Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1991results about How to "Improve computing power" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
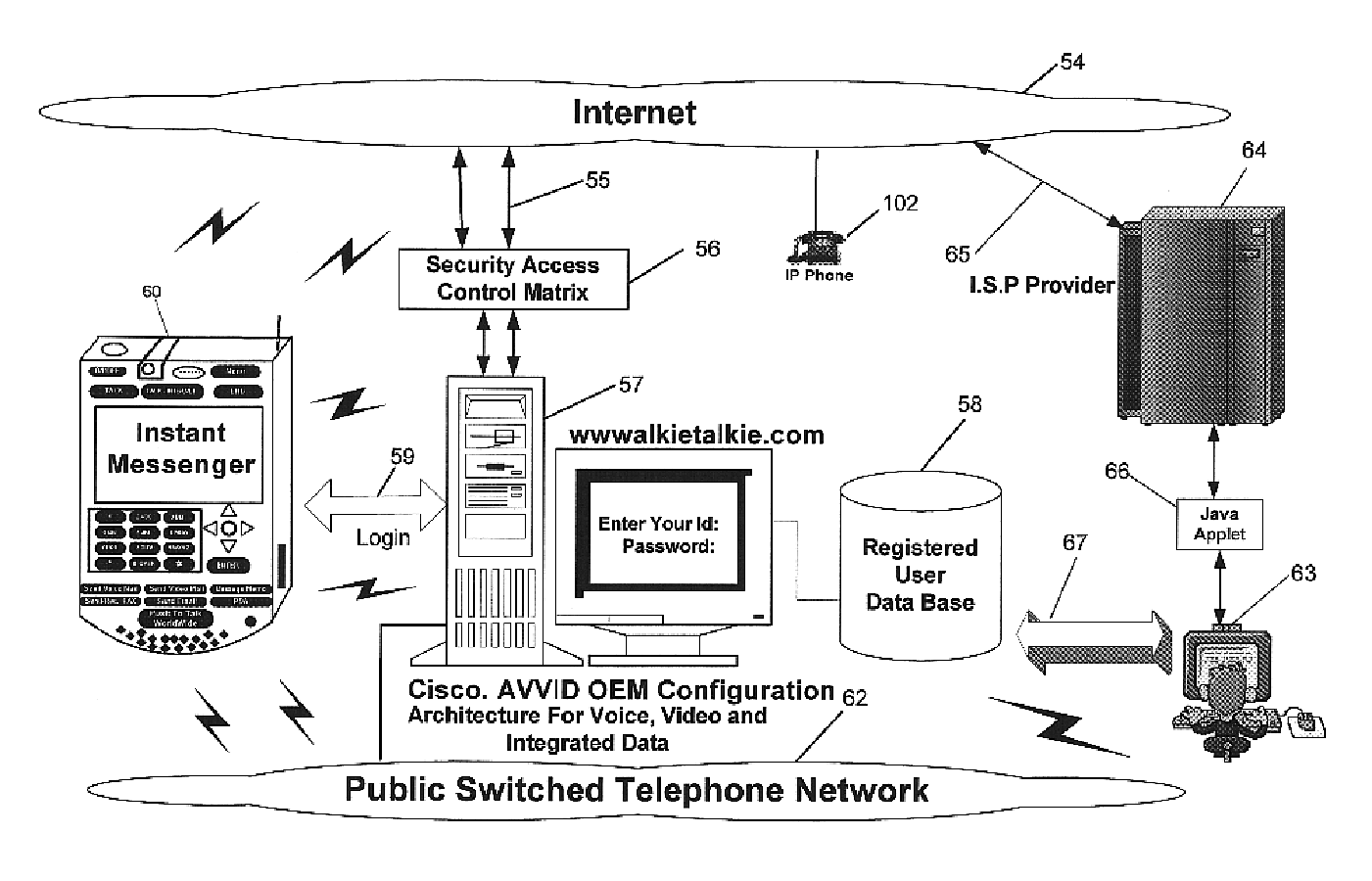
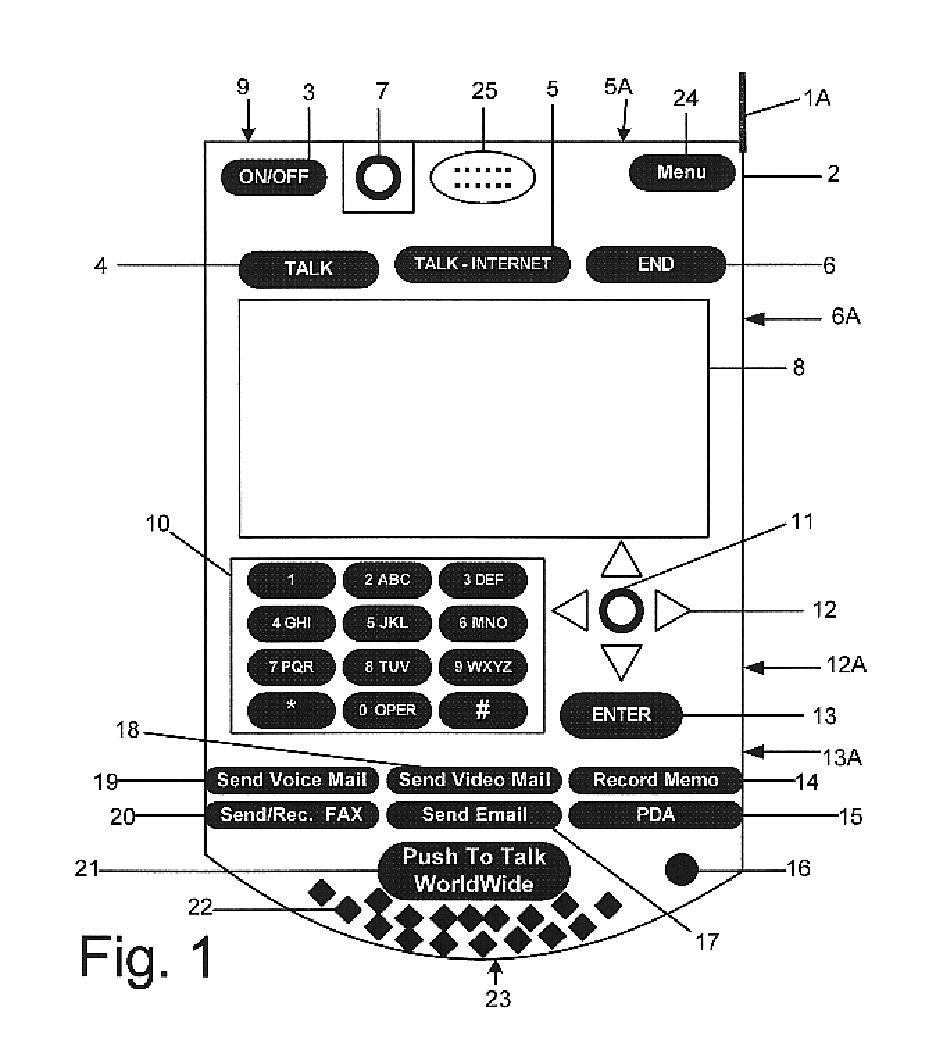
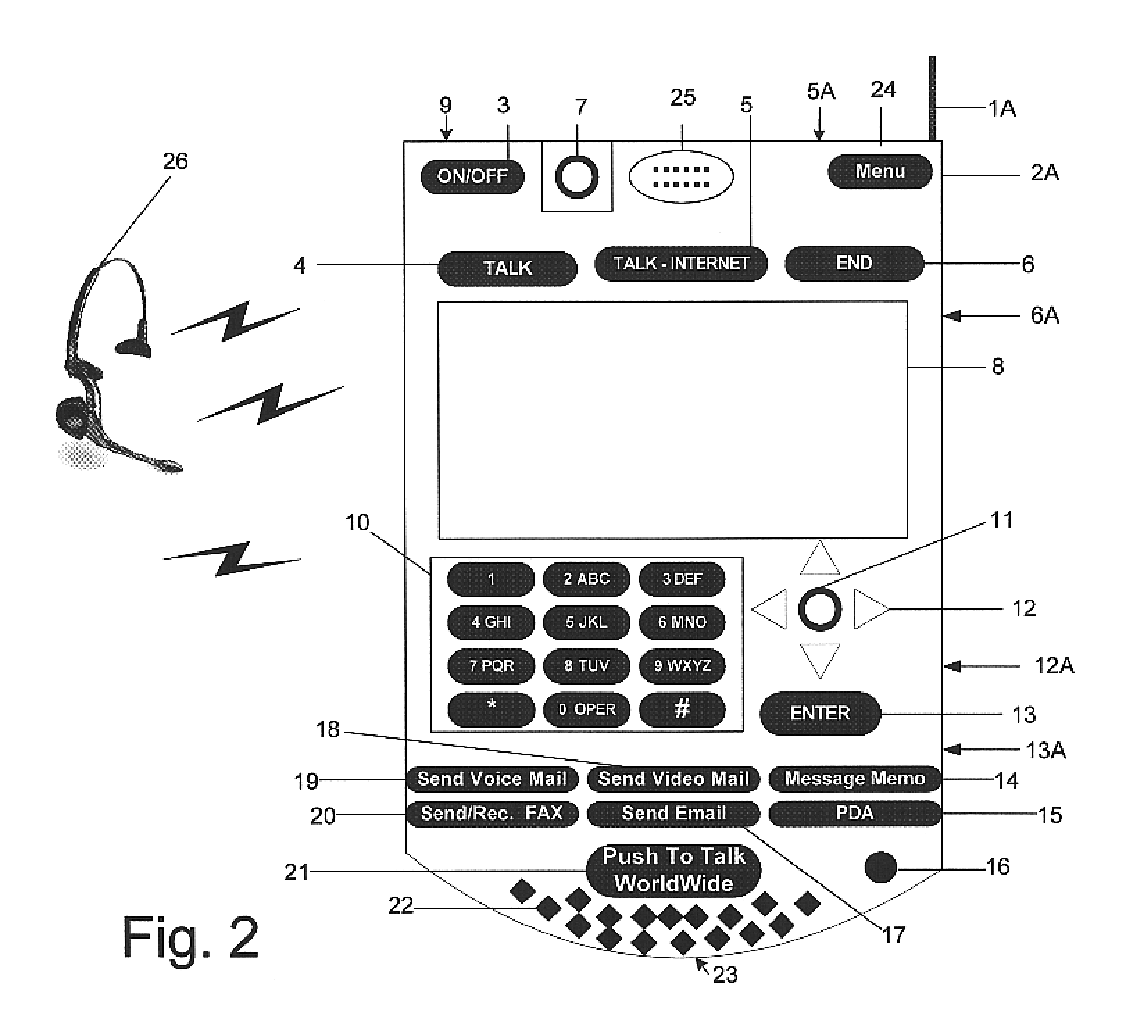
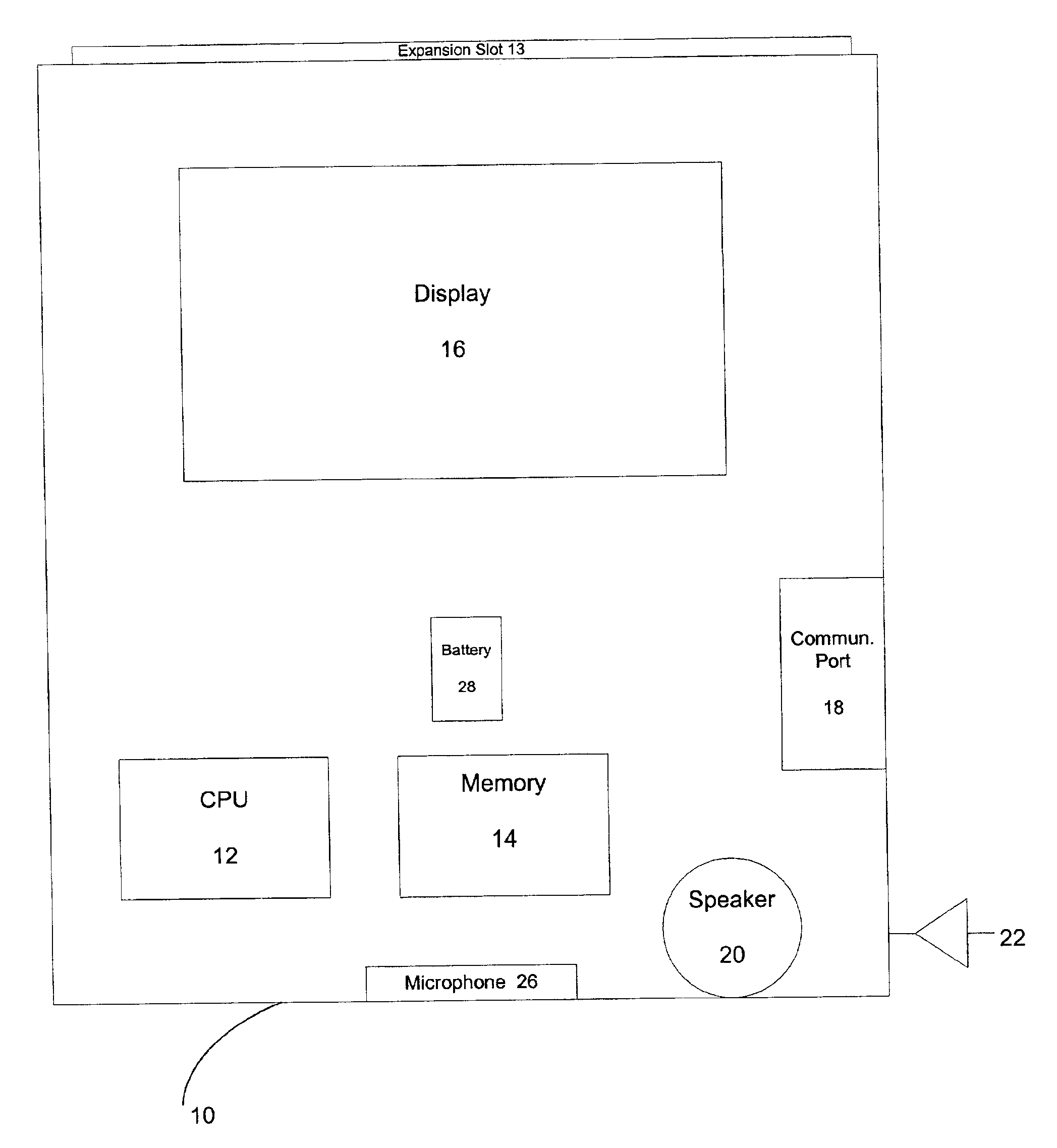
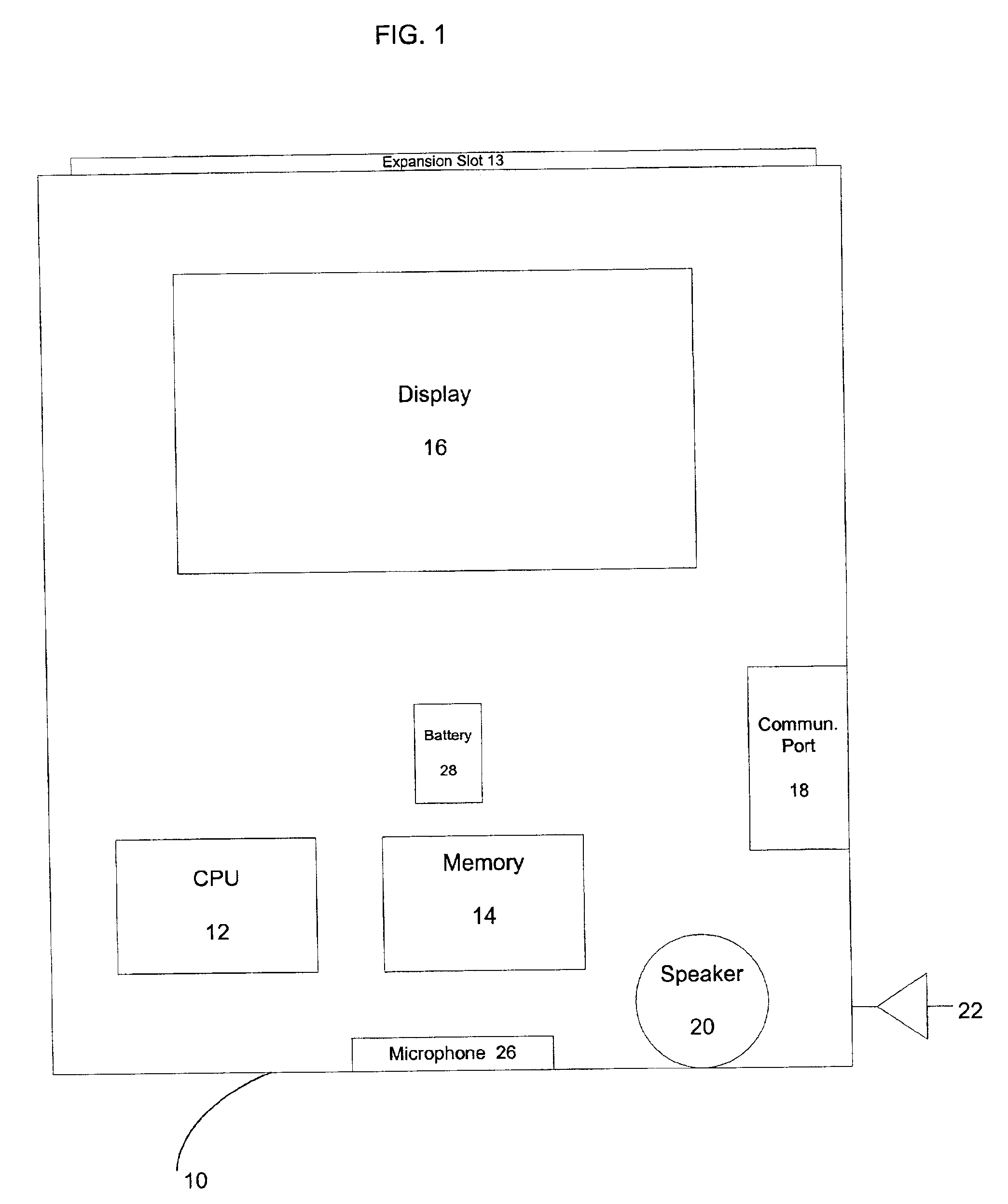
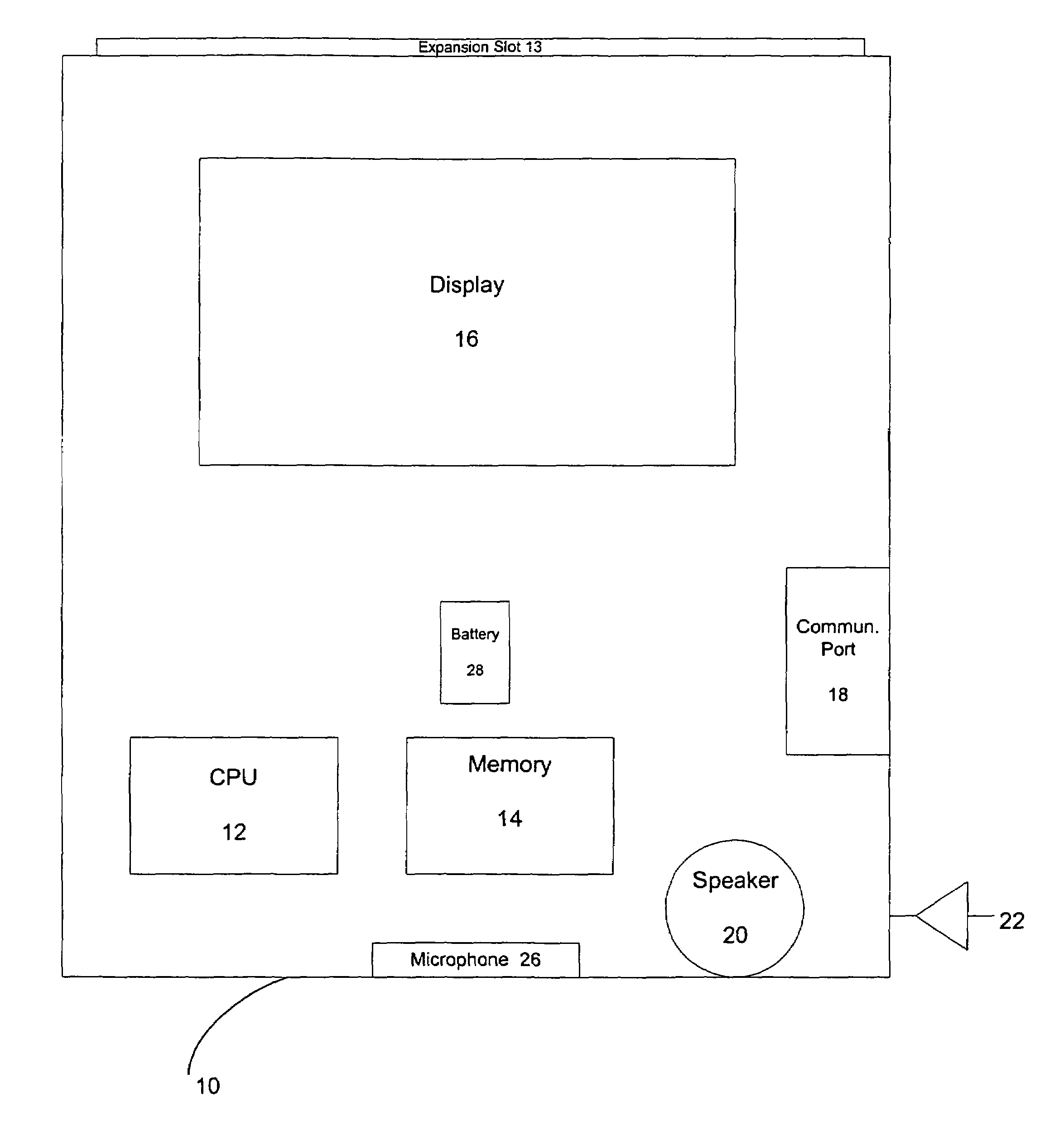
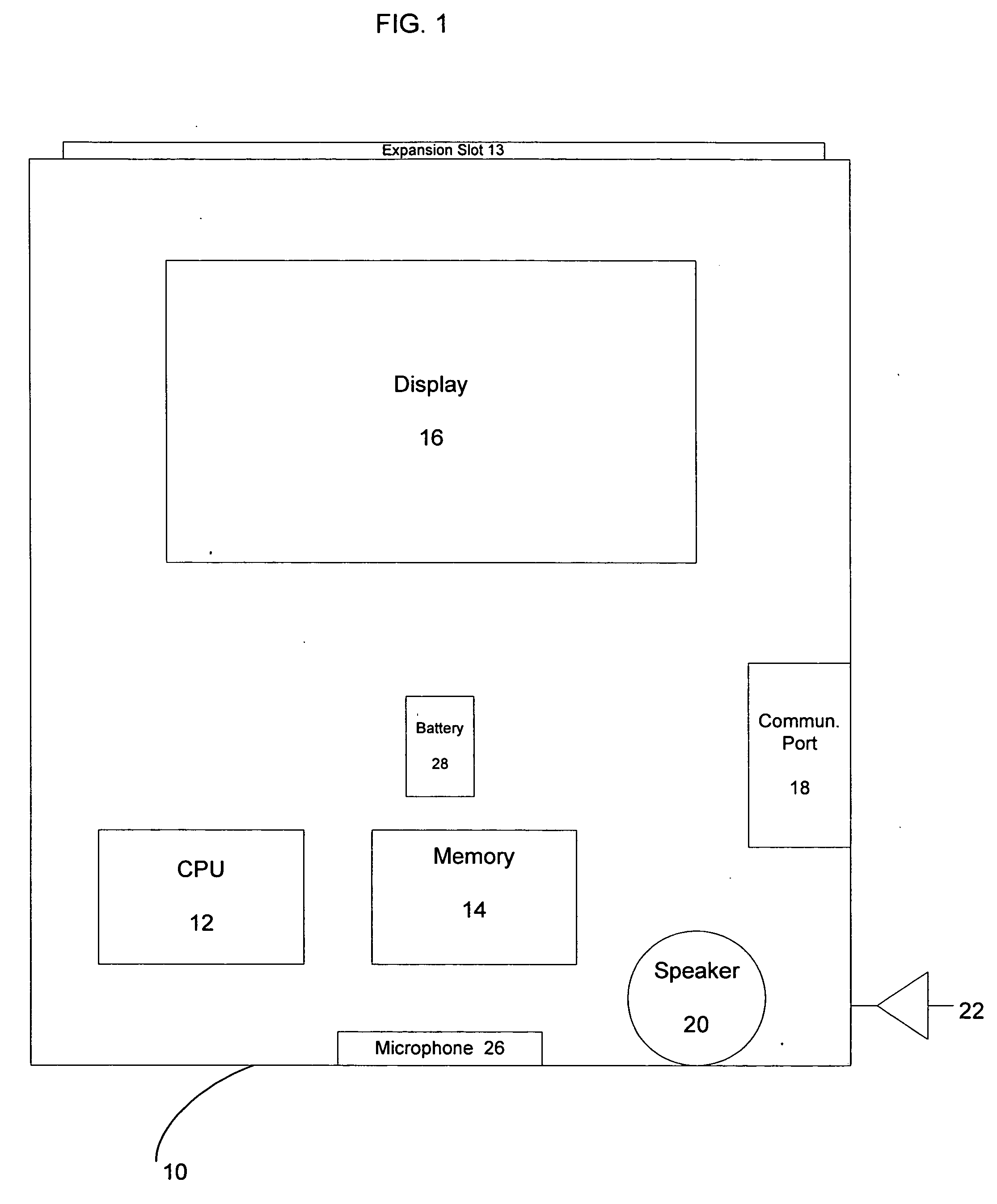
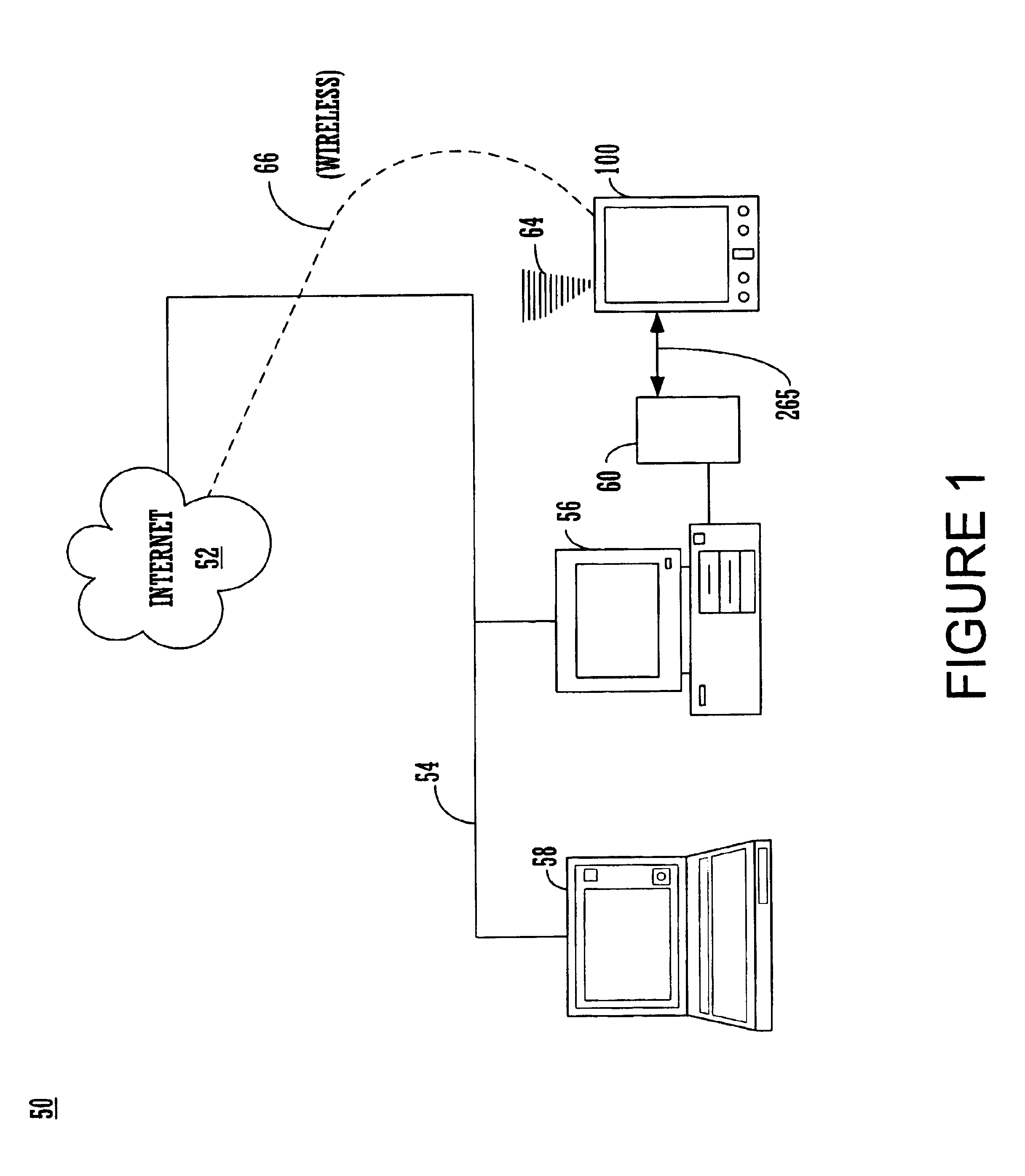
Multifunctional world wide walkie talkie, a tri-frequency cellular-satellite wireless instant messenger computer and network for establishing global wireless volp quality of service (QOS) communications, unified messaging, and video conferencing via the internet
InactiveUS6763226B1High quality voice and data communicationMinimal costCordless telephonesInterconnection arrangementsQuality of serviceMass storage
World-Wide-Walkie-Talkie, a high speed multifunction interstellar wireless computer / instant messenger communicator, Personal Digital Assistant (PDA), coupled with a resilient, robust, VoIP data network and internet server method, deploying multiple wireless networks and protocols such as Voice Over IP, GPRS, WAP, Bluetooth, PCS, I-Mode, comprising a high speed Intel Pentium 4 Mobile(TM) or compatible Processor, to formulate a internet gateway system (99) and network bridge (150) for establishing instant low cost, real time global communications to the Public Switched Telephone Network via the internet (54). A PUSH-TO-TALK-WORLDWIDE button (21) instantly initiates global bisynchronous communications, or videoconferencing sessions. Fax, VideoMail, and unified messaging services are immediately available. GPS and mass memory provides global navigational tracking and data storage. Internet users, telephones, and cellular / satellite phone users can intercommunicate with the invention via VoIP / IM services. The invention provides uniformed global wireless communications, eliminates traditional long distance costs, and operates anywhere on earth.
Owner:COMP SCI CENT
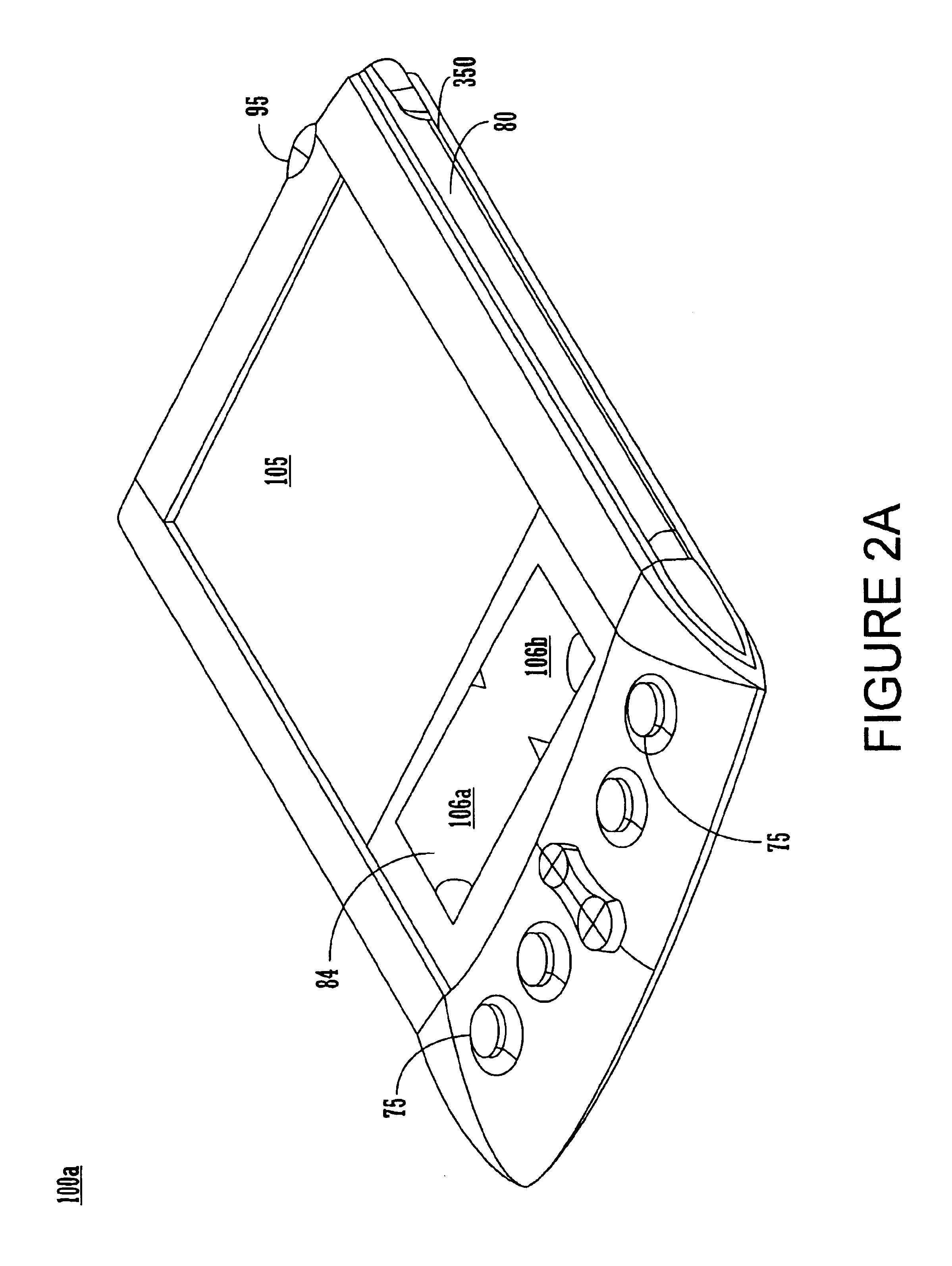
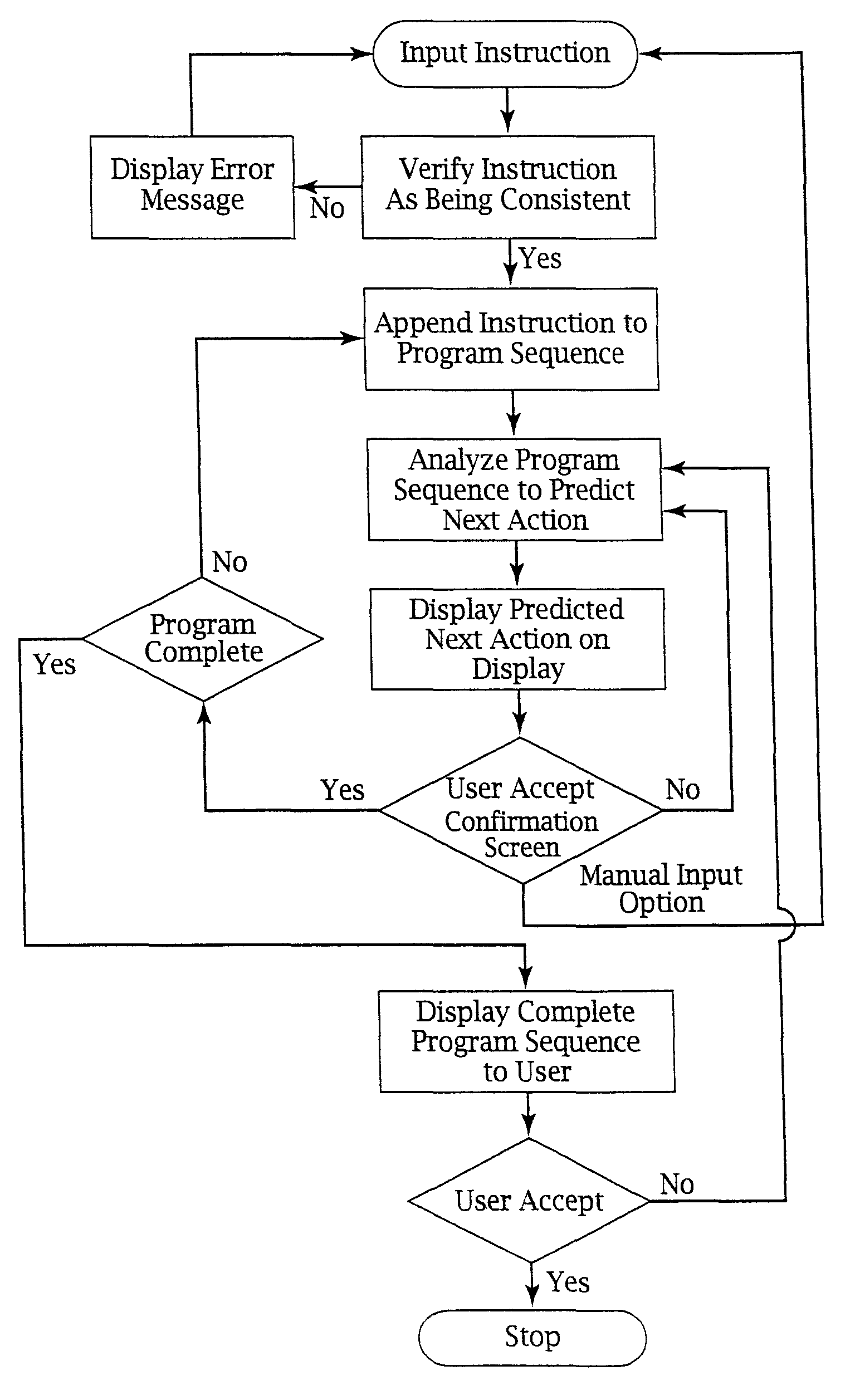
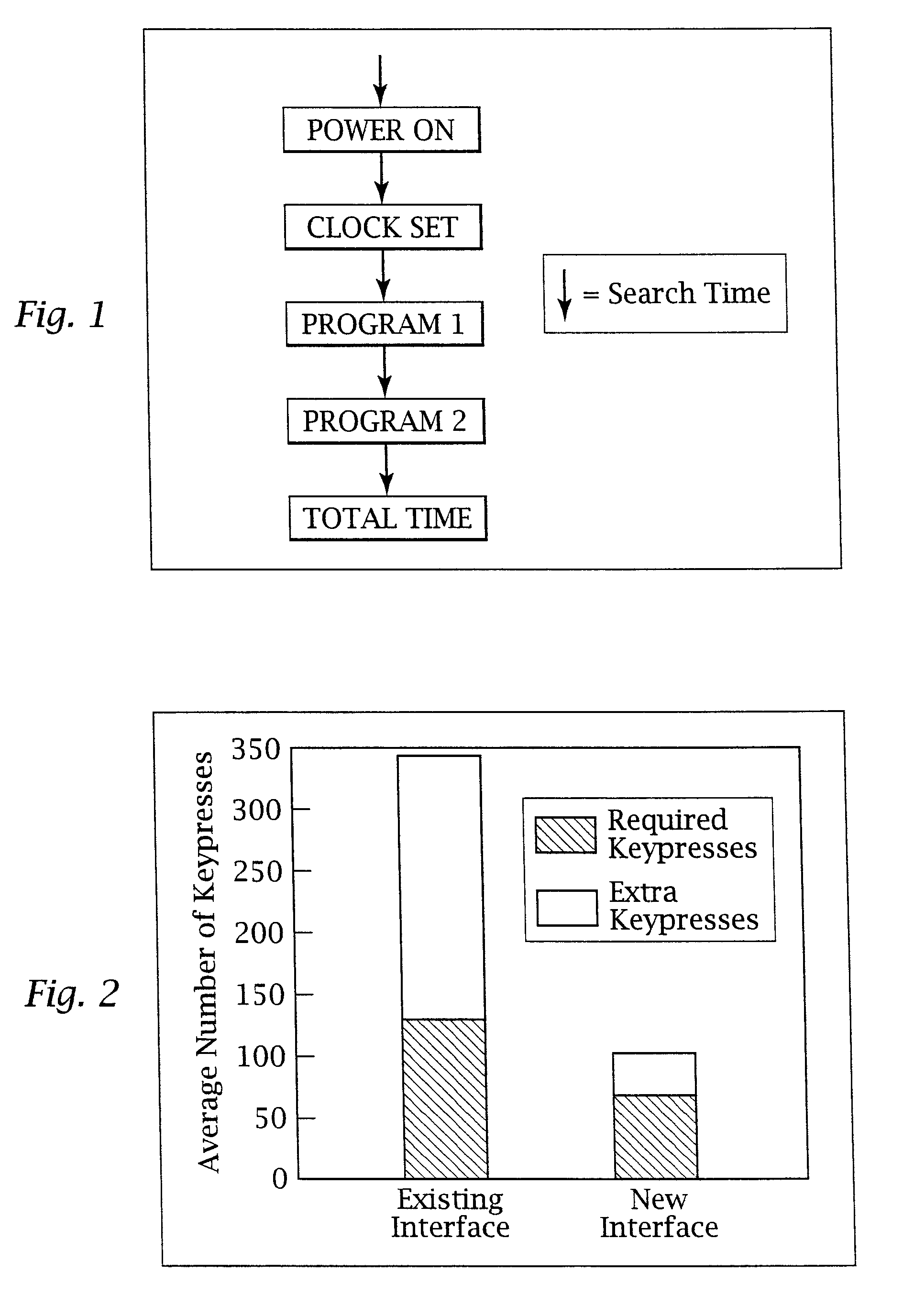
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
ActiveUS7136710B1Significant to useImprove computing powerComputer controlAnalogue secracy/subscription systemsConceptual basisHuman–machine interface
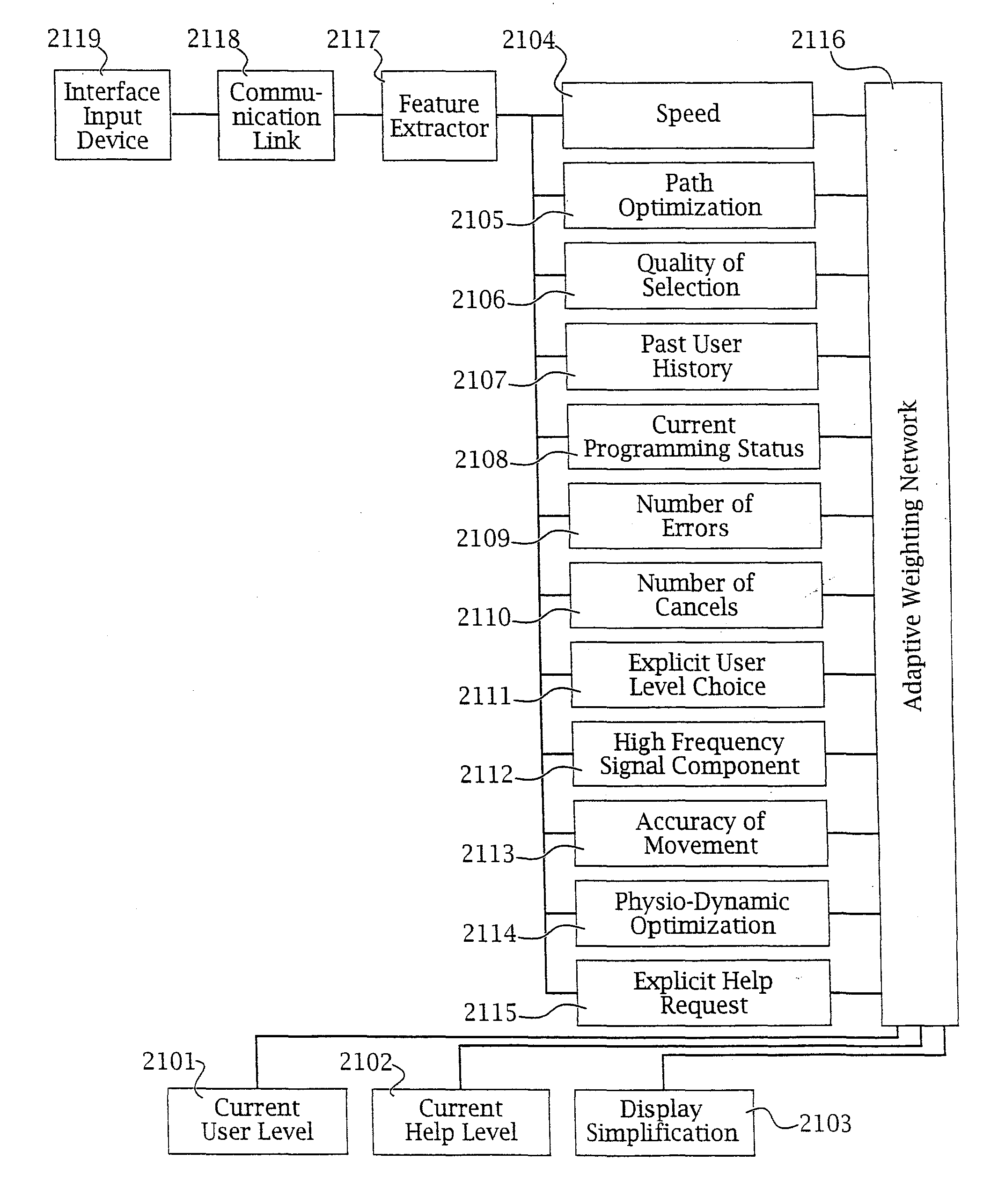
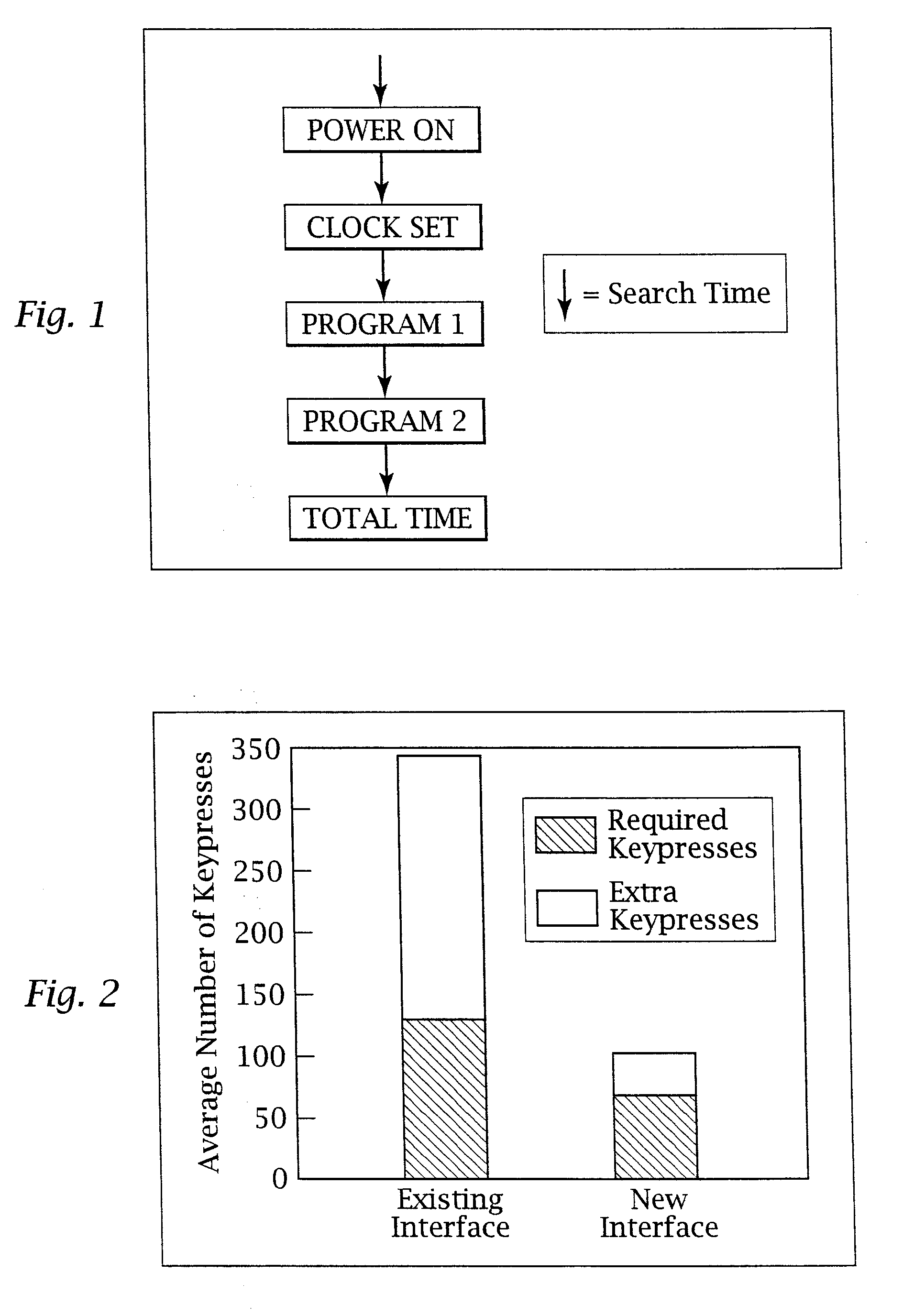
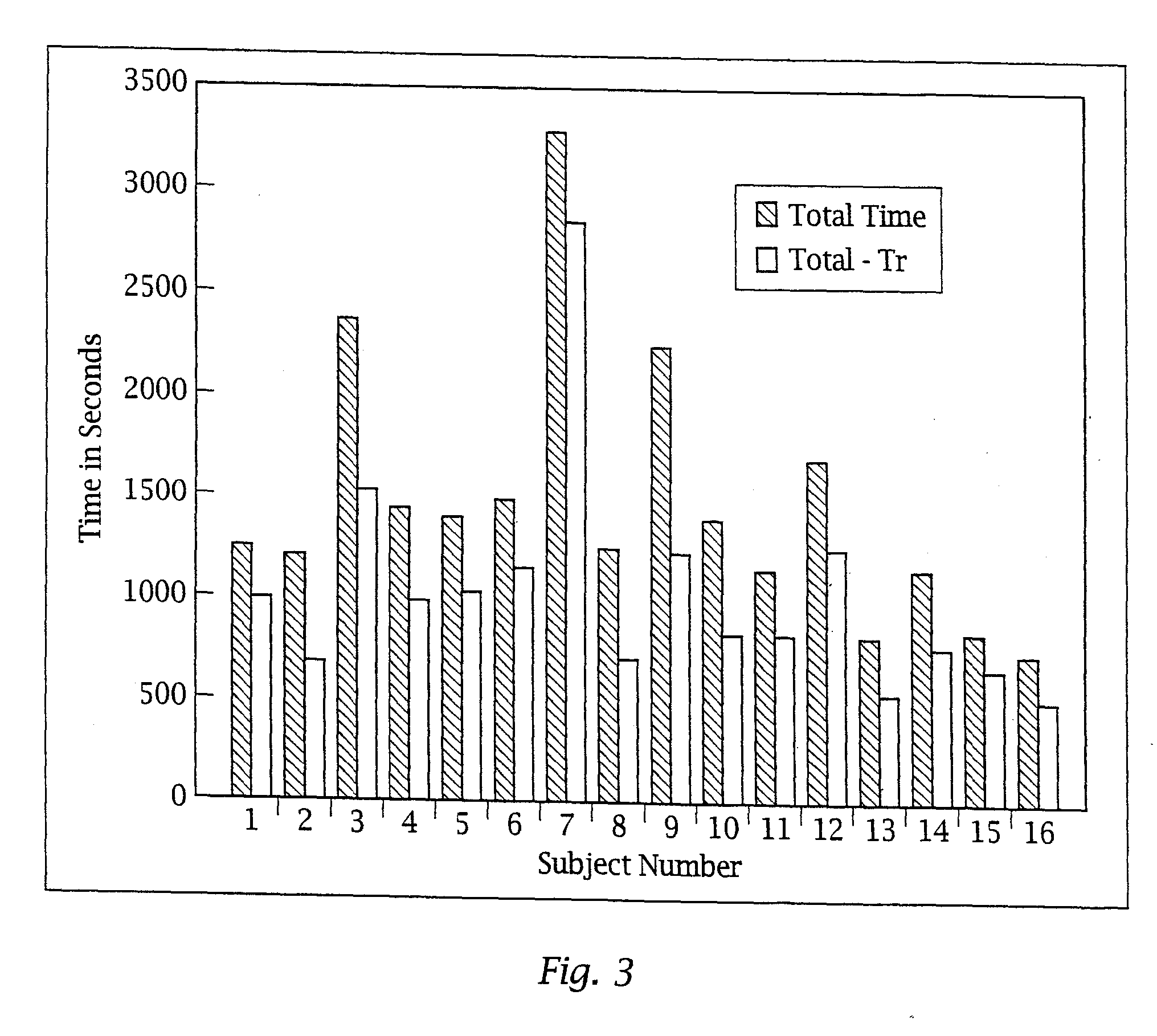
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP +1
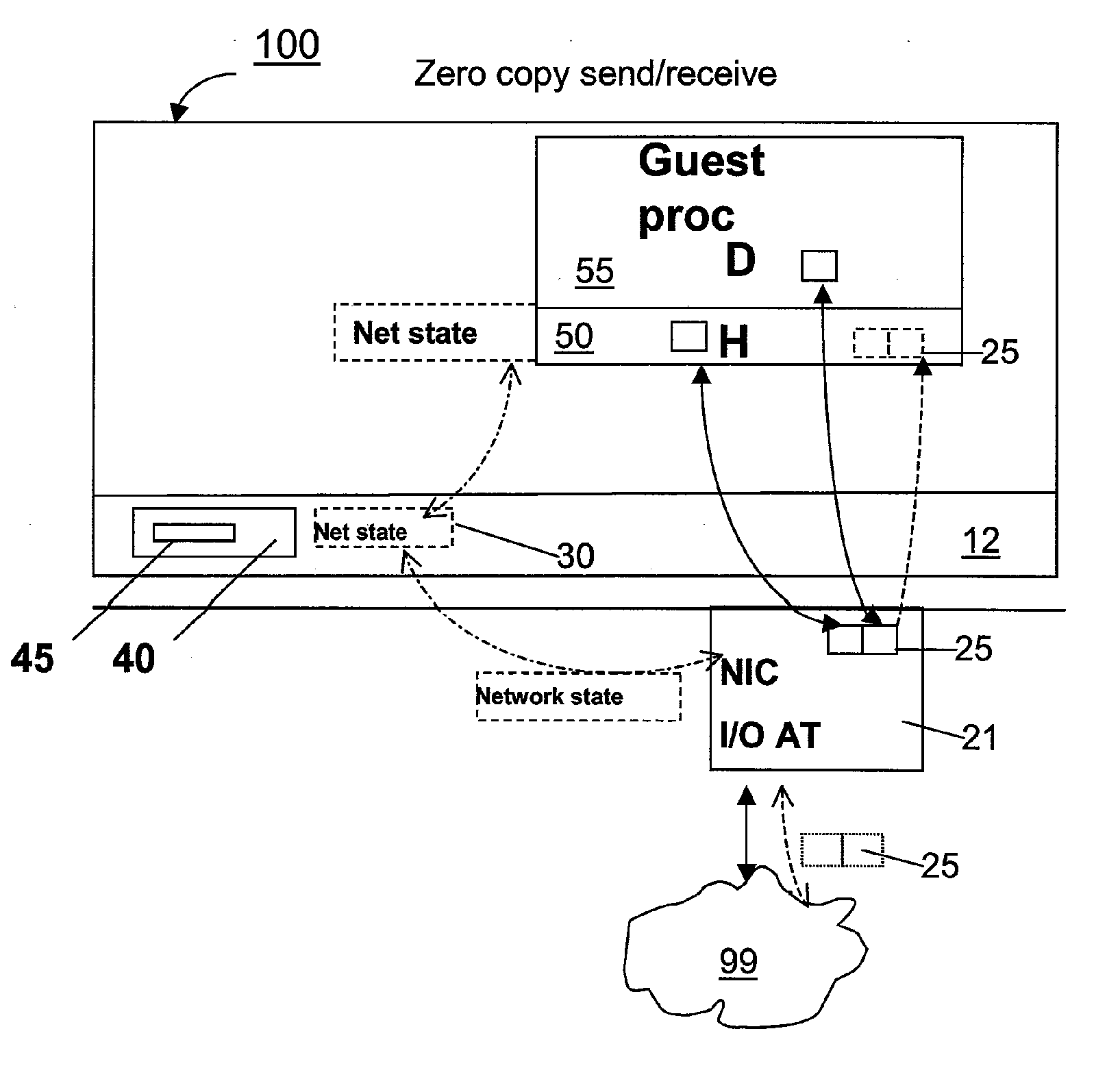
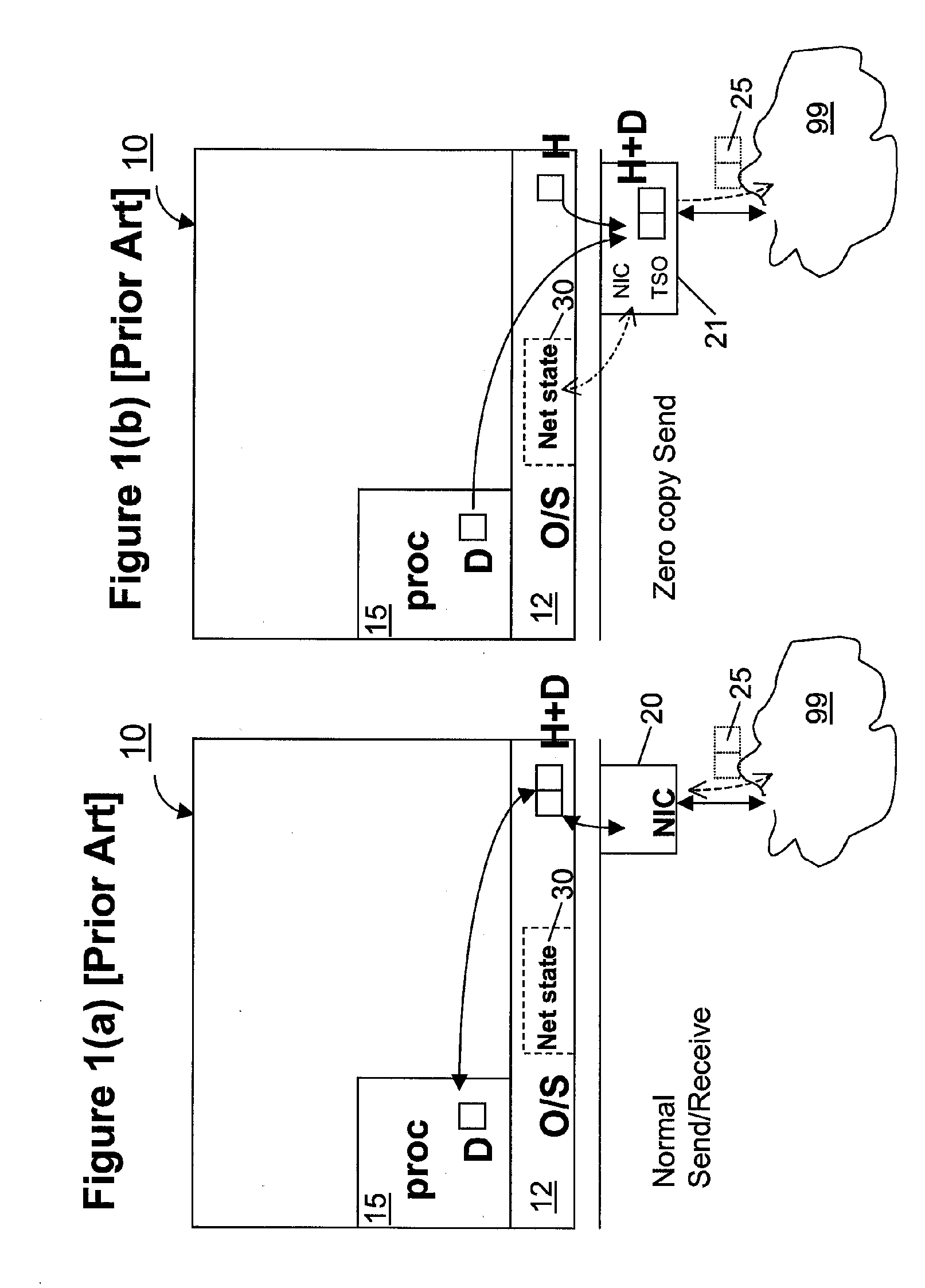
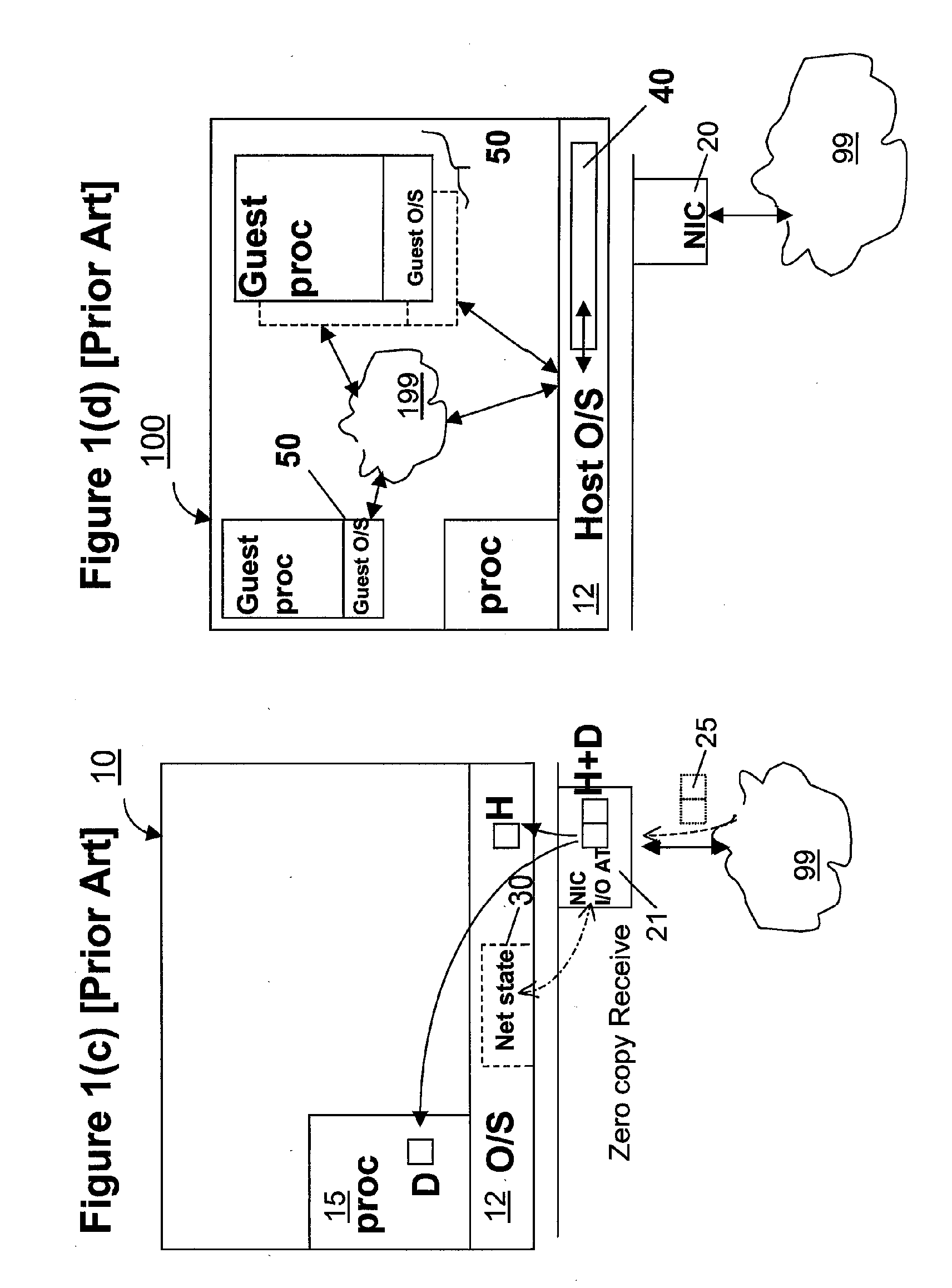
Zero-copy network I/O for virtual hosts
ActiveUS20070061492A1Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionData packVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
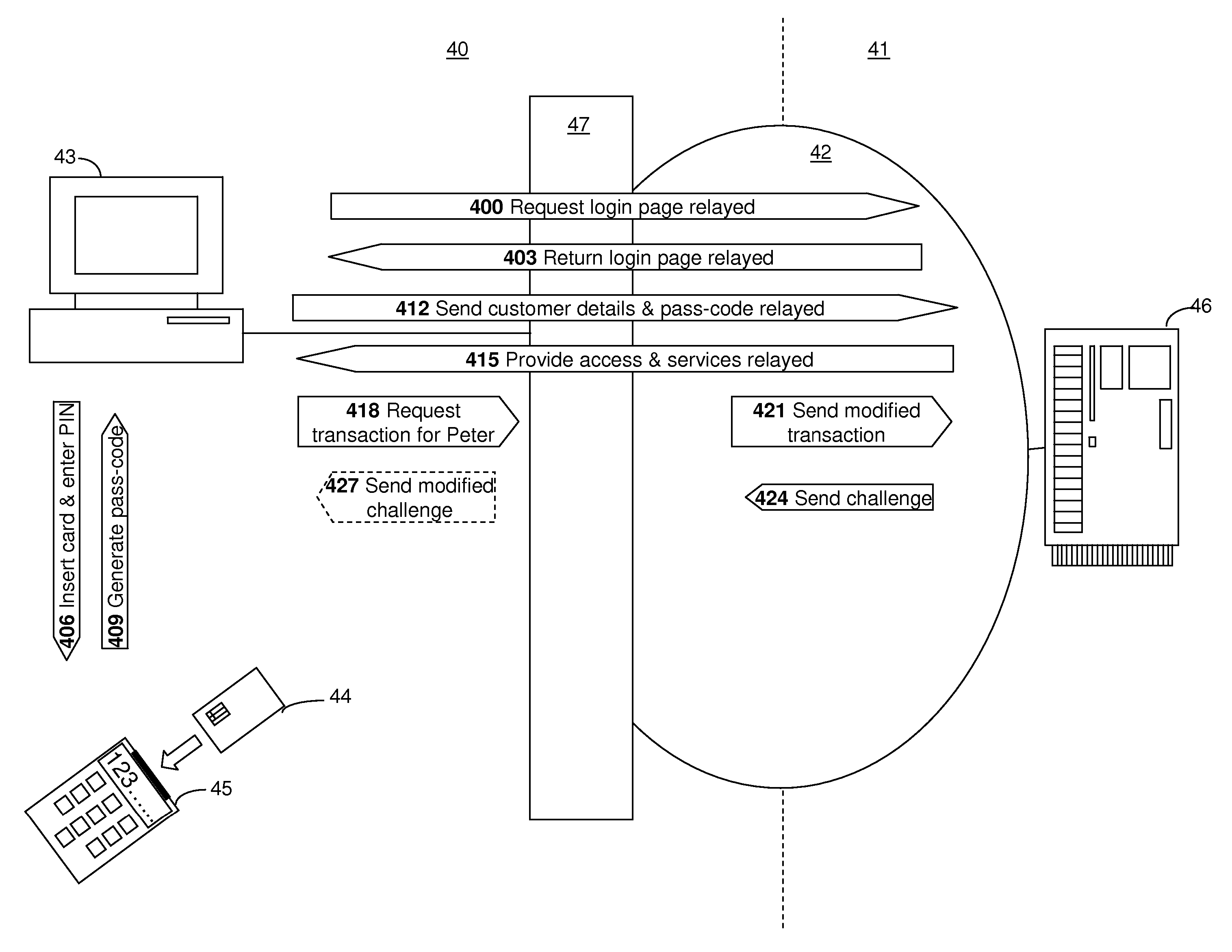
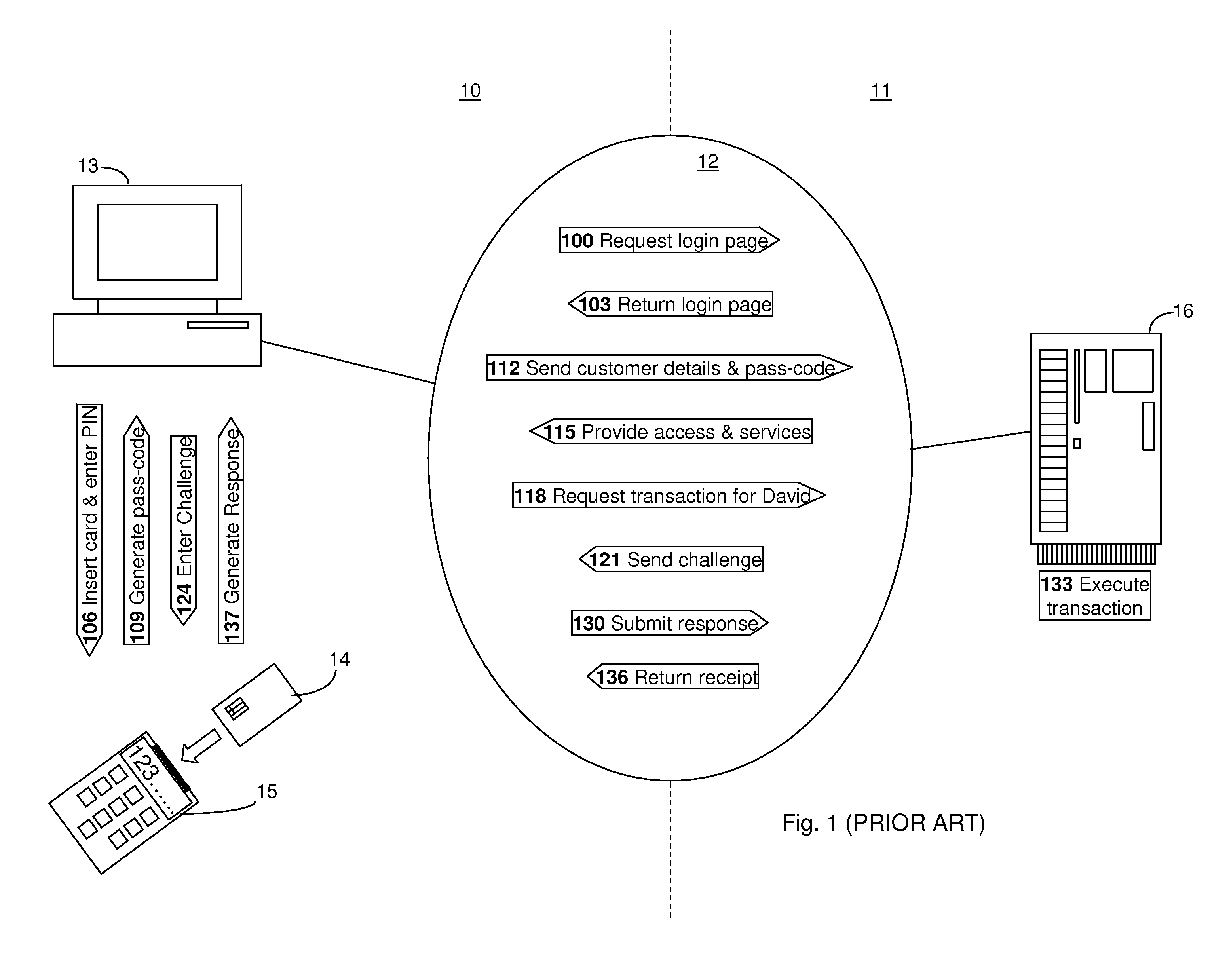
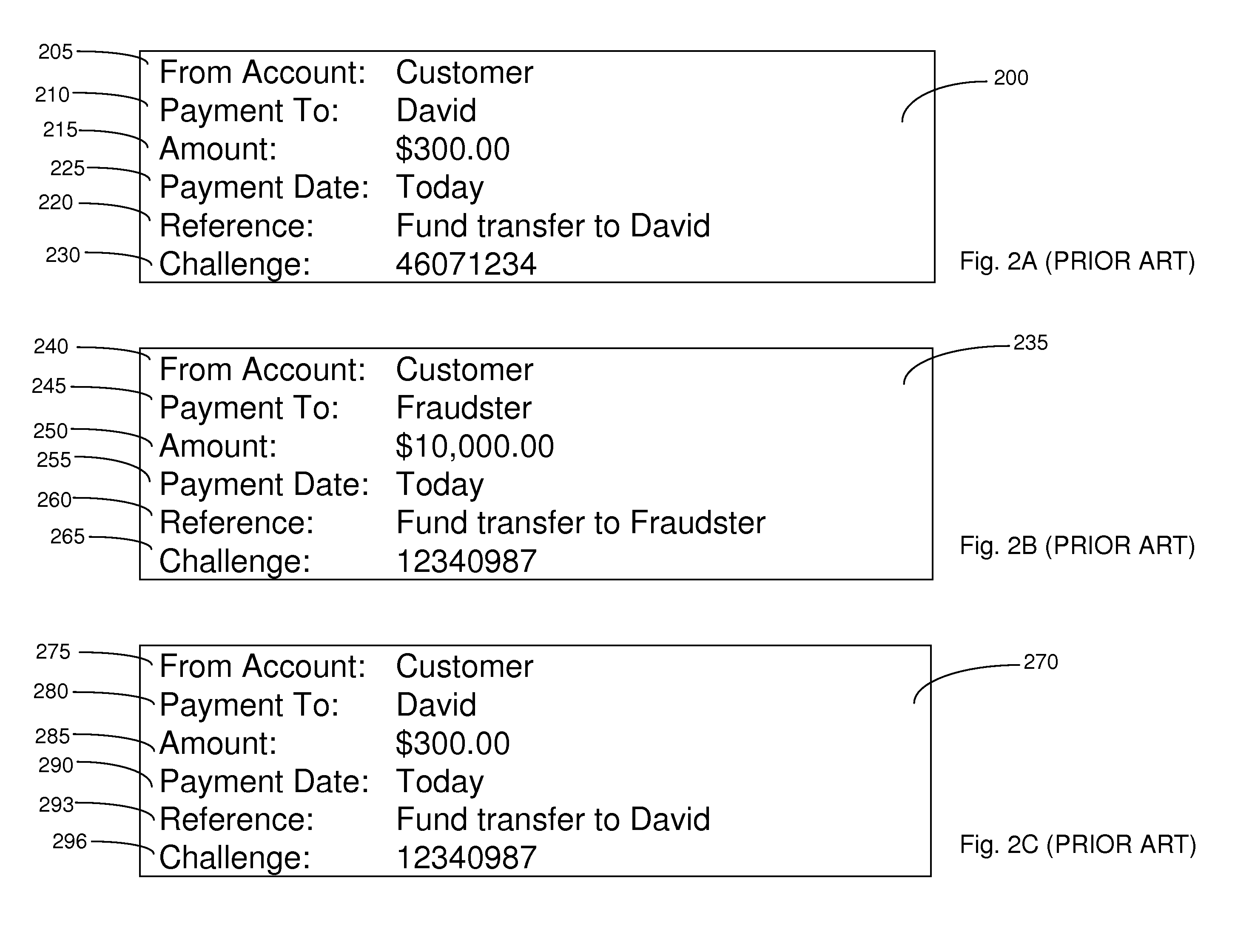
Online transactions systems and methods
InactiveUS20070043681A1Improve securityImprove computing powerAcutation objectsDigital data authenticationMan-in-the-middle attackInternet privacy
Embodiments of the present invention relate to an online transaction method enacted between a first party and a second party, for example a customer and a bank respectively. The method of the embodiment includes the steps of the first party transmitting a transaction request comprising transaction details and the second party receiving the transaction request and generating, for the first party, an authentication request, comprising transaction details and challenge data. In order to increase the security of the overall transaction, the authentication request is adapted so that it is difficult for an automated process to use or modify information therein to generate a replacement authentication request. Such a method finds application in reducing the potential for a man-in-the-middle attack, wherein an intermediate, subversive process can behave as a legitimate second party in order to steal money from the first party.
Owner:THE ROYAL BANK OF SCOTLAND PLC
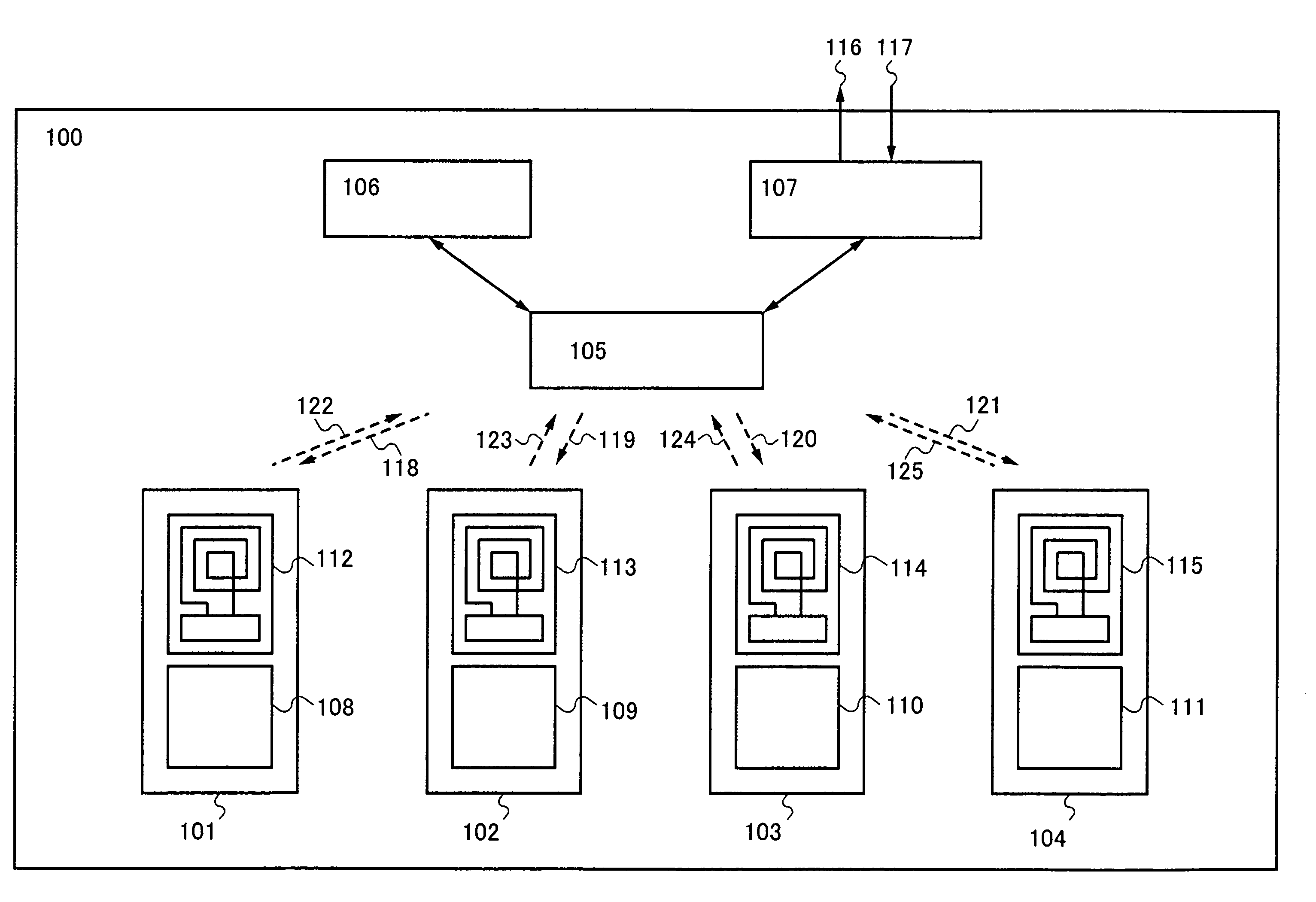
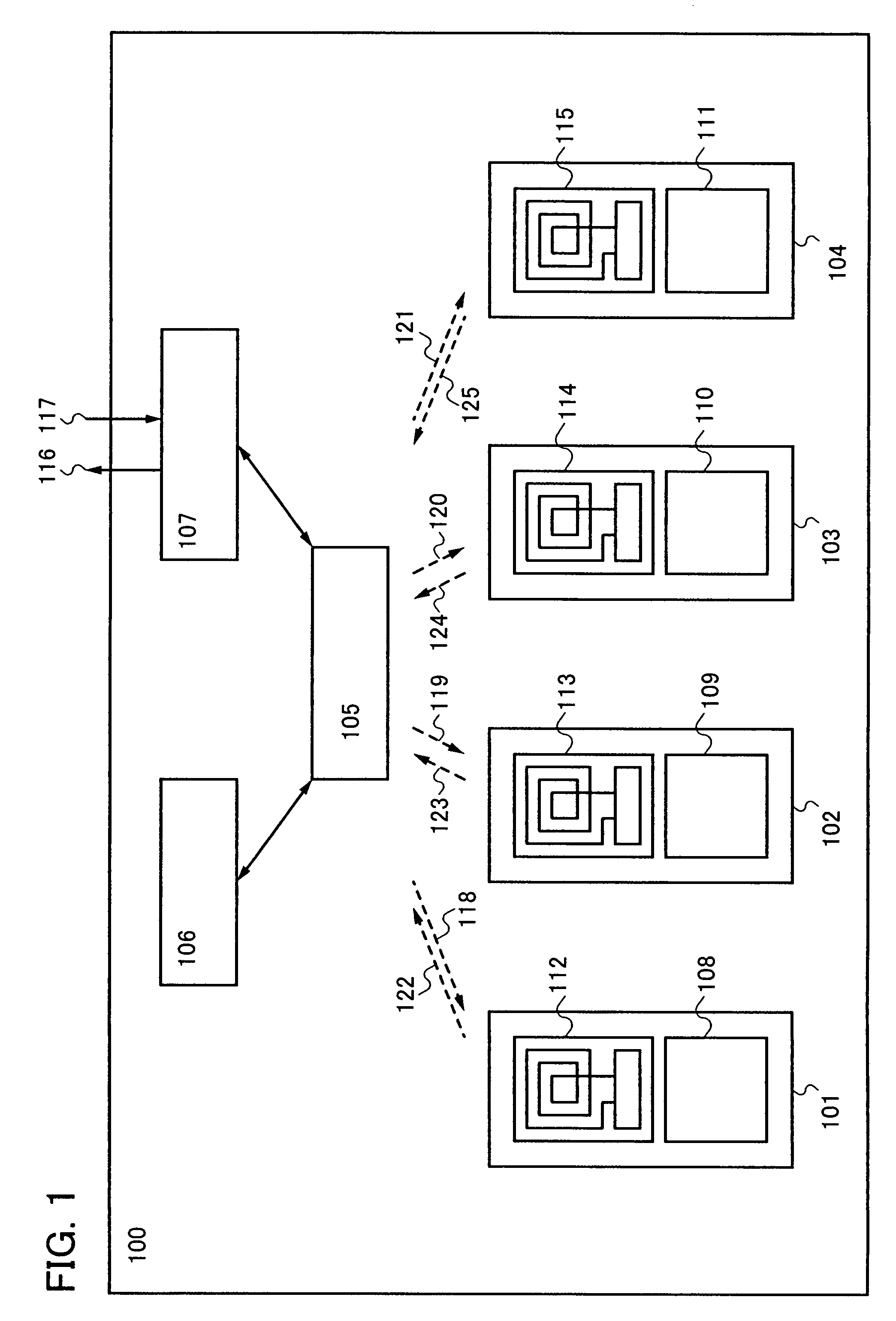
Digital watermarking apparatus and methods
InactiveUS7024016B2Improve computing powerReduced portabilitySpeech analysisCharacter and pattern recognitionDisplay deviceInventory management
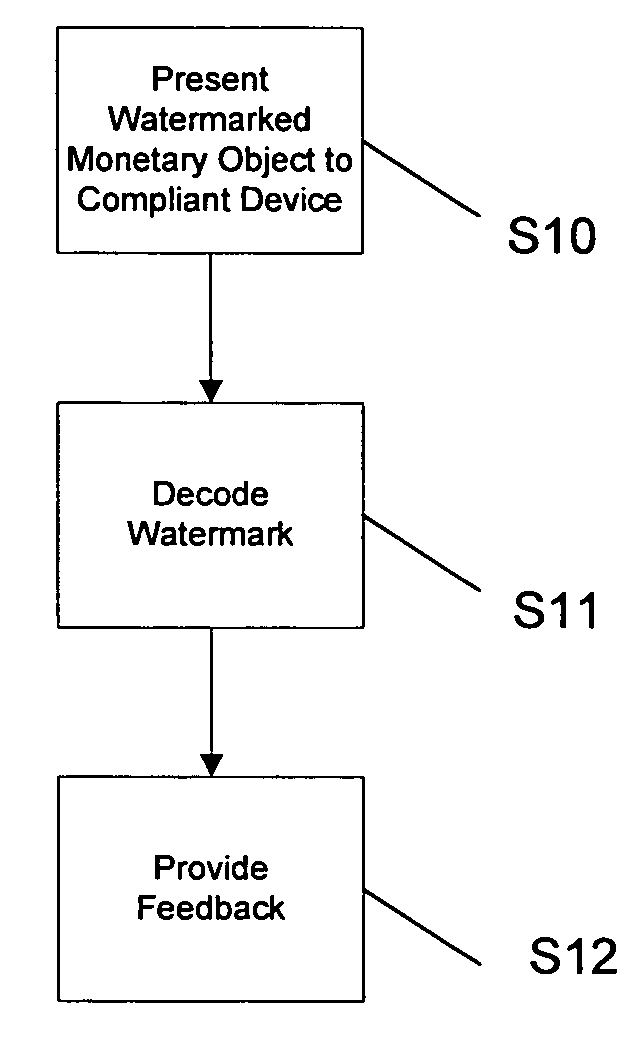
The present invention relates to various digital watermarking methods and systems. In one embodiment, a handheld device displays a digitally watermarked ticket image at an event center. At the event center, a watermark decoder extracts the watermark to determine authorized entry. In another embodiment, a plurality of microlenses can provide a polarized luminance pattern on a display. The pattern corresponds to (or conveys) a unique device identifier. In yet another embodiment, monetary objects are watermarked with payload information to signify currency denomination. The payload information, once extracted, is used to provide feedback regarding the currency denomination. An audio signal or Braille output can be provided as feedback. In still another embodiment, a document management system is based on watermarks. Embedded watermarks are used to track document history, determine document version information, and enhance overall security. In still another embodiment, an inventory system reads watermarks that have been directly applied to inventory items. Inventory management is greatly enhanced. Handheld computing devices are advantageously employed with these embodiments.
Owner:DIGIMARC CORP
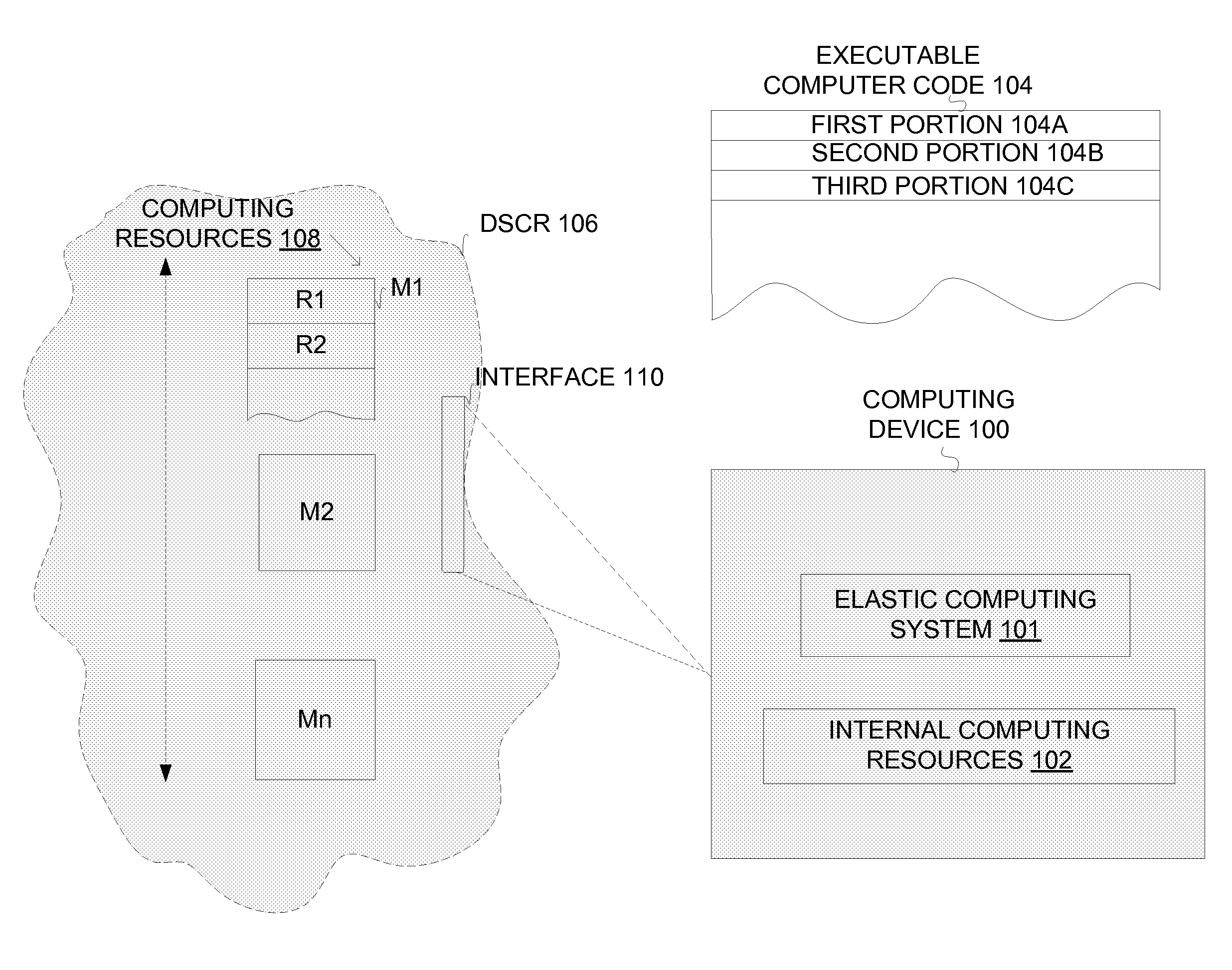
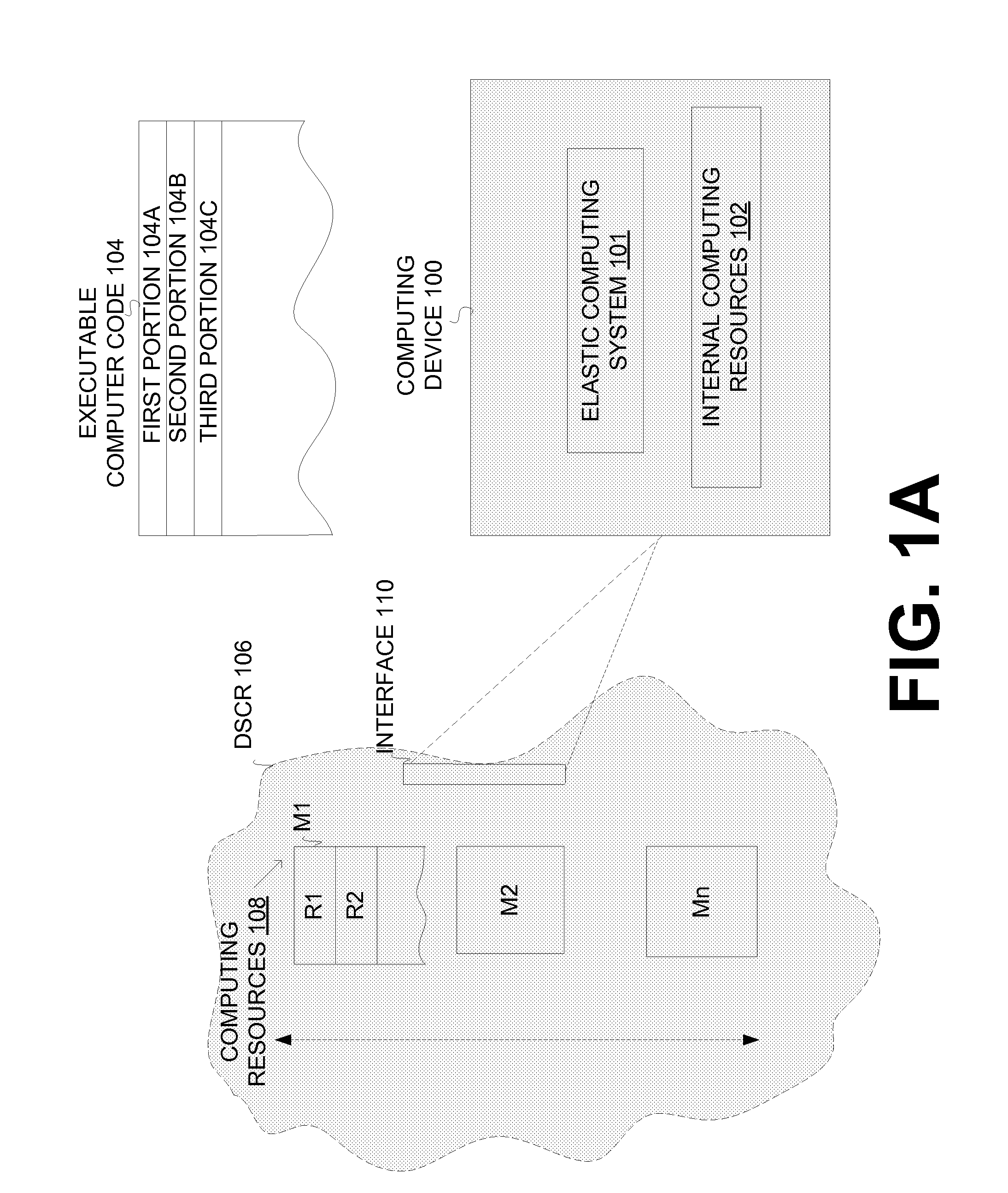
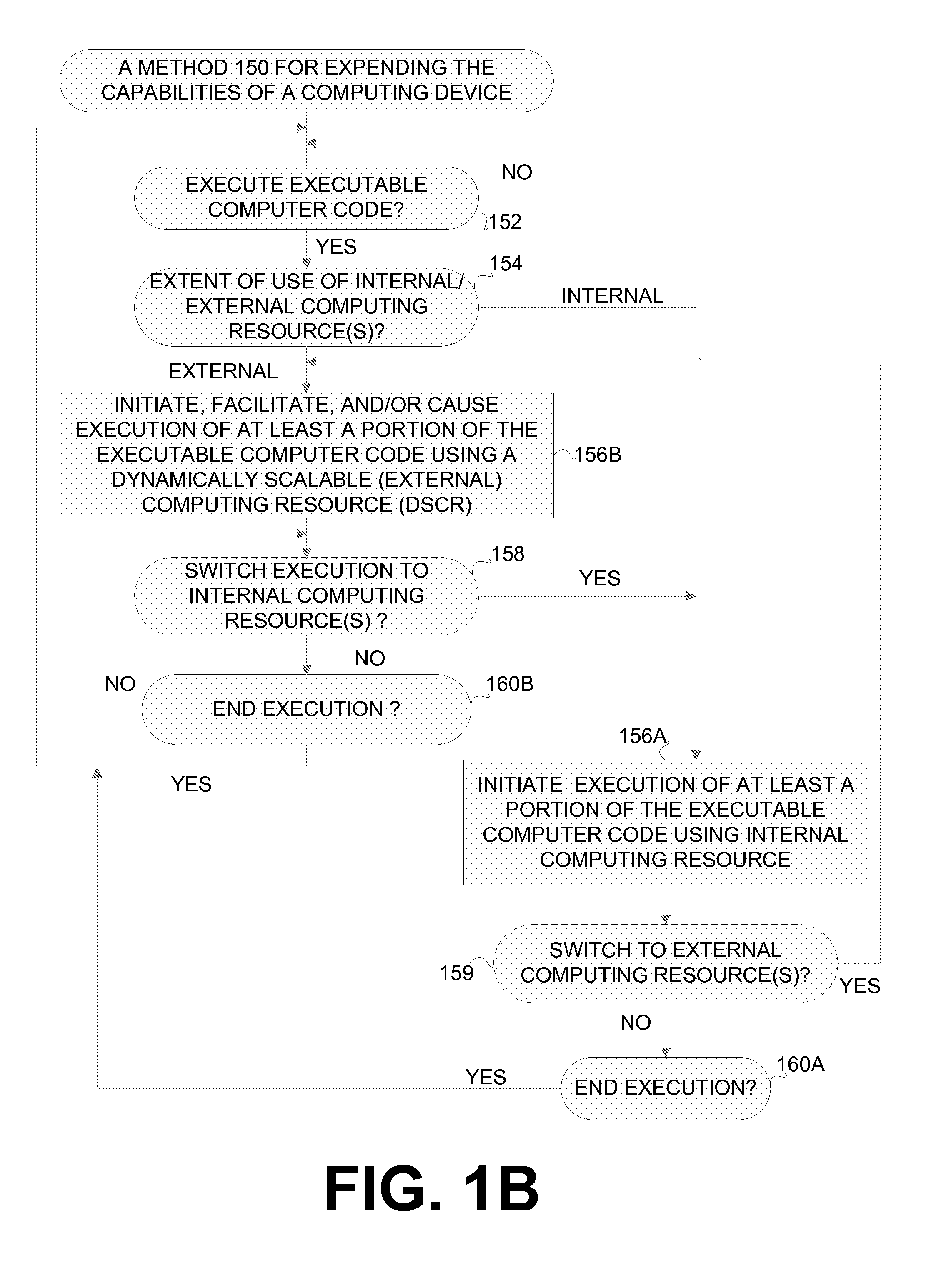
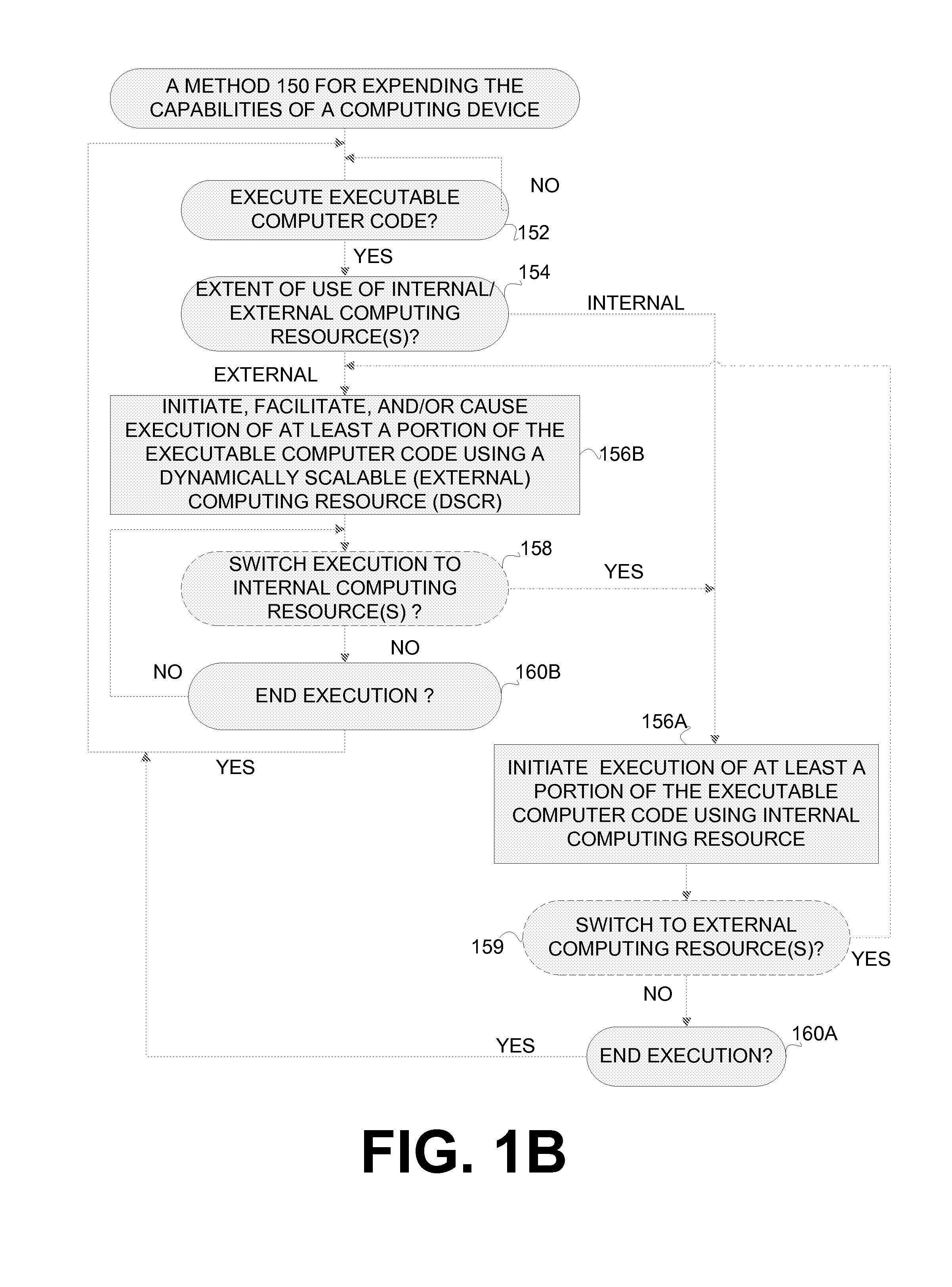
Extending the capability of computing devices by using dynamically scalable external resources
InactiveUS20100131590A1Limited and/or reduce computing resourceEffective migrationResource allocationMultiple digital computer combinationsDynamic ExtensionOn demand
Techniques for extending the capabilities of computing environments and / or systems are disclosed. A scalable and dynamic external computing resource can be used in order to effectively extend the internal computing capabilities of a computing environment or system. The scalable and dynamic external computing resource can provide computing resources that far exceed the internal computing resources, and provide the services as needed, and in a dynamic manner at execution time. As a result, a computing device may function with relatively limited and / or reduced computing resources (e.g., processing power, memory) but have the ability to effectively provide as much computing services as may be needed, and provide the services when needed, on demand, and dynamically during the execution time.
Owner:SAMSUNG ELECTRONICS CO LTD
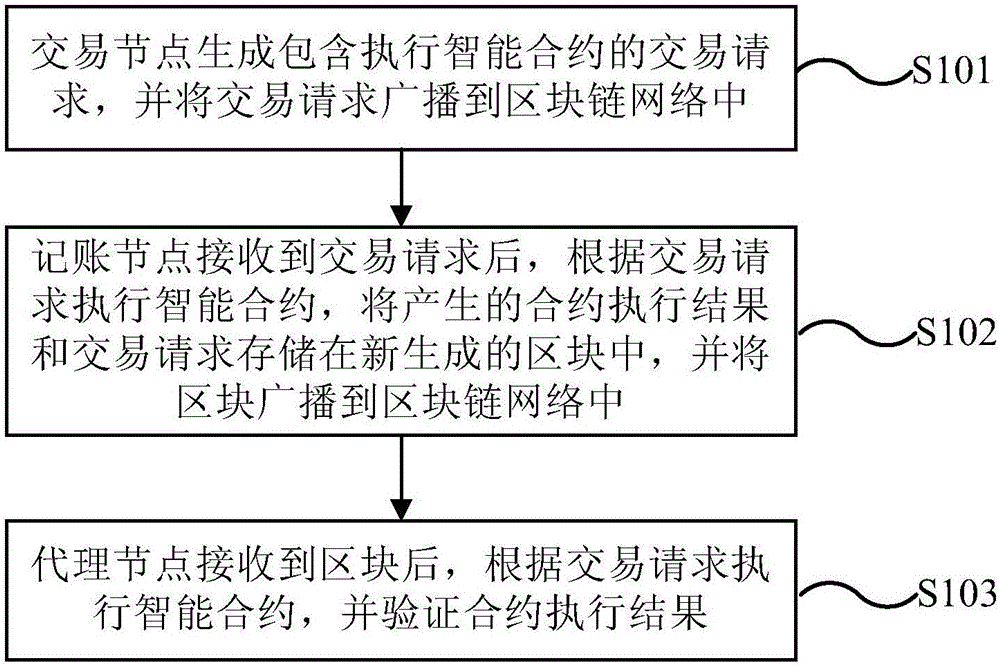
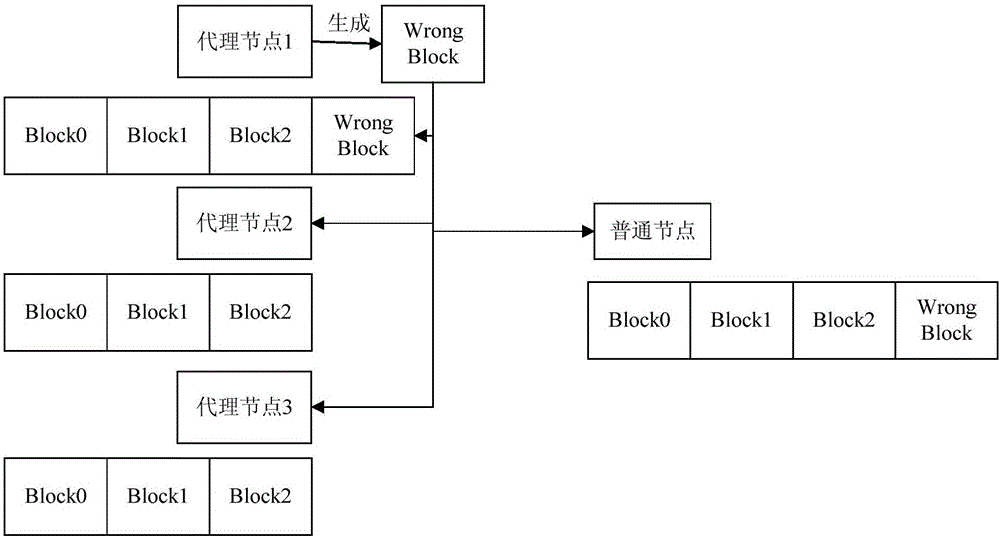
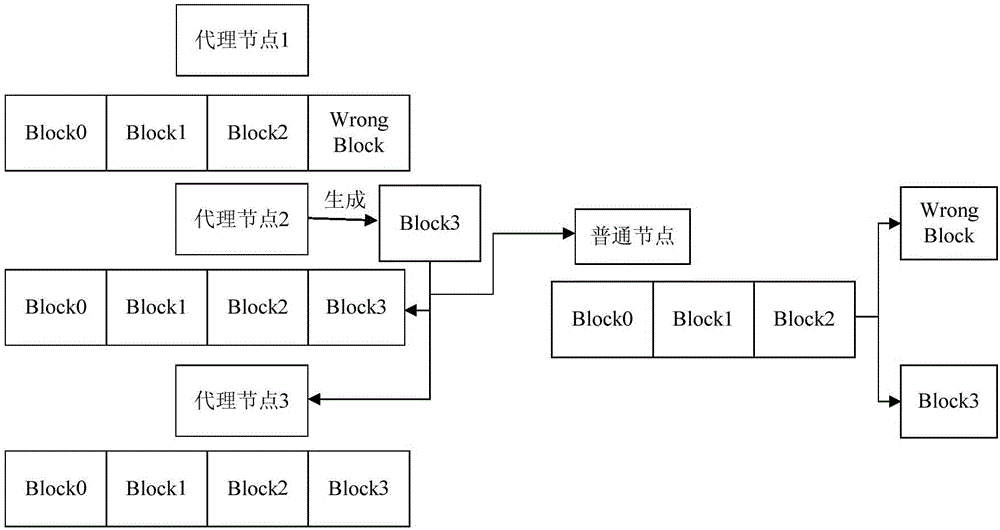
Block chain consensus method based on DPOS and nodes
The invention provides a block chain consensus method based on a DPOS and nodes. The method comprises the following steps that a transaction node generates a transaction request of executing an intelligent contract and broadcasts the transaction request to a block chain network; an accounting node receives the transaction request, then executes the intelligent contract according to the transaction request, stores a generated contract execution result and a transaction request in a newly-generated block and broadcasts the block to the block chain network; and an agent node receives the block, then executes the intelligent contract according to the transaction request and verifies the contract execution result. By using the technical scheme provided in the invention, a common node does not need to verify the contract execution result so that a calculating capability of a whole network can be effectively increased.
Owner:北京果仁宝科技有限公司
Digital watermarking apparatus and methods
InactiveUS7164780B2Improve computing powerReduced portabilityPaper-money testing devicesCharacter and pattern recognitionUnique identifierHand held devices
The present invention relates to various steganographic methods and apparatus. In one embodiment, a plurality of microlenses can provide a steganographic signal for a handheld device. The pattern corresponds to (or conveys) a device identifier. In another embodiment, a handheld computing device includes: a plurality of pixel elements; a set of microlenses; and electronic circuitry communicating with the set of microlenses. The set of microlenses are arranged to create a pattern, the pattern providing a plural-bit identifier. The electronic circuitry operates to change the unique identifier. Other embodiments are also provided.
Owner:DIGIMARC CORP
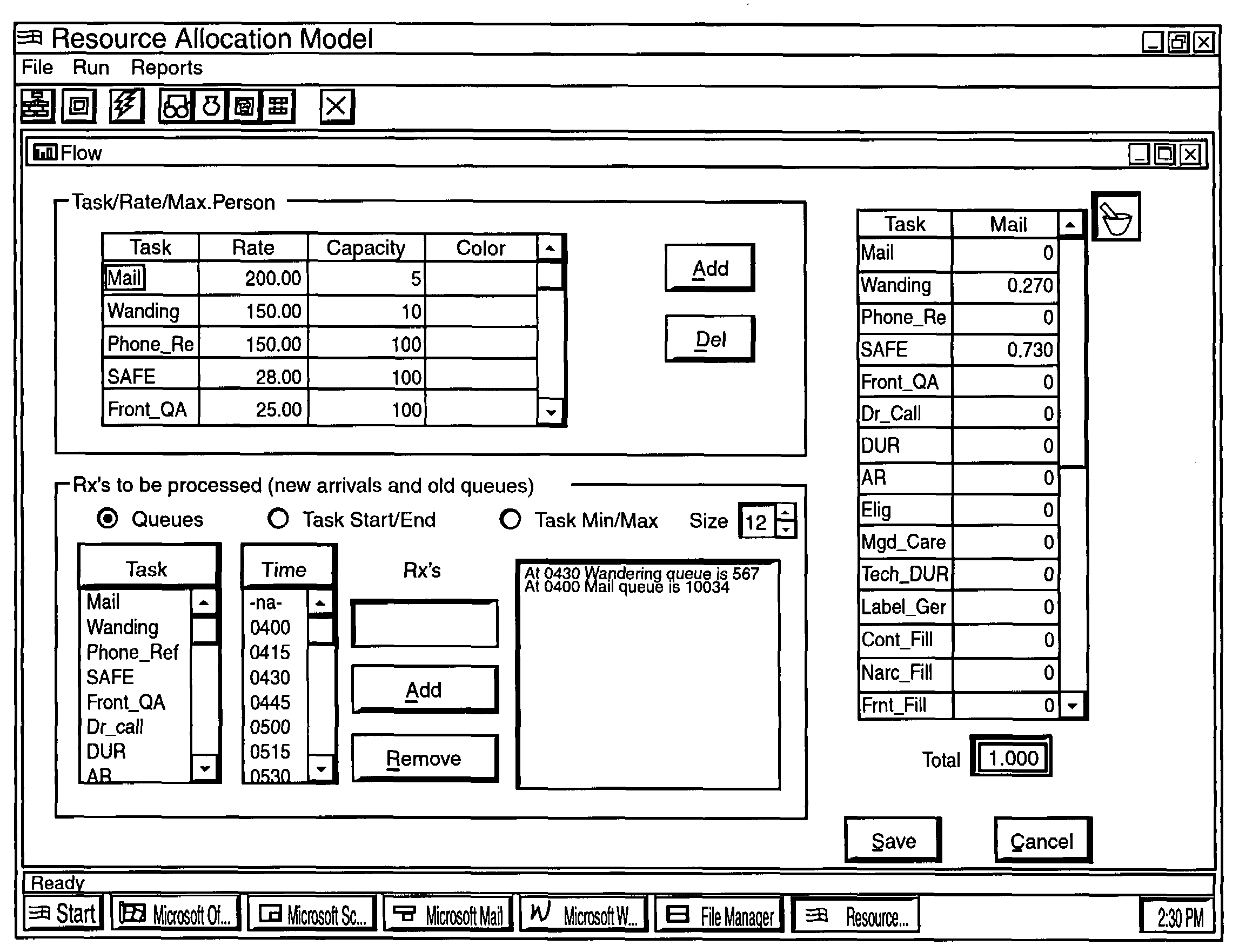
Computer implemented resource allocation model and process to dynamically and optimally schedule an arbitrary number of resources subject to an arbitrary number of constraints in the managed care, health care and/or pharmacy industry
InactiveUS7003475B1Enhanced method and apparatusImprove computing powerDigital computer detailsResourcesPharmacyResource allocation
A method of allocating resources includes scheduling jobs from among a plurality of resources of a work-producing system. The work producing system is a pharmacy. The method includes the steps of sorting, in a predetermined order, available resources to be utilized in the pharmacy by a last task assignment, a number of tasks performable, rate per task, and / or cost per hour, and determining one or more queues responsive to the sorting. The method also includes the step of normalizing the queue by dividing a current task queue by an average rate of the available resources for each task in the current task queue. The method also includes the step of assigning the available resources to one or more tasks with a predetermined normalized queue, subject to at least one task constraint.
Owner:EXPRESS SCRIPTS STRATEGIC DEV INC
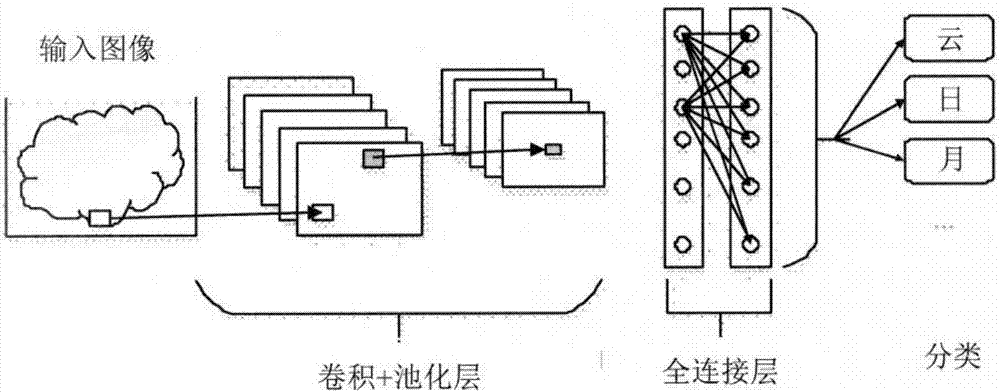
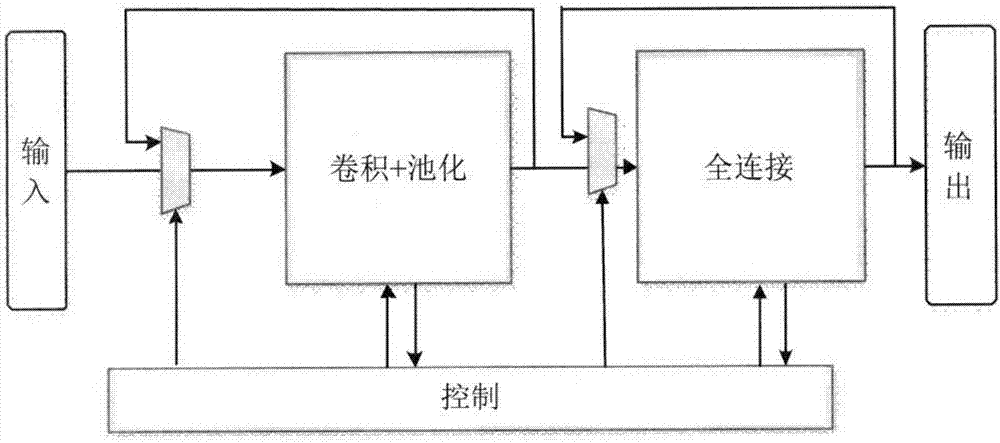
Apparatus and method for realizing accelerator of sparse convolutional neural network
InactiveCN107239824AImprove computing powerReduce response latencyDigital data processing detailsNeural architecturesAlgorithmBroadband
The invention provides an apparatus and method for realizing an accelerator of a sparse convolutional neural network. According to the invention, the apparatus herein includes a convolutional and pooling unit, a full connection unit and a control unit. The method includes the following steps: on the basis of control information, reading convolutional parameter information, and input data and intermediate computing data, and reading full connected layer weight matrix position information, in accordance with the convolutional parameter information, conducting convolution and pooling on the input data with first iteration times, then on the basis of the full connected layer weight matrix position information, conducting full connection computing with second iteration times. Each input data is divided into a plurality of sub-blocks, and the convolutional and pooling unit and the full connection unit separately operate on the plurality of sub-blocks in parallel. According to the invention, the apparatus herein uses a specific circuit, supports a full connected layer sparse convolutional neural network, uses parallel ping-pang buffer design and assembly line design, effectively balances I / O broadband and computing efficiency, and acquires better performance power consumption ratio.
Owner:XILINX INC
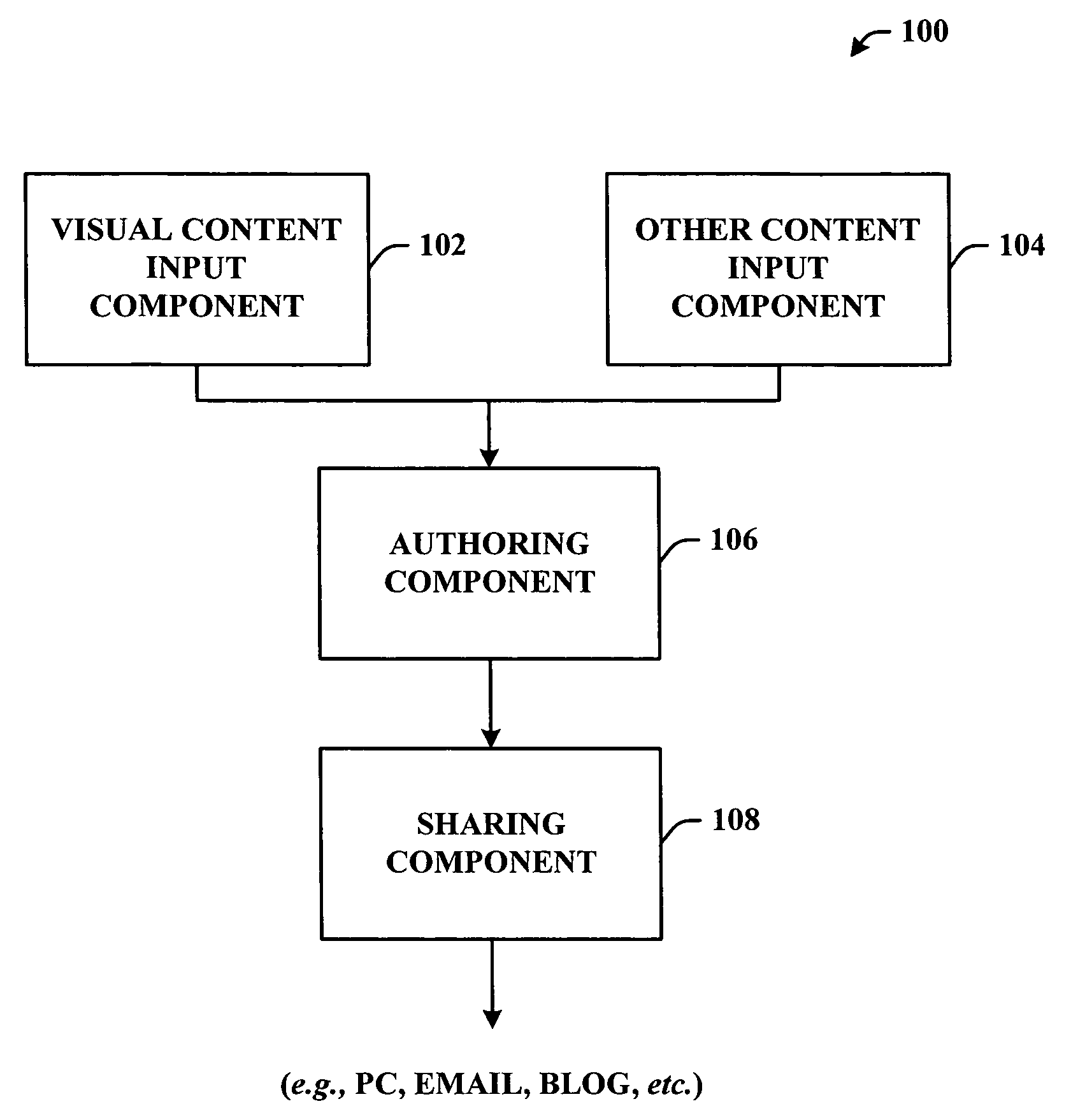
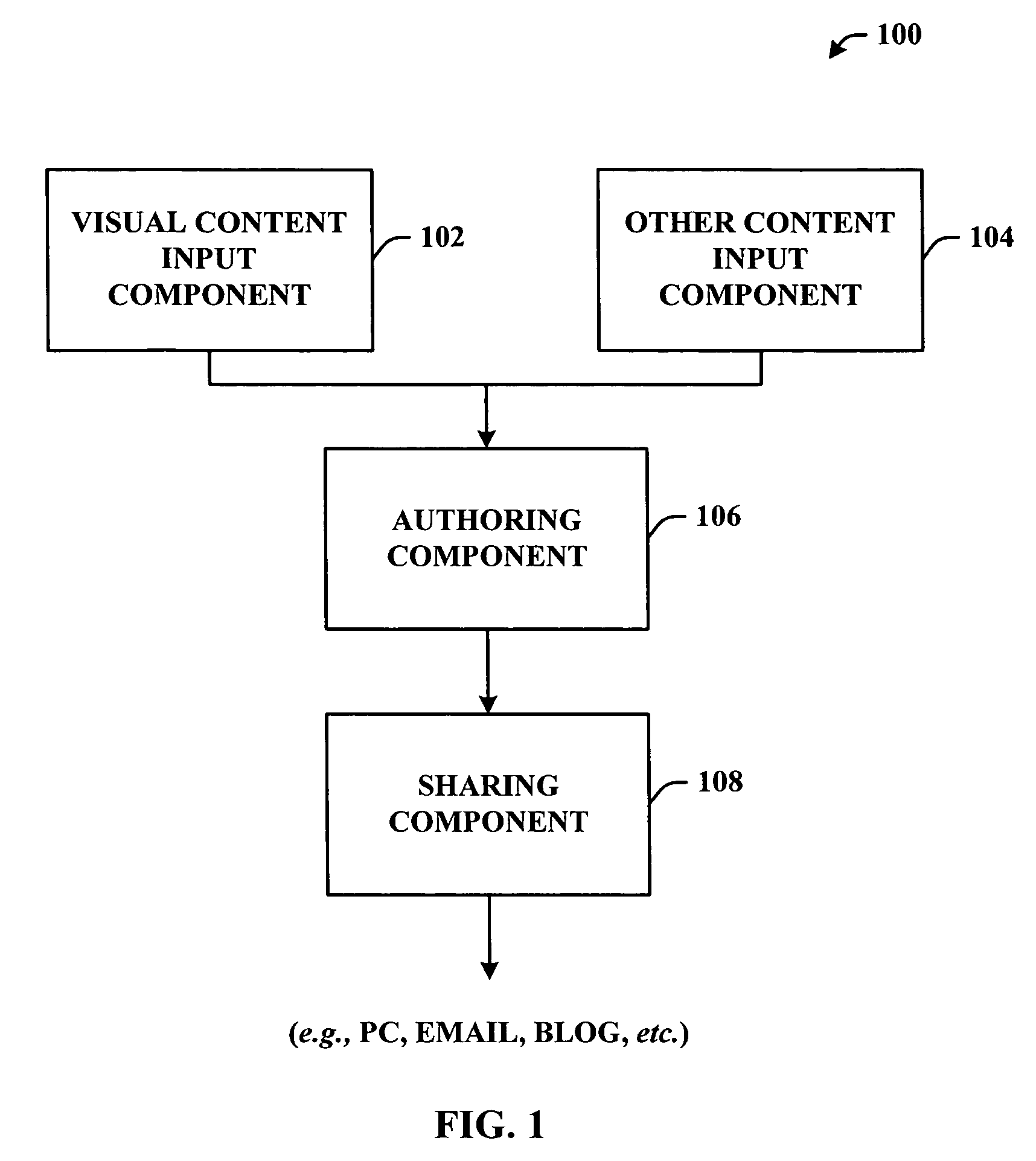
System and method to associate content types in a portable communication device
InactiveUS20060041632A1Easy to demonstrateOptimize allocationMetadata multimedia retrievalMultiple digital computer combinationsContent typePortable communications device
A system and or / methodology that facilitates organizing content on a portable communications device to generate a compilation (e.g., presentation) containing the organized content. The system and / or methodology includes an authoring component that associates content of a first type with a subset of other content and a sharing component that communicates and distributes the associated content. The subject invention can include a visual content input component that receives visual content and another content input component that can generate and organize other content in accordance with a user preference. The other content can include any content type known in the art including, but not limited to, visual, audible, text or the like.
Owner:MICROSOFT TECH LICENSING LLC
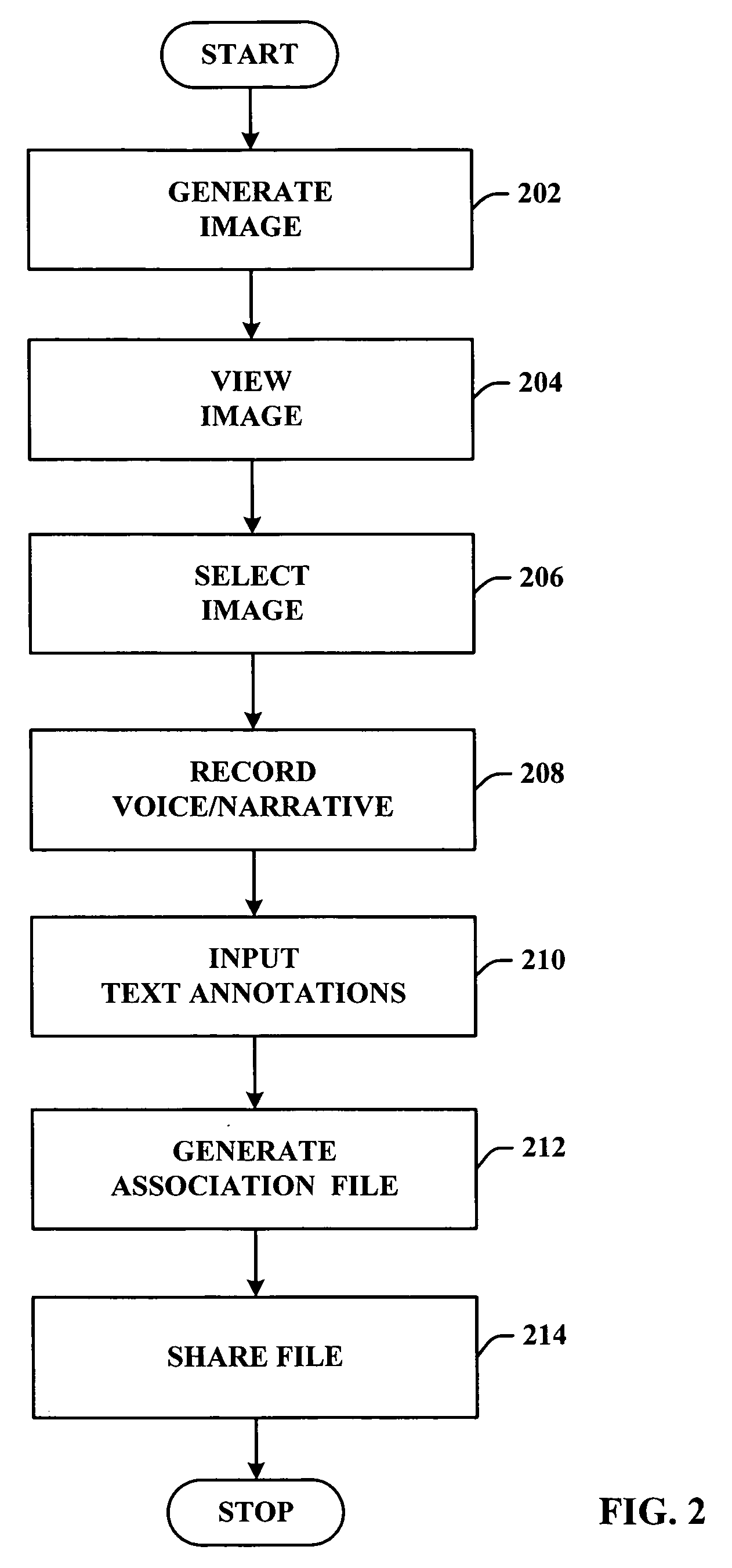
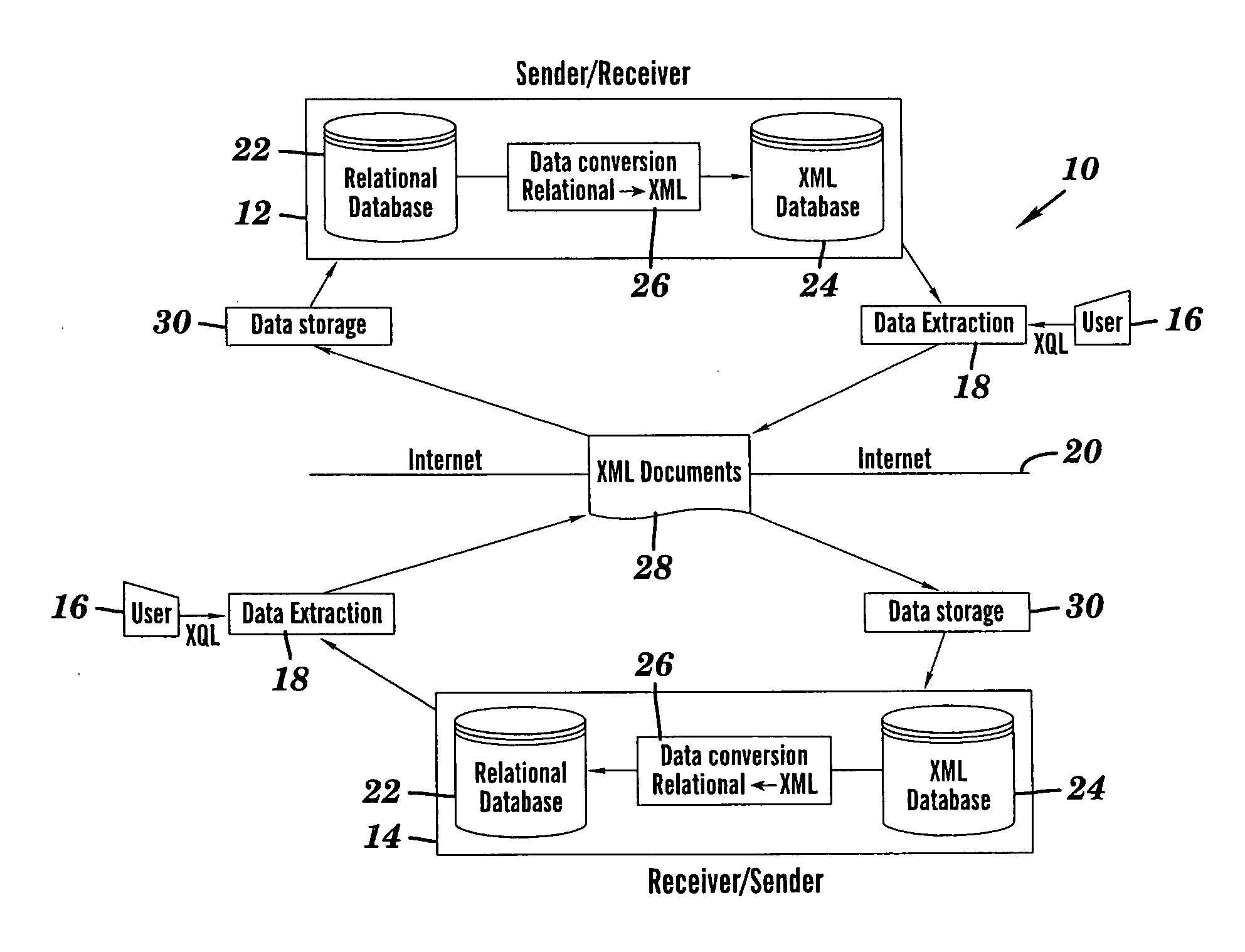
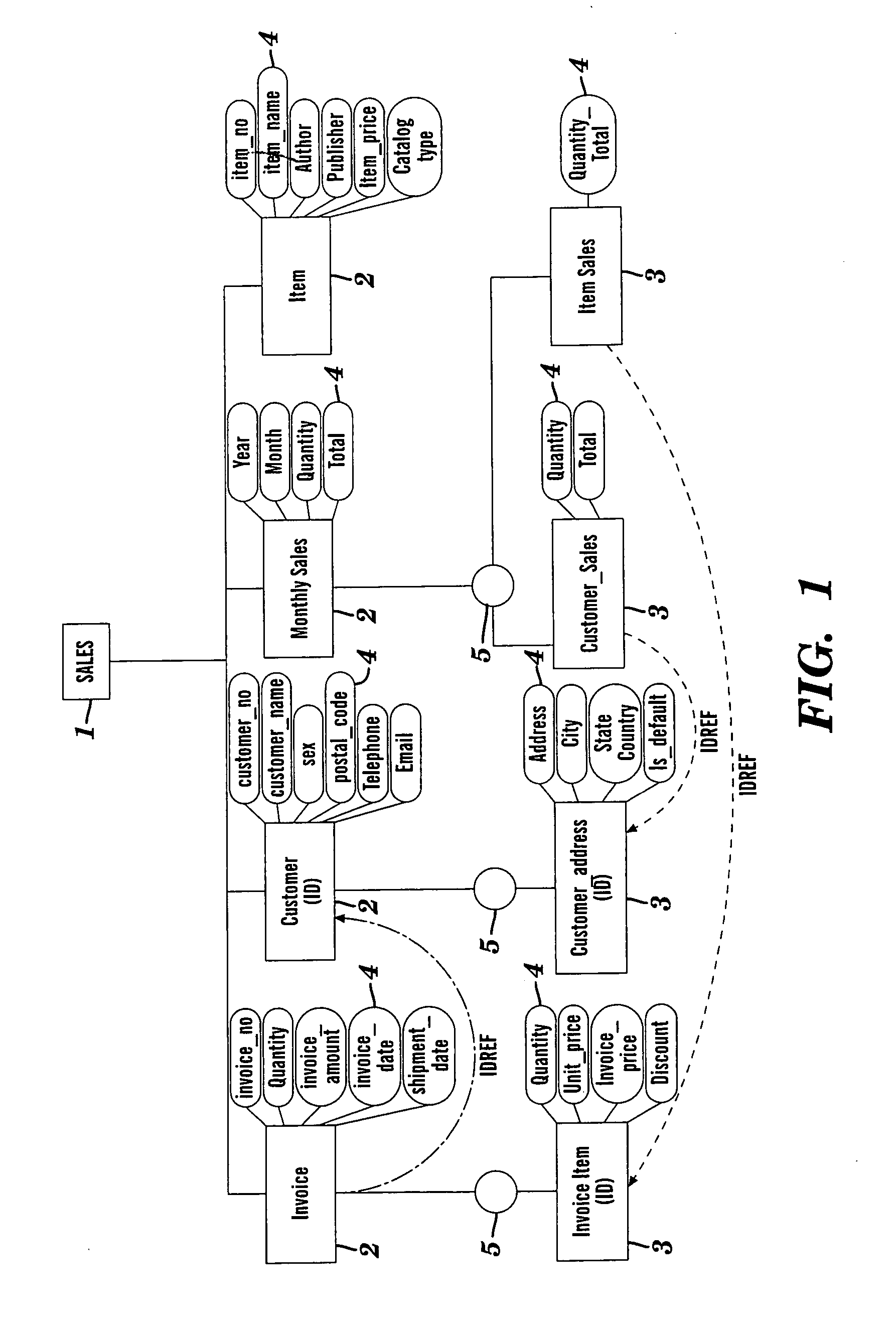
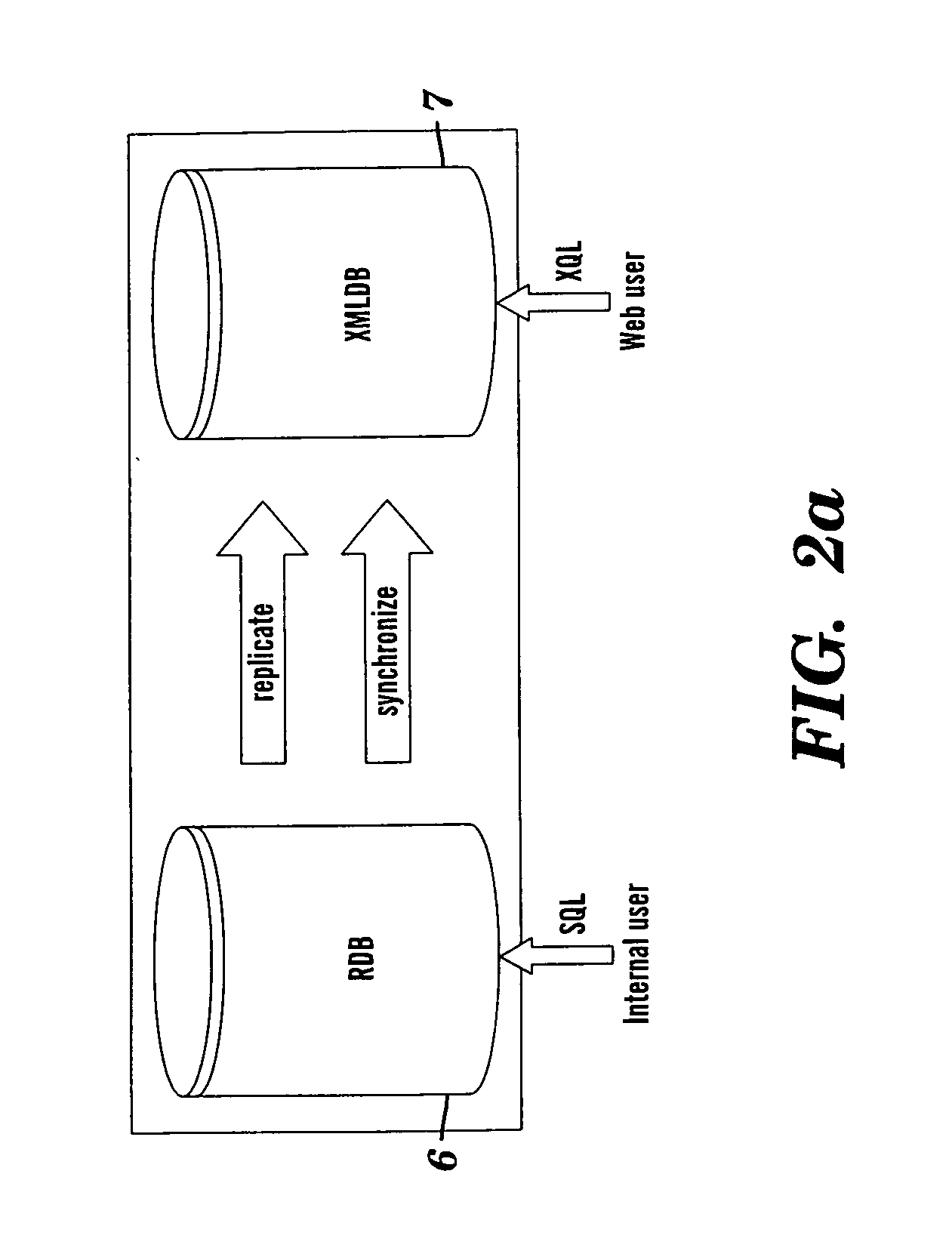
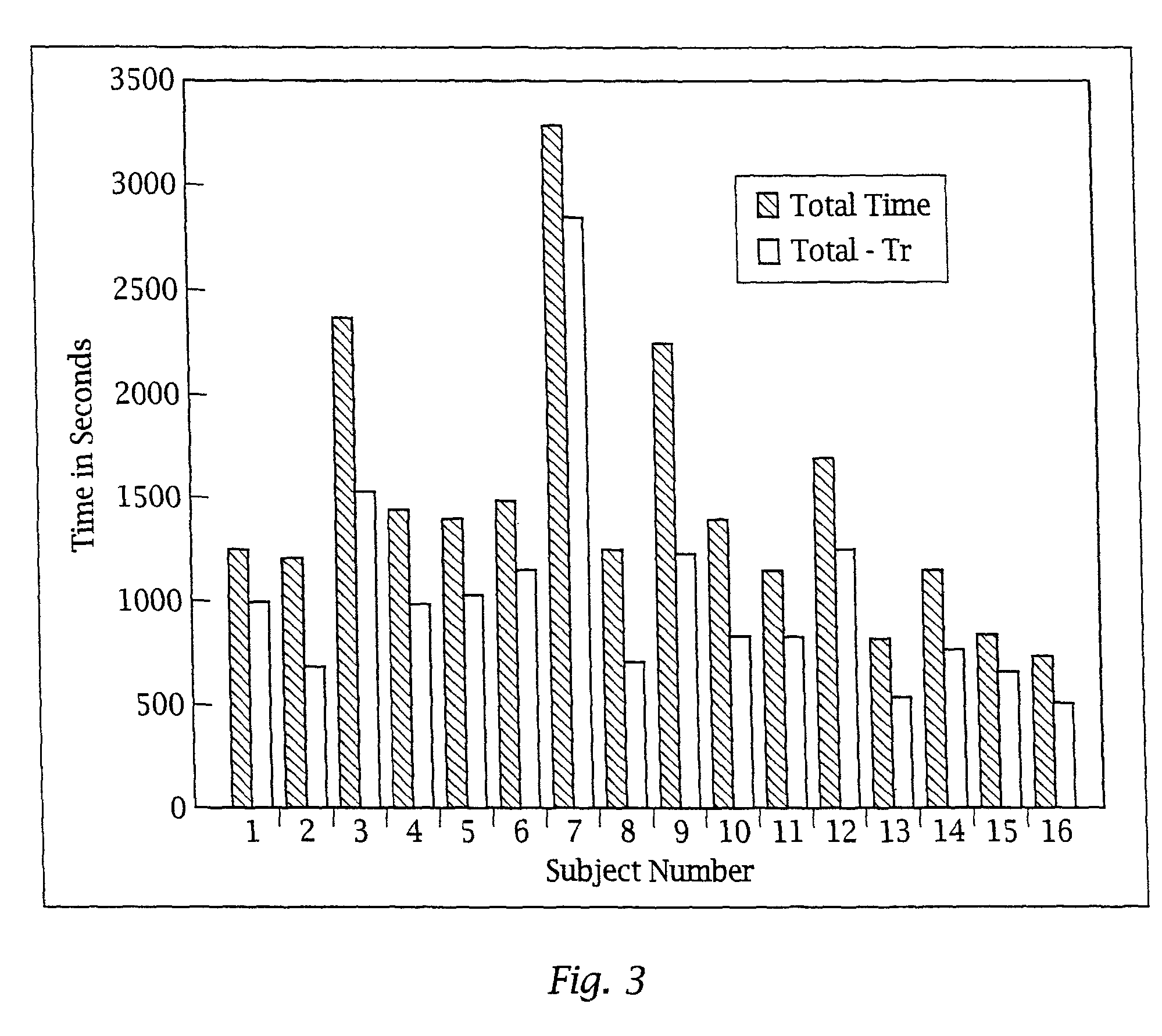
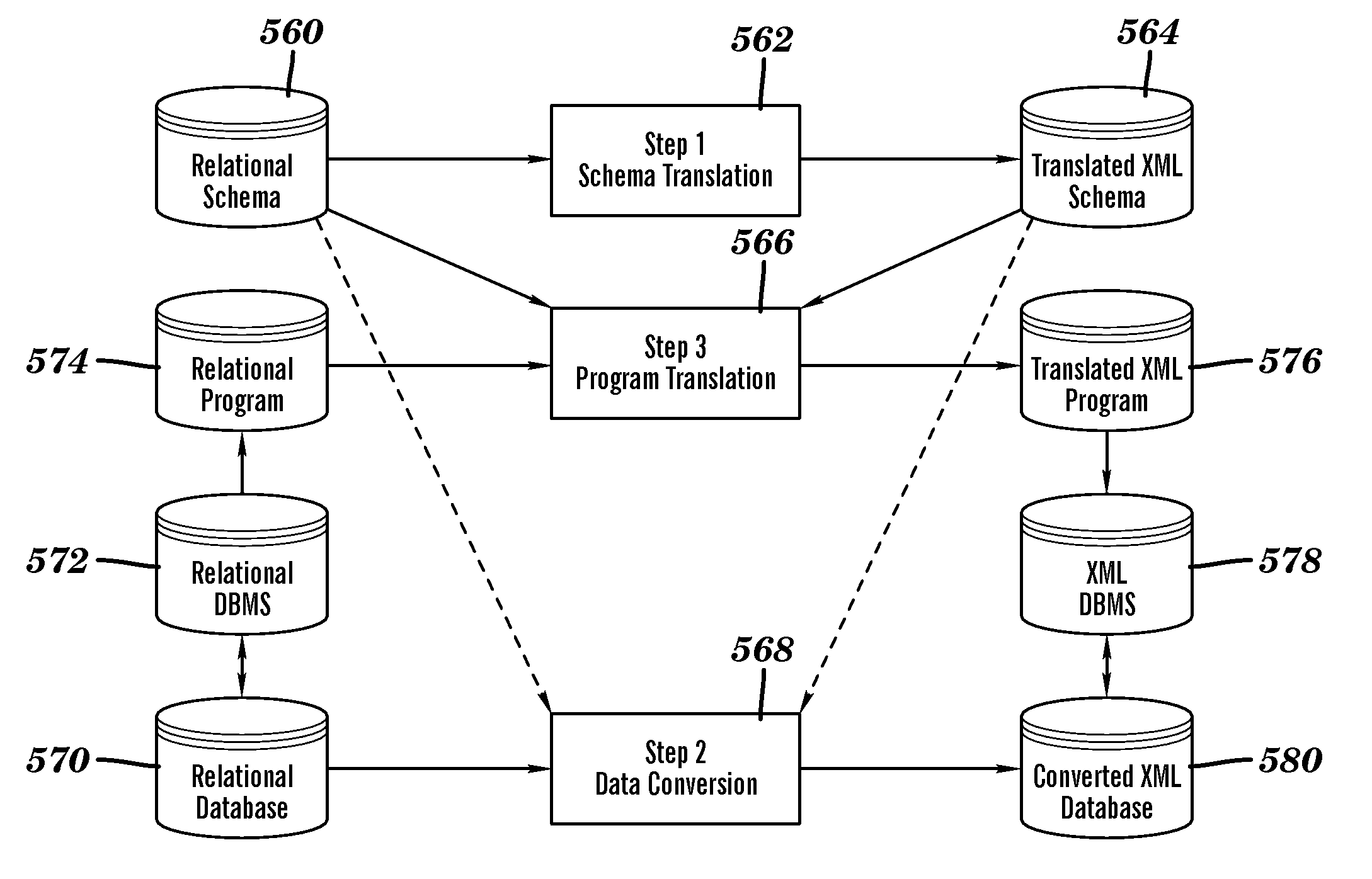
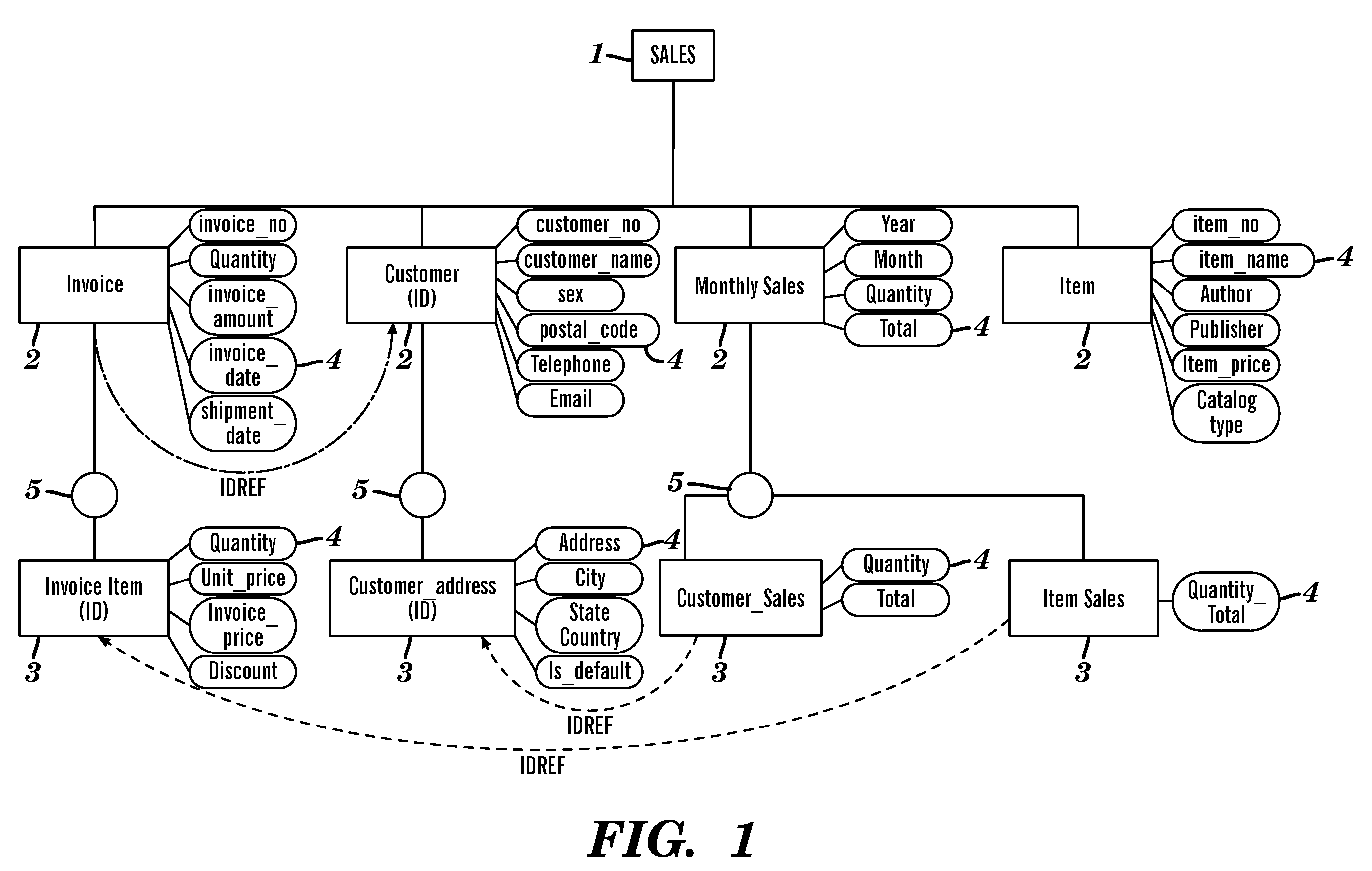
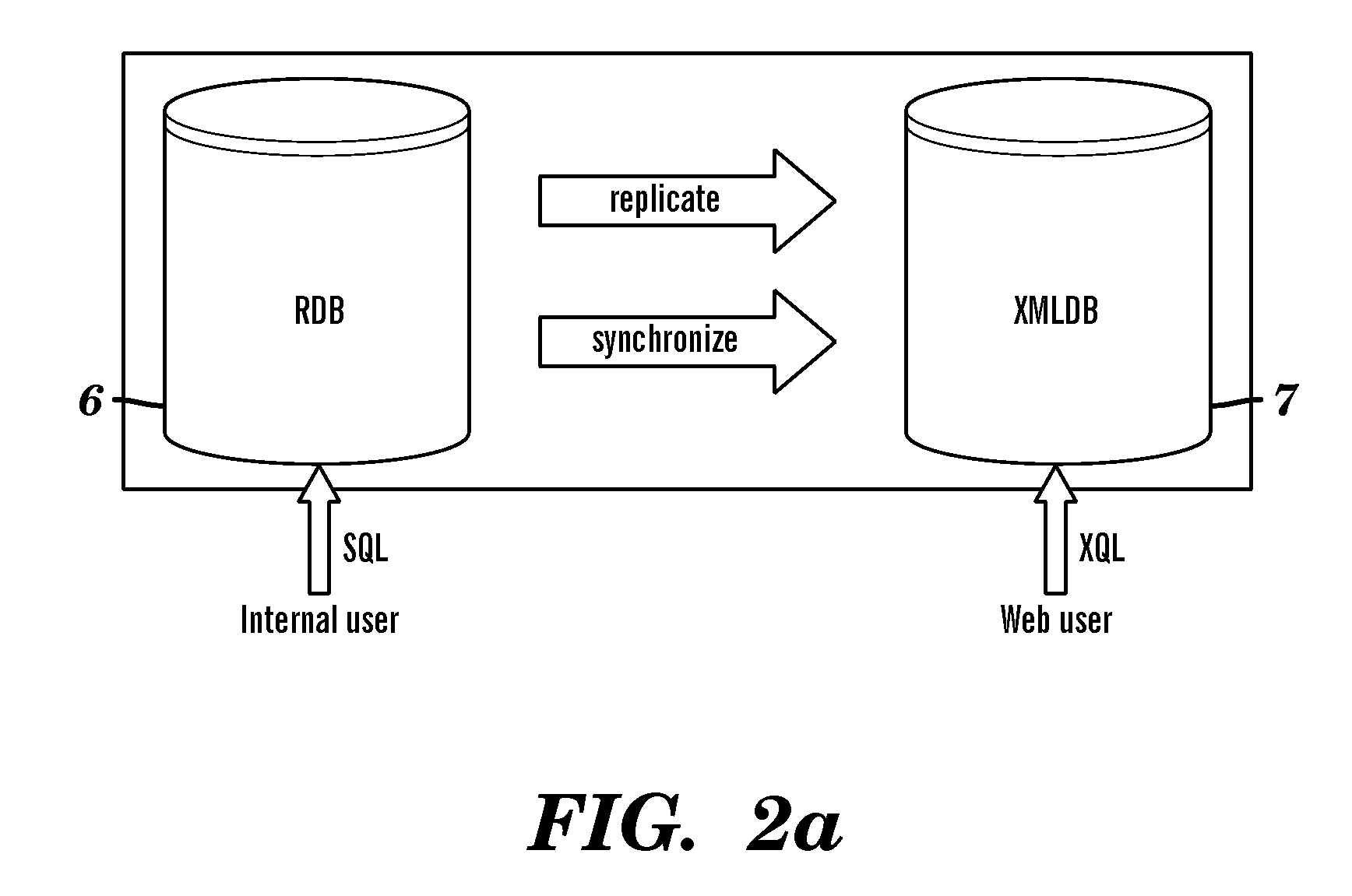
System and method of translating a relational database into an XML document and vice versa
InactiveUS20060173865A1Easy to useImprove performanceDigital data processing detailsNatural language data processingEntity relationship modellingXML tree
A method of translating a relational database into an XML document comprises generating an Extended Entity Relationship model from relational schema associated with the relational database and applying a schema translation process to the Extended Entity Relationship model to map the relational schema into a Document Type Definition (DTD) of an XML schema. An XML Tree Model is then generated from the Document Type Definition, the XML Tree Model being representative of one or more data semantics of the relational schema which are preserved as one or more data semantics in the XML document. Relational data from the relational database is then converted into the XML document using the relational schema and the XML schema from the Document Type Definition and / or the XML Tree Model. There is also described a method of translating an XML database into a relational database which comprises the reversal of the steps of the aforementioned method, and a system for implementing both methods.
Owner:CITY UNIVERSITY OF HONG KONG
Semiconductor device
InactiveUS7840188B2Reduce the amount requiredReduce total powerEnergy efficient ICTNear-field transmissionThread schedulingControl circuit
In a multi-core semiconductor device, a data bus between CPUs or the like consumes a larger amount of power. By provision of a plurality of CPUs which transmit data by a backscattering method of a wireless signal, a router circuit which mediates data transmission and reception between the CPUs or the like, and a thread control circuit which has a thread scheduling function, a semiconductor device which consumes less power and has high arithmetic performance can be provided at low cost.
Owner:SEMICON ENERGY LAB CO LTD
Digital watermarking apparatus and methods
ActiveUS20050111723A1Broaden applicationIncrease flexibilityElectric signal transmission systemsDigital data processing detailsOptical scannersHand held devices
The present invention relates to digital watermarking methods and systems. In one embodiment, a handheld device displays a digitally watermarked image at an event center. An optical scanner captures optical scan data representing the device display. A watermark decoder analyzes the captured optical scan data to obtain the watermark. The watermark is used to determine authorized entry. The handheld device may include a cell phone or other portable computing device.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
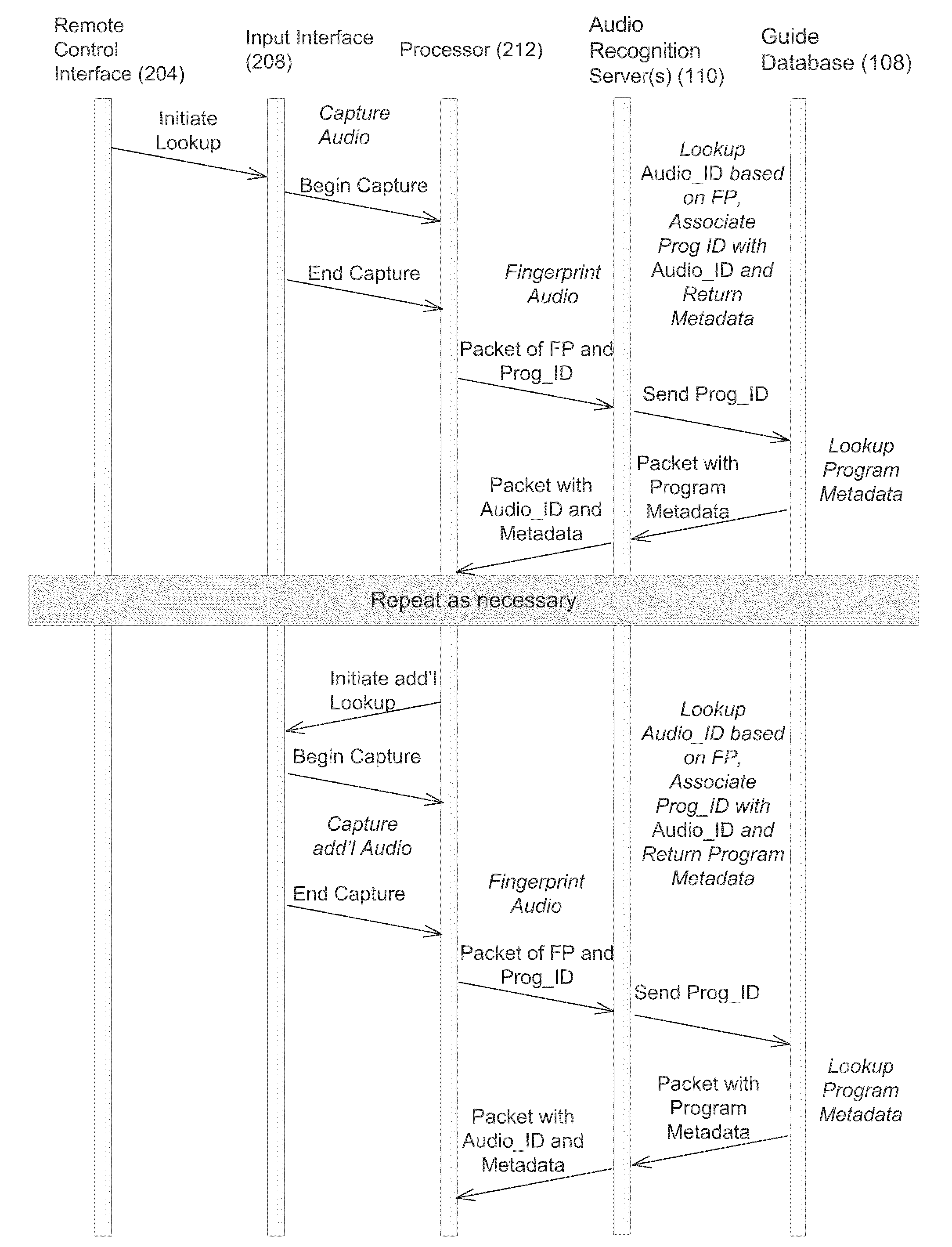
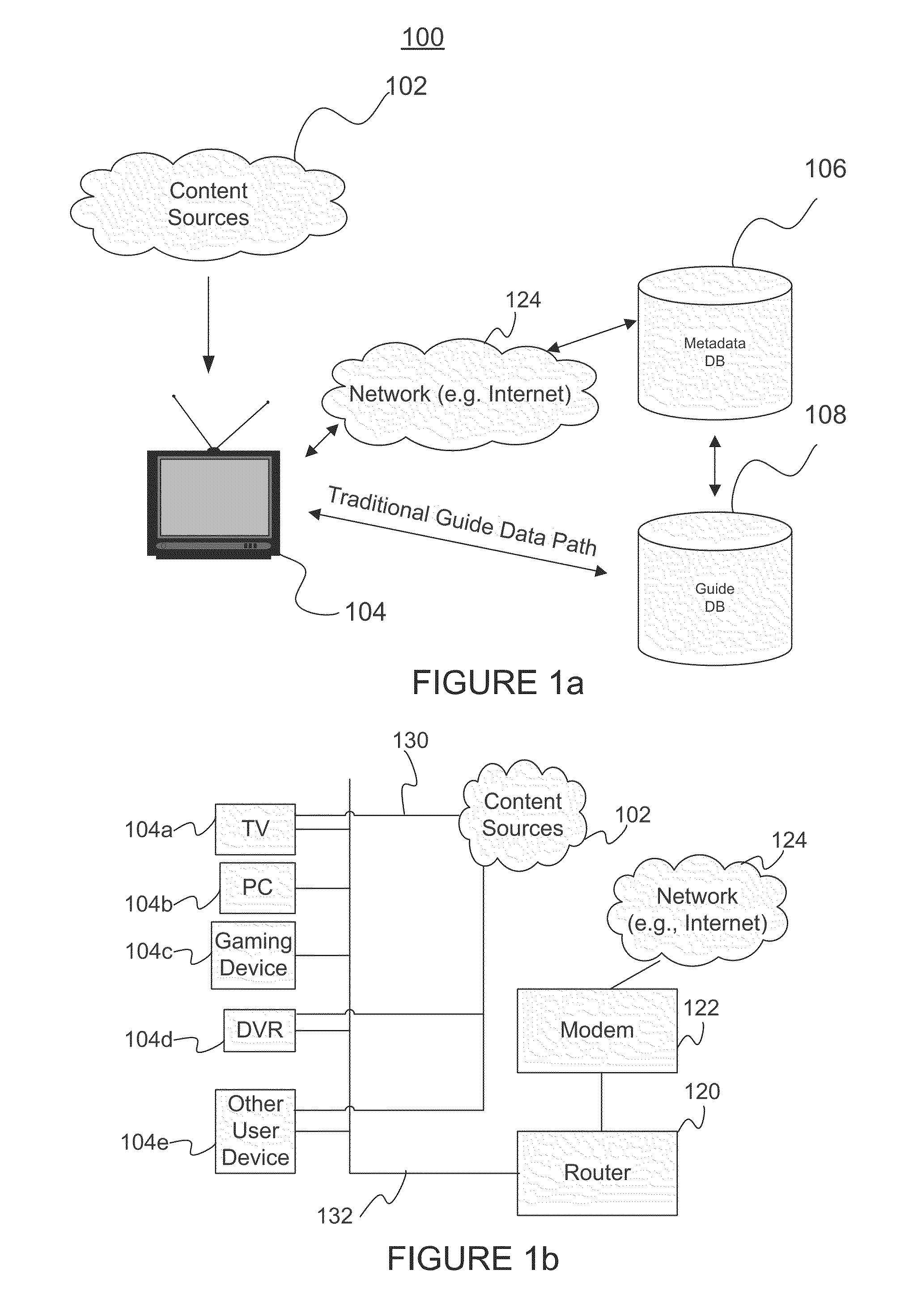
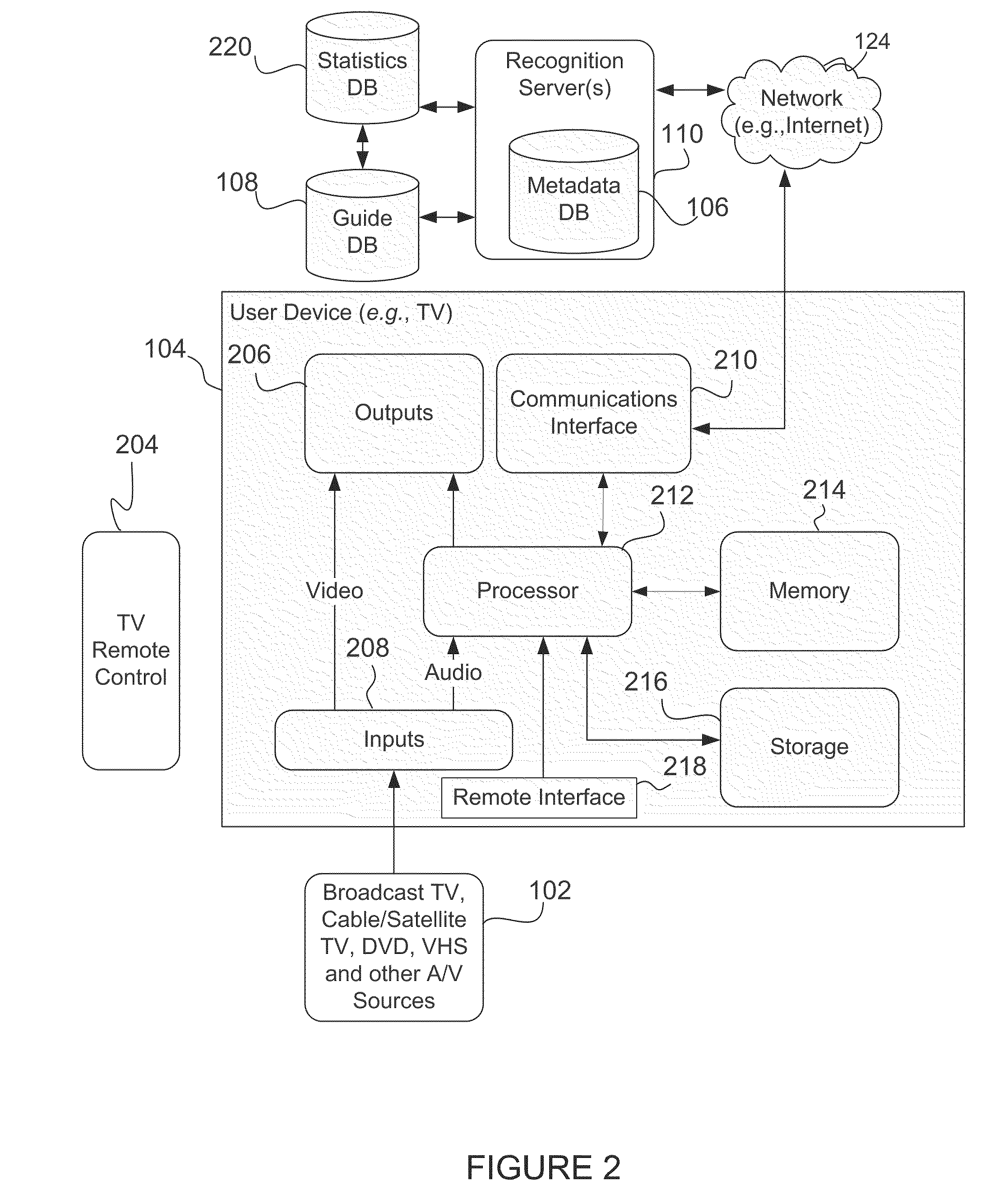
Content Recognition and Synchronization on a Television or Consumer Electronics Device
InactiveUS20110041154A1Improve computing powerTelevision system detailsDigital data information retrievalUser deviceMetadata
An audio portion of content, such as an audio stream, is associated with a multimedia program. A server receives an audio fingerprint and a program identifier from a network and associates the audio fingerprint with an audio identifier. A request packet including the program identifier is transmitted over the network to request program guide information associated with the program identifier. The program data including the program guide information is received from the network and metadata associated with the audio identifier and the program data are transmitted onto the network. A user device initiates a request for the metadata by using an audio fingerprint and the program identifier.
Owner:ROVI TECH CORP
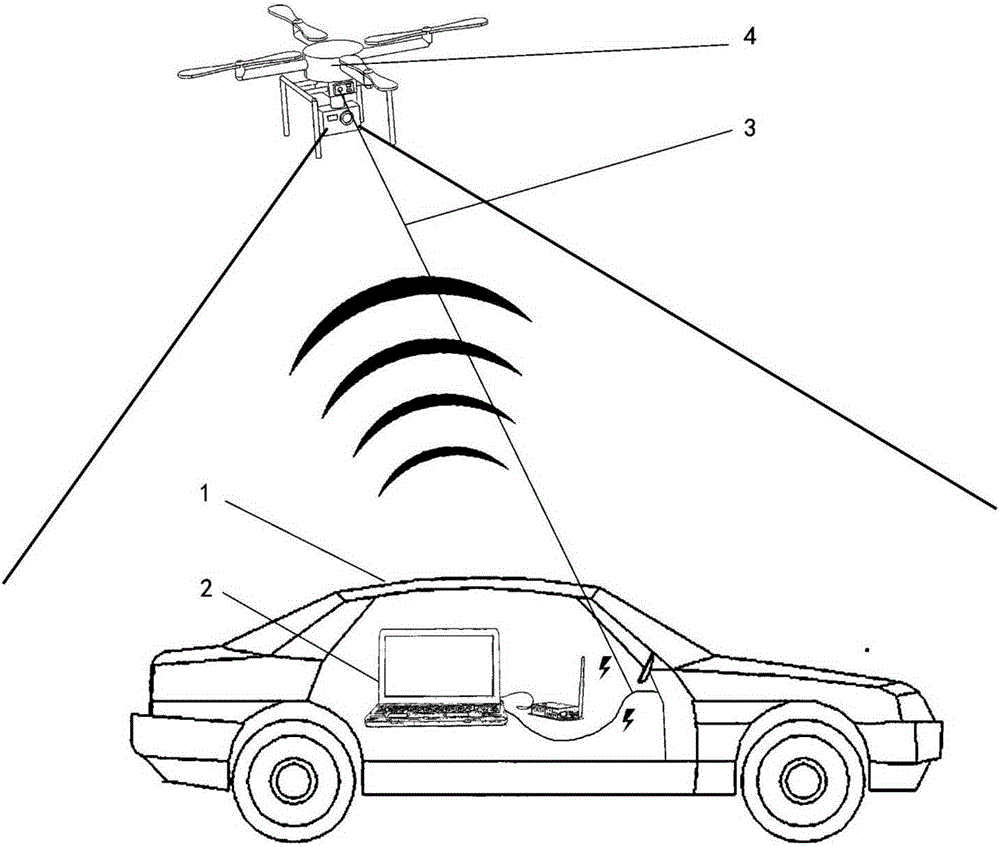
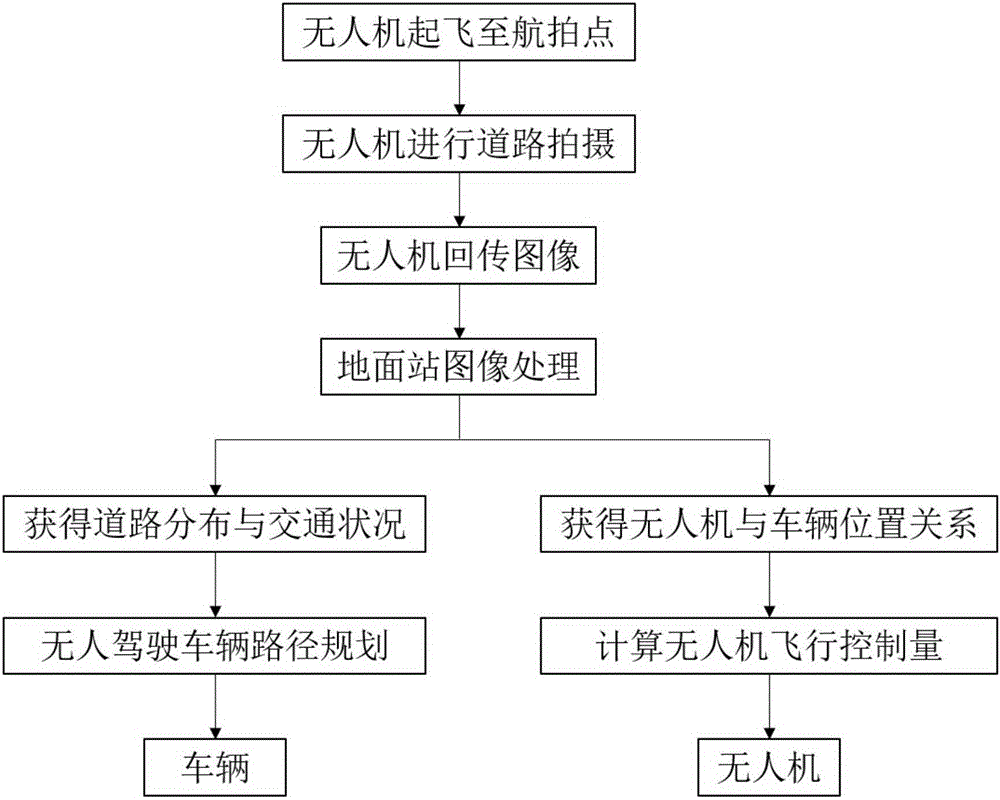
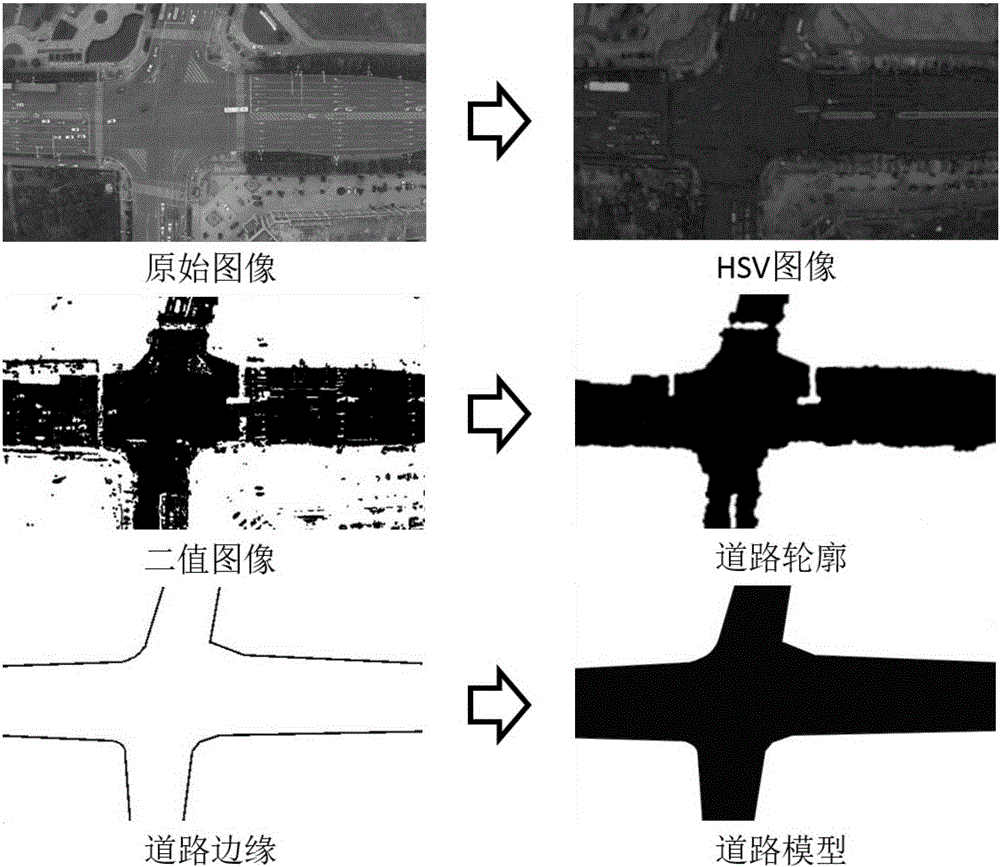
Unmanned perception based unmanned aerial vehicle route planning method
ActiveCN105318888AStable working conditionWide coverageInstruments for road network navigationControl signalVehicle driving
The invention discloses an unmanned perception based unmanned aerial vehicle route planning method for rapidly planning the vehicle driving route. According to the invention, based on the unmanned flight perception system, road video images around a target vehicle are photographed by utilizing an unmanned flight to be sent to a ground station; the ground station receives the video images and processes the video images so as to obtain the vehicle and road messages, route planning is carried out according to the vehicle position, and the route is transmitted to the unmanned aerial vehicle; and a computer module of the ground station calculates a flight control signal to control the unmanned aerial vehicle to follow the vehicle to proceed, and corrects the route in real time. According to the invention, based on an unmanned flight platform, the operation state is stable; and the road environment around the vehicle is photographed from a great height, the coverage area is wide, and the observed road traffic information is distinct and clear, so that the road distribution condition and the traffic condition around the target vehicle can be obtained rapidly, the reasonable route planning can be obtained, the route is more precise, and the road condition analysis is more timely and accurate.
Owner:BEIHANG UNIV
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS20070070038A1Significant to useImprove computing powerAnalogue secracy/subscription systemsCharacter and pattern recognitionHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Automatic driving system for automobile information sharing between automobile and its control method
InactiveCN101101702AReduce fatigueReduce accident rateAnti-collision systemsExternal condition input parametersInformation sharingDriver/operator
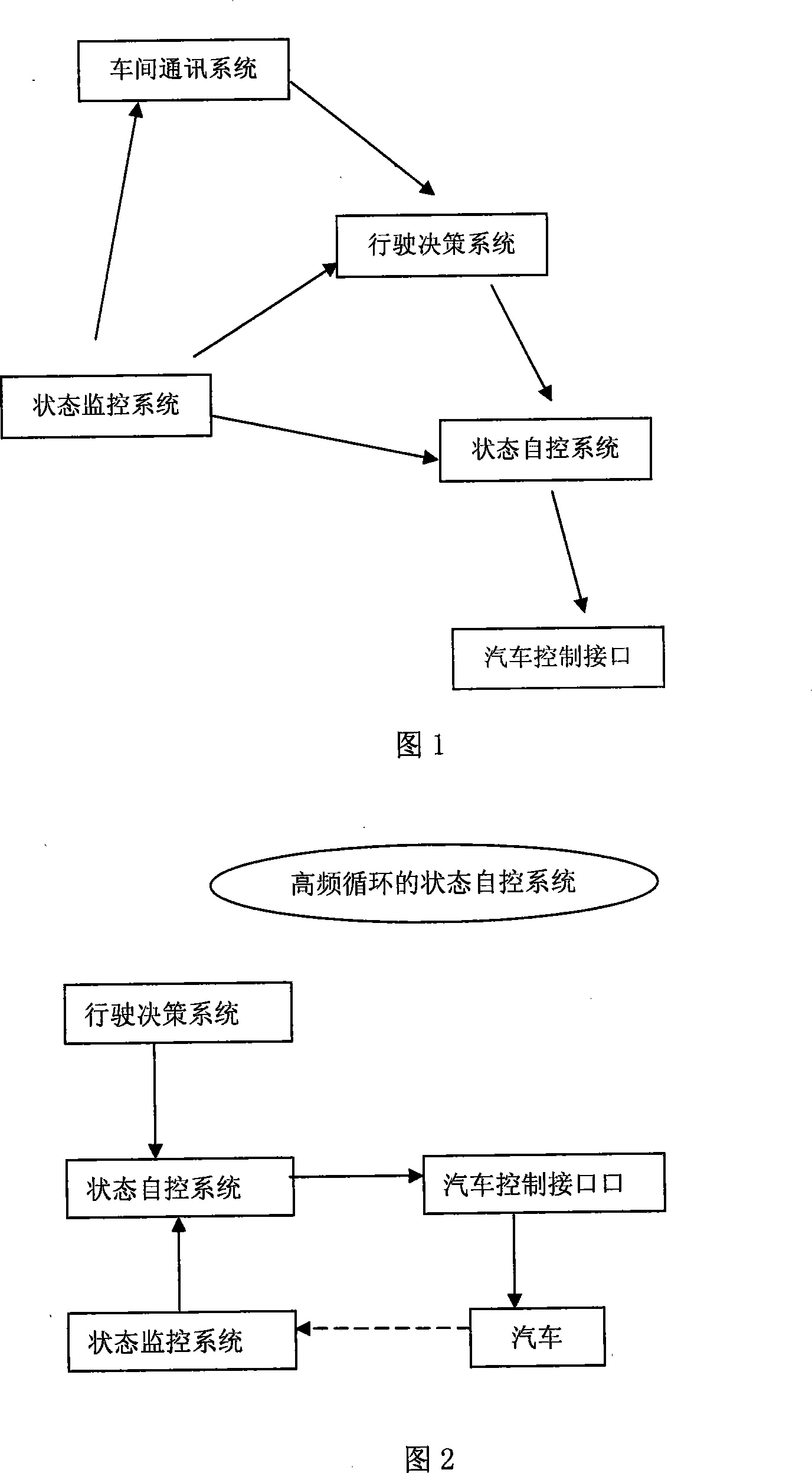
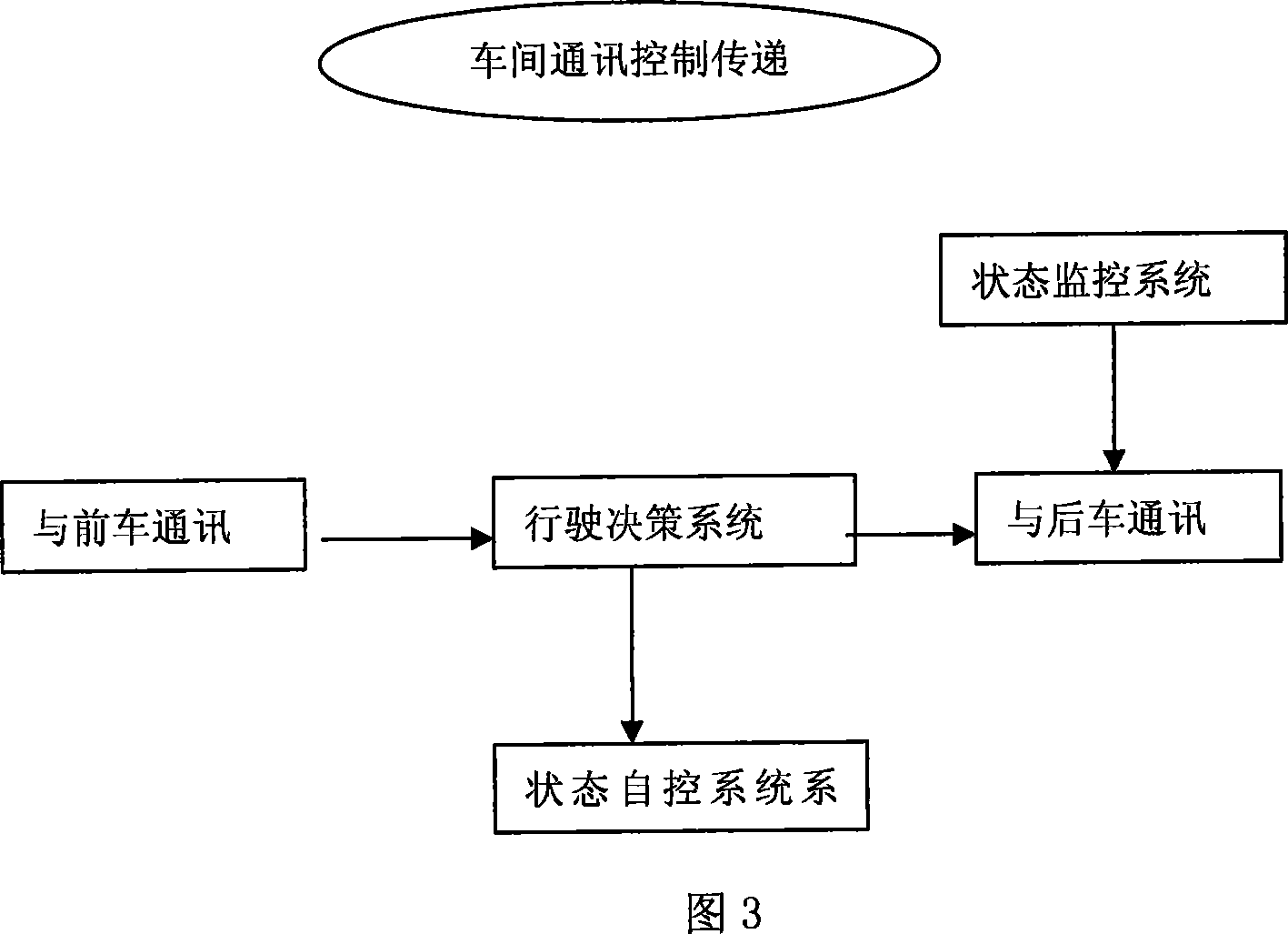
This system includes a car series consisting of at least two cars. The inter-car comm. sub-system (ICS) of the leading car sends the running and situation info to the car behind. ICS of the latter sends info to the driving decision-making system (DD) of this car. When DD receives info, the situation supervision sub-system (SS) of this car offers the Driving Situation of this Car (DSC) to DD, too. DD combines and analyzes these two info then sends instruction to the situation self-control sub-system (SC). SC combines the instruction and the info from SS, then finally real time controls DSC via the car control port sub-system. This invention reduces the driver's tired degree, the accident occurring rate and driving cost.
Owner:陈拙夫
Driver fatigue monitoring device based on multivariate information fusion and monitoring method thereof
InactiveCN101540090AImprove computing powerMeet the requirementsCharacter and pattern recognitionAlarmsDriver/operatorInformation integration
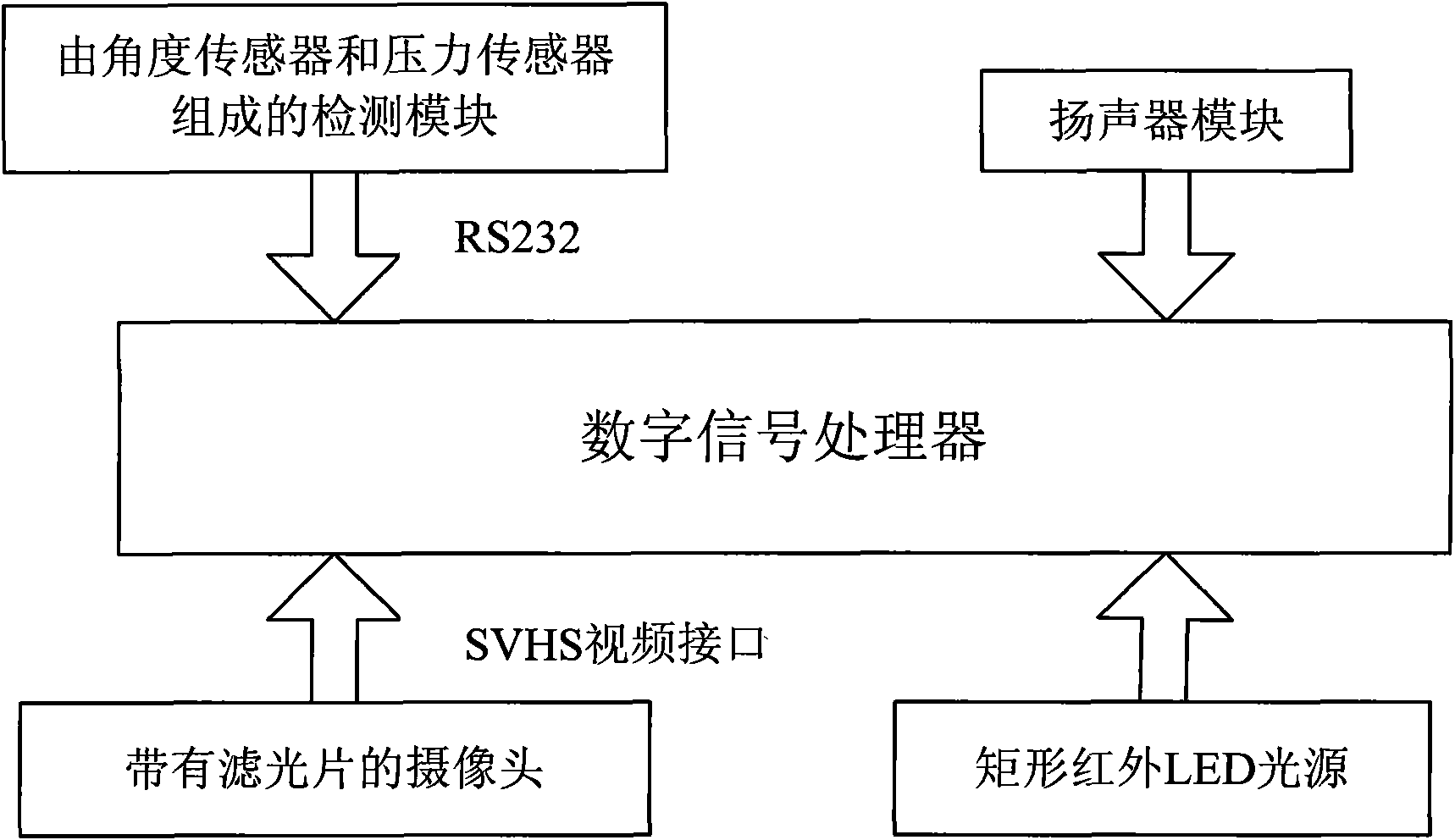
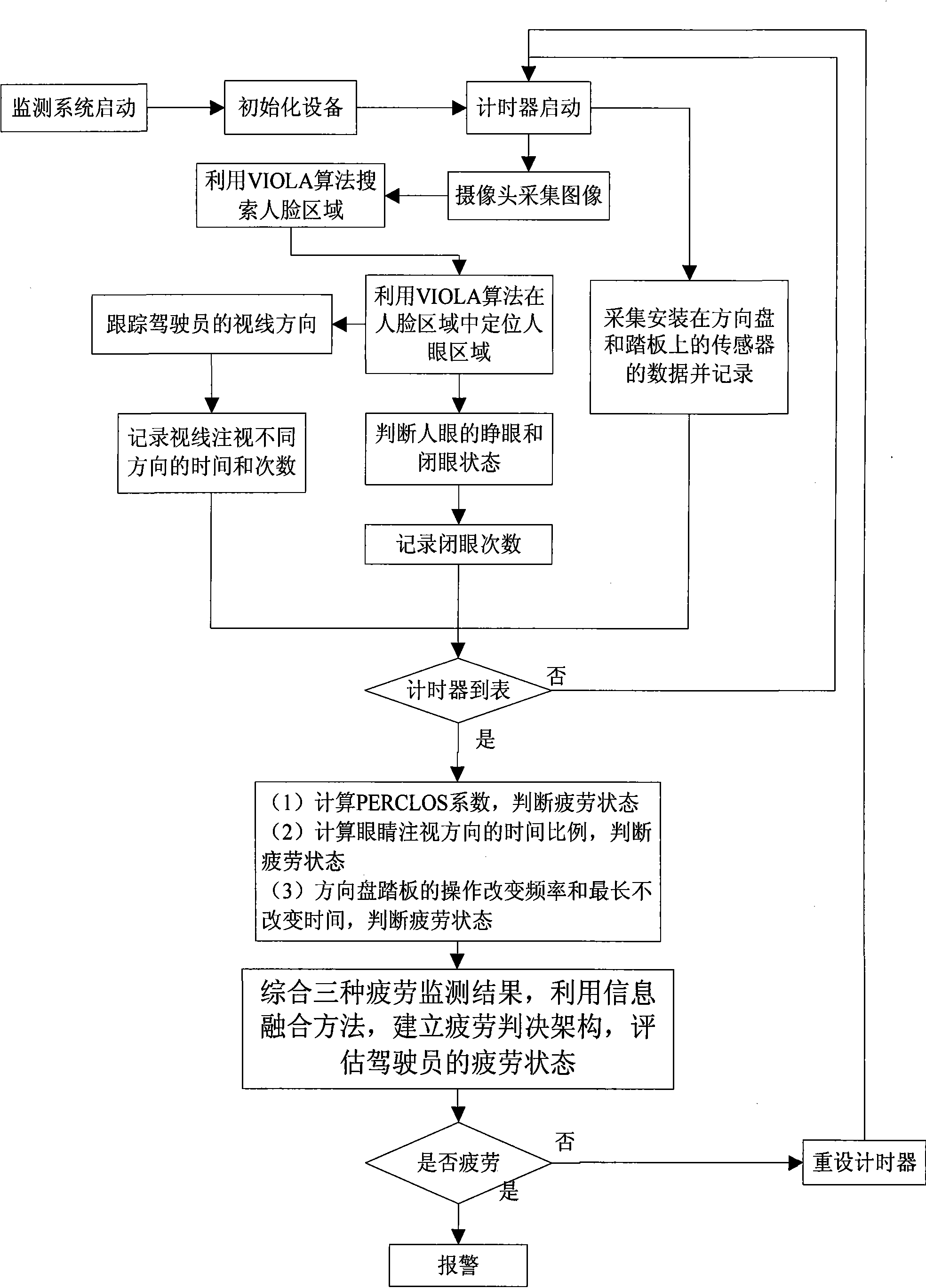
The invention discloses a driver fatigue monitoring device based on multivariate information fusion and a monitoring method thereof. The device comprises a digital signal processor, a camera head with a filter, a rectangular ultrared LED light source module mounted on a car windshield, a speaker module and a sensor module comprising an angular sensor and a pressure sensor, wherein the camera head, the rectangular ultrared LED light source module, the speaker module and the sensor module are respectively connected with the digital signal processor. The monitoring method comprises four procedures, namely eye characteristic identification, view line track, driving activity monitoring and fatigue characteristic judgment which merges the fatigue judgment results of the eye characteristic identification, the view line track and the driving activity monitoring to accurately judge the fatigue states of a driver. The invention utilizes an information merging technology to further develop and improve a fatigue driving detection technology, can objectively, rapidly and accurately judge the fatigue state of the driver in real time and avoids traffic accidents caused by fatigue driving.
Owner:SOUTH CHINA UNIV OF TECH
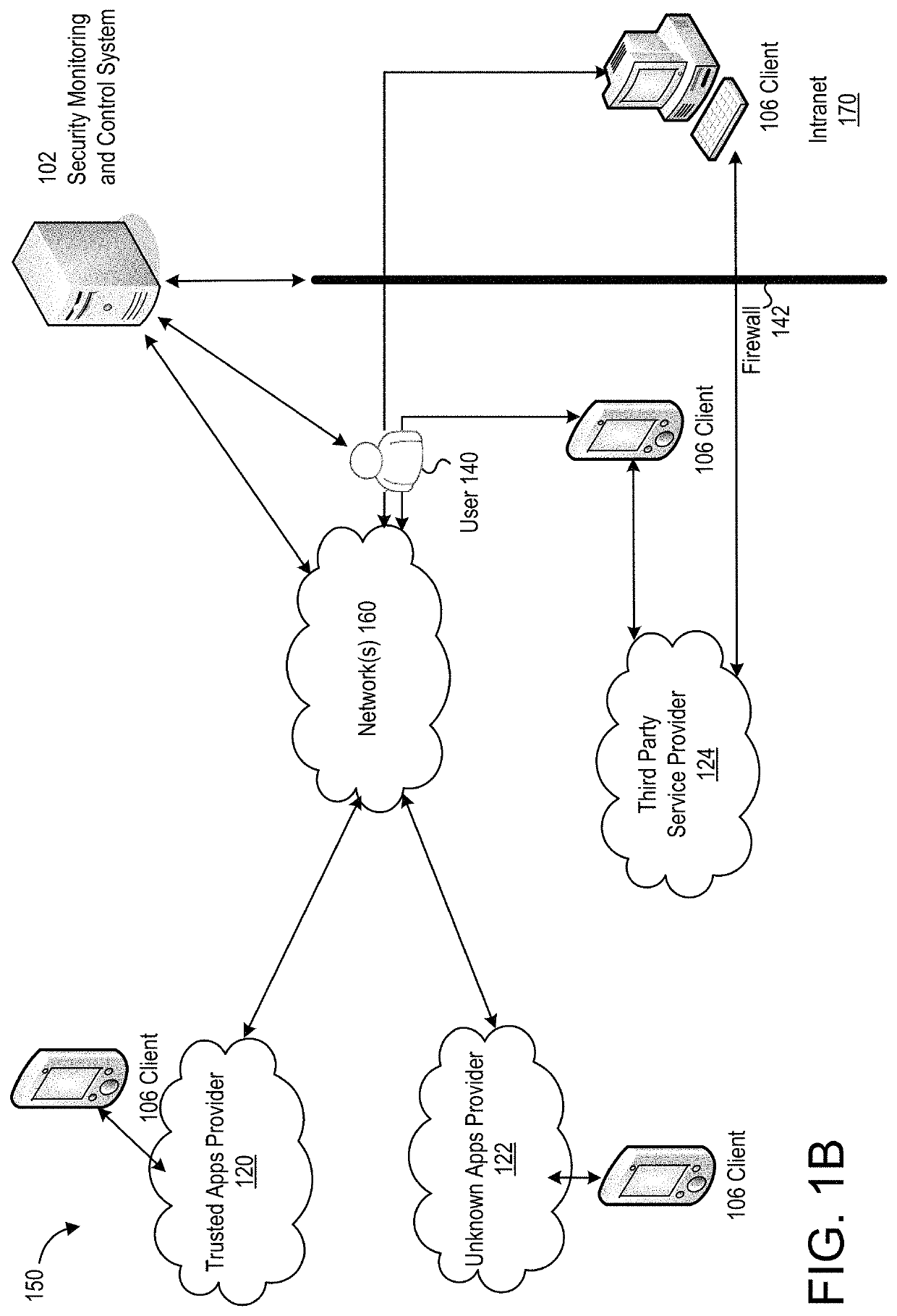
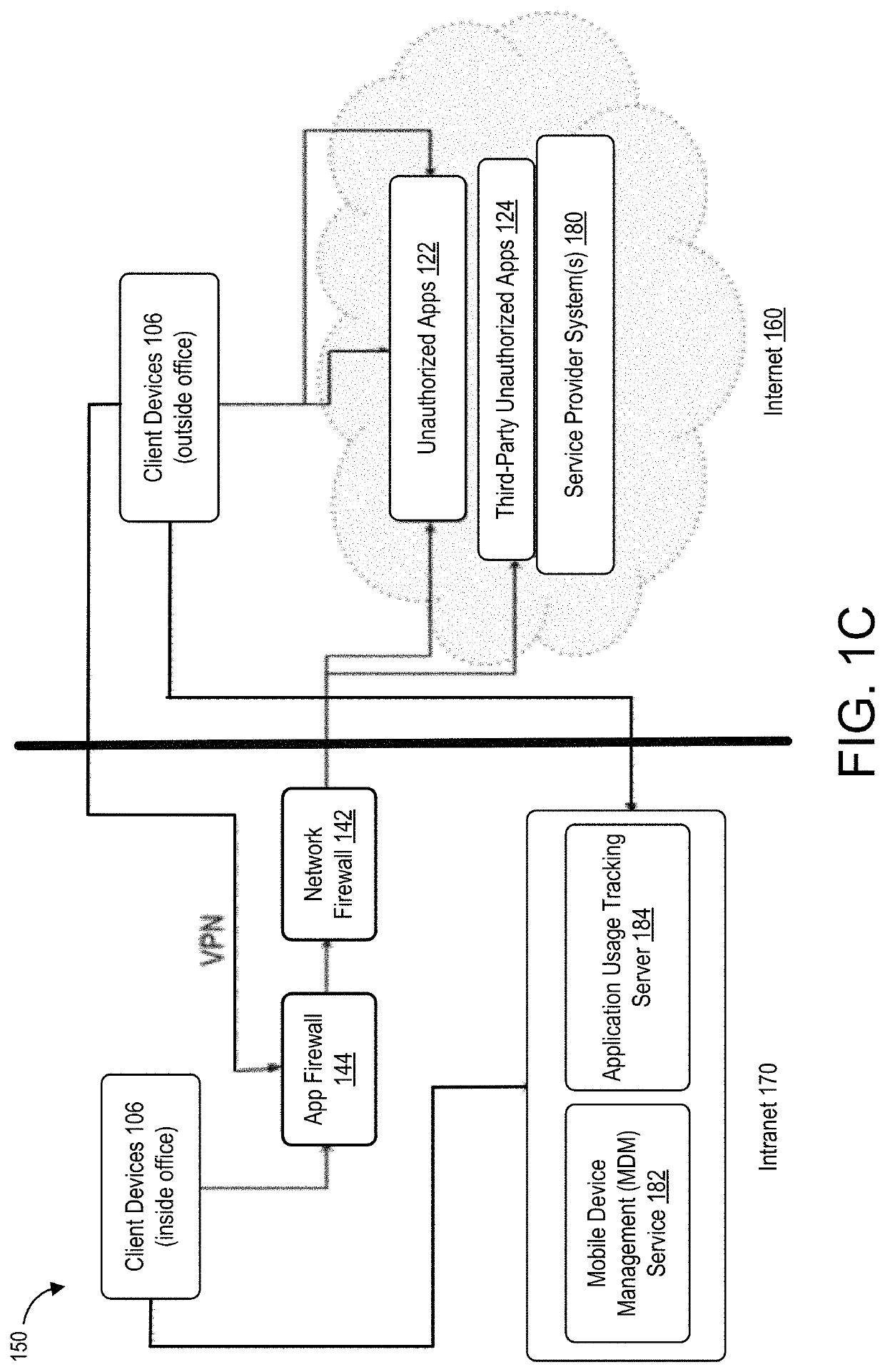
Techniques for discovering and managing security of applications
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
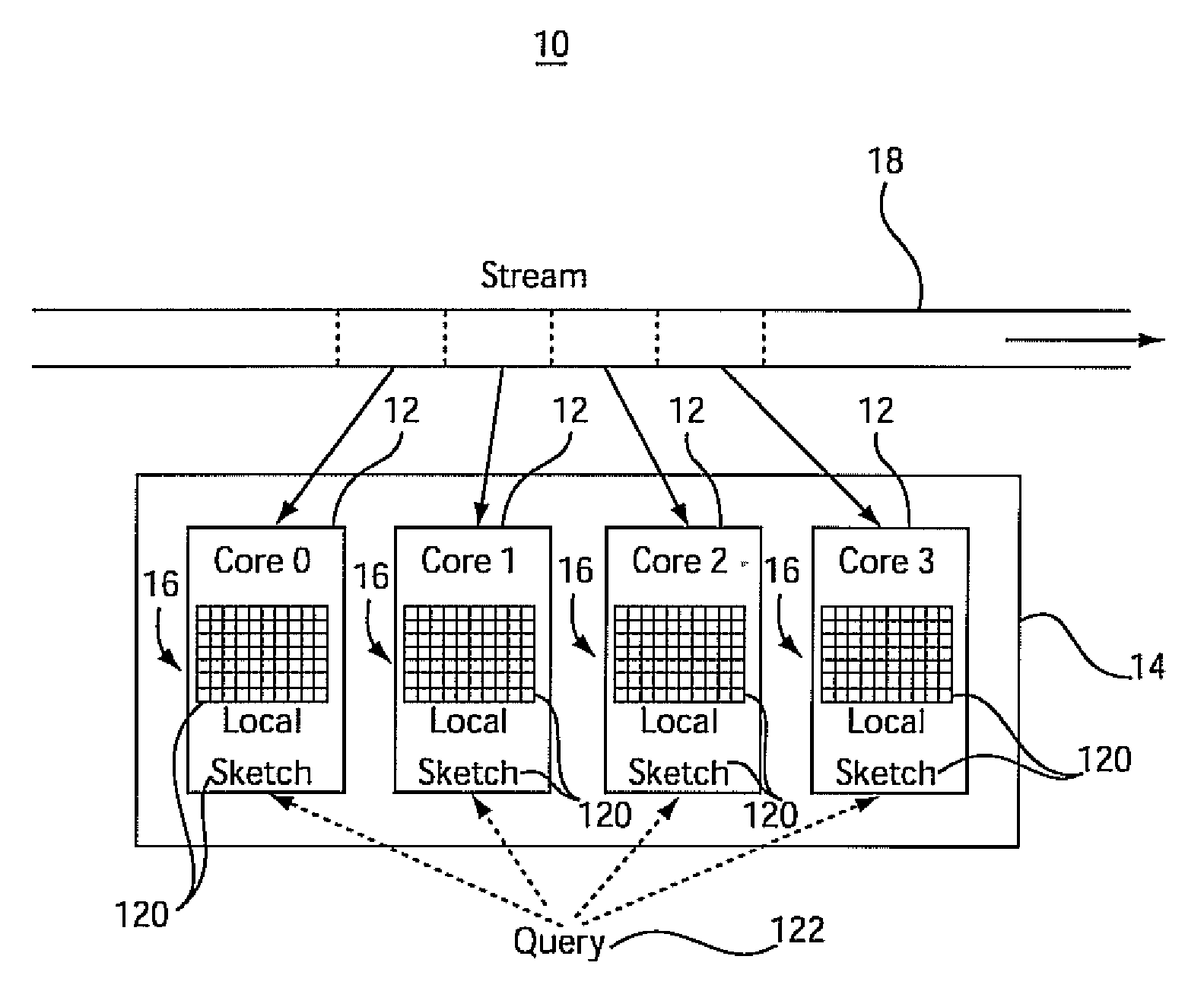
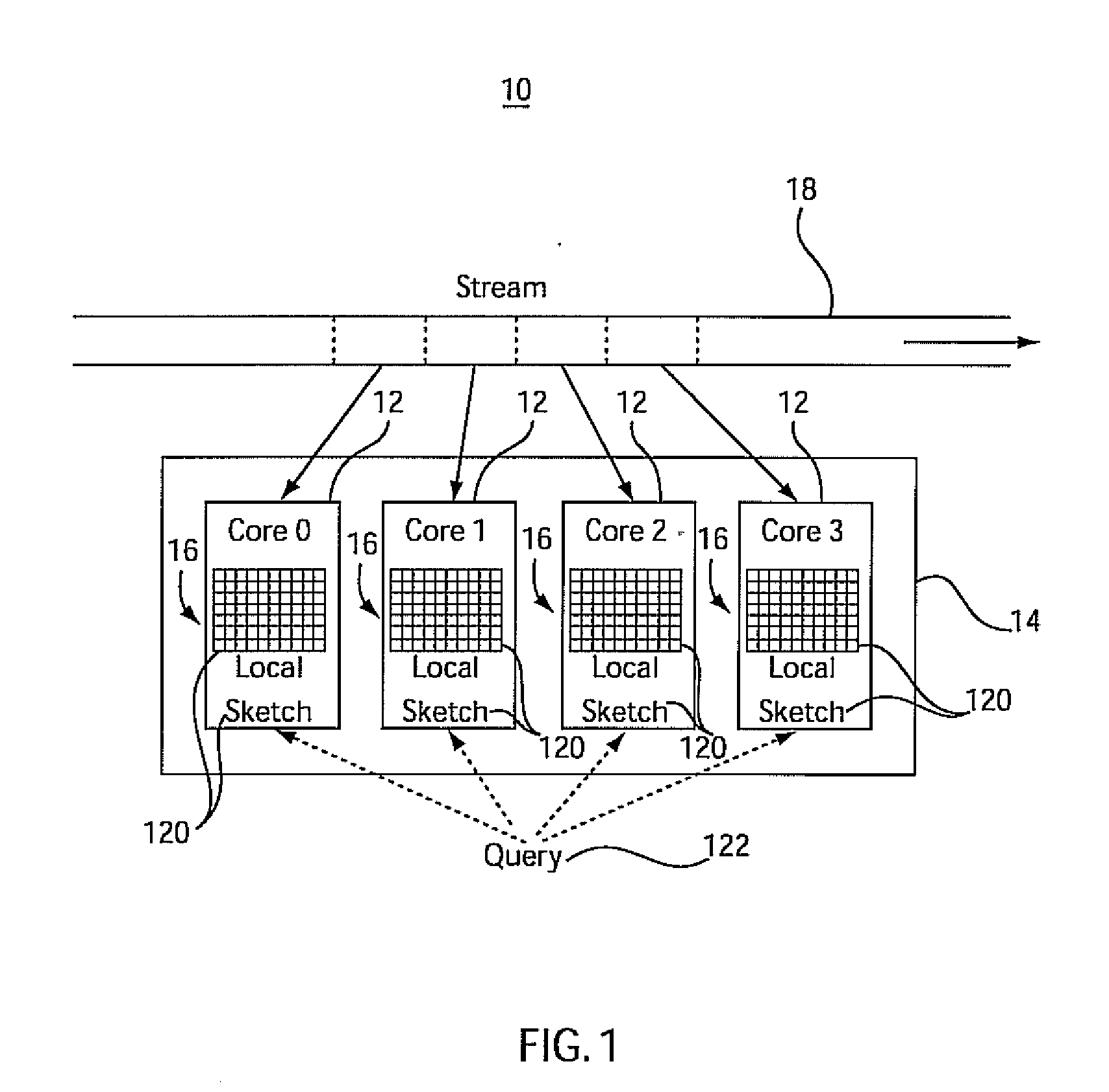
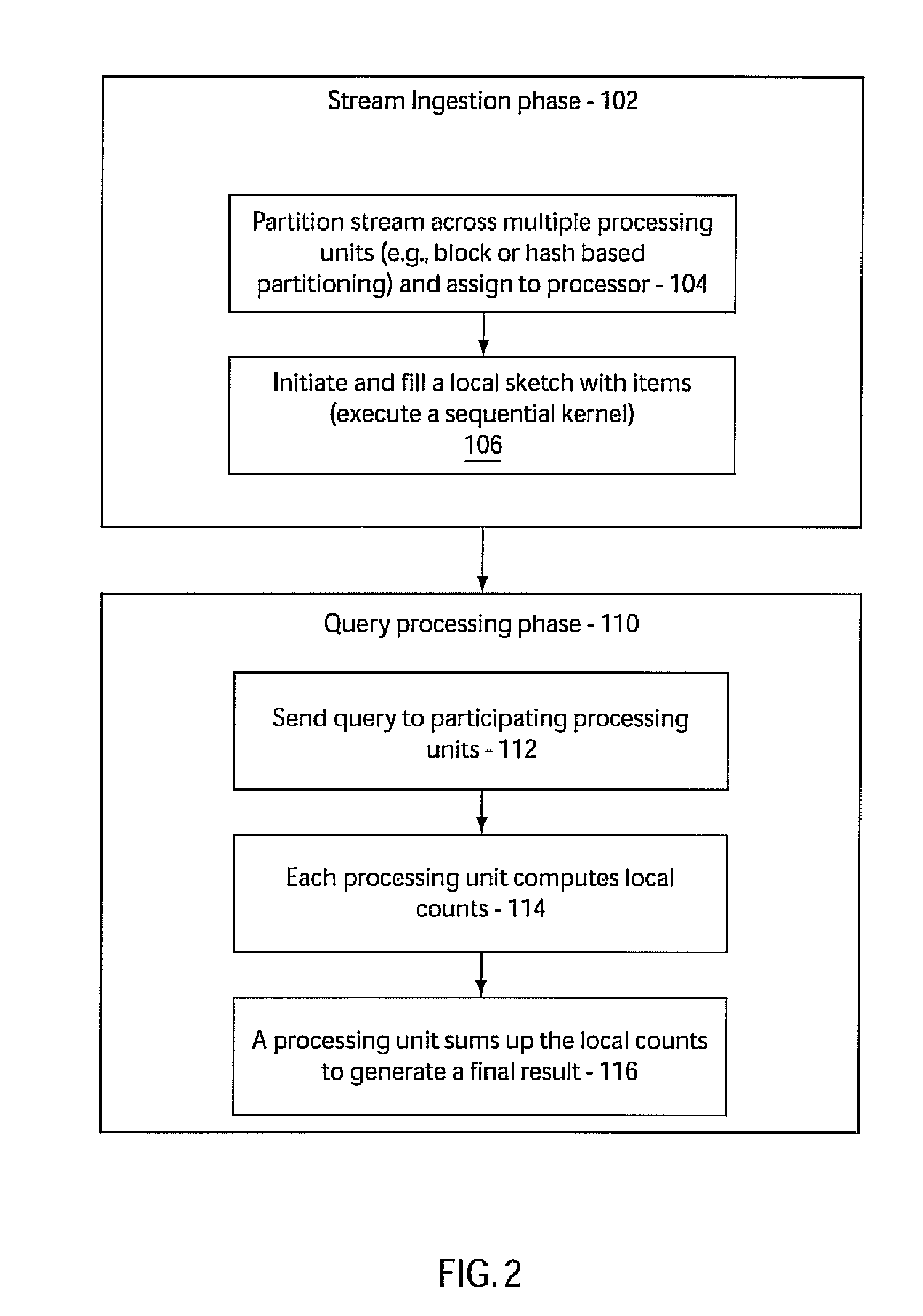
System and method for analyzing streams and counting stream items on multi-core processors
InactiveUS20090031175A1Improve computing powerImprove performanceProgram control using stored programsError detection/correctionMulti-core processorZero frequency
Systems and methods for parallel stream item counting are disclosed. A data stream is partitioned into portions and the portions are assigned to a plurality of processing cores. A sequential kernel is executed at each processing core to compute a local count for items in an assigned portion of the data stream for that processing core. The counts are aggregated for all the processing cores to determine a final count for the items in the data stream. A frequency-aware counting method (FCM) for data streams includes dynamically capturing relative frequency phases of items from a data stream and placing the items in a sketch structure using a plurality of hash functions where a number of hash functions is based on the frequency phase of the item. A zero-frequency table is provided to reduce errors due to absent items.
Owner:IBM CORP
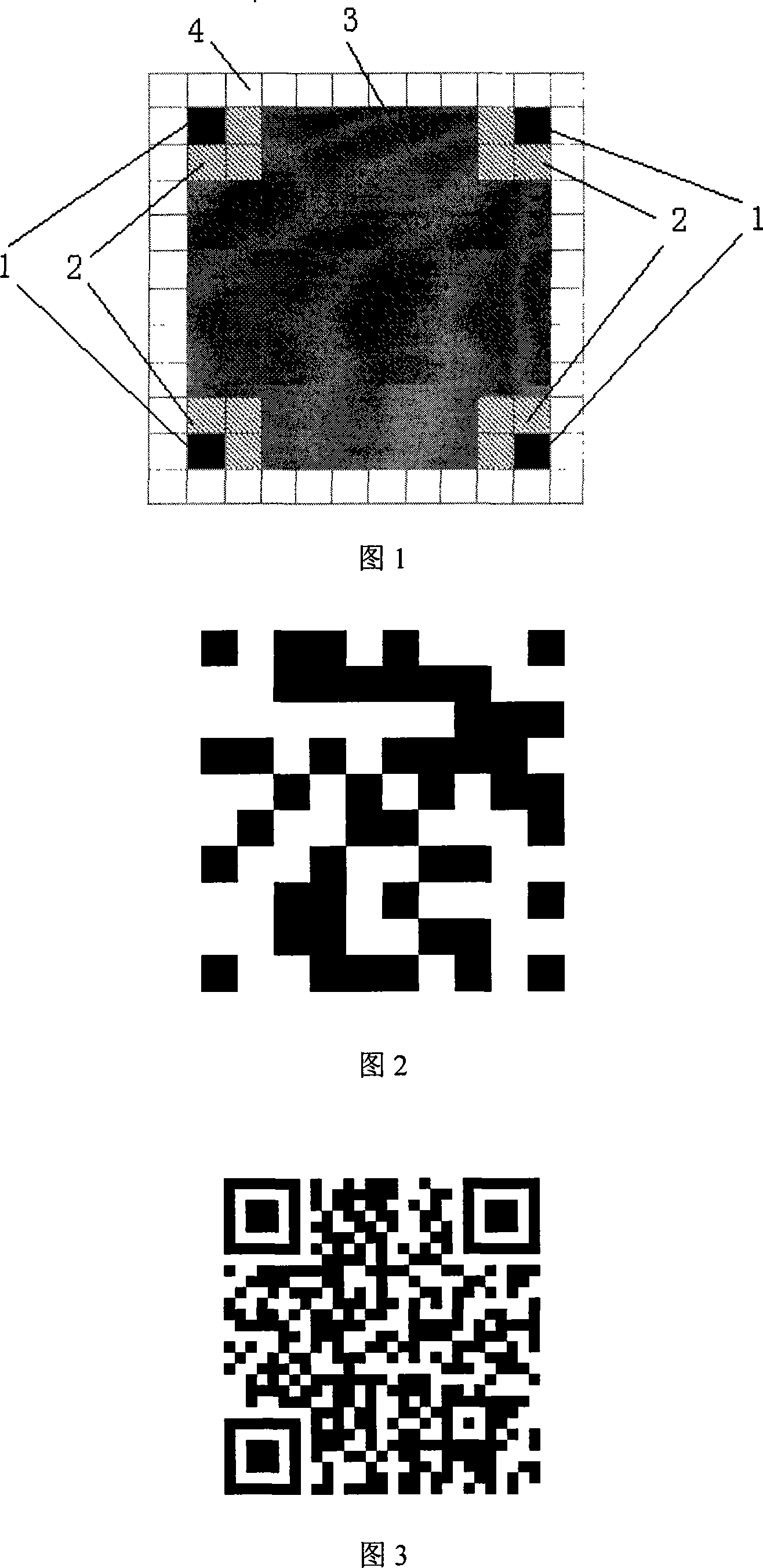
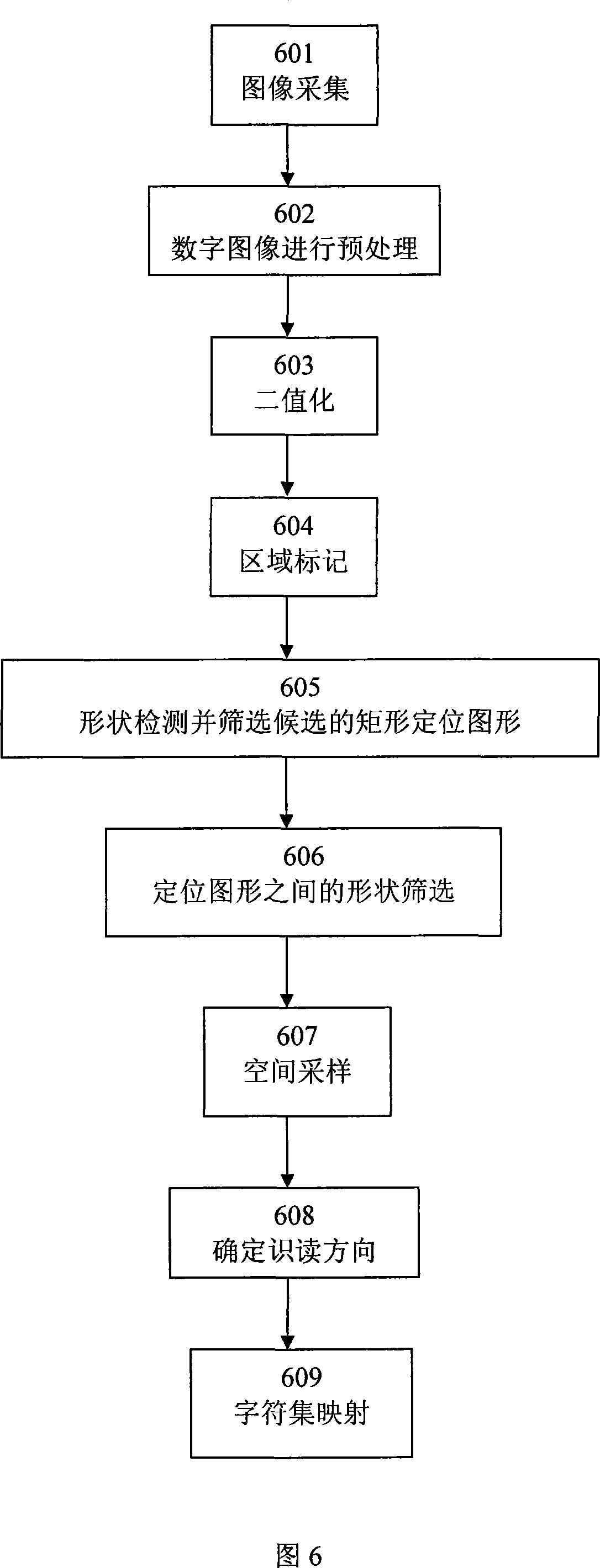
2D code system, and identification method
InactiveCN101093553ALarge codeword capacitySimple structureCharacter and pattern recognitionRecord carriers used with machinesGraphicsDark color
A 2-D code system is prepared for forming code character by arranging square unit blocks, dividing code character region to positioning region and positioning space region as well as data region, using four the same dark-color square positioning patterns to from said positioning region, applying coding method with unique identification-direction to generate data in said data region and using light-color unit block as positioning space region being used to isolate four square positioning patterns from said data region.
Owner:BOGUTIANBO TECH
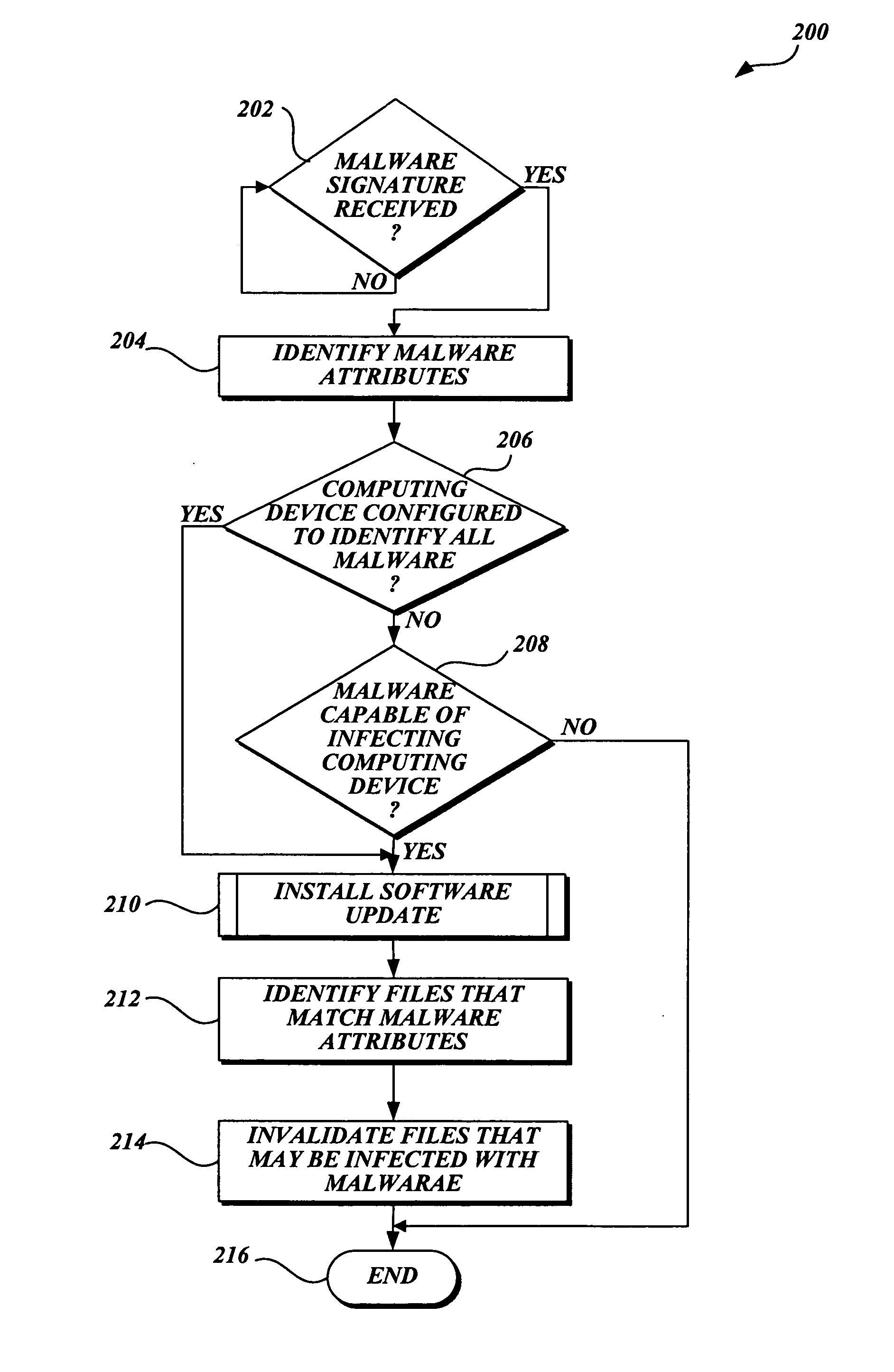
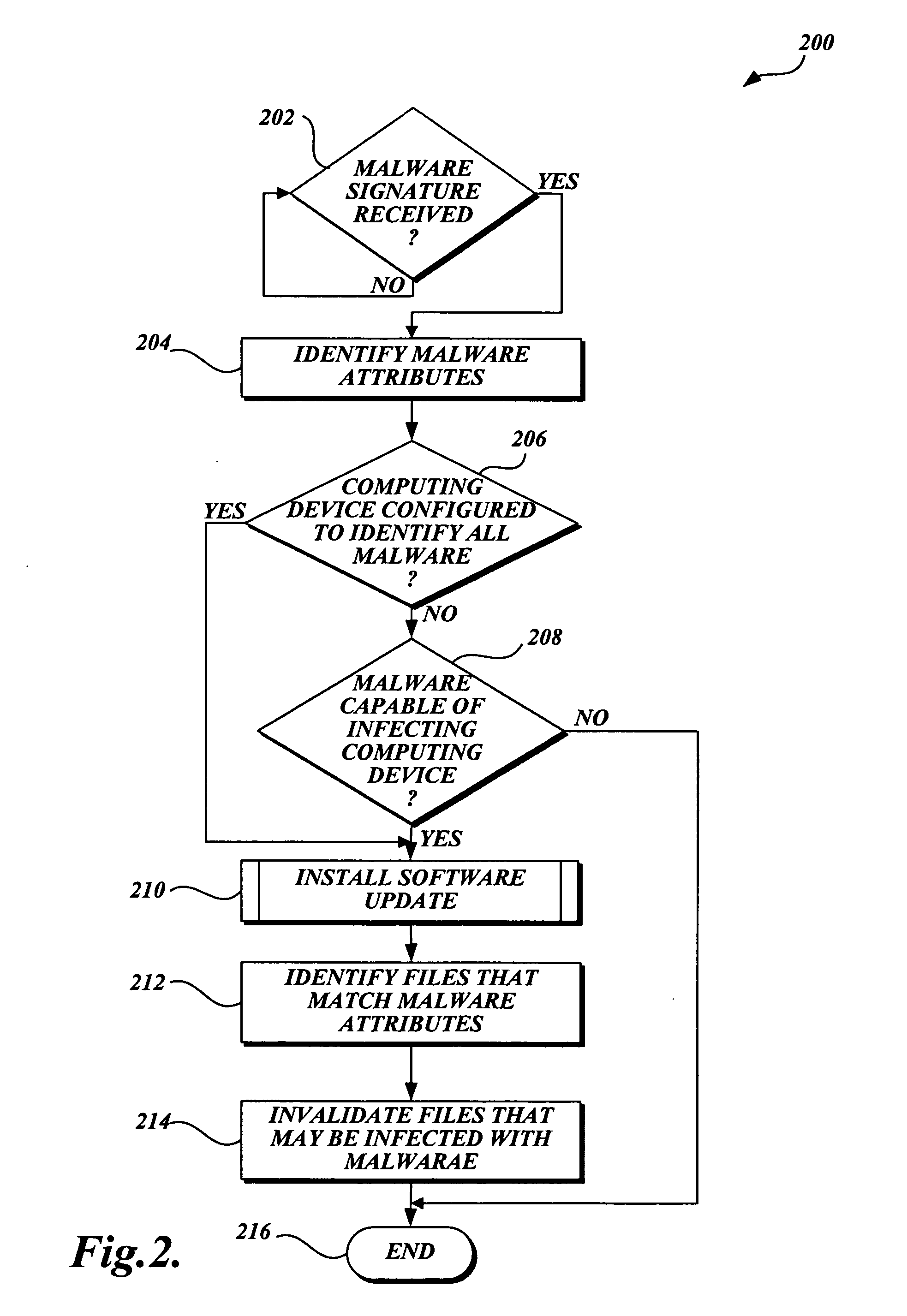
System and method of caching decisions on when to scan for malware
InactiveUS20060174344A1Improve computing powerReduce the amount requiredMemory loss protectionUnauthorized memory use protectionSoftware updateMalware
In accordance with this invention, a system, method, and computer-readable medium that selectively scans files stored on a computing device for malware is provided. One aspect of the present invention includes identifying files that need to be scanned for malware when a software update that includes a malware signature is received. More specifically, attributes of the new malware are identified by searching metadata associated with the malware. Then, the method searches a scan cache and determines whether each file with an entry in the scan cache is the type that may be infected by the malware. If a file is the type that may be infected by the malware, the file is scanned for malware when a scanning event such as an I / O request occurs. Conversely, if the file is not the type that may be infected by the malware, the file may be accessed without a scan being performed.
Owner:MICROSOFT TECH LICENSING LLC
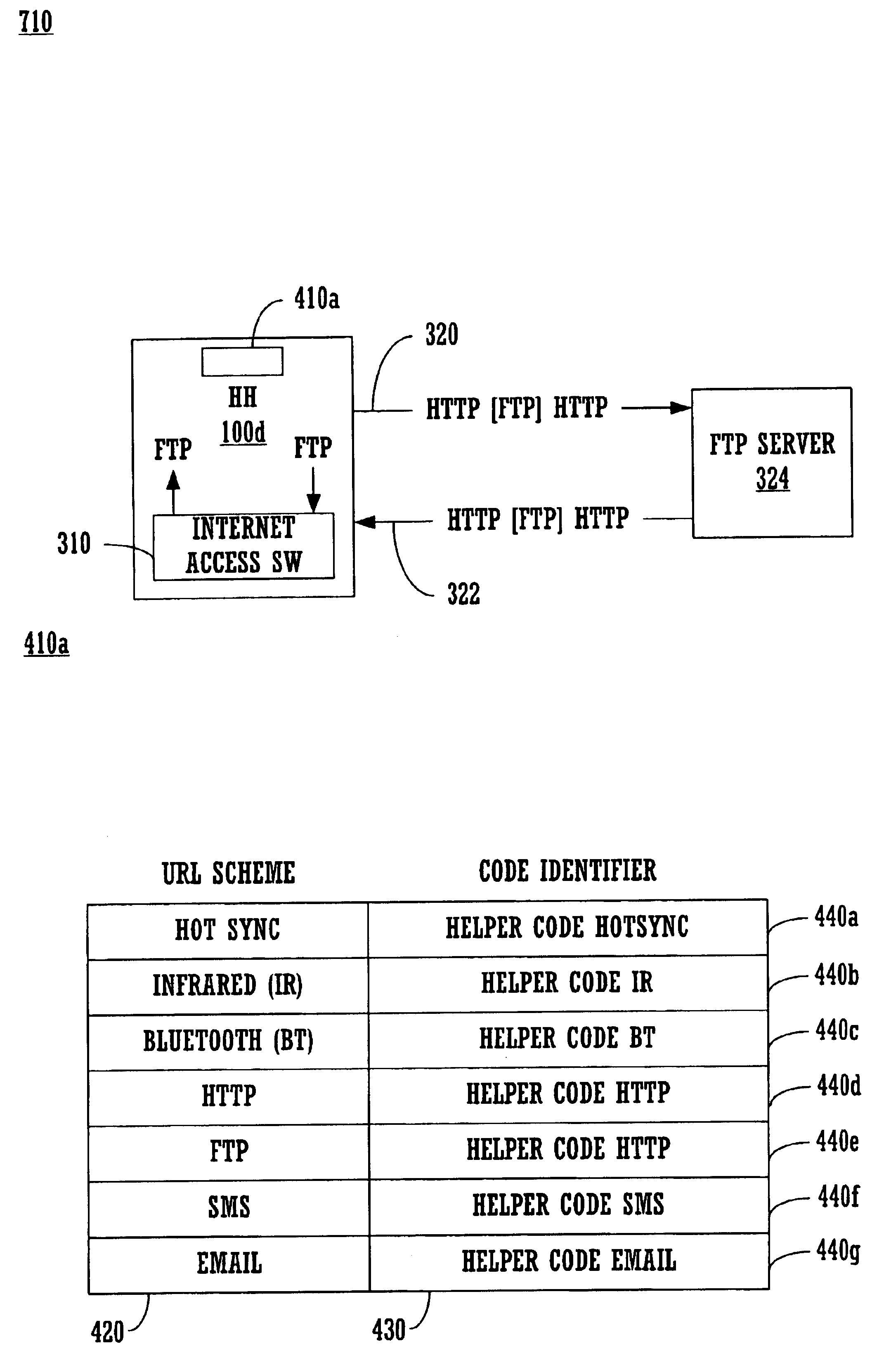
Method and system for implementing URL scheme proxies on a computer system
InactiveUS6850986B1Increase compute capacityImprove computing powerTime-division multiplexMultiple digital computer combinationsComputer securityApplication software
A method and system for implementing URL scheme proxies. Embodiments of the invention allow URL schemes that are not natively supported by a computer to be supported via proxy, e.g., using a URL scheme that is native to the computer to forward the non-native transport. More specifically, embodiments of the invention allow a first computer system to support a first URL scheme by encapsulating its transport information into another URL scheme that is natively supported by the first computer. The encapsulated information is then forwarded to a second computer system or server which can provide support for the first URL scheme transport. For instance, if the first computer supports http but does not support ftp, then an ftp transport can be encapsulated inside an http transport and then forwarded to an ftp server which can then extract and process the ftp transport. The ftp response can be handled in an analogous fashion. The invention increases the native URL scheme capabilities of a computer system by proxy. In one embodiment, a system registry is used in order to determine which helper code to use for a particular URL scheme. The selection of helper code and whether native or proxy support is selected are tasks that are transparent to the application. The invention can allow a device with no Internet access to act, transparently, as if it has Internet access.
Owner:ACCESS
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS8046313B2Significant to useImprove computing powerAnalogue secracy/subscription systemsCharacter and pattern recognitionHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
System and method of translating a relational database into an XML document and vice versa
ActiveUS20080320023A1Easy to useImprove performanceDigital data processing detailsNatural language data processingXML schemaRelational model
A method of translating a relational database into an XML document comprises generating an Extended Entity Relationship model from relational schema associated with the relational database and applying a schema translation process to the Extended Entity Relationship model to map the relational schema into a Document Type Definition (DTD) of an XML schema. An XML Tree Model is then generated from the Document Type Definition, the XML Tree Model being representative of one or more data semantics of the relational schema which are preserved as one or more data semantics in the XML document. Relational data from the relational database is then converted into the XML document using the relational schema and the XML schema from the Document Type Definition and / or the XML Tree Model. There is also described a method of translating an XML database into a relational database which comprises the reversal of the steps of the aforementioned method, and a system for implementing both methods.
Owner:FONG JOSEPH S P
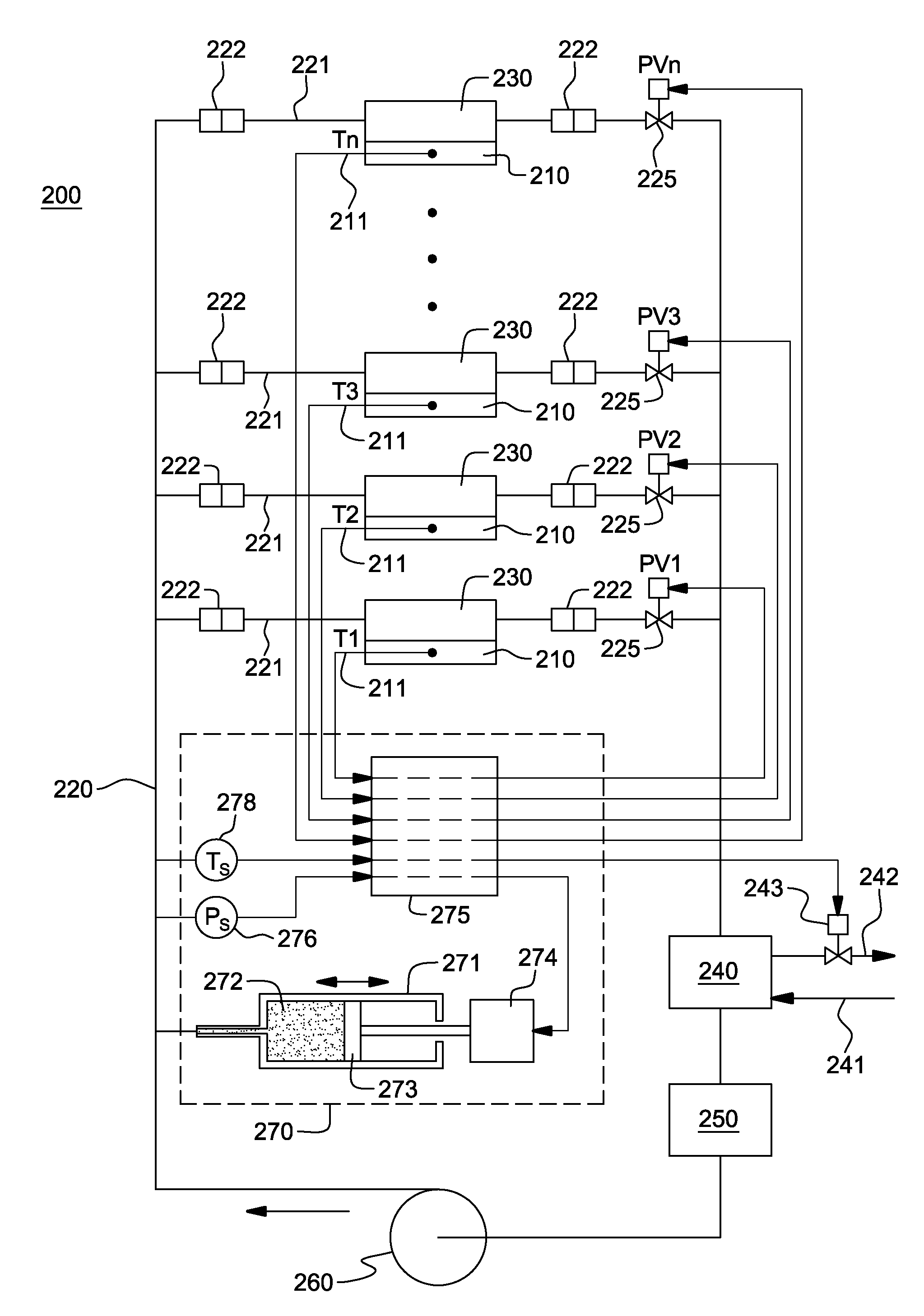
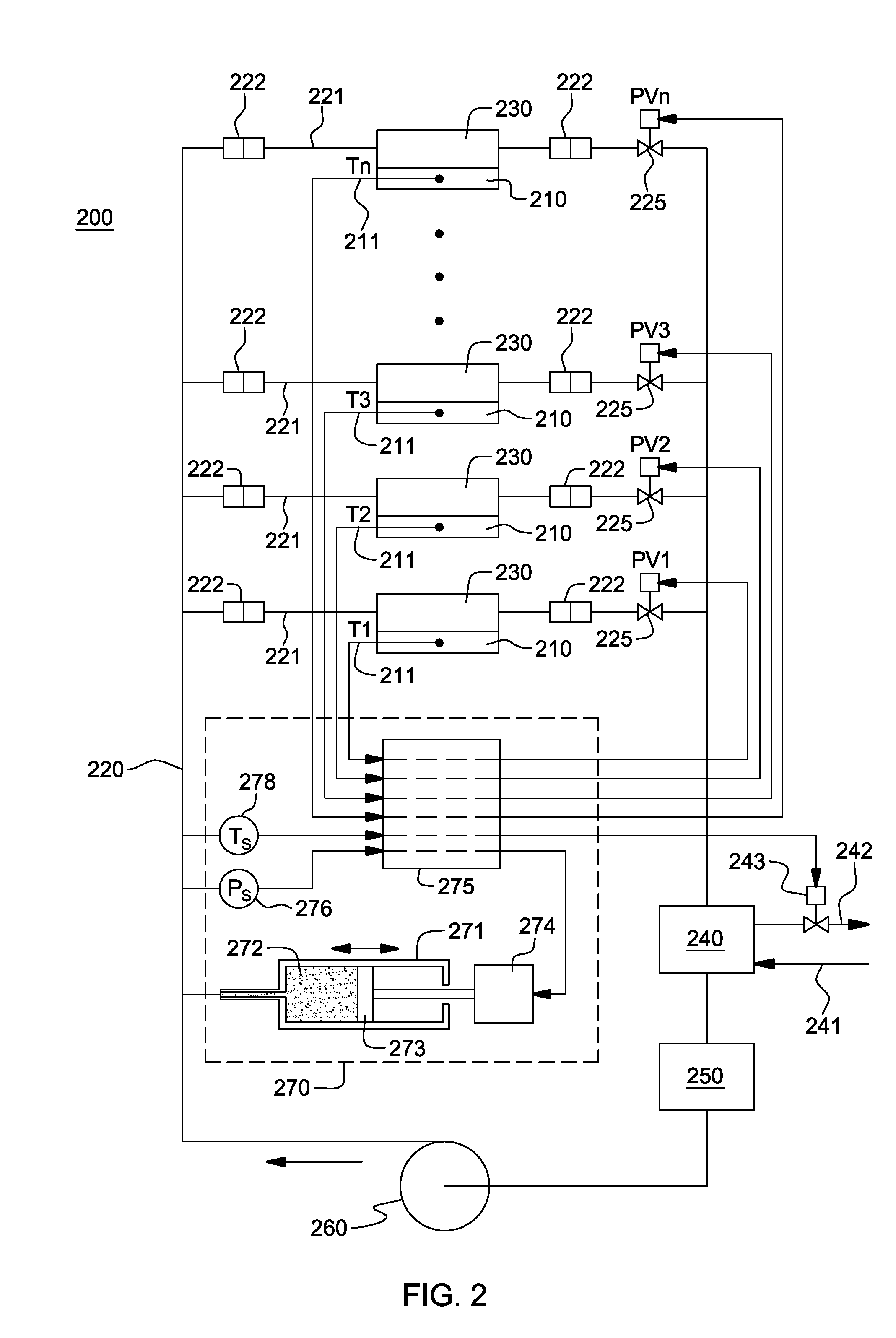
Control of system coolant to facilitate two-phase heat transfer in a multi-evaporator cooling system
ActiveUS20110056225A1Increase the amount of heatingHigh heat densitySpace heating and ventilation safety systemsSpace heating and ventilation control systemsElectronic systemsNuclear engineering
A cooling system and method are provided for facilitating two-phase heat transfer from an electronics system including a plurality of electronic devices to be cooled. The cooling system includes a plurality of evaporators coupled to the electronic devices, and a coolant loop for passing system coolant through the evaporators. The coolant loop includes a plurality of coolant branches coupled in parallel, with each coolant branch being coupled in fluid communication with a respective evaporator. The cooling system further includes a control unit for maintaining pressure of system coolant at a system coolant supply side of the coolant branches within a specific pressure range at or above saturation pressure of the system coolant for a given desired saturation temperature of system coolant into the evaporators to facilitate two-phase heat transfer in the plurality of evaporators from the electronic devices to the system coolant at the given desired saturation temperature.
Owner:LENOVO GLOBAL TECH INT LTD
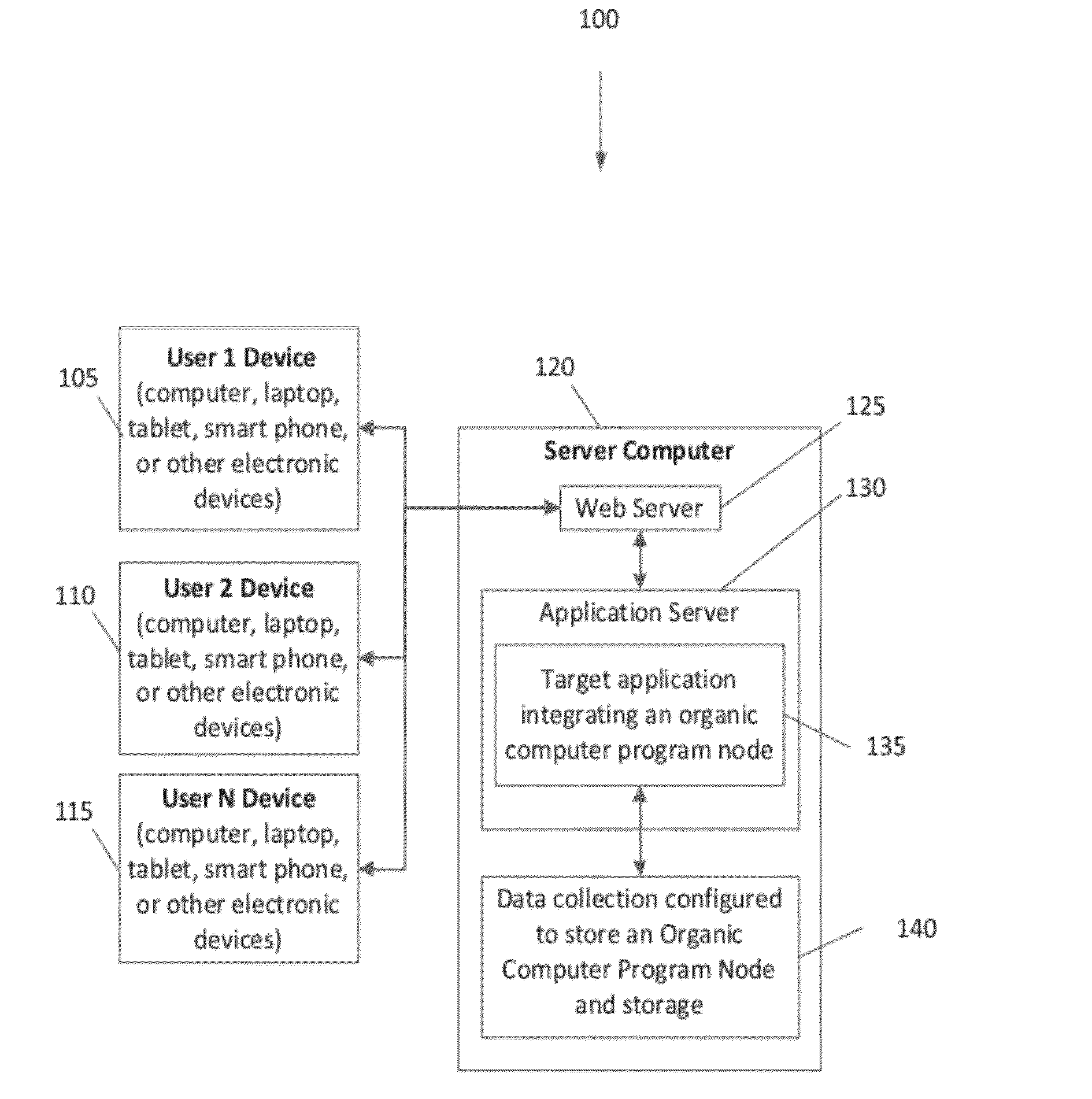
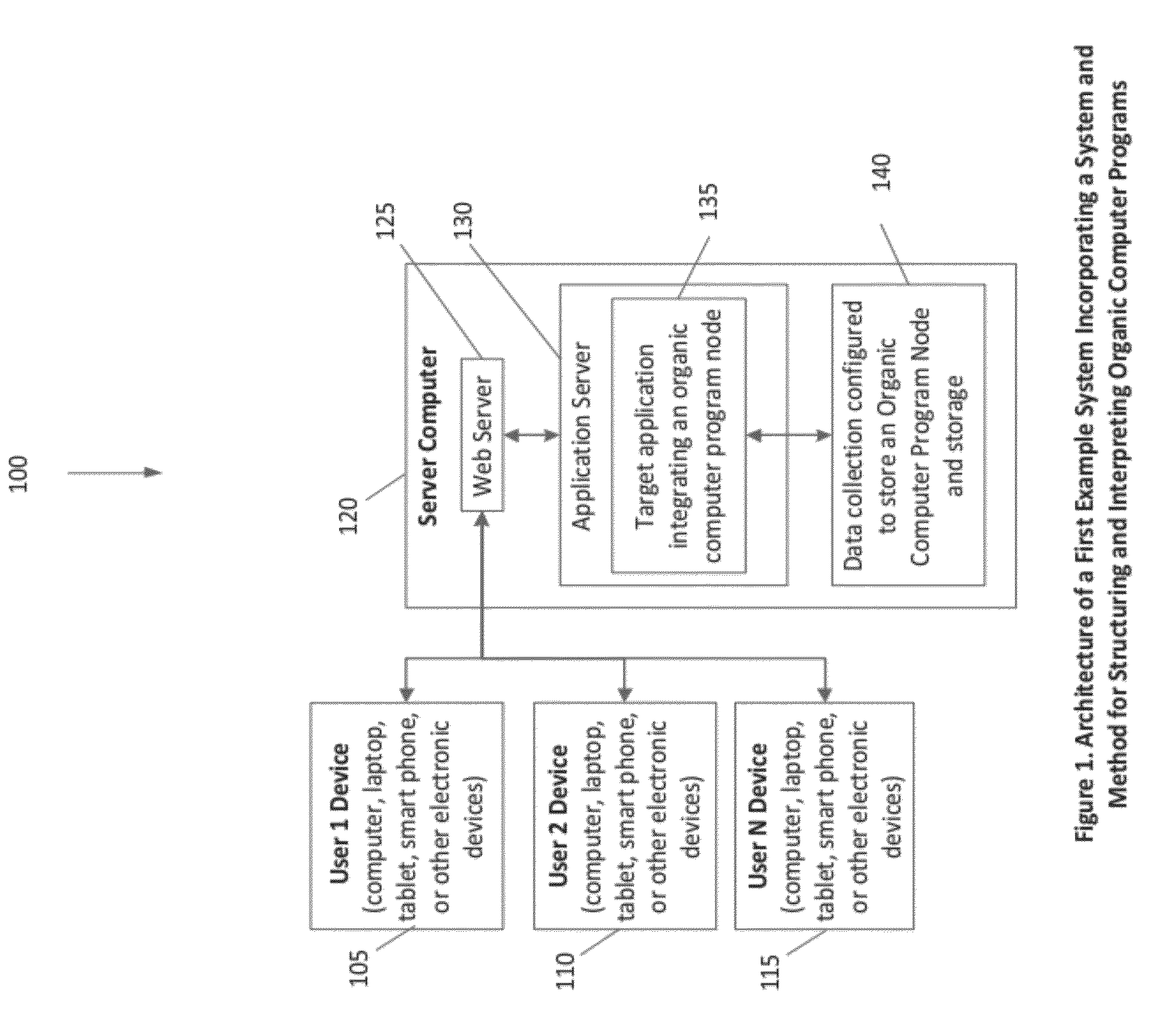
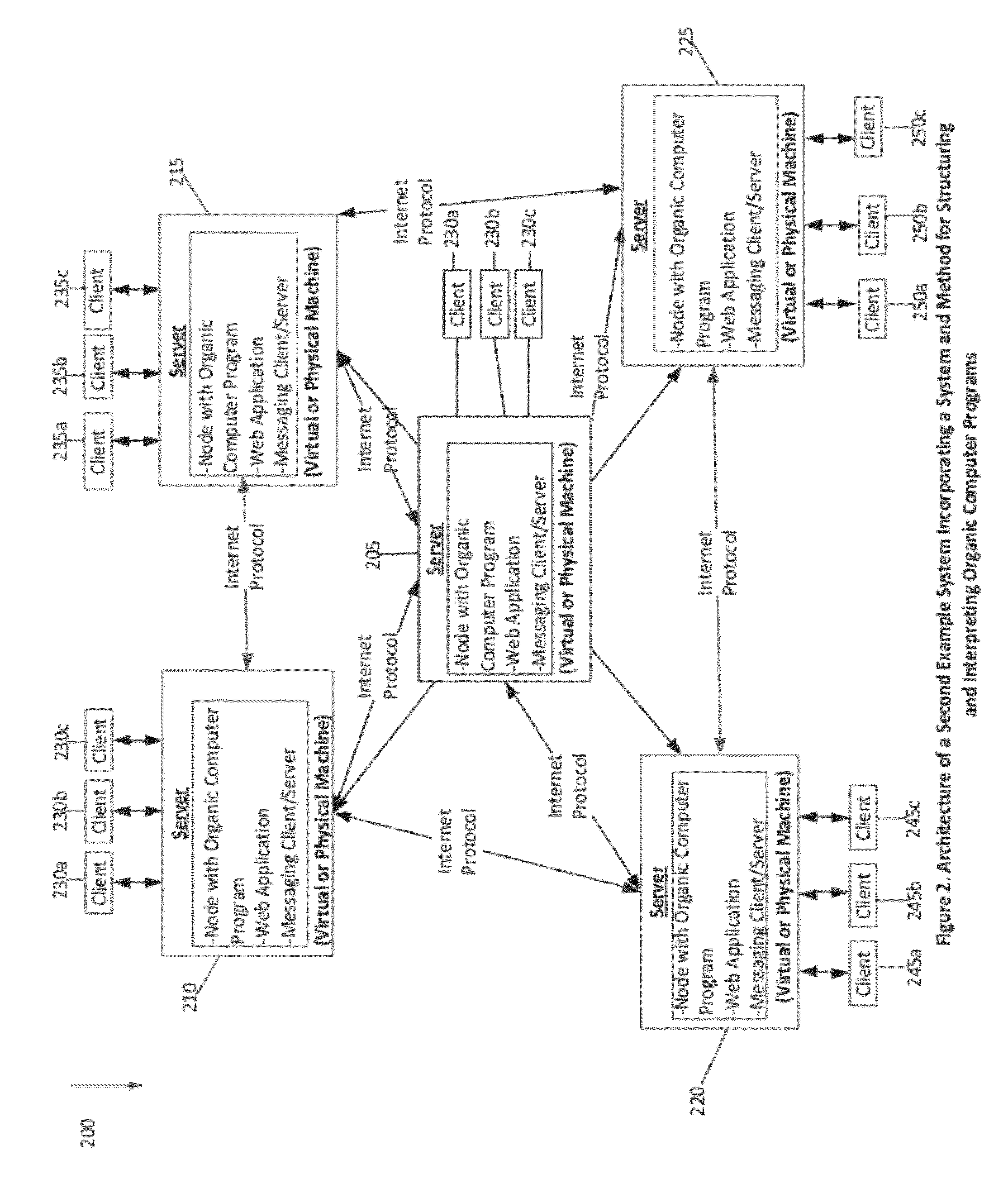
System and method for the structuring and interpretation of organic computer programs
InactiveUS20120254842A1Improve operational capabilitiesImprove computing powerProgram code adaptionSoftware designComputer programmingRunning time
In various aspects, a system and method for structuring and interpreting organic computer programs may provide for programs to expand, grow and evolve analogous to the way plants, animals, and organisms in nature grow and evolve. The organic computing system and method may unify program design time and program run time, may provide for program structure and program state to change at run time, and may provide for programs to continuously change and evolve through the addition of member functions, inputs, and outputs as the program is running. The organic computing system provides continuous means of differentiation, creating asymmetries and the opportunity for competition, and integration, creating symmetries and the opportunity for cooperation. Together, these factors provide a programming system wherein normalization occurs over time through the exchange and integration of differences and evolution and diversification through the creation of new differences, thereby introducing a differential form of computer science.
Owner:SKAI
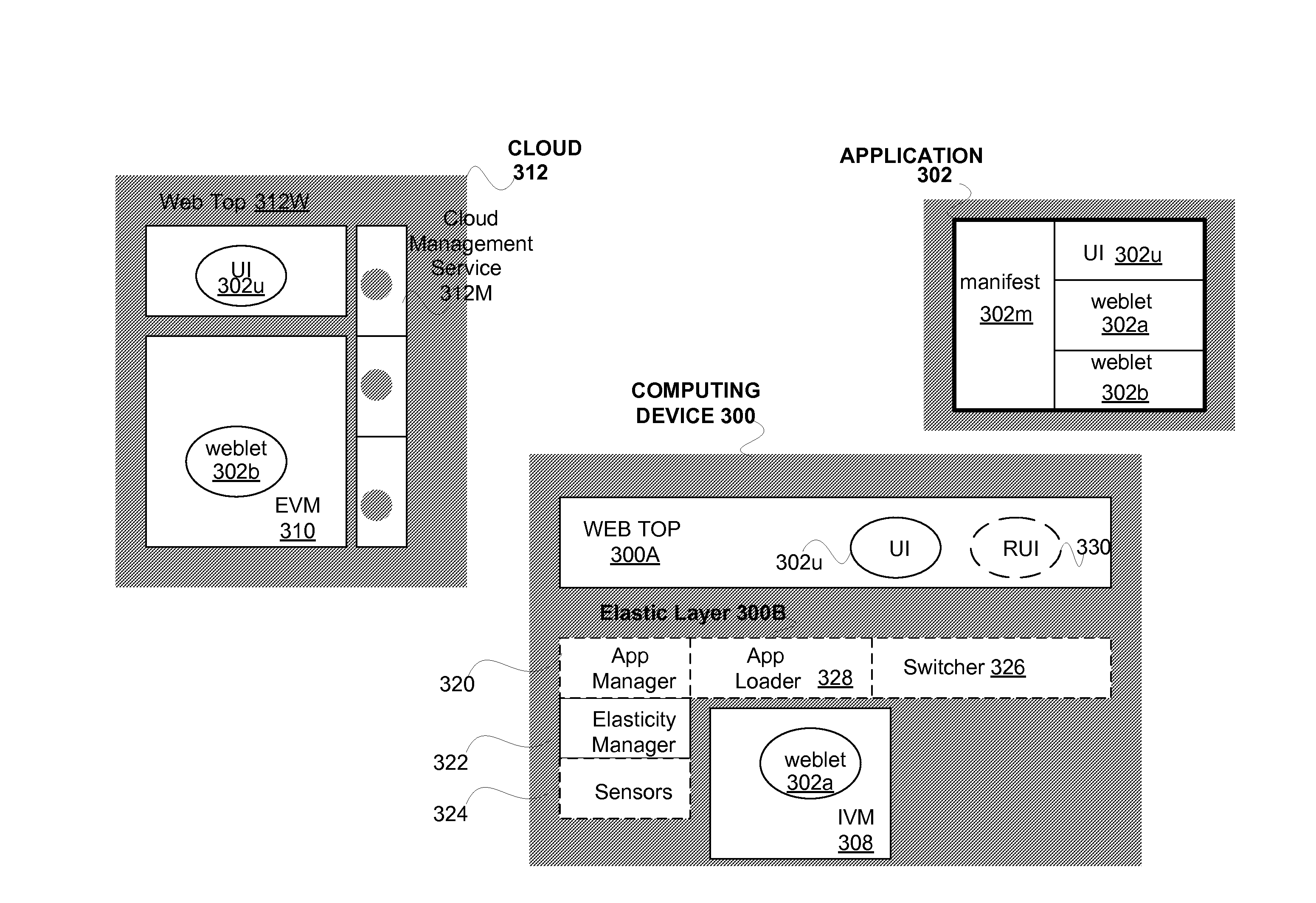
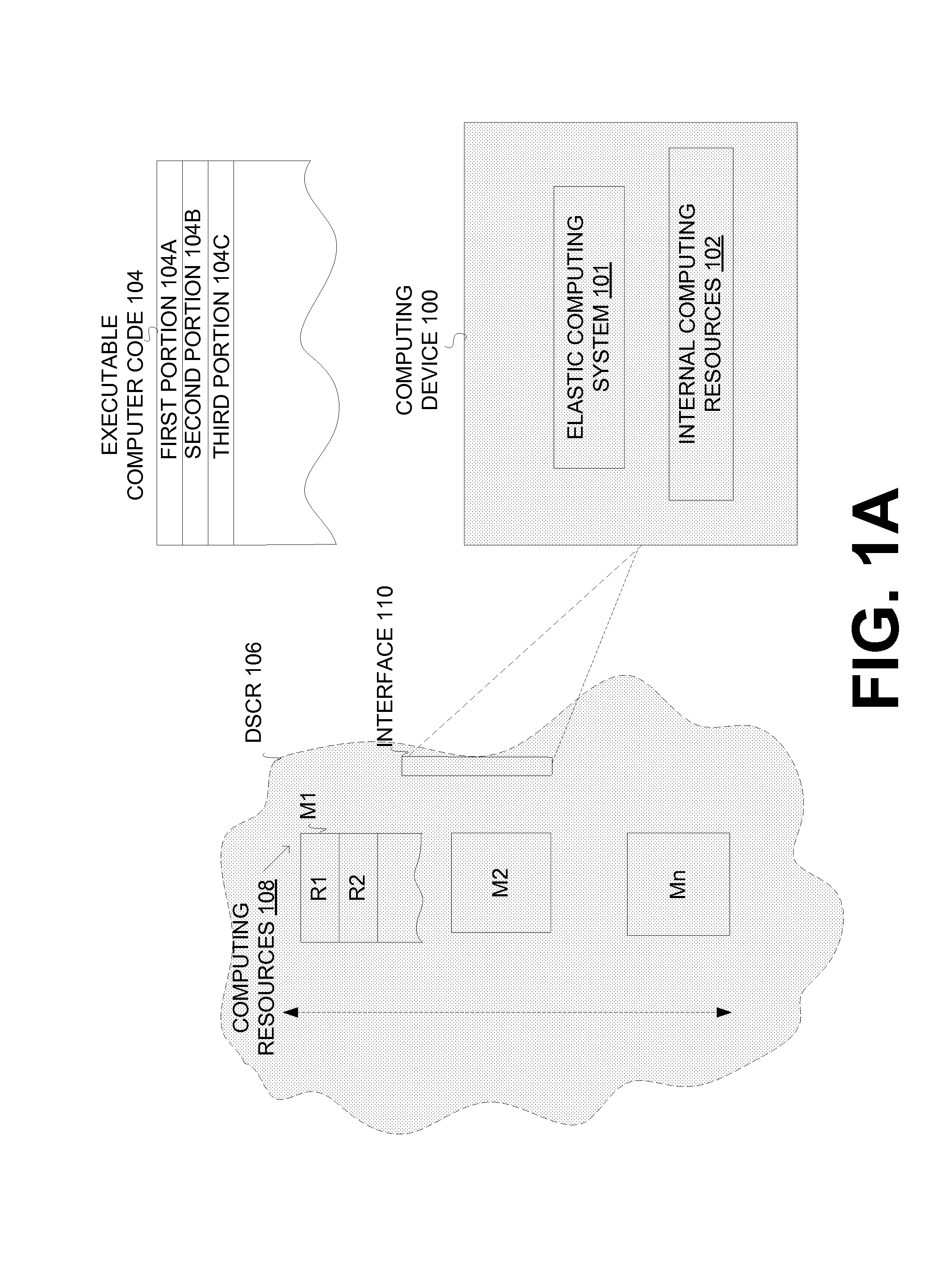
Execution allocation cost assessment for computing systems and environments including elastic computing systems and environments
InactiveUS20100131592A1Limited and reduced computing resourceEfficiently provideEnergy efficient ICTResource allocationMobile telephonyComputing systems
Techniques for assessing the cost of allocation of execution and affecting the allocation of execution are disclosed. The cost of allocation of execution to or between a first computing device (e.g., a mobile device) and one or more computing resource providers (e.g., one or more Clouds) can be determined during runtime of the executable code. It will be appreciated that a computing system can operate independently of the first computing device and one or more computing resource providers and provide execution allocation cost assessment as a service to the first computing device and / or one or more computing resource providers. Execution allocation cost can be assessed (or determined) based on execution allocation data pertaining to the first computing device and / or one or more computing resource providers. By way of example, power consumption of a mobile device can be used as a factor in determining how to allocate individual components of an application program (e.g., weblets) between a mobile phone and a Cloud. The invention is especially suited for Elastic computing environment and systems. In an Elastic computing environment, scalable and dynamic external computing resources can be used in order to effectively extend the computing capabilities beyond that which can be provided by internal computing resources of a computing system or environment.
Owner:SAMSUNG ELECTRONICS CO LTD
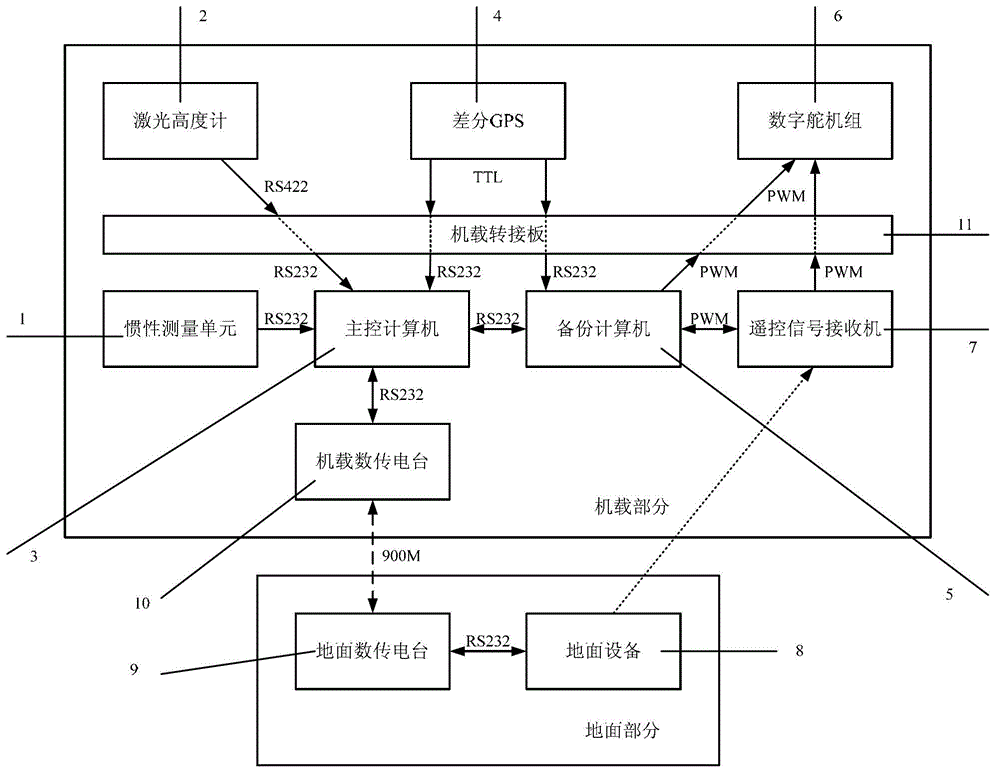
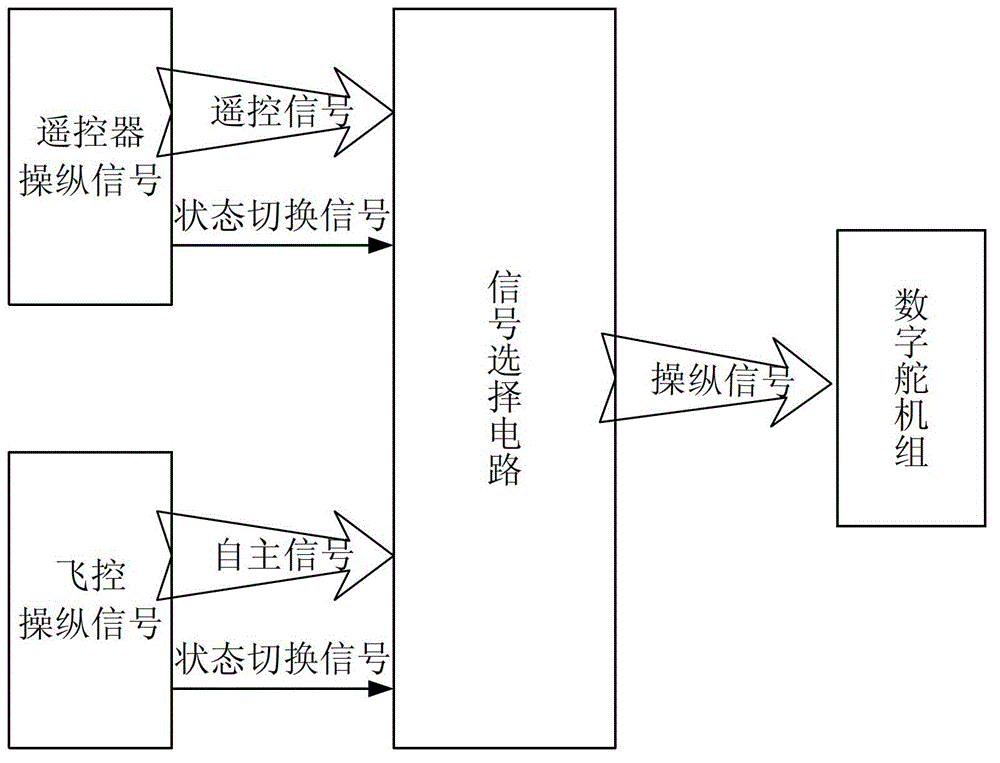
Dual-redundancy autonomous flight control system for micro-miniature unmanned helicopters
InactiveCN102915038AImprove computing powerImprove securityPosition/course control in three dimensionsFly controlRemote control
The invention discloses a dual-redundancy autonomous flight control system for micro-miniature unmanned helicopters, which comprises an airborne control system and a ground remote control and remote measuring system, wherein the airborne control system acquires the flight data of a helicopter, controls the unmanned helicopter to fly in accordance with scheduled subjects according to a flight control algorithm, and sends the flight data and algorithm results to the ground remote control and remote measuring system through an airborne data transfer radio in the airborne control system; and the ground remote control and remote measuring system receives the data sent by the airborne control system, displays the data through a ground station so as to enable ground experimenters to know the flight and control states of the helicopter, and uploads a control instruction in real time through the ground station so as to adjust and change the flight subjects and control state of the helicopter. According to the invention, the autonomous capacity of small unmanned helicopters can be improved, and the reliability of the system can be increased; and especially, when a flight control computer has failures, the safety of a test platform can be ensured to the maximum extent.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com