Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
34144results about "Machine learning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Automatic, personalized online information and product services
InactiveUS6981040B1Improve performanceManage efficiently enormousDigital data information retrievalMultiple digital computer combinationsLearning machinePersonalized search
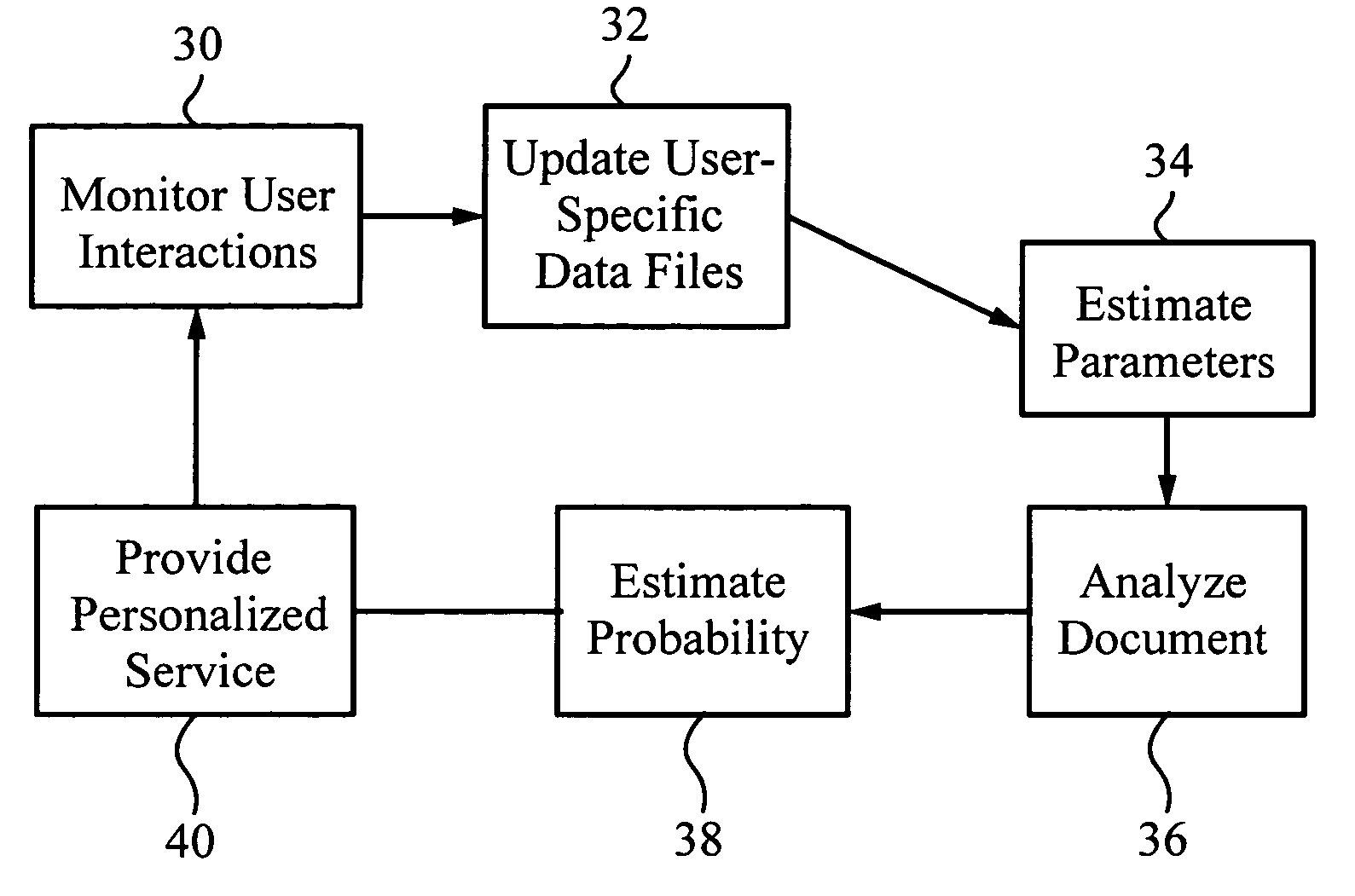
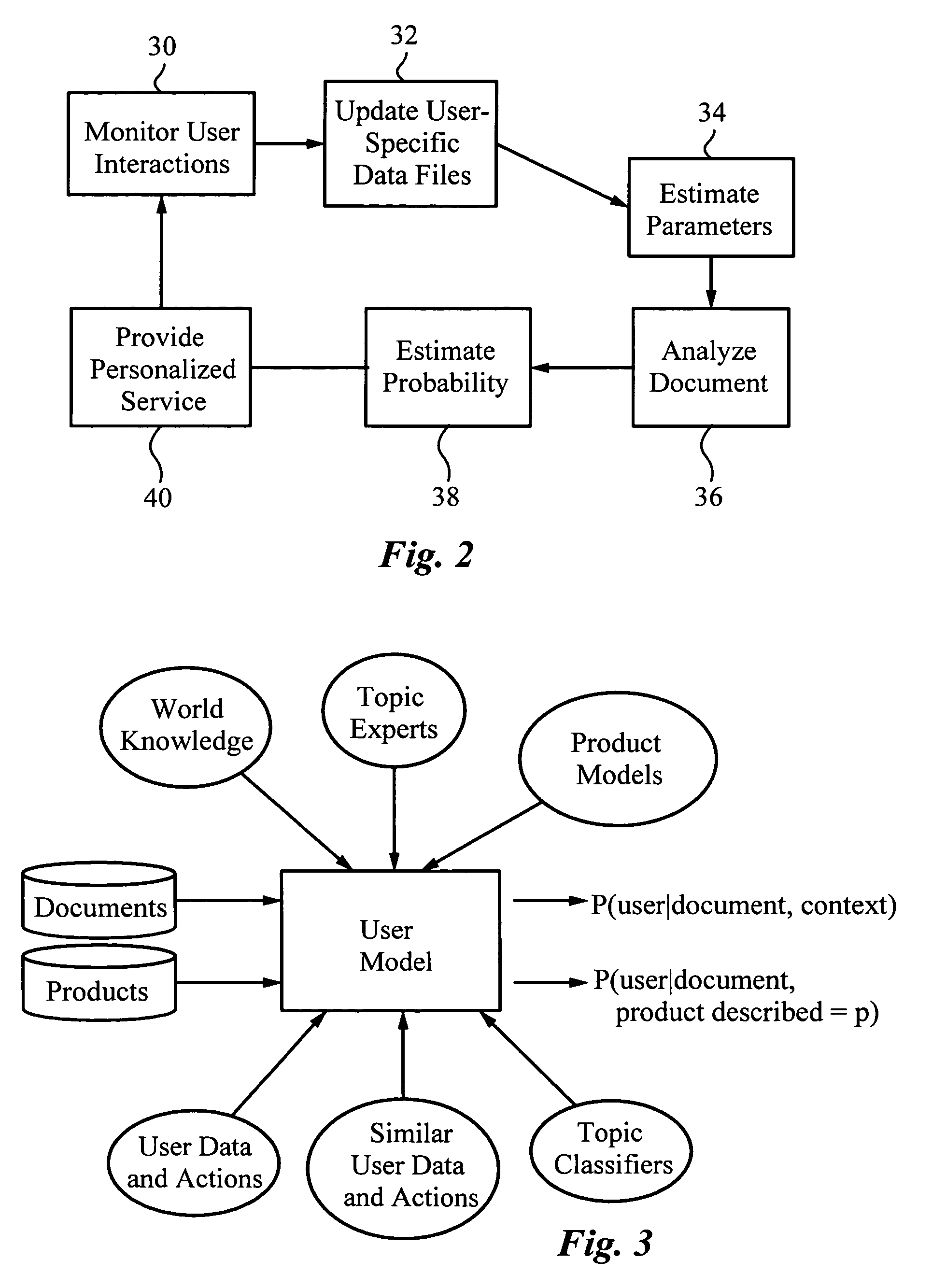
A method for providing automatic, personalized information services to a computer user includes the following steps: transparently monitoring user interactions with data during normal use of the computer; updating user-specific data files including a set of user-related documents; estimating parameters of a learning machine that define a User Model specific to the user, using the user-specific data files; analyzing a document to identify its properties; estimating the probability that the user is interested in the document by applying the document properties to the parameters of the User Model; and providing personalized services based on the estimated probability. Personalized services include personalized searches that return only documents of interest to the user, personalized crawling for maintaining an index of documents of interest to the user; personalized navigation that recommends interesting documents that are hyperlinked to documents currently being viewed; and personalized news, in which a third party server customized its interaction with the user. The User Model includes continually-updated measures of user interest in words or phrases, web sites, topics, products, and product features. The measures are updated based on both positive examples, such as documents the user bookmarks, and negative examples, such as search results that the user does not follow. Users are clustered into groups of similar users by calculating the distance between User Models.
Owner:PERSONALIZED USER MODEL PUM
Contextual responses based on automated learning techniques
InactiveUS6842877B2Input/output for user-computer interactionComputer security arrangementsRepetitive taskUser interface
Techniques are disclosed for using a combination of explicit and implicit user context modeling techniques to identify and provide appropriate computer actions based on a current context, and to continuously improve the providing of such computer actions. The appropriate computer actions include presentation of appropriate content and functionality. Feedback paths can be used to assist automated machine learning in detecting patterns and generating inferred rules, and improvements from the generated rules can be implemented with or without direct user control. The techniques can be used to enhance software and device functionality, including self-customizing of a model of the user's current context or situation, customizing received themes, predicting appropriate content for presentation or retrieval, self-customizing of software user interfaces, simplifying repetitive tasks or situations, and mentoring of the user to promote desired change.
Owner:MICROSOFT TECH LICENSING LLC
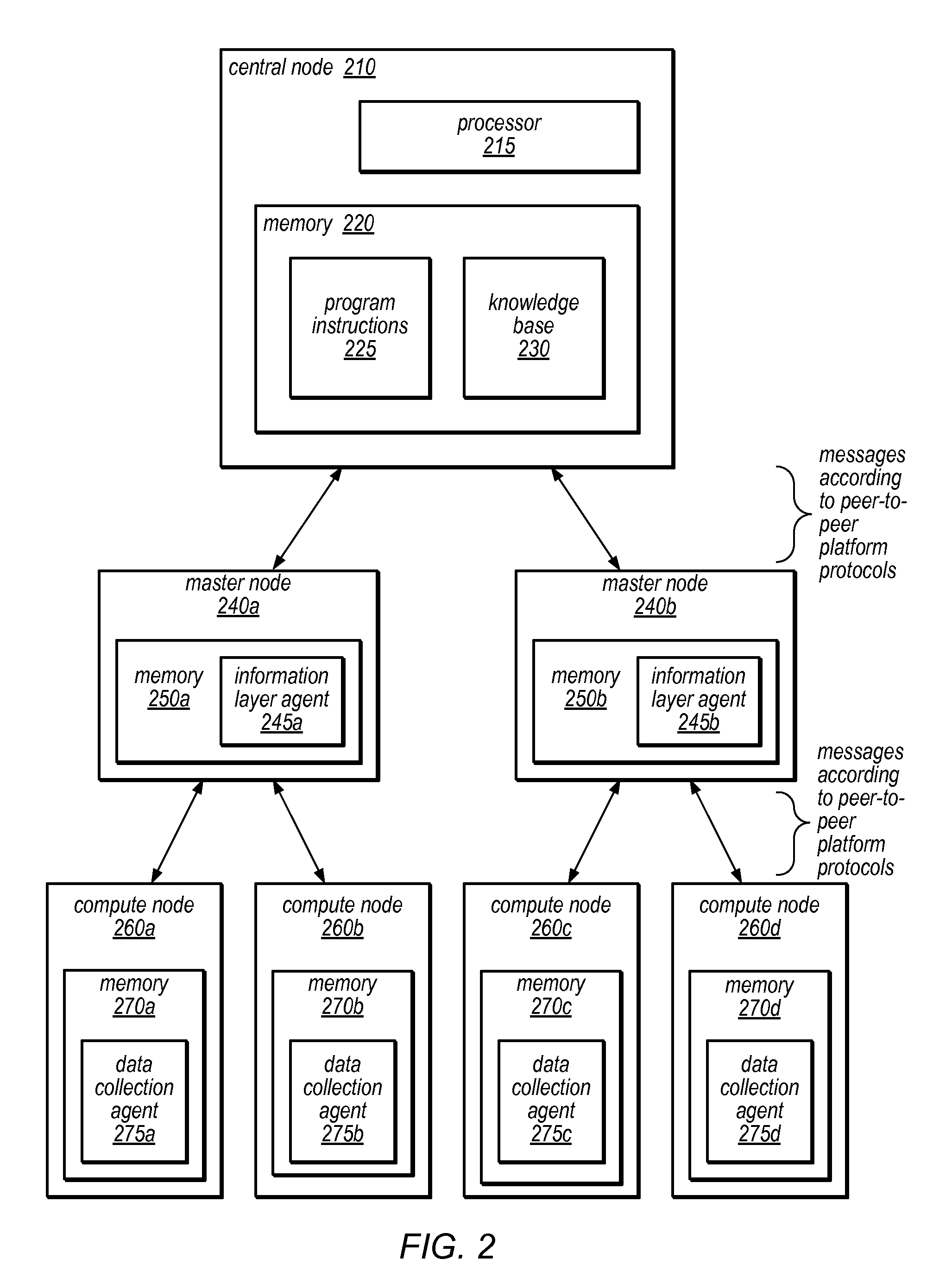
System and Method for Distributed Denial of Service Identification and Prevention
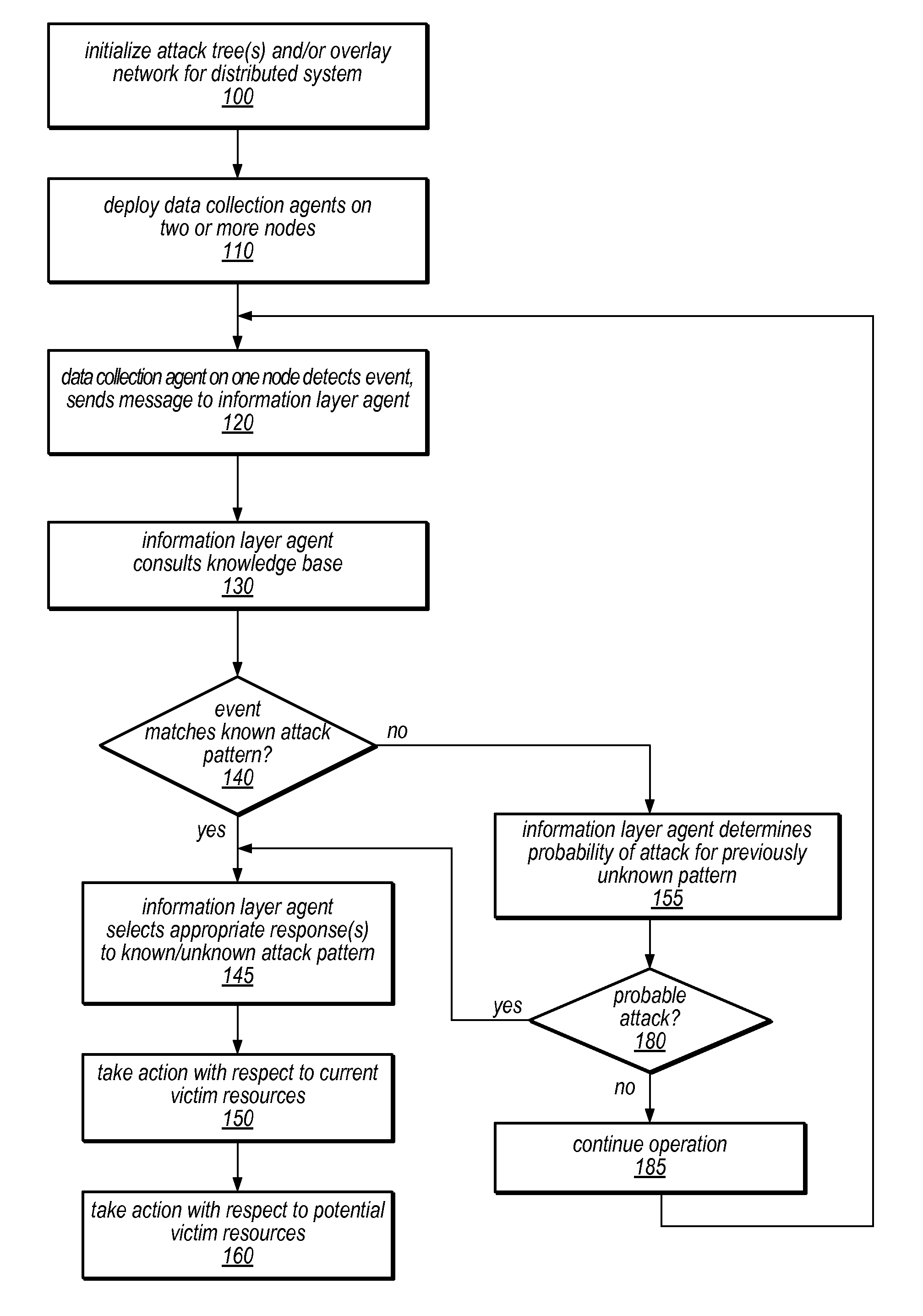
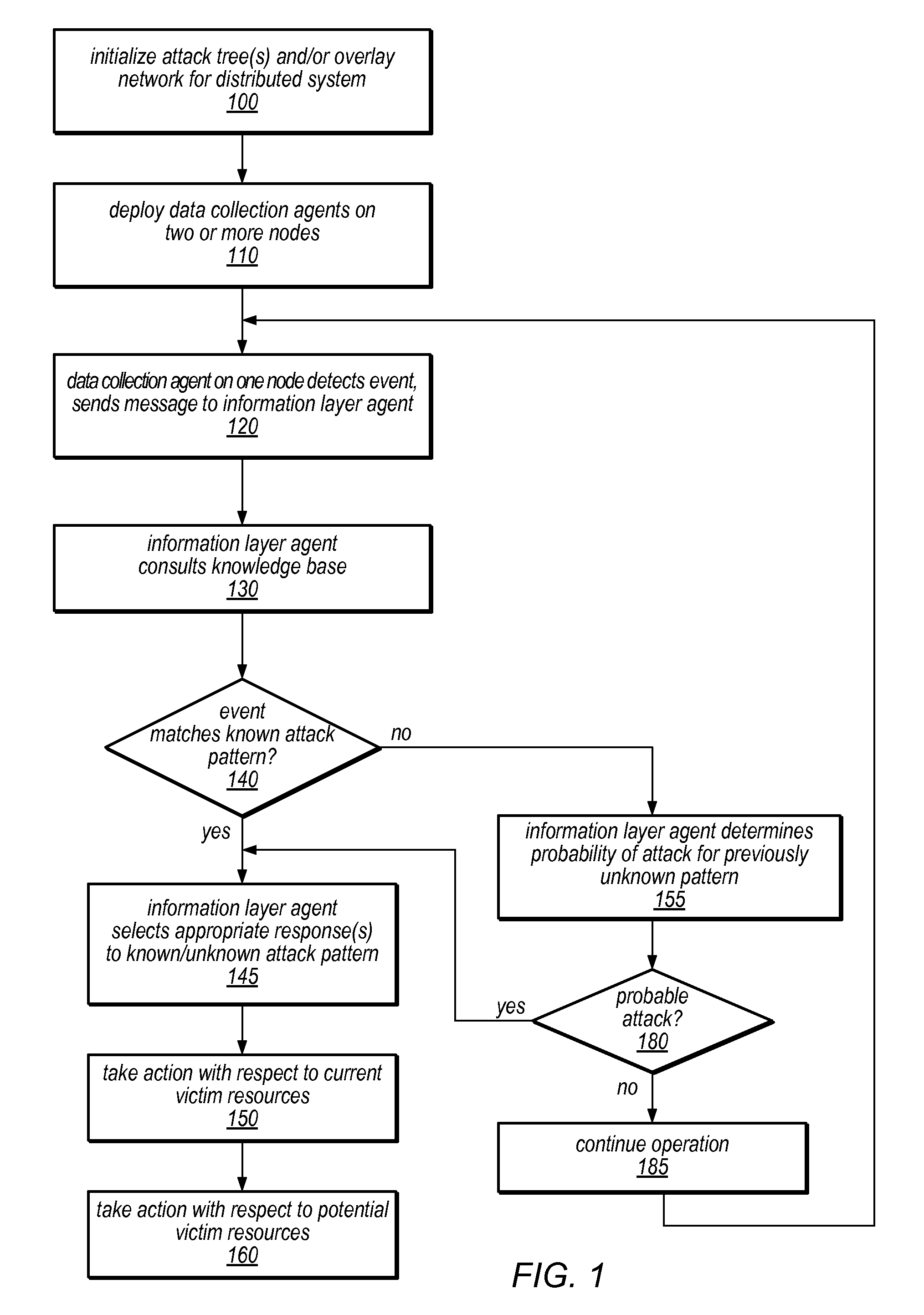
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
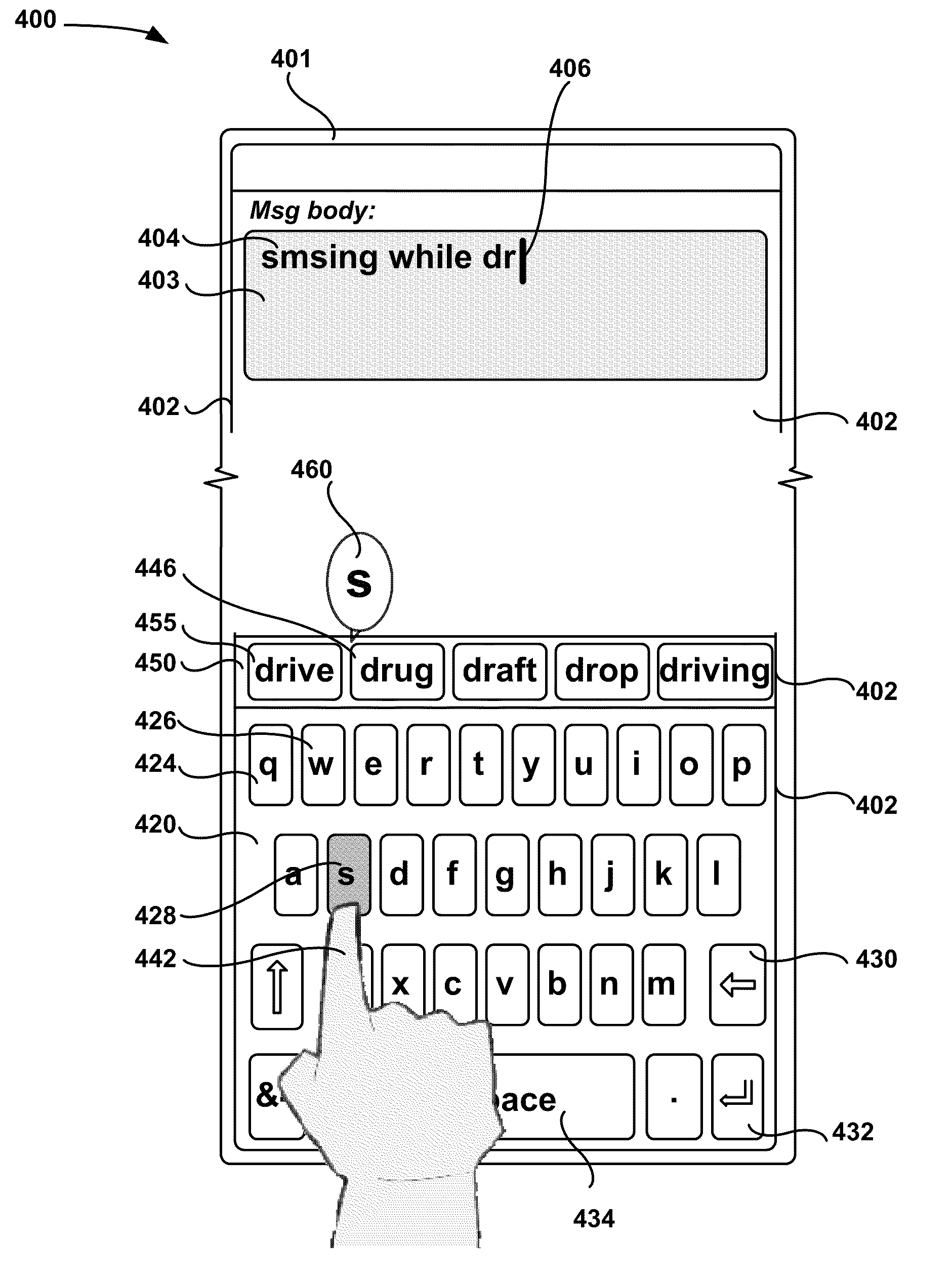
Real-time typing assistance
InactiveUS20110201387A1Improve experienceImprove performanceInput/output for user-computer interactionCathode-ray tube indicatorsText entry
An apparatus and method are disclosed for providing feedback and guidance to touch screen device users to improve the text entry user experience and performance through the use of indicators such as feedback semaphores. Also disclosed are suggestion candidates, which allow a user to quickly select next words to add to text input data, or replacement words for words that have been designated as incorrect. According to one embodiment, a method comprises receiving text input data, providing an indicator for possible correction of the text input data, displaying suggestion candidates associated with alternative words for the data, receiving a single touch screen input selecting one of the suggestion candidates, and modifying the input data using the word associated with the selected suggestion candidate.
Owner:MICROSOFT TECH LICENSING LLC
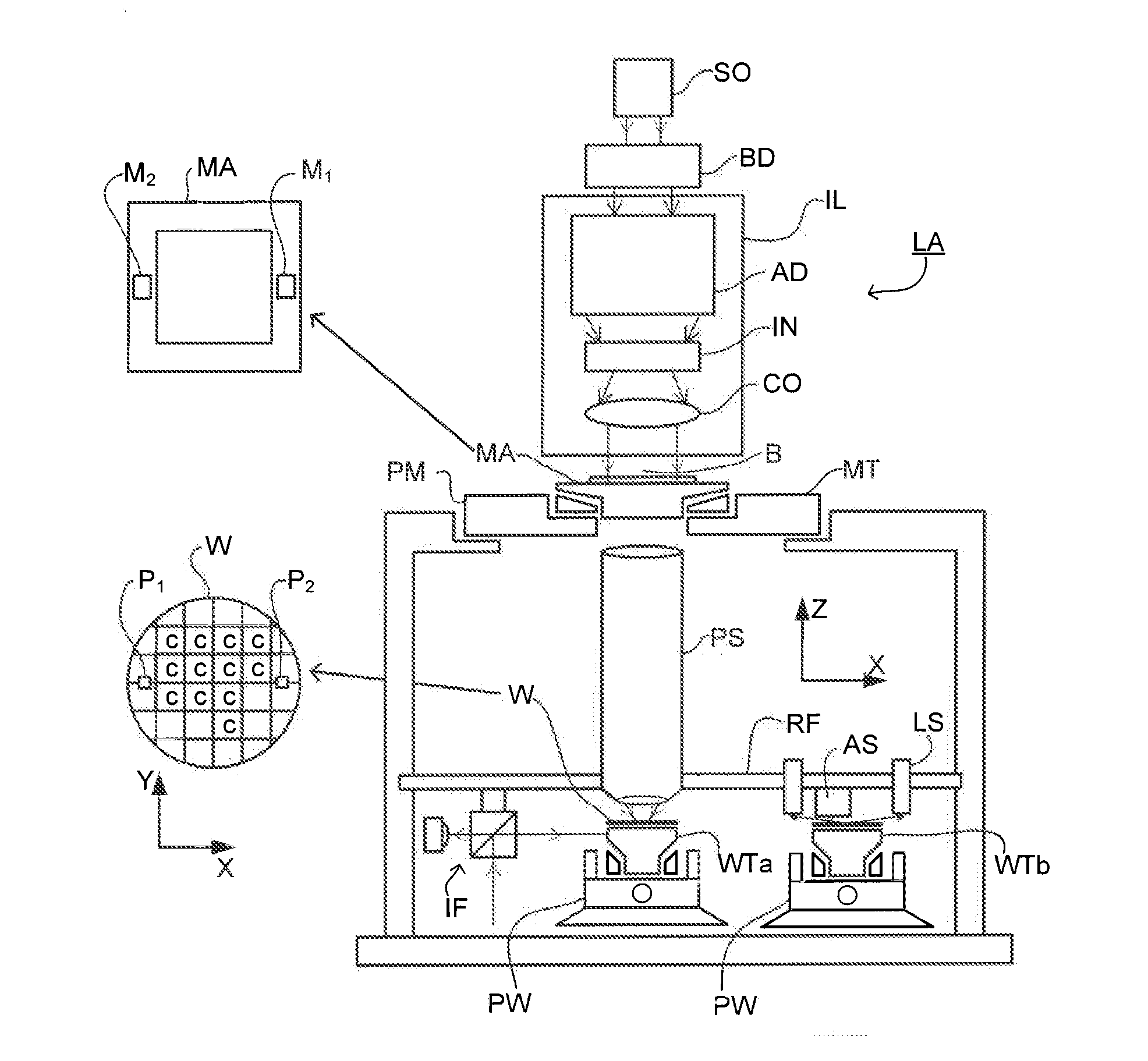
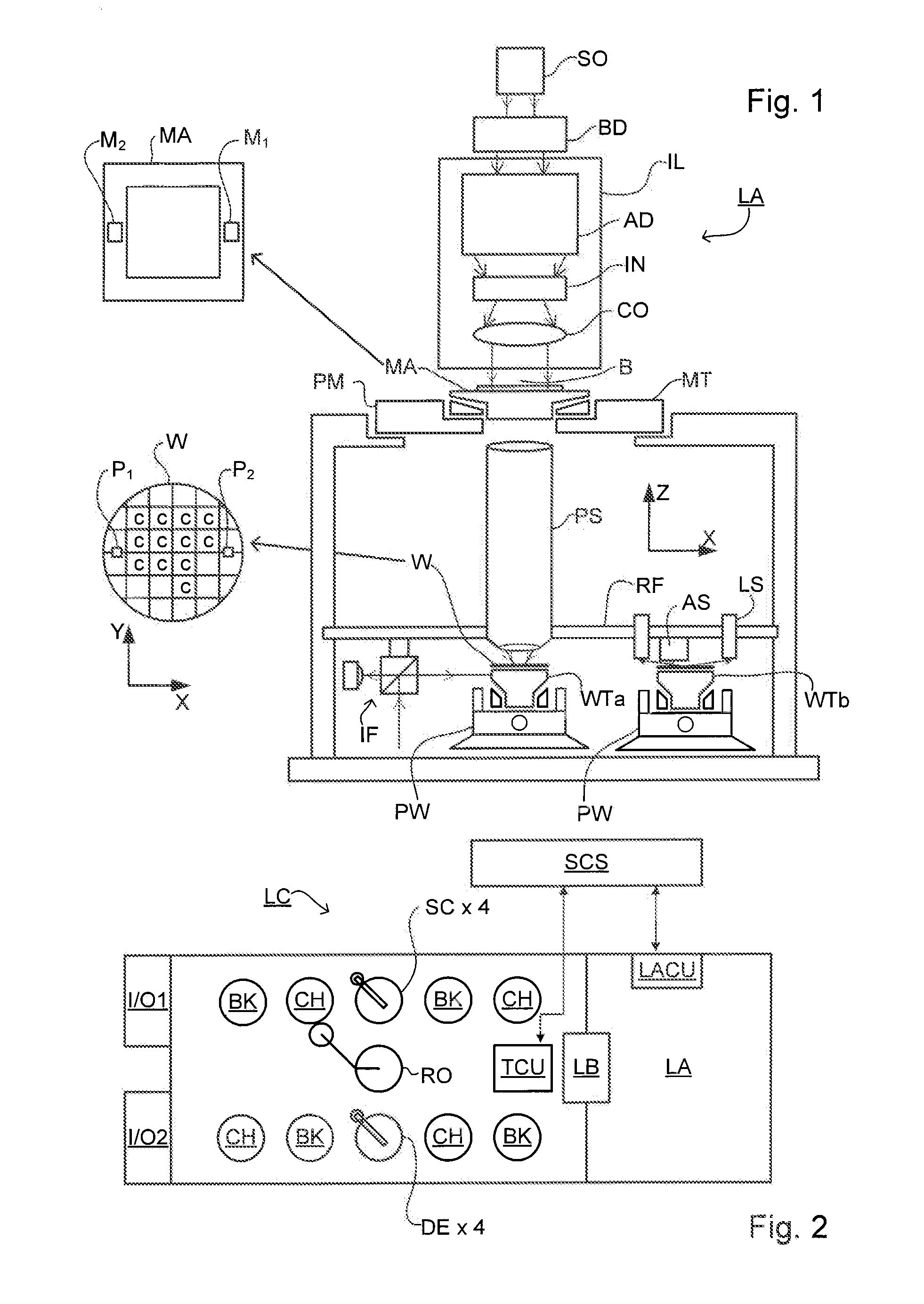
Metrology Method and Inspection Apparatus, Lithographic System and Device Manufacturing Method
ActiveUS20120123581A1Improve accuracyImprove throughputPhotomechanical apparatusScattering properties measurementsUltrasound attenuationSpatial light modulator
Methods are disclosed for measuring target structures formed by a lithographic process on a substrate. A grating structure within the target is smaller than an illumination spot and field of view of a measurement optical system. The optical system has a first branch leading to a pupil plane imaging sensor and a second branch leading to a substrate plane imaging sensor. A spatial light modulator is arranged in an intermediate pupil plane of the second branch of the optical system. The SLM imparts a programmable pattern of attenuation that may be used to correct for asymmetries between the first and second modes of illumination or imaging. By use of specific target designs and machine-learning processes, the attenuation patterns may also be programmed to act as filter functions, enhancing sensitivity to specific parameters of interest, such as focus.
Owner:ASML NETHERLANDS BV
Internet appliance system and method
InactiveUS20060200253A1Minimize timeTelevision system detailsAdvertisementsPhysical securityThe Internet
An Internet appliance, comprising, within a single housing, packet data network interfaces, adapted for communicating with the Internet and a local area network, at least one data interface selected from the group consisting of a universal serial bus, an IEEE-1394 interface, a voice telephony interface, an audio program interface, a video program interface, an audiovisual program interface, a camera interface, a physical security system interface, a wireless networking interface; a device control interface, smart home interface, an environmental sensing interface, and an environmental control interface, and a processor, for controlling a data transfer between the local area network and the Internet, and defining a markup language interface communicated through a packet data network interface, to control a data transfer or control a remote device.
Owner:BLANDING HOVENWEEP
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
ActiveUS7136710B1Significant to useImprove computing powerComputer controlAnalogue secracy/subscription systemsConceptual basisHuman–machine interface
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP +1
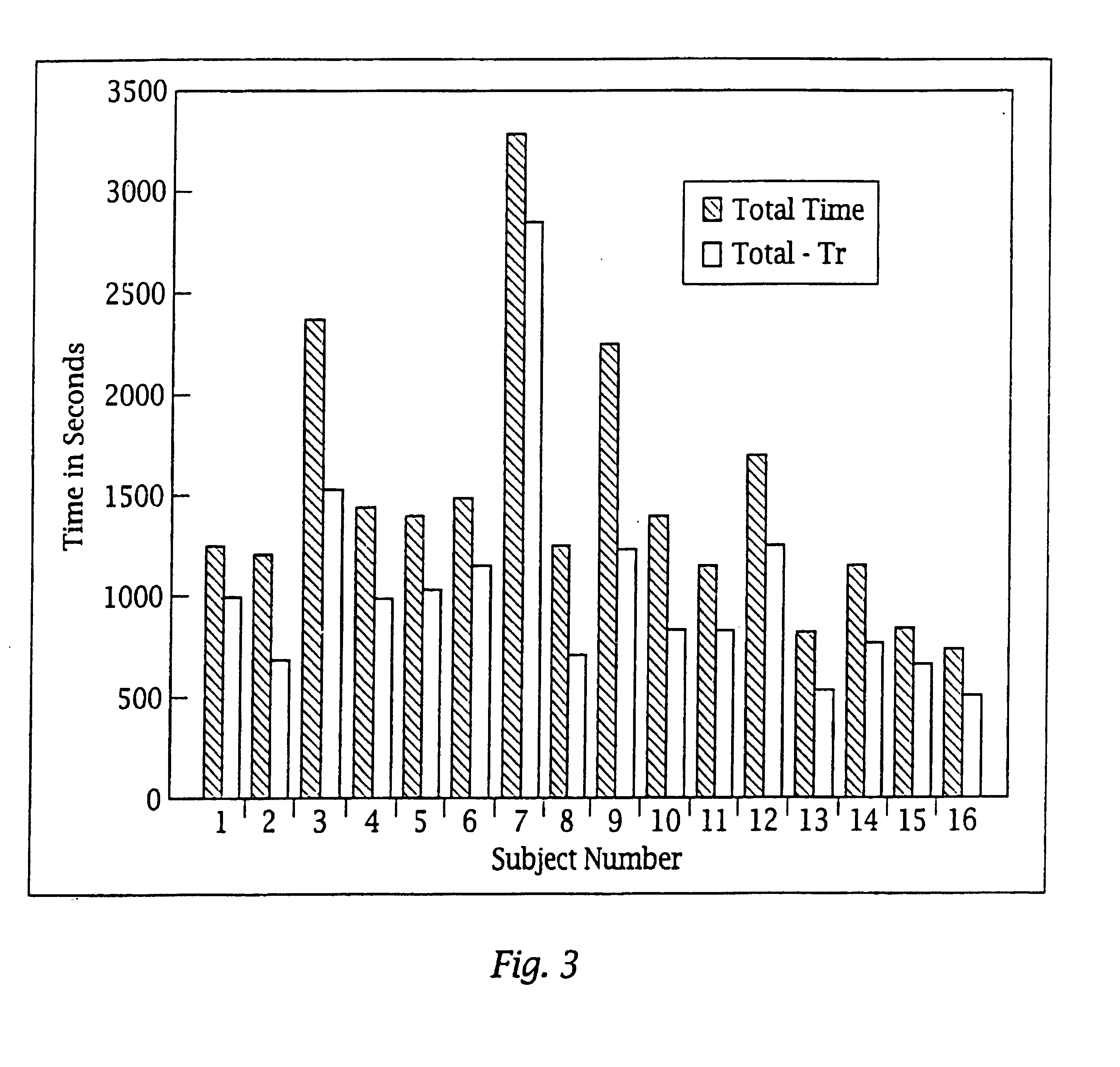
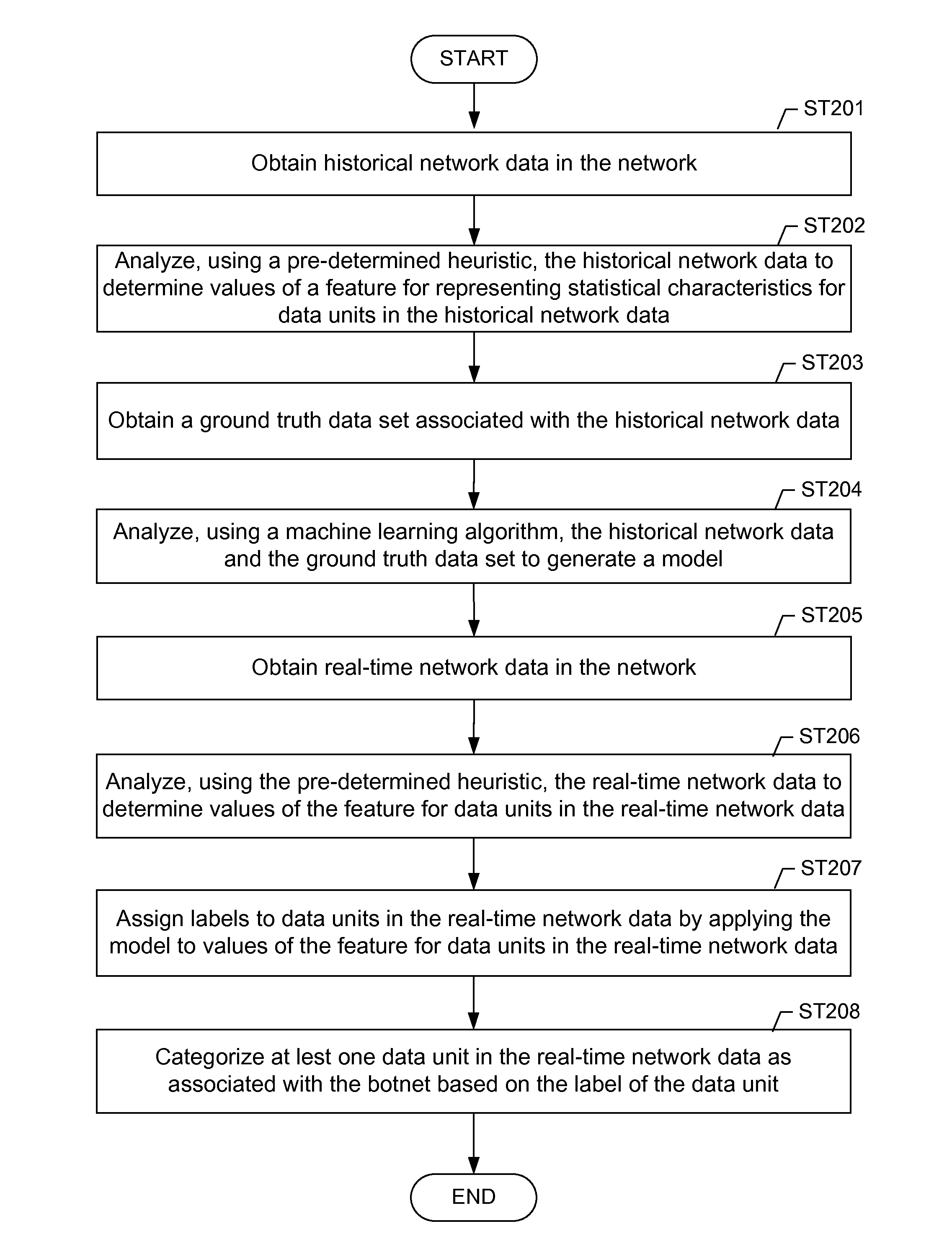
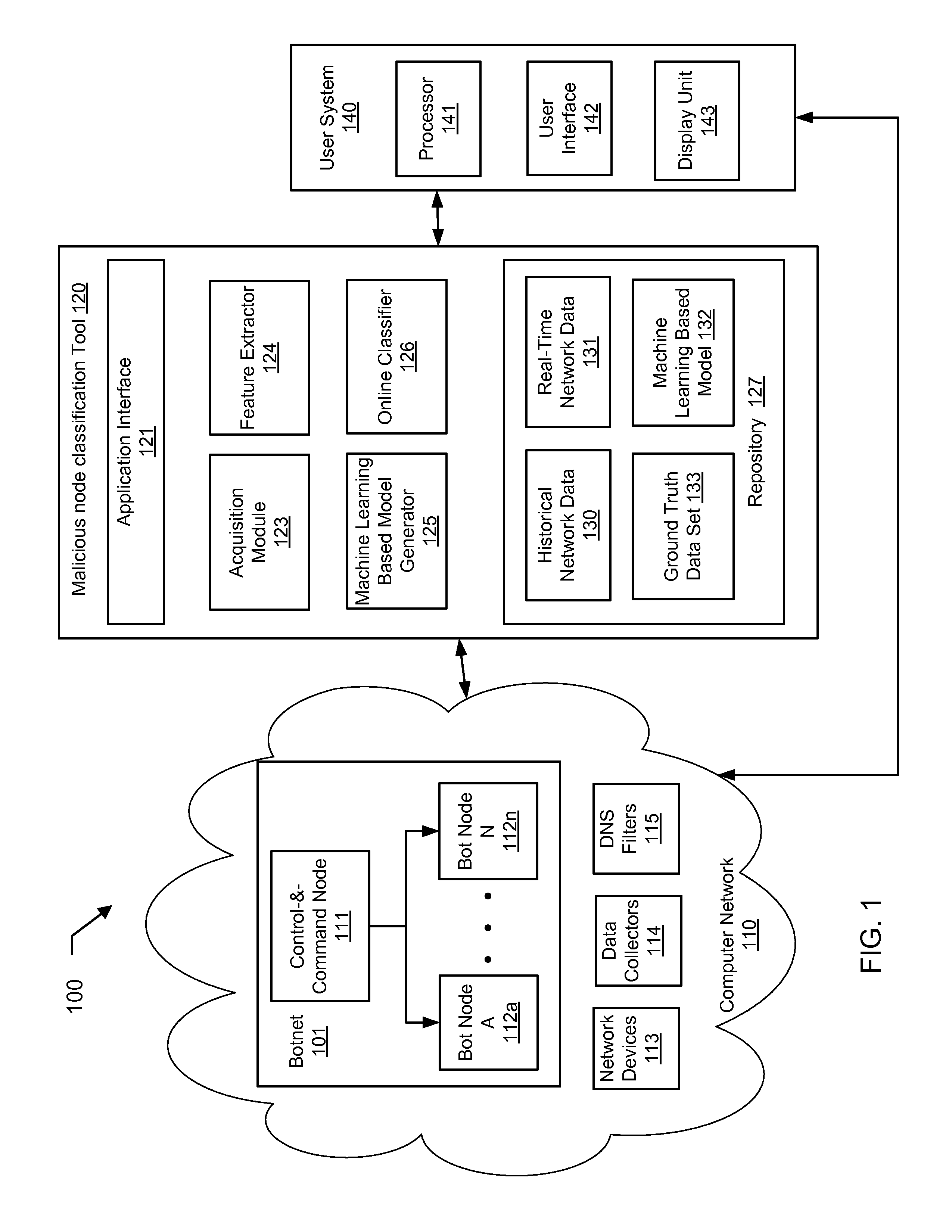
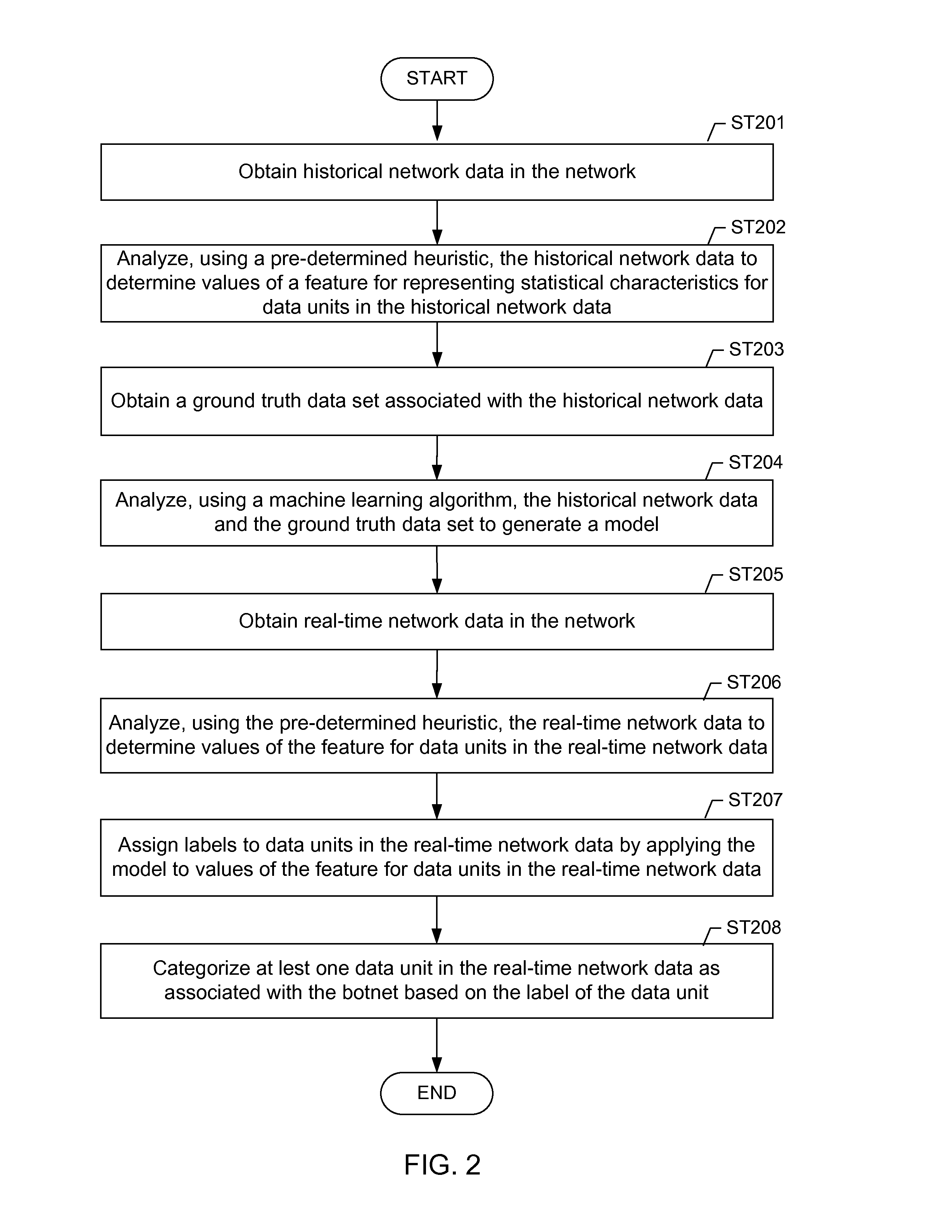
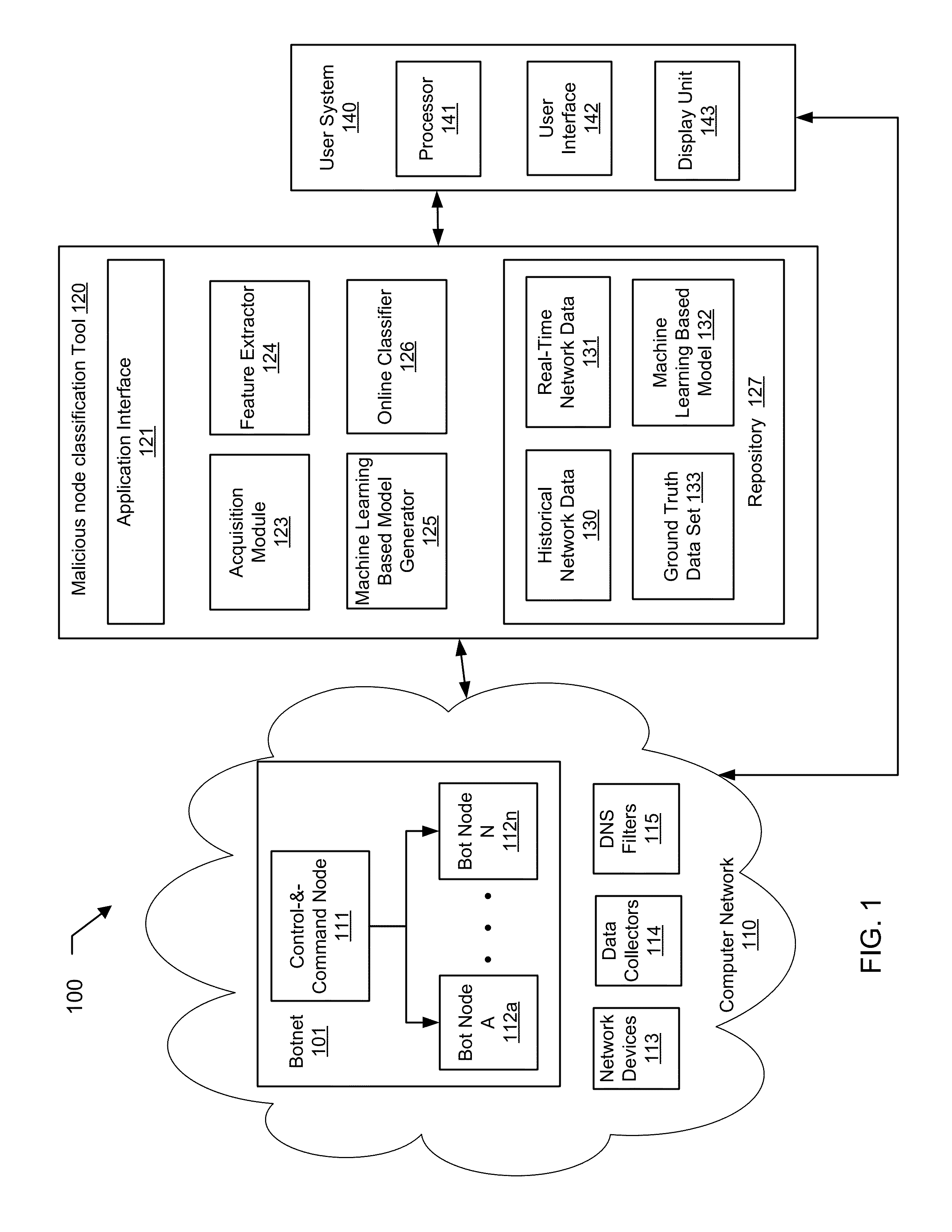
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
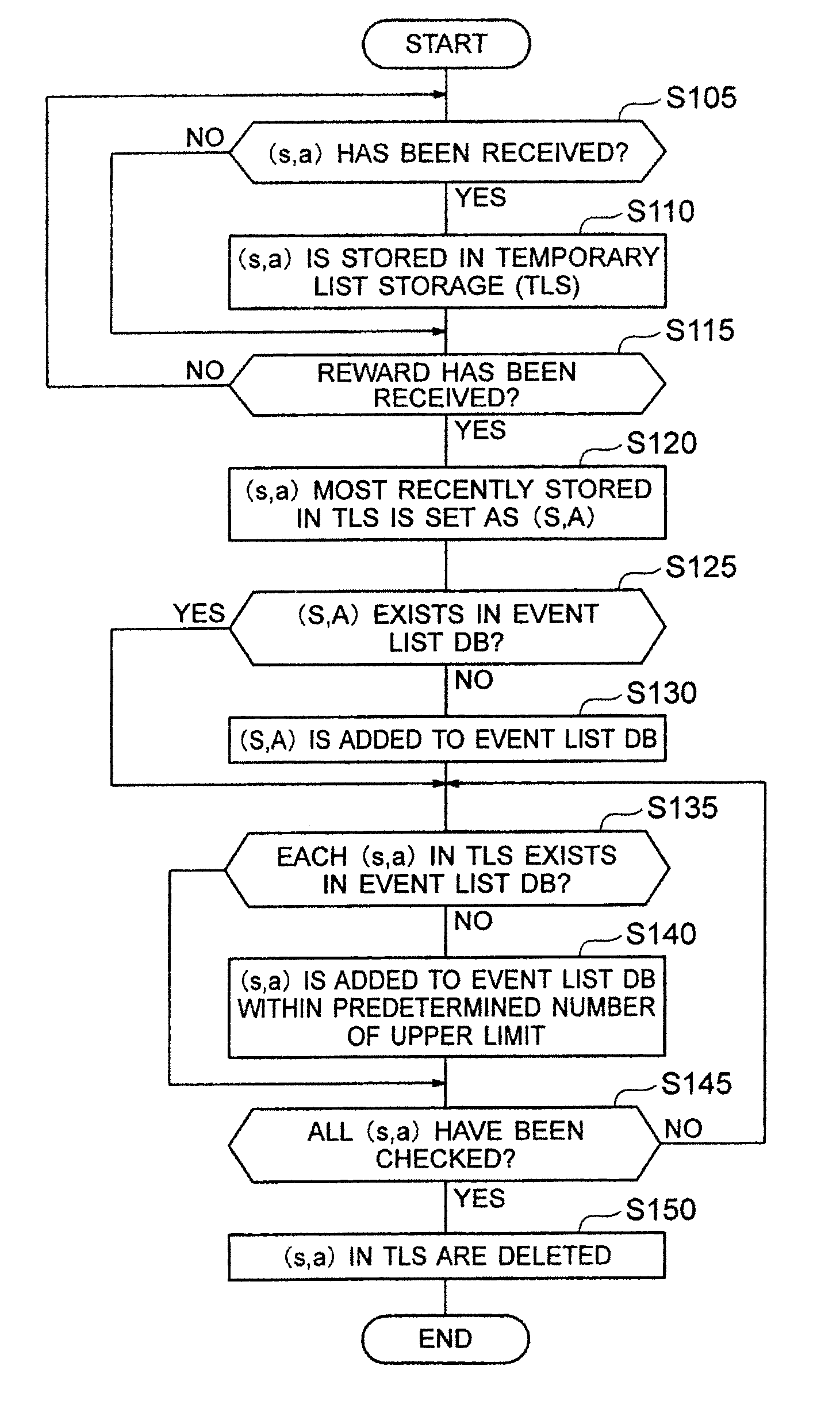
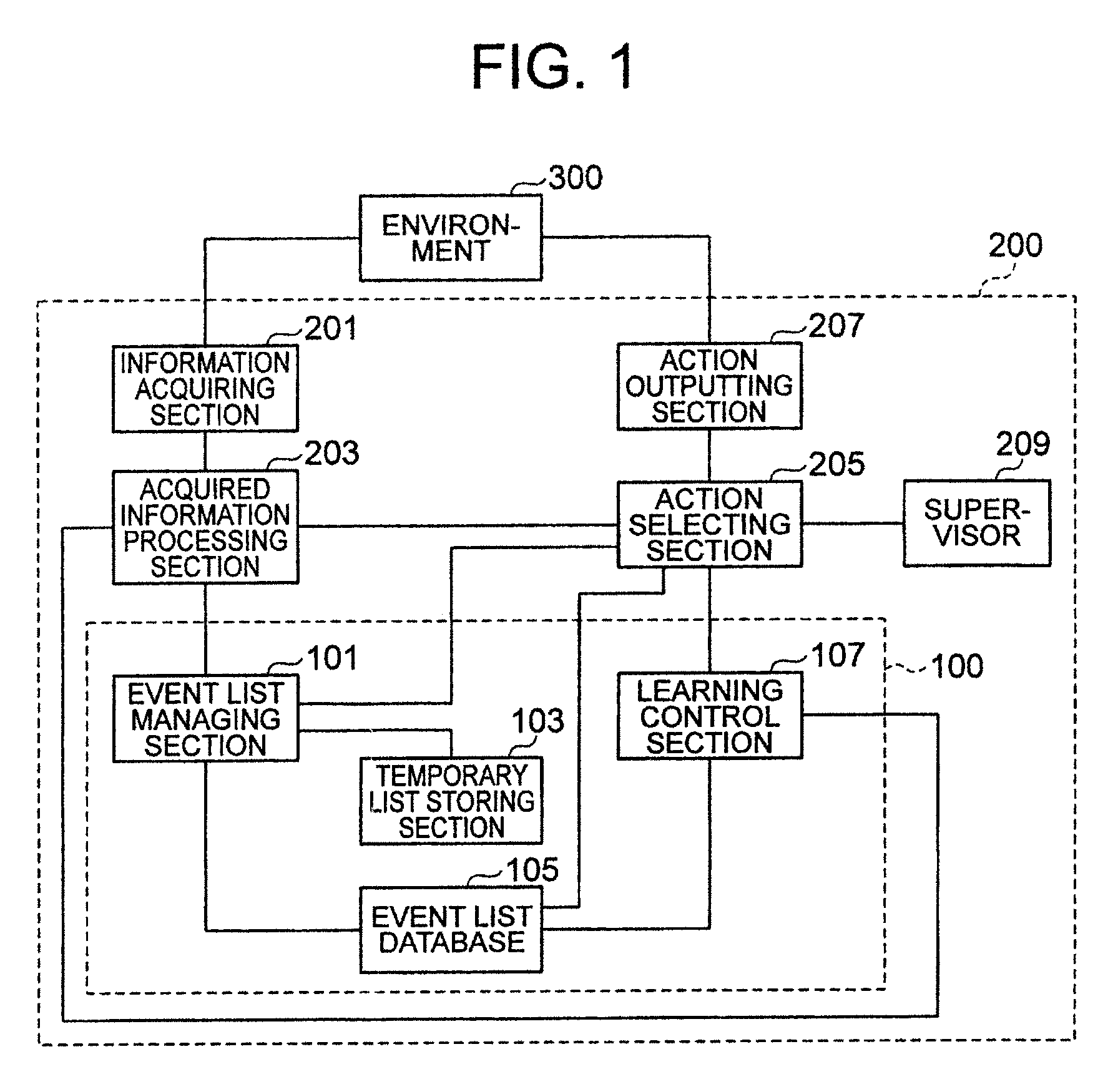
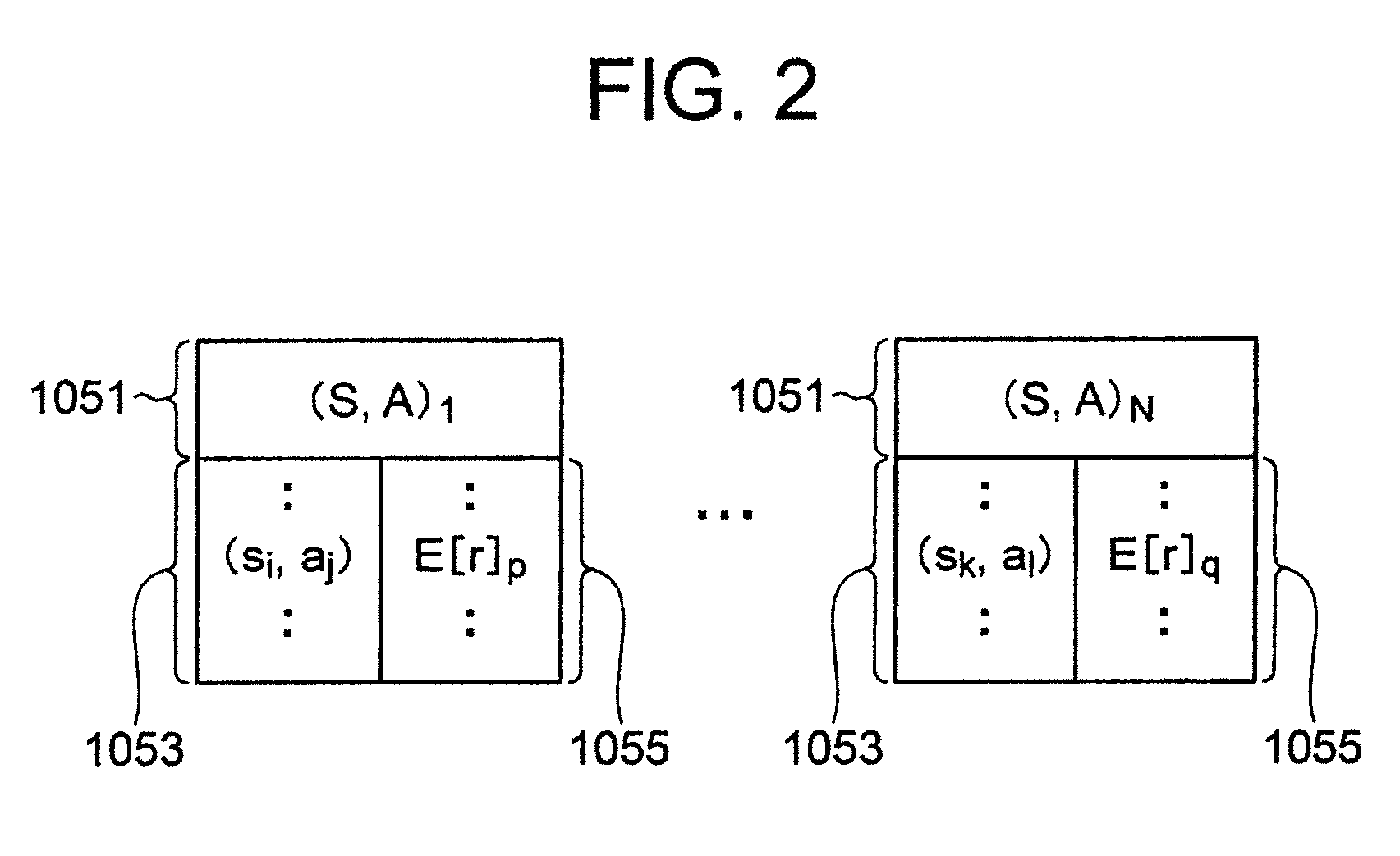
Learning system and learning method comprising an event list database
InactiveUS8290883B2Adaptable to changeImprove efficiencyDigital computer detailsMachine learningStudy methodsLearning methods
A learning system according to the present invention includes an event list database for storing a plurality of event lists, each of the event lists being a set including a series of state-action pairs which reaches a state-action pair immediately before earning a reward, an event list managing section for classifying state-action pairs into the plurality of event lists for storing, and a learning control section for updating expectation of reward of a state-action pair which is an element of each of the event lists.
Owner:HONDA MOTOR CO LTD
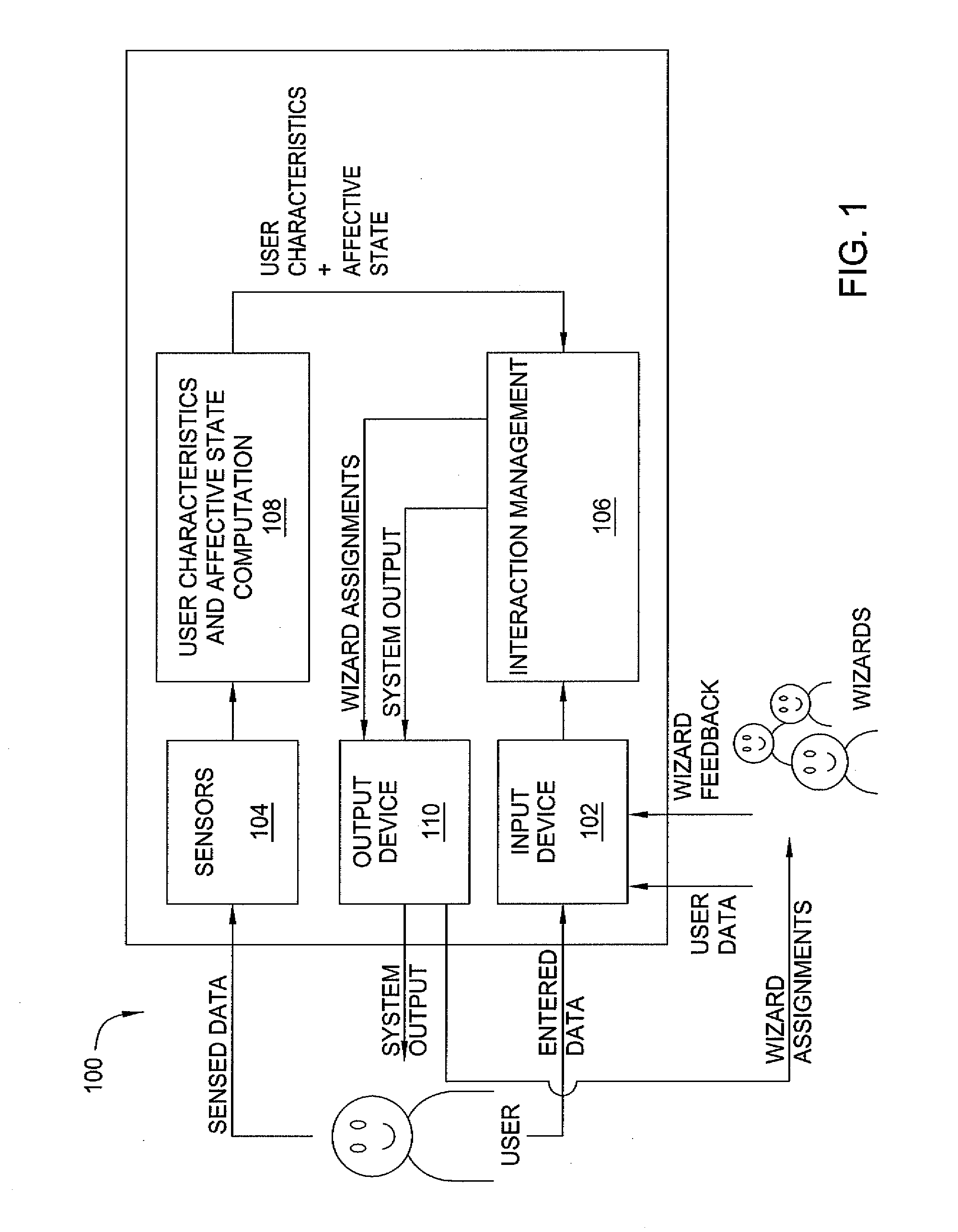
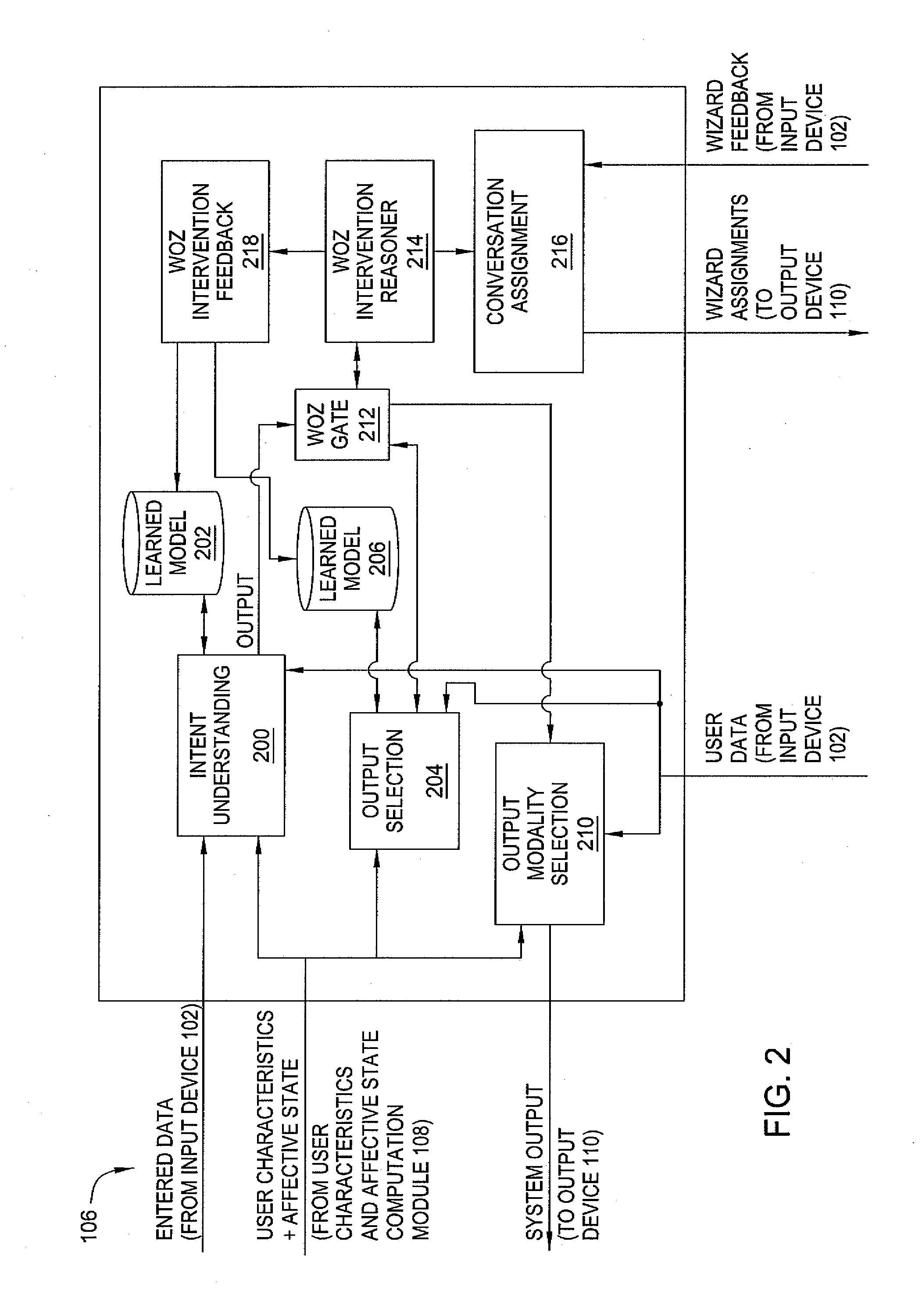
Method and apparatus for exploiting human feedback in an intelligent automated assistant
Owner:HEWLETT PACKARD DEV CO LP +2
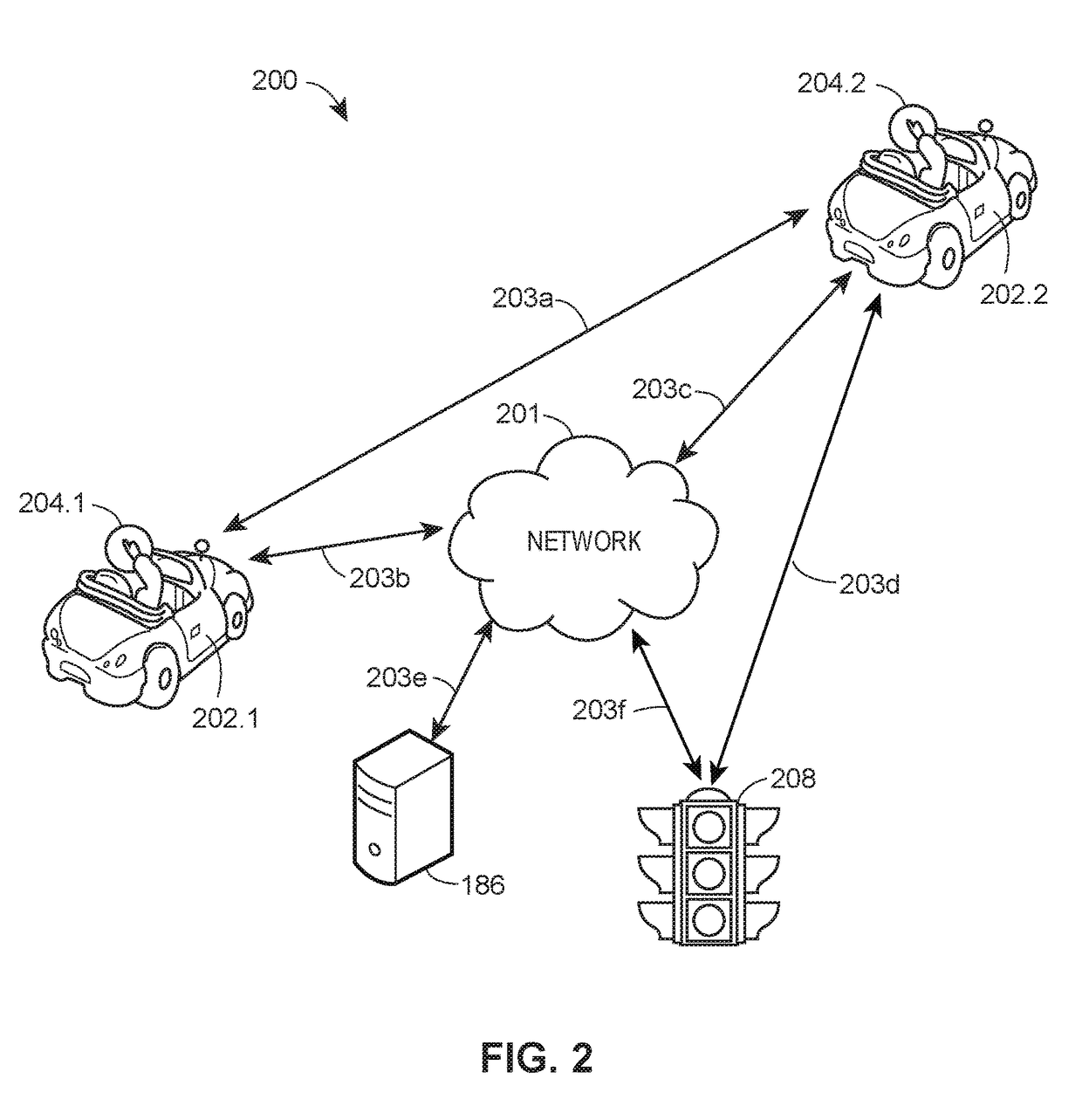
Vehicular traffic alerts for avoidance of abnormal traffic conditions
ActiveUS9805601B1Accurately reflectPrice may become excessiveControlling traffic signalsTelevision system detailsTransceiverEngineering
Methods and systems are described for generating a vehicle-to-vehicle traffic alert. Various aspects may include detecting that an abnormal traffic condition exists in an operating environment of a vehicle and generating a related electronic message. The electronic message may be transmitted via the vehicle's transceiver using a wireless communication to a nearby vehicle to alert the nearby vehicle of the abnormal traffic condition and to allow the nearby vehicle to avoid the abnormal traffic condition.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
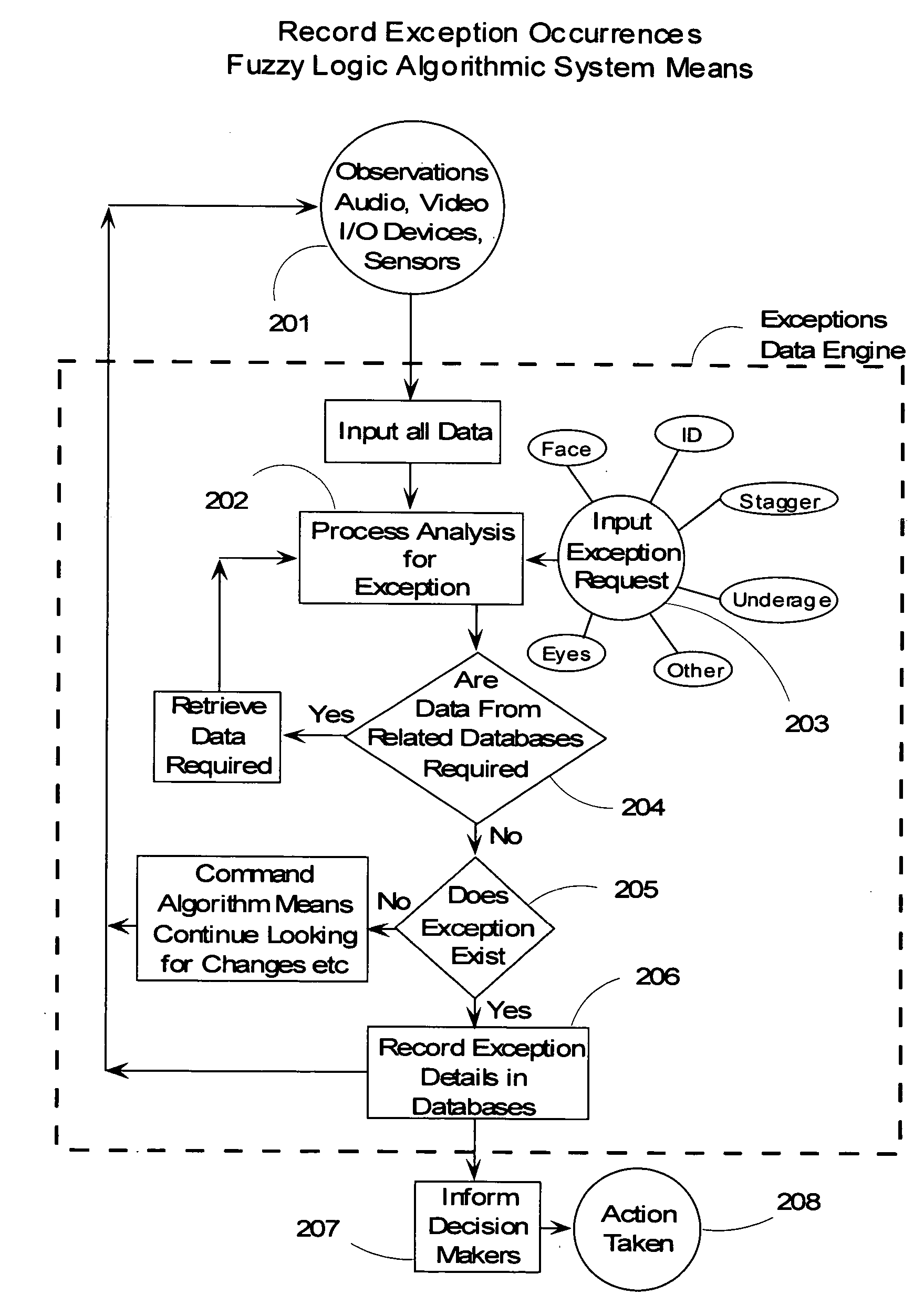
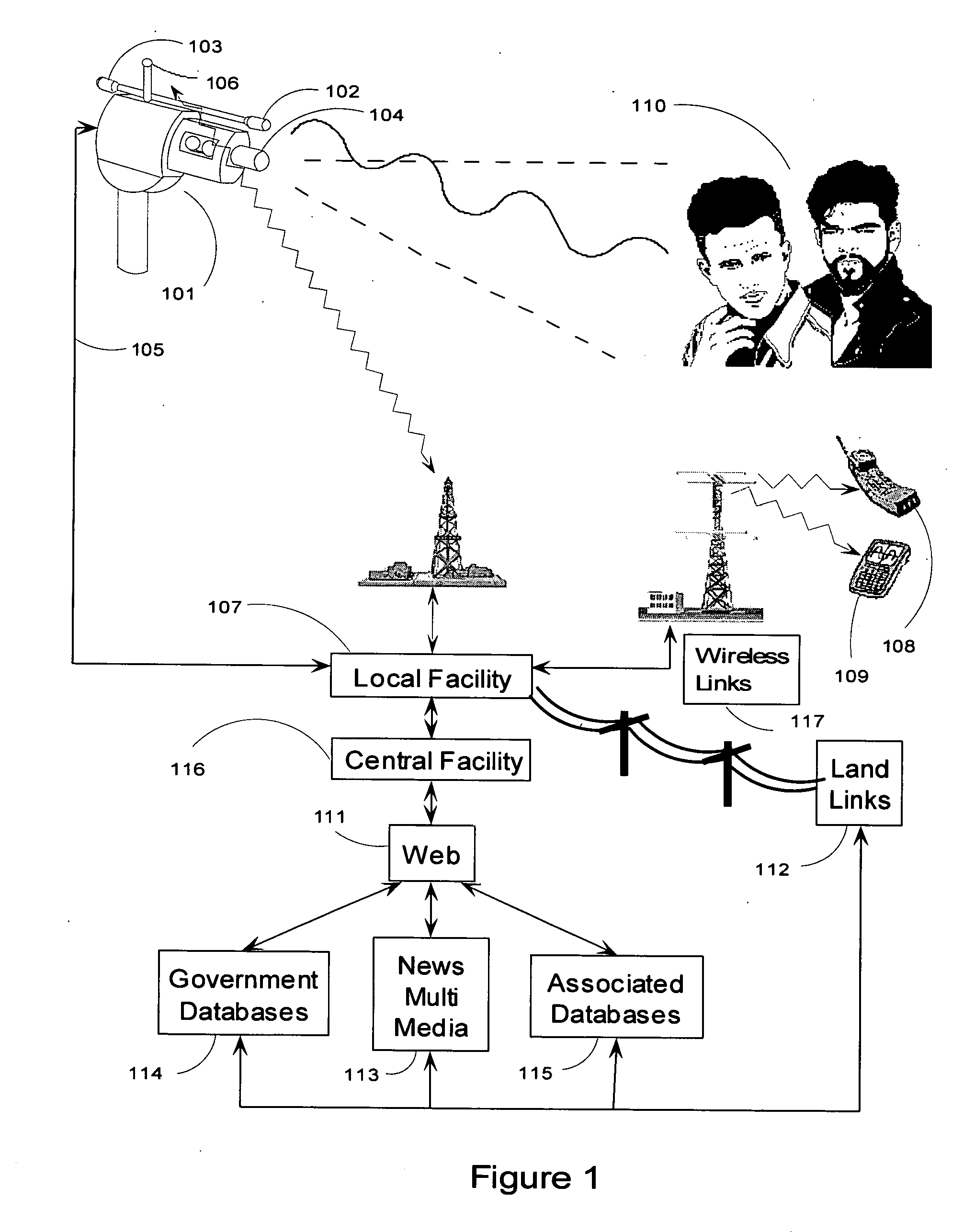
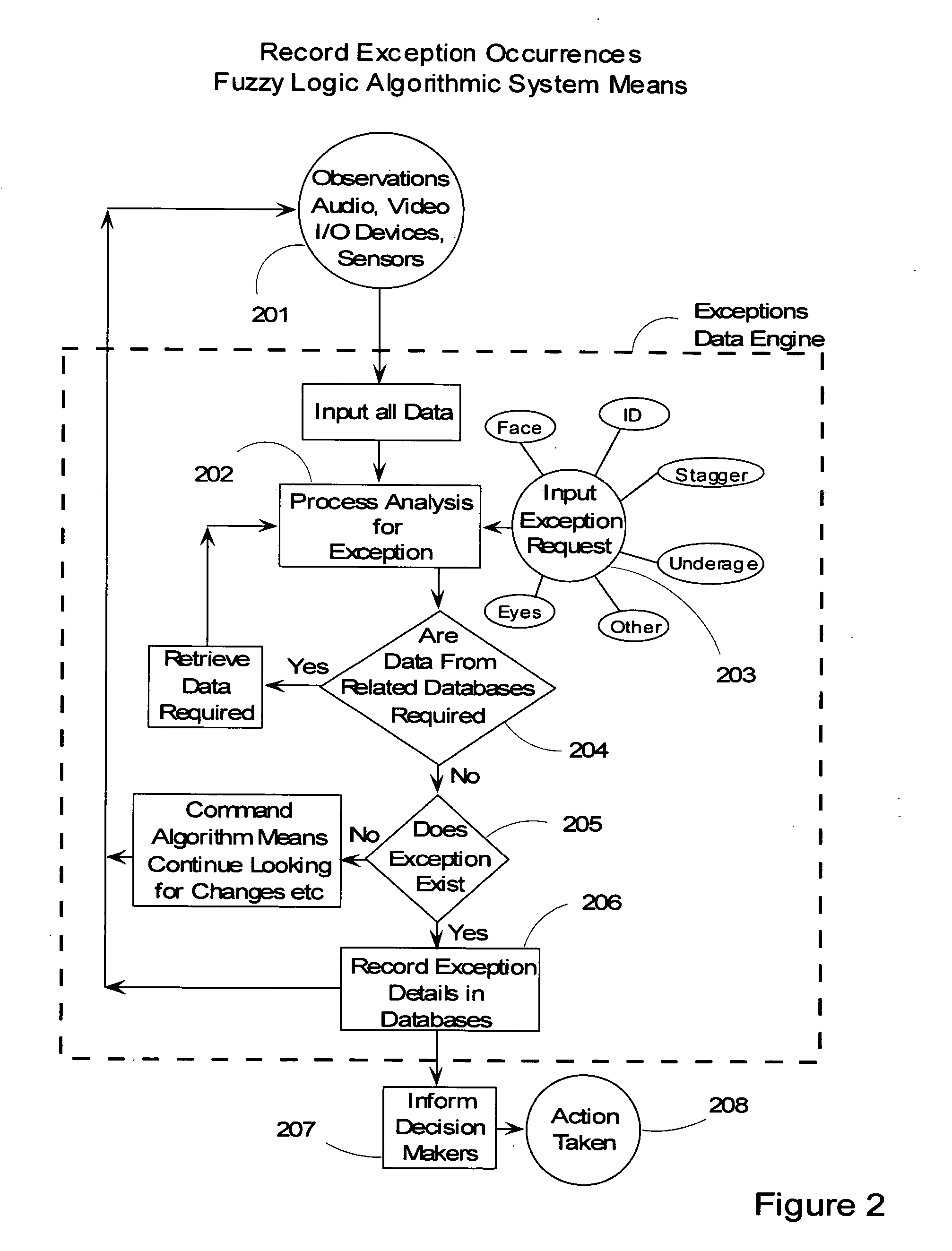
Video surveillance data analysis algorithms, with local and network-shared communications for facial, physical condition, and intoxication recognition, fuzzy logic intelligent camera system
InactiveUS20060190419A1Minimum storage levelReduce data storageDigital computer detailsCharacter and pattern recognitionPattern recognitionVideo monitoring
This invention relates to intelligent video surveillance fuzzy logic neural networks, camera systems with local and network-shared communications for facial, physical condition and intoxication recognition. The device we reveal helps reduce underage drinking by detecting and refusing entrance or service to subjects under legal drinking age. The device we reveal can estimate attention of viewers of advertising, entertainment, displays and the like. The invention also relates to method, and Vision, Image and related-data, database-systems to reduce the volume of surveillance data through automatically recognizing and recording only occurrences of exceptions and elimination of non-events thereby achieving a reduction factor of up to 60,000. This invention permits members of the LastCall™ Network to share their databases of the facial recognition and identification of subjects recorded in the exception occurrences with participating members' databases: locally, citywide, nationally and internationally, depending upon level of sharing permission.
Owner:BUNN FR E +1
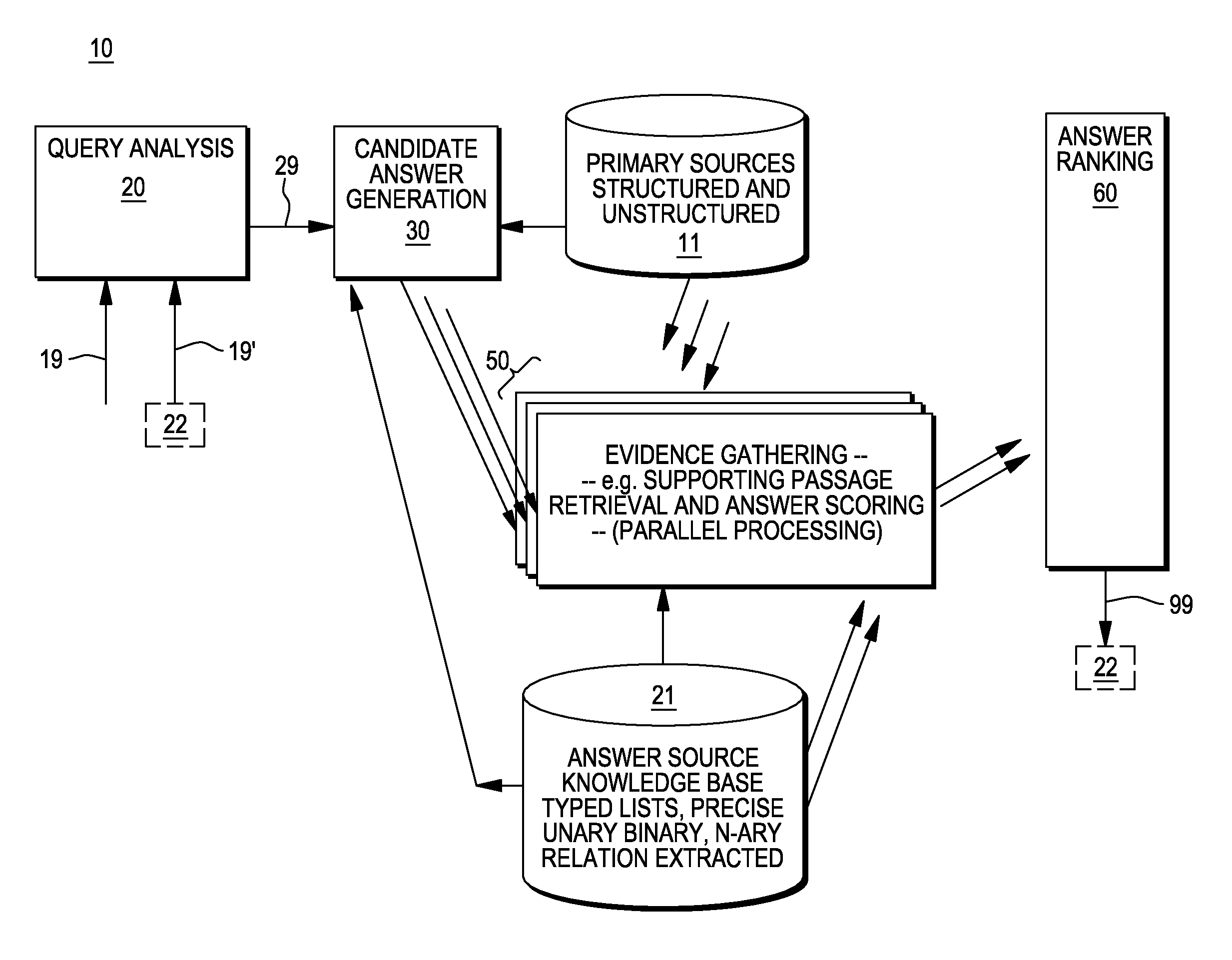
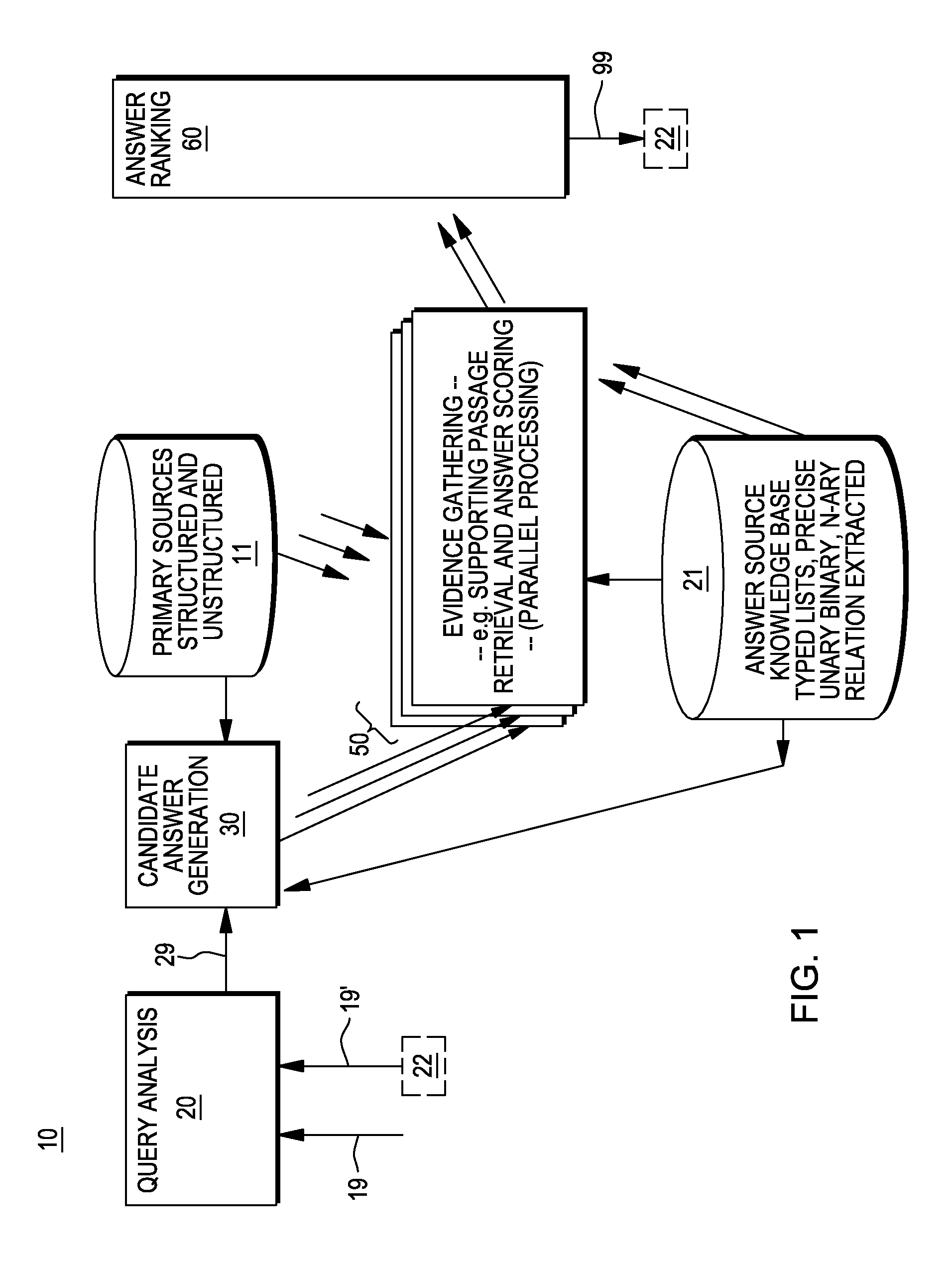
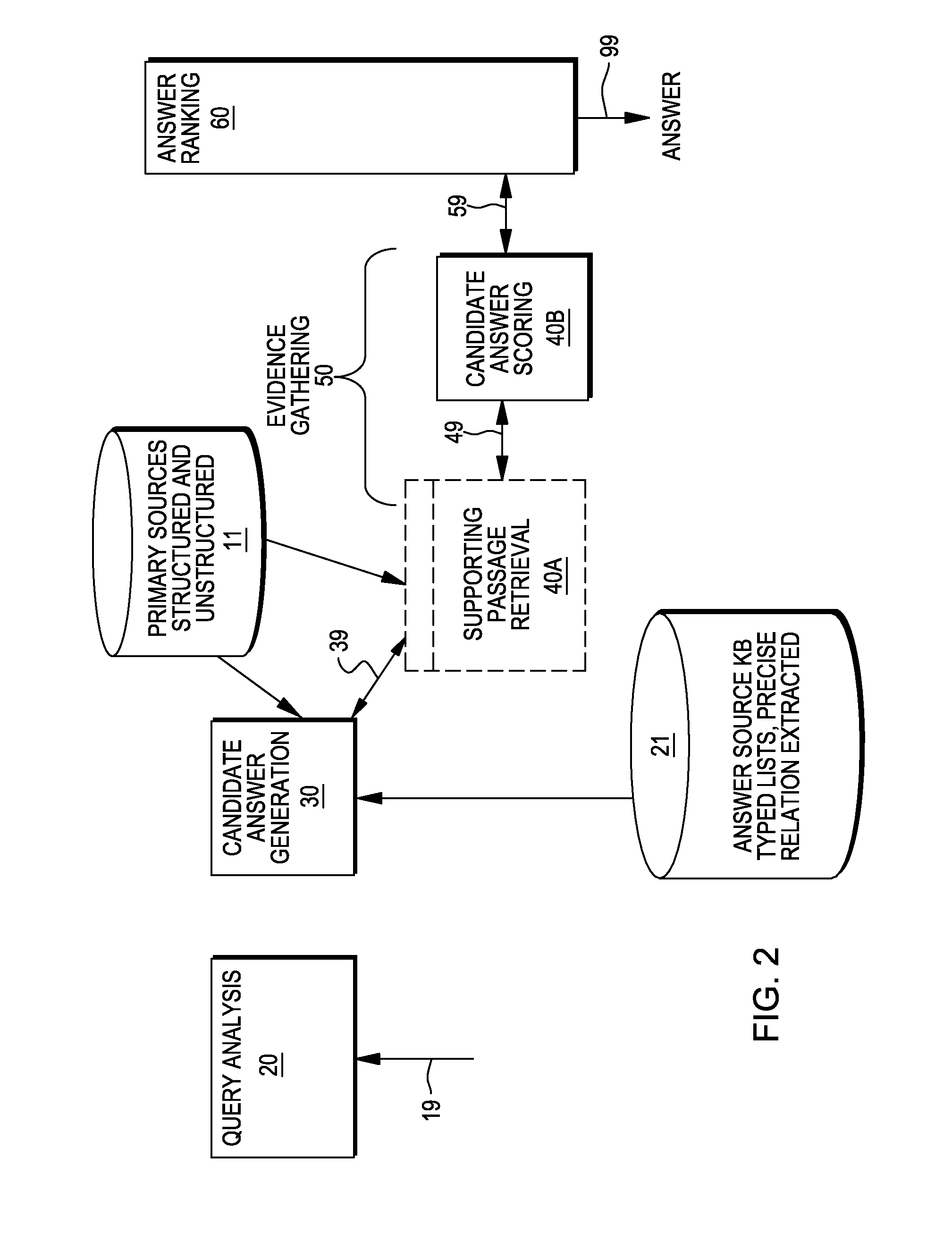
Providing answers to questions using multiple models to score candidate answers
ActiveUS20130007055A1Digital data information retrievalDigital data processing detailsRankingMultiple Models
A method, system and computer program product for generating answers to questions. In one embodiment, the method comprises receiving an input query; conducting a search to identify candidate answers to the input query, and producing a plurality of scores for each of the candidate answers. For each of the candidate answers, one, of a plurality of candidate ranking functions, is selected. This selected ranking function is applied to the each of the candidate answers to determine a ranking for the candidate answer based on the scores for that candidate answer. One or more of the candidate answers is selected, based on the rankings for the candidate answers, as one or more answers to the input query. In an embodiment, the ranking function selection is performed using information about the question. In an embodiment, the ranking function selection is performed using information about each answer.
Owner:INT BUSINESS MASCH CORP
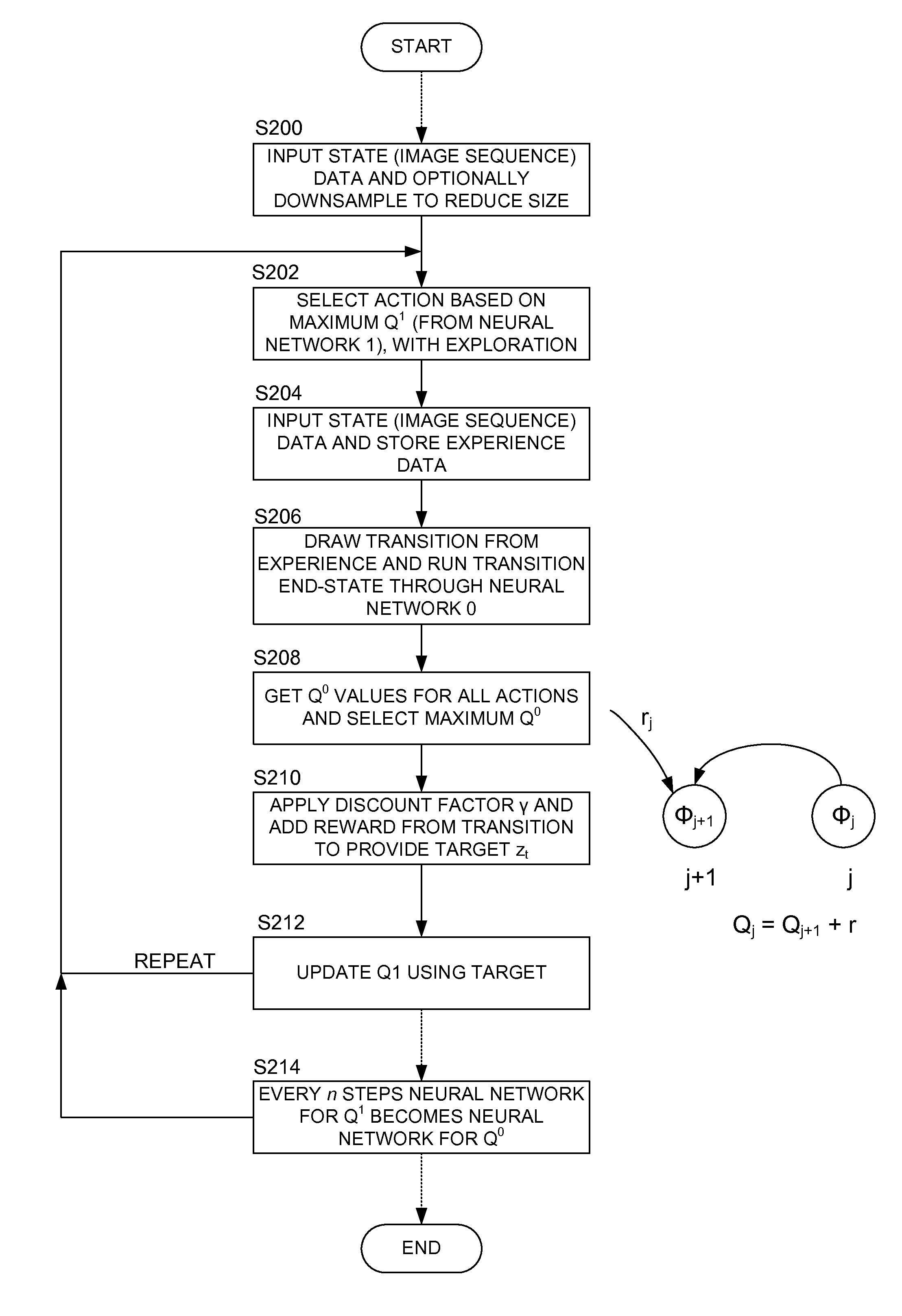
Methods and apparatus for reinforcement learning
ActiveUS20150100530A1Reduce computing costLarge data setDigital computer detailsArtificial lifeAlgorithmReinforcement learning
Owner:DEEPMIND TECH LTD
Robust anomaly detection and regularized domain adaptation of classifiers with application to internet packet-flows
InactiveUS20120284791A1Maximize aggregate statistical significanceMaximizesMathematical modelsMemory loss protectionCredit cardAlgorithm
Sound, robust methods identify the most suitable, parsimonious set of tests to use with respect to prioritized, sequential anomaly detection in a collected batch of sample data. While the focus is on detecting anomalies in network traffic flows and classifying network traffic flows into application types, the methods are also applicable to other anomaly detection and classification application settings, including detecting email spam, (e.g. credit card) fraud detection, detecting imposters, unusual event detection (for example, in images and video), host-based computer intrusion detection, detection of equipment or complex system failures, as well as of anomalous measurements in scientific experiments.
Owner:PENN STATE RES FOUND
Malicious software detection in a computing system
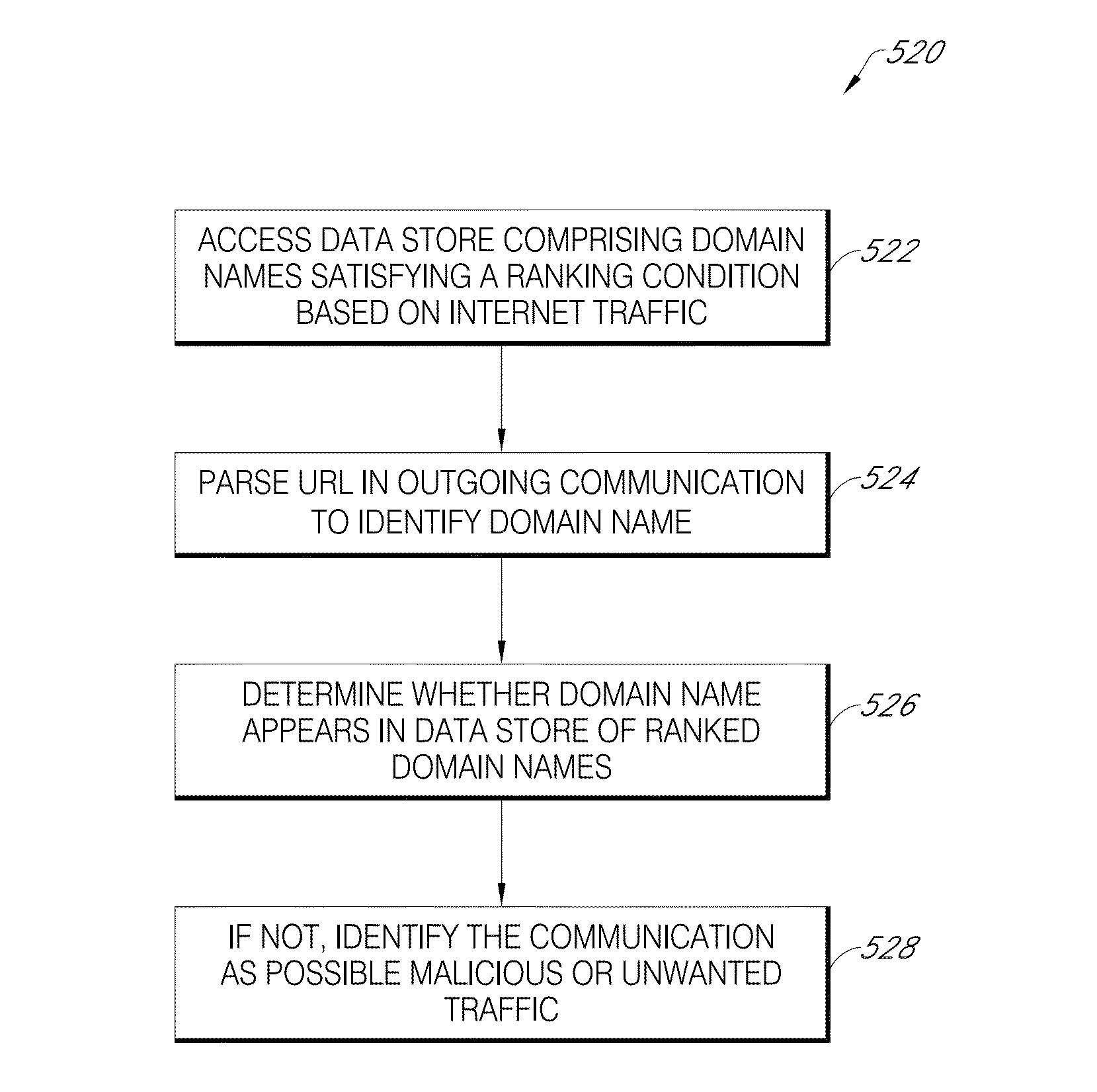
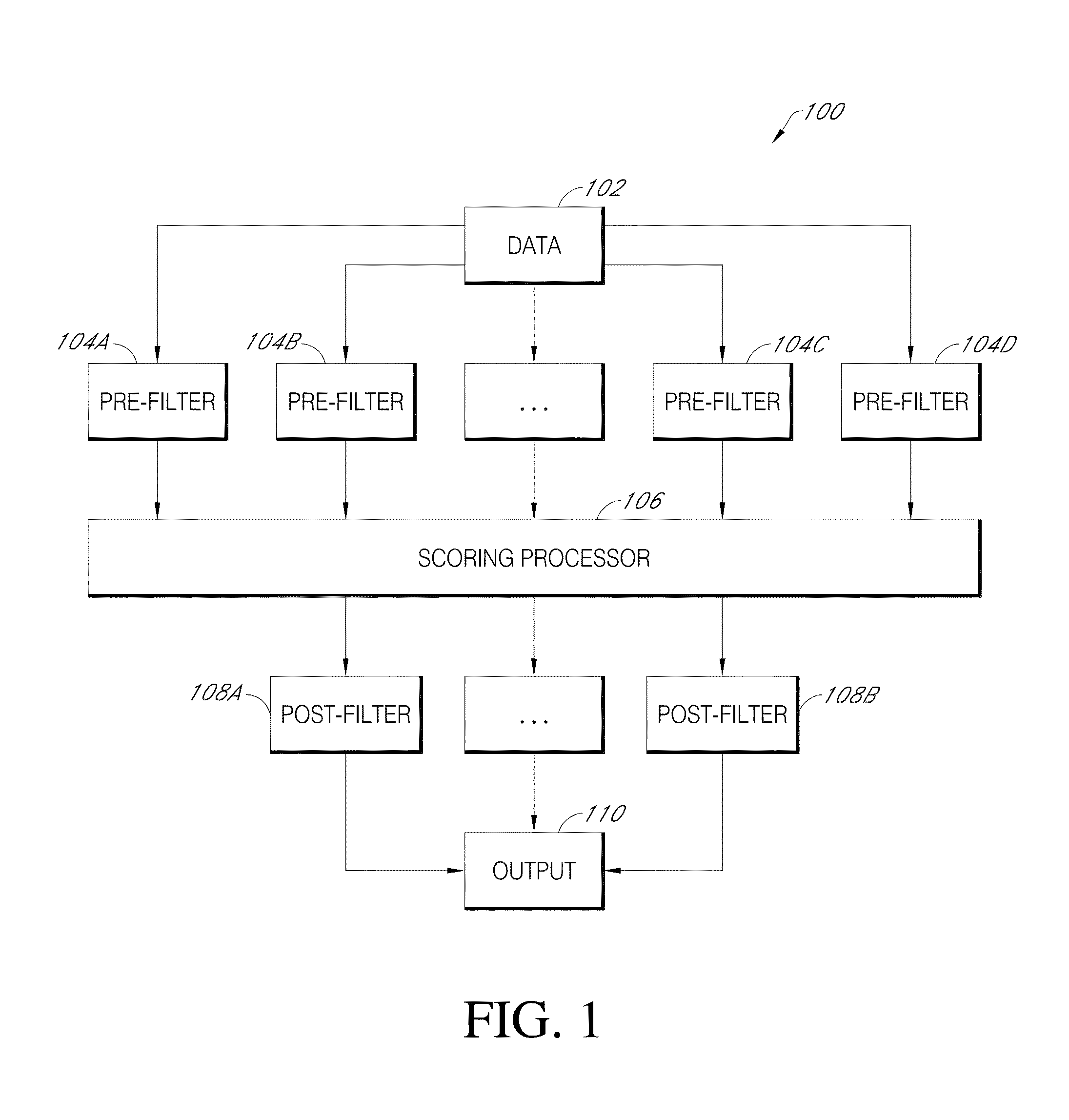
ActiveUS9043894B1Function increaseConsume significant storageComputer security arrangementsMultiple digital computer combinationsComputerized systemMalware
A computer system identifies malicious Uniform Resource Locator (URL) data items from a plurality of unscreened data items that have not been previously identified as associated with malicious URLs. The system can execute a number of pre-filters to identify a subset of URLs in the plurality of data items that are likely to be malicious. A scoring processor can score the subset of URLs based on a plurality of input vectors using a suitable machine learning model. Optionally, the system can execute one or more post-filters on the score data to identify data items of interest. Such data items can be fed back into the system to improve machine learning or can be used to provide a notification that a particular resource within a local network is infected with malicious software.
Owner:PALANTIR TECHNOLOGIES
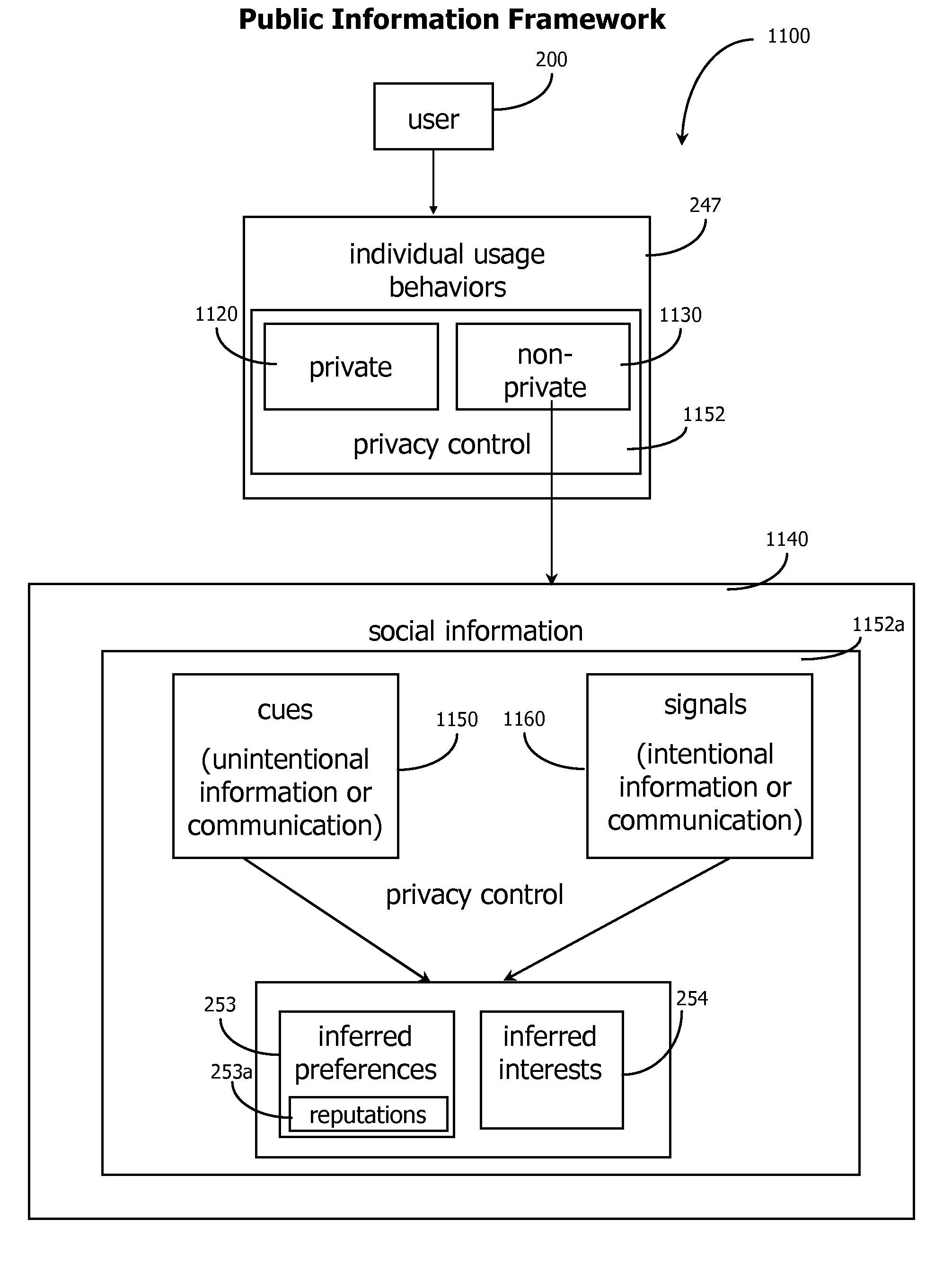
Adaptive Social Computing Methods
ActiveUS20060200435A1Easy to adaptEfficiently navigateDigital computer detailsMachine learningVision basedSelf adaptive
Methods of applying adaptive social computing systems are disclosed. The social computing systems include capabilities to generate adaptive recommendations and representations of social networks derived, at least in part, from inferences of the preferences and interests of system users based on a plurality of usage behaviors, spanning a plurality of usage behavior categories. The behavioral categories include system navigation behaviors, content referencing behaviors, collaborative behaviors, and the monitoring of physical location and changes in location. Privacy control functions and compensatory functions related to insincere usage behaviors can be applied. Adaptive recommendation delivery can take the form of visual-based or audio-based formats.
Owner:WORLD ASSETS CONSULTING AG
Inferring user preferences from an internet based social interactive construct
ActiveUS20100312724A1Improve future questionImprove decisionDigital data processing detailsNatural language data processingGraphicsInternet based
In embodiments of the present invention improved capabilities are described for a computer program product embodied in a computer readable medium that, when executing on one or more computers, helps determine an unknown user's preferences through the use of internet based social interactive graphical representations on a computer facility by performing the steps of (1) ascertaining preferences of a plurality of users who are part of an internet based social interactive construct, wherein the plurality of users become a plurality of known users; (2) determining the internet based social interactive graphical representation for the plurality of known users; and (3) inferring the preferences of an unknown user present in the internet based social interactive graphical representation of the plurality of known users based on the interrelationships between the unknown user and the plurality of known users within the graphical representation.
Owner:EBAY INC
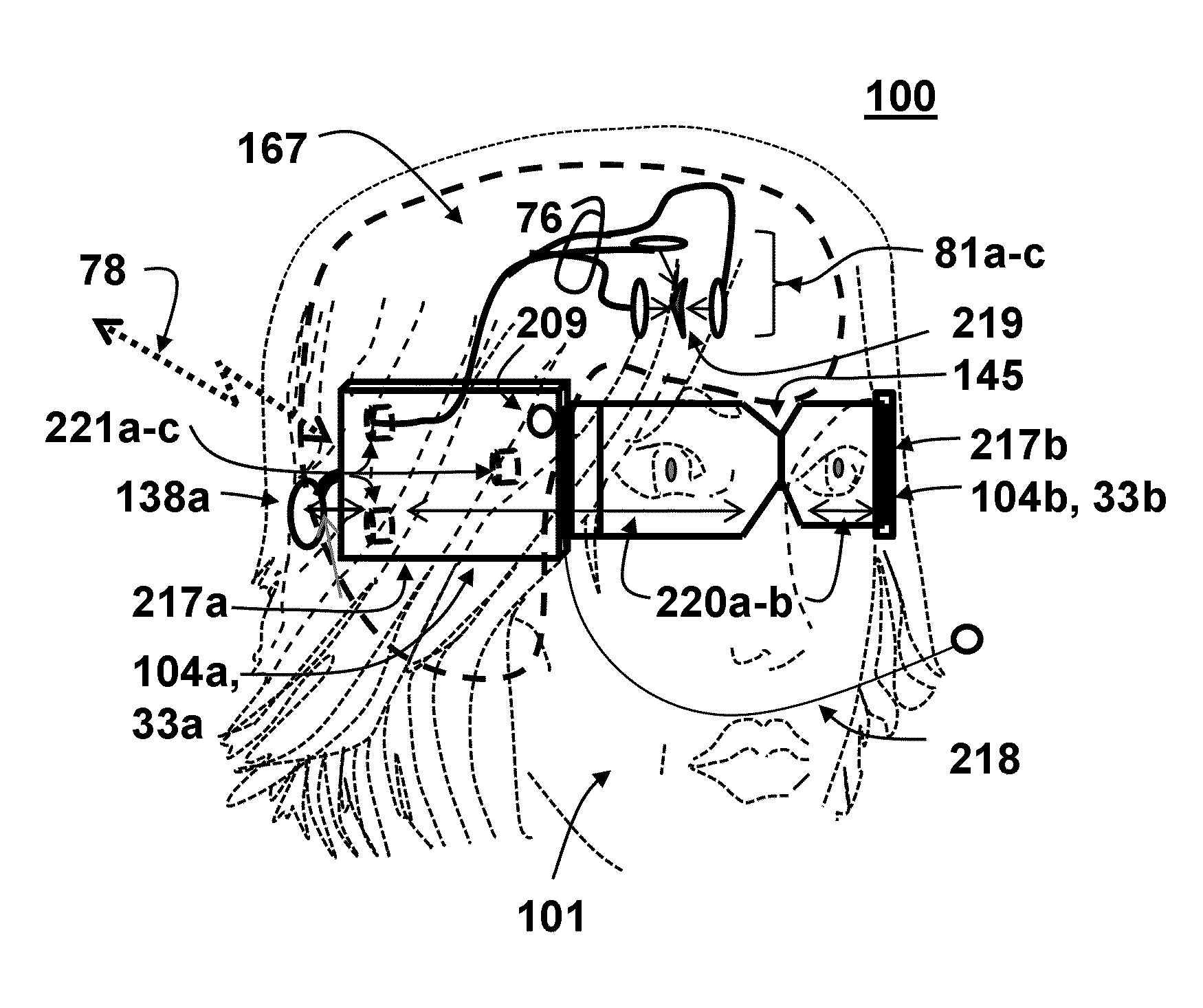
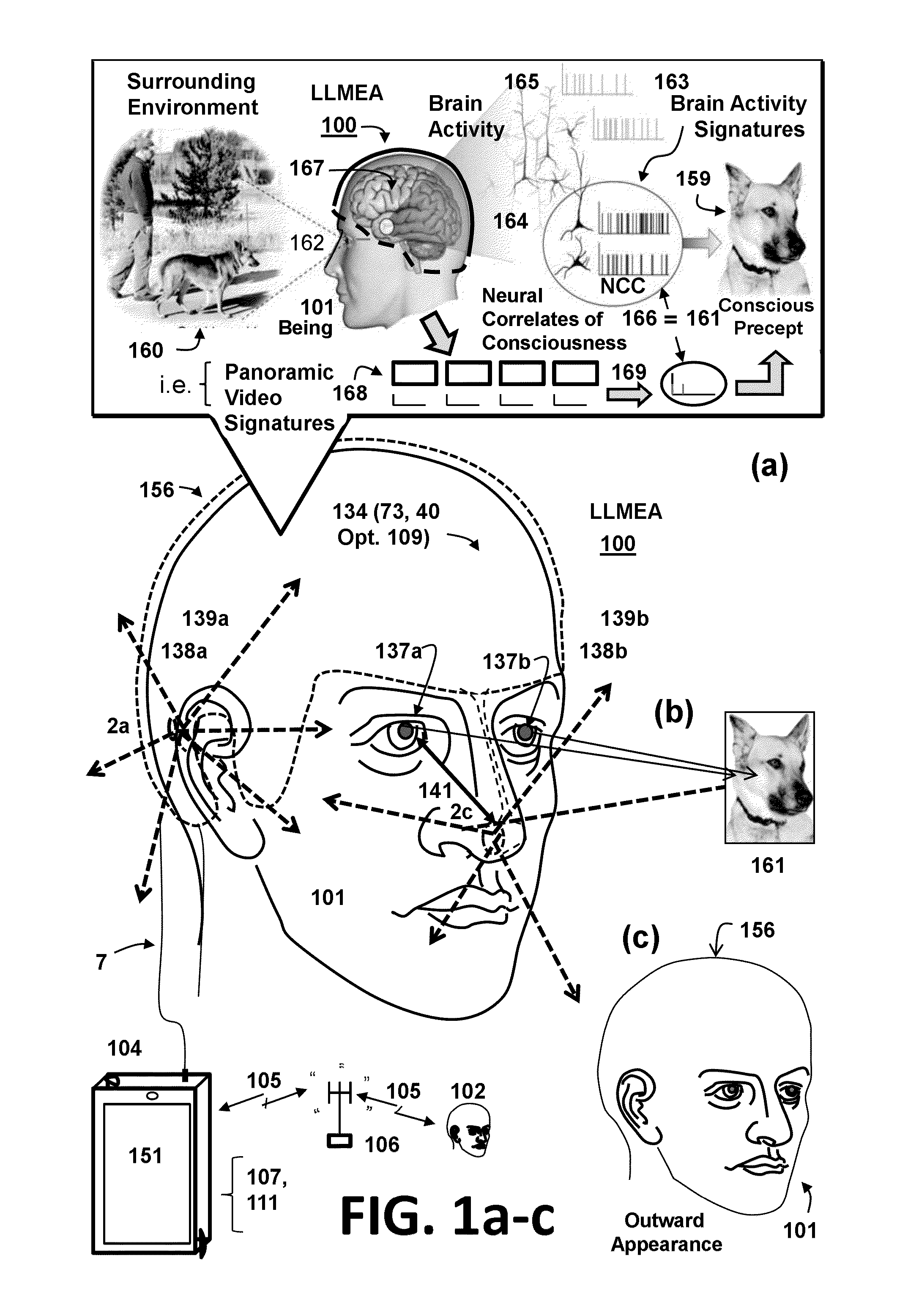
Human environment life logging assistant virtual esemplastic network system and method
ActiveUS20130063550A1Promote reconstructionHigh resolutionTelevision system detailsBioelectric signal measurementRelational databaseDisplay device
A user borne portable personal digital assistant, a brain activity sensing system, a surround sensing system, and correlation system are provided for video logging and memory enhancement. Signatures simultaneously input from the brain system and surround system representing the environment around the user at a given time and place are correlated into a historical relational database. Real-time query means for identifying correlations between the historical database and current internal and external signatures as the user moves through space and time are provided. Body integrated sensor, processing, and display devices are provided to accomplish statistically valid neural representations within the brain correlated to externally originated geo-spatial information and sensory representations surrounding the user. Methods and systems are disclosed for using the resultant data from the data logging system as input into a simulation, stimulation, search engine, social network, telecommunication, or emulation system within a biological, mechanical, and bio-mechanical system.
Owner:VIRTUAL VIDEO BY RITCHEY LLC
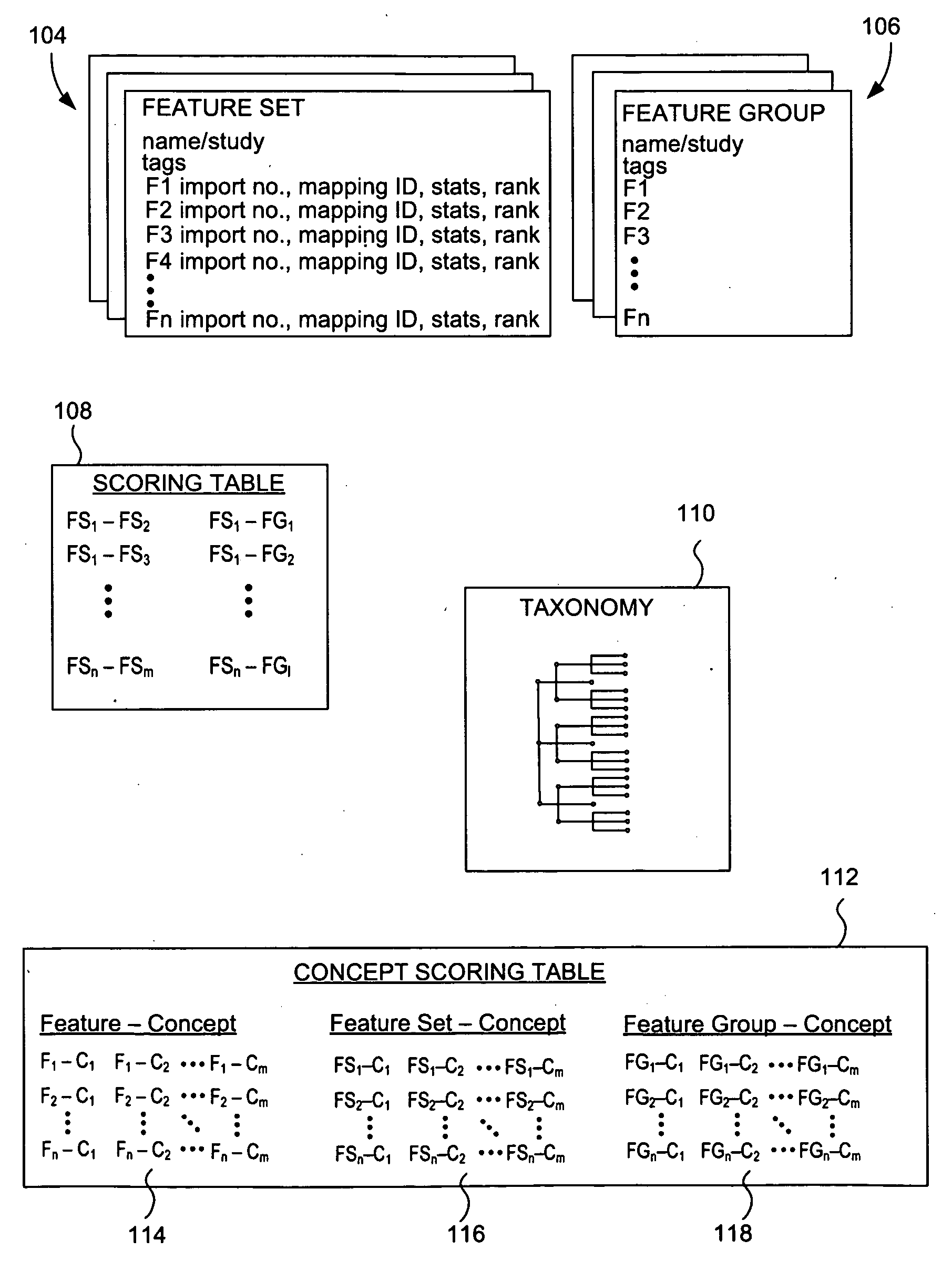
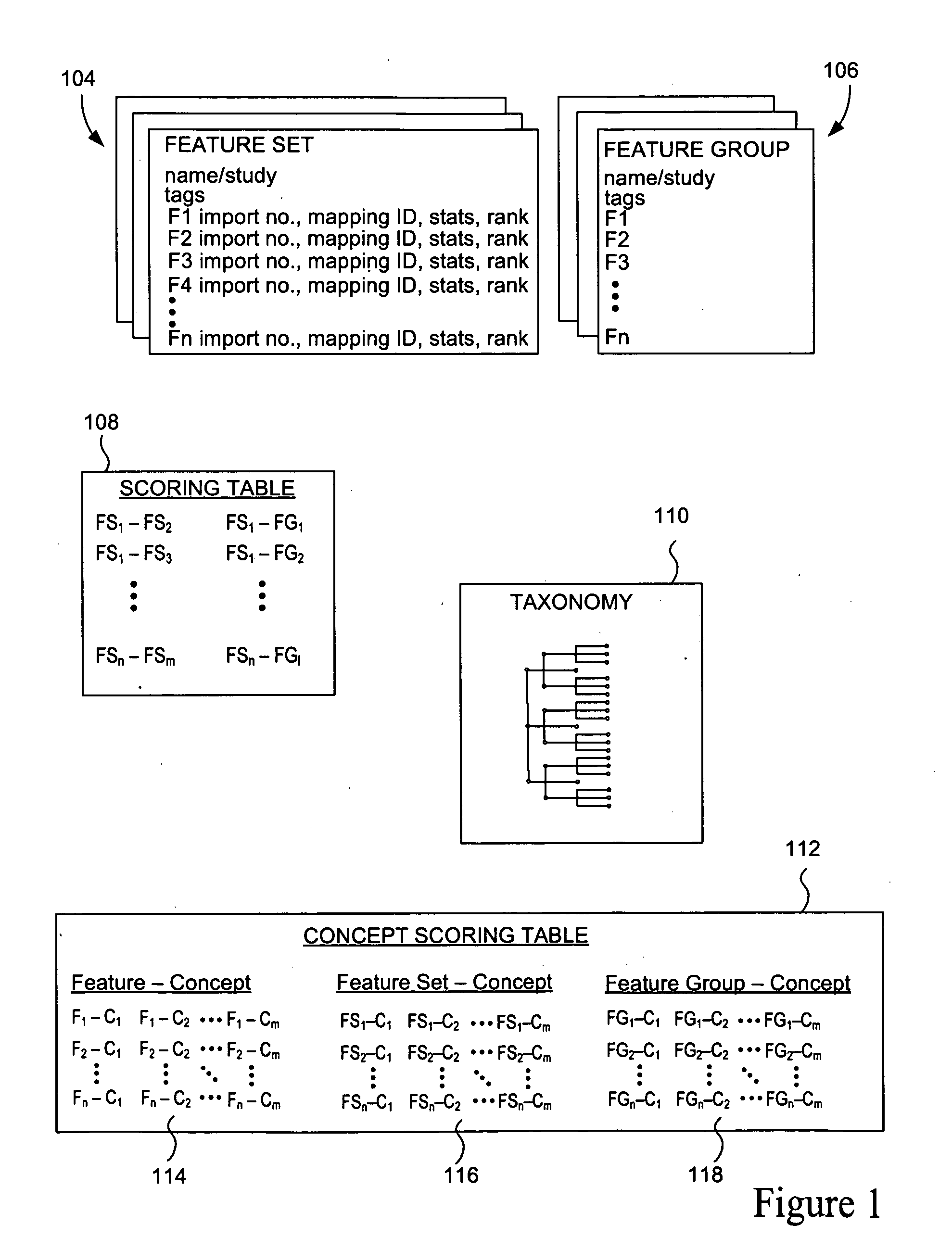
Categorization and filtering of scientific data
ActiveUS20090222400A1Improve efficiencyChaos modelsNon-linear system modelsBiological bodyMeta-analysis
The present invention relates to methods, systems and apparatus for capturing, integrating, organizing, navigating and querying large-scale data from high-throughput biological and chemical assay platforms. It provides a highly efficient meta-analysis infrastructure for performing research queries across a large number of studies and experiments from different biological and chemical assays, data types and organisms, as well as systems to build and add to such an infrastructure. According to various embodiments, methods, systems and interfaces for associating experimental data, features and groups of data related by structure and / or function with chemical, medical and / or biological terms in an ontology or taxonomy are provided. According to various embodiments, methods, systems and interfaces for filtering data by data source information are provided, allowing dynamic navigation through large amounts of data to find the most relevant results for a particular query.
Owner:ILLUMINA INC
Mobile user borne brain activity data and surrounding environment data correlation system
ActiveUS9101279B2High resolutionEasy to navigateTelevision system detailsBioelectric signal measurementActivity sensingHuman–computer interaction
A mobile user borne brain activity data and surrounding environment data correlation system comprising a brain activity sensing subsystem, a recording subsystem, a measurement computer subsystem, a user sensing subsystem, a surrounding environment sensing subsystem, a correlation subsystem, a user portable electronic device, a non-transitory computer readable medium, and a computer processing device. The mobile user borne system collects and records brain activity data and surrounding environment data and statistically correlates and processes the data for communicating the data into a recipient biological, mechanical, or bio-mechanical system.
Owner:VIRTUAL VIDEO BY RITCHEY LLC
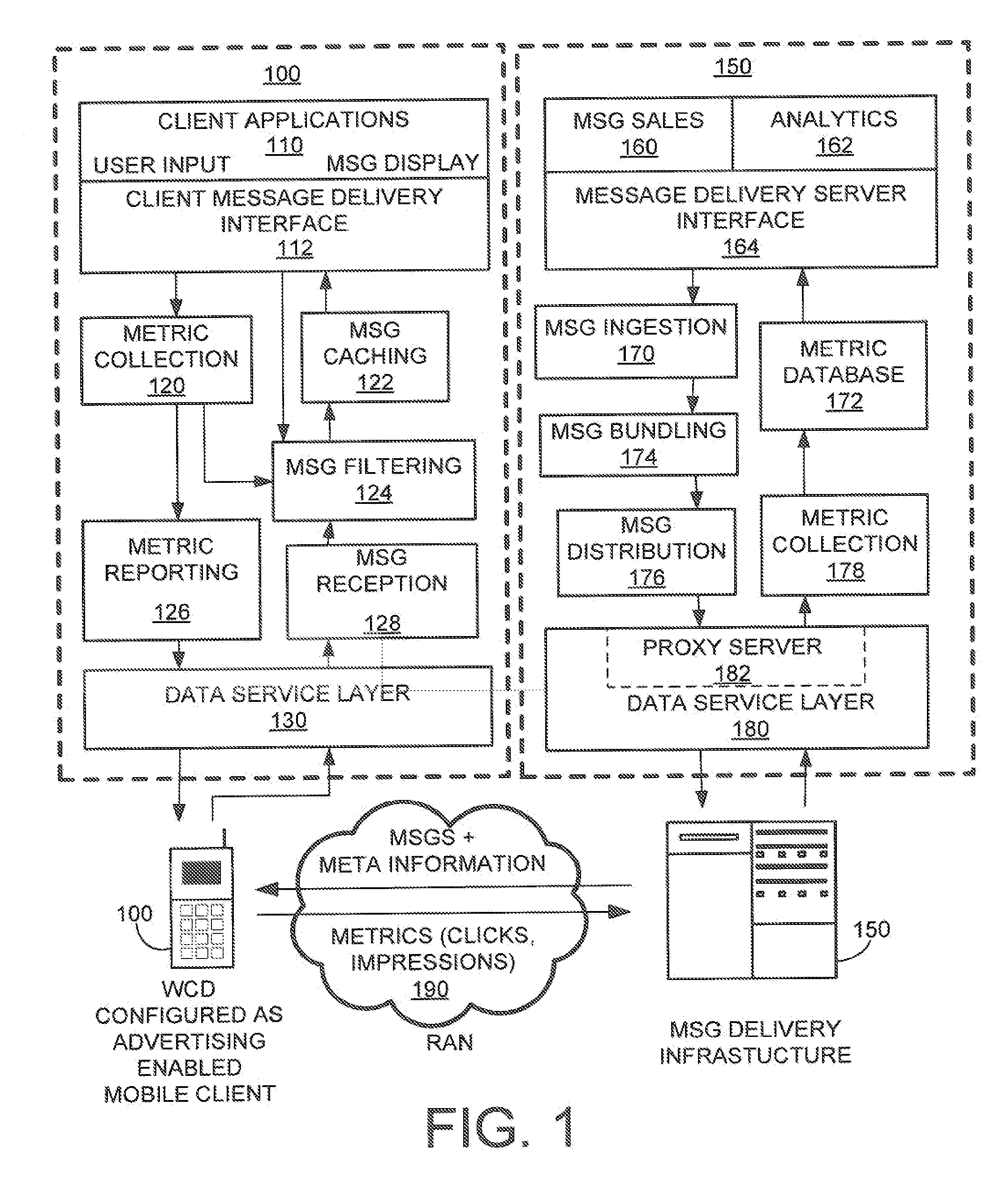
Method and system for user profile match indication in a mobile environment
Methods and systems for determining a suitability for a mobile client to display information are disclosed. For example, a method for determining a suitability for a mobile client to receive a targeted content message includes generating user profile data by the mobile client, receiving a set of target profile data associated with the targeted content message, the set of target profile data being descriptive of the targeted content message, comparing the user profile data with the target set of profile data to produce a set of confidence-level data, a target set of profile data describing the content of a respective targeted-content message, and storing the targeted content message in the mobile client based upon the set of confidence-level data.
Owner:QUALCOMM INC
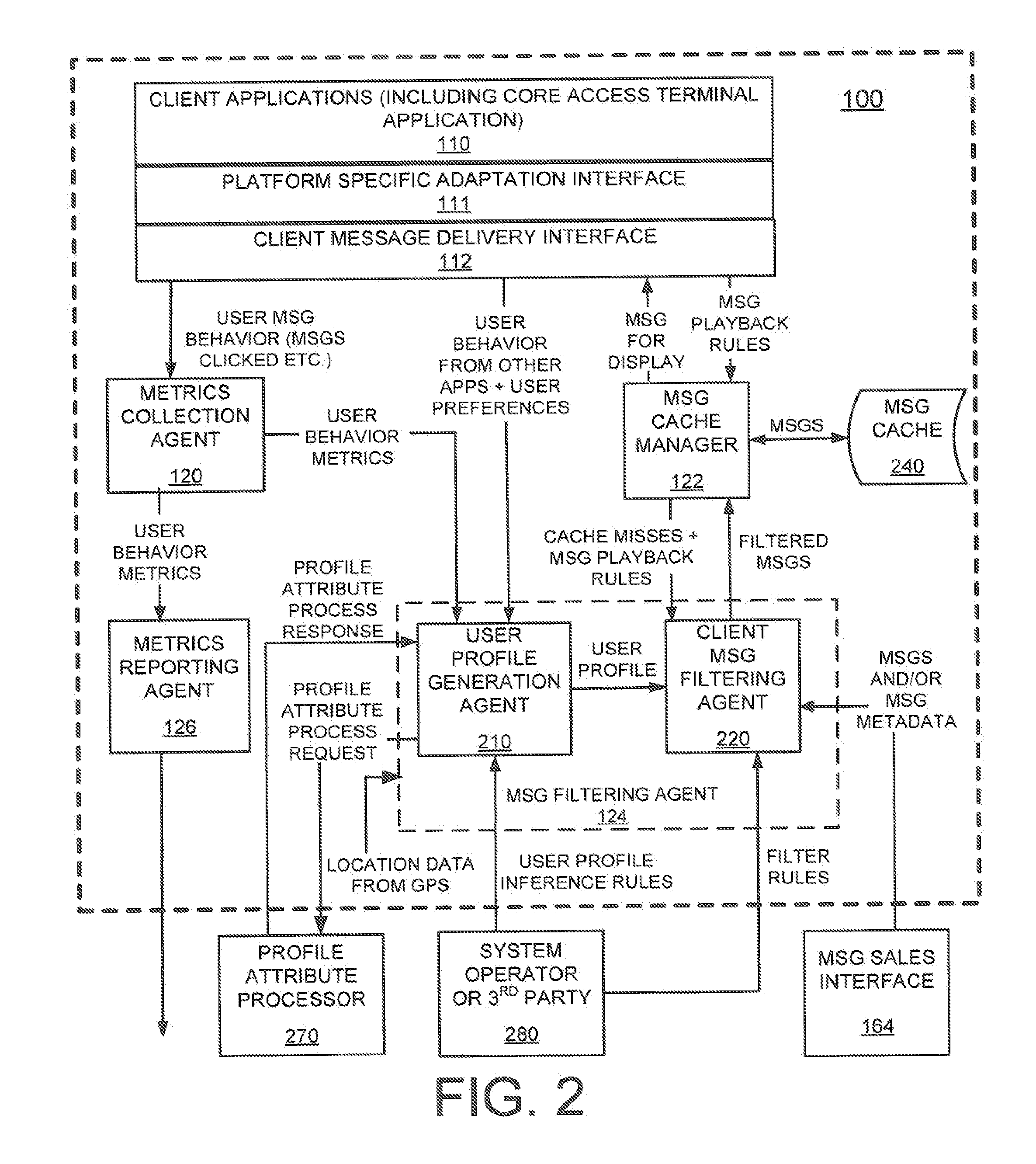
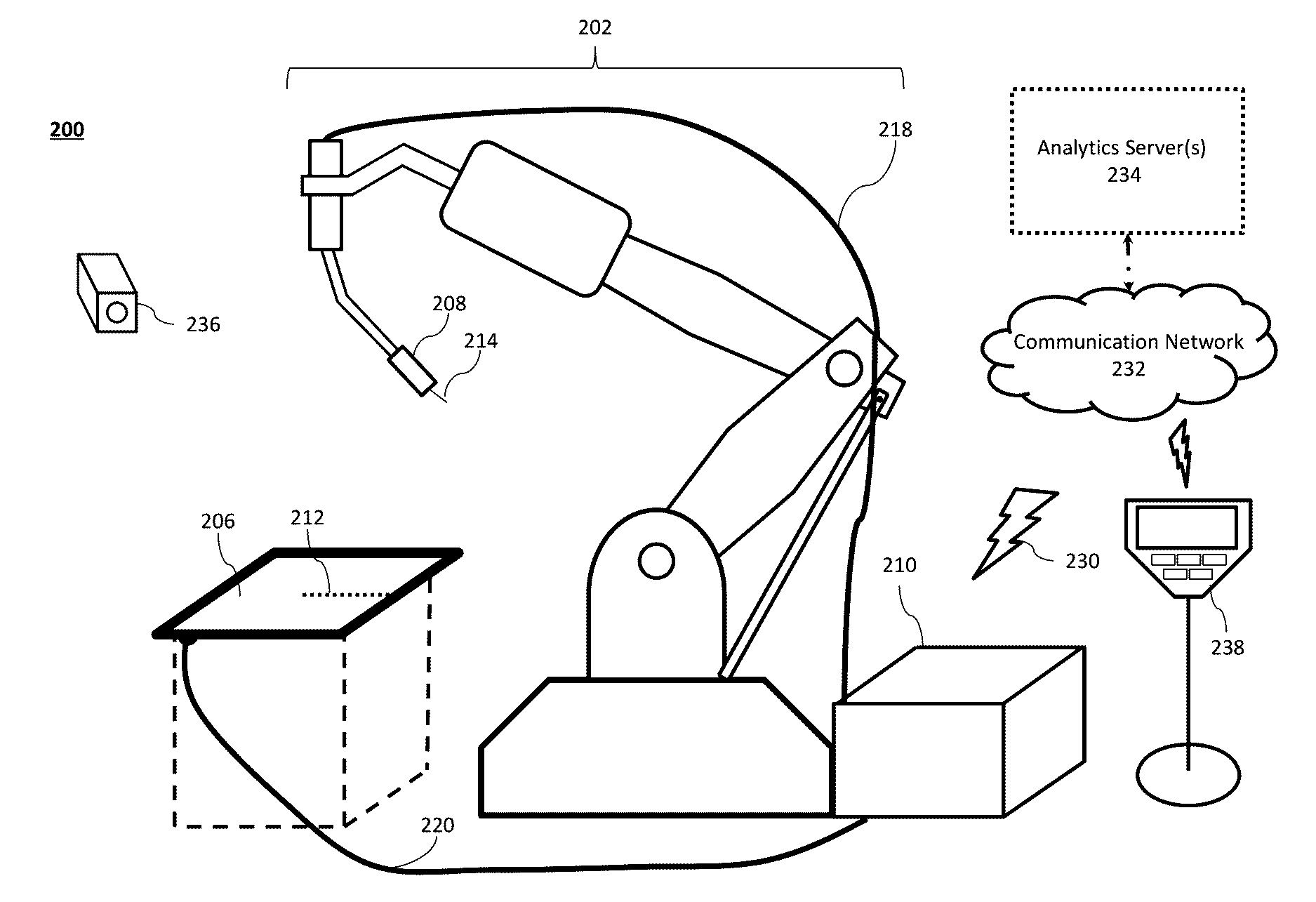
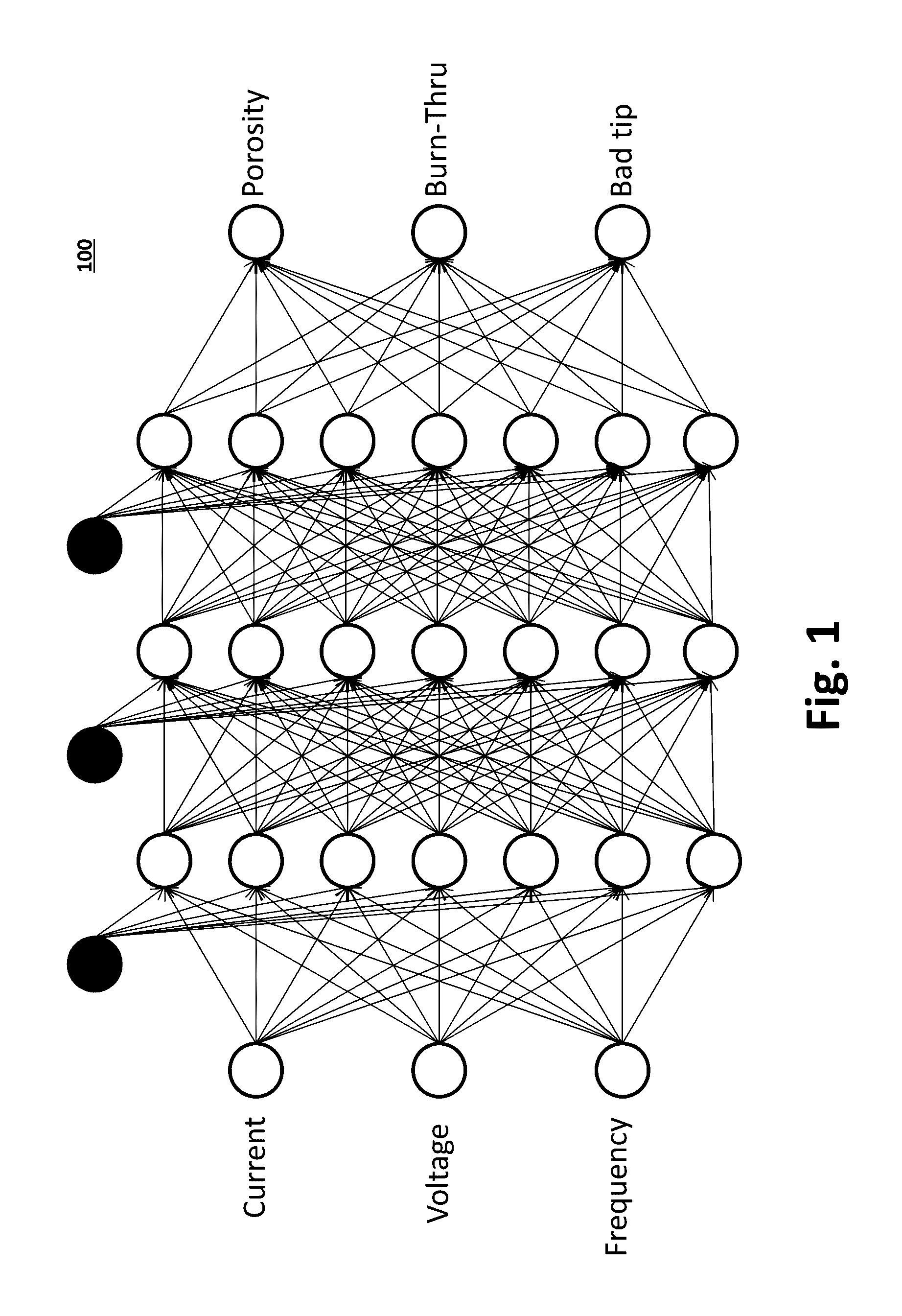
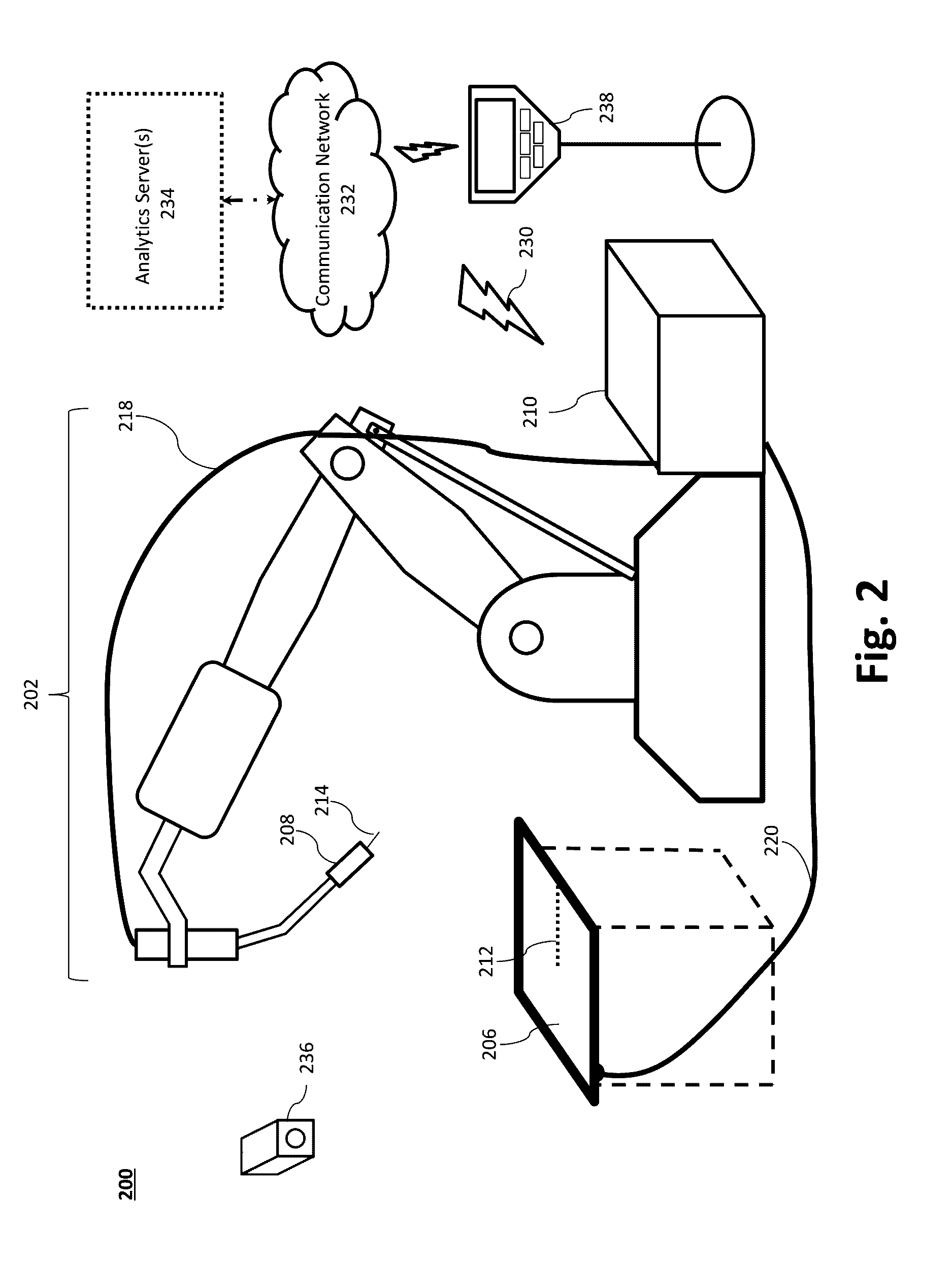
System and Method to Facilitate Welding Software as a Service
ActiveUS20170032281A1Minimizing human interactionScalable and cost-effective mass customization approachProgramme controlTesting/monitoring control systemsCommunication interfaceData set
A weld production knowledge system for processing welding data collected from one of a plurality of welding systems, the weld production knowledge system comprising a communication interface communicatively coupled with a plurality of welding systems situated at one or more physical locations. The communication interface may be configured to receive, from one of said plurality of welding systems, welding data associated with a weld. The weld production knowledge system may comprise an analytics computing platform operatively coupled with the communication interface and a weld data store. The weld data store employs a dataset comprising (1) welding process data associated with said one or more physical locations, and / or (2) weld quality data associated with said one or more physical locations. The analytics computing platform may employ a weld production knowledge machine learning algorithm to analyze the welding data vis-à-vis the weld data store to identify a defect in said weld.
Owner:ILLINOIS TOOL WORKS INC
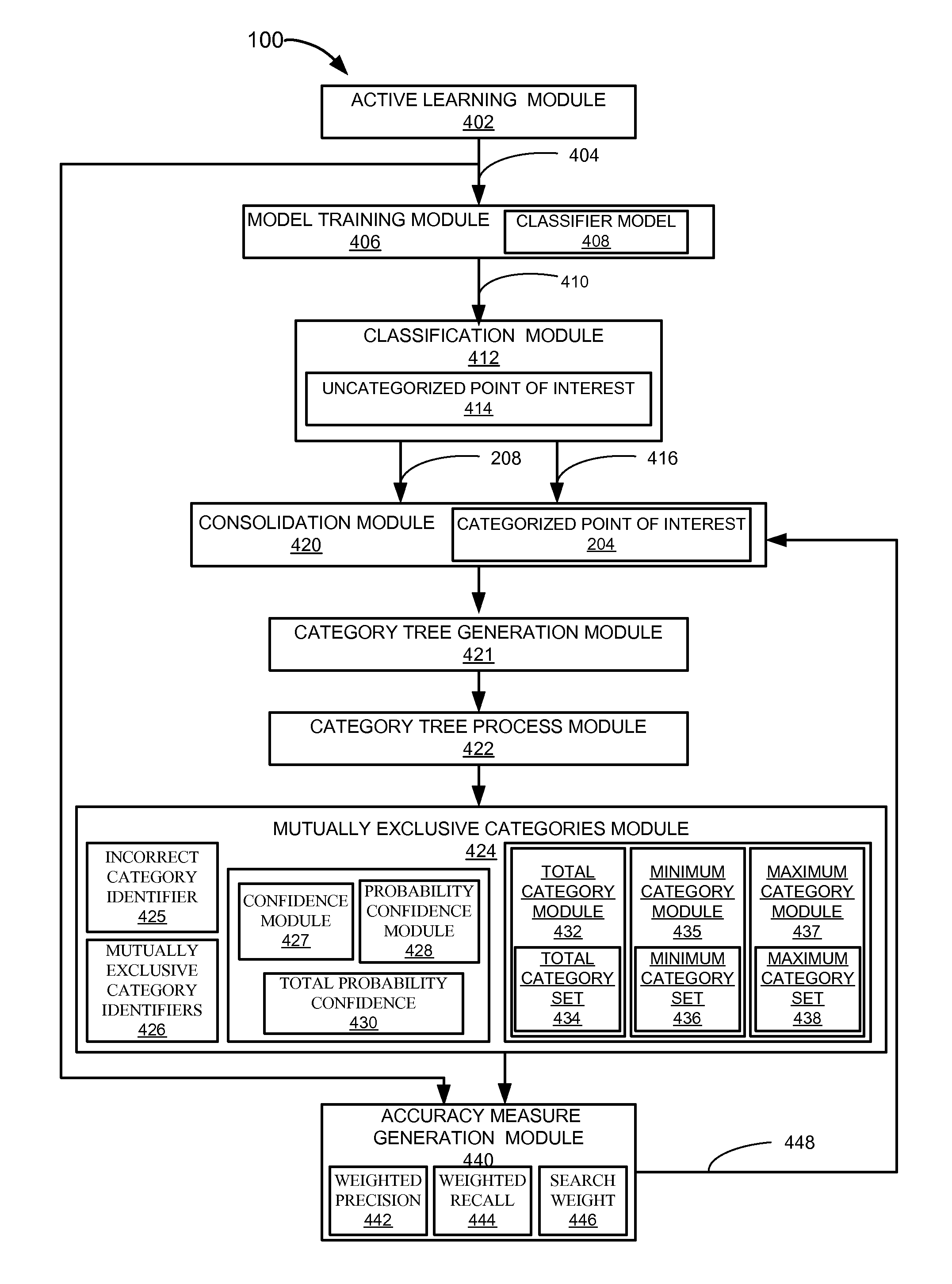
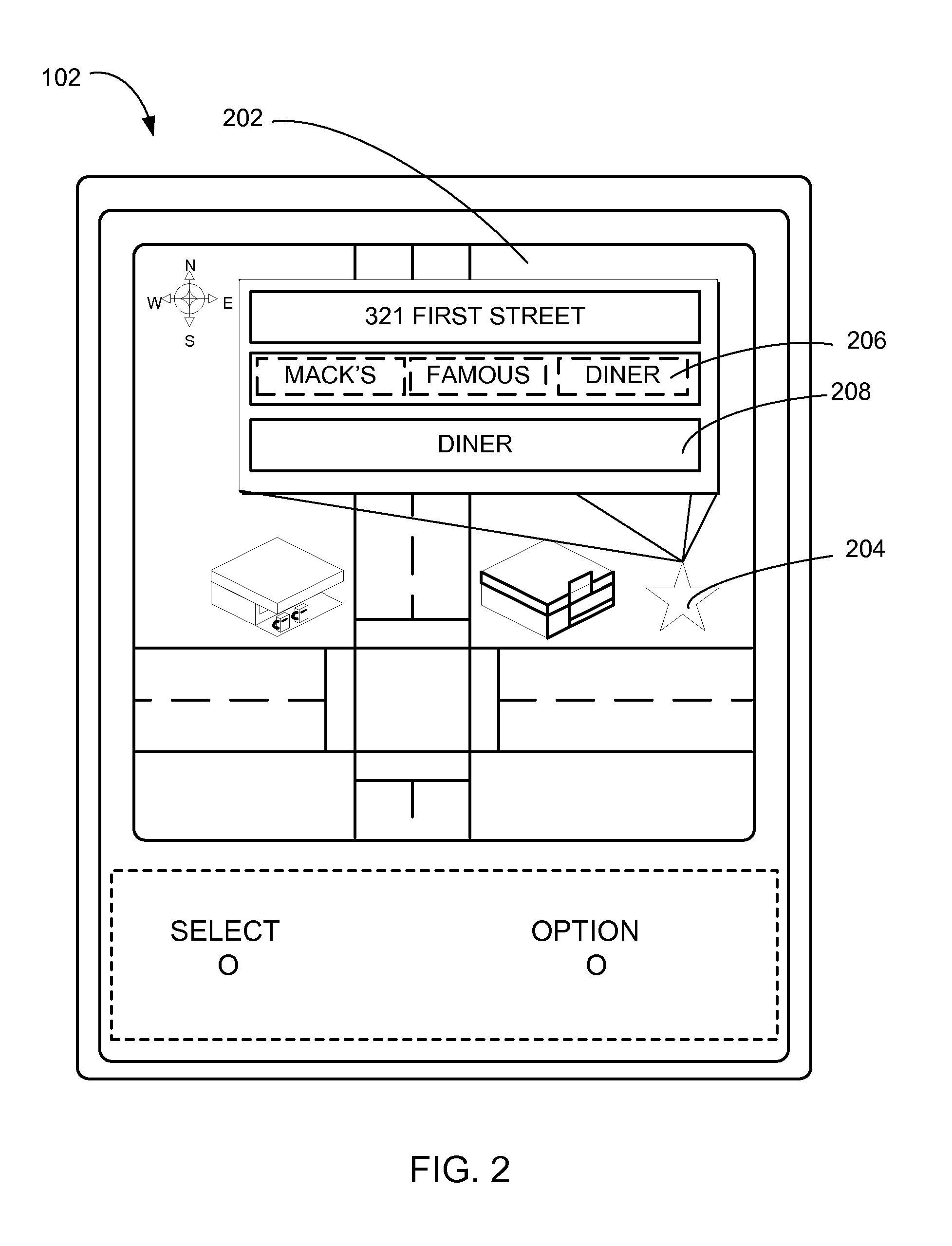
Navigation system with point of interest classification mechanism and method of operation thereof
A method of operation of a navigation system includes: generating a training data from a randomly sampled uncategorized point of interest; generating a trained classifier model by training a classifier model using the training data; generating a category identifier, a confidence score, or a combination thereof for an uncategorized point of interest using the trained classifier model; generating a categorized point of interest by assigning the category identifier to the uncategorized point of interest; calculating a weighted confidence score based on a weighted F-measure for the category identifier, a pair of the category identifier and the confidence score; and consolidating the categorized point of interest based on the weighted confidence score for the category identifier being meeting or exceeding a threshold for displaying on a device.
Owner:TELENAV INC
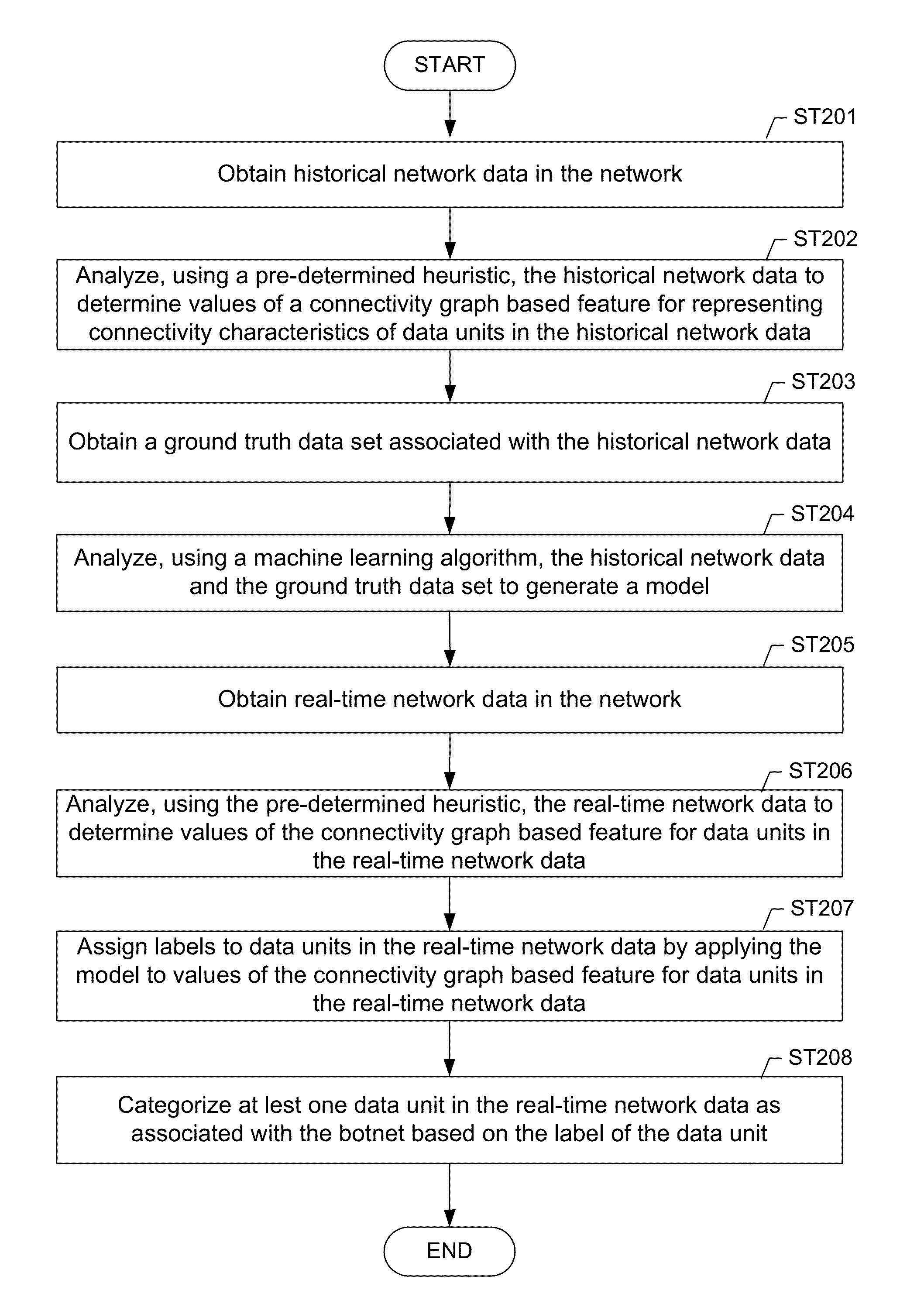
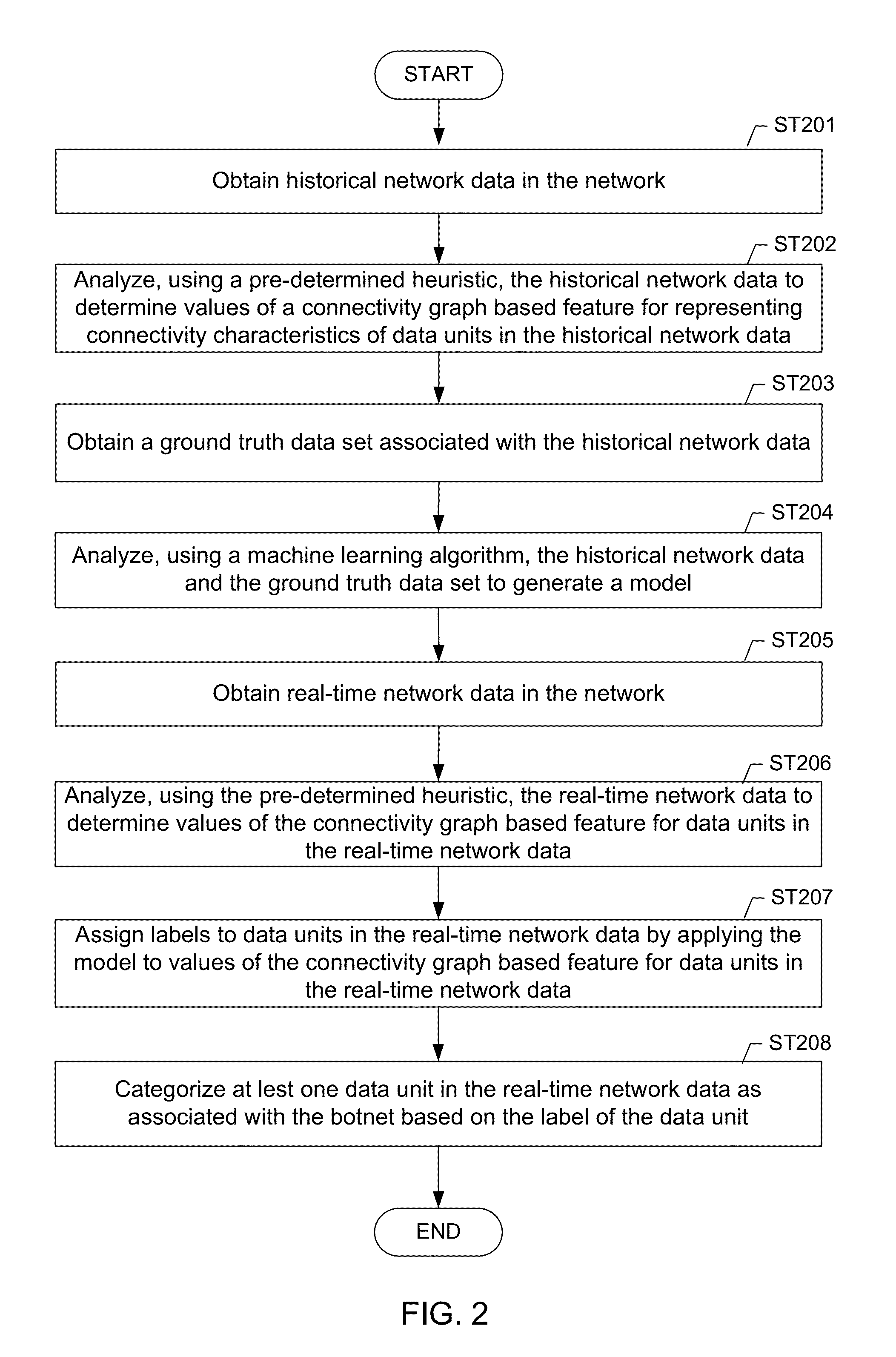
Machine learning based botnet detection using real-time connectivity graph based traffic features
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a connectivity graph based feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the connectivity graph based feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the connectivity graph based feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the connectivity graph based feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
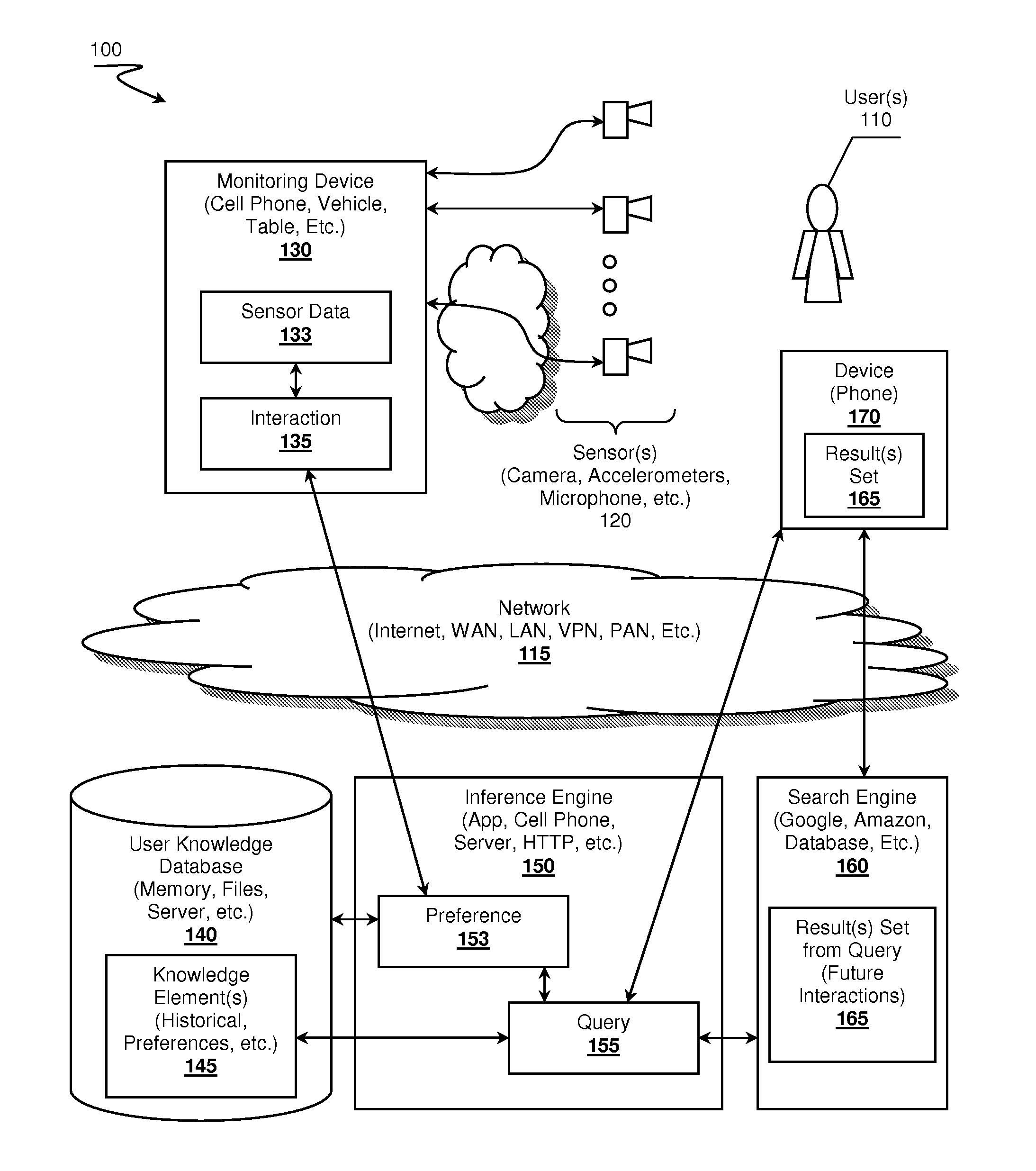
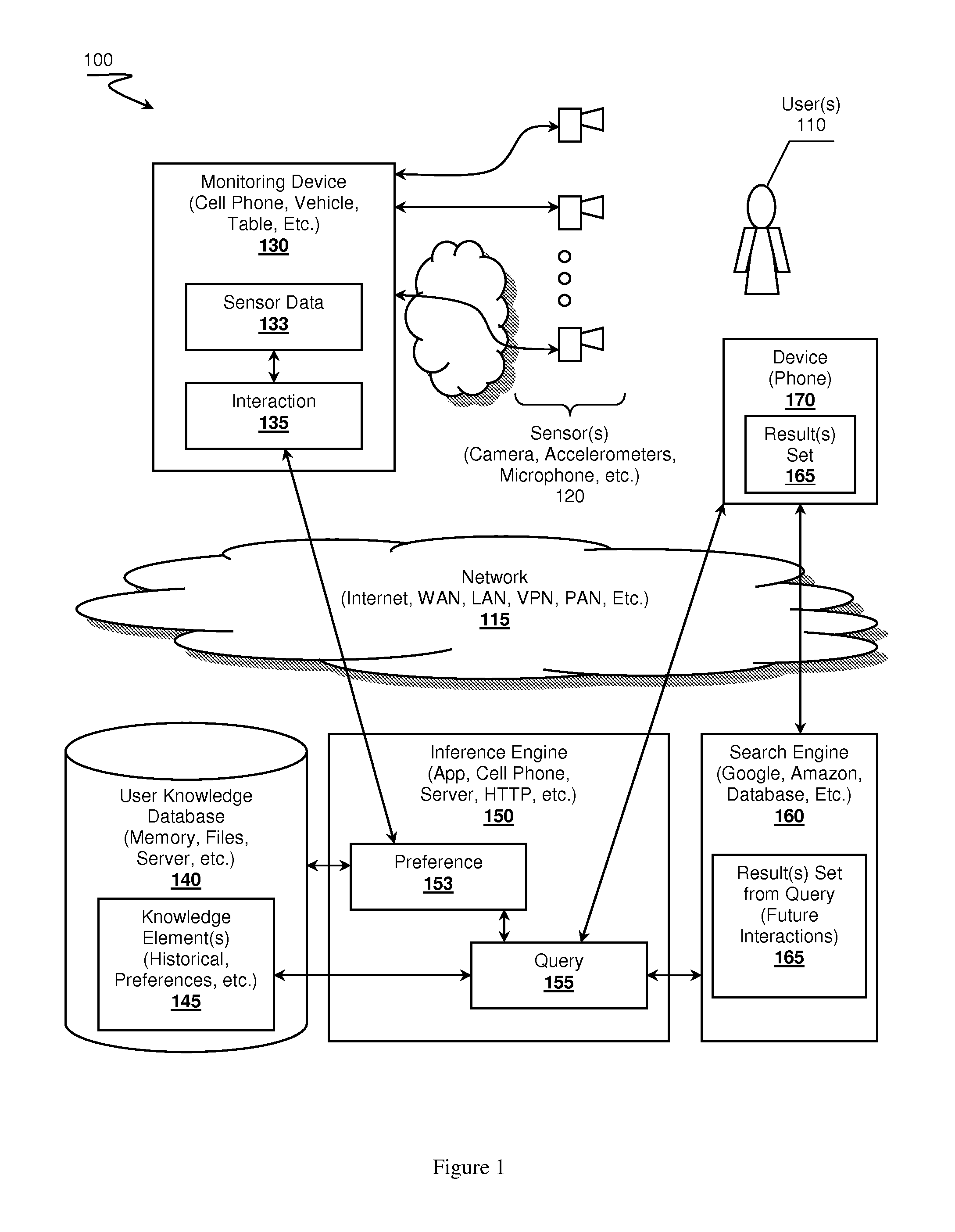
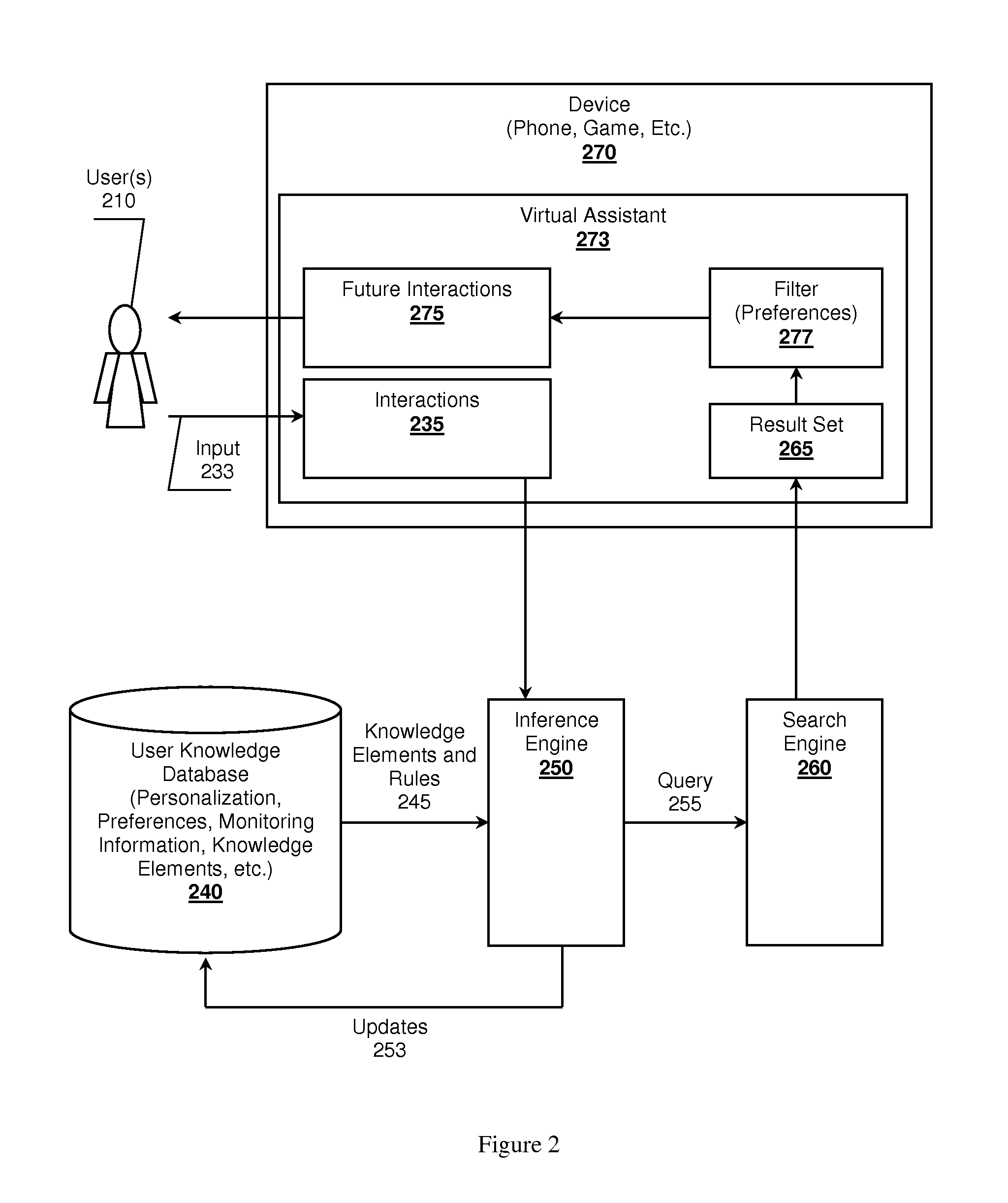
Self-learning, context aware virtual assistants, systems and methods
A virtual assistant learning system is presented. A monitoring device, a cell phone for example, observes user interactions with an environment by acquiring sensor data. The monitoring device uses the sensor data to identify the interactions, which in turn is provided to an inference engine. The inference engine leverages the interaction data and previously stored knowledge elements about the user to determine if the interaction exhibits one or more user preferences. The inference engine can use the preferences and interactions to construct queries targeting search engines to seek out possible future interactions that might be of interest to the user.
Owner:NANT HLDG IP LLC
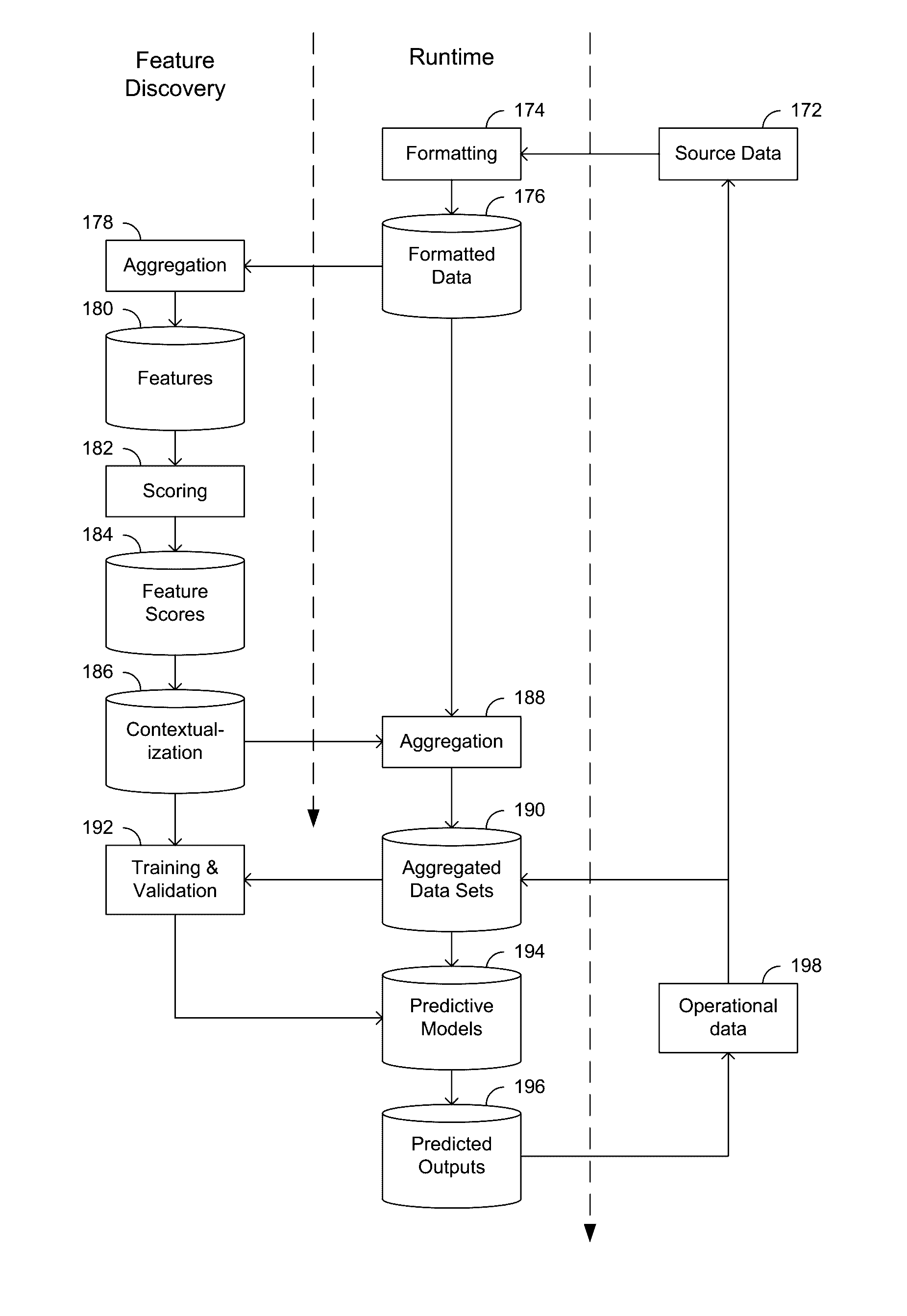
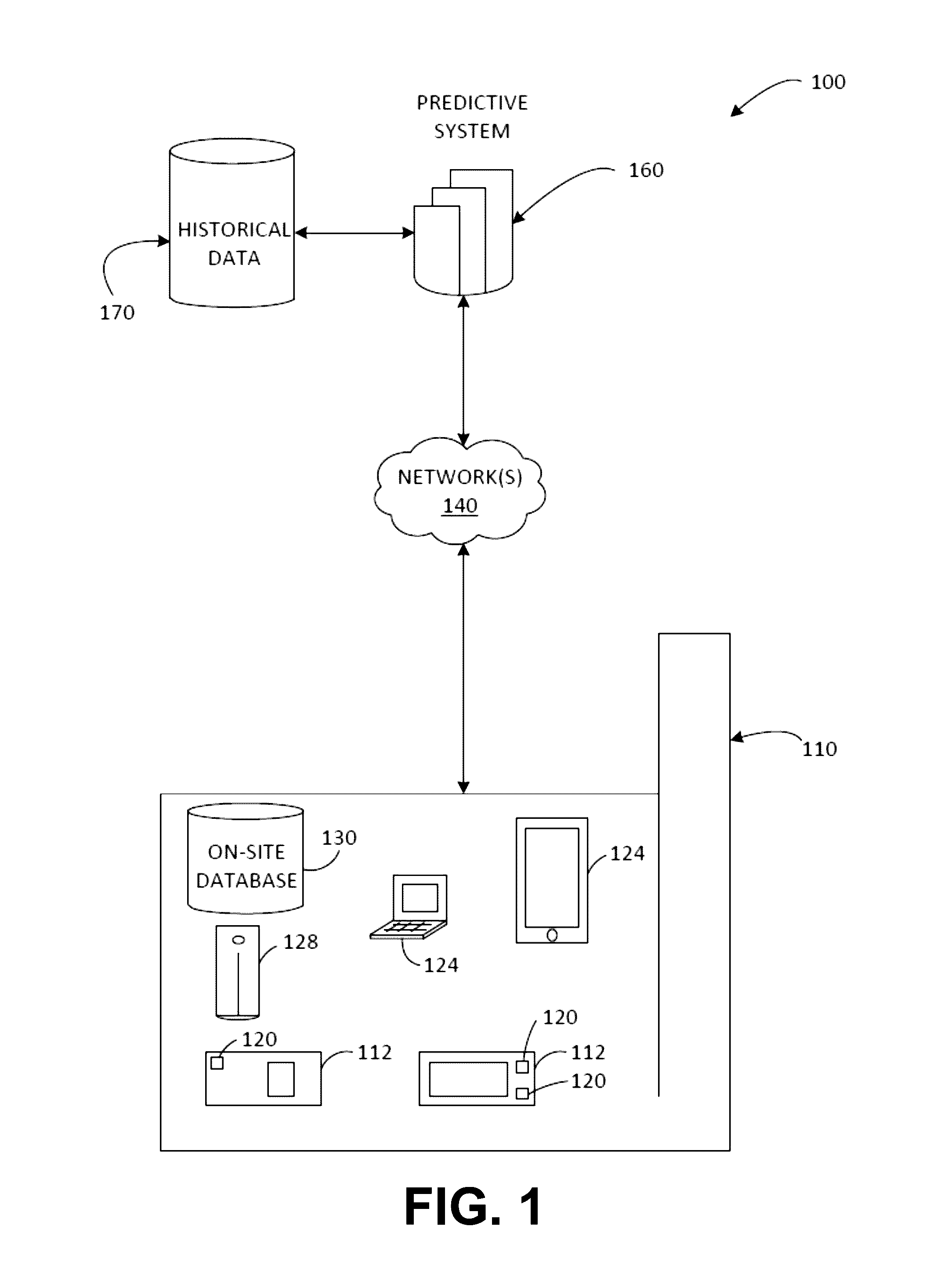
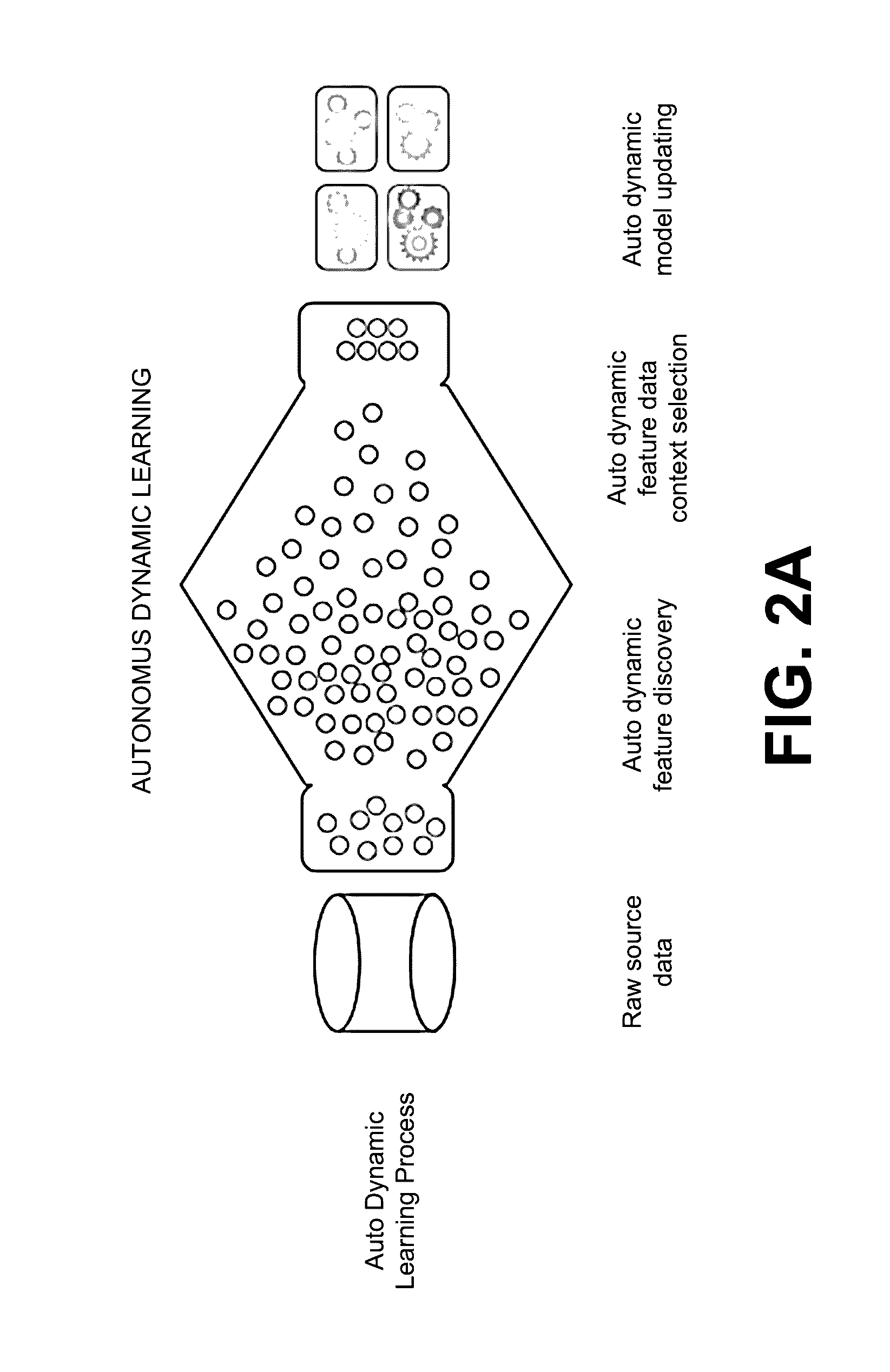
Dynamically updated predictive modeling of systems and processes
ActiveUS20160350671A1Testing/monitoring control systemsProbabilistic networksSufficient timeOperational system
Various examples are provided for dynamically updating or adapting predictive modeling for prediction of outcomes of interest for operating systems and processes. Embodiments of the disclosure may provide systems, apparatus, processes, and methods for generating and deploying dynamically updated predictive models. In some embodiments, the predictive model may be deployed for the purpose of predicting operational outcomes of interests in operating systems, hardware devices, machines and / or processes associated therewith prior to the operational outcomes of interest occurring. The predictions can, for example, provide sufficient time for maintenance or repairs to be scheduled and carried out to avoid the predicted operational outcome. Autonomous evaluation of features allows the predictive models to be dynamically updated in response to changes in the environment or monitored data.
Owner:RAYTHEON TECH CORP
Methods for generating natural language processing systems
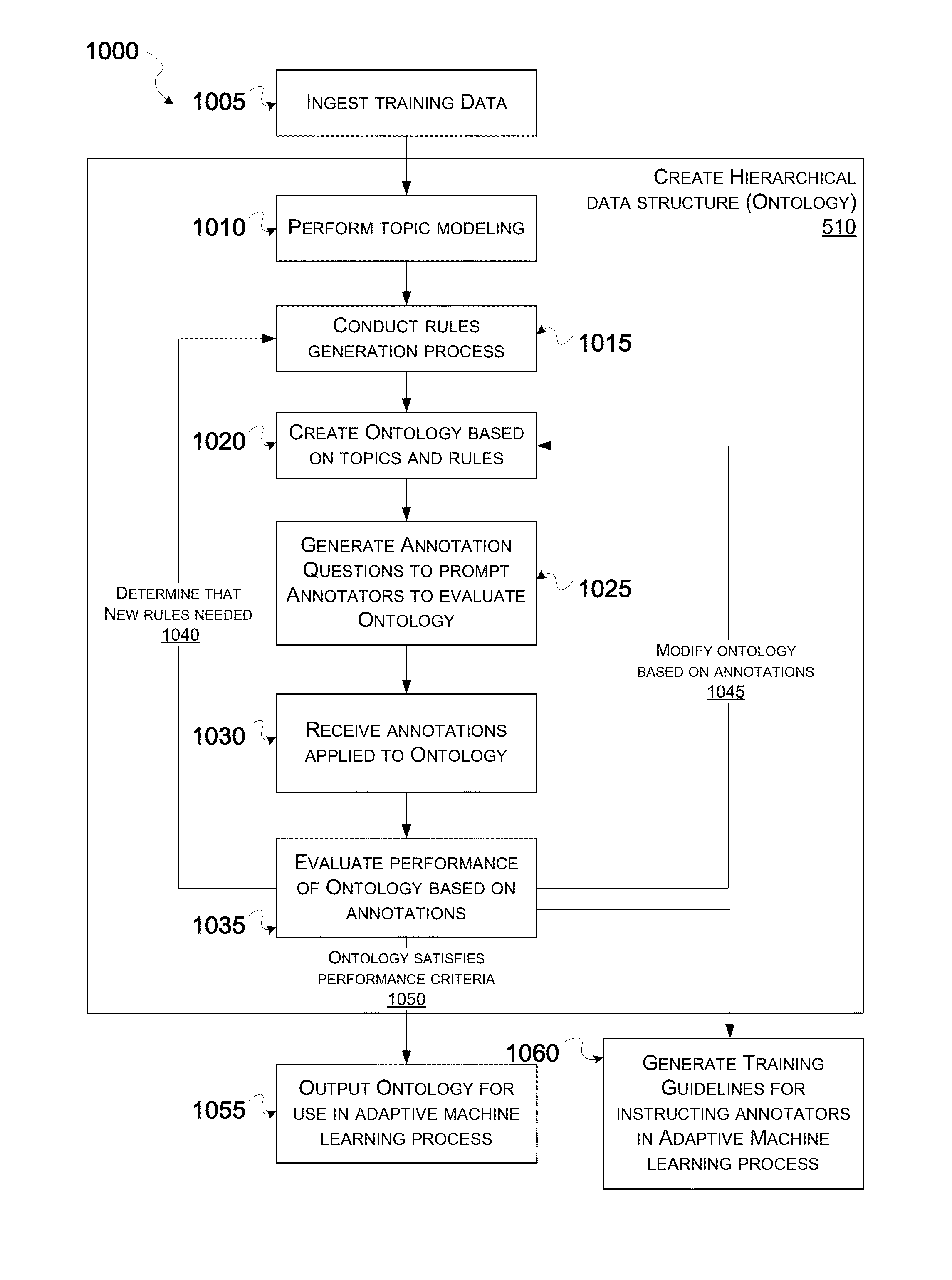
ActiveUS20160162456A1Low degree of certaintyNatural language translationData processing applicationsNODALDocumentation
Methods are presented for generating a natural language model. The method may comprise: ingesting training data representative of documents to be analyzed by the natural language model, generating a hierarchical data structure comprising at least two topical nodes within which the training data is to be subdivided into by the natural language model, selecting a plurality of documents among the training data to be annotated, generating an annotation prompt for each document configured to elicit an annotation about said document indicating which node among the at least two topical nodes said document is to be classified into, receiving the annotation based on the annotation prompt; and generating the natural language model using an adaptive machine learning process configured to determine patterns among the annotations for how the documents in the training data are to be subdivided according to the at least two topical nodes of the hierarchical data structure.
Owner:100 CO GLOBAL HLDG LLC
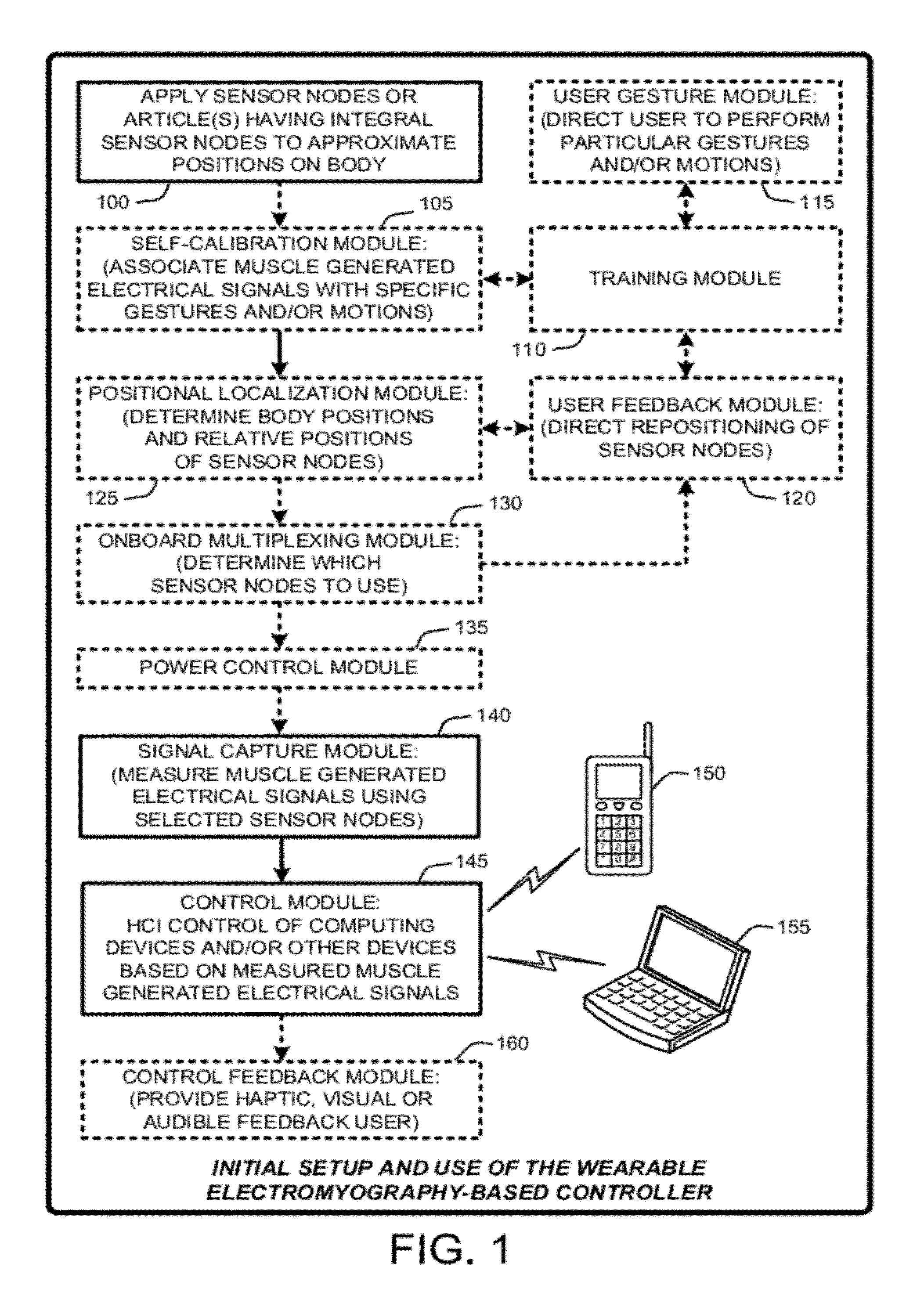
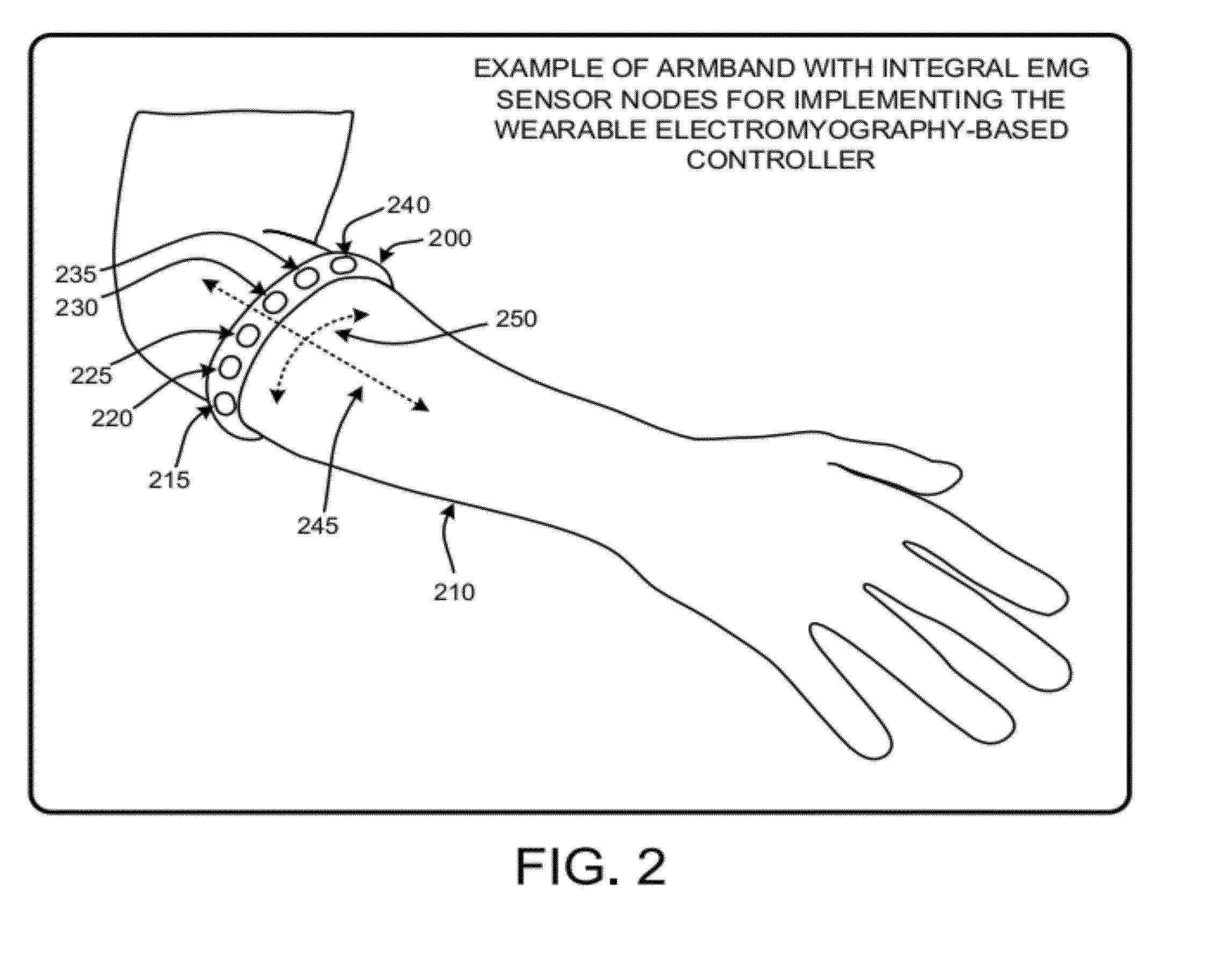
Wearable electromyography-based human-computer interface
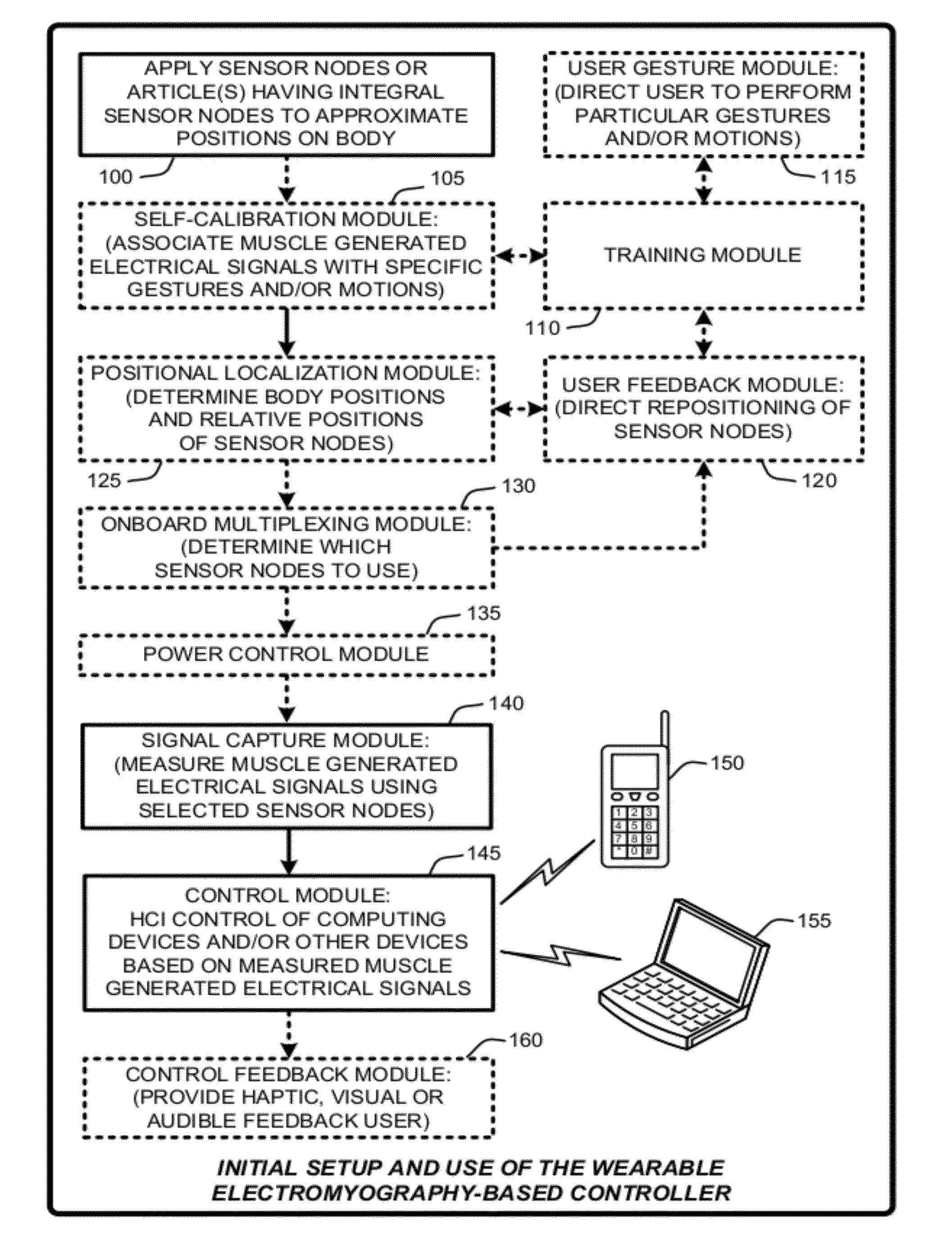
ActiveUS20120188158A1Input/output for user-computer interactionElectromyographyHuman–machine interfacePhysical medicine and rehabilitation
A “Wearable Electromyography-Based Controller” includes a plurality of Electromyography (EMG) sensors and provides a wired or wireless human-computer interface (HCl) for interacting with computing systems and attached devices via electrical signals generated by specific movement of the user's muscles. Following initial automated self-calibration and positional localization processes, measurement and interpretation of muscle generated electrical signals is accomplished by sampling signals from the EMG sensors of the Wearable Electromyography-Based Controller. In operation, the Wearable Electromyography-Based Controller is donned by the user and placed into a coarsely approximate position on the surface of the user's skin. Automated cues or instructions are then provided to the user for fine-tuning placement of the Wearable Electromyography-Based Controller. Examples of Wearable Electromyography-Based Controllers include articles of manufacture, such as an armband, wristwatch, or article of clothing having a plurality of integrated EMG-based sensor nodes and associated electronics.
Owner:MICROSOFT TECH LICENSING LLC
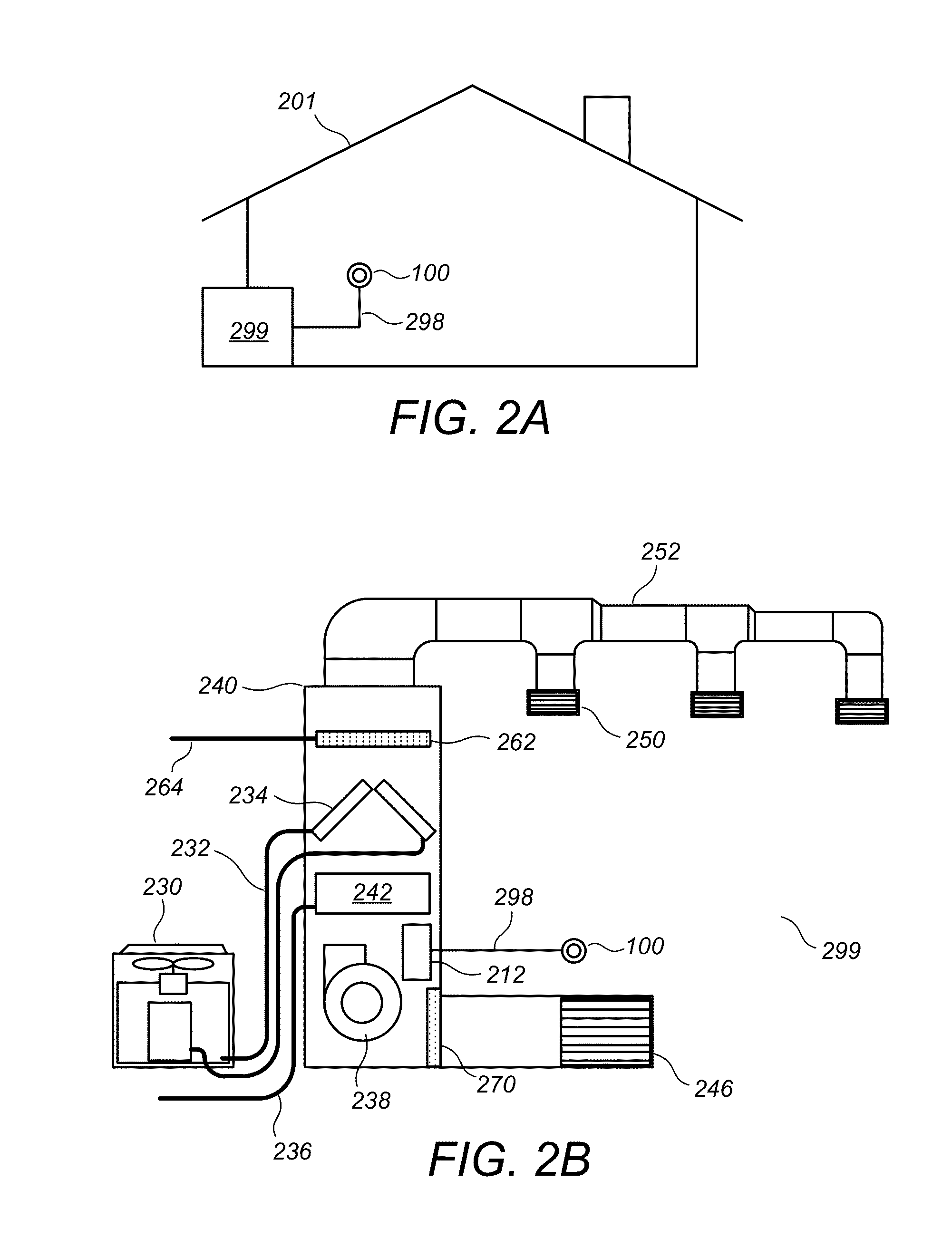
User-friendly, network connected learning thermostat and related systems and methods
ActiveUS20130173064A1Improve energy efficiencyLarge energy expenseOptical radiation measurementSpace heating and ventilationMicrocontrollerDisplay device
A user-friendly, network-connected learning thermostat is described. The thermostat is made up of (1) a wall-mountable backplate that includes a low-power consuming microcontroller used for activities such as polling sensors and switching on and off the HVAC functions, and (2) separable head unit that includes a higher-power consuming microprocessor, color LCD backlit display, user input devices, and wireless communications modules. The thermostat also includes a rechargeable battery and power-stealing circuitry adapted to harvest power from HVAC triggering circuits. By maintaining the microprocessor in a “sleep” state often compared to the lower-power microcontroller, high-power consuming activities, such as learning computations, wireless network communications and interfacing with a user, can be temporarily performed by the microprocessor even though the activities use energy at a greater rate than is available from the power stealing circuitry.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com