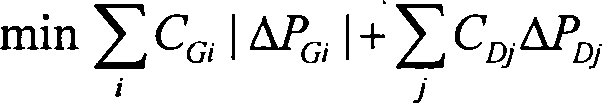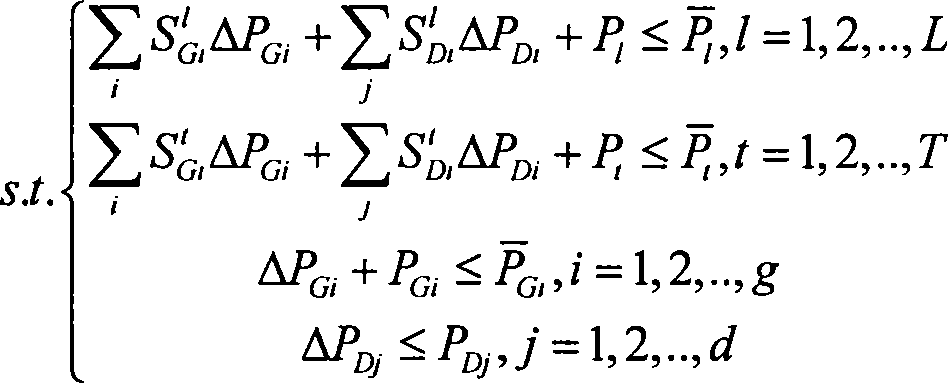Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4428results about How to "Fix security issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
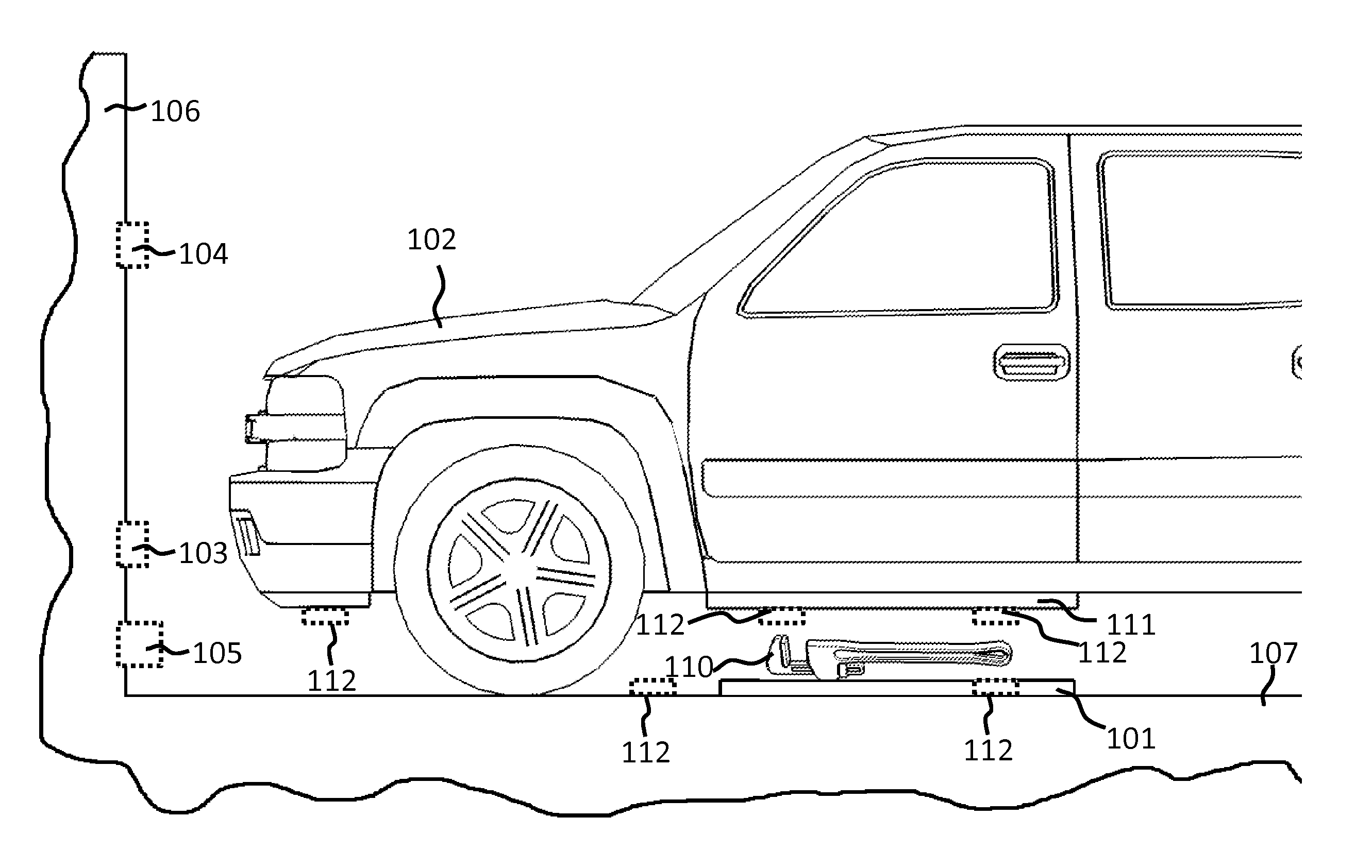
Vehicle charger safety system and method
InactiveUS20110074346A1Safety concern can be addressedFix security issuesMultiple-port networksBatteries circuit arrangementsForeign objectSystem identification
Wireless vehicle charger safety systems and methods use a detection subsystem, a notification subsystem and a management subsystem. The detection subsystem identifies a safety condition. The notification subsystem provides an indication of the safety condition. The management subsystem addresses the safety condition. In particular, undesirable thermal conditions caused by foreign objects between a source resonator and a vehicle resonator are addressed by sensing high temperatures, providing a warning and powering down a vehicle charger, as appropriate for the environment in which the charger is deployed.
Owner:WITRICITY CORP
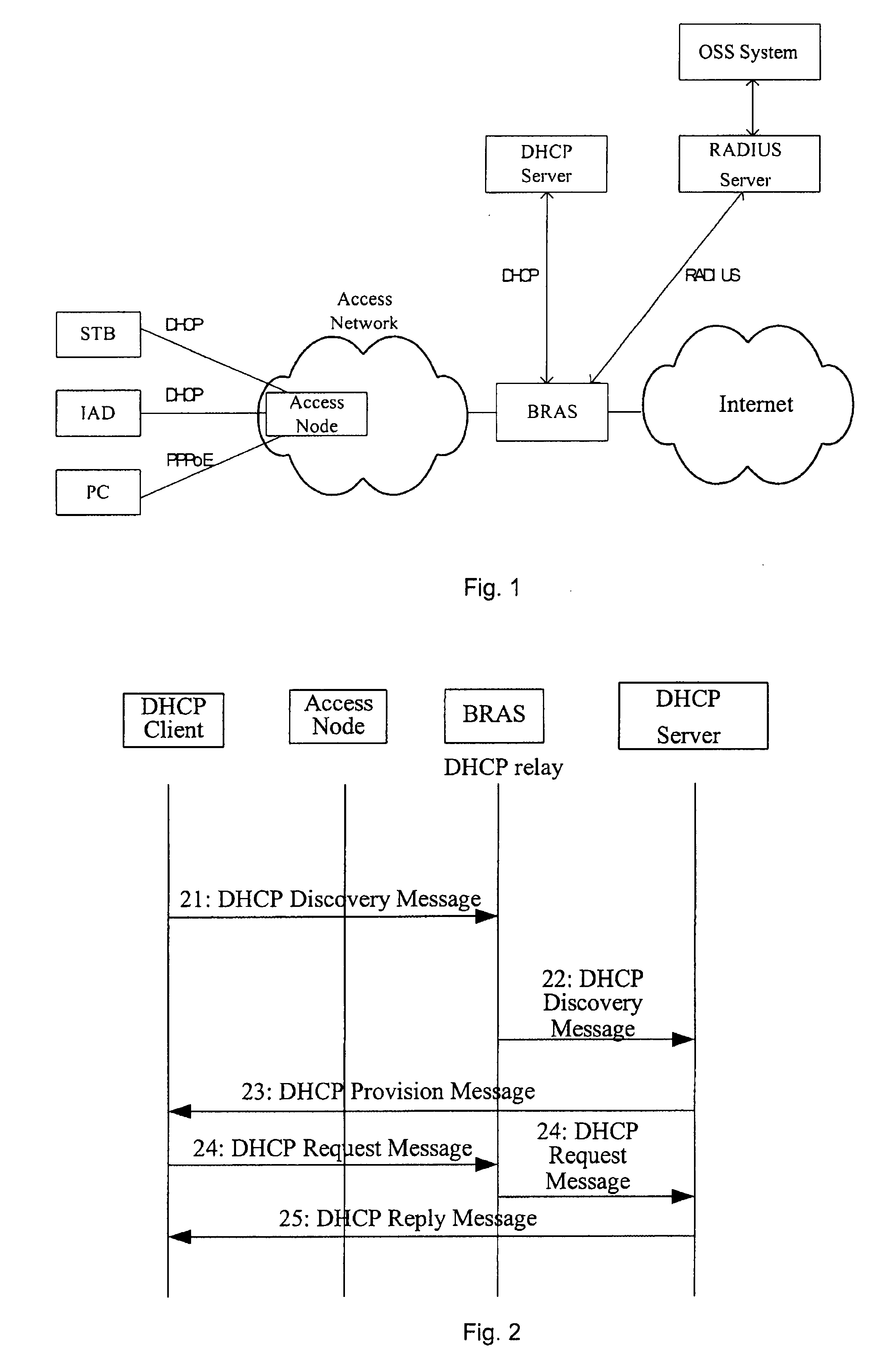
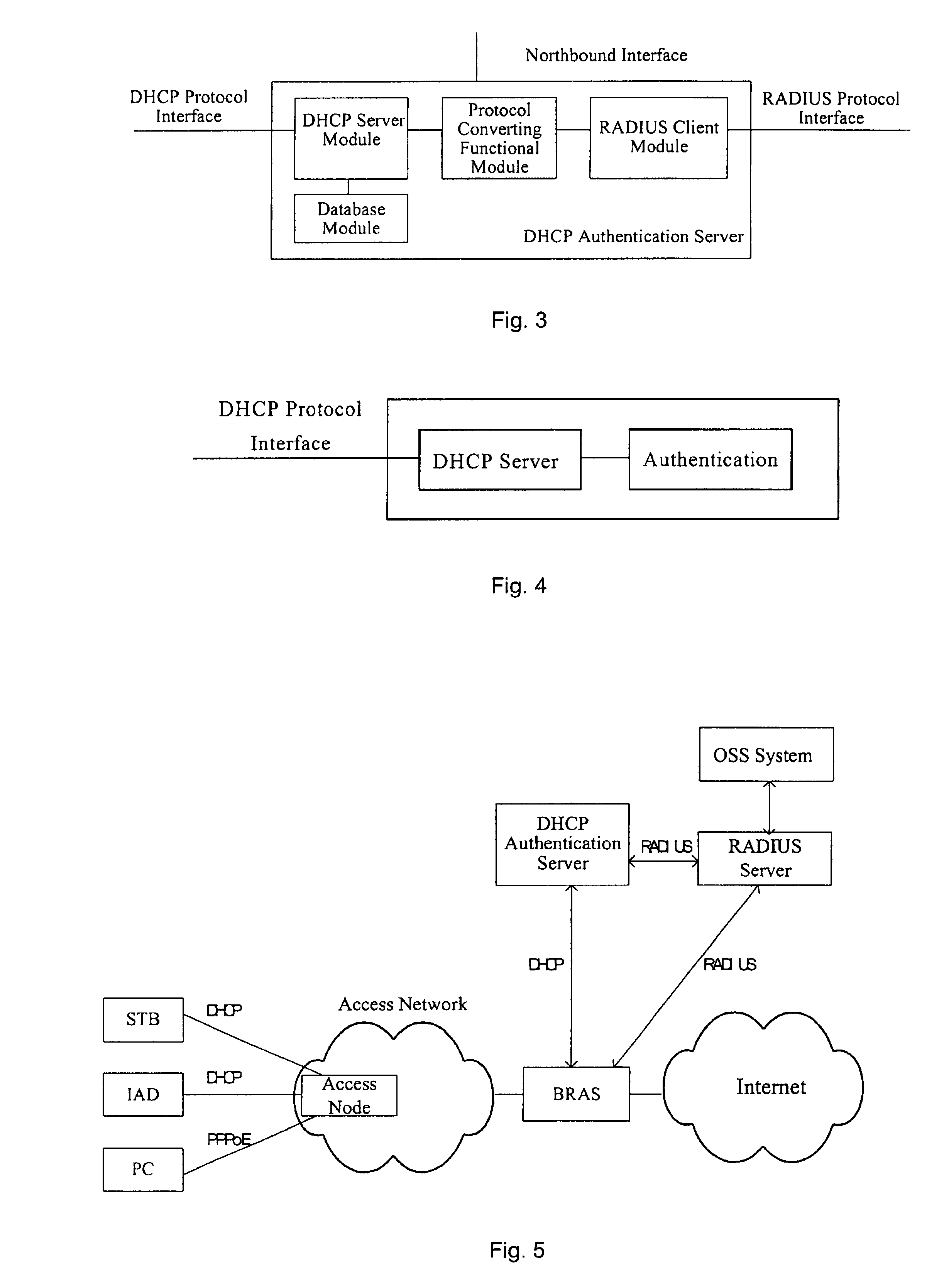
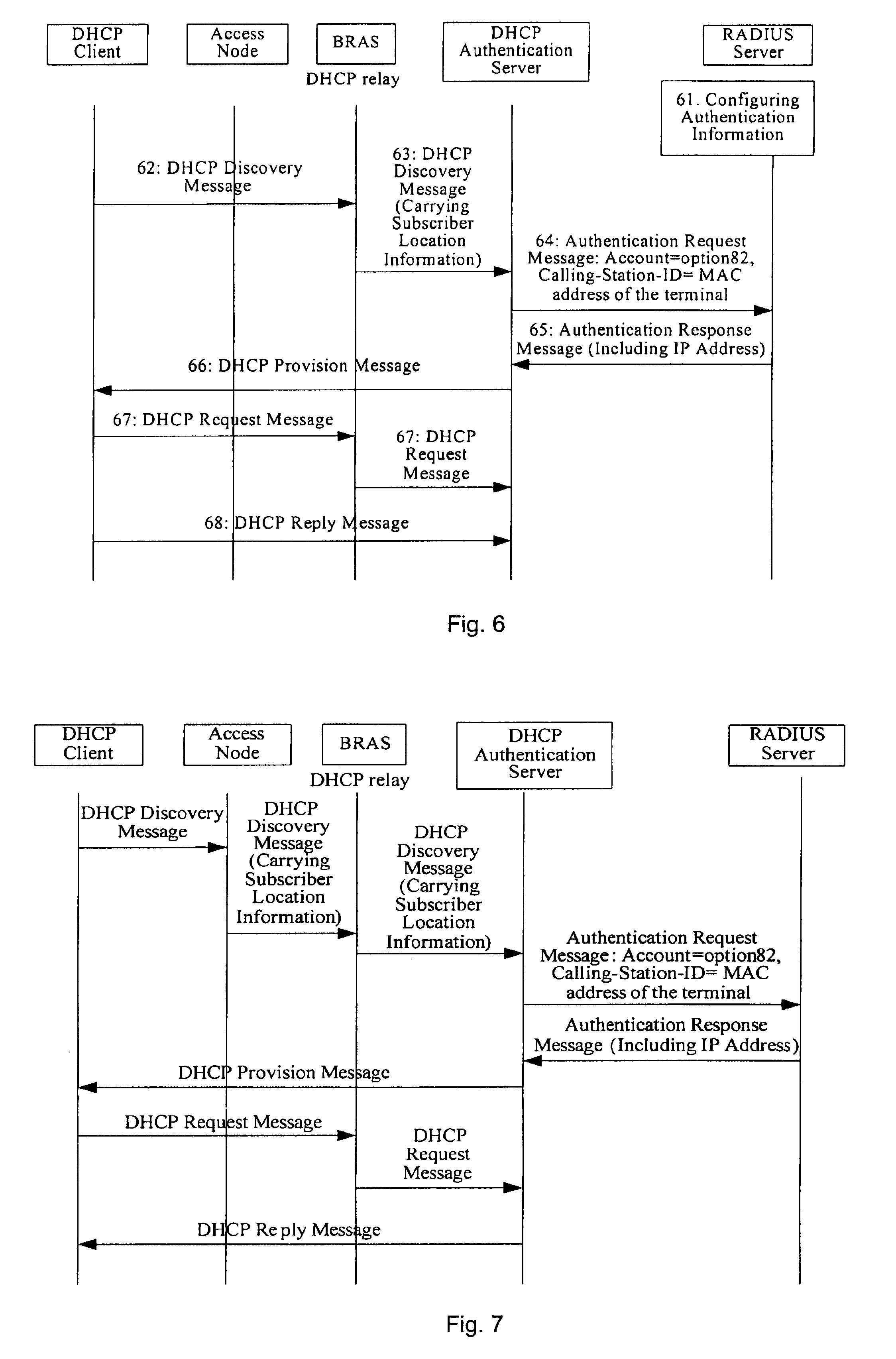
Method, system and server for realizing secure assignment of DHCP address
InactiveUS20080092213A1Enhanced securityNetwork cost be lowerDigital data processing detailsComputer security arrangementsClient-sideIp address
A method, a system and an authentication server for realizing a secure assignment of a DHCP address are disclosed. The method includes: sending a DHCP Discovery message via an access network; obtaining the identification information of the DHCP client and performing an authenticating to the DHCP client based on the identification information; and only assigning the address to the DHCP client has passed the authentication. Therefore, in the present invention, access authentication may be performed on a subscriber according to location information, and IP address is only assigned to the valid subscriber and terminal. Therefore, the security of the address assignment in DHCP mode may be enhanced greatly. Moreover, in the present invention, addresses may be managed by an AAA server unitedly, or the addresses may be assigned after being authenticated by the AAA server successfully.
Owner:HUAWEI TECH CO LTD
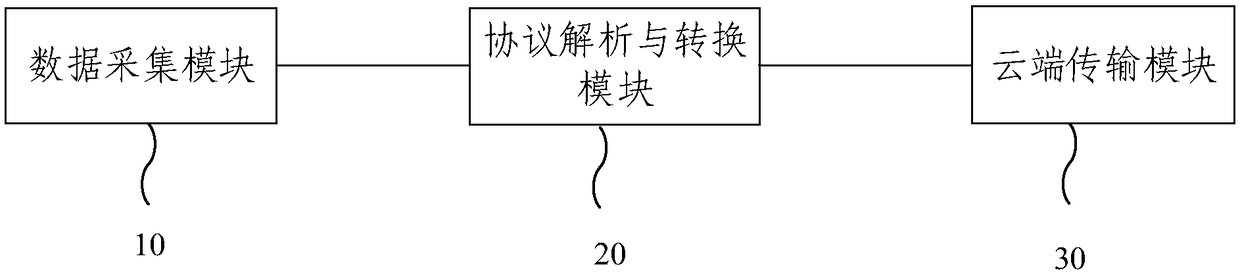
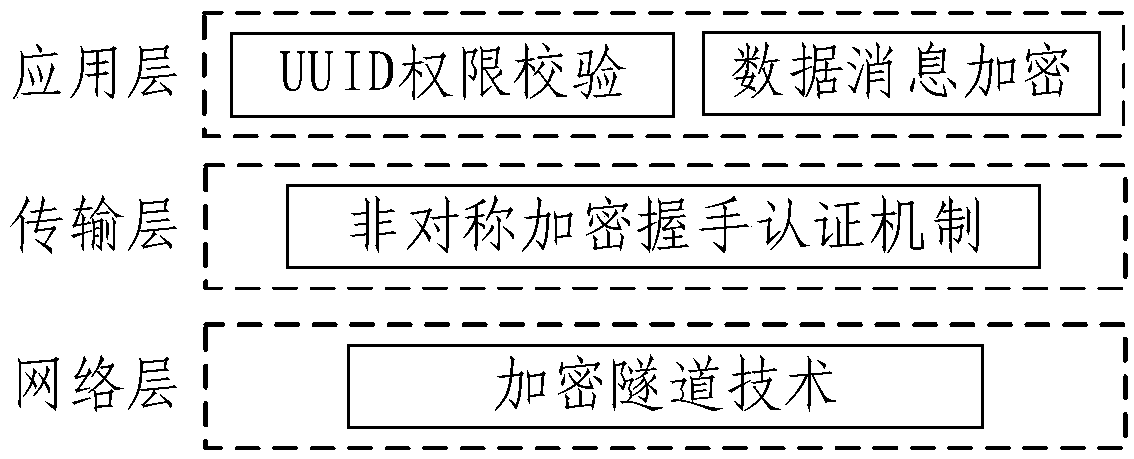
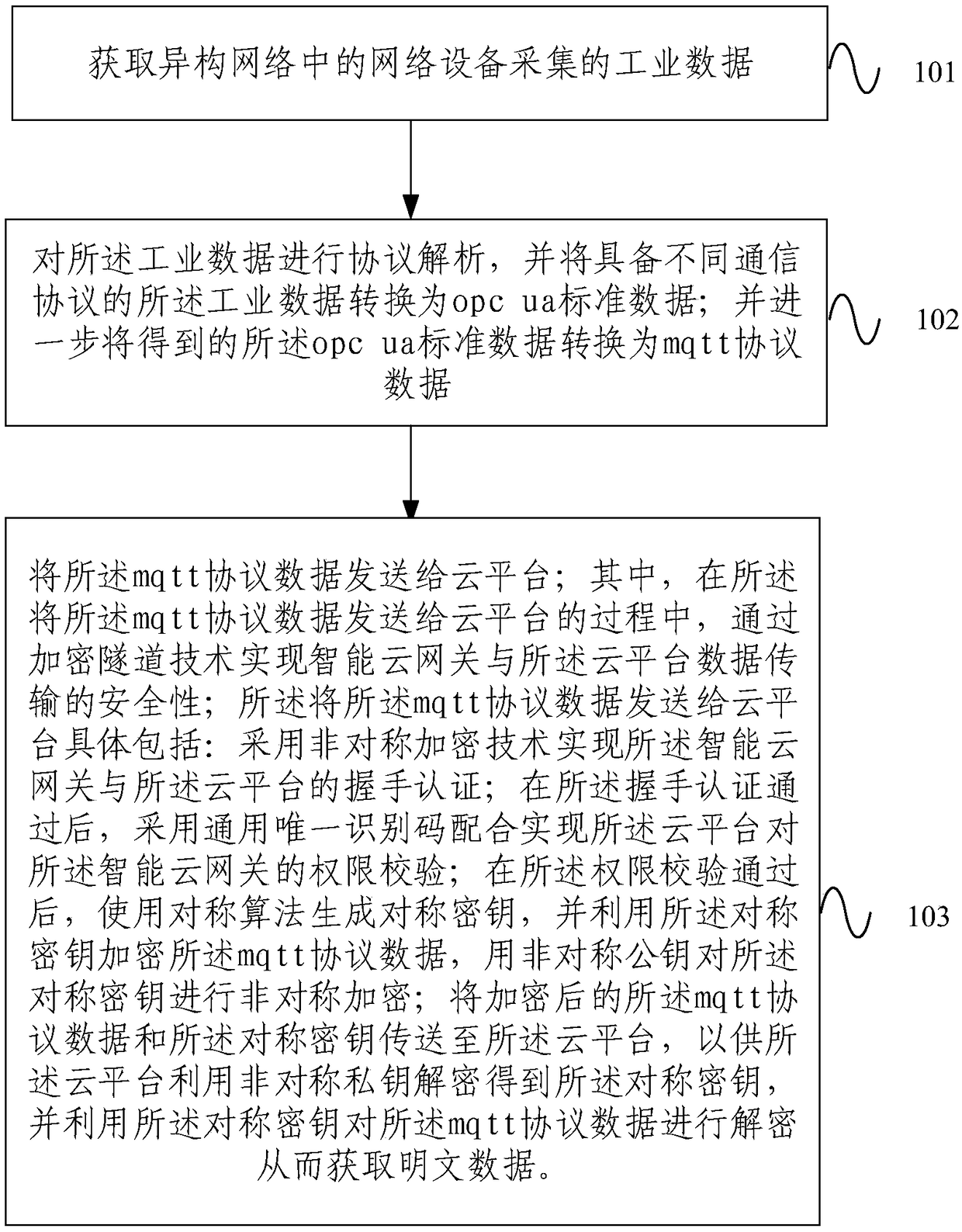
Intelligent cloud gateway of industrial IoT (Internet of Things) and communication method of gateway
ActiveCN109150703ASolve the problem of going to the cloudFix security issuesNetwork connectionsData transformationNetwork Communication Protocols
The invention provides an intelligent cloud gateway of the industrial IoT and a communication method of the gateway. The gateway comprises a data collection module, a protocol analysis and conversionmodule and a cloud transmission module; the data collection module obtains industrial data collected by network equipment in the heterogeneous network; the protocol analysis and conversion module analyzes protocols of the industrial data, converts the industrial data with the different communication protocols into OPC UA standard data, and further converts the obtained OPC UA standard data into MQTT protocol data; and the cloud transmission module transmits the MQTT protocol data to a cloud platform. Thus, the industrial data with the different protocols is sent to the cloud via the single gateway, different network device access schemes are provided, and the difficulty in transmitting the multi-protocol industrial data to the cloud in the heterogeneous network is solved; and the securityof data transmission is ensured comprehensively in the network, transmission and application layers, and a complete security guarantee system is formed.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
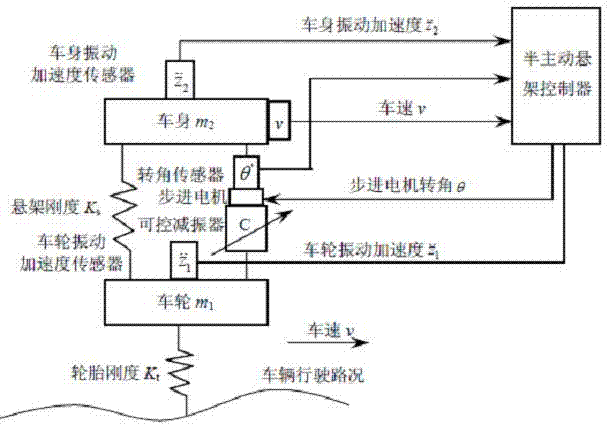
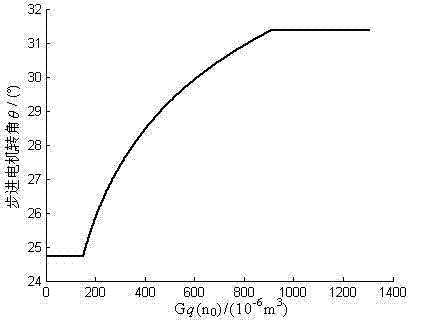
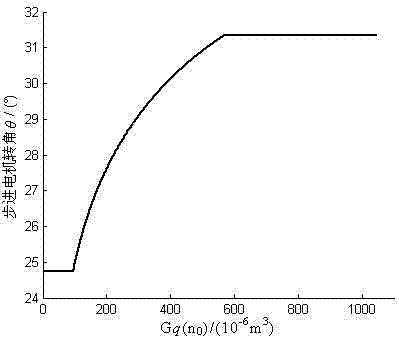
Real-time optimal damping control algorithm of automobile semi-active suspension system
InactiveCN102729760AImprove performanceSolve ride comfortResilient suspensionsVibration accelerationControl signal
The invention relates to an optimal damping control algorithm of a continuous-control-type semi-active suspension system, and the optimal damping control algorithm is researched and developed for meeting the taking comfort of people and automobile driving safety requirements well. The control algorithm comprises the following steps of: measuring automobile body vibration acceleration signals, automobile speed signals and rotation angle signals by utilizing a sensor; sensing the automobile driving road condition and suspension system damping ratio according to the signals measured by the sensor; according to the measured automobile body and automobile wheel vibration acceleration, obtaining the automobile body and automobile wheel vertical motion speed and the relative motion speed between an automobile body and automobile wheels; determining the optimal damping coefficient and the damping force of a shock absorber required under the current automobile speed and road condition according to automobile parameters, outputting stepping motor rotation angle control signals through a controller, and controlling and regulating the area of the damping throttling hole of a controllable shock absorber, so that the semi-active suspension system achieves the required optimal damping and damping force. The semi-active suspension optimal damping control algorithm provided by the invention is simple and easy to implement, has low requirements for the dynamic property of an actuating element, and is beneficial to the applications and popularization of the semi-active suspension.
Owner:SHANDONG UNIV OF TECH
Power circuit scanning test robot airplane and controlling system
InactiveCN1645284ANo casualtiesAvoid lostToy aircraftsCable installation apparatusNavigation systemElectric power
A robot airplane for tour inspection of power line in counterwise driving structure of coxial double propeller uses two engines to control flight stability, GPS and GIS to confirm flight path, computer processor to adjust flight attitute and battery to provide power for motor, transducer and data link system. Its control system consists of navigation system, autonomous planning system, data link system and on line detection system.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Method and system for internet of things information transmission
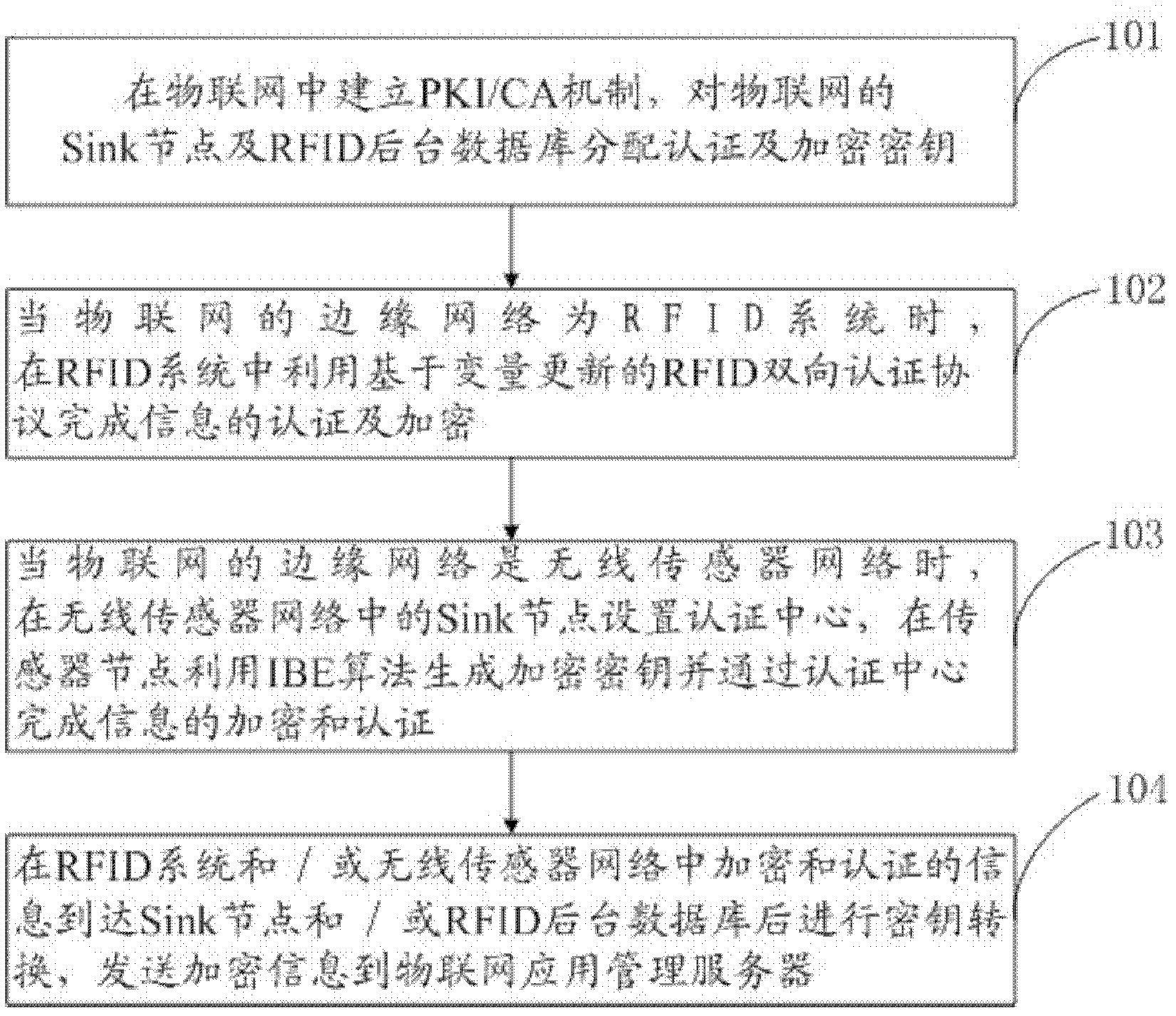
ActiveCN103166919AImprove securityGuaranteed privacyUser identity/authority verificationInformation transmissionThe Internet
The invention discloses a method and a system for internet of things information transmission. Firstly, a public key infrastructure / certificate authority (PKI / CA) mechanism is established in the internet of things and an authentication key and an encryption key are distributed to an aggregation node of the internet of things; transmitted information is encrypted and authorized in an edge network of the internet of things; and key conversion is conducted after the encrypted and authorized information reaches the aggregation node of the internet of things and the information encrypted again is sent to an application management server of the internet of things. According to the method and the system for the internet of things information transmission, the internet of things can effectively resist interior attack, information safety transmission level is improved and complexity of encryption and safety authentication calculation in the edge network of the internet of things is reduced.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
Network security situation sensing system and method based on multi-layer multi-angle analysis
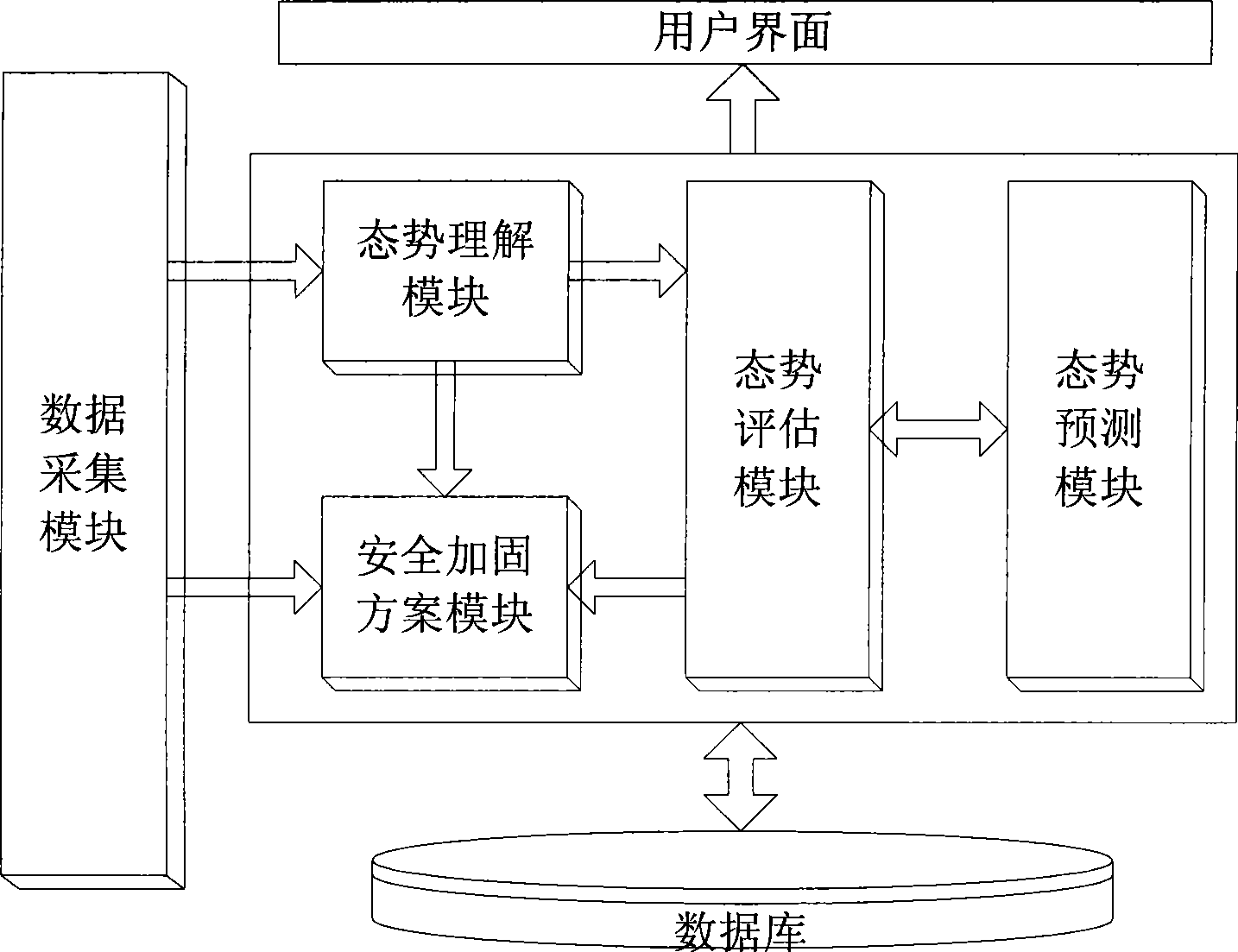
InactiveCN101459537AThe evaluation results are systematic and comprehensiveFix security issuesData switching networksData acquisition moduleNetworked system
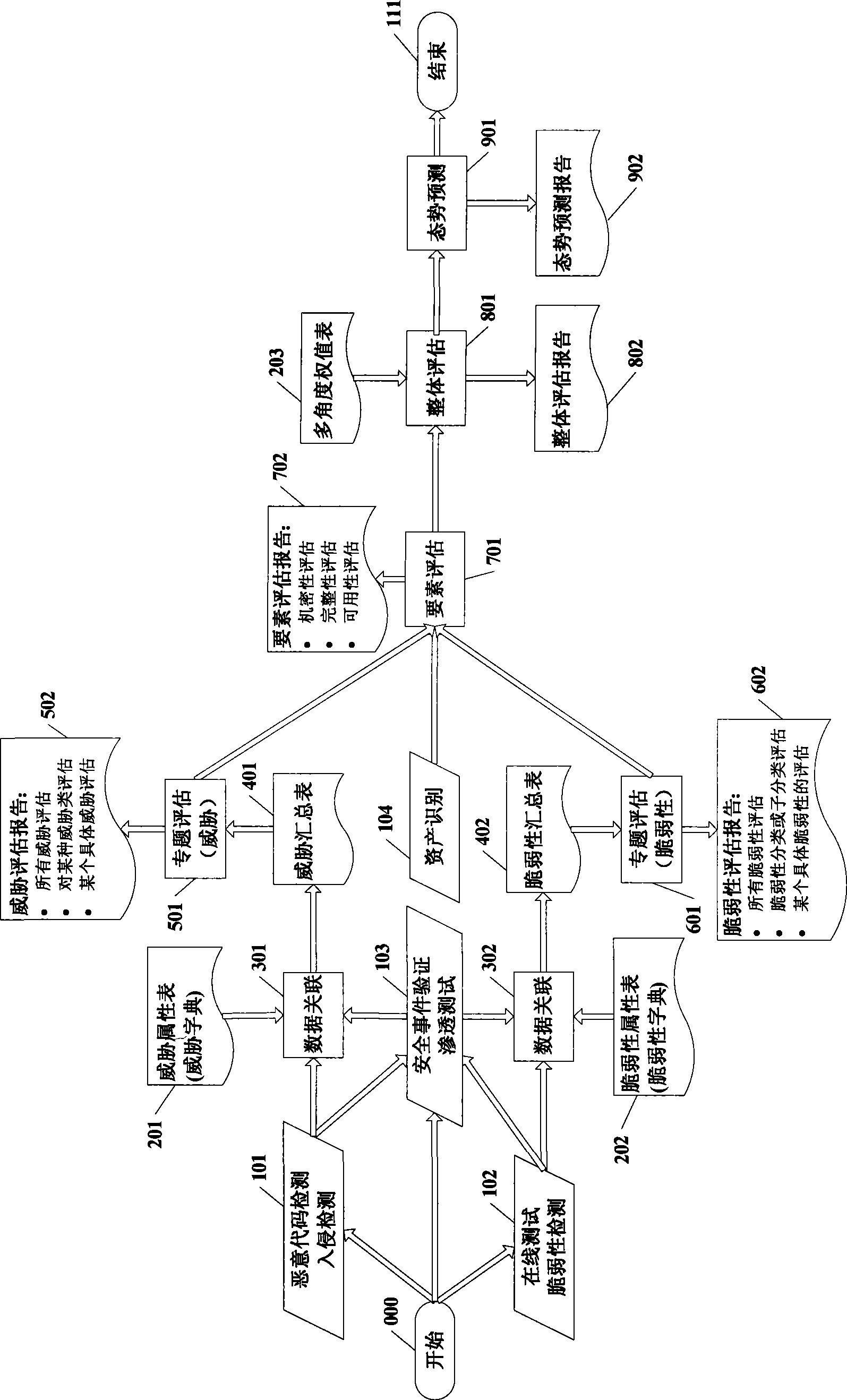
The invention discloses a network security situation perception system and a method based on multilevel multi-angle analysis, wherein the system comprises a data gathering module, a network security situation understanding module, a network security situation estimation module and a network security situation forecasting module. The method for achieving the network security situation perception system comprises the following steps: firstly, doing statistical data fusion and association analysis to data in the aspects of assets, intimidation and vulnerability of a network system gathered by a sensor, and getting normalized data, secondly, analyzing the normalized data after the fusion of the step one, and doing network security situation special subject estimation, thirdly, doing network security situation factor estimation according to the normalized data obtained in the step one and the estimation result of the step two, fourthly, doing the integral estimation of network security situation according to the estimation result of the step three, fifthly, doing network security situation forecast according to the estimation result of the step D. The invention analyzes the security situation of network from multi levels and multi angles, and guarantees a result perception system to be more accurate and comprehensive.
Owner:UNIV OF SCI & TECH OF CHINA
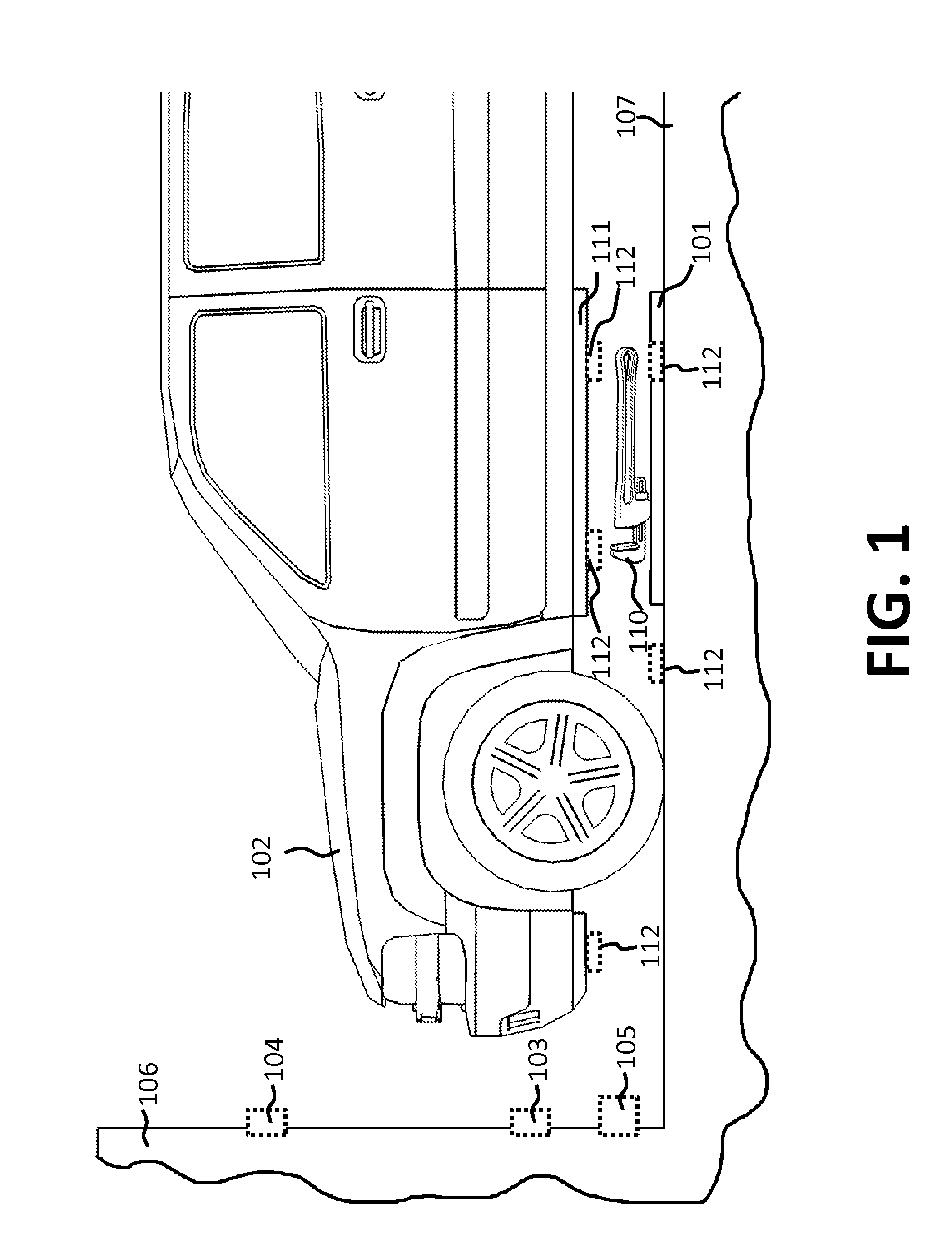
Vehicle Charger Safety System and Method
InactiveUS20140084859A1Fix security issuesMultiple-port networksBatteries circuit arrangementsForeign objectSystem identification
Wireless vehicle charger safety systems and methods use a detection subsystem, a notification subsystem and a management subsystem. The detection subsystem identifies a safety condition. The notification subsystem provides an indication of the safety condition. The management subsystem addresses the safety condition. In particular, undesirable thermal conditions caused by foreign objects between a source resonator and a vehicle resonator are addressed by sensing high temperatures, providing a warning and powering down a vehicle charger, as appropriate for the environment in which the charger is deployed.
Owner:WITRICITY CORP
Nuclear power plant working robot and control system thereof
InactiveCN101774170ACapable of autonomous navigationRealize online monitoringEndless track vehiclesManipulatorTerrainOperational costs
The invention relates to a nuclear power plant working robot and a control system thereof, which belong to the fields of robots and automation equipment. The nuclear power plant working robot is a crawler-type mobile manipulator and is composed of a mobile platform driven by double crawlers and a four freedom degree manipulator carried on the mobile platform. The nuclear power plant working robot can move inside a nuclear power plant, has two control modes of manual remote control and autonomous control, and is remotely controlled by a wireless or wired mode. The control system of the nuclear power plant working robot includes a host monitoring and planning control system and a robot control system which are matched to control the operation of the robot. The robot operates autonomously, is safe and reliable, can complete certain dangerous tasks in high radioactivity environment; the robot has small size, stable performance, great maneuverability and low operation cost; a crawler-type chassis has strong gripping force as well as certain climbing and obstacle clearing ability, and is suitable to walking over complex terrains; and the robot has high intelligence degree and can realize autonomous control and manual remote control.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
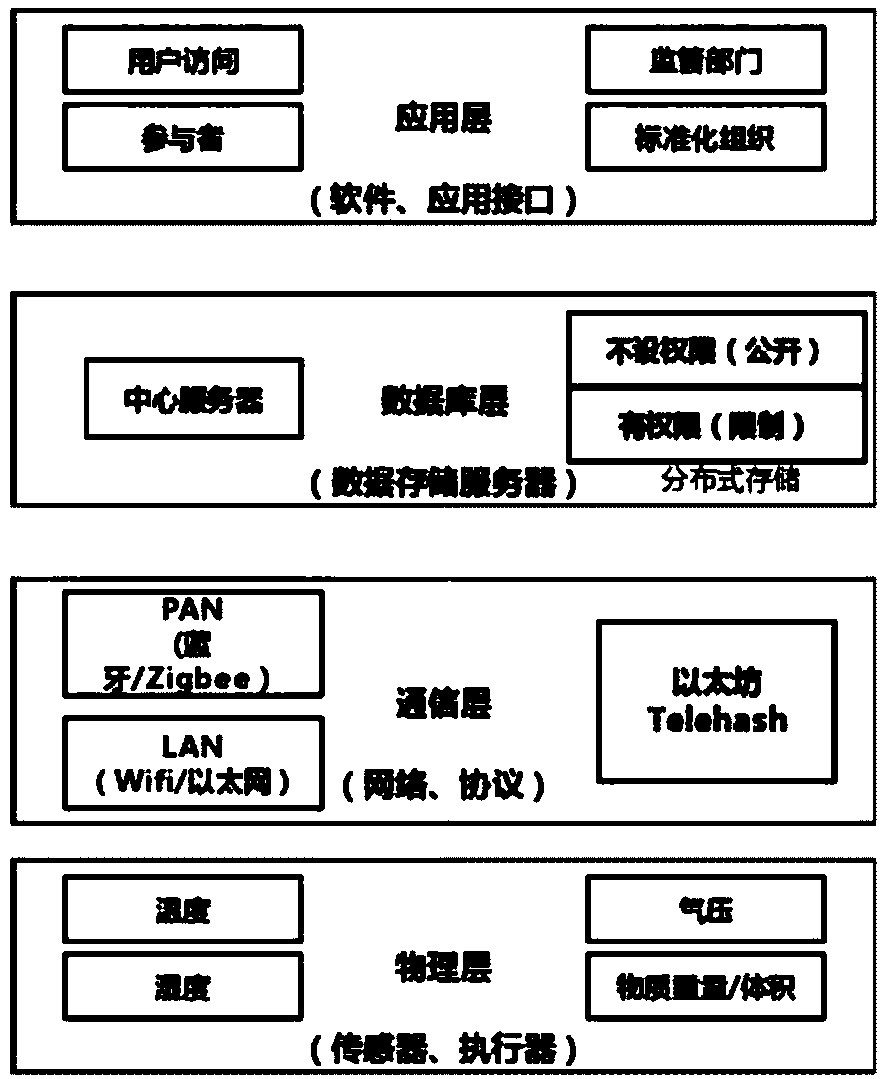
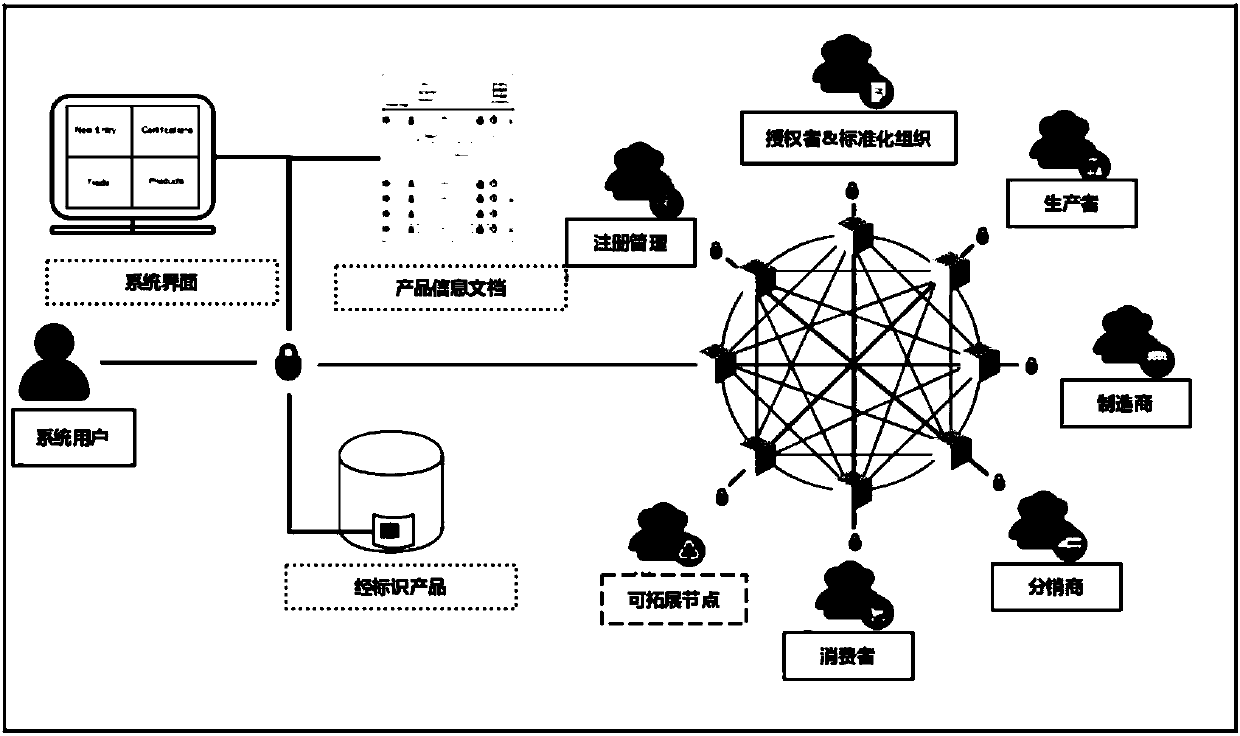
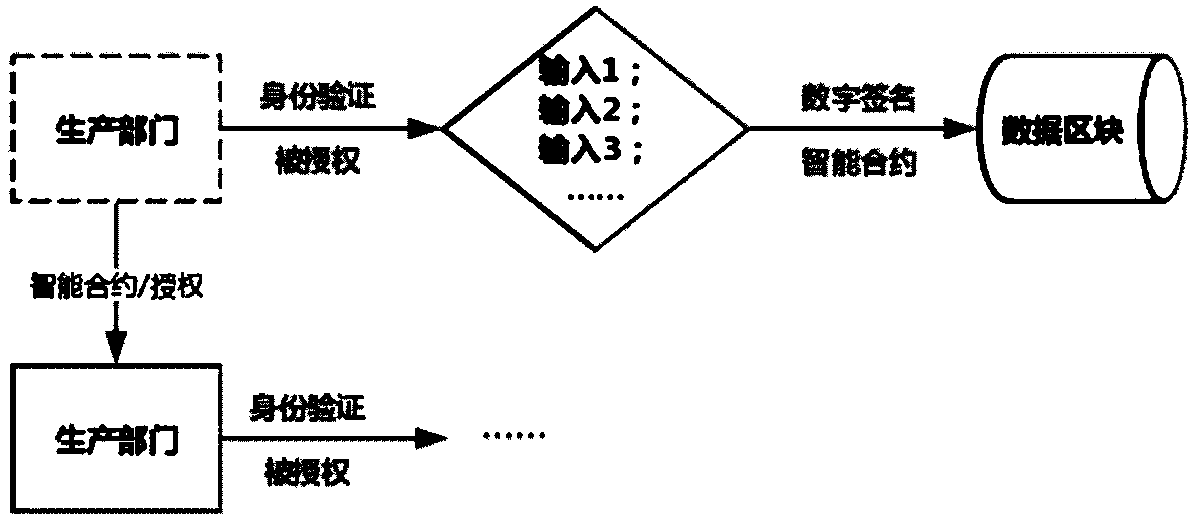
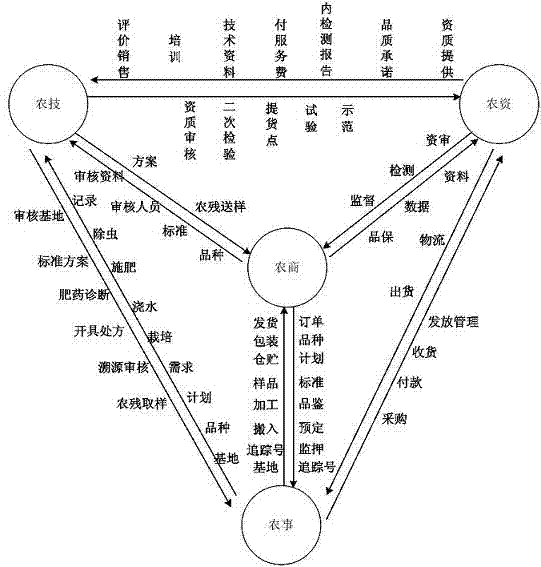
Blockchain technology-base agricultural product traceability method
InactiveCN107909372ASolve non-standard collectionFix security issuesCommerceDigital signatureData access
The invention relates to a blockchain technology-base agricultural product traceability method. According to the method, a block chain technology is applied to the database layer and communication layer of a system; agricultural products are coded through a global unified identification system; a data entry process uses digital signatures and smart contracts, so that it can be ensured that data are not tampered; all the data are stored in a blockchain and can be accessed by authorized nodes; and the right of data access depends on the roles and functions of participants in a supply chain. Withthe method adopted, problems such as non-standard information collection, insecure data storage, the vulnerability of a central system to attacks and failure to ensuring privacies in the process of information exchange between enterprises of a traditional agricultural product traceability system can be solved.
Owner:FUDAN UNIV
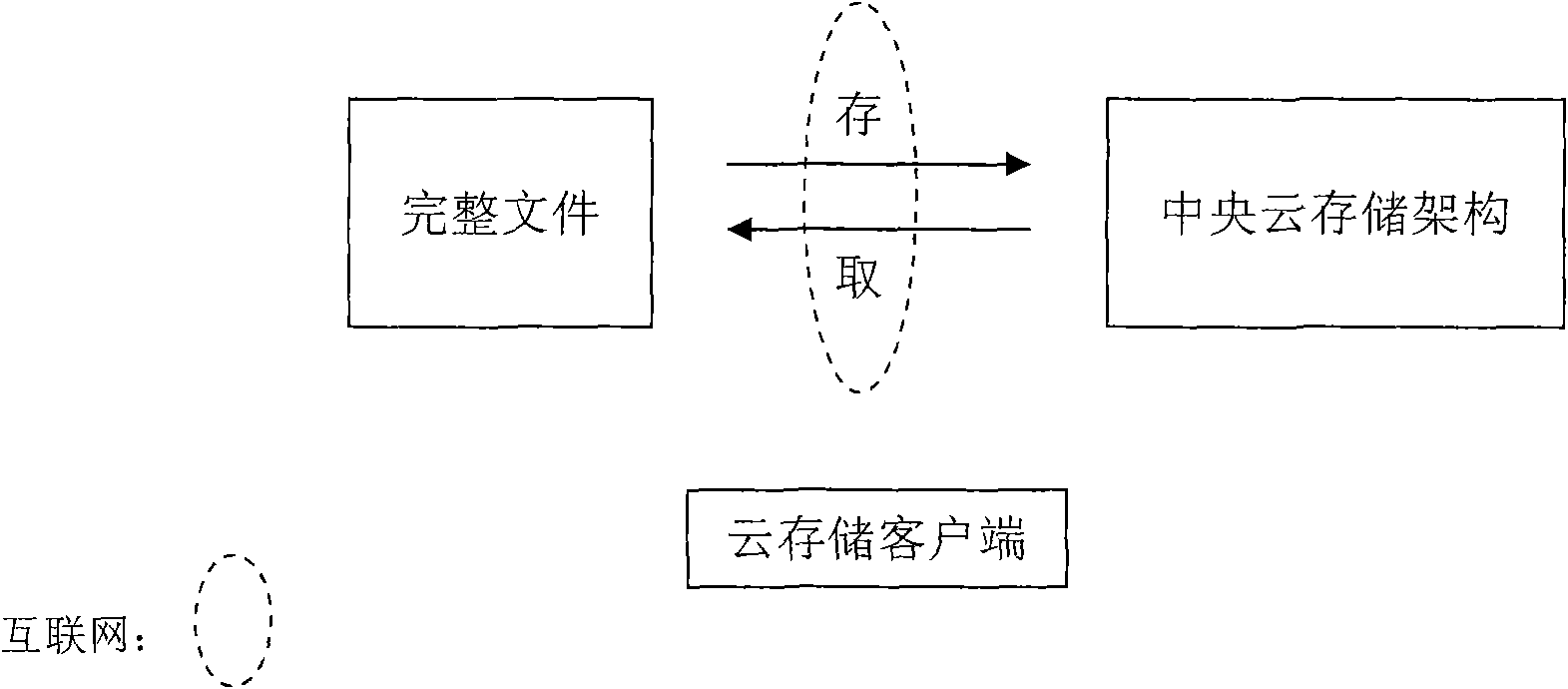
Method for structuring parallel system for cloud storage
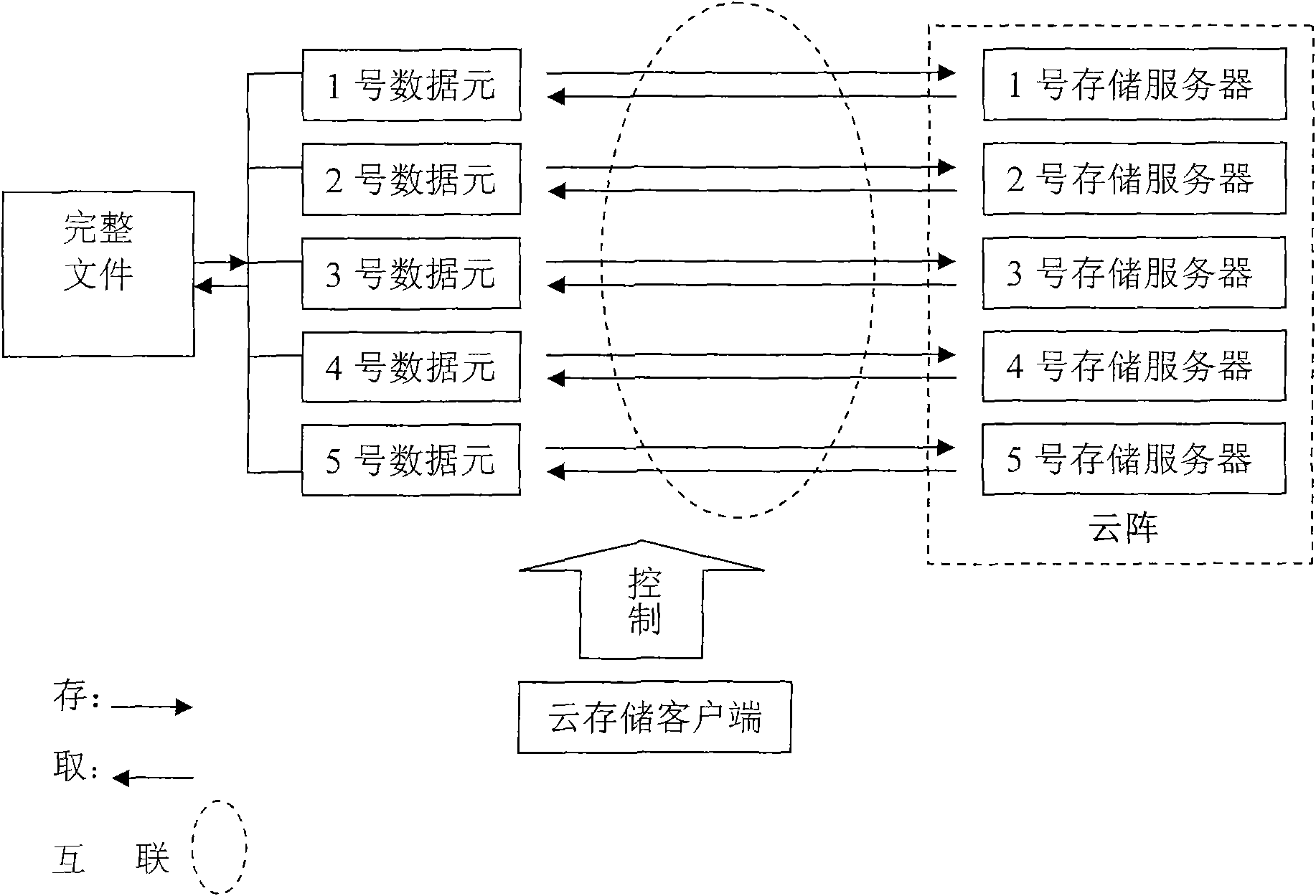
The invention is mainly characterized in that: (1) a novel technical proposal for decentralizing network central storage is established, namely before being stored, a master file is broken into a plurality of sub-files known as data elements, as the smallest units for storage, by a program; (2) a prior network central storage method is replaced by cloud array storage technology, wherein a cloud array consists of a plurality of servers set by special serial numbers; an access relation of the data elements corresponding to the servers is established according to the serial numbers; and an original file is broken into the data elements respectively stored in the cloud arrays; (3) the storage of the data elements adopts a multi-process parallel mode, namely one process executes the storage of one data element, and N processes execute the storage of N data elements; and due to the parallel processes, the storage speed can be improved; (4) the data elements are encrypted and compressed, and an original password is not allowed to save; and (5) an operating system of the servers is Unix. The method for structuring a parallel system for the cloud storage can effectively solve the problem of the security of cloud storage data, and has important value for cloud storage structuring and application development.
Owner:何吴迪
Spinel nickel manganese acid lithium and layered lithium-rich manganese-based composite cathode material with core-shell structure and preparation method thereof
ActiveCN104157831APromote circulationRaise the ratioCell electrodesSecondary cellsComposite cathodeMaterial synthesis
The invention relates to a spinel nickel manganese acid lithium and layered lithium-rich manganese-based composite cathode material with a core-shell structure and a preparation method thereof, which belongs to the technical field of material synthesis. The prepared lithium ion composite cathode material takes a layered lithium-rich manganese-based Li[Lia(NixCoyMnz)]O2 as a core material, takes spinel nickel manganese acid lithium LiNi0.5Mn1.5O4 as a shell material; a coprecipitation method is employed to obtain a core-shell precursor, the core-shell precursor and the lithium source are uniformly mixed and calcined to obtain the spinel nickel manganese acid lithium and layered lithium-rich manganese-based composite cathode material with the core-shell structure. According to the invention, the layered lithium-rich manganese-based is taken as the core material, and the spinel nickel manganese acid lithium is taken as the shell material; under the prerequisite that material gram capacity is kept, material structural stability is increased, material cycle, multiplying power and safety performances are improved, function composite and complementation of the core material and the shell layer material can be realized, and the problem that high capacity and high security can not be achieved simultaneously is solved. The composite cathode material has the advantages of simple process and obviously increased performance.
Owner:南京时拓能源科技有限公司
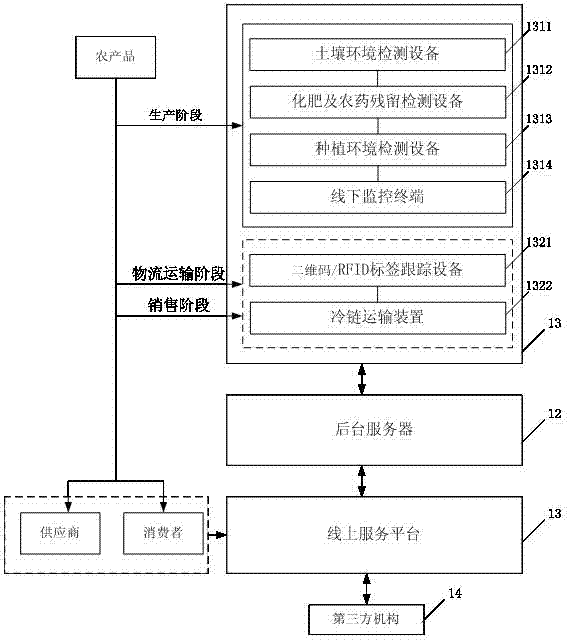
Supply chain control system for ensuring agricultural product safety
InactiveCN104715330ARealize the purchaseFix security issuesBuying/selling/leasing transactionsResourcesRelevant informationControl system
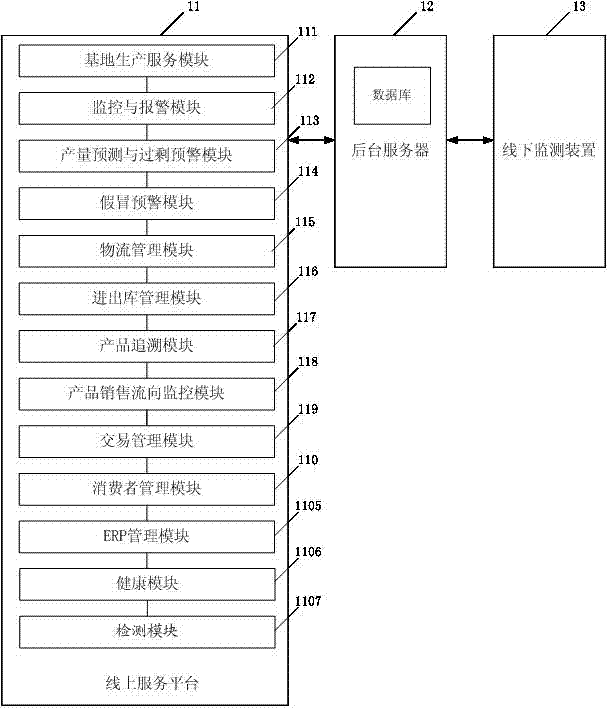
The invention discloses a supply chain control system for ensuring agricultural product safety. The system is used for achieving the control management over agricultural product information for the whole process ranging from the production stage to the transportation stage to the sales stage. The system comprises an on-line service platform, a background server and an off-line monitoring device; the off-line monitoring device comprises detection equipment which is arranged in the production stage, in the transportation stage and in the sales stage and serves for detecting and acquiring corresponding relevant information in the production stage, relevant information in the transportation stage and relevant information in the sales stage; all the acquired information is sent into a database of the background server; the on-line service platform communicates with the background server to acquire the relevant information, corresponding control signals are sent to the off-line monitoring device through the background server, and to be specific, the on-line service platform comprises multiple control modules which correspond to information in the production stage, information in the transportation stage and information in the sales stage, so that it is achieved that the whole process ranging from the production stage to the transportation stage to the sales stage of agricultural products is monitored effectively in a seamlessly flowing mode.
Owner:厦门绿链集成服务有限公司
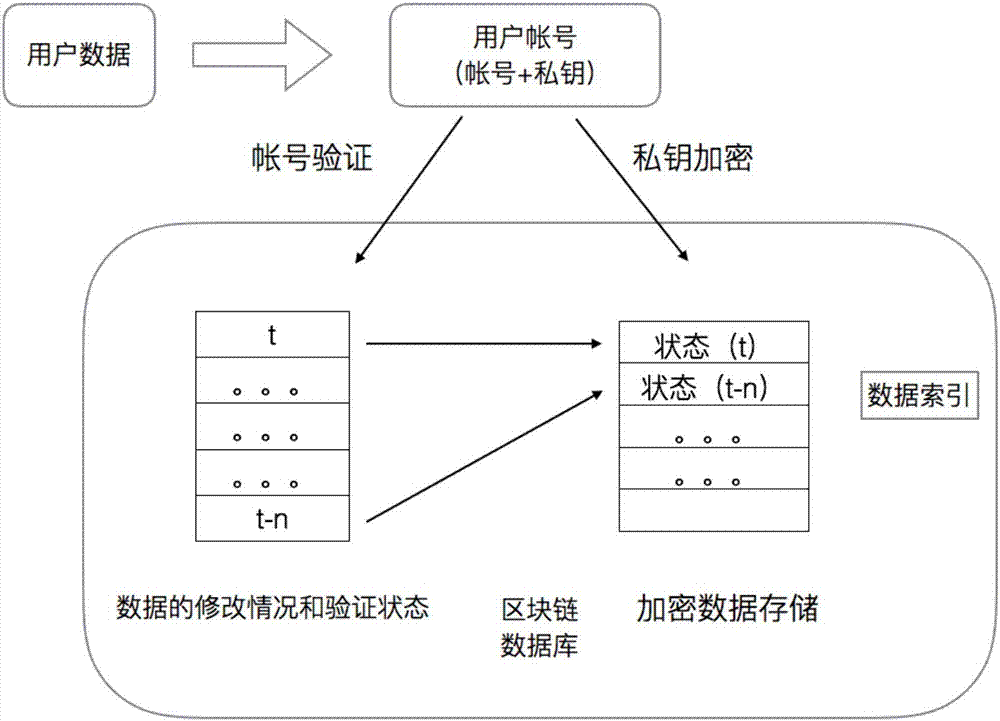
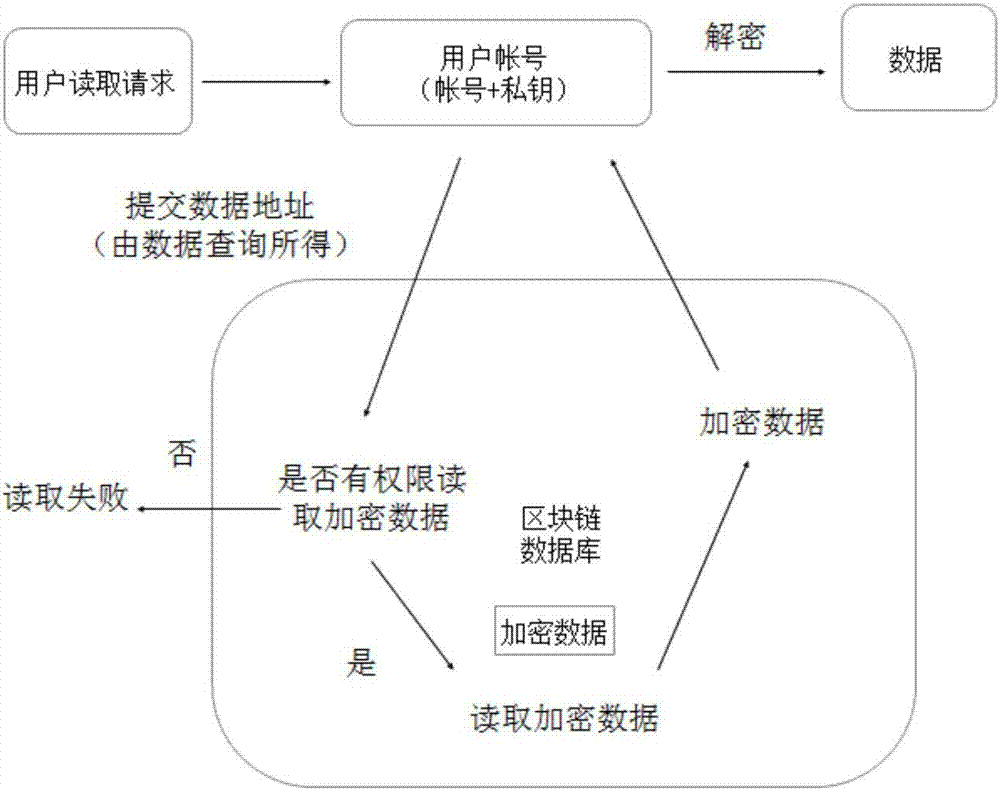
Blockchain-based database system and method of using same
ActiveCN107292181AFix permission issuesSolve the problem of excessive permissionsDigital data protectionSpecial data processing applicationsConfidentialityCentral database
The invention discloses a blockchain-based database system, comprising a client, an access server and a blockchain verification server. A method of using the blockchain-based database system comprises the steps of 1, registering a blockchain account on the blockchain verification server through the client, or registering, by the blockchain verification server itself, the blockchain account on the blockchain verification server, and acquiring a public key and a private key; 2, writing, by a user, data into the access server through the client; 3, transmitting, by the access server, a request to the blockchain verification server to perform data co-recognition; 4, submitting, by the user, a query request to the access server through the client to perform related query; 5, after the user obtains data query results, directly using, by the user, the results to read data, or otherwise the user having the need to perform data query; after data reading, unlocking the data by the user through his or her own account private key. The problems are solved that data in a central database are insecure and it is difficult for a distributed database to arrive at uniformity and data confidentiality.
Owner:无锡井通网络科技有限公司
Digital signature method, digital signature system and quantum key card
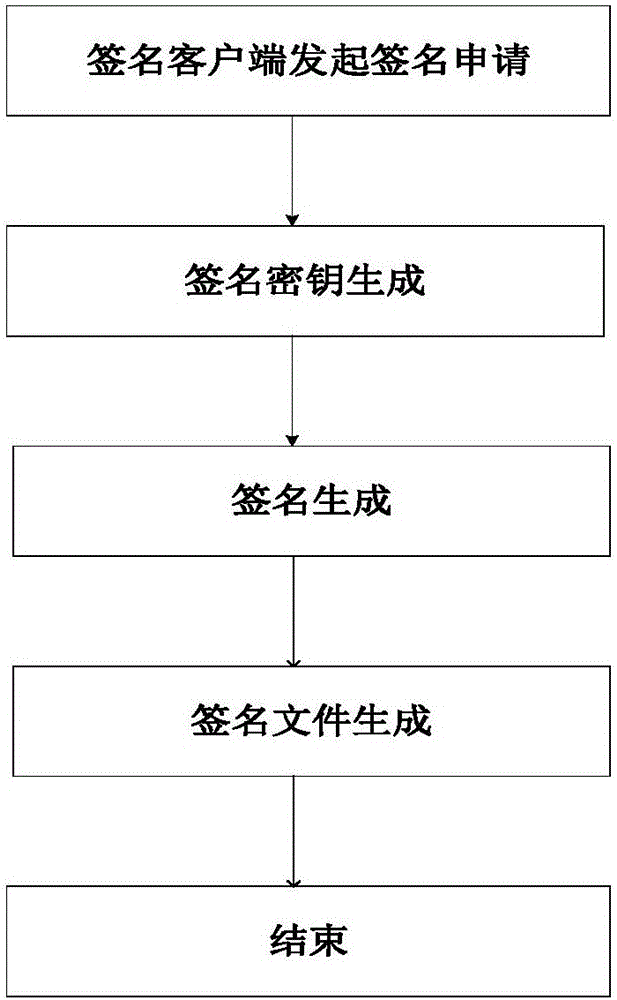
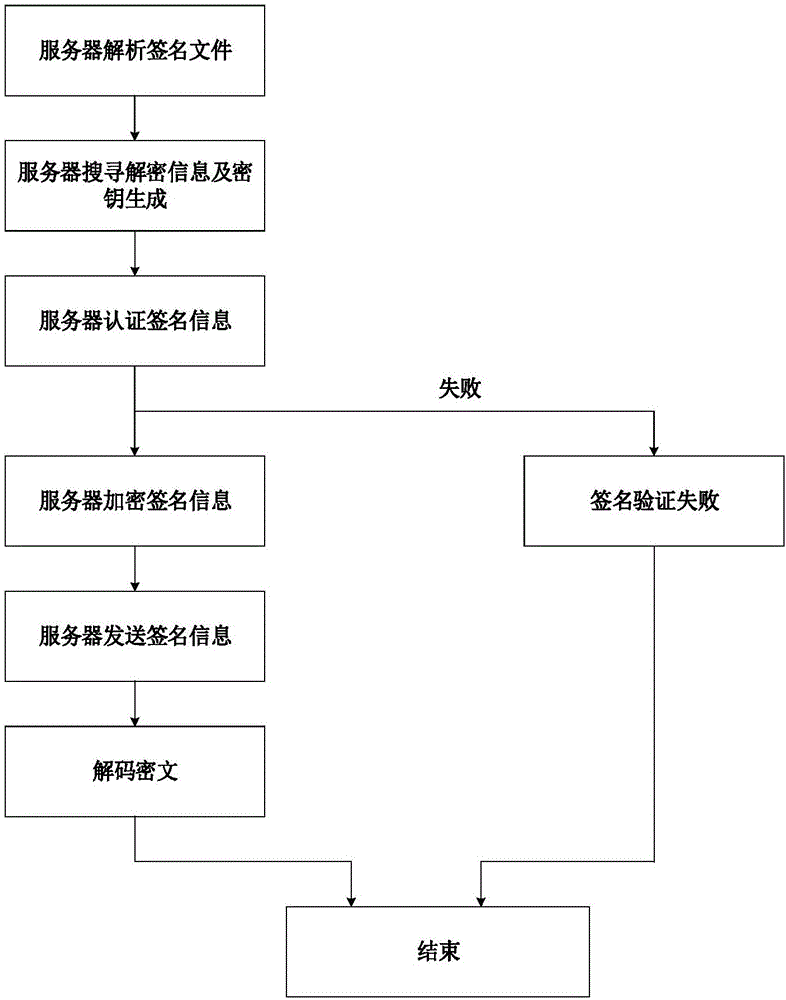
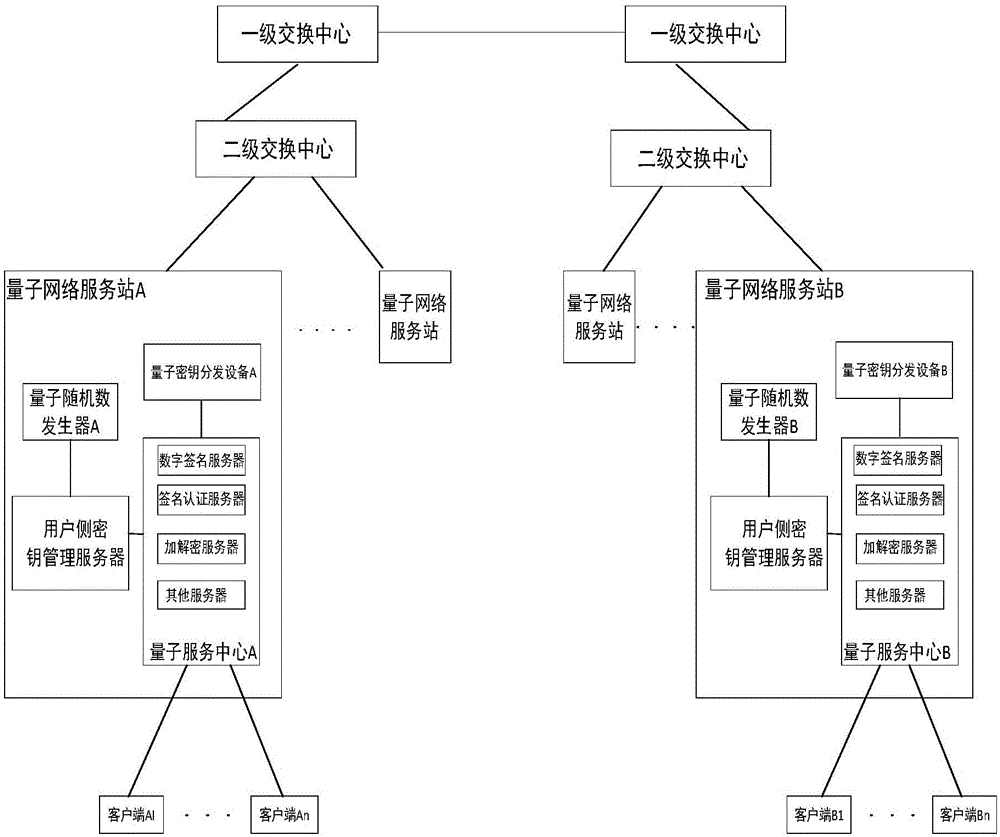
ActiveCN106357396AFix security issuesReduce the risk of being crackedKey distribution for secure communicationUser identity/authority verificationSignature fileDigital signature
The invention discloses a digital signature method, a digital signature system and a quantum key card. The digital signature system comprises quantum network service stations, signature client sides, authentication client sides and quantum key cards, wherein the quantum network service stations are configured on the network side, and the signature client sides and the authentication client sides are configured on the user side. The digital signature method includes that a true random number is generated on the network side and then stored in the corresponding quantum key card and on the network side respectively to form a corresponding user-side key; the quantum key card matching with the signature client side uses the stored user-side key to generate a signature file, the signature file is sent to the authentication client side via the signature client side, and the authentication client side sends the received signature file to the current quantum network service station, acquires the corresponding user-side key from the network side to perform signature authentication on the signature file and sends signature authentication results to the corresponding authentication client side. The digital signature method, the digital signature system and the quantum key card have the advantage that key seeds are stored in the quantum key cards and the quantum network service stations, so that the problems of access use and safety of quantum network terminals are solved.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
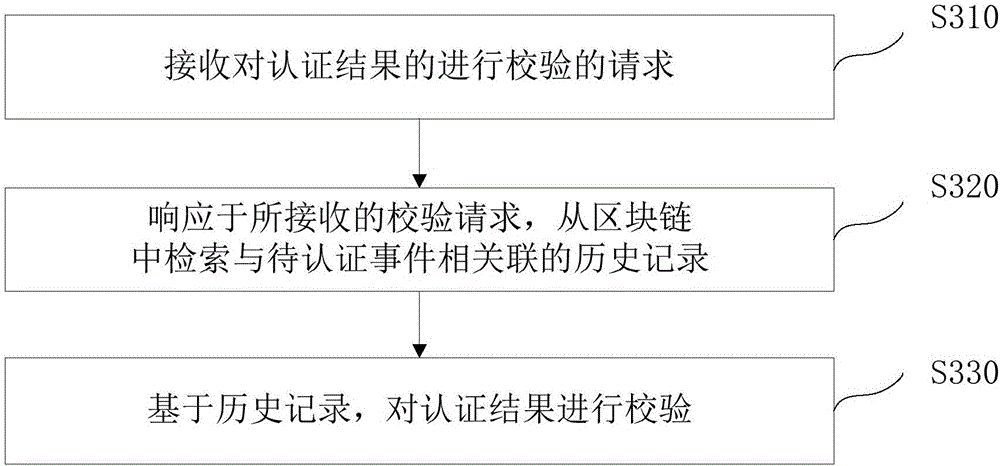
Event authentication method and device
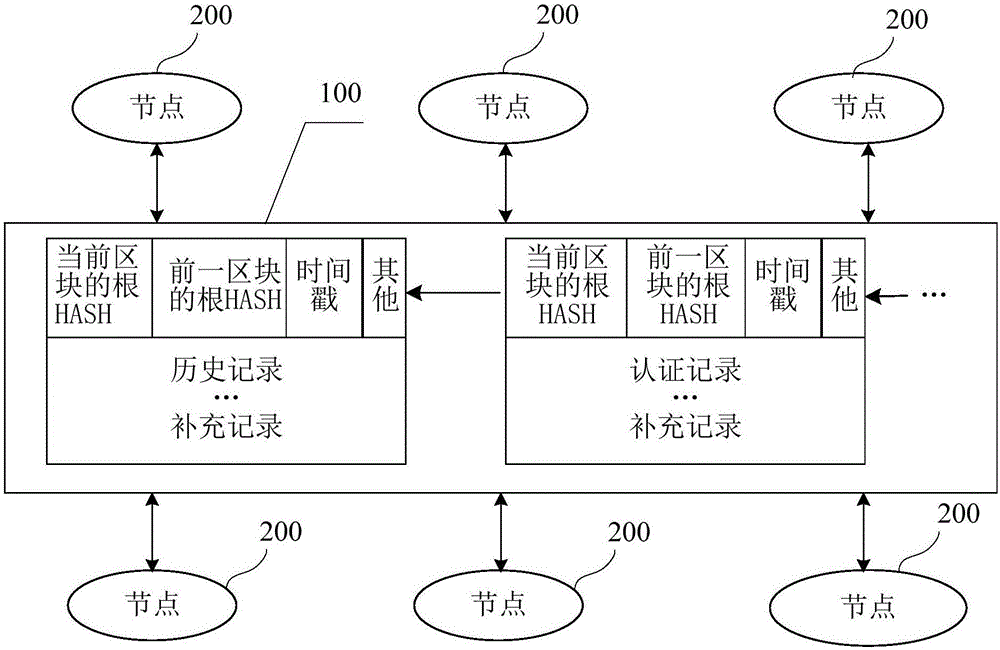
InactiveCN106845210AFix security issuesAddress reliabilityDigital data authenticationRelevant informationDependability
The invention discloses an event authentication method and device. The method includes: collecting the related information of a to-be-authenticated event; generating an authentication request for performing authentication on the to-be-authenticated event when the related information meets the triggering conditions of the to-be-authenticated event; responding to the generated request to retrieve historical records associated with the requested to-be-authenticated event from a block chain; authenticating the to-be-authenticated event according to the historical records. The method has the advantages that the collected event information is compared with preset event information to trigger the event authentication flow, and the problems that an existing authentication program is complex, long in authentication time, non-objective in authentication, and the like are solved; the authentication is performed on the basis of the historical records, which cannot be tampered and are high in reliability, in the block chain, and high authentication result reliability and high safety node are achieved.
Owner:BUBI BEIJING NETWORK TECH CO LTD
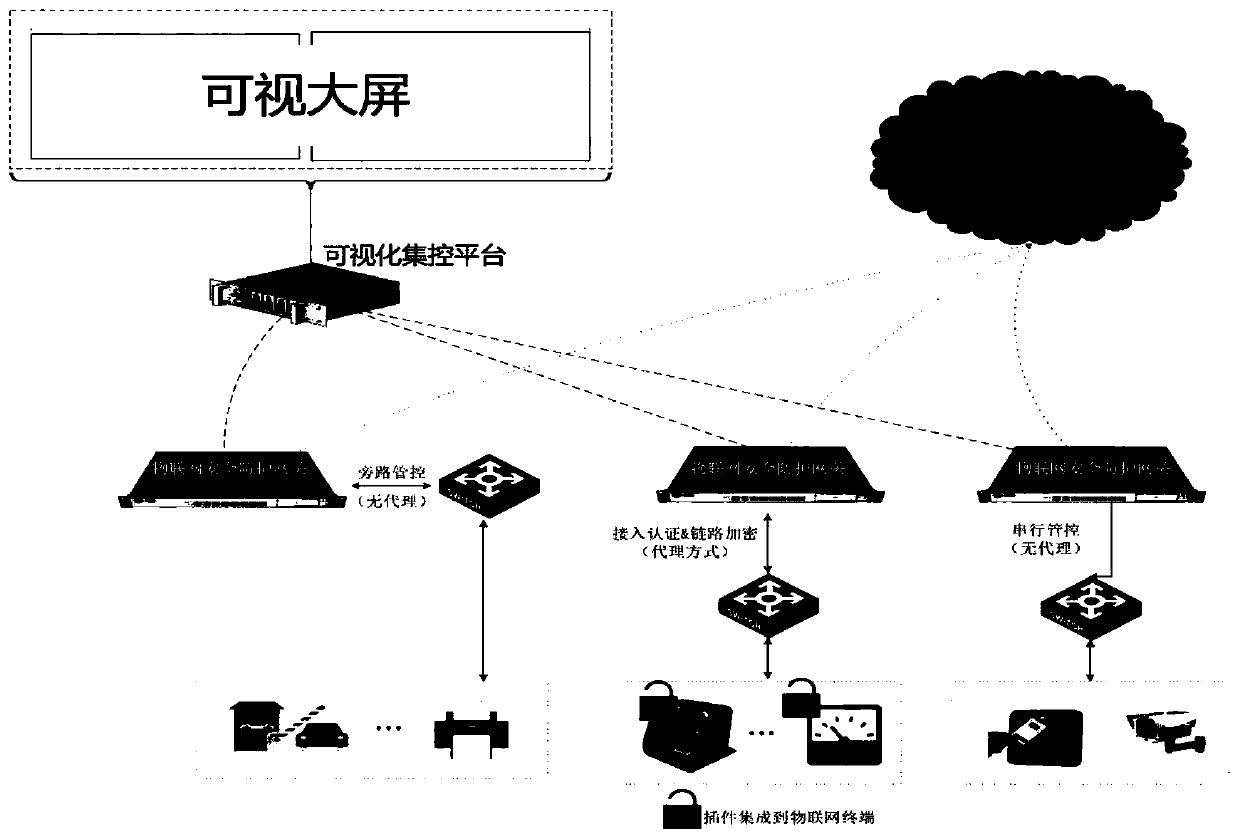
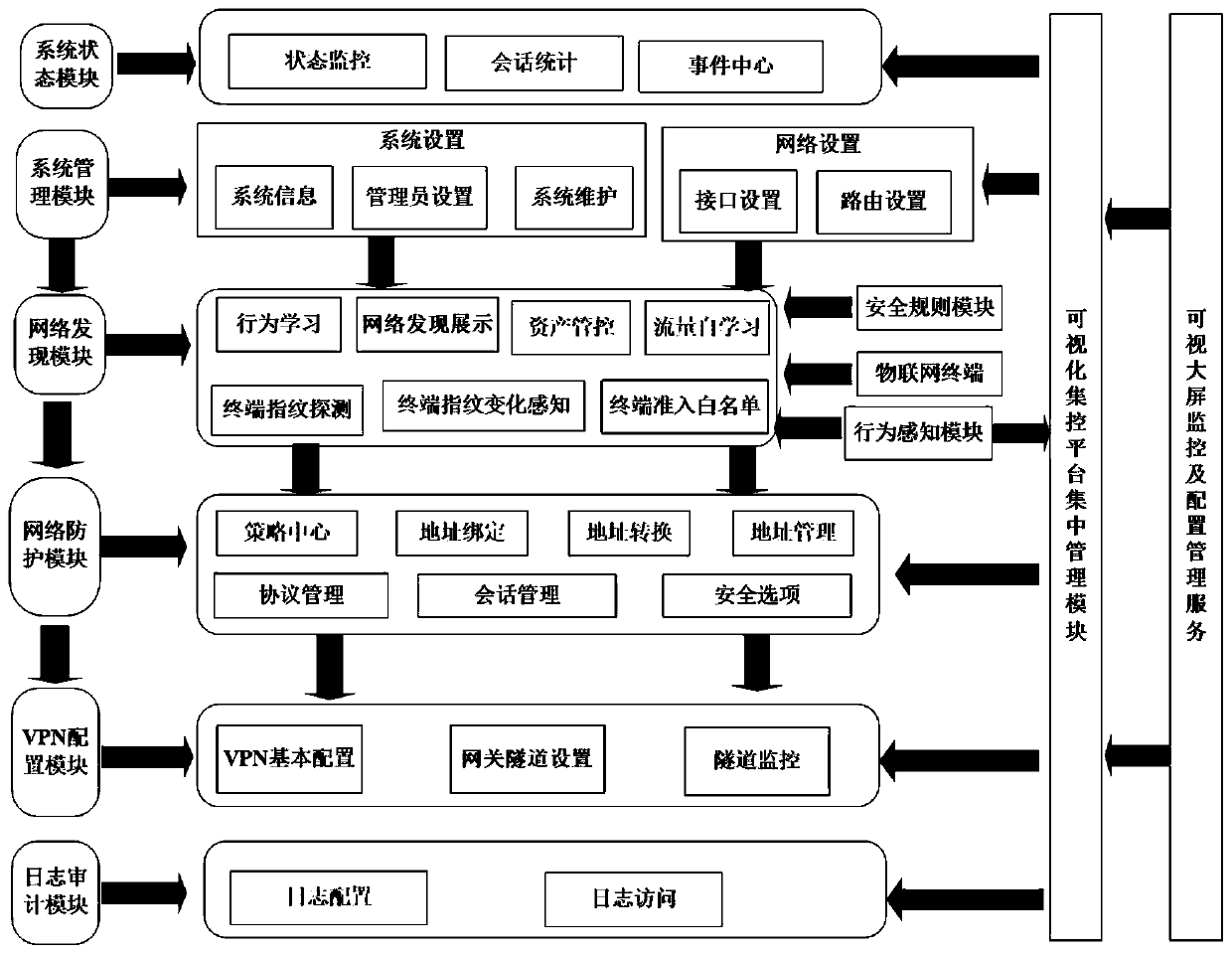
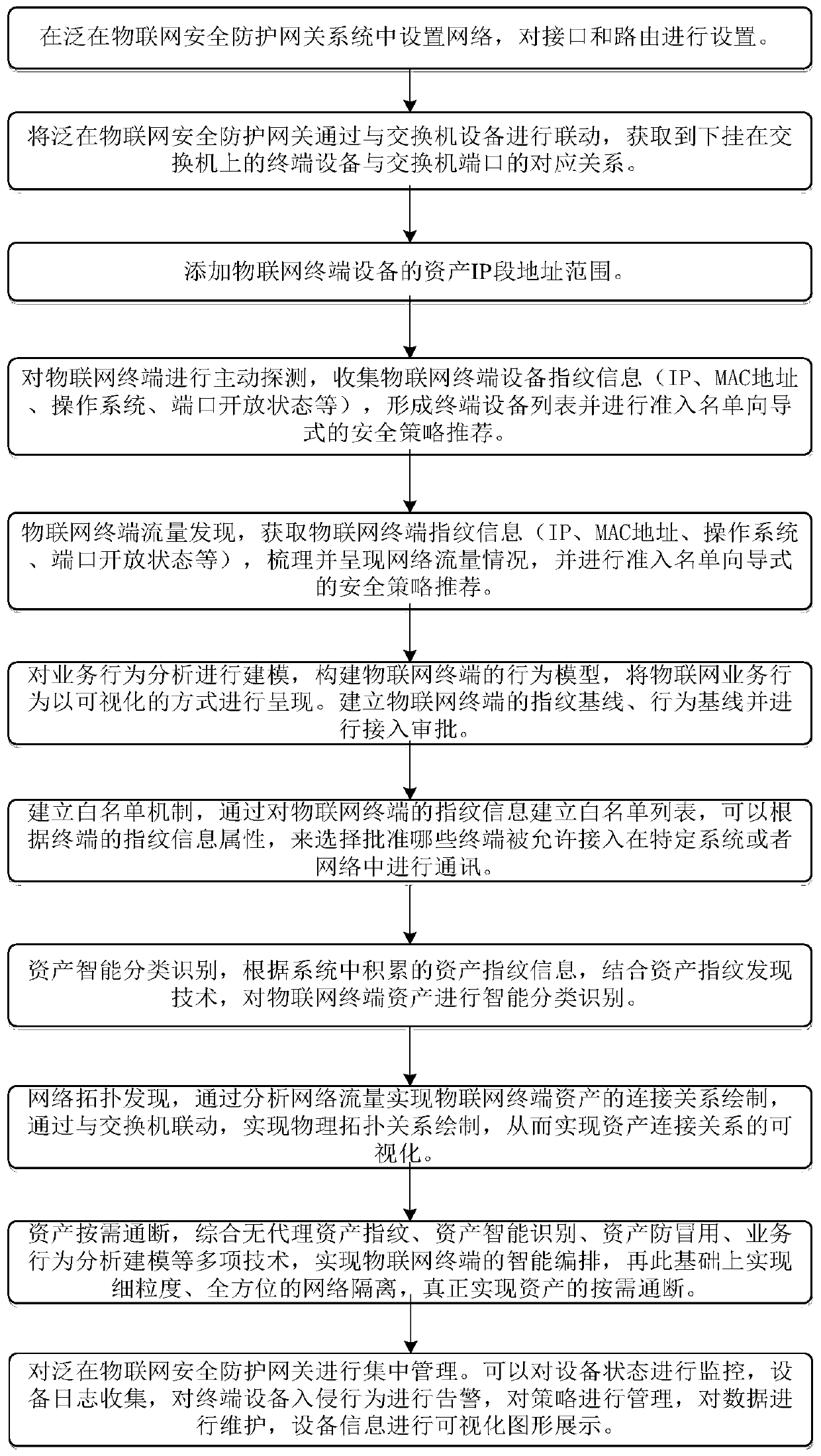
Electric power industry ubiquitous Internet of Things security protection gateway system, method and deployment architecture
InactiveCN110958262ARealize visualizationEfficient identificationTransmissionVisual presentationAttack
The invention discloses an electric power industry ubiquitous Internet of Things security protection gateway system, method and deployment architecture. The method is oriented to a ubiquitous electricpower Internet of Things full-scene safety protection application scene. A terminal identification technology is adopted, fingerprint information of Internet of Things terminal device in a network isidentified in two modes of active detection and flow discovery, asset conditions of Internet of Things terminals in the network are identified through active scanning, visual presentation is realized, and various terminals such as a traditional PC, a dumb terminal and intelligent equipment can be effectively identified. An identity baseline is established for the identified Internet of Things terminal and approval is carried out, so that counterfeit attack protection of the Internet of Things terminal is realized. Security situation evaluation of the Internet of Things terminal can be realized, and protection suggestions and means are effectively given. By performing effective admission control on the identified Internet of Things terminal, the problems of access authentication and security management and control of massive IP devices can be effectively solved, and a user is helped to construct a secure and controllable ubiquitous power Internet of Things.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
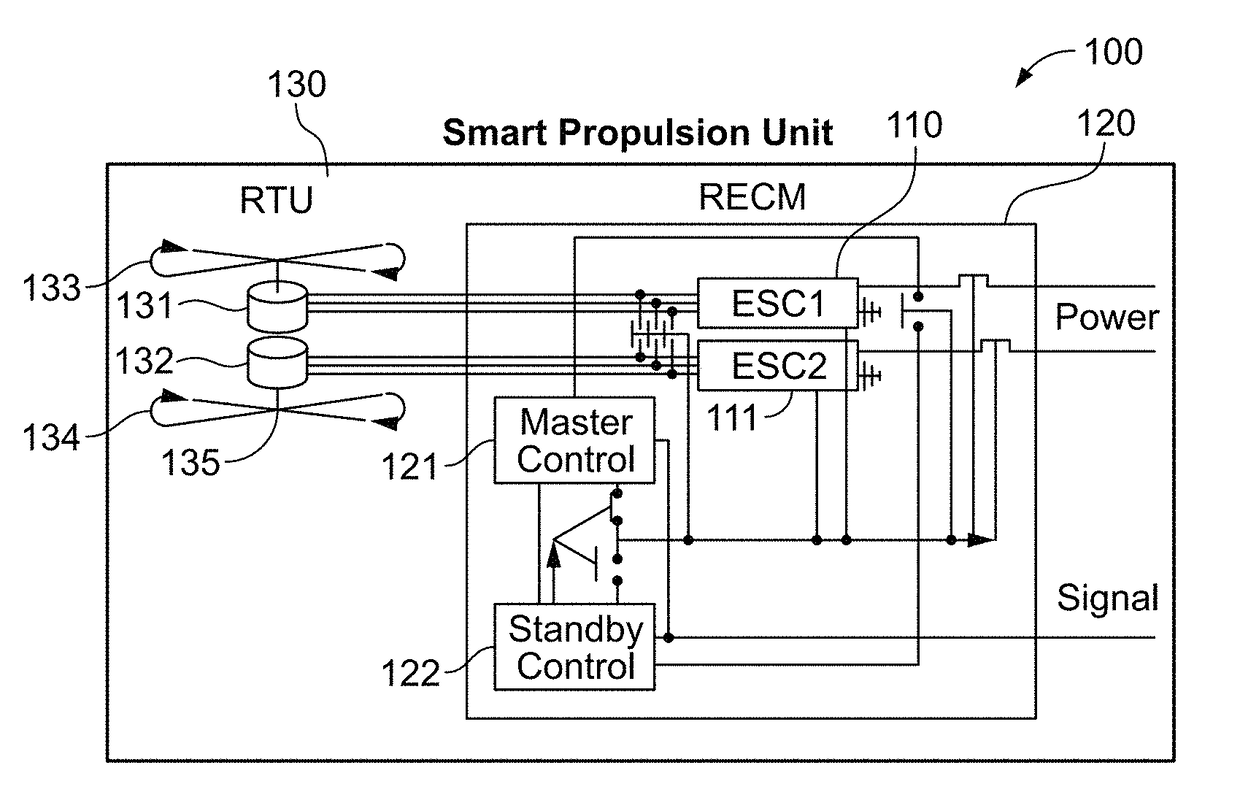
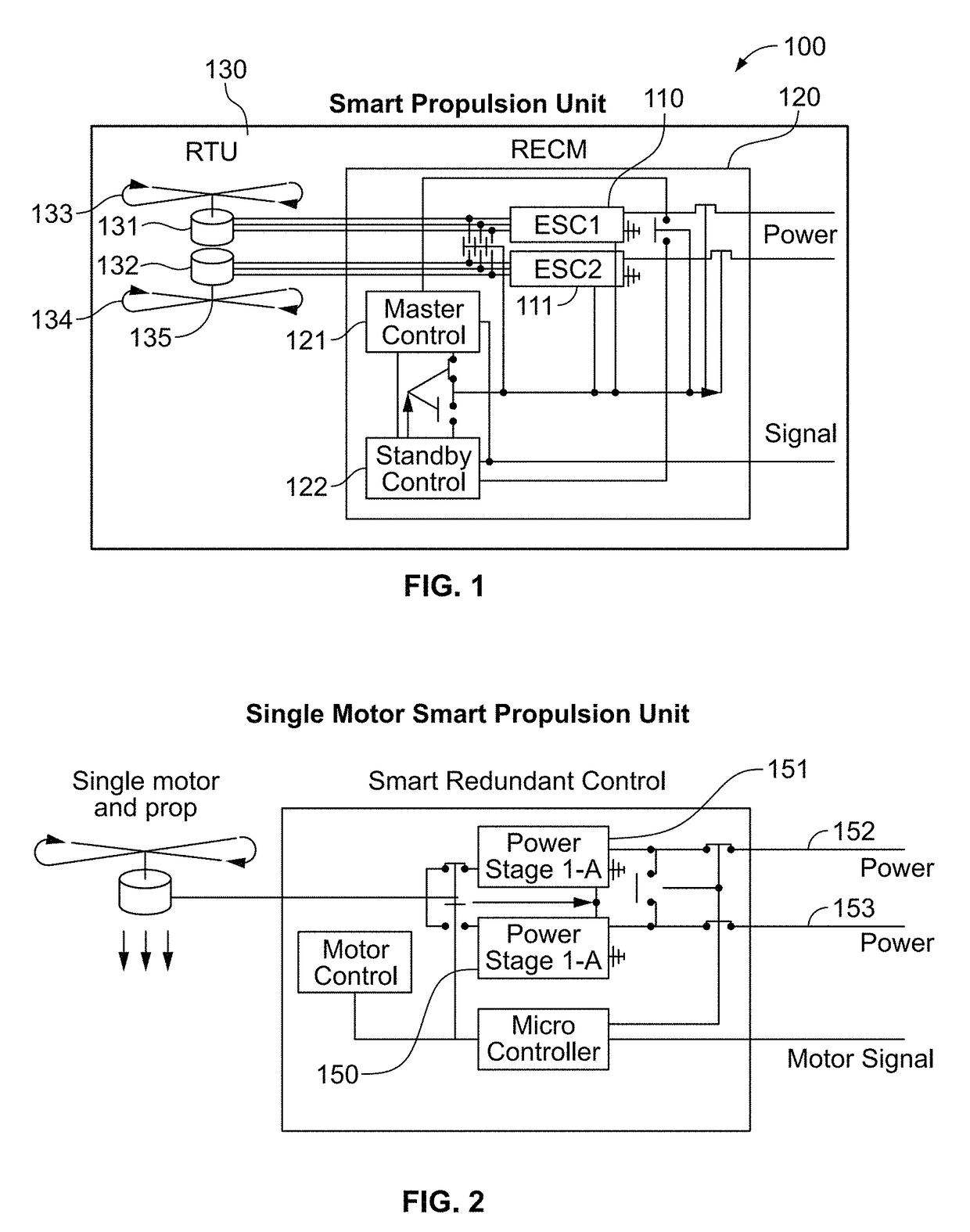
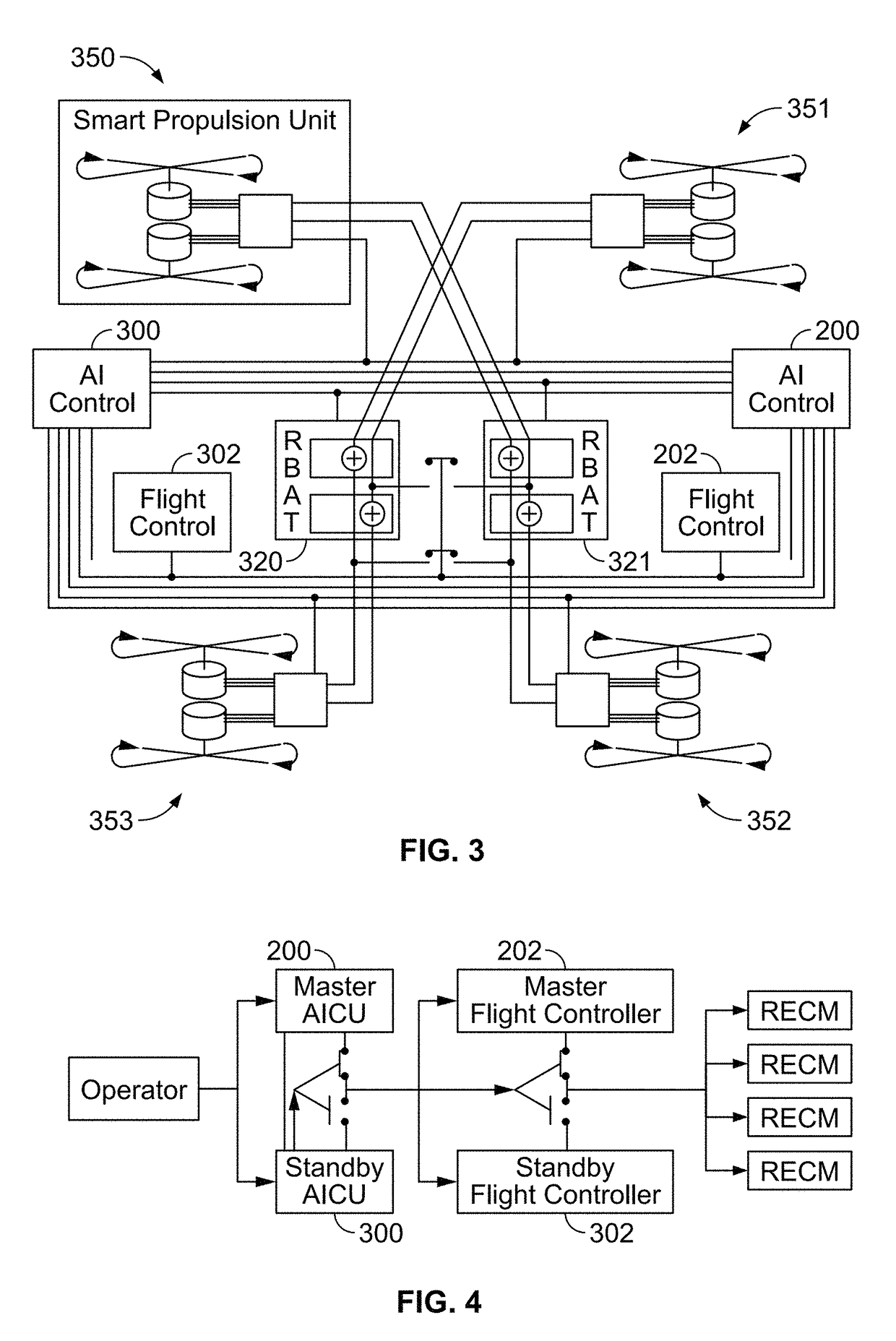
Redundant component and intelligent computerized control system for multi-rotor VTOL aircraft
ActiveUS9828107B1Transportation safetyAffordable and safe and redundantDigital data processing detailsActuated automaticallyLinear motionControl system
The present invention provides a vehicle with redundant systems to increase the overall safety of the vehicle. In other aspects, the present invention provides a method for learning control of non-linear motion systems through combined learning of state value and action-value functions.
Owner:STC UNM
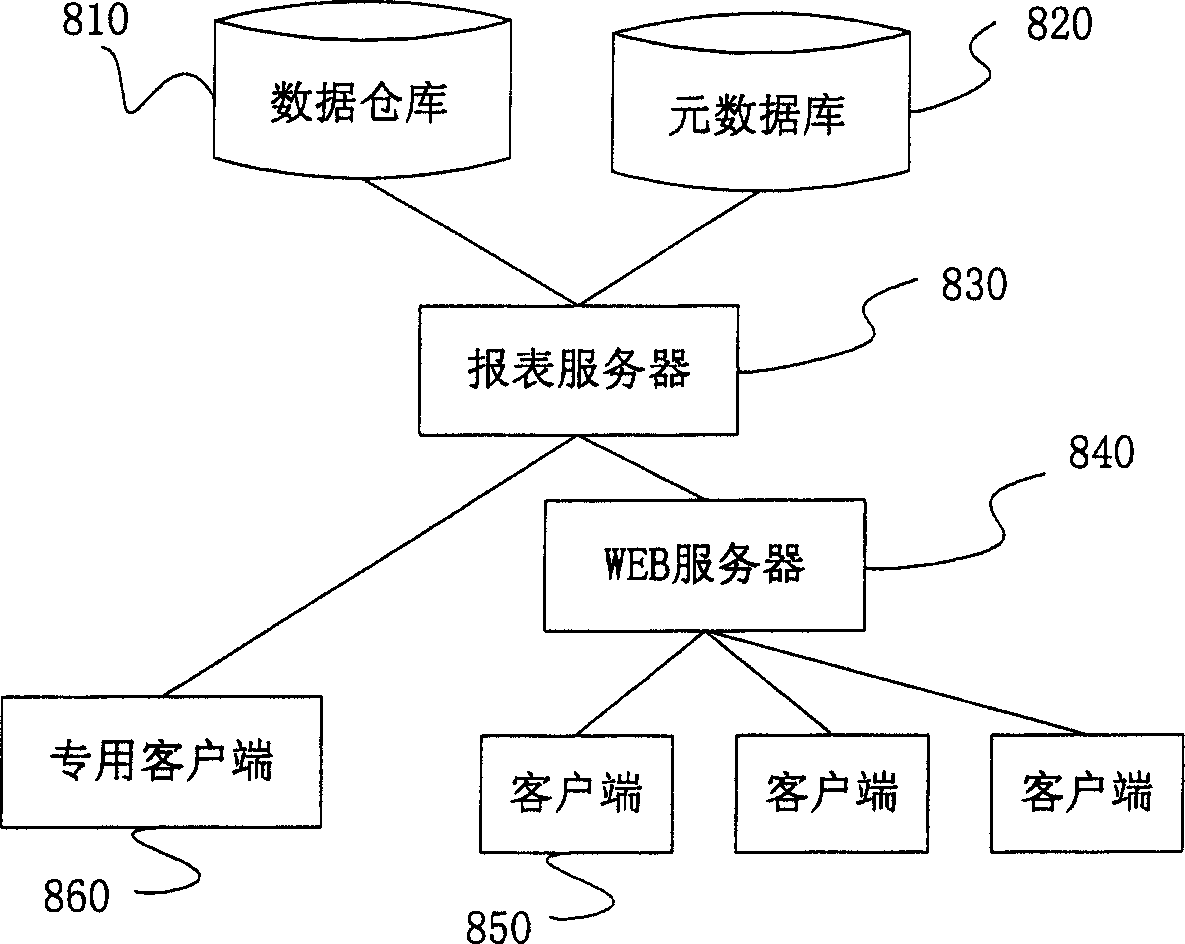
Relation type data base system and its search and report method
InactiveCN1588369AAchieve independenceAchieve type independenceSpecial data processing applicationsData centerClient-side
The relation-type data base system of the present invention includes data center for storing data object; metadata base for storing metadata; client sides; report server connected to the client sides; and intermediate server connected to the data center, the metadata base and the report server. The inquiry and report process includes the client side to input inquiry and report request, the report server to send metadata inquiry request, for the intermediate server to obtain metadata from the metadata base, for the report server to send metadata to the client side, for the client to input inquiring and report condition based on the metadata, for the report server to create command, for the intermediate server to execute the command in the data center and to return result to the report server, for the report server to store the result and return it to the client side, and for the client to show the result.
Owner:HUNDSUN TECH
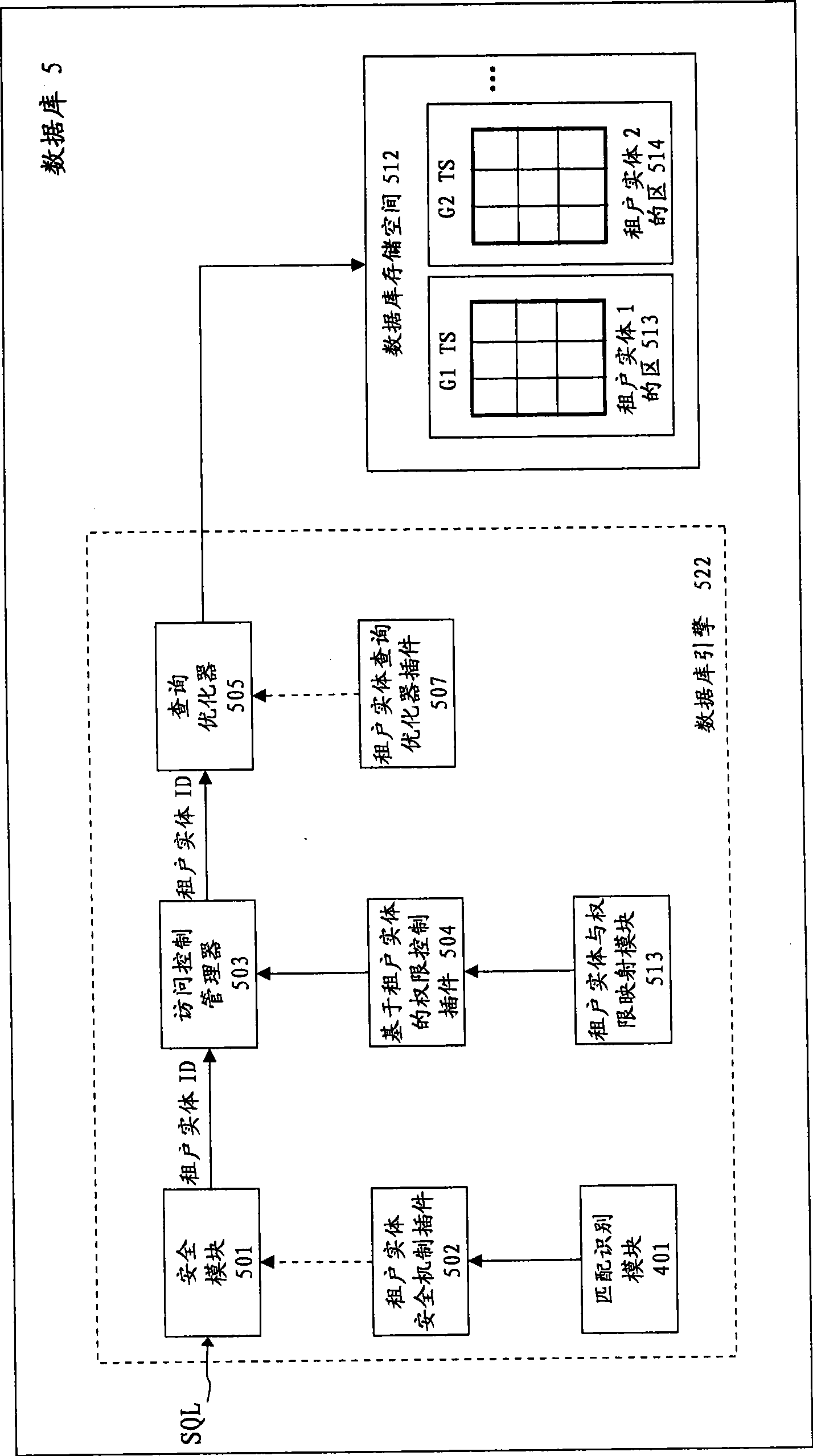
Multi-tenant oriented database engine and its data access method
InactiveCN101499061AImprove search efficiencyLow costSpecial data processing applicationsExtensibilityAccess method
A database engine facing multiple tenancies and data accessing method thereof are provided. The method of the invention includes: receiving a data access request of tenancy; determining the tenancy entity corresponding to the tenancy, wherein multiple tenancy entities share one logic table in the database; processing the data access request of the tenancy according to the configuration information of the tenancy entity. The invention introduces the concept of tenancy entity to the database: a plurality of tenancy entities shares one logic table such that the development and management costs are reduced; meanwhile, every tenancy entity has independent database access account number such that the security problem of the database access is solved; when the tenancy request comes, the data access request of the tenancy is processed according to the authority of the account number of the tenancy. Due to the introduced concept of the tenancy entity in the invention, the data of the tenancy is physically separated from each other and thus it is possible to improve performance, excellent isolation and expandability; and it is possible to realize the service quality management for the tenancy at the same time.
Owner:IBM CORP
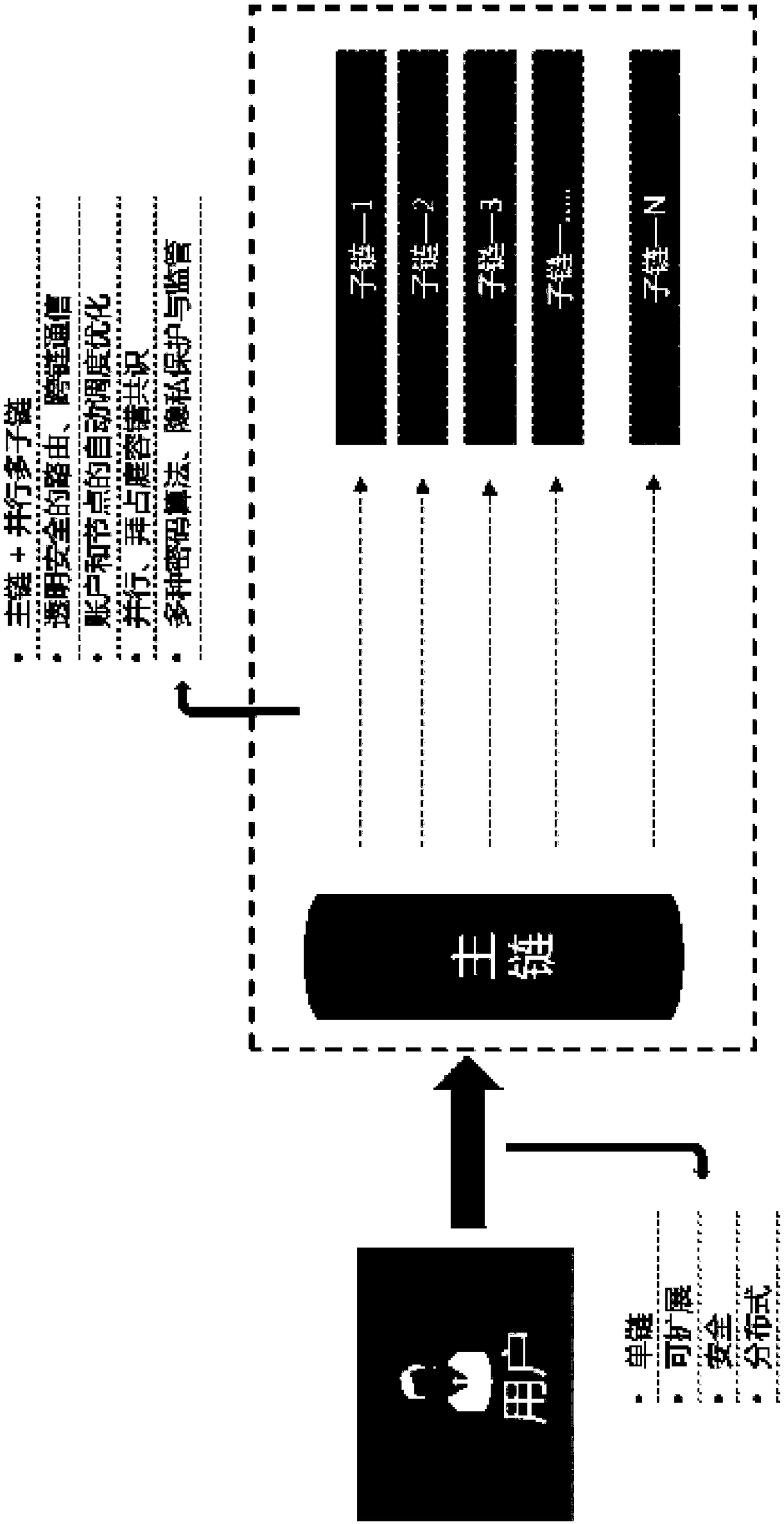
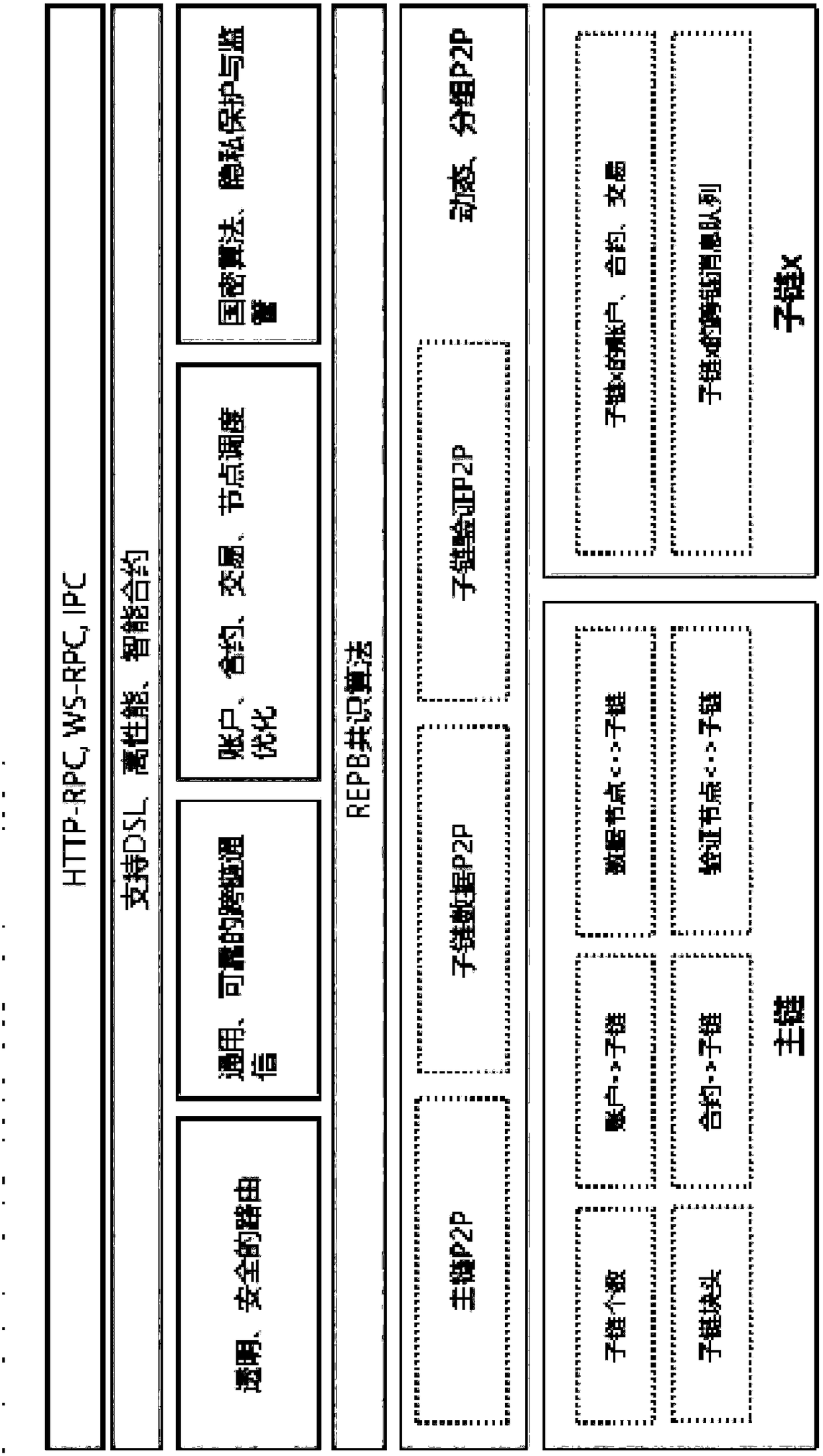
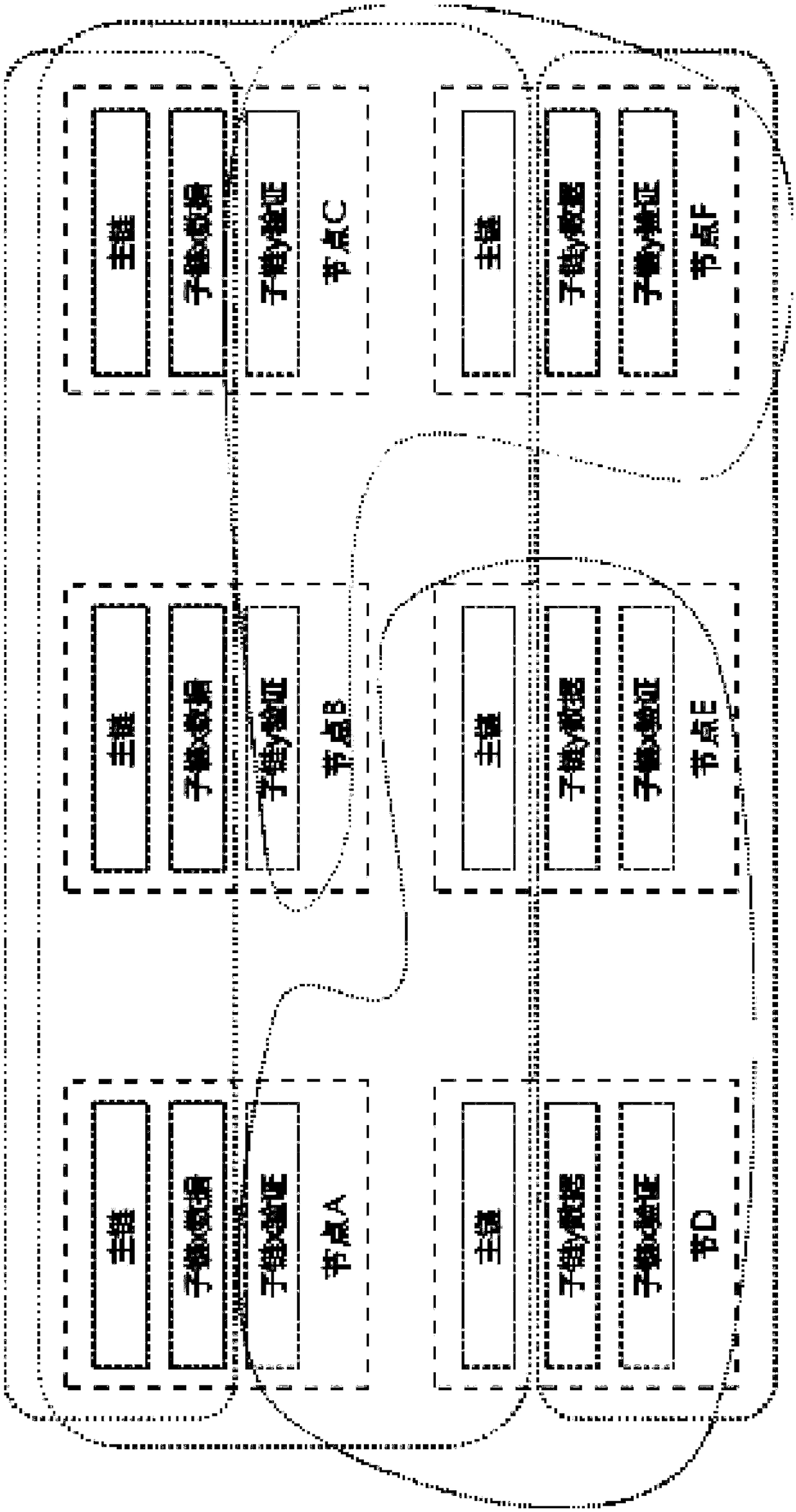
REPB consensus based on block chain backbone plus parallel multi-subchains
ActiveCN109508982AFix security issuesImprove scalabilityEncryption apparatus with shift registers/memoriesPayment protocolsByzantine fault toleranceMulti link
The invention is based on the REPB consensus of the block chain main chain and the parallel multi-sub-chain, and solves the problems of safety and decentralization by randomly selecting the consensusnode, and has high scalability. Encryption is performed to ensure the security of random values. Parallel processing of multi-linked data is carried out to solve performance problems. Byzantine fault-tolerant mechanism to quickly reach consensus, prevent bifurcation, and solve performance problems. Through an effective fusion of the above four technologies, the problems of decentralization, security and performance in the consensus algorithm are solved.
Owner:北京蓝石环球区块链科技有限公司
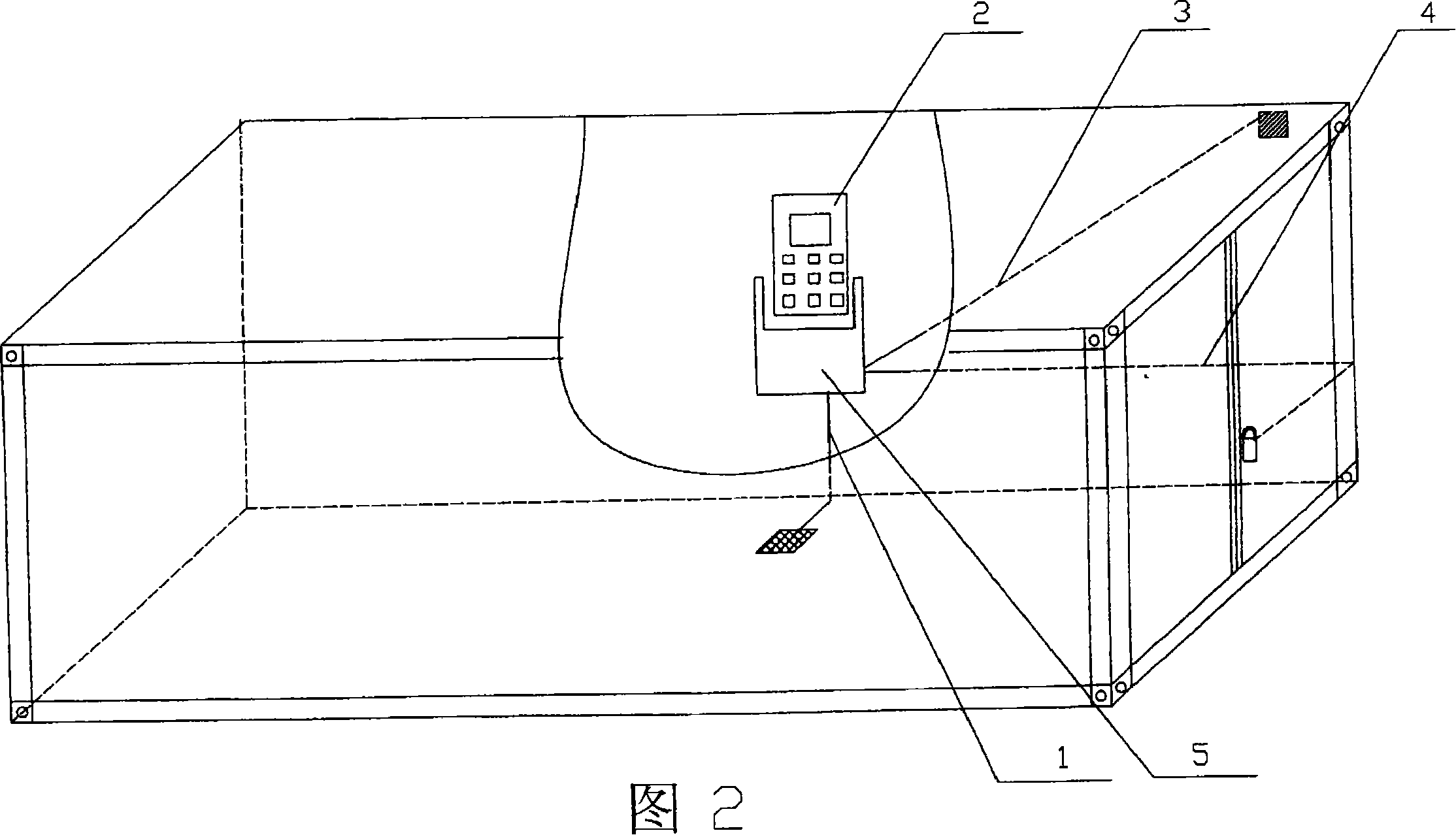
Intelligent container or the like and use thereof
InactiveCN101229869AIncrease useReduce volumeTemperatue controlLarge containersIntelligent NetworkLogistics management
The invention relates to an intelligent container or the analogs thereof, which is technologically characterized in that the invention consists of two parts of the installation power and an intelligent terminal with an entrance guard and an electronic lock (an intelligent lock) which is built-in arranged in an antenna integration; by combining with a lifting device, the invention is provided with an intelligent container with a function of lifting self-loading and unloading or the analogs. By integrated application of the technology such as the intelligent terminal combining with satellite positioning, the wireless communication, the RFID radio frequency identification, the network and the computer calculation, the real-time performance, the controllability and the security of freight transportation in the container can be solved and extend to a client as a temporary warehouse, which saves the automobile resources and waiting time and realizes the freight path information management which is a highest level of logistics business that anyone loads or unloads the freight anywhere and at anytime, the freight is in any location and in any status, the recording and monitoring of the freight environmental status in transporting the freight and the freight information and flow business can be inquired, traded and stowage planned on the network.
Owner:沈军
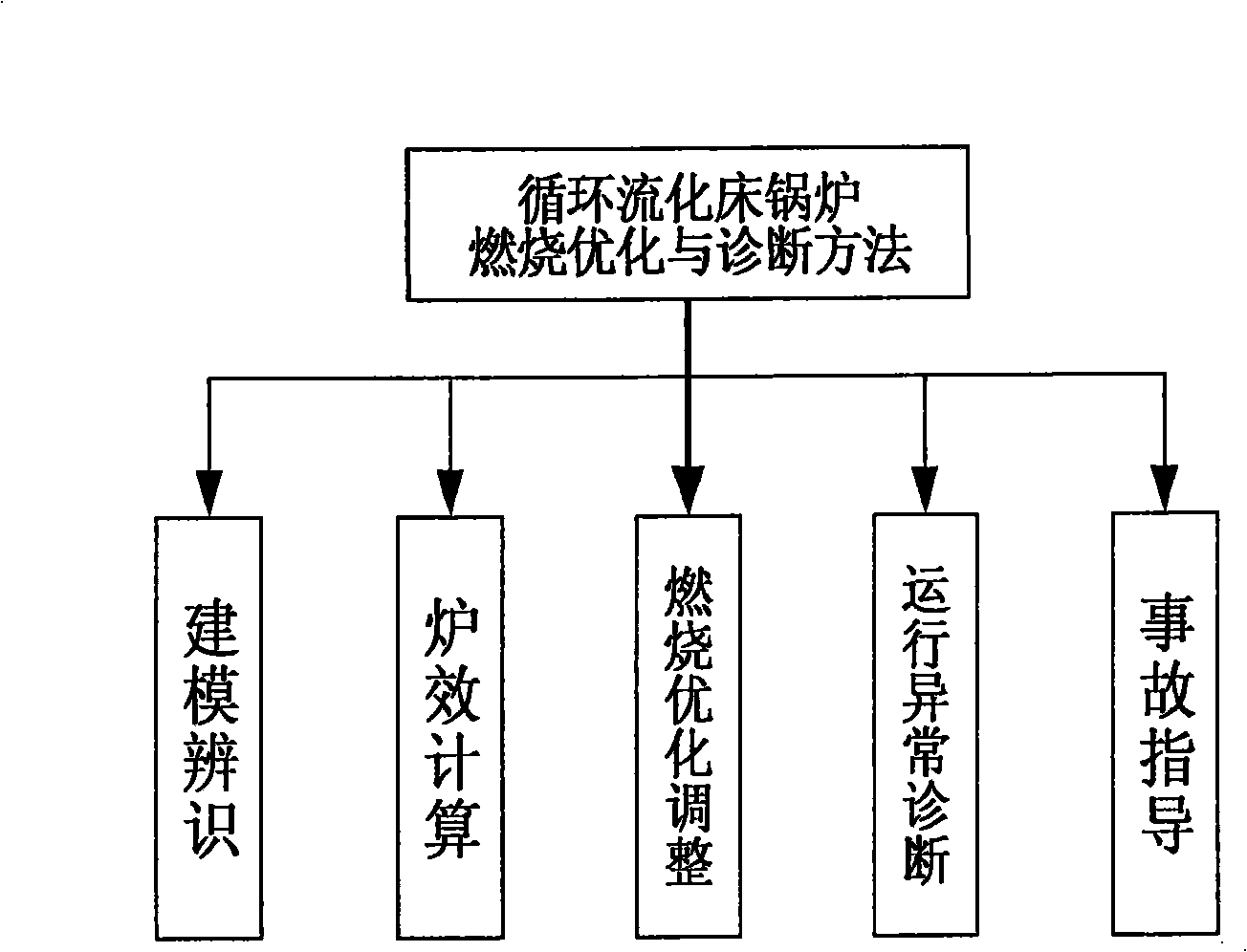
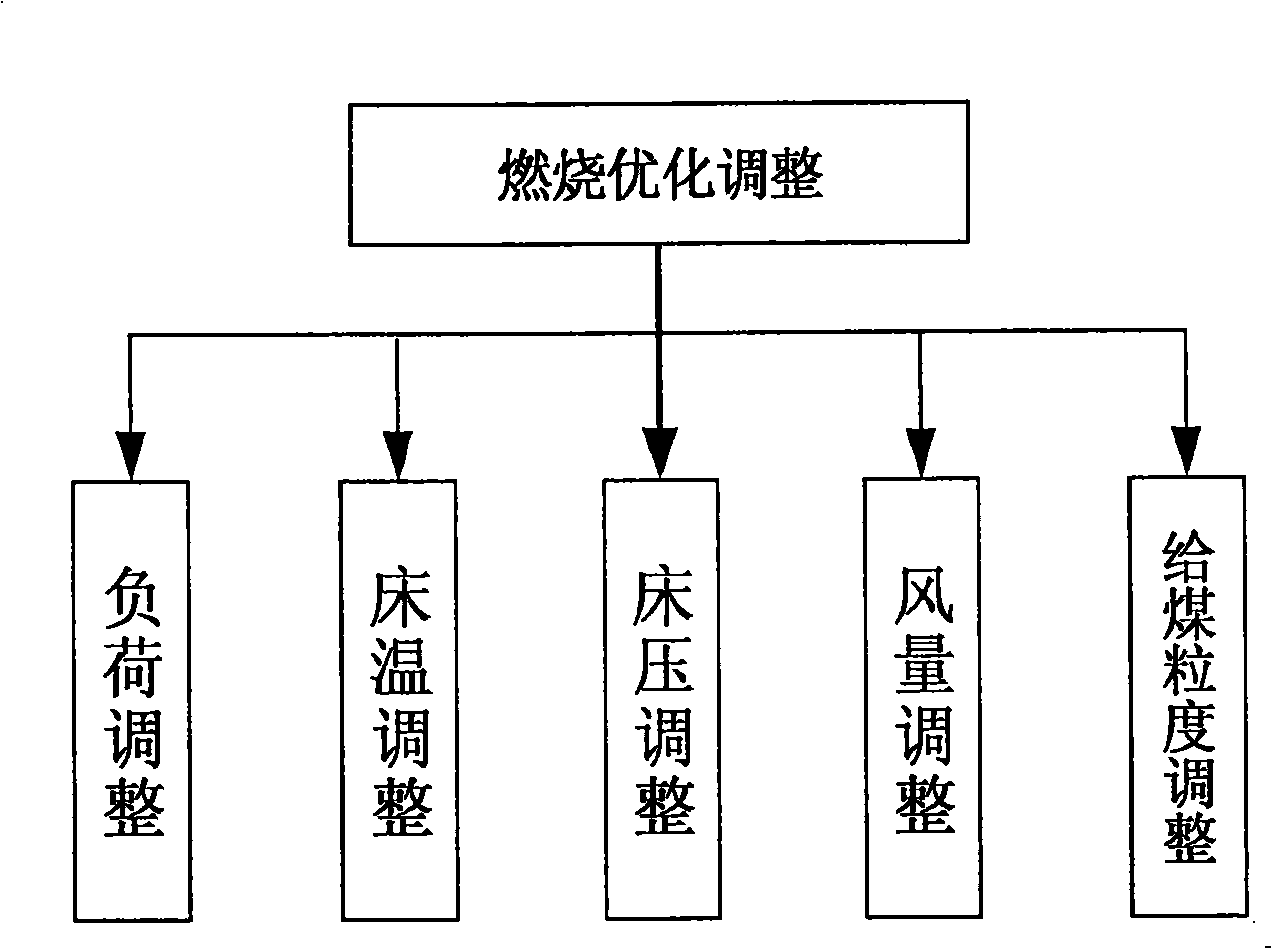
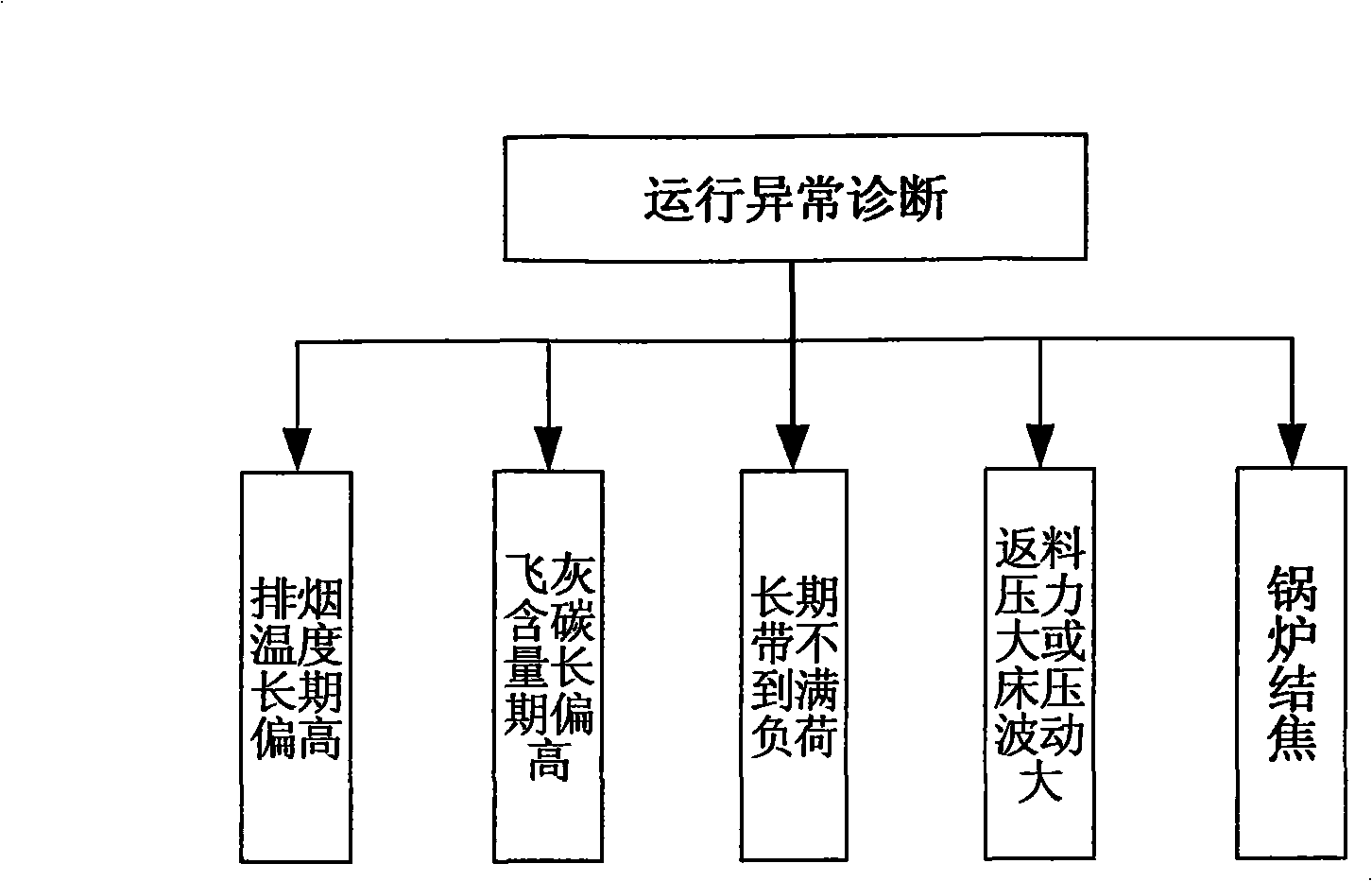
Method for optimizing and diagnosing circulating fluid bed boiler combustion
InactiveCN101329582AImprove economyFix security issuesElectric testing/monitoringAdaptive controlAir volumeEngineering
The invention relates to a circulating fluidized bed boiler combustion optimization and diagnosis method for acquiring and sorting out operation data such as bed temperature, bed pressure, load, efficiency, coal supply amount, limestone supply amount, primary air volume, primary wind pressure, upper secondary air volume and wind pressure, lower secondary air volume and wind pressure, oxygen content, induced air volume, slagging amount, NOx, Sox, etc., to build a neural network model as the basis for optimization adjustment and diagnosis. Field data of design value, measured value during operation, fuel chemistry assay value and etc. of the circulating fluidized bed boiler are utilized as the basis for optimization adjustment and diagnosis to calculate boiler efficiency as the basis for optimization adjustment and diagnosis; a judgment criterion for the optimization adjustment of combustion work condition is established and a corresponding solution is proposed, and therefore, optimization adjustment can be carried out when the circulating fluidized bed boiler deviates from the optimum combustion work condition; a judgment criterion for abnormal operation is established and a solution thereof is proposed; and therefore, problems which can not be solved after optimization adjustment can be diagnosed and analyzed. Common accident phenomena are summarized and processing strategies can be proposed, and therefore, guidance can be provided to accident handling.
Owner:SOUTHEAST UNIV
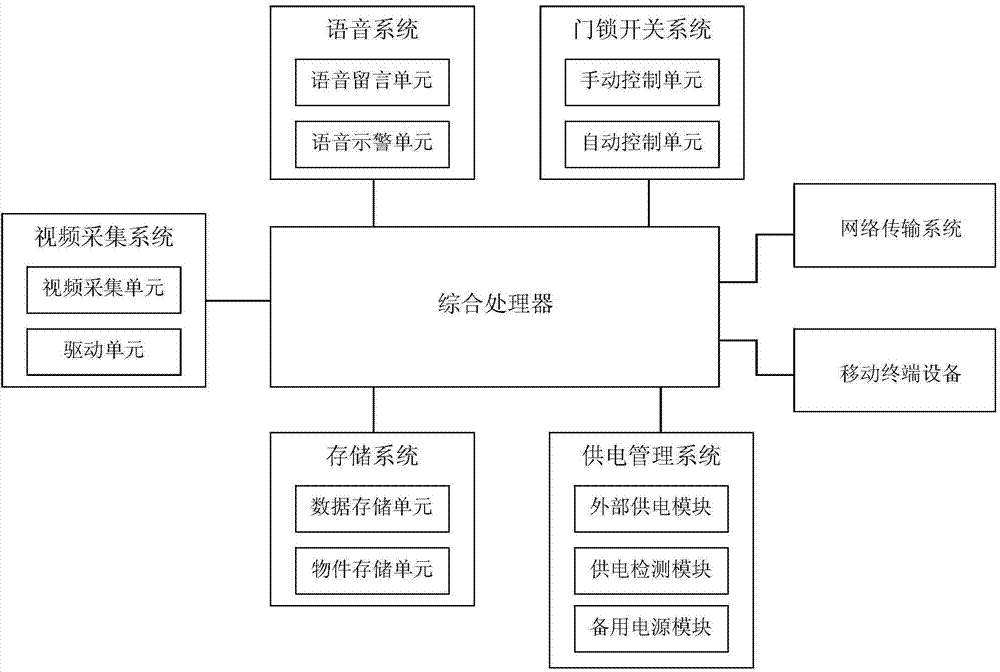
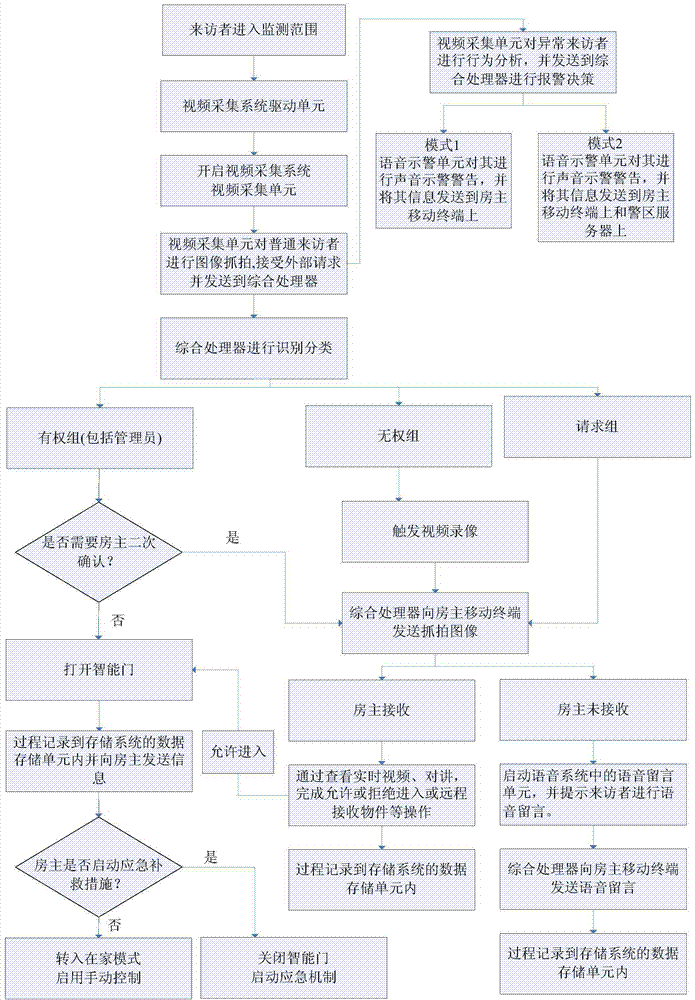
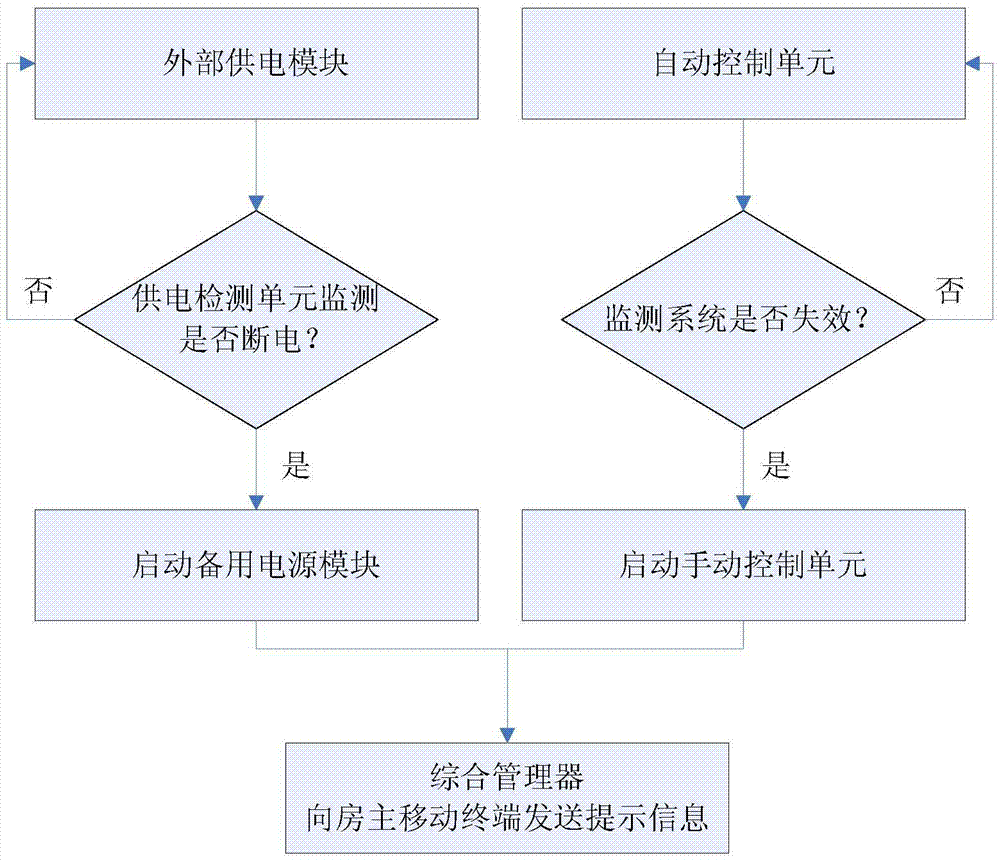
Intelligent door safety control system based on video service and intelligent door safety control method based on video service
InactiveCN104504793AImprove securityRealize smart functionsClosed circuit television systemsIndividual entry/exit registersVideo monitoringSafety control
The invention provides an intelligent door safety control system based on video service and an intelligent door safety control method based on video service. The intelligent door safety control system comprises a video image acquiring system, a voice system, a network transmitting system, a storage system, a door switch system, mobile terminal equipment, a power supply system and an integrated processor. According to the intelligent door safety control system, by virtue of the three main systems of the video image acquiring system, the voice system and the mobile terminal system and by means of the network transmitting system, multiple intelligent functions of an access control system are realized, and comprise visitor video image acquisition, visitor identification and classification, voice message, voice warning, automatic material receiving, automatic / manual door control switching, power supply detection switching, visitor behavior judging, pre-warning, multiple signal transfer outputs and the like. By virtue of front-end video monitoring, middle-end network transmitting and terminal mobile equipment, a house owner, a visitor and an intelligent door perform an interactive action, so that the service range and applicability of the intelligent door are enhanced. The safety and user use experience of the intelligent door are greatly improved.
Owner:TIANJIN YAAN TECH CO LTD
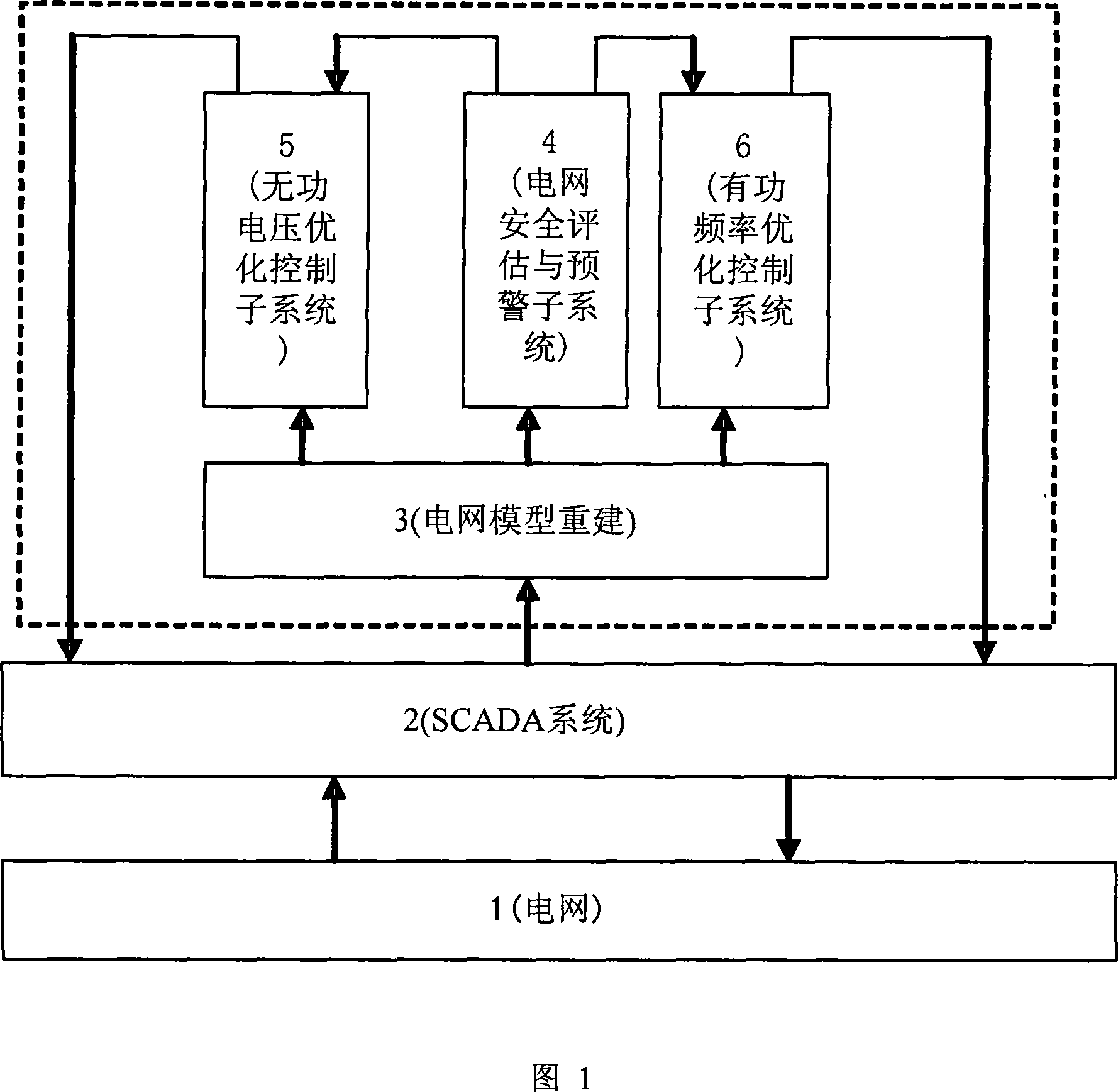
Three-dimensional coordinated electric network energy managing system and method for controlling and evaluating electric network
InactiveCN101232182ARealize online trackingRealize closed-loop controlData processing applicationsSpecial data processing applicationsPower qualityLoop control
The invention relates to a 3D-coordinated power grid energy management system and a power grid evaluation and control method, which belongs to the field of scheduling automation of power system. The system comprises a power grid model reconstruction sub-system, a power grid safety evaluation and alarm sub-system, an active frequency optimization control sub-system and a passive voltage optimization control sub-system, and a background calculation sub-system and a system foreground. The method comprises following steps: tracking isoline of an external power grid and automatically reconstructing a global power grid model; automatically executing online safety analysis integrated with static power grid, dynamic power grid, voltage stabilization, coordination of relay protection setting values, etc., and online recognizing the safety state of the power grid; alarming for normal unsafe condition, and carrying out prevention control; alarming for emergent conditions, and carrying out correction control calculation; and carrying out realtime active scheduling closed-loop control and passive voltage optimized closed-loop control under normal safety condition. The invention can achieve comprehensive and coordinated closed-loop control for the safety of the power grid, the economy and the electric energy quality.
Owner:TSINGHUA UNIV
Integrated identity based encryption (IBE) data encryption system
InactiveCN102932149AEasy accessSolve the convenienceUser identity/authority verificationService systemKey issues
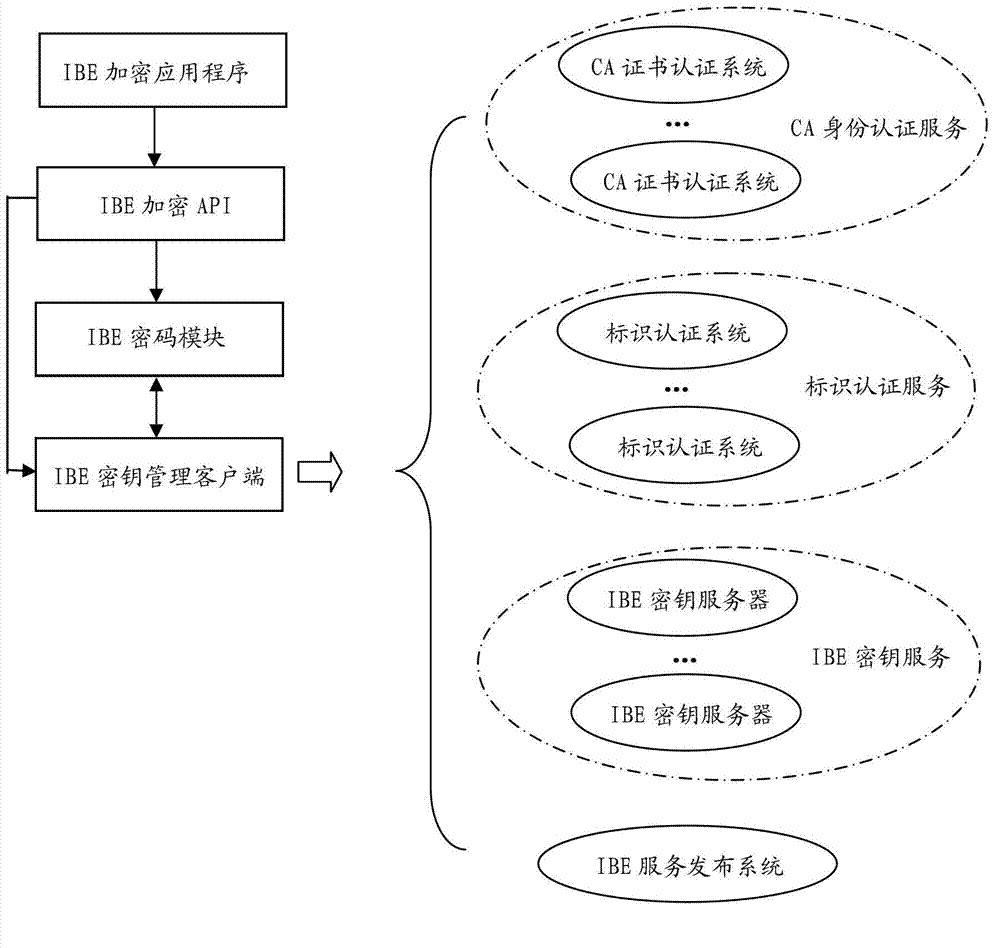
The invention relates to an integrated IBE data encryption system. The system comprises an IBE key server, a certification authority (CA) system, an identification authority system, an IBE service publication system, an IBE encryption application program, an IBE encryption application program interface (API), an IBE crypto module and an IBE key management client. The IBE service publication system publishes related service system information on line, and the encryption application program calls the IBE crypto module through the IBE encryption API to complete IBE data encryption and decryption functions; the IBE crypto module is connected with the IBE key server through the IBE key management client to obtain IBE public parameters and IBE private keys needed for the encryption and decryption; when the private keys are obtained, the IBE key management client obtains identification certifications from the CA system; and in an online interaction process, the key management client proves identities of users by using the identification certifications signed by the CA system. The system solves the key problems of identification safety, identification attribution confirmation, obtaining convenience of the public parameters and the like in IBE encryption.
Owner:WUHAN UNIV OF TECH +1
Keypress behavior pattern construction and analysis system of touch screen user and identity recognition method thereof
ActiveCN105279405AFix security issuesThe realization process is convenientDigital data authenticationTransmissionIdentity recognitionData acquisition
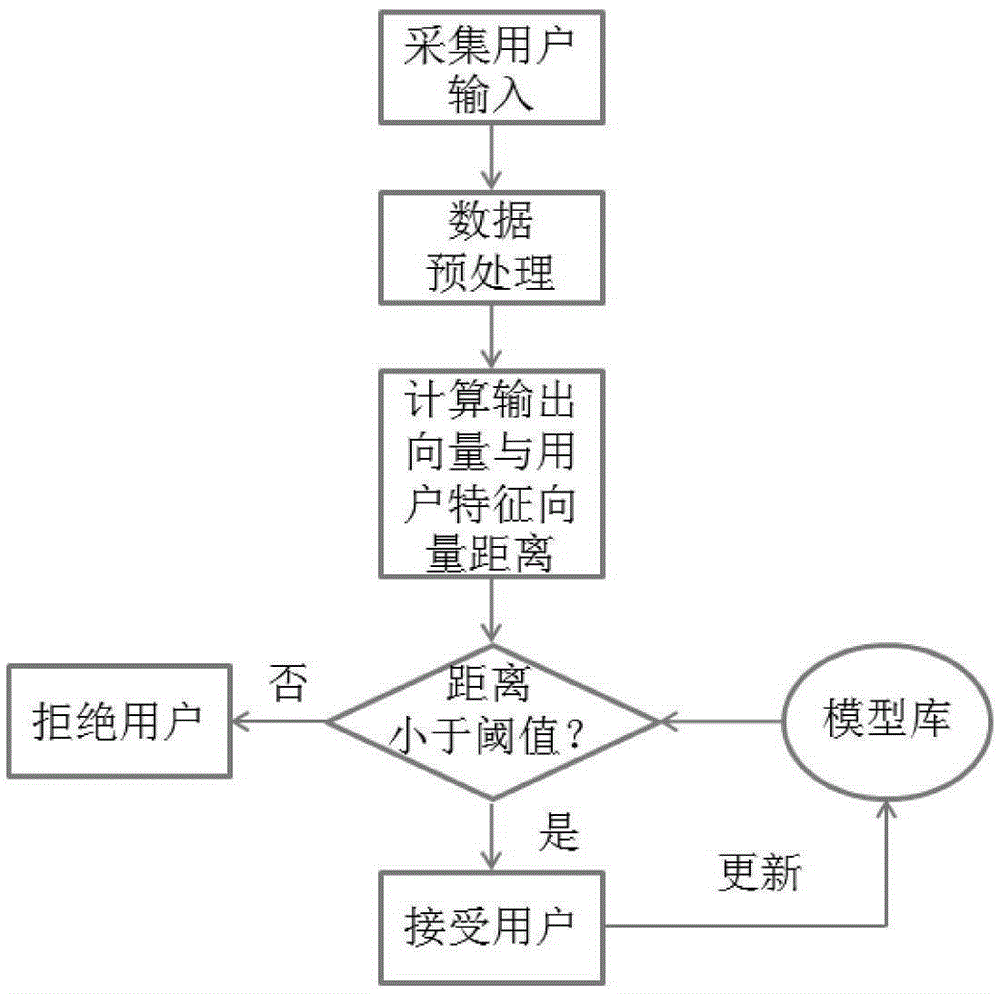
The invention provides a keypress behavior pattern construction and analysis system of a touch screen user and an identity recognition method thereof. According to the invention, data analysis is performed by using history keypress information of inputting a password by a soft keyboard on a mobile phone touch screen; a corresponding neural network model is established; and model calculation is performed on new to-be-tested data, to recognize a user identity. The system comprises a user data acquisition module, a data pre-processing module, a model training module, and a user identity identification module. The user data acquisition module is responsible for acquiring time series information of a user clicking the soft keyboard and inputting the password, and pressure and contact area information. The data pre-processing module is responsible for pre-processing the acquired data, removing dirty data, and performing normalization on the data. The model training module is responsible for performing analysis and modeling on a key-in mode of all users. The user identity identification module is responsible for performing model calculation on the new to-be-tested data, to recognize the user identity and improve security of a user account password.
Owner:TONGJI UNIV
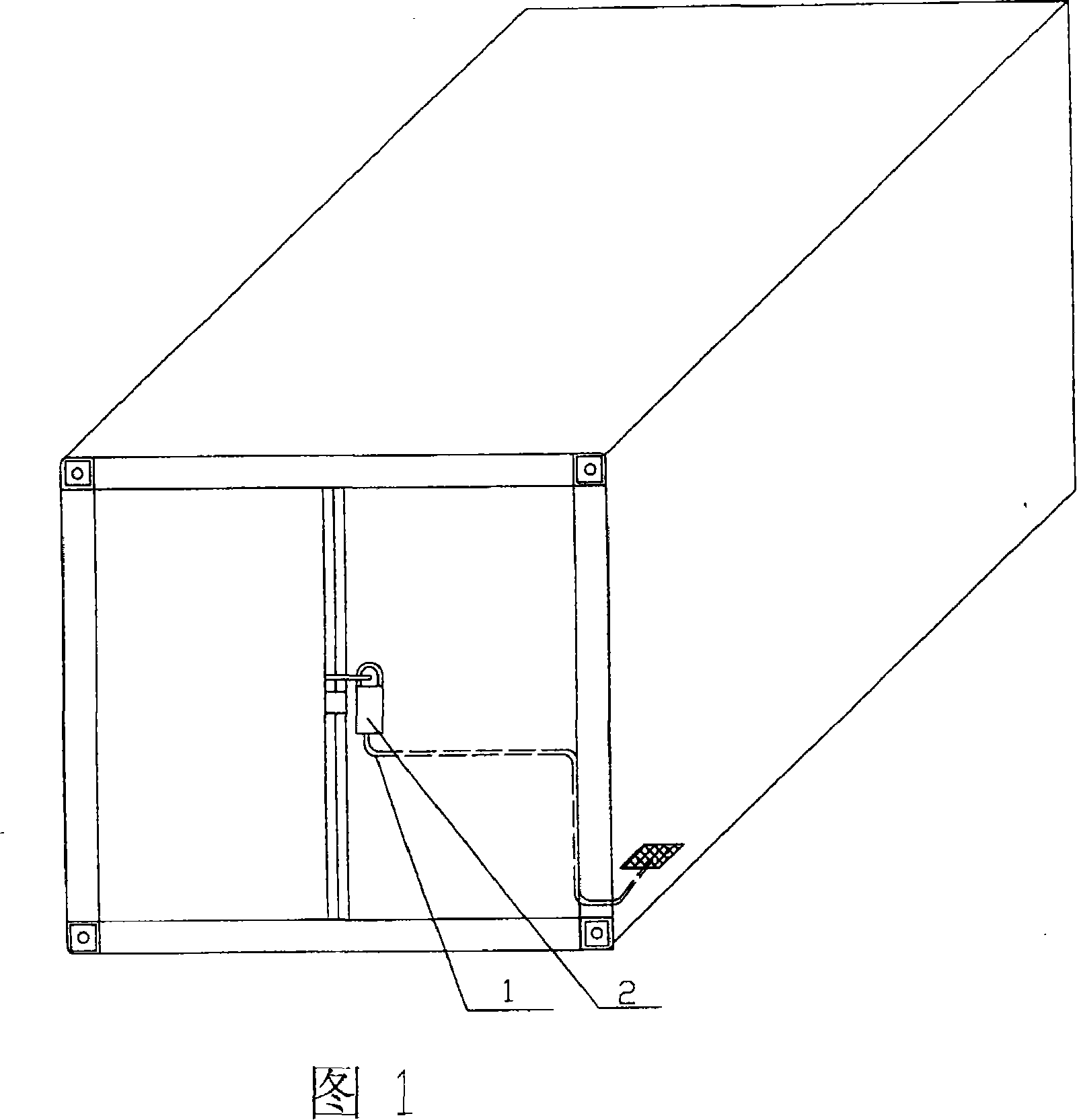
Test system for monitoring pipe leakage and early warning safety
The invention provides a conduit leakage inspection and safety early warning test system for oil-gas transportation conduit leakage inspection and corresponding early warning technique tests, relating to mechanical vibration or sound wave impact metering and conduit system technique field, comprising a circular conduit (53) which is connecting with a storage can region (2) and a pump (9) to be a close ring, is imbedded underground, is antiseptically treated and is cathodic protected, and a circular optical fibre (54) imbedded in one ditch. The circular conduit (53) has two lead-out branch pipes and a plurality of relief valve wells. A plurality of valves, volume meters and pressure instruments are provided on the conduit. An air compressor (26) is provided on one lead-out branch pipe, and another lead-out branch pipe is unloaded. A plurality of valves, pressure instruments and gas flowmeters are provided on the circular conduit. Pressure sensors of a circular conduit on-site instruments and remote transmitting cables transmit pressure signals to a central control room.
Owner:PIPECHINA SOUTH CHINA CO
Positioning method and system of automatic driving automobile
ActiveCN109581449ASolve the errorFix security issuesSatellite radio beaconingSatellite positioningMarine navigation
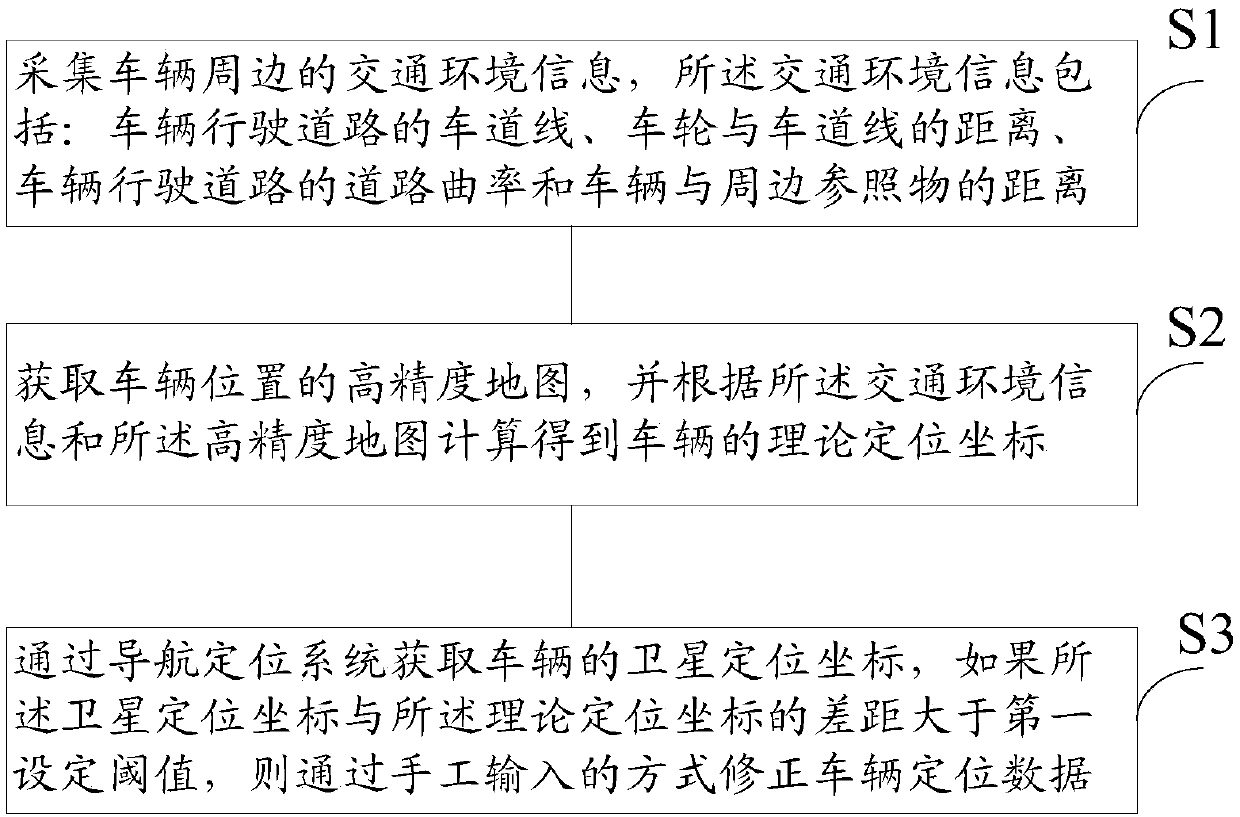
The invention provides a positioning method and system of an automatic driving automobile. The positioning method of the automatic driving automobile comprises the following steps: collecting trafficenvironment information around a vehicle, wherein the traffic environment information includes: a lane line of a road on which the vehicle travels, a distance between a wheel and the lane line, a roadcurvature of the road on which the vehicle travels, and a distance between the vehicle and a surrounding reference object; obtaining a high-precision map of the vehicle position, and calculating a theoretical positioning coordinate of the vehicle according to the traffic environment information and the high-precision map; and obtaining a satellite positioning coordinate of the vehicle through a navigation and positioning system, and correcting the vehicle positioning data through a manual input manner if the difference between the satellite positioning coordinate and the theoretical positioning coordinate is greater than a first preset threshold. The invention can improve the positioning accuracy and safety of the automatic driving automobile.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
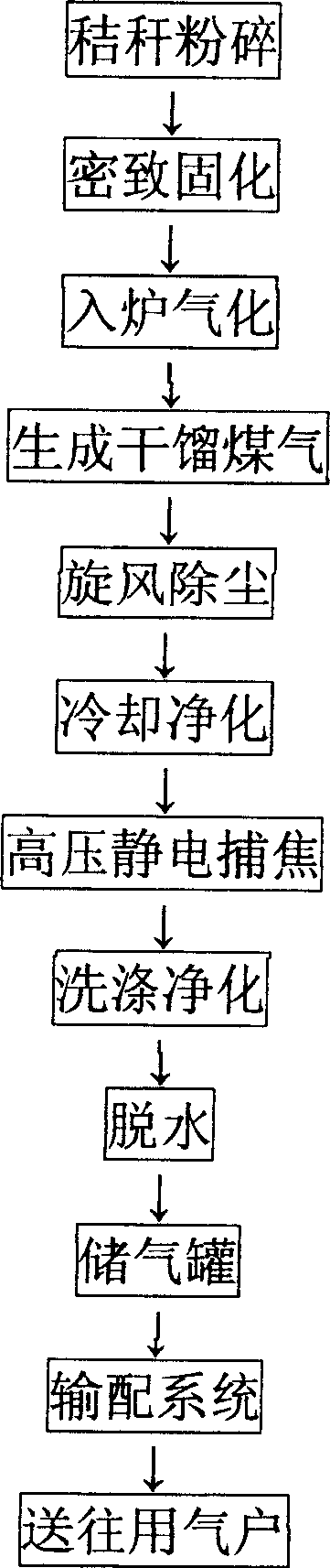
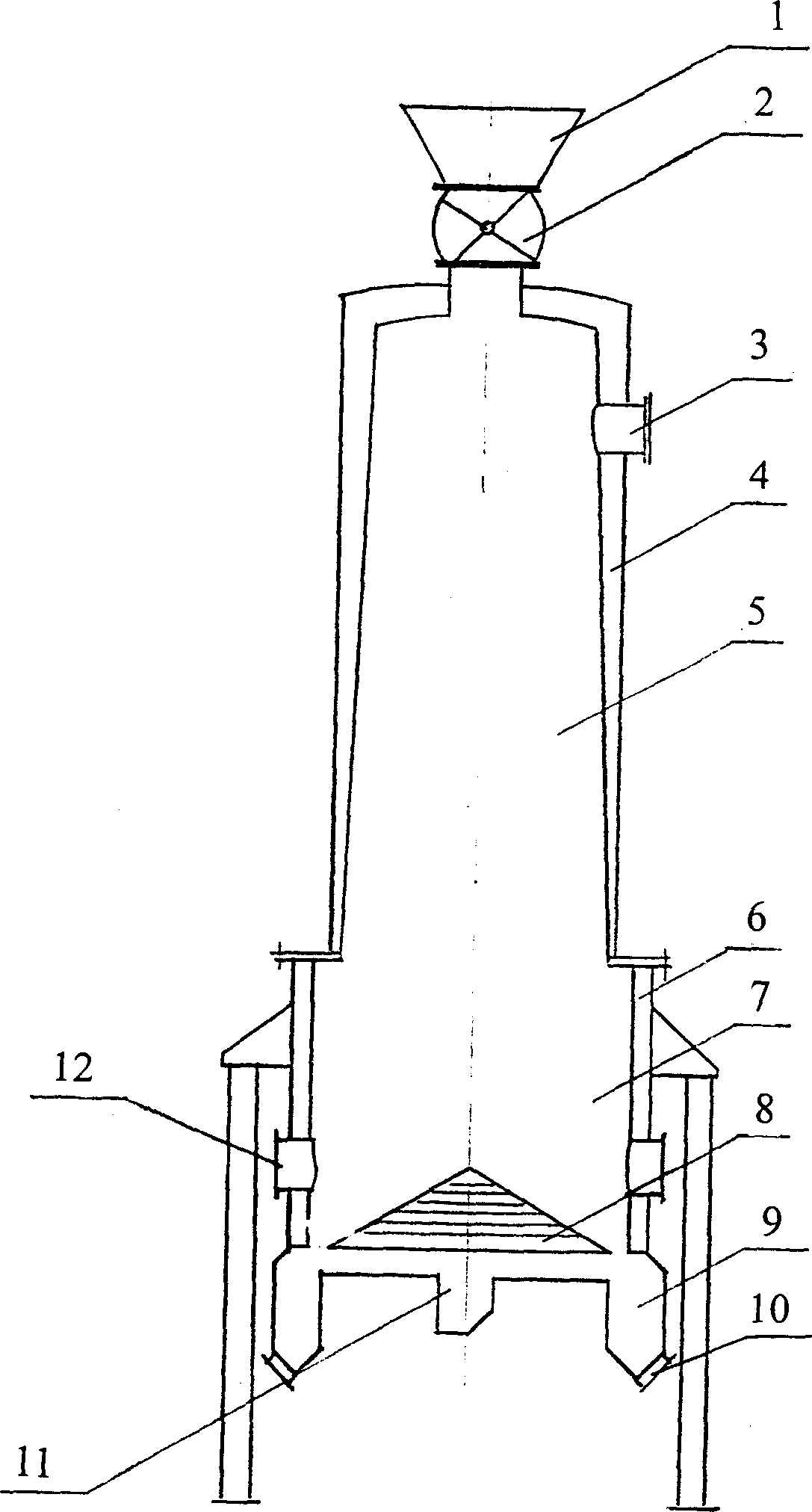
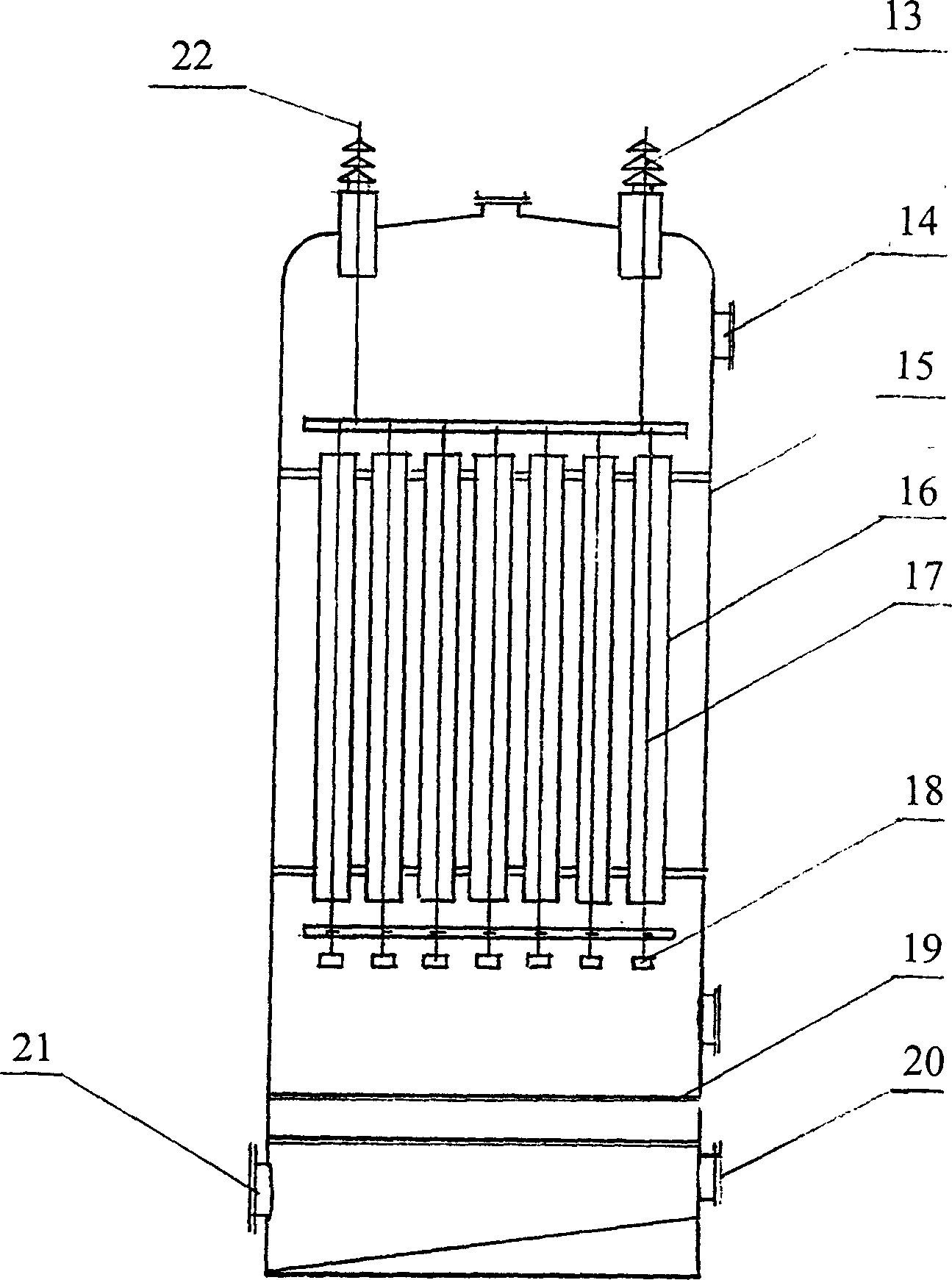
Biomass pyrogenation gasification and purification method
InactiveCN1730609AHigh calorific valueHigh hydrogen contentBiofuelsCombustible gas purificationCyclonePurification methods
The invention provides a biological mass thermal decomposition, gasification and purification method which comprises, disintegrating the biological mass, gasifying in a furnace, obtaining retort gas, cyclone dedusting, cooling down and purifying, high voltage static coke trapping, making the coke tar bubbles and dust in the coal gas deposit onto the coke collection poles, thus purifying the coal gas, finally washing and dewatering.
Owner:MIANYANG TONGMEI ENERGY SCI & TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com