Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
379 results about "Security guarantee" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A security guarantee is a type of guarantee where the guarantor provides real estate as additional security for the borrower’s loan.
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
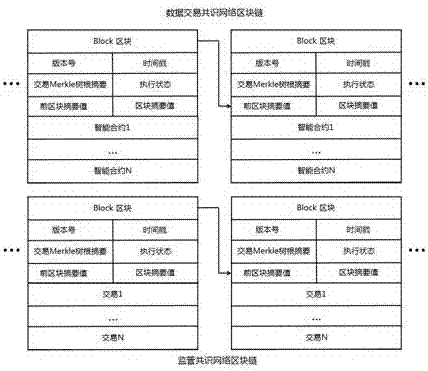
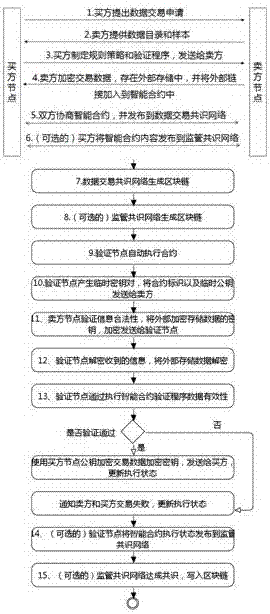
Block chain smart contract-based data transaction method
InactiveCN107464118AReduce storage costsGuaranteed execution efficiencyFinanceDatabase distribution/replicationThird partyExternal data
The invention relates to the technical field of big data, block chains and smart contracts, and in particular to a block chain smart contract-based data transaction method. According to the block chain smart contract-based data transaction method, purchase and sale behaviors of purchasers and sellers of transactions are recorded through block chains, automatic execution of the transactions is realized by utilizing smart contracts, and big data for the transactions is not recorded in the block chains and is encrypted and stored in an external data memory, so that the purchasers only can obtain the data after the smart contracts are successfully transacted; and moreover, the purchasers can publish transactions through a supervisory block chain consensus network, so that third-party witness is realized and the security guarantee of data transactions is increased.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
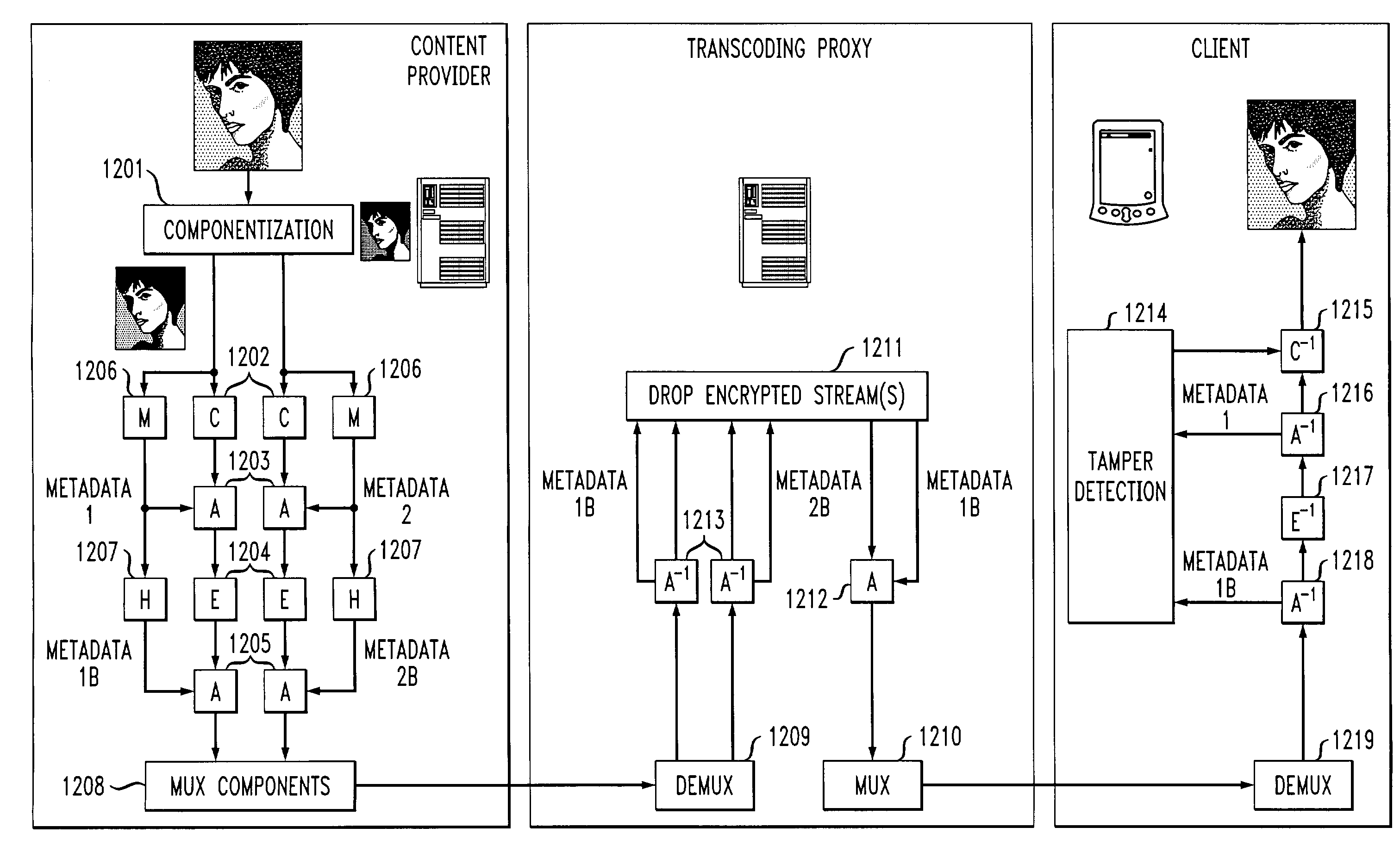
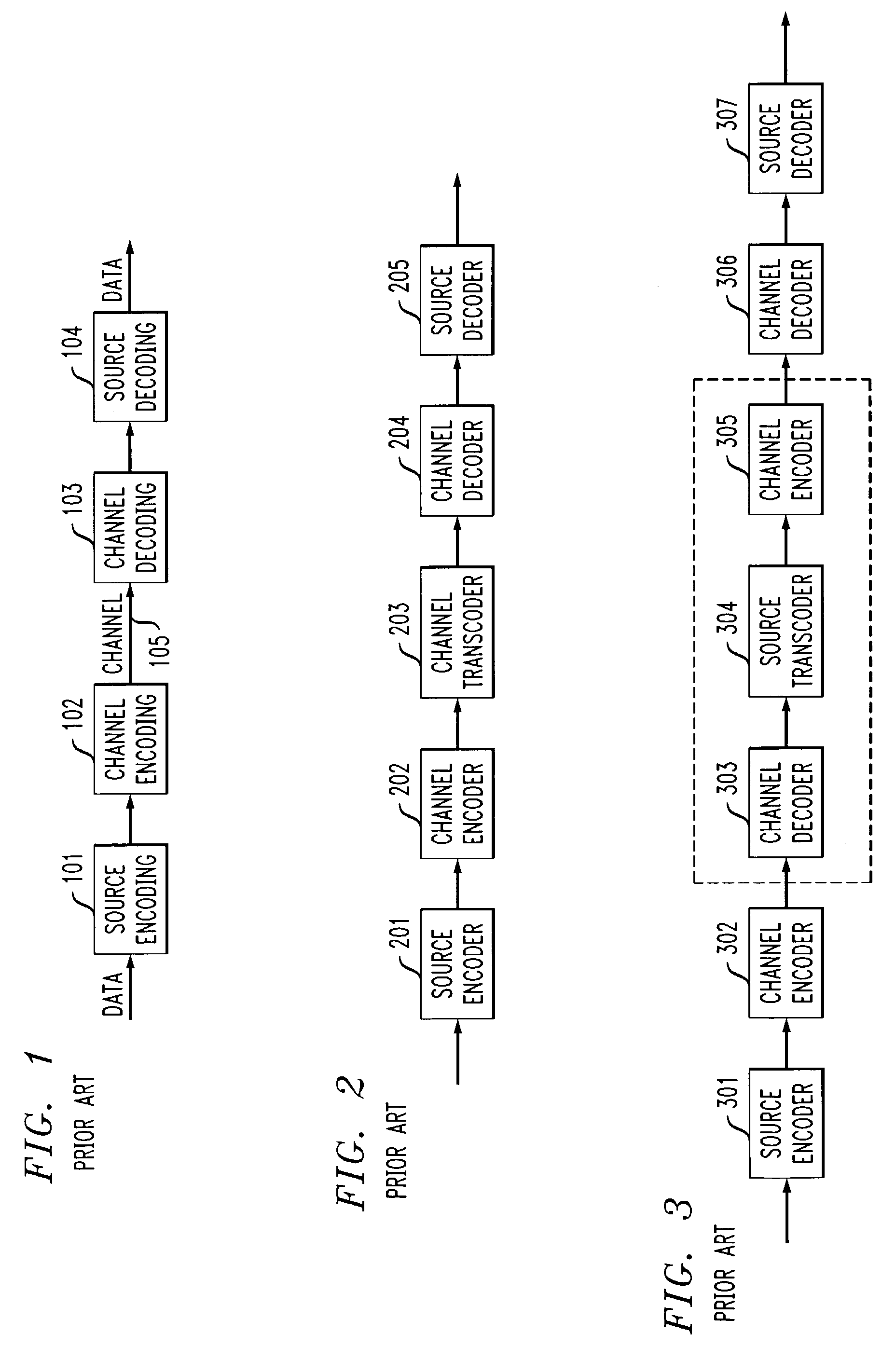
Method and apparatus for networked information dissemination through secure transcoding
ActiveUS6963972B1Improve speedIncrease speedUnauthorized memory use protectionHardware monitoringClient-sideMetadata
A method and system enables network intermediaries such as proxies to transcode multimedia data without violating end-to-end security guarantees. In one embodiment, a content provider decomposes a data stream into a plurality of components, each of which are independently encrypted. In a preferred embodiment, an intermediary or proxy performs transcoding of the components by prioritizing and dropping predetermined components, in accordance with unencrypted clear-text metadata associated with each component, without the need for decrypting the components. Clear-text metadata preferably provides a semantic understanding of the absolute or relative importance / priority of the components with respect to each other, thereby facilitating the transcoding process. The destination / client device can subsequently decrypt the components transmitted by the transcoding proxy and reassemble them into a representation of the original data content.
Owner:AWEMANE LTD
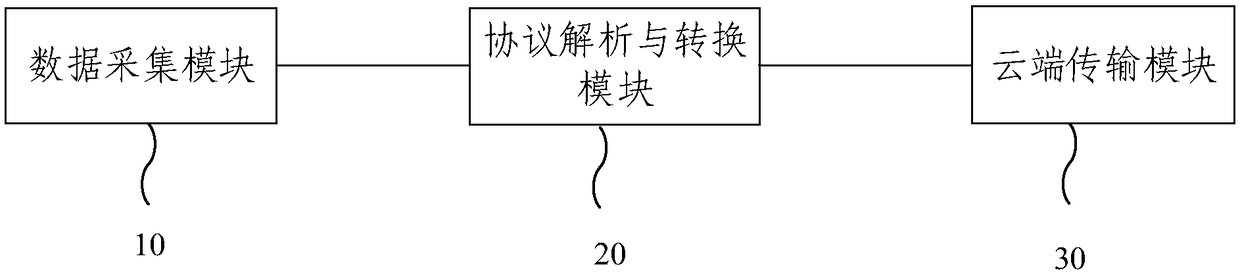
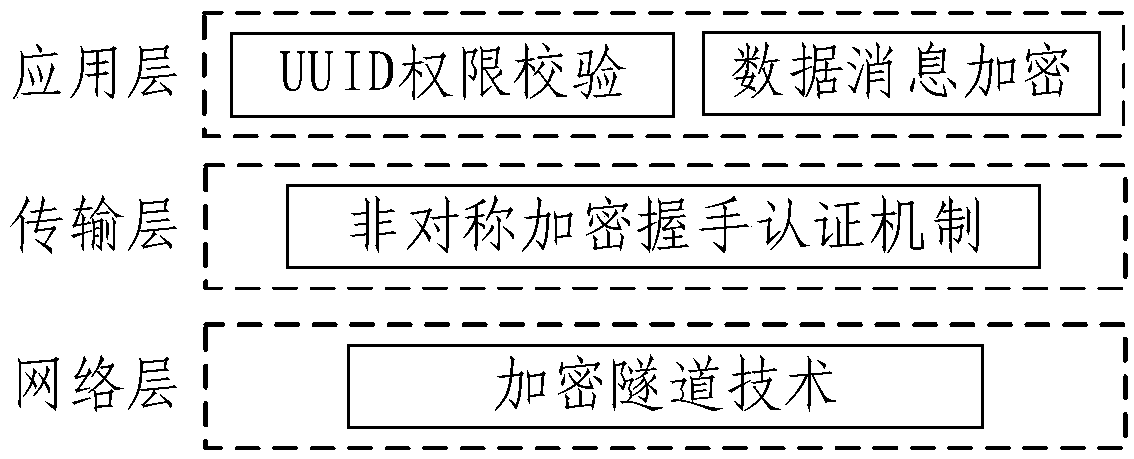
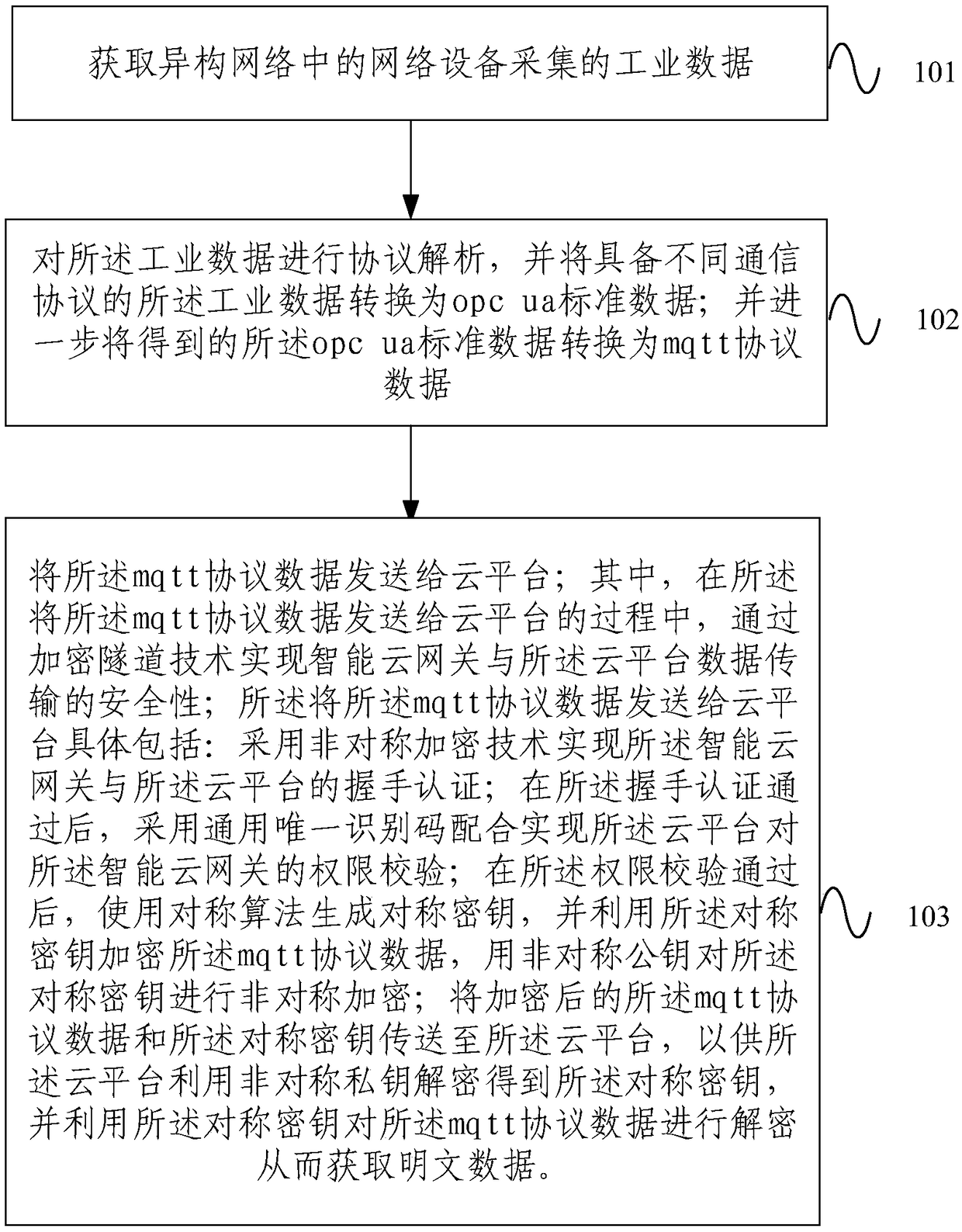
Intelligent cloud gateway of industrial IoT (Internet of Things) and communication method of gateway
ActiveCN109150703ASolve the problem of going to the cloudFix security issuesNetwork connectionsData transformationNetwork Communication Protocols
The invention provides an intelligent cloud gateway of the industrial IoT and a communication method of the gateway. The gateway comprises a data collection module, a protocol analysis and conversionmodule and a cloud transmission module; the data collection module obtains industrial data collected by network equipment in the heterogeneous network; the protocol analysis and conversion module analyzes protocols of the industrial data, converts the industrial data with the different communication protocols into OPC UA standard data, and further converts the obtained OPC UA standard data into MQTT protocol data; and the cloud transmission module transmits the MQTT protocol data to a cloud platform. Thus, the industrial data with the different protocols is sent to the cloud via the single gateway, different network device access schemes are provided, and the difficulty in transmitting the multi-protocol industrial data to the cloud in the heterogeneous network is solved; and the securityof data transmission is ensured comprehensively in the network, transmission and application layers, and a complete security guarantee system is formed.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
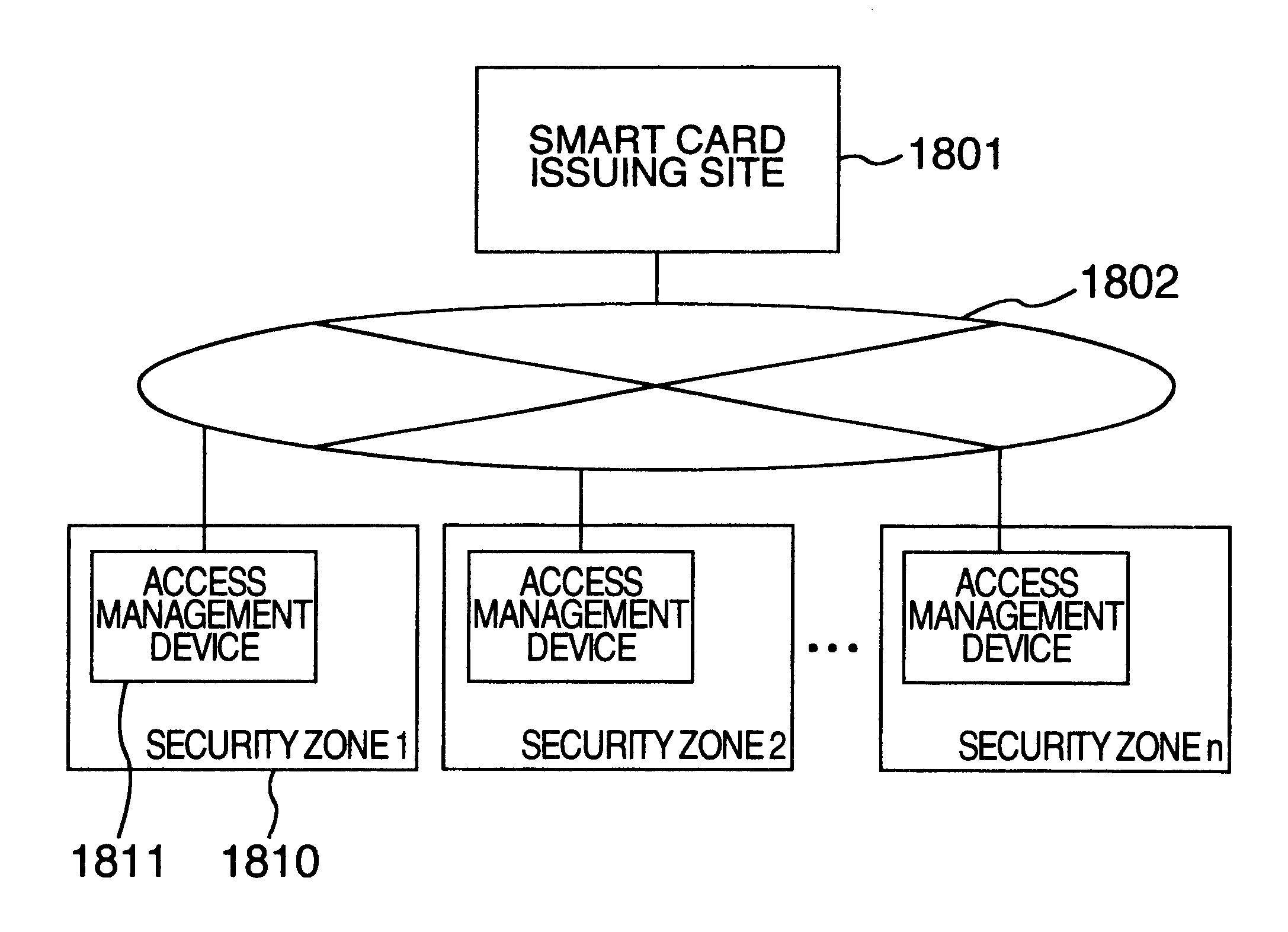
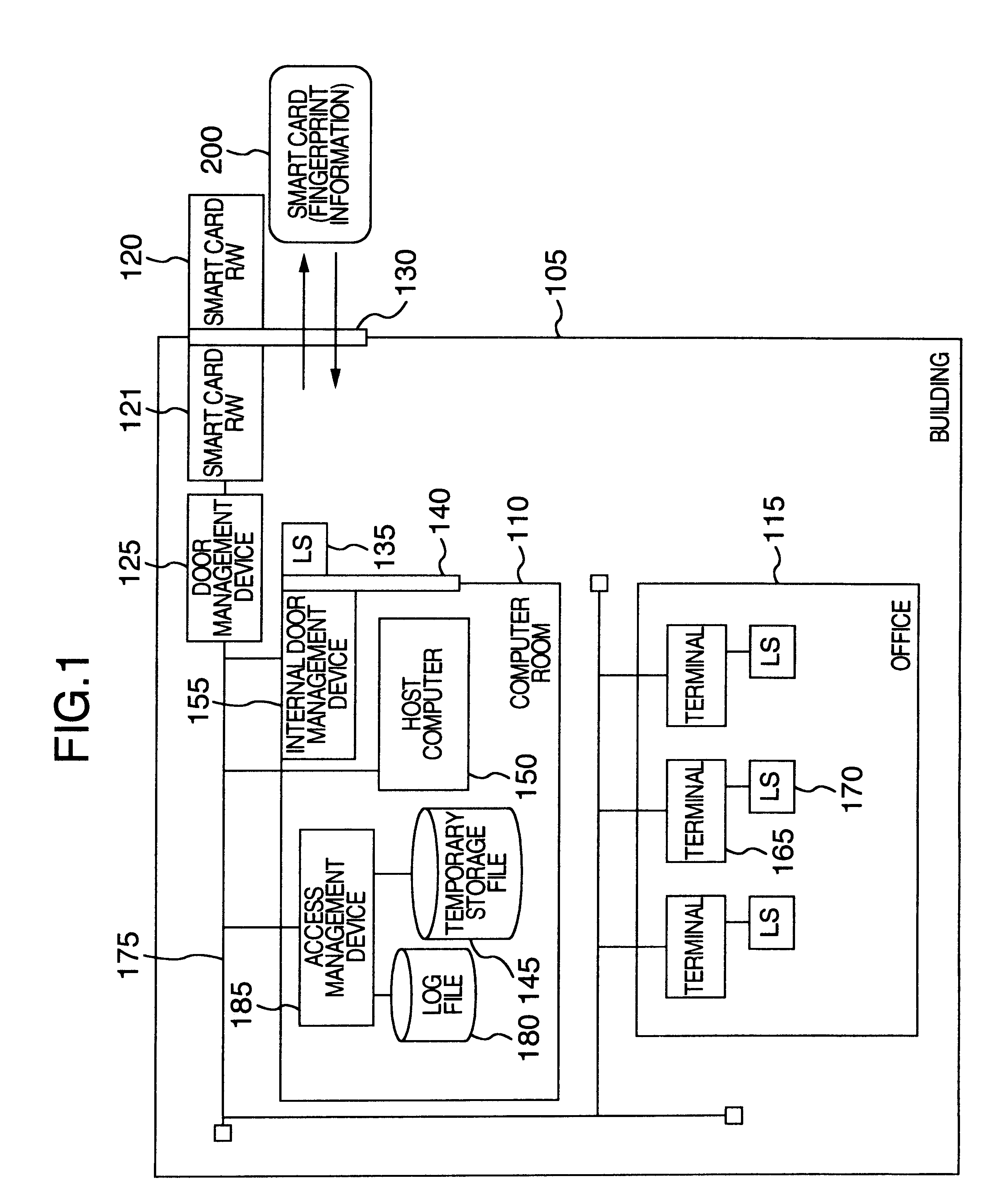
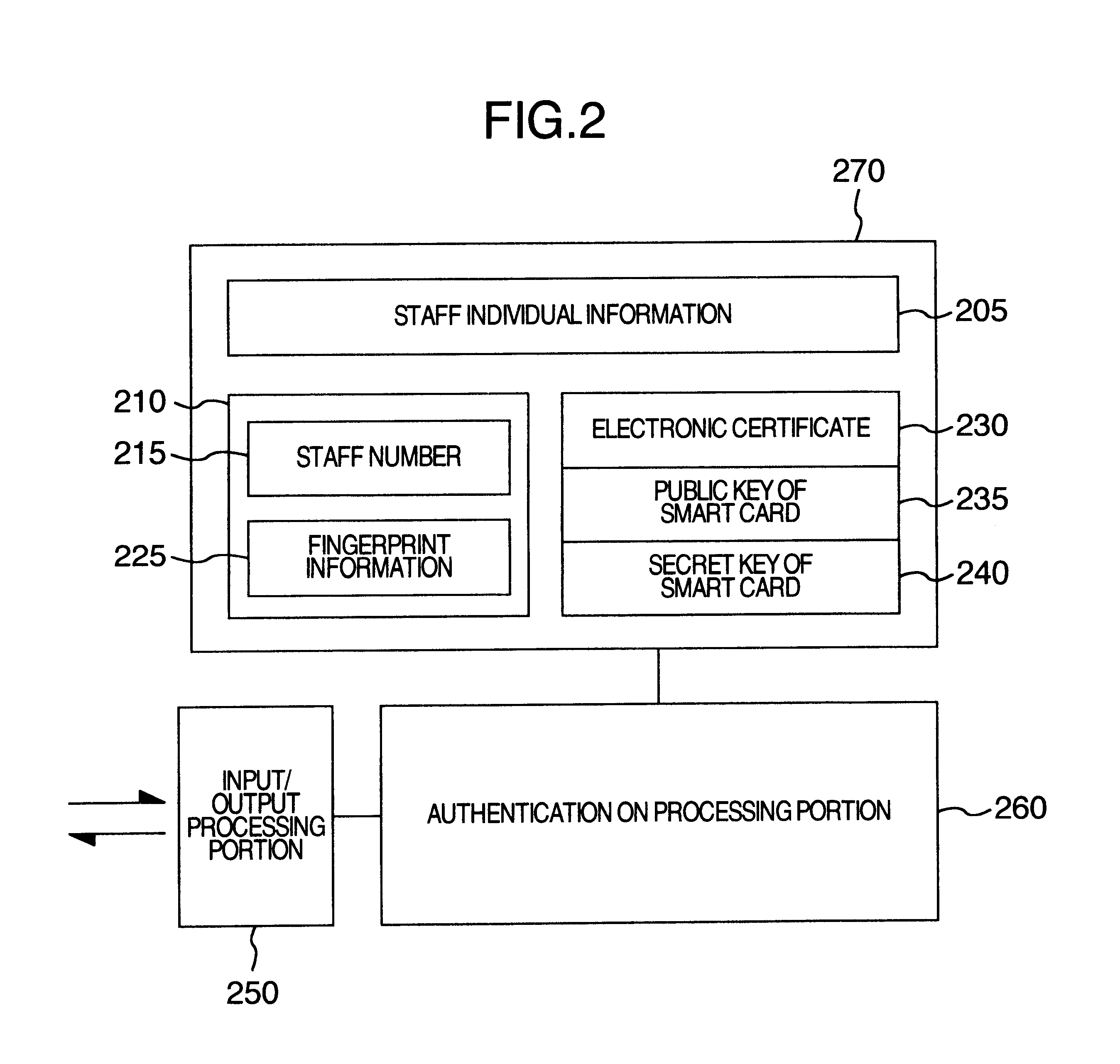
Security guarantee method and system
InactiveUS6747564B1Low costImprove securityElectric signal transmission systemsImage analysisEmployee numberSmart card
A security system wherein, when a staff enters a building, a smart card carried by the staff is verified, and staff information inclusive of a staff number and fingerprint information is read from the smart card and is stored temporarily in a temporary storage file. When the staff logs on to a terminal, the fingerprint of the staff is read by a fingerprint input device (LS) and verified with the fingerprint information of the temporary storage file for verification. When the staff leaves the building, the staff number is read from the smart card the staff carries, and the corresponding staff information is erased from the temporary storage file. Security of a security object inside a security zone can be improved.
Owner:HITACHI LTD
Credit-based blockchain consensus method for large-scale e-commerce
ActiveCN107395403APerformance is not affectedImprove consensus efficiencyFinanceData switching networksPublic environmentThe Internet
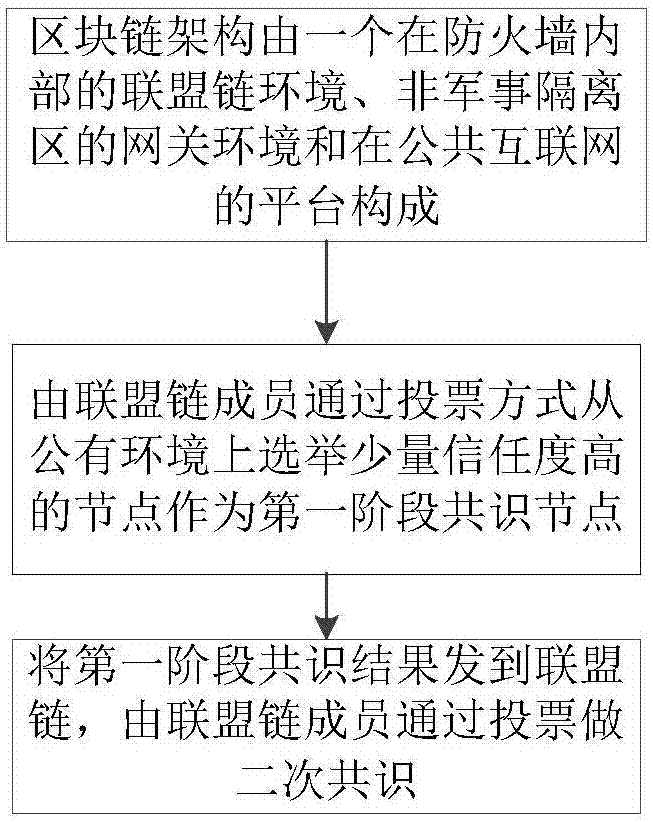
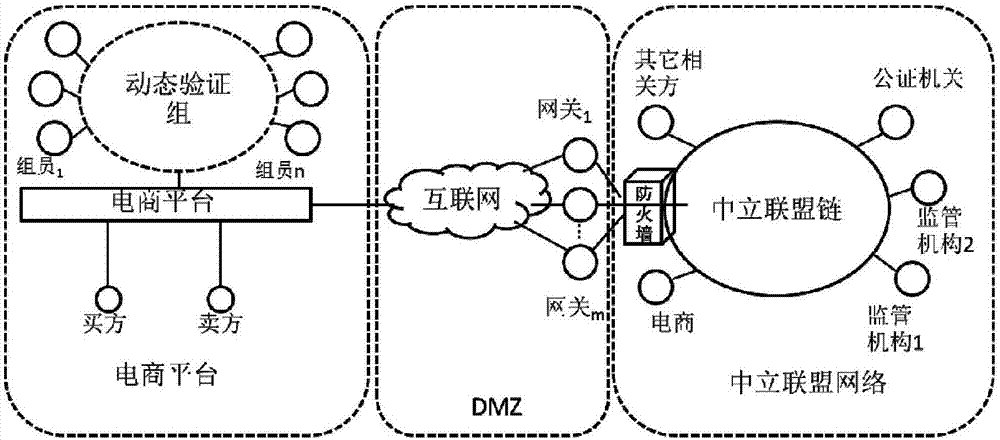
The invention discloses a credit-based blockchain consensus method for large-scale e-commerce. According to the method, by applying a blockchain to the large-scale e-commerce application scene, the scalability needed by the large-scale e-commerce scene can be achieved, millions of nodes can be supported, the consensus requirement that the service speed of the e-commerce is ten millions per second can be met, energy consumption such as Bitcoins is not needed, and the problem that a blockchain adopting proof of stake (POS) is lack of security guarantee is solved. The method comprises the steps that 1, the structure of the blockchain is composed of an alliance chain environment in a firewall, a gateway environment in a non-military isolation area and a platform in the public Internet; 2, alliance chain members elect a few nodes with a high trust degree from a public environment to serve as first-stage consensus nodes; and 3, a first-stage consensus result is sent to a alliance chain, the alliance chain members perform secondary consensus through voting to ensure the accuracy of the consensus result from the public environment, and then the security requirement is met.
Owner:北京区块链云科技有限公司
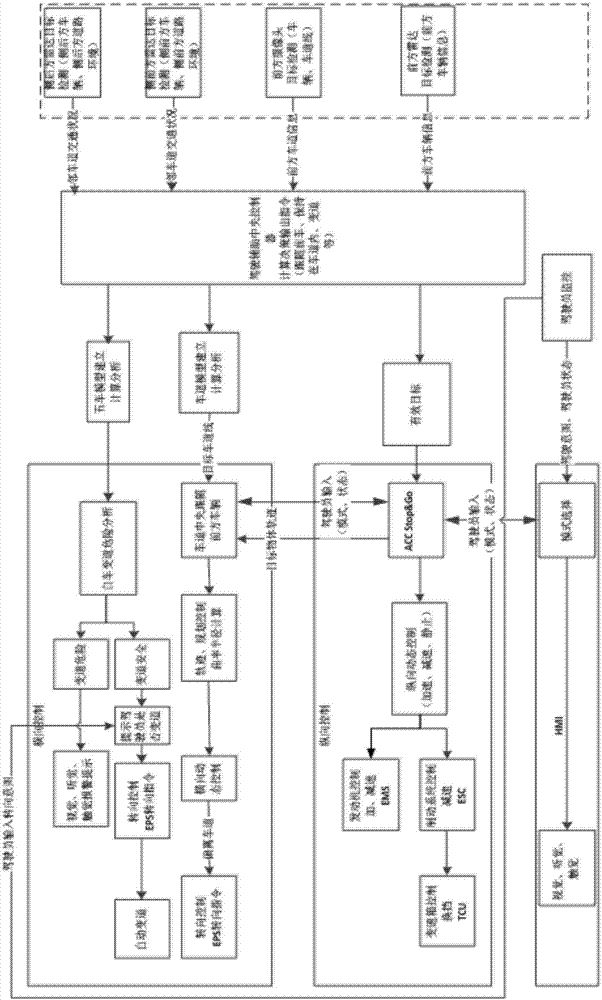
Super highway auxiliary system
The invention provides a super highway auxiliary system, and belongs to the field of safe driving of automobiles. The super highway auxiliary system comprises a radar sensor, a camera sensor, a central controller and a vehicle-mounted ECU execution unit, wherein the radar sensor is used for detecting environmental information and vehicle information around a current vehicle; the camera sensor is used for collecting the environmental information around the current vehicle; the central controller is used for receiving the information transmitted from the radar sensor and the camera sensor, collecting the vehicle information of the current vehicle transmitted by an ECU, integrating the information for processing and judgment, and issuing an instruction to the relevant vehicle-mounted ECU execution unit; and the vehicle-mounted ECU execution unit is used for receiving the instruction and controlling the current vehicle to execute the instruction. Through the adoption of the super highway auxiliary system provided by the invention, the hands and feet of a driver are liberated to the greatest extent, so that driver fatigue due to a monotonous driving mode is avoided; the seamless connection between super highway assist and traffic jam assist is realized; and two cases that changing lanes is dangerous and changing lanes is safe are distinguished by the system, and different assists are provided for the driver, so that not only is the lane change security guaranteed, but also the convenience of lane change is provided, and the driving pleasure is improved.
Owner:GEELY AUTOMOBILE INST NINGBO CO LTD +1
Information interaction method and system for electronic cigarettes
InactiveUS20150288468A1Promote exchangeEasy to buildBroadcast specific applicationsNetwork topologiesBroadcast domainElectronic cigarette
An information interaction method and system for electronic cigarettes is provided in the present invention; the method comprises the following steps: at least one of the electronic cigarettes sending broadcast information containing electronic cigarette information of the one electronic cigarette to one or more of the other electronic cigarettes, and / or sending request information containing obtaining request for electronic cigarette information to one or more of the other electronic cigarettes, and / or sending response information which is generated to response request information; at least one of the electronic cigarettes receiving broadcast information, requesting information or responding information from one or more of the other electronic cigarettes. When implementing the present invention, the following advantageous effects can be achieved: it is convenient for users to exchange electronic cigarettes information and establish social intercourse; users can be helped to choose suitable electronic cigarettes for themselves; the uses can obtain security guarantee.
Owner:XIANG ZHIYONG
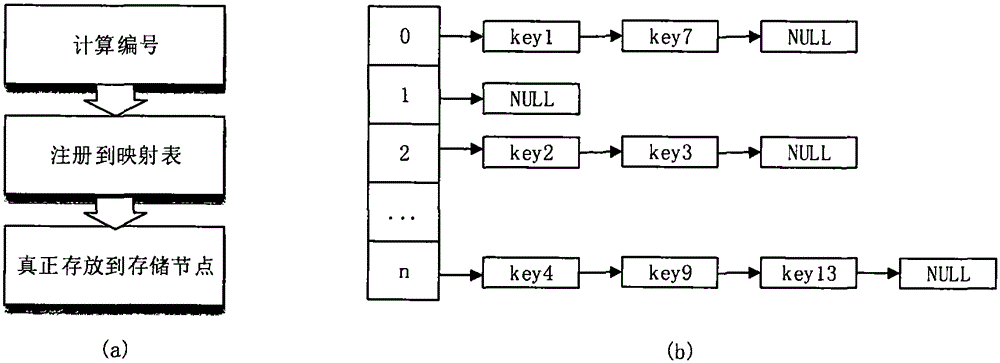
Log recovery method in memory data management and log recovery simulation system in memory data management
ActiveCN105159818AReduce complexityIncrease speedHardware monitoringRedundant operation error correctionRecovery methodSelf recovery
The invention discloses a log recovery method in memory data management and a log recovery simulation system in memory data management, and relates to the technical field of data management. The method comprises the following steps that: (1) a main node obtains a node ID (identification) of a cluster node; a data write-in command is sent to the cluster node; the cluster node performs data storage; and the main node forms a mapping table; (2) the main node sends a cluster node log command to a log node matched with the cluster mode according to the node ID; and the log node stores the log, performs persistence on the log, and then successfully records information into the main node log; and (3) when the cluster node fails, the transaction execution is stopped; and the main node obtains a fault node ID and obtains log records in the log node for recovery. Partial fault nodes in the cluster node can achieve the self recovery state; the mutual transmission of relevant data item information is not needed; the log recovery complexity is reduced; the log recovery speed is accelerated; and the security guarantee is achieved.
Owner:NORTHEASTERN UNIV
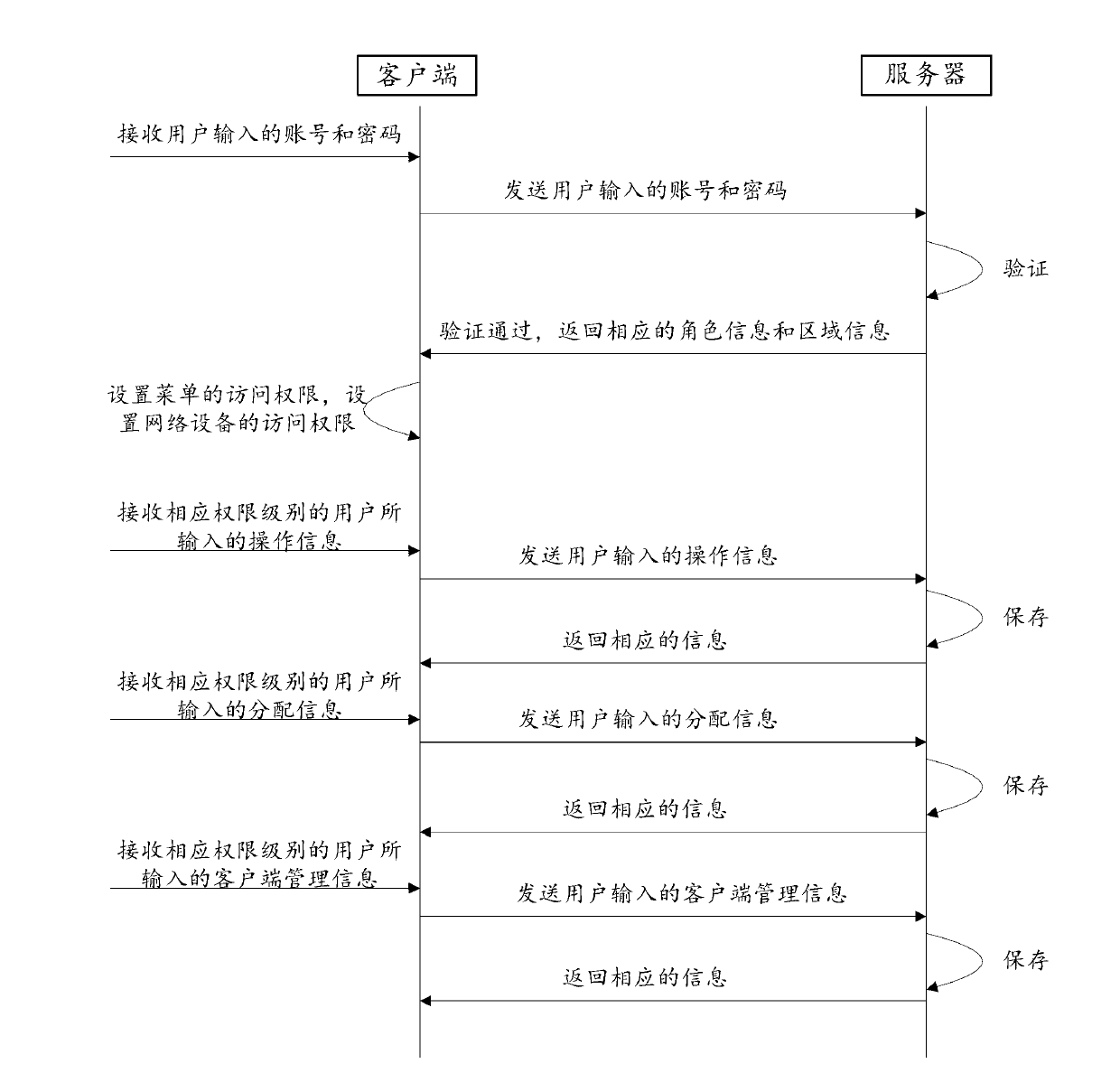
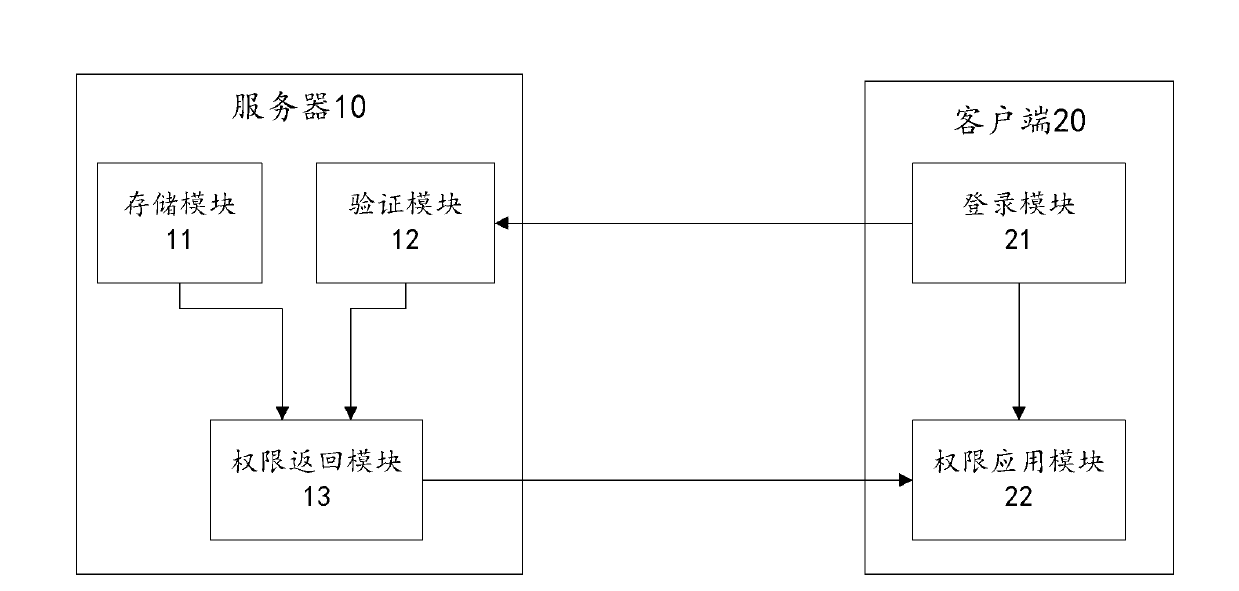
Method and system for achieving right management in network management
InactiveCN103001803AAvoid duplicationAvoid the problem of ultra vires managementData switching networksUser inputPassword
The invention discloses a method and a system for achieving right management in network management. The method includes that a server stores a plurality of pieces of user information including an account number, a password, role information and zone information, wherein the role information is used for indicating access rights of a menu and the zone information is used for indicating access rights of network equipment; a client receives and sends the account number and the password which are input by a user to the server for verification when the user logs in at the client; if the verification by the server is passed, the server returns the corresponding role information and the zone information to the client; and after the user logs in at the client, access rights of menus are set according to the role information and access rights of the network equipment are set according to the zone information. According to the method and the system, not only the problems of management repetition and management in excess of rights are solved, but also security guarantee is provided for maintenance of the network equipment, and safety of network management is safeguarded.
Owner:PHICOMM (SHANGHAI) CO LTD
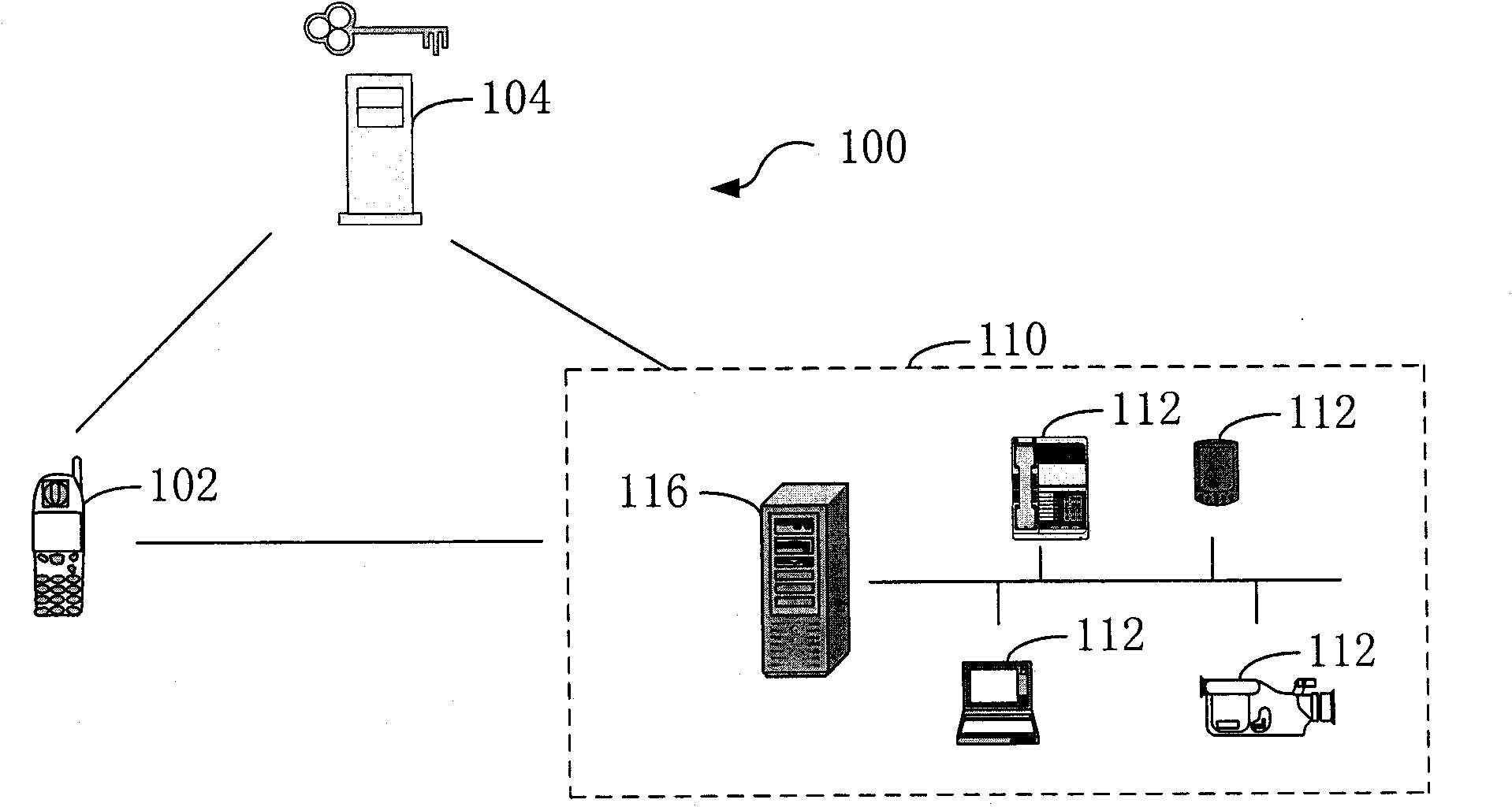
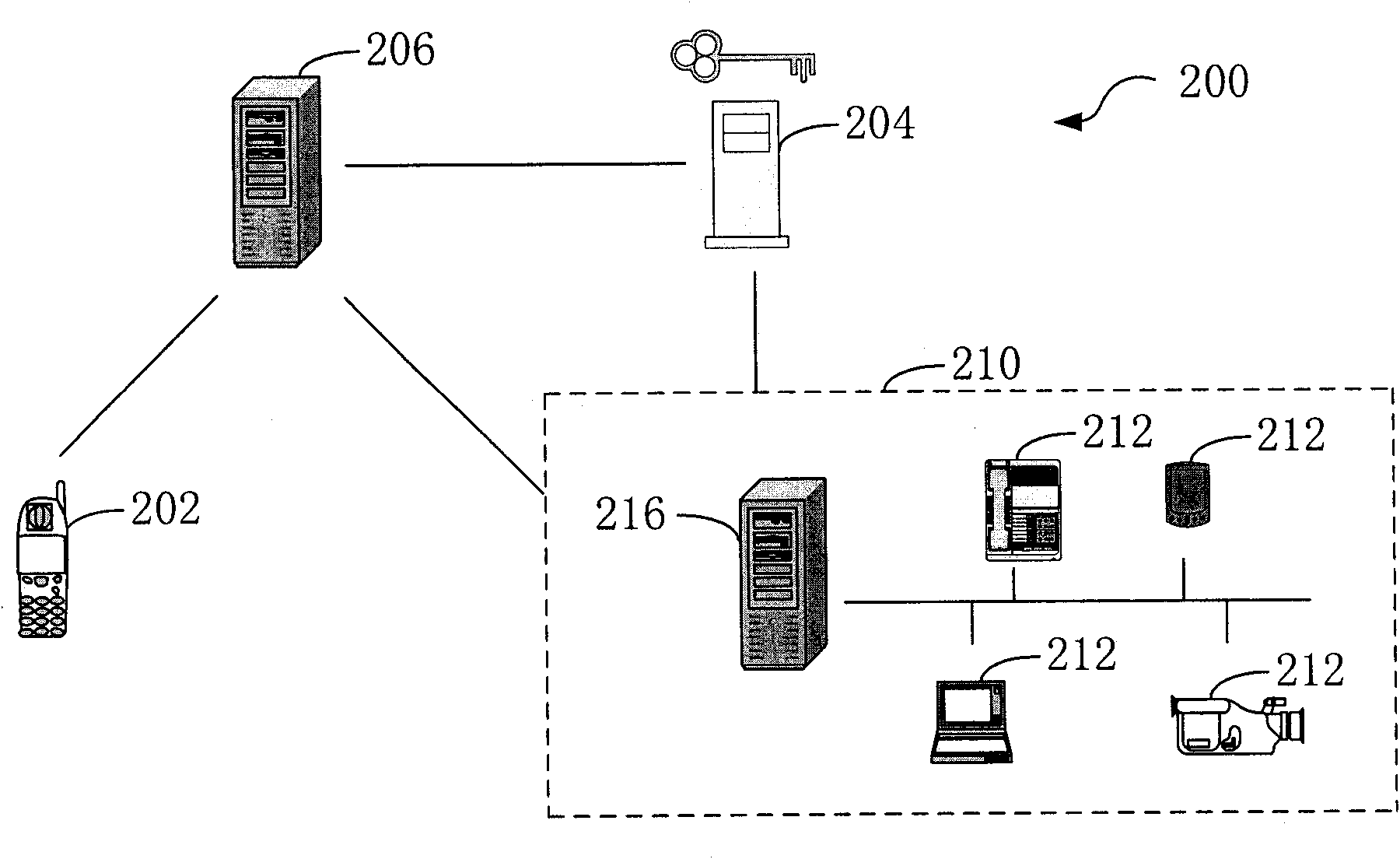
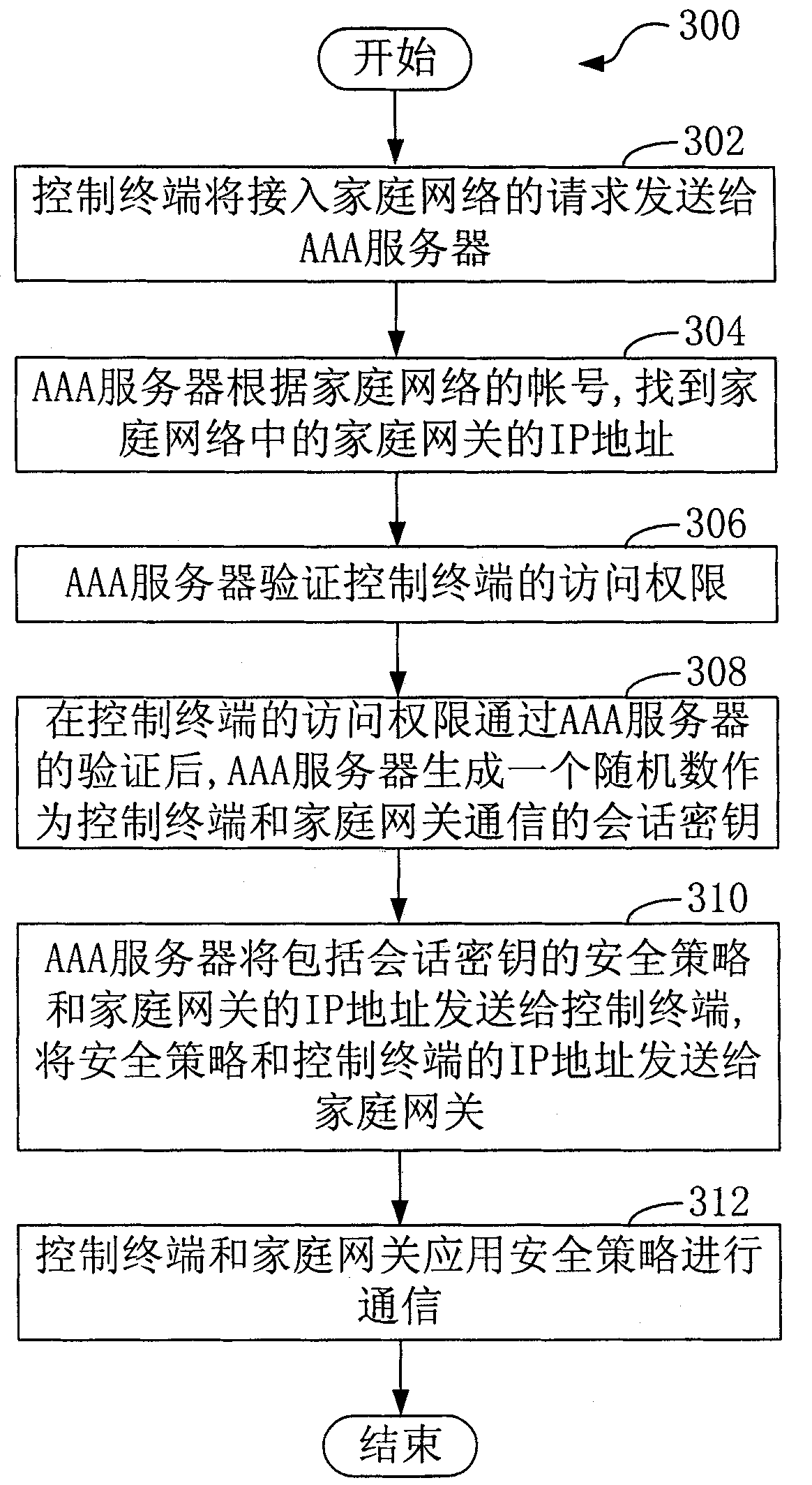
AAA server, home network access method and system
ActiveCN101820344AThe Method of Realizing Remote Security AccessEasy to useUser identity/authority verificationData switching by path configurationAccess methodIp address
The invention provides an AAA server and a home network access method and a system, relating to the field of network security, wherein the home network access method comprises the following steps of: sending a request of accessing a home network to an AAA server by a control terminal, wherein the access request comprises the account number of the home network; finding the IP address of the home gateway in the home network by the AAA server according to the account number of the home network; verifying the access right of the control terminal by the AAA server; after the access right of the control terminal passes the verification of the AAA server, generating a random number by the AAA server to serve as a session key of the communication of the control terminal and the home gateway; sending a security policy comprising the session key and the IP address of the home gateway to the control terminal by the AAA server; sending the security policy and the IP address of the control terminal to the home gateway; and carrying out communication between the control terminal and the home gateway by applying the security policy. The invention realizes the remote safe access of the home network by means of the security guarantee of network access.
Owner:CHINA TELECOM CORP LTD
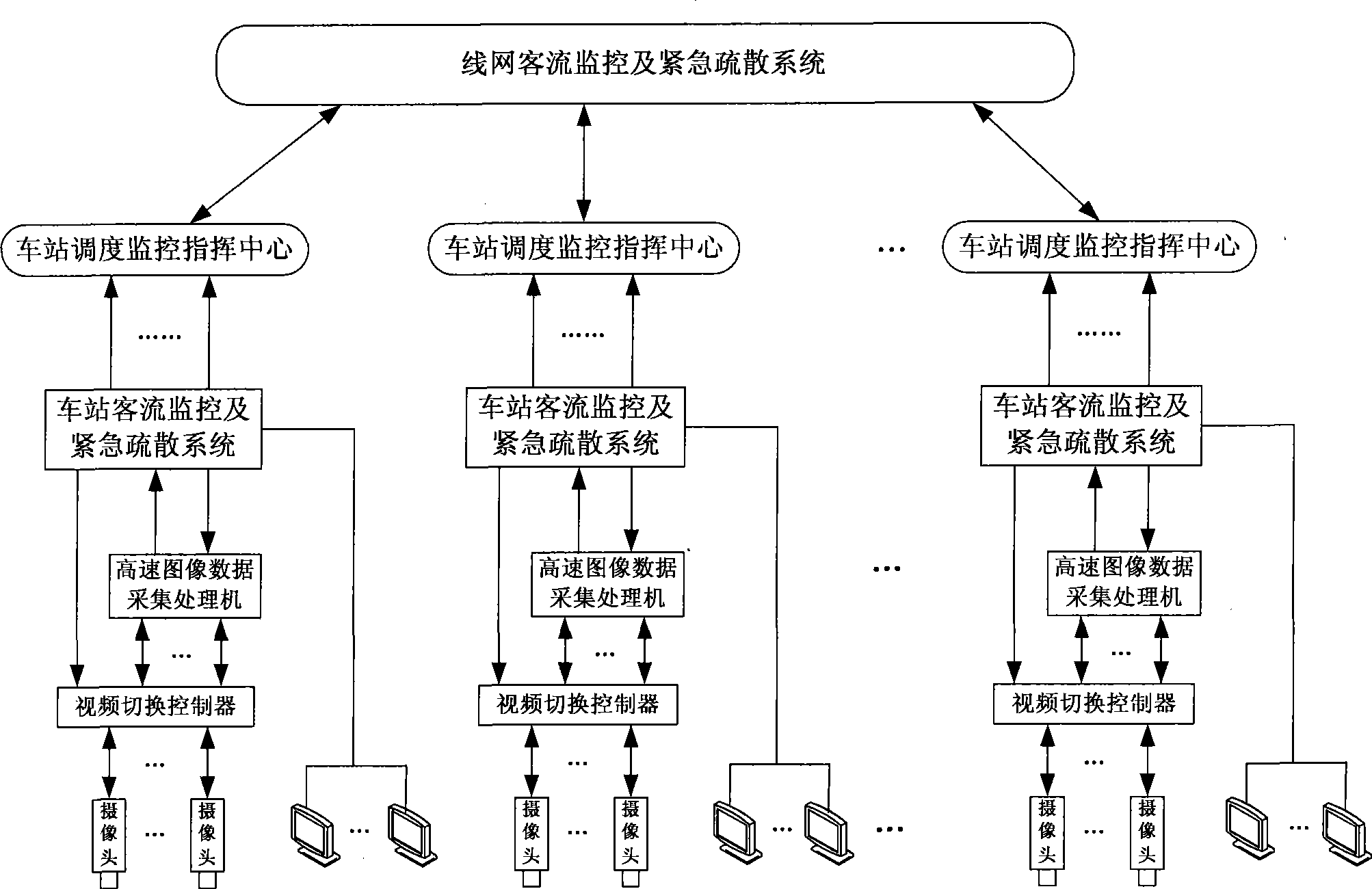
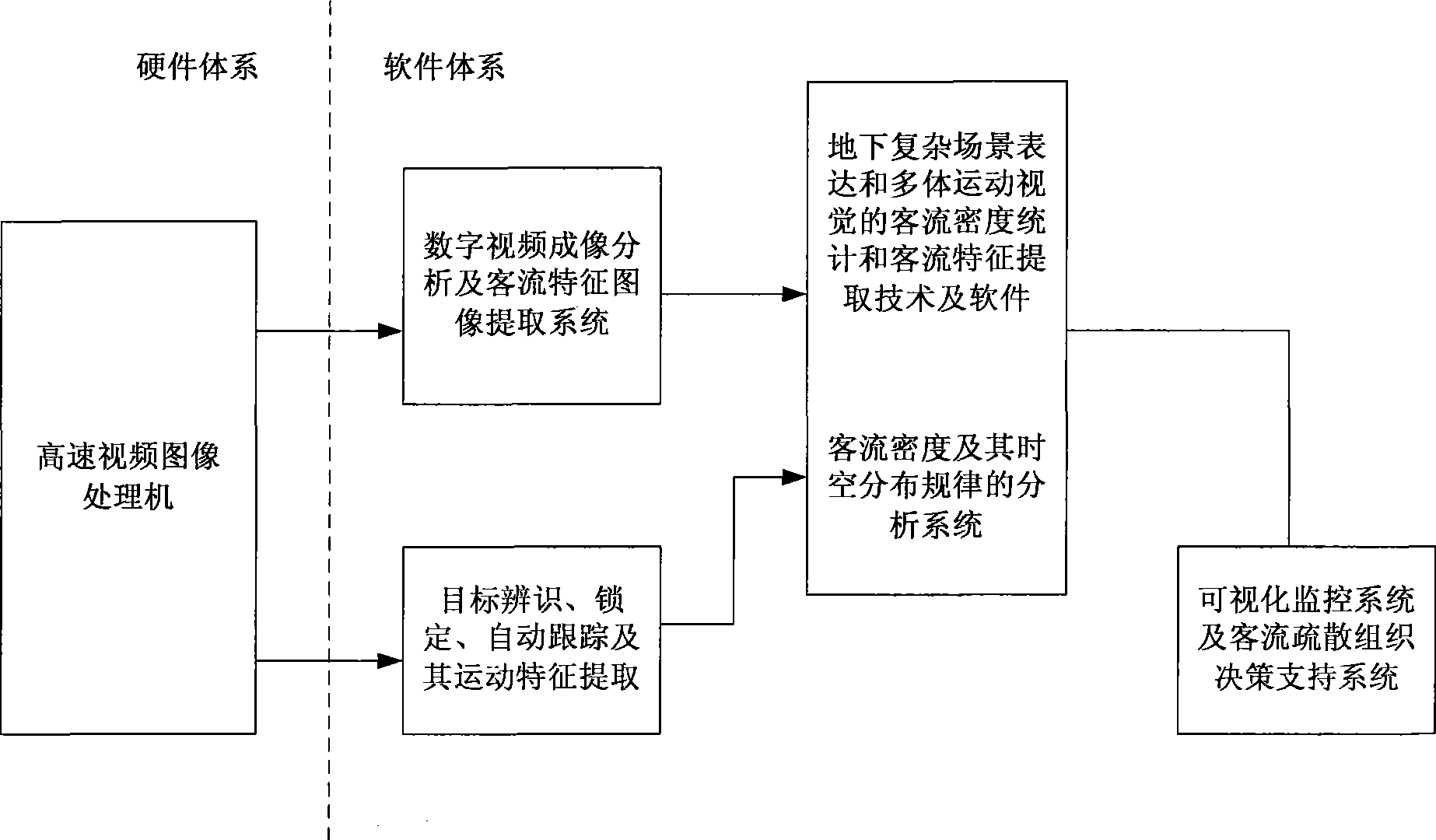
System of urban track traffic for passenger flow monitor and emergency evacuation
ActiveCN101445122AAuto Start TuningRailway traffic control systemsClosed circuit television systemsDigital videoData acquisition
The invention discloses a system of an urban track traffic for passenger flow monitor and emergency evacuation in the technical field of subway passenger flow security guarantee, which has the technical scheme that the system comprises a hardware part and a software part; the hardware part comprises a station camera, a multi-channel video switching controller, a high-speed image data acquisition processor, a station dispatching centre processor and a line network command center processor; the station camera is connected with the high-speed image data acquisition processor through the multi-channel video switching controller; the high-speed image data acquisition processor is connected with the station dispatching centre processor which is connected with the line network command center processor; and the software part comprises a digital video imaging and analyzing programme, a station passenger flow monitor and emergency evacuation system and a line network passenger flow monitor and emergency evacuation system. The system monitors the passenger flow volume and the passenger flow distribution in a real-time manner, and can start up the emergency handling process automatically to adjust a service system as needed in a real-time manner.
Owner:BEIJING JIAOTONG UNIV
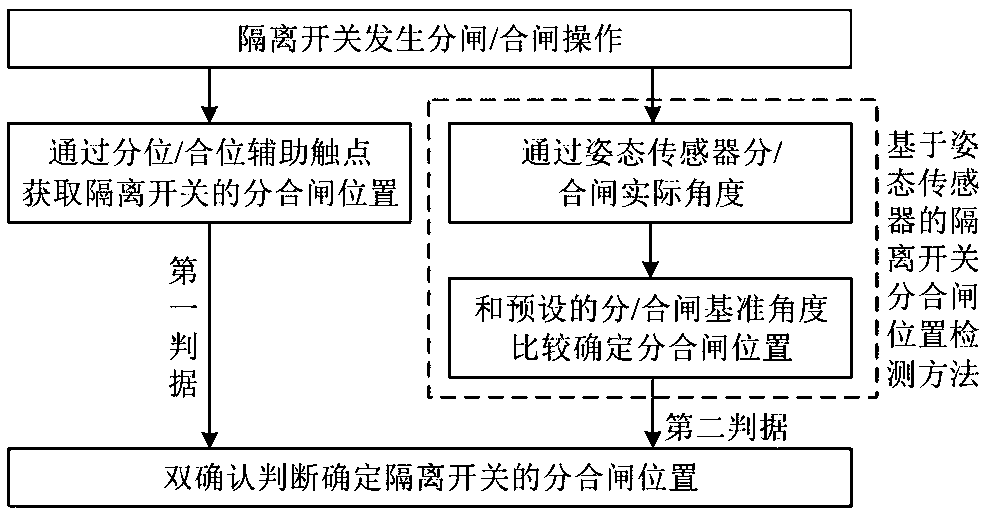
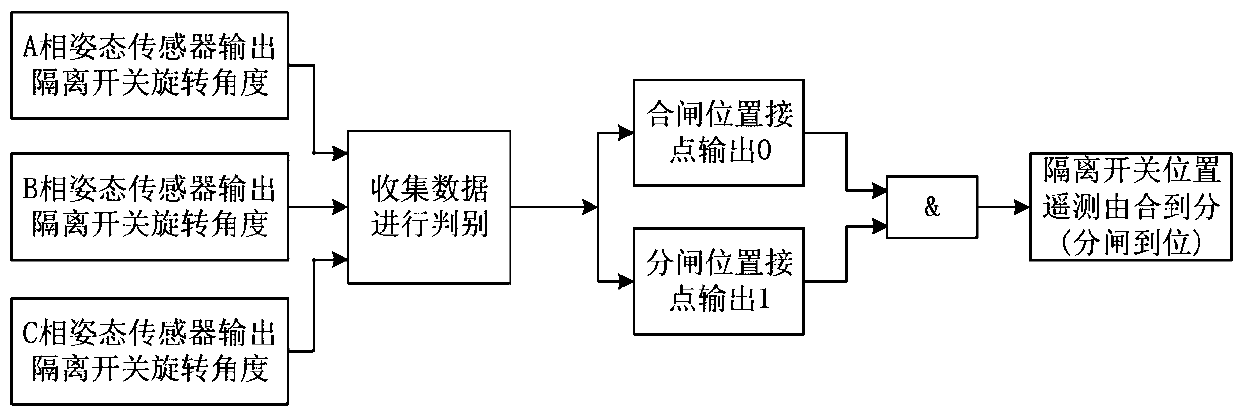
Attitude sensor-based isolating switch opening and closing position detection and double confirmation detection method and system and medium
InactiveCN110018415AAvoid influenceHigh precisionCircuit interrupters testingLocation detectionState switching
The invention discloses an attitude sensor-based isolating switch opening and closing position detection and double confirmation detection method and system and a medium. The double confirmation method of the invention includes the following steps of after an isolating switch is opened / closed, obtaining the opening and closing position of the isolating switch through opening / closing auxiliary contacts to form a first criterion; recording the opening / closing actual angle of the isolating switch in the opening / closing process by using an attitude sensor, comparing the opening / closing actual angle with a preset opening / closing reference angle, and determining the opening and closing position of the isolating switch to form a second criterion; and performing double confirmation according to the first criterion and the second criterion to determine the opening and closing position of the isolating switch. According to the scheme of the invention, after the operation of the isolating switch,operation and maintenance personnel can accurately determine the opening and closing state of the isolating switch, the accuracy of equipment state discrimination can be greatly improved, the openingand closing state of an intelligent isolating switch can be reliably and effectively determined, and the security guarantee can be provided for realizing one-key sequential control operation of statetransition of substation isolating switches.
Owner:STATE GRID HUNAN ELECTRIC POWER +3
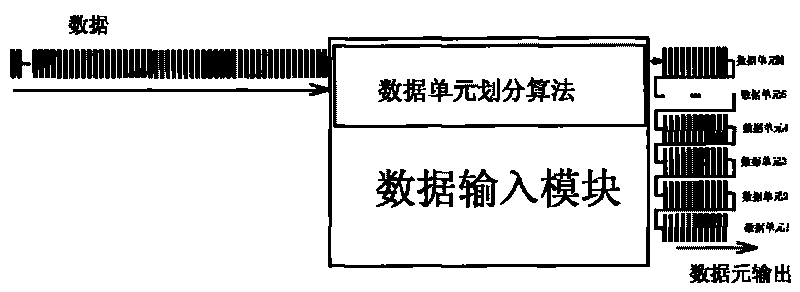
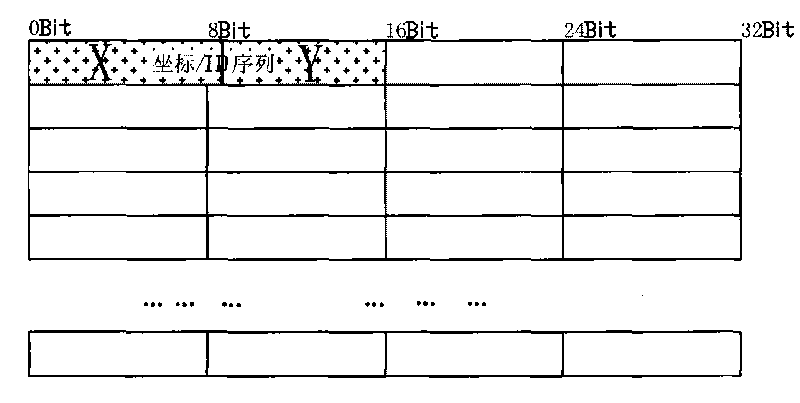
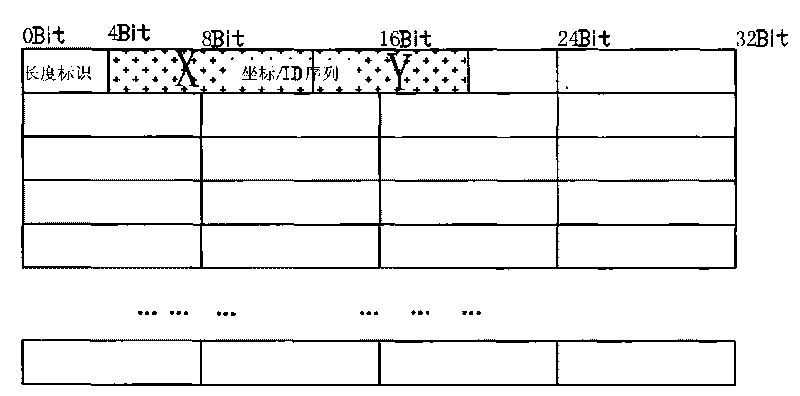
Data element and coordinate algorithm-based method and device for encrypting mixed data
InactiveCN101692636AImprove securityDiversity guaranteedEncryption apparatus with shift registers/memoriesSpecial data processing applicationsComputer hardwareHybrid type
The invention relates to the field of data encryption, and discloses a method and a device for encrypting by performing data element division on data, performing coordinate distribution on each data element and adopting different algorithms and keys. The device is characterized in that: the security guarantee of the data does not depend on the complexity of a certain encryption algorithm or the length of a key for encrypting any more. By introducing various custom simple algorithms which cannot be predicted outside and mixing various different encryption algorithms to encrypt the same document, the advantages of the algorithms are effectively integrated, the computational load and cost for encrypting are greatly reduced, and the method and the device have significant beneficial effects and technical progress.
Owner:广东宽提科技有限公司
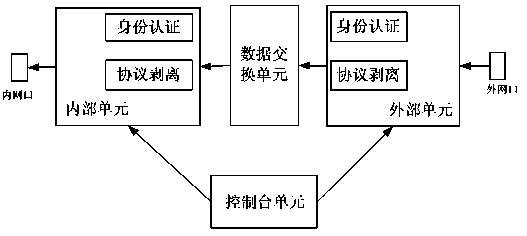
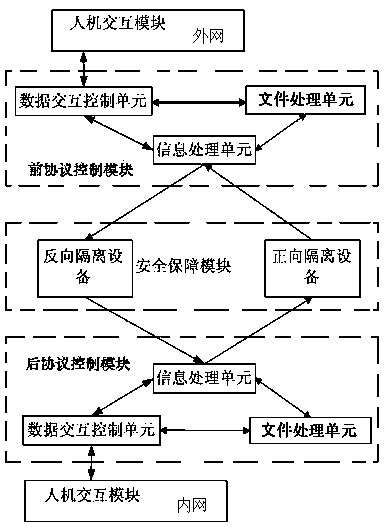
Security isolation file transmission control method
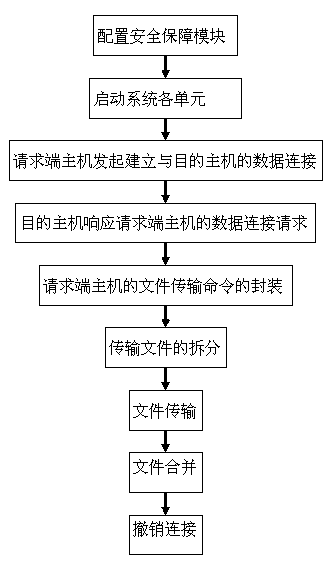
InactiveCN103997495AStrong process controllabilityImprove efficiencyTransmissionData connectionFile transmission
The invention discloses a security isolation file transmission control method. Security internal and external network file transmission is achieved through one-way transmission network architecture of a protocol control module and a security guarantee module. The method mainly comprises the steps that the security guarantee module is configured, all units of a system are started, a request end host initiates data connection with a target host, the target host responds to a data connection request of the request end host, a file transmission order of the request end host is packaged, a transmission file is detached, files are transmitted and merged, and connection is withdrawn. The request end host can send the files to the target host and can download the files from the target host, and concurrent file sending and file downloading of multiple tasks and multiple users can be achieved. According to the security isolation file transmission control method, internal and external data based on one-way network isolation equipment can be transparently transmitted, and the internal and external data transmission efficiency can be improved through a soft exchange protocol.
Owner:PLA UNIV OF SCI & TECH
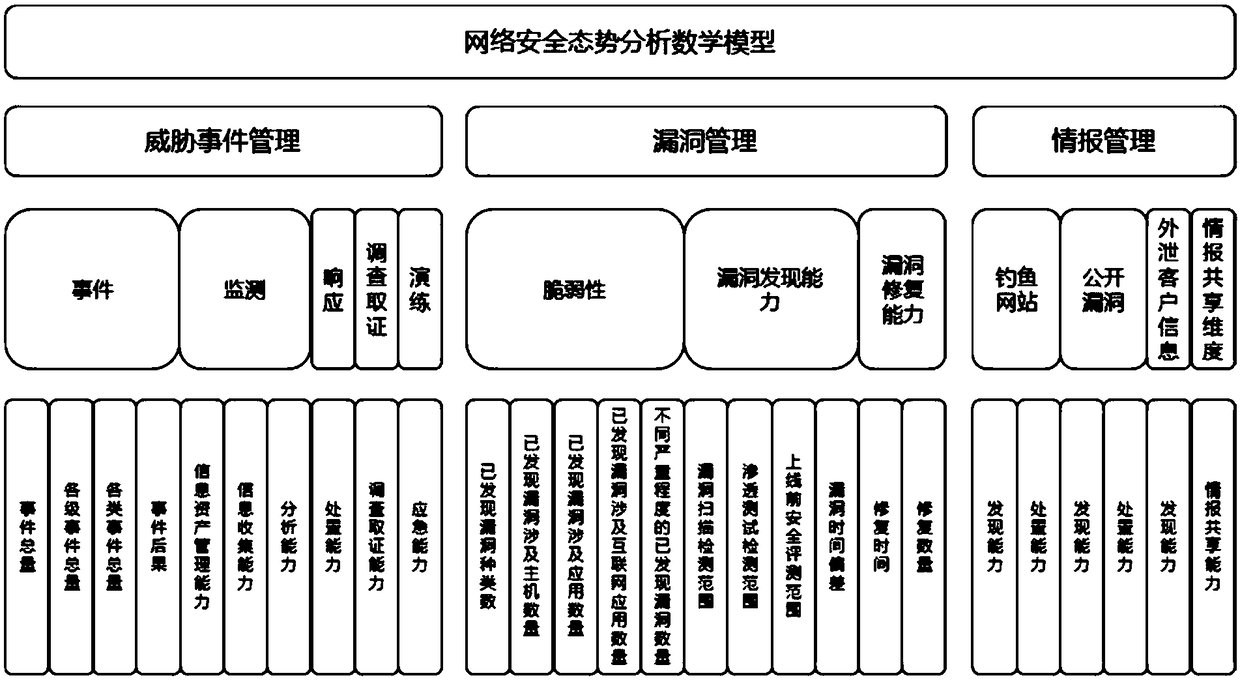
Network security situation analysis model and network security assessment method
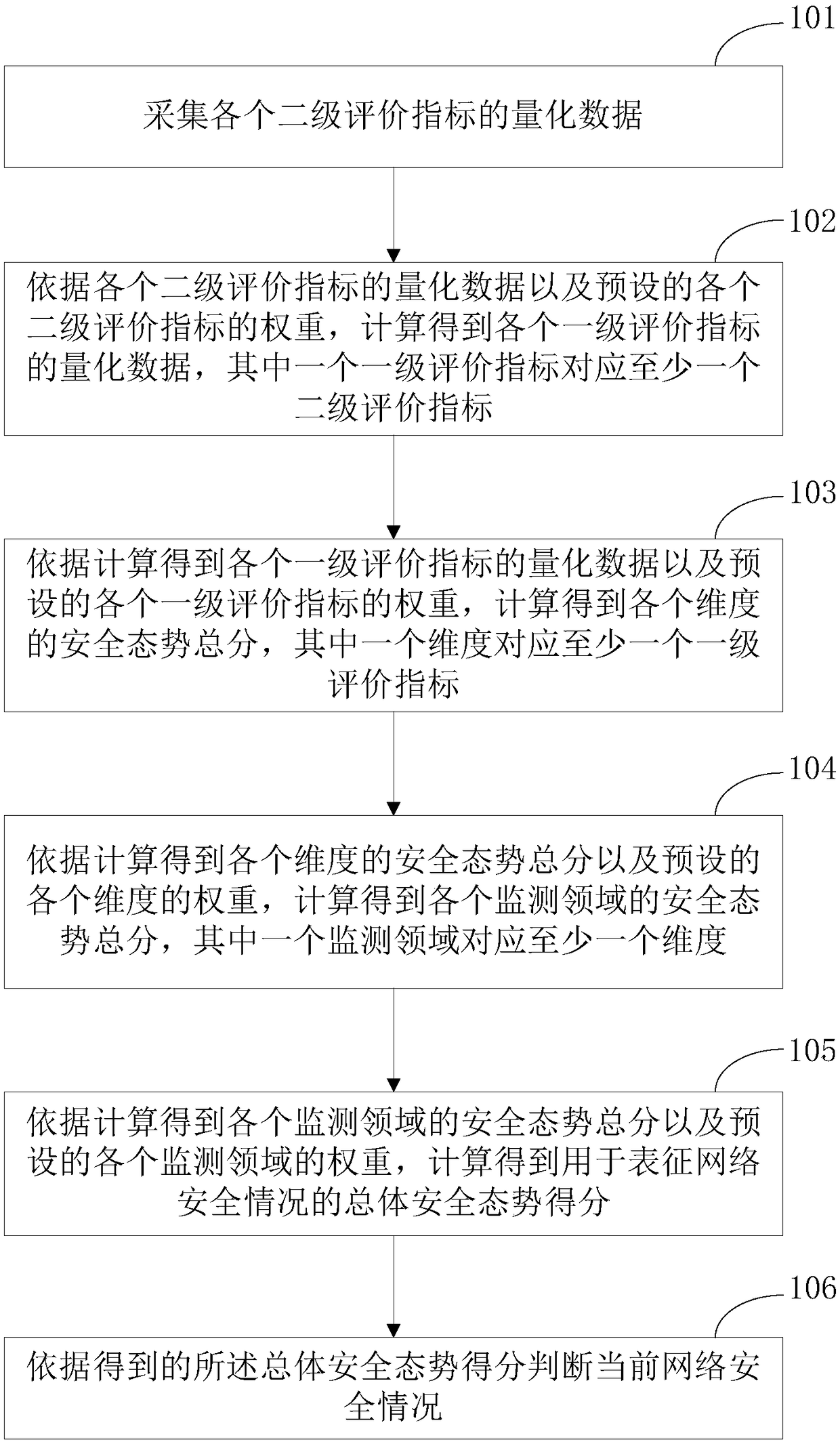
The invention provides a network security situation analysis model and a network security assessment method, wherein the total security situation score of each level evaluation index in the third level is calculated based on each level evaluation index corresponding to the level evaluation index and the weight of each level evaluation index, the security situation total score of each dimension inthe second level is calculated based on each level evaluation index corresponding to the dimension and the weight of each level evaluation index, the total security situation score of each monitoringdomain in the first level is calculated based on the corresponding dimensions of the monitoring domain and the weight of each dimension, and the overall security situation score of the network security situation analysis model is calculated based on the weight of each monitoring domain and each monitoring domain. The invention takes the security defense technology as the main visual angle, comprehensively considers the security guarantee ability to deal with the network attack in multiple dimensions, and can reflect the external network attack condition in real time, identify the medium-and long-term defense emphases, and classify and measure the robustness of the information system.
Owner:BANK OF CHINA
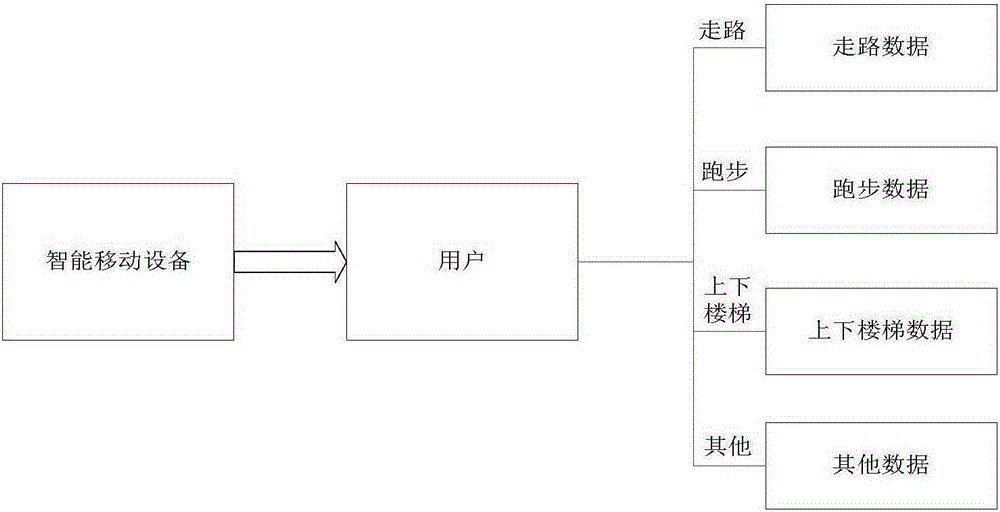
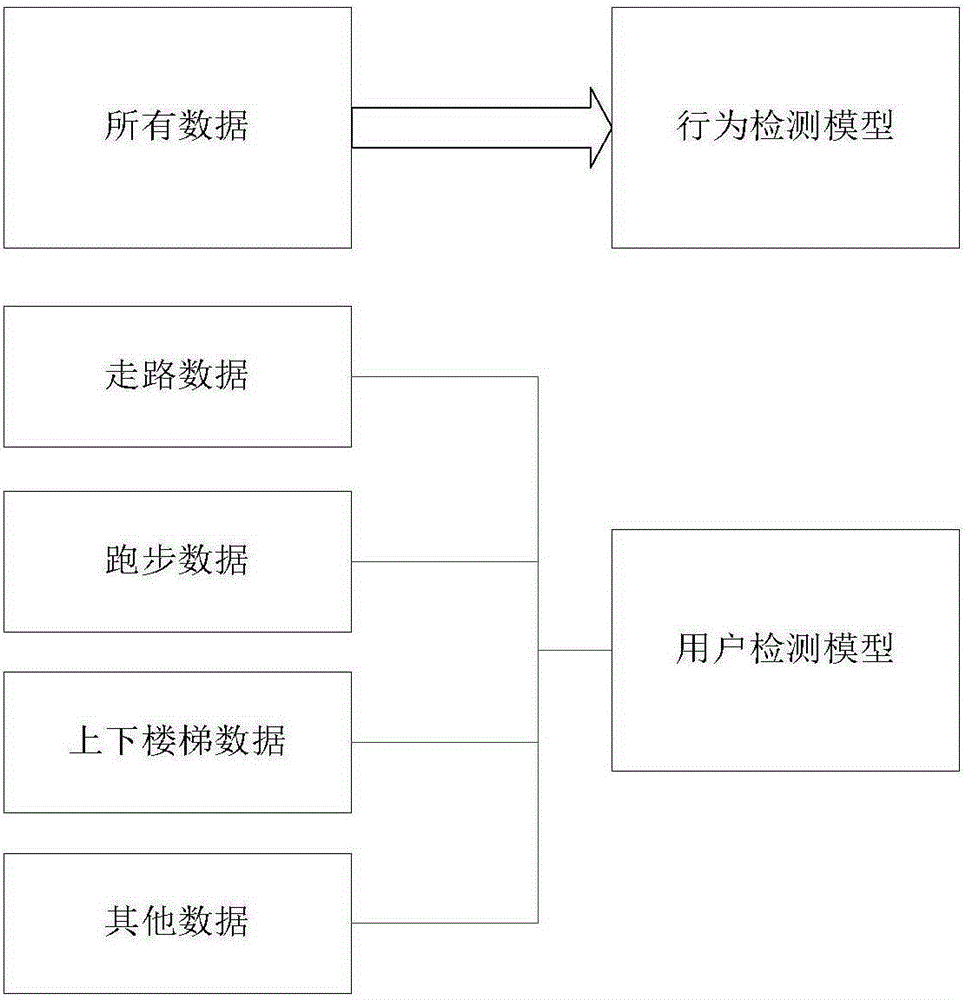
Gait bio-feature based mobile device identity recognition method
The invention provides a gait bio-feature based mobile device identity recognition method. The method is combined with a mobile terminal and is perfection and expansion of an existing bio-identification technology. The method consists of two parts of a training module and an identification module. The training module comprises three steps of data acquisition, feature extraction and model establishment; and the identification module comprises to-be-identified user data collection, model matching and notification response. According to the method, by utilizing self functions and convenience of the mobile terminal, data is completely acquired, a scientific mathematic basic model is constructed, and gait information of a user is obtained, so that user uniqueness is ensured. A system adopts a national SMS4 symmetric encryption algorithm to perform encryption, so that the data transmission security is well ensured. The method has the advantages that rich sensor and network functions of the mobile device are fully utilized, a modeling process is combined with daily gaits of the user, and the bio-identification technology can be continuously perfected without the need for a deliberate operation. Compared with other identification modes, the security system is relatively high in concealing property and difficult to target. Meanwhile, no contact is required, the concealing is difficult, and remote identification can be performed, so that the user security guarantee is greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Industrial field intelligent monitoring terminal based on internet of things
InactiveCN104298202AImprove securityImprove reliabilityTotal factory controlProgramme total factory controlReliable transmissionThe Internet
The invention discloses an industrial field intelligent monitoring terminal based on the internet of things. The terminal can collect electric power parameters and a switching value input state on site and can collect other monitoring parameters through a wireless network built through an RS485 bus of an industrial field layer or a field layer wireless ad hoc network module. The terminal carries out comprehensive computation and analysis on the collected parameters and carries out intelligent control. Wireless application communication between the industrial field layer and an application layer of the internet of things can be further achieved through the terminal, a data encryption and identity verification anti-counterfeiting mechanism is built through an encryption unit, and reliable technical guarantees are provided for wireless transmission through a controllable DC-DC power supply. By means of the terminal, the technical problems such as security guarantee, reliable transmission and intelligent control existing in an industrial field monitoring terminal are solved, and accordingly industrial field monitoring based on the internet of things is safer, more reliable, more instantaneous and more intelligent.
Owner:张晓华 +1
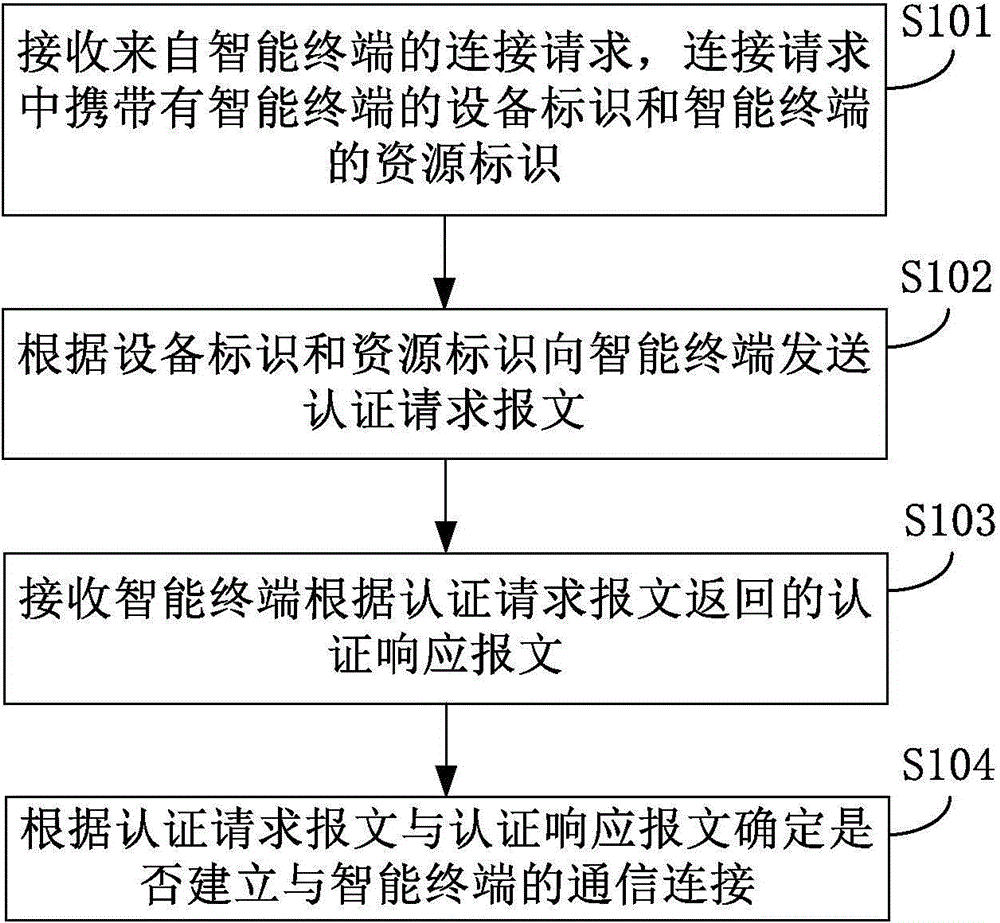
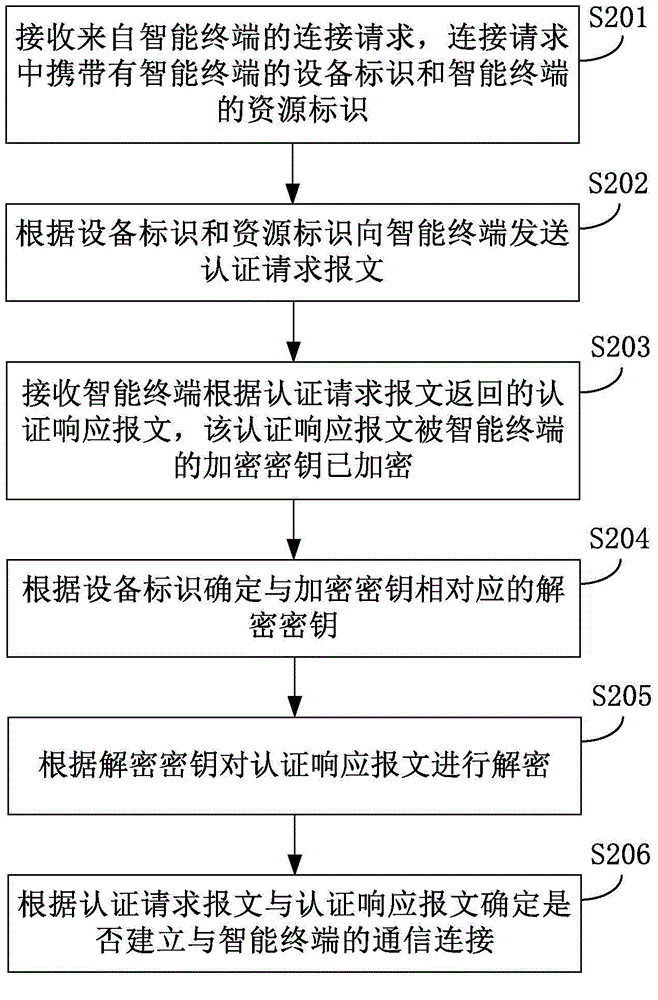
Method and device for establishing communication connection of intelligent terminal
ActiveCN104980920AAccess supportReliable interconnectionConnection managementSecurity arrangementAccess networkThird party
The invention discloses a method and a device for establishing a communication connection of an intelligent terminal. The method comprises: receiving a connection request from the intelligent terminal, wherein the connection request carries an equipment identifier of the intelligent terminal and a resource identifier of the intelligent terminal, and the resource identifier is generated by the intelligent terminal in a networking initialization process; sending an authentication request message to the intelligent terminal according to the equipment identifier and the resource identifier; receiving an authentication response message returned by the intelligent terminal according to the authentication request message; and determining whether establishing the communication connection of the intelligent terminal according to the authentication request message and the authentication response message. The method provided by the technical scheme in the invention can be used for avoiding the identify identifier of the intelligent terminal of being guessed, resulting in that a malicious third party forges and attacks the server, and the method can bring more reliable security guarantee to the interconnection and interworking of the intelligent terminal and can support an access network of a large-scale intelligent terminal.
Owner:XIAOMI INC
Remote communication security management architecture of ubiquitous green community control network and method for constructing the same
ActiveCN102724175AGuaranteed experienceRealize reasonable schedulingTransmissionNetwork architectureDistributed security
The invention discloses a remote communication security management architecture of a ubiquitous green community control network and a method for constructing the same. For a remote communication process of a ubiquitous green community control network, information transmission and invoking are carried out by a backbone network based on a TCP / IP protocol. According to the security management architecture, on the basis of a ubiquitous green community control network, a new security management center is deployed; security management modules are added to a gateway and terminal equipment, so that the gateway and the terminal equipment are updated as a secure gateway and a secure terminal; and a memory is divided into a general-purpose memory and a core memory and an application unit is further divided into a service type application unit and a user type application unit. According to the disclosed security management method, distributed security management is realized and level-to-level security management with different security levels is supported. And under the precondition that an original network architecture is changed little, effective security guarantees can be realized for the remote communication process of the ubiquitous green community control network by supports for distributed and level-to-level management.
Owner:下一代互联网关键技术和评测北京市工程研究中心有限公司
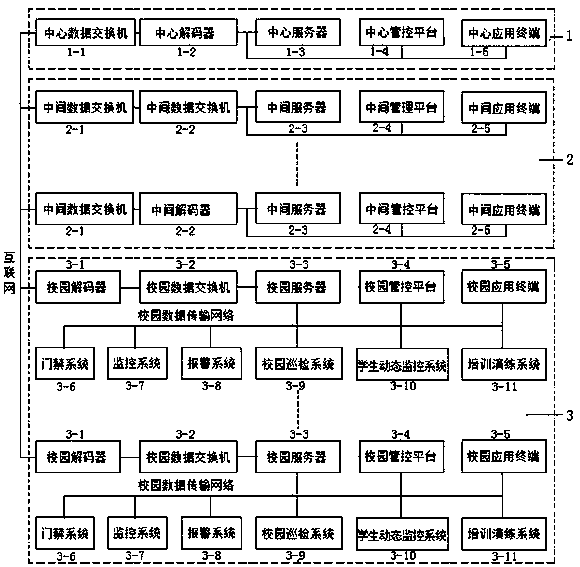
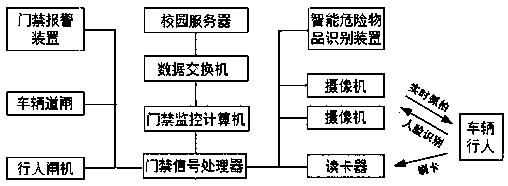
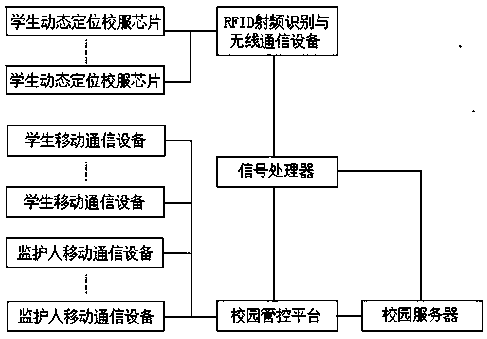
Intelligent monitoring and early warning system for campus security guarantee
PendingCN107730681AImprove security monitoring and early warning capabilitiesWide coverage of security monitoringInput/output for user-computer interactionTelevision system detailsIntelligent lightingThe Internet
The invention relates to an intelligent monitoring and early warning system for campus security guarantee, and belongs to the technical field of security guarantee. The system comprises a central management and control scheduling system, a plurality of intermediate management and control scheduling systems and a campus management and control scheduling system, and all the management and control dispatching systems are connected with one another through the internet. The central and intermediate management and control scheduling systems each comprise a data switch, a decoder, a server, a management and control platform and an application terminal. The servers and the management and control platforms are connected with the internet through the decoders and the data switches, and the application terminals are connected with the management and control platforms. The campus management and control scheduling system comprises a data switch, a decoder, a server, a management and control platform, an application terminal, an entrance guard system, a monitoring system, an alarm system, a tour inspection system, a student dynamic monitoring system and a training exercise system; all the systems are connected with a campus server and a campus management and control platform through a campus data transmission network. The system has the advantages of being wide in security monitoring coverage, high in system integration degree, multifunctional, intelligent, capable of achieving multi-level supervision and fast responding and the like.
Owner:长春北电软件有限公司 +3
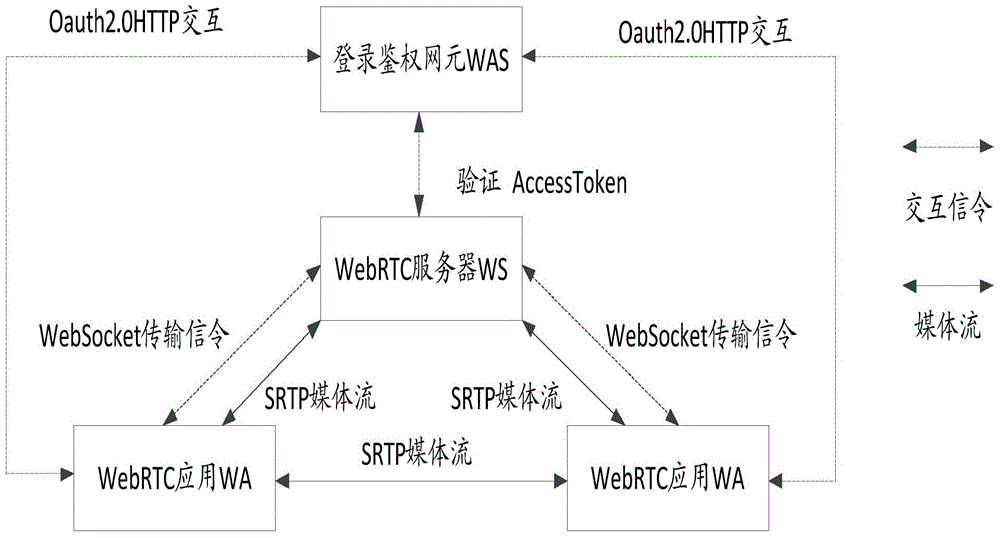
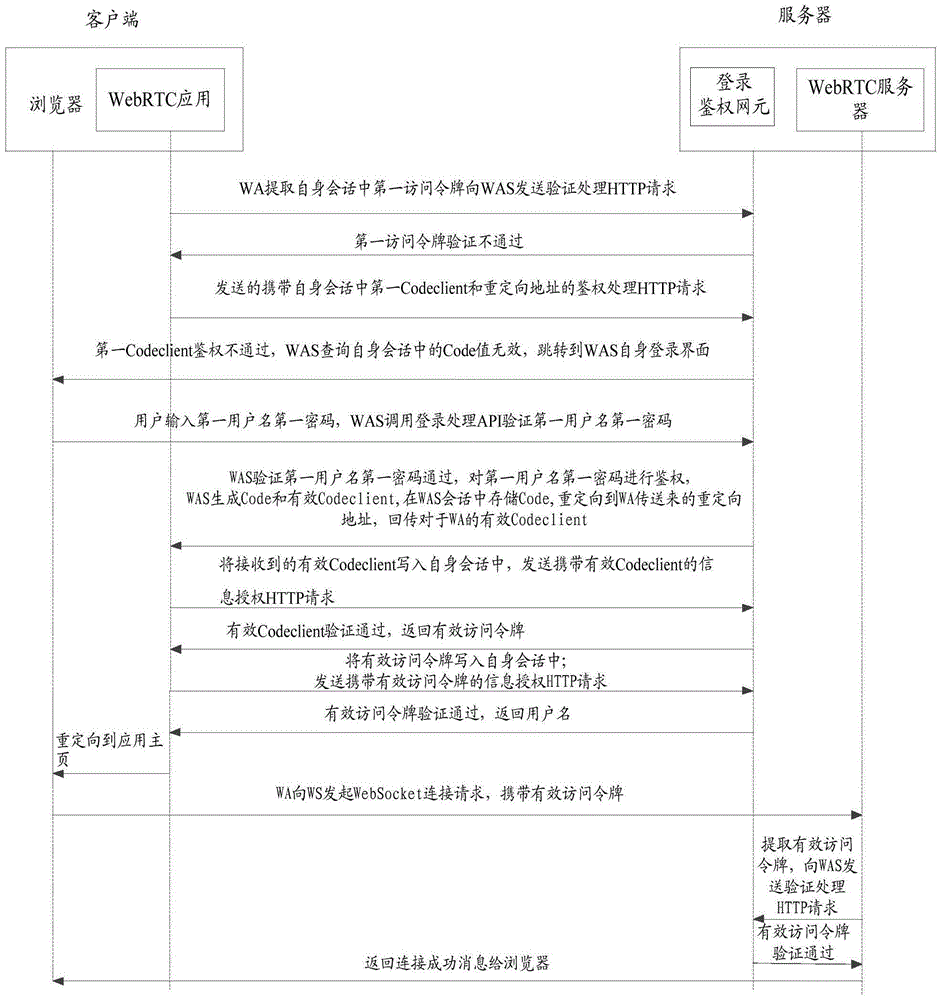
Authentication access method and apparatus of Web real-time communication platform
The invention provides an authentication access method and apparatus of a Web real-time communication platform. The method includes: receiving a login request carrying verification information and sent by a Web real-time communication application, verifying the login request sent by the Web real-time communication application, and returning a login verification success message after successful login verification of the verification information; and performing authentication verification on the verification information after successful login verification, and sending an effective access token and a unique identity identifier to the Web real-time communication application after successful authentication verification so that the Web real-time communication application directs a user to a Web real-time communication application homepage according to the received unique identity identifier and establishes the connection with a Web real-time communication server WS according to the effective access token. According to the method and apparatus, the security of user accounts of the Web real-time communication service platform can be improved, and a security guarantee is provided for the users for Web real-time communication service and the Web real-time communication service platform.
Owner:ZTE CORP
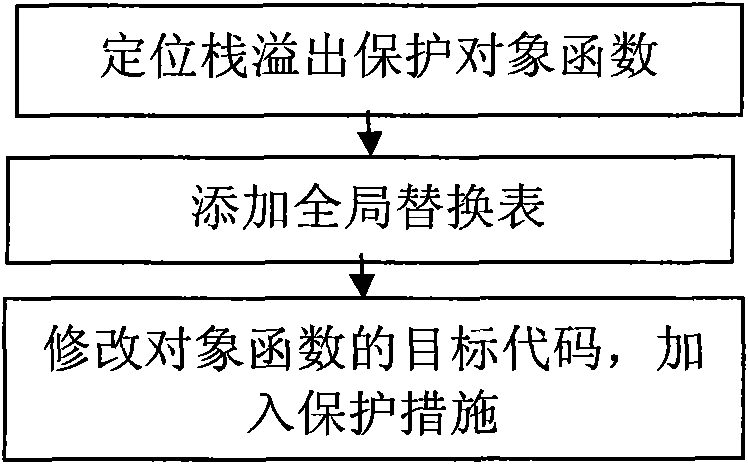
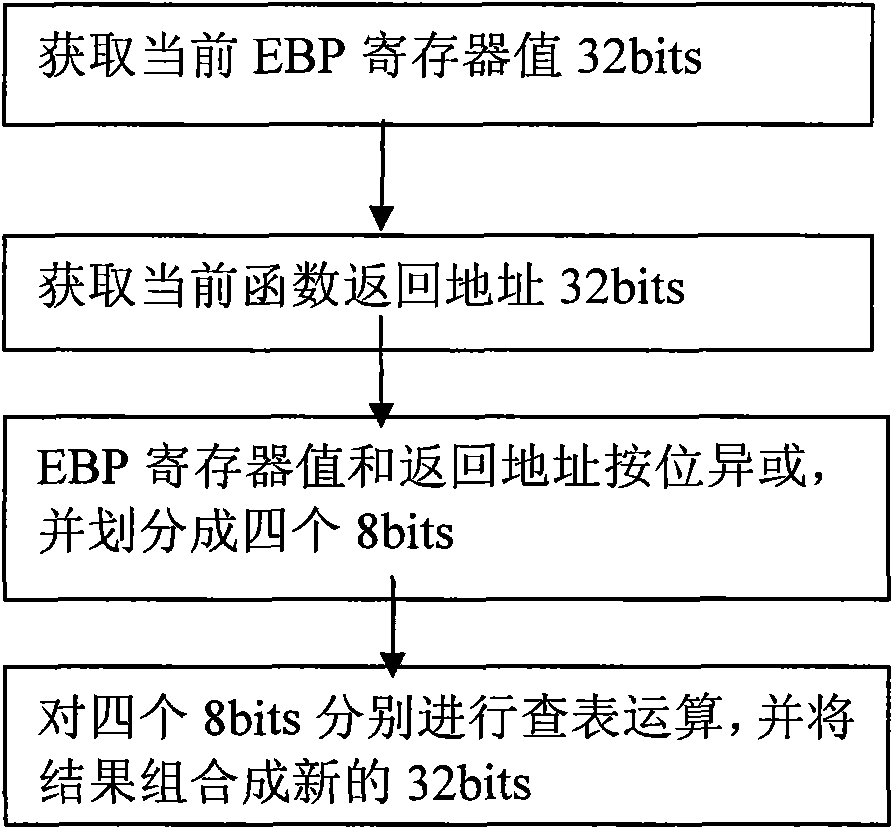
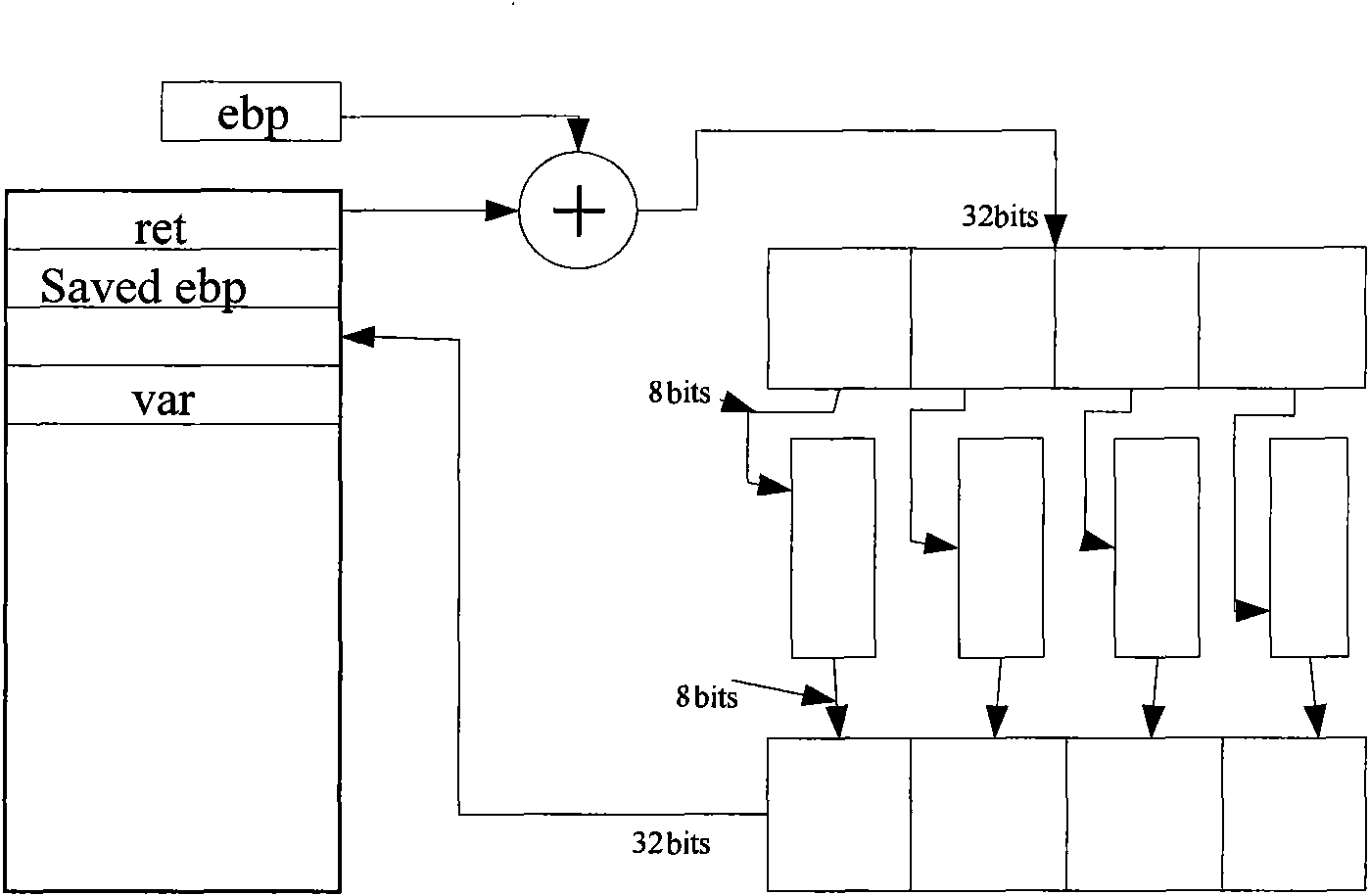
Stack overflow attack defense method
The invention discloses a stack overflow attack defense method, which belongs to the field of security guarantee of a computer system. The method comprises the following steps of: a) positioning a function with potential stack overflow defect in a program; b) before the function is executed, encrypting a return address to obtain first encrypted message by using a key register and storing the encrypted message; and c) before the function is returned, encrypting the return address to obtain second encrypted message by using the key register likewise, and if the first encrypted message and the second encrypted message are different, showing that the stack overflow attack exists. The method can be used for stack overflow attack defense, and is applicable in multiple fields of aerospace, finance, manufacture, communication, energy, medicinal treatment, education and the like.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Lightweight authentication and key agreement protocol applicable to electric information acquisition
InactiveCN102882688AReduce the number of interactionsResistance to asynchronous attacksUser identity/authority verificationAttackKey-agreement protocol
The invention relates to a lightweight authentication and key agreement protocol applicable to electric information acquisition. An identify authentication stage is completed on the basis of communication of a digital certificate of an authentication center of a state grid cooperation of China and a shared key. In a key agreement stage, new and old parameter protection keys which are updated dynamically are utilized, and lightweight operators are utilized for computation, and the key agreement is completed by communication circulations only. In a key updating stage, a session key group and the new and old parameter protection keys are synchronized. During key agreement, parameters are protected alternatively by the new and old parameter protection keys so that nonsynchronous attack can be resisted effectively. The protocol can be analyzed by combination of BAN logic formal analysis and informal analysis methods, can be approved to have safety attributes such as two-way entity authentication, perfect forward security and the like when reaching first-level faith and second-level faith, resists to various attacks, and can complete identify authentication and key agreement in real time effectively on the premises of security guarantee and meet requirements of an electric information acquisition system to key application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Dynamic cipher method, system and dynamic cipher card
InactiveCN1987938AAchieving Security GuaranteesGood development environmentFinancePayment architecturePaymentSecure authentication
The invention provides a method and system of dynamic PIN and dynamic PIN card, the referred dynamic PIN method includes that a group of dynamic PIN is random generated, each dynamic PIN has the character of uniqueness. The dynamic PIN is stored and the corresponding relation between the each dynamic PIN and a coordinate data is established. When in the course of dynamic PIN confirmation: prompting the coordinate data; inputting the PIN corresponding to the coordinate data; judging whether the referred coordinate data is consistent with the dynamic PIN. If they are identical, then the input dynamic PIN passes the security qualification. The cost of this invention lower than the certification qualification, but the security, operationality is between the certification qualification and static PIN qualification, the security guarantee of payment is fulfilled.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Network contraction secure service system
InactiveCN101123505AUser identity/authority verificationCommerceThird partyElectronic identification
The present invention relates to a security service system of contract signing on the Internet, which includes a contract-signing applicant, contracting parties and a guarantor, wherein the contract-signing applicant and the contracting parties can be administrative organs, enterprises and institutions, and social groups along with legal representatives or ordinary natural persons, and the guarantor is a specific website service institution. Each of the contract-signing parties cooperates with the guarantor to synchronize the security service system of witness and verification by guarantor-provided email boxes, registration and encryption of emails, electronic anti-counterfeiting stamps and come-and-go registered emails, thus ensuring the authenticity and integrity of the signature of electronic contracts or texts. The system realizes the effective integration of three security service functions that includes the registration and encryption of ordinary emails, electronic anti-counterfeiting stamps and certifications and the third-party notarization, which provides security guarantee to the integrity and authenticity of the electronic information of the electronic business on the Internet, electronic government affairs, and other business transactions of electronic information.
Owner:张伟民
Blockchain consensus method
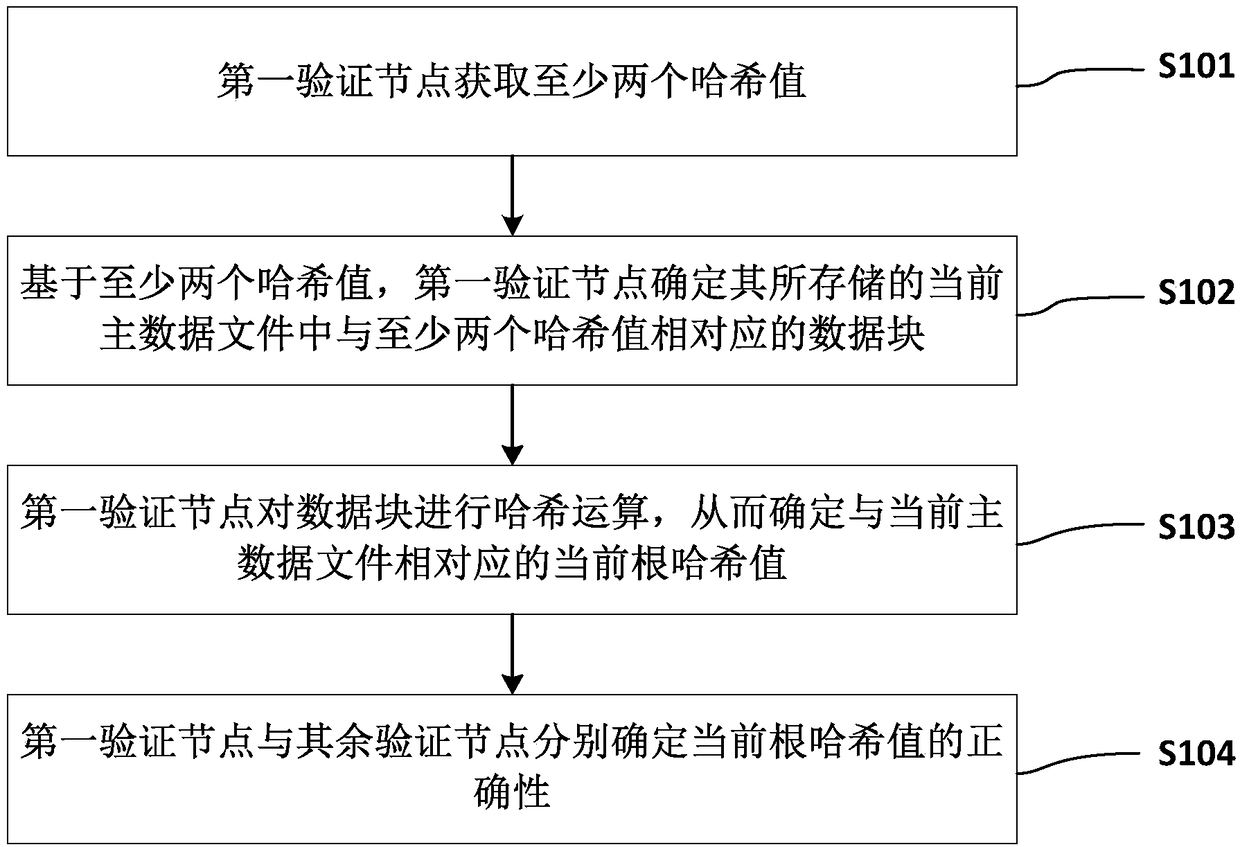
ActiveCN108667836AGuaranteed safe operationImprove verification efficiencyUser identity/authority verificationData fileHash table
The invention discloses a blockchain consensus method. The method comprises the following steps: a first verification node obtains at least two hash values; based on the at least two hash values, thefirst verification node determines data blocks corresponding to the at least two hash values in a current main data file stored in the first verification node; the first verification node performs hash operation on the data blocks to determine a current root hash value corresponding to the current main data file; and the first verification node and the remaining verification nodes respectively determine the correctness of the current root hash value. By adoption of the blockchain consensus method, a large amount of CPU calculation does not need to be consumed, and meanwhile the network participants can be stimulated in a reward and punishment mode to provide security guarantee for blockchain data.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD +1
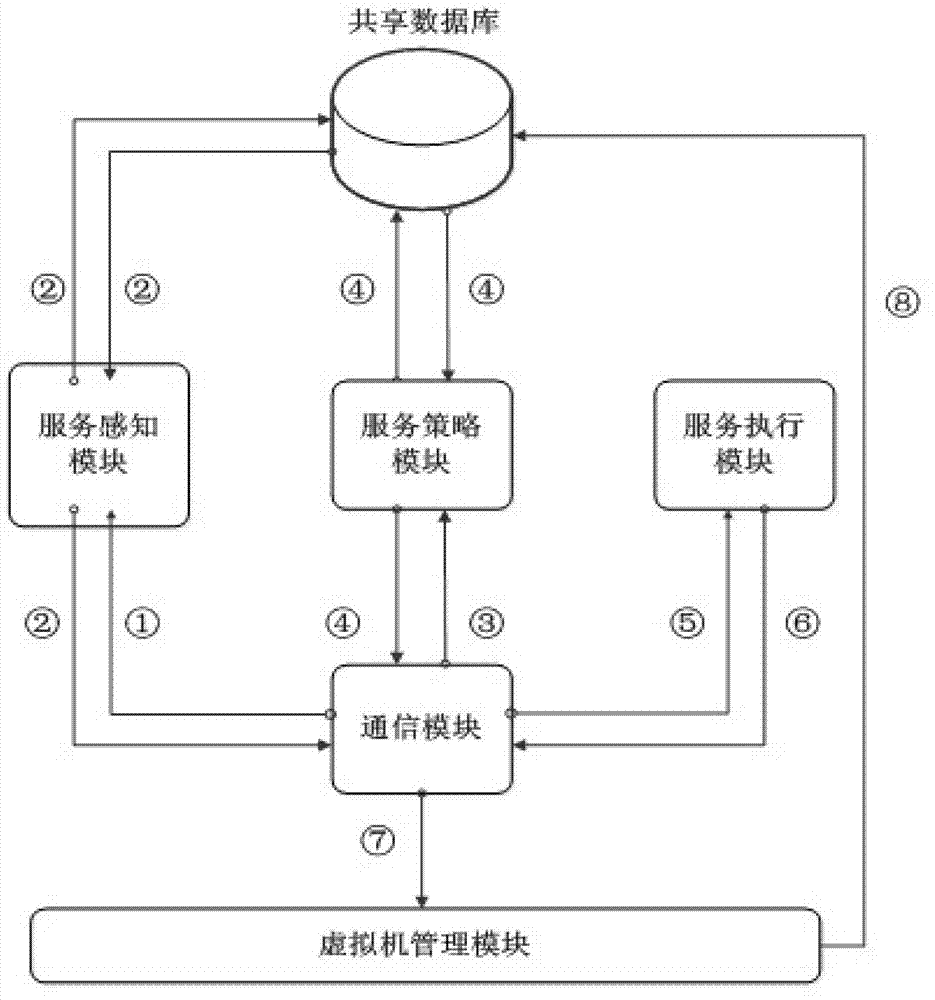
Guarantee method and guarantee system for improving usability of virtual machine application
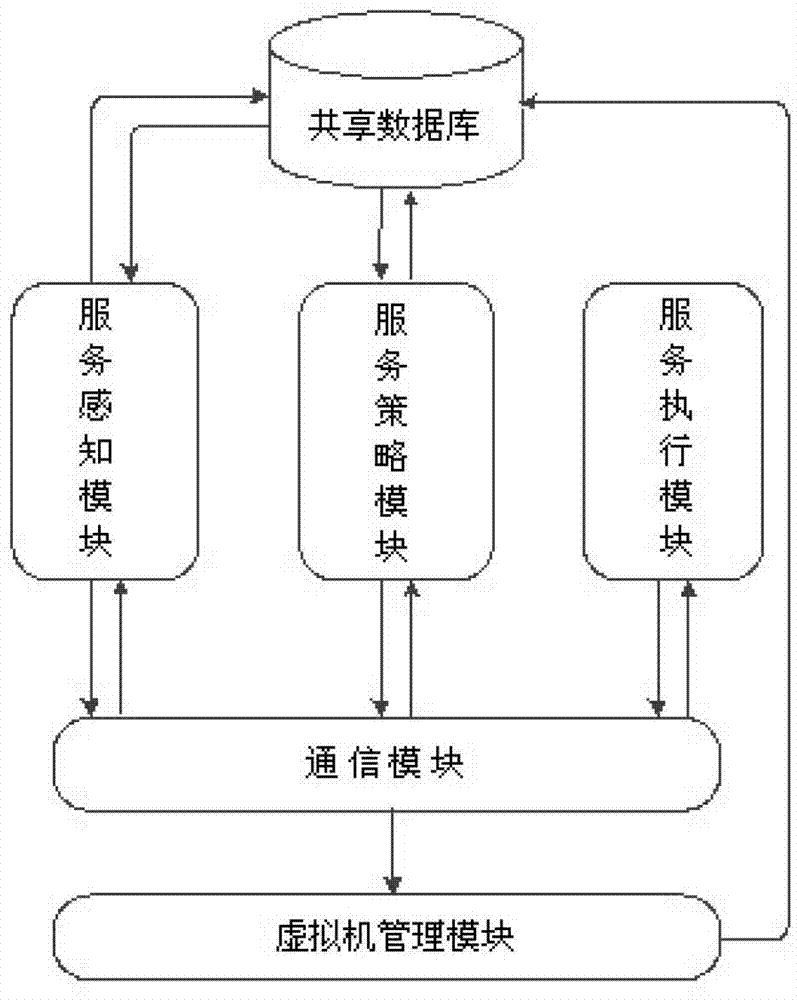
InactiveCN103118100AGuaranteed uptimeApplication service is stableData switching networksSoftware simulation/interpretation/emulationHigh availabilityUsability
The invention relates to the technical field of computers, in particular to a guarantee method and a guarantee system for improving usability of virtual machine application. The system realizes communications by means of an event communication mechanism for performing communications, and mainly comprises a shared data base, a communication module, a service perceiving module, a service strategy module, a service execution module and a virtue machine management module. The service perceiving module is used for perceiving application state; the service strategy utilizes the state perceived by the service perceiving module for selecting high availability strategy; the service execution module transfers in turn related functions of the virtue machine management module in corresponding orders according to the high availability strategy; and the shared data base provides information required in operation for the modules. The guarantee method and the guarantee system for improving usability of virtual machine application have the advantages of being capable of providing sustained security guarantee for application business (operational procedure installed to operate in a virtue machine) of the virtue machine, and guaranteeing stable and reliable operation of application services.
Owner:WUHAN UNIV
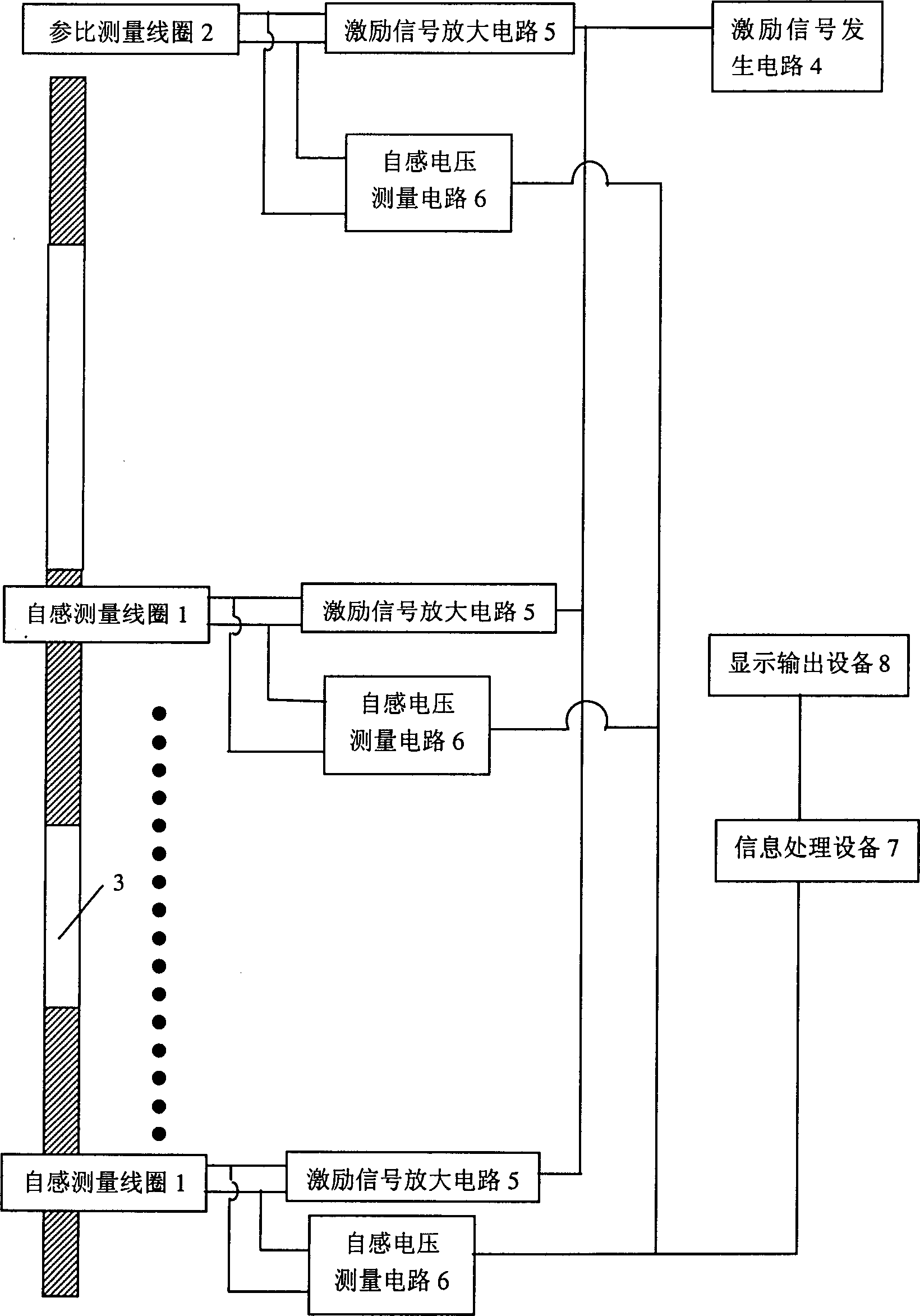
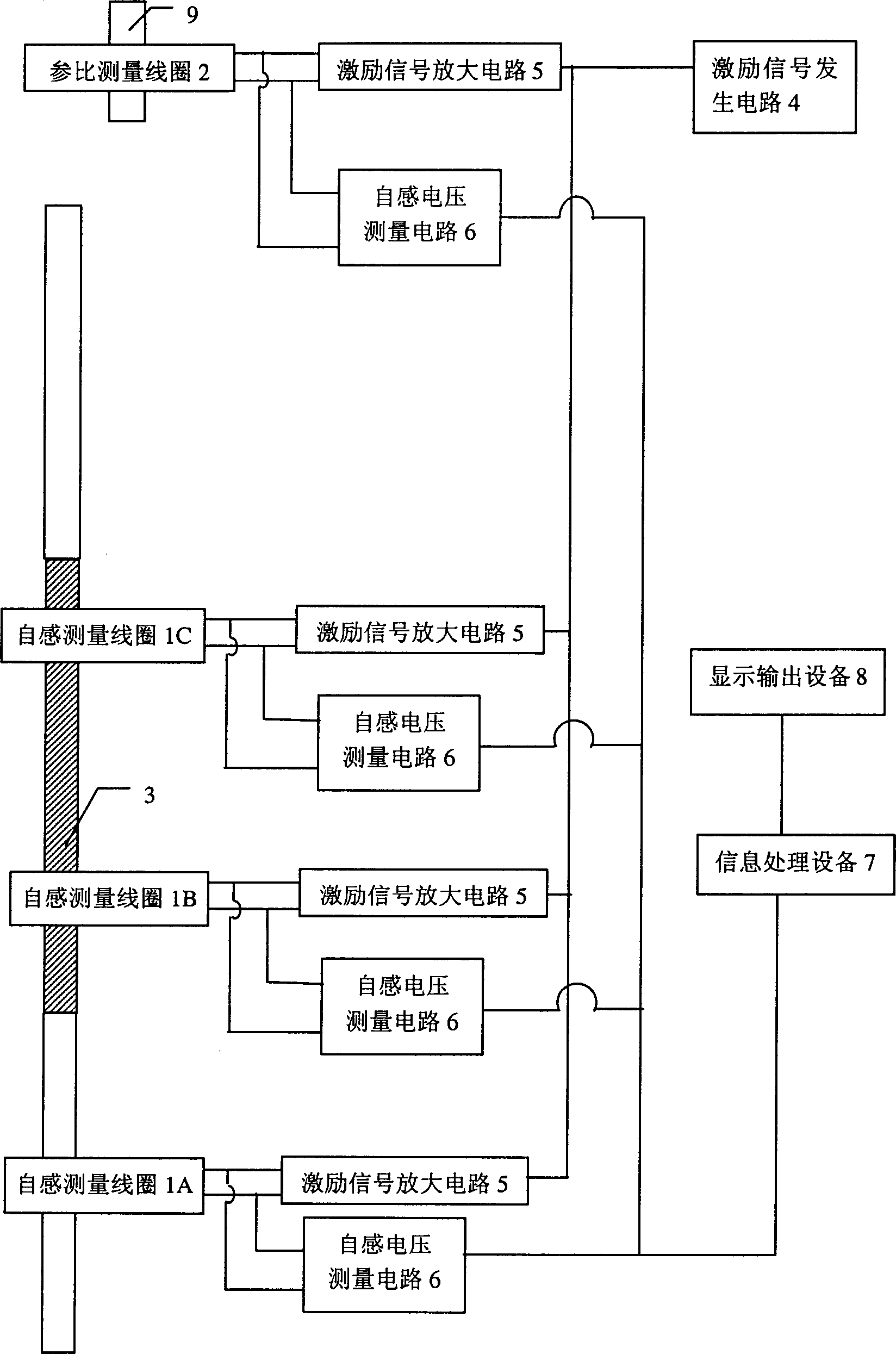
Coil self-inductance based control rod position measuring system
ActiveCN1808629AReduce installation difficultyReduce volumeNuclear energy generationNuclear monitoringInformation processingSelf induction
The disclosed single-coil measurement system for position of control rod based on coil self-induction principle in reactor measuring and controlling technique comprises a measurement sensor for rod position, a reference signal sensor, a measurement mandrel space arranged with the magnetic inductive material and non-inductive material connected to the control rod, and the information processing device with ADC to analyze by the dc signal with linear relation with self-inductive voltage from sensors. This invention has small volume and stable running with convenient maintenance to provide security guarantee for reactor.
Owner:TSINGHUA UNIV
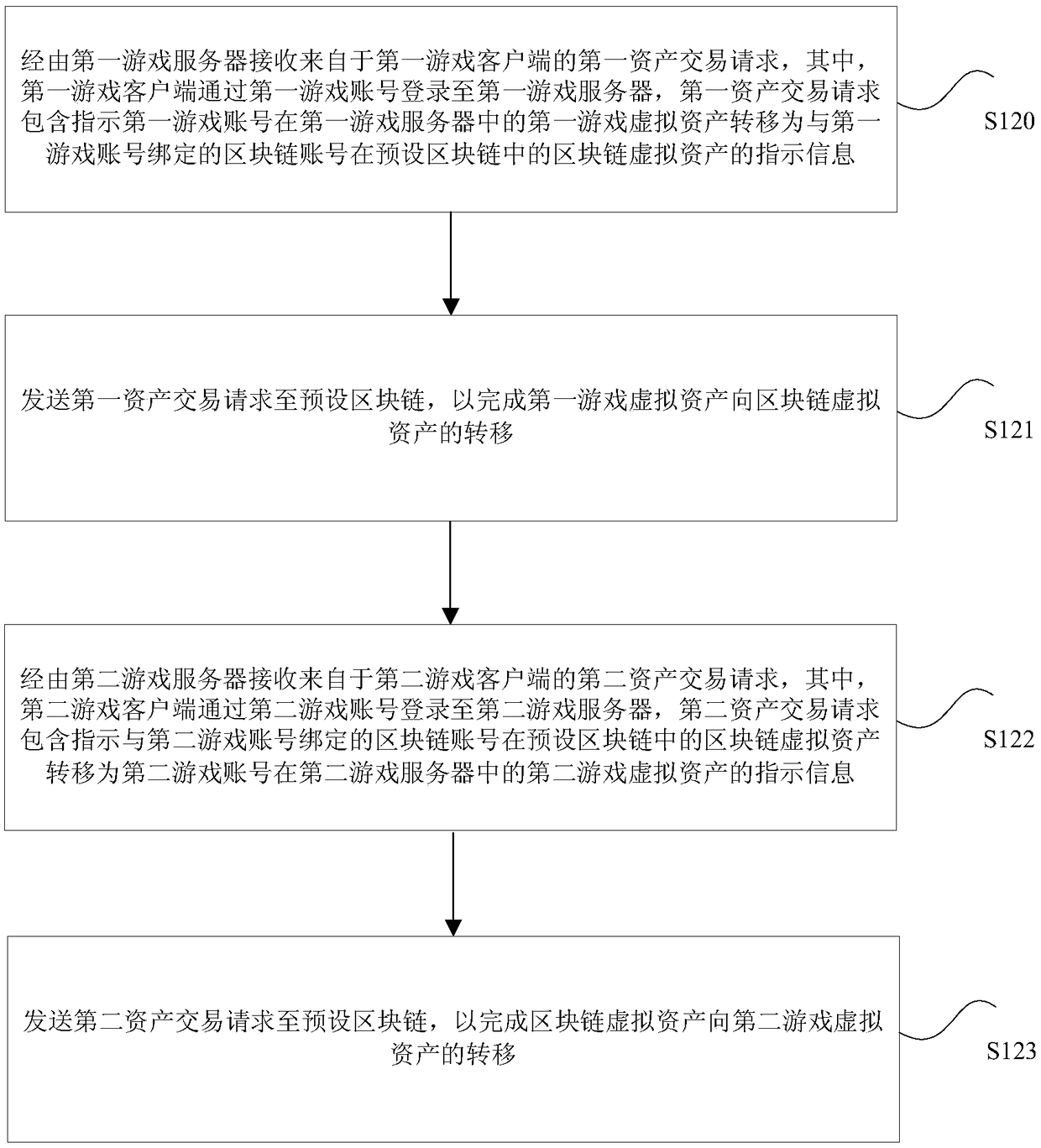
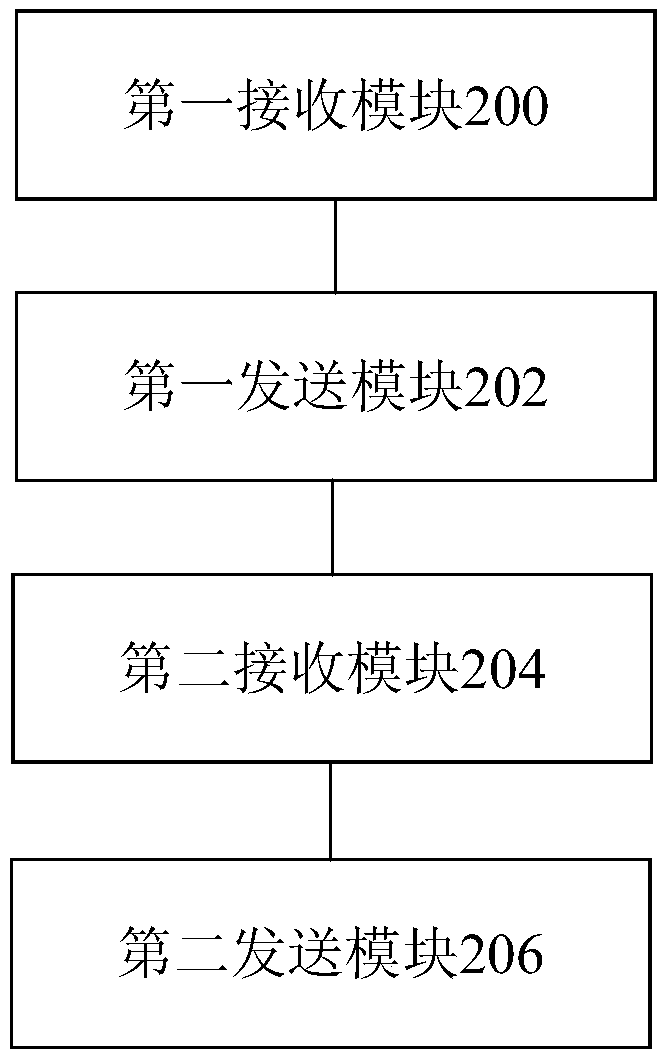
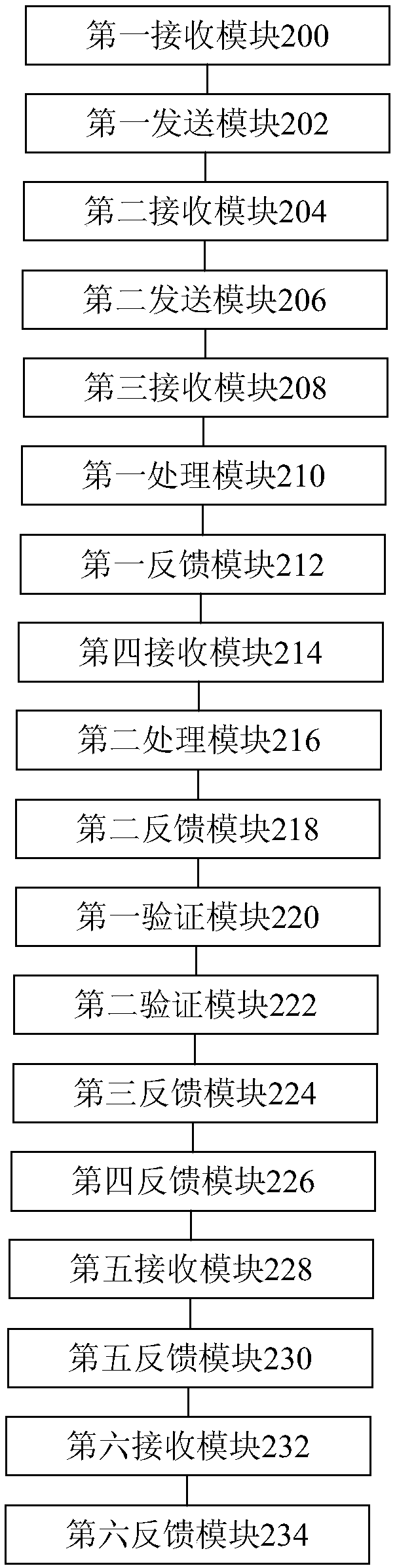
A method and device for processing virtual assets across games, a processor and a server
The invention discloses a method and device for processing virtual assets across games, a processor and a server. The method includes receiving a first asset transaction request from a first game client via a first game server; sending a first asset transaction request to a preset block chain to complete the transfer of the first game virtual asset to the block chain virtual asset; receiving, viathe second game server, a second asset transaction request from the second game client; sending a transaction request of the second asset is sent to the preset block chain to complete the transfer ofthe block chain virtual asset to the second game virtual asset. The invention solves the technical problems in the related art that the game assets of a game player are managed and controlled only bya game server, and the game assets are short of security guarantee and easy to depreciate.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com