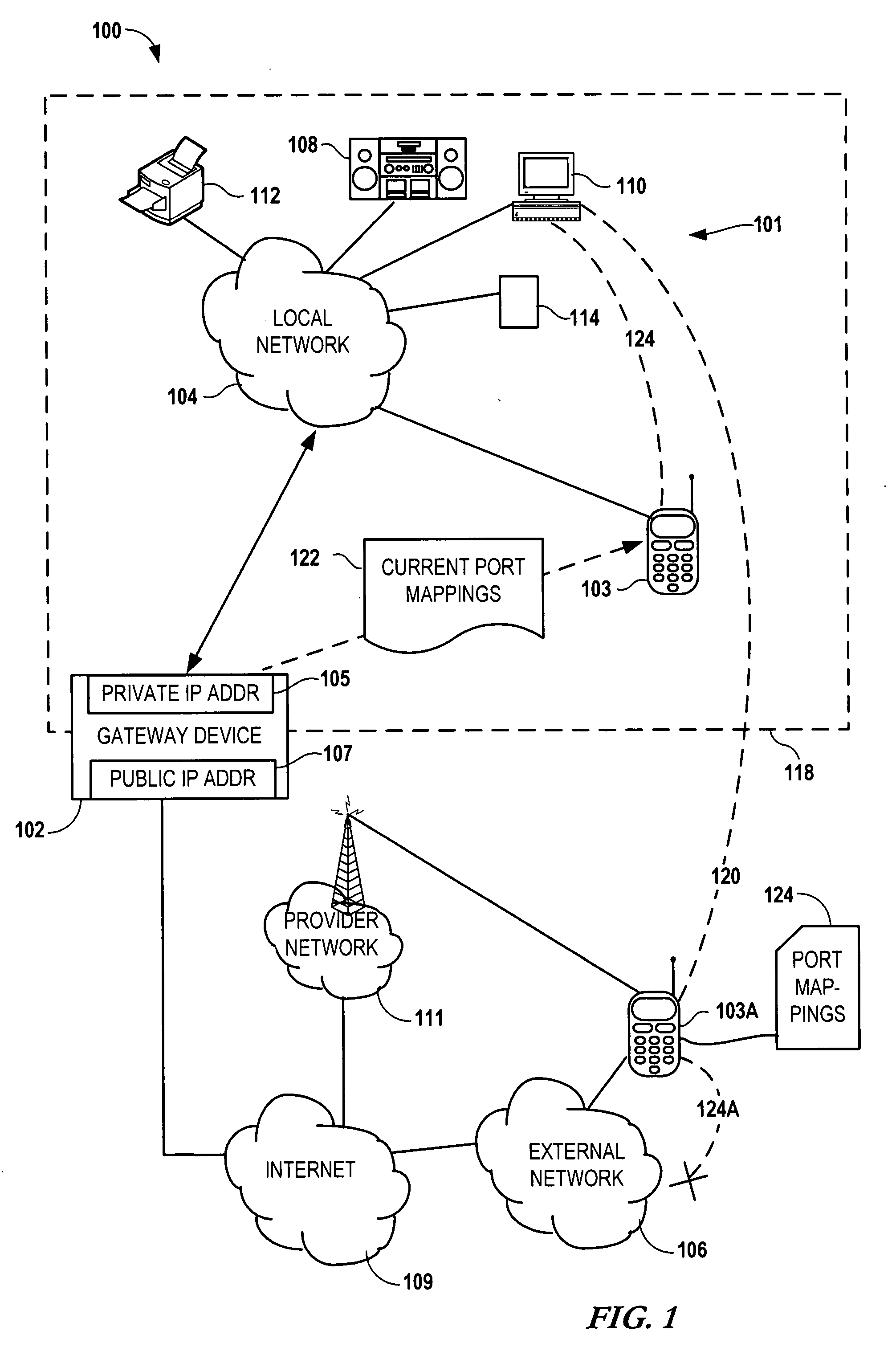
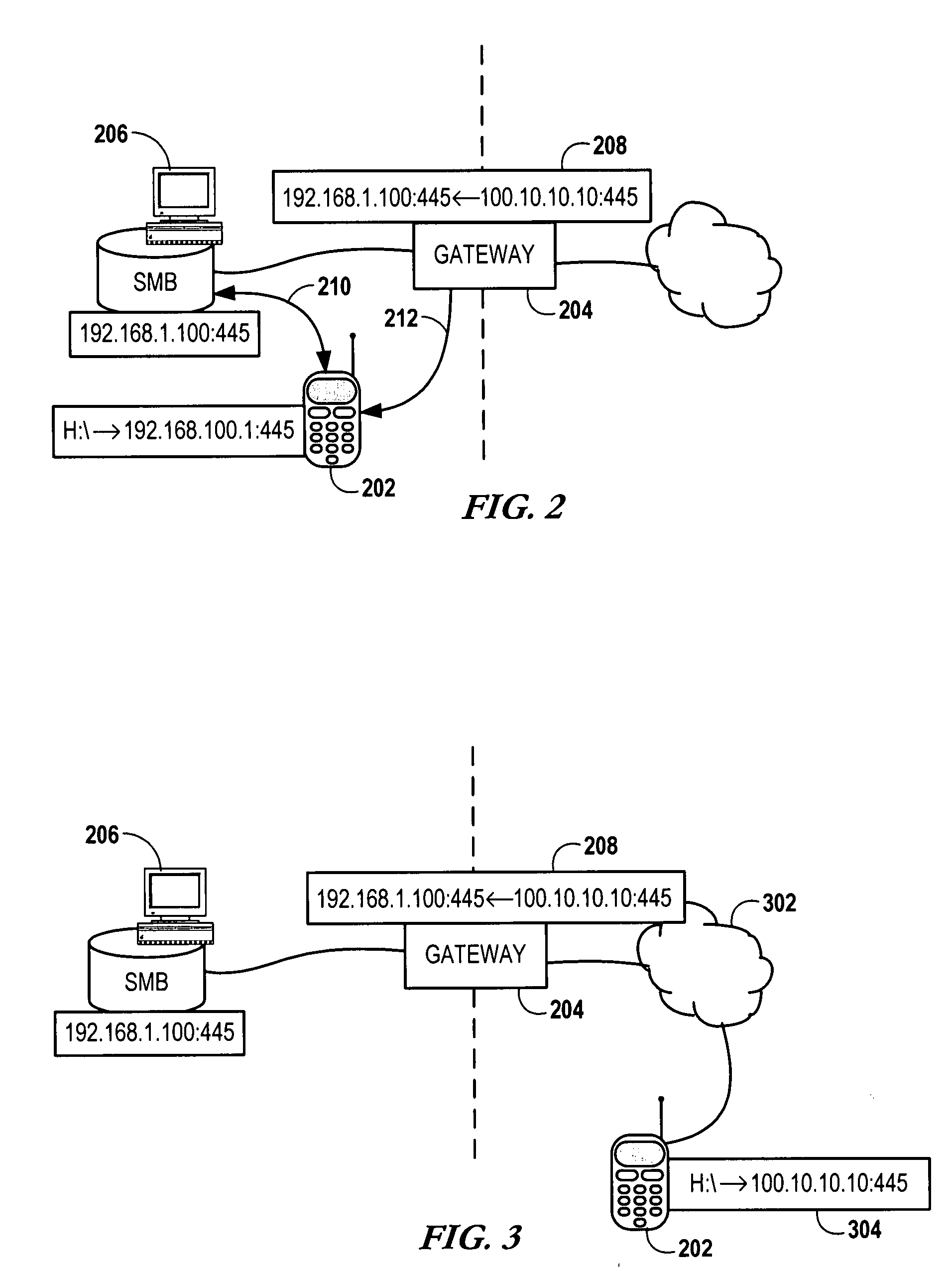
Configuring a user device to remotely access a private network
InactiveUS20090129301A1Network traffic/resource managementRadio transmissionPrivate networkPublic network
Configuring a mobile device to remotely access a private network involves determining, via the private network, first network parameters that enable the mobile device utilize to a computing service of the private network. The device also determines, via a gateway coupled to the private network, second network parameters that allow the mobile to utilize the computing service via a public network. The first and second network parameters are stored on the mobile device. A request is received from a user of the mobile device to access the computing service. It is determined that the mobile device is not on the private network. In response to determining that the mobile device is not on the private network, the second network parameters are utilized to access the computing service via the gateway in response to the request.
Owner:NOKIA CORP
Smart and selective synchronization between databases in a document management system
InactiveUS20050216524A1Efficient transportGuaranteed normal transmissionDigital data information retrievalSpecial data processing applicationsData synchronizationData set
A smart synchronization method and system for use in a document management system is disclosed. Upon a request for data synchronization from a remote location, the management software determines, based on network parameters and data types, the most effective algorithms for efficiently transporting the data to be synchronized over the network. In another aspect, a selective synchronization method and system is disclosed wherein the management software uses a summary of data in a request for synchronization to determine which data sets require updating. The management software synchronizes the databases using only those updates, rather than entire data sets. Network efficiency is maximized as a result.
Owner:INTEGRATED DATA CORP
Systems and methods for video stream selection
InactiveUS20070024705A1Maximize efficiencyShort response timeTelevision system detailsColor television detailsComputer graphics (images)Multi stream
Systems and methods for selecting reception of video streams in an adaptive fashion, for example, from a multi-stream video source. In one implementation, reception of the video streams may be dynamically switched such that optimal bandwidth is selected in adaptive fashion using a set of video parameters, such as the size or dimensions of the viewing window, and / or a set of system and network parameters, to ascertain the optimal stream selection.
Owner:UTC FIRE & SECURITY AMERICAS CORPORATION INC
Efficient handover of media communications in heterogeneous IP networks using handover procedure rules and media handover relays
ActiveUS8228861B1Reduce complexityIncrease speedError detection/prevention using signal quality detectorChannel coding adaptationMedia controlsCable Internet access
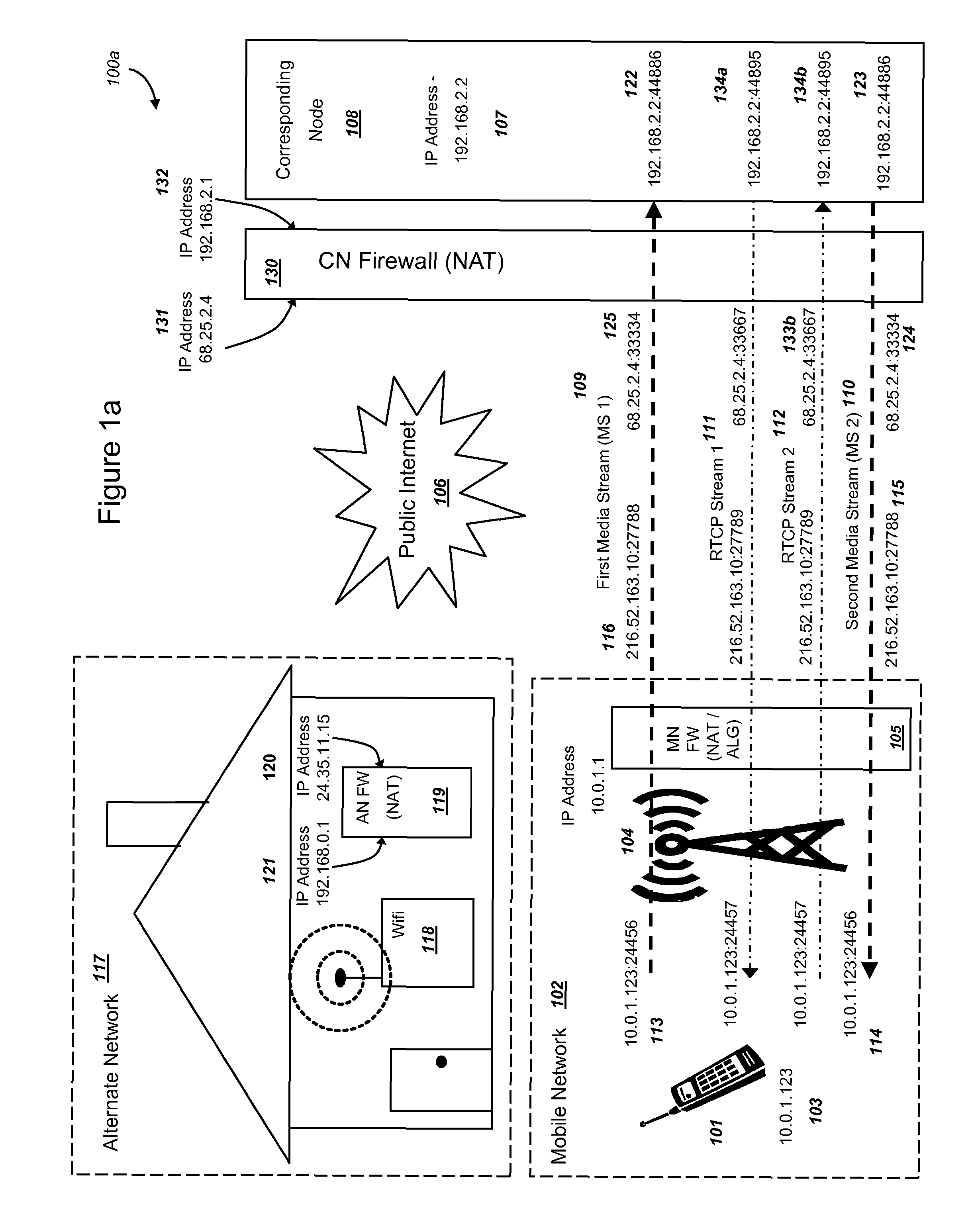
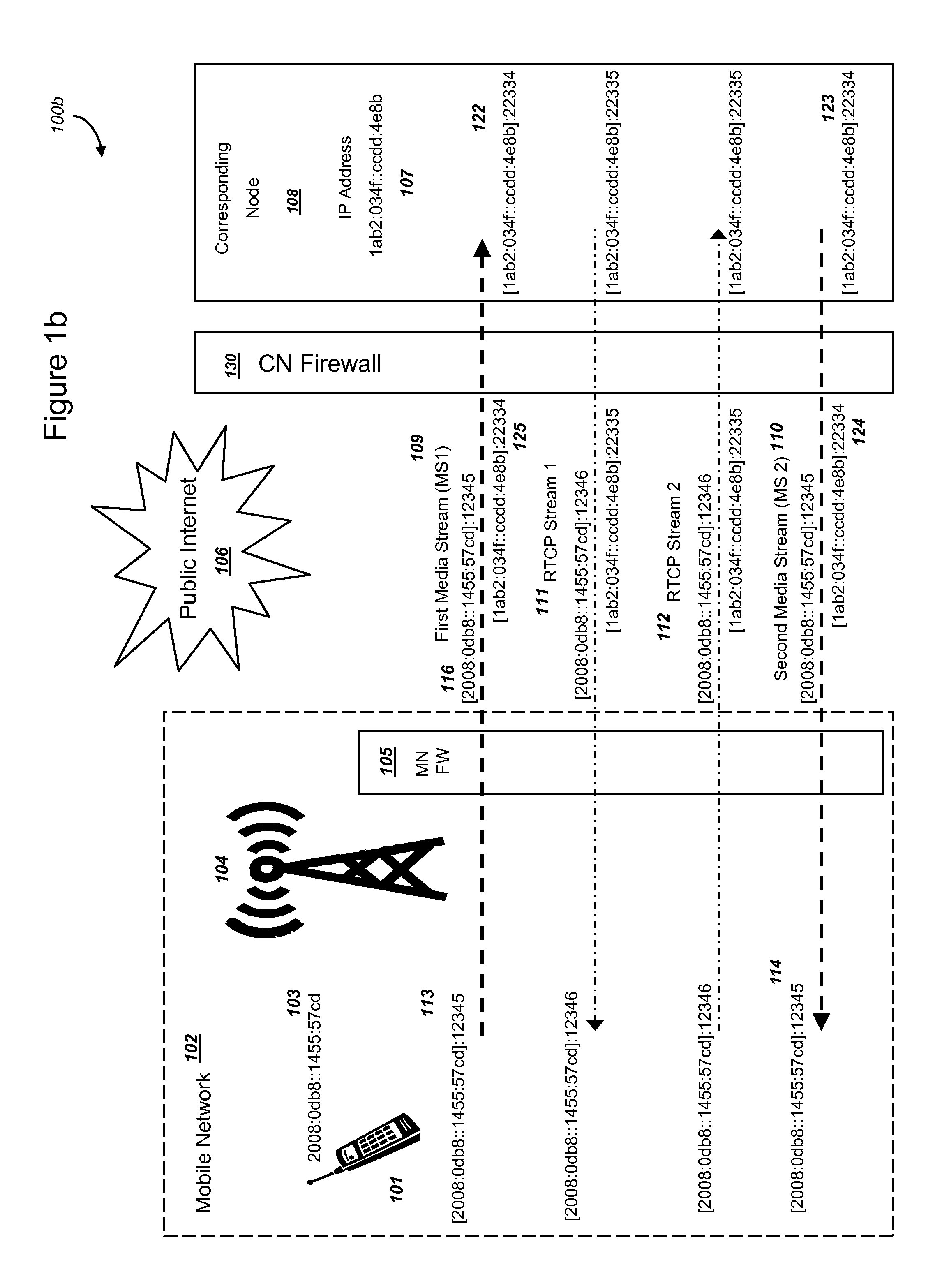
Methods and systems are provided for efficient handover of a media session between heterogeneous Internet Protocol (IP) networks. A mobile device with Internet access can operate a software program to communicate with a corresponding node. The corresponding node may access the Internet through a firewall which may include Network Address Translation (NAT)-routing functionality. The mobile device establishes a media session with a corresponding node via the transmission of a first media stream and receipt of a second media stream, and a media-control channel can optionally be implemented. The mobile device can acquire Internet access through a second IP address, and packets routed between the second IP address and the Internet may traverse a firewall. The mobile device can evaluate a set of network parameters at the second IP address from a stored Local Area Network (LAN) profile. A software routine can (i) evaluate that handover of the media session from the first IP address to the second IP address is preferred and (ii) select an efficient handover procedure according to handover procedure rules.
Owner:GOOGLE LLC
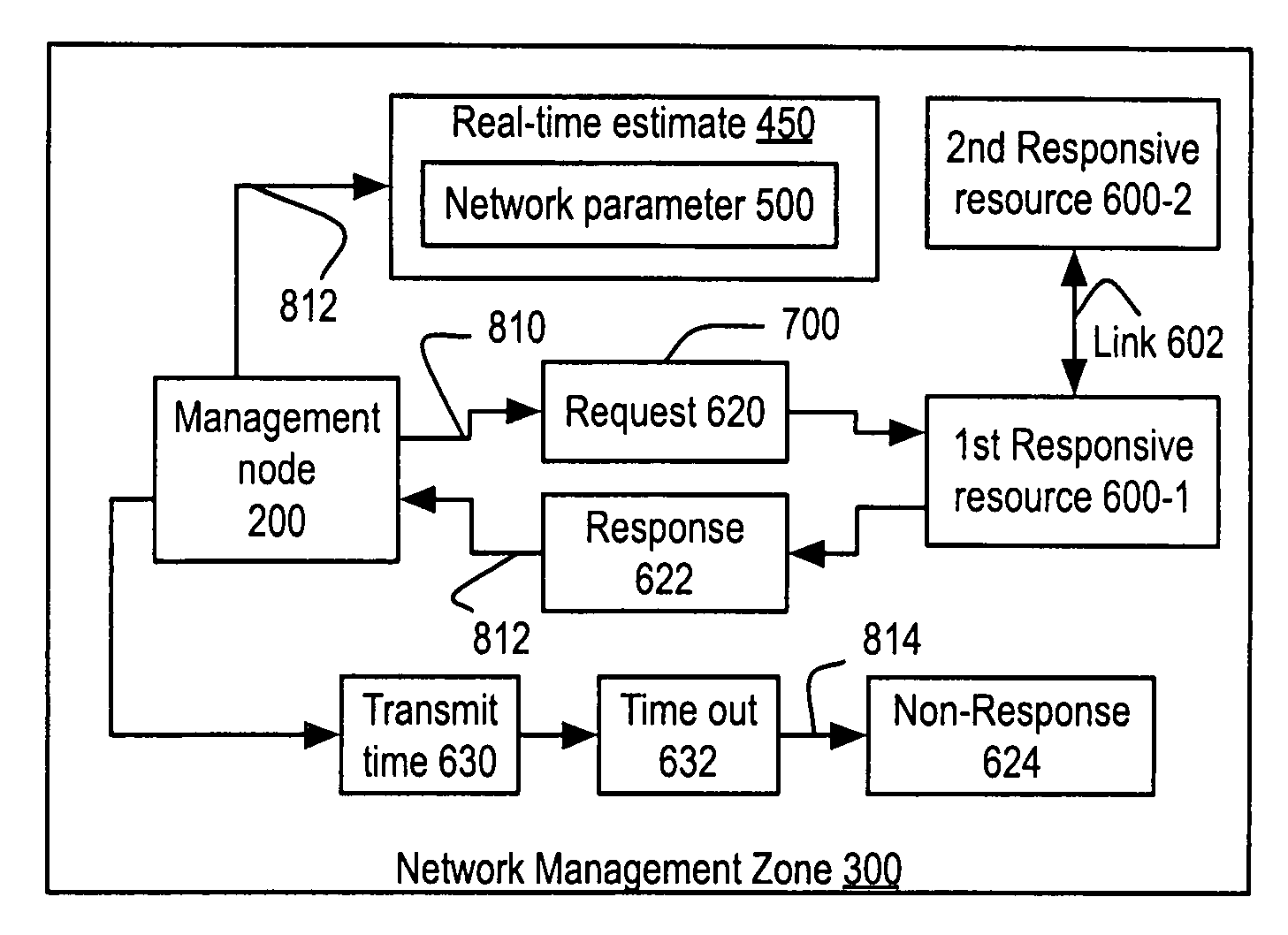
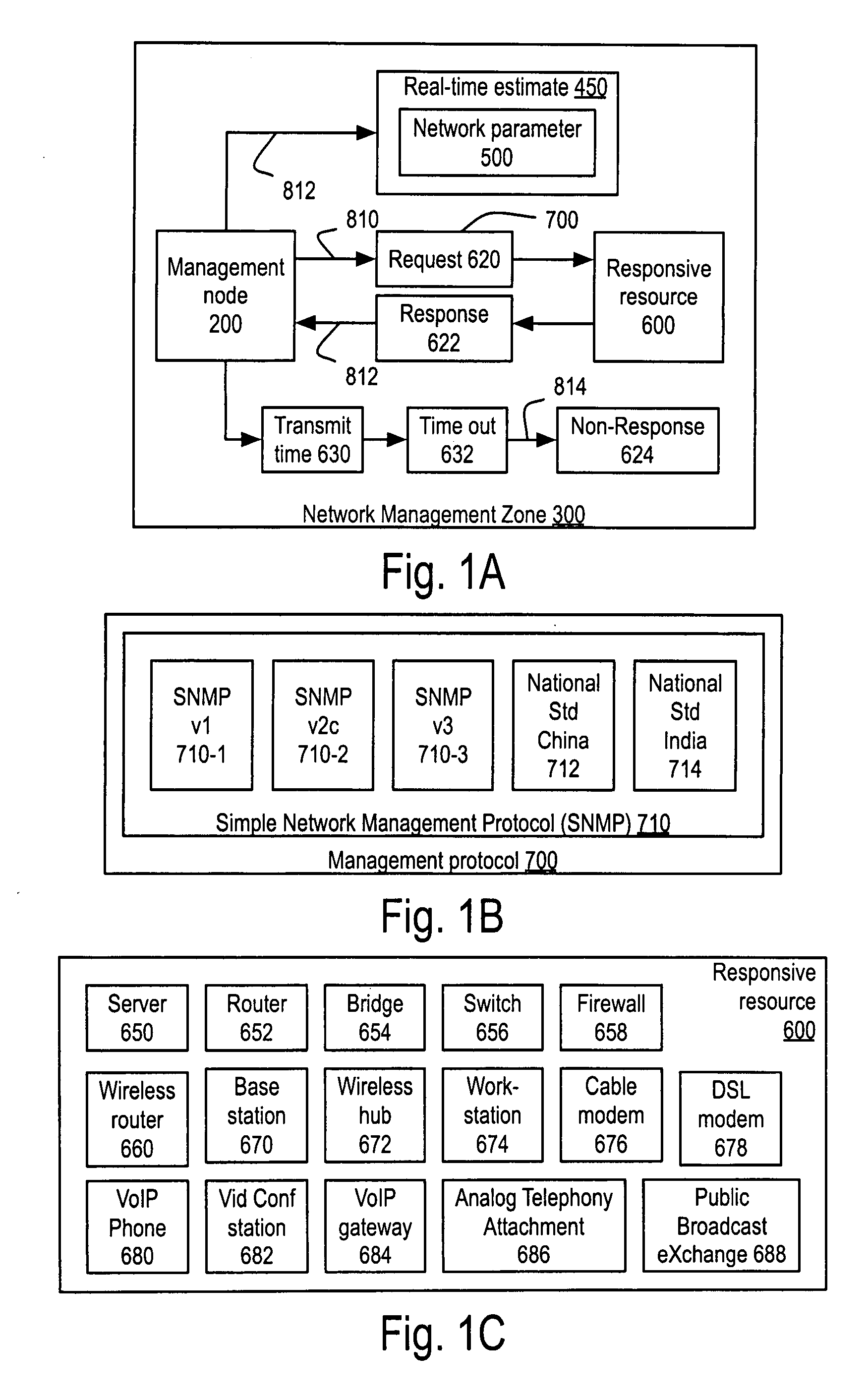
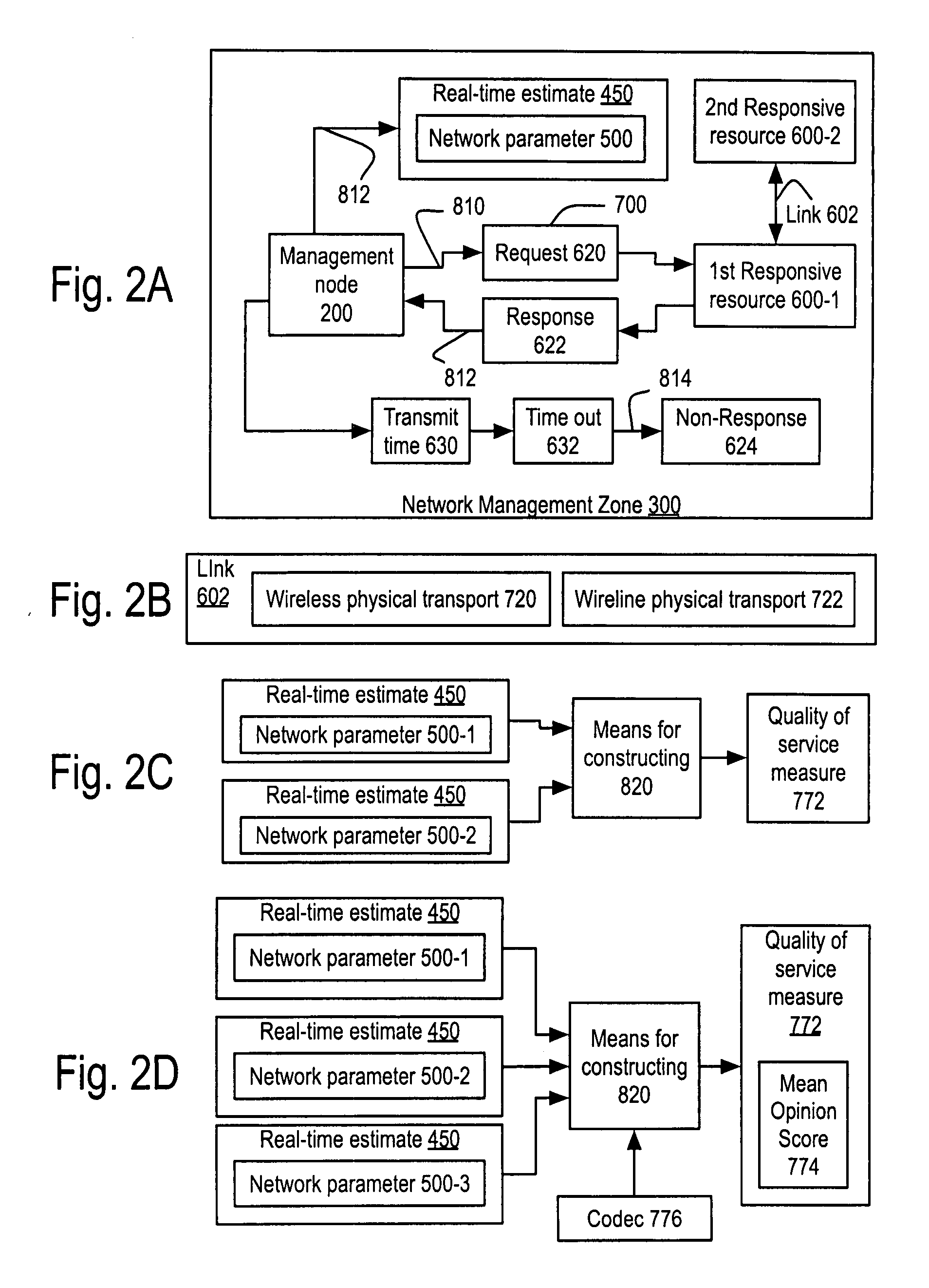
Apparatus and method for measuring and using response to SNMP requests to provide real-time network parameter estimates in a network management zone
InactiveUS20080201468A1Digital computer detailsData switching networksReal-time webQuality of service
Method creates Real-Time Estimates (RTE) of network parameters for responsive resources of a network management zone (NMZ) by sending requests in a management protocol and uses those real-time estimates to present a resource map of the NMZ, possibly altering a responsive resource, possibly posting a service schedule request. The invention includes implementation mechanisms and installation packages. The RTE of network parameter is a product of the process. Constructing a quality of service measure from RTE of at least two network parameters. Quality of service measure as a product of the process. The quality of service measure may include or be the Mean Opinion Score.
Owner:PATH SOLUTIONS
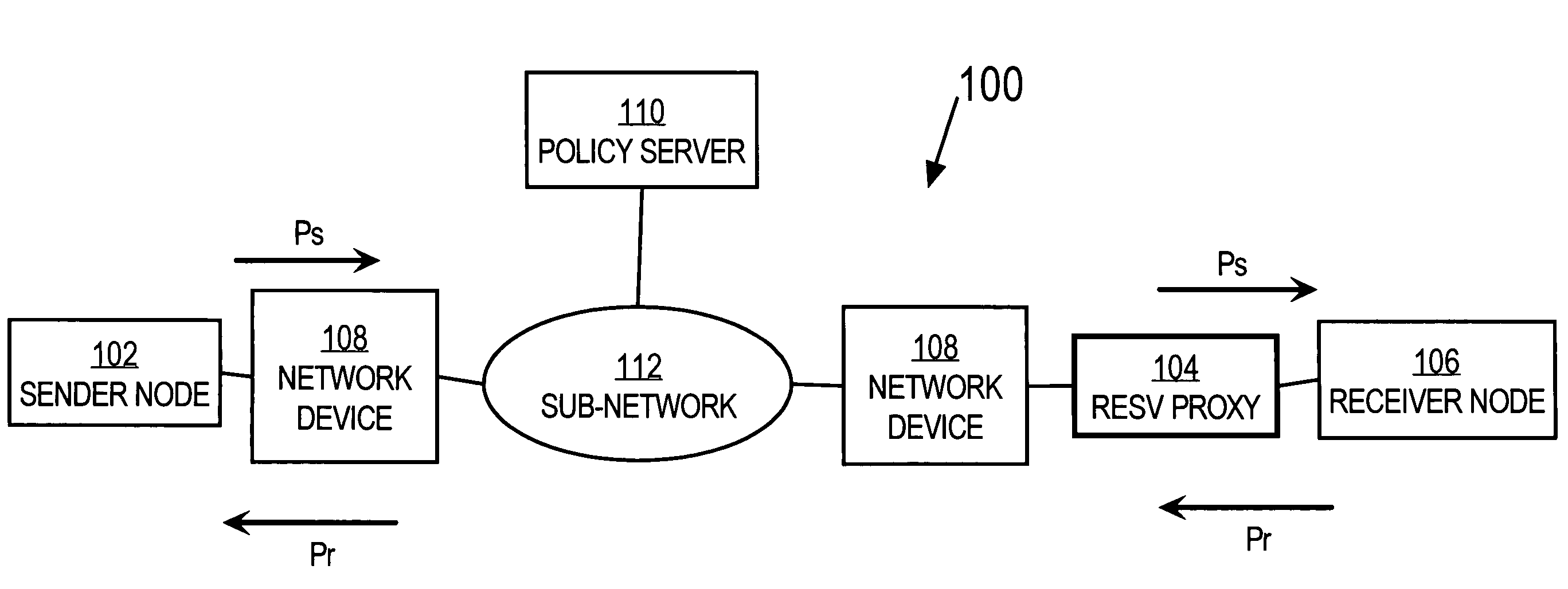
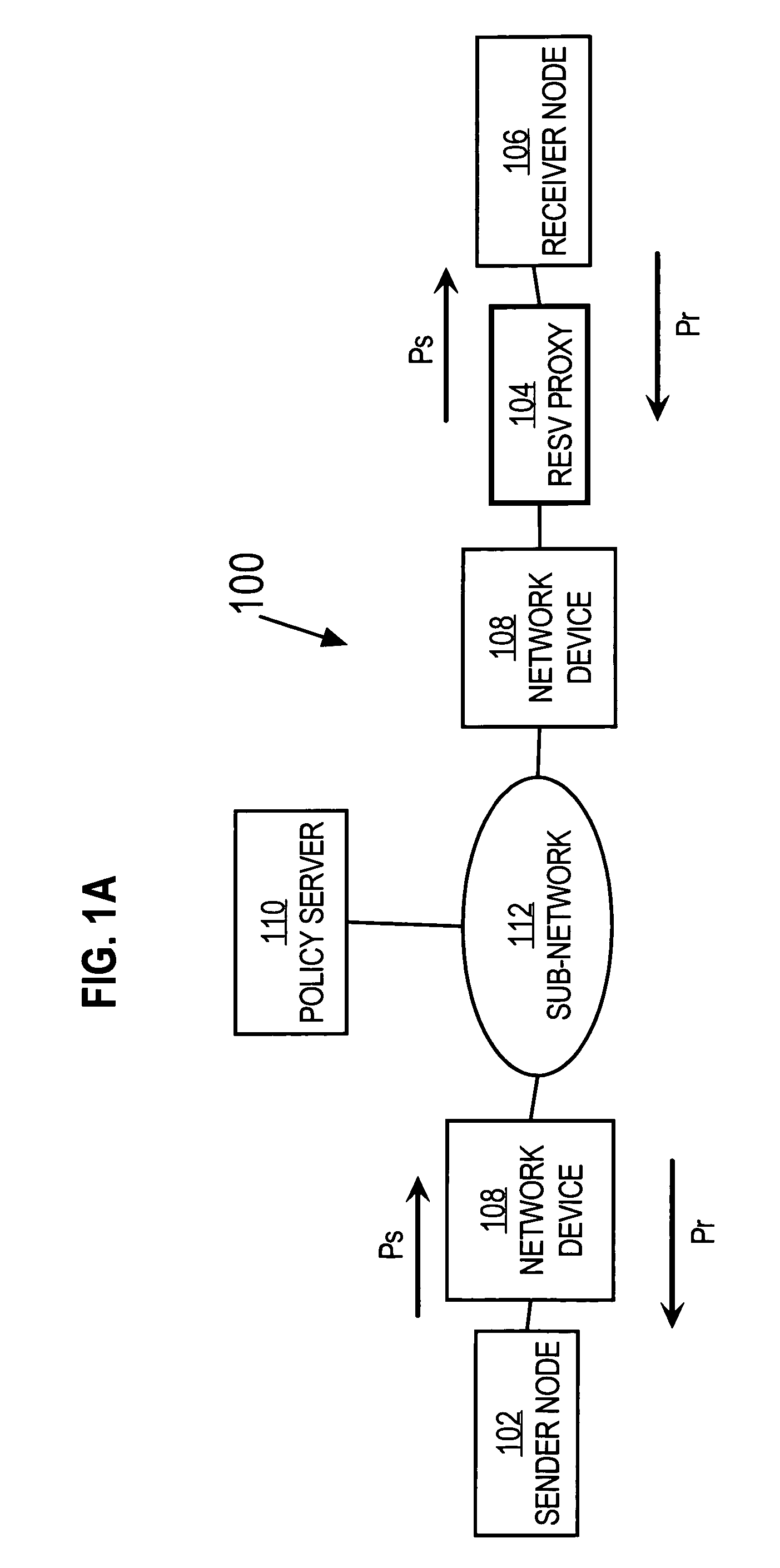
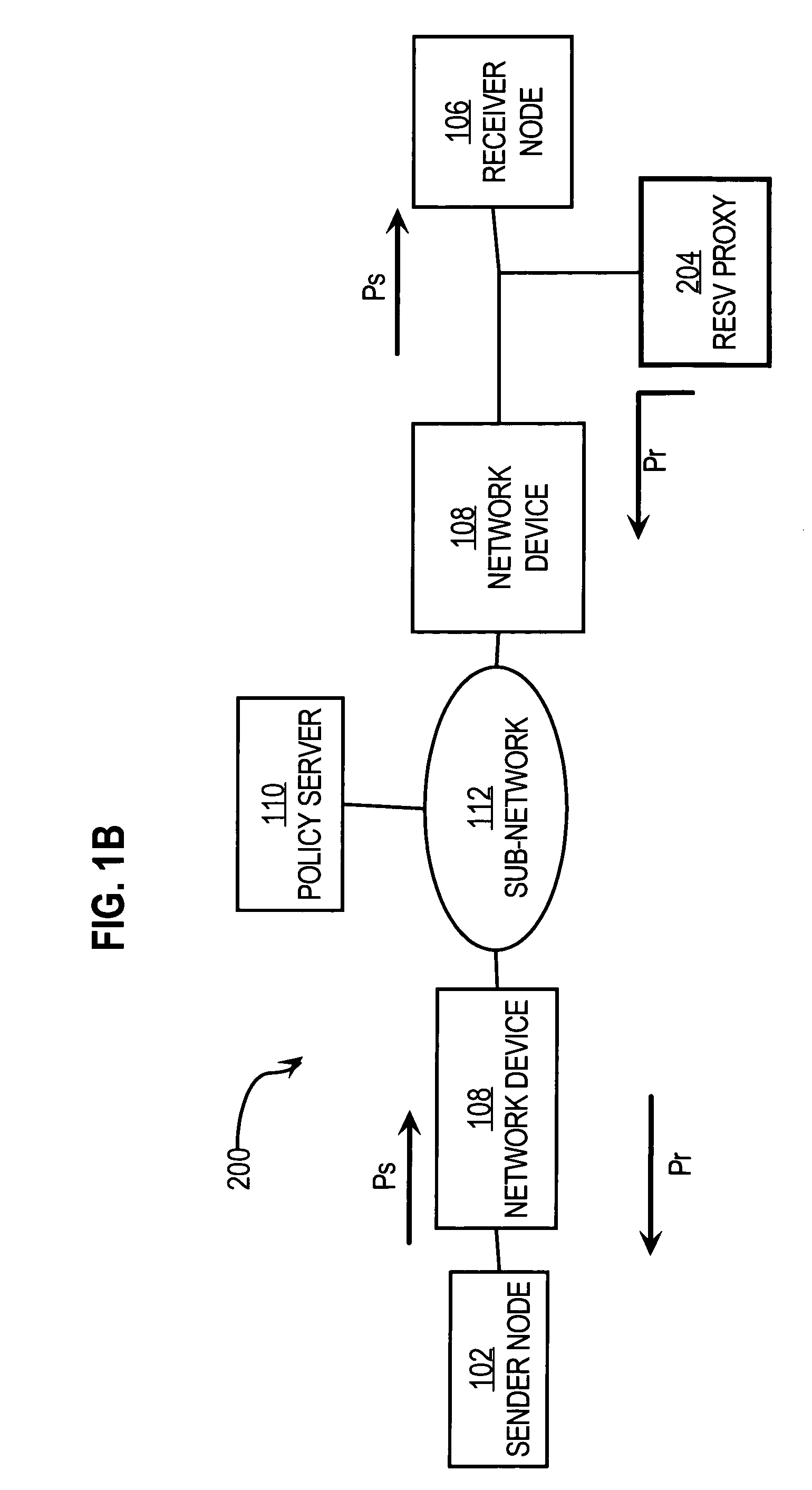
Method and apparatus providing automatic RESV message generation for non-RESV-capable network devices
A method and apparatus for providing network resource reservation capability for receiver nodes that either cannot or do not facilitate RSVP processes is provided. A RESV proxy is connected between an anticipated sender node and an anticipated receiver node in a computer network, e.g., a voice over IP network. The RESV proxy can detect an RSVP Path message and determine whether a RESV message is appropriate for the anticipated traffic flow. If it is so determined, the RESV proxy generates and communicates a RESV message through the network back to the anticipated sender node. The appropriateness of a RESV message can be based upon predetermined relationships or logic involving one or more of network parameters, transport parameters, and characteristics of the anticipated traffic flow, and other traffic flow attributes determined from analyzing the RSVP Path message. The RESV proxy can also interface with a policy server on the network to facilitate generation of the RESV message according to one or more of the anticipated traffic flow attributes. Alternatively, the RESV proxy can include the policy server functionality itself.
Owner:CISCO TECH INC
System and method for automatic detection and configuration of network parameters
ActiveUS7051087B1Automatically network operationReduce errorsMultiple digital computer combinationsTransmissionComputerized systemAutomatic testing
The present invention relates to a system for automatic detection and configuration of network parameters. The system includes a first computer system for communicating to a network and at least a second computer system for providing network information. The first computer system queries the network and receives network information from the at least a second computer system before a network identification has been established for the first computer system. The system further includes a storage for storing at least one configuration associated with a network interface. The first computer system configures the network interface based upon the network information received from the at least a second computer system. Also, the first computer system may configure the network interface by determining a network identification associated with the network information and matching the at least one configuration with the network identification.
Owner:MICROSOFT TECH LICENSING LLC
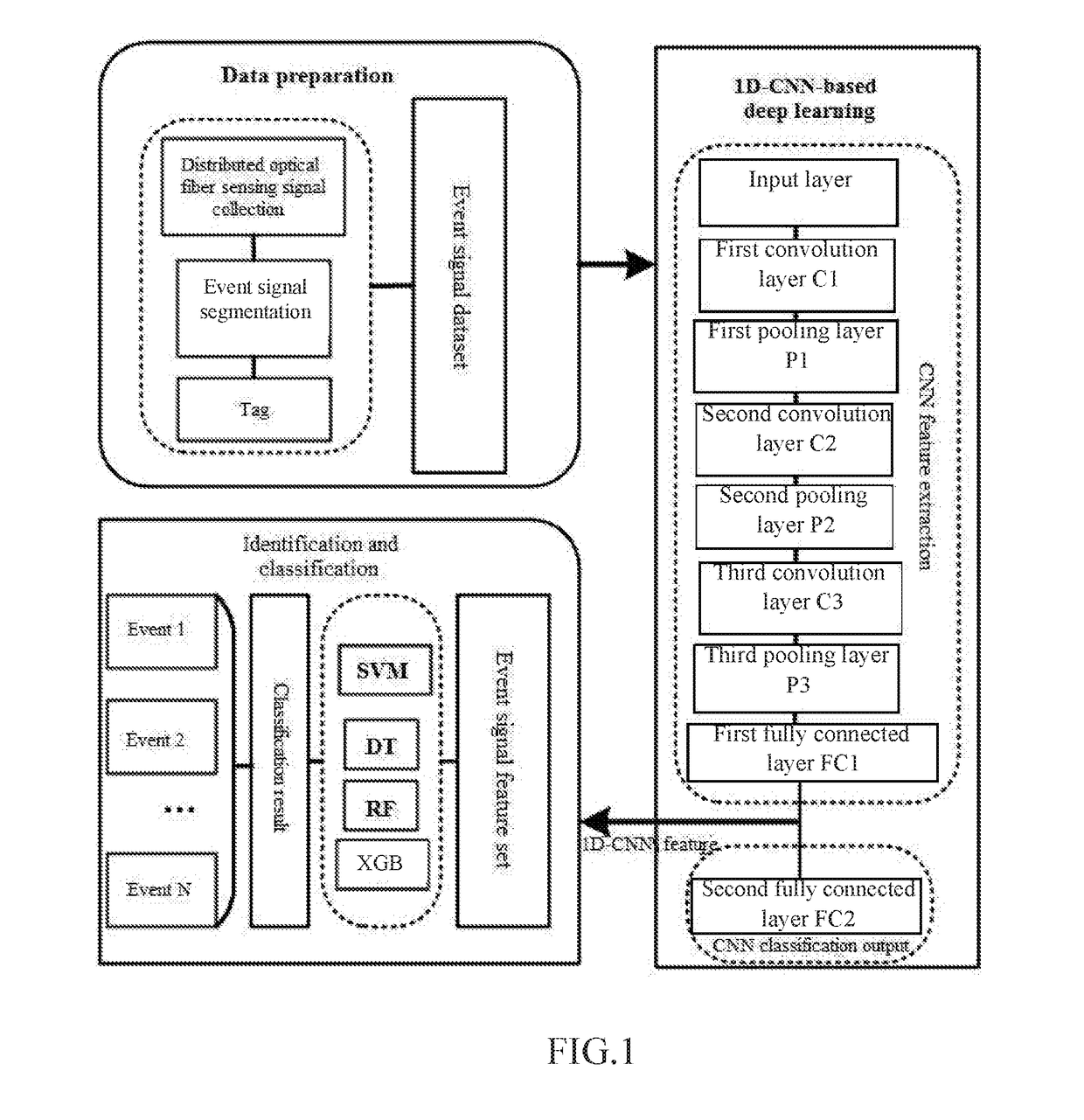
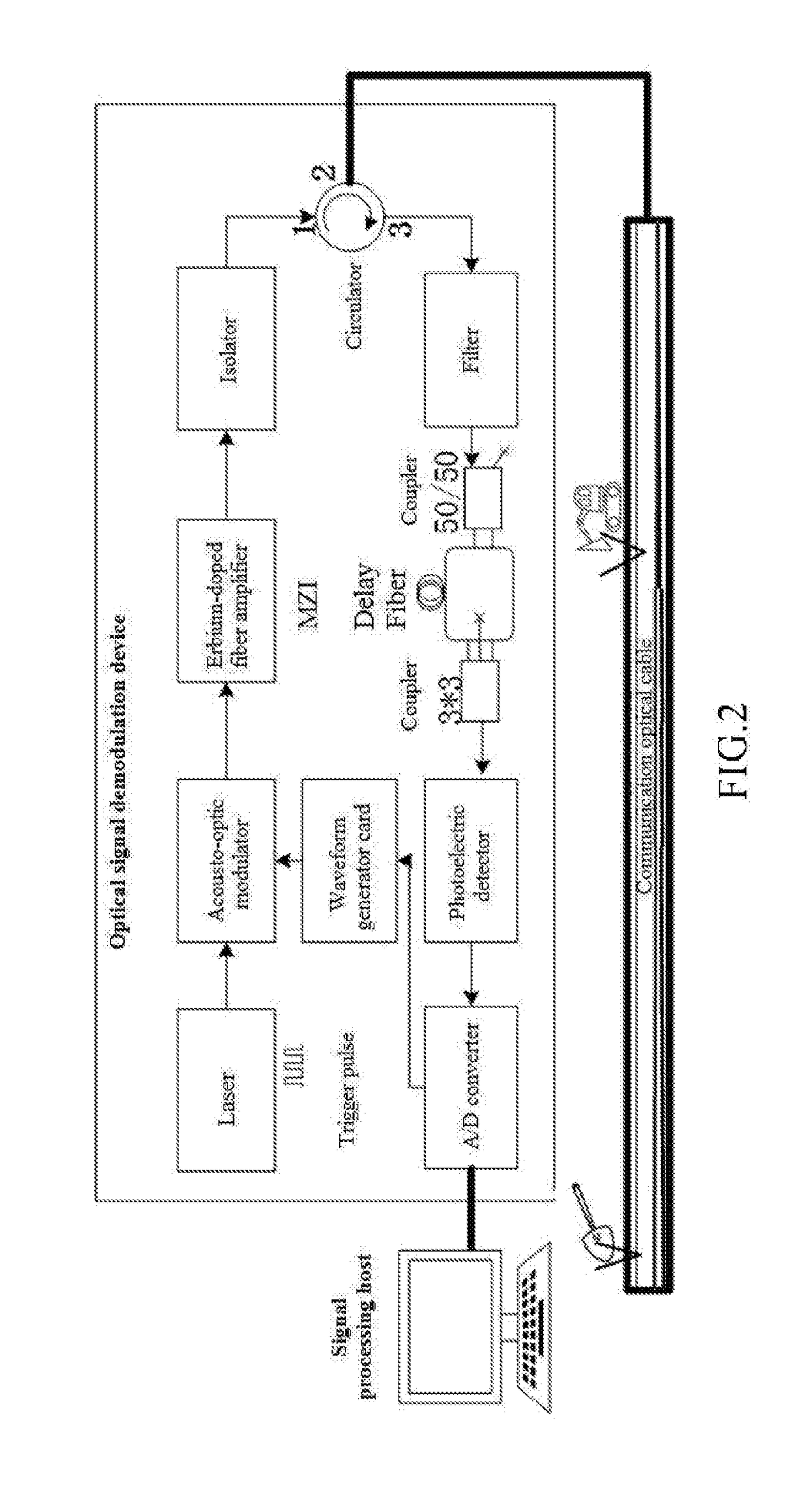
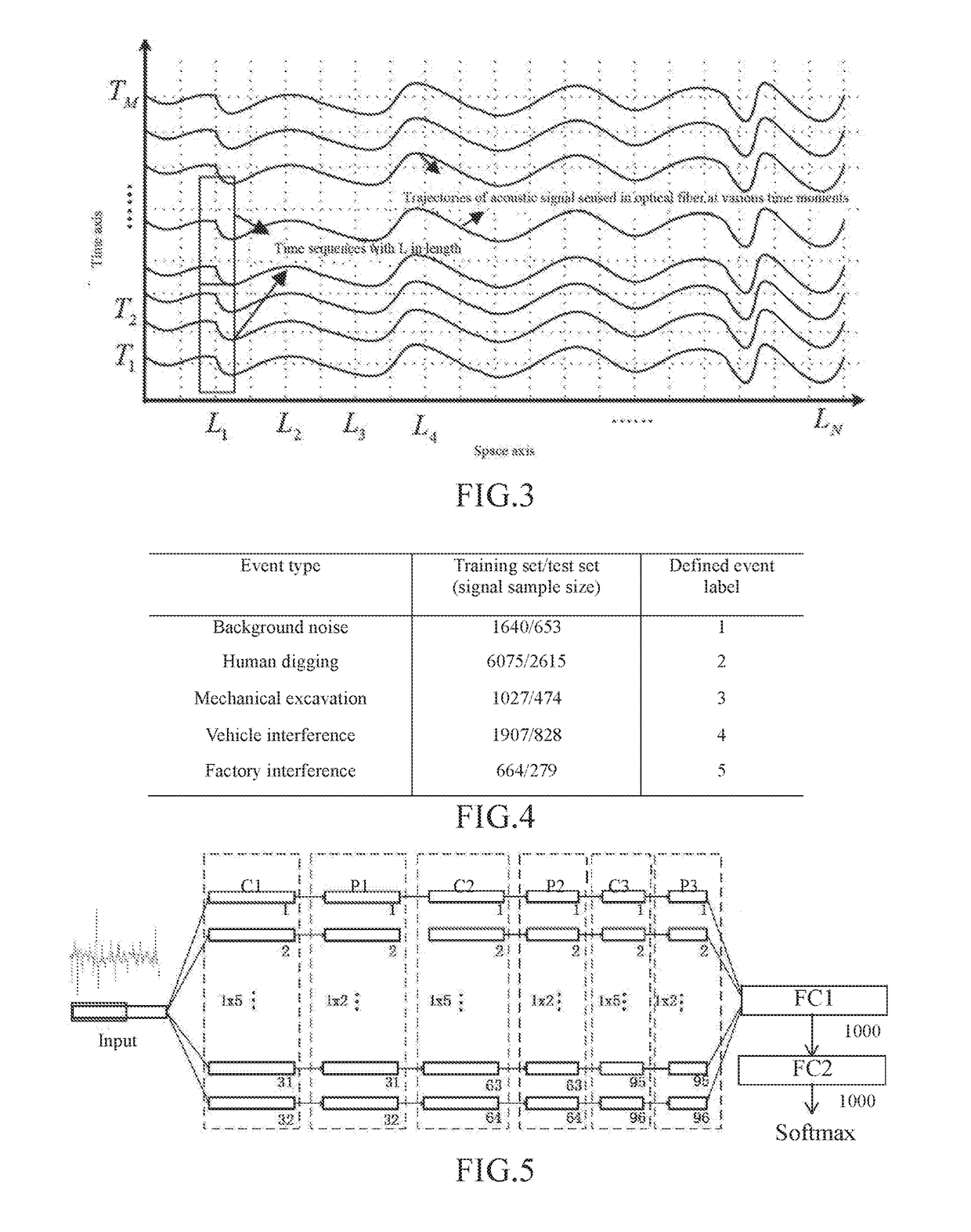
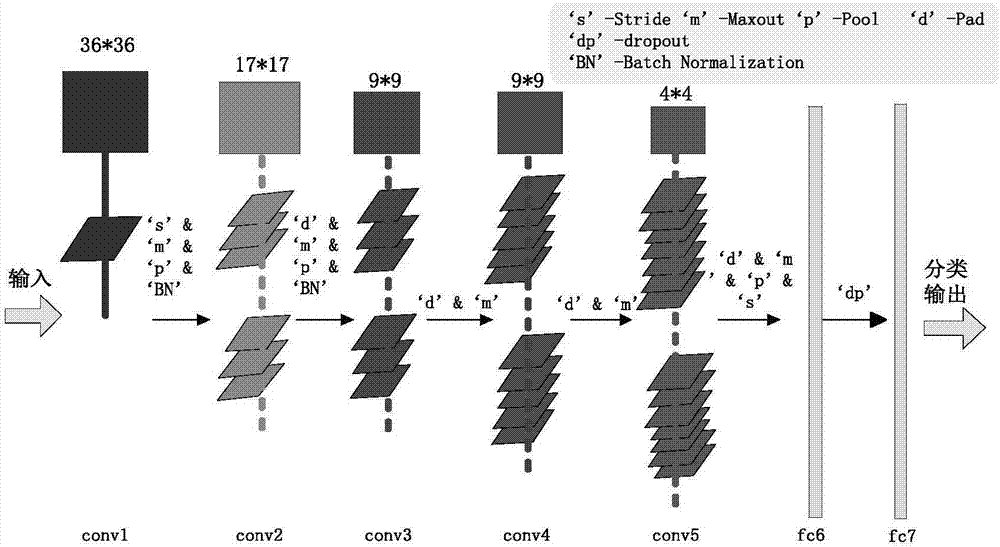
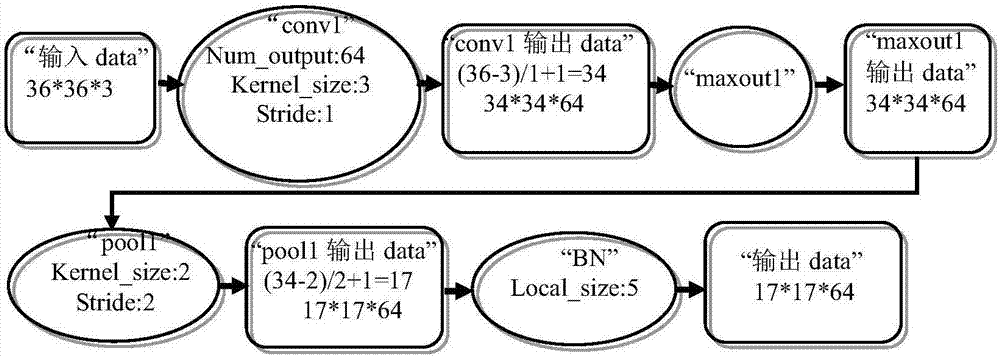
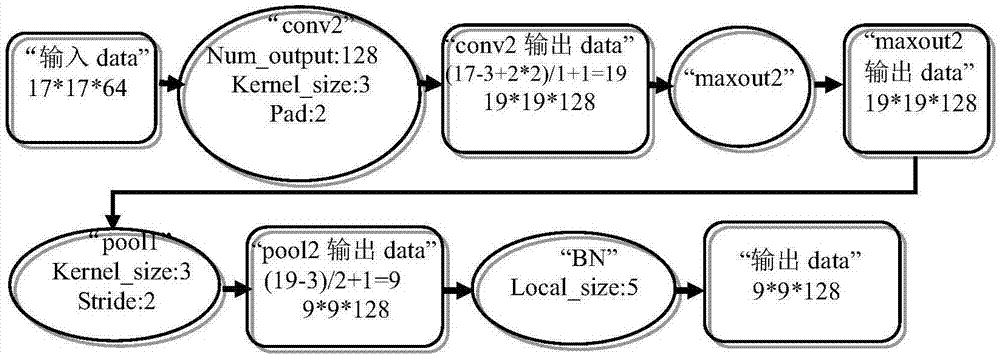
1D-CNN-Based Distributed Optical Fiber Sensing Signal Feature Learning and Classification Method
A 1D-CNN-based ((one-dimensional convolutional neural network)-based) distributed optical fiber sensing signal feature learning and classification method is provided, which solves a problem that an existing distributed optical fiber sensing system has poor adaptive ability to a complex and changing environment and consumes time and effort due to adoption of manually extracted distinguishable event features, The method includes steps of: segmenting time sequences of distributed optical fiber sensing acoustic and vibration signals acquired at all spatial points, and building a typical event signal dataset; constructing a 1D-CNN model, conducting iterative update training of the network through typical event signals in a training dataset to obtain optimal network parameters, and learning and extracting 1D-CNN distinguishable features of different types of events through an optimal network to obtain typical event signal feature sets; and after training different types of classifiers through the typical event signal feature sets, screening out an optimal classifier.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Skypoint for mobile hotspots
A system and method for dynamically planning a network is presented. One method may begin by determining network parameters for connecting nodes to a network and decision variables associated with radios and / or nodes in the network. Constraints may be established to narrow possible values of the network parameters and / or the decision variables. The constraints may be based on one or more of: values associated with connecting a radio to a node in the network, values associated with connecting two nodes in the network together over a communication link, whether a node can connect to a GIG node and a flow balance in the GIG node. To find possible links in the network that are optimal, the method may minimize an equation based on the network parameters, constraints and decision variables to determine optimal communication links between pairs of nodes in the network, pairs of nodes and radios and / or pairs of radios.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
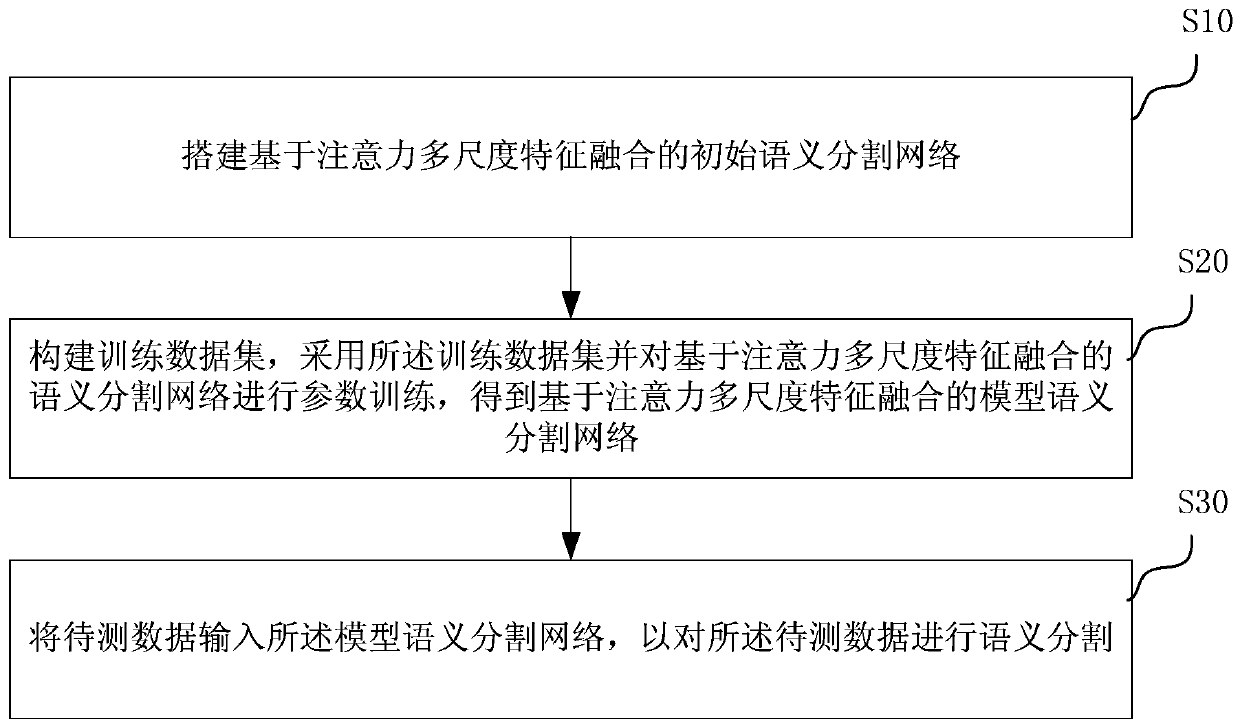
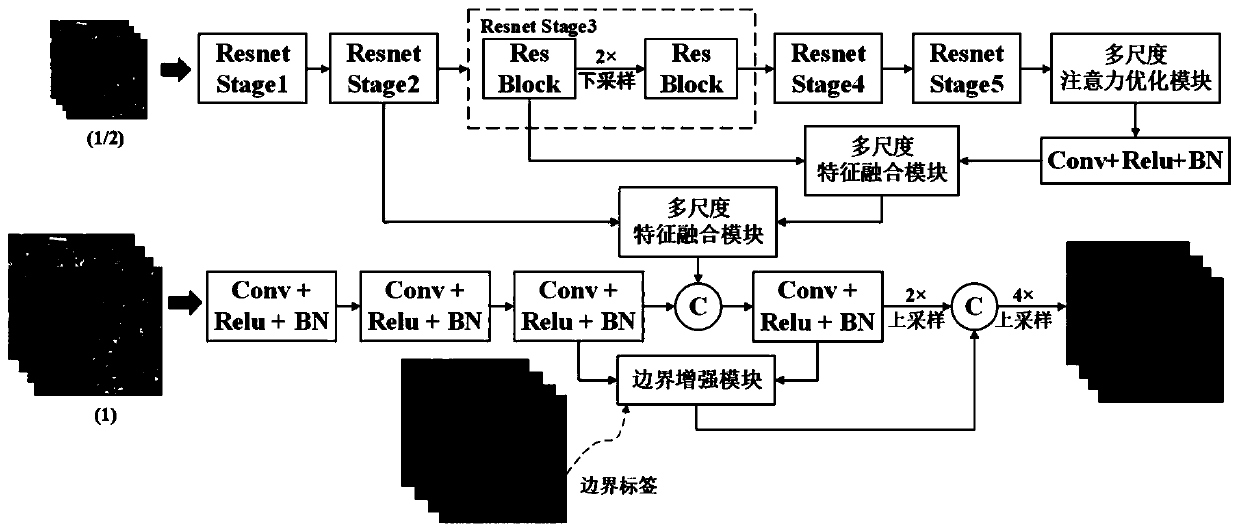
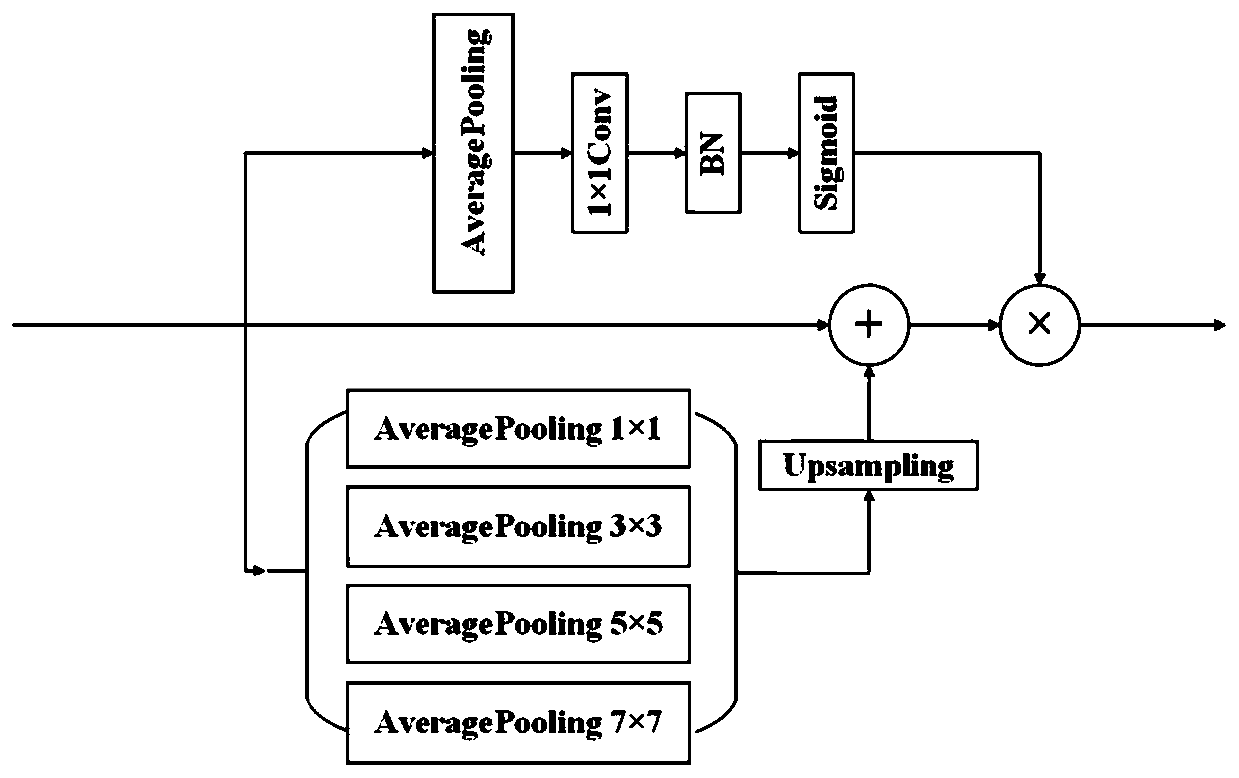
Remote sensing image semantic segmentation method based on attention multi-scale feature fusion
PendingCN111127493AImprove performanceReduce the amount of parametersImage enhancementImage analysisPattern recognitionEncoder decoder
The invention discloses a remote sensing image semantic segmentation method based on attention multi-scale feature fusion, and the method comprises the steps: establishing a semantic segmentation network based on attention multi-scale feature fusion, building a training data set, and carrying out the network parameter training through employing the training data set. And performing semantic segmentation on to-be-tested data by using the trained network during testing. And the network is a lightweight encoder-decoder structure. Wherein the idea of an image cascade network is introduced; meanwhile, coding features and decoding features are optimized by using an attention mechanism, a multi-scale attention optimization module, a multi-scale feature fusion module and a boundary enhancement module are constructed, feature maps of different scales are extracted and fused, training is guided by using multi-scale semantic tags and boundary tags, and semantic segmentation of remote sensing images can be effectively carried out.
Owner:CHINA UNIV OF MINING & TECH
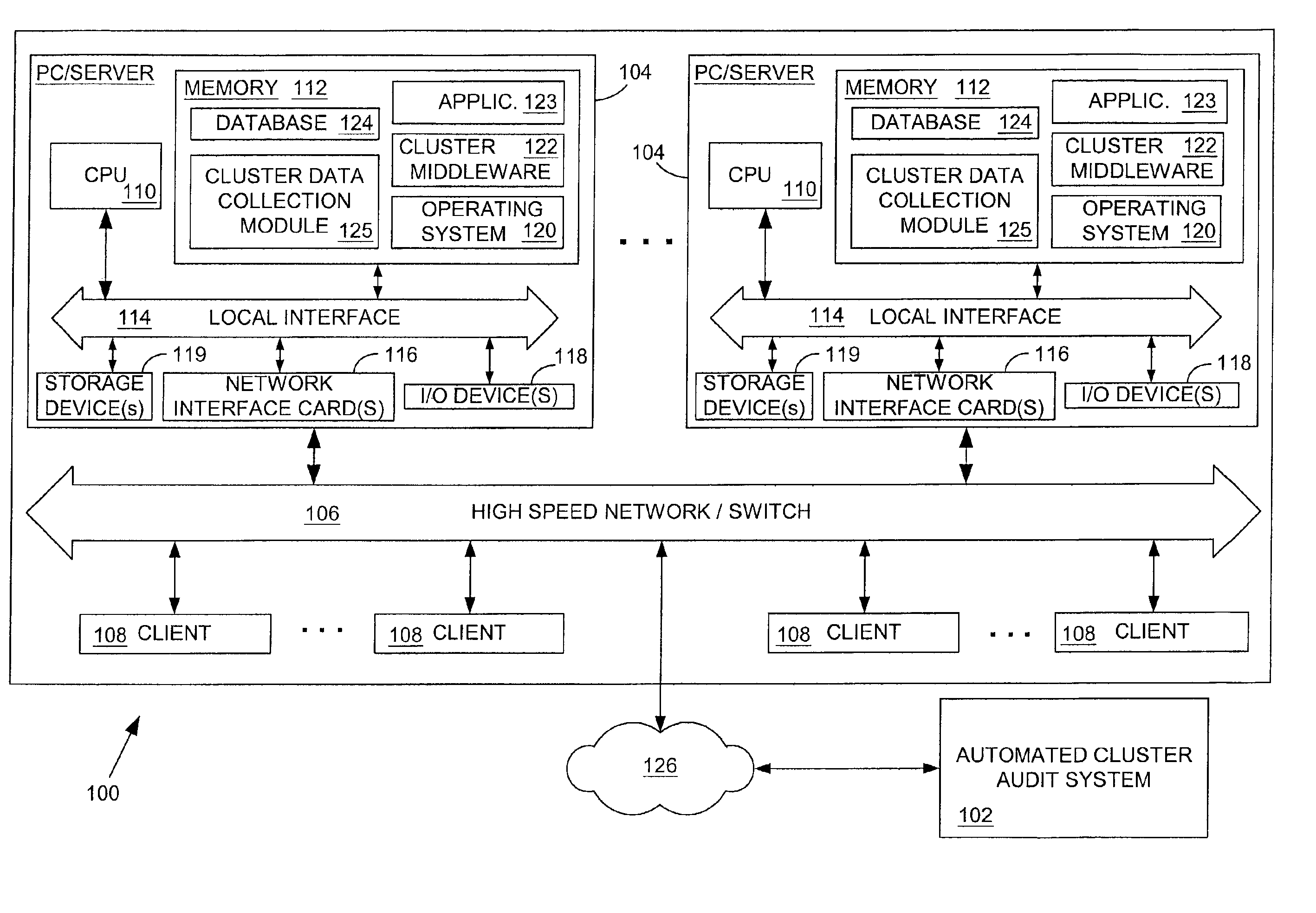
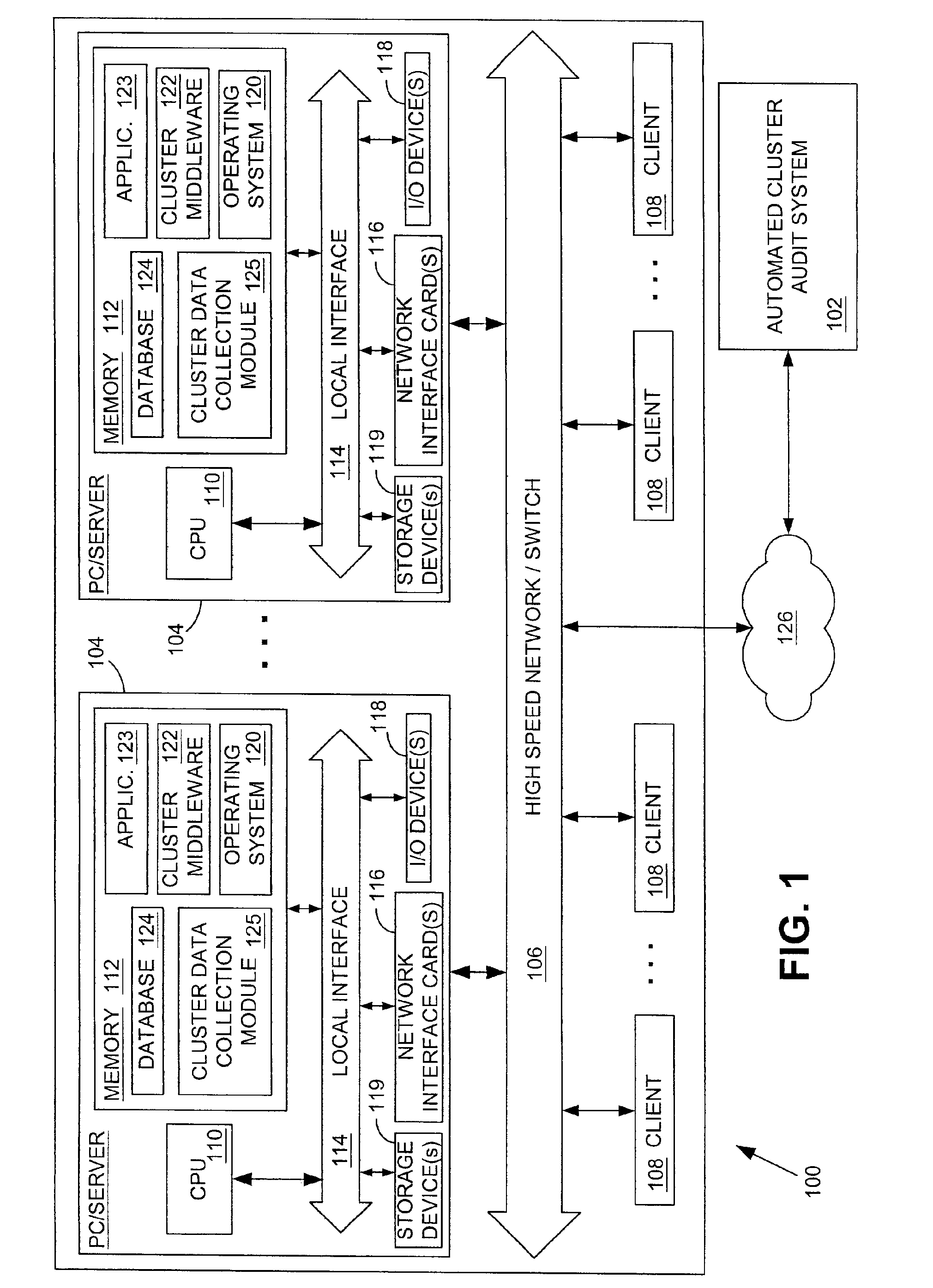
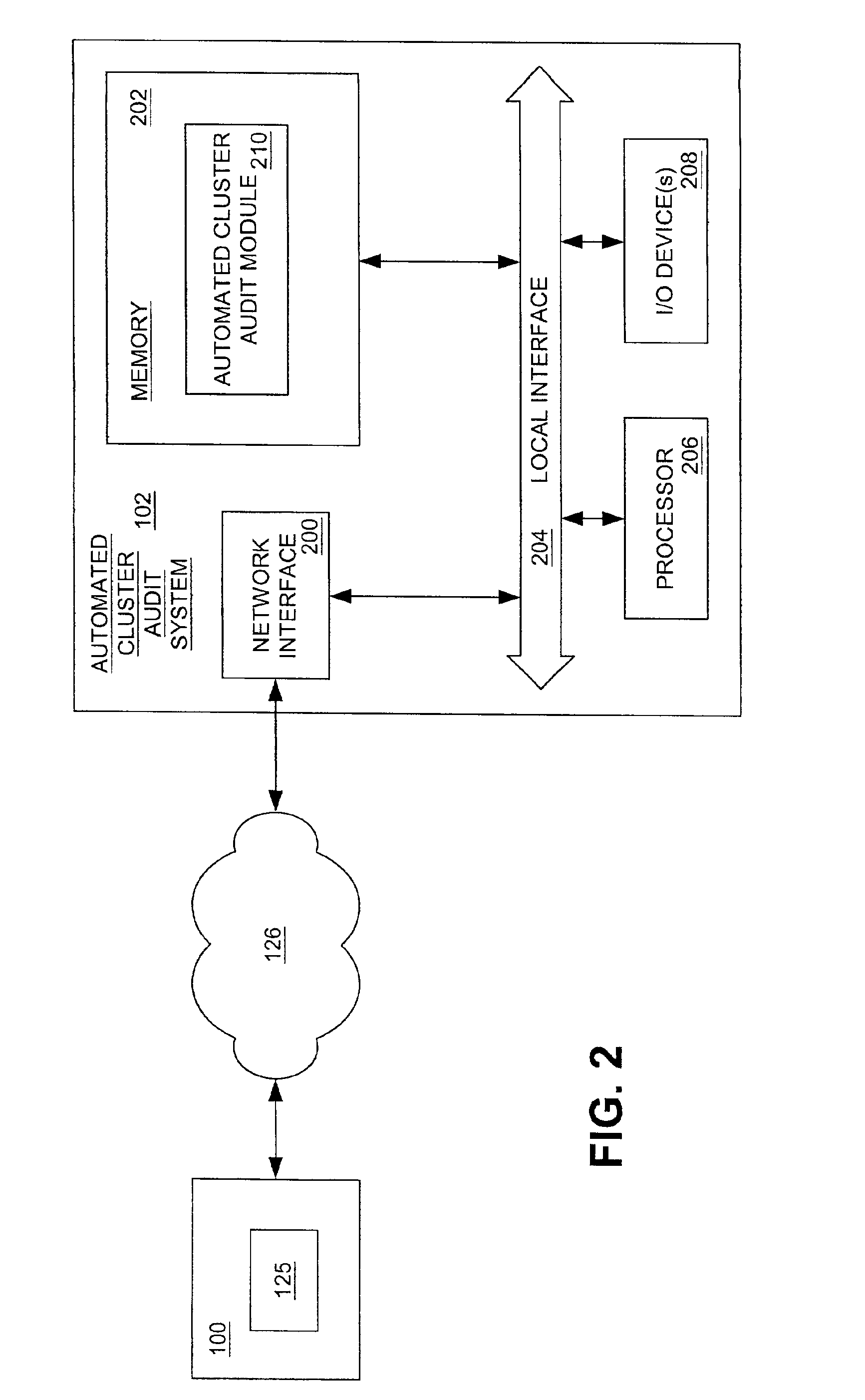
Systems and methods for providing automated diagnostic services for a cluster computer system
InactiveUS6895534B2Reliability increasing modificationsHardware monitoringMiddlewareNetwork parameter
Systems and methods for providing automated diagnostic services for a cluster computer system are provided. One embodiment is a method for providing automated diagnostic services for a cluster computer system comprising a plurality of nodes. Each of the plurality of nodes may provide an application to a plurality of clients. Briefly described, one such method comprises the steps of: receiving a current value of a network parameter related to cluster middleware associated with the cluster computer system; analyzing the current value of the network parameter relative to a predetermined reference value for the network parameter; and providing information based on the analysis of the current value relative to the predetermined reference value.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
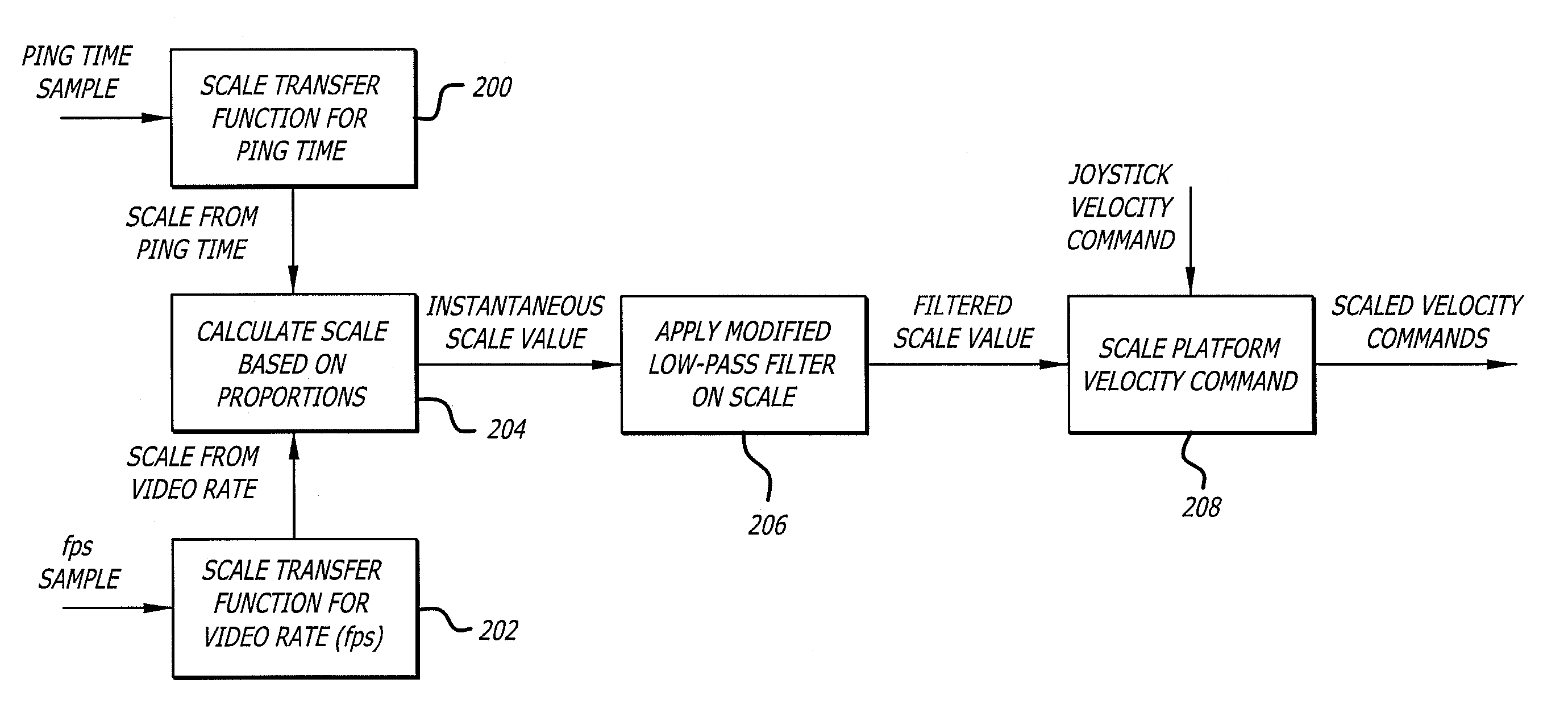
Mobile videoconferencing robot system with network adaptive driving
A remote control station that controls a robot through a network. The remote control station transmits a robot control command that includes information to move the robot. The remote control station monitors at least one network parameter and scales the robot control command as a function of the network parameter. For example, the remote control station can monitor network latency and scale the robot control command to slow down the robot with an increase in the latency of the network. Such an approach can reduce the amount of overshoot or overcorrection by a user driving the robot.
Owner:TELADOC HEALTH INC +1
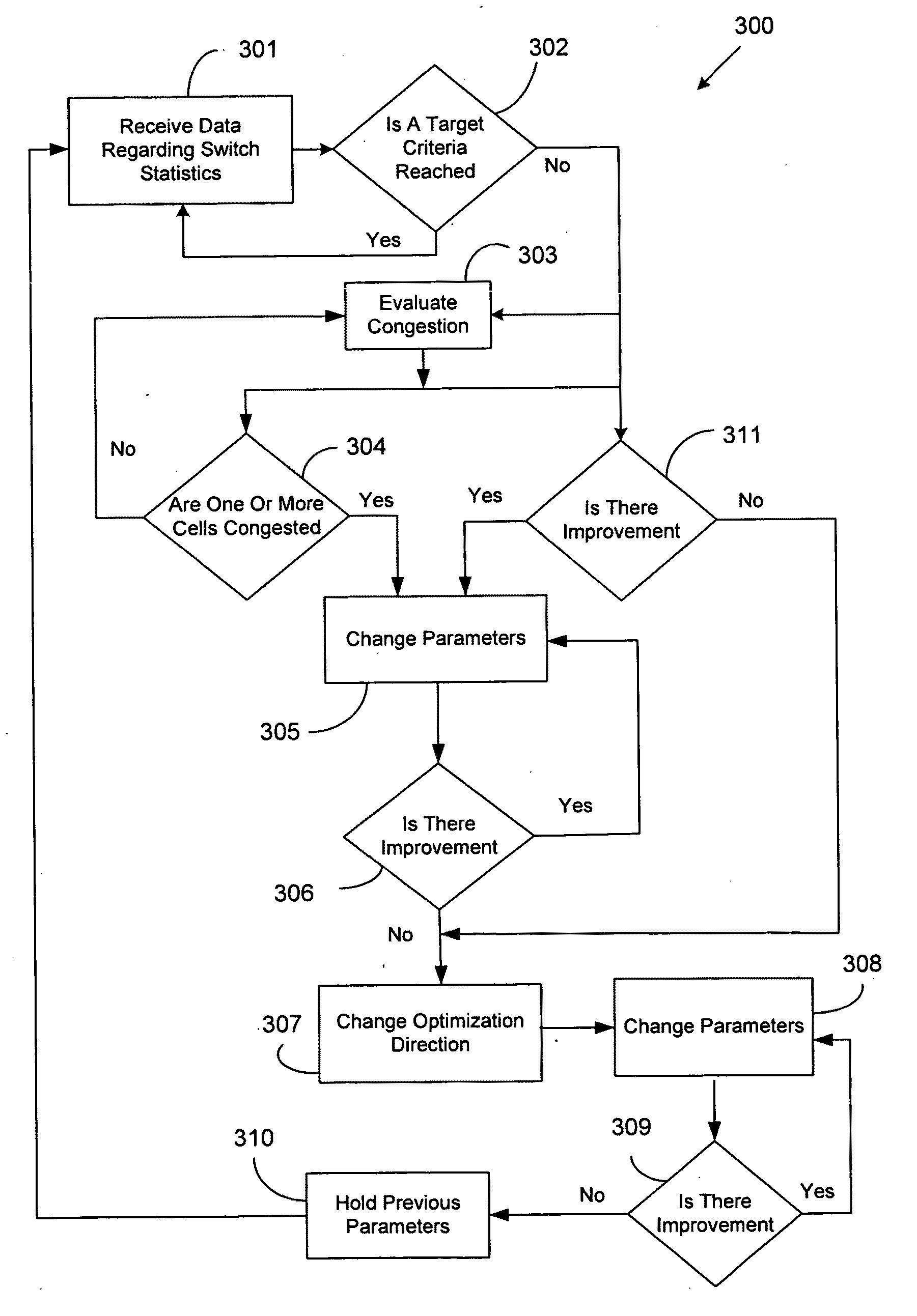
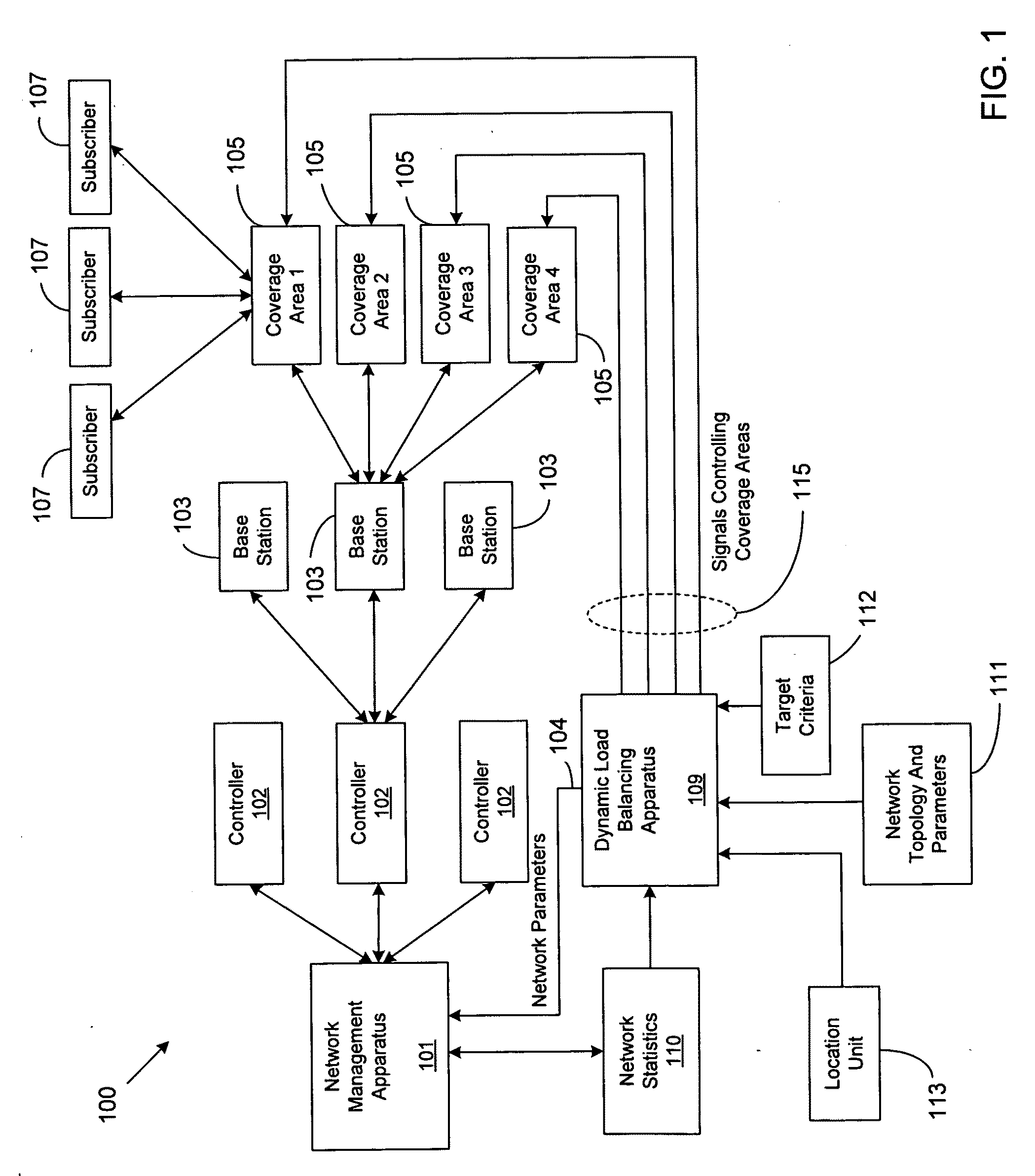
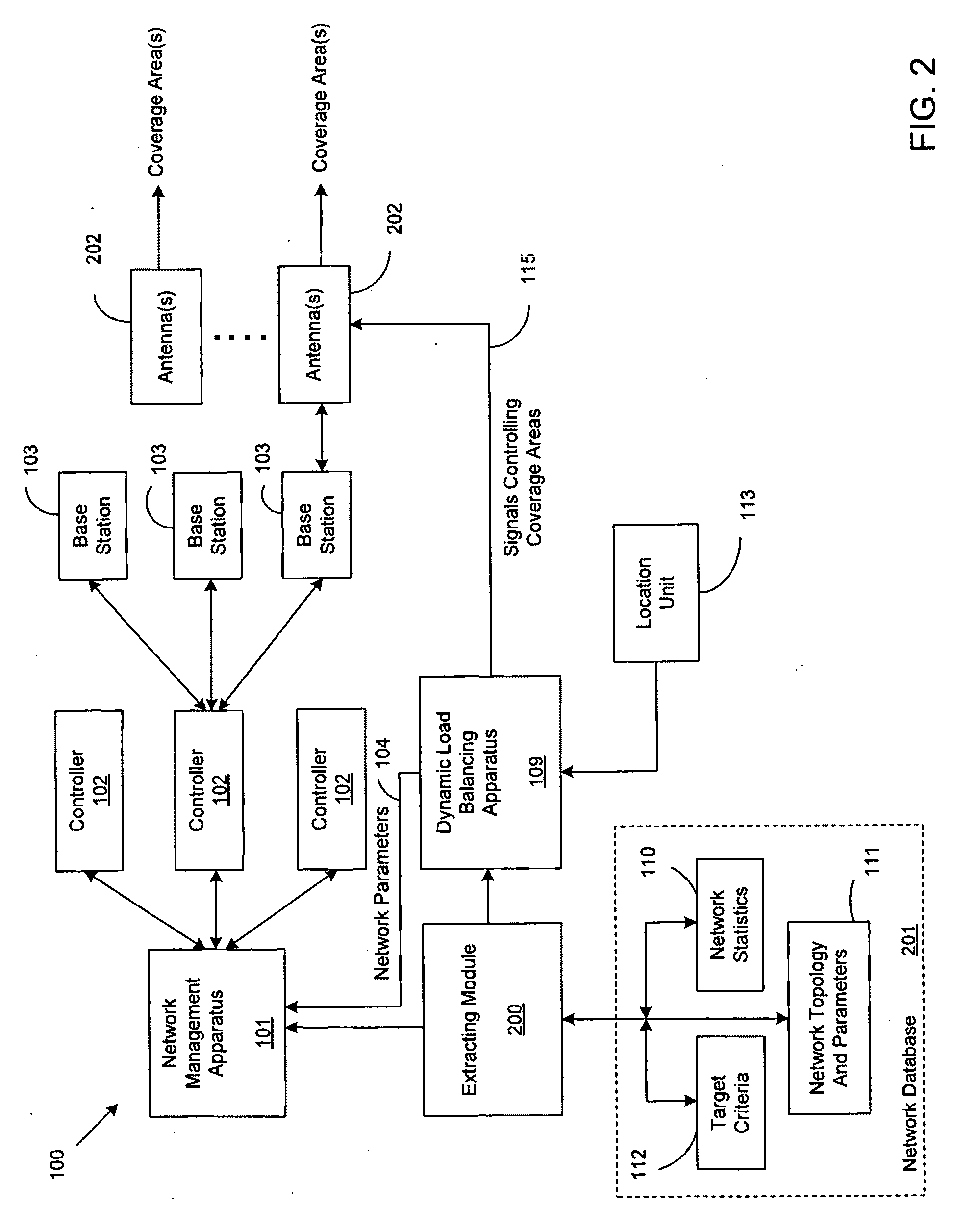
Dynamic load balancing
ActiveUS20090323530A1Increase rangeReduce in quantityError preventionTransmission systemsQuality of serviceDynamic load balancing
A method, program, system and apparatus perform dynamic load balancing of coverage areas in a wireless communication network. The dynamic load balancing is performed by evaluating cell congestion based on location information of subscribers in the wireless communication network, collecting network parameters related to the wireless communication network and altering network parameters based on the evaluated cell congestion. After the network parameter is altered, the coverage areas are narrowed. Improvements in cell congestion and quality of server are then determined based on the narrowing of the coverage areas. Altering of the plurality of network parameters and evaluating of the cell congestion are performed continuously until a target quality of service is achieved.
Owner:VIAVI SOLUTIONS INC
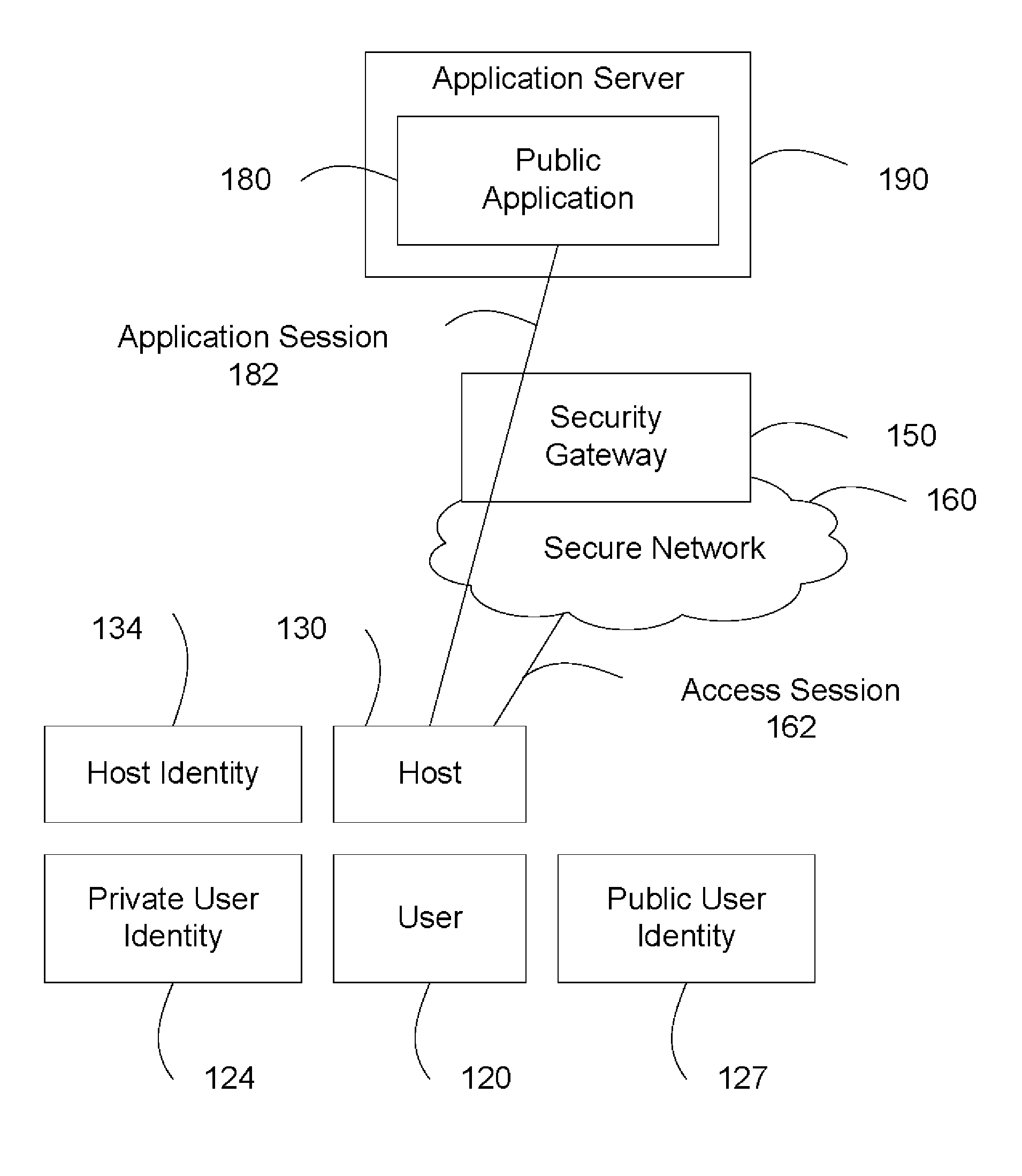
System and Method to Apply Network Traffic Policy to an Application Session
ActiveUS20100235880A1Digital data processing detailsMultiple digital computer combinationsTraffic capacityApplication software
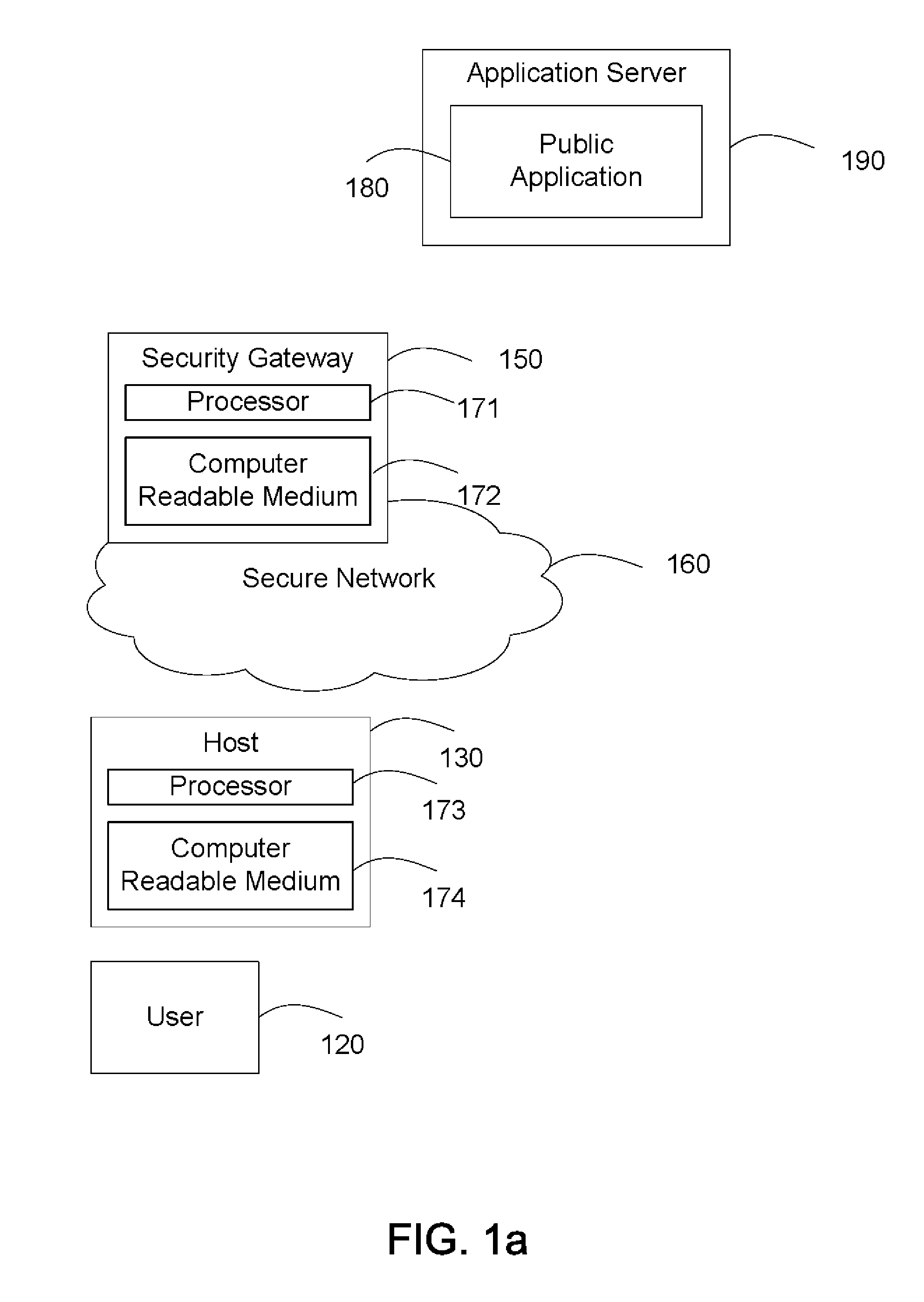
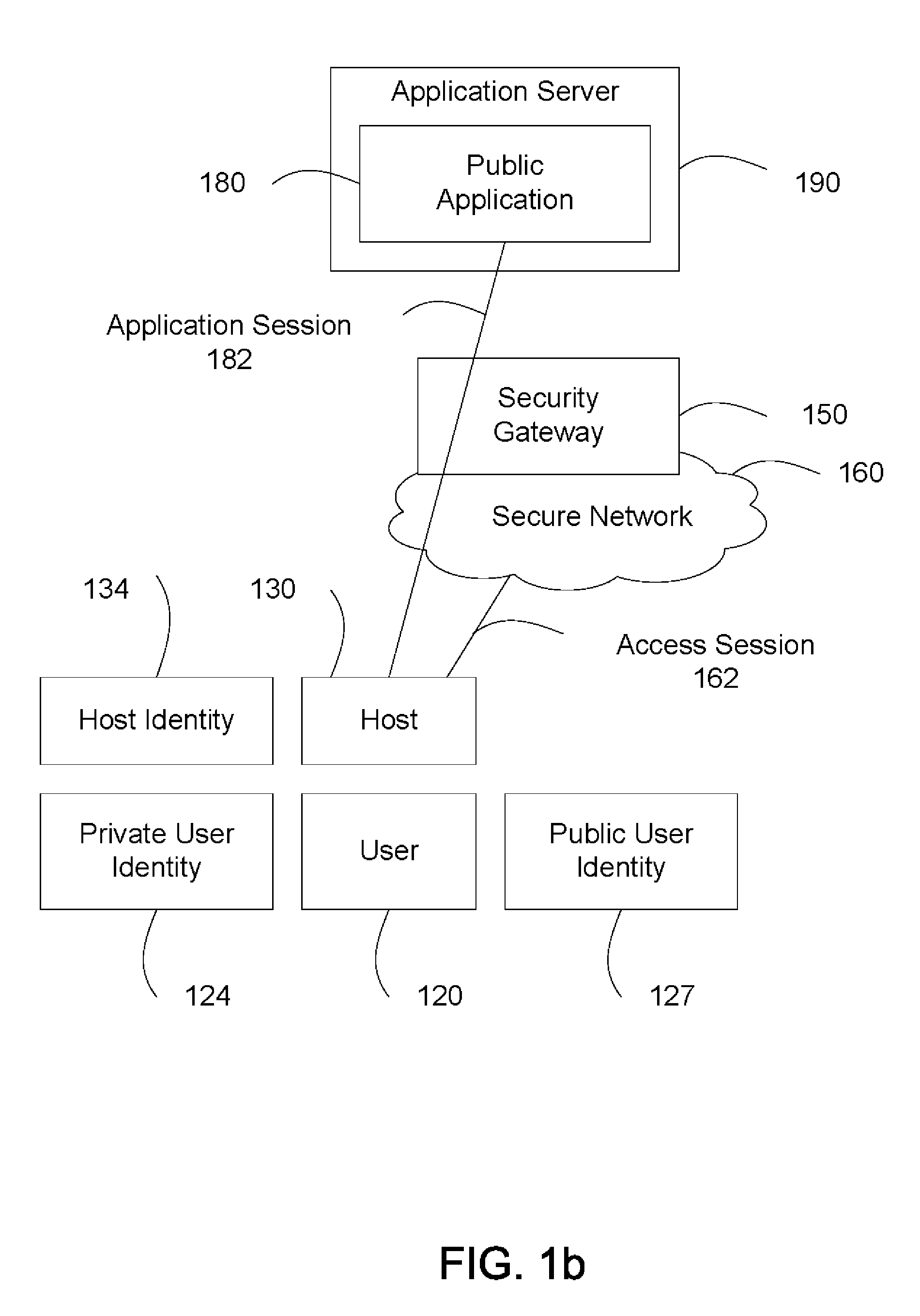
Method for applying a security policy to an application session, includes: recognizing the application session between a network and an application via a security gateway; determining by the security gateway a user identity of the application session using information about the application session; obtaining by the security gateway the security policy comprising network parameters mapped to the user identity; and applying the security policy to the application session by the security gateway. The user identity may be a network user identity or an application user identity recognized from packets of the application session. The security policy may comprise a network traffic policy mapped and / or a document access policy mapped to the user identity, where the network traffic policy is applied to the application session. The security gateway may further generate a security report concerning the application of the security policy to the application session.
Owner:A10 NETWORKS
Performance logging using relative differentials and skip recording
ActiveUS20070140301A1Minimizing storage resourceImprove accuracyDigital computer detailsTime-division multiplexTimestampOperating system
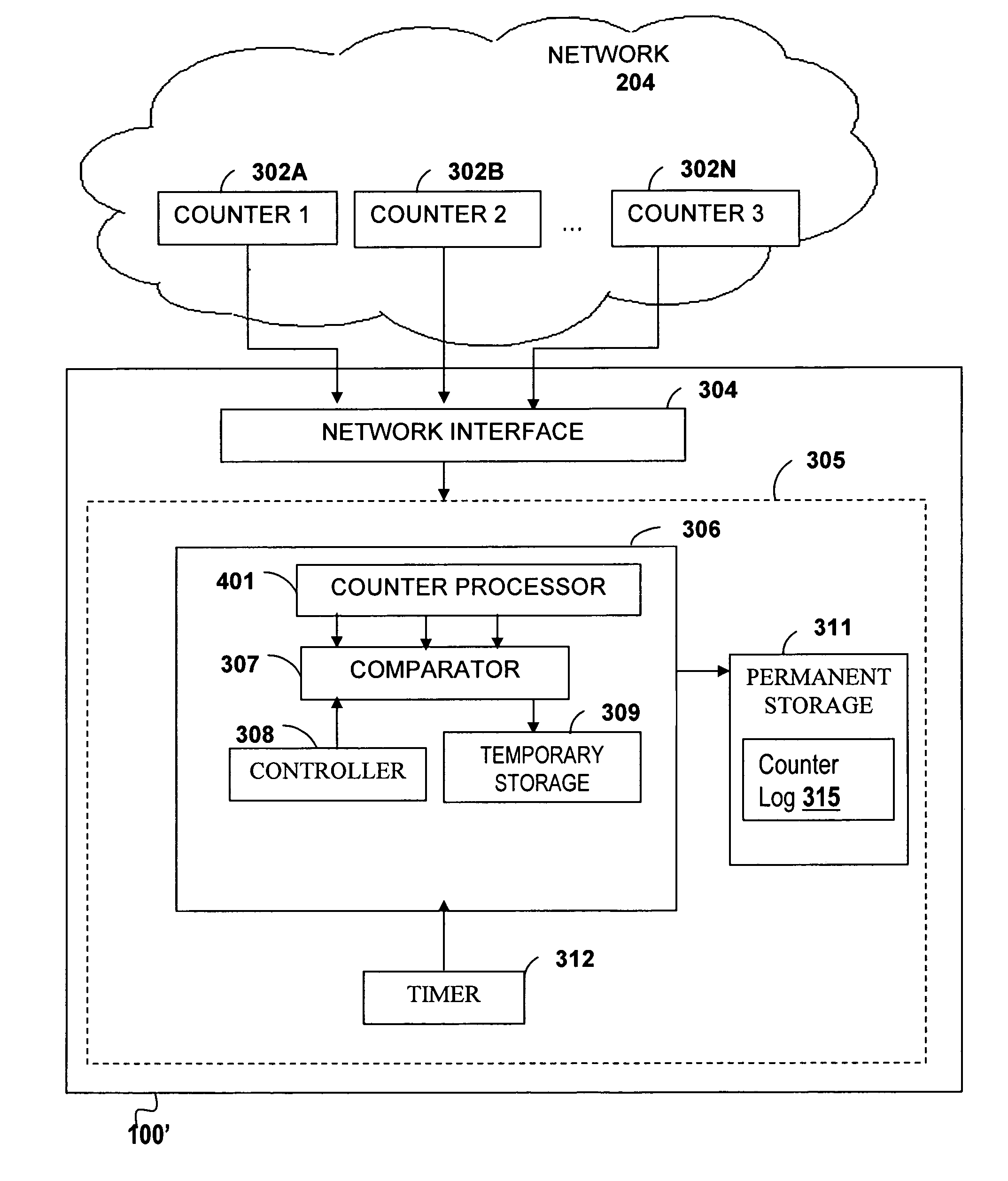
The present invention is directed towards “skip” and “differential” recording techniques for recording values of network parameter to a log in a lossless manner while reducing storage resources used to record such values. The counter monitor of the present invention monitors and records values of counters at time intervals to generate a counter log provided via temporary or permanent storage. The counter monitor compares a reading of the value of the counter to a previously obtained value of the counter. If the value of the counter has not changed, the counter monitor records only the timestamp to the counter log, thereby “skipping” the recording of the unchanged value. If there is any change in the value of the counter, then the change in value of the counter, i.e., a “differential” value, along with the timestamp is stored in the counters log. To further reduce storage resource usage, the counter monitor also stores changes to the timestamps as differential changes in time values.
Owner:CITRIX SYST INC
Image classification method based on convolution neural network
PendingCN107341518AImprove accuracyImprove recognition rateCharacter and pattern recognitionNeural learning methodsClassification methodsNetwork structure
The invention discloses an image classification method based on a convolution neural network. The method comprises the following steps: constructing a deep convolution neural network; improving the deep convolution neural network; training and testing the deep convolution neural network; and optimizing the network parameter. By using the image classification method disclosed by the invention, the improvement and the optimization are respectively performed on the network structure and multiple parameters of the convolution neural network, the recognition rate of the deep convolution neural network can be effectively improved, and the accuracy of the image classification is improved.
Owner:EAST CHINA UNIV OF TECH
Method for managing the quality of encrypted voice over IP to teleagents
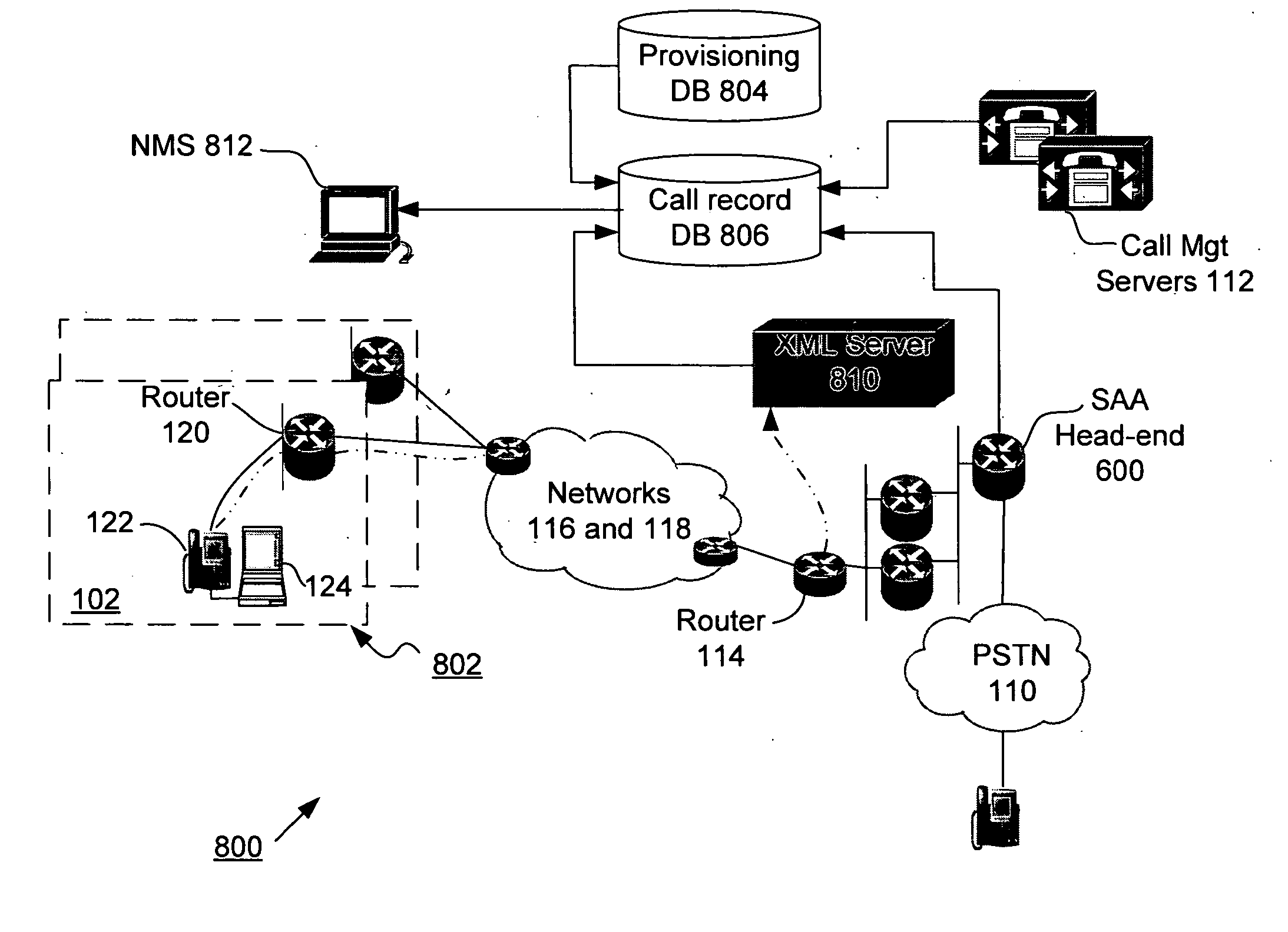
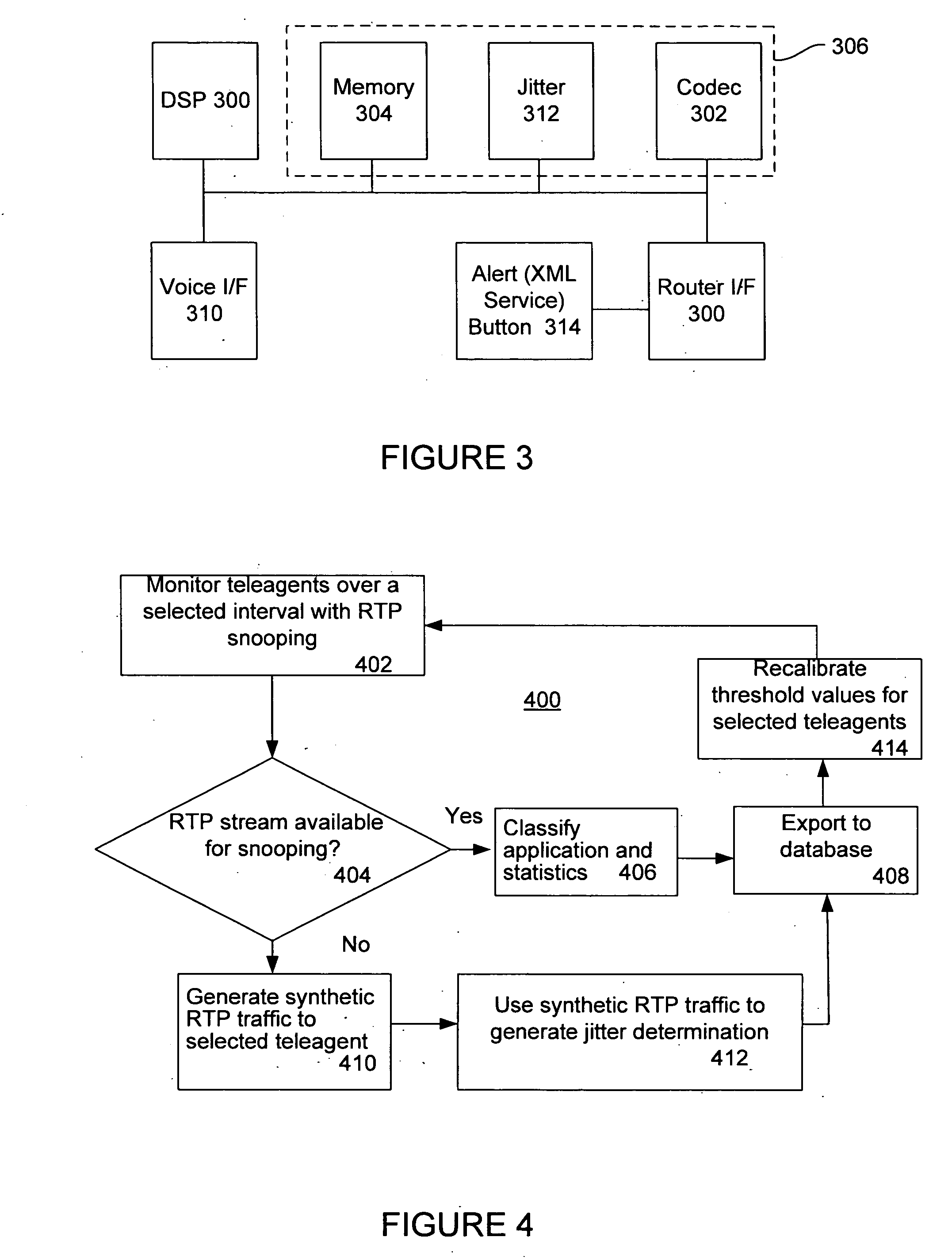
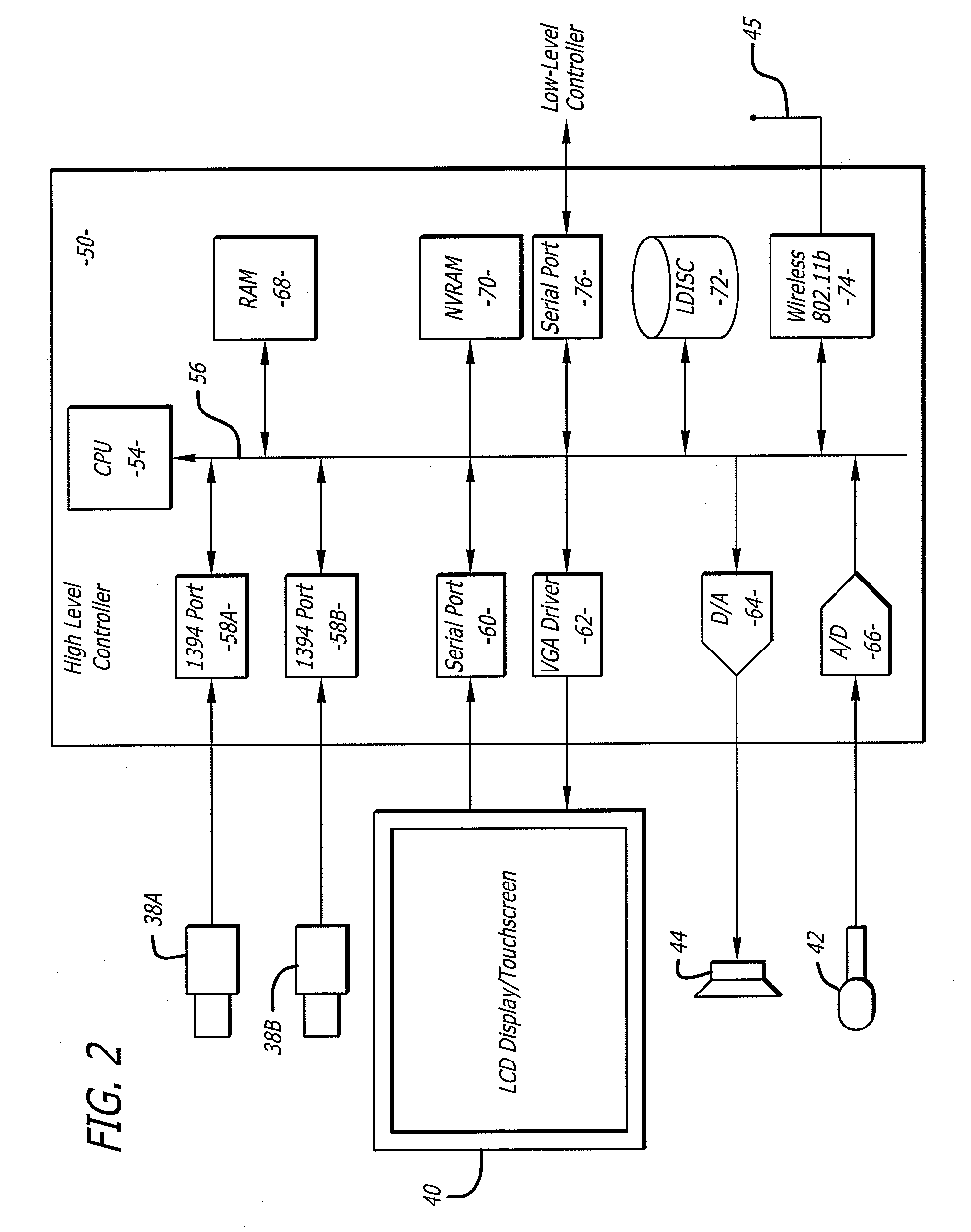
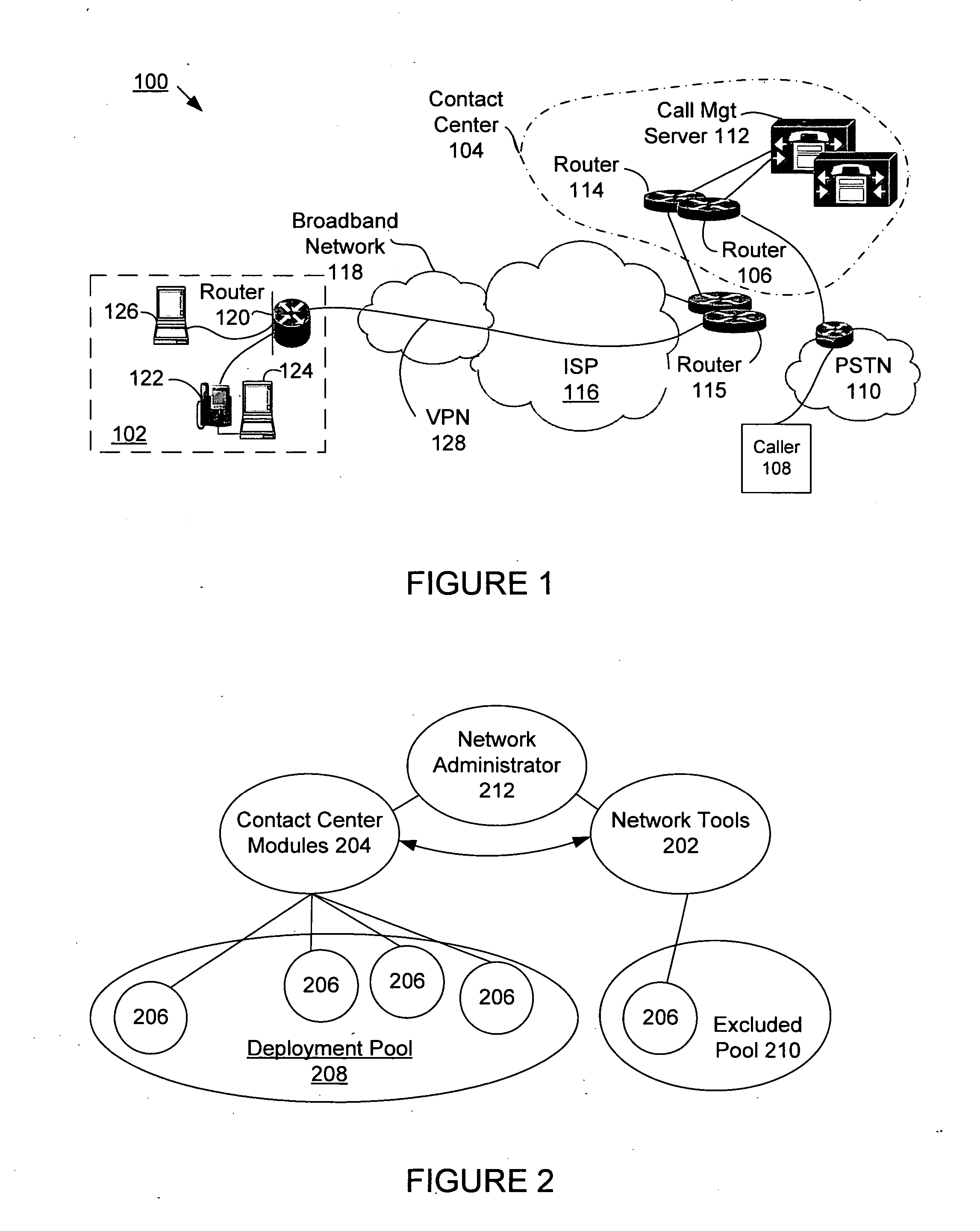
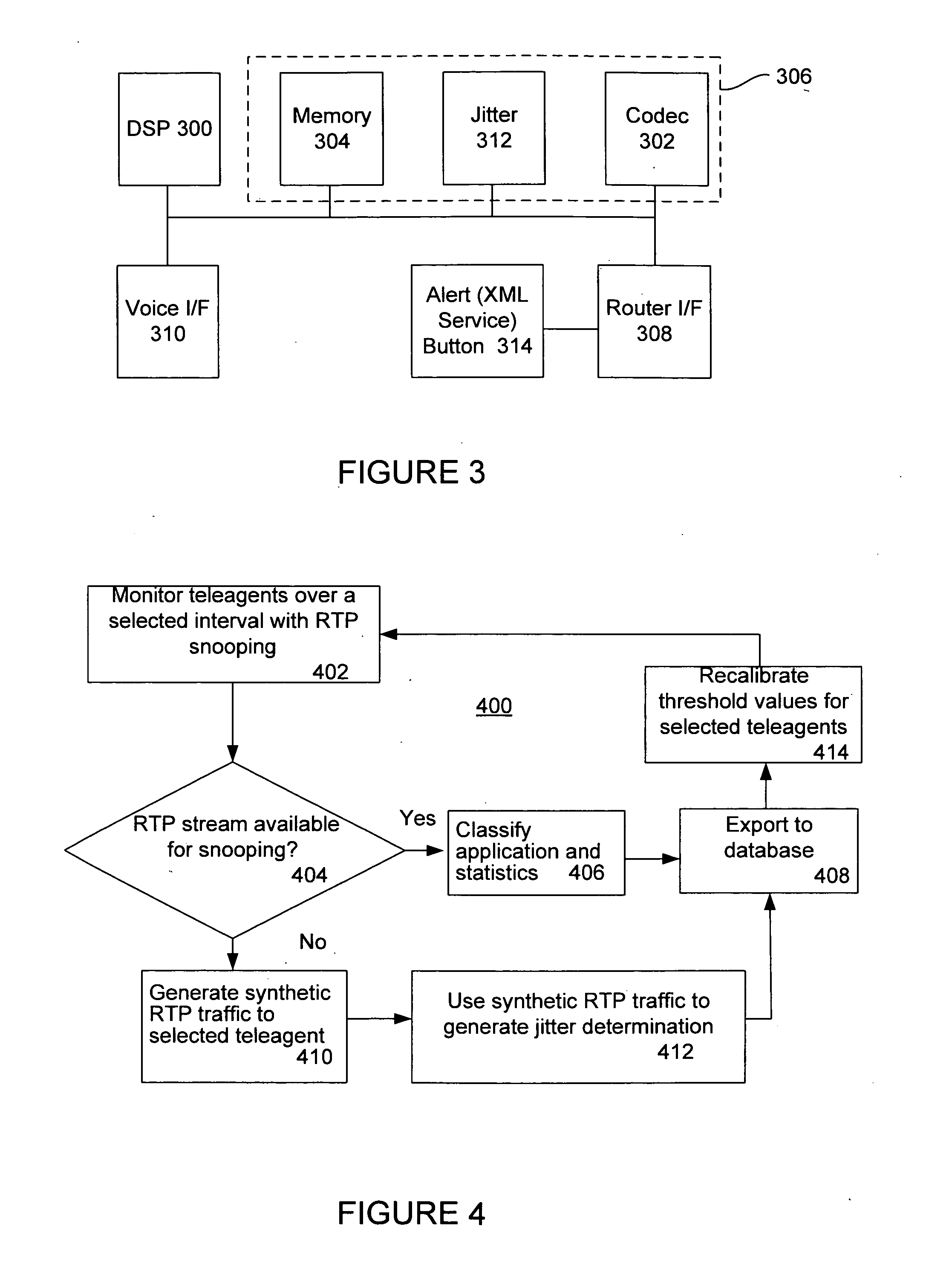
A voice over Internet protocol (VoIP) system and more particularly, an improved VoIP system serving a distributed group of teleagents. Network parameters that affect voice quality over broadband connections are rapidly detected by generating both detected and subjective alerts when problems with the quality of a IP telephone connection are detected and correcting the detected problems. Network parameters are monitored during an actual VoIP telephone call or by using synthetic traffic. If the voice quality degrades for a particular teleagent, the teleagent is removed from the pool of available agents until voice quality improves. Alternatively, the voice quality of each teleagent may be ranked according to the service provided.
Owner:CISCO TECH INC
Method and computing system for transparence computing on the computer network
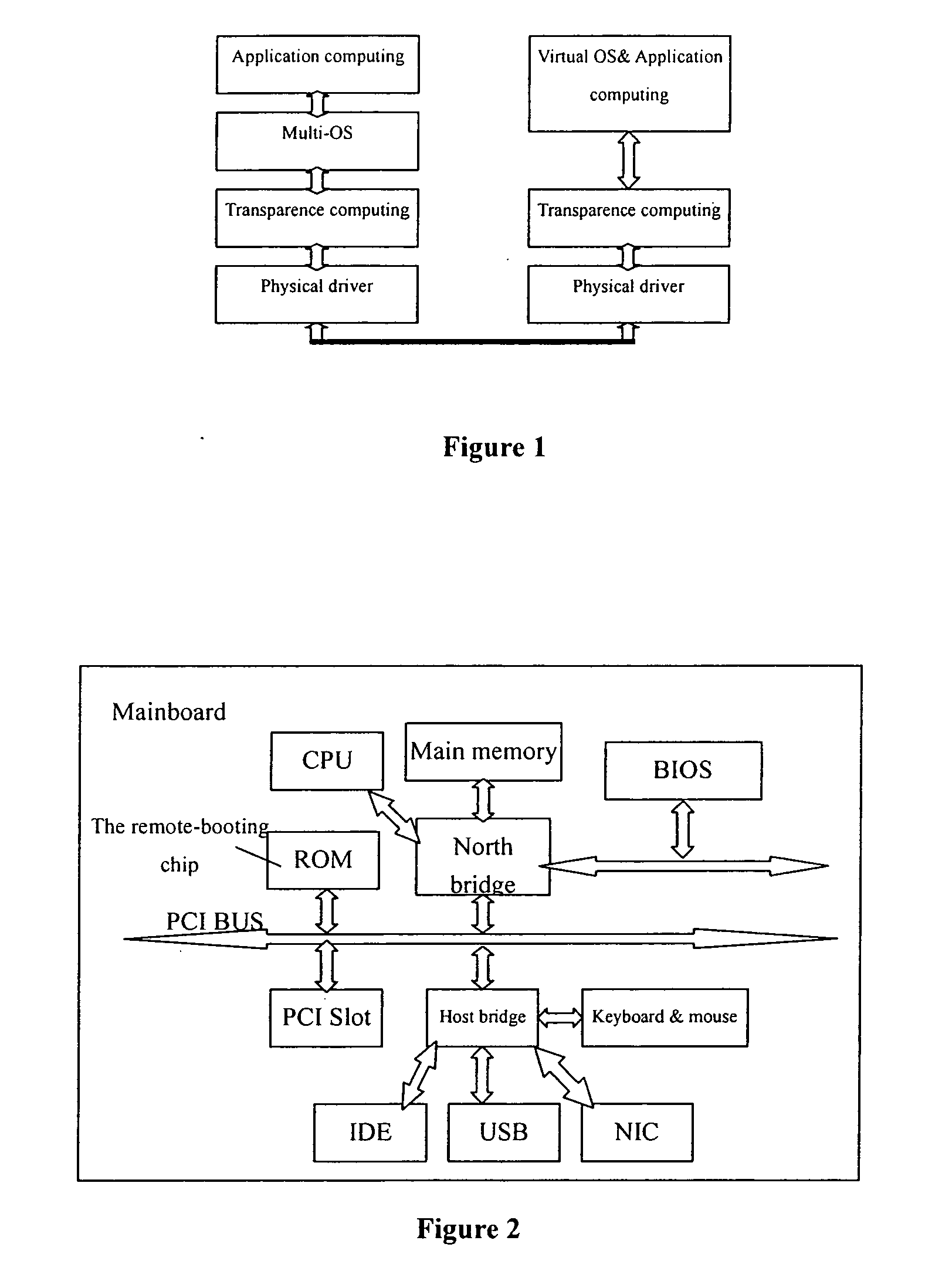
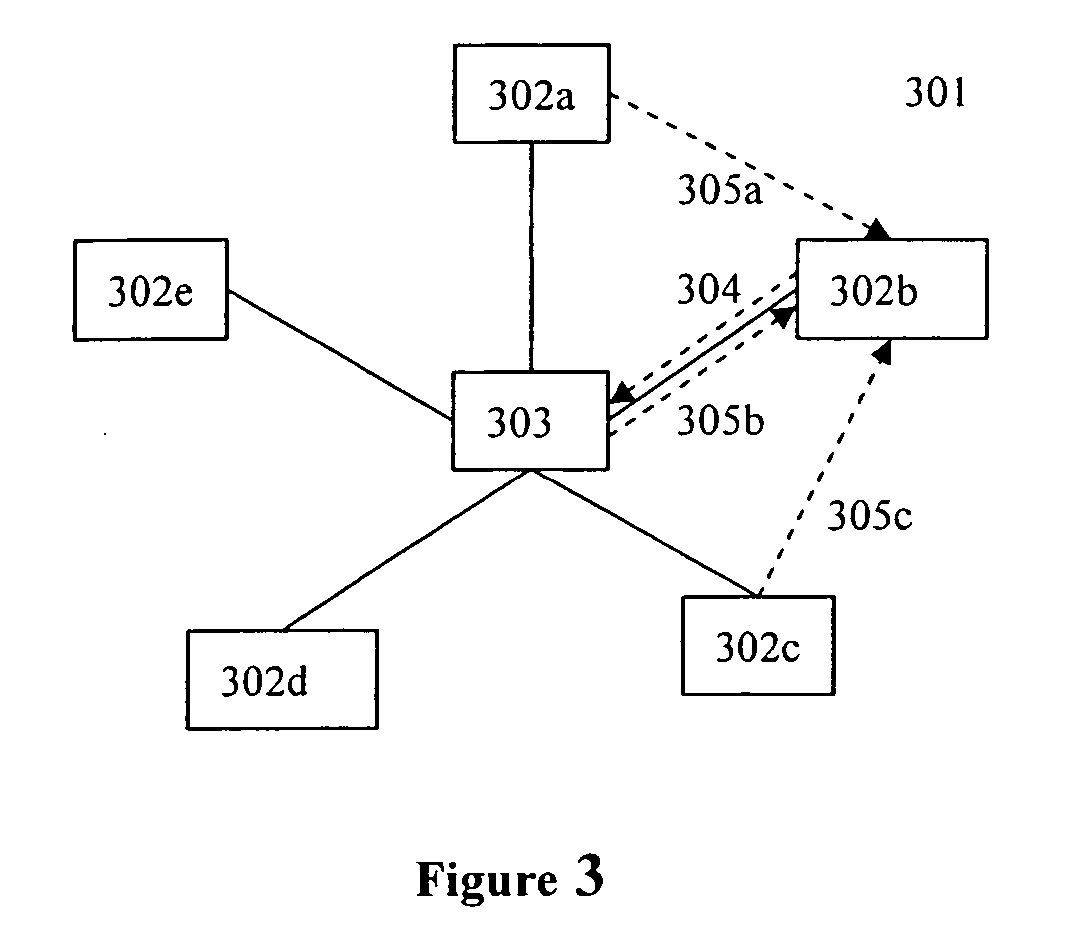
ActiveUS20060117172A1Improve performanceImprove availabilityDigital computer detailsData resettingOperational systemTransparent computing
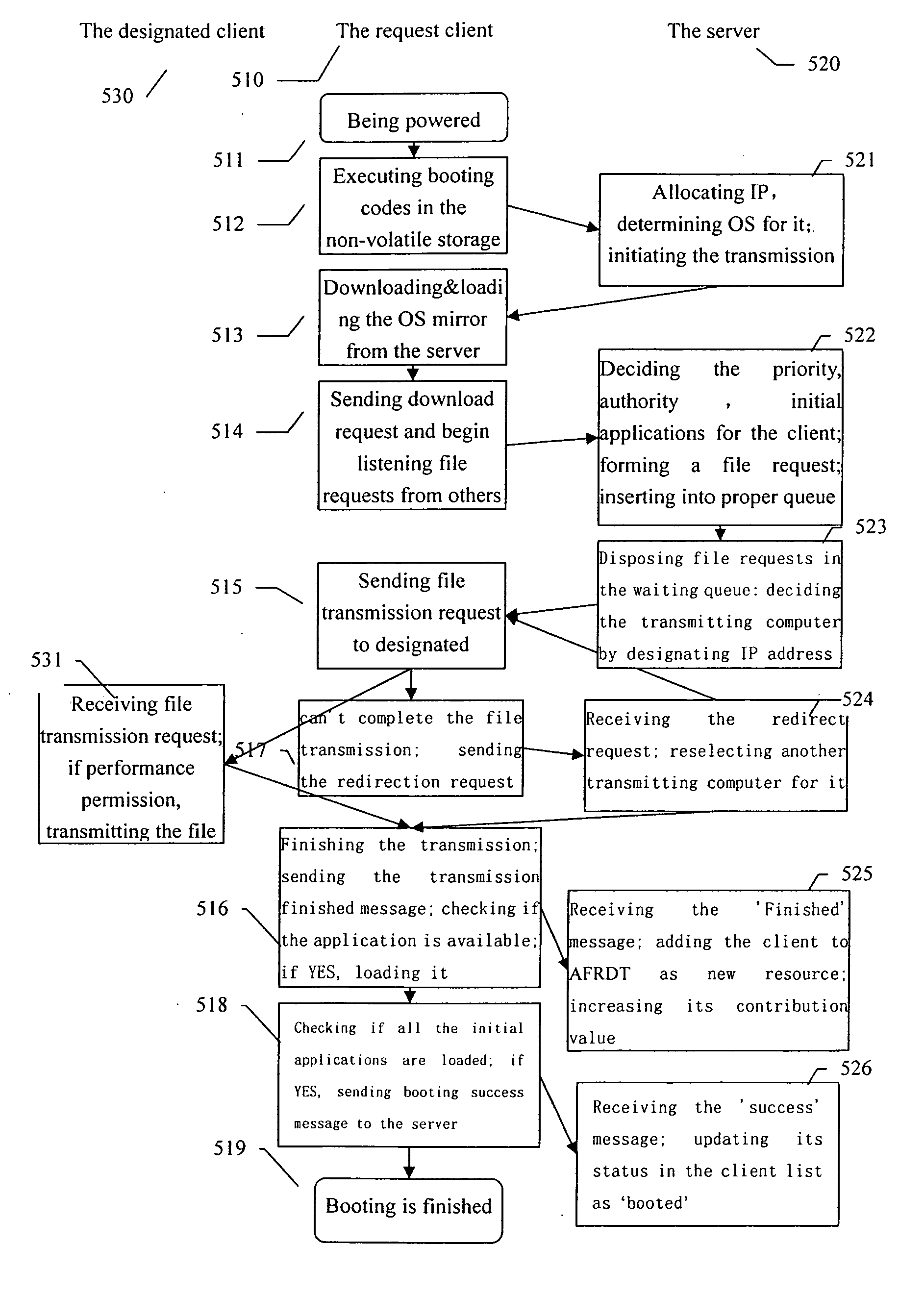
A computing system based on Transparence Computing consists of clients and a server. There is no disk and no preinstalled OS on the client; a remote booting chip is set on the client's mainboard for downloading and loading the OS. Boot-supporting services, OS kernel mirrors, and applications are preset on the server; After being powered, the client broadcasts the boot request to the network and the server allocates network parameters for it. The client downloads an OS-selecting script from the server. After the user selects the needed OS, the client downloads and loads the selected OS from the server. Hence, the client fulfills the user's computing requirements just as a normal PC. The computing work is implemented on the client-side, during which the client can acquire corresponding resources such as applications, data, and documents from the server on demand. The client can be provided with private storage across the network by presetting a service in the mirror for creating virtual disks on the server, and thus data generated during or after the computing can be persistently stored on the server's storage.
Owner:TSINGHUA UNIV
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
InactiveUS7295960B2Significant valueEasy to explainGeometric CADAnalogue computers for electric apparatusHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
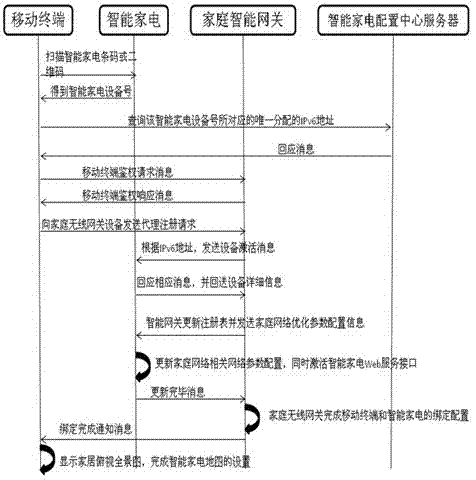
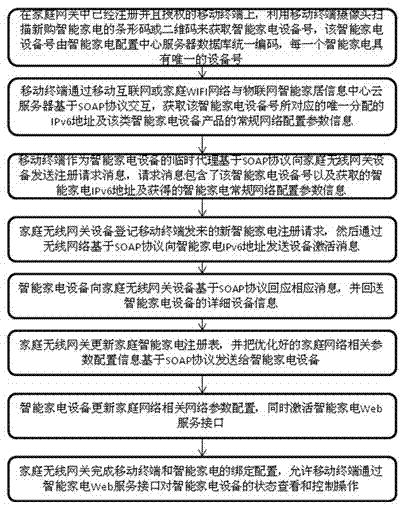
Method for automatically registering intelligent home appliance in network by one key
InactiveCN102769619ASimplify complex configurationEasy remote controlTransmissionWeb serviceRemote control
The invention discloses a method for automatically registering an intelligent home appliance in a network by one key. The method comprises the following steps: obtaining the device number of the newly purchased intelligent home appliance by scanning; obtaining the IPv6 address and the general network configuration parameters of the home appliance from a server; sending registration request information to a home wireless gateway by a mobile terminal; sending device activation information to the home appliance by the home wireless gateway; returning detailed device information to the home wireless gateway by the home appliance; updating a home appliance registry and sending optimized home network configuration parameters to the home appliance by the home wireless gateway; updating home network relevant parameter configuration and activating a home appliance Web service interface by the home appliance; and finishing the binding configuration of the mobile terminal and the home appliance by the home wireless gateway. By the method, the configuration for finishing the registration of the intelligent home appliance in a computer is simplified for users and professional staffs, the binding of the mobile terminal and the intelligent home appliance is finished automatically, and the later safer remote control on the Web service interface of the intelligent home appliance through an authorized mobile terminal is facilitated.
Owner:NANJING XIAOWANG SCI & TECH
Mobile videoconferencing robot system with network adaptive driving
Owner:TELADOC HEALTH INC +1
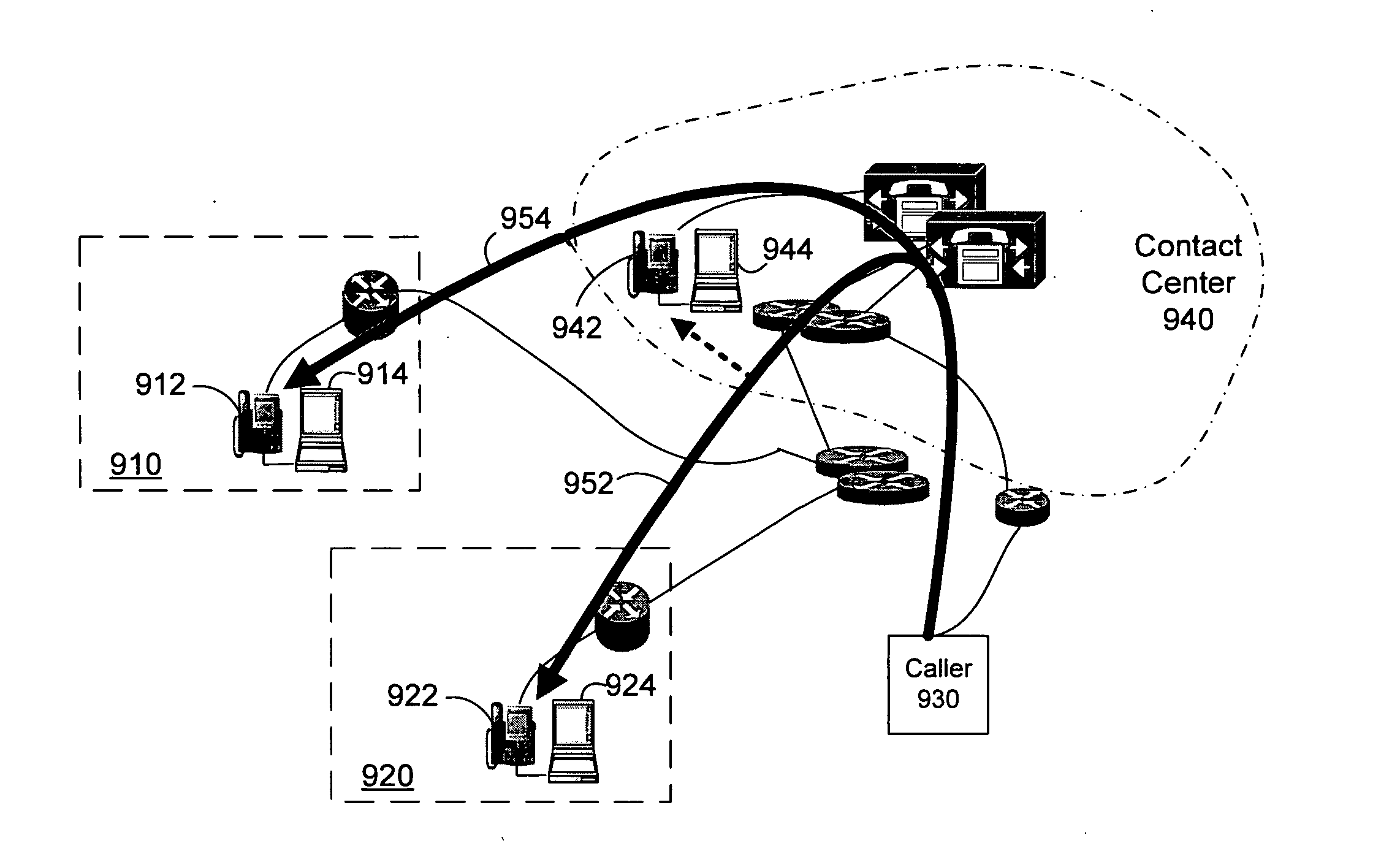
Supervisor intercept for teleagent voice over internet protocol communications
ActiveUS20070019618A1Special service for subscribersNetwork connectionsTelecommunications linkCommunications system
A system for transferring a call from one teleagent to another in response to a loss of voice quality in a voice over Internet protocol (VoIP) communication system. Network parameters that affect voice quality over broadband connections are detected manually or automatically and an alert is generated. In response to the alert, a supervisor can transfer the call in progress to a second agent so that a better communication link can be provided and voice quality restored. Such transfer can be seamless to the caller. In different embodiments, transfer, or intercept, can occur manually or automatically (e.g., without supervisor intervention).
Owner:CISCO TECH INC
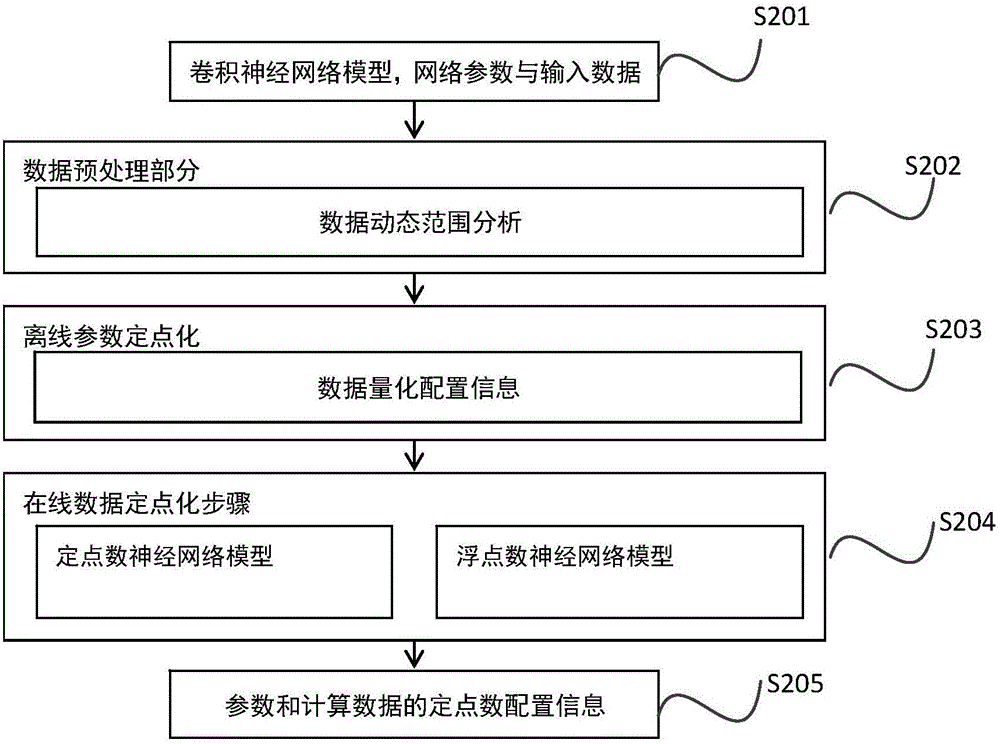
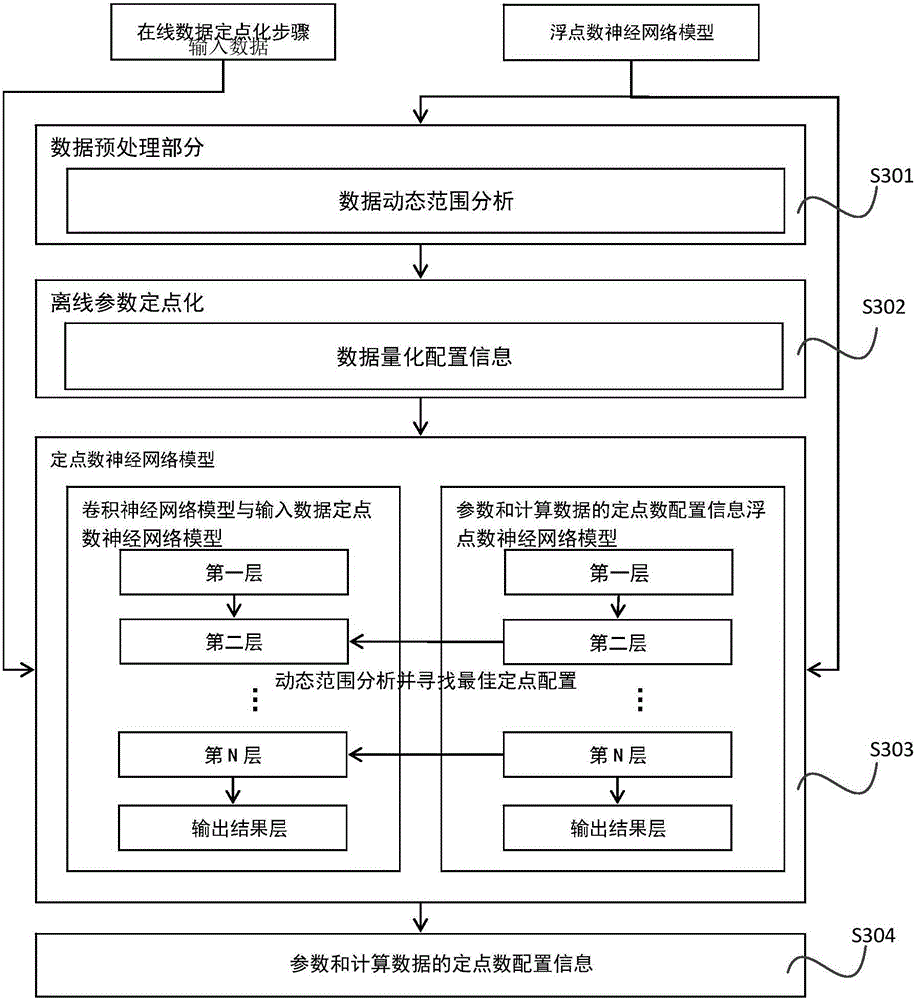
Method and apparatus for fixed-pointing layer-wise variable precision in convolutional neural network
InactiveCN105760933AReduce precision lossFast transmissionNeural learning methodsFloating pointNetwork data
The invention discloses a method and an apparatus for fixed-pointing the layer-wise variable precision in a convolutional neural network. The method comprises the following steps: estimating fixed-pointing configuration input to various layers in the convolutional neural network model respectively in accordance with input network parameters and a value range of input data; based on the acquired fixed-point configuration estimation and the optimal error function, determining the best fixed-point configuration points of the input data and network parameters of various layers and outputting the best fixed-point configuration points; inputting respectively the input data which is subject to fixed-pointing and an input data of an original floating-point number as a first layer in the convolutional neural network and computing the optimal fixed-point configuration point of the output data of the layer, and inputting the output result and an output result of the original first layer floating-point number as a second layer. The rest of the steps can be done in the aforementioned manner until the last layer completes the whole fixed-pointing. The method of the invention guarantees the minimum precision loss of each layer subject to fixed-pointing of the convolutional neural network, can explicitly lower space required by storing network data, and can increase transmitting velocity of network parameters.
Owner:BEIJING DEEPHI INTELLIGENT TECH CO LTD
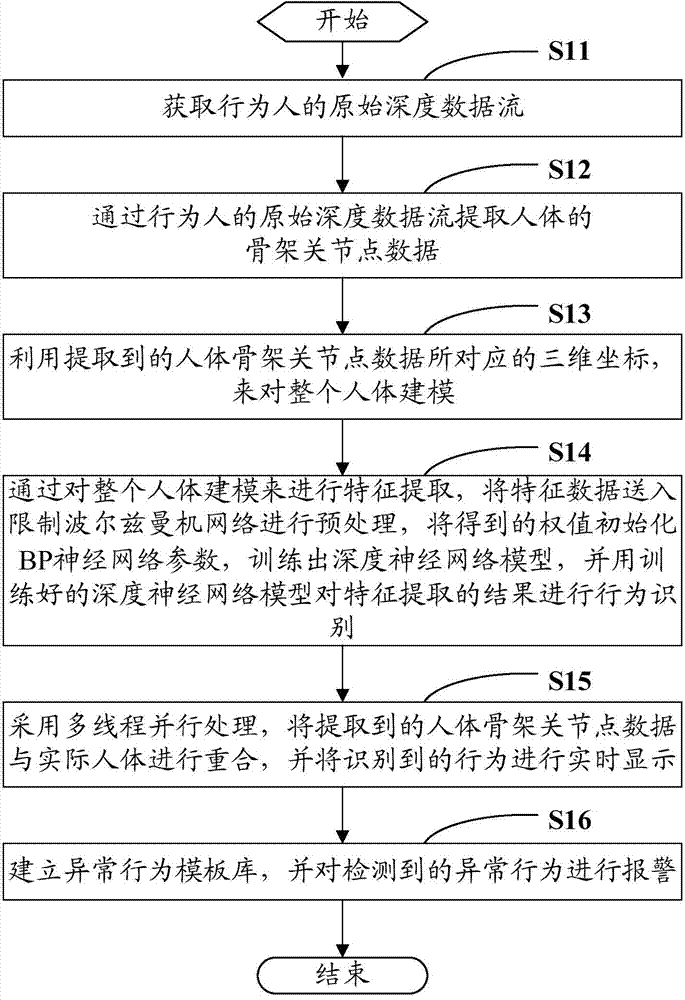
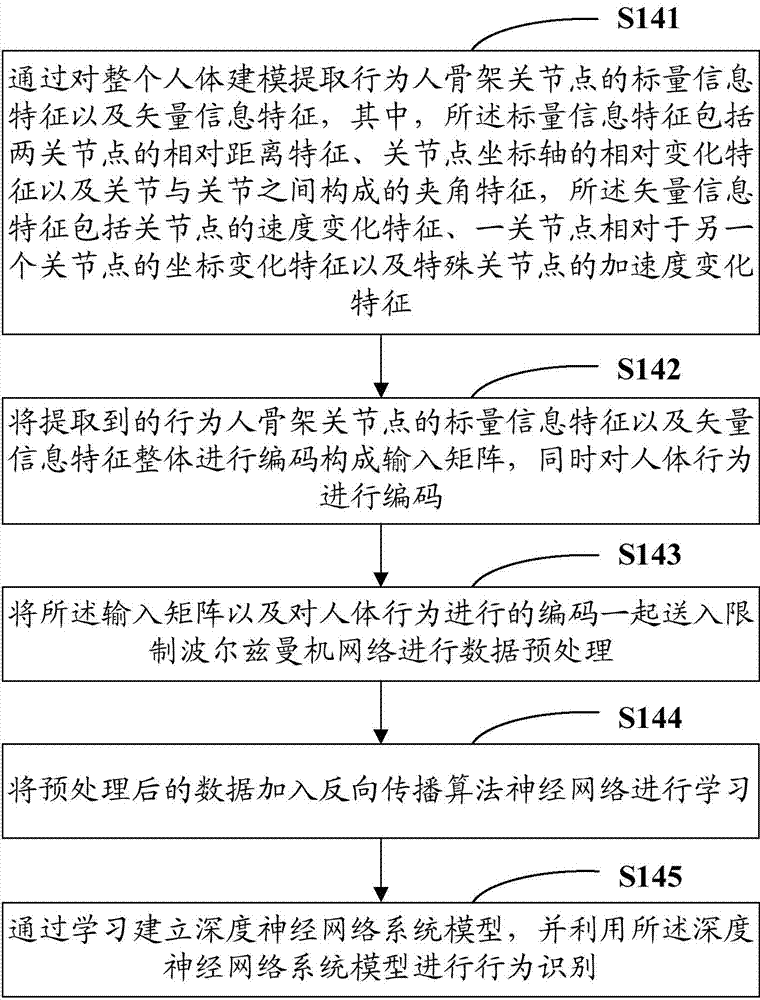
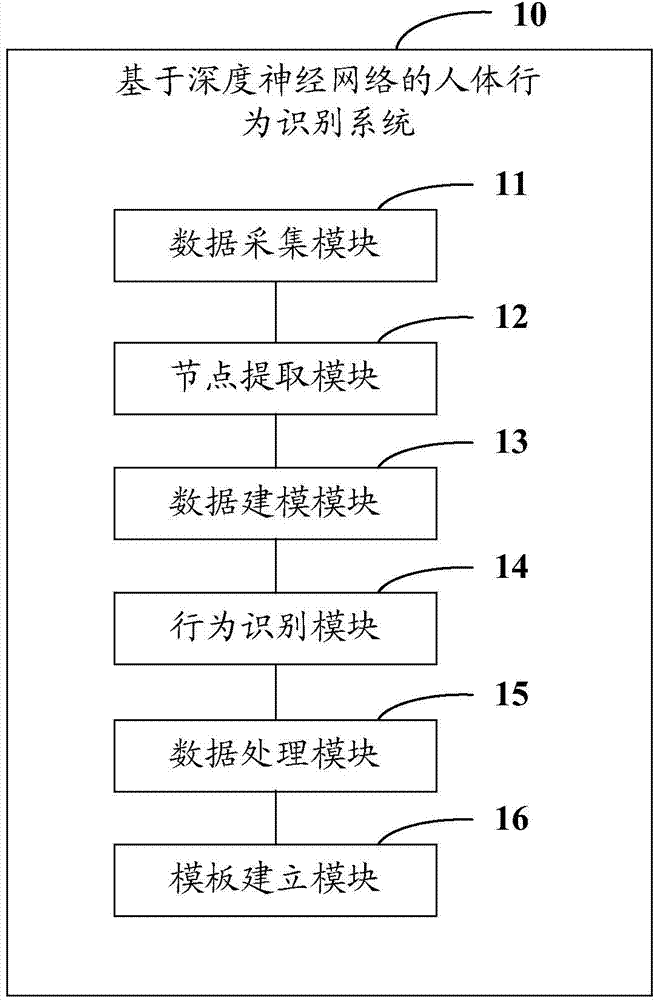
Human behavior recognition method and human behavior recognition system based on depth neural network
InactiveCN104850846APrivacy protectionImprove accuracyCharacter and pattern recognitionNeural learning methodsHuman behaviorHuman body
The invention provides a human behavior recognition method based on a depth neural network, comprising the following steps: acquiring original depth data stream of an actor; extracting human skeleton joint data from the original depth data stream of the actor; modeling the entire human body with three-dimensional coordinates corresponding to the extracted human skeleton joint data; extracting features by modeling the entire human body, sending feature data to a restricted Boltzmann machine network for preprocessing, training out a depth neural network model based on received weight initialization BP neural network parameters, and identifying a behavior from a feature extraction result; overlapping the extracted human skeleton joint data and the actual human body through multi-threaded parallel processing, and displaying the identified behavior in real time; and establishing an abnormal behavior template library and alarming for a detected abnormal behavior. The change of human behavior can be detected in real time, and alarm can be raised for abnormal behaviors (such as fall) of a human body.
Owner:SHENZHEN UNIV
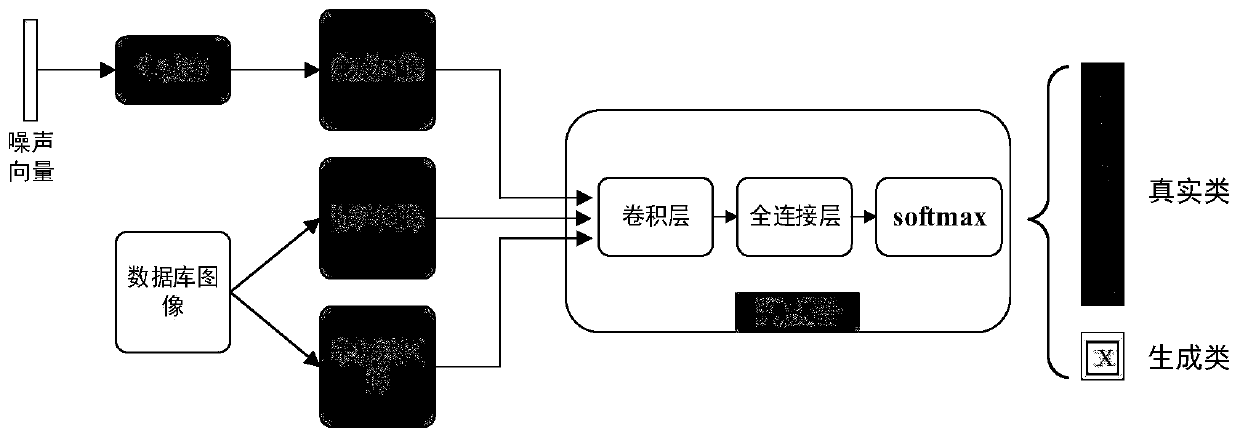
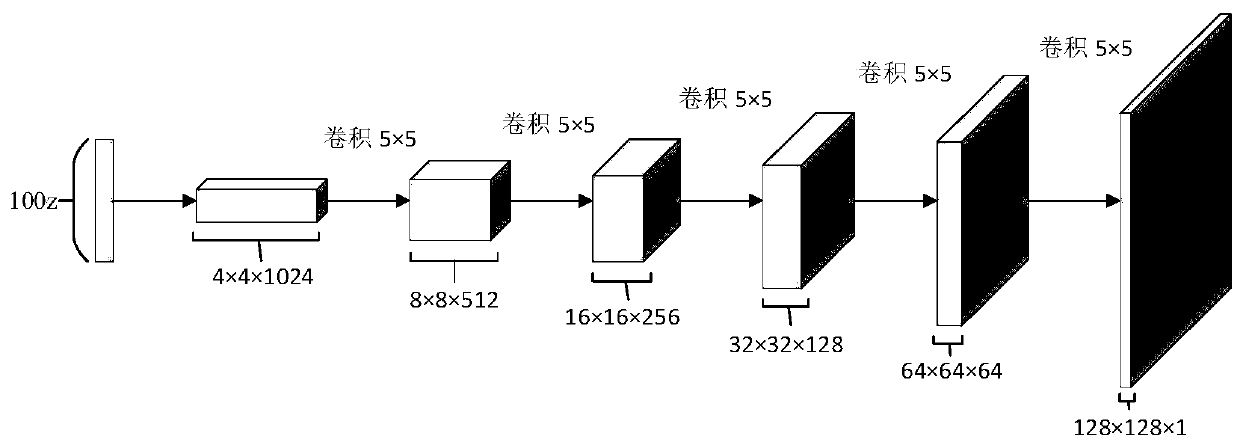
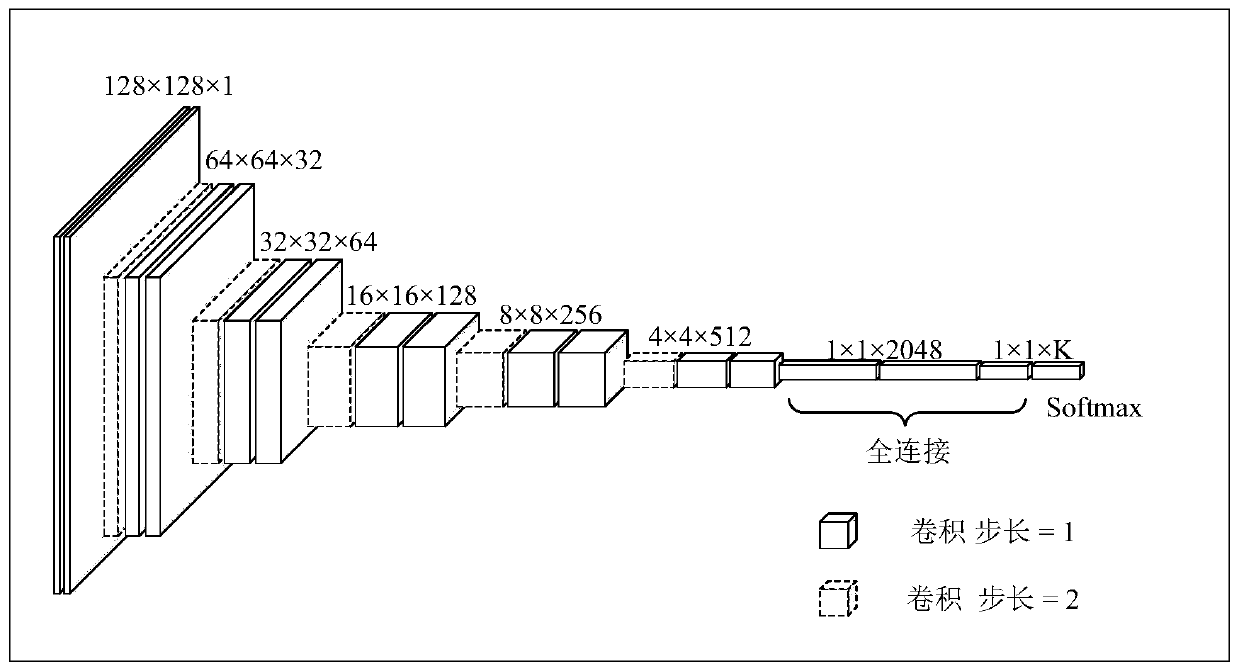
Semi-supervised X-ray image automatic labeling based on generative adversarial network
InactiveCN110110745ACharacter and pattern recognitionNeural architecturesX-rayGenerative adversarial network
The invention provides a semi-supervised X-ray automatic labeling method based on a generative adversarial network. A traditional training method is improved on the basis of an existing generative adversarial network method, and a semi-supervised training method combining supervised loss and unsupervised loss is used for carrying out image classification recognition based on a small number of labeled samples. The problem of data scarcity annotation of the X-ray image is studied. The method comprises: firstly, on the basis of a traditional unsupervised generative adversarial network, using a softmax for replacing a final output layer; expanding the X-ray image into a semi-supervised generative adversarial network, defining additional category label guide training for the generated sample, optimizing network parameters by adopting the semi-supervised training, and finally, automatically labeling the X-ray image by adopting a trained discriminant network. Compared with traditional supervised learning and other semi-supervised learning algorithms, the method has the advantage that in the aspect of medical X-ray image automatic labeling, the performance is improved.
Owner:SHANGHAI MARITIME UNIVERSITY
System and method for analyzing the performance of multiple transportation streams of streaming media in packet-based networks
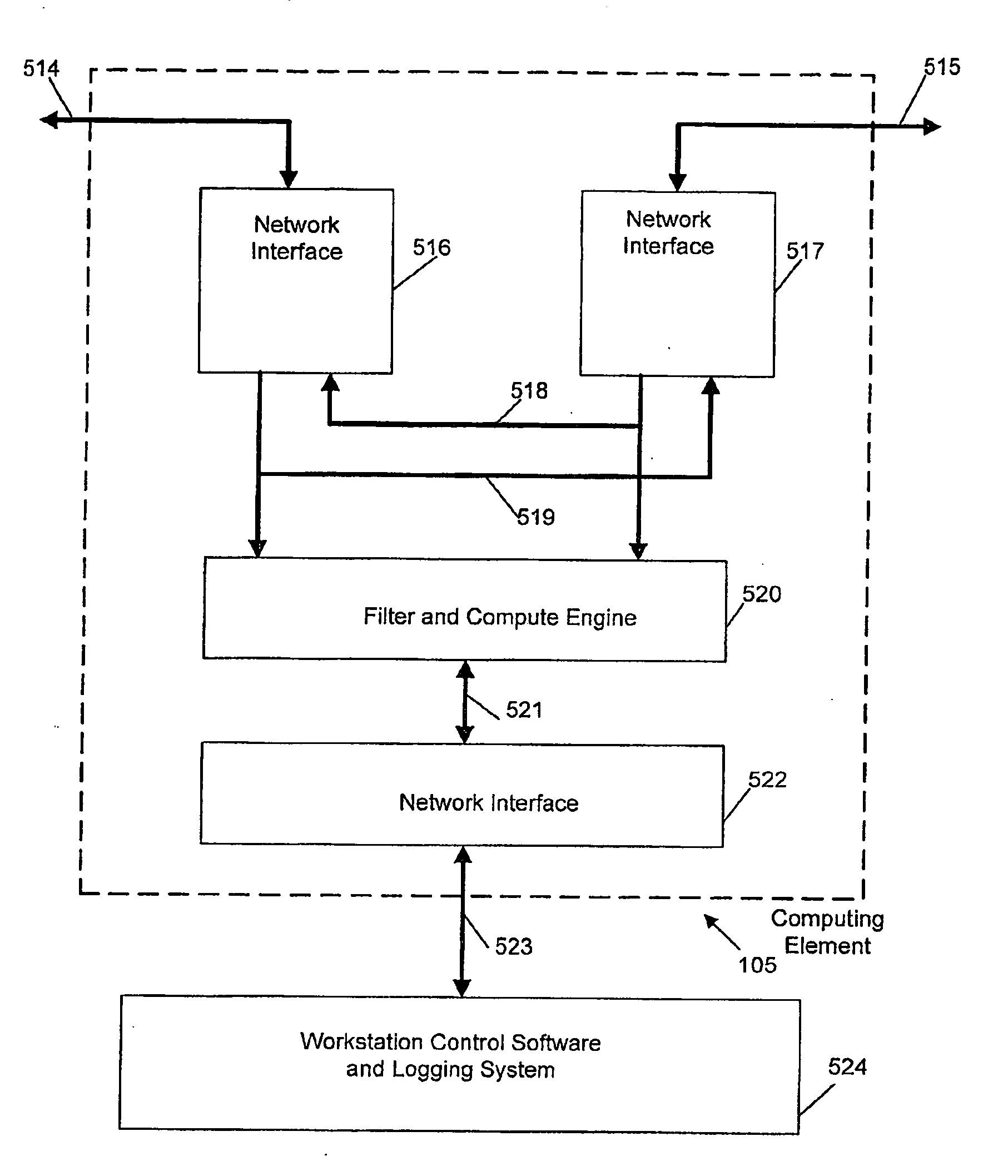
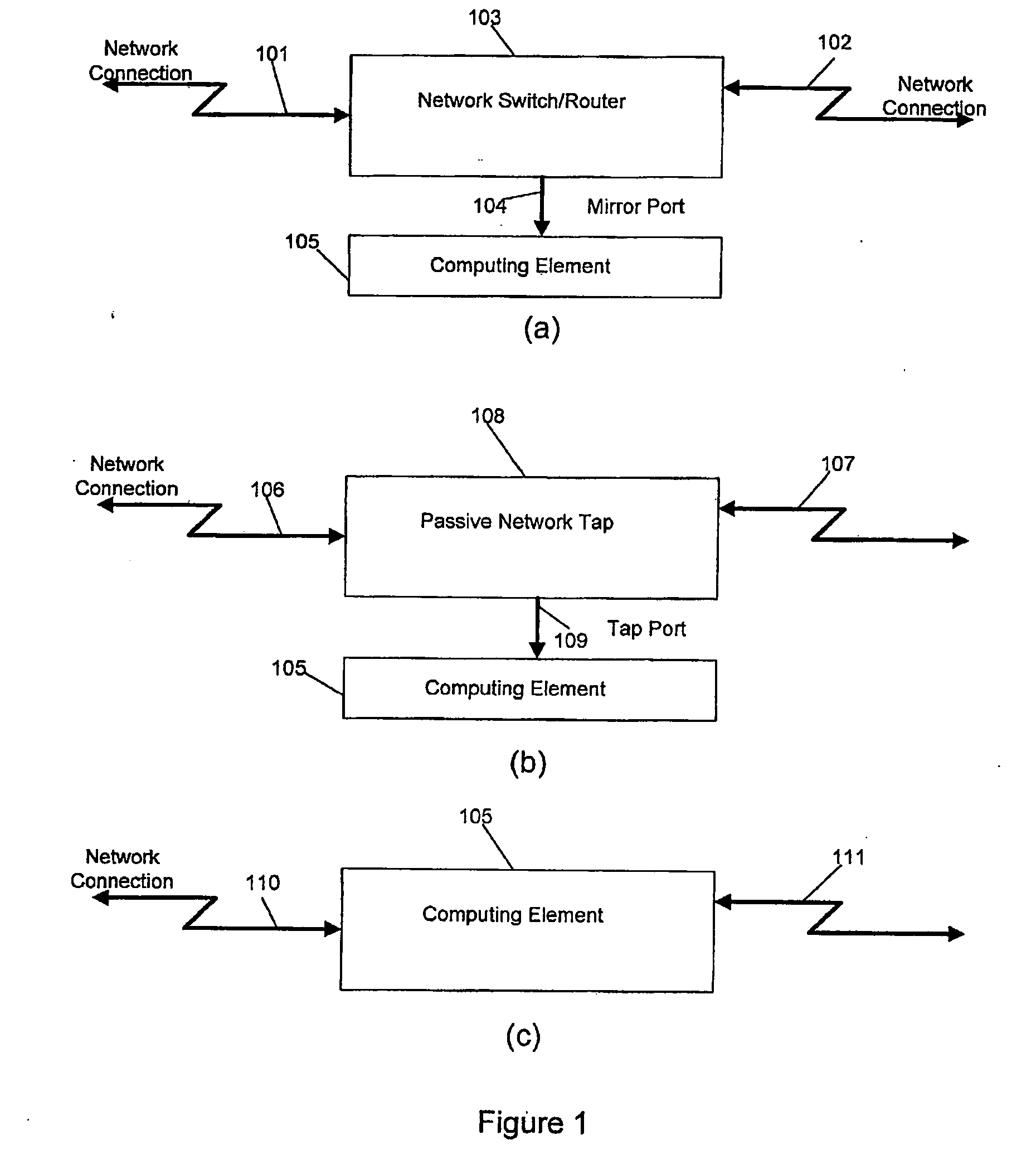
Streaming media network parameters are measured using an electronic system and displayed directly to a user or transmitted via an electronic interface such as an existing system network conduit, either in or out-of-band. A scalable hardware and / or software compute engine filters and reduces network parameters to simplify tracking the instantaneous and long term streaming media performance of the network. Hence, the entire set of active media streams is continuously monitored concurrently, thereby providing the ability to detect impairments as well as predict impending impairments. In one example, an existing packetized network conduit containing streaming media is tapped to concurrently and objectively analyze the streaming media streams, producing statistics (such as delay factor and media loss rate) and alarm-type events according to predetermined rules. Tapping the existing packetized network in multiple points provides comparison points and assists in pinpointing the source(s) of the impairment(s).
Owner:INEOQUEST TECH
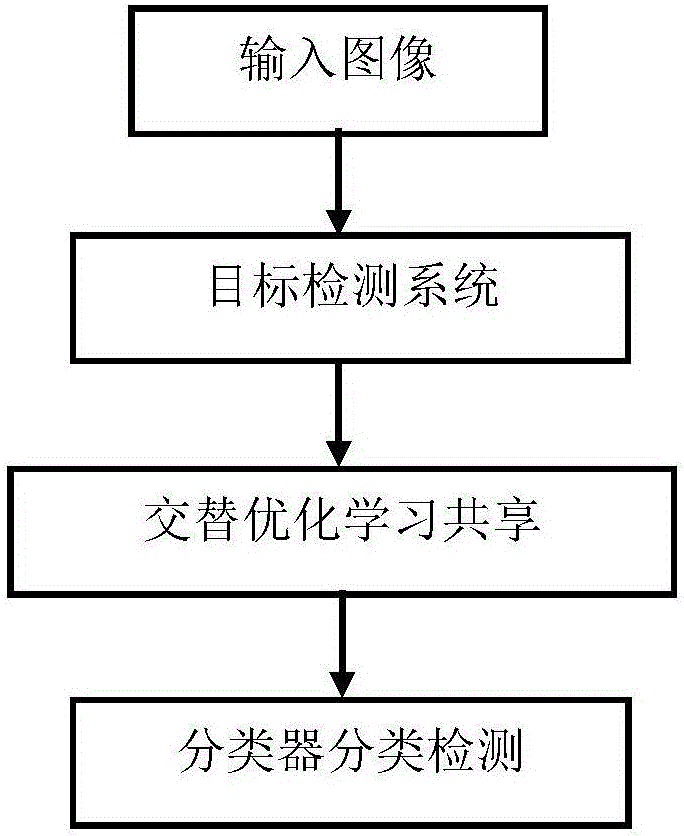
Real-time target detection method based on region convolutional neural network
InactiveCN106599939ACharacter and pattern recognitionNeural learning methodsPattern recognitionRegion of interest
The invention provides a real-time target detection method based on a region convolutional neural network. The real-time target detection method mainly comprises an input image, a target detection system, alternative optimization learning and sharing, and classifier classification and detection. The real-time target detection method comprises the steps of: regarding an image of any size as input, inputting a plurality of regions of interest (RoIs) while inputting the image, proposing a detection region by means of a region proposal network (RPN), utilizing the proposed detection region by an R-CNN detector, sharing all spatial positions by means of complete connection layers, learning shared characteristics by adopting alternative training optimization, and carrying out classification detection by using the classifier. According to the real-time target detection method, the RPNs are used for generating region proposals, and the network parameters are reduced by using shared weights, thus the region proposing step costs almost nothing; and the region proposal network (RPN) and the region convolutional neural network (R-CNN) share two network between a convolutional layer, thereby the cost is significantly reduced, the detection speed is fast, and the efficiency is high.
Owner:SHENZHEN WEITESHI TECH
Short-term electric power load prediction method considering meteorological factors
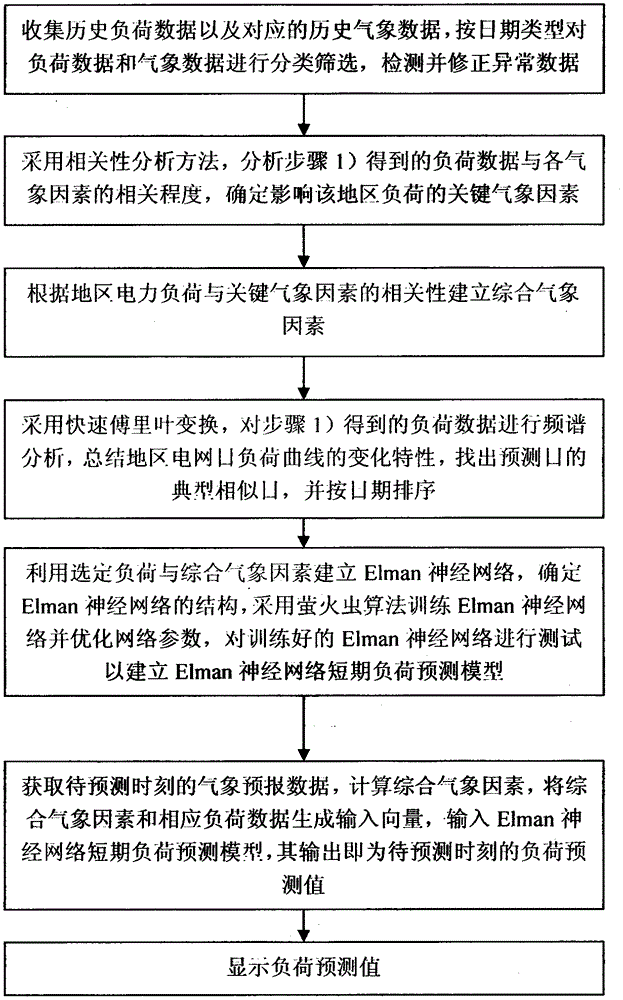
InactiveCN106779129AReduce workloadImprove forecast accuracyClimate change adaptationForecastingLoad forecastingPower grid
The invention discloses a short-term electric power load prediction method considering meteorological factors, and belongs to the technical field of electric power load prediction. The method includes: collecting historical load data and meteorological data, and detecting and correcting abnormal data; analyzing the relevance between the load data and the meteorological factors, and determining key meteorological factors; establishing comprehensive meteorological factors according to the relevance between the load and the key meteorological factors; summarizing change characteristics of a daily load curve of a regional power grid, and finding out typical similar days of a prediction day; establishing an Elman neural network short-term load prediction model by employing the selected load and the comprehensive meteorological factors, and training network parameters by employing a firefly algorithm; inputting the comprehensive meteorological factors of a to-be-predicted moment and the corresponding load data to the Elman neural network short-term load prediction model, and outputting a load prediction value of the to-be-predicted moment; and displaying the load prediction value. According to the method, the load data of weekdays, weekends, and official holidays can be accurately predicted, the prediction precision is high, the applicability is high, and reliable basis is provided for making of generation plans for operation personnel of the power grid.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com