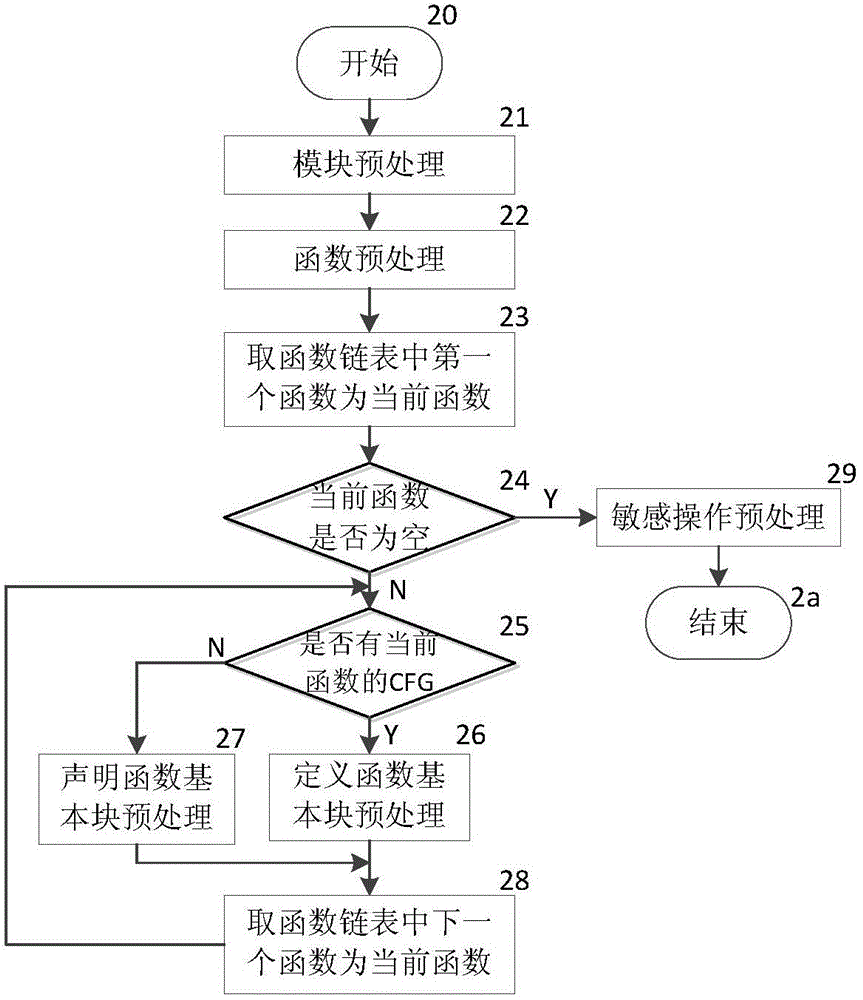
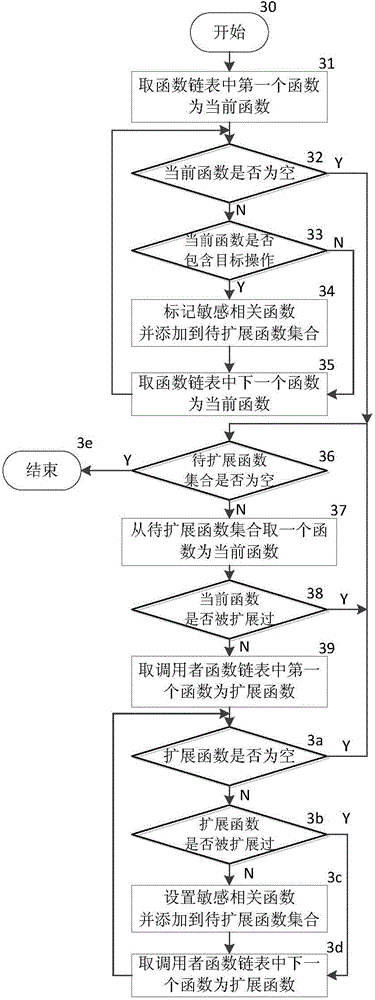
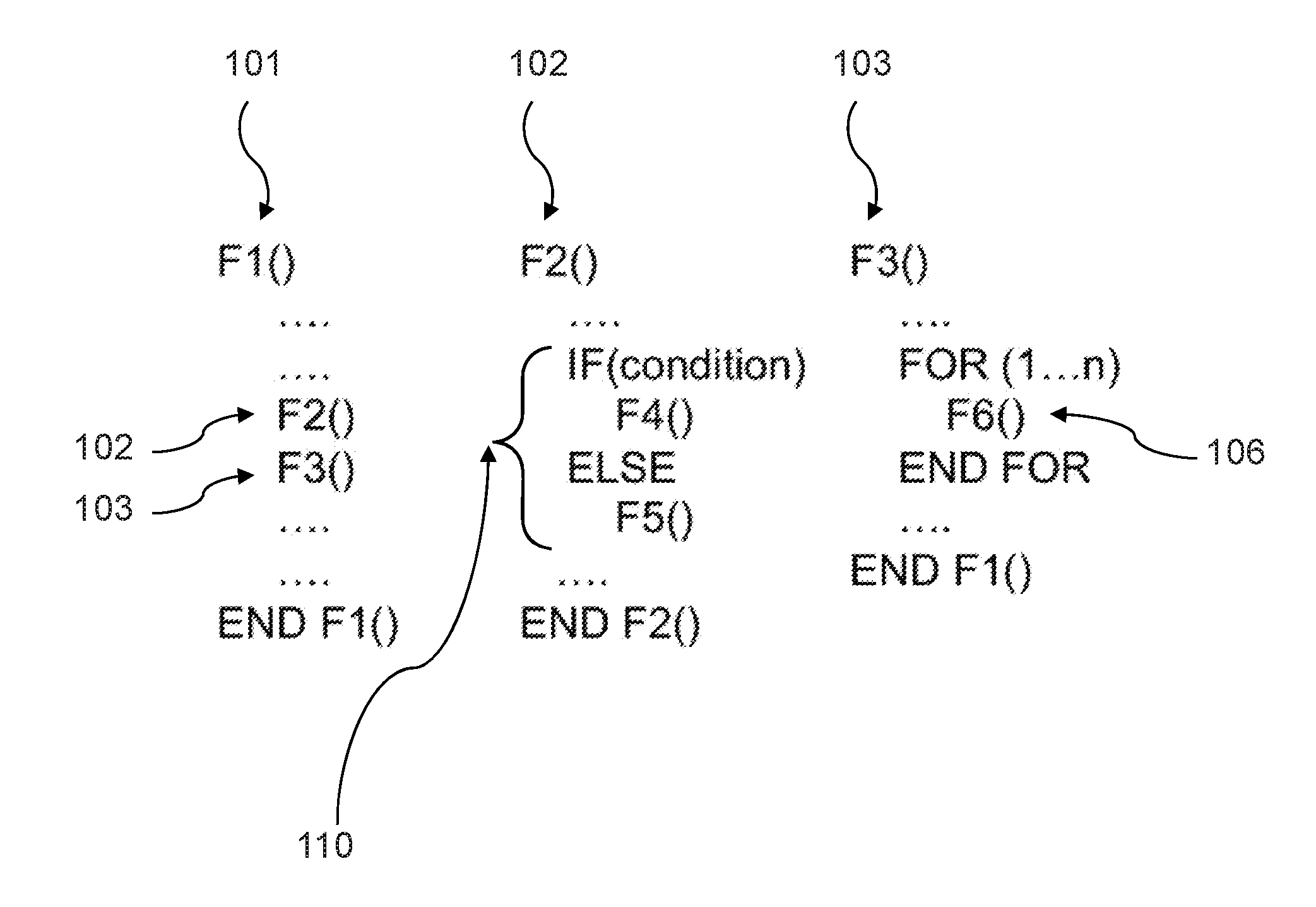
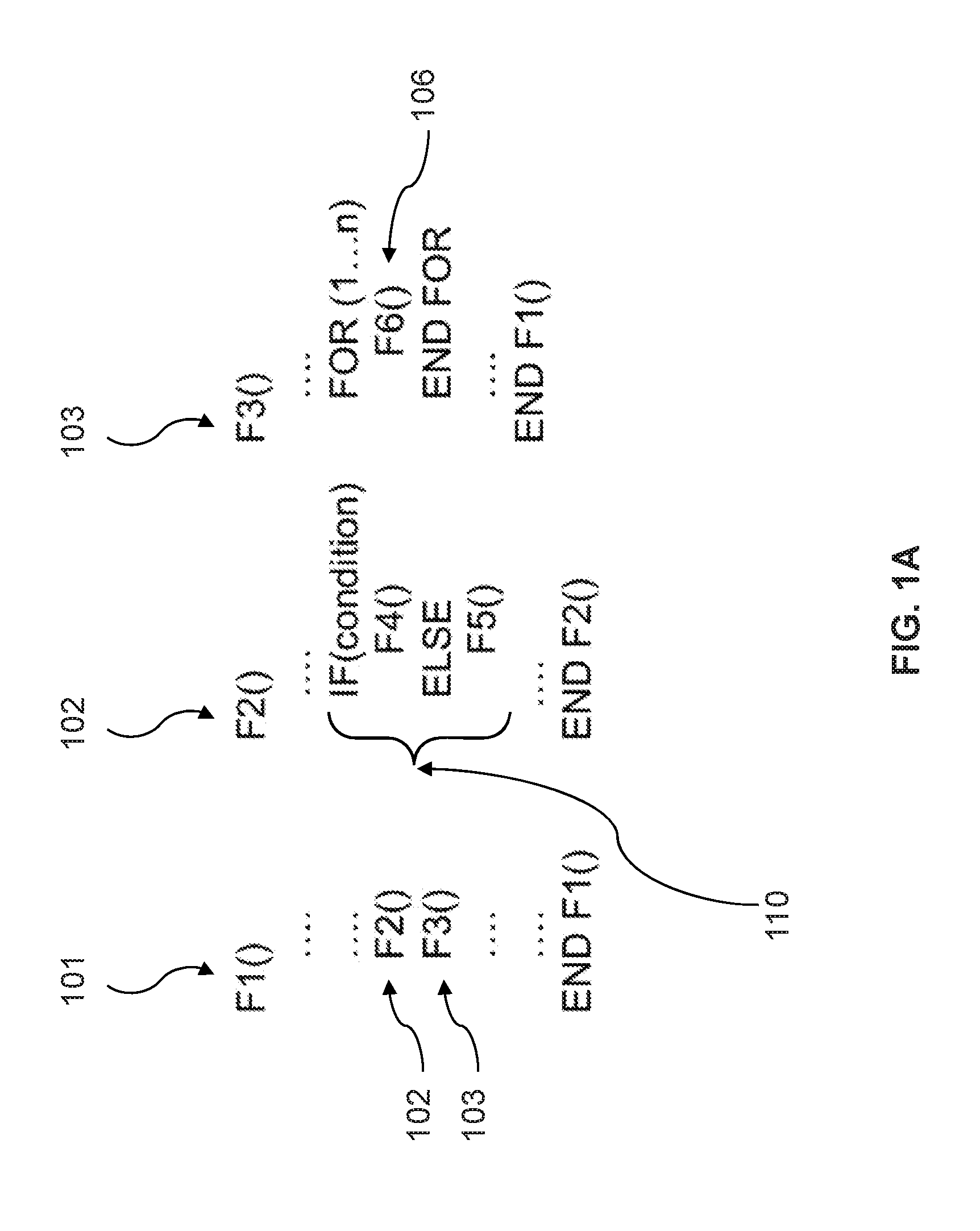
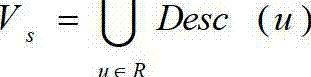Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
169 results about "Call graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
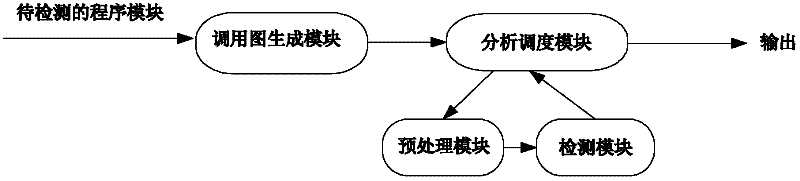
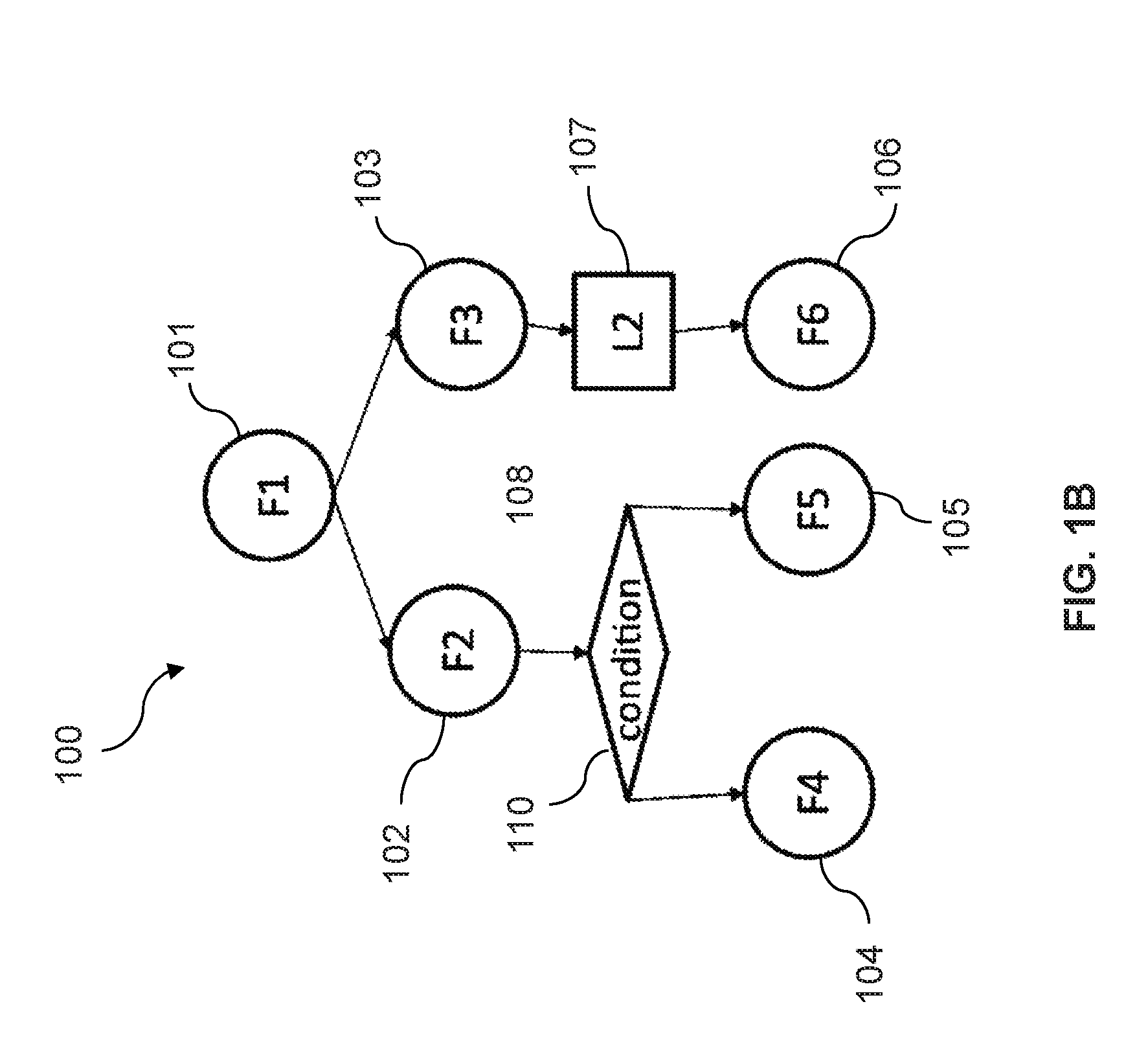
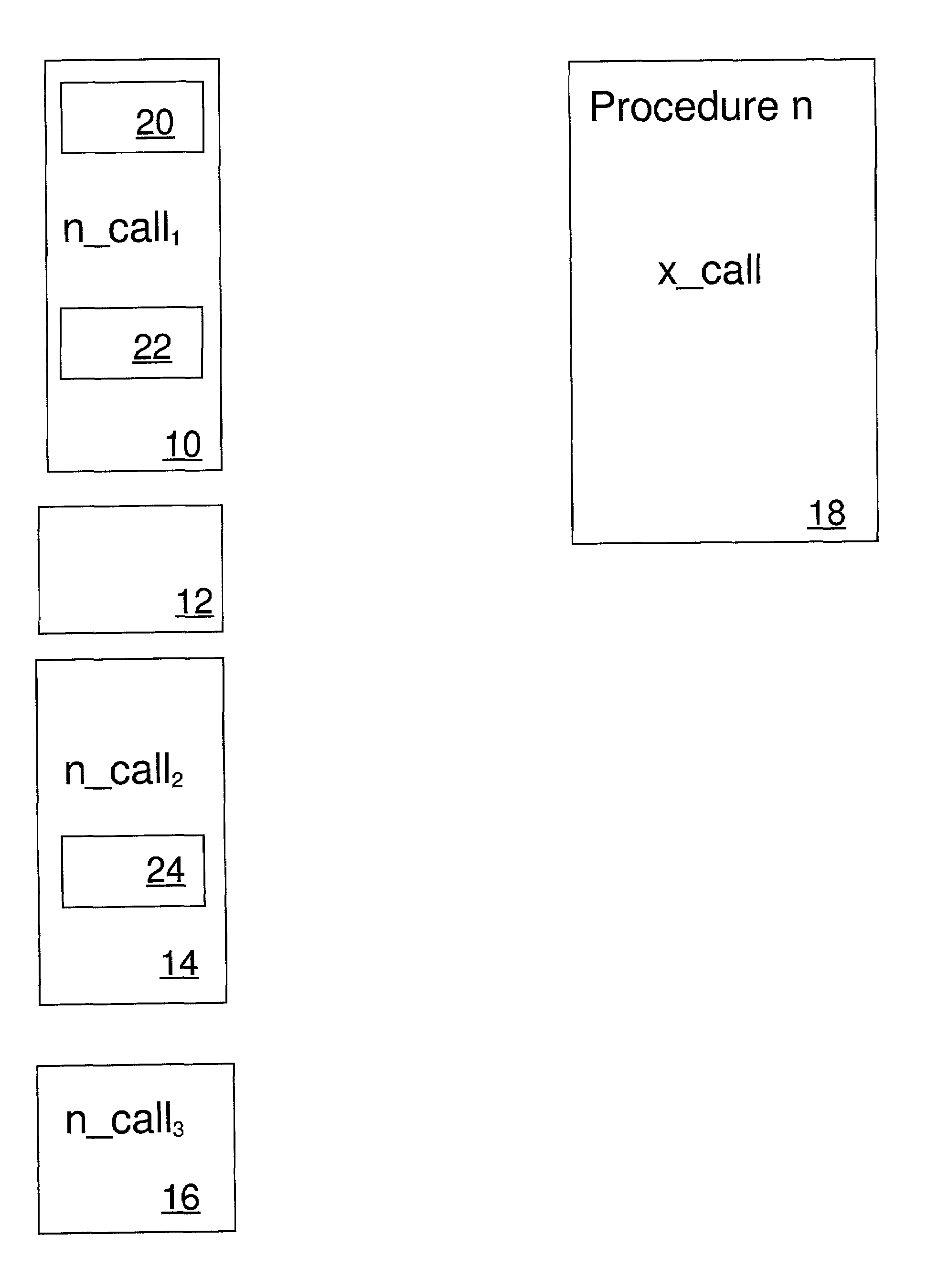
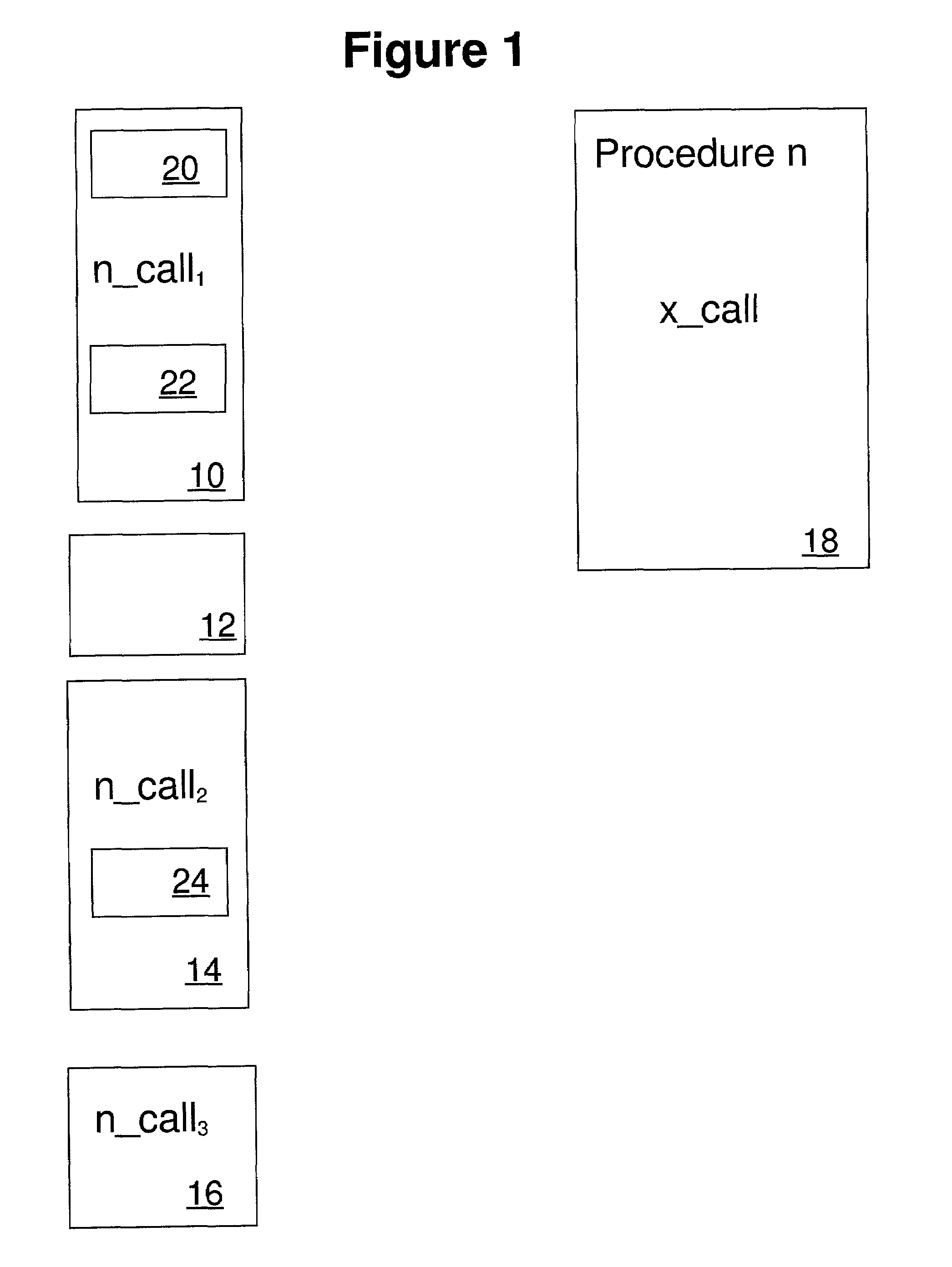
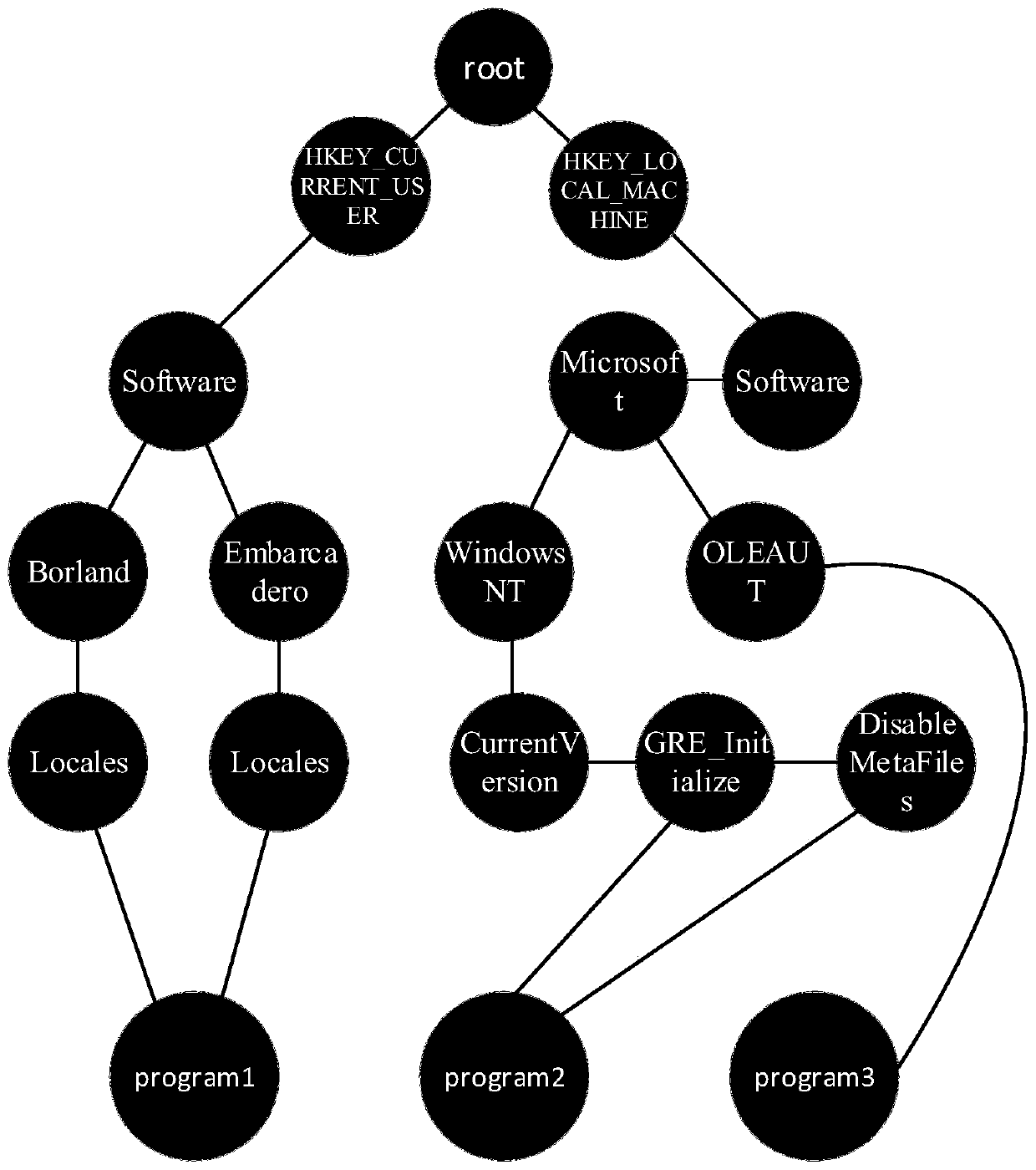
A call graph (also known as a call multigraph) is a control flow graph, which represents calling relationships between subroutines in a computer program. Each node represents a procedure and each edge (f, g) indicates that procedure f calls procedure g. Thus, a cycle in the graph indicates recursive procedure calls.
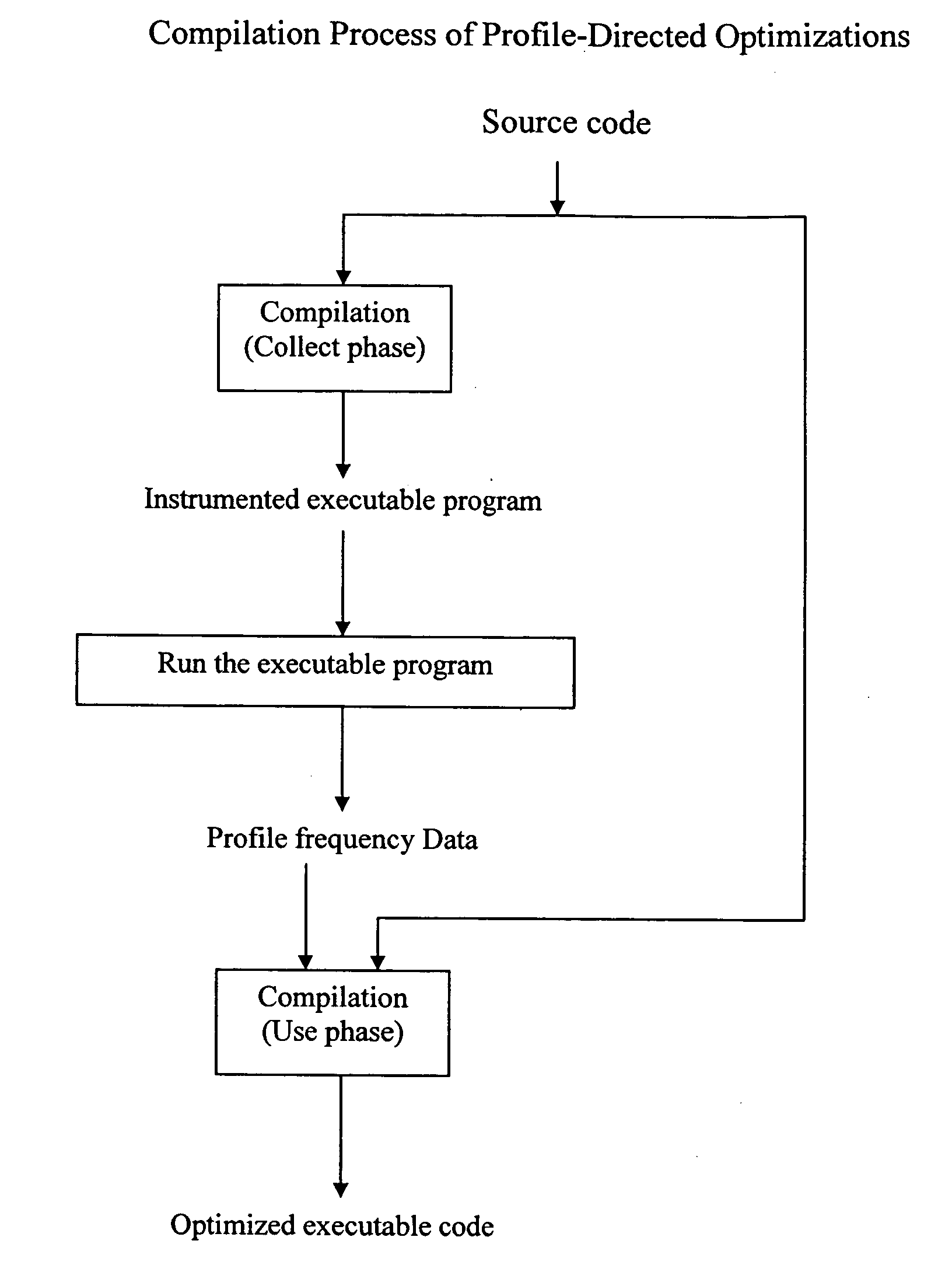
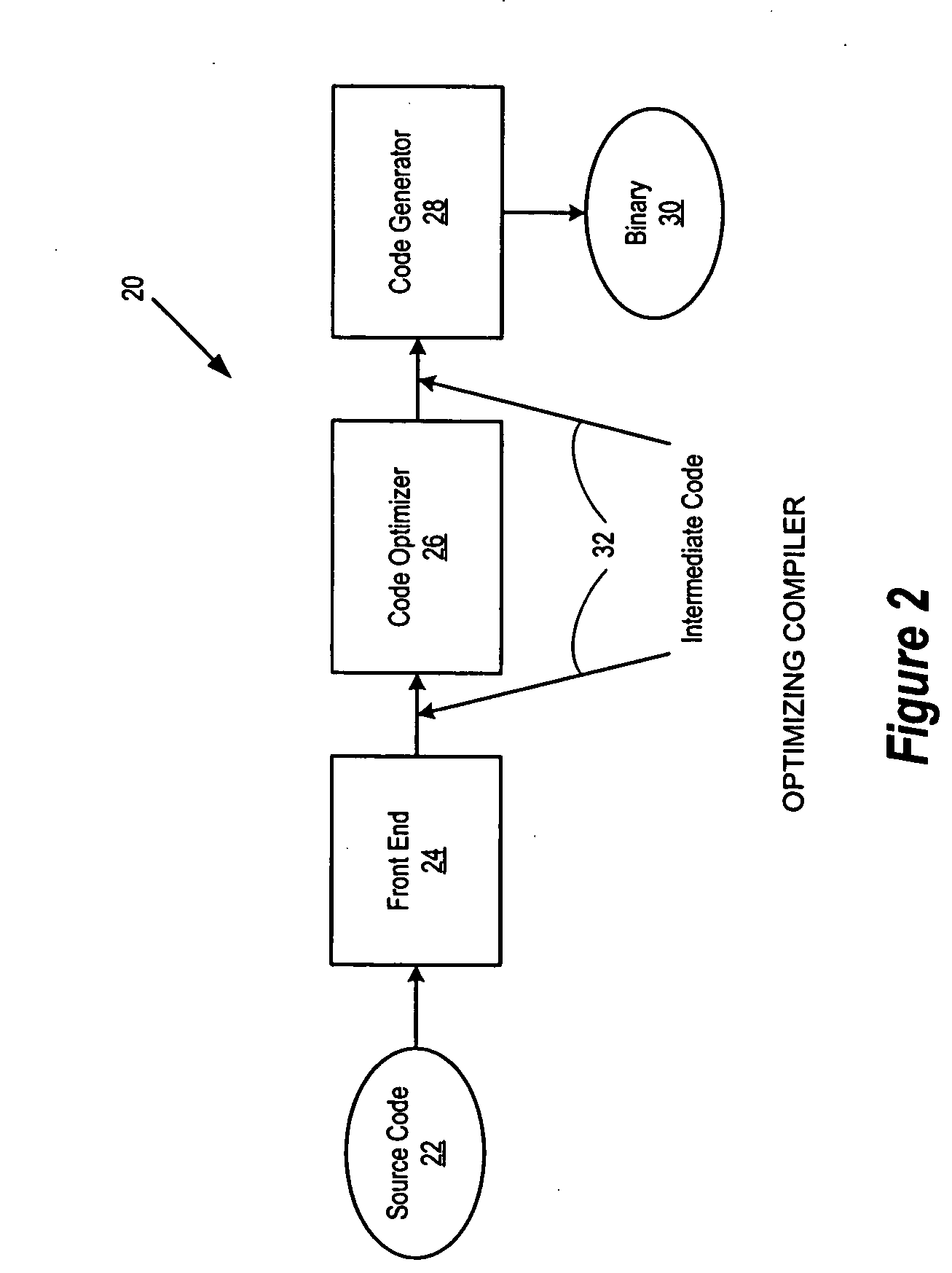
Method and apparatus for accurate profiling of computer programs
InactiveUS6934935B1Precise maintenanceHardware monitoringMultiprogramming arrangementsGraphicsOperational system
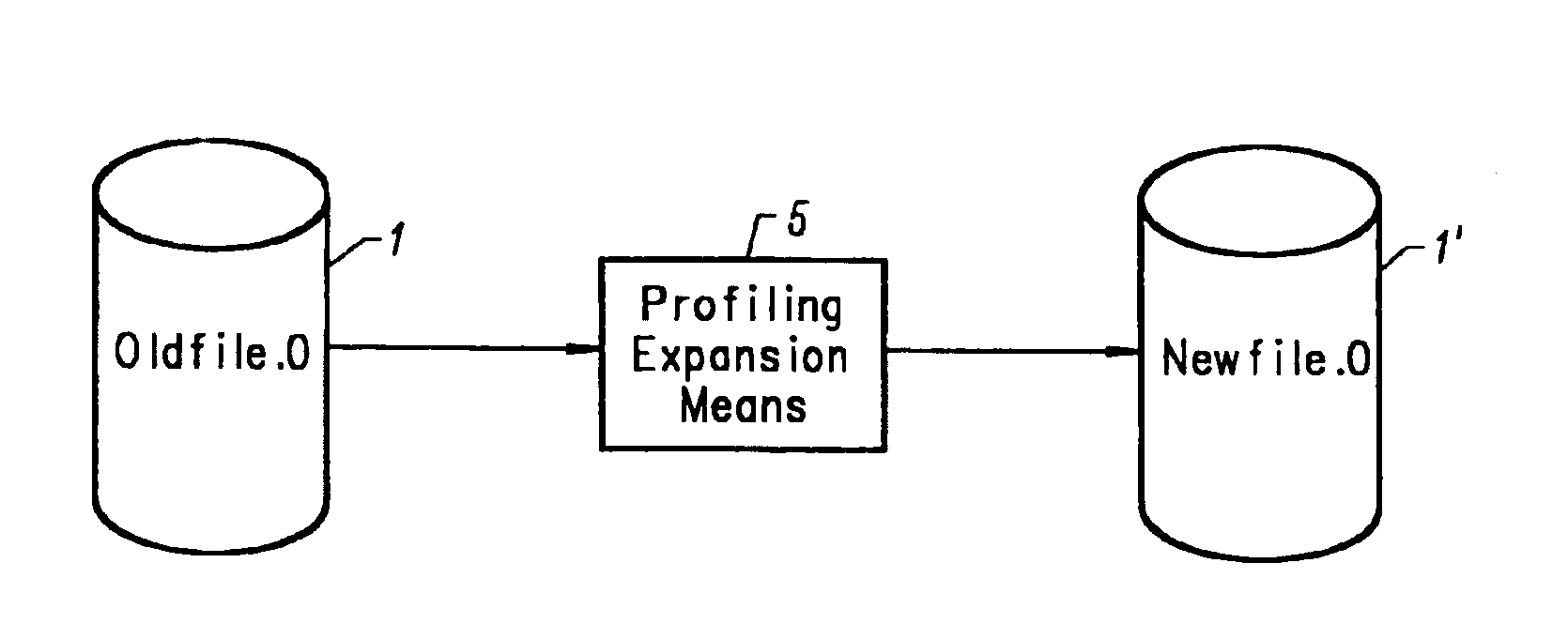
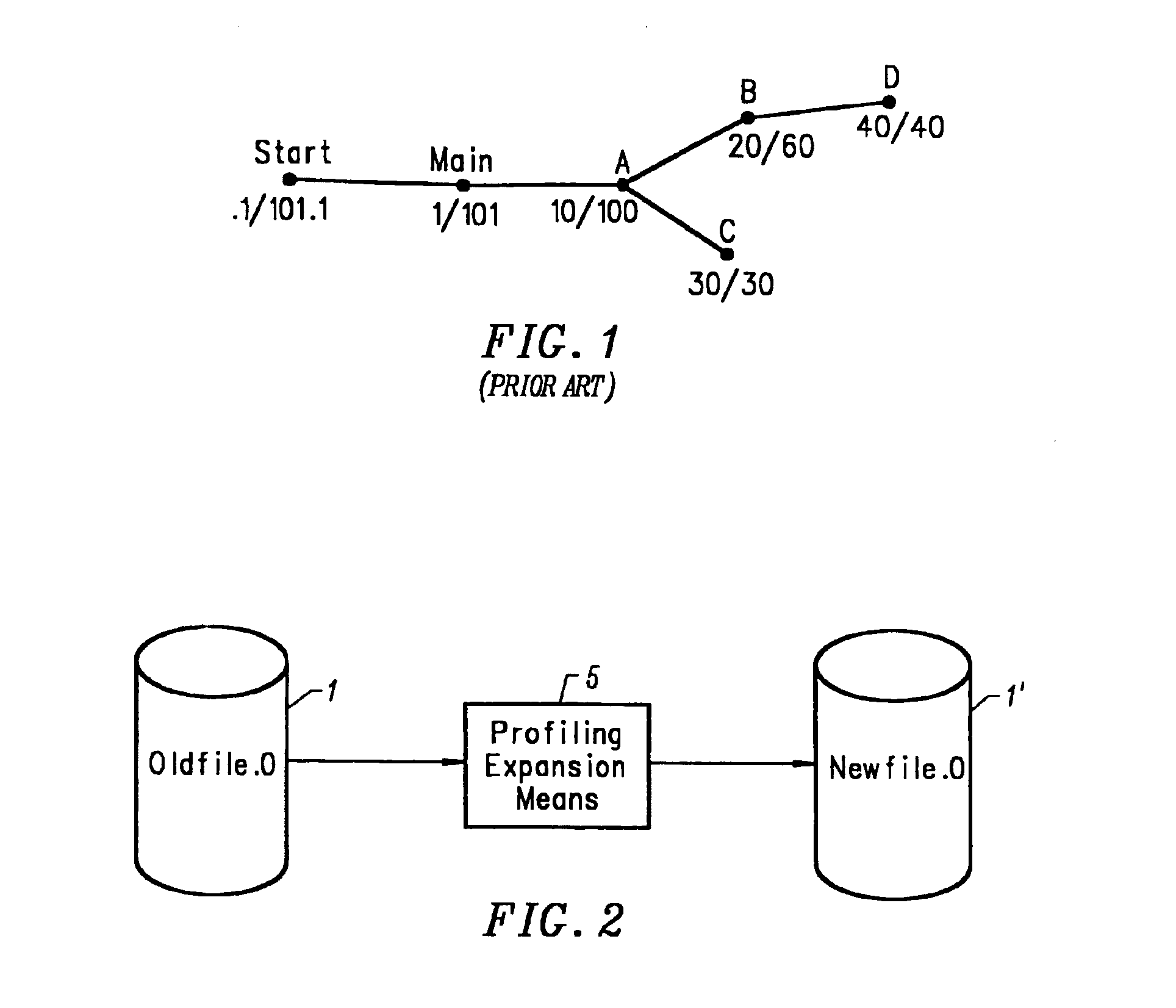
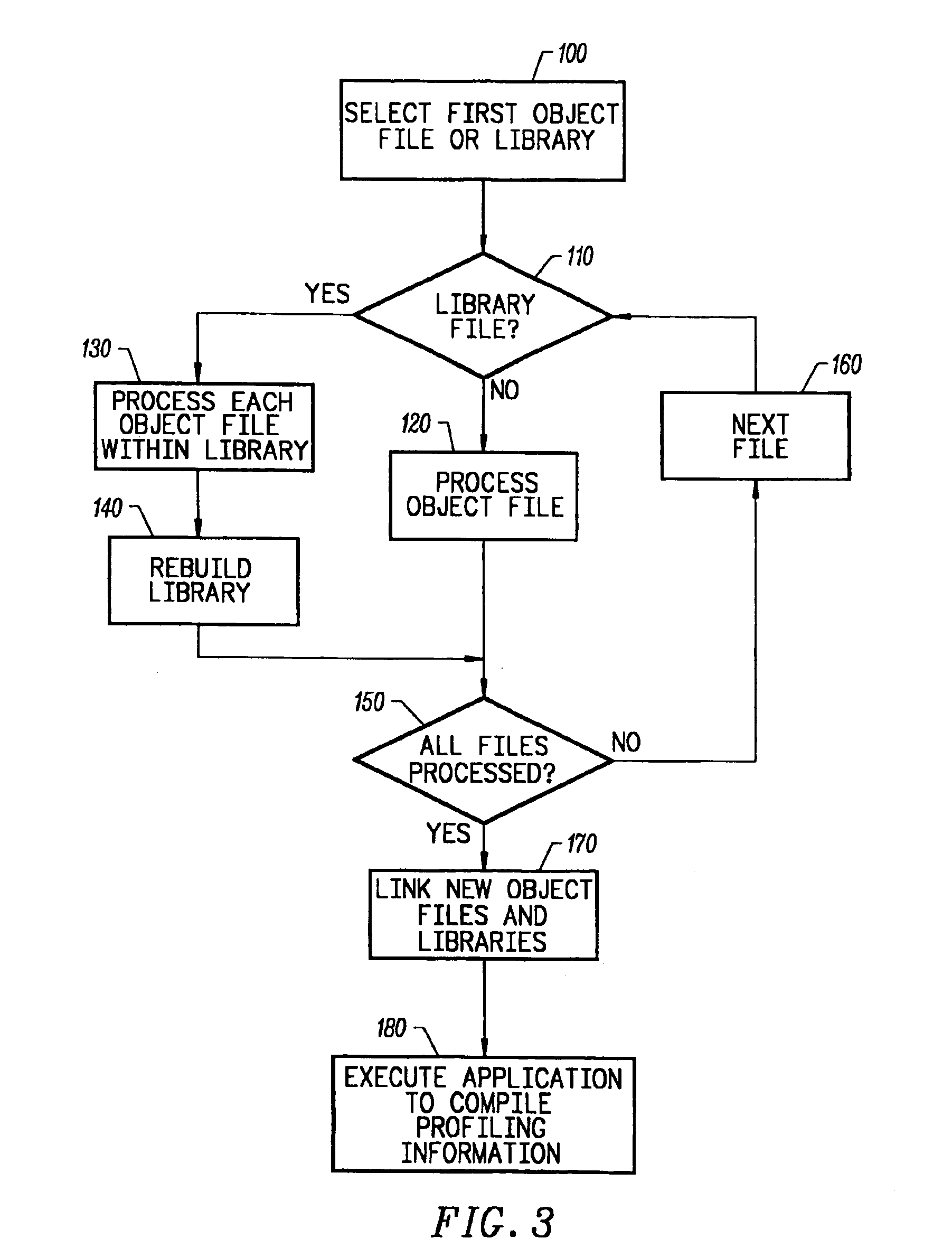
An object code expansion profiler equips a program for execution profiling by preprocessing the object code files of the program so as to add profiling monitoring code to the beginning of all or substantially all functions. The preprocessing includes, for each function, the steps of grouping the function's instructions into basic blocks, counting the number of cycles required to execute the instructions of the basic block, and inserting special monitoring code with the basic block. The special monitoring code is executed each time the basic block is executed, and updates the profiling information to reflect the number of cycles required to execute the basic block. Special handling is provided for profiling calls to the Operating System (OS). The resultant profiling information is converted into a call graph image most useful for human users. For each arc in the graph connecting a calling-function / parent-node to a called-function / child node, the displayed arc image has a width logarithmically proportional to the self+descendants time for the called function.
Owner:IBM CORP
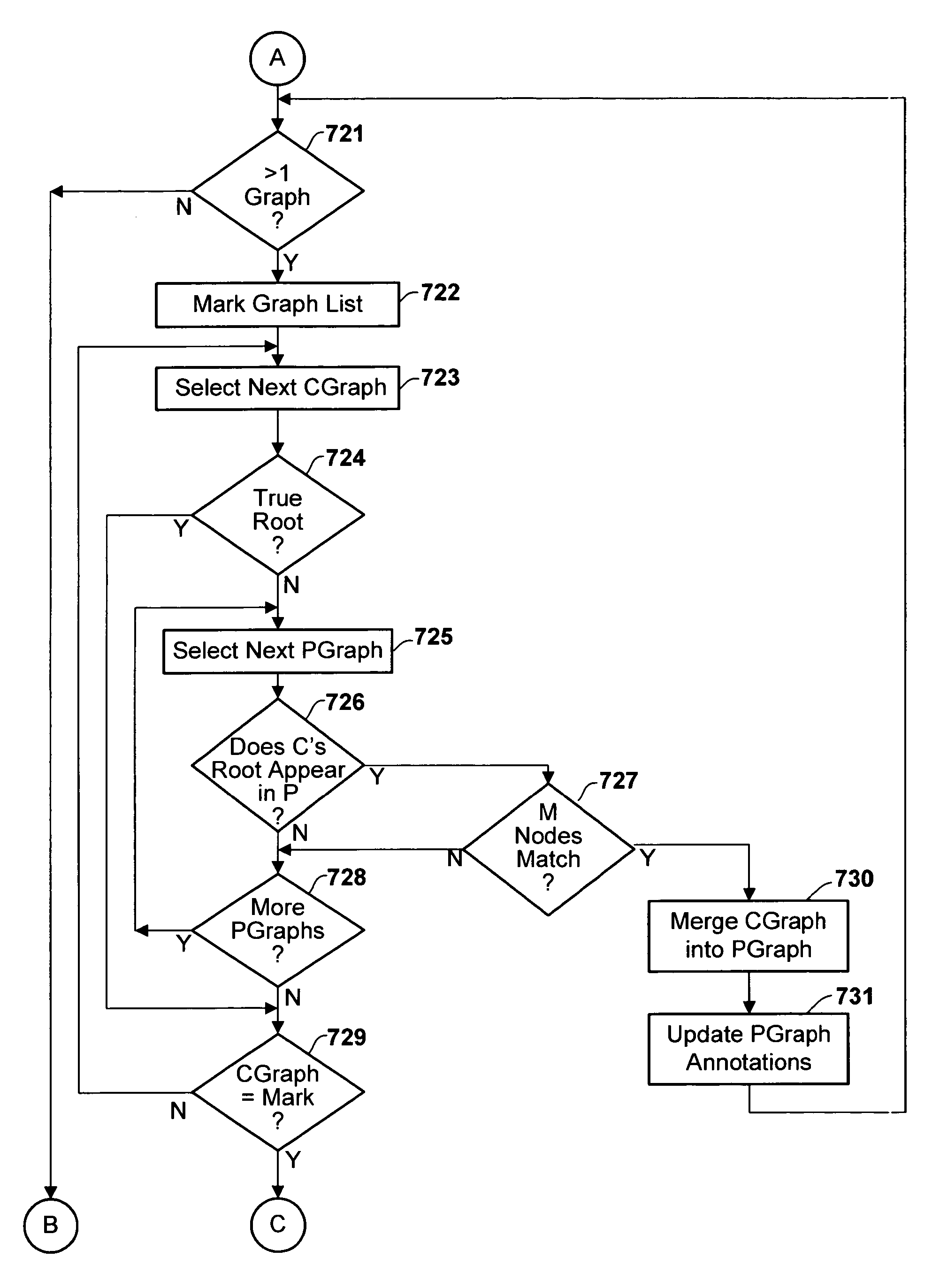
Method and apparatus for analyzing call history data derived from execution of a computer program
InactiveUS20060218543A1Data is very largeReduce overheadError detection/correctionSpecific program execution arrangementsGraphicsGraphical user interface
Call history data is sampled at fixed intervals during run-time, each sample representing only a limited portion of the stack. These data samples are subsequently automatically analyzed by merging overlapping sampled call history sequences to build larger call graphs, according to some pre-specified merge criterion. Preferably, the call history graphs are annotated with counts of the execution frequency (number of times a particular procedure was executing when the sample was collected) and the stack frequency (number of times the procedure appeared in the sampled stack portion) associated with each respective called procedure. Preferably, a graphical user interface presents the user with a graphical representation of the call graph(s) and annotations.
Owner:IBM CORP
Method and apparatus for analyzing call history data derived from execution of a computer program
InactiveUS7509632B2Reduce overheadWithout distortionError detection/correctionSpecific program execution arrangementsGraphicsGraphical user interface
Owner:INT BUSINESS MASCH CORP
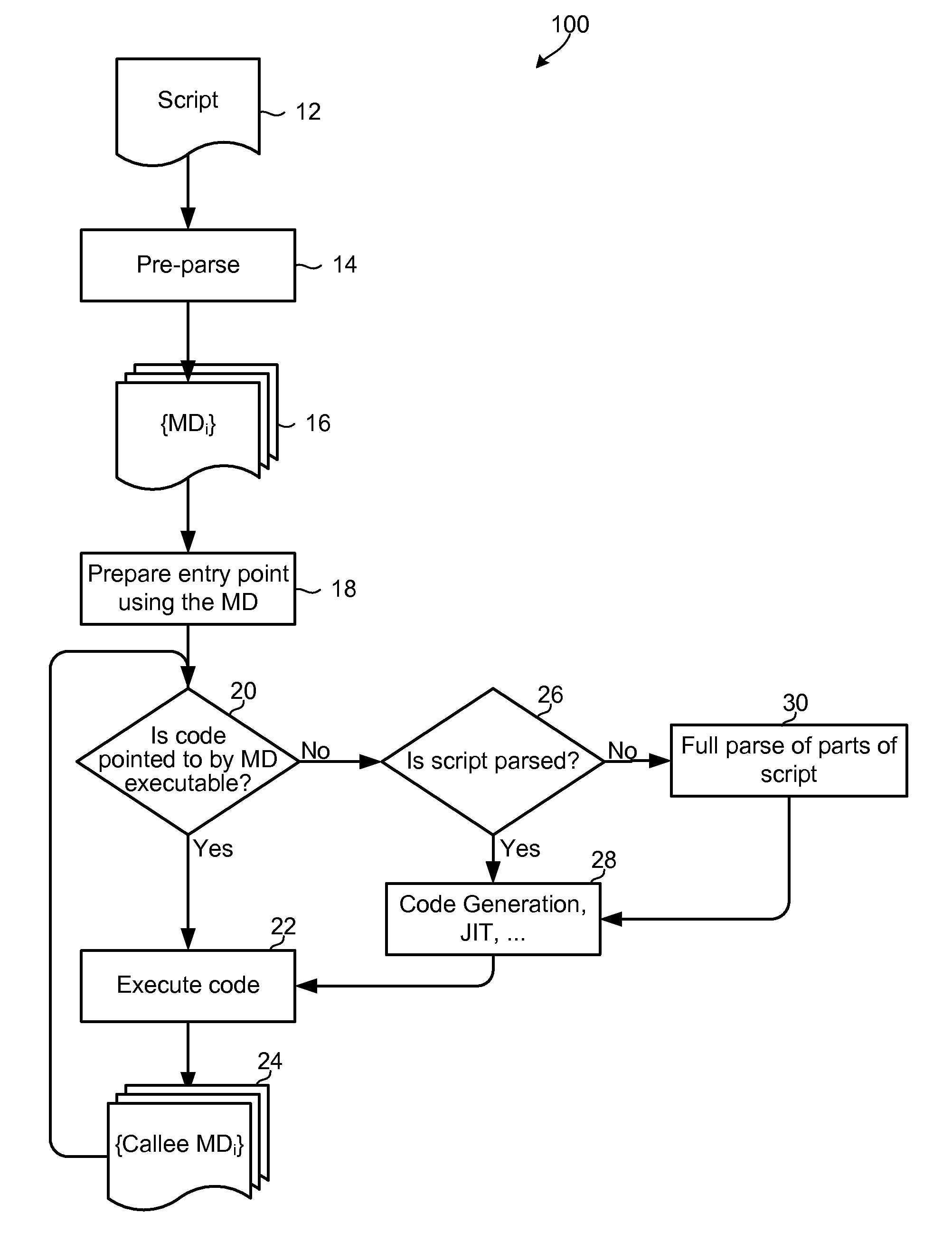
Execution of dynamic languages via metadata extraction
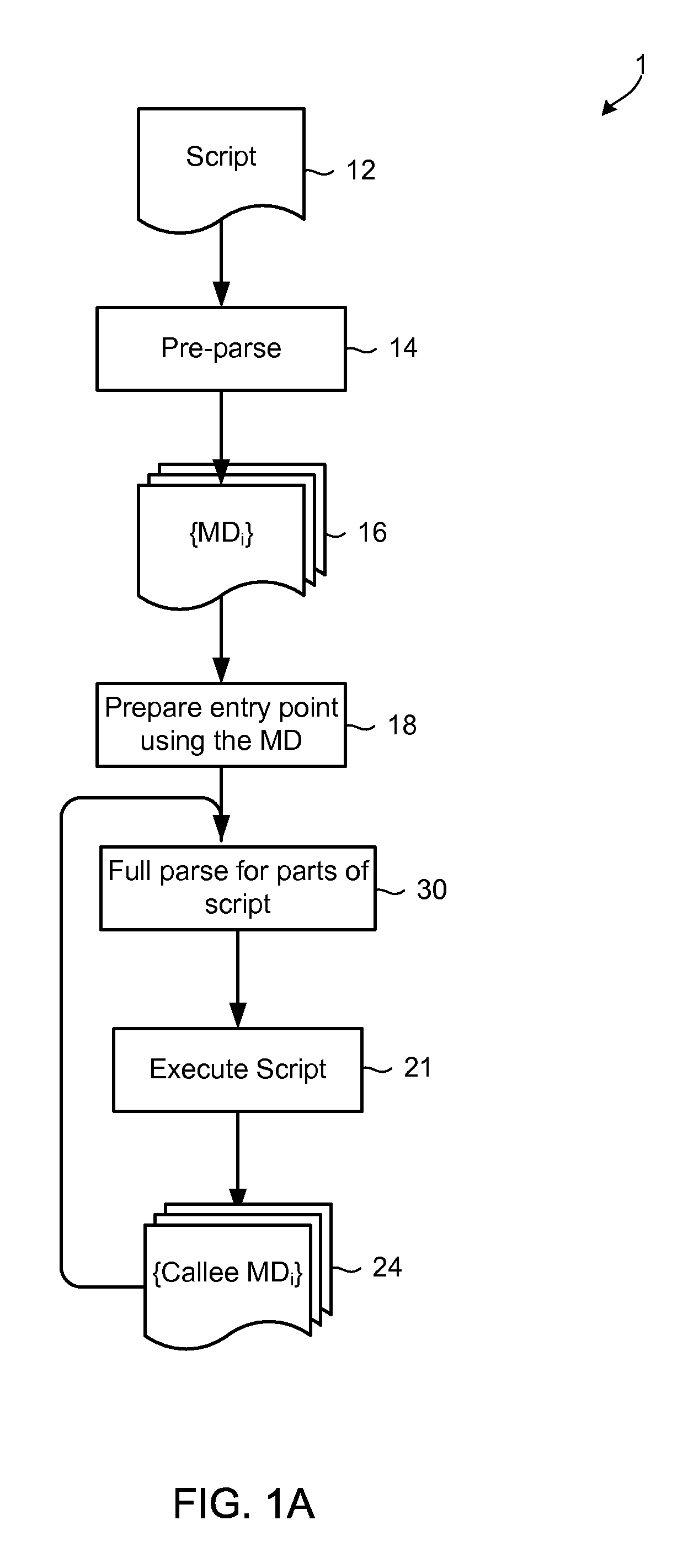
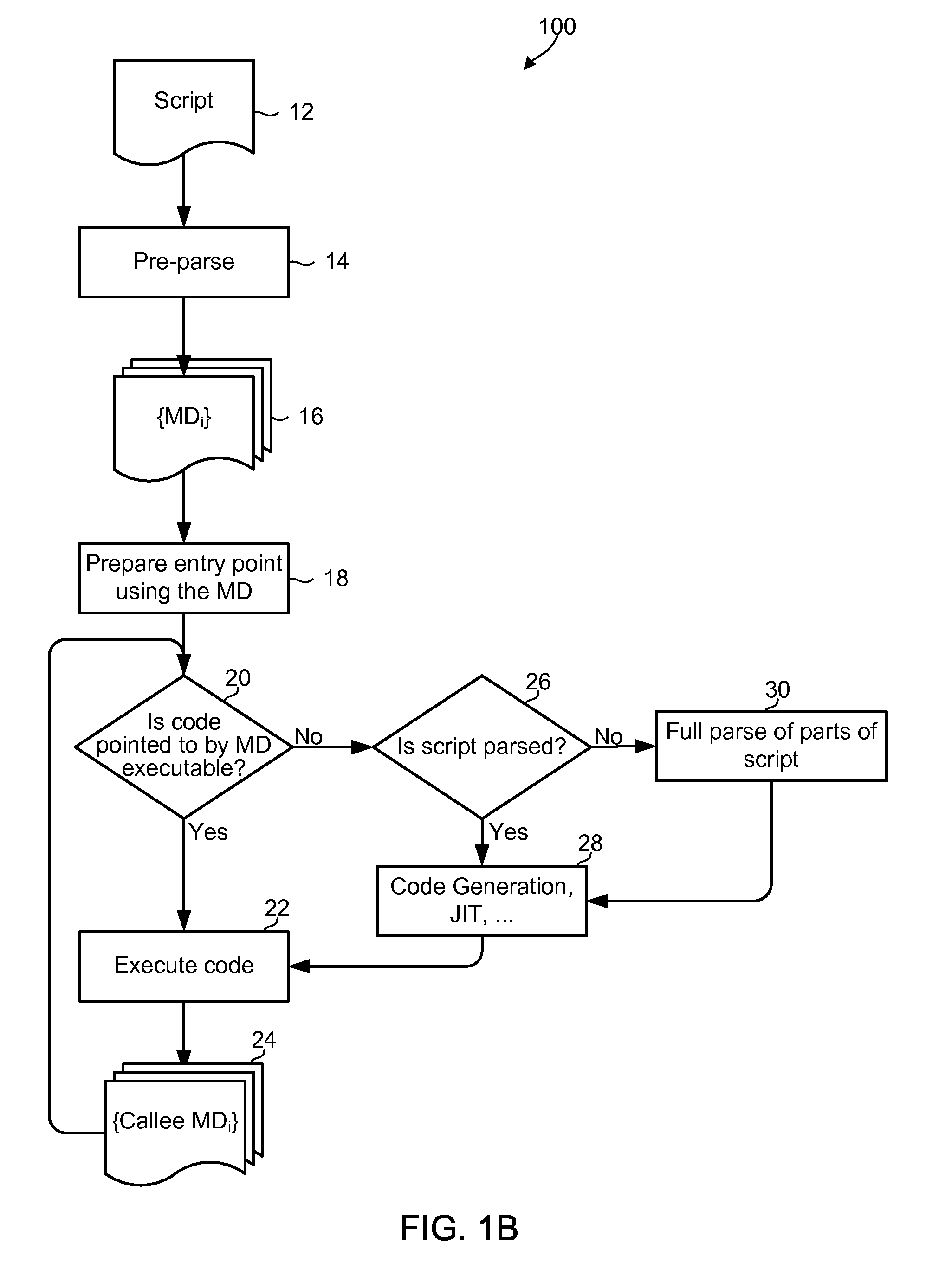
Methods and devices for executing scripts written in a dynamic scripting language include parsing scripts in two stages, a pre-parse using a simplified grammar to generate script metadata regarding the high level structure of the script, and a full parse using the grammar and syntax of the dynamic scripting language and generated script metadata. The generated metadata may describe the high level structure that is present in the language of the script such as functions, object methods, and a top level call graph. The script metadata may be used during the full parse to determine the parts of the code to be fully parsed. The aspects minimize processing time spent in the parsing at run-time, and may eliminate processing required to interpret or compile sections of code that will not be executed. Script metadata as well as results of full parsing may also be cached to provide further processing efficiencies.
Owner:QUALCOMM INC
Automatic software fault diagnosis by exploiting application signatures
InactiveUS7877642B2Reduce in quantityExcessive weightDatabase updatingError detection/correctionProgram tracingSoftware fault
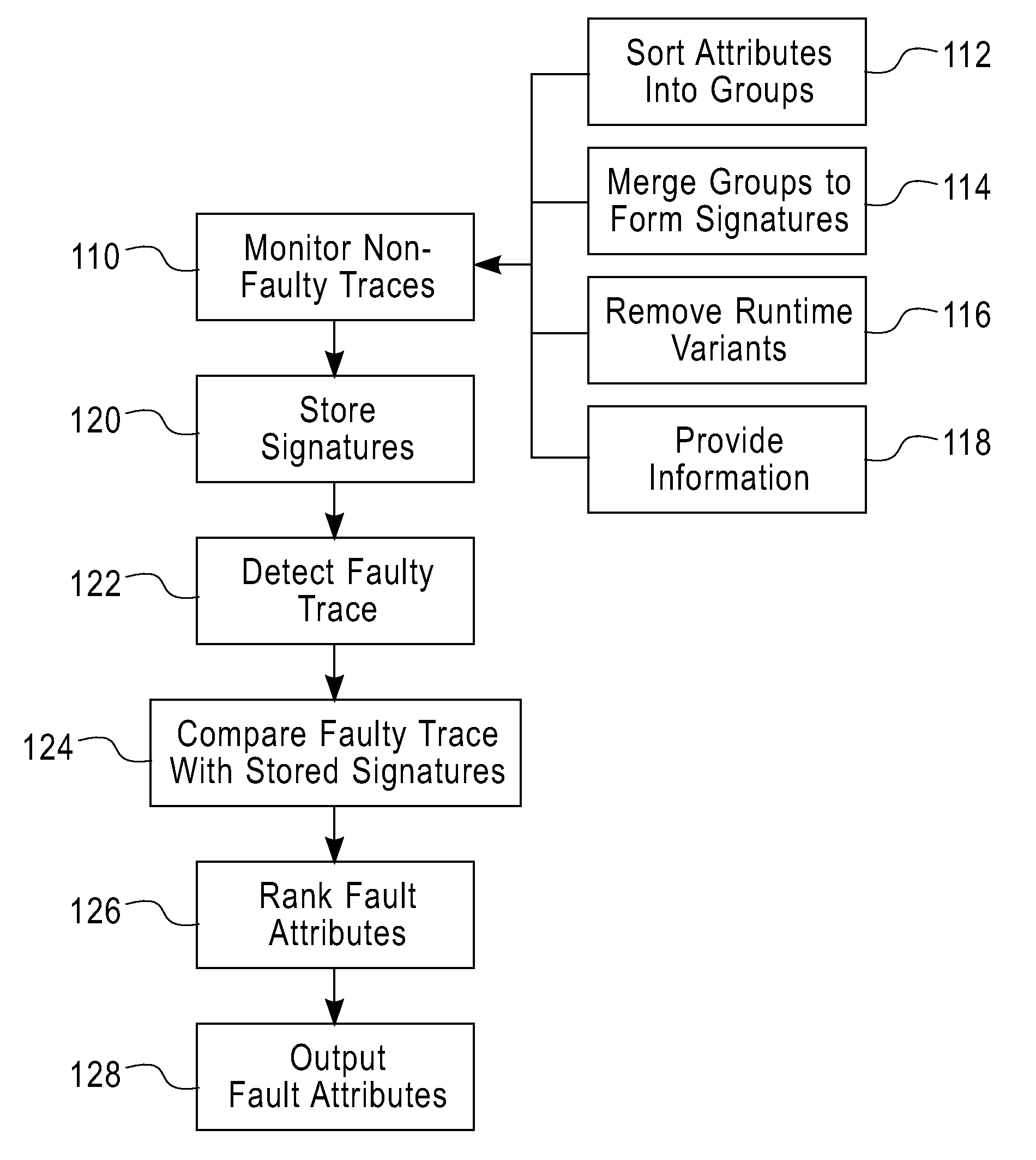
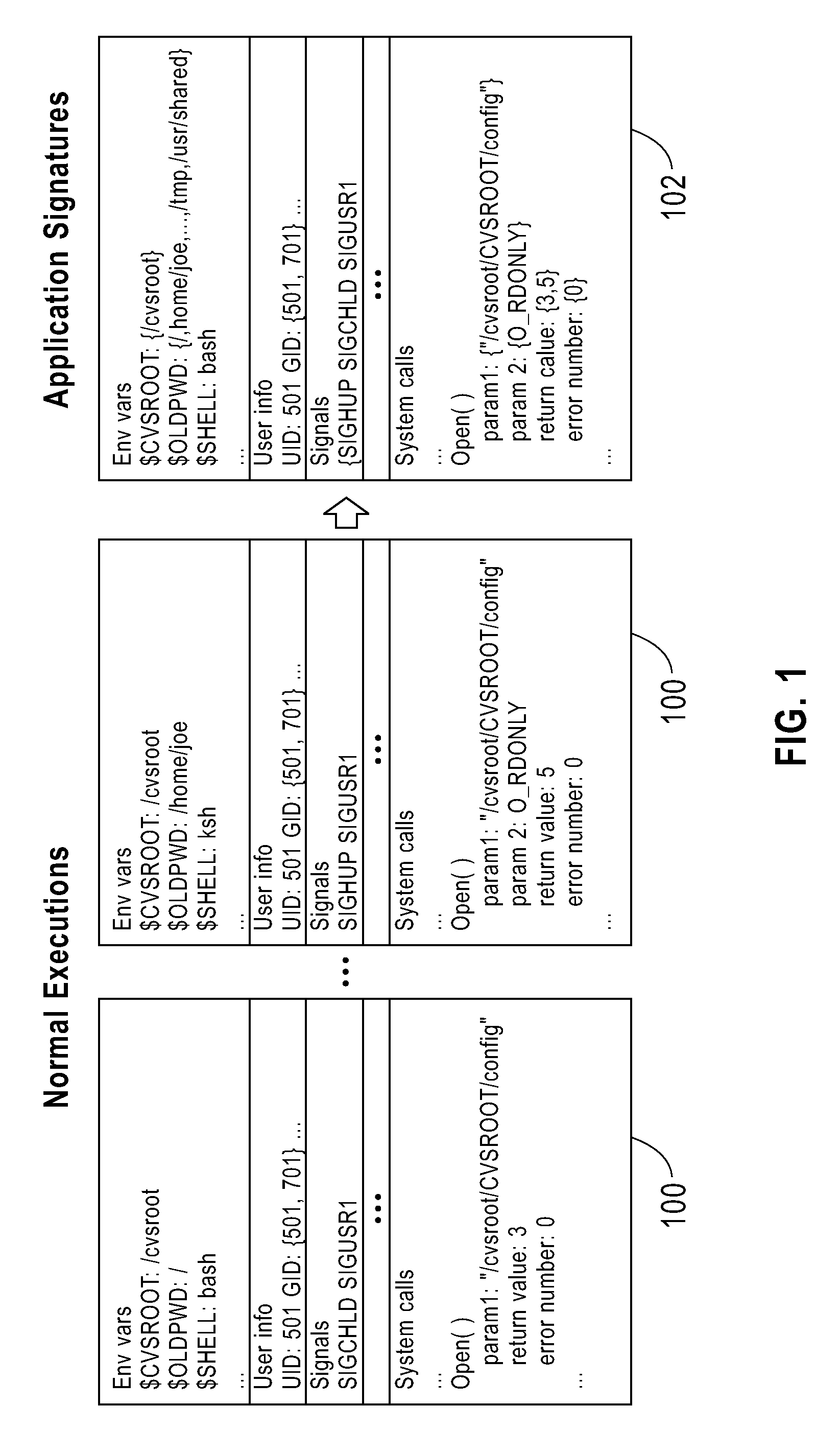
A method monitors non-faulty application traces of a computer application with the runtime environment during fault-free activities to create non-faulty runtime signatures for the computer application. Once obtained, the method stores the non-faulty runtime signatures. The method then detects a faulty application trace of the computer application and compares the faulty application trace with the non-faulty runtime signatures by comparing a call graph of the faulty application trace with call graphs of non-faulty application traces of the application signatures to identify differences between the two (e.g., fault attributes). Then the invention outputs the fault attributes to allow the user to identify a fault cause.
Owner:GLOBALFOUNDRIES INC
Code static analysis-based data race detecting method and system thereof
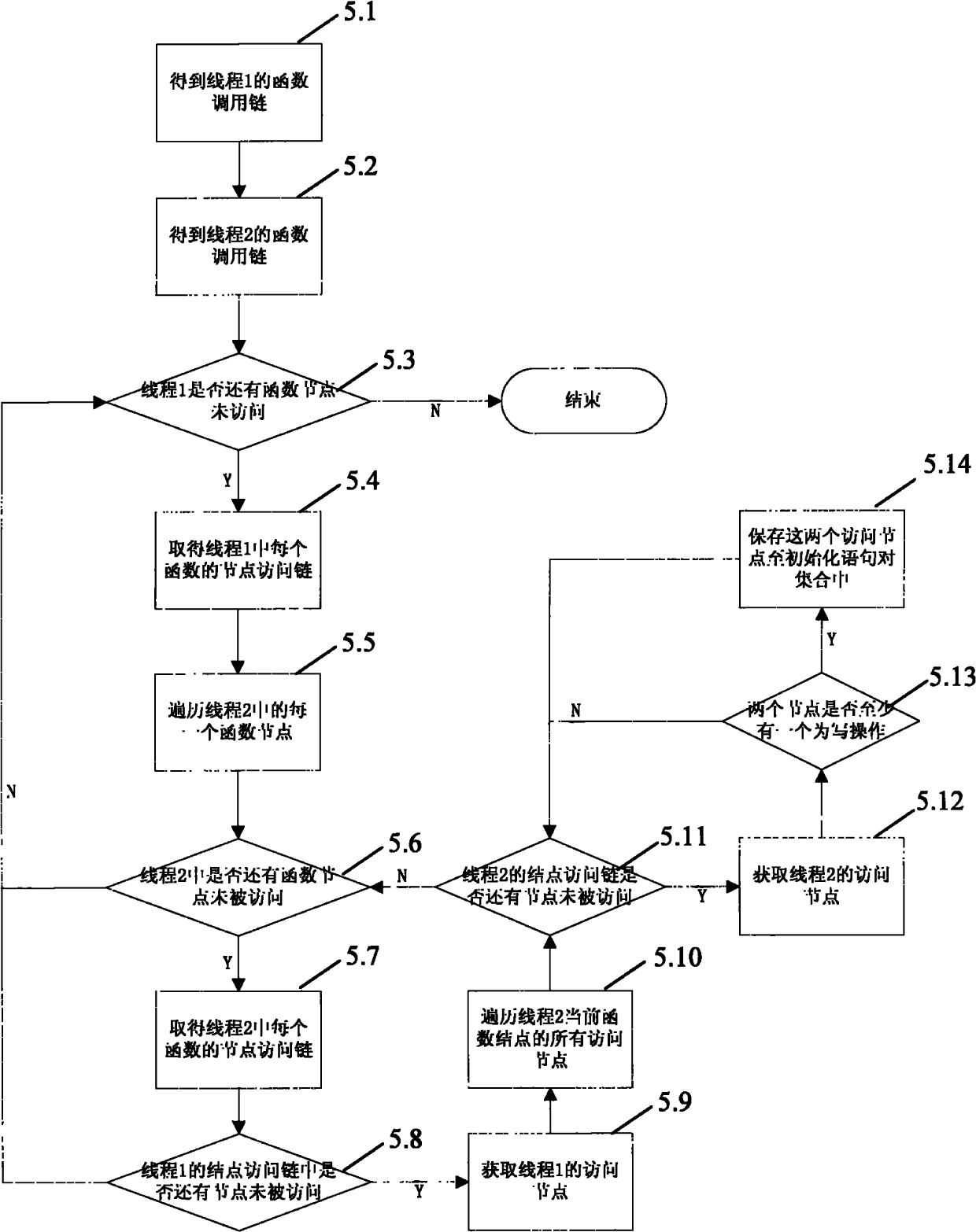
The invention discloses a code static analysis-based data race detecting method and a system of the detecting method. The method comprises the following steps of: reading software to be detected, statically analyzing a source program of the software to be detected, and generating an abstract syntax tree, a control flow graph and a global function call graph of the software to be detected; on thatbasis, computing alias information in each function, outlet alias information among functions, lock assembly information, an access link of an access escapable variable quantity in each function and a thread building relational graph; computing a plurality of initialized sentence pair sets of a plurality of access nodes in every two threads; and gradually eliminating the sets according to the alias information, the lock assembly information and a concurrency relation to obtain a sentence pair which can finally have the data race. The detecting method and the detecting system can effectively detect the data race of a multi-thread program compiled by C / C++, thereby having the characteristics of high test precision and high automaticity, and being applied to detecting the data race caused bytwo threads or multiple threads.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Dynamic and static combined software security test method
InactiveCN102360334AIncreased security testing productivitySolve the path space explosion problemSoftware testing/debuggingCall graphBasic block
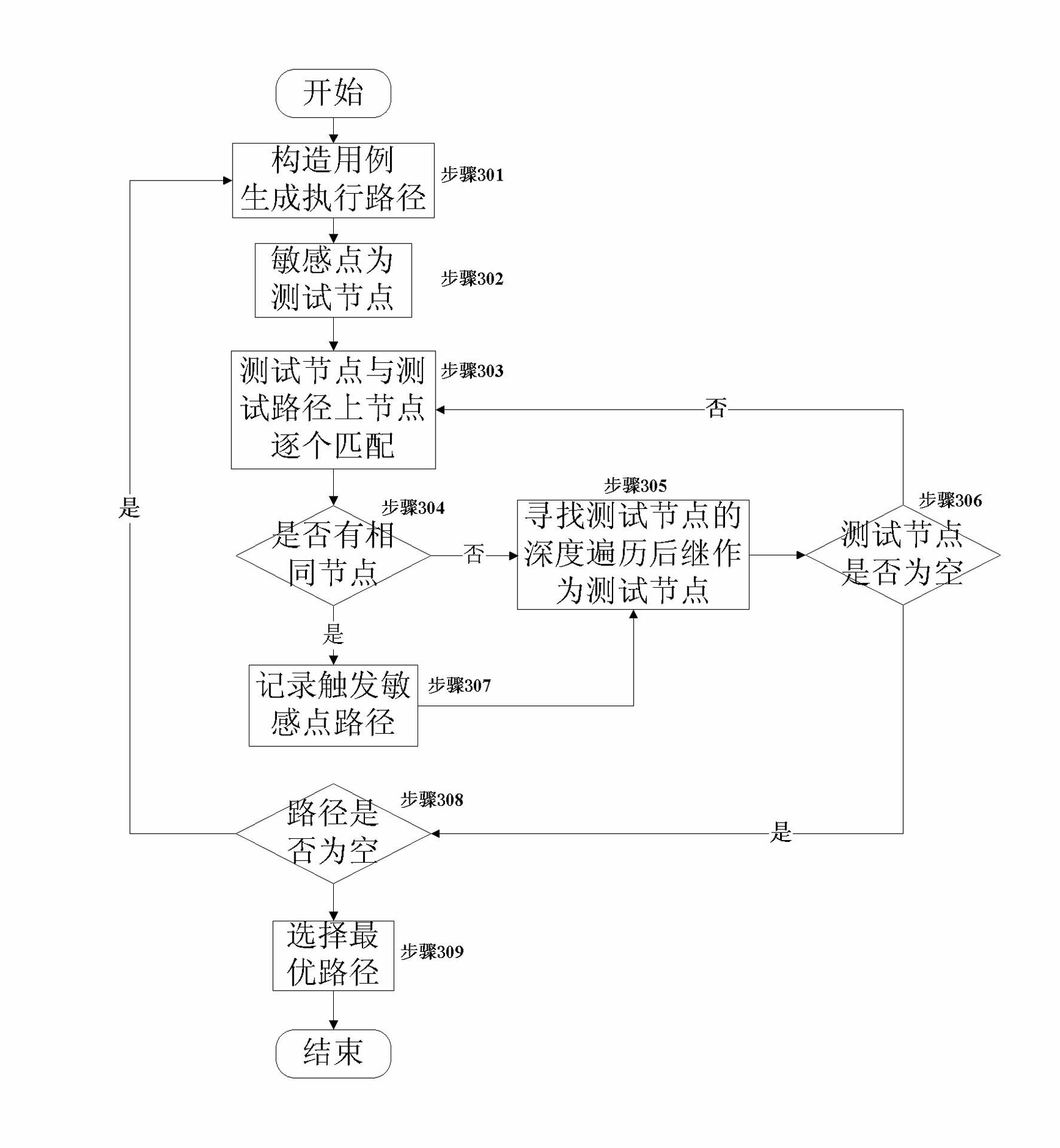
The invention relates to a computer software security test method, and in particular relates to a dynamic and static combined software security test method. The test method comprises the following steps: firstly carrying out disassembly and intermediate language transformation on an executable program so as to generate a function call graph (CG) and a control flow graph (CFG) of a file; finding out a vulnerable point of a system by means of static analysis of the function CG, and constructing a test case generation execution path by virtue of a dynamic analysis method; searching a called function based on the function CG, finding out a specific path for triggering the vulnerable point on a first-grade basic block according to the CFG if the function is located on the generated execution path, and then ending the loophole mining process corresponding to the sensitive point; and if the path can not be found, reconfiguring the test case generation execution path and then searching the called function in a cyclic manner. The dynamic and static combined software security test method has the advantages of better solving the problem of path state space blast caused by single Fuzz dynamic test, and greatly improving the path coverage hit rate and the software test analysis efficiency.
Owner:THE PLA INFORMATION ENG UNIV
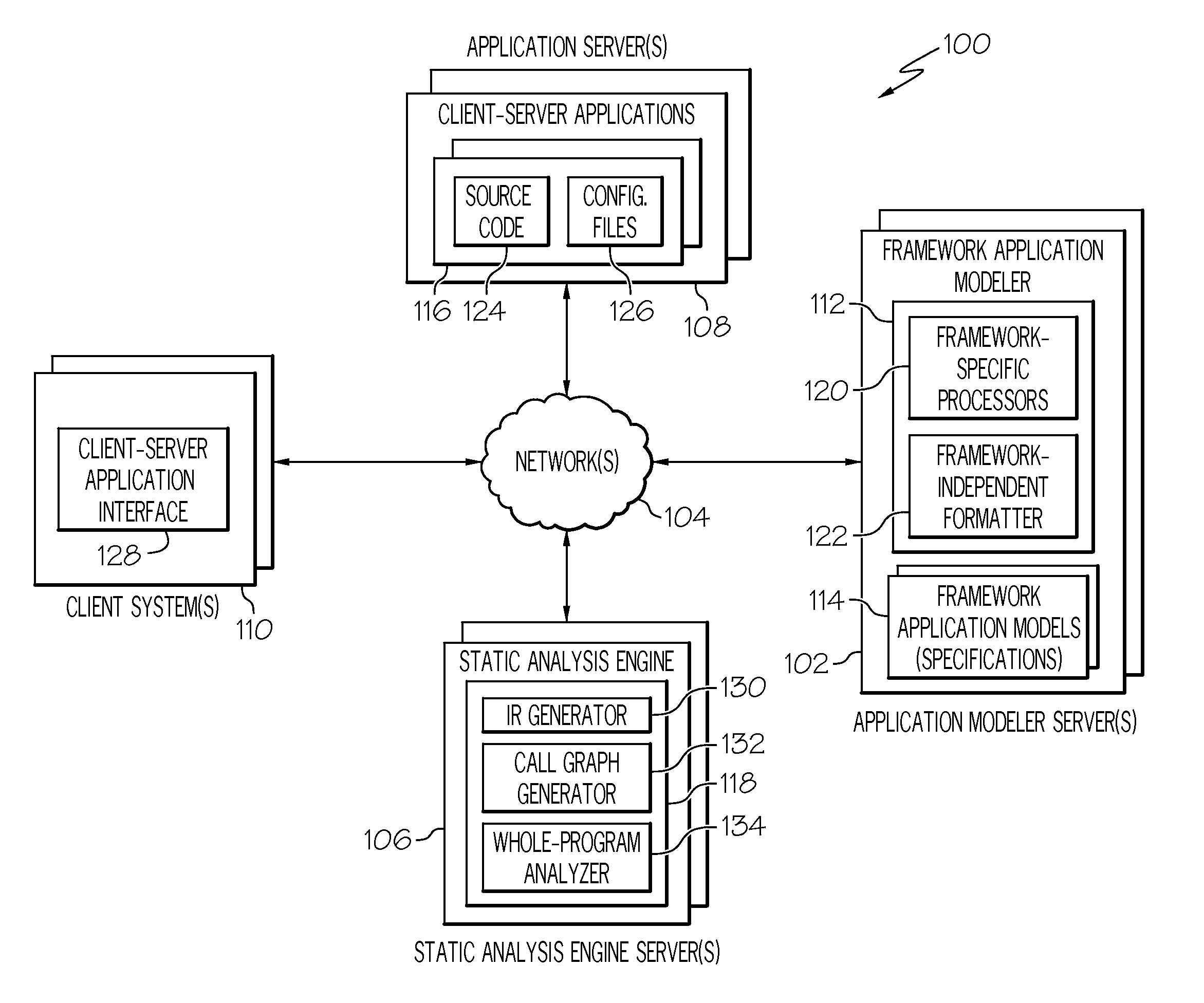
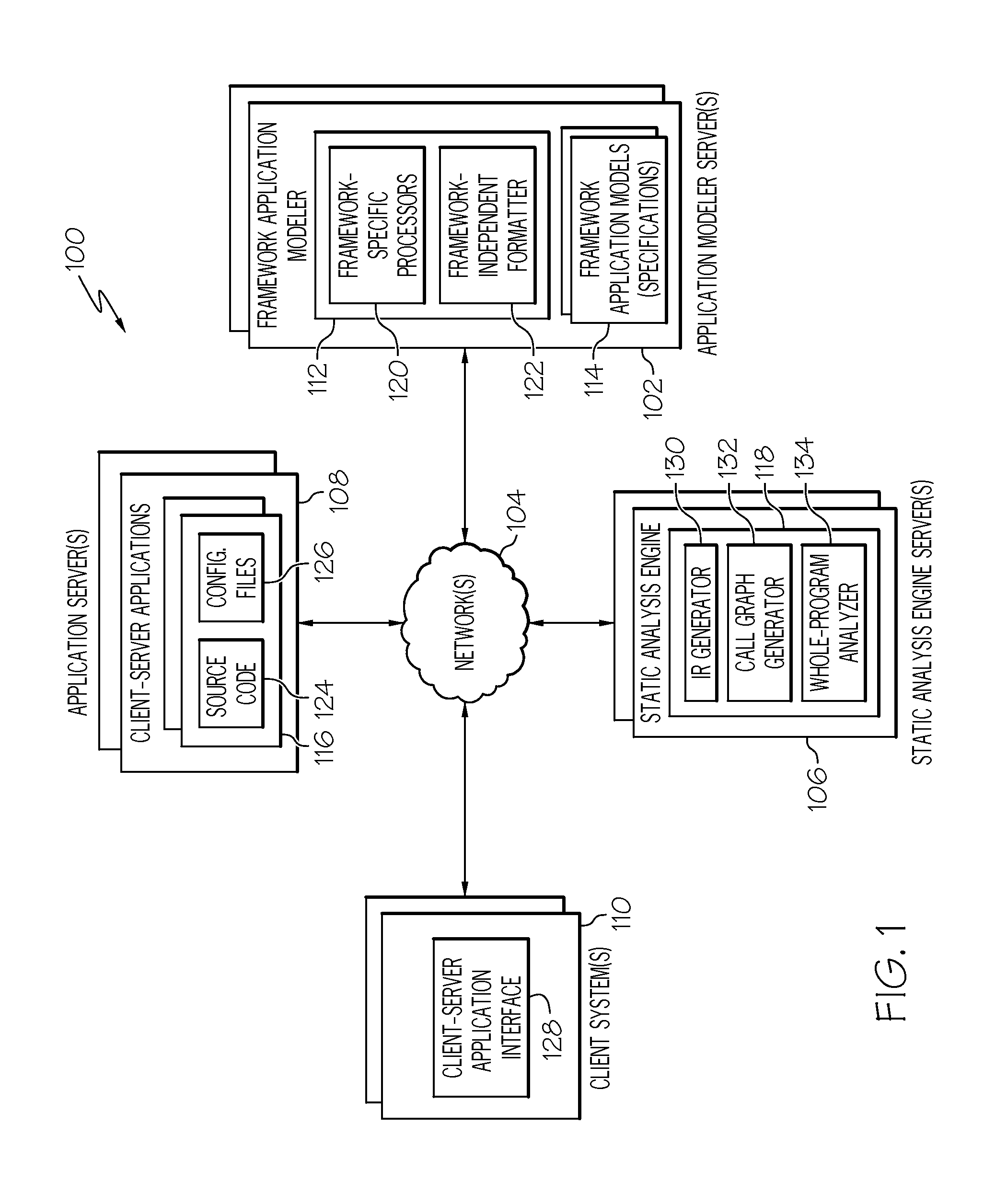
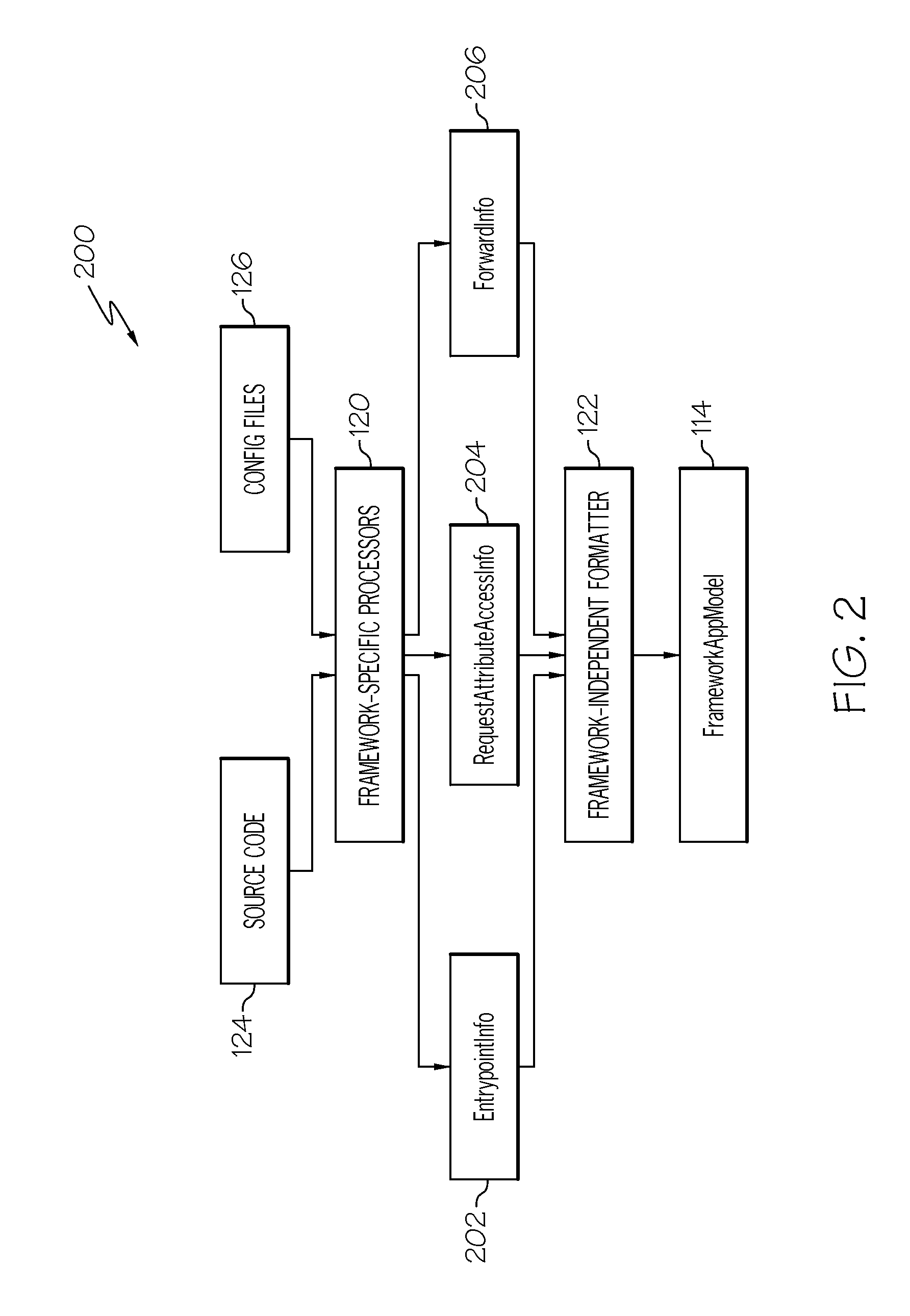
Static analysis of client-server applications using framework independent specifications
InactiveUS20120102474A1Computer security arrangementsReverse engineeringStatic timing analysisCall graph
Systems and methods are provided for statically analyzing a software application that is based on at least one framework. According to the method, source code of the software application and a specification associated with the software application are analyzed. The specification includes a list of synthetic methods that model framework-related behavior of the software application, and a list of entry points indicating the synthetic methods and / or application methods of the software application that can be invoked by the framework. Based on the source code and the specification, intermediate representations for the source code and the synthetic methods are generated. Based on the intermediate representations and the specification, call graphs are generated to model which application methods of the software application invoke synthetic methods or other application methods of the software application. The software application is statically analyzed based on the call graphs and the intermediate representations so as to generate analysis results for the software application.
Owner:IBM CORP
Parallelization security hole detecting method based on function call graph
InactiveCN102567200AEasy to analyzeEasy to detectSoftware testing/debuggingPlatform integrity maintainanceCall graphAccessibility
The invention relates to a parallelization security hole detecting method based on a function call graph, which is characterized in that a function set to be detected is determined by analyzing the function call relation in a C language module, instrumentation and assert analysis are performed for the function set by means of the preprocessing technology, and then security holes of a program are detected by the aid of model checking and the parallelization technology. The method mainly includes the steps: generating the function relation call graph, and determining C function information to be detected by analyzing the function relation call graph; extracting attribute information of a buffer area related to C program source codes by the aid of the constraint analysis technology, and inserting corresponding ASSERT statement information in a variable declaration, an assignment and a function call point by means of the attribute information of the buffer area; and performing accessibility judgment for the instrumented codes, and analyzing whether a dangerous point in the program includes an accessible path to discover the security holes in the source codes or not. The method detects the security holes such as buffer area overflow and the like by combining the constraint analysis static detecting technology, model checking and the parallelization technology, and the detecting precision of the method is higher than that of the general static detecting technology.
Owner:BEIHANG UNIV
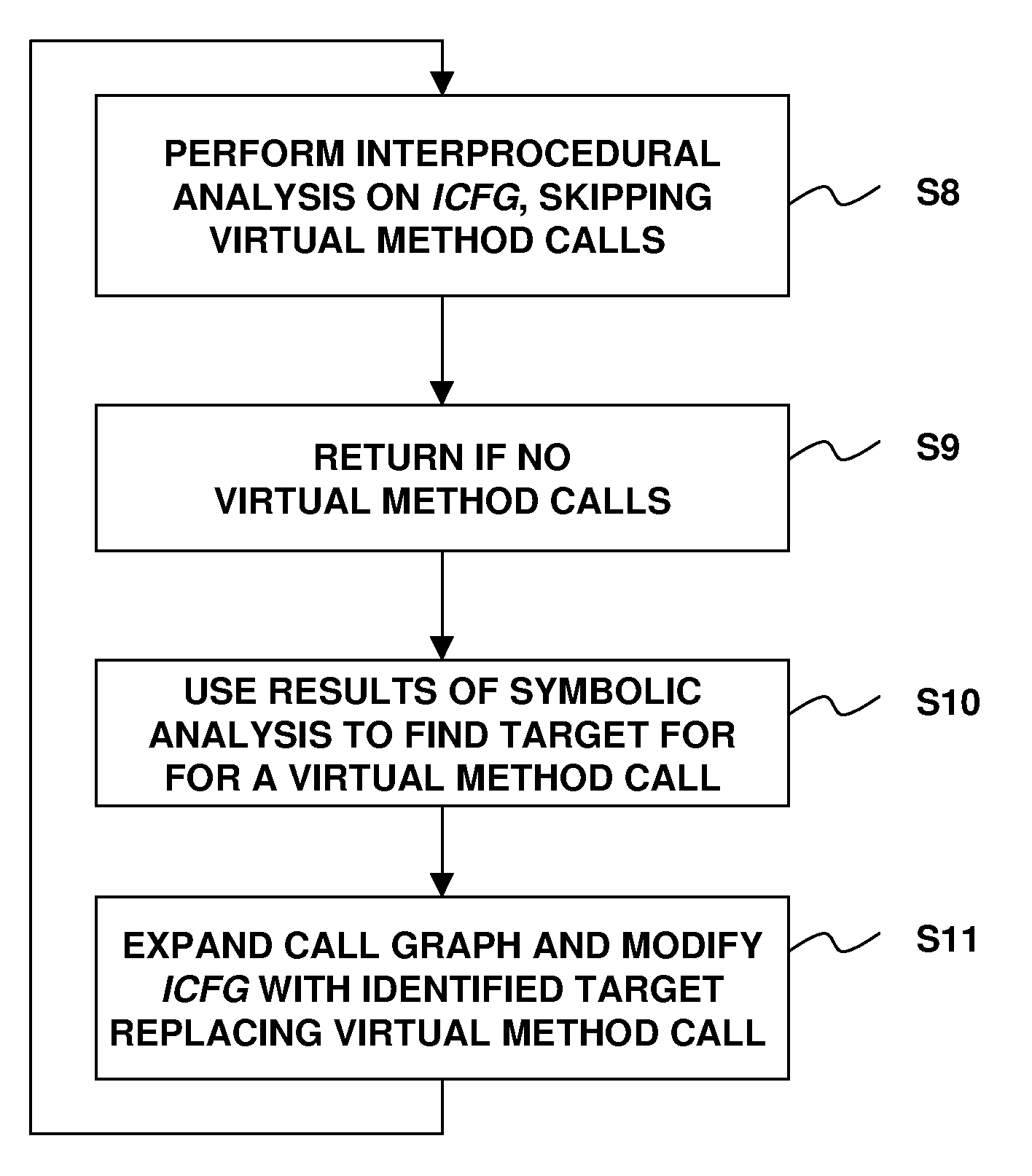
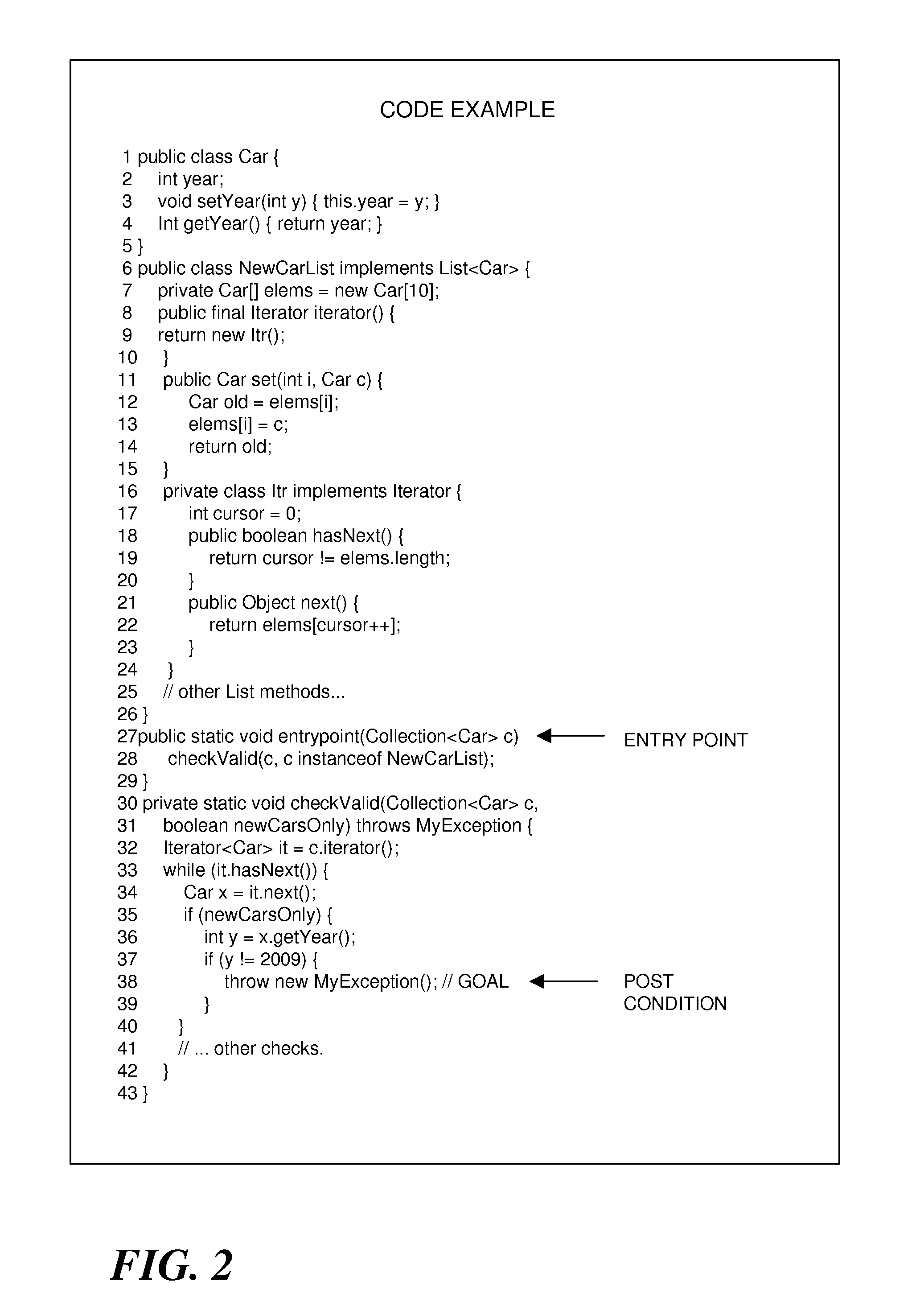
Feedback-Directed Call Graph Expansion
InactiveUS20110138369A1Software engineeringSpecific program execution arrangementsProgramming languageCall graph
A technique for feedback-directed call graph expansion includes performing symbolic analysis on an interprocedural control flow graph representation of software code, skipping over a virtual method call in the control flow graph, using information obtained from the symbolic analysis as feedback to identify a target of the virtual method call, and iterating the symbolic analysis on a modified version of the control flow graph that associates the target with the virtual method.
Owner:IBM CORP +1
Behavior specification, finding main, and call graph visualizations
A process transforms compiled software into a semantic form. The process transforms the code into a semantic form. The process analyzes behavior functionality by processing precise programming behavior abstractions stored in a memory and classifies the code as malware based on the code behavior. Another method identifies the starting point of execution of a compiled program. The method calculates a complexity measure by calculating the number of potential execution paths of local functions; identifies the number of arguments passed to local functions; and identifies the starting point of execution of the compiled program. Another method provides interactive, dynamic visualization of a group of related functions wherein a user can explore the rendered graph and select a specific function and display functions that are color coded by their ancestral relation and their function call distance to the selected function.
Owner:UT BATTELLE LLC
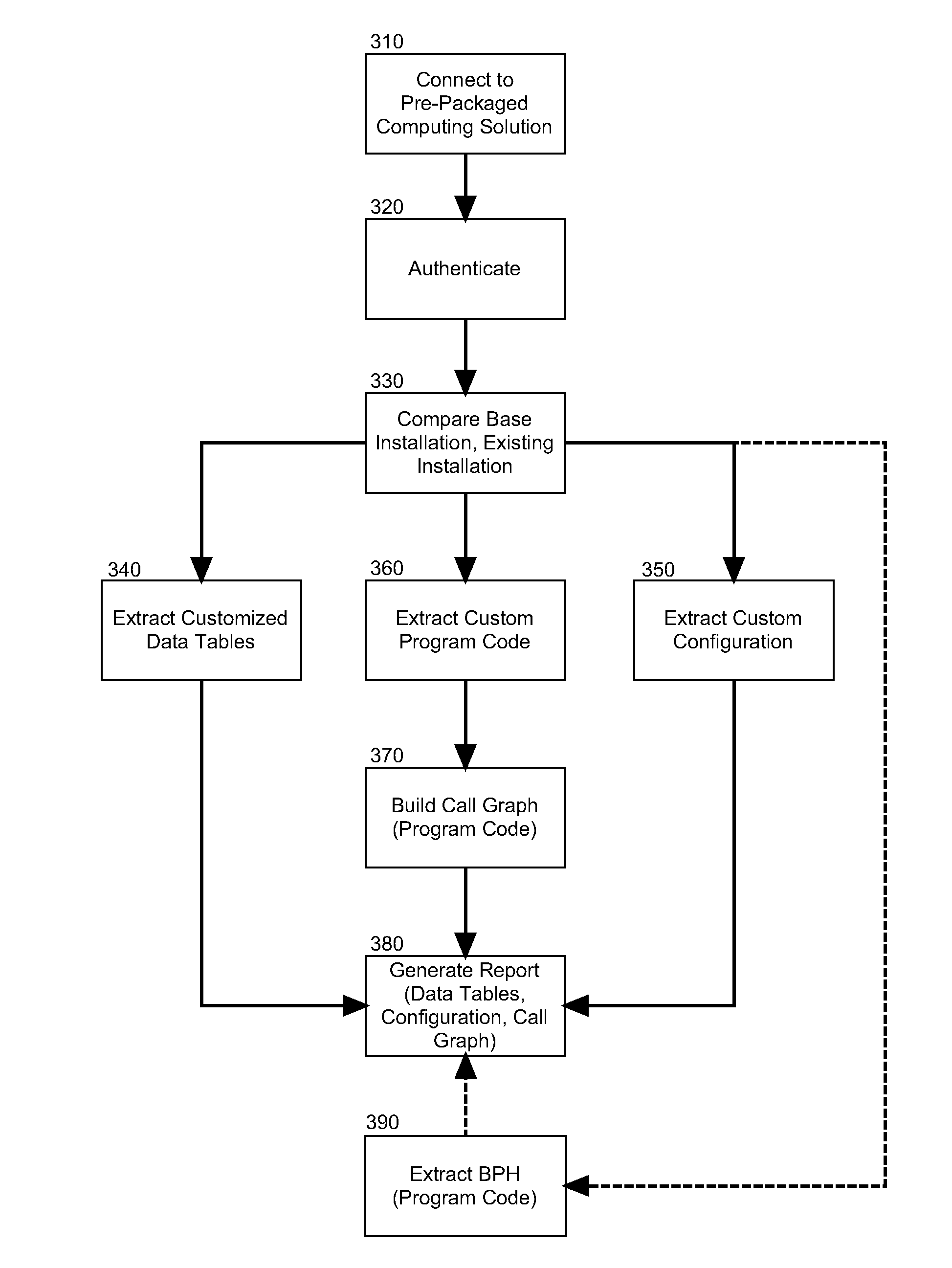
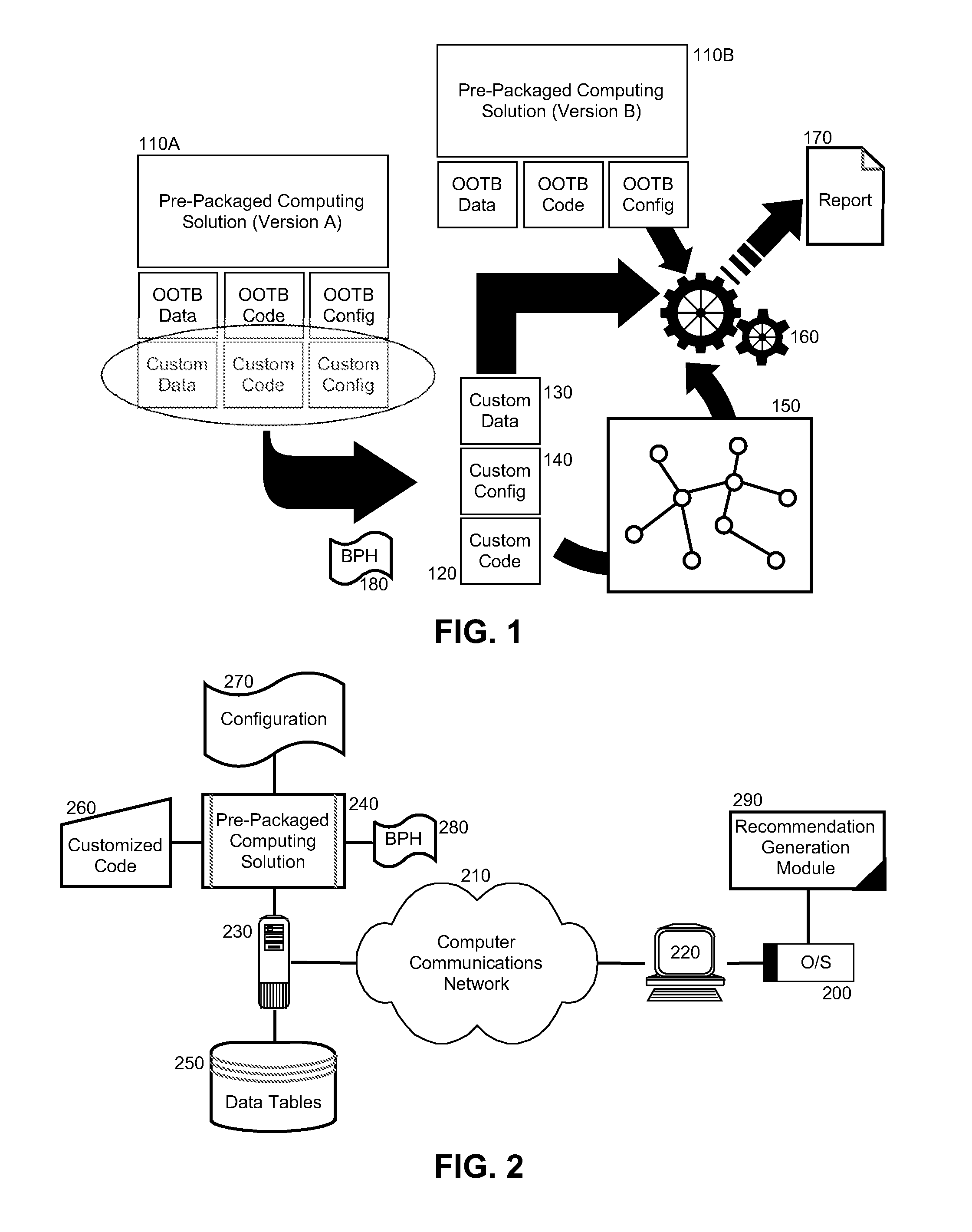
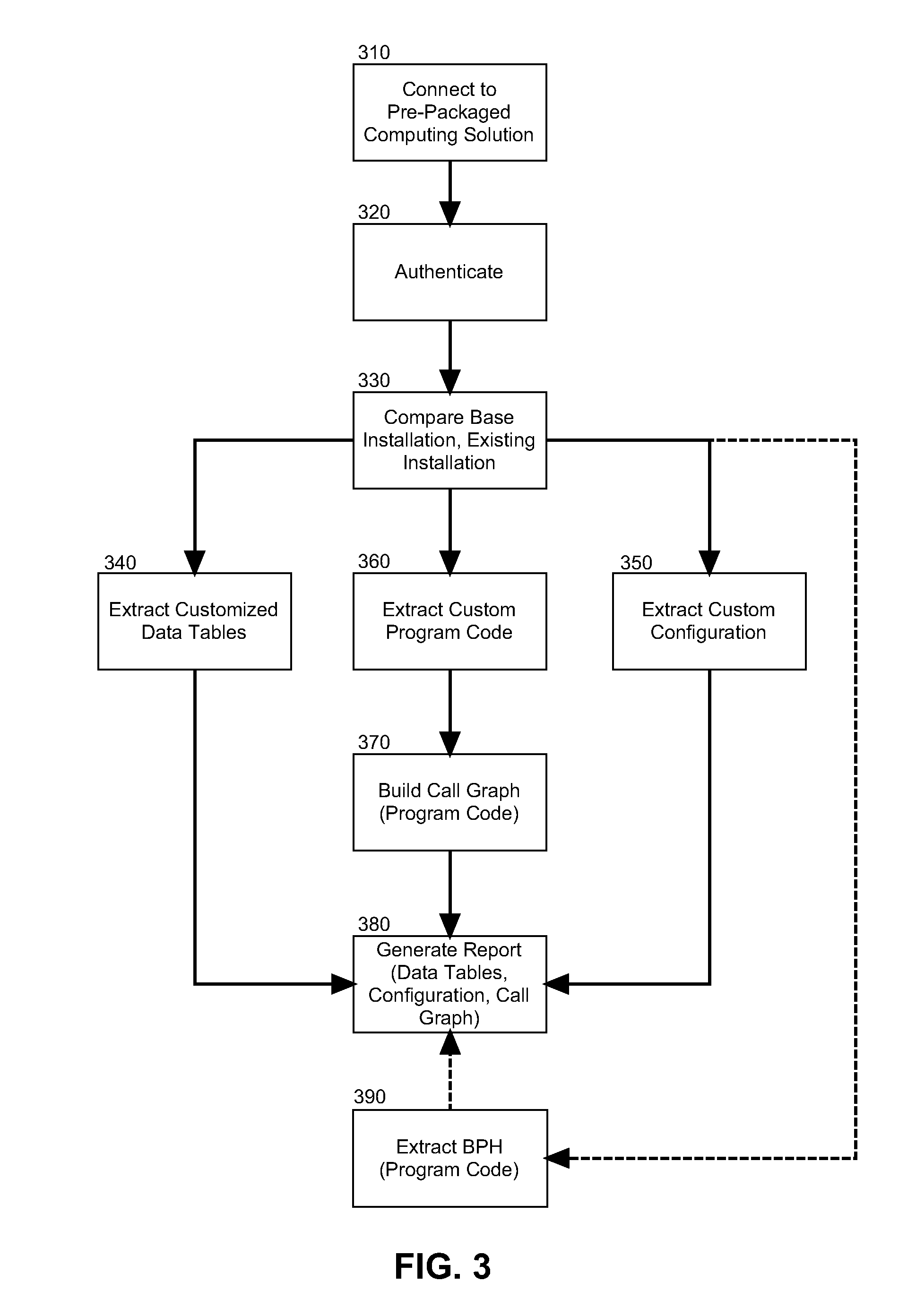
Static code analysis for packaged application customization
A method for static code analyzing customizations to a pre-packaged computing solution can include establishing a communicative connection from a recommendation generation module to a pre-packaged computing solution and authenticating into the pre-packaged computing solution. Customized program code can be extracted from the pre-packaged computing solution and a call graph of the customized program code can be constructed such that the call graph indicates method calls to different interfaces for program code of the pre-packaged computing solution. Finally, a report can be generated identifying customized program code to be adapted to a new version of the pre-packaged computing solution based upon changes in the different interfaces shown by the call graph to be used in the new version of the pre-packaged computing solution and modifications required for the customized program code to call the different interfaces in the new version of the pre-packaged computing solution.
Owner:IBM CORP +1
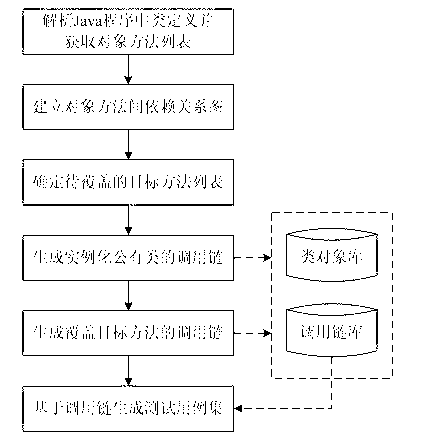
Random test case generation method facing Java program
The invention discloses a random test case generation method facing a Java program. The random test case generation method comprises the following steps of: (1) resolving a class definition of the Java program, and acquiring an object method list; (2) establishing a dependency relation graph comprising a method calling graph and a property dependency graph among object methods; (3) determining a target method list to be covered; (4) generating a calling chain by aiming at instantiation for public classes, and maintaining a class object base; (5) generating a calling chain by aiming at covering target methods, and maintaining a calling chain base; and (6) generating a test case set for the Java program based on the calling chain base. The method can be widely applied to automatic test work of medium-and large-size Java software systems and can automatically generate test cases completely; the highest code coverage rate is achieved by the least number of test cases; complicated data structures can be processed; test assertion can be automatically generated; and the test case generation method is simple and effective, and has high applicability and expandability.
Owner:NANJING UNIV
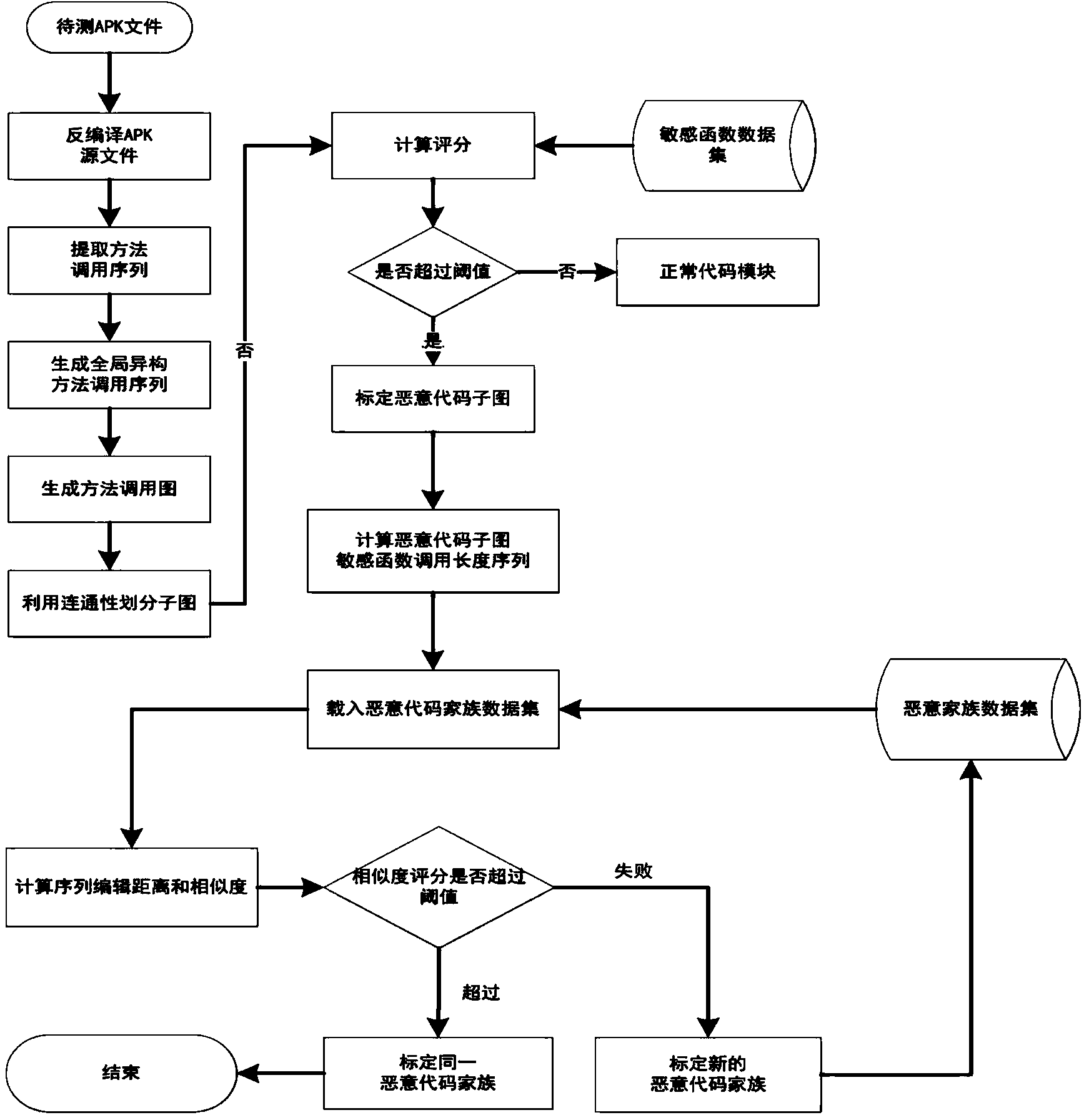
Android malicious software detection method based on method call graph
ActiveCN103473507AEasy to identifyGood killing effectPlatform integrity maintainanceCode moduleThird party
The invention provides an Android malicious software detection method based on a method call graph. A heterogeneous method call graph for constructing Android application Apk software is adopted, a sensitivity function is calibrated, and malicious codes are subjected to location and family classification by using the connectivity of the graph. The specific flow comprises the following steps: scanning the connectivity of the graph on the heterogeneous method call graph to obtain each sub-graph; grading the sensitivity function of each sub-graph, wherein the sub-graphs surpassing a threshold value are determined as malicious code modules, and similar malicious code sub-graph structures in different Android software are determined as malicious code families. According to the Android malicious software detection method, unknown malicious software can be found heuristically, families of the unknown malicious software are calibrated, and safe scanning and protection are provided for broad Android third-party markets and personal users.
Owner:XI AN JIAOTONG UNIV
Updating profile frequency for procedure inlining
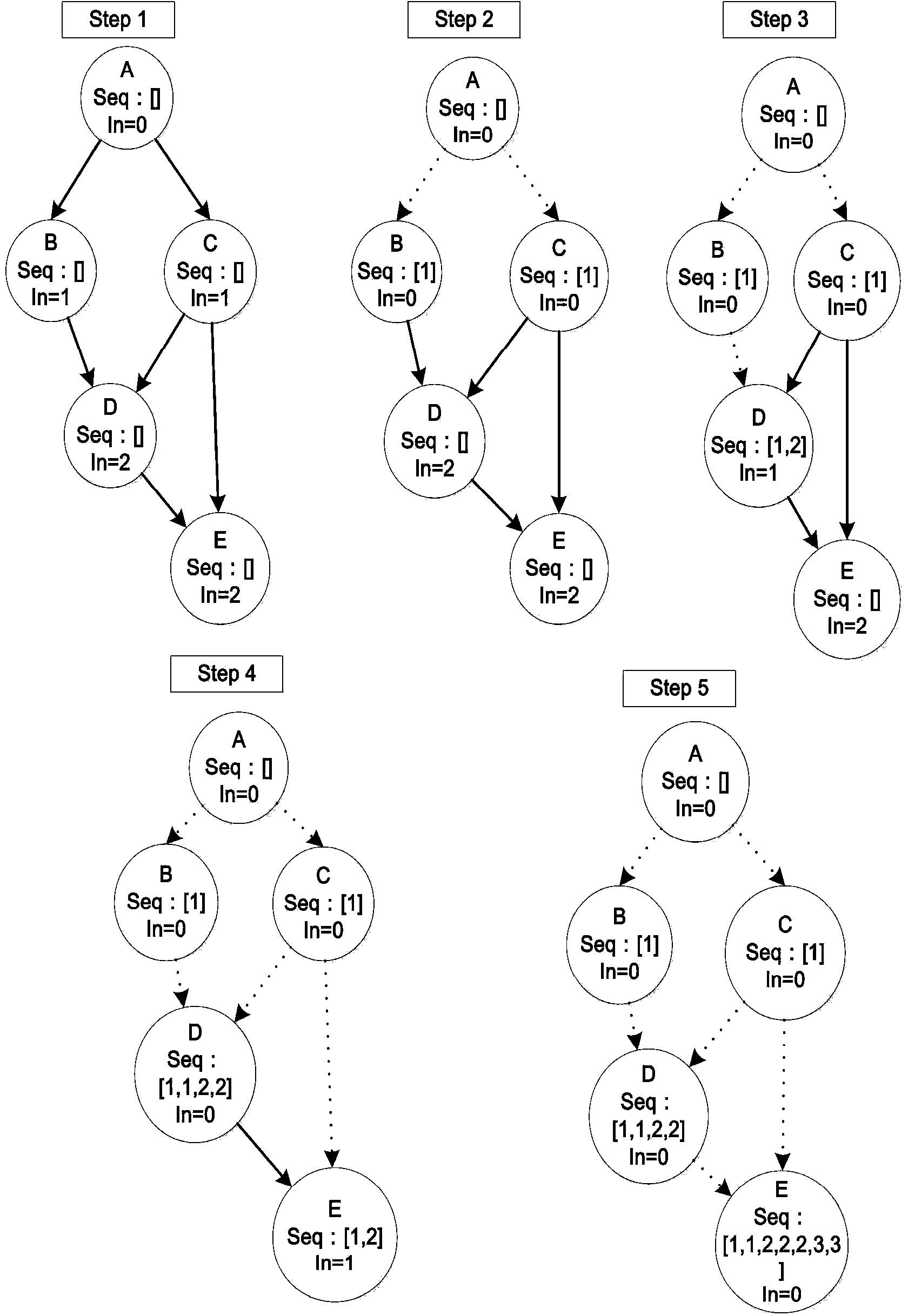
ActiveUS20050262491A1Improve performanceAccurate frequencySoftware engineeringProgram controlCall siteCall graph
A method and apparatus for frequency-updating for procedure inlining. The frequency-updating scheme assumes the call graph of a program has no cycles. It keeps the frequency for each procedure as accurate as that before inlining. Using the present invention, the runtime performance of a source program by a compiler is improved. A source program is analyzed to generate a call graph of the source program, wherein each of the procedures has a first known execution frequency. The call graph is used in conjunction with inlining plans by an inlining algorithm to generate an inlined version of the source program wherein selected call sites have been inlined. An updated execution frequency is generated for each of the procedures and the updated execution frequency for each of the procedures is used to generate optimized executable code for the source program. In various embodiments of the invention, heuristics can be used to calculate cost / benefit ratios for calls in the procedures of the source program to generate a ranking of the call sites and to select calls in the subroutines for inlining. The selected calls are inlined until a predetermined resource limit has been reached. An updated execution frequency is computed each time any of the call sites is inlined. In an embodiment of the invention, the updated execution frequency of the procedures determined by proportional adjustment, wherein the ratio between a procedure's frequency and its statement frequency remains unchanged.
Owner:ORACLE INT CORP
Scalable propagation-based methods for call graph construction
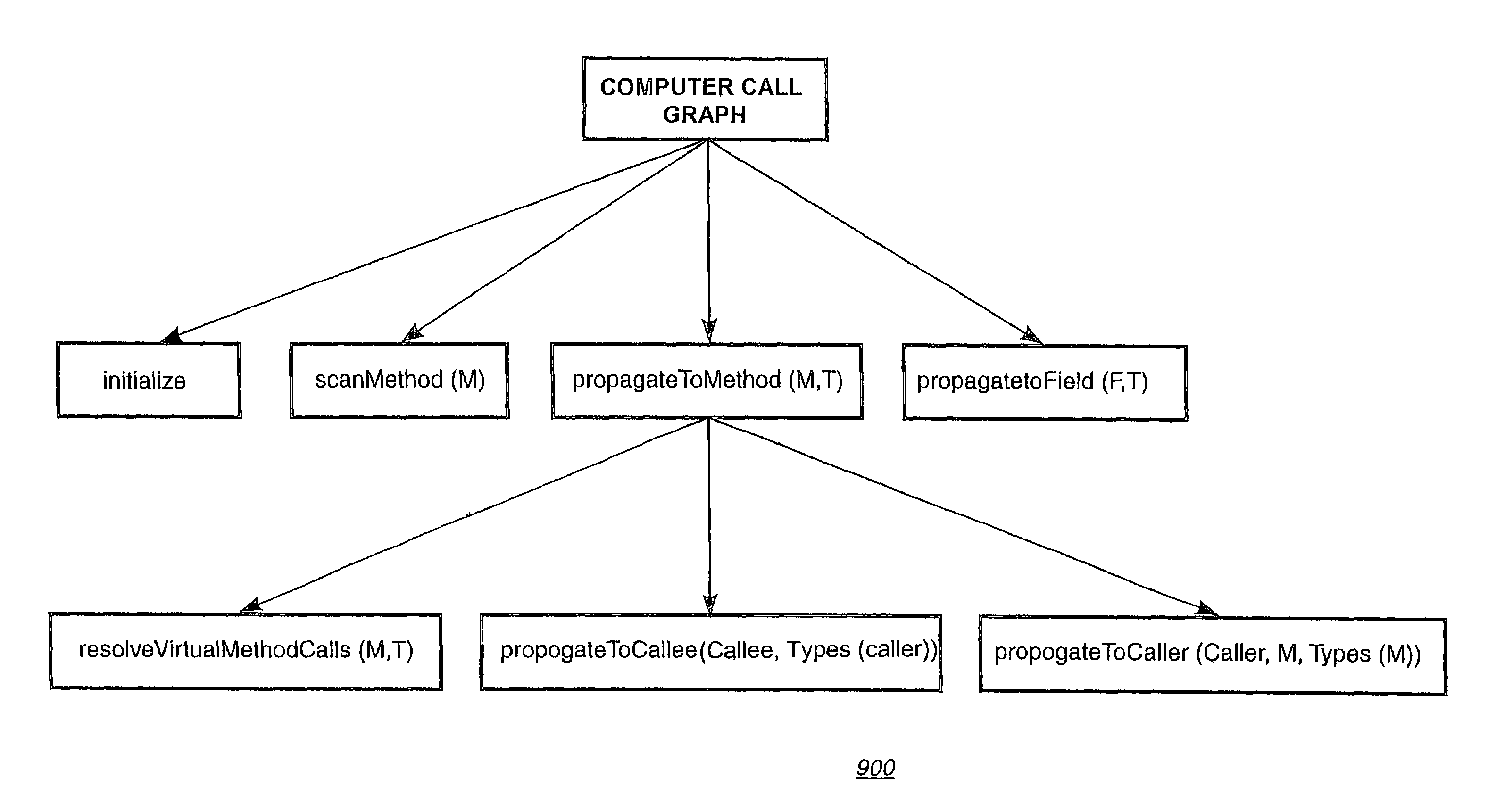
InactiveUS7003507B2Easy to implementImprove efficiencyData processing applicationsExecution paradigmsComputer scienceAllocation site
A program storage device, readably by a machine, tangibly embodying instructions to perform method steps for constructing a call graph whereby for each method M, a set of types SM of objects that may occur in method M is determined for each field F, a set of types SF of objects is determined that may be stored in field F, the method comprising: determining the allocation sites inside the body of method M; determining the set of directly called methods M′ inside the body of method M; and determining the set of virtually called methods M″ inside the body of method M.
Owner:IBM CORP
Static-analysis-assisted symbolic execution vulnerability detection method
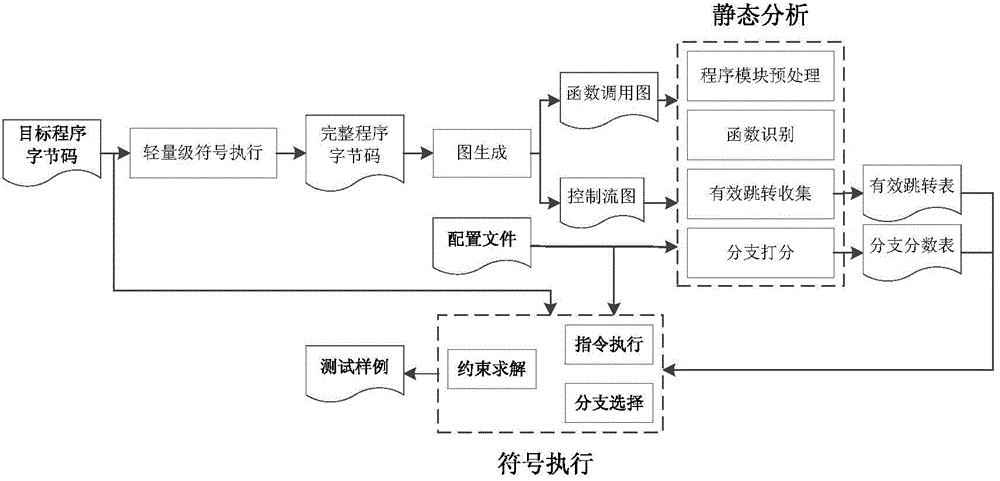
ActiveCN104794401AImprove detection efficiencyReduce computing timePlatform integrity maintainanceControl flowCall graph
A static-analysis-assisted symbolic execution vulnerability detection method includes the light-weight symbolic execution stage, the graph generation stage, the static analysis stage, the symbolic execution stage and the like. At the light-weight symbolic execution stage, symbolic execution is conducted on a target program byte code file under the small time expenditure through a simple symbolic strategy by means of a KLEE symbolic execution tool so as to obtain a bite code of a complete program after the linking process is completed; at the graph generation stage, on the basis of the bite code of the complete program, function calling graphs of the complete program and control flow graphs of the functions are generated through a concentrated opt tool of an LLVM3.1 tool; at the static analysis stage, the function calling graphs of the complete program, the control flow graphs of the functions and configuration files are used as input; at the symbolic execution stage, an effective skip table and a branch marking table are used for assisting in vulnerability detection symbolic execution.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Global call control flow graph for optimizing software managed manycore architectures
InactiveUS20160170725A1Easy to useEfficient implementationSoftware engineeringProgram controlControl flowGraphics
Software Managed Manycore (SMM) architectures with scratch pad memory for reach core are a promising solution for scaling memory. In these architectures the code and data of the tasks mapped to the cores is explicitly managed by the compiler and often require inter-procedural information and analysis. But, a call graph of the program does not have enough information, and the Global CFG has too much information. Most new techniques informally define and use GCCFG (Global Call Control Flow Graph)—a whole program representation that succinctly captures the control-flow and function call information—to perform inter-procedural analysis. Constructing GCCFGs for several cases in common applications. The present disclosure provides unique graph transformations to formally and correctly construct GCCFGs for optimal compiler management of manycore systems.
Owner:ARIZONA STATE UNIVERSITY
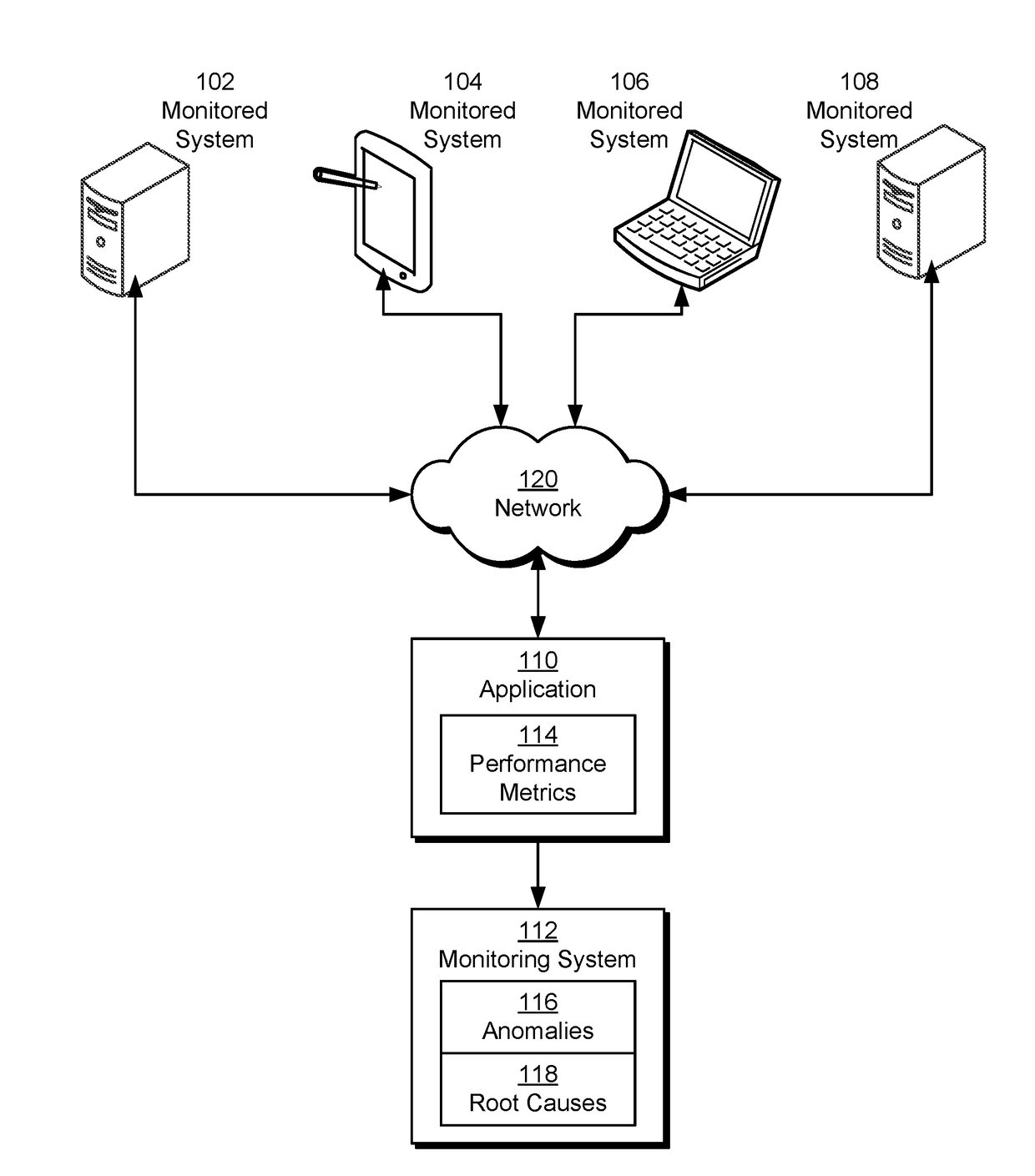
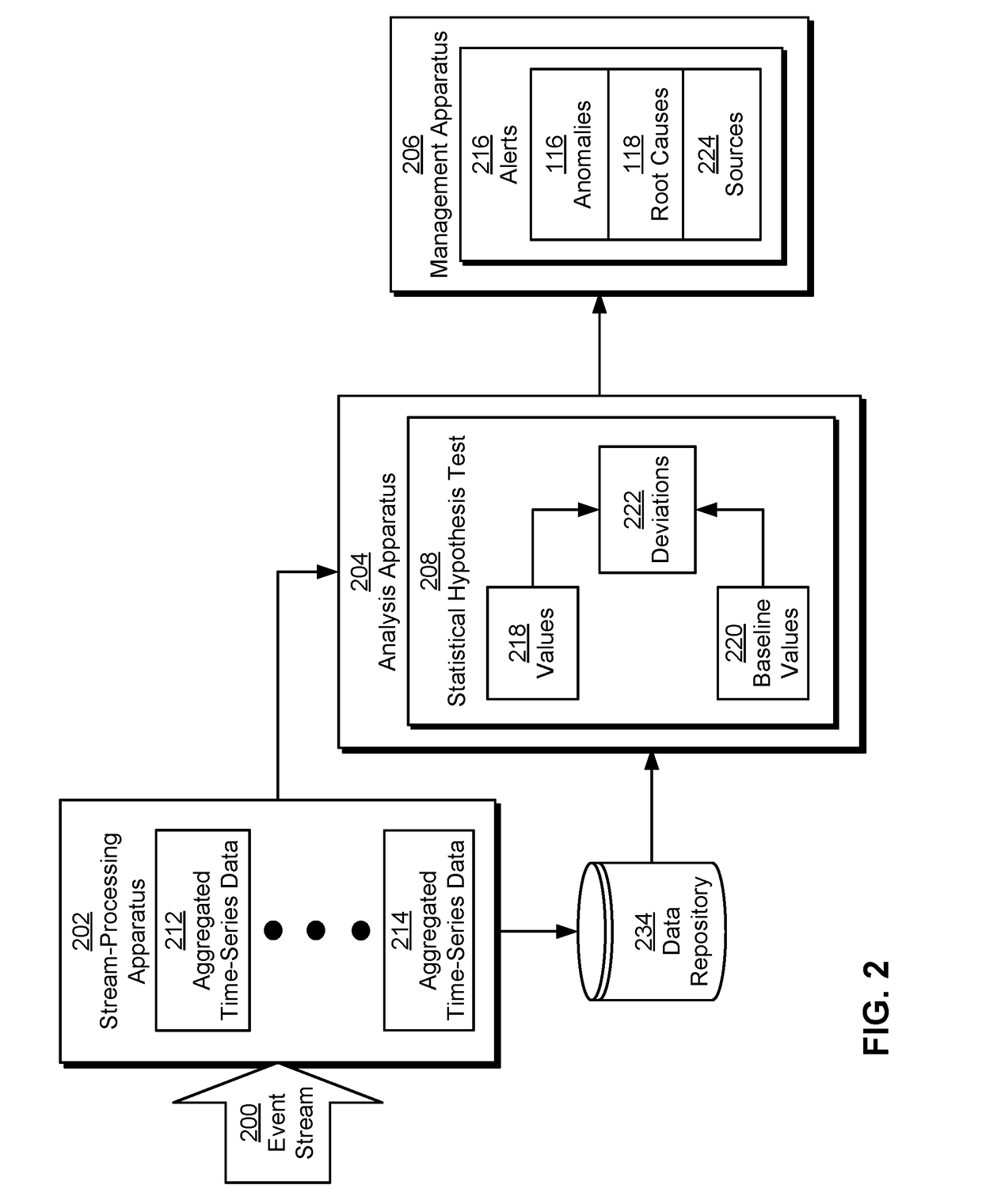
Analysis of site speed performance anomalies caused by server-side issues
The disclosed embodiments provide a system for processing data. During operation, the system obtains a component of a time-series performance metric associated with a server-side root cause of an anomaly in the time-series performance metric. Next, the system obtains a call graph representation of the component, wherein the call graph representation includes a parent node having a parent value of the component and a set of child nodes of the parent node, each child node having a corresponding child value of the component. The system then analyzes the call graph representation to identify one or more of the child nodes as sources of the anomaly. Finally, the system outputs an alert that identifies the sources of the anomaly.
Owner:MICROSOFT TECH LICENSING LLC
Method for micro service of monolithic application
ActiveCN108279926ALow costReduce investmentCode refactoringProgram code adaptionCall graphSoftware engineering
The invention discloses a method for micro service of monolithic application. The method mainly comprises the steps of a call analysis stage, a module resolution stage and a framework adaptation stage, wherein a method call relationship among classes in application codes is obtained by analyzing byte codes in a package file, and thereby a call chain in the application is analyzed and a call graphis generated; for the call graph, all codes of which in-degree is zero are taken as entries, the entries are taken as starting points in turn to conduct breadth first search on a digraph to find all lower nodes, the starting point and the search result are taken as a to-be-split out micro service module together, according to the rule, an integrated item is divided into a plurality of independentmicro service modules, each module can be separately conducted with development and deployment, and the monolithic application also achieves quick micro service. The method for micro service of the monolithic application has the advantages that the input of the process for a monolithic framework to be converted into a micro service framework is reduced, the learning cost of the development is reduced, and the method can help the item be smoothly transferred into the micro service framework.
Owner:浙江网新恒天软件有限公司
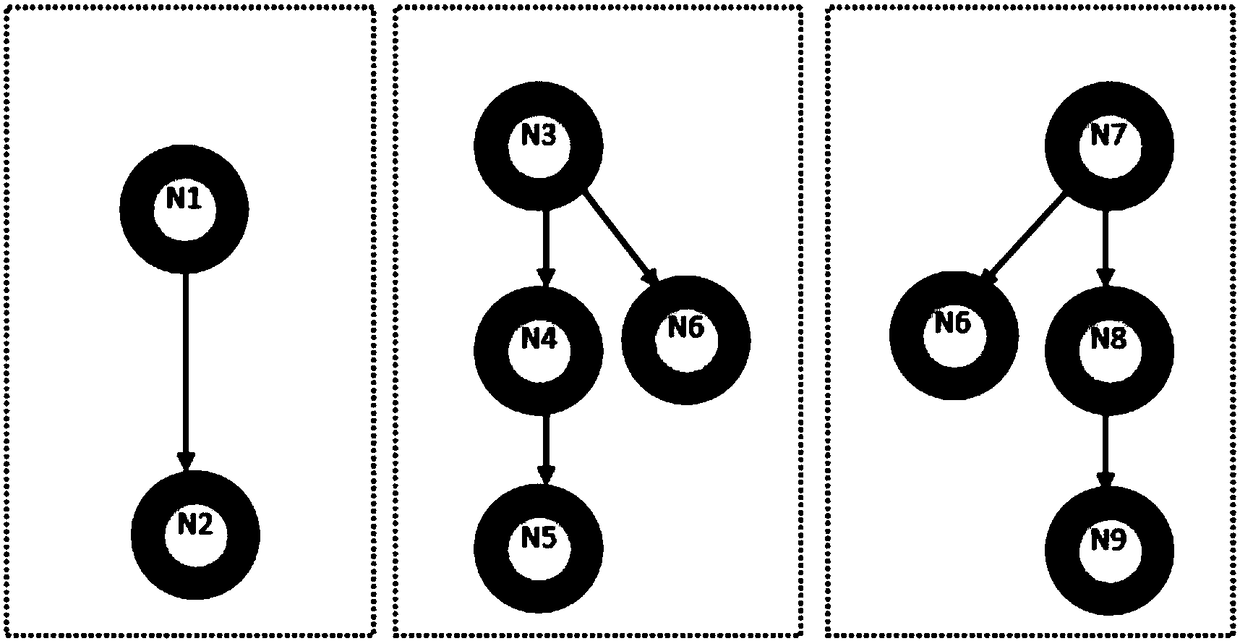
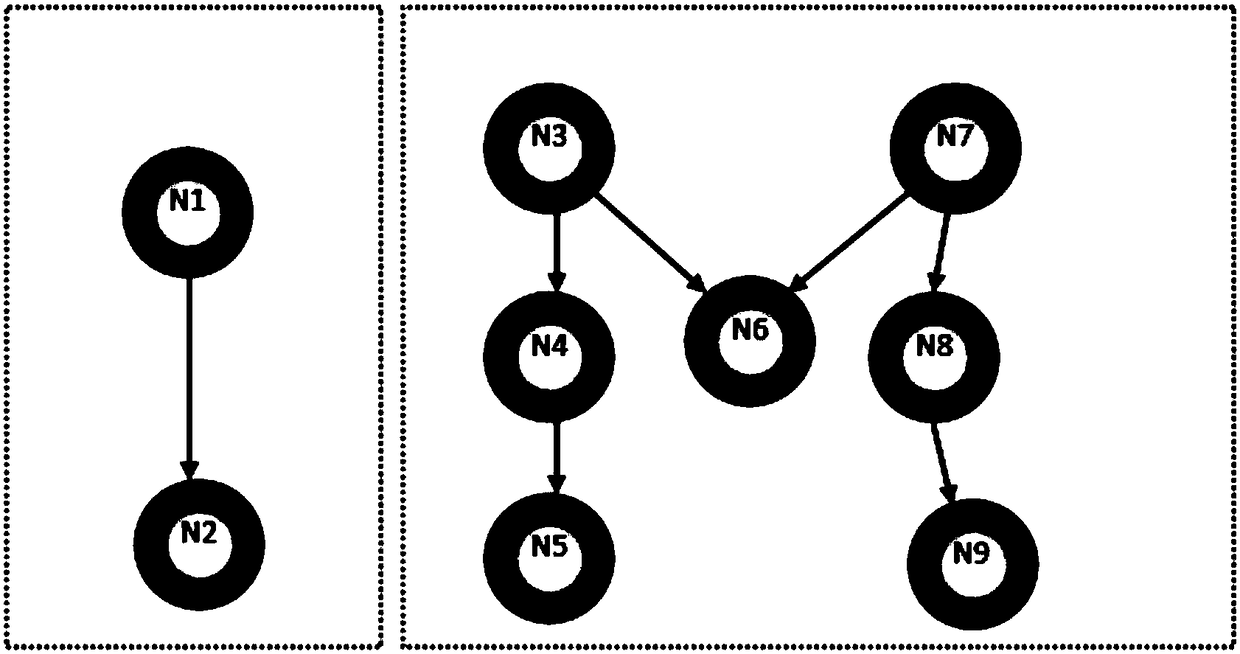
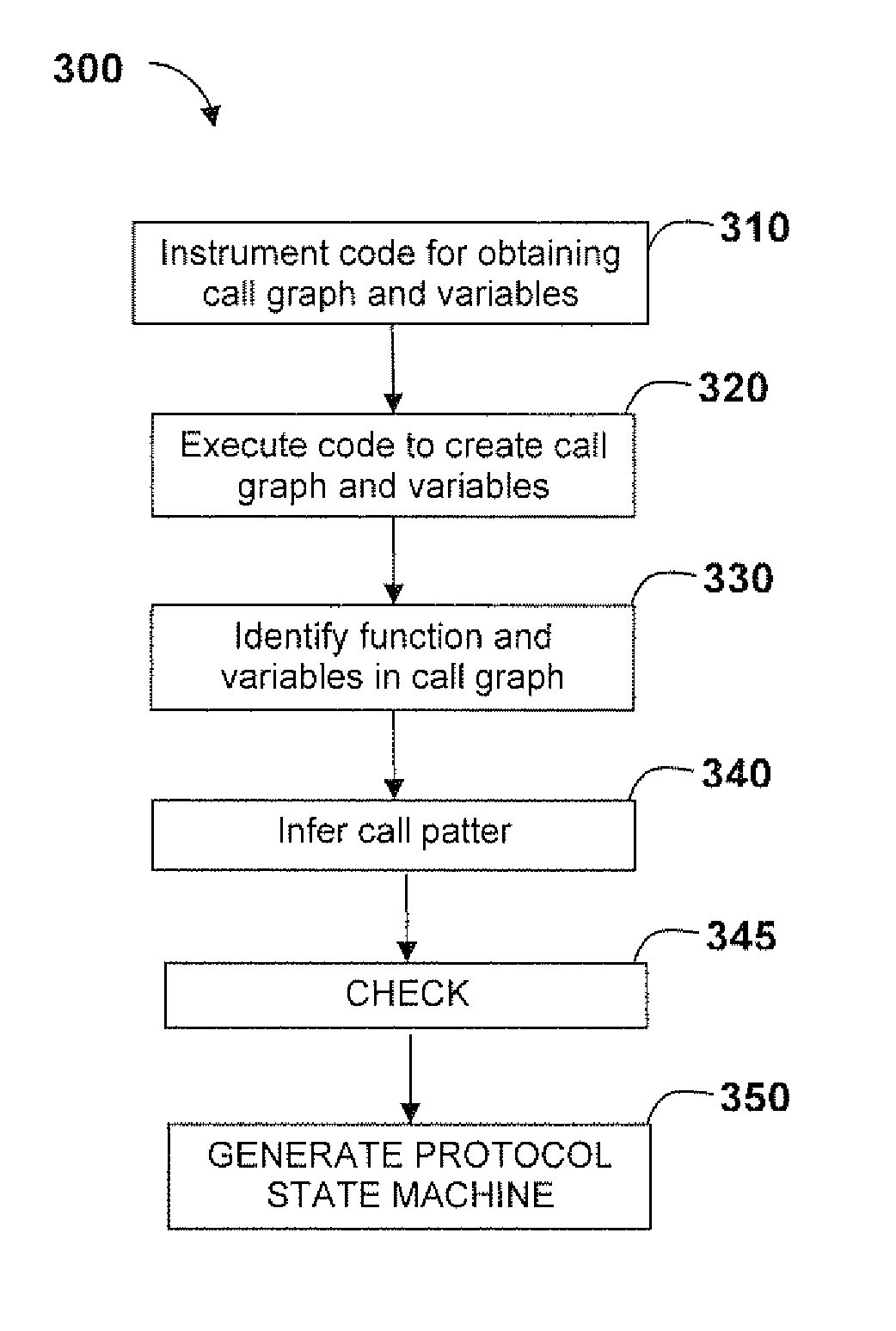
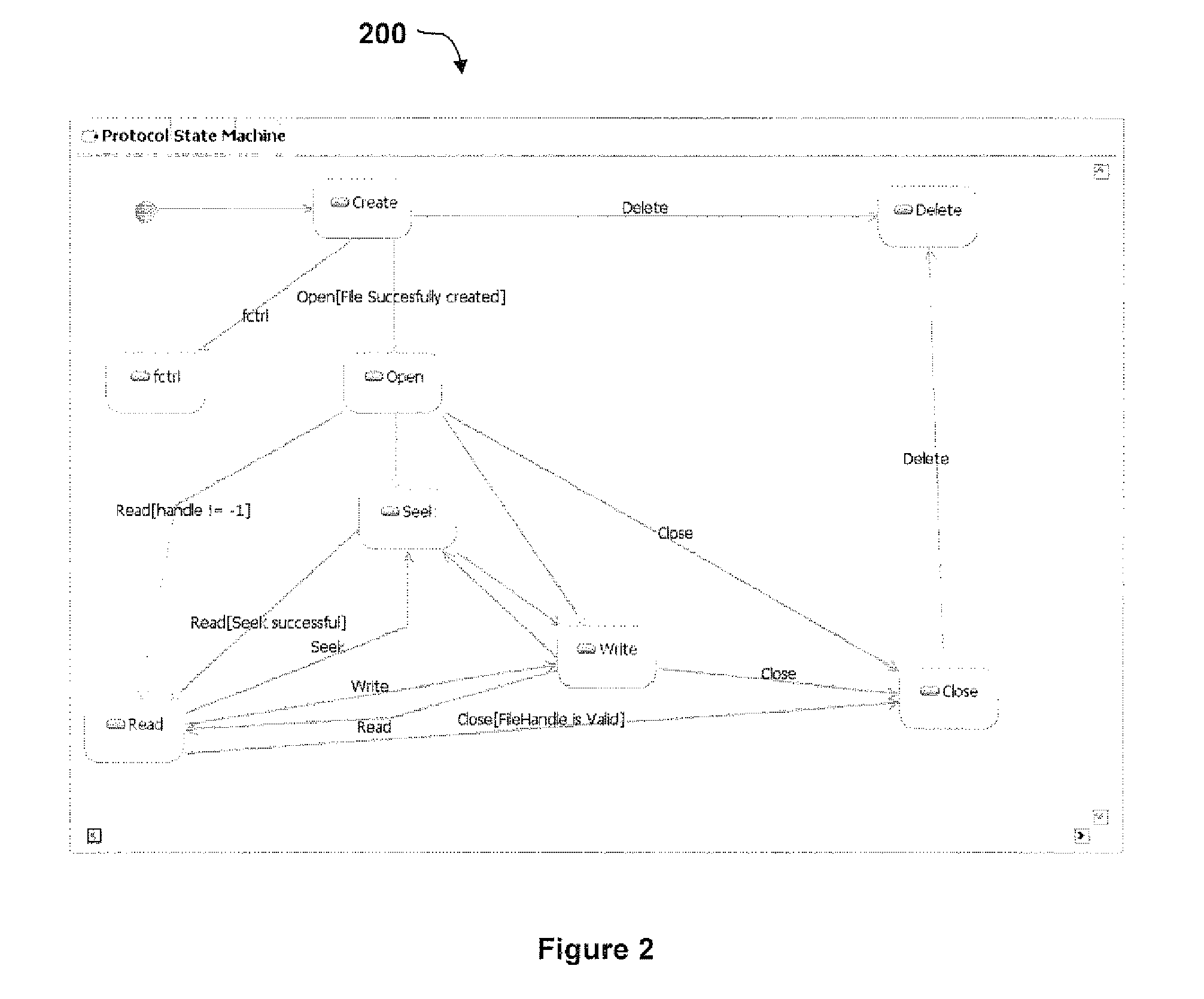
Using Dynamic Call Graphs For Creating State Machines
InactiveUS20080288931A1Visual/graphical programmingSpecific program execution arrangementsCall graphClass variable
A method and system capable of creating UML protocol state machine for classes and interfaces of a software, by instrumenting the software to obtain a call graph comprising classes and interfaces and respective values associated with class variables and interface variables; identifying particular classes and interfaces in the call graph; identifying call patterns from the call graph to generate a protocol state machine.
Owner:IBM CORP
Interprocedural dead store elimination
InactiveUS7100156B2Improvement in code optimizationReduce needSoftware engineeringDigital computer detailsProgramming languageFunction definition
A system for optimizing computer code generation by carrying out interprocedural dead store elimination. The system carries out a top down traversal of a call graph in an intermediate representation of the code being compiled. Live on exit (LOE) sets are defined for variables at call points for functions in the code being compiled. Bit vectors representing the LOE sets for call points for functions are stored in an LOE table indexed or hashed by call graph edges. For each function definition reached in the call graph traversal, a LOE set for the function itself is generated by taking the union of the LOE call point sets. The entries in the LOE table for the LOE call point sets are then removed. The LOE set for each function is used to determine if variables that are the subject of a store operation in a function may be subject to a dead store elimination optimization.
Owner:IBM CORP
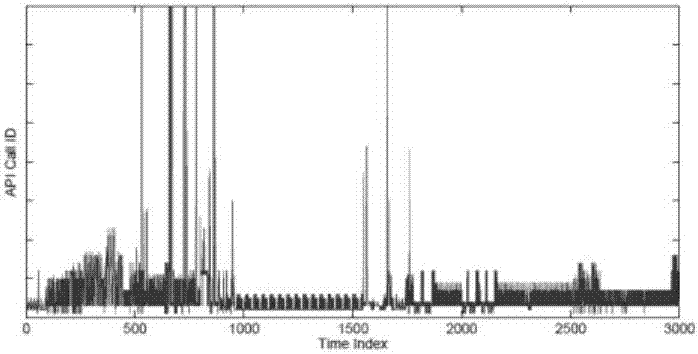
Malicious software API call sequence detection method based on graph convolution
ActiveCN111259388AImprove bindingFlexible organizational structurePlatform integrity maintainanceNeural architecturesCall graphAlgorithm
Owner:SUN YAT SEN UNIV
C-program parallel region detecting method
ActiveCN104536898AStatistics overheadStatistics call relationshipSoftware testing/debuggingCall graphCombined method
The invention discloses a C-program parallel region detecting method. The C-program parallel region detecting method is characterized by comprising the following steps of 1 pre-compiling the portion except system header files in source files, 2 compiling pre-compiled source codes and the system header files and performing dynamic analysis, 3 inserting dynamic analysis results into the source codes obtained after pre-compiling to obtain intermediate files, 4 conducting static analysis on the intermediate files to generate a program calling graph, and 5 detecting a task parallel region, a pipelining task parallel region and a data parallel region in a C-program according to the program calling graph. The C-program parallel region detecting method is a dynamic state and static state combined method. By means of the C-program parallel region detecting method, the parallel possibility of various particle sizes of all portions of the program is further dynamically analyzed on the basis that the program calling graph using functions and loops as units can be obtained.
Owner:ZHEJIANG UNIV
Graph theoretical method for quickly and accurately detecting zero-day malicious software
InactiveCN107315956AQuick checkAccurate detectionPlatform integrity maintainanceCall graphFeature extraction
The invention discloses a graph theoretical method MalZero for quickly and accurately detecting zero-day malicious software. The method is characterized in that features are extracted from API calling graphs to establish a classifier model, benign software and malicious software have different graph theoretical properties in respective API calling graphs, and the graph theoretical features extracted from the API calling graphs can be used for distinguishing the malicious software from the benign software effectively and efficiently. Three modules, namely a graph construction module, a feature extraction module and a graph classification module are involved in the method. Through the MalZero, the malicious software can be quickly and accurately detected on a terminal host, high efficiency is achieved in terms of storage space and detection time, and the MalZero can supplement an existing malicious software detection scheme of the terminal host due to low overhead.
Owner:DONGGUAN UNIV OF TECH
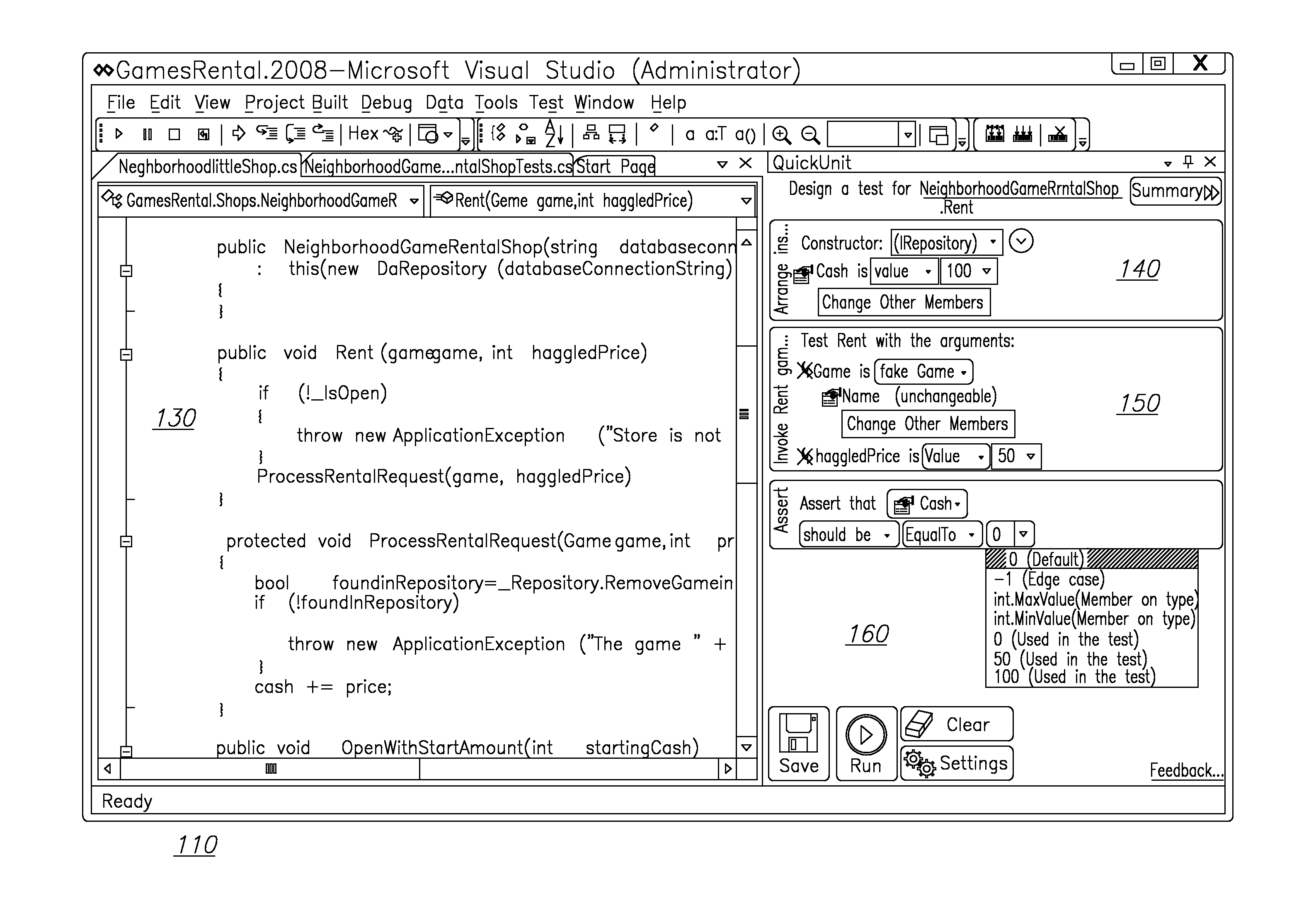
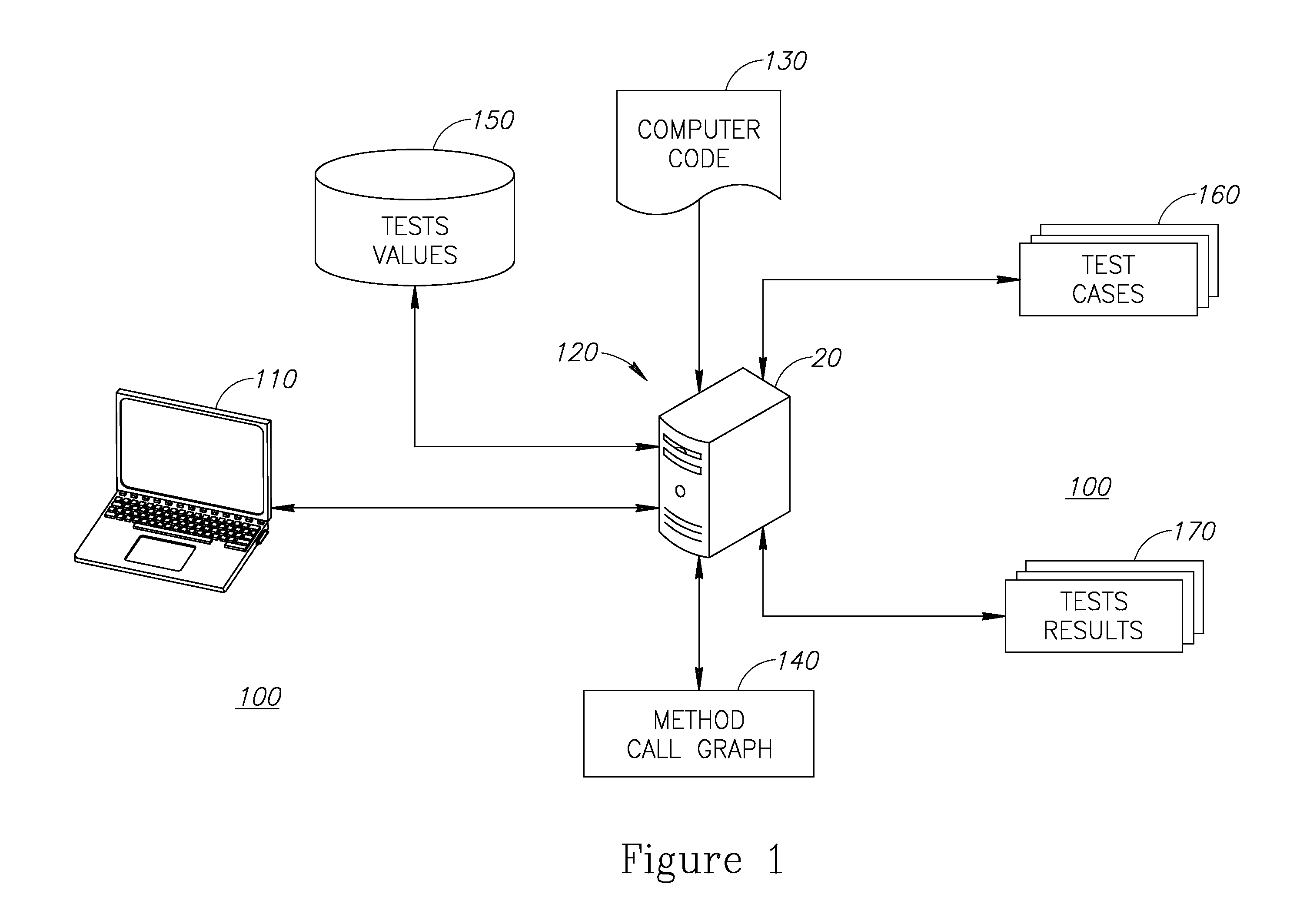
Interactive environment for test case generation associated with a computer code
InactiveUS20110321013A1Software testing/debuggingSpecific program execution arrangementsCoded elementTest data generation
A method of generating test cases for a given computer code is provided. The method includes: building a method call graph for a computer code under test, wherein the method call graph holds method calls between code elements of the code; presenting code elements having relevancy for testing for a portion of the computer code in response to a selection of the portion, wherein the relevancy is determined using the method call graph; associating test values for code elements in response to selection from a suggested range of test values generated for each selected code element respectively; and generating a test case useable for testing the selected portion of computer code, wherein the test case refers to the selected code elements relevant for the selected portion with the associated selected values, wherein at least one of the building, the presenting, the associating, and the generating is executed by a processor.
Owner:QUICKUNIT
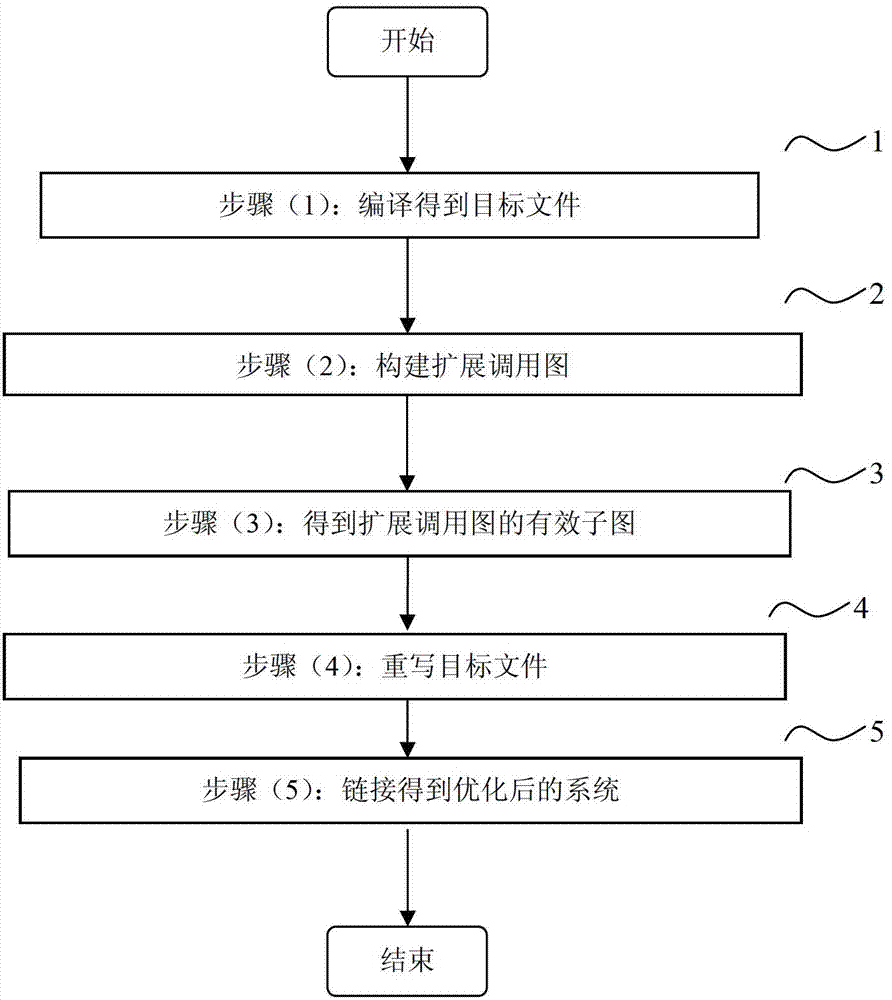
Automatic optimization method based on full-system expansion call graph for mobile terminal operation system
The invention discloses an automatic optimization method based on a full-system expansion call graph for a mobile terminal operation system, relating to the field of mobile terminal software. The method is suitable for the mobile terminal operation system and can be used to realize the elimination of useless codes in a full system range, reduce the volume of system codes on the premise of not reducing system performance and thus reduce the hardware manufacture cost of a mobile terminal. The method comprises the following main steps of: compiling a source code to obtain a target document; structuring an expansion call graph for all local codes in the full system by starting from the target document; analyzing the expansion call graph, and obtaining effective sub-graphs of the expansion call graph by starting from an entrance point; rewriting the target document generated through compiling, and deleting all codes which are not located in the effect sub-graphs; and linking to generate optimized binary codes. The automatic optimization method disclosed by the invention has the characteristics of wide application range, high automation degree, convenience in use, obvious optimization effect and the like.
Owner:TSINGHUA UNIV
Parallel symbolic execution method based on path cluster reductions
ActiveCN103049377AReduce time overheadImprove abilitiesSoftware testing/debuggingCall graphEntry point
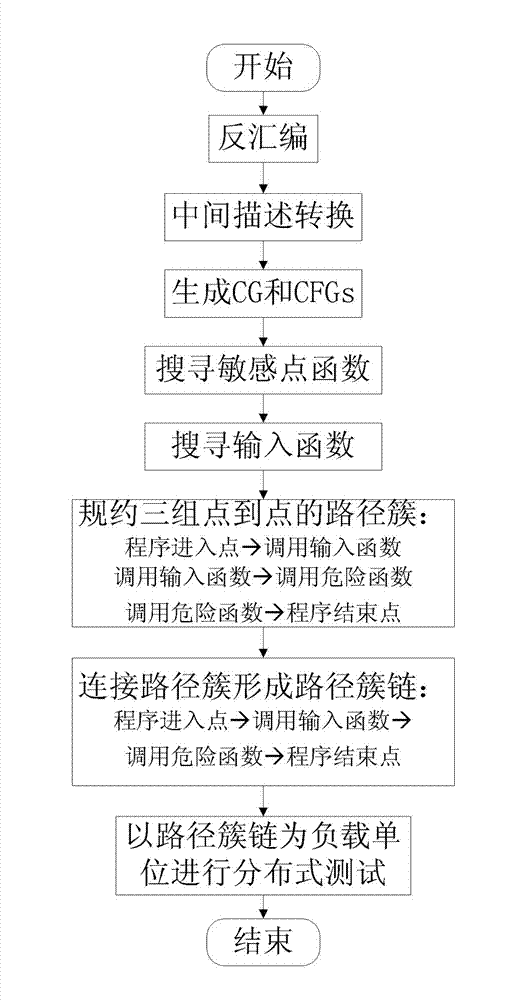
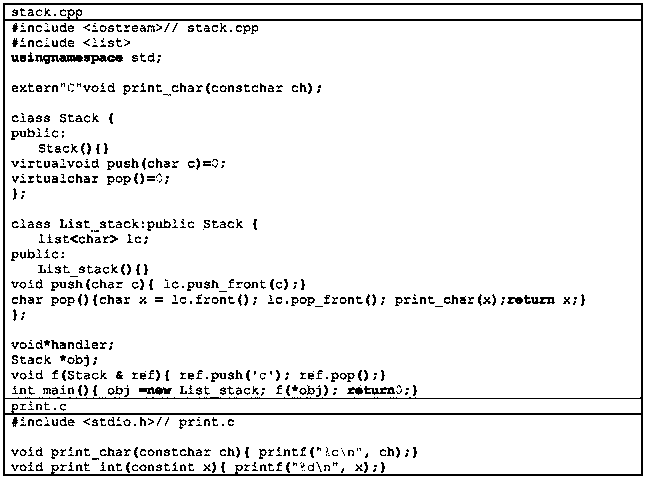
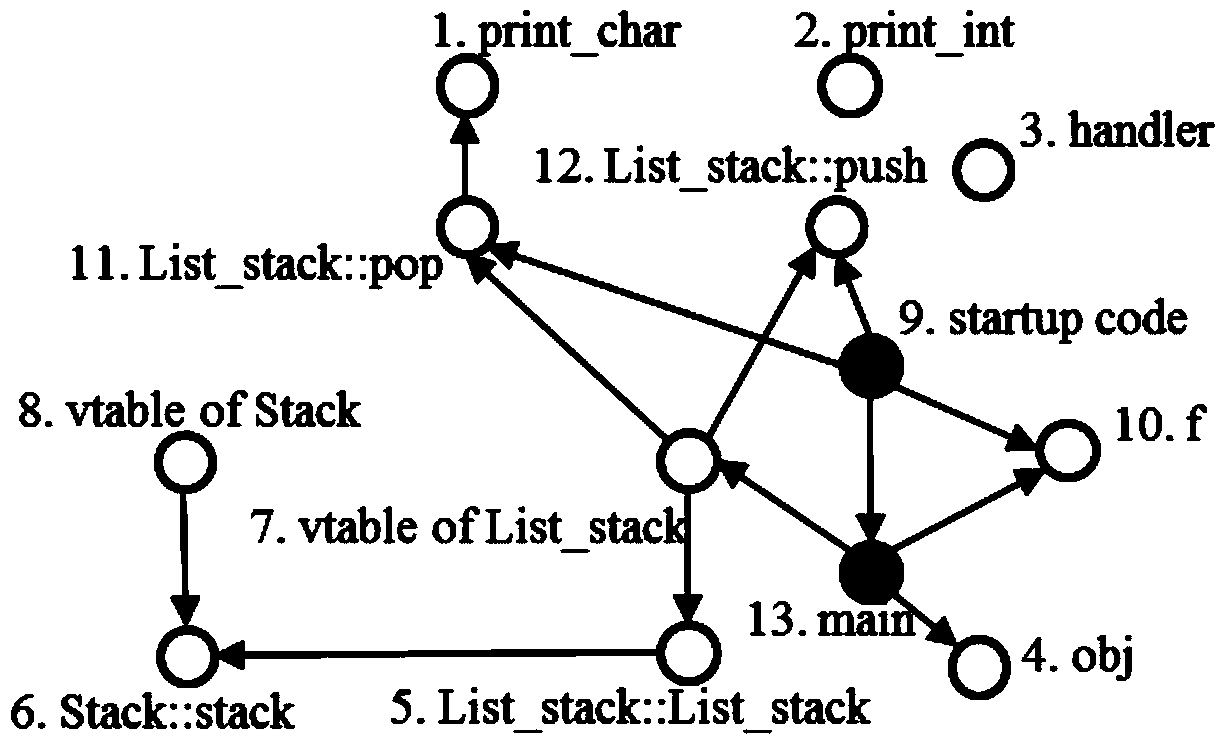
The invention relates to a computer software safety testing method based on program symbolic execution path cluster partitions. The parallel symbolic execution method based on path cluster reductions includes the steps of: (1) disassembling an tested executable program, (2) obtaining assembly codes of the tested executable program and transferring into uniform intermediate assembly language forms, (3) generating a function call graph and a control flow diagram of the tested executable program according to intermediate assembly language forms, (4) finding a dangerous function and an input function according to a static analysis of the function call graph; (5) respectively creating a path between a program entry point and a call input function, between the call input function and a call dangerous function, and between the call dangerous function and a program end point and reducing into path cluster, (6) subjecting the obtained paths to point-to-point connection to form an integral path cluster chain assembly from program entry point to program end point, and (7) generating corresponding test cases to perform actual program safety tests with an integral path cluster chain from program entry point to program end point formed in step (6) serving as a load unit.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
Extension call graph based software system node importance evaluation method
InactiveCN104035773AFully consider the life cycleImprove accuracySpecific program execution arrangementsSorting algorithmCall graph
The invention relates to the field of software engineering, in particular to an extension call graph based software system node importance evaluation method. The method is applicable to a software system, can give importance indexes of functions and data nodes in the entire software system, and performs sorting according to the importance indexes so as to quickly find key nodes in the software system. The method includes the main steps: compiling source codes to obtain object files; starting from the object files, creating an extension call graph of all native codes of the software system; analyzing the extension call graph, and utilizing a node sorting algorithm to compute the importance index of each node in the extension call graph, wherein the importance index represents the importance of each node in the software system. The method has the advantages of wide application range, high accuracy, reasonability in evaluation, high automation degree, convenience in use and the like.
Owner:TSINGHUA UNIV
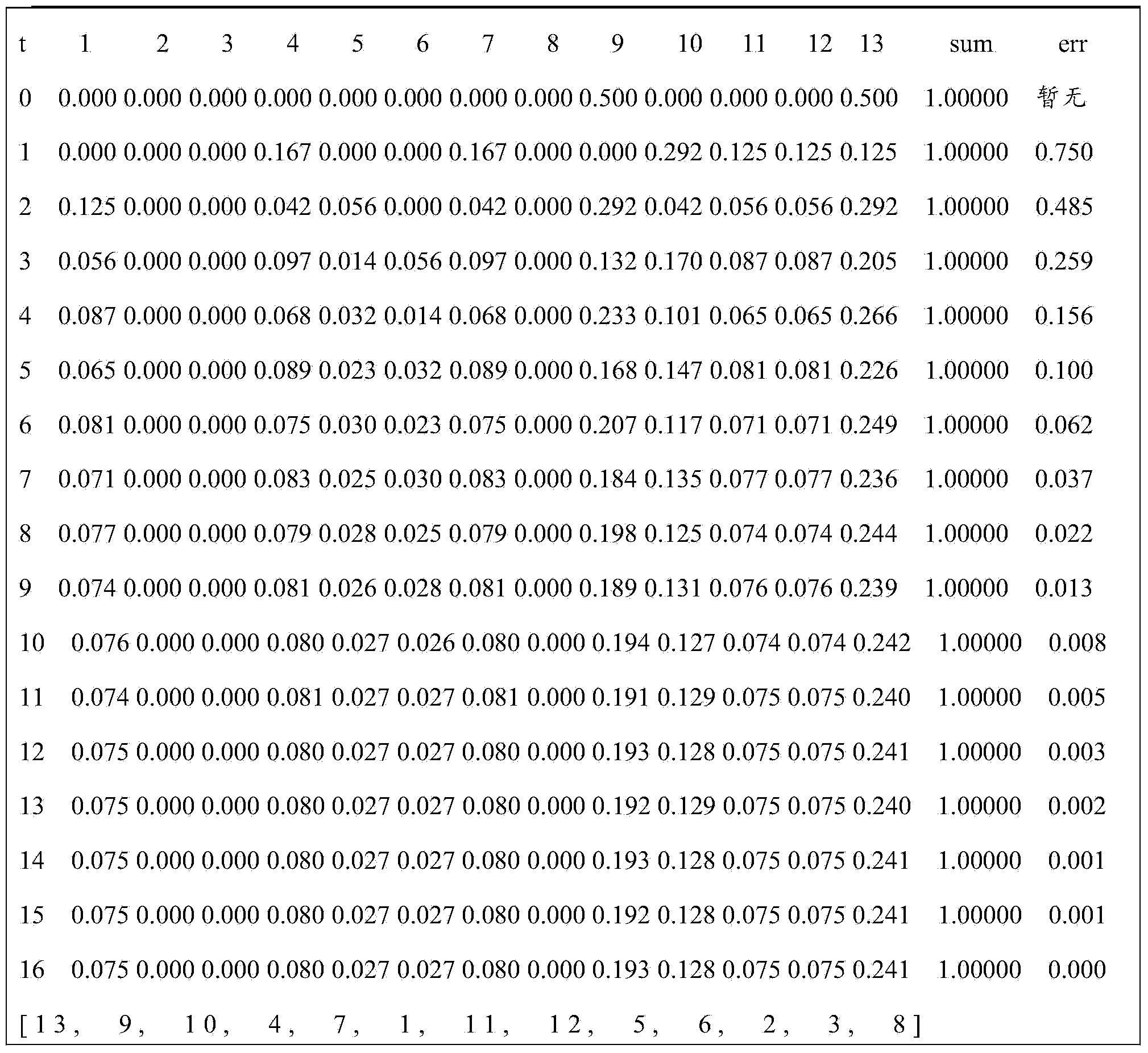
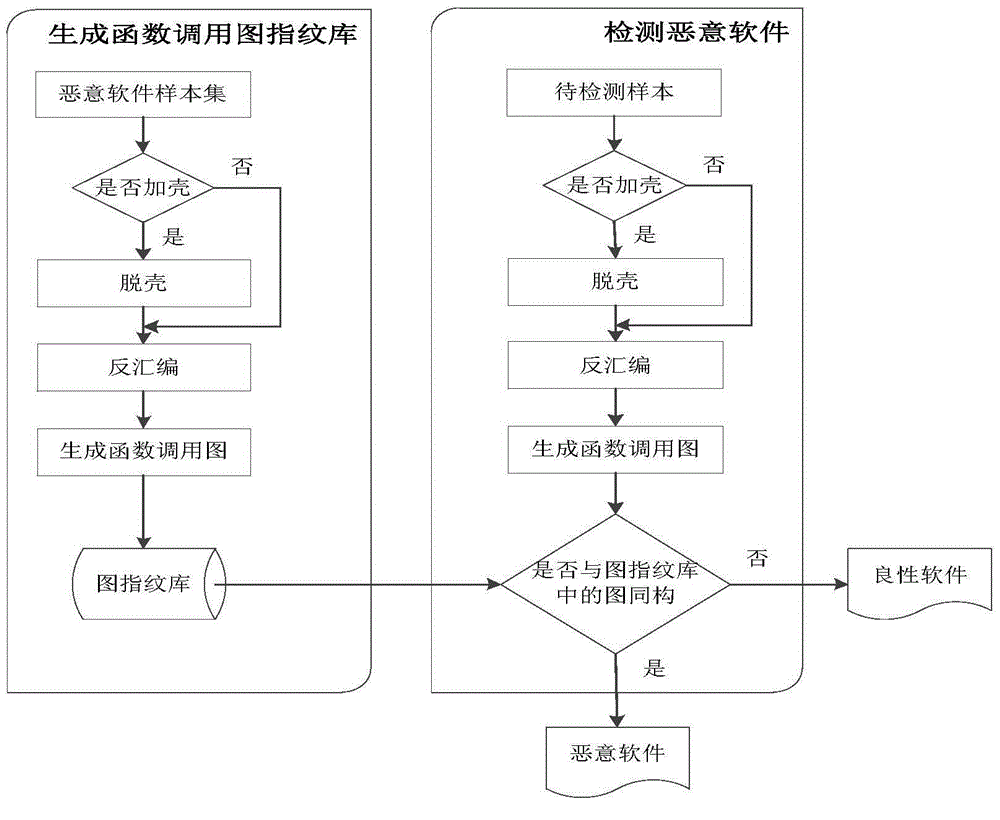
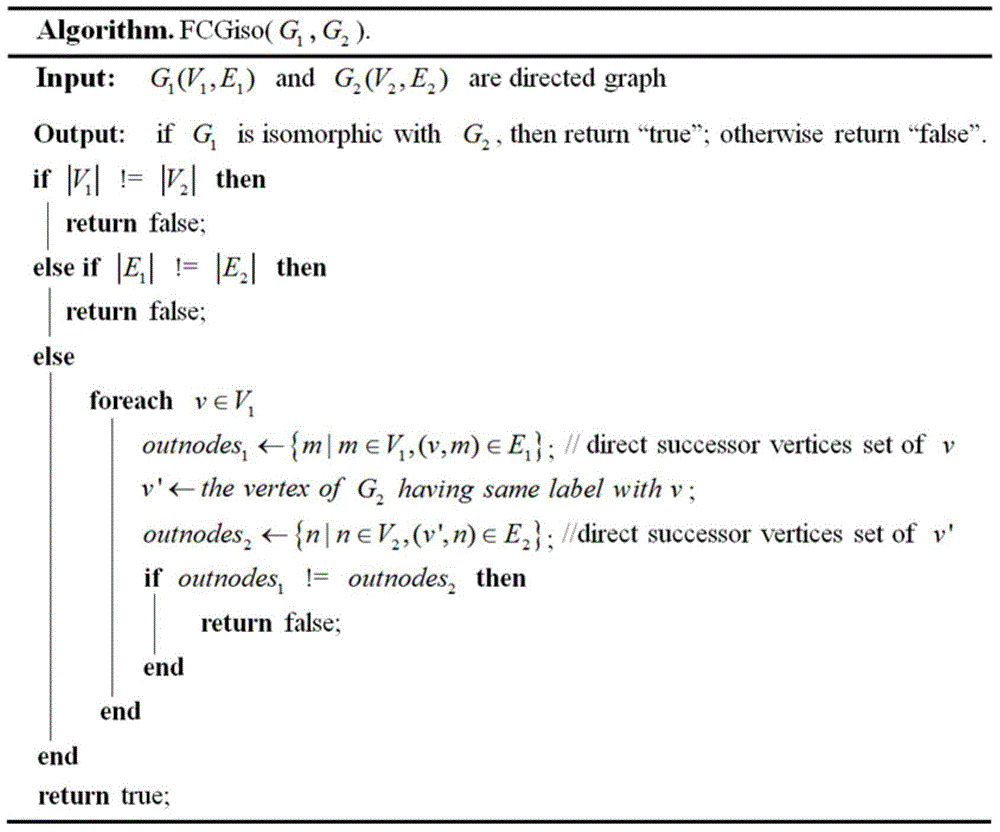
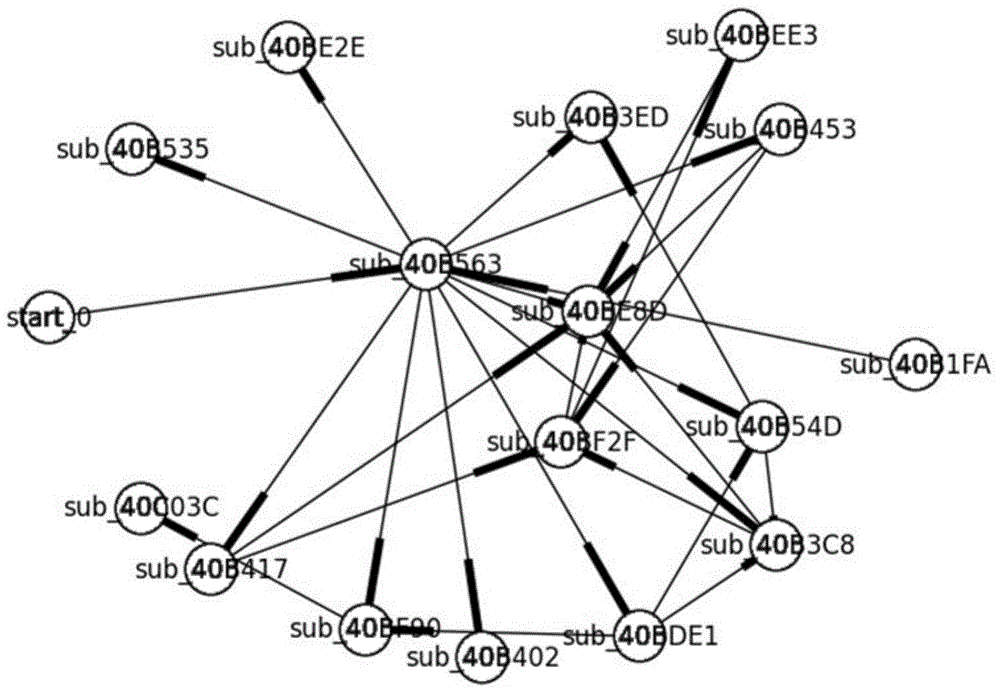
Function call graph fingerprint based malicious software detection method
The invention provides a function call graph fingerprint based malicious software detection method, comprising: judging whether a known malicious software sample is packed; performing disassembly processing to obtain an assembly code of the malicious software sample; by taking a function as a node and inter-function call as an edge, generating a function call graph; adding the function call graph as a fingerprint of the sample into a graph fingerprint library; judging whether the to-be-detected sample is packed; performing disassembly processing to obtain an assembly code of the to-be-detected sample; based on the assembly code, generating the function call graph of the to-be-detected sample, wherein the graph serves as the fingerprint of the detected sample; and performing isomorphism judgment on the function call graph fingerprint of the to-be-detected sample and each graph in the graph fingerprint library. According to the method, the function call graph is used as the fingerprint of the software, and most malicious software and malicious software variants are identified by fully utilizing a characteristic that the functional call graph is a special graph, so that the identification time is short and the efficiency is high.
Owner:SICHUAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com