Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5701results about How to "Avoid security issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
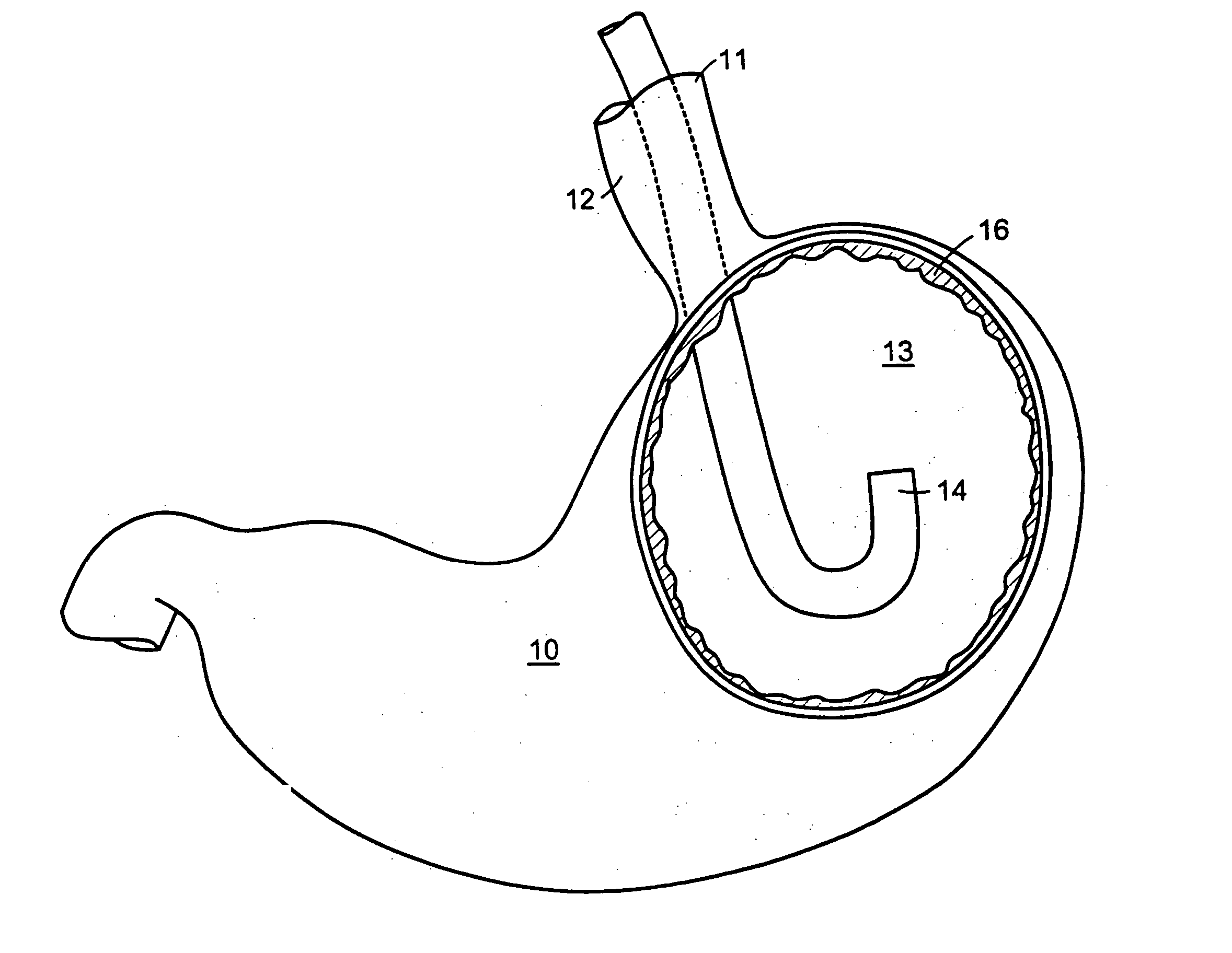
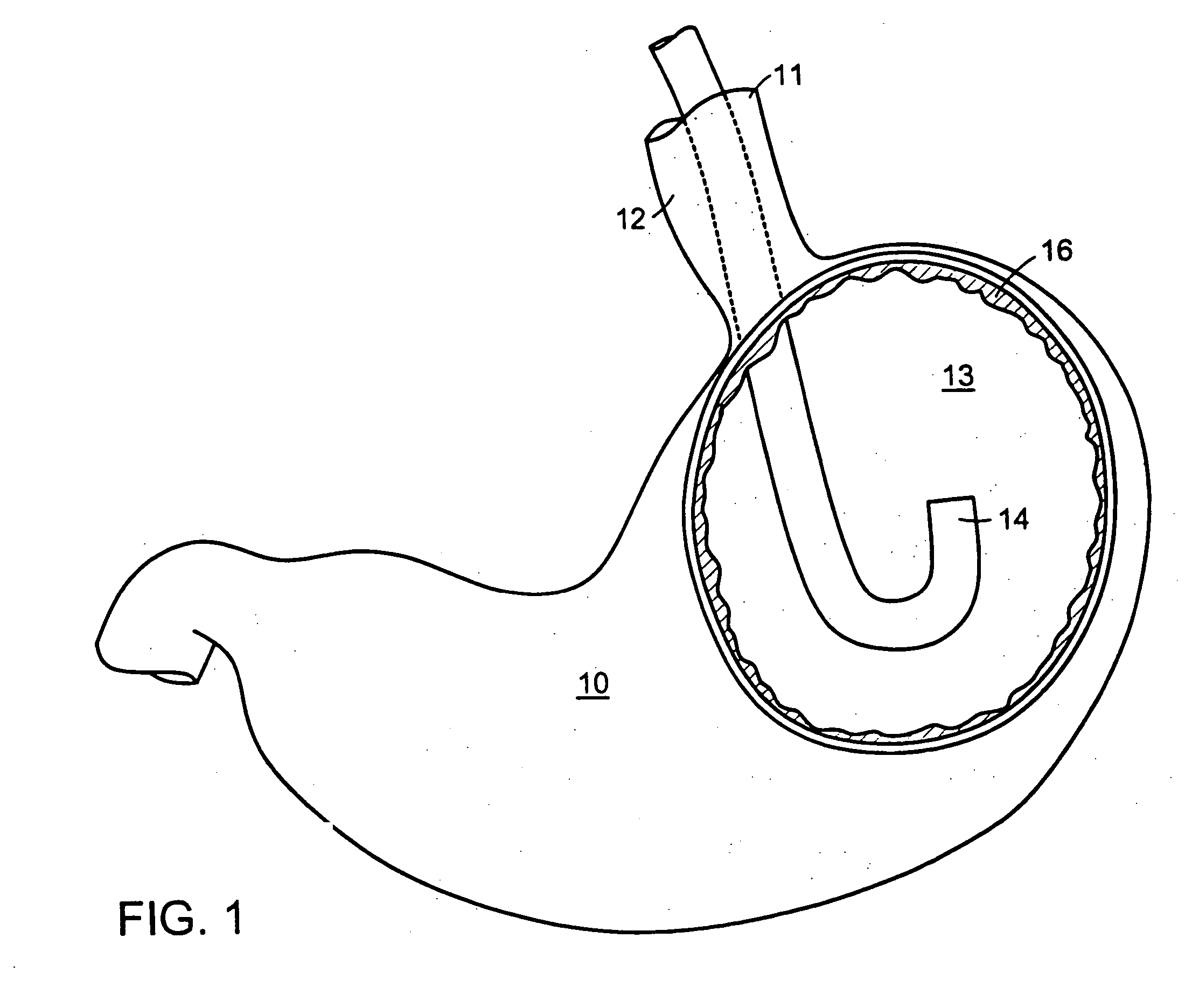
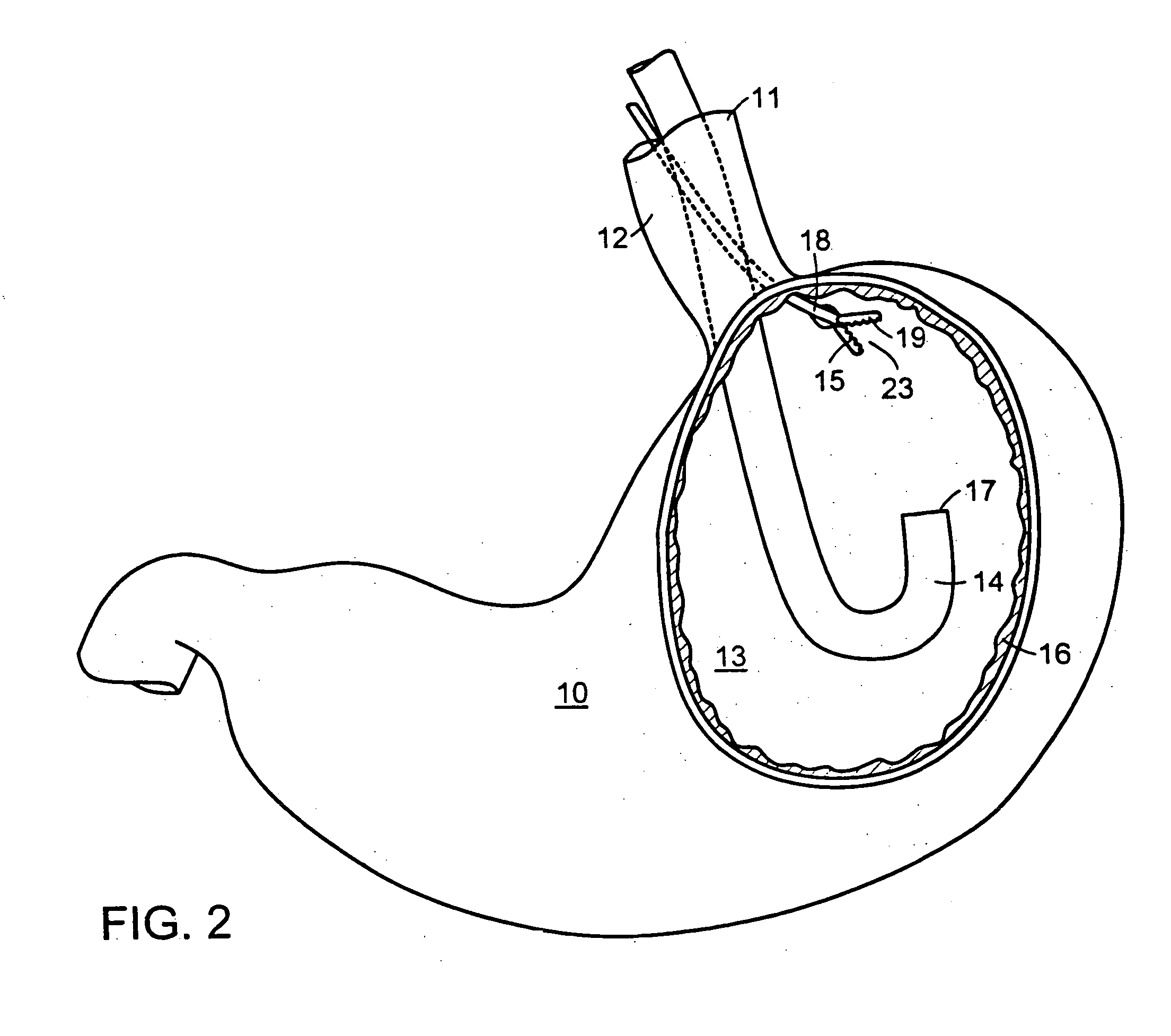
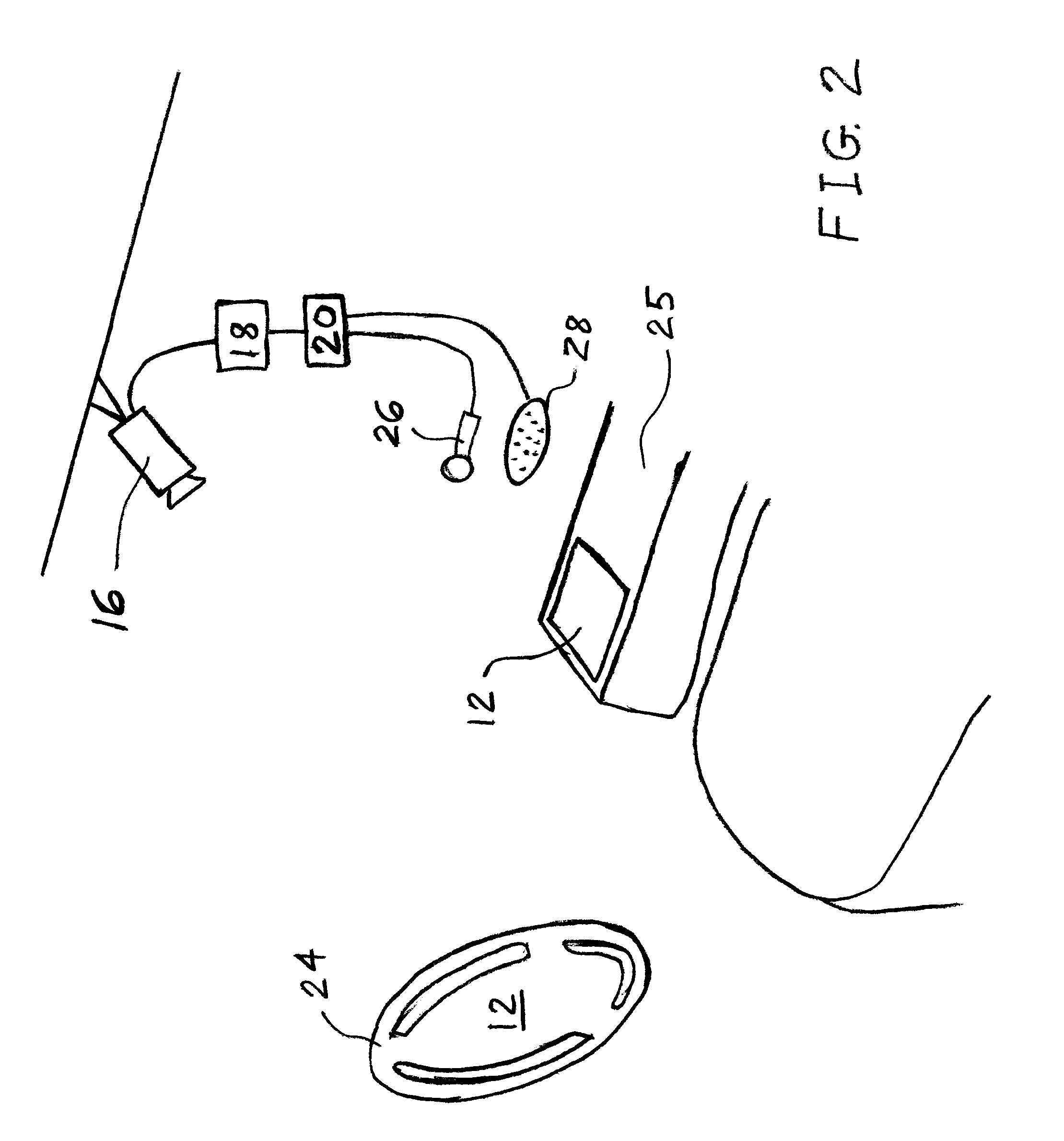
Methods and devices for tissue reconfiguration
InactiveUS20050033328A1Reduce trafficReduce morbiditySuture equipmentsSurgical needlesBody organsEndoscope
Owner:ETHICON ENDO SURGERY INC
Integrated rule network management system
InactiveUS20030110262A1Low costMinimizing cross-configurationDigital computer detailsCathode-ray tube indicatorsNetwork managementService configuration
A network service administration system including a plurality of service objects, a plurality of address objects; and a service configuration application for a multifunction appliance running on a client computer coupled to the appliance via a network. The service configuration application includes an interface allowing subscribers to configure at least a subset of application content services provided by the appliance and including a rule set implementing rules in ones of said application content services in said subset based on changes to configurations of any other of said application content services. Each of said service objects may comprise an individual network service definition.
Owner:JUMIPER NETWORKS INC +1
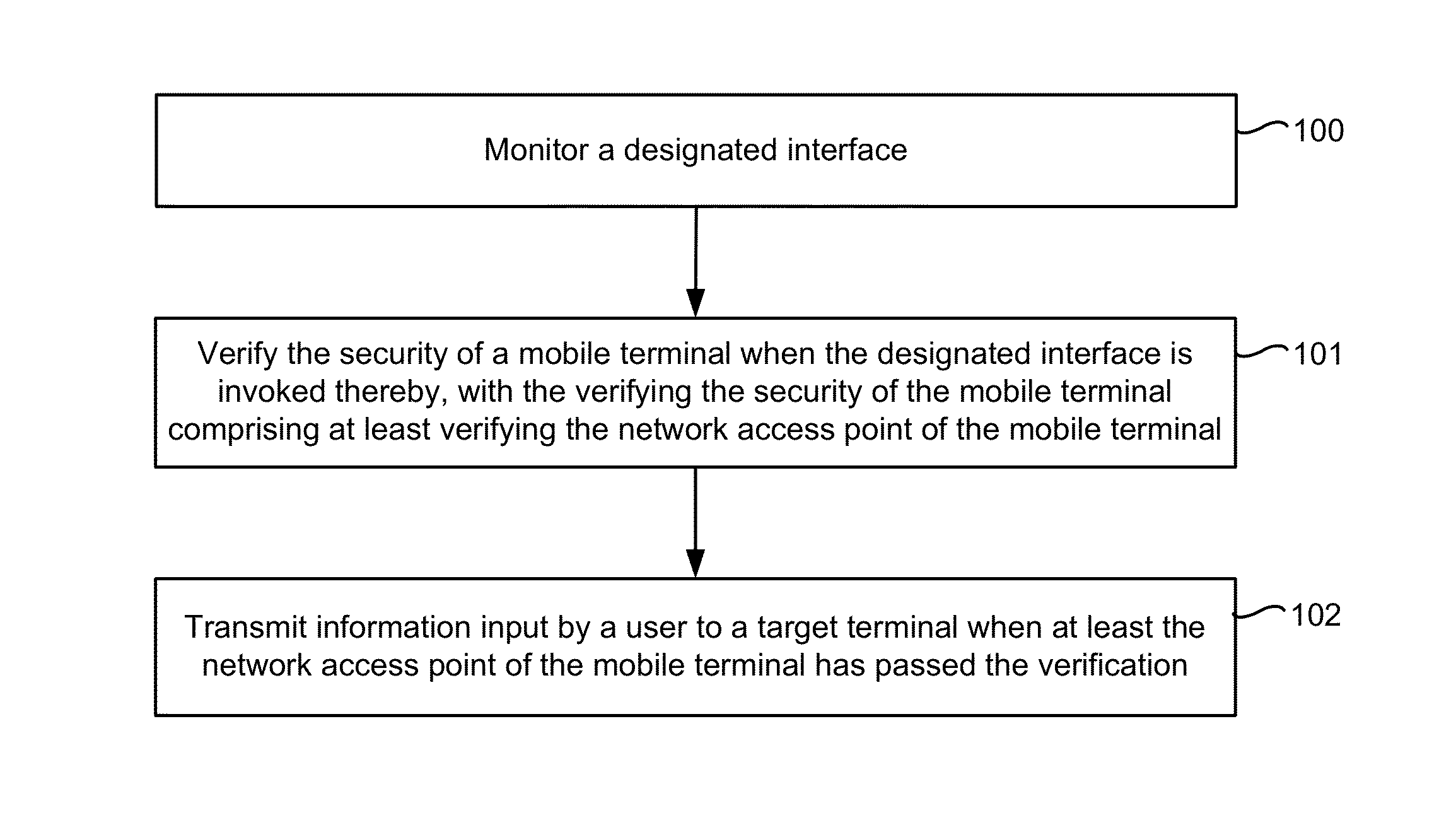
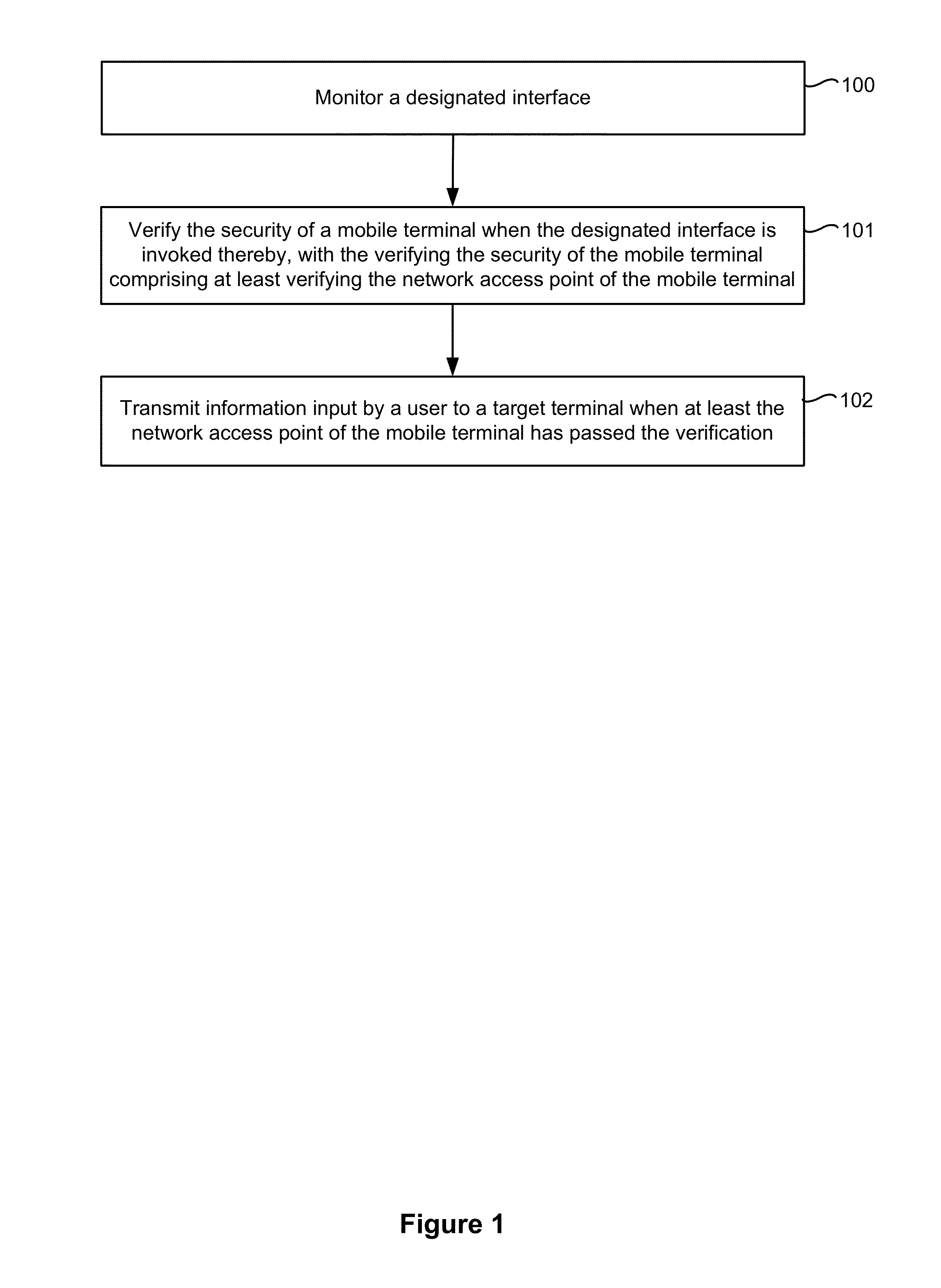
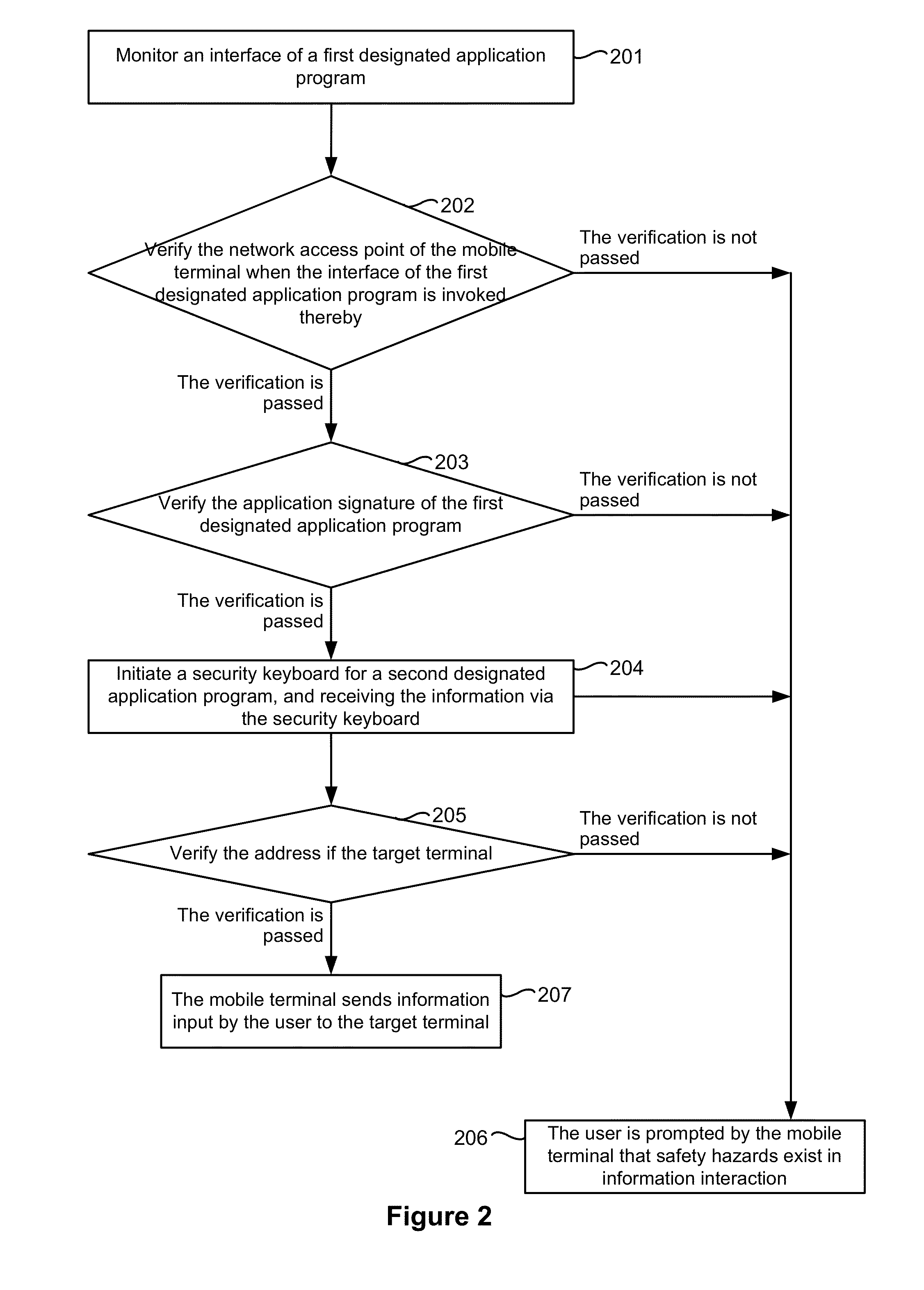
Method and device for securing an information interaction process
ActiveUS20140074716A1Improve securityAvoid security issuesFinanceComputer security arrangementsDisplay deviceComputer terminal
An electronic device with one or more processors, memory, and a display detects a user interaction with a user interface of a first application and, in response to detecting the user interaction with the user interface of the first application, determines whether one or more security parameters are satisfied, where a first security parameter is satisfied when a network access point being used by the electronic device satisfies predefined criteria. In accordance with a determination that the one or more security parameters are satisfied, the device: displays a security keyboard on the display corresponding to a second application different from the first application; and receives user information input via the security keyboard by a user of the electronic device. The device transmits the user information to a target terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
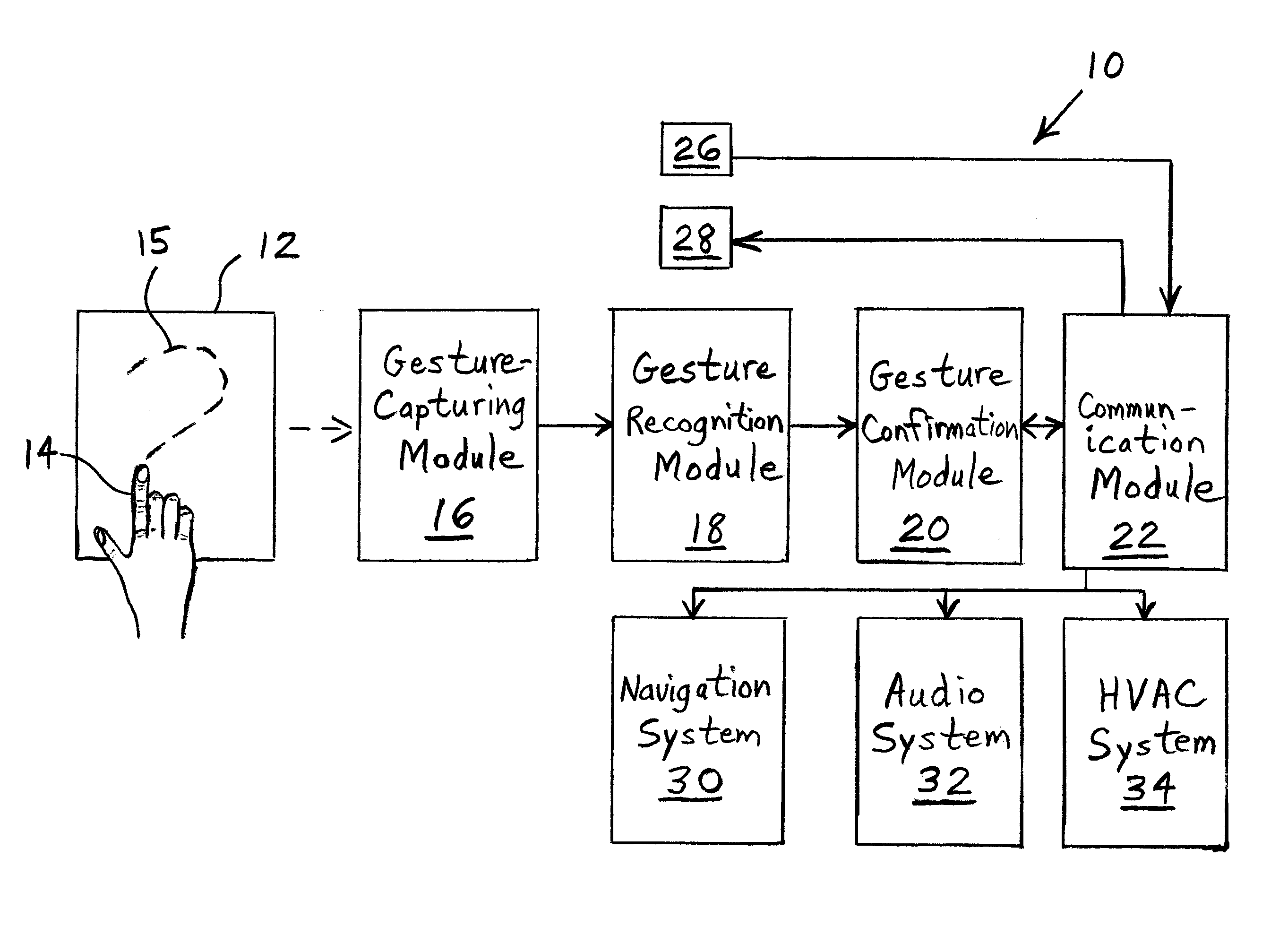
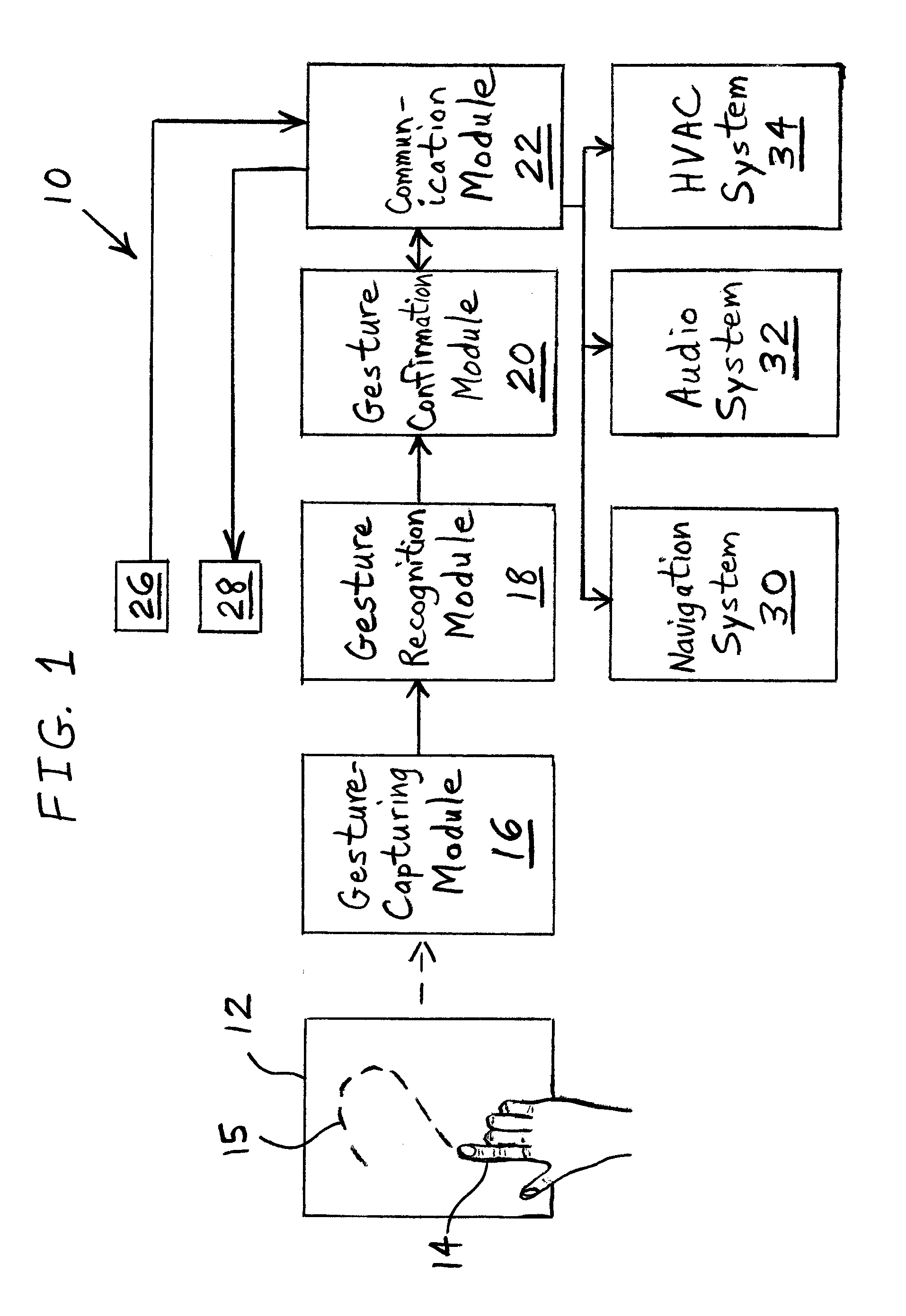
Gesture-based information and command entry for motor vehicle
ActiveUS20110050589A1Safer and easy to learnEasy to learnDashboard fitting arrangementsInstrument arrangements/adaptationsHuman–computer interactionVisual perception
A method of receiving input from a user includes providing a surface within reach of a hand of the user. A plurality of locations on the surface that are touched by the user are sensed. An alphanumeric character having a shape most similar to the plurality of touched locations on the surface is determined. The user is audibly or visually informed of the alphanumeric character and / or a word in which the alphanumeric character is included. Feedback is received from the user regarding whether the alphanumeric character and / or word is an alphanumeric character and / or word that the user intended to be determined in the determining step.
Owner:ROBERT BOSCH GMBH
High-capacity lithium-ion electrolyte, battery and preparation method of battery
ActiveCN101771167AIncrease capacityLow costFinal product manufactureCell electrodesElectrolytic agentPhysical chemistry
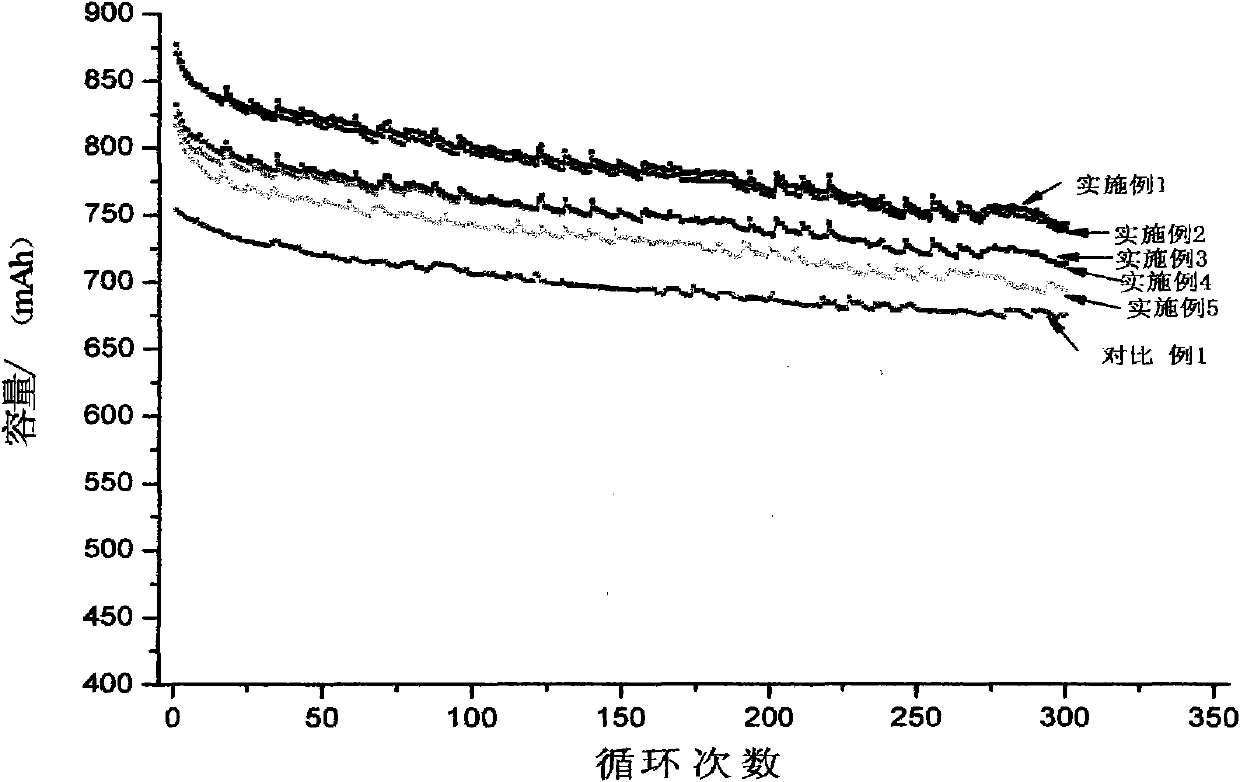
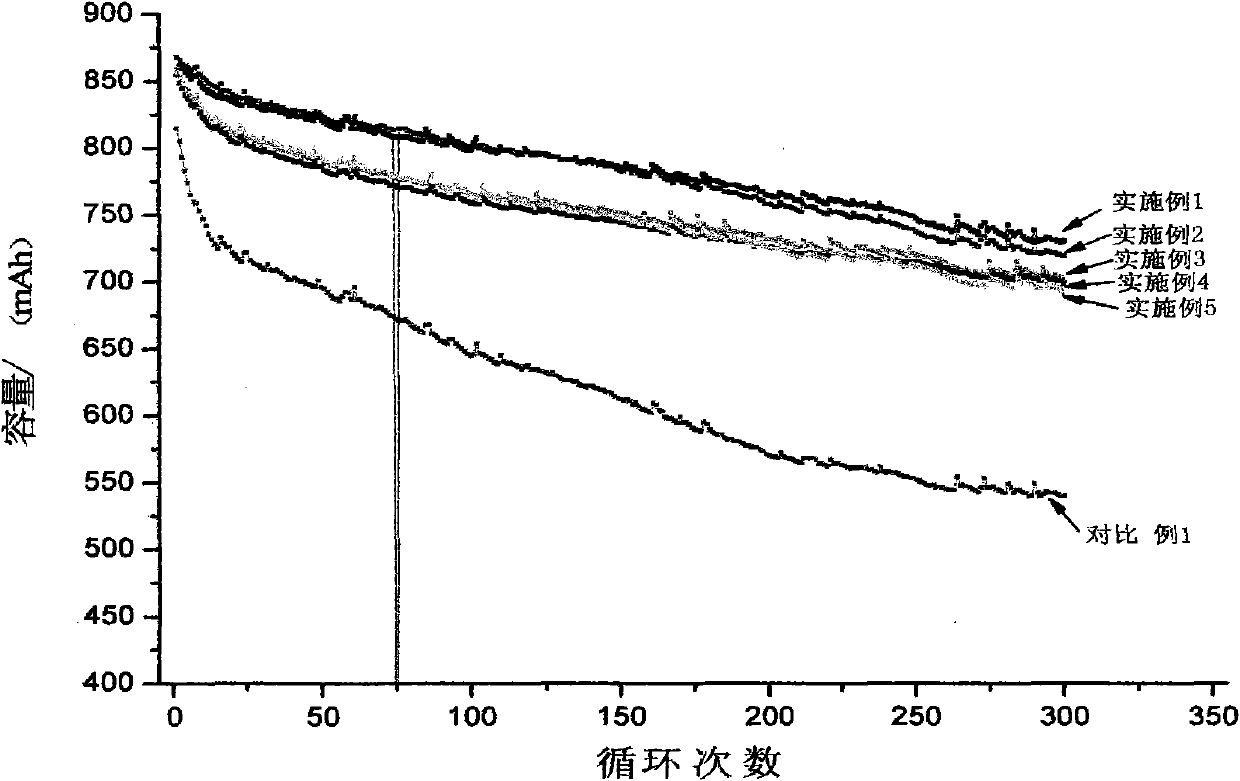
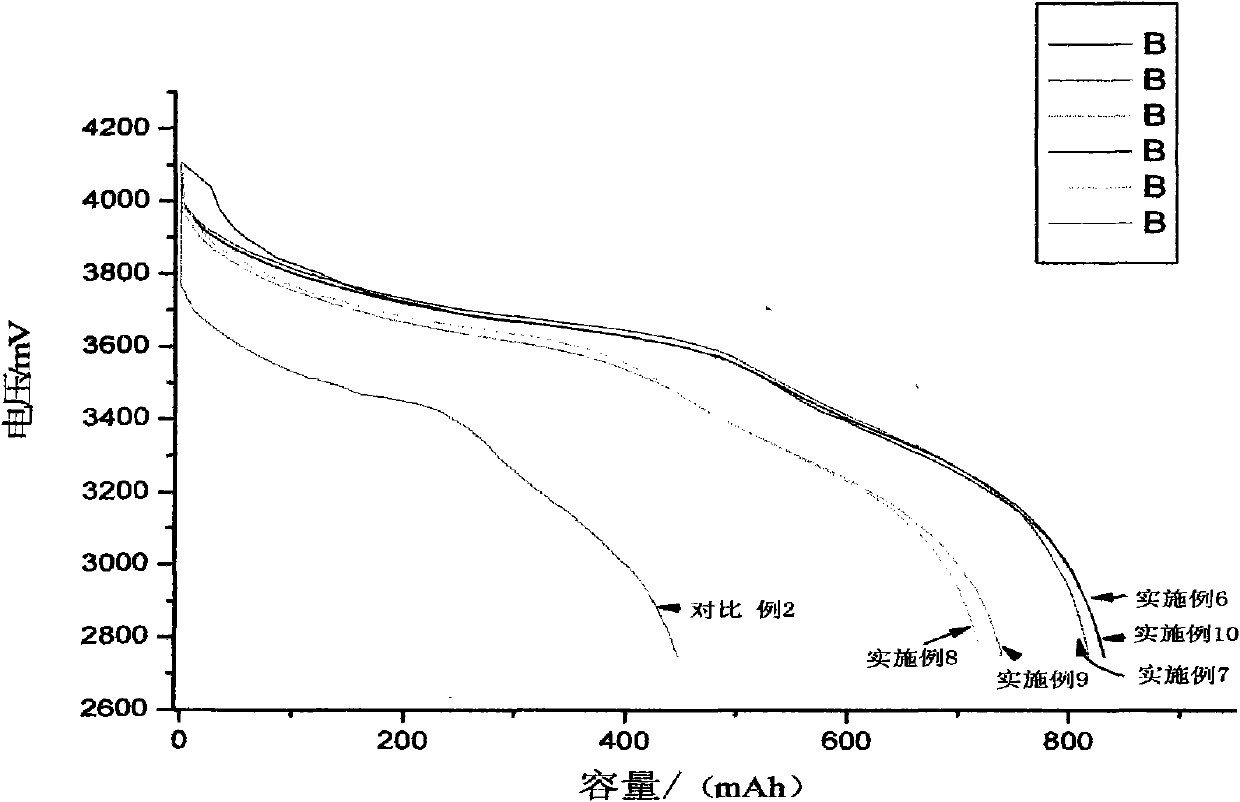
The invention relates to a high-capacity lithium-ion electrolyte, a battery and a preparation method of a battery, in particular to the high-capacity lithium-ion electrolyte and the battery using the high-capacity lithium-ion electrolyte and the preparation method of the battery. The electrolyte disclosed by the invention comprises lithium salt and non-aqueous organic solvent, and also consists of the following components in weight percent in terms of the total weight of the electrolyte: 0.5-7% of film-forming additive, 0-15% of flame-retardant additive, 2-10% of antiovefill additive, 0.01-2% of stabilizer and 0.01-1% of wetting agent; the electrolyte can enable the anode with high Ni content to work stably, and reduce the battery cost; the high-capacity lithium-ion battery can perform high ratio capacity and excellent safety and high temperature property and cyclic life fully due to the addition and synergetic functions of various functional additives.
Owner:JIUJIANG TINCI ADVANCED MATERIALS CO LTD
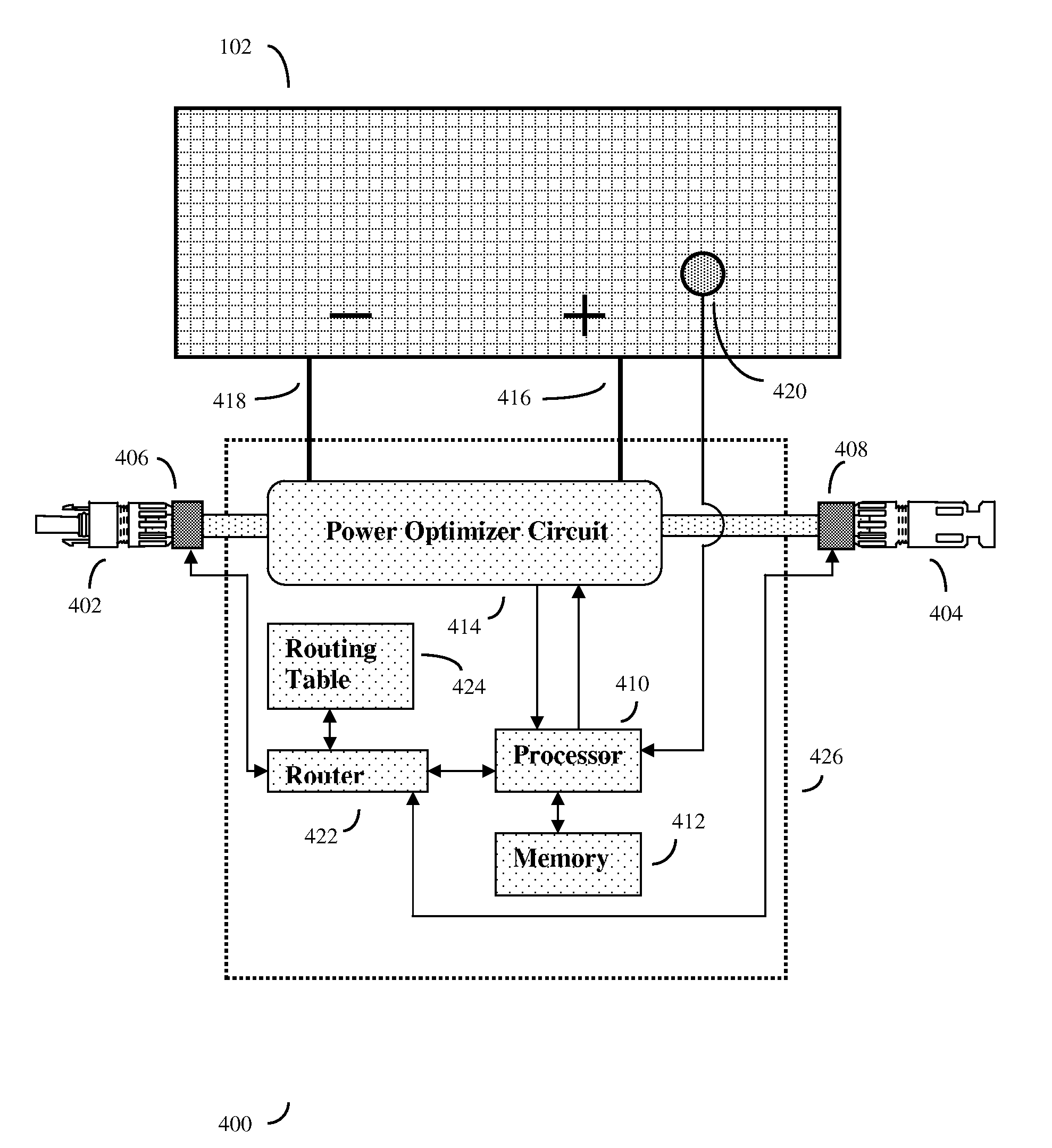
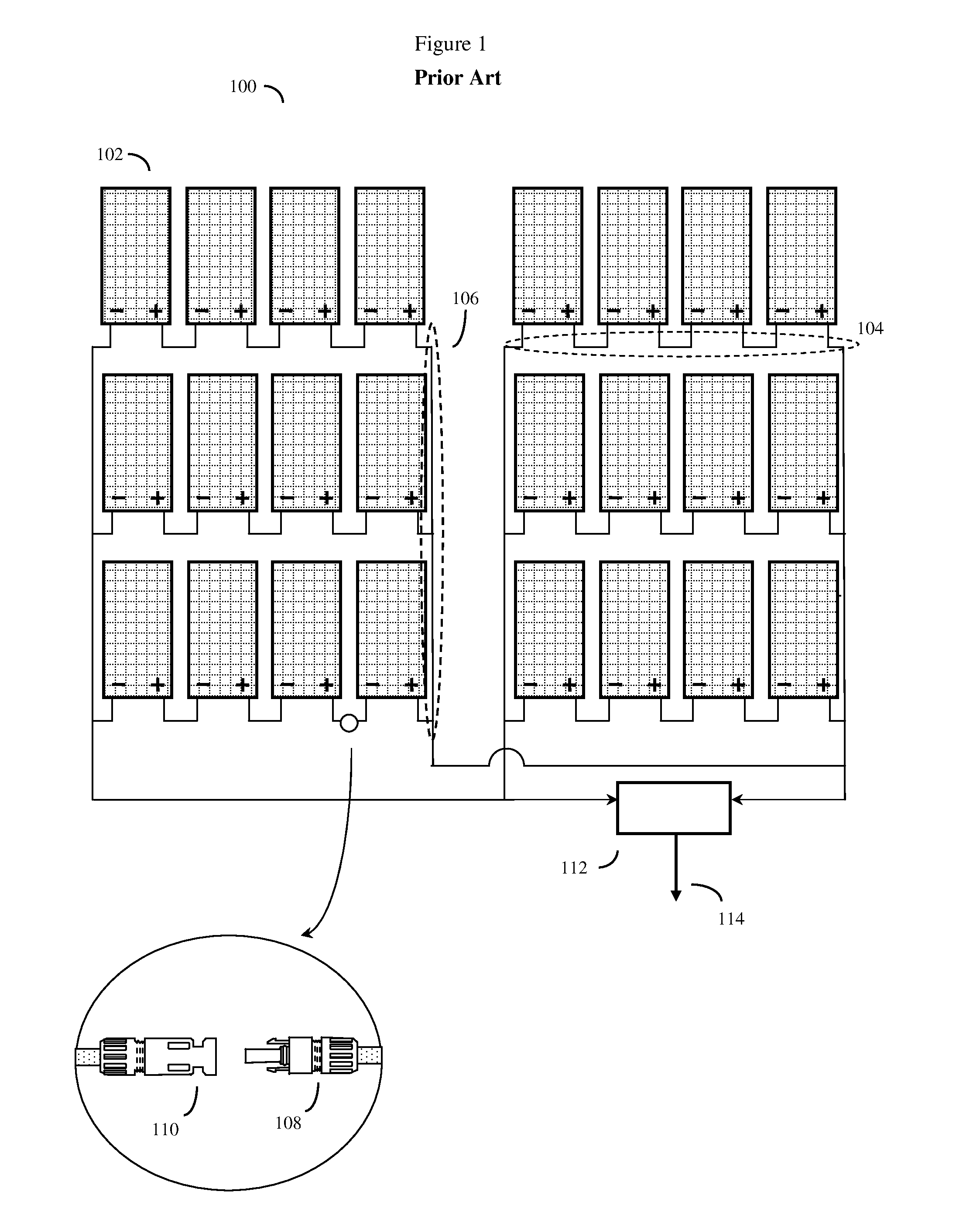
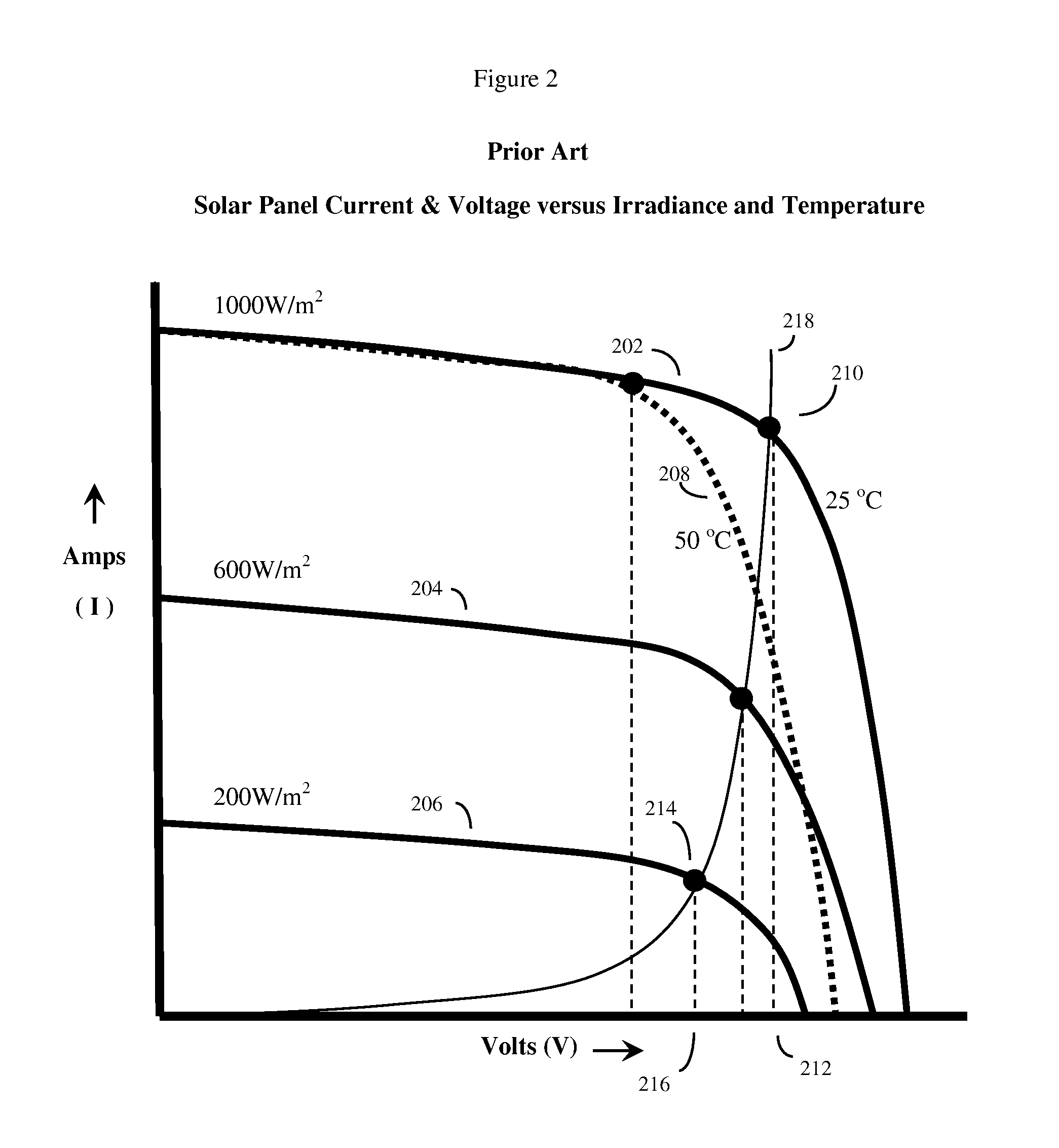
Vibration mediated networks for photovoltaic arrays
ActiveUS20110132424A1Improve coordinationInexpensive and robustPhotovoltaic monitoringSonic/ultrasonic/infrasonic transmissionPhotovoltaic solar energyNetwork packet
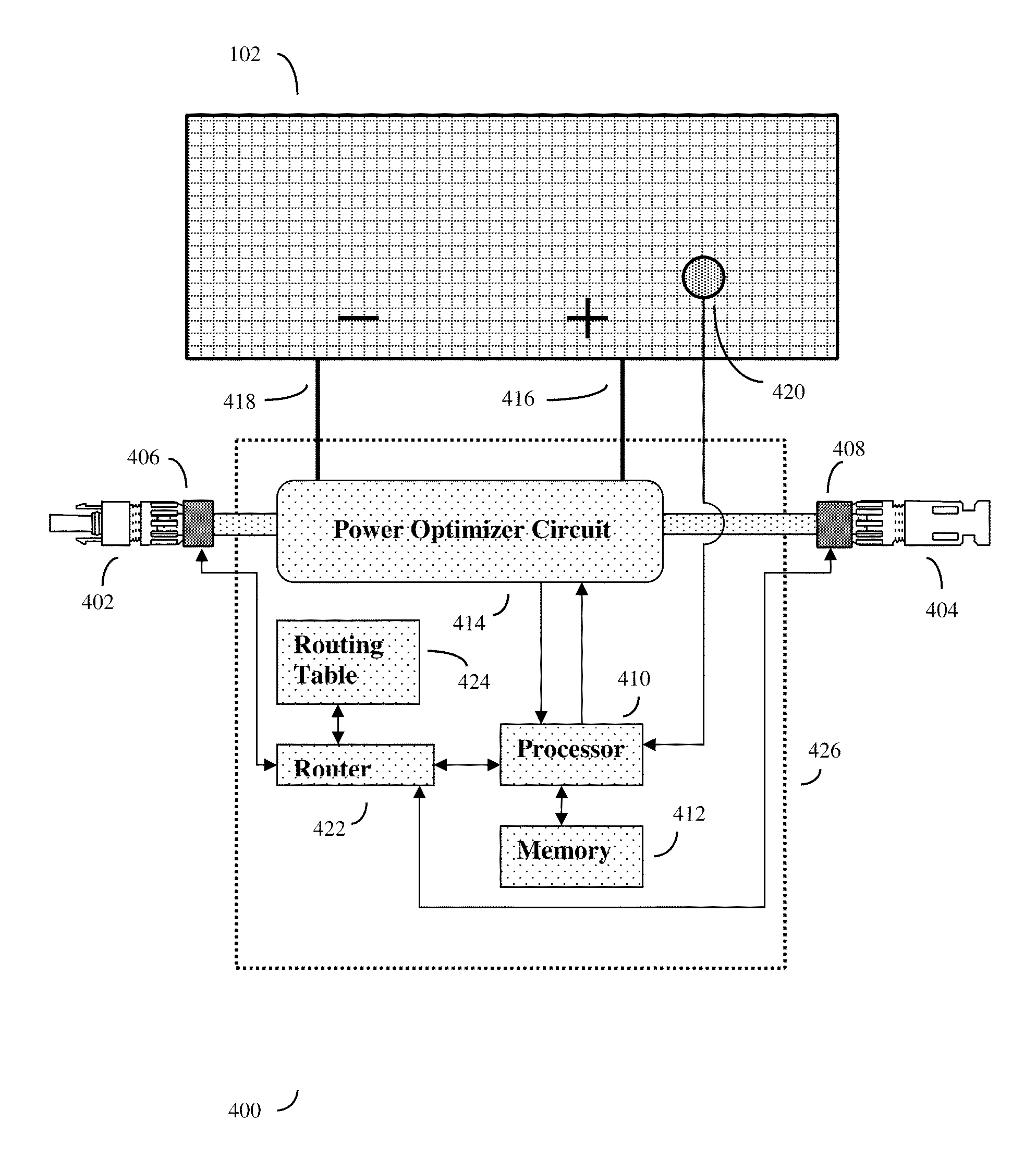
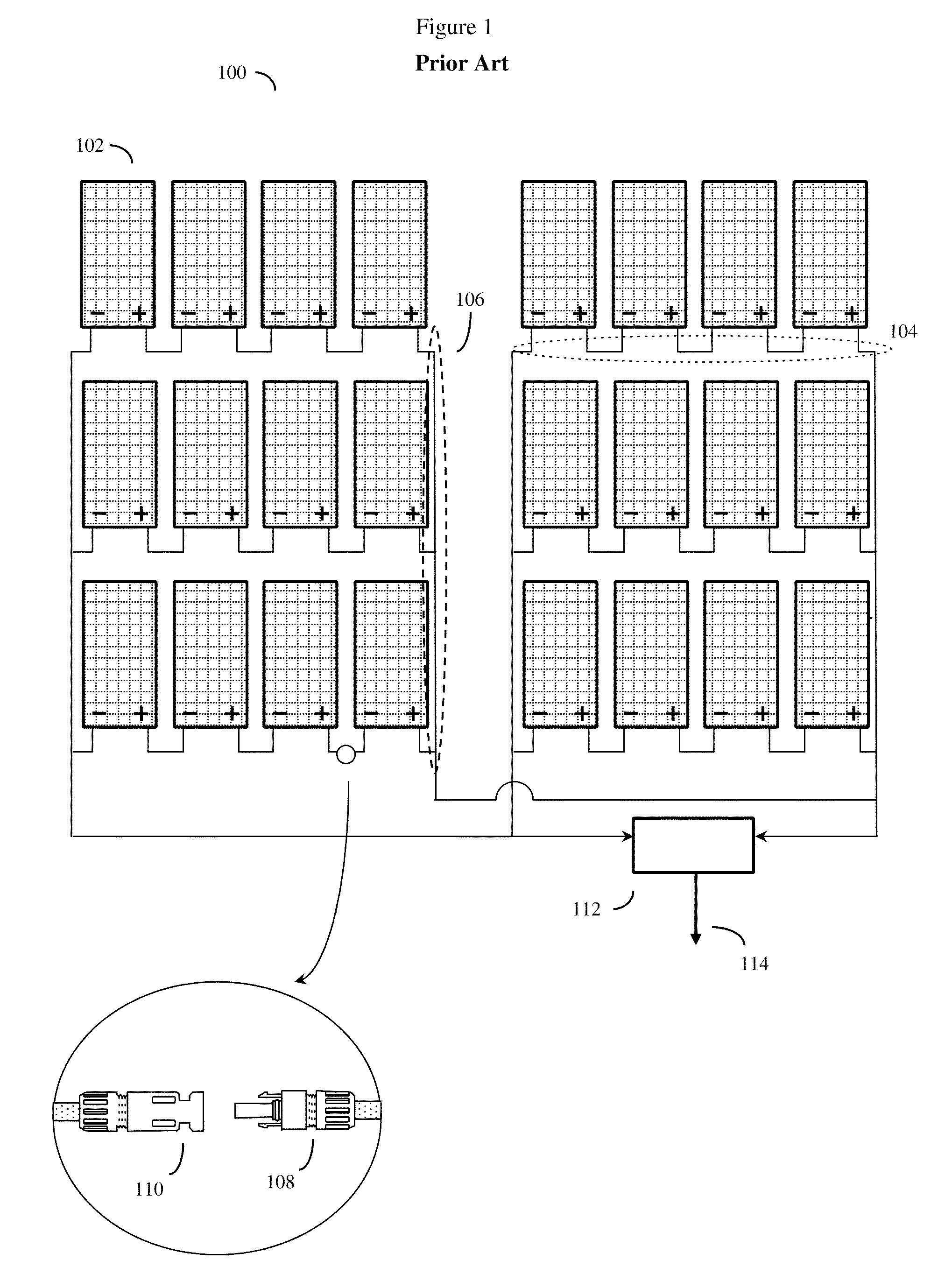
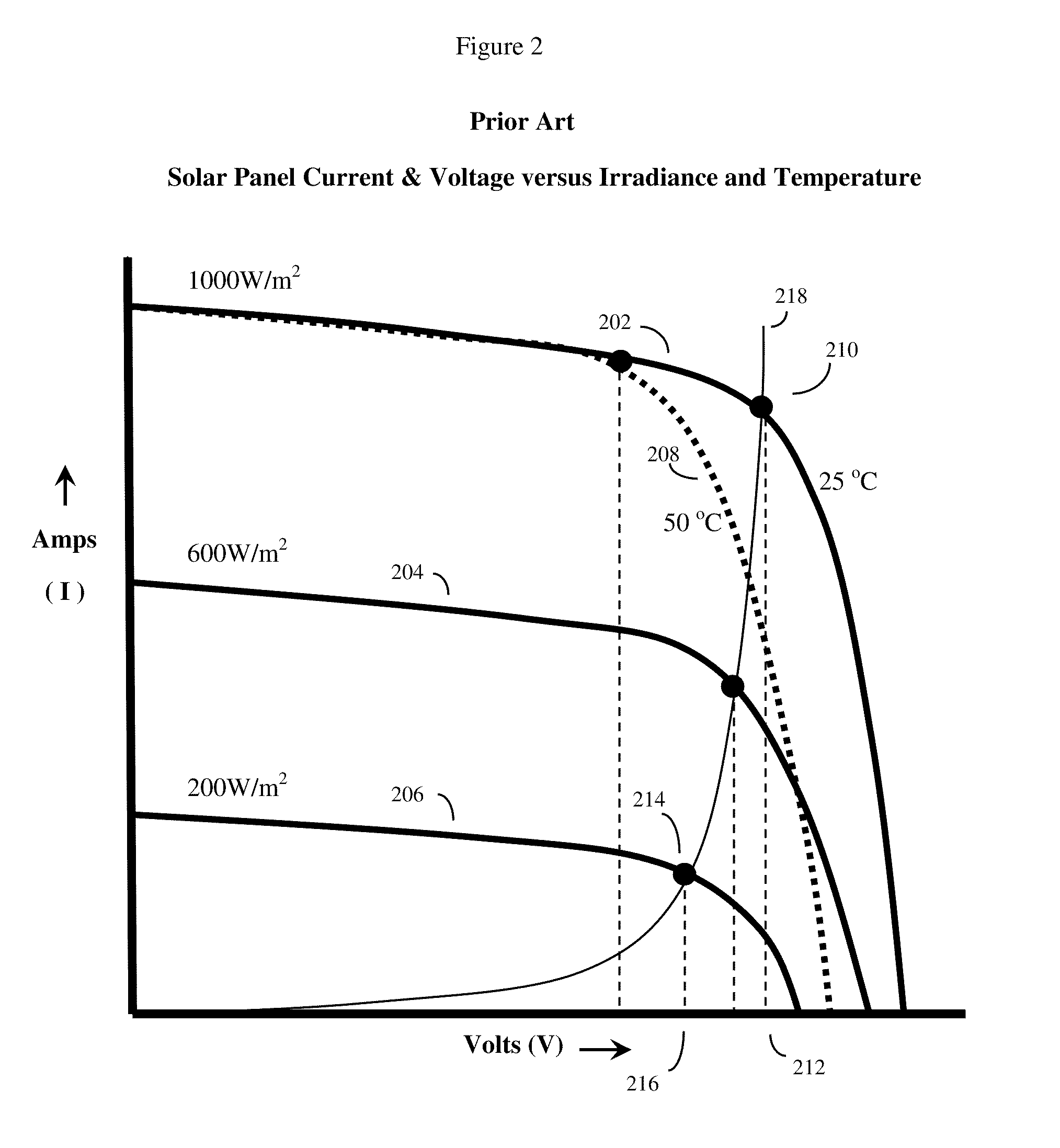
A system and method to optimize the overall power output of a photovoltaic solar array. The solar panels are connected to software adjustable power optimizing devices, which in turn are connected to a mesh network with individual router devices. The individual router devices will send and receive data packets by creating or detecting vibrations in a solid vibration conducting media (such as the solar power wiring) that connects the individual photovoltaic solar panels. Often at least one centralized control device is used to periodically request sensor data packets from the individual router devices and solar panels. The centralized control device will typically compute the proper adjustments for the individual adjustable power optimizing devices that will optimize the overall power output from the photovoltaic solar array. The control device will then send adjustment data packets back to the individual router devices through the mesh network, thus optimizing overall power output.
Owner:RAKIB SELIM SHLOMO
Industrial control network security protection monitoring system
InactiveCN109474607AReal-time preventionReal-time protectionTransmissionData informationData modeling
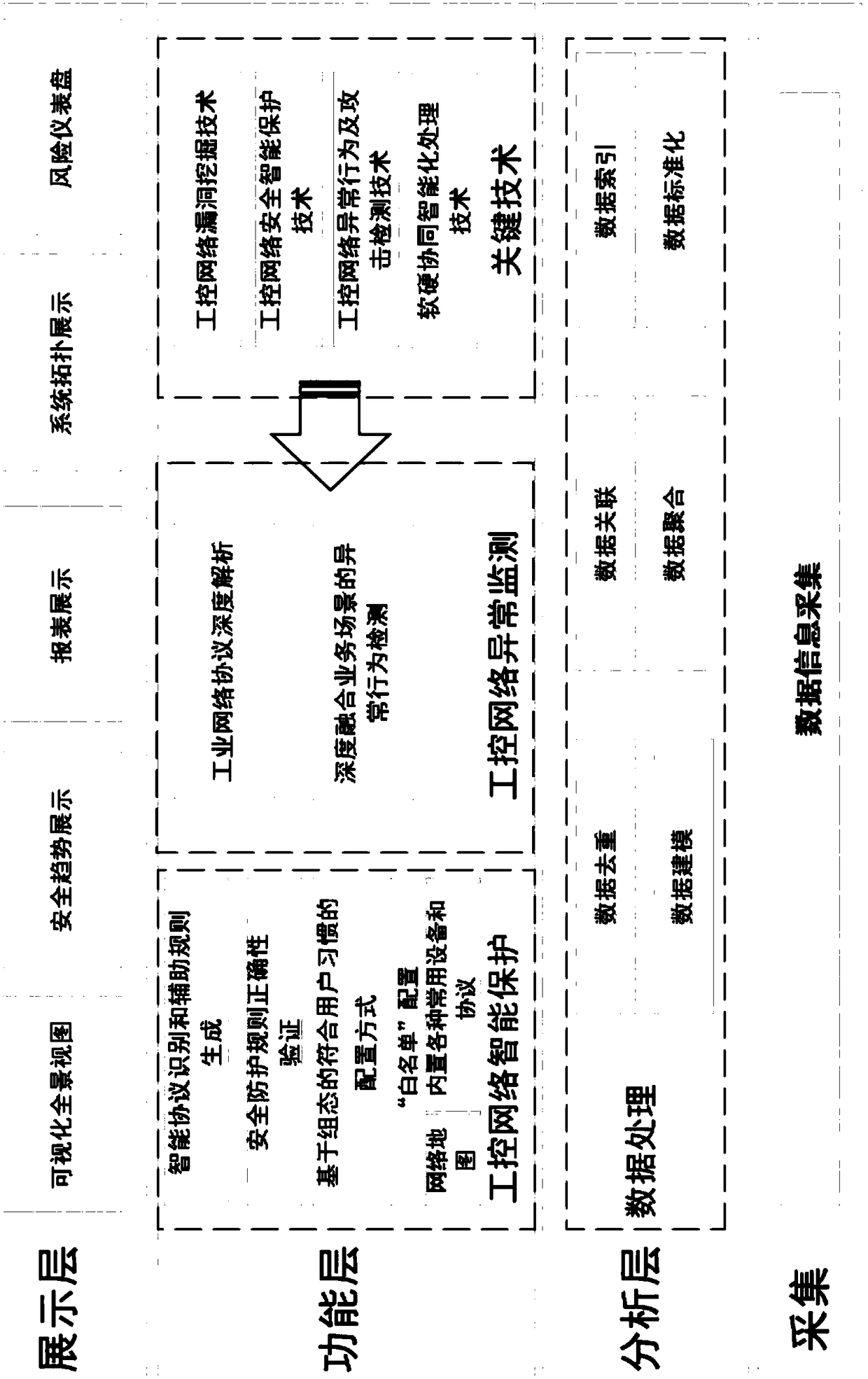
An industrial control network security protection monitoring system performs real-time prevention and protection on industrial equipment of the industrial control network, and realizes network security protection monitoring through an acquisition layer, an analysis layer, a function layer and a display layer based on an integrated application platform, wherein the display layer mainly displays security trend, system topology and industrial control panorama; the acquisition layer comprises the acquisition of network data traffic and the recording of industrial control network operations; the analysis layer mainly comprises data processing, data association, data aggregation, data modeling, and integrated interfaces of other function modules; and the function layer mainly comprises monitoring audit, intrusion prevention, vulnerability mining, and data isolation. The system provided by the invention protects and protects industrial equipment in real time through the intelligent protectiontechnology of the industrial network control system, monitors and audits the data information of the entire industrial control network through the monitoring and auditing technology to prevent the industrial control network from being attacked externally, and can also have the vulnerability mining function of the industrial control network to escort the entire industrial control network security.
Owner:中船重工信息科技有限公司
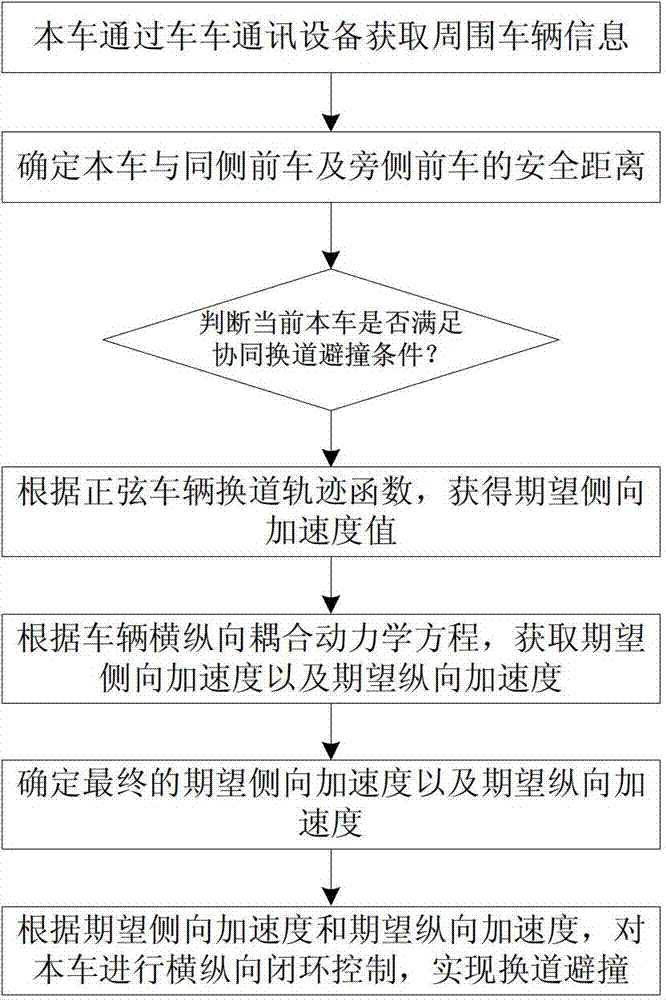
Active-lane-changing collision-avoidance control method and device based on vehicle-vehicle coordination
ActiveCN103496366AEnsure safetyAvoid security issuesExternal condition input parametersActive safetyRear-end collision
The invention provides an active-lane-changing collision-avoidance control method and device based on vehicle-vehicle coordination and belongs to the technical field of intelligent traffic / automobile active safety control. The active-lane-changing collision-avoidance control device comprises a vehicle-vehicle communication unit, a distance measuring sensor, a three-axis acceleration sensor, a vehicle speed sensor, an electronic control unit, an ESP control unit, a driver auxiliary operation unit, a tail lamp control unit and a vehicle inner warning unit. According to the active-lane-changing collision-avoidance control method, surrounding vehicle information is obtained through the vehicle-vehicle communication unit, the safety distance between a vehicle and a front vehicle on the same lane and the safety distance between the vehicle and a front vehicle on the side lane are determined; then, whether the vehicle meets the coordinated lane-changing collision-avoidance requirement is judged, if yes, the expectant lateral and the longitudinal acceleration of the vehicle is calculated, and control over the direction and the speed of the vehicle are conducted, and if not, lane-changing danger warning is conducted. By the adoption of the active-lane-changing collision-avoidance control method and device based on vehicle-vehicle coordination, active-lane-changing collision-avoidance control is achieved, driver safety accidents caused by emergency brake and rear-end collision accidents caused by emergency brake can be avoided, manual operation errors are avoided, and the safety of driving the vehicle is guaranteed.
Owner:北京踏歌智行科技有限公司
Vibration mediated networks for photovoltaic arrays
ActiveUS8509032B2Improve coordinationInexpensive and robustPhotovoltaic monitoringSonic/ultrasonic/infrasonic transmissionPhotovoltaic solar energyNetwork packet
Owner:RAKIB SELIM SHLOMO
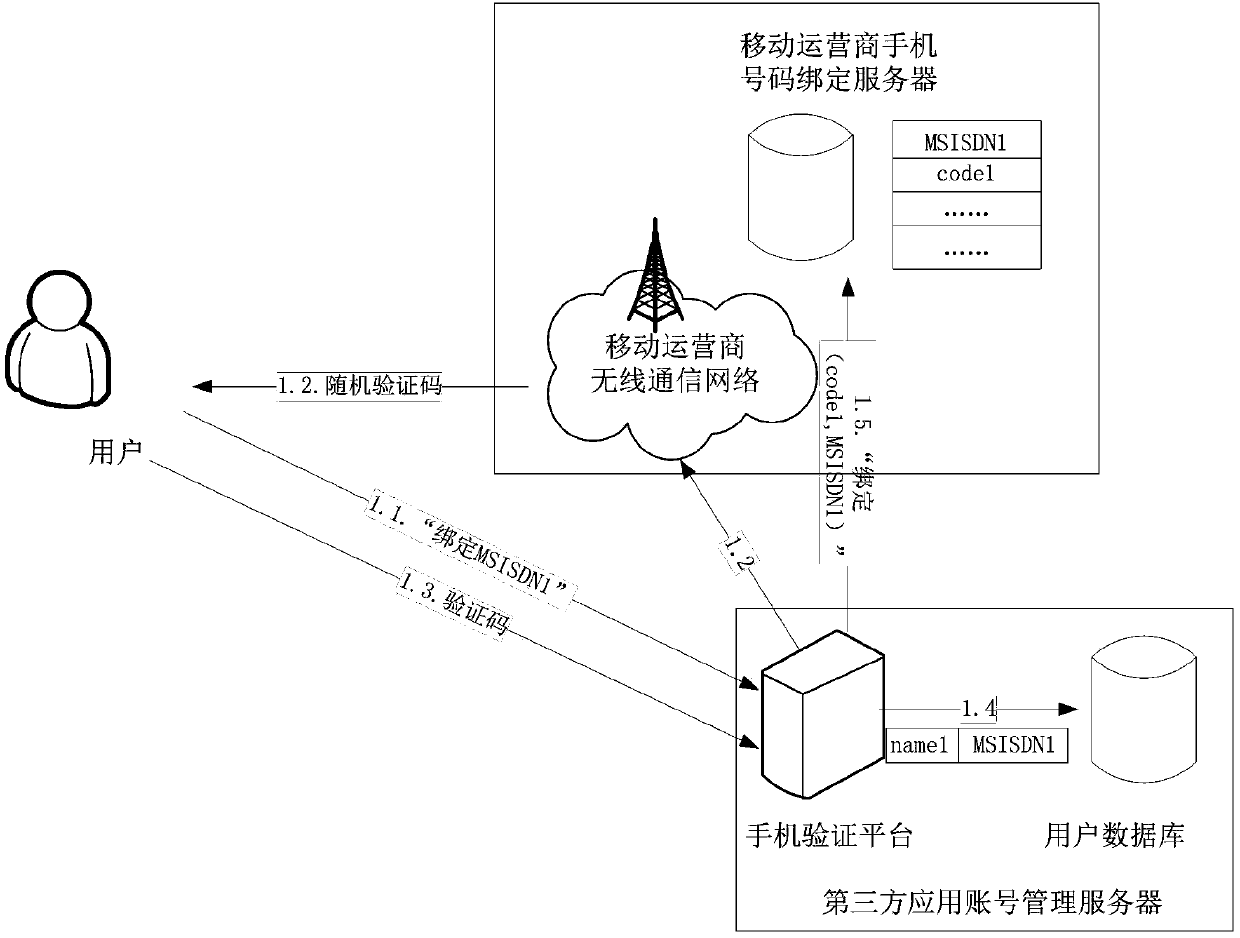
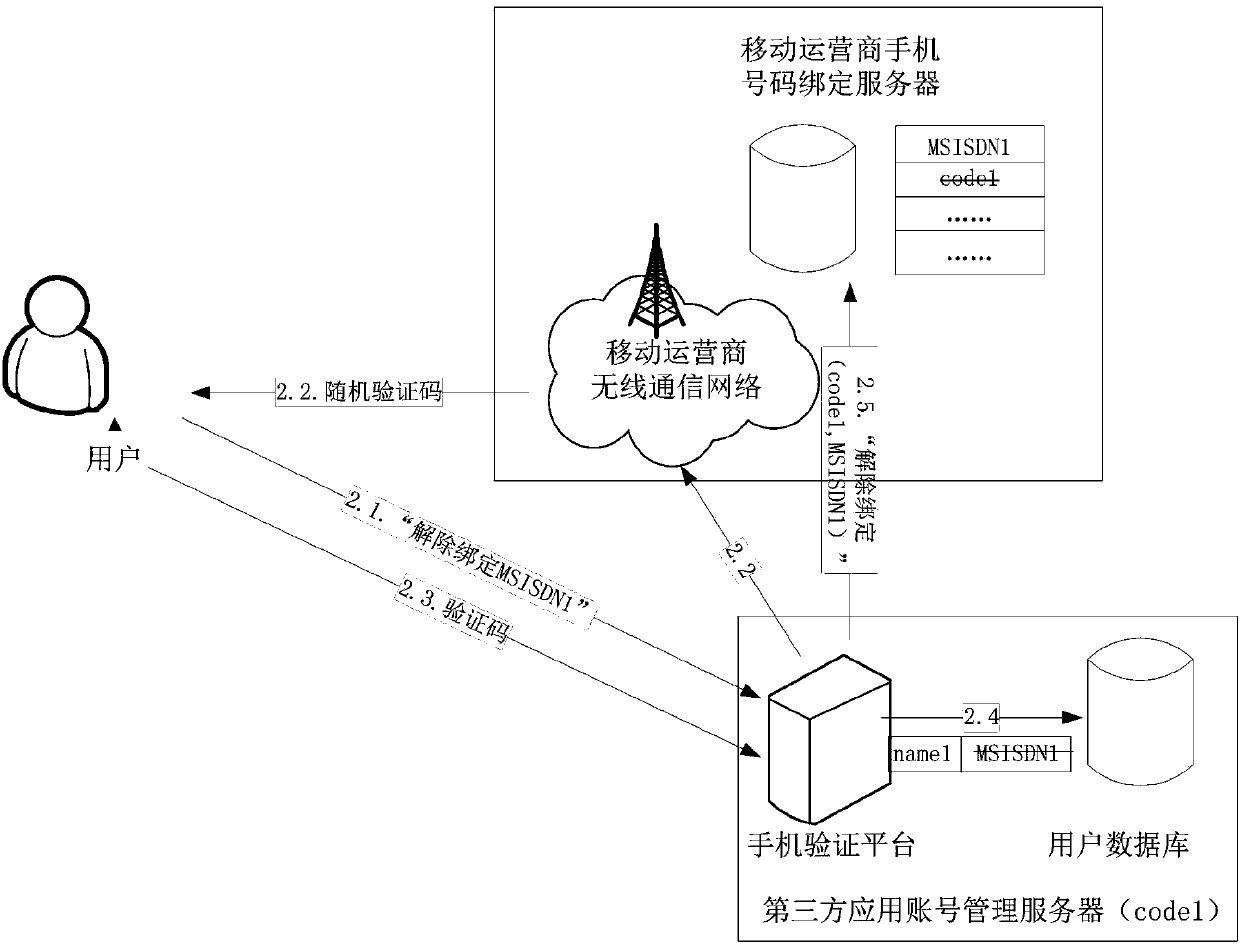
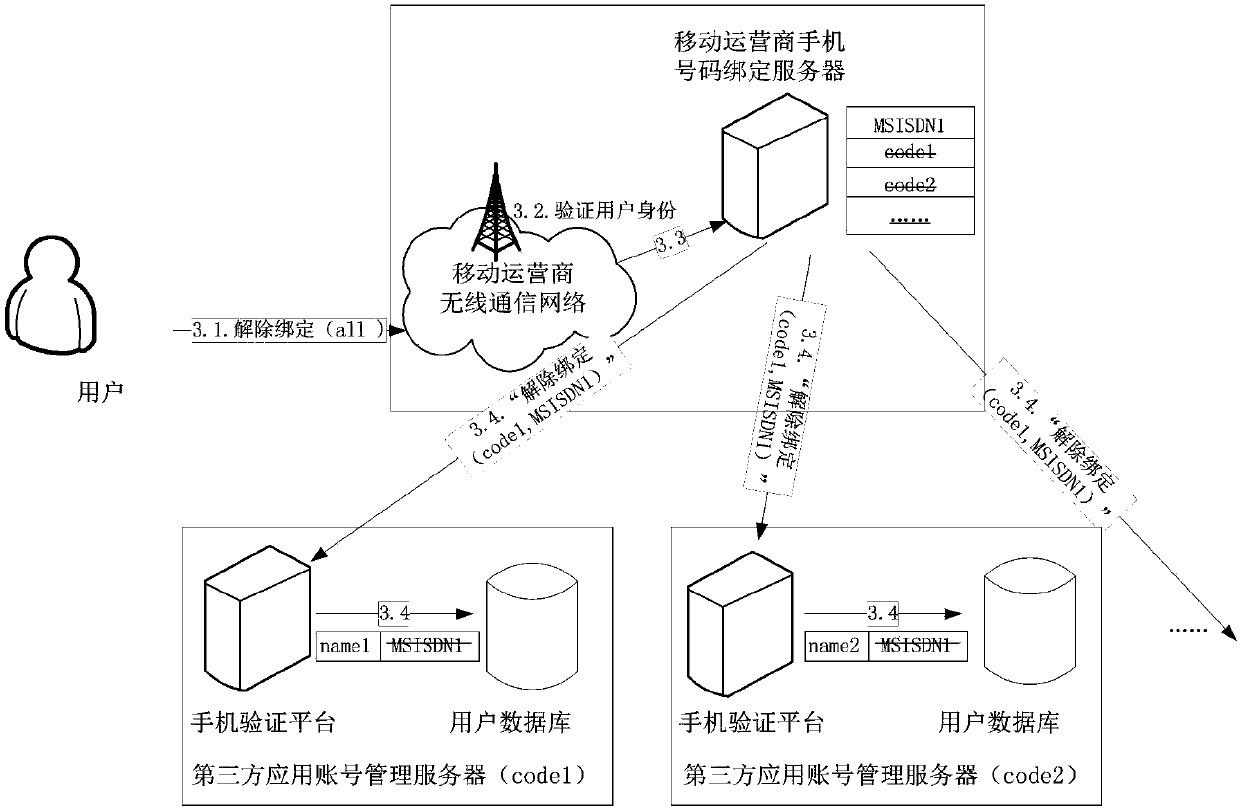
Binding, unbinding and binding updating method for third-party application account and mobile phone number
ActiveCN103746792AImprove privacy and securityEasy to moveSpecial data processing applicationsSecuring communicationMobile Telephone NumberThird party
The invention discloses a binding method, an unbinding method and a binding updating method for a third-party application account and a mobile phone number. The binding method comprises the following steps that (1) a user transmits a mobile phone number to be bound to a mobile phone verification platform of a third-party application account management server; (2) the mobile phone verification platform of the third-party application account management server generates a random verification code, and transmits the random verification code to the user of the mobile phone number to be bound through a mobile operator network; (3) the user receives a verification short message, and transmits the verification code back to the mobile phone verification platform of the third-party application account management server; (4) a user database of the third-party application account management server records an association relationship between an account of the user and the mobile phone number; (5) the mobile phone verification platform of the third-party application account management server transmits a service name code and the mobile phone number to a mobile phone binding server of the mobile operator through a binding message, and associates the mobile phone number of the user and the bound third-party application service name code.
Owner:郑盈盈
Wireless power system for portable devices under rotational misalignment
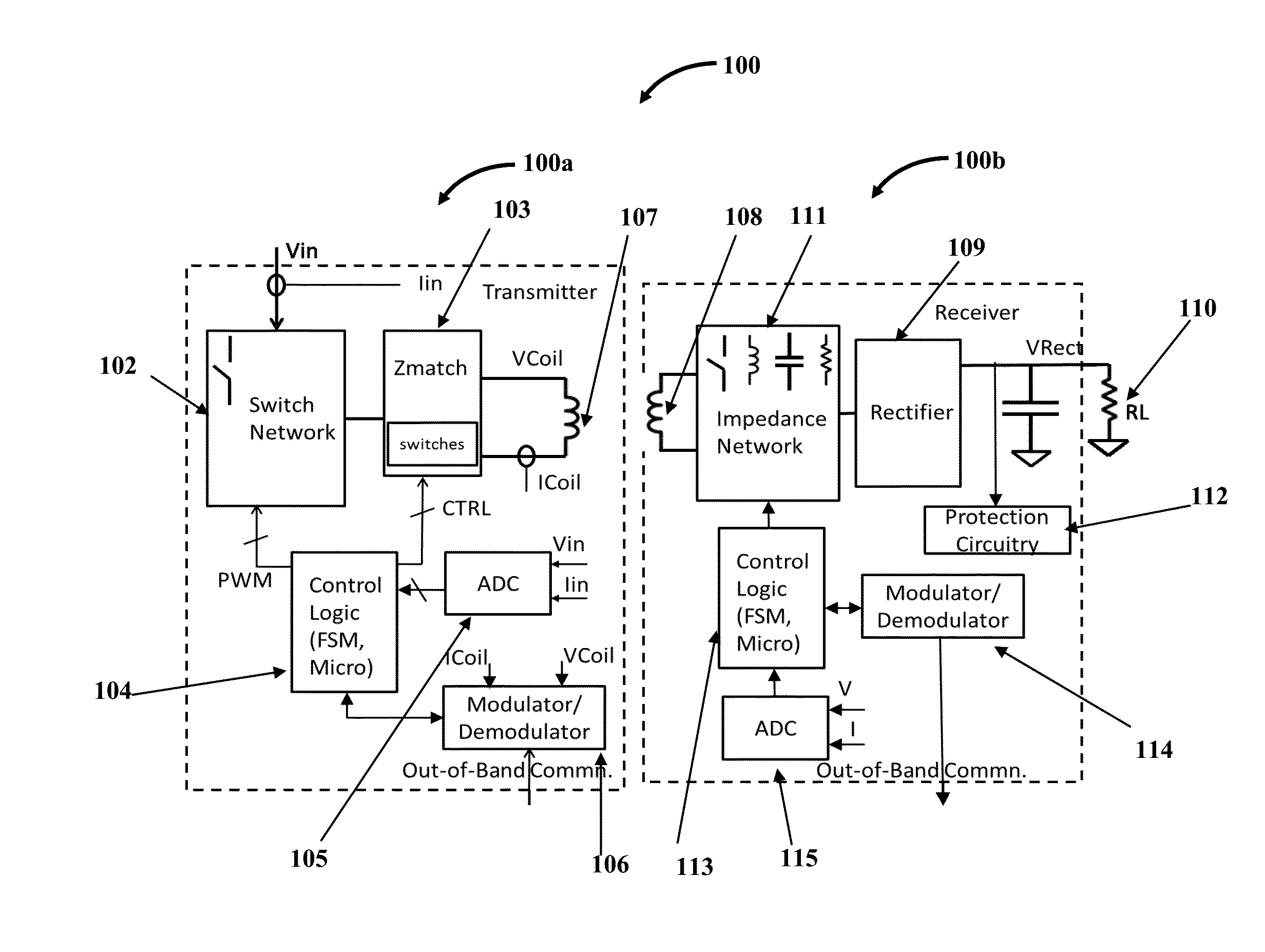
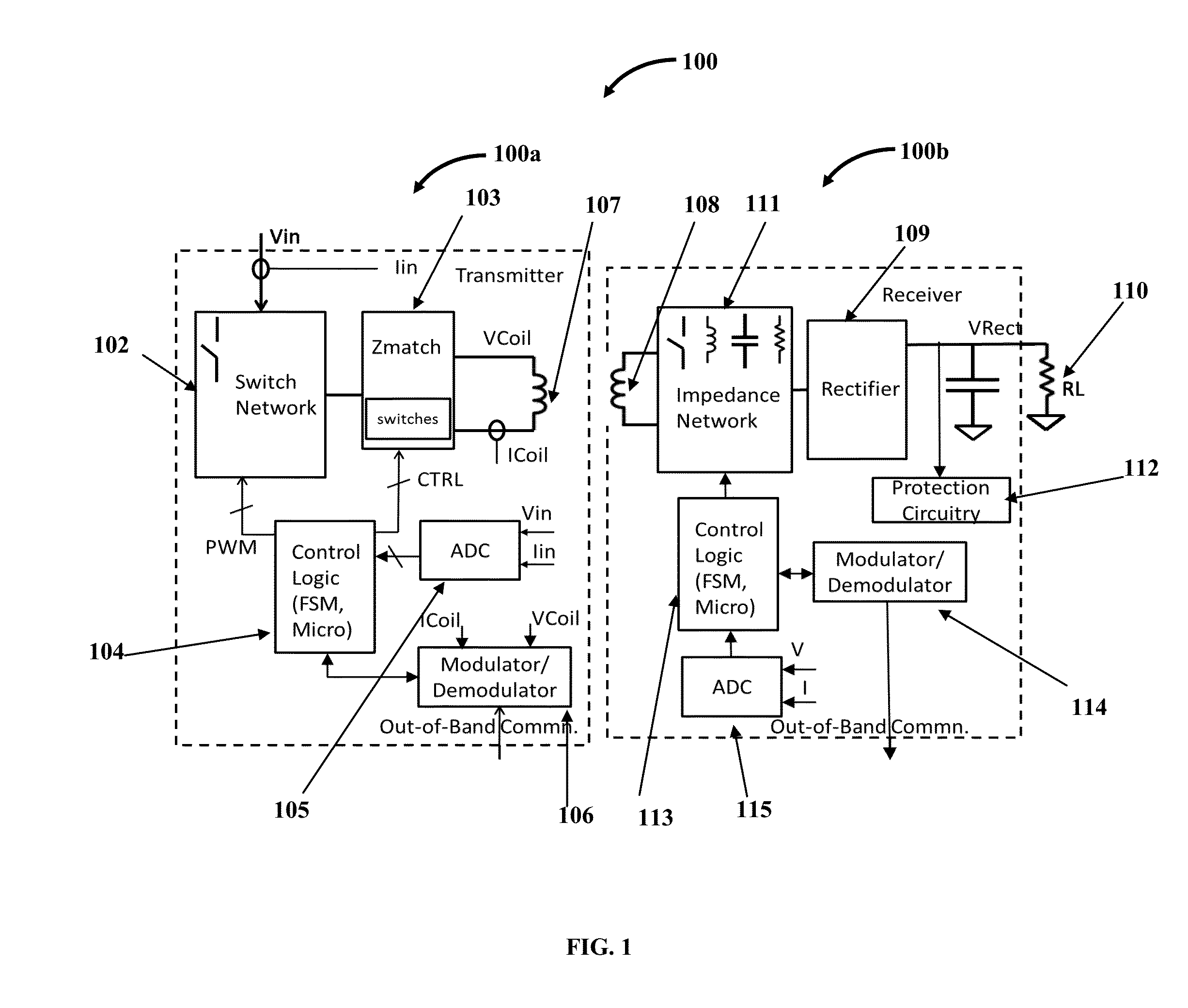
InactiveUS20150372493A1Avoid security issuesEfficient detectionTransformersTransformers/inductances circuitsElectric power transmissionElectricity
A wireless power transmitter (WPT) including a first, second, third circuit and a transmit coil for wirelessly delivering power to a wireless power receiver (WPR) including a receiver coil, rectifier, impedance network, protection circuitry, control logic, modulator / demodulator and ADC is provided. A method that enables WPT and WPR to deliver the required power to the WPR's downstream load in planar, orthogonal and intermediate modes of WPR placement on WPT is provided. The WPR is integrated into the strap / frame or in the vital area of the device. To avoid a heated metal object safety issue, the WPT implements a metal object detect algorithm to detect metal objects and terminate transmission of power. To protect their circuitry from induced voltage spikes in excess of acceptable levels, the WPR includes a simple protection circuitry that naturally turns on and siphons out the excess power when the acceptable threshold levels are exceeded.
Owner:WIPQTUS
Vending machines with field-programmable locks
InactiveUS6900720B2Easily and inexpensively programmedImprove the level ofFrequency-division multiplex detailsDigital data processing detailsBiological activationHome based
Owner:MICRO ENHANCED TECH
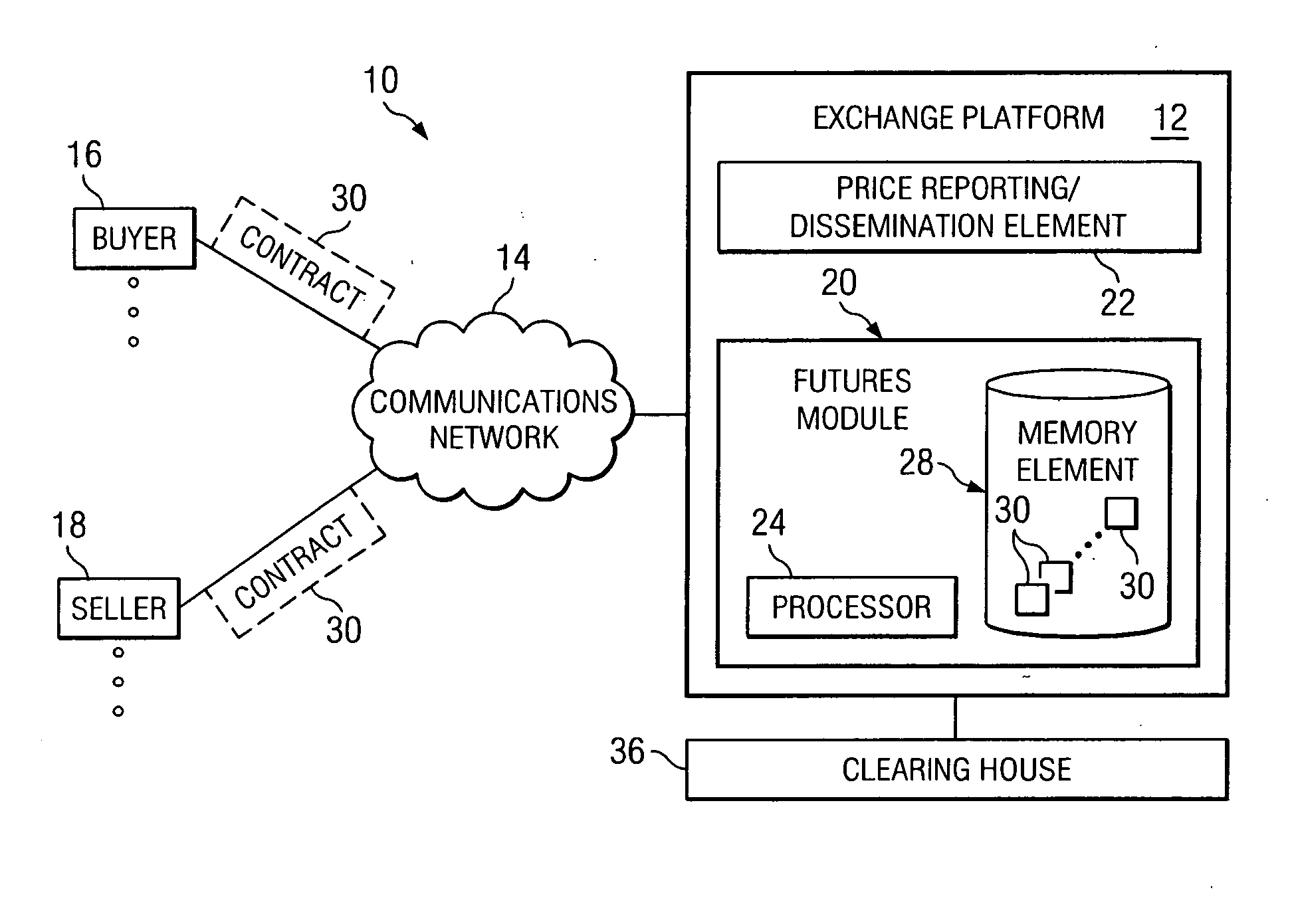
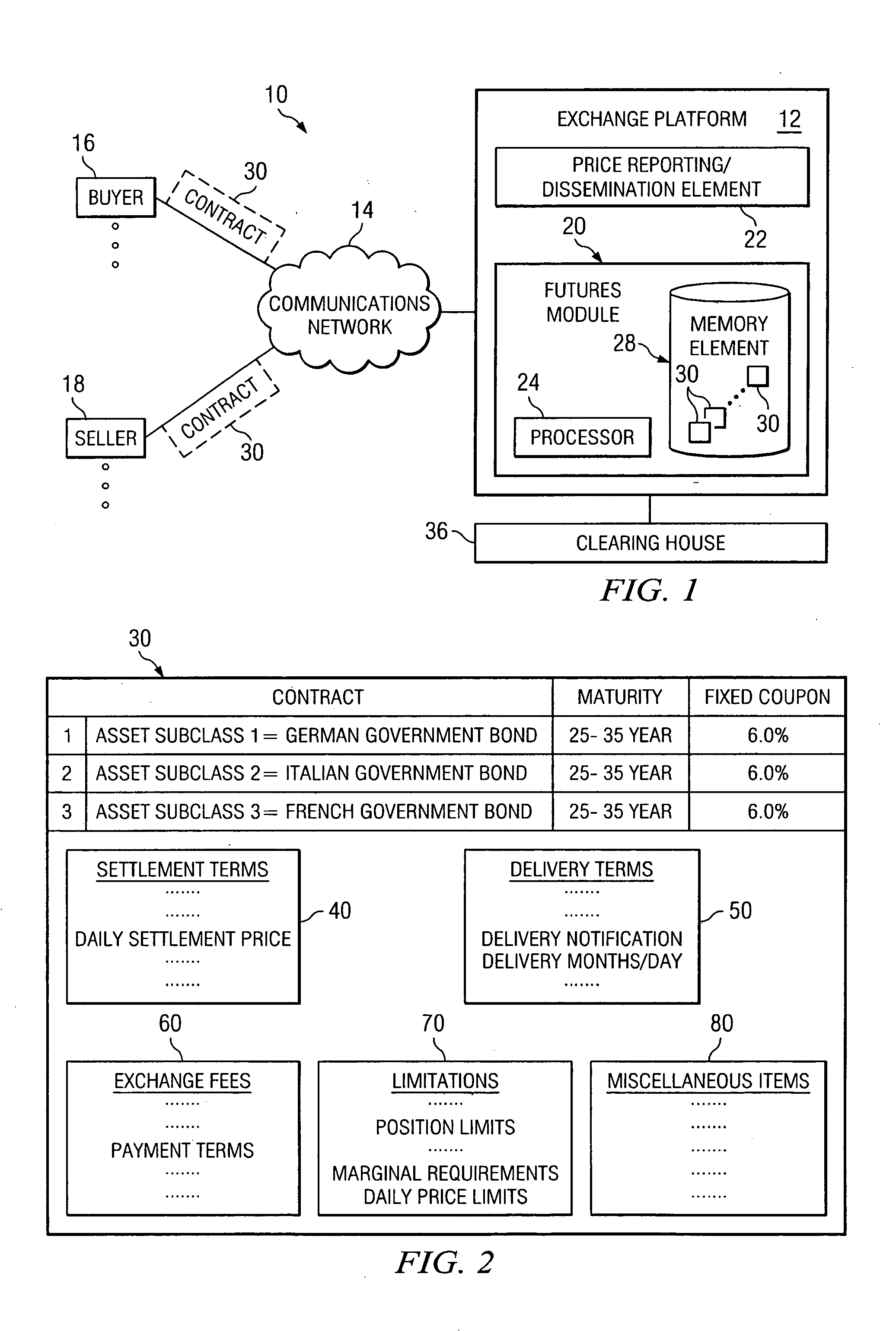
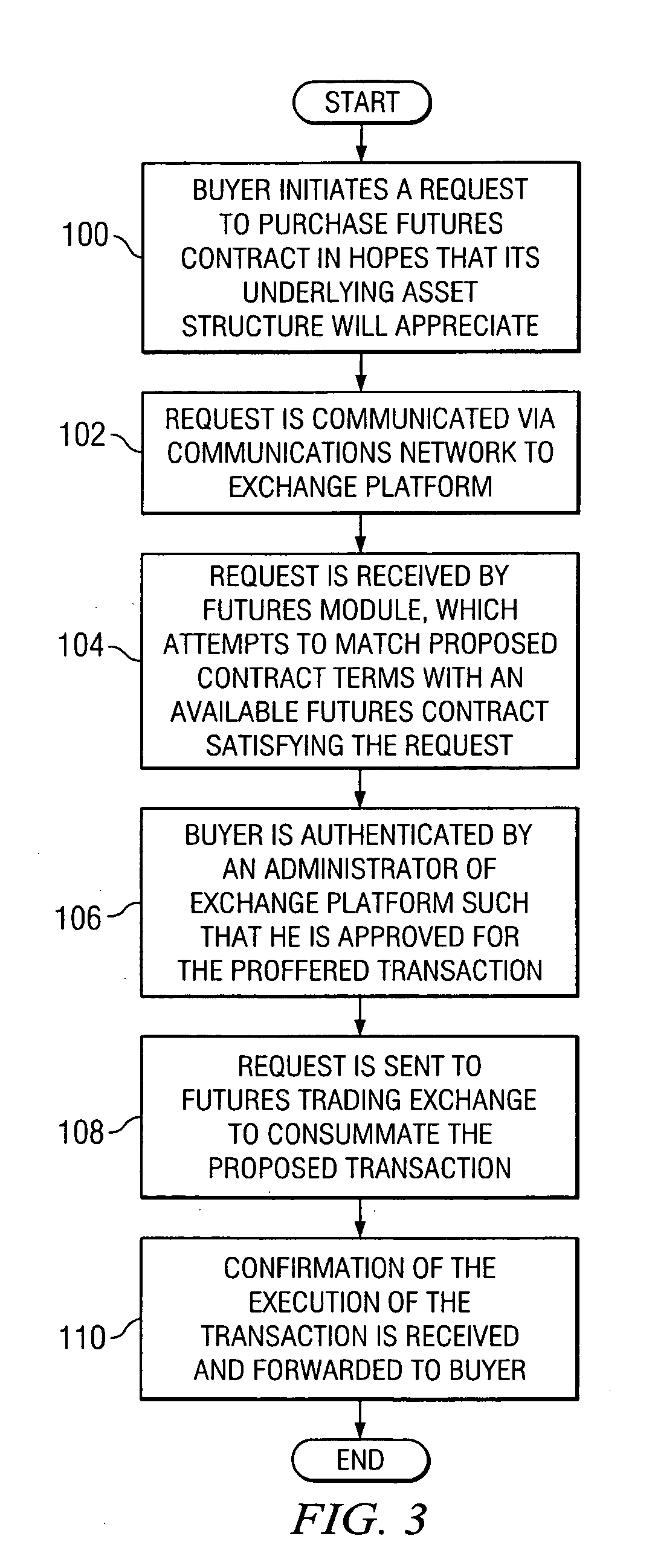
System and method for providing futures contracts in a financial market environment
ActiveUS20050086152A1Protect an investor against sharp marketplace fluctuationsEnhanced flexibility and liquidity and diversificationFinanceSpecial data processing applicationsPurchasingOperating system
A method for offering an asset in a financial environment is provided that includes receiving a request to perform a selected one of a purchasing and a selling operation for a futures contract. The futures contract includes a first asset class having a first value associated therewith and a second asset class having a second value associated therewith. A price for the futures contract is determined at least partially by the first and second values.
Owner:BGC PARTNERS LP
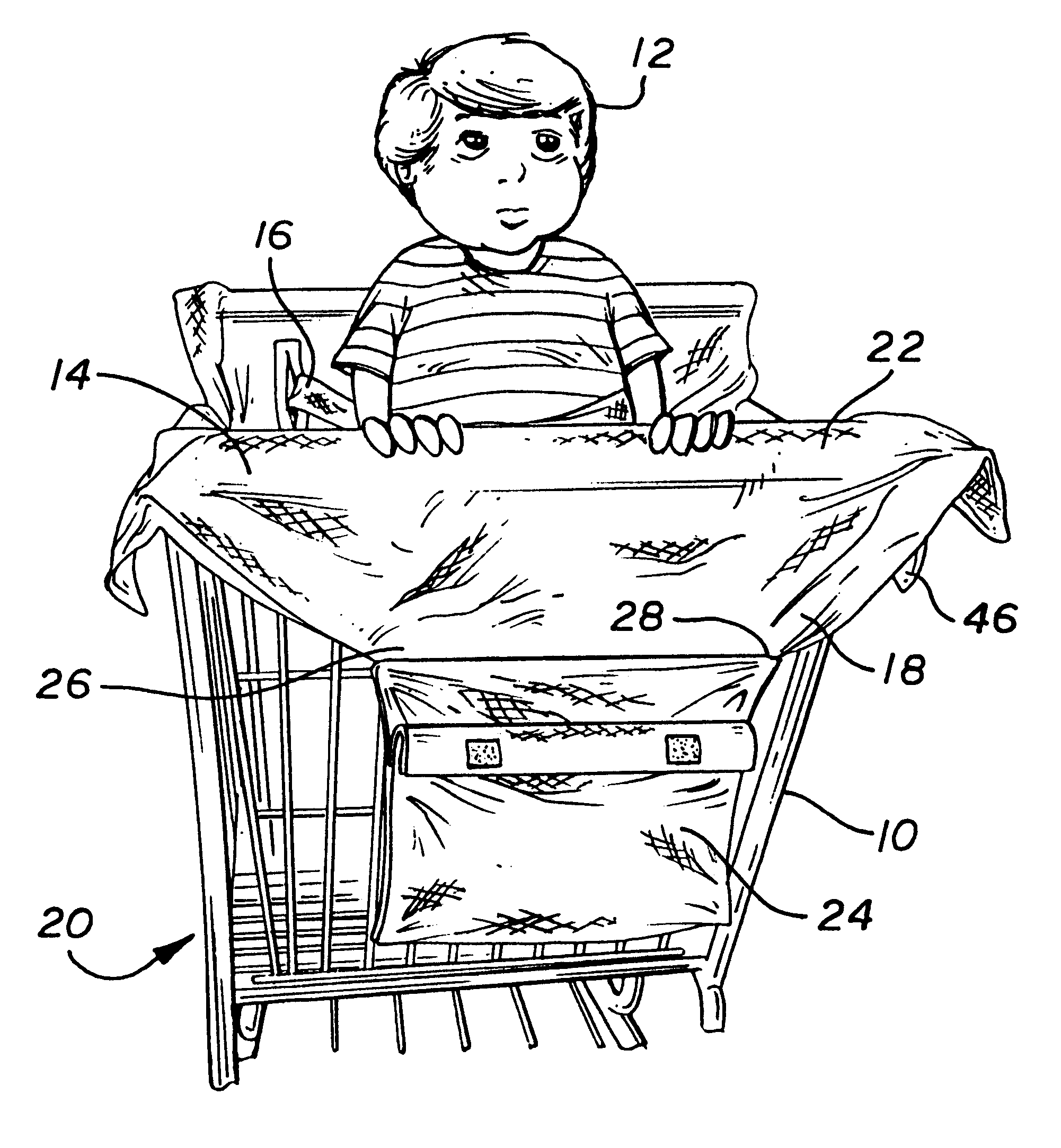
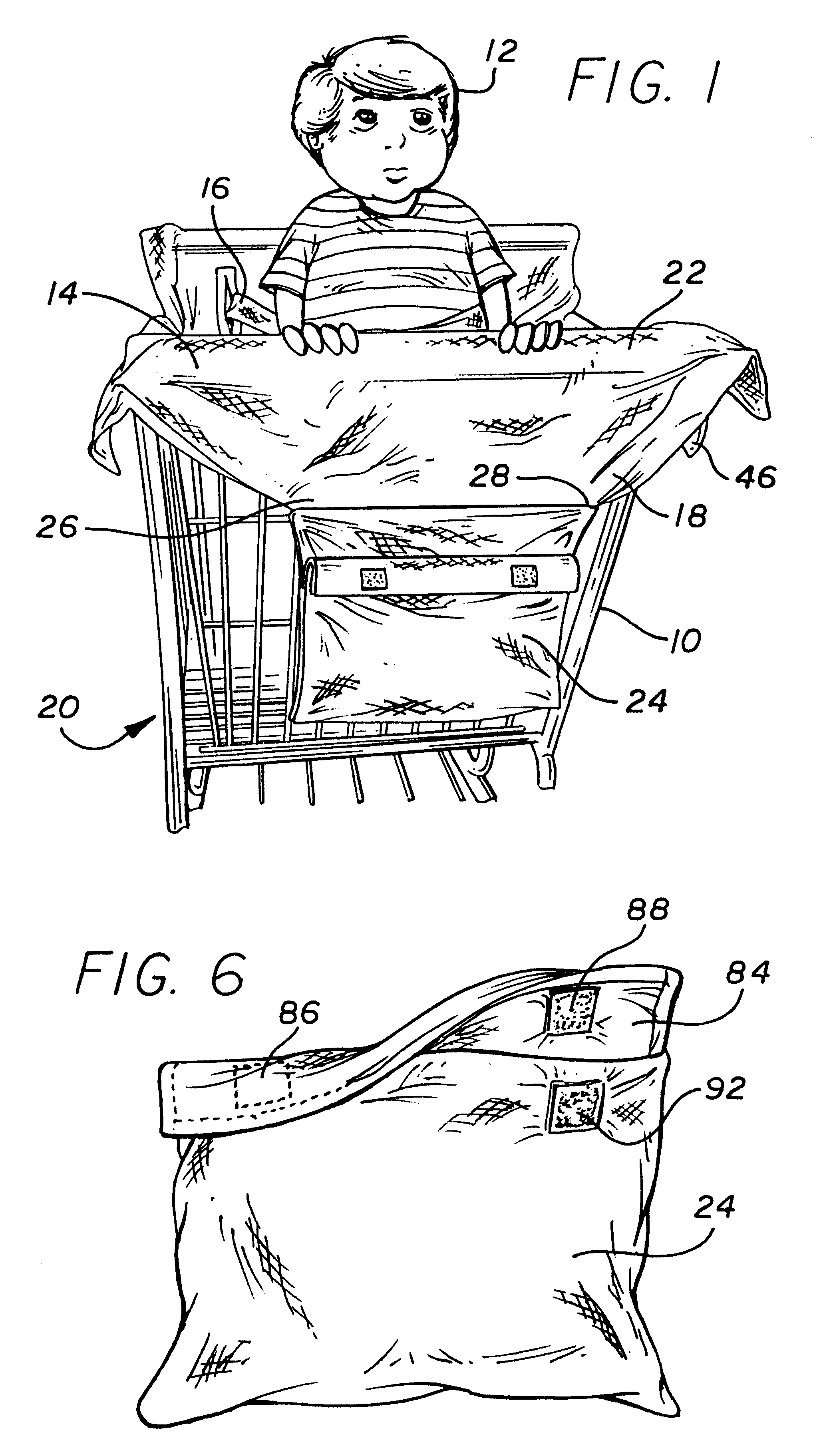
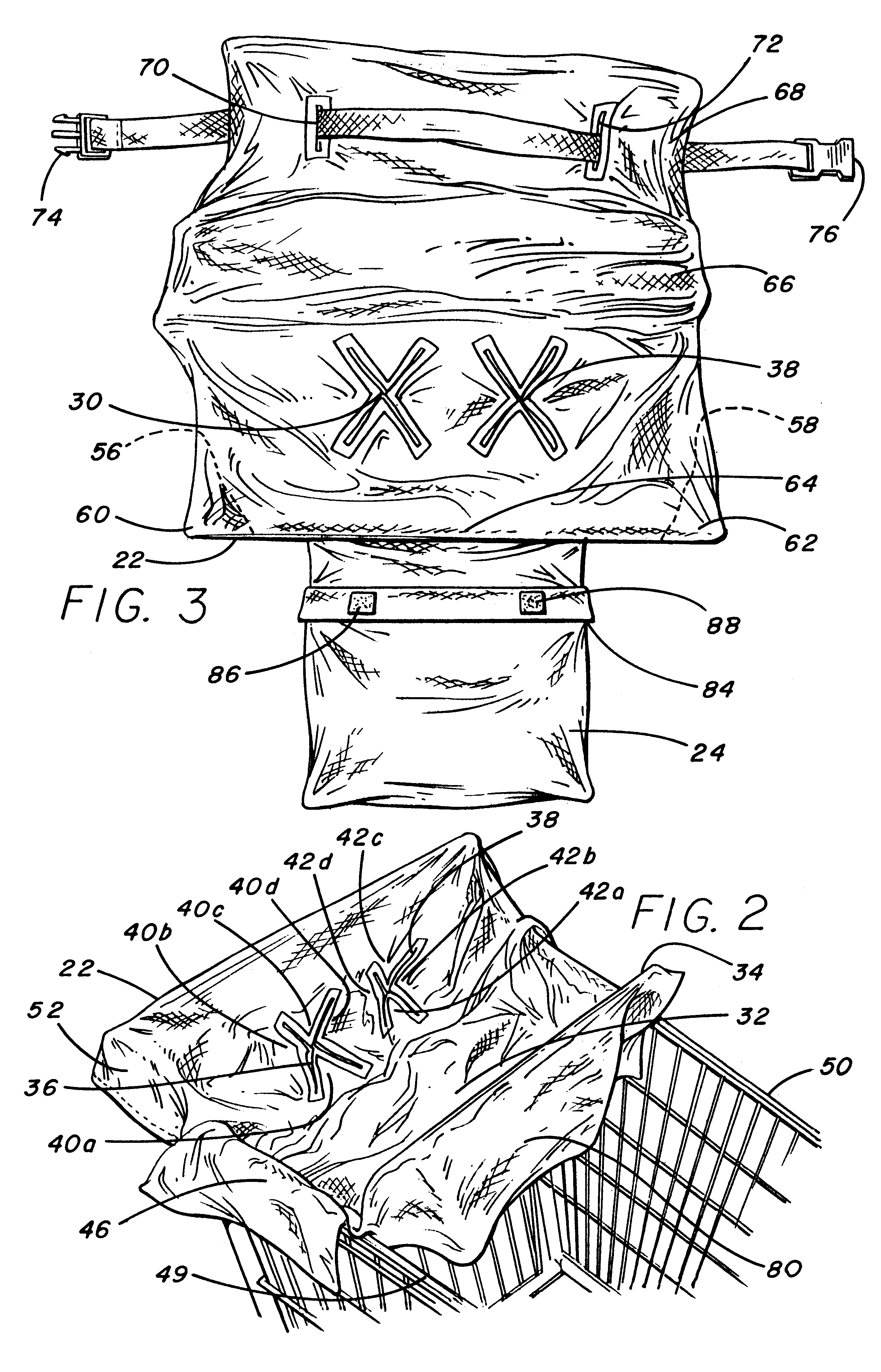
Baby seat cover
InactiveUS6237998B1Overcome deficienciesAvoid security issuesStoolsKids chairsEngineeringBelt safety
Owner:APRILE SANDRA STEPHENS
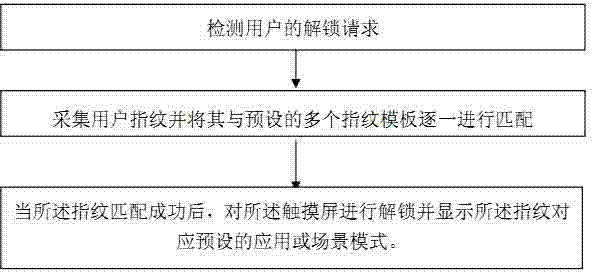
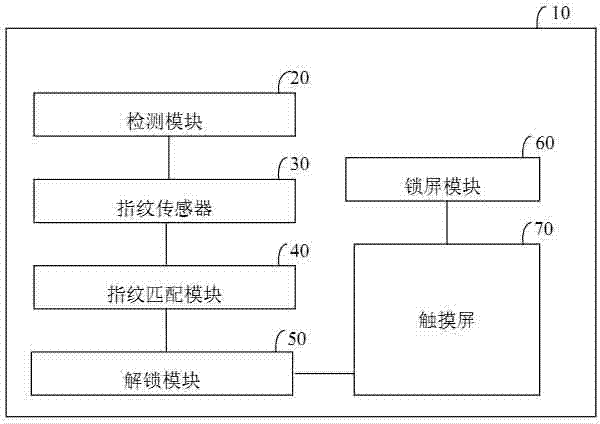
Control method and system for electronic device with fingerprint sensor and touch screen
InactiveCN103886237AImprove securityImprove privacyDigital data authenticationAcquiring/reconising fingerprints/palmprintsPersonalizationControl system
The invention discloses a control method for an electronic device with a fingerprint sensor and a touch screen. The control method includes the steps that an unlocking request of a user is detected; a fingerprint of the user is collected and matched with preset multiple fingerprint templates of the user fingers one by one; after fingerprint matching is successful, the touch screen is unlocked, and a preset application or scene mode corresponding to the fingerprint is displayed. In addition, correspondingly, the invention further provides a control system for the electronic device with the fingerprint sensor and the touch screen. The fingerprint is verified to improve safety and privacy of the electronic device, meanwhile, after fingerprints of different fingers are unlocked, different application or scene modes set in a personalized mode are displayed, tedious step-by-step operation application and scene setting are avoided, and operation experience of the user is improved.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
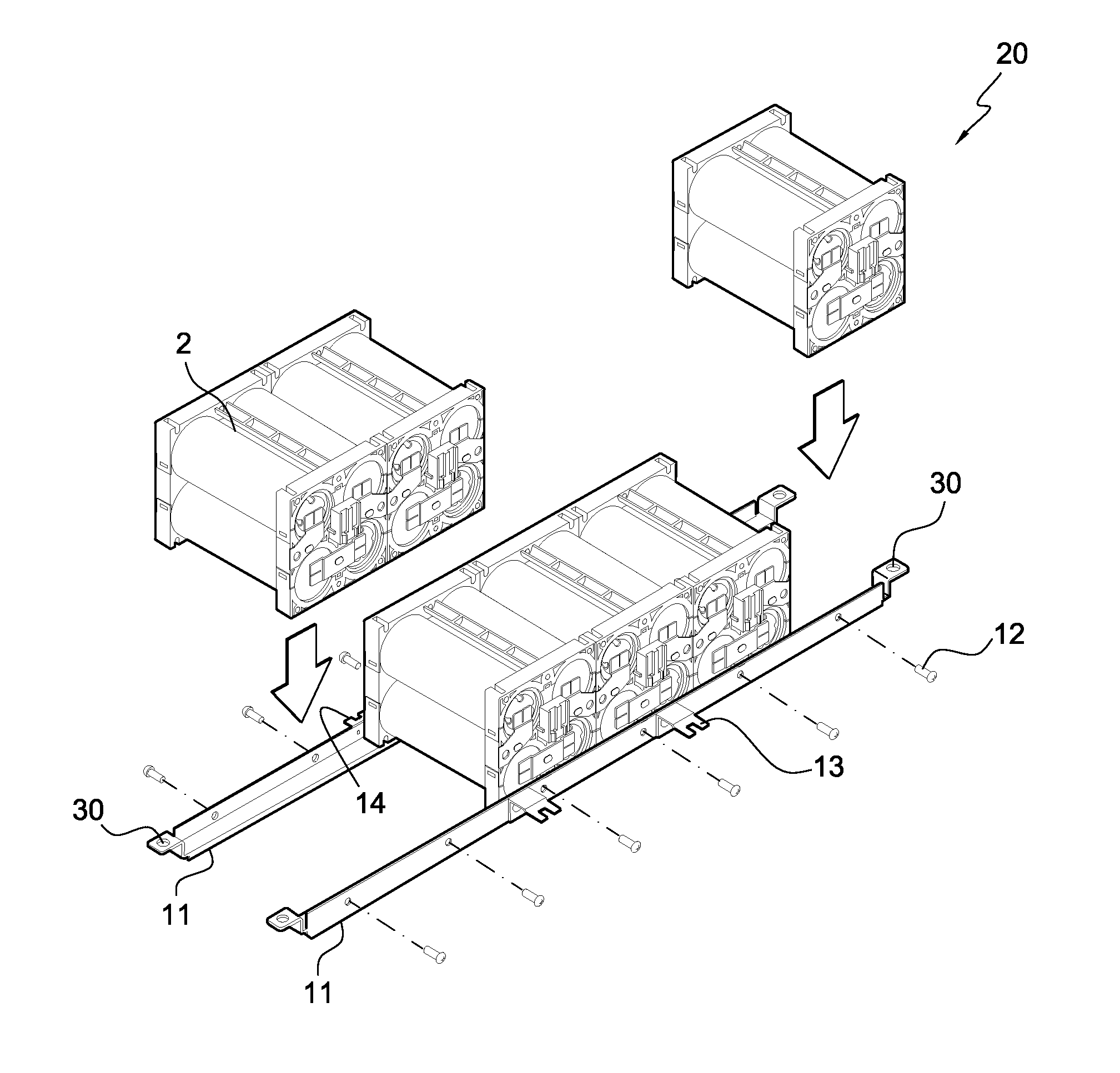
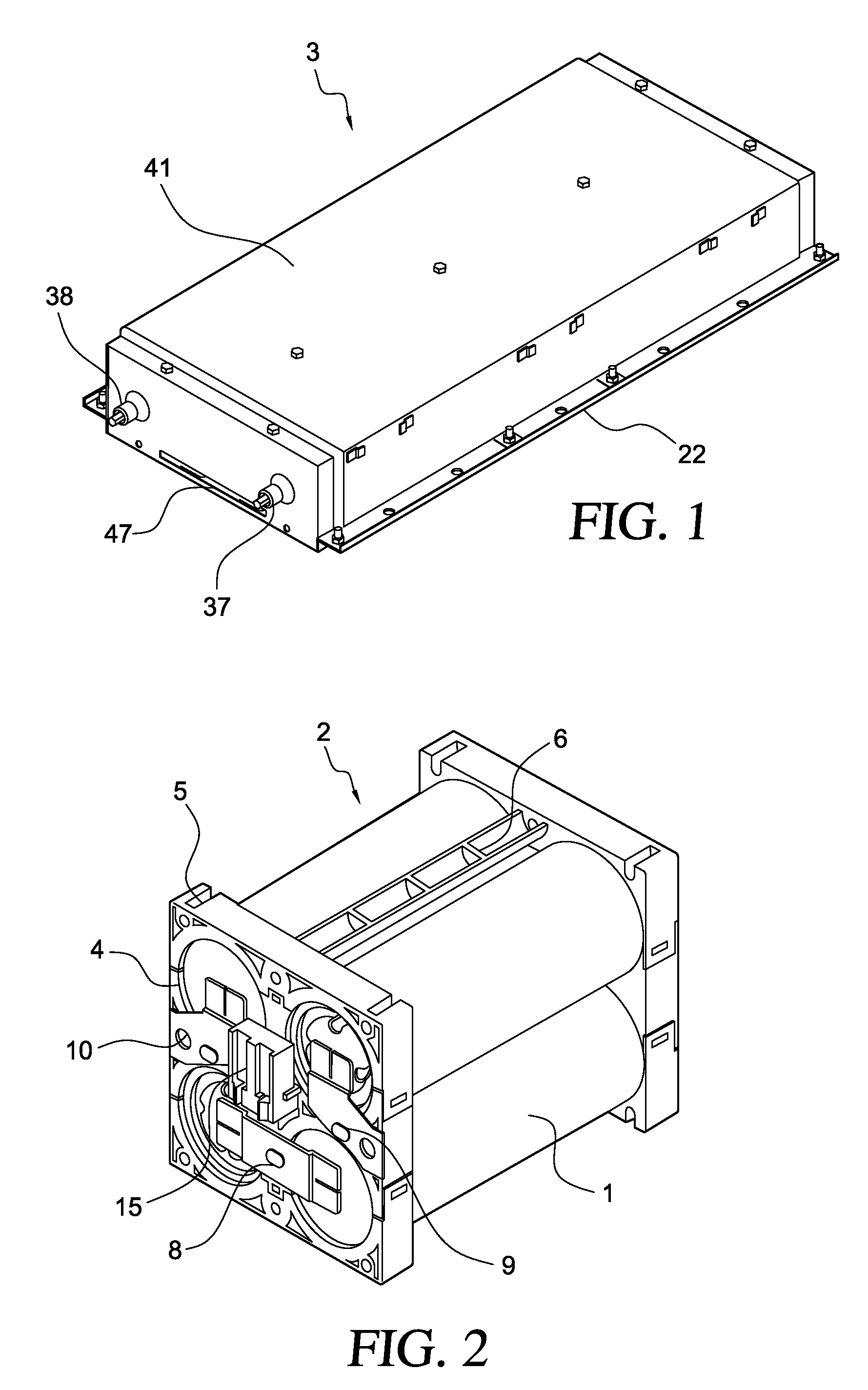
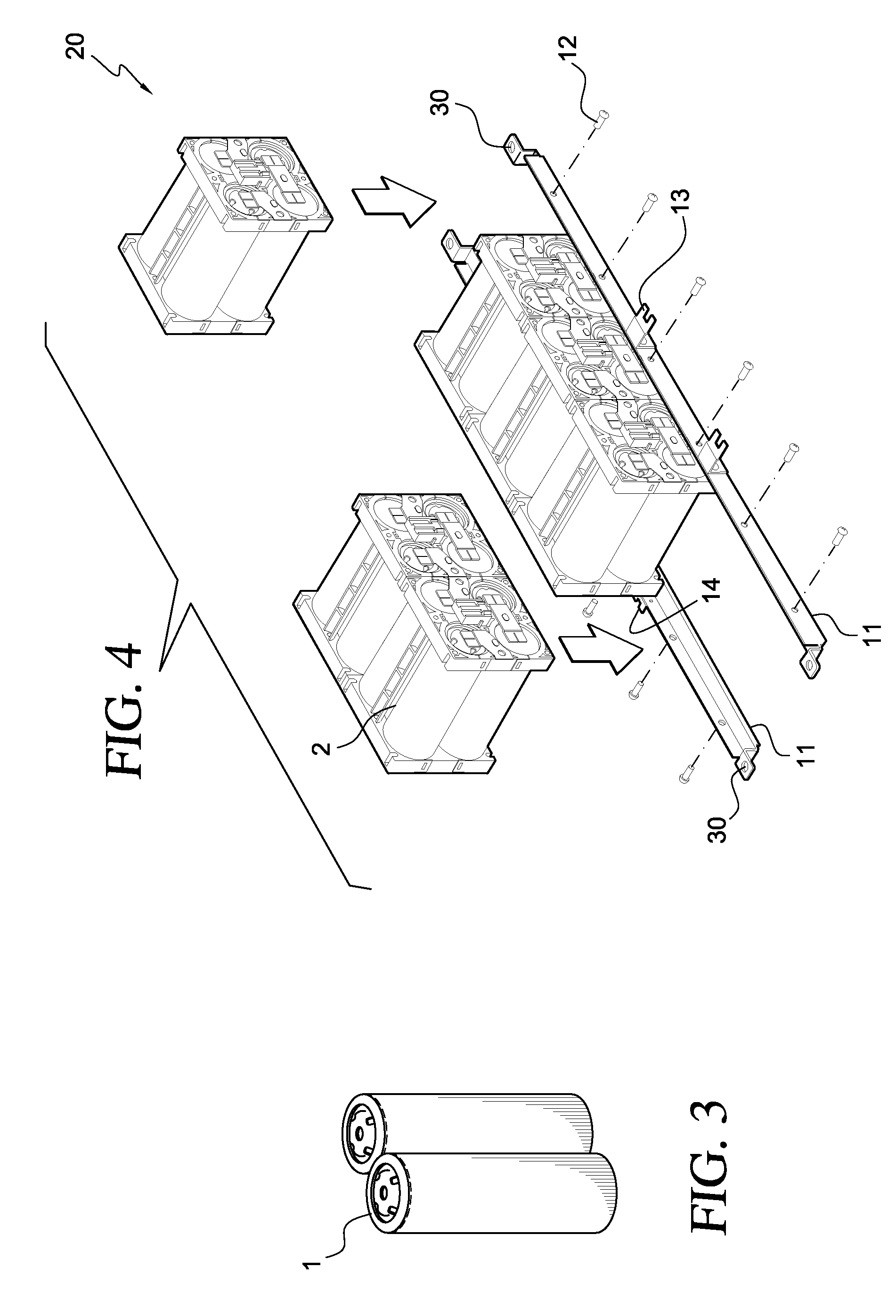
Battery module
ActiveUS20070141459A1Excellent in cooling easinessLow costPrimary cell to battery groupingCell temperature controlElectrical polarityElectrical and Electronics engineering
Owner:HITACHI VEHICLE ENERGY
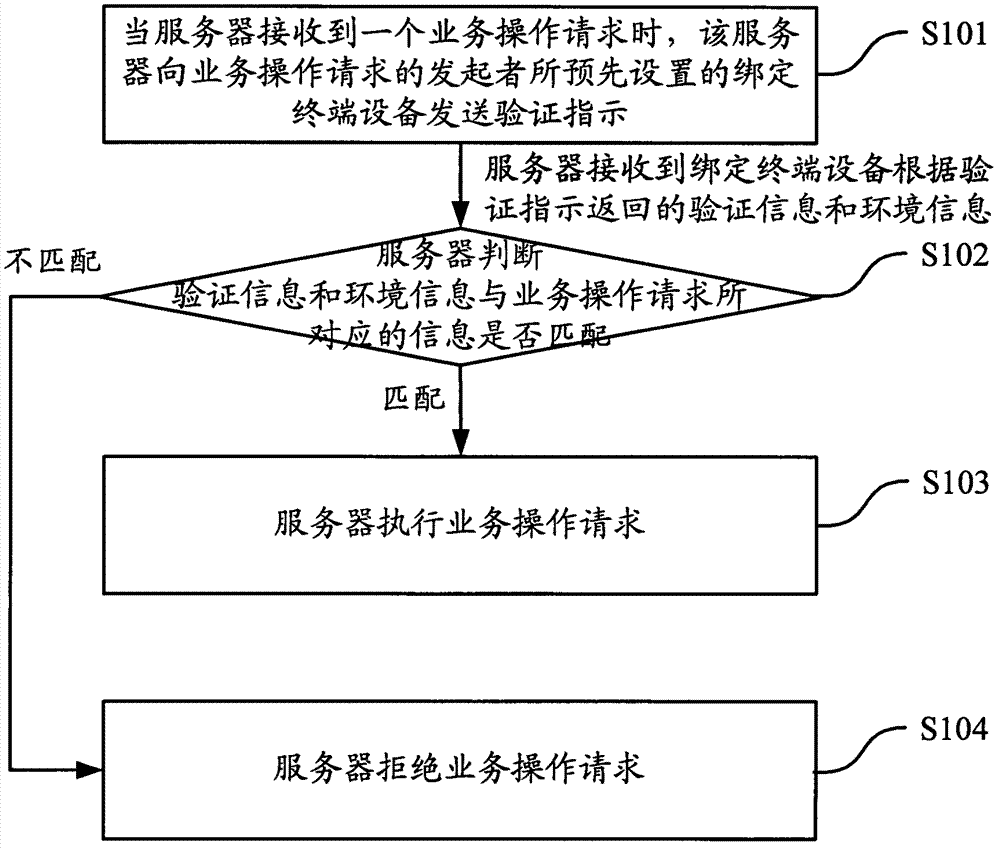
Authentication method, equipment and system
ActiveCN102790674AImprove securitySimplify operating proceduresUser identity/authority verificationTerminal equipmentComputer terminal
The embodiment of the invention discloses an authentication method, authentication equipment and an authentication system. By applying the technical scheme adopted by the embodiment of the invention, when a service operation request is received, preset binding terminal equipment can be triggered to carry out authentication, the matching judgment is carried out on information corresponding to the service operation request according to returned authentication information and environment information and the corresponding service operation request can be executed only under the condition of successful matching, so that the operation program of an operator is simplified and the fussy operation and the security hole which are caused by manual input of authentication information are avoided; and meanwhile, under the assist of authentication of the environment information, the matching of characteristic information such as an actual position of a user and the like and the information corresponding to the service operation request is ensured, so that the safety of the service processing is further improved.
Owner:ALIBABA GRP HLDG LTD
Network security situation sensing system and method based on multi-layer multi-angle analysis
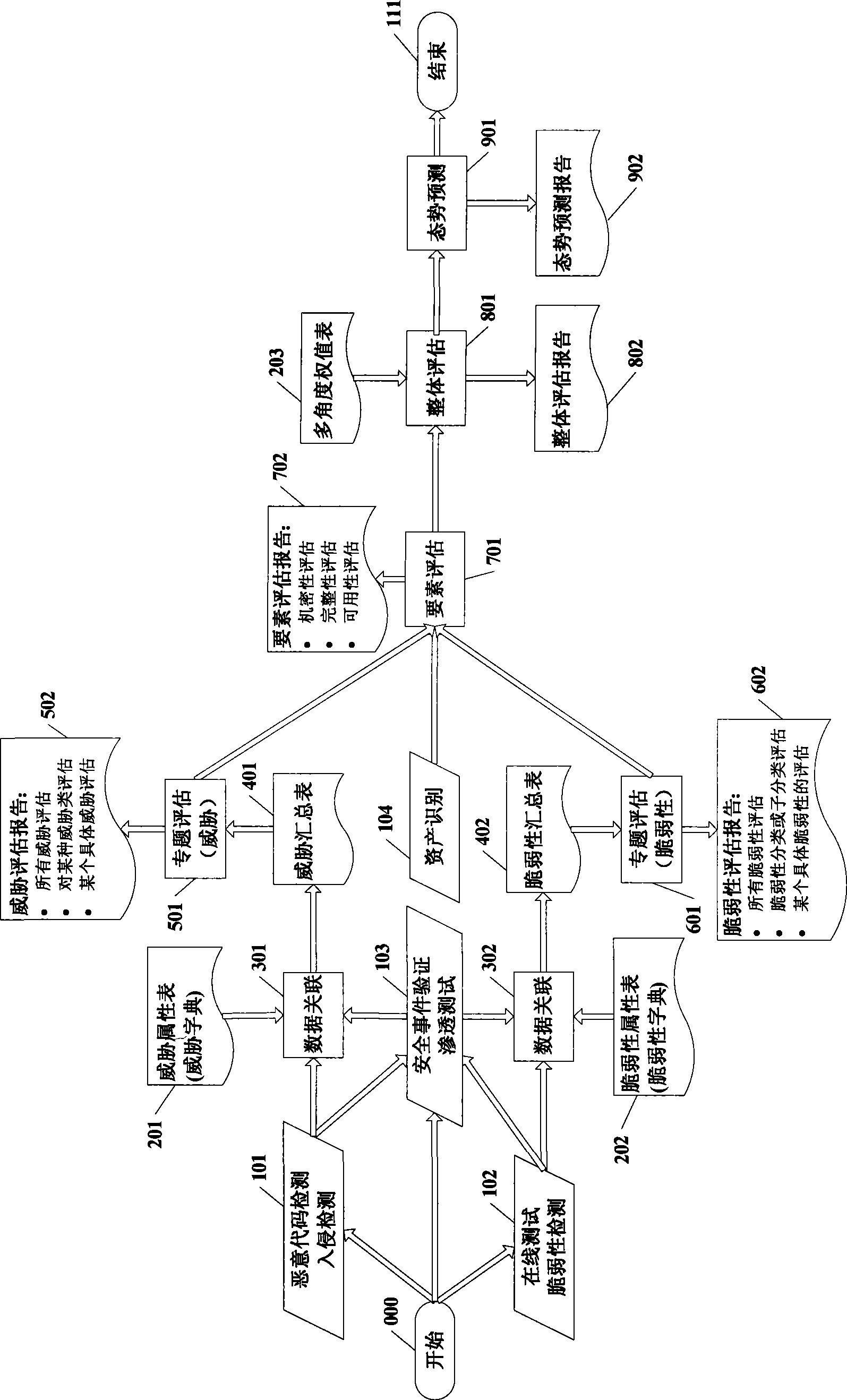
InactiveCN101459537AThe evaluation results are systematic and comprehensiveFix security issuesData switching networksData acquisition moduleNetworked system
The invention discloses a network security situation perception system and a method based on multilevel multi-angle analysis, wherein the system comprises a data gathering module, a network security situation understanding module, a network security situation estimation module and a network security situation forecasting module. The method for achieving the network security situation perception system comprises the following steps: firstly, doing statistical data fusion and association analysis to data in the aspects of assets, intimidation and vulnerability of a network system gathered by a sensor, and getting normalized data, secondly, analyzing the normalized data after the fusion of the step one, and doing network security situation special subject estimation, thirdly, doing network security situation factor estimation according to the normalized data obtained in the step one and the estimation result of the step two, fourthly, doing the integral estimation of network security situation according to the estimation result of the step three, fifthly, doing network security situation forecast according to the estimation result of the step D. The invention analyzes the security situation of network from multi levels and multi angles, and guarantees a result perception system to be more accurate and comprehensive.
Owner:UNIV OF SCI & TECH OF CHINA
Device for monitoring medical equipment
InactiveUS20050193279A1Increase probabilityImprove reliabilitySafety arrangmentsPulse automatic controlMedical equipmentSafety control
A medical instrument, in particular a generator for high-frequency surgery, comprises setting elements for presetting functions, and also functional elements for performing functions according to the settings. A controller interrogates the setting elements and controls the functional elements accordingly. Furthermore, a safety controller is provided for performing plausibility checks with the aid of information from the setting elements and also the functional elements, and for deactivating, or putting into a safe operating condition, the functional elements in the case of inadmissible working conditions.
Owner:STORZ ENDOSKOP PROD GMBH
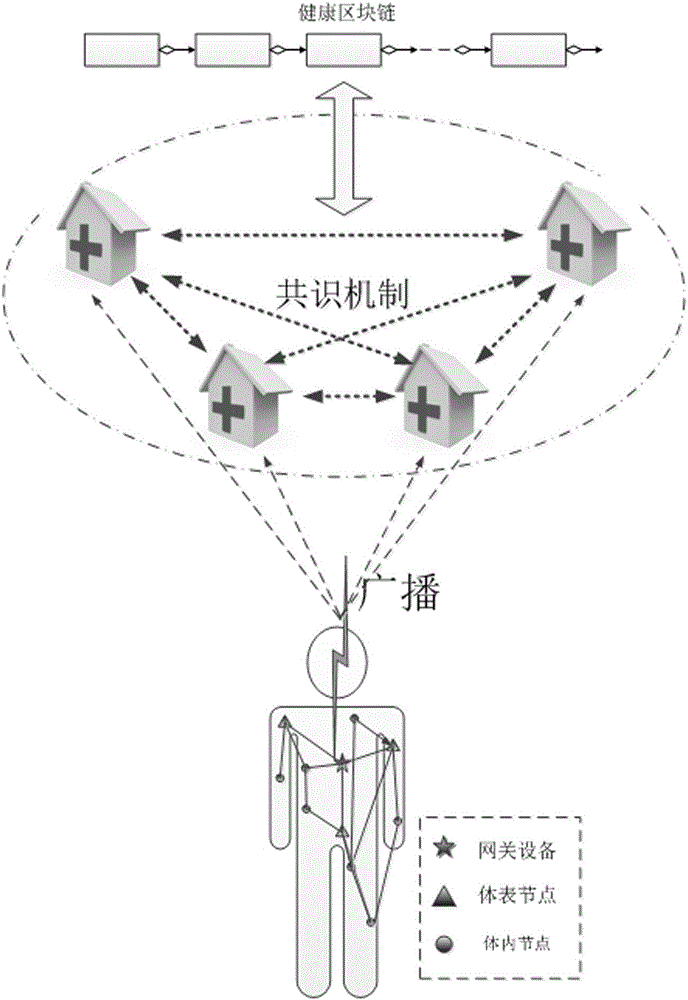
Lightweight back-up and efficient restoration method of health block chain data encryption keys
InactiveCN105812126AReduce management complexityAvoid heavy burdenKey distribution for secure communicationBody area networkRestoration method
The invention provides a lightweight back-up and efficient restoration method of health block chain data encryption keys.Body area networks achieve physiological parameters acquisition of healthy body health, health block chains are produced by a group of credible IT devices appointed by multiple health institutions and used for receiving and storing health data of the body area networks, the health block chain data encryption keys are produced by utilizing a fuzzy technology fuzzy vault and physiological signals acquired by the body area networks, human physiological data acquired in different time periods is encrypted by utilizing different data encryption keys and then is saved in the block chains of the IT devices without storage of historical data encryption keys; historical secret keys are restored by utilizing the health data acquired by the body area networks in real time.The lightweight back-up and efficient restoration method integrates the body area networks with the health block chains, avoids huge burden brought by secret key splitting related in a traditional secret key restoration method and safe storage and retrieval of shadow secret keys and greatly reduces management complexity of the health block chain data encryption keys.
Owner:QILU UNIV OF TECH
Device for monitoring medical equipment
InactiveUS7203556B2Increase probabilityImprove reliabilitySafety arrangmentsPulse automatic controlMedical equipmentEngineering
A medical instrument, in particular a generator for high-frequency surgery, comprises setting elements for presetting functions, and also functional elements for performing functions according to the settings. A controller interrogates the setting elements and controls the functional elements accordingly. Furthermore, a safety controller is provided for performing plausibility checks with the aid of information from the setting elements and also the functional elements, and for deactivating, or putting into a safe operating condition, the functional elements in the case of inadmissible working conditions.
Owner:STORZ ENDOSKOP PROD GMBH
Dual-signal independent chimeric antigen receptors (dsCAR) and uses thereof
ActiveCN103483452APromote proliferationHigh activityPeptide/protein ingredientsAntibody mimetics/scaffoldsAntigen receptorsViral infectious disease
The invention relates to chimeric antigen receptors (CAR), particularly relates to dual-signal independent chimeric antigen receptors (dsCAR), and also relates to immune response cells of the dual-signal independent chimeric antigen receptors (dsCAR) and uses of the immune response cells in preparation of drugs for treatment of malignant tumor and virus infected diseases. In detail, the dual-signal independent chimeric antigen receptors (dsCAR) can respectively identify two different family antigens of tumor cells and can respectively transmit two T-cell-activation related signals. One of the CAR can transmit a first T-cell-activation related signal by combing a ligand of a tumor specific antigen or a tumor-associated antigen to decide T-cell killing specificity, and the other CAR can transmit a second T-cell-activation related signal by combing a ligand of a membrane receptor (such as EGFR (epidermal growth factor receptor) family protein) widely expressed by the tumor cells to promote T cell activation, proliferation and survival. The dual-signal independent chimeric antigen receptors (dsCAR) can avoid the potential safety problems on the basis of maintaining curative effects of second generation and third generation CAR.
Owner:SHANGHAI CELL THERAPY GRP CO LTD
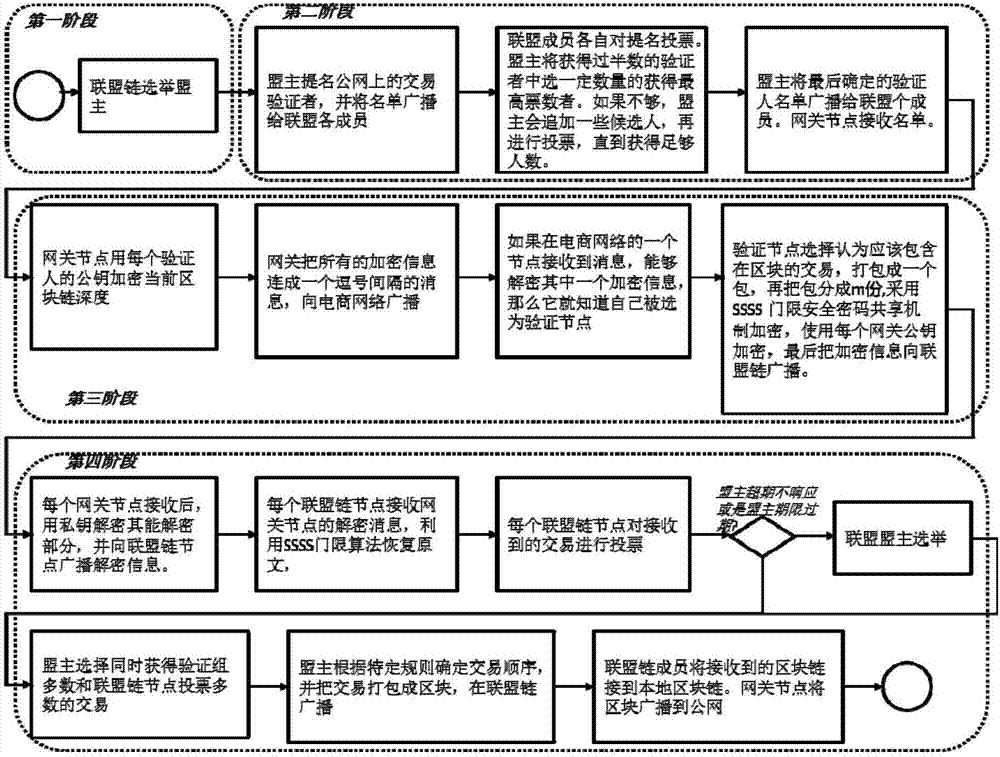
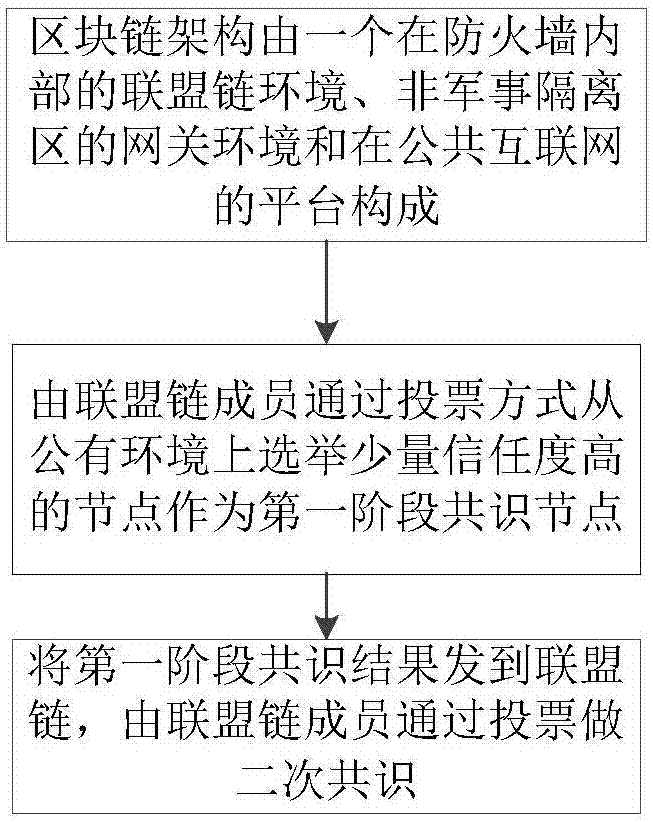
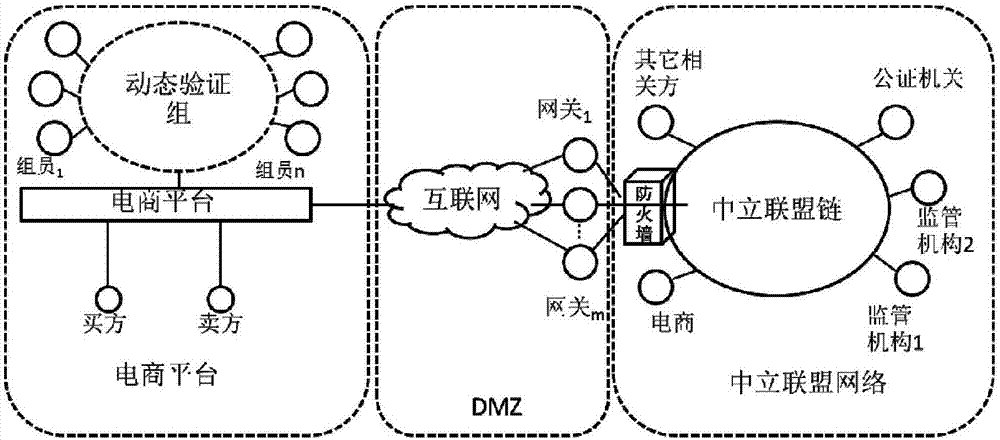
Credit-based blockchain consensus method for large-scale e-commerce
ActiveCN107395403APerformance is not affectedImprove consensus efficiencyFinanceData switching networksPublic environmentThe Internet
The invention discloses a credit-based blockchain consensus method for large-scale e-commerce. According to the method, by applying a blockchain to the large-scale e-commerce application scene, the scalability needed by the large-scale e-commerce scene can be achieved, millions of nodes can be supported, the consensus requirement that the service speed of the e-commerce is ten millions per second can be met, energy consumption such as Bitcoins is not needed, and the problem that a blockchain adopting proof of stake (POS) is lack of security guarantee is solved. The method comprises the steps that 1, the structure of the blockchain is composed of an alliance chain environment in a firewall, a gateway environment in a non-military isolation area and a platform in the public Internet; 2, alliance chain members elect a few nodes with a high trust degree from a public environment to serve as first-stage consensus nodes; and 3, a first-stage consensus result is sent to a alliance chain, the alliance chain members perform secondary consensus through voting to ensure the accuracy of the consensus result from the public environment, and then the security requirement is met.
Owner:北京区块链云科技有限公司
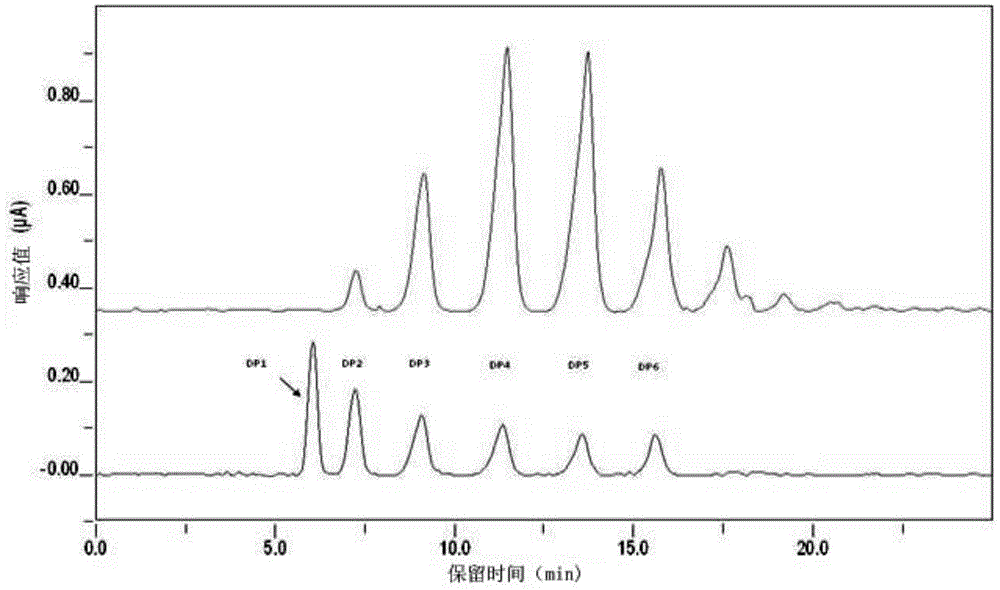
Chitosan oligosaccharide compounded preparation and application in prolonging shelf life of fruits
InactiveCN104642528AExtend fruit shelf lifeReduce usageFruit and vegetables preservationChemistryOrganic acid
A chitosan oligosaccharide compounded preparation for prolonging shelf life of fruits contains 0.3-5% of chitosan oligosaccharide with a fresh-keeping function, 0.1-2% of organic acid and 0.03-0.5% of a growth inhibitor. The compounded preparation is applied to fruits. By introducing chitosan oligosaccharide with the fresh-keeping function into a fruit preservative, the chitosan oligosaccharide compounded preparation has a double effect of sterilization and preservation. In addition, a medicament with chitosan oligosaccharide and organic acid as main components has advantages of safety, nontoxicity, low cost and low dosage, and is environmentally friendly.
Owner:DALIAN INST OF CHEM PHYSICS CHINESE ACAD OF SCI
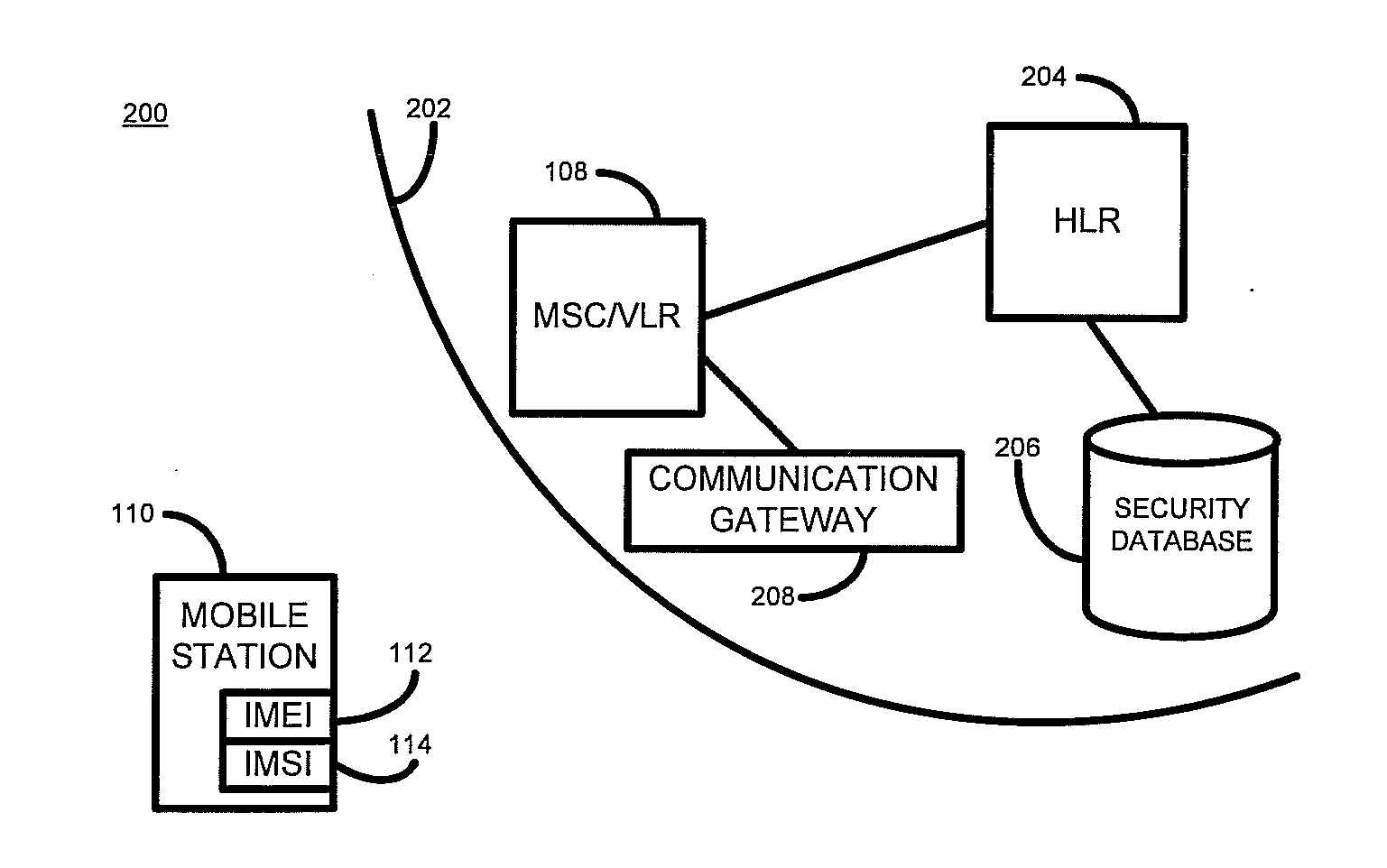
Network access control
ActiveUS20110086612A1Reduce the valueAvoid security issuesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData memoryUser identifier
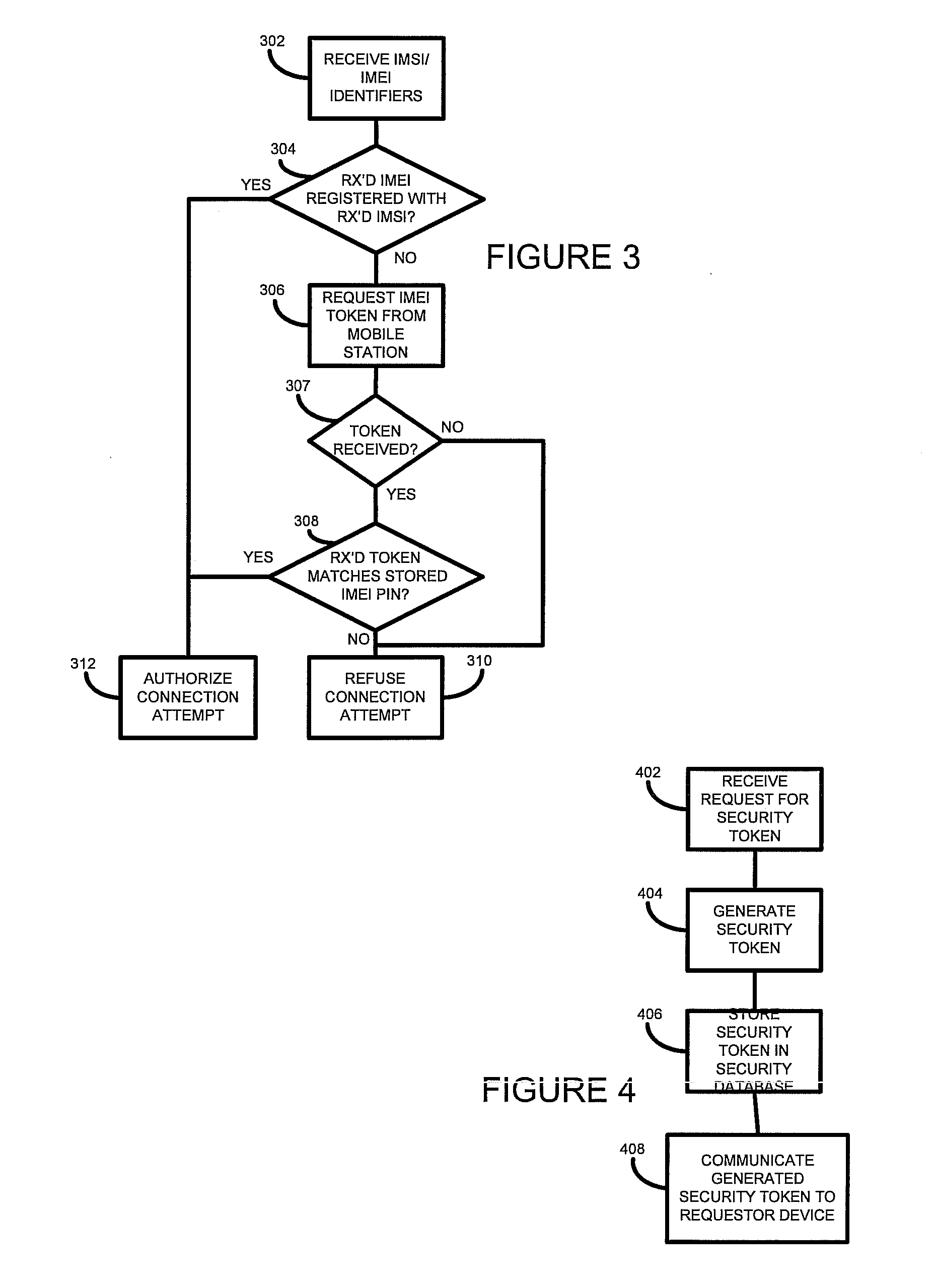
According to one embodiment of the present invention, there is provided a method of authorizing a communication device to connect to a network. The method comprises receiving, at a processor, a communication device identifier and a subscriber identifier, determining, by the processor, whether the received communication device identifier is associated with the received subscriber identifier in a data store. Where it is determined that the received identifiers are not so associated the method further comprise requesting, by the processor, a security token associated with the communication device, receiving, at the processor, a security token, determining, by the processor, whether the received security token matches a stored security token associated with the received communication device identifier in the data store, and where it is so determined, authorizing the communication device to connect to the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and system for payment of NFC mobile phone-POS machine
InactiveCN101567108AInput less informationReduce the probability of errorComplete banking machinesAccounting/billing servicesMobile paymentMobile phone
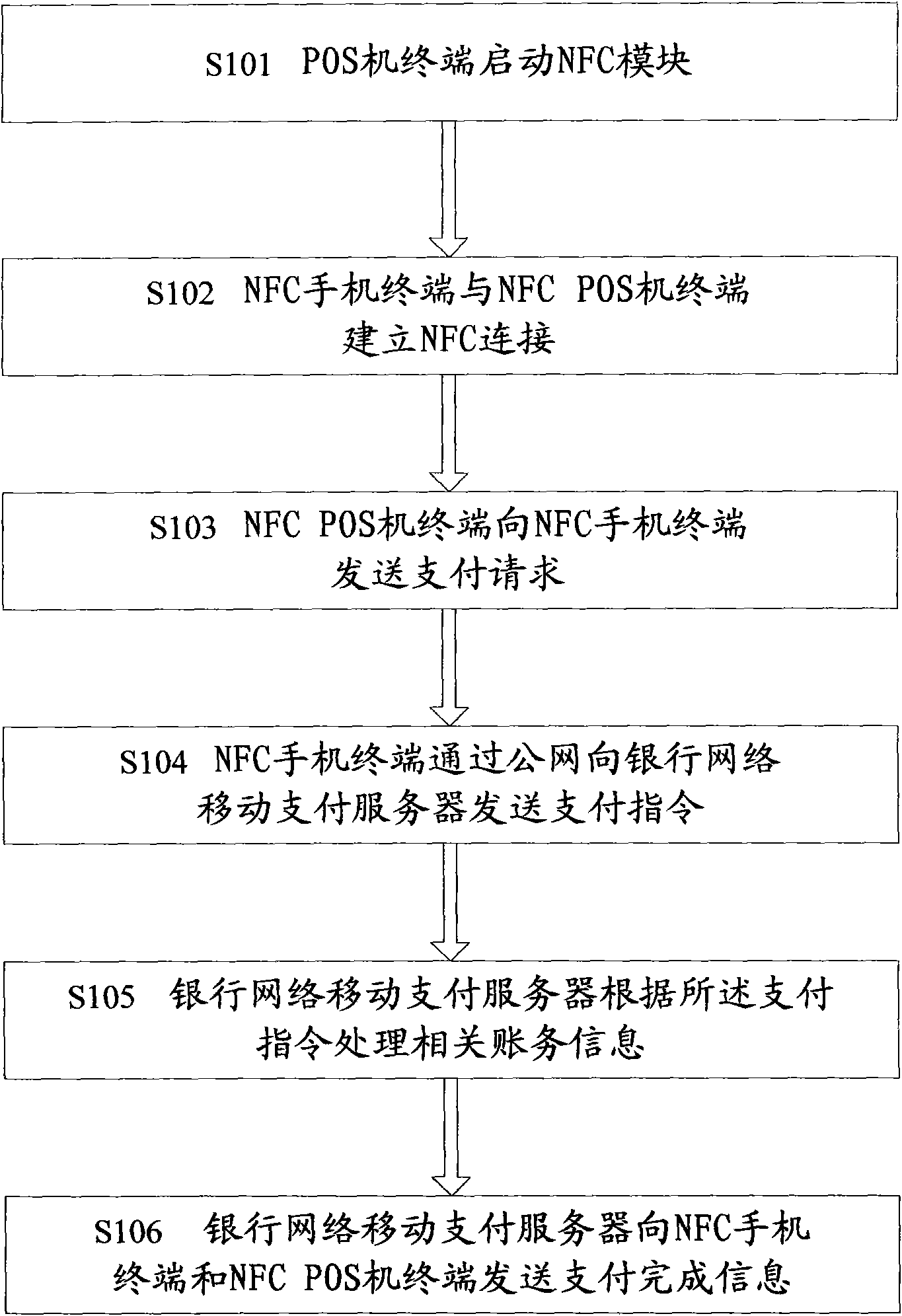
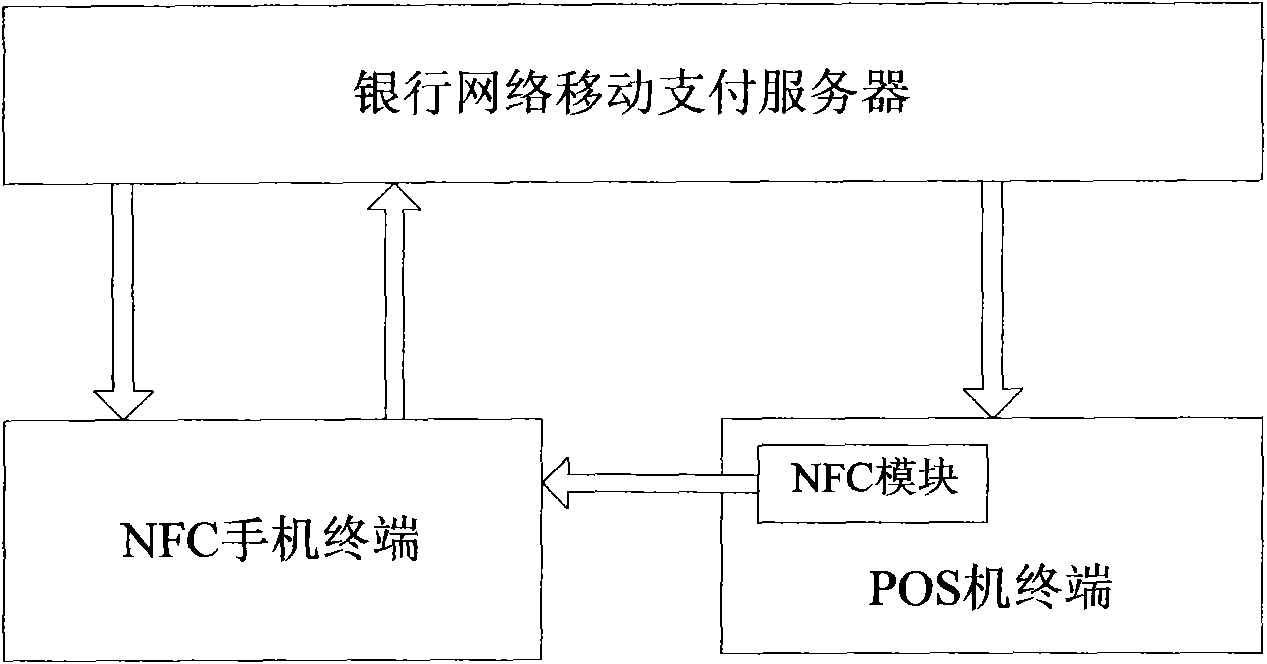
The invention discloses a method and a system for payment of an NFC mobile phone-POS machine, which are designed to solve the problems of complicated operation and easy mistakes in the prior mobile phone payment mode. The system comprises an NFC mobile phone terminal, an NFC POS machine terminal and a bank network mobile payment server; the NFC POS machine terminal is used for sending a payment request to the NFC mobile phone terminal through NFC signals; the NFC mobile phone terminal is used for receiving the payment request and sending a payment instruction to the bank network mobile payment server according to the payment request; and the bank network mobile payment server receives the payment instruction, processes related financial information and sends an operation result to the NFC POS machine terminal and the NFC mobile phone terminal. The method and the system are suitable for consumption settlement between consumers and trade companies.
Owner:BEIJING AIO TIME INFORMATION TECH
Device, method and system for preventing web page from being distorted
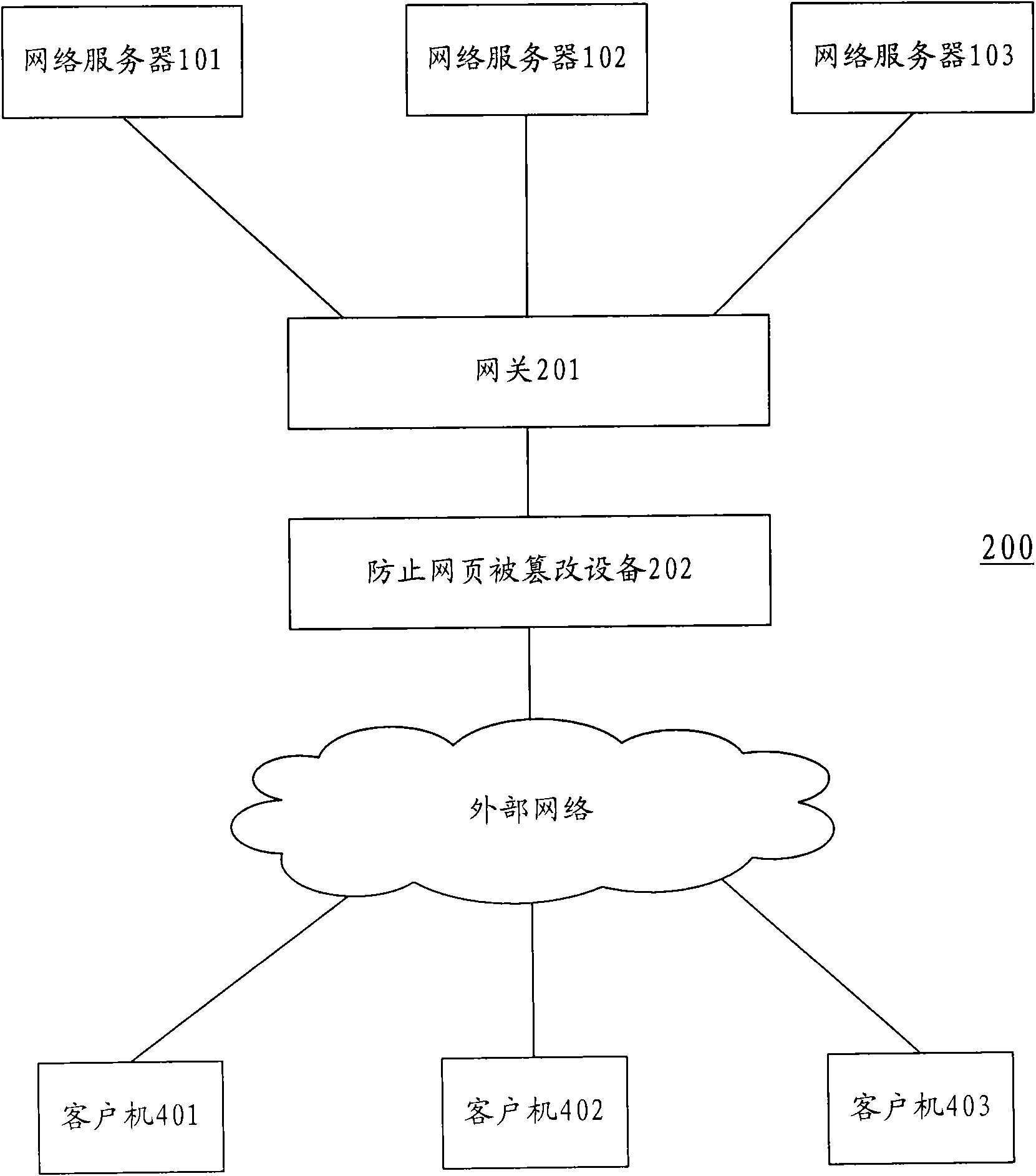
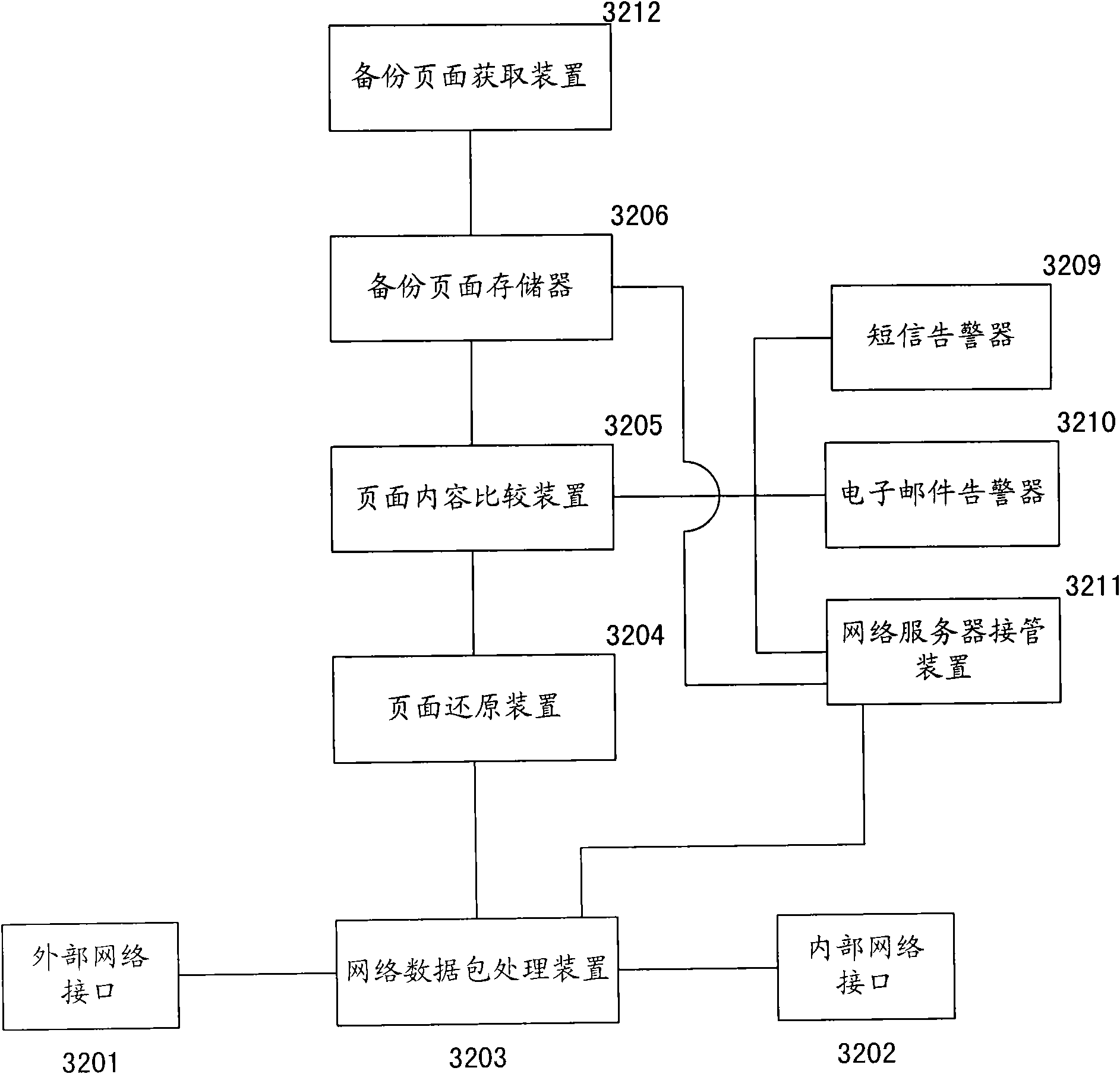
InactiveCN101626368APrevent secondary tamperingPrevent tamperingDigital data protectionData switching networksNetwork packetNetwork data
The invention discloses a device for preventing a web page from being distorted, wherein in the device for preventing the web page from being distorted, a network data pack processing device intercepts a network data pack returned from a network server, a page restoring device receives the network data pack intercepted by the network data pack processing device and restores the network data pack into the web page content, a page content comparing unit compares the web page content restored by the page restoring device with a pre-backup web page content corresponding to the restored web page content to determine whether the restored web page content is distorted and notifies a network server takeover device about the information on the distortion of the web page when the restored web page content is determined to be distorted, and when receiving the information on the distortion of the web page, the network server takeover device returns the pre-backup web page content corresponding to the restored web page content to external network users. The invention also provides a method used in the device for preventing the web page from being distorted, and a system using the device for preventing the web page from being distorted.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD
Lithium transition metal complex oxide for lithium ion secondary battery cathode active material and method for producing the same, lithium ion secondary battery cathode active material, and lithium ion secondary battery
InactiveUS20080241693A1Improve featuresAvoid security issuesIron compoundsCobalt compoundsLithium compoundSilicon
A lithium transition metal complex oxide for a lithium ion secondary battery cathode active material contains 100 to 1000 ppm of silicon and 300 to 900 ppm of fluorine. A method for producing the lithium transition metal complex oxide includes the step of mixing a lithium compound, a transition metal compound, a fluorine compound, and a silicon compound to prepare a raw material mixture, and the step of firing the raw material mixture to produce the lithium transition metal complex oxide.
Owner:NIPPON CHECMICAL IND CO LTD
Flight training data acquisition and quality evaluation system of analog machine
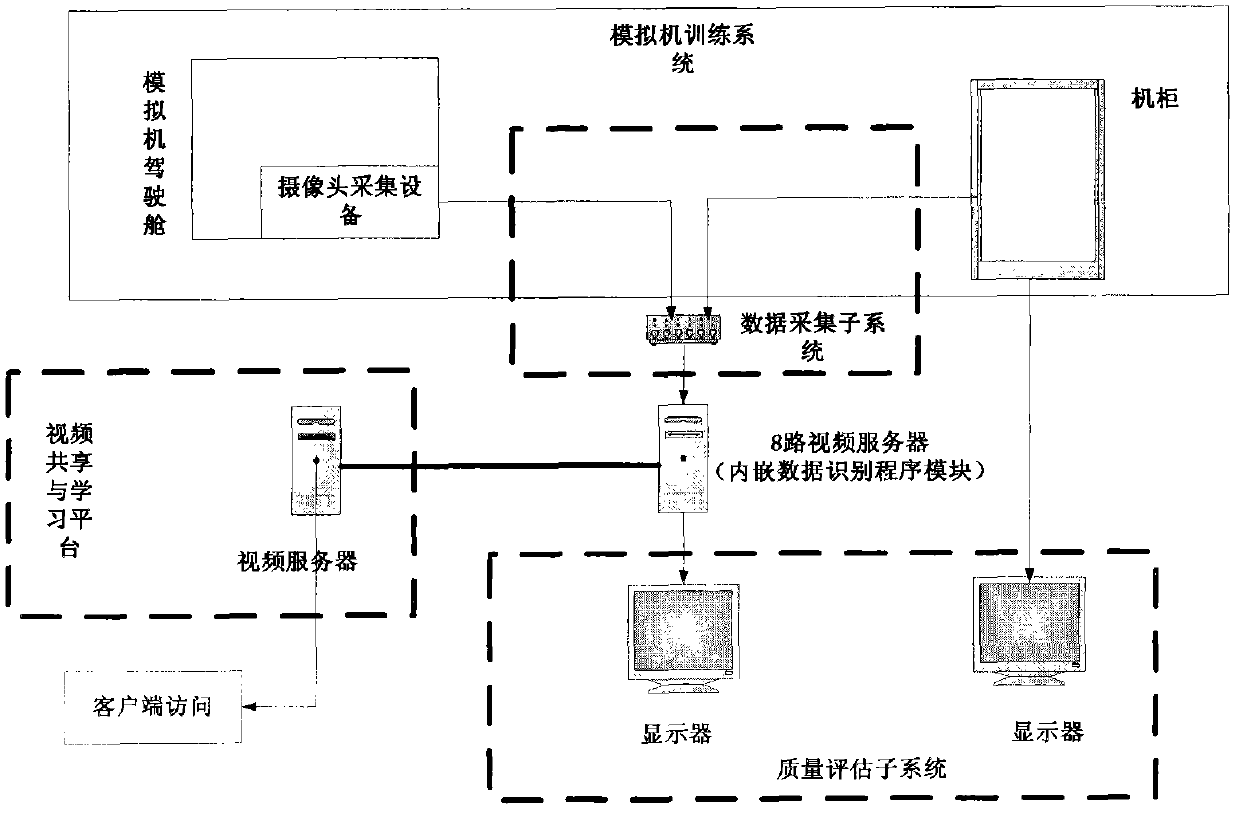
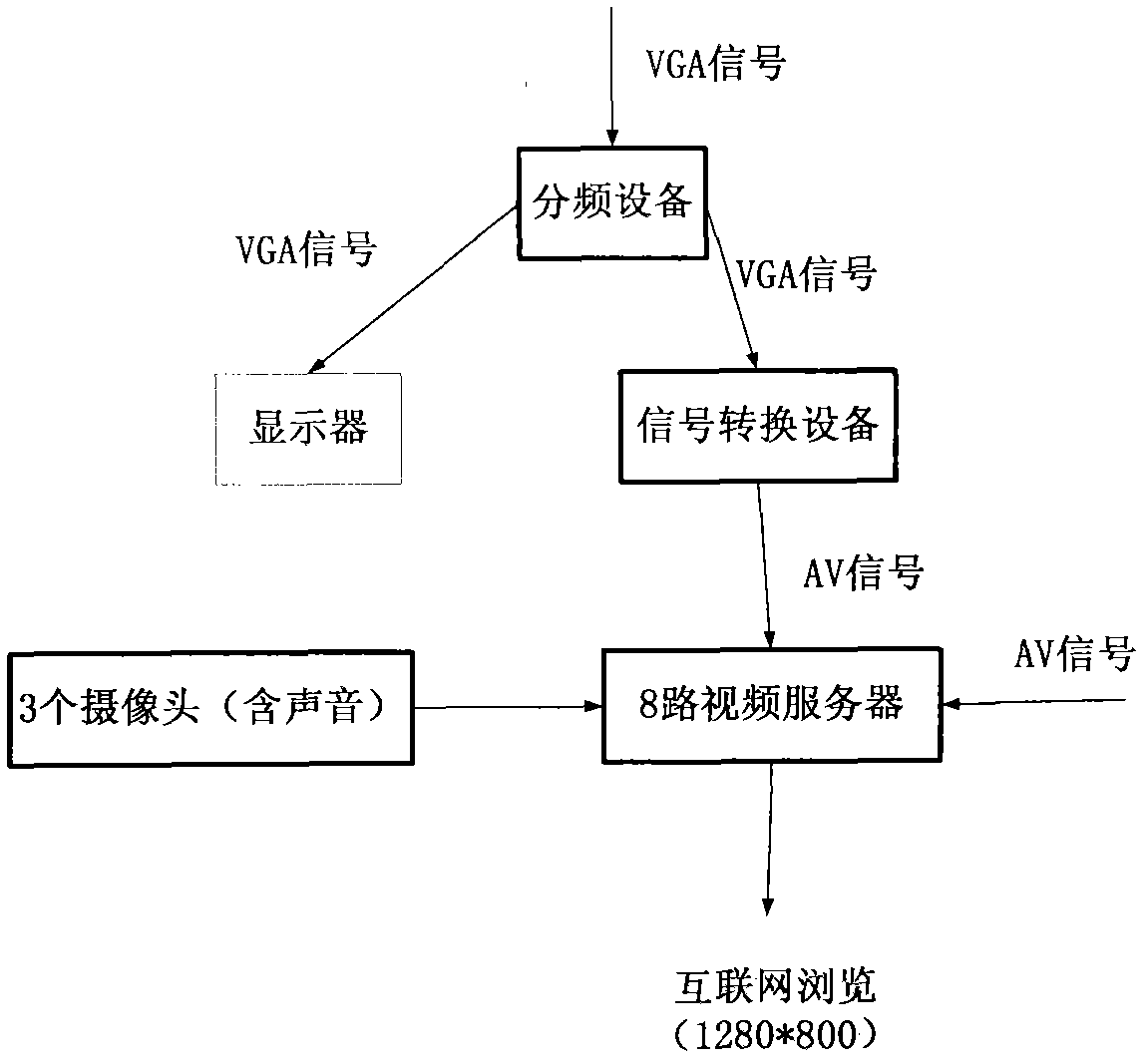
InactiveCN102053563AEase of evaluationRealize simultaneous playbackCosmonautic condition simulationsSimulator controlAviationThree dimensional simulation
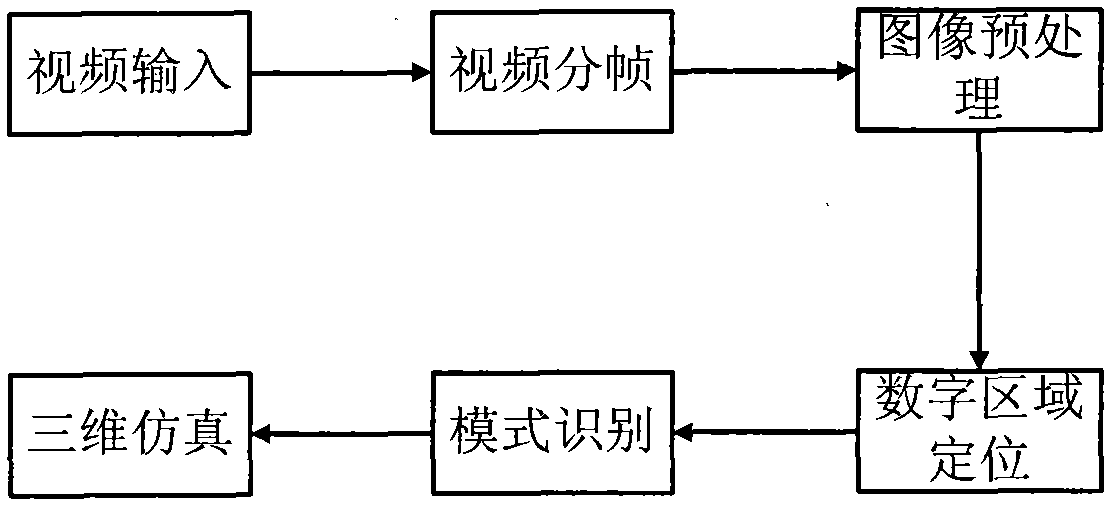
The invention belongs to the field of aviation training, relating to a flight training data acquisition and quality evaluation system of an analog machine and a technical scheme thereof, in particular to the problems of acquiring the videos of flight data in a training system monitor of the analog machine, preprocessing an image after video frame graduation by applying an image processing technology, recognizing the flight data in the image by using a pattern recognition technology, carrying out three-dimensional simulation on a flight path in the training process of the analog machine so as to further carry out teaching evaluation, generalizing and summarizing typical problems, submitting the problems and flight training videos to a video server and providing a share and study platform. Under the conditions of keeping fully isolation with an analog machine system and avoiding a data communication channel with the analog machine system, the flight training data acquisition and quality evaluation system provided by the invention accurately acquires the flight data, reproduces the training process of a pilot and evaluates the quality.
Owner:刘宇
Apparatus and method for identity-based encryption within a conventional public-key infrastructure
InactiveUS20070199071A1Avoid security issuesKey distribution for secure communicationDigital data processing detailsMaster keyCommon key
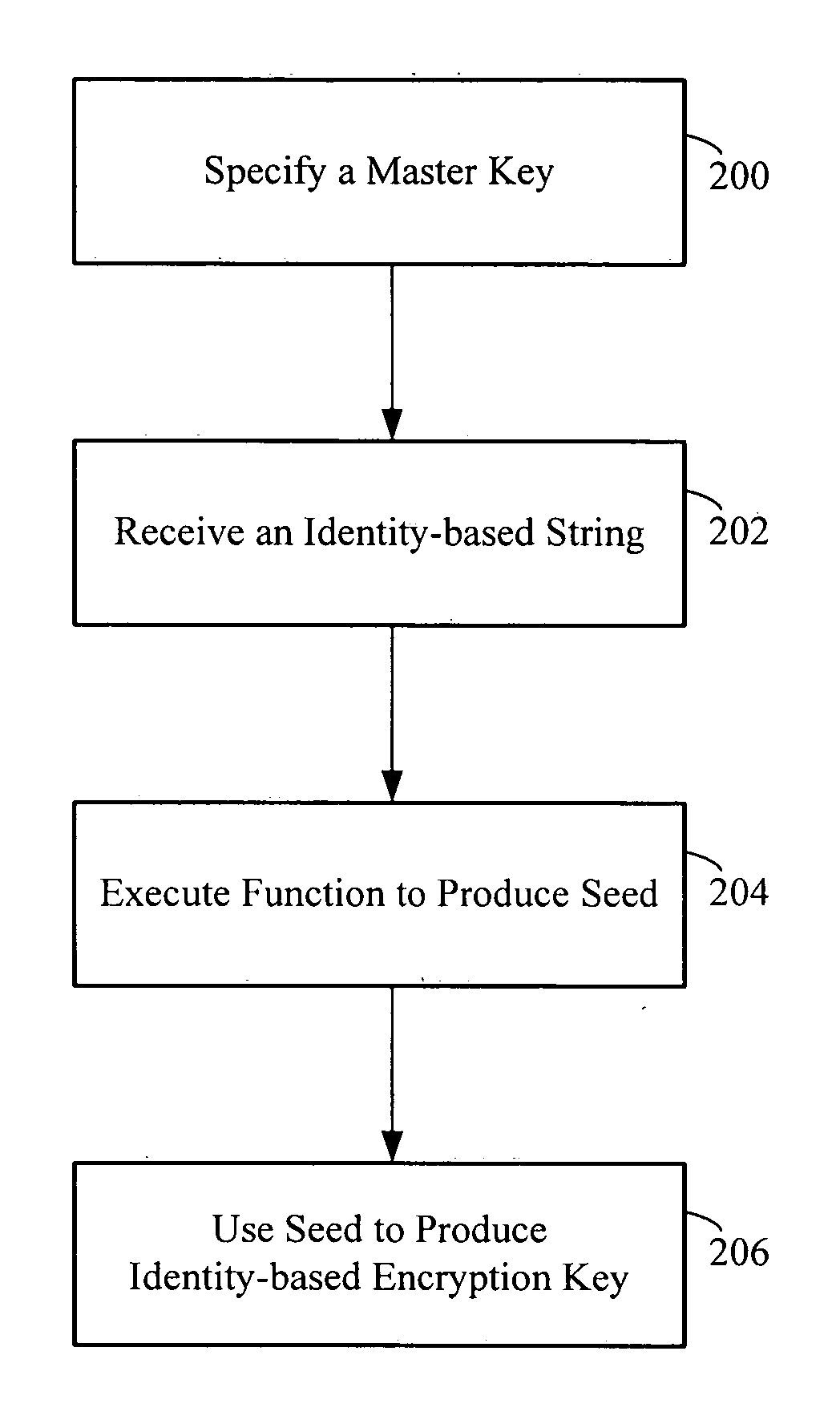
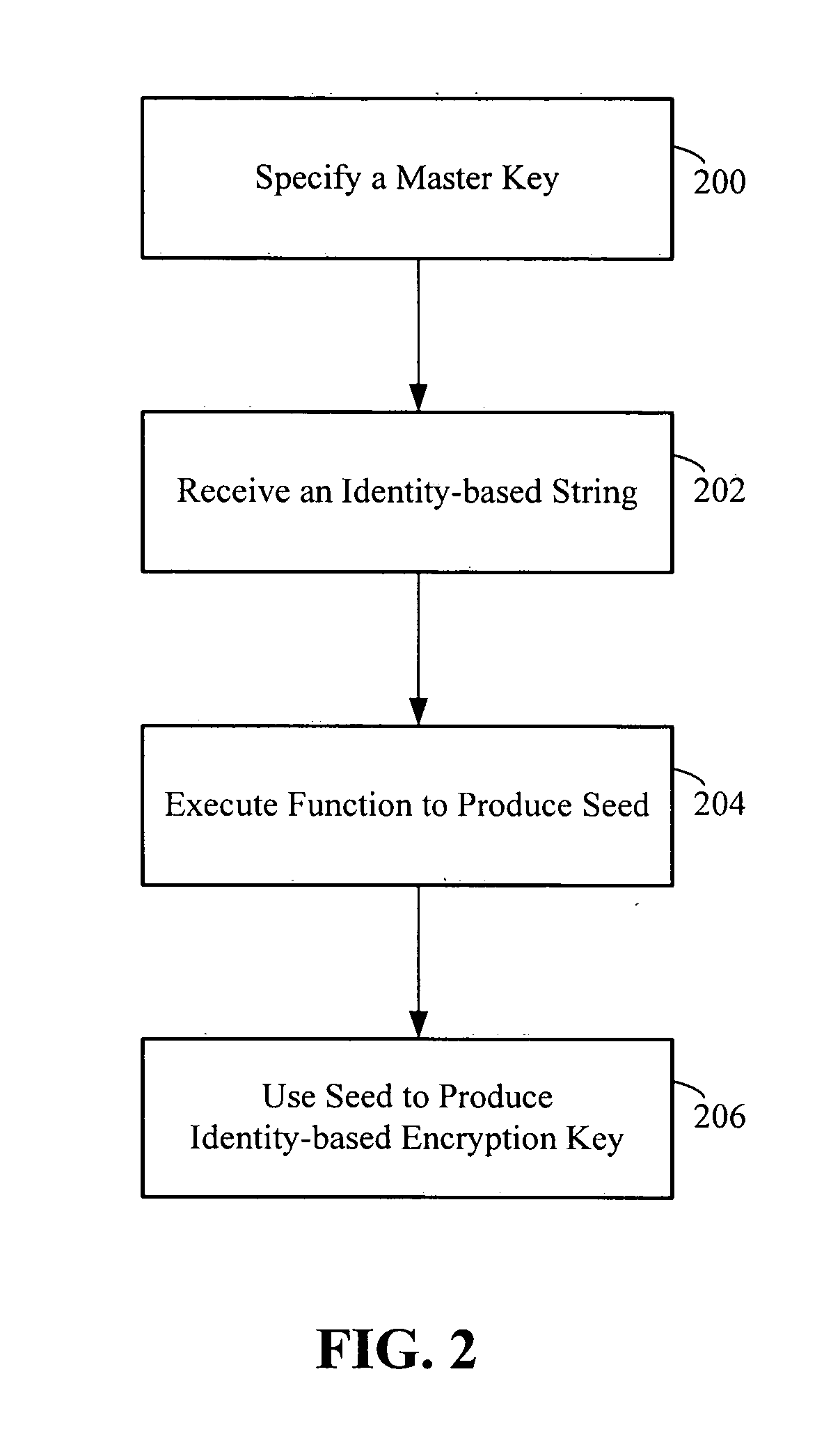
A method of generating an identity-based encryption key includes specifying a master key; receiving an identity-based string; executing a function that processes the master key and the identity-based string to produce a seed; and using the seed to produce an identity-based encryption key.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com