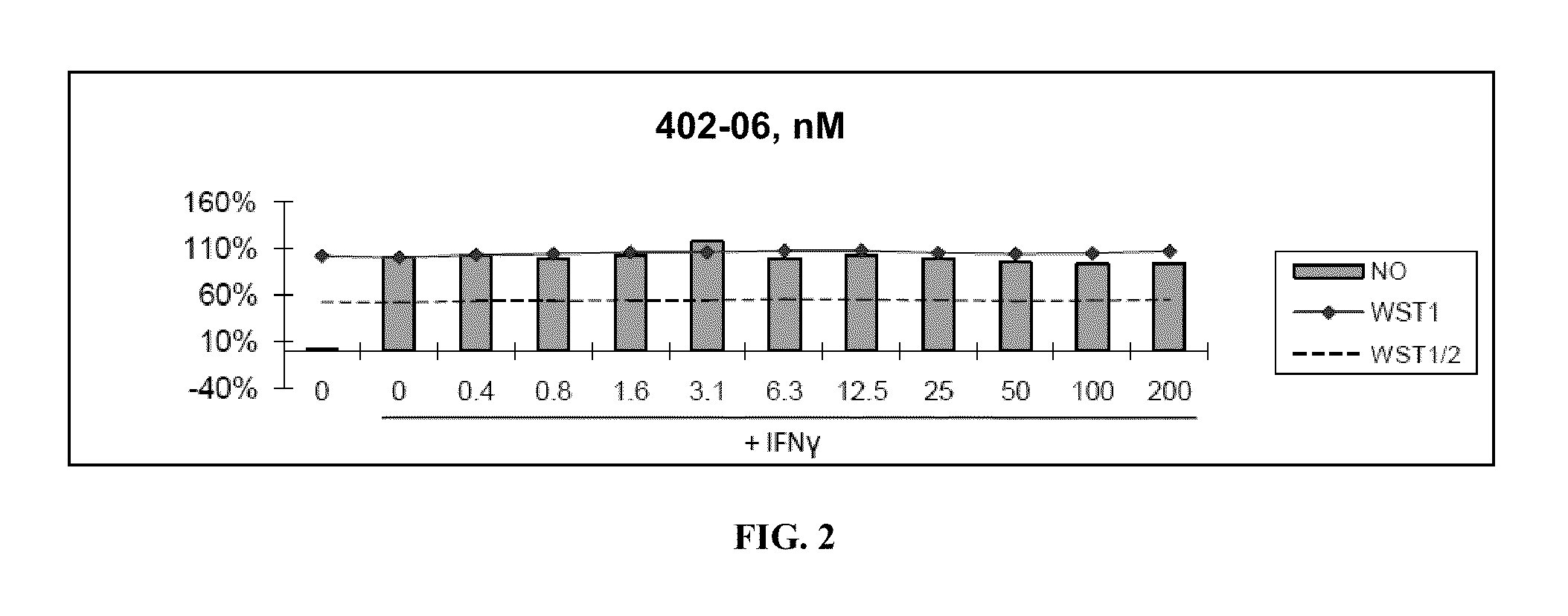
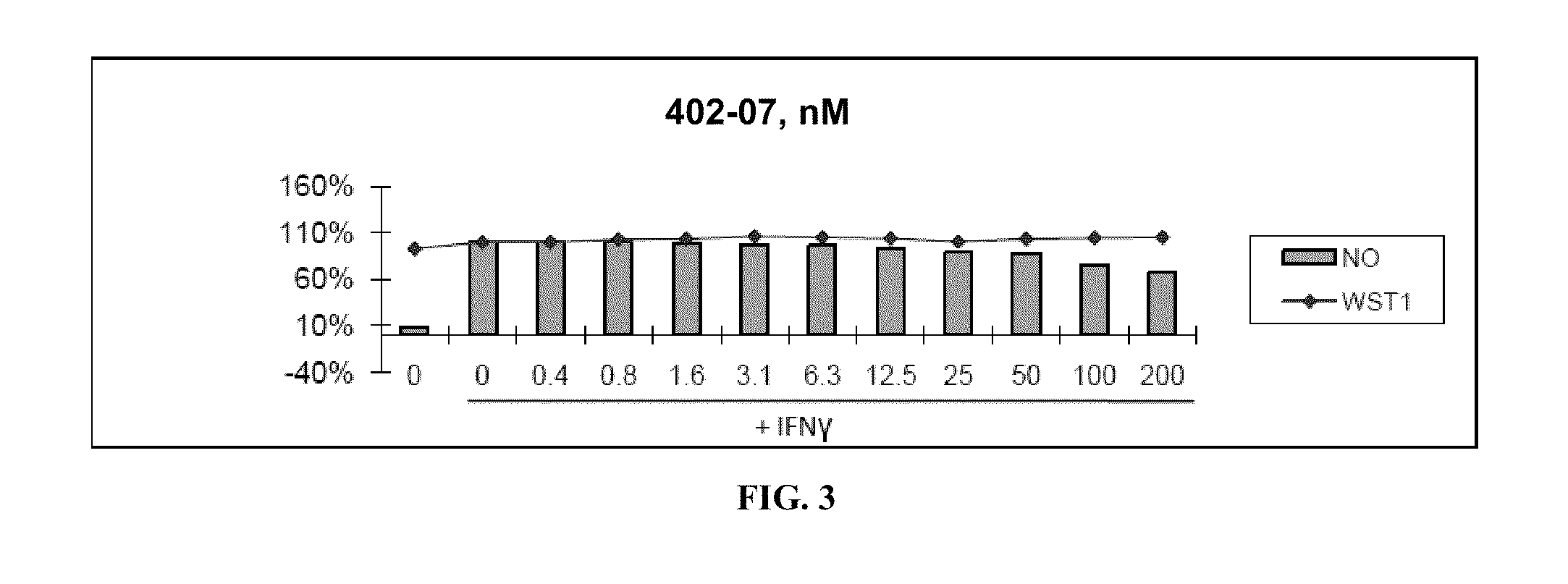
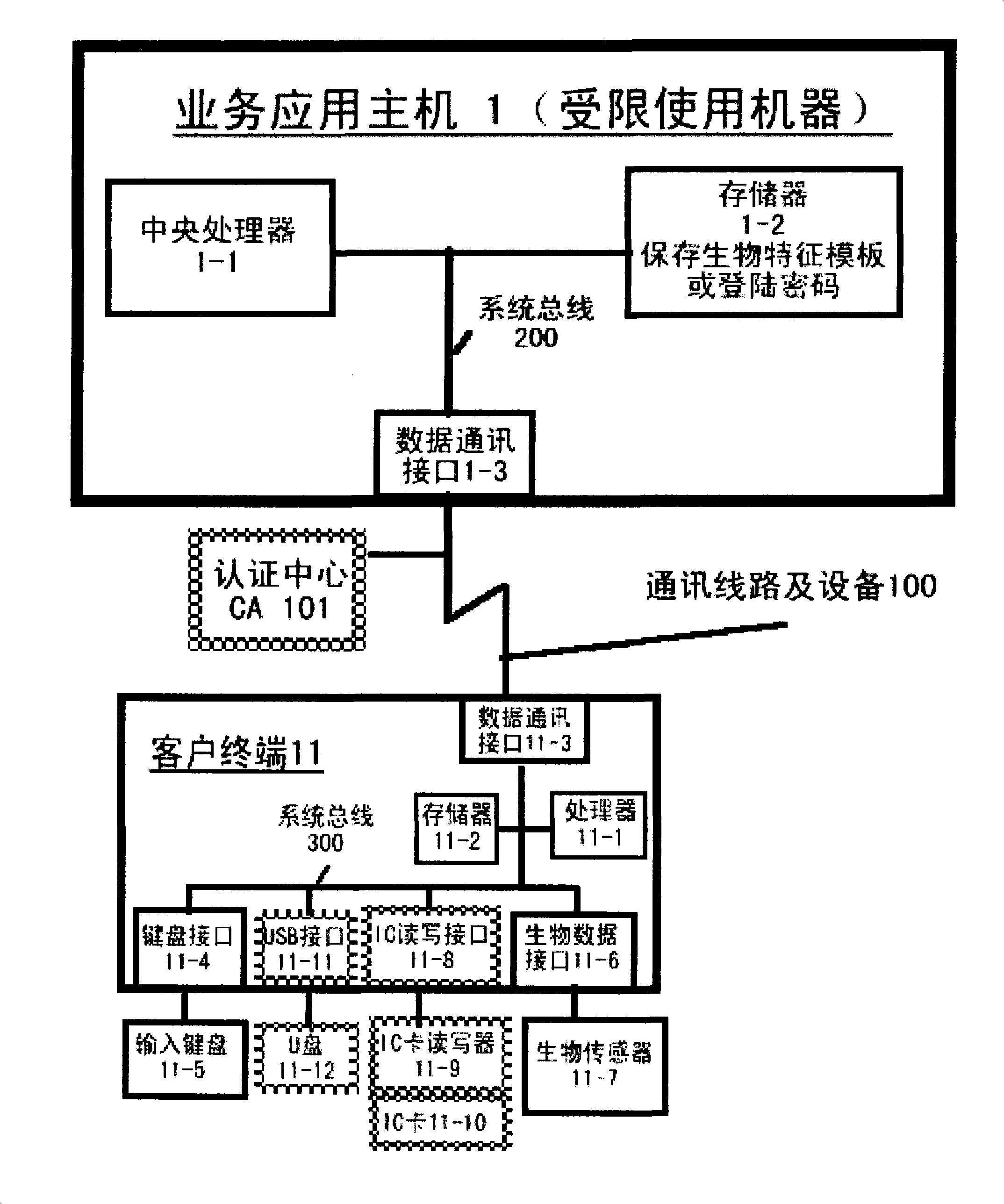
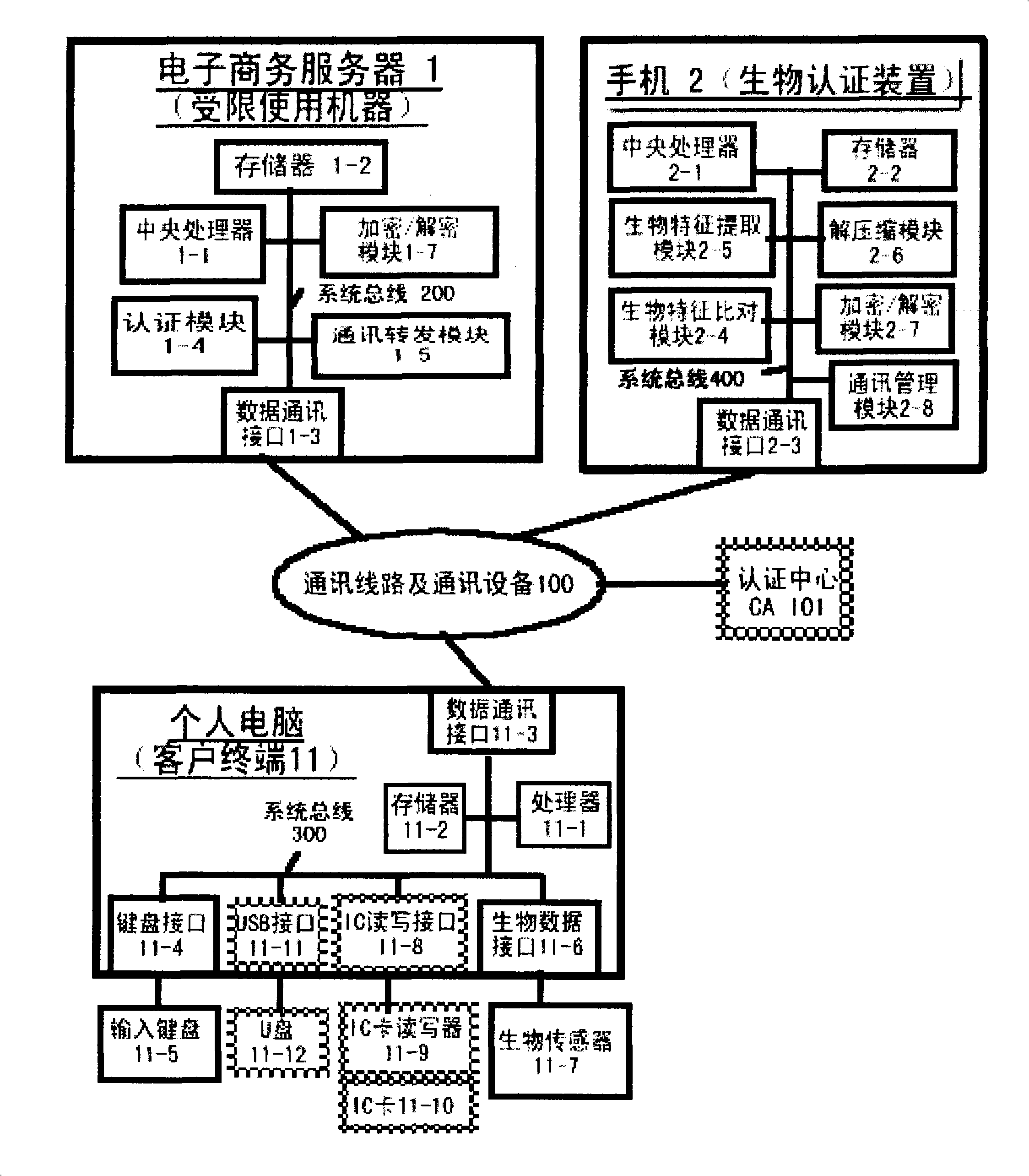
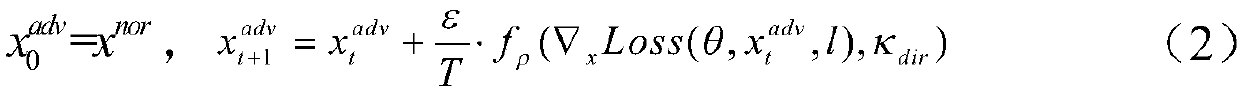Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2871results about How to "Avoid attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
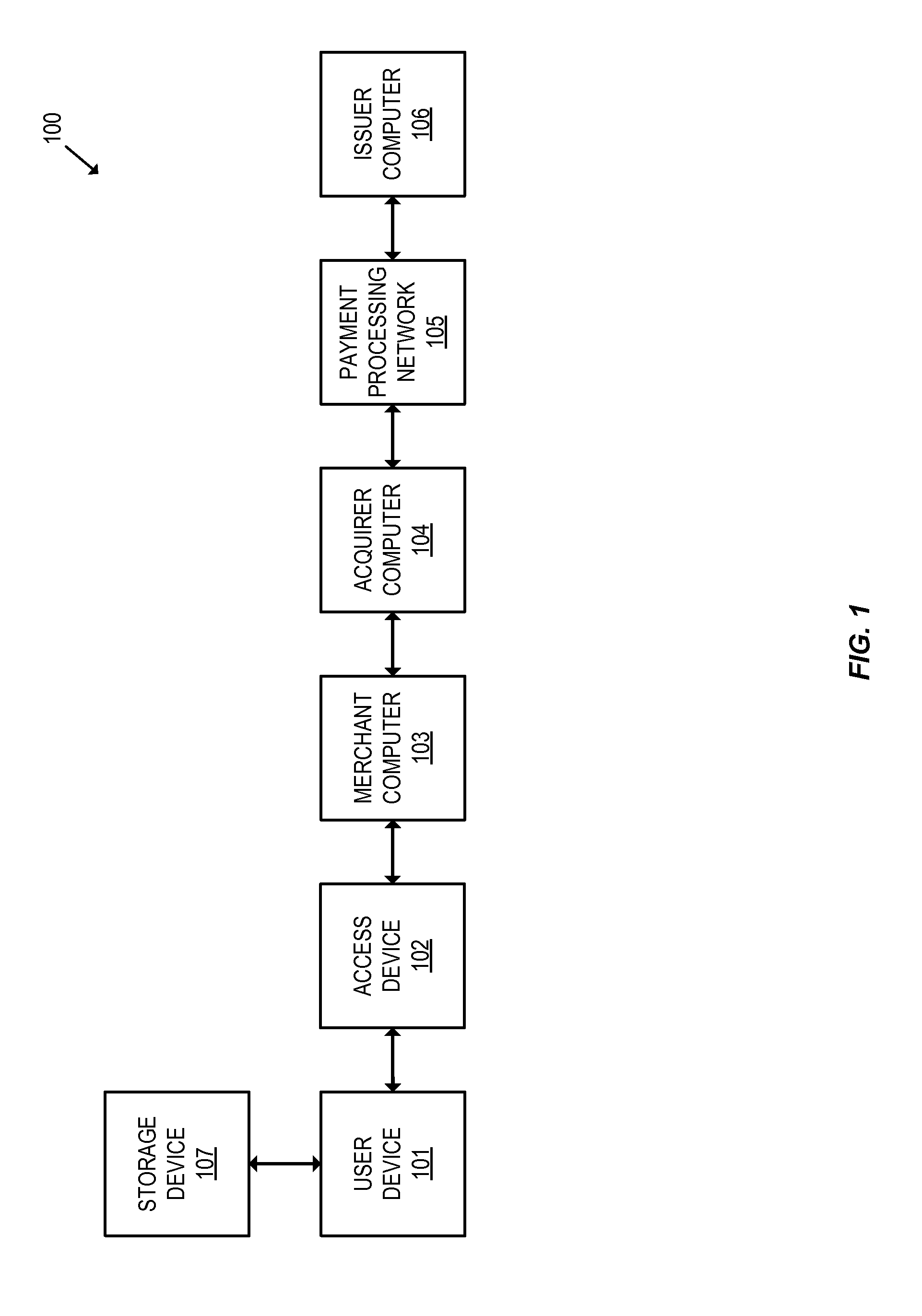
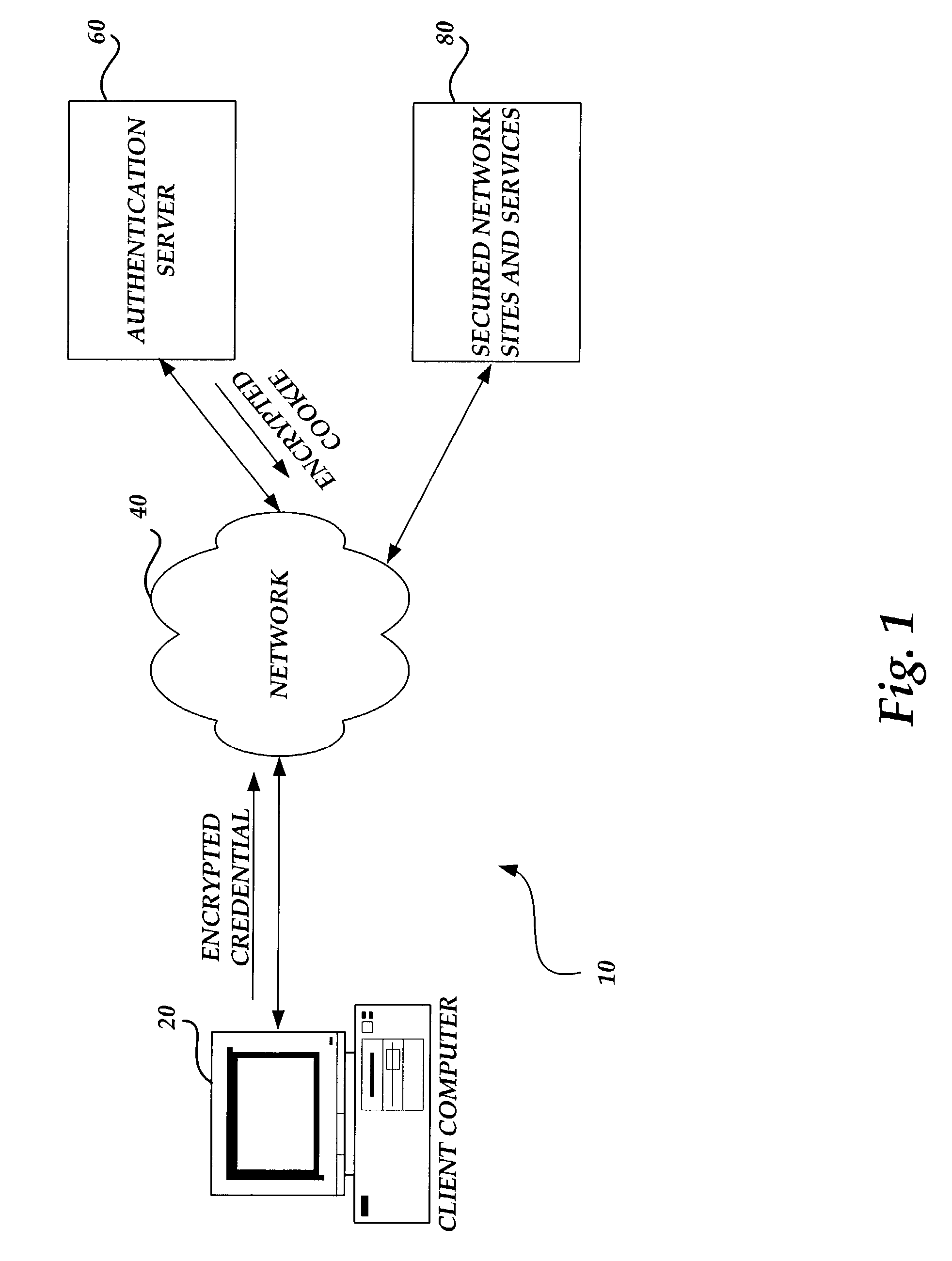
Systems and methods for secure client applications
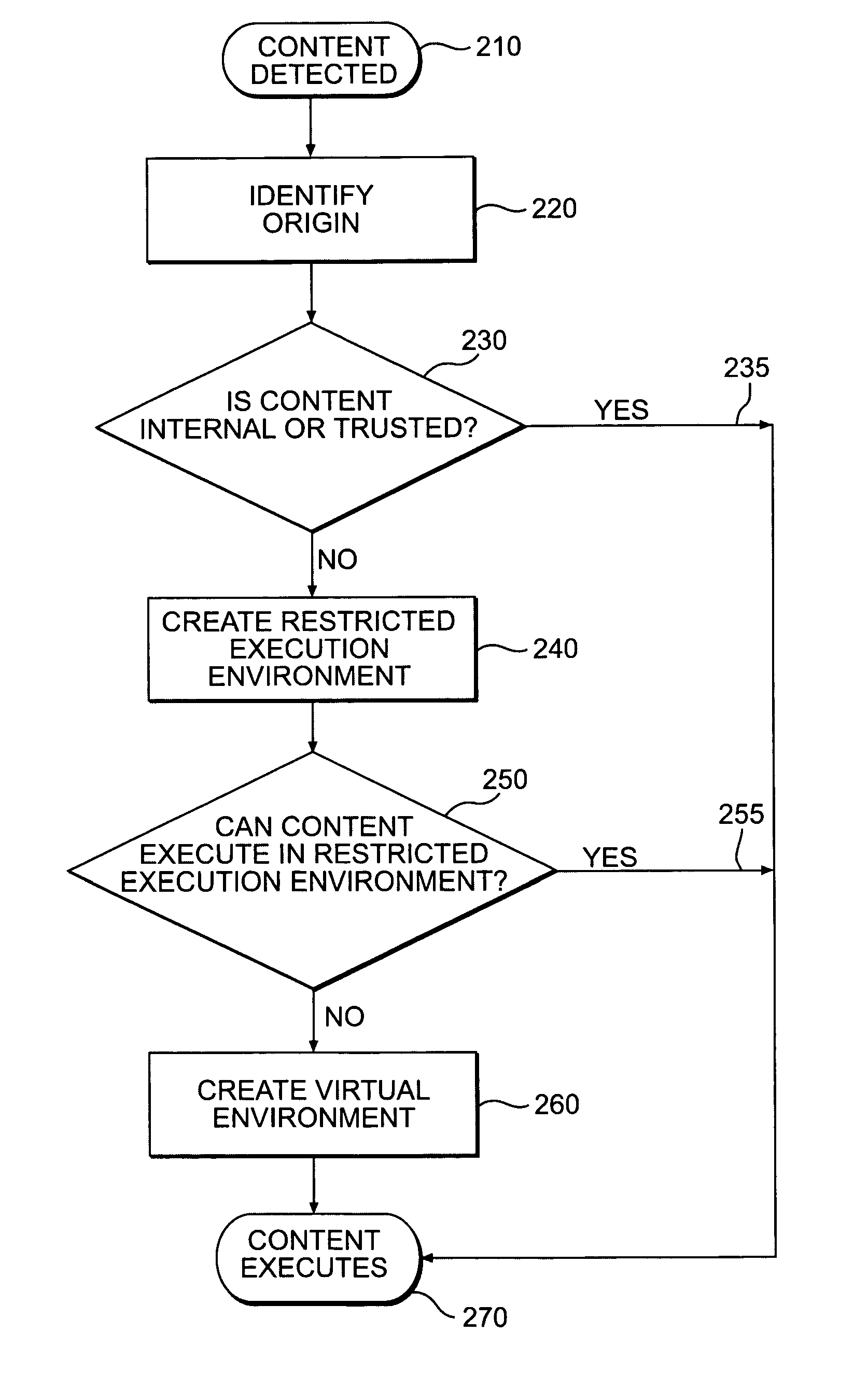
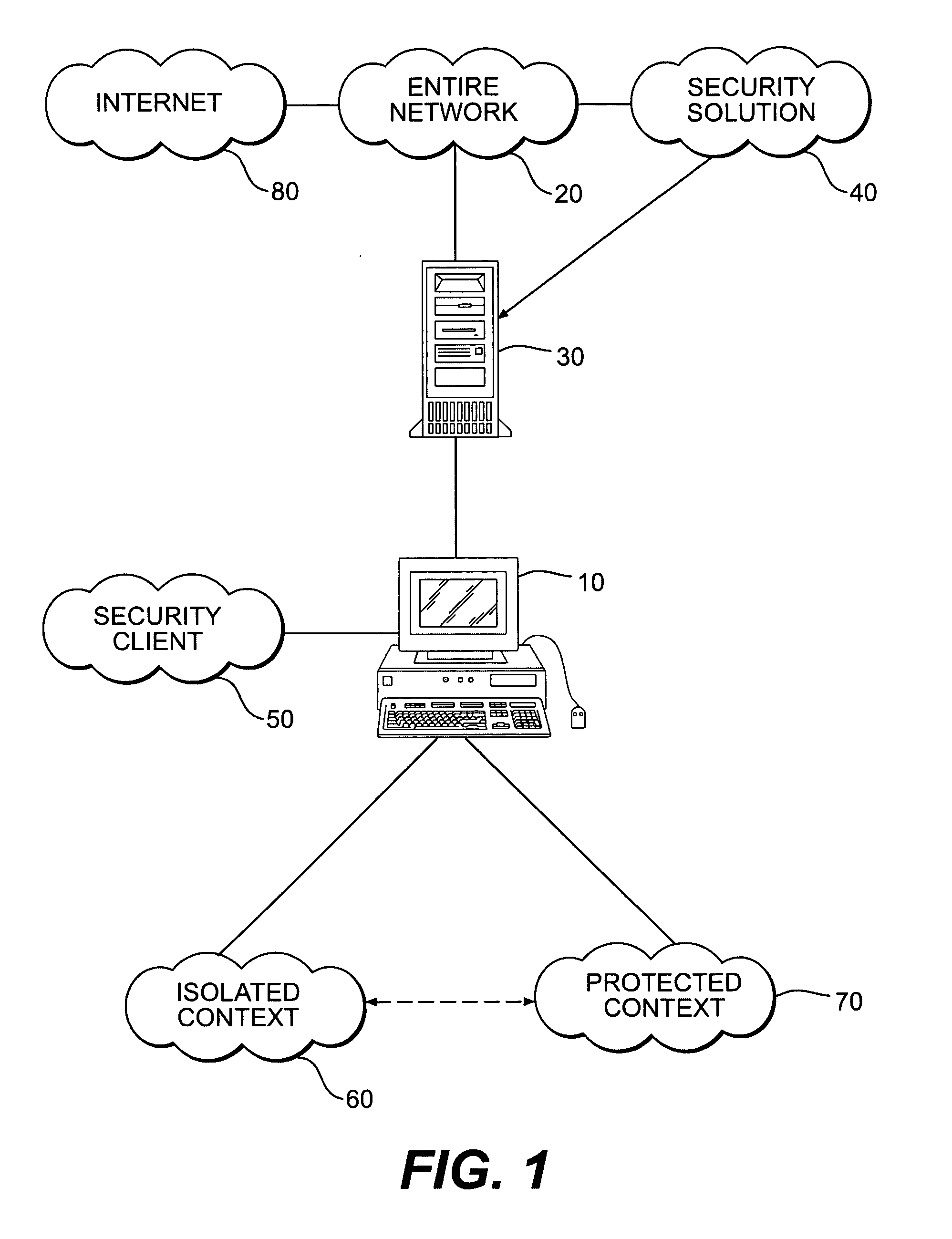
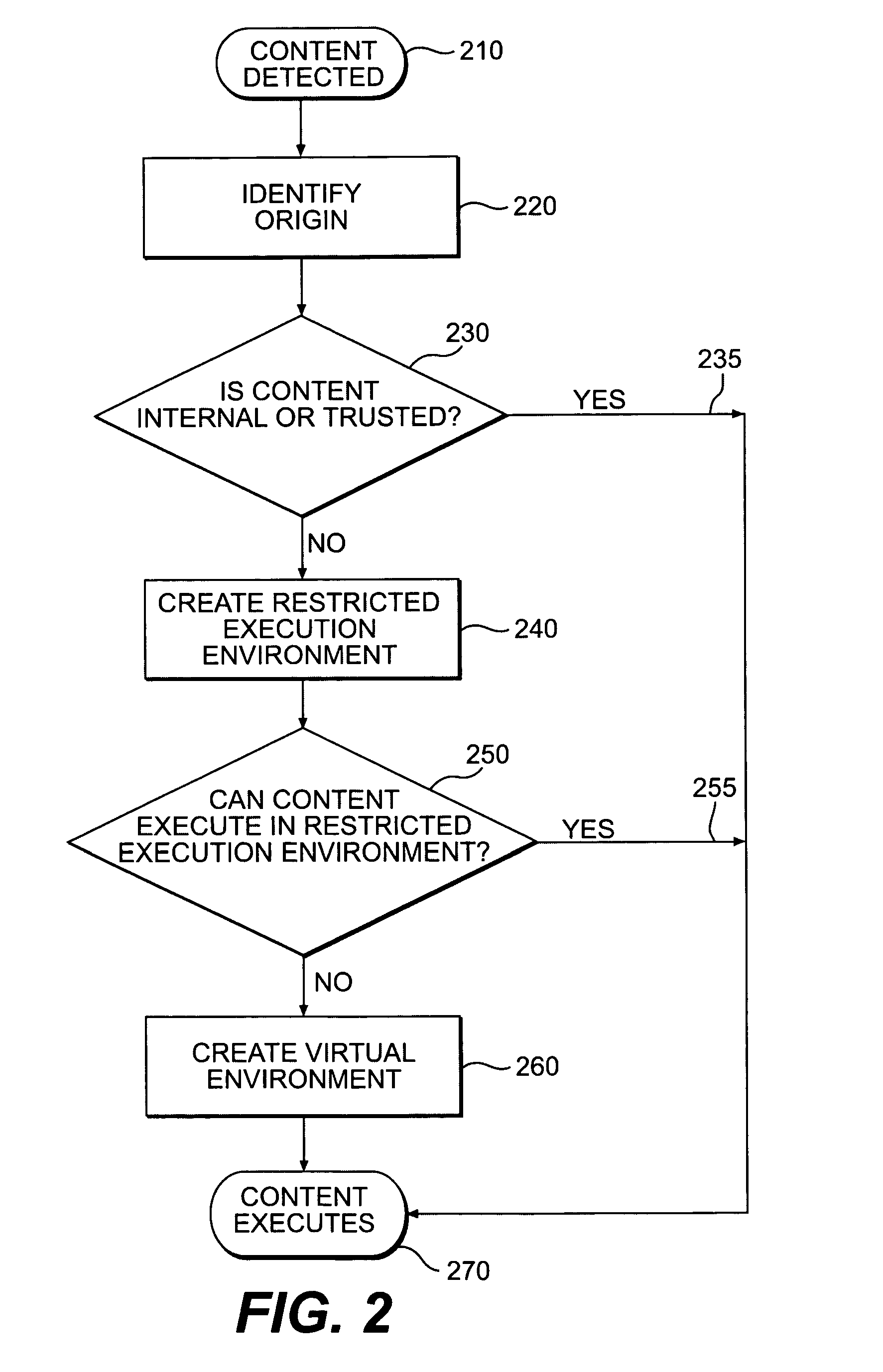
ActiveUS20050149726A1Avoid attackMinimize impactDigital data processing detailsHardware monitoringVirtualizationClient-side
An innovative security solution which separates a client into a Protected Context, which is the real files and resources of the client, and an Isolated Context, which is a restricted execution environment which makes use of virtualized resources to execute applications and modify content in the Isolated Context, without allowing explicit access to the resources in the Protected Context. The solution further consolidates user interfaces to allow users to seamlessly work with content in both contexts, and provide a visual indication of which display windows are rendered from content executed in the Isolated Context.
Owner:GOOGLE LLC
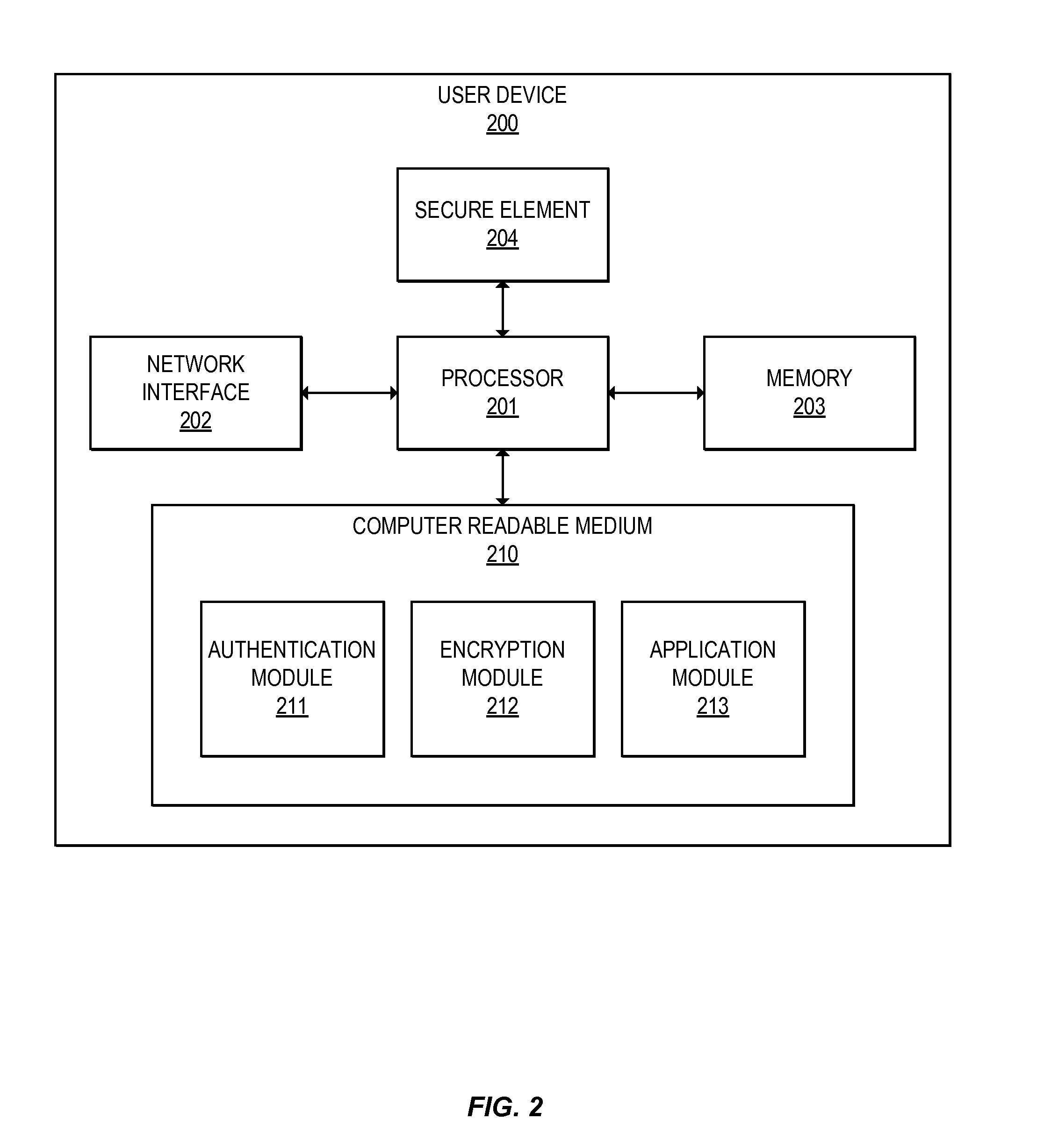
Methods for secure cryptogram generation
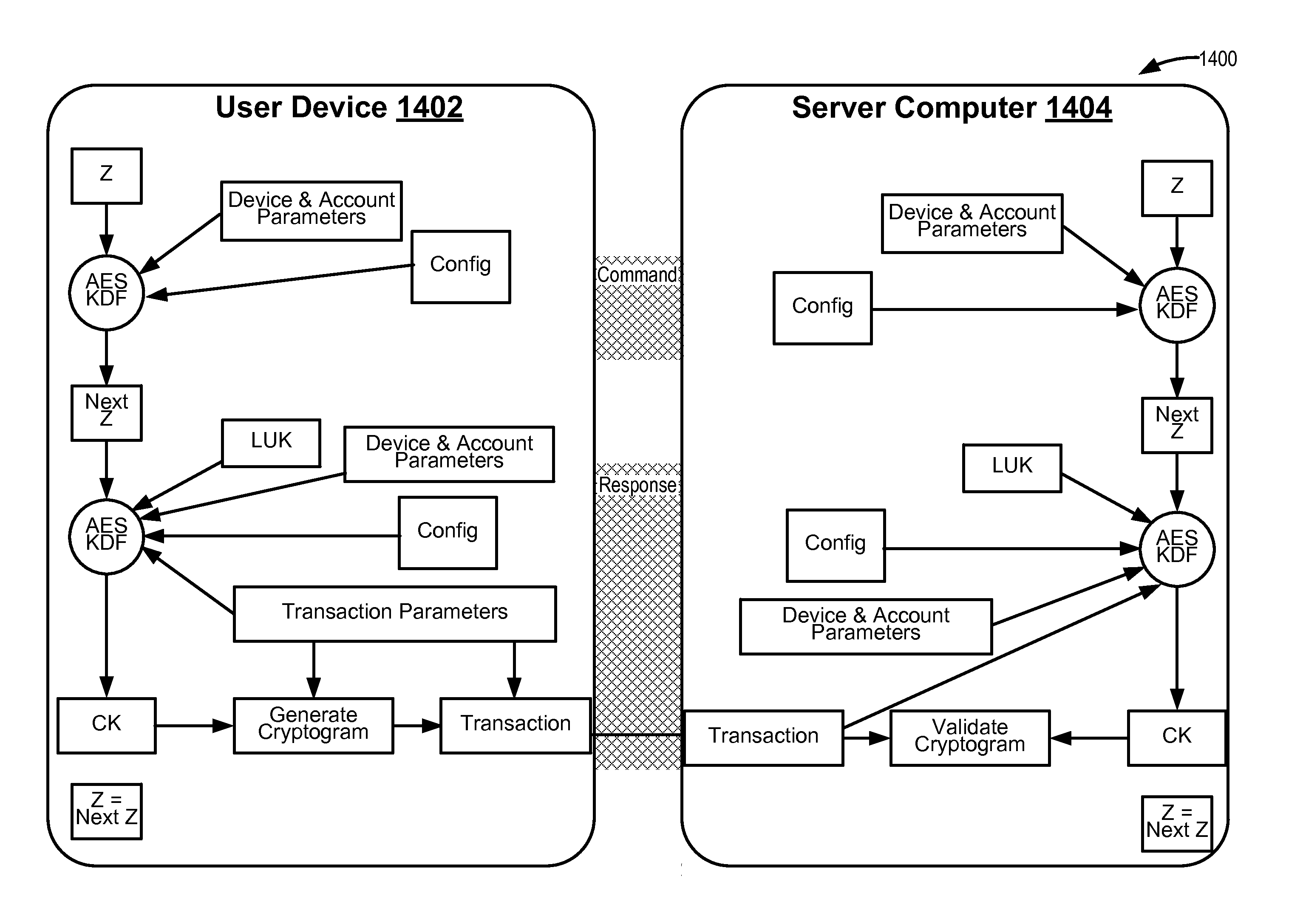
ActiveUS20160065370A1Avoid attackKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationUser device
Embodiments of the invention introduce efficient methods for securely generating a cryptogram by a user device, and validating the cryptogram by a server computer. In some embodiments, a secure communication can be conducted whereby a user device provides a cryptogram without requiring the user device to persistently store an encryption key or other sensitive data used to generate the cryptogram. For example, the user device and server computer can mutually authenticate and establish a shared secret. Using the shared secret, the server computer can derive a session key and transmit key derivation parameters encrypted using the session key to the user device. The user device can also derive the session key using the shared secret, decrypt the encrypted key derivation parameters, and store the key derivation parameters. Key derivation parameters and the shared secret can be used to generate a single use cryptogram key. The cryptogram key can be used to generate a cryptogram for conducting secure communications.
Owner:VISA INT SERVICE ASSOC
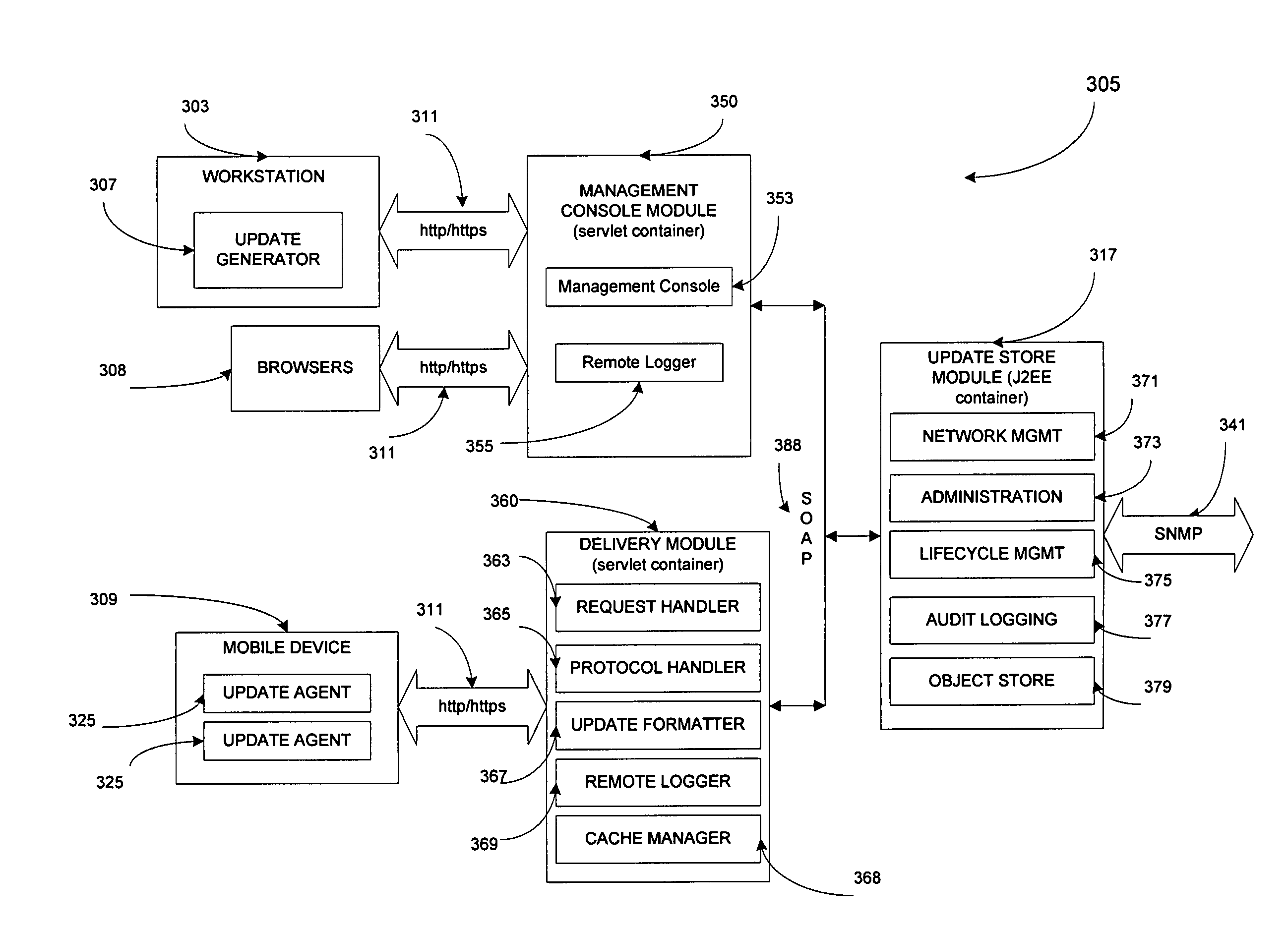
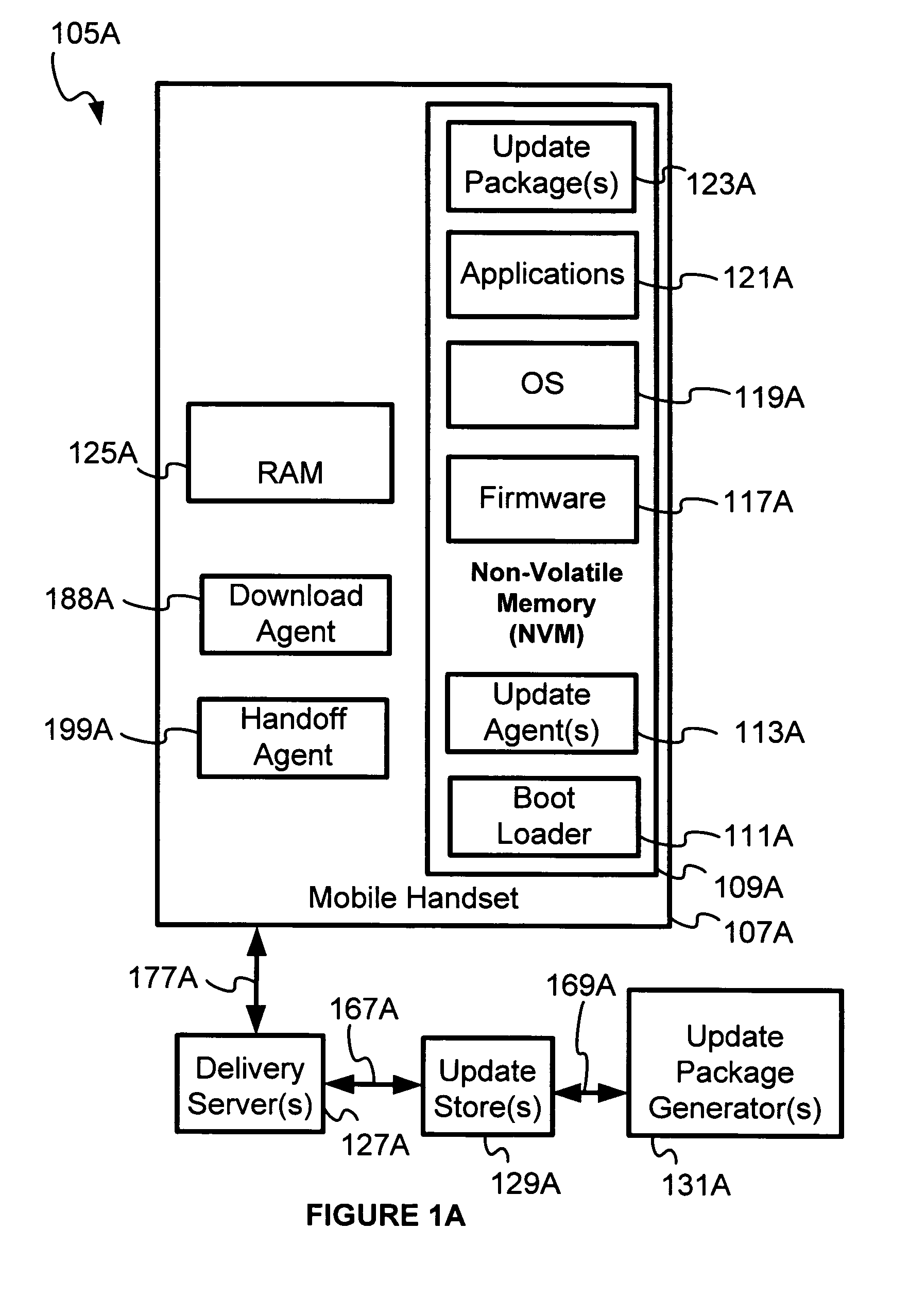
Network for updating electronic devices
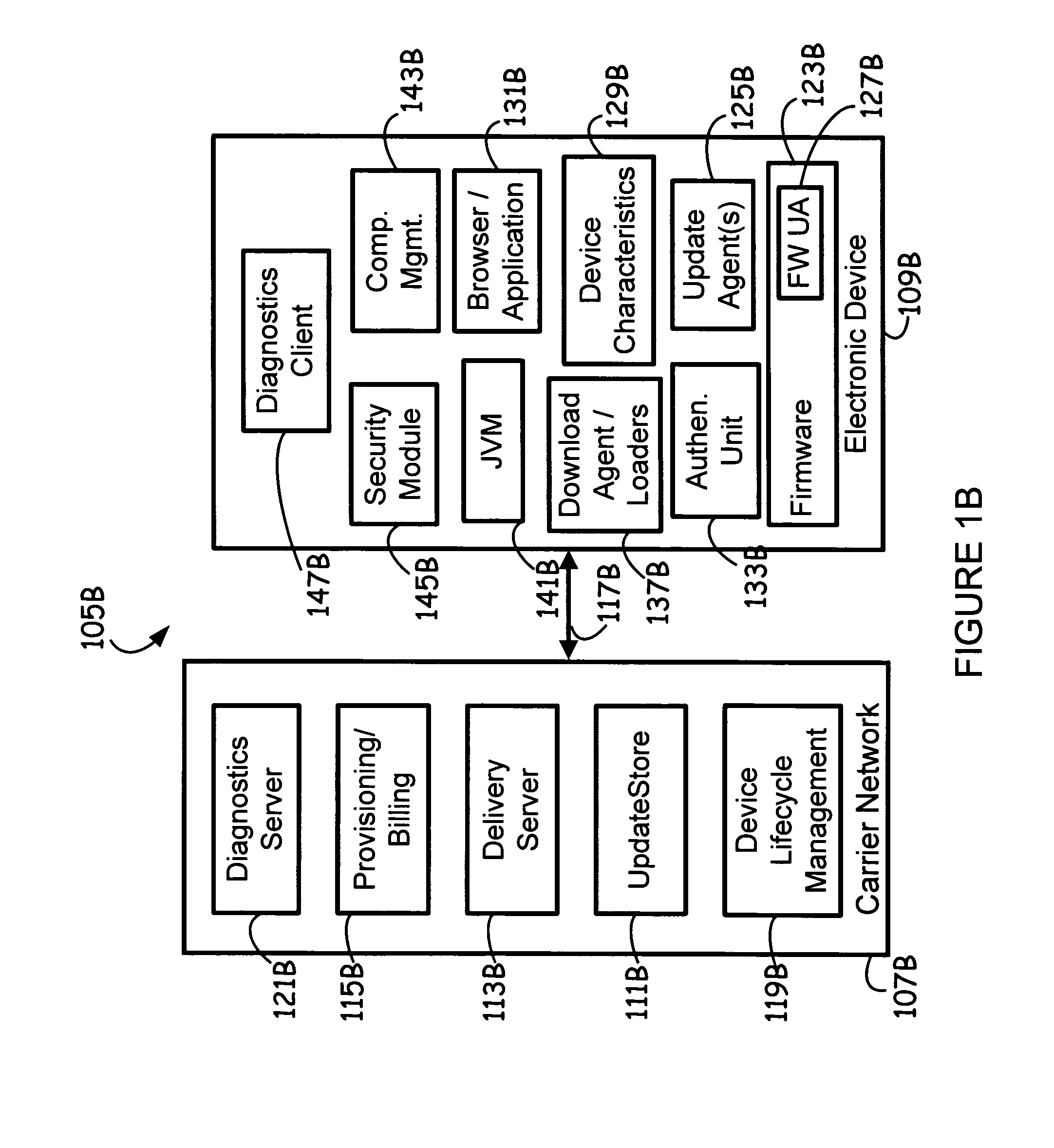
InactiveUS8555273B1Small sizeAvoid attackSoftware engineeringSpecific program execution arrangementsSoftwareVolatile memory
Disclosed herein is an electronic device network for lifecycle management of firmware and software in electronic devices. The electronic device network may also be adapted to manage configuration parameters in the electronic devices. Lifecycle management provided by the electronic device network may include firmware and software downloading, firmware and software updating, and remote locking and remote enabling of electronic device capability. An update store module in the electronic device network may be adapted to dispense update packages to requesting electronic devices. The electronic devices may employ one or a plurality of update agents to update software and firmware therein. A boot loader in the electronic device is capable of determining whether an update agent is to be invoked or whether a previous backup copy of the update agent in non-volatile memory is to be invoked upon determining, based upon status information, that an update is to be conducted, rather than a normal startup operation without updates.
Owner:QUALCOMM INC
Remote printing of secure and/or authenticated documents
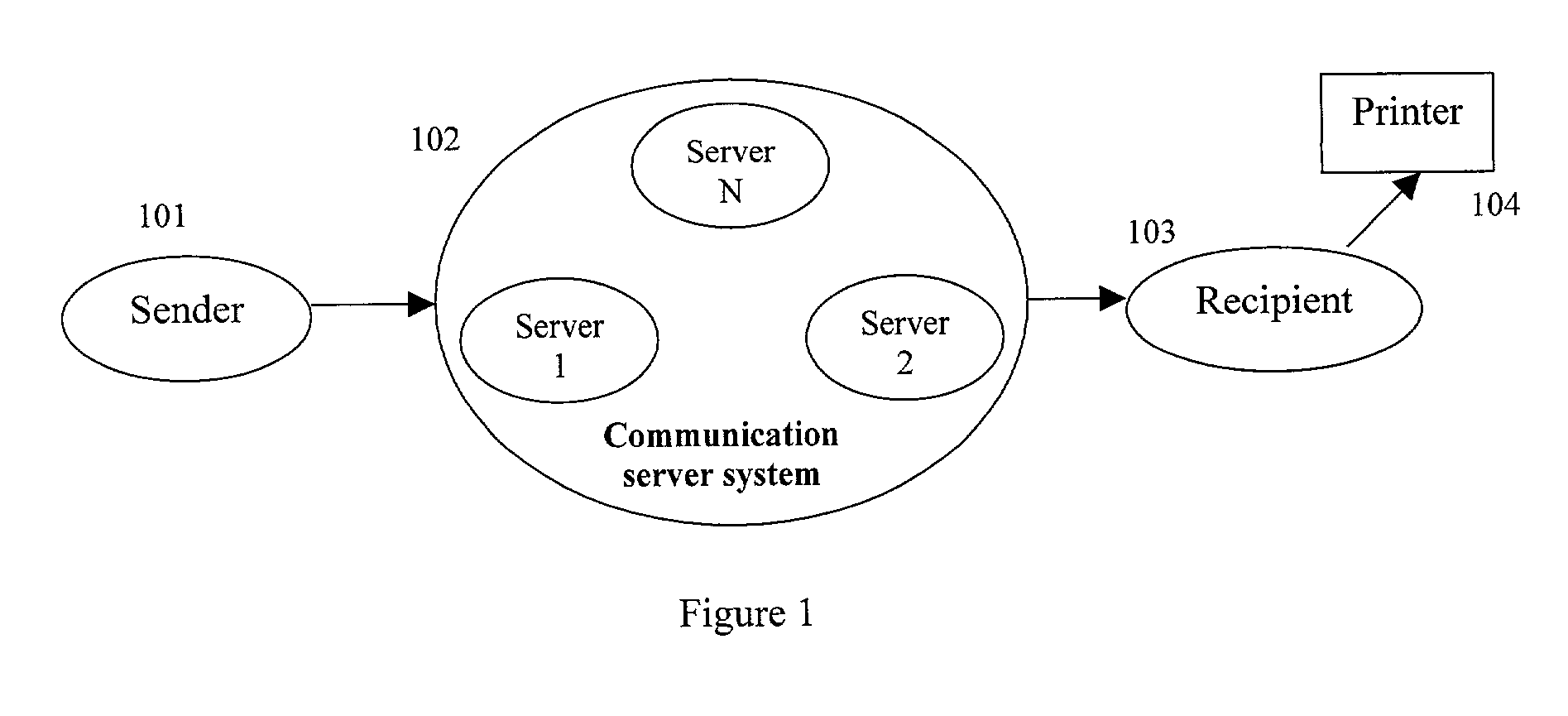
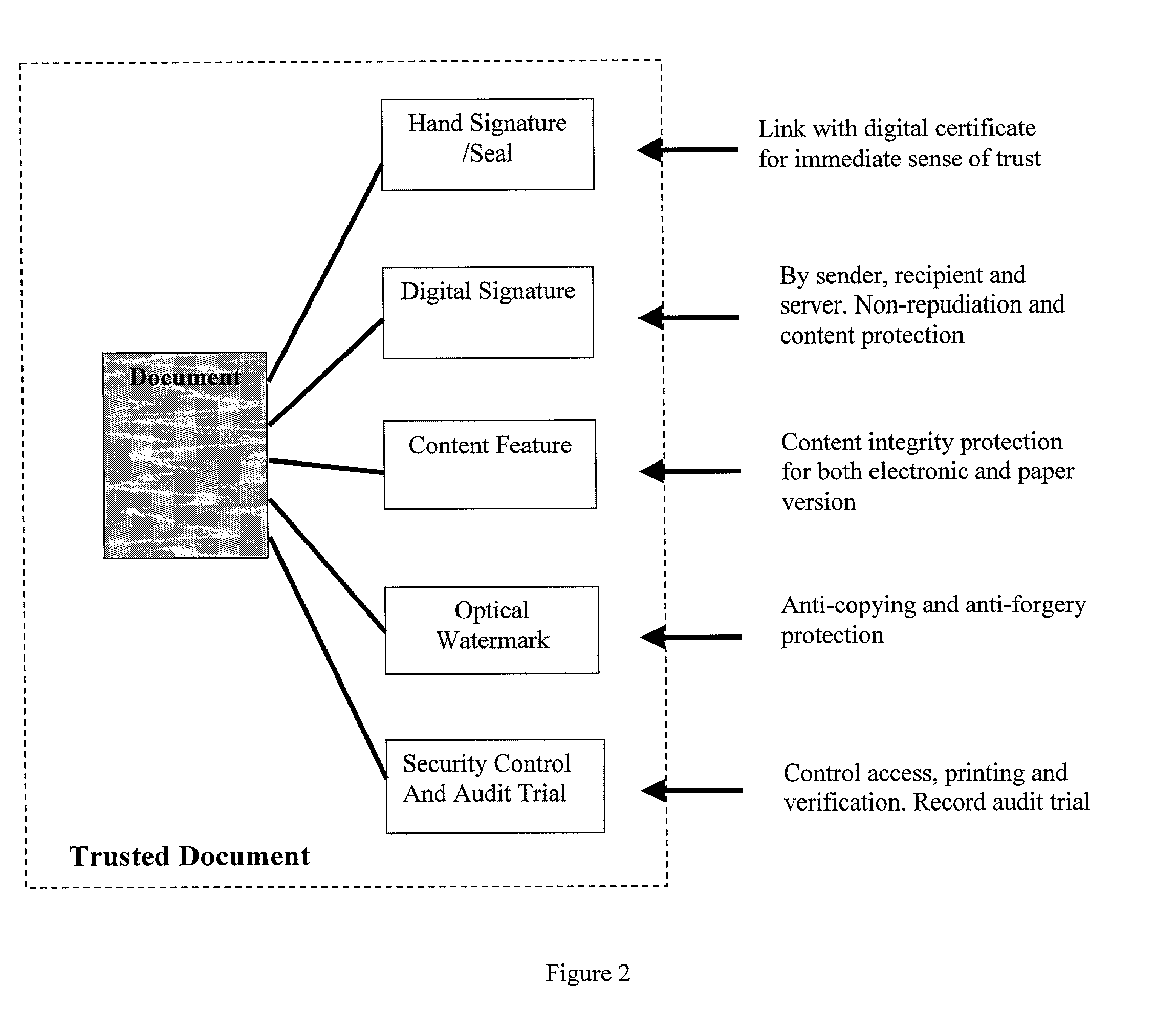
InactiveUS20020042884A1Improve performanceAvoid attackDigital data processing detailsUnauthorized memory use protectionDocumentationDatabase
A method for the remote printing of a document by use of a network, the method including the steps of: (a) receiving at a server the document as sent from a sender; (b) the server forwarding the document to a recipient; (c) the document being authenticated prior to being forwarded to the recipient; and (d) the server receiving instructions from the sender regards printing controls and the server implementing those controls on the recipient. A hardware device to support the printing controls is also disclosed.
Owner:TRUSTCOPY PTE
Method for Protecting IC Cards Against Power Analysis Attacks
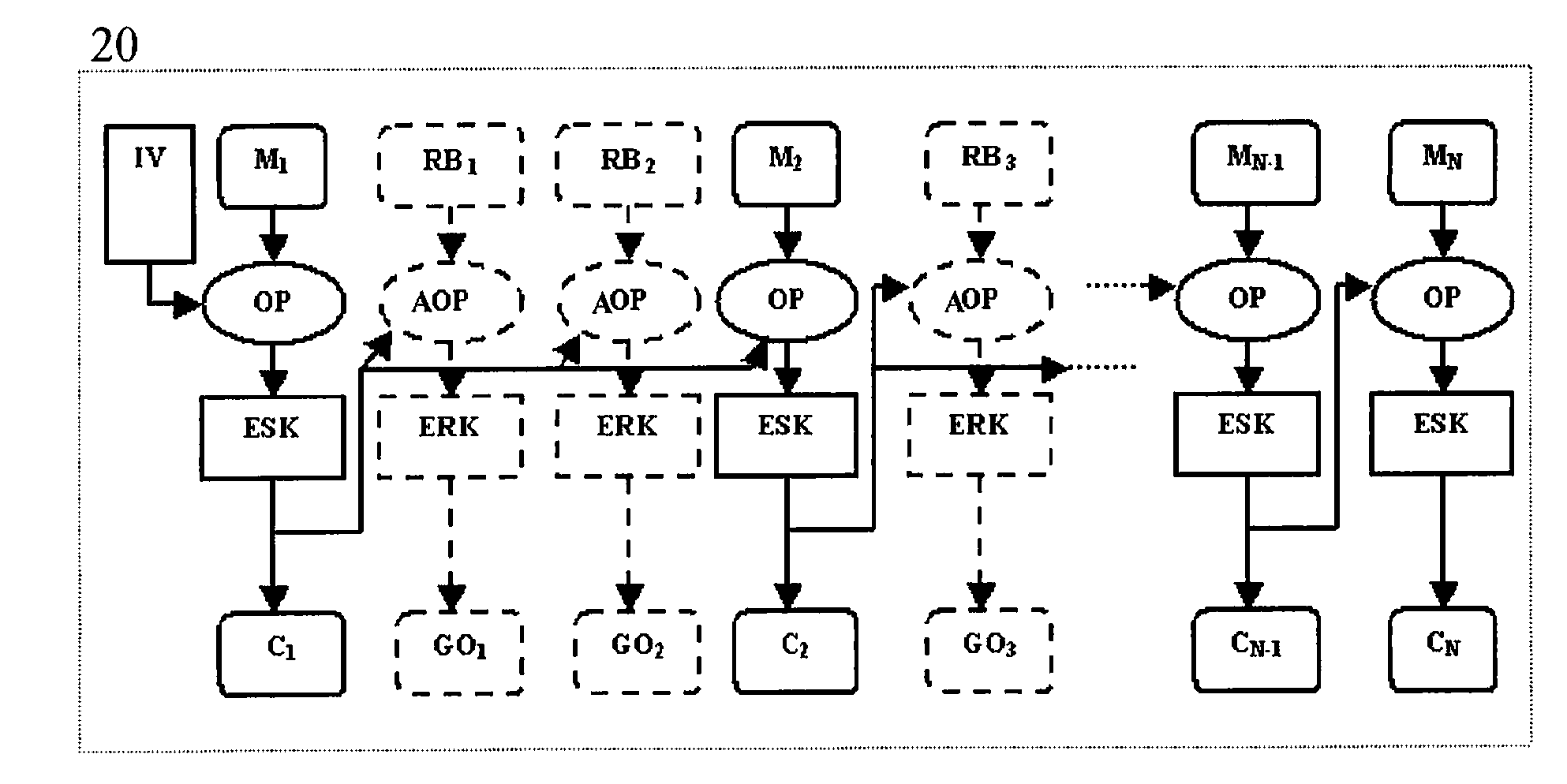
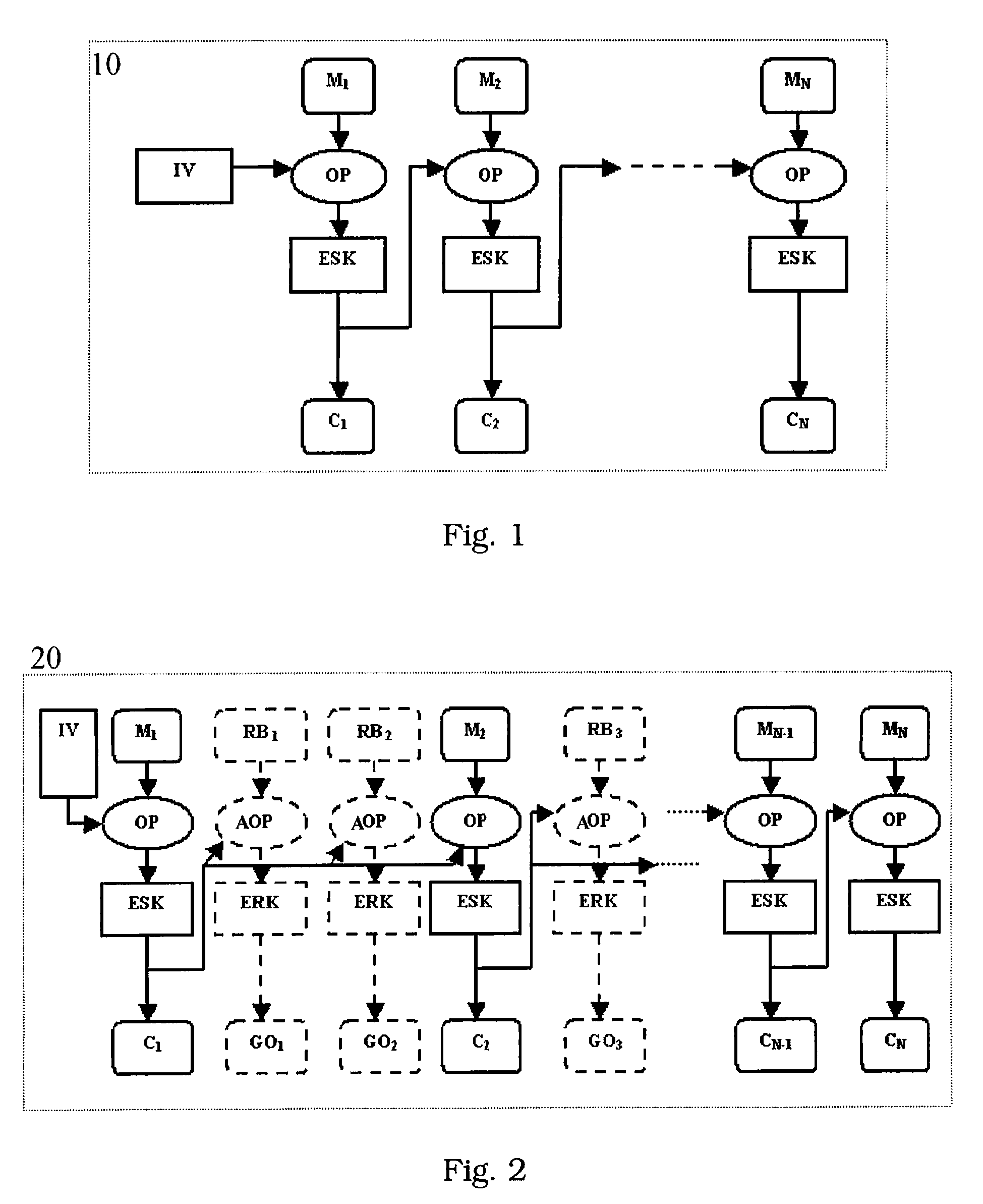
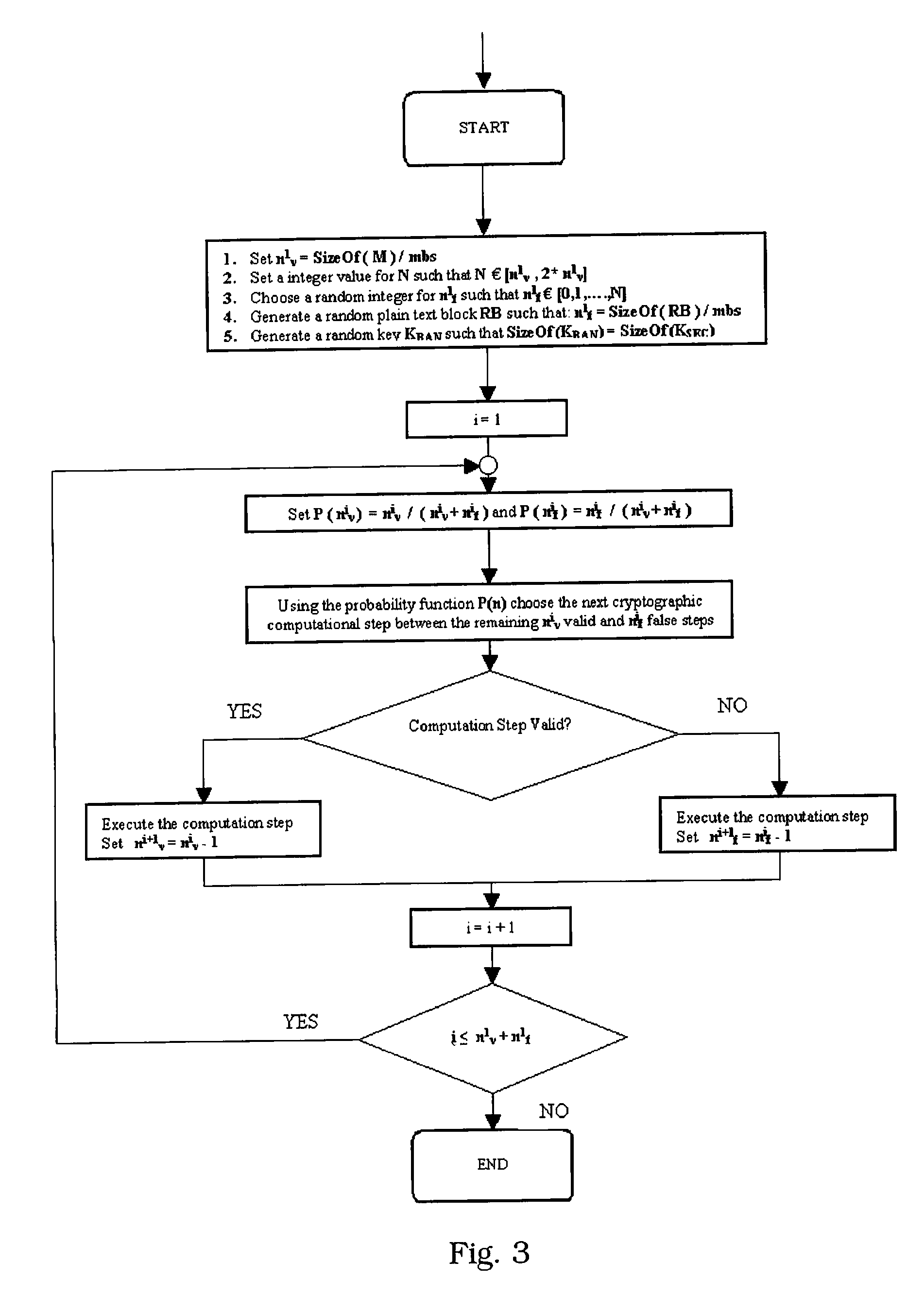
ActiveUS20080019507A1Prevent power analysis attackImprove automationInternal/peripheral component protectionSecret communicationComputer hardwarePower analysis
A method for protecting data against power analysis attacks includes at least a first phase of executing a cryptographic operation for ciphering data in corresponding enciphered data through a secret key. The method includes at least a second phase of executing an additional cryptographic operation for ciphering additional data in corresponding enciphered additional data. An execution of the first and second phases is undistinguishable by the data power analysis attacks. Secret parameters are randomly generated and processed by the at least one second phase. The secret parameters include an additional secret key ERK for ciphering the additional data in the corresponding enciphered additional data.
Owner:STMICROELECTRONICS INT NV
Plasma for patterning advanced gate stacks
InactiveUS20070099428A1Avoid attackSemiconductor/solid-state device manufacturingSemiconductor devicesPlasma compositionNitrogen
A plasma composition and its use in a method for the dry etching of a stack of at least one material chemically too reactive towards the use of a Cl-based plasma are provided. Small amounts of nitrogen (5% up to 10%) can be added to a BCl3 comprising plasma and used in an anisotropical dry etching method whereby a passivation film is deposited onto the vertical sidewalls of stack etched for protecting the vertical sidewalls from lateral attack such that straight profiles can be obtained.
Owner:INTERUNIVERSITAIR MICRO ELECTRONICS CENT (IMEC VZW)
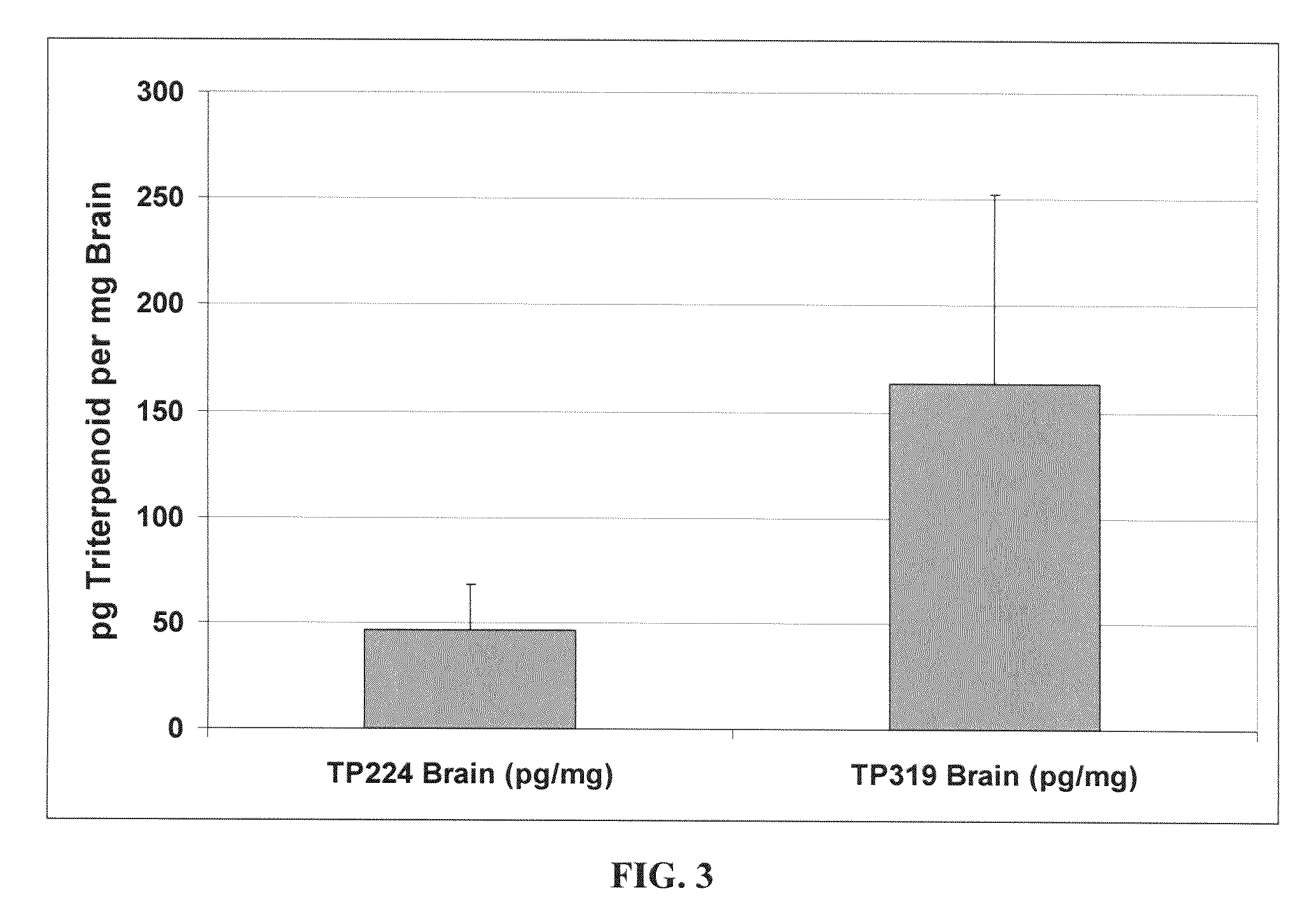
Novel synthetic triterpenoids and methods of use in the treatment and prevention of multiple scleroris
InactiveUS20090060873A1Improving glomerular filtration rateImproving creatinine clearanceBiocideSalicyclic acid active ingredientsDiseaseBipolar mood disorder
The present invention overcomes limitations of the prior art by providing new compounds and methods for the treatment of conditions, such as neurodegenerative diseases (e.g., multiple sclerosis), psychiatric disorders (e.g., psychosis, bipolar disorder, depression, neuropathic pain), conditions involving CNS-mediated chronic pain, spinal cord injuries, and other diseases or injuries.
Owner:TRUSTEES OF DARTMOUTH COLLEGE THE +1
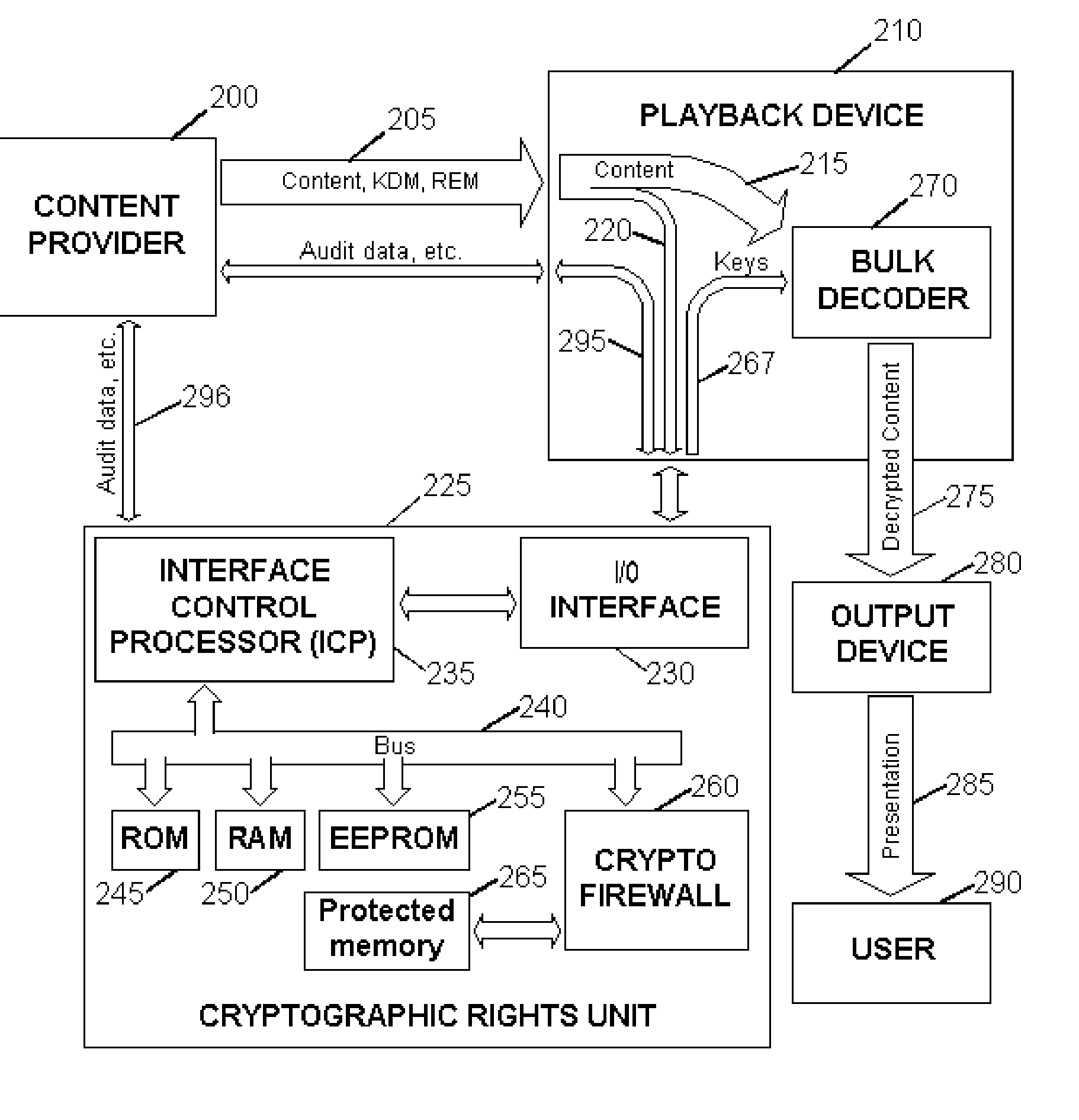
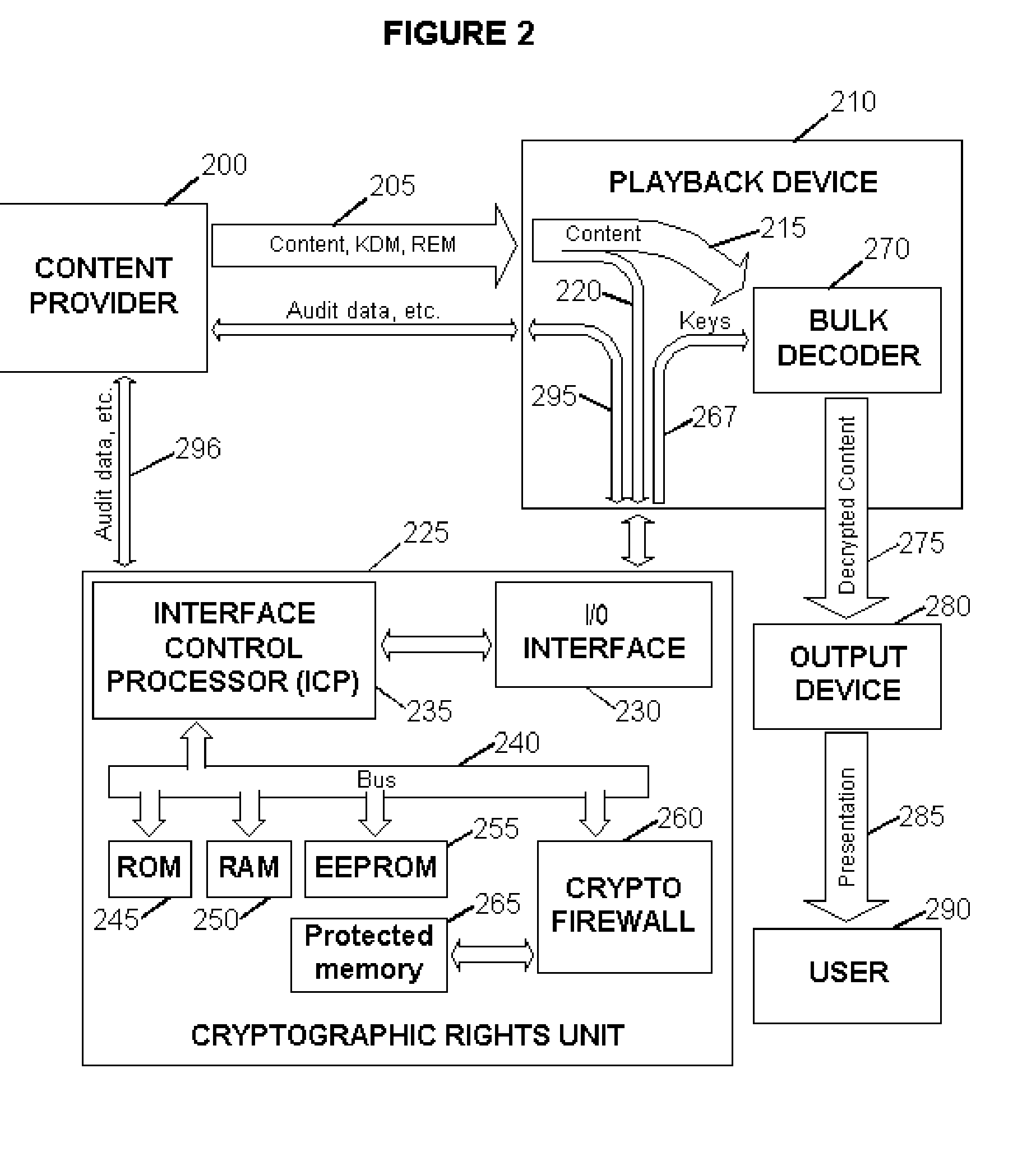
Digital Content Protection Method and Apparatus
InactiveUS20020099948A1Improve securityMinimizes probabilityKey distribution for secure communicationDigital data processing detailsDigital signatureDigital content
<heading lvl="0">Abstract of Disclosure< / heading> Before use, a population of tamper-resistant cryptographic enforcement devices is partitioned into groups and issued one or more group keys. Each tamper-resistant device contains multiple computational units to control access to digital content. One of the computational units within each tamper-resistant device communicates with another of the computational units acting as an interface control processor, and serves to protect the contents of a nonvolatile memory from unauthorized access or modification by other portions of the tamper-resistant device, while performing cryptographic computations using the memory contents. Content providers enforce viewing privileges by transmitting encrypted rights keys to a large number of recipient devices. These recipient devices process received messages using the protected processing environment and memory space of the secure unit. The processing result depends on whether the recipient device was specified by the content provider as authorized to view some encrypted digital content. Authorized recipient devices can use the processing result in decrypting the content, while unauthorized devices cannot decrypt the content. A related aspect of the invention provides for securing computational units and controlling attacks. For example, updates to the nonvolatile memory, including program updates, are supported and protected via a cryptographic unlocking and validation process in the secure unit, which can include digital signature verification.
Owner:CRYPTOGRAPHY RESEARCH
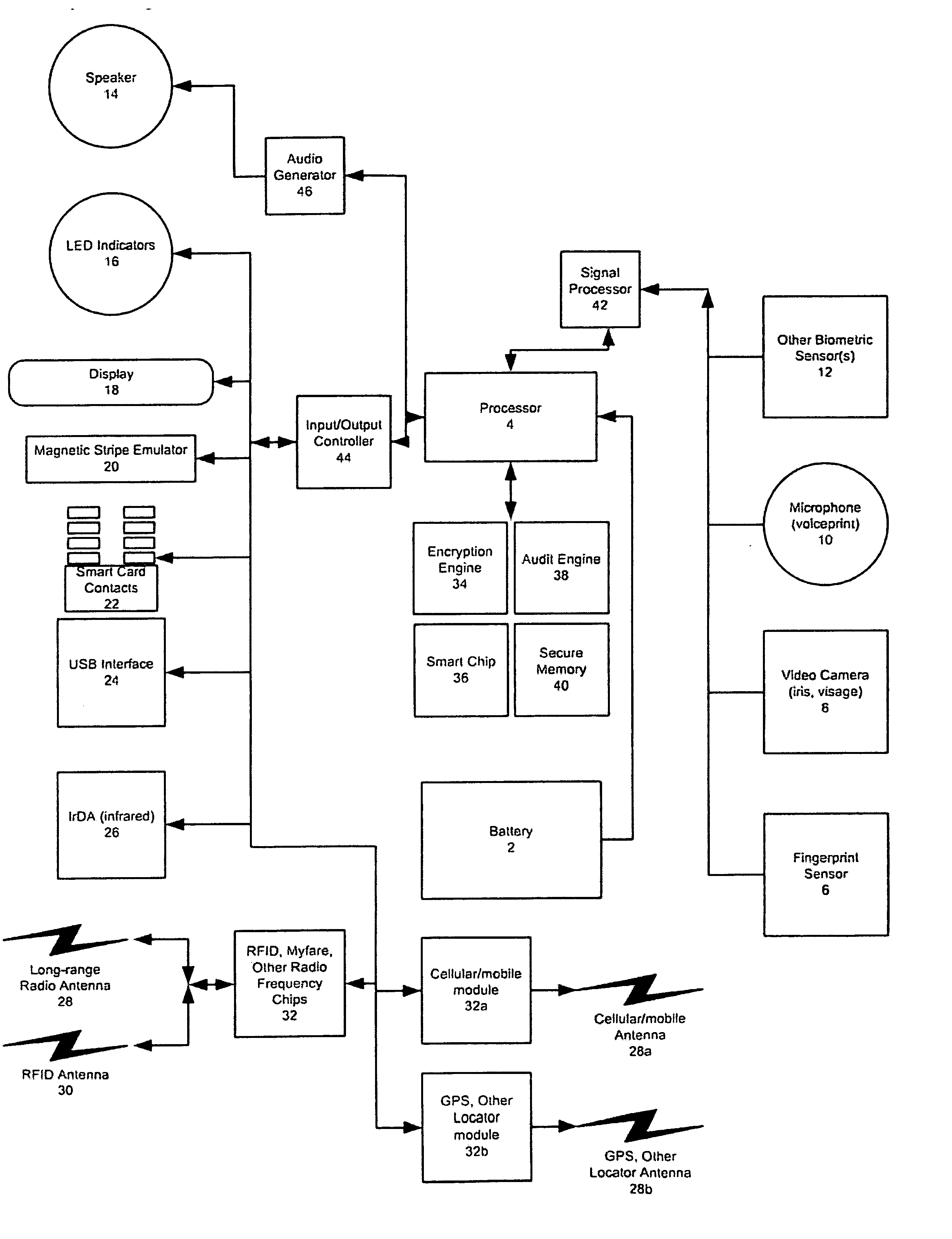
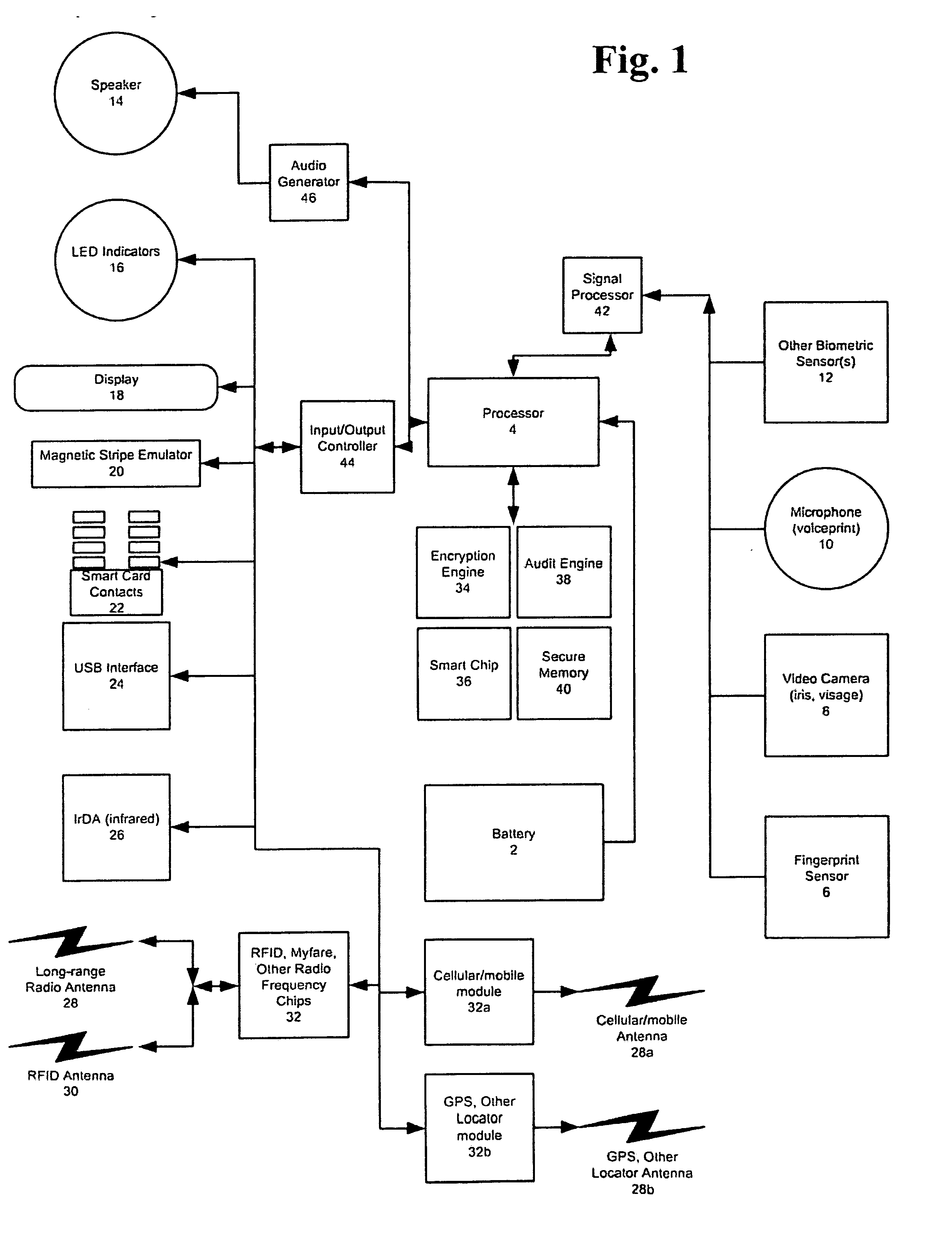
Universal, Biometric, Self-Authenticating Identity Computer Having Multiple Communication Ports
InactiveUS20080148059A1Maintain securityLimited accessUser identity/authority verificationPayment architectureSmart cardCard reader
An improved device for use in authorizing transactions, supplying information and performing applications is provided by the present invention, effectively implementing a secured individual and portable Public Key Infrastructure (PKI) terminal. The device uses a local processor and secure data storage in conjunction with a variety of sensors to perform authentication processes that establish an individuals identity and provide authority to perform a desired transaction. The sensors allow the device to directly scan biometric identifying information from an individual. A card swipe interface and a proximity antenna are provided to facilitate communication between the device and remote interface devices such as magnetic swipe card readers, smart card readers, infrared communications ports and proximity and long range radio scanners. In addition, the local processor, memory, display and user inputs allow the device to run applications such as those performed by a traditional computer, gaming device, personal data assistant and smart phone.
Owner:SHAPIRO MICHAEL F
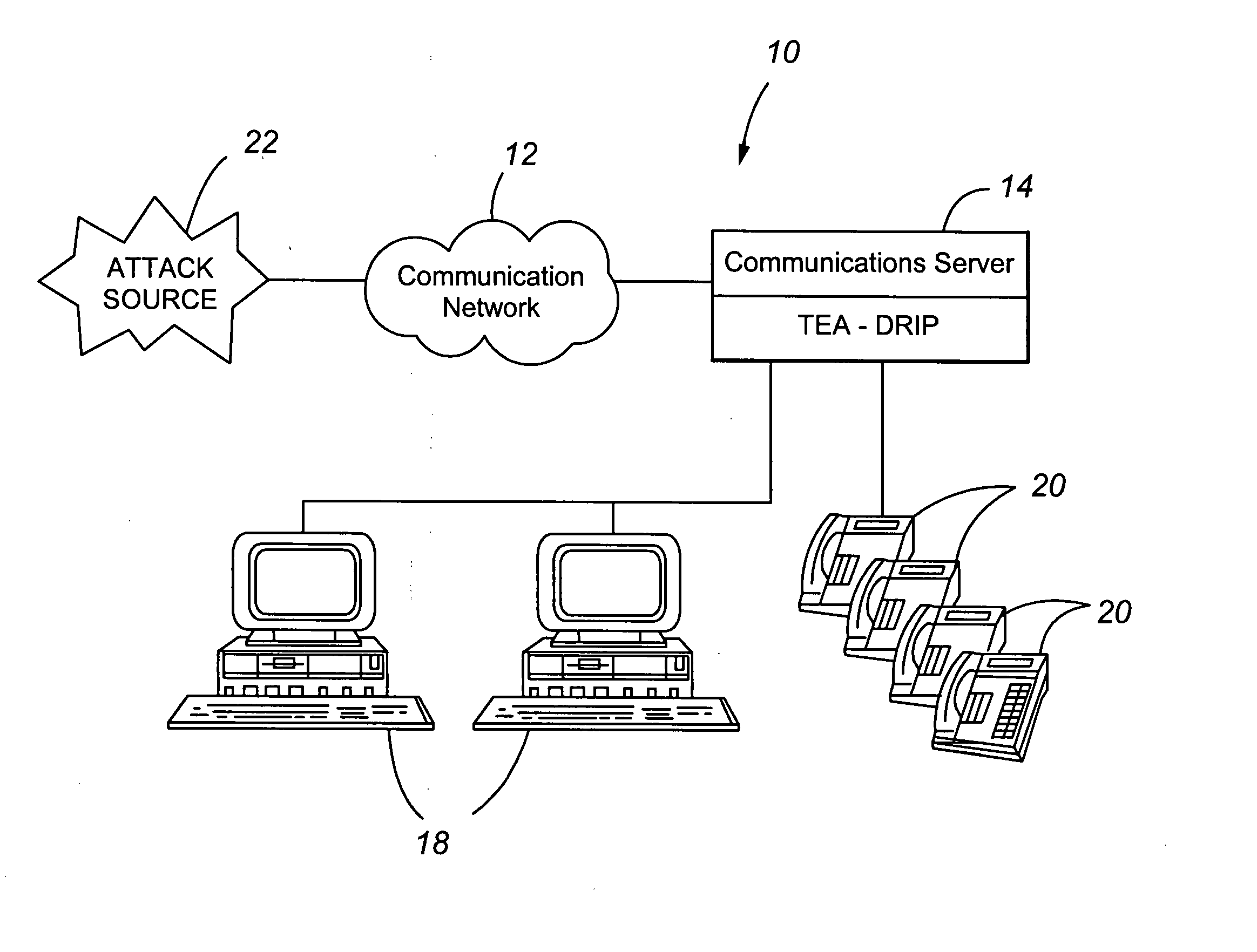
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS20070036314A1Effectively prevent future attackAvoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
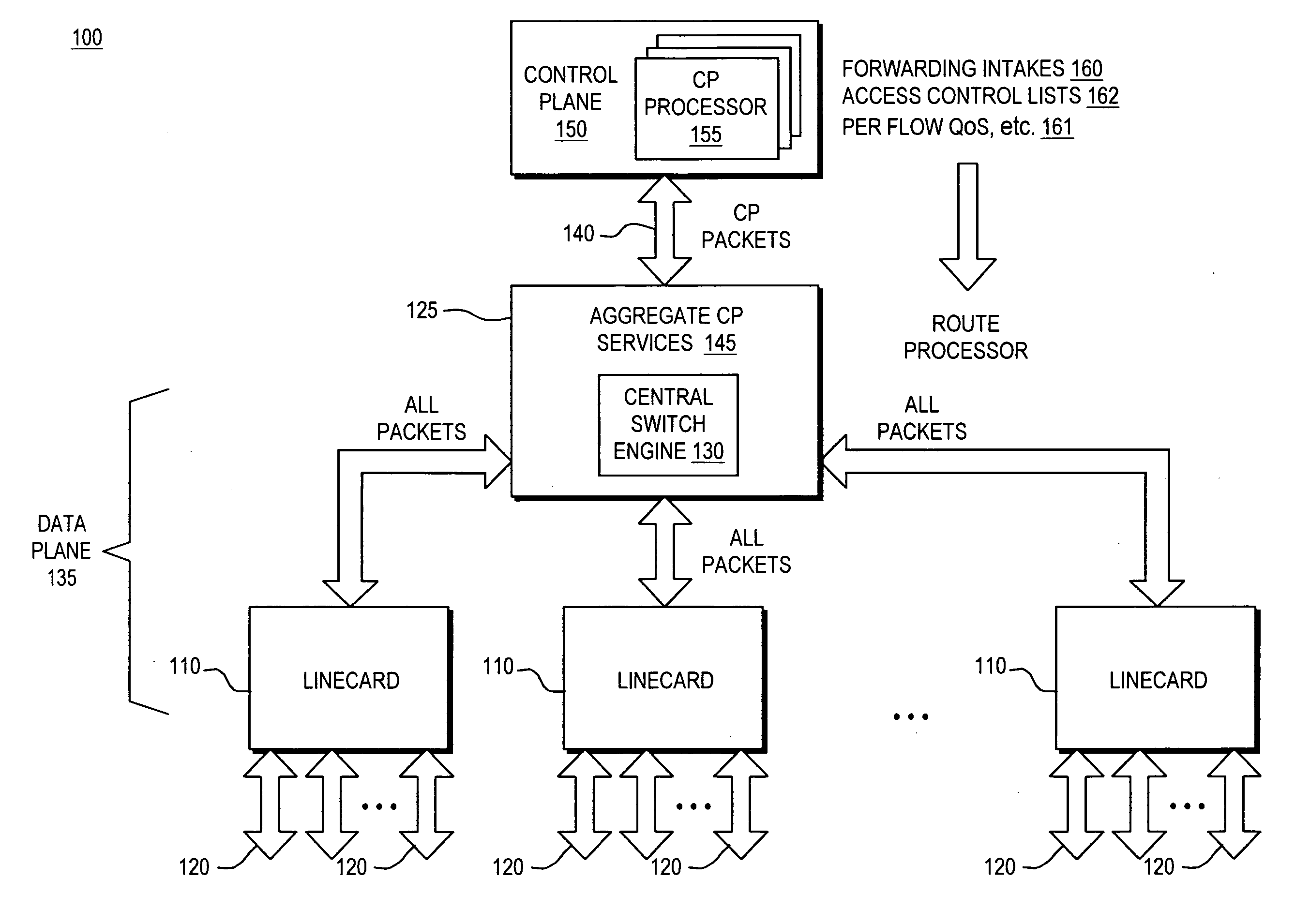
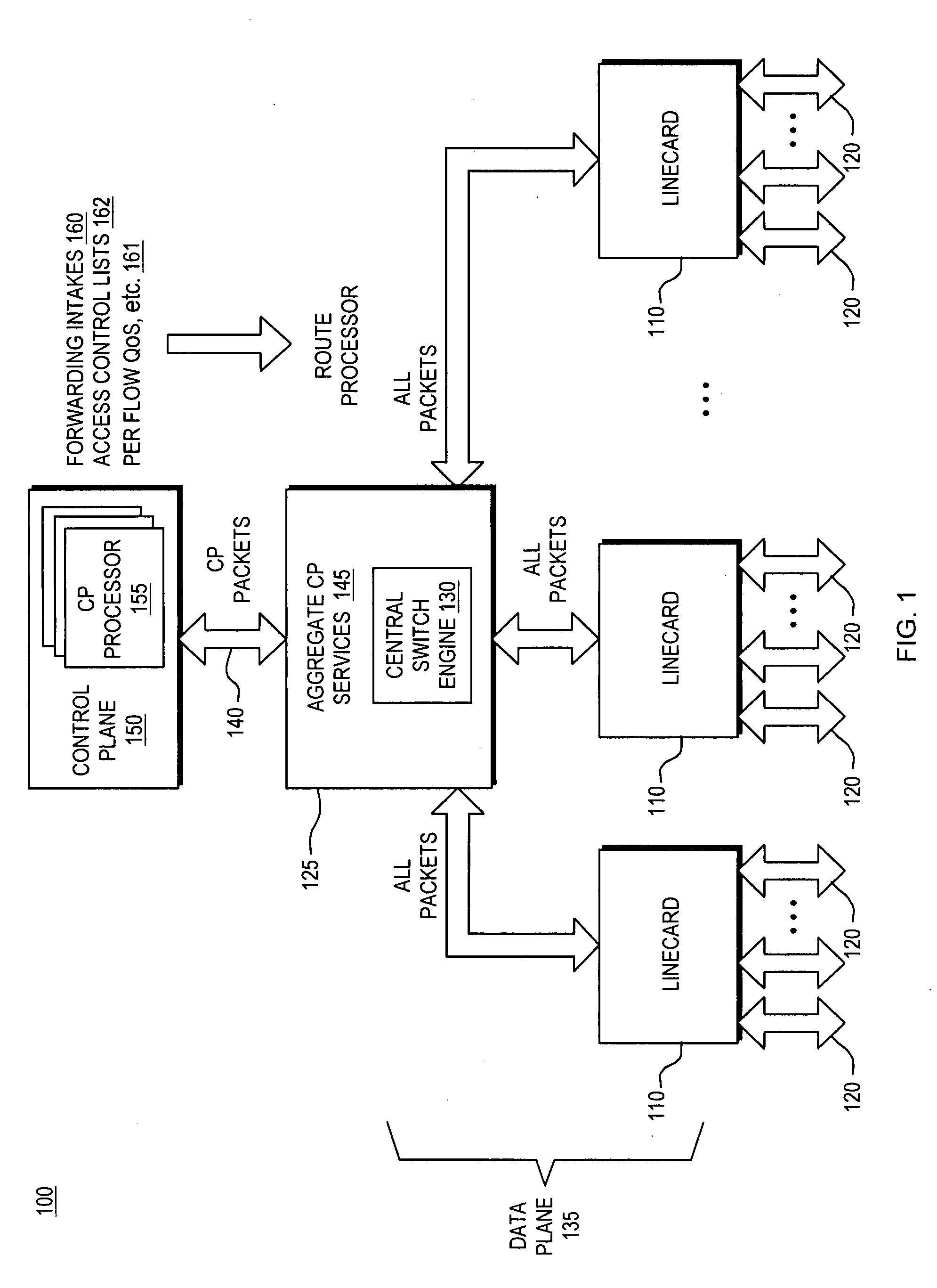
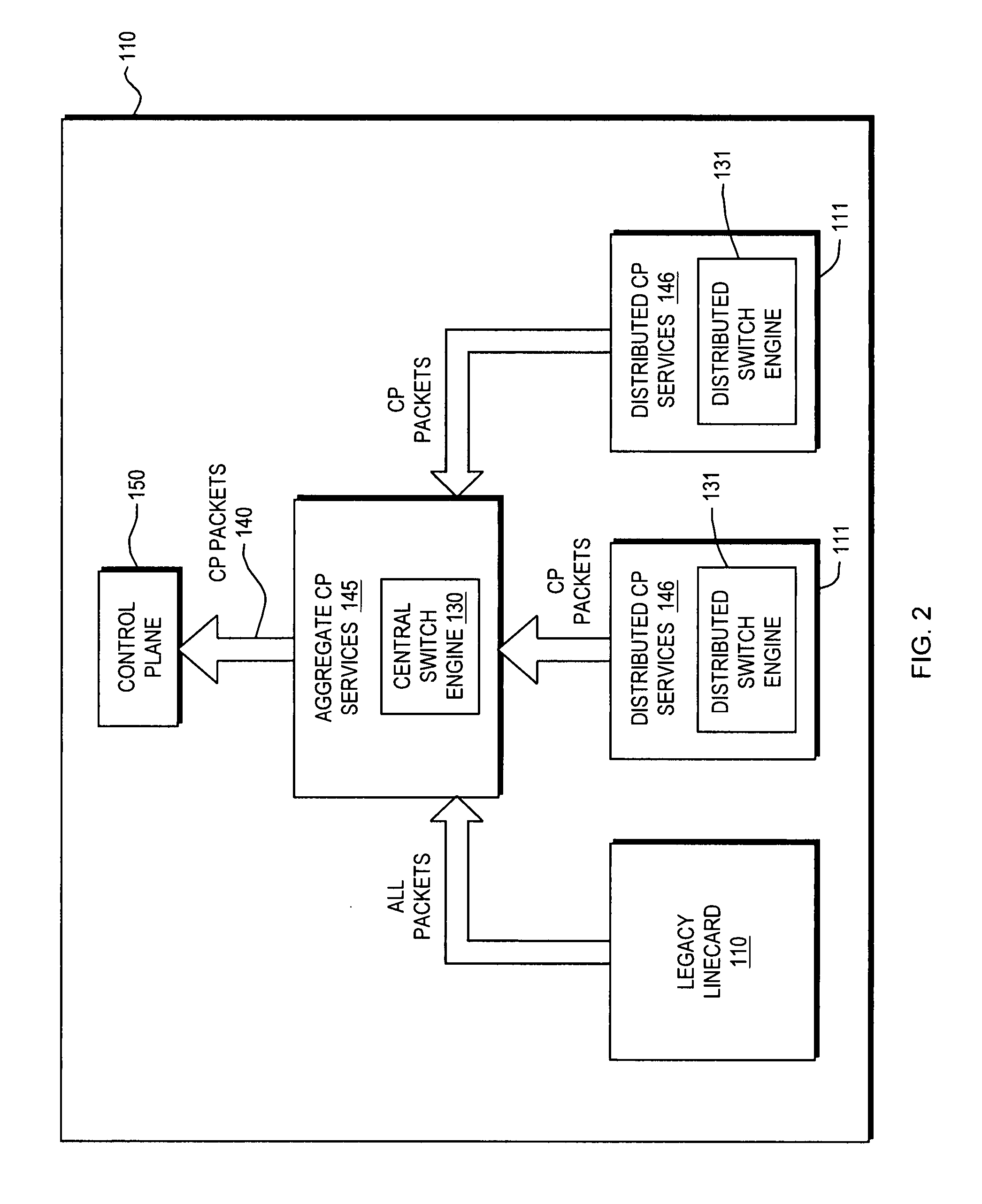
Control plane security and traffic flow management
InactiveUS20070201357A1Improve immunityImprove service qualityMultiplex system selection arrangementsInterconnection arrangementsTraffic capacityQuality of service
An internetworking device that provides improved immunity to Denial of Service attacks, and in general, improved Quality of Service (QoS). An internetworking element or other route processor is composed of two main parts, including a data forwarding plane and a control plane; the control plane runs routing, signaling and control protocols that are responsible for determining the packet forwarding behavior by the data plane. Independent control plane processes may be provided; however, they are considered to be a single network entity that is a uniquely addressable port. Packets thus intended for the control plane always pass through a designated point. As a result, a set of port services unique to the control plane may be applied to the control plane port. These control plane port services thus can be utilized to control all packet traffic entering and exiting the control plane processes as a whole.
Owner:CISCO SYSTEMS INC
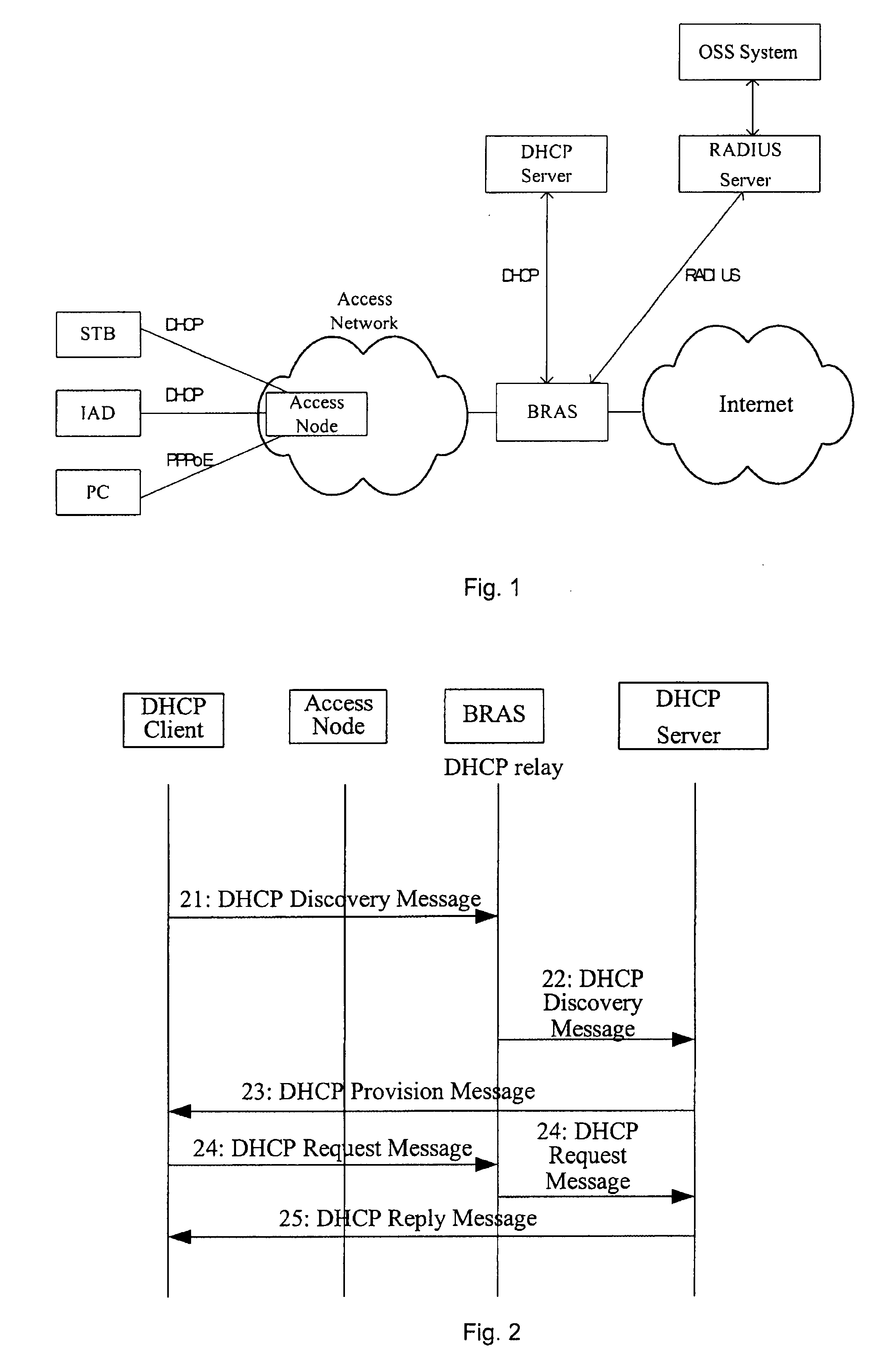
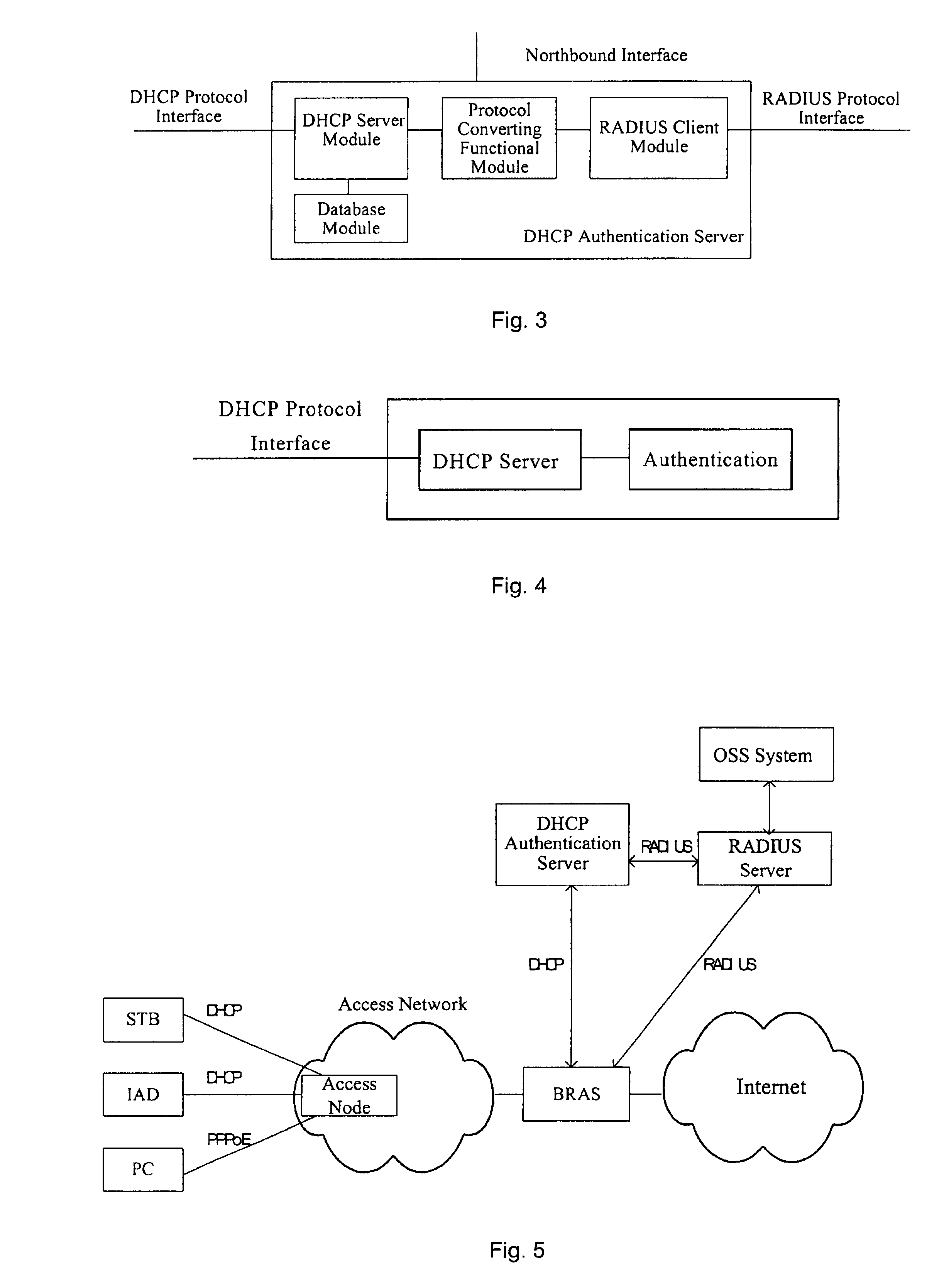
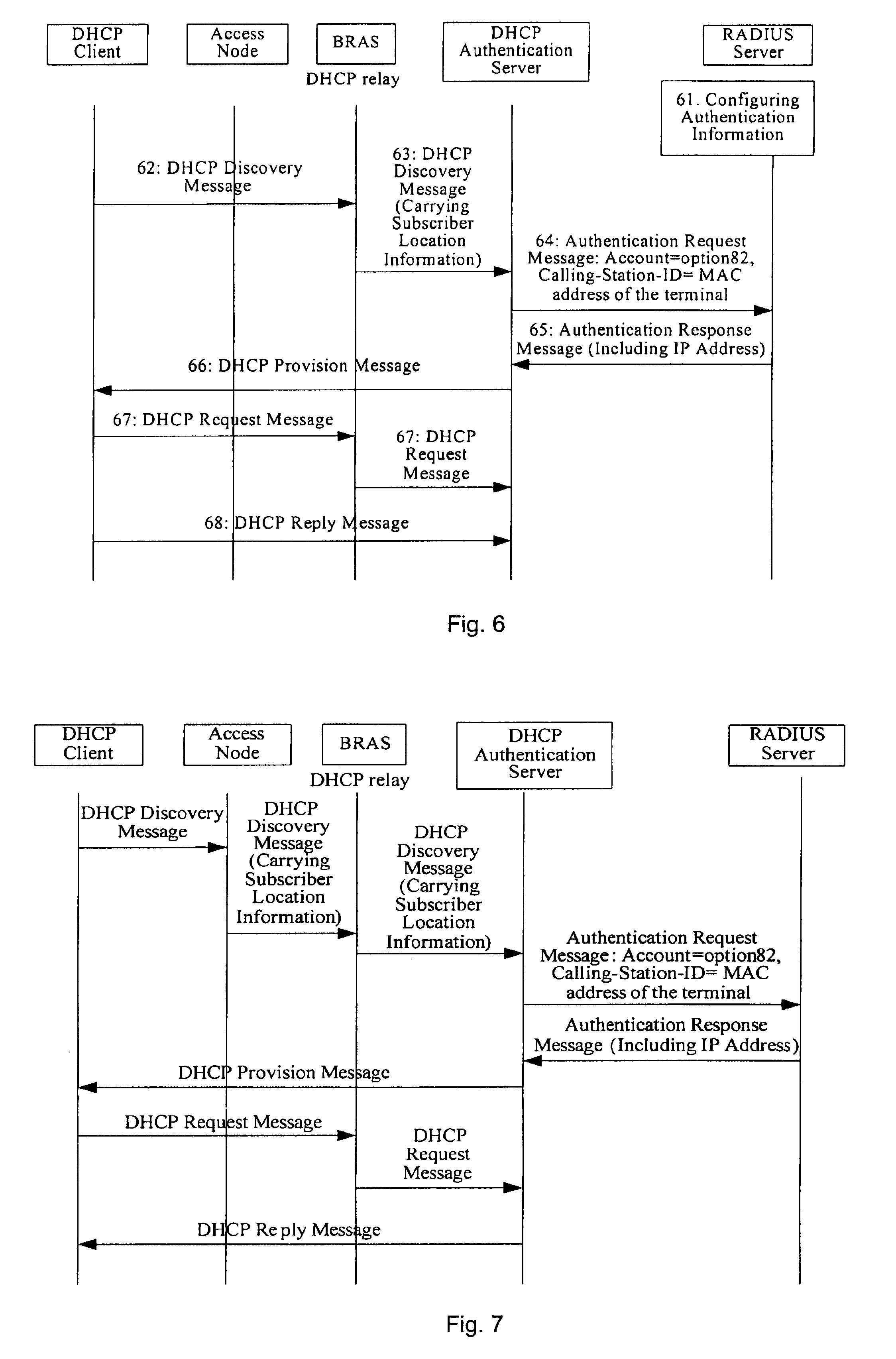
Method, system and server for realizing secure assignment of DHCP address
InactiveUS20080092213A1Enhanced securityNetwork cost be lowerDigital data processing detailsComputer security arrangementsClient-sideIp address
A method, a system and an authentication server for realizing a secure assignment of a DHCP address are disclosed. The method includes: sending a DHCP Discovery message via an access network; obtaining the identification information of the DHCP client and performing an authenticating to the DHCP client based on the identification information; and only assigning the address to the DHCP client has passed the authentication. Therefore, in the present invention, access authentication may be performed on a subscriber according to location information, and IP address is only assigned to the valid subscriber and terminal. Therefore, the security of the address assignment in DHCP mode may be enhanced greatly. Moreover, in the present invention, addresses may be managed by an AAA server unitedly, or the addresses may be assigned after being authenticated by the AAA server successfully.
Owner:HUAWEI TECH CO LTD
Method to support mobile IP mobility in 3GPP networks with SIP established communications
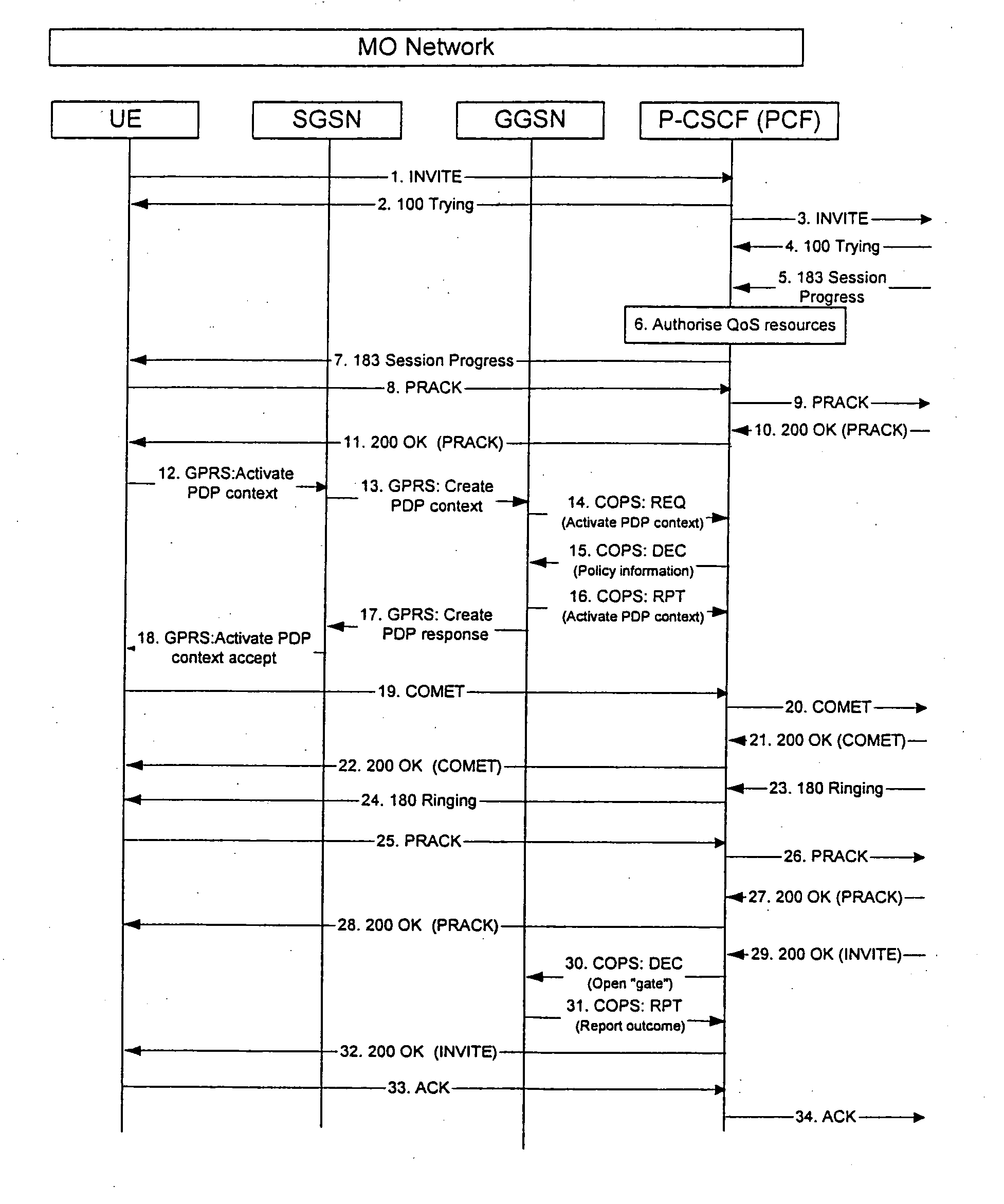
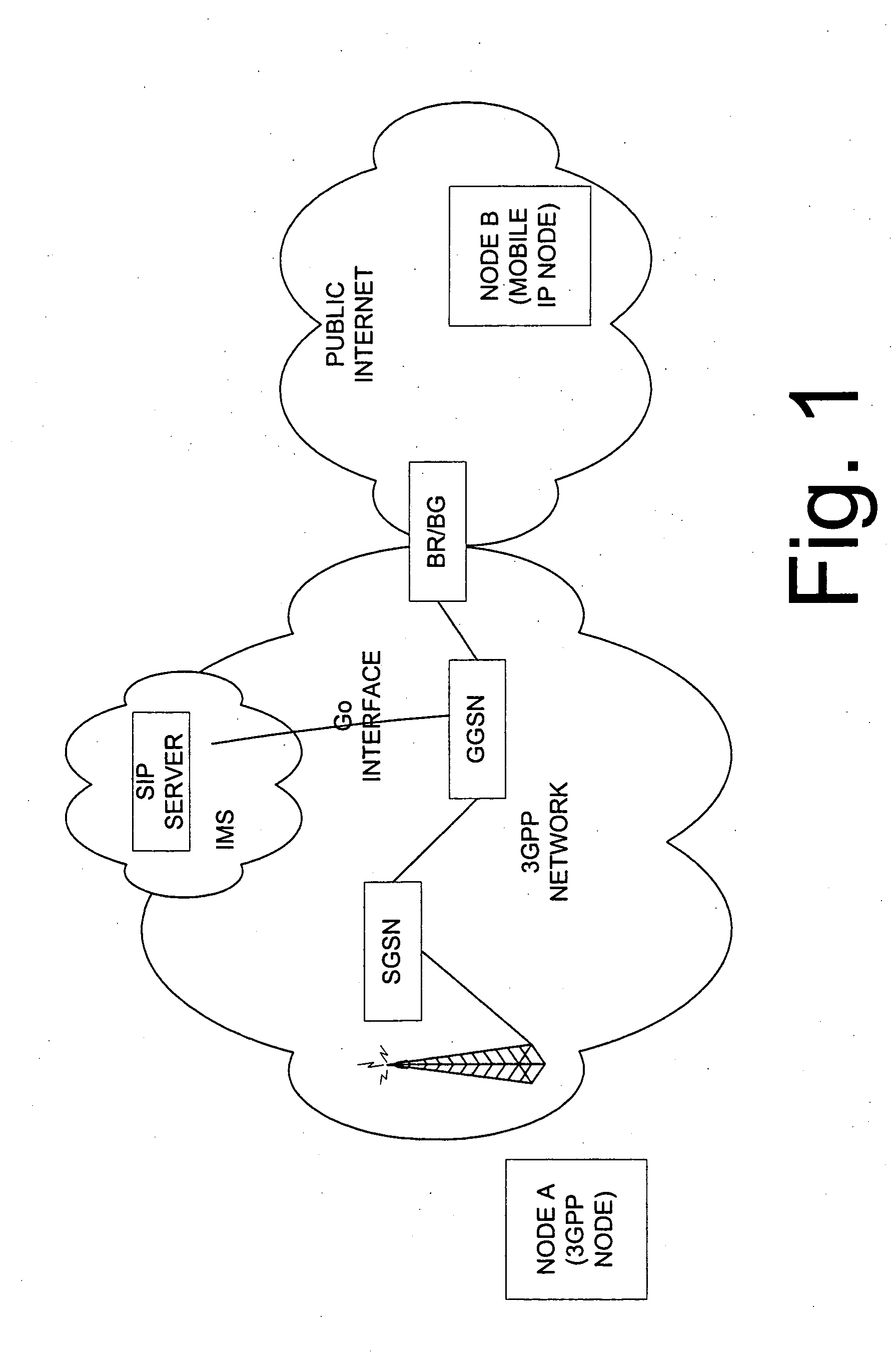
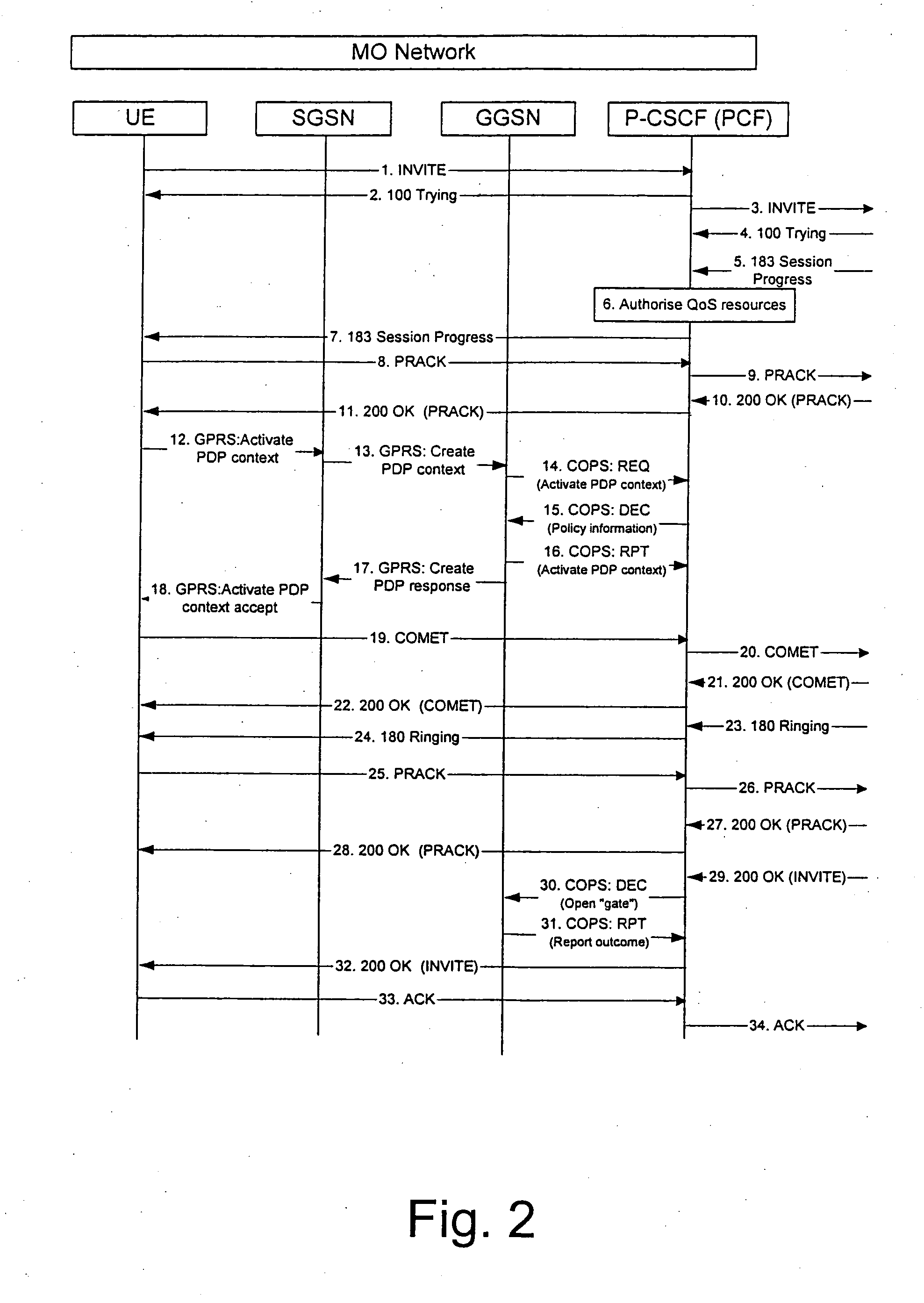
InactiveUS20050165917A1Service is blockedAvoid attackMemory loss protectionError detection/correctionNetwork elementNetworked system
The invention proposes a method for controlling a connection between a first network node and a second network node, wherein the connection is controlled by a packet filtering function filtering packets such that a packet is discarded in case a source address and / or a destination address do not comply with a filtering rule, wherein the packet filtering function is configured at a connection set up, and at least one of the first or second network node is adapted to change its address, the method comprising the steps of informing, the packet filtering function about the new address of the network node having changed its address, and updating the packet filter of the packet filtering function by using the new address of the network node having changed its address. The invention also proposes a corresponding network system comprising at least a network node and a packet filtering network element. Furthermore, the invention proposes a corresponding packet filtering network device.
Owner:NOKIA CORP
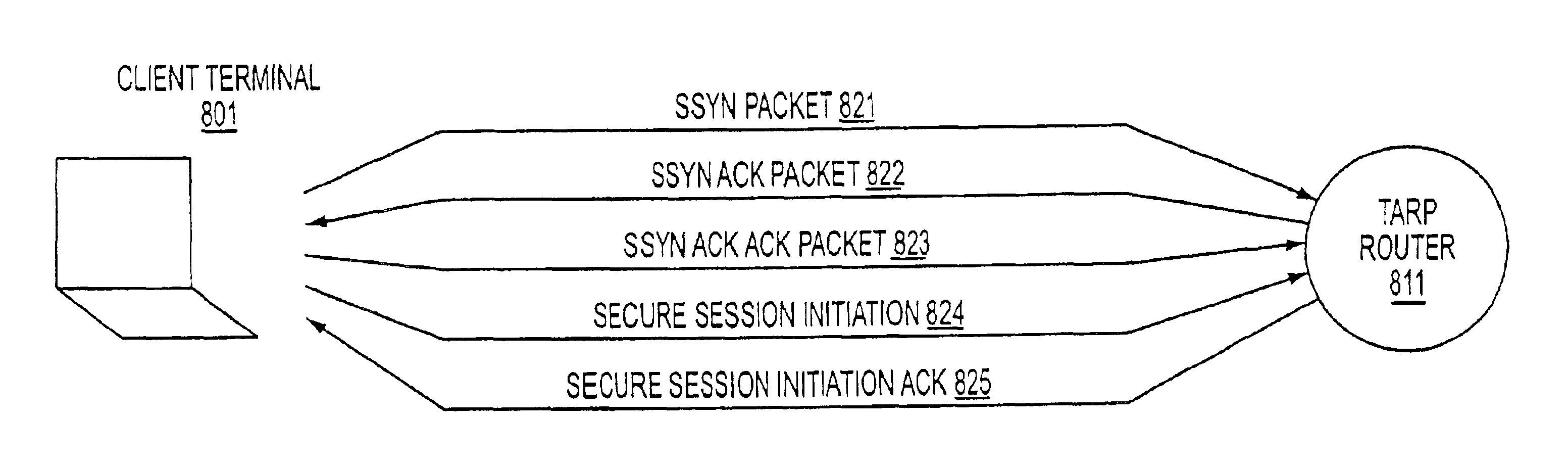
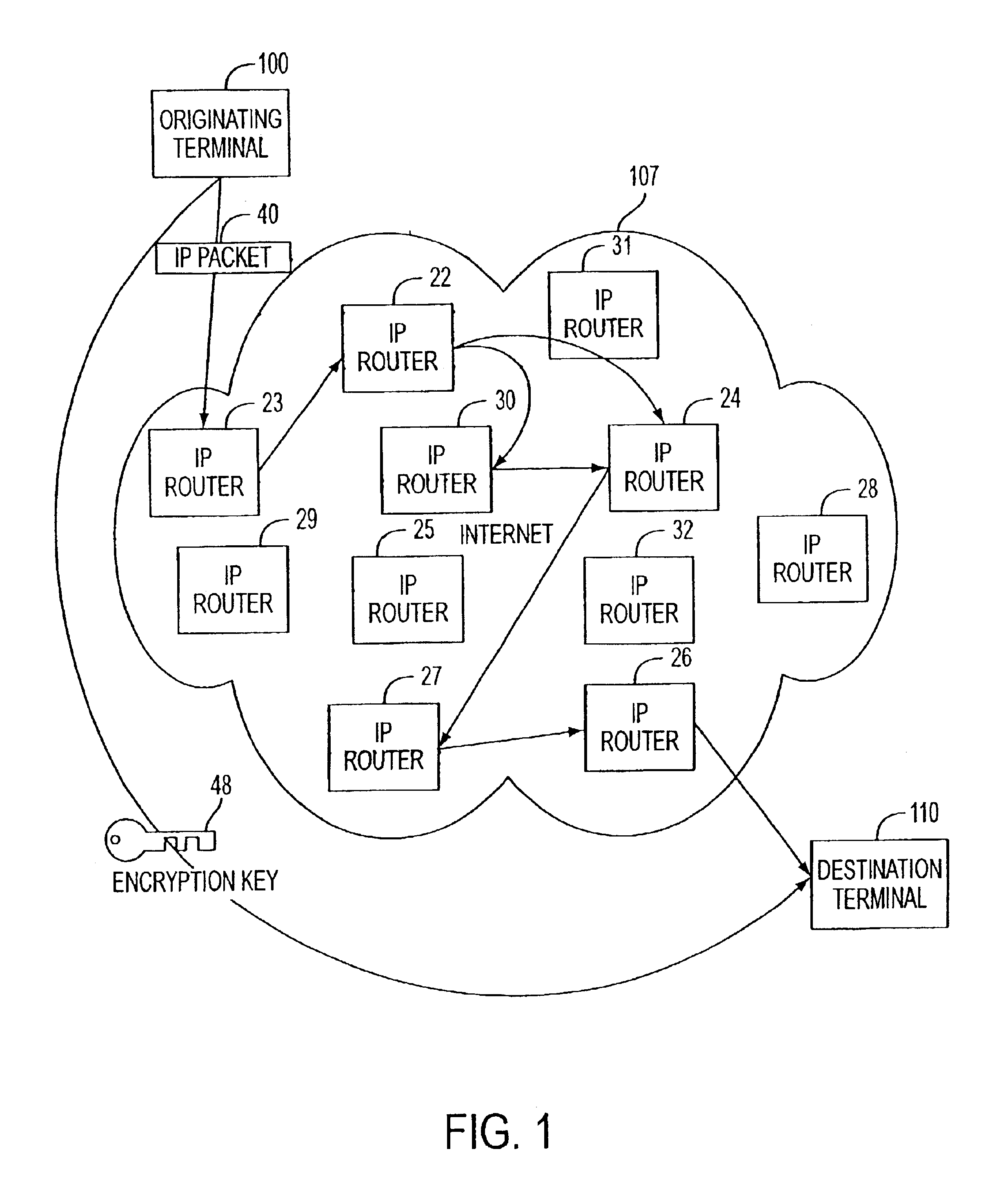
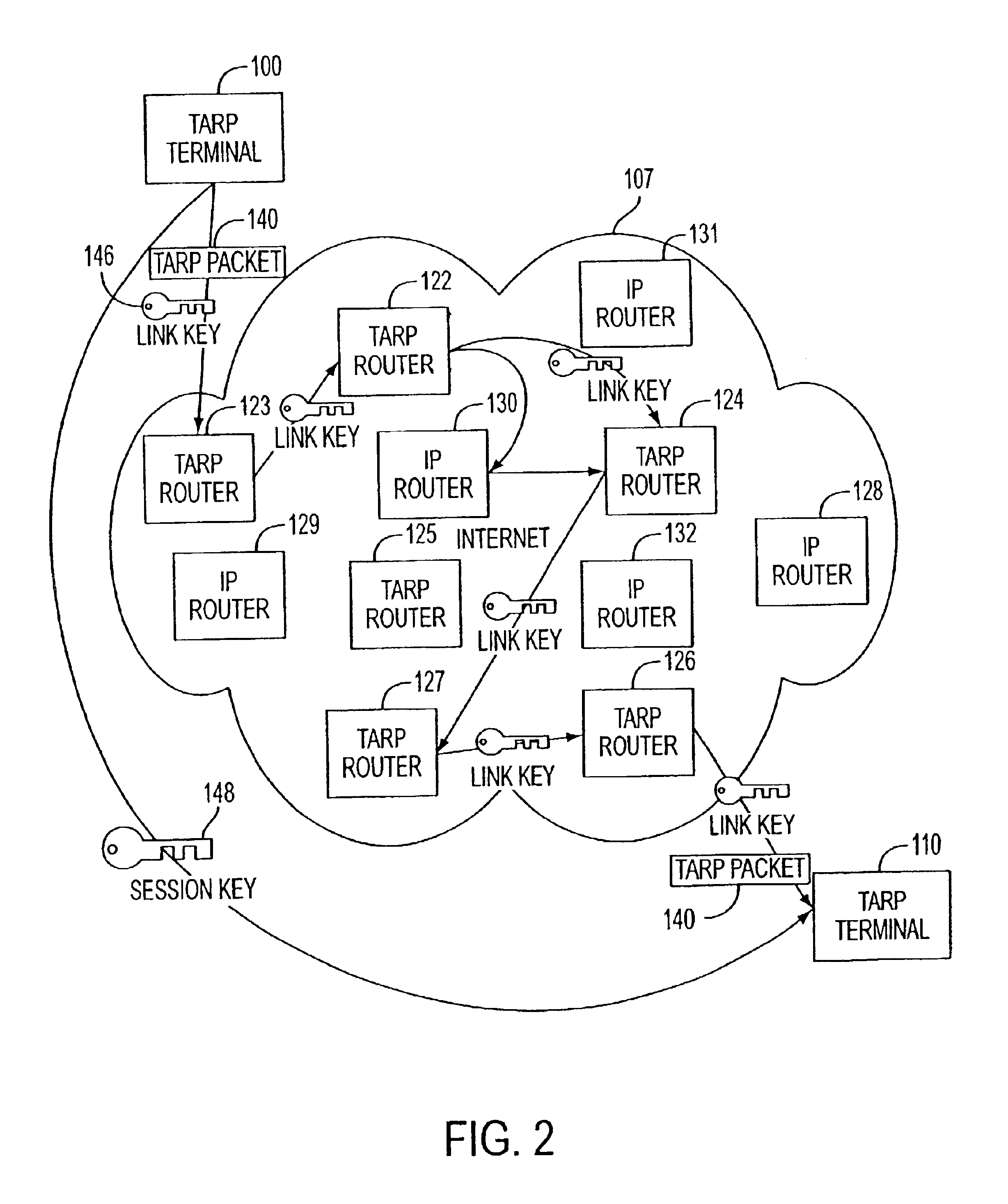
Agile network protocol for secure communications with assured system availability
InactiveUS6907473B2Prevents denial-of-service attackAvoid attackError detection/correctionMultiple digital computer combinationsSecure communicationPrivate network
A plurality of computer nodes communicate using seemingly random Internet Protocol source and destination addresses. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are quickly rejected. Improvements to the basic design include (1) a load balancer that distributes packets across different transmission paths according to transmission path quality; (2) a DNS proxy server that transparently creates a virtual private network in response to a domain name inquiry; (3) a large-to-small link bandwidth management feature that prevents denial-of-service attacks at system chokepoints; (4) a traffic limiter that regulates incoming packets by limiting the rate at which a transmitter can be synchronized with a receiver; and (5) a signaling synchronizer, that allows a large number of nodes to communicate with a central node by partitioning the communication function between two separate entities.
Owner:VIRNETX
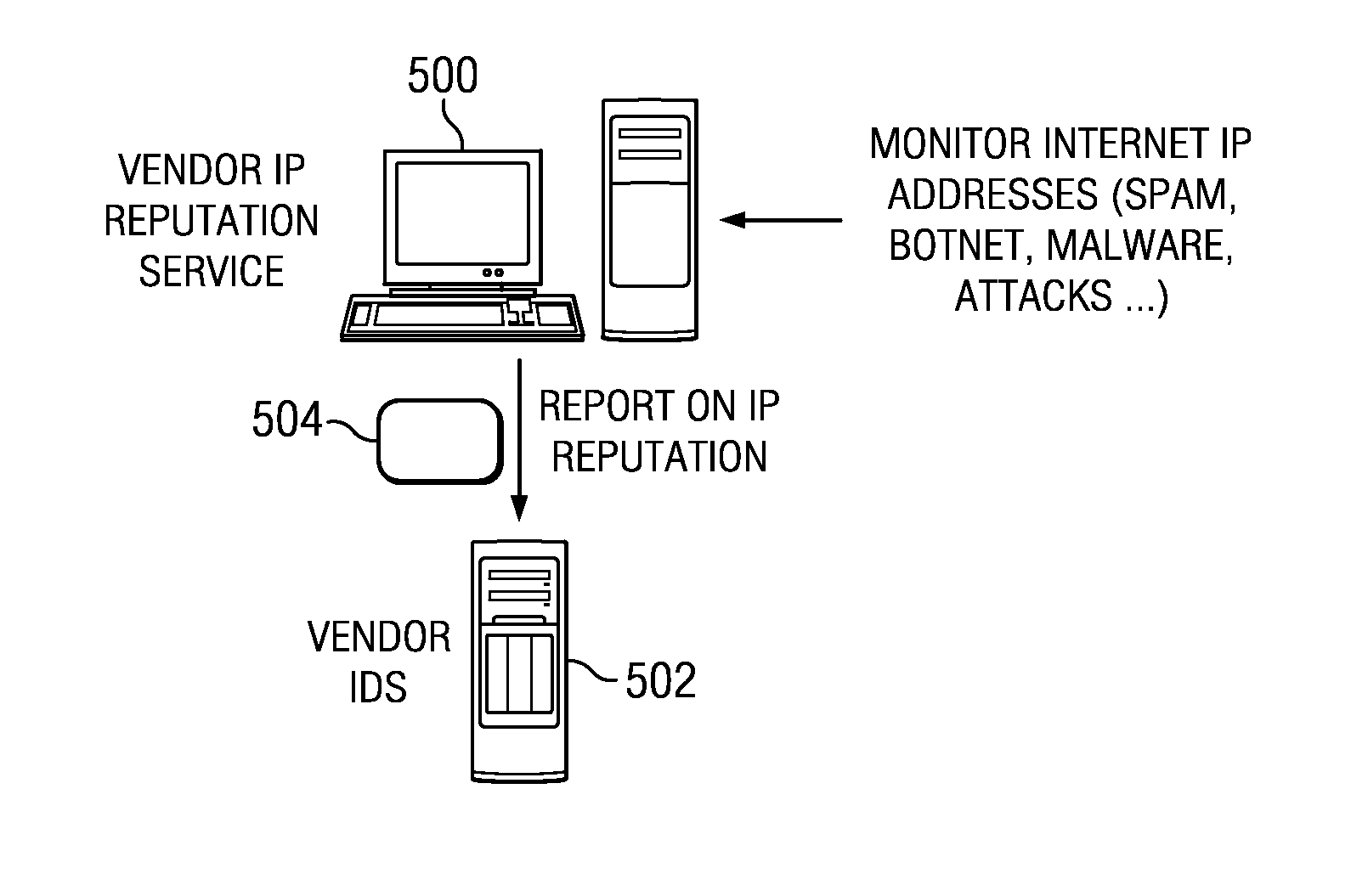
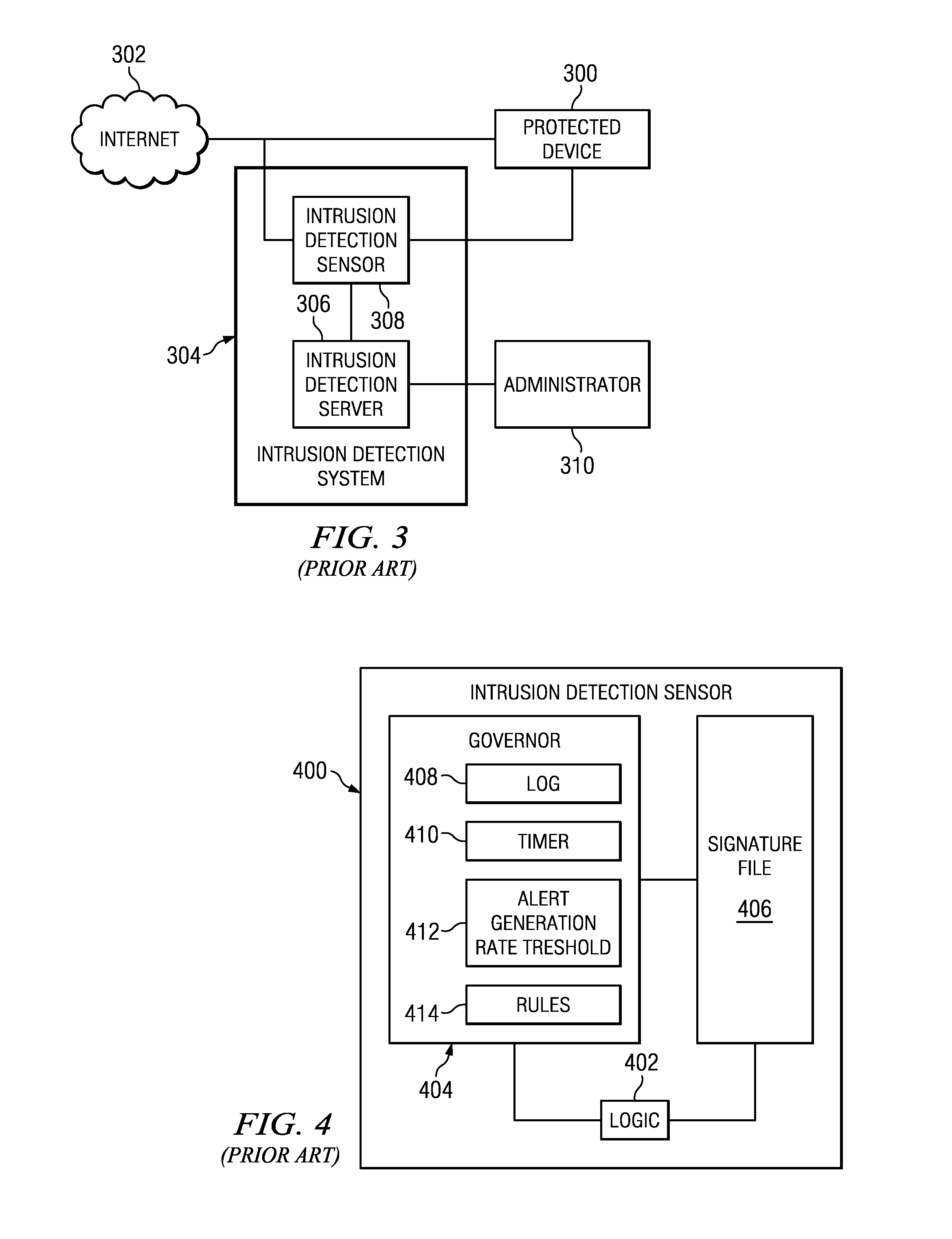
Cooperative intrusion detection ecosystem for IP reputation-based security
ActiveUS20140059683A1Easy to operateImprove system response timeMemory loss protectionError detection/correctionPattern matchingContinuous data
An intrusion detection system (IDS) is enhanced to operate in a cluster of such systems, and IDSs organized into a cluster cooperate to exchange IP reputation influencing events information between or among the cooperating systems in real-time to enhance overall system response time and to prevent otherwise hidden attacks from damaging network resources. An IDS includes an IP reputation analytics engine to analyze new and existing events, correlate information, and to raise potential alerts. The IP reputation analytics engines may implement an algorithm, such as a pattern matching algorithm, a continuous data mining algorithm, or the like, to facilitate this operation. Clustering IDS endpoints to share IP reputation influencing events, using the cluster-wide view to determine IP reputation, and feeding the cluster-wide view back to the IDS endpoints, provides for enhanced and early detection of threats that is much more reliable and scalable as compared to prior art techniques.
Owner:IBM CORP
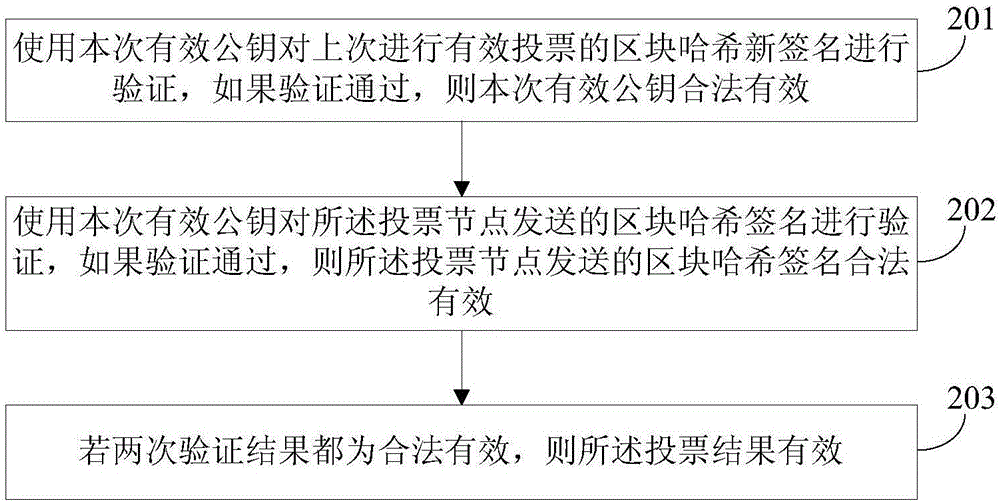
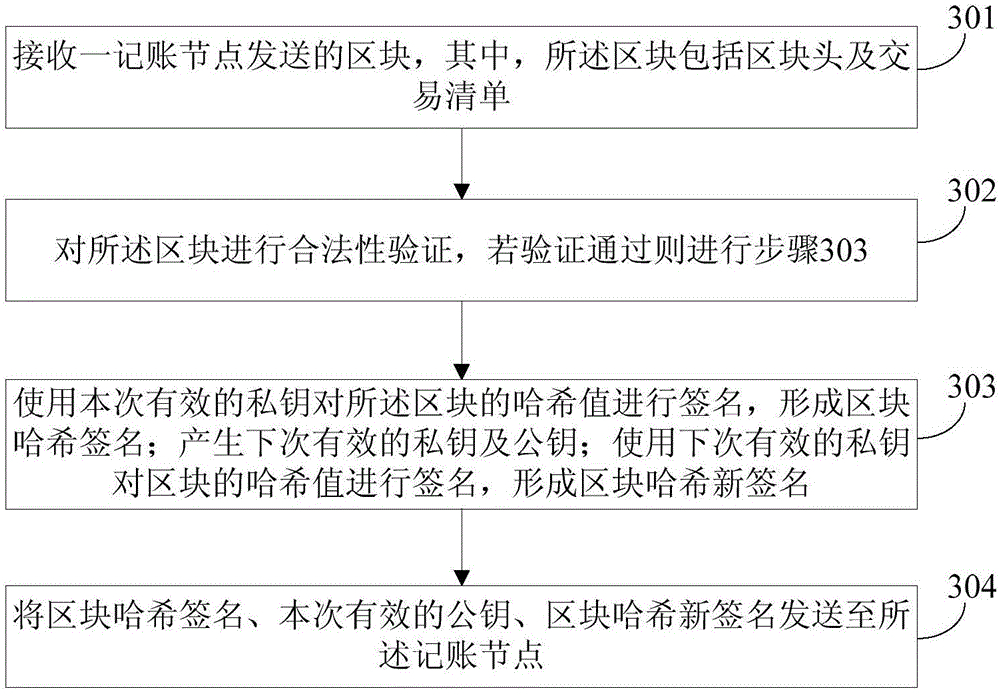
Accounting method, accounting system, voting node and accounting node under block chain voting and accounting mode
ActiveCN106411503AImprove securityVerify validityKey distribution for secure communicationVoting apparatusAccounting methodBlockchain
The application provides an accounting method, an accounting system, a voting node and an accounting node under a block chain voting and accounting mode. The method comprises the following steps: an accounting node sends a block to voting nodes; each voting node dynamically generates a private key and a public key which are valid next time, signs the Hash value of the block with a current valid private key to form a block Hash signature, signs the Hash value of the block with the next-time valid private key to form a new block Hash signature, and sends the block Hash signature, a current valid public key and the new block Hash signature to the accounting node; the accounting node verifies whether the voting results are valid; and the voting nodes of which the voting results are valid are counted, and if the calculated number of voting nodes meets conditions, all the valid voting results are input to the block header, stored in an accounting book and sent to all other accounting nodes. After each vote, a private key / public key pair becomes invalid, and a new private key and a new public key are generated. The keys only work once, and the accounting security is improved greatly.
Owner:BANK OF CHINA
Antioxidant inflammation modulators: oleanolic acid derivatives with saturation in the C-ring
ActiveUS7915402B2Suppresses demyelinationSuppresses transectionNervous disorderAntipyreticPerylene derivativesPharmaceutical Substances
This invention provides, but is not limited to, novel oleanolic acid derivatives having the formula:wherein the variables are defined herein. Also provided are pharmaceutical compositions, kits and articles of manufacture comprising such compounds, methods and intermediates useful for making the compounds, and methods of using the compounds and compositions.
Owner:REATA PHARMA INC
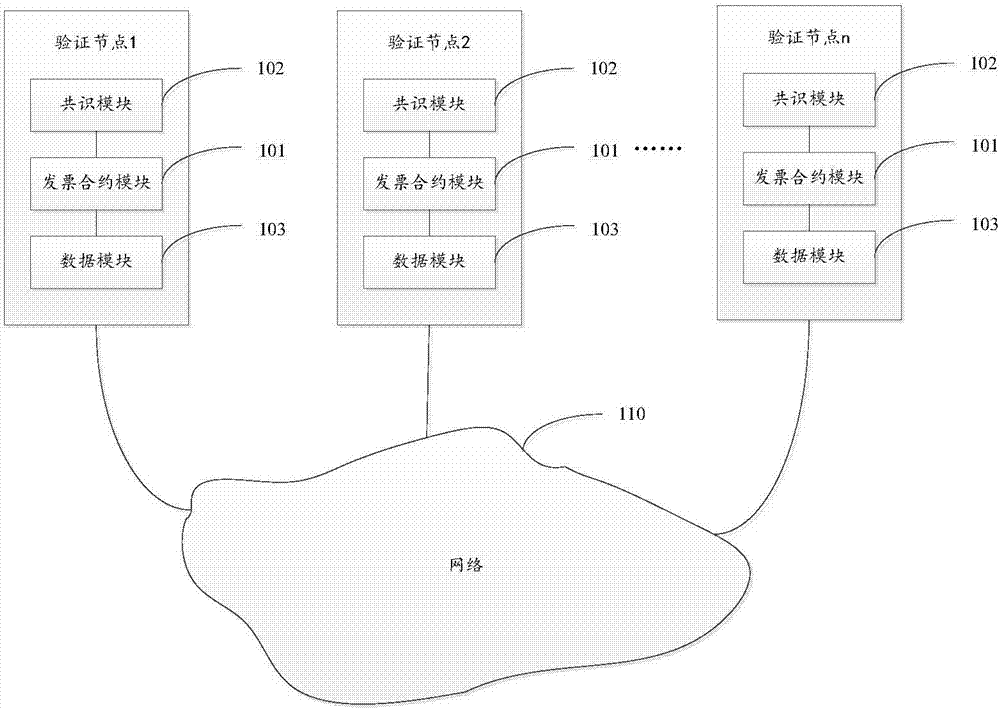
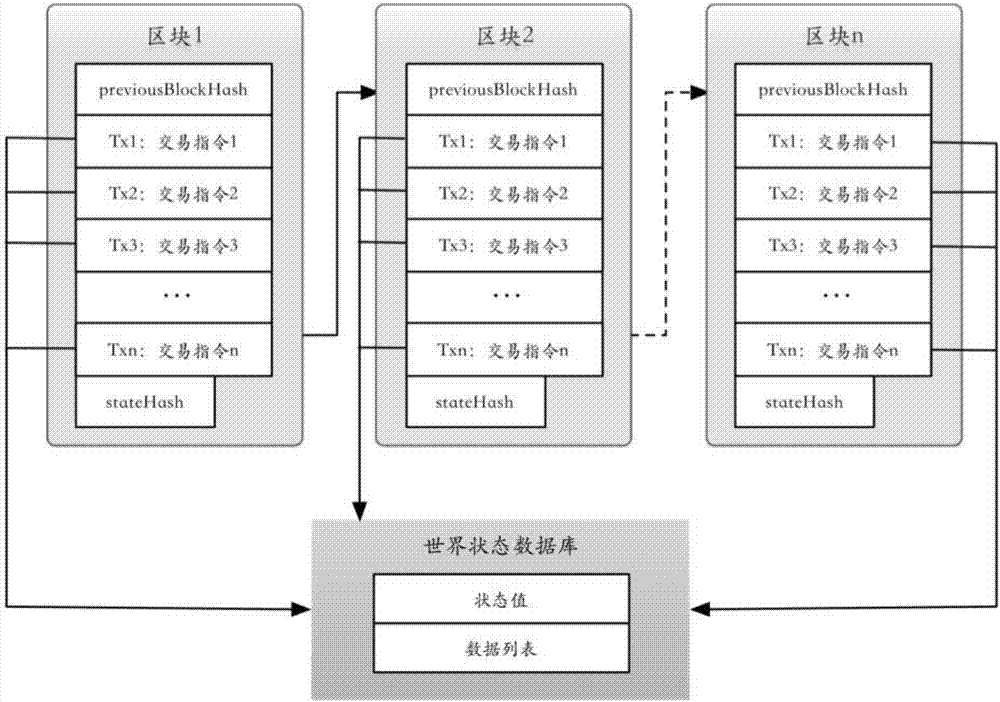
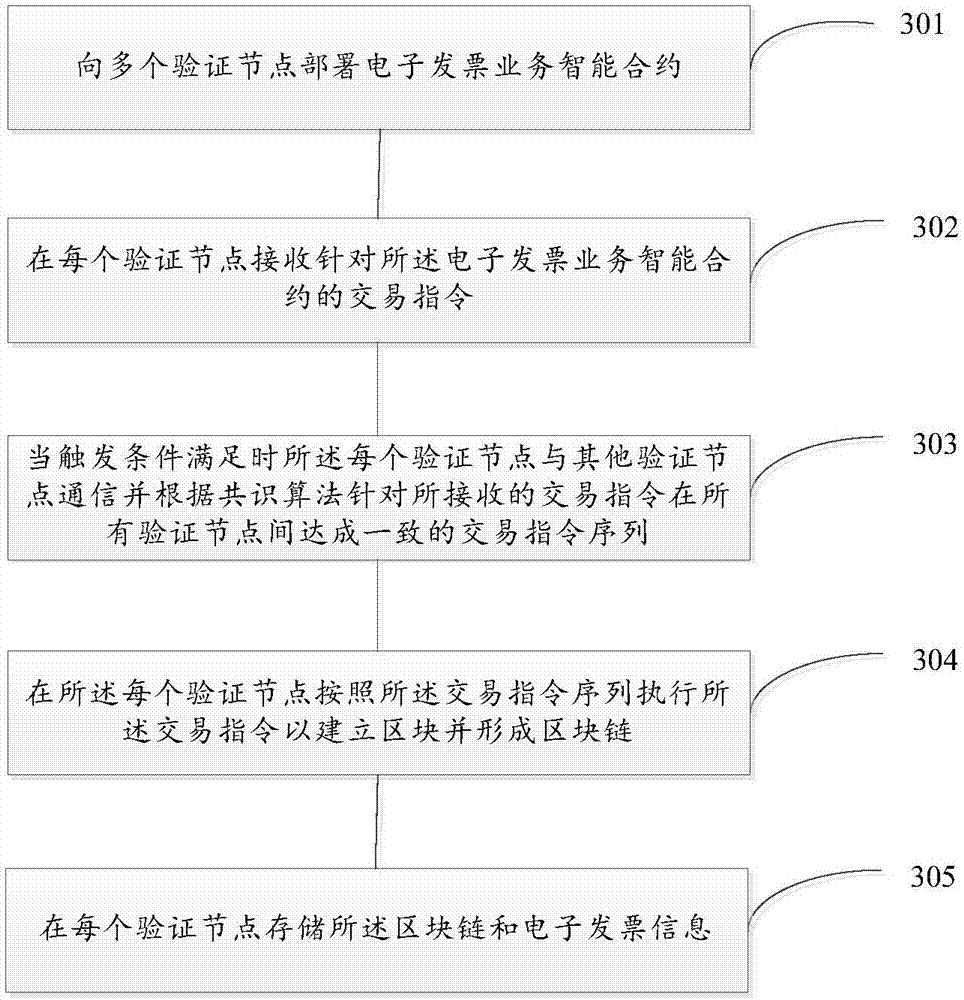
Electronic invoice management system and method based on distributed accounting
InactiveCN106952124APrevent tamperingAvoid attackUser identity/authority verificationBilling/invoicingTamper resistanceInvoice
The invention discloses an electronic invoice management system and a method based on distributed accounting. The system comprises multiple verification nodes. Each verification node comprises an electronic invoice contract module and an agreement module, wherein the electronic invoice contract module comprises an electronic invoice service intelligent contract and is configured to be used for receiving a transaction command of the electronic invoice service intelligent contract and executing the transaction command according to a result of the agreement module so as to establish a block and form a block link, and the electronic invoice service intelligent contract is operation performed on an electronic invoice. The agreement module is configured to be used for communicating with other verification nodes when being triggered and making an agreement on a transaction command sequence between all verification nodes for the received transaction command according to an agreement algorithm. According to the invention, tamper-proofing is realized and the system and the method are cost-effective.
Challenge-response user authentication
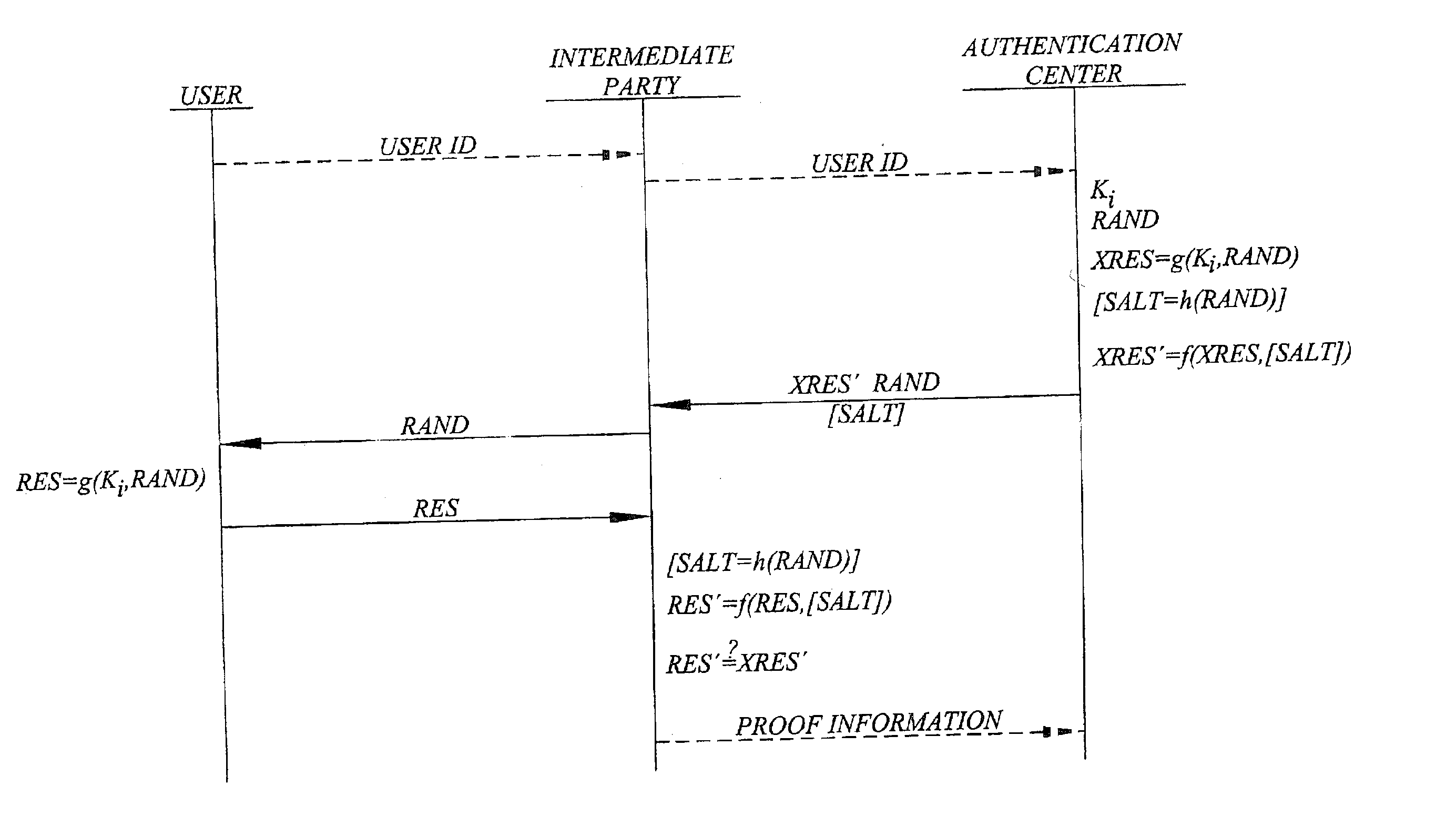
ActiveUS20030233546A1Easy to migrateAvoid attackUser identity/authority verificationDigital data authenticationInternet privacyUser authentication
A challenge-response authentication procedure includes masking of the expected response (XRES) generated by an authentication center by means of a masking function (f), and transmission of the masked expected response (XRES'), instead of the expected response itself, to an intermediate party at which the actual user authentication takes place. The intermediate party also receives a user response (RES) from the user and generates a masked user response (RES') using the same masking function (f) as the authentication center did. In order to authenticate the user, the intermediate party then verifies that the masked user response (RES') corresponds to the masked expected response (XRES') received from the authentication center. The above procedure enables the intermediate party to prove that user authentication has taken place, keeping in mind that only the legitimate user knows the response beforehand.
Owner:TELEFON AB LM ERICSSON (PUBL)
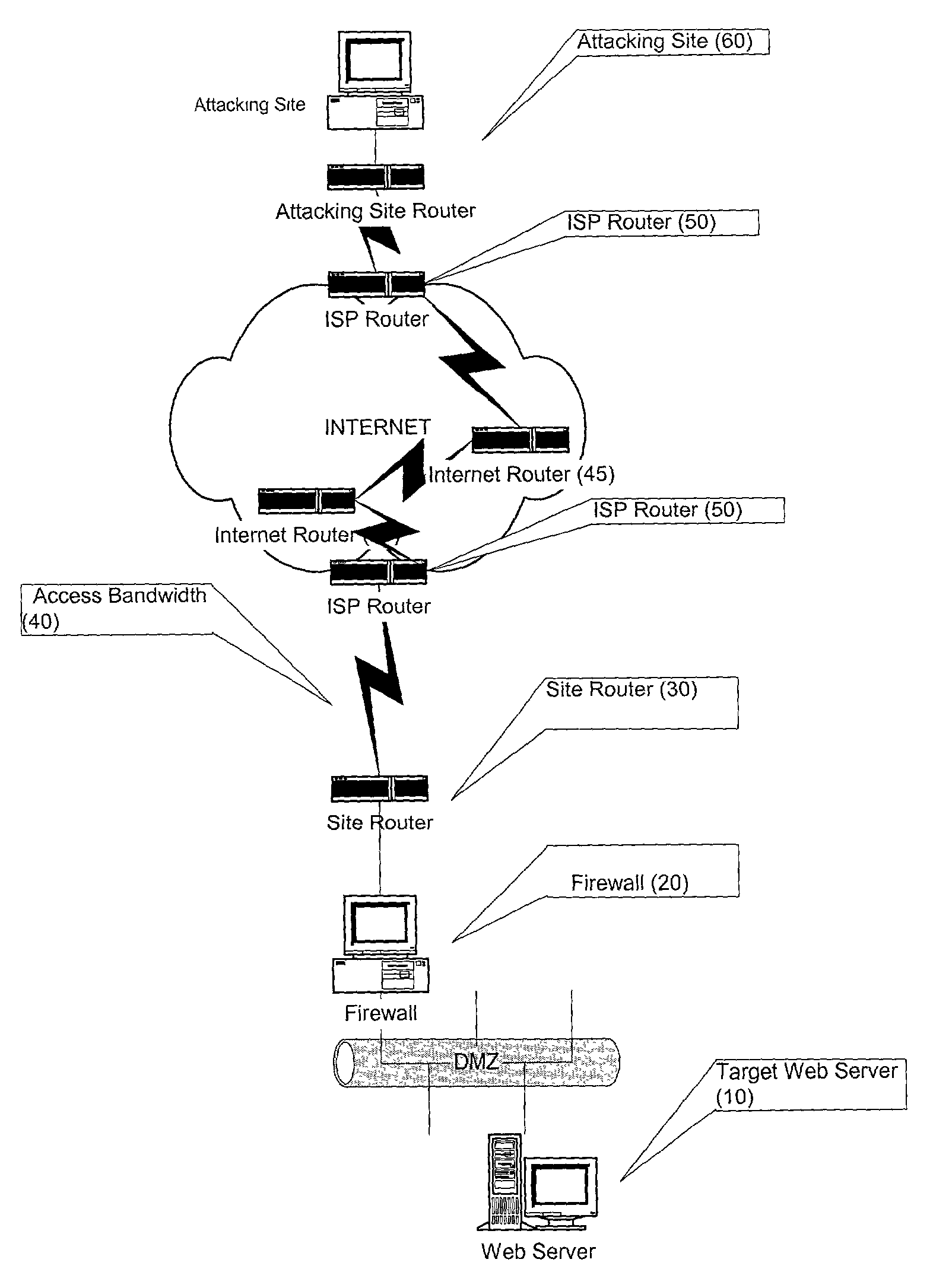
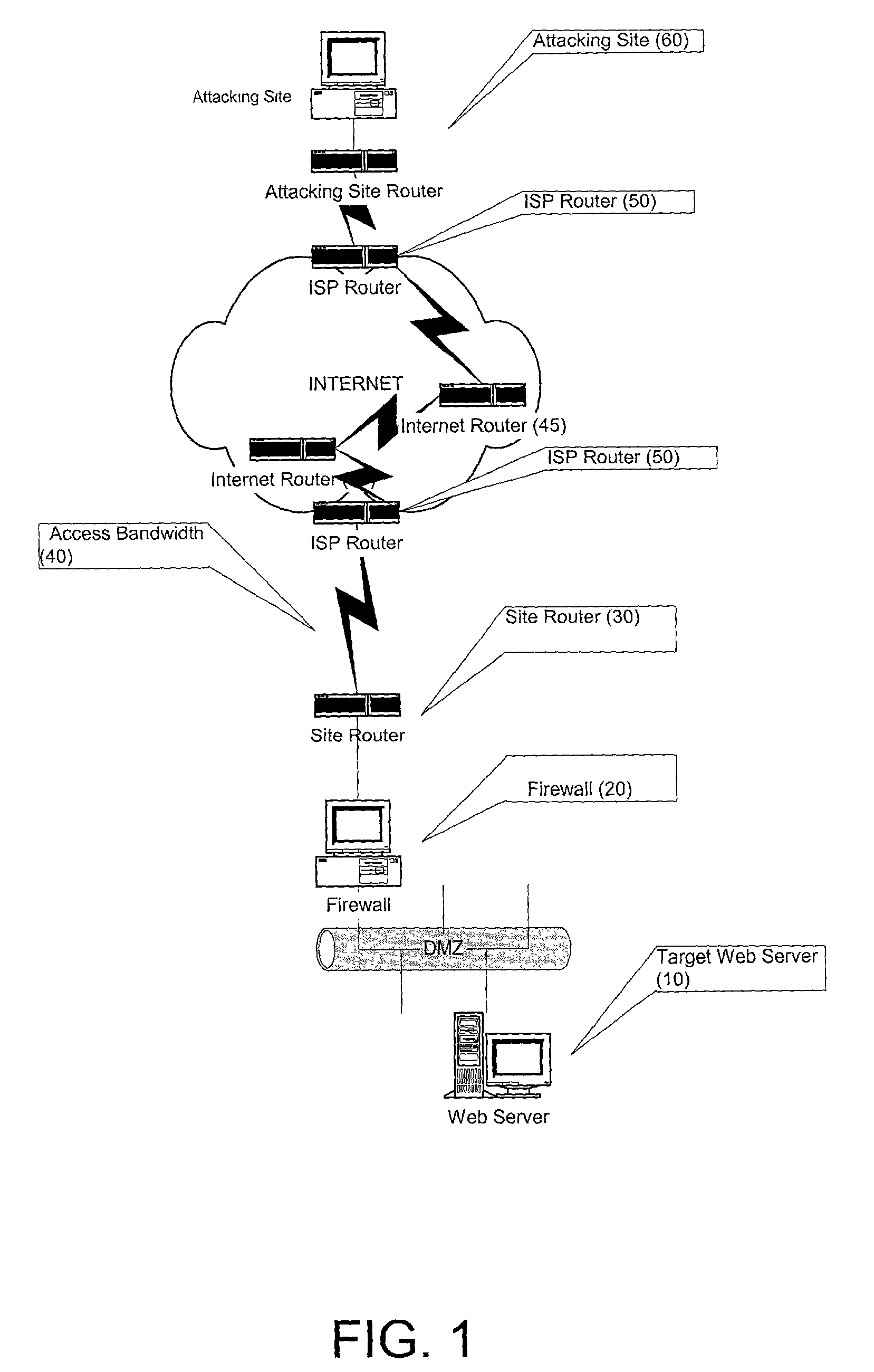
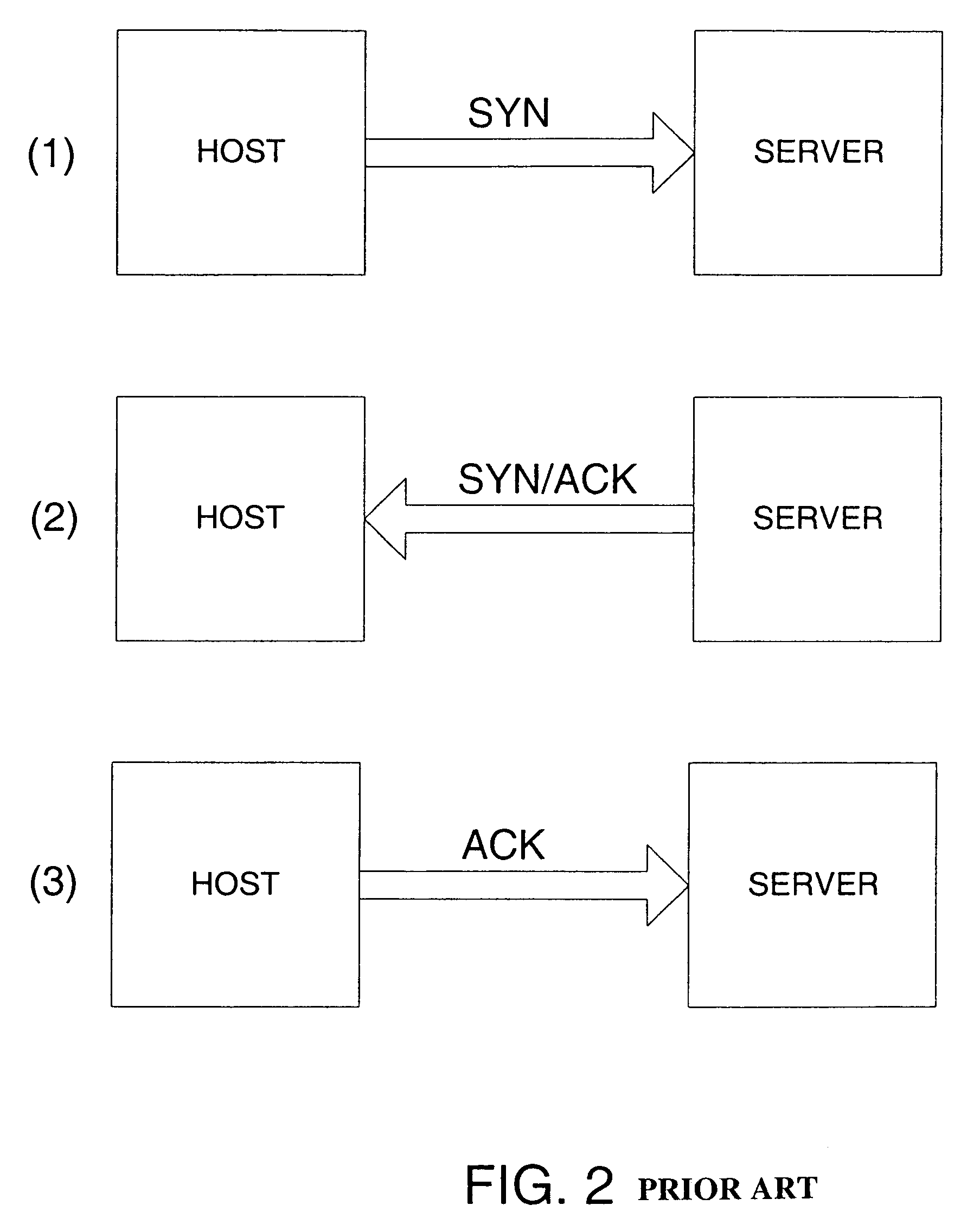
Prevention of bandwidth congestion in a denial of service or other internet-based attack
InactiveUS7301899B2Avoid attackAutomatic detectionError preventionTransmission systemsIp addressClient-side
A method and apparatus for preventing a Denial of Service attack directed at a target that is hosted on a server. The attack is detected and the IP address of the source client of the attack is identified. The IP address of the source of the attack is then communicated upstream to router devices close to the attacking source and the attacker is prevented from further attacks until it is determined that the attacker poses no threat. The detection of the attack and the communication of the identity of the attacker to upstream routers is performed automatically or by human intervention.
Owner:COMVERSE
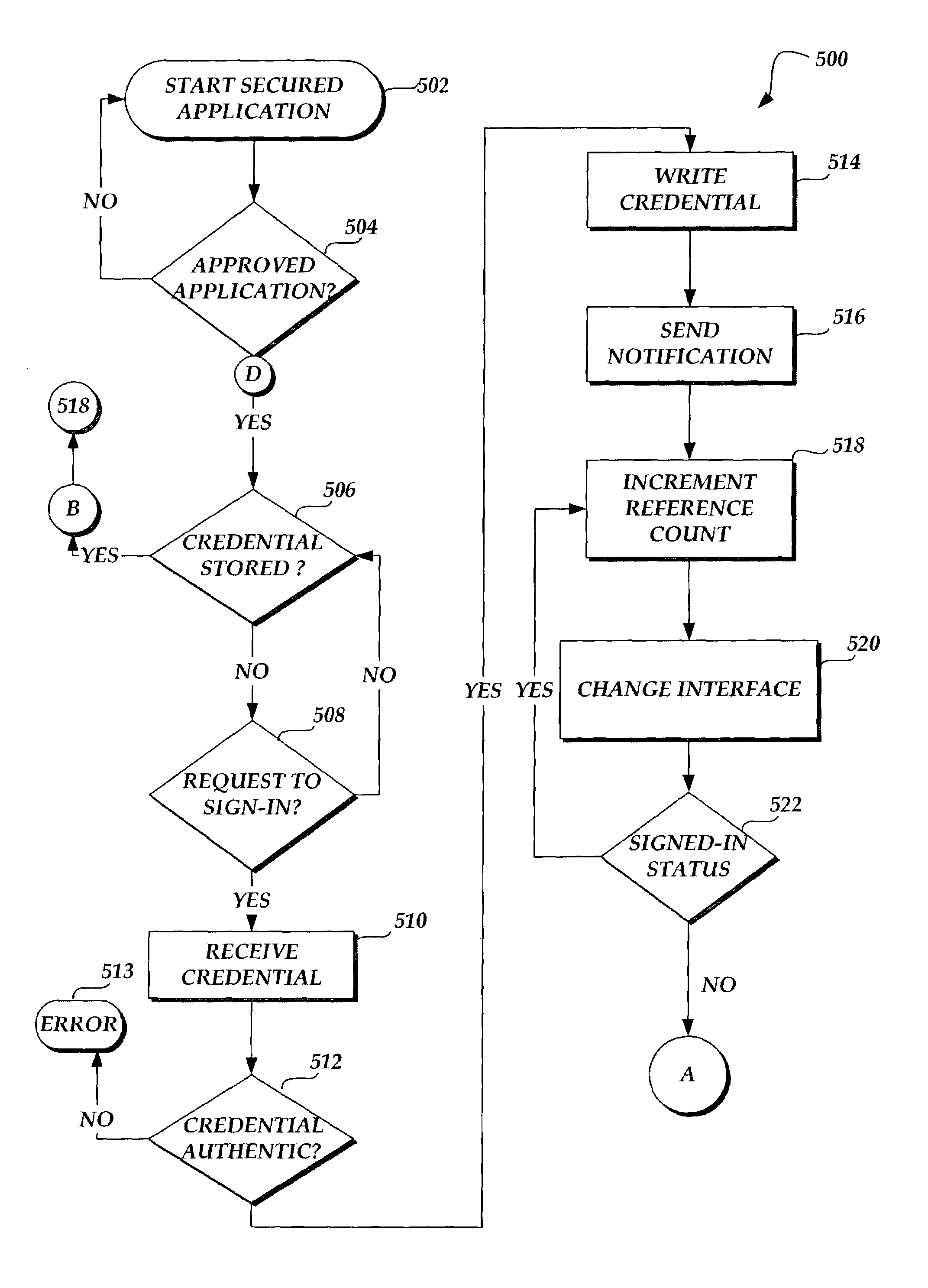
Sharing a sign-in among software applications having secured features
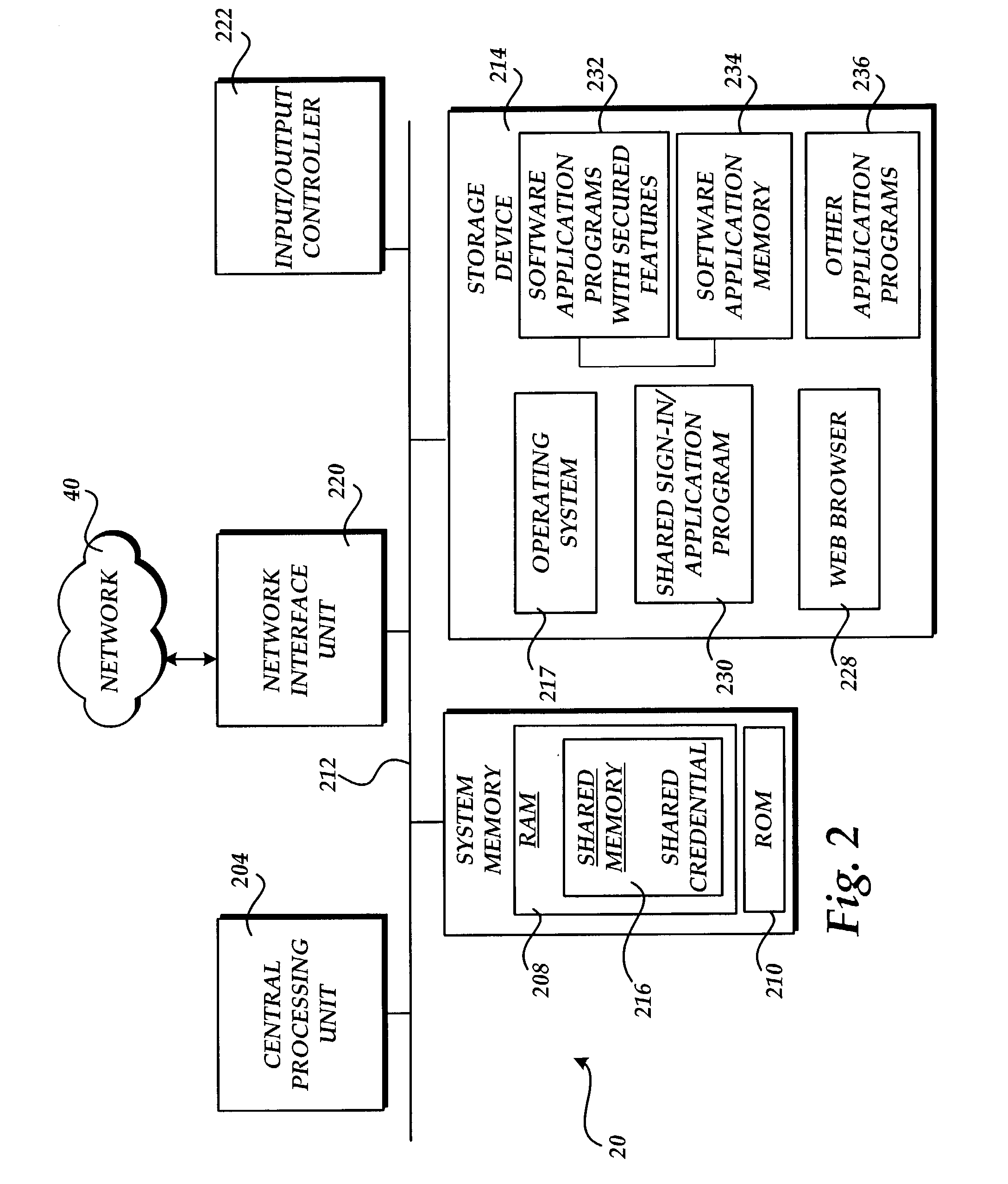
ActiveUS7254831B2Improve network efficiencyReduce network trafficDigital data processing detailsMultiple digital computer combinationsPasswordApplication software
In the present invention, when one open or running software application having secured features enters an access signed-in or logged-in state, other open or running software applications having secured features enter a ready signed-in state automatically, without prompting user intervention. The same operation that signed-in or logged-in the initial software application will transition other software applications that are presently open, active to run, or that start in run mode to a ready signed-in state. The access signed-in state fully authenticates the user's identity and grants access to secured features. The ready signed-in state places the software application in a state of readiness to authenticate and access secured features without prompting user intervention. One feature of the present invention is the sharing of a sign-in or login credential (e.g. username and password) and the processing of the shared credential in order to provide a universal, shared sign-in session between open software applications having secured features. This feature helps provide a user experience that in effect, has only one sign-in or login session for software applications with secured features.
Owner:MICROSOFT TECH LICENSING LLC
Bidirectional identification method and system
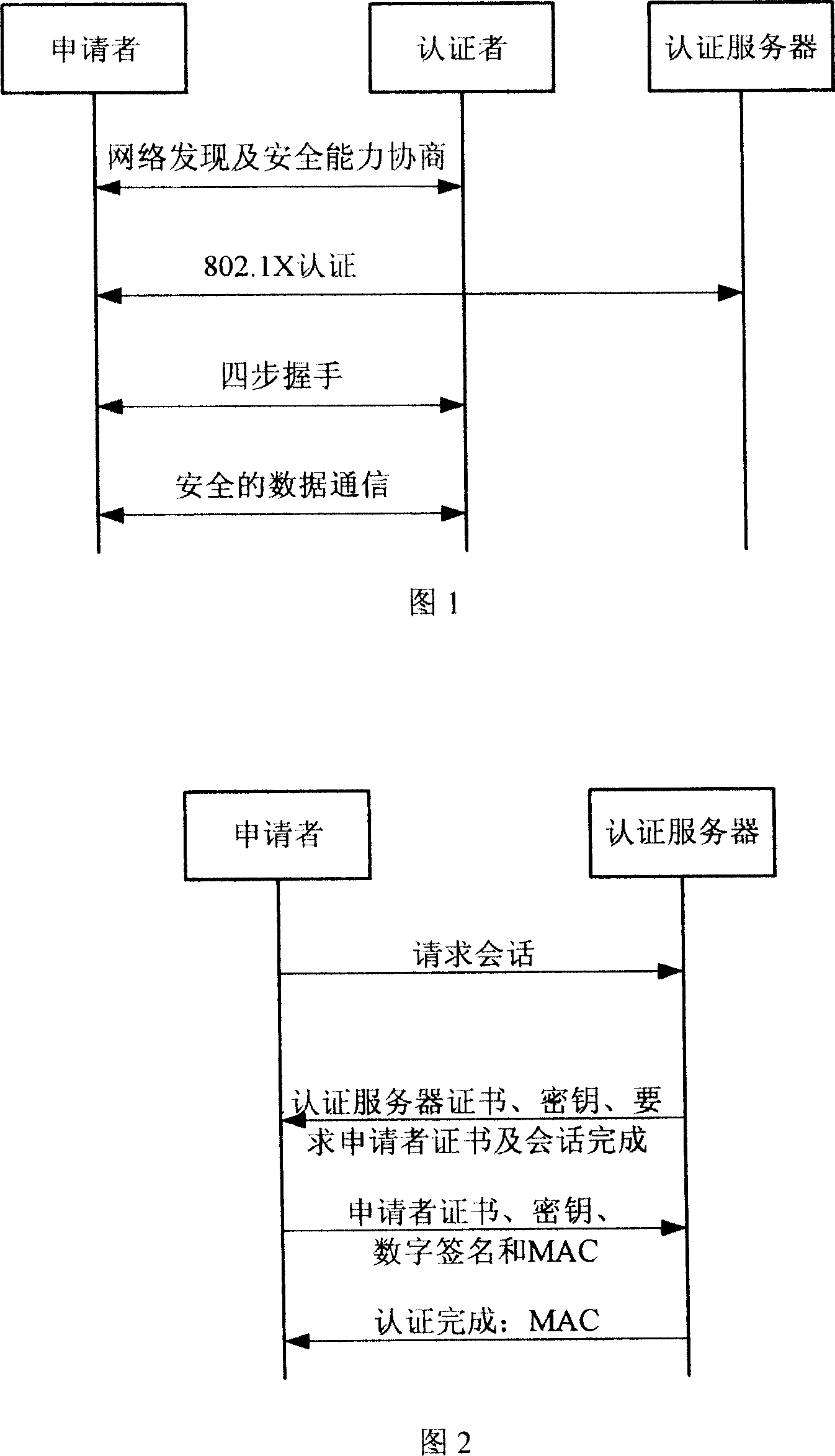
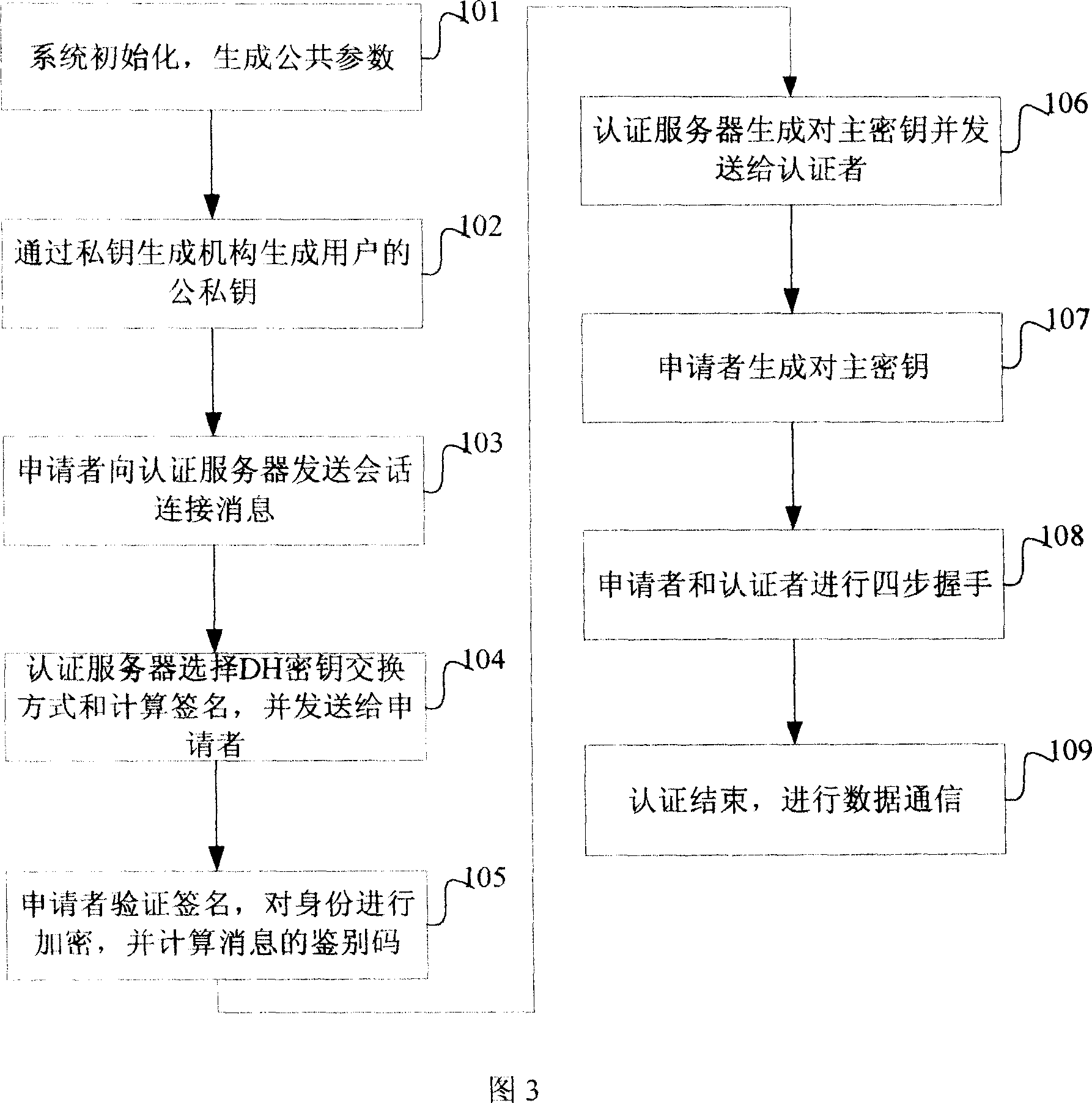
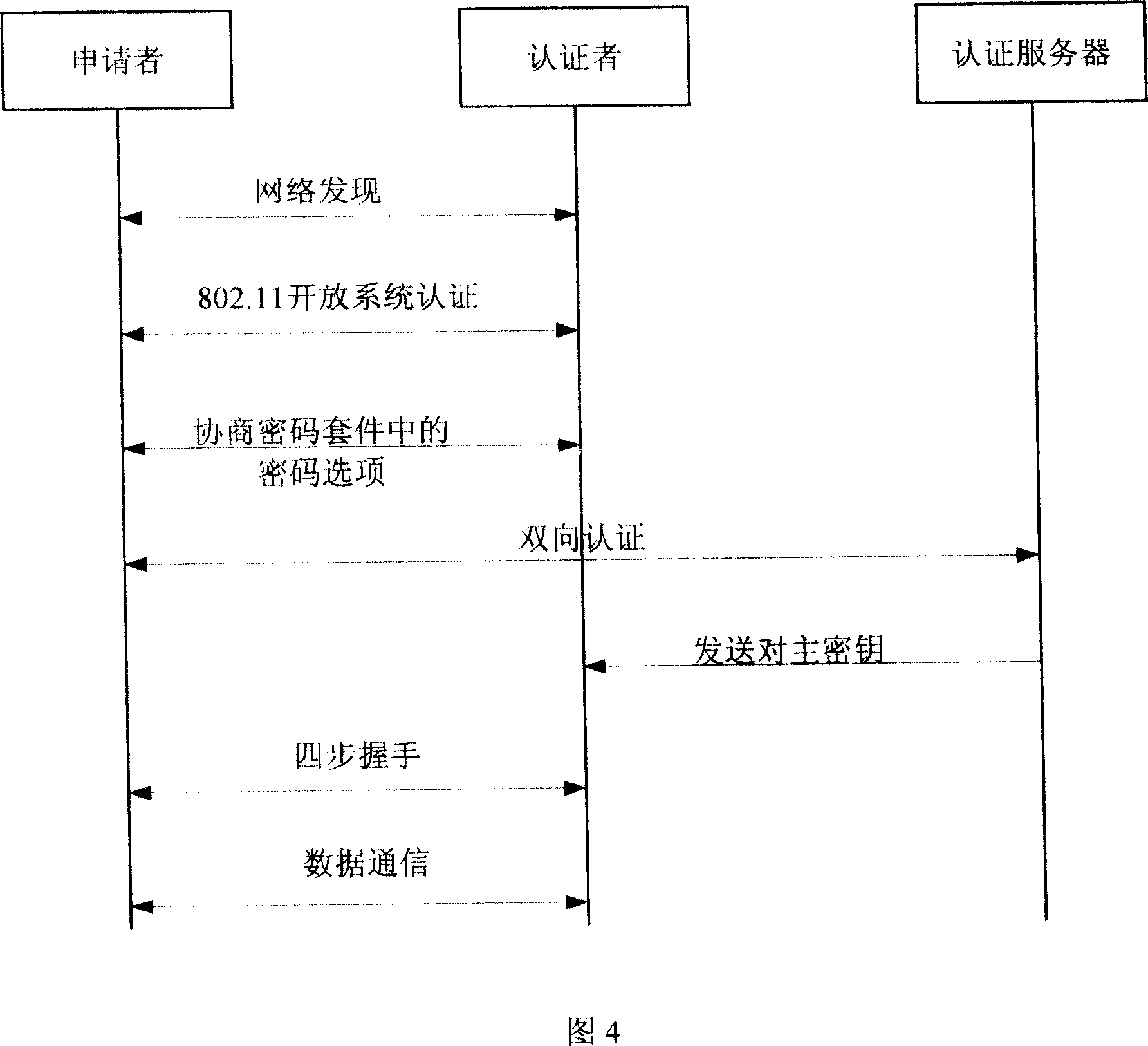
InactiveCN101119196AEffective calculationImprove security strengthUser identity/authority verificationHand shakesNetwork communication
The present invention provides a bi-direction authentication method and system which belongs to the field of network communication. The present invention aims at solving the problems that certificate management in present private key authority technology is complex and the certificate management can not protect the identity of the users. The present invention provides a bi-direction authority method. The present invention includes the procedures of the system initialization and generating system parameters, an applicant initializing a dialogue request to establish connection with an authorization server, the applicant and the authorization server mutually check identity and generate a pair of main key which is used for the four-procedure-hand-shaking. The present invention also provides a bi-direction authorization system. The system includes a parameter initialization module, an establishing dialogue connecting module, a server identity verification module and an applicant identify verification. Applications of the technical proposal of the present invention can reduce the establishing and maintenance cost of the system, to enhance the running efficiency of the system, and to realize the target of protecting applicants.
Owner:XIDIAN UNIV +1
Antioxidant inflammation modulators: C-17 homologated oleanolic acid derivatives
ActiveUS7943778B2Suppresses demyelinationSuppresses transectionAntibacterial agentsSenses disorderAntioxidantMedicinal chemistry
This invention provides, but is not limited to, novel oleanolic acid derivatives having the formula:wherein the variables are defined herein. Also provided are pharmaceutical compositions, kits and articles of manufacture comprising such compounds, methods and intermediates useful for making the compounds, and methods of using the compounds and compositions.
Owner:REATA PHARMA INC
Methods in Mixed Network and Host-Based Mobility Management
InactiveUS20100313024A1Increases handover delayReduce switching delayKey distribution for secure communicationUser identity/authority verificationMix networkMobility management
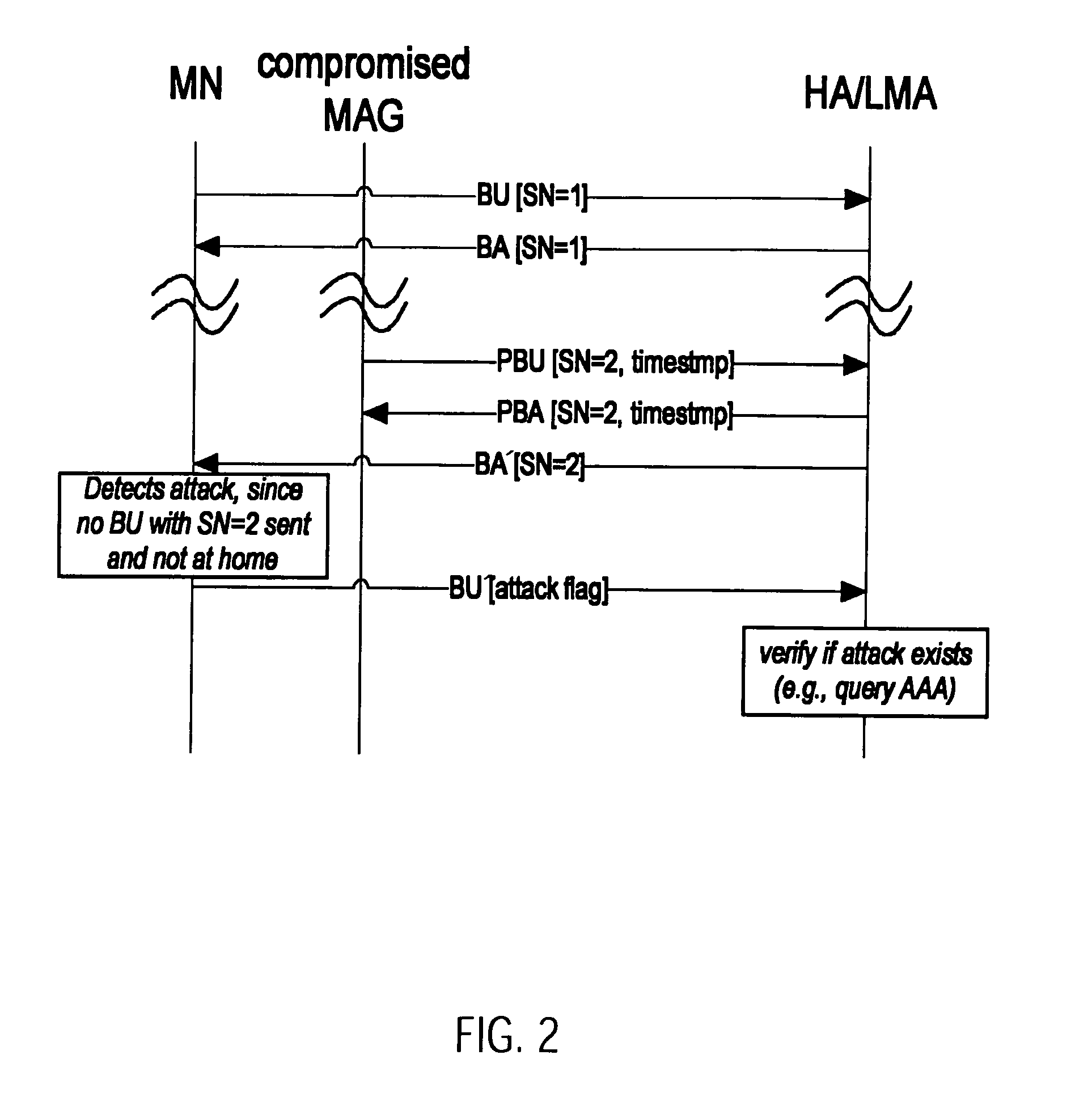
A first aspect of the invention relates to a method for verifying an attachment of a mobile node to a network element in a network. A second aspect of the invention relates to a method to be implemented in a mobility anchor node, which detects whether a race condition between registration messages occurs and resolves the most recent location of a mobile node. A third aspect of the invention relates to a method for detecting whether a binding cache entry for a mobile at a correspondent node has been spoofed and to a method for registering a care-of address of a mobile node at a correspondent node. A fourth aspect of the invention relates to a method for providing from a mobile node to a local mobility anchor information on an attachment of a mobile node to a network element.
Owner:PANASONIC CORP
Application-layer security method and system
InactiveUS7313822B2Avoid attackMemory loss protectionUnauthorized memory use protectionConfidentialityApplication software
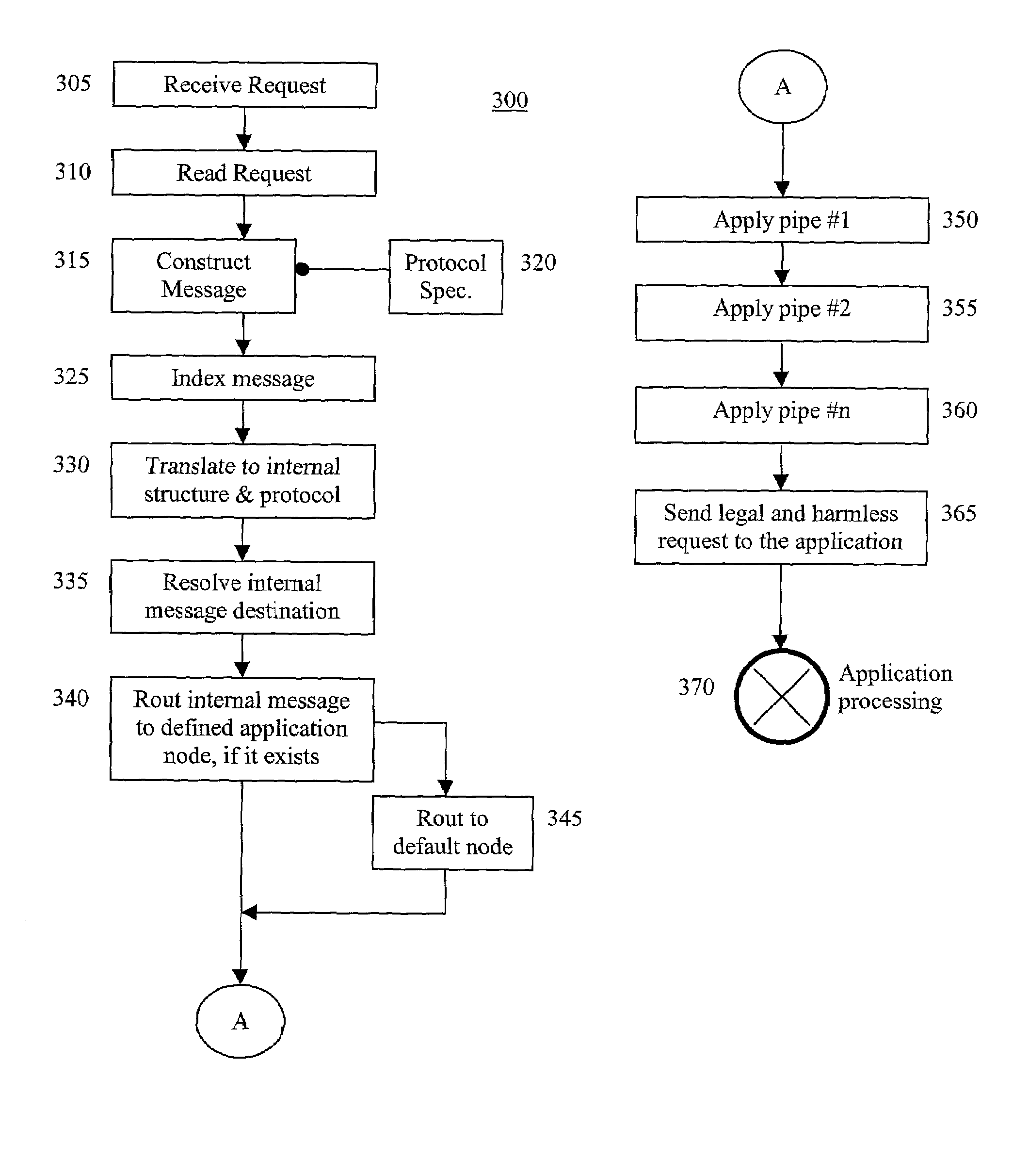
The present invention secures applications from executing illegal or harmful operation requests received from a distrusted environment, thereby, preventing an application from damaging itself, other applications, performance, files, buffers, databases, and confidentiality of information. An operation reverse engineering layer is positioned in front of an application in a trusted environment and between the application and the incoming application operation requests that are received from an unknown or distrusted environment. The operation reverse engineering layer checks the requests for either form, content, or both, to insure that only legal and harmless requests will pass to the given application. Hardware, software, or both, are employed to implement the operation reverse engineering layer.
Owner:KAVADO
Antioxidant inflammation modulators: novel derivatives of oleanolic acid
ActiveUS20100048911A1Suppresses demyelinationSuppresses transectionBiocideNervous disorderAntioxidantCancer
Disclosed herein are novel oleanolic acid derivatives. Methods of preparing these compounds are also disclosed. The oleanolic acid derivatives of this invention may be used for the treatment and prevention of many diseases, including cancer, neurological disorders, inflammation, and pathologies involving oxidative stress.
Owner:REATA PHARM INC
Authentication system based on biological characteristics and identification authentication method thereof
InactiveCN101330386AAttack is notAttacks are not directlyUser identity/authority verificationCharacter and pattern recognitionInternet privacyComputer terminal
The invention relates to an authentication system and an authentication method based on biological features. The method comprises the steps of conducting centralized storage and biological feature comparison operation for a large quantity of user biological feature templates according to user ID identifiers stored on a memory on a limited use machine and corresponding biding ID identifiers thereof on a biological authentication device of a digital processing terminal; separating the biological feature templates from the authentication function of the limited use machine; allocating to digital processing terminals (including PCs, notebooks or mobile phones, PDAs of users)of users as biological authentication device-storing the biological feature templates with decentralization and operating and processing biological features to be authenticated with decentralization so as to conduct comparison with the biological feature templates pre-stored on the respective digital processing terminals; feeding back comparison and verification results to the limited use machines; authorizing to conduct equal authentication of the biological authentication device ID identifier on the digital processing terminal for the corresponding binding user ID identifiers by the centralized authentication of the limited use machine according to the comparison verification result data.
Owner:刘洪利
Secure data storage for protecting digital content
InactiveUS8452988B2The implementation process is simpleConvenient for userKey distribution for secure communicationUnauthorized memory use protectionDigital dataPaper data storage
Owner:WANG MICHAEL SUJUE
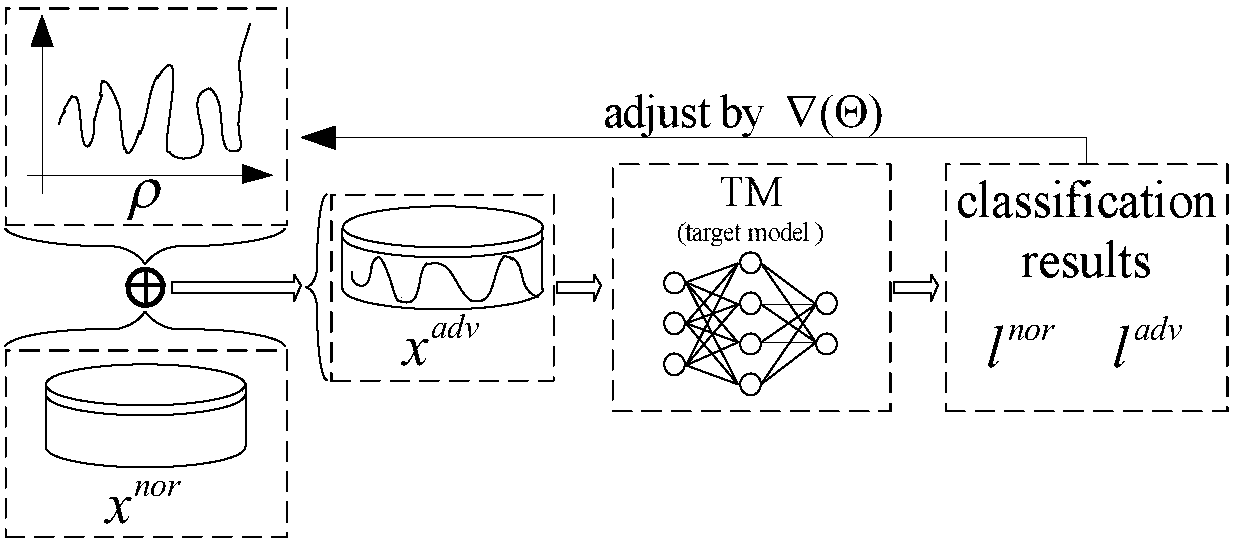
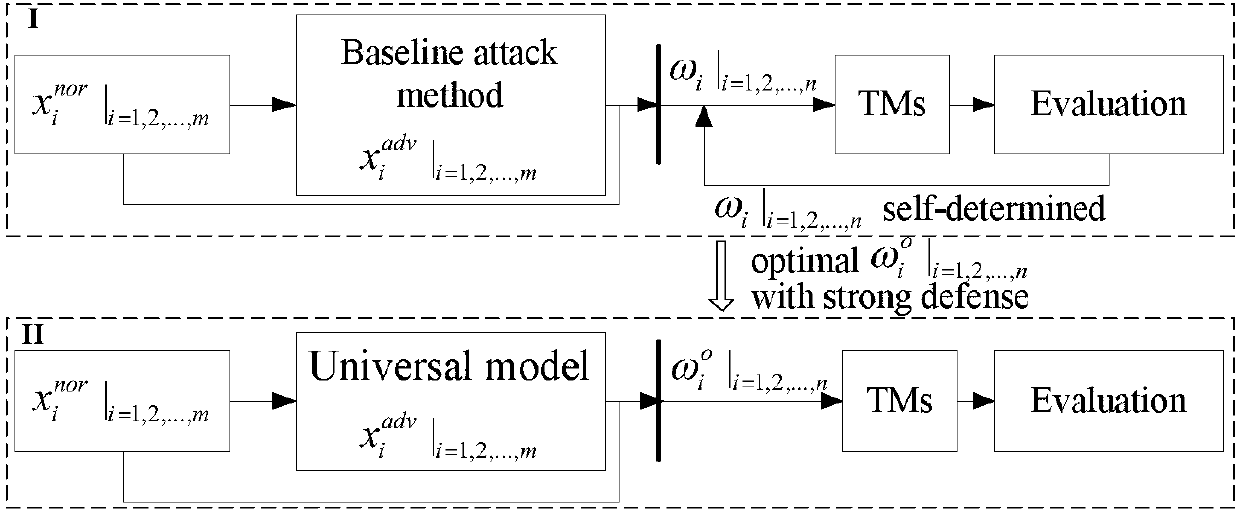
Multi-model cooperative defense method facing deep learning antagonism attack
InactiveCN108446765AEffective defense against attacksAvoid attackCharacter and pattern recognitionNeural learning methodsSubstitution modelAdaBoost
A multi-model cooperative defense method facing deep learning antagonism attack comprises the following steps of: 1) performing unified modeling based on a gradient attack to provide a [Rho]-loss model; 2) according to design of a unified model, for an countering attack of a target model fpre(x), according to a generation result of a countering sample, classifying a basic expression form of an attack into two classes; 3) analyzing the parameters of the model, performing parameter optimization of the [Rho]-loss model and search step length optimization of a disturbance solution model for the countering sample; and 4) for the mystique of a black box attack, designing an experiment based on an adaboost concept, generating a plurality of different types of substitution models, used to achievethe same task, for integration, designing a multi-model cooperative defense method with high defense capability through an attack training generator of an integration model with high defense capability, and providing multi-model cooperative detection attack with weight optimal distribution. The multi-model cooperative defense method is high in safety and can effectively defense the attack of a deep learning model for the antagonism attack.
Owner:ZHEJIANG UNIV OF TECH
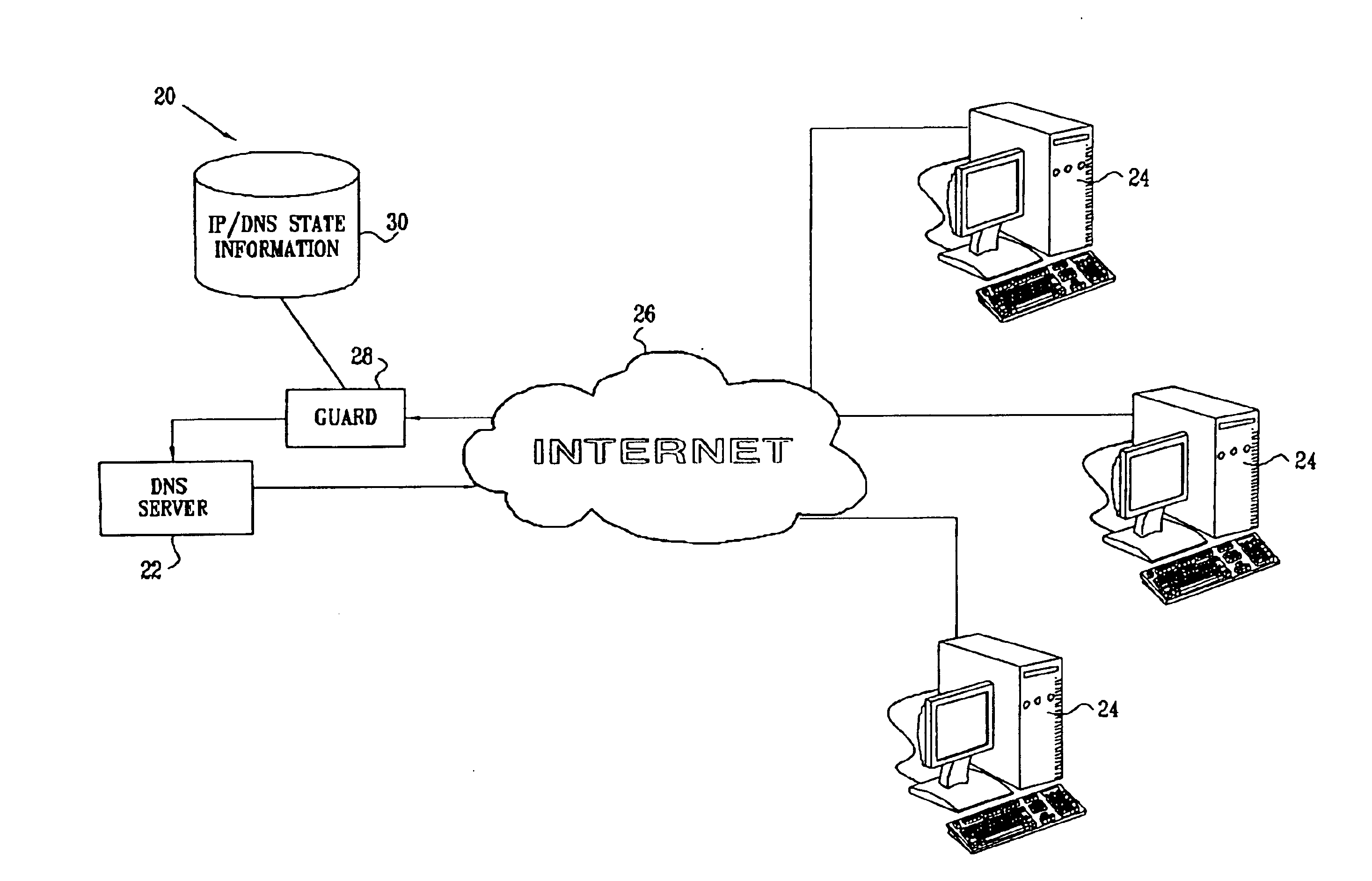
Protecting against spoofed DNS messages
InactiveUS6907525B2Avoid attackMemory loss protectionError detection/correctionDomain nameComputer network
A method for authenticating communication traffic includes receiving a first request, such as a DNS request, sent over a network from a source address, to provide network information regarding a given domain name. A response is sent to the source address in reply to the first request. When a second request is from the source address in reply to the response, the authenticity of the first request is assessed based on the second request.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com