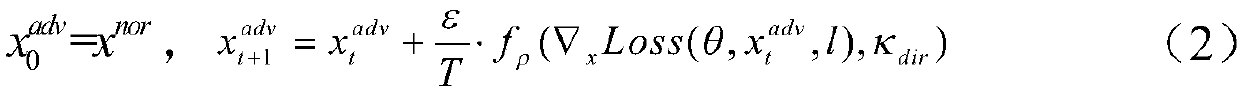Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1209 results about "Black box" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In science, computing, and engineering, a black box is a device, system or object which can be viewed in terms of its inputs and outputs (or transfer characteristics), without any knowledge of its internal workings. Its implementation is "opaque" (black). Almost anything might be referred to as a black box: a transistor, an algorithm, or the human brain.
Method and system for sleep monitoring, regulation and planning
InactiveUS20110230790A1Accurately determineGood user interfaceAcoustic time signalsPerson identificationActigraphyAnalysis data
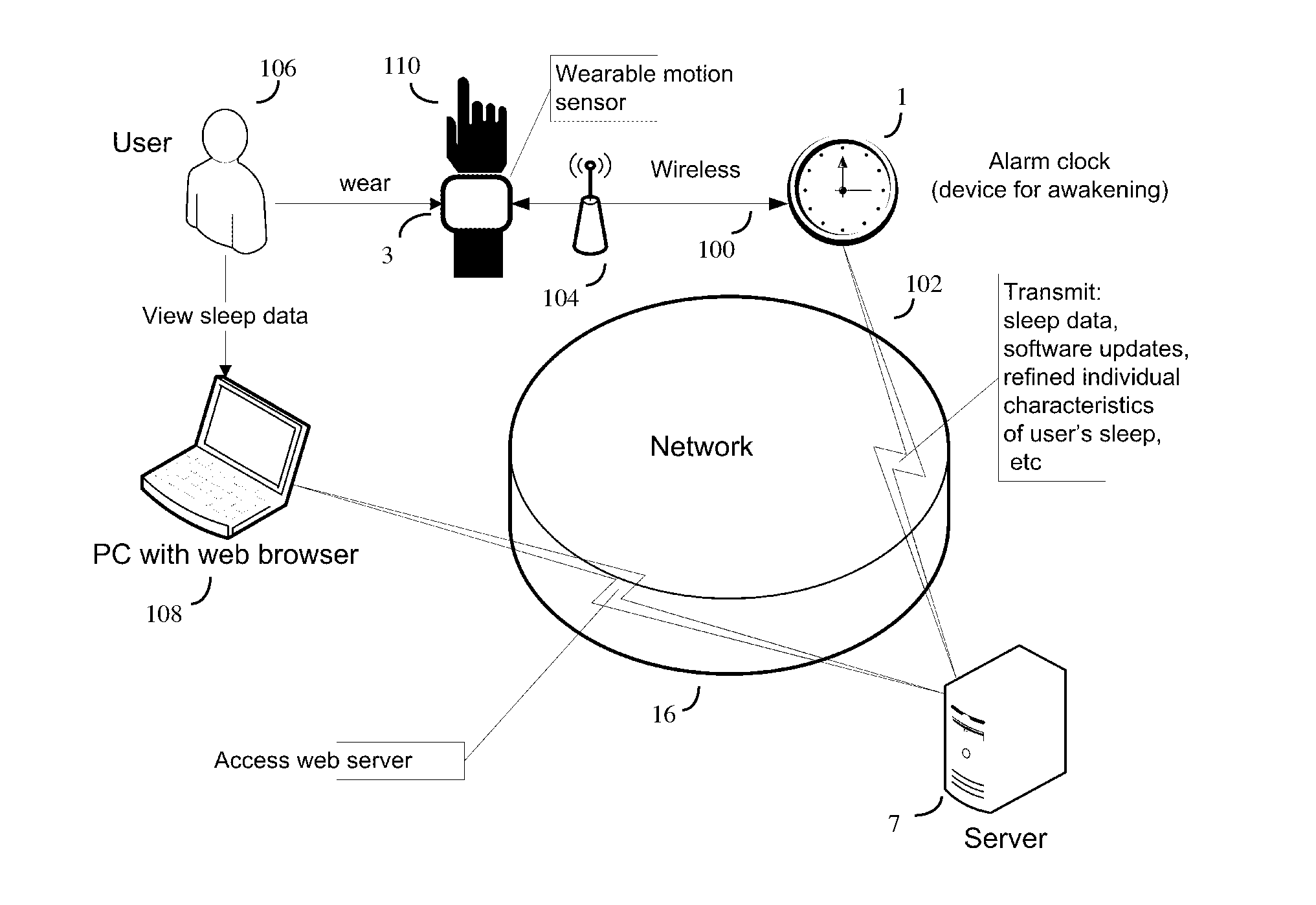
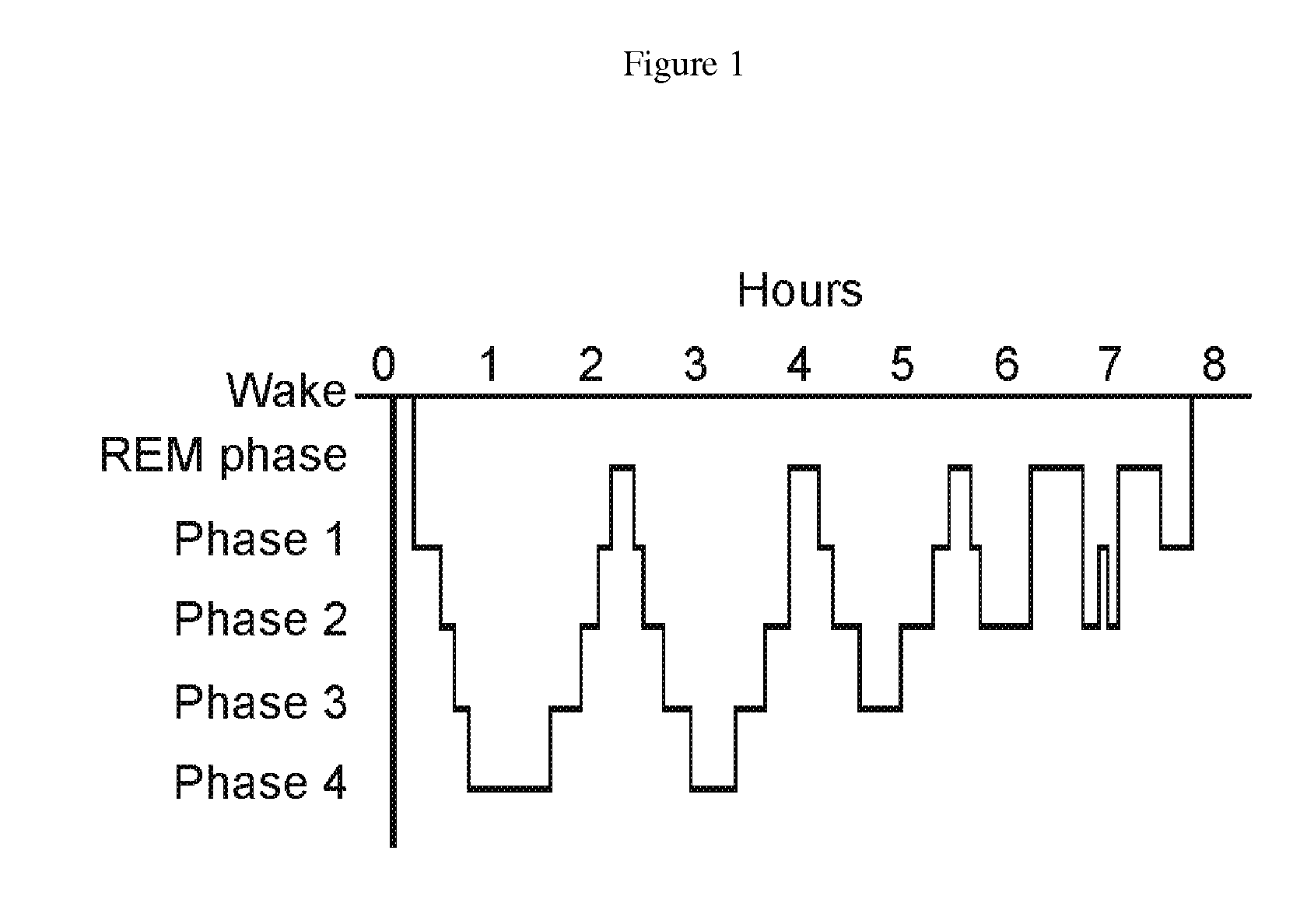
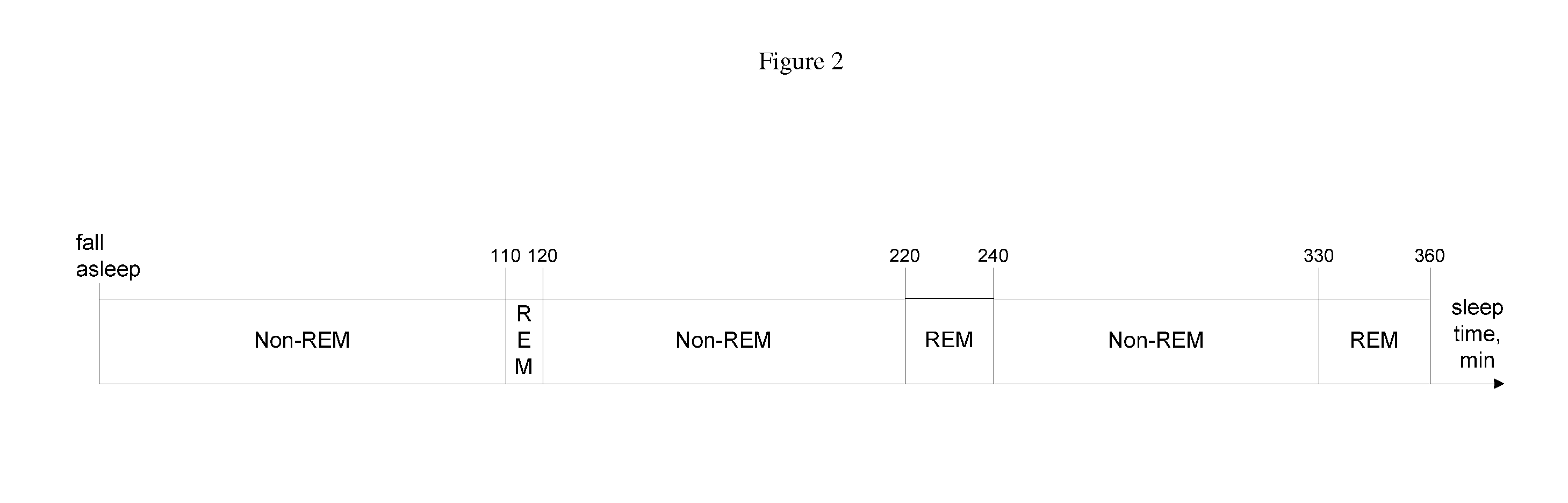
A method for operating a sleep phase actigraphy synchronized alarm clock that communicates with a remote sleep database, such as an internet server database, and compares user physiological parameters, sleep settings, and actigraphy data with a large database that may include data collected from a large number of other users with similar physiological parameters, sleep settings, and actigraphy data. The remote server may use “black box” analysis approach by running supervised learning algorithms to analyze the database, producing sleep phase correction data which can be uploaded to the alarm clock, and be used by the alarm clock to further improve its REM sleep phase prediction accuracy.
Owner:KOZLOV VALERIY
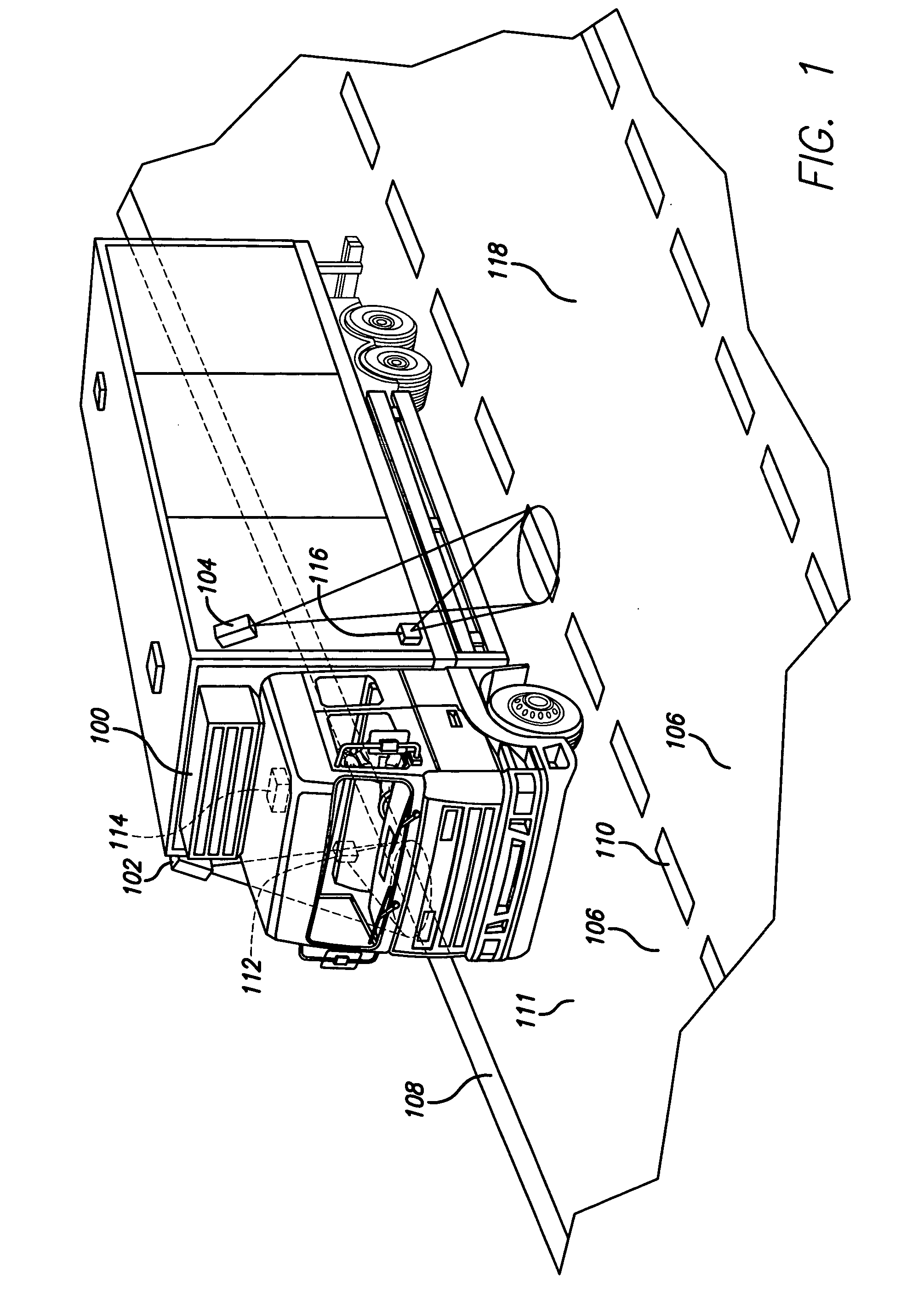
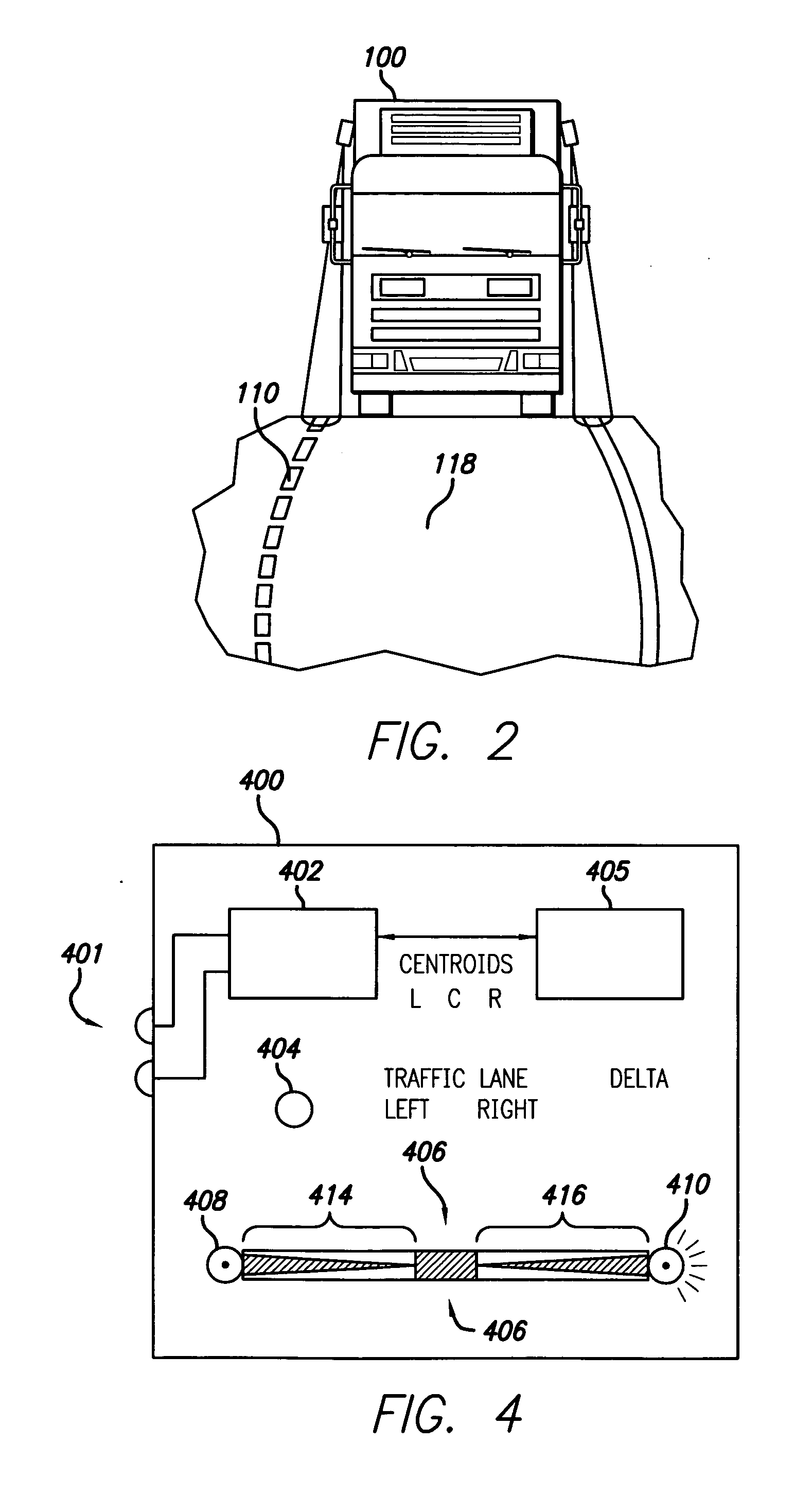
Vehicular black box monitoring system
InactiveUS6894606B2Evaluate performanceRegistering/indicating working of vehiclesAnti-collision systemsMonitoring systemEngineering
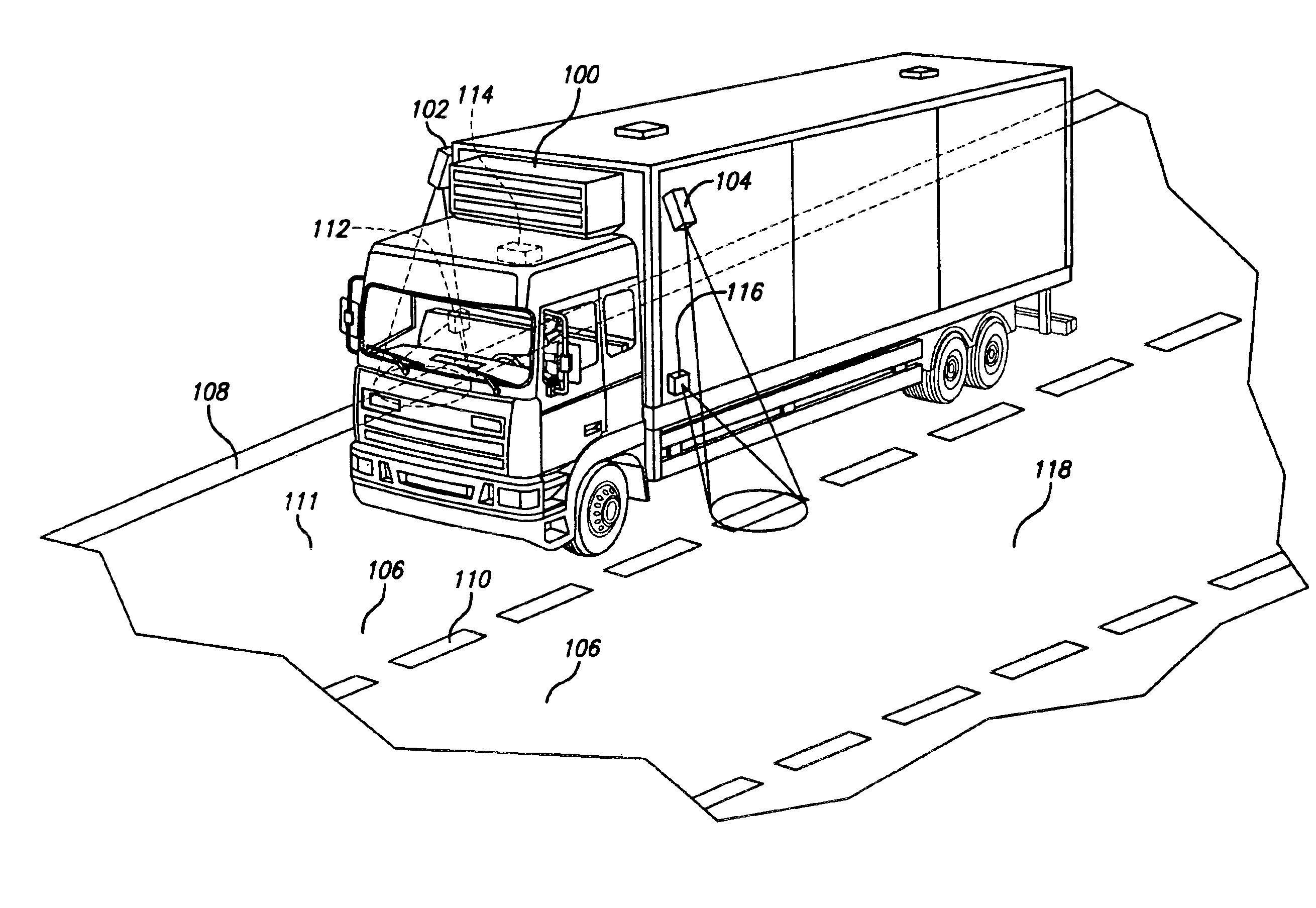
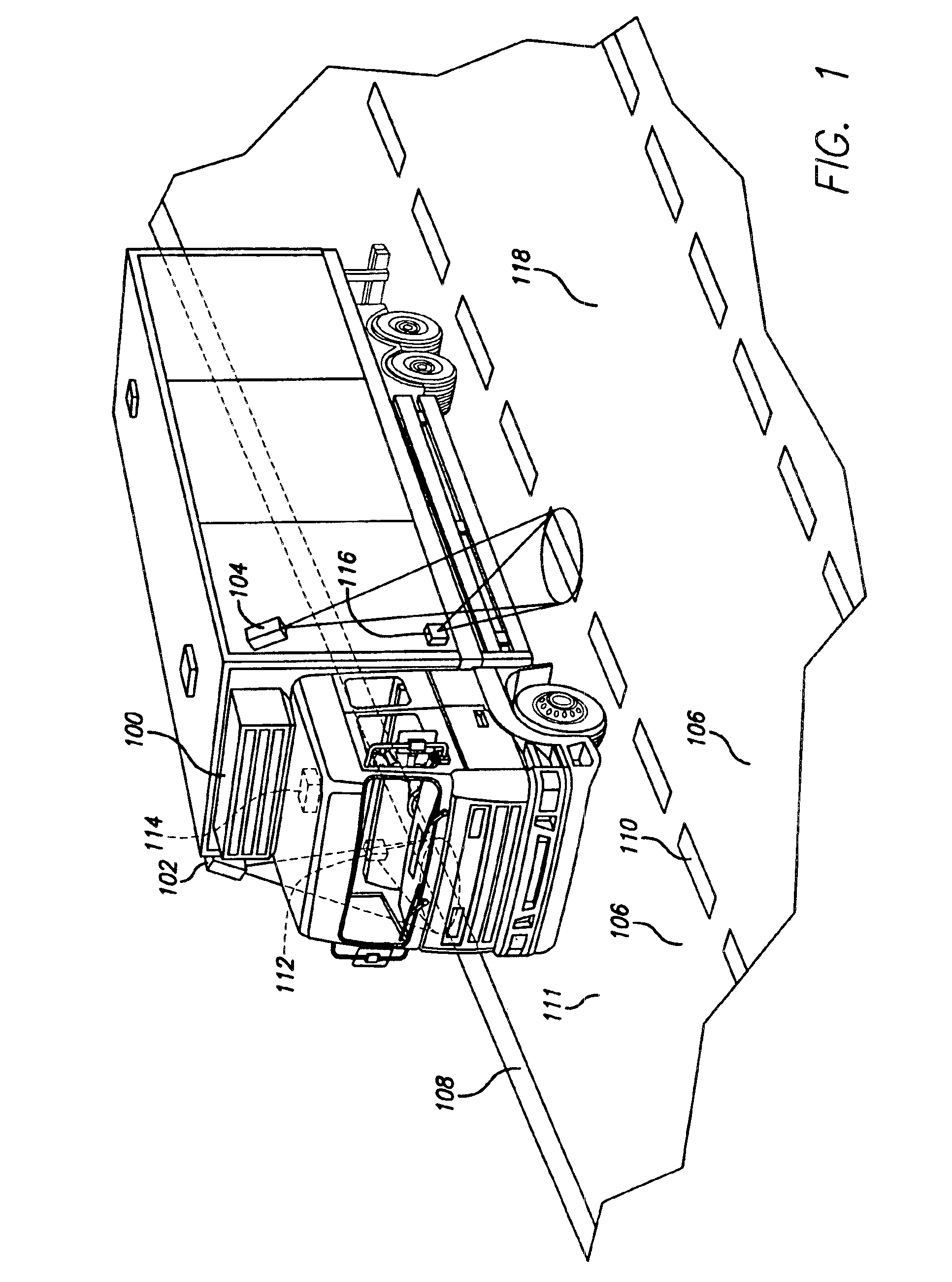
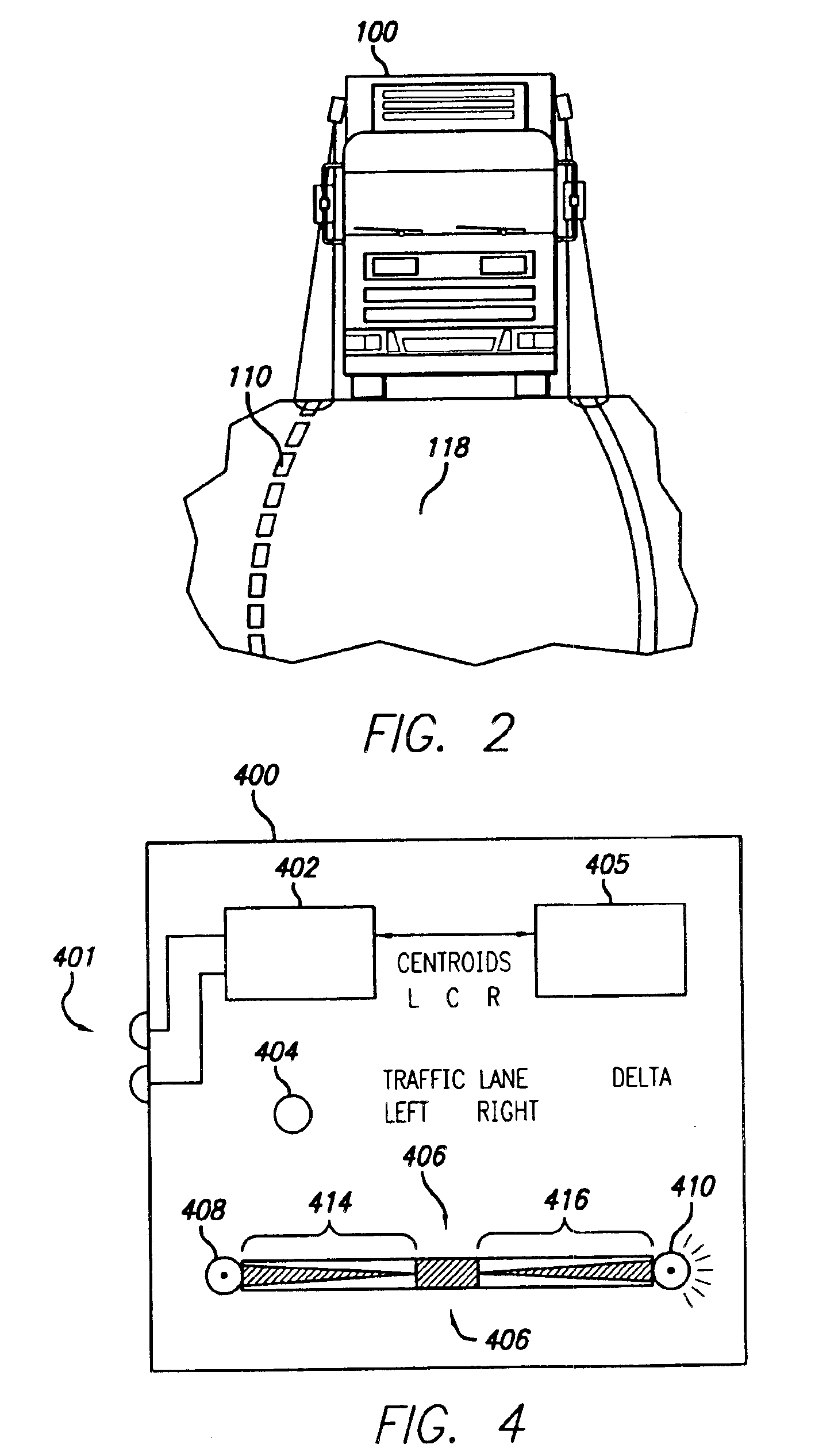
A vehicular “black box” provides recording means by which driver action can be reviewed after an accident or collision, as well as indicating immediate vehicle disposition status to the driver. Using cameras (which may be very small), the disposition of the vehicle in its lane is determined by detecting the highway lines painted on the road.The data is also recorded so that should an accident or collision occur, the events leading up to such an event are made available for later review and analysis.
Owner:FORBES FRED +3
Vehicular black box monitoring system
InactiveUS20020105438A1Easy to driveFewer accidents on the highwaysRegistering/indicating working of vehiclesAnti-collision systemsMonitoring systemEngineering
A vehicular "black box" provides recording means by which driver action can be reviewed after an accident or collision, as well as indicating immediate vehicle disposition status to the driver. Using cameras (which may be very small), the disposition of the vehicle in its lane is determined by detecting the highway lines painted on the road. The data is also recorded so that should an accident or collision occur, the events leading up to such an event are made available for later review and analysis.
Owner:FORBES FRED +3
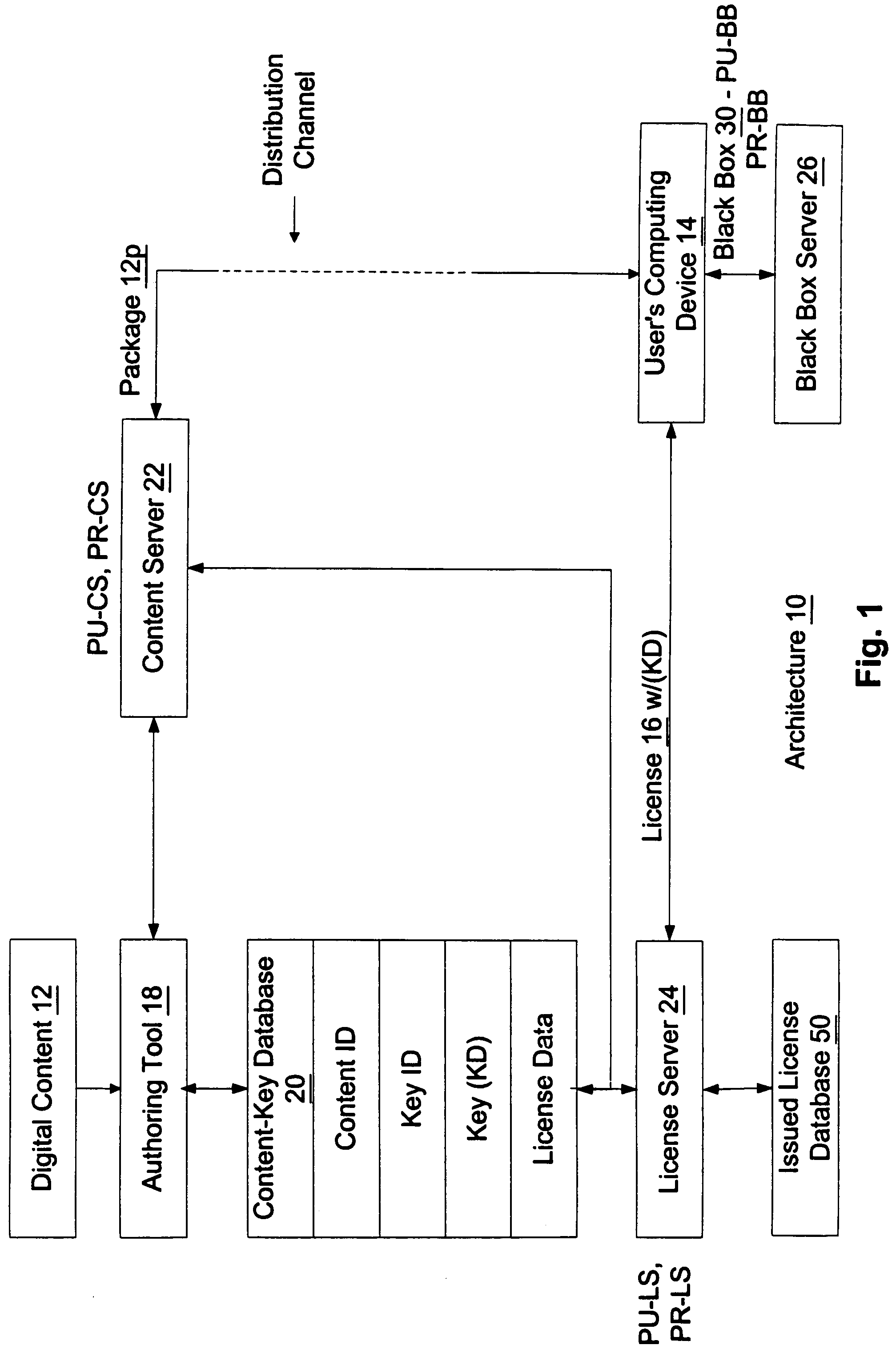
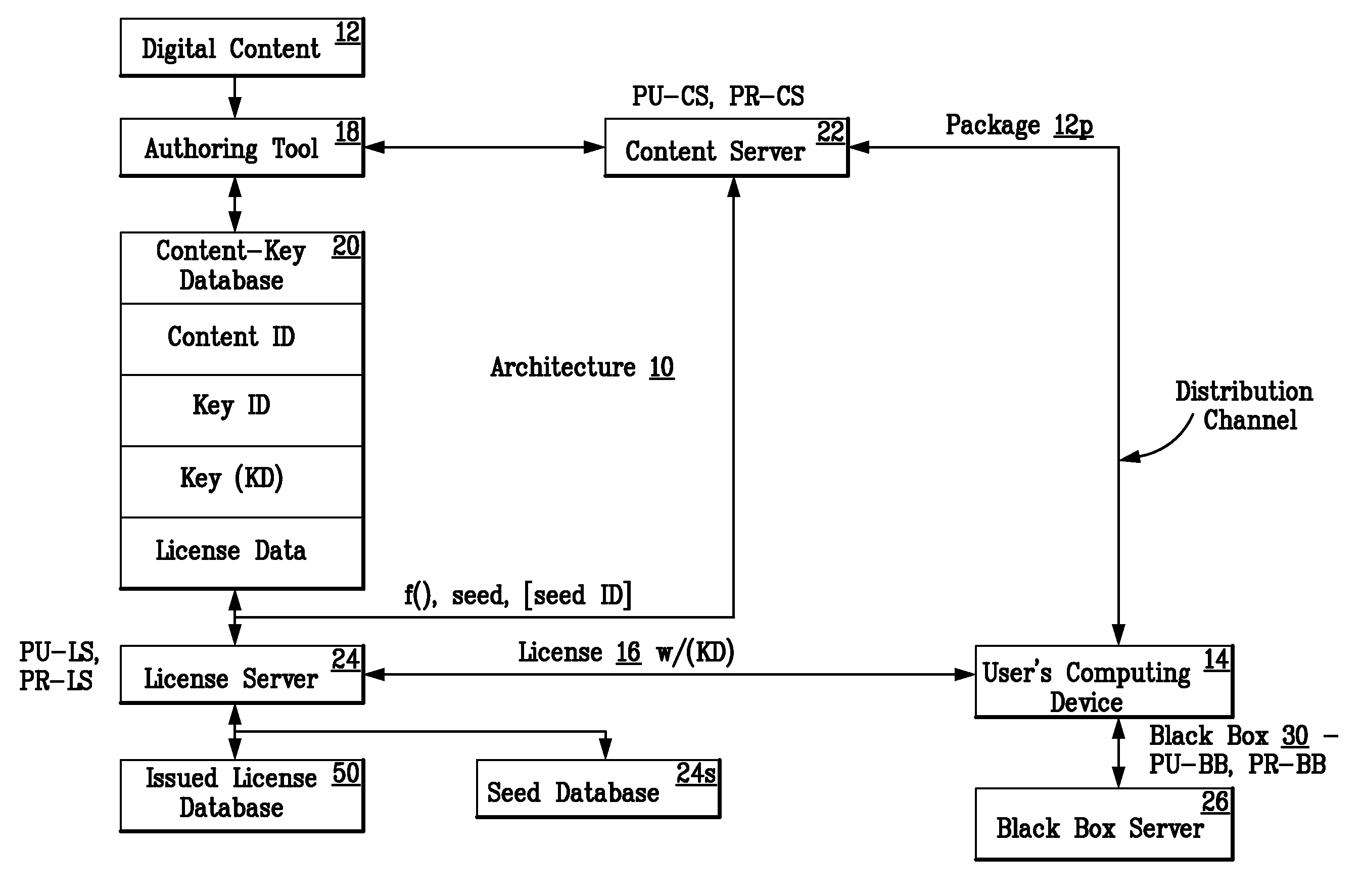
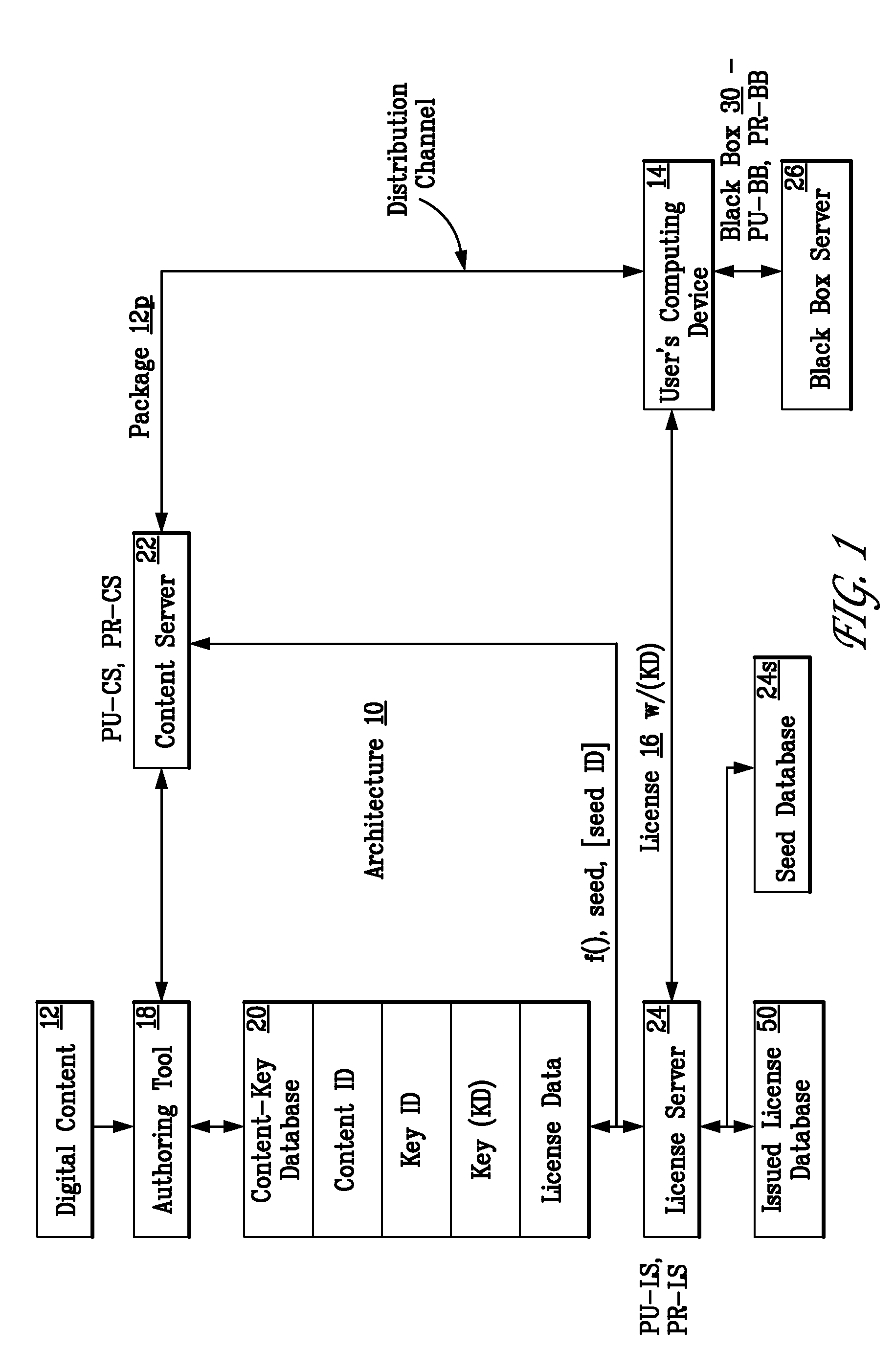
Method for obtaining a black box for performing decryption and encryption functions in a digital rights management (DRM) system
InactiveUS7051005B1Satisfies needDigital data processing detailsCoin-freed apparatus detailsDigital rights managementBlack box
A digital rights management (DRM) system operates on a computing device and requires a black box for performing decryption and encryption functions. To obtain the black box from a black box server, the DRM system requests such black box from such black box server. The black box server in response generates the black box, where such black box is unique and has a public / private key pair. The black box server then delivers the generated black box to the DRM system and the DRM system installs the delivered black box in such DRM system.
Owner:MICROSOFT TECH LICENSING LLC
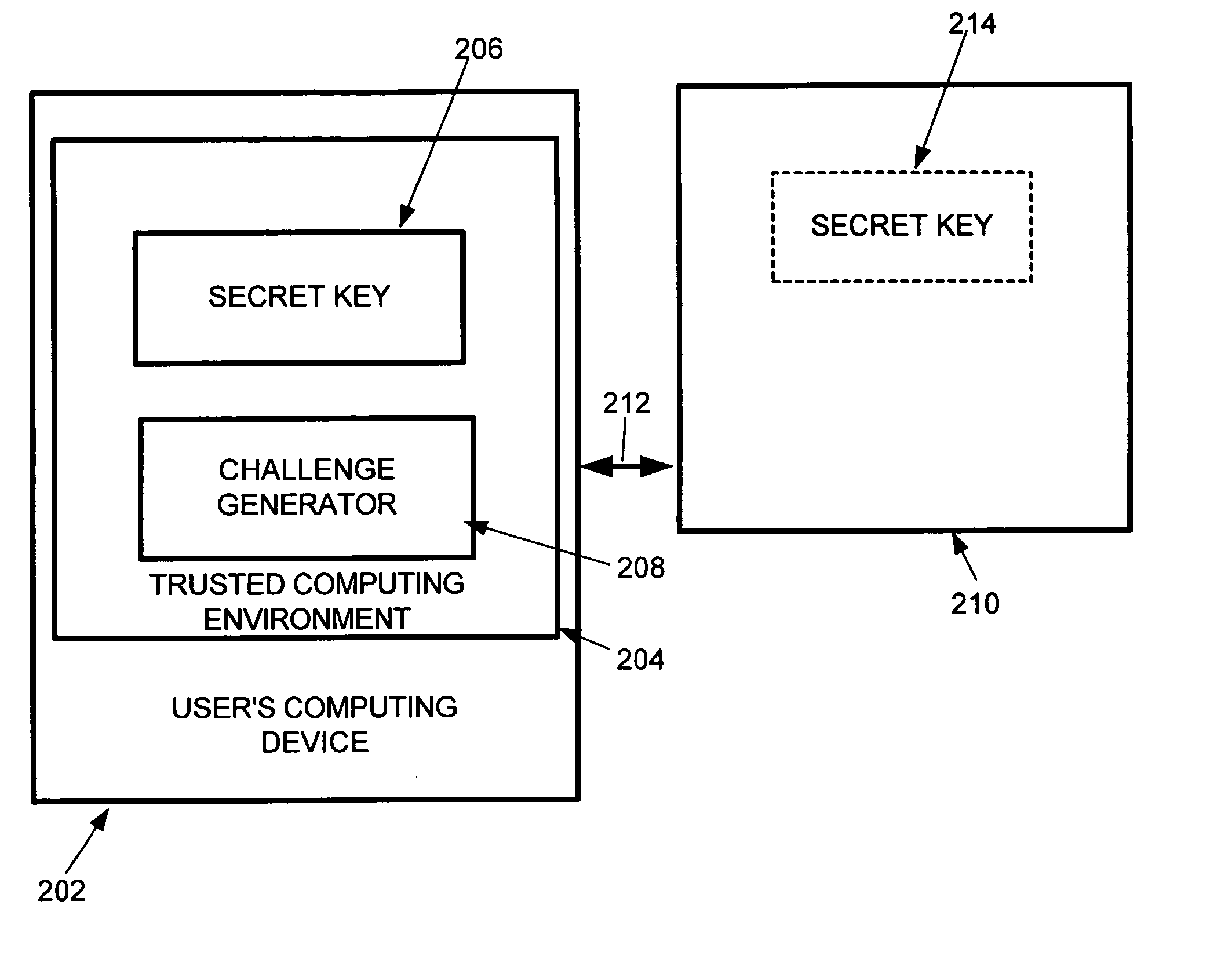
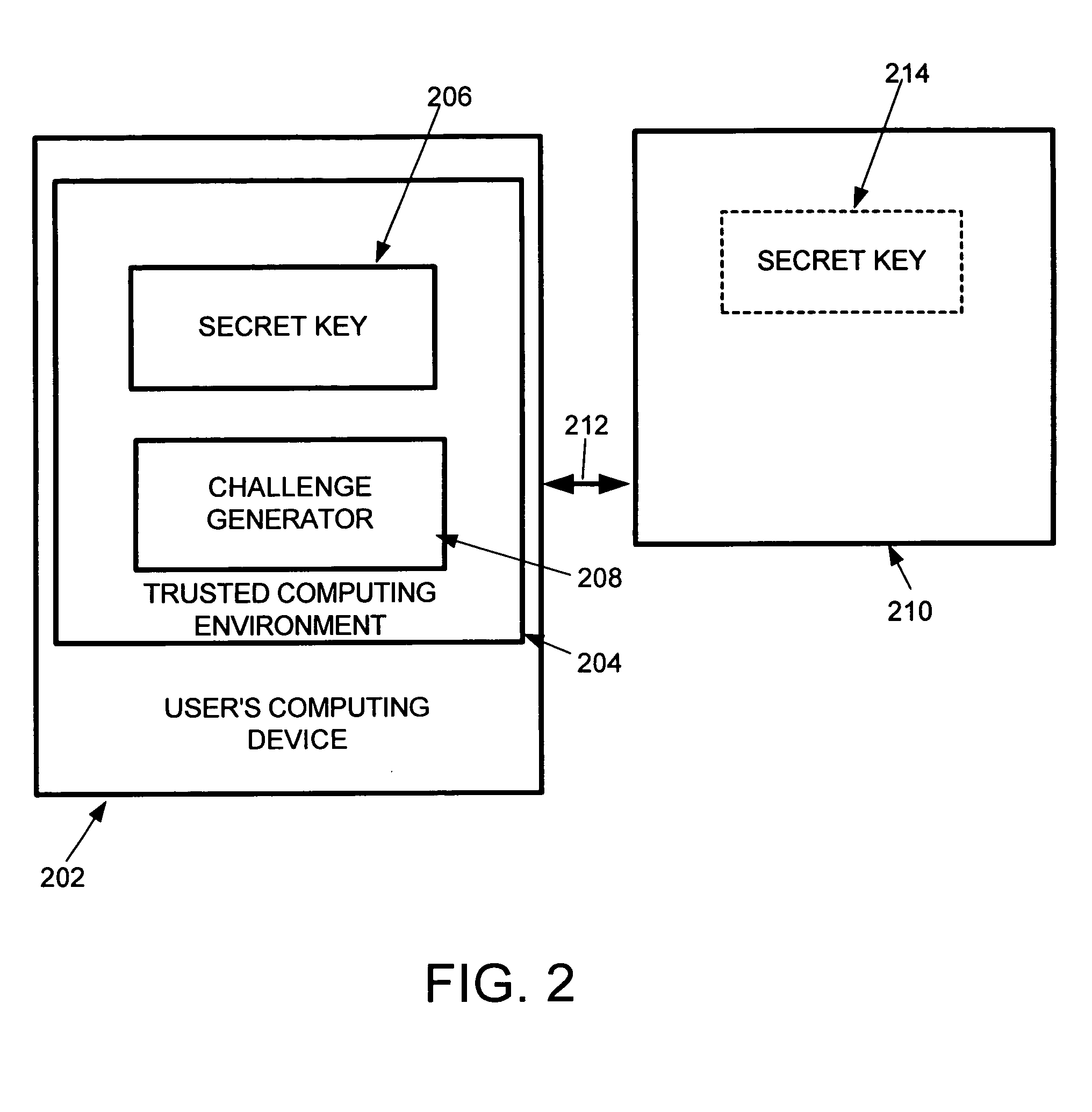
System and method for non-interactive human answerable challenges
InactiveUS20050120201A1Good delayNeed greatDigital data processing detailsUser identity/authority verificationComputer usersService provision
A system and method for automatically determining if a computer user is a human or an automated script. Human interactive proofs (HIPs) are currently used to deter automated registration for web services by automated computer scripts. Unfortunately, HIPs entail multiple steps (request service, receive challenge, respond to challenge) that can be burdensome. The system and method of the invention in one embodiment provides a “black-box” to potential users consisting of a challenge generator and a secret key. The challenge is generated for the user and the response can be provided as part of the service request, eliminating the need for a separate challenge from a service provider and response to the challenge.
Owner:MICROSOFT TECH LICENSING LLC
System and methods for automated airport air traffic control services
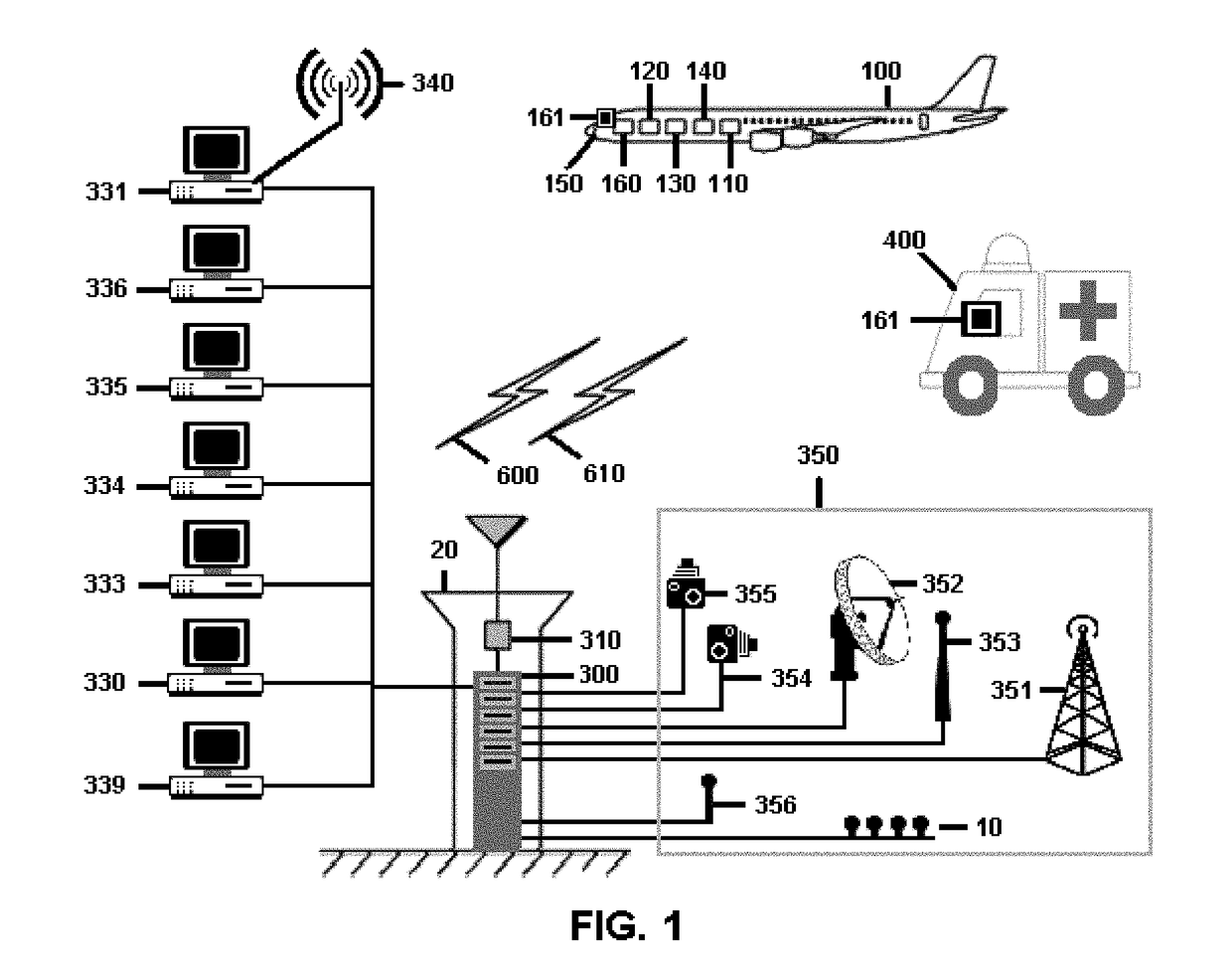
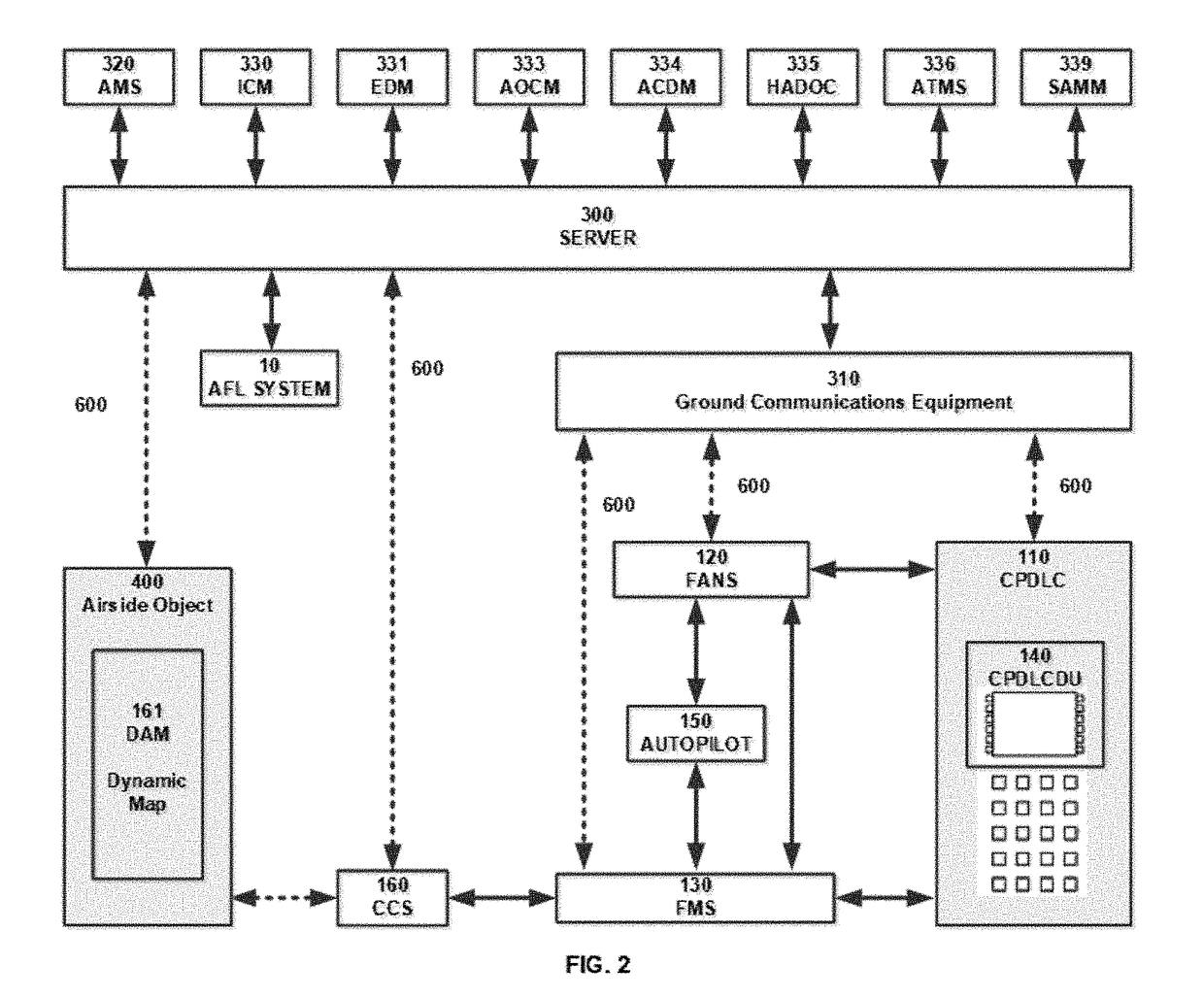
InactiveUS20180061243A1Extension of timeMaximized situational awarenessNatural language translationTelevision system detailsNetwork operations centerAirplane
A system and method for automating Air Traffic Control operations at or near an airport. as a complete standalone automated system replacing the need for a human controller to make aircraft movement decisions nor the need communicate with pilots, or as semi-automated, where a controller controls how the system operates. The system with related methods and computer hardware and computer software package, automatically manages manned aircraft, remote controlled UAV and airborne-able vehicles traffic at or near an airport, eliminates ATC-induced and reduce pilot-induced runway incursions and excursions, processes control messages related to aircraft or Pilots, communicates with Pilot over ATC radio frequency, receives aircraft positions, communicates control messages with the aircraft avionics, provides pilots a dynamic map with continuous display of nearby traffic operations, shows clearance and information related to runway operations, warns pilot of runway conditions and turbulence from other operations, warns when landing gear is not locked, displays the pilot emergency exits during takeoff roll, shows the pilot when and where to exit from the runway, shows the pilot where and when to cross a junction, calculates and displays pilot optimal speed and timing on taxiways and junctions for saving fuel, calculates congestions, calculates best taxiway routes, calculates when aircraft can cross a runway, provides directives and information to pilot over CPDLC display or dynamic map for airside operations, alerts and triggers breaks of the aircraft on wrong path or when hold-short bar is breached, displays emergency personnel with routing map and final aircraft resting position for emergency operations, takes over an aircraft operation when aircraft is hijacked or deviates from the flight plan, provide standalone or manned Remote Tower functionality, Records and retains all information related to airport airside operations including aircraft positions and conditions from sensors and reports for runways, junctions and taxiways, Records and retains aircraft data and cockpit voice to ground-based servers to eliminate black-box requirements, calculate future weather and airport capacity from aircraft at or nearby airport, coordinates handoff operations with other ATC positions, interfaces with ACDM systems, airport operations center, flow center and network operations center.
Owner:IATAS AUTOMATIC AIR TRAFFIC CONTROL
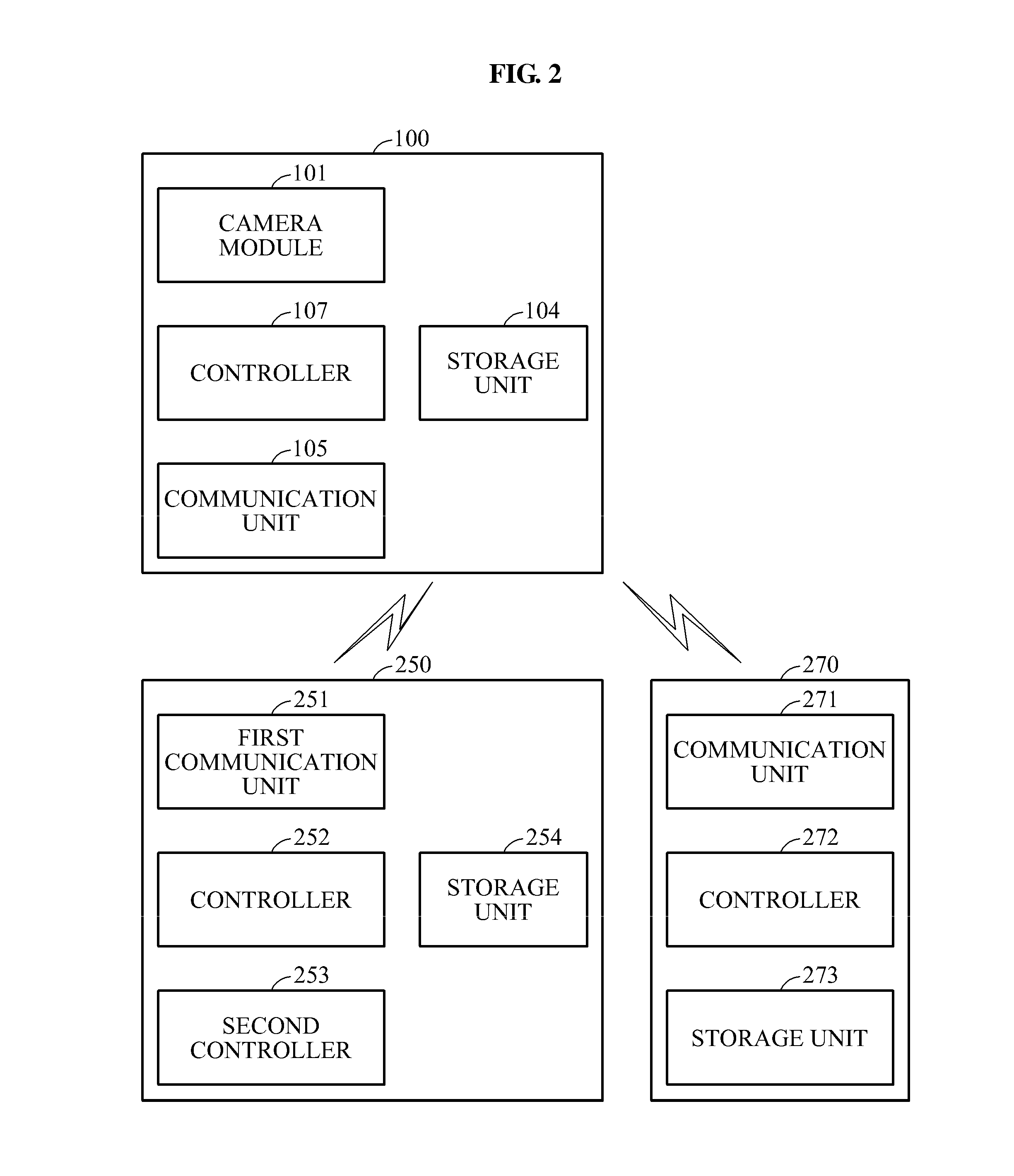
Vehicular image processing apparatus and method of sharing data using the same
ActiveUS20140324247A1Data augmentationImprove utilizationRegistering/indicating working of vehiclesDigital data processing detailsImaging processingBlack box
Provided are a vehicular image processing apparatus and a method of sharing data using the same that may verify a driving route of a vehicle or detect and share a location of a vehicle by analyzing recorded images of the image processing apparatus, for example, a black box, thereby increasing data usage and utilization.
Owner:THINKWARE +1
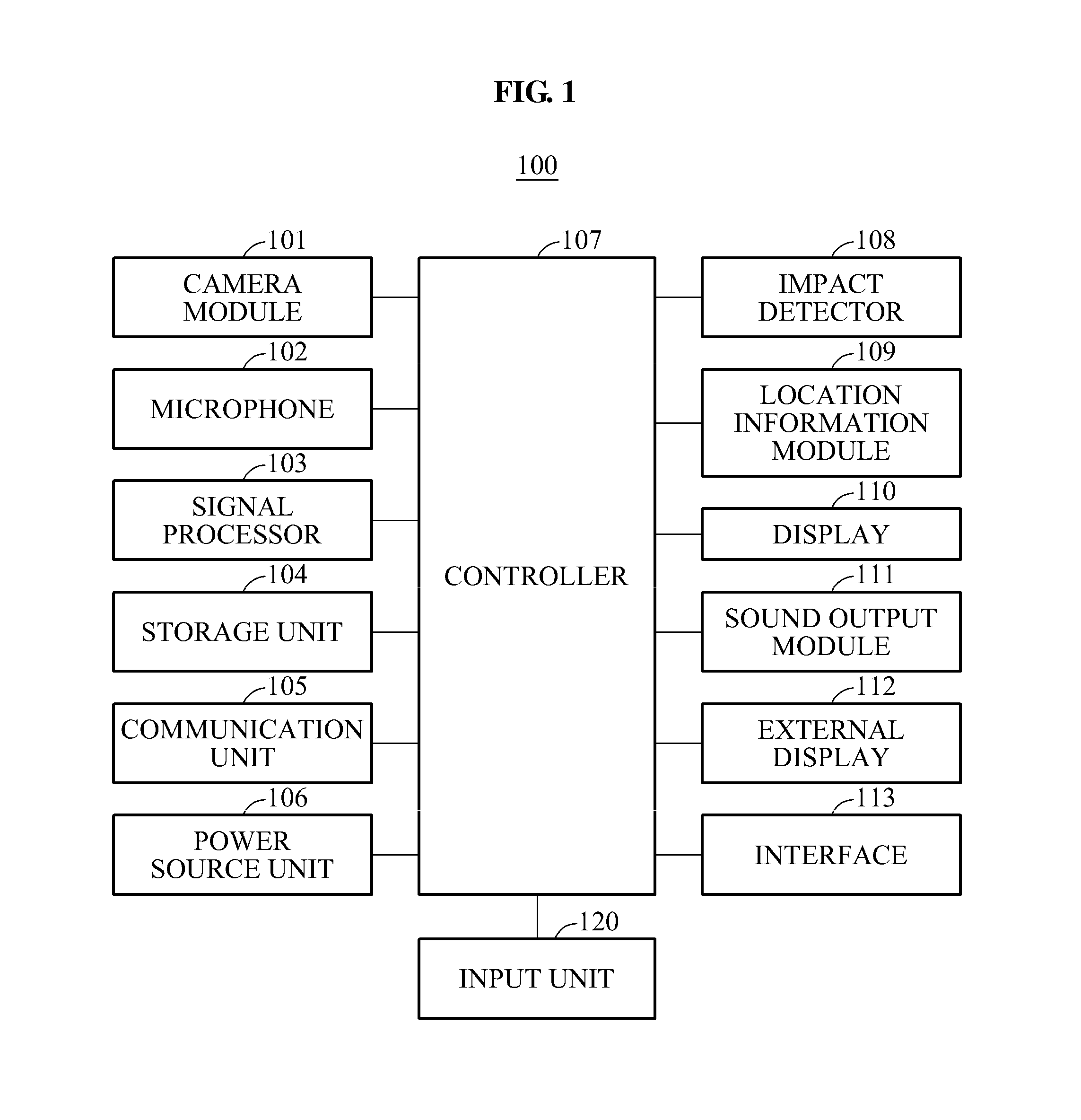
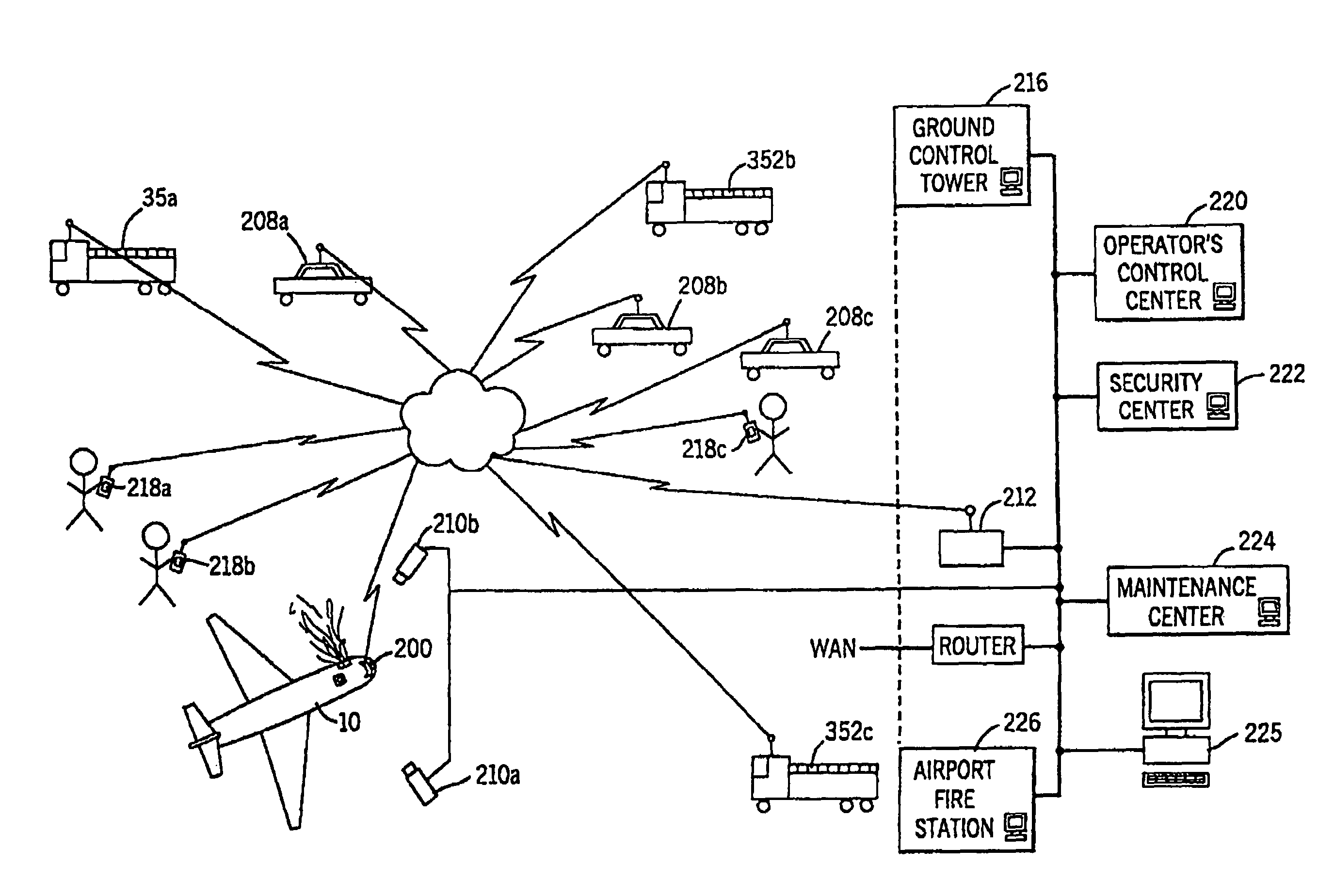
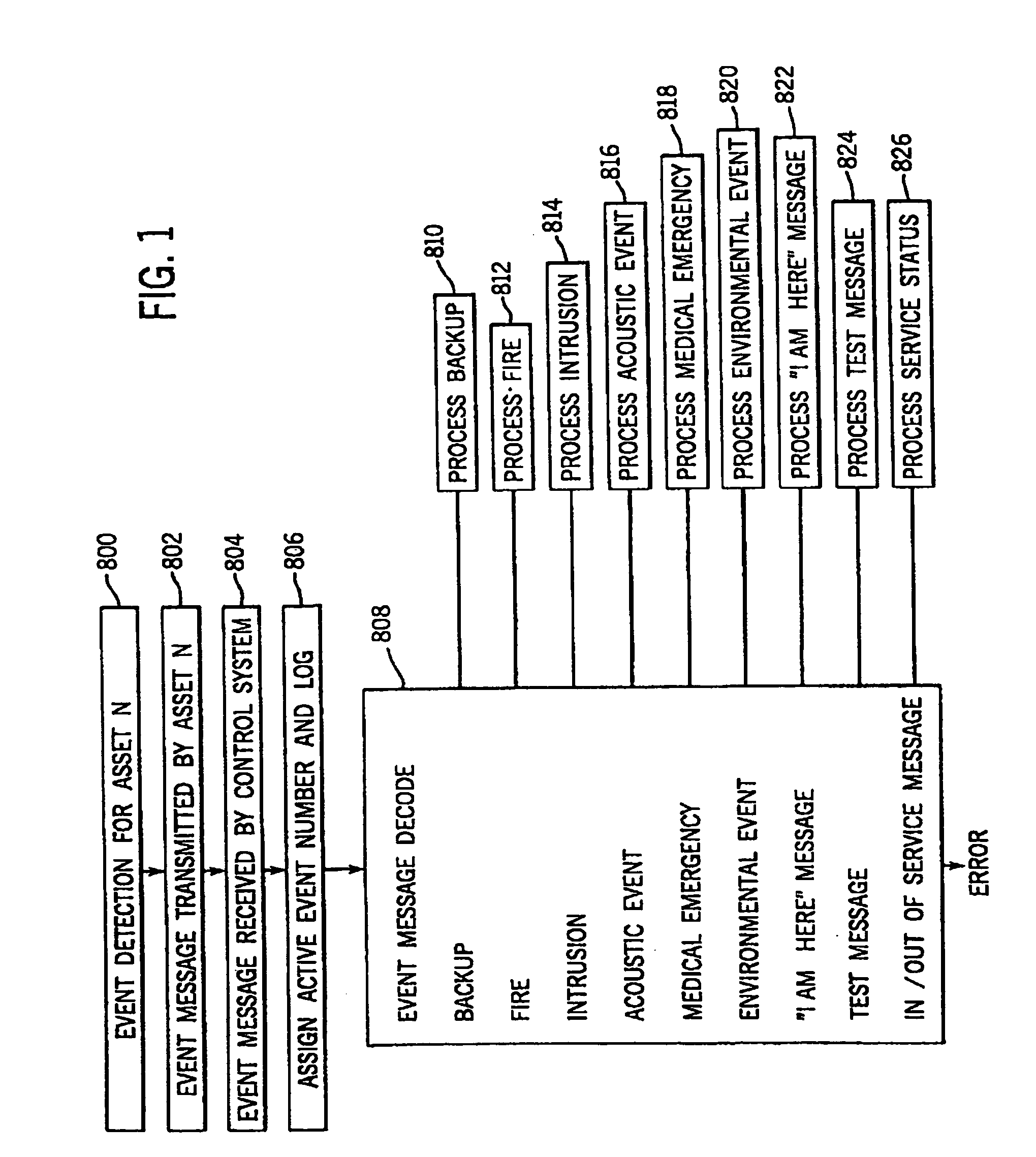
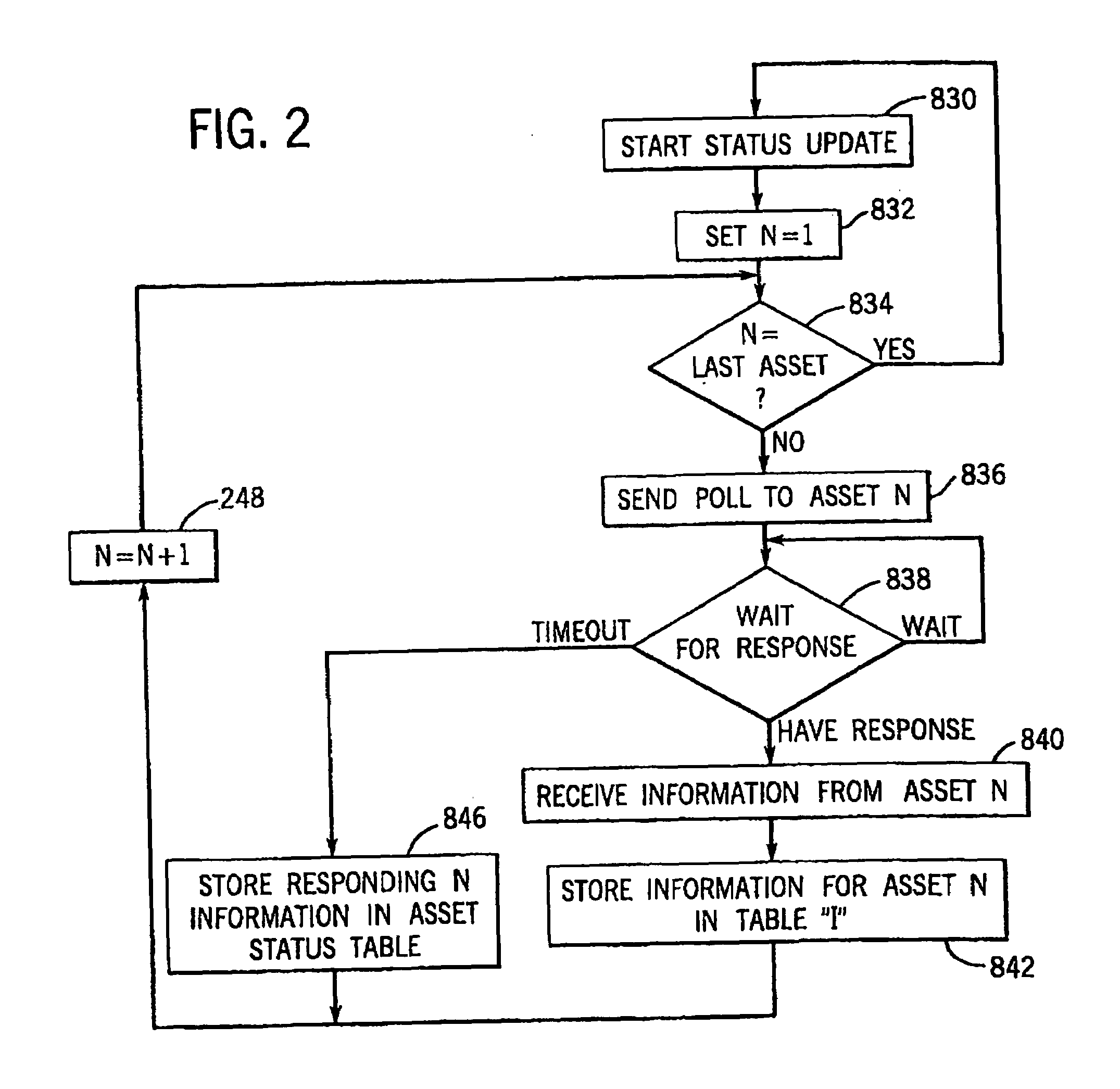
Apparatus for and method of collecting and distributing event data to strategic security personnel and response vehicles
InactiveUS7561037B1Minimize the numberFrequency-division multiplex detailsRoad vehicles traffic controlSmoke detectorsMotion detector
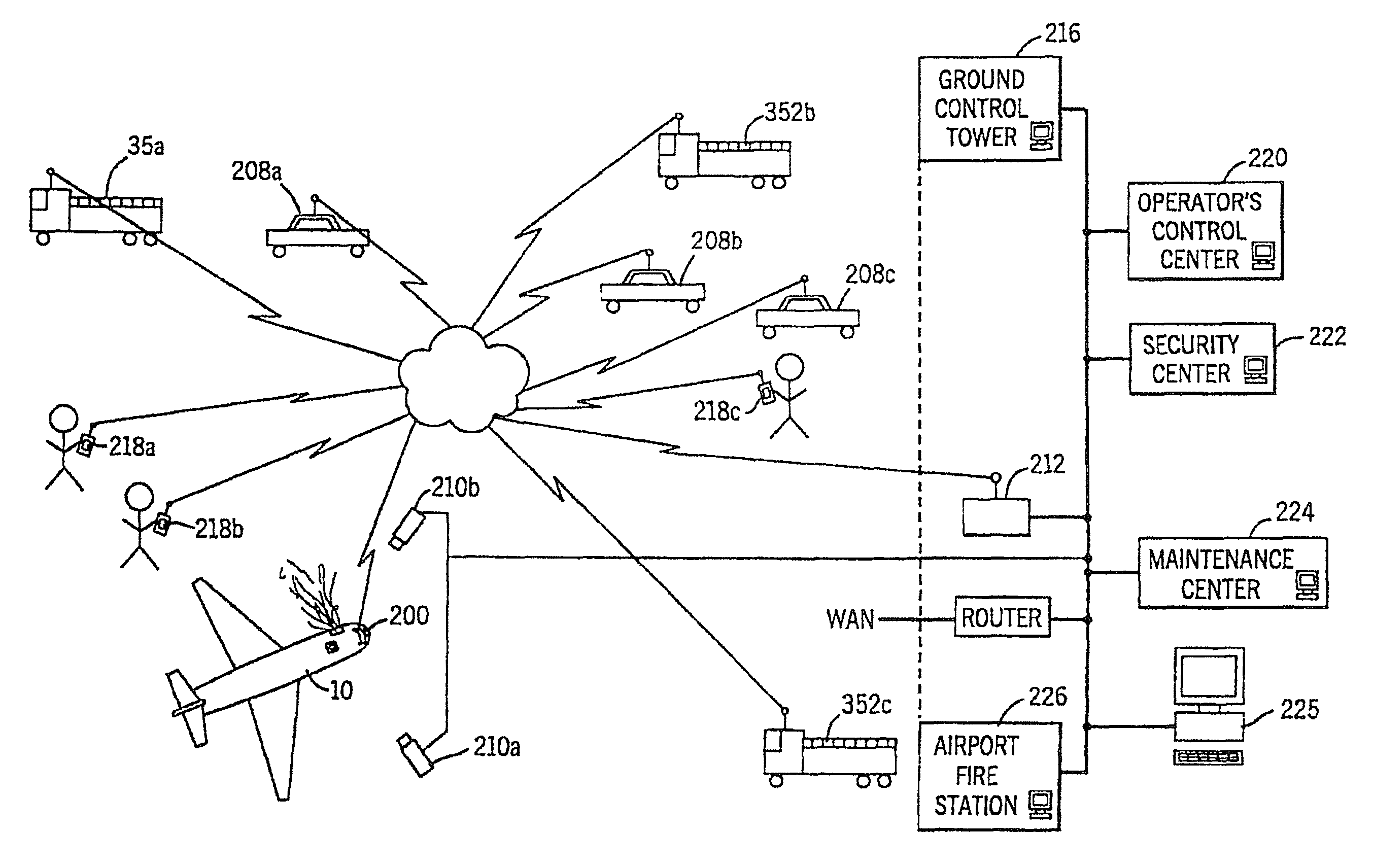
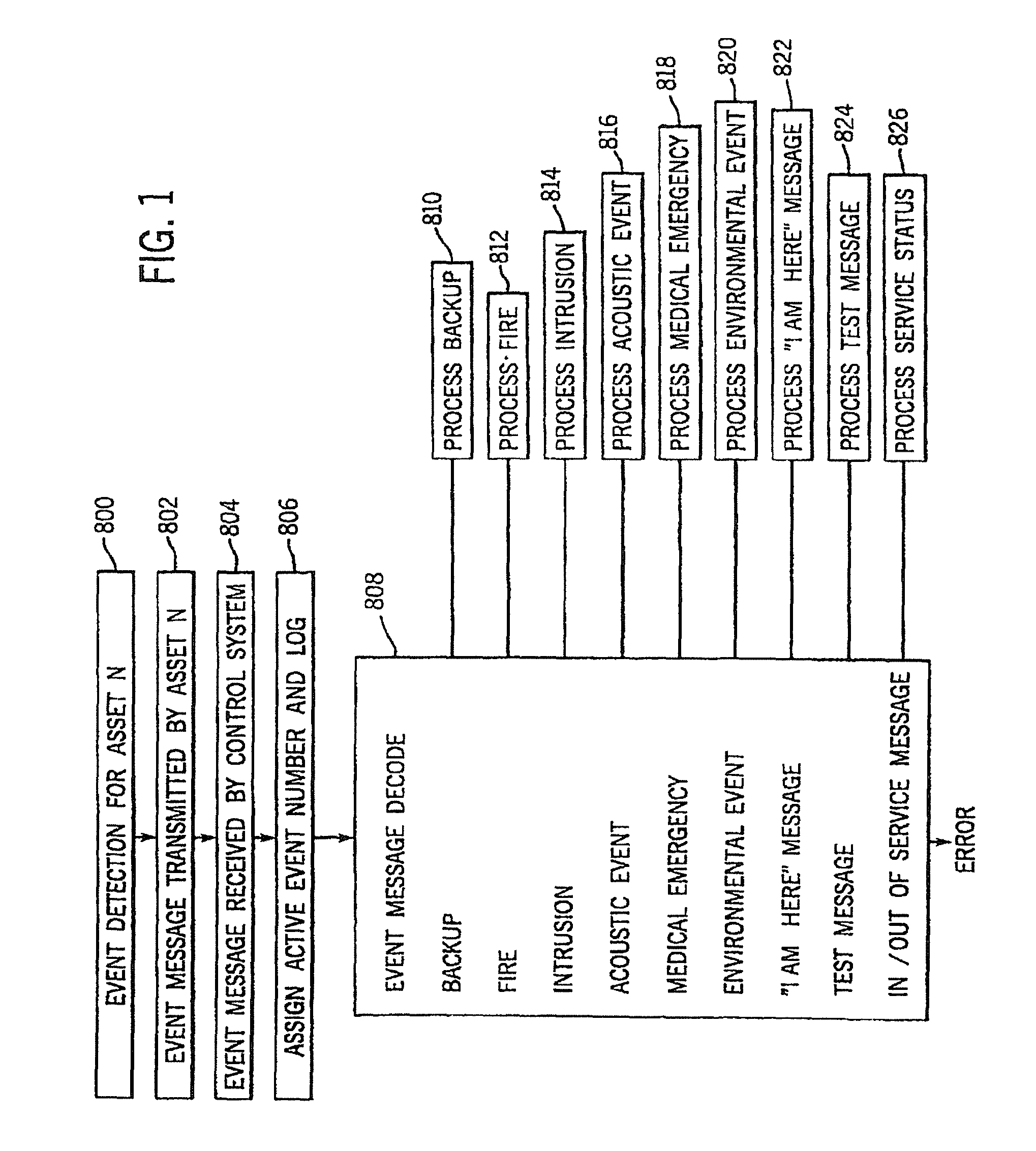
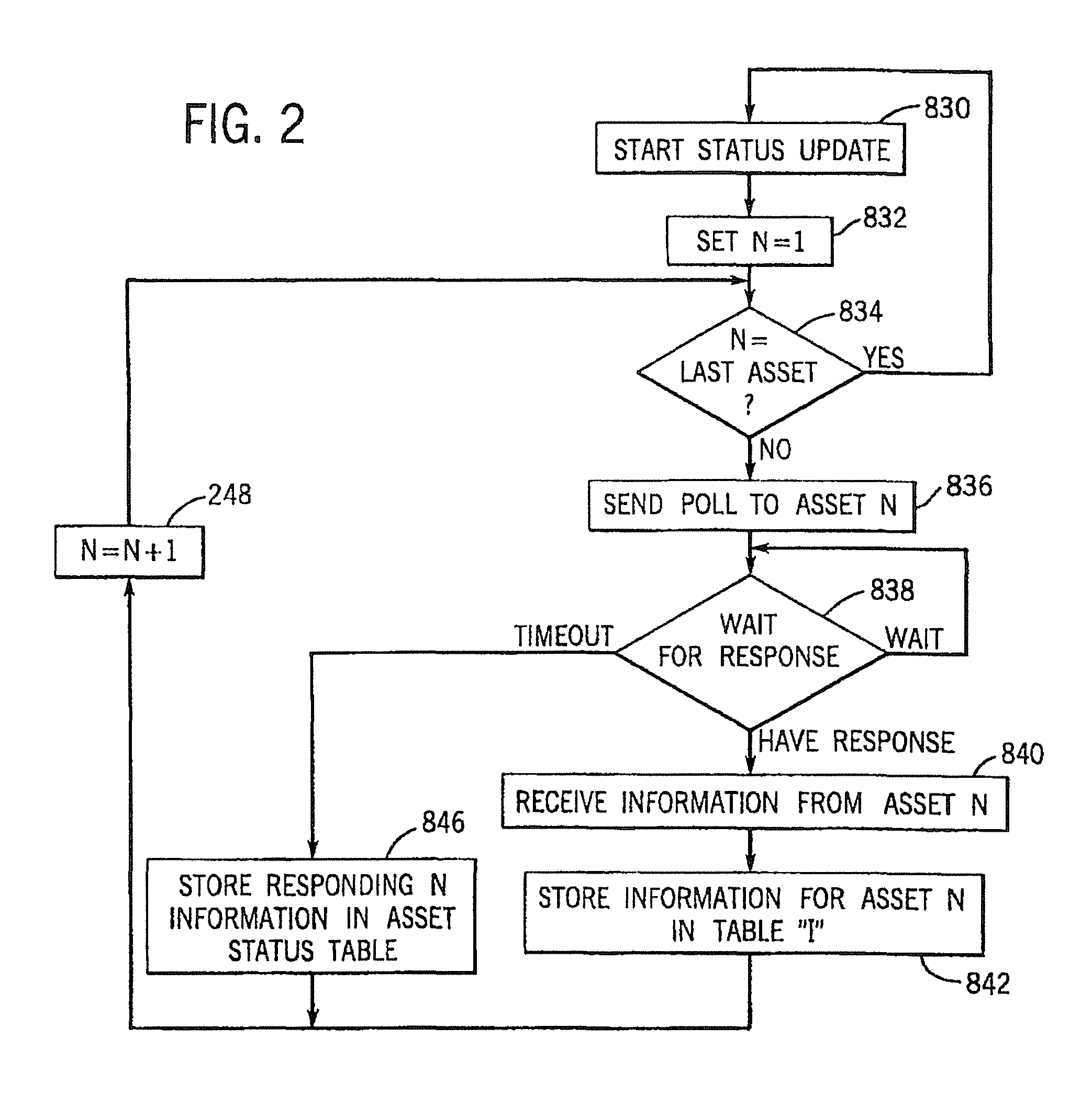
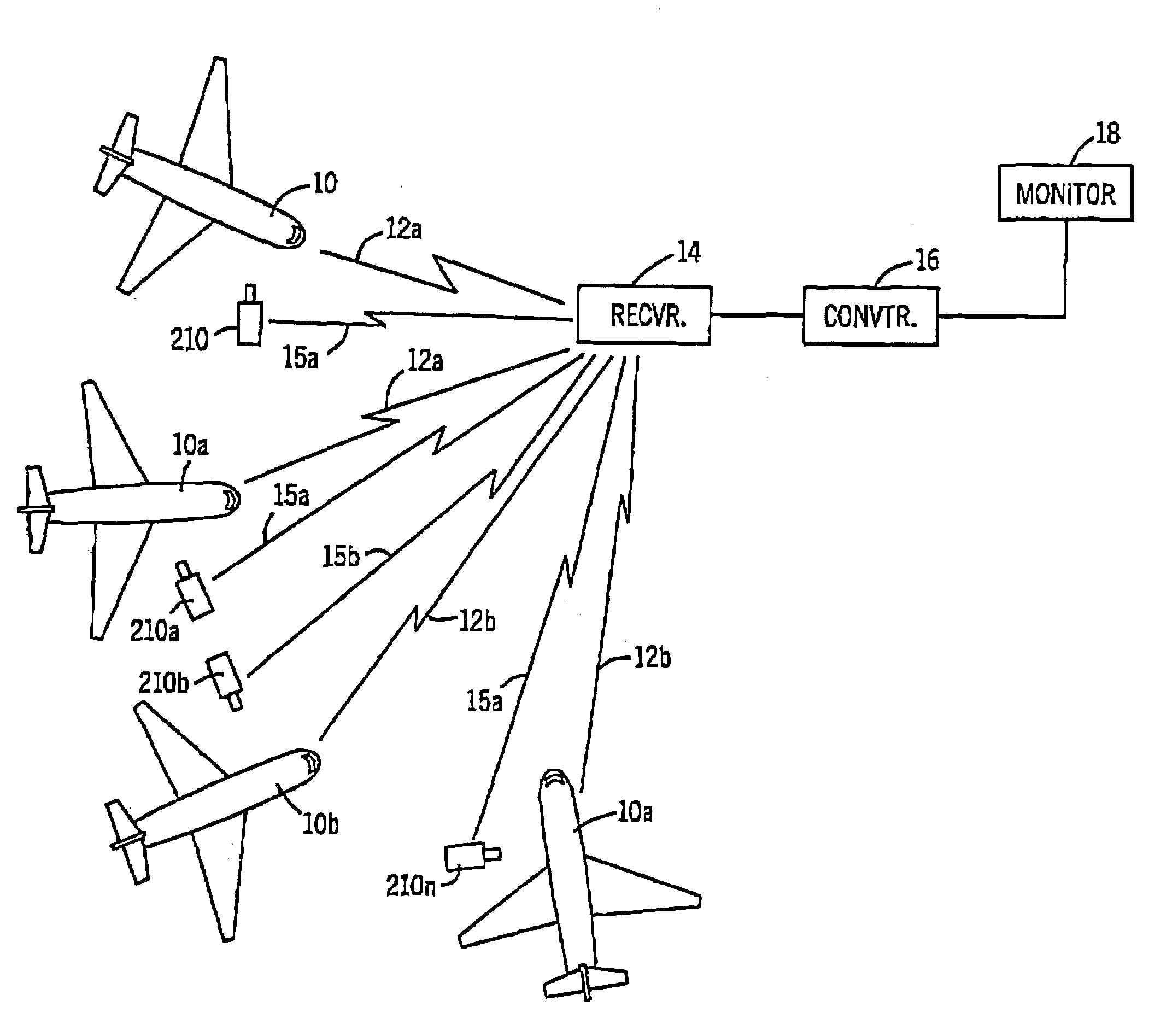
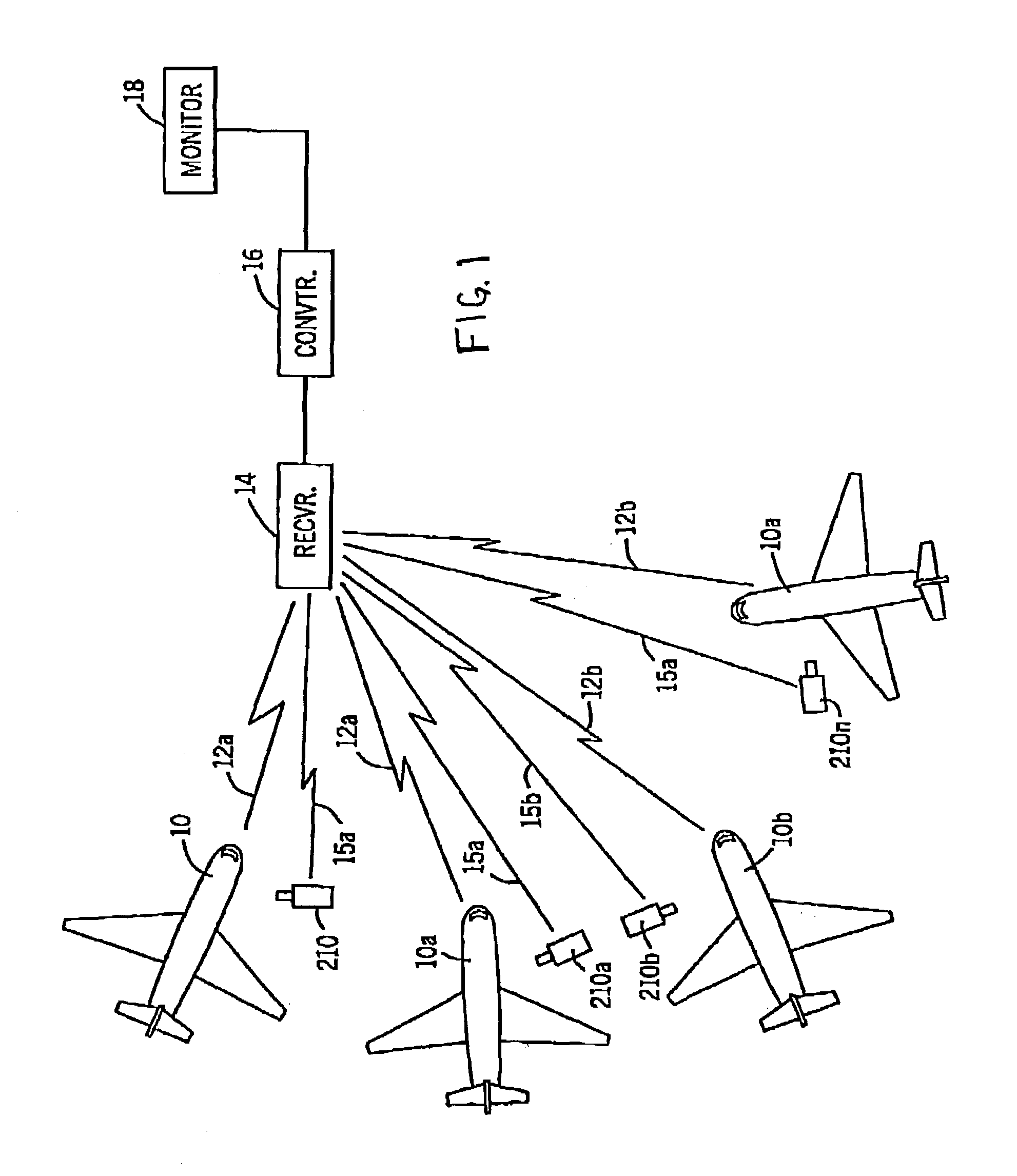
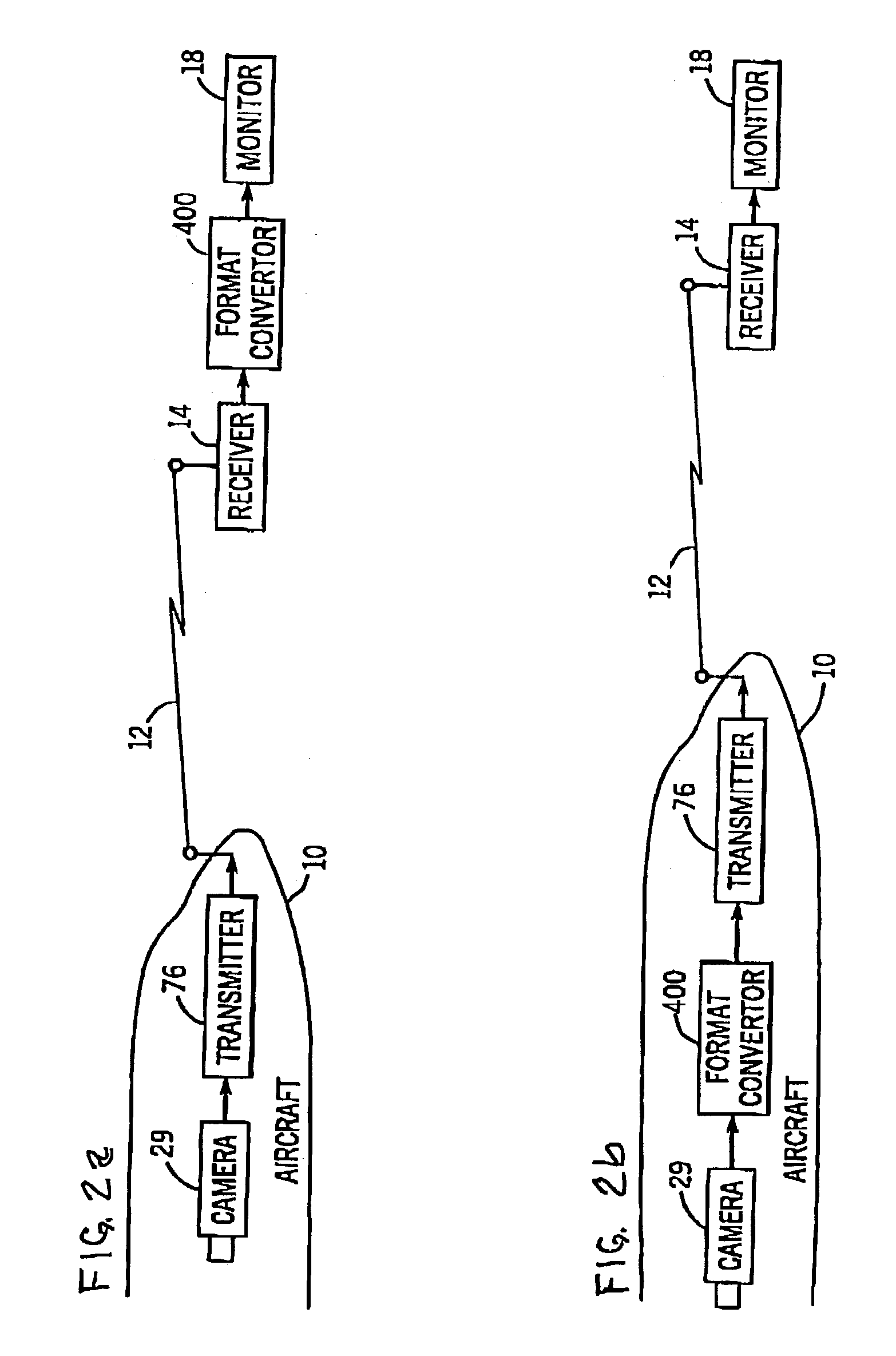
A security and surveillance system for aircraft on the ground incorporates a plurality of strategically spaced sensors including video imaging generators, audio sensors, motion detectors, and fire and smoke detectors for monitoring critical components and critical areas of both the interior and the exterior of the a commercial transport such as an aircraft. The system is a comprehensive multi-media safety, tracking and / or surveillance system, which provides both visual and / or audio information as well as critical data such as location, direction, intrusion, fire and / or smoke detection and / or status of environmental conditions and / or asset systems status. The collected information is analyzed and prioritized according to type of event, location and nature of required response for automatically dispatching the proper response. The captured data and images are transmitted to a ground based security station for display on a monitor and may be recorded on a “black box” recorder as well as on a ground based recording system.
Owner:PR NEWSWIRE
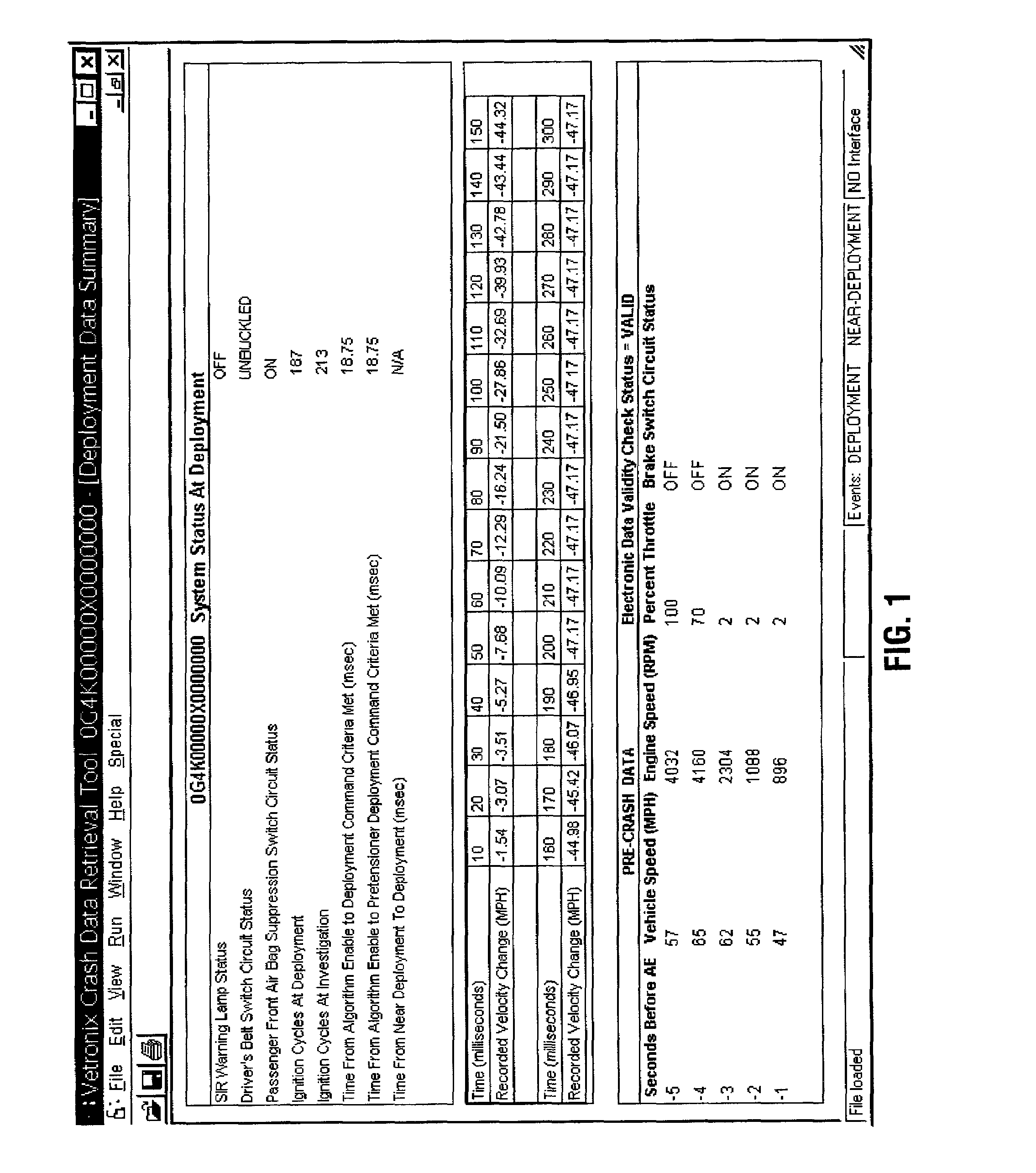
Methods and apparatus for using black box data to analyze vehicular accidents
Disclosed are methods and apparatus for using black box data to analyze vehicular accidents. The methods include obtaining information from an event data recorder associated with a vehicle and using the data obtained therefrom in determining and analyzing the vehicular accident. Attributes to be analyzed include impact severity, change in velocity, and other desired parameters. Further disclosed are methods to securely communicate the downloaded black box information to a secure location for later analysis and processing.
Owner:CCC INFORMATION SERVICES
Dynamical methods for solving large-scale discrete and continuous optimization problems
InactiveUS7050953B2Easy to solveSimple methodDigital computer detailsComputation using non-denominational number representationLocal optimumDynamic method
Dynamical methods for obtaining the global optimal solution of general optimization problems having closed form or black box objective functions, including the steps of first finding, in a deterministic manner, one local optimal solution starting from an initial point, and then finding another local optimal solution starting from the previously found one until all the local optimal solutions starting from any initial point are found, and then finding from said points the global optimal solution.
Owner:BIGWOOD SYST
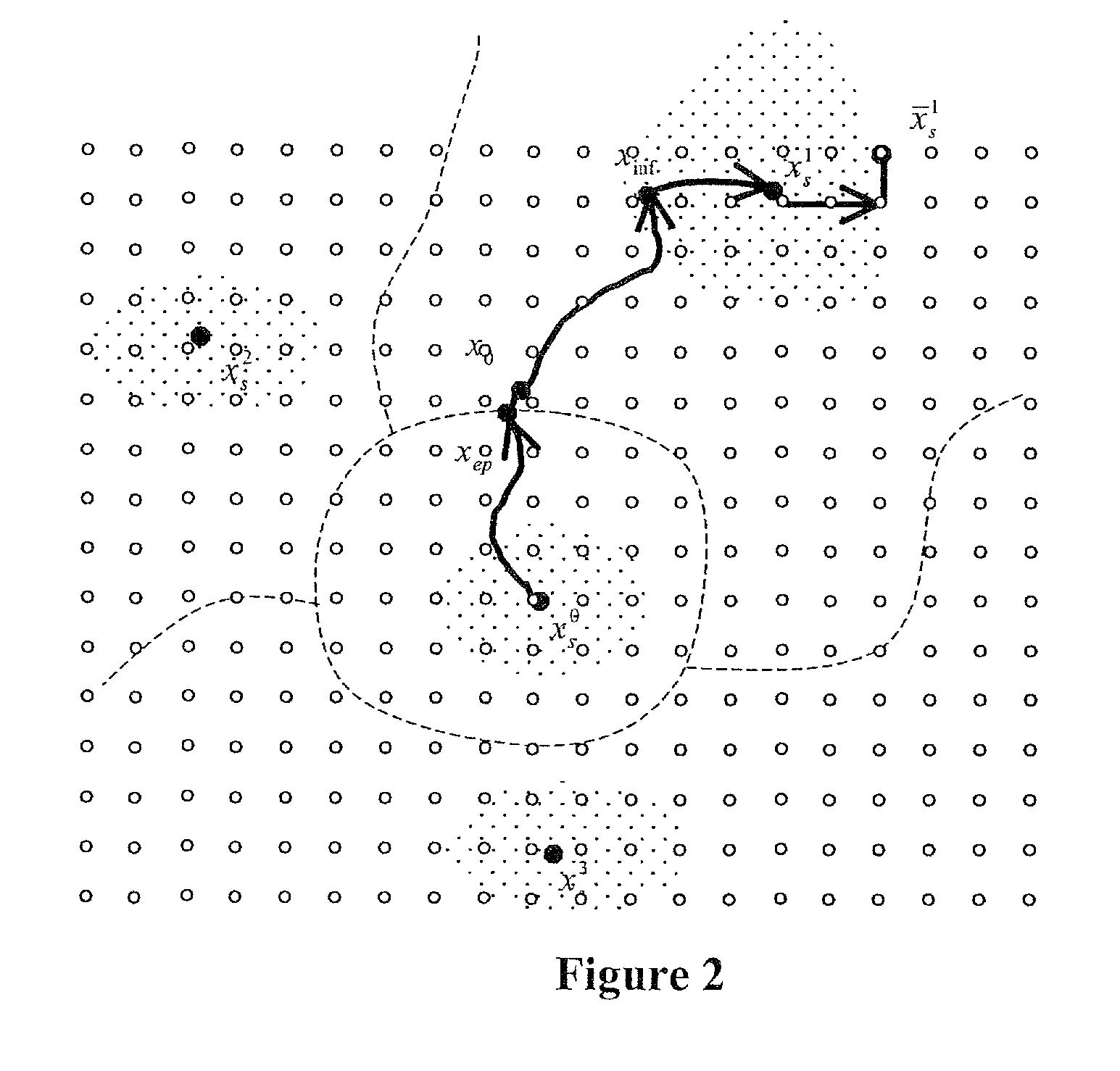
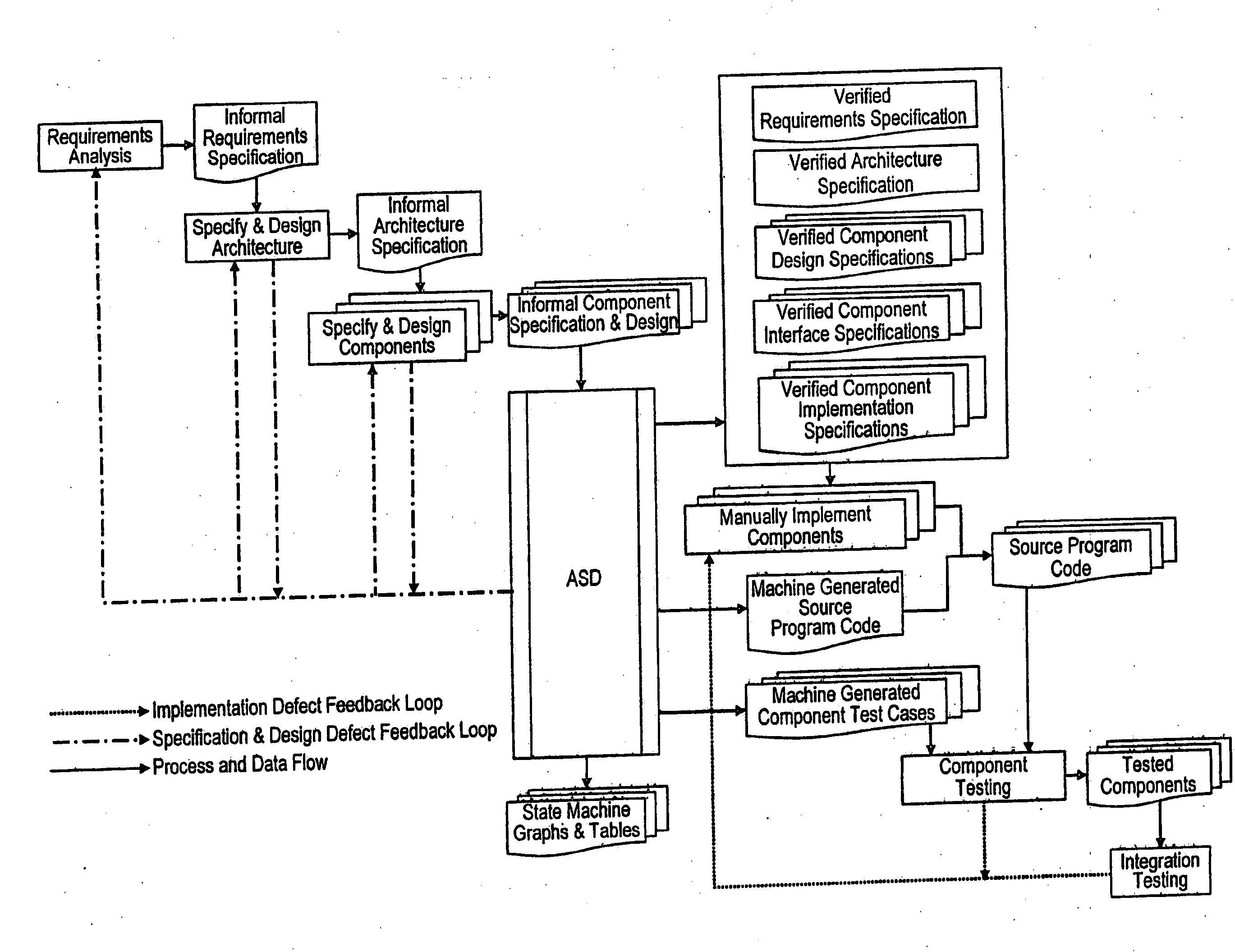
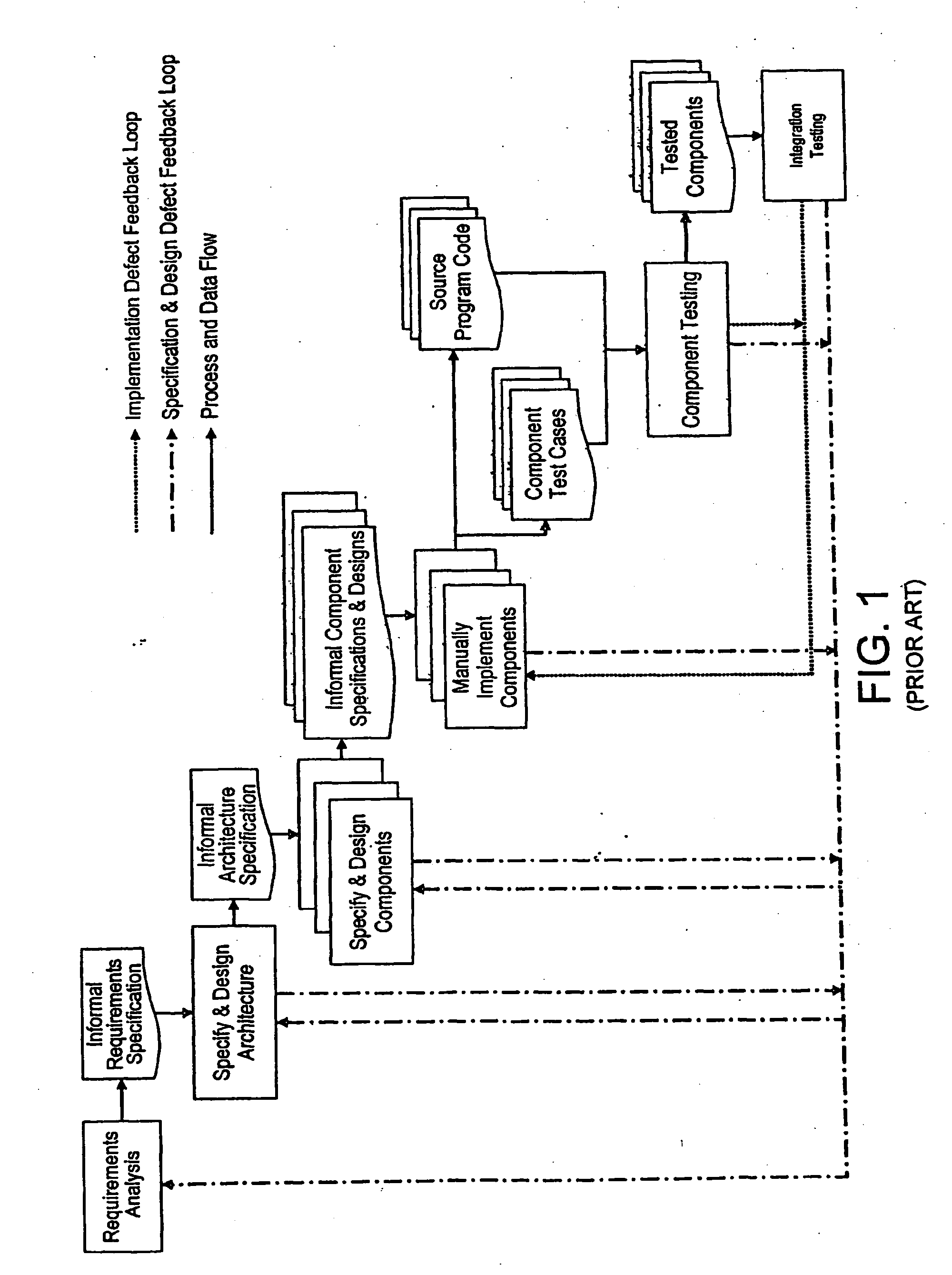
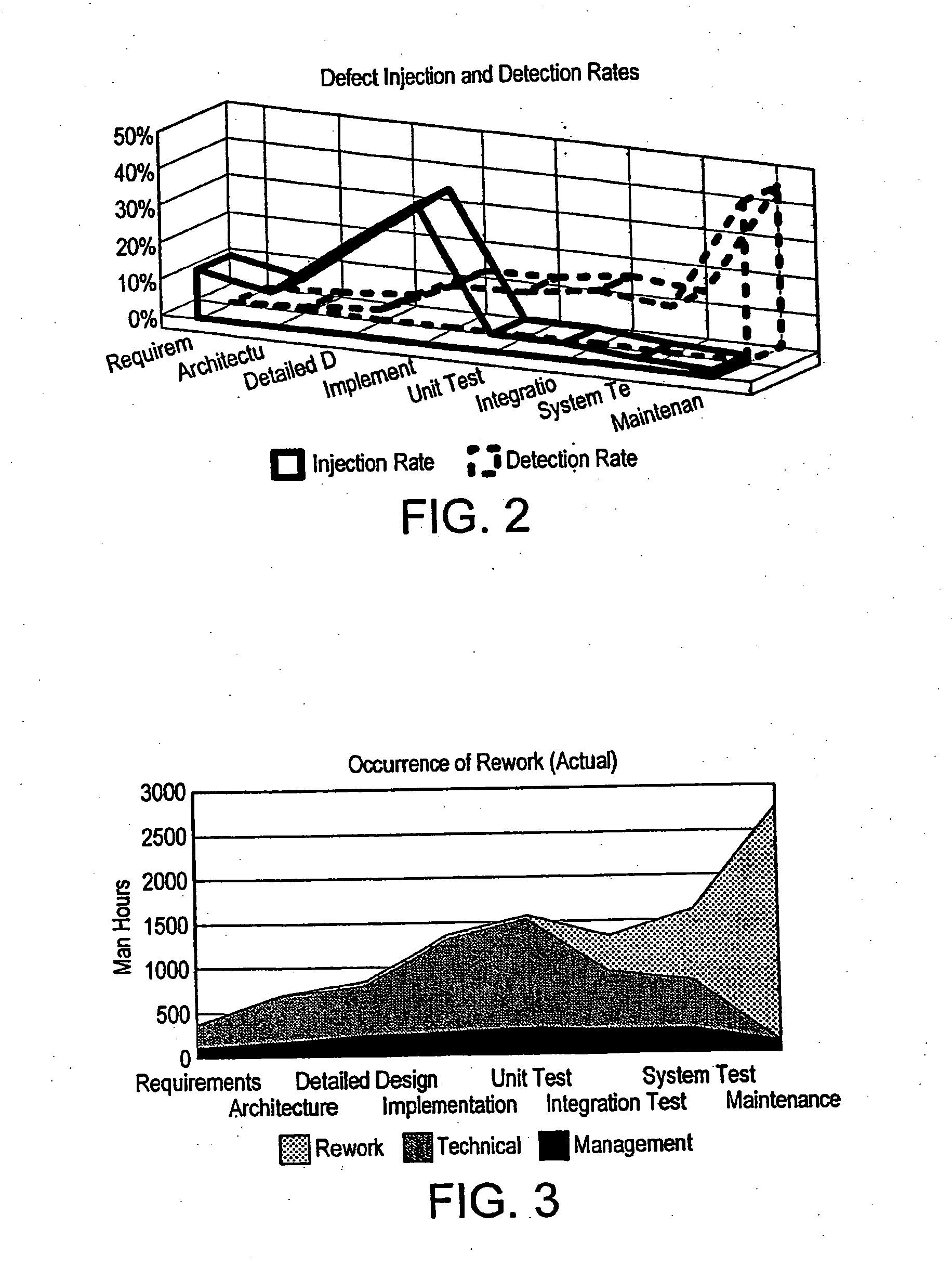
Analytical Software Design System
ActiveUS20080263506A1Improve effectivenessExpand coverageSoftware designRequirement analysisSystems designMathematical model
An analytical software design system arranged to receive informal system design specifications and to convert them into verified design specifications for use in creating source code and carrying out implementation testing of the source code is described. The system comprises a verified black box specification generator arranged to process the received informal system design specifications to create formal specifications; to generate from the formal specifications mathematical models representing the system behaviour; to analyse the mathematical models to determine if they have the required behaviour; to adjust the formal specifications until the required behaviour is achieved; and to derive the required verified design specifications from the mathematical models.
Owner:COCOTEC LTD
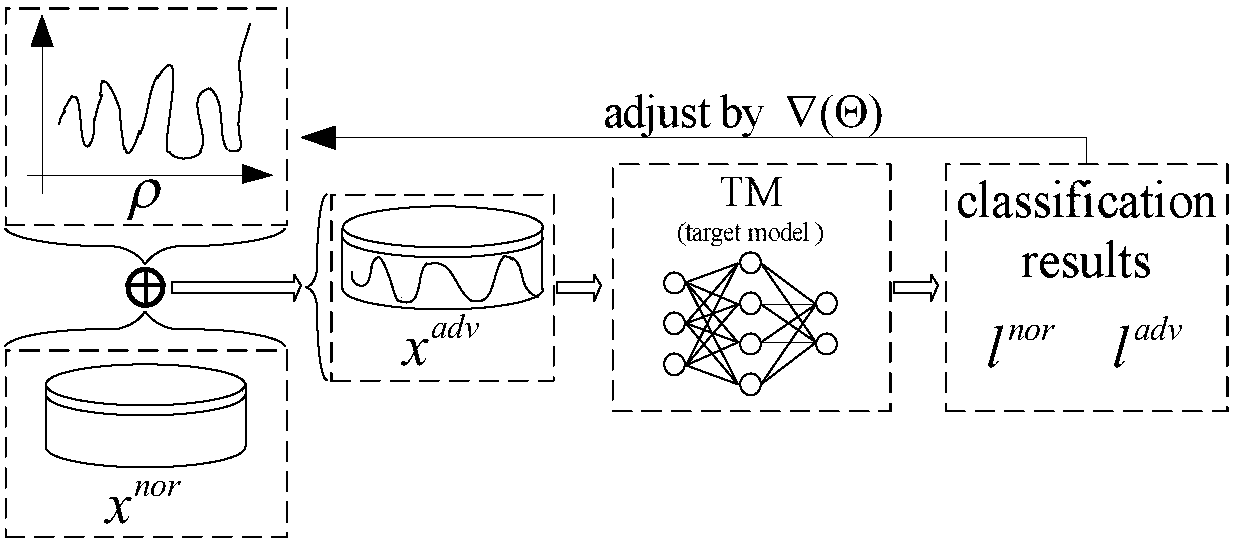
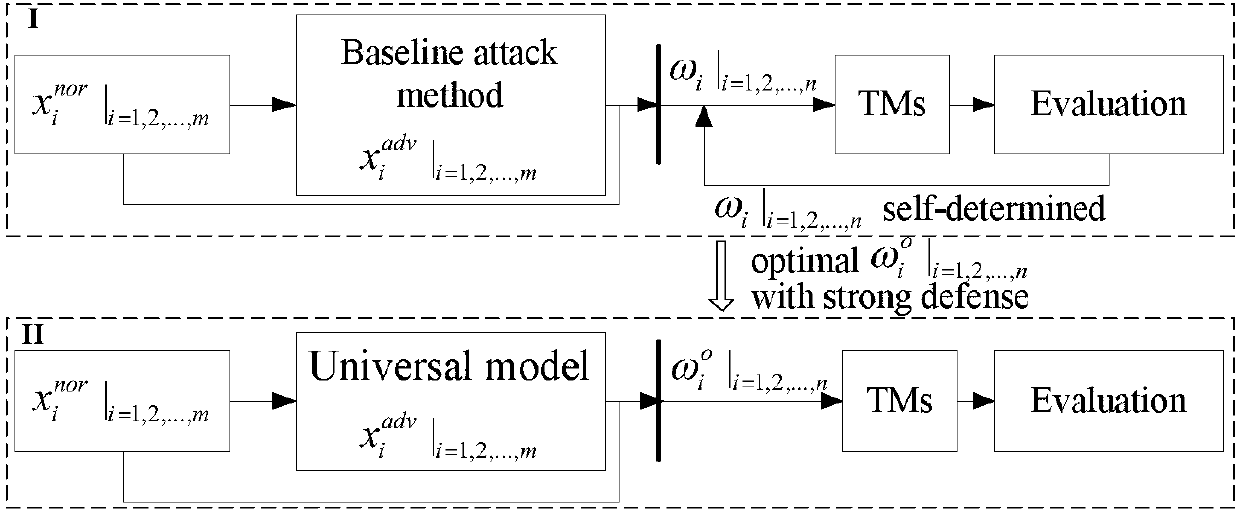
Multi-model cooperative defense method facing deep learning antagonism attack
InactiveCN108446765AEffective defense against attacksAvoid attackCharacter and pattern recognitionNeural learning methodsSubstitution modelAdaBoost
A multi-model cooperative defense method facing deep learning antagonism attack comprises the following steps of: 1) performing unified modeling based on a gradient attack to provide a [Rho]-loss model; 2) according to design of a unified model, for an countering attack of a target model fpre(x), according to a generation result of a countering sample, classifying a basic expression form of an attack into two classes; 3) analyzing the parameters of the model, performing parameter optimization of the [Rho]-loss model and search step length optimization of a disturbance solution model for the countering sample; and 4) for the mystique of a black box attack, designing an experiment based on an adaboost concept, generating a plurality of different types of substitution models, used to achievethe same task, for integration, designing a multi-model cooperative defense method with high defense capability through an attack training generator of an integration model with high defense capability, and providing multi-model cooperative detection attack with weight optimal distribution. The multi-model cooperative defense method is high in safety and can effectively defense the attack of a deep learning model for the antagonism attack.
Owner:ZHEJIANG UNIV OF TECH
Vehicle black box
InactiveUS20120109447A1Vehicle testingRegistering/indicating working of vehiclesRecording durationReal-time data
A vehicle black box includes a memory device for receiving and storing real-time data associated with the vehicle during a recording time window. Upon determining that an accident has occurred, circuitry freezes the recording time window and stores the real-time data within the frozen recording time window within a one-time programmable (OTP) memory.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and method of targeting advertisements and providing advertisements management
InactiveUS20110078018A1Slow searchesSpecial service provision for substationWeb data indexingOperational systemStructure of Management Information
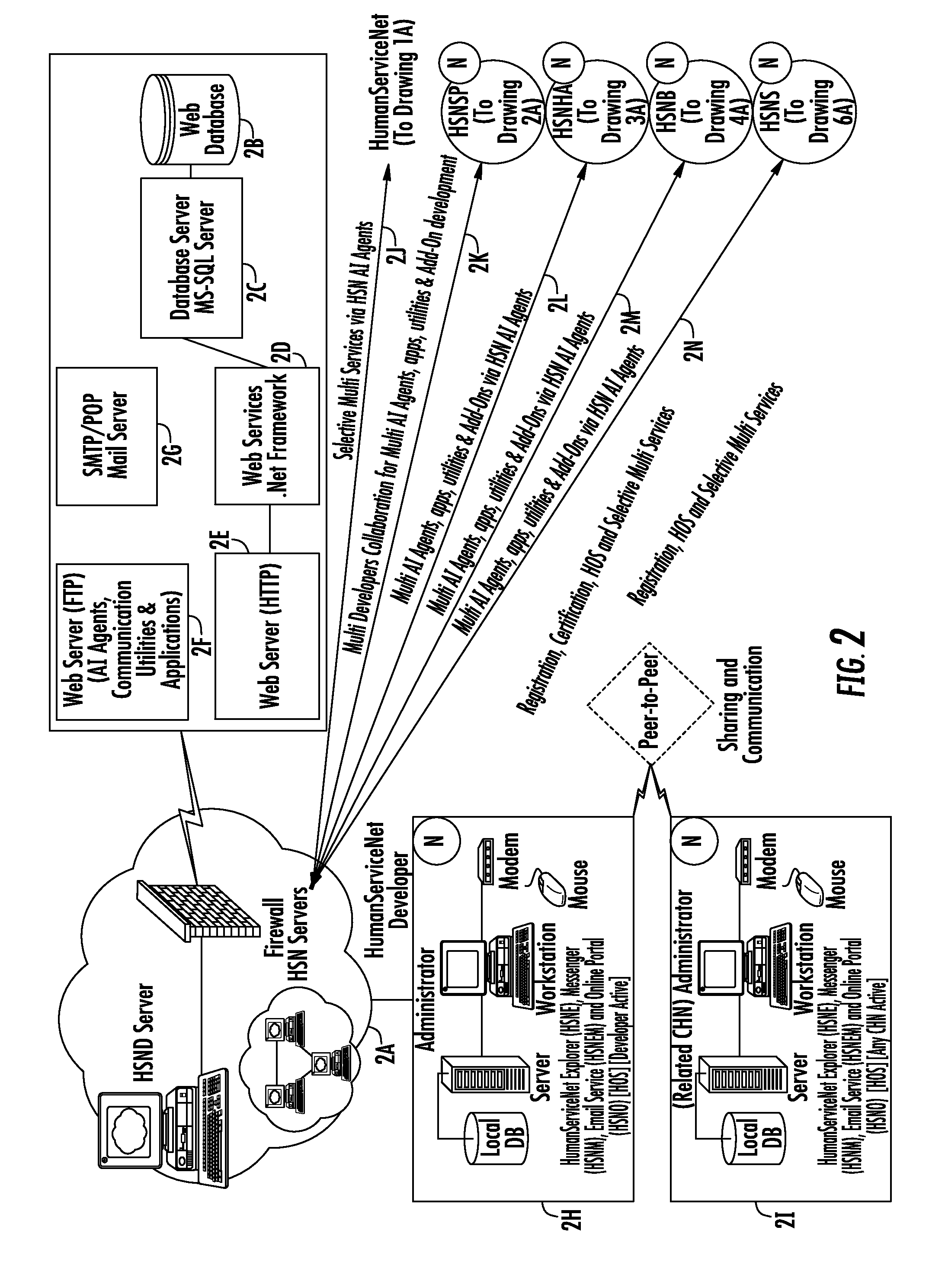
A system for transmission, reception and accumulation of the knowledge packets to plurality of channel nodes in the network operating distributedly in a peer to peer environment via installable one or more role active Human Operating System (HOS) applications in a digital devise of each of channel node, a network controller registering and providing desired HOS applications and multiple developers developing advance communication and knowledge management applications and each of subscribers exploiting the said network resources by leveraging and augmenting taxonomically and ontologically classified knowledge classes expressed via plurality search macros and UKID structures facilitating said expert human agents for knowledge invocation and support services and service providers providing information services in the preidentified taxonomical classes, wherein each of channel nodes communicating with the unknown via domain specific supernodes each facilitating social networking and relationships development leading to human grid which is searchable via Universal Desktop Search by black box search module.
Owner:ONEPATONT SOFTWARE LTD
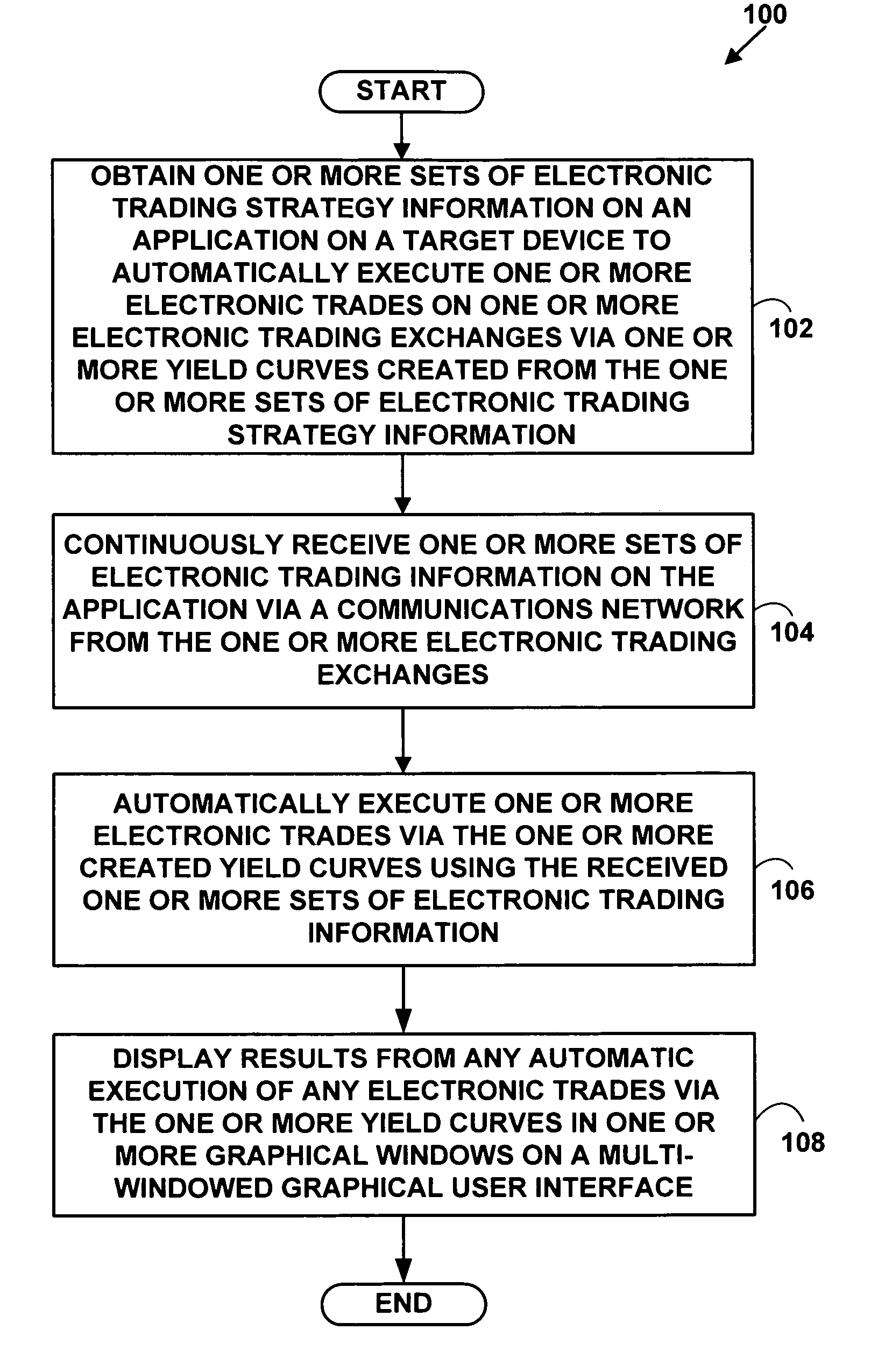
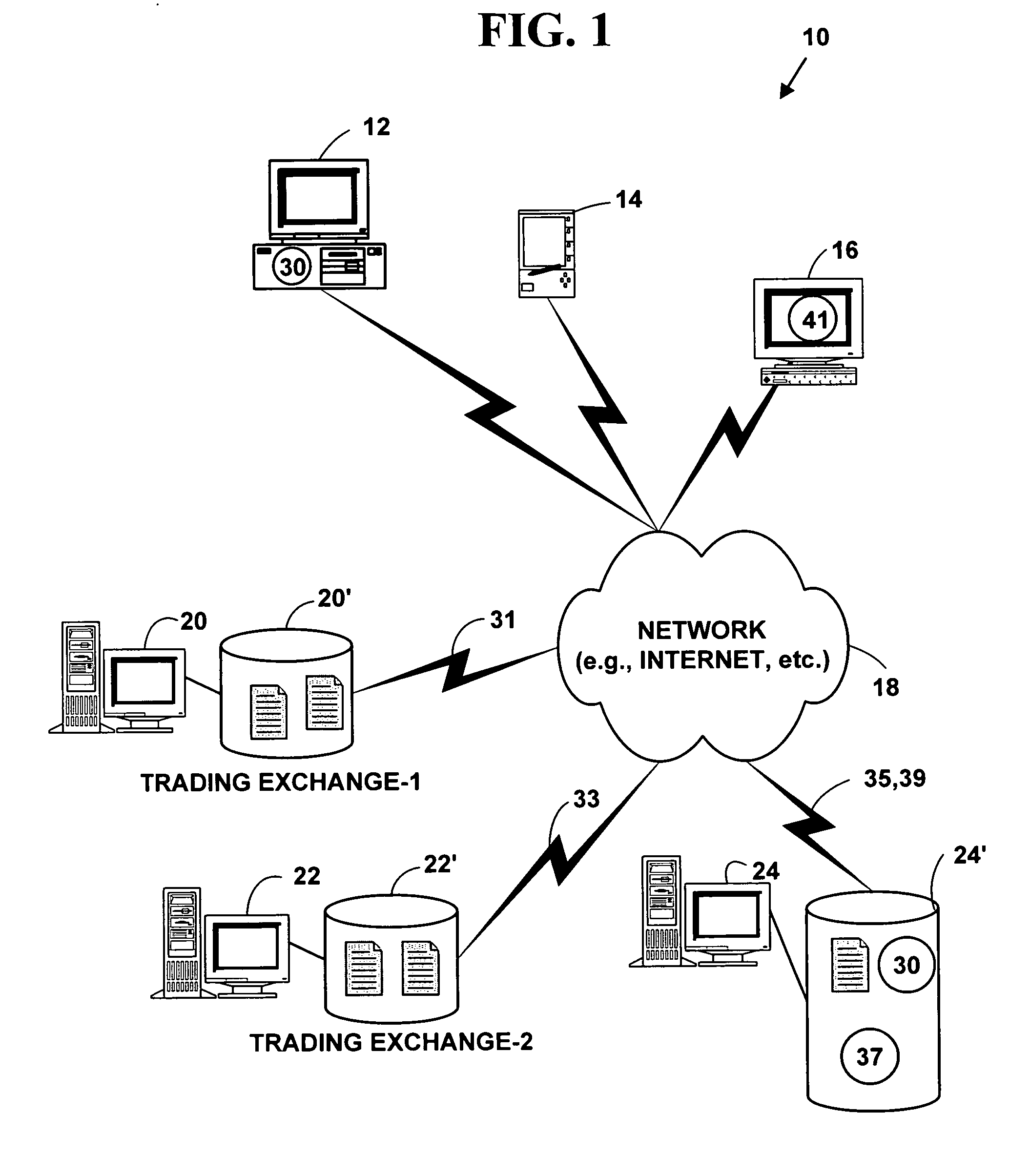
Method and system for electronic trading via a yield curve
A method and system for providing electronic trading via yield curves. The method and system allow automatic execution of electronic trades with yield curve trading strategies using real, synthetic, black box, spread, and supply differential yield curve trading information.
Owner:PRIME TRADING LLC +1
Method and apparatus for extraction of nonlinear black-box behavioral models from embeddings of the time-domain measurements
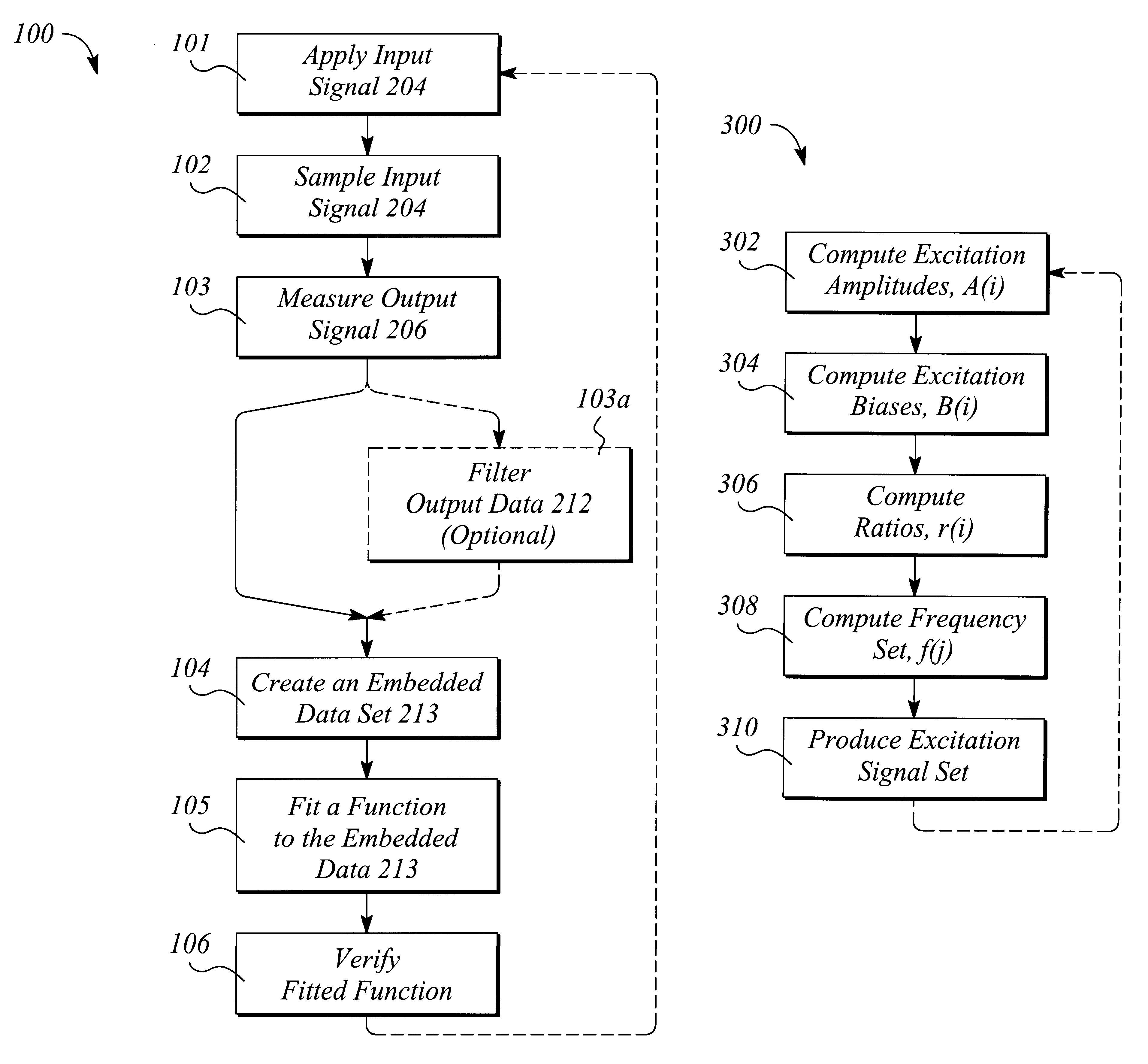
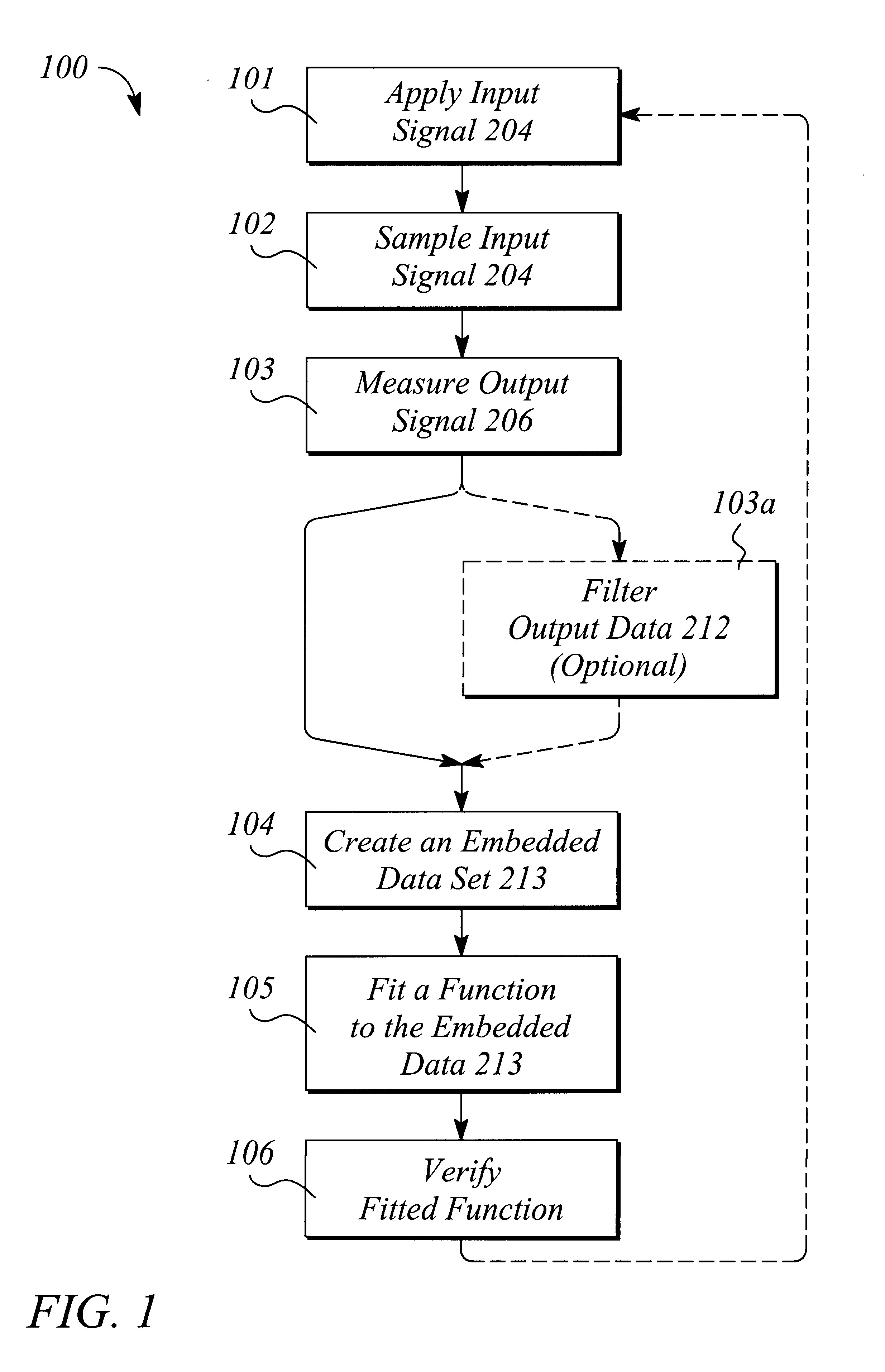
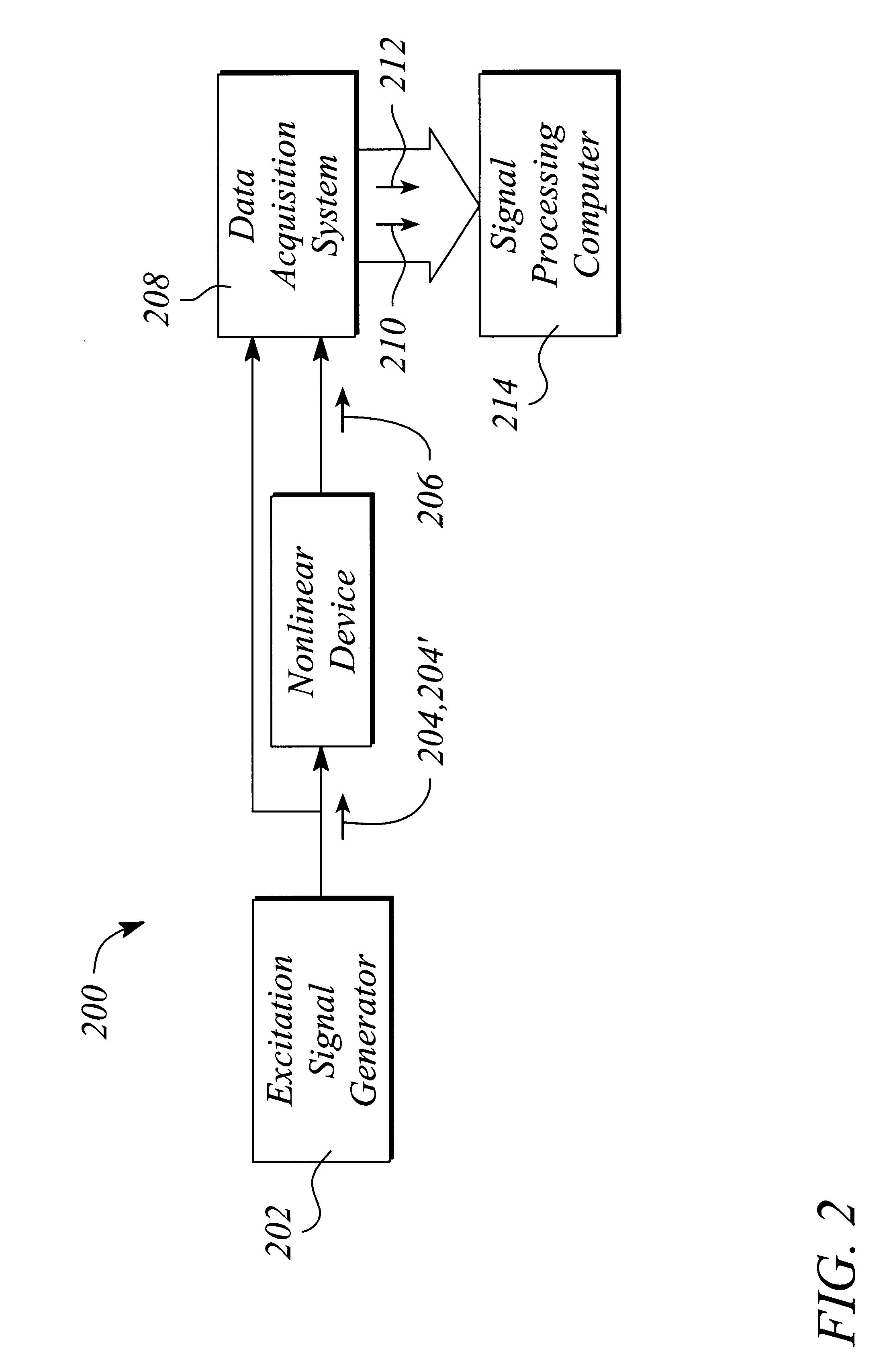
A method and apparatus that utilize time-domain measurements of a nonlinear device produce or extract a behavioral model from embeddings of these measurements. The method of producing a behavioral model comprises applying an input signal to the nonlinear device, sampling the input signal to produce input data, measuring a response of the device to produce output data, creating an embedded data set, fitting a function to the embedded data set, and verifying the fitted function. The apparatus comprises a signal generator that produces an input signal that is applied to the nonlinear device, the device producing an output signal in response. The apparatus further comprises a data acquisition system that samples and digitizes the input and output signals and a signal processing computer that produces an embedded data set from the digitized signals, fits a function to the embedded data set, and verifies the fitted function.
Owner:AGILENT TECH INC
Method and system for electronic trading via a yield curve
A method and system for providing electronic trading via yield curves. The method and system allow automatic execution of electronic trades with yield curve trading strategies using real, synthetic, black box, spread, and supply differential yield curve trading information.
Owner:PRIME TRADING LLC +1
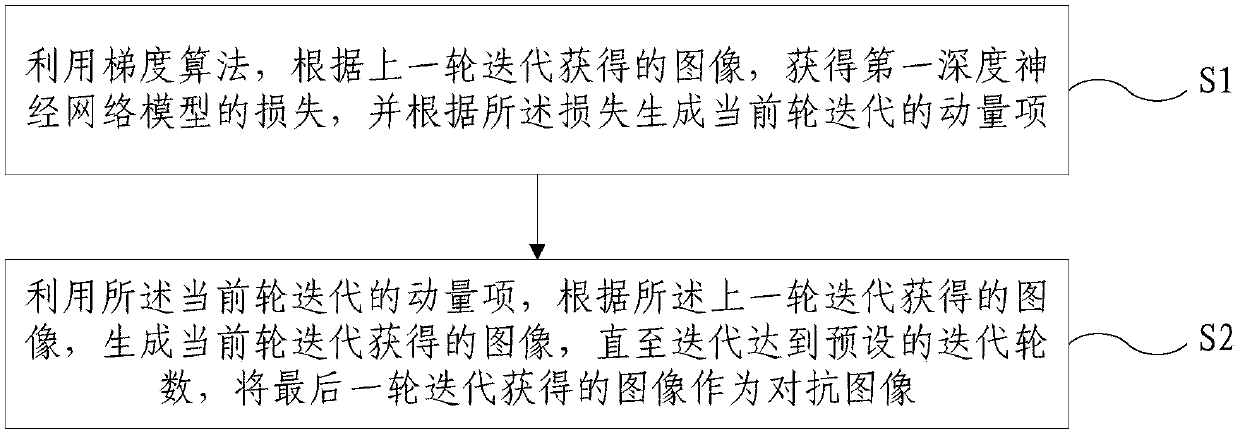
Method for generating adversarial image
InactiveCN108257116AImprove robustnessImprove accuracyImage enhancementImage analysisMomentumAlgorithm
The invention provides a method for generating an adversarial image. The method comprises: on the basis of a gradient algorithm, a loss value of a first deep neural network model is obtained accordingto an image obtained by last-turn iteration, and a momentum of current-turn iteration is generated based on the loss value; and on the basis of the momentum of current-turn iteration, an image obtained by current-turn iteration is generated based on the image obtained by the last-turn iteration until iteration reaches a preset iteration turn number, and the image obtained by the last-turn iteration is used as an adversarial image. According to the method provided by the invention, iteration of an original image is carried out by using the momentum and the adversarial image being capable of attach the deep neural network model is obtained, so that coupling between a white-box attack success rate and a migration performance is reduced effectively. The high attack success rates of the whitebox model and the black box model are realized. The method can be used for adversarial training, thereby improving the correction rate of image classification by using the deep neural network model and also can be used for attacking the deep neural network model.
Owner:TSINGHUA UNIV
Vehicular black box monitoring system
InactiveUS20050099279A1Evaluate performanceRegistering/indicating working of vehiclesColor television detailsMonitoring systemEngineering
A vehicular “black box” provides recording means by which driver action can be reviewed after an accident or collision, as well as indicating immediate vehicle disposition status to the driver. Using cameras (which may be very small), the disposition of the vehicle in its lane is determined by detecting the highway lines painted on the road. The data is also recorded so that should an accident or collision occur, the events leading up to such an event are made available for later review and analysis.
Owner:FORBES FRED +3
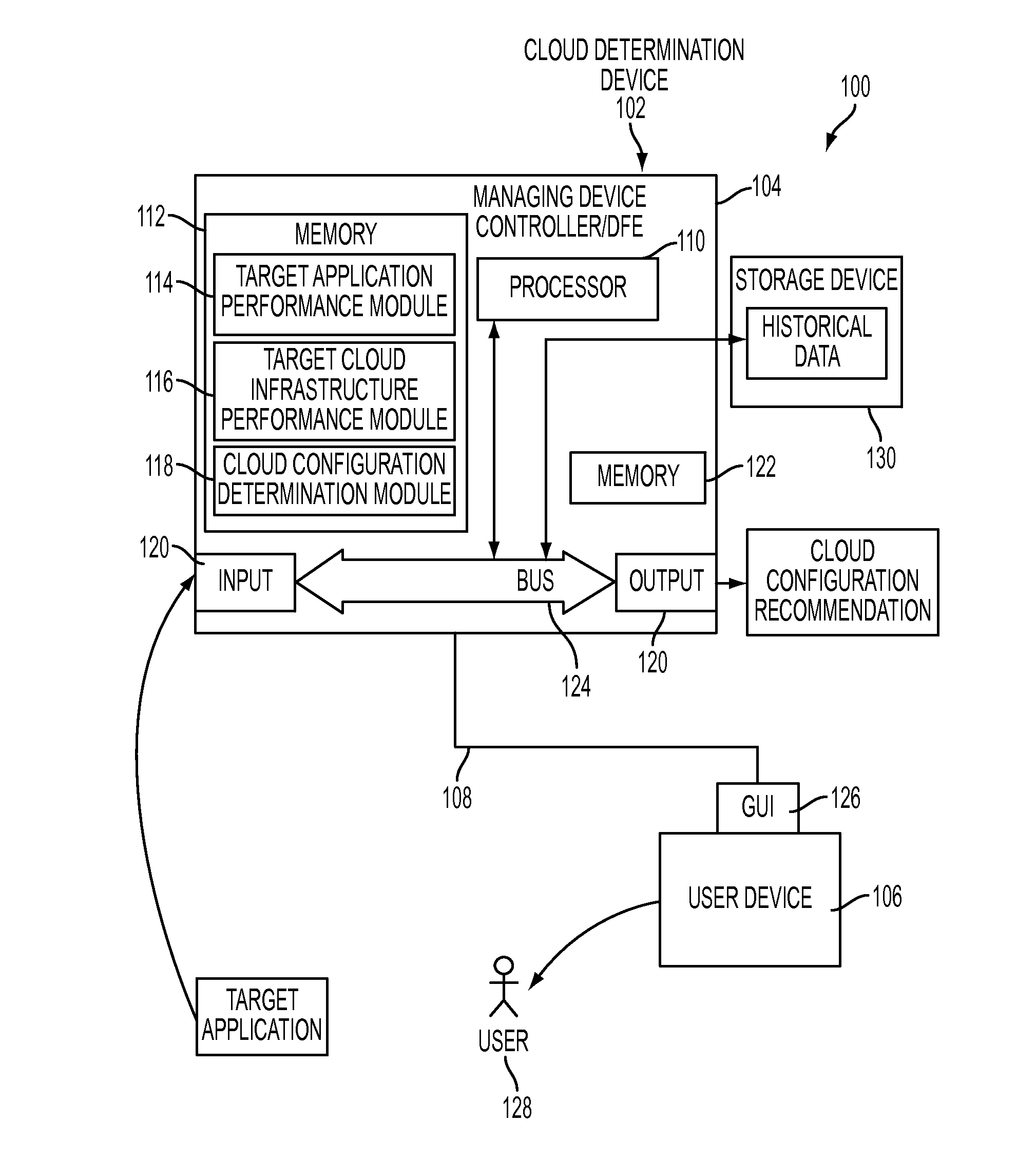
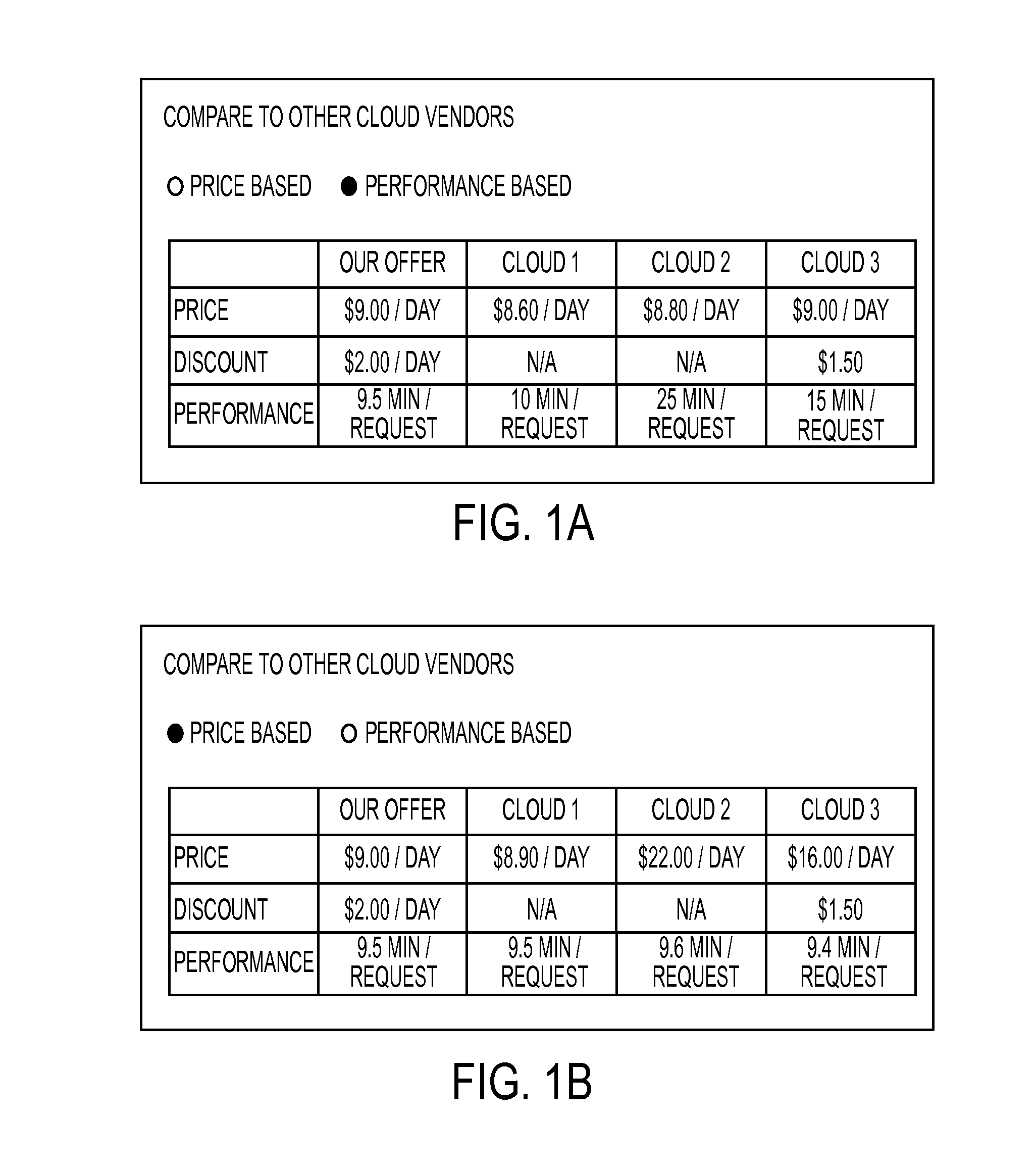
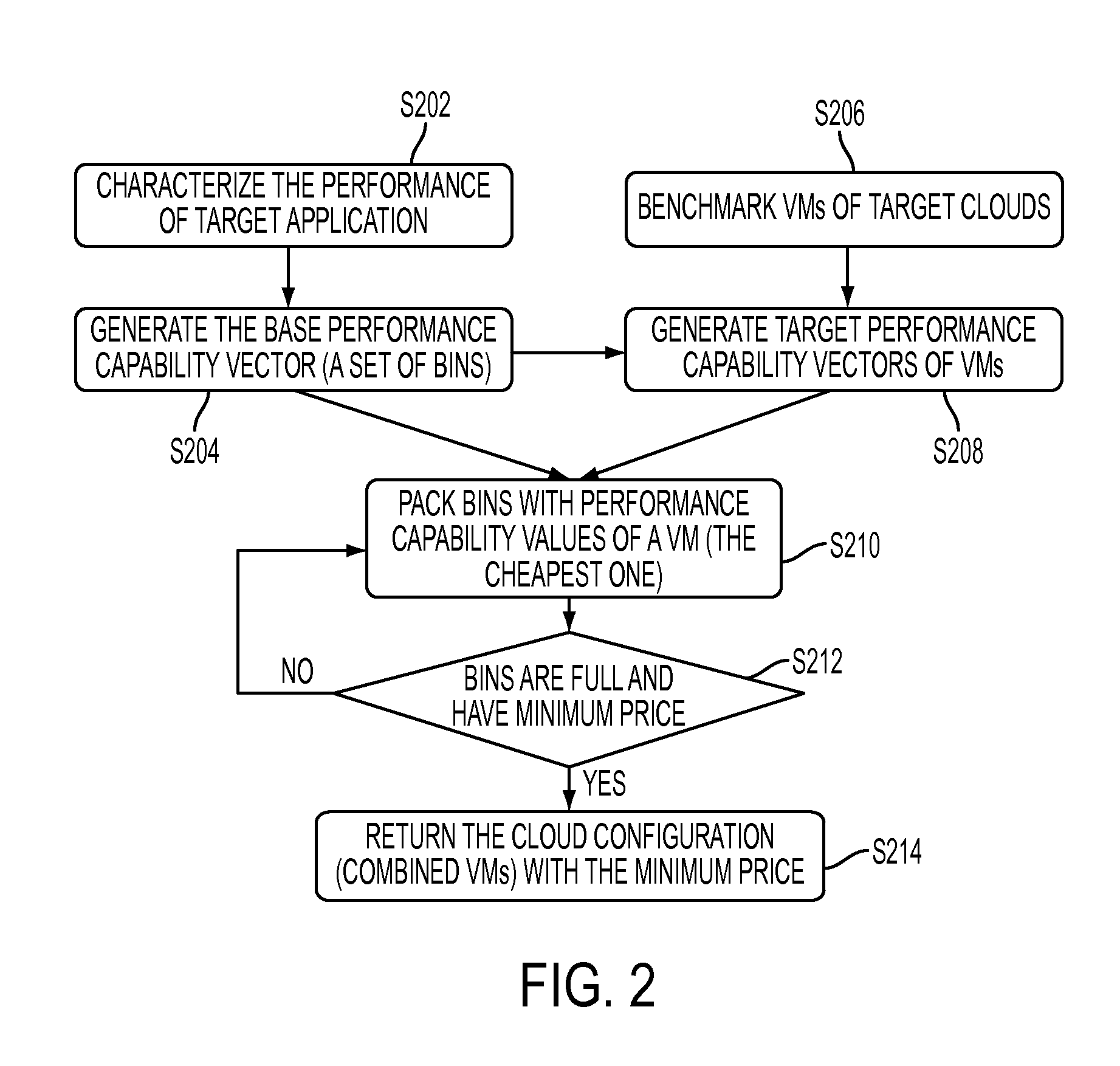
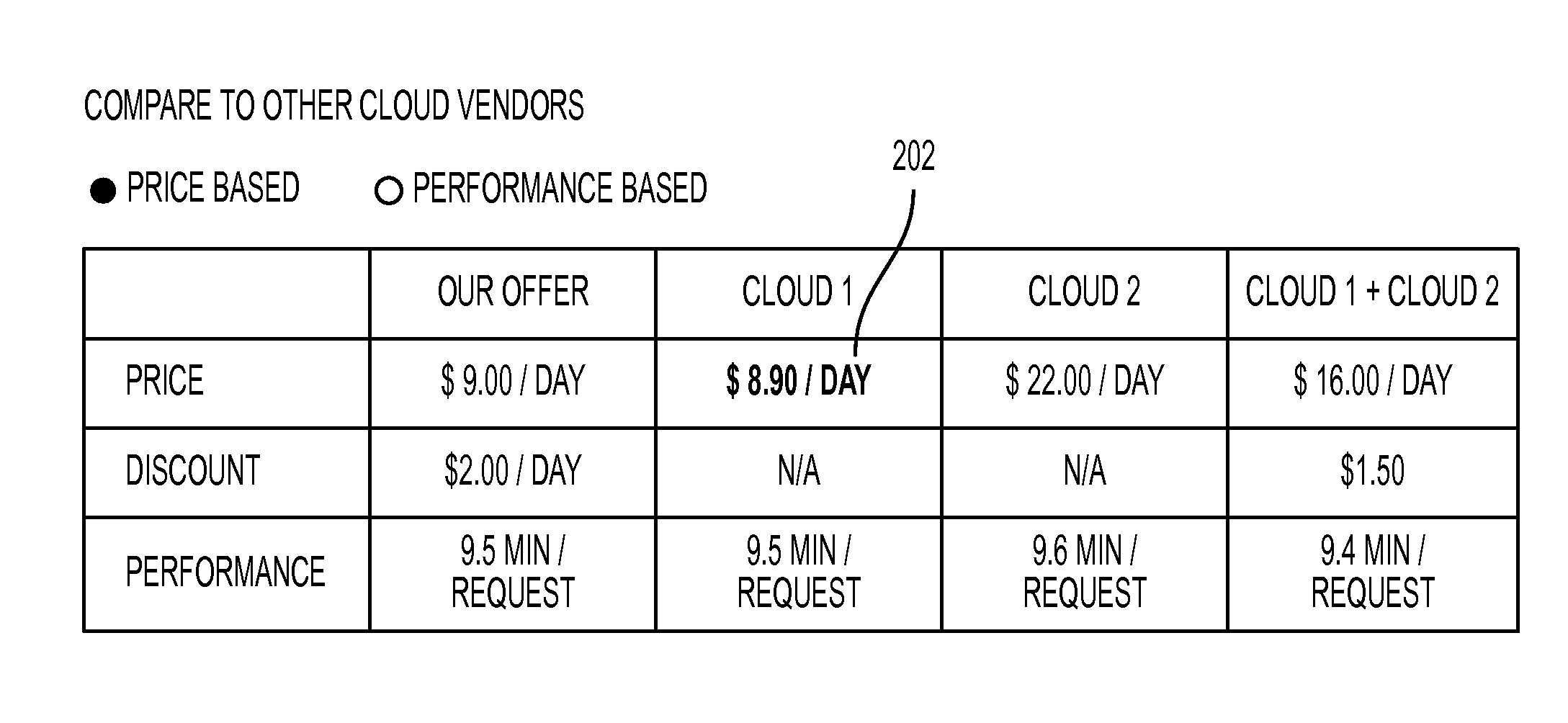
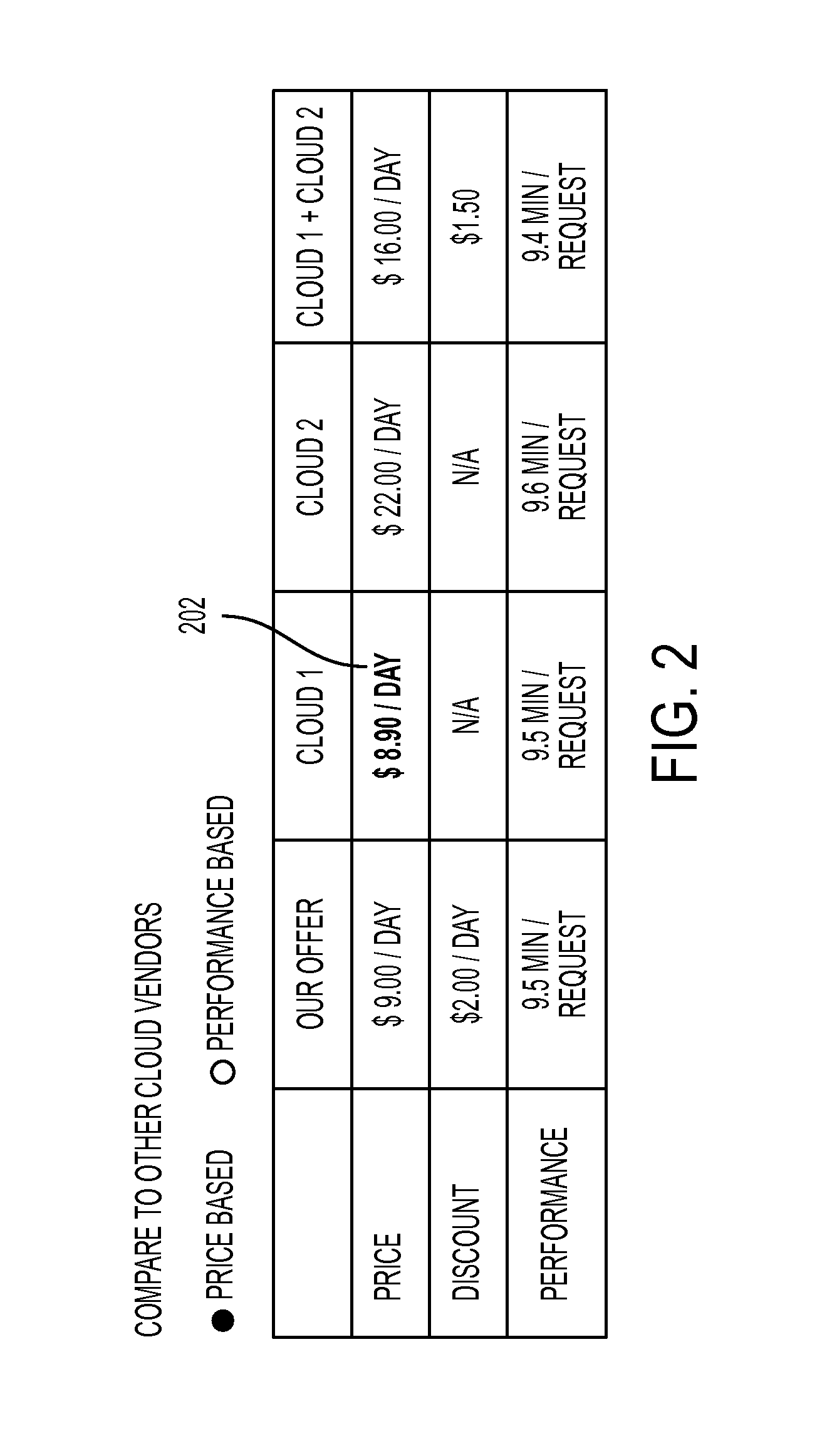
System and method for identifying optimal cloud configuration in black-box environments to achieve target throughput with best price based on performance capability benchmarking
A method and system identifies a cloud configuration for deploying a software application. A performance of a target application and workload is characterized. A set of benchmark applications is then deployed into at least one target cloud infrastructure. The target infrastructure is characterized using the set of benchmarking applications. The performance of the target application is represented with a set of bins each corresponding to a resource subsystem of a virtual machine and a performance score that is required to deploy the target application and meet the target performance. The bins are filled with performance values for selected target virtual machines. Using the filled bins, a set of virtual machines needed to satisfy the target cloud infrastructure is determined. A recommendation is provided for the set of virtual machines to use in deploying the software application.
Owner:XEROX CORP
Apparatus and method of collecting and distributing event data to strategic security personnel and response vehicles
InactiveUS7173526B1Good informationEffective trackingFrequency-division multiplex detailsRoad vehicles traffic controlSmoke detectorsMotion detector
A security and surveillance system for aircraft on the ground incorporates a plurality of strategically spaced sensors including video imaging generators, audio sensors, motion detectors, and fire and smoke detectors for monitoring critical components and critical areas of both the interior and the exterior of the a commercial transport such as an aircraft. The system is a comprehensive multi-media safety, tracking and / or surveillance system, which provides both visual and / or audio information as well as critical data such as location, direction, intrusion, fire and / or smoke detection and / or status of environmental conditions and / or asset systems status. The collected information is analyzed and prioritized according to type of event, location and nature of required response for automatically dispatching the proper response. The captured data and images are transmitted to a ground based security station for display on a monitor and may be recorded on a “black box” recorder as well as on a ground based recording system.
Owner:PR NEWSWIRE
Ground based security surveillance system for aircraft and other commercial vehicles
InactiveUS7049953B2Enhanced monitoring and/orresponseEnhances maintenance procedureRoad vehicles traffic controlColor television detailsMotion detectorSmoke detectors
A security and surveillance system for aircraft on the ground incorporates a plurality of strategically spaced sensors including video imaging generators, audio sensors, motion detectors, and fire and smoke detectors for monitoring critical components and critical areas of both the interior and the exterior of the a commercial transport such as an aircraft. The captured data and images are transmitted to a ground based security station for display on a monitor and may be recorded on a “black box” recorder as well as on a ground based recording system. The multiple audio and image signals are multiplexed and sequenced utilizing split screen technology in order to minimize the recording and monitoring hardware required to process the images.
Owner:PR NEWSWIRE
Producing a new black box for a digital rights management (DRM) system
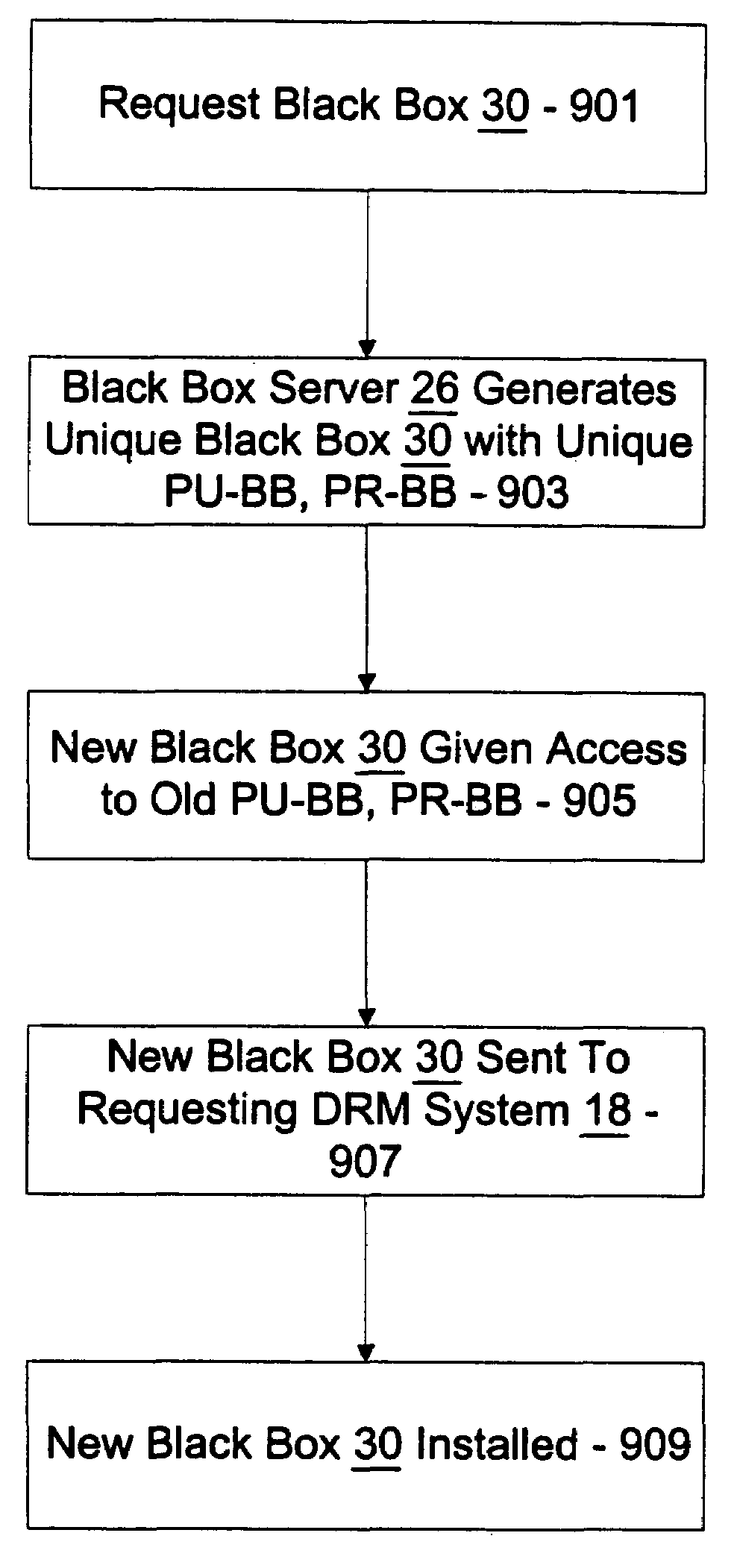
InactiveUS20080195871A1Encryption apparatus with shift registers/memoriesUnauthorized memory use protectionComputer hardwareDigital rights management
A new ((n)th) black box is produced for a digital rights management (DRM) system. The (n)th black box is for being installed in and for performing decryption and encryption functions in the DRM system. The (n)th black box is produced and delivered to the DRM system upon request and includes a new ((n)th) executable and a new ((n)th) key file. The (n)th key file has a new ((n)th) set of black box keys and a number of old sets of black box keys. The request includes an old ((n-1)th) key file having the old sets of black box keys. A code optimizer / randomizer receives a master executable and randomized optimization parameters as inputs and produces the (n)th executable as an output. A key manager receives the (n-1)th key file and the (n)th set of black box keys as inputs, extracts the old sets of black box keys from the (n-1)th key file, and produces the (n)th key file including the (n)th set of black box keys and the old sets of black box keys as an output. The (n)th executable and the (n)th key file are forwarded to the requesting DRM system.
Owner:MICROSOFT TECH LICENSING LLC
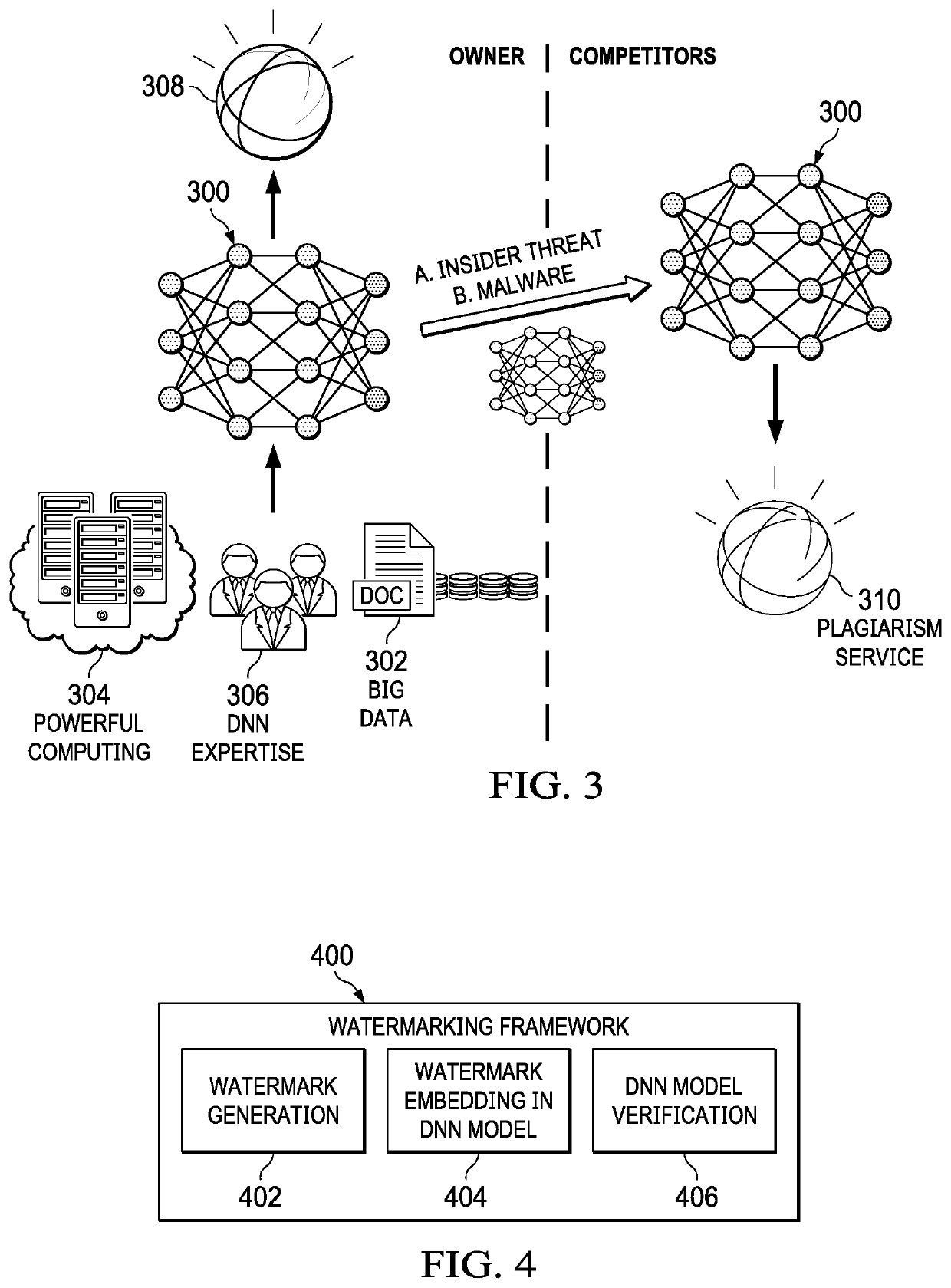
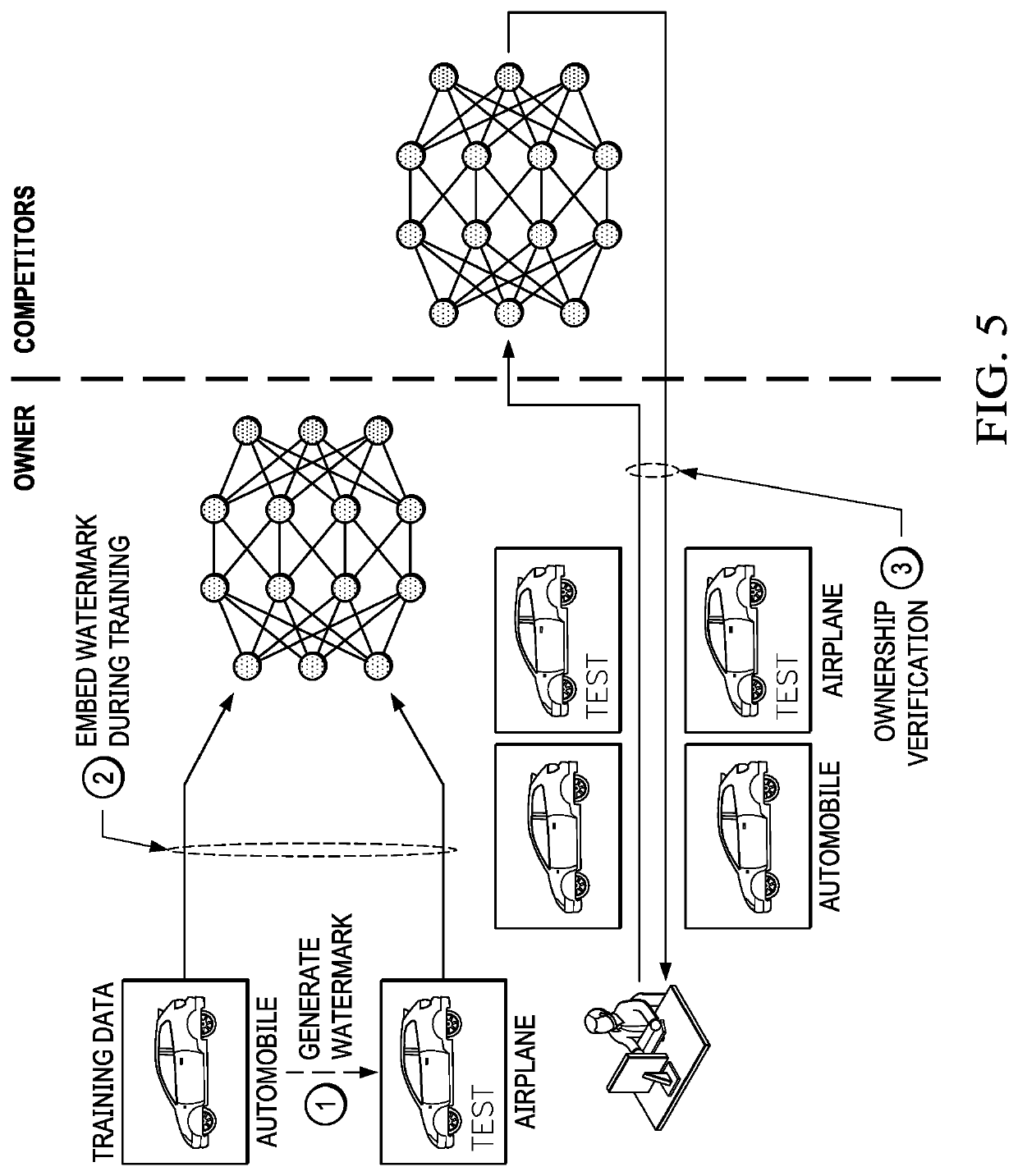
Protecting deep learning models using watermarking
ActiveUS20190370440A1Carry-out efficiently and reliablyProtect intellectual propertyProgram/content distribution protectionNeural learning methodsBlack boxLearning models
A framework to accurately and quickly verify the ownership of remotely-deployed deep learning models is provided without affecting model accuracy for normal input data. The approach involves generating a watermark, embedding the watermark in a local deep neural network (DNN) model by learning, namely, by training the local DNN model to learn the watermark and a predefined label associated therewith, and later performing a black-box verification against a remote service that is suspected of executing the DNN model without permission. The predefined label is distinct from a true label for a data item in training data for the model that does not include the watermark. Black-box verification includes simply issuing a query that includes a data item with the watermark, and then determining whether the query returns the predefined label.
Owner:IBM CORP
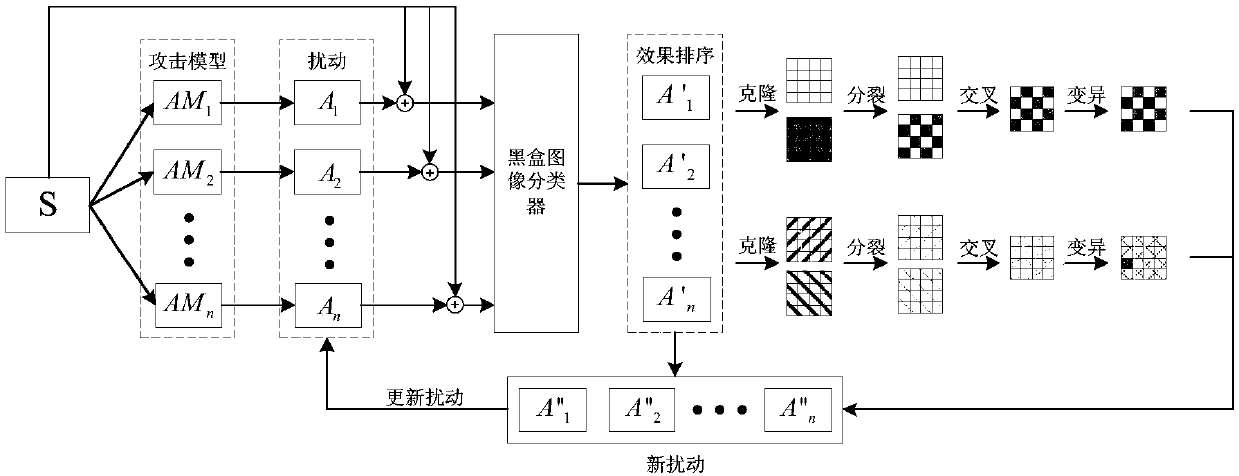
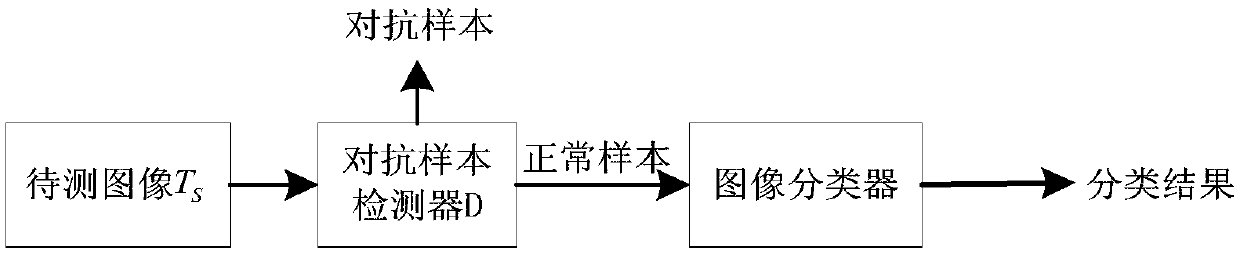
Image classifier adversarial attack defense method based on disturbance evolution
ActiveCN108615048AIncrease diversityEfficient detectionCharacter and pattern recognitionGenetic algorithmsAttack modelBox model
The invention discloses an image classifier adversarial attack defense method based on disturbance evolution. The method comprises the following steps that 1) the sample is attacked by different attack models so as to obtain different types of disturbance; 2) a block box model is attached by the adversarial sample corresponding to the disturbance and the attack effect is ordered; 3) cloning, crossing, variation and other operation are performed on the disturbance of great attack effect so as to obtain the new disturbance; 4) the disturbance is updated by using the parent-child hybrid selectionmode so as to achieve the objective of disturbance evolution; 5) an adversarial sample detector is trained by the adversarial sample corresponding to the evolved disturbance and the normal sample; and 6) when the detection sample is detected, detection is performed by using the adversarial sample detector firstly and then the normal sample is inputted to the black box model and the class is returned so as to achieve the adversarial attack defense effect.
Owner:ZHEJIANG UNIV OF TECH
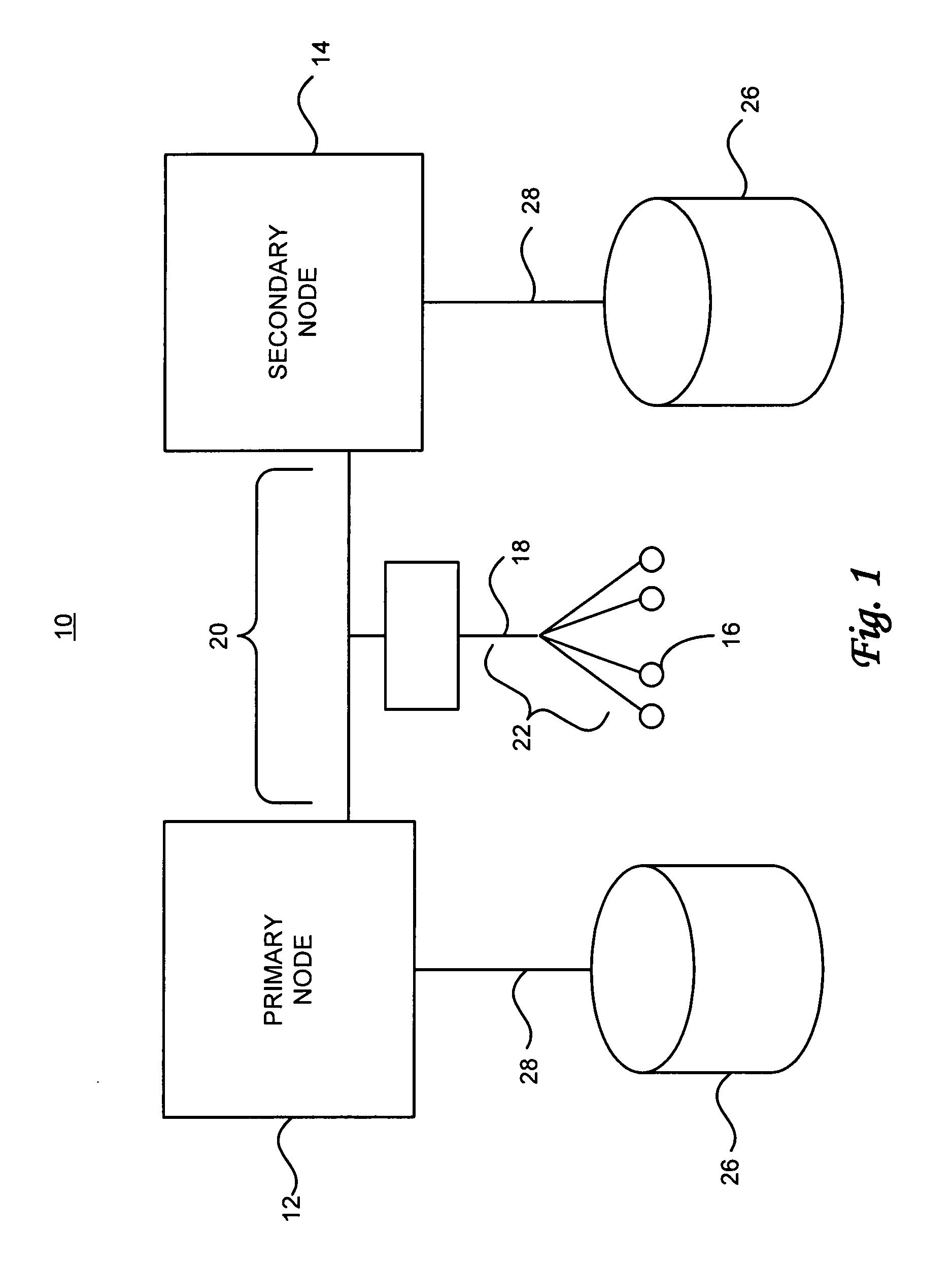
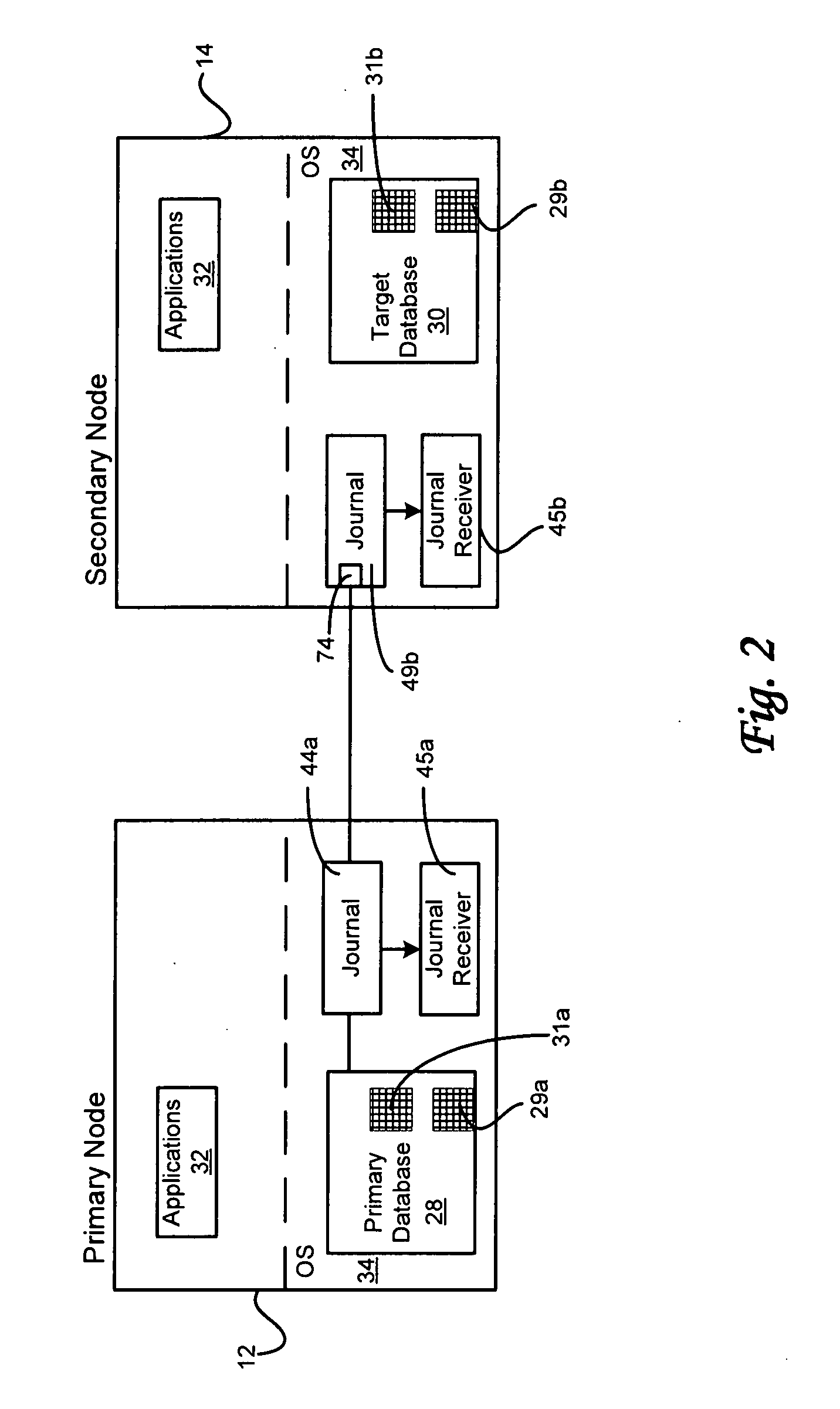
Method for auditing data integrity in a high availability database
ActiveUS20080189498A1Digital data information retrievalError detection/correctionThird partyData integrity
A method for maintaining the integrity of a backup database table on a secondary node against a continuously replicated and dynamically changing original database table on a primary node includes generating an original checksum of a segment of the original database table between a beginning record and an ending record. The checksum and identification data may be stored in an original control database table. The original control database table may be replicated to a backup control database table. Thereafter, a backup checksum of a segment of the backup database table between a beginning record and an ending record is generated. A comparison between the backup checksum and the original checksum is made in response to a triggering update to the backup control database table. Collisions by application generate transactions in the source and target databases may be detected despite the use of third party “black box” replication processes.
Owner:PRECISELY SOFTWARE INC
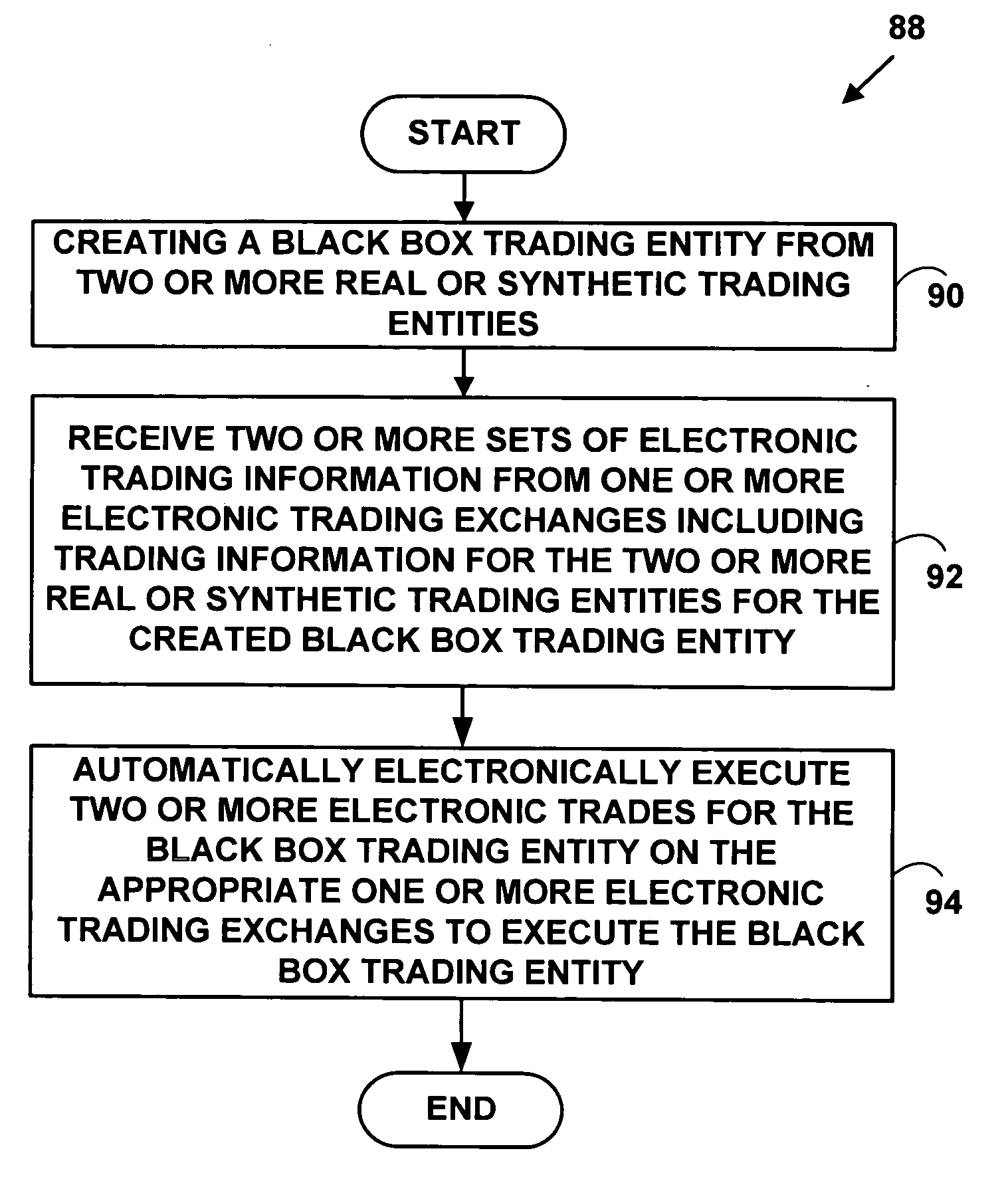
Method and system for providing automatic execution of black box strategies for electronic trading
InactiveUS20060259407A1FinanceInput/output processes for data processingSimulationElectronic trading
A method and system for providing automatic execution of black box trading strategies for electronic trading. A black box trading entity is created from two or more real or synthetic trading entities including real or synthetic contracts or financial instruments. The black box trading entity is automatically traded via one or more electronic trading exchanges.
Owner:ROSENTHAL COLLINS GROUP
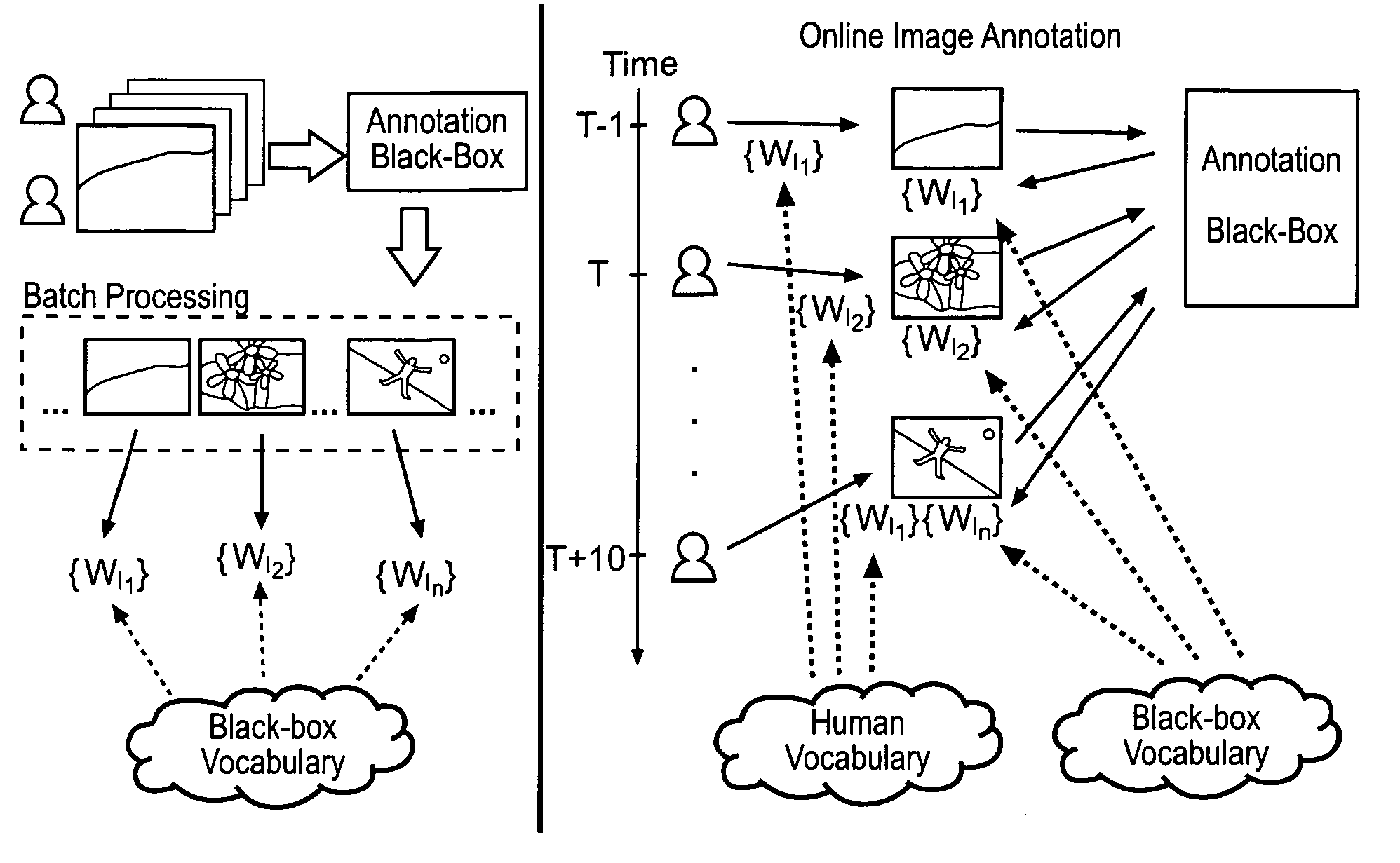
Tagging over time: real-world image annotation by lightweight metalearning
InactiveUS20090083332A1Improve annotation performanceIncur some computational overheadCharacter and pattern recognitionMetadata still image retrievalSemantic lexiconComputer science
A principled, probabilistic approach to meta-learning acts as a go-between for a ‘black-box’ image annotation system and its users. Inspired by inductive transfer, the approach harnesses available information, including the black-box model's performance, the image representations, and a semantic lexicon ontology. Being computationally ‘lightweight.’ the meta-learner efficiently re-trains over time, to improve and / or adapt to changes. The black-box annotation model is not required to be re-trained, allowing computationally intensive algorithms to be used. Both batch and online annotation settings are accommodated. A “tagging over time” approach produces progressively better annotation, significantly outperforming the black-box as well as the static form of the meta-learner, on real-world data.
Owner:PENN STATE RES FOUND
System and method for cloud capability estimation for user application in black-box environments using benchmark-based approximation
A system and method for providing cloud performance capability estimation and supporting recommender systems by simulating bottleneck and its migration for any given complex application in a cost-efficient way are provided. To do this, first, the system and method builds an abstract performance model for an application based on the resource usage pattern of the application in an in-house test-bed (i.e., a white-box environment). Second, it computes relative performance scores of many different cloud configurations given from black-boxed clouds using a cloud metering system. Third, it applies the collected performance scores into the abstract performance model to estimate performance capabilities and potential bottleneck situations of those cloud configurations. Finally, using the model, it can support recommender systems by providing performance estimates and simulations of bottlenecks and bottleneck migrations between resource sub-systems while new resources are added or replaced.
Owner:XEROX CORP
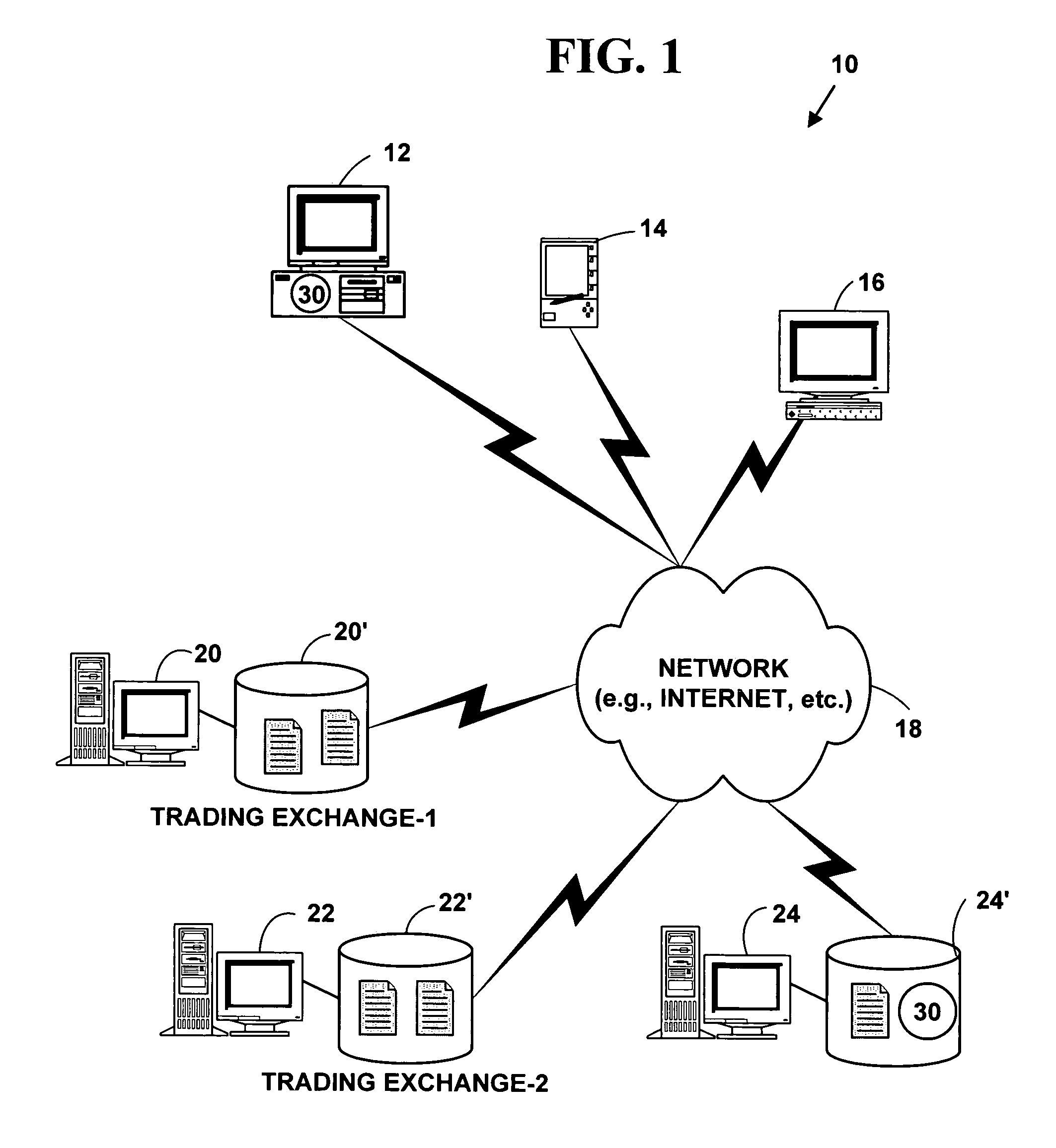
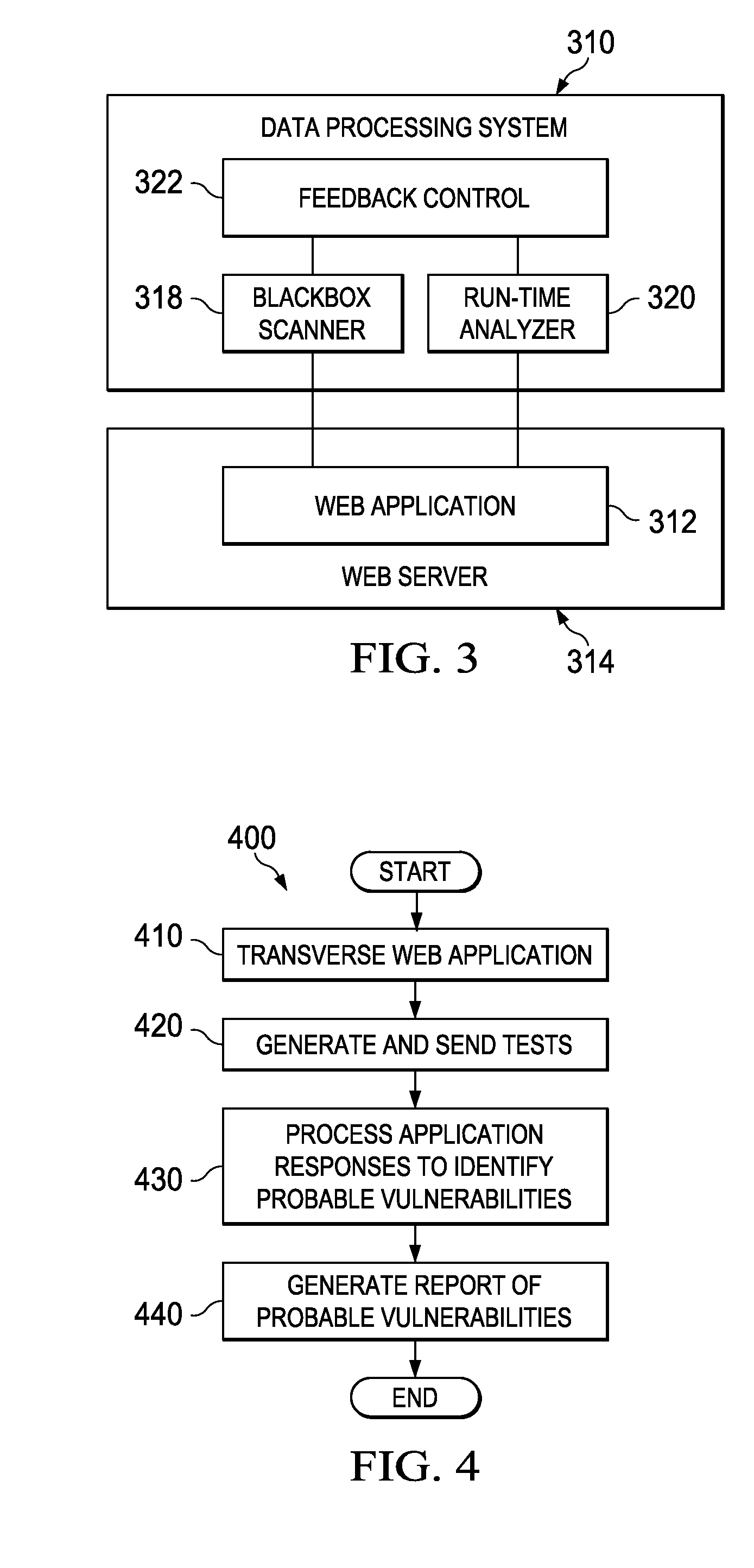
Measuring Coverage of Application Inputs for Advanced Web Application Security Testing
ActiveUS20100169974A1Memory loss protectionError detection/correctionData processing systemWeb application
A computer implemented method, a data processing system, and a computer usable recordable-type medium having a computer usable program code monitor a black box web application security scan. A black box scan of a web application is initiated. The black box scan sends a test is sent to a plurality of web application inputs of the web application. A runtime analysis is performed on the black box scan of the web application. Based on the run time analysis of the black box scan, the black box scan is modified.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com