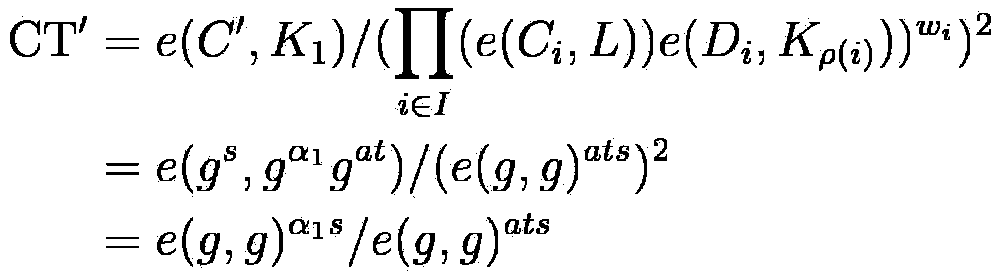Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
621 results about "Cloud service provider" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A cloud service provider, or CSP, is a company that offers some component of cloud computing -- typically infrastructure as a service (IaaS), software as a service (SaaS) or platform as a service (PaaS) -- to other businesses or individuals.
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
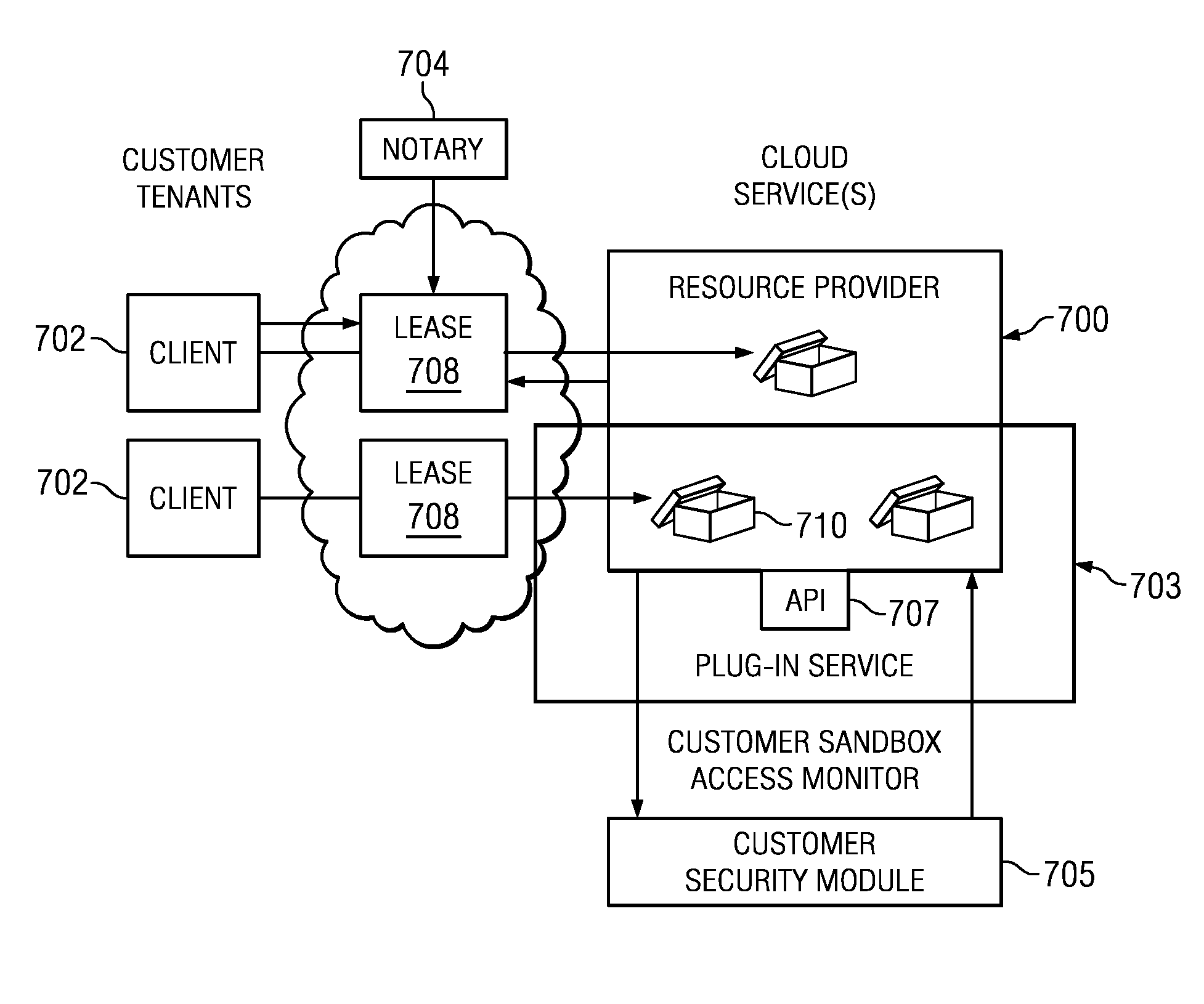
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Authentication and authorization methods for cloud computing security platform
ActiveUS20130007845A1Retain controlDigital data processing detailsUser identity/authority verificationThird partyResource pool
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
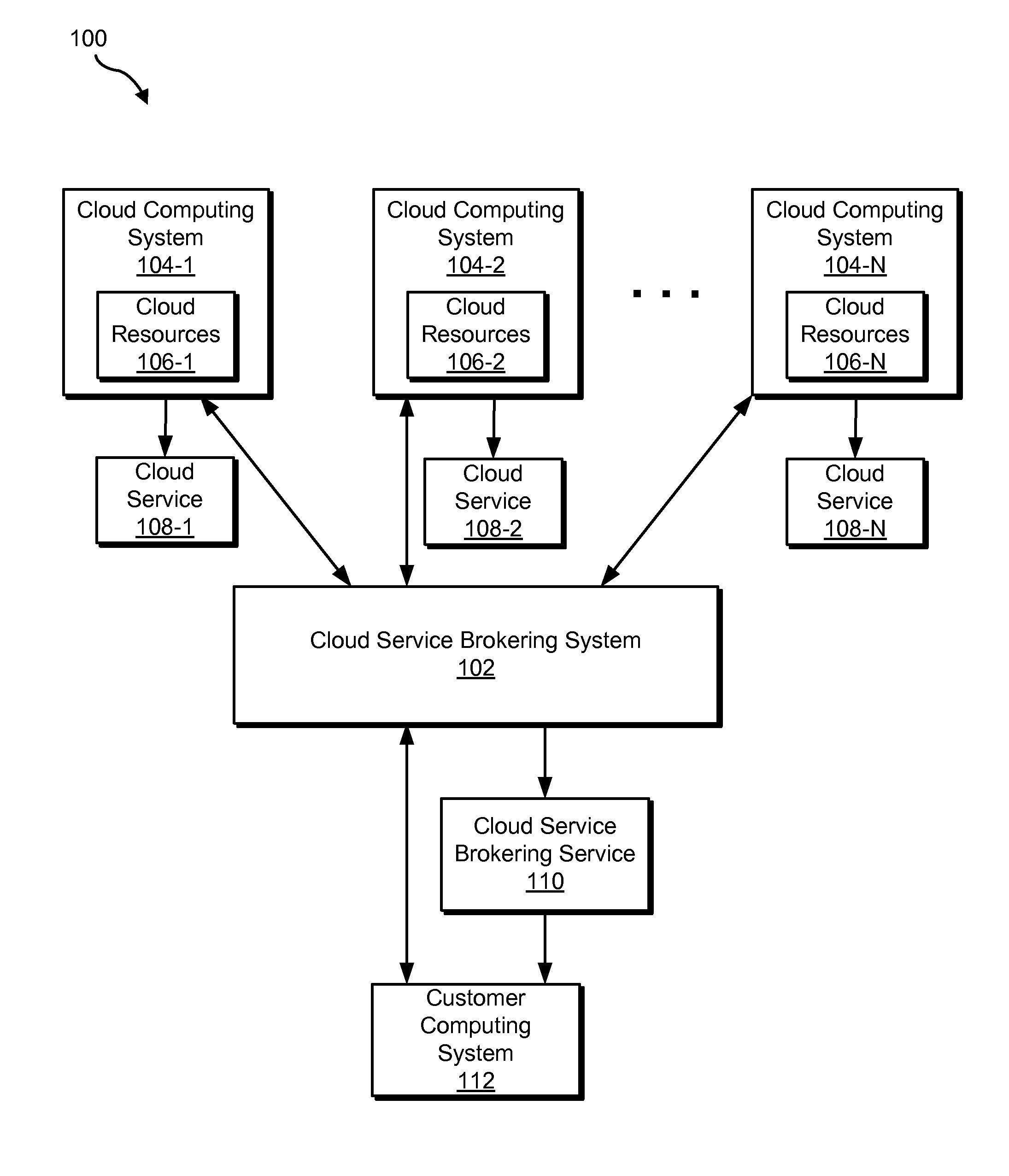
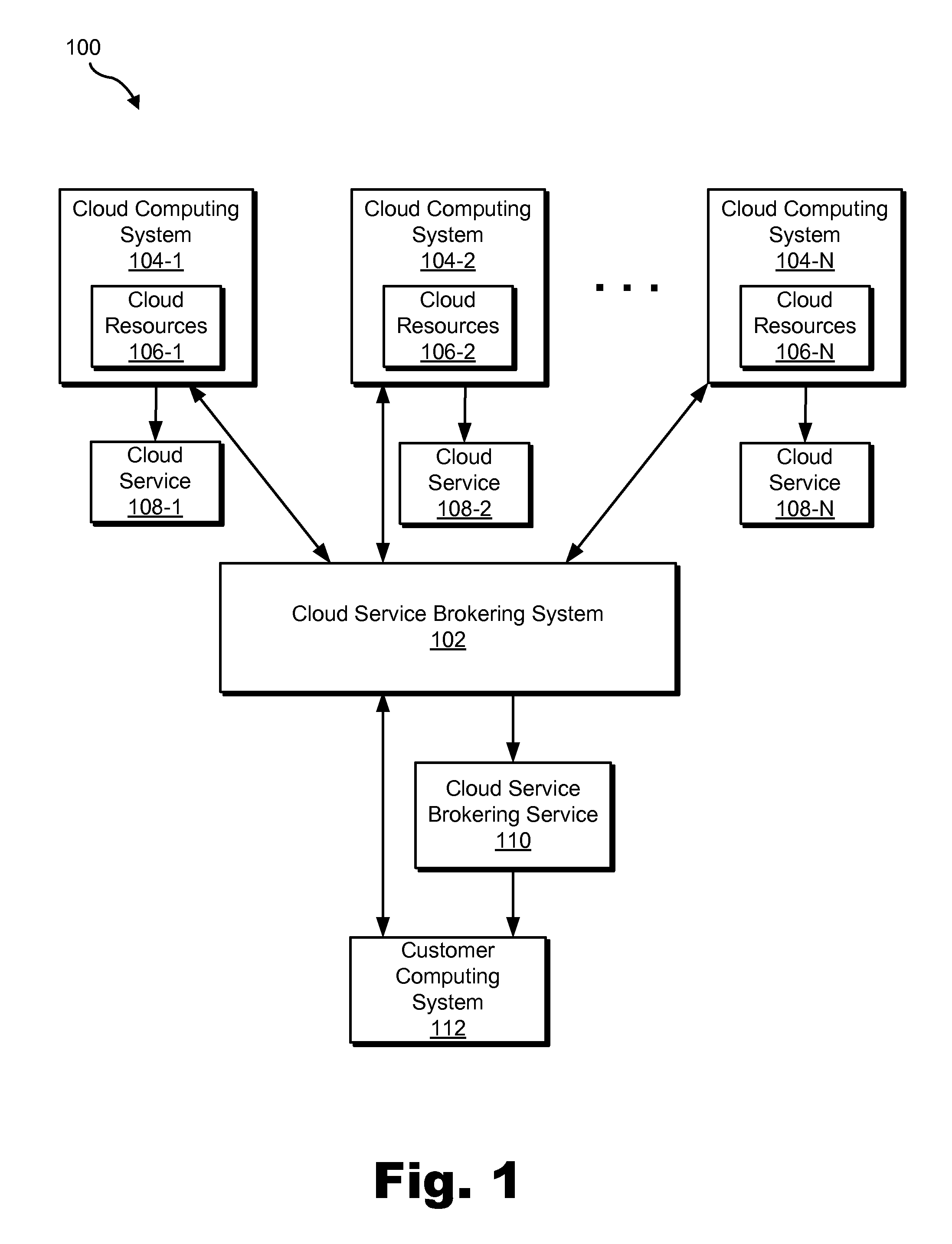
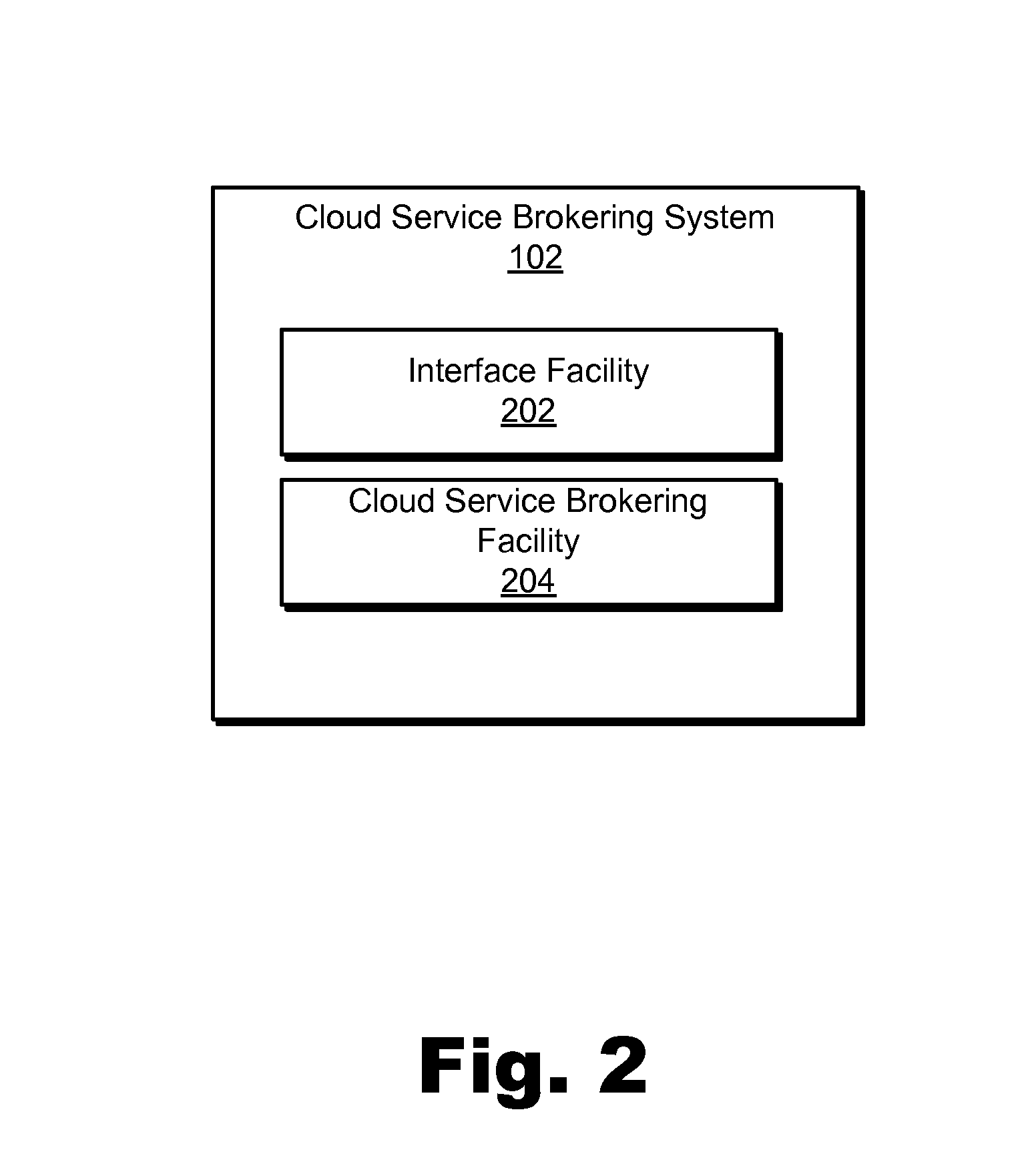
Cloud service brokering systems and methods
An exemplary method includes a computer-implemented cloud service brokering system that provides a cloud service brokering service 1) registering a plurality of cloud services with the cloud service brokering service, the plurality of cloud services provided by a plurality of cloud service providers and configured to provide distinct sets of cloud computing resources as a service, 2) receiving, from a customer of the cloud service brokering service, cloud service request information, 3) selecting, based on the cloud service request information, a cloud computing resource from the distinct sets of cloud computing resources provided by the plurality of cloud services registered with the cloud service brokering service, and 4) allocating the selected cloud computing resource for use by the customer. In certain examples, the allocating may be supported by the system configuring a customer network to support implicit and / or explicit transport requirements. Corresponding systems and methods are also described.
Owner:VERIZON PATENT & LICENSING INC
Systems and methods for cloud bridging between intranet resources and cloud resources
Embodiments of the present solution provide a cloud bridge to bring network transparency between the otherwise disparate networks of the datacenter and cloud service provider. For example, appliances may be deployed in the datacenter and on the edge of the cloud. These appliances may be configured or designed and constructed to communicate with each other and recognize and understand the local IP and / or public IP network information of the on-premise datacenter of the enterprise and the cloud datacenter. These appliances may manage the flow of network traffic between the on-premise and cloud datacenters in a manner to appear and act seamlessly and transparently as a single network spanning both the on-premise and cloud data centers.
Owner:CITRIX SYST INC
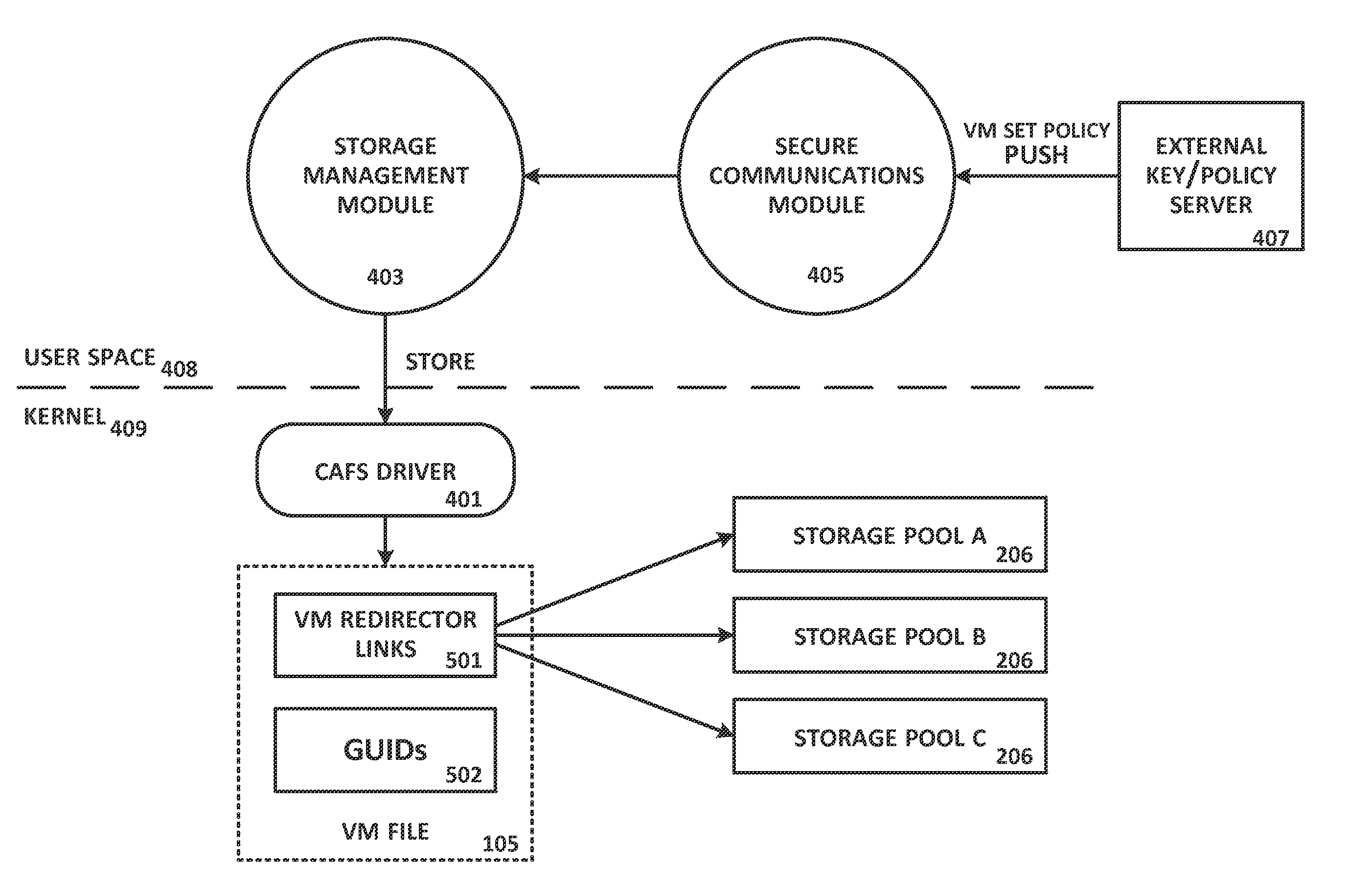
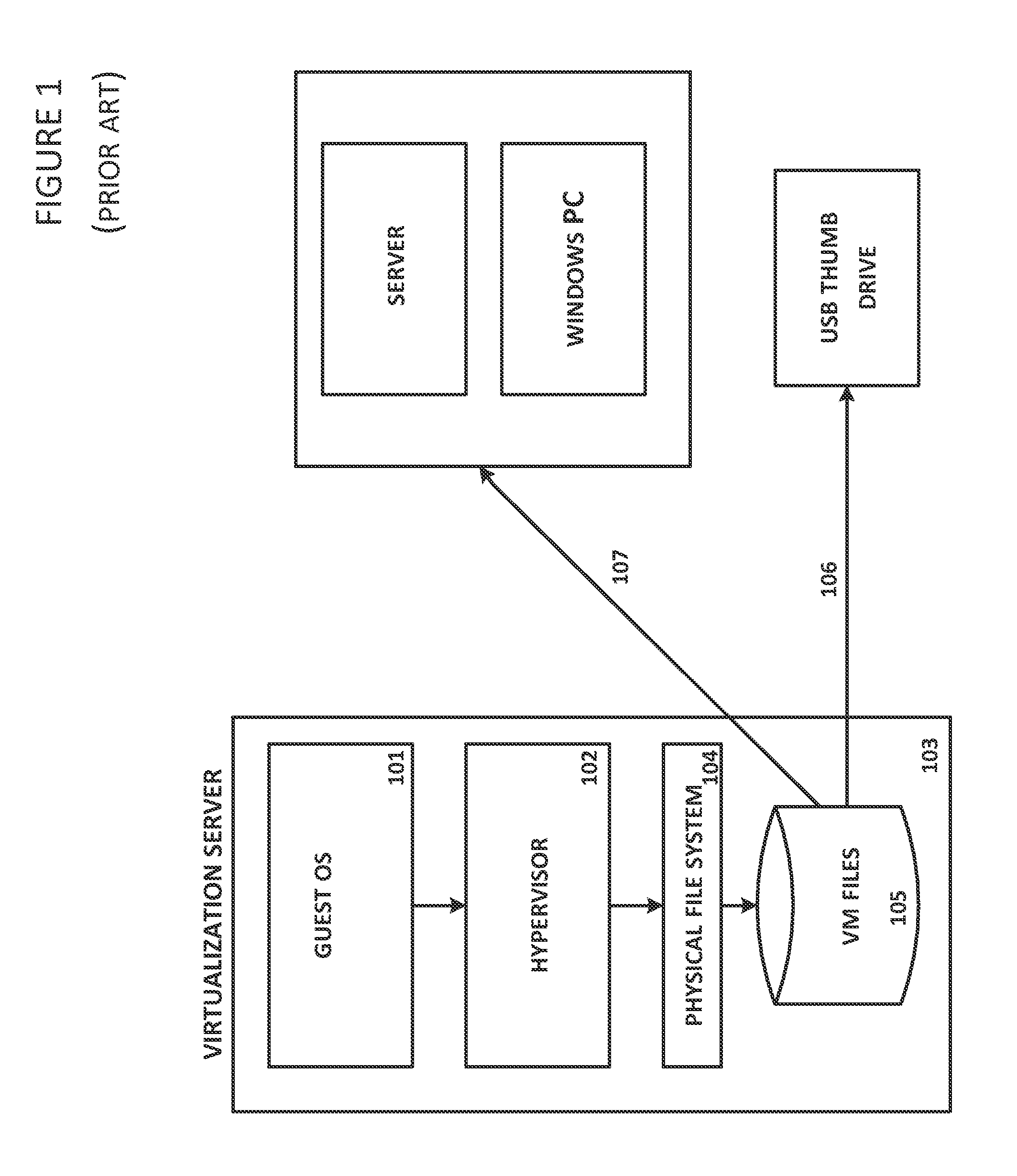
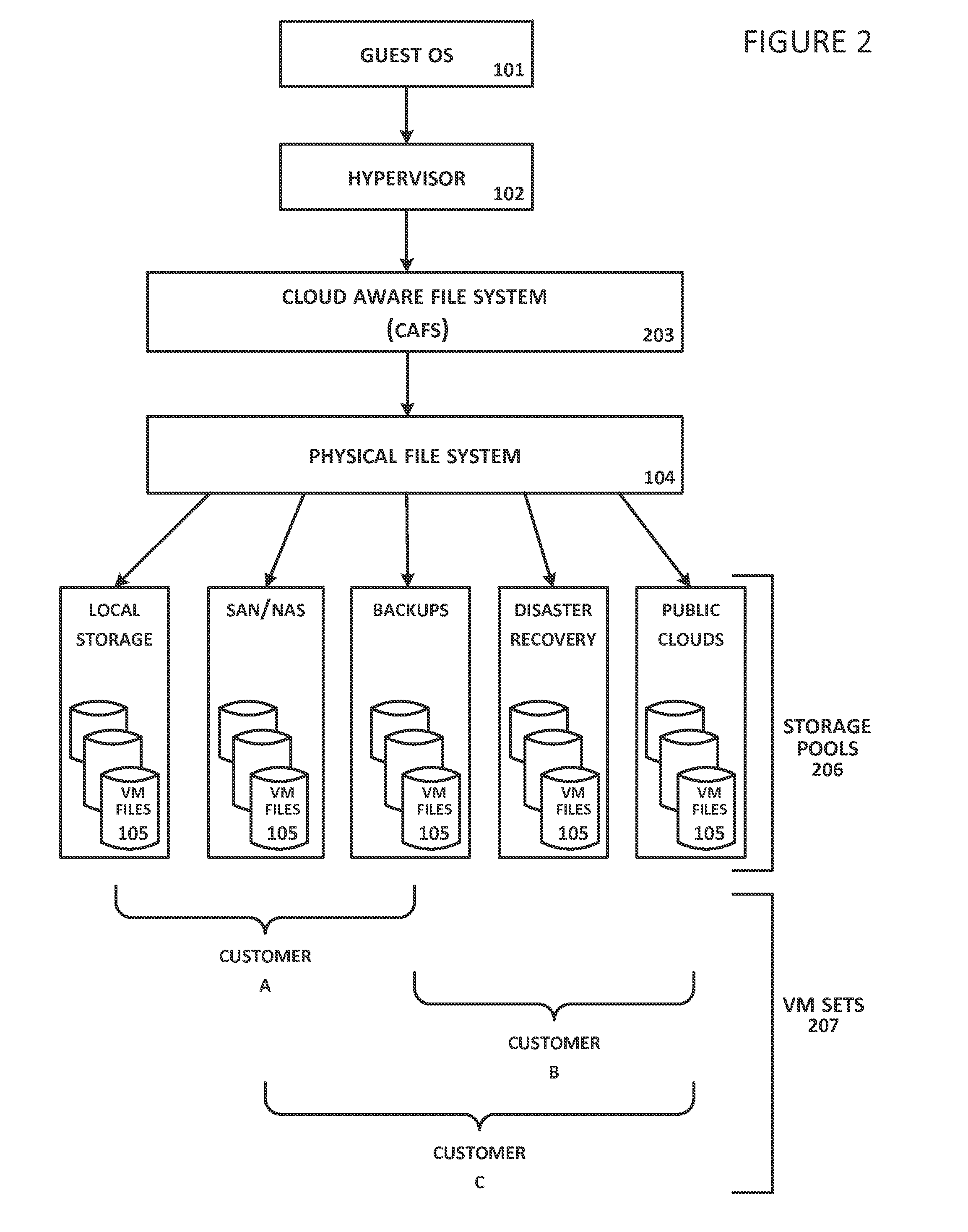
System and Method For Secure Storage of Virtual Machines
ActiveUS20120110328A1Safe storageDigital data information retrievalInternal/peripheral component protectionVirtual file systemData center
A virtual file system is described that is implemented in a virtualization platform as a stackable file system layer that intercepts file operations between a hypervisor and a physical file system. The virtual file system encrypts (at least in part) VM files to be stored, organizes the encrypted VM files into VM sets, and then maps and stores the encrypted VM sets into storage pools. Storage and access to files within the VM sets is controlled through the use of administrator-determined policies governing storage, security, access control, authentication, and auditing. The system and method described herein allow a seamless integration between a data center (e.g., a private cloud) and computing resources served across the internet and supported by cloud service providers (e.g., public clouds) while ensuring that the security needs of customers and cloud service providers are met.
Owner:HYTRUST
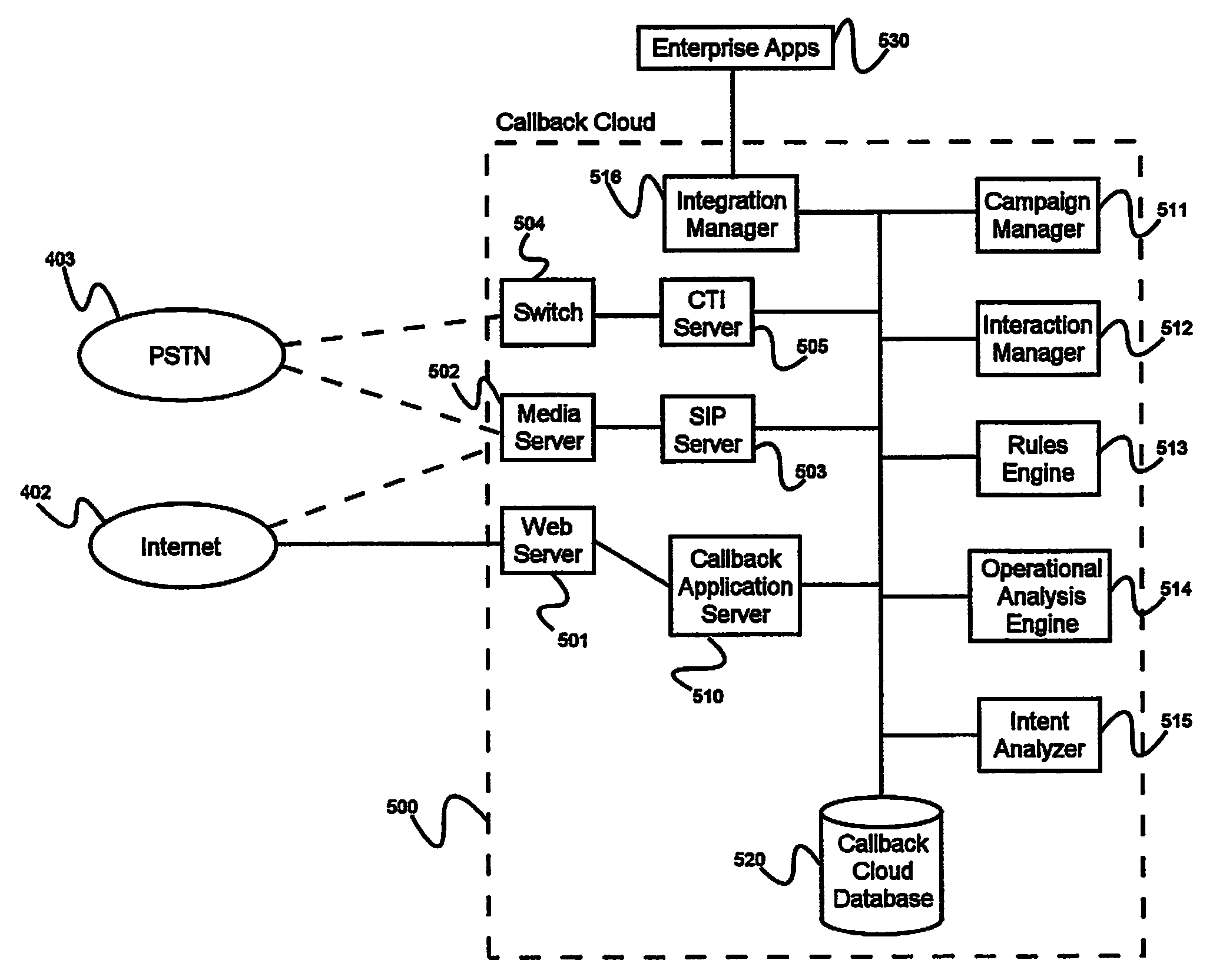
System and method for providing a callback cloud
ActiveUS20130054684A1Avoid the needIncrease contactDigital data information retrievalReservationsSession managementMedia type
A system for providing a callback cloud, comprising an application server operated by a callback cloud service provider, a media server, a session management server, an interaction manager, and an intent analysis engine. The application server receives registrations from callback providers unaffiliated with the callback service provider. The application server is adapted to receive callback requests from users, comprising a specific callback provider from whom a callback is requested, when a requested callback should be made, and allowable media types. The application server directs the callback request to the interaction manager, and the interaction manager sends data elements pertaining to the request to the intent analysis engine and receives therefrom data elements pertaining to the callback request determined based on an analysis of the requester's intent. The interaction manager directs the session management server to initiate a callback, and the session management server provides signaling to the media server to conduct the callback.
Owner:VIRTUAL HOLD TECH
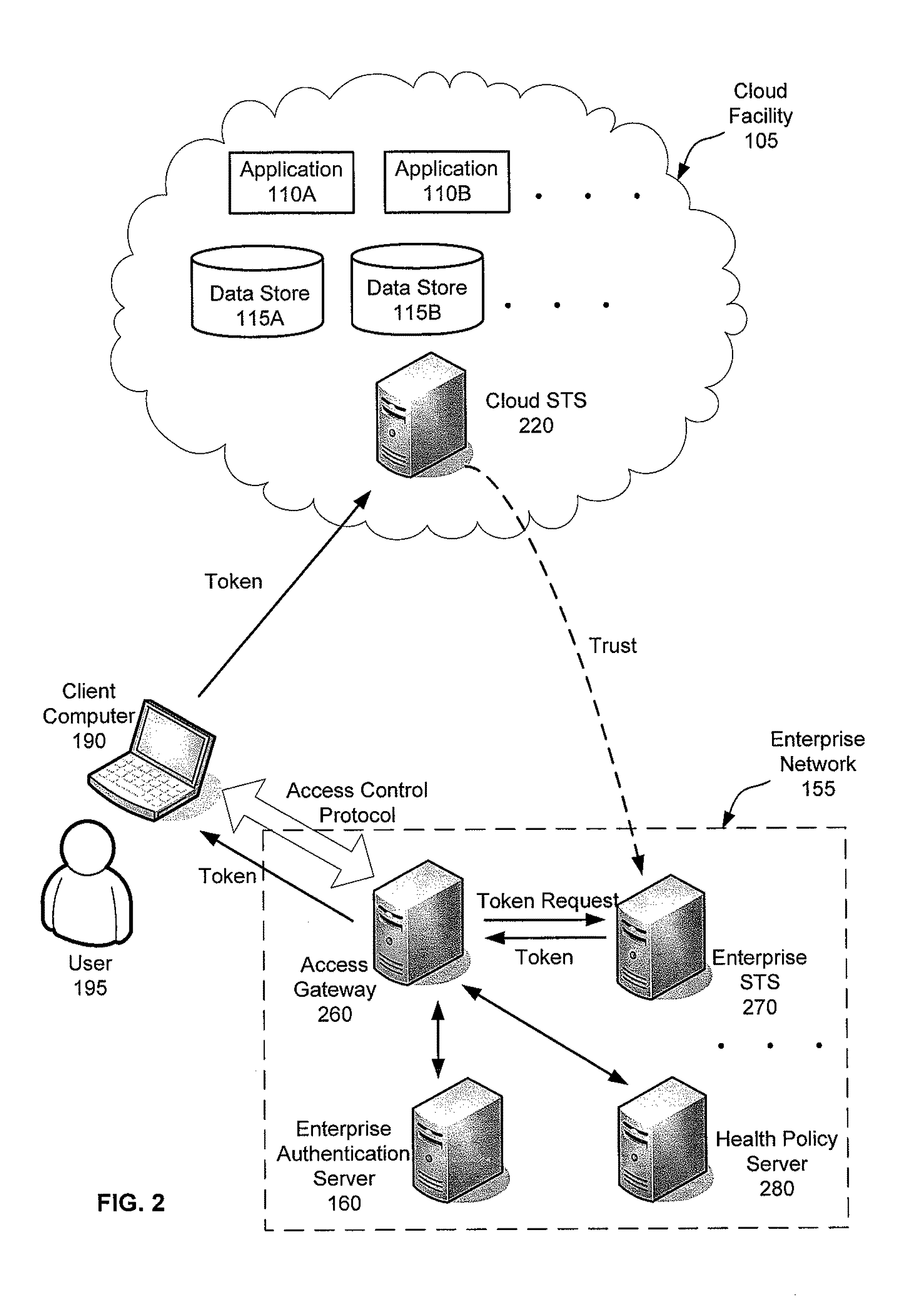
Flexible end-point compliance and strong authentication for distributed hybrid enterprises
ActiveUS20110307947A1Digital data processing detailsMultiple digital computer combinationsUser authenticationClient-side
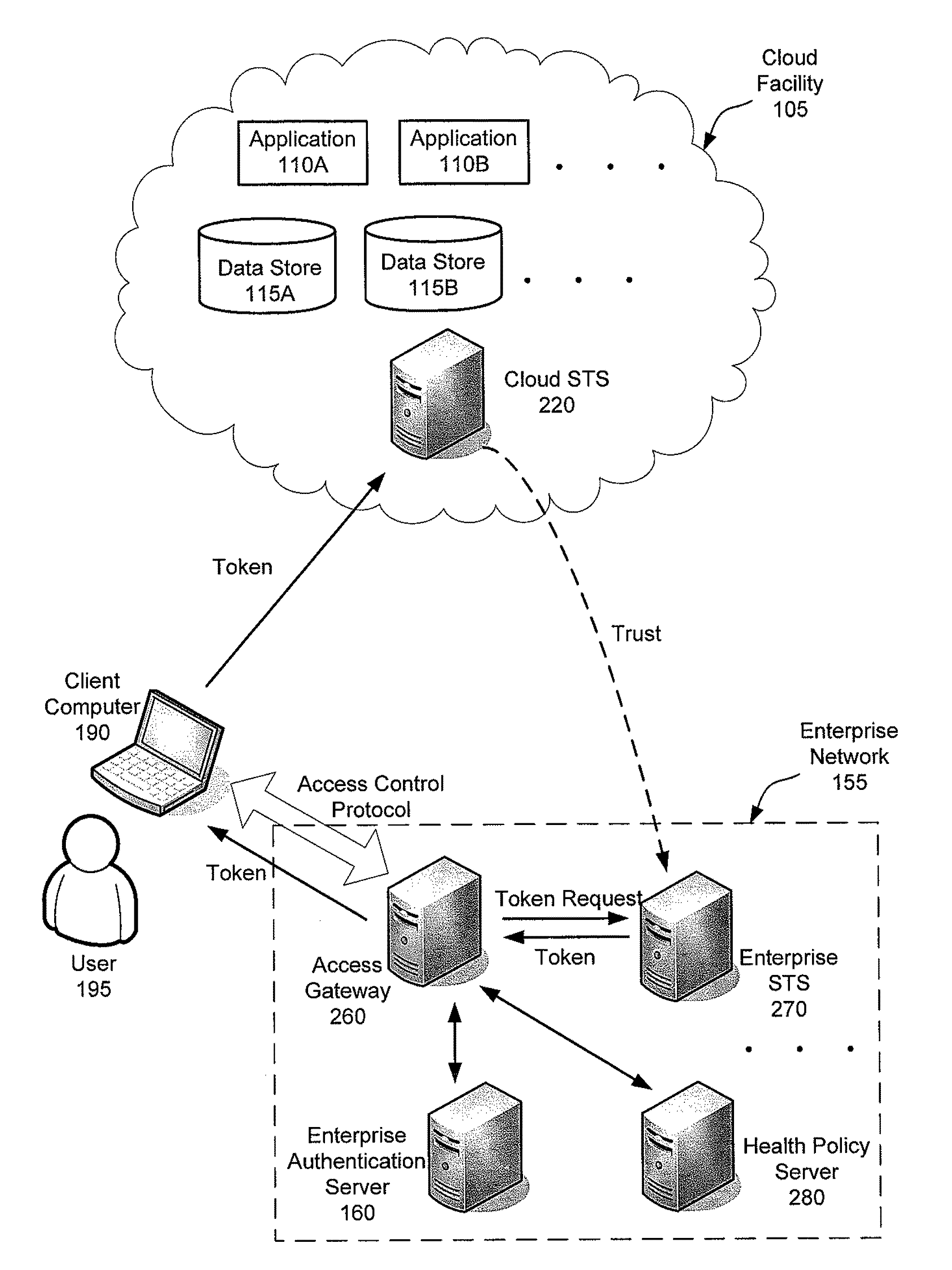
Systems, methods and apparatus for accessing at least one resource hosted by at least one server of a cloud service provider. In some embodiments, a client computer sends authentication information associated with a user of the client computer and a statement of health regarding the client computer to an access control gateway deployed in an enterprise's managed network. The access control gateway authenticates the user and determines whether the user is authorized to access the at least one resource hosted in the cloud. If the user authentication and authorization succeeds, the access control gateway requests a security token from a security token service trusted by an access control component in the cloud and forwards the security token to the client computer. The client computer sends the security token to the access component in the cloud to access the at least one resource from the at least one server.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for adaptive application provisioning
ActiveUS20130297802A1Error detection/correctionDigital computer detailsApplication softwareSelf adaptive
The present application is directed towards systems and methods for adaptive application provisioning for cloud services. An appliance deployed in a network as a gateway may be able to transparently monitor application activity in a cloud computing environment provided by one or more servers, including servers executed by virtual machines, bare-metal or non-virtual servers, or other computing devices. In some embodiments, the appliance may monitor one or more network metrics, including bandwidth usage, latency, congestion, or other issues; and / or may monitor application health or server or virtual machine statistics, including memory and processor usage, bandwidth usage, latency, or other metrics. Responsive to one or more metrics exceeding a threshold, the appliance may automatically provision or start, or deprovision or shut down, one or more virtual or physical machines from a cloud service provider, and may provide configuration information to the provisioned or started machines as needed.
Owner:CITRIX SYST INC
Optimizing cloud service delivery within a cloud computing environment
This invention provides a system or method to provide dynamically packaged Cloud services to customers via a Cloud services registry. The Cloud services registry is dynamic and operates by polling different Cloud service providers and Cloud service databases to ensure that the Cloud services registry is up to date with the latest available Cloud services. The Cloud services registry is available for queries from Cloud customers and abstracts multiple Cloud service providers. By abstracting the Cloud services, the dynamic Cloud services registry creates a modular package of different services from different Cloud service providers based on the query and requested priority for services. The dynamic Cloud registry is dynamically updated based on the level of services that the provider has available. The dynamic registry determines what service best matches the requirements from a Cloud service request (CSR) and returns a personalized set of matching services.
Owner:IBM CORP
Implementing comparison of cloud service provider package offerings
ActiveUS20140278808A1Enhancing cloud serviceEfficient and effectiveMarket predictionsService provisionArchitecture specification
A computer-implemented method of implementing comparison of cloud service provider package offerings comprises a plurality of operations. An operation of creating a cloud services architecture specification defining a cloud infrastructure that supports deployment of an application thereto is performed. An operation of determining a cloud services offering price for each one of the plurality of cloud service offerings to characterize implementation of the cloud infrastructure using cloud services thereof on a basis of pricing of such cloud services is performed. Determining the cloud services offering price for a particular one of the cloud service offerings includes mapping the cloud services architecture specification to cloud service pricing information for the particular one of the cloud service offerings.
Owner:HCL TECH LTD
System and method for providing a callback cloud
A system for providing a callback cloud, comprising an application server operated by a callback cloud service provider, a media server, a session management server, an interaction manager, and an intent analysis engine. The application server receives registrations from callback providers unaffiliated with the callback service provider. The application server is adapted to receive callback requests from users, comprising a specific callback provider from whom a callback is requested, when a requested callback should be made, and allowable media types. The application server directs the callback request to the interaction manager, and the interaction manager sends data elements pertaining to the request to the intent analysis engine and receives therefrom data elements pertaining to the callback request determined based on an analysis of the requester's intent. The interaction manager directs the session management server to initiate a callback, and the session management server provides signaling to the media server to conduct the callback.
Owner:VIRTUAL HOLD TECH
Resource exchange management within a cloud computing environment
ActiveUS20110145413A1Improve usabilityReduce unavailabilityFinanceGroup 8/9/10/18 element organic compoundsResource managementResource based
The present invention provides a solution for resource sharing (e.g., inter-Cloud) within a Cloud-computing environment. One objective of the present invention is to better utilize idle public or private Cloud infrastructures and improve the availability of Cloud services by allowing different Cloud service providers to virtually combine their services and infrastructures. In the event that there is not enough capacity for a single Cloud service provider to manage its workload, the workload may be shifted to additional infrastructures within the Cloud. The result of the workload shift may reduce the unavailability of Cloud services to the Cloud end-user by allowing another Cloud service provider to temporarily handle the workload. Based on the resource sharing activities, compensation (e.g., credits / tokens) can be exchanged between the participating Cloud providers to reflect their participation in the resource exchange.
Owner:KYNDRYL INC
Integrated Metering of Service Usage for Hybrid Clouds
InactiveUS20130185413A1Error detection/correctionDigital computer detailsEvent dataCloud service provider
An embodiment is directed to a hybrid cloud environment wherein a user of cloud computing services is disposed to consume cloud provided services delivered by each of a plurality of cloud computing service providers. Specified event data is received at an MCS component, wherein the event data pertains to metering events related to consumed services delivered by one or more cloud service providers. Event data includes event data furnished by one or more entities that actively monitor metering events at one or more local or remote cloud service provider locations. Event data is sent from the MCS component to a metering system, and the metering system generates reports from the event data that contains usage information on services provided by one or more cloud service providers, wherein information for a provider specifies amounts and quality of each type of service delivered to users by the provider.
Owner:IBM CORP
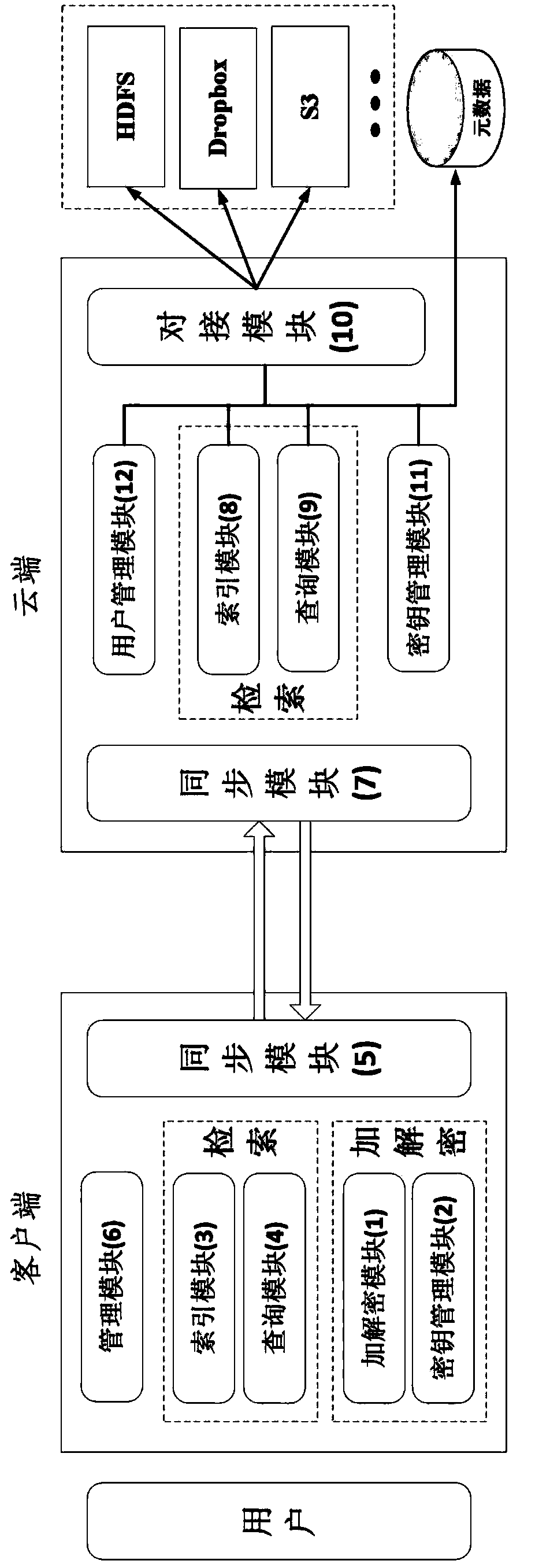
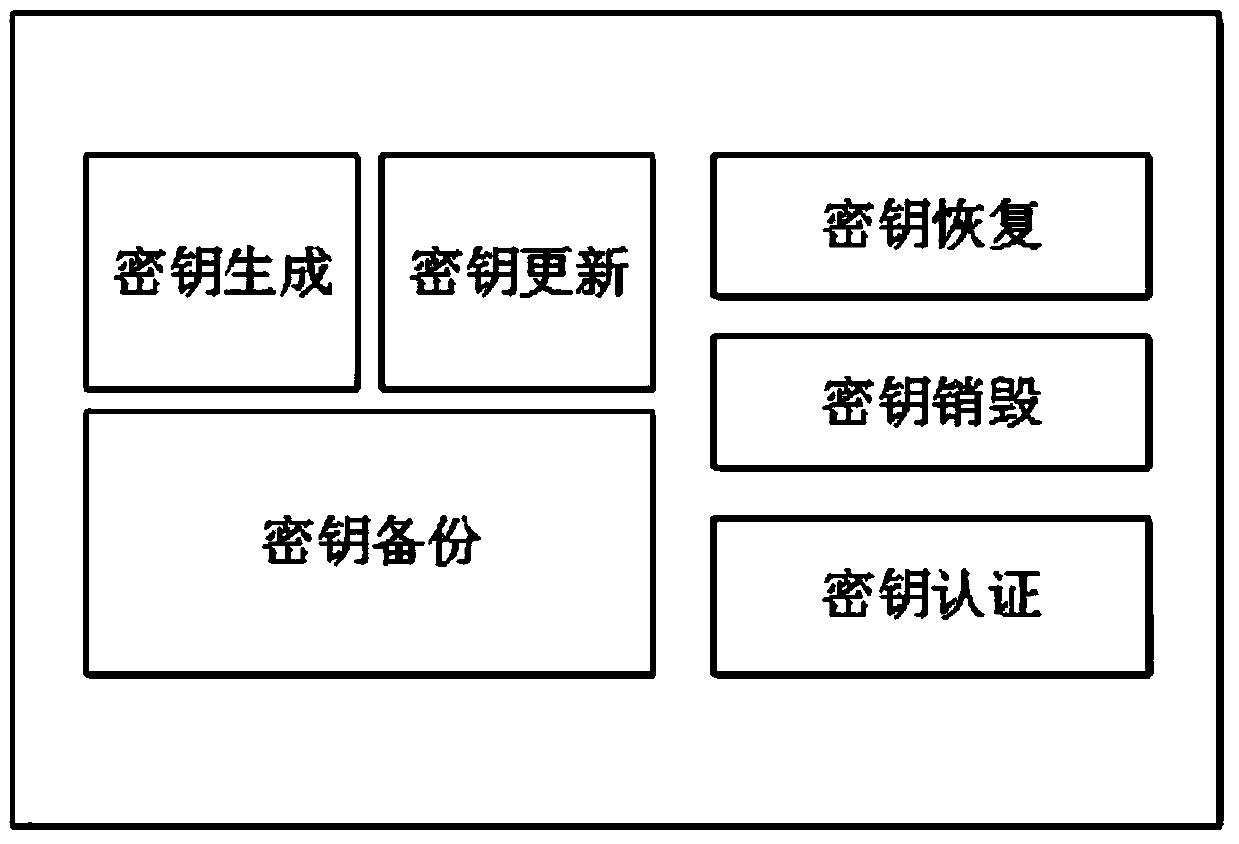
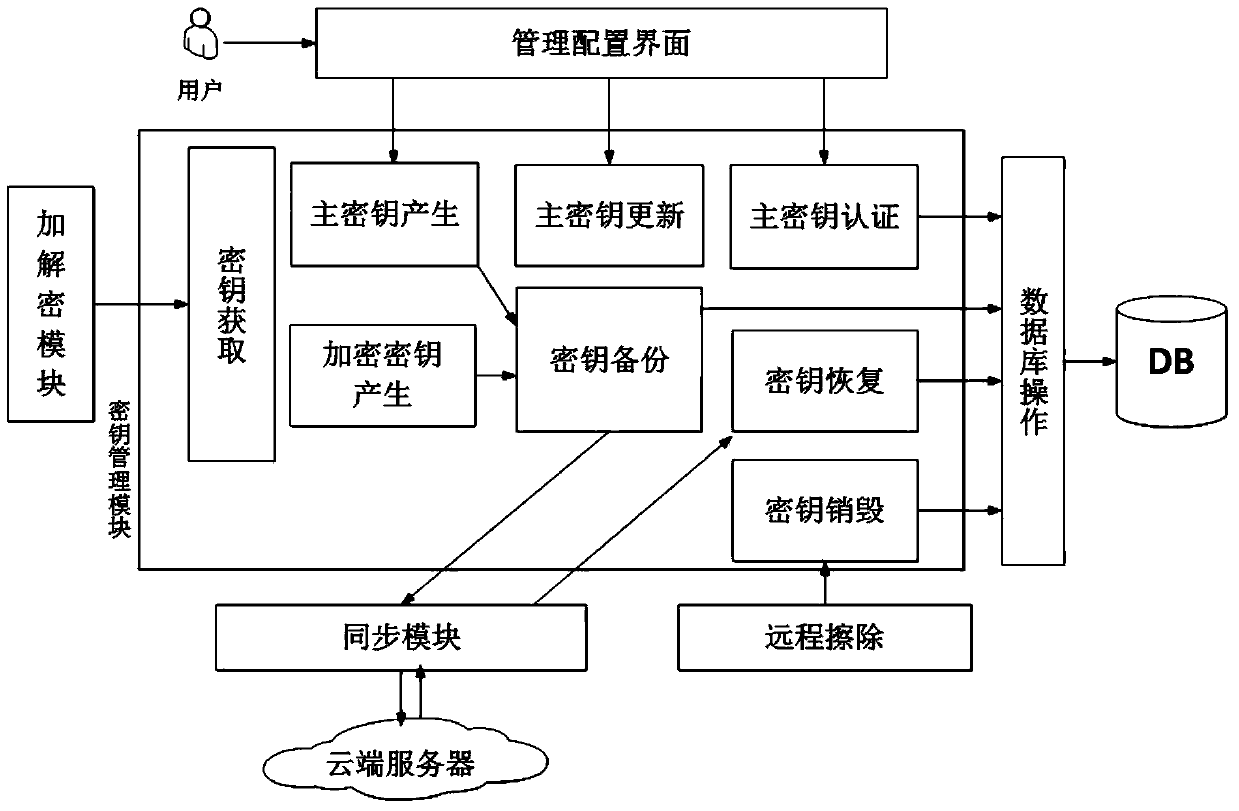
Ciphertext cloud storage method and system
InactiveCN103595730AWon't leakDoes not affect survivalTransmissionComputer hardwareData synchronization
The invention relates to a ciphertext cloud storage method and system. In the ciphertext cloud storage method system composed of at least one client terminal and a cloud terminal server, the ciphertext cloud storage method comprises the steps that (1) a user adopts a ciphertext and / or a plaintext to conduct data synchronism on the client terminal in the process of data storage and selects an encryption algorithm for the ciphertext; (2) authentication parameters provided based on the identity of the user is used for generating a master key, synchronous data of the ciphertext are encrypted on the client terminal through two-level keys comprising the master key and an encryption and decryption key, and the master key is backed up; (3) the ciphertext and a ciphertext index are synchronized on the client terminal and a cloud terminal, or a plaintext index is established after synchronous data of the plaintext are synchronized on the cloud terminal and the client terminal; (4) the plaintext and / or ciphertext is / are stored in a local private cloud storage server or in a storage server of a cloud storage provider according to a mount point requested by the user. By the adoption of the ciphertext cloud storage method and system, the data cannot be lost when the terminal is lost, if protection is inappropriate, only the ciphertext form of a file is damaged, and the ciphertext cloud storage system can dock with multiple cloud server providers.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
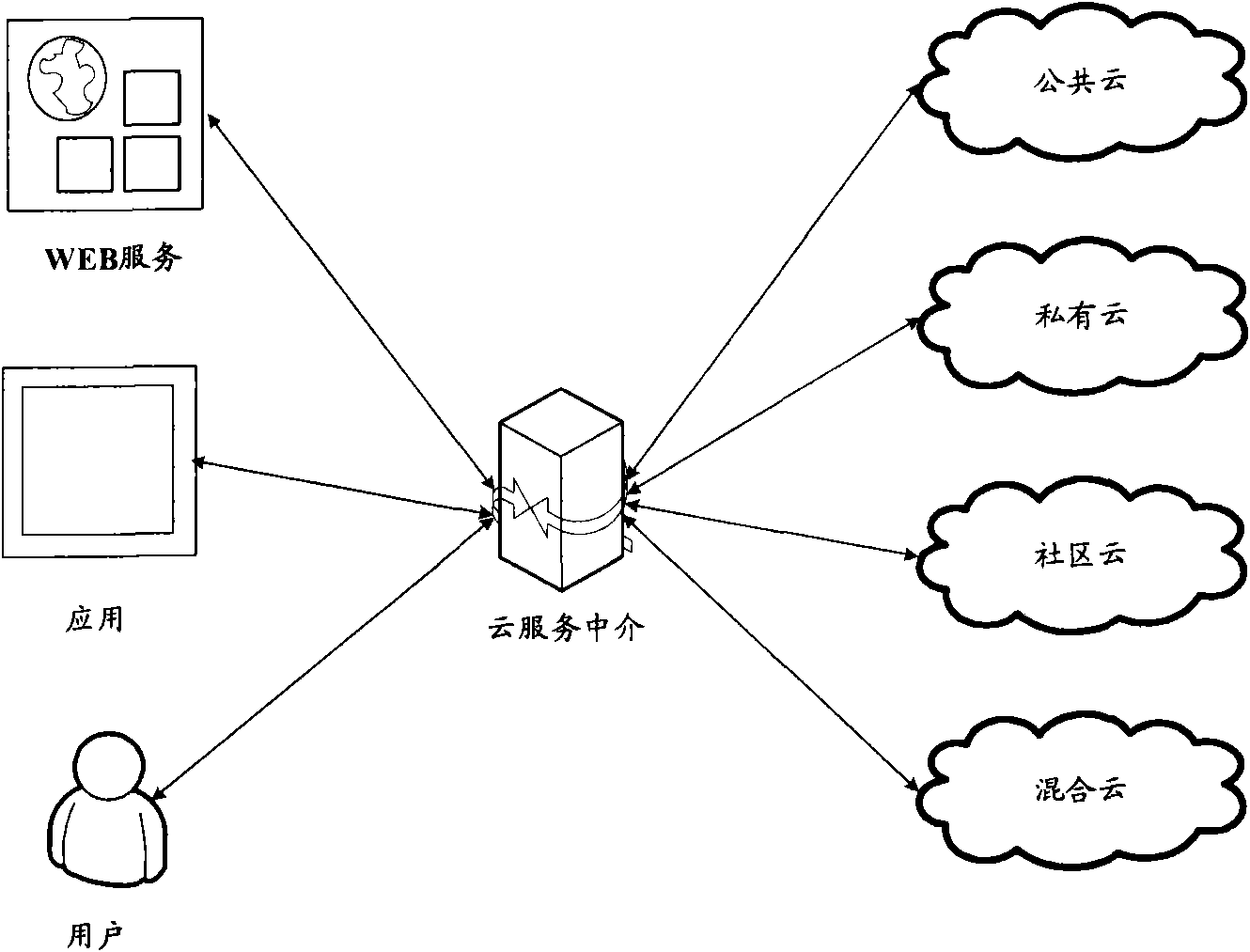
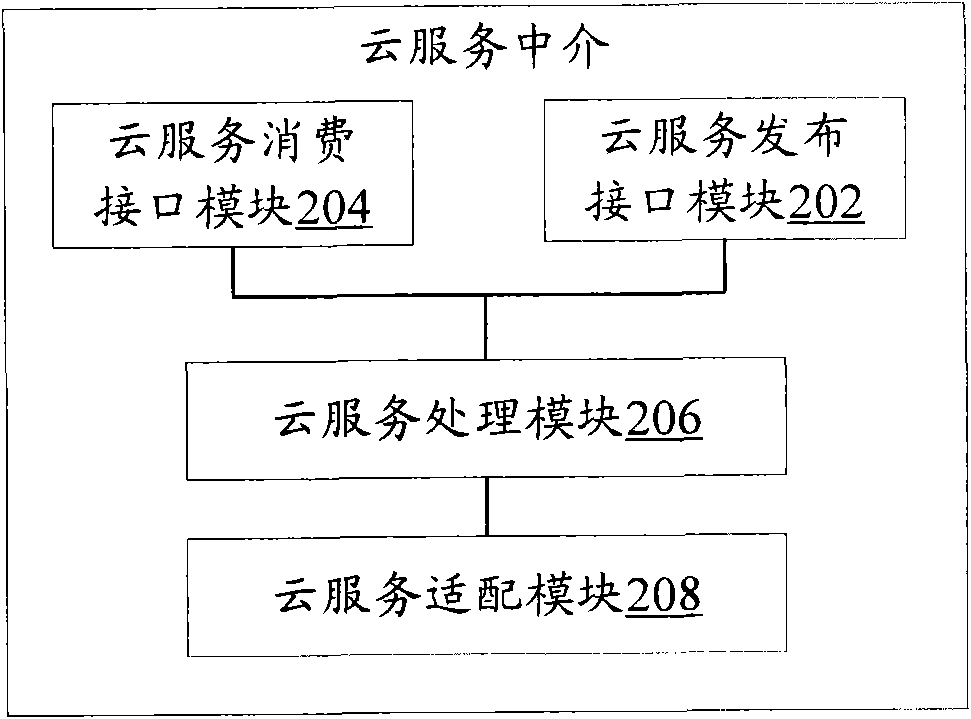
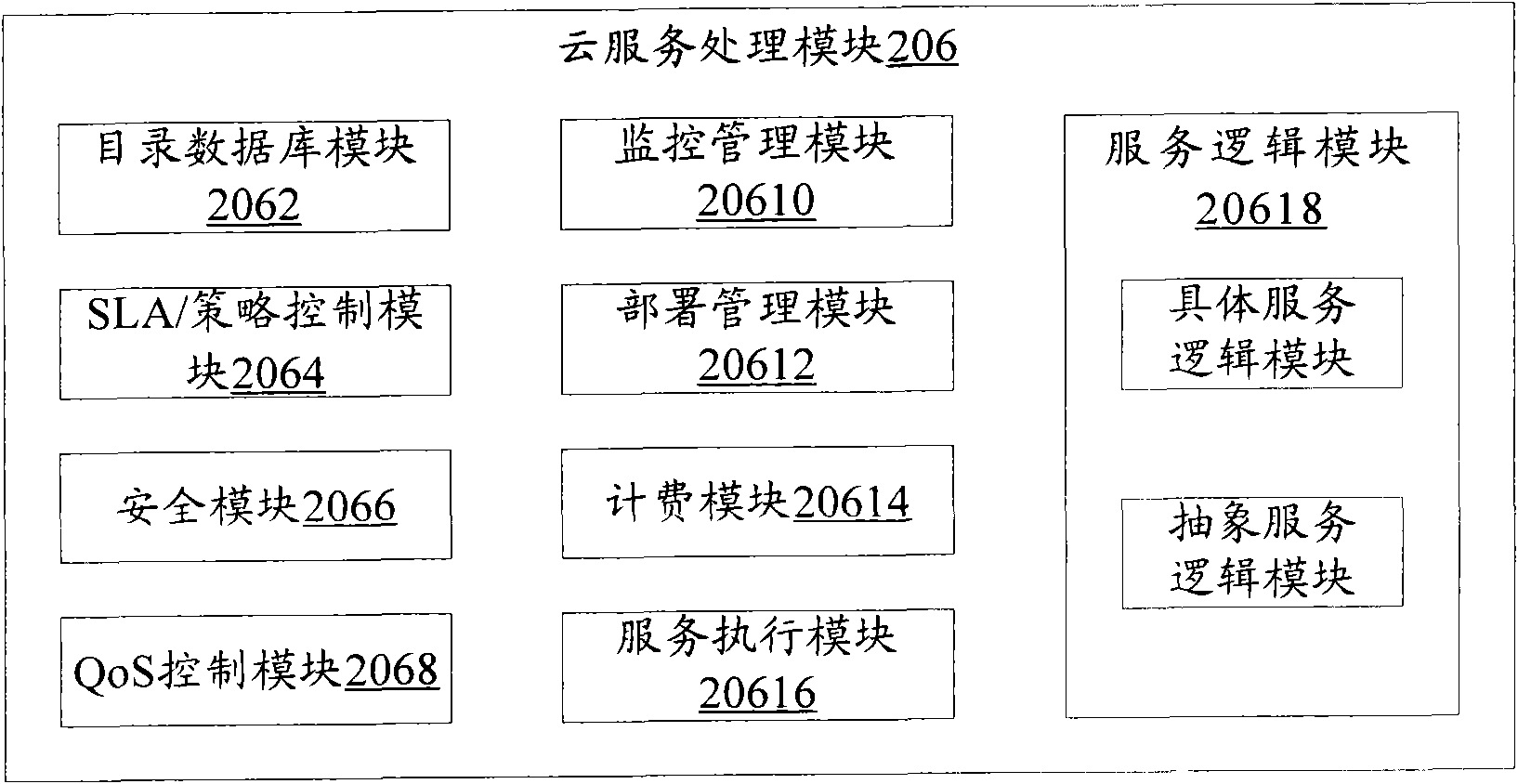
Cloud service medium, cloud computing method and cloud system
InactiveCN102255933ASolve wasteSolve efficiency problemsMetering/charging/biilling arrangementsCommerceResource informationCloud service provider
The invention discloses a cloud service medium, a cloud computing method and a cloud system. The cloud service medium comprises a cloud service releasing interface module, a cloud service consuming interface module, a cloud service processing module and a cloud service adapting module, wherein the cloud service releasing interface module is used for subscribing for cloud computing services and resource information which are provided by multiple cloud service providers; the cloud service consuming interface module is used for providing a consuming interface by which cloud service requestors can be accessed to the cloud service providers for the cloud service requestors; the cloud service processing module is used for processing the cloud service consumption requests of the cloud service providers; and the cloud adapting module is used for adapting the cloud computing services and resources provided by the cloud service providers for the cloud service requestors according to the cloud service consumption requests. According to the invention, the cloud service requestors can use the cloud services provided by different cloud service providers, the system resource is saved and the system efficiency is improved.
Owner:ZTE CORP
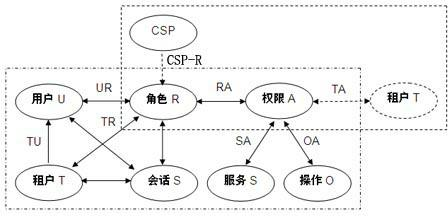
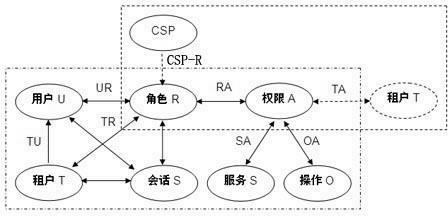
Cloud security access control model
InactiveCN102571821AReasonable designSimple structureData switching networksData access controlMedia access control
The invention discloses a cloud security access control model. The model is characterized in that: aiming at the multi-tenant architecture characteristic of cloud computing, by combining a role-based access control (RBAC) model, a tenant concept and a cloud service provider concept are introduced to an access control model, and a uniform tenant access control model and a user access control model are formed by defining model elements and formally describing model functions. The cloud security access control model can adapt to the characteristic of multi-tenant of the cloud computing, improves the flexibility of user authority management in a cloud computing environment, can reduce the complexity of authorization management and management overhead, and can effectively ensure the security and integrity of user data in the cloud computing environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
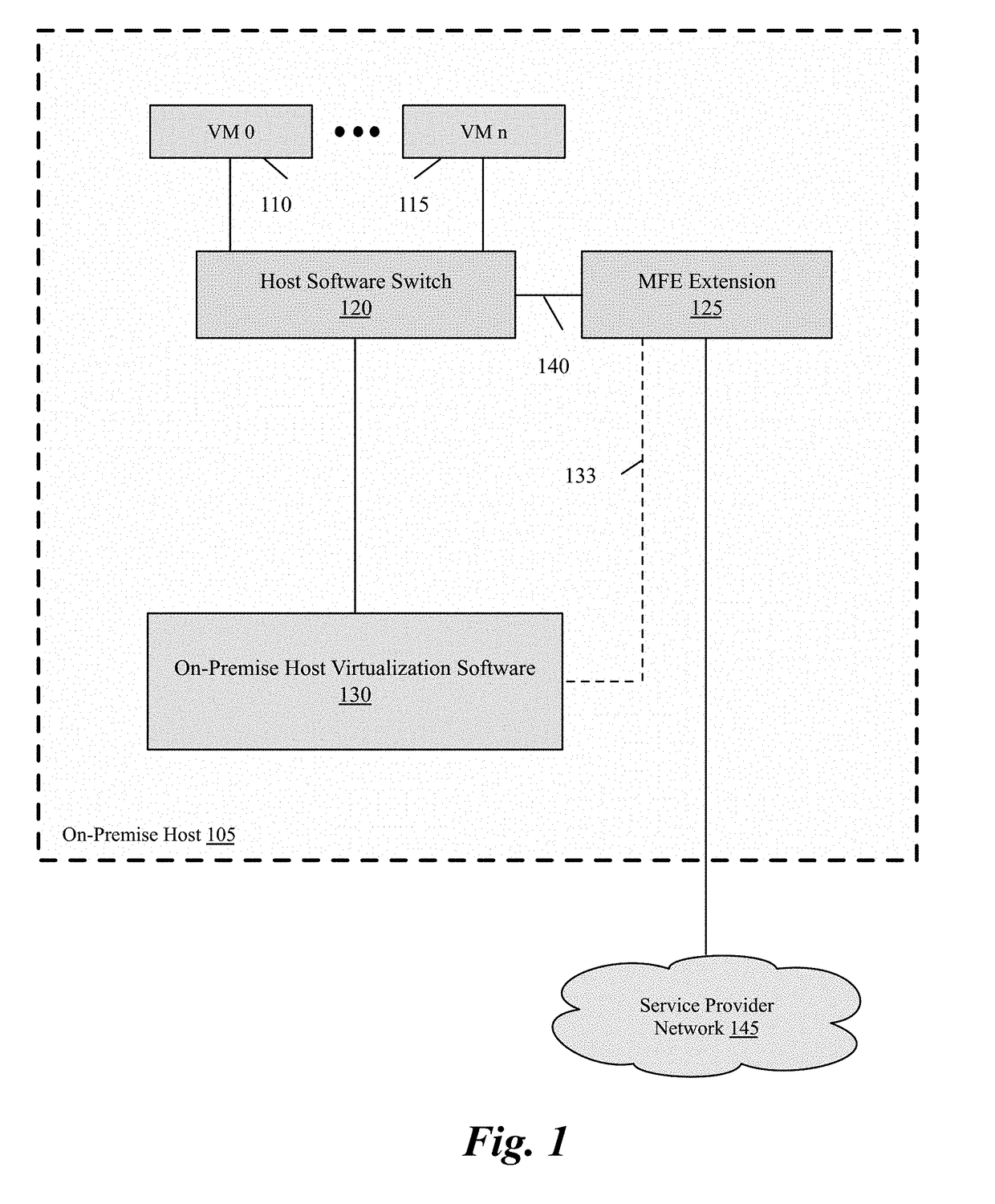
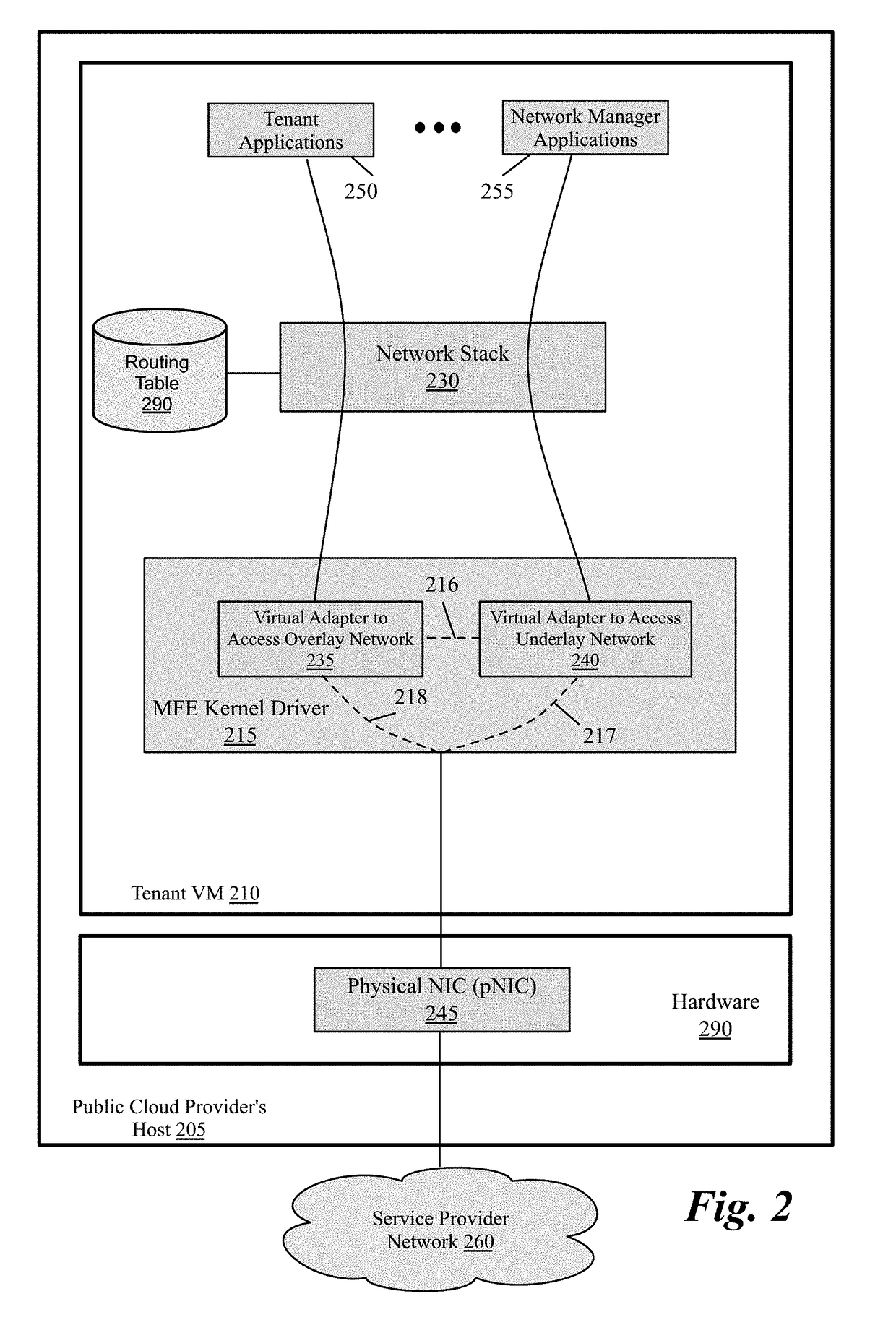
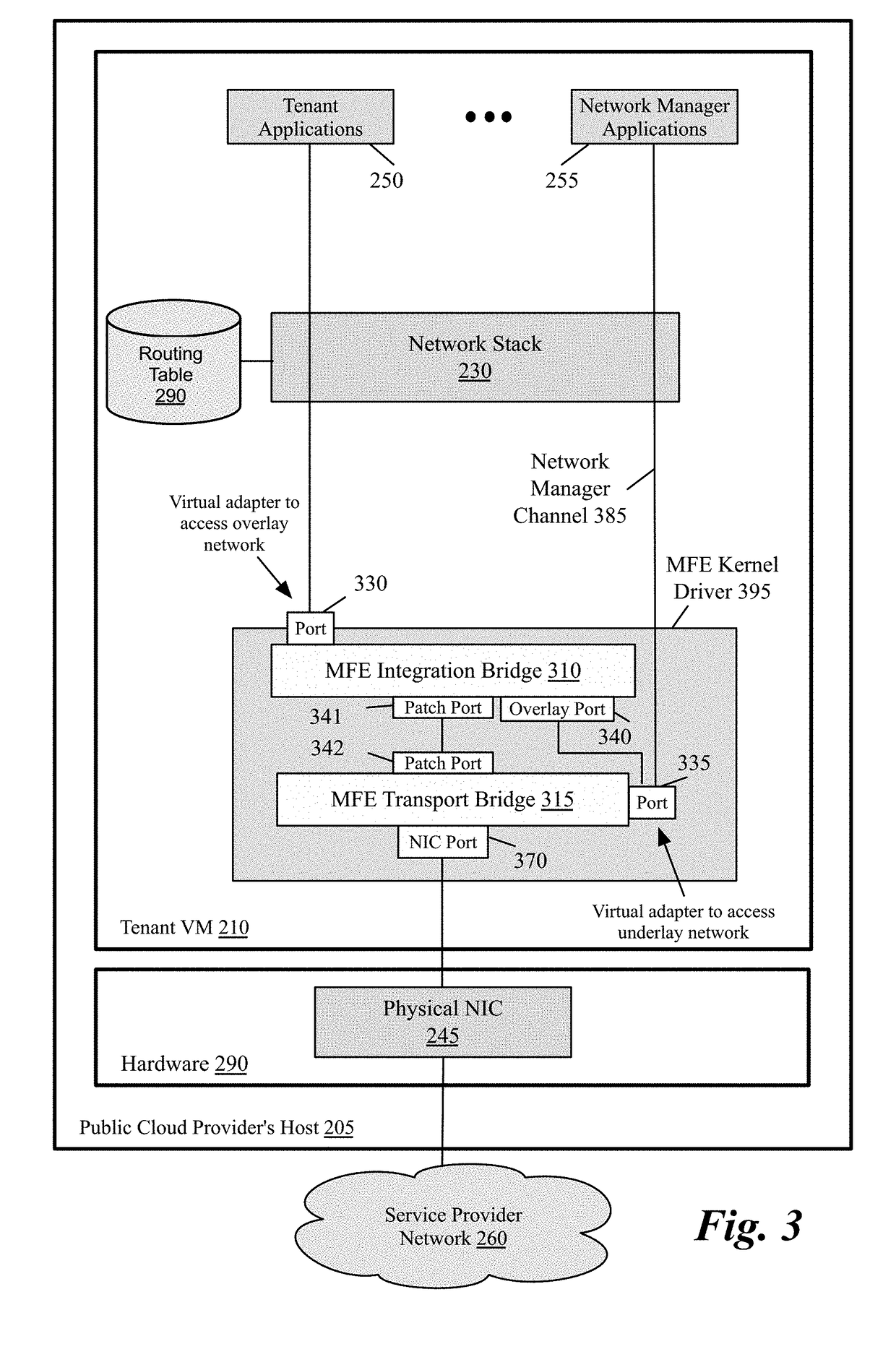
Packet communication between logical networks and public cloud service providers native networks using a single network interface and a single routing table
A data compute node executes (i) a set of tenant applications connected to a third party overlay network, (ii) a set of network manager applications, and (iii) a managed forwarding element that includes a pair of overlay and underlay network virtual adapters. A packet that is received from a network manager application and addressed to an underlay network destination is sent to the underlay network destination address through a physical NIC of the host without network address translation or encapsulation. A packet that is received from a tenant application and addressed to an underlay network destination is subject to SNAT and is sent to the underlay network destination address. A packet that is received from a tenant application and is addressed an overlay destination address is encapsulated with the header of the overlay network and is sent to the overlay network destination address through the underlay virtual adapter.
Owner:NICIRA
Methods and systems relating to optical networks
ActiveUS20170019168A1Reduce restrictionsMultiplex system selection arrangementsWavelength-division multiplex systemsFiberData center
Data center interconnections, which encompass WSCs as well as traditional data centers, have become both a bottleneck and a cost / power issue for cloud computing providers, cloud service providers and the users of the cloud generally. Fiber optic technologies already play critical roles in data center operations and will increasingly in the future. The goal is to move data as fast as possible with the lowest latency with the lowest cost and the smallest space consumption on the server blade and throughout the network. Accordingly, it would be beneficial for new fiber optic interconnection architectures to address the traditional hierarchal time-division multiplexed (TDM) routing and interconnection and provide reduced latency, increased flexibility, lower cost, lower power consumption, and provide interconnections exploiting N×M×D Gbps photonic interconnects wherein N channels are provided each carrying M wavelength division signals at D Gbps.
Owner:AEPONYX
Supporting Compliance in a Cloud Environment
InactiveUS20120096525A1Error detection/correctionDigital data processing detailsData exchangeClient-side
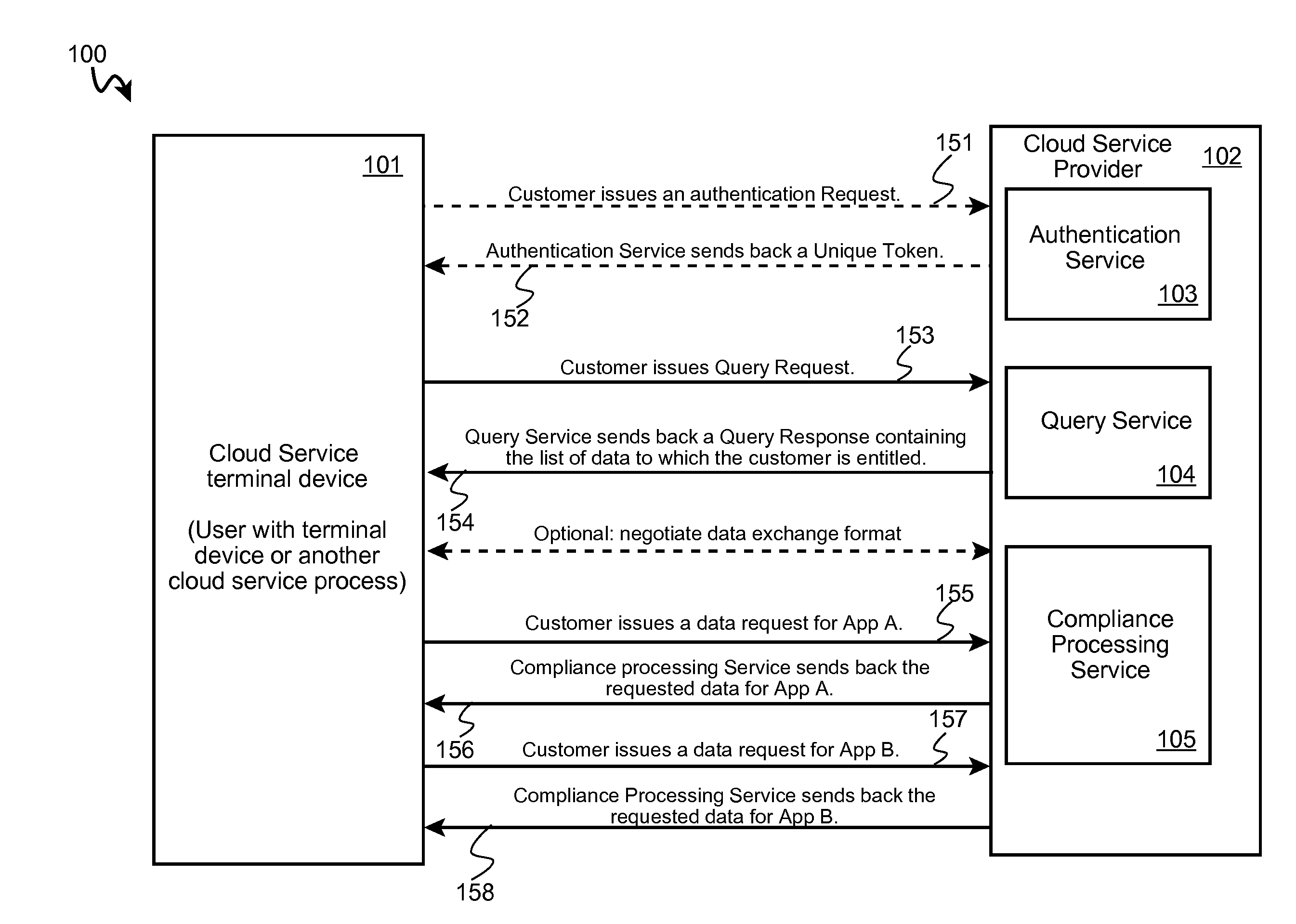
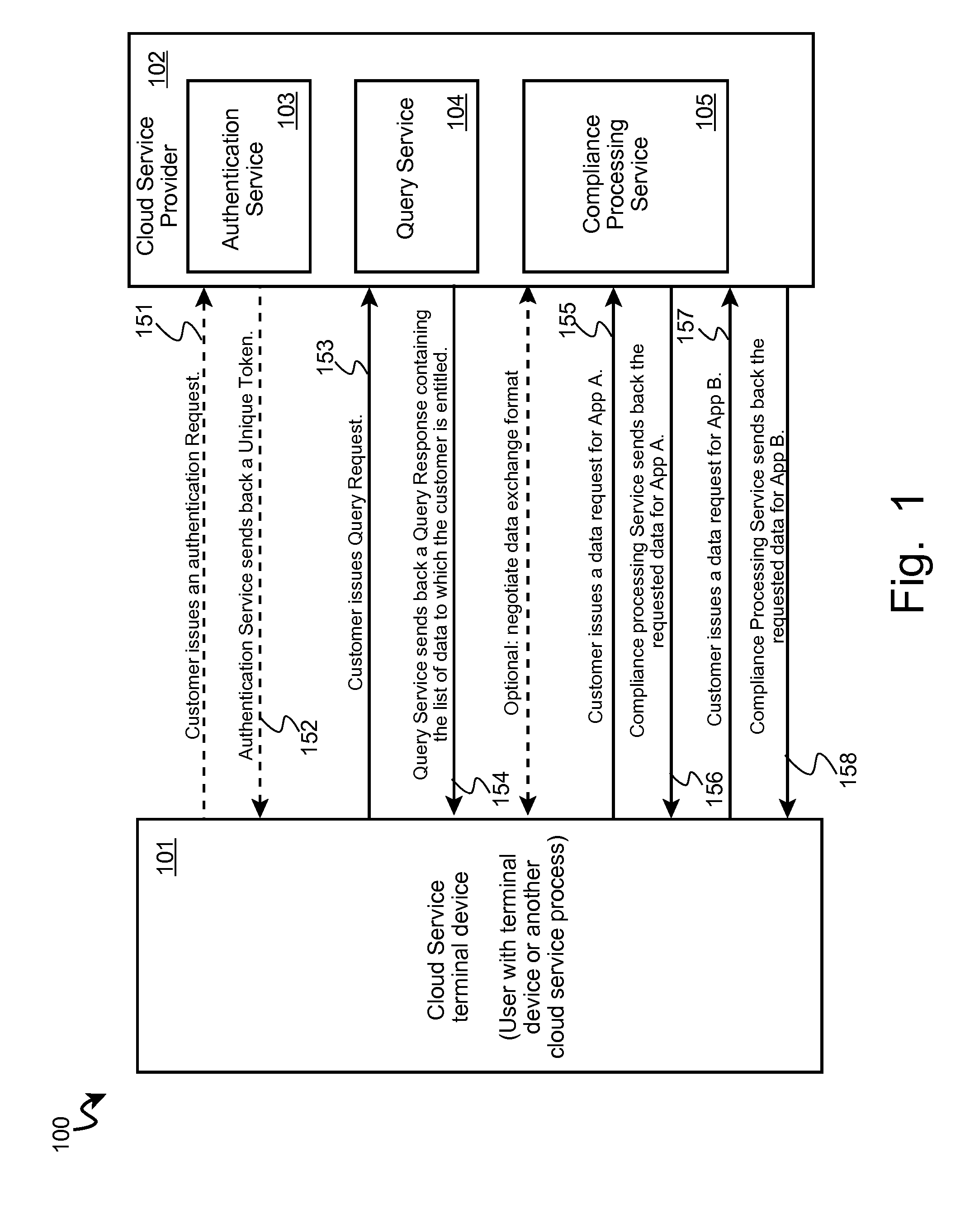
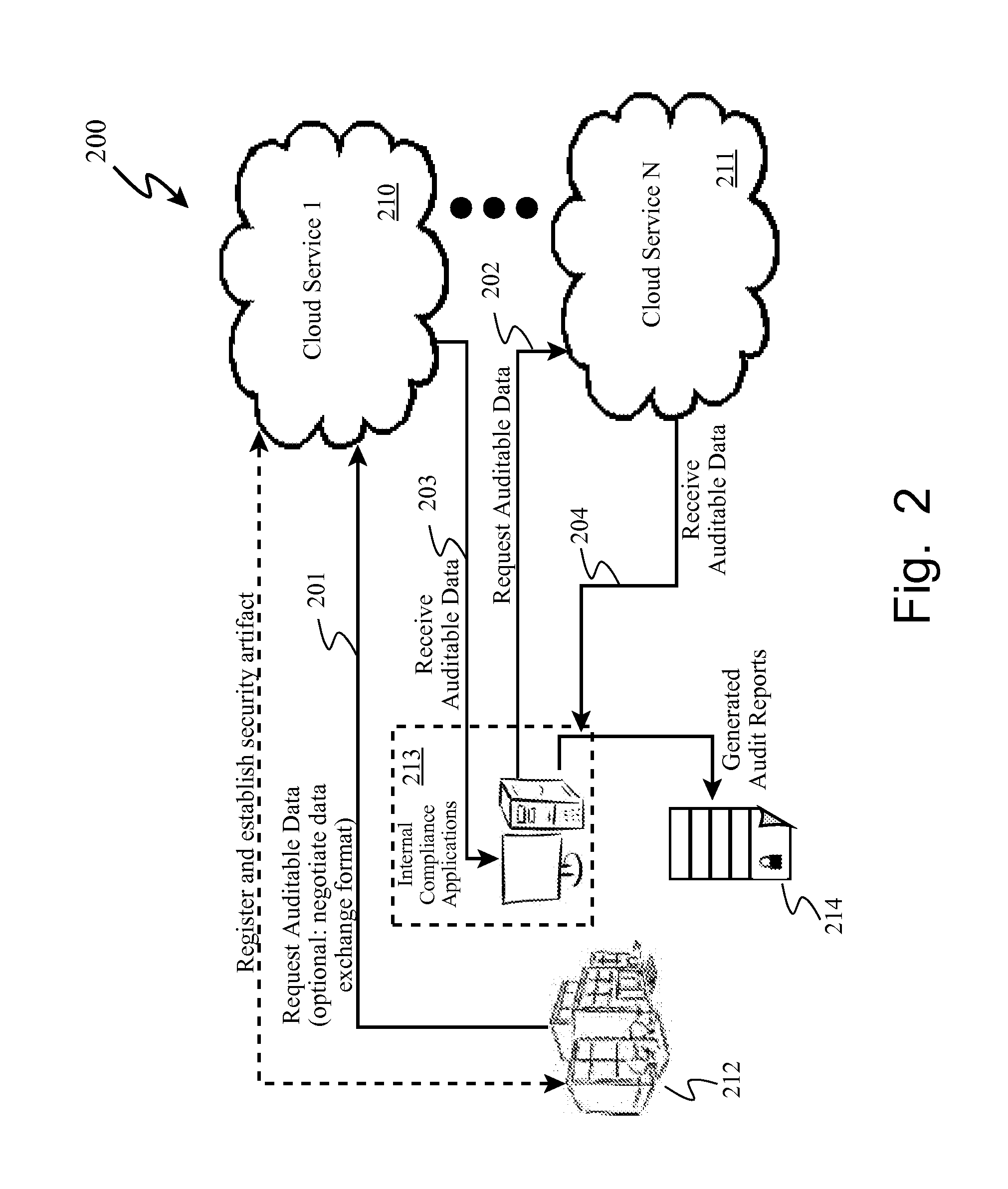
Gathering auditable data concerning actions in a cloud computing environment is automated by determining that one or more auditable data items are available associated with a requester and with at least one application program; responsive to determining that data items are available, transmitting a list of the available auditable data items to a requesting cloud client computer; subsequent to transmitting the list, receiving a data request from the cloud client computer for one or more particular auditable data items from the list; preparing the requested particular auditable data items for transmission according to a predetermined format; and transmitting the prepared requested particular auditable data items to the cloud client computer. Optionally, in some embodiments, the requesting cloud client computer may negotiate a data exchange format with the cloud service provider for receipt of the requested auditable information.
Owner:IBM CORP
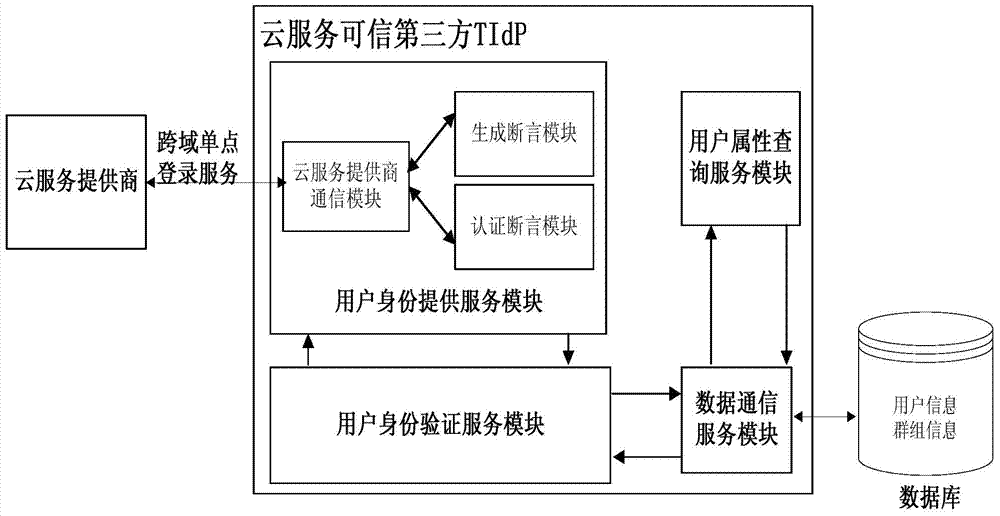
Identity escrow and authentication cloud resource access control system and method for multiple tenants
InactiveCN103532981AImprove qualityReduce management costsUser identity/authority verificationThird partyControl system
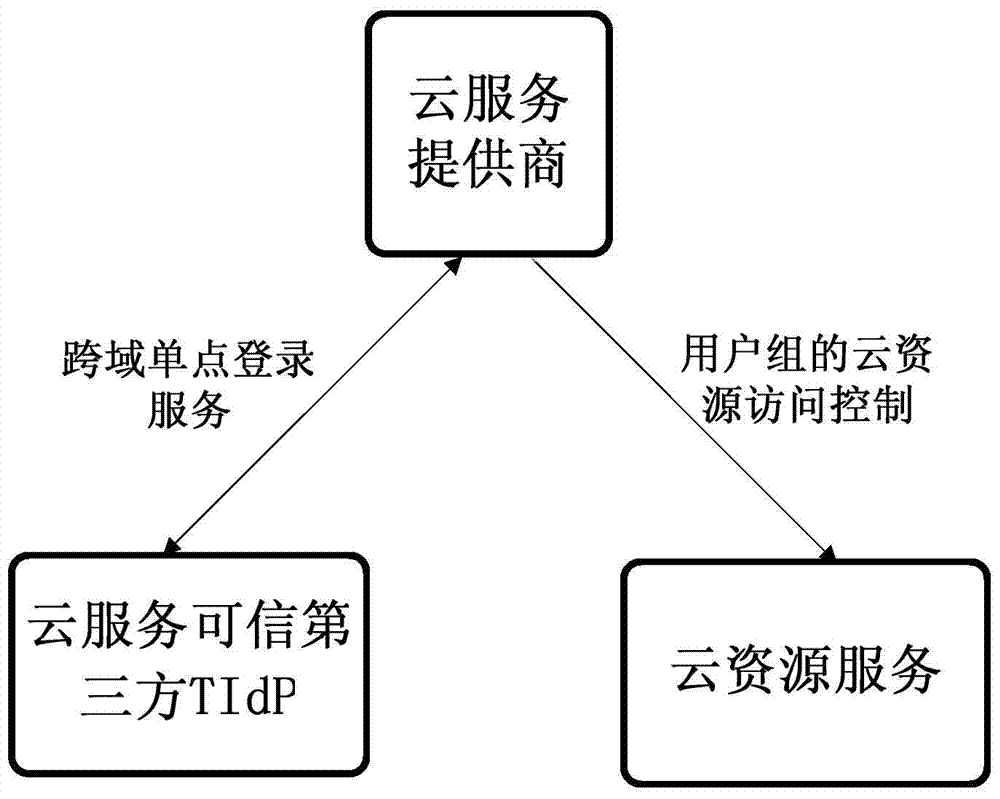
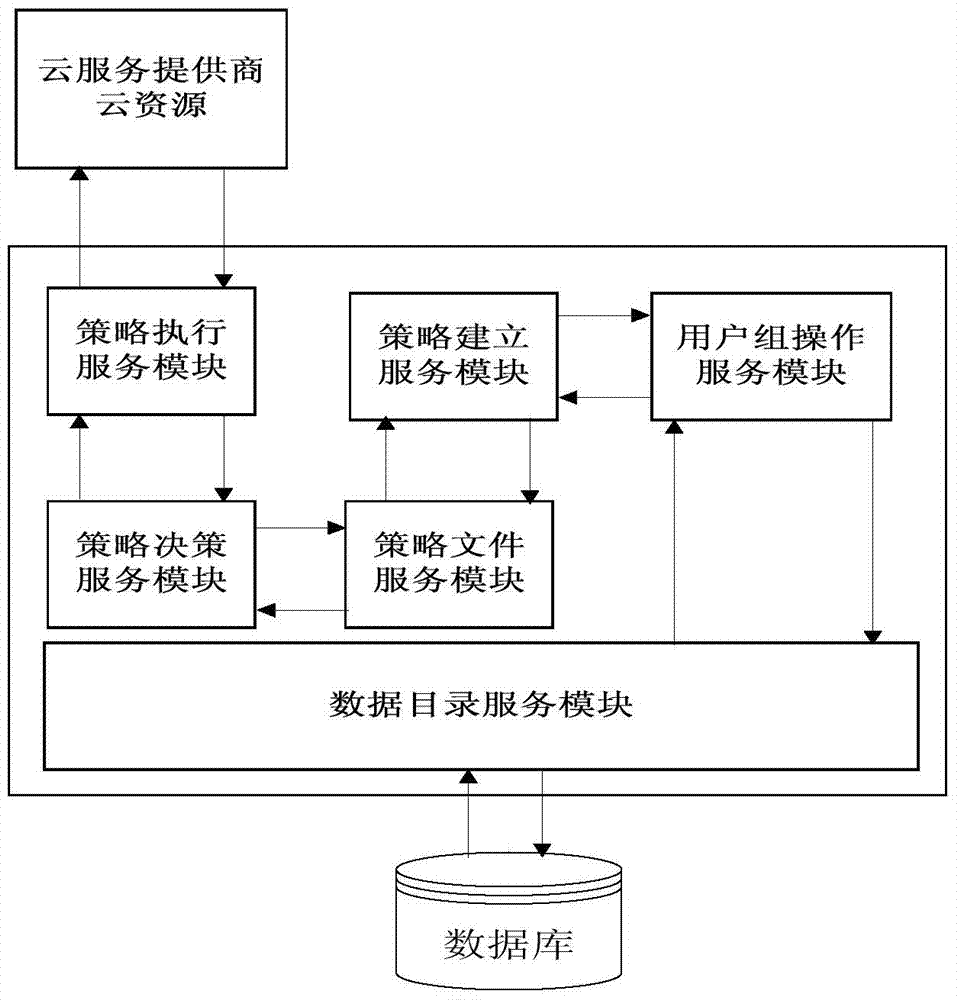
The invention provides an identity escrow and authentication cloud resource access control system and an identity escrow and authentication cloud resource access control method for multiple tenants. The system is characterized in that the cloud service business of a cloud service provider is divided into two parts of an identity authentication permission part and a cloud resource access control part, wherein the business of the identity authentication permission part is hosted by a credible third party TIdP of the cloud service, and the TIdP is in charge of governing hosted user information and group information of the tenant, completes the user identity authentication work of a hosting user and generates cross-domain security credential service containing identity recognition information; the cloud resource access control part is responsible for assigning corresponding permission for a group where the user is located, and analyzes the access request of the user and implements an access control decision according to the existing resource access control strategy when the user accesses to the cloud resource, so as to achieve safety access control over the cloud resource.
Owner:INST OF INFORMATION ENG CAS
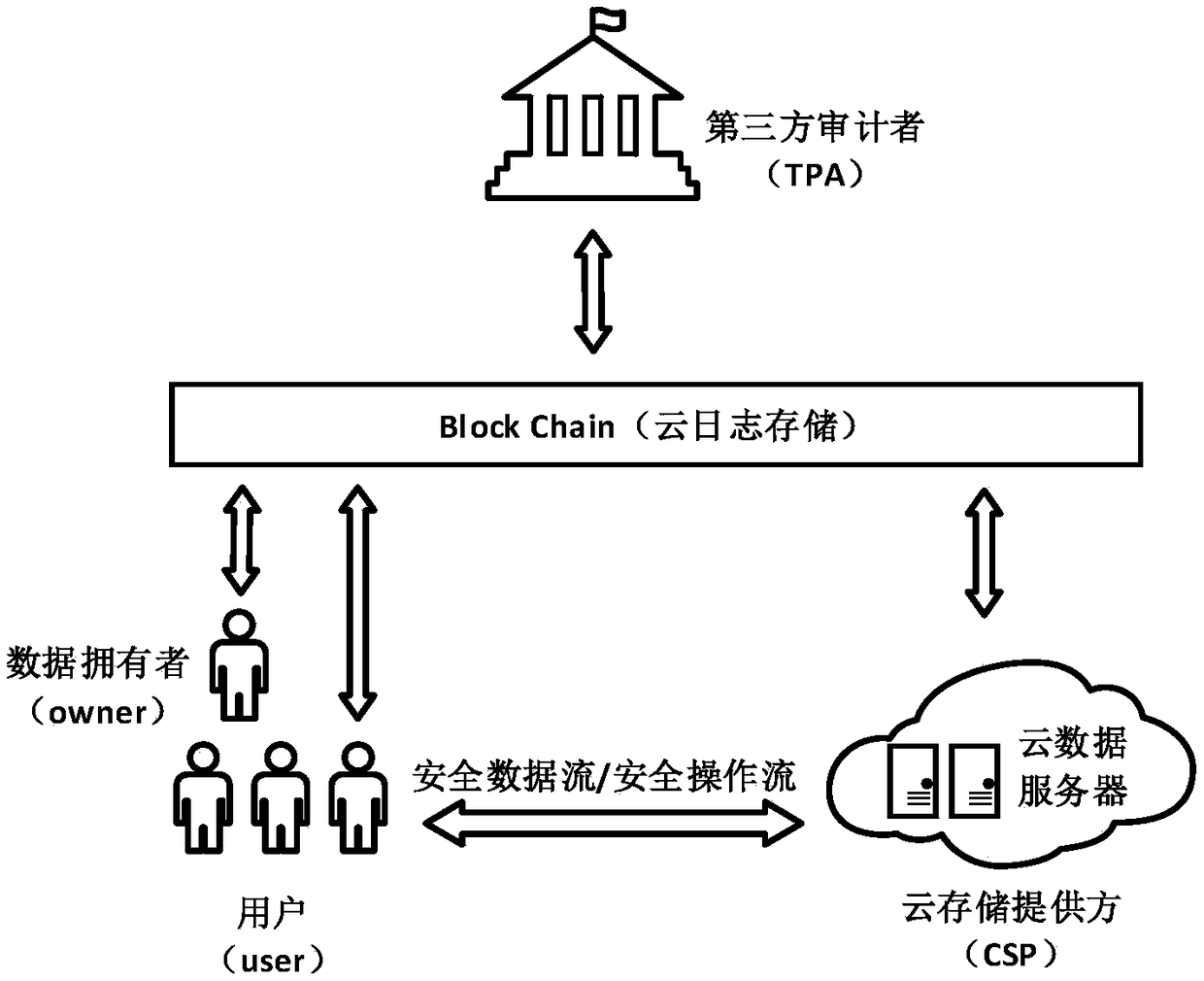
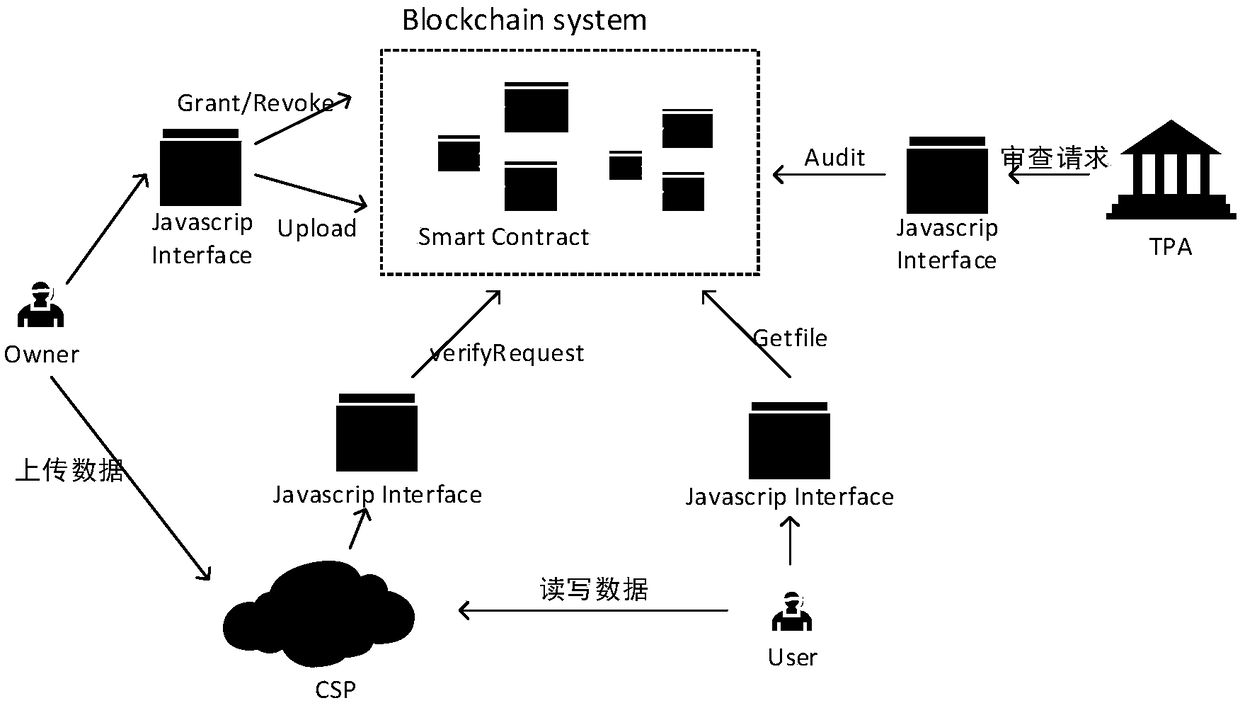
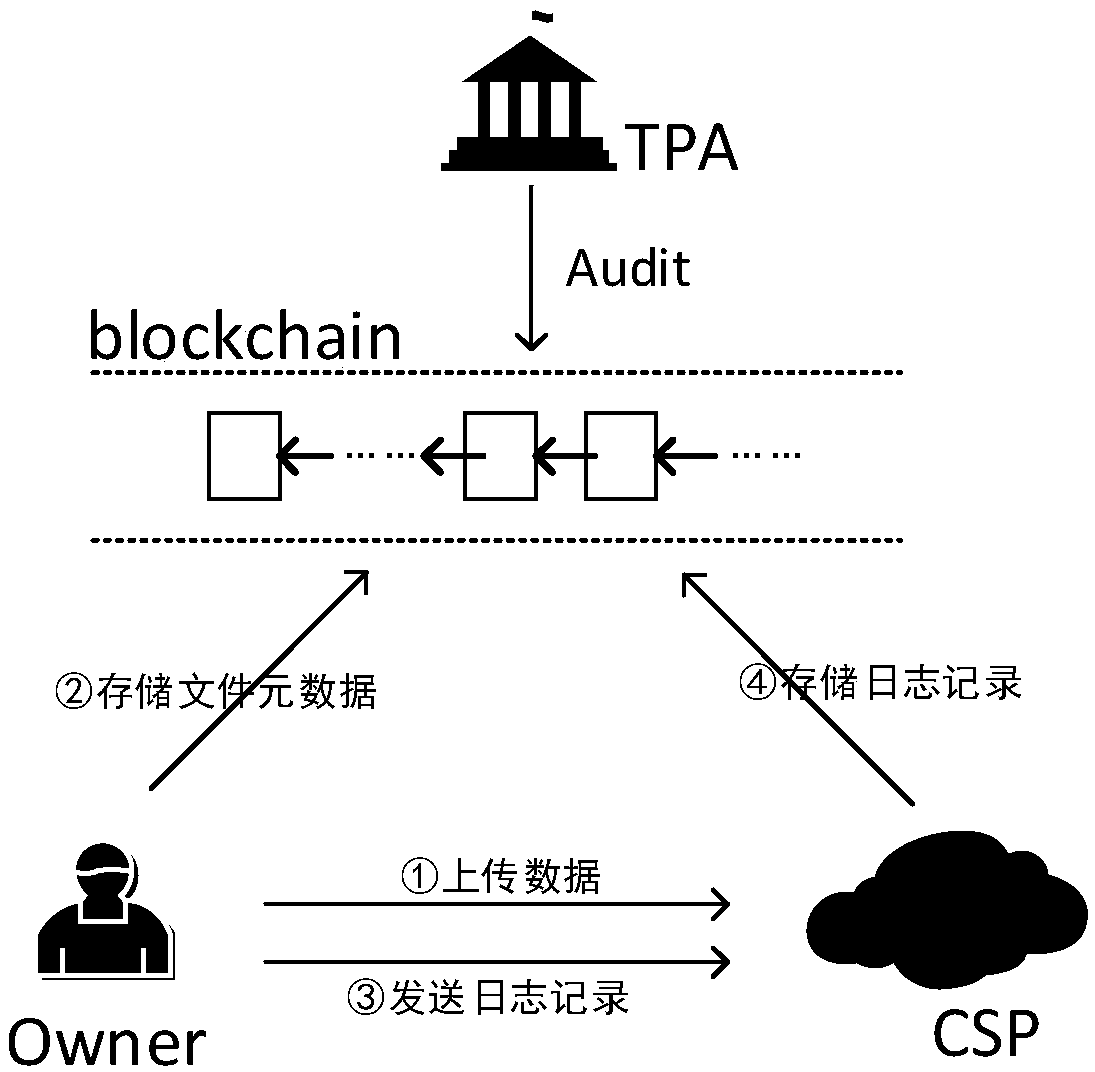
A log behavior audit method based on a block chain in cloud storage environment
The invention discloses a log behavior audit method based on a block chain in a cloud storage environment. Each interface required in the flow of the method is compiled by an intelligent contract, which ensures that both sides cannot deny the behavior of the log behavior, so that the log record in the block chain network is completely trusted. The audit interface of the intelligent contract is called when there is an audit requirement, and the log records are reviewed by the intelligent contract and the results are returned to the requesting user. By transferring the cloud log storage from thecloud storage provider to the block chain, the invention ensures the safety and integrity of the log data by utilizing the characteristics of decentralization, decentralization and high reliability of the block chain. The intelligent contract is used to make the block chain network provide the log read-write interface and audit structure, and the data access process is designed for the interaction between users and cloud service providers, which can ensure that users and cloud storage parties can record the log completely on the block chain network, and the log record cannot be denied and tampered with.
Owner:HUAZHONG UNIV OF SCI & TECH
Cloud computing resource scheduling method based on scheduling object space
InactiveCN102780759ARealize personalized schedulingImprove efficiencyData switching networksAdaptive optimizationDecision taking
The invention discloses a cloud computing resource scheduling method based on scheduling object space. According to the method, the concept of scheduling object space is introduced for setting a flexible standard framework, so that a user can explain the requirement on service resource scheduling, namely the user can select required scheduling attribute for optimization, wherein a multi object resource distribution scheduling mechanism can make adaptive resource scheduling decision under the driving of the expandable user scheduling object space. The method can dynamically deploy cloud computing resource according to the requirement of the user on resource scheduling, and realizes the adaptive optimal distribution of the cloud computing resource driven by the user requirement. Moreover, the scheduling strategy can avoid over turning-on of a cloud computing server as much as possible, thereby improving the utility ratio of resources and reducing the cost of a cloud service provider.
Owner:HEFEI UNIV OF TECH
System and method for reducing latency time with cloud services
ActiveUS20110173405A1Reduce service latencyDatabase updatingError detection/correctionSoftware updateData management
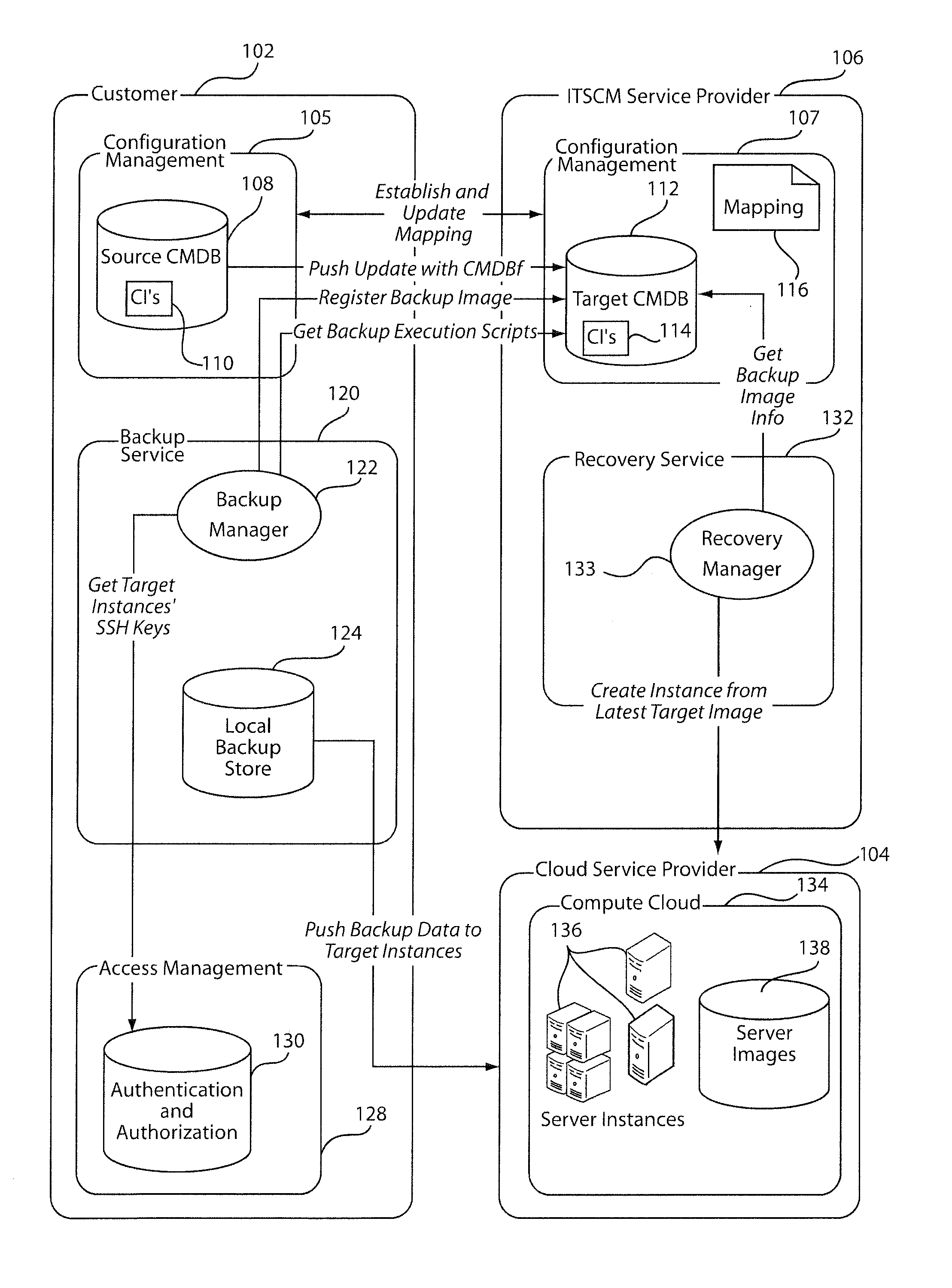
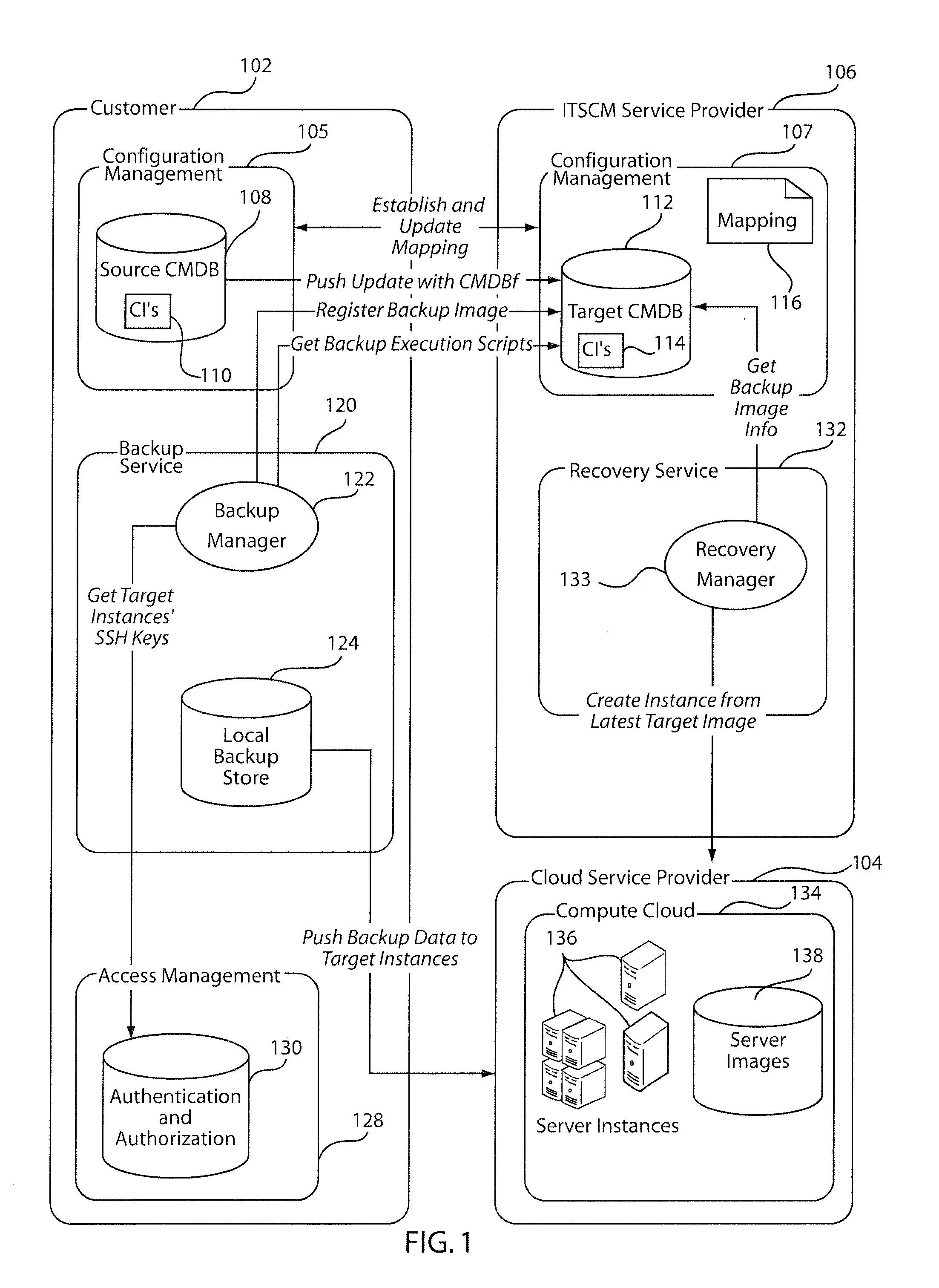
A system and method for reducing service latency includes dividing an information technology service for a customer into an infrastructure management service and a data management service. Data associated with the information technology service is stored in a backup memory. A set of infrastructure images related to the information technology service is stored at a cloud service provider. The infrastructure images are updated with software updates and hardware updates, as needed, and the data associated with the information technology service is updated through backup and restore mechanisms. The set of infrastructure images that have been updated with data with latest updates are started for recovery, continuity, testing, etc.
Owner:KYNDRYL INC
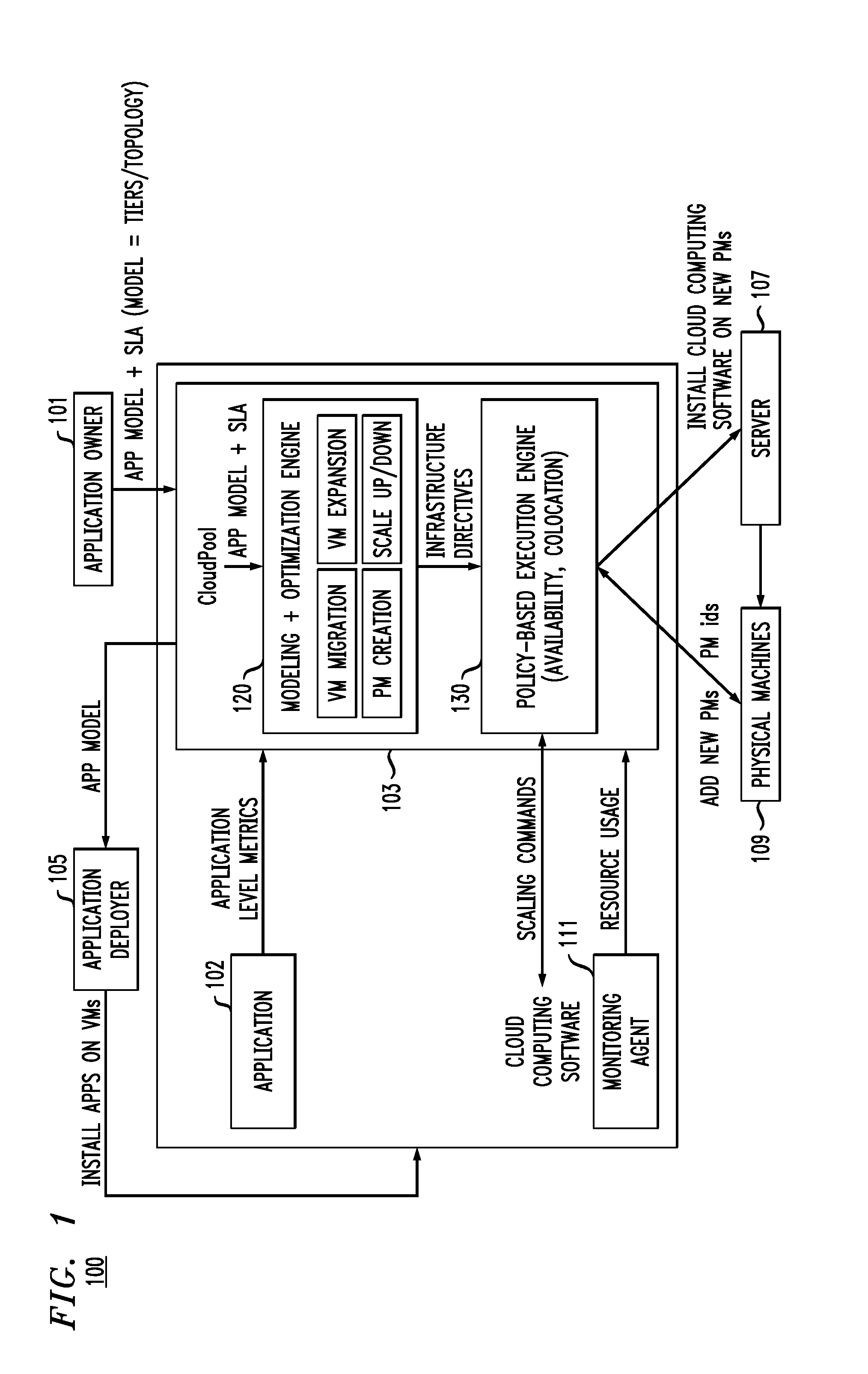
Systems and methods for scaling a cloud infrastructure
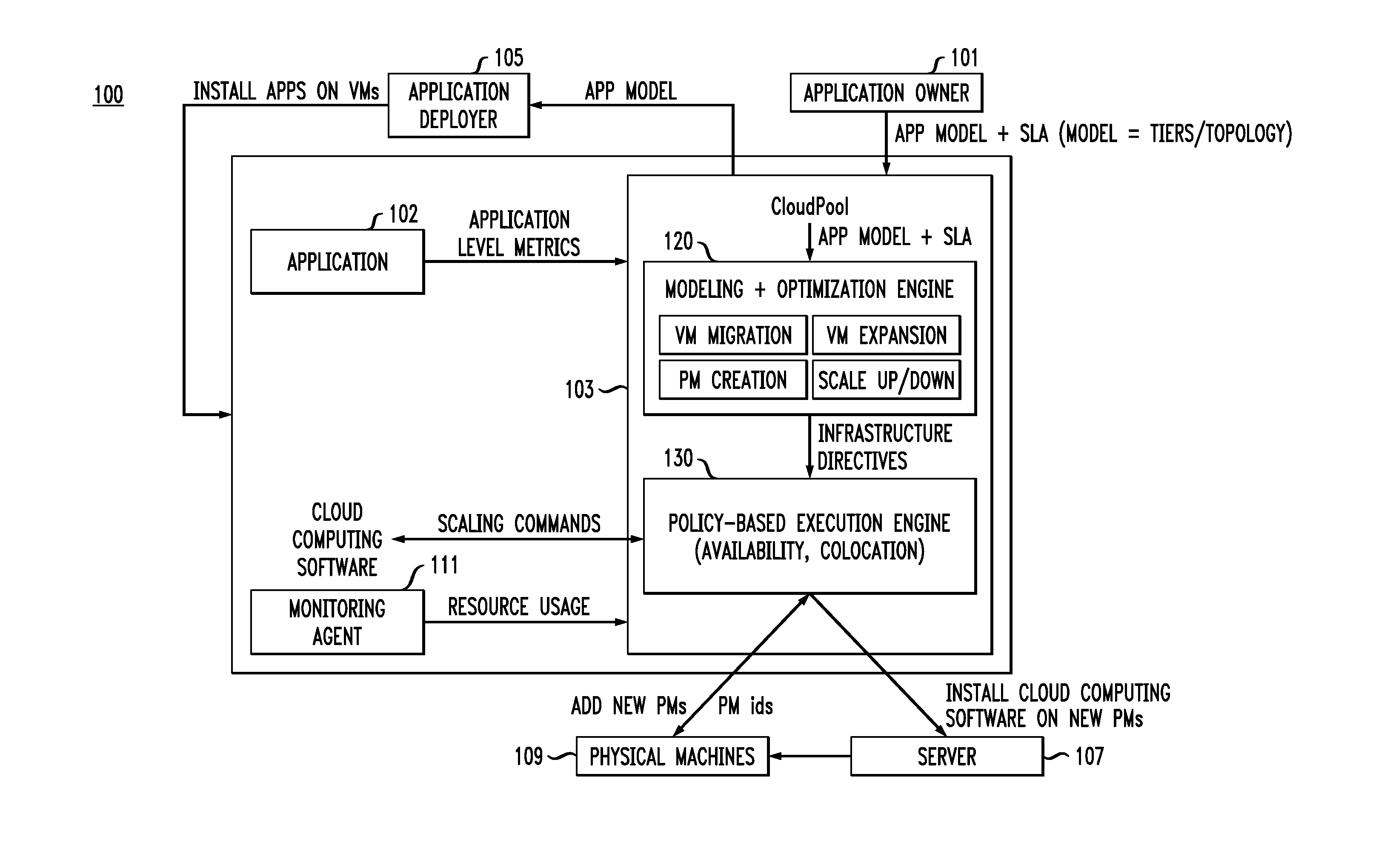
ActiveUS20150169291A1Minimizing resource consumptionRobustnessSoftware designSoftware metricsCloud service providerDistributed computing
A method for scaling a cloud infrastructure, comprises receiving at least one of resource-level metrics and application-level metrics, estimating parameters of at least one application based on the received metrics, automatically and dynamically determining directives for scaling application deployment based on the estimated parameters, and providing the directives to a cloud service provider to execute the scaling.
Owner:IBM CORP
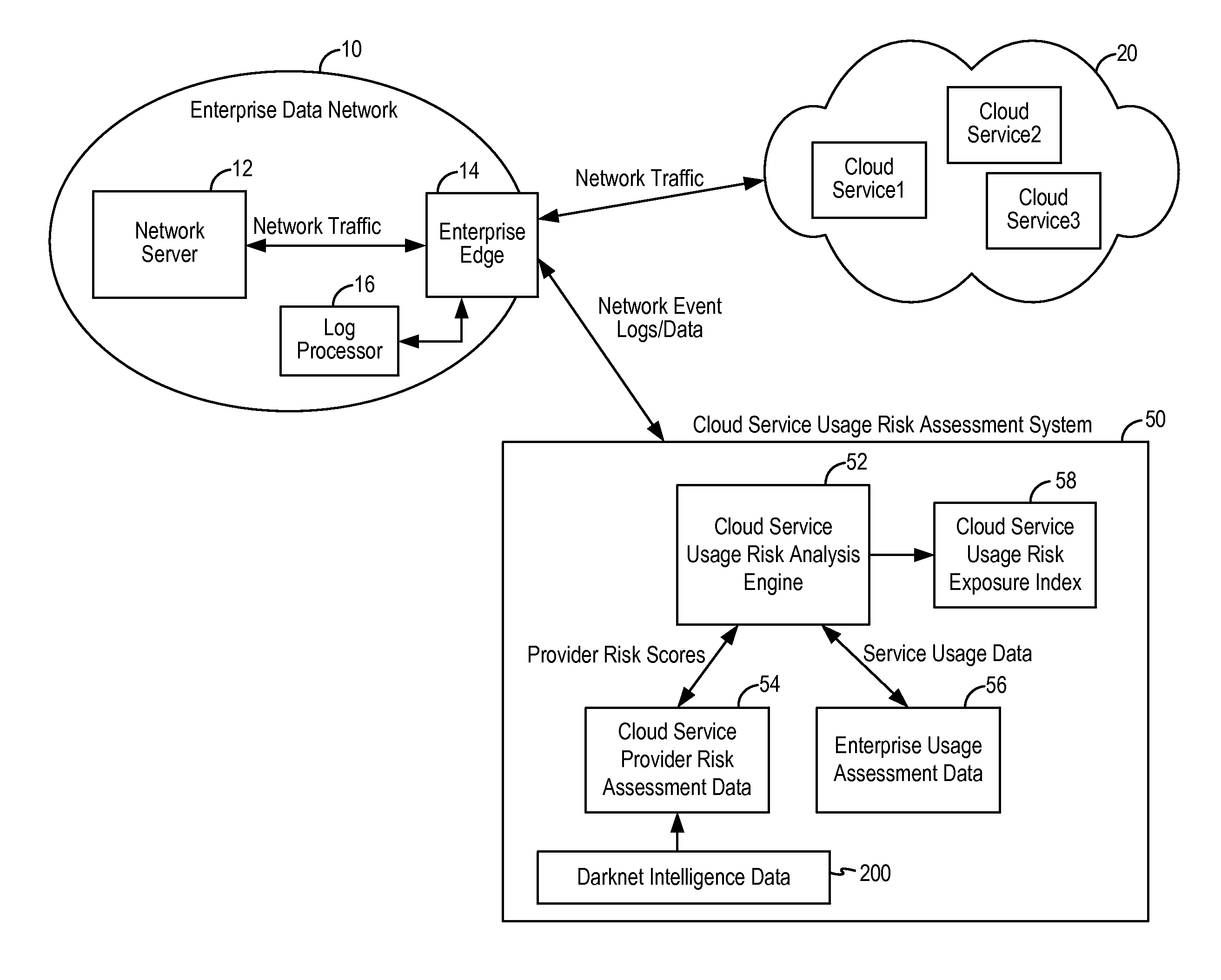
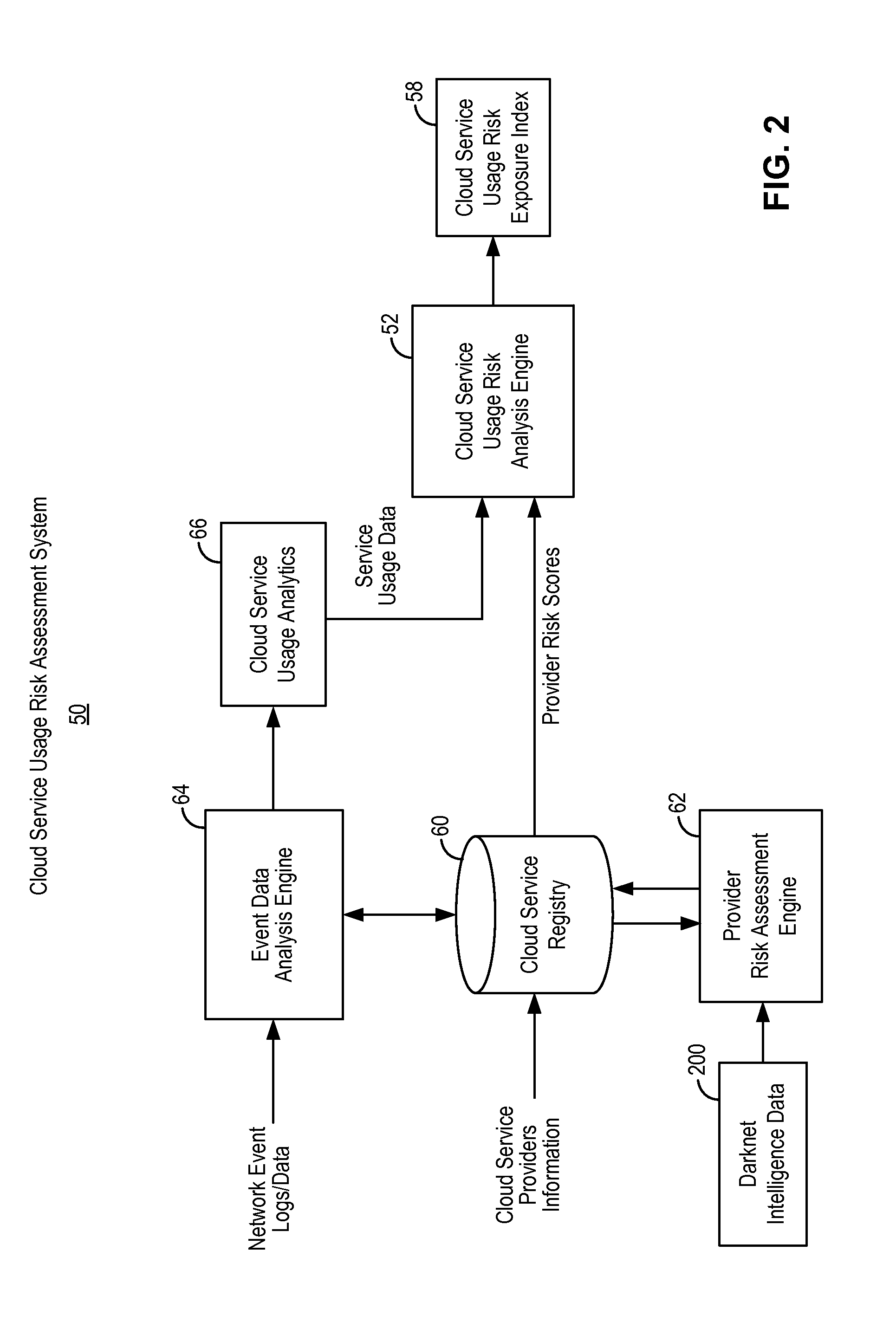
Cloud service usage risk assessment using darknet intelligence
A method of assessing a risk level of an enterprise using cloud-based services from one or more cloud service providers includes assessing provider risk scores associated with the one or more cloud service providers and in view of darknet intelligence data; assessing cloud service usage behavior and pattern of the enterprise; and generating a risk score for the enterprise based on the provider risk scores and on the cloud service usage behavior and pattern of the enterprise. The risk score is indicative of the risk of the enterprise relating to the use of the cloud-based services from the one or more cloud service providers.
Owner:SKYHIGH SECURITY LLC
Outsourcing decryption method of attribute-based encryption based on ciphertext policy
InactiveCN104022868AReduce the burden onEfficient and safe decryptionKey distribution for secure communicationUser identity/authority verificationThird partyCiphertext
The invention provides a highly-efficient safe outsourcing decryption method based on the attribute encryption in mobile cloud computing environment. The method comprises the following steps: system initialization; a data owner encrypting a file and uploading the file to a cloud service provider; an authorization organization generating secret keys; a third party transforming ciphertexts; and a mobile terminal user decrypting the file. According to the method, targeted for the mobile cloud computing environment, by utilizing a ciphertext policy attribute-based encryption shared data method, according to the requirement of limited operation and storage capacity of a mobile terminal, and under the premise of guaranteeing data security, a portion of complex decryption tasks are outsourced to the third party; and by utilizing outsourcing decryption, secret key decomposition technique and matching algorithm, unnecessary bilinearity pairing operation is reduced, and a reliable method is provided for the mobile terminal to carry out rapid decryption.
Owner:HANGZHOU NORMAL UNIVERSITY
Resource exchange management within a cloud computing environment
ActiveUS8037187B2Improve usabilityReduce unavailabilityFinanceGroup 8/9/10/18 element organic compoundsResource managementResource based
The present invention provides a solution for resource sharing (e.g., inter-Cloud) within a Cloud-computing environment. One objective of the present invention is to better utilize idle public or private Cloud infrastructures and improve the availability of Cloud services by allowing different Cloud service providers to virtually combine their services and infrastructures. In the event that there is not enough capacity for a single Cloud service provider to manage its workload, the workload may be shifted to additional infrastructures within the Cloud. The result of the workload shift may reduce the unavailability of Cloud services to the Cloud end-user by allowing another Cloud service provider to temporarily handle the workload. Based on the resource sharing activities, compensation (e.g., credits / tokens) can be exchanged between the participating Cloud providers to reflect their participation in the resource exchange.
Owner:KYNDRYL INC
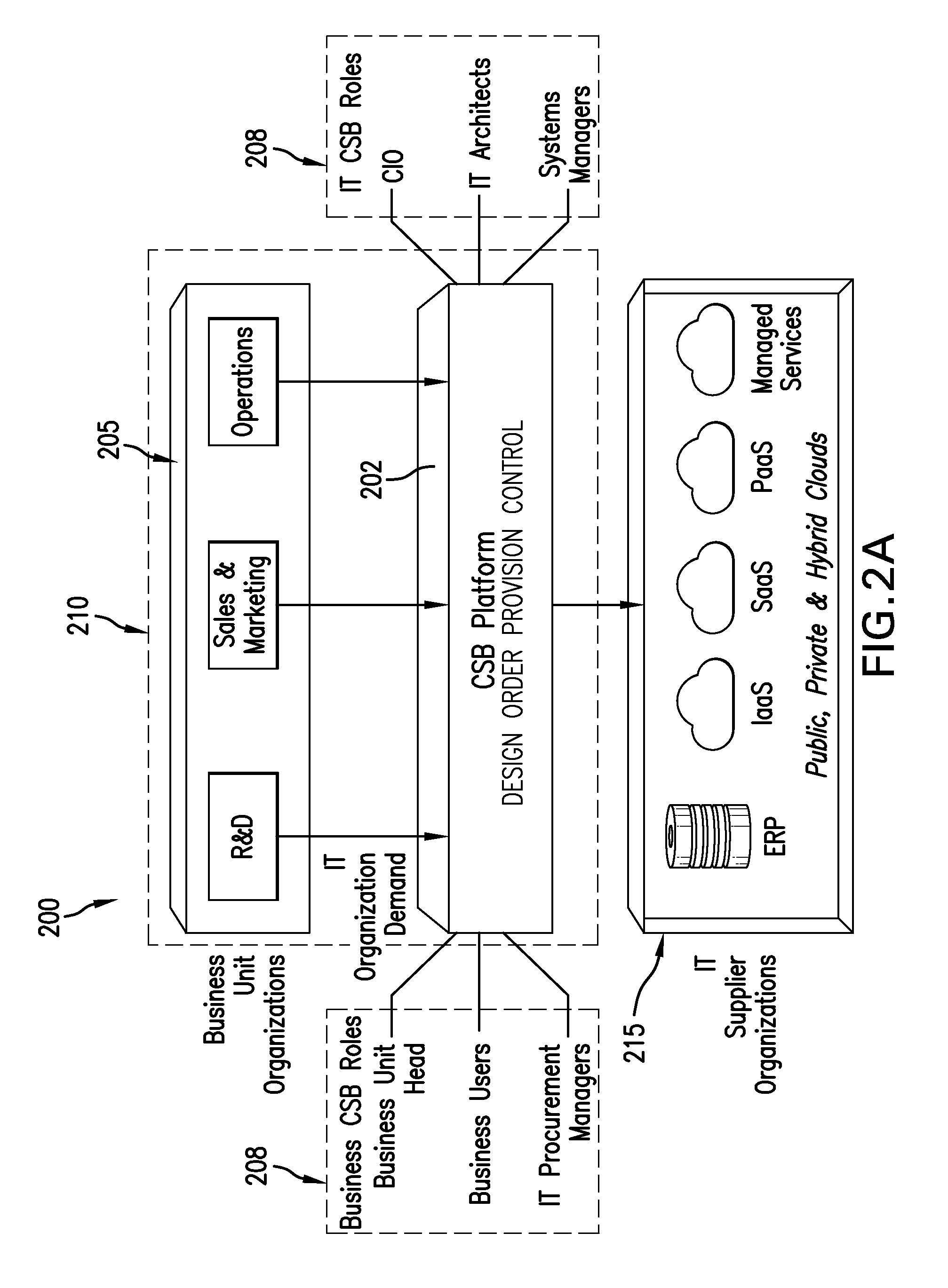
Integrated cloud service brokerage (CSB) platform functionality modules
InactiveUS20140280966A1Enhancing cloud serviceEfficient and effectiveFinanceDigital computer detailsCloud service providerService resource
A non-transitory computer-readable storage medium has tangibly embodied thereon and accessible therefrom instructions interpretable by at least one data processing device. The instructions are configured for causing the at least one data processing device to perform a method for enabling a user thereof to select one or more cloud service providers that offer cloud service resources fulfilling cloud service resource requirements of a cloud service solution, to procure the cloud service resources from the one or more cloud service providers and to provision the cloud service resources in accordance with the service resource requirements of the cloud service solution.
Owner:HCL TECH LTD
Cloud computing roaming services
The present invention provides a system and method to provide Cloud roaming services. It allows Cloud services to be offered to requesters that are abstracted from the underlying Cloud provider used to fulfill those services. The present invention provides the ability for Cloud providers to be dynamically associated with currently available Cloud services for requesters. The system and method describes two scenarios—a pull and push model—to align requester required services to currently available services from Cloud providers. The requester has a profile determining a prioritized list of Cloud providers that may be used, or the primary Cloud provider may delegate services to a partner cloud. The algorithm of the invention shows how the provider decides which requesters have access to which services—based on current utilization and forecasting. Also, from a requester perspective, location, roaming, network bandwidth and requester processing capabilities (not all-inclusive) may be sent to the provider of Cloud services to determine whether a change is needed.
Owner:KYNDRYL INC
System for allowing handheld client side to network with charging pile to display payment
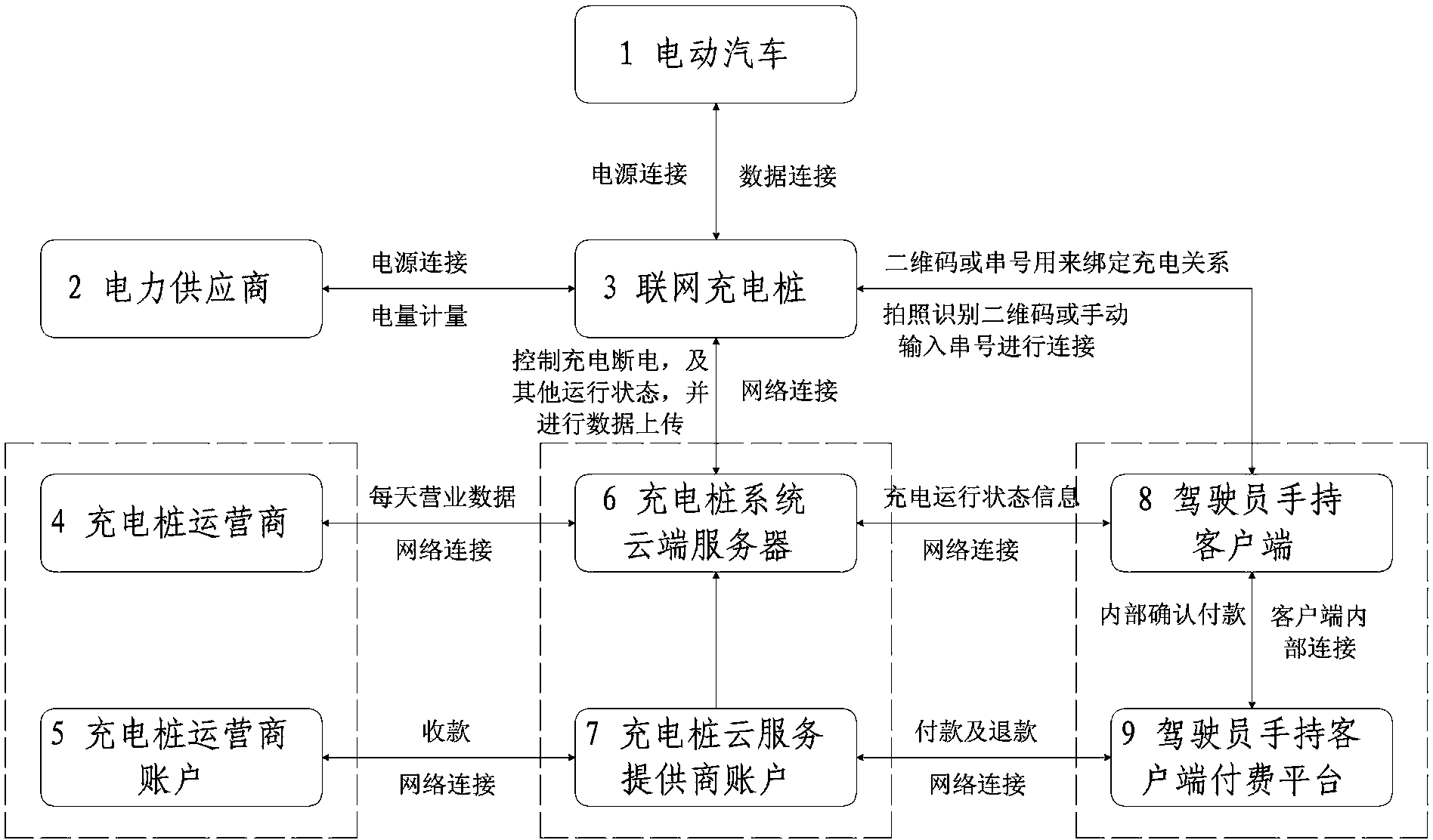
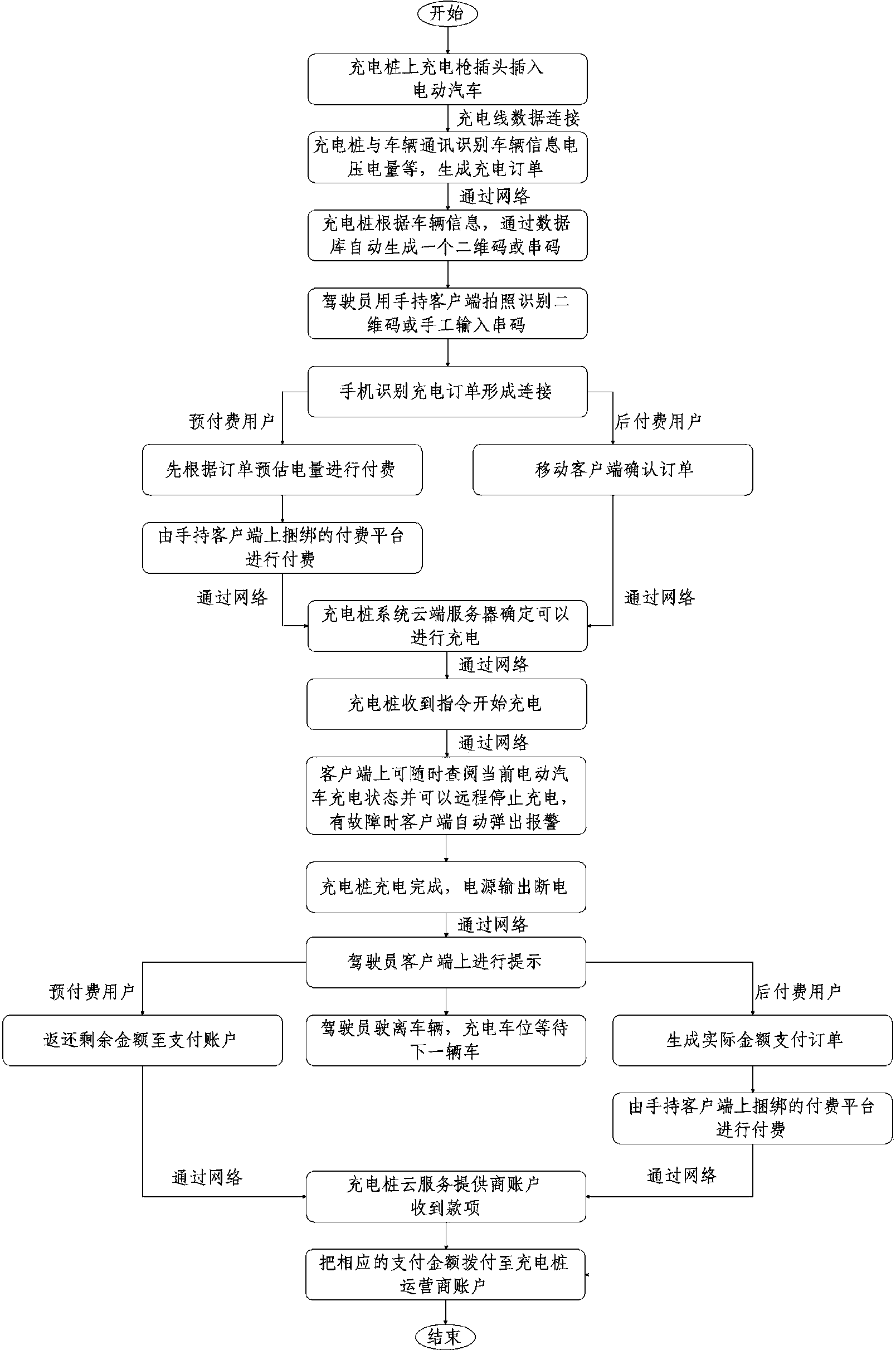
The invention discloses a system for allowing a handheld client side to network with a charging pile to display payment. The system is characterized by comprising an electric automobile (1), a power supplier (2), the networking charging pile (3), a charging pile operator (4), a charging pile operator account (5), a charging pile system cloud server (6), a charging pile cloud service provider account (7), the driver handheld client side (8) and a payment platform (9) interconnected with the driver handheld client side. The payment methods include the prepayment method and the post-payment method. By means of the system, a driver can online check the real-time state of the charging pile for charging the electric automobile through the handheld client side. The advantage of paying the bill directly through the bound payment platform on the handheld client side can be achieved. The charging pile operator can also check the operation condition of charging piles within the jurisdiction in a certain period of time.
Owner:陈明辉
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com