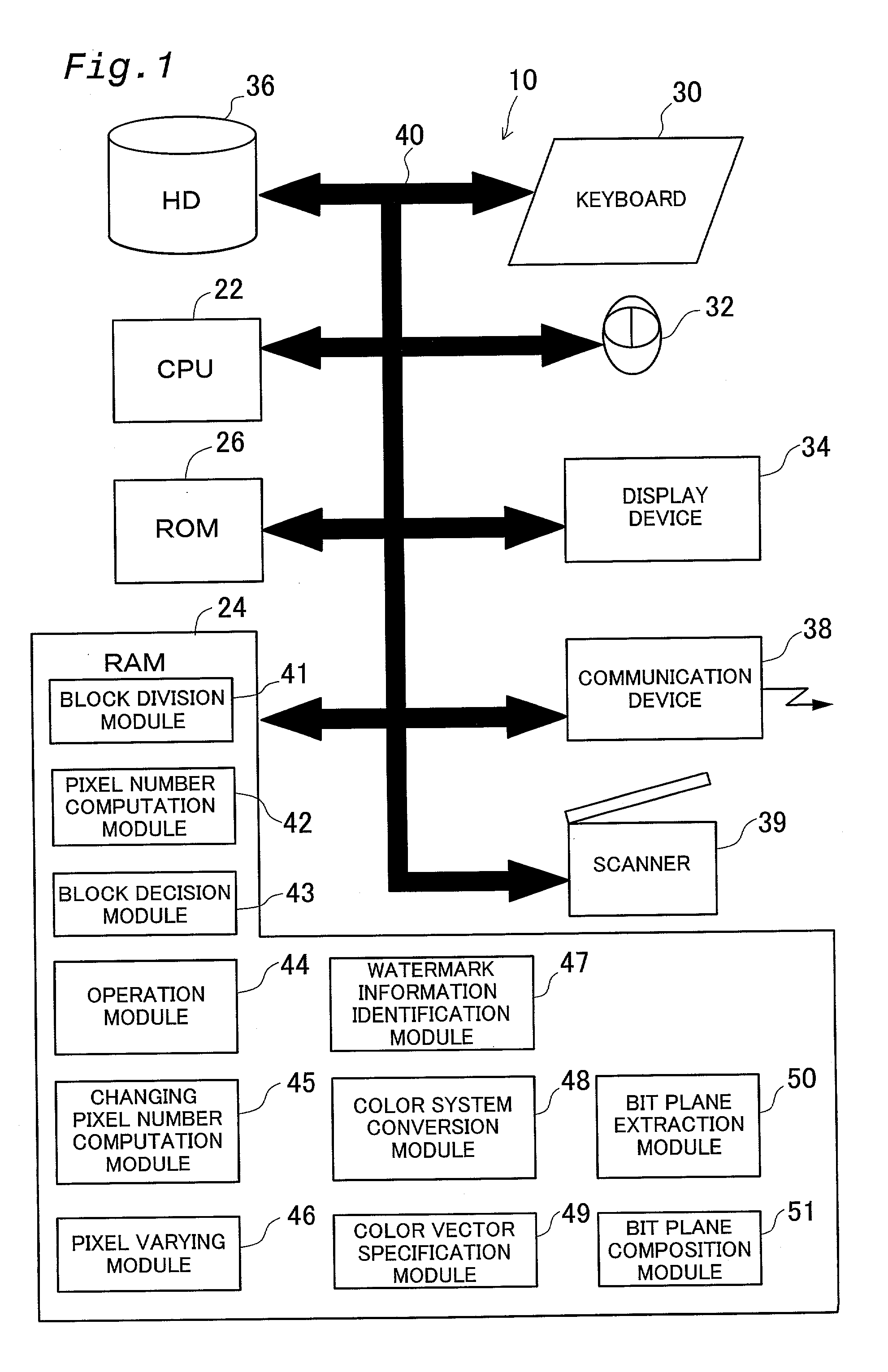
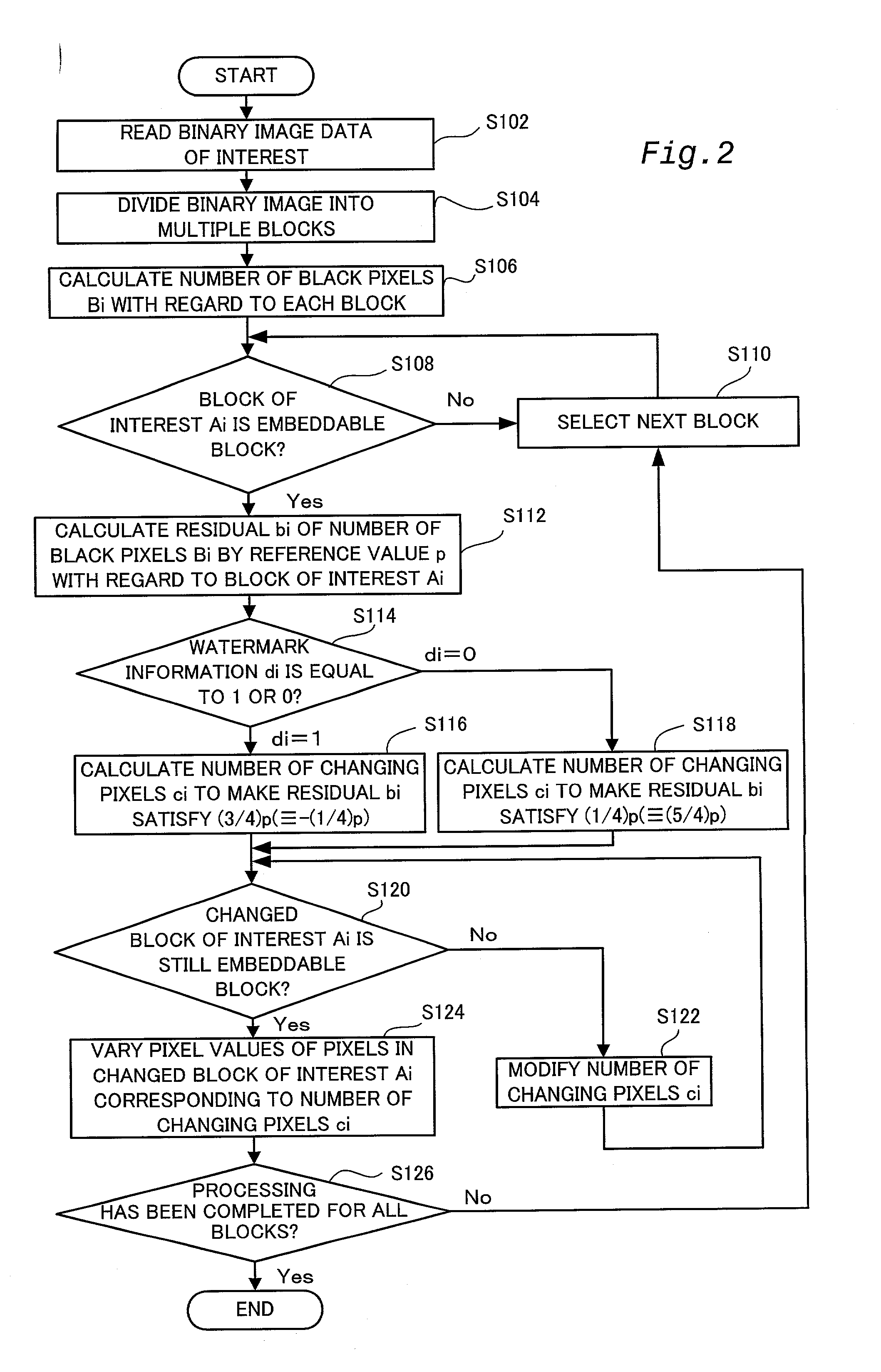
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1281 results about "Watermark" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
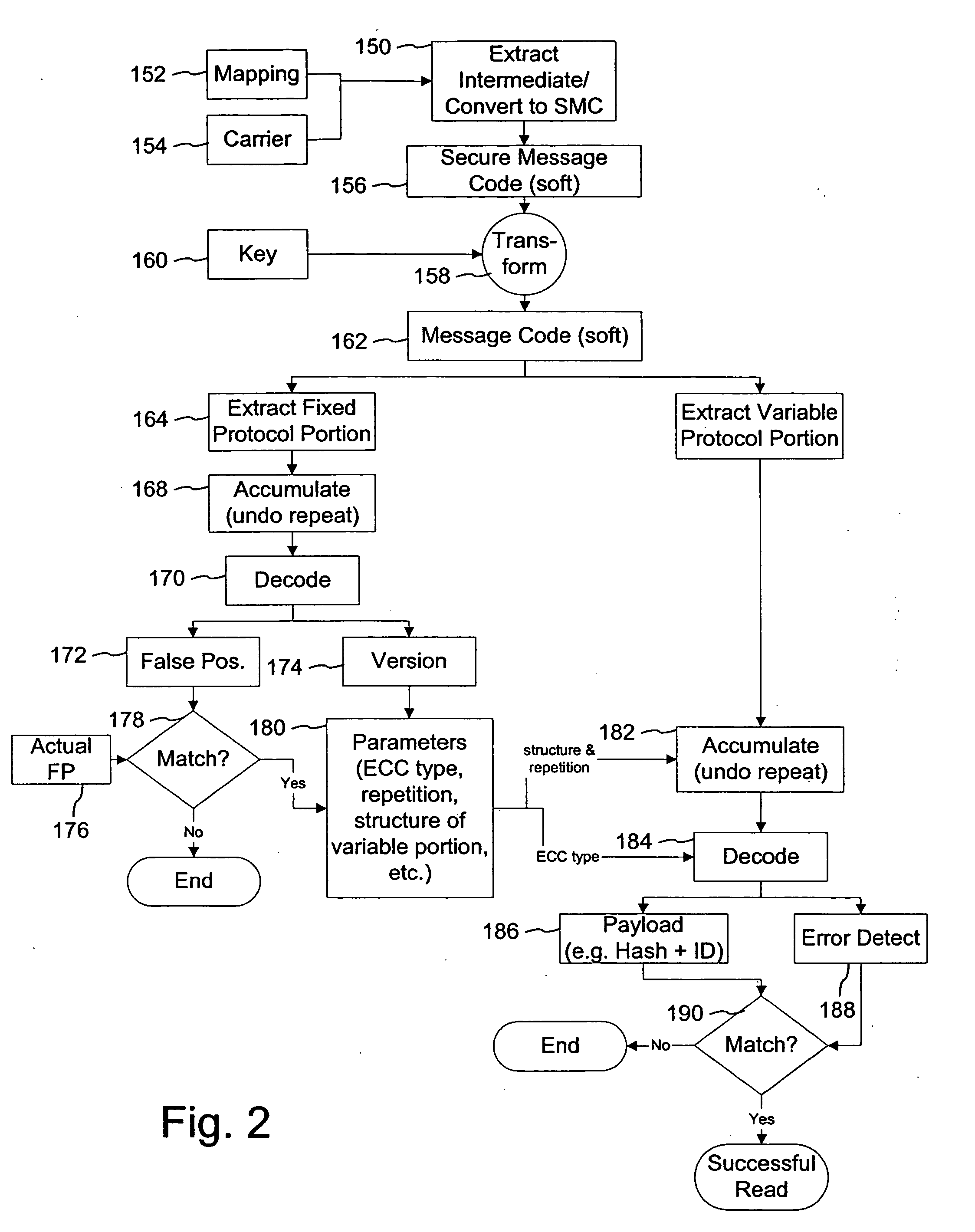
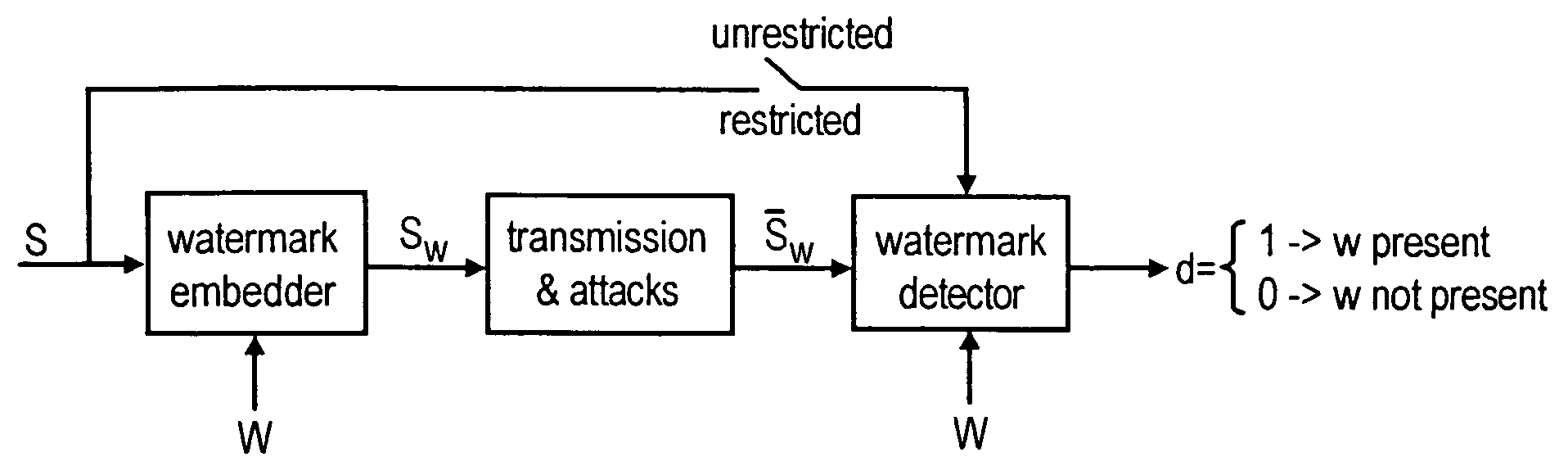
A watermark stored in a data file refers to a method for ensuring data integrity which combines aspects of data hashing and digital watermarking. Both are useful for tamper detection, though each has its own advantages and disadvantages.
Content security layer providing long-term renewable security
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
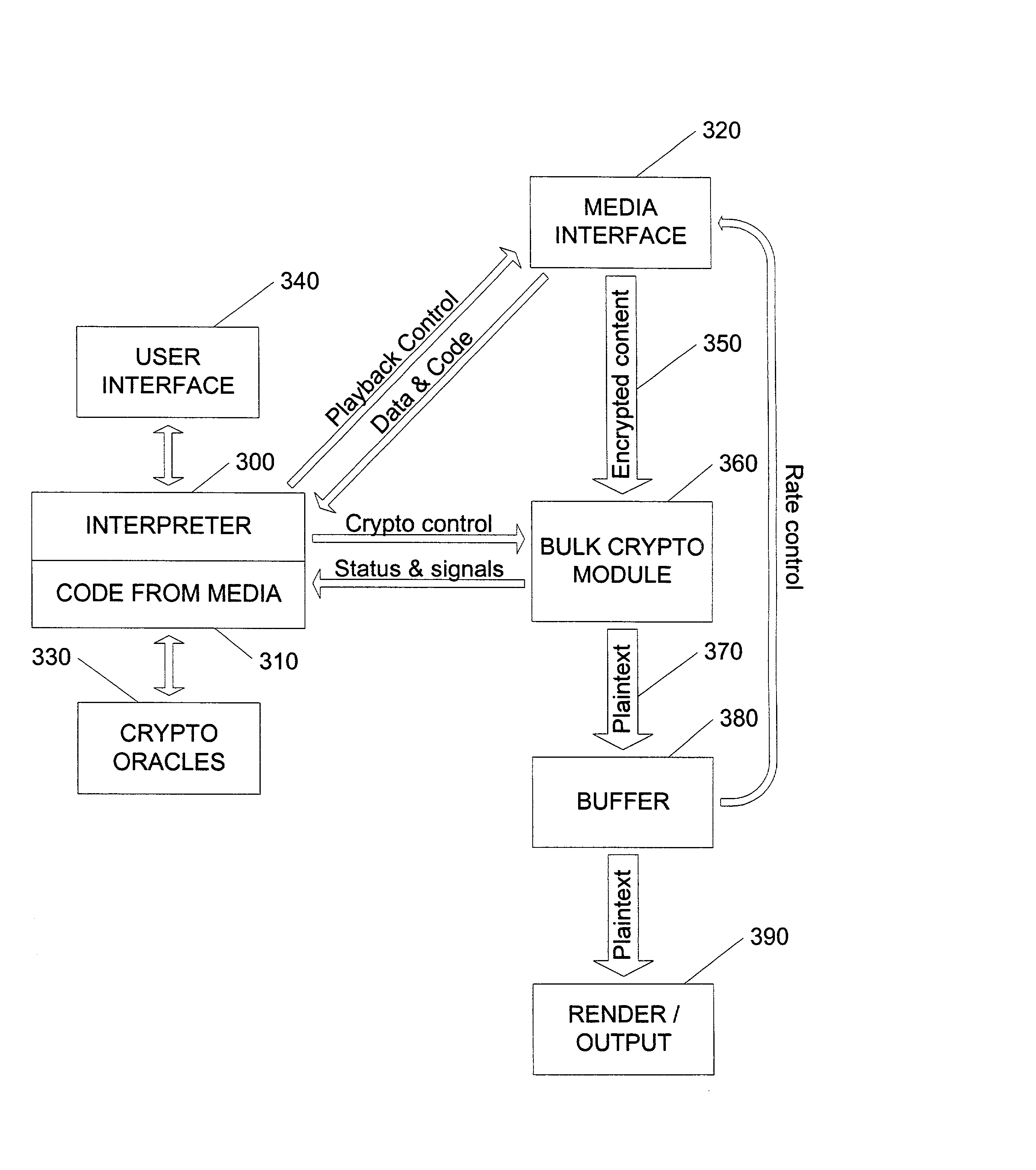
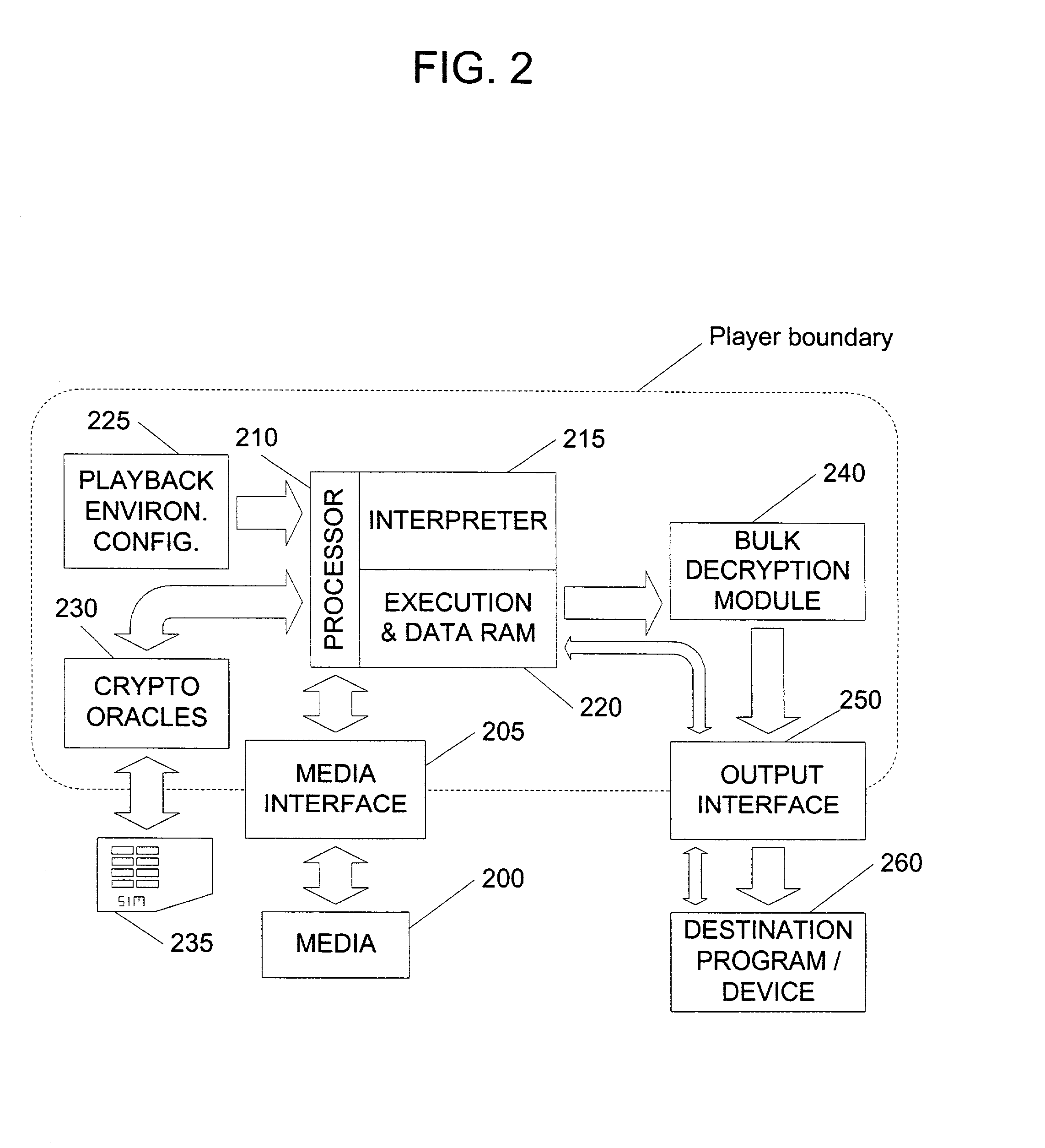
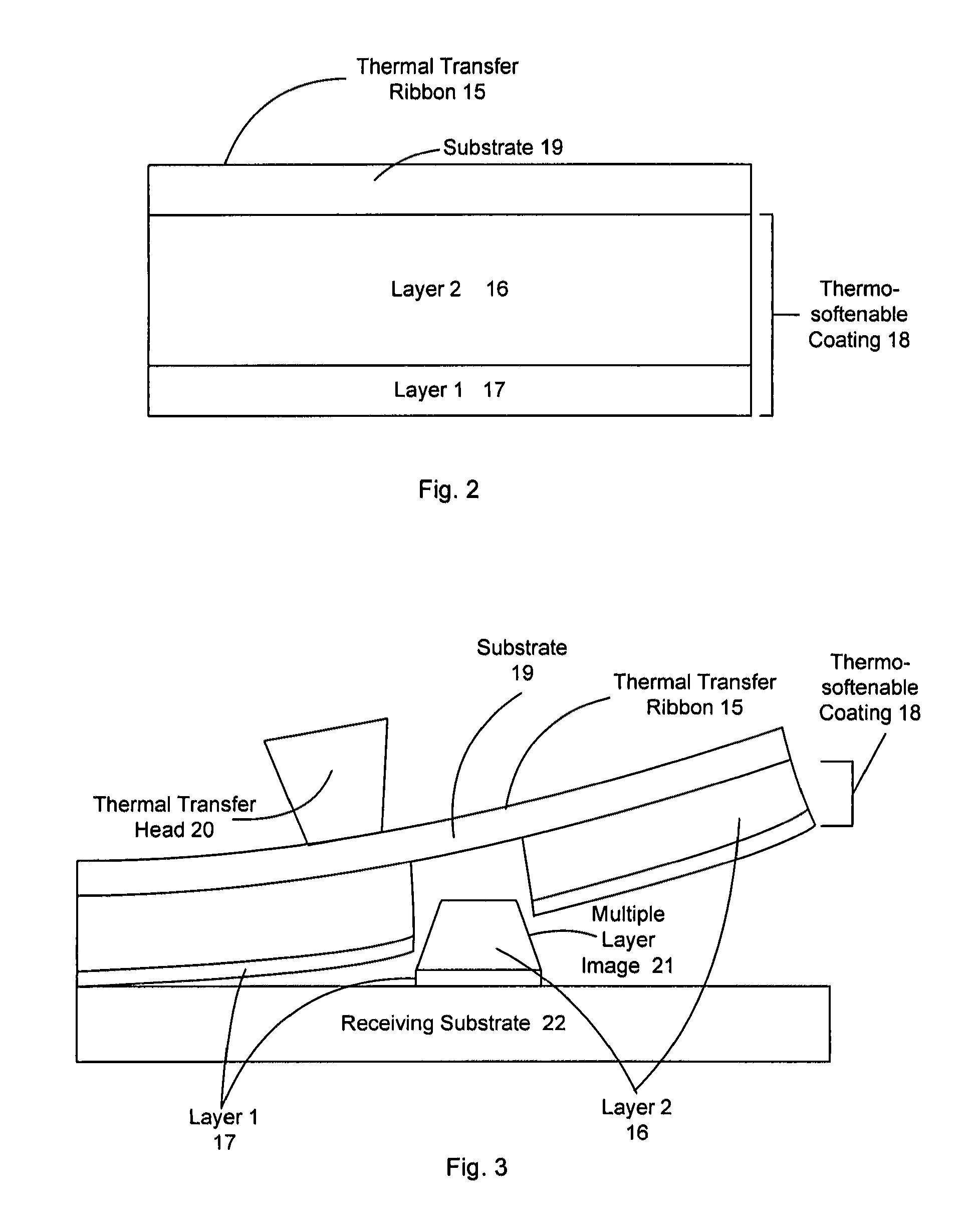
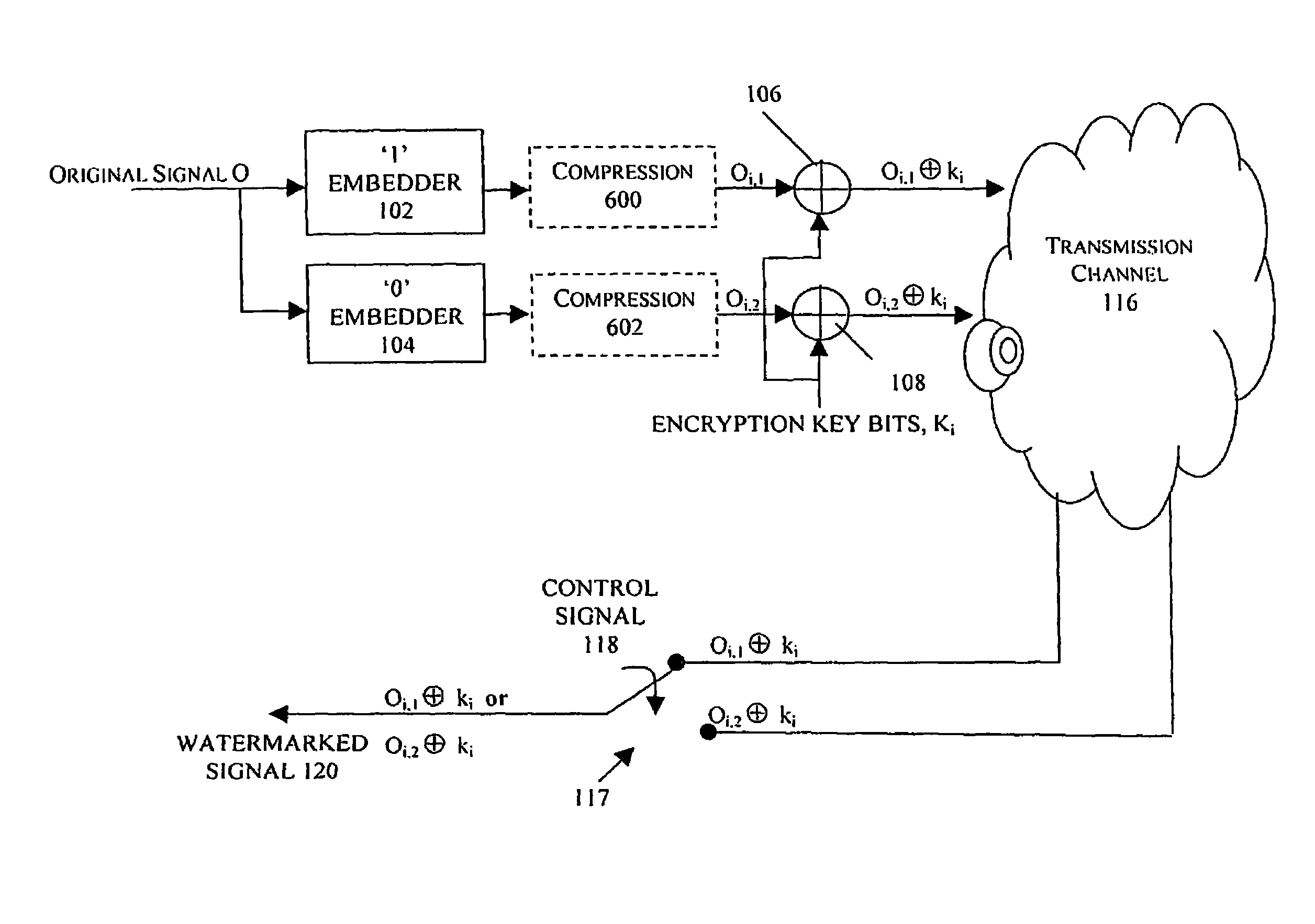
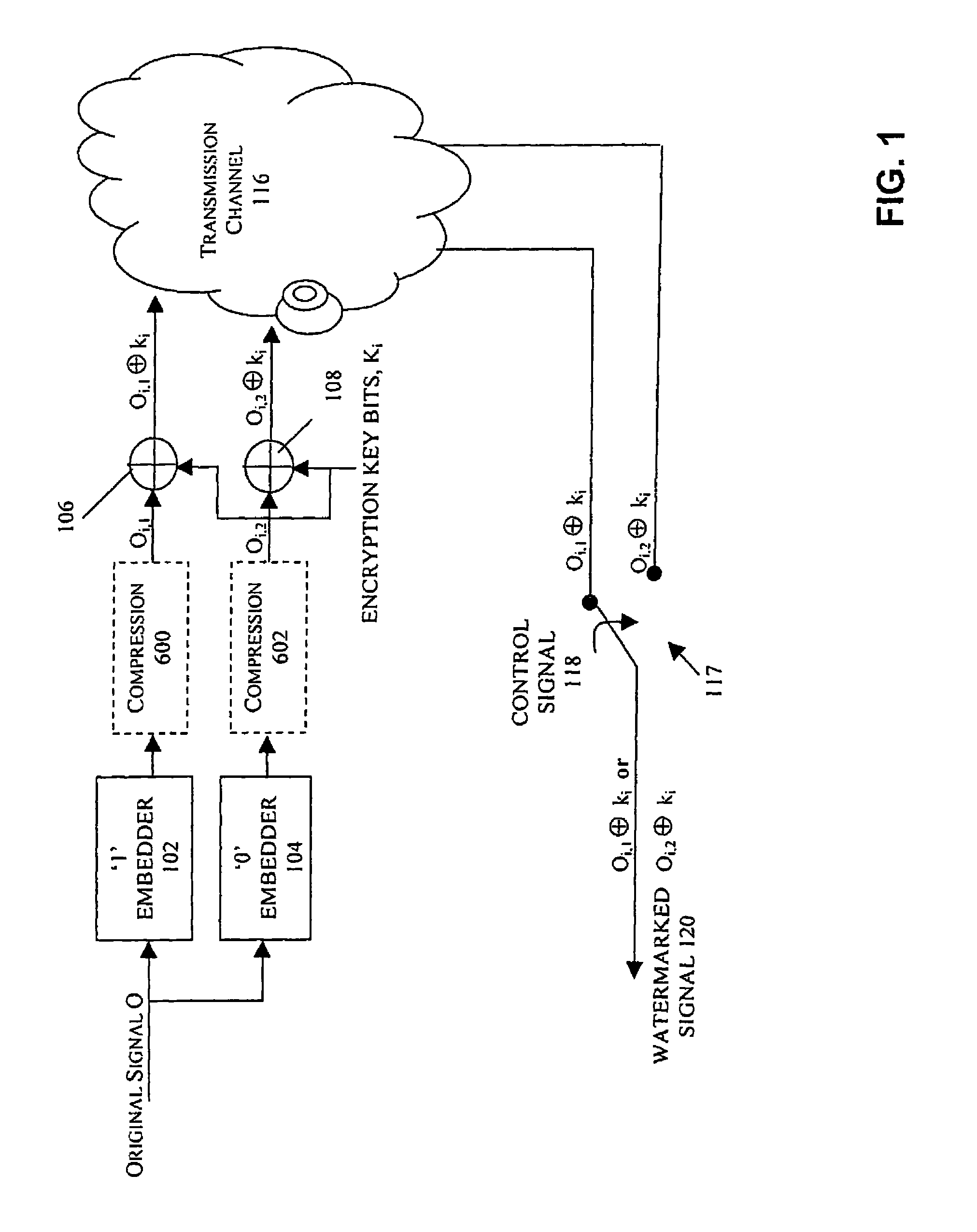
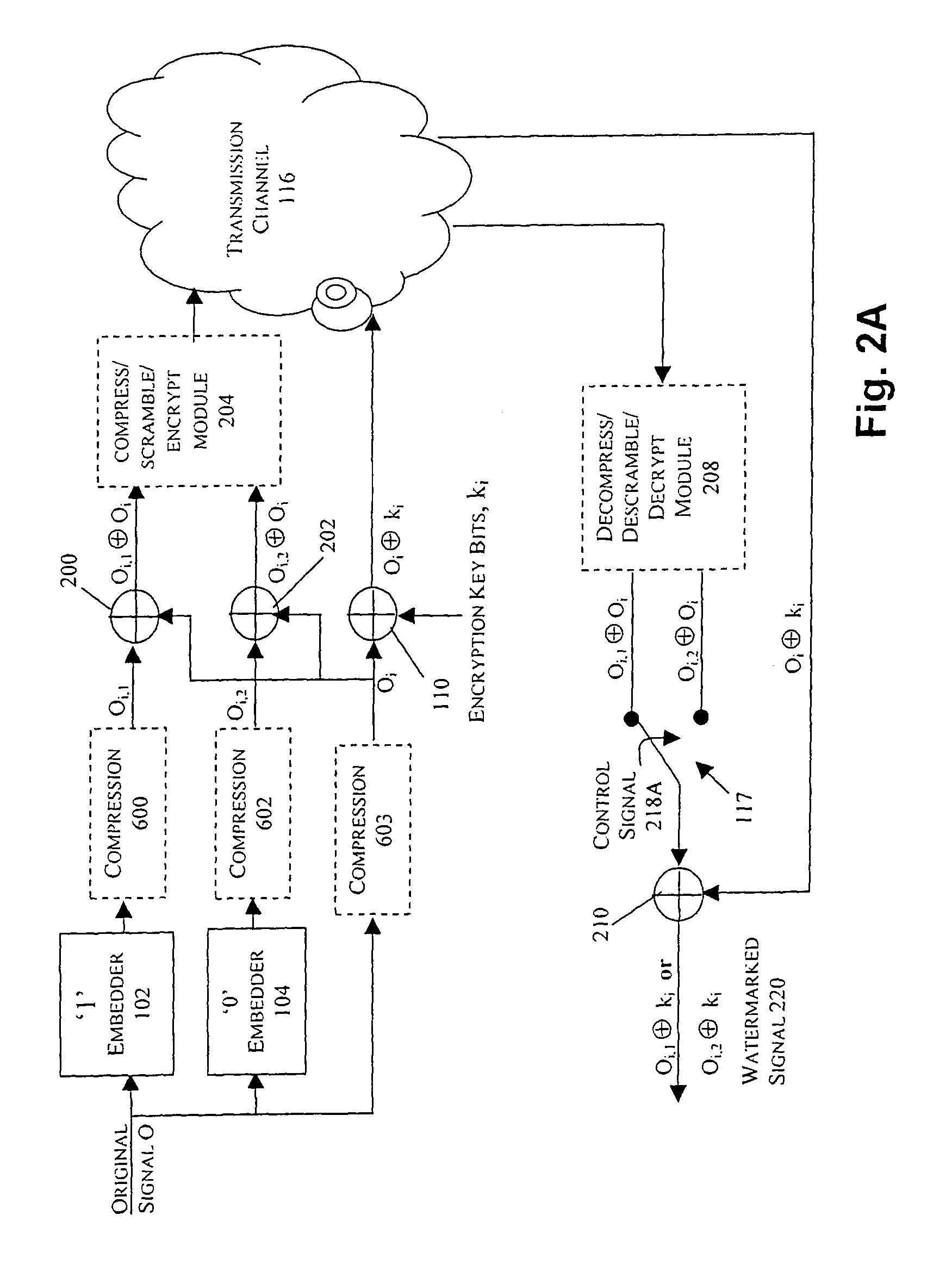
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
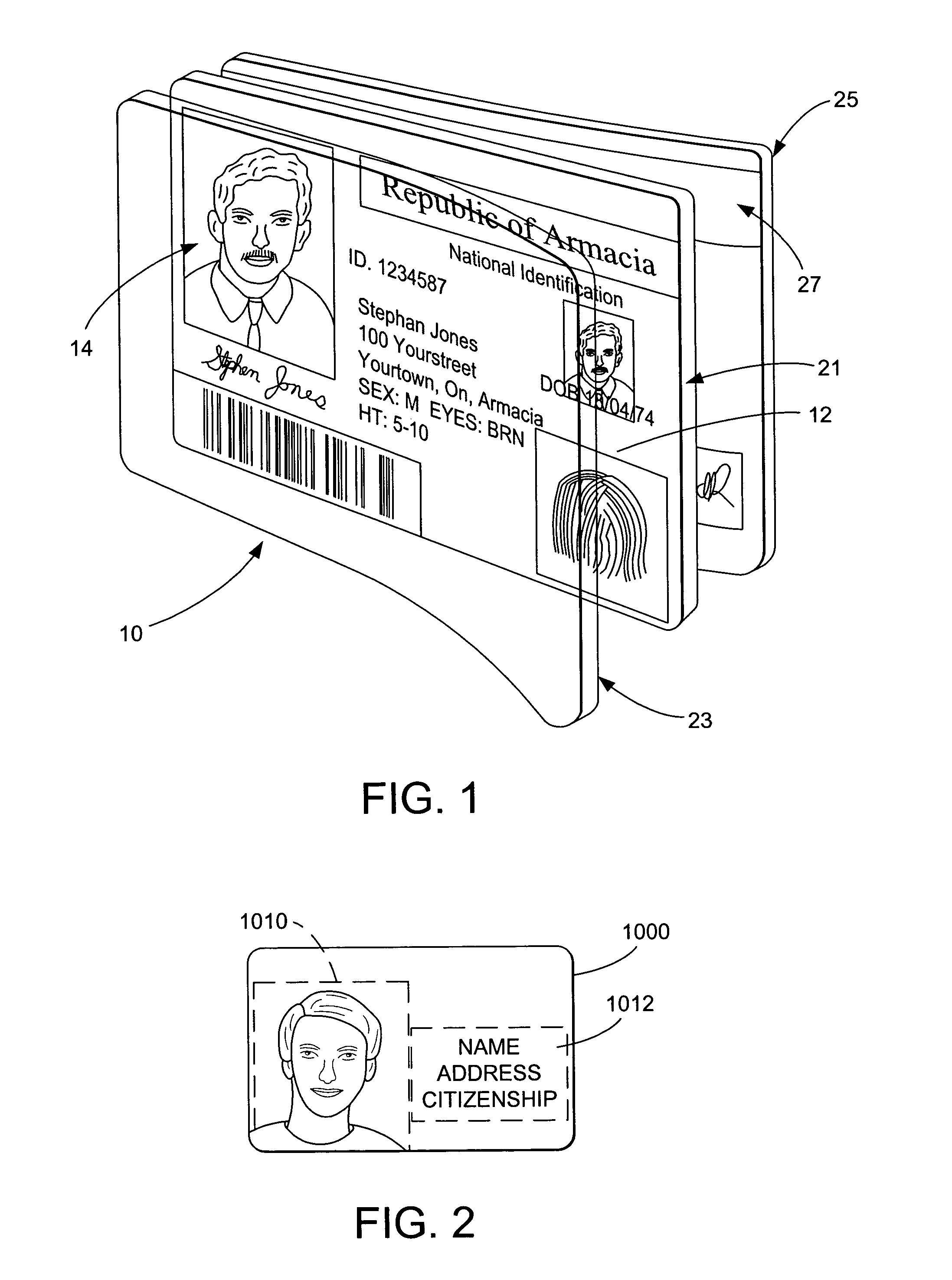
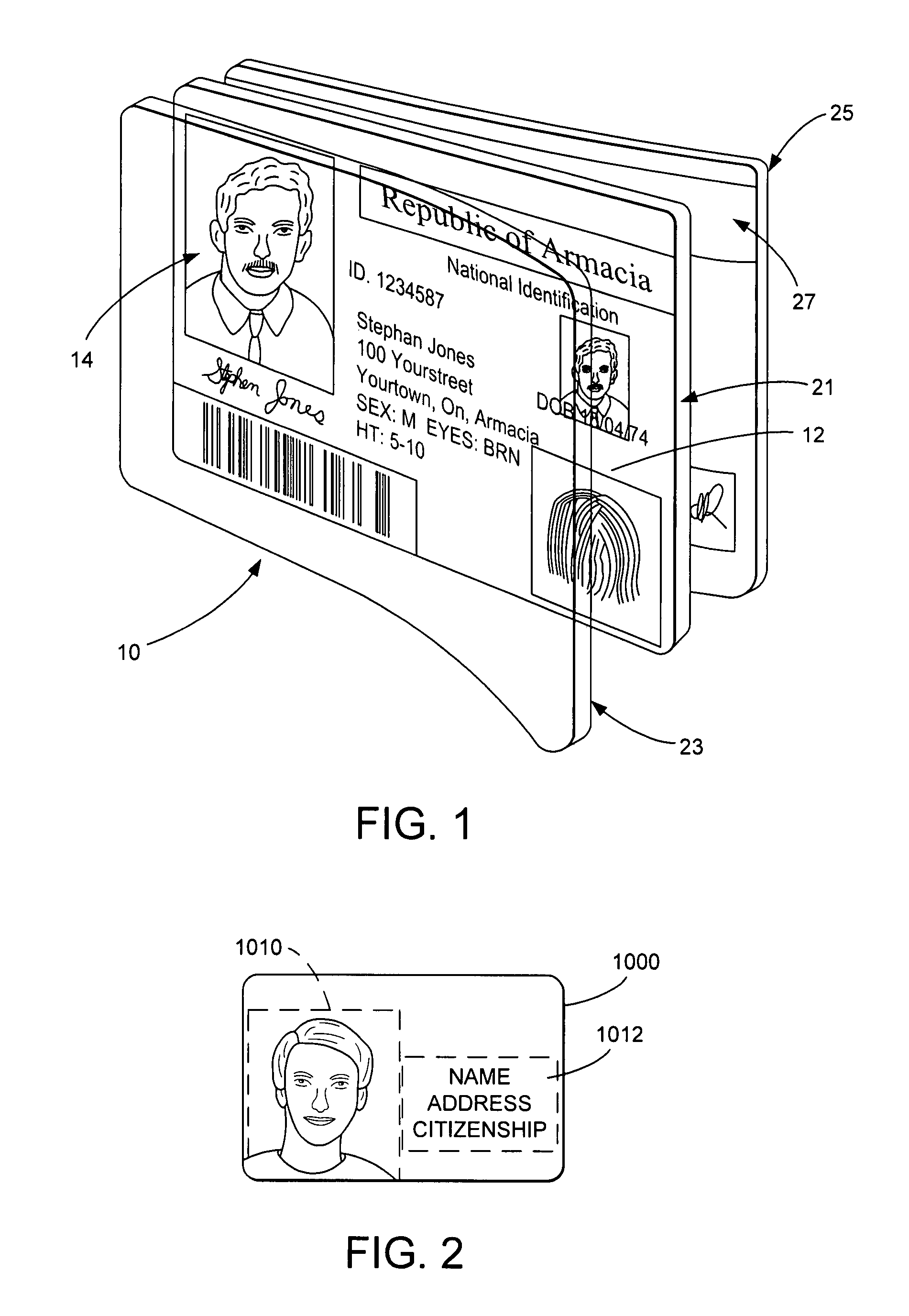
Identification document and related methods
InactiveUS20050160271A9Level of protectionEasy to useOther printing matterPaper-money testing devicesDocumentationComputer science
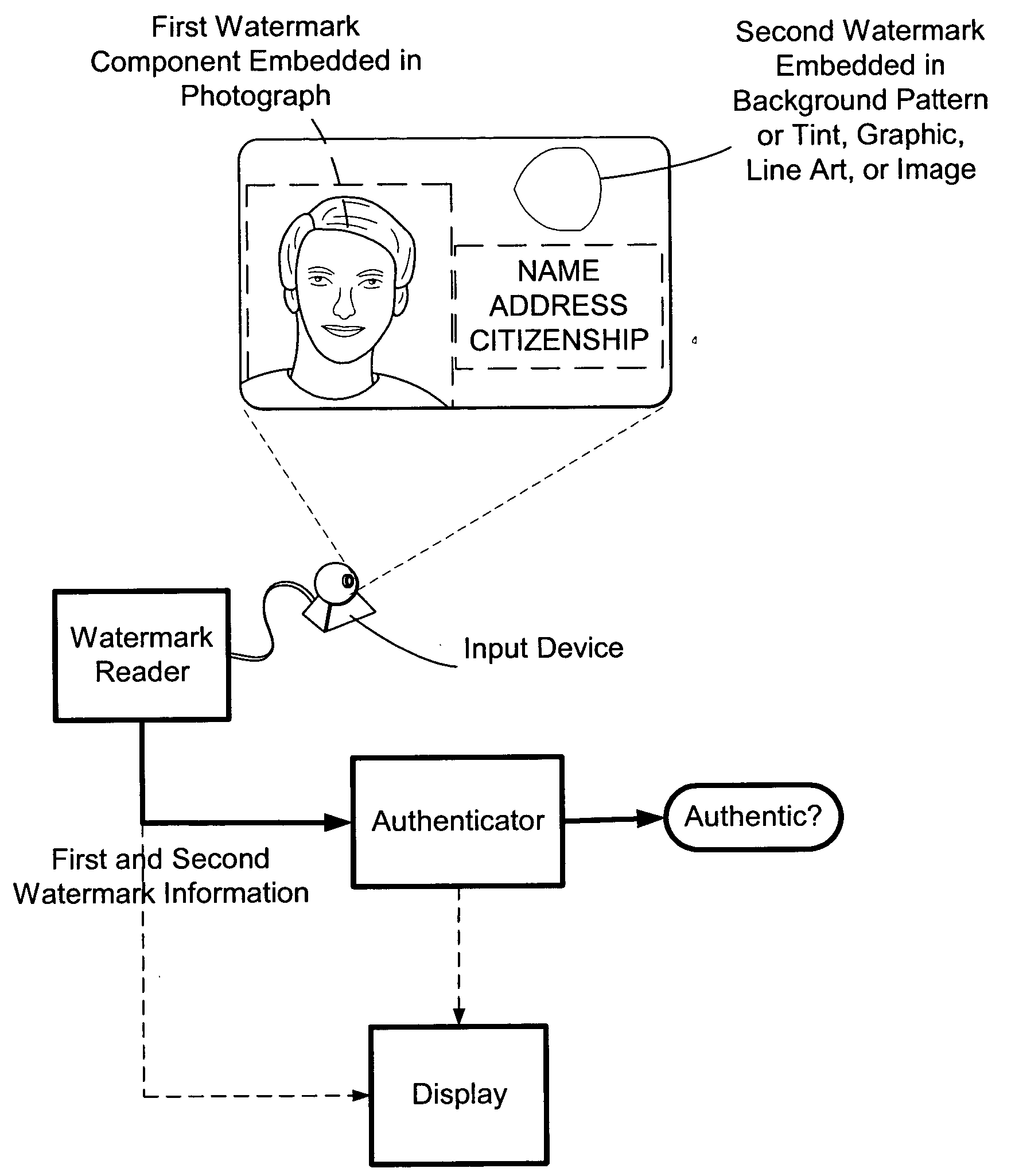
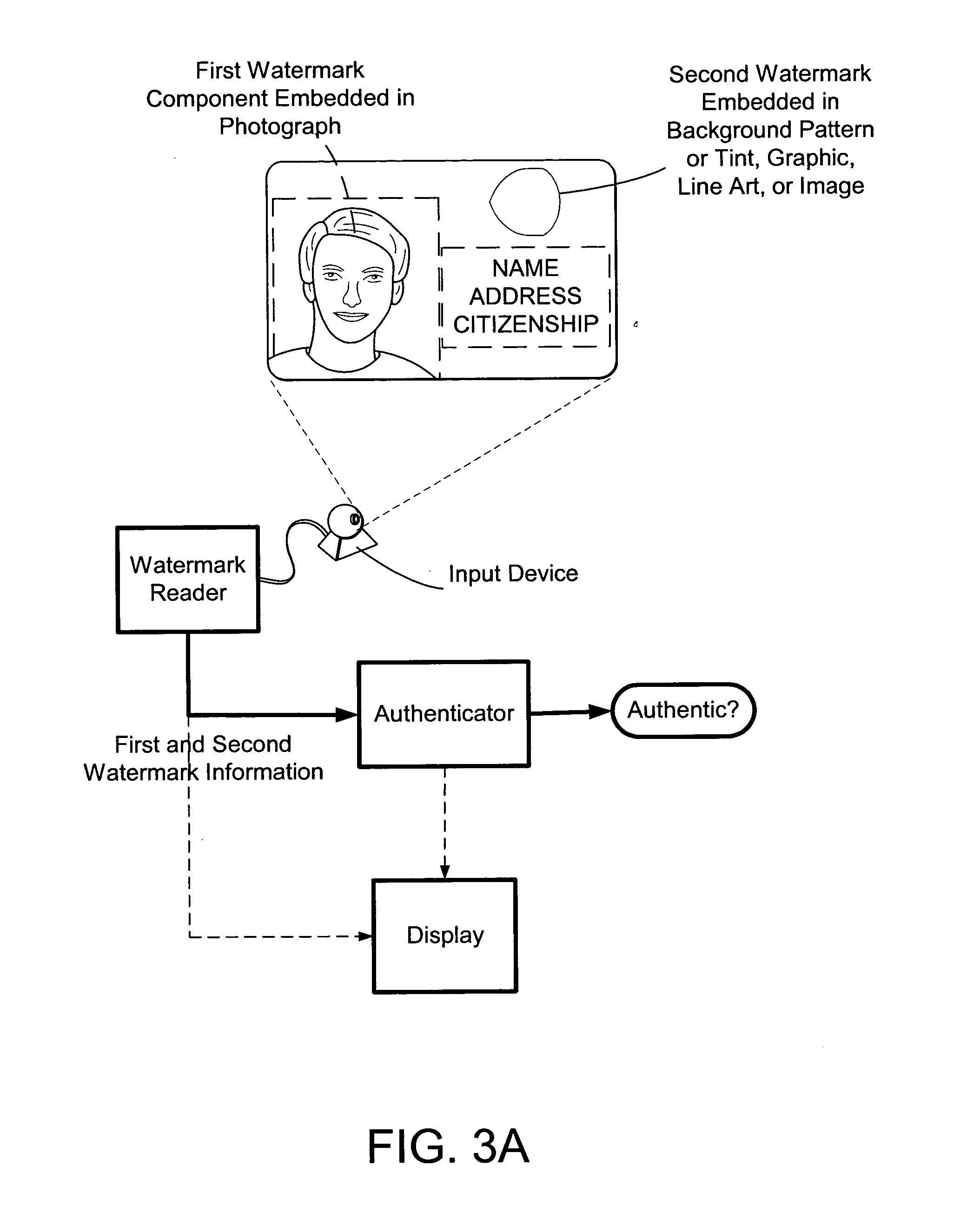
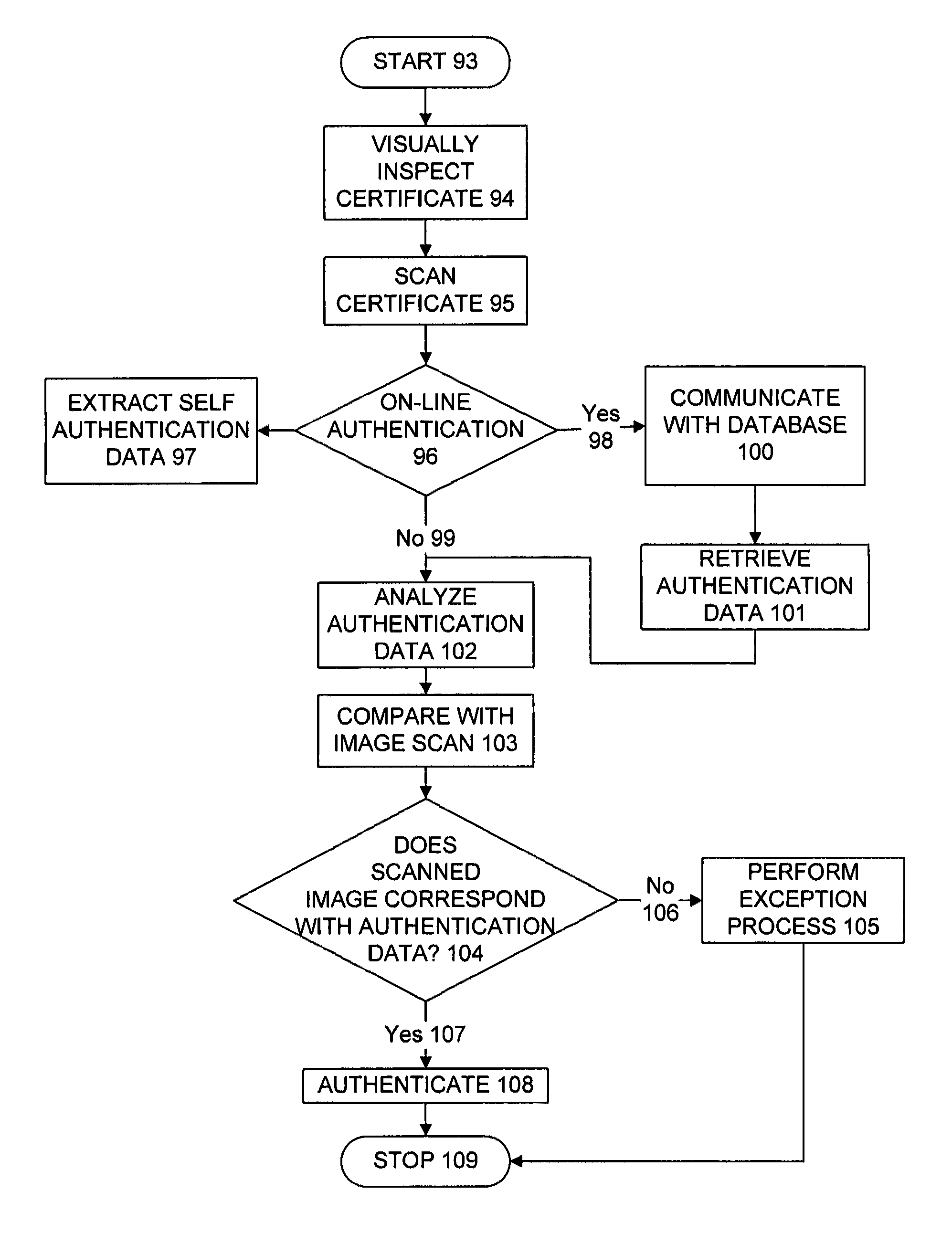
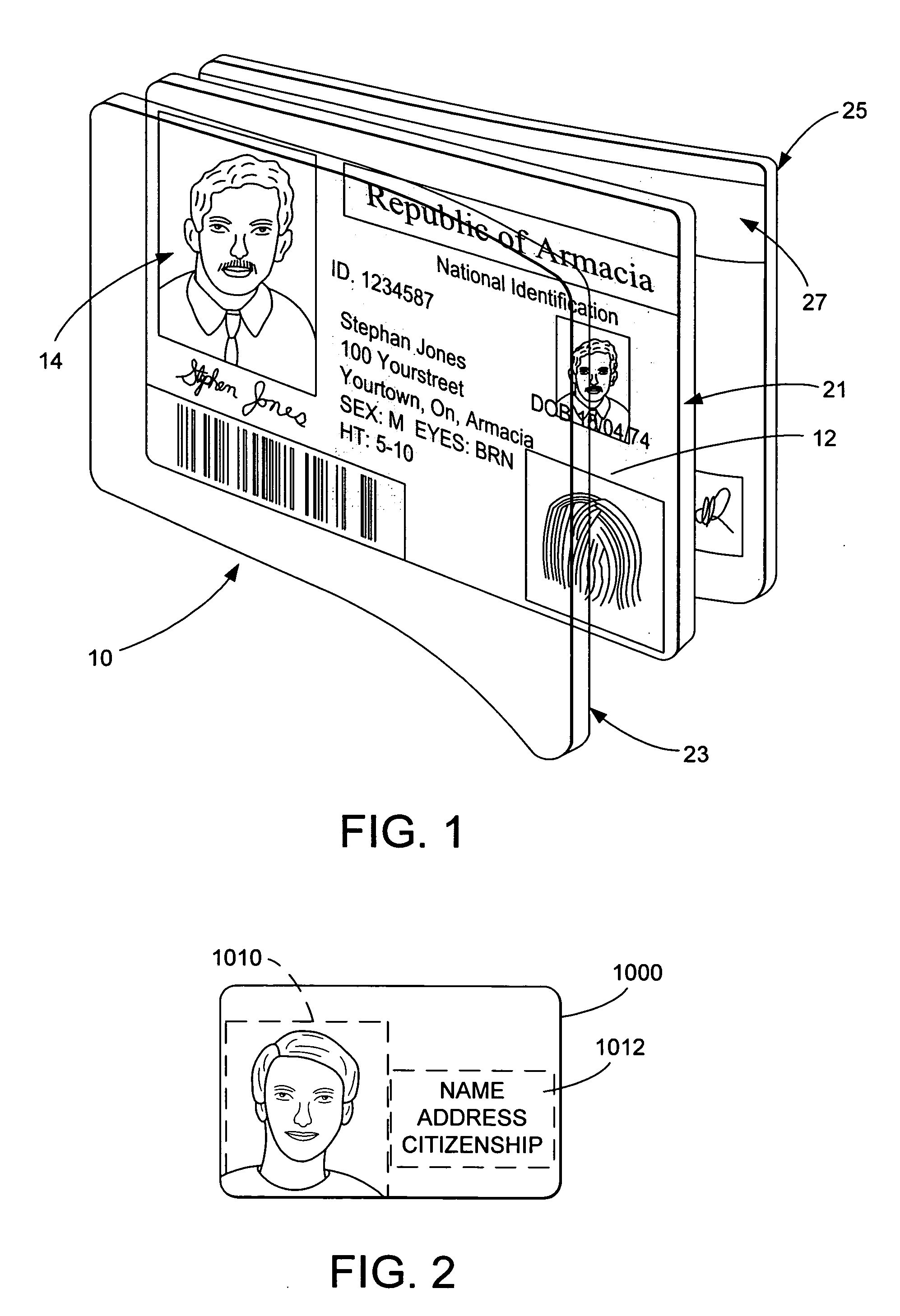
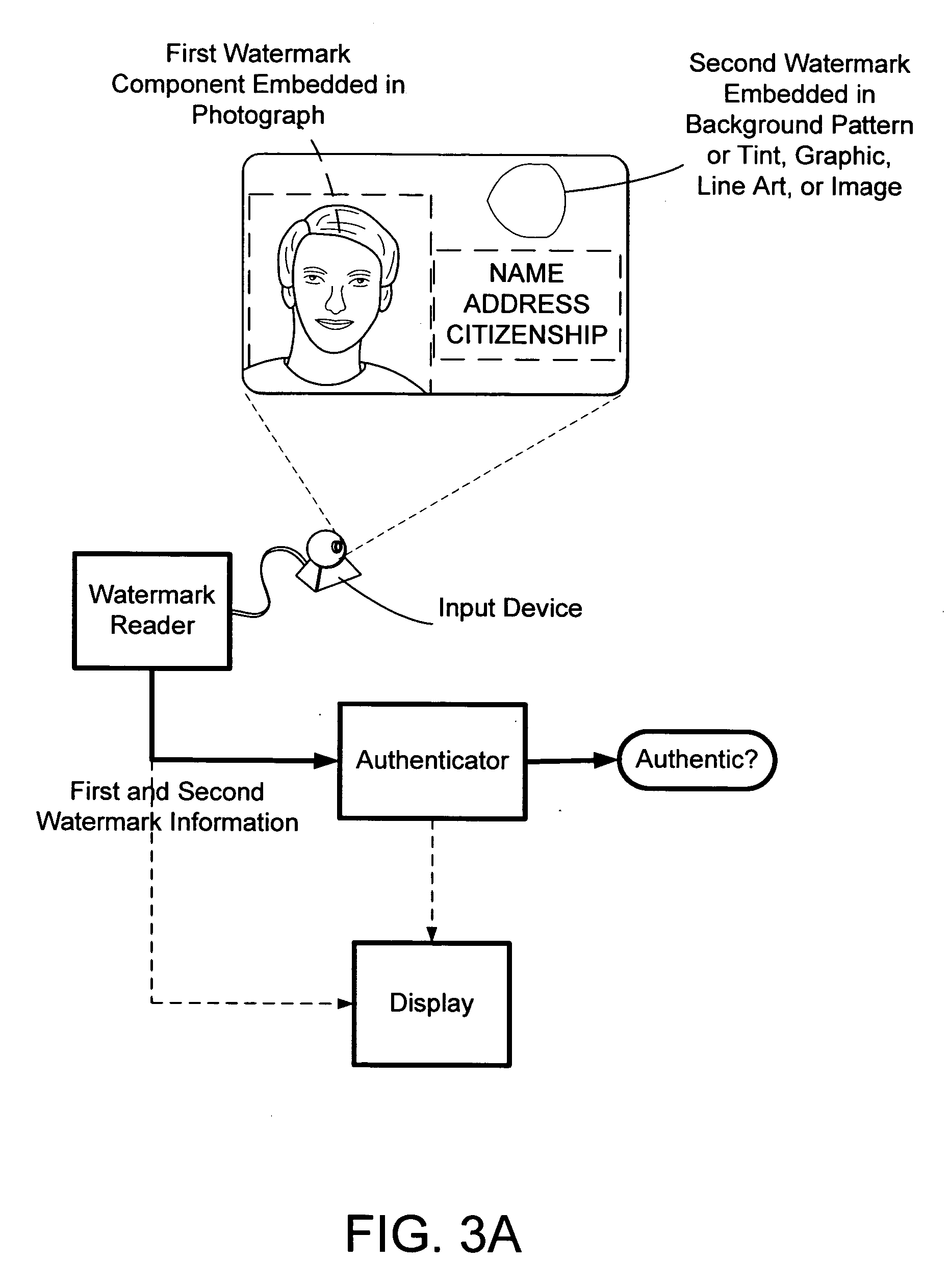
The present invention provides methods and systems for authenticating identification documents. We also teach an identification document including two or more digital watermarks. The watermarks correspond with each other or with indicia carried by the identification document. The correspondence can be verified to determine authenticity. We also provide digital watermark detection methods and systems to identify the different watermarks through embedded orientation components. We then focus watermark message-decoding efforts on areas identified as likely including watermark orientation components. In one implementation we provide a watermark detection trigger to identify so-called legacy documents. The trigger may indicate the presence or expected absence of a digital watermark. In other implementations we provide a versatile document authenticator to toggle between watermarking and non-watermarking authentication processes depending on a detection trigger.
Owner:DIGIMARC CORP
Authentication method and system
InactiveUS8171567B1Low densityStable positionDigital data processing detailsUser identity/authority verificationEngineeringReproduction
The present invention provides a method and apparatus for the production and labeling of objects in a manner suitable for the prevention and detection of counterfeiting. Thus, the system incorporates a variety of features that make unauthorized reproduction difficult. In addition, the present invention provides a system and method for providing a dynamically reconfigurable watermark, and the use of the watermark to encode a stochastically variable property of the carrier medium for self-authentication purposes.
Owner:COPILOT VENTURES FUND III
Identification document and related methods
ActiveUS20070016790A1Level of protectionEasy to useOther printing matterPaper-money testing devicesPaper documentDocument preparation
The present invention provides methods and systems for authenticating identification documents. We also teach an identification document including two or more digital watermarks. The watermarks correspond with each other or with indicia carried by the identification document. The correspondence can be verified to determine authenticity. We also provide digital watermark detection methods and systems to identify the different watermarks through embedded orientation components. We then focus watermark message-decoding efforts on areas identified as likely including watermark orientation components. In another implementation we provide a watermark detection trigger to identify so-called legacy documents. The trigger may indicate the presence or expected absence of a digital watermark. In other implementations we provide a versatile document authenticator to toggle between watermarking and non-watermarking authentication processes depending on a detection trigger. Other implementations are provided as well.
Owner:DIGIMARC CORP
System reactions to the detection of embedded watermarks in a digital host content
InactiveUS7369677B2Increase payload capacitySacrificing complexityUser identity/authority verificationSpeech analysisSystem requirementsSystem recovery
Methods for adapting the operation of a system in response to the detection of embedded watermarks from a digital host content are provided. A digital host content is received and examined for the presence of watermarks. In response to the detection of embedded watermarks and in accordance with the value, type, density or spacing of the detected watermarks, one or more system reactions may take place. These reactions include conditionally allowing the system to resume its normal operation, prohibiting the system from resuming its normal operation, degrading the quality of the digital host content or changing the security status of the digital host content. In response to the extraction of weak watermarks that do not meet the desired system requirements, the extraction operation may be modified or extended to enable the detection of strong watermarks.
Owner:IP ACQUISITIONS LLC
Method for robust watermarking of content
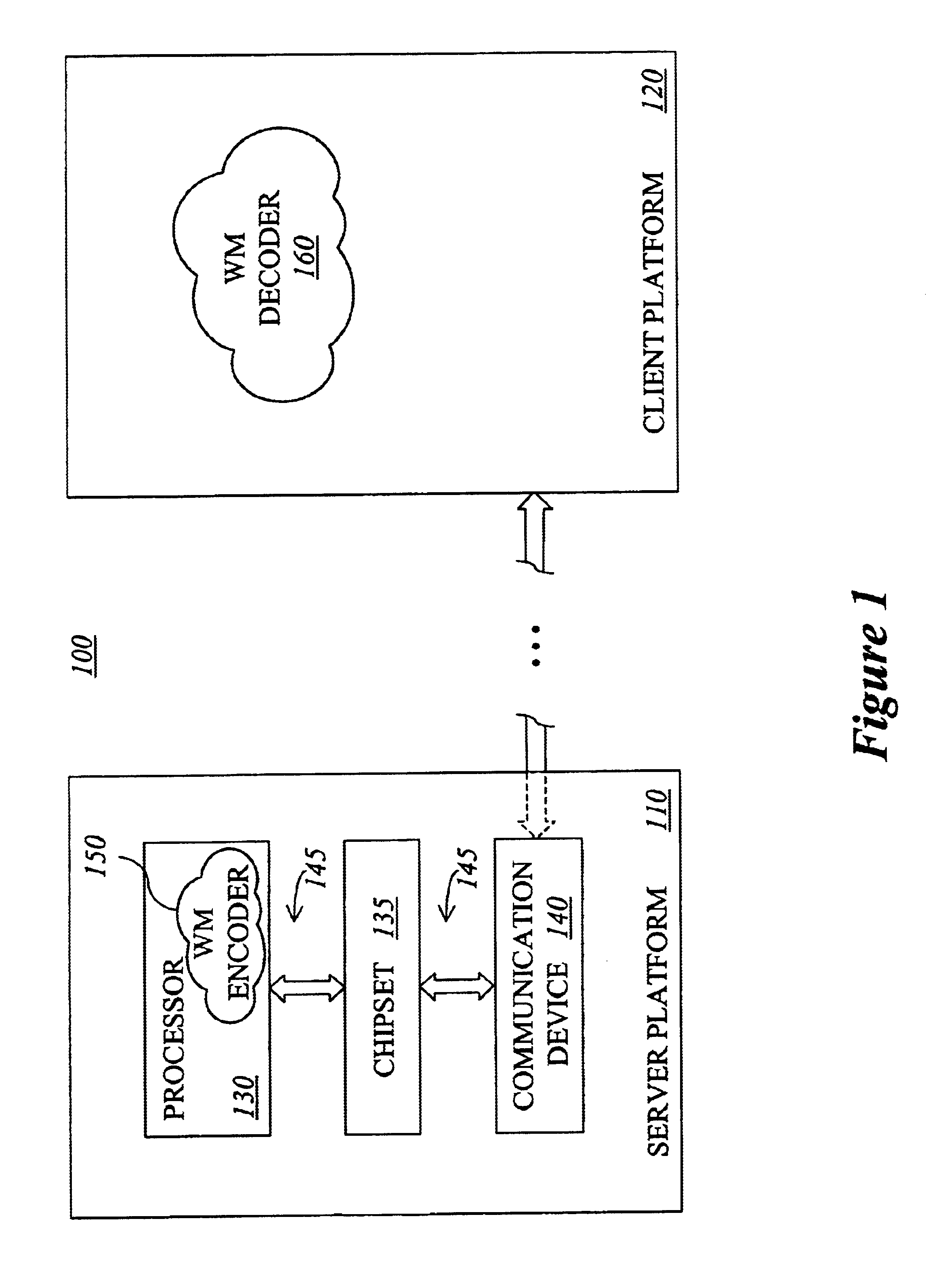
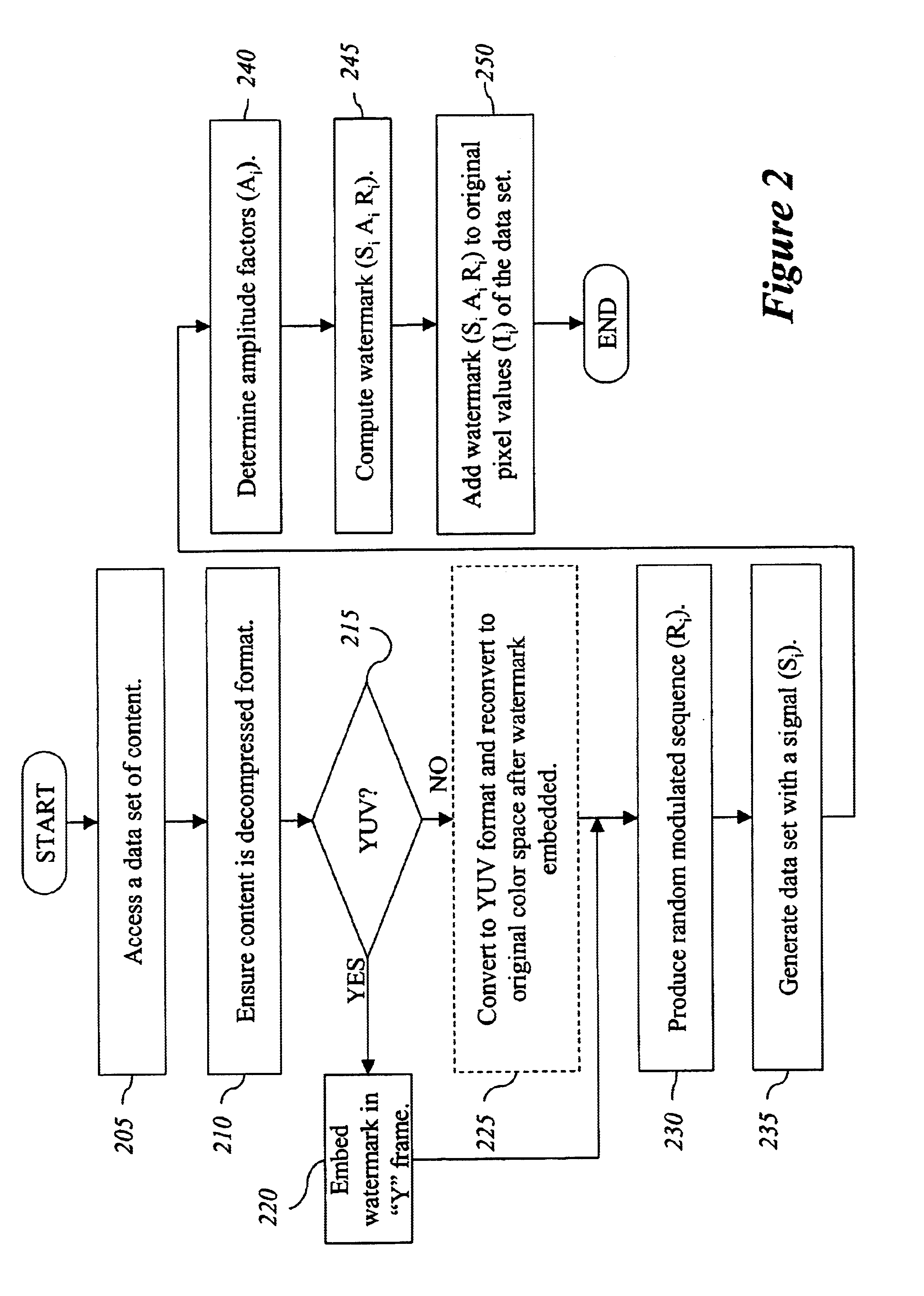
One inventive aspect pertains to a watermarking mechanism that allows a watermark to be determined from only a part of the video sequence without human intervention and without reference to the original watermarked frames. This watermark has improved invisibility, detection reliability and robustness. Invisibility is improved through the inclusion of frame difference parameters to calculate the amplitude of the watermark. Detection reliability and robustness can be improved by assuring that opposite signed values for the pseudo-random number sequence are spatially near each other and using data blocks forming the data sets, respectively. Another inventive aspect pertains to a watermarking mechanism that is exclusively dependent on the data contained in the data sets and is completely interoperable between spatial and compressed domains.
Owner:INTEL CORP
Optimization methods for the insertion, protection, and detection of digital watermarks in digital data
Disclosed herein are methods and systems for encoding digital watermarks into content signals. Also disclosed are systems and methods for detecting and / or verifying digital watermarks in content signals.According to one embodiment, a system for encoding of digital watermark information includes: a window identifier for identifying a sample window in the signal; an interval calculator for determining a quantization interval of the sample window; and a sampler for normalizing the sample window to provide normalized samples.According to another embodiment, a system for pre-analyzing a digital signal for encoding at least one digital watermark using a digital filter is disclosed.According to another embodiment, a method for pre-analyzing a digital signal for encoding digital watermarks comprises: (1) providing a digital signal; (2) providing a digital filter to be applied to the digital signal; and (3) identifying an area of the digital signal that will be affected by the digital filter based on at least one measurable difference between the digital signal and a counterpart of the digital signal selected from the group consisting of the digital signal as transmitted, the digital signal as stored in a medium, and the digital signal as played backed.According to another embodiment, a method for encoding a watermark in a content signal includes the steps of (1) splitting a watermark bit stream; and (2) encoding at least half of the watermark bit stream in the content signal using inverted instances of the watermark bit stream.Other methods and systems for encoding / decoding digital watermarks are also disclosed.
Owner:WISTARIA TRADING INC
Methods and apparatus for watermarking and distributing watermarked content
ActiveUS20120308071A1Easy to identifyCharacter and pattern recognitionImage data processing detailsContent distributionImage processing
Methods and apparatus for generating and distributing watermarked content are described. Content to be distributed is sliced into a plurality of segments, e.g., short portions. Individual segments are subjected to watermarking with multiple watermarked versions of a segment being generated. Different watermarked versions of a segment communicate different information, e.g., one or more numbers. Sets of watermarked segments corresponding to a program are supplied to a content distribution device. Based on a session number or other information corresponding to the destination of the content, the content distribution device selects watermarked segments from the sets of segments to provide to the user. The combination of segments communicates, via the watermarks, a sequence of numbers used to identify the streamed content without requiring the distribution node to perform image processing to generate the watermarks. When the segments are communicated sequentially, the watermarks can be detected and the identifying numerical sequence extracted.
Owner:TIME WARNER CABLE ENTERPRISES LLC
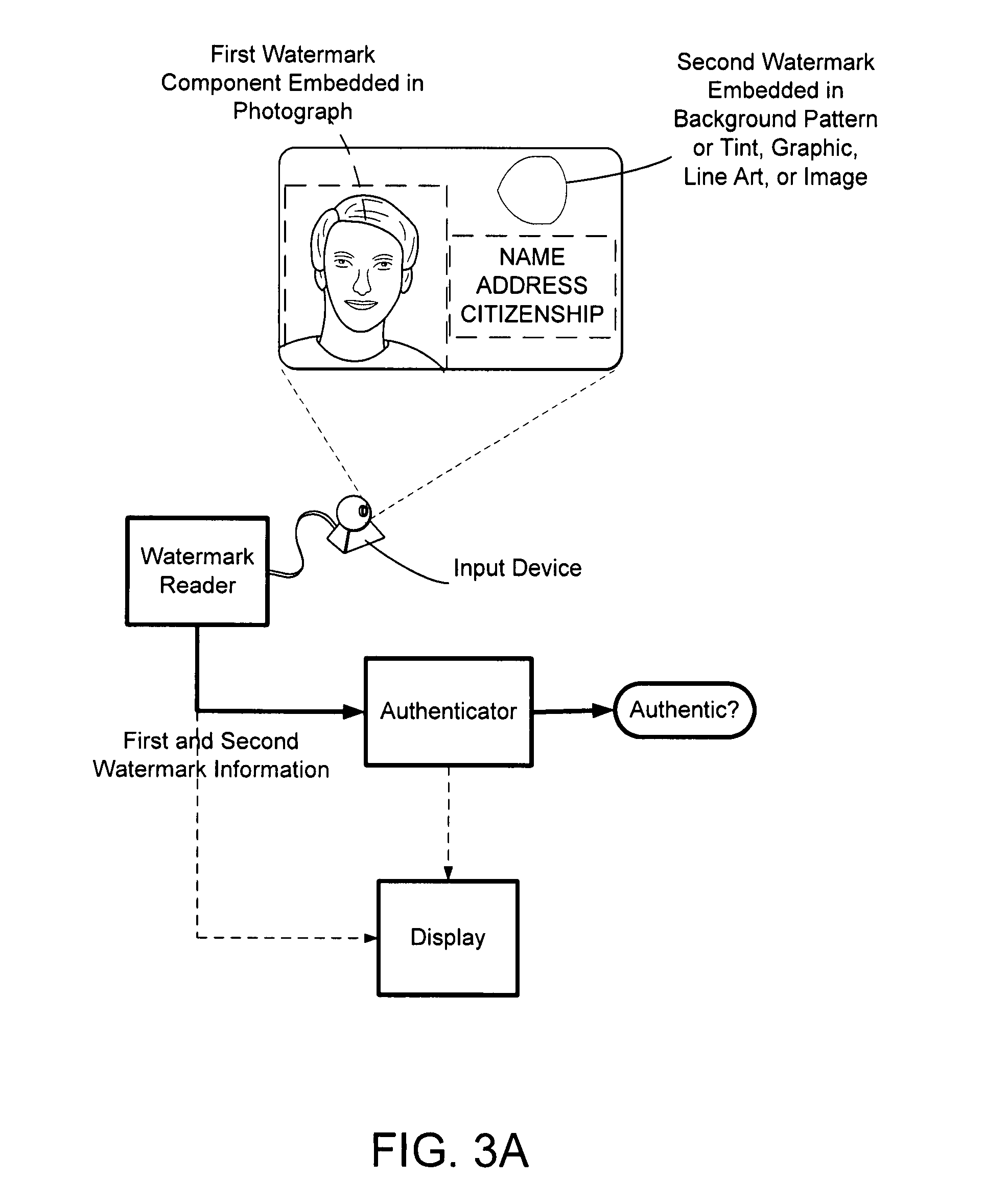
Watermark payload encryption methods and systems
InactiveUS20050271246A1User identity/authority verificationCharacter and pattern recognitionInternet privacyChecksum
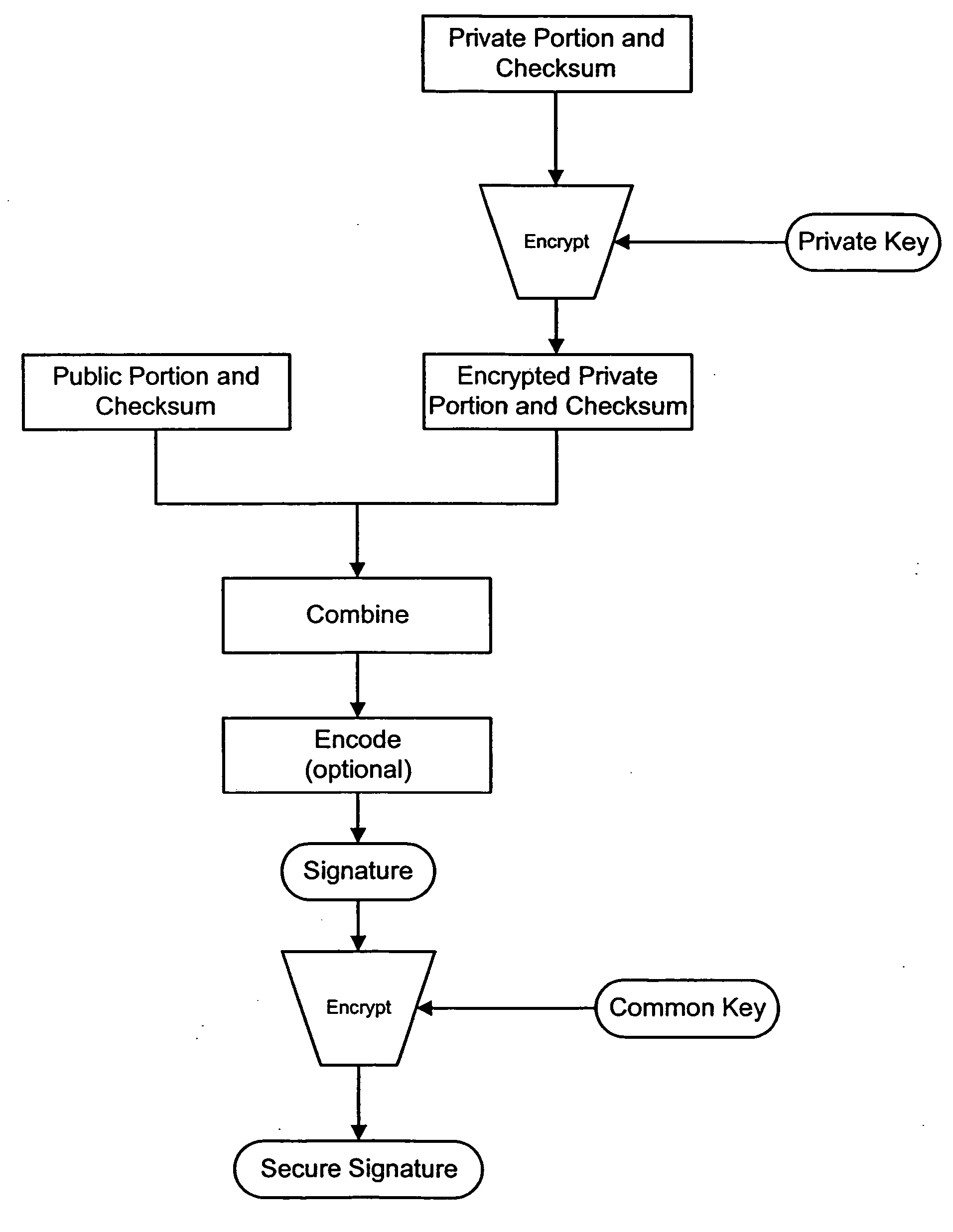
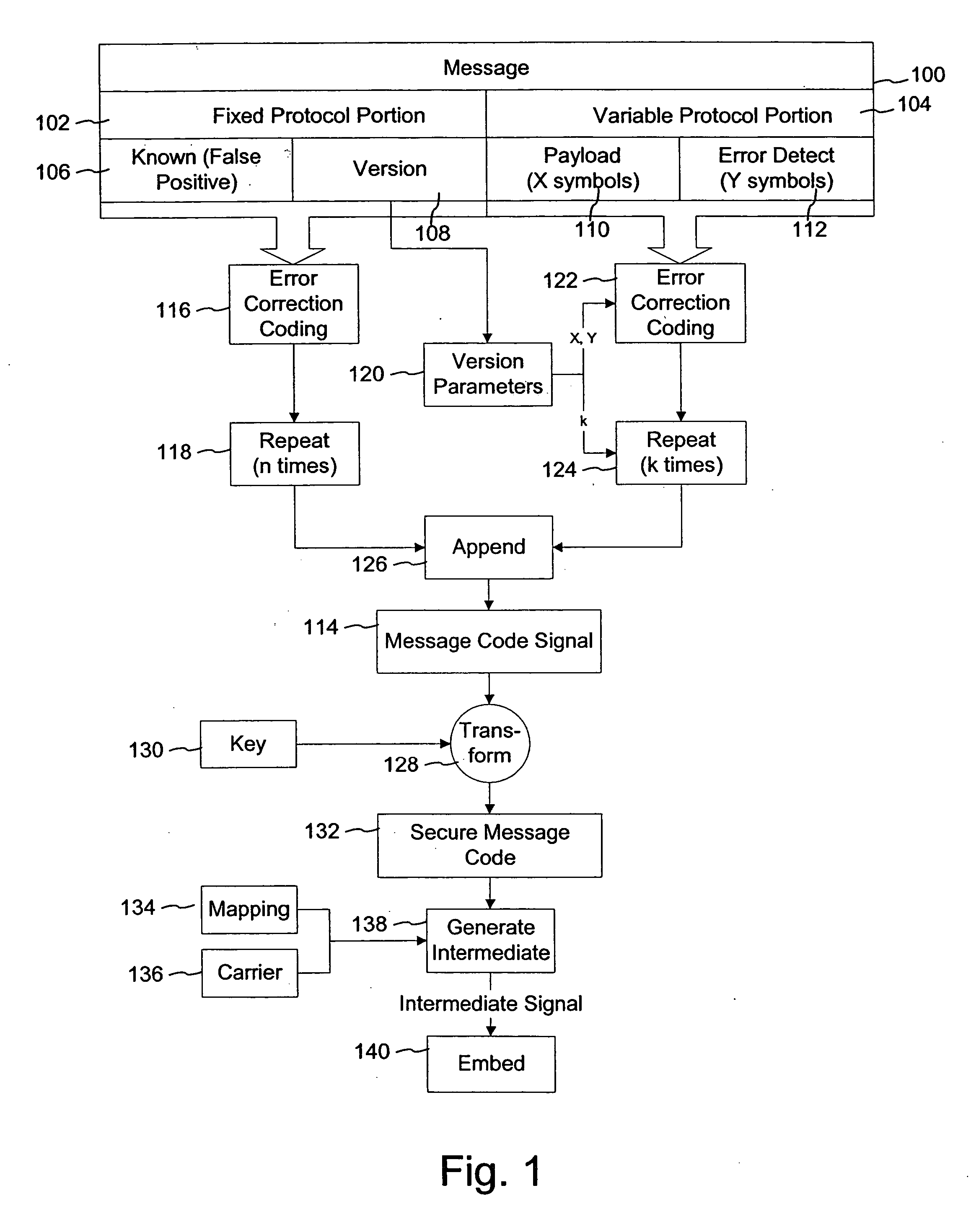
The present invention provides a method of securing messages steganographically embedded in media (e.g., printed or electronic objects, audio and video). In one implementation, a message includes a first portion and a second portion. The first portion includes a first message and a first checksum, which are encrypted with a private key. The encrypted first portion is combined with the second portion. The second portion includes a second message and as second checksum. The combined encrypted first portion and the second portion form a signature. The signature is encrypted with a common or universal key, perhaps after error correction coding. The private key is uniquely associated with an entity such as a document issuing jurisdiction. In another implementation, a method appends information to a watermark message received from a remote device. The information preferably corresponds to the remote device or to a user of the remote device. In yet another implementation, a method provides standardized watermark payloads from various input data, regardless of the size of the input data.
Owner:DIGIMARC CORP
Software self-defense systems and methods
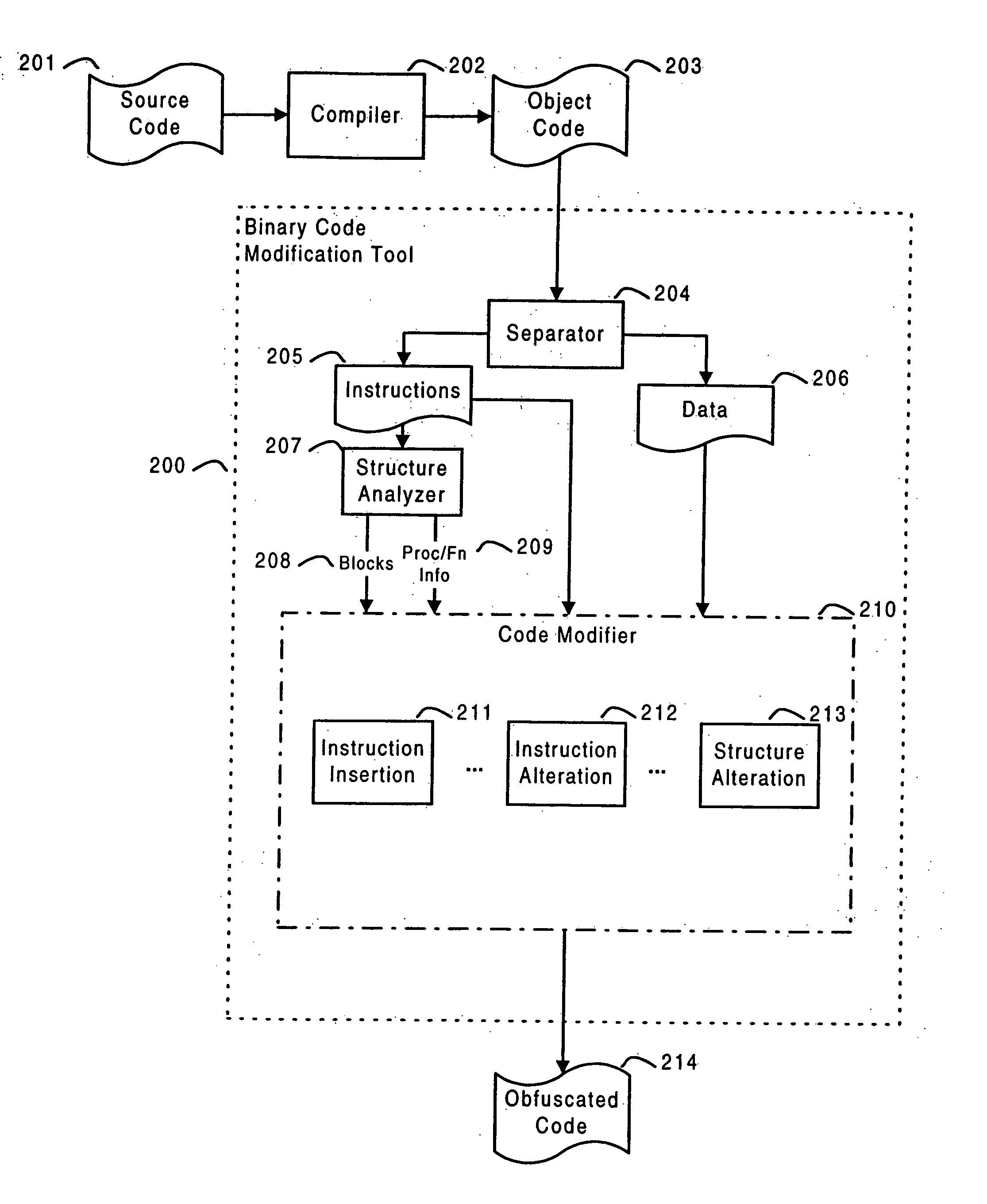
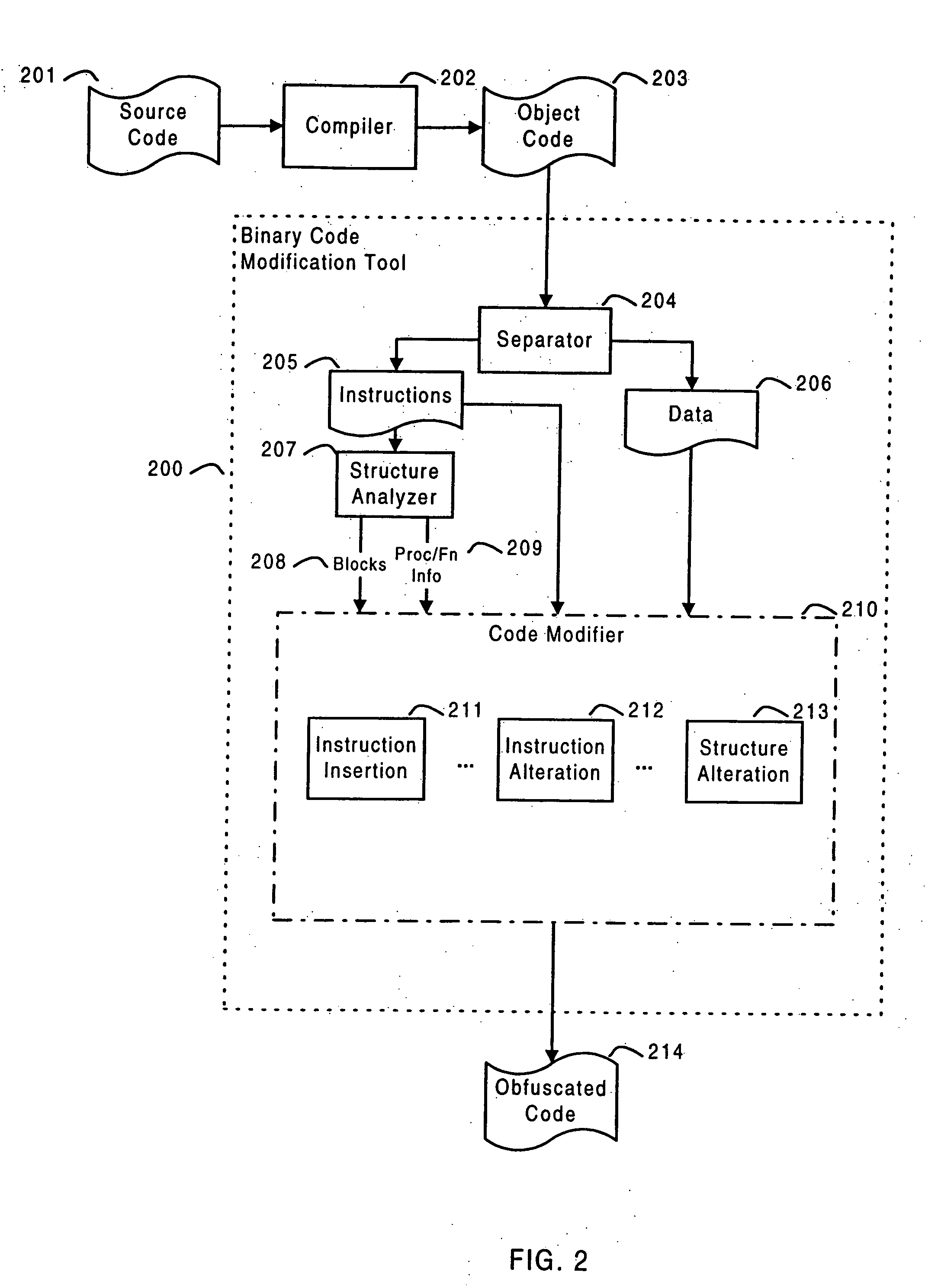
ActiveUS20050204348A1Error detection/correctionProgram/content distribution protectionTamper resistanceObfuscation
Systems and methods are disclosed for protecting a computer program from unauthorized analysis and modification. Obfuscation transformations can be applied to the computer program's local structure, control graph, and / or data structure to render the program more difficult to understand and / or modify. Tamper-resistance mechanisms can be incorporated into the computer program to detect attempts to tamper with the program's operation. Once an attempt to tamper with the computer program is detected, the computer program reports it to an external agent, ceases normal operation, and / or reverses any modifications made by the attempted tampering. The computer program can also be watermarked to facilitate identification of its owner. The obfuscation, tamper-resistance, and watermarking transformations can be applied to the computer program's source code, object code, or executable image.
Owner:INTERTRUST TECH CORP
Rights Management System and Methods
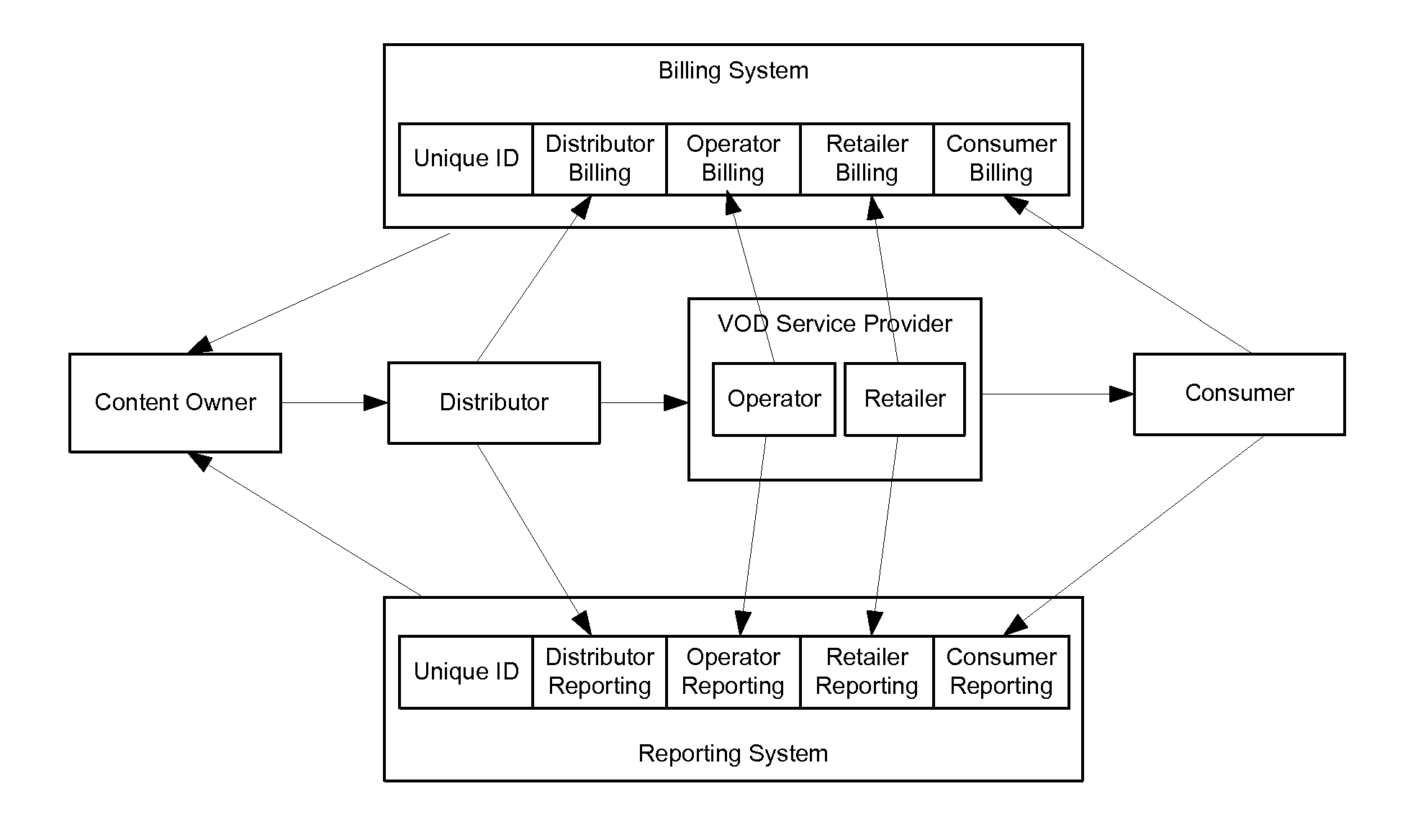
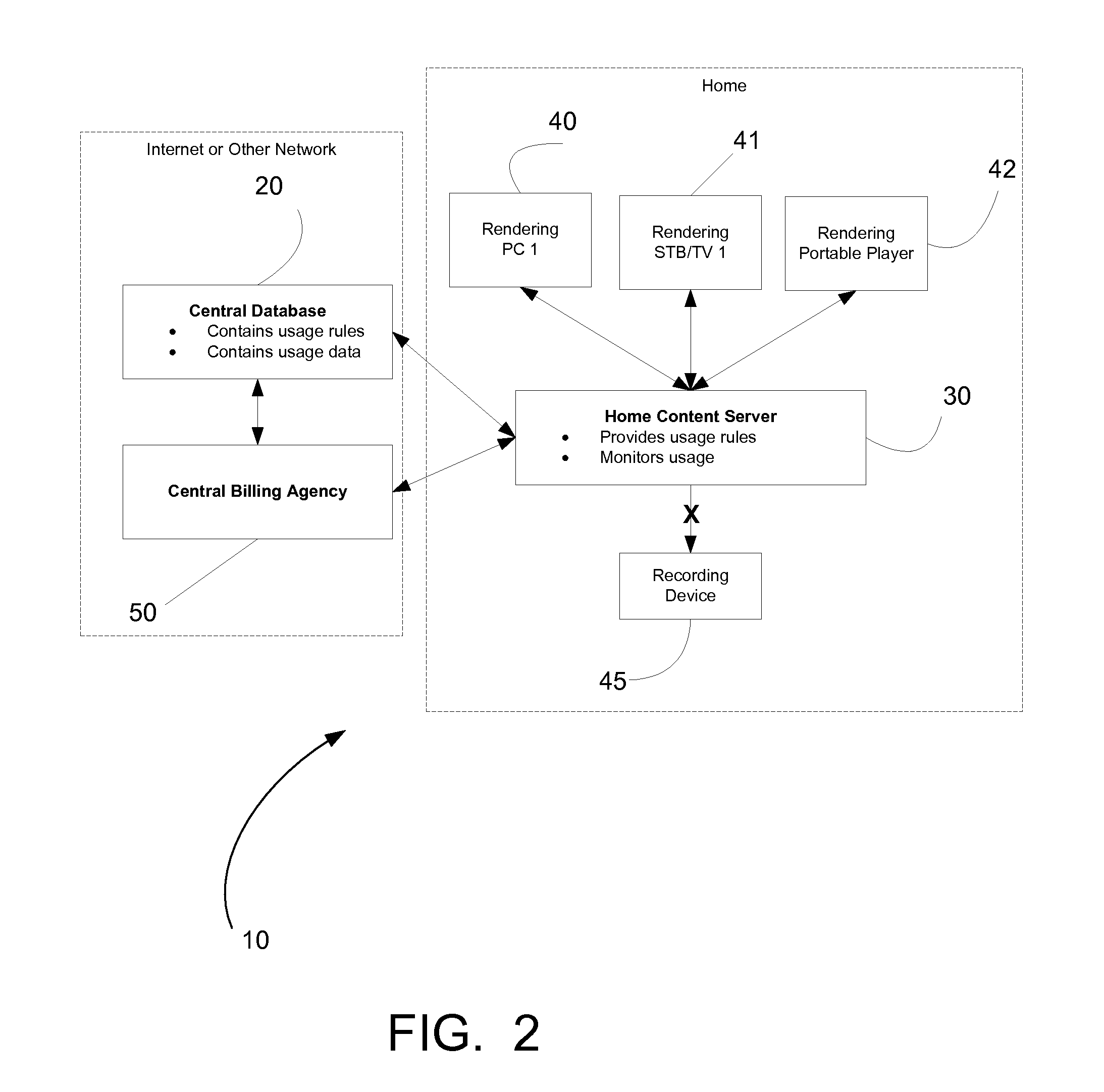
ActiveUS20070294173A1Difficult to controlDifficult to trackDigital data processing detailsRecord information storageContent IdentifierRights management
A method of performing digital asset management of content is provided. The content is identified with an identifier. The identifier can be identified with a digital watermark, header file, or both. The identifier is linked to usage rules to regulate usage and protect the content. The usage rules can be maintained on a remote or local database or server. Once extracted, an identifier is used to index the database to locate a corresponding usage rule, and can be used to override copy control information with proper purchase and subsequent protection. Content can be managed from such. In another embodiment, an identifier is used to track usage, such as amount of content viewed, time played, and copies made. In yet another embodiment, a content identifier is used to regulate content throughout a distribution chain, and a distributed set of databases with information relevant only to the owner of the database act as one database due to a central router.
Owner:DIGIMARC CORP
Systems and methods for authenticating video using watermarks
ActiveUS20180121635A1User identity/authority verificationProgram/content distribution protectionData streamDigital content
Disclosed are blockchain-based methods and systems for watermarking digital content. In an exemplary aspect, a method for watermarking digital content is provided, by receiving, by a processor, a data stream comprising audio and / or video content; receiving watermark data, by a processor, from a computing node communicatively linked to a blockchain-based distributed ledger; and applying at least one watermark to the data stream based upon the watermark data, wherein the watermark comprises at least one hash based on one or more data blocks stored in the blockchain-based distributed ledger.
Owner:MIDCAP FINANCIAL TRUST
Watermarking
InactiveUS7130443B1Reliably embedded in pictureRendering detection simple and reliableTelevision system detailsUser identity/authority verificationVisibilityComputer science
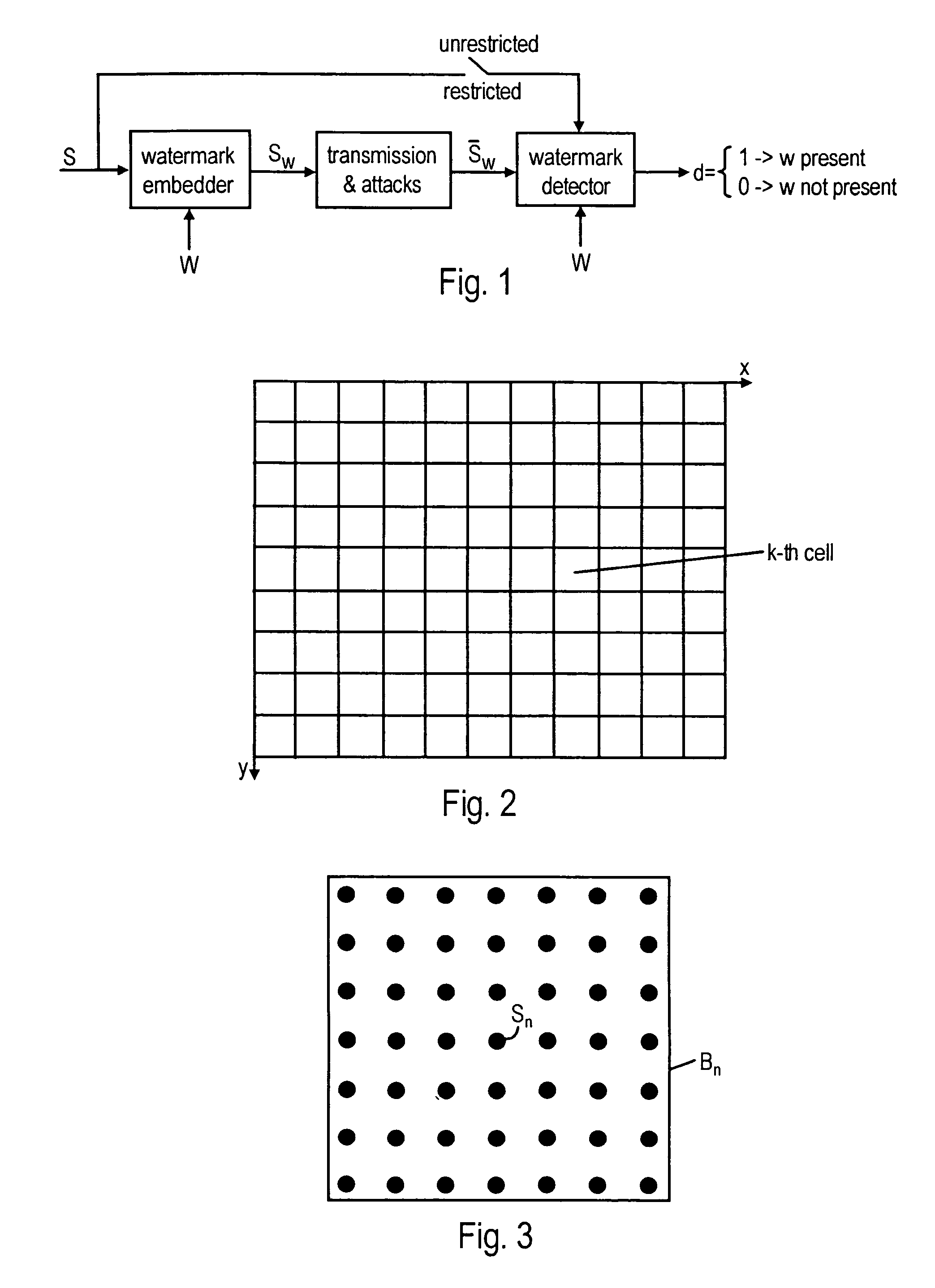
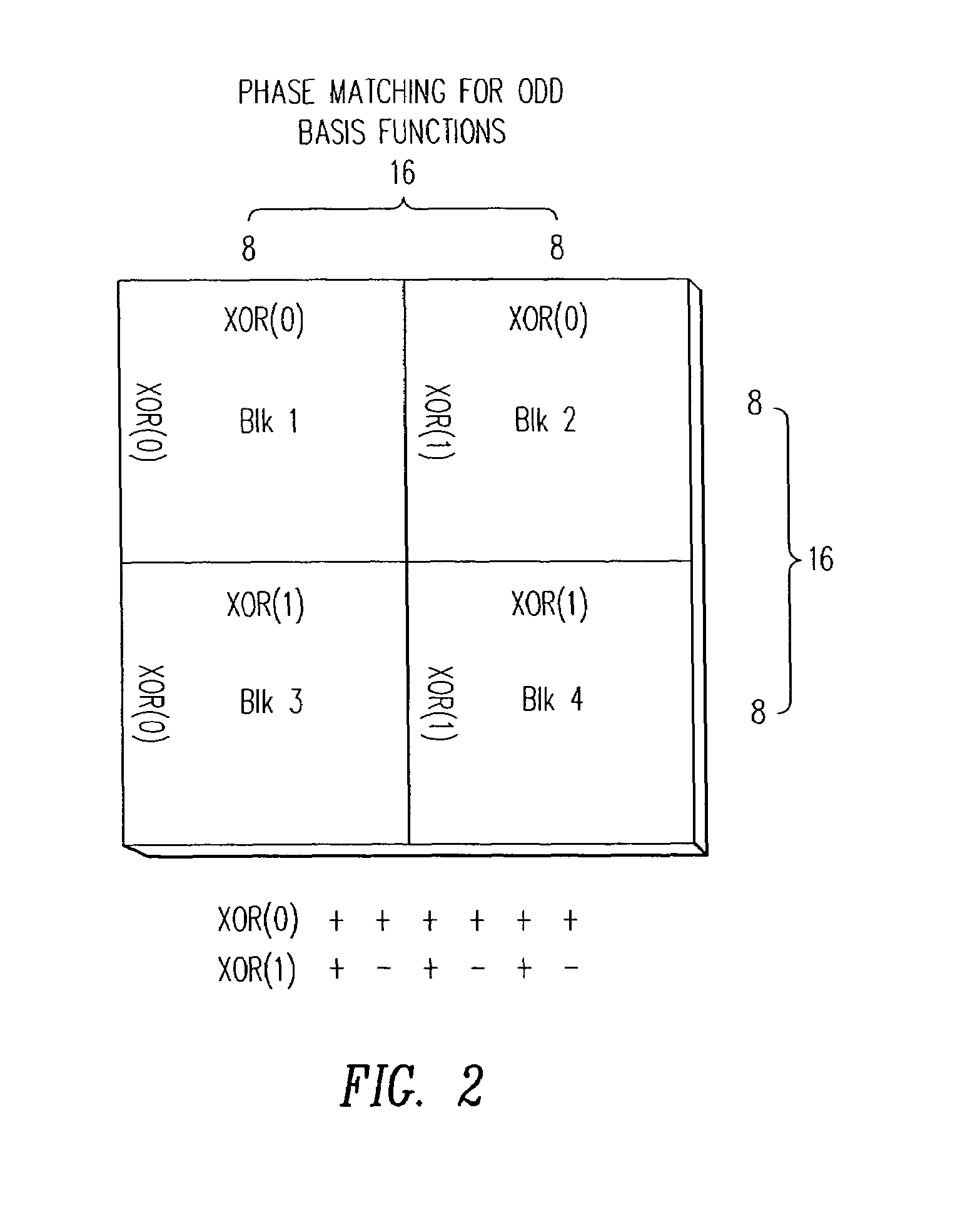
A watermarking system and method is proposed for still or moving pictures in which a watermark is embedded robustly and simply into DC-values, but without causing unacceptable visible picture degradation. The watermark is secure and can be readily detected, and the method can be used to convey additional data. Also disclosed is a method for watermarking a sequence of pictures in which the visibility of artifacts is reduced. The watermark may carry data and may be used to label a program.
Owner:BRITISH BROADCASTING CORP
Transform domain watermarking of image signals
InactiveUS7139408B2Increased incentives for both casual and professional unauthorized copyingAvoid repetitionTelevision system detailsSpeech analysisJPEGImage signal
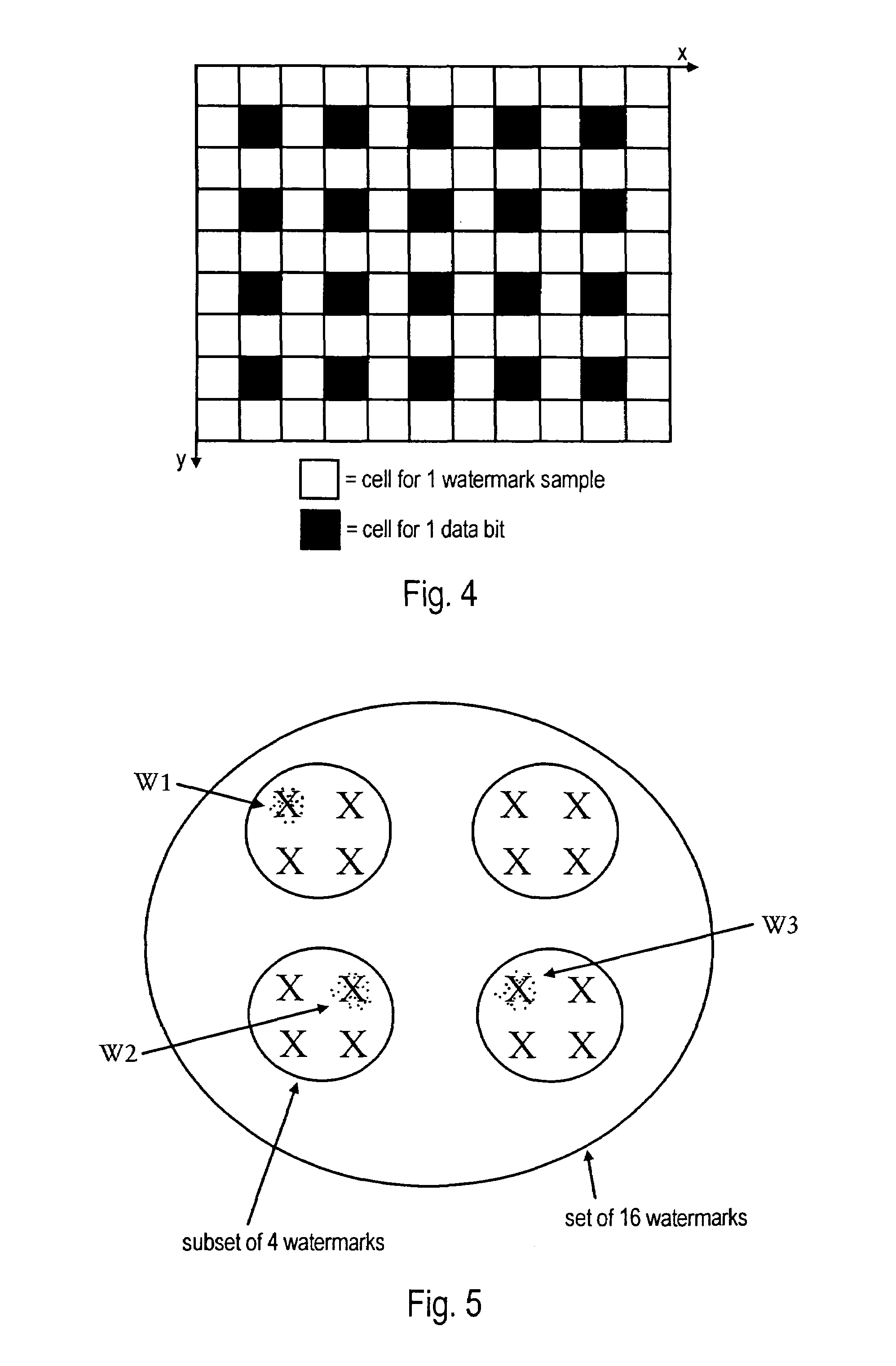
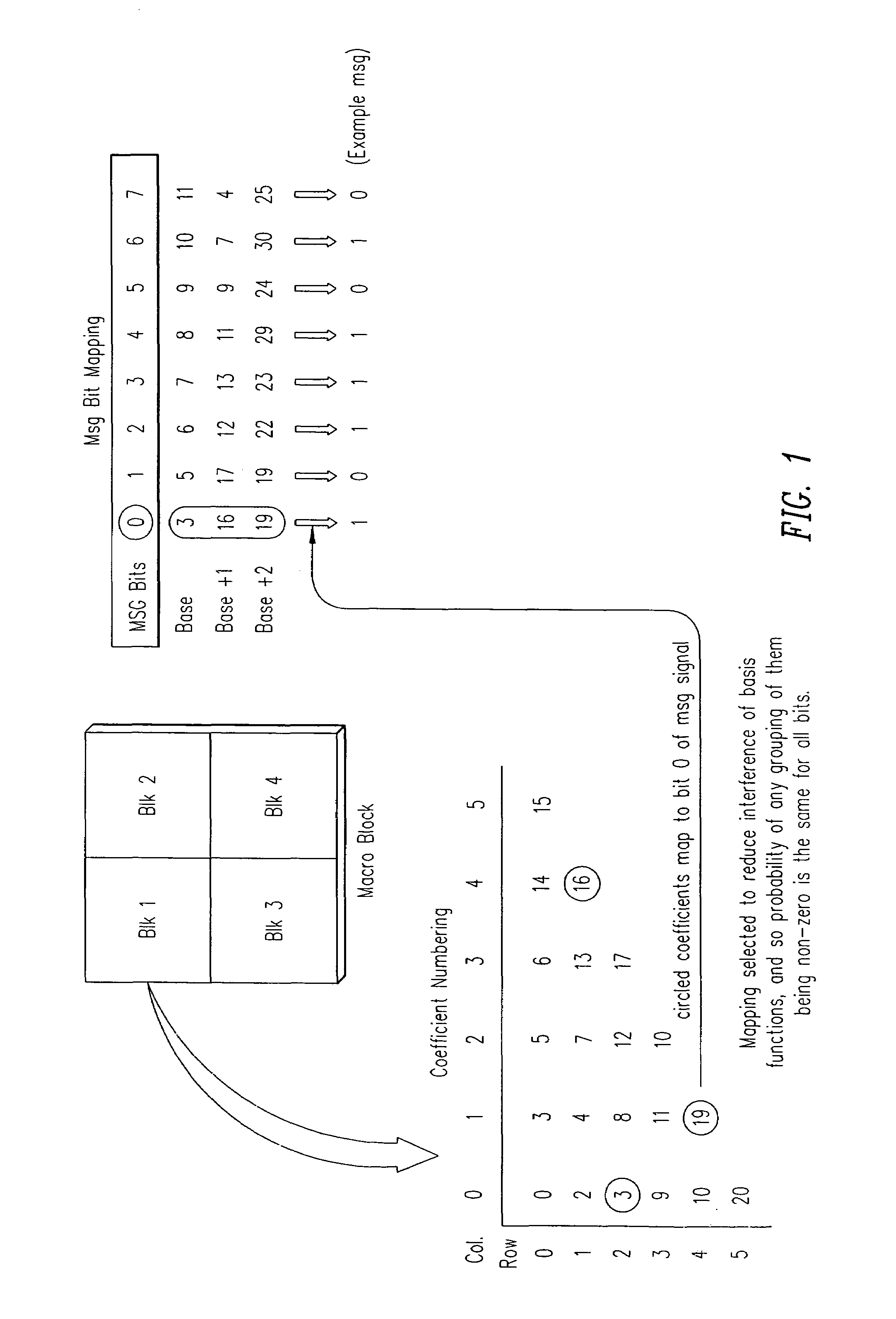
The invention provides methods and related systems for embedding and detecting watermarks in images, such as JPEG or MPEG formatted images as well as other types of image signals. One method receives transform coefficients of the image, and changes the value of selected coefficients to embed watermark data in the coefficients. The changing of the coefficients is controlled such that it both embeds the data and forms an orientation signal that facilitates determination of rotation or scale of the image. Another aspect of the invention is a variation of embedding a watermark in an image. This method receives message bits to be embedded in the image, receives transform coefficients of the image, and maps the message bits to selected transform coefficients. The method changes the value of selected coefficients to embed data in the coefficients. The characteristics of the image are used to control the change of transform coefficients to embed the watermark, and a bit rate control is used to modify the change of transform coefficients to embed the watermark according to a bit rate limit.
Owner:DIGIMARC CORP
Applying informed coding, informed embedding and perceptual shaping to design a robust, high-capacity watermark
InactiveUS6996249B2Small distortionMinimize perceptual impactCode conversionCharacter and pattern recognitionAlgorithmPost embedding
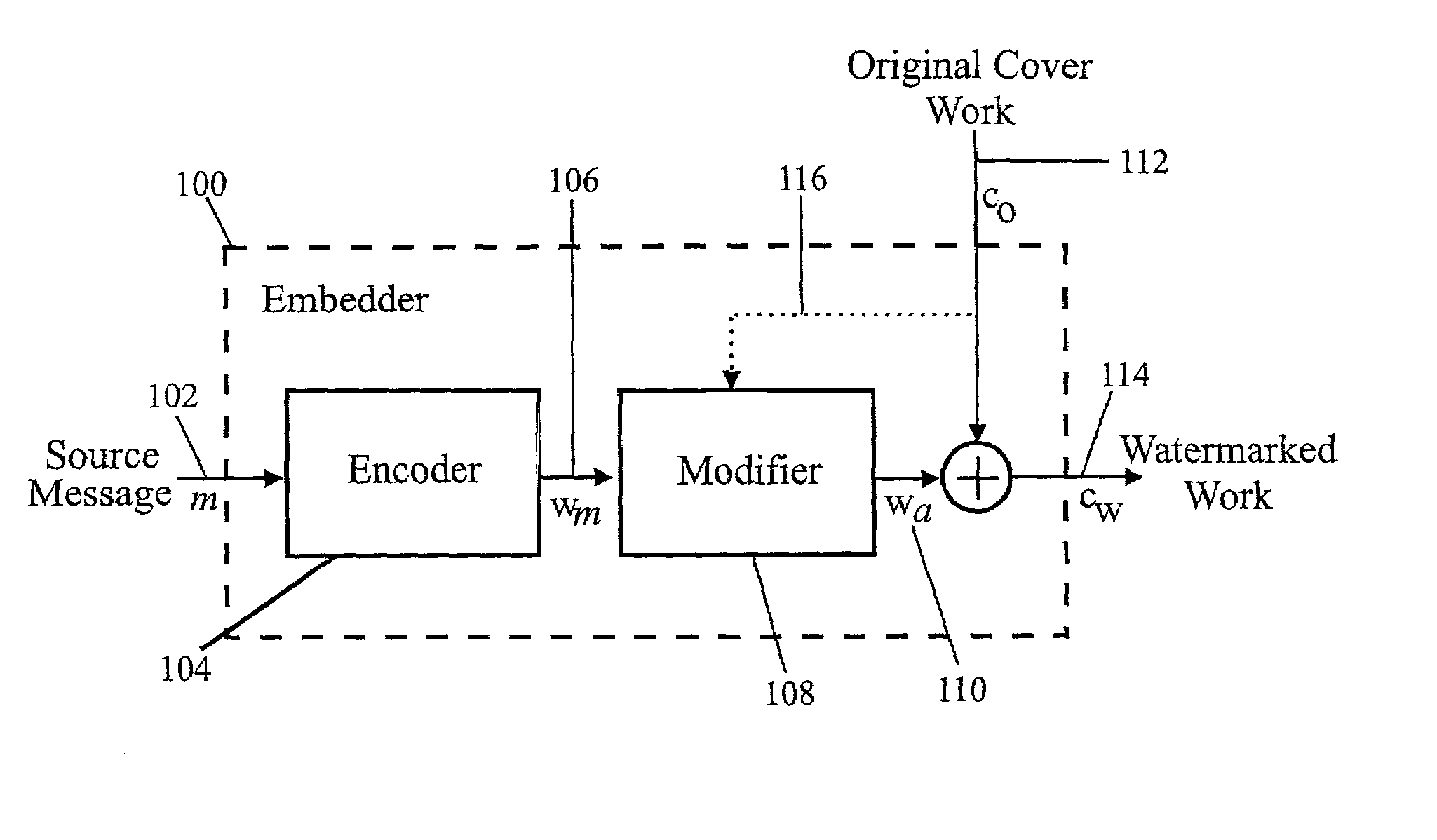
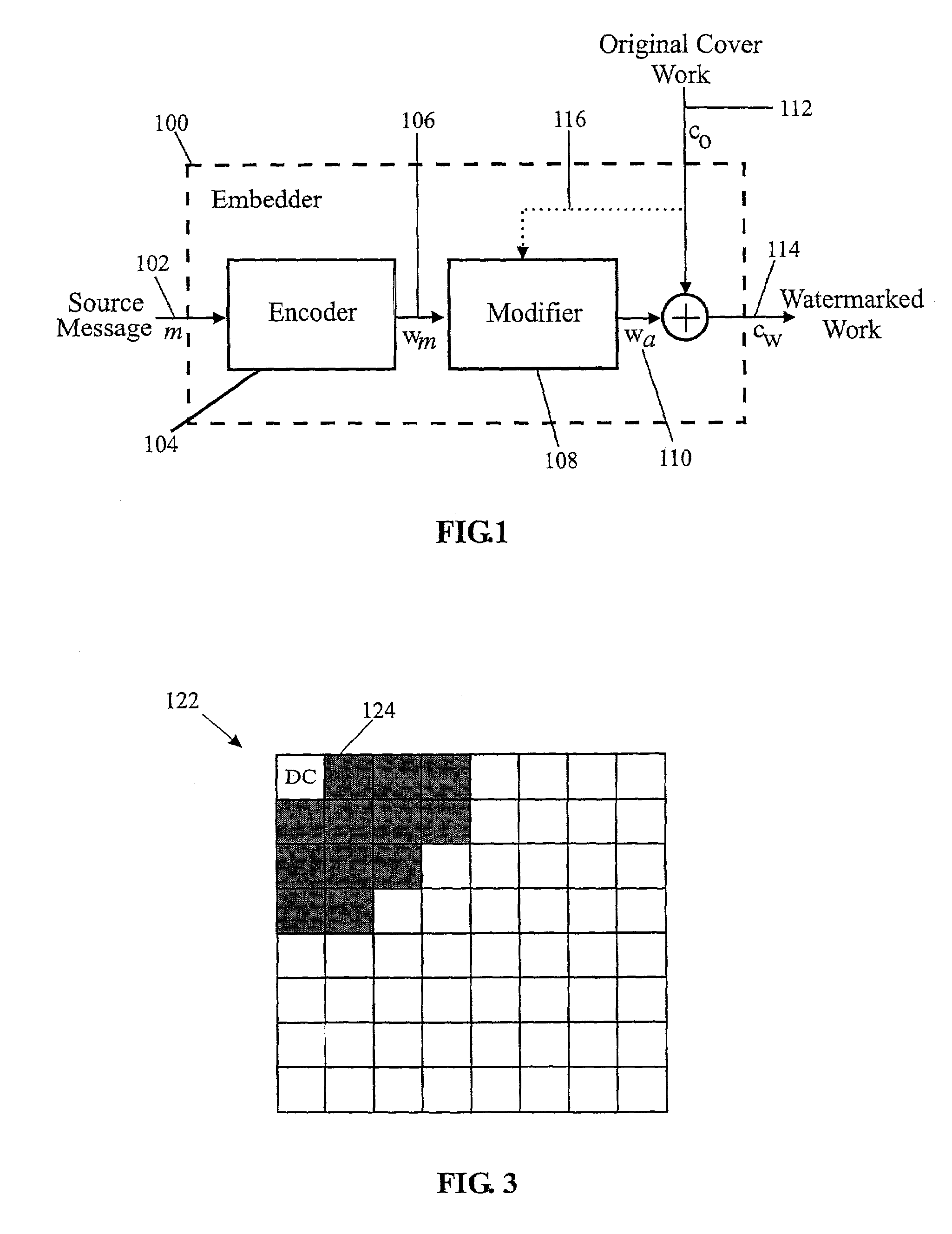
A watermark message embedded in a cover work can be made robust to various types of post-embedding operations, while simultaneously minimizing perceptual impact on the cover work. This is accomplished by the informed coding of the watermark message to be embedded. This is also accomplished by the informed embedding of the watermark message code in the cover work. Finally, the watermark message code may be perceptually shaped to minimize impact on the fidelity of the watermarked work. Further, these techniques may be combined for maximum effect.
Owner:NEC CORP
Detecting media areas likely of hosting watermarks
ActiveUS8301893B2Level of protectionEasy to useAcutation objectsPaper-money testing devicesPattern recognitionDigital data
The present invention relates generally to digital watermarking and steganographic encoding. One claim recites a method including: receiving data corresponding to at least a portion of digital data; separating the data into a plurality of portions; determining a measure relative to a predetermined measure for each of the portions, wherein the measure comprises a measure related to a predetermined digital watermark signal; based at least in part on the measure, identifying which out of the plurality of portions are likely to host digital watermarking therein. Of course, other combinations are provided as well.
Owner:DIGIMARC CORP
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
ActiveUS20080005571A1Fine granularityEffective distributionUser identity/authority verificationDigital data protectionComputer networkDigital signature
Disclosed herein are methods and systems for transmitting streams of data. The present invention also relates to generating packet watermarks and packet watermark keys. The present invention also relates to a computerized system for packaging data for transmission to a user. The system may utilize computer code to generate a bandwidth rights certificate that may include: at least one cryptographic credential; routing information for the transmission; and, optionally, a digital signature of a certificate owner; a unique identification code of a certificate owner; a certificate validity period; and pricing information for use of bandwidth. The present invention also relates to an electronic method and system for purchasing good and services by establishing an account whereby a customer is credited with a predetermined amount of bandwidth usage, and then charges are assessed against the account in an amount of bandwidth usage which corresponds to the agreed upon purchase value for the selected item.
Owner:WISTARIA TRADING INC
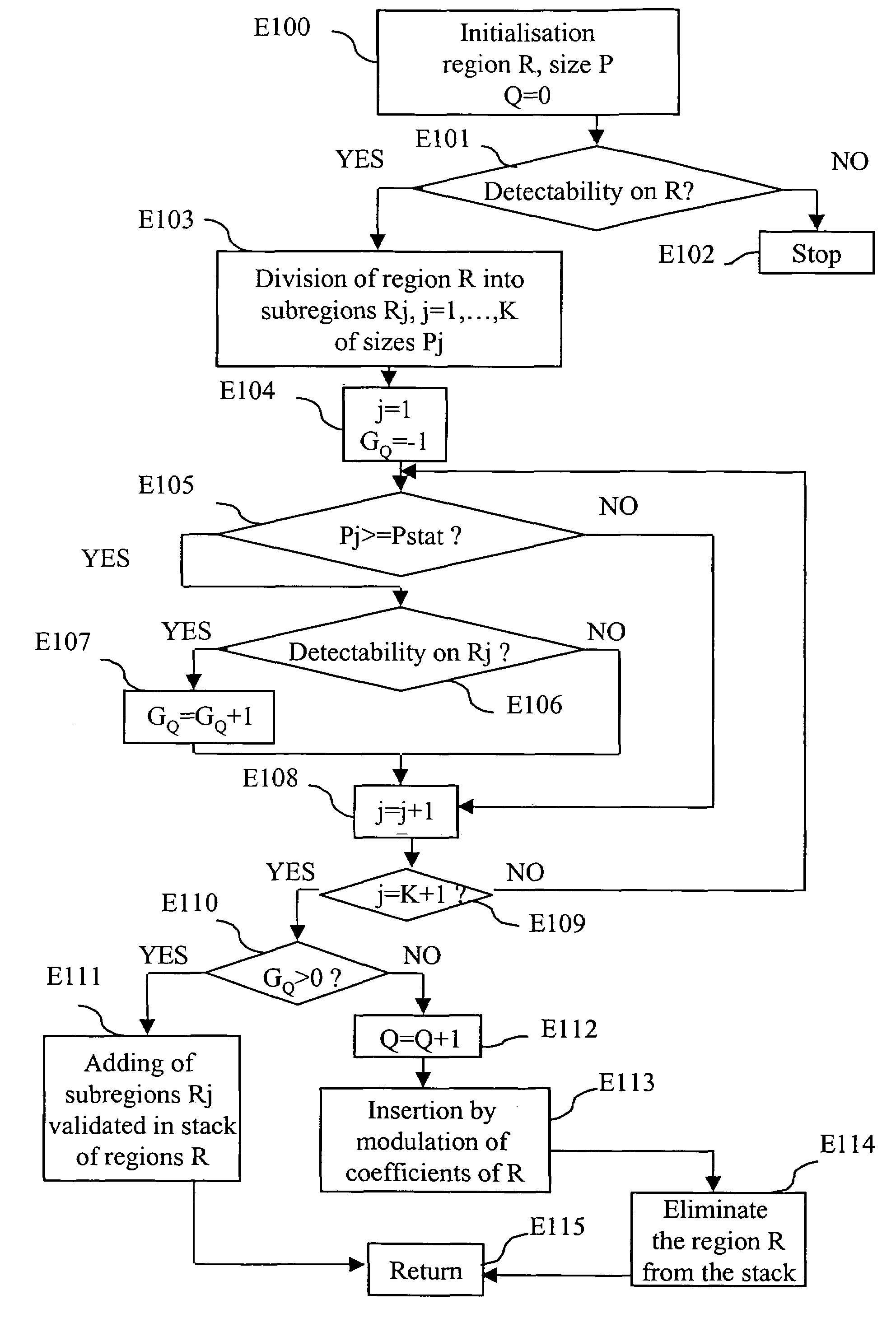
Method for determining a partition in order to insert a watermark, and associated insertion and decoding methods
InactiveUS7031491B1Guaranteed detection effectEnsuring imperceptibilityUser identity/authority verificationCharacter and pattern recognitionPseudo random sequenceDecoding methods
A method of determining a partition into distinct regions of a set of coefficients representative of at least a part of an image in order to insert a watermark comprises the following steps:generation (E501) of a centred pseudo-random sequence (w) equal in size to the cardinal number (N) of the said set of coefficients, formed from centred pseudo-random sub-sequences;modulation (E502) of the said set of coefficients by the said centred pseudo-random sequence (w) in order to insert the same information bit on the said set of coefficients; andchecking (E504–E508), over each region, of a criterion of detectability of the information bit inserted by modulation.Use especially for determining an adaptative partition as a function of a criterion of detectability of an information bit inserted on each region.
Owner:CANON KK
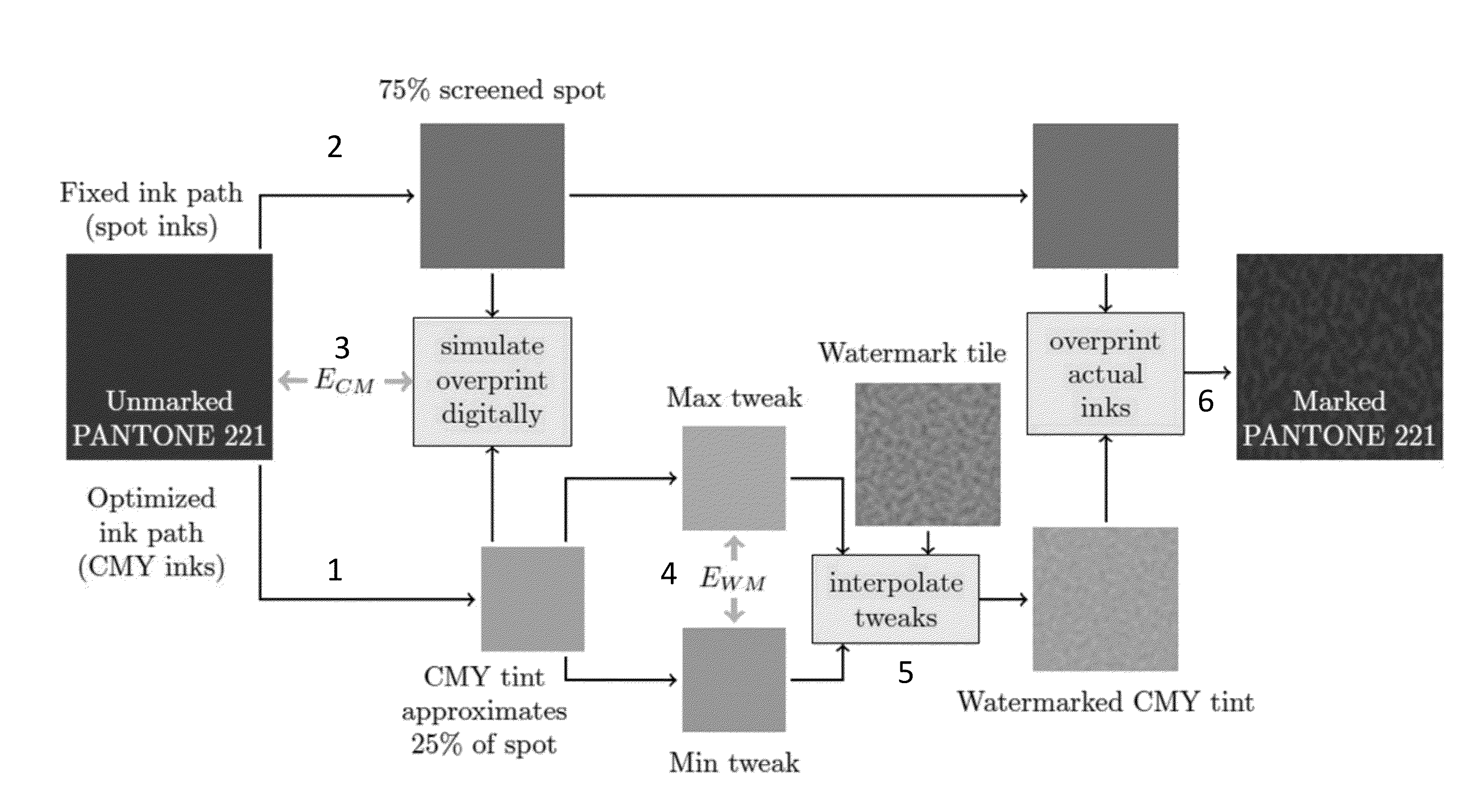
Spot color substitution for digital watermarking
ActiveUS20160198064A1Character and pattern recognitionImage watermarkingComputer visionDigital watermarking
The present disclosure relates generally to digital watermarking for spot colors. In one implementation a substitute spot color+CMY tint is selected to replace an original spot color. The CMY tint can be transformed to carry a digital watermark signal. Of course, other features, combinations and technology are described herein.
Owner:DIGIMARC CORP
Watermarking in an encrypted domain
Methods, apparatus and systems for embedding auxiliary information in encrypted host signals are provided. The present invention enables secure application of digital watermarks at any point in the transmission and / or distribution of digital content by enabling the insertion of a plurality of digital watermarks, without the knowledge of the encryption / decryption keys, into a digital host content that has been encrypted with an encryption key. The embedded watermarks persist throughout the content subsequent to the decryption of the content. The disclosed techniques are applicable to content that has been encrypted using a variety of different encryption techniques and algorithms, including stream ciphers, block ciphers, symmetric and asymmetric encryption algorithms. These methods are further adapted to enable the insertion of watermarks into a content that is compressed prior to encryption.
Owner:VERANCE
Method of embedding digital watermark, method of extracting embedded digital watermark and apparatuses for the same
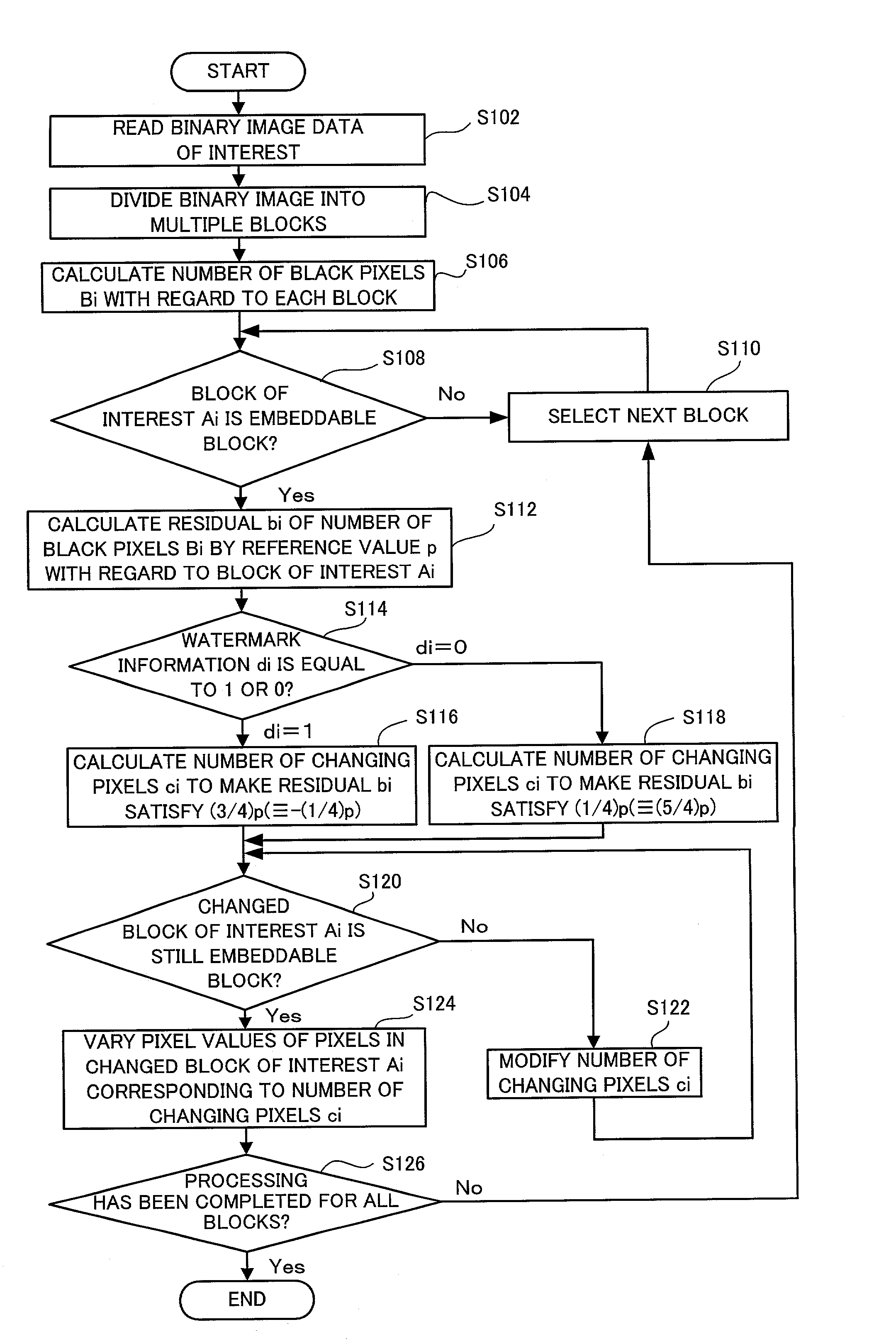
InactiveUS20030076979A1Easy to processIncrease resistanceCharacter and pattern recognitionImage data processing detailsColor imageColor transformation
A color conversion module 42 carries out color conversion of original color image data Grgb from the RGB color system into the CMYK color system to obtain color-converted original color image data Gcmyk (step S104). A DCT module 44 applies DCT (discrete cosine transform) over the whole color-converted original color image data Gcmyk to generate DCT coefficients Dcmyk (step S106). An embedding module 46 embeds the watermark information s into the components C, M, Y, and K of the DCT coefficients Dcmyk (step S108). An IDCT module 48 applies IDCT (inverse discrete cosine transform) onto DCT coefficients D'cmyk with the watermark information s embedded therein to generate embedding-processed color image data G'cmyk (step S110). The color conversion module 42 carries out color conversion of the embedding-processed color image data G'cmyk from the CMYK color system into the RGB color system to obtain embedding-processed color image data G'rgb (step S112). This arrangement does not require any correction of the position or the shape of image blocks in the process of extracting the embedded watermark information.
Owner:KOWA CO LTD
Inlaying method and device of digital watermarks in text documents
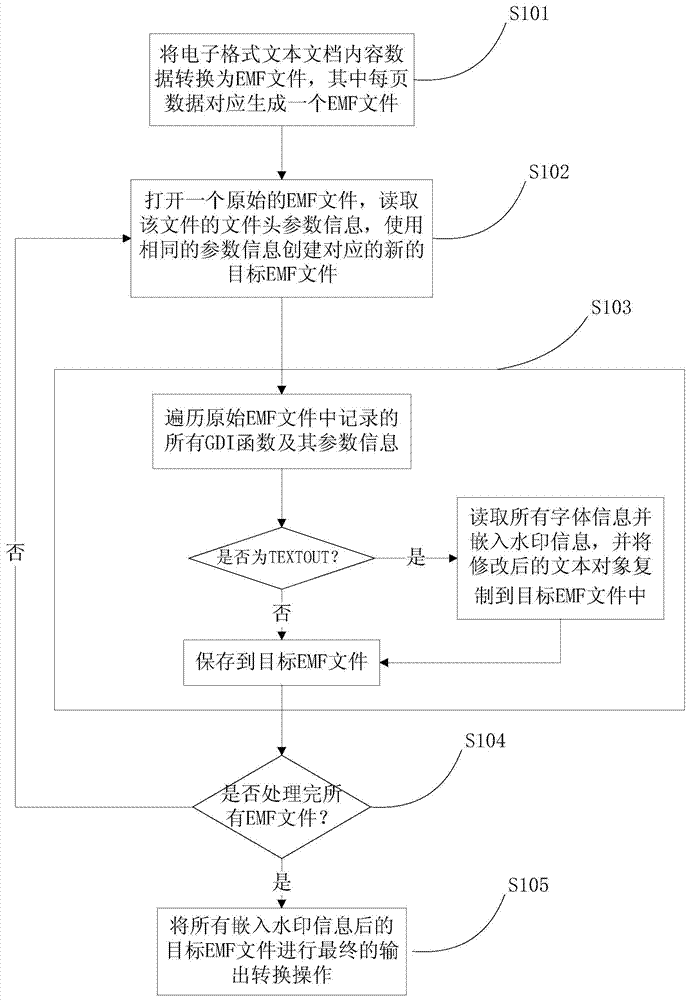
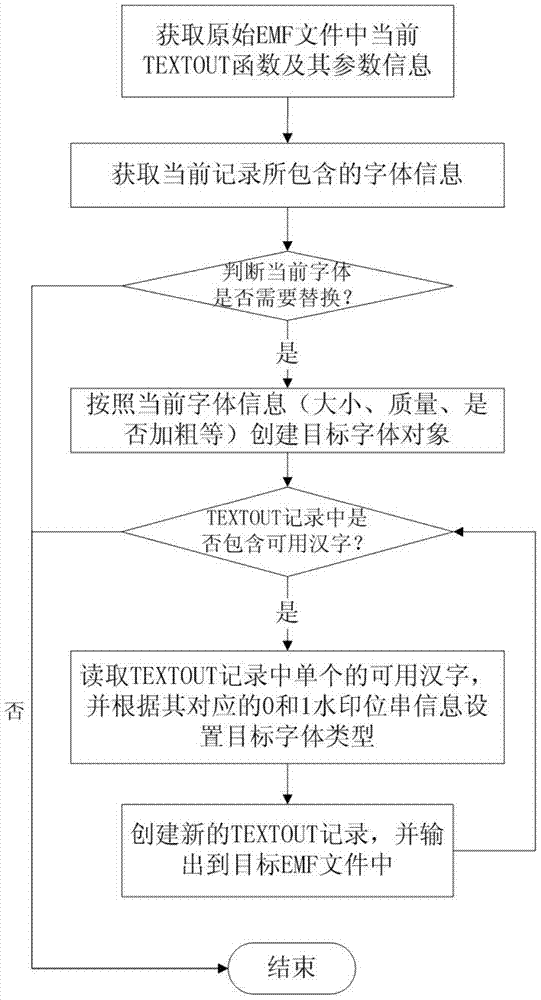
ActiveCN103500296ARealize security prevention and controlRealize traceabilityImage data processing detailsProgram/content distribution protectionElectronic formInformation embedding
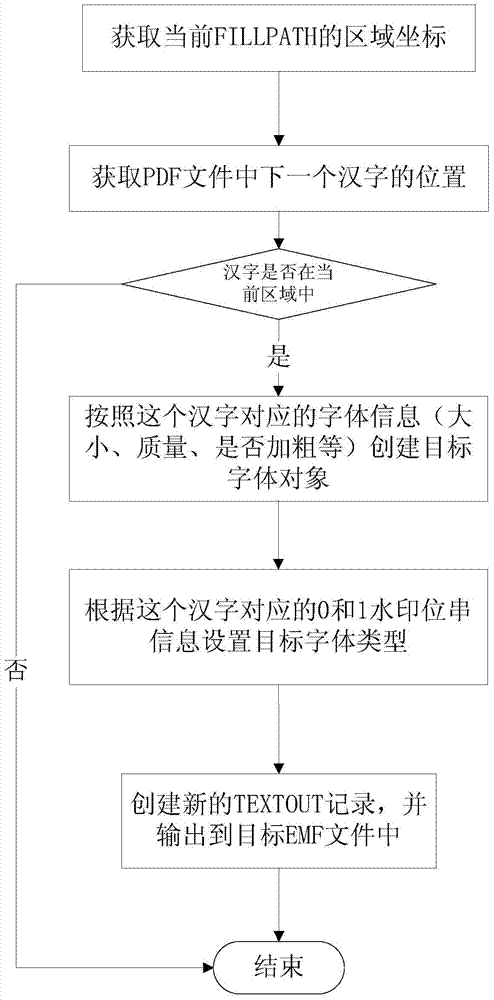
The invention relates to an inlaying method and device of digital watermarks in text documents. The method comprises the steps that electronic form text documents are converted to EMF documents, the converted initial EMF documents are opened, document header parameter information is used for setting up corresponding target EMF documents, all GDI functions and parameter information of the GDI functions in the initial EMF documents are all searched, whether the DGI functions are TEXTOUT is judged, if yes, all font information is read and watermark information is inlaid, and then the GDI functions are copied to the target EMF documents, if not, the DGI functions are directly copied to the target EMF documents, and after all the initial EMF documents are processed, all target EMF documents inlaid with the watermark information are subjected to the final output conversion operation. According to the method and device, the problem of watermark information inlaying of various electronic form text documents and paper text documents is solved, and safety monitoring and controlling, source tracing and content protection of important text documents are achieved.
Owner:李晓妮
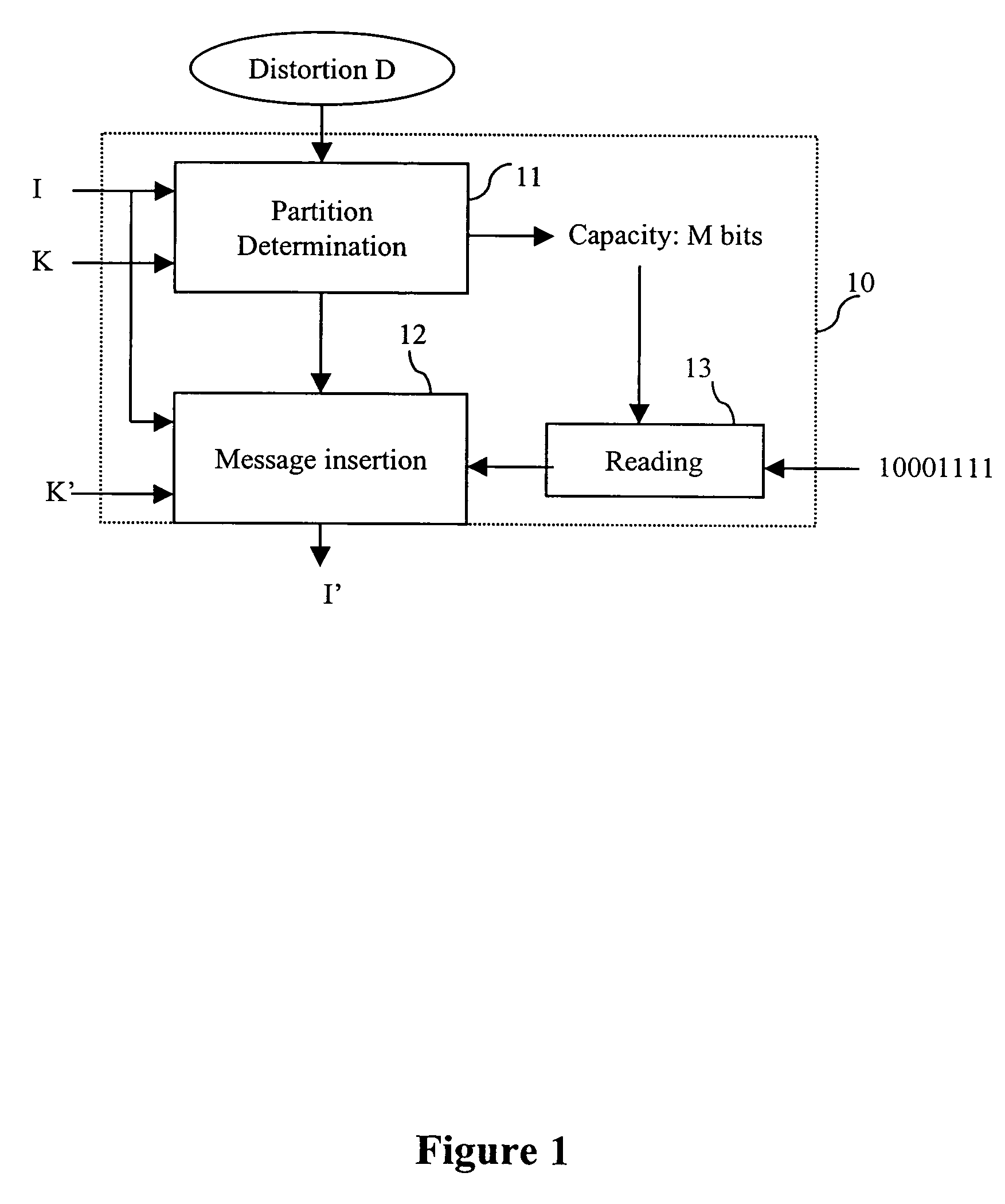
Method for the prior monitoring of the detectability of a watermarking signal
InactiveUS7058200B2Guaranteed robustnessCharacter and pattern recognitionImage data processing detailsArray data structureDigital image
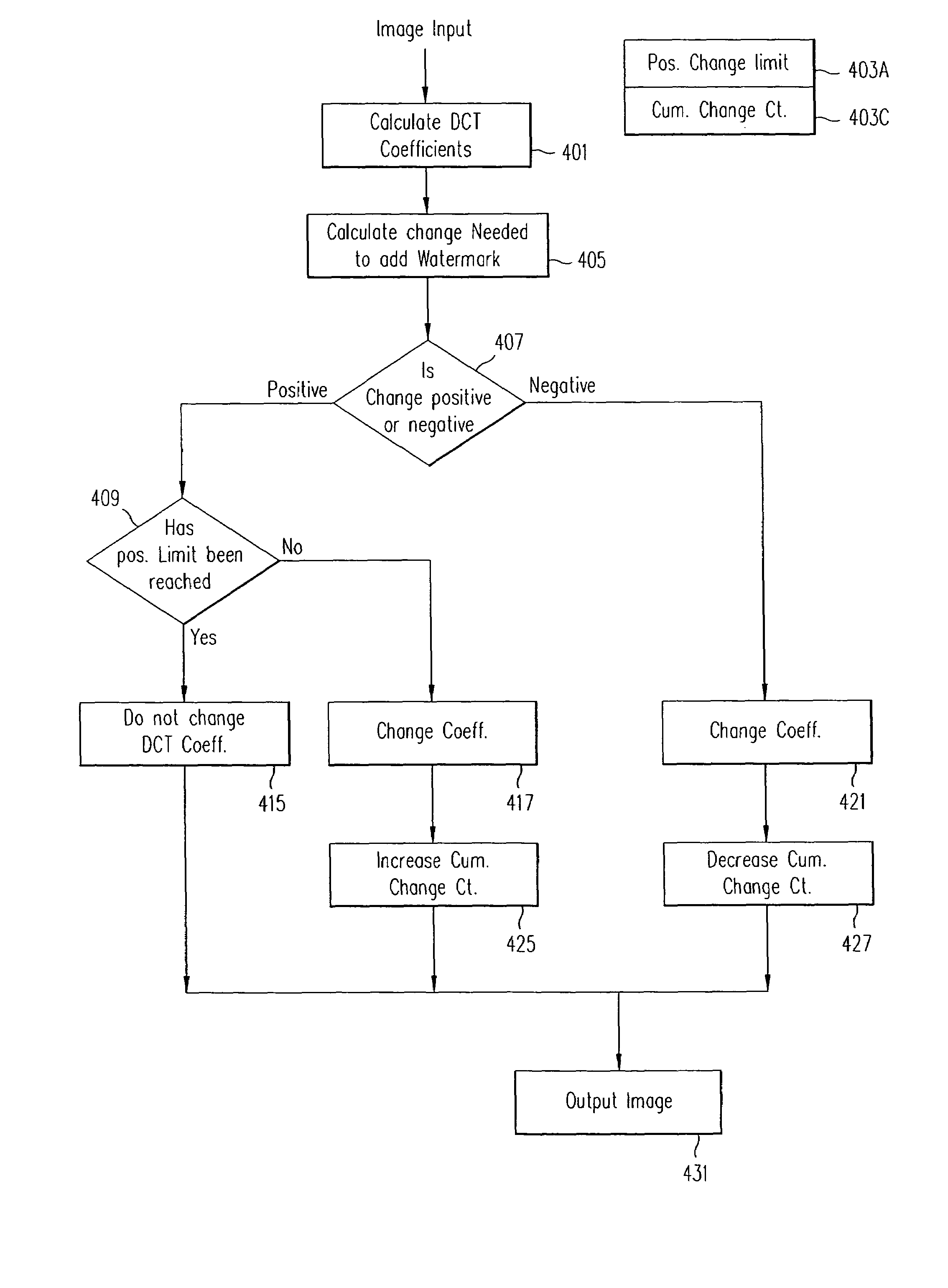
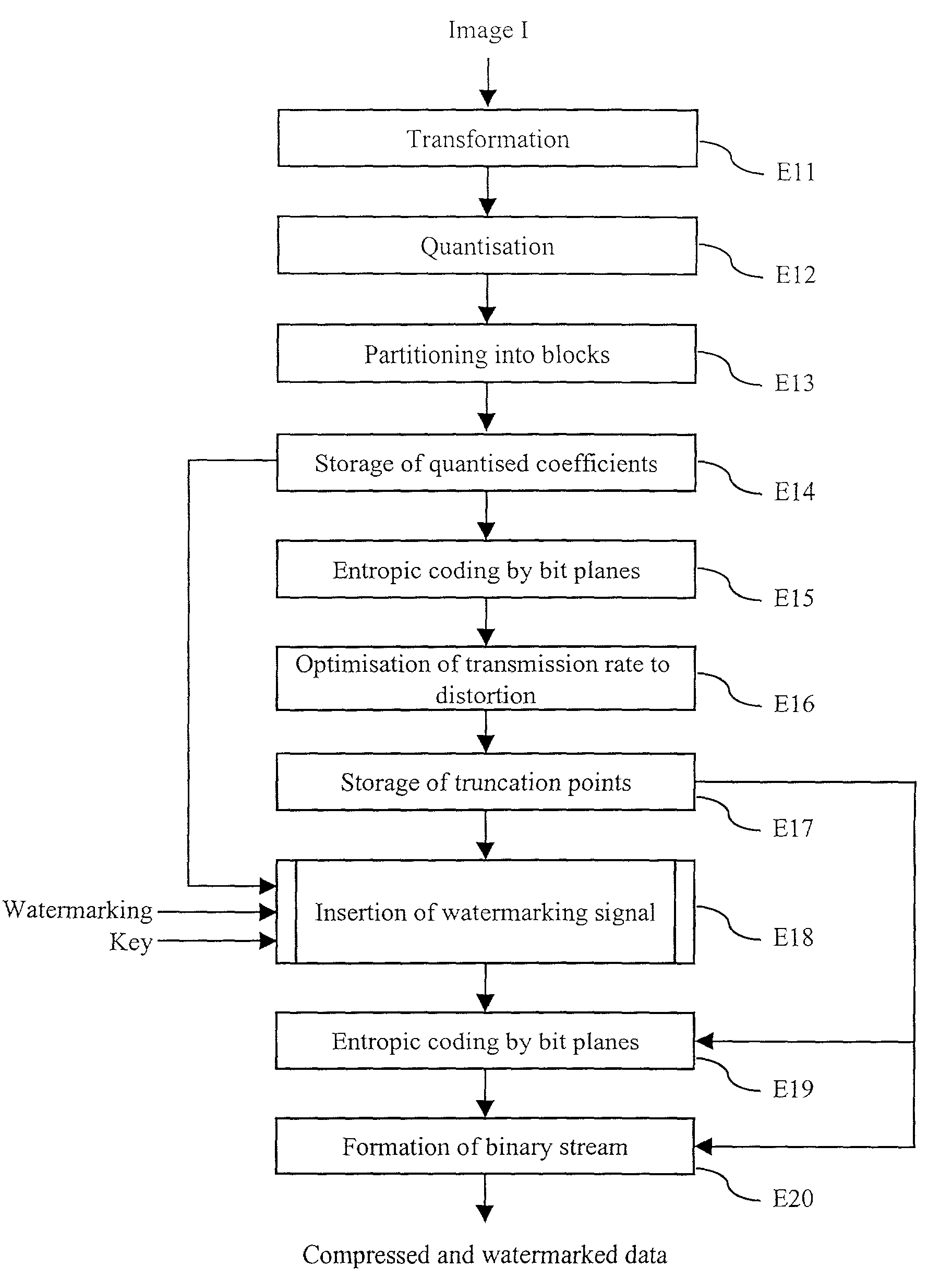
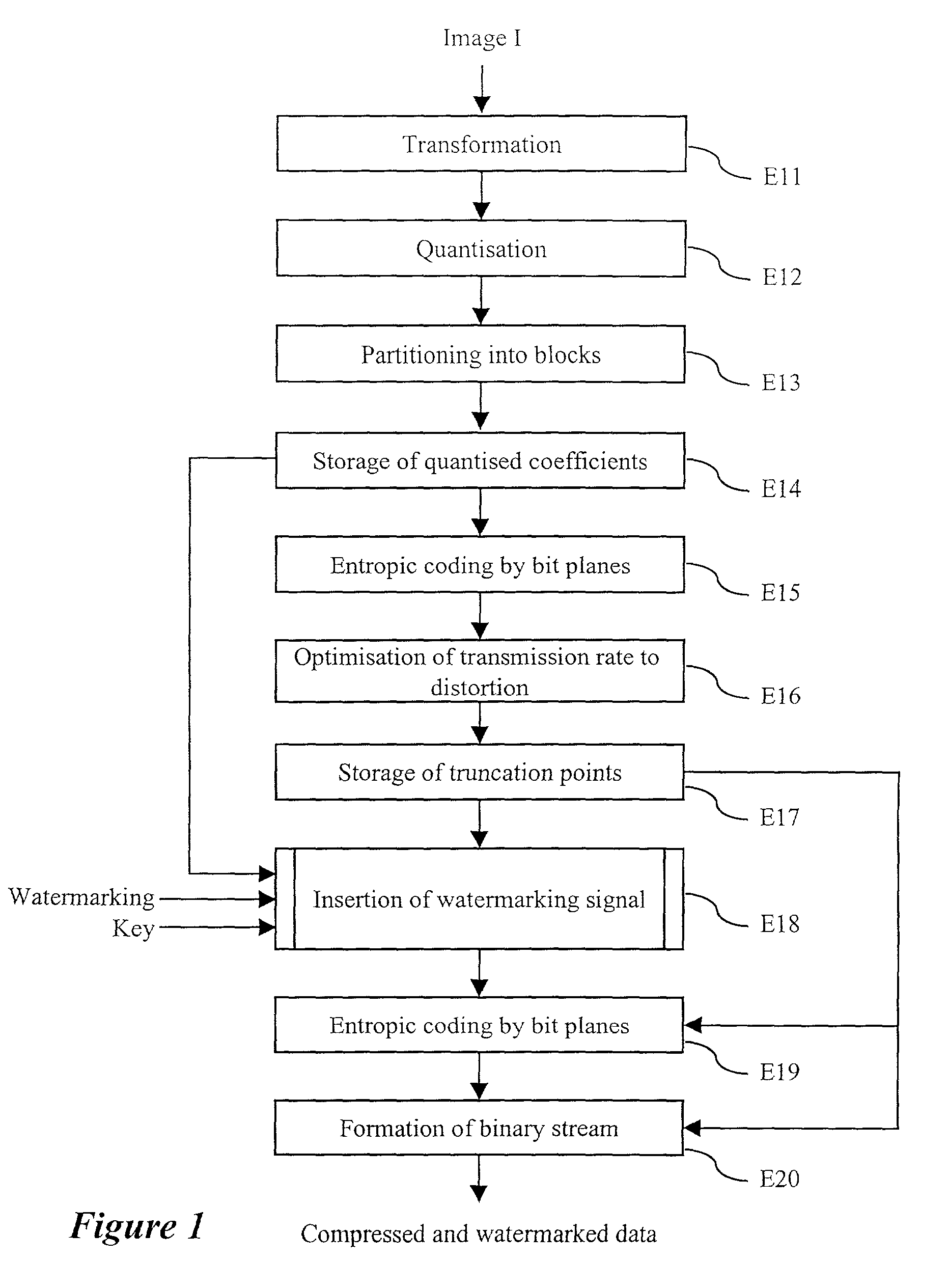
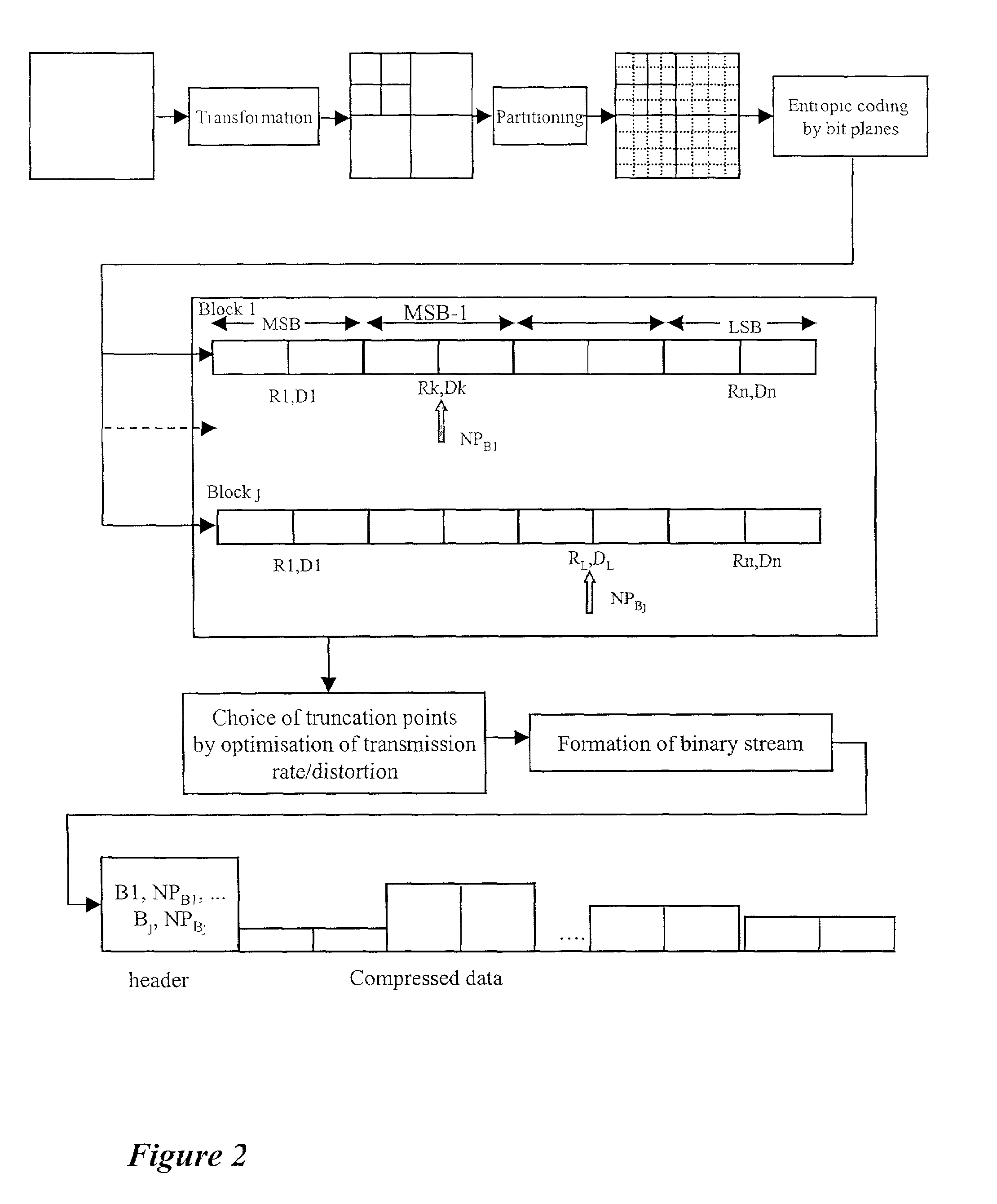
A method for the prior monitoring of the detectability of a watermarking signal inserted by modulation in a set of coefficients representing for example a digital image. The method comprises the step of simulating a distortion on the set of modulated coefficients, the distortion corresponding to a given compression level of the set of coefficients before modulation, determined by optimisation of a ratio of transmission rate to distortion. The method further comprises the step of calculating a detectability test on the set of modulated coefficients after distortion, and a step of comparing the detectability test with a threshold detection value. The method is used notably for inserting a watermarking signal during the compression of a digital image.
Owner:CANON KK
Information processing apparatus and processing method therefor
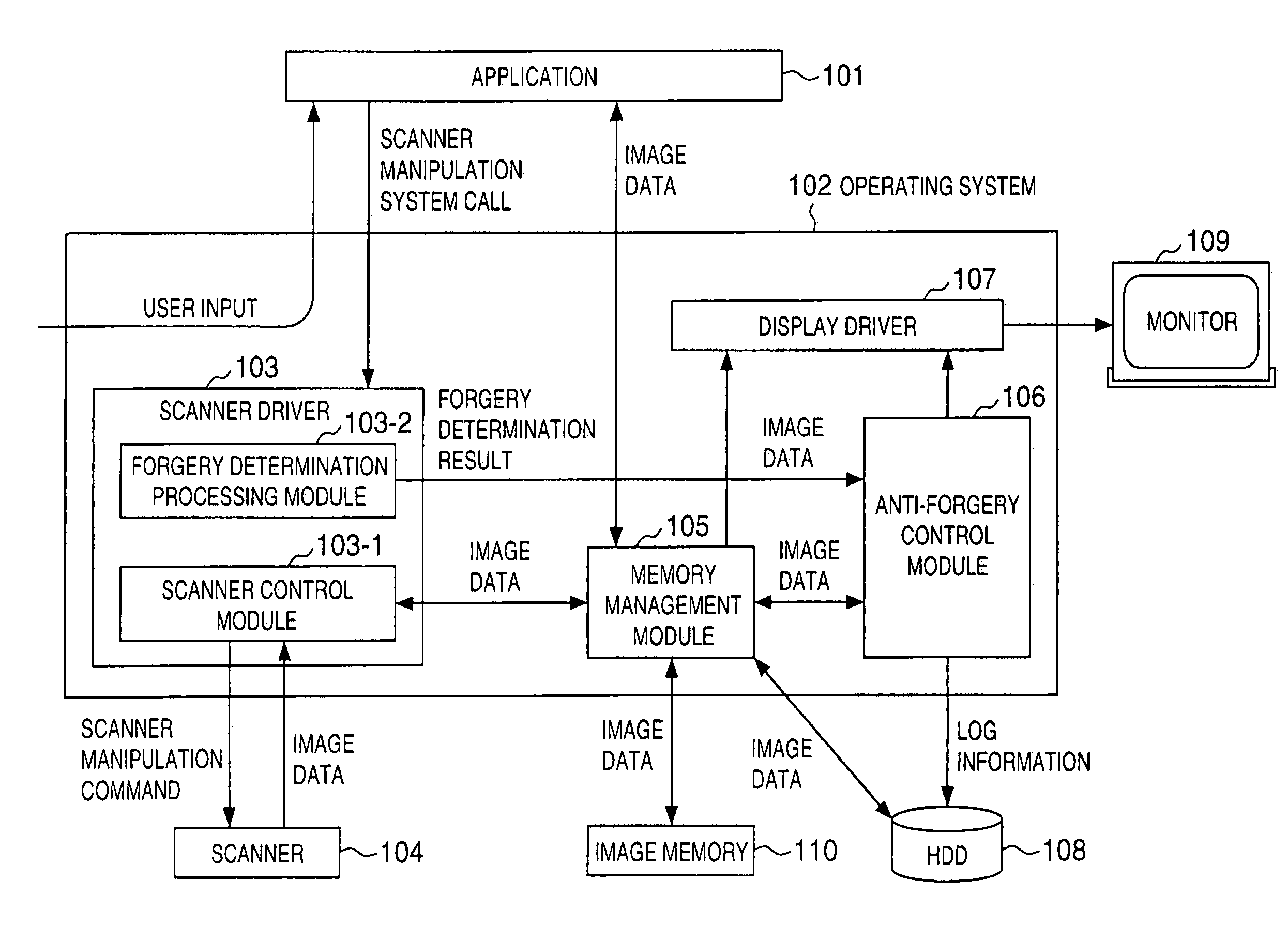
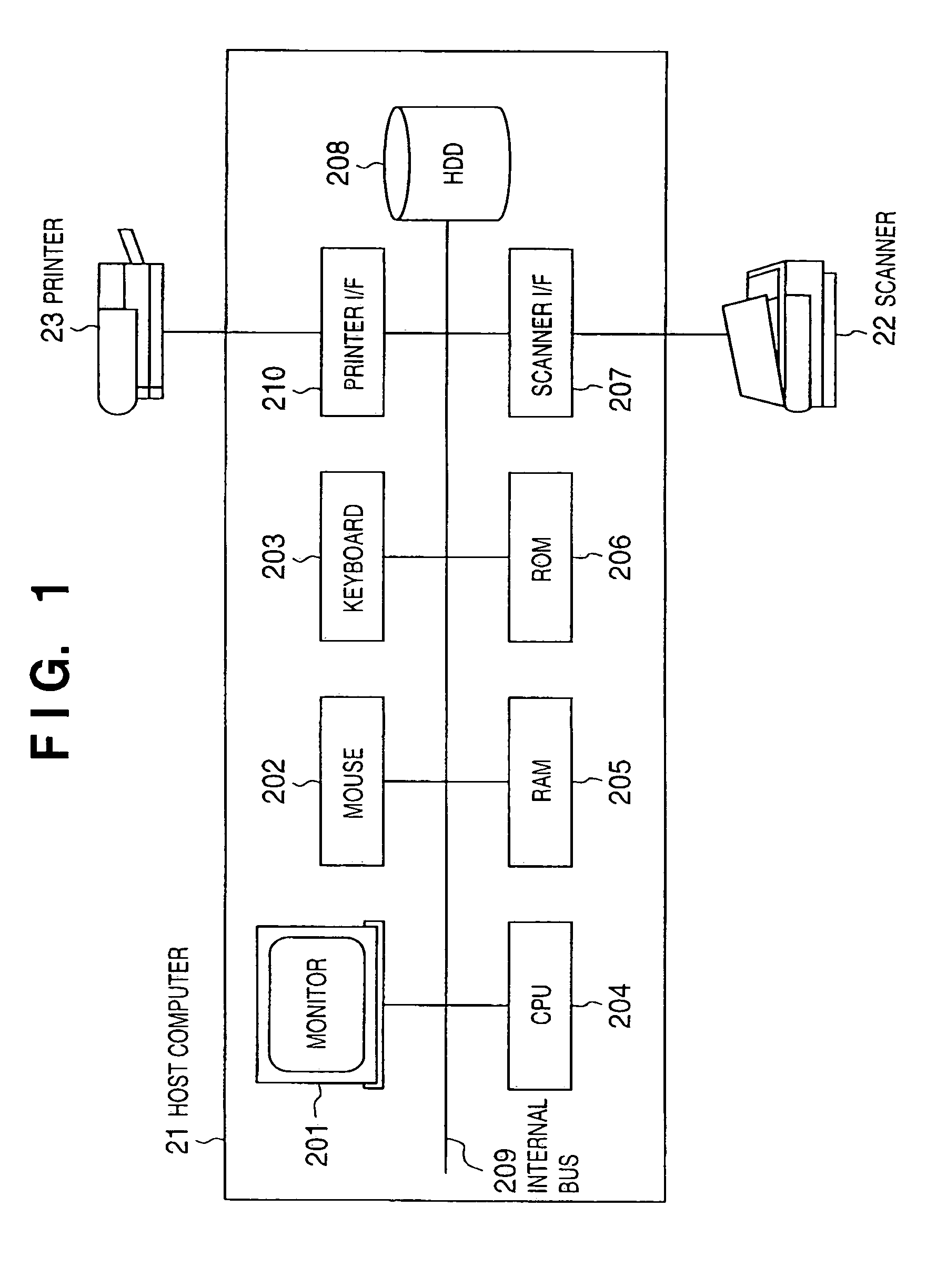
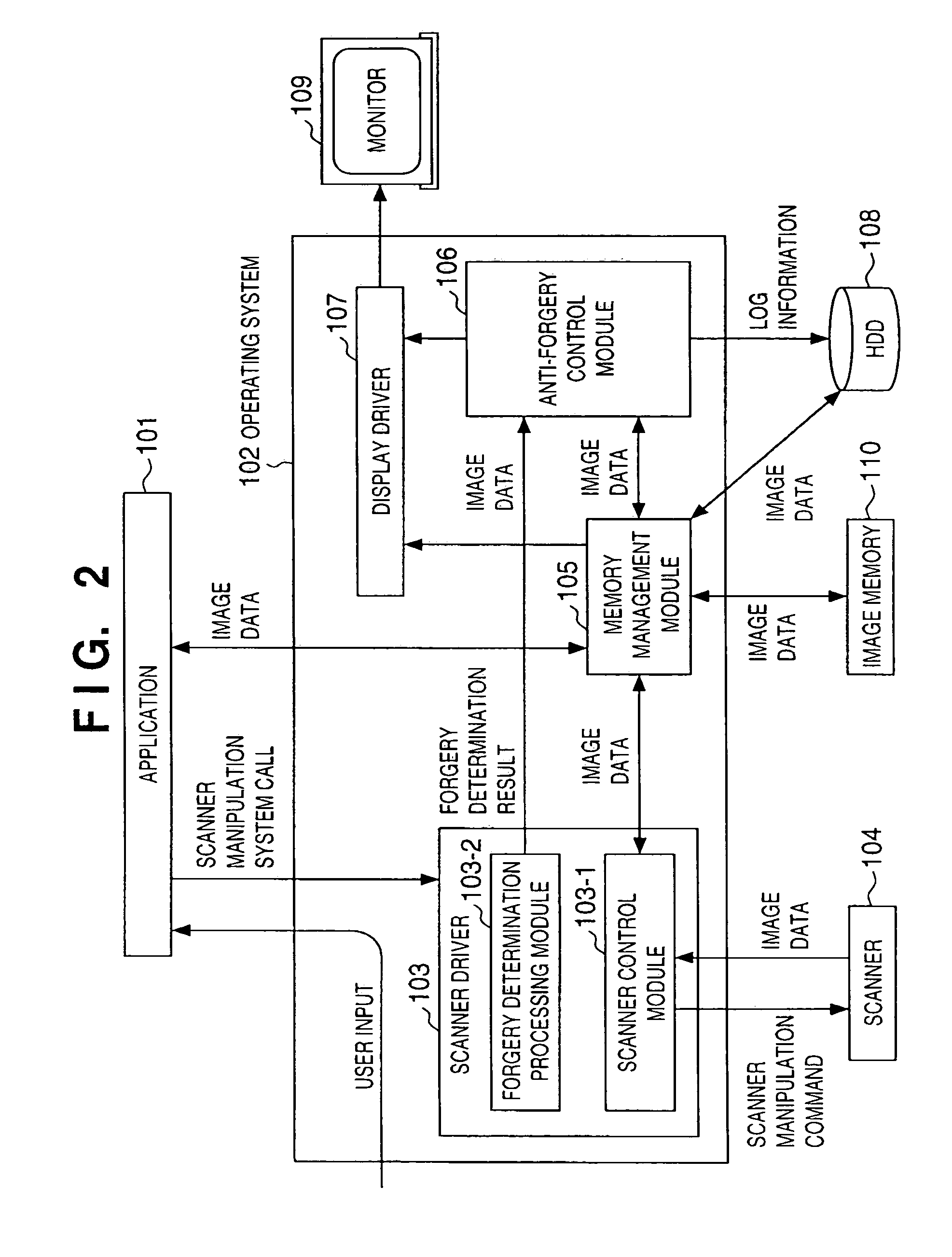
ActiveUS6930803B1Television system detailsCharacter and pattern recognitionInformation processingImaging processing
In an image processing apparatus which has an operating system (102) and scanner driver (103), is connected to a scanner (104) for reading an original and converting it into an image signal, and stores image data read by manipulating the scanner (104), a forgery determination processing module (103-2) of the scanner driver (103) compares the read digital watermark data with specific image data to determine the matching degree, and an anti-forgery control module (106) controls predetermined image processing on the basis of the determination result for the image data read by the scanner driver (103).
Owner:CANON KK
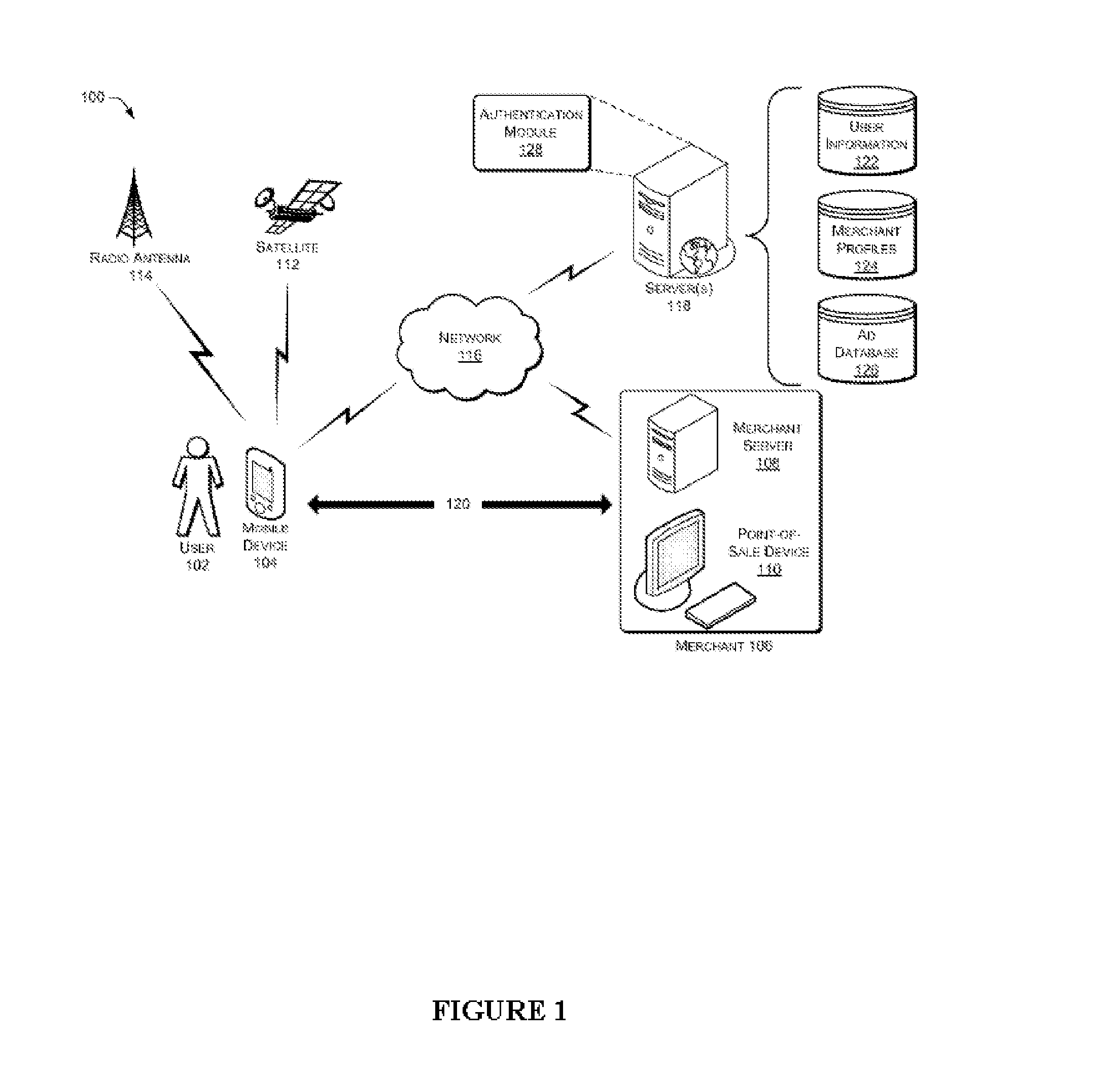
Location Based Mobile User Selected Time, Location, and Number Limited Automatic Location Based Reserve and Redeem Discounts on Products or Services with Automatic Security and Feedback Features
Methods, systems, software, computer readable non-transitory media, applications, devices, and the like for providing location based, mobile, user selected, time, location, and number limited or unlimited electronic coupon card selection of automatic location based reserve and redeem discounts on products or services with a profile picture, tag, motion enabled watermark, or other visual, 2D or mechanism for security purposes.
Owner:RANDELL JASON MATTHEW +1
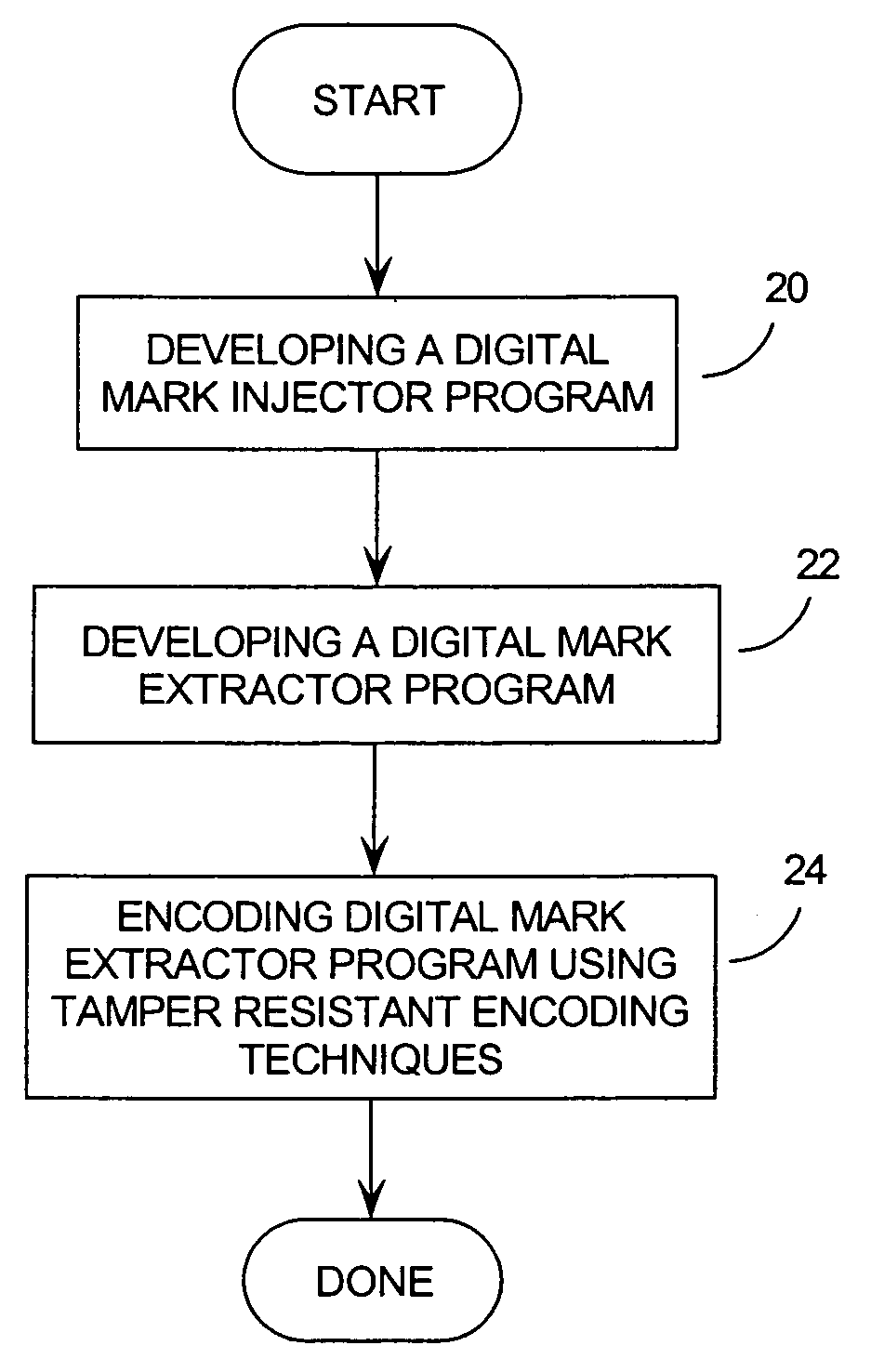
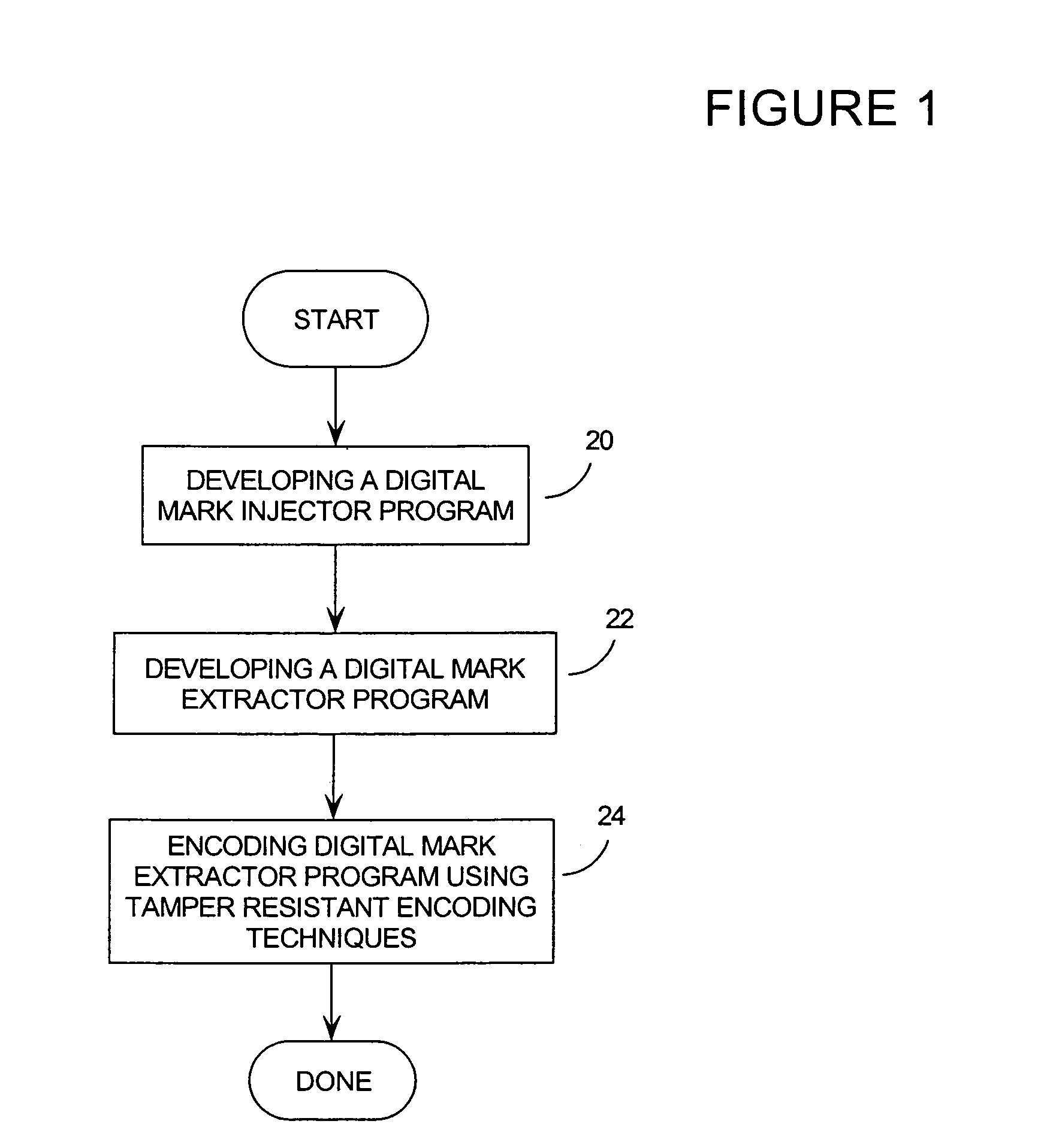
Method and system for sustainable digital watermarking
InactiveUS7395433B2User identity/authority verificationUnauthorized memory use protectionTamper resistanceInternet privacy
Digital marks (so-called fingerprints and watermarks) serve two basic purposes: (1) Investigative: the owner reads a fingerprint to determine how the marked entity leaked; and (2) Legal: the owner must prove in court that (a) there is a watermark (a concealed copyright message), and (b) it is the owner's. The main difficulty of item (2) is that the first use of the watermark software reveals the watermarking method to the public so that hostile parties are equipped to remove or damage its watermarks. The invention uses tamper-resistant software encoding techniques to protect the digital mark extractor algorithm, frustrating the attacks of hostile parties in two ways: the resulting code is obscure (that is, its inner workings are incomprehensible; and chaotic (that is, a modification at any point will almost certainly produce a nonsense program.
Owner:IRDETO CANADA CORP
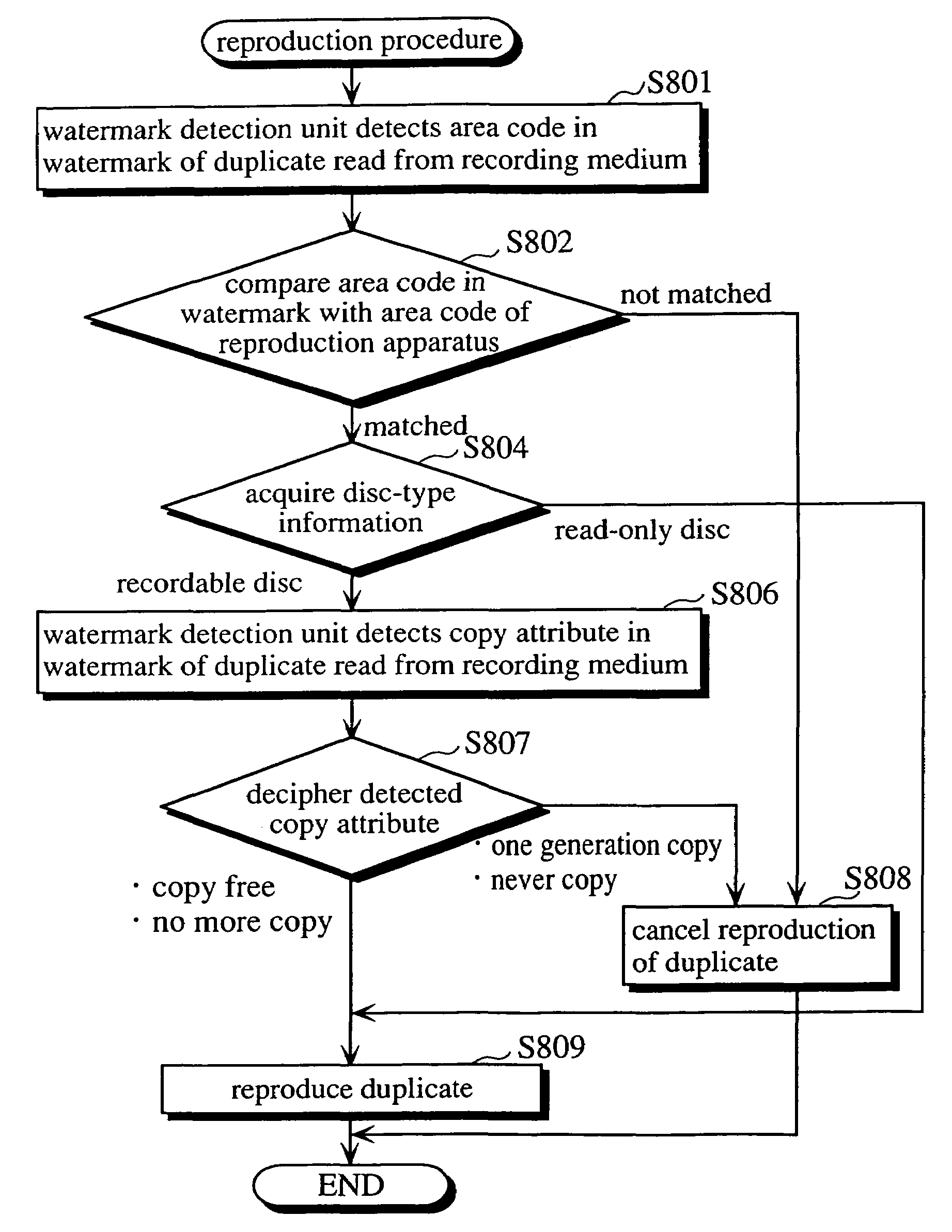
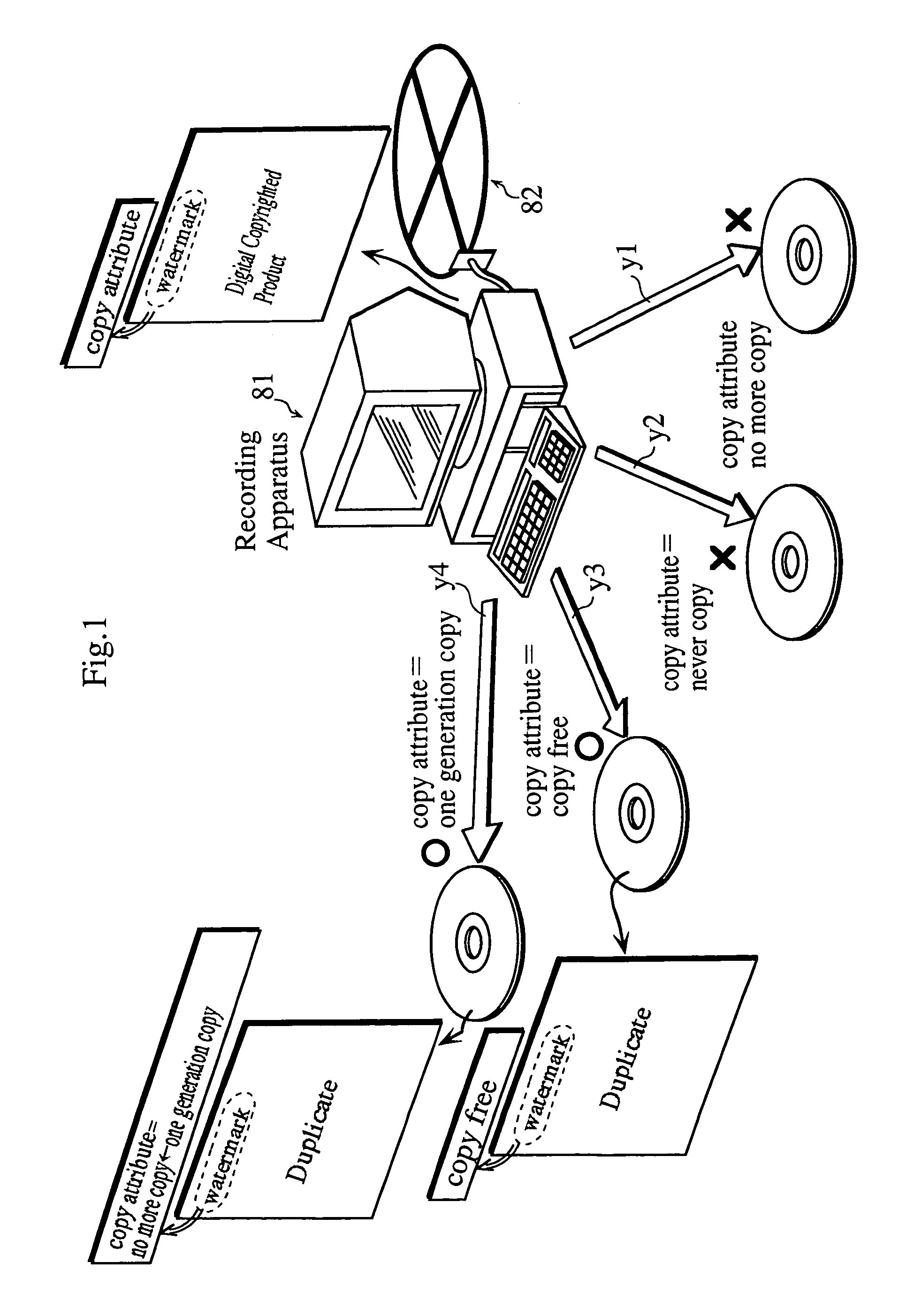
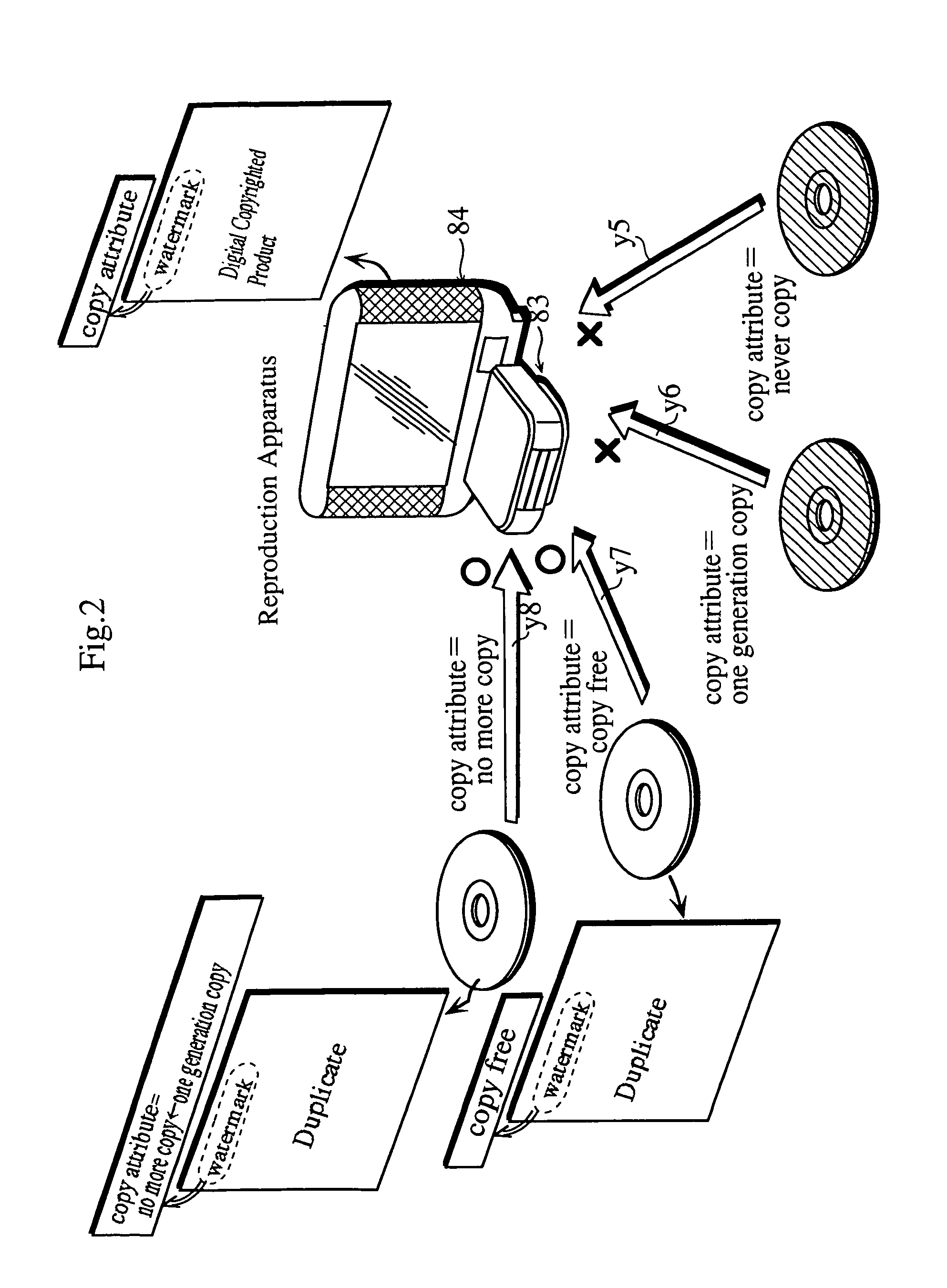
Recorder for recording copy of production on the basis of copy attribute embedded as electronic watermark in the production, reproducing device for reproducing recorded copy, recorded medium, recording method, and reproducing method
InactiveUS6937553B1Inhibition of reproductionReduce riskTelevision system detailsOptical re-recordingComputer hardwareRecording media
A recording apparatus for recording a duplicate of a product onto a recording medium, the product being a copyrighted digital product having a copy attribute embedded as a watermark thereon and the recording apparatus including (a) an acquiring unit for acquiring the copy attribute embedded on the product, (b) a changing unit for changing the acquired copy attribute into a copy attribute showing no more copy when the acquired copy attribute shows one generation copy, (c) a reading unit for reading from the recording medium at least a part of medium ID information recorded on the recording medium in an unalterable state, and (d) a recording unit for recording onto the recording medium the duplicate having both the copy attribute showing no more copy and the read medium ID information embedded as a watermark thereon.
Owner:PANASONIC CORP
Method for measuring multimedia video communication quality
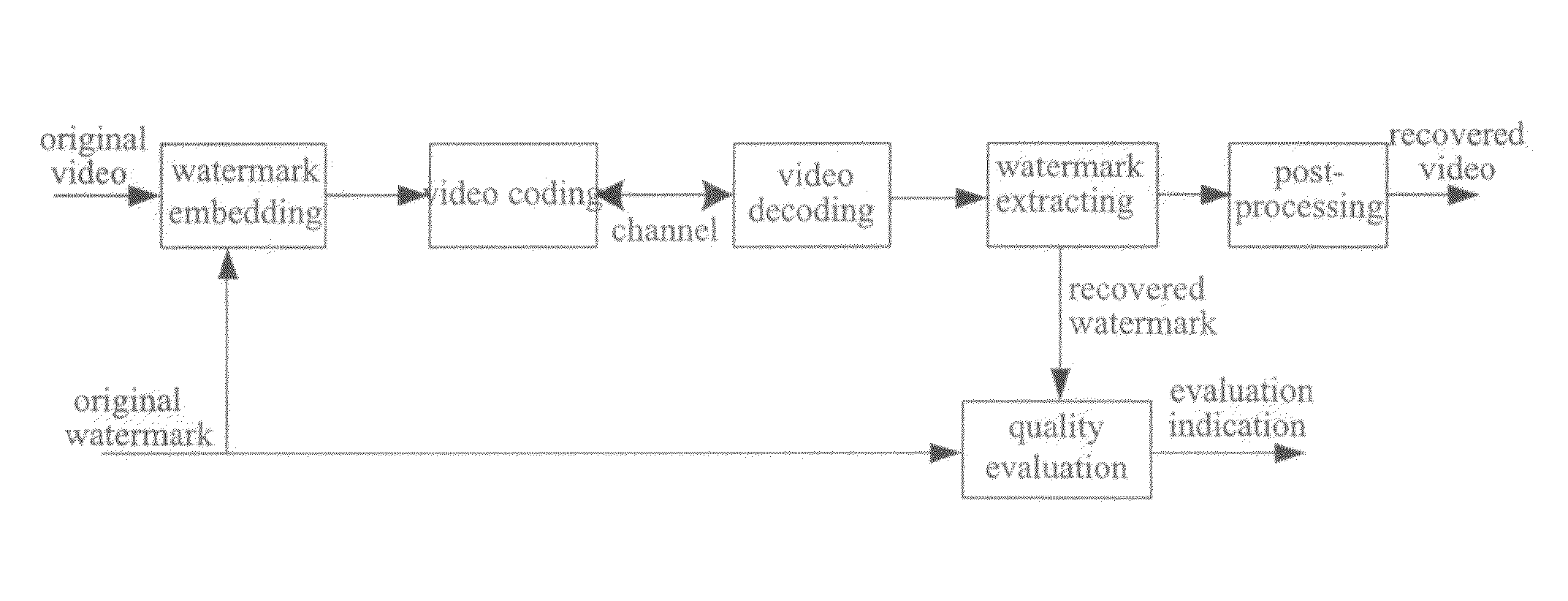
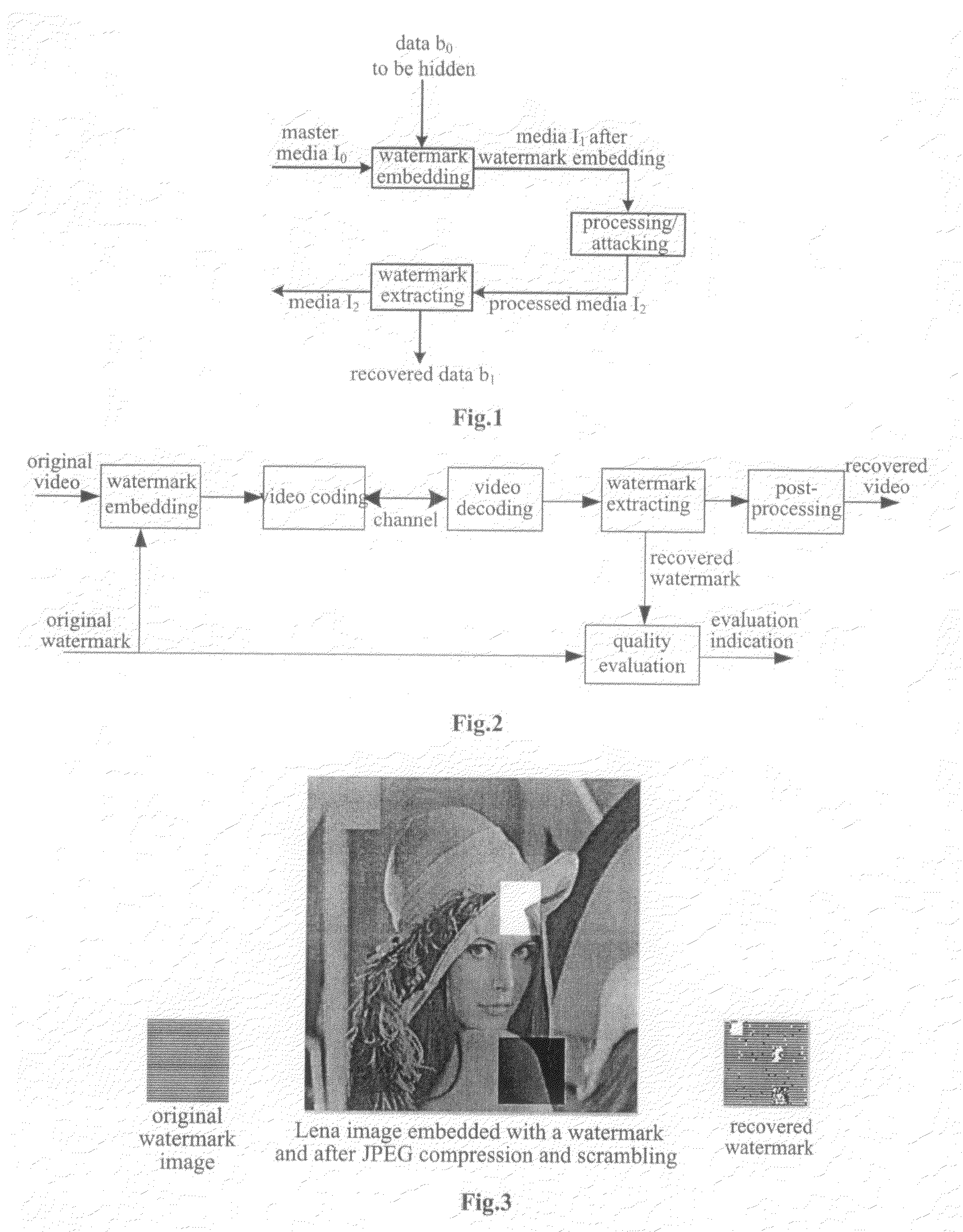
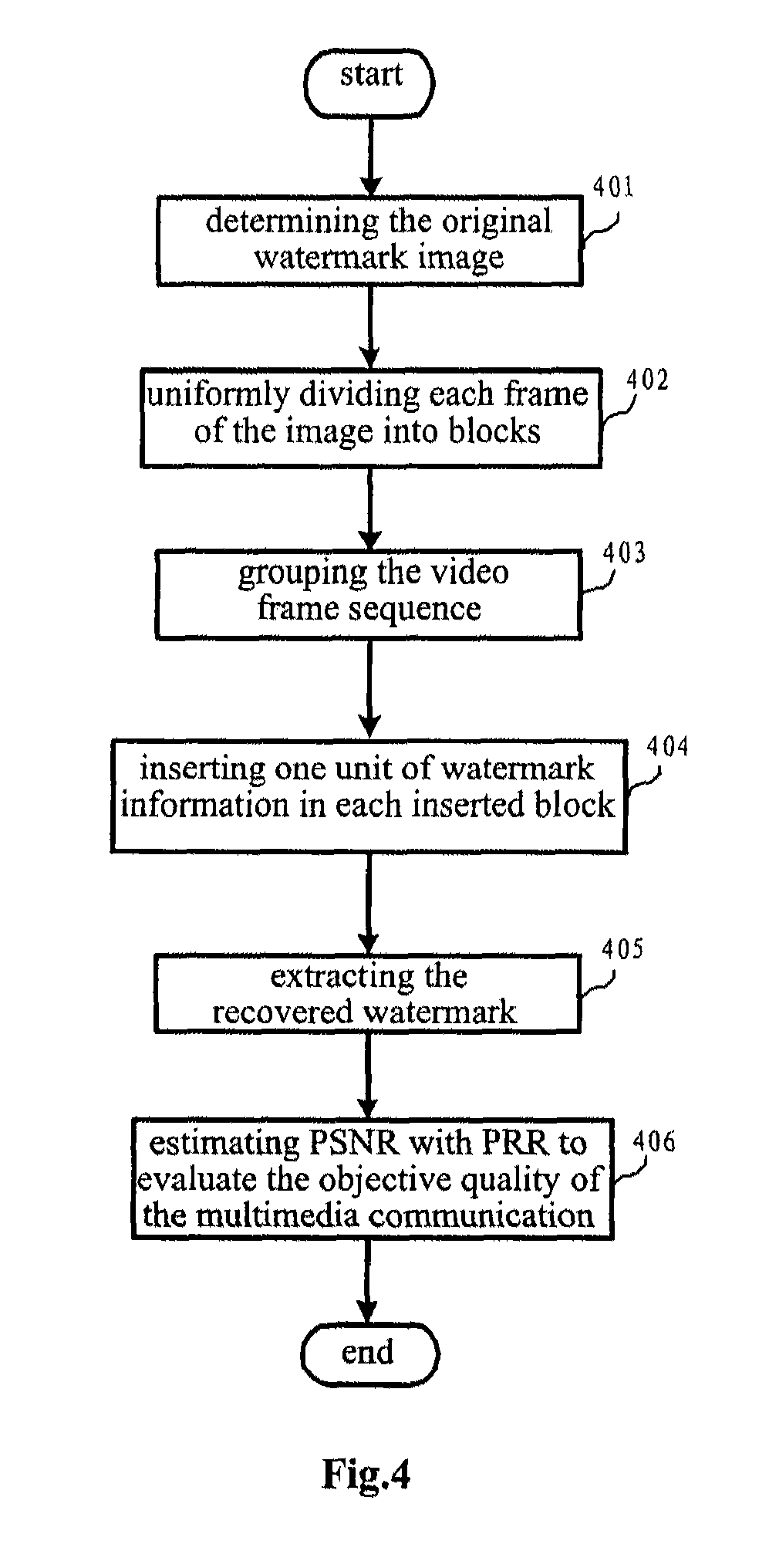
InactiveUS8184164B2Improve accuracyOptimize networkTelevision system detailsNoise figure or signal-to-noise ratio measurementTelecommunicationsCommunication quality
A method for measuring multimedia communication quality is disclosed. The multimedia video communication quality may be objectively reflected through the embedment and extraction of digital watermark under a precondition that the quality of the multimedia video data is not obviously affected. In the invention, each frame of the multimedia video data is uniformly divided into blocks of equal size and watermark data is embedded in each of the blocks, so that the watermark may be uniformly distributed. The multimedia video data are divided into groups, and the watermark is embedded in a part of the frames with equal interval between the frames in each group to reduce the effect of the watermark on the data. The watermark information is directly embedded in the spatial domain of the original video data. The PSNR of the video data is linearly fitted using the accuracy rate of the recovered watermark relative to the original watermark, and the fitted PSNR is regarded as a measurement indication of the multimedia video communication quality. Post-processing such as smoothing filtering is performed on video frames after watermark extraction to eliminate the effect of the watermark on the multimedia video data quality.
Owner:RPX CORP
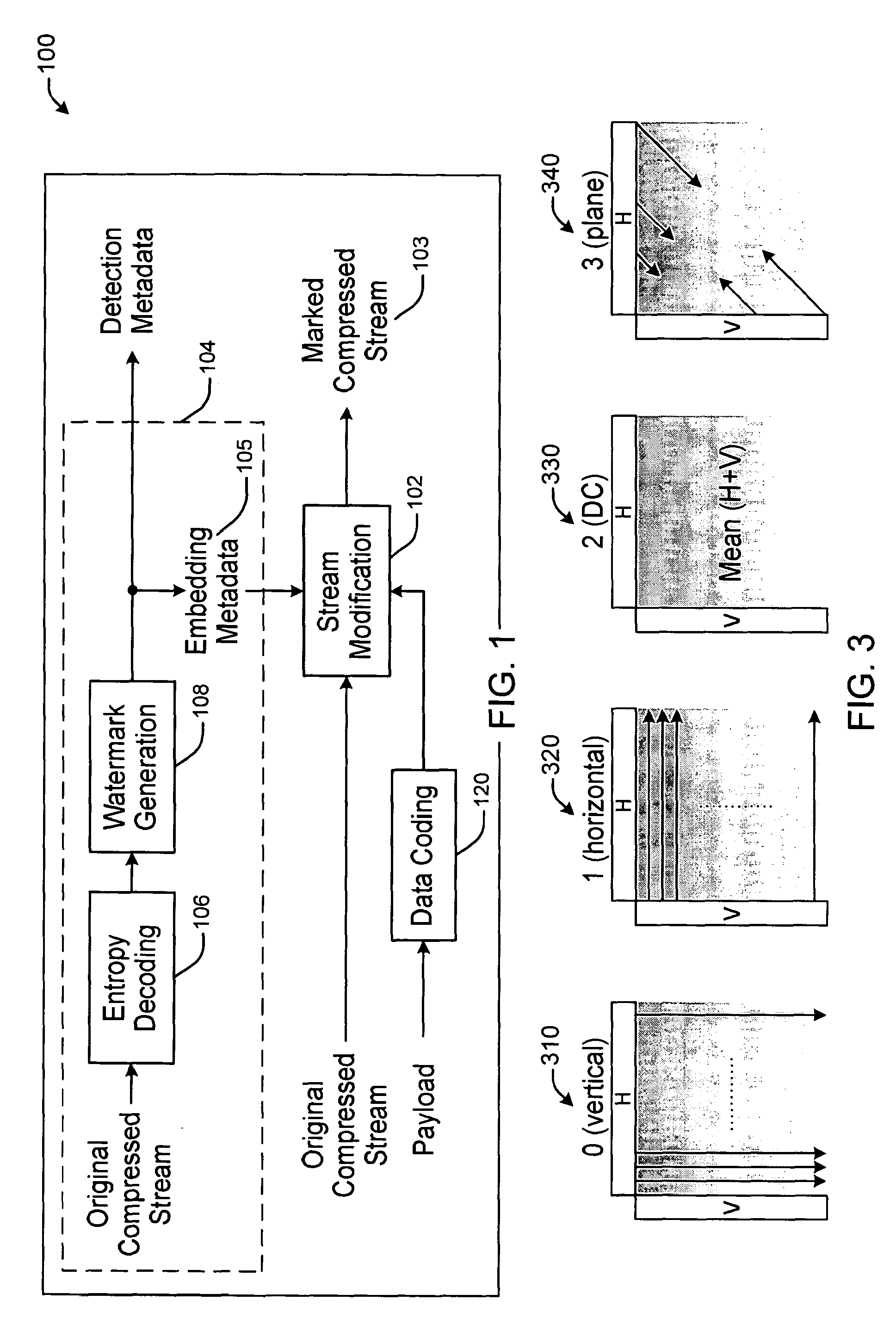
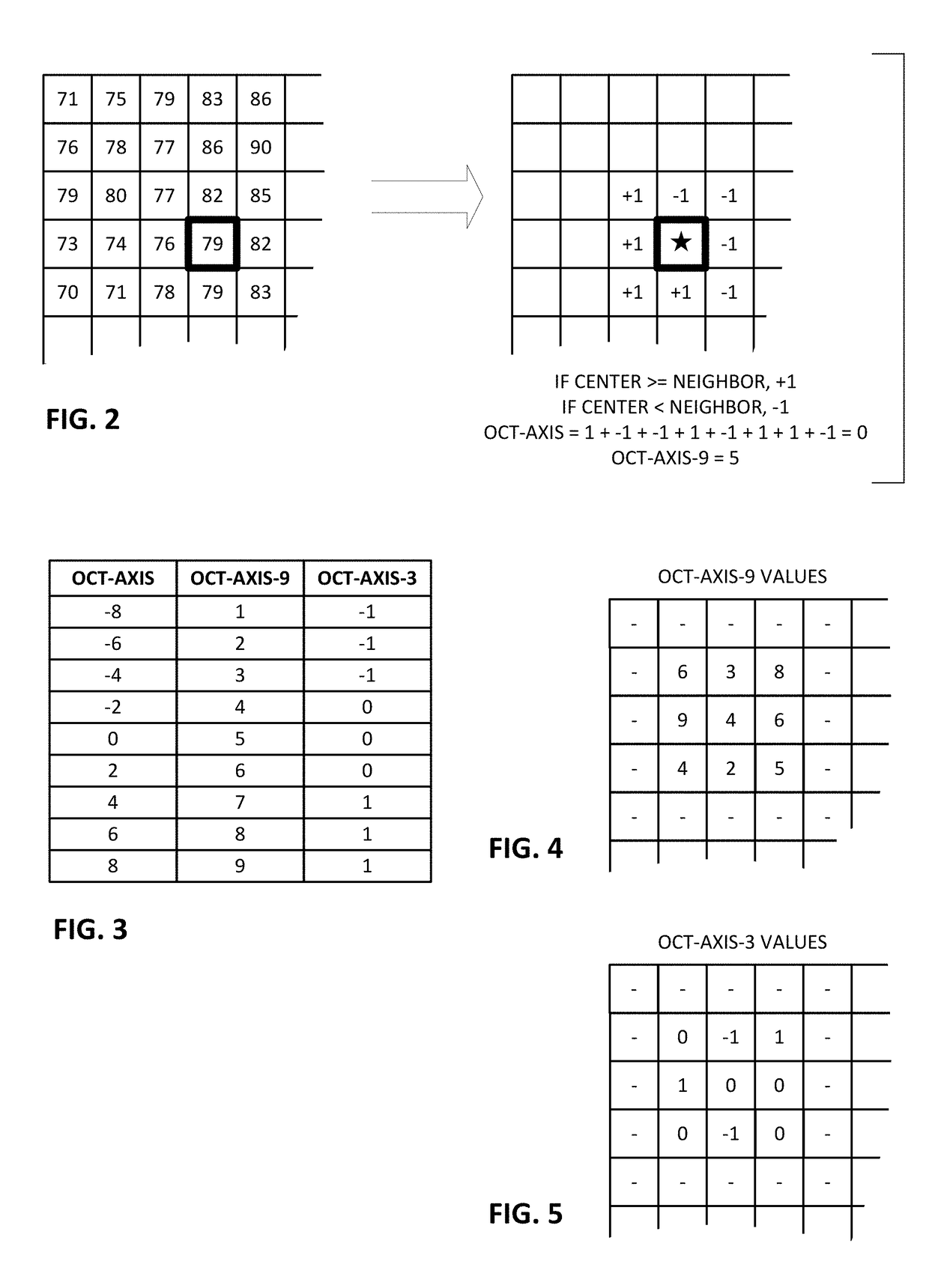
Modifying a coded bitstream
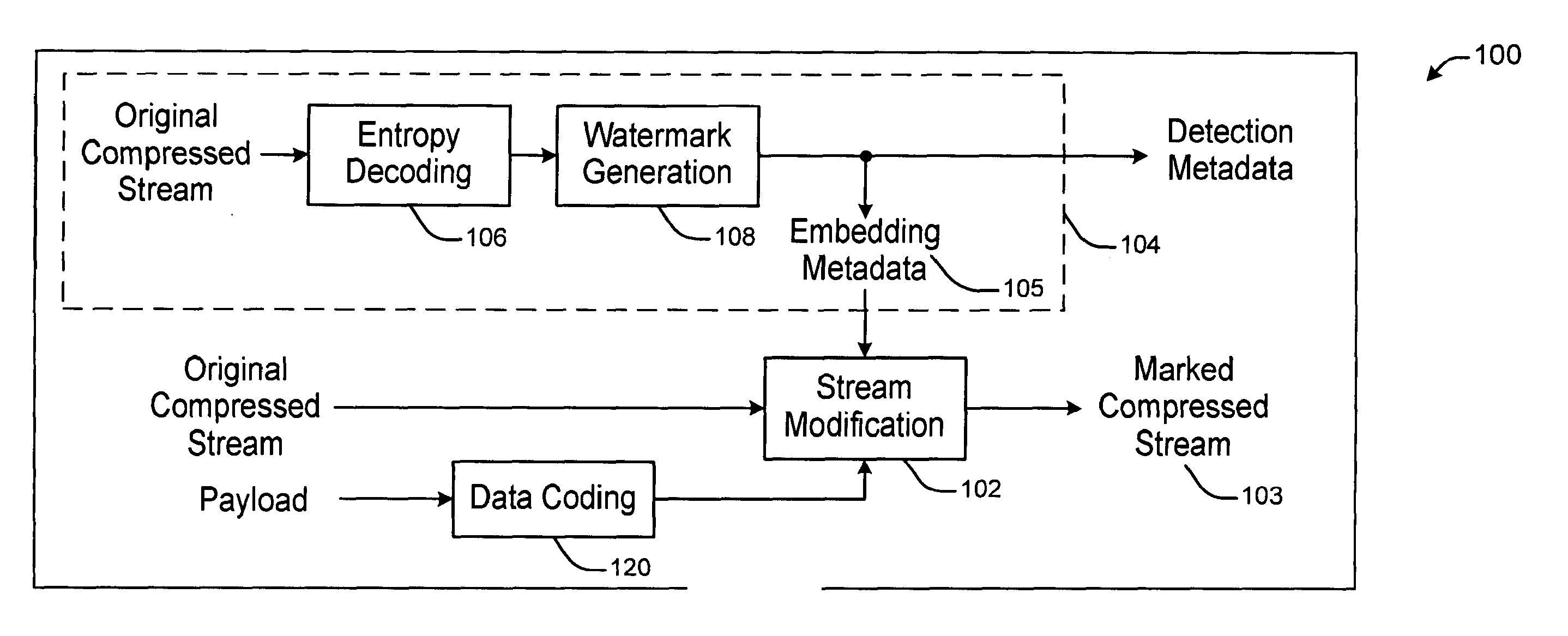
ActiveUS8588459B2Character and pattern recognitionImage data processing detailsData packTheoretical computer science
Various implementations are provided for, for example, determining watermarking data, performing the watermarking, and processing watermarked data. At least one implementation watermarks AVC bitstream that uses CAVLC entropy coding. The watermarking data may be determined in a pre-processing stage and stored for later use in watermark a bitstream. One method accesses variable-length encoded data including an encoding of information identifying an actual reference used to predictively encode an image. The encoding of the information has a particular value. The method determines an alternative value that is different from the particular value, such that the alternative value is an encoding of alternative information that identifies a different reference from the actual reference. The alternative value is for use in watermarking the variable-length encoded data.
Owner:CONTENTARMOR
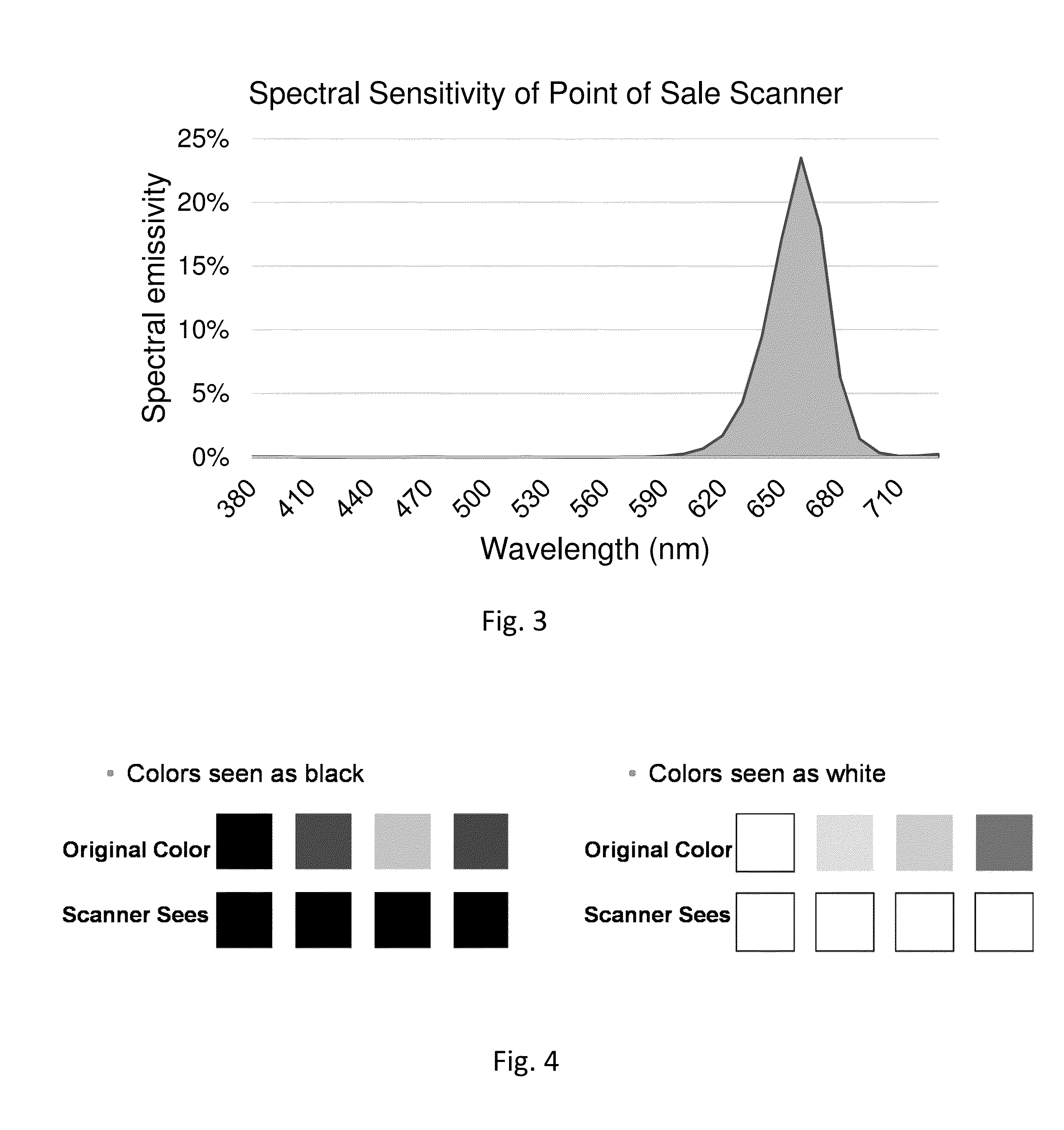
Image-based pose determination
ActiveUS20180005343A1Efficient implementationCorrectly extract payloadImage enhancementImage analysisPattern recognitionEngineering
A steganographic digital watermark signal is decoded from host imagery without requiring a domain transformation for signal synchronization, thereby speeding and simplifying the decoding operation. In time-limited applications, such as in supermarket point-of-sale scanners that attempt watermark decode operations on dozens of video frames every second, the speed improvement allows a greater percentage of each image frame to be analyzed for watermark data. In battery-powered mobile devices, avoidance of repeated domain transformations extends battery life. A great variety of other features and arrangements, including machine learning aspects, are also detailed.
Owner:DIGIMARC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com