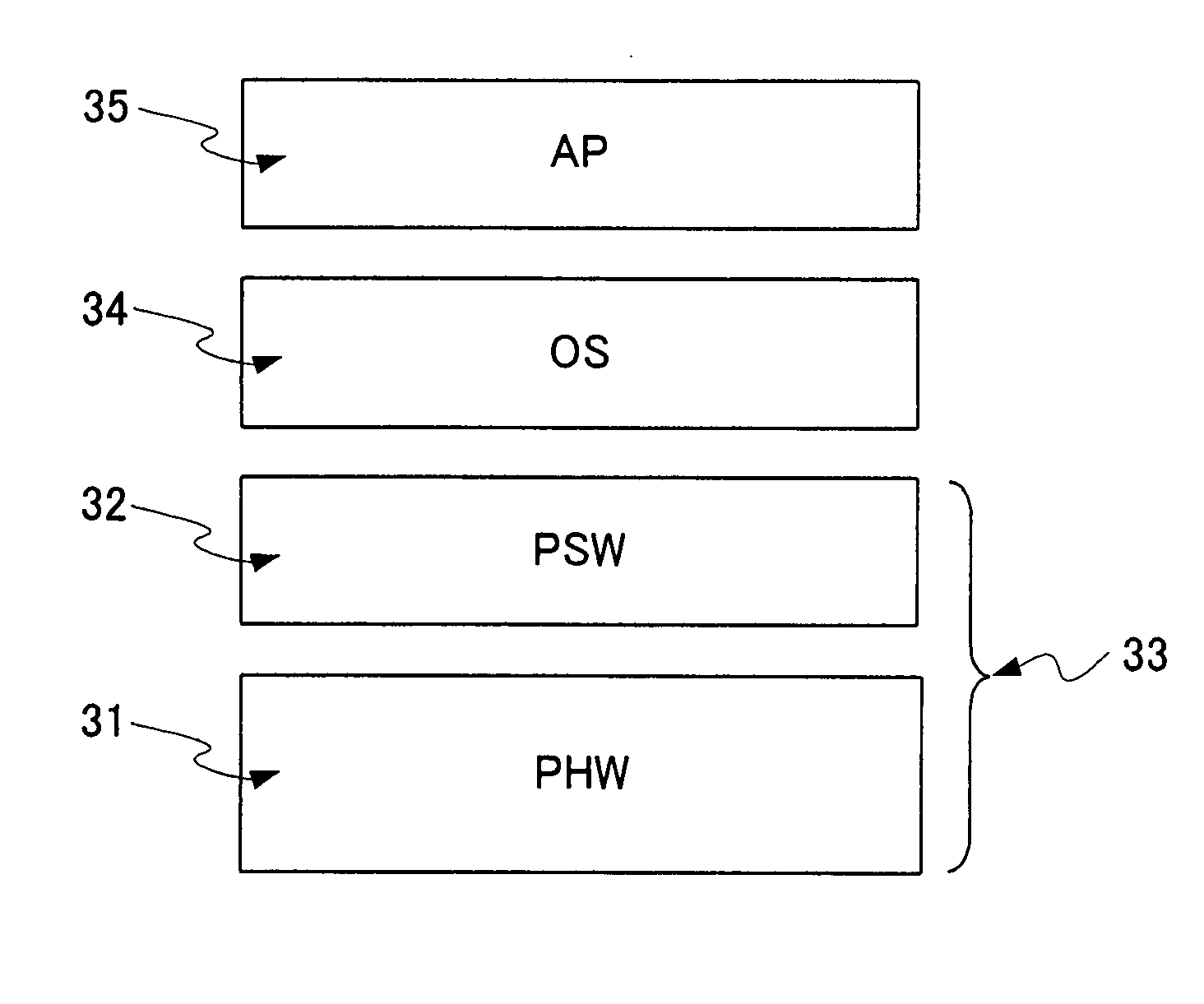
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1412 results about "Object code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
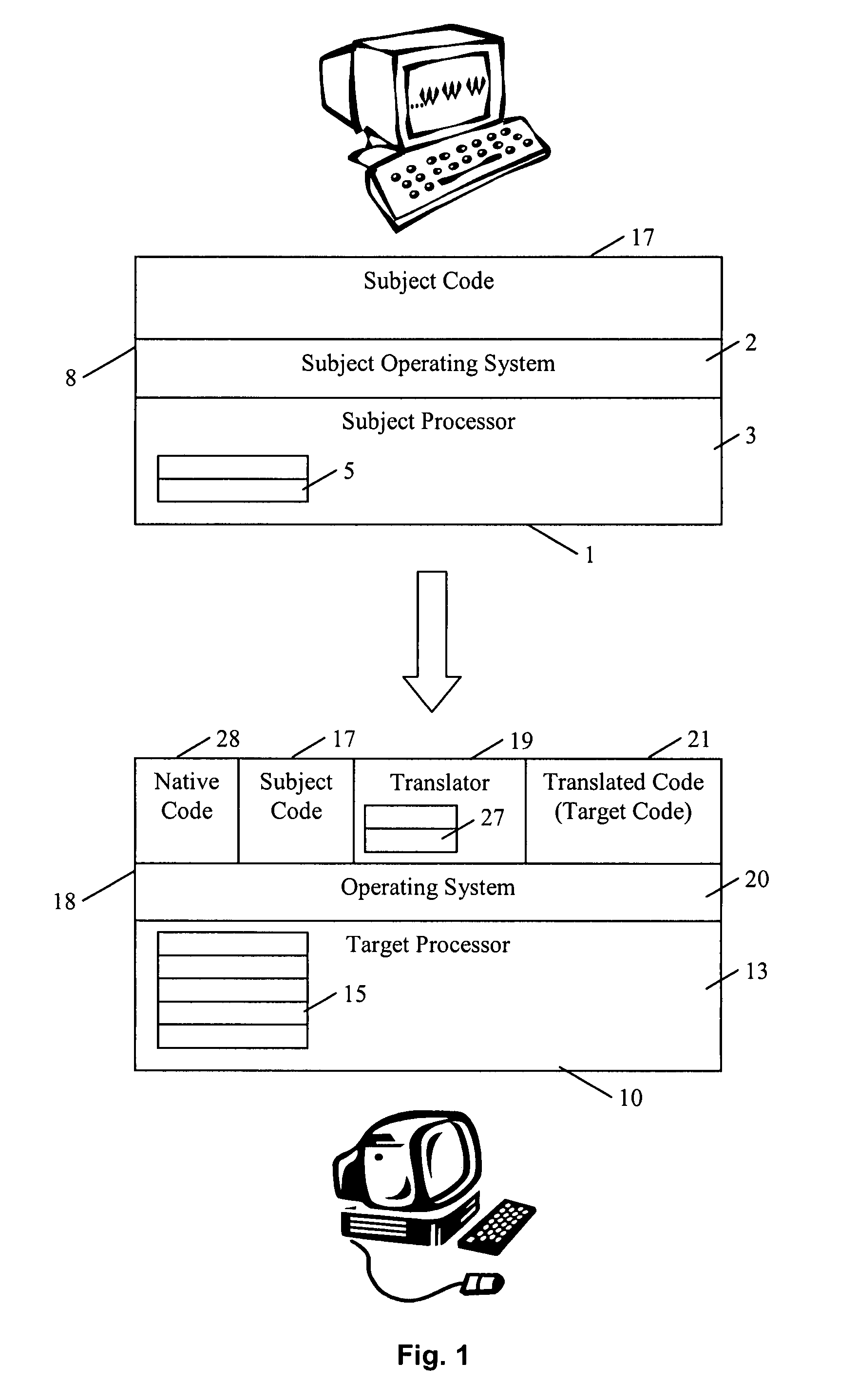
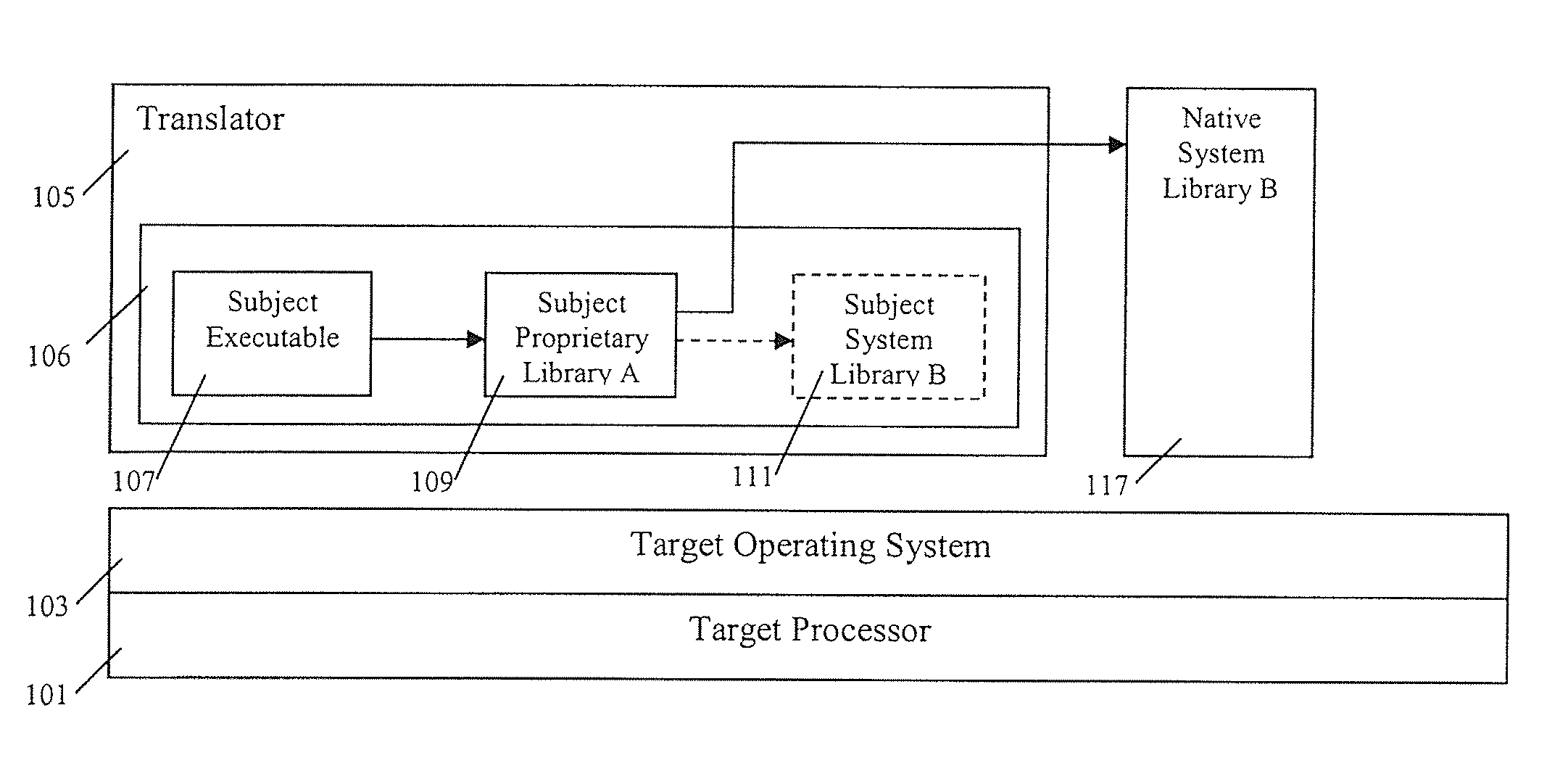
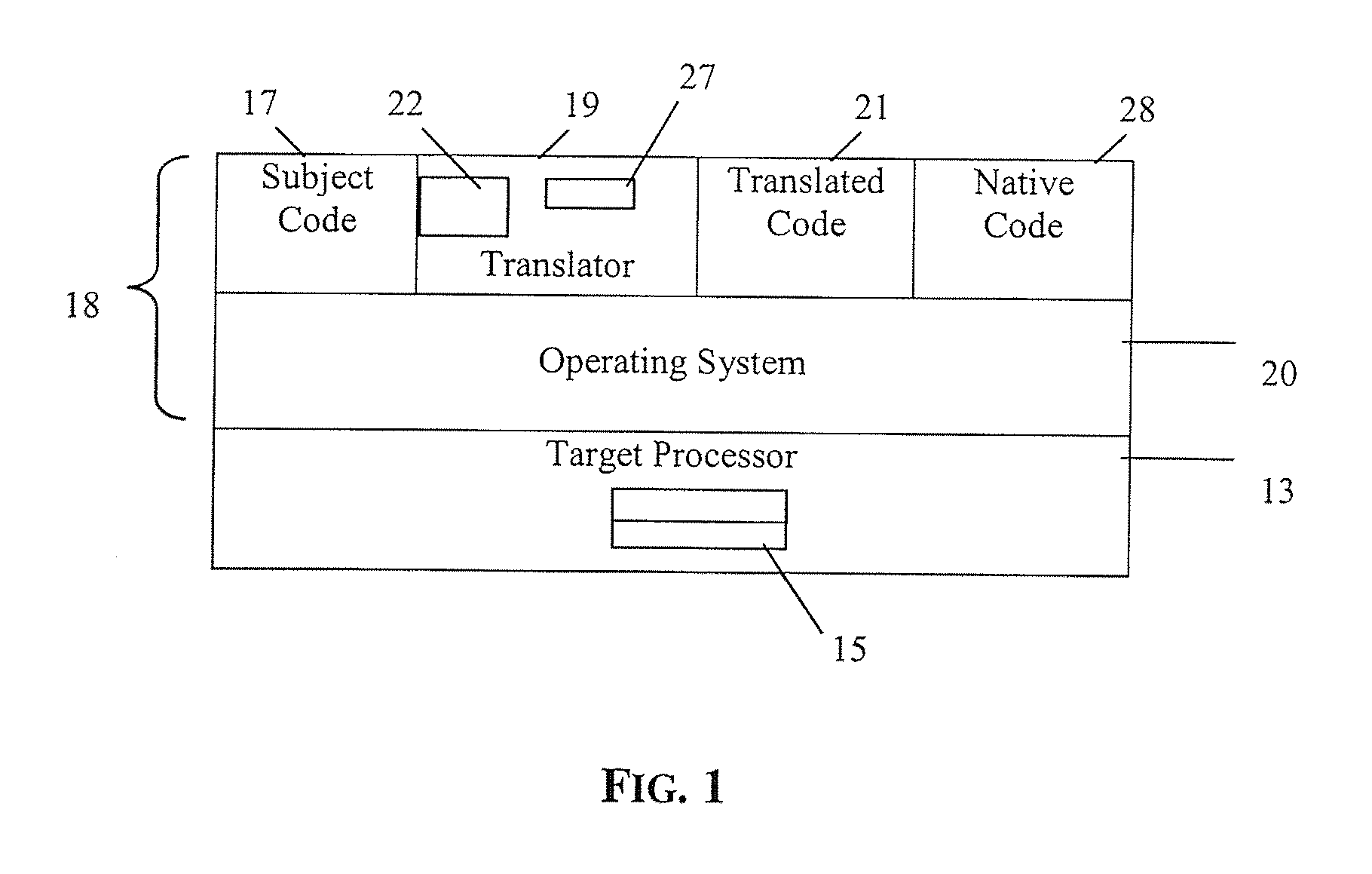
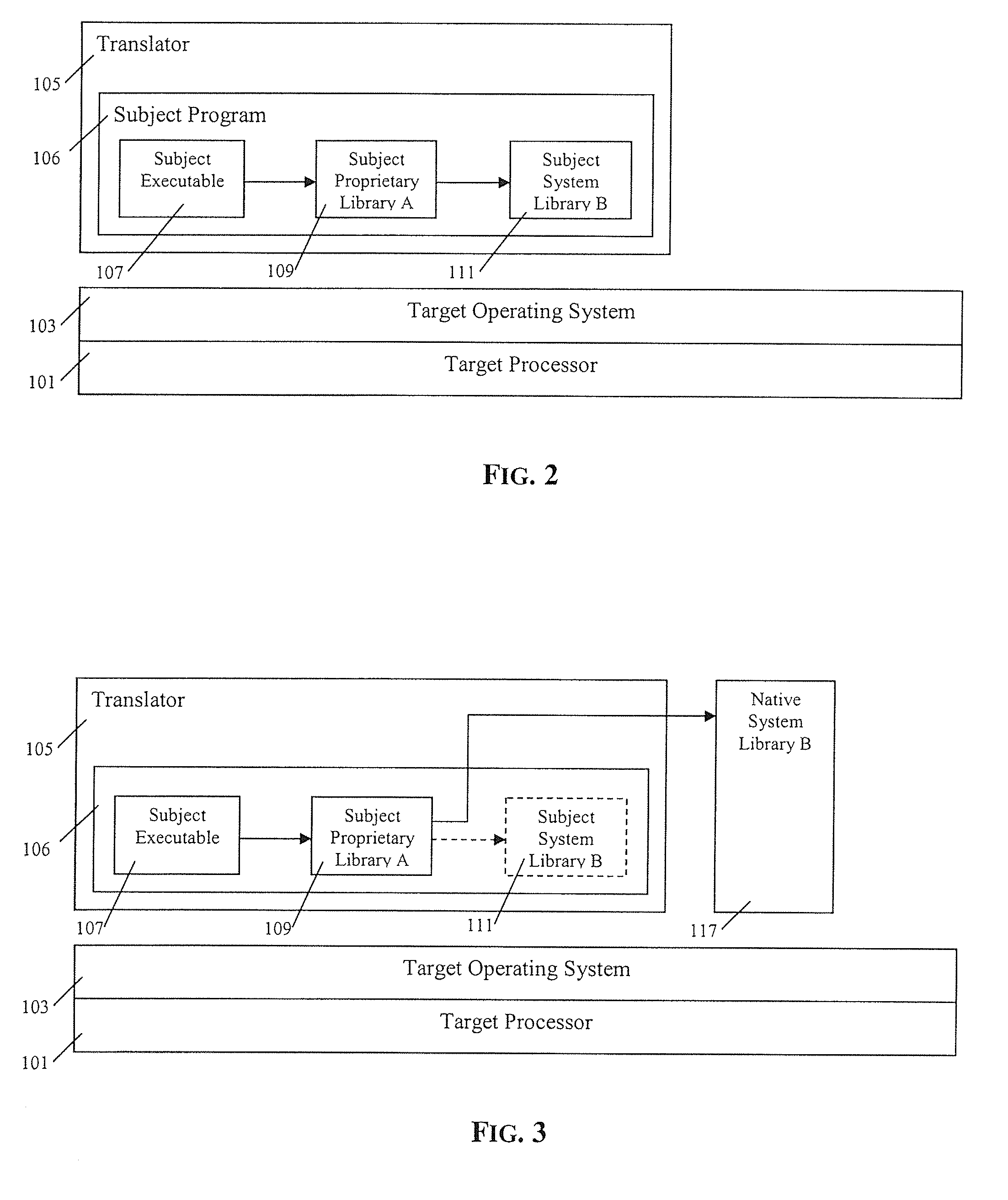
In computing, object code or object module is the product of a compiler. In a general sense object code is a sequence of statements or instructions in a computer language, usually a machine code language (i.e., binary) or an intermediate language such as register transfer language (RTL). The term indicates that the code is the goal or result of the compiling process, with some early sources referring to source code as a "subject program."
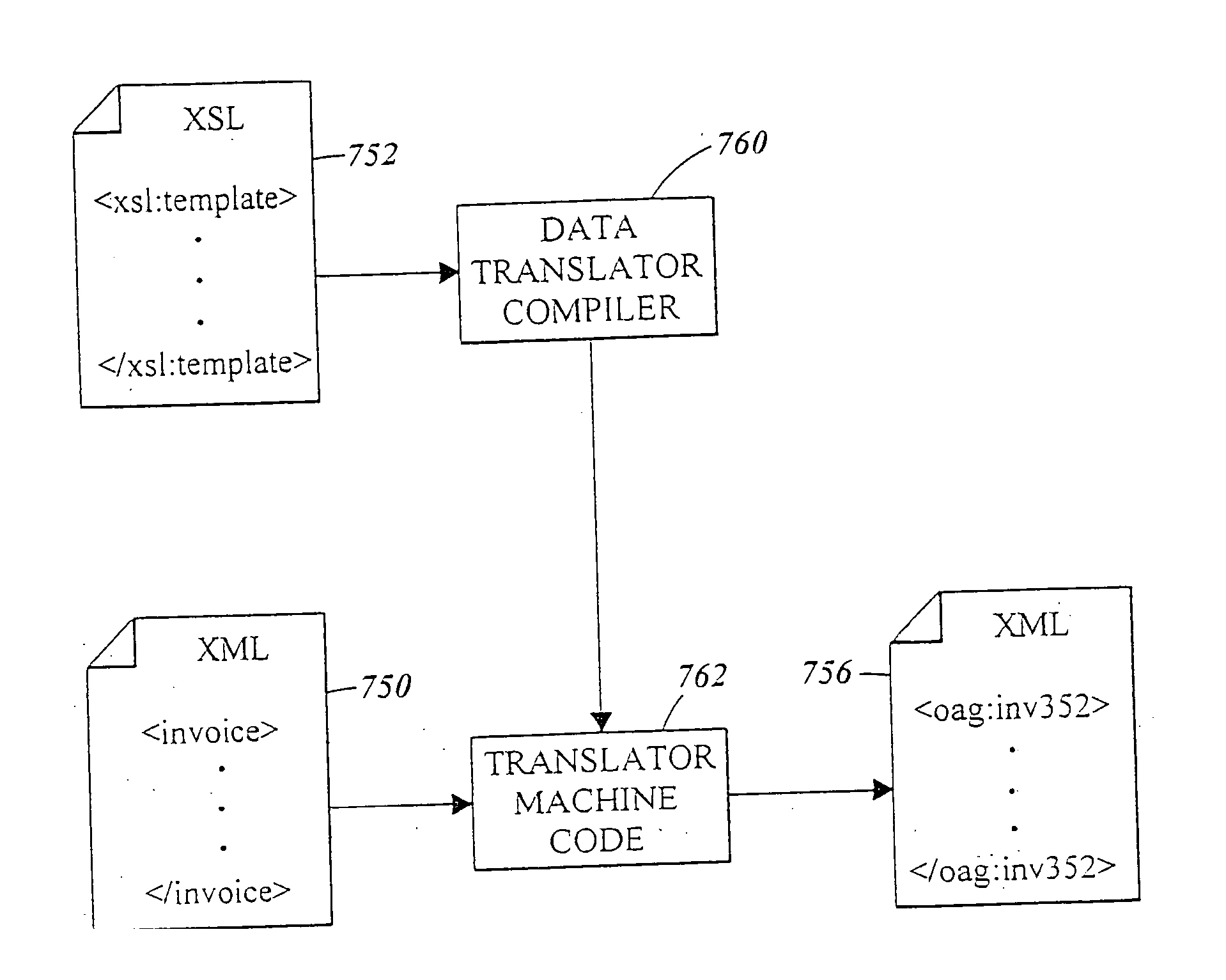
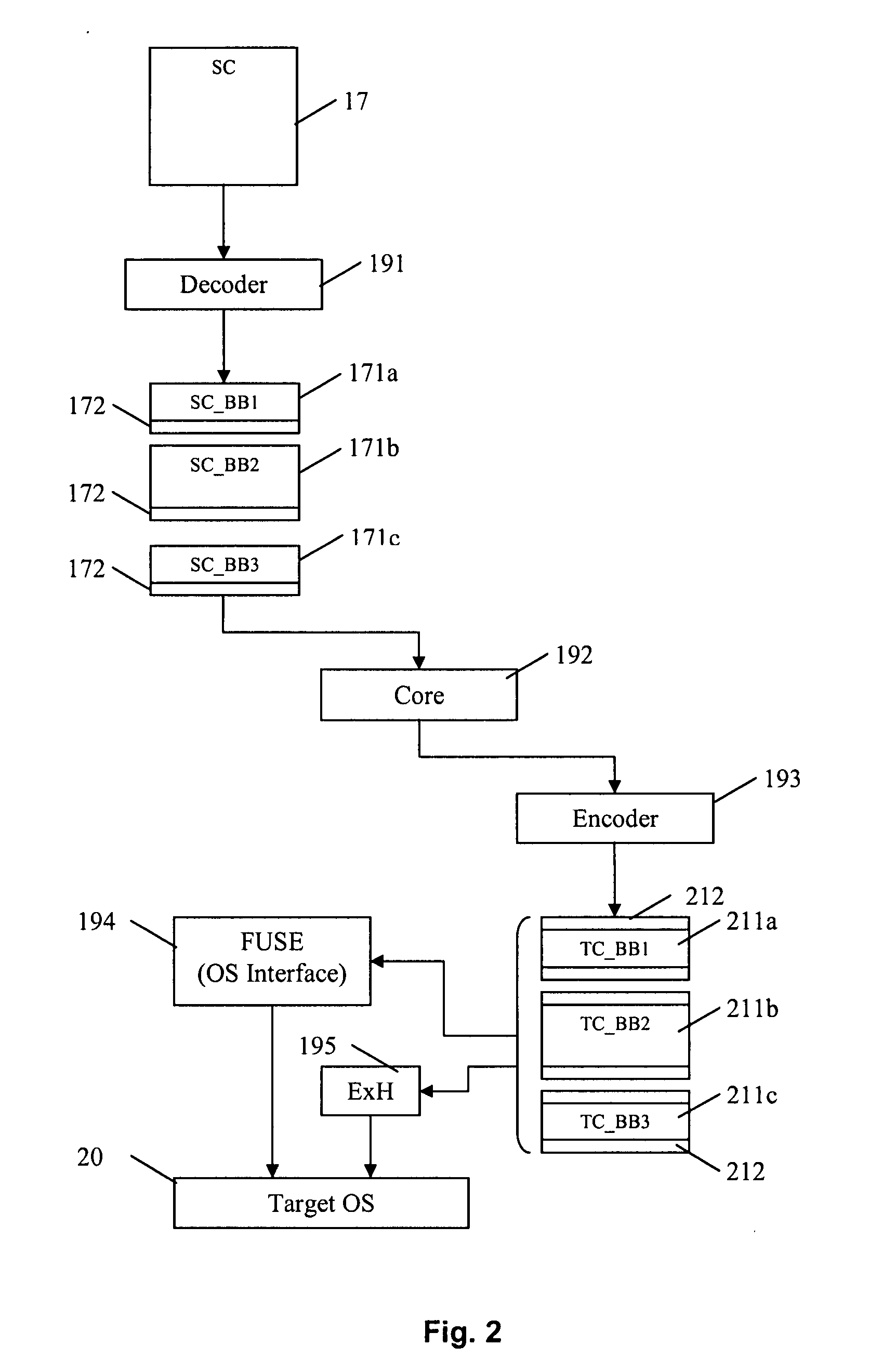
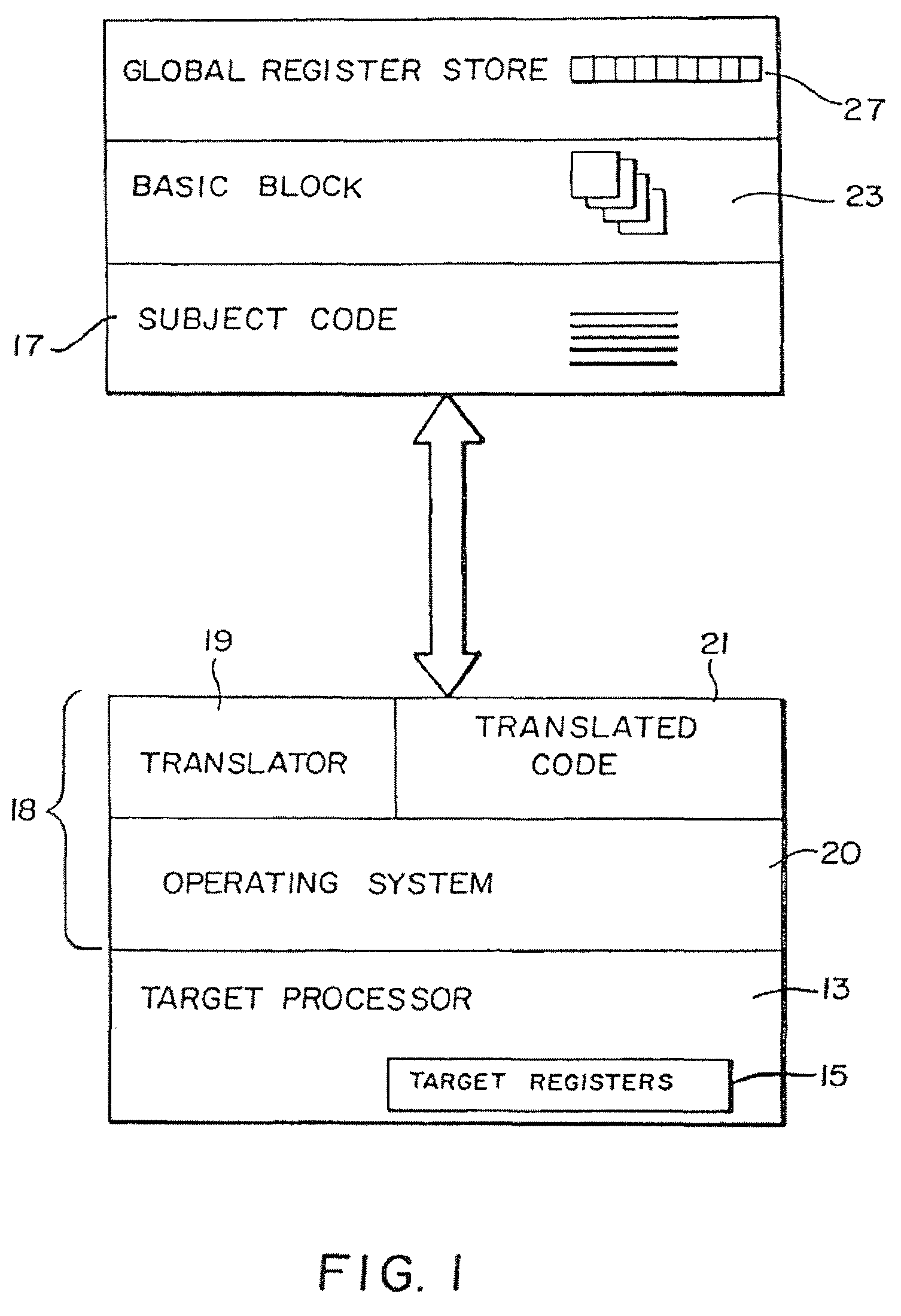
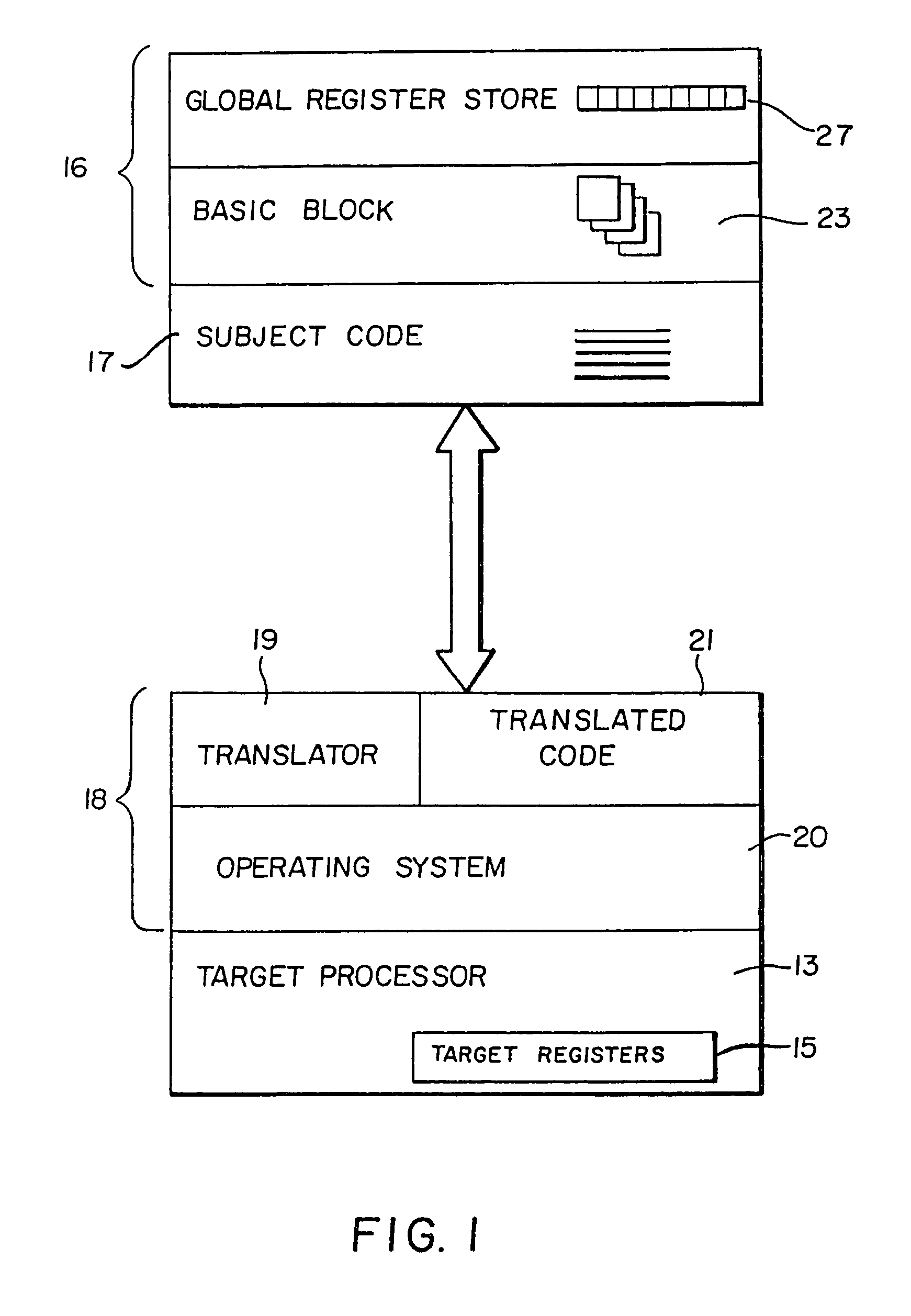
Method and apparatus of streaming data transformation using code generator and translator
InactiveUS20050273772A1Promote generationStay flexibleNatural language data processingMultiple digital computer combinationsStreaming dataObject code
A high level transformation method and apparatus for converting data formats in the context of network applications, among other places. A flexible transformation mechanism is provided that facilitates generation of translation machine code. A translator is dynamically generated by a translator compiler engine. When fed an input stream, the translator generates an output stream by executing the native object code generated on the fly by the translator compiler engine. In addition, the translator may be configured to perform a bi-directional translation between the two streams as well as translation between two distinct protocol sequences. Further a translator may working in streaming mode, to facilitate streaming processing of documents.
Owner:IBM CORP
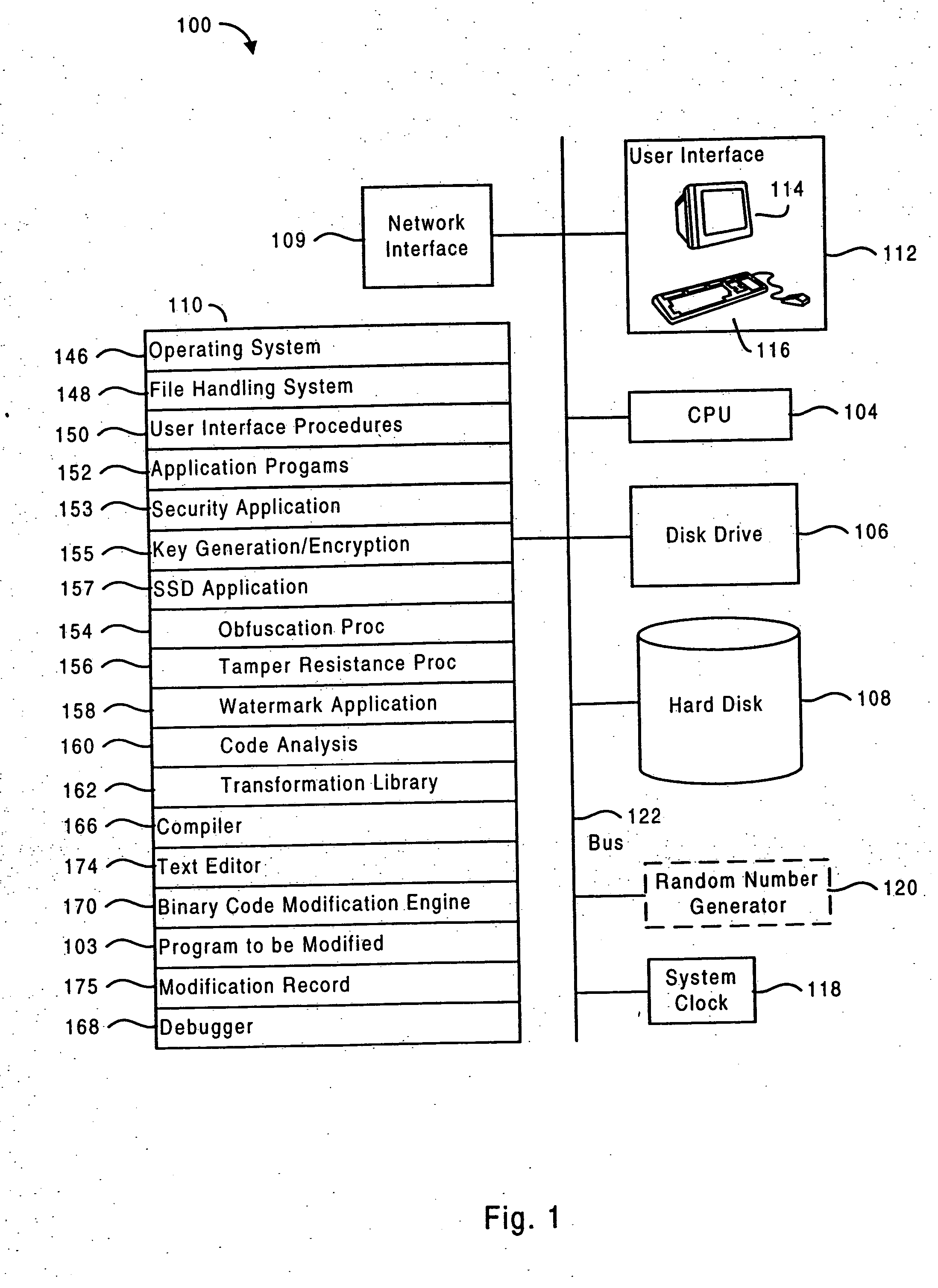
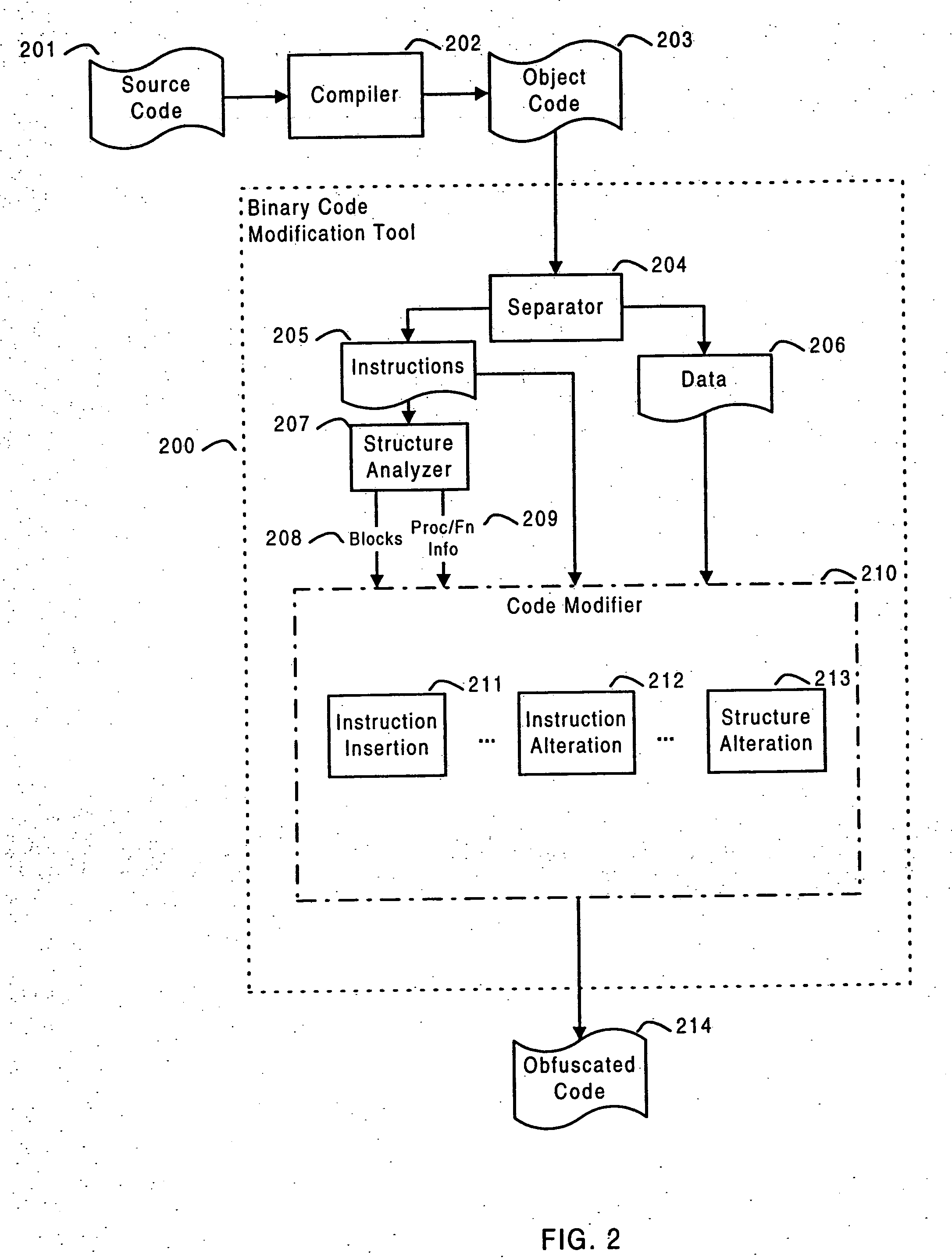
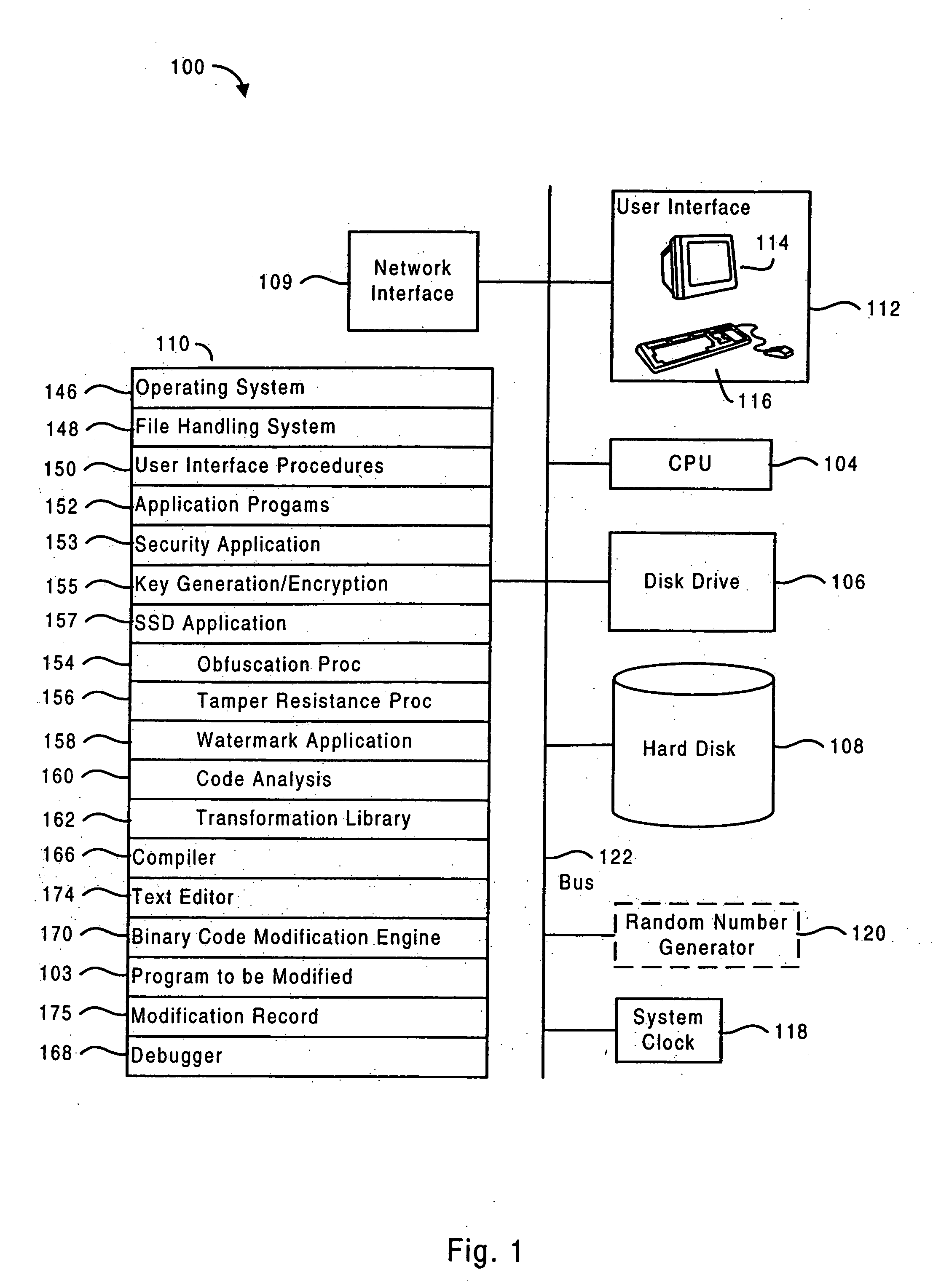
Software self-defense systems and methods
ActiveUS20050183072A1Error detection/correctionProgram/content distribution protectionTamper resistanceObfuscation
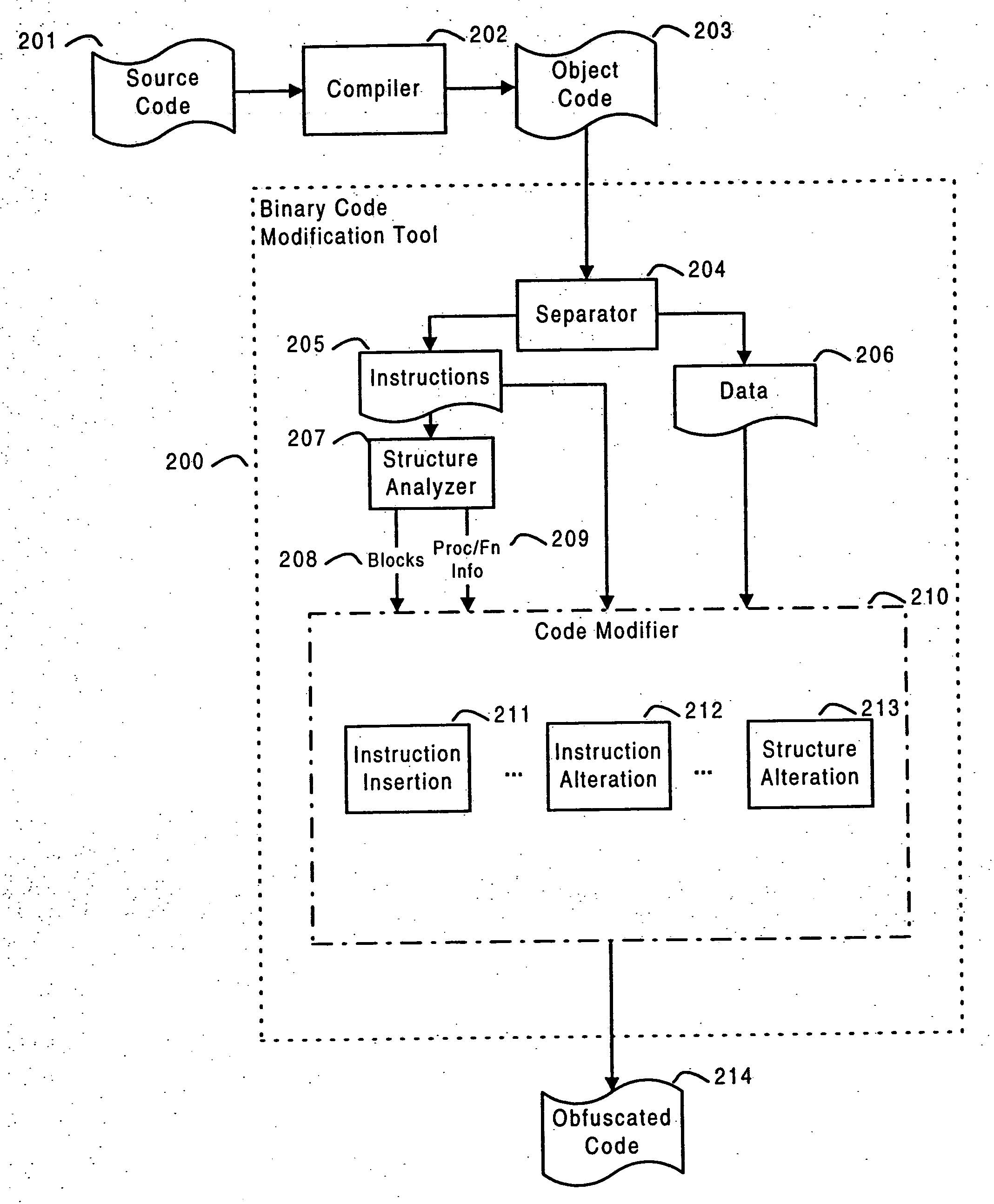
Systems and methods are disclosed for protecting a computer program from unauthorized analysis and modification. Obfuscation transformations can be applied to the computer program's local structure, control graph, and / or data structure to render the program more difficult to understand and / or modify. Tamper-resistance mechanisms can be incorporated into the computer program to detect attempts to tamper with the program's operation. Once an attempt to tamper with the computer program is detected, the computer program reports it to an external agent, ceases normal operation, and / or reverses any modifications made by the attempted tampering. The computer program can also be watermarked to facilitate identification of its owner. The obfuscation, tamper-resistance, and watermarking transformations can be applied to the computer program's source code, object code, or executable image.
Owner:INTERTRUST TECH CORP
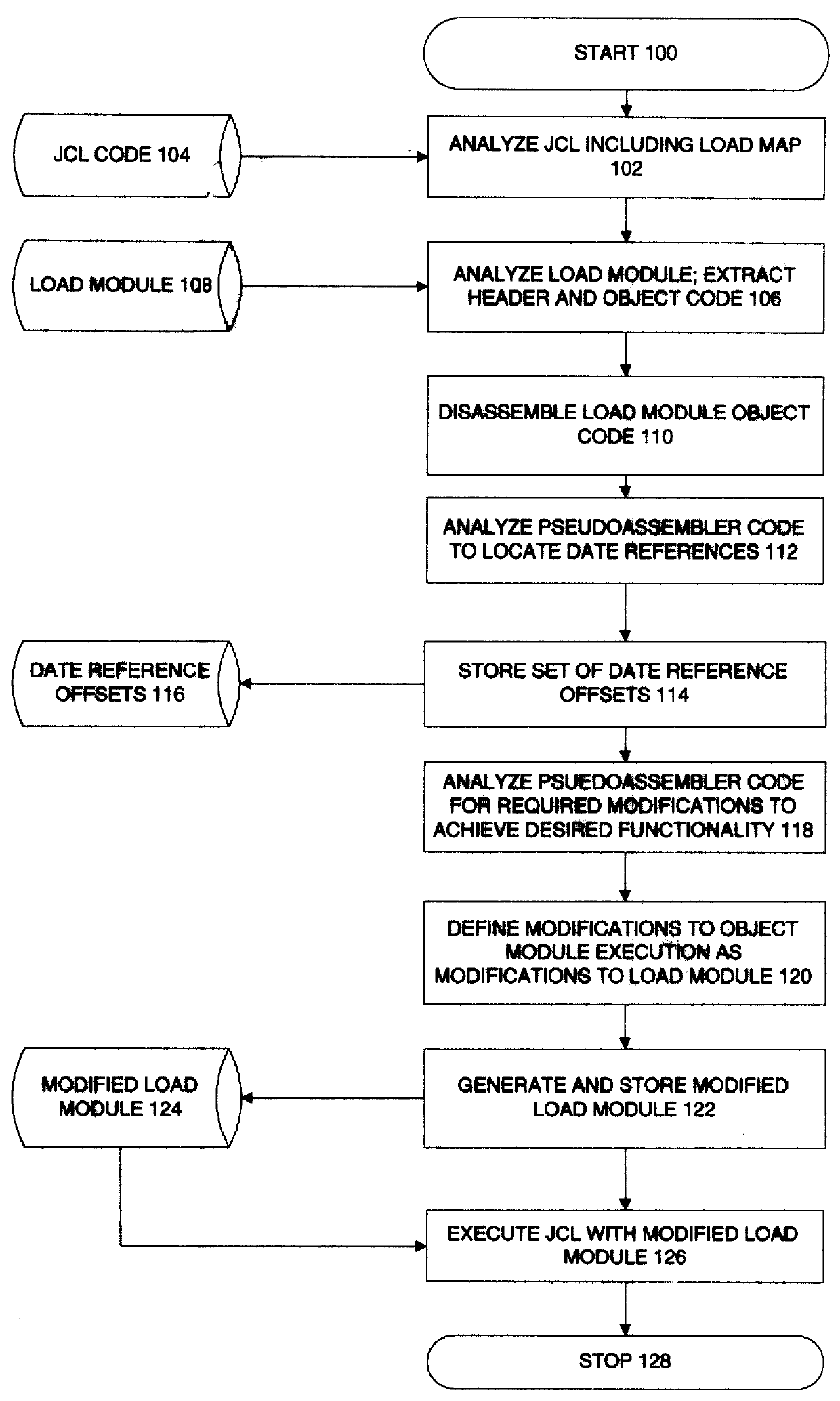
Object code logic analysis and automated modification system and method
InactiveUS6071317ALow costImprove automationSoftware maintainance/managementProgram loading/initiatingOperational systemObject code
A method and system for modifying computer program logic with respect to a predetermined aspect, comprising (a) before run time: analyzing compiled computer program logic of a module for processes involving the predetermined aspect before run time, substantially without decompilation or reference to computer program source code; and storing a set of modifications relating to computer program logic modifications of the module relating to the predetermined aspect; and (b) at run time: based on the stored set of modifications, selectively transferring program control from the module to a separate logical structure, executing modified logical operations with respect to the predetermined aspect, and subsequently returning program control to the module. The predetermined aspect may be, for example, a data type, algorithm type, or interface specification. In a preferred embodiment, the predetermined aspect is date related data, and more particularly, to logical operations relating to date related data which are flawed. The system preferably operates in a mainframe environment, wherein the compiled computer program constitutes one or more load modules, executing under an operating system, wherein the computer program logic modifications preferably comprise program flow control diversions in an original object module, which selectively transfer logical control to a separate object module to effect modifications to the computer program logic, followed by a return of control to the original object module.
Owner:HANGER SOLUTIONS LLC +1
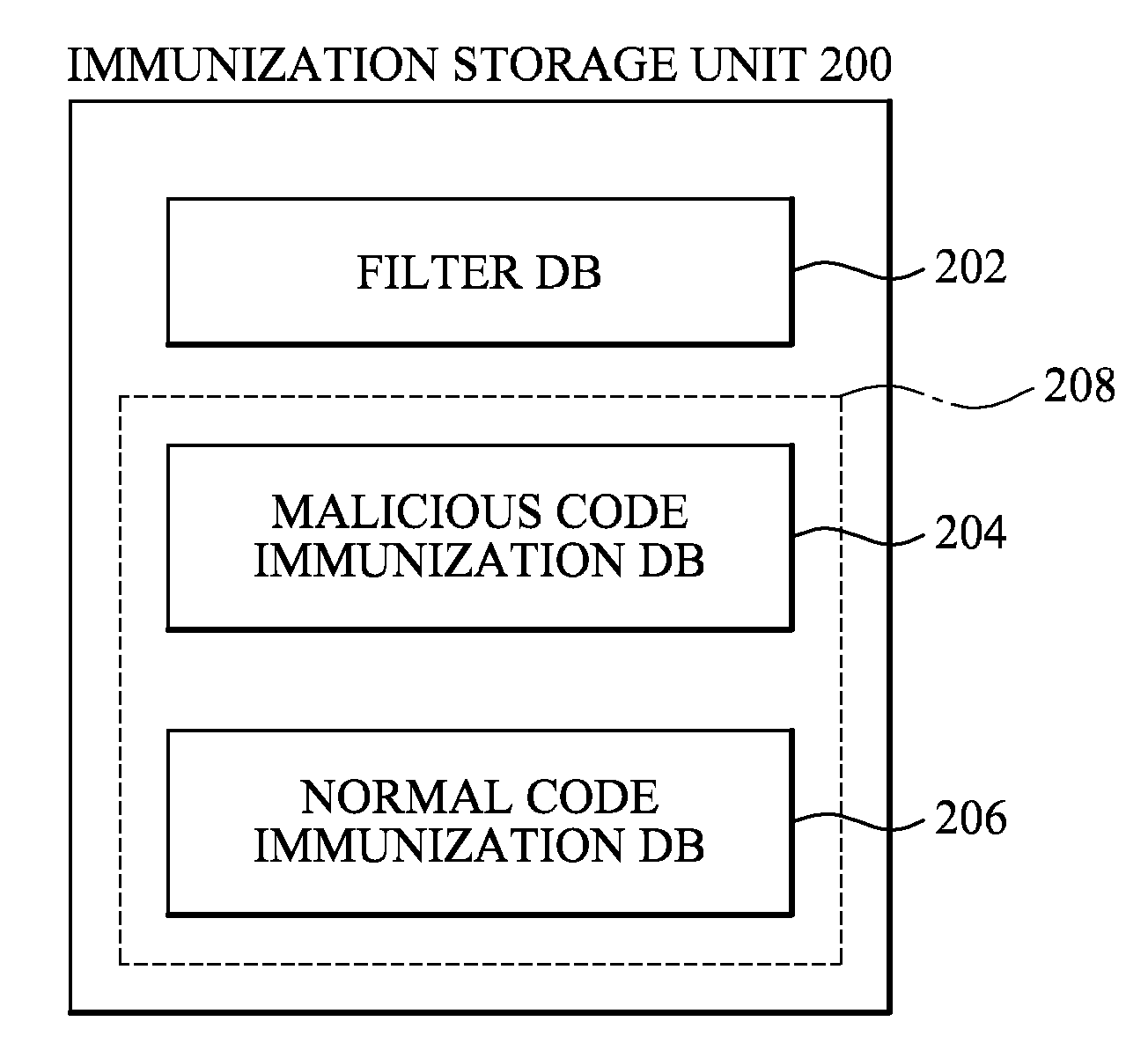
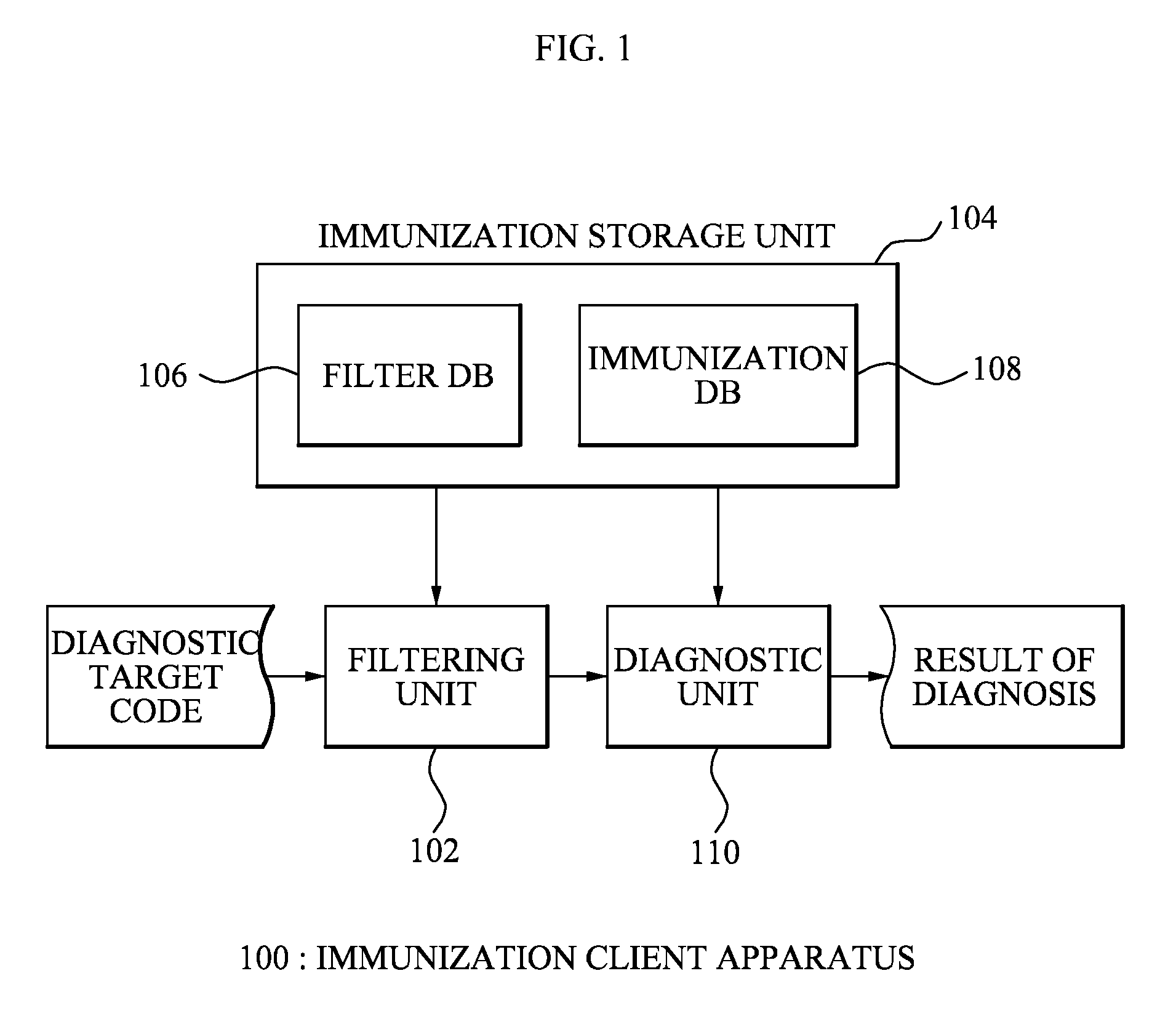
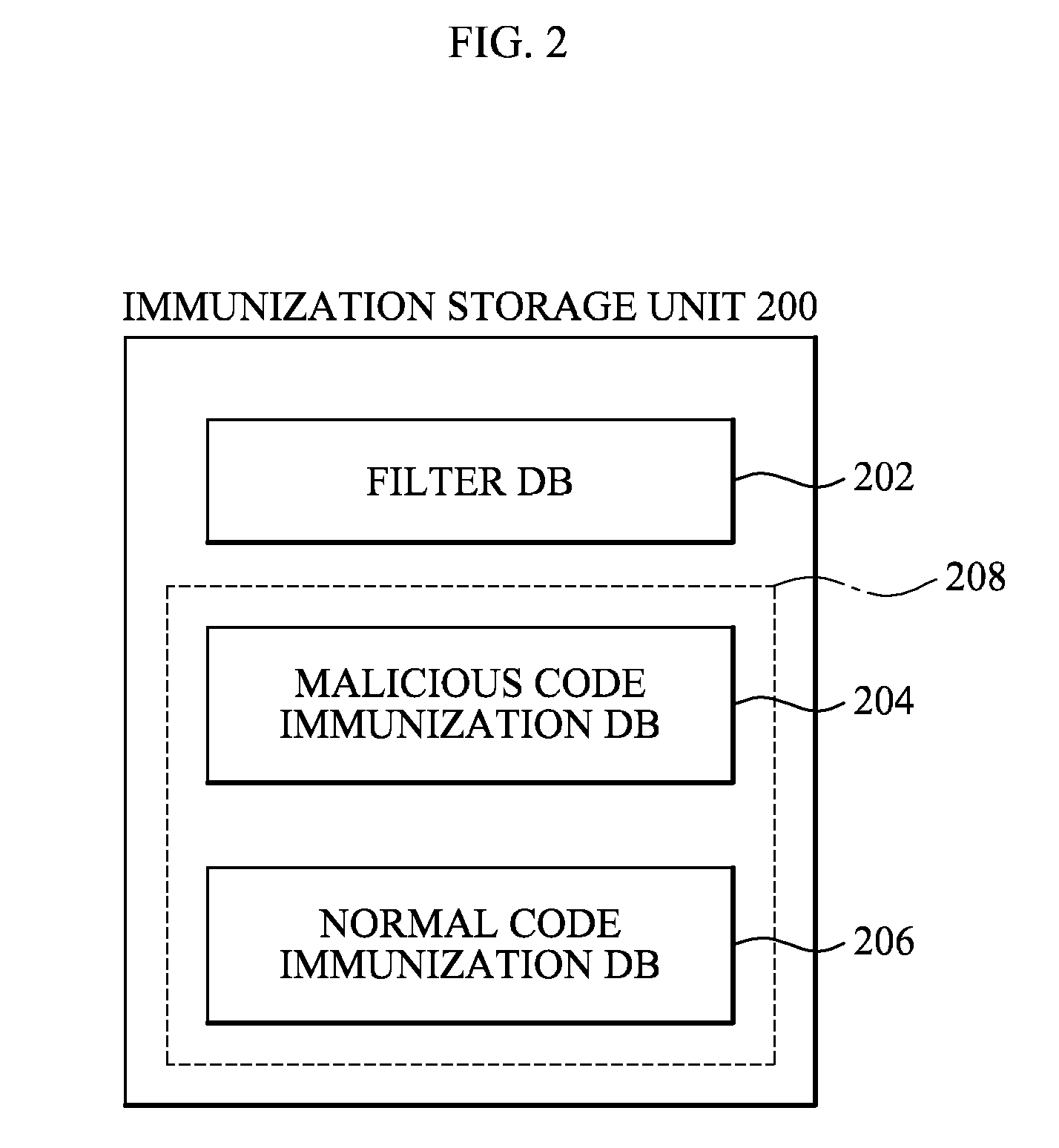
System, apparatus and method of malware diagnosis mechanism based on immunization database
ActiveUS8464340B2Small sizeShorten operation timeMemory loss protectionError detection/correctionObject codeMalware
An immunization system including: an immunization client apparatus which determines whether a target code is a malicious code by performing an immunization operation with respect to a first immunization signature and a code signature that is extracted from the target code and reports the result of the determination to an immunization server; and the immunization server which diagnoses whether the target code is the malicious code, updates a second immunization signature based on the reported result of the determination, and transmits to the immunization client apparatus an update message about the updated second immunization signature, wherein the immunization client apparatus updates the first immunization signature based on the received update message is provided.
Owner:SAMSUNG ELECTRONICS CO LTD
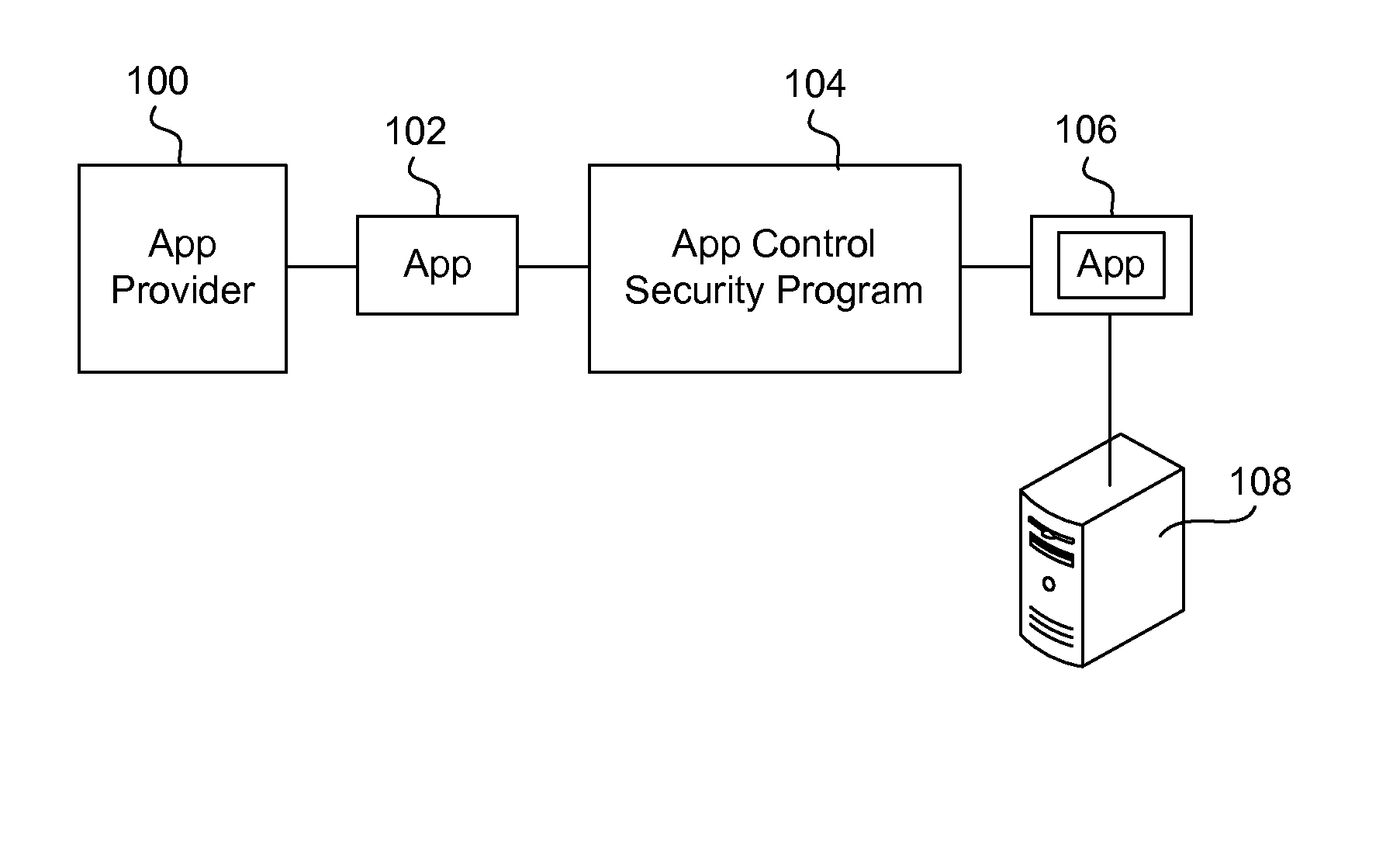
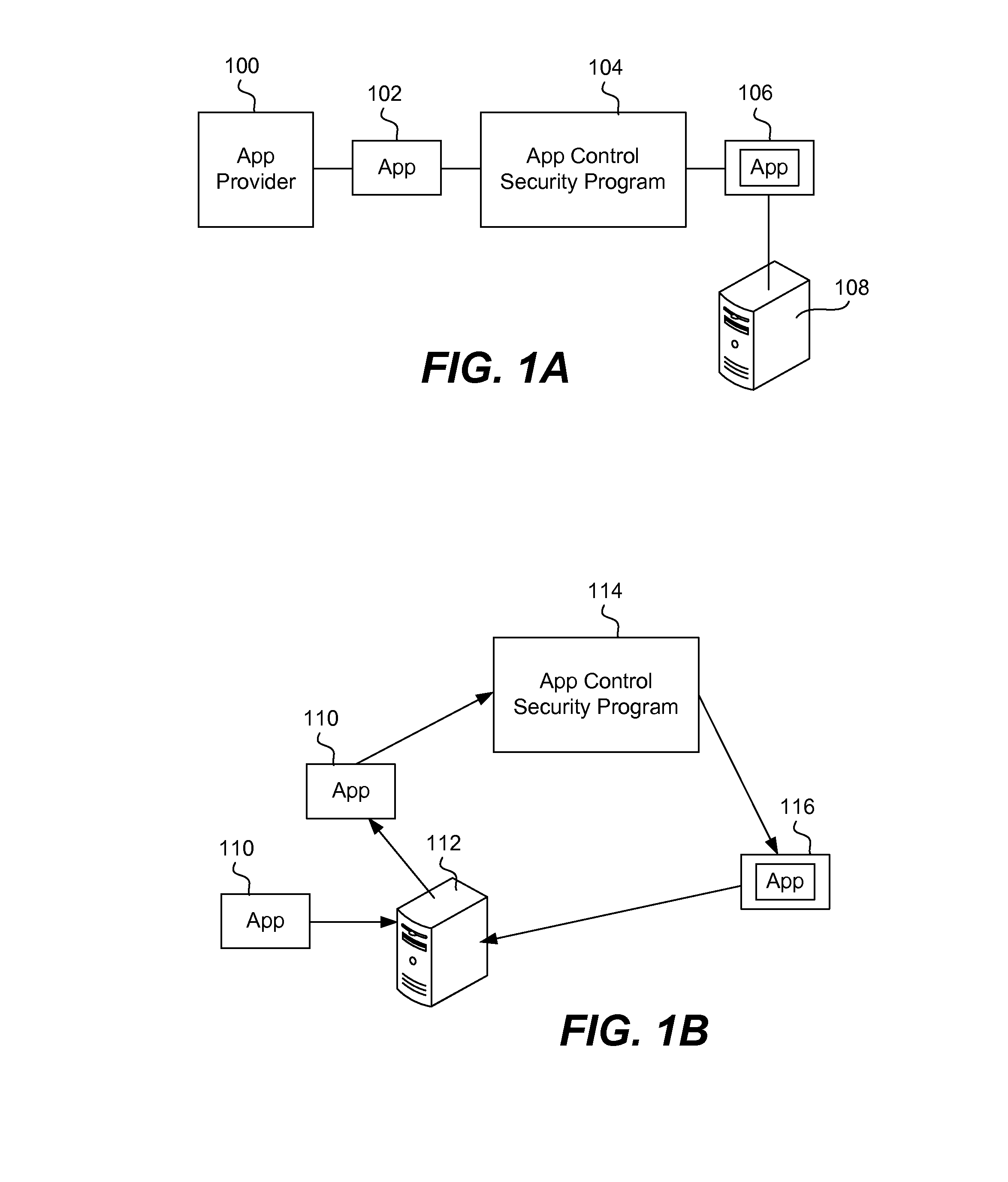
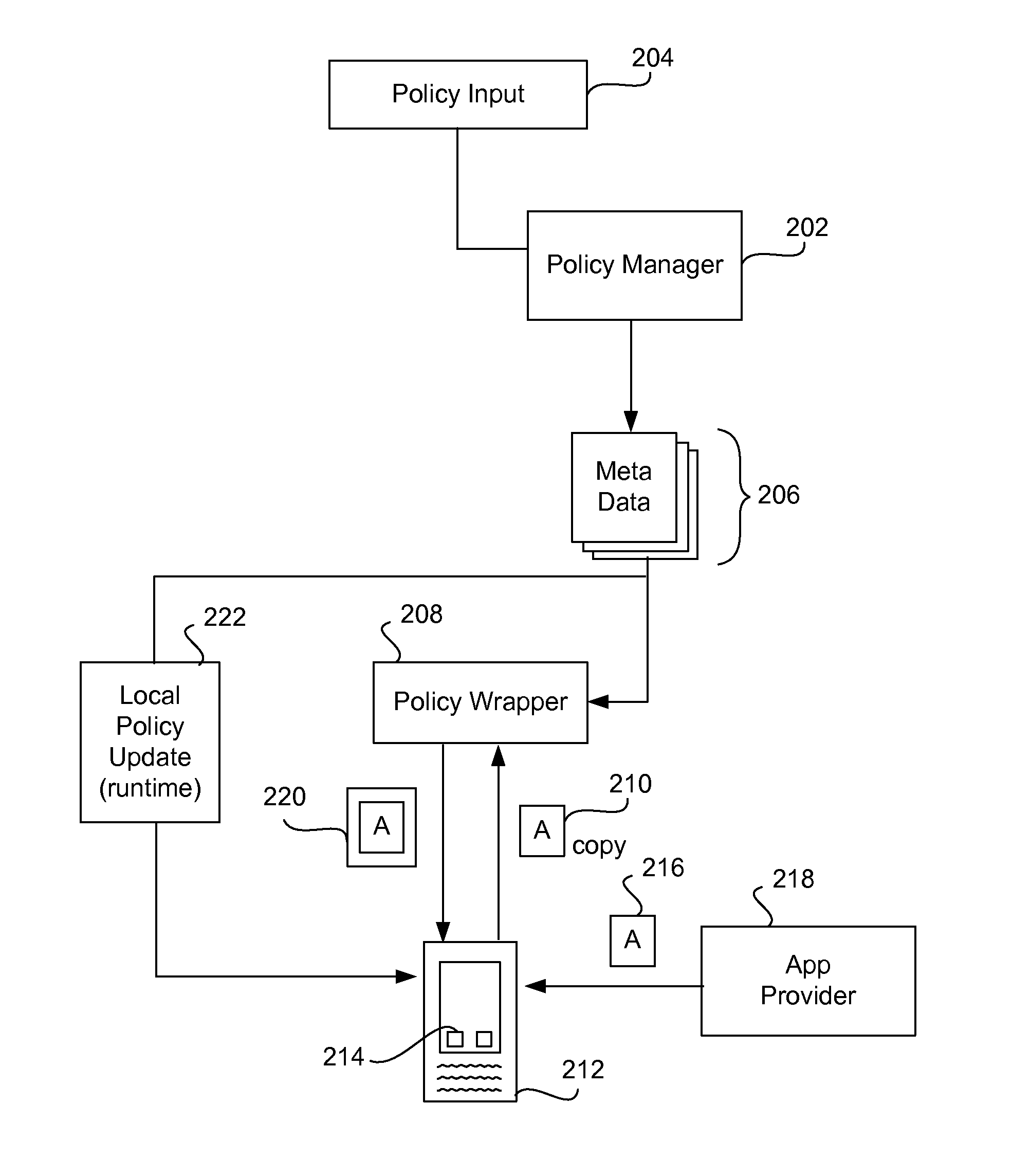
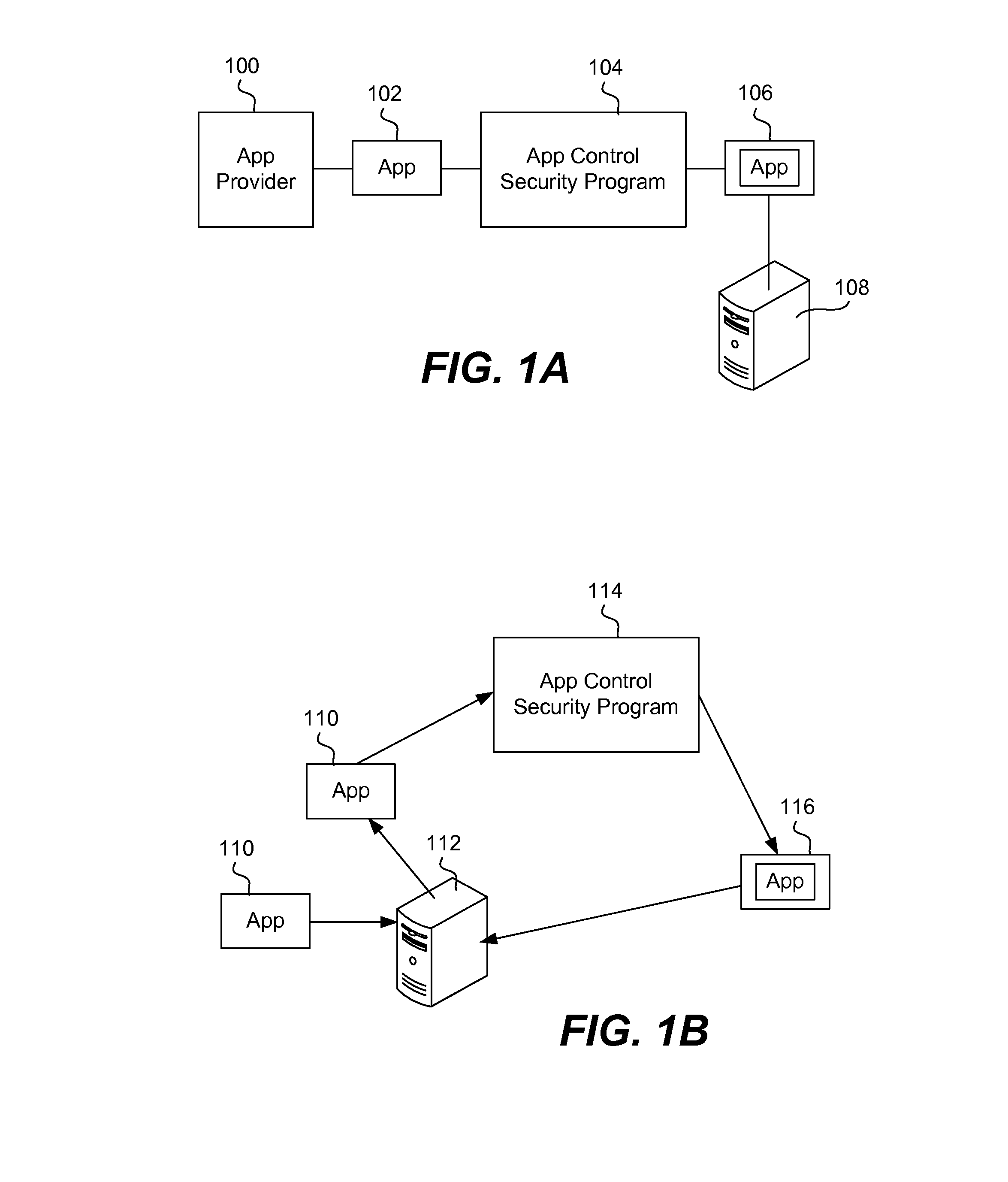
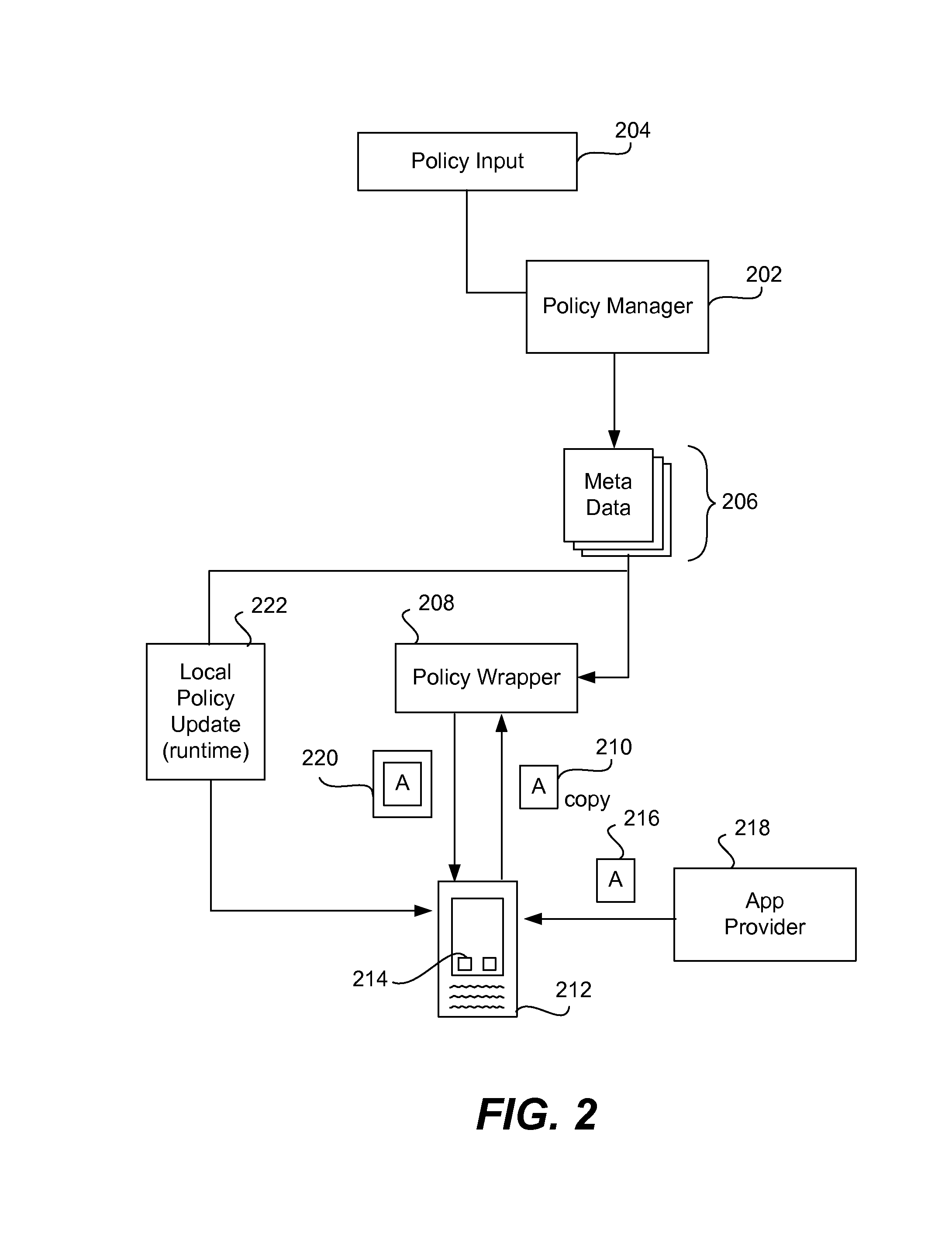
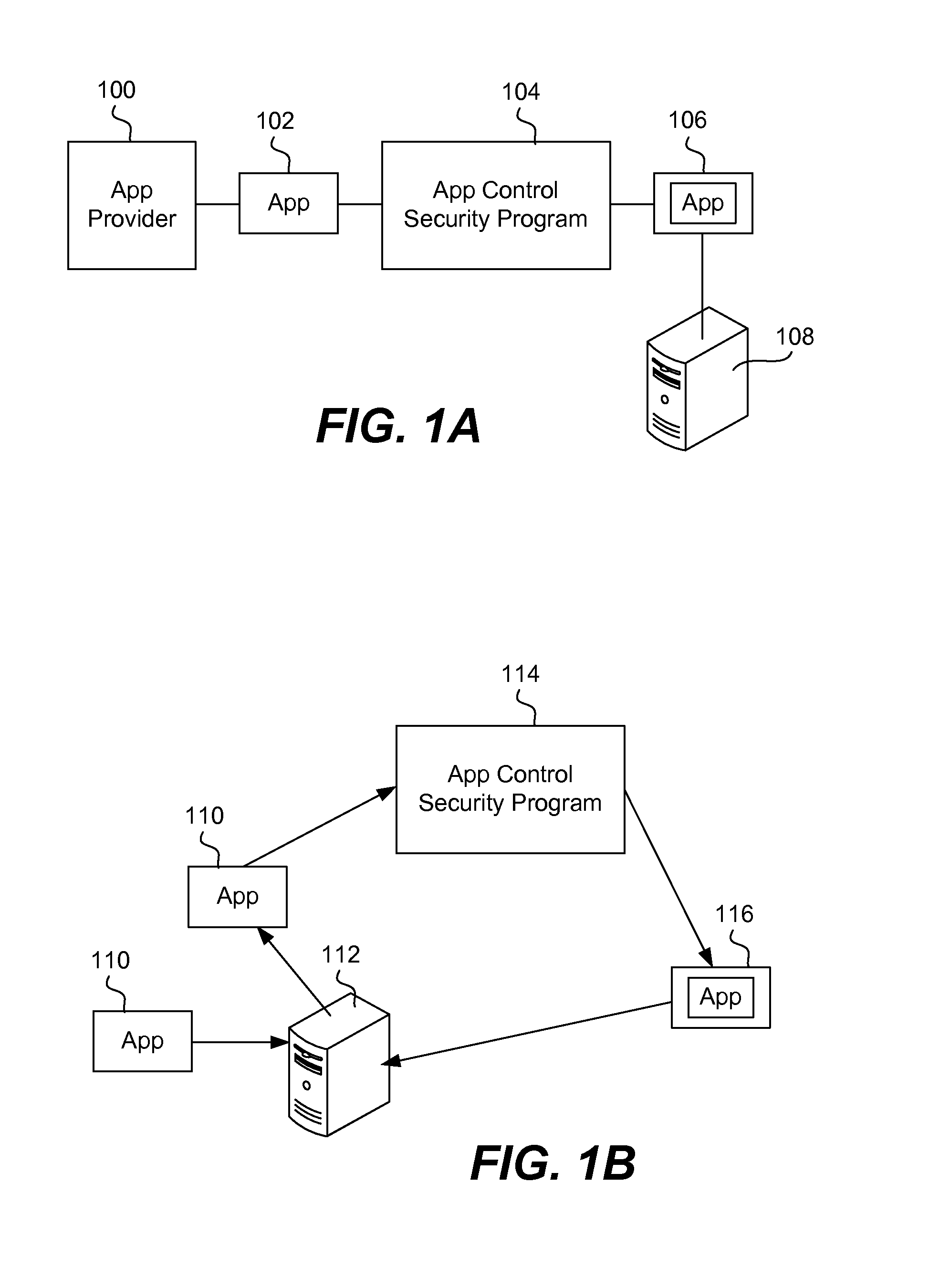
Securing and managing apps on a device
ActiveUS20120210443A1Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Method and apparatus of streaming data transformation using code generator and translator
InactiveUS7590644B2Promote generationStay flexibleDigital data processing detailsNatural language data processingStreaming dataObject code
A high level transformation method and apparatus for converting data formats in the context of network applications, among other places. A flexible transformation mechanism is provided that facilitates generation of translation machine code. A translator is dynamically generated by a translator compiler engine. When fed an input stream, the translator generates an output stream by executing the native object code generated on the fly by the translator compiler engine. In addition, the translator may be configured to perform a bi-directional translation between the two streams as well as translation between two distinct protocol sequences. Further a translator may working in streaming mode, to facilitate streaming processing of documents.
Owner:INT BUSINESS MASCH CORP
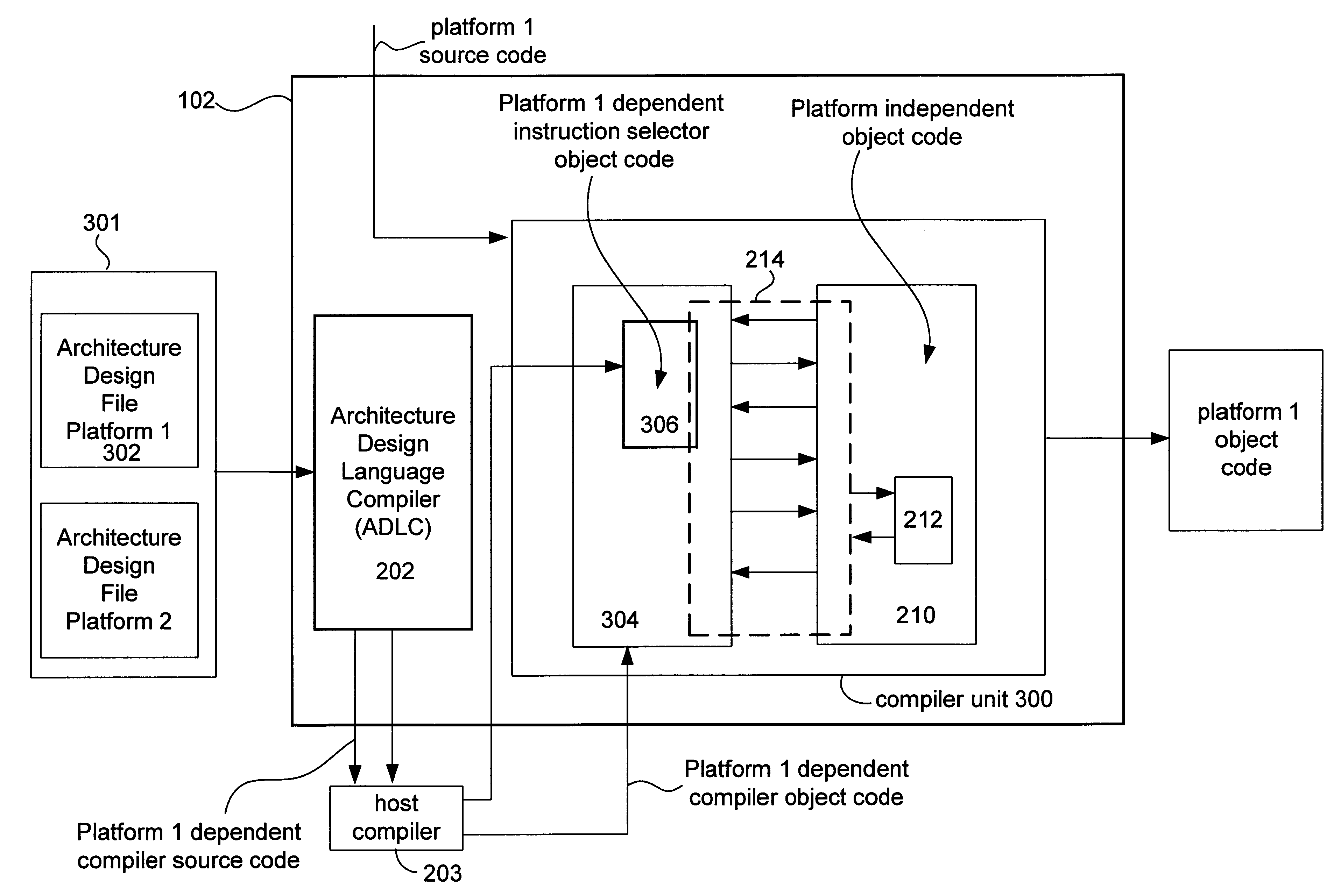
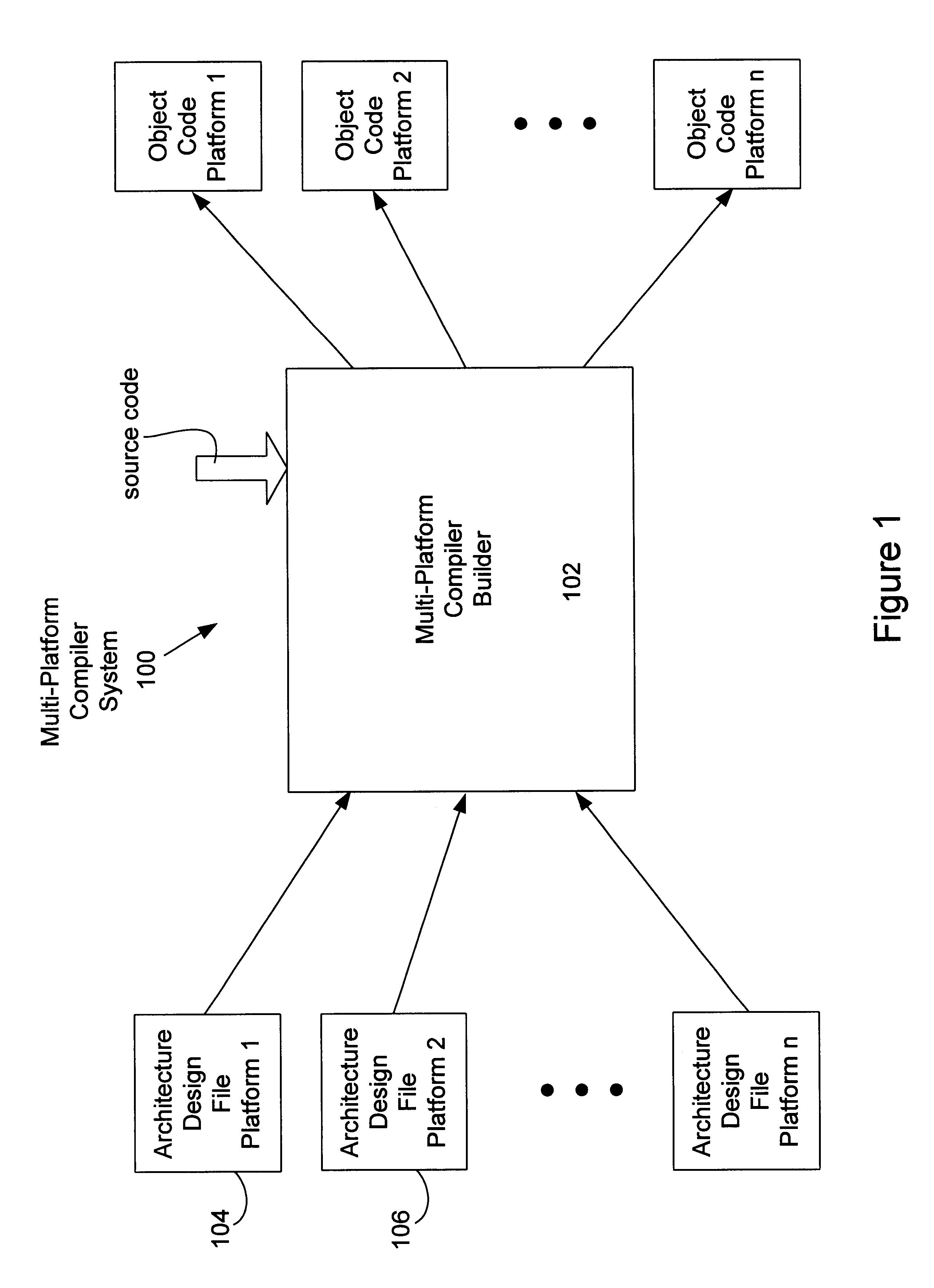
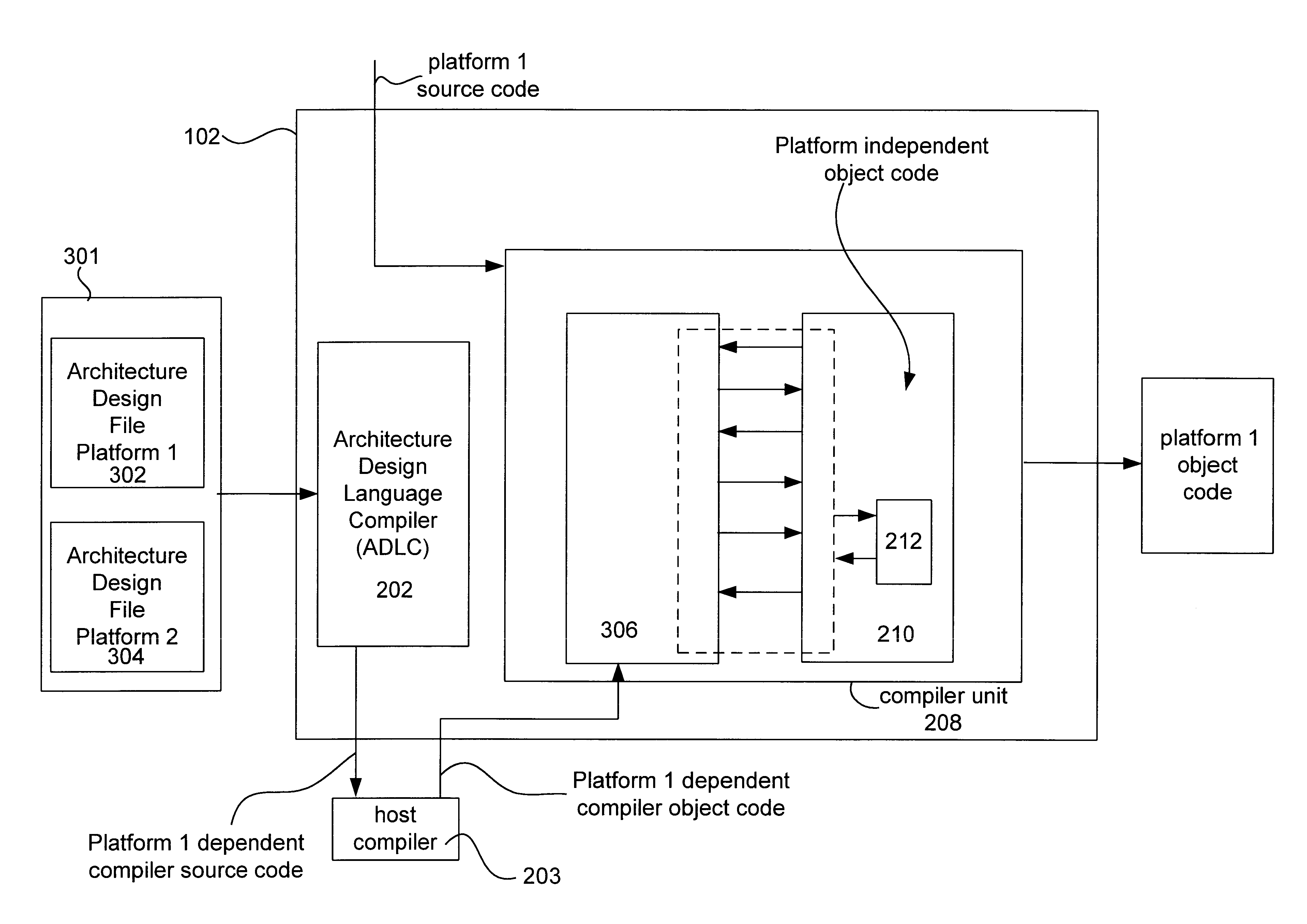
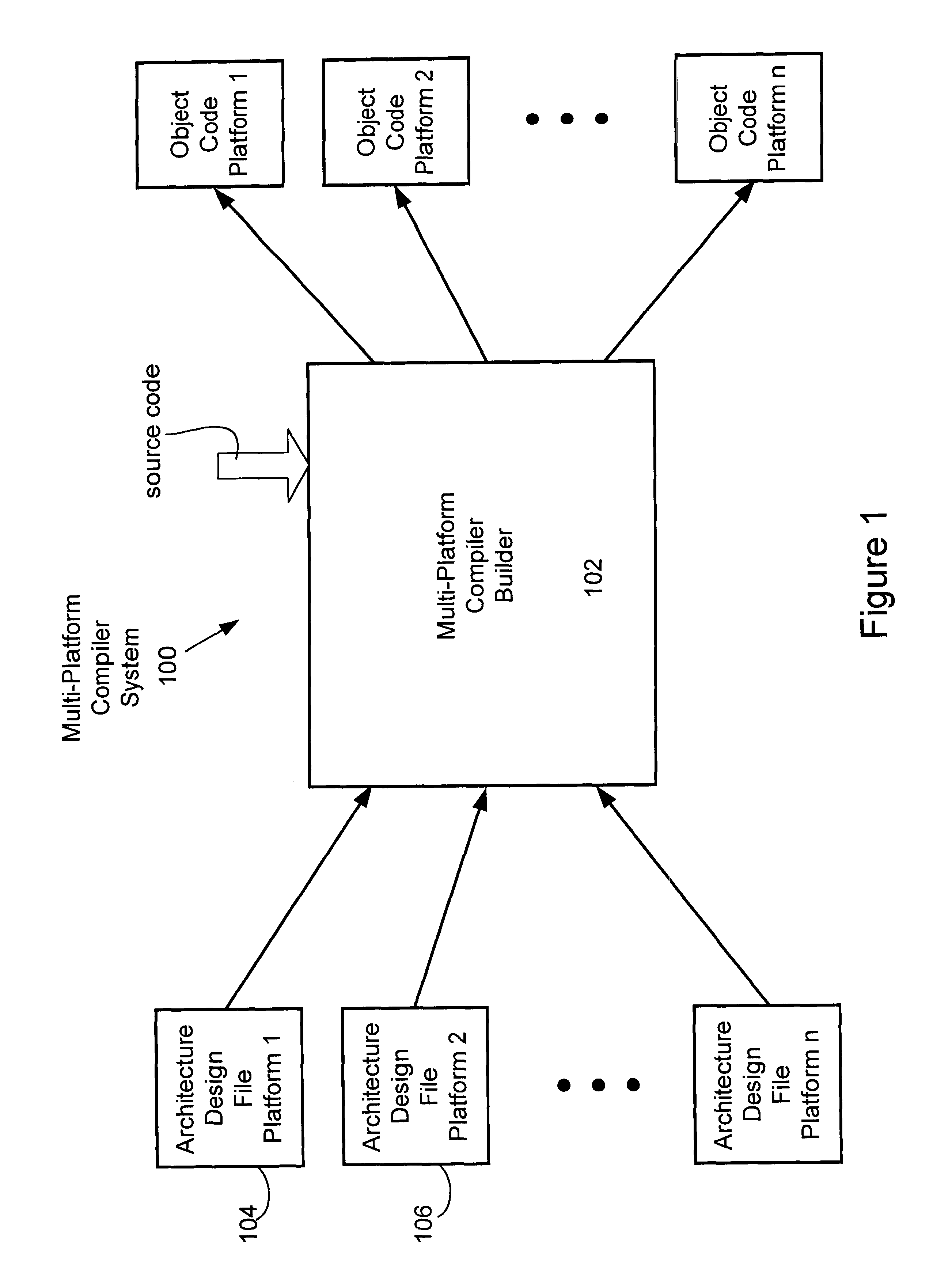
Instruction selection in a multi-platform environment
Systems and methods for building a platform specific compiler having an embedded instruction selector in a multi-platform environment are provided. A set of user defined platform dependent compiler architecture descriptors that describe corresponding architectural features and a set of instruction predicates defining those instructions to be selected are converted to platform dependent compiler object code and instruction selector object code, respectively. The platform specific compiler having the embedded instruction selector is formed from the platform dependent compiler object code, the instruction selector object code, and the platform independent compiler object code.
Owner:ORACLE INT CORP
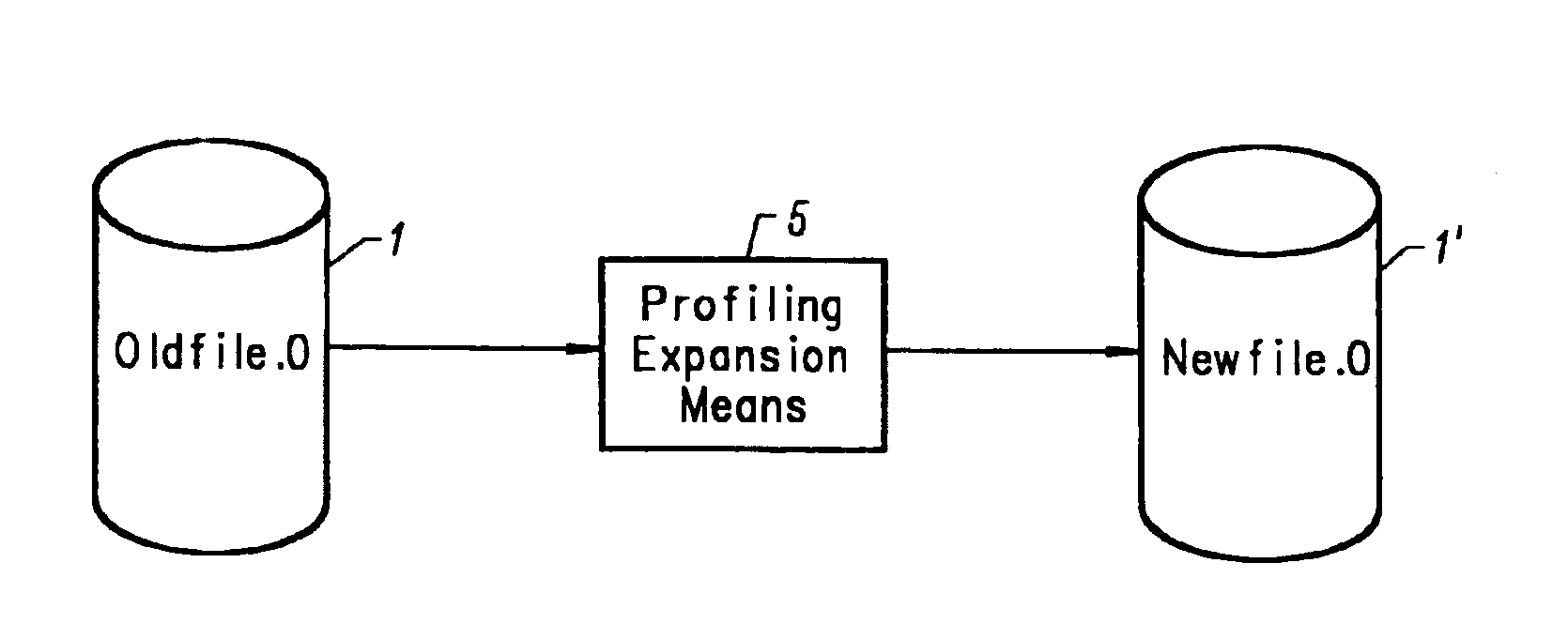
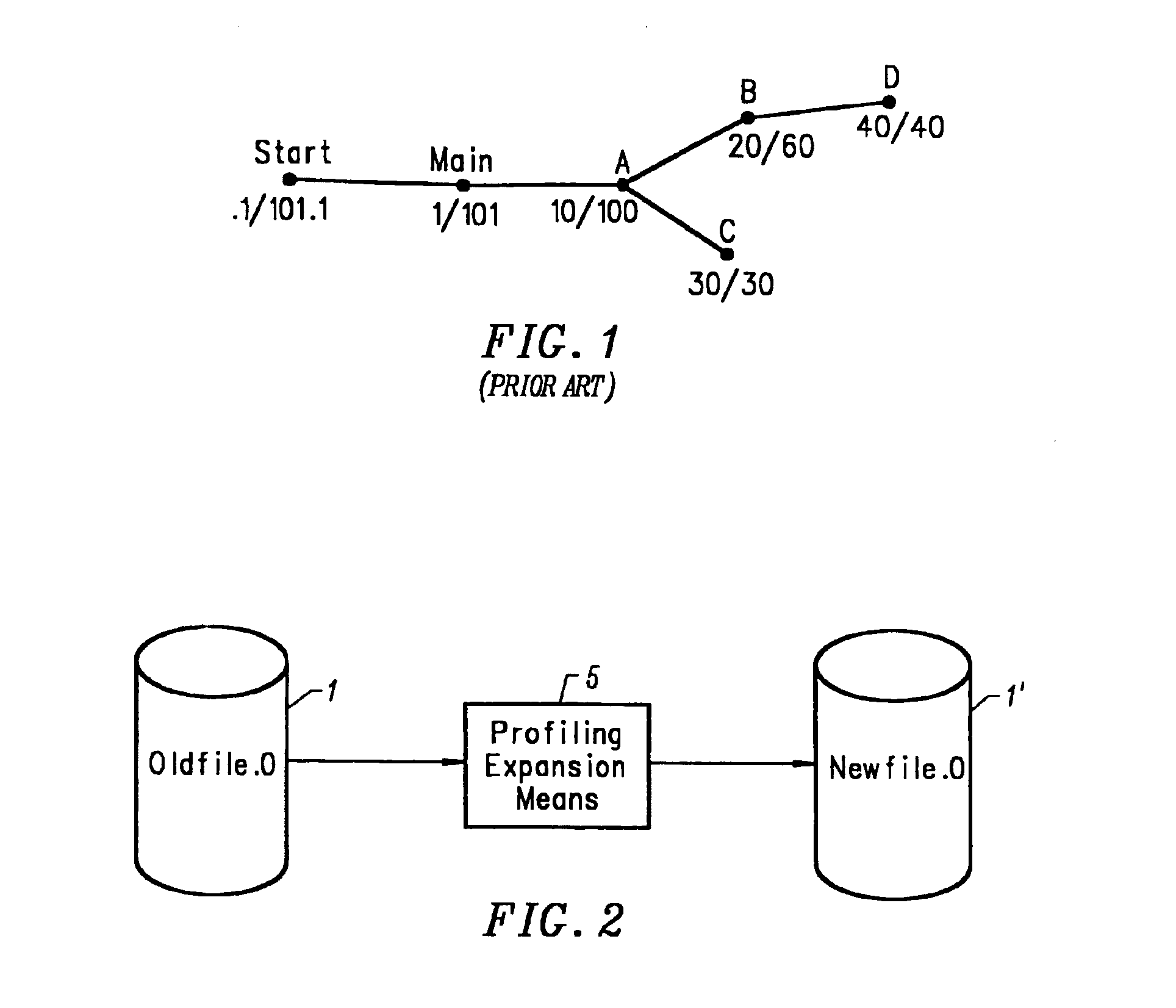
Method and apparatus for accurate profiling of computer programs
InactiveUS6934935B1Precise maintenanceHardware monitoringMultiprogramming arrangementsGraphicsOperational system
An object code expansion profiler equips a program for execution profiling by preprocessing the object code files of the program so as to add profiling monitoring code to the beginning of all or substantially all functions. The preprocessing includes, for each function, the steps of grouping the function's instructions into basic blocks, counting the number of cycles required to execute the instructions of the basic block, and inserting special monitoring code with the basic block. The special monitoring code is executed each time the basic block is executed, and updates the profiling information to reflect the number of cycles required to execute the basic block. Special handling is provided for profiling calls to the Operating System (OS). The resultant profiling information is converted into a call graph image most useful for human users. For each arc in the graph connecting a calling-function / parent-node to a called-function / child node, the displayed arc image has a width logarithmically proportional to the self+descendants time for the called function.
Owner:IBM CORP
Securing and managing apps on a device
ActiveUS8549656B2Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Software self-defense systems and methods
ActiveUS20050204348A1Error detection/correctionProgram/content distribution protectionTamper resistanceObfuscation
Systems and methods are disclosed for protecting a computer program from unauthorized analysis and modification. Obfuscation transformations can be applied to the computer program's local structure, control graph, and / or data structure to render the program more difficult to understand and / or modify. Tamper-resistance mechanisms can be incorporated into the computer program to detect attempts to tamper with the program's operation. Once an attempt to tamper with the computer program is detected, the computer program reports it to an external agent, ceases normal operation, and / or reverses any modifications made by the attempted tampering. The computer program can also be watermarked to facilitate identification of its owner. The obfuscation, tamper-resistance, and watermarking transformations can be applied to the computer program's source code, object code, or executable image.
Owner:INTERTRUST TECH CORP
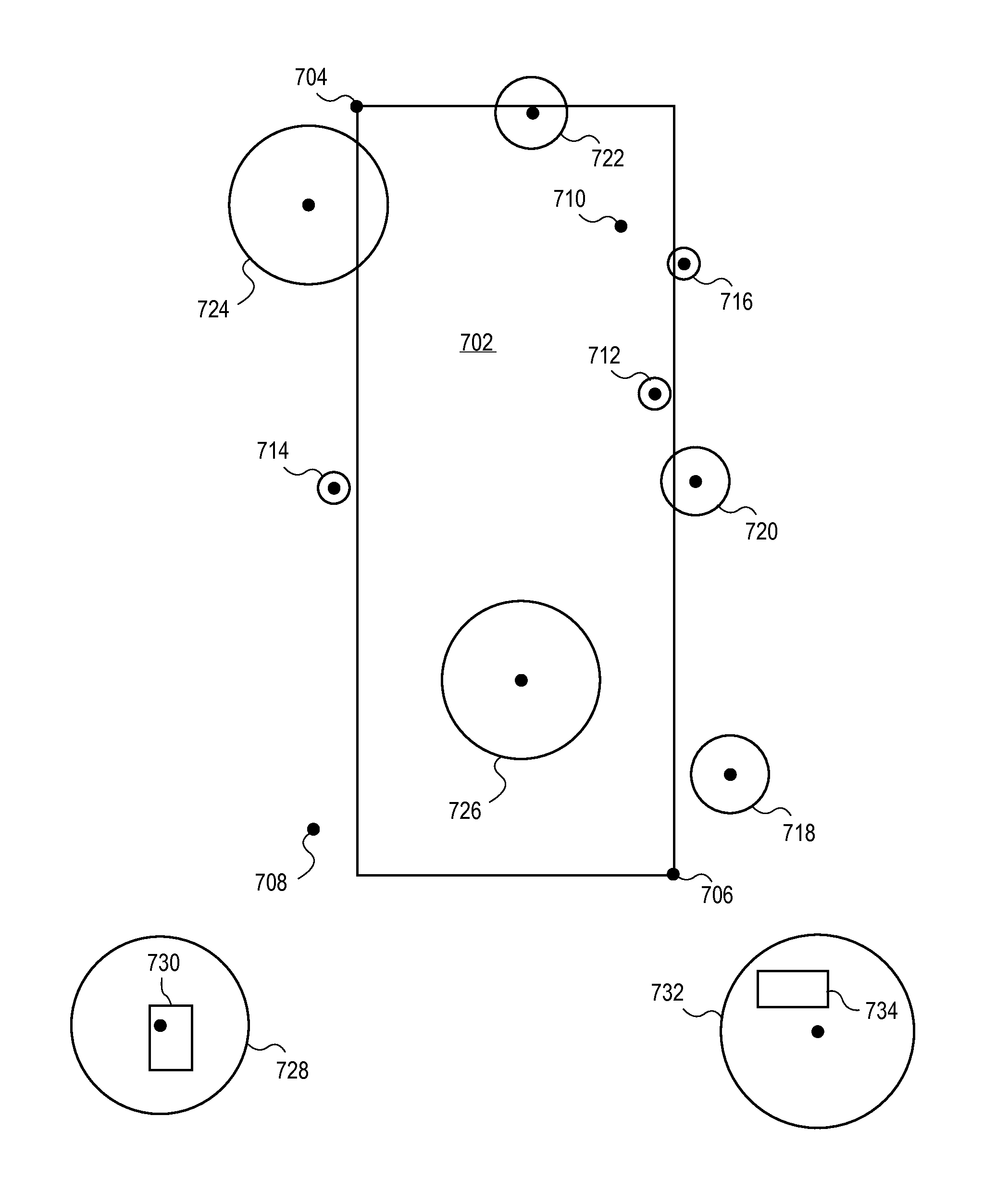
Geographical restrictions for application usage on a mobile device
ActiveUS20140208397A1Digital data processing detailsComputer security arrangementsOperational systemObject code
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smart phone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. App object code is substituted with security program object code, thereby creating a security-wrapped app. The app is provisioned with a geo-fencing policy which prevents execution of an app outside a pre-defined geographical area. If the device is within the defined area, the app is allowed to execute. The geographical area, such as a building or company campus, is defined using longitude and latitude coordinates and a location accuracy value. Device location is obtained using location / GPS services on the device.
Owner:BLUE CEDAR NETWORKS INC
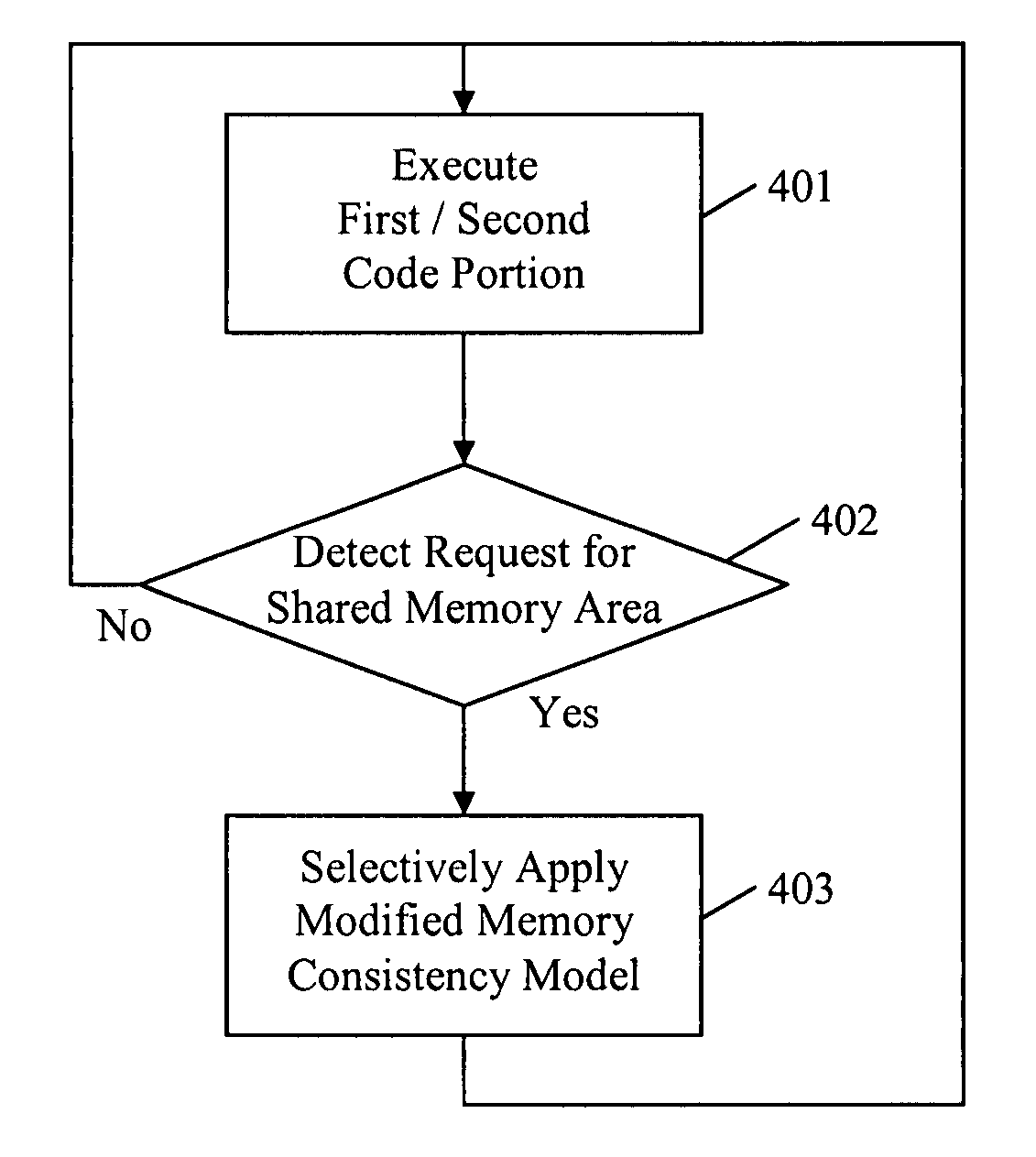
Memory consistency protection in a multiprocessor computing system
InactiveUS20080140971A1Low-cost and effectiveImproved memory consistencyResource allocationMemory adressing/allocation/relocationMulti processorObject code
A method and apparatus to protect memory consistency in a multiprocessor computing system are described, in particular relating to program code conversion such as dynamic binary translation. The exemplary system provides a memory, processors and a controller / translator unit (CTU) arranged to convert subject code into at least first and second target code portions executable on the processors. The CTU comprises an address space allocation unit to provide virtual address space regions and direct the target code portions to access the memory therethough; a shared memory detection unit to detect a request to access a shared memory area, accessible by both target code portions, and to identify at least one group of instructions in the first target code portion which access the shared memory area; and a memory protection unit to selectively apply memory consistency protection in relation to accesses to the shared memory area by the identified group of instructions.
Owner:IBM CORP
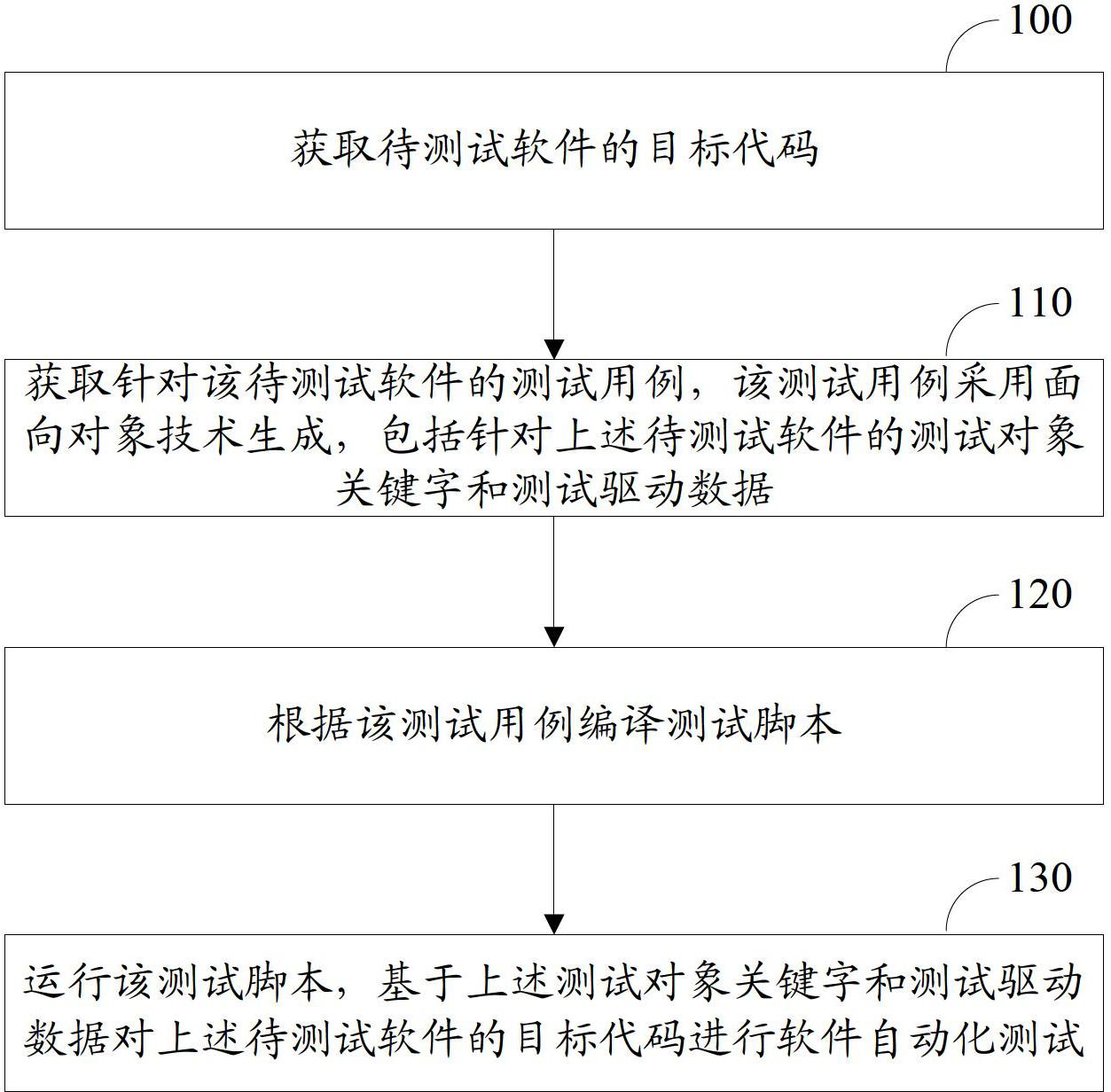
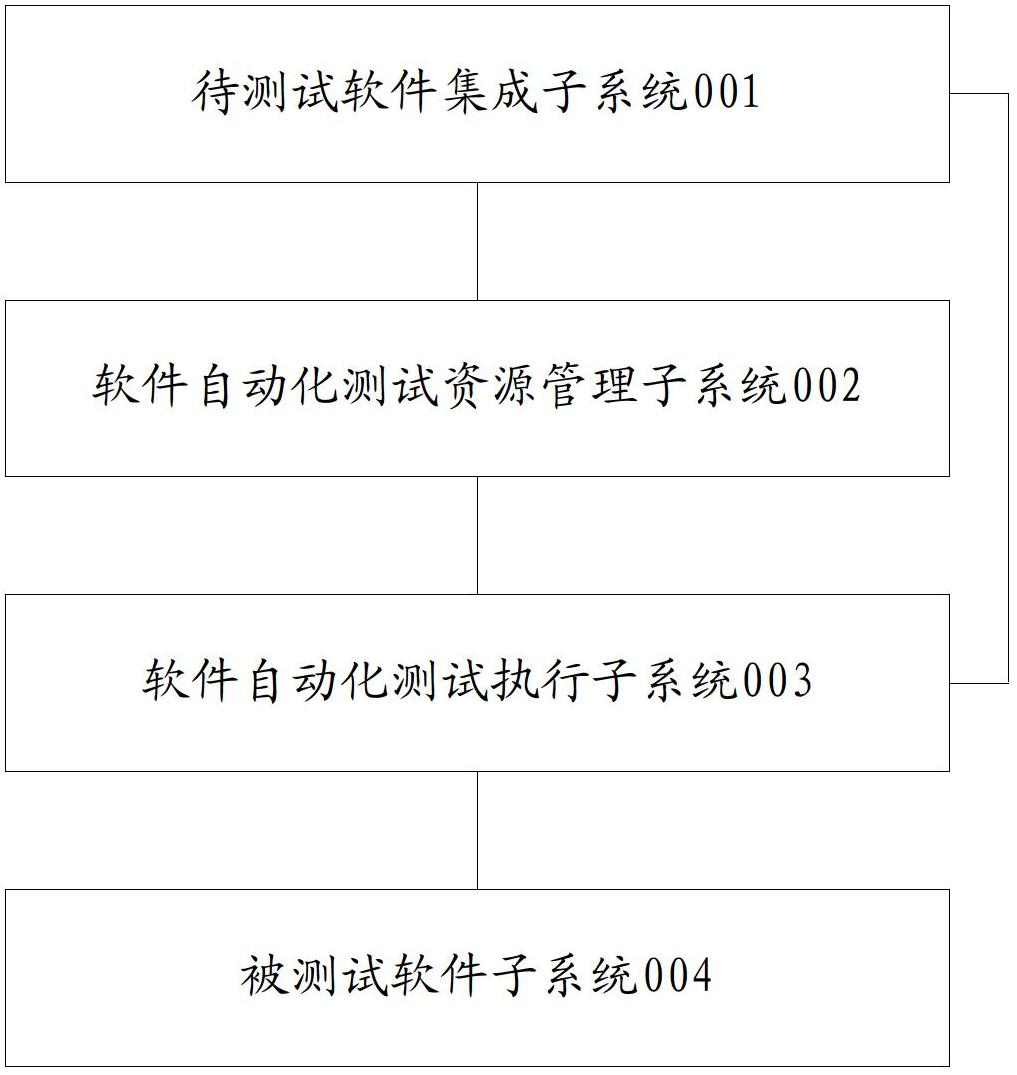
Method and system for realizing automatic software testing
ActiveCN102693183AImprove performanceImprove automated testingSoftware testing/debuggingTest scriptObject code
The invention discloses a method and a system for realizing automatic software testing. The method includes the following steps: obtaining the object code of the to-be-tested software; obtaining the test case for the to-be-tested software, wherein the test case is generated by adopting the oriented object technology and includes a test object key word and a test drive data for the to-be-tested software; compiling and saving the test script according to the test case; running the test script, so as to carry out the automatic software testing of the object code of the to-be-tested software based on the test object key word and the test drive data. By adopting the solution of automatic testing and utilizing the object oriented test case to carry out the automatic testing based on the assemblage of the test object key word and the test drive data, the automatic software testing can be realized without the participation of any operator, and the method and the system for realizing automatic software testing are applicable to all the stages of software testing.
Owner:RAISECOM TECH
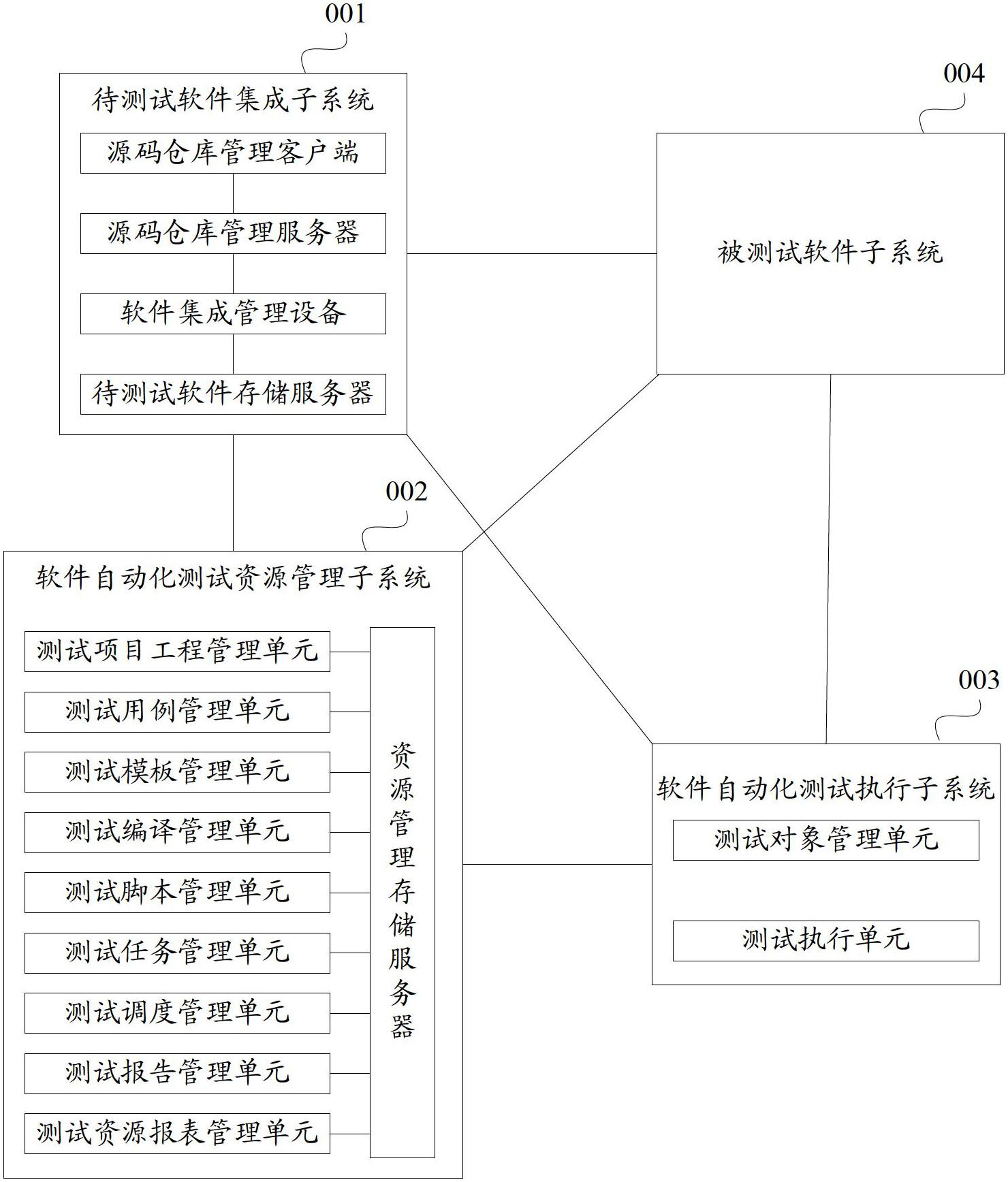
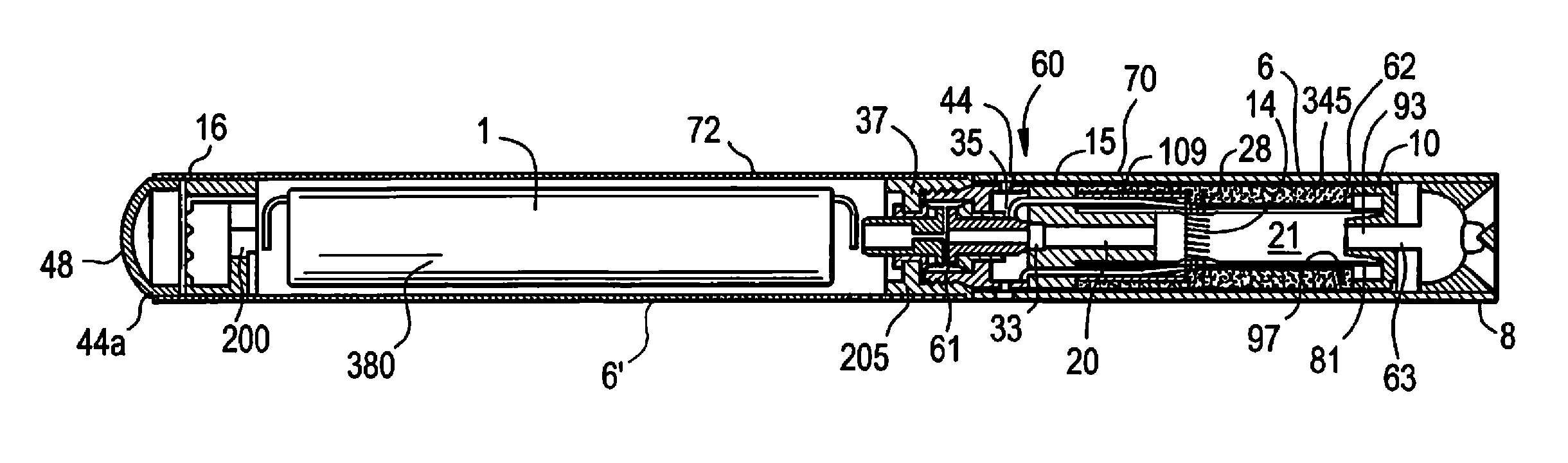
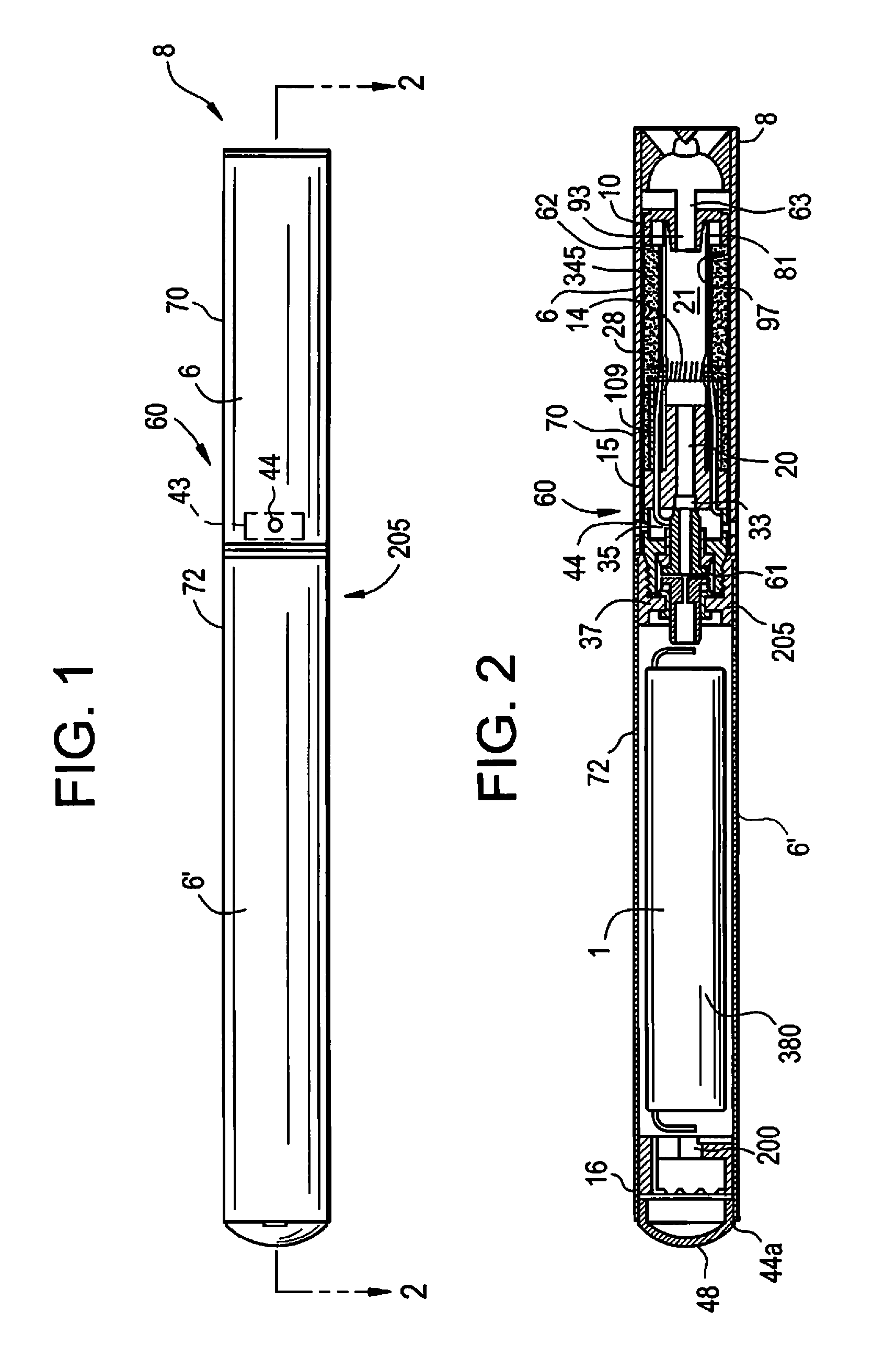
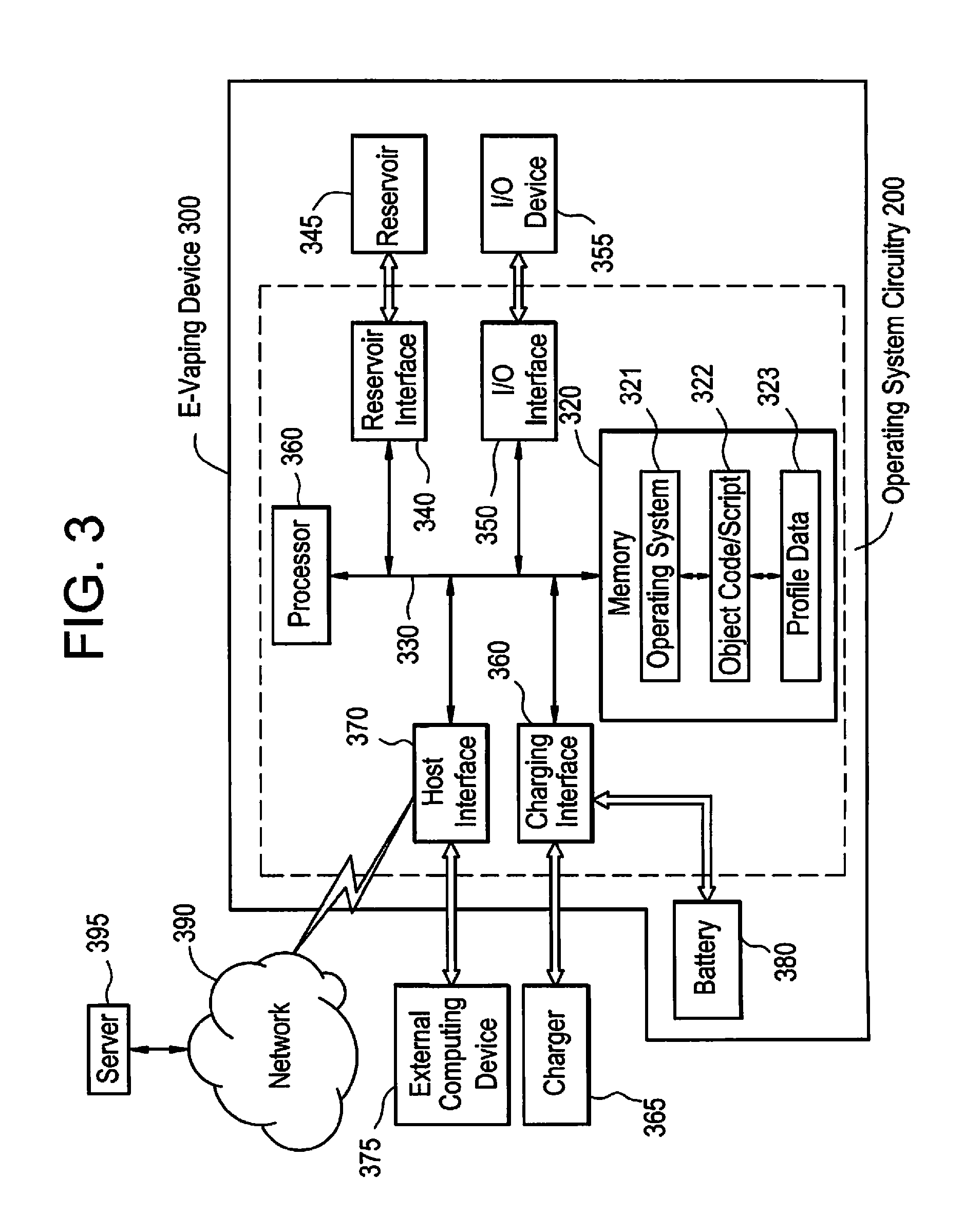
Method and device for executing an e-vaping device operating system, e-vaping programming language, and e-vaping application programming interface
ActiveUS20160143361A1Steam generation heating methodsTobacco devicesApplication programming interfaceObject code
An electronic vaping device includes a housing extending in a longitudinal direction, the housing including a mouth-end and a connection-end, a reservoir containing a pre-vapor formulation, the reservoir in the housing, a heating element in the housing, the heating element in fluid communication with the reservoir, the heating element configured to generate a vapor, and a rechargeable battery configured to power at least the heating element and any other potential power consuming element(s) such as electronic circuits. The electronic vaping device also includes a first memory having stored thereon computer readable instructions relating to an electronic vaping operating system (OS), and at least one processor configured to execute the OS computer readable instructions to execute the operating system, the operating system including a real-time kernel configured to operate the electronic vaping device, and execute object code related to electronic vaping device functionality.
Owner:AKRIA CLIENT SERVICES LLC
Dynamic native binding
ActiveUS20090100416A1Avoid overheadEfficient implementationBinary to binarySoftware simulation/interpretation/emulationObject codeFunction prototype
Owner:IBM CORP
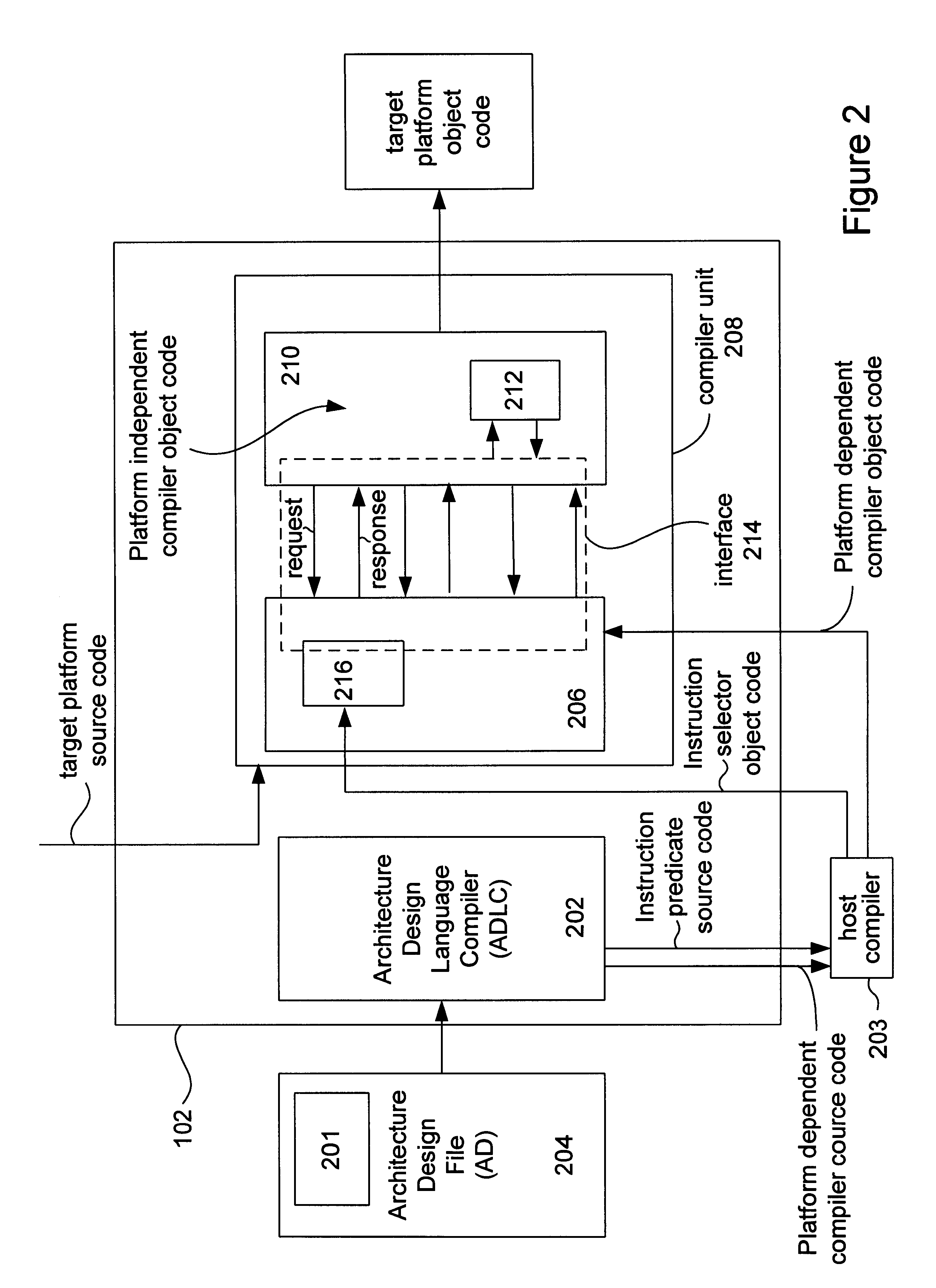
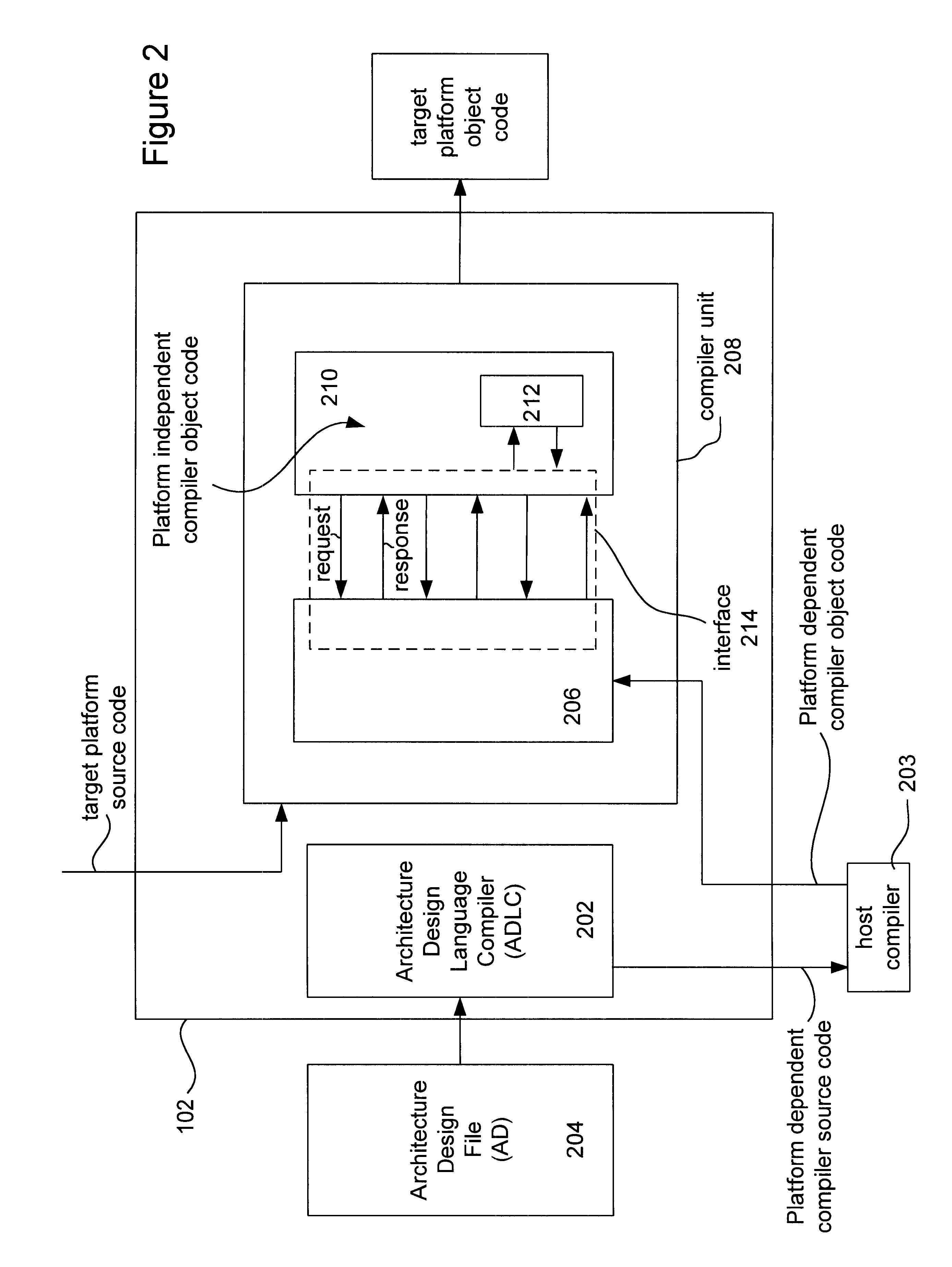
File portability techniques
InactiveUS6526570B1Program code adaptionSpecific program execution arrangementsObject codeMulti platform
Systems and methods for building a platform specific compiler in a multi-platform environment are provided. A set of user defined platform dependent compiler architecture descriptors that describe corresponding architectural features of a particular hardware platform dependent compiler are provided. The descriptors are converted into the platform dependent compiler source code which is compiled into platform dependent compiler object code. The platform specific compiler is formed from the platform dependent compiler object code and platform independent compiler object code already provide. During compiler run time an interface mediates the flow of information between the platform dependent compiler object code and the platform independent compiler object code.
Owner:ORACLE INT CORP
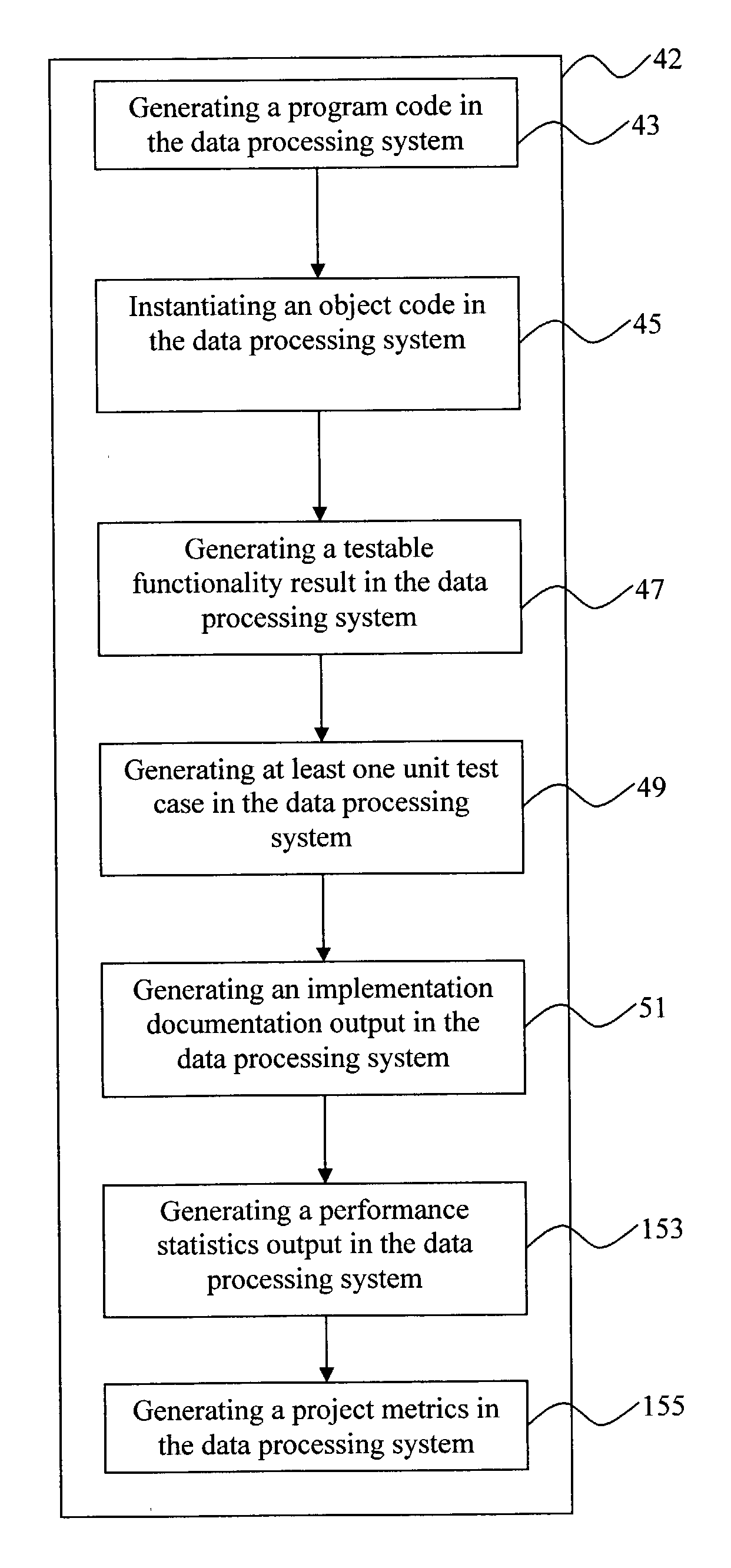
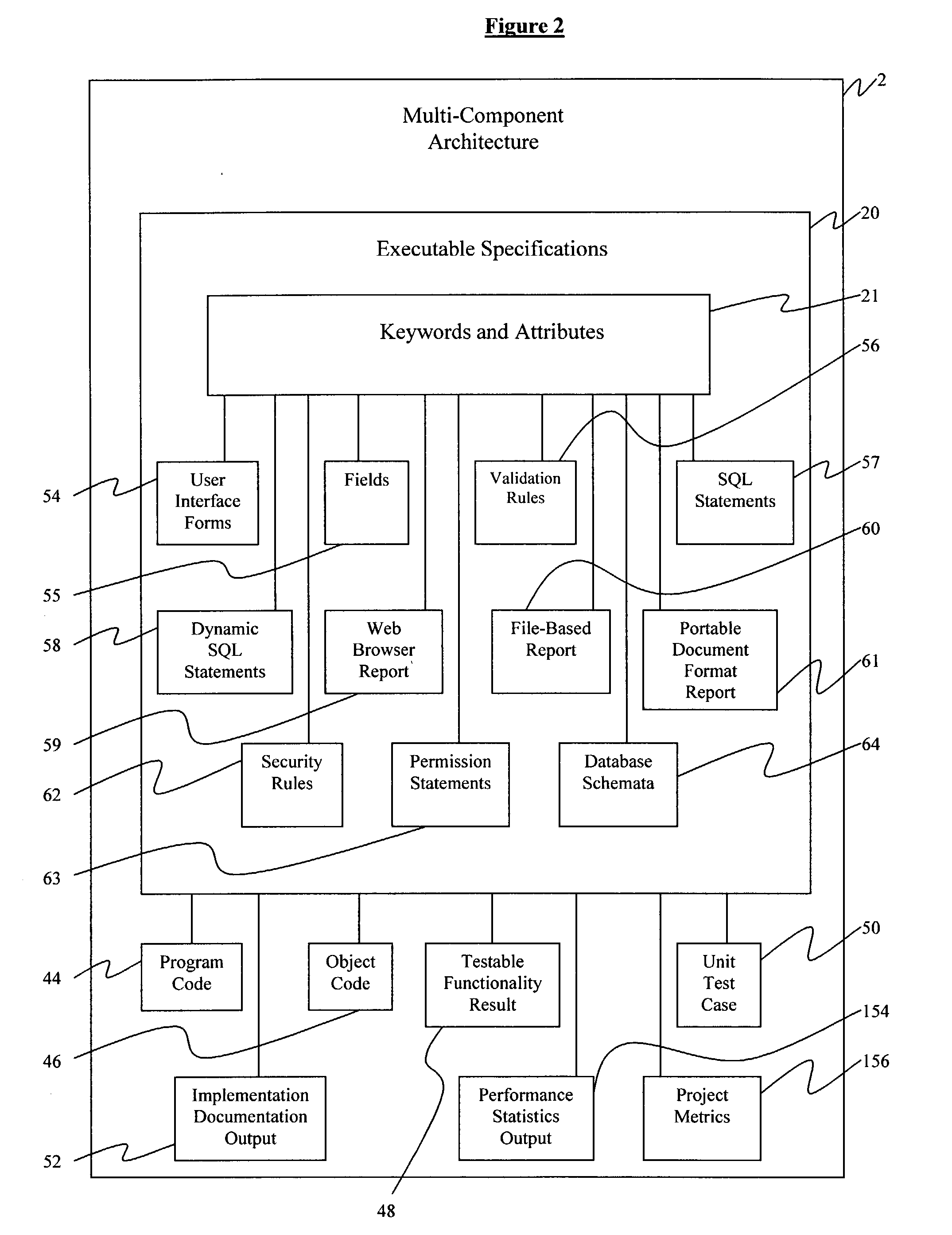
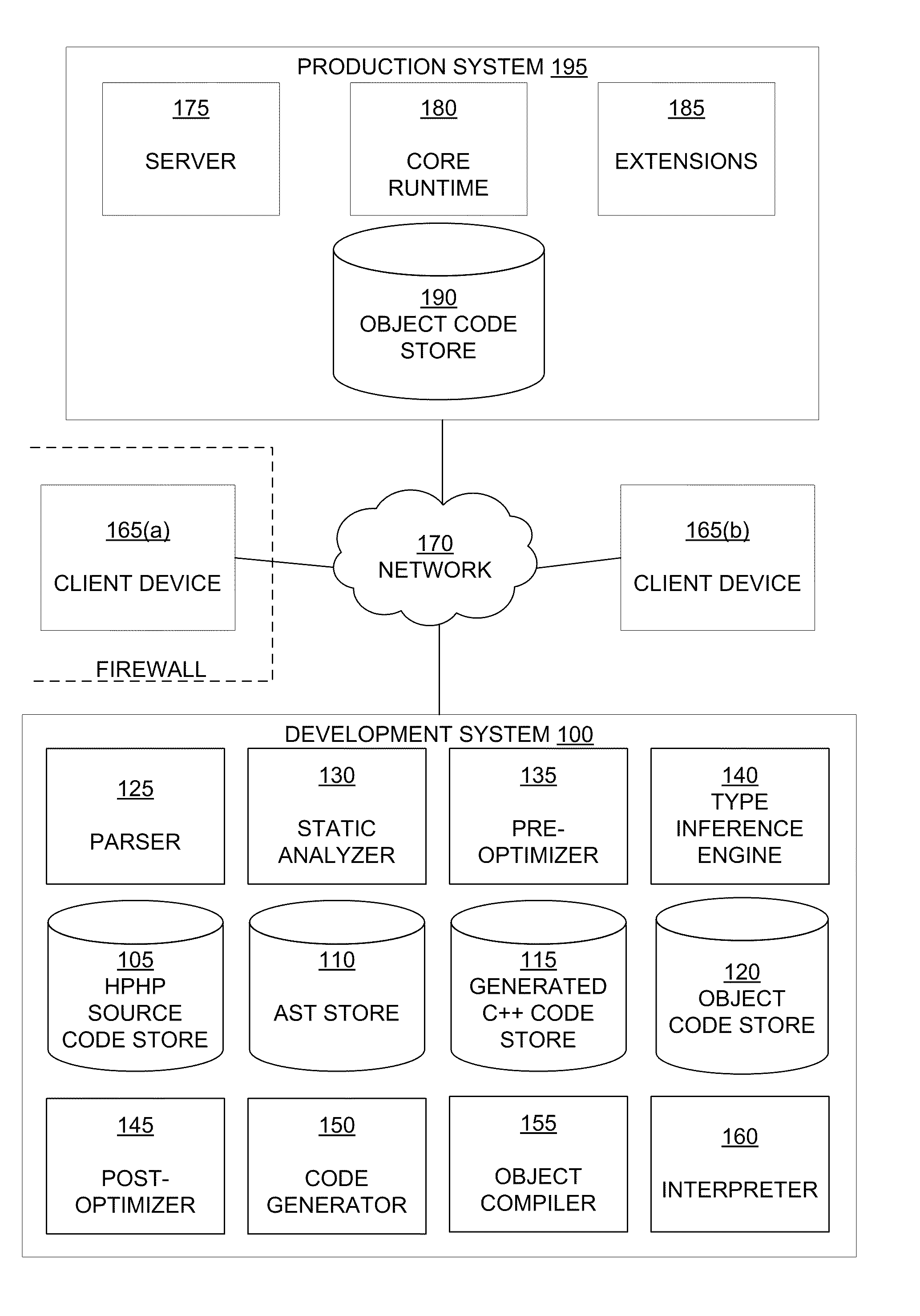
Computer system for performing reusable software application development from a set of declarative executable specifications
InactiveUS20040010776A1Time can be spentEasy to manageSoftware testing/debuggingSpecific program execution arrangementsDocumentation procedureProject metrics
A computer system executing a method for performing reusable software application development comprises integrating a data processing system, providing a set of keywords and attributes, and declaring a set of executable specifications using the keywords and attributes, further comprising generating a program code, instantiating an object code, generating a testable functionality result, generating at least one unit test, generating an implementation documentation output, generating a performance statistics output, and generating a project metrics in the data processing system. The step of providing a set of keywords and attributes comprises generating a set of user interface forms, fields, and validation rules, generating a library of structured query language statements, generating a library of rules for generating dynamic structured query language statements, generating one of a web browser report, a file-based report, and a portable document format report, generating a library of security rules and permission statements, and generating database schemata.
Owner:RPX CORP
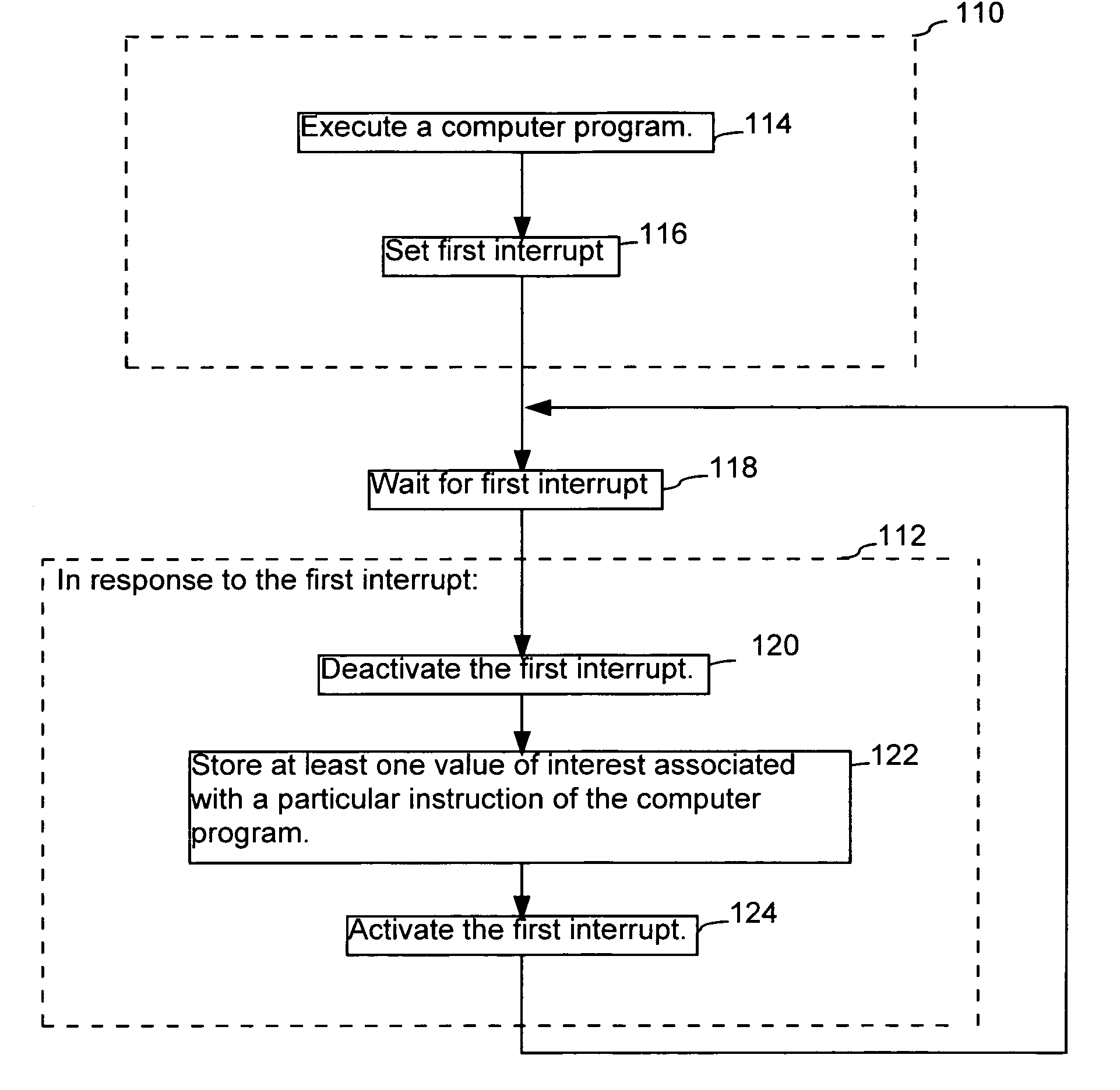
Efficient, transparent and flexible latency sampling
InactiveUS6961930B1Enabling profilingIncrease coverageError detection/correctionSpecific program execution arrangementsObject codeParallel computing
The performance of an executing computer program on a computer system is monitored using latency sampling. The program has object code instructions and is executing on the computer system. At intervals, the execution of the computer program is interrupted including delivering a first interrupt. In response to at least a subset of the first interrupts, a latency associated with a particular object code instruction is identified, and the latency is stored in a first database. The particular object code instruction is executed by the computer such that the program remains unmodified.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
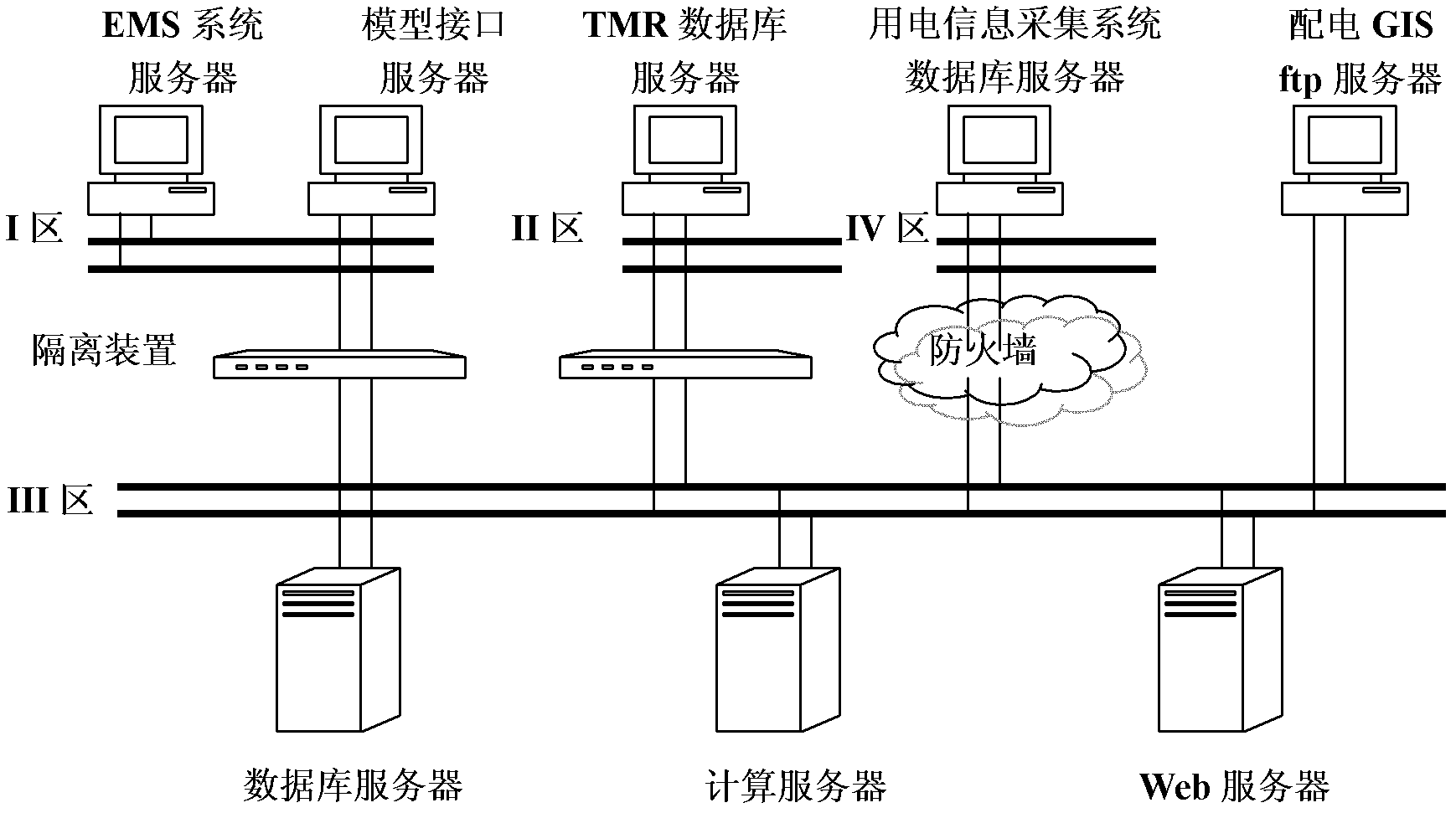
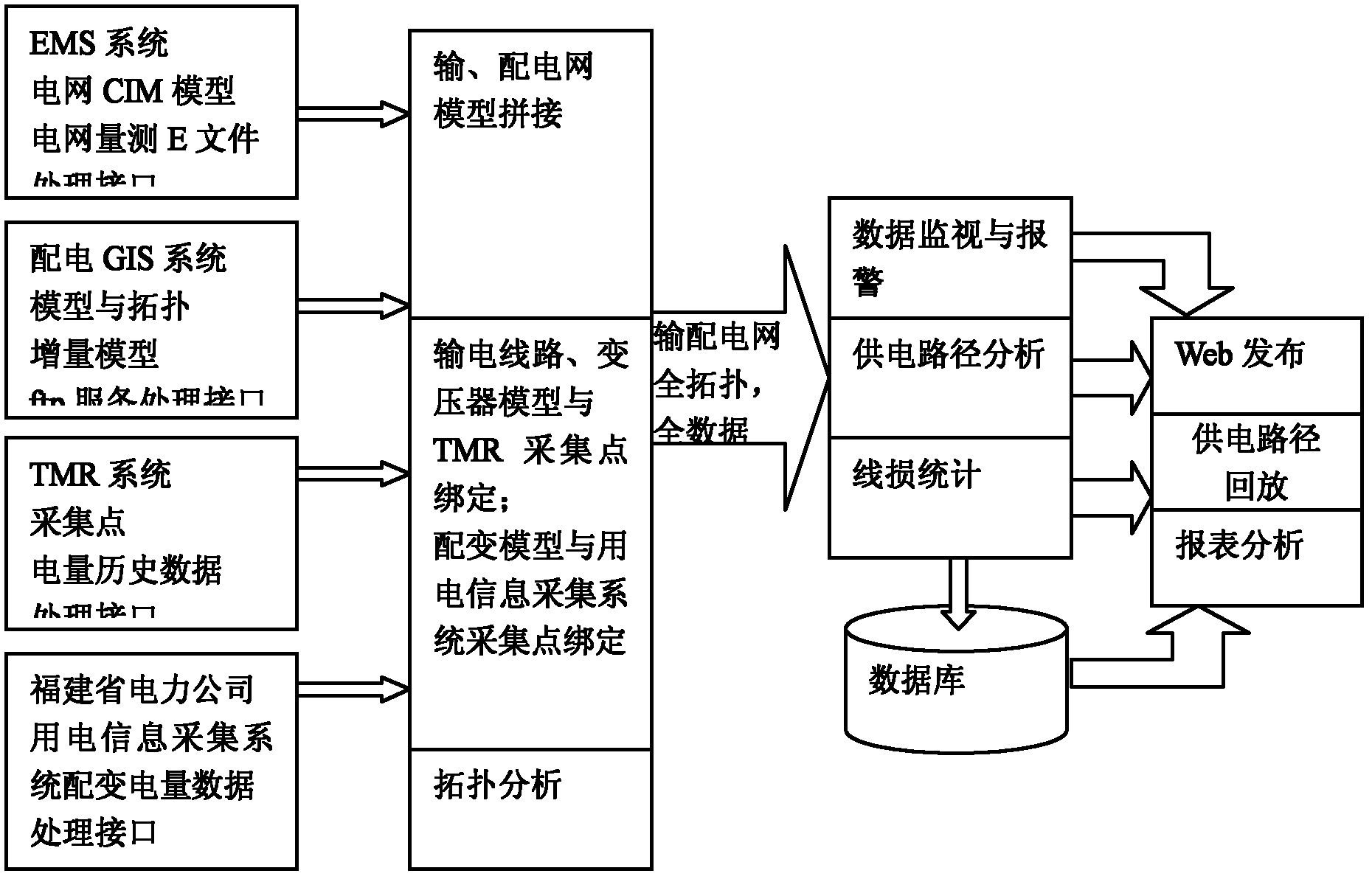
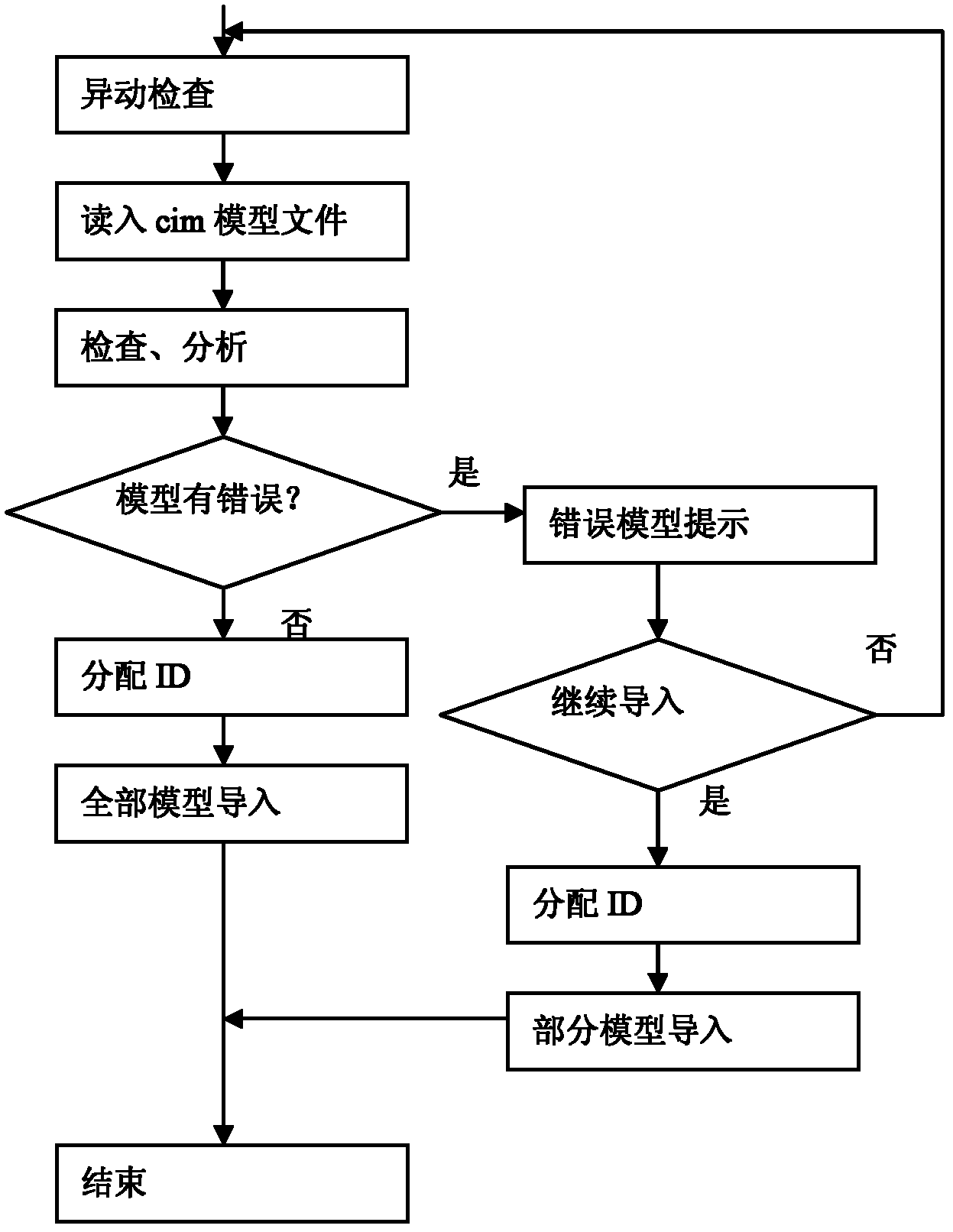
Transmission and distribution network integration comprehensive line loss management analysis system and processing flow thereof
InactiveCN102254256AReal time serviceReal-time (quasi-real-time serviceData processing applicationsAc network circuit arrangementsLoss rateWeb service
The invention discloses a transmission and distribution network integration comprehensive line loss management analysis system and a processing flow thereof. The processing flow comprises the following steps of: obtaining the required network topology, line parameters, real-time data and history data from an EMS (energy management system), a power distribution GIS (geographic information system), a TMR (tele-meter reading) system and an electricity consumption information acquiring system through a processing interface, finishing integrating of the network topology, the line parameters, the real-time data and the history data based on unified object code and management service through model splitting software; and storing the analysis result into a database through digital monitoring and alarm software, power supply path analysis software, transmission and distribution network integration line loss counting and analysis software, and transmitting the result to the Web server to produce report forms. The system and processing flow disclosed by the invention provide suggestions for performing omnibearing and multi-angle monitoring and analysis on the full network loss, and also provide suggestions for a power grid to carry out the work of operation way optimization, technical reconstruction and the like with reduced grid loss rate.
Owner:STATE GRID CORP OF CHINA +1
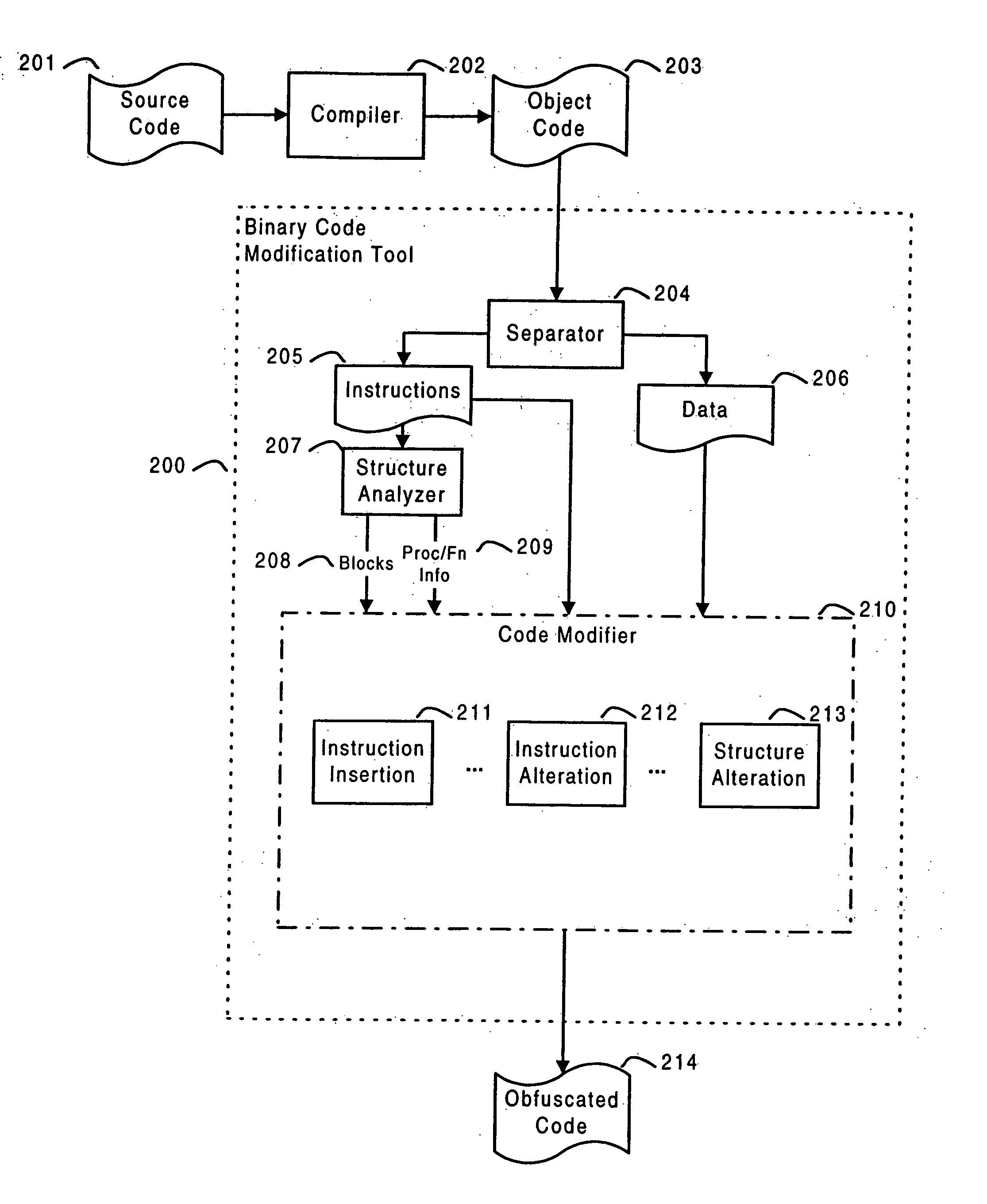
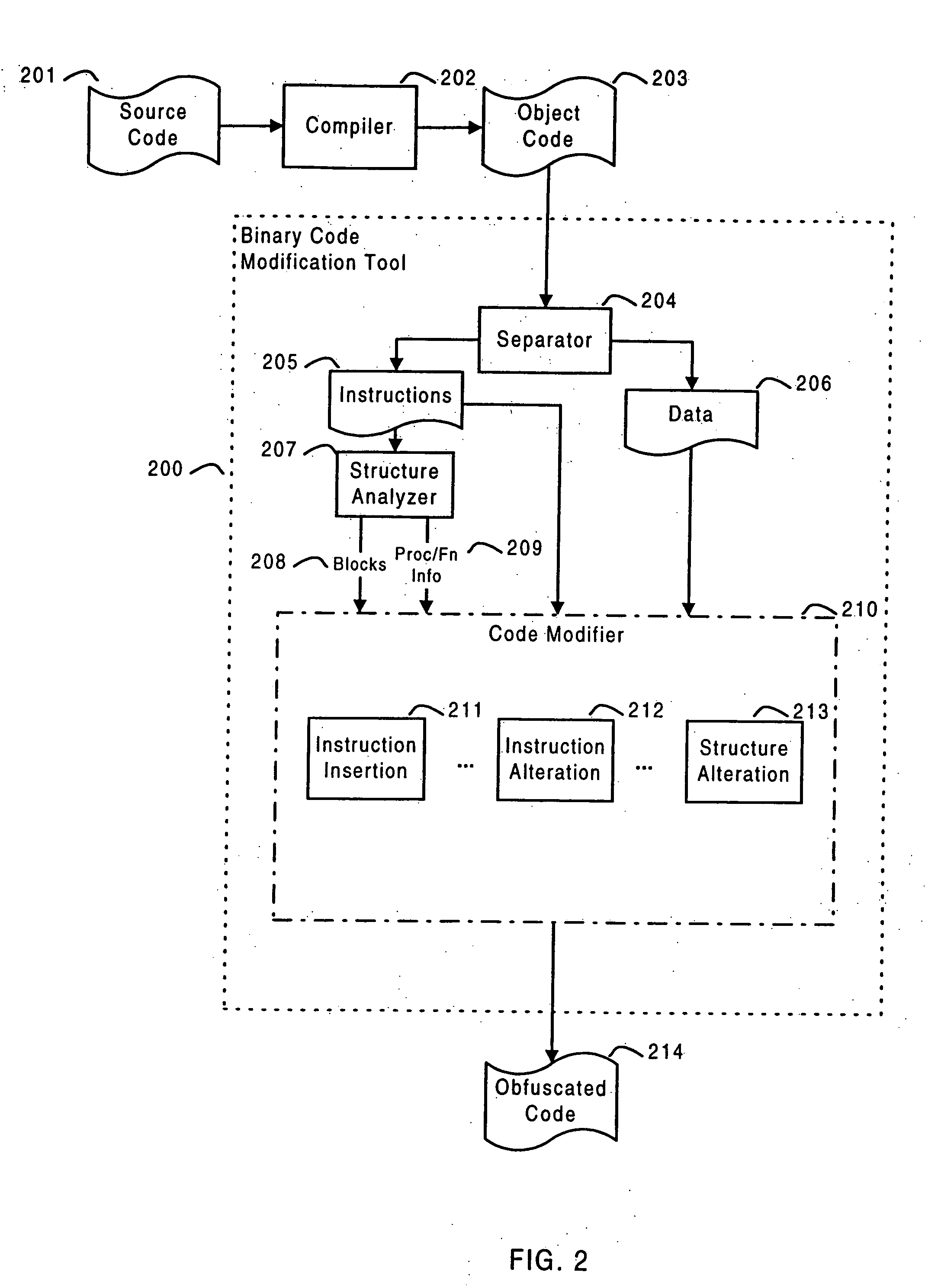
Post-compile instrumentation of object code for generating execution trace data
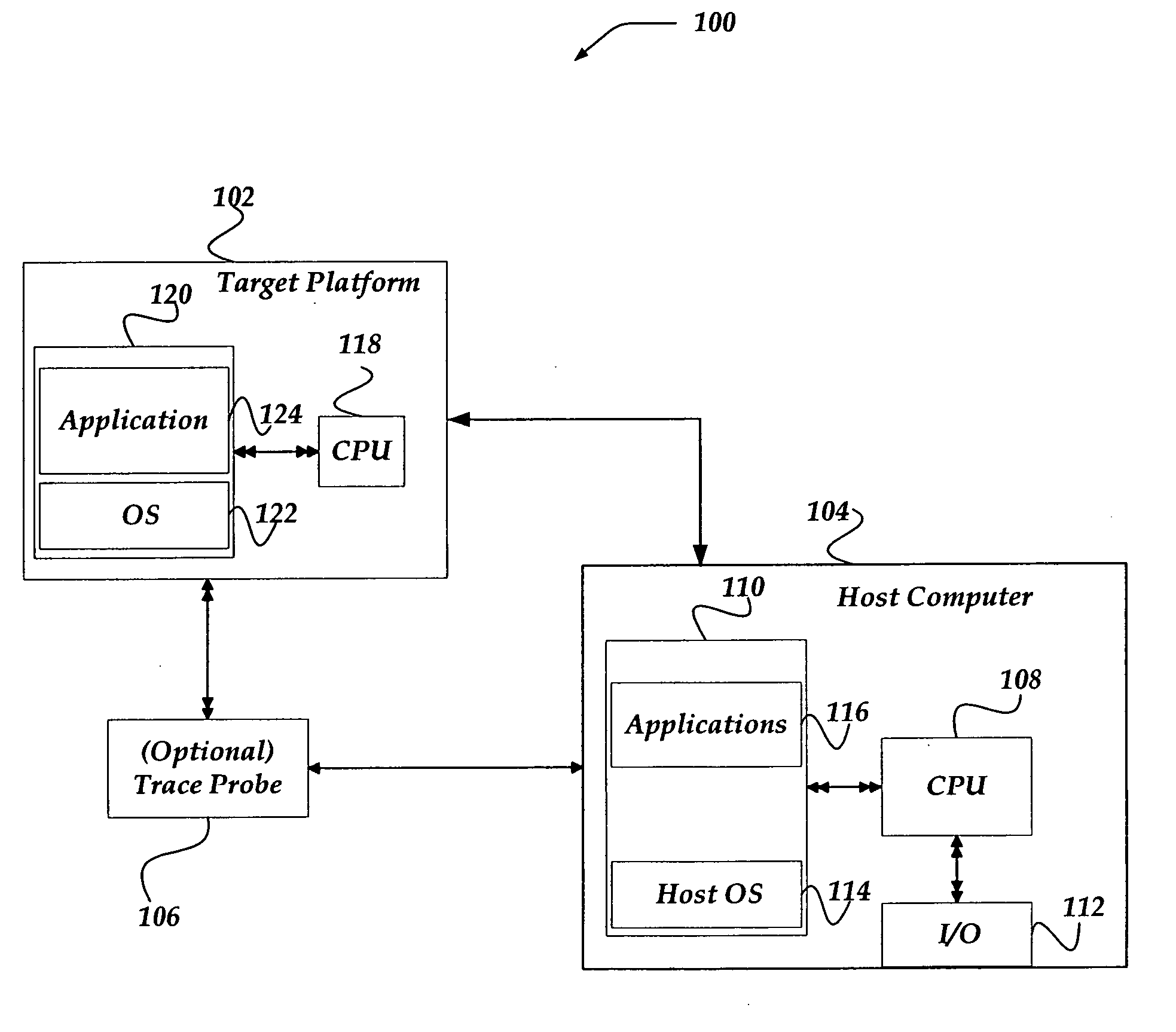
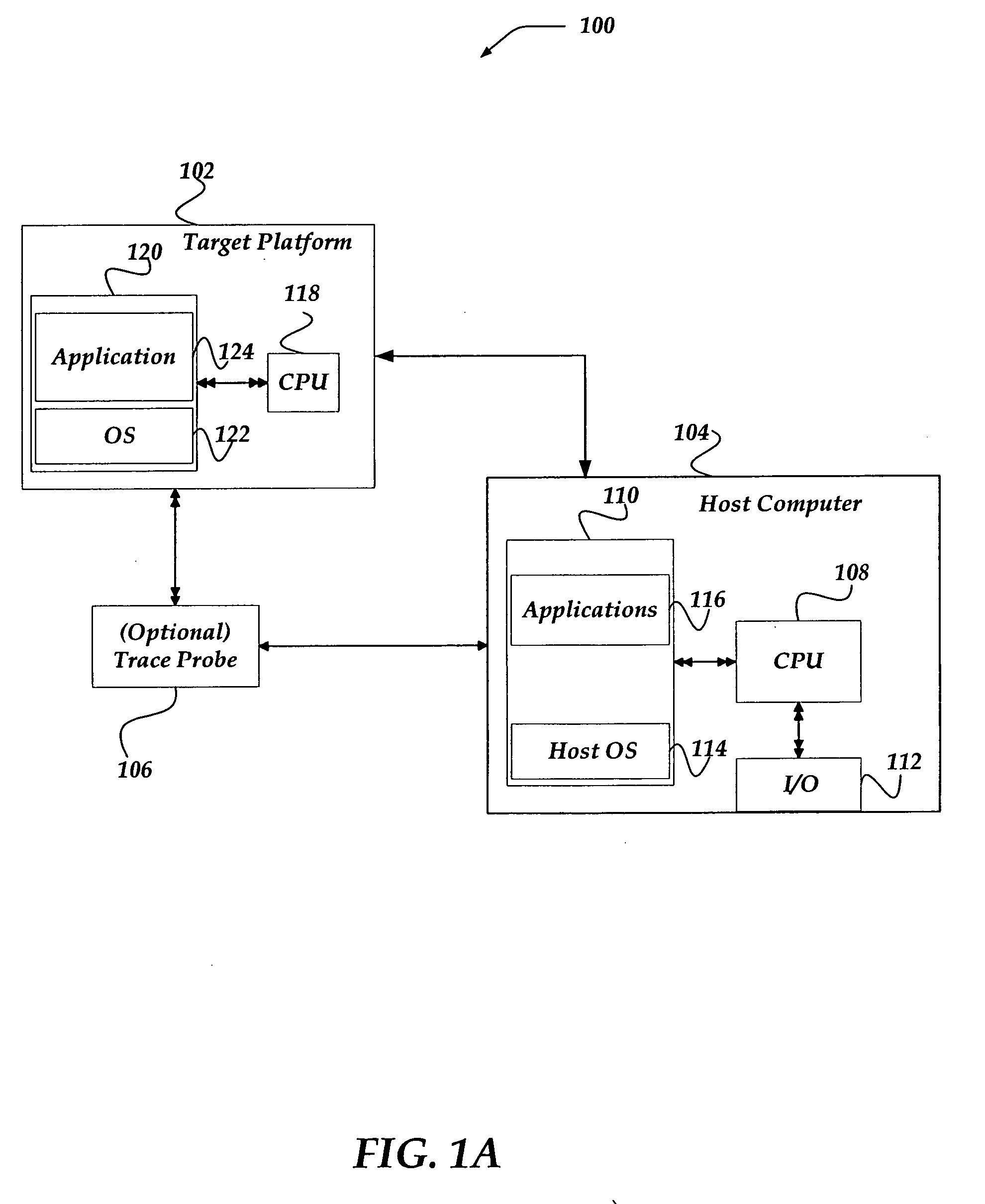
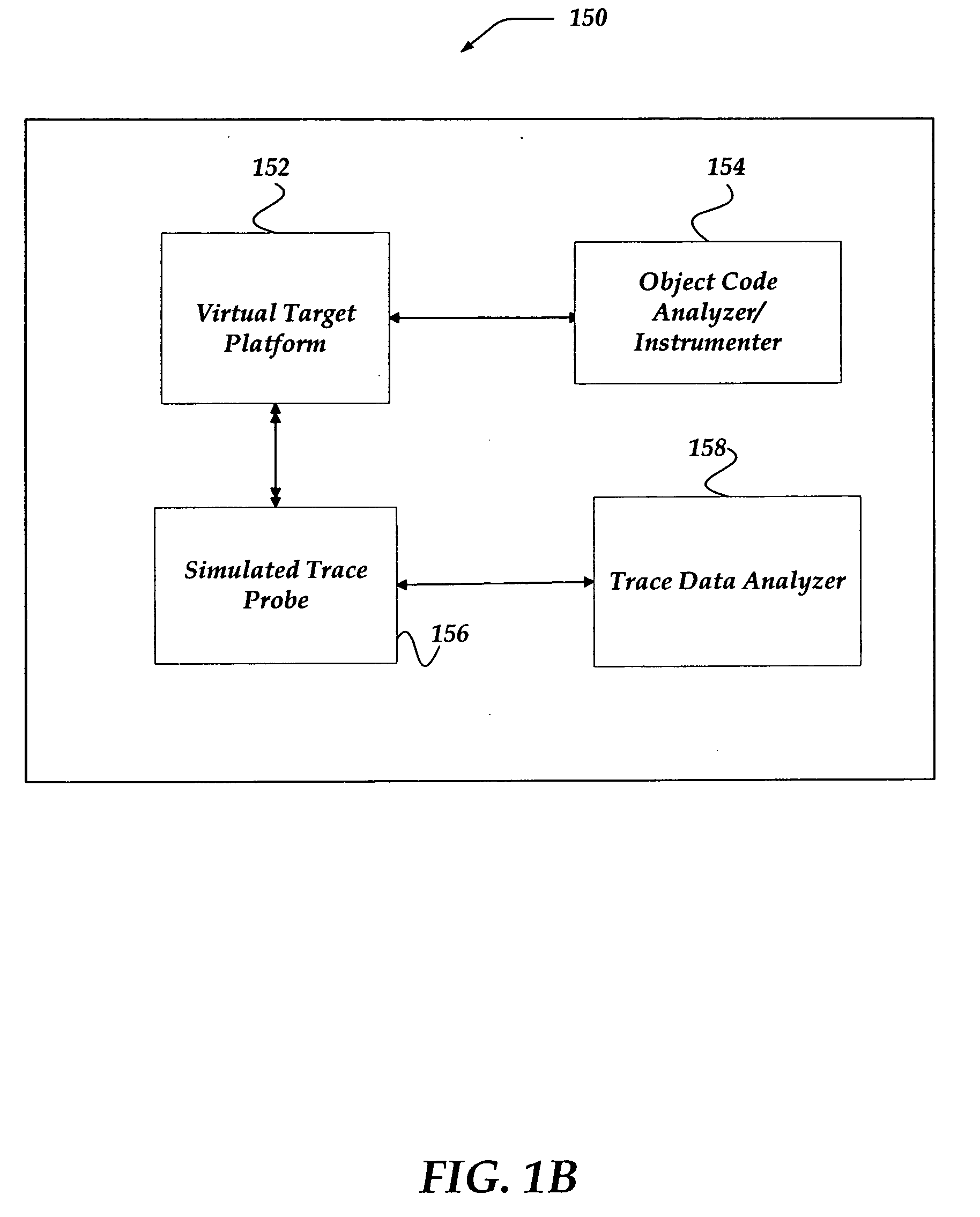
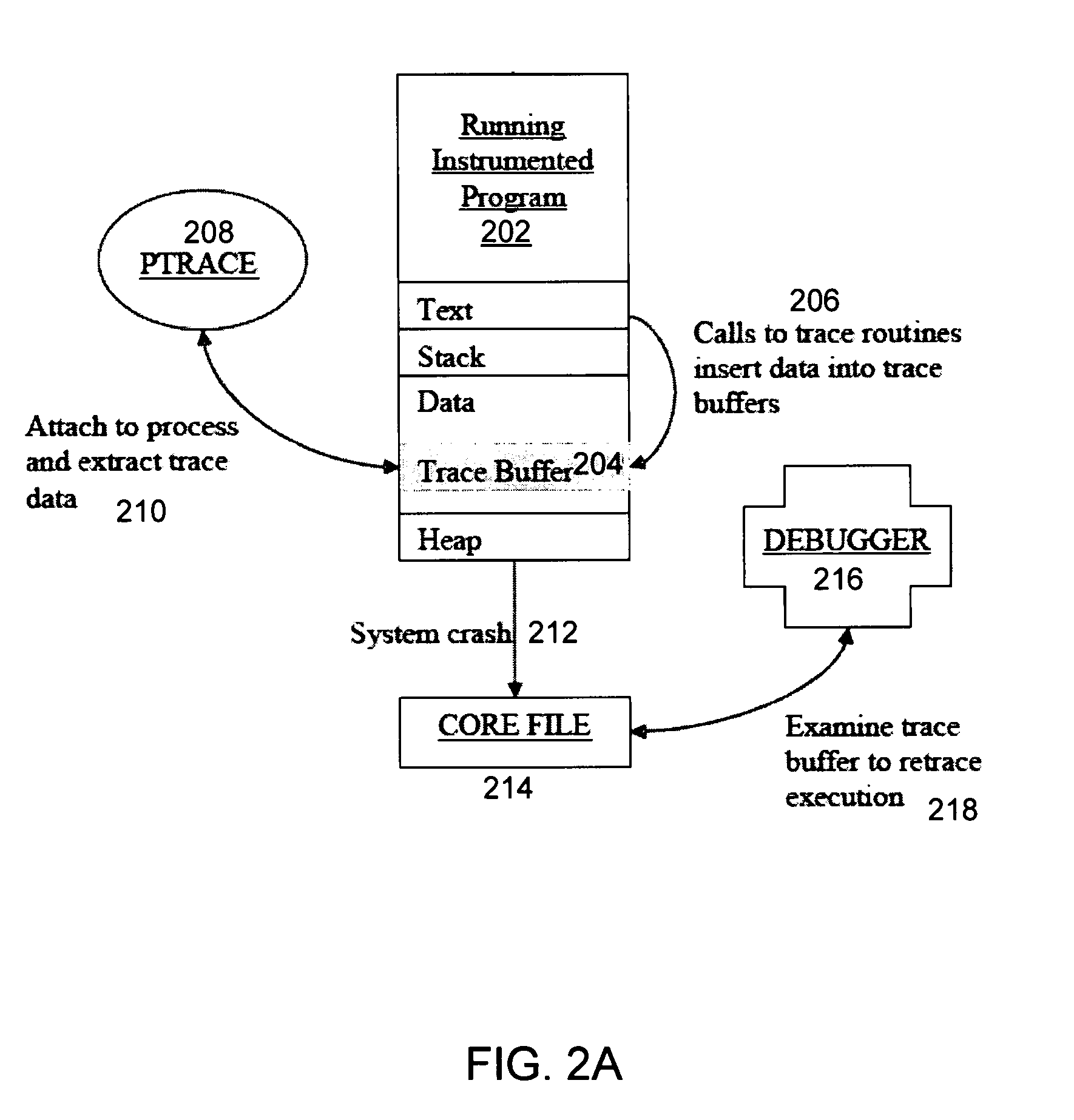
ActiveUS20060190930A1Error detection/correctionSpecific program execution arrangementsVisibilityOperational system
The invention is directed to instrumenting object code of an application and / or an operating system on a target machine so that execution trace data can be generated, collected, and subsequently analyzed for various purposes, such as debugging and performance. Automatic instrumentation may be performed on an application's object code before, during or after linking. A target machine's operating system's object code can be manually or automatically instrumented. By identifying address space switches and thread switches in the operating system's object code, instrumented code can be inserted at locations that enable the execution trace data to be generated. The instrumentation of the operating system and application can enable visibility of total system behavior by enabling generation of trace information sufficient to reconstruct address space switches and context switches.
Owner:GREEN HILLS SOFTWARE
Compiler-inserted predicated tracing
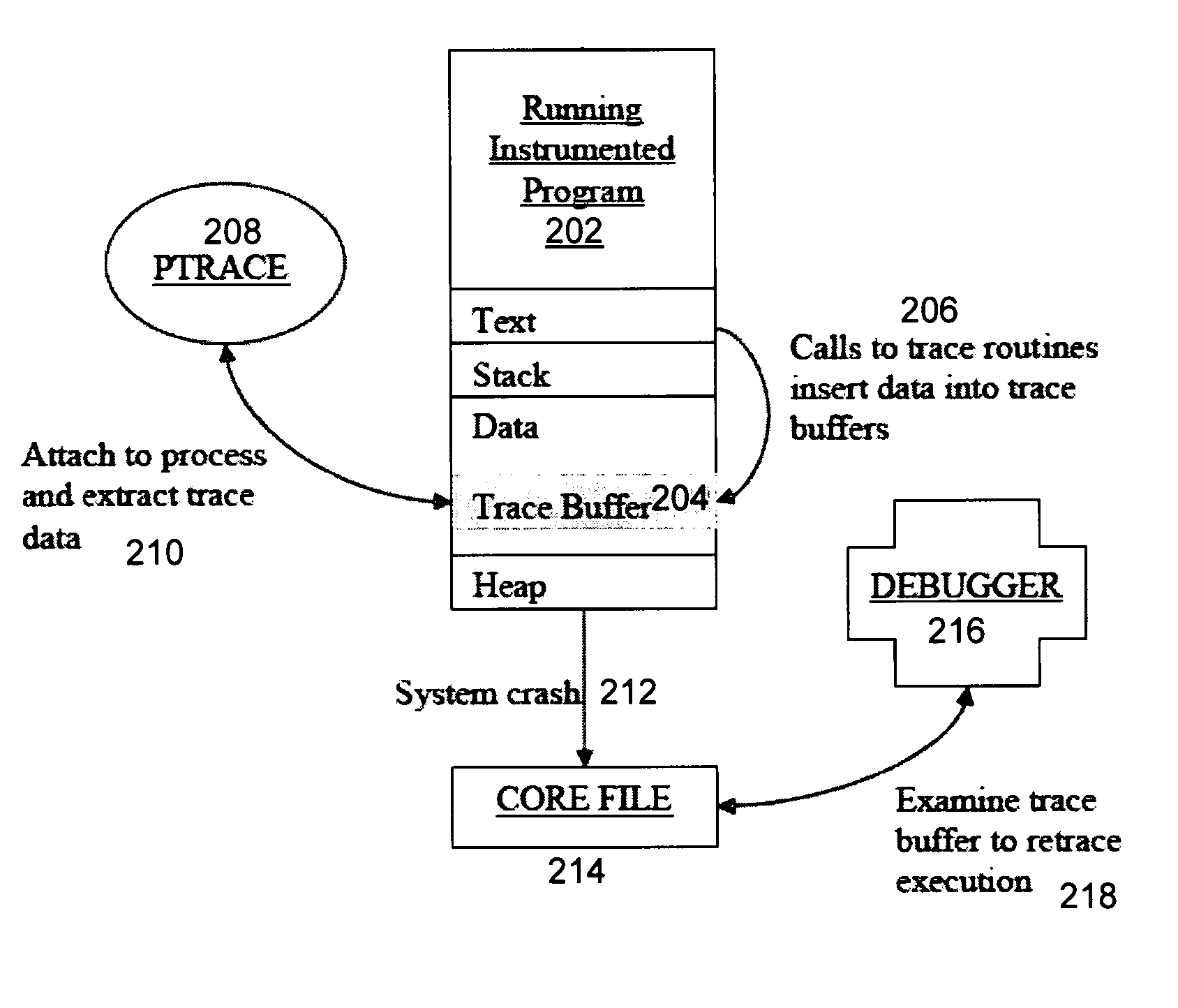
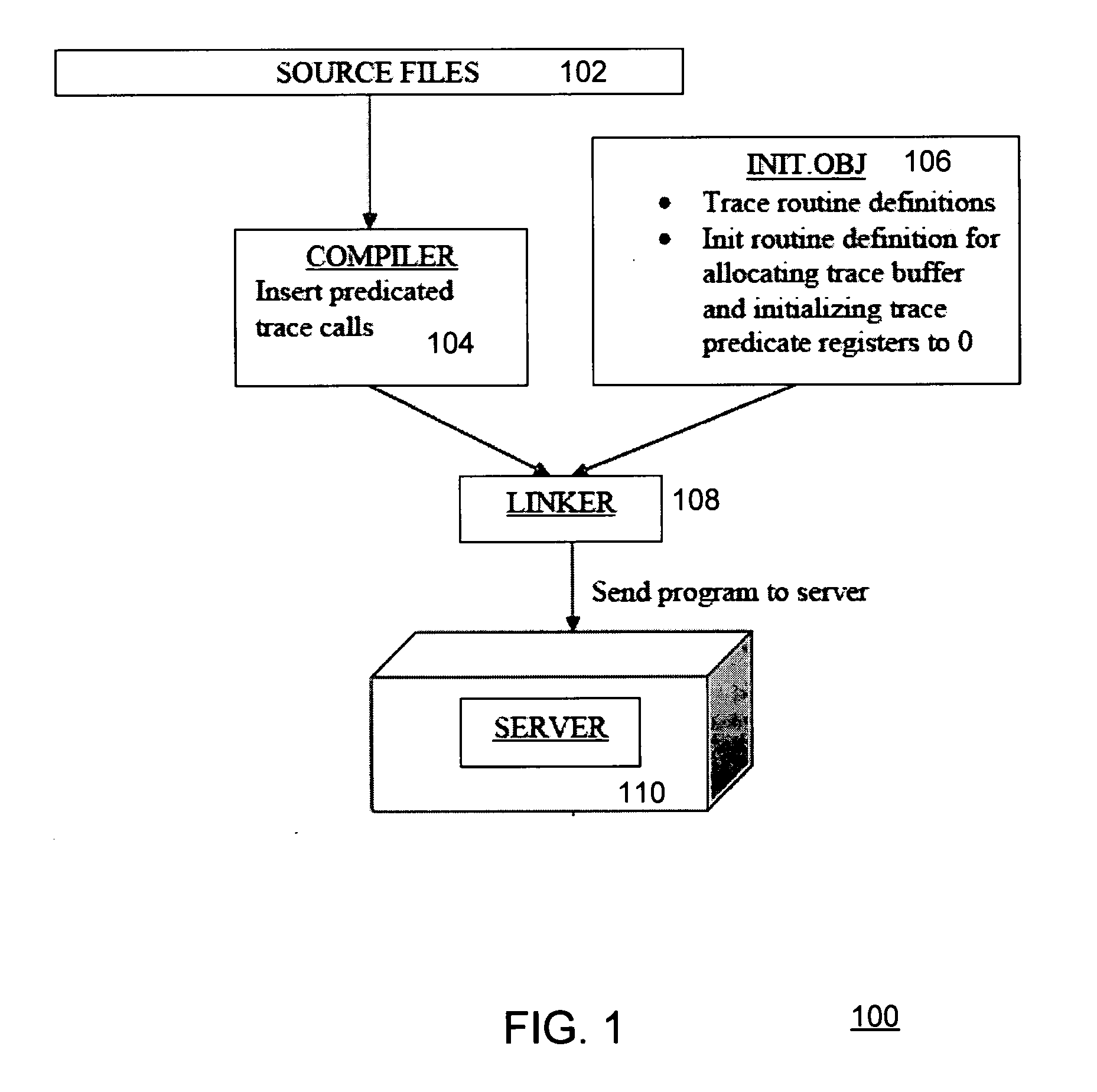
InactiveUS20090037887A1Error detection/correctionSpecific program execution arrangementsObject codeParallel computing
One embodiment relates to a computer-implemented method of generating an executable program which includes inserting predicated calls to trace routines during compilation of the source code. Each predicated call comprises a function call that is conditional upon a value stored in a predicate register. The object code generated from compiling said source code is subsequently linked with object code which includes the trace routines. Another embodiment relates to a computer-implemented method of executing a deployed computer program with low-level tracing using compiler-inserted predicated tracing calls. A tracing mode is enabled by setting one or more predicate register bits in a microprocessor. Predicated calls to trace routines insert trace data into at least one trace buffer. Upon a system crash, a core file including said trace data is written out. Other embodiments, aspects and features are also disclosed.
Owner:HEWLETT PACKARD DEV CO LP
Methods and apparatus to iteratively compile software to meet user-defined criteria
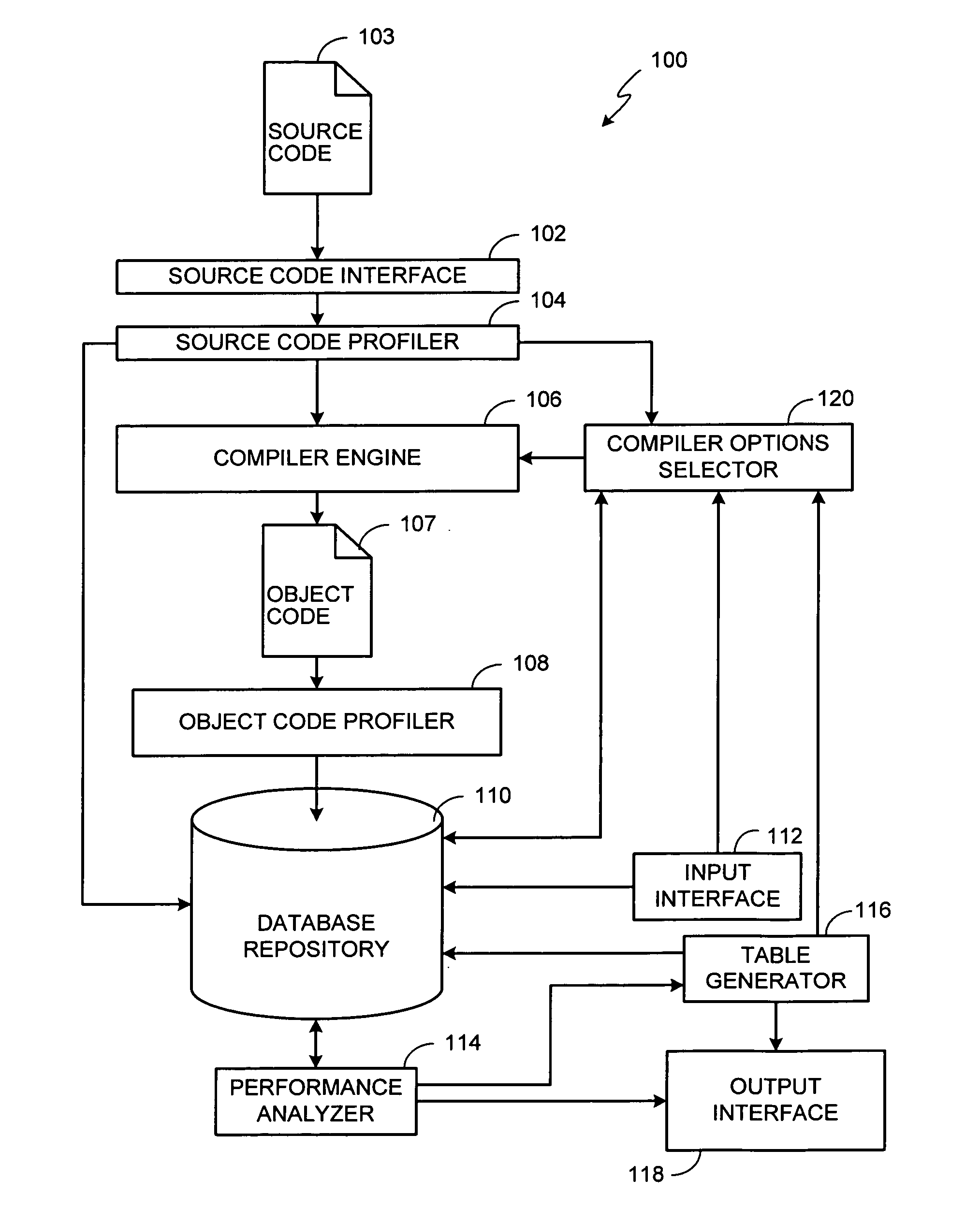
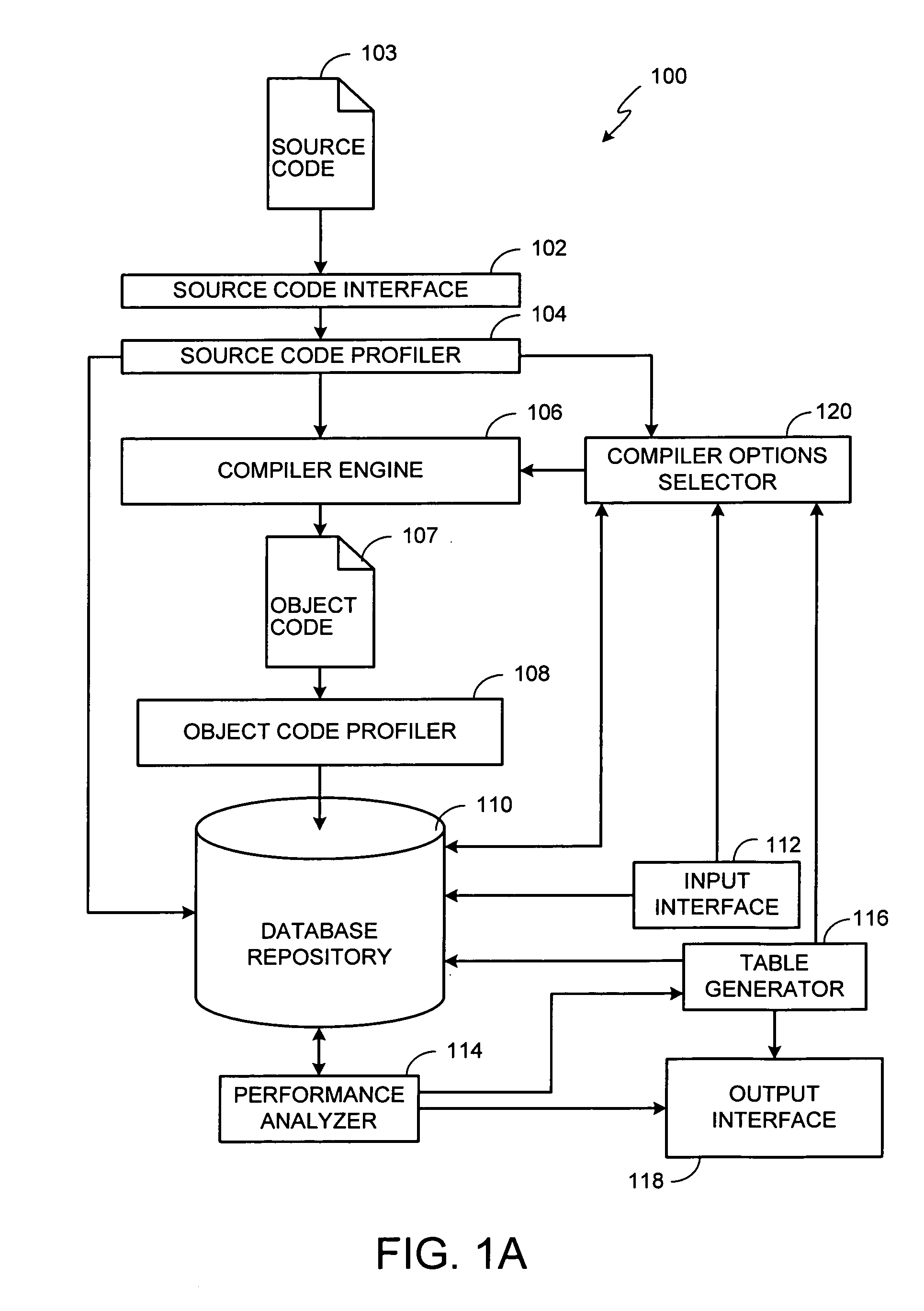
Methods, apparatus, and articles of manufacture to iteratively compile software to meet user-defined criteria are disclosed. A disclosed example method receives target performance characteristics from a user and compiles source code to generate object code. The object code is then analyzed to determine measured performance characteristics. The measured performance characteristics are then compared to the target performance characteristics. If the measured performance characteristics are unacceptable based on the target performance characteristics, the one of a plurality of compiler options configurations is selected based on empirical data correlating the compiler options configurations to structural characteristics of at least one of the source code or the object code. Without obtaining further user input, the operations are repeated one or more times until the measured performance characteristics are substantially equal to the target performance characteristics or until a predetermined number of recompilations have occurred.
Owner:INTEL CORP
Microprocessor using genetic algorithm
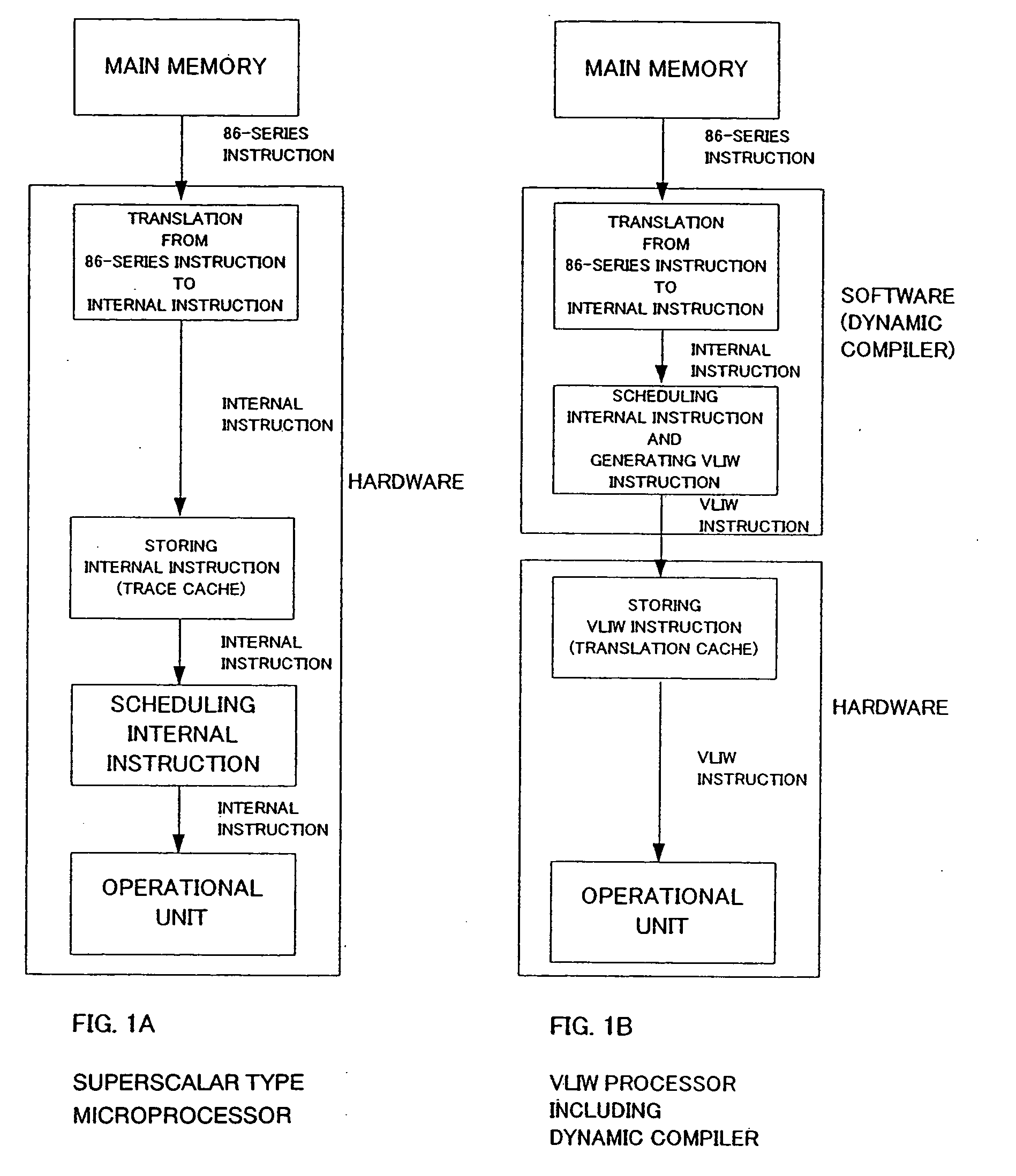
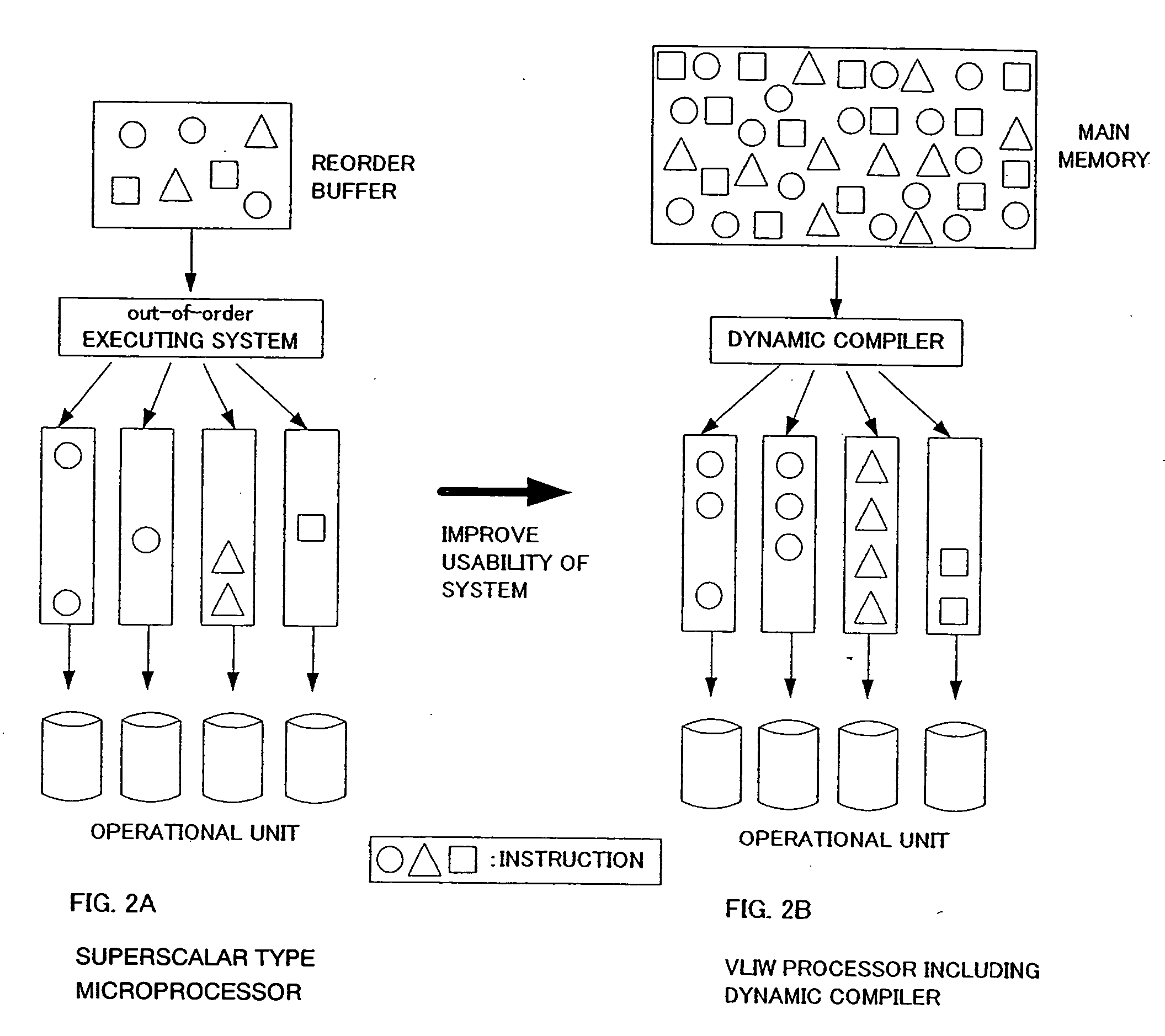
InactiveUS20050005085A1Excessive overheadImprove business performanceSoftware engineeringGeneral purpose stored program computerDynamic compilationObject code
The present invention reduces overhead in a VLIW type microprocessor including a dynamic compiler or controls a memory capacity for storing an object code after scheduling. The present invention relates to a VLIW microprocessor including a dynamic compiler and improves operation performance of a microprocessor by executing instructions more efficiently. Specifically, one feature of the present invention is to reduce overhead accompanying execution of a dynamic compiler and to control a memory capacity for storing an object code after scheduling internal instructions by using genetic algorithm (GA) in an execution of instructions in a VLIW microprocessor including a dynamic compiler.
Owner:SEMICON ENERGY LAB CO LTD
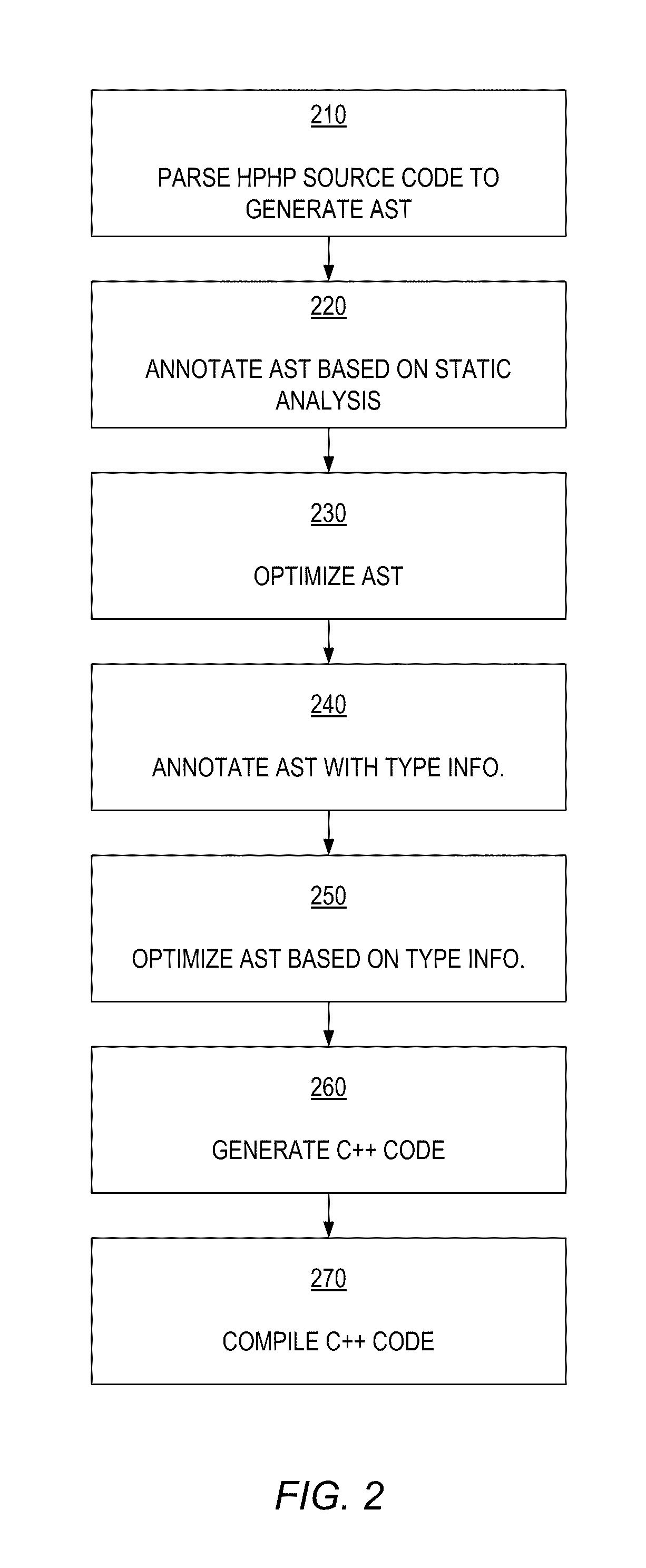
High performance php
ActiveUS20110179347A1Programming languages/paradigmsNatural language data processingObject codeDocument preparation
Markup language documents including server side scripting code using PHP syntax are executed efficiently in response to requests received by a server. The processing of the markup language document results in generation of a transformed markup language document that is returned in response to the request. The server side script code is input to a compiler that generates C++ code (or code in any object-based language based on C language) implementing the functionality of the server side script code. The C++ code is compiled to generated object code which is executed in order to process the markup language document. The generated C++ code includes functionality supported by PHP language including redeclaration of functions, dynamic variables, global variables, and the like. The generated C++ code invokes memory allocation code that allocates and deallocates objects obtained by instantiating the generated C++ classes.
Owner:META PLATFORMS INC
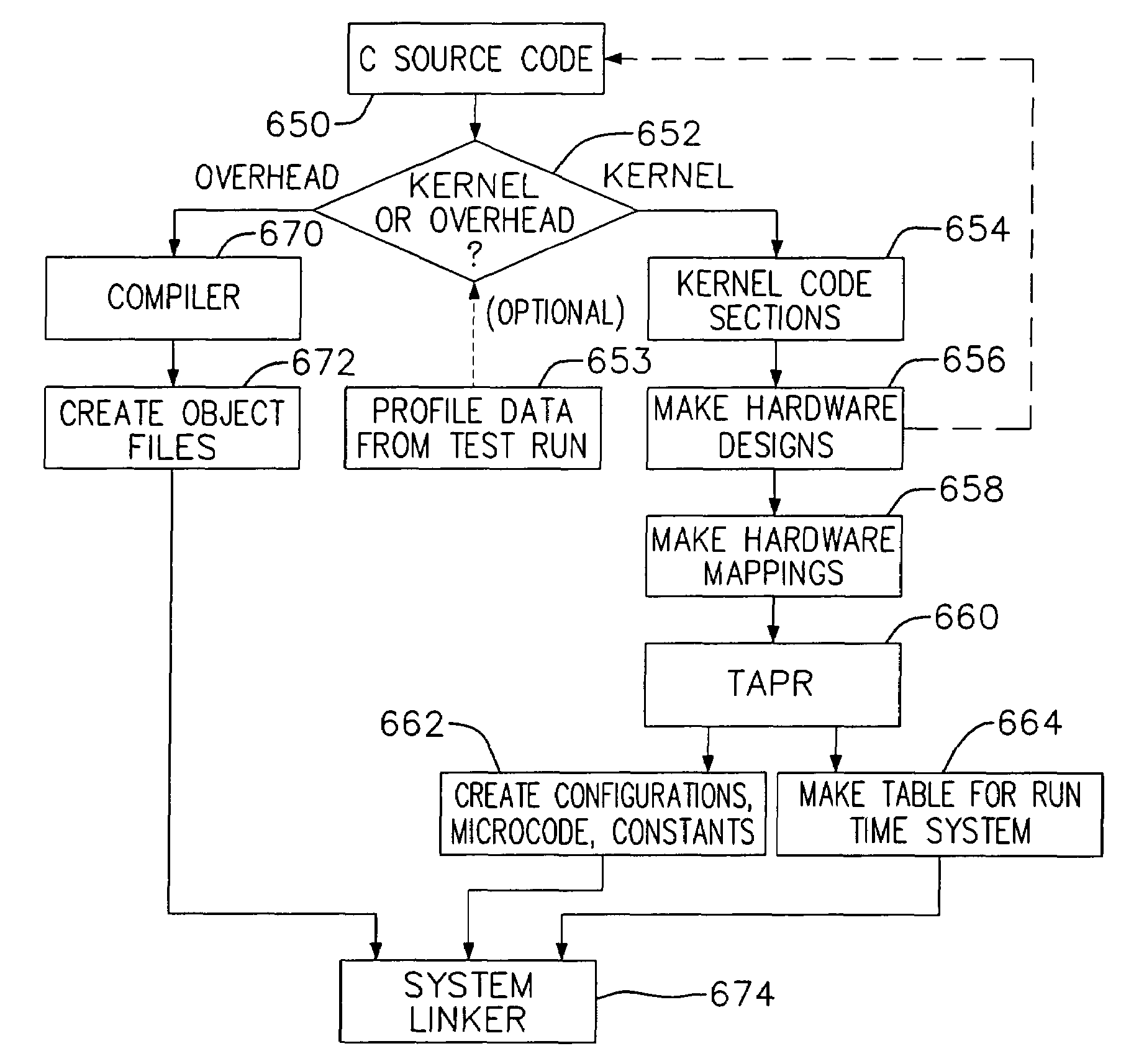
System and method for preparing software for execution in a dynamically configurable hardware environment
A system and method for creating run time executables in a configurable processing element array is disclosed. This system and method includes the step of partitioning a processing element array into a number of defined sets of hardware accelerators, which in one embodiment are processing elements called “bins”. The system and method then involves decomposing a program description in object code form into a plurality of “kernel sections”, where the kernel sections are defined as those sections of object code which are candidates for hardware acceleration. Next, mapping the identified kernel sections into a number of hardware dependent designs is performed. Finally, a matrix of the bins and the designs is formed for use by the run time system.
Owner:QUALCOMM INC
System and method for detecting release-to-release binary compatibility in compiled object code
InactiveUS6658421B1Not slow down field access and method invocationOptimize timingSpecial data processing applicationsSpecific program execution arrangementsProgramming languageDigital signature
Digital signatures of various aspects or characterizing indicia of object code classes are used to determine whether a compiled class has built-in assumptions about external classes that are incorrect due to modification and recompilation of the external class. The indicia generally involve an encoding of the layout of various run time structures in the external class such as field tables or method tables.
Owner:IBM CORP
Shared code caching for program code conversion
ActiveUS7805710B2General purpose stored program computerProgram loading/initiatingCode TranslationObject code
Subject program code is translated to target code in basic block units at run-time in a process wherein translation of basic blocks is interleaved with execution of those translations. A shared code cache mechanism is added to persistently store subject code translations, such that a translator may reuse translations that were generated and / or optimized by earlier translator instances.
Owner:IBM CORP
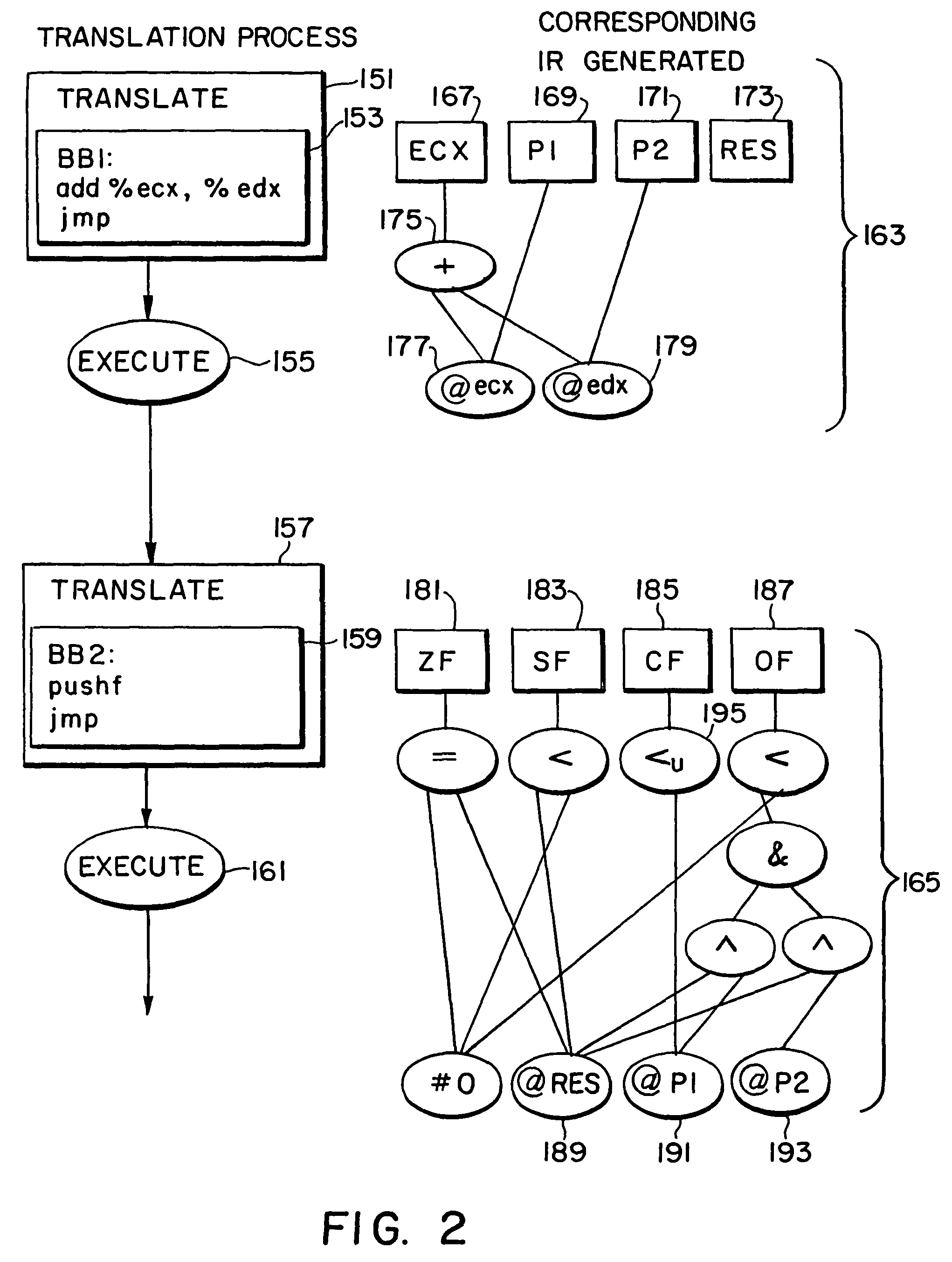
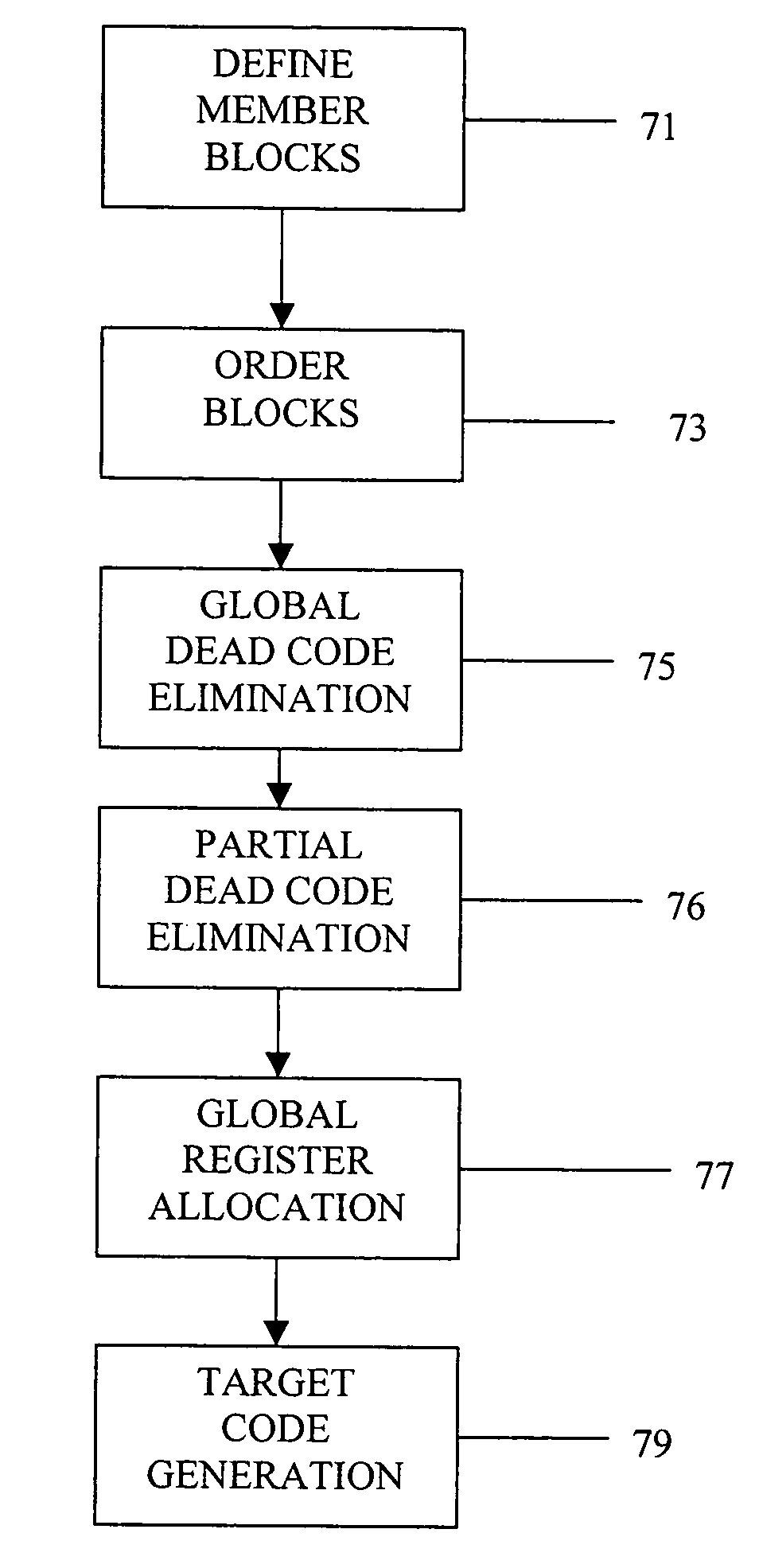
Partial dead code elimination optimizations for program code conversion
InactiveUS7543284B2Generate efficientlyAvoid it happening againSoftware engineeringSpecific program execution arrangementsProcessor registerObject code
An improved method and apparatus for performing program code conversion is provided and, more particularly, for generating improved intermediate representations for use in program code conversion. During program code conversion, a partial dead code elimination optimization technique is implemented to identify partially dead register definitions within a block of program code being translated. The partial dead code elimination is an optimization to the intermediate representation in the form of code motion for blocks of program code ending in non-computed branches or computed jumps, where target code for all dead child nodes of a partially dead register definition is prevented from being generated and target code for partially dead child nodes of a partially dead register definition is delayed from being generated until after target code is generated for all fully live child nodes for the partially dead register definition.
Owner:IBM CORP
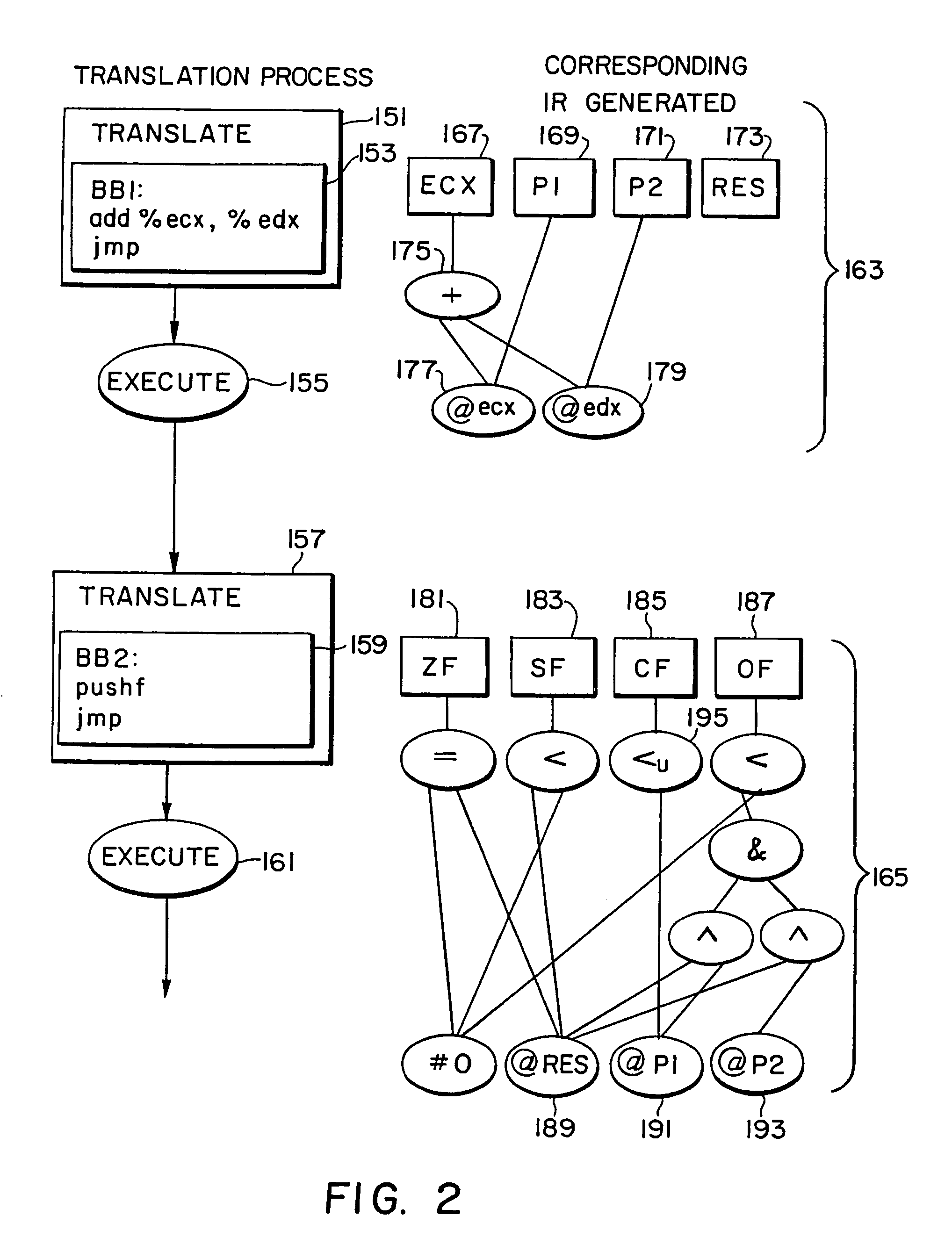
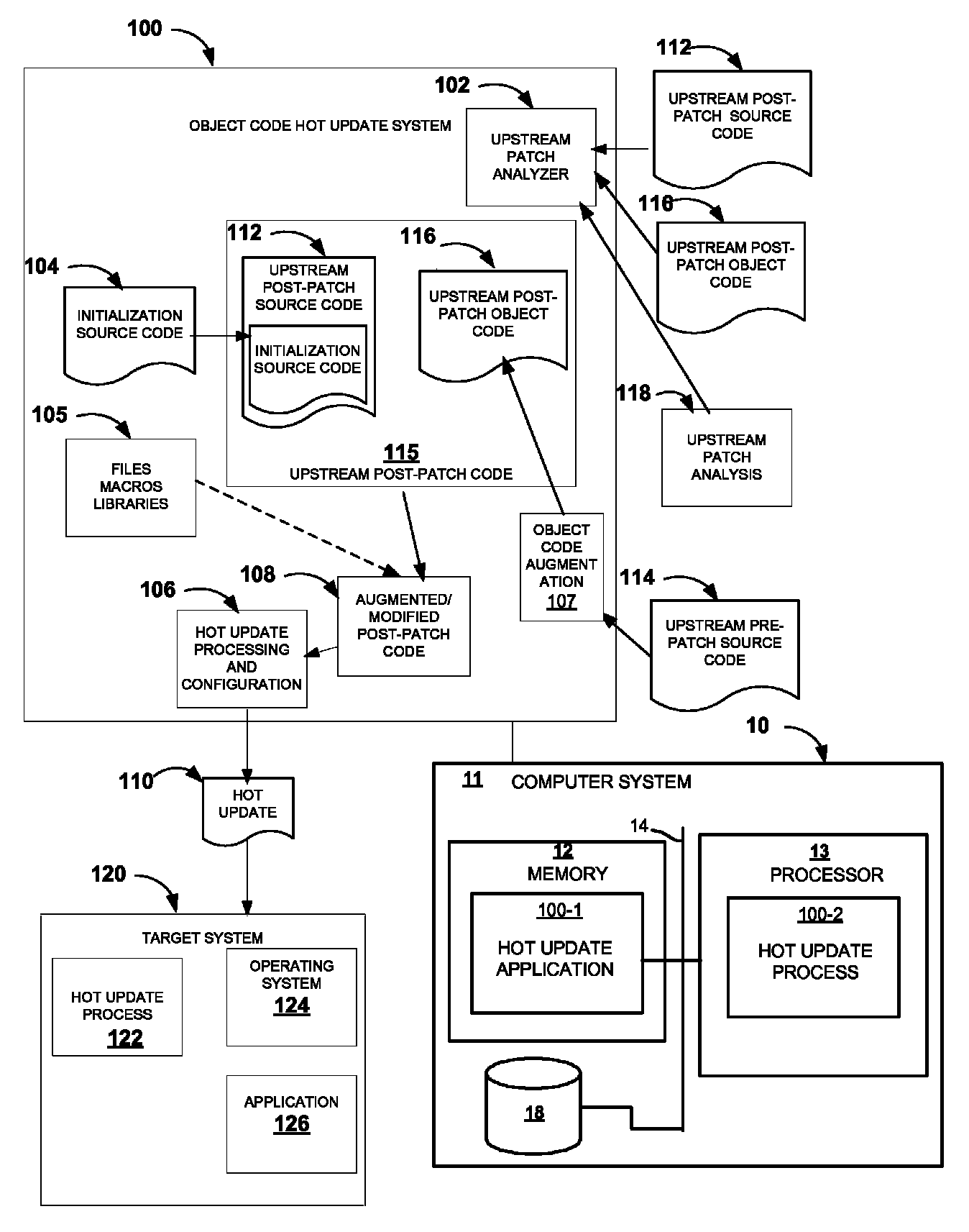
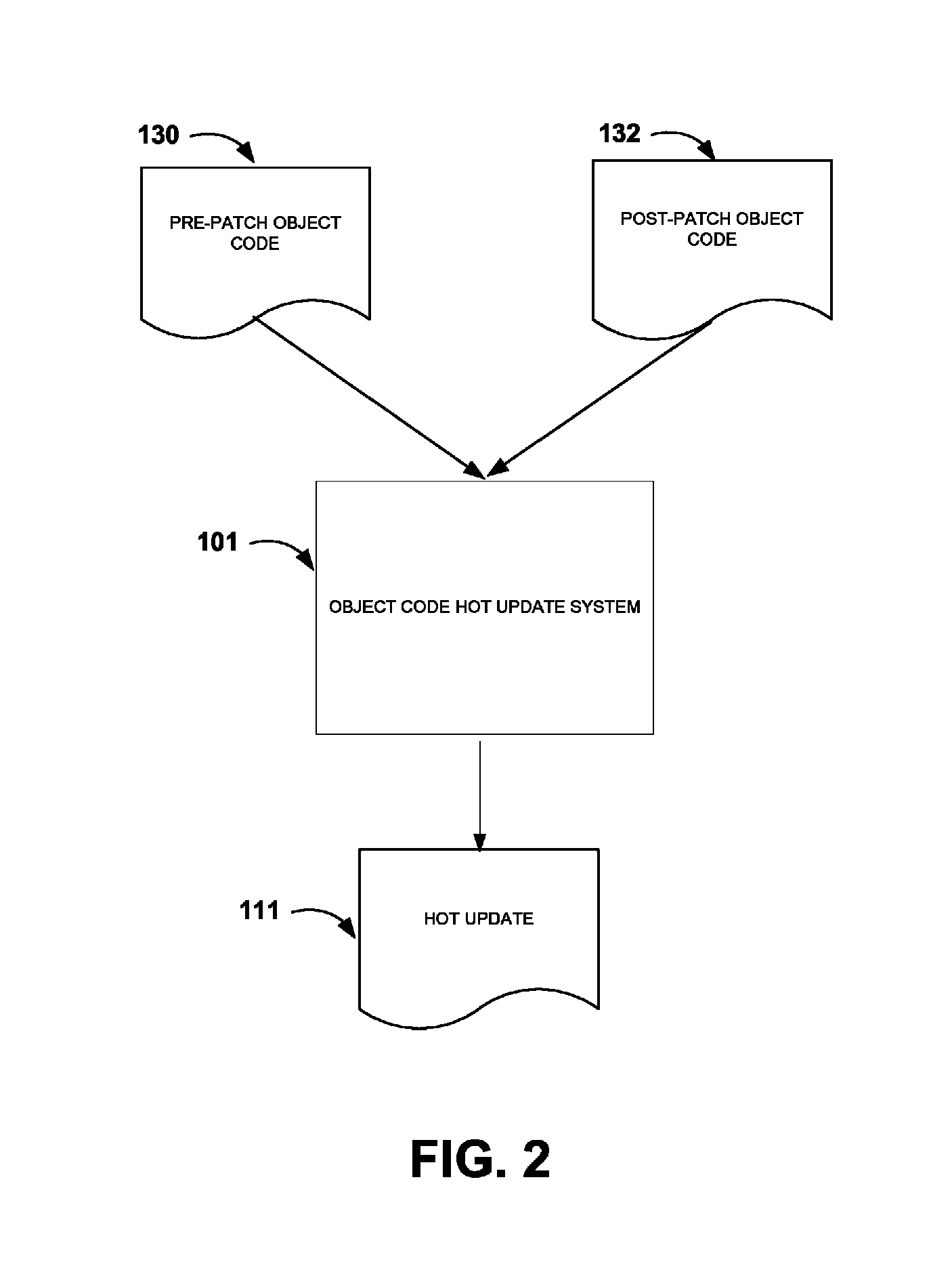
System and methods for object code hot updates
ActiveUS8607208B1Minimizes unnecessary modificationQuantity minimizationSoftware engineeringMultiprogramming arrangementsObject codeParallel computing
An object code hot update system generates hot updates for patching running programs by analyzing upstream post-patch code, augmenting the upstream post-patch code to provide augmented post-patch code with additional initialization functionality. The system further provides techniques to identify a candidate extra-change site in upstream post-patch code and modify the upstream post-patch code to generate a hot update.
Owner:ORACLE INT CORP
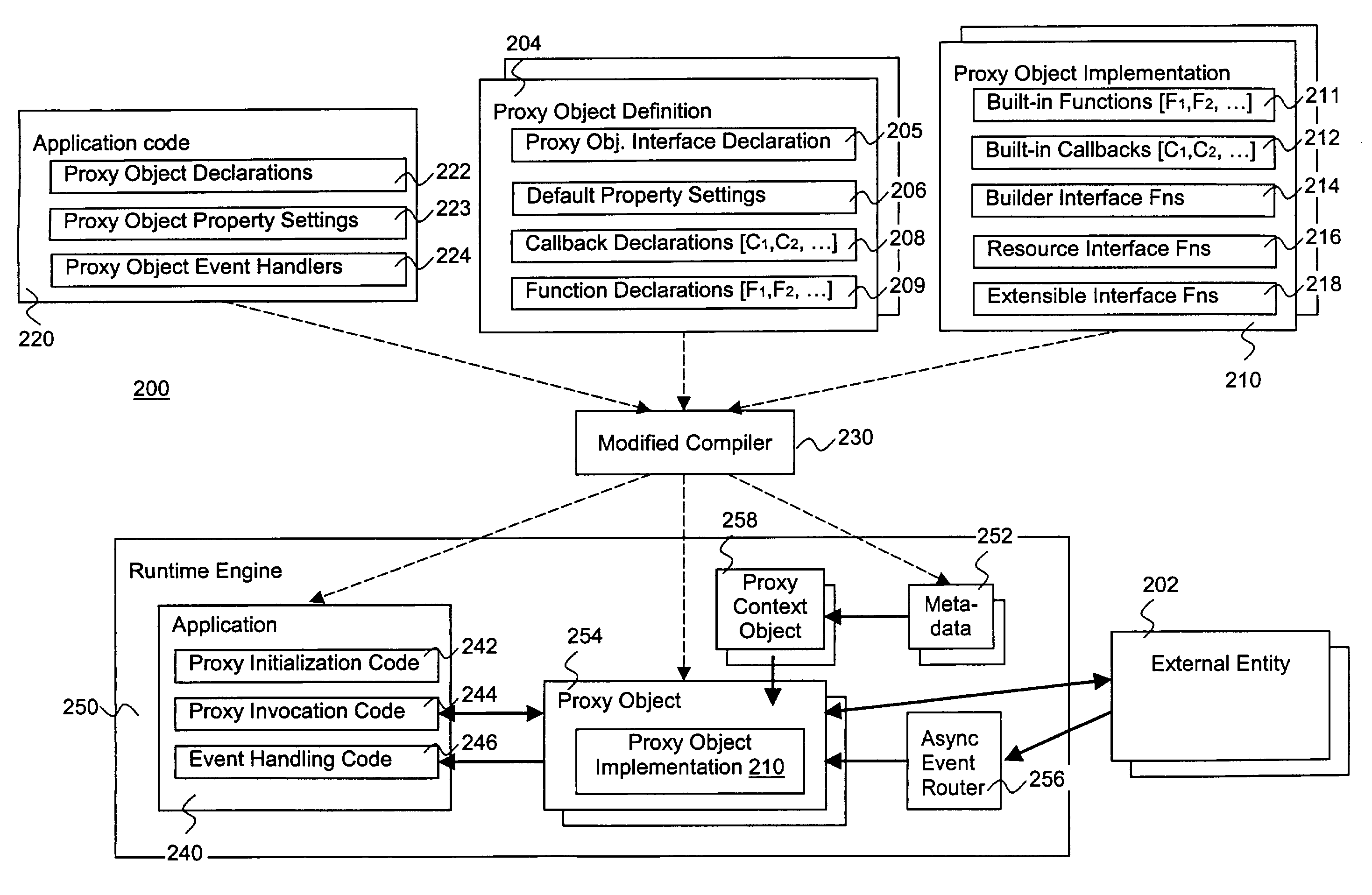
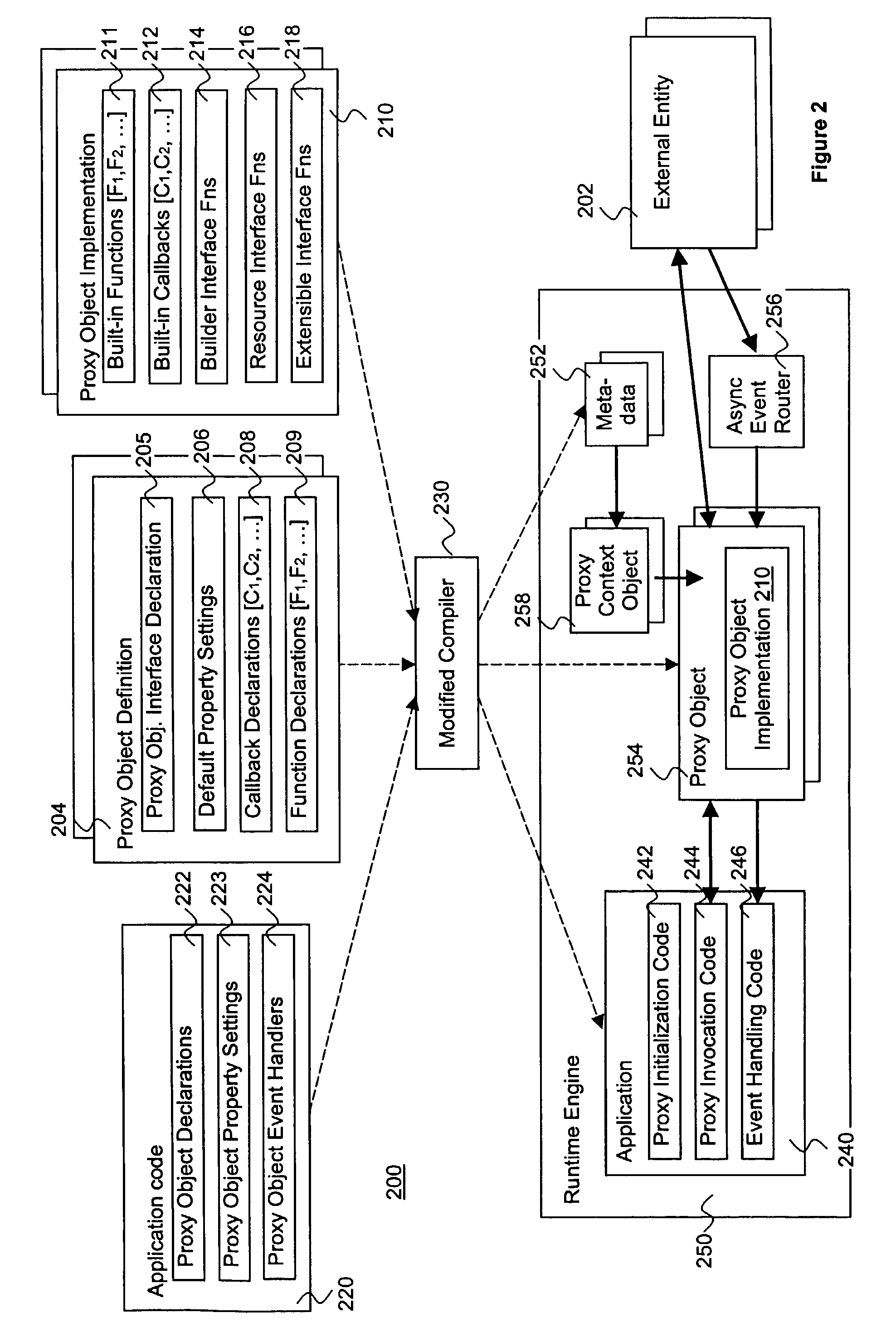
Methods and apparatus for building, customizing and using software abstractions of external entities
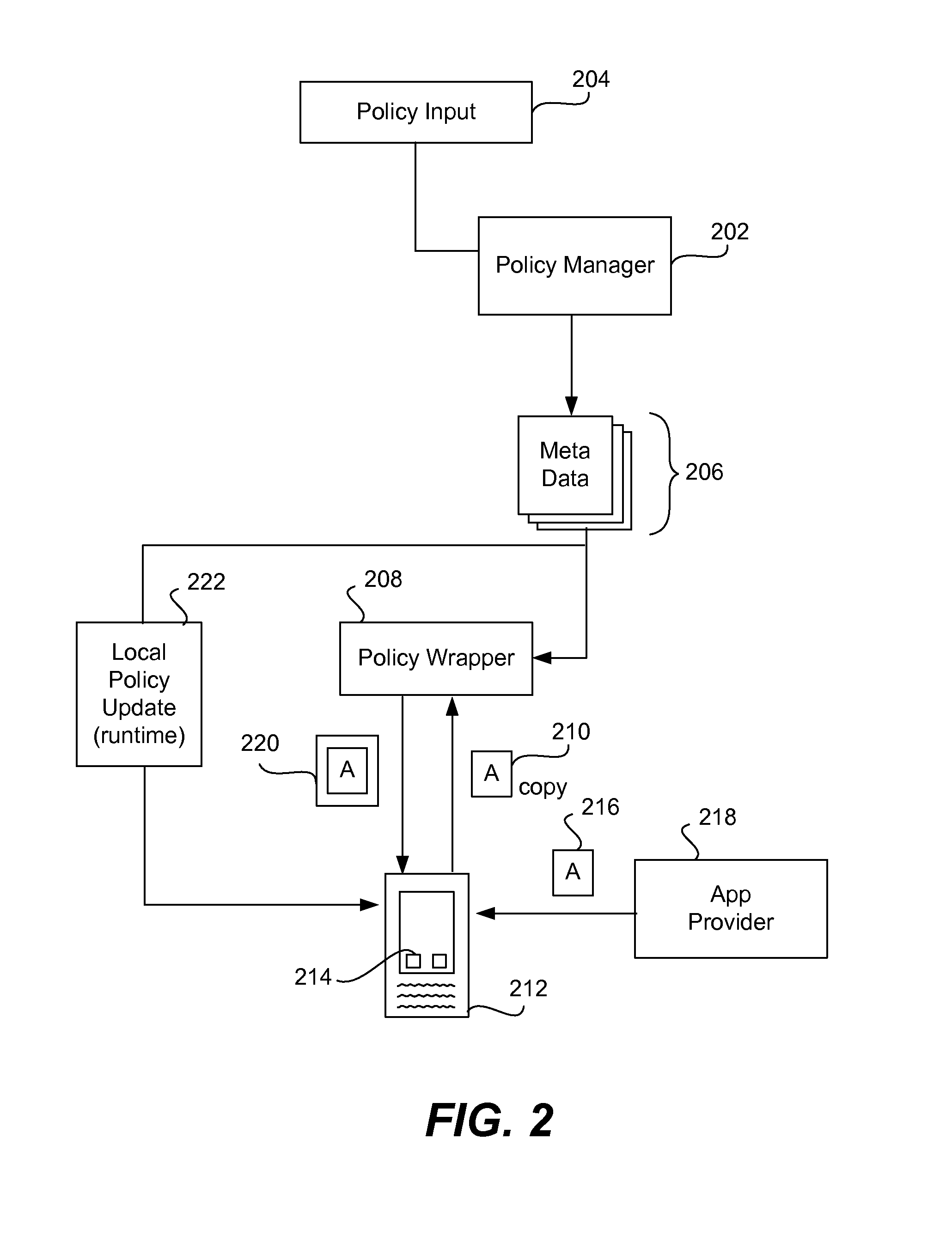
InactiveUS7516447B2Facilitate generation and routingSpecific program execution arrangementsMemory systemsObject codeObject definition
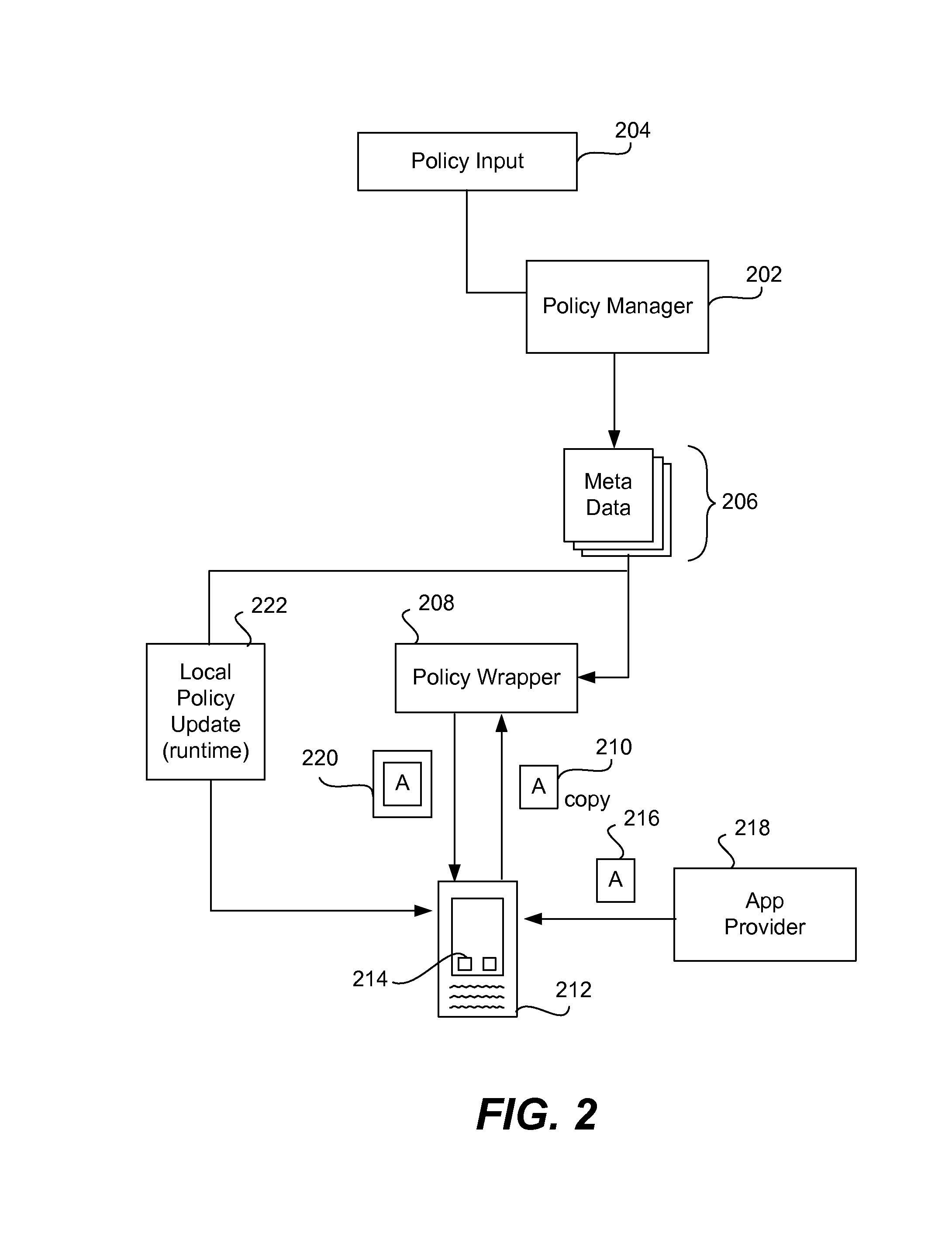
An entity is abstracted through implementation of a proxy object of the present invention, including functions for a software application to programmatically interact with the entity at runtime, as well as optional compile and design time implementation classes to support the development and customization of declarative proxy object definitions. In one embodiment, builder and resource interfaces are provided to assist in the creation of the implementation classes. In one embodiment, an extension interface is also provided to facilitate extension of an implementation of the proxy object. Software applications including programmatic usage of proxy object functions are compiled into object codes with proxy objects and meta data files. The compiled object codes are executed using a runtime engine, which includes proxy context objects to facilitate interaction on an instance basis, and an asynchronous event router to route asynchronous events for the entity.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com