Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
115662results about "Neural learning methods" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and Method for Distributed Denial of Service Identification and Prevention
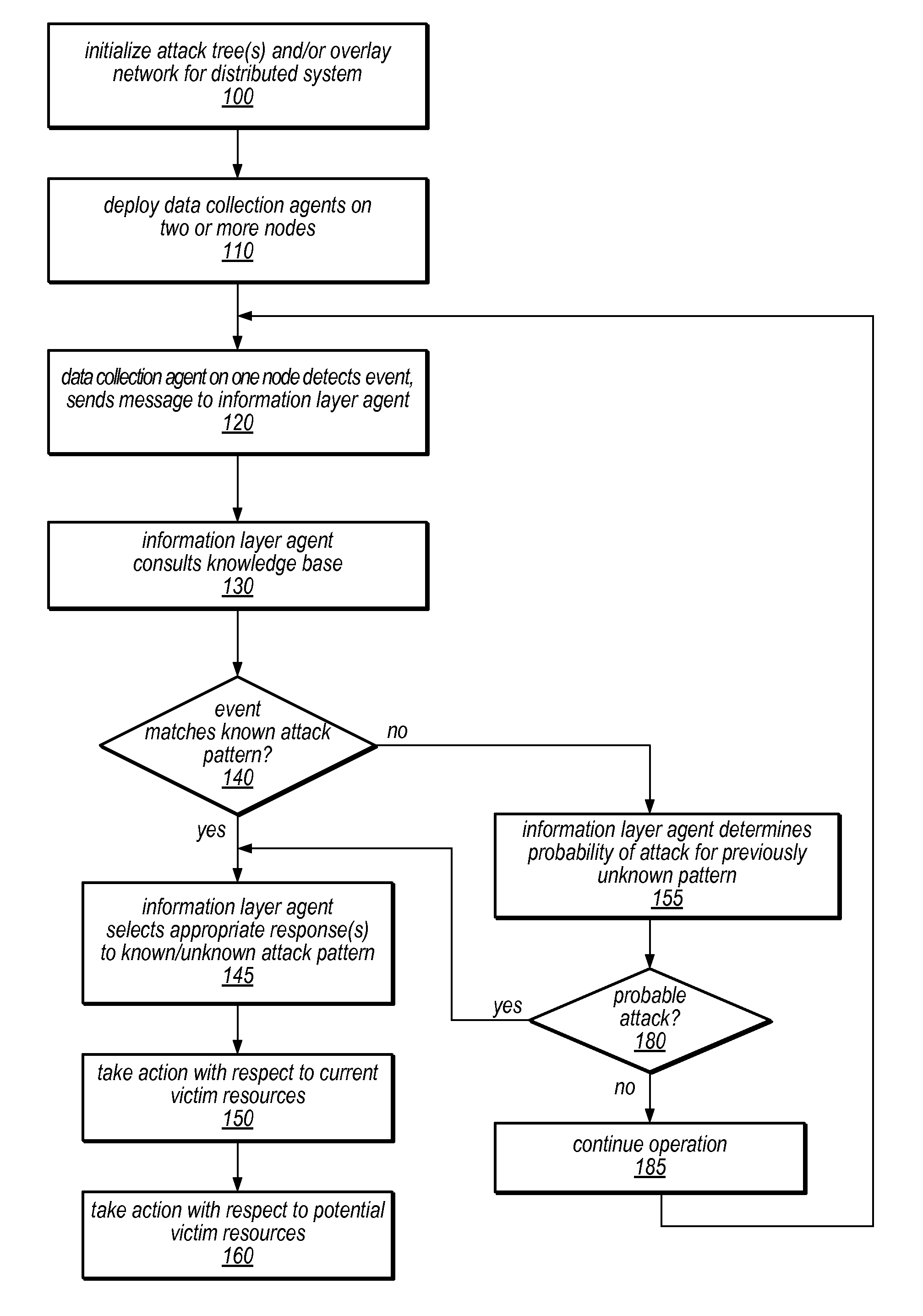
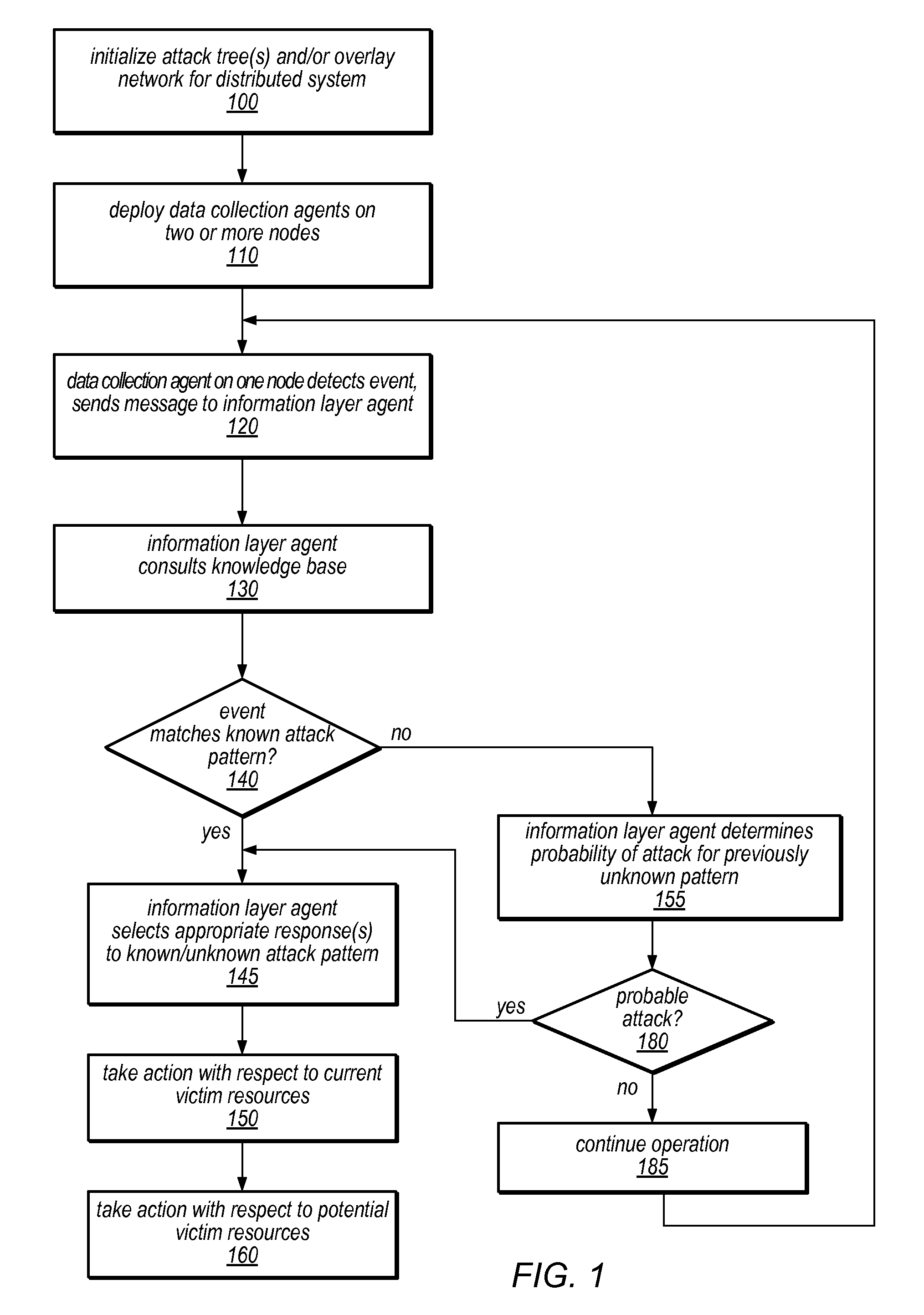
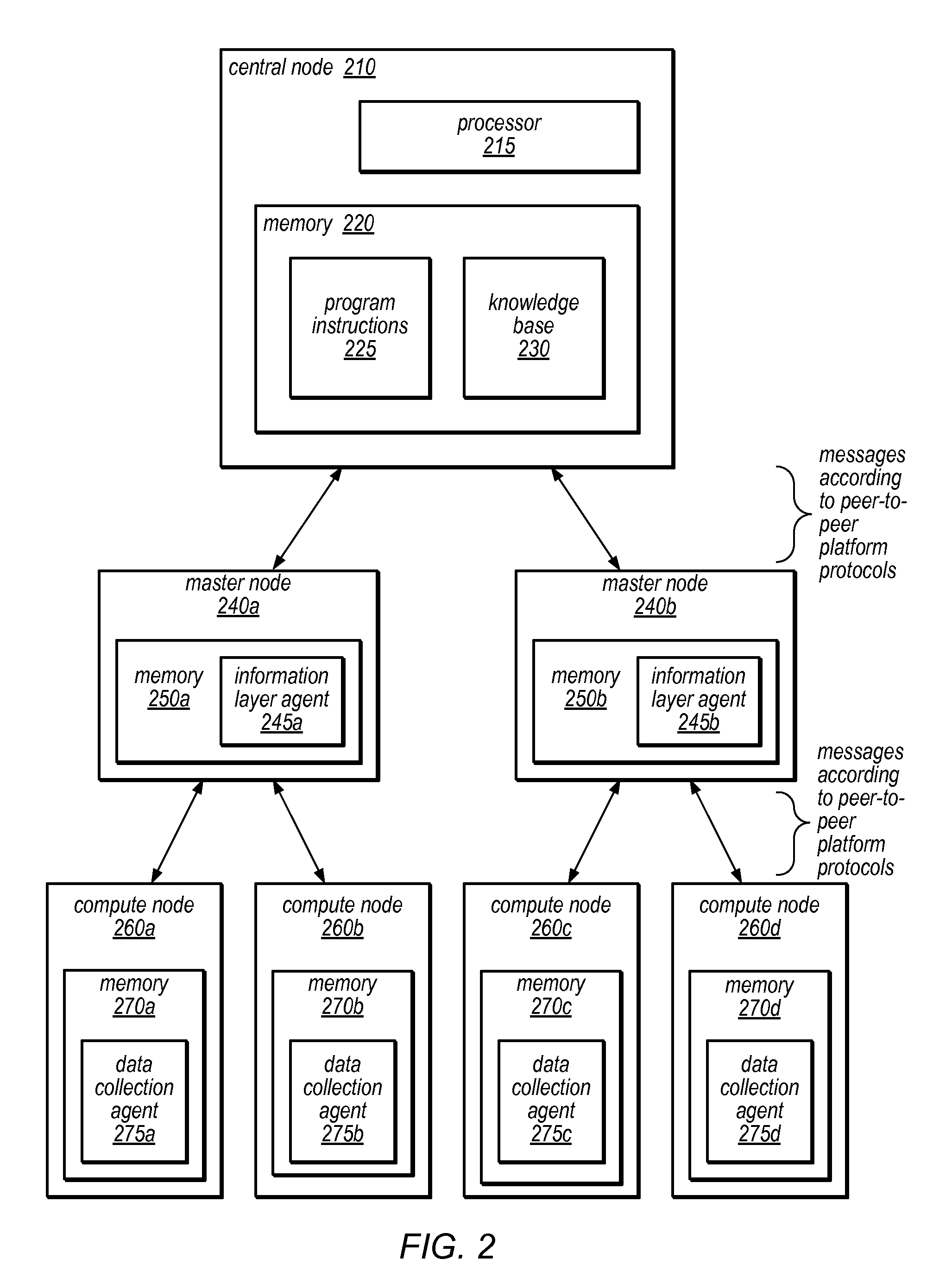
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
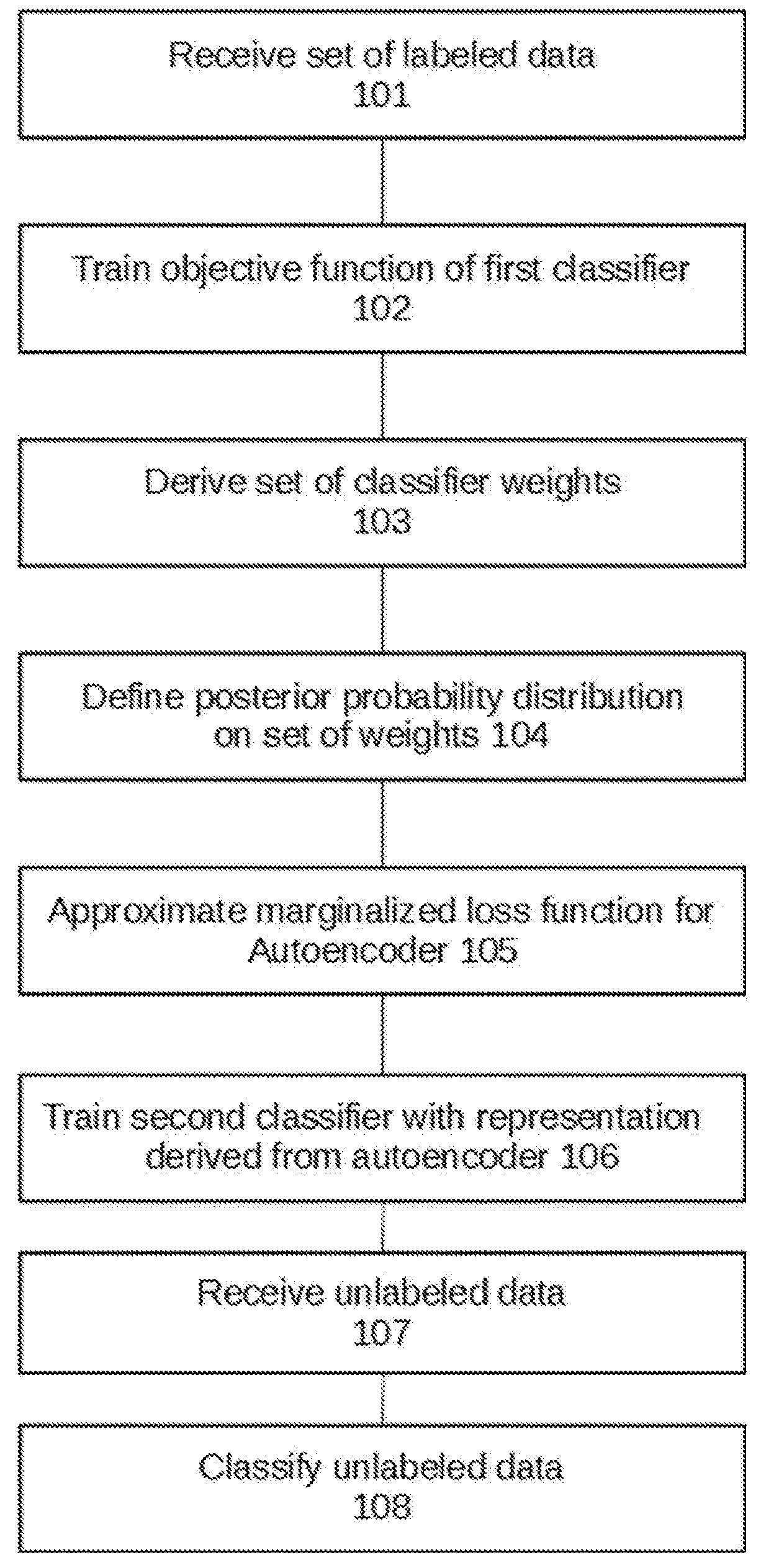
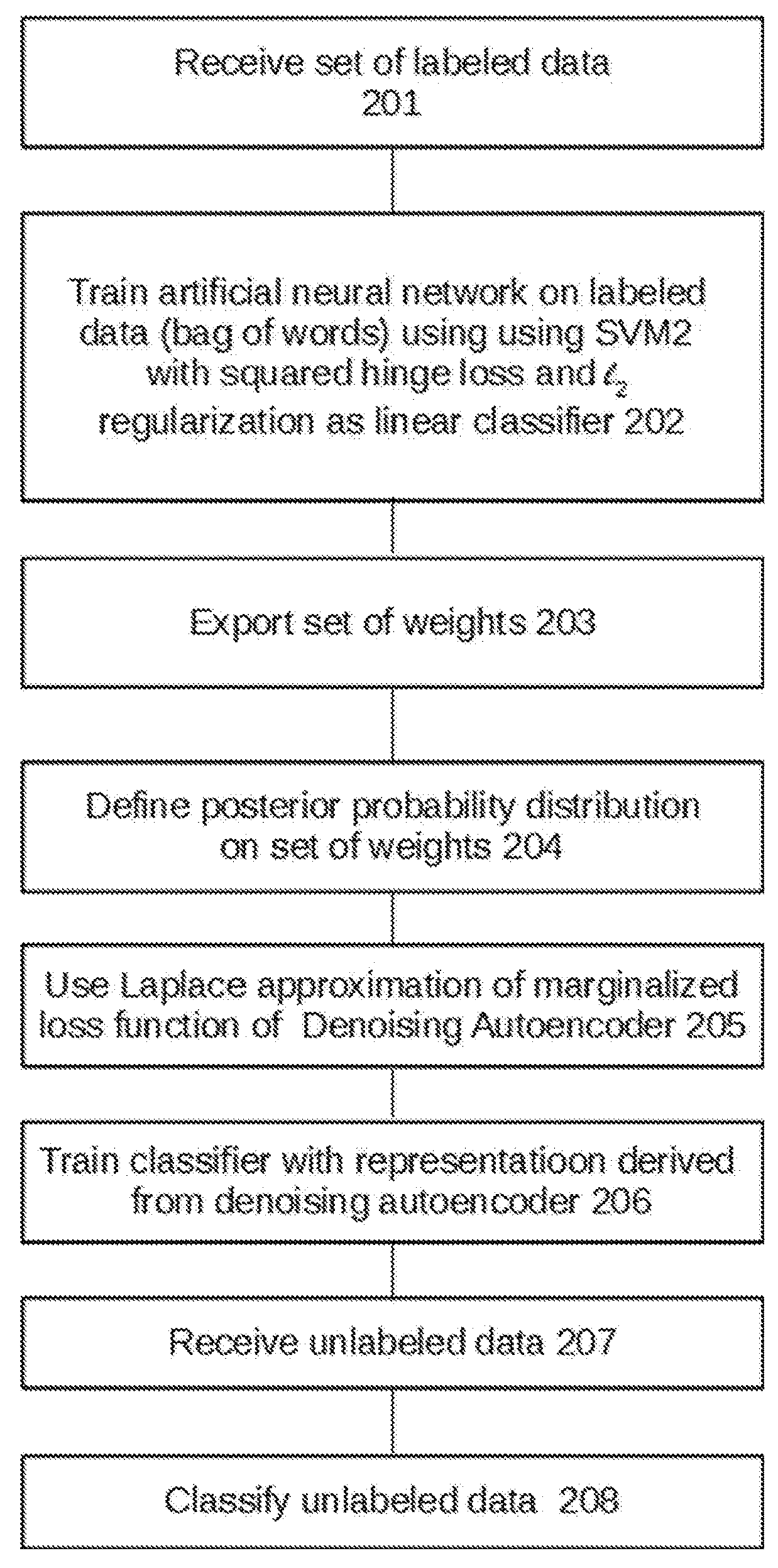
Semisupervised autoencoder for sentiment analysis
ActiveUS20180165554A1Reduce biasImprove performanceMathematical modelsKernel methodsLabeled dataComputer science
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
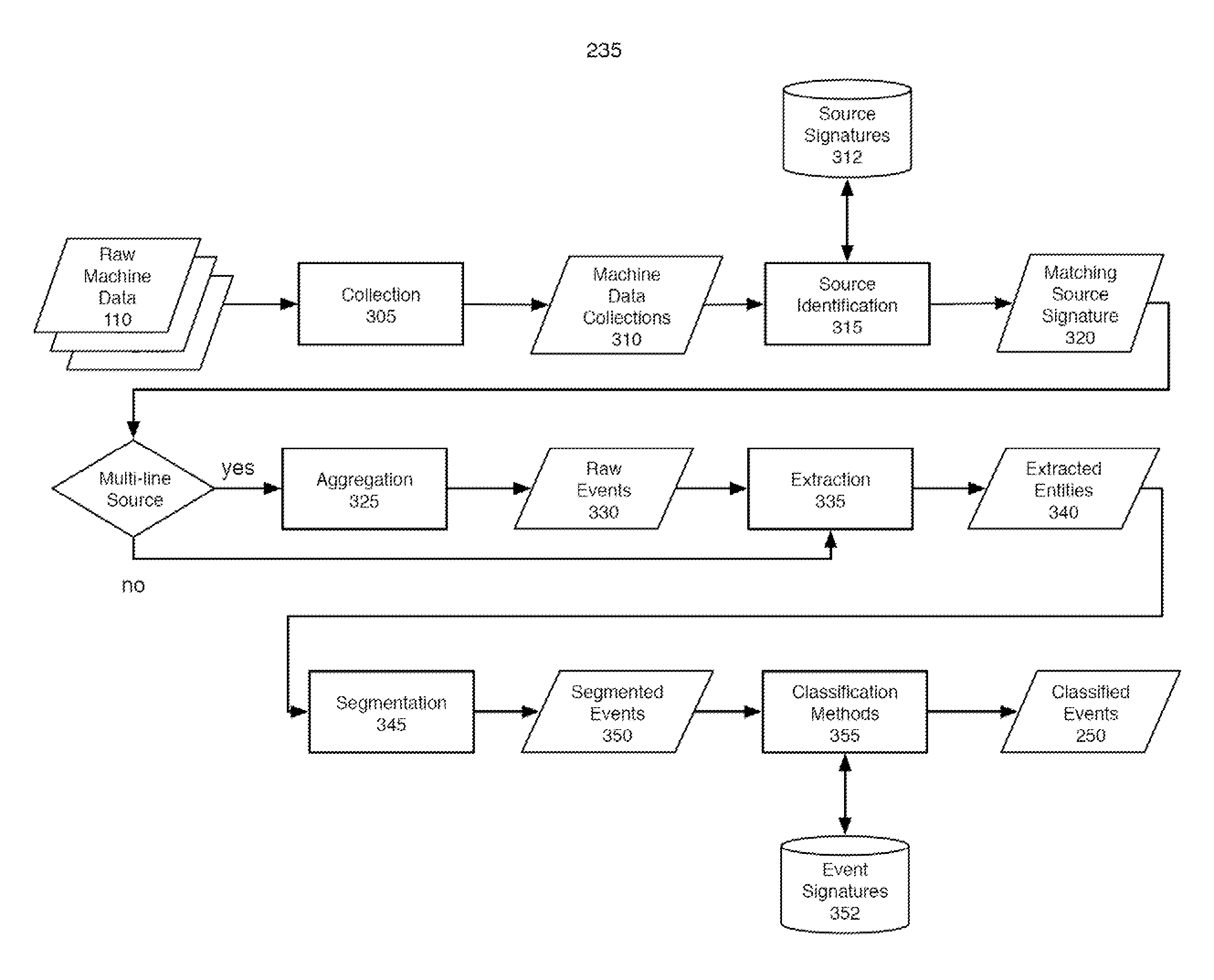
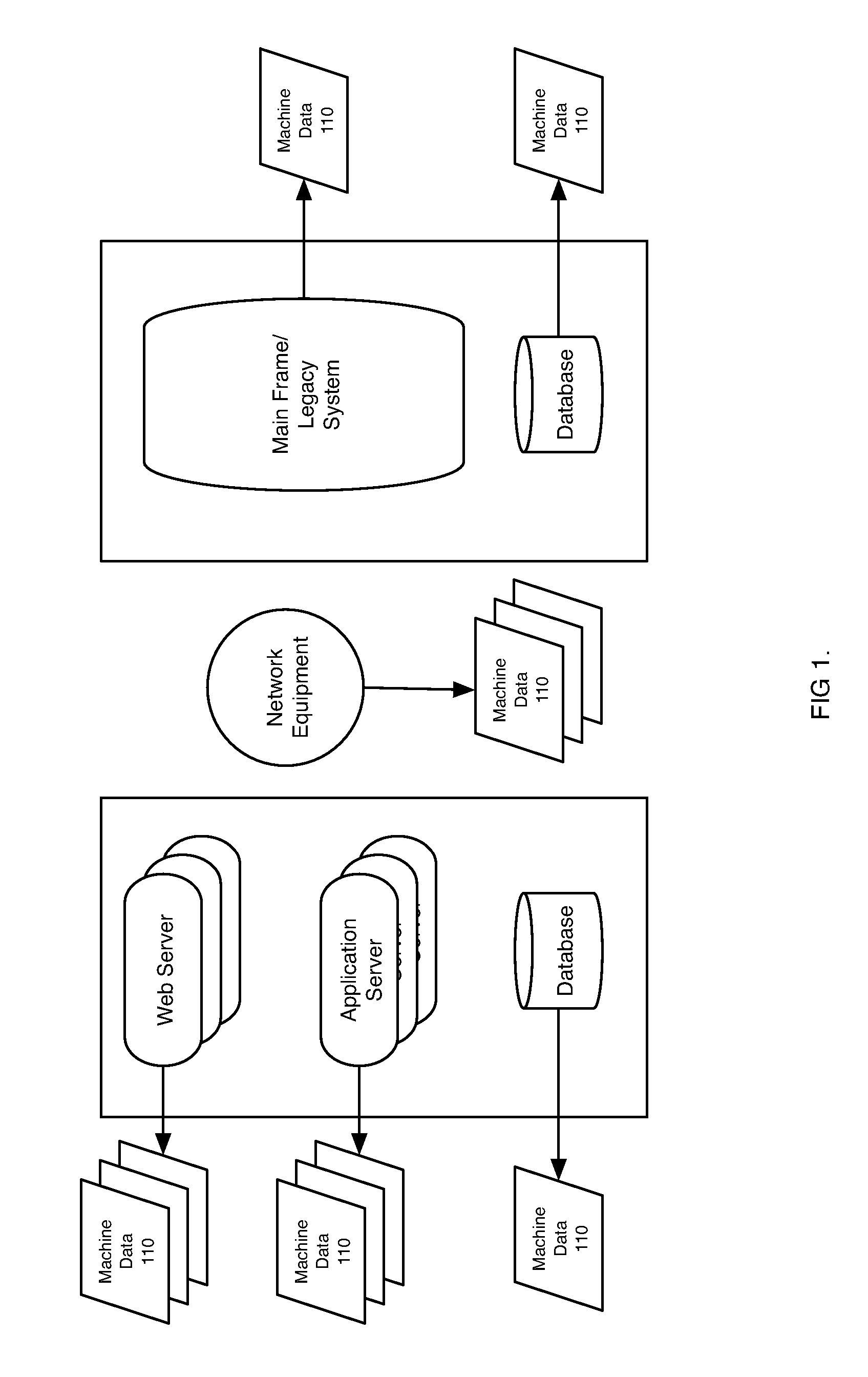
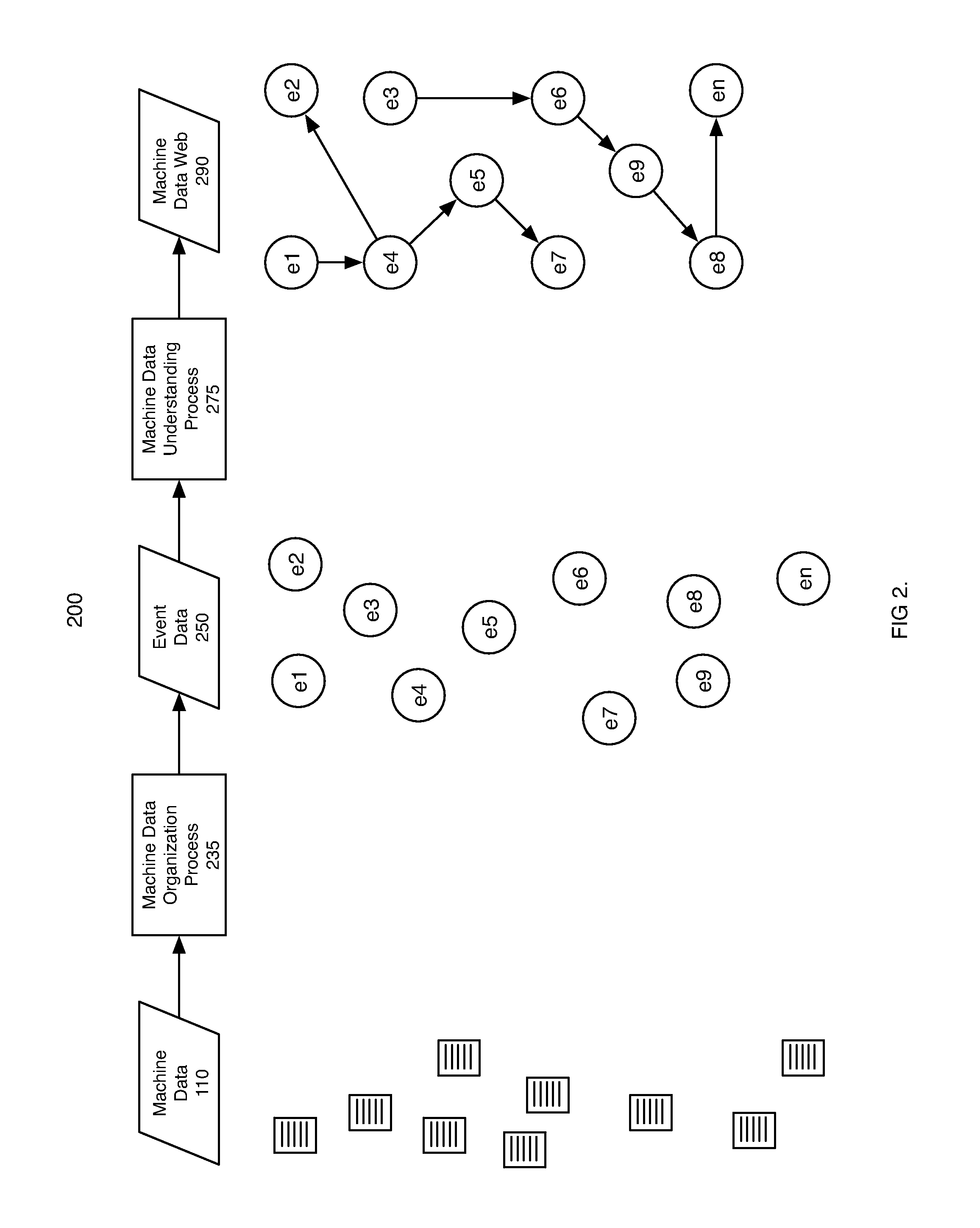
Machine data web
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
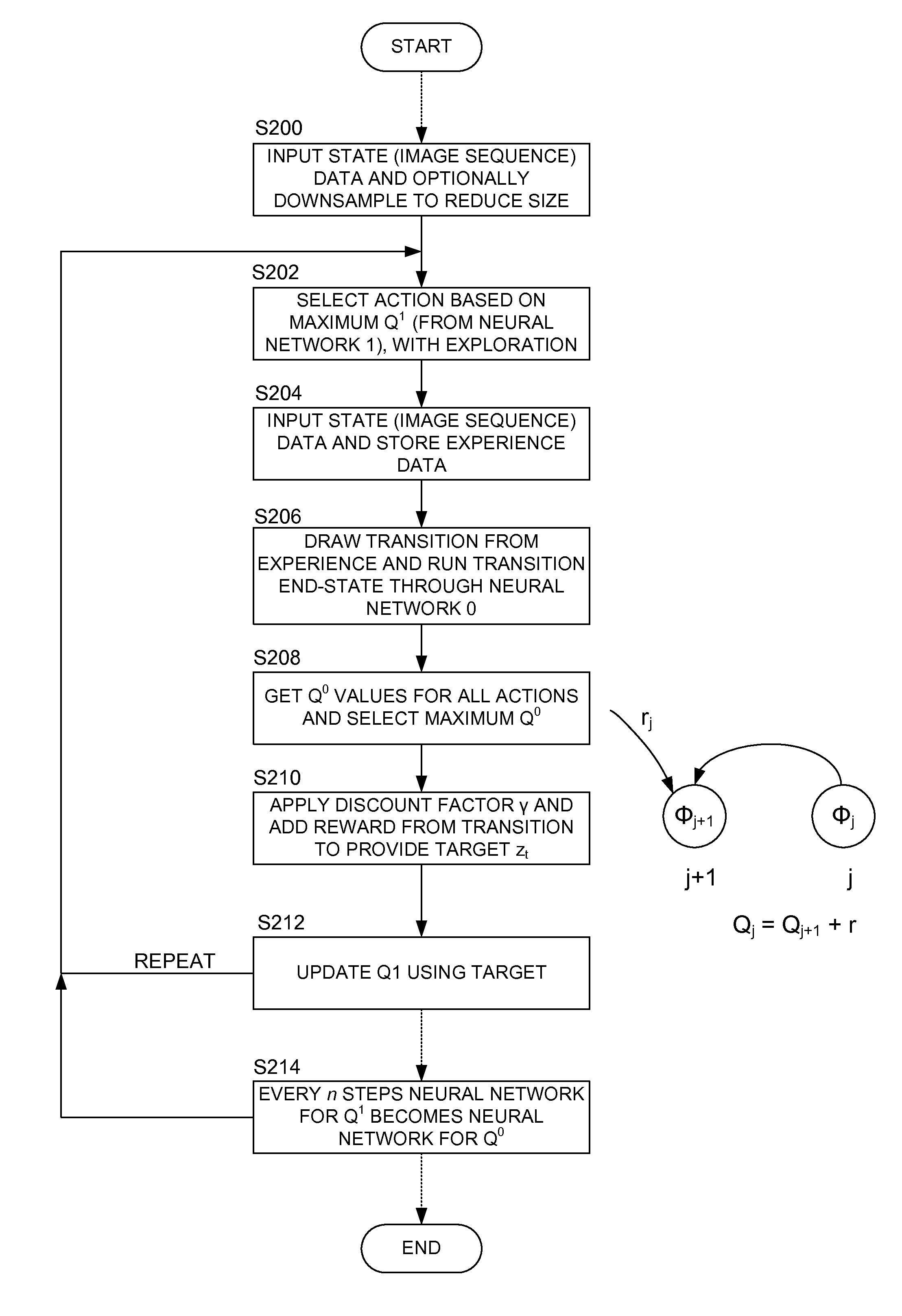
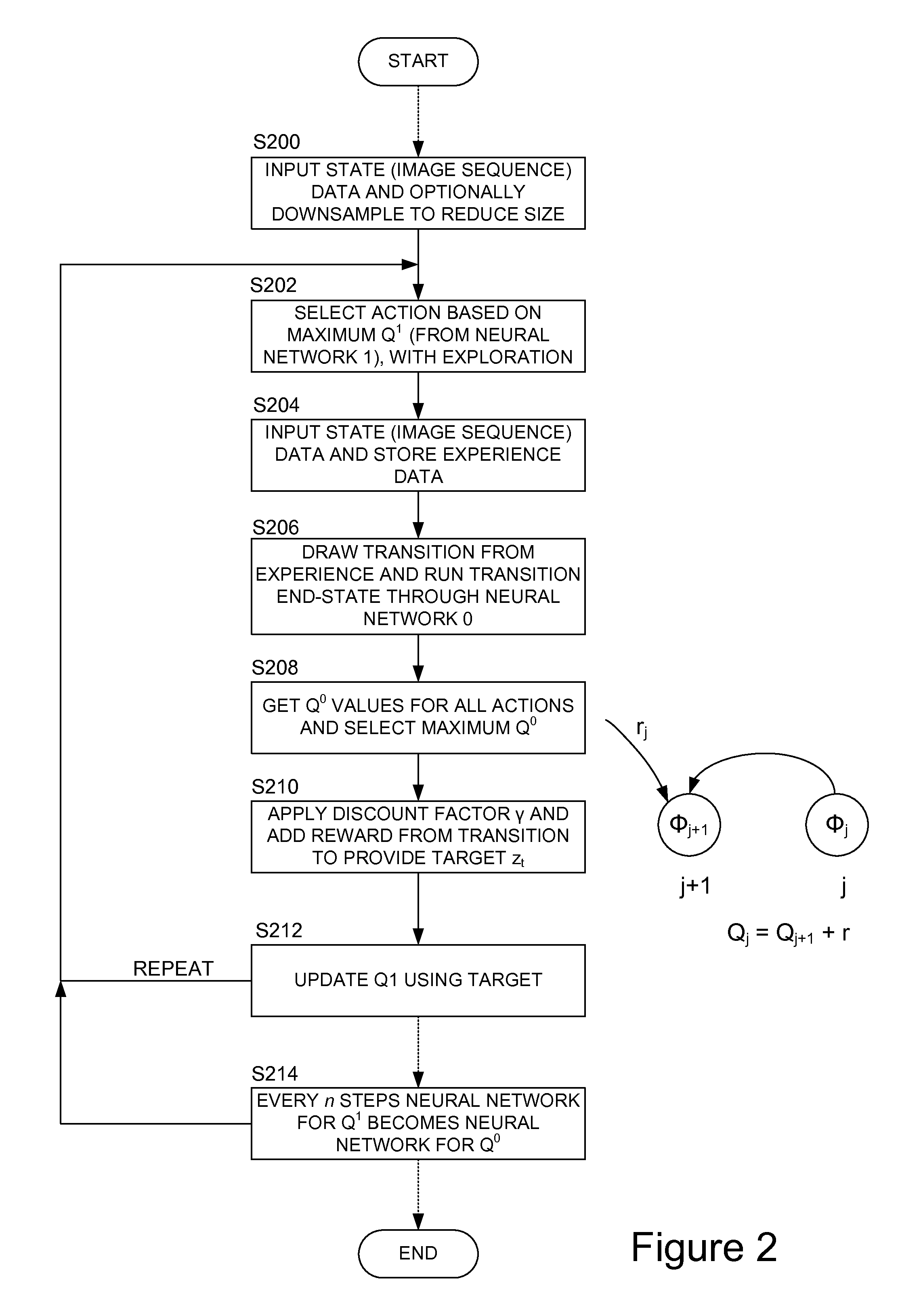
Methods and apparatus for reinforcement learning
ActiveUS20150100530A1Reduce computing costLarge data setDigital computer detailsArtificial lifeAlgorithmReinforcement learning
Owner:DEEPMIND TECH LTD
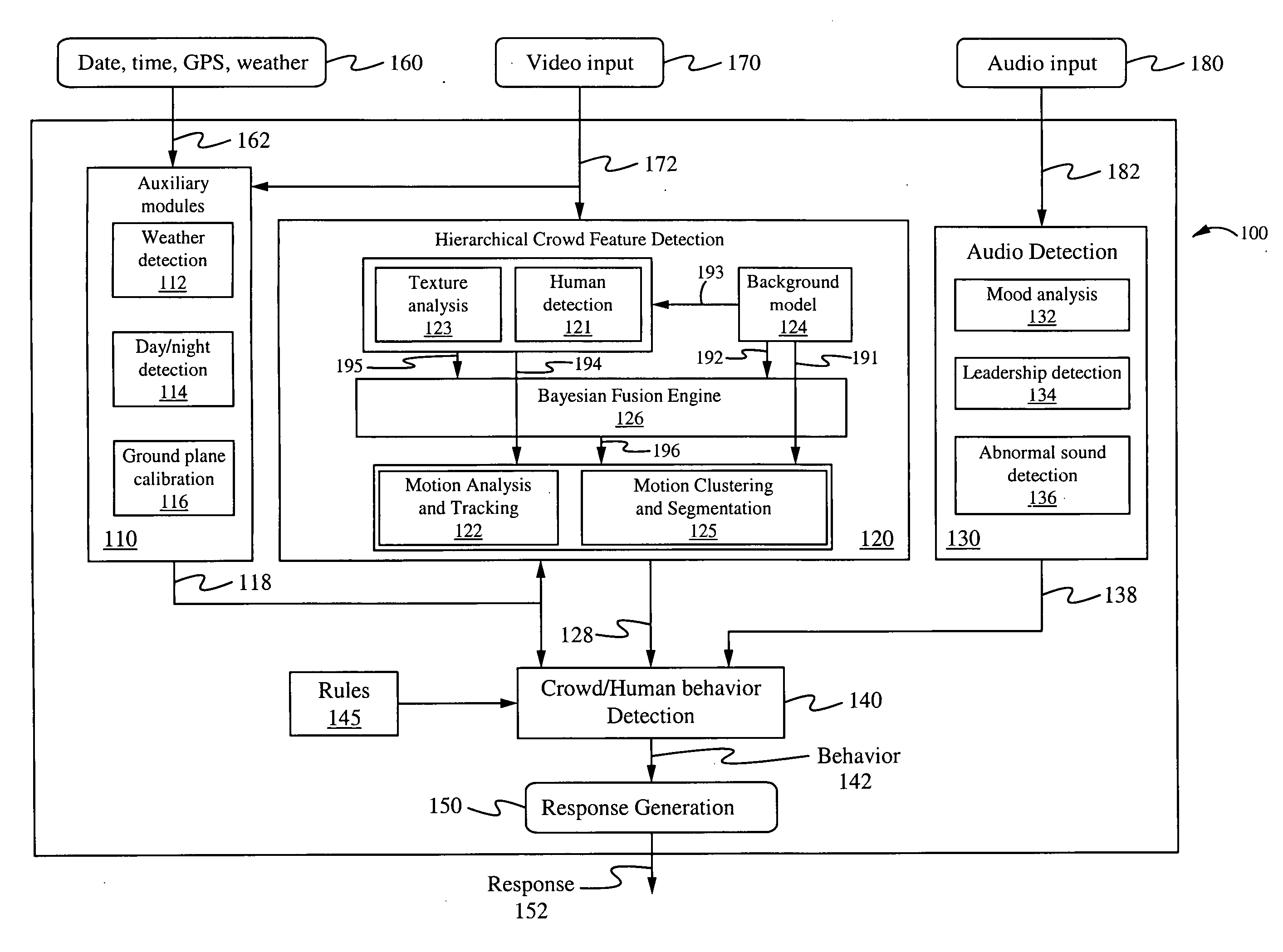
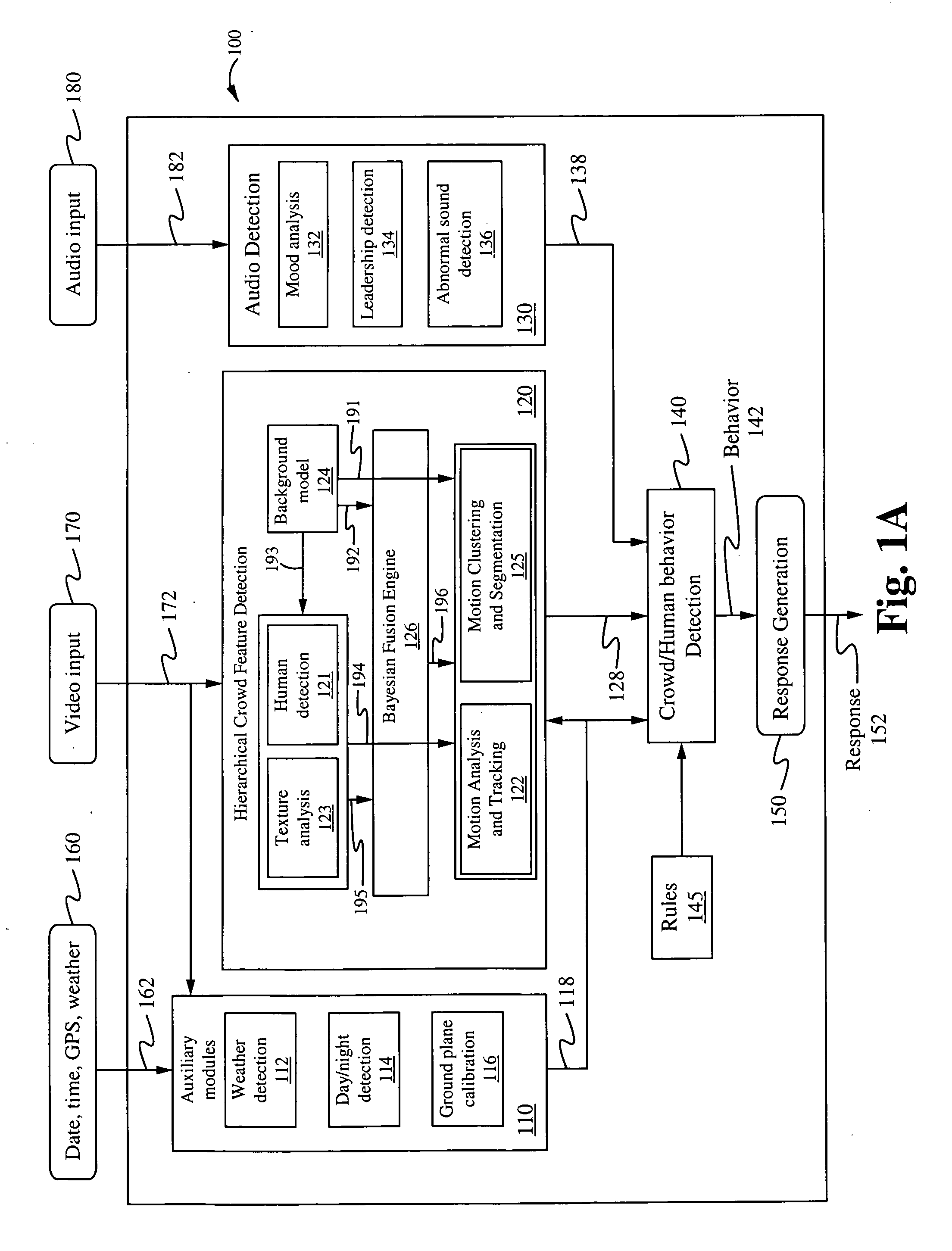
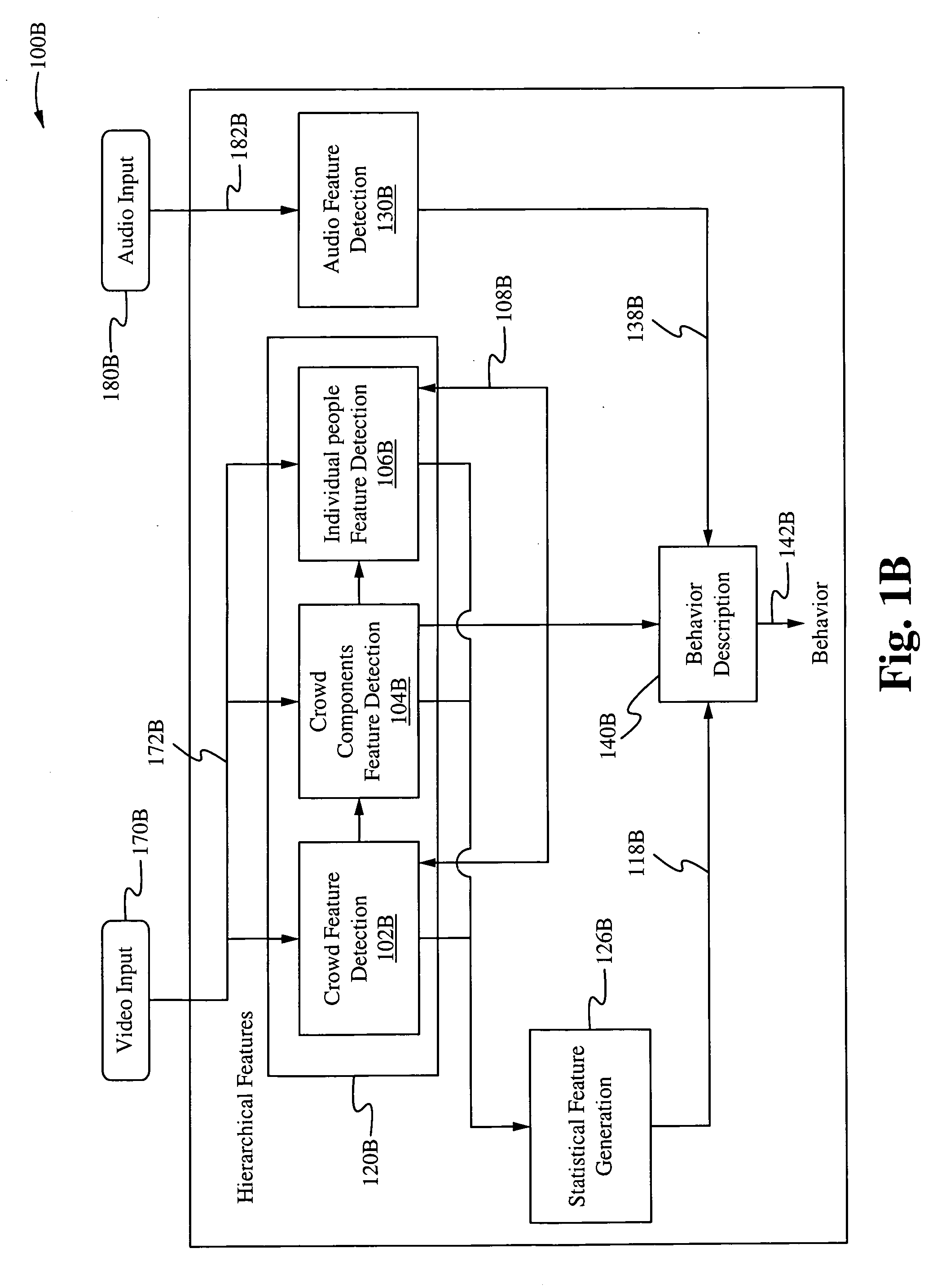
Method of and system for hierarchical human/crowd behavior detection
ActiveUS20090222388A1Improved crowd featureAdd featureKernel methodsDigital computer detailsAdaBoostCrowds
The present invention is directed to a computer automated method of selectively identifying a user specified behavior of a crowd. The method comprises receiving video data but can also include audio data and sensor data. The video data contains images a crowd. The video data is processed to extract hierarchical human and crowd features. The detected crowd features are processed to detect a selectable crowd behavior. The selected crowd behavior detected is specified by a configurable behavior rule. Human detection is provided by a hybrid human detector algorithm which can include Adaboost or convolutional neural network. Crowd features are detected using textual analysis techniques. The configurable crowd behavior for detection can be defined by crowd behavioral language.
Owner:AXIS
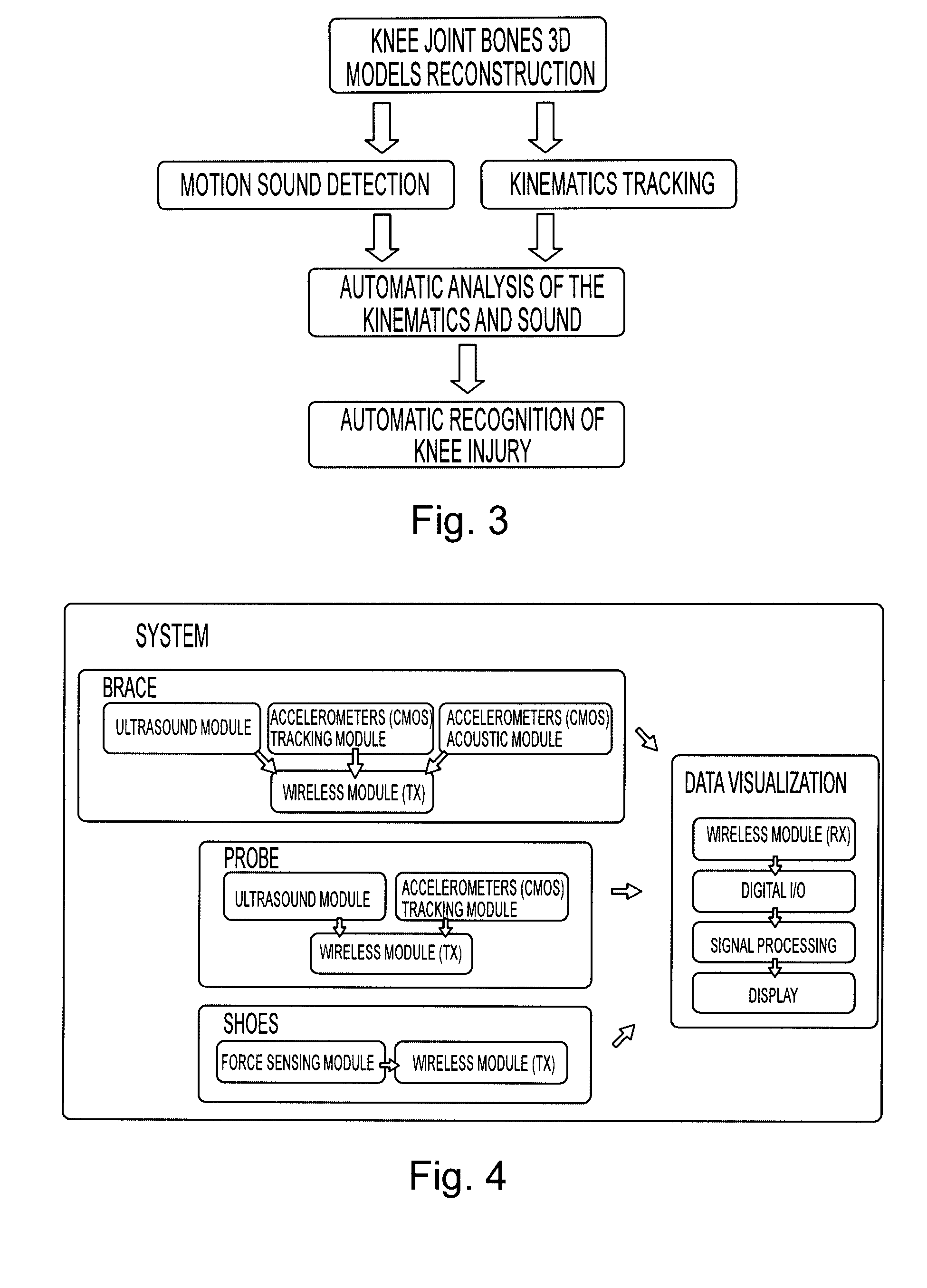
Noninvasive Diagnostic System
ActiveUS20100198067A1Big gapPhysical therapies and activitiesUltrasonic/sonic/infrasonic diagnosticsRange of motionSacroiliac joint
A method for diagnosing a joint condition includes in one embodiment: creating a 3d model of the patient specific bone; registering the patient's bone with the bone model; tracking the motion of the patient specific bone through a range of motion; selecting a database including empirical mathematical descriptions of the motion of a plurality actual bones through ranges of motion; and comparing the motion of the patient specific bone to the database.
Owner:JOINTVUE
Vehicle type recognition method based on rapid R-CNN deep neural network
ActiveCN106250812AScalableQuick Subclass IdentificationCharacter and pattern recognitionNeural learning methodsCategory recognitionNerve network
The invention discloses a vehicle type recognition method based on a rapid R-CNN deep neural network, which mainly comprises unsupervised deep learning, a multilayer CNN (Convolutional Neural Network), a regional advice network, network sharing and a softmax classifier. The vehicle type recognition method realizes a framework for implementing end-to-end vehicle detection and recognition by using one rapid R-CNN network in a real sense, and is capable of carrying out quick vehicle sub-category recognition with high accuracy and robustness under the environment of being applicable to the shape diversity, the illumination variation diversity, the background diversity and the like of vehicle targets.
Owner:汤一平
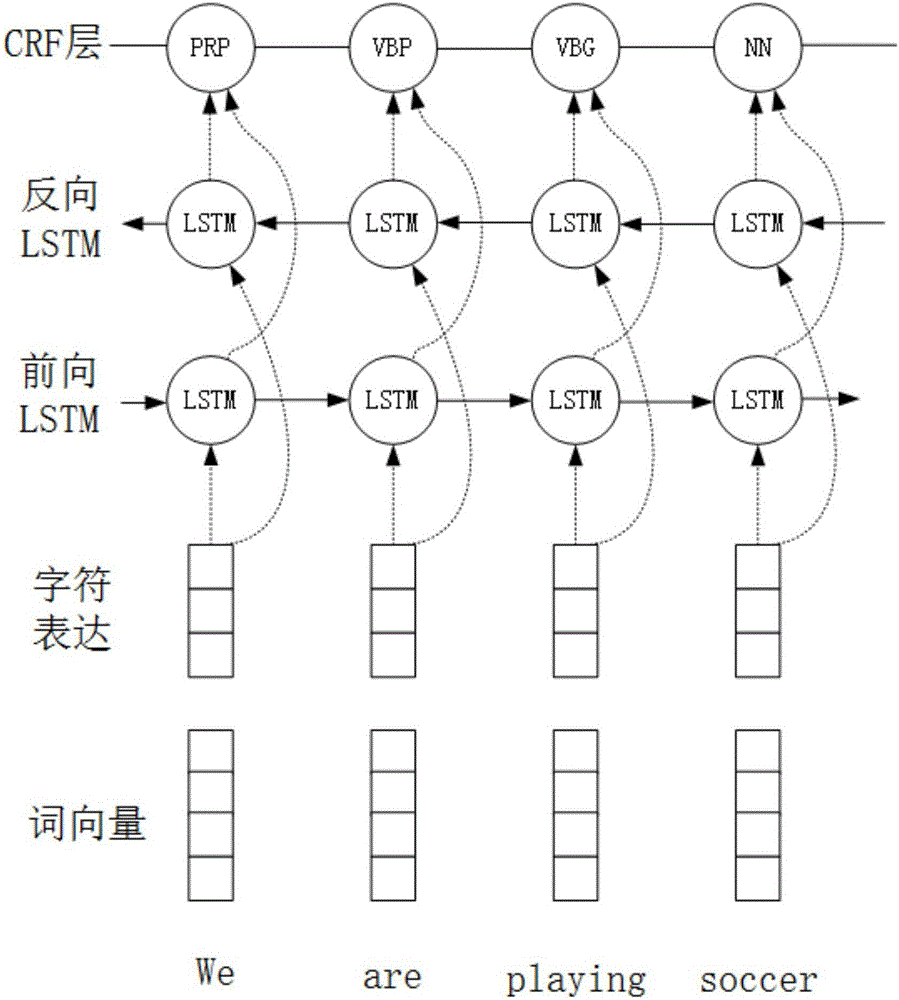
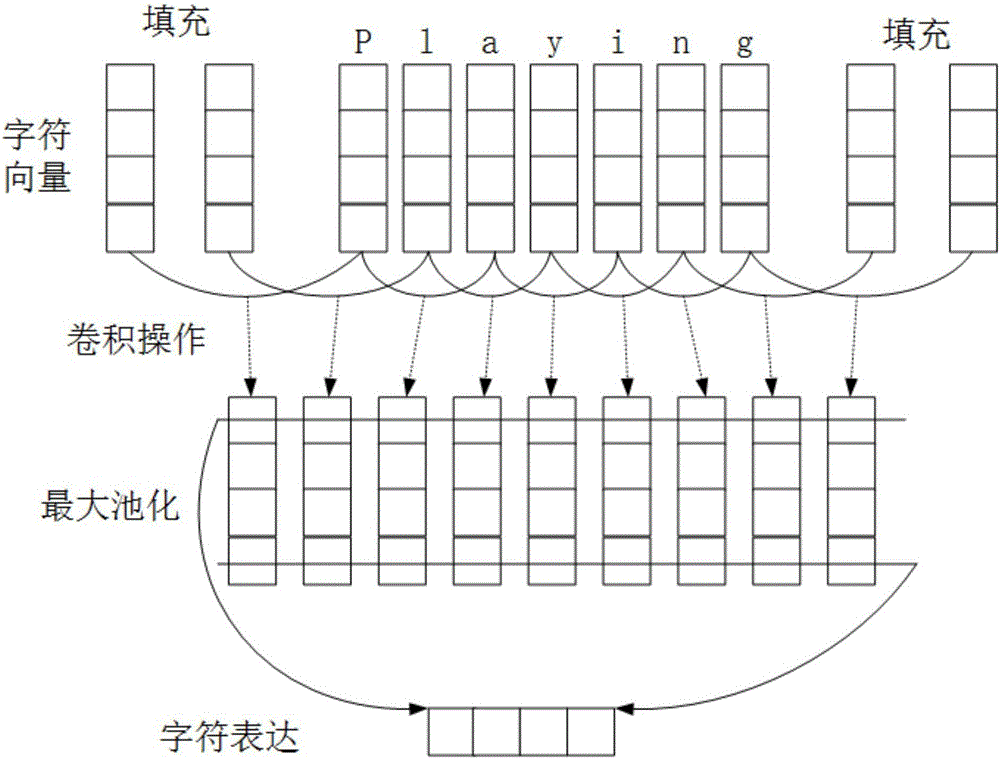
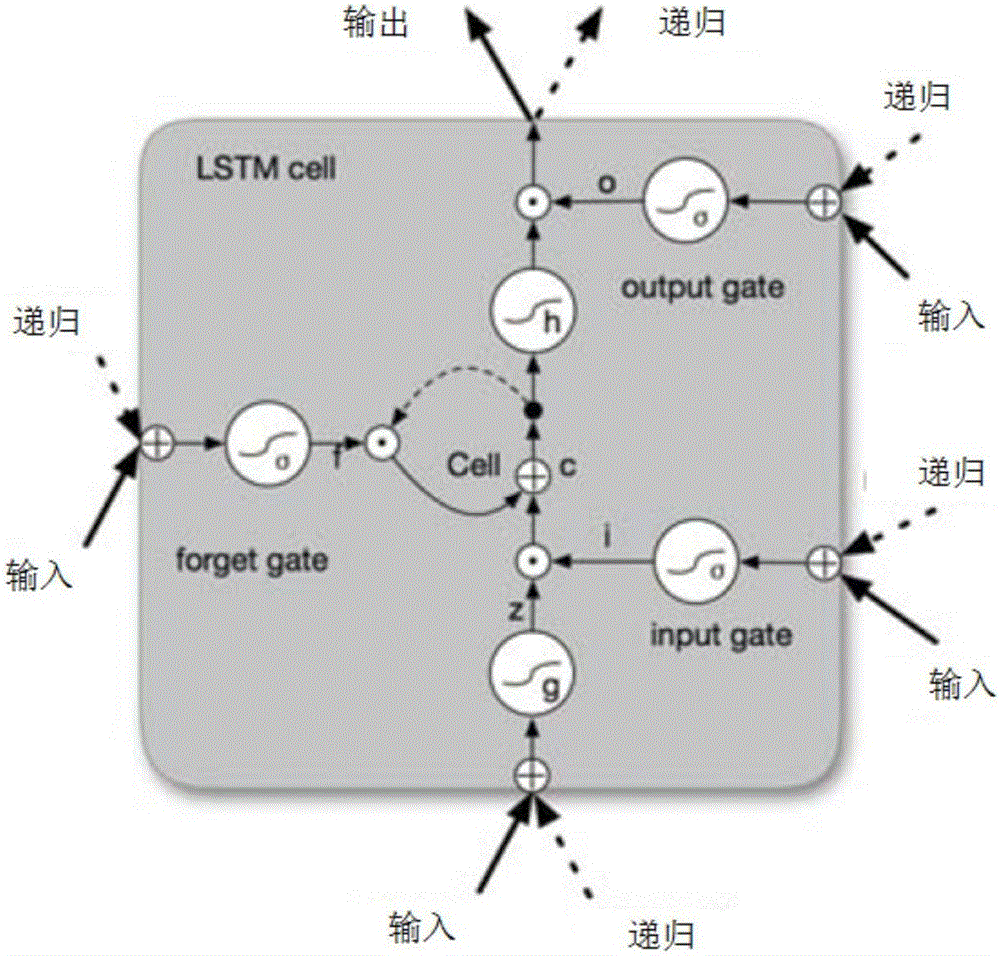
Text named entity recognition method based on Bi-LSTM, CNN and CRF
InactiveCN106569998ASolving the Named Entity Labeling ProblemNatural language data processingNeural learning methodsConditional random fieldNerve network
The invention discloses a text named entity recognition method based on Bi-LSTM, CNN and CRF. The method includes the following steps: (1) using a convolutional nerve network to encode and convert information on text word character level to a character vector; (2) combining the character vector and word vector into a combination which, as an input, is transmitted to a bidirectional LSTM neural network to build a model for contextual information of every word; and (3) in the output end of the LSTM neural network, utilizing continuous conditional random fields to carry out label decoding to a whole sentence, and mark the entities in the sentence. The invention is an end-to-end model without the need of data pre-processing in the un-marked corpus with the exception of the pre-trained word vector, therefore the invention can be widely applied for statement marking of different languages and fields.
Owner:ZHEJIANG UNIV
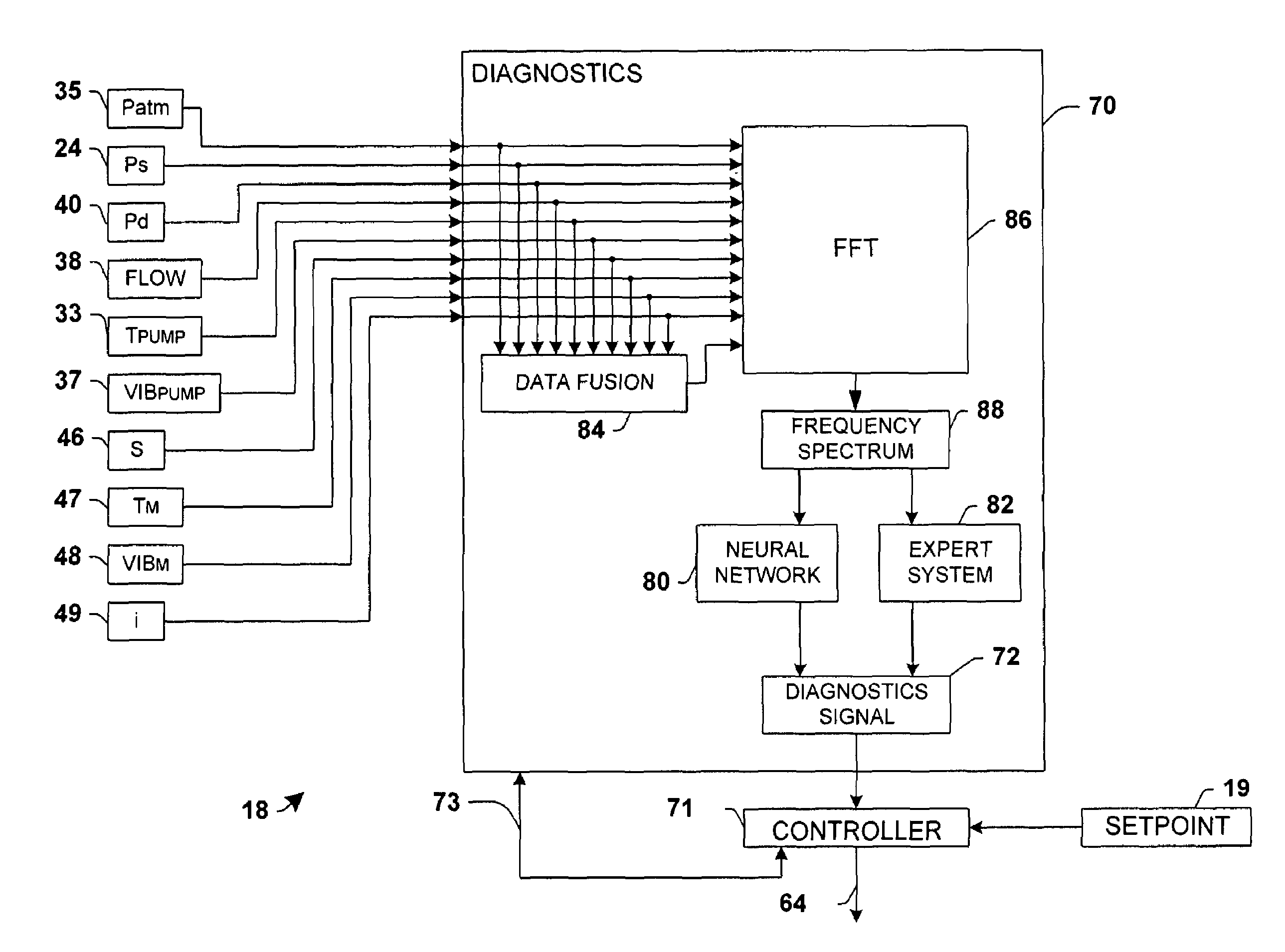
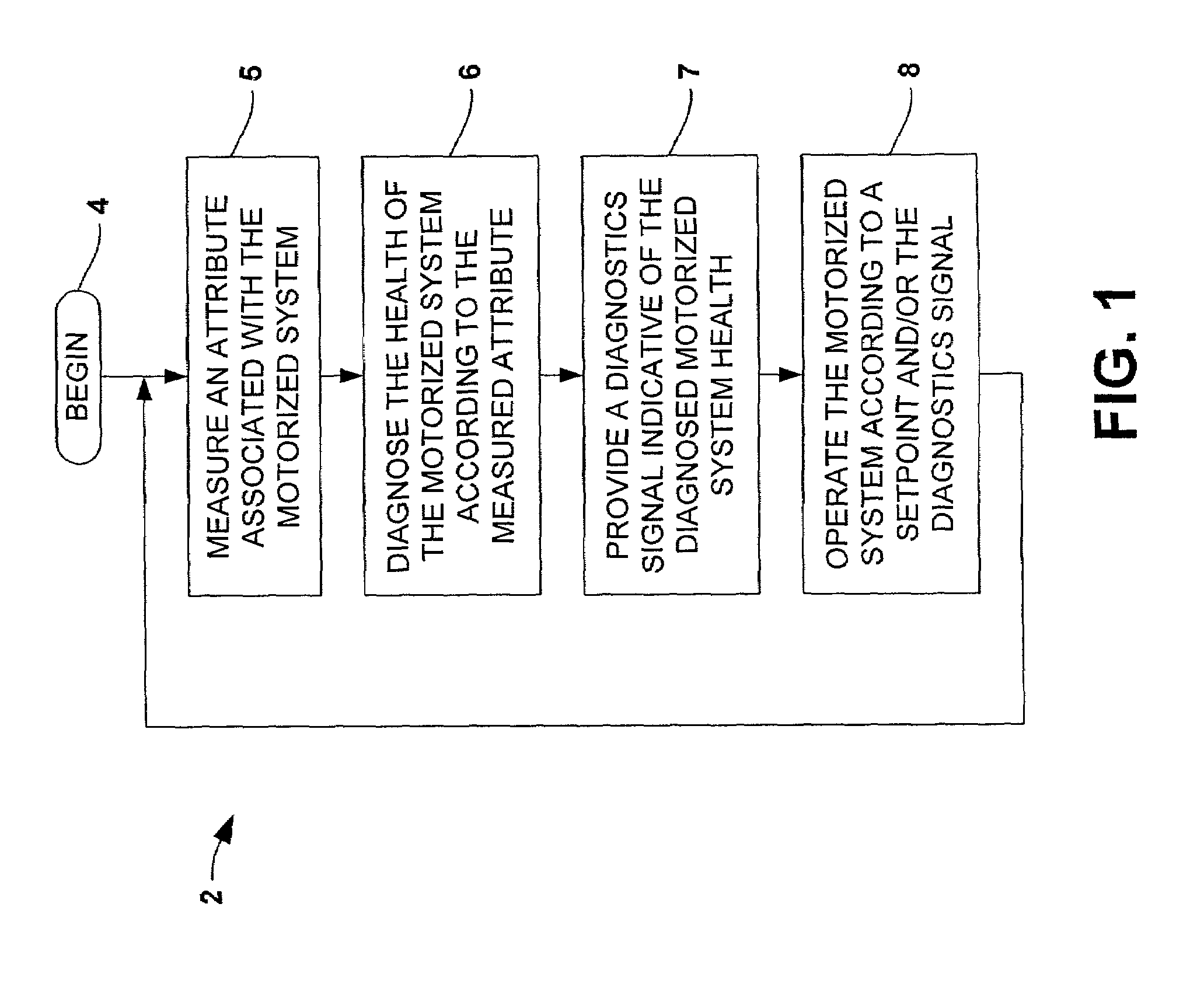
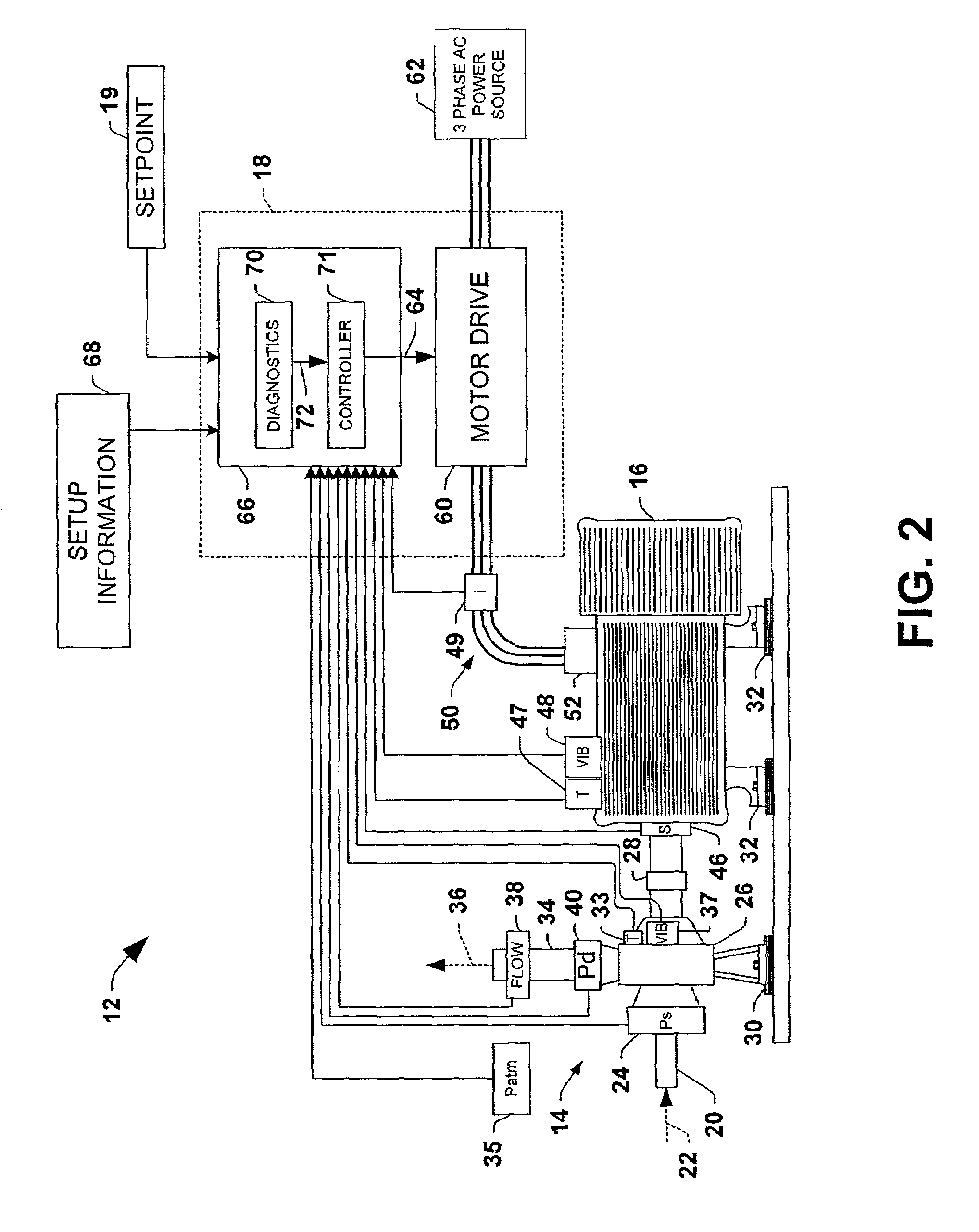
Motorized system integrated control and diagnostics using vibration, pressure, temperature, speed, and/or current analysis
InactiveUS7539549B1Condition be reduced and eliminatedAdvantageously employedPump componentsTesting/monitoring control systemsCurrent analysisDiagnostic system
Systems and methods are disclosed for controlling and diagnosing the health of a motorized system. The systems may comprise a diagnostics system and a controller, wherein the diagnostics system employs a neural network, an expert system, and / or a data fusion component in order to assess the health of the motorized system according to one or more attributes associated therewith. The controller may operate the motorized system in accordance with a setpoint and / or a diagnostics signal from the diagnostics system. Also disclosed are methodologies for controlling and diagnosing the health of a motorized system, comprising operating a motor in the motorized system in a controlled fashion, and diagnosing the health of the motorized system according to a measured attribute associated with the motorized system, wherein the motor may be operated according to a setpoint and / or the diagnostics signal.
Owner:ROCKWELL AUTOMATION TECH
Unified language modeling framework for word prediction, auto-completion and auto-correction
ActiveUS20170091168A1Natural language data processingKnowledge representationProgramming languageAutocorrection
Systems and processes for unified language modeling are provided. In accordance with one example, a method includes, at an electronic device with one or more processors and memory, receiving a character of a sequence of characters and determining a current character context based on the received character of the sequence of characters and a previous character context. The method further includes determining a current word representation based on the current character context and determining a current word context based on the current word representation and a previous word context. The method further includes determining a next word representation based on the current word context and providing the next word representation.
Owner:APPLE INC
Intelligent control with hierarchical stacked neural networks
ActiveUS8775341B1Increased complexityComplex mathematical operationDigital data information retrievalSemantic analysisSemantic propertyNerve network
A system and method of detecting an aberrant message is provided. An ordered set of words within the message is detected. The set of words found within the message is linked to a corresponding set of expected words, the set of expected words having semantic attributes. A set of grammatical structures represented in the message is detected, based on the ordered set of words and the semantic attributes of the corresponding set of expected words. A cognitive noise vector comprising a quantitative measure of a deviation between grammatical structures represented in the message and an expected measure of grammatical structures for a message of the type is then determined. The cognitive noise vector may be processed by higher levels of the neural network and / or an external processor.
Owner:COMMONS MICHAEL LAMPORT
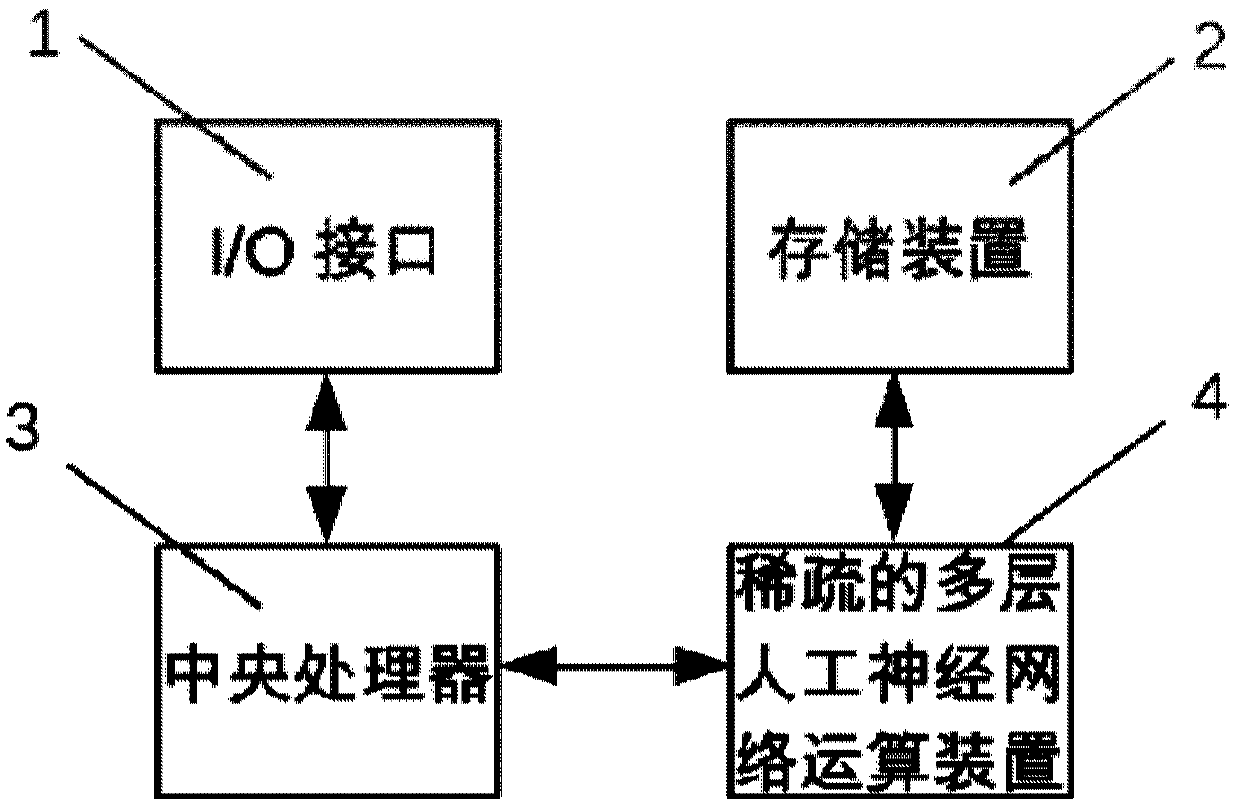
Artificial neural network calculating device and method for sparse connection
ActiveCN105512723ASolve the problem of insufficient computing performance and high front-end decoding overheadAdd supportMemory architecture accessing/allocationDigital data processing detailsActivation functionMemory bandwidth
An artificial neural network calculating device for sparse connection comprises a mapping unit used for converting input data into the storage mode that input nerve cells and weight values correspond one by one, a storage unit used for storing data and instructions, and an operation unit used for executing corresponding operation on the data according to the instructions. The operation unit mainly executes three steps of operation, wherein in the first step, the input nerve cells and weight value data are multiplied; in the second step, addition tree operation is executed, the weighted output nerve cells processed in the first step are added level by level through an addition tree, or the output nerve cells are added with offset to obtain offset-added output nerve cells; in the third step, activation function operation is executed, and the final output nerve cells are obtained. By means of the device, the problems that the operation performance of a CPU and a GPU is insufficient, and the expenditure of front end coding is large are solved, support to a multi-layer artificial neural network operation algorithm is effectively improved, and the problem that memory bandwidth becomes a bottleneck of multi-layer artificial neural network operation and the performance of a training algorithm of the multi-layer artificial neural network operation is solved.
Owner:CAMBRICON TECH CO LTD
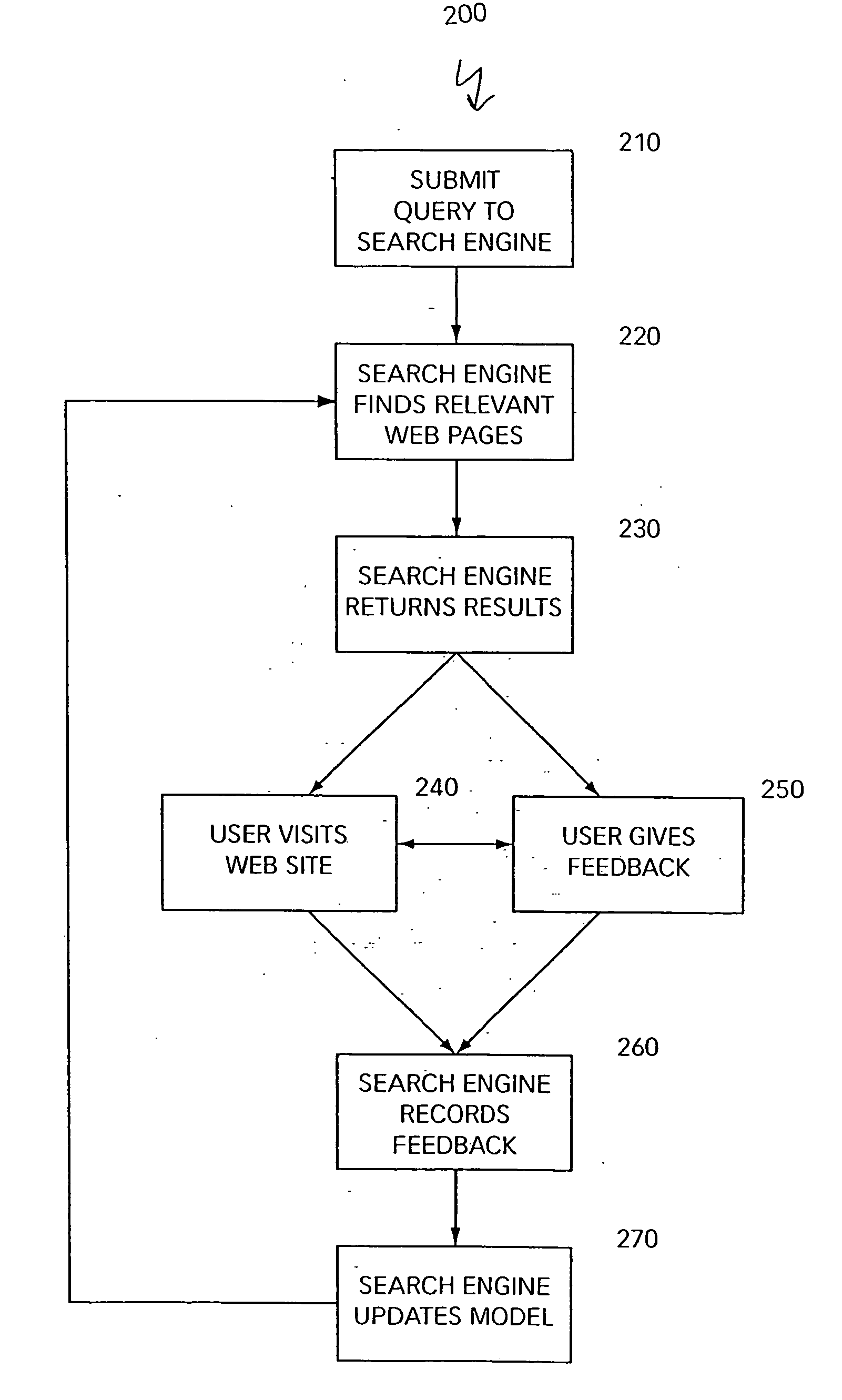
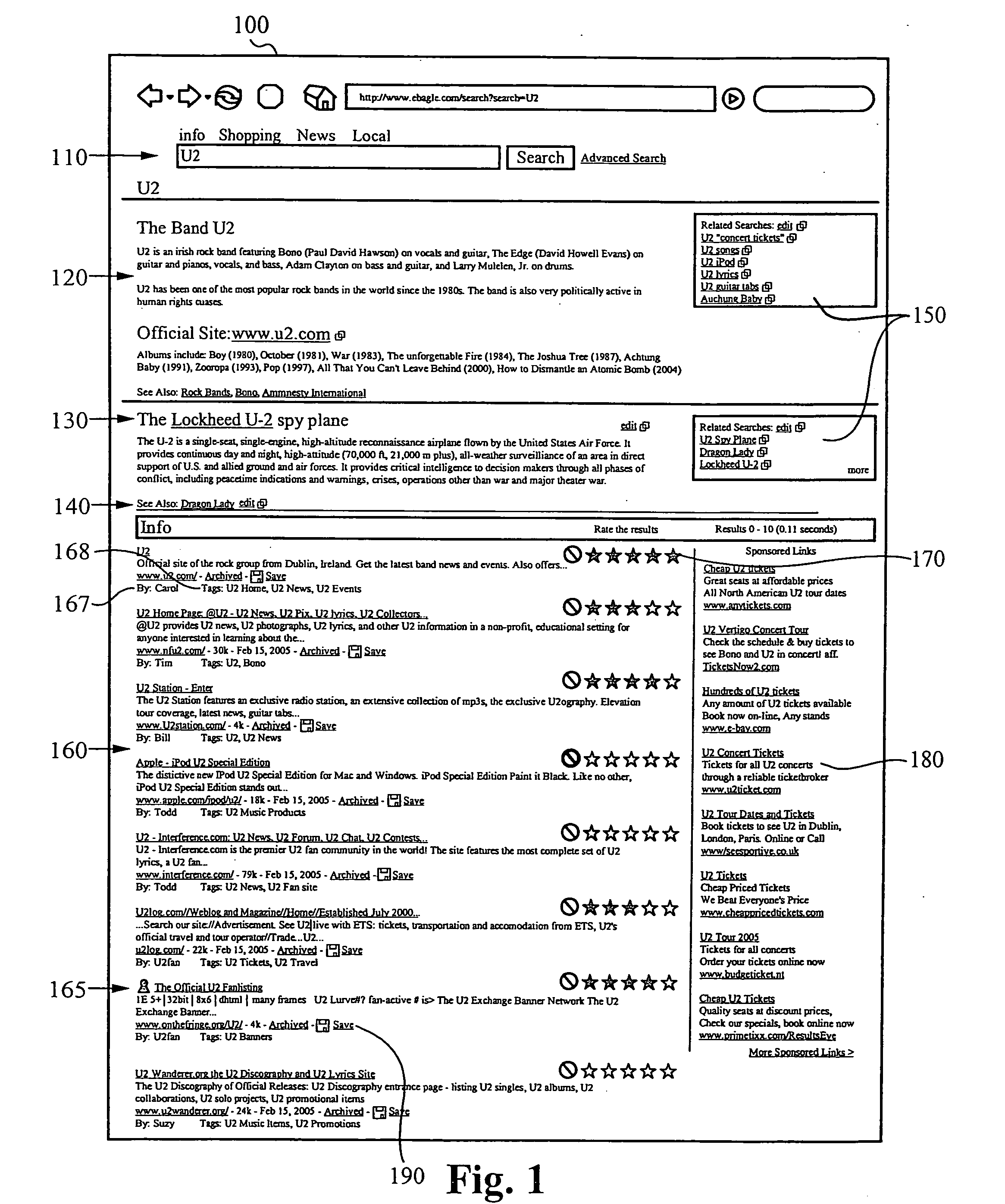
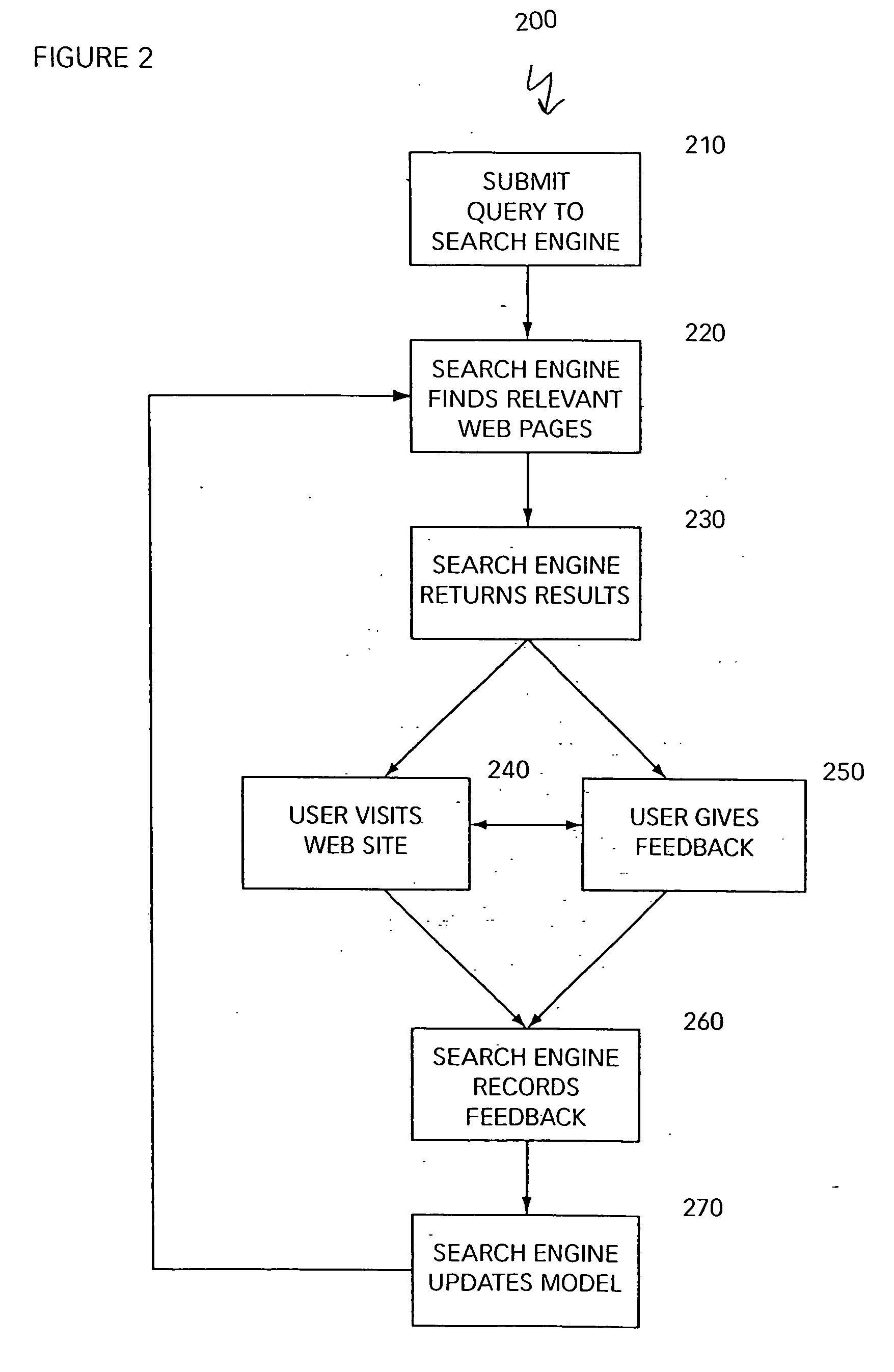
Search engine that applies feedback from users to improve search results
ActiveUS20070106659A1Raise the possibilityData processing applicationsNeural learning methodsStatistical classificationUser input
The present invention is directed to methods of and systems for ranking results returned by a search engine. A method in accordance with the invention comprises determining a formula having variables and parameters, wherein the formula is for computing a relevance score for a document and a search query; and ranking the document based on the relevance score. Preferably, determining the formula comprises tuning the parameters based on user input. Preferably, the parameters are determined using a machine learning technique, such as one that includes a form of statistical classification.
Owner:PINTEREST
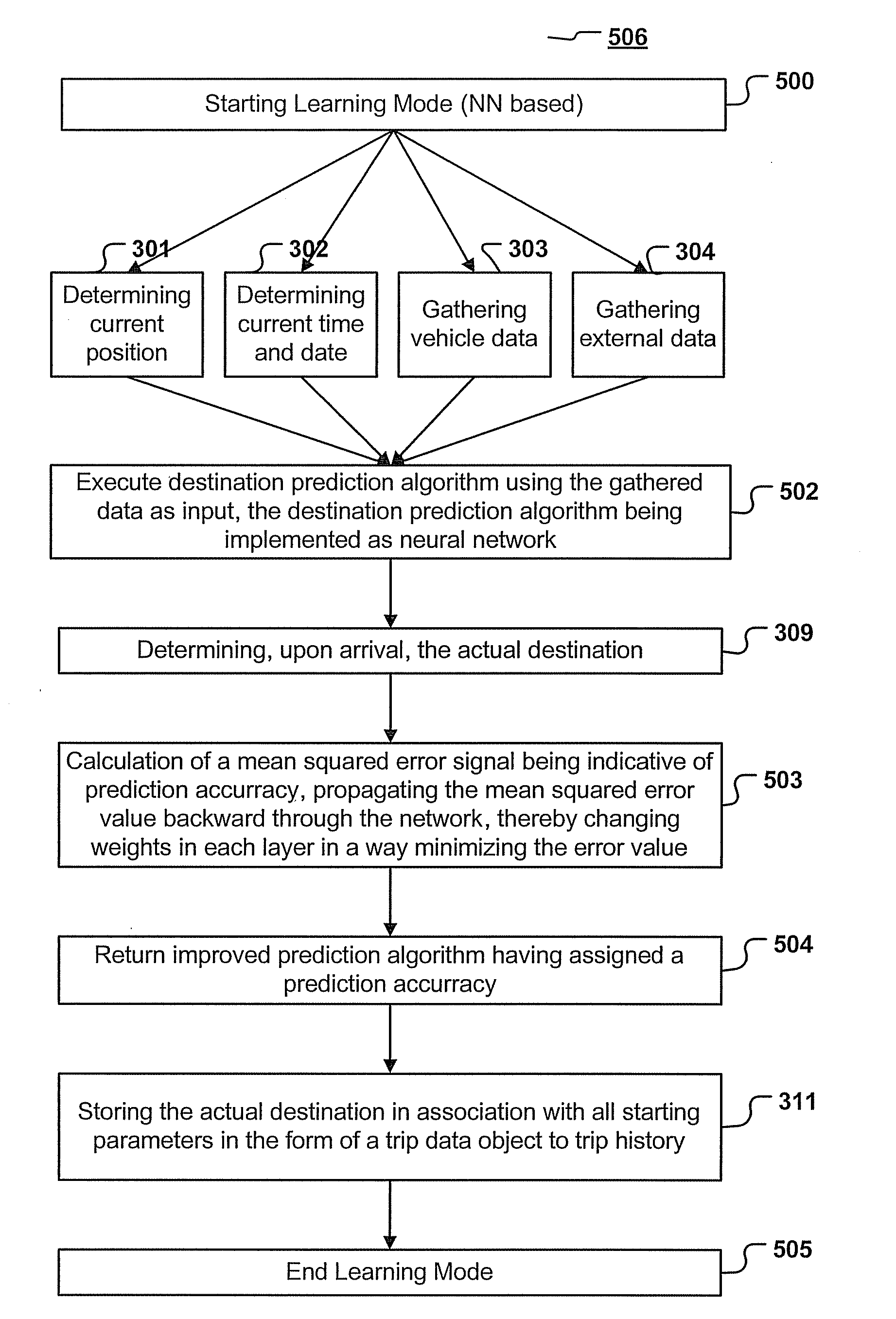
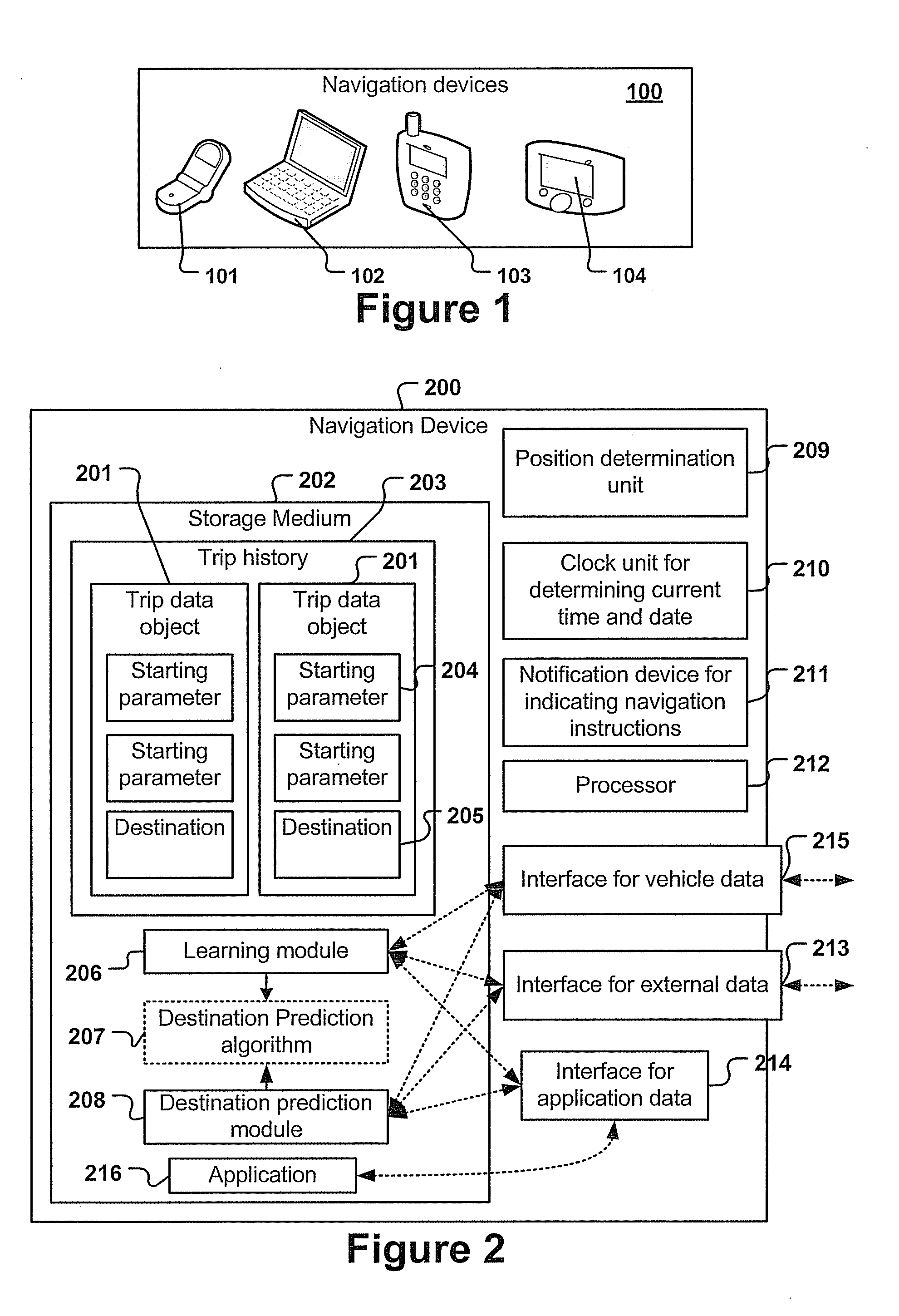
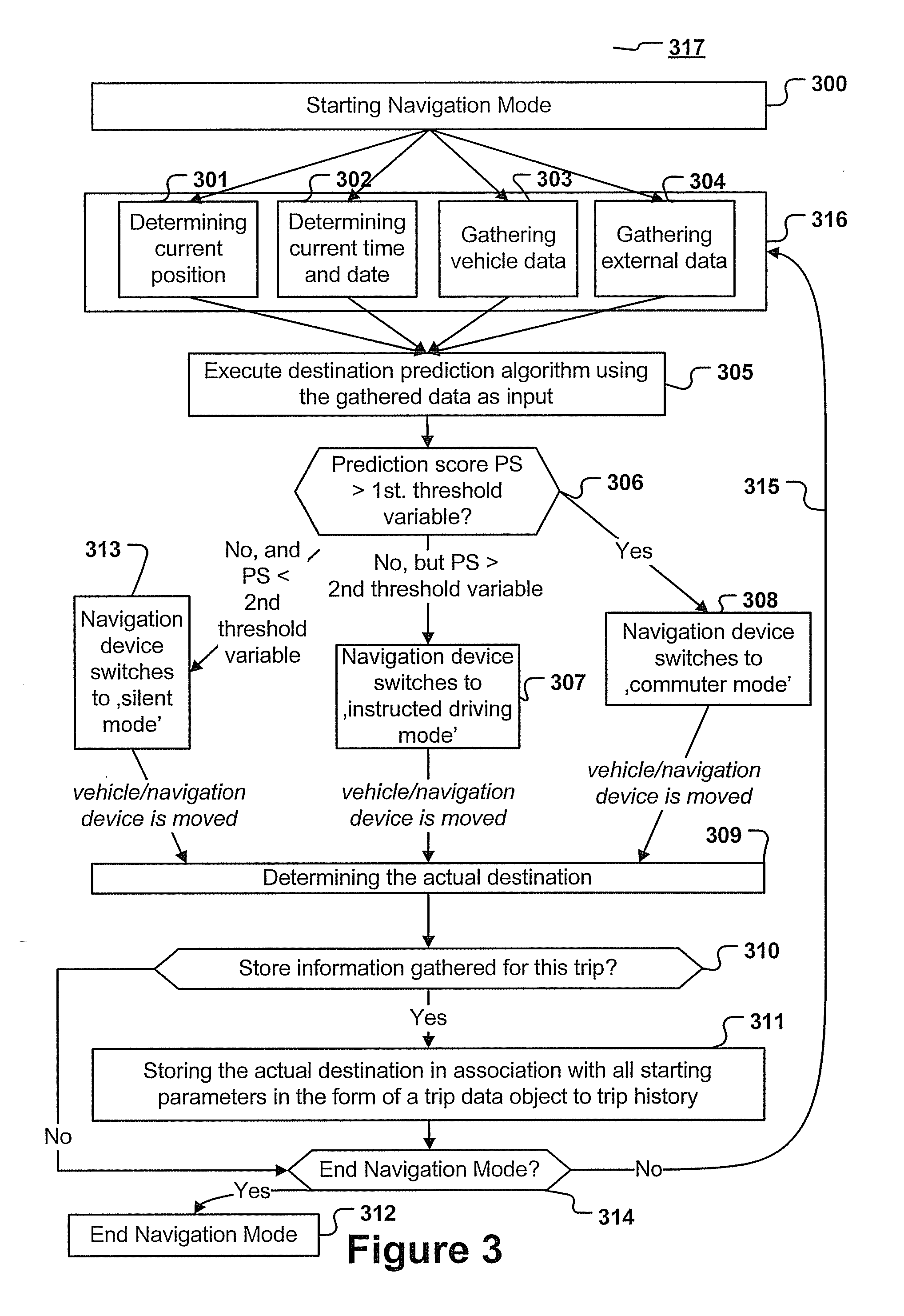
Navigation device and method for predicting the destination of a trip
ActiveUS20110238289A1Improve efficiencyImprove accuracyInstruments for road network navigationDigital data processing detailsStart timePrediction algorithms
A navigation device and computer implemented method for predicting the destination of a trip, the method being executed by a navigation device, the method comprising the steps of: determining starting parameters, the starting parameters comprising at least the starting point, starting time and date of the trip, executing a destination prediction algorithm, the destination prediction algorithm taking the starting parameters as input and predicting a destination, wherein the destination prediction algorithm is generated by using information of a trip history; determining, upon arrival at the predicted or another destination, the actual destination.
Owner:SAP AG
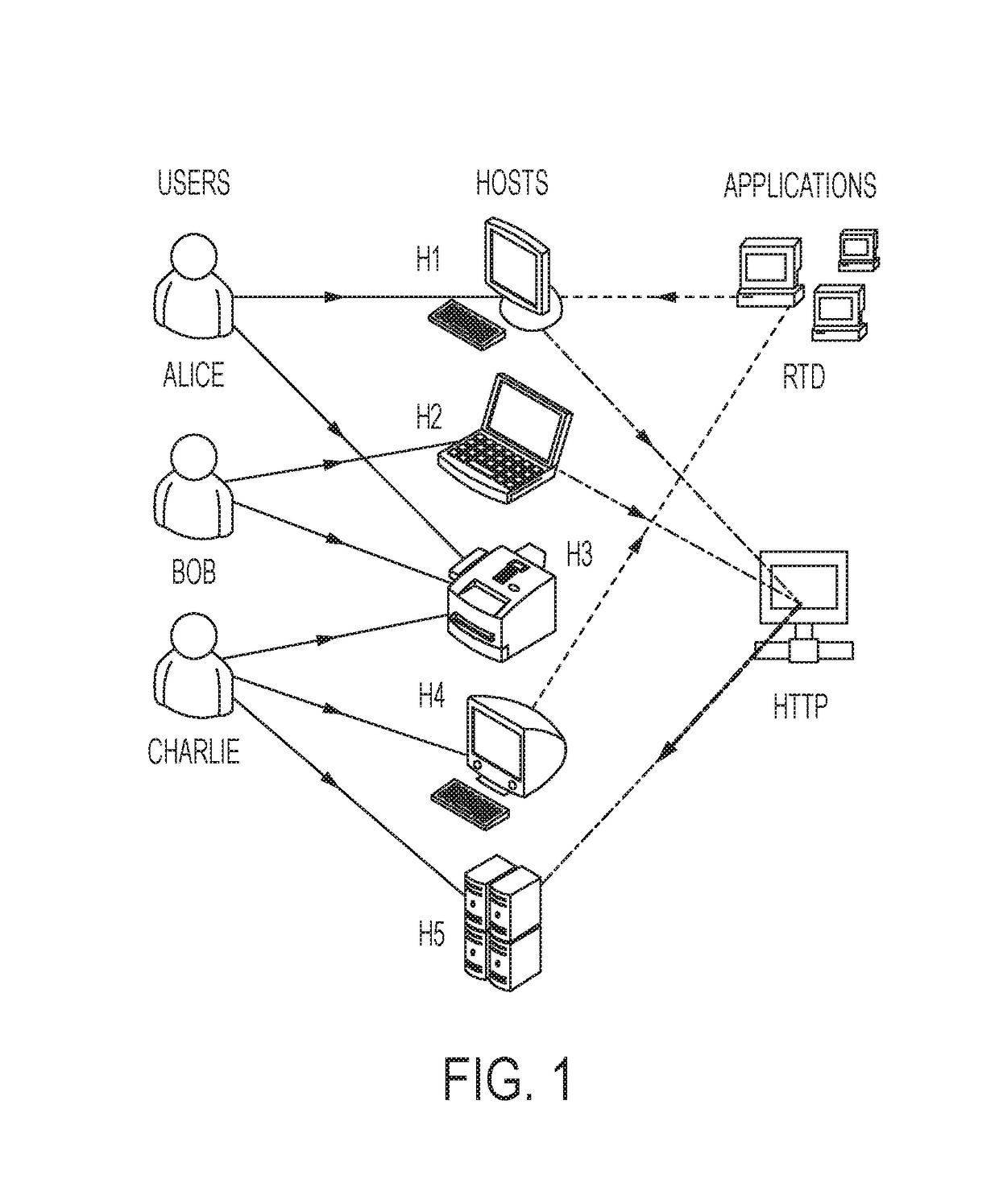
Data services handler
A data services handler comprises an interface between a data store and applications that supply and consume data, and a real time information director (RTID) that transforms data under direction of polymorphic metadata that defines a security model and data integrity rules for application to the data.
Owner:VALTRUS INNOVATIONS LTD
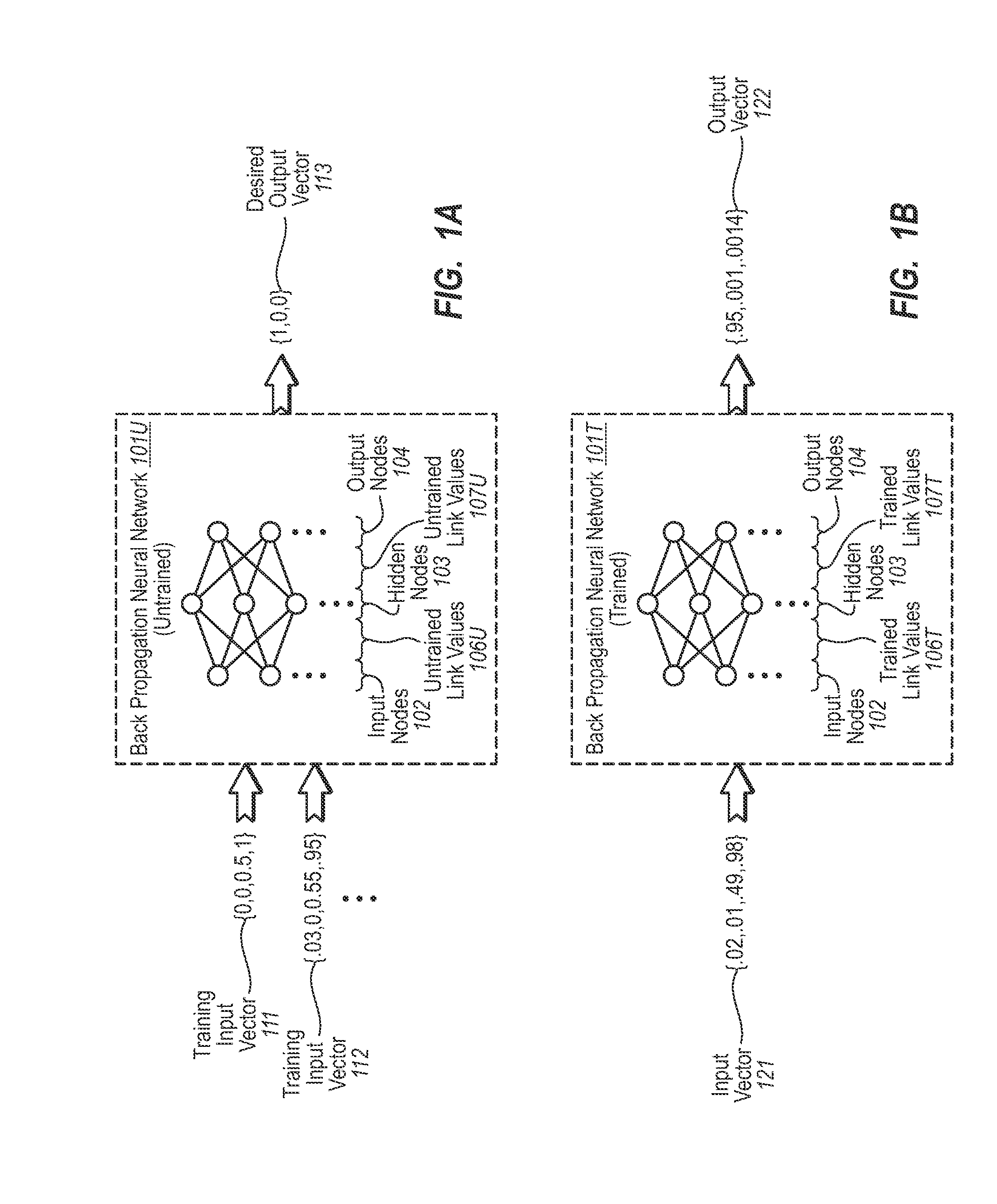
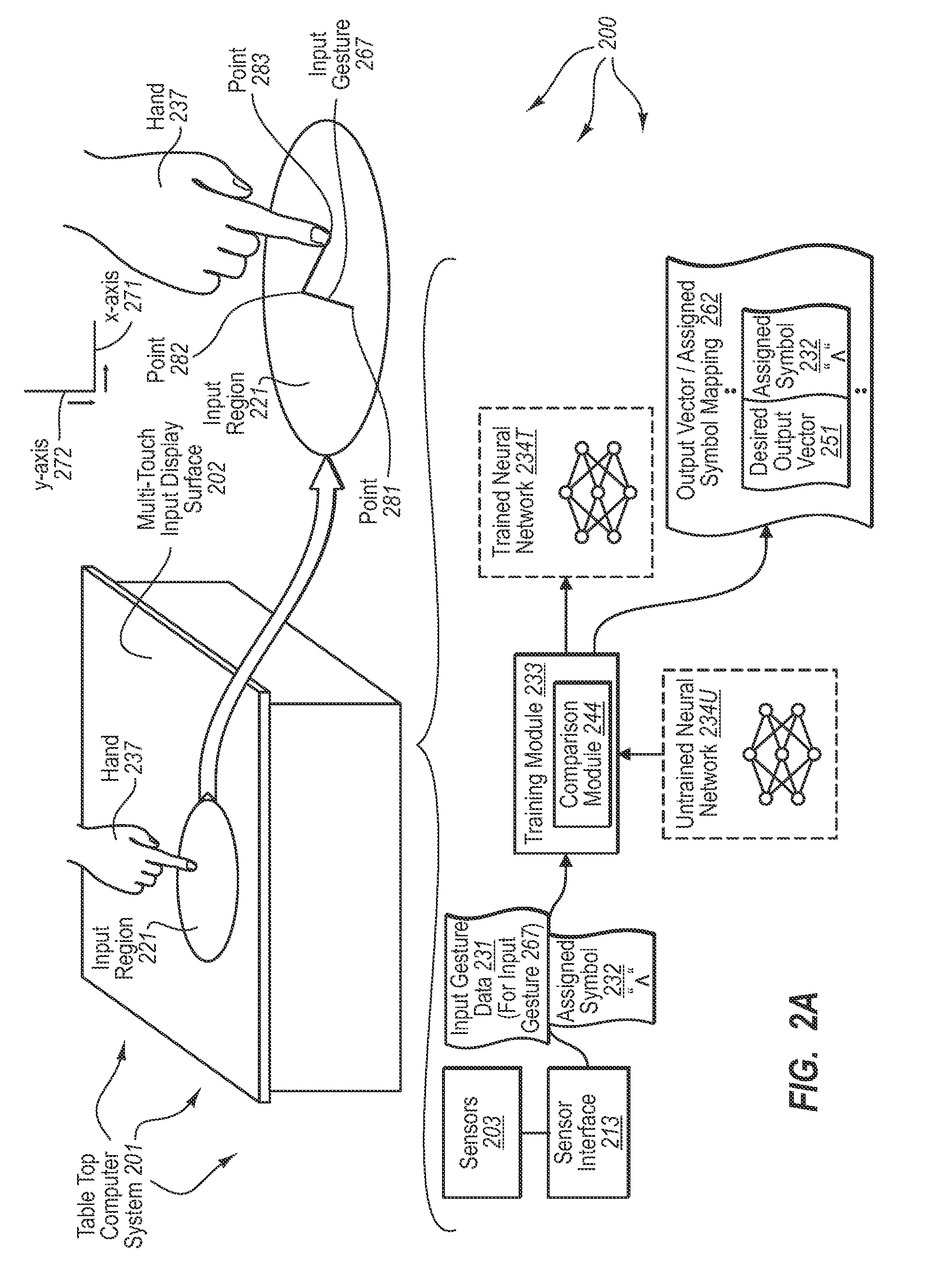
Recognizing input gestures
The present invention extends to methods, systems, and computer program products for recognizing input gestures. A neural network is trained using example inputs and backpropagation to recognize specified input patterns. Input gesture data is representative of movements in contact on a multi-touch input display surface relative to one or more axes over time. Example inputs used for training the neural network to recognize a specified input pattern can be created from sampling input gesture data for example input gestures known to represent the specified input pattern. Trained neural networks can subsequently be used to recognize input gestures that are similar to known input gestures as the specified input pattern corresponding to the known input gestures.
Owner:MICROSOFT TECH LICENSING LLC
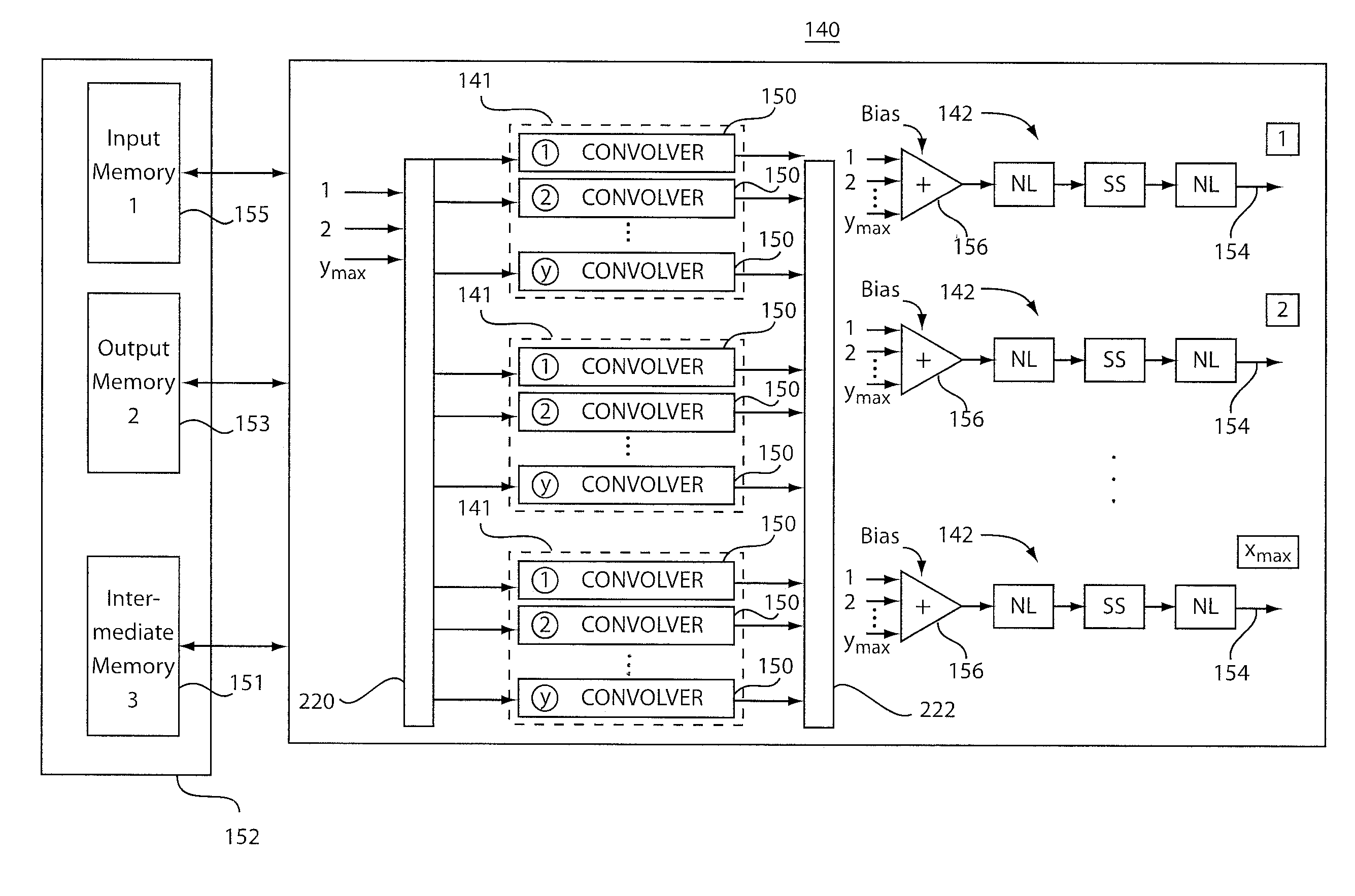
Dynamically configurable, multi-ported co-processor for convolutional neural networks
ActiveUS20110029471A1Improve feed-forward processing speedGeneral purpose stored program computerDigital dataCoprocessorControl signal
A coprocessor and method for processing convolutional neural networks includes a configurable input switch coupled to an input. A plurality of convolver elements are enabled in accordance with the input switch. An output switch is configured to receive outputs from the set of convolver elements to provide data to output branches. A controller is configured to provide control signals to the input switch and the output switch such that the set of convolver elements are rendered active and a number of output branches are selected for a given cycle in accordance with the control signals.
Owner:NEC CORP
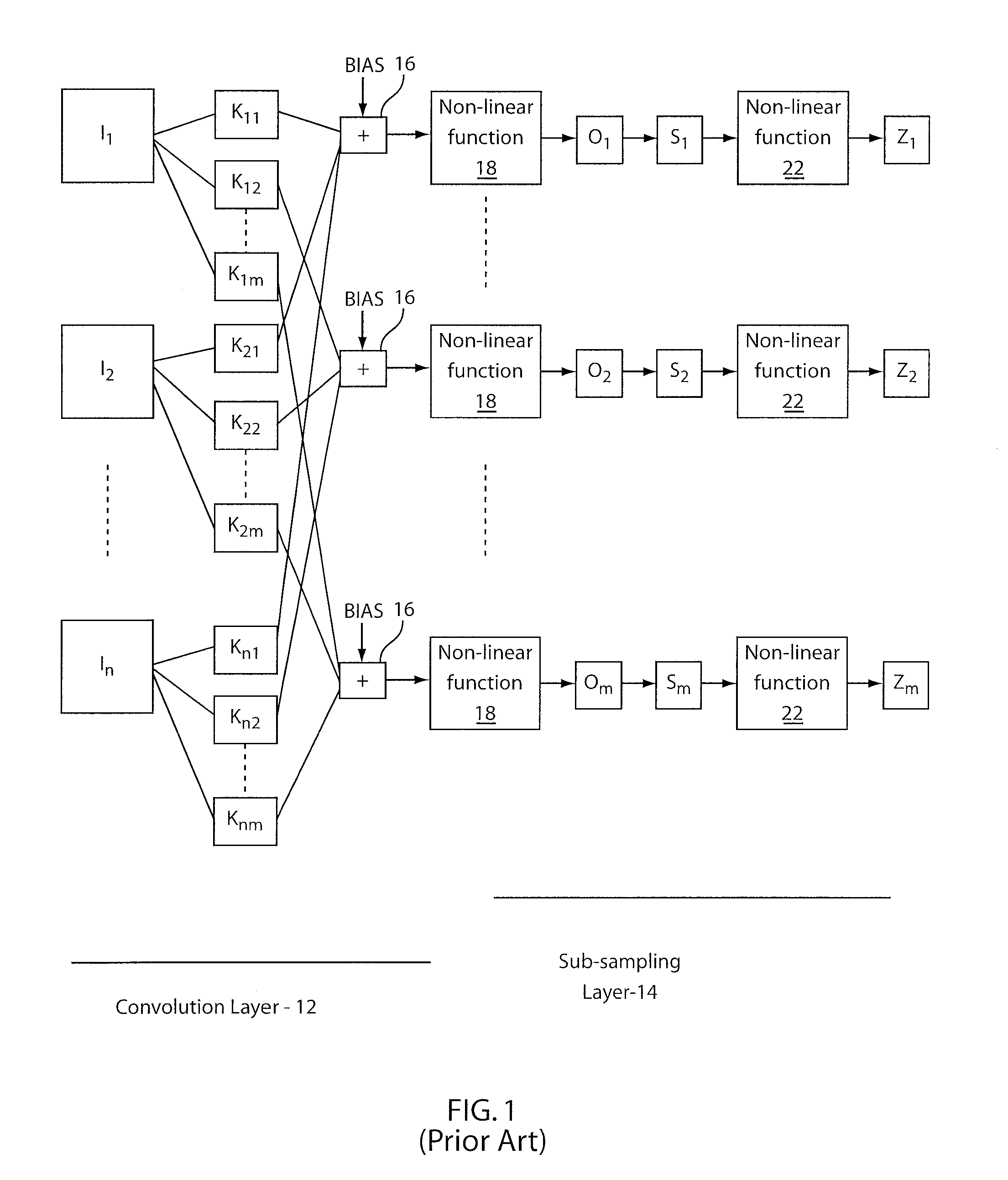
Convolutional-neural-network-based classifier and classifying method and training methods for the same
InactiveUS20150036920A1Character and pattern recognitionNeural learning methodsClassification methodsNeuron
The present invention relates to a convolutional-neural-network-based classifier, a classifying method by using a convolutional-neural-network-based classifier and a method for training the convolutional-neural-network-based classifier. The convolutional-neural-network-based classifier comprises: a plurality of feature map layers, at least one feature map in at least one of the plurality of feature map layers being divided into a plurality of regions; and a plurality of convolutional templates corresponding to the plurality of regions respectively, each of the convolutional templates being used for obtaining a response value of a neuron in the corresponding region.
Owner:FUJITSU LTD
Database security via data flow processing
InactiveUS20110219035A1Easy to detectPreventing data flowDigital data information retrievalDigital data processing detailsComputer moduleData stream processing
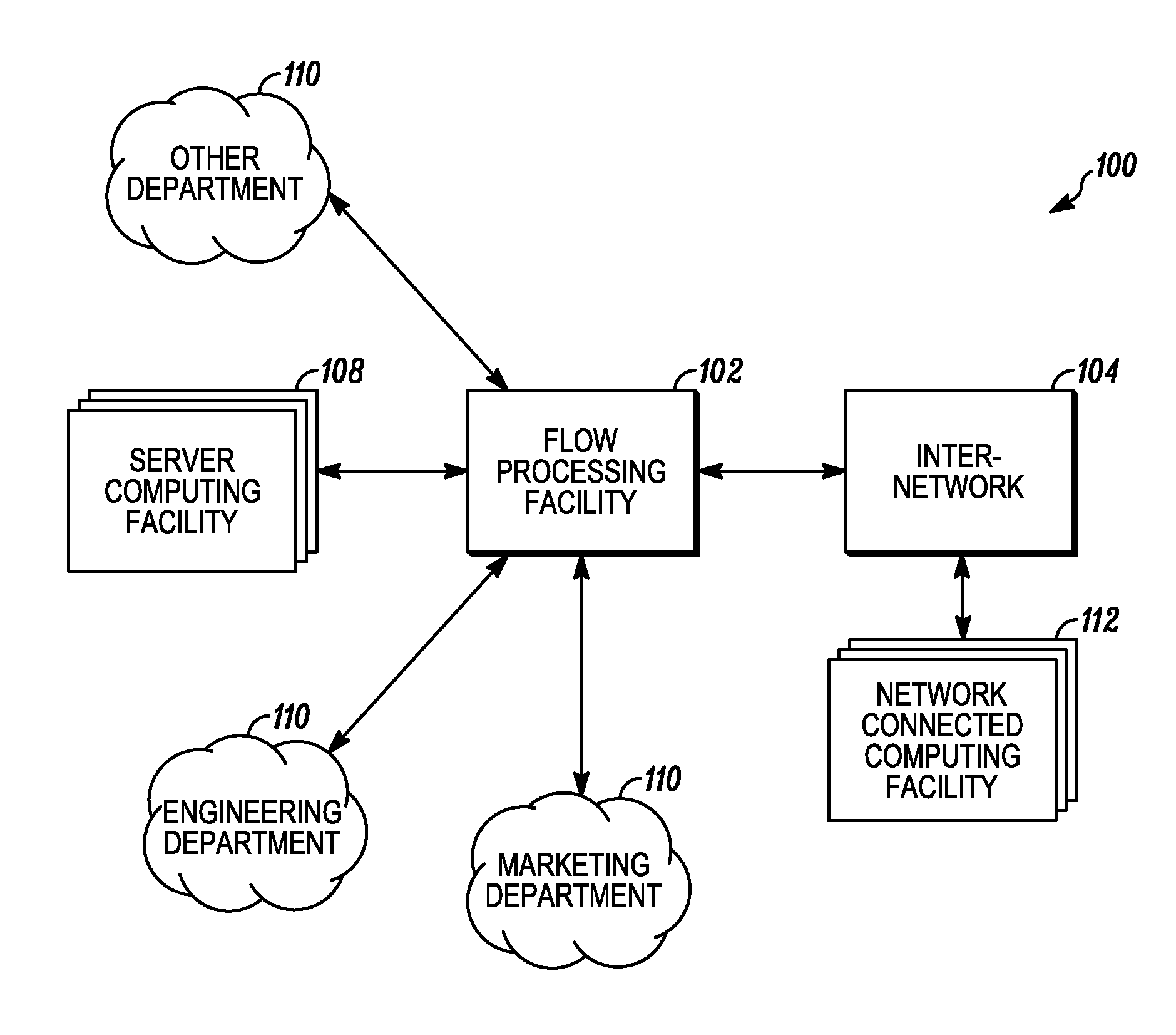
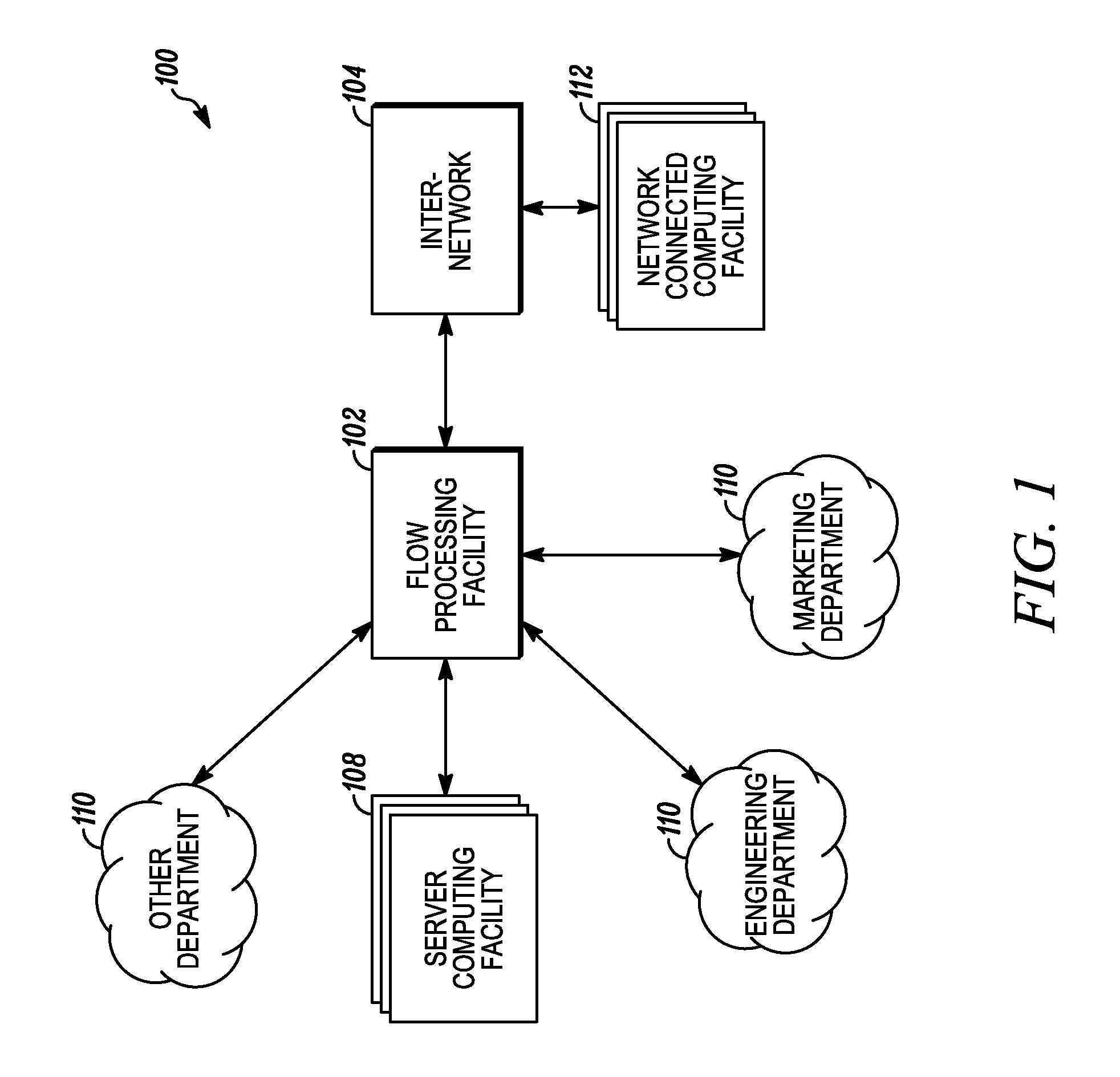
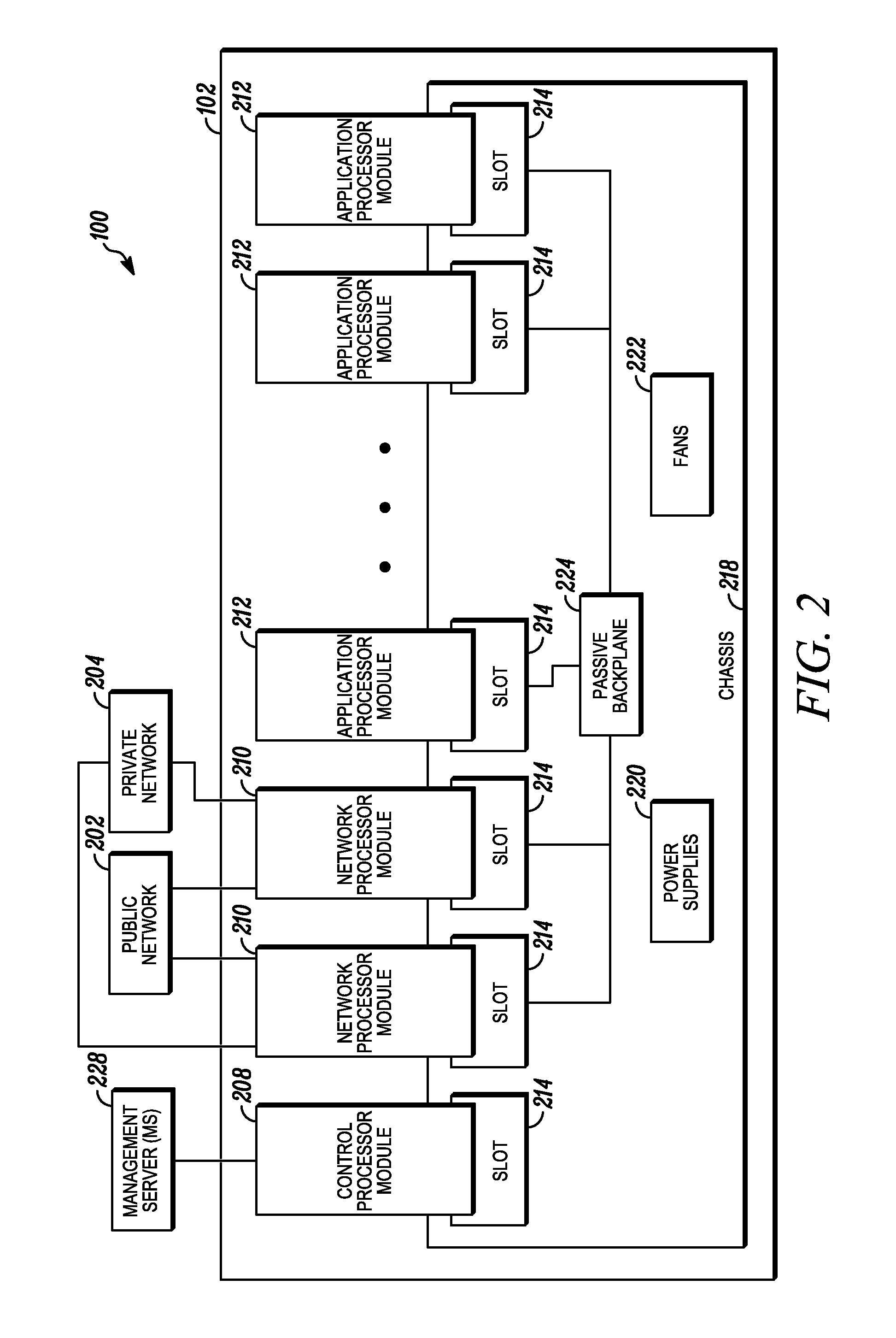
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
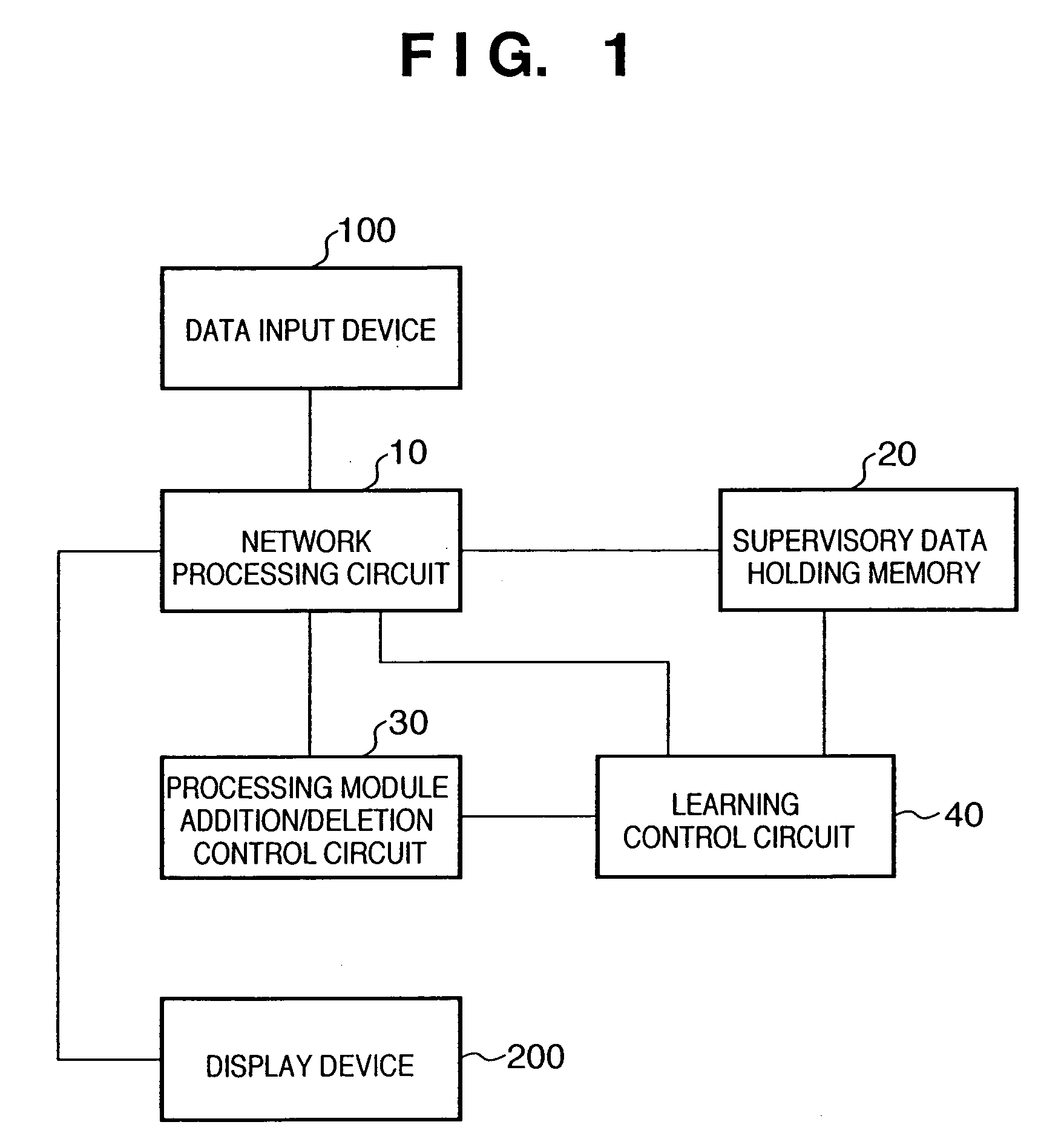
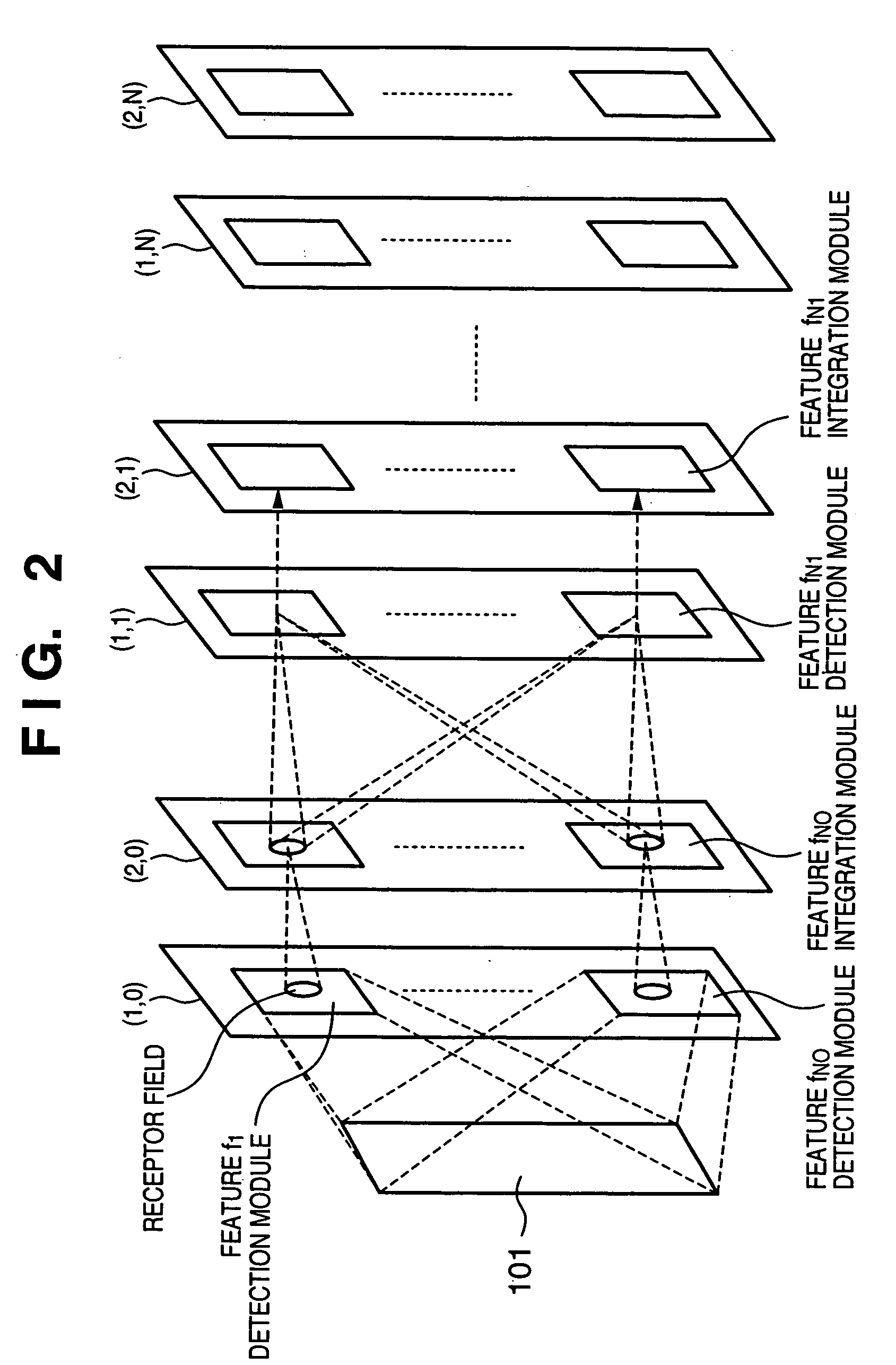
Information processing apparatus, information processing method, pattern recognition apparatus, and pattern recognition method
InactiveUS20050283450A1Image analysisDigital computer detailsPattern recognitionInformation processing
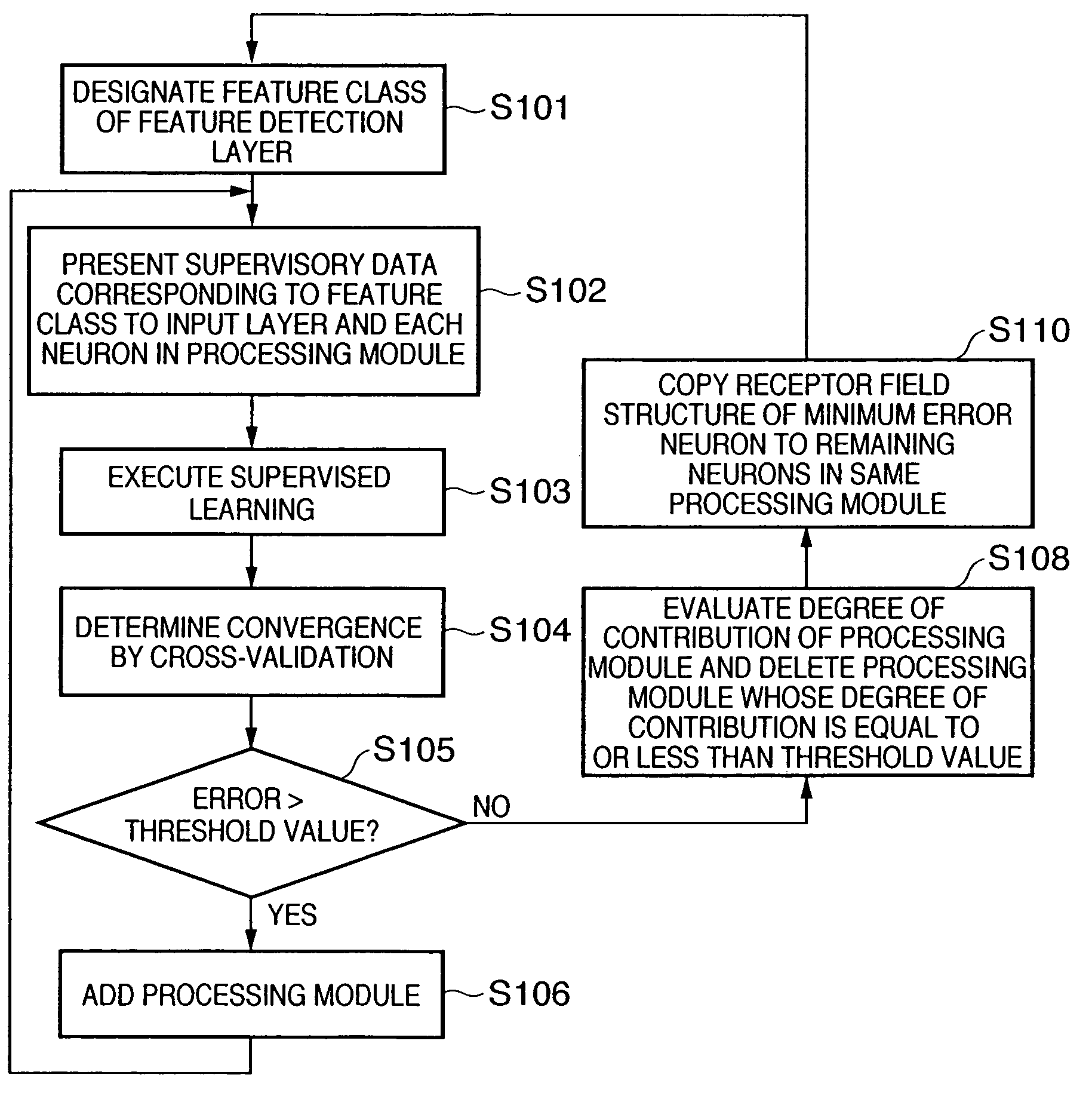
In a hierarchical neural network having a module structure, learning necessary for detection of a new feature class is executed by a processing module which has not finished learning yet and includes a plurality of neurons which should learn an unlearned feature class and have an undetermined receptor field structure by presenting a predetermined pattern to a data input layer. Thus, a feature class necessary for subject recognition can be learned automatically and efficiently.
Owner:CANON KK
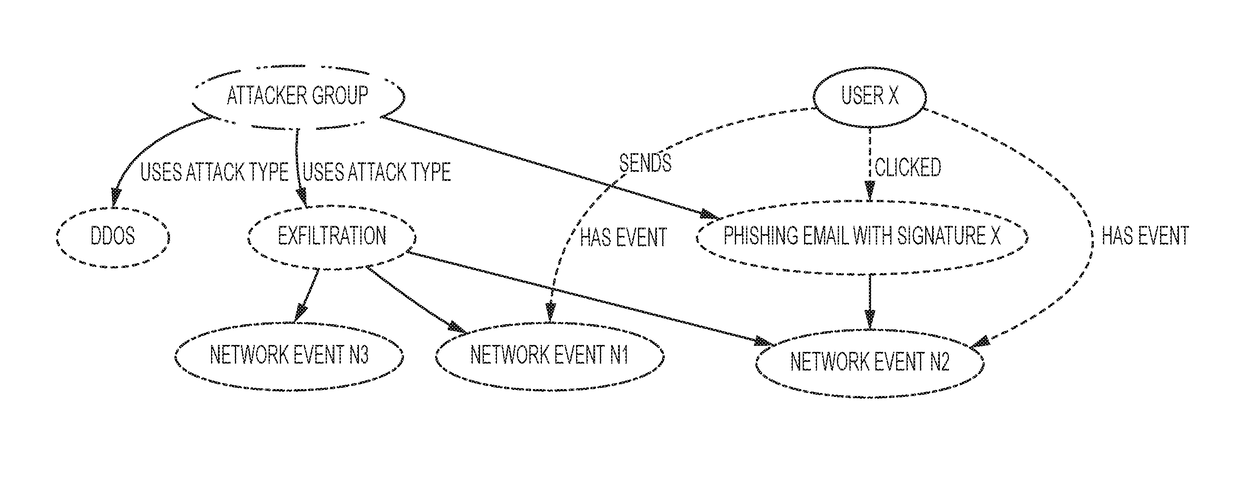
System and methods for automated detection, reasoning and recommendations for resilient cyber systems
ActiveUS20180103052A1Improve applicabilityLarge capacityDigital data information retrievalComputer security arrangementsElastic networkKnowledge extraction
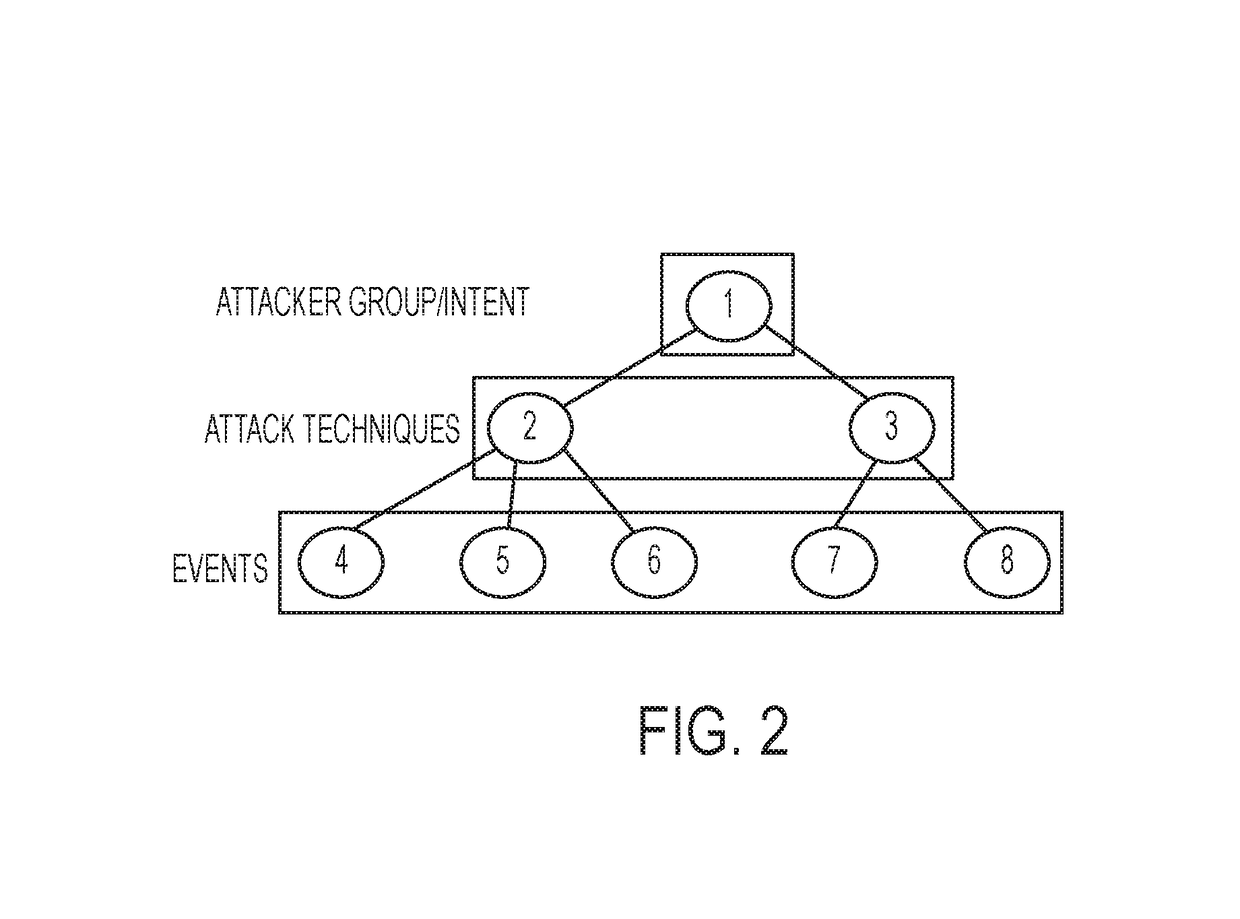
A method for securing an IT (information technology) system using a set of methods for knowledge extraction, event detection, risk estimation and explanation for ranking cyber-alerts which includes a method to explain the relationship (or an attack pathway) from an entity (user or host) and an event context to another entity (a high-value resource) and an event context (attack or service failure).
Owner:BATTELLE MEMORIAL INST
Active adaptation of networked compute devices using vetted reusable software components
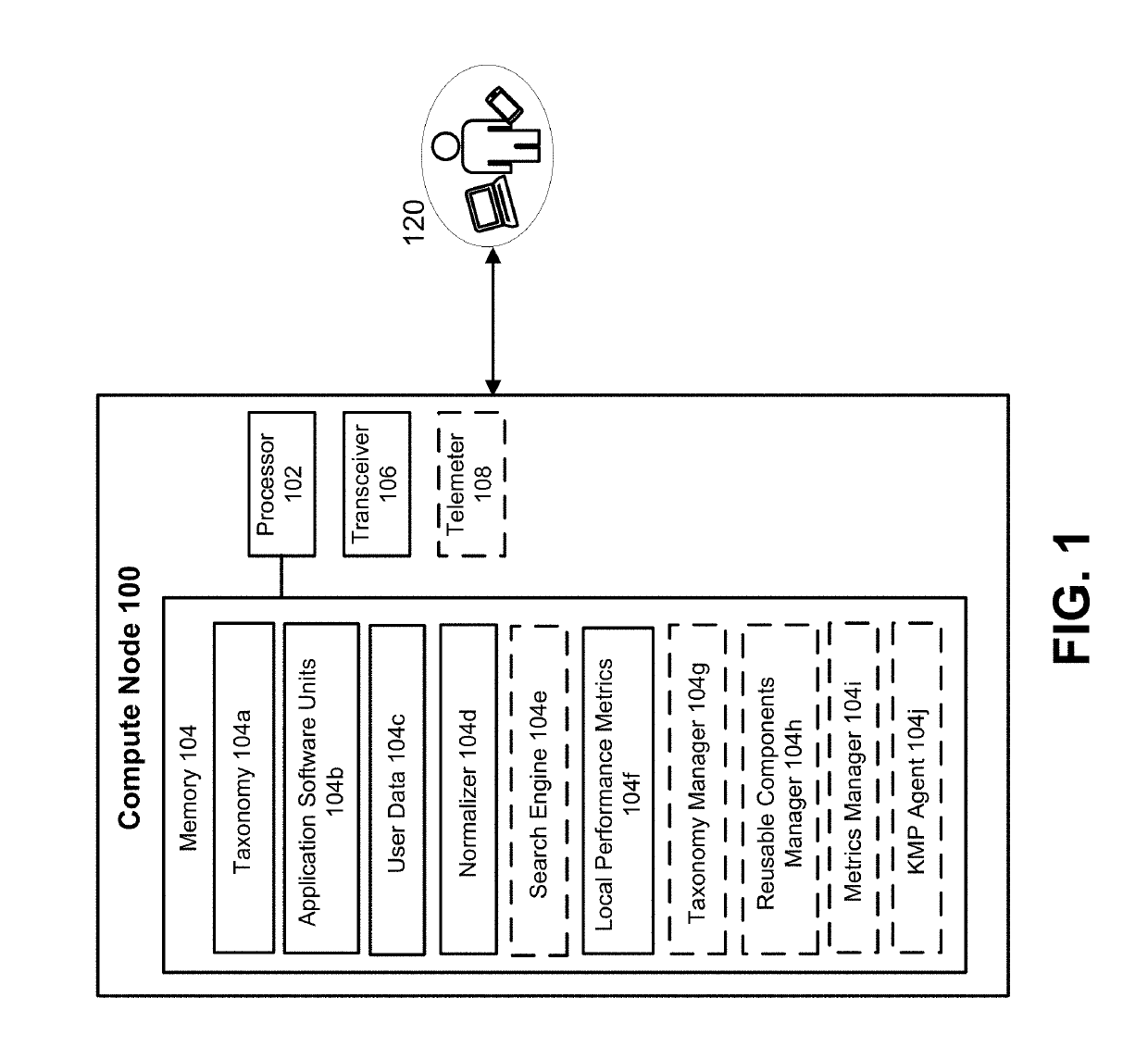
ActiveUS20190171438A1Other databases queryingKnowledge representationReusable softwareParallel computing
A method includes receiving a text description of a system capability request, and converting the text description into a normalized description of the system capability request. A repository is then queried, based on the normalized description and using a search algorithm, to identify multiple candidate application software units (ASUs). The candidate ASUs are displayed to a user for selection. The user-selected ASU is then deployed, either locally or to at least one remote compute device, in response to receiving the user selection. Deployment can include the user-selected candidate ASU being integrated into a local or remote software package, thus defining a modified software package that is configured to provide the system capability.
Owner:ARCHEMY INC
Hardware system design improvement using deep learning algorithms
Methods and apparatus for deep learning-based system design improvement are provided. An example system design engine apparatus includes a deep learning network (DLN) model associated with each component of a target system to be emulated, each DLN model to be trained using known input and known output, wherein the known input and known output simulate input and output of the associated component of the target system, and wherein each DLN model is connected as each associated component to be emulated is connected in the target system to form a digital model of the target system. The example apparatus also includes a model processor to simulate behavior of the target system and / or each component of the target system to be emulated using the digital model to generate a recommendation regarding a configuration of a component of the target system and / or a structure of the component of the target system.
Owner:GENERAL ELECTRIC CO
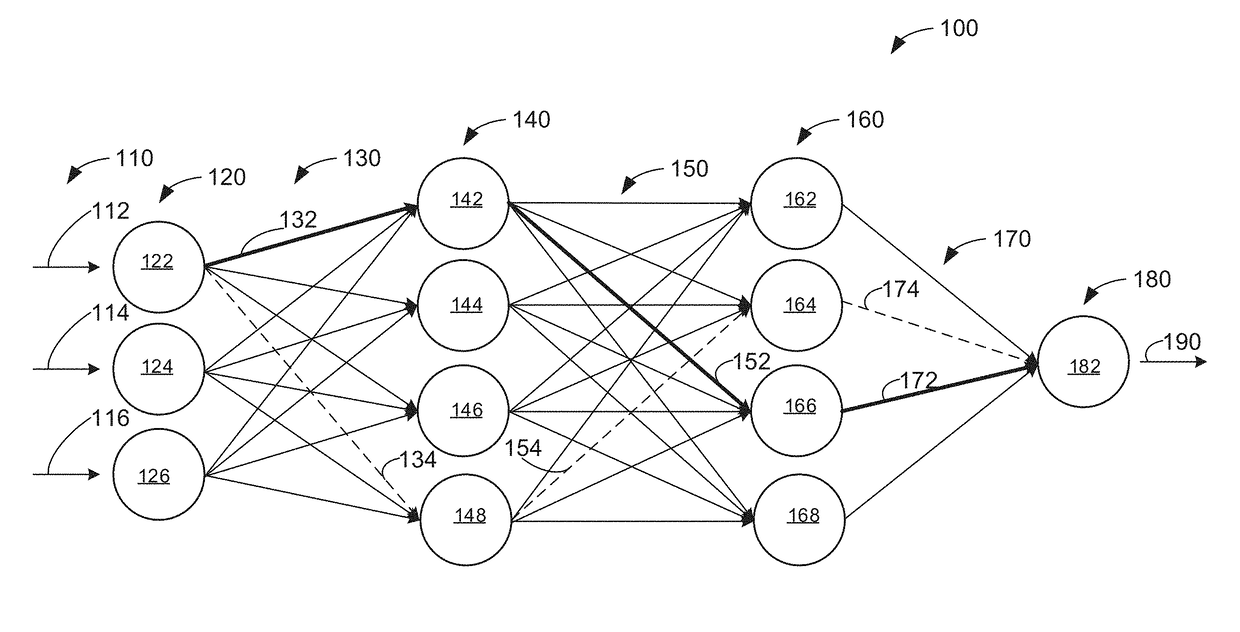
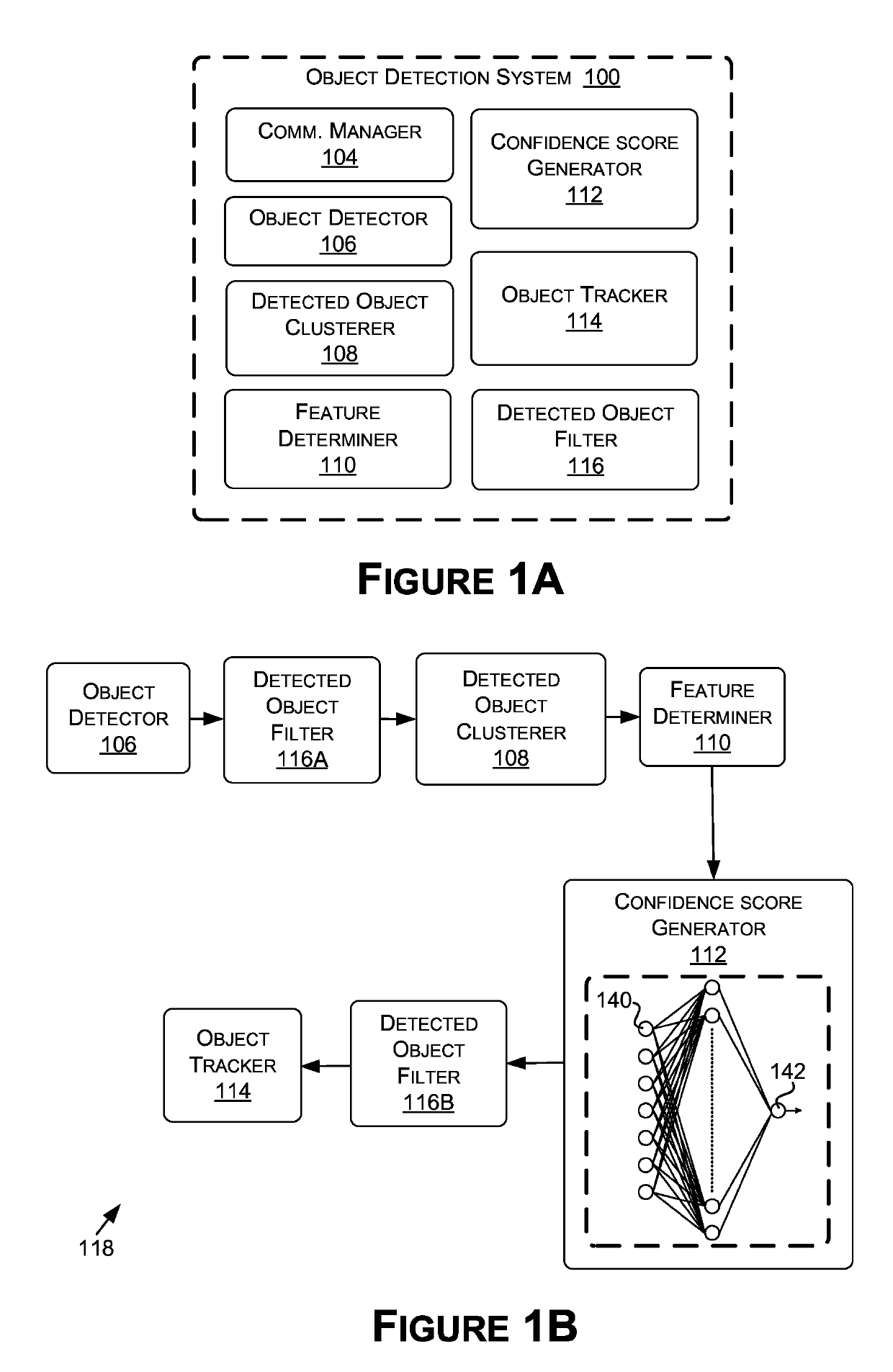
Object detection and detection confidence suitable for autonomous driving
ActiveUS20190258878A1Accurately indicatedFalse detectionScene recognitionMachine learningGround truthObject-class detection
In various examples, detected object data representative of locations of detected objects in a field of view may be determined. One or more clusters of the detected objects may be generated based at least in part on the locations and features of the cluster may be determined for use as inputs to a machine learning model(s). A confidence score, computed by the machine learning model(s) based at least in part on the inputs, may be received, where the confidence score may be representative of a probability that the cluster corresponds to an object depicted at least partially in the field of view. Further examples provide approaches for determining ground truth data for training object detectors, such as for determining coverage values for ground truth objects using associated shapes, and for determining soft coverage values for ground truth objects.
Owner:NVIDIA CORP
Deep learning medical systems and methods for image reconstruction and quality evaluation
Methods and apparatus to automatically generate an image quality metric for an image are provided. An example method includes automatically processing a first medical image using a deployed learning network model to generate an image quality metric for the first medical image, the deployed learning network model generated from a digital learning and improvement factory including a training network, wherein the training network is tuned using a set of labeled reference medical images of a plurality of image types, and wherein a label associated with each of the labeled reference medical images indicates a central tendency metric associated with image quality of the image. The example method includes computing the image quality metric associated with the first medical image using the deployed learning network model by leveraging labels and associated central tendency metrics to determine the associated image quality metric for the first medical image.
Owner:GENERAL ELECTRIC CO
Computer intrusion detection system and method based on application monitoring
InactiveUS7181768B1Reduced false positive falseReduce false negative rateMemory loss protectionError detection/correctionNerve networkPrediction algorithms
An intrusion detection system (IDS) that uses application monitors for detecting application-based attacks against computer systems. The IDS implements application monitors in the form of a software program to learn and monitor the behavior of system programs in order to detect attacks against computer hosts. The application monitors implement machine learning algorithms to provide a mechanism for learning from previously observed behavior in order to recognize future attacks that it has not seen before. The application monitors include temporal locality algorithms to increased the accuracy of the IDS. The IDS of the present invention may comprise a string-matching program, a neural network, or a time series prediction algorithm for learning normal application behavior and for detecting anomalies.
Owner:SYNOPSYS INC
Knowledge Discovery Agent System and Method
ActiveUS20070203693A1Maximizes rangeFacilitate communicationWeb data indexingNatural language data processingUnstructured dataConditional probability
A system and method for processing information in unstructured or structured form, comprising a computer running in a distributed network with one or more data agents. Associations of natural language artifacts may be learned from natural language artifacts in unstructured data sources, and semantic and syntactic relationships may be learned in structured data sources, using grouping based on a criteria of shared features that are dynamically determined without the use of a priori classifications, by employing conditional probability constraints.
Owner:DIGITAL REASONING SYST
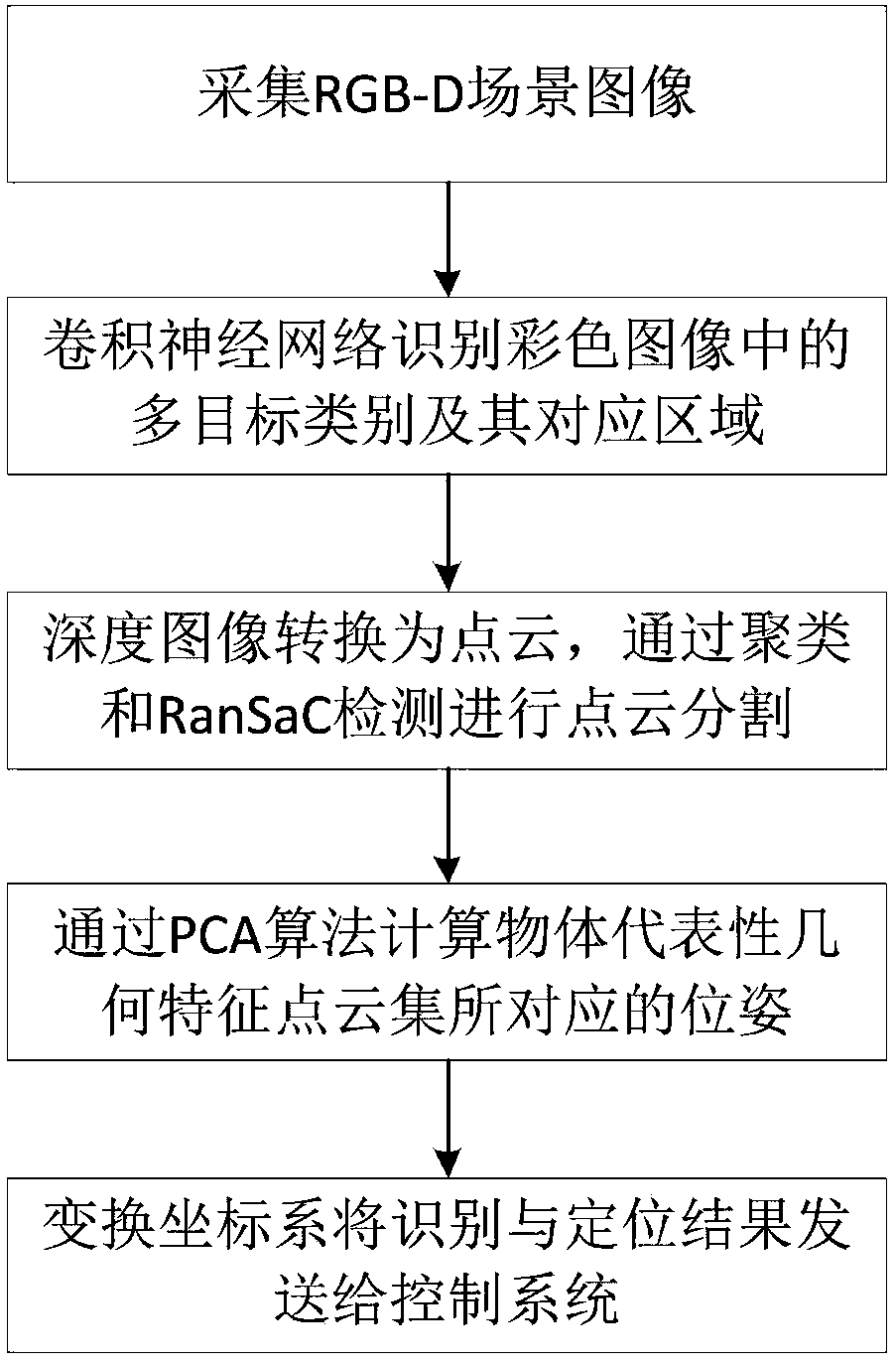
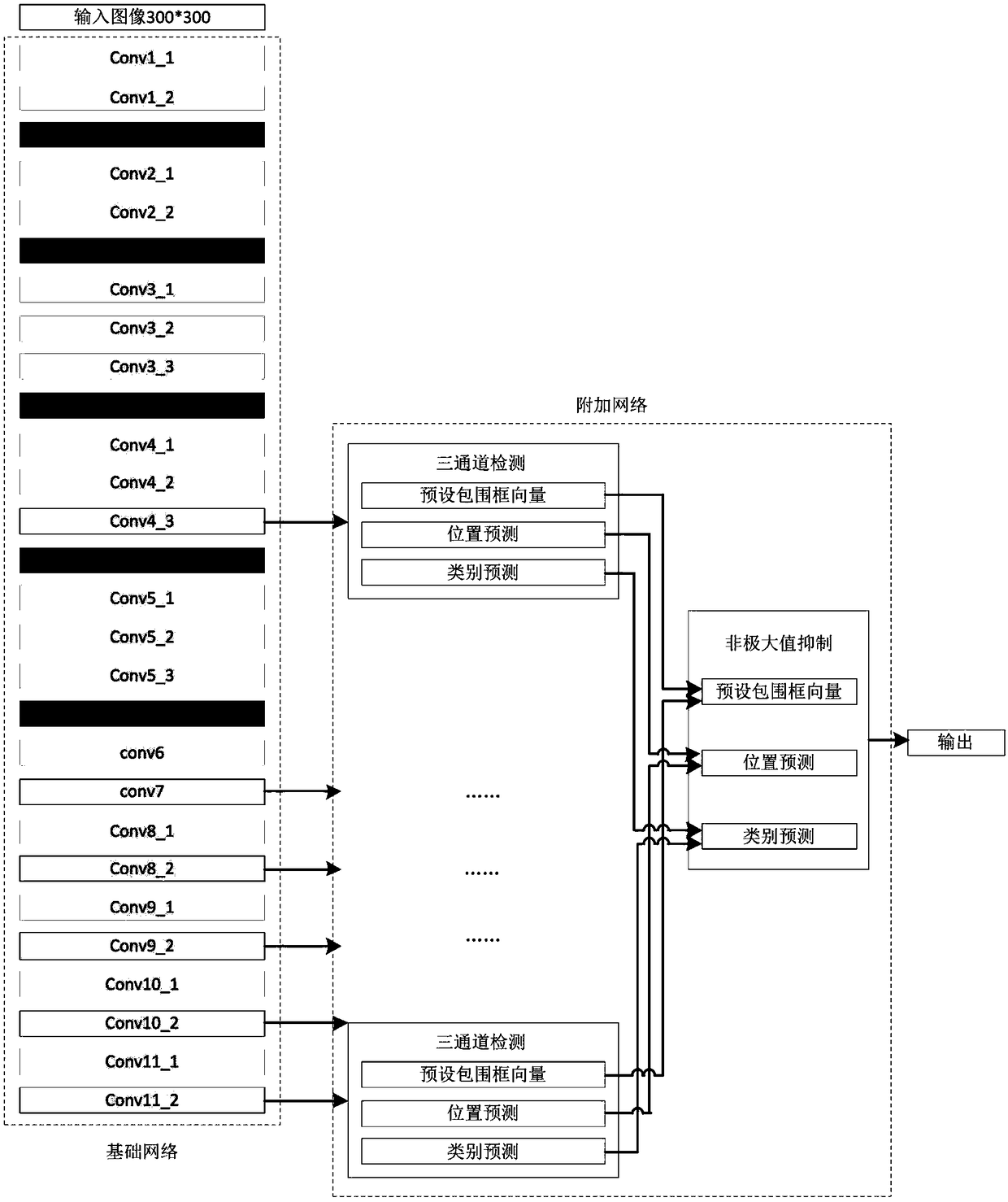
Visual recognition and positioning method for robot intelligent capture application
The invention relates to a visual recognition and positioning method for robot intelligent capture application. According to the method, an RGB-D scene image is collected, a supervised and trained deep convolutional neural network is utilized to recognize the category of a target contained in a color image and a corresponding position region, the pose state of the target is analyzed in combinationwith a deep image, pose information needed by a controller is obtained through coordinate transformation, and visual recognition and positioning are completed. Through the method, the double functions of recognition and positioning can be achieved just through a single visual sensor, the existing target detection process is simplified, and application cost is saved. Meanwhile, a deep convolutional neural network is adopted to obtain image features through learning, the method has high robustness on multiple kinds of environment interference such as target random placement, image viewing anglechanging and illumination background interference, and recognition and positioning accuracy under complicated working conditions is improved. Besides, through the positioning method, exact pose information can be further obtained on the basis of determining object spatial position distribution, and strategy planning of intelligent capture is promoted.
Owner:合肥哈工慧拣智能科技有限公司
Noninvasive diagnostic system
InactiveUS20120029345A1Physical therapies and activitiesUltrasonic/sonic/infrasonic diagnosticsUltrasonic sensorProximate
A device for acquiring data and diagnosing a musculoskeletal injury. The device includes a semi-flexible housing, at least one ultrasonic transducer, a positional localizer, and a transmission system. The semi-flexible housing is positioned proximate a portion of the musculoskeletal system of a patient and supports the at least one ultrasonic transducer and the positional localizer. The at least one ultrasonic transducer is configured to acquire an ultrasonic data indicative of a bone surface. The positional localizer is positioned at a select location relative to the at least one ultrasonic transducer and tracks movement of the housing. The transmission system transmits the ultrasonic data of the at least one ultrasonic transducer and the movement data of the positional localizer to a data analyzer for analysis and diagnosis.
Owner:JOINTVUE LLC
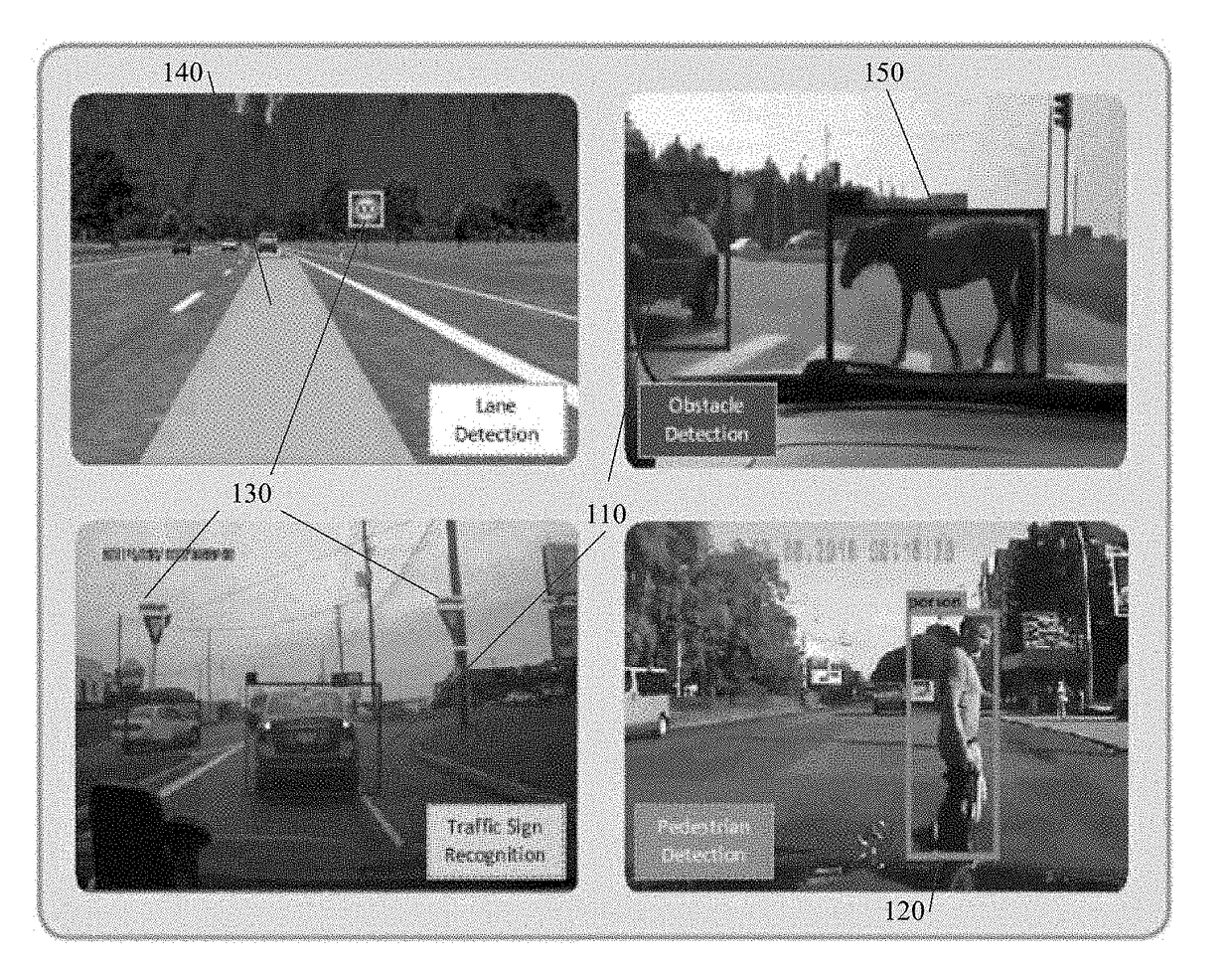
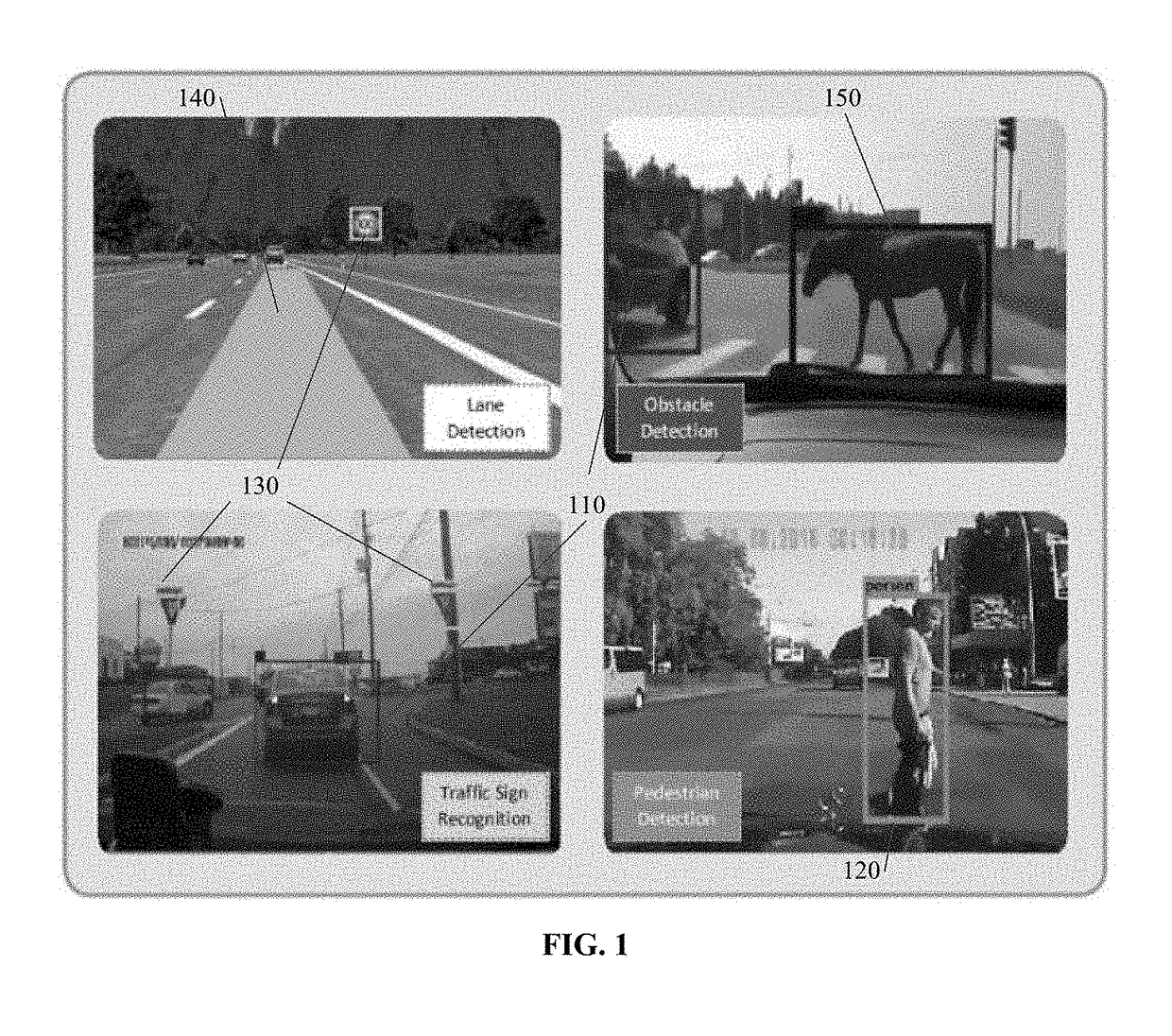
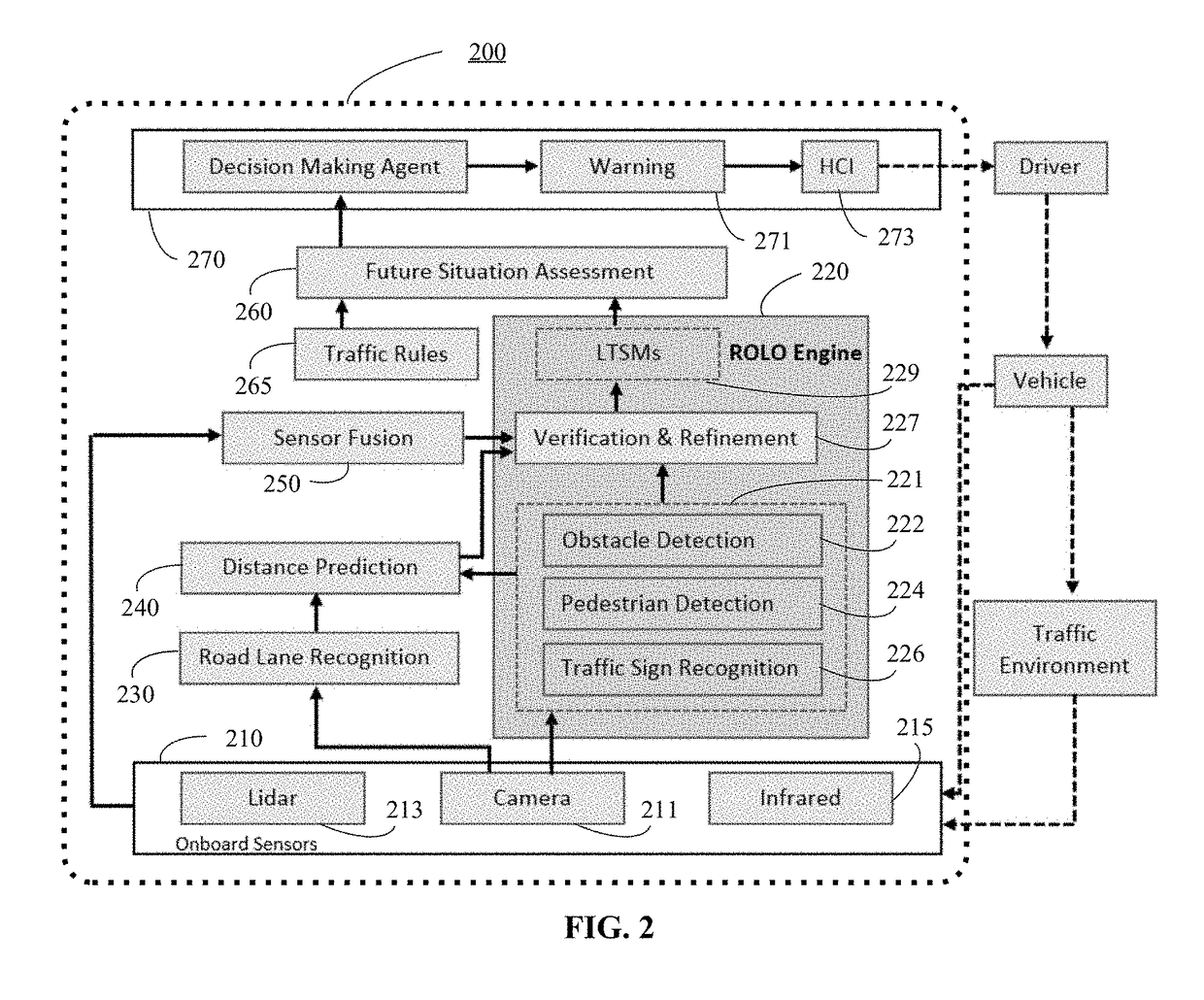
Method and system for vision-centric deep-learning-based road situation analysis
In accordance with various embodiments of the disclosed subject matter, a method and a system for vision-centric deep-learning-based road situation analysis are provided. The method can include: receiving real-time traffic environment visual input from a camera; determining, using a ROLO engine, at least one initial region of interest from the real-time traffic environment visual input by using a CNN training method; verifying the at least one initial region of interest to determine if a detected object in the at least one initial region of interest is a candidate object to be tracked; using LSTMs to track the detected object based on the real-time traffic environment visual input, and predicting a future status of the detected object by using the CNN training method; and determining if a warning signal is to be presented to a driver of a vehicle based on the predicted future status of the detected object.
Owner:TCL CORPORATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com