Patents
Literature
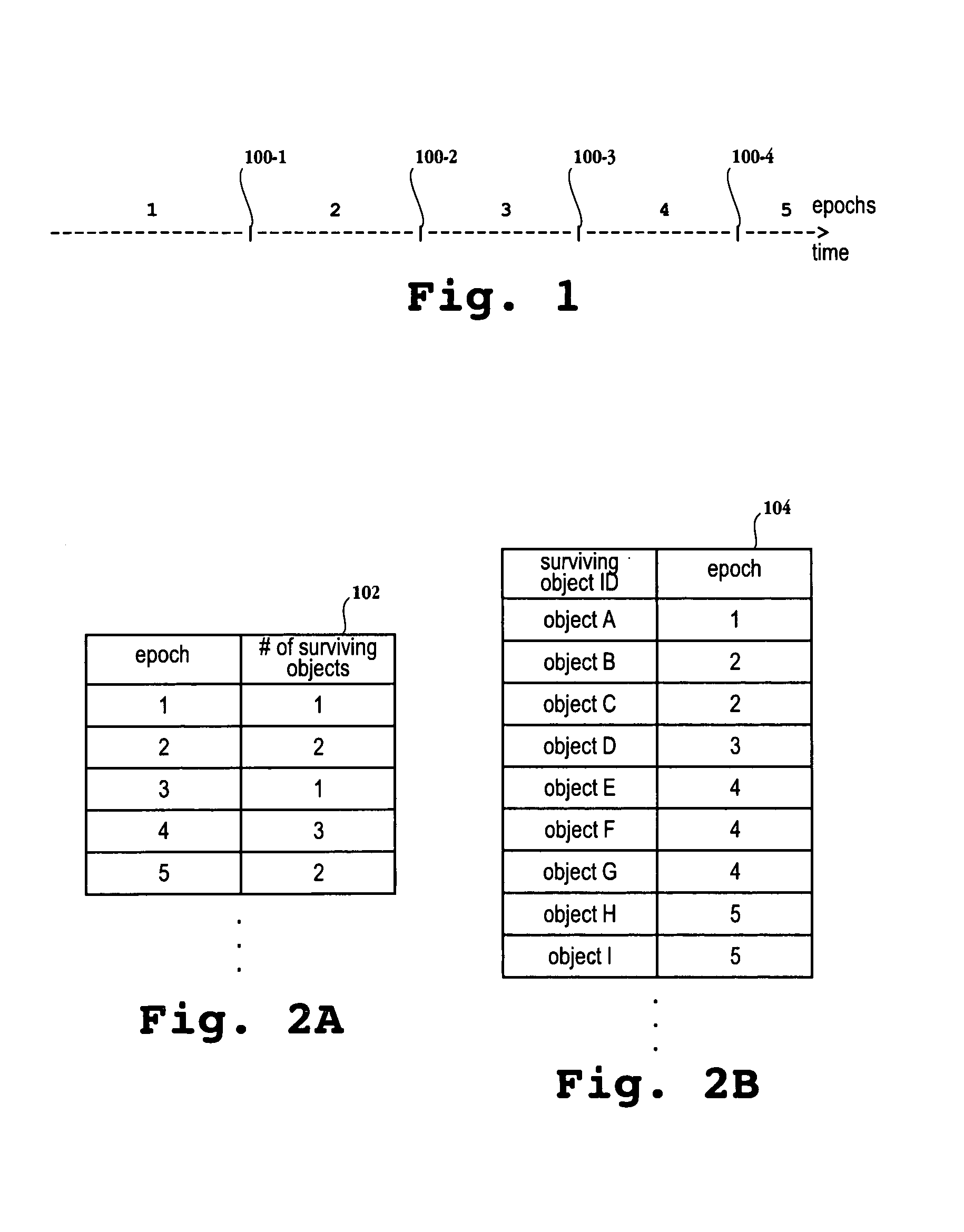
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
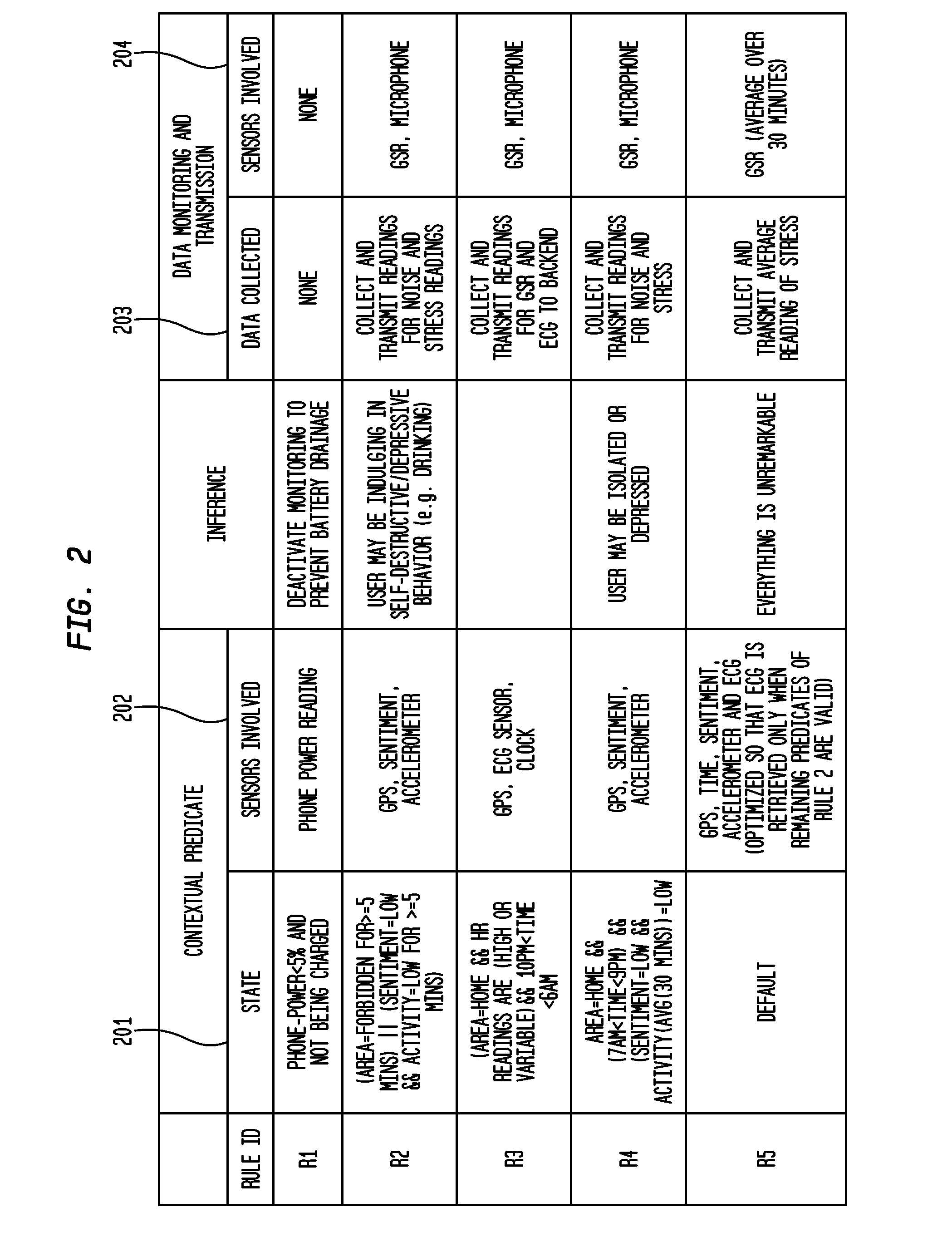
585 results about "Low overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
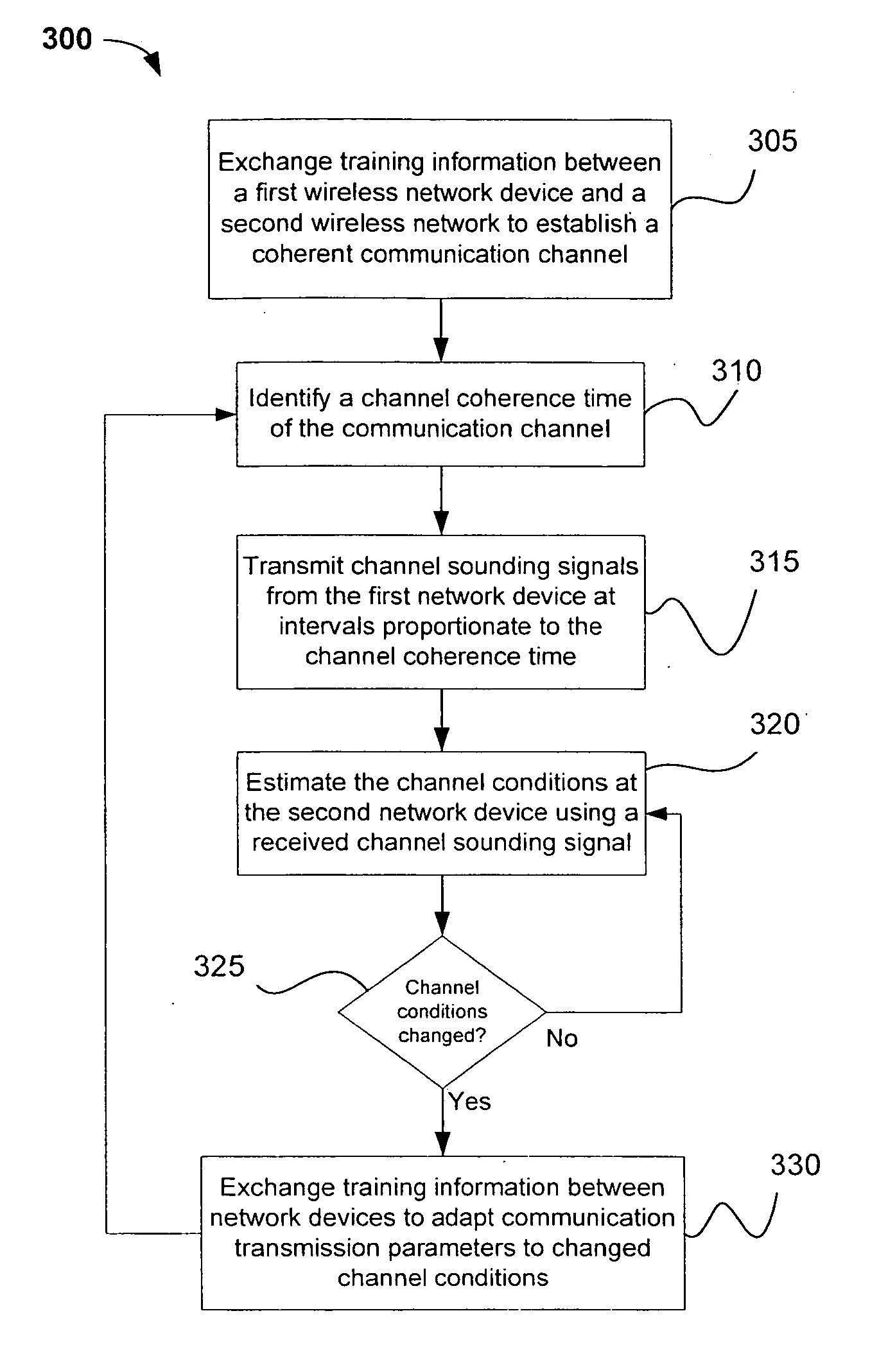
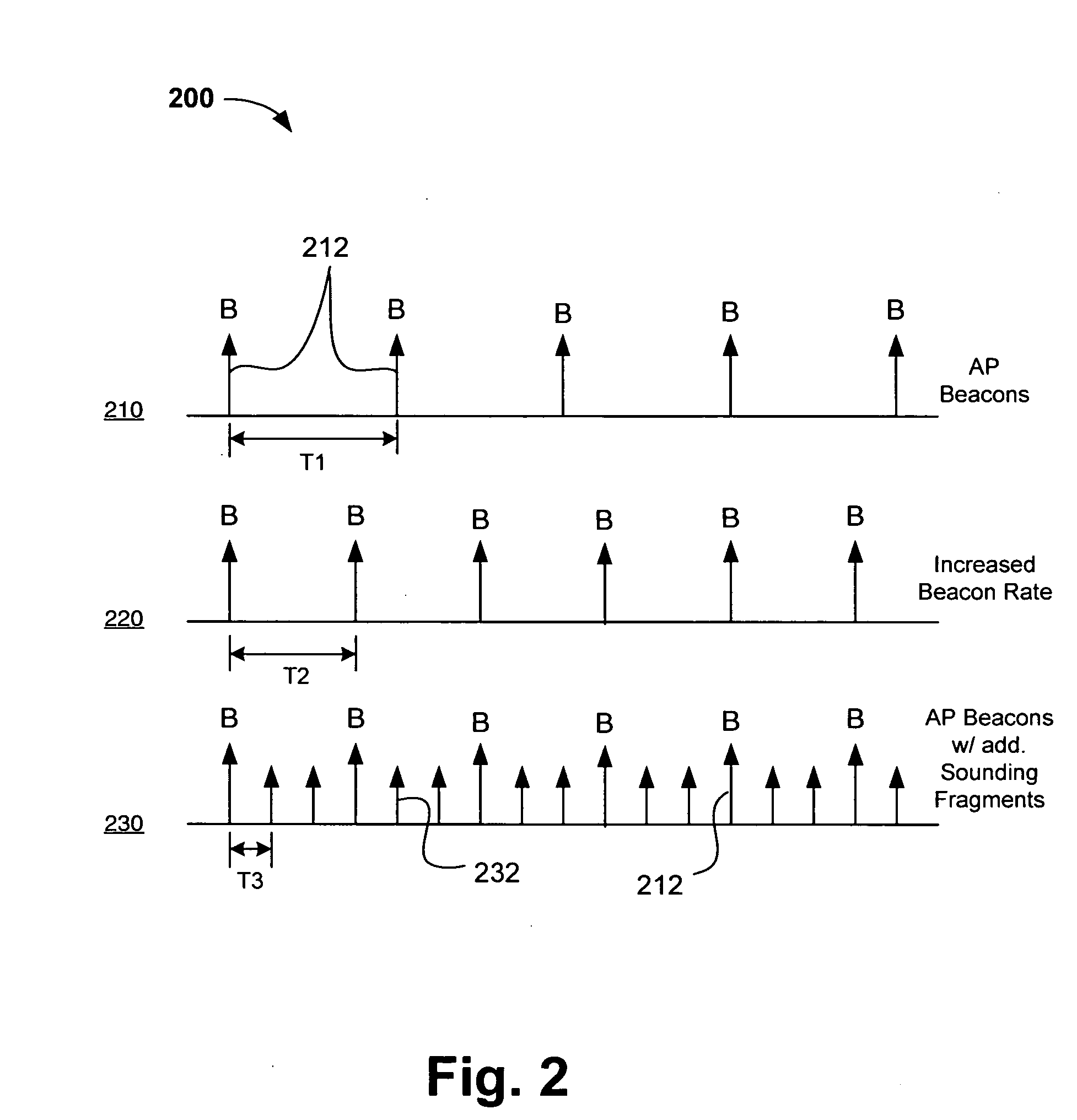
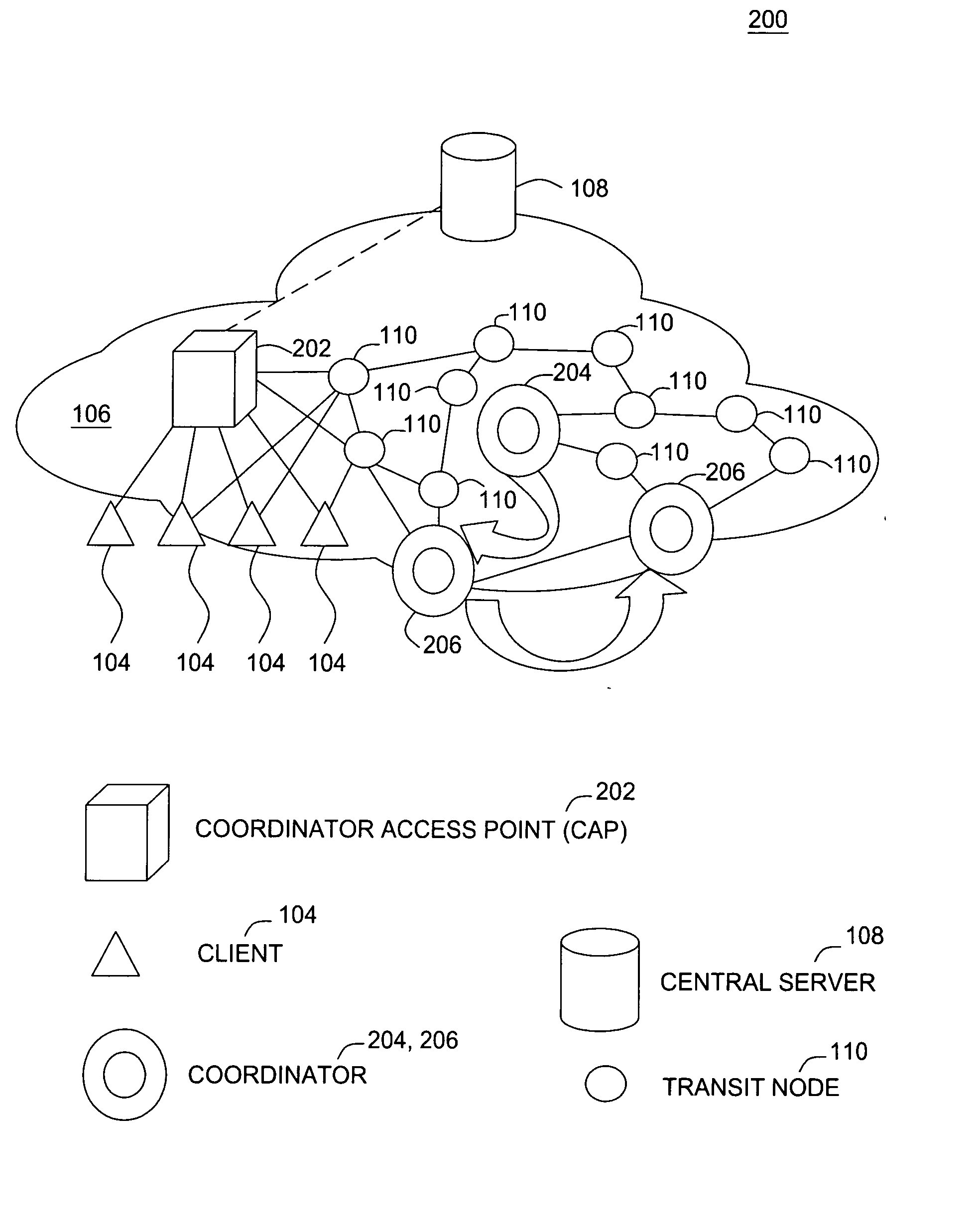
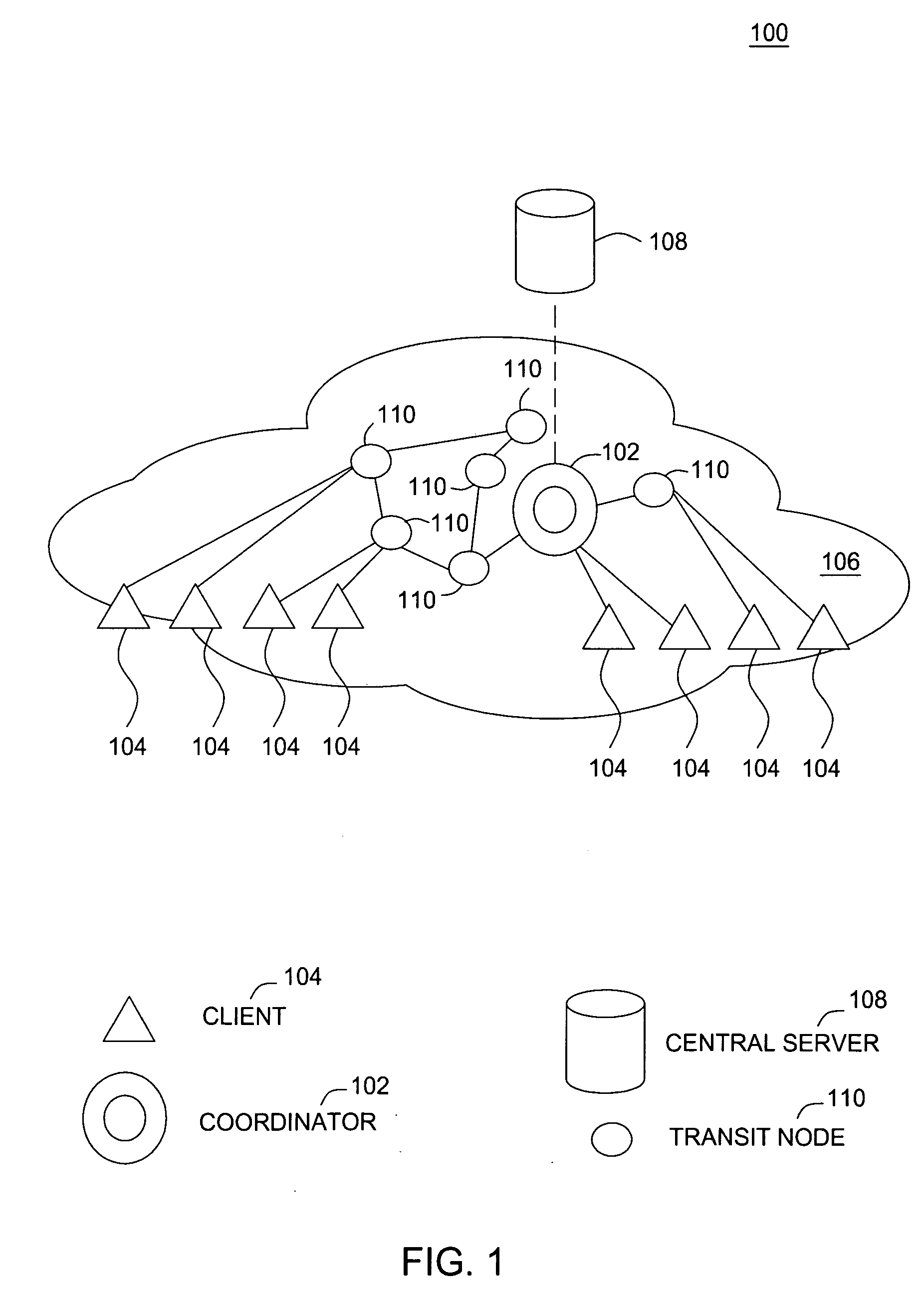
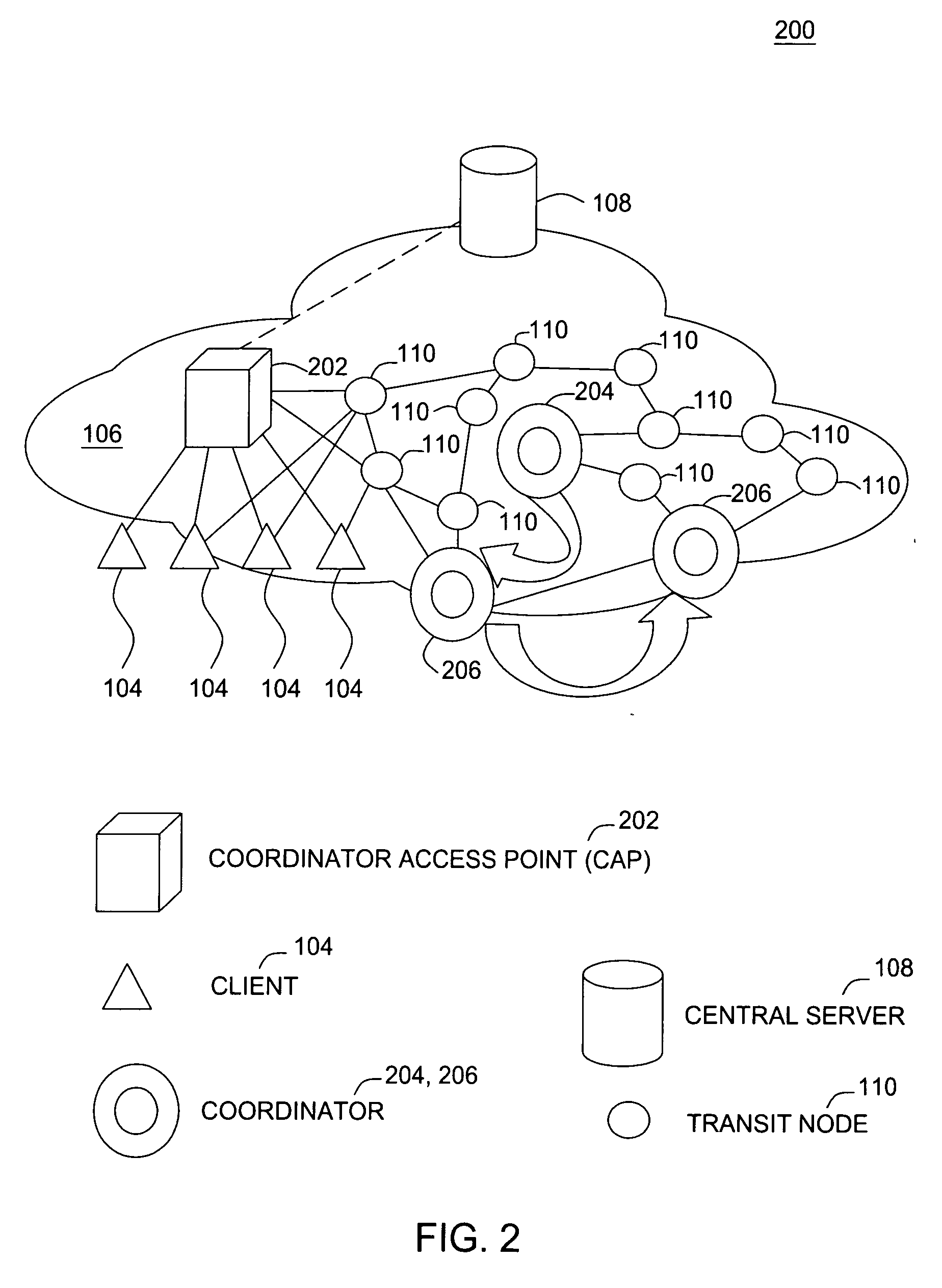
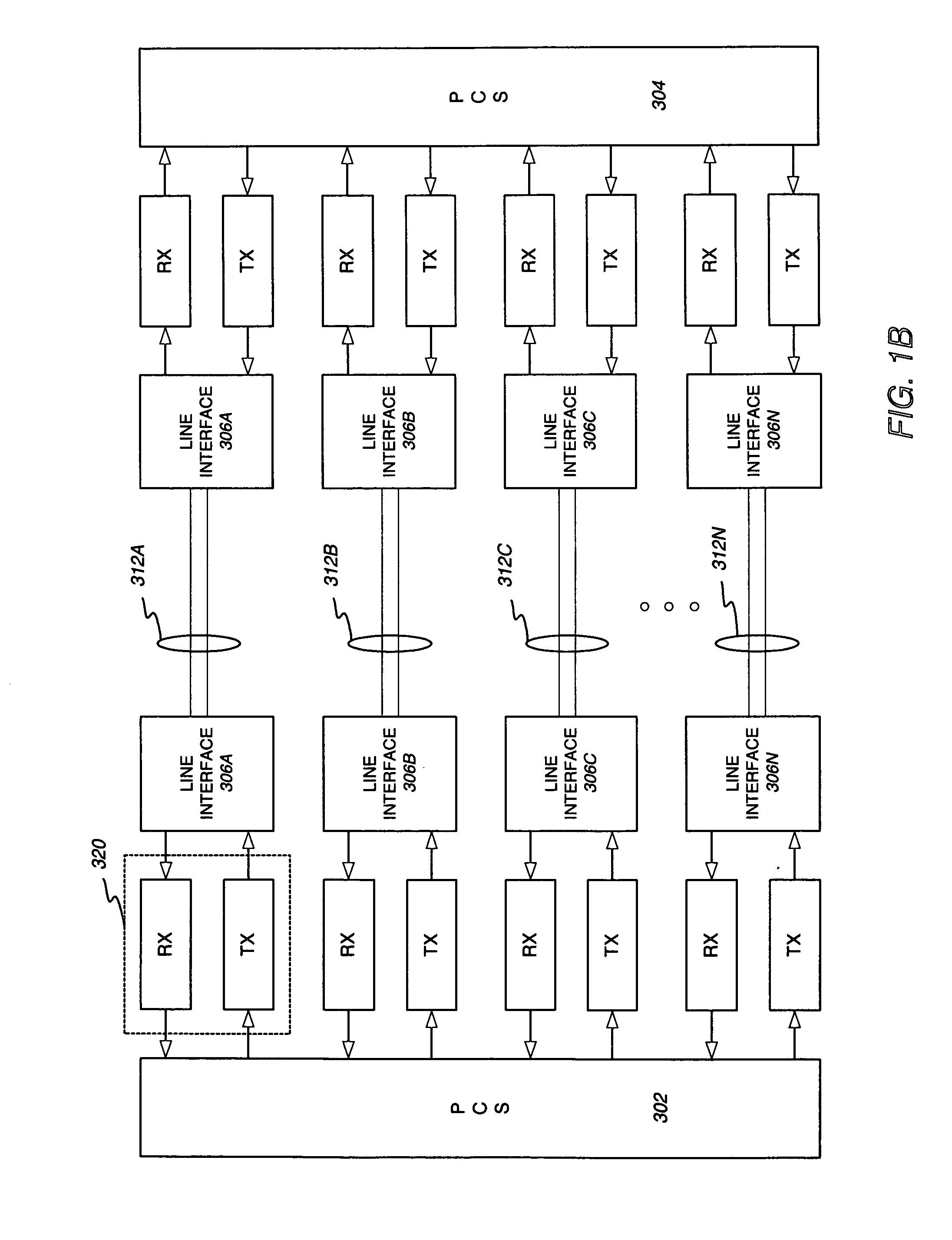
Channel adaptation using variable sounding signal rates
InactiveUS20050170781A1Error detection/prevention using signal quality detectorFrequency-division multiplex detailsCoherence timeLink adaptation
Systems, devices and methods for updating link adaptations in multi-carrier modulated signals between an access point (AP) and a wireless local area network (WLAN) station (STA) include (are configured for) periodically transmitting a channel sounding signal from the AP. The STA receives each unsolicited channel sounding signal and evaluates the current channel conditions between the AP and STA. The AP adjusts a rate of transmission of the channel sounding signals in accordance with the channel coherence time so that the channel estimates performed by the STA will be valid within the time varying characteristics of the channel. Depending on the length of the coherence time for network environment, the channel sounding signals may be AP beacons, low overhead signal fragments with no payload, or a combination of both.
Owner:INTEL CORP
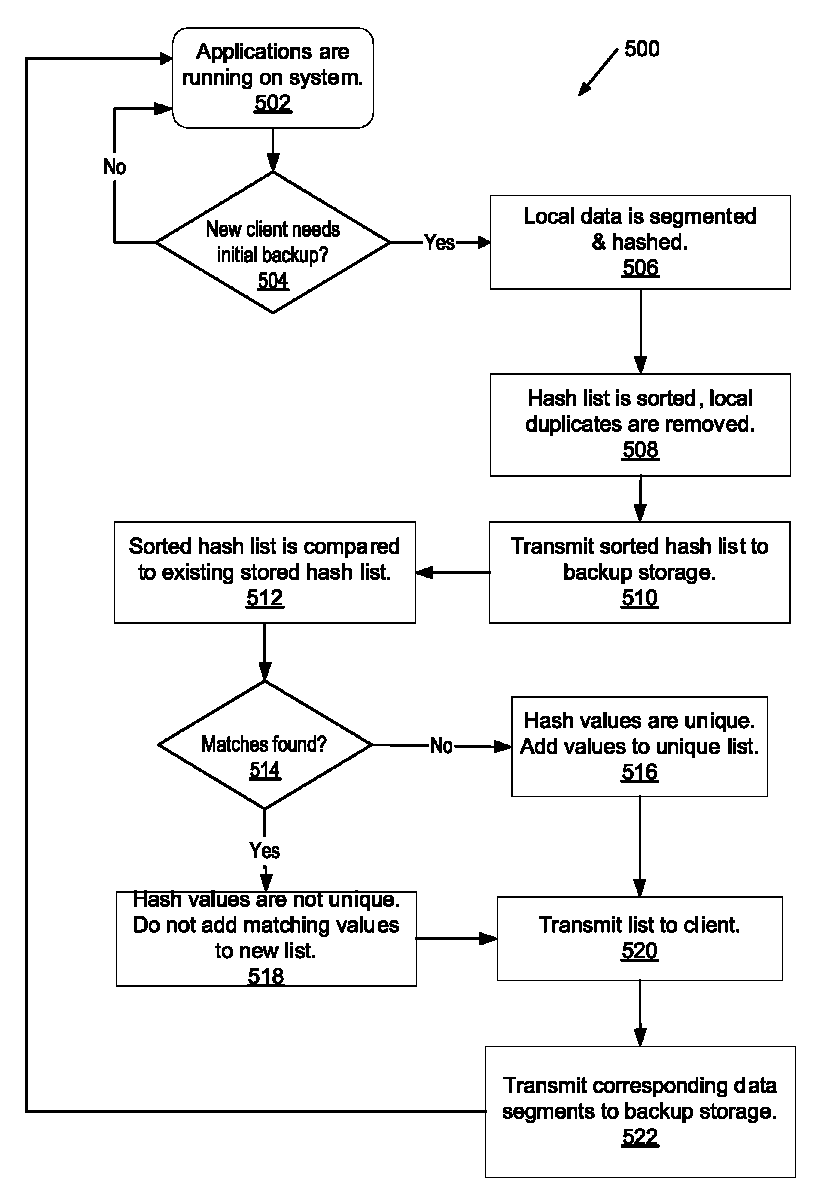
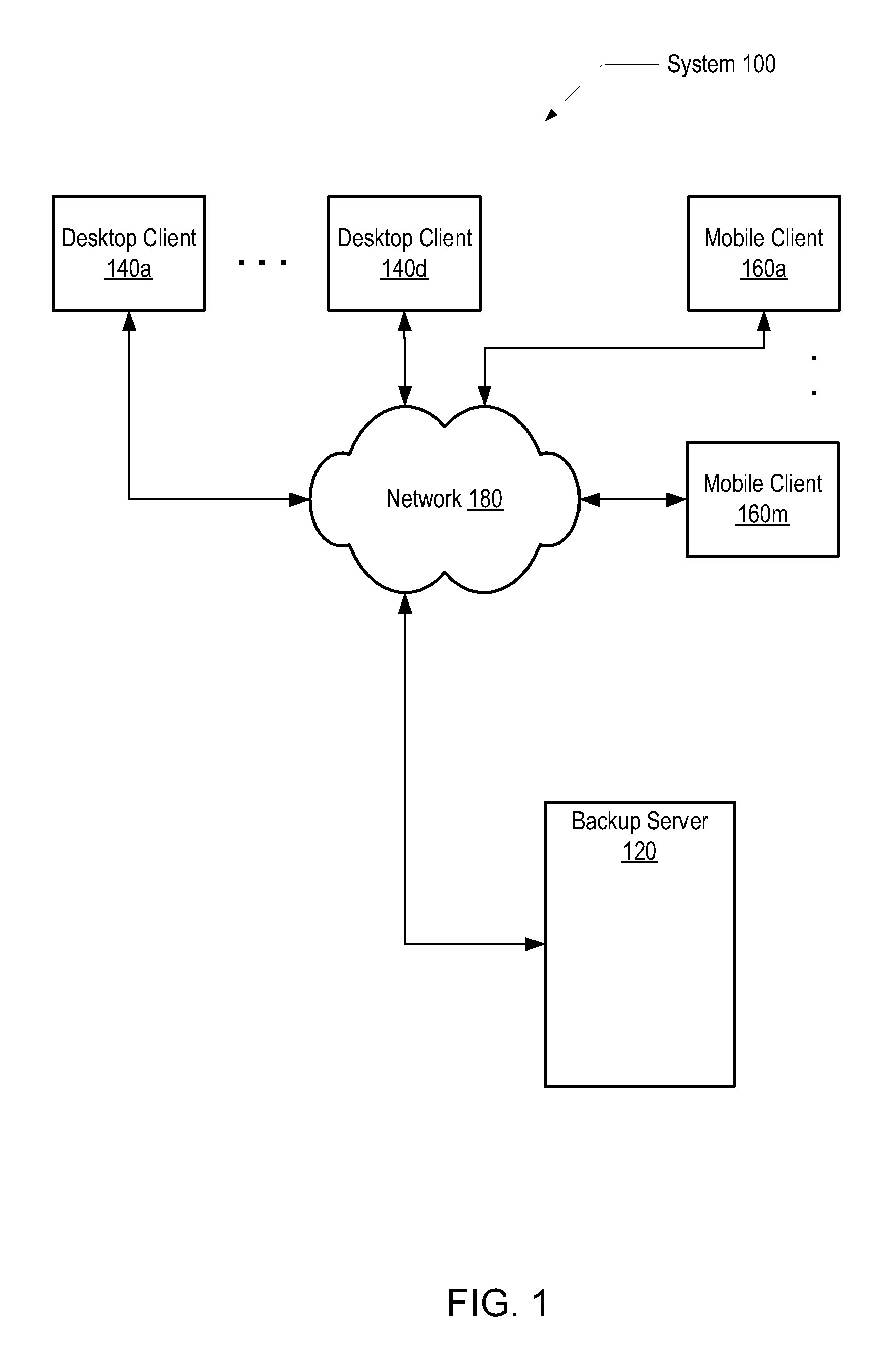
Low-overhead means of performing data backup
ActiveUS7761425B1Data efficientError detection/correctionDigital data processing detailsData segmentComputerized system
A system and method for data backup. A computer system includes clients coupled to backup server and single instance store via a network. Prior to requesting an initial data backup, a new client segments and fingerprints the data to be backed up. The new client creates a sorted list of hash values and removes duplicate values in the list. In response to receiving the sorted list, a backup server may further reduce the sorted list to a unique list by removing hash values corresponding to data segments already residing on the single instance store. In response to receiving the unique list, the new client may transmit corresponding data segments to the backup server via the network. The transmitted data segments are added to a single instance store.
Owner:VERITAS TECH
Managing uplink resources in a cellular radio communications system
ActiveUS20090225709A1Increase data rateEasy to handleNetwork topologiesData switching by path configurationCellular radioCommunications system
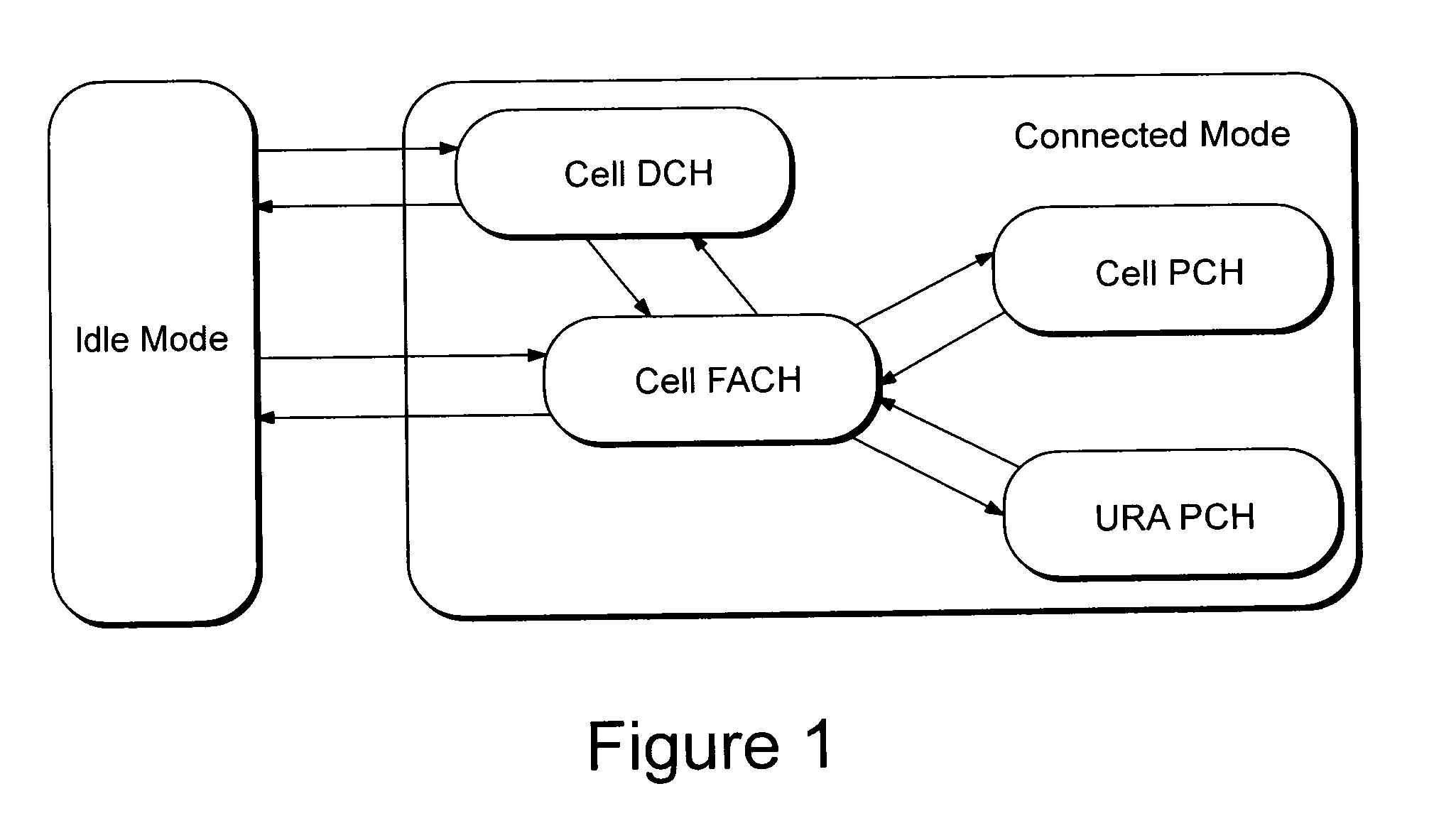
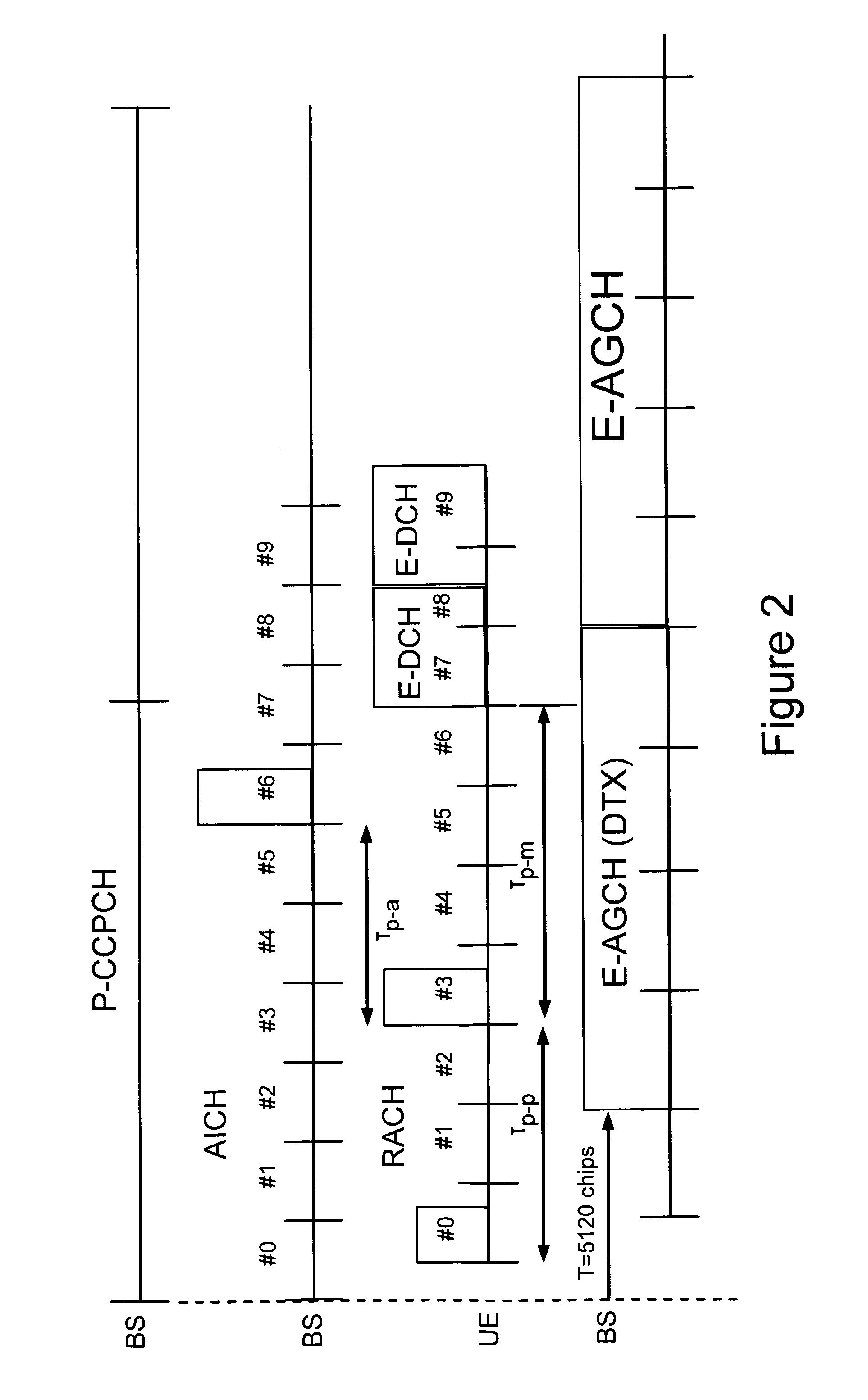
The technology in this application provides a method and apparatus for efficiently using common uplink radio resources, e.g. a common uplink enhanced-dedicated physical channel (E-DCH) resource. A UE releases a common E-DCH resource very quickly after a completed transmission. In addition or alternatively, a base station may release a common E-DCH resource configuration from the network side to free up common E-DCH resources for use by other UEs. A low overhead signaling scheme for quickly and effectively releasing of common E-DCH resources between a UE and a base station is also described. For example, existing signaling fields on protocol layer 2 (L2) or layer 1 (L1) may be used. In one preferred example embodiment, signaling fields already in use in a CELL_DCH service state are given a different meaning for UEs in a CELL_FACH service state so that common E-DCH resources are quickly and effectively released.
Owner:TELEFON AB LM ERICSSON (PUBL)
Acorn: providing network-level security in P2P overlay architectures
InactiveUS20070149279A1Broadcast specific applicationsDigital computer detailsObfuscationComputer science
To address the problem of providing network-based security to mitigate and detect cheating in peer-to-peer (P2P) gaming architecture, an architecture suite called architectures with coordinator obfuscation for resilient P2P gaming networks (ACORN) is presented that uses a combination of low overhead, per-packet access authentication, moving-coordinator and cheat detection mechanisms to effectively mitigate security threats.
Owner:RPX CORP
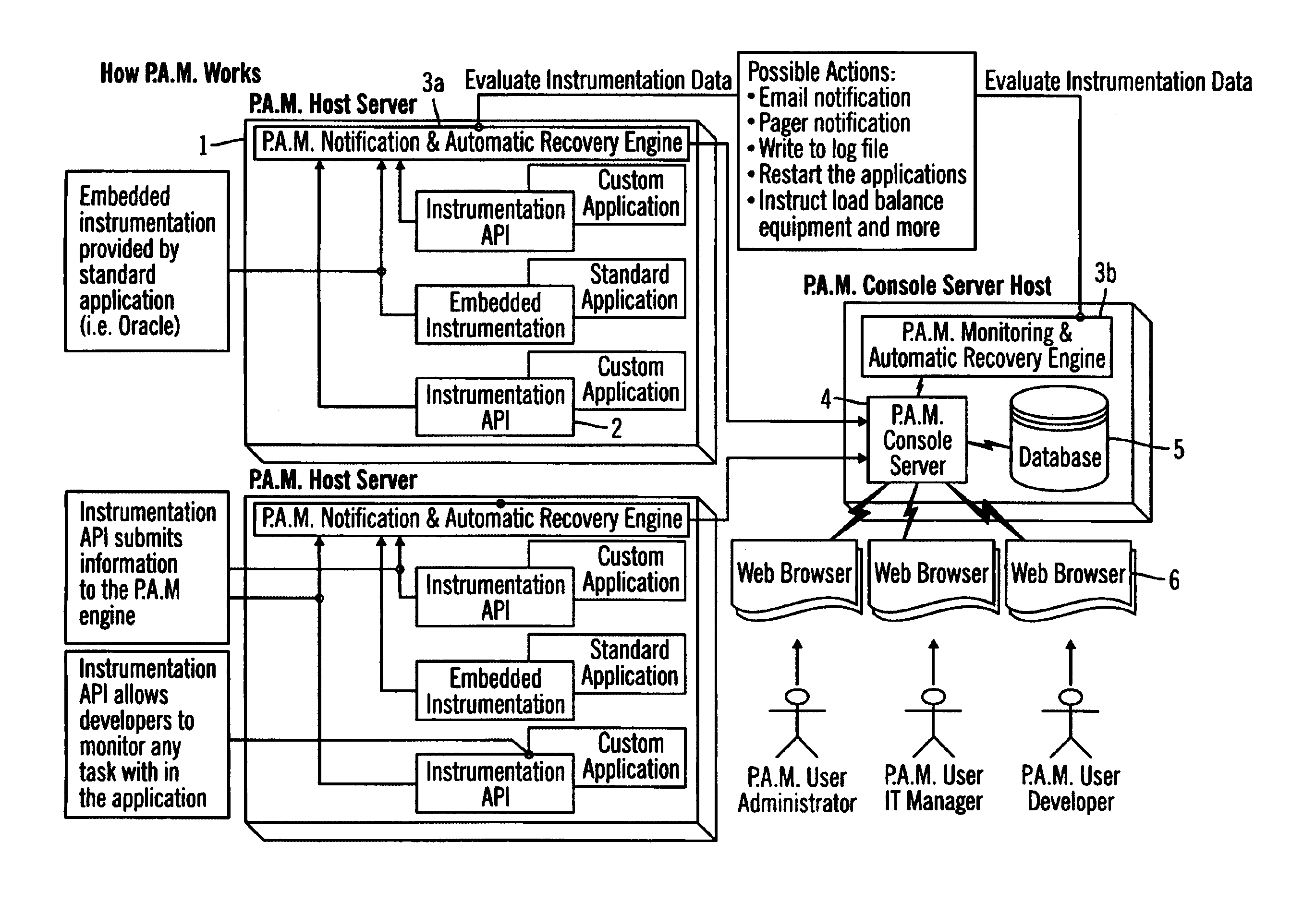
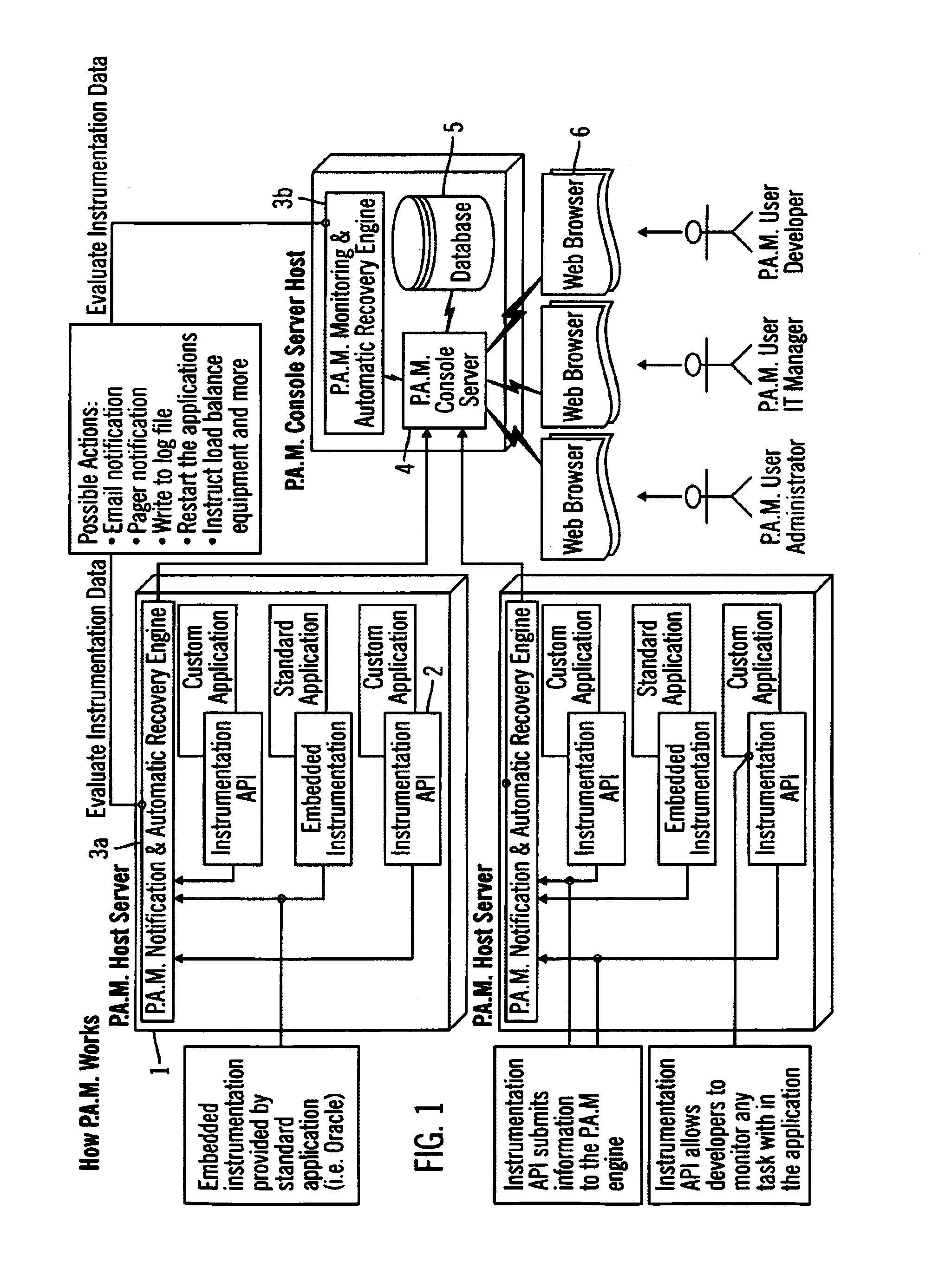
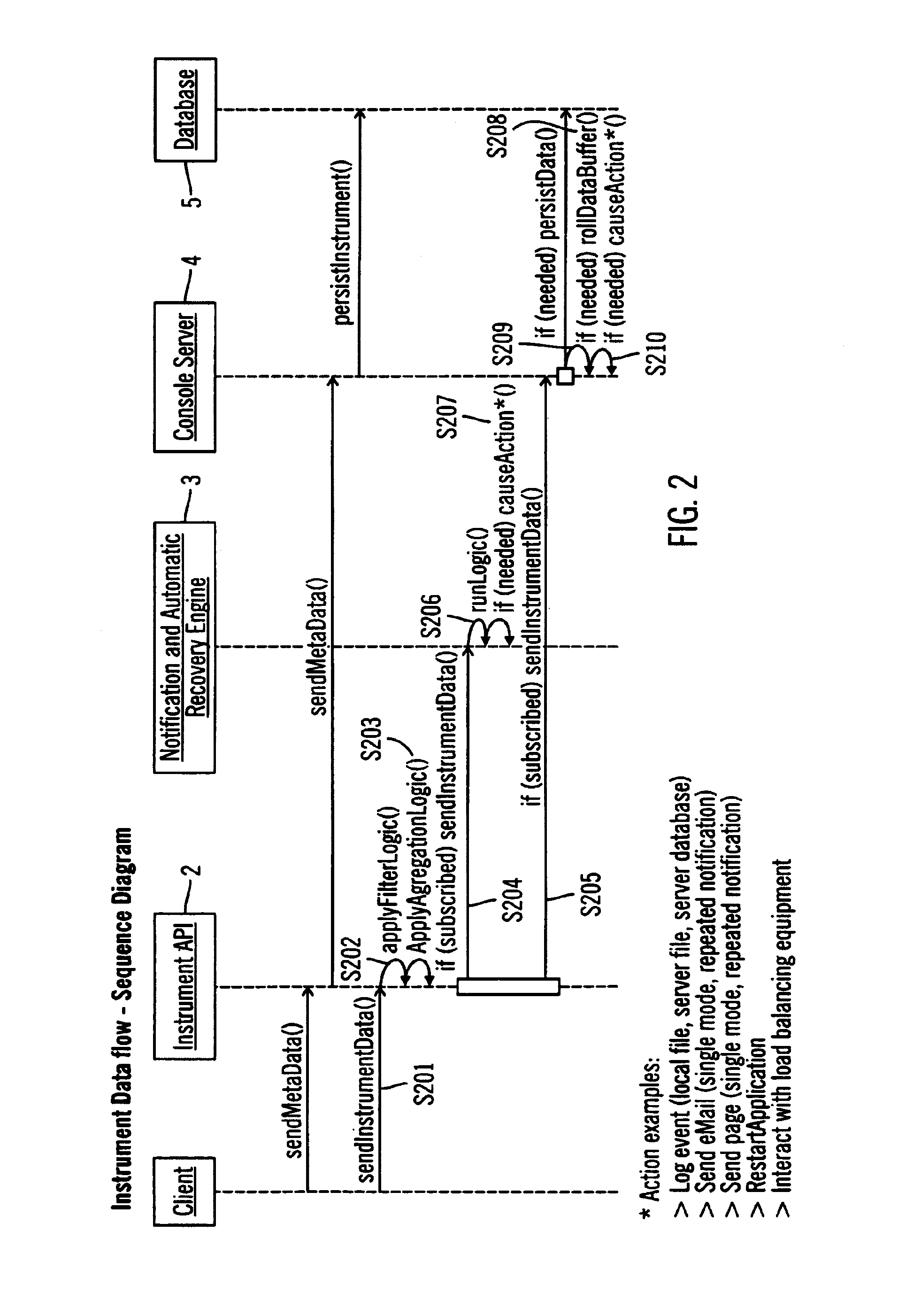
Application manager for monitoring and recovery of software based application processes
InactiveUS7028225B2Reduce overheadShorten the timeDigital computer detailsNuclear monitoringPagerGranularity
A constant monitoring and recovery system that enables the measurement of task usage / metrics and performance of software-based business applications. These metrics can then be evaluated by logic, in combination with each other and / or a timer, in a distributed environment. This is accomplished with the introduction of an extremely low overhead to the application host. The results of the logic evaluation can cause real-time and real-world responses such as application restart, interaction with load balancing equipment, or notification (via email, pager, etc.). Data can also be persisted to a database for later archival or evaluation, with the ability to reduce granularity over time. Specifically, an application manager monitors business application processes, notifies failure and automatically recovers software based business applications based on the logic of the underlying applications. The application manager comprises three main components that work together: Instrumentation API for setting up monitoring parameters; Event Notification and Automatic Recovery Evaluation Engine; Monitoring Console Server.
Owner:PATH RELIABILITY
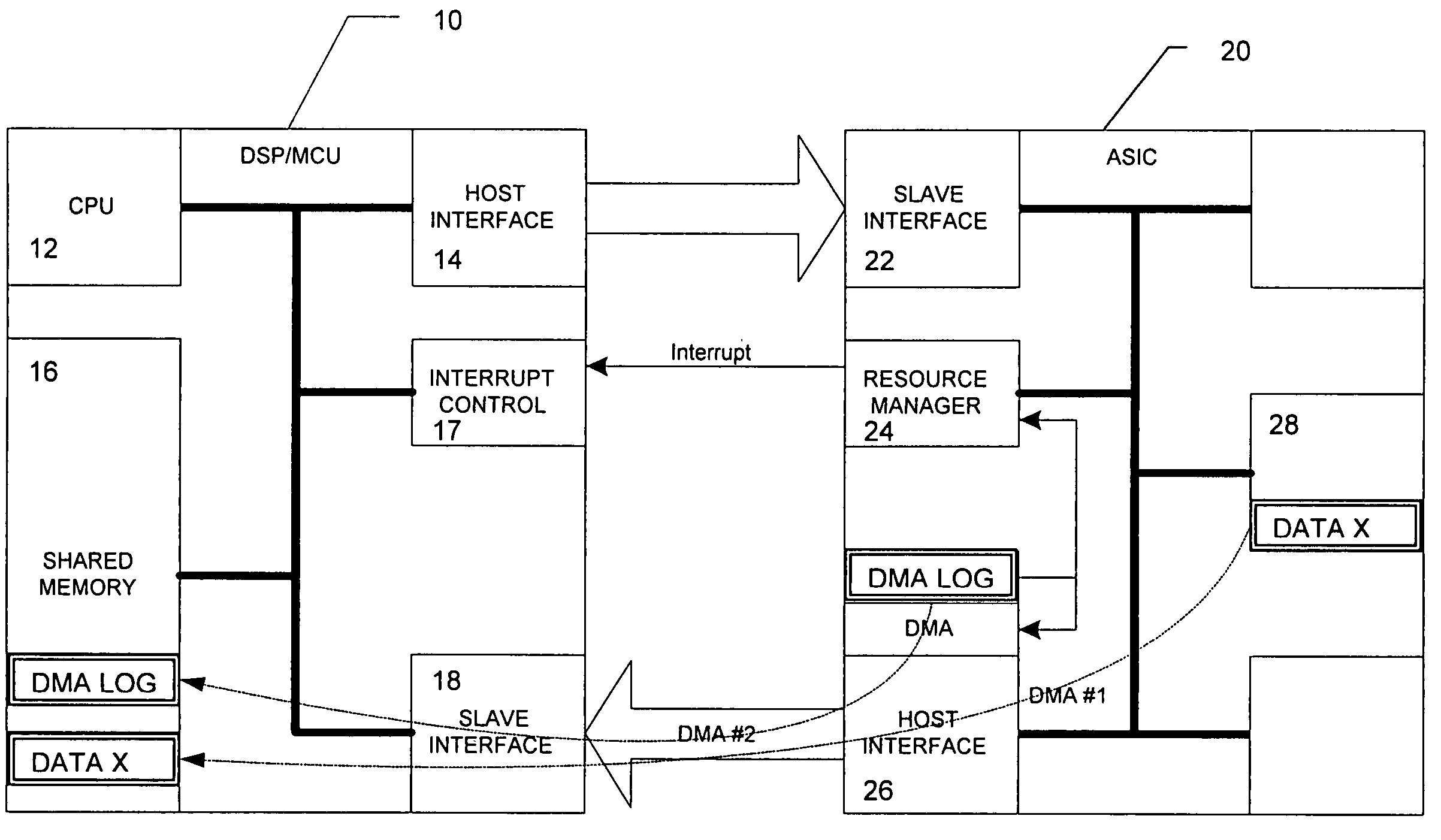
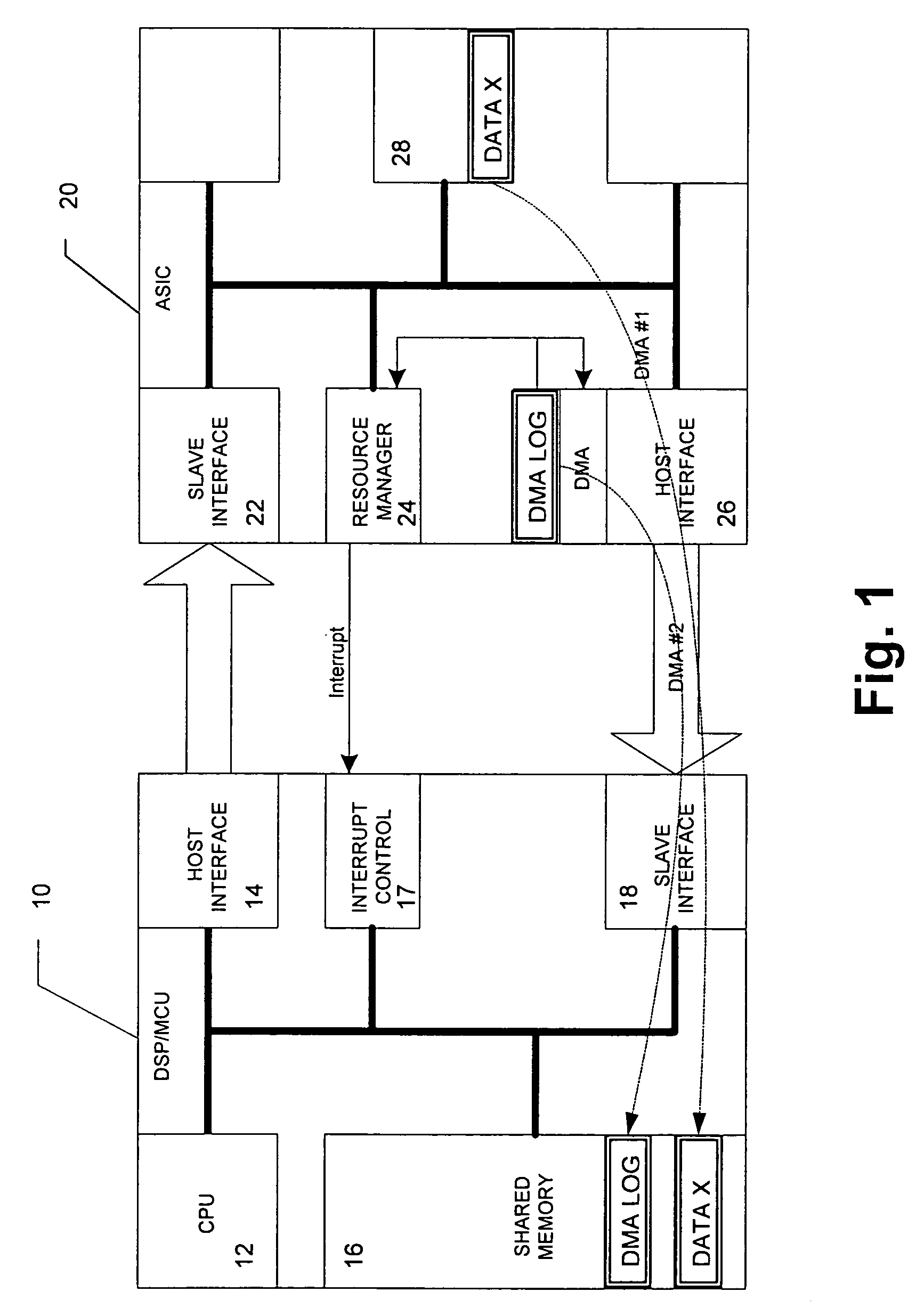
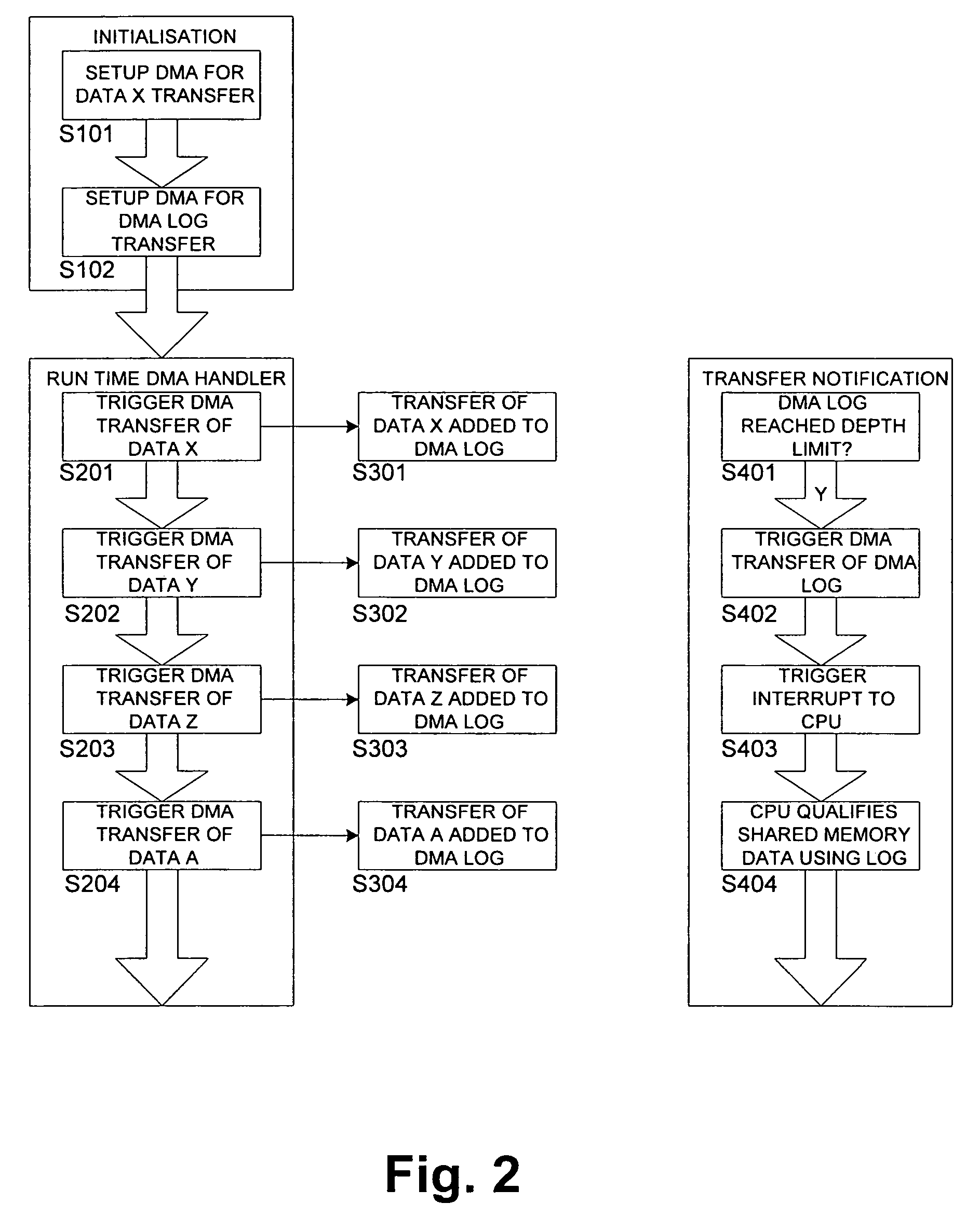
DMA data transfer between low-overhead processor and connected external circuitry using transactions log
InactiveUS7293119B2Reduce loadReduce overheadDigital computer detailsSpecific program execution arrangementsTransaction logData transmission
Owner:NOKIA SOLUTIONS & NETWORKS OY
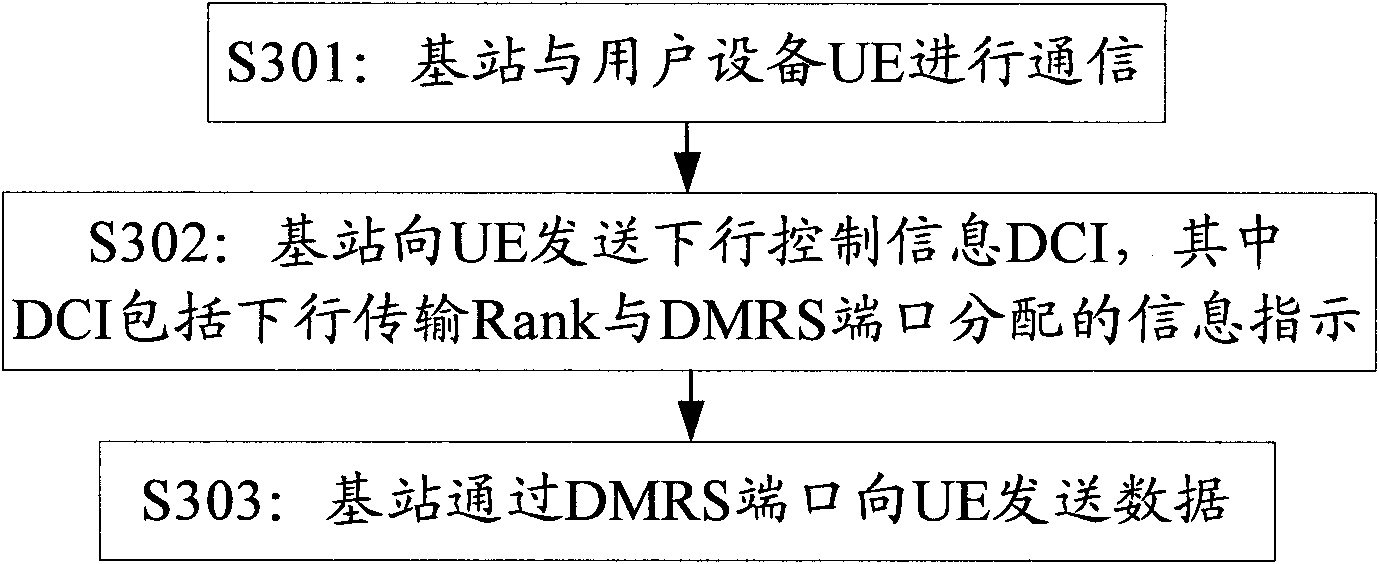
Method and device for indicating information
ActiveCN102158302AReduce overheadMinor changesError preventionHigh level techniquesUser equipmentDemodulation
The embodiment of the invention provides a method for indicating information, and the method comprises the following steps: a base station communicates with user equipment (UE) and allocates a corresponding dataflow to the UE according to the attribute of the UE; the base station sends downlink control information (DCI) to the UE, wherein the DCI contains information indications allocated to a downlink transmission Rank and a demodulation reference sign (DMRS) port; and the base station sends the corresponding dataflow to the UE through the DMRS port. By using the technical scheme provided bythe invention, the signaling overhead is reduced by using a transmission block switch and through the combined coding of NDI (non-damage inspection) bits in the mono-code transmission, thereby supporting the combined indication of the DMRS port and bus Rank with a lower overhead.
Owner:DATANG MOBILE COMM EQUIP CO LTD
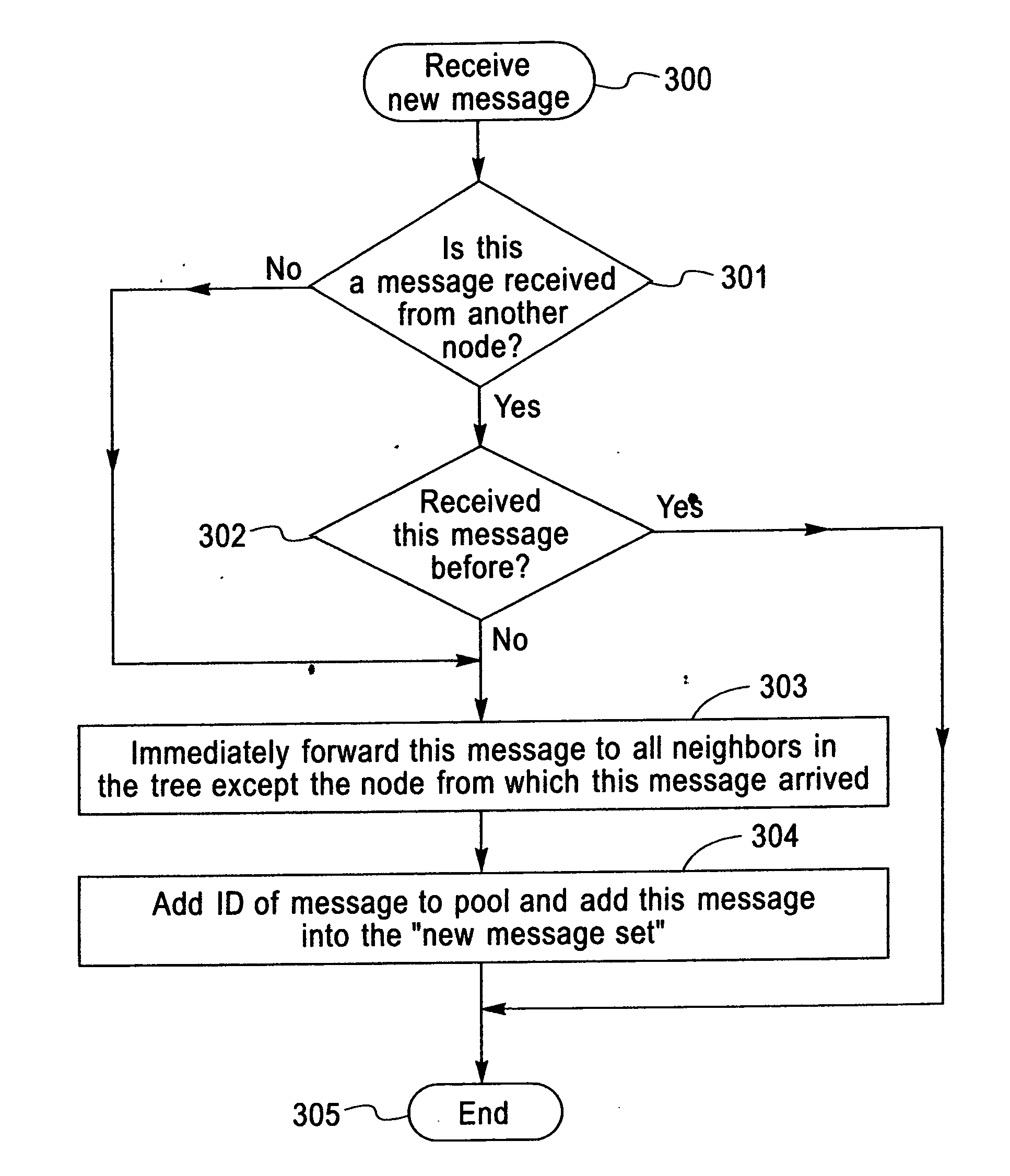
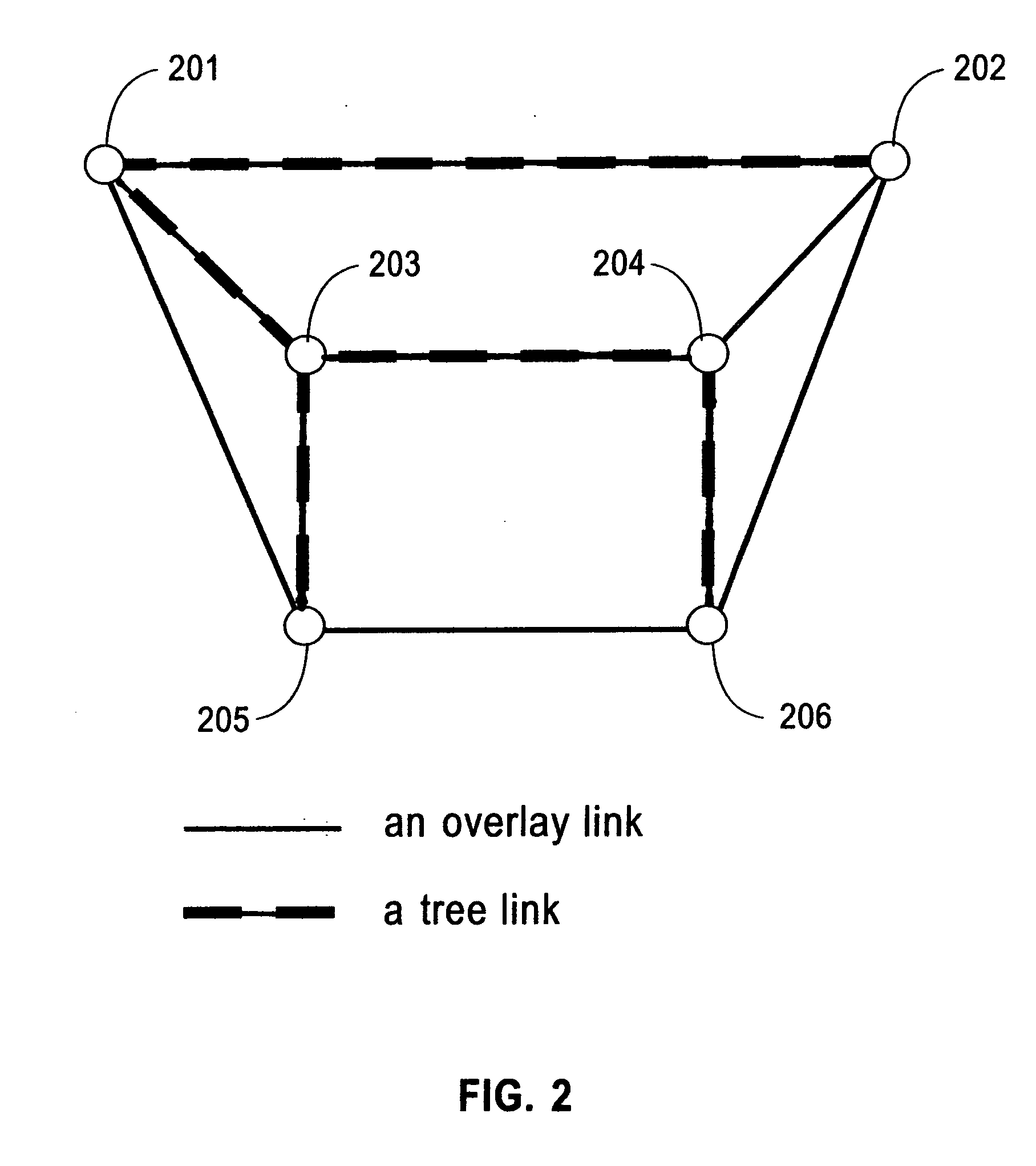
Apparatus, system, and method for reliable, fast, and scalable multicast message delivery in service overlay networks
InactiveUS20070110063A1Reduce overheadIncrease delayTime-division multiplexData switching by path configurationOverlay networkMulticast message
A method to organize nodes into an overlay network and to disseminate multicast messages within this overlay both through an efficient tree embedded in the overlay and through gossips exchanged between overlay neighbors. Regardless of the size of the system, this invention incurs a constant low overhead on each node.
Owner:IBM CORP
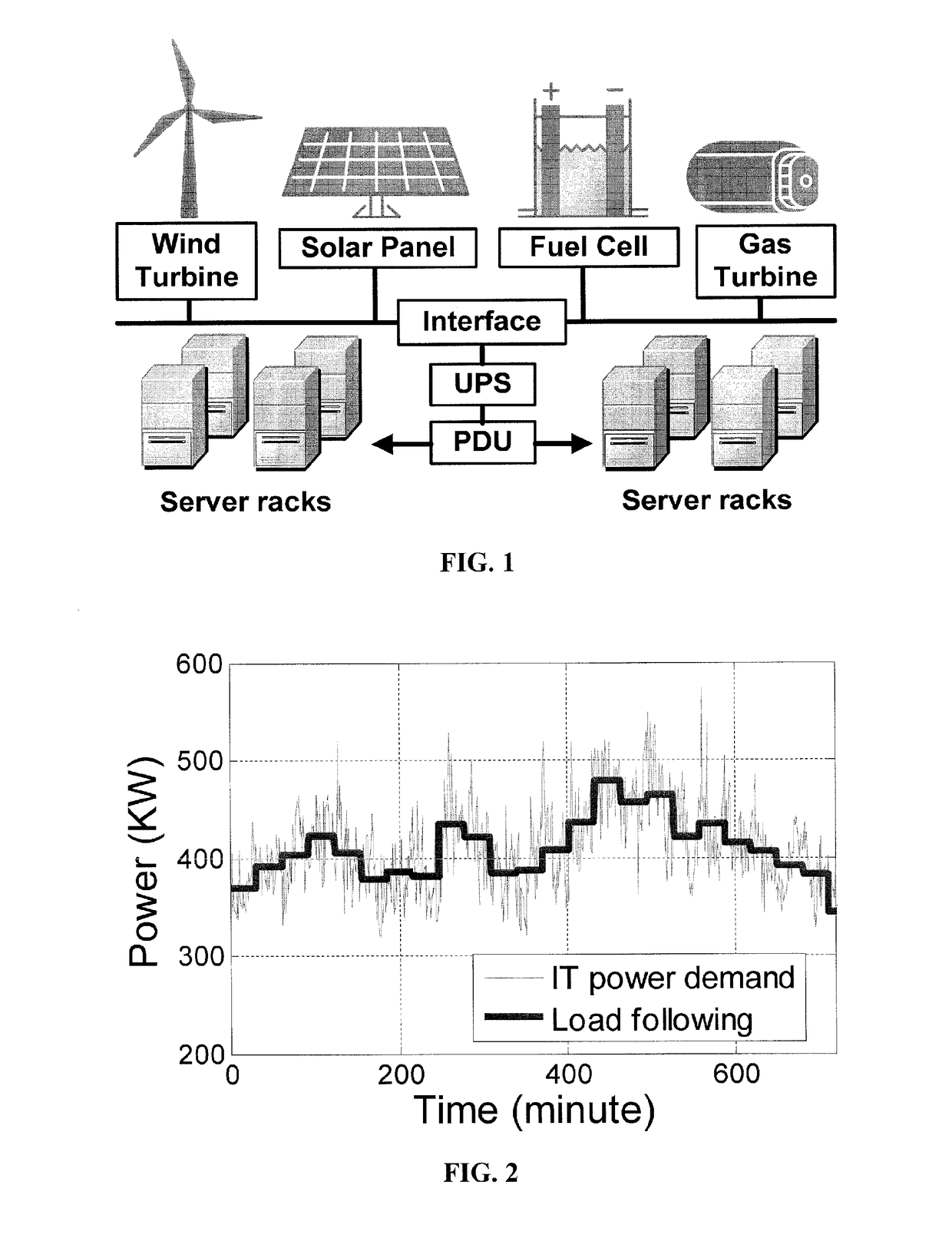
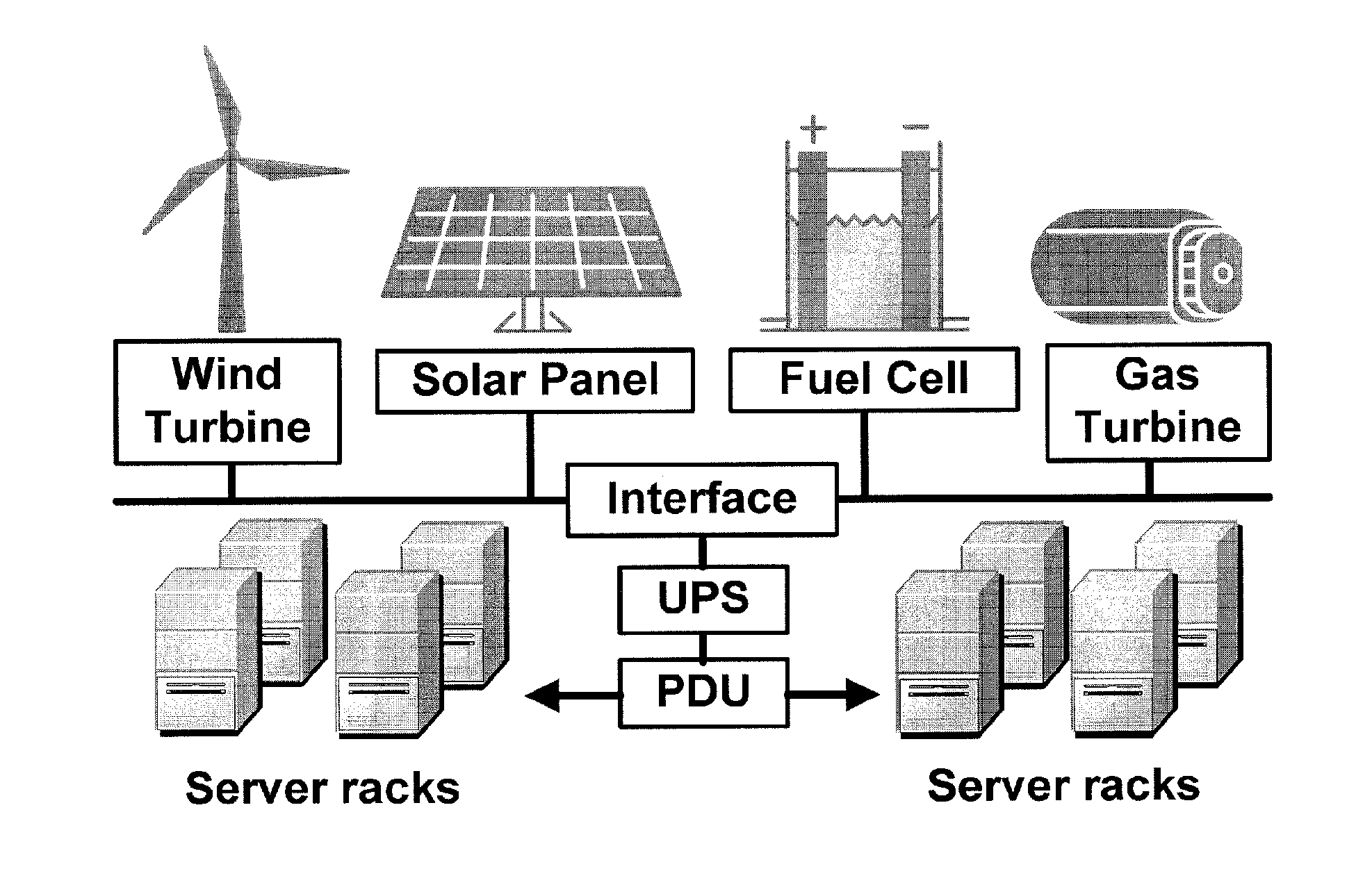
Method and apparatus for power management using distributed generation
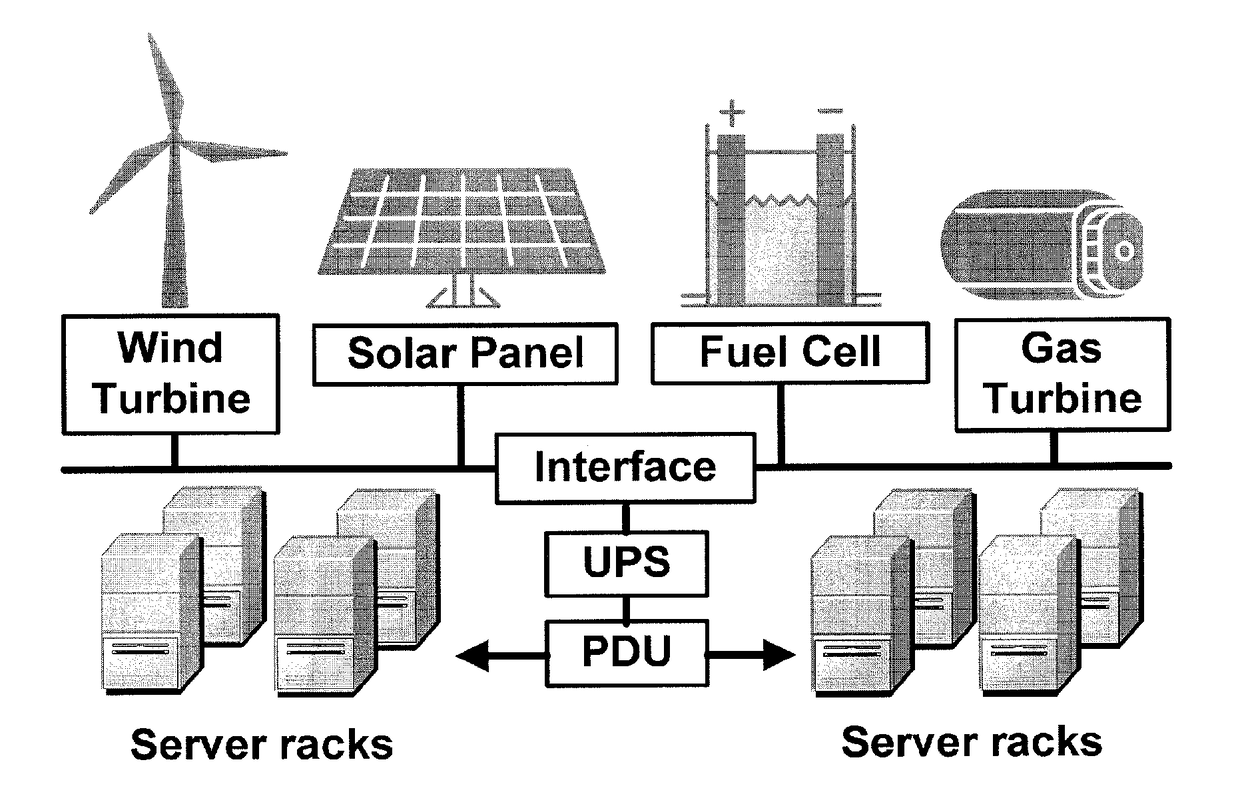
ActiveUS9800052B2Improve performanceReduce electricity loadGeneration forecast in ac networkSingle network parallel feeding arrangementsData centerEngineering
Embodiments relate to a method and system for power demand shaping (PDS) so as to manage power generation and use. Specific embodiments relate to data center power demand shaping to achieve high-performance low-overhead data center operation. Specific embodiments can incorporate standard (utility power) energy sources, renewable energy sources, or a combination of standard (utility power) energy sources and renewable energy sources. Embodiments of the subject PDS techniques can incorporate trimming the data center load power so as to allow DG systems to follow the power demand efficiently and / or incorporate two adaptive load tuning schemes that can boost data center performance and enable near-oracle operation during power demand trimming process. To implement a cross-layer power optimization scheme, embodiments of the subject invention relate to a power management module that can reside between front-end distributed generation and back-end computing facilities to provide a coordinated tuning between the supply and load.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
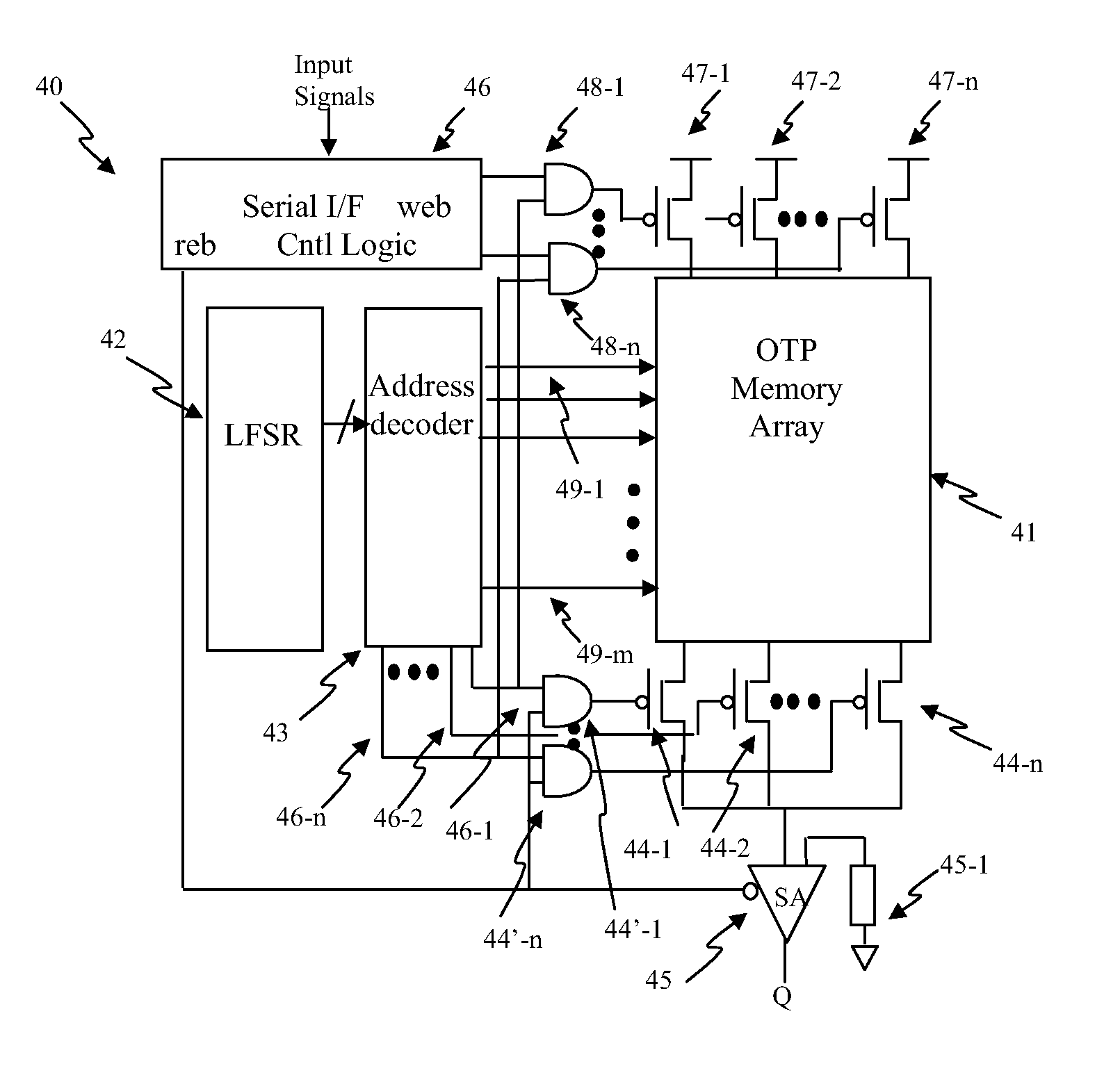
Circuit and System of a Low Density One-Time Programmable Memory
InactiveUS20130201745A1Low density OTPsReduce memory sizeElectric analogue storesRead-only memoriesAddress generatorHemt circuits
A low density One-Time Programmable (OTP) memory is disclosed to achieve low gate count and low overhead in the peripheral circuits to save the cost. A maximum-length Linear Feedback Shift Register (LFSR) can be used to generate 2n−1 address spaces from an n-bit address. The registers used in the address generator can have two latches. Each latch has two cross-coupled inverters with two outputs coupled to the drains of two MOS input devices, respectively. The inputs of the latch are coupled to the gates of the MOS input devices, respectively. The sources of the MOS input devices are coupled to the drains of at least one MOS device(s), whose gate(s) are coupled to a clock signal and whose source(s) are coupled to a supply voltage. The two latches can be constructed in serial with the outputs of the first latch coupled to the inputs of the second latch.
Owner:ATTOPSEMI TECH CO LTD
Cloud money-based hierarchical cloud computing system excitation method
InactiveCN101719930ARealize distributed payment behaviorAvoid bottleneck nodesMultiprogramming arrangementsTransmissionPaymentHigh effectiveness
In order to improve the running stability of a system, an excitation mechanism is necessary to facilitate a terminal node to stably and truthfully contribute resources and perform teamwork, namely, the node is facilitated to flow from an unreliable end node layer to a reliable end node layer. The invention discloses a cloud money-based hierarchical cloud computing system excitation method. In the method, the principles of simplicity, high efficiency, low overhead and easy implementation are taken as main ideas; the train of thought of remuneration according to work in the human society is borrowed; and a cloud money-based reliable end node excitation mechanism is disclosed, which excites the node to actively provide services by adopting virtual money named as cloud money. Therefore, distributed payment in a cloud computing environment is realized, the end node can more stably and truthfully provide personal resources to finish assigned tasks, the function of the end node in an outer cloud layer is maximally developed and the system is finally optimized.
Owner:NANJING UNIV OF POSTS & TELECOMM
Efficient genomic read alignment in an in-memory database
ActiveUS20140214334A1Great processing timeConvenient timeData visualisationBiological testingIn-memory databaseAlgorithm
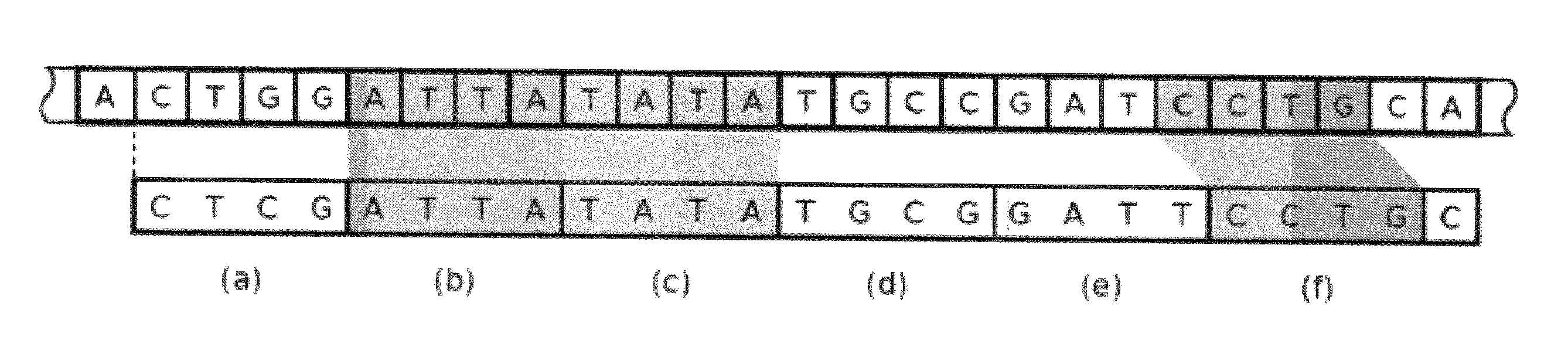
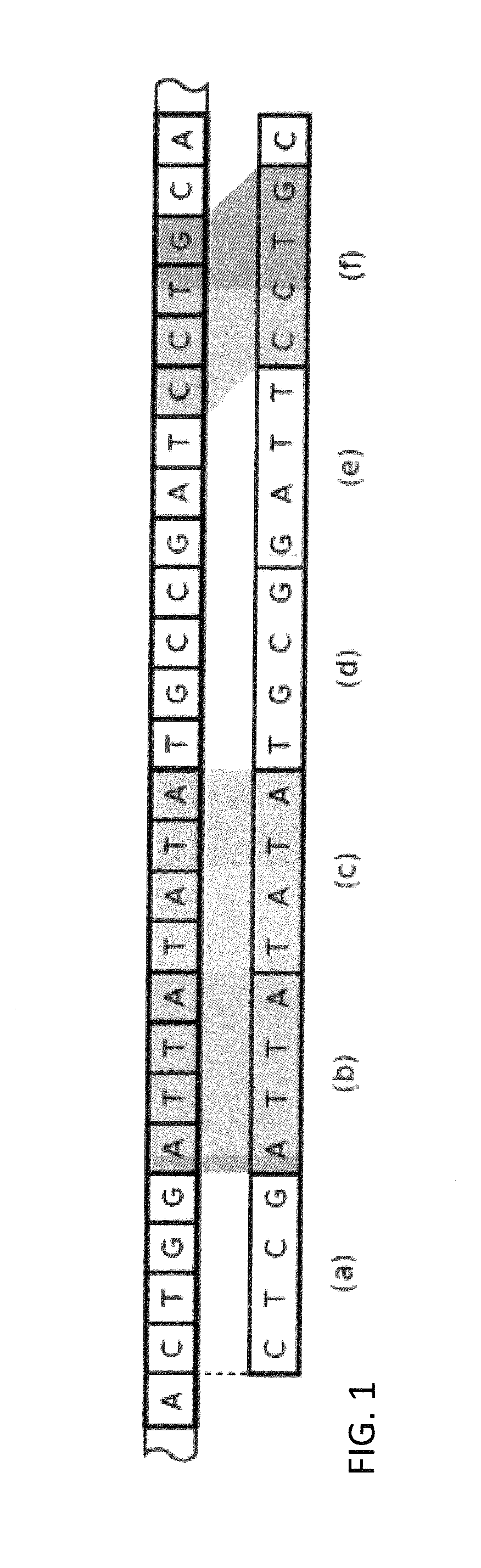
A high performance, low-cost, gapped read alignment algorithm is disclosed that produces high quality alignments of a complete human genome in a few minutes. Additionally, the algorithm is more than an order of magnitude faster than previous approaches using a low-cost workstation. The results are obtained via careful algorithm engineering of the seeding based approach. The use of non-hashed seeds in combination with techniques from search engine ranking achieves fast cache-efficient processing. The algorithm can also be efficiently parallelized. Integration into an in-memory database infrastructure (IMDB) leads to low overhead for data management and further analysis.
Owner:HASSO PLATTNER INSTITUT FUR SOFTWARESYSTTECHN
Enabling capture, transmission and reconstruction of relative causitive contextural history for resource-constrained stream computing applications
InactiveUS20110238379A1Guaranteed normal transmissionEfficiently replayingDigital computer detailsTelemedicineData streamSystem usage
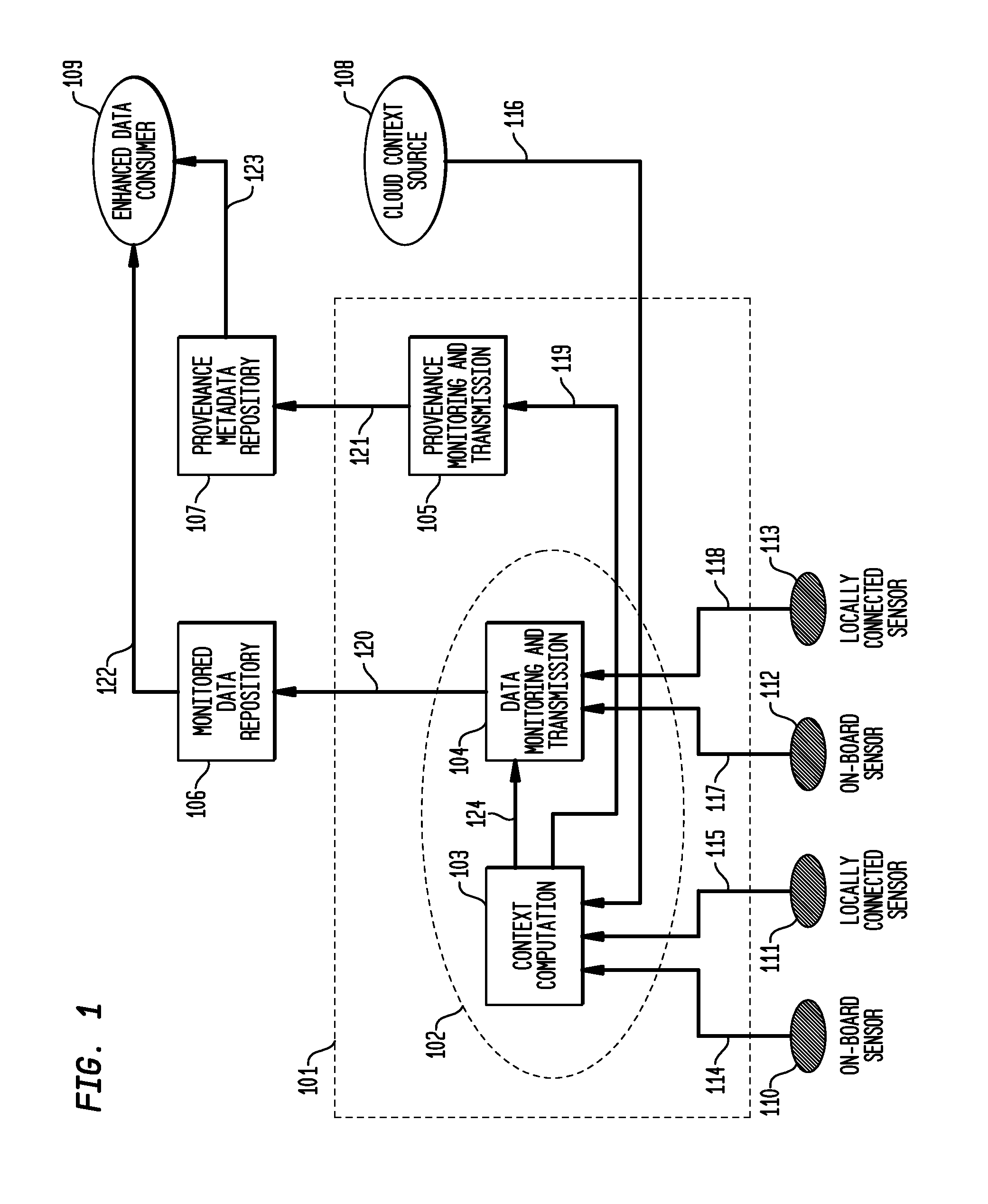
A scalable middleware for supporting energy-efficient, long-term remote health monitoring and the capture and transmission of relative causative contextual history where data is collected using physiological sensors and transported back to the middleware through a mobile device serving as a gateway. The key to energy efficient operations lies in the adoption of an Activity Triggered Deep Monitoring paradigm, where data collection episodes are triggered only when the system is determined to possess a specified set of causative contexts. The system supports on-demand collection of causative contextual history using a low-overhead provenance collection sub-system. In a preferred embodiment the behavior of this sub-system is configured using an application-defined context composition graph. The resulting causative context history stream provides valuable insight into the states and conditions surround sensor readings and allows improved human interpretation of the ‘episodic’ sensor data streams.
Owner:TELCORDIA TECHNOLOGIES INC
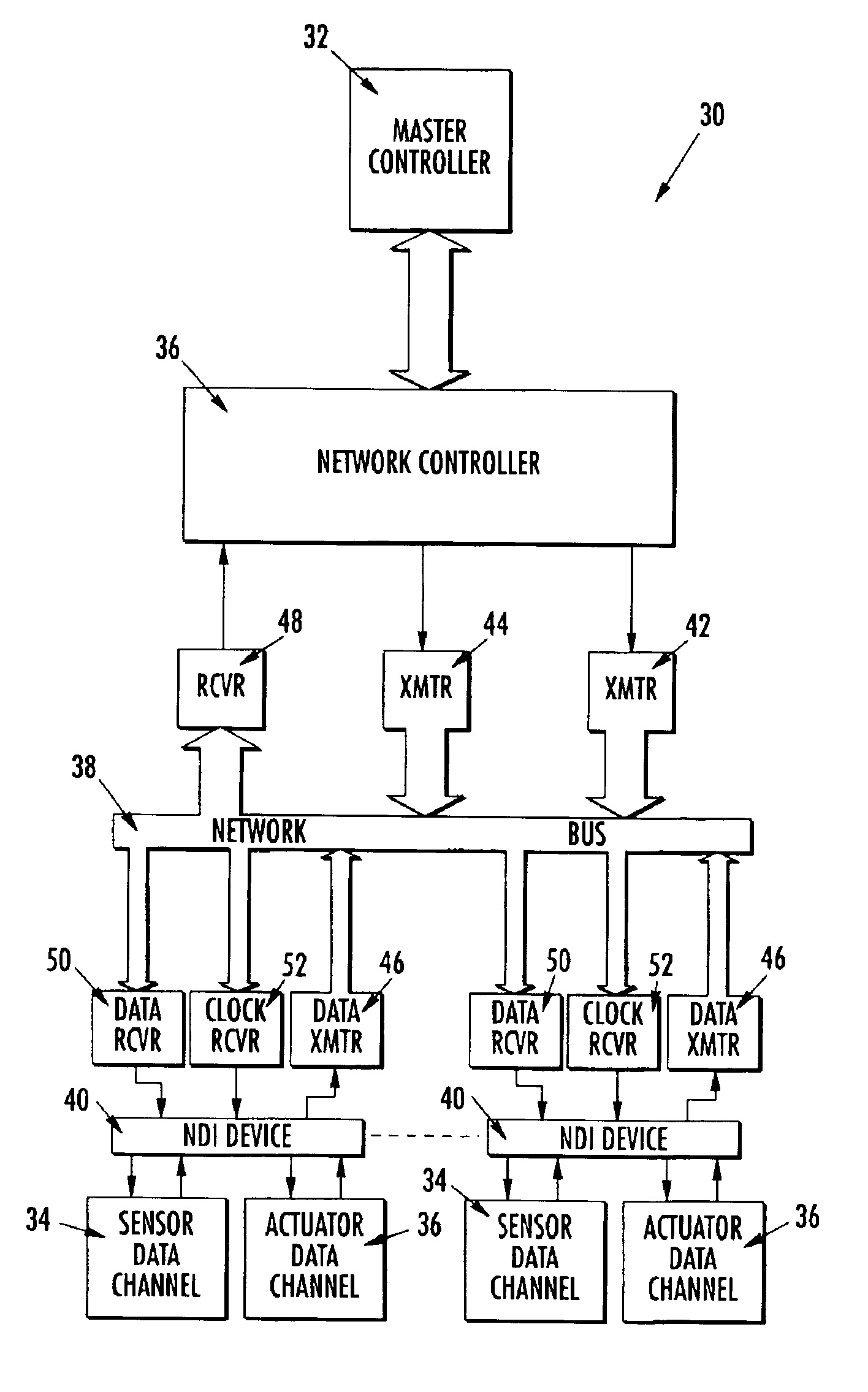
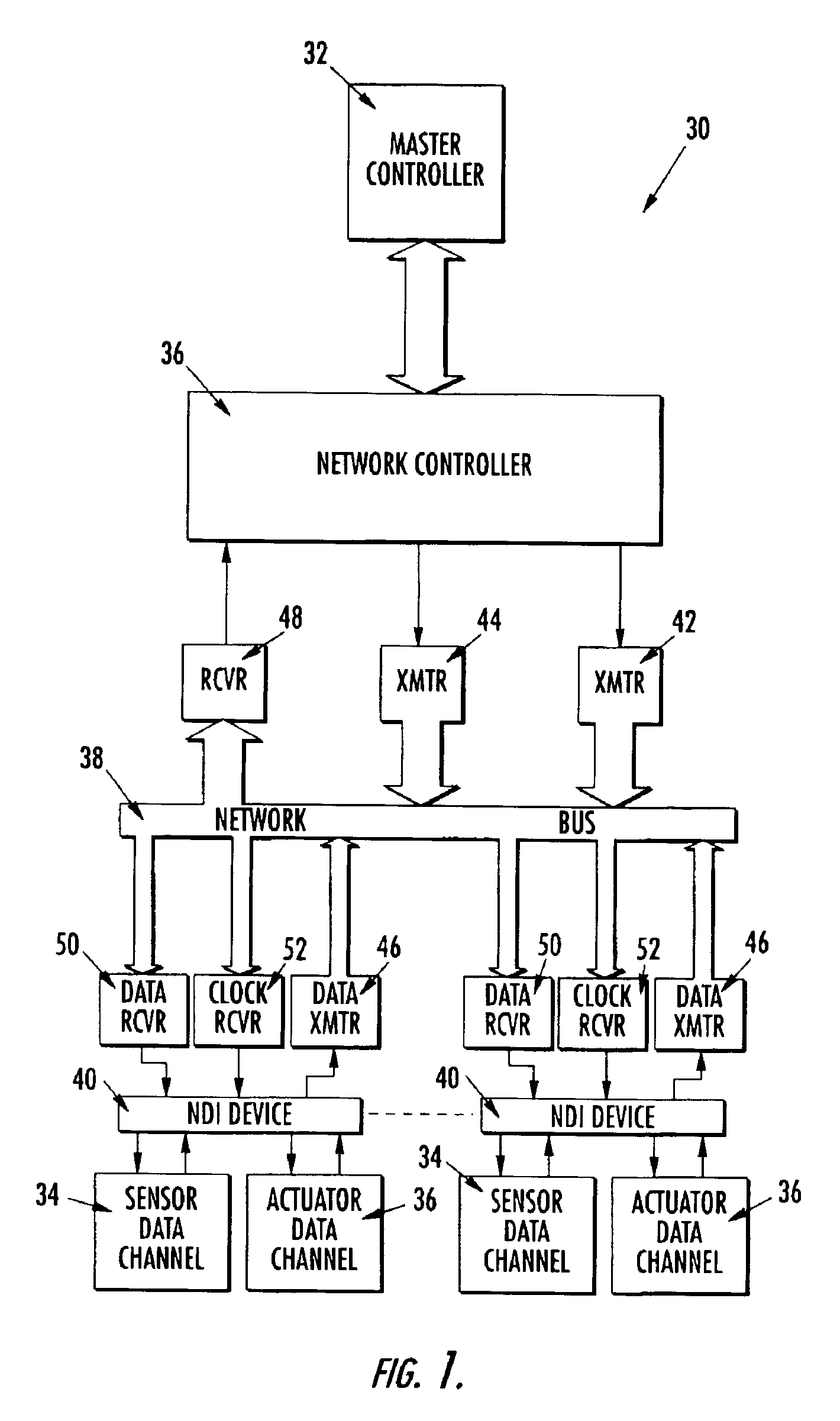
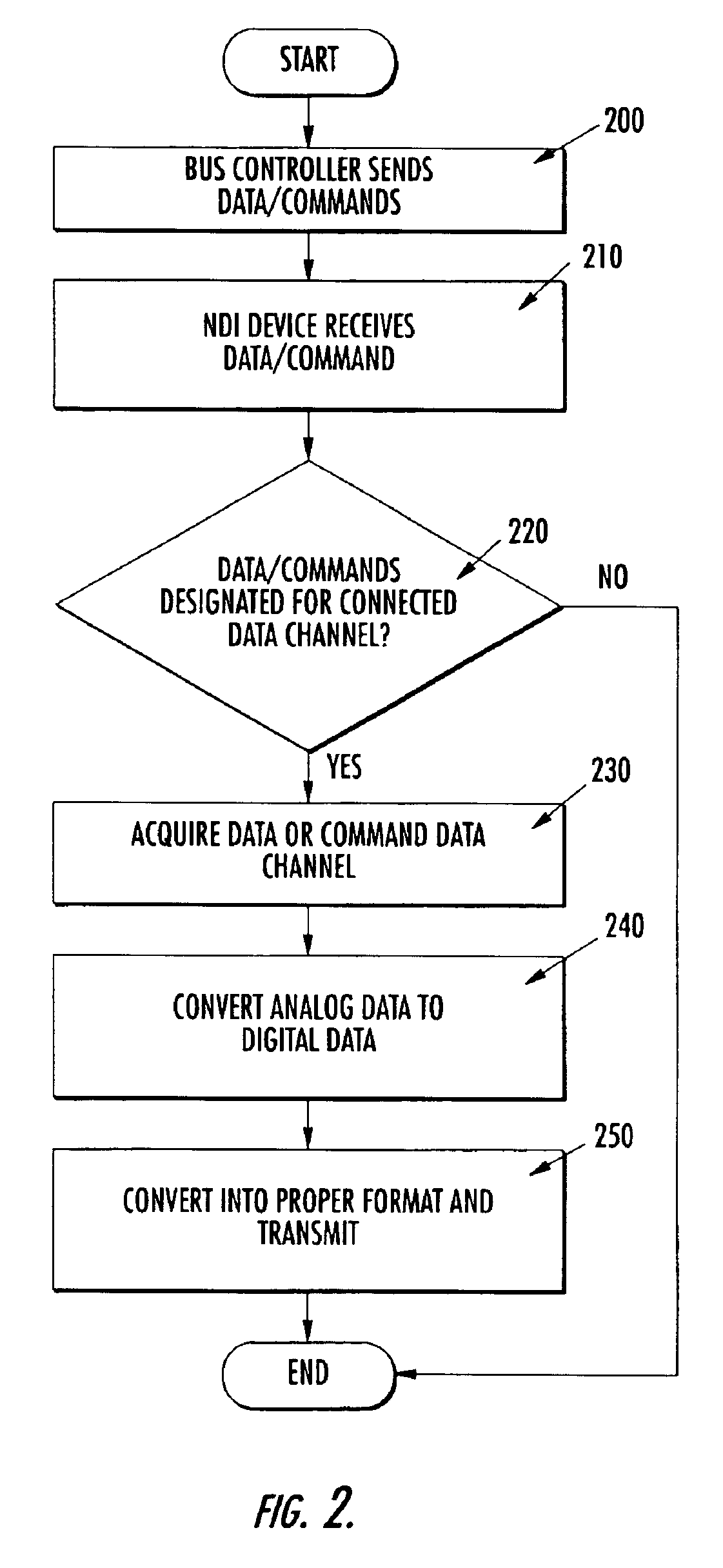
Network device interface for digitally interfacing data channels to a controller via a network
InactiveUS6938106B2Easy extractionLarge deviationGeneral purpose stored program computerSynchronisation signal speed/phase controlActuatorDigital signal
The present invention provides a network device interface and method for digitally connecting a plurality of data channels, such as sensors, actuators, and subsystems, to a controller using a network bus. The network device interface interprets commands and data received from the controller and polls the data channels in accordance with these commands. Specifically, the network device interface receives digital commands and data from the controller, and based on these commands and data, communicates with the data channels to either retrieve data in the case of a sensor or send data to activate an actuator. Data retrieved from the sensor is then converted by the network device interface into digital signals and transmitted back to the controller. In one advantageous embodiment, the network device interface uses a specialized protocol for communicating across the network bus that uses a low-level instruction set and has low overhead for data communication.
Owner:THE BOEING CO
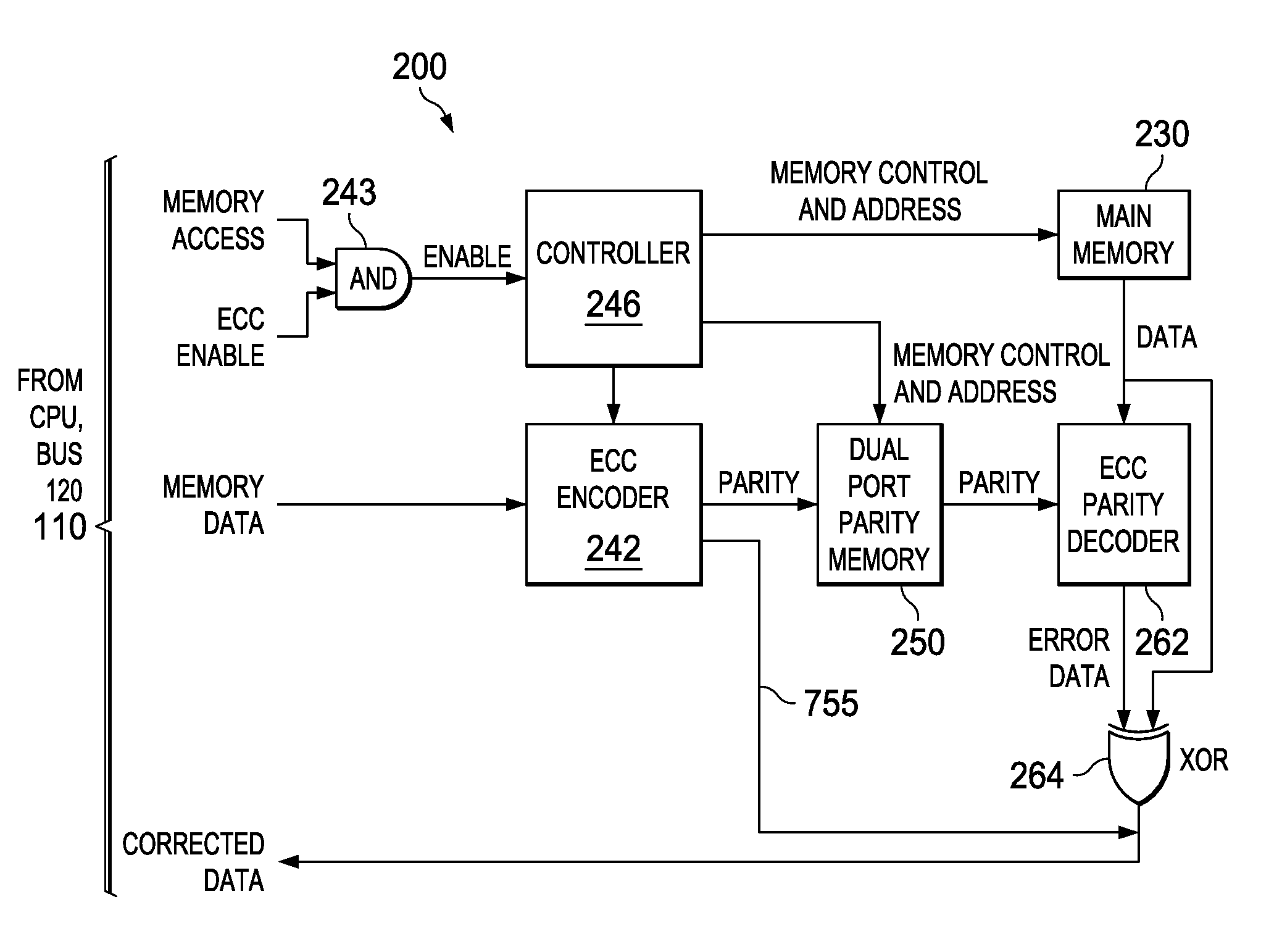
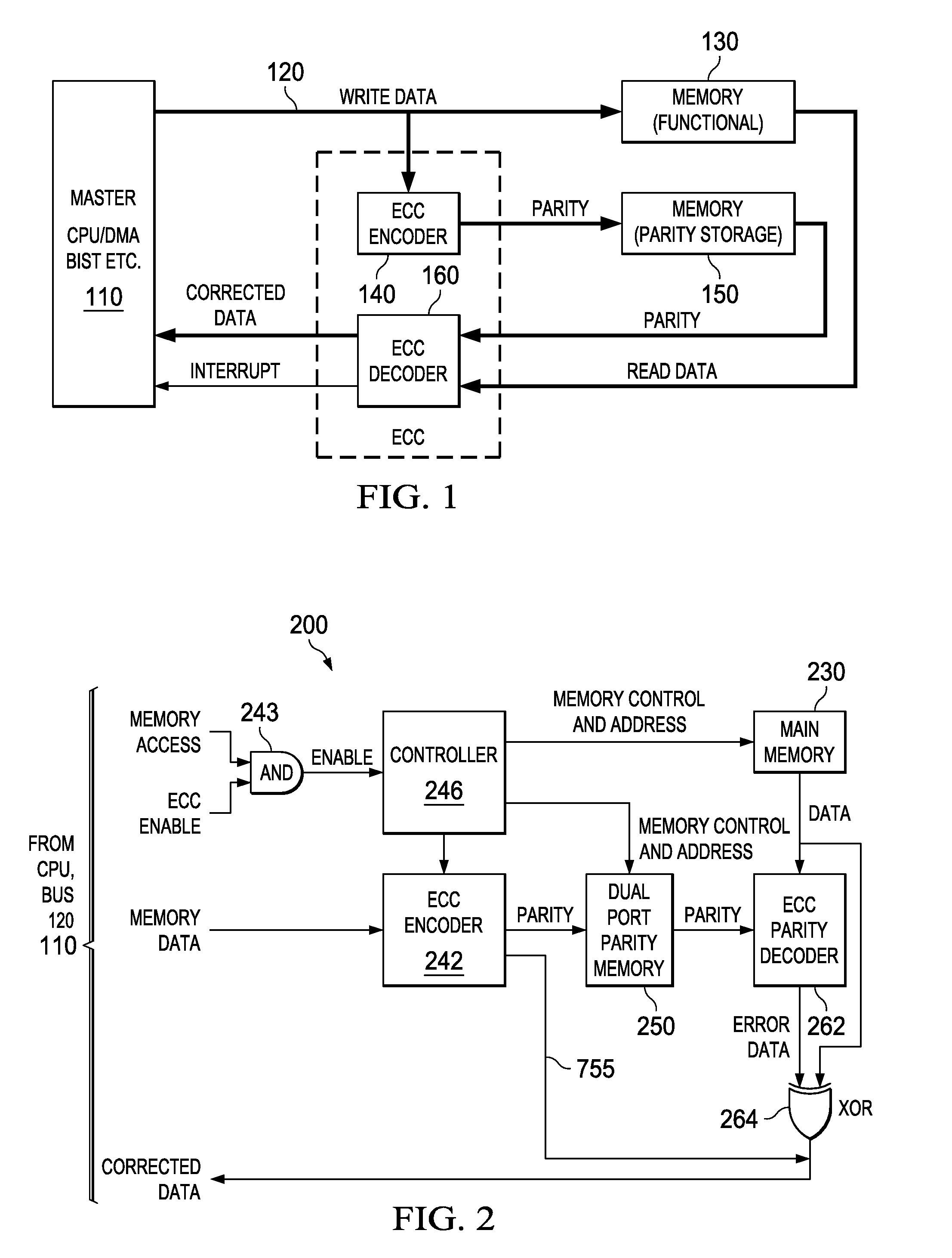
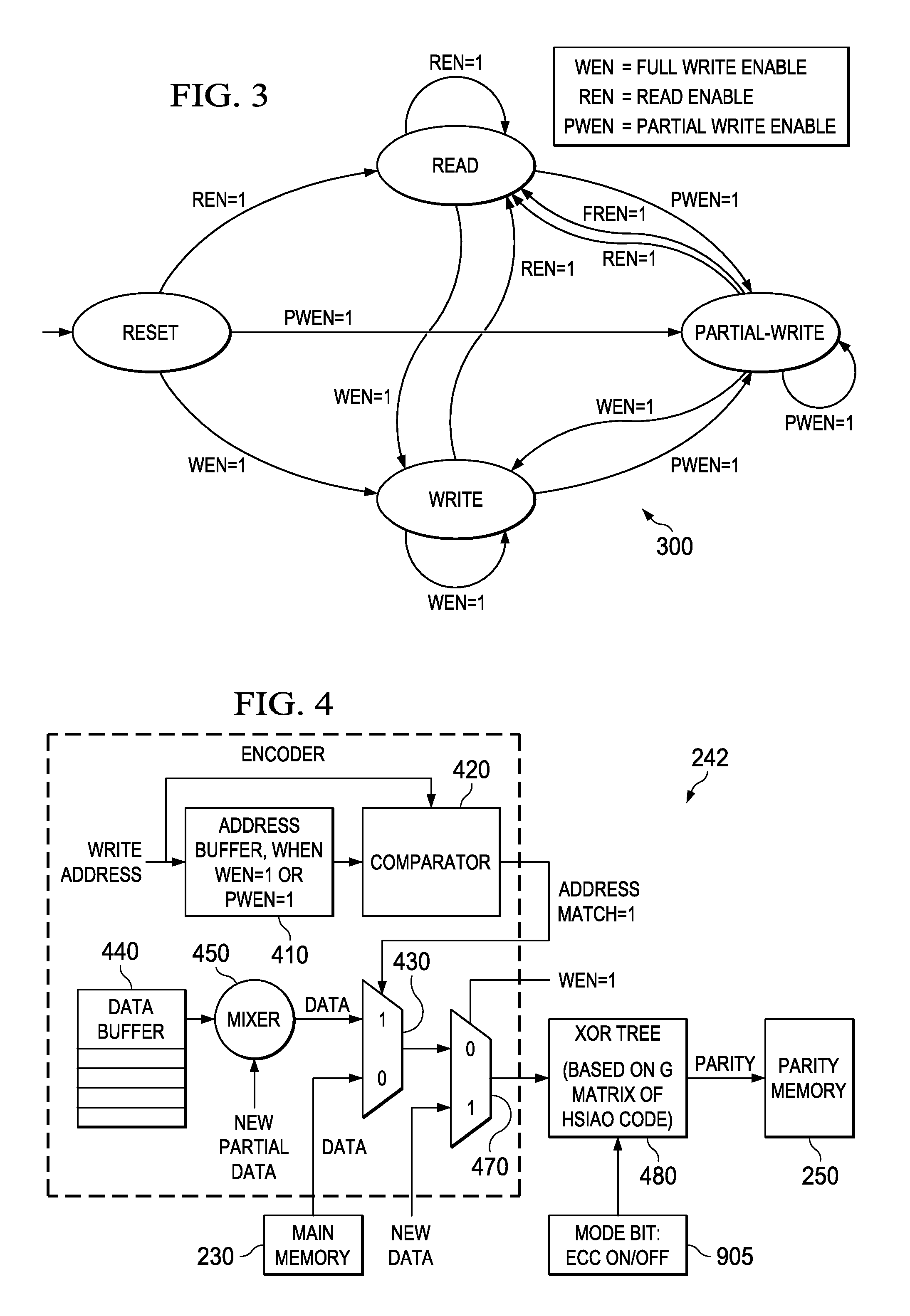
Low overhead and timing improved architecture for performing error checking and correction for memories and buses in system-on-chips, and other circuits, systems and processes
An electronic circuit (200) for use with an accessing circuit (110) that supplies a given address and a partial write data portion and also has dummy cycles. The electronic circuit (200) includes a memory circuit (230) accessible at addresses, an address buffer (410), a data buffer (440) coupled to the memory circuit (230), and a control circuit (246) operable in the dummy cycles to read data from the memory circuit (230) to the data buffer (440) from a next address location in the memory circuit (230) and to store that next address in the address buffer (410). The electronic circuit further includes a multiplexer (430), a comparing circuit (420) responsive to the given address and a stored address in the address buffer (410), to operate the multiplexer (430) to pass data from the data buffer (440) or to pass data from the memory circuit (230) instead; and a mixer circuit (450) operable to put the partial write data portion into the data taken from the selected one of the data buffer (440) or memory circuit (230). Other circuits, devices, systems, processes of operation and processes of manufacture are also disclosed.
Owner:TEXAS INSTR INC
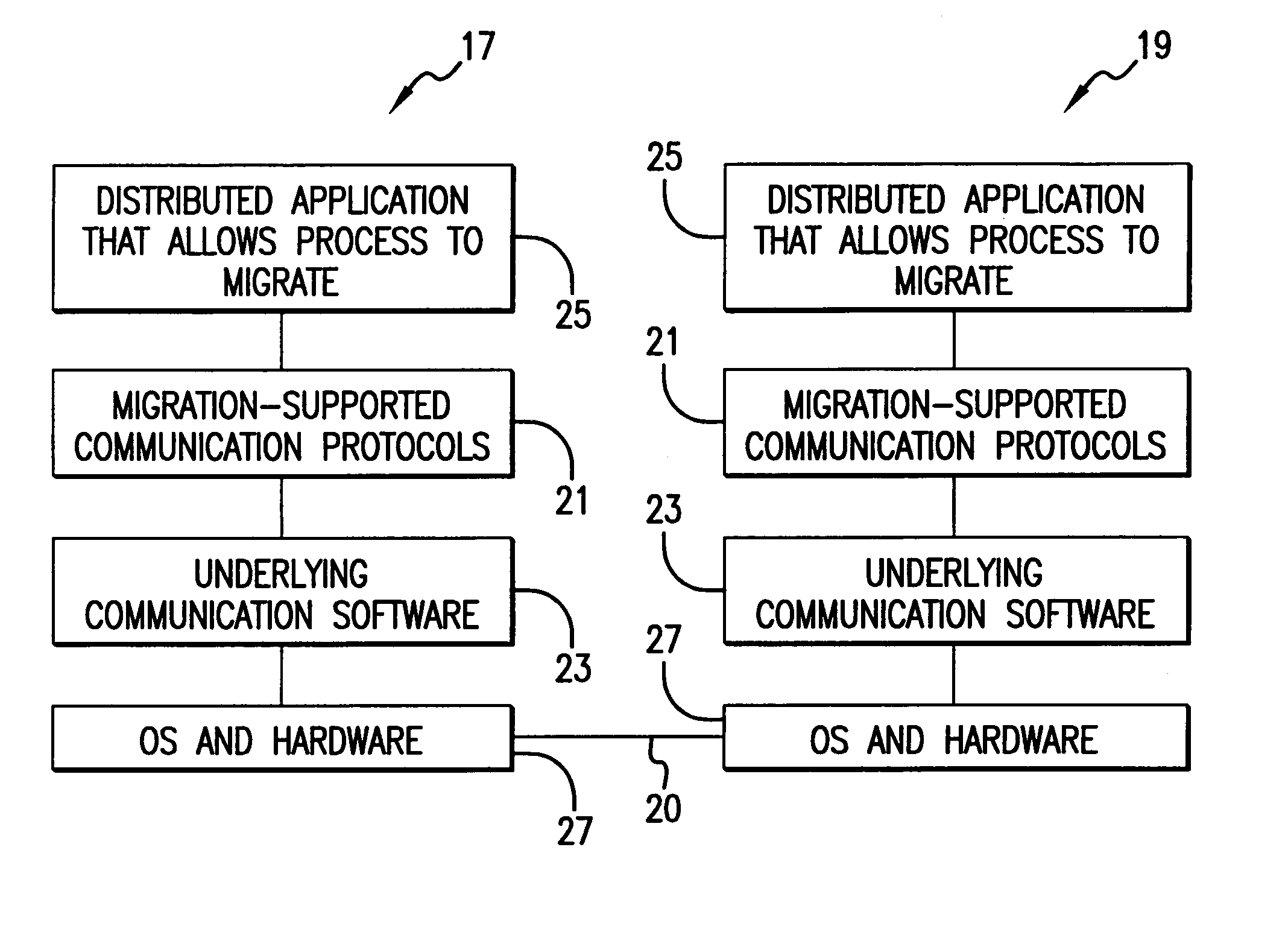
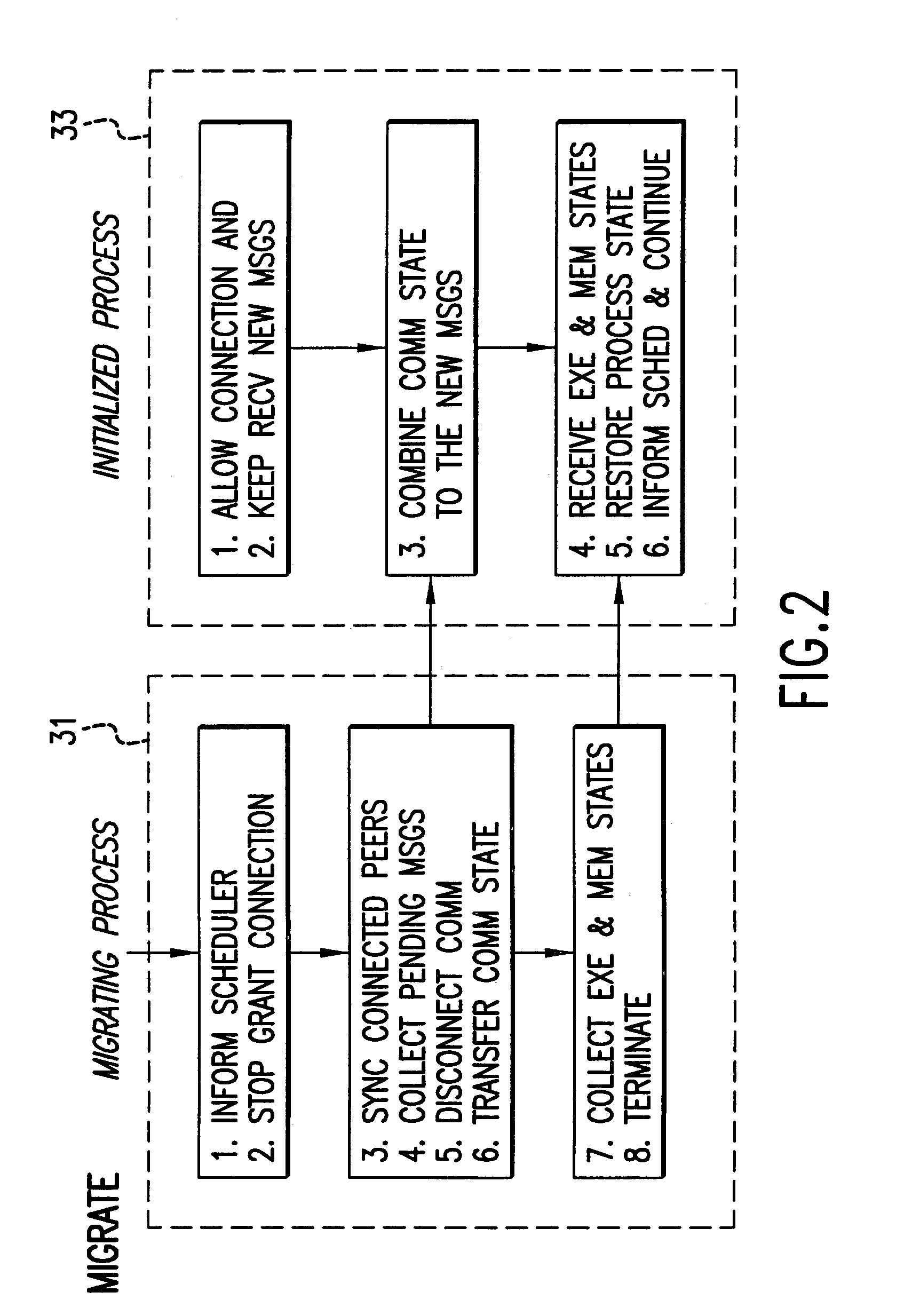
Communication and process migration protocols for distributed heterogeneous computing
ActiveUS7065549B2Effective supportSmall communication overheadMultiprogramming arrangementsMultiple digital computer combinationsTraffic capacityHigh effectiveness
Communication and Process Migration Protocols instituted in an independent layer of a virtual machine environment allow for heterogeneous or homogeneous process migration. The protocols manage message traffic for processes communicating in the virtual machine environment. The protocols manage message traffic for migrating processes so that no message traffic is lost during migration, and proper message order is maintained for the migrating process. In addition to correctness of migration operations, low overhead and high efficiency is achieved for supporting scalable, point-to-point communications.
Owner:ILLINOIS INSTITUTE OF TECHNOLOGY
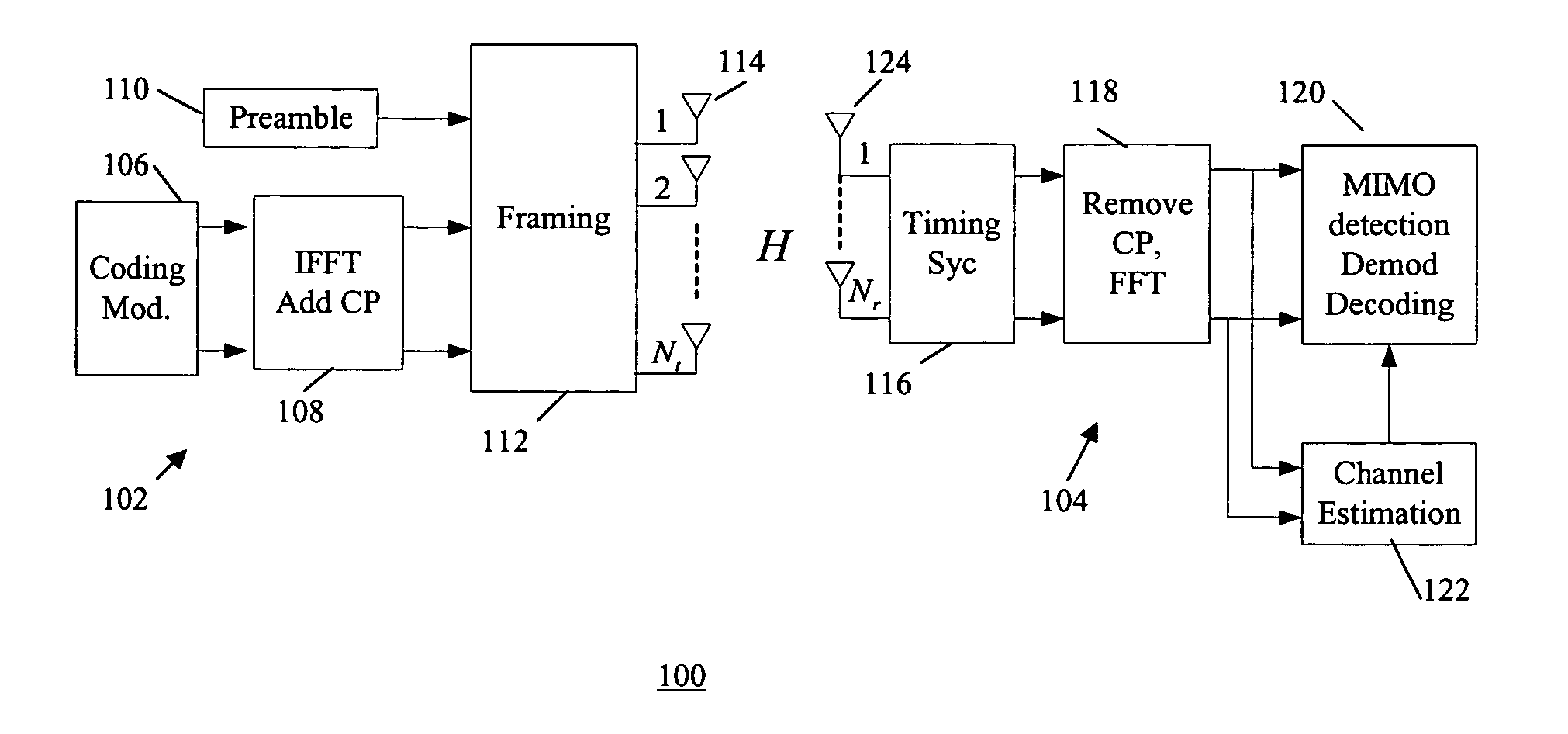
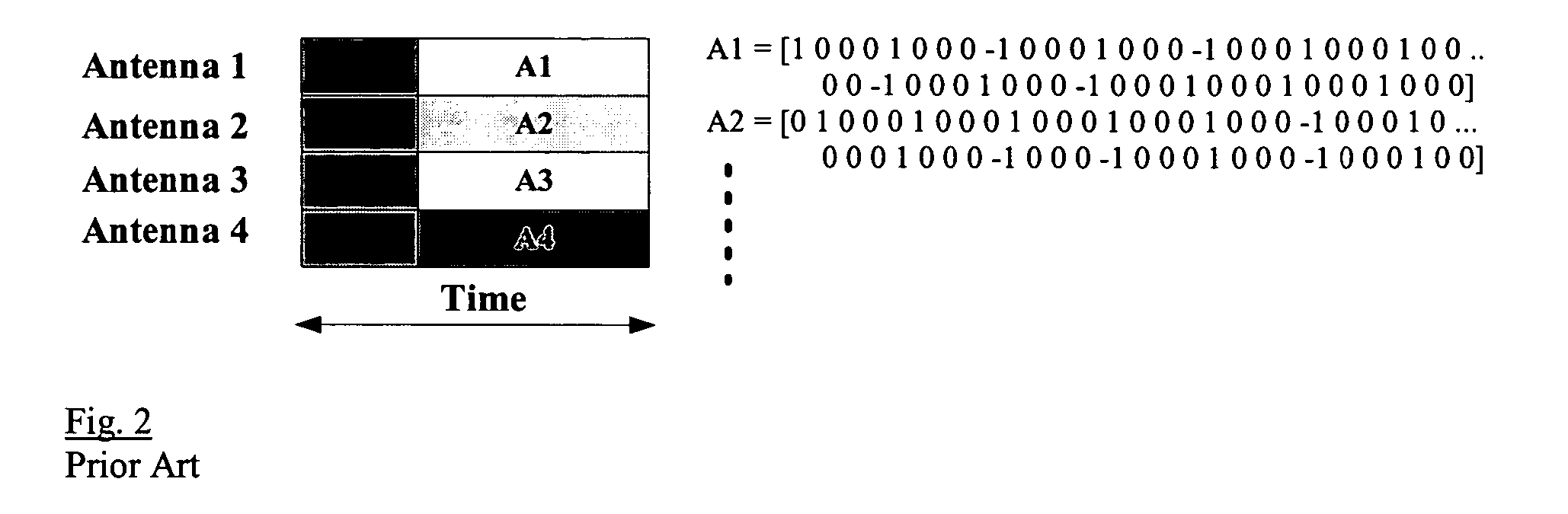
Method of channel estimation for MIMO-OFDM using phase rotated low overhead preamble
InactiveUS20060227891A1Simple scalabilityReduce overheadModulated-carrier systemsDiversity/multi-antenna systemsEngineeringMIMO-OFDM
A low overhead long preamble and the corresponding channel estimator for MIMO-OFDM systems that are backward compatible with current 802.11a systems. The preamble has a first training sequence and a second training sequence, wherein the second training sequence is a phase rotation of the first training sequence. The first training sequence comprises a 802.11a training sequence. The preamble can further include multiple training sequences, wherein each training sequence is a different phase rotation of the first training sequence.
Owner:SAMSUNG ELECTRONICS CO LTD
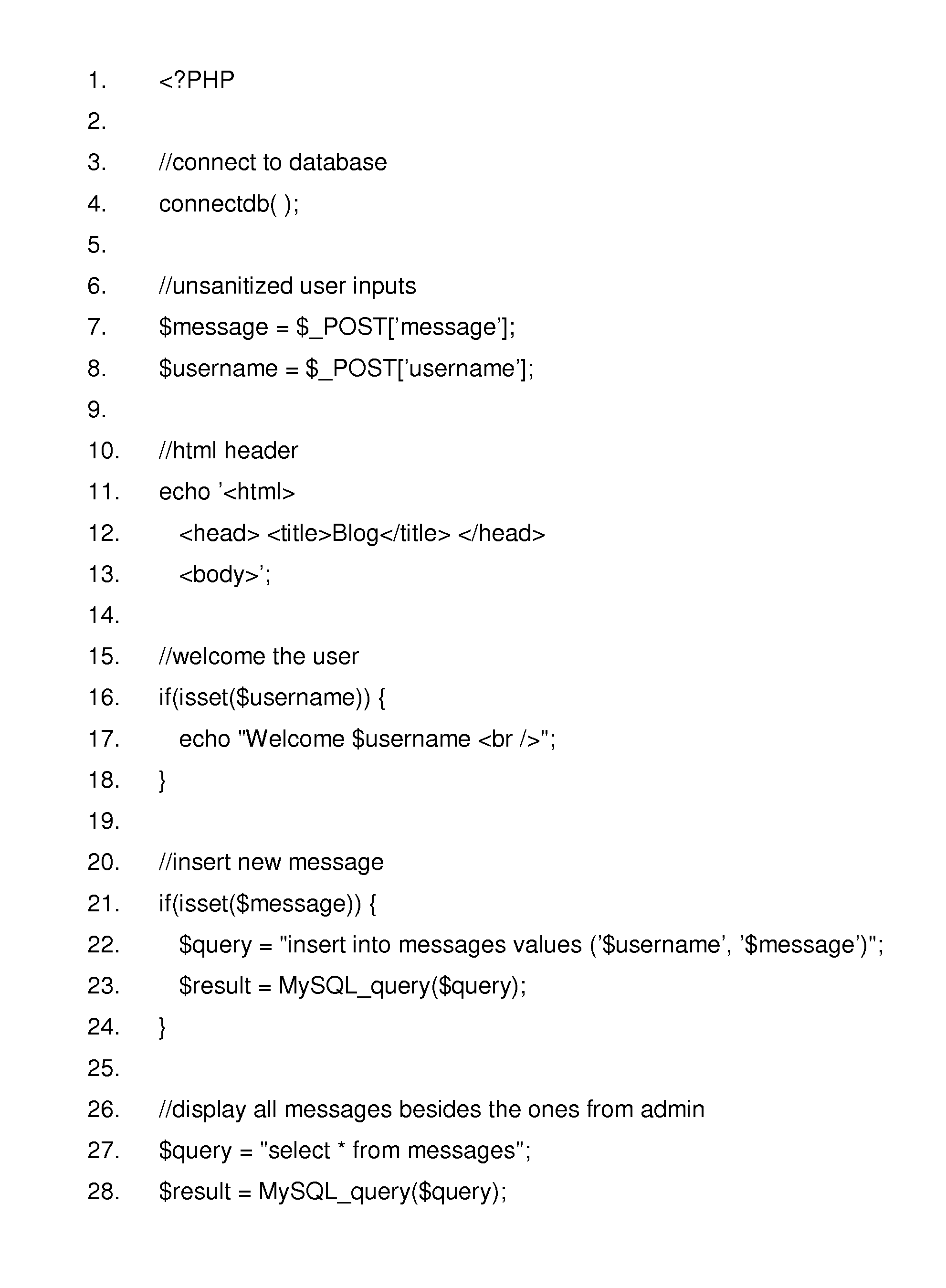
Complementary Character Encoding for Preventing Input Injection in Web Applications
InactiveUS20110252475A1Reduce overheadPreventing executionMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
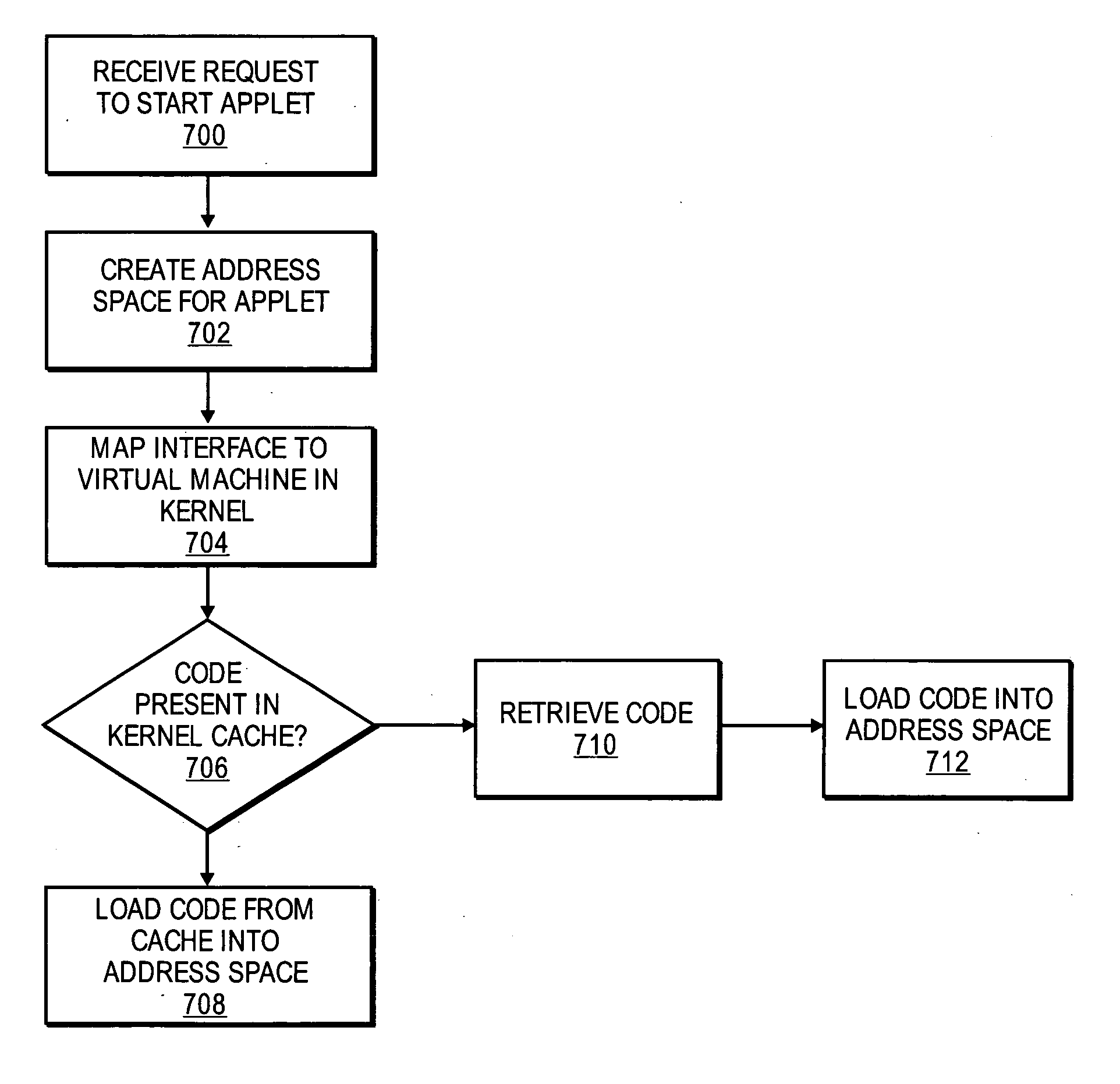
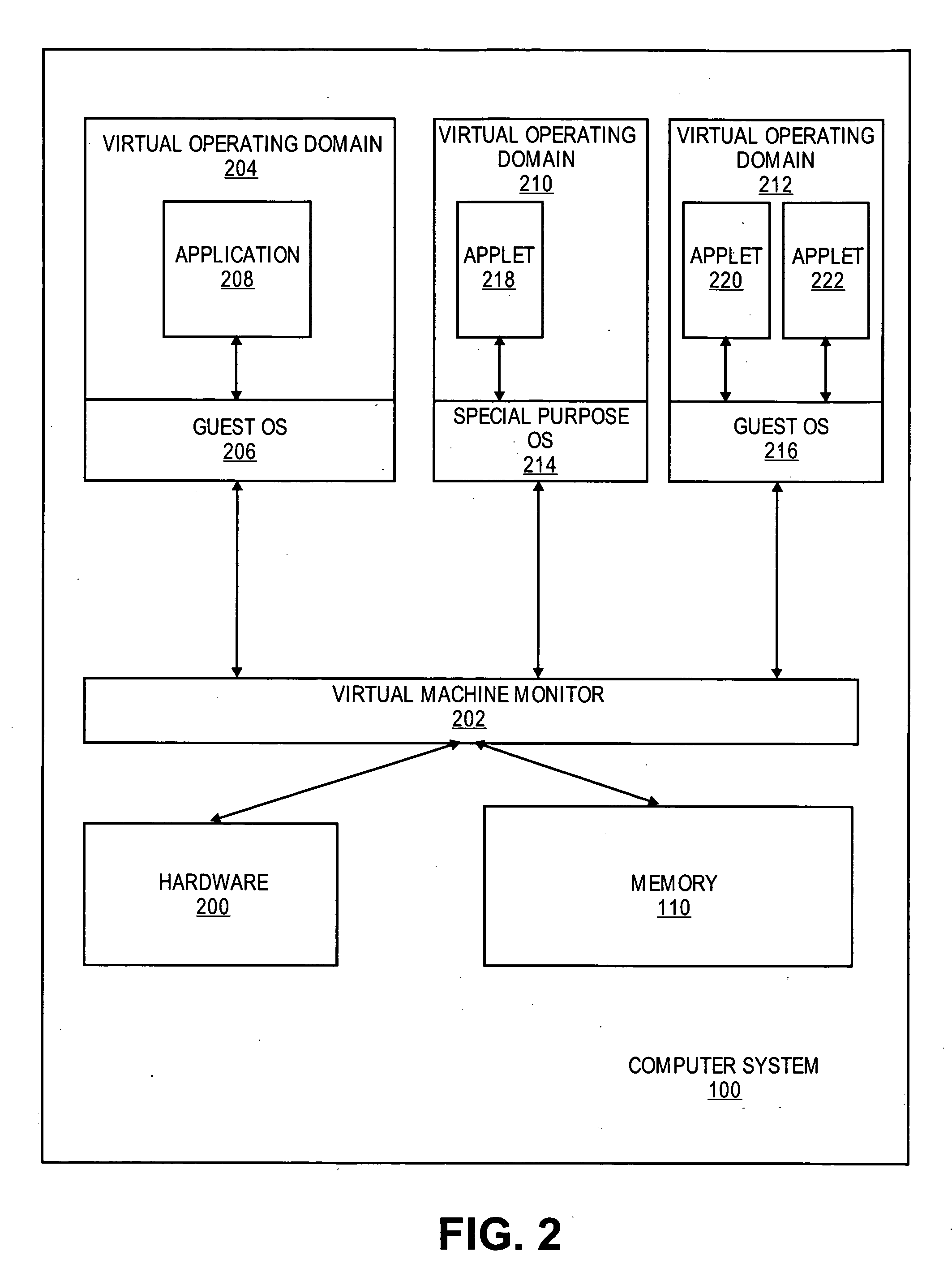
Purpose domain for in-kernel virtual machine for low overhead startup and low resource usage
ActiveUS20070169024A1Software simulation/interpretation/emulationMemory systemsOperational systemAnalog computer
Embodiments of the present invention provide an architecture for securely and efficiently executing byte code generated from a general programming language. In particular, a computer system is divided into a hierarchy comprising multiple types of virtual machines. A thin layer of software, known as a virtual machine monitor, virtualizes the hardware of the computer system and emulates the hardware of the computer system to form a first type of virtual machine. This first type of virtual machine implements a virtual operating domain that allows running its own operating system. Within a virtual operating domain, a byte code interpreter may further implement a second type of virtual machine that executes byte code generated from a program written in a general purpose programming language. The byte code interpreter is incorporated into the operating system running in the virtual operating domain. The byte code interpreter implementing the virtual machine that executes byte code may be divided into a kernel component and one or more user level components. The kernel component of the virtual machine is integrated into the operating system kernel. The user level component provides support for execution of an applet and couples the applet to the operating system. In addition, an operating system running in a virtual operating domain may be configured as a special purpose operating system that is optimized for the functions of a particular byte code interpreter.
Owner:RED HAT
Synchronization of time in a mobile ad-hoc network
ActiveUS20120127977A1Reduce overheadEfficient communicationSynchronisation arrangementNetwork topologiesObservational errorSynchronous network
Methods and systems are disclosed herein for synchronizing network time in a mobile ad-hoc network (MANET). Each node in the MANET may be synchronized with all of its neighbors for effective communications. More specifically, a local timing reference may be adjusted according to measured errors in incoming control packets so that time slotted transmissions can be scheduled without collisions with other nodes. The method and system is a low overhead protocol that only requires a small amount of data attached to each scheduled transmission avoiding the requirement for separate messaging. This may reduce the overhead of maintaining the MANET providing additional efficiency and robustness.
Owner:POWERWAVE COGNITION INC
Method for monitoring heap for memory leaks
A low overhead method for identifying memory leaks is provided. The low overhead method includes a) detecting completion of a garbage collection cycle; and b) identifying a boundary between used objects in memory and free memory space. The steps of a) and b) are repeated and then it is determined if there is an existing memory leak based upon evaluation of boundary identifiers. A computer readable media and a system for identifying memory leaks for an object-oriented application are also provided.
Owner:ORACLE INT CORP
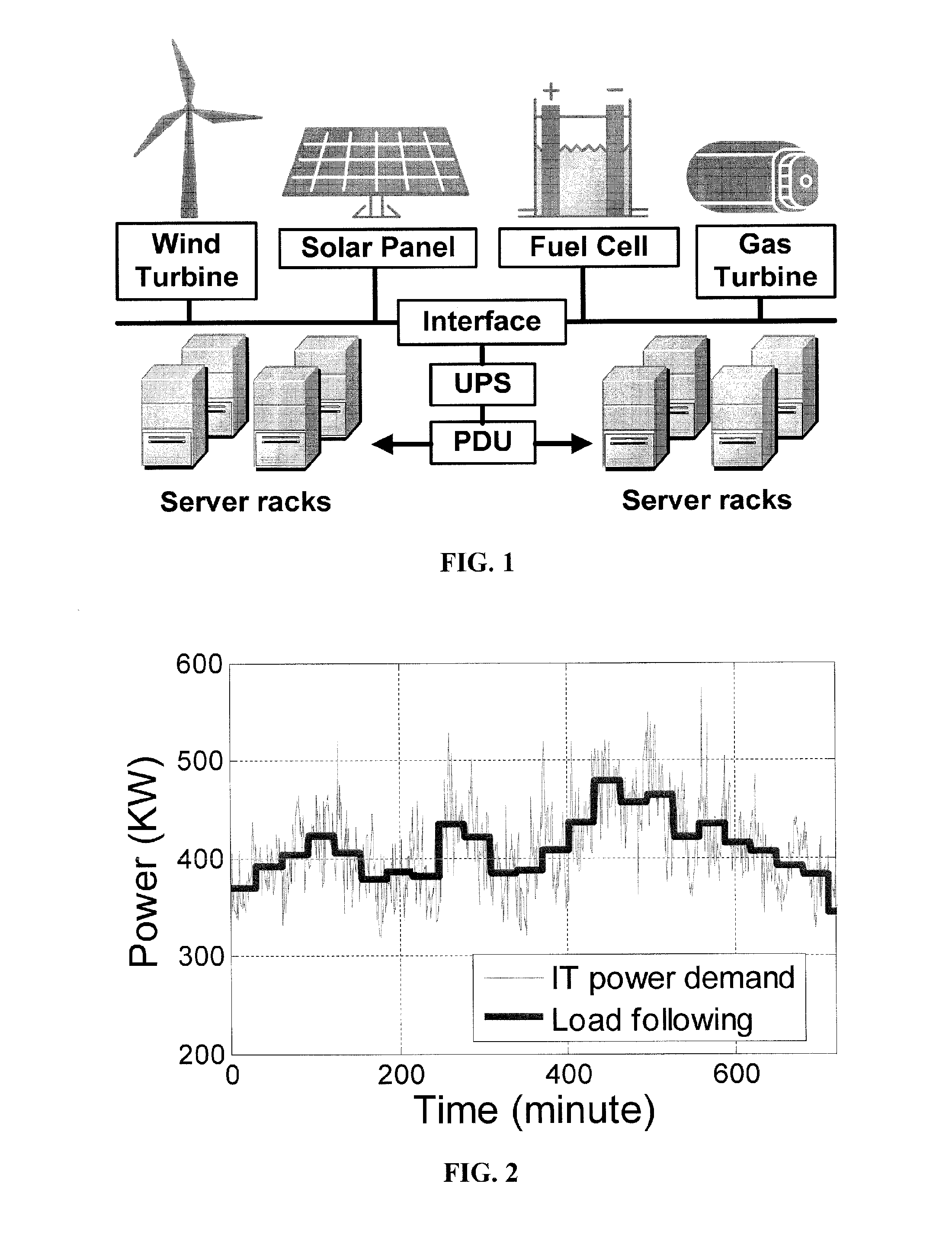
Method and apparatus for power management using distributed generation
ActiveUS20160013652A1Sufficient performanceImprove load following efficiencyGeneration forecast in ac networkSingle network parallel feeding arrangementsData centerEngineering
Embodiments relate to a method and system for power demand shaping (PDS) so as to manage power generation and use. Specific embodiments relate to data center power demand shaping to achieve high-performance low-overhead data center operation. Specific embodiments can incorporate standard (utility power) energy sources, renewable energy sources, or a combination of standard (utility power) energy sources and renewable energy sources. Embodiments of the subject PDS techniques can incorporate trimming the data center load power so as to allow DG systems to follow the power demand efficiently and / or incorporate two adaptive load tuning schemes that can boost data center performance and enable near-oracle operation during power demand trimming process. To implement a cross-layer power optimization scheme, embodiments of the subject invention relate to a power management module that can reside between front-end distributed generation and back-end computing facilities to provide a coordinated tuning between the supply and load.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Cluster fault-tolerance system, apparatus and method
InactiveCN101369241AGuaranteed to recover correctlyQuick checkError detection/correctionExtensibilityFault tolerance
The invention discloses a cluster fault tolerance system, a device and a method. The system includes: a remote checkpoint server which is used to respond the remote checkpoint request from a faulty node and execute the checkpoint operation; a node faulty checking module which is used to monitor the operating system of a local node and the running state of an assigned process and to trigger a remote checkpoint; and a communication system checkpoint module which is used to realize the checkpoint of the communication device and support the recovery function of communication breakpoint. The invention provides localized fast fault restoration for the parallel processing cluster, has a lower overhead and good expansibility, and makes ideal availability for the cluster system with ten billions and hundred billions calculation scale.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Circuit and system of a low density one-time programmable memory
InactiveUS8861249B2Low density OTPsReduce memory sizeElectric analogue storesRead-only memoriesIp addressAddress generator
A low density One-Time Programmable (OTP) memory is disclosed to achieve low gate count and low overhead in the peripheral circuits to save the cost. A maximum-length Linear Feedback Shift Register (LFSR) can be used to generate 2n−1 address spaces from an n-bit address. The registers used in the address generator can have two latches. Each latch has two cross-coupled inverters with two outputs coupled to the drains of two MOS input devices, respectively. The inputs of the latch are coupled to the gates of the MOS input devices, respectively. The sources of the MOS input devices are coupled to the drains of at least one MOS device(s), whose gate(s) are coupled to a clock signal and whose source(s) are coupled to a supply voltage. The two latches can be constructed in serial with the outputs of the first latch coupled to the inputs of the second latch.
Owner:ATTOPSEMI TECH CO LTD
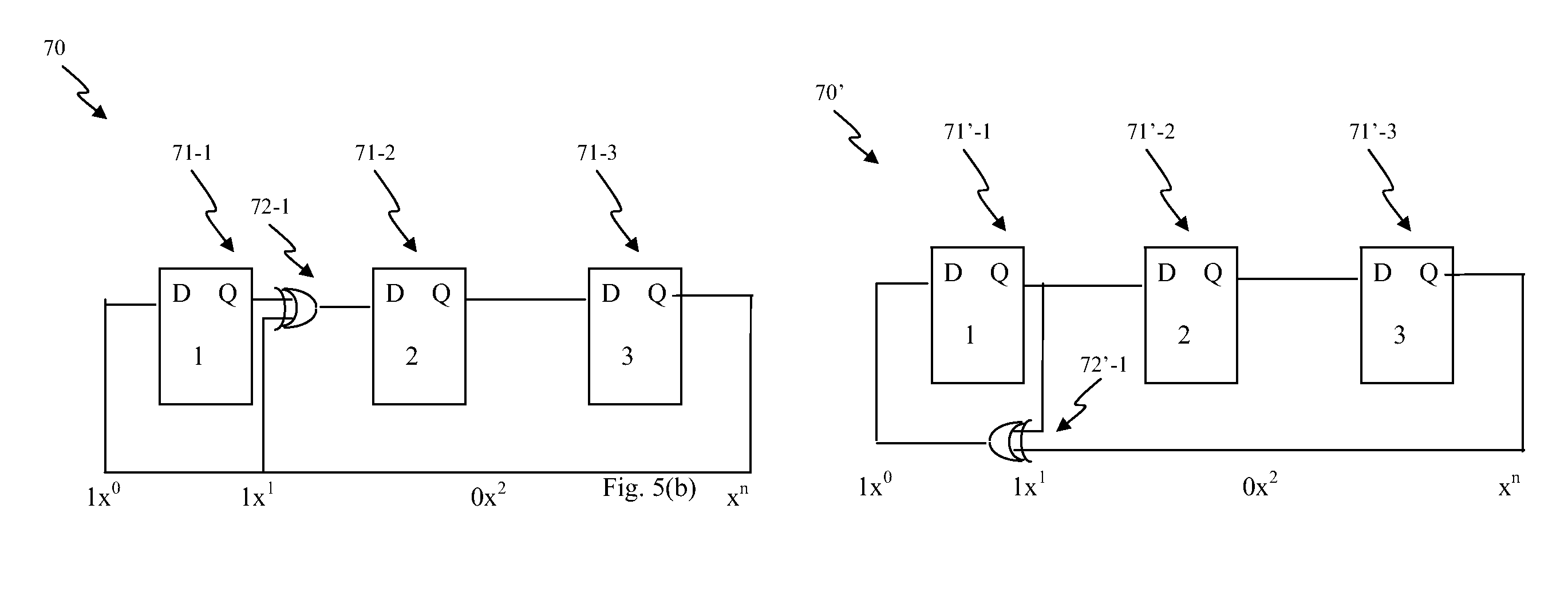
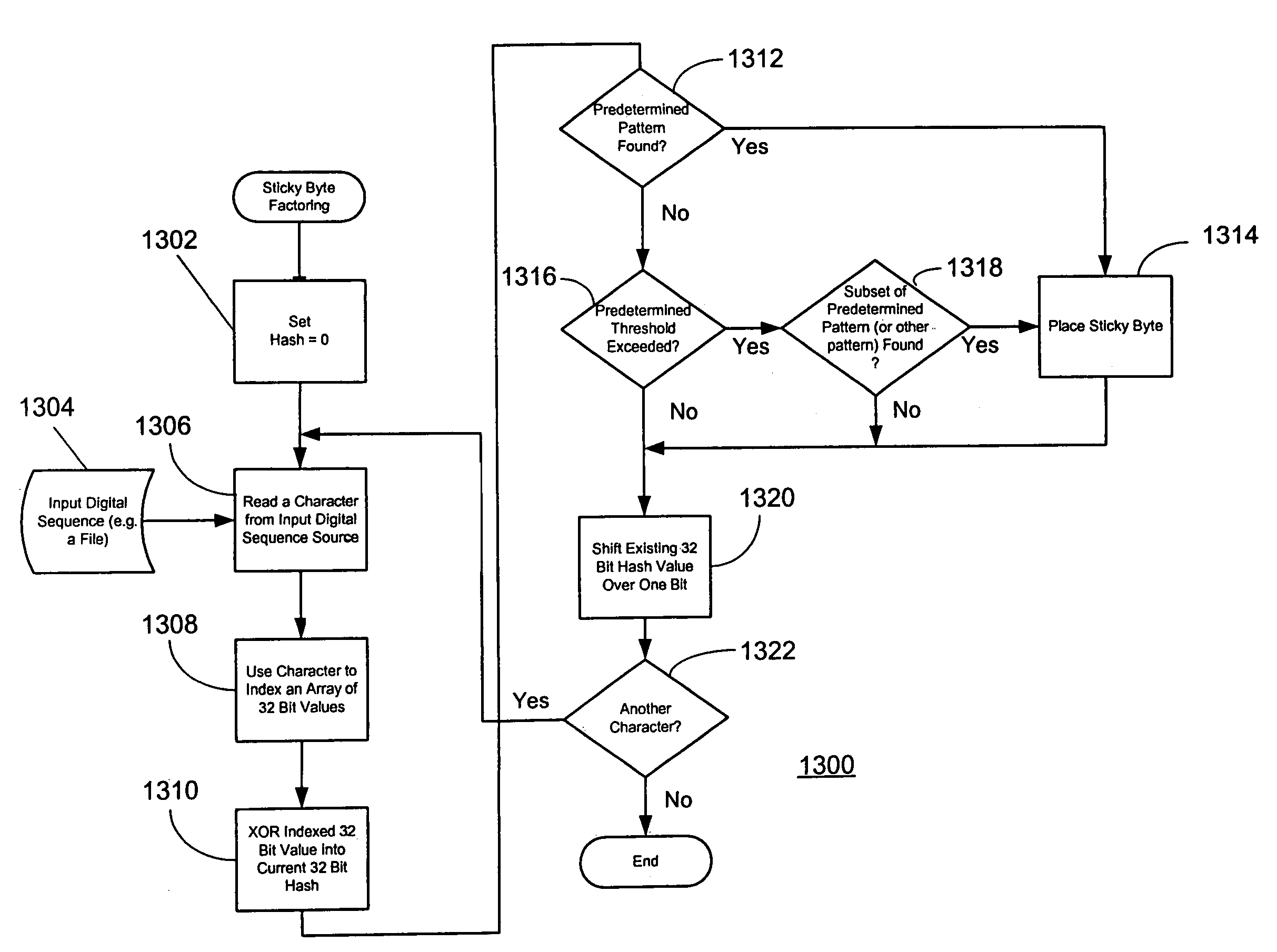
System and method for unorchestrated determination of data sequences using sticky byte factoring to determine breakpoints in digital sequences
InactiveUS7272602B2Near optimal commonalityMinimal computationData processing applicationsDigital data information retrievalData setRolling hash
A system and method for unorchestrated determination of data sequences using “sticky byte” factoring to determine breakpoints in digital sequences such that common sequences can be identified. Sticky byte factoring provides an efficient method of dividing a data set into pieces that generally yields near optimal commonality. This is effectuated by employing a rolling hashsum and, in an exemplary embodiment disclosed herein, a threshold function to deterministically set divisions in a sequence of data. Both the rolling hash and the threshold function are designed to require minimal computation. This low overhead makes it possible to rapidly partition a data sequence for presentation to a factoring engine or other applications that prefer subsequent synchronization across the data set.
Owner:EMC IP HLDG CO LLC
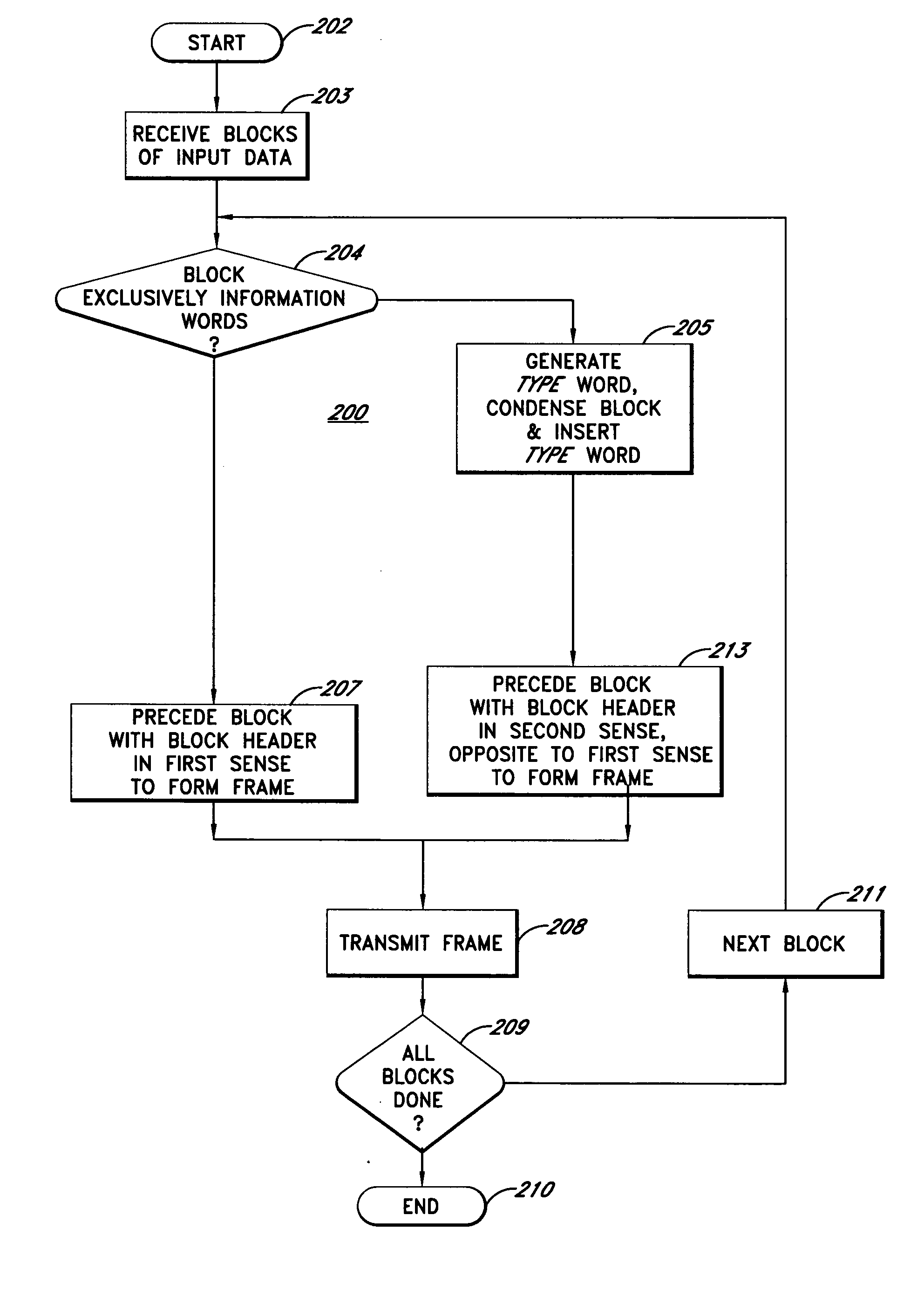
Communication system and encoding method having low overhead
ActiveUS20060256875A1Reduce overheadError preventionTime-division multiplexComputer hardwareCommunications system
A communication system processes blocks of input data that include control words and a packet of information words are received. The packet has a start preceded by ones of the control words and an end followed by others of the control words. When the block consists exclusively of information words, a one bit block header having a first sense is appended to the block to form a frame. When the block does not consist exclusively of information words, the block is condensed to accommodate a TYPE word, the TYPE word is generated and inserted into the block and a one bit block header is appended to the block to form the frame. When the block does not consist exclusively of information words the one bit block header has a second sense, opposite to the first sense. Use of a one bit block header reduces overhead. Forward error correction is also utilized.
Owner:MARVELL ASIA PTE LTD
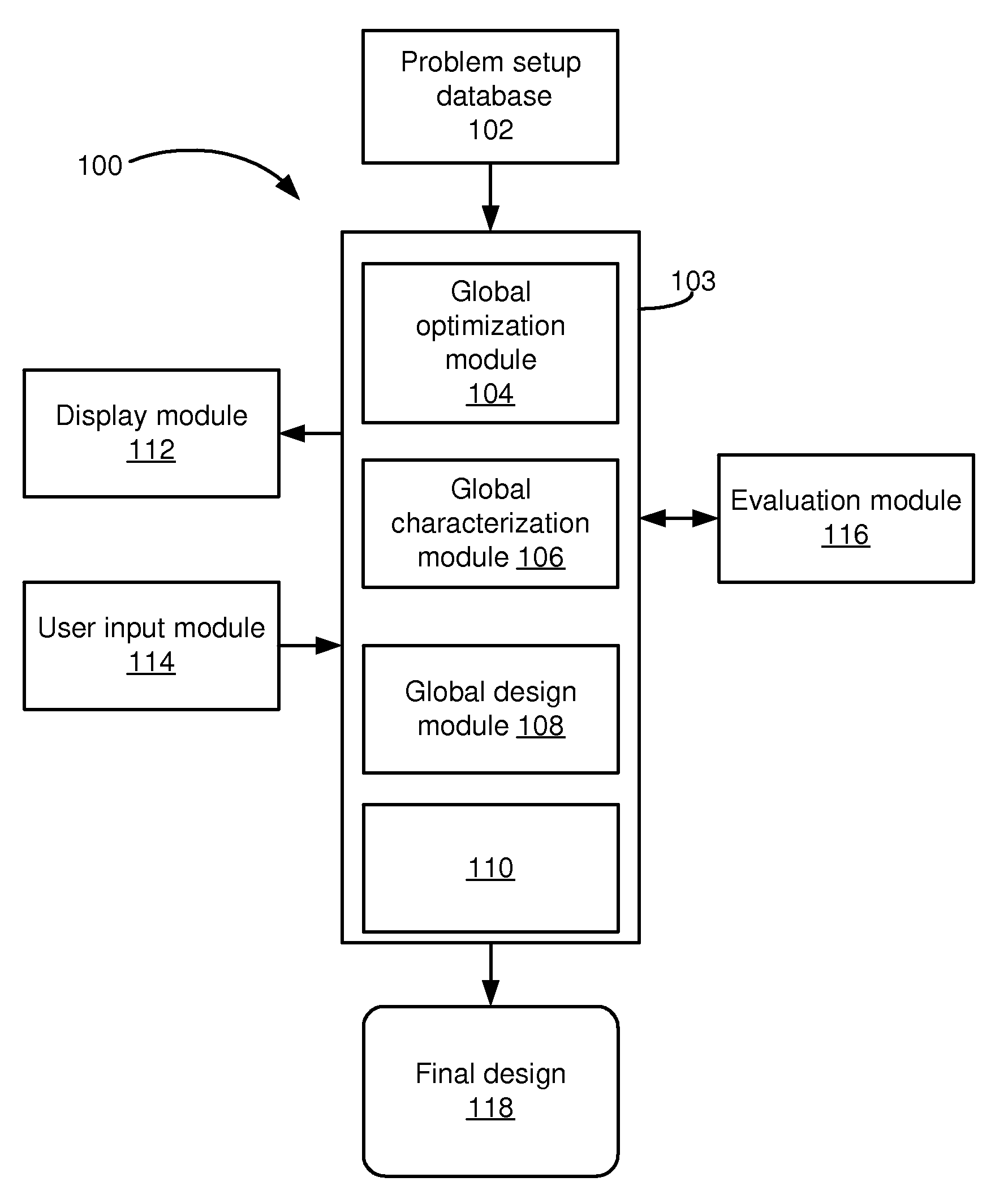
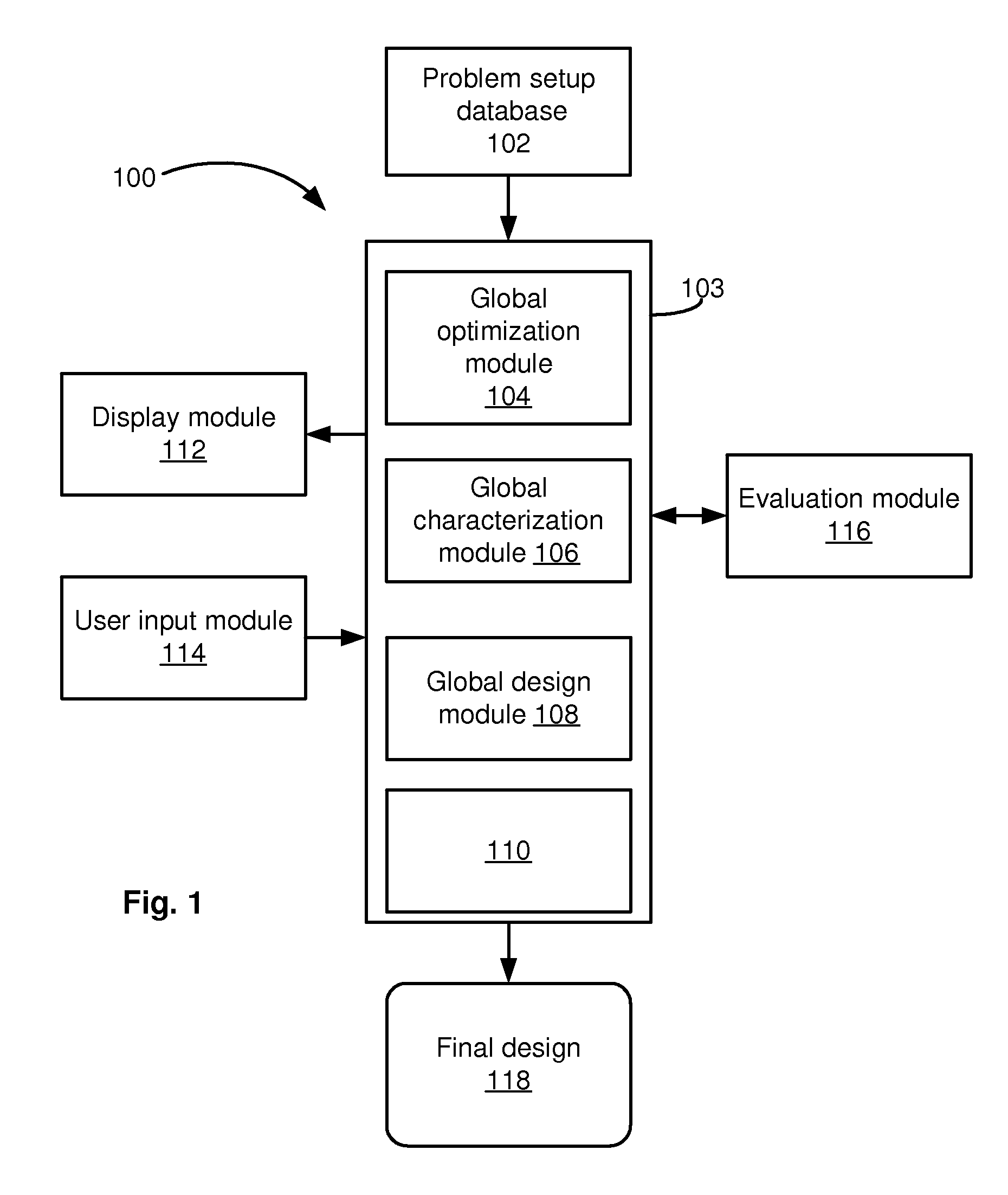
Global statistical optimization, characterization, and design
ActiveUS20090228846A1Low costChange its valueDetecting faulty computer hardwareCAD circuit designTime rangeTheoretical computer science
For application to analog, mixed-signal, and custom digital circuits, a system and method to do: global statistical optimization (GSO), global statistical characterization (GSC), global statistical design (GSD), and block-specific design. GSO can perform global yield optimization on hundreds of variables, with no simplifying assumptions. GSC can capture and display mappings from design variables to performance, across the whole design space. GSC can handle hundreds of design variables in a reasonable time frame, e.g., in less than a day, for a reasonable number of simulations, e.g., less than 100,000. GSC can capture design variable interactions and other possible nonlinearities, explicitly capture uncertainties, and intuitively display them. GSD can support the user's exploration of design-to-performance mappings with fast feedback, thoroughly capturing design variable interactions in the whole space, and allow for more efficiently created, more optimal designs. Block-specific design should make it simple to design small circuit blocks, in less time and with lower overhead than optimization through optimization.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
System, method and computer program product for protecting software via continuous anti-tampering and obfuscation transforms
InactiveUS20110035601A1Efficiently translatedAvoid modificationUnauthorized memory use protectionHardware monitoringObfuscationApplication software
Method, system and computer program product for applying existing anti-tampering and obfuscation technique to virtual machine technology and offers several distinct advantages. The anti-tampering and obfuscation transforms can be applied continuously to prevent adversaries from gaining information about the program through emulation or dynamic analysis. In addition, the encryption can be used to prevent hackers from gaining information using static attacks. The use of a virtual machine also allows for low overhead execution of the obfuscated binaries as well as finer adjustment of the amount of overhead that can be tolerated. In addition, more protection can be applied to specific portions of the application that can tolerate slowdown. The incorporation of a virtual machine also makes it easy to extend the technology to integrate new developments and resistance mechanisms, leading to less development time, increased savings, and quicker deployment.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND
Piggy-backed key exchange protocol for providing secure, low-overhead browser connections when a client requests a server to propose a message encoding scheme
InactiveUS7039946B1Minimal numberMaintain integrityKey distribution for secure communicationDigital data processing detailsKey exchangeSecurity parameter
A method, system, and computer program product for establishing security parameters that are used to exchange data on a secure connection. A piggy-backed key exchange protocol is defined, with which these security parameters are advantageously exchanged. By piggy-backing the key exchange onto other already-required messages (such as a client's HTTP GET request, or the server's response thereto), the overhead associated with setting up a secure browser-to-server connection is minimized. This technique is defined for a number of different scenarios, where the client and server may or may not share an encoding scheme, and is designed to maintain the integrity of application layer communication protocols. In one scenario, a client requests a server to propose a message encoding scheme. If the client has security-sensitive data to transmit with its request, it waits for the proposed scheme before sending this sensitive data to the server. Otherwise, the server may inform the client of the message encoding scheme in the same transmission used to send a response to a client's request.
Owner:IBM CORP
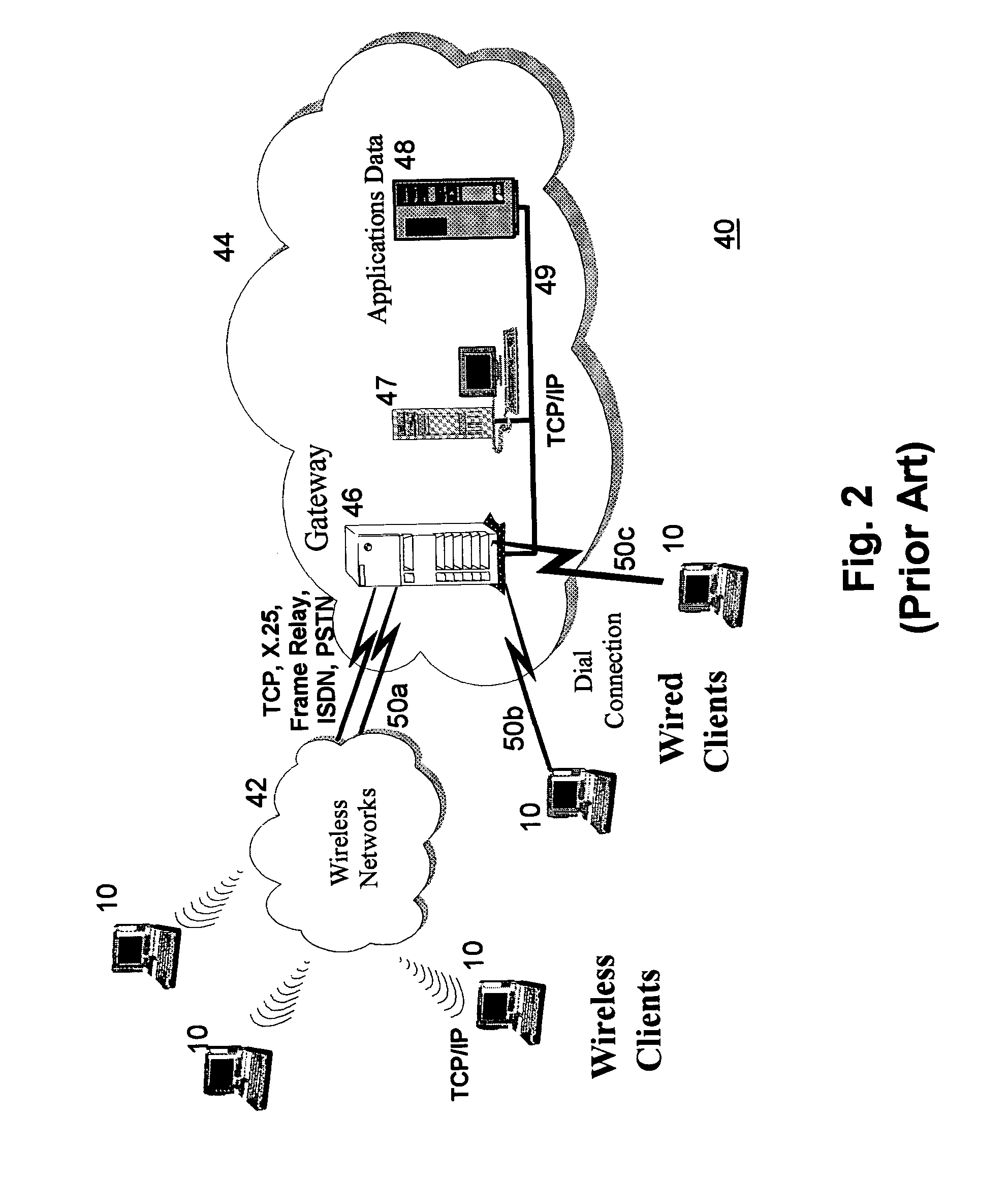
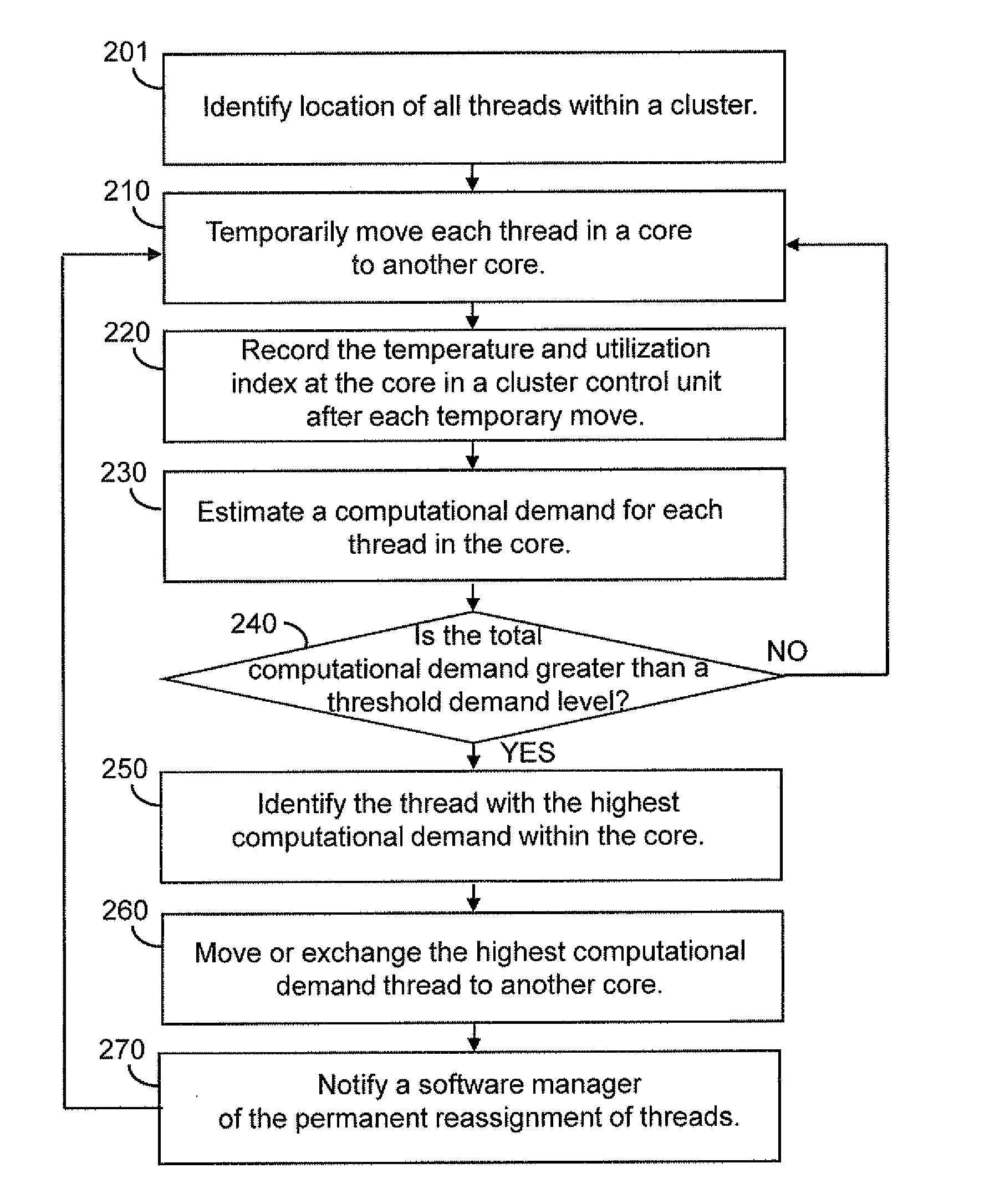
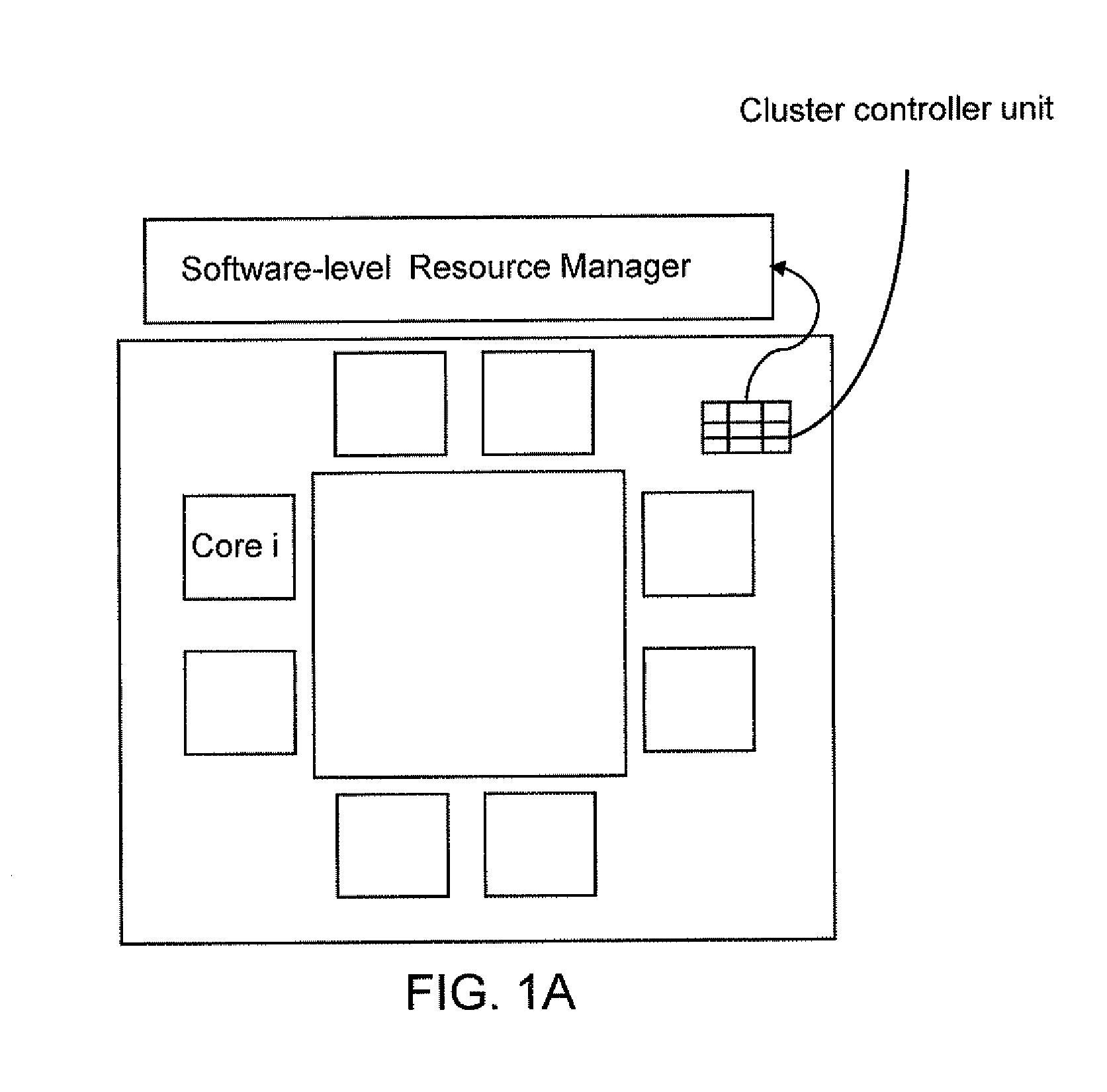
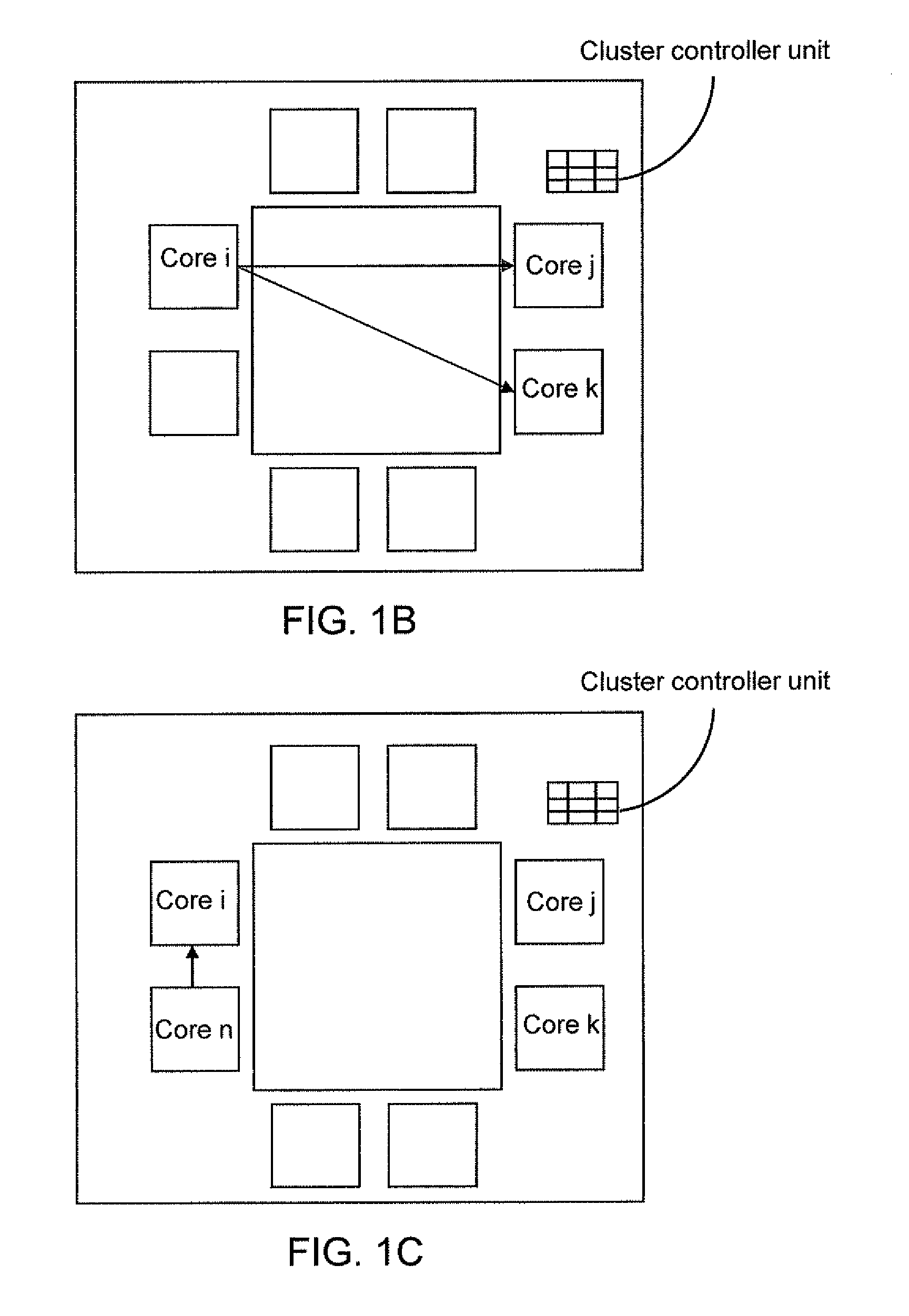
Low overhead dynamic thermal management in many-core cluster architecture
InactiveUS20110191776A1Digital data processing detailsMultiprogramming arrangementsSemiconductor chipEngineering
A semiconductor chip includes a plurality of multi-core clusters each including a plurality of cores and a cluster controller unit. Each cluster controller unit is configured to control thread assignment within the multi-core cluster to which it belongs. The cluster controller unit monitors various parameters measured in the plurality of cores within the multi-core cluster to estimate the computational demand of each thread that runs in the cores. The cluster controller unit may reassign the threads within the multi-core cluster based on the estimated computational demand of the threads and transmit a signal to an upper-level software manager that controls the thread assignment across the semiconductor chip. When an acceptable solution to thread assignment cannot be achieved by shuffling of threads within the multi-core cluster, the cluster controller unit may also report inability to solve thread assignment to the upper-level software manager to request a system level solution.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com