Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
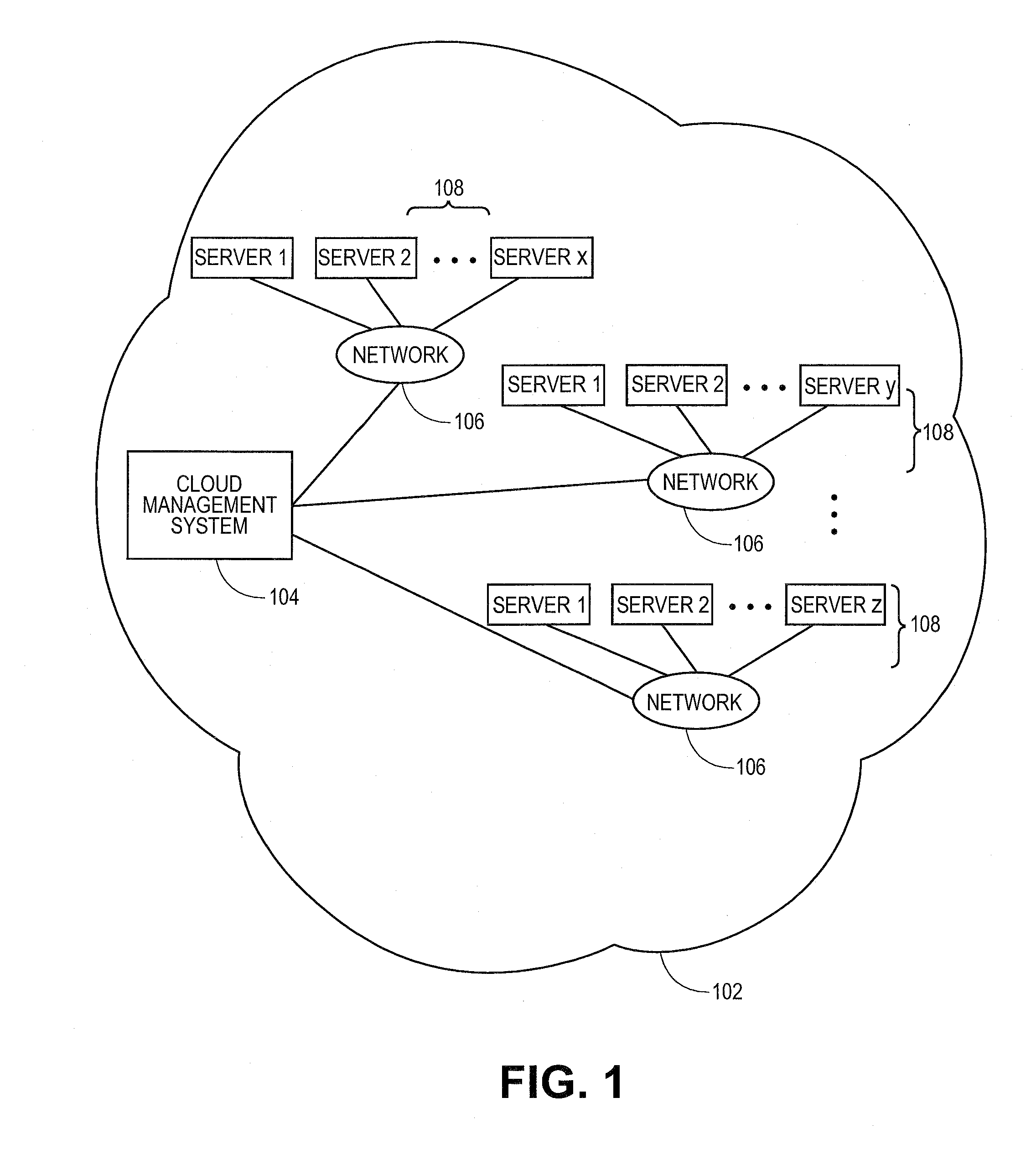
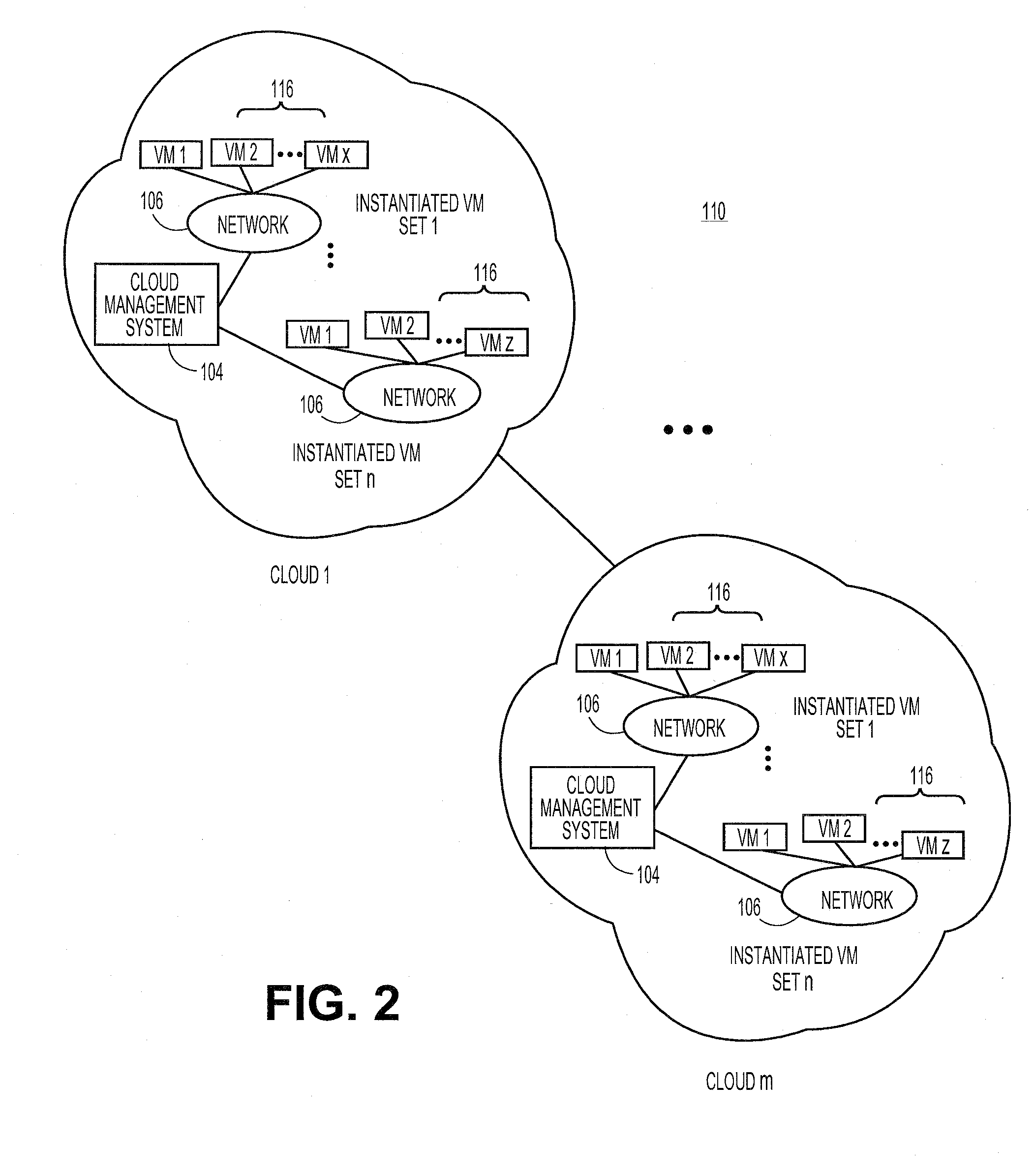
10383 results about "Cloud computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
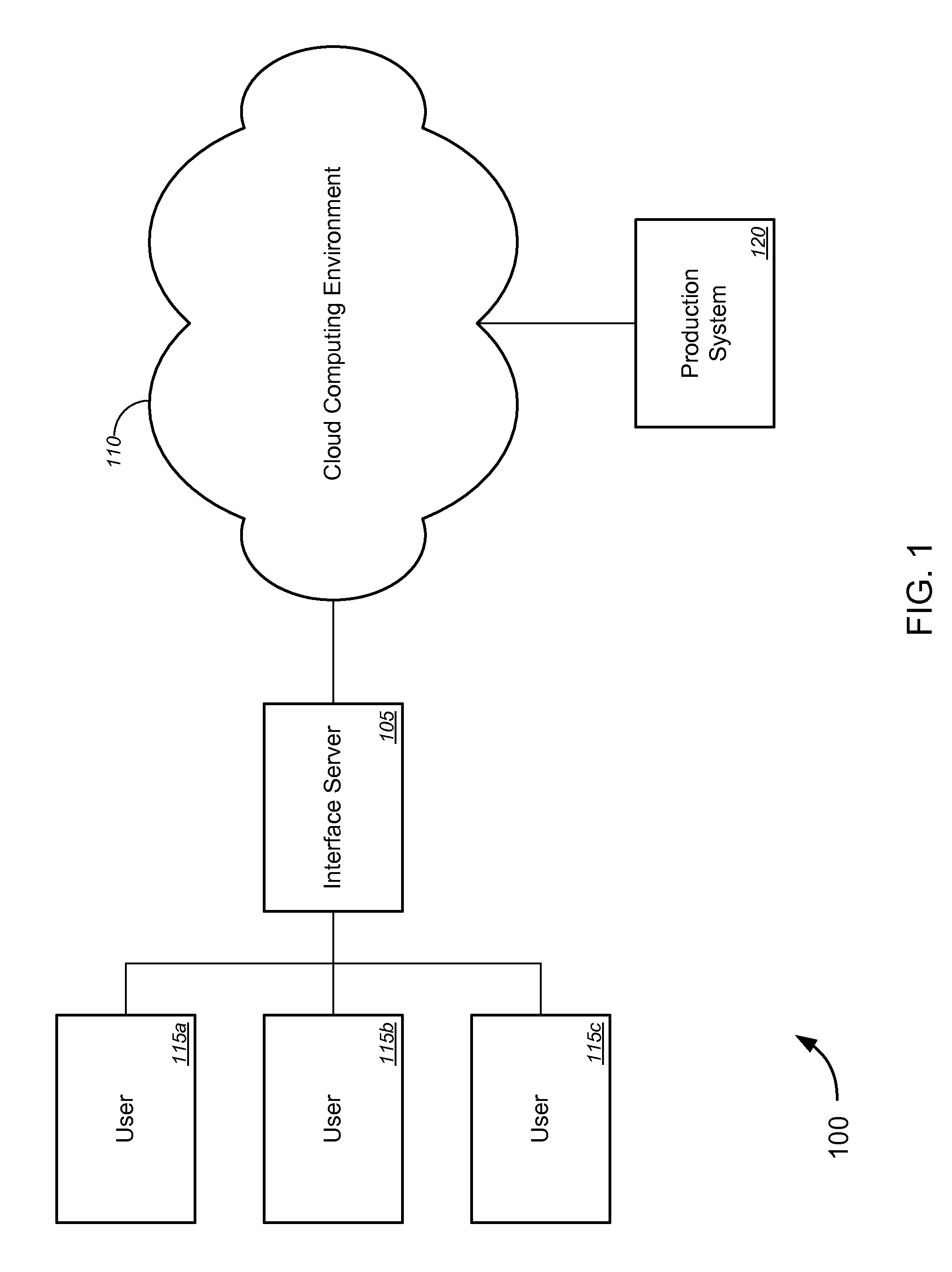
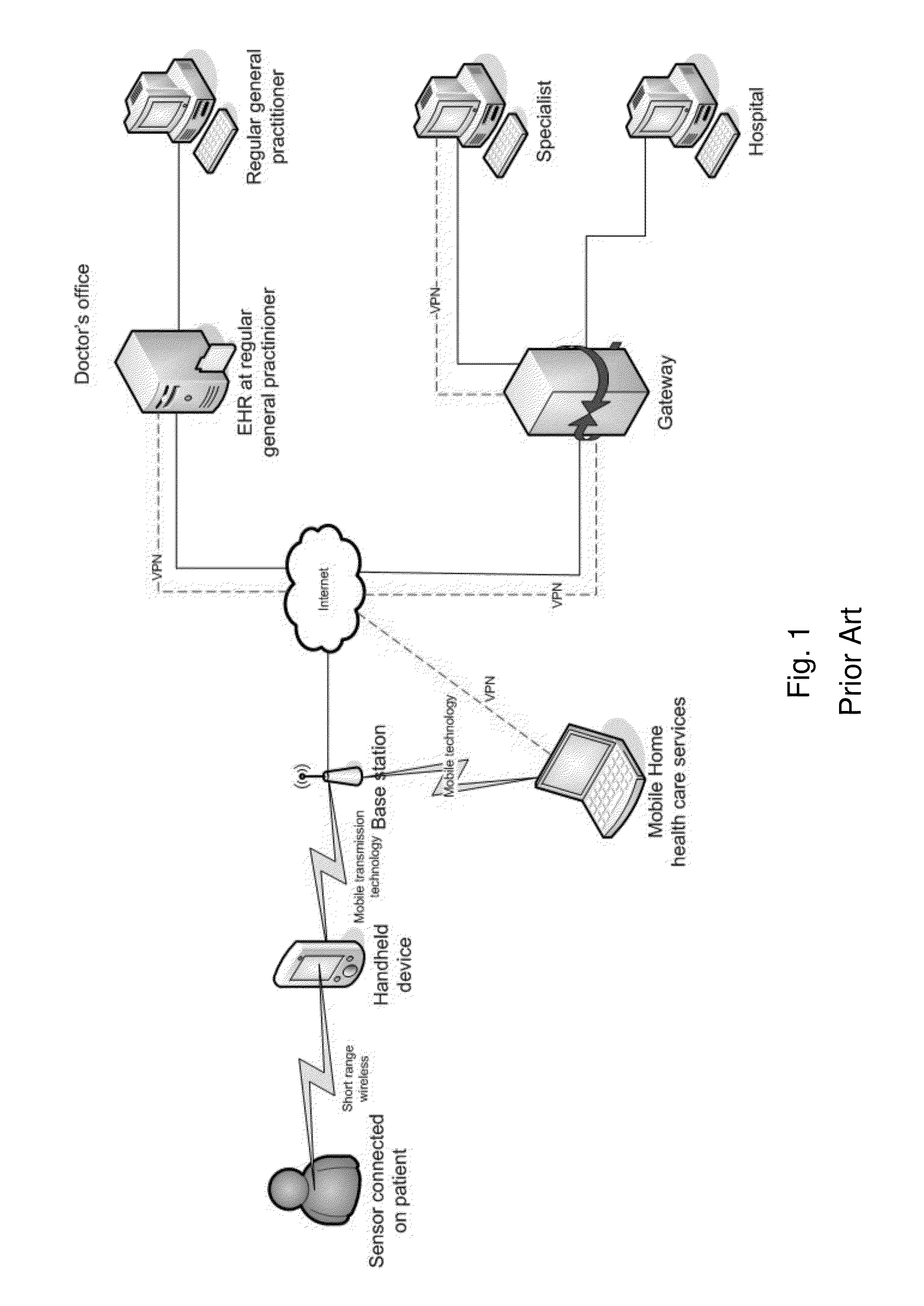
Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. The term is generally used to describe data centers available to many users over the Internet. Large clouds, predominant today, often have functions distributed over multiple locations from central servers. If the connection to the user is relatively close, it may be designated an edge server.
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
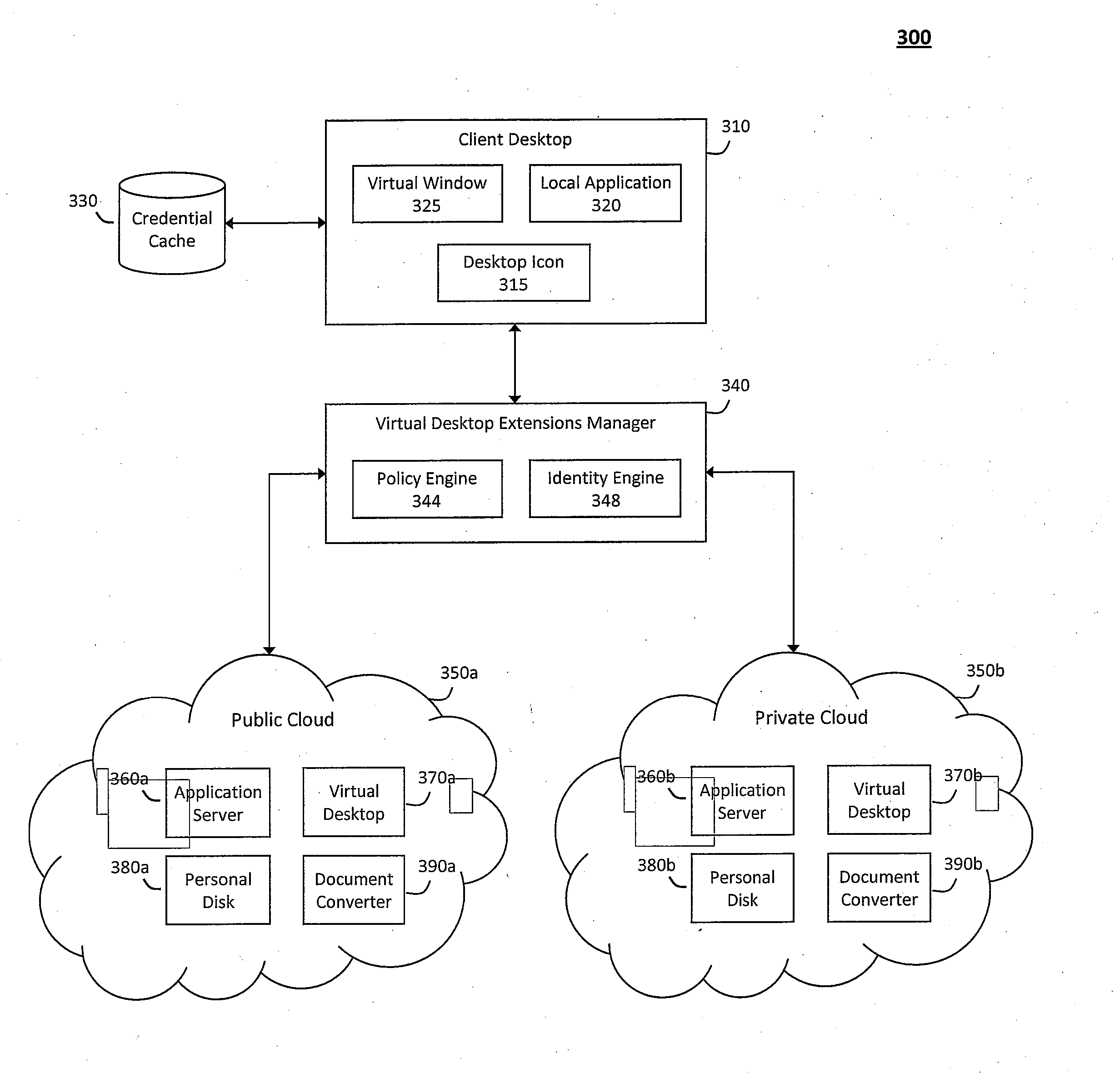
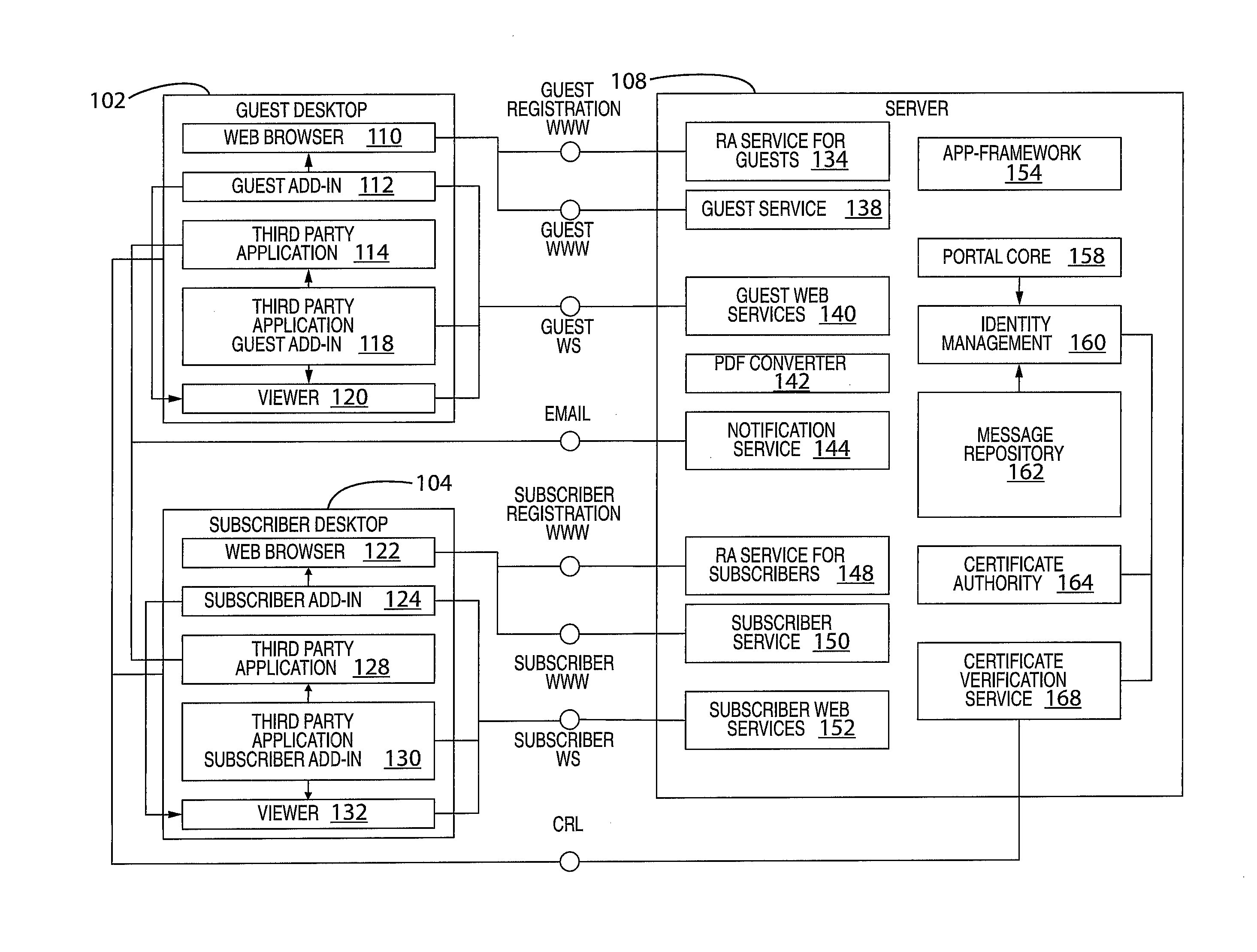
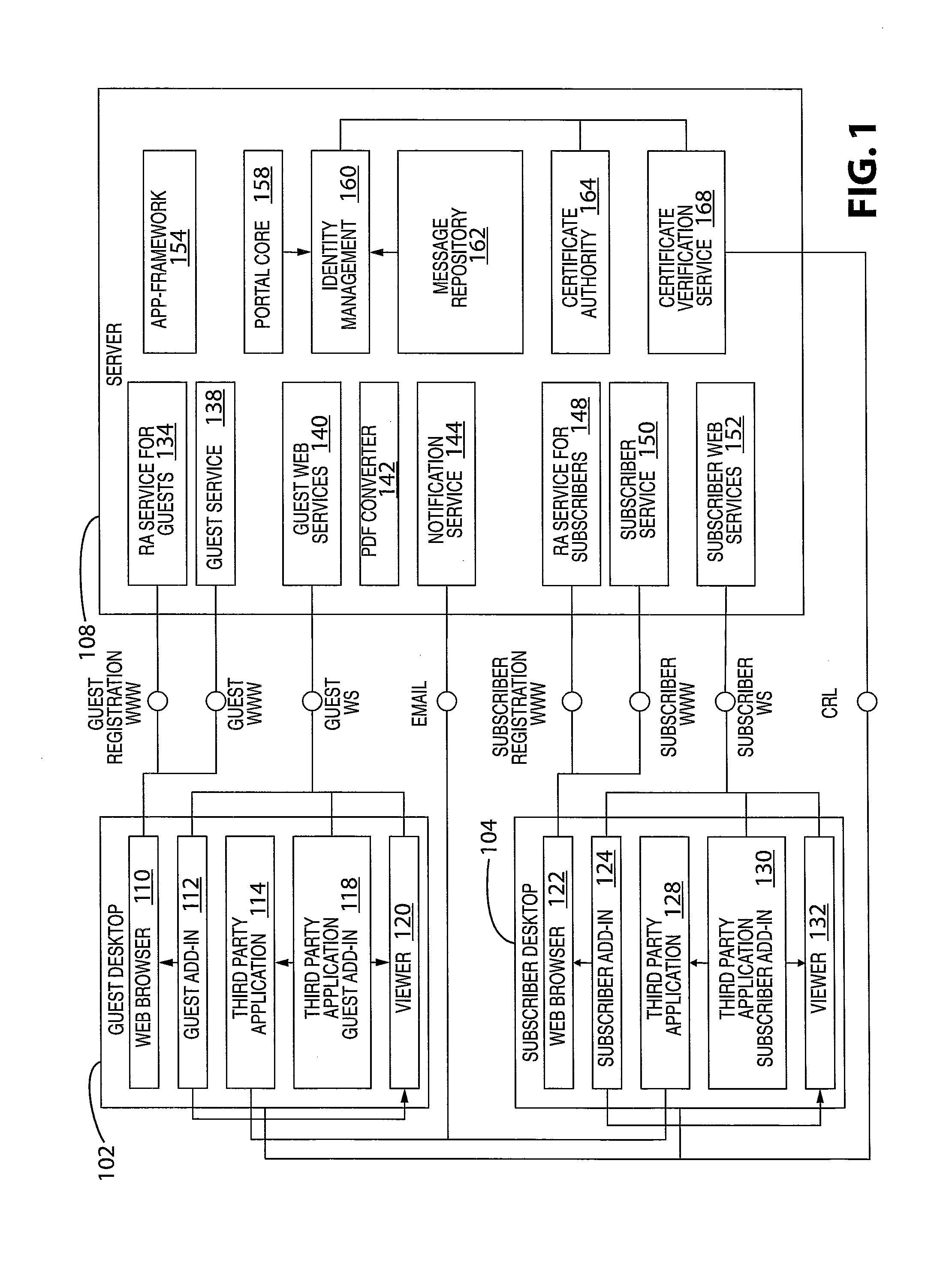
System and method for providing virtual desktop extensions on a client desktop
ActiveUS20110209064A1Simplify complexityProvide capabilityInput/output for user-computer interactionDigital data processing detailsClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
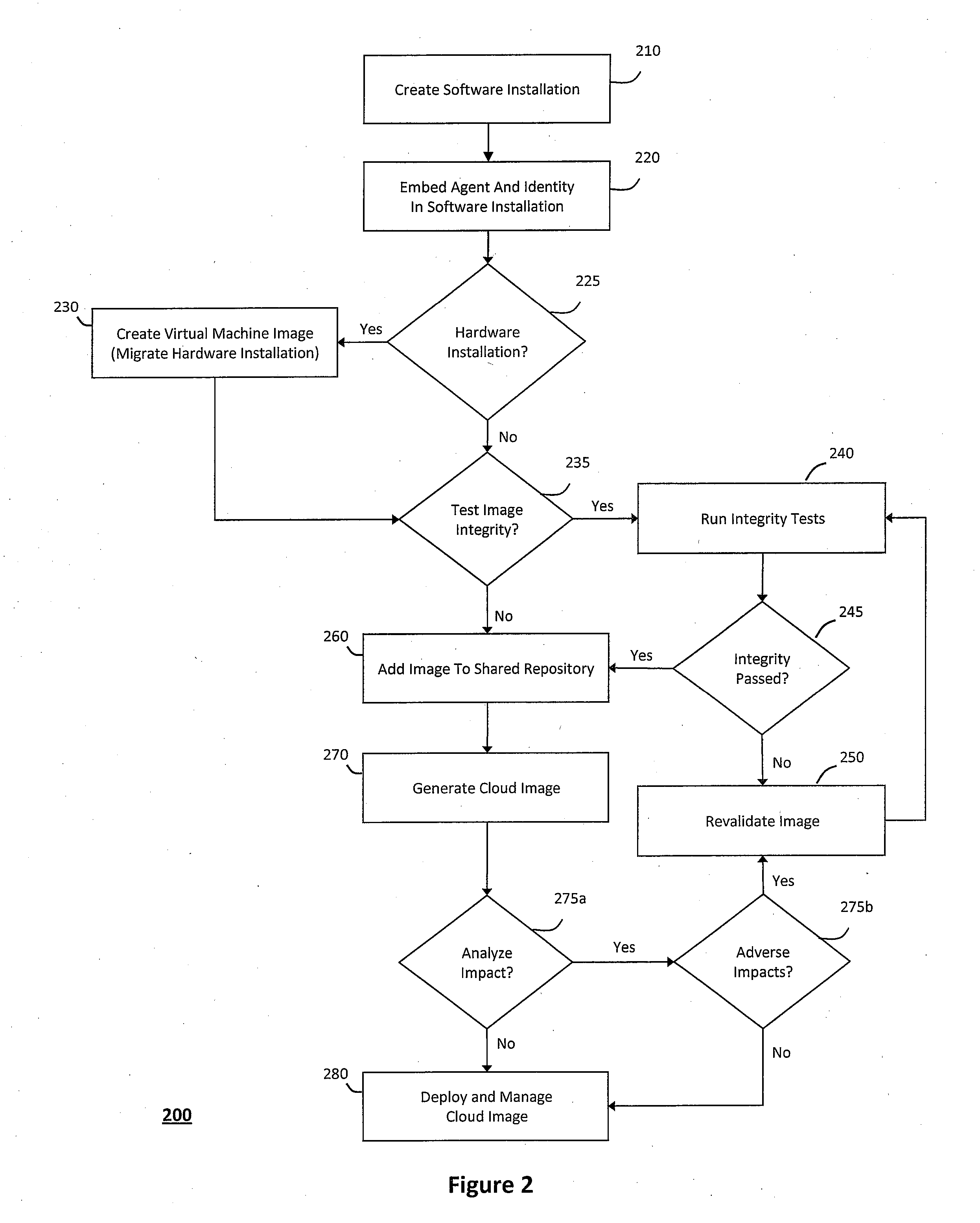
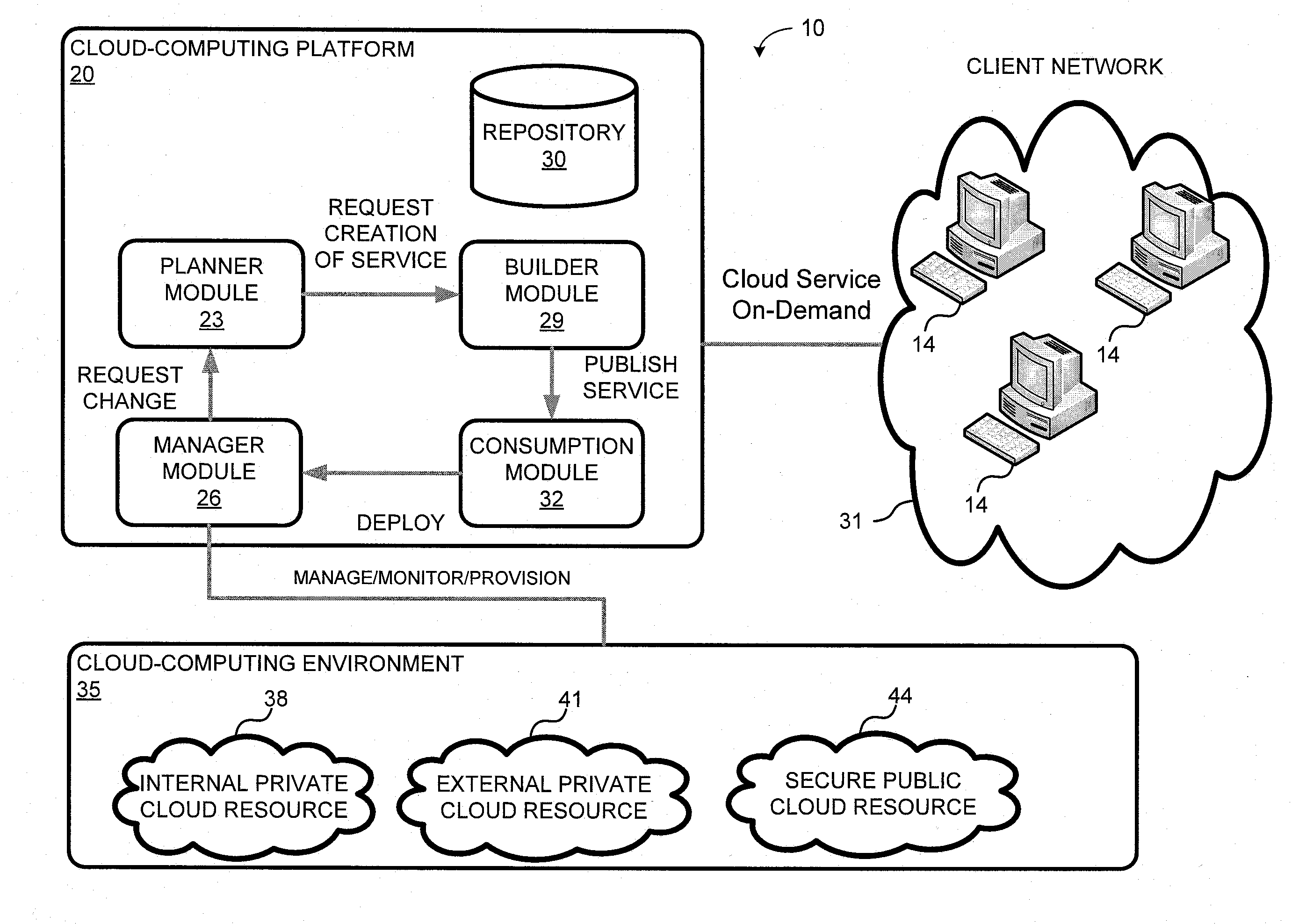
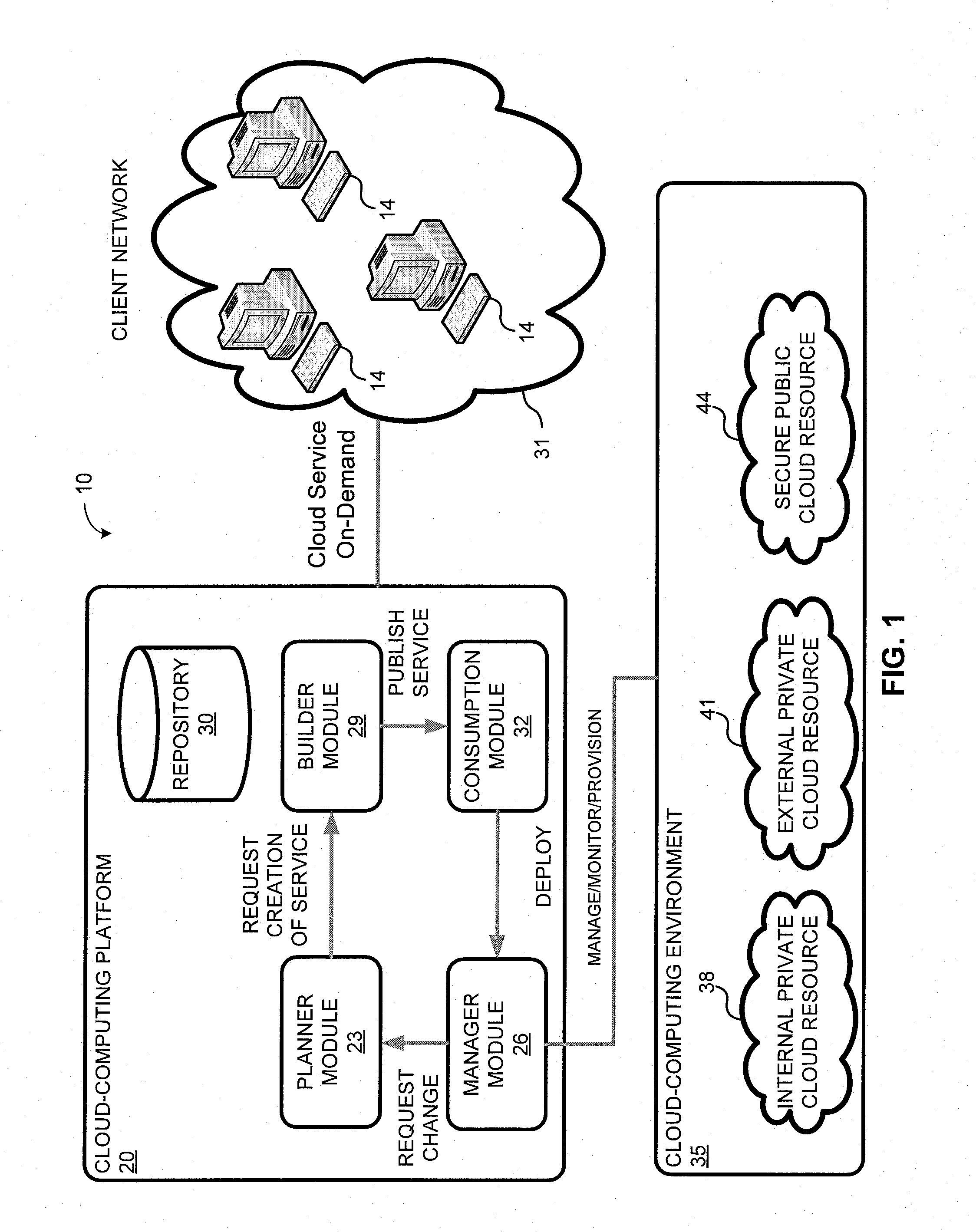
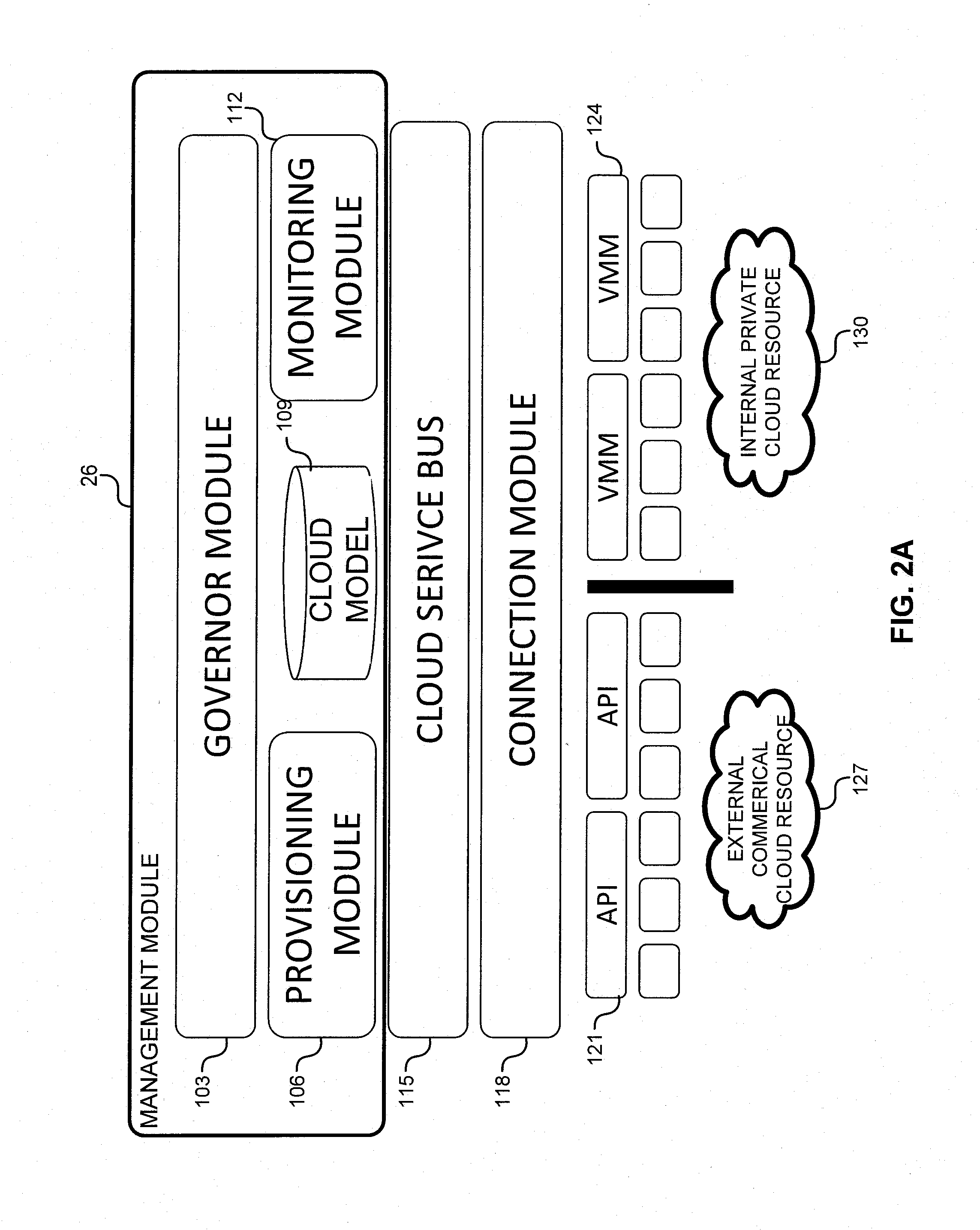
System and method for a cloud computing abstraction layer
ActiveUS20110231899A1Rapid and dynamic deployment and scalingShorten the timeDigital computer detailsComputer security arrangementsAbstraction layerWorkload
According to one system of the invention, the system provides a cloud-computing service from a cloud-computing environment comprising a plurality of cloud-computing resources. The system may comprise: a management module configured to manage a cloud-computing resource of the plurality of cloud-computing resources as a cloud-computing service, wherein the cloud-computing service performs a computer workload; an adapter configured to connect to the cloud-computing resource to the system and translate a management instruction received from the management module into a proprietary cloud application program interface call for the cloud-computing resource; a cloud service bus configured to route the management instruction from the management module to the adapter; a consumption module configured to allow a user to subscribe the cloud-computing service; a planning module configured to plan the cloud-computing service; and a build module configured to build the cloud-computing service from the cloud-computing resource and publish the cloud-computing service to the consumption module.
Owner:DXC US AGILITY PLATFORM INC
Methods and Systems for Automated Management of Virtual Resources In A Cloud Computing Environment
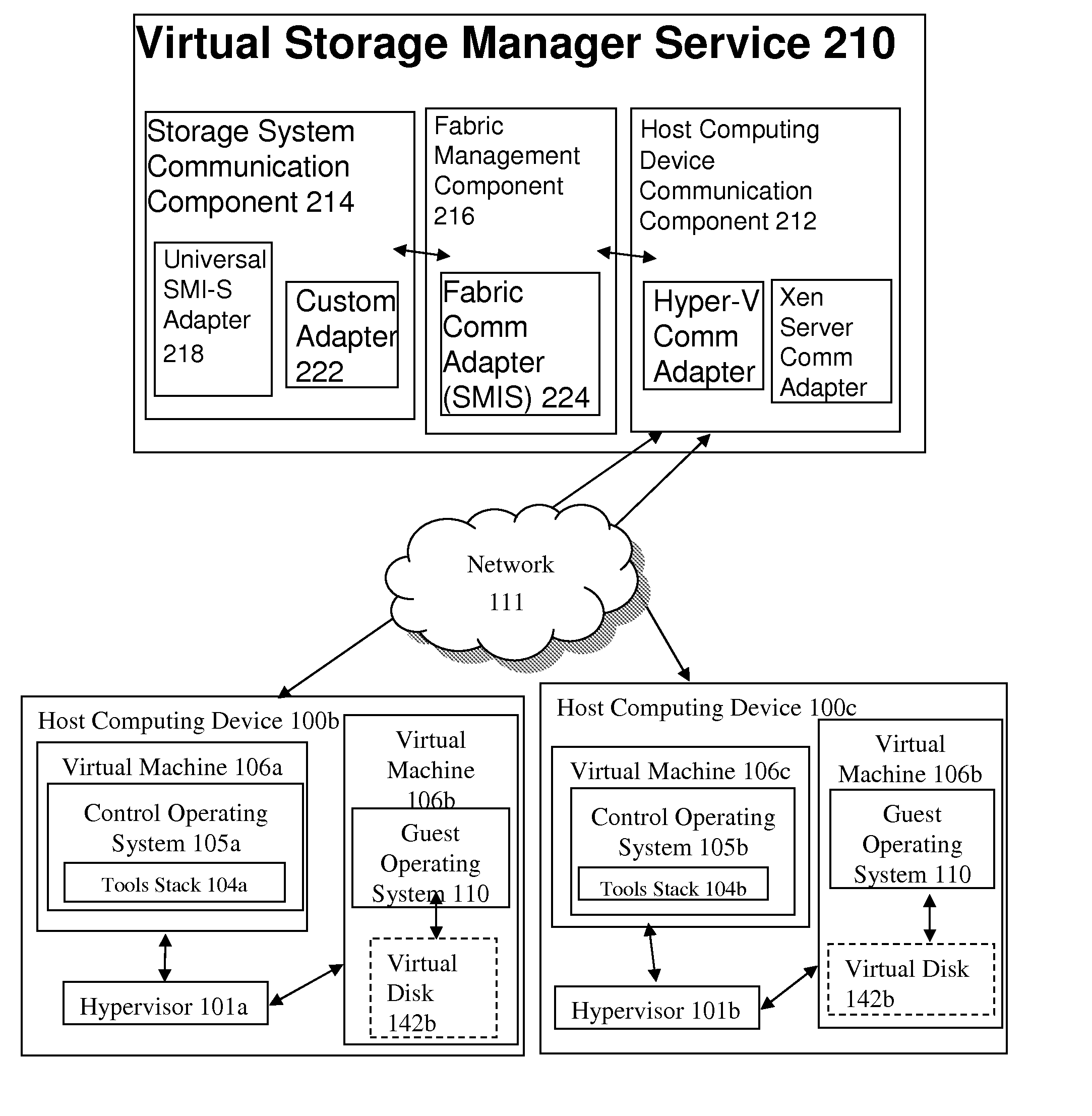
ActiveUS20100198972A1Multiple digital computer combinationsProgram controlStorage area networkCloud computing
A system for automated management of virtual resources in a cloud computing environment includes a host computing device communication component and a storage system communication component. The storage system communication component is executed by a storage delivery management service, communicates with a storage system adapter in a storage area network to identify a storage system in a storage area network, and directs the automated provisioning of a virtual storage resource on the identified storage system, the storage system providing resources for provisioning the virtual drive. The host computing device communication component receives a request for access by a host computing device to the virtual storage resource, and responds, to the host computing device, with an identification of a network port of the identified storage system and an identification of the provisioned virtual storage resource.
Owner:CITRIX SYST INC
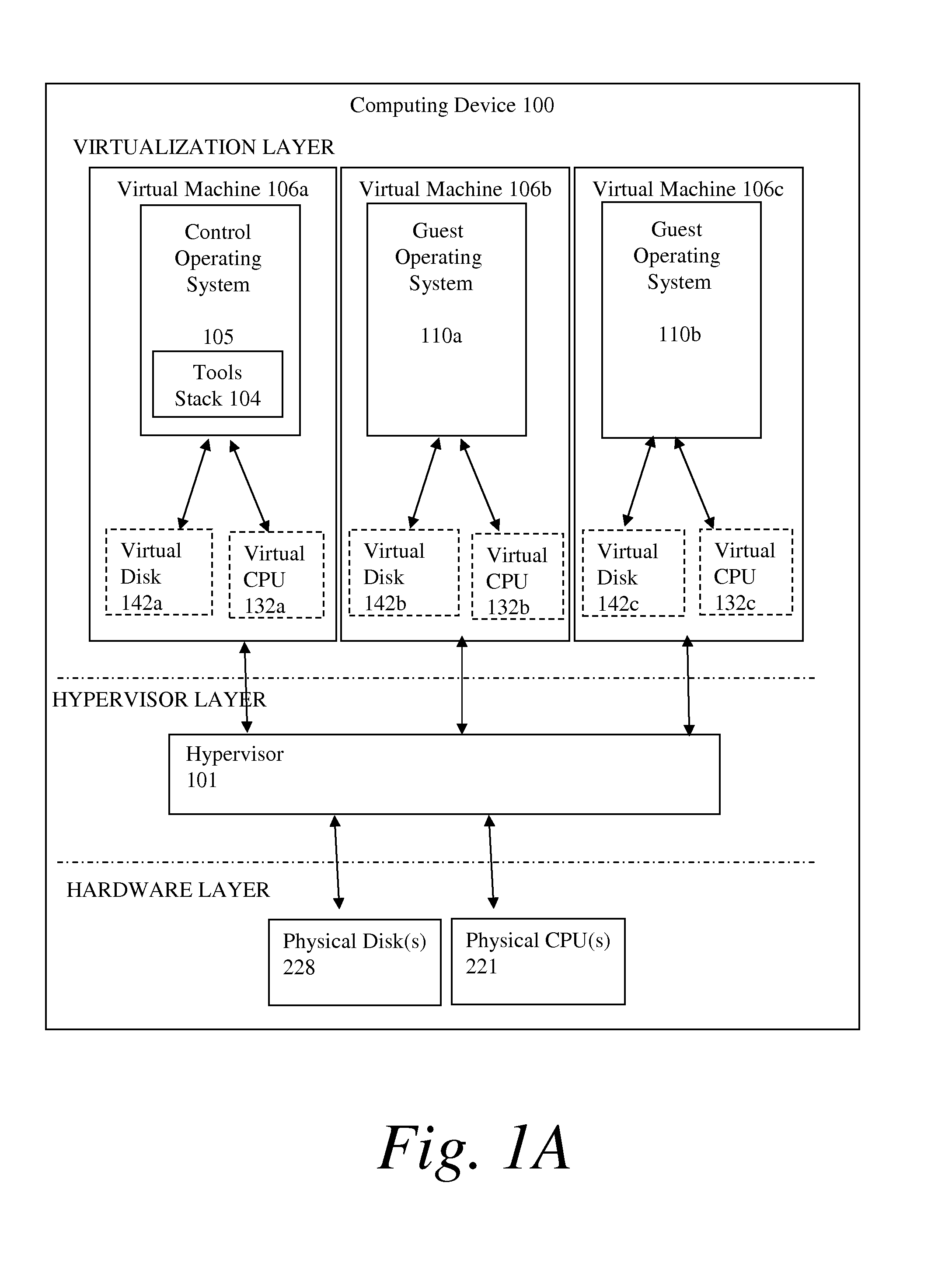
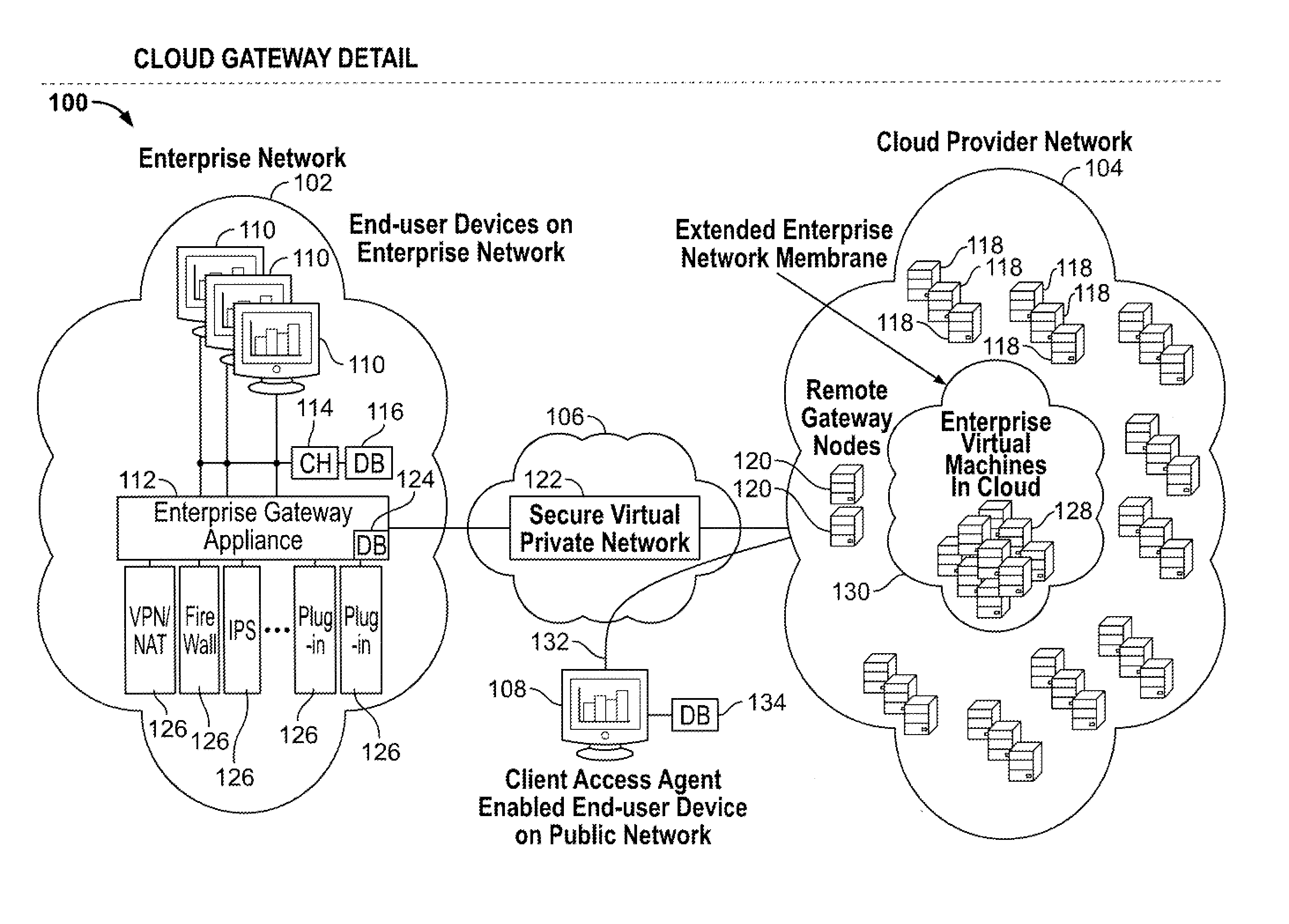
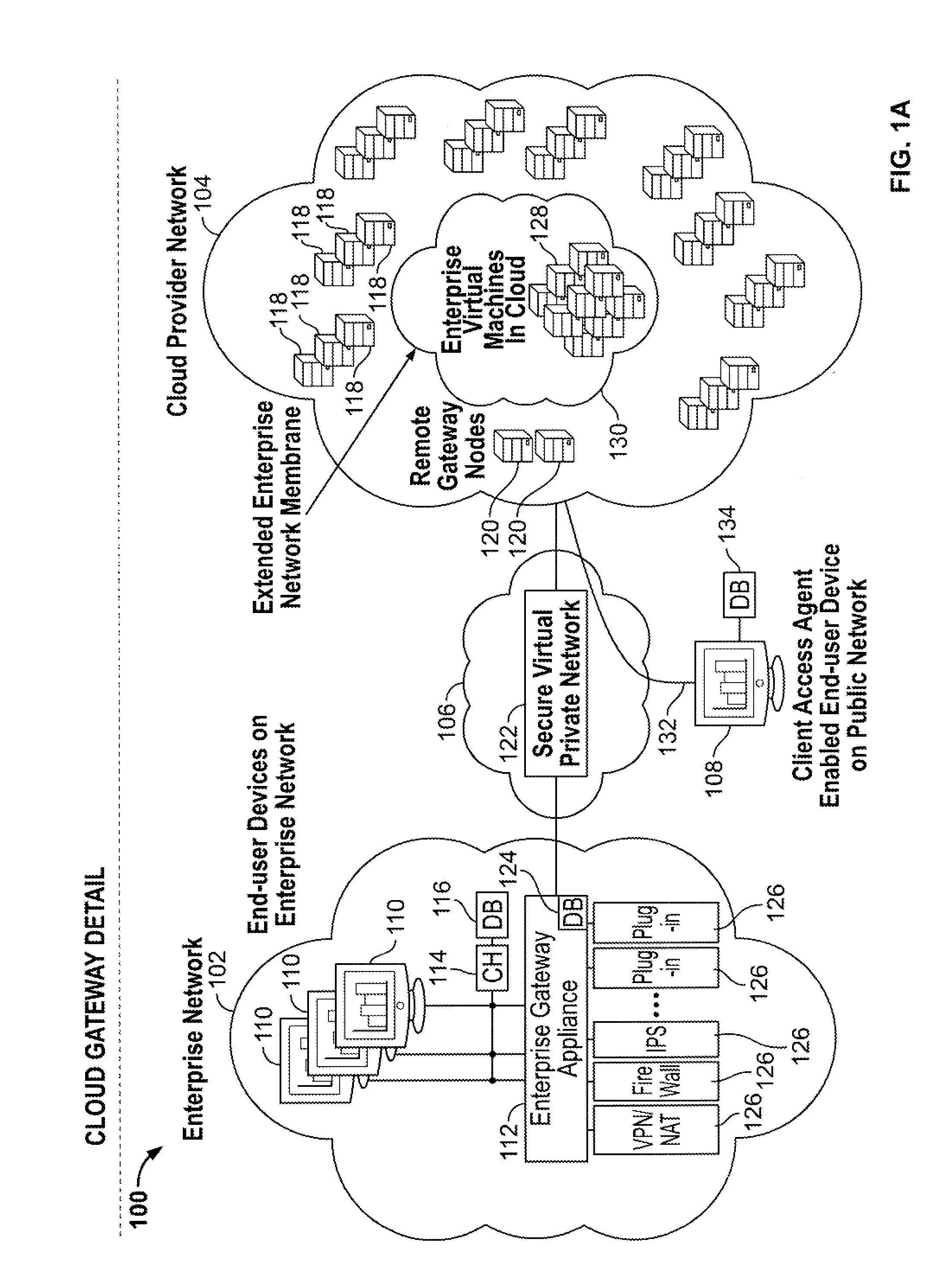
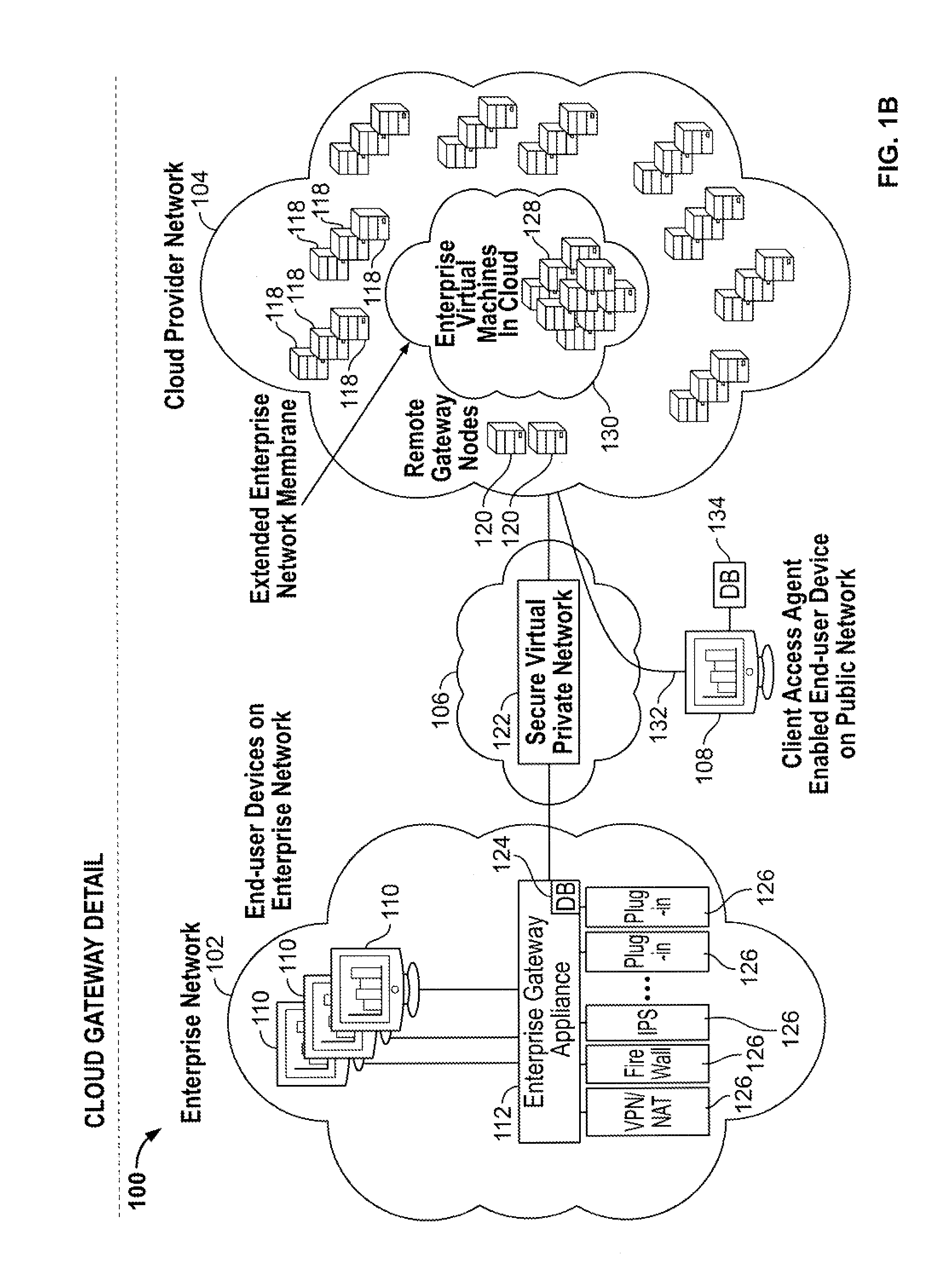
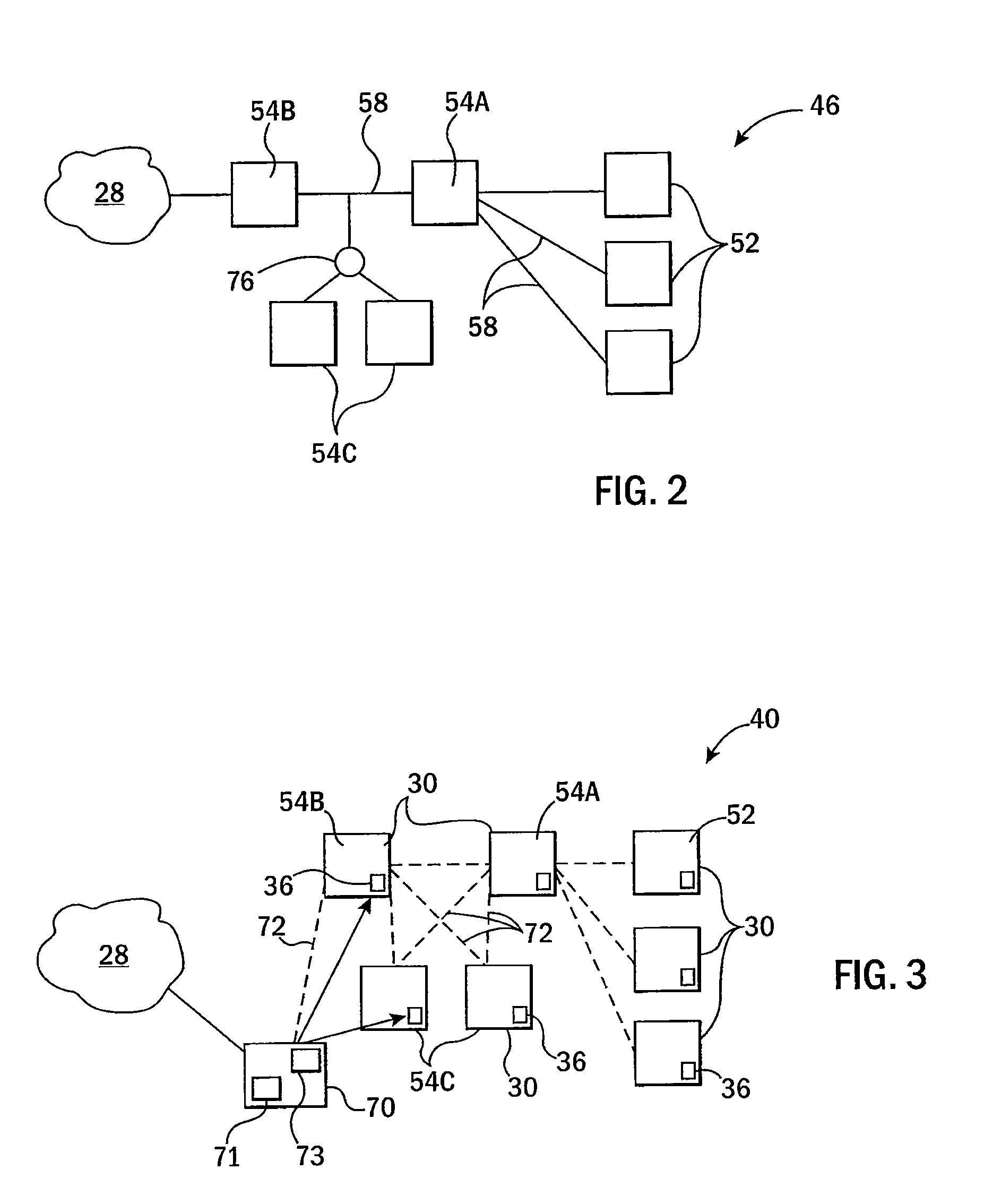
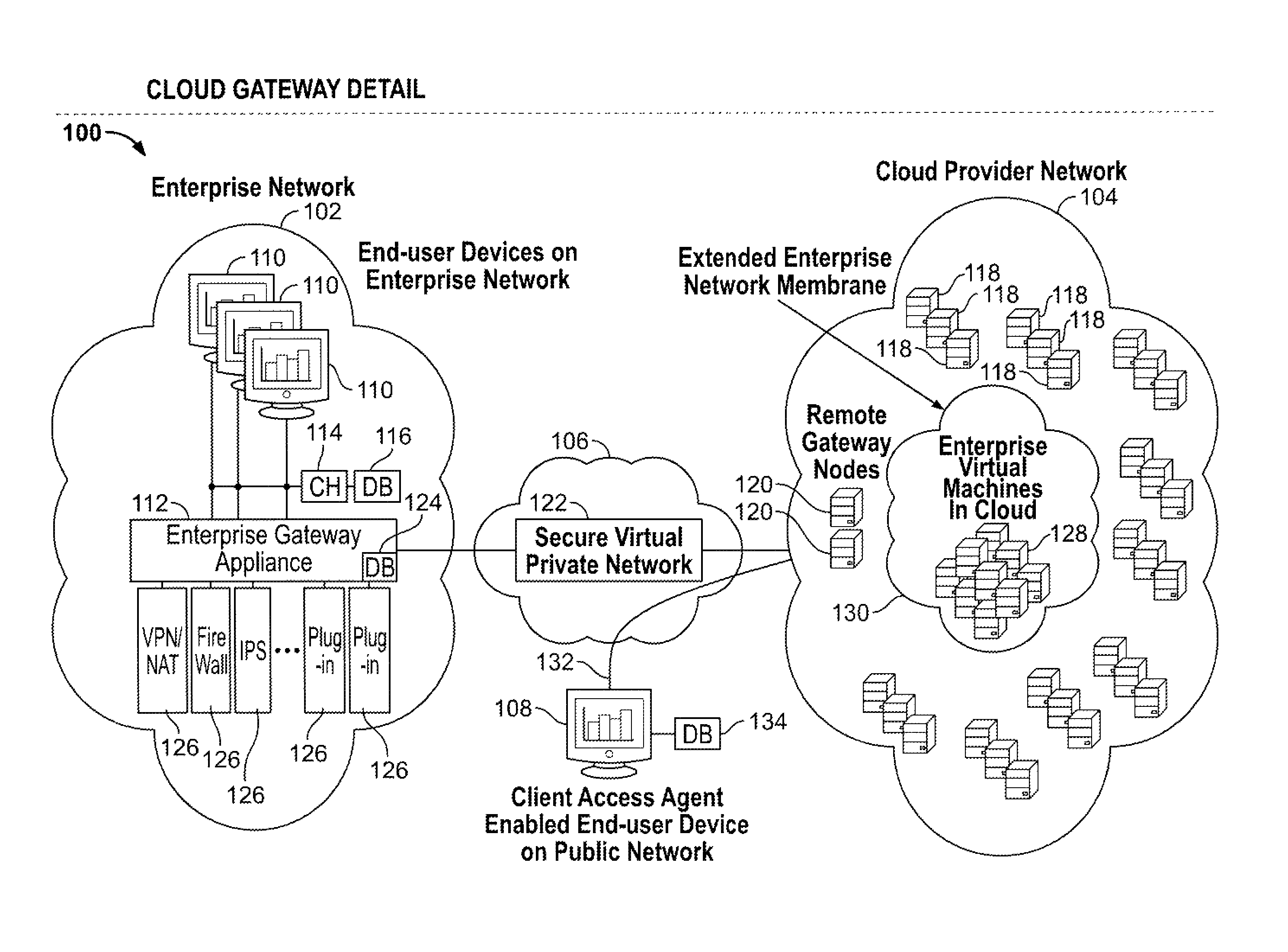
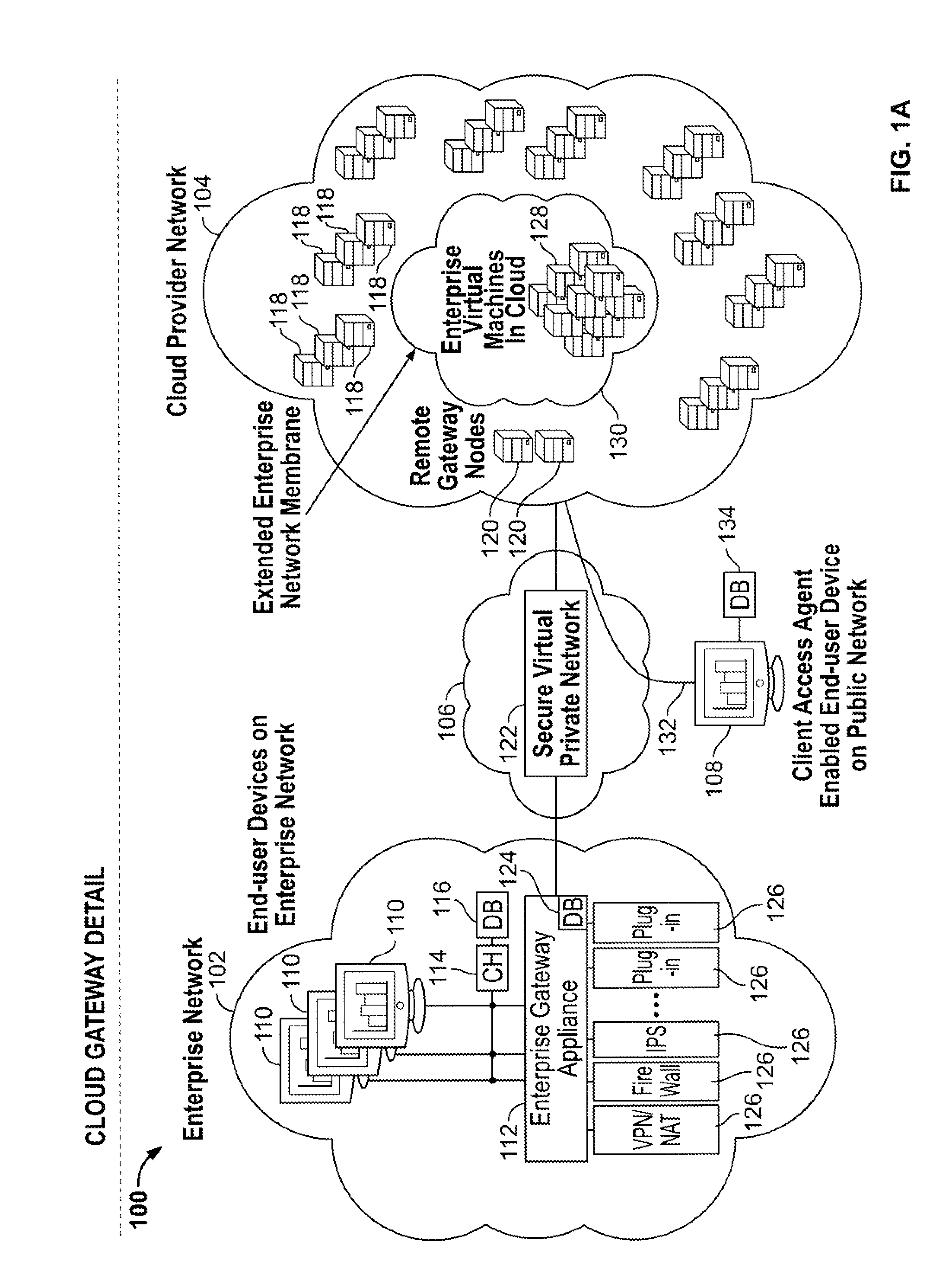
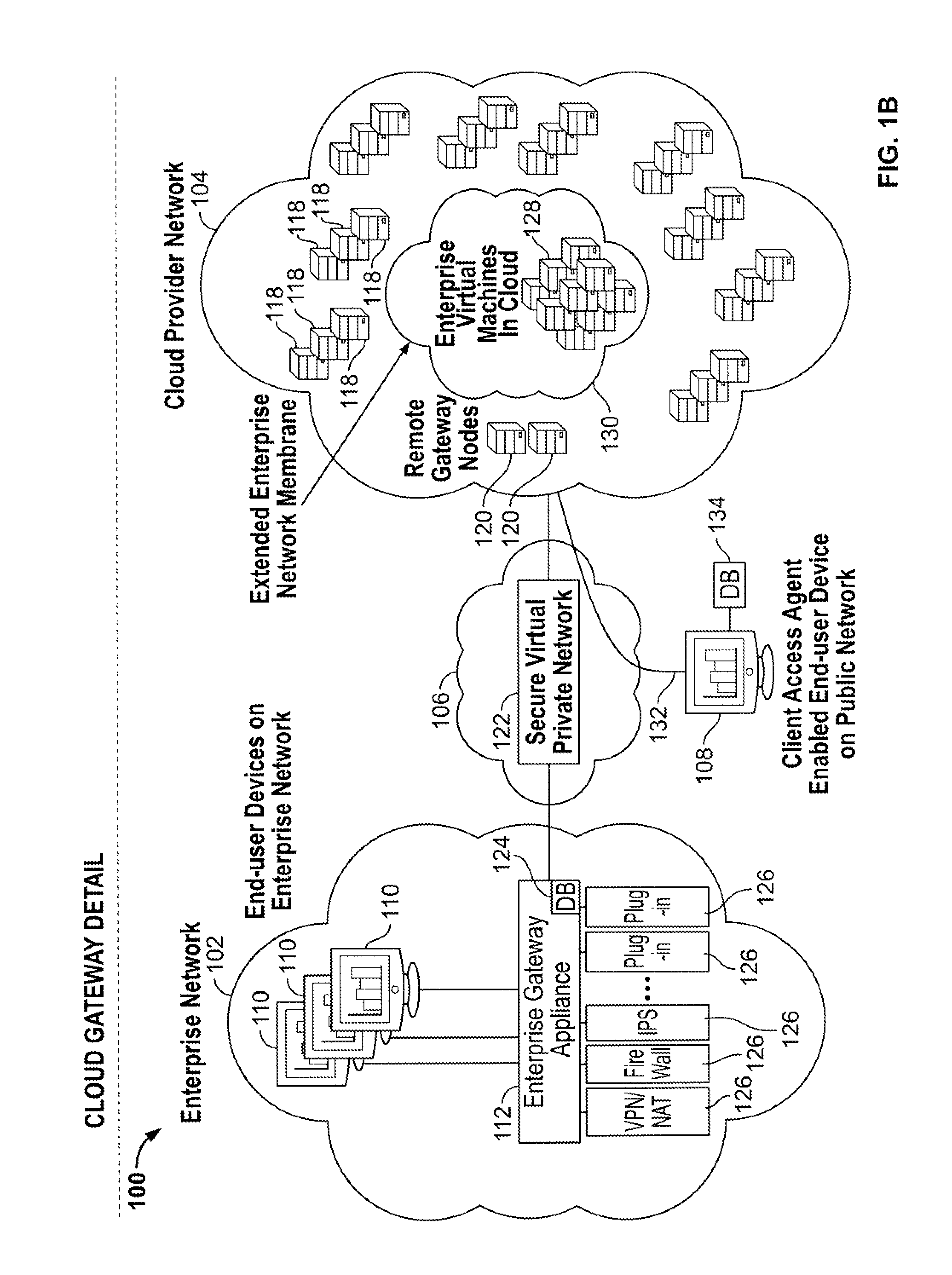
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS20100027552A1Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
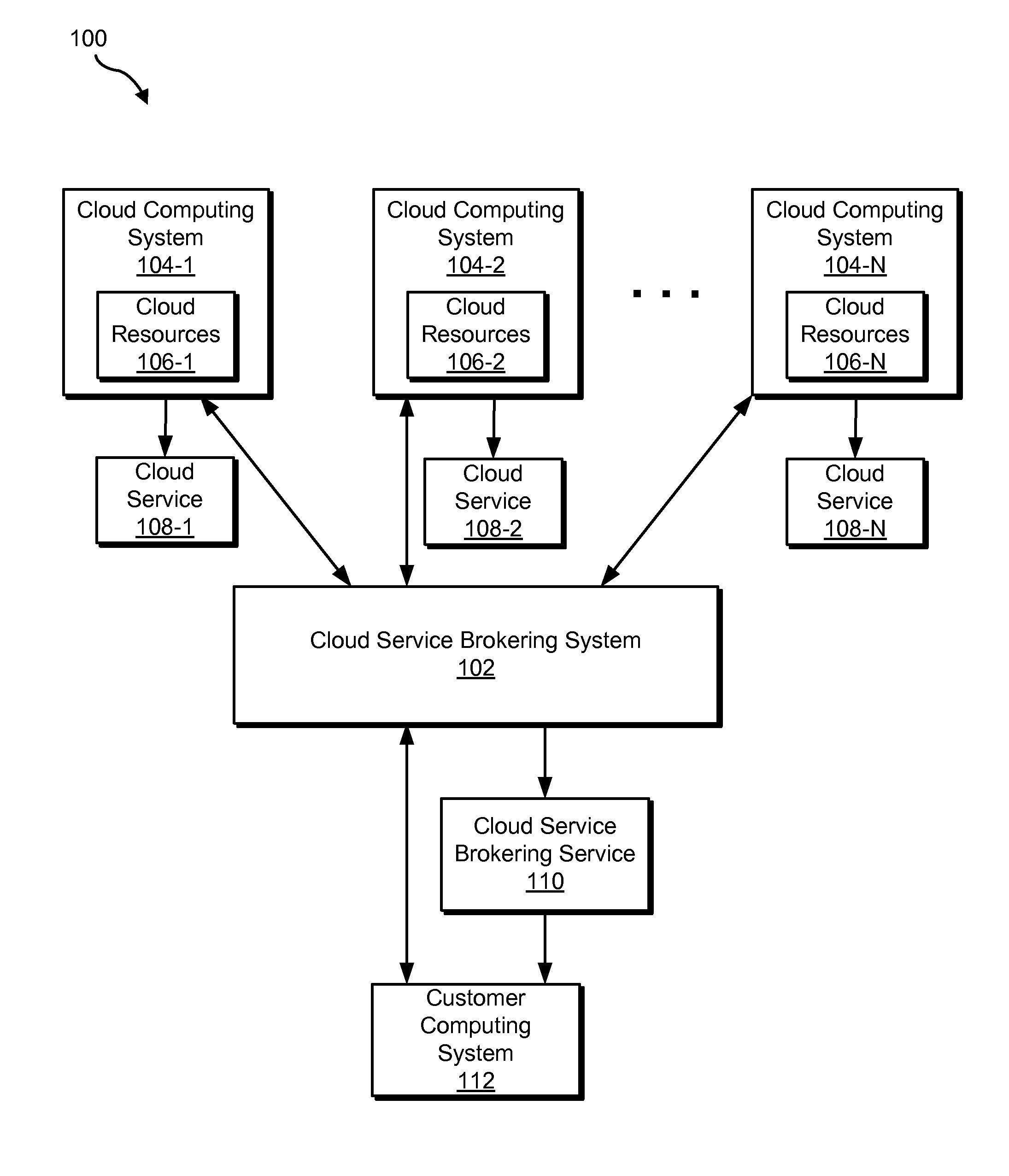
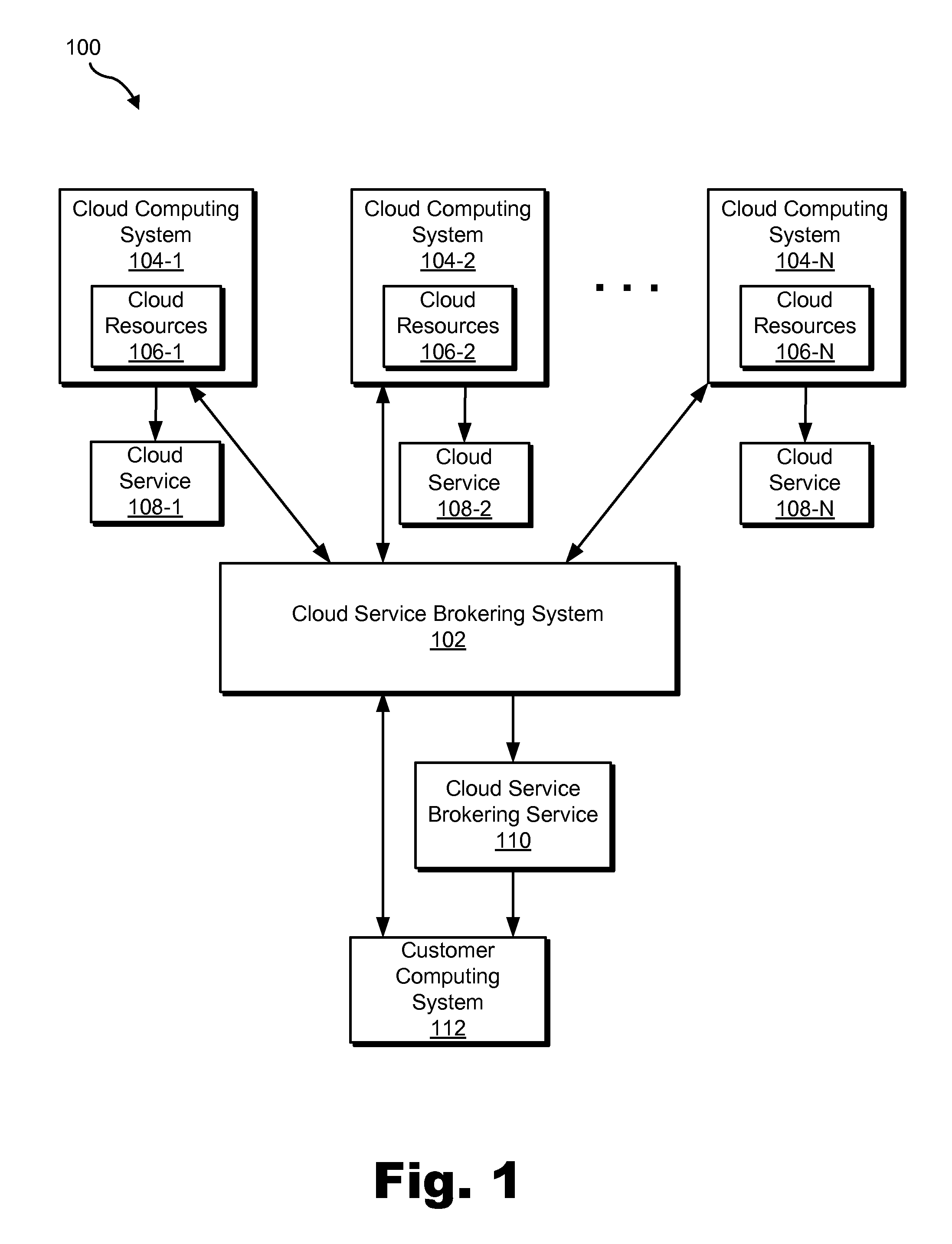
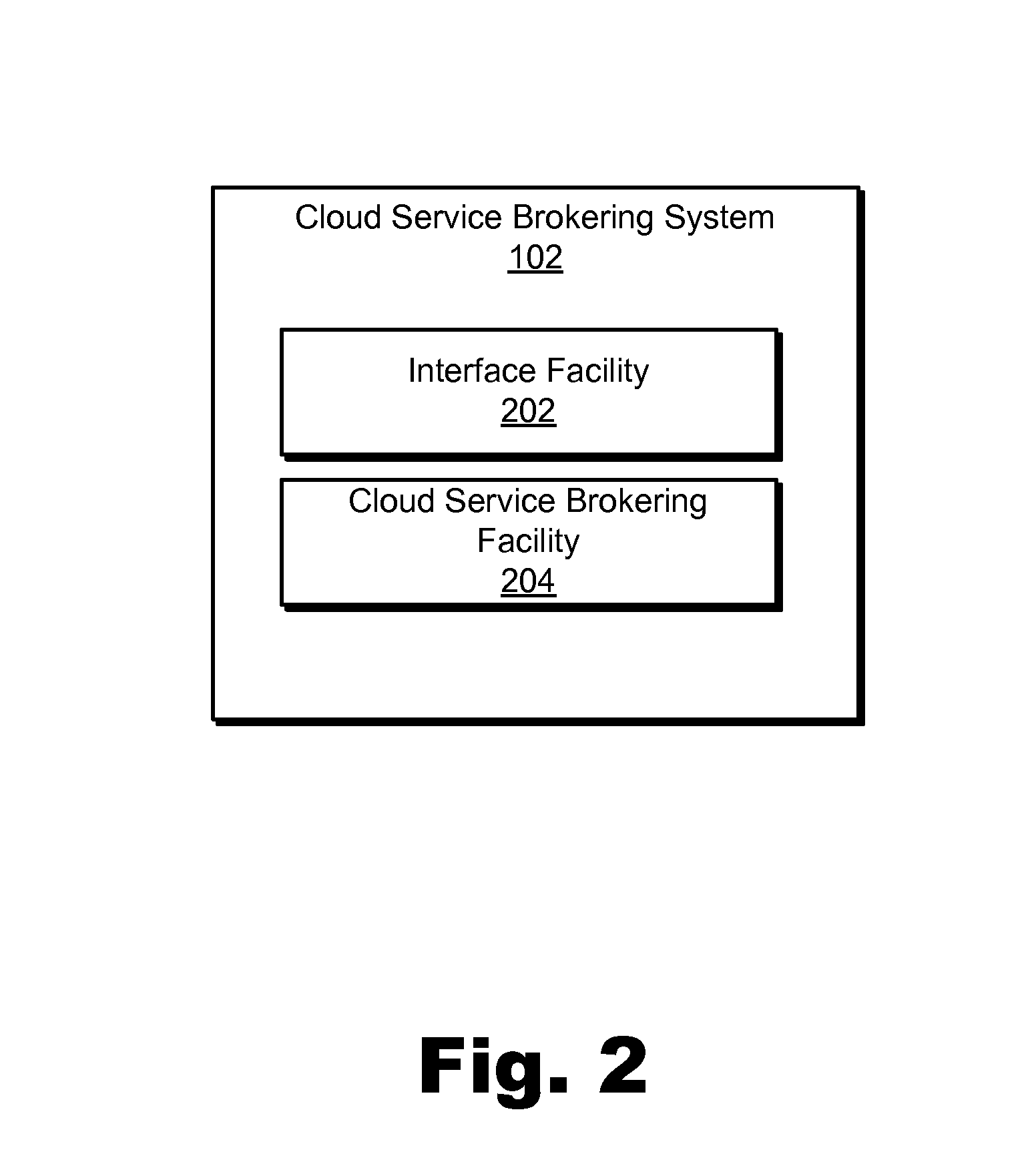
Cloud service brokering systems and methods
An exemplary method includes a computer-implemented cloud service brokering system that provides a cloud service brokering service 1) registering a plurality of cloud services with the cloud service brokering service, the plurality of cloud services provided by a plurality of cloud service providers and configured to provide distinct sets of cloud computing resources as a service, 2) receiving, from a customer of the cloud service brokering service, cloud service request information, 3) selecting, based on the cloud service request information, a cloud computing resource from the distinct sets of cloud computing resources provided by the plurality of cloud services registered with the cloud service brokering service, and 4) allocating the selected cloud computing resource for use by the customer. In certain examples, the allocating may be supported by the system configuring a customer network to support implicit and / or explicit transport requirements. Corresponding systems and methods are also described.
Owner:VERIZON PATENT & LICENSING INC
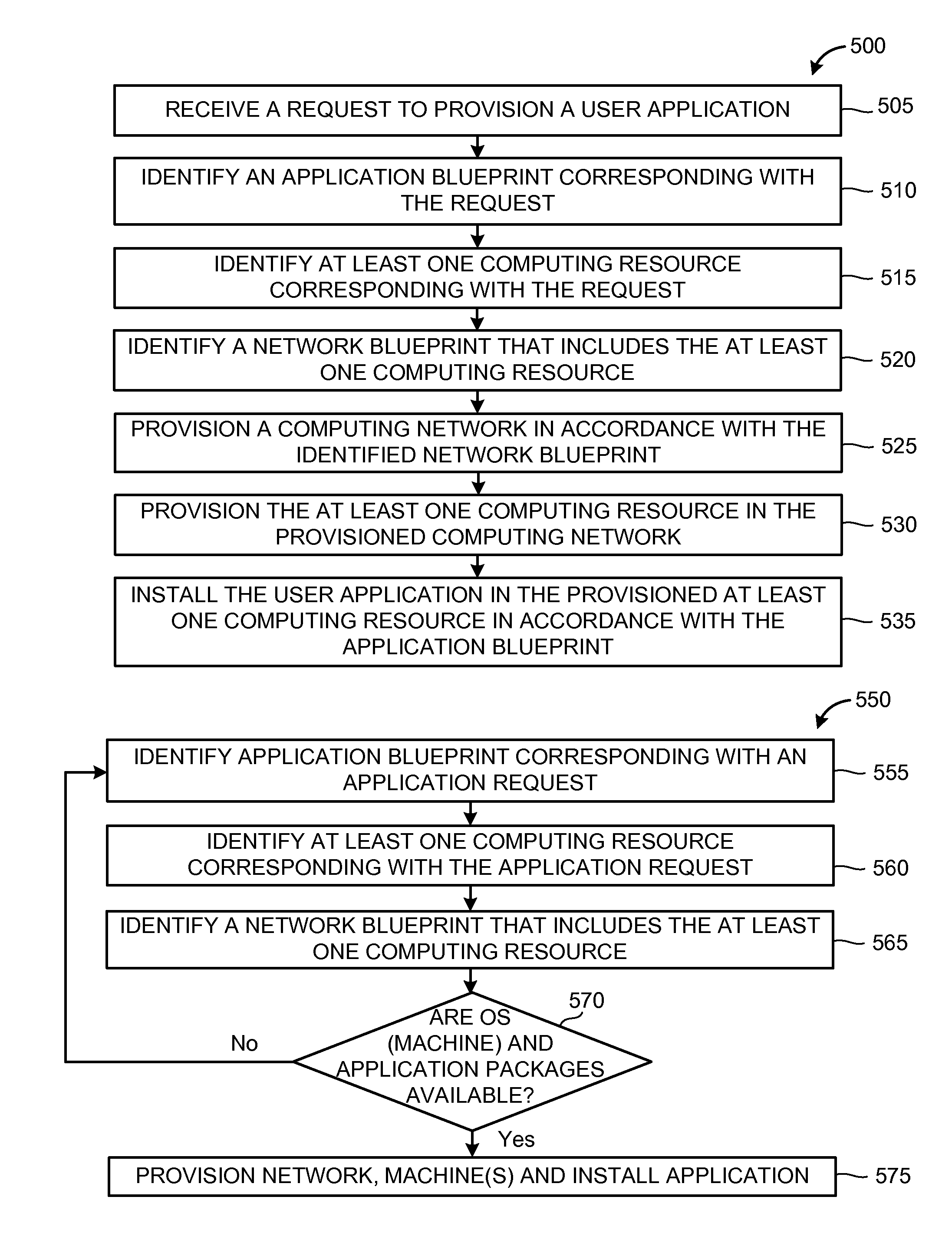
Hybrid cloud infrastructures
Methods and apparatus for implementing hybrid-cloud computing networks are disclosed. An example computer-implemented method includes receiving, at a computing device, a request to provision a user application. The method further includes identifying an application blueprint corresponding with the request and identifying at least one computing resource corresponding with the request. The method still further includes identifying a network blueprint that includes the at least one computing resource, provisioning a computing network in accordance with the identified network blueprint and provisioning the at least one computing resource in the provisioned computing network. The method also includes, installing the user application in the provisioned at least one computing resource in accordance with the application blueprint.
Owner:BLADELOGIC
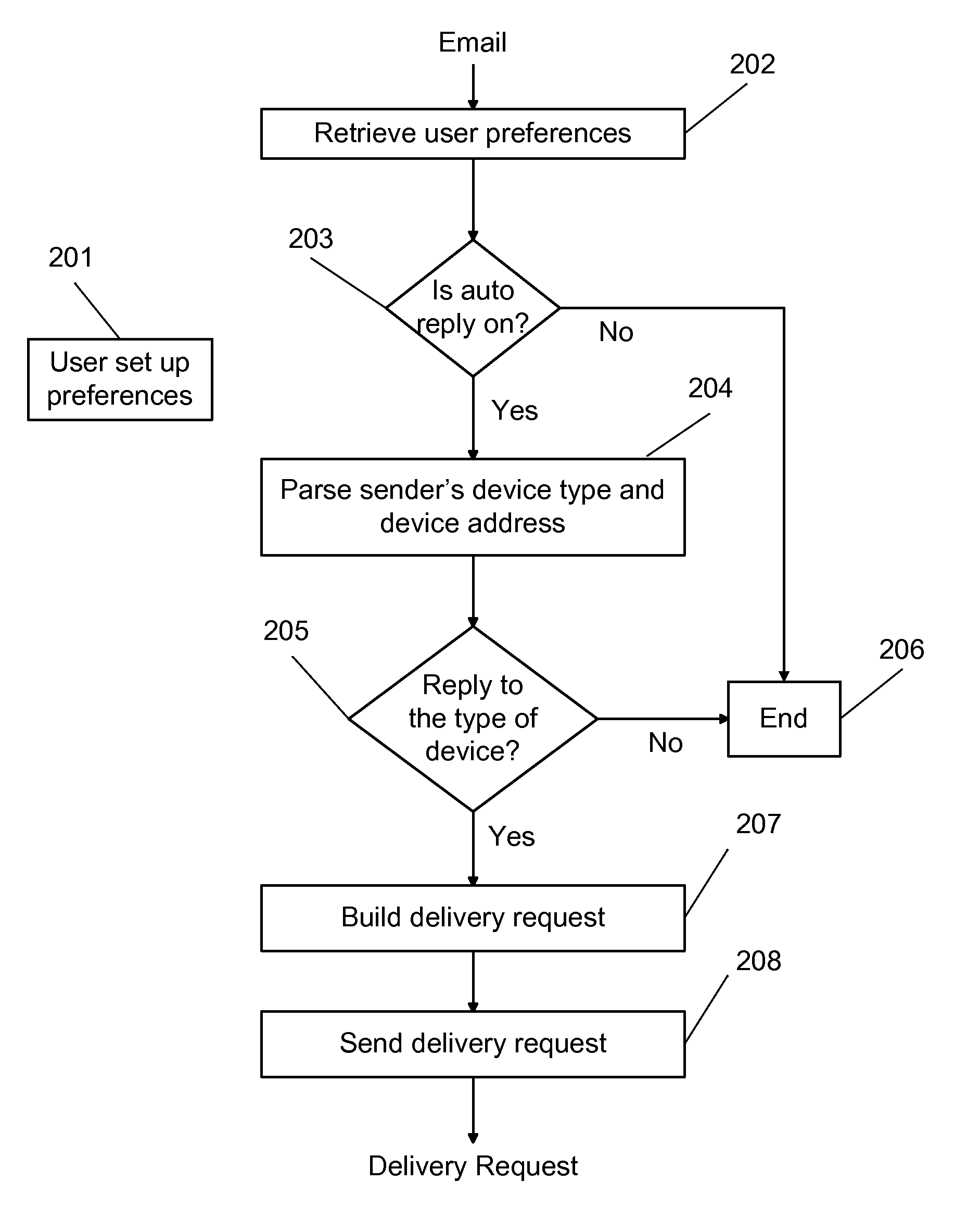
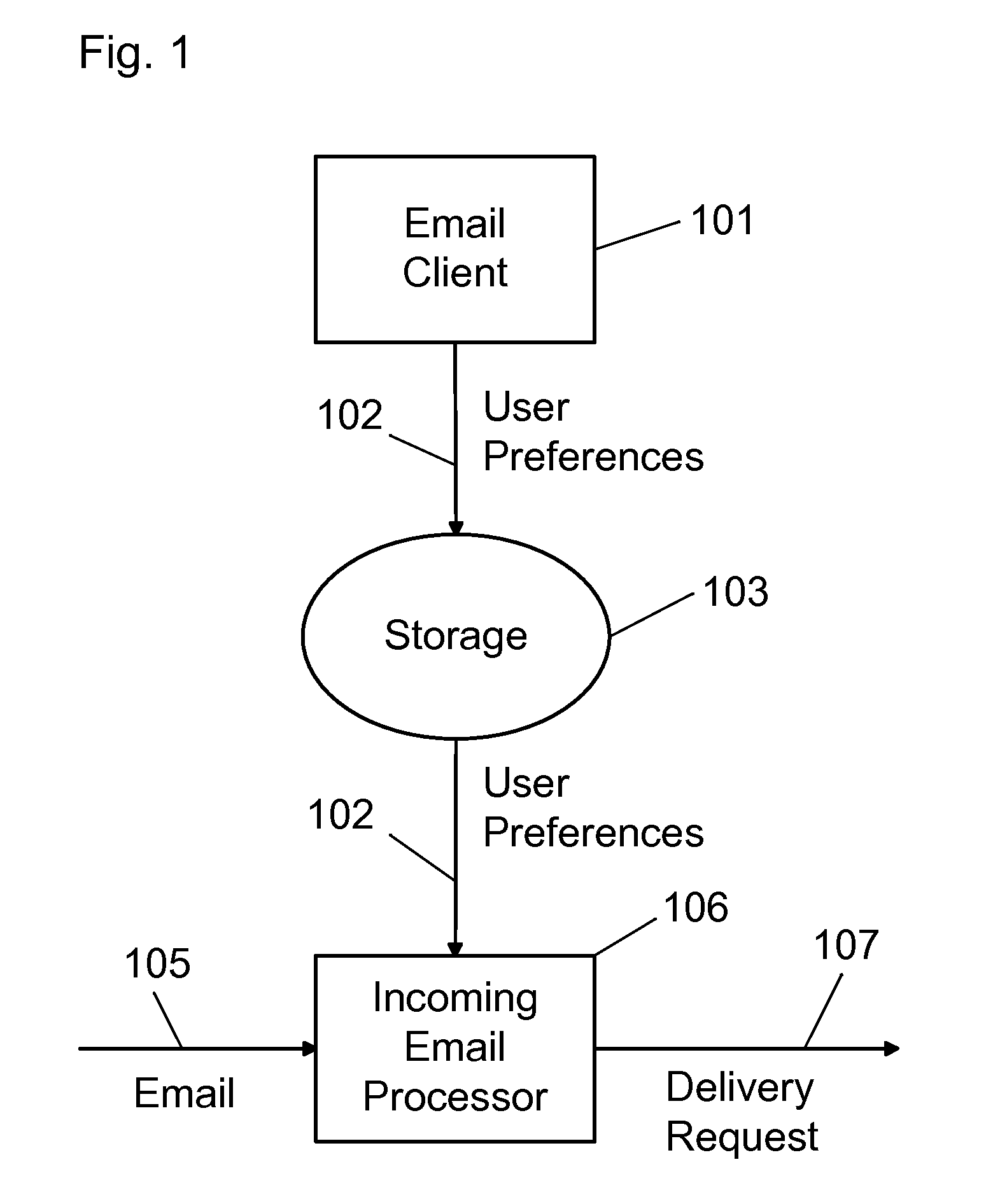
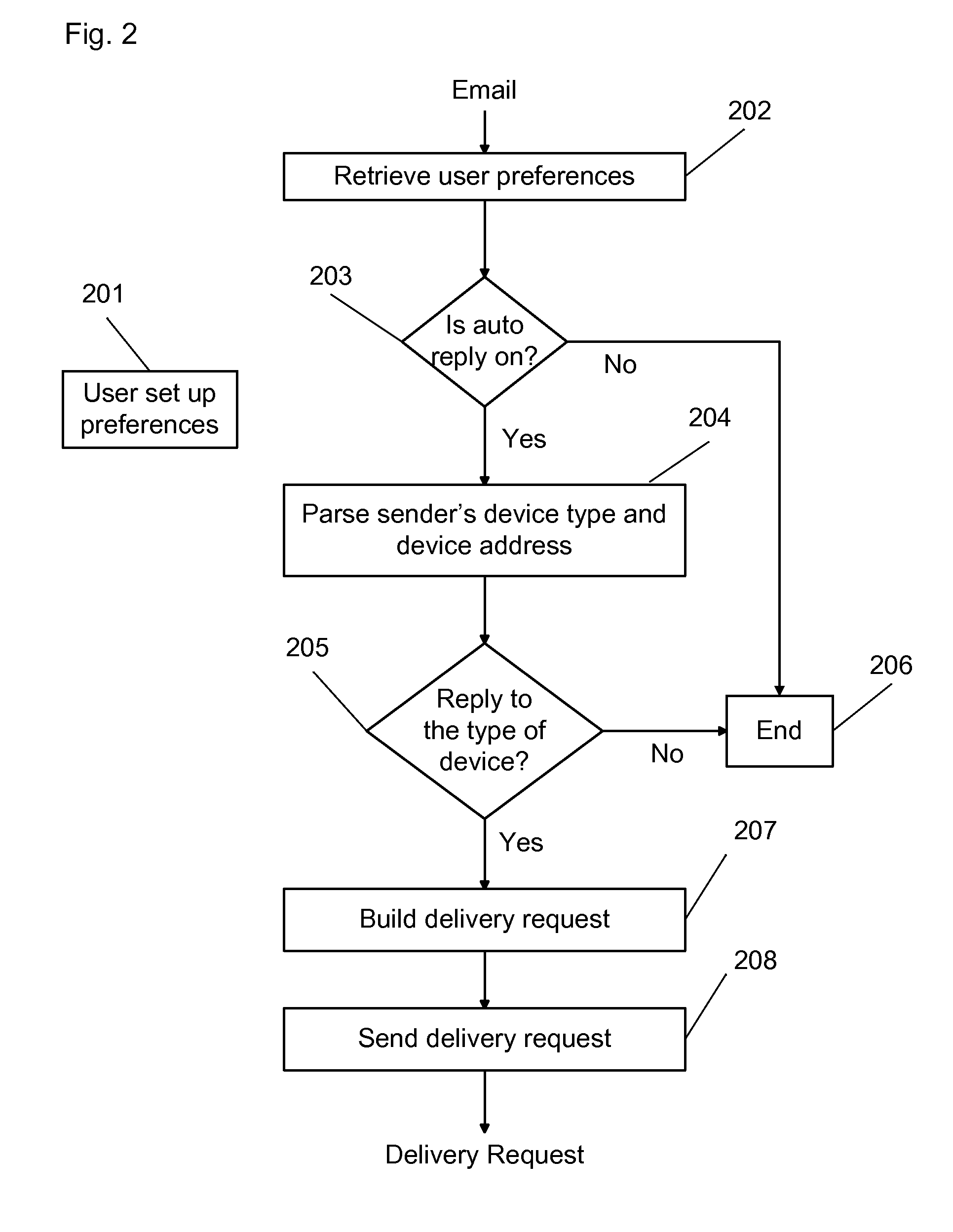
Unified auto-reply to an email coming from unified messaging service
InactiveUS20110029616A1Easily enlistedMultiple digital computer combinationsMessage deliveryCommunication device
A system and method for providing an auto-reply message in response to an incoming message sent from a message sending device and delivered by a unified messaging service as an email encoded with information about the sending device's type and address. The incoming messages may be coming from email, fax, phone, text message, instant message, MMS, TV, or other communication devices. The auto-reply function of this invention is capable of replying to the messages regardless of what type of message sending device is used. The system is preferably implemented by integrating the new technologies of unified messaging service and unified message delivery service with the email tool, and by employing the new design methodology of cloud computing.
Owner:WANG GUANMING +1
Managing services in a cloud computing environment
What is provided are a system and method which enables an organization or user to manage computational services in a cloud computing network for security, compliance and governance. The management including creating a trusted virtual network including encrypted data storage, encrypted data transport, and trusted instances of servers all communicatively coupled together forming a trusted cloud computing environment that is associated with the organization. A web portal running on a web server provides a point of access to the cloud computing environment. A workflow is accessed to implement one or more policies in trusted computing environment to manage the trusted cloud computing environment, the workflow customized to the organization. The access control; and to the trusted cloud computing environment is used to ensure access by users authorized by the organization to ensure compliance with adopted standards.
Owner:CLOUDNEXA
Secure virtual network platform for enterprise hybrid cloud computing environments
ActiveUS20140244851A1Broaden applicationEasy to deployMultiple digital computer combinationsData switching networksVirtual platformCloud computing
A secure virtual network platform connects two or more different or separate network domains. When a data packet is received at an end point in one network domain, a determination is made as to whether the data packet should be forwarded outside the virtual network platform, or transmitted via the virtual network to a destination in another network domain connected by the virtual network platform.
Owner:ZENTERA SYST
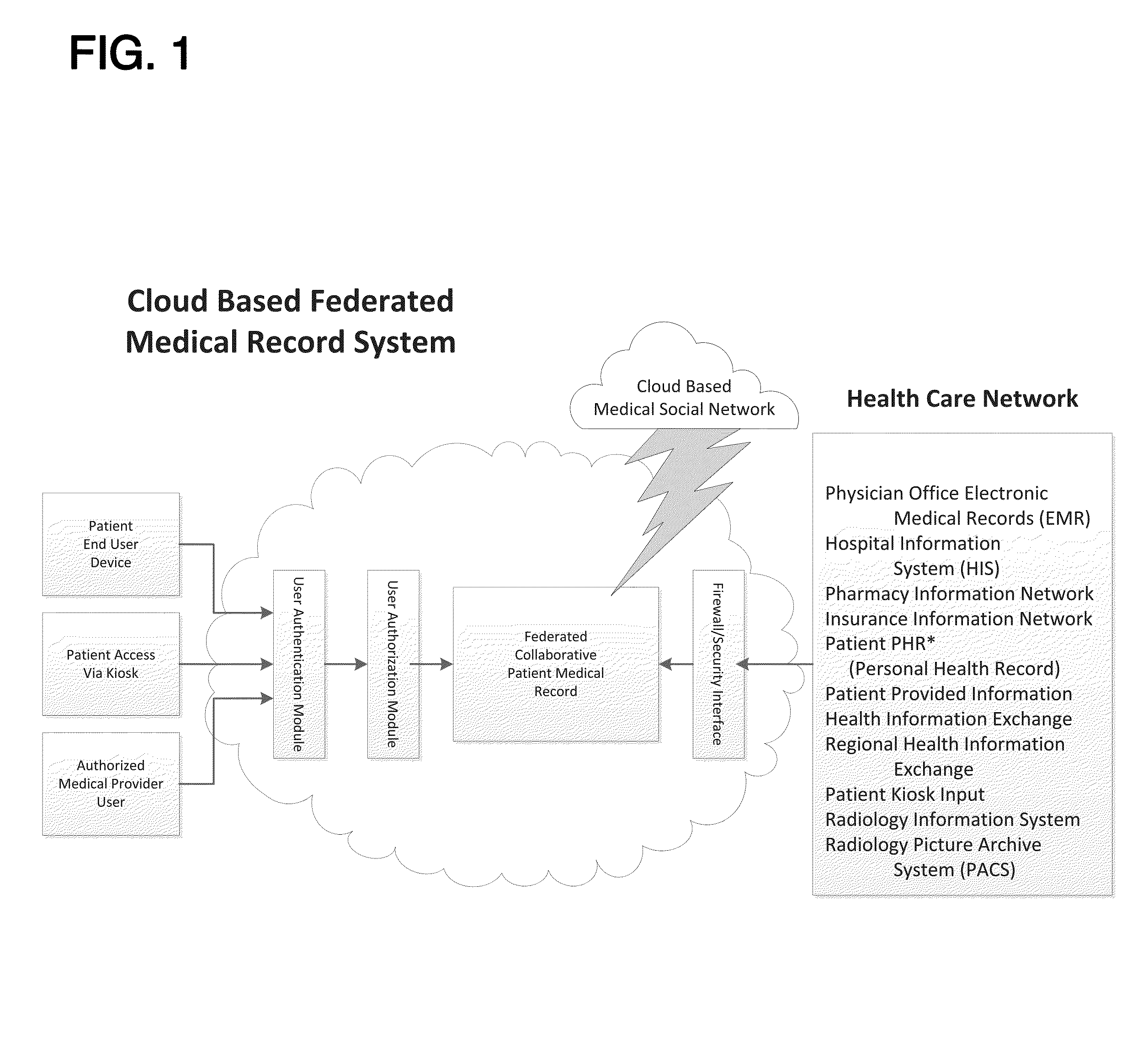
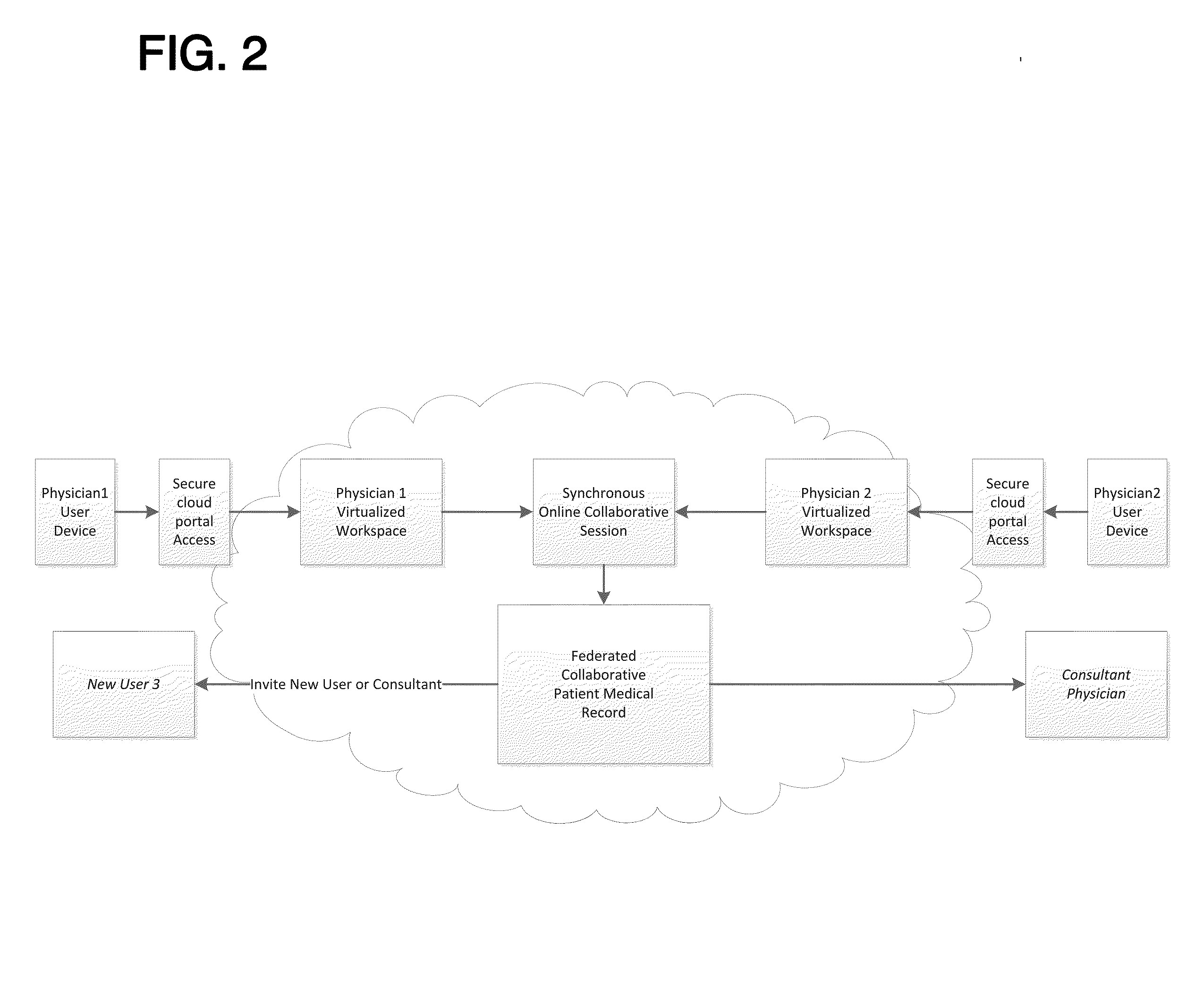
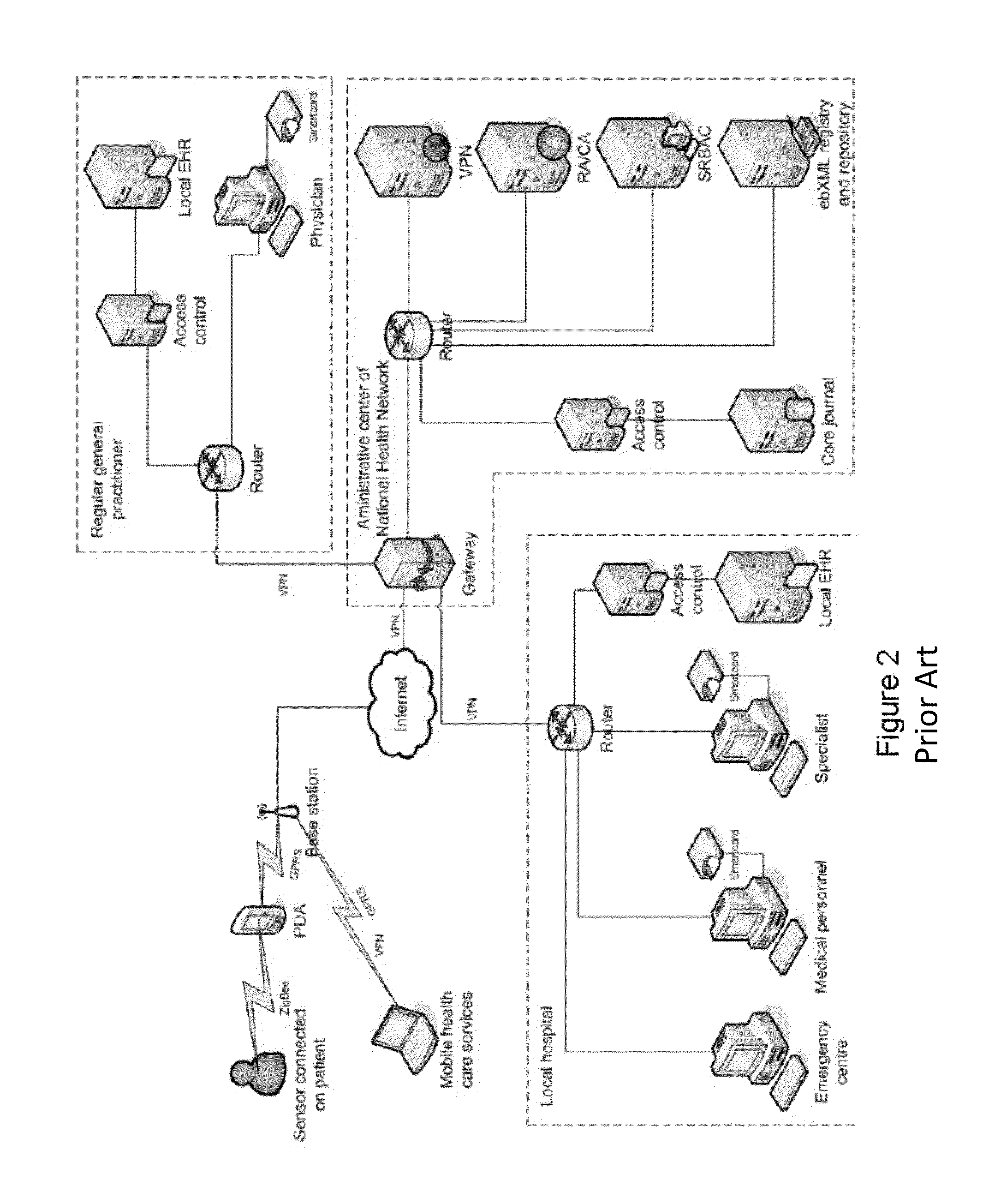
Federated Collaborative Medical Records System Utilizing Cloud Computing Network and Methods
InactiveUS20150261917A1Digital data protectionPatient personal data managementMedical recordComputer terminal
A cloud-based, federated collaborative medical records system and methods, in the preferred embodiments, features a variety of mechanisms to enable end users to store, access, edit, and share health information, on demand. A key aspect of said embodiments involves the circumvention of barriers preventing the transfer of health information placed upon other electronic medical records systems and related systems preventing users who are not part of a specific business entity from accessing the records. The preferred embodiments of the present invention delegate control over medical information to those individuals who need access to such medical information at the appropriate time.
Owner:SMITH DOUGLAS K
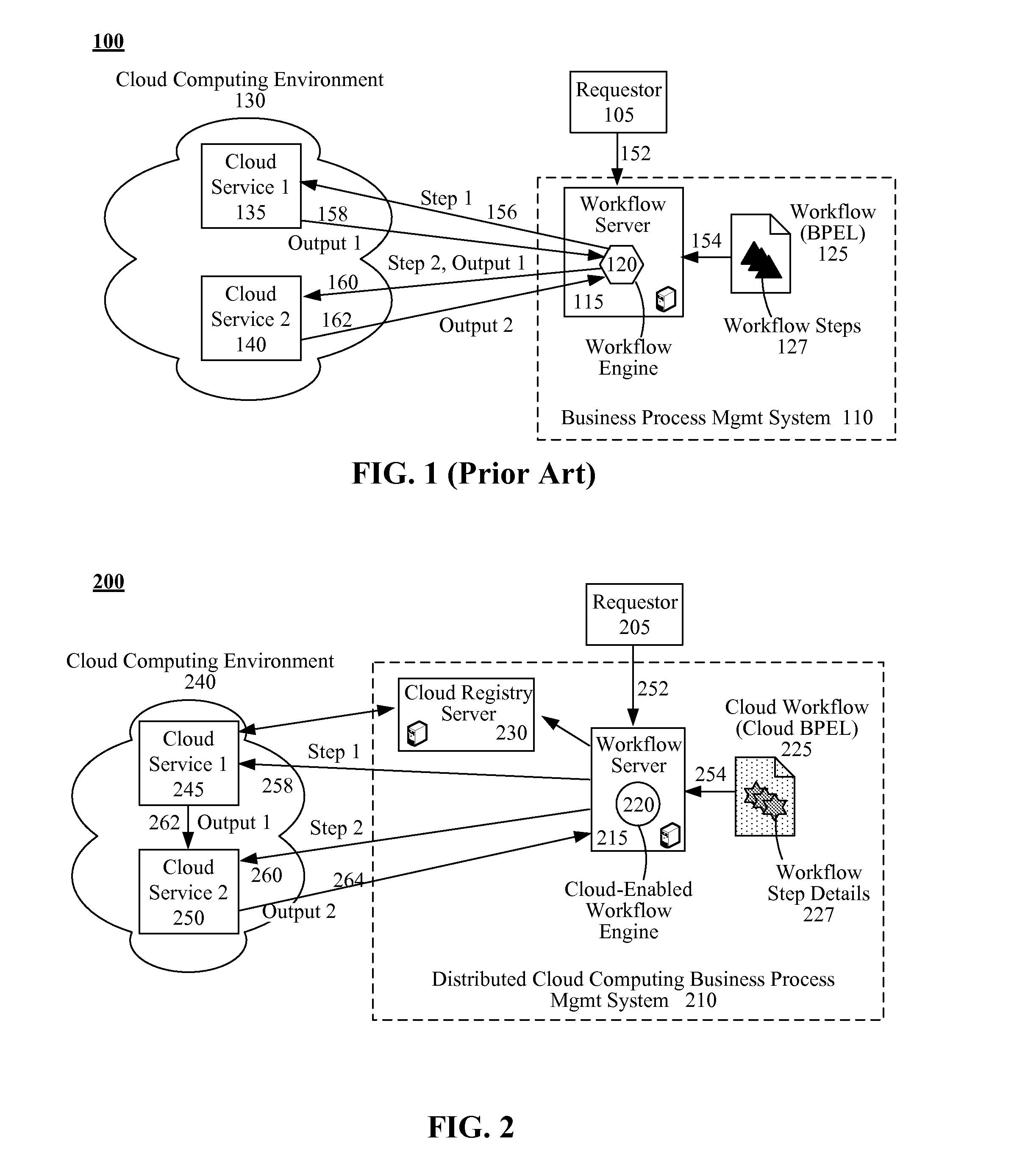
Dynamically optimized distributed cloud computing-based business process management (BPM) system
InactiveUS20110238458A1Short timeLow costMultiple digital computer combinationsProgram controlService provisionBusiness management
A workflow server can receive requests, each for a business process workflow conforming to a business process model. Each business process workflow can include a set of interdependent tasks. The workflow server can satisfy received requests by assigning tasks to different service providers that provide software services. Each of the tasks can be assigned to corresponding ones of the software services. For each task, the workflow server can also defines an allocated cost per software service, and a time allocation per software service for completing the corresponding one of the tasks. Different service providers, including those assigned to tasks, can receive information for ones of the tasks not directly assigned to them by the workflow server. The different service providers can then bid on these tasks. Wherein when bids are won, tasks for a business process flow can be reassigned based on winning bids.
Owner:IBM CORP
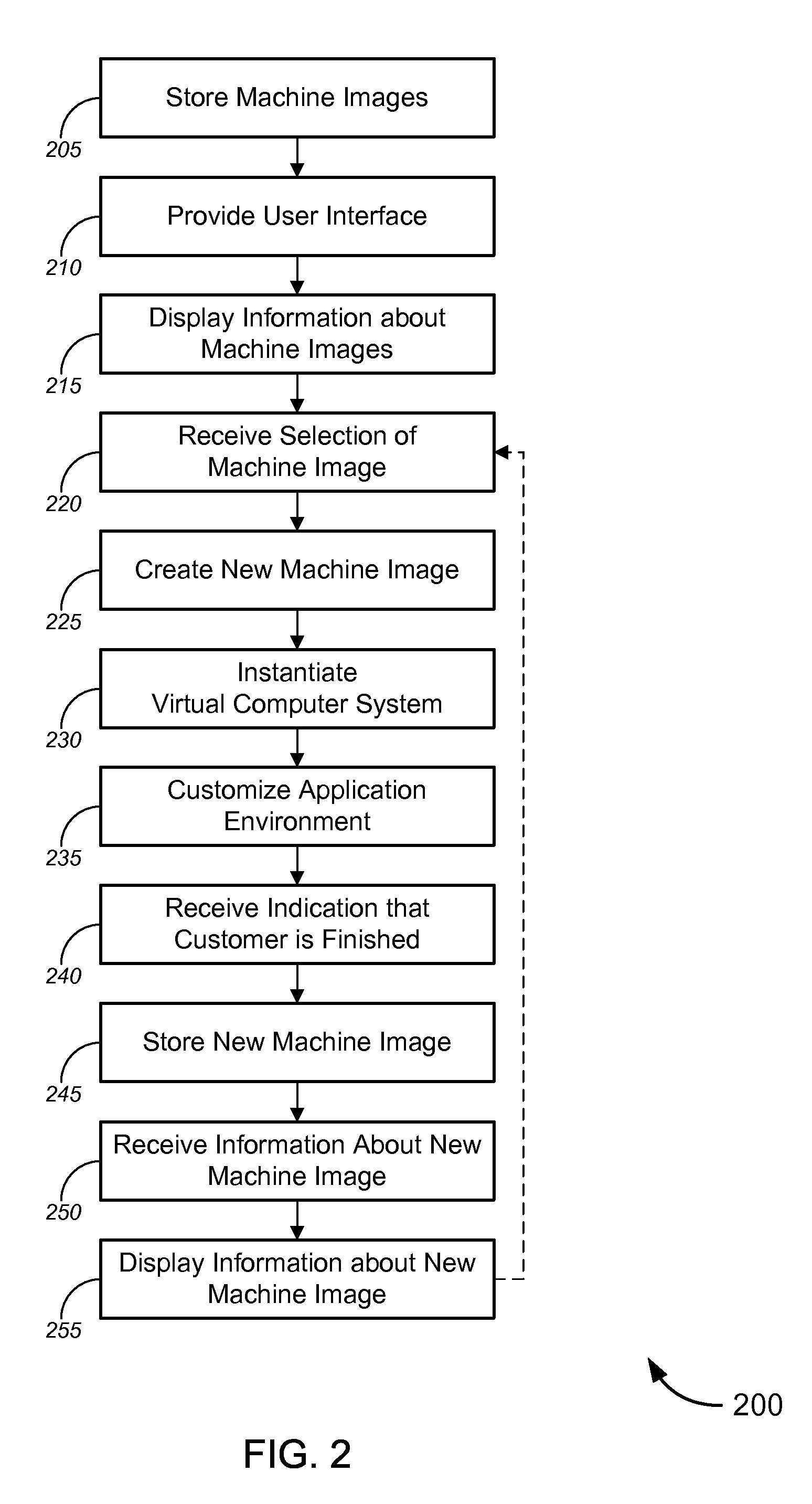
Managing virtual machines
ActiveUS20110055714A1Multiple digital computer combinationsProgram loading/initiatingComputerized systemUser interface
Tools and techniques for managing virtual machines, including without limitation virtual machines running in a cloud computing environment. Certain tools provide a user interface that allows a user to browse machine images to find an image that meets the user's needs. In some aspects, these tools and techniques can provide the ability for users to customize machine images to meet their own needs and / or to share their customized machine images with other users. In other aspects, these tools and techniques can provide users with the ability to export virtual machines for use on an actual computer system.
Owner:ORACLE INT CORP
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Online systems and methods for advancing information organization sharing and collective action
ActiveUS9253609B2Easily scaledHighly versatileInput/output for user-computer interactionData processing applicationsKnowledge organizationMobile device
Methods and systems and mobile device interfaces for creating, joining, organizing and managing via mobile devices affinity groups in a cloud computing environment for social and business purposes.
Owner:HOSIER DOUG
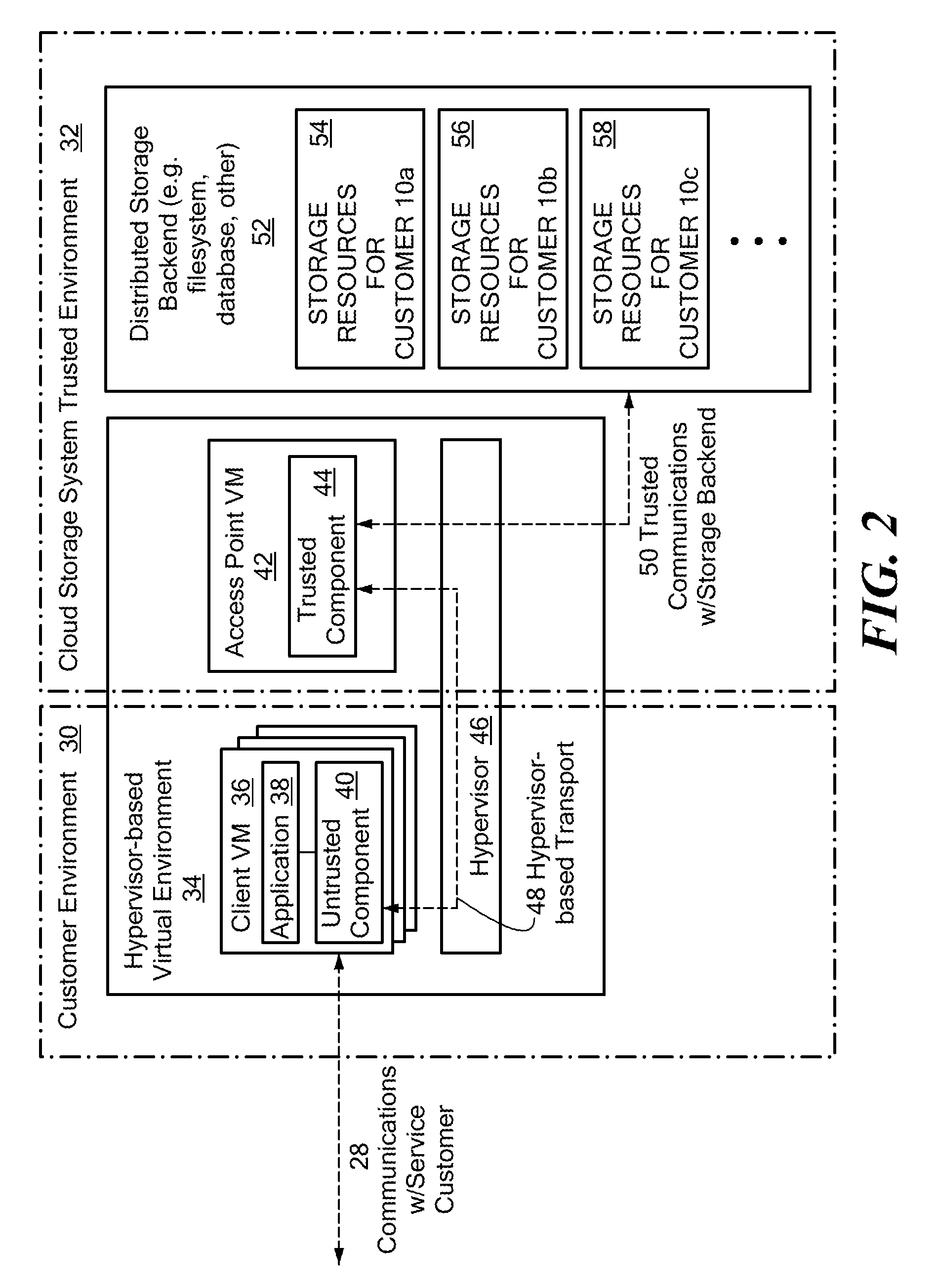
Scalable and secure high-level storage access for cloud computing platforms
ActiveUS8352941B1Effective segmentationImprove the level ofMultiprogramming arrangementsSoftware simulation/interpretation/emulationTrusted componentsTrust relationship
An untrusted component exposing a high level storage object interface within an untrusted client virtual machine accepts application level storage object operations. Responsive to a storage object operation, the untrusted component passes a message through the underlying hypervisor to an associated trusted component. The trusted component processes the message by authenticating the client virtual machine and locating an internal mapping between the client virtual machine and an associated customer-specific set of backend storage resources to which the requested storage object operation is to be applied. The trusted component uses a trust relationship with the backend storage system to securely communicate the storage object operation to the backend storage system, and passes the operation results through the hypervisor back to the untrusted component in the source client virtual machine from which the storage object request originated.
Owner:EMC IP HLDG CO LLC
Systems and methods for bridging and managing media content associated with separate media content networks
ActiveUS20120304233A1Digital data processing detailsMultiple digital computer combinationsCloud computingService networks
An exemplary system includes at least one computing device located within a local media content network and configured to 1) generate a media index of local media content stored by one or more media content access devices located within the local media content network and cloud media content stored by one or more cloud computing devices located within a cloud media content service network and 2) manage the local media content and the cloud media content based on the media index and on a predefined media management heuristic. Corresponding methods, systems, and apparatus are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
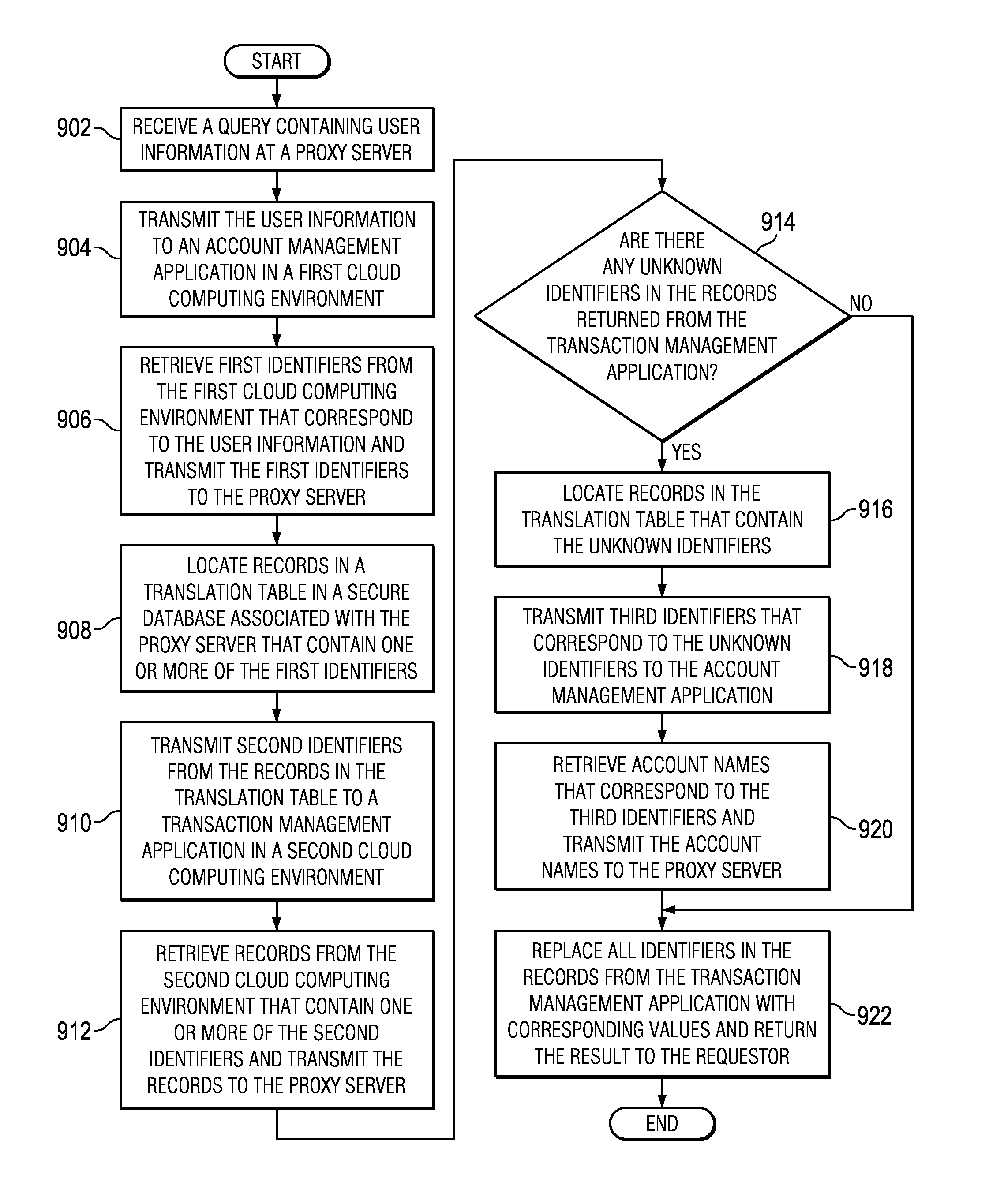
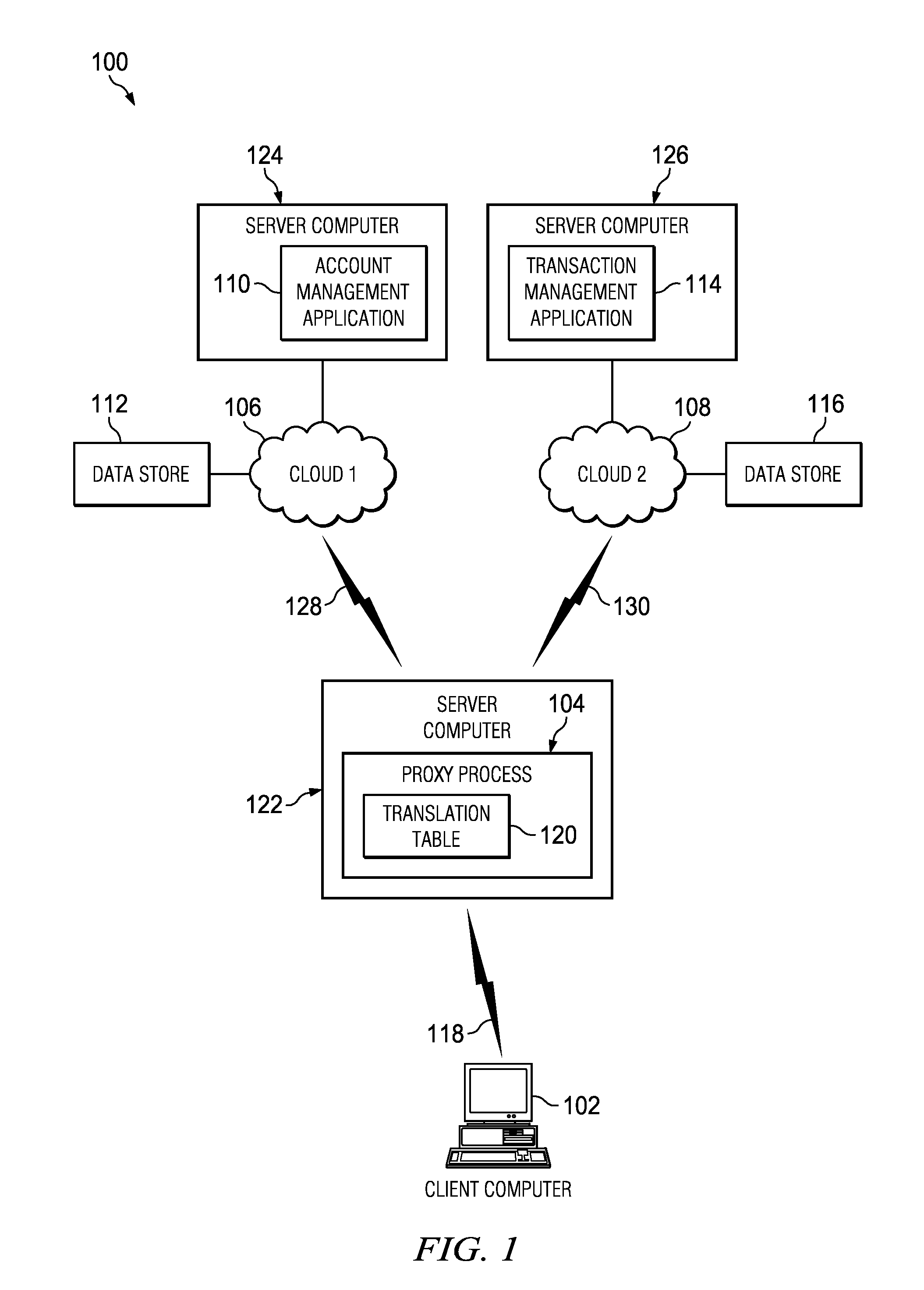
Managing sensitive data in cloud computing environments
ActiveUS9460307B2Digital data processing detailsDigital data protectionTranslation tableCloud computing
The illustrative embodiments provide a method, computer program product, and apparatus for managing collectively sensitive data. Collectively sensitive data is divided into a first partition for reassembly data, a second partition of the collectively sensitive data, and a third partition of the collectively sensitive data. Each of the second partition and the third partition are collectively nonsensitive in isolation. The first partition is stored in a translation table in a secure database. The translation table is configured for use in assembling collectively sensitive data from the second partition and the third partition. The second partition of the collectively sensitive data is stored in a first database associated with a first cloud computing environment. The third partition of collectively sensitive data is stored in a second database associated with a second cloud computing environment.
Owner:INT BUSINESS MASCH CORP
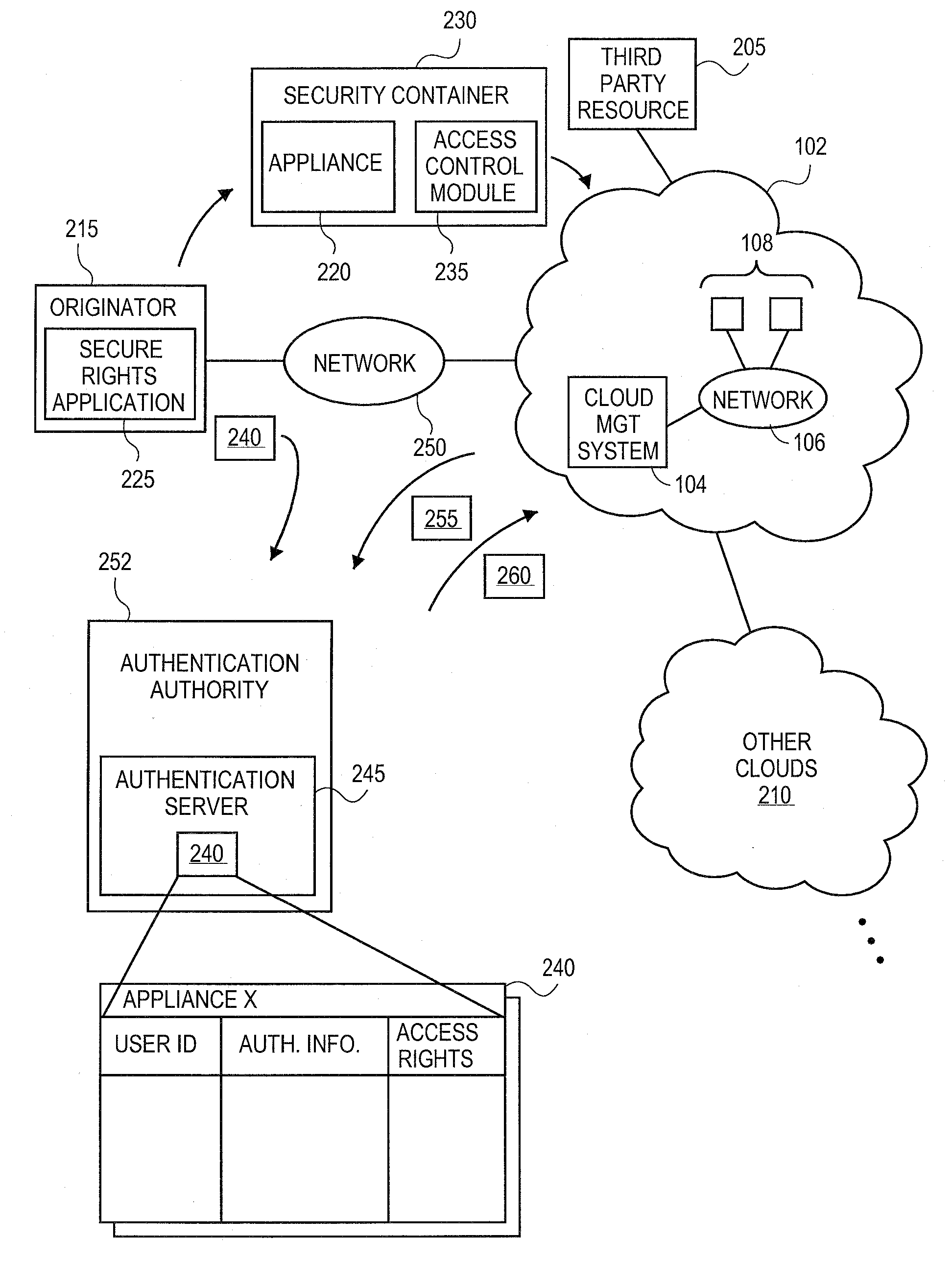
Methods and systems for securing appliances for use in a cloud computing environment
ActiveUS20100132016A1Digital data processing detailsUser identity/authority verificationOperational systemSecurity level
An originator of an appliance can independently secure the appliance for instantiation in the cloud, separate from the security level of the cloud. The originator can secure the appliance utilizing a secure rights application. The secure rights application can be configured to “wrap” an appliance in a security container. The security container can limit access to the applications and operating systems contained in the appliance, but allow the appliance to operate normally once instantiated in the cloud. The secure rights application can be configured to cryptographically secure the appliance in order limit the ability of unauthorized parties from accessing the components of the appliance while maintaining the functionality of the appliance.
Owner:RED HAT
Cloud-Based Middlebox Management System
ActiveUS20140068602A1Effectively scaledData switching networksSoftware simulation/interpretation/emulationApplication softwareMiddleware
A virtual network virtual machine may be implemented on a cloud computing facility to control communication among virtual machines executing applications and virtual machines executing middlebox functions. This virtual network virtual machine may provide for automatic scaling of middleboxes according to a heuristic algorithm that monitors the effectiveness of each middlebox on the network performance as application virtual machines are scaled. The virtual machine virtual network may also locate virtual machines in actual hardware to further optimize performance.
Owner:WISCONSIN ALUMNI RES FOUND
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS8514868B2Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
Secure Workflow and Data Management Facility
ActiveUS20100299763A1Digital data processing detailsAnalogue secracy/subscription systemsCommunications managementSecure communication
Disclosed is a computer program that provides a secure workflow environment through a cloud computing facility, wherein the secure workflow environment may be adapted to (1) provide a plurality of users with a workspace adaptable to provide secure document management and secure communications management, wherein the users comprise at least two classes of user, including a participant and a subscriber, the subscriber having control authority within the workspace that exceeds that of the participant and the participant having control over at least some of the participants own interactions with the workspace, (2) maintain a secure instance of each communication provided by each of the users such that each communication can be managed, (3) maintain a secure instance of each document interaction provided by each user such that each interaction can be managed; and extending the secure workflow environment to the users through a secure network connection.
Owner:PALO ALTO NETWORKS INC
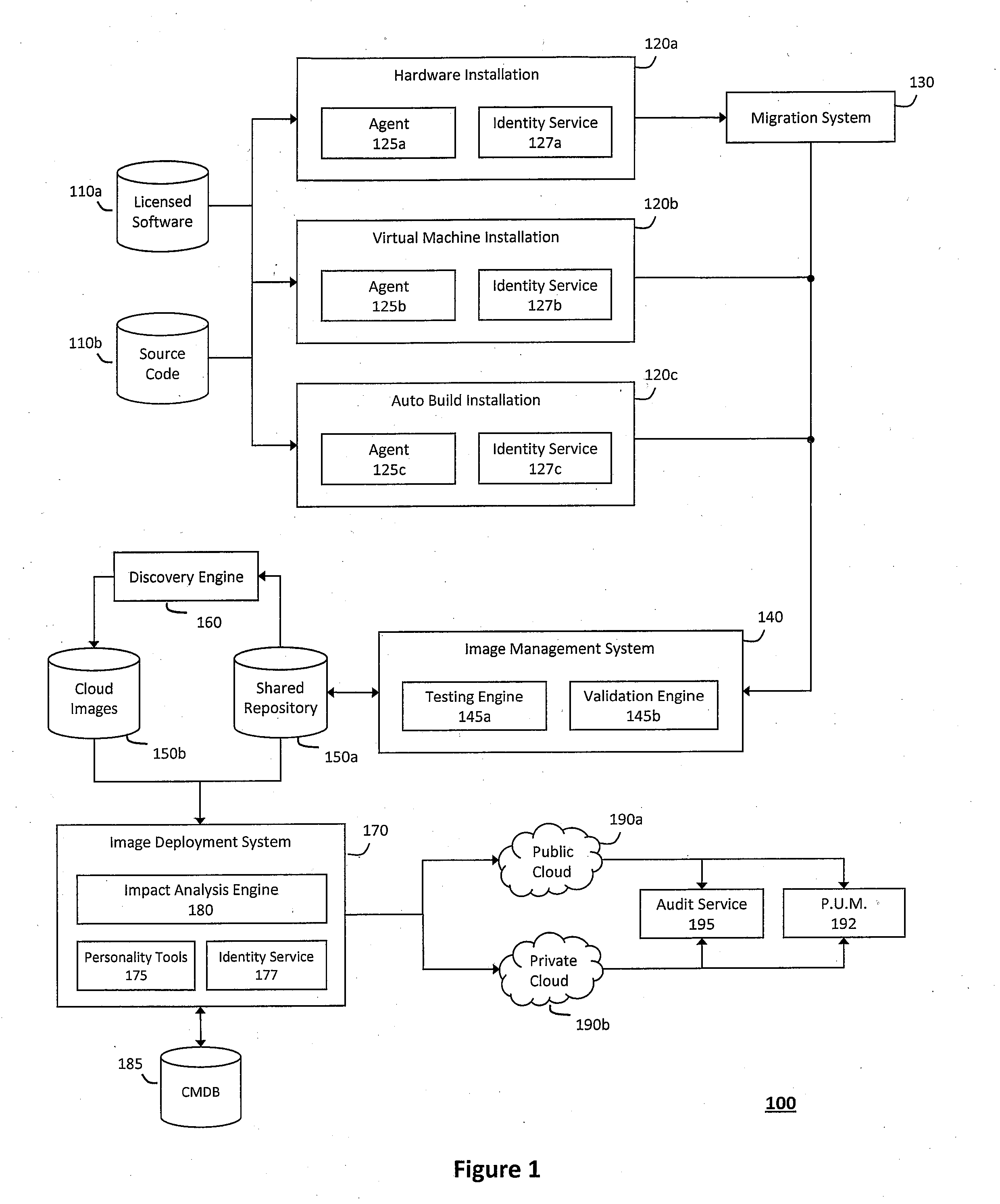
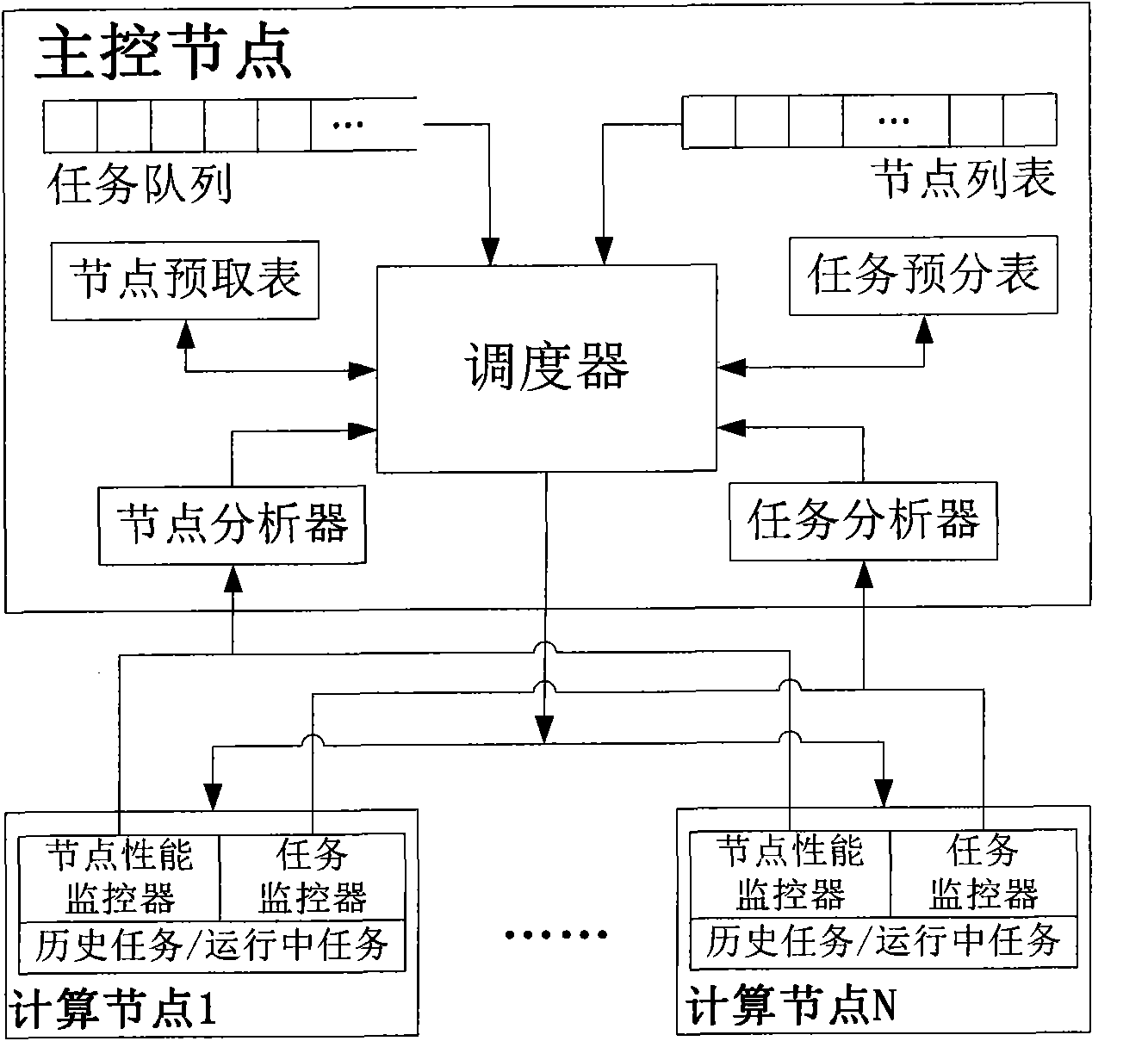
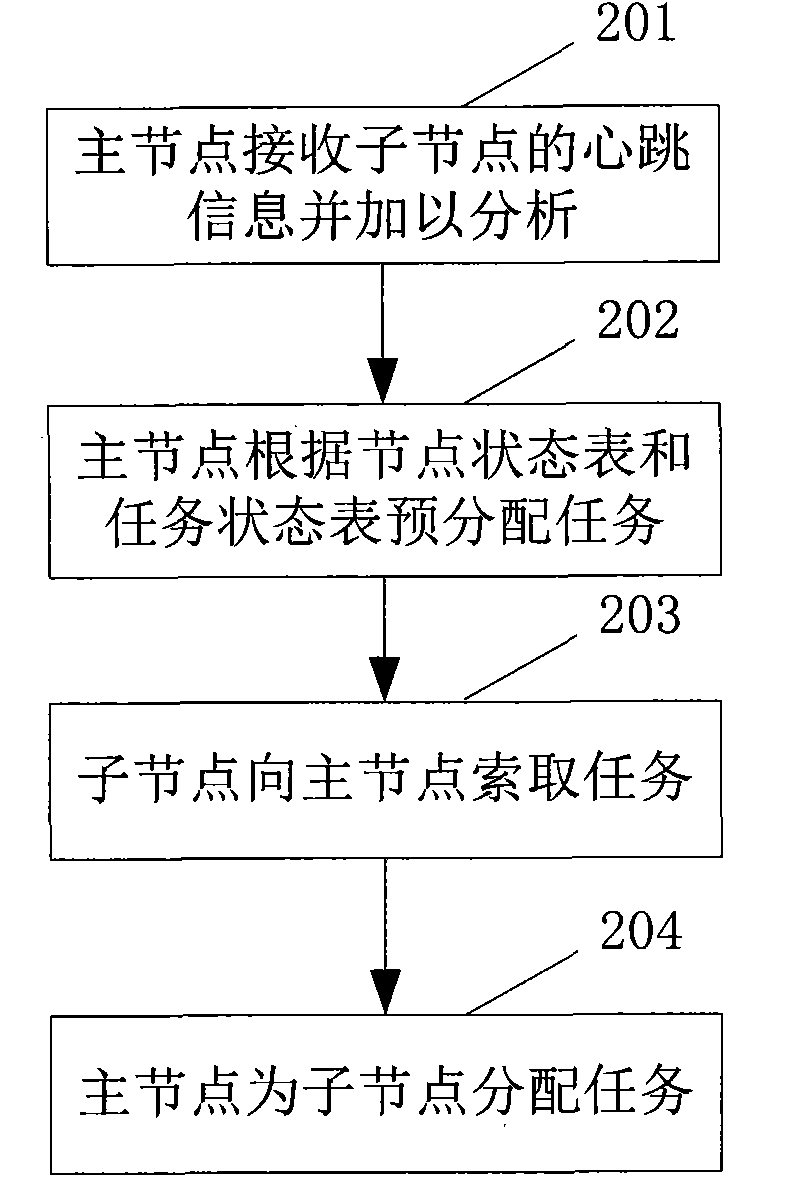
Task-dynamic dispatching method under distributed computation mode in cloud computing environment
InactiveCN102073546AReasonable distributionSolve bottlenecksResource allocationResource utilizationCloud computing
The invention provides a task-dynamic dispatching method under a distributed computation mode in a cloud computing environment, which comprises the following four steps: 1. a main node receives and analyzes heartbeat information of a subsidiary node; 2. the main node previously distributes the task according to a node state table and a task state table; 3. the subsidiary node demands the task from the main node; and 4. the main node distributes the task to the subsidiary node. The method firstly considers the resource demand of the task and the performance information of the nodes, and dynamically controls the distribution of the task under the condition that the requirement is met, so that the response speed of the work and the resource utilization of the nodes are improved. The method has wide practical value and application prospect in the technical field of the distributed computation in the cloud computing environment.
Owner:SHANGHAI JUNESH INFORMATION TECH CO LTD
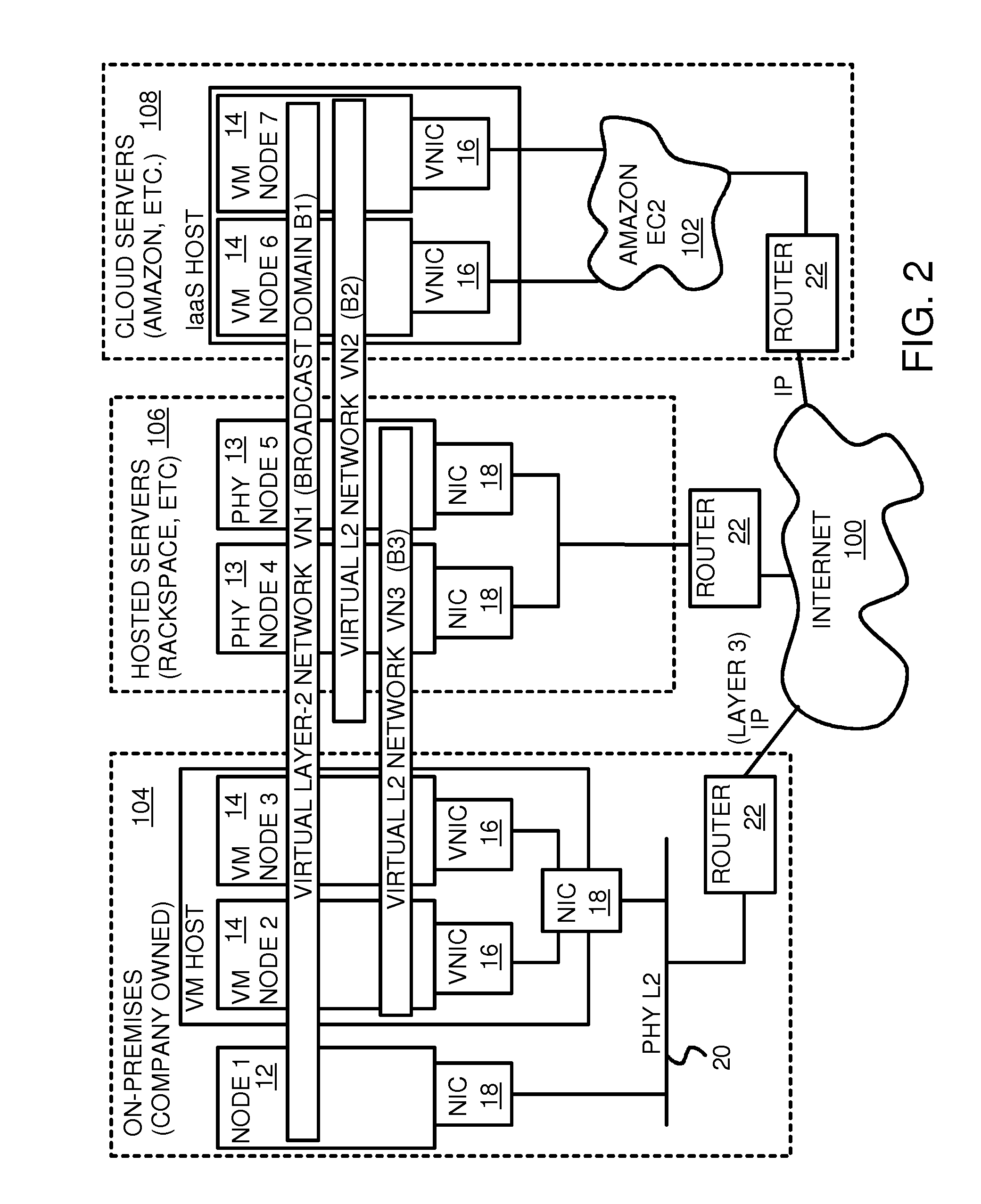
User-configured on-demand virtual layer-2 network for infrastructure-as-a-service (IaaS) on a hybrid cloud network
A virtual network is overlaid upon physical networks. The virtual network is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. A VN device driver shim intercepts LAN packets and their virtual MAC and IP addresses and encapsulates them with physical packets that can be routed over the Internet. As new nodes are created, a VN switch table is expanded so that all nodes on the virtual network can reach the new node. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A VN configuration controller in a central server updates the VN switch tables. Organizations can expand their virtual network as nodes are created at remote cloud computing providers without action by the staff at the cloud computing provider. Hybrid cloud virtual networks include on-premises physical and virtual-machine nodes, and off-premises guest nodes and instances.
Owner:CISCO TECH INC
Online Systems and Methods for Advancing Information Organization Sharing and Collective Action
ActiveUS20140282016A1Easy to scaleWide range of functionsInput/output for user-computer interactionData processing applicationsKnowledge organizationMobile device
Methods and systems and mobile device interfaces for creating, joining, organizing and managing via mobile devices affinity groups in a cloud computing environment for social and business purposes.
Owner:HOSIER DOUG
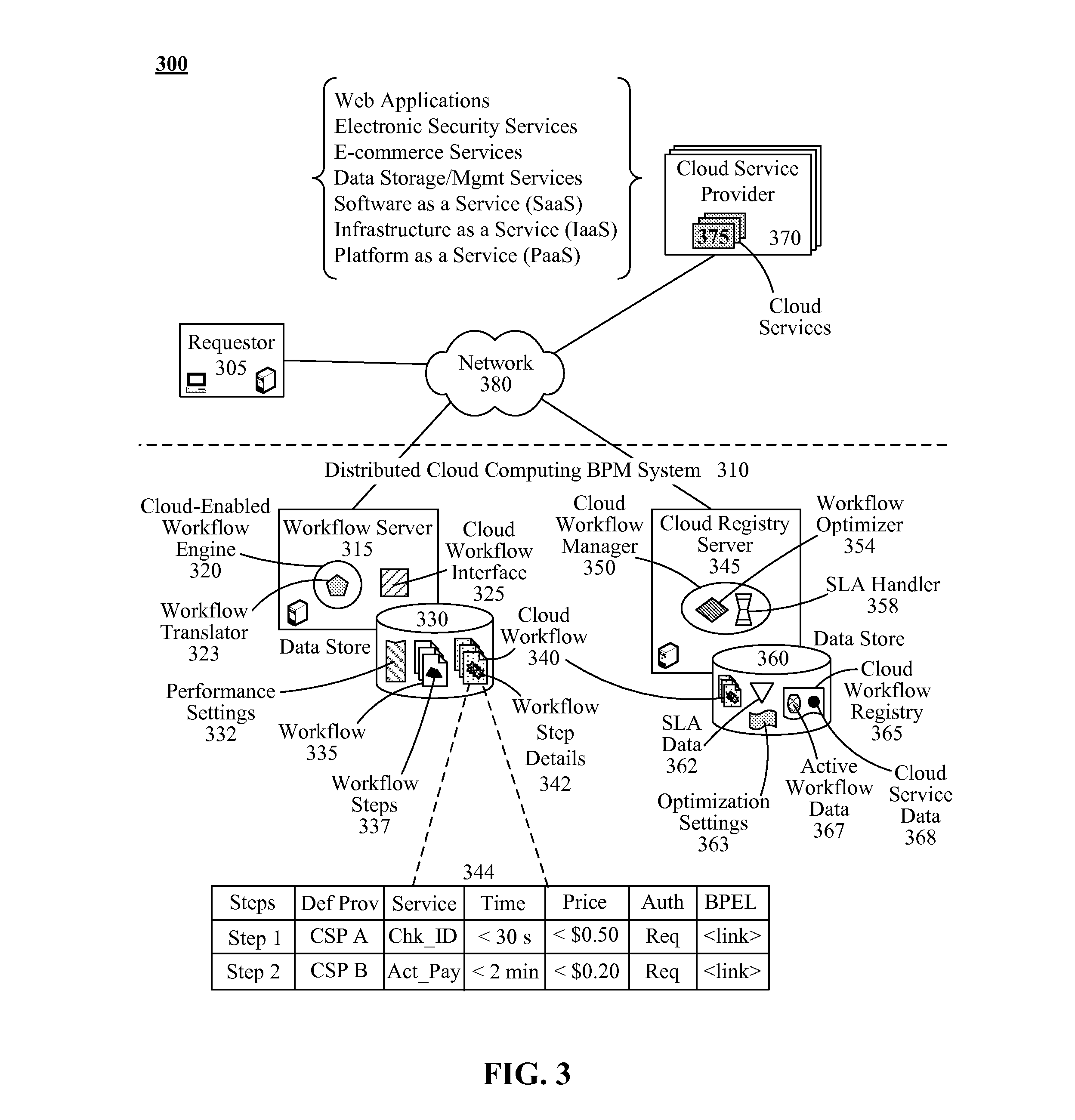
Provisioning services using a cloud services catalog
The present invention provides a system and method for provisioning Cloud services by establishing a Cloud services catalog using a Cloud service bus within a Cloud computing environment. In one embodiment, there is a Cloud services catalog manager configured to connect a plurality of Clouds in a Cloud computing environment; maintain a catalog of integrated Cloud services from the plurality of connected Clouds; and display an index of the integrated services on a user interface. Using this system and method will allow for multiple disparate services, offered by different partners, across unrelated, physically distinct Clouds to be presented as an index of integrated services.
Owner:IBM CORP
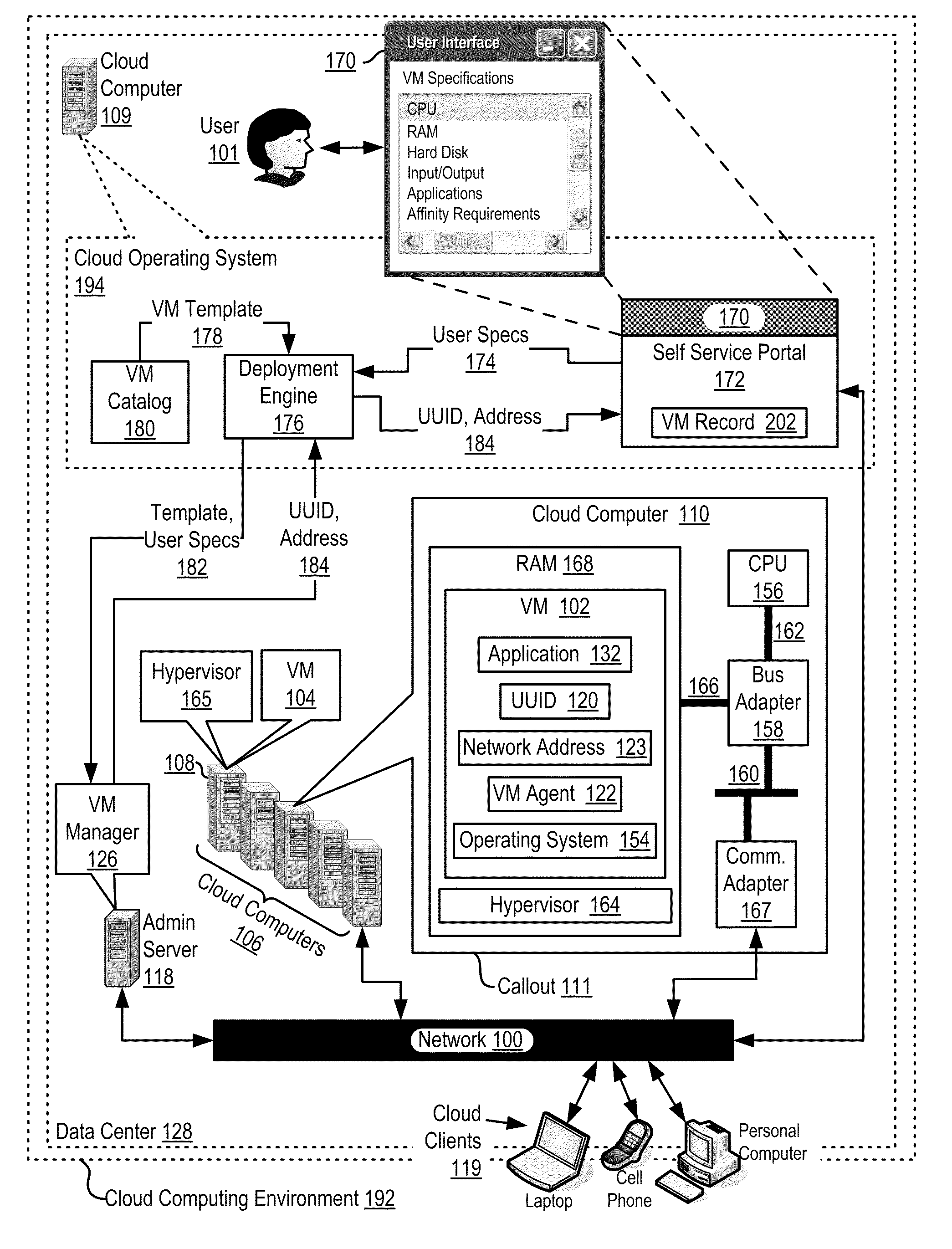
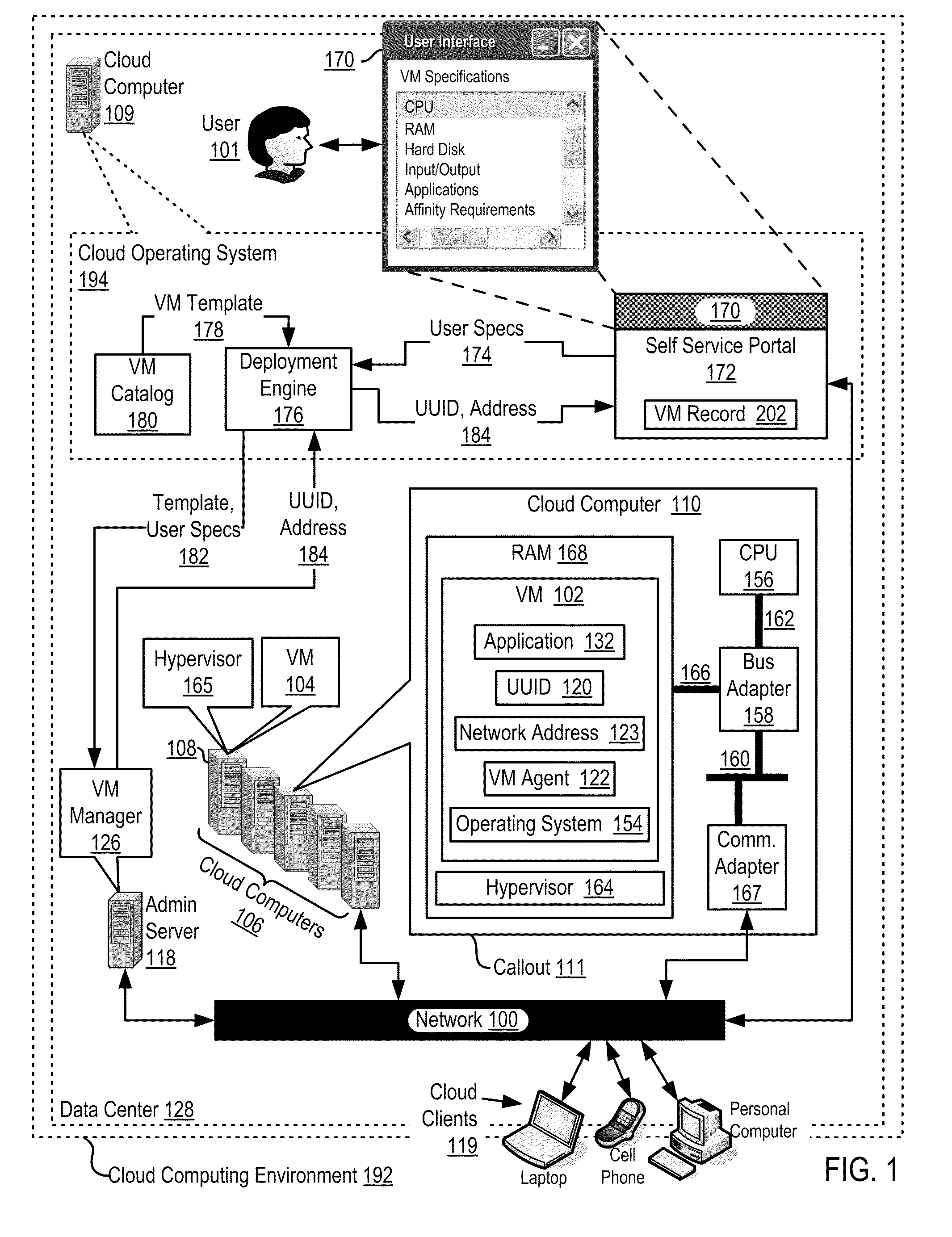
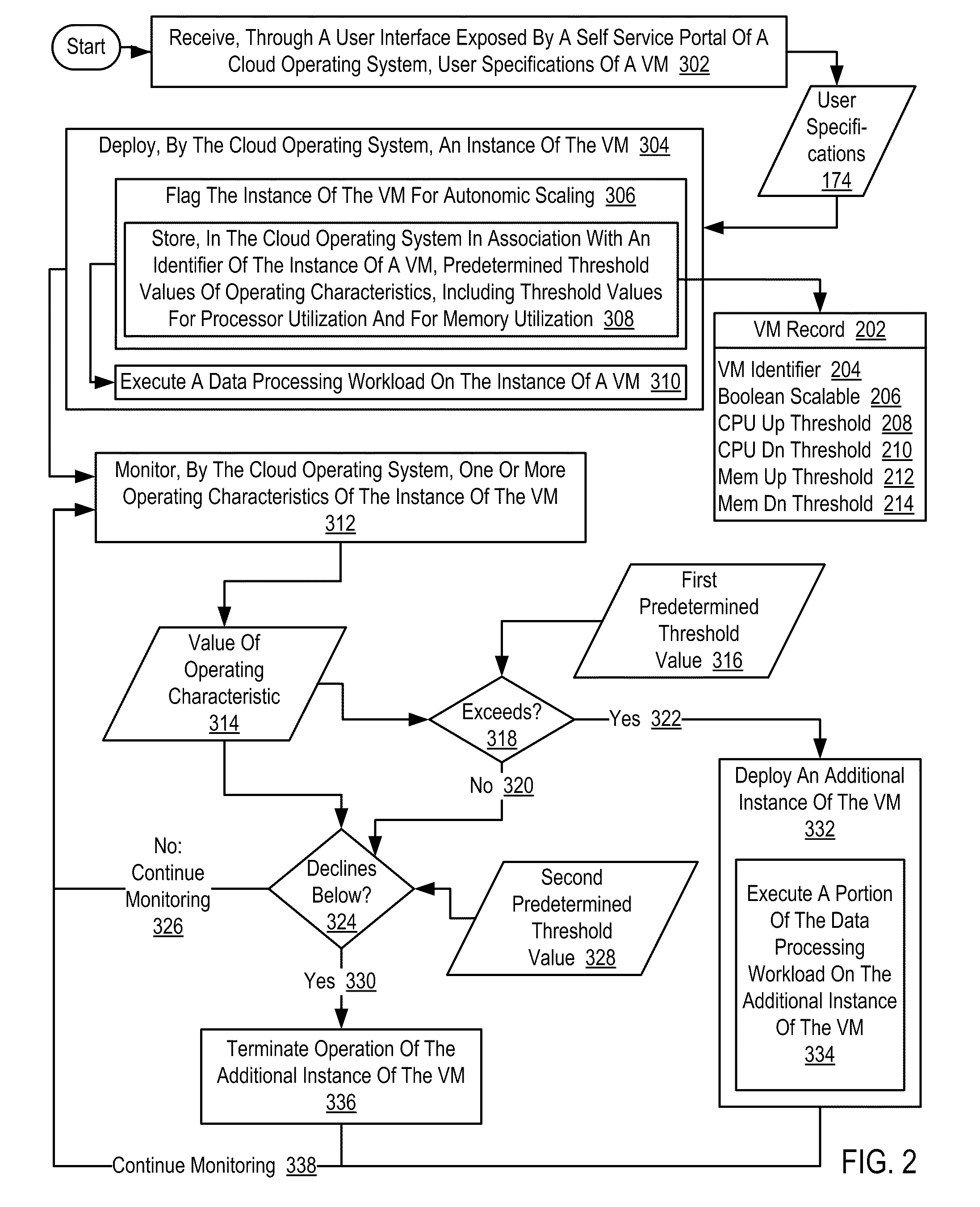
Autonomic Scaling Of Virtual Machines In A Cloud Computing Environment
ActiveUS20110258621A1Program loading/initiatingSoftware simulation/interpretation/emulationOperational systemData center
Autonomic scaling of virtual machines in a cloud computing environment, the cloud computing environment including virtual machines (‘VMs’), the VMs installed upon cloud computers disposed within a data center, also including a cloud operating system and a data center administration server operably coupled to the VMs, including deploying, by the cloud operating system, an instance of a VM, flagging the instance of a VM for autonomic scaling; monitoring, by the cloud operating system, one or more operating characteristics of the instance of the VM; deploying, by the cloud operating system, an additional instance of the VM if a value of an operating characteristic exceeds a first predetermined threshold value, including executing a portion of the data processing workload on the additional instance of the VM; and terminating operation of the additional instance of the VM if a value of an operating characteristic declines below a second predetermined threshold value.
Owner:DAEDALUS BLUE LLC
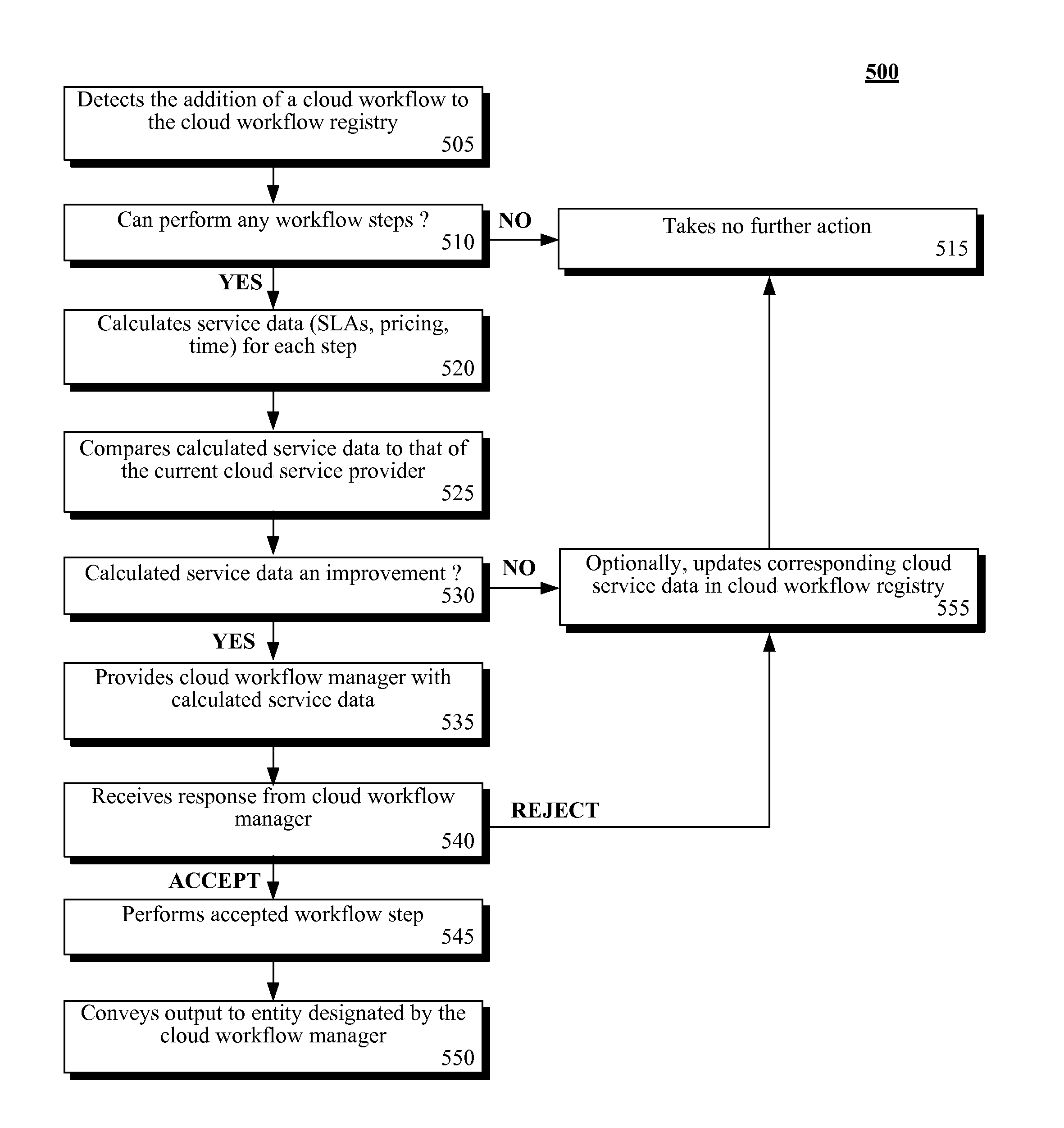
Optimizing cloud service delivery within a cloud computing environment
This invention provides a system or method to provide dynamically packaged Cloud services to customers via a Cloud services registry. The Cloud services registry is dynamic and operates by polling different Cloud service providers and Cloud service databases to ensure that the Cloud services registry is up to date with the latest available Cloud services. The Cloud services registry is available for queries from Cloud customers and abstracts multiple Cloud service providers. By abstracting the Cloud services, the dynamic Cloud services registry creates a modular package of different services from different Cloud service providers based on the query and requested priority for services. The dynamic Cloud registry is dynamically updated based on the level of services that the provider has available. The dynamic registry determines what service best matches the requirements from a Cloud service request (CSR) and returns a personalized set of matching services.
Owner:IBM CORP
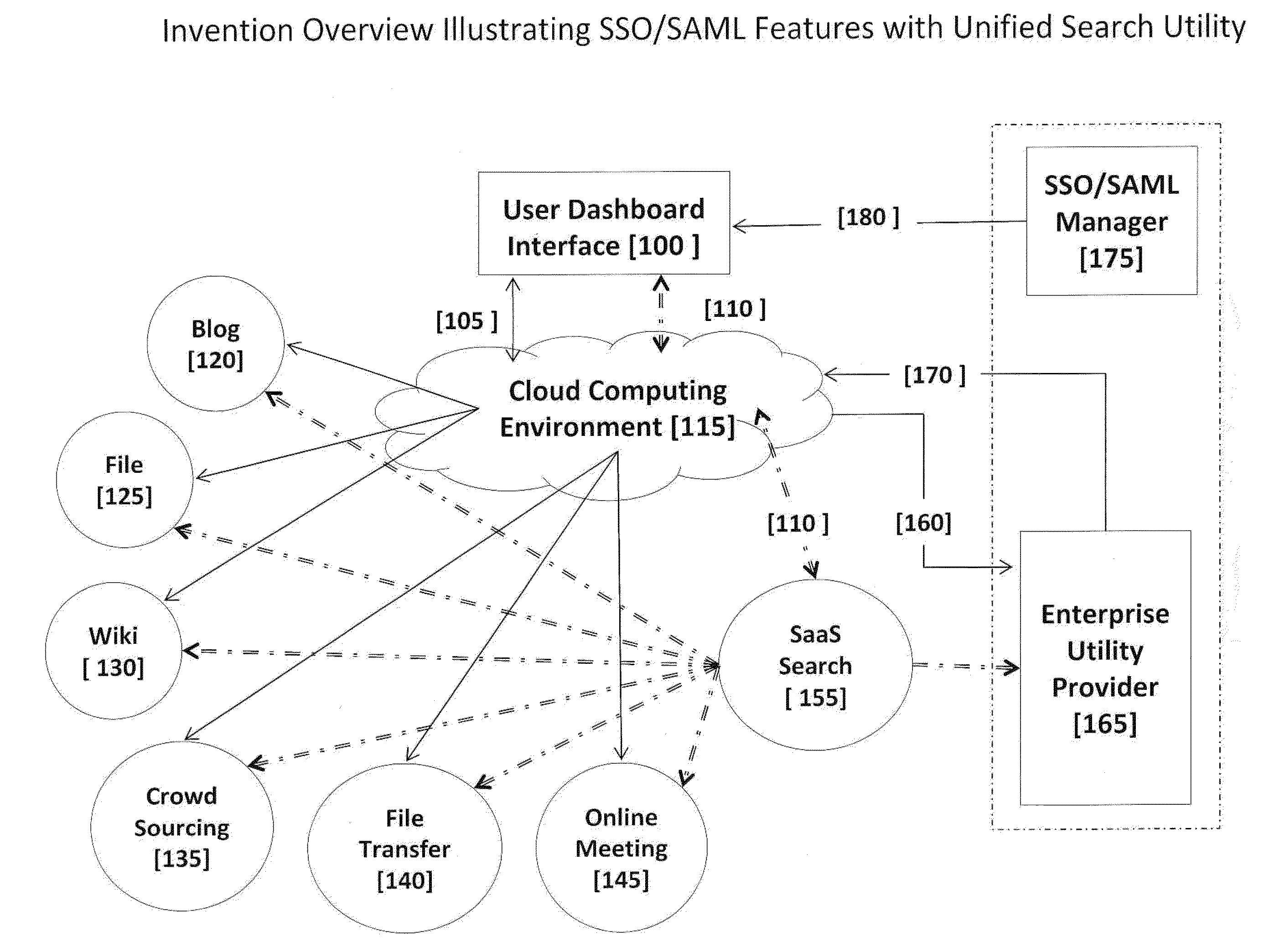
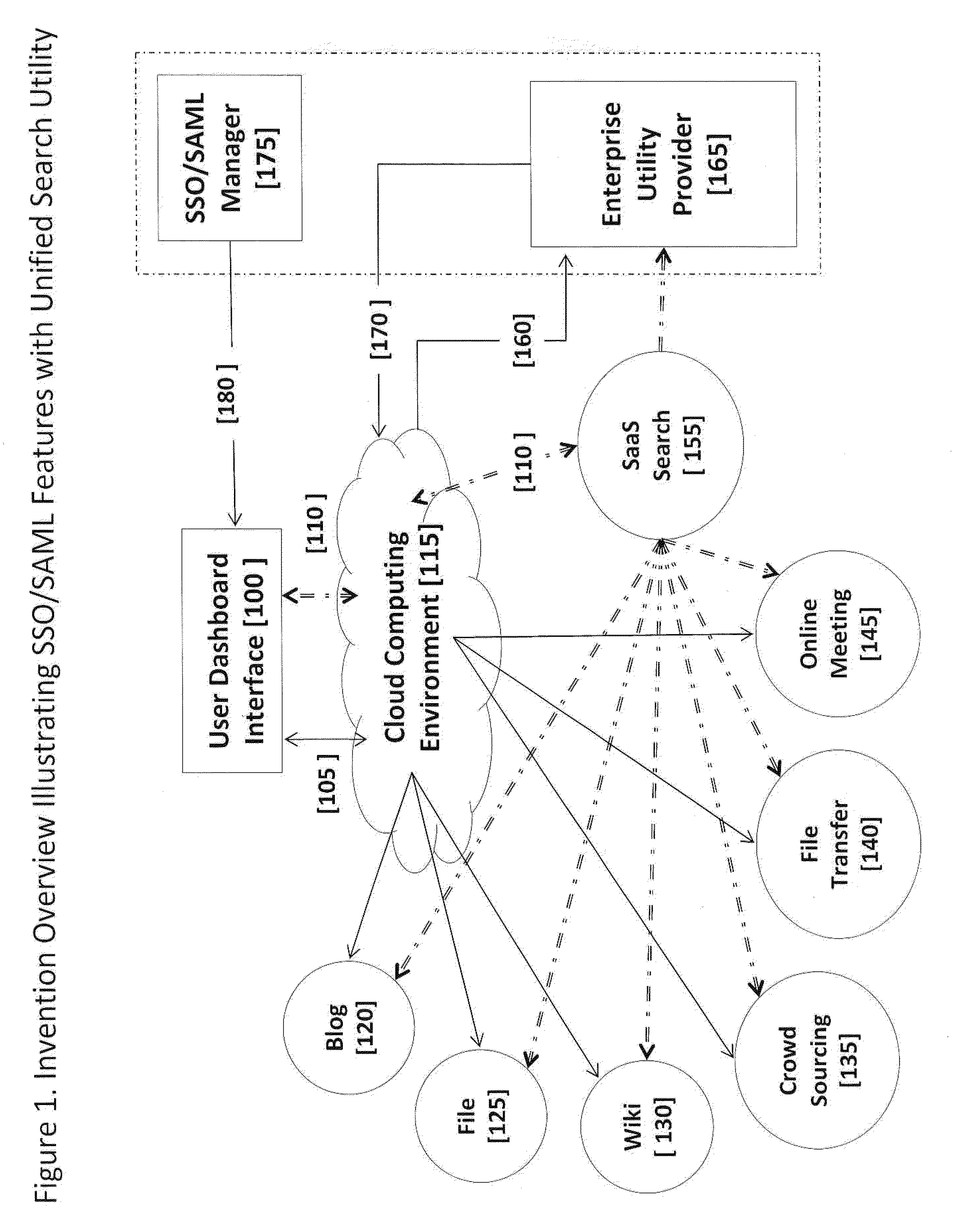
Integrated Enterprise Software and Social Network System User Interfaces Utilizing Cloud Computing Infrastructures and Single Secure Portal Access
InactiveUS20120216125A1Reduced revenue opportunityInput/output for user-computer interactionMultiple digital computer combinationsDashboardCommunications system
A software-based method and system to provide a secure user interface on multiple and diverse electronic computing devices with a customized and secure dashboard feature. The systems and methods simultaneously integrate internally generated software utilities of an enterprise with externally accessed software operating in a ‘cloud computing’ environment. The systems and methods can be used in management and operations that use computer based software, data management, creative processes and communication systems. The systems and methods reduce the requirement for additional programming to integrate or interchange equivalent and independently developed software for use within an enterprise. The systems and methods permit social network communications between members of an enterprise and an external community. The security features of the user interface portal permit collaborations between parties in an external community and enterprise members that can develop new processes that remain proprietary to the enterprise and parties of an external community.
Owner:ZAMA INNOVATIONS LLC
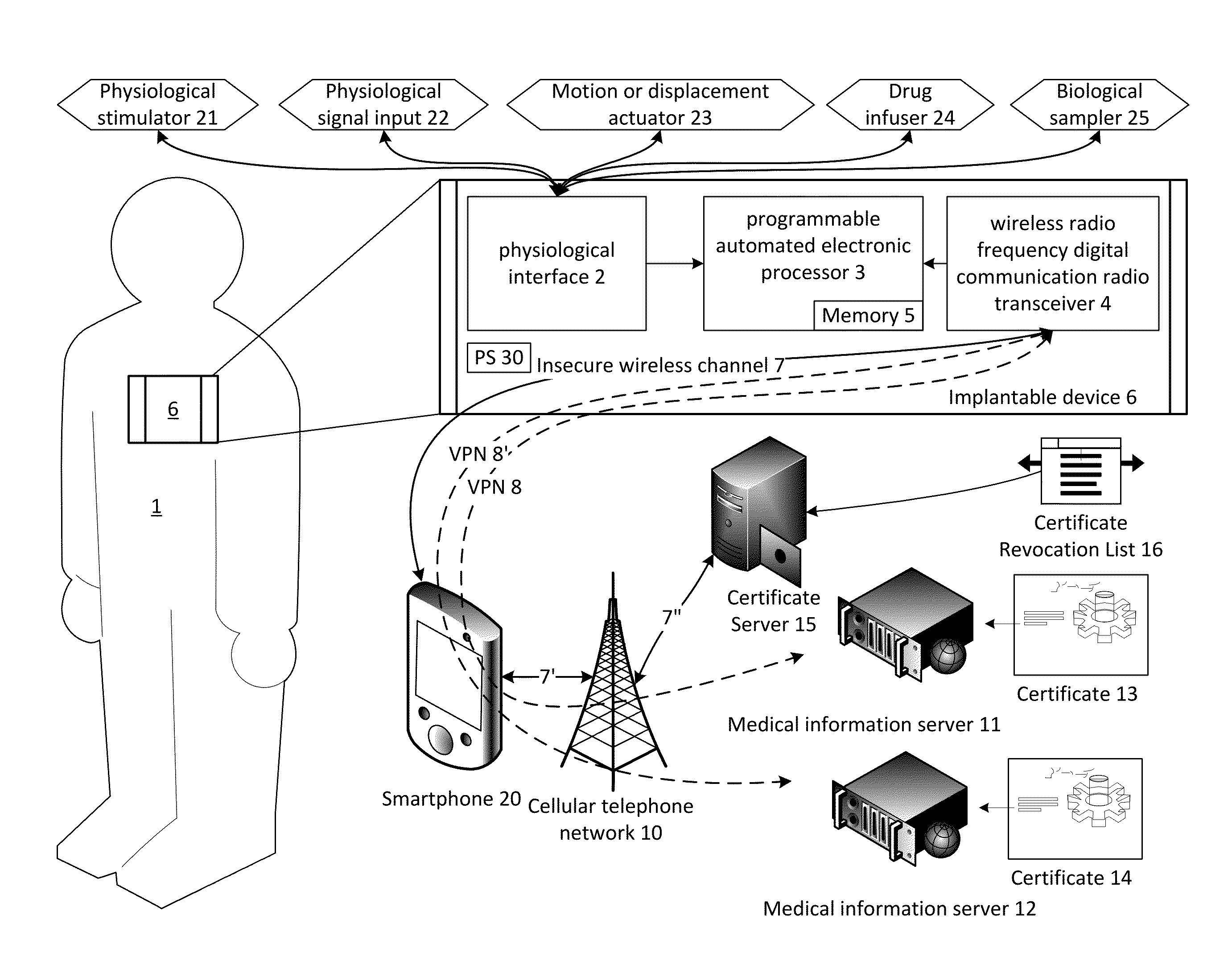
System and method for secure relayed communications from an implantable medical device
ActiveUS9215075B1Good security mechanismLarge block sizePhysical therapies and activitiesDrug and medicationsSecure communicationMedical equipment
The present invention provides systems and methods for supporting encrypted communications with a medical device, such as an implantable device, through a relay device to a remote server, and may employ cloud computing technologies. An implantable medical device is generally constrained to employ a low power transceiver, which supports short distance digital communications. A relay device, such as a smartphone or WiFi access point, acts as a conduit for the communications to the internet or other network, which need not be private or secure. The medical device supports encrypted secure communications, such as a virtual private network technology. The medical device negotiates a secure channel through a smartphone or router, for example, which provides application support for the communication, but may be isolated from the content.
Owner:POLTORAK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com