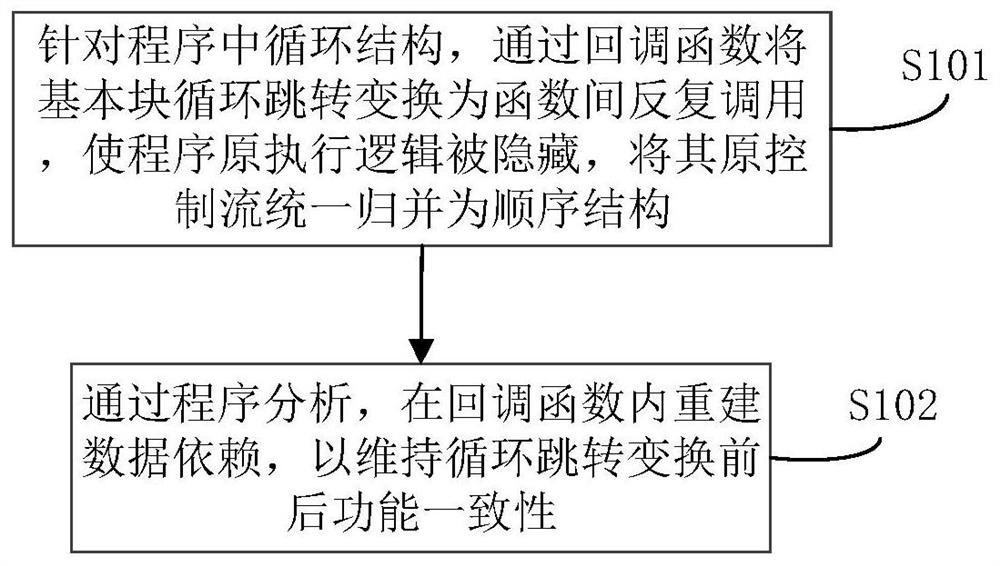
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
275 results about "Callback" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
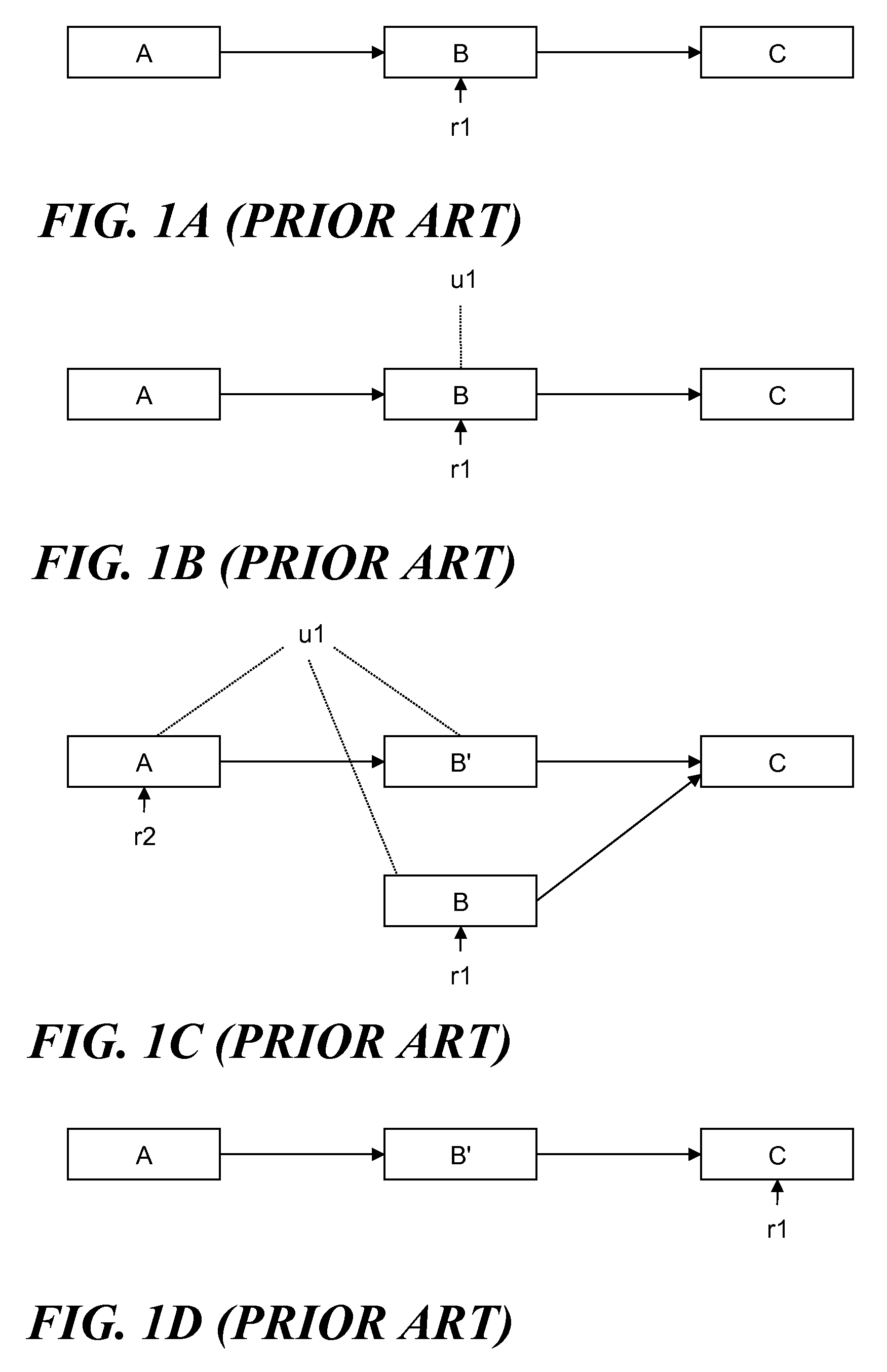
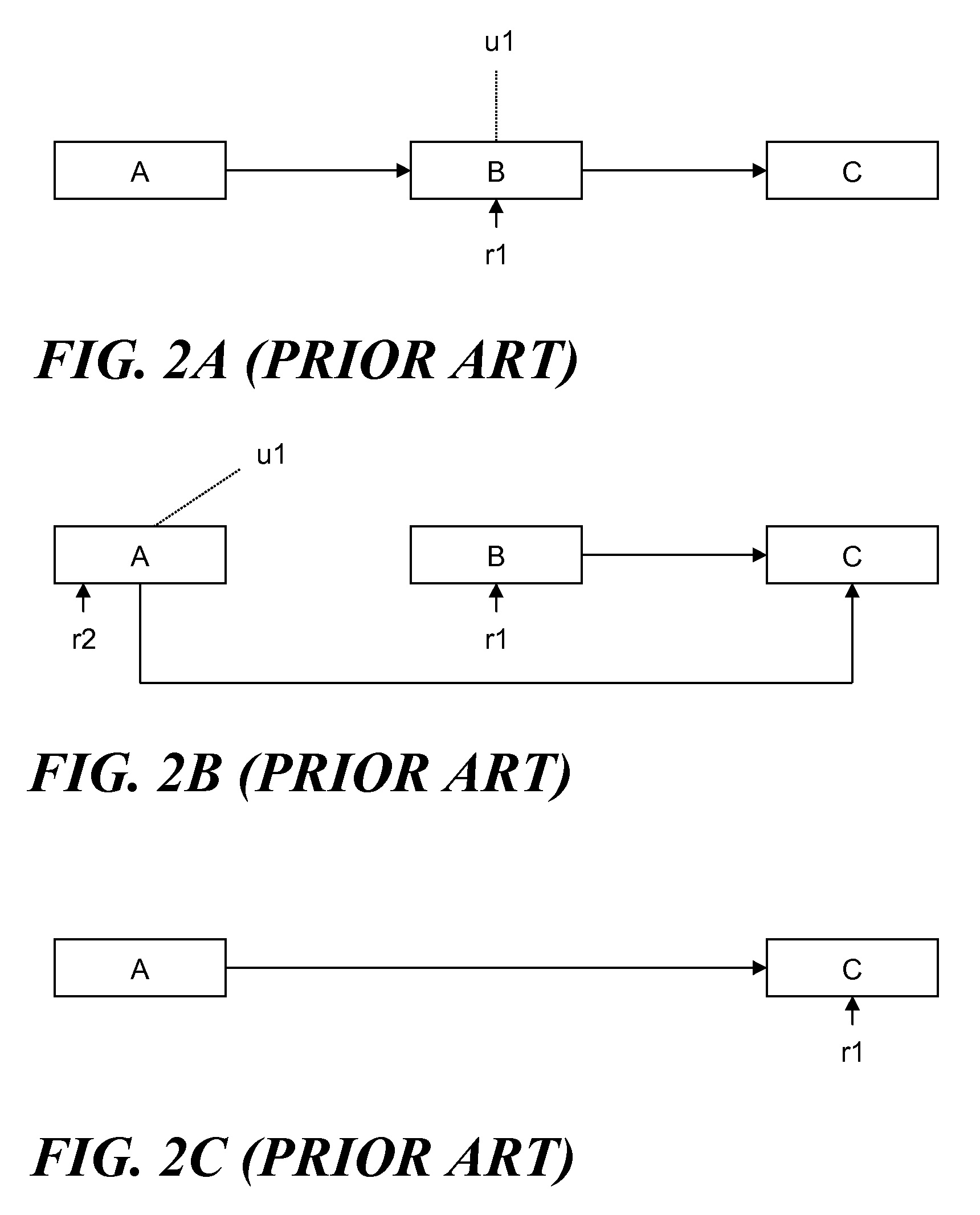
In computer programming, a callback, also known as a "call-after" function, is any executable code that is passed as an argument to other code that is expected to call back (execute) the argument at a given time. This execution may be immediate as in a synchronous callback, or it might happen at a later time as in an asynchronous callback. Programming languages support callbacks in different ways, often implementing them with subroutines, lambda expressions, blocks, or function pointers.
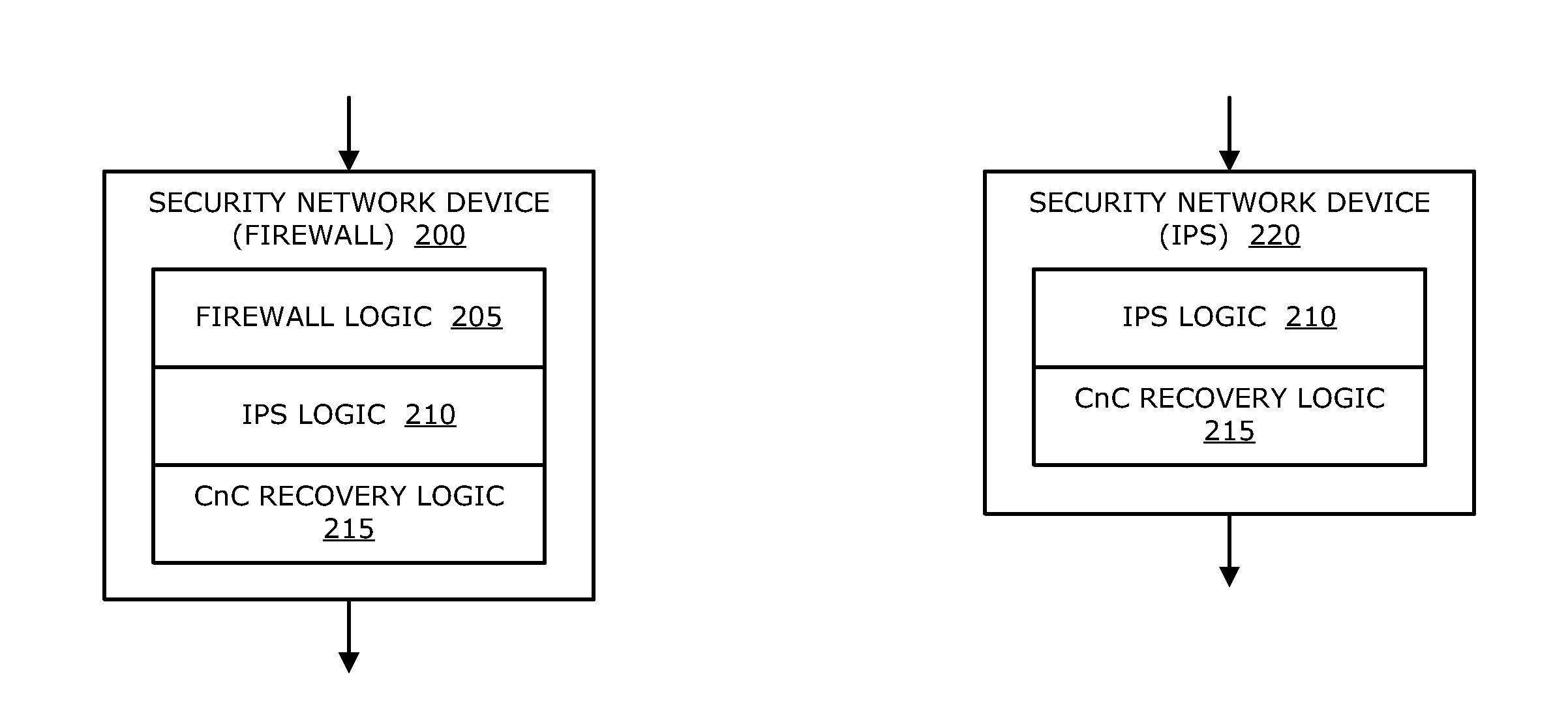
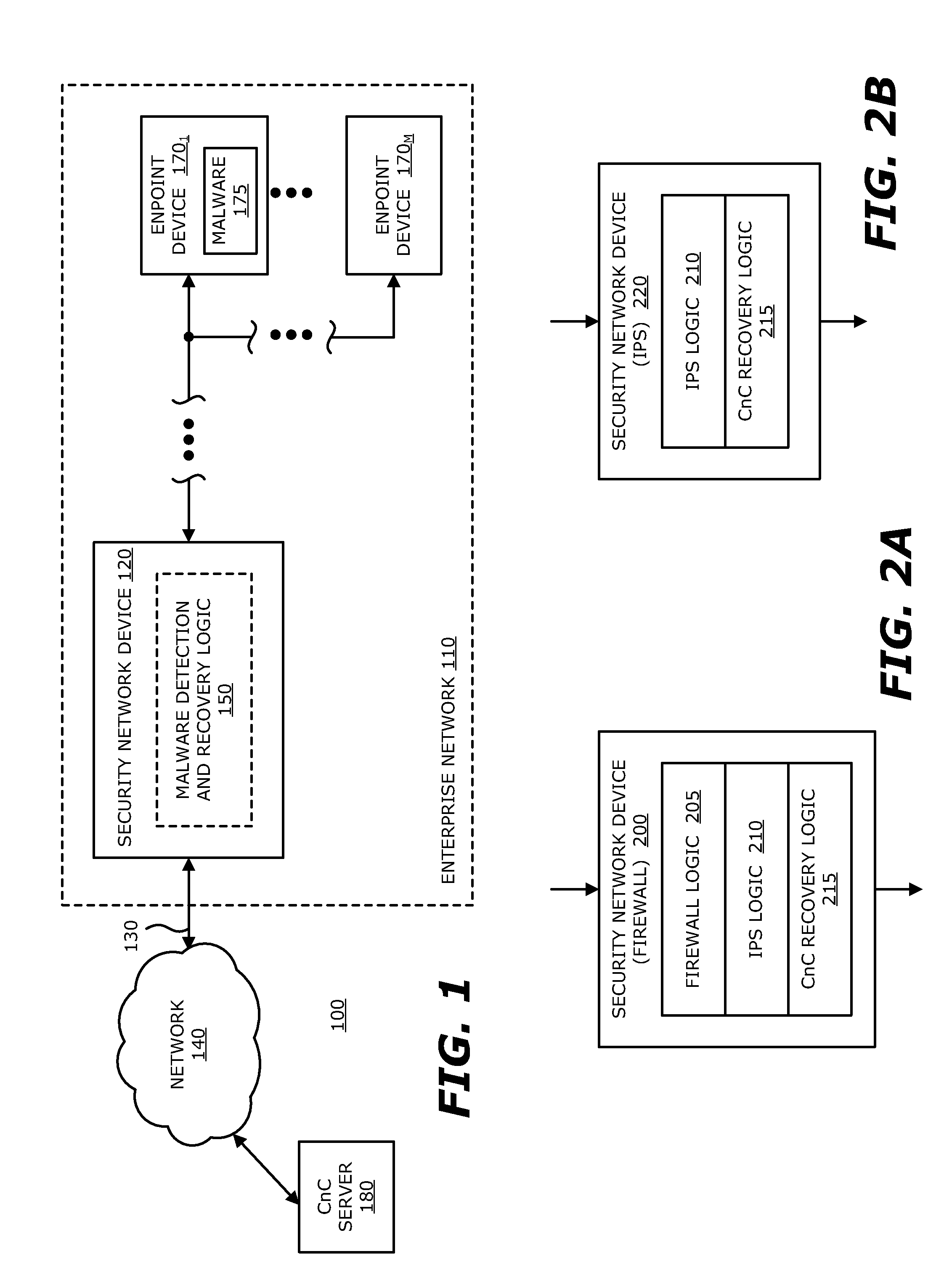
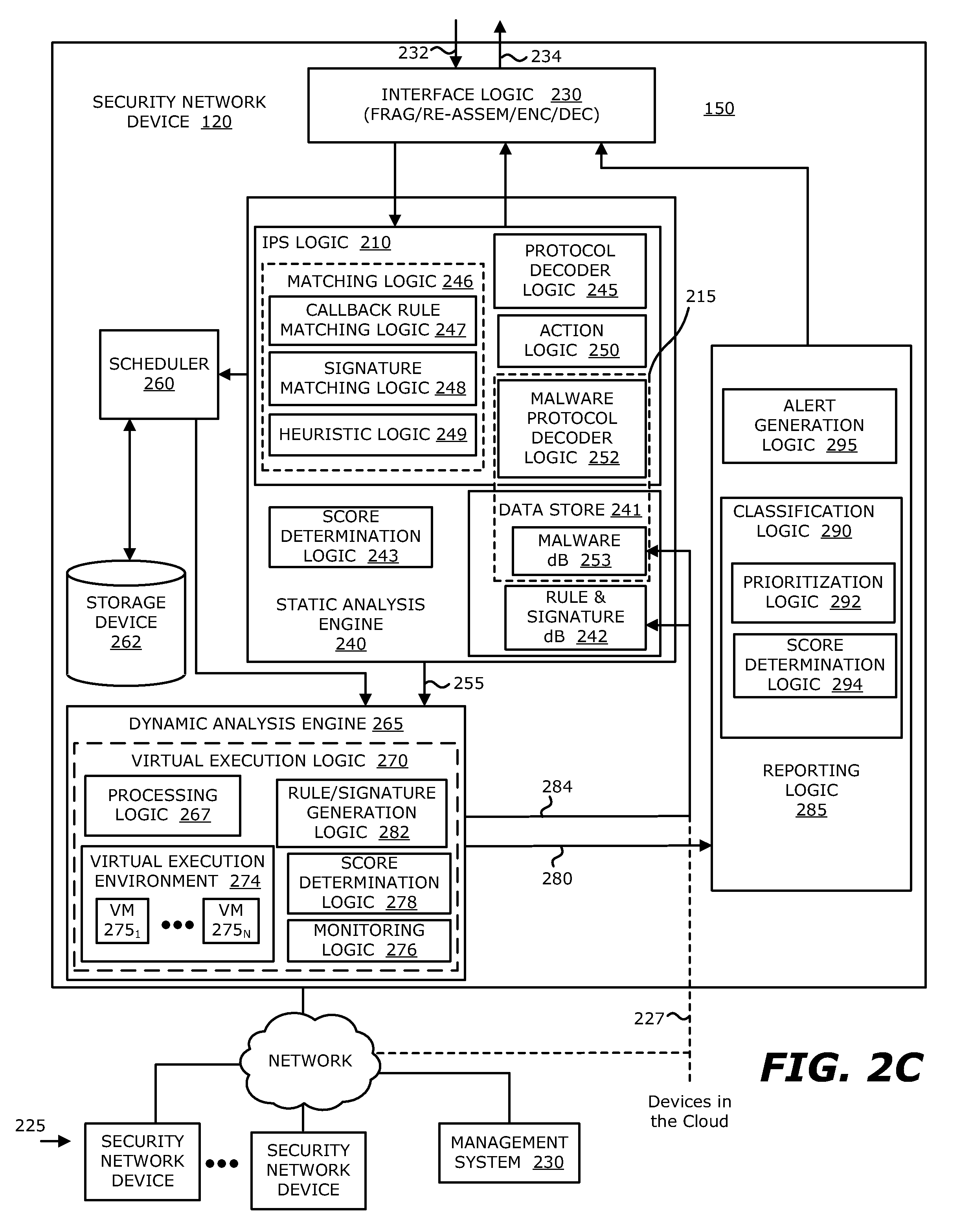
Intrusion prevention and remedy system
According to one embodiment, a computerized method is directed to neutralizing callback malware. This method involves intercepting an incoming message from a remote source directed to a compromised endpoint device. Next, a first portion of information within the incoming message is substituted with a second portion of information. The second portion of information is designed to mitigate operability of the callback malware. Thereafter, the modified incoming message, which includes the second portion of the information, is returned to the compromised endpoint device.
Owner:FIREEYE SECURITY HLDG US LLC
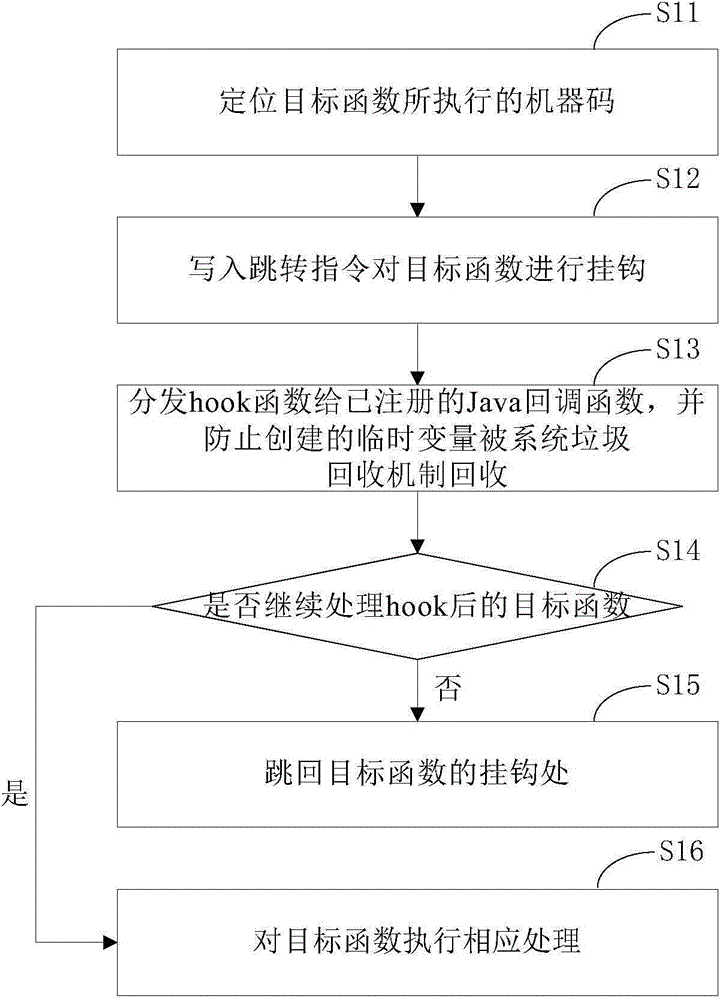
Program monitoring method and defending method thereof, as well as relevant device
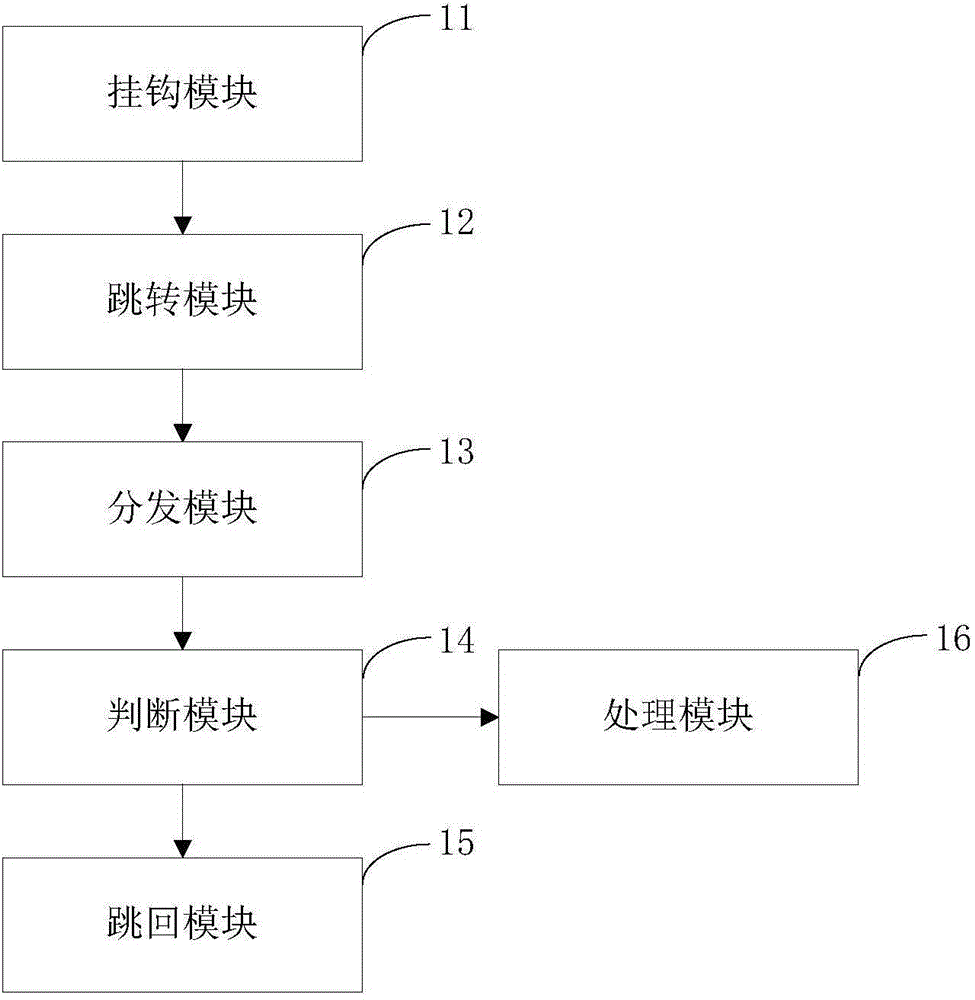
ActiveCN104598809AHook implementationAvoid markingPlatform integrity maintainanceTemporary variableProgram monitoring
The invention provides a program monitoring method and device. The program monitoring method comprises the following steps: writing in a skip instruction for positioned objective functions so as to perform a hook operation; distributing hook functions to registered Java callback functions, and preventing created temporary variables from being collected by a garbage collection mechanism of a system; enabling the objective functions which are not processed to skip back to hook positions, or else, continuing to process the objective functions. Through the adoption of the program monitoring method disclosed by the invention, any Java function of an Android system under an ART mode can be monitored without destroying the stack of the objective functions, so that the garbage collection mechanism of the ART can perform normal memory collection. The invention further provides a program defending method and device, which realize a defending mechanism of the Android system under the ART mode by adopting the program monitoring method disclosed by the invention.
Owner:BEIJING QIHOO TECH CO LTD
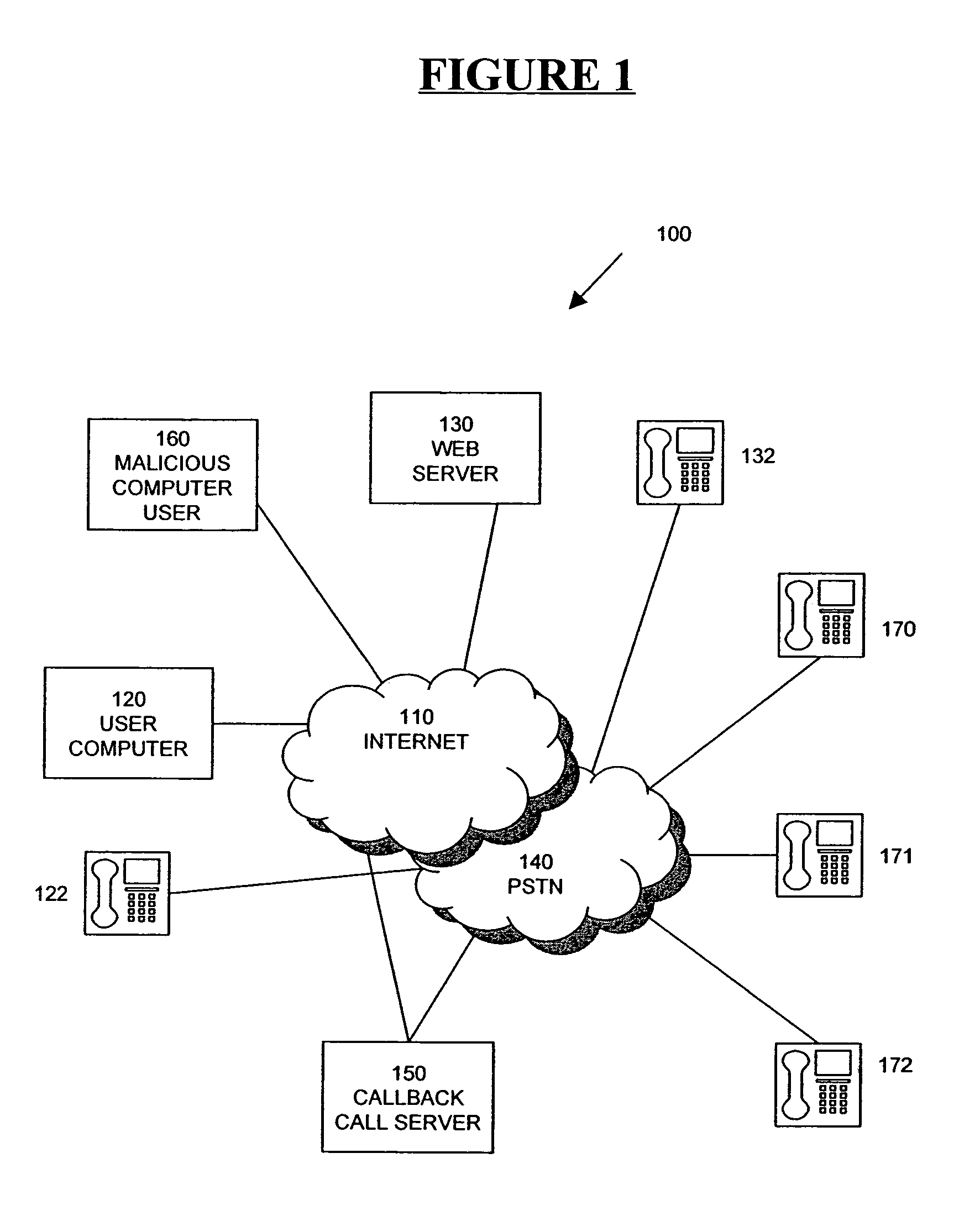
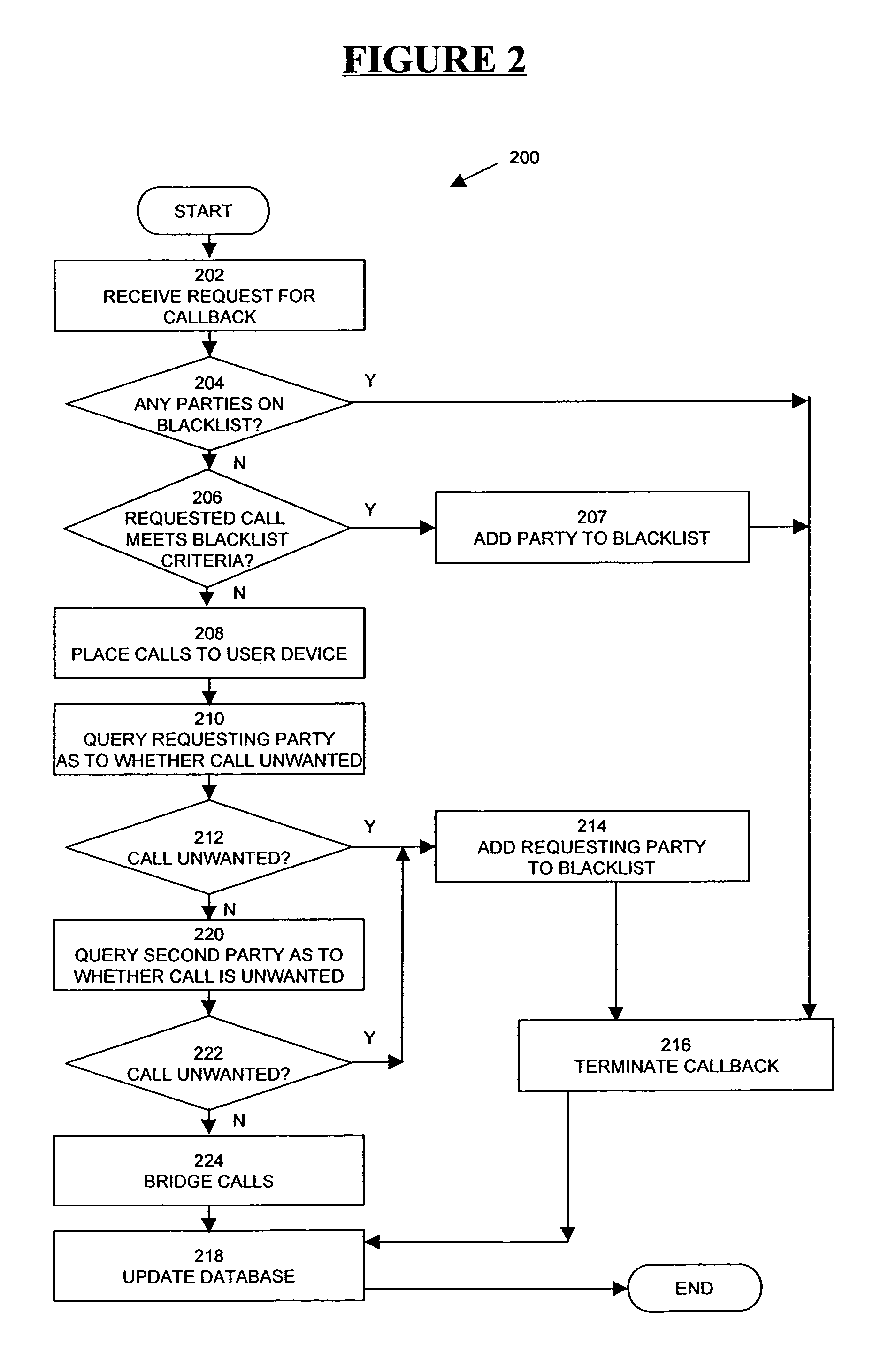
Method and apparatus for the prevention of unwanted calls in a callback system
ActiveUS7315518B1Prevent unwanted callsMultiplex system selection arrangementsSpecial service provision for substationTelecommunicationsUser device
In one method and apparatus for blocking unwanted calls in a callback system, parameters associated with a callback request (e.g., the user device to which the call is to be directed, the IP address from which the request originated or an identifier of the source computer from which the callback request originated, the party from whom the call is requested) are tracked for each call. A decision to automatically block the requested callback is made based on one or more criteria based on a combination of these parameters, which may be a total over a period of time. In a second method, one or both of the parties to the callback is queried as to whether the callback is unwanted and, if so, one or more parameters associated with the request are blacklisted.
Owner:ORACLE OTC SUBSIDIARY
Game data monitoring method and game data monitoring device
ActiveCN106294166AImprove securityTimely Locating Security VulnerabilitiesSoftware testing/debuggingComputer scienceObject function
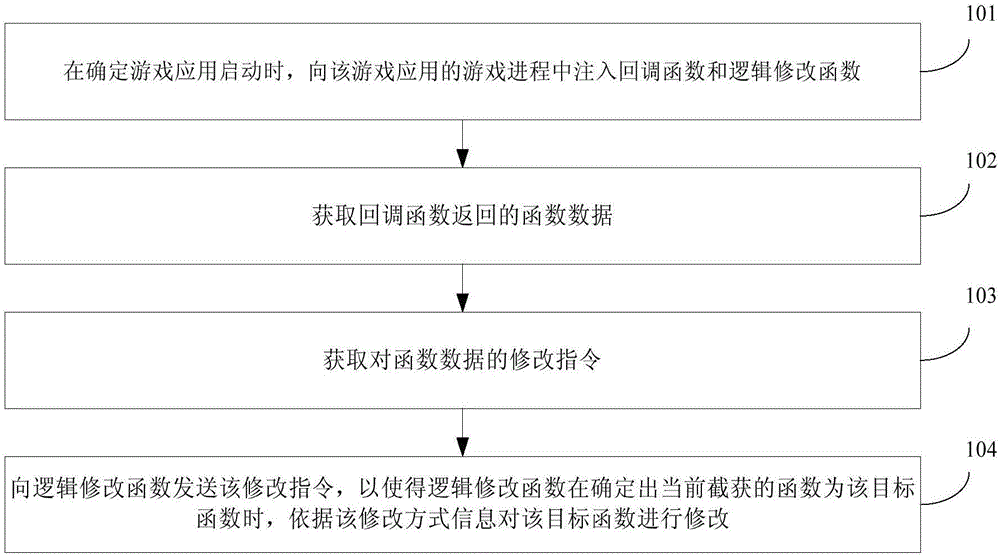
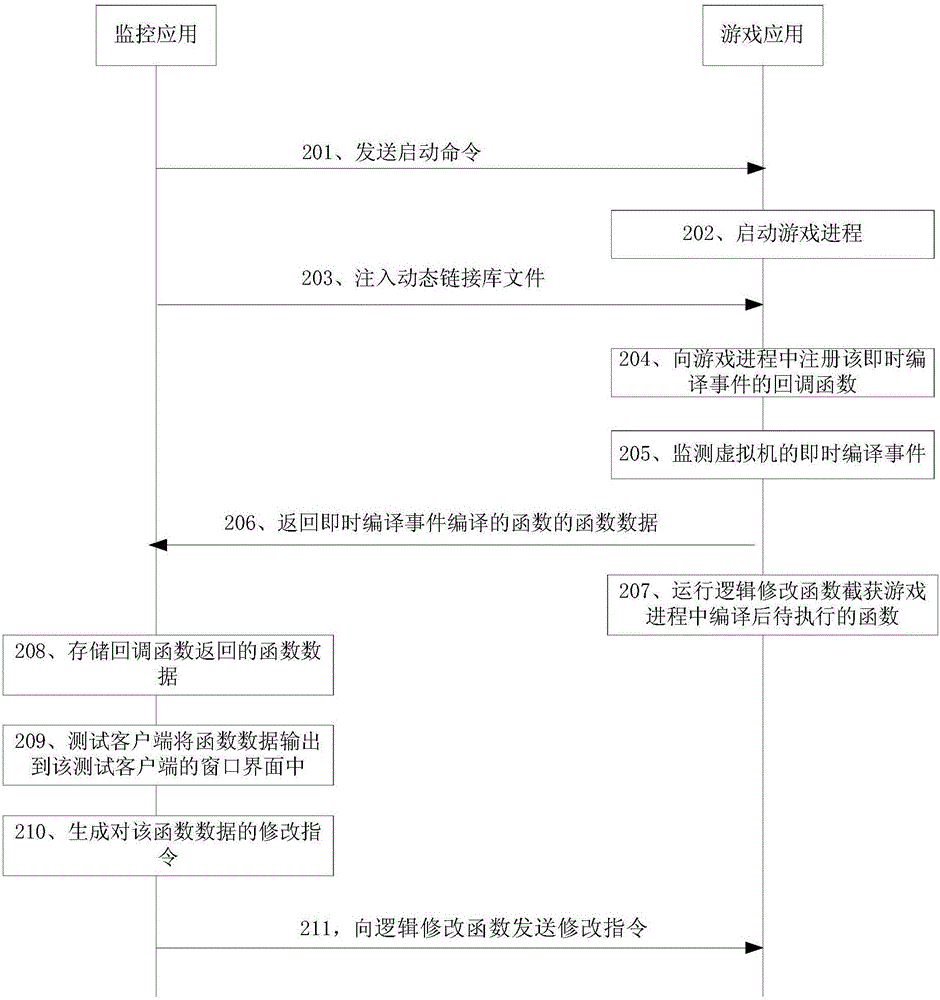
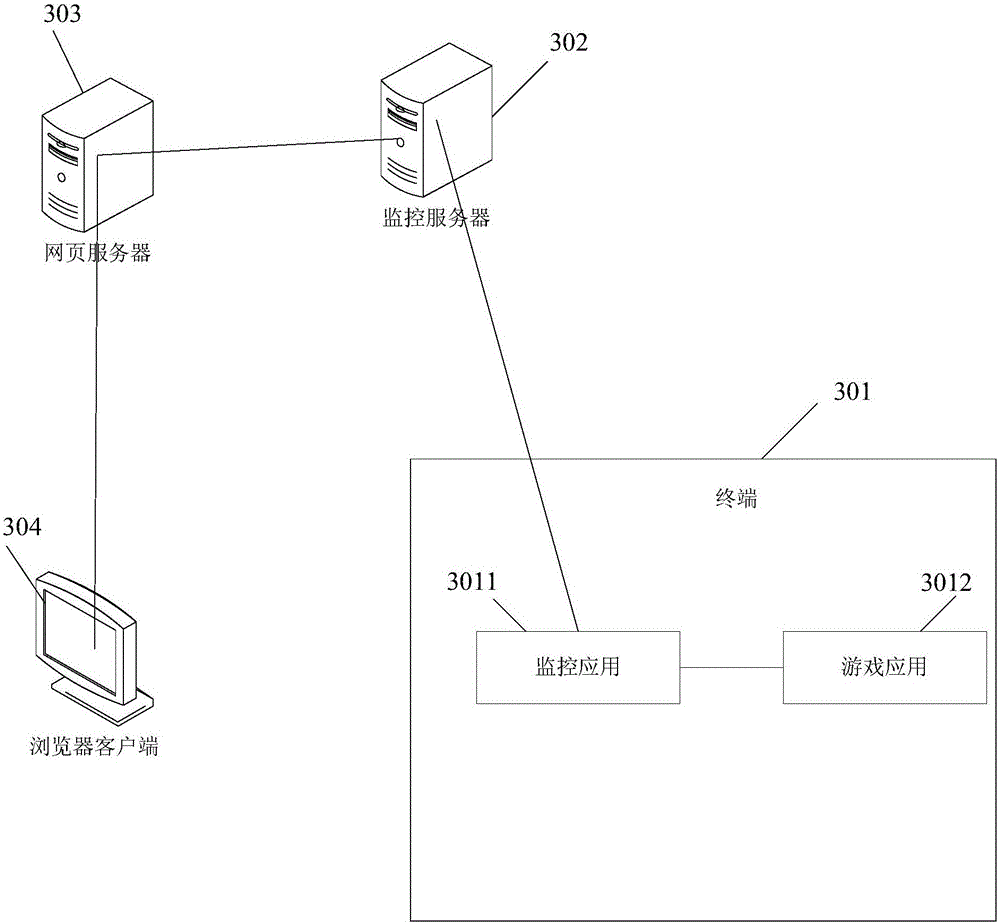
The invention provides a game data monitoring method and a game data monitoring device. In the scheme adopted in the invention, when a monitored game application is started up, a callback function and a logic modification function are injected into a game process of the game application, the callback function is used for capturing function data of at least one function currently operated in the game process, the logic modification function is used for intercepting and capturing a function currently operated in the game process; function data is acquired by virtue of the callback function; after a modification instruction for the acquired function data is acquired, the modification instruction can be sent to the logic modification function injected into the game process, so that when the logic modification function determines that the currently intercepted and captured function is an objective function required to be modified by the modification instruction, the objective function is modified according to modification mode information in the modification instruction. The method and the device can be used for improving the safety of function data operated by the game application.
Owner:TENCENT TECH (SHENZHEN) CO LTD
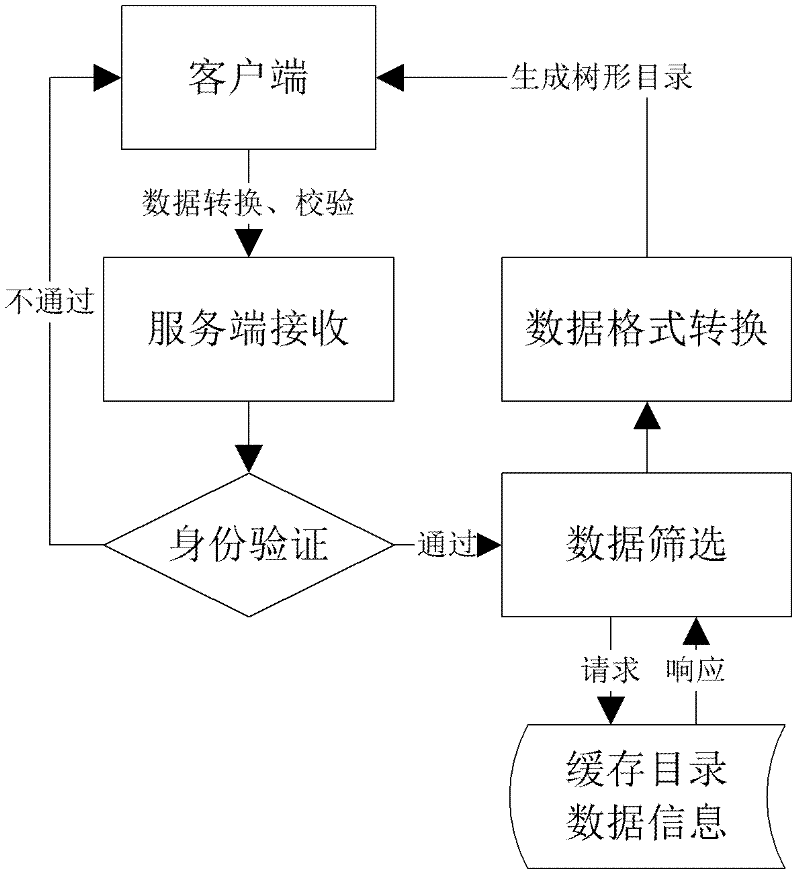
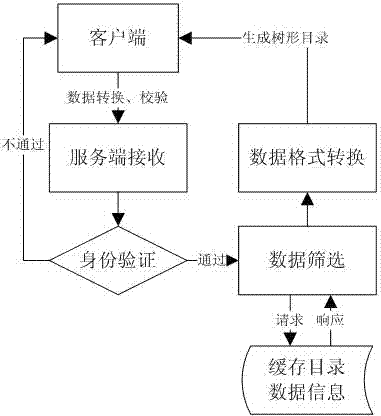
Dynamic tree structured directory retrieval method in BS (browser/server) structure software
The invention discloses a dynamic tree structured directory retrieval method in BS (browser / server) structure software. The method comprises the following steps: 1) taking out the information of a tree node; 2) carrying out data caching; 3) judging whether the node contains retrieval items; 4) carrying out structure transformation on expected data; and 5) carrying out data interaction. In the step 4), the expected data is used for synchronously generating a data format required by a tree directory structure according to JSON (java-script serialized object notation) specification; and in the step 5), the background processing contents of a WEB page timely return the expected JSON-format data to a foreground WEB page by a preset Ajax (Asynchronous JavaScript and XML) callback function, and the JSON-format data is analyzed by using a JavaScript built-in method so as to generate a tree structured expression of the expected data.
Owner:LINKAGE SYST INTEGRATION
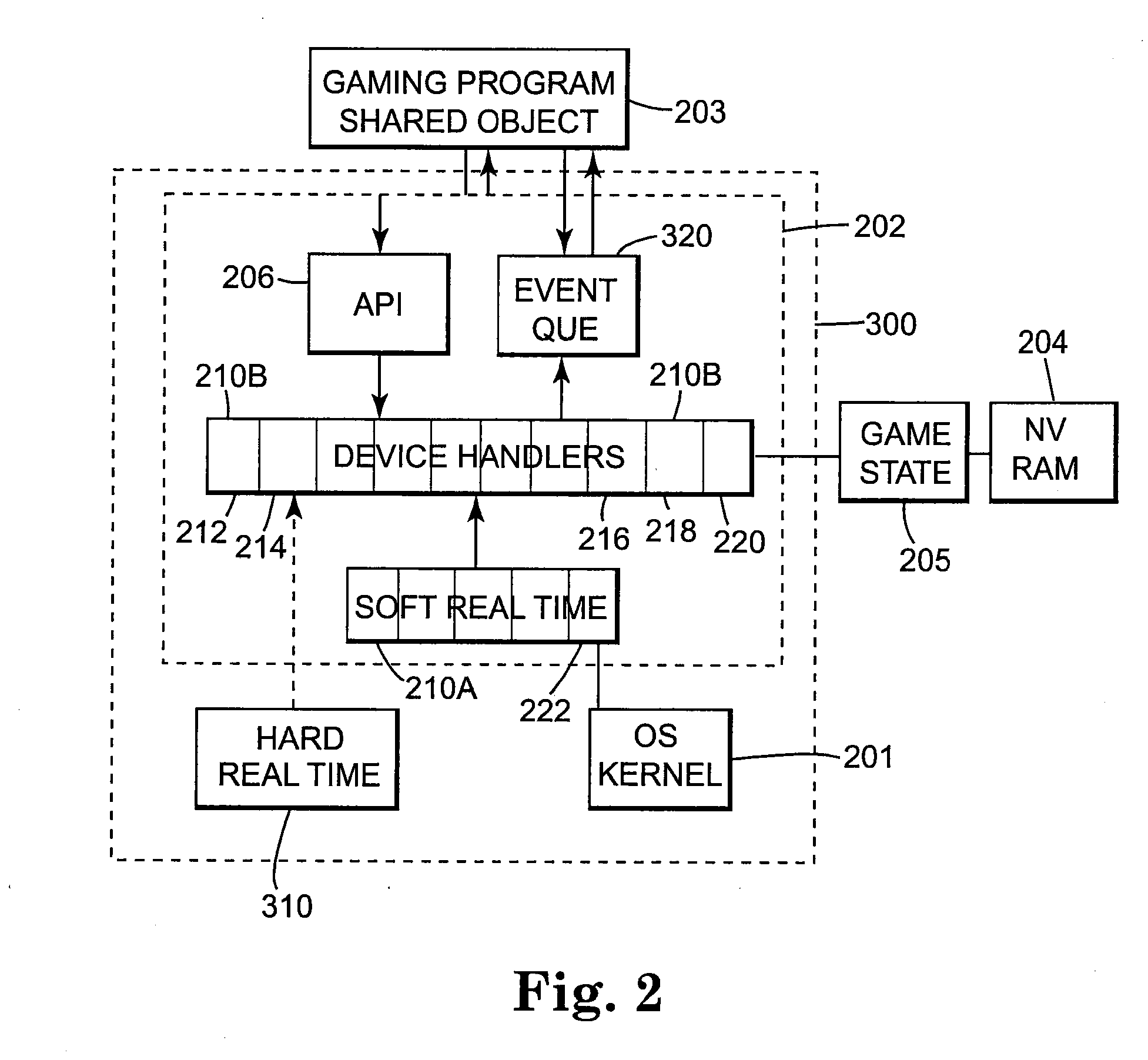
Computerized gaming system, method and apparatus
InactiveUS20080058097A1Facilitate useFacilitate information sharingApparatus for meter-controlled dispensingVideo gamesPower lossInformation sharing
The present invention in various embodiments provides a computerized wagering game method and apparatus that features an operating system kernel, a system handler application that loads and executes gaming program shared objects and features nonvolatile storage that facilitates sharing of information between gaming program objects. The system handler of some embodiments further provides an API library of functions callable from the gaming program objects, and facilitates the use of callback functions on change of data stored in nonvolatile storage. The nonvolatile storage also provides a nonvolatile record of the state of the computerized wagering game, providing protection against loss of the game state due to power loss. The system handler application in various embodiments includes a plurality of device handlers, providing an interface to selected hardware and the ability to monitor hardware-related events.
Owner:IGT
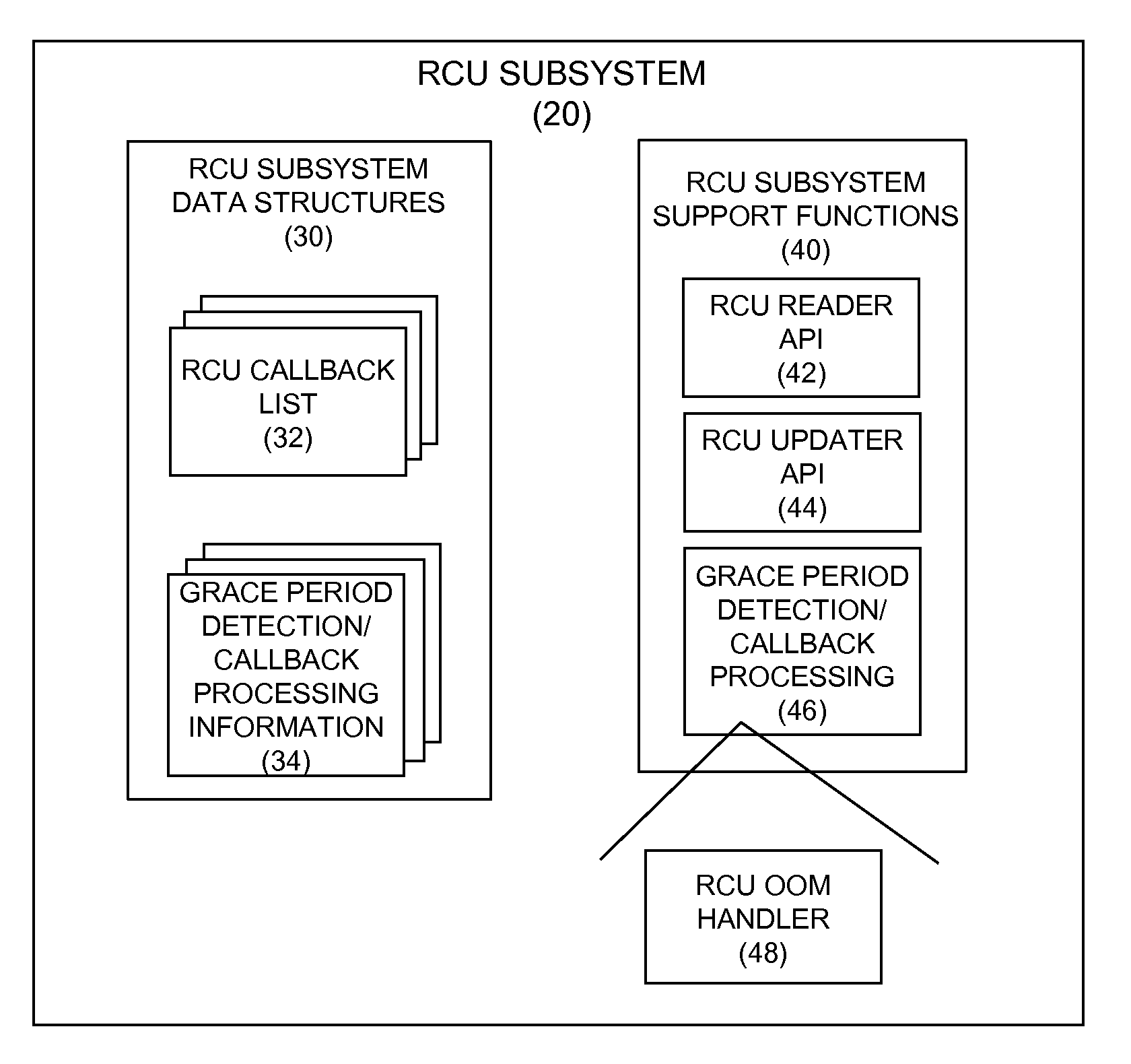
Motivating lazy RCU callbacks under out-of-memory conditions
InactiveUS8972801B2Input/output to record carriersError detection/correctionOut of memoryEmbedded system
Owner:INT BUSINESS MASCH CORP
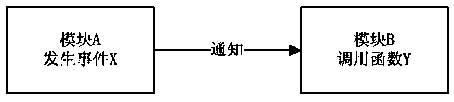
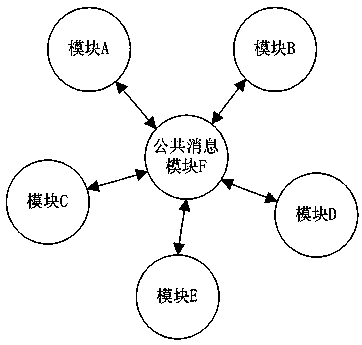
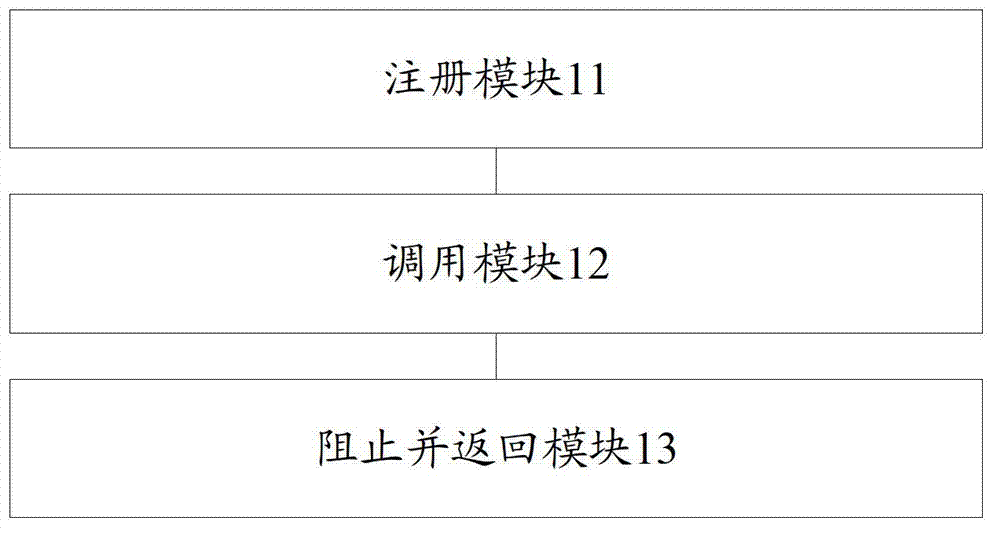
Intermodule notification callback method and module interaction structure
InactiveCN103995752AReduce couplingEasy maintenanceInterprogram communicationSoftware systemCoupling
The invention discloses an intermodule notification callback method. The method includes the steps that a common information module is established, and the common information module is connected with all function modules respectively; callback functions of events or response events of all the function modules are registered in the common information module; after the common information module receives the information sent from other function modules, all the callback functions of the events which are registered in advance are called, and accordingly interaction amoung the function modules can be achieved. According to the intermodule notification callback method, module interaction work is completed by one independent common information module in a unified mode, coupling of a plurality of modules is lowered, and a software system can be maintained easily; interaction among the modules can be achieved more simply only through simple registration in the common information module; a header file of the common information module is directly cited in all the modules in which interaction is needed, the inconsistent definition condition among the modules is avoided, and the stability of the system is improved.
Owner:PHICOMM (SHANGHAI) CO LTD
Course handling method and device
ActiveCN102831344APrevent intrusionBlock callMultiprogramming arrangementsComputer security arrangementsComputer hardwareSecurity software
The invention provides a course handling method and a device. By the method and device, hostile courses can be prevented from invading security software by using dynamic link library (DLL) files and global message hooks, so that the detection of security software cannot be restrained by hostile courses. The method comprises the following steps of: during creation of threads, registering various local message hooks in the system, wherein correspondence is established between the local message hook and the message function in the system; calling the corresponding local message hook through the message function when the message function is called by the thread, wherein the message function includes a window creating function; and calling a callback function of the local message hook to prevent the global message hook from being called and returning to execute the message function.
Owner:三六零数字安全科技集团有限公司
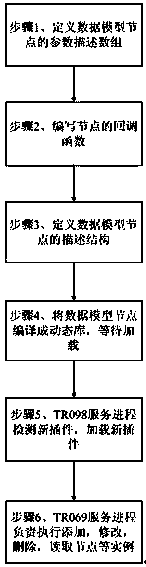
Method for dynamically loading data model based on plug-in
InactiveCN103761136AAchieve scalabilityImprove maintainabilityProgram loading/initiatingExtensibilityComputer architecture
The invention relates to a method for dynamically loading a data model based on a plug-in. Firstly, a description structure of a data model node is defined; secondly, the data model node is compiled into a dynamic depot and when a TR098 service process detects the new plug-in, the new plug-in is loaded. An external progress adds, alters, deletes and reads the data node loaded in the third step. In the time of reading operation, a TR069 service procress is used for adding, altering, deleting and reading a node example and calling the corresponding callback function to execute the specific function. The description of the data model and the TR098 service process are separated and the description of the data model is compiled into the dynamic depot and exists as the plug-in. The plug-in is dynamically loaded in the TR098 service process and high expandability and maintainability of the system can be achieved.
Owner:PHICOMM (SHANGHAI) CO LTD
Automated self-service callback for proactive and dynamic user assistance
ActiveUS10917520B1Special service for subscribersNon-redundant fault processingCallbackTelephone number
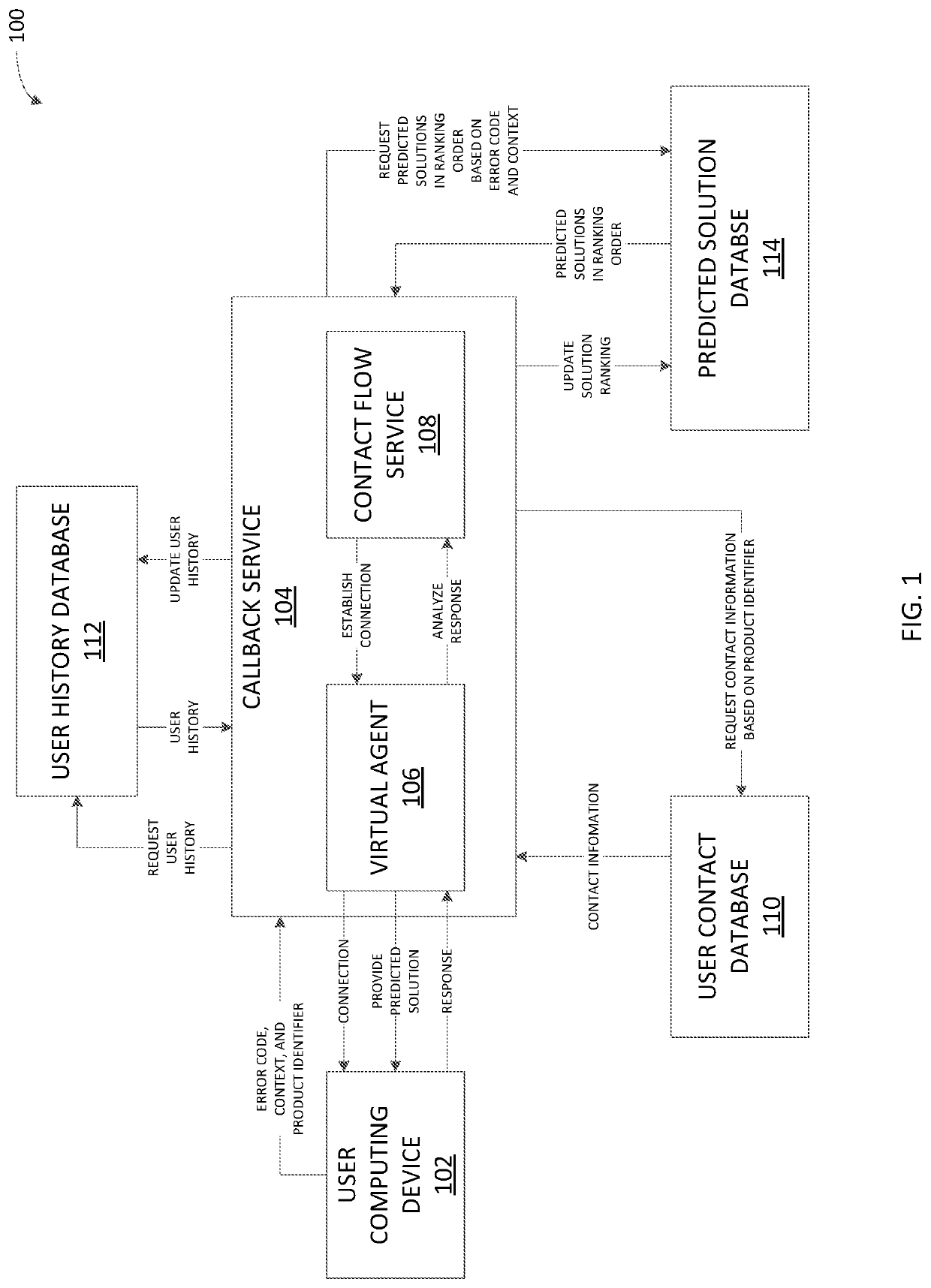
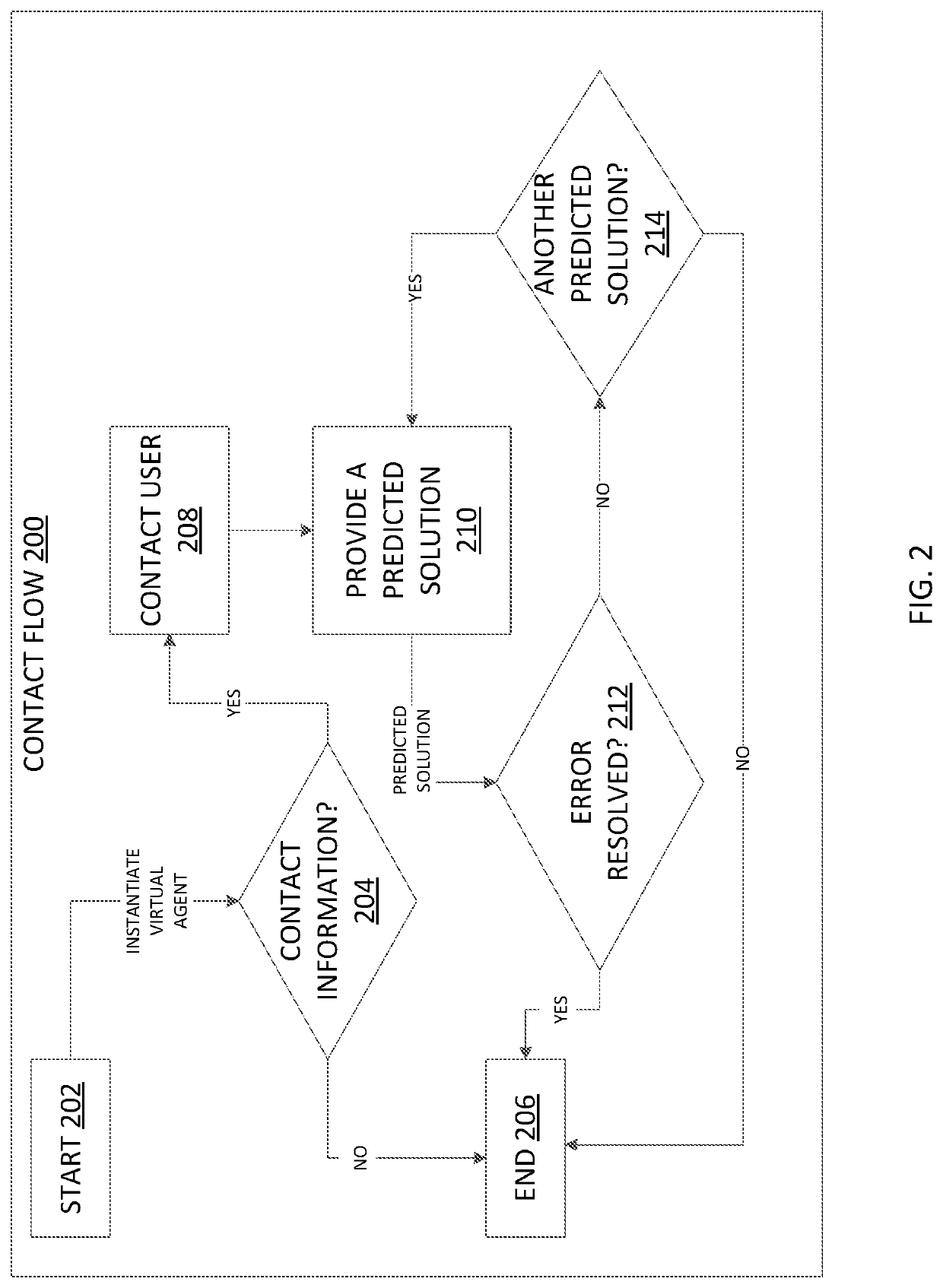
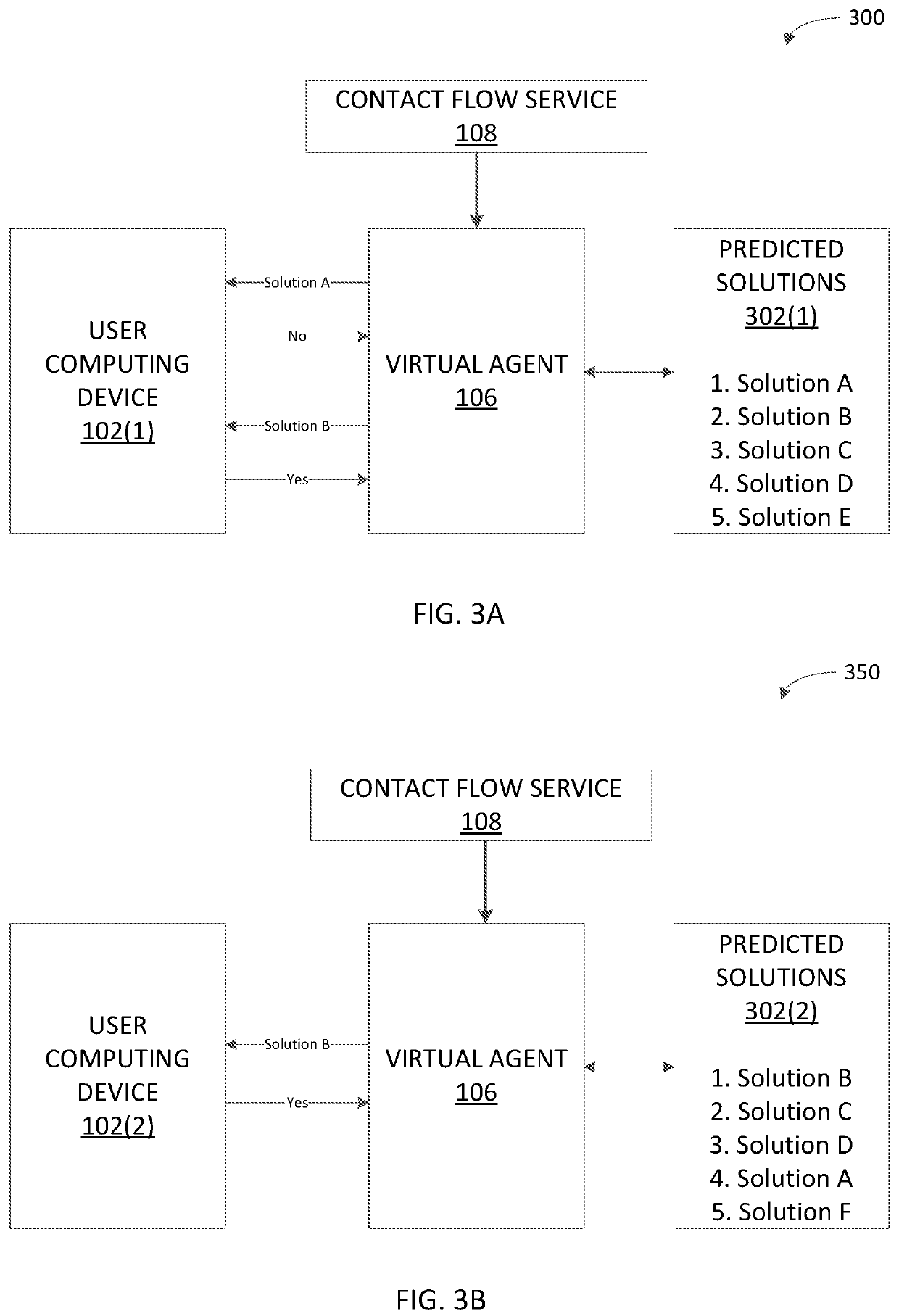
Certain aspects of the present disclosure provide techniques for providing an automated callback service to a user. An example technique includes receiving an indication of a product installation failure, which includes an error code, a context of the computing device, and a product identifier. Based on the product identifier, a phone number is retrieved that is associated with the user of the computing device. A set of solutions predicted to resolve the installation failure is retrieved, based on the error code and the context. A callback is established to the user, and the user is connected with a virtual agent that will provide solutions from the set of solutions in the ranking order retrieved until a solution is determined to resolve the product installation error. The ranking of the predicted solutions is updated for other users in the future who may face a similar product installation error.
Owner:INTUIT INC
Method and module for data asynchronous processing with synchronous information callback function
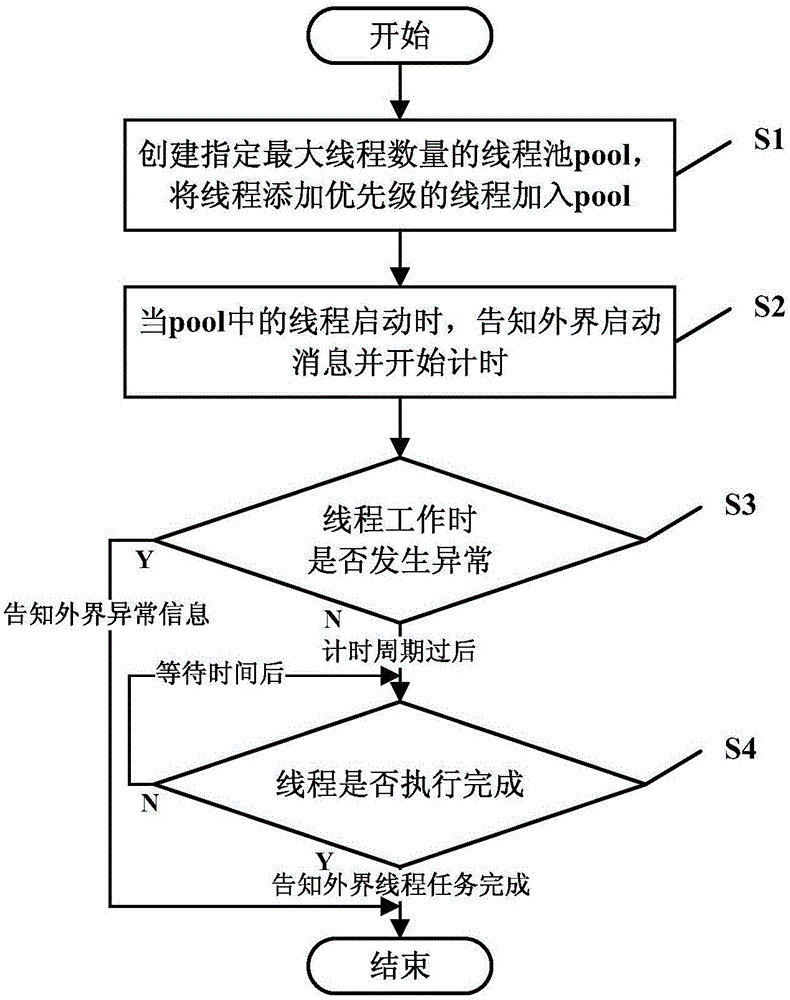
ActiveCN106502773AEfficient use ofProblems that don't waste system resourcesProgram initiation/switchingHardware monitoringComputer moduleThread pool
The invention discloses a method and module for data asynchronous processing with a synchronous information callback function and relates to the field of asynchronous data processing. The method comprises the steps that a thread pool with a designated maximum thread quantity is established, a priority is added to a thread of each asynchronous data processing task, and the threads are added into the pool; when the threads in the pool are started, information executed by the asynchronous data processing task corresponding to the current thread is returned; time counting is started for the current thread according to a preset time counting cycle; the pool is used to call the current thread to start working, and stack information during abnormity occurrence is determined and returned when an abnormity takes place during work of the current thread; and whether the current thread is completed is detected at scheduled time. According to the invention, the running quantity of the multiple threads can be controlled, and whether execution of the threads is completed is detected at scheduled time; and execution states of the asynchronous data processing tasks can be known, occupied resources of a CPU and consumed electric energy are reduced, and system performance can be ensured.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
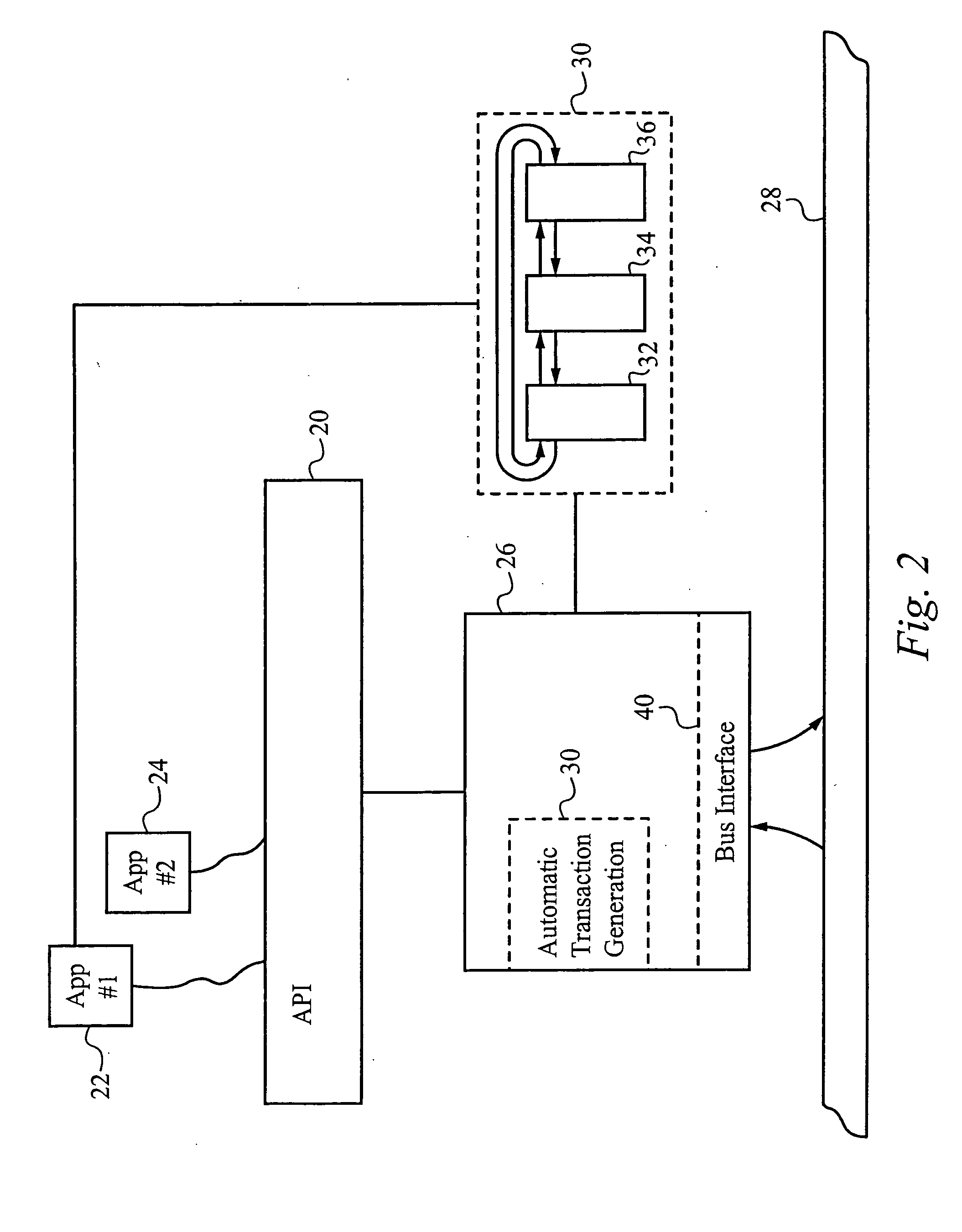
Application programming interface for data transfer and bus management over a bus structure
InactiveUS20050097245A1Hybrid switching systemsInput/output processes for data processingData streamApplication programming interface
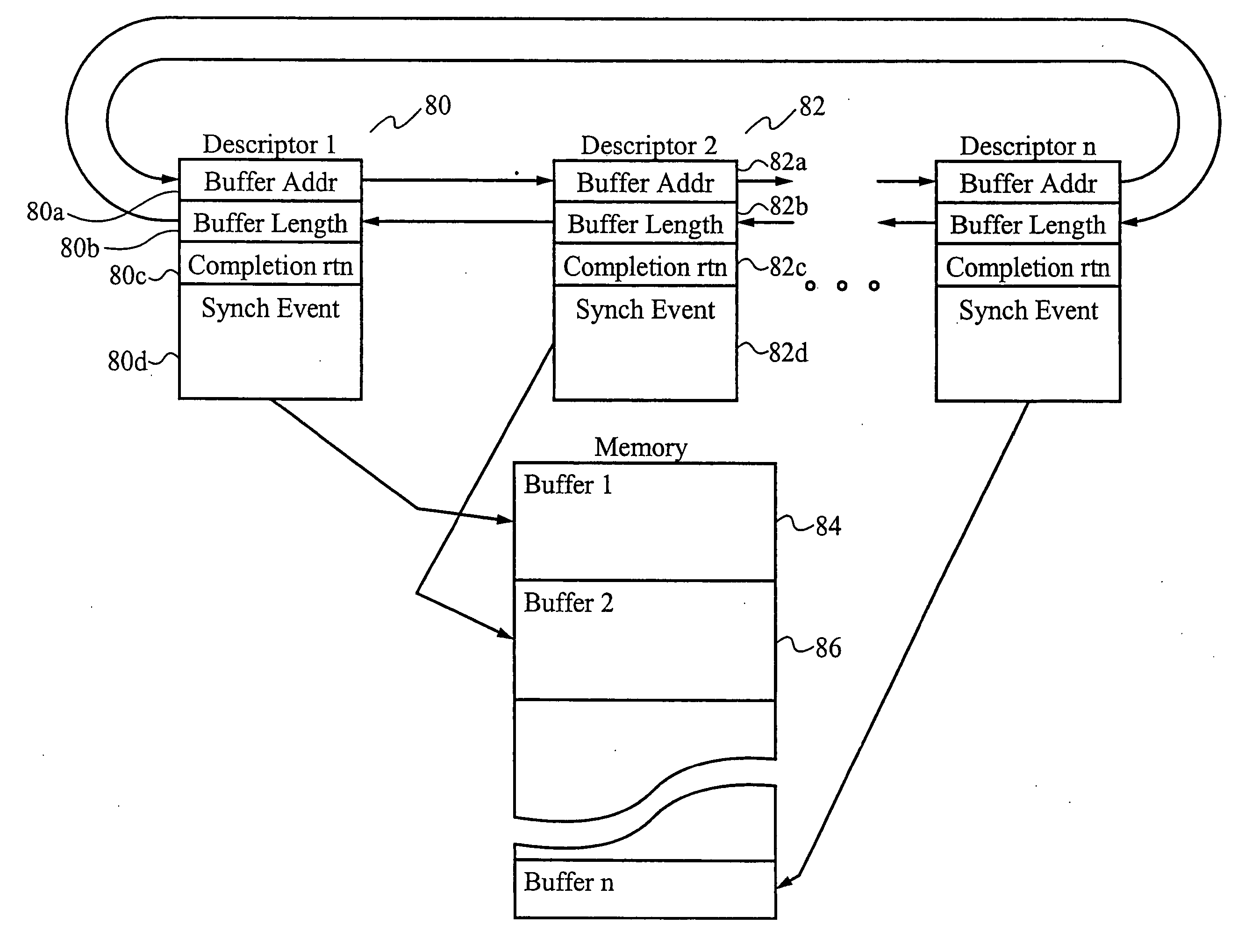
In a first embodiment, an applications programming interface (API) implements and manages isochronous and asynchronous data transfer operations between an application and a bus structure. During an synchronous transfer the API includes the ability to transfer any amount of data between one or more local data buffers within the application and a range of addresses over the bus structure using one or more asynchronous transactions. An automatic transaction generator may be used to automatically generate the transactions necessary to complete the data transfer. The API also includes the ability to transfer data between the application and another node on the bus structure isochronously over a dedicated channel. During an isochronous data transfer, a buffer management scheme is used to manage a linked list of data buffer descriptors. During isochronous transfers of data, the API provides implementation of a resynchronization event in the stream of data allowing for resynchronization by the application to a specific point within the data. Implementation is also provided for a callback routine for each buffer in the list which calls the application at a predetermined point during the transfer of data. An isochronous API of the preferred embodiment presents a virtual representation of a plug, using a plug handle, to the application. The isochronous API notifies a client application of any state changes on a connected plug through the event handle. The isochronous API also manages buffers utilized during a data operation by attaching and detaching the buffers to the connected plug, as appropriate, to manage the data flow.
Owner:SONY CORP +1
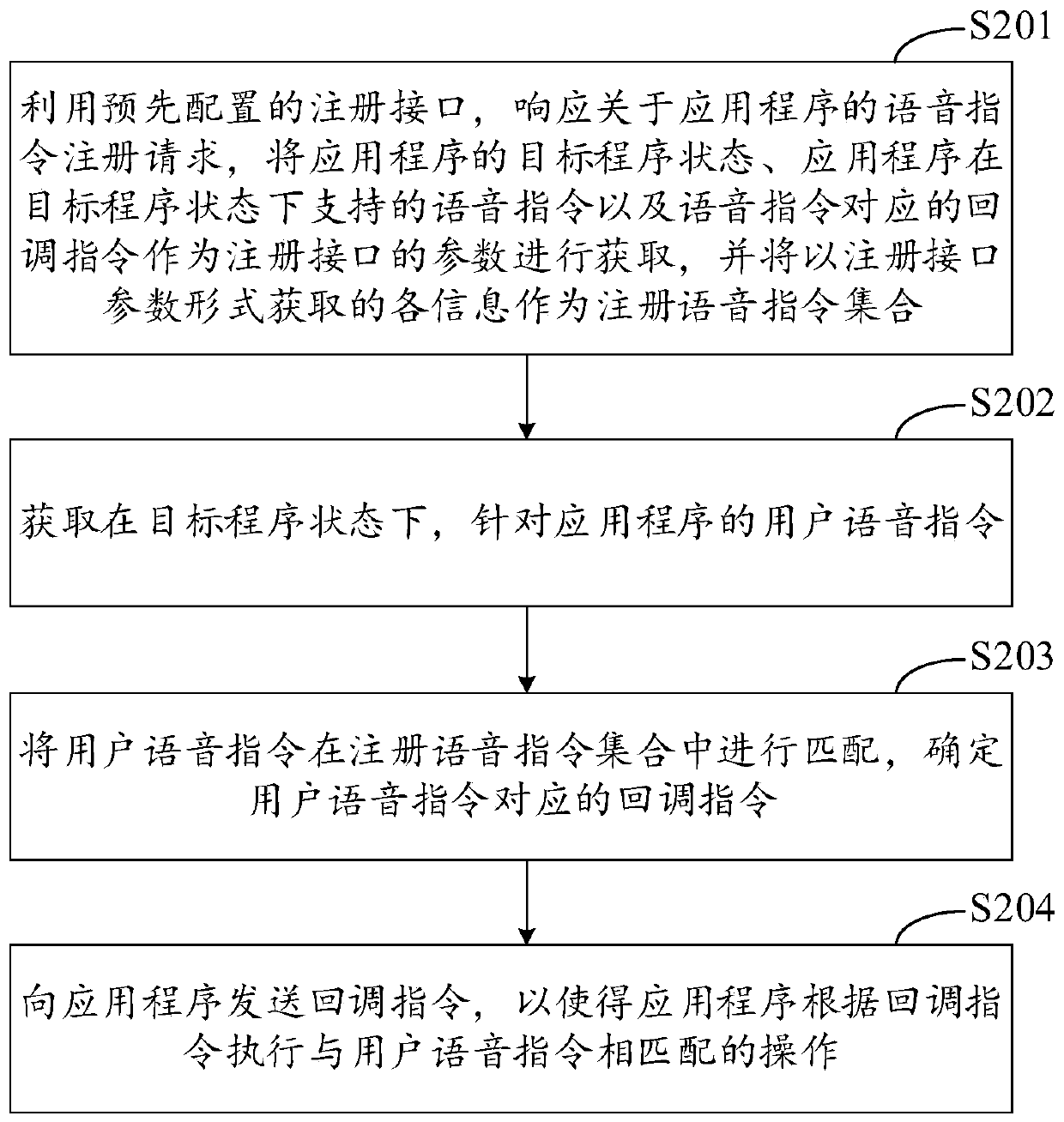
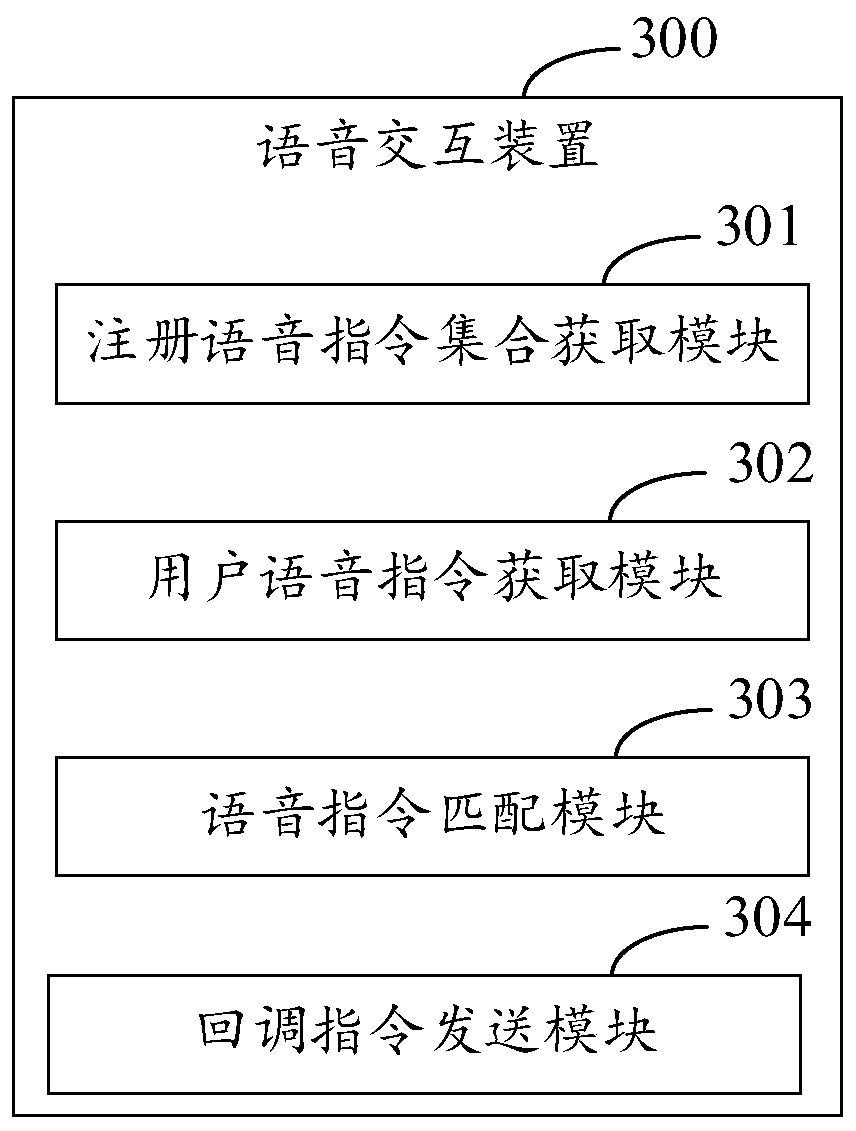
Voice interaction method and device of application program, equipment and medium
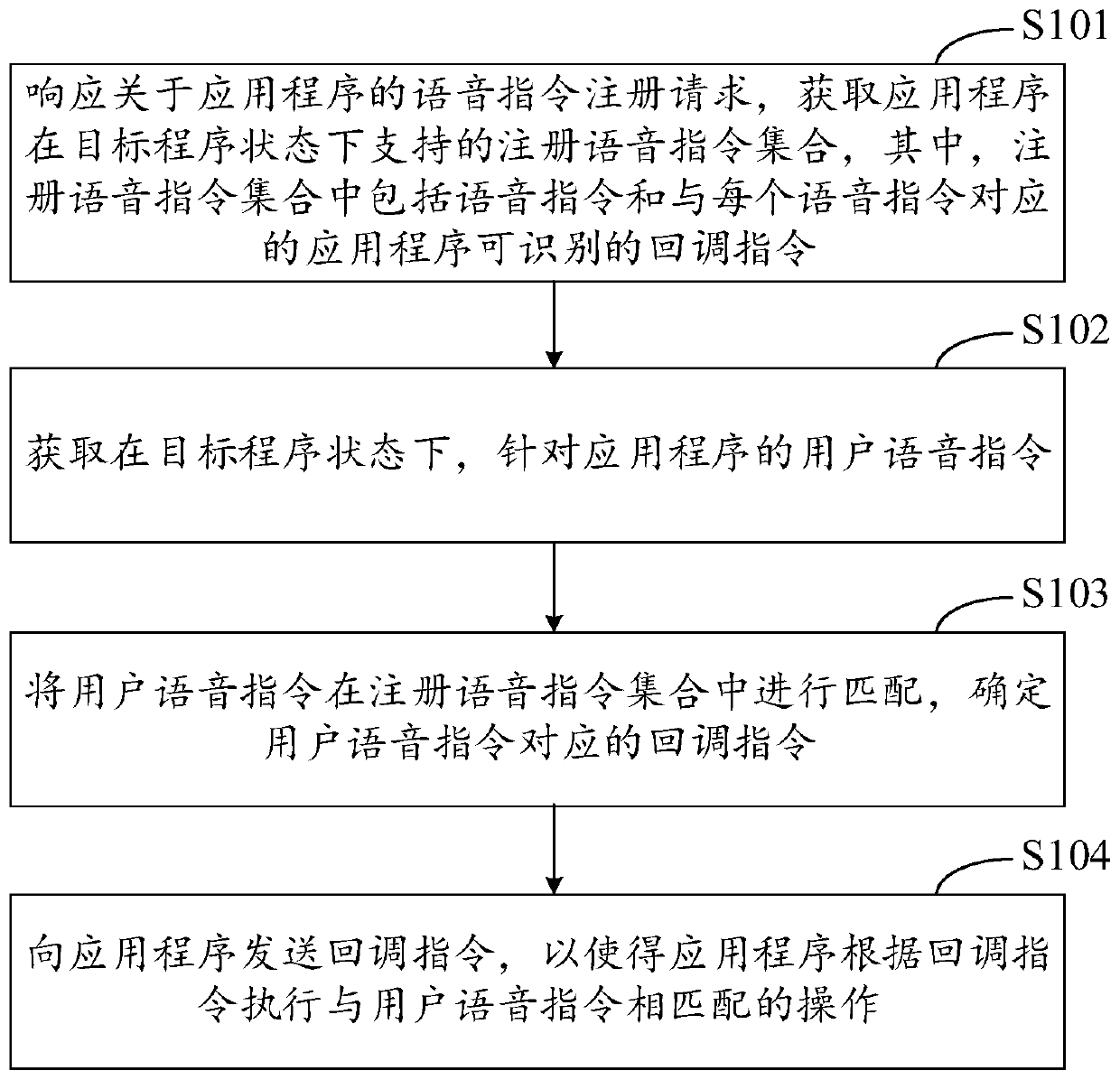
PendingCN110647305AImprove response efficiencyImprove recognition accuracySound input/outputCallbackApplication procedure
The embodiment of the invention discloses a voice interaction method and device of an application program, equipment and a medium, and relates to the technical field of voice. According to the specific implementation scheme, a voice instruction registration request about an application program is responded, a registration voice instruction set supported by the application program in a target program state is obtained, and the registration voice instruction set comprises voice instructions and callback instructions which correspond to the voice instructions and can be recognized by the application program; a user voice instruction is acquired for the application program in the target program state; the user voice instruction matches in a registered voice instruction set, and a callback instruction corresponding to the user voice instruction is determined; and a callback instruction is sent to the application to enable the application to execute an operation matched with the user voice instruction according to the callback instruction. According to the embodiment of the invention, the response accuracy of the user voice instruction can be improved, and the implementation process of the voice interaction function of each application program is simplified.
Owner:APOLLO INTELLIGENT CONNECTIVITY (BEIJING) TECH CO LTD
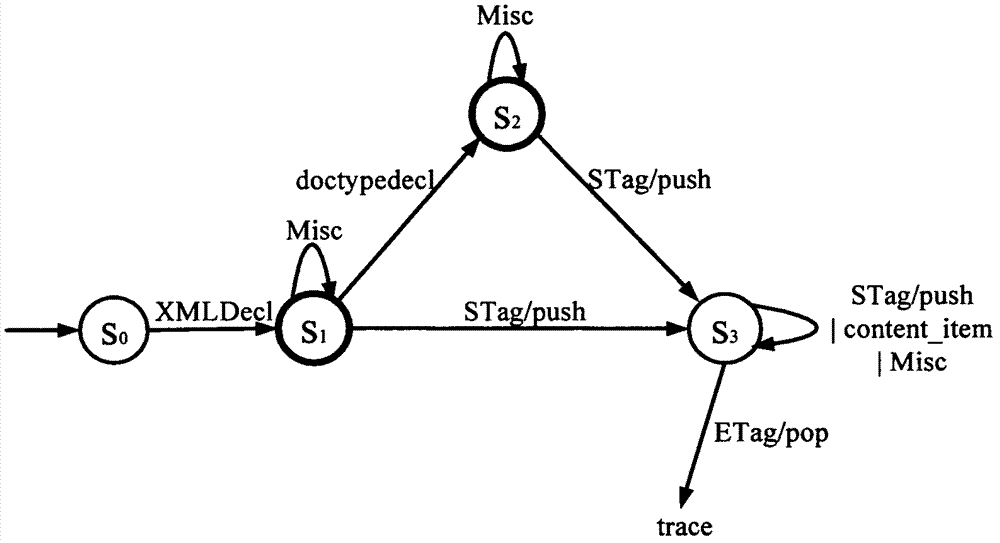
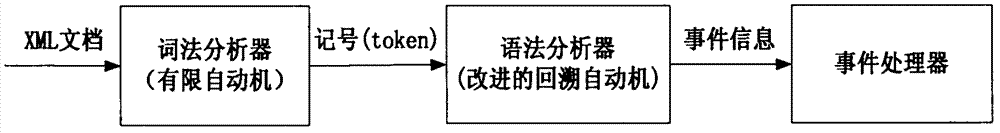
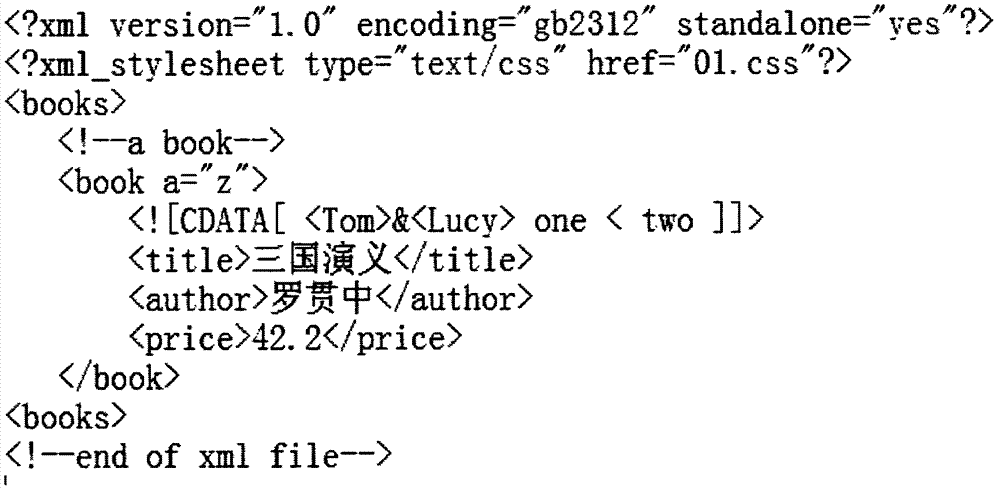
JSAX (joint simple API (application program interface) for XML (extensible markup language)) parser and parsing method based on syntactic analysis of backtracking automaton
ActiveCN102708155ASimplify the design processImprove efficiencySpecial data processing applicationsLexical analysisCallback
The invention relates to a JSAX (joint simple API (application program interface) for XML (extensible markup language)) parser and a parsing method based on syntactic analysis of a backtracking automaton. An action transfer rule delta of the backtracking automaton is redefined and the improved backtracking automaton is applied to a syntactic parser, so that the design and the implementation of the syntactic parser are simplified, and the efficiency of the XML parser is effectively improved. During the syntactic parse, the backtracking automaton uses a mark flow provided by a lexer parser as the input and compresses the current state to the stack top when the mark read by the backtracking automaton is a start mark; when the read mark is an end mark, the automaton pops a state out of the stack top as the next state of the automaton; and the automaton does not carry out any stack operation for other marks. During the syntactic parse, the XML document information meeting the syntactic specifications returns to the user through a standard callback function. The JSAX parser and the parsing method solve the problems that the syntactic parser of the XML document parser is complex in structure and low in performance, have the characteristics of easy implementation and high efficiency, and can be applied to parsing the XML documents.
Owner:XIDIAN UNIV
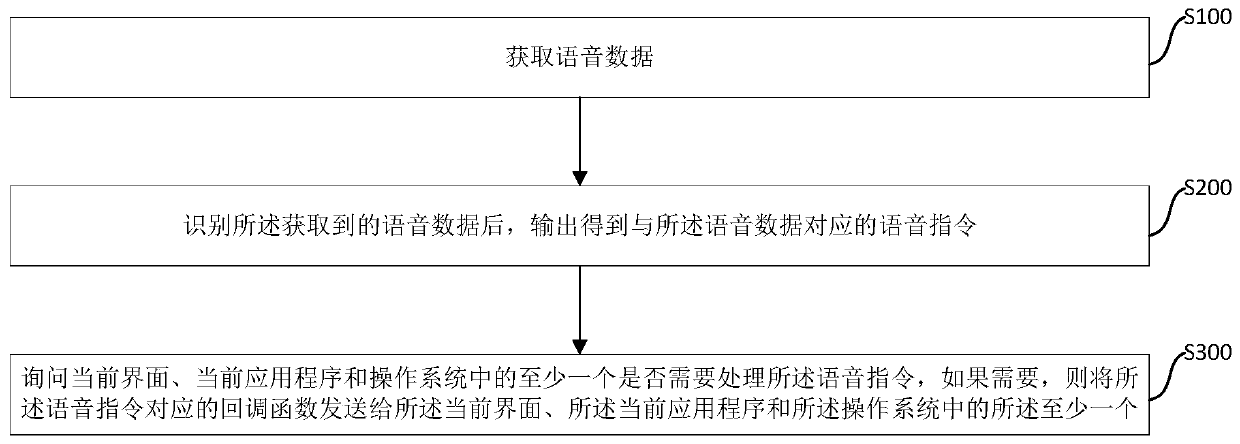
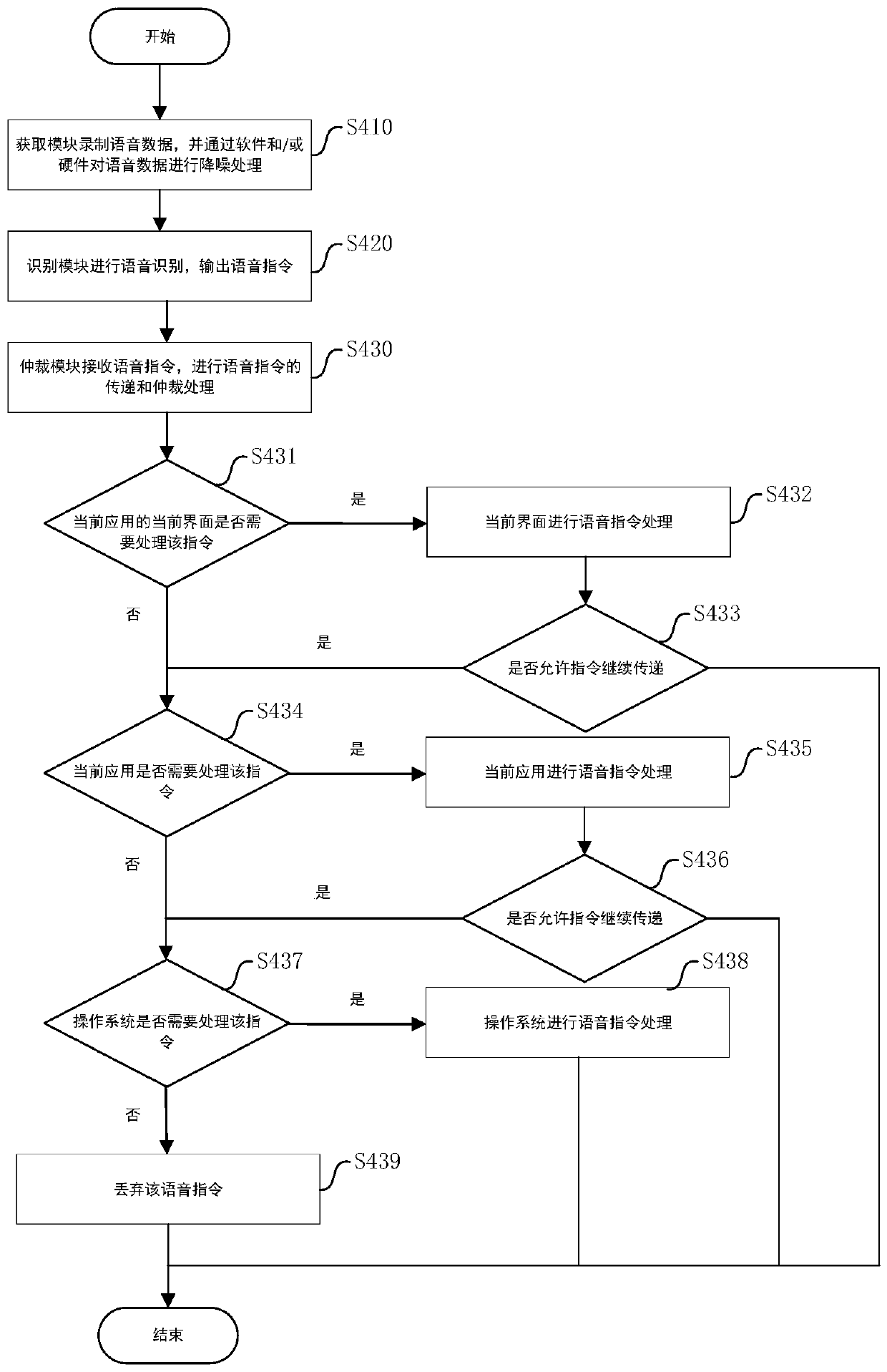
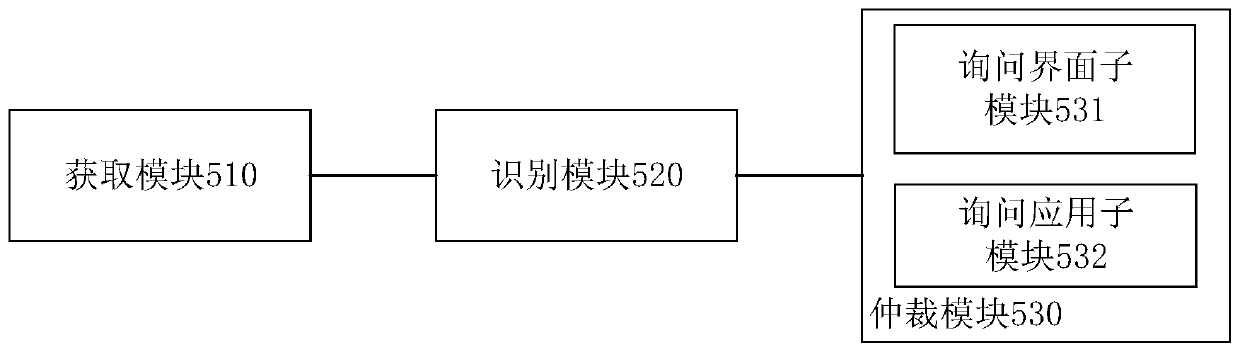
Voice command arbitration method and device
ActiveCN110223682AImprove processing efficiencyImprove reusabilitySpeech recognitionVoice dataReusability
The embodiment of the invention provides a voice command arbitration method and device, and belongs to the technical field of computers. The voice command arbitration method comprises the steps: voicedata are obtained; the obtained voice data are recognized, and a voice command corresponding to the voice data is obtained; and whether one or more of a current interface, a current application program and an operating system need to process the voice command or not is inquired, and if yes, a callback function corresponding to the voice command is sent to one or more of the current interface, thecurrent application program and the operating system. According to the voice command arbitration method and device, through unified execution of recording, recognition and analysis of the voice data,and hierarchical execution of arbitration and distribution of the voice command, the reusability of a code is improved, the complexity of the code is also lowered, and the processing efficiency of the voice command is improved.
Owner:APOLLO INTELLIGENT CONNECTIVITY (BEIJING) TECH CO LTD
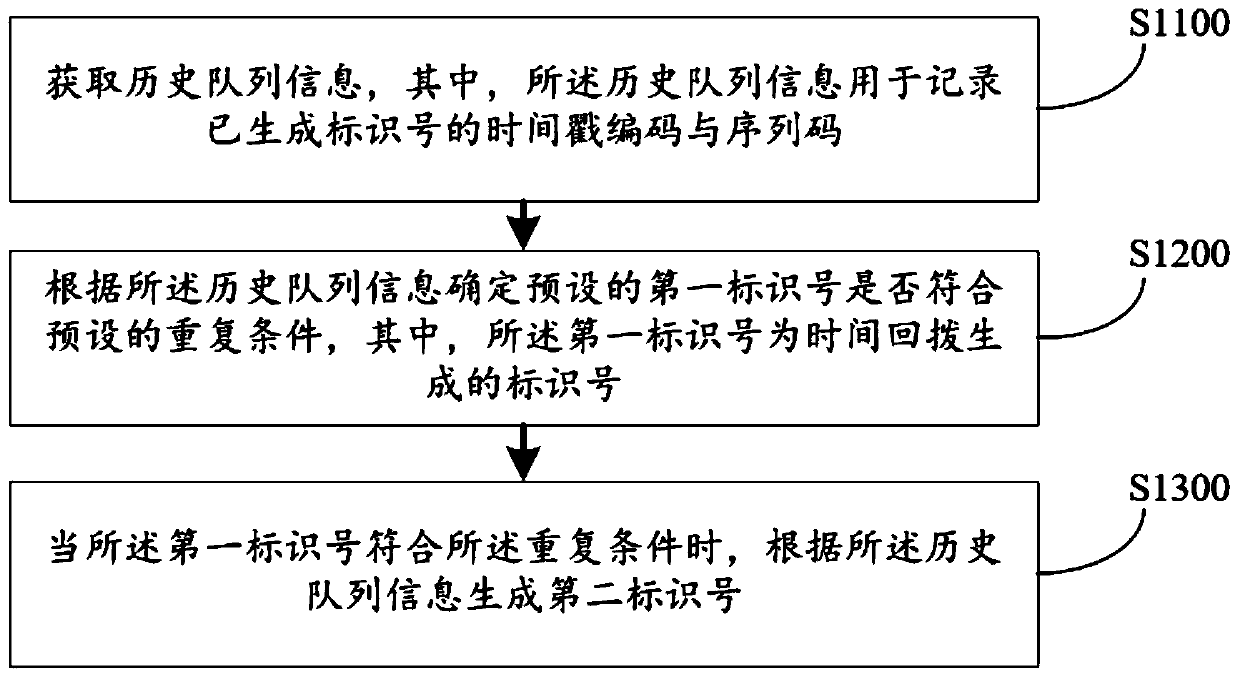
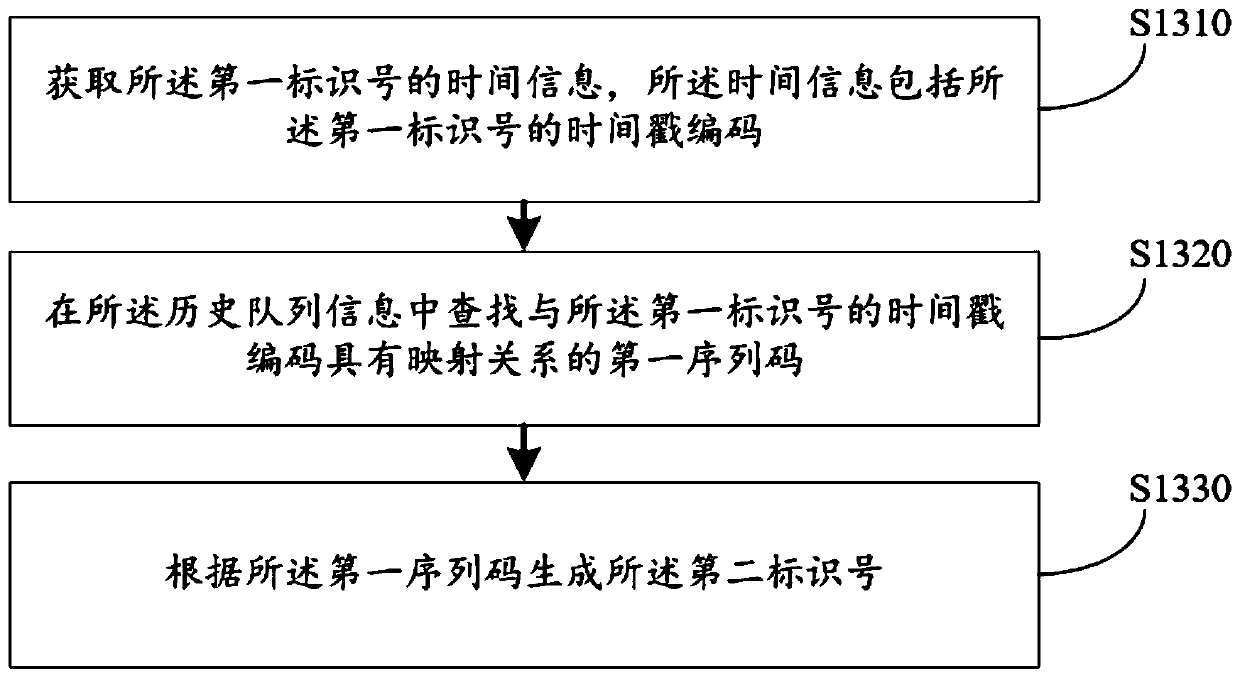
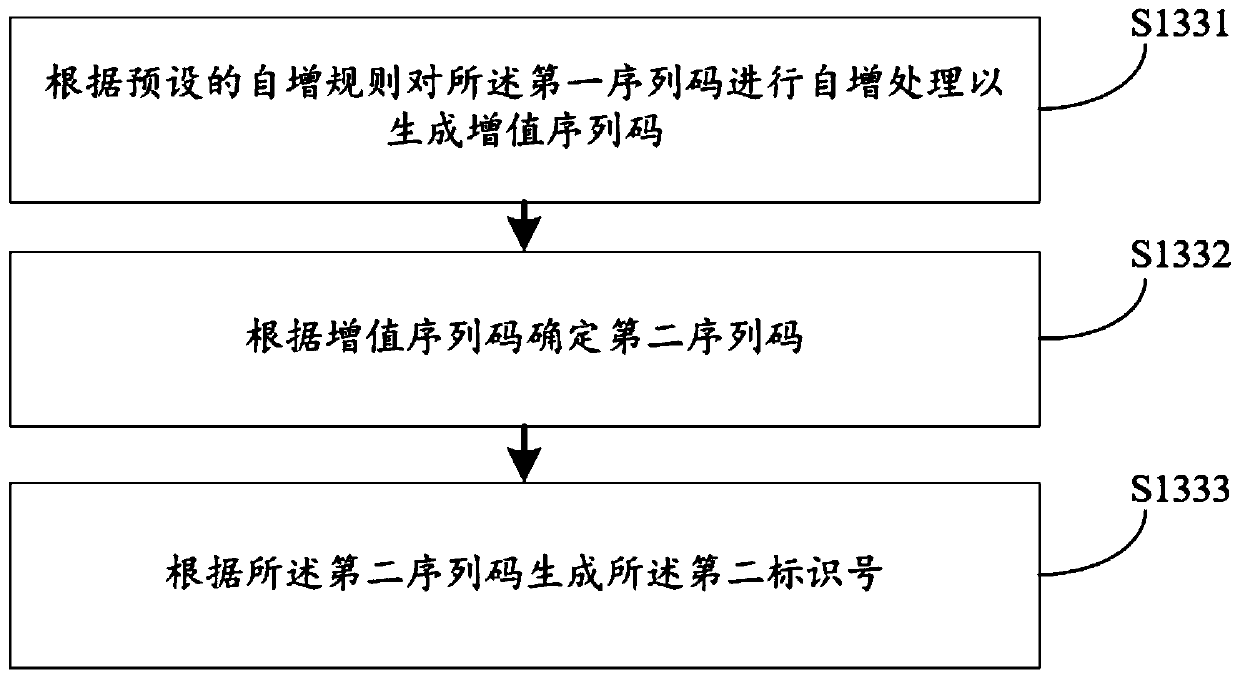
Identification number generation method and device, computer equipment and storage medium
ActiveCN111291424AMake sure not to repeatSolve the problem of duplicate identification numbersInternal/peripheral component protectionCallbackTimestamping
The embodiment of the invention discloses an identification number generation method and device, computer equipment and a storage medium, and the method comprises the following steps: obtaining historical queue information which is used for recording a timestamp code and a sequence code of a generated identification number; determining whether a preset first identification number meets a preset repetition condition according to the historical queue information, the first identification number being an identification number generated by time callback; and when the first identification number meets the repetition condition, generating a second identification number according to the historical queue information. A used timestamp and a used sequence code are recorded by setting historical queue information; whether the identification number is repeated or not is determined according to the historical queue when the identification number is generated by time callback, and when the identification number is repeated, the new identification number is generated by using the sequence code which is not used before according to the historical queue information, so that the generated identification number is effectively ensured not to be repeated.
Owner:望海康信(北京)科技股份公司
Web service broadcast engine
ActiveUS8423602B2Eliminate connectionMultiple digital computer combinationsTransmissionWeb serviceApplication software
A system, computer architecture, and method of enabling asynchronous callback and broadcast notification between a server and a client software application in a network, wherein the method comprises processing computer logic instructions in the network; requesting a notification of a completion of the processing of the computer logic instructions; storing the notification request in a registry; queuing the notification request according to a response to the notification request and a list of user endpoints requesting the notification of a completion of the processing of the computer logic instructions; and notifying a recipient system of the completion of the processing of the computer logic instructions upon execution of the queued notification request.
Owner:INT BUSINESS MASCH CORP
Implementation method for retransmitting and controlling congestion control in separating system
InactiveCN103051560AImprove QoS performanceProspects for widespread practical useData switching networksQuality of serviceData pack
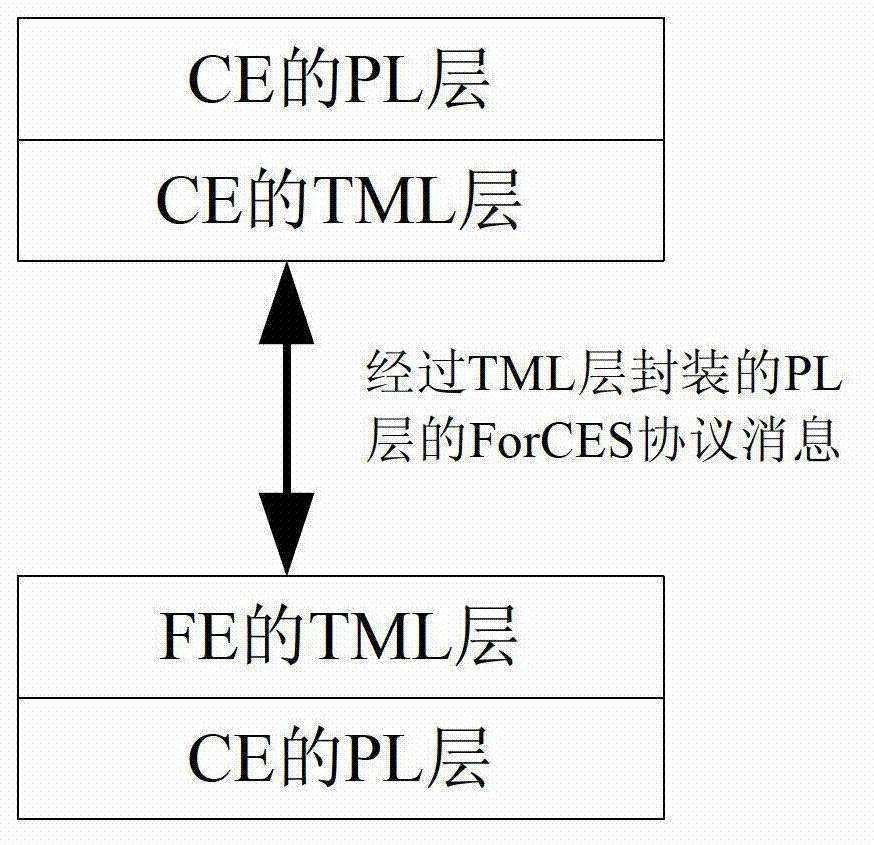
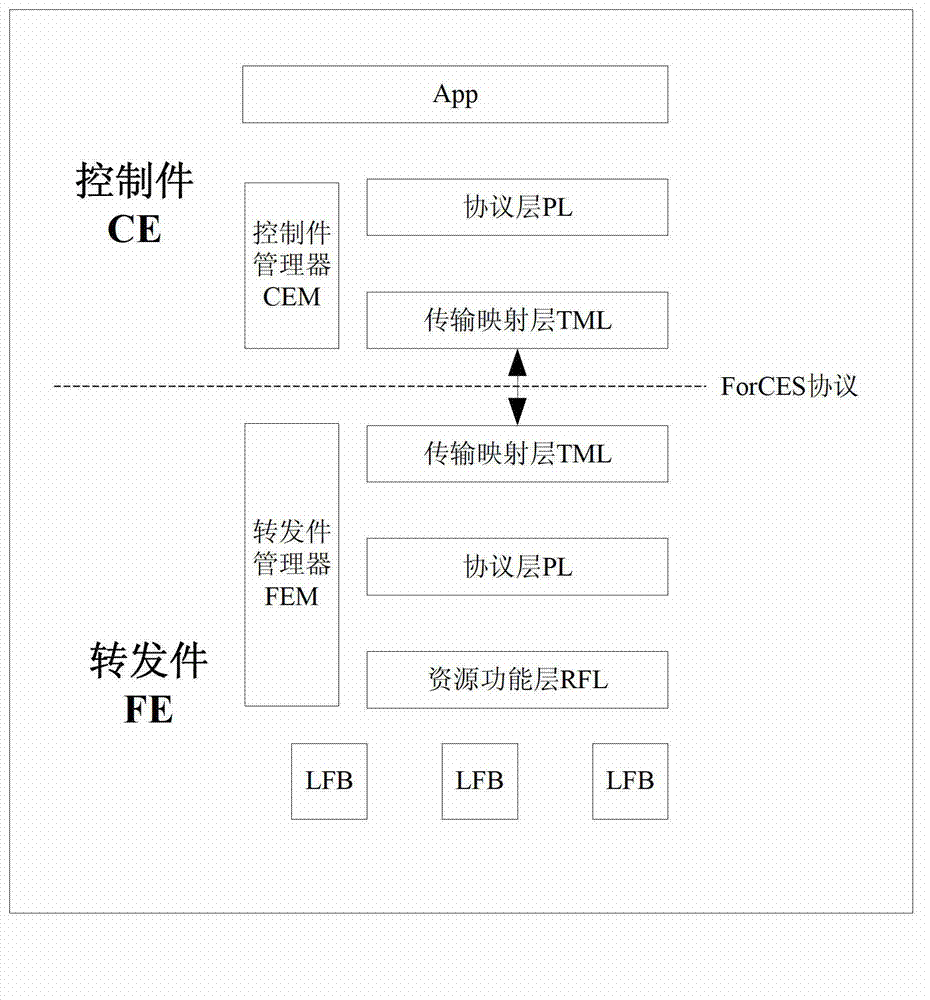
The invention discloses an implementation method for retransmitting and controlling congestion control in a separating system. The implementation method comprises the following steps of: 1.calculating whether the occupying ratio of a total buffer-area queue exceeds a preset threshold value or not by a control element according to a dispatcher in a transmission mapping layer; 2. if judging that a message in the queue is in a local congestion state, redistributing the residual service time of the round by the dispatcher to meet the requirement of the queue to the greatest degree; 3. managing a module through the control element by a transmission-mapping layer module and notifying a protocol-layer module in the mode of a callback function; and constructing a congestion feedback message by the protocol-layer module and sending the congestion feedback message to the opposite end of the transmission mapping layer through the transmission-mapping layer module; and 4. delivering the congestion feedback message to the protocol-layer module through the module at the opposite end of the transmission mapping layer, and actively adjusting the sending rate of a data packet by the protocol-layer module in the modes of additive increase and multiplicative decrease. The implementation method is applied to an existing ForCES prototype system, so that the overall QoS (Quality of Service) performance of the system is improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Method of using cryptographic equipment by JAVASCRIPT
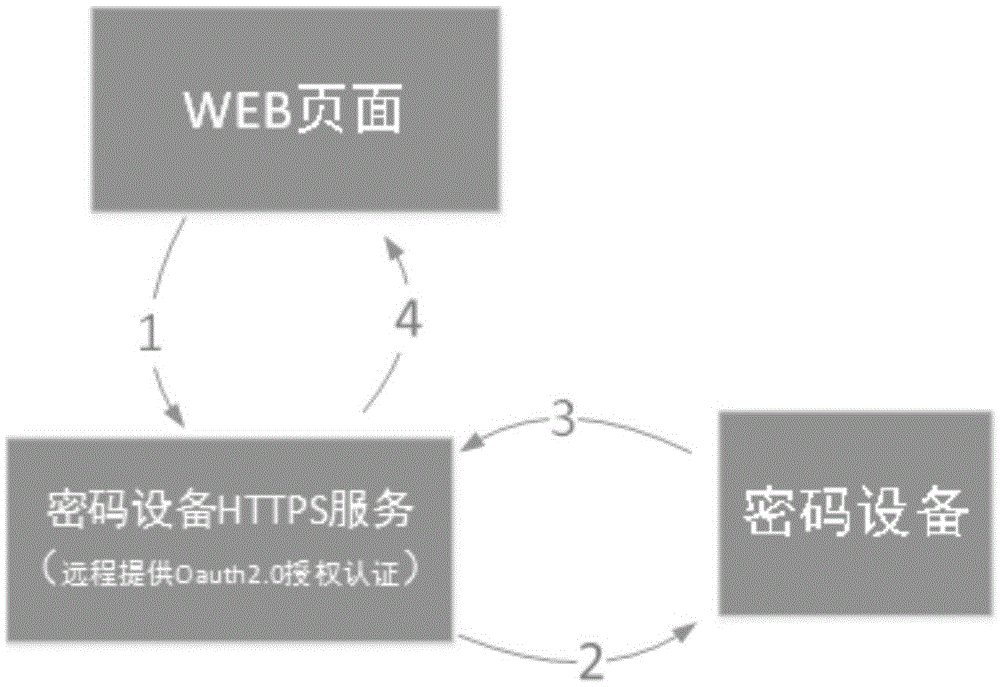
InactiveCN105071922AAvoid instability, security and other issuesDon't worry about updatingSecuring communicationCallbackSoftware engineering
The invention relates to a Method of using cryptographic equipment by JAVASCRIPT. The method comprises the following steps: step 1) of accessing the HTTPS (Hyper Text Transfer Protocol) service of the cryptographic equipment by the applied WEB page JavaScript script through an SRC (Source) attribute of a <script> tag by an HTTPS protocol, and putting the parameter data into an URL (Uniform Resource Locator) link; step 2) of requiring a caller to verify the identity after acquiring the parameters in the URL required by the HTTPS by the HTTPS service of the cryptographic equipment, after the identity verification is passed, operating the cryptographic equipment according to the parameters; step 3) of returning an operating result of the cryptographic equipment by means of balling back a JavaScript function in the WEB page after the operation is finished; acquiring the operating result in the JavaScript callback function by the applied WEB page, and then processing the operating result according to an own business process. The method of using the cryptographic equipment by JAVASCRIPT provided by the invention has the advantages of being free from a browser plug-in, cross-platform, flexible in deployment, high in security, convenient, supporting very long data and saving cost and the like.
Owner:ZHEJIANG ICINFO TECH
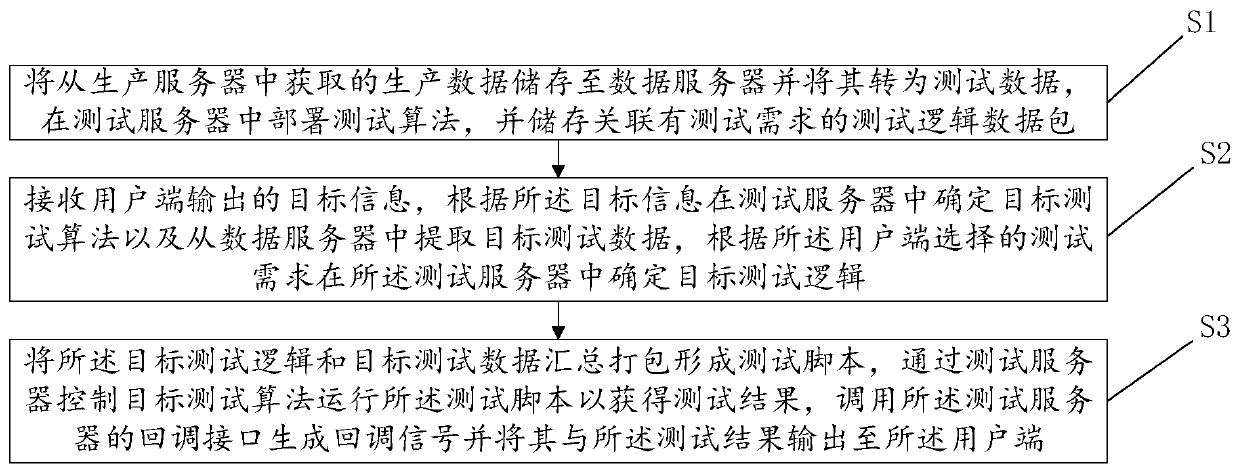
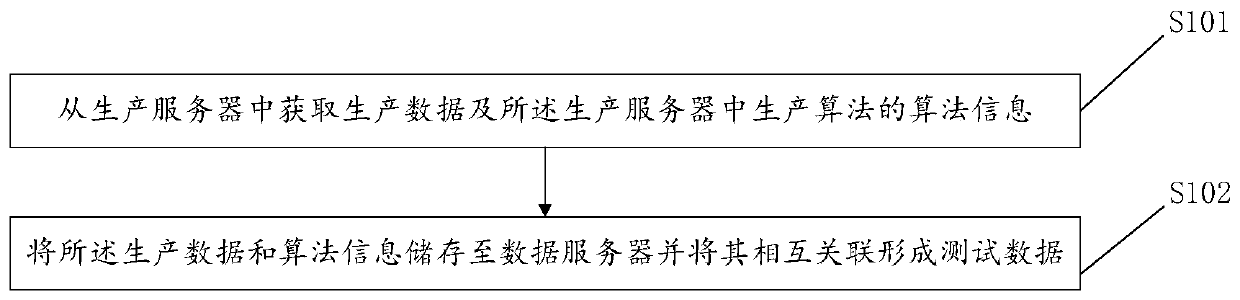
Automatic algorithm testing method and device, computer system and readable storage medium
PendingCN111258913AImprove acquisition efficiencyReduce fatigue strengthSoftware testing/debuggingData packTest script
The invention discloses an automatic algorithm testing method and device, a computer system and a readable storage medium. Based on the technical field of testing, the method comprises the following steps: storing production data obtained from a production server into a data server, converting the production data into test data, deploying a test algorithm in a test server, and storing a test logicdata packet associated with a test demand; receiving target information output by the user side, determining a target test algorithm in the test server according to the target information, extractingtarget test data from the data server, and determining target test logic in the test server according to test requirements; and summarizing and packaging the target test logic and the target test data to form a test script, controlling a target test algorithm to run the test script to obtain a test result, calling a callback interface to generate a callback signal, and outputting the callback signal and the test result to the user side. According to the invention, the effect of automatically testing the algorithm is realized, and the problems of low working efficiency and high randomness of the current test are avoided.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
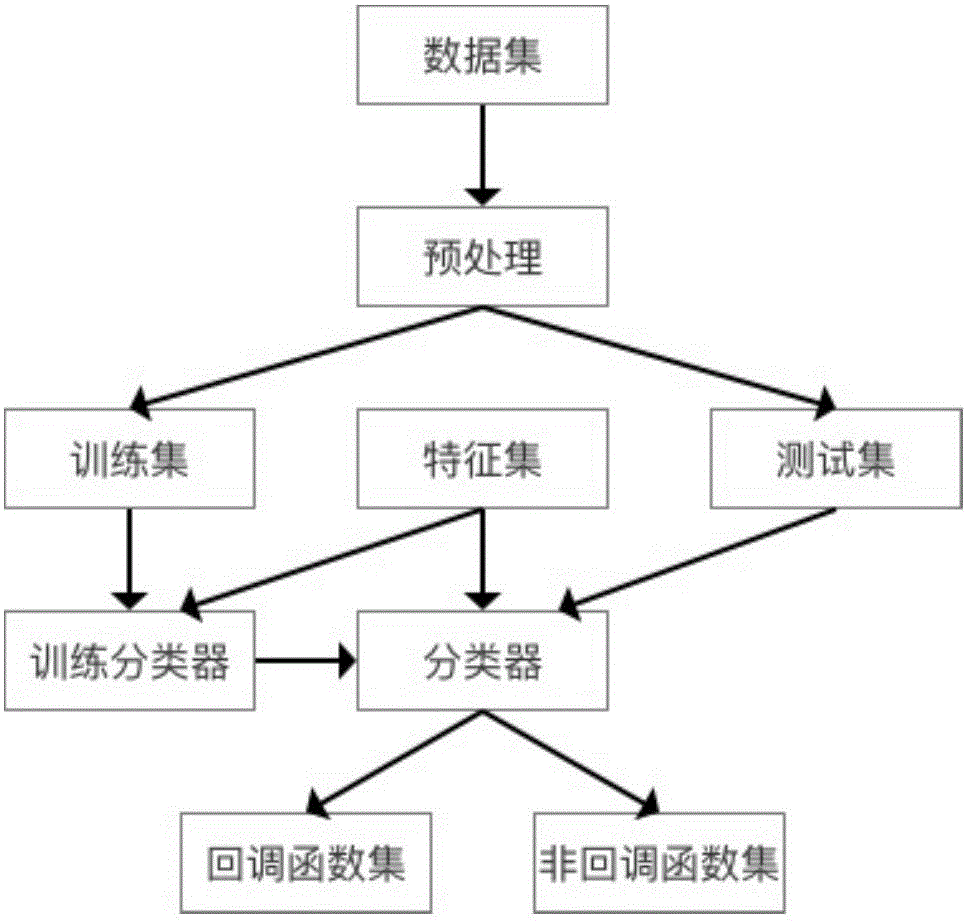
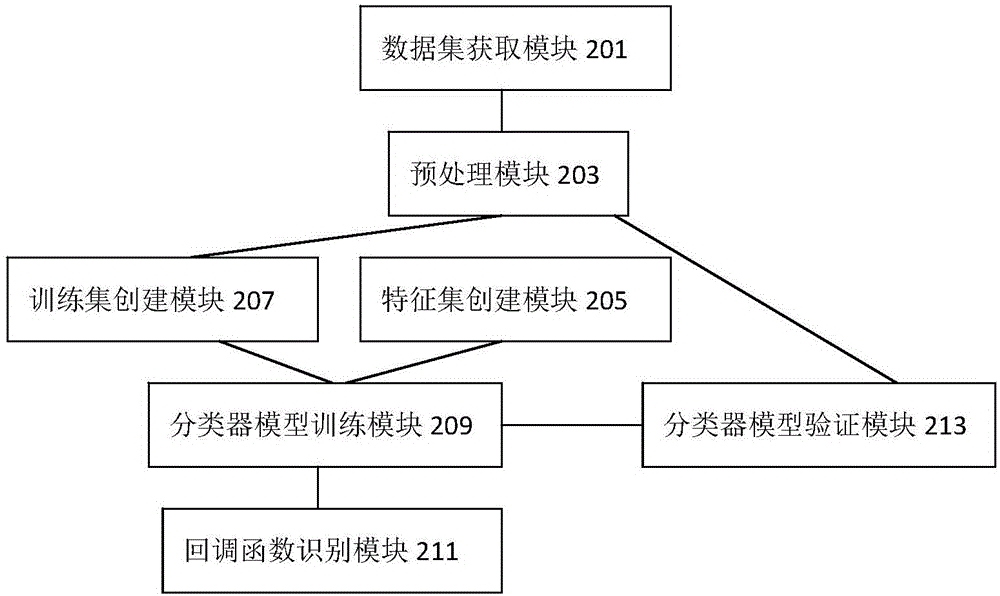
Android platform callback function detecting method based on machine learning method
ActiveCN106845235AEfficient identificationAccurate identificationCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorData set
The invention discloses an Android platform callback function detecting method based on a machine learning method. The method includes the following steps that data sets are obtained; the obtained data sets are pre-processed; feature sets are established by using specific syntax and semantics of an Android platform, and the feature sets serves as feature vectors of the machine learning algorithm; the data sets are randomly selected to form a training set, and callback functions in the training set are manually labeled; a classifier is trained by using the training set, and a classifier model is obtained; according to the classifier model, the machine learning algorithm is adopted, all functions in the data sets are mapped to callback function sets or non-callback function sets respectively, and the identification of the callback functions is completed. The method takes the advantage of the machine learning algorithm, the callback functions and non-callback functions of the Android platform can thus be effectively and accurately identified, and the method is suitable for Android operating systems different in version.
Owner:KUNSHAN BRANCH INST OF MICROELECTRONICS OF CHINESE ACADEMY OF SCI
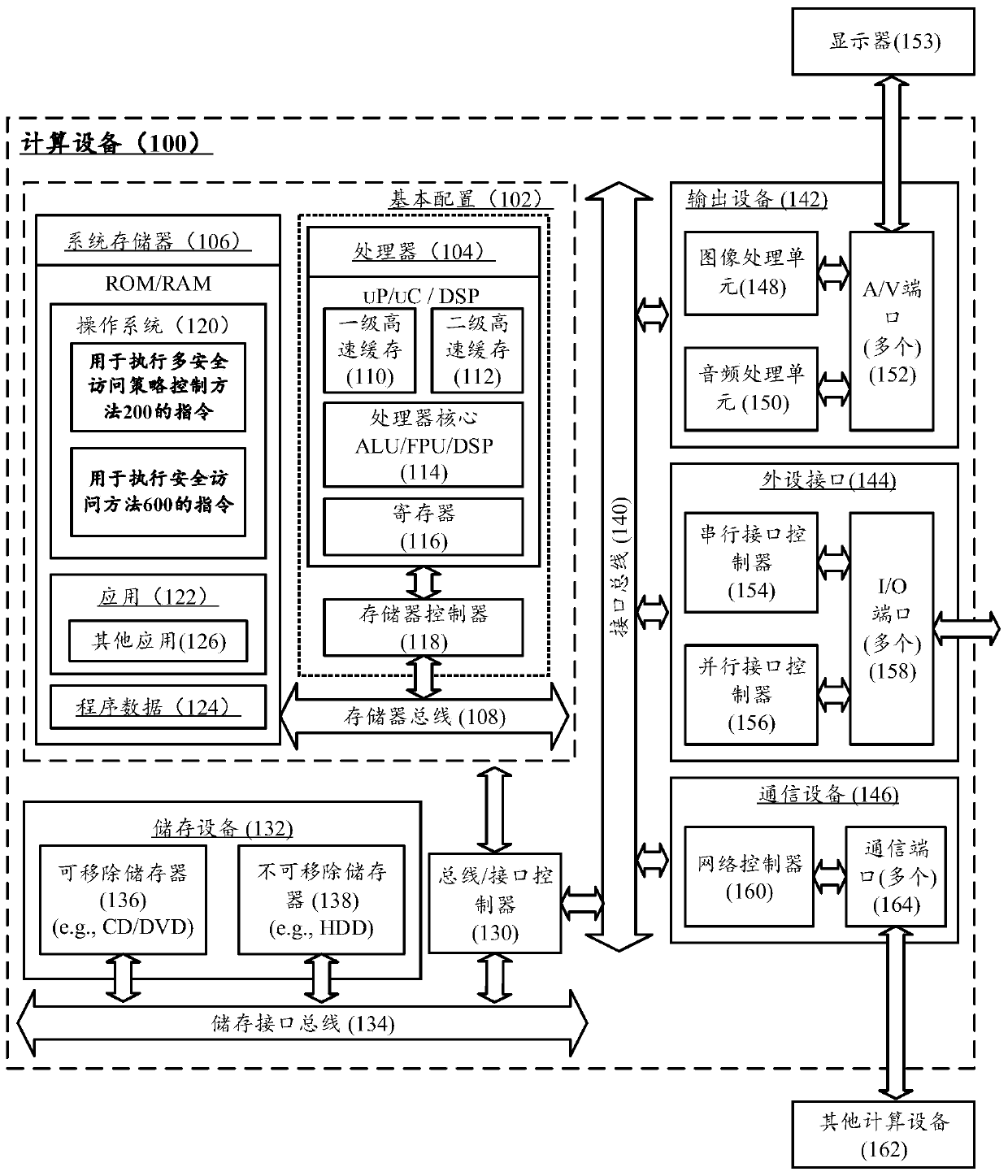
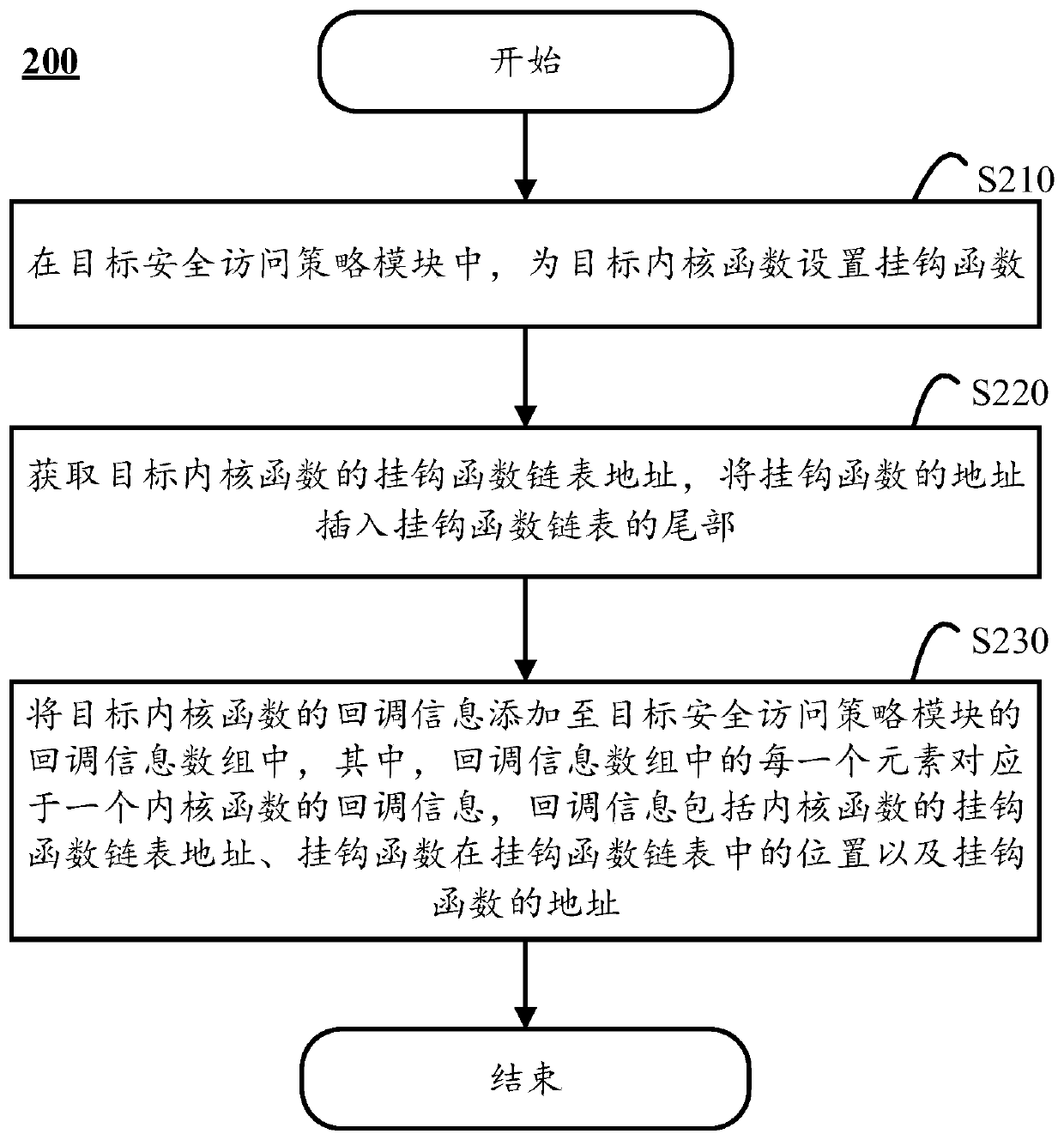
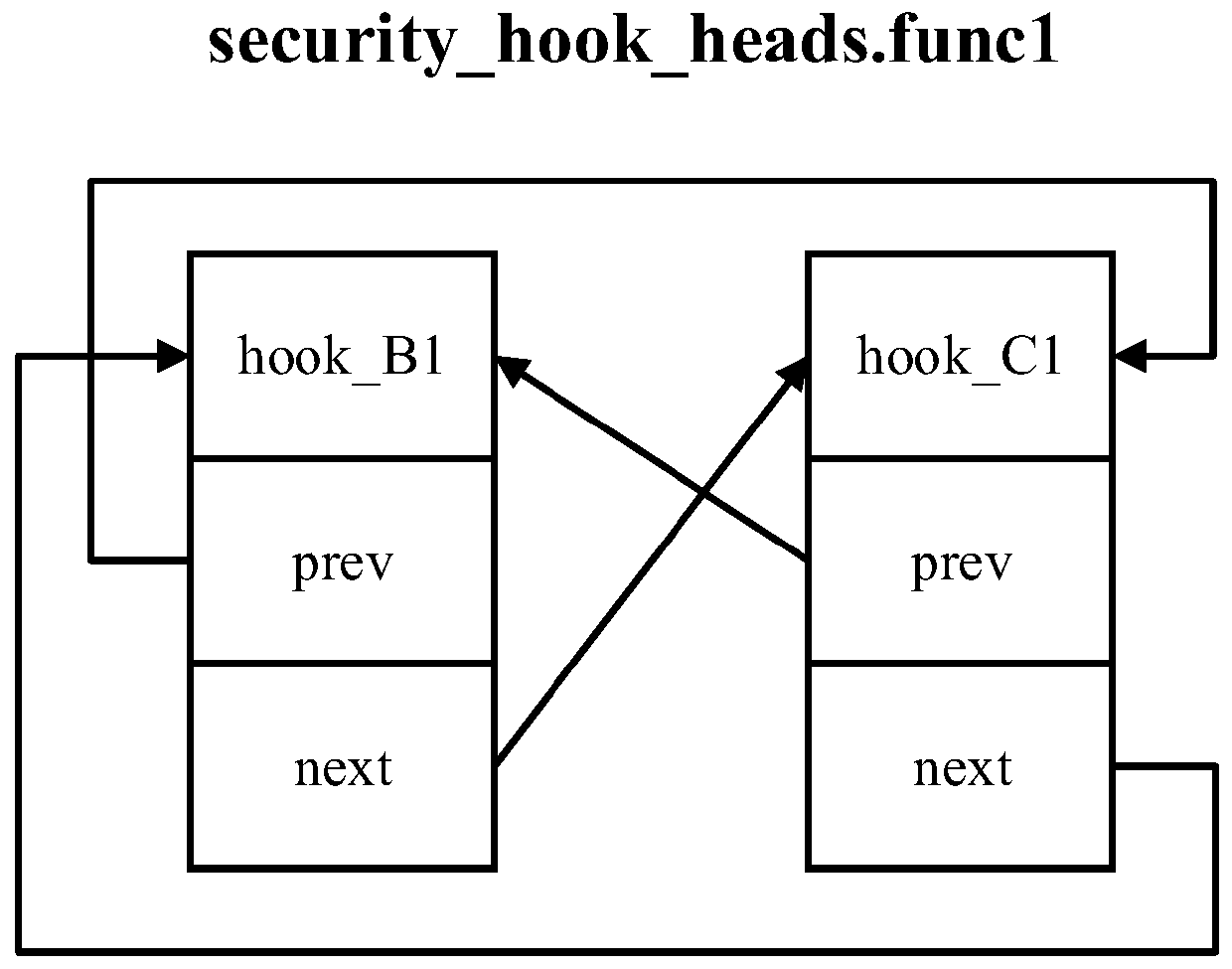
Multi-security access strategy control method and computing equipment
The invention discloses a multi-security access strategy control method, which is executed in computing equipment and comprises the following steps of: setting a hook function for a target kernel function in a target security access strategy module; acquiring the hook function linked list address of the target kernel function, and inserting the address of the hook function into the tail part of the hook function linked list; and adding the callback information of the target kernel function to the callback information array of the target security access strategy module, wherein each element inthe callback information array corresponds to the callback information of one kernel function, and the callback information comprises the hook function linked list address of the kernel function, theposition of the hook function in the hook function linked list and the address of the hook function. The invention also discloses a corresponding security access method and computing equipment.
Owner:北京统信软件技术有限公司
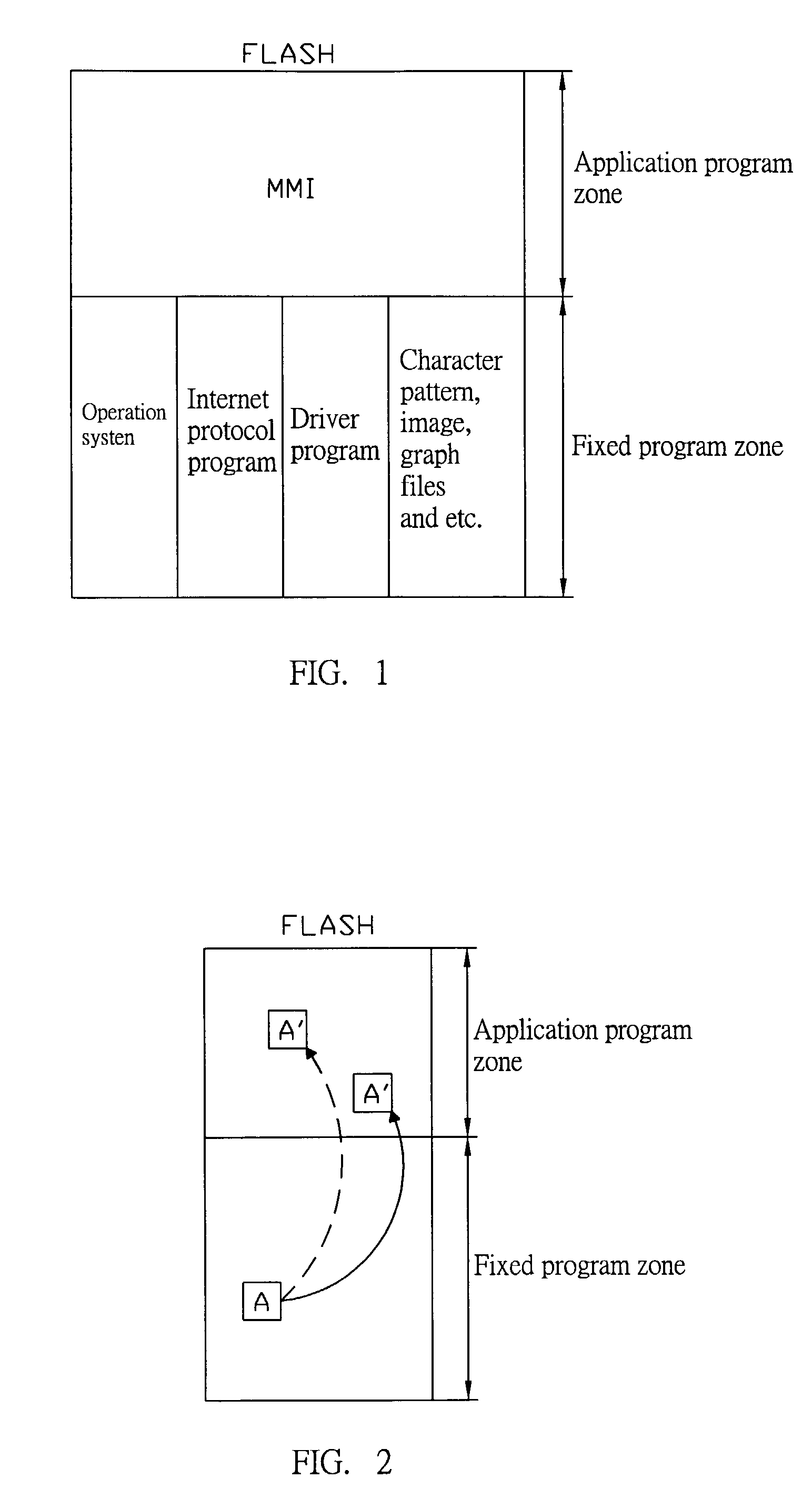
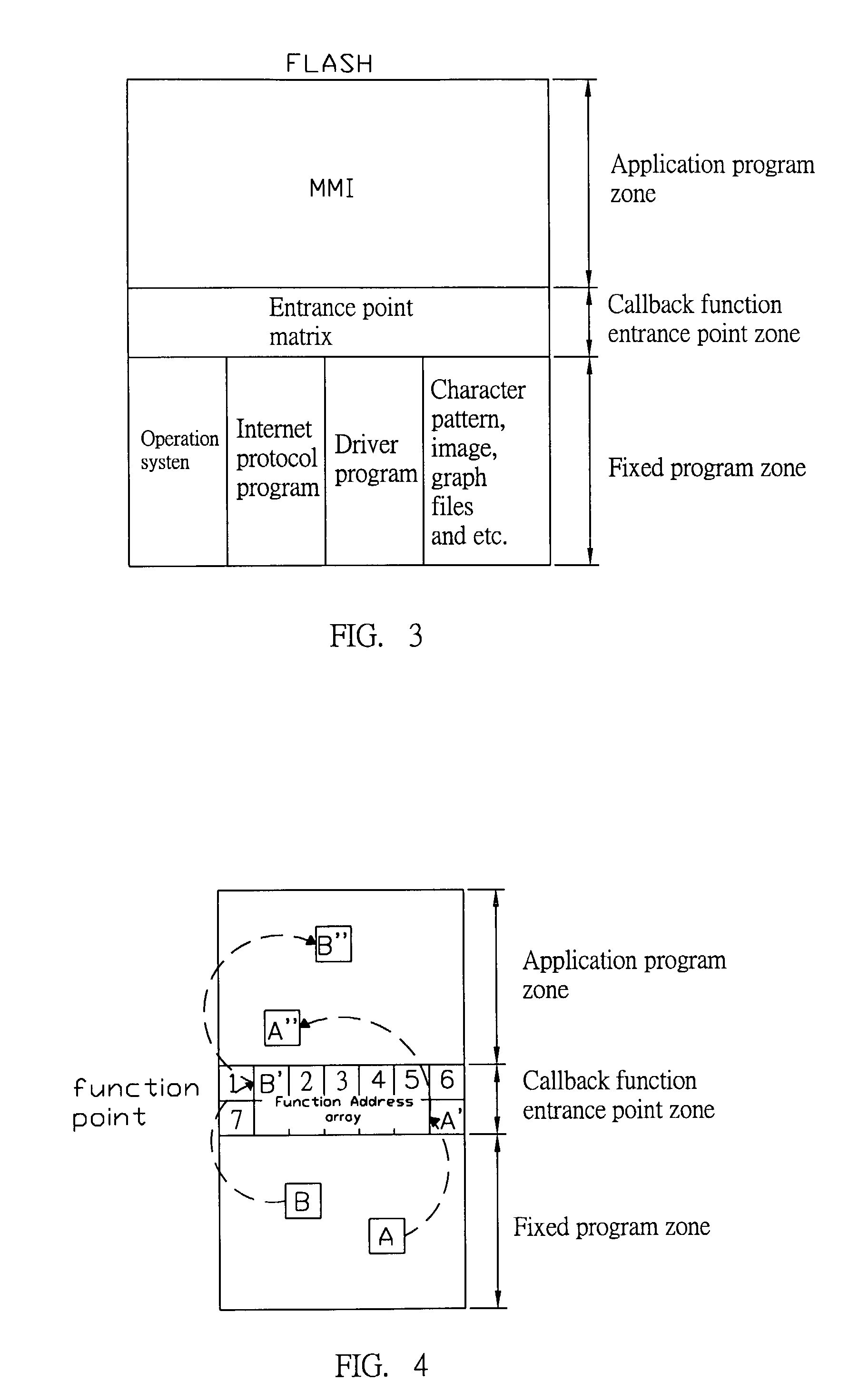
Method for repeatedly recording program in flash memory
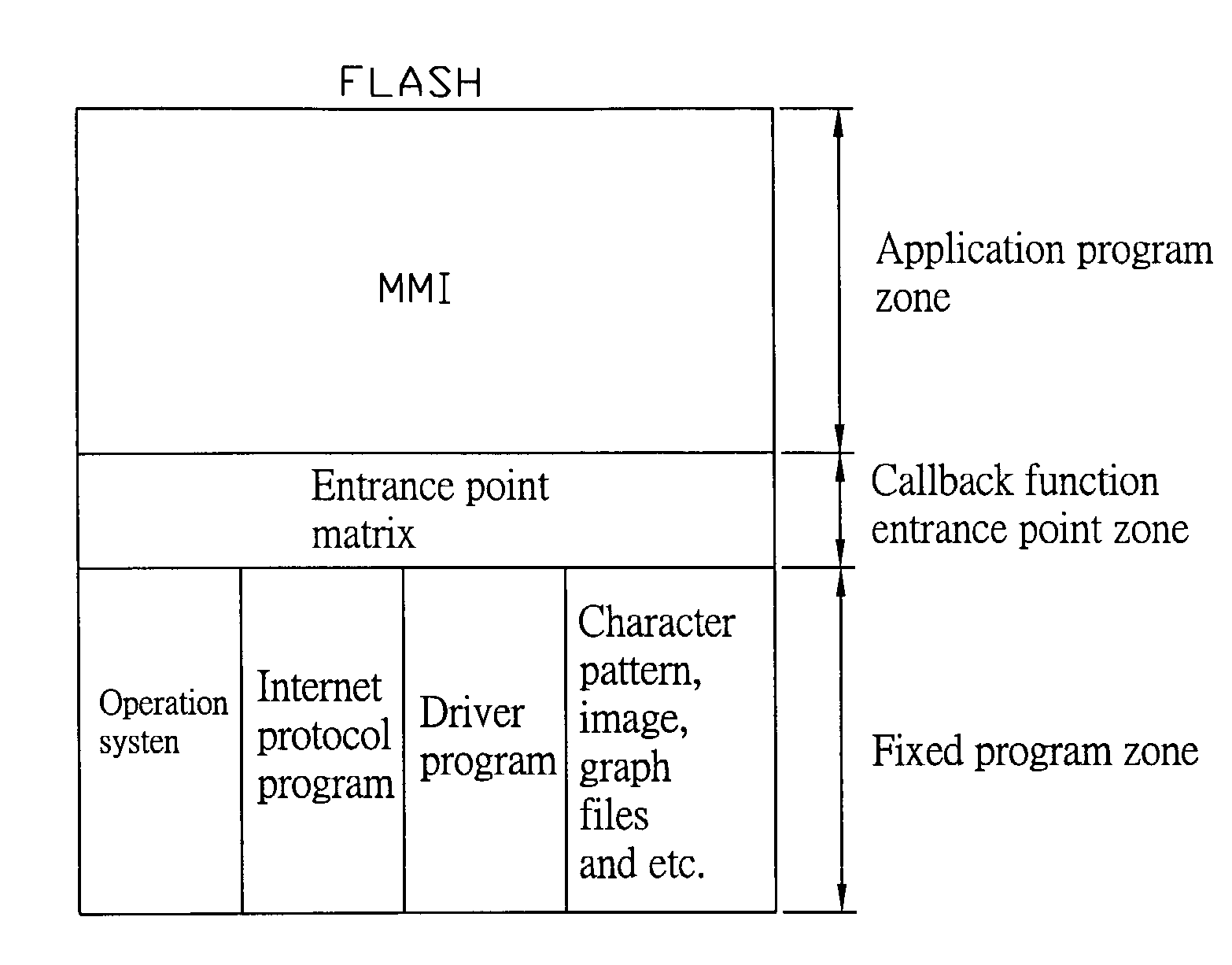
InactiveUS20030236940A1Reduce recording timeImprove recording efficiencyRead-only memoriesProgram loading/initiatingCallbackSoftware engineering
A Method for repeatedly recording a program in a flash memory is utilized to record a revised application program into a planned flash memory after the program is edited. The flash memory comprises a fixed program zone used to store never-revised fixed programs, an application program zone used to store revisable application programs and a callback function entrance point zone used to store an entrance point matrix. The starting address values of all callback functions in the application zone called by the fixed programs are stored in the entrance point zone. Therefore, only the program codes of the callback entrance point zone and the application program zone parts need to be recorded when the flash memory is recorded. Consequently, recording efficiency can be upgraded and program maintenance time can be reduced.
Owner:LITE ON TECH CORP
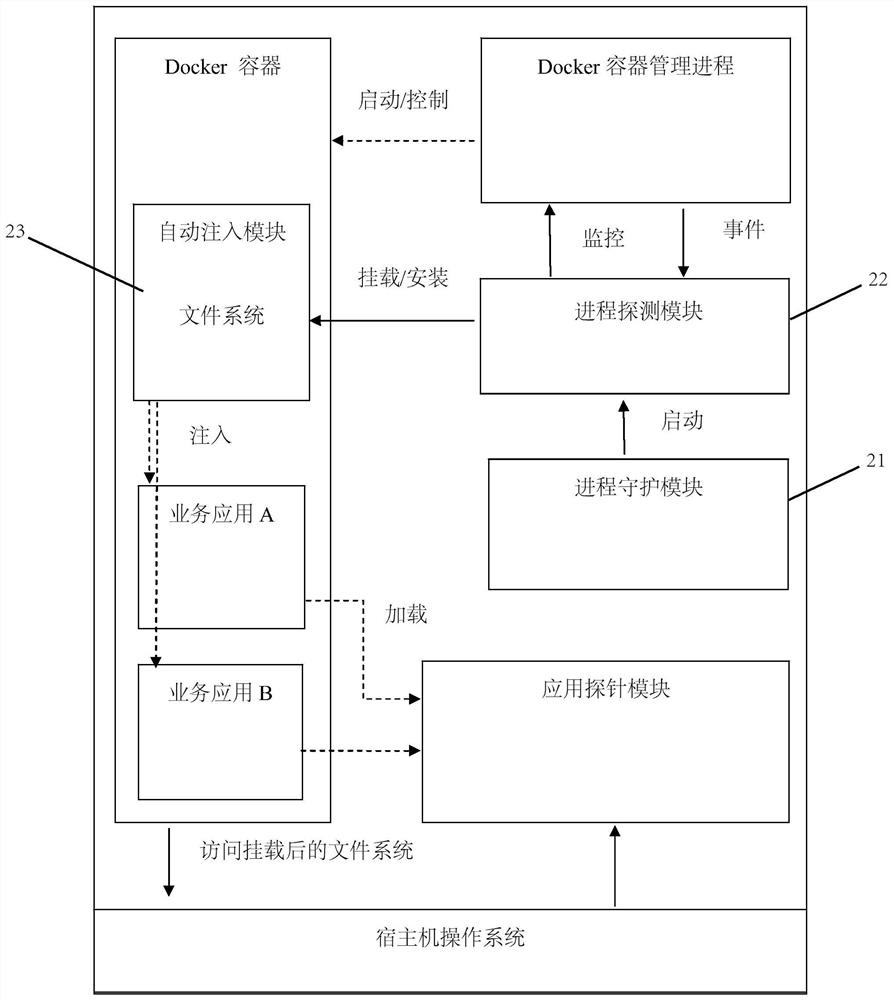
Method and device for injecting application probe in docker container environment
ActiveCN111813646AImplement automatic injectionTo achieve the purpose of performance monitoringHardware monitoringEnergy efficient computingOperational systemFile system
The invention relates to the technical field of computers. The invention provides a method and a device for injecting an application probe in a docker container environment. The method comprises the following steps: a process detection step: establishing a callback channel, monitoring a docker container management process, and automatically mounting a file directory where an application probe module is located to a corresponding directory in a file system of a new container when monitoring that the docker container management process starts the new container; a step of automatically injectinga probe: when it is monitored that a new application process is started on a docker container, starting the new application process, analyzing an execution environment of the new application process,setting an environment variable of the new application process or changing a starting parameter of the new application process after determining that the new application process meets the condition ofautomatically injecting the application probe, and injecting the corresponding application probe before the new application process executes the service logic. Through the technical scheme, the problem that in the docker container environment in the prior art, an operating system cannot monitor the transaction-level performance of the application process in the container is solved.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Vulnerability detection method and device, computer equipment and storage medium
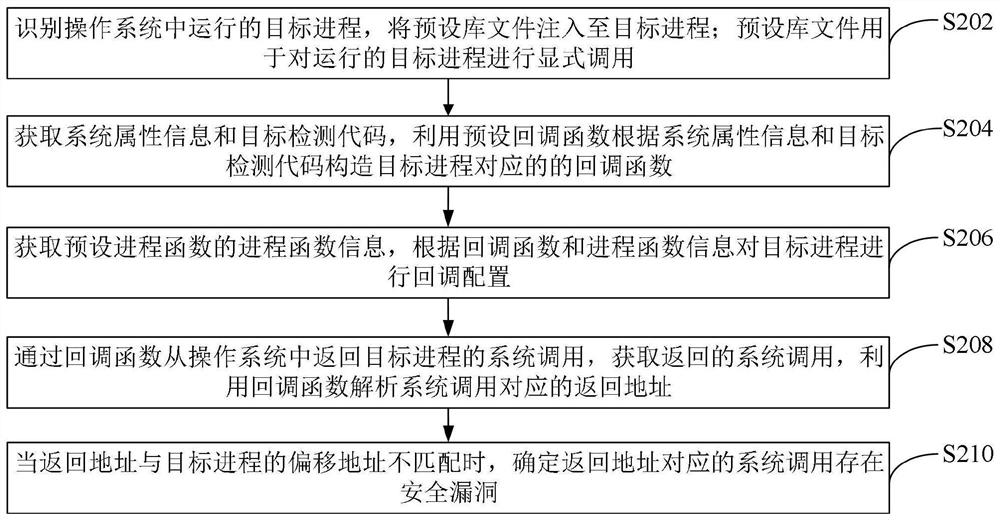
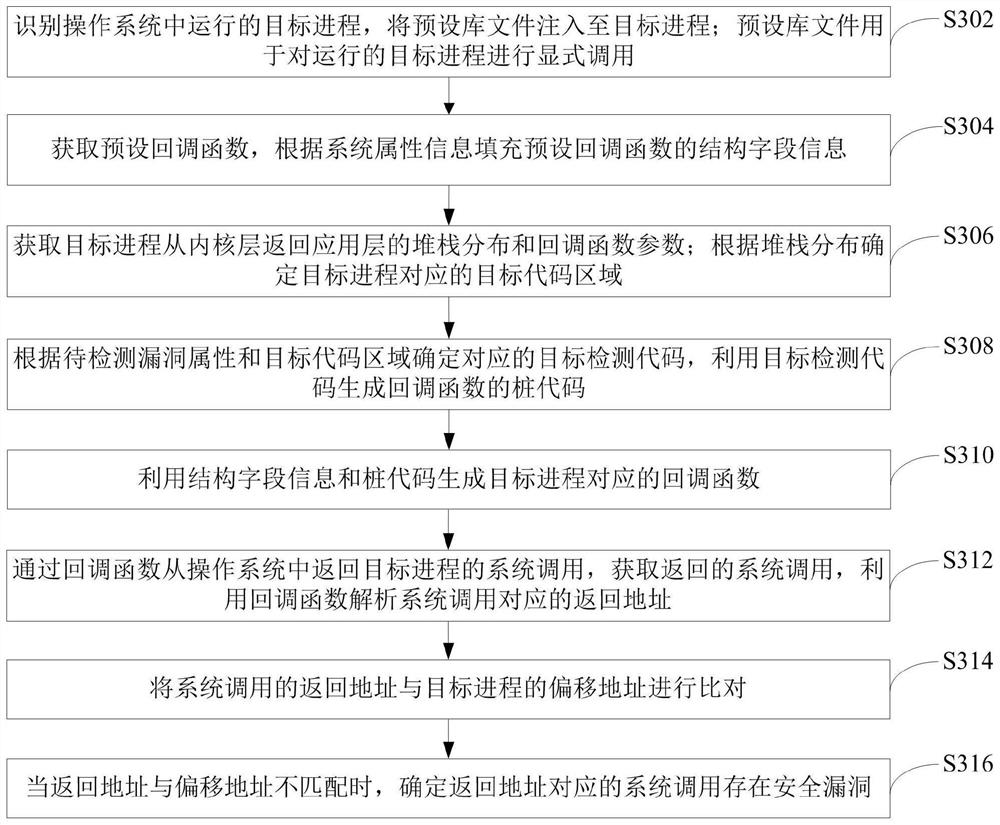
PendingCN113569246AImprove efficiencyHigh precisionPlatform integrity maintainanceOperational systemCallback
The invention relates to a vulnerability detection method and device, computer equipment and a storage medium. The method comprises the following steps: identifying a target process running in an operating system, and injecting a preset library file into the target process; wherein the preset library file is used for performing explicit calling on a running target process; obtaining system attribute information and a target detection code, and constructing a callback function corresponding to the target process by utilizing a preset callback function according to the system attribute information and the target detection code; performing callback configuration on the target process by utilizing a preset process function and a callback function; returning the system call of the target process from the operating system through the callback function, obtaining the returned system call, and analyzing a return address corresponding to the system call by utilizing the callback function; and when the return address is not matched with the offset address of the target process, determining that the system call corresponding to the return address has security vulnerabilities. By adopting the method, the vulnerability detection efficiency and accuracy can be effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Dynamic link library injection method and device, equipment and storage medium
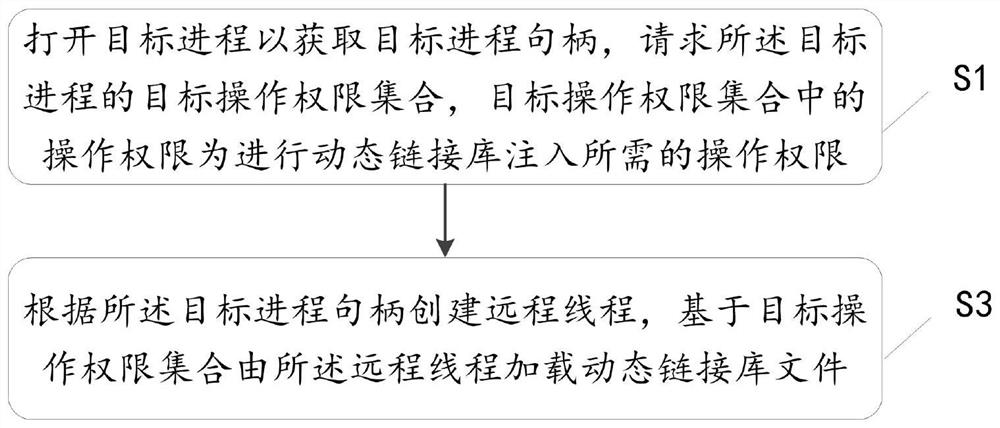
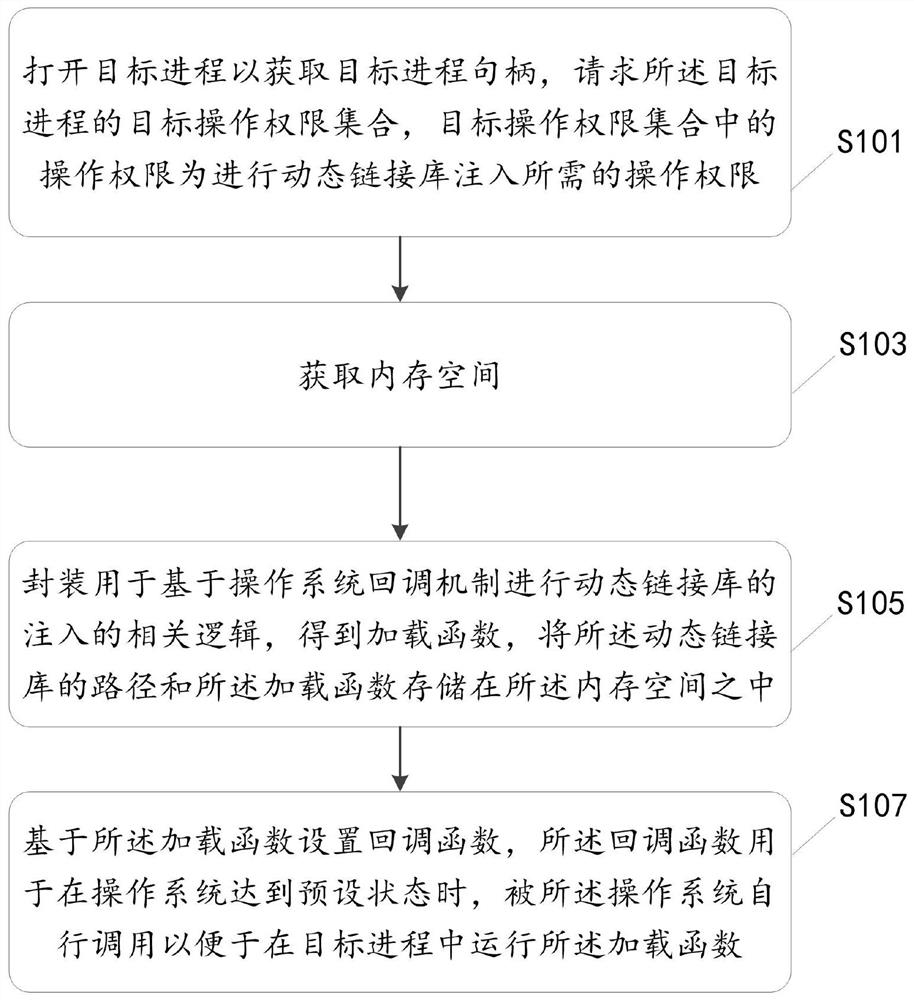
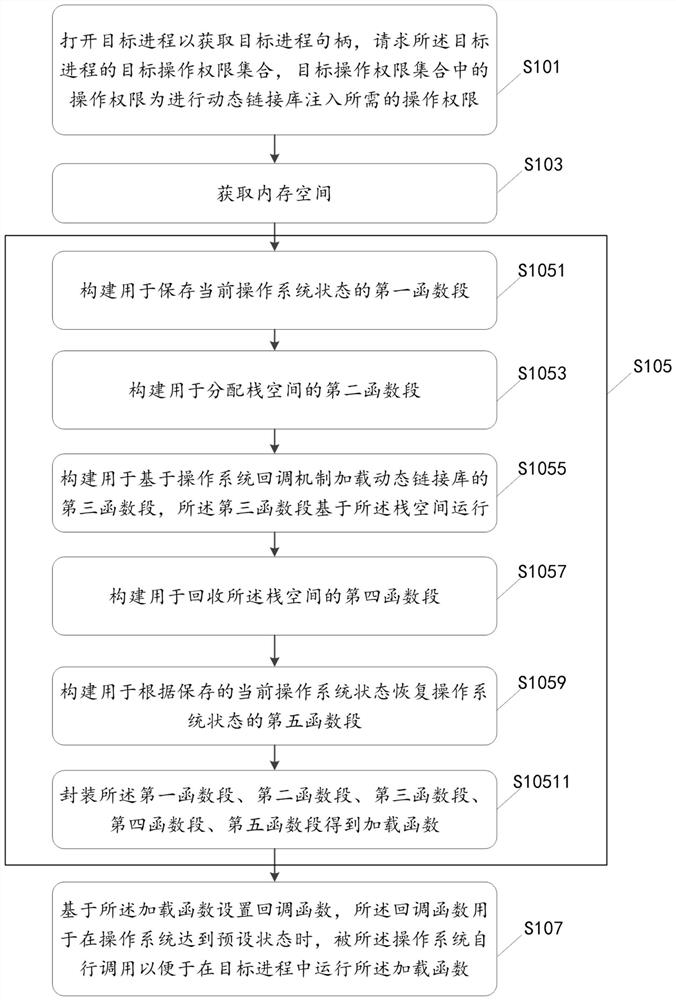
PendingCN113703859AHigh injection success rateThe target operation permission is lowResource allocationProgram loading/initiatingPathPingOperational system
The invention discloses a dynamic link library injection method and device, equipment and a storage medium; the method comprises the steps of opening a target process to obtain a target process handle, requesting a target operation authority set of the target process, wherein operation authorities in the target operation authority set are operation authorities needed for dynamic link library injection; obtaining a memory space; packaging related logic used for injecting the dynamic link library based on an operating system callback mechanism to obtain a loading function, and storing a path of the dynamic link library and the loading function in the memory space; and setting a callback function based on the loading function, the callback function being used for being automatically called by the operating system when the operating system reaches a preset state so as to run the loading function in a target process. According to the invention, the required target operation authority is few, the thread management and monitoring in the target process can be bypassed, and less callback function information is disclosed, so that the dynamic link library injection success rate is higher.
Owner:TENCENT TECH (SHENZHEN) CO LTD
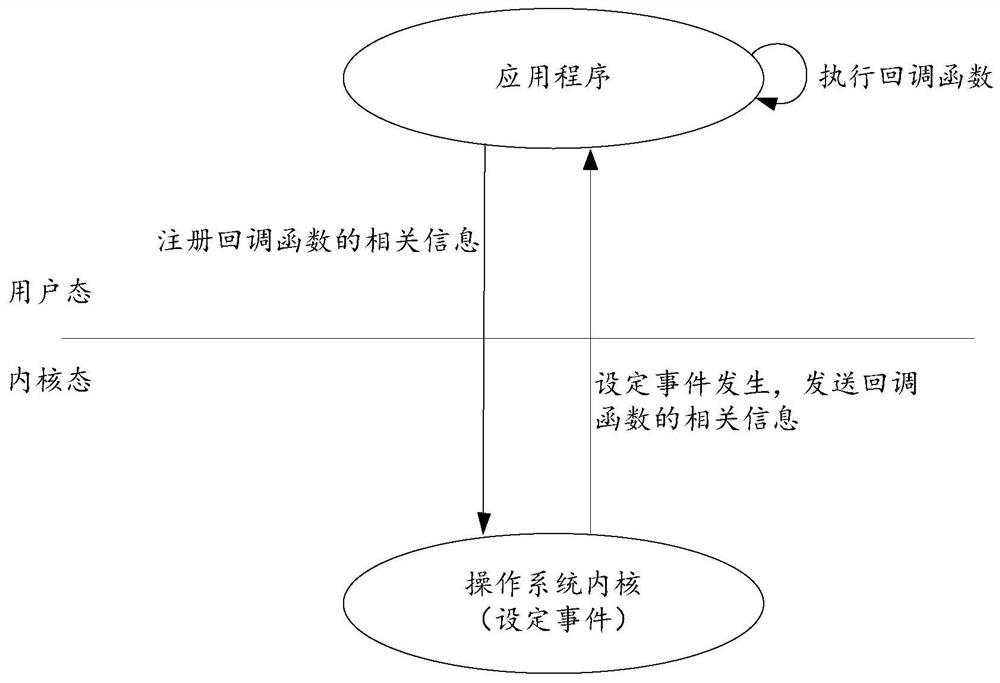
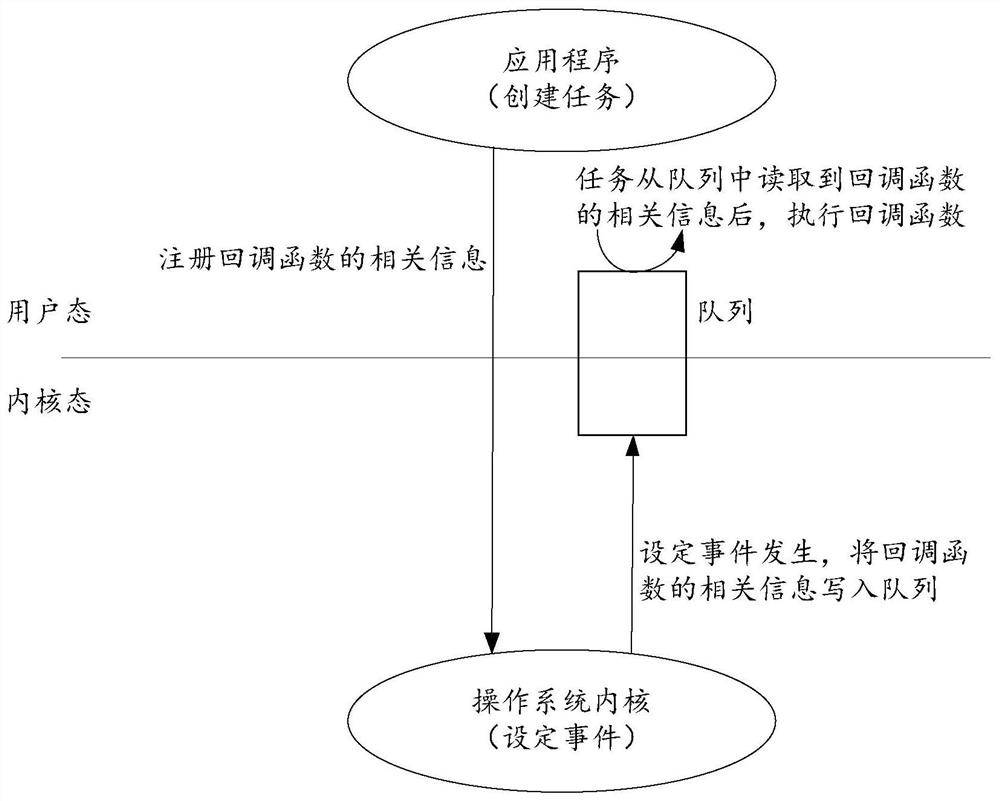
Function calling method and device, medium, embedded equipment and operating system
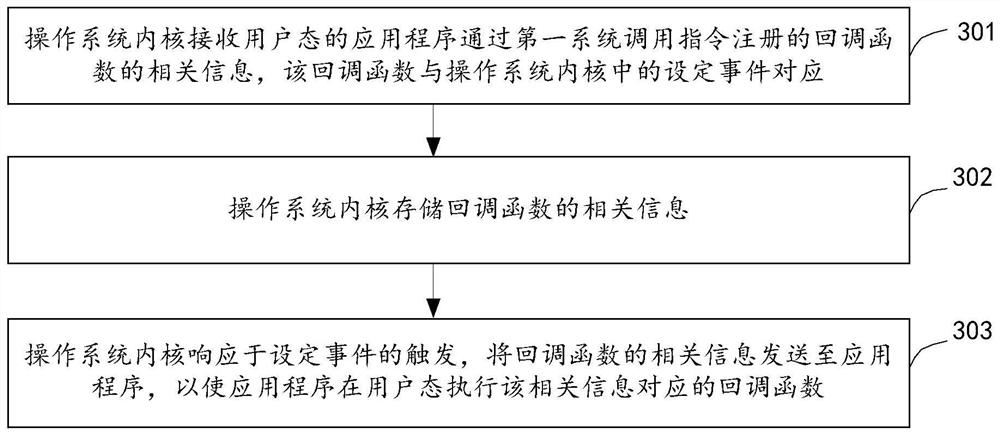
PendingCN114281431AAvoid security issuesProgram initiation/switchingInterprogram communicationCallbackApplication procedure
The embodiment of the invention provides a function calling method and device, a medium, embedded equipment and an operating system, and the function calling method comprises the steps that an operating system kernel receives related information of a callback function registered by an application program in a user mode through a first system calling instruction, and stores the related information of the callback function, the callback function corresponds to a set event in an operating system kernel; and in response to triggering of the set event, the operating system kernel sends related information of the callback function to the application program, so that the application program executes the callback function in a user mode.
Owner:ALIBABA GRP HLDG LTD
Method, device and equipment for determining program by utilizing privileged bug and storage medium
PendingCN111191226AImprove accuracyImprove detection efficiencyPlatform integrity maintainanceCallbackSoftware engineering
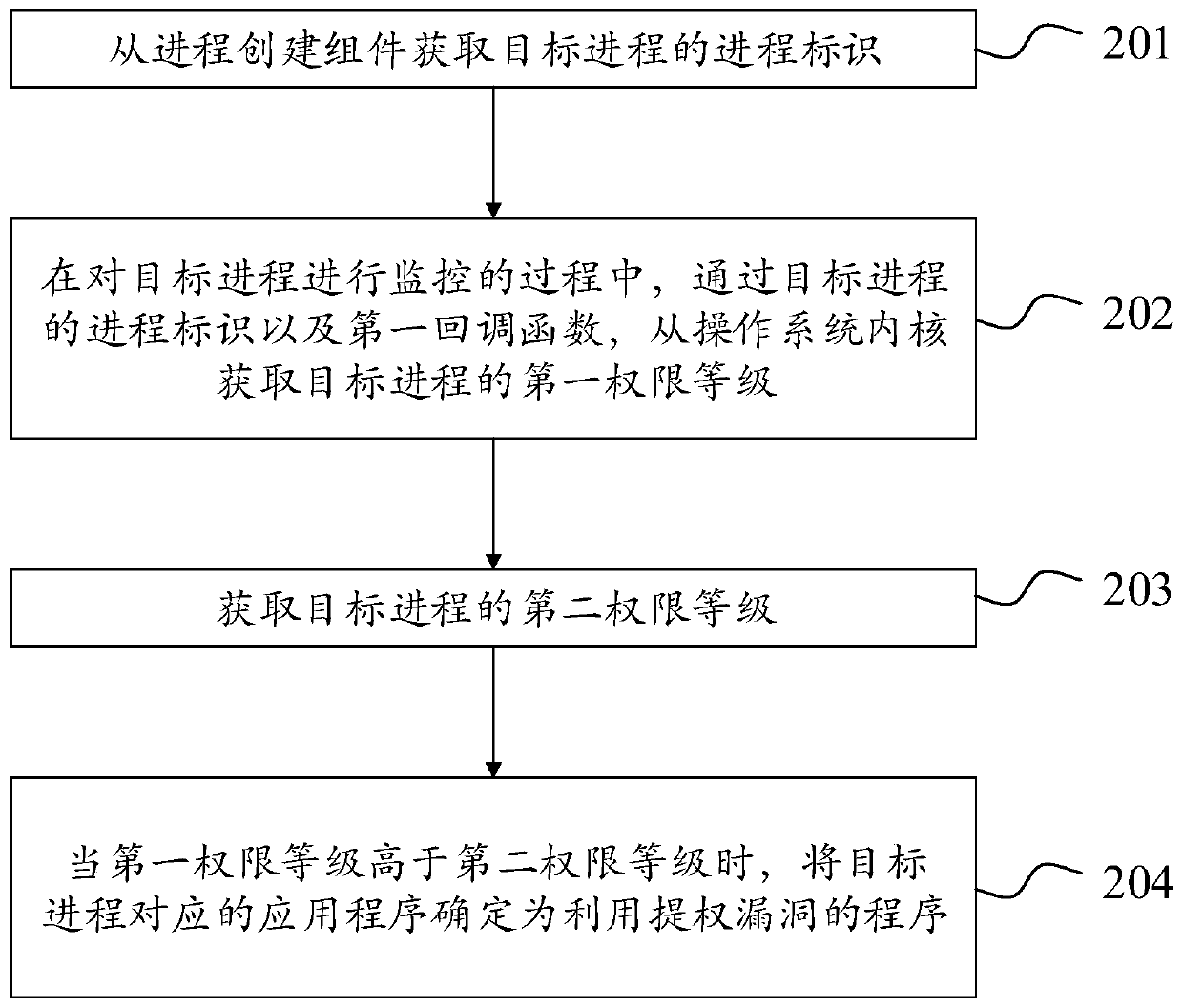
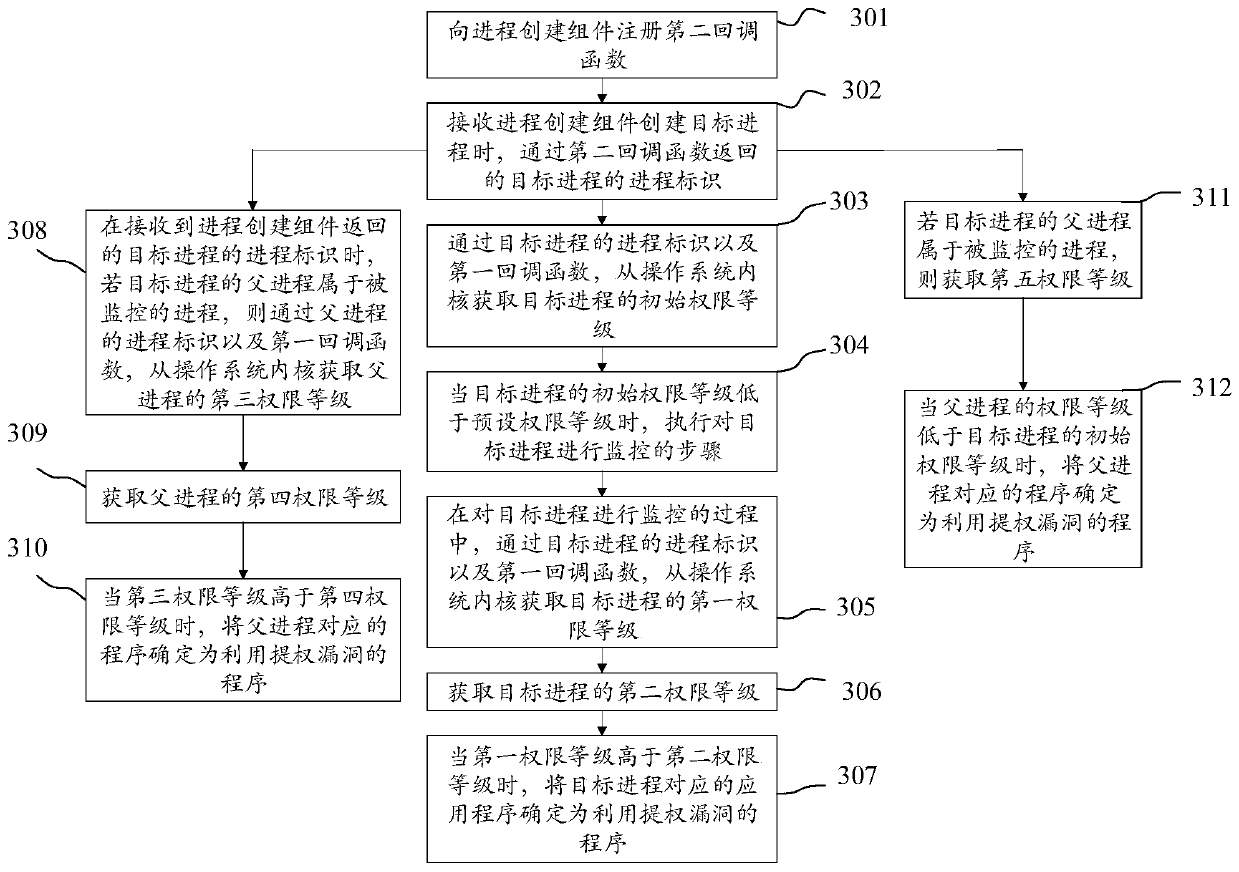
The invention discloses a method for determining a program by utilizing a privileged bug, and belongs to the technical field of computers. The method comprises the steps of obtaining a process identifier of a target process from a process creation component; in the process of monitoring the target process, obtaining a first permission level of the target process from a system kernel through a process identifier of the target process and a first callback function; obtaining a second permission level; and when the first permission level is higher than the second permission level, obtaining a program corresponding to the target process as a program utilizing the permission-enhancing vulnerability. The method comprises the steps of obtaining a process identifier of a target process from a process creation component; obtaining an authority level of the target process from a system kernel according to the process identifier, and determining whether the program corresponding to the target process utilizes the privilege-offering vulnerability or not according to the privilege levels acquired twice successively; the process does not need to monitor various privilege-offering behaviors in the system, and which processes utilize the privilege-offering vulnerability is judged according to the privilege change of the processes, so that the detection accuracy and the detection efficiency areimproved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Control flow obfuscation method and system based on a callback function
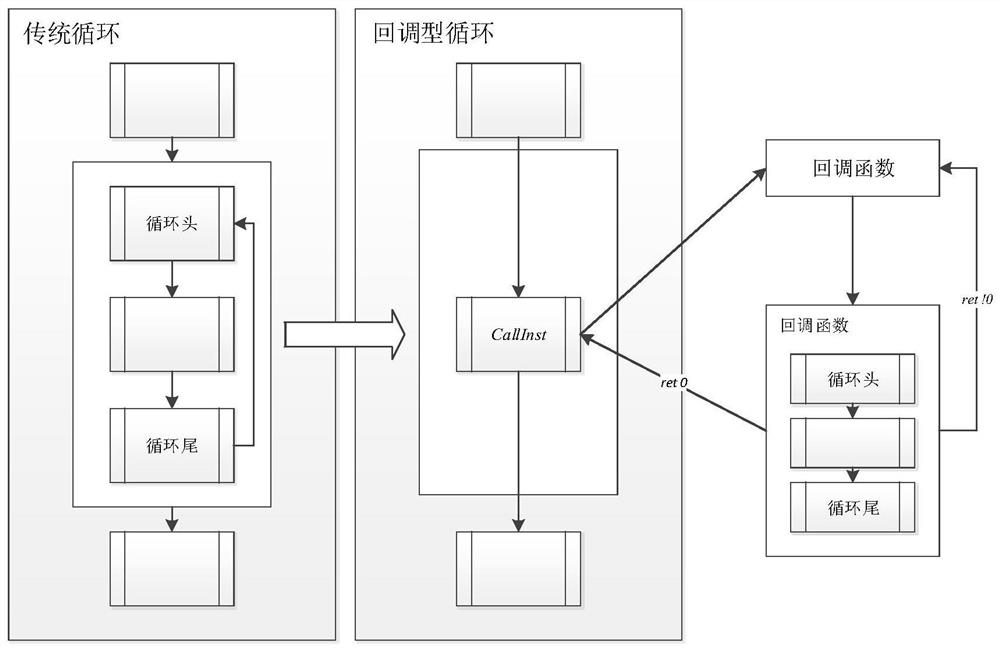
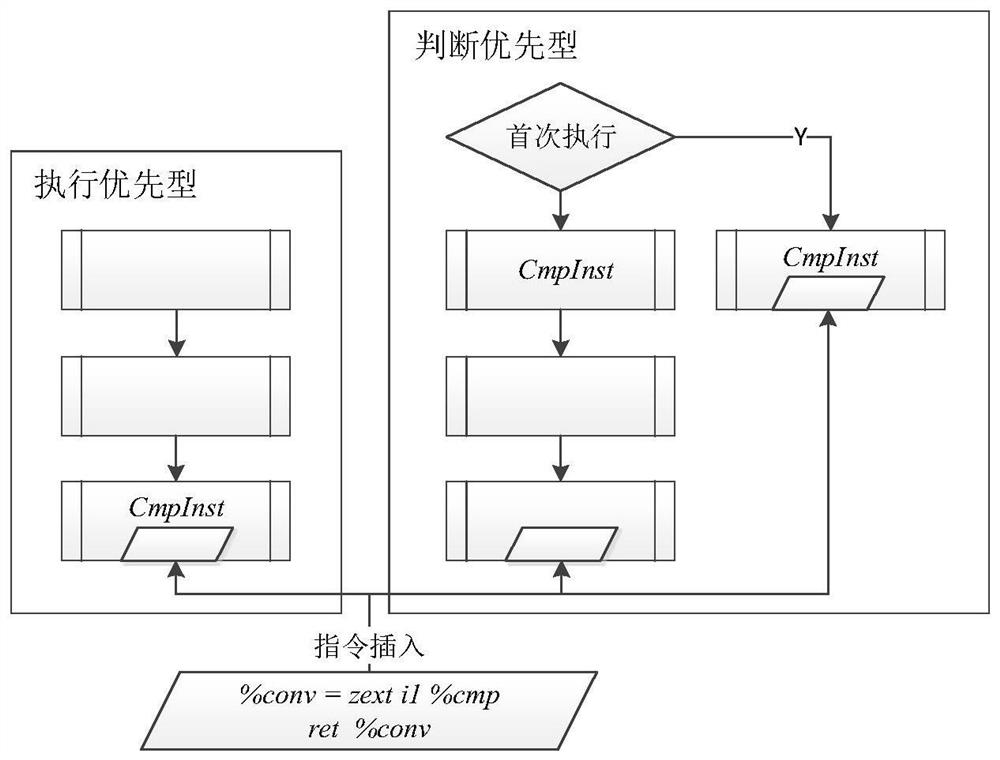
ActiveCN111723345AEffective cost impactGuaranteed execution efficiencyProgram/content distribution protectionCode compilationEngineeringConfusion
The invention belongs to the technical field of network security, and particularly relates to a control flow obfuscation method and system based on a callback function, aiming at a loop structure in aprogram, a basic block loop hop is converted into inter-function repeated calling through the callback function, so that the original execution logic of the program is hidden, and the original control flow of the program is merged into a sequence structure in a unified manner; through program analysis, data dependence is reconstructed in a callback function so as to maintain functional consistency before and after cyclic jump conversion. According to the method, the callback function is cyclically called; program key algorithm logic is hidden; the detection cannot be easily performed by an automatic analysis technology; the problem that a traditional confusion method is difficult to confront an automatic analysis means is effectively solved; because only a small number of function calls and necessary parameter transfer instructions are introduced into the original program, the influence on the program overhead is effective, the anti-analysis capability is greatly enhanced under the condition of ensuring the program execution efficiency, the program size and the execution efficiency are not obviously changed before and after an actual application test, and the method has good applicability.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com