Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6606 results about "Computer software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
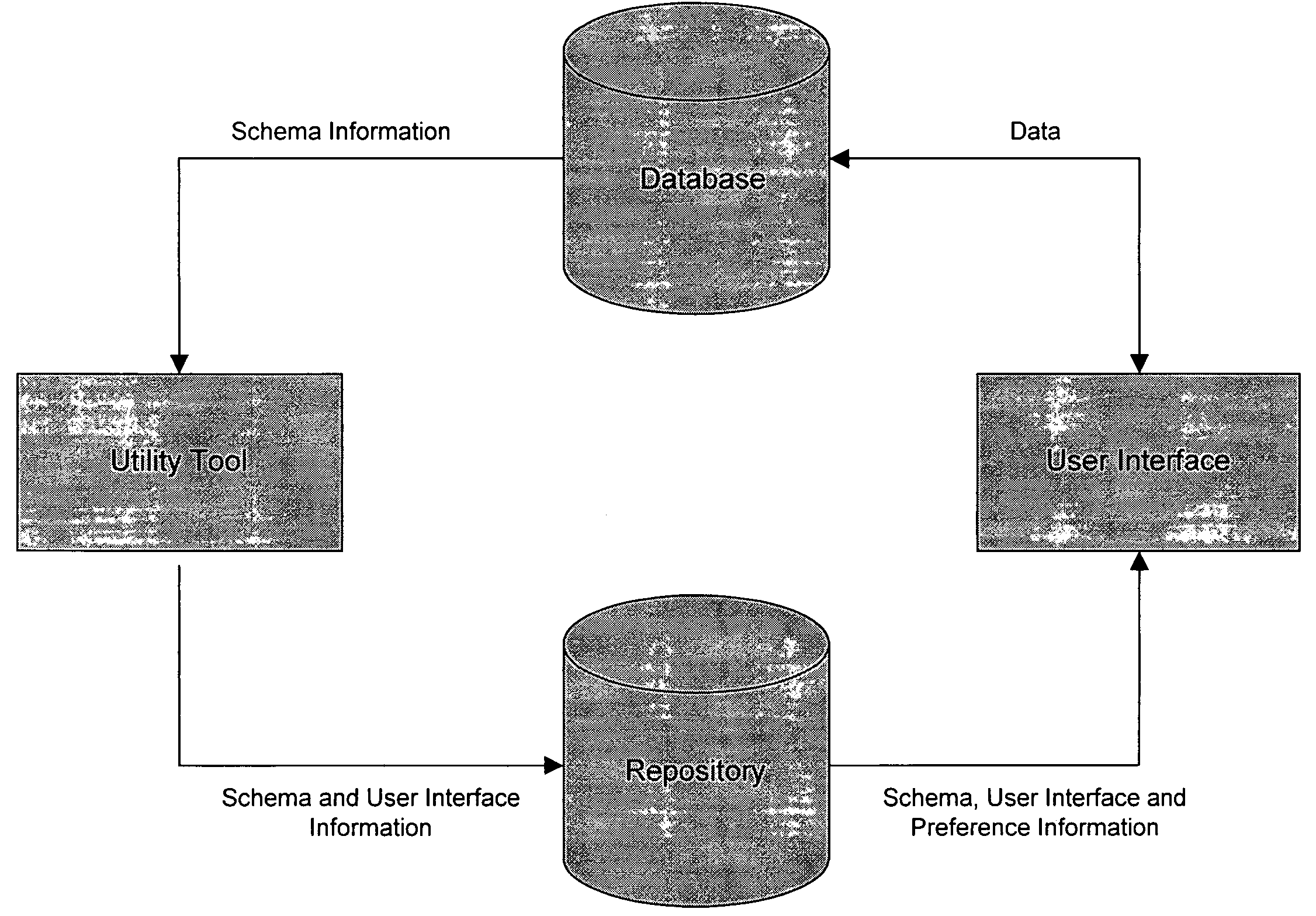
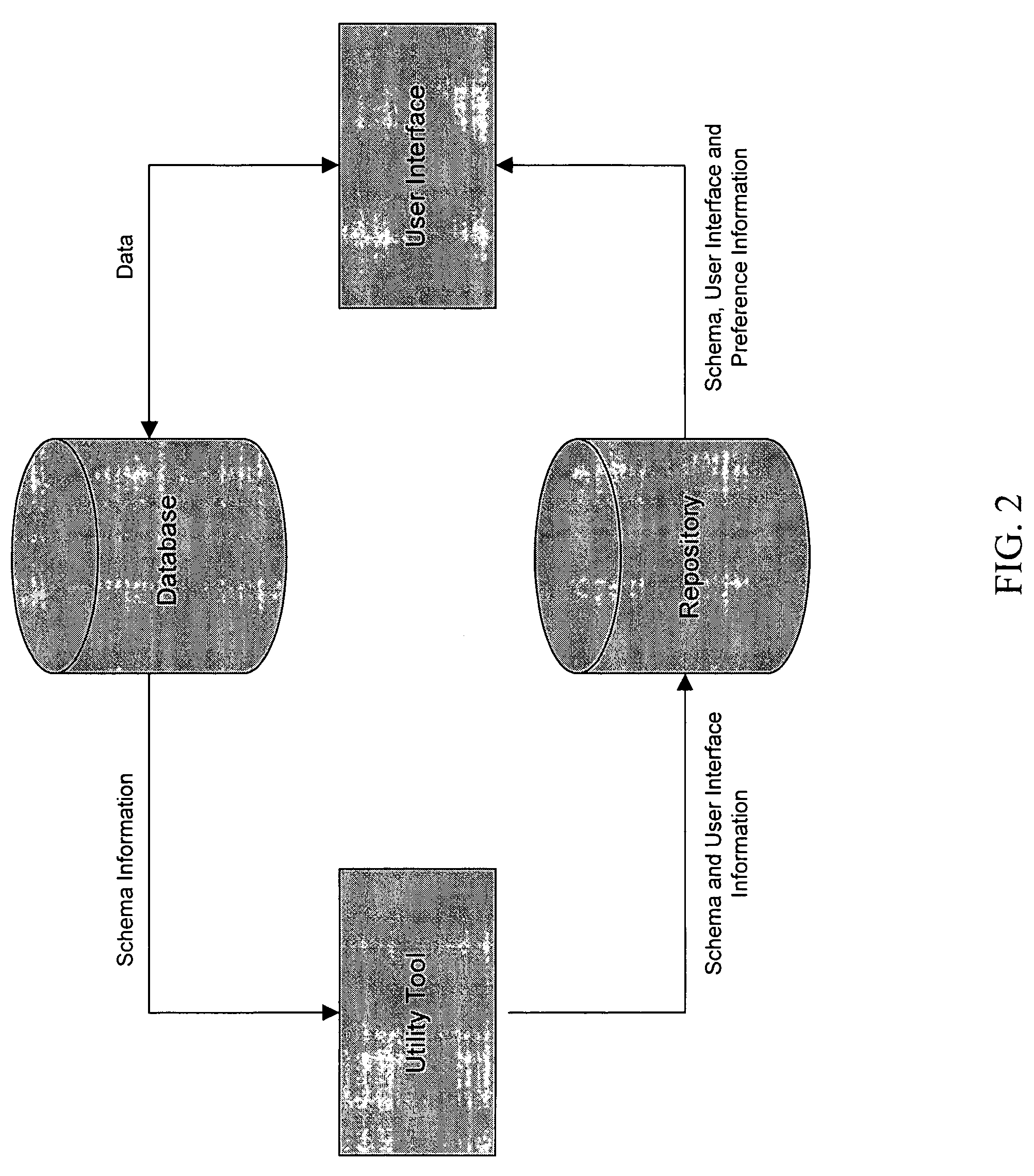
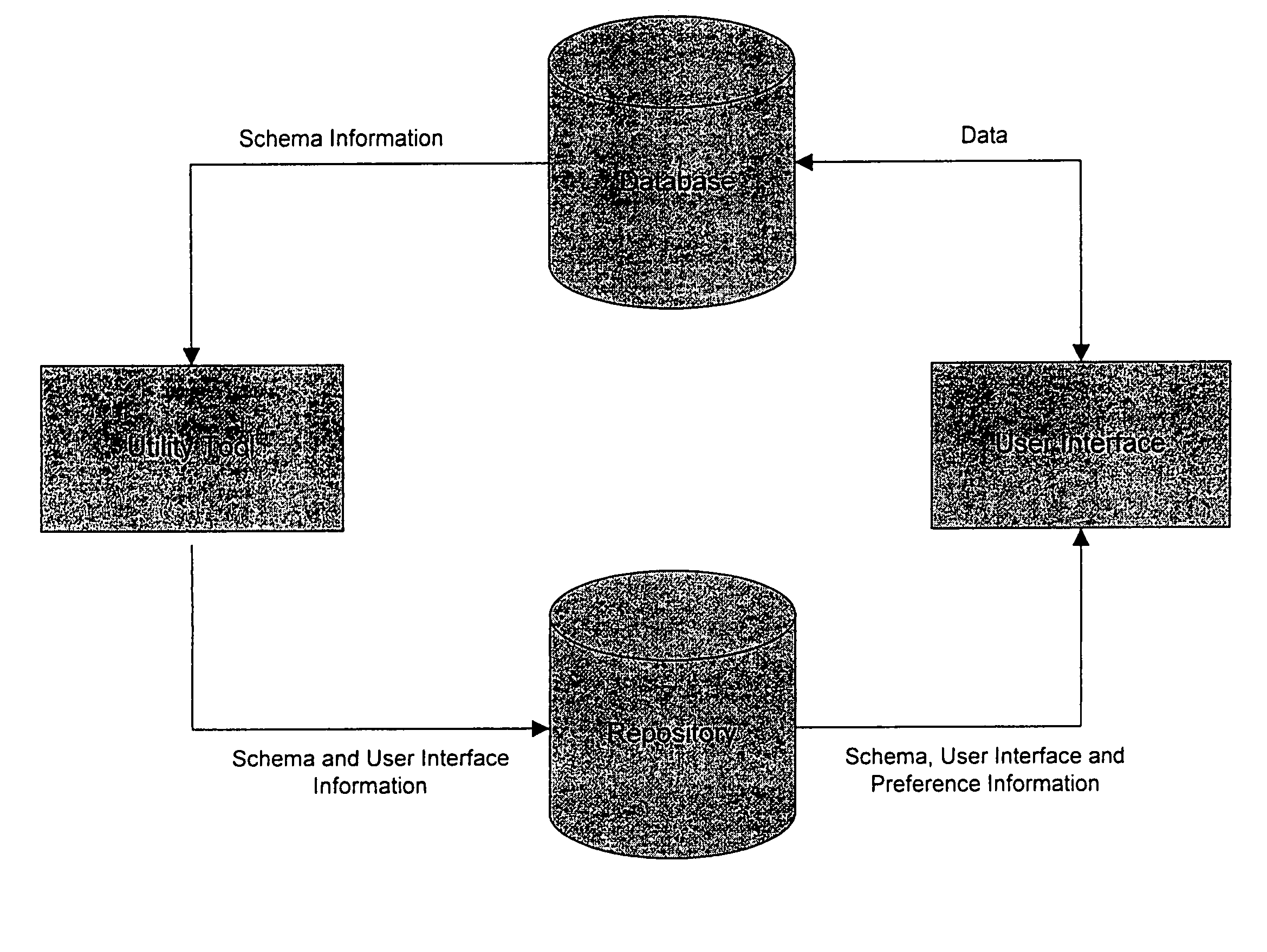
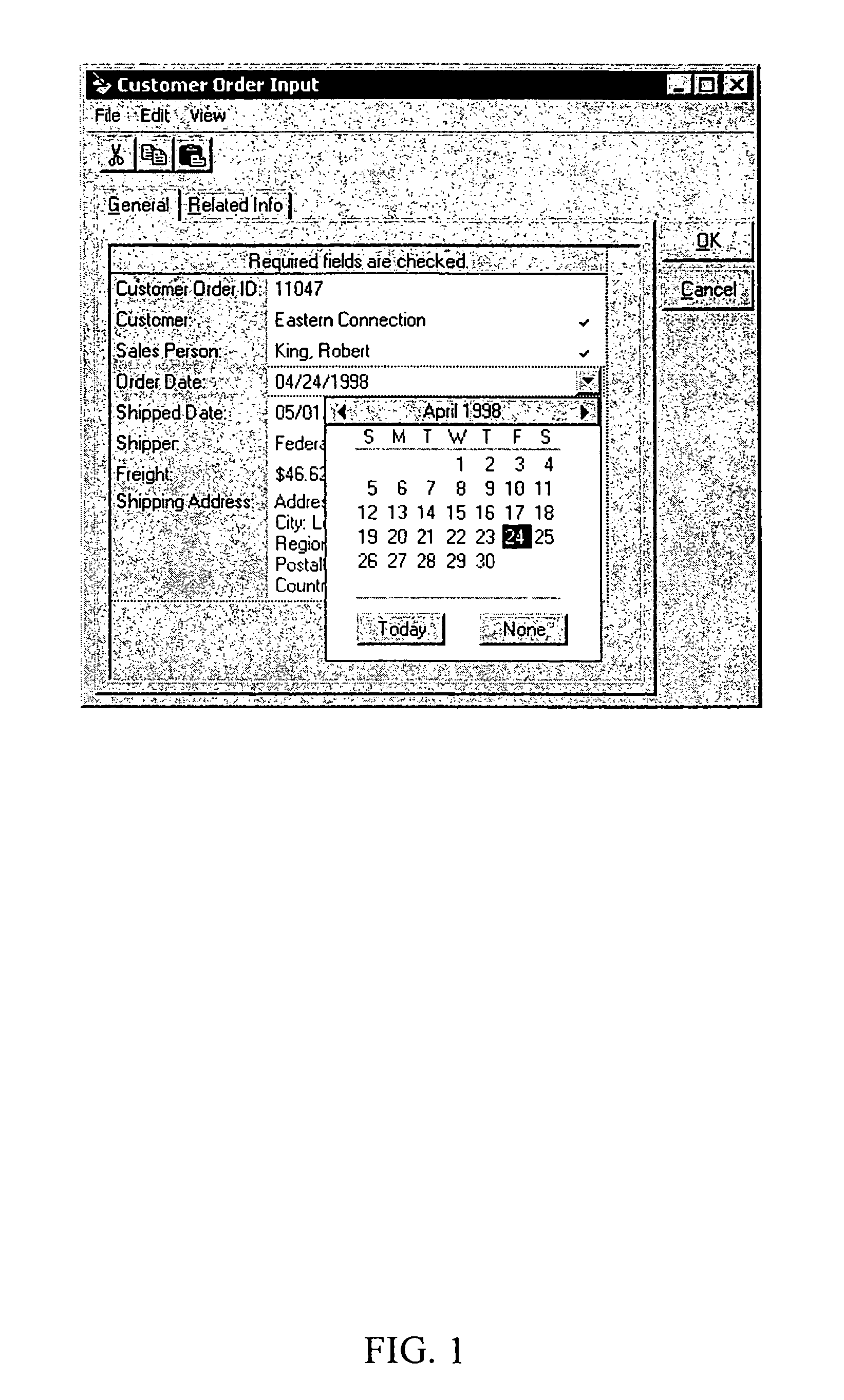
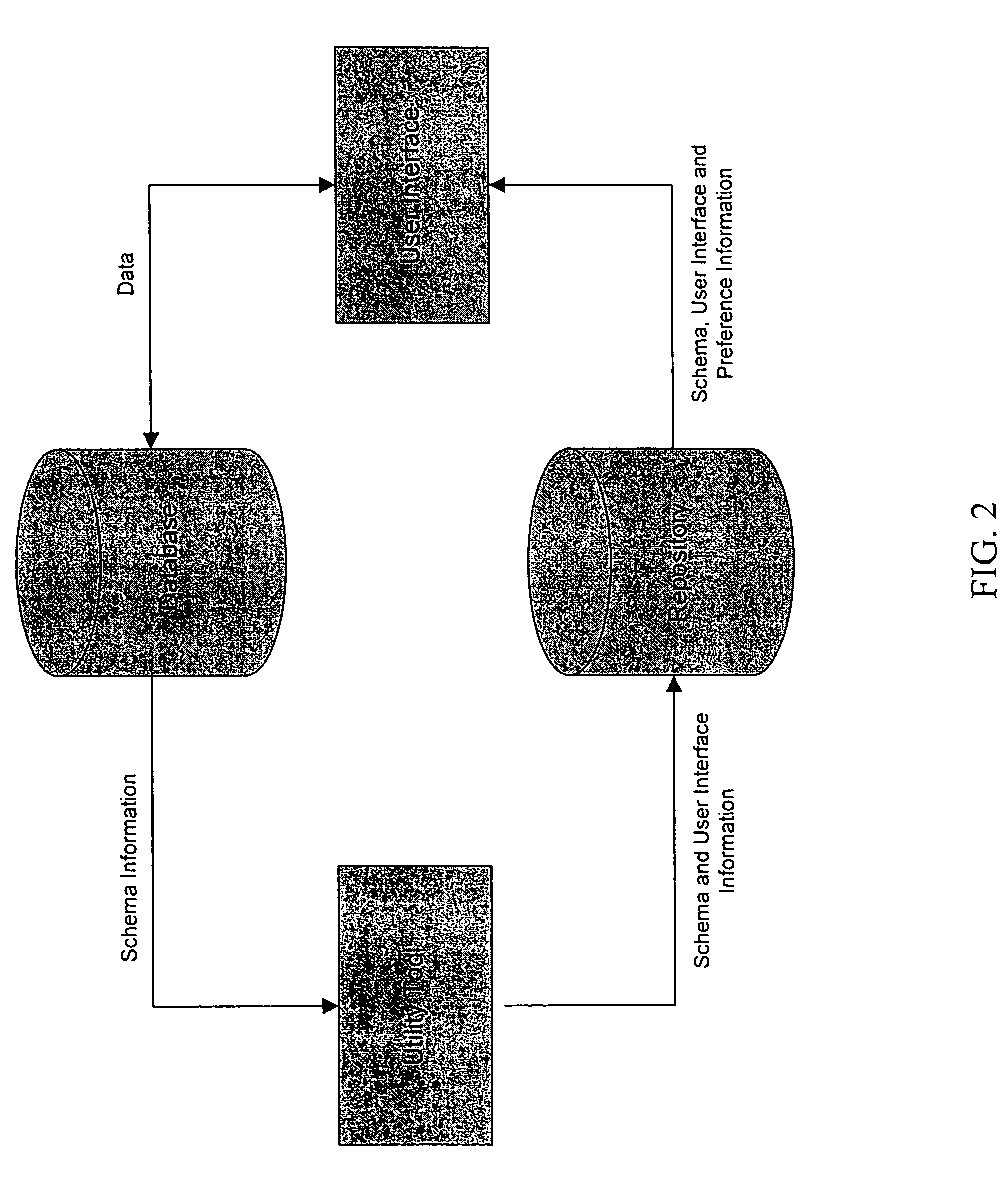
Automated generation of dynamic data entry user interface for relational database management systems
InactiveUS7062502B1Easy to navigateData processing applicationsMultiple digital computer combinationsRelational database management systemComputer software
Computer software for, computer apparatus for, and a method of automatically generating a user interface for a relational database comprising extracting schema information from the relational database and automatically generating corresponding schema and user interface metadata, storing the metadata in a repository, and automatically developing from the metadata a user interface appropriate to the relational database.
Owner:ADVANCED DYNAMIC INTERFACES
Automated generation of dynamic data entry user interface for relational database management systems
InactiveUS7401094B1Easy to navigateData processing applicationsDigital data processing detailsRelational database management systemComputer software
Owner:ADVANCED DYNAMIC INTERFACES
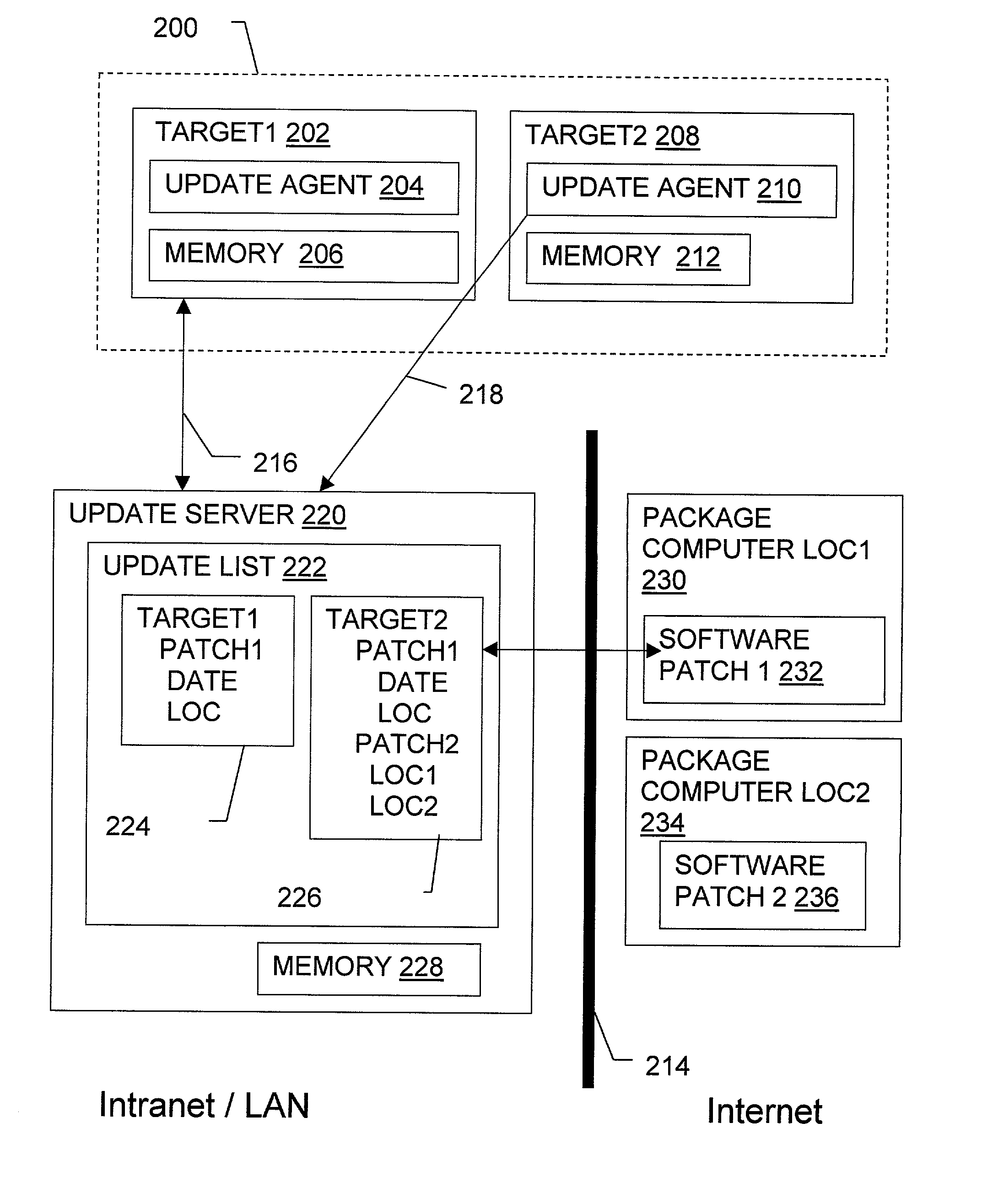
Non-invasive automatic offsite patch fingerprinting and updating system and method
InactiveUS20020100036A1Error detection/correctionDigital computer detailsSoftware updateNon invasive
Methods, systems, and configured storage media are provided for discovering software updates, discovering if a given computer can use the software update, and then updating the computers with the software as needed automatically across a network without storing the updates on an intermediate machine within the network. Furthermore, when a failure is detected, the rollout is stopped and the software can be automatically removed from those computers that already were updated. The software update can be stored originally at an address that is inaccessible through the network firewall by intermediately uploading the software update to an update computer which is not a part of the network but has access through the firewall, which is then used to distribute the update.
Owner:HEAT SOFTWARE USA
Computerized smart gaming tournament system for the internet
Owner:MURDOCK WILBERT Q +1
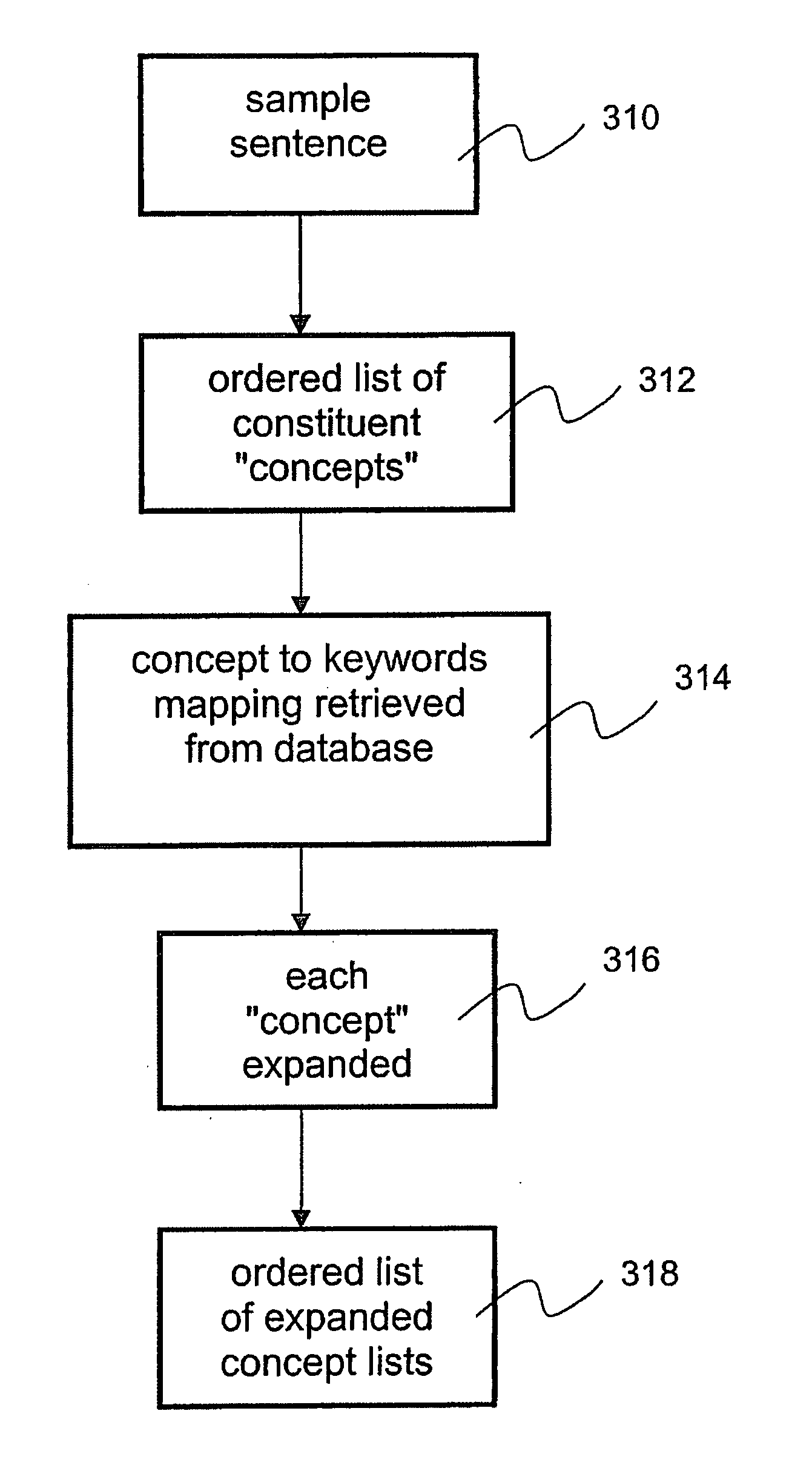
System and methods for improving accuracy of speech recognition
The invention provides a system and method for improving speech recognition. A computer software system is provided for implementing the system and method. A user of the computer software system may speak to the system directly and the system may respond, in spoken language, with an appropriate response. Grammar rules may be generated automatically from sample utterances when implementing the system for a particular application. Dynamic grammar rules may also be generated during interaction between the user and the system. In addition to arranging searching order of grammar files based on a predetermined hierarchy, a dynamically generated searching order based on history of contexts of a single conversation may be provided for further improved speech recognition. Dialogue between the system and the user of the system may be recorded and extracted for use by a speech recognition engine to refine or create language models so that accuracy of speech recognition relevant to a particular knowledge area may be improved.
Owner:INAGO CORP
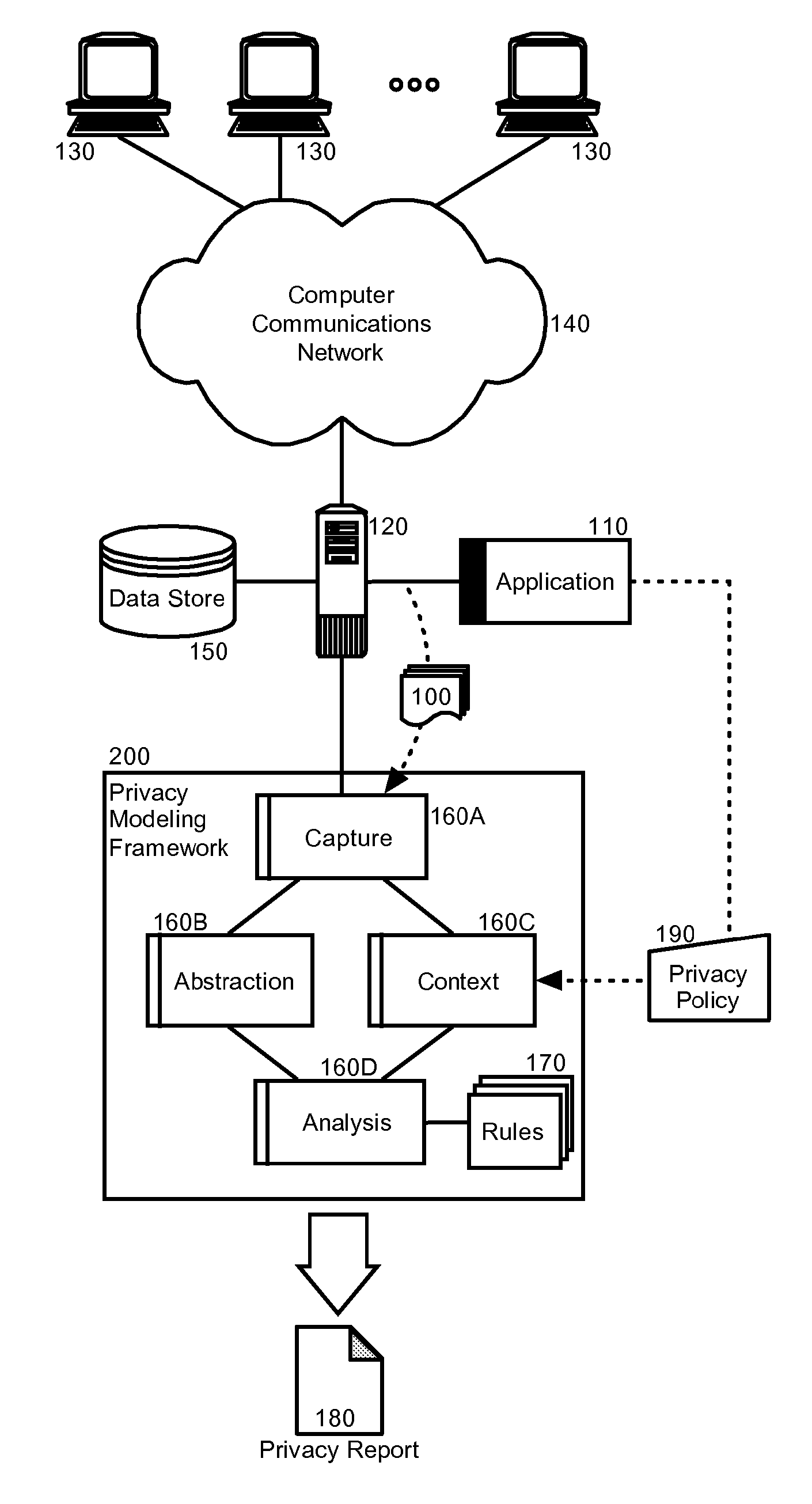
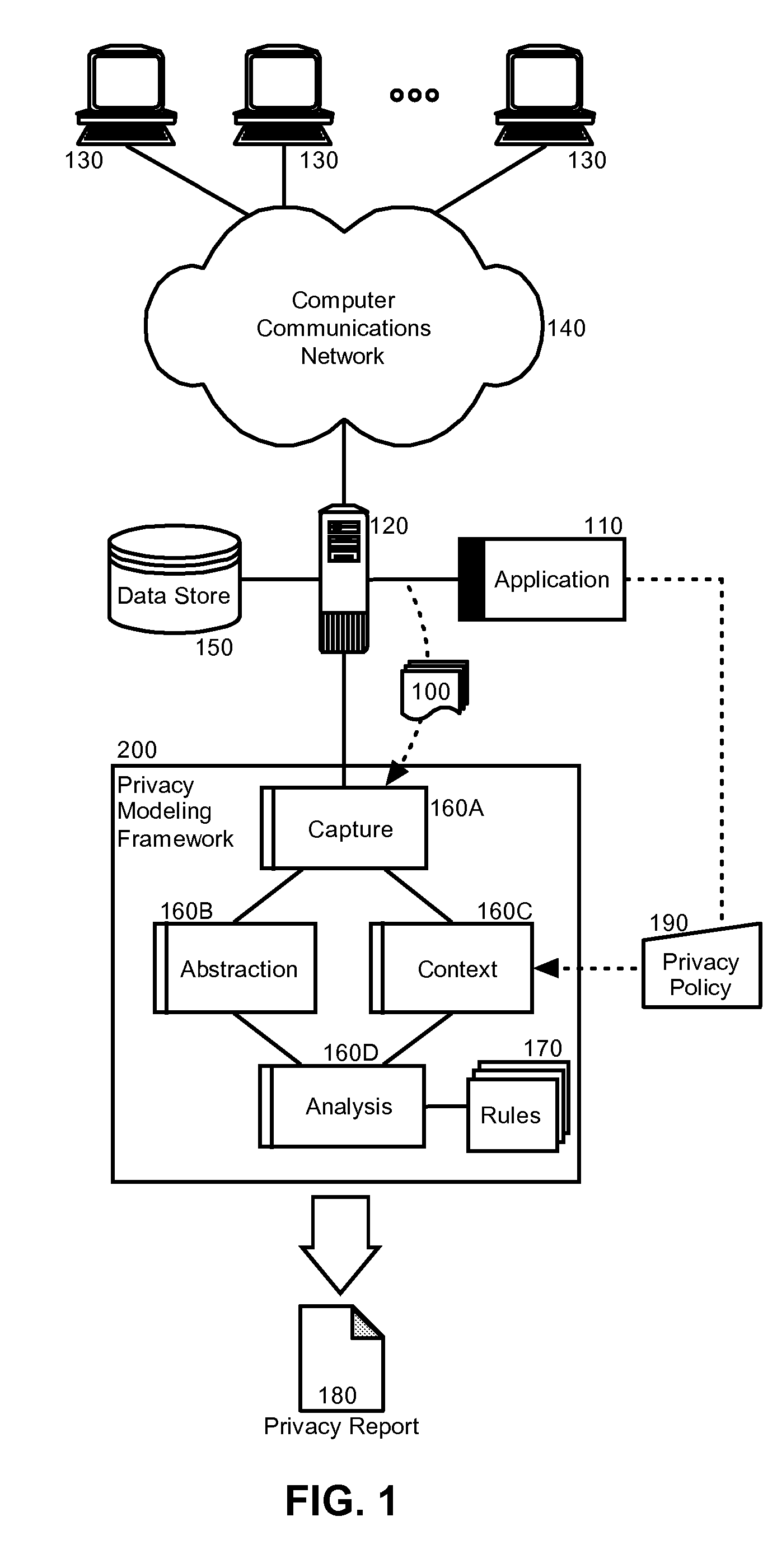
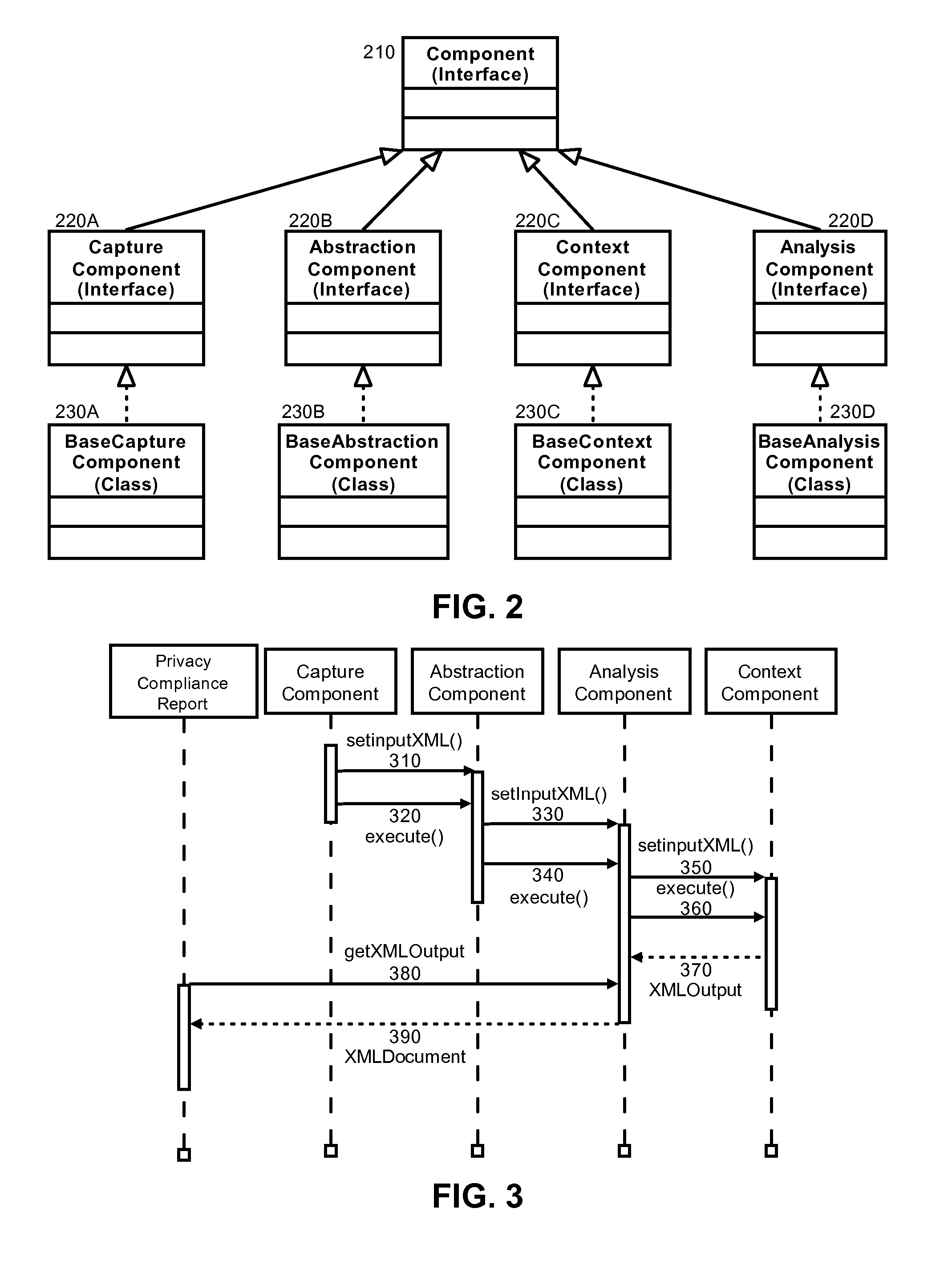
Privacy modeling framework for software applications
InactiveUS20070266420A1Computer security arrangementsOffice automationData processing systemCoupling
Embodiments of the present invention address deficiencies of the art in respect to privacy compliance assessment for computer software and provide a method, system and computer program product for a privacy model framework for software applications. In one embodiment, a privacy modeling data processing system can be provided. The privacy modeling data processing system can include a modeling framework configured for communicative coupling to a software application. The modeling framework can capture information flows from requests to and responses from a coupled software application, and can rules-based process the captured information flows for privacy rules to generate a privacy compliance report for the software application.
Owner:IBM CORP
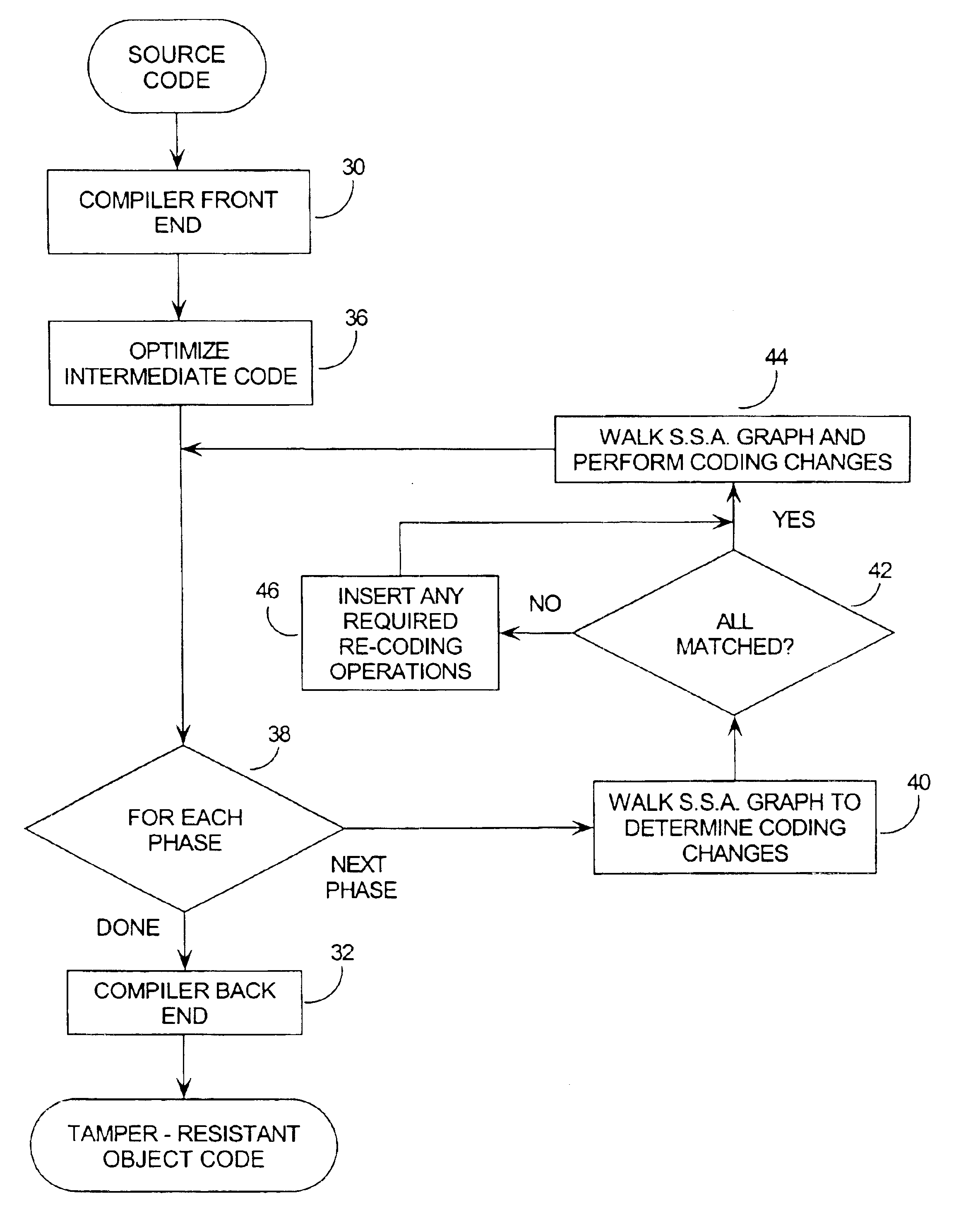
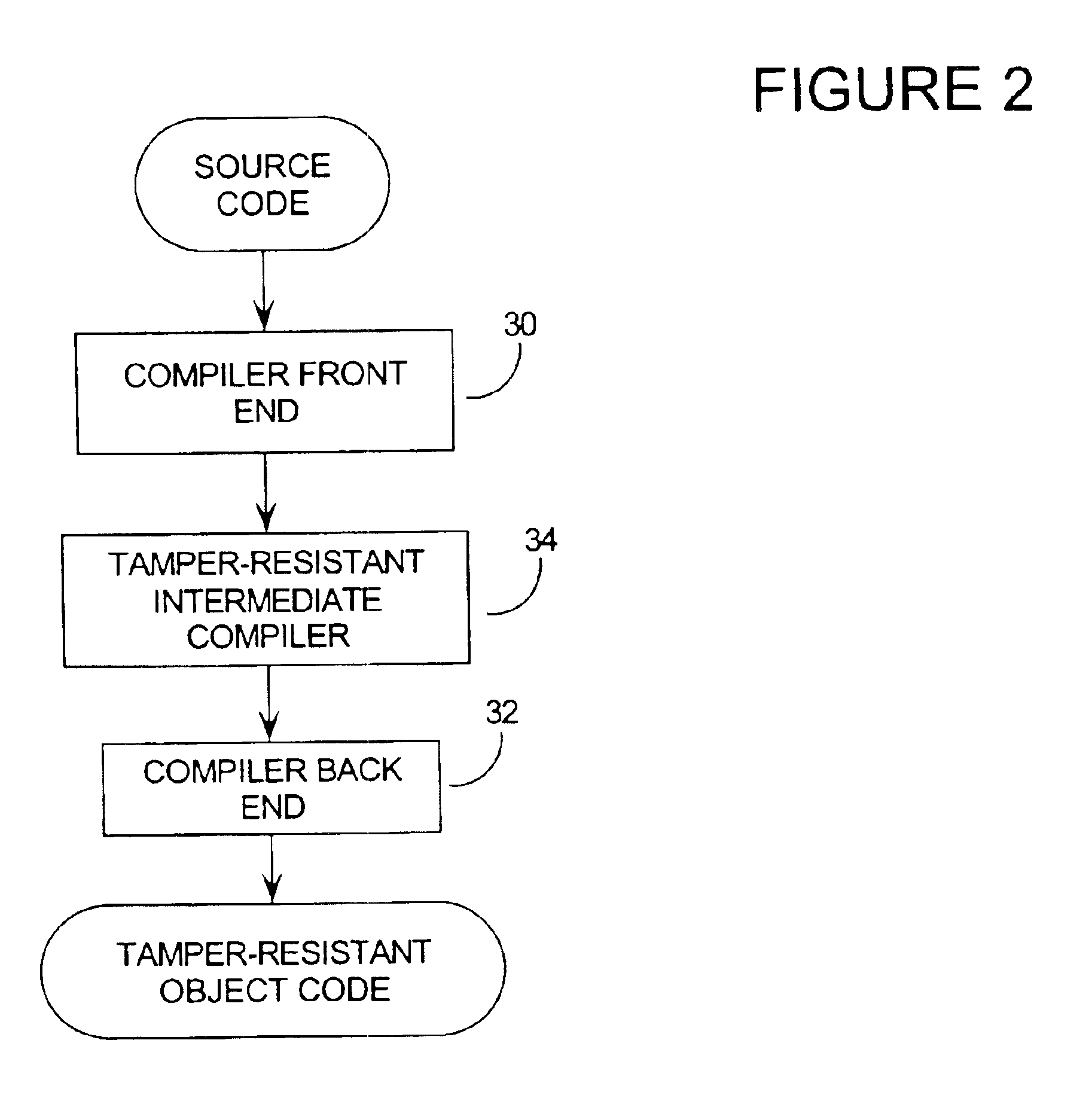
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
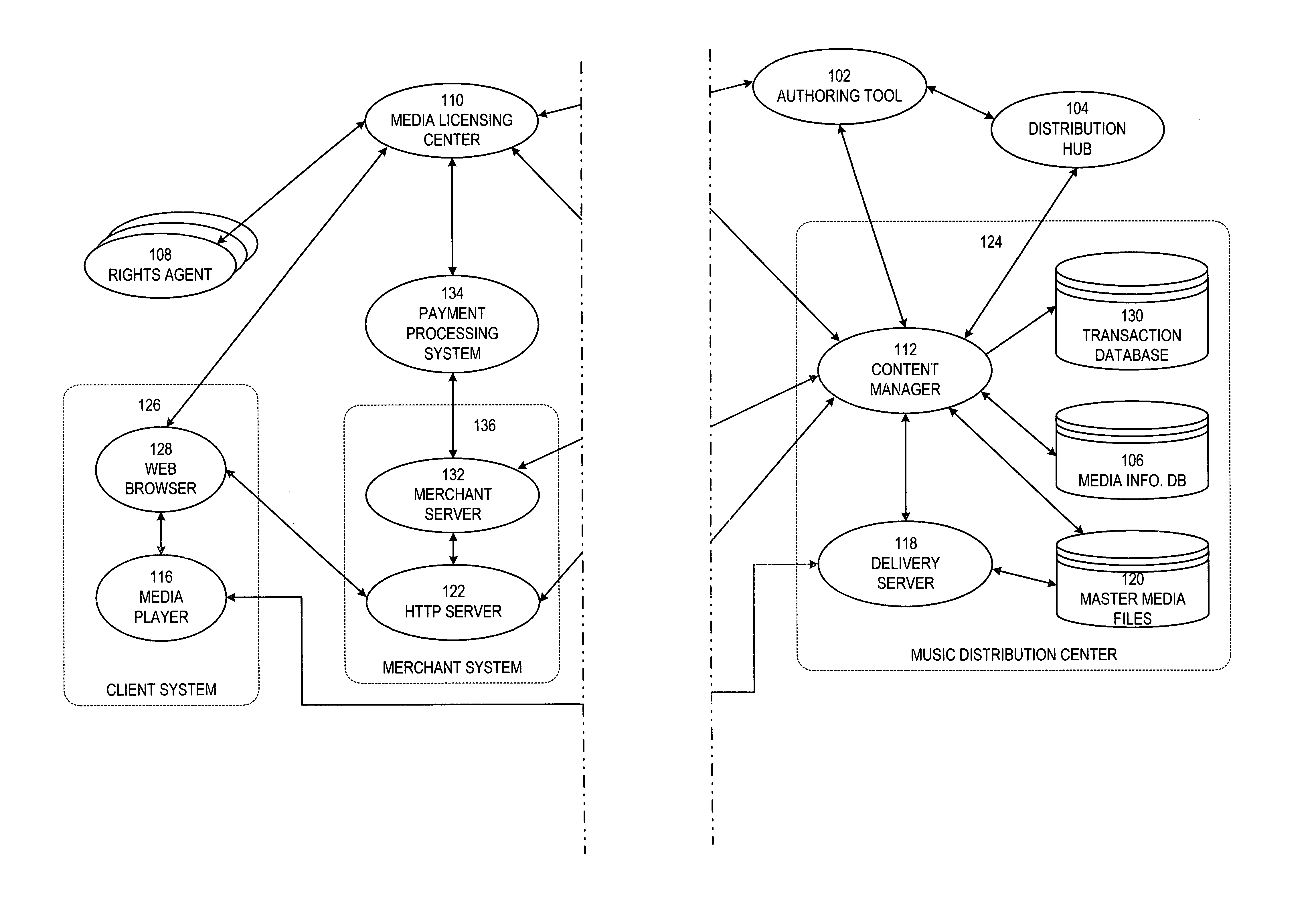
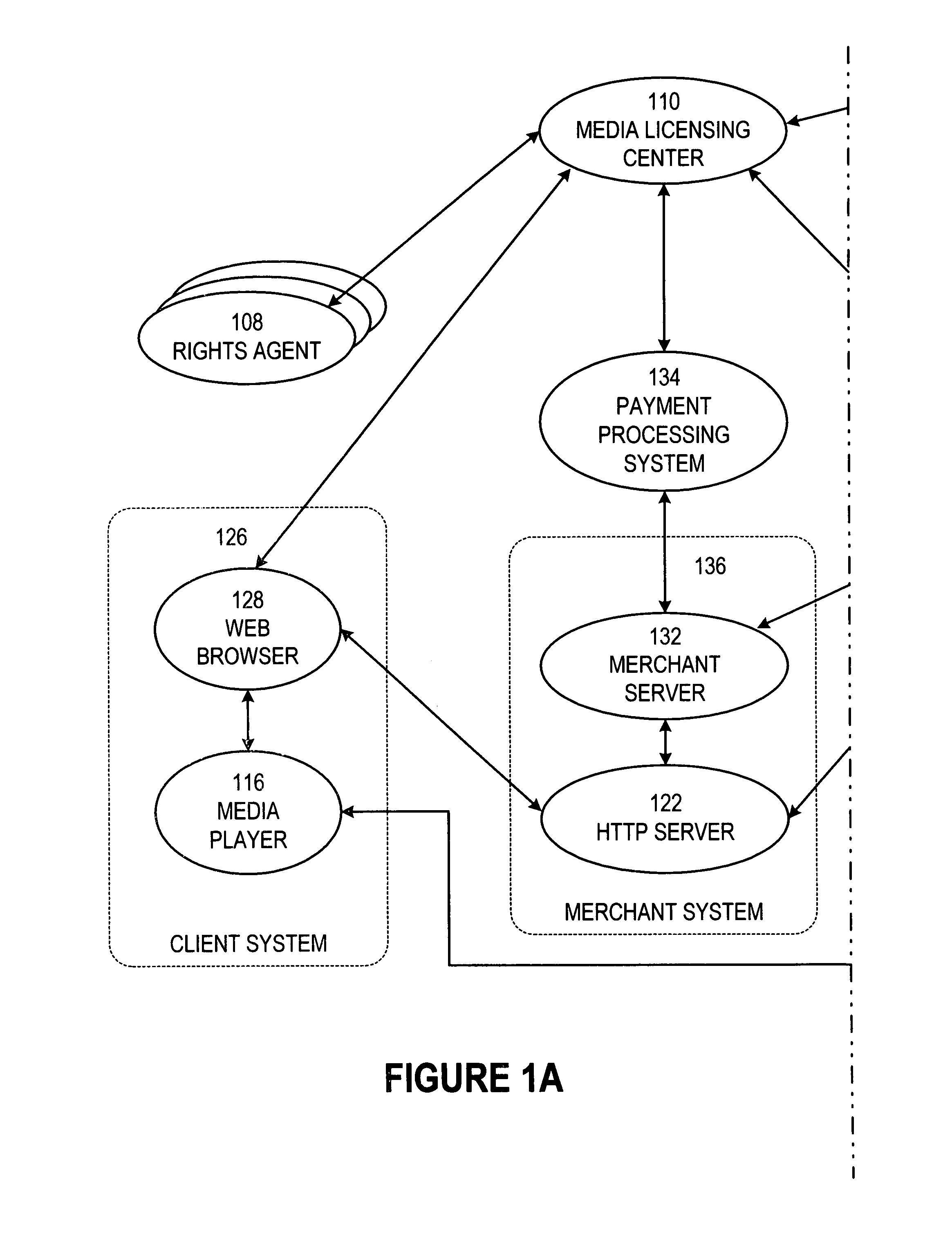
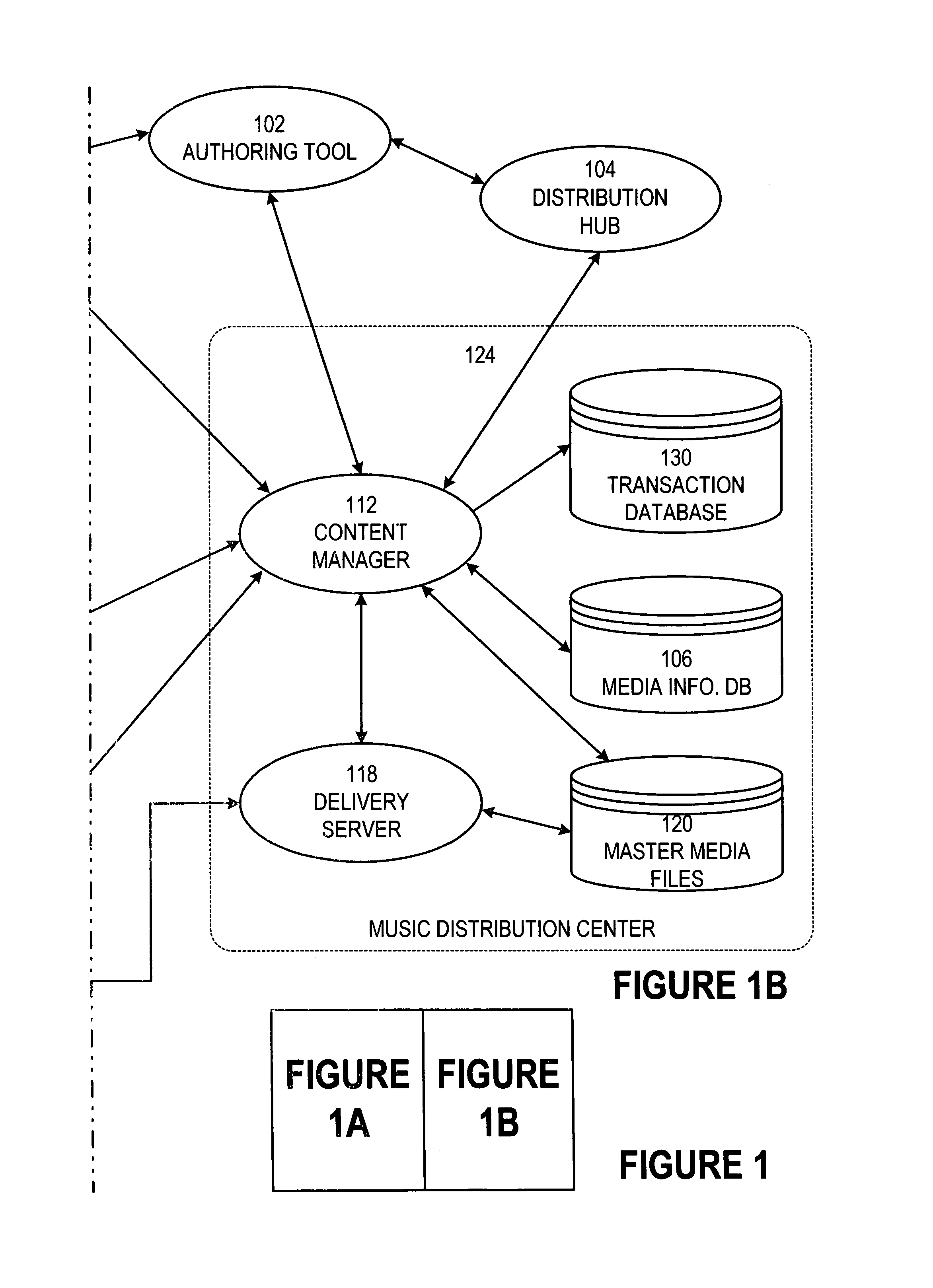
Secure online music distribution system
InactiveUS7263497B1Flexibility and ease of useGood flexibilityComputer security arrangementsPayment architectureContent managementInformation data
A secure music distribution system securely distributes digital products such as music, video, and / or computer software along with related media over a public telecommunications network, such as the Internet, employing a client-server architecture. The digital products are stored and controlled by a content manager computer system and are sold by separate merchant computer systems. The secure music distribution system includes a music distribution center which operates with any number of client systems and with any number of merchant systems. The music distribution center includes a content manager and at least one delivery server. The content manager maintains a media information database, a master media file system, and a transaction database. In addition, the music distribution center interfaces with a media licensing center, which in turn communicates with one or more distributed rights agent servers and the merchant servers. The merchant server executes in a merchant computer system, which also includes an HTTP (HyperText Transfer Protocol) server. The merchant servers interface with various payment processing systems. The client systems include a media player and a Web browser. Additional delivery servers and media licensing centers operate independently and externally to the music distribution center and interface with the music distribution center.
Owner:MICROSOFT TECH LICENSING LLC
Digital interactive delivery system for TV/multimedia/internet
InactiveUS20050028206A1Television system detailsAnalogue secracy/subscription systemsSignal onIP multicast
Owner:IMAGICTV
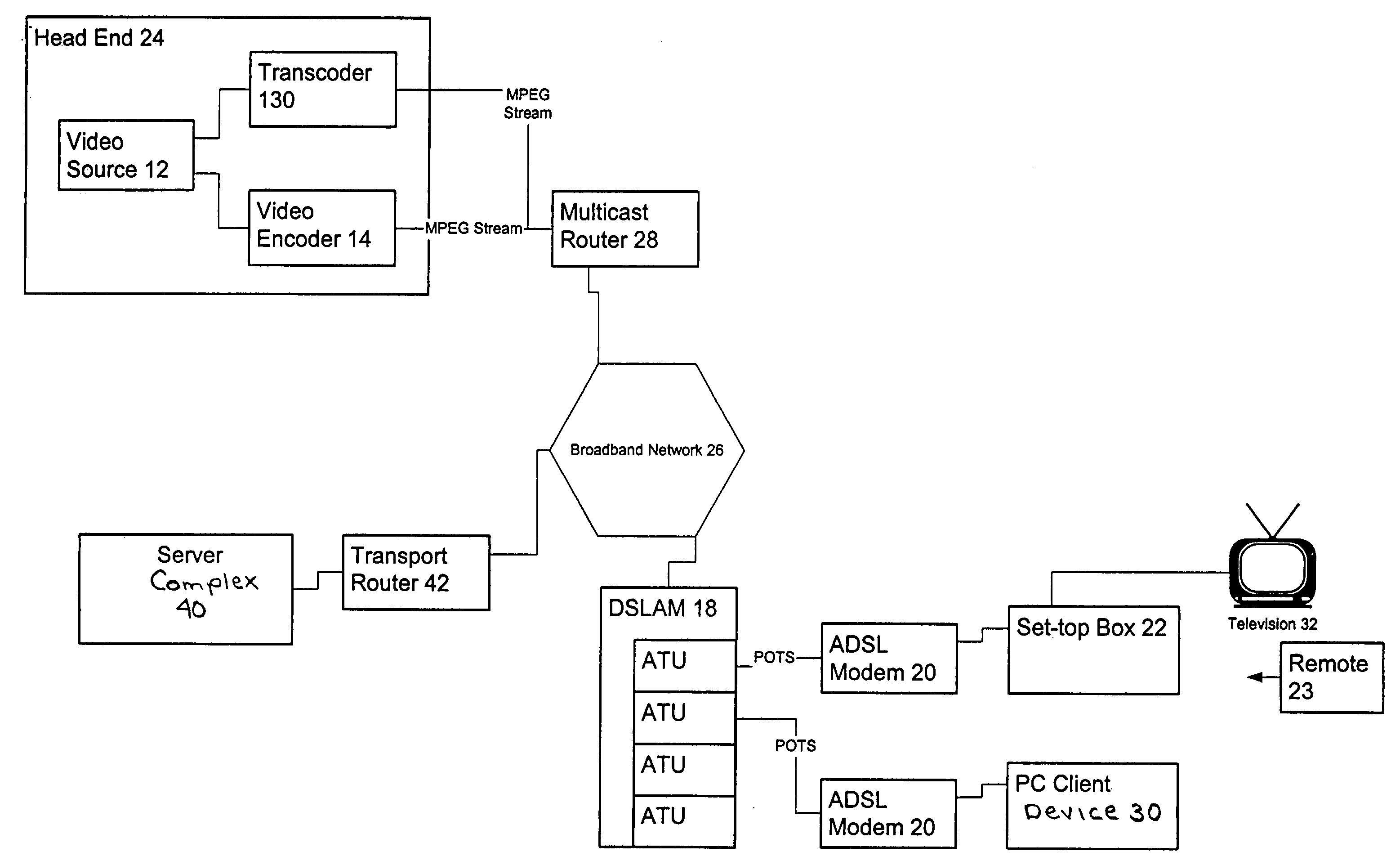
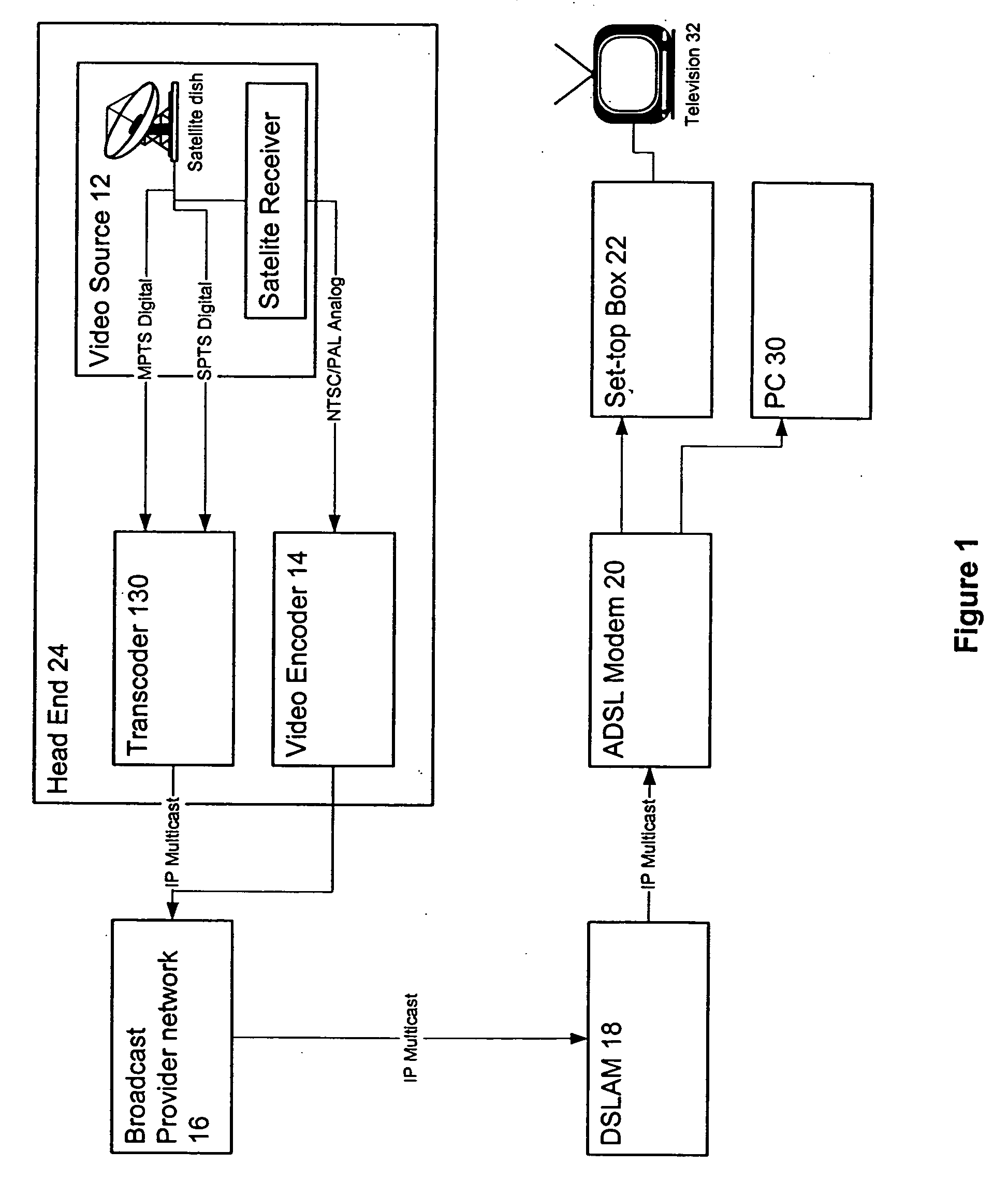
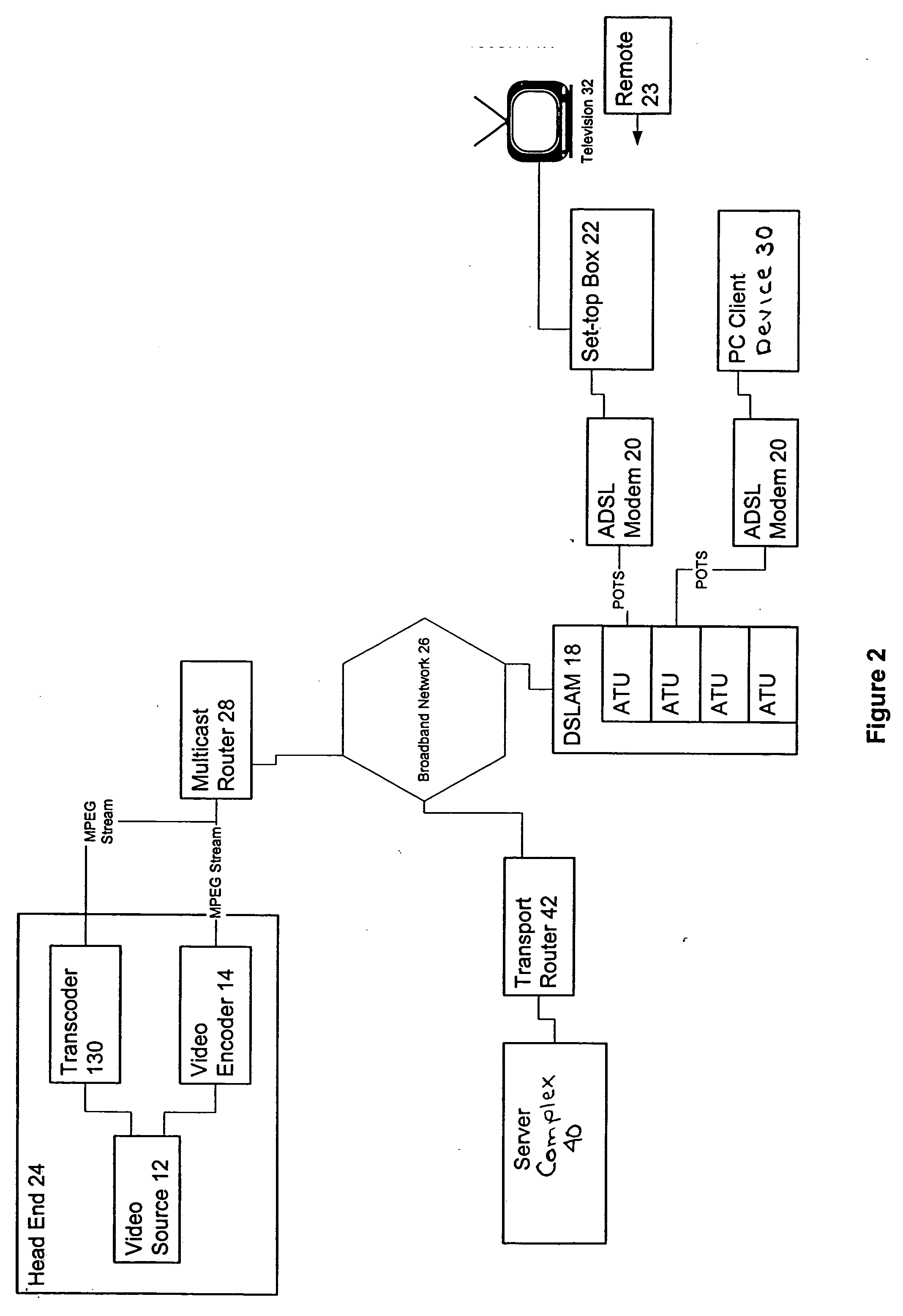
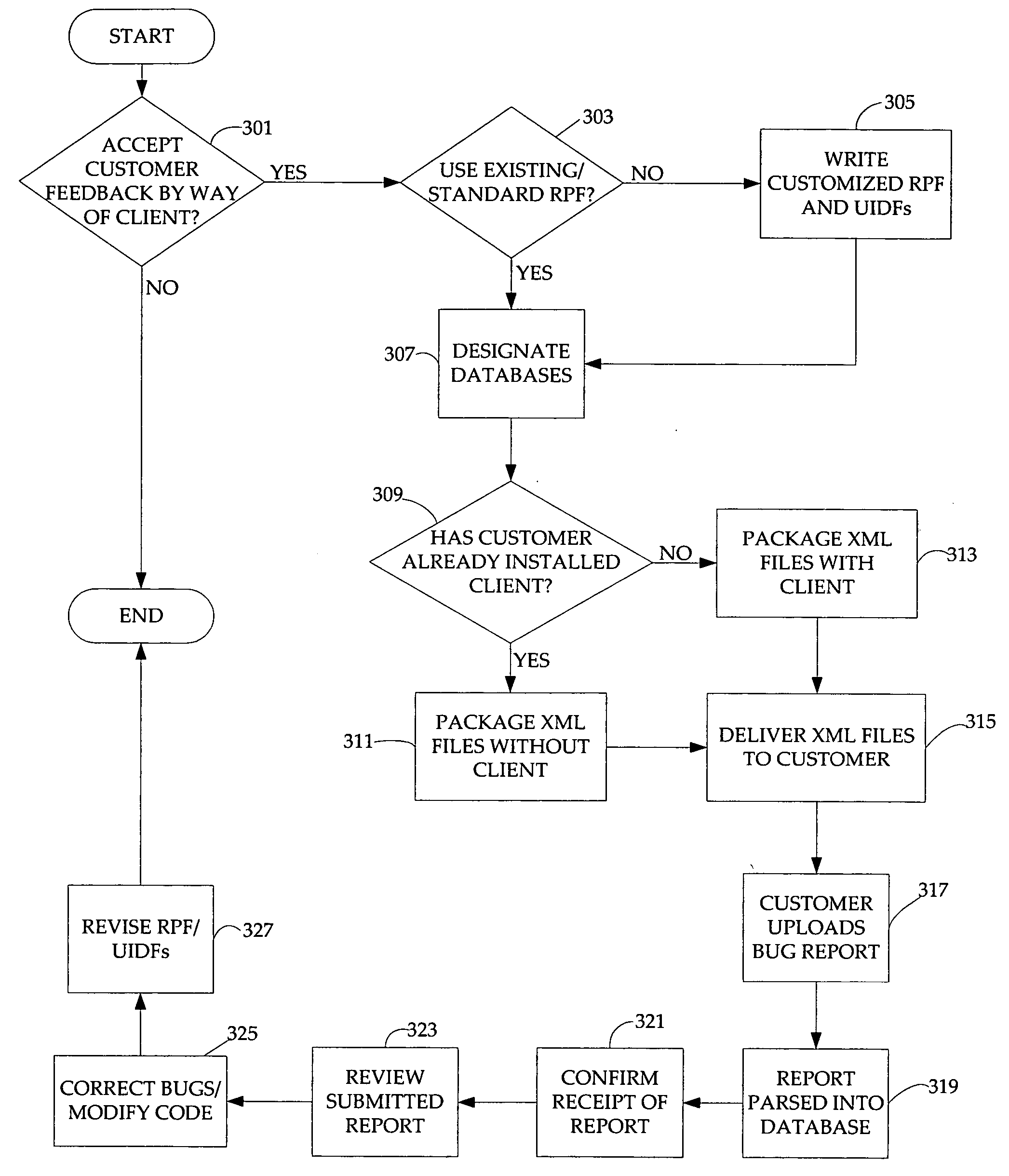
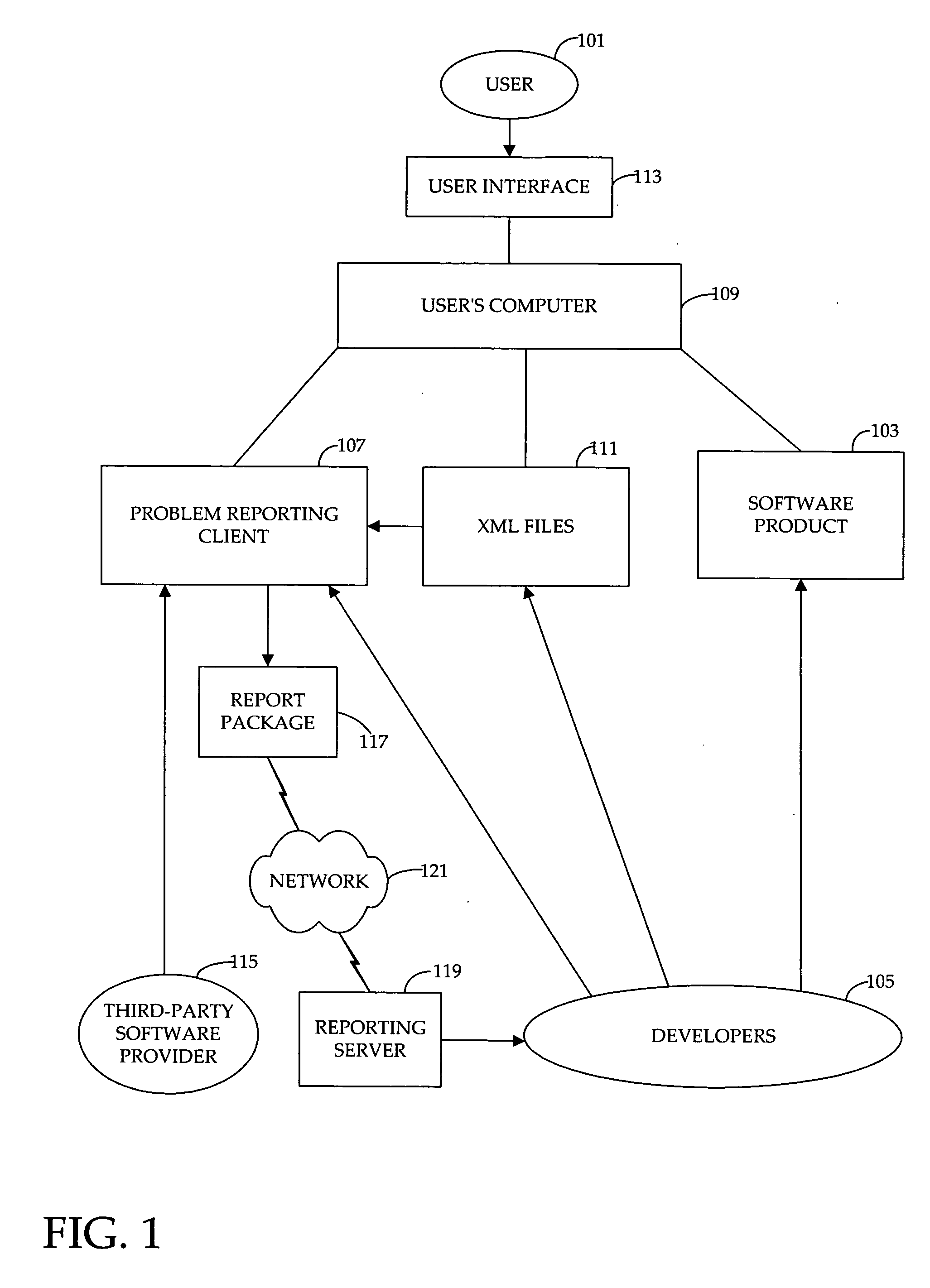
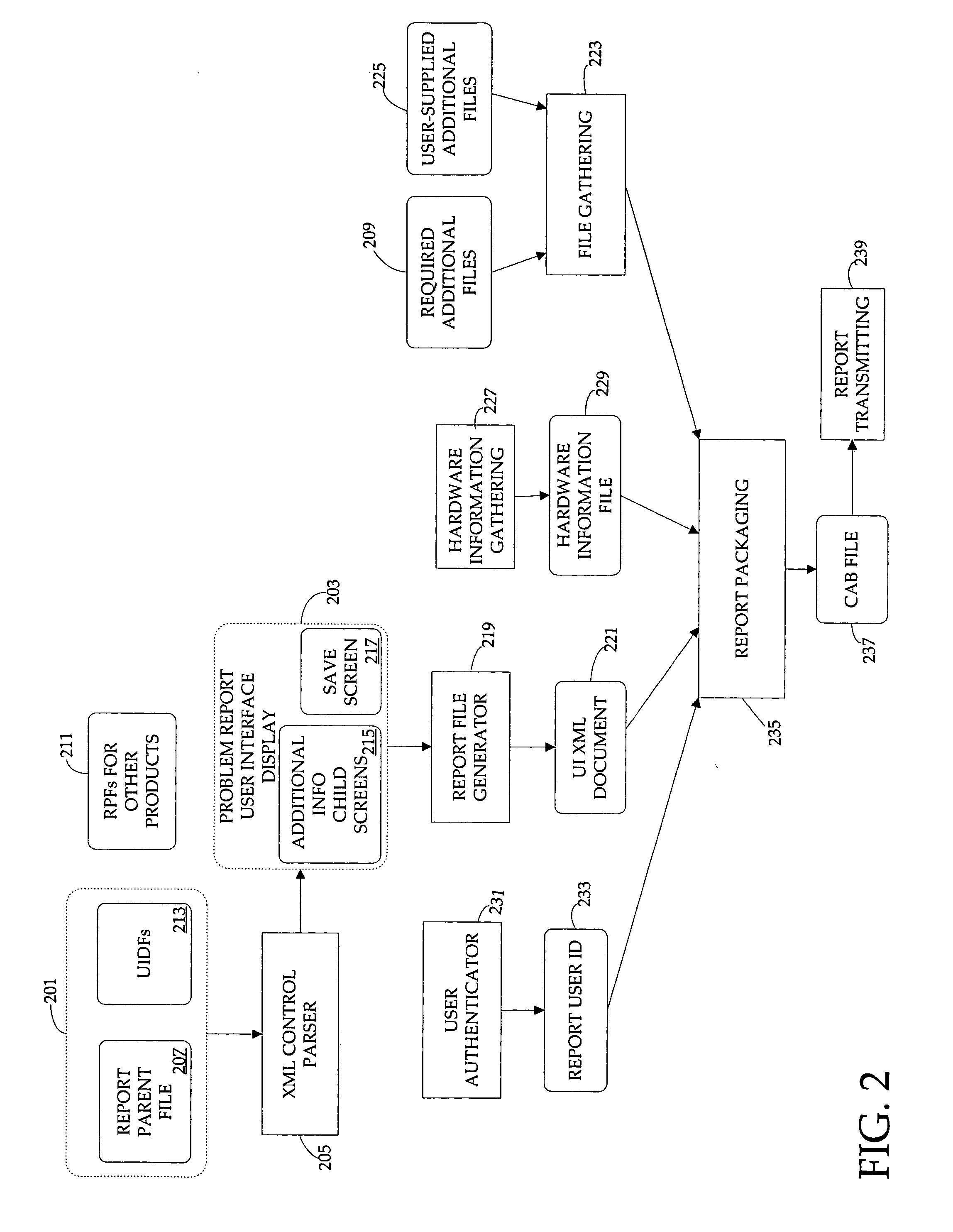
Extensible and dynamically-configurable problem-reporting client
A system and method is disclosed for facilitating the reporting of information regarding a computer software product by way of a dynamically-configurable general report client. The general report client is used along with a set of report user interface definition files that is specific to each software product for which a report can be prepared. A set of report user interface definition files customizes the report user interface for reporting information relating to the software product with which it is associated. The invention provides for dynamic configurability in that, by entering certain values by way of the report user interface, the user may cause the client to load additional report user interface definition files and present additional user interface child screens accordingly. The invention provides methods by which software developers, software providers and others obtain user feedback for such purposes as beta-testing and debugging.
Owner:MICROSOFT TECH LICENSING LLC
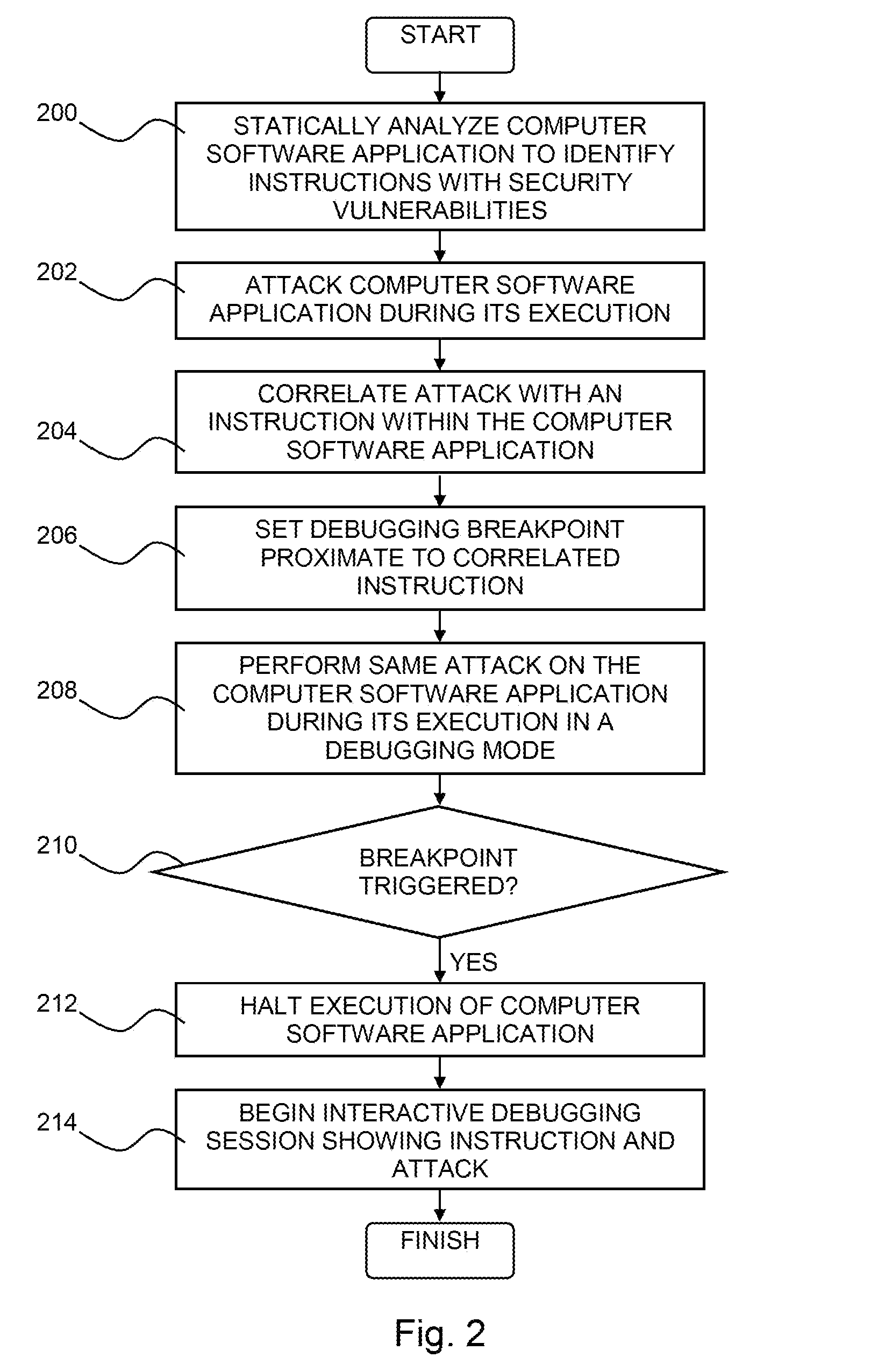
Pinpointing security vulnerabilities in computer software applications
ActiveUS8510842B2Memory loss protectionUnauthorized memory use protectionSoftware engineeringApplication software
Owner:FINJAN BLUE INC
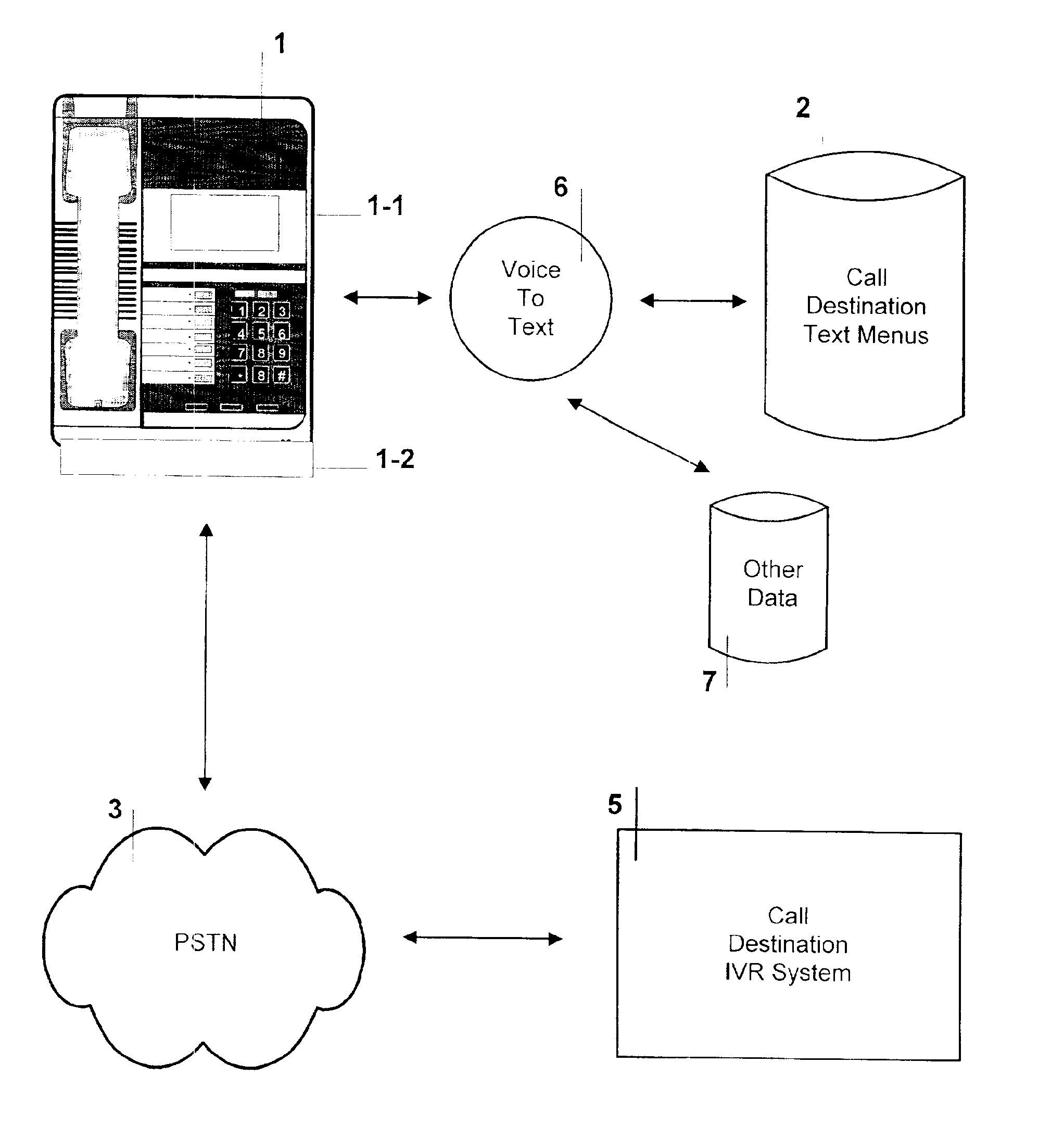
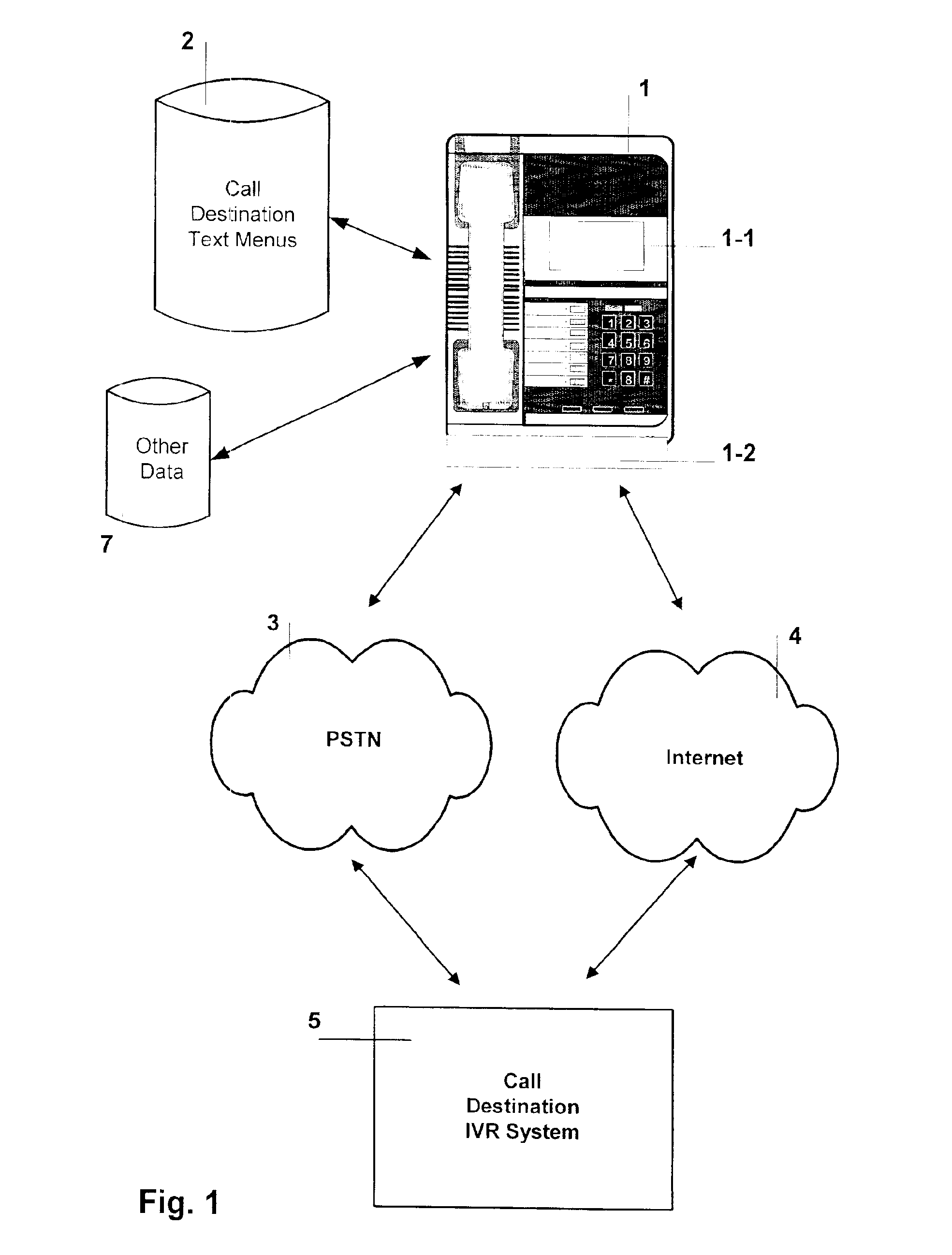
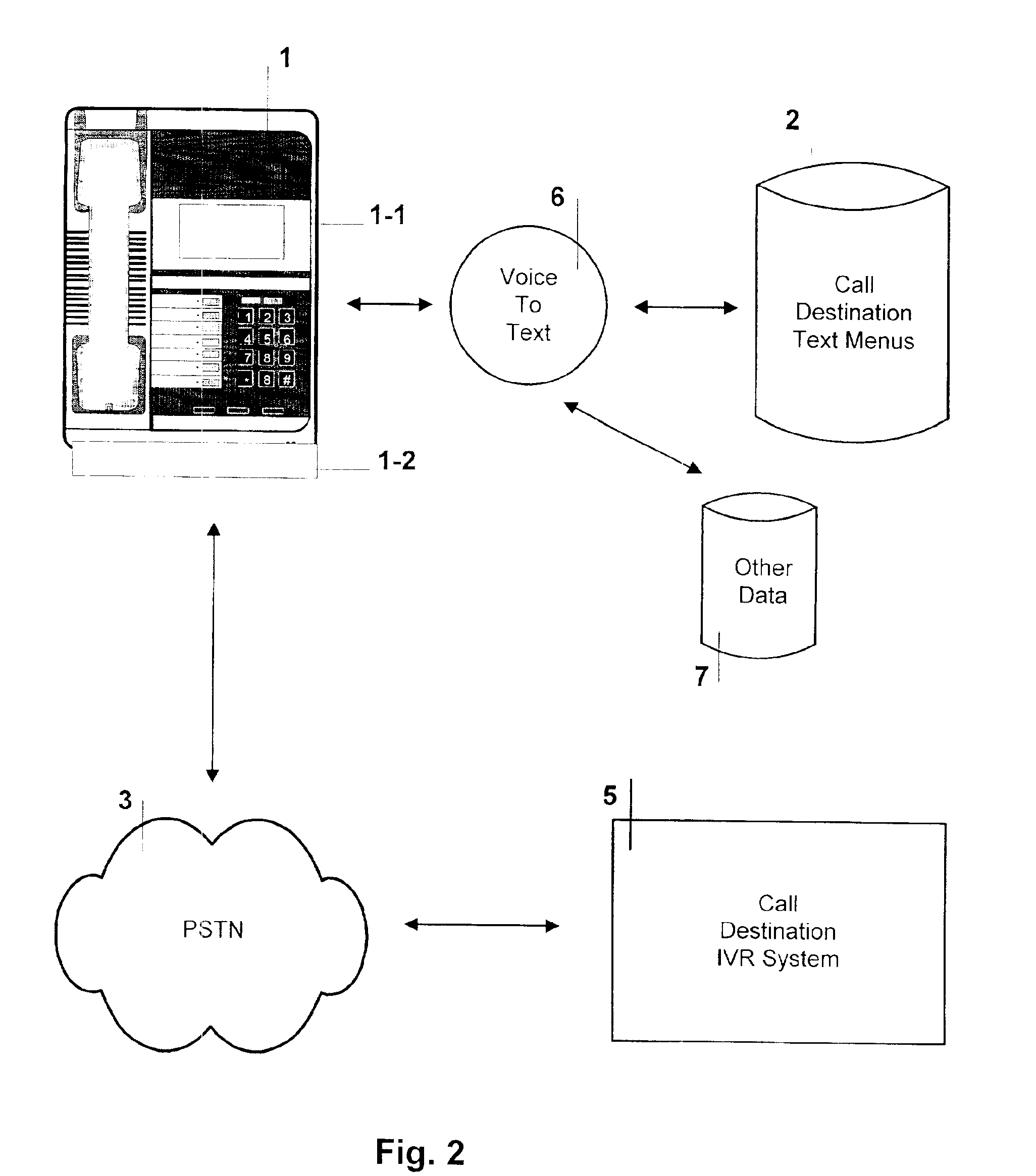
System and method for integrating the visual display of text menus for interactive voice response systems
InactiveUS7027990B2Telephone data network interconnectionsArrangements for variable traffic instructionsModem deviceThe Internet
The present invention solves the serial nature of today's Interactive Voice Response (IVR) telephony menu systems, by means of visually “looking ahead” and in any direction in the nested audio IVR menus. Computer software in the telephone, or associated hardware, provides a graphical user interface that enables the user to navigate related IVR text menus that are displayed on the telephone. The present invention provides a variety of means to store, display, select and update associated text menus and other data with an IVR system. The various communication means include analog modems, broadband modems, and VoIP connectivity. The present invention provides the means to convert the audio IVR menus to text menus, as well as the means to download the associated IVR text menus from the Internet.
Owner:SUSN LESTER
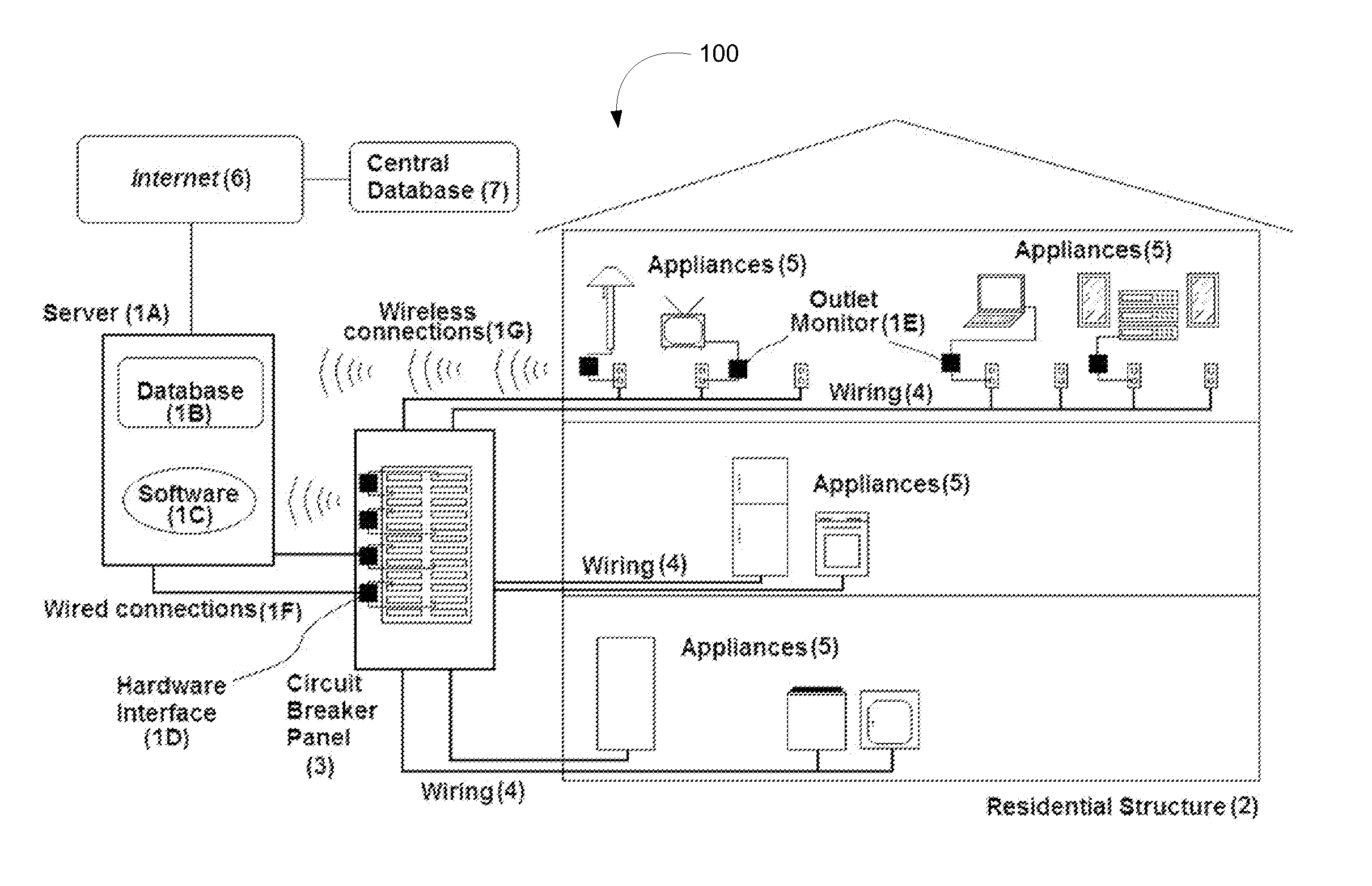
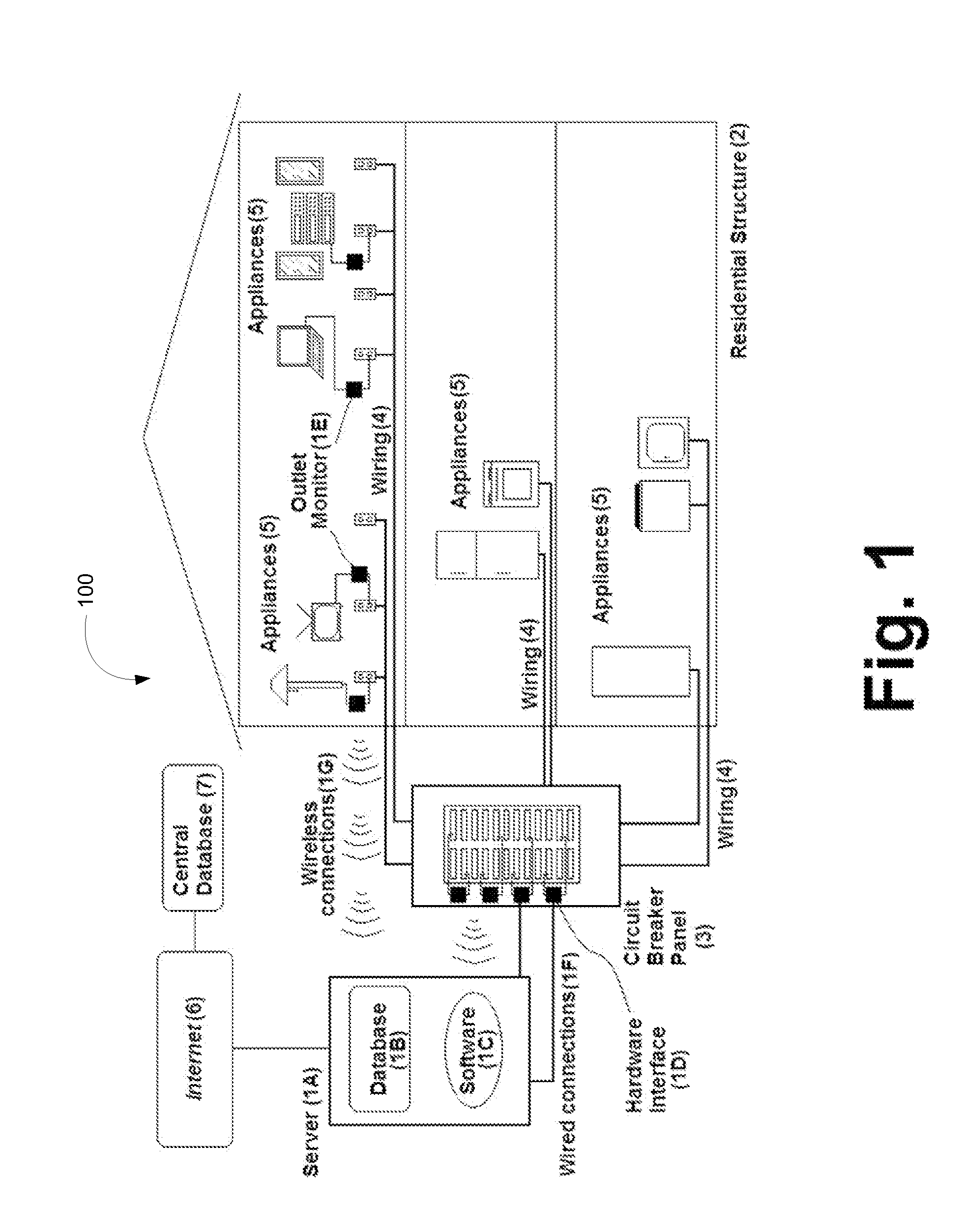
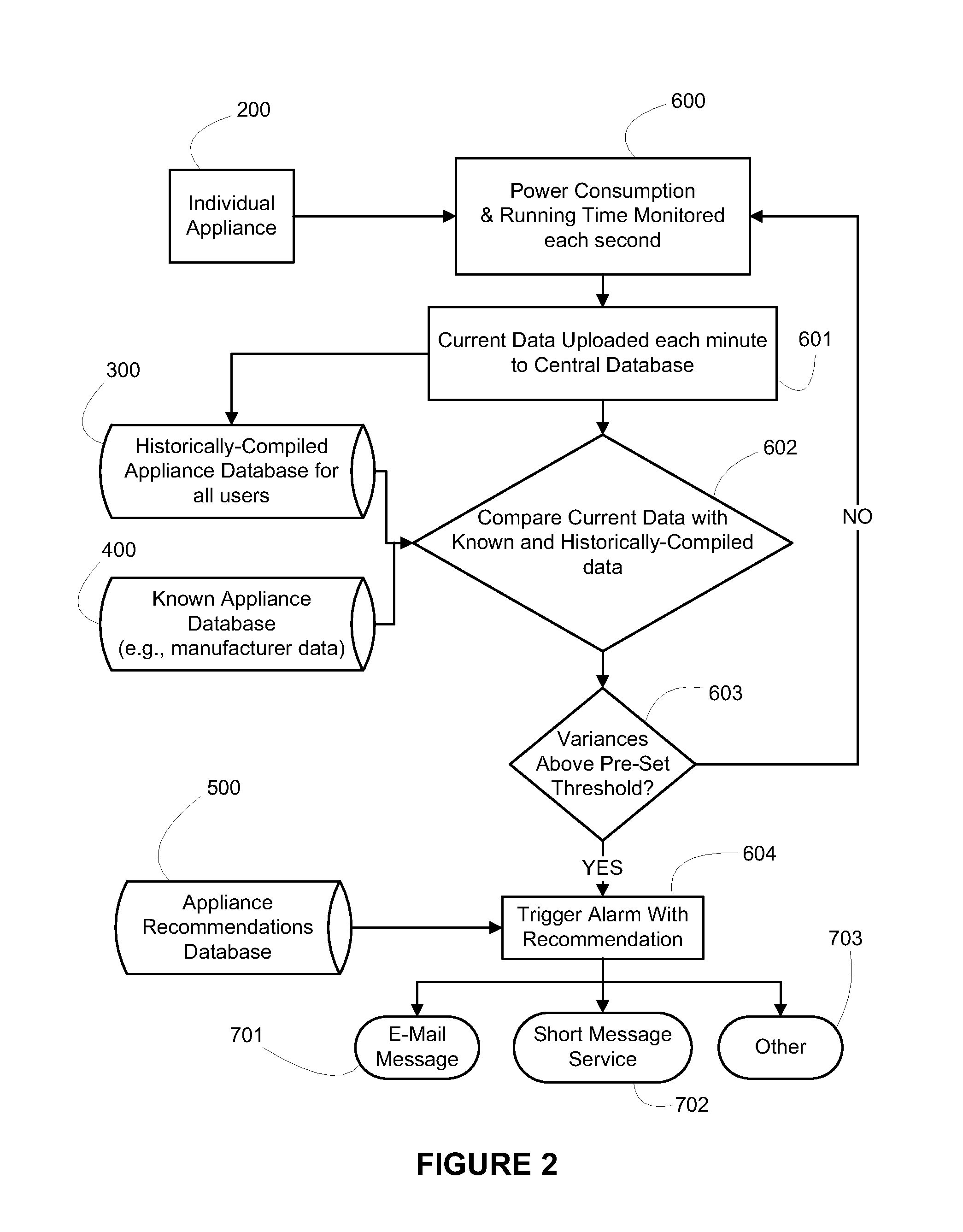
System and method to monitor and manage performance of appliances
ActiveUS20110040785A1Reduce energy consumptionSimple addressingDigital data processing detailsTesting/monitoring control systemsDecision takingComputer software
A system and method providing home and small business owners to monitor and manage one or more appliances. This enables a use to understand in detail their electrical consumption, to make informed decisions based on factual data about energy-saving upgrades to their current systems / appliances, and to provide Internet-based surveillance and control of systems for prevention of freezing, breakdown, or possible fire-related losses, including possible loss-of-life. The system and method includes through the use of Internet based computer software and databases, a hardware interface with electrical circuit panel(s) or fuse boxes in communication with the software and databases and optional wireless outlet monitoring units in communication with the software and databases. The databases being formed and created by the system and method for determining performance of appliances.
Owner:POWERHOUSE DYNAMICS
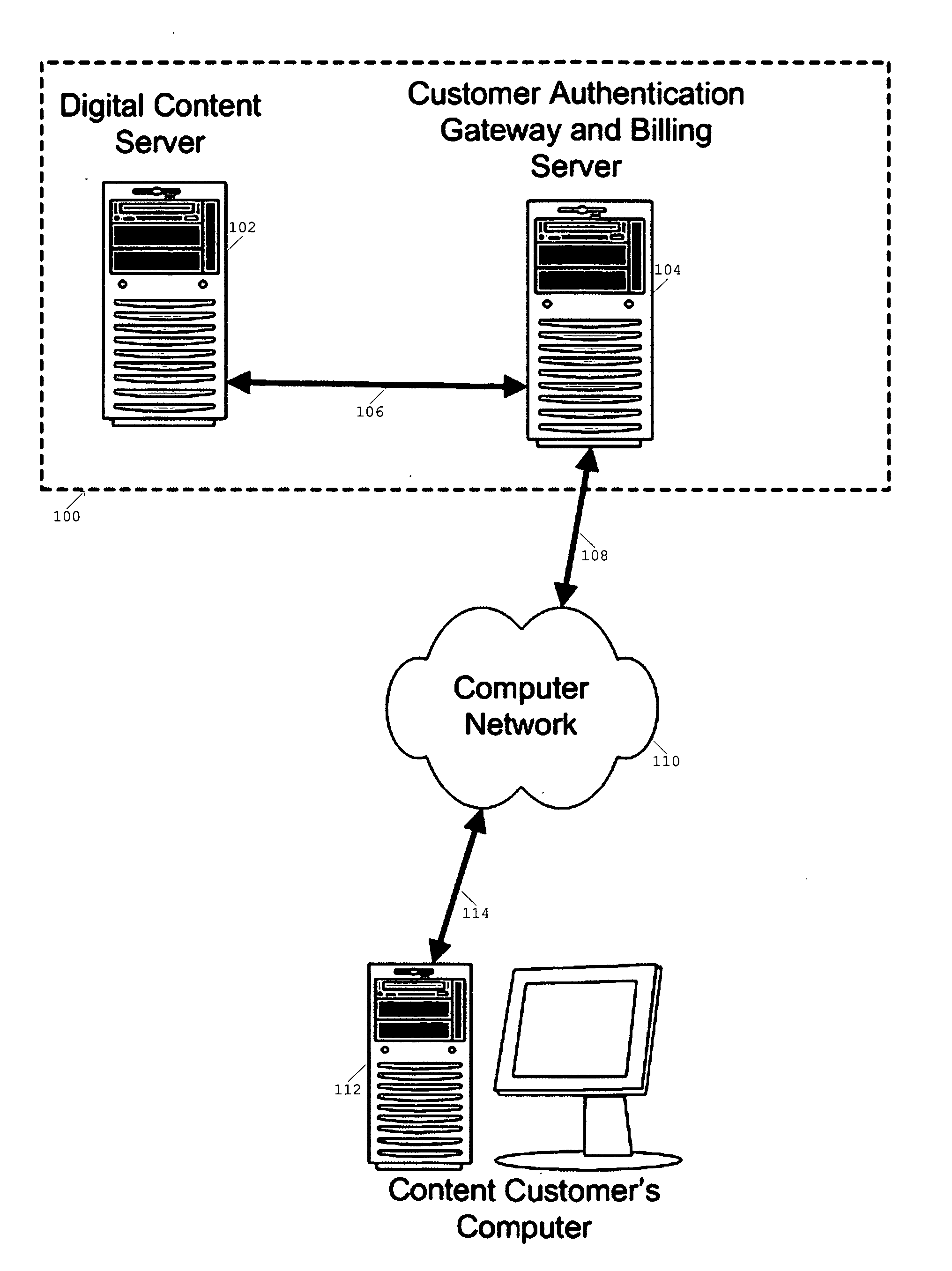
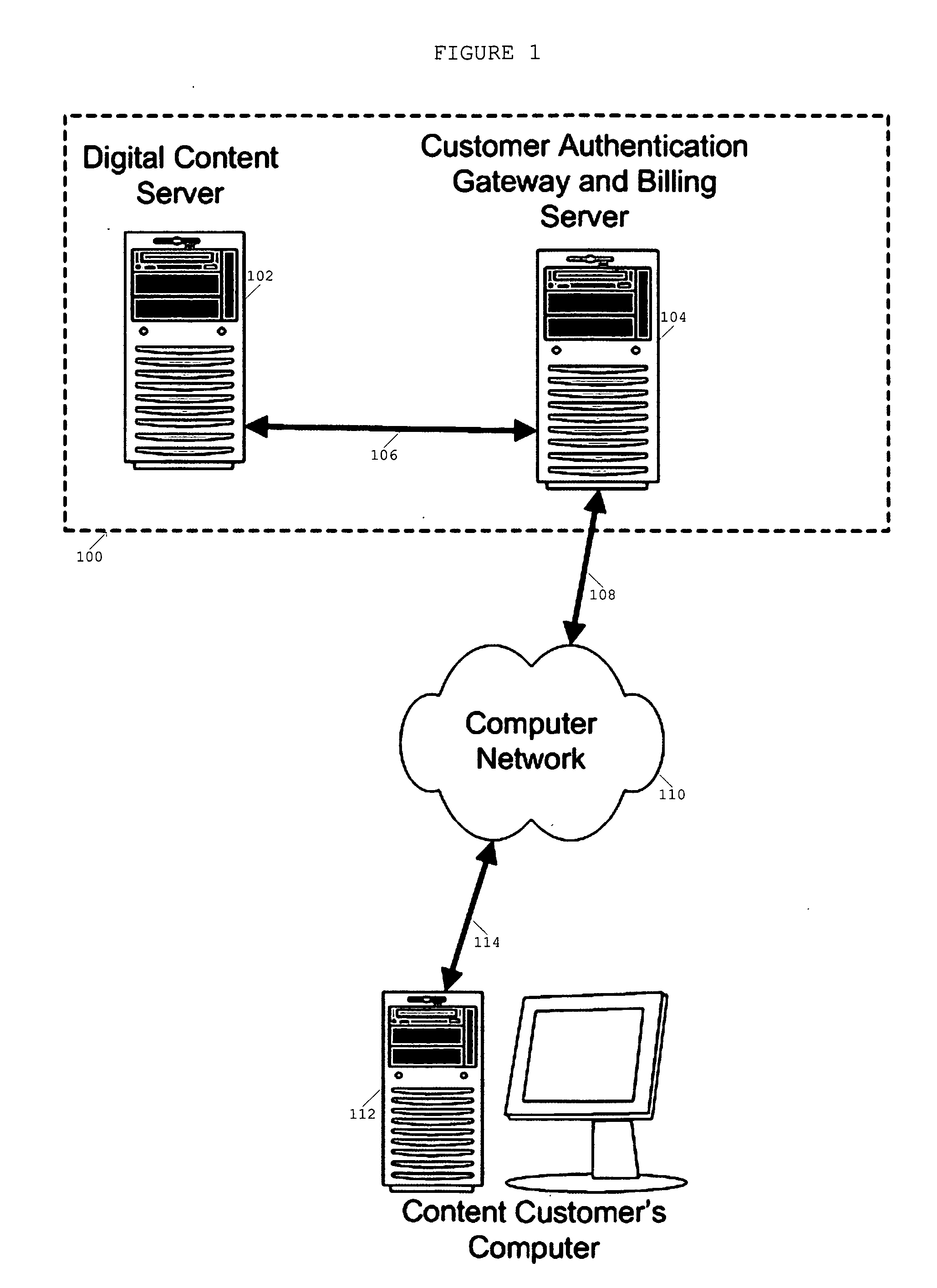
Method and apparatus for the rental or sale, and secure distribution of digital content
A method for the rental or sale, and distribution of digital content via the Internet. This method ensures enforcement of copyrights and end-use licensing. The invention consists of one or more databases, for the storage of digital content, and also for storage of customer profile and billing information. These databases are housed in multiple networked computers, sharing a private connection to an Internet firewall, gateway computer. This computer hosts an electronic commerce web site for customer purchase transactions and encryption of digital content prior to customer download. The invention also includes a software client application for decrypting and using the digital content. The invention also provides for computer software to manage the digital content inventory of each customer.
Owner:VARBLE THOMAS BRYAN
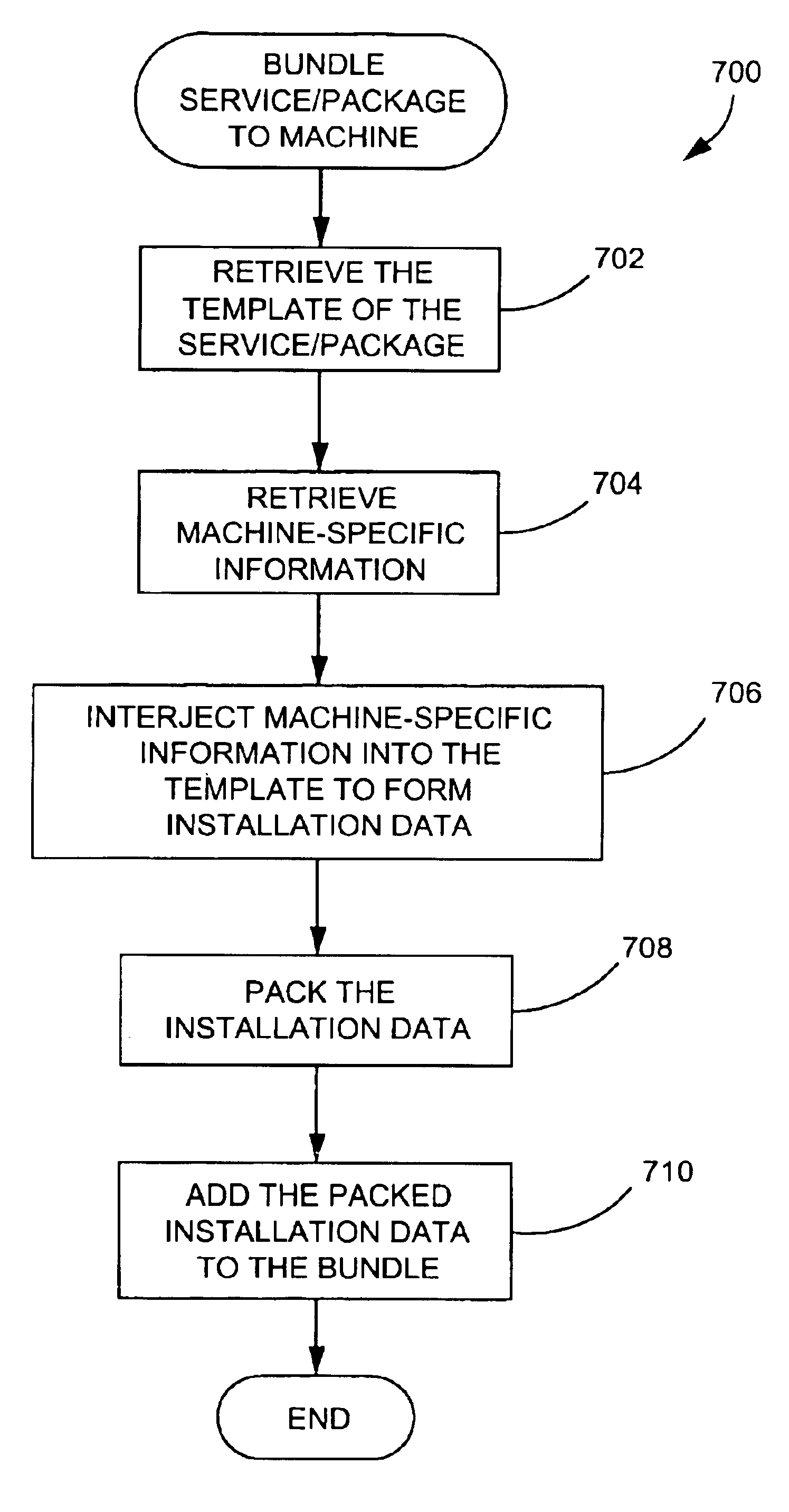
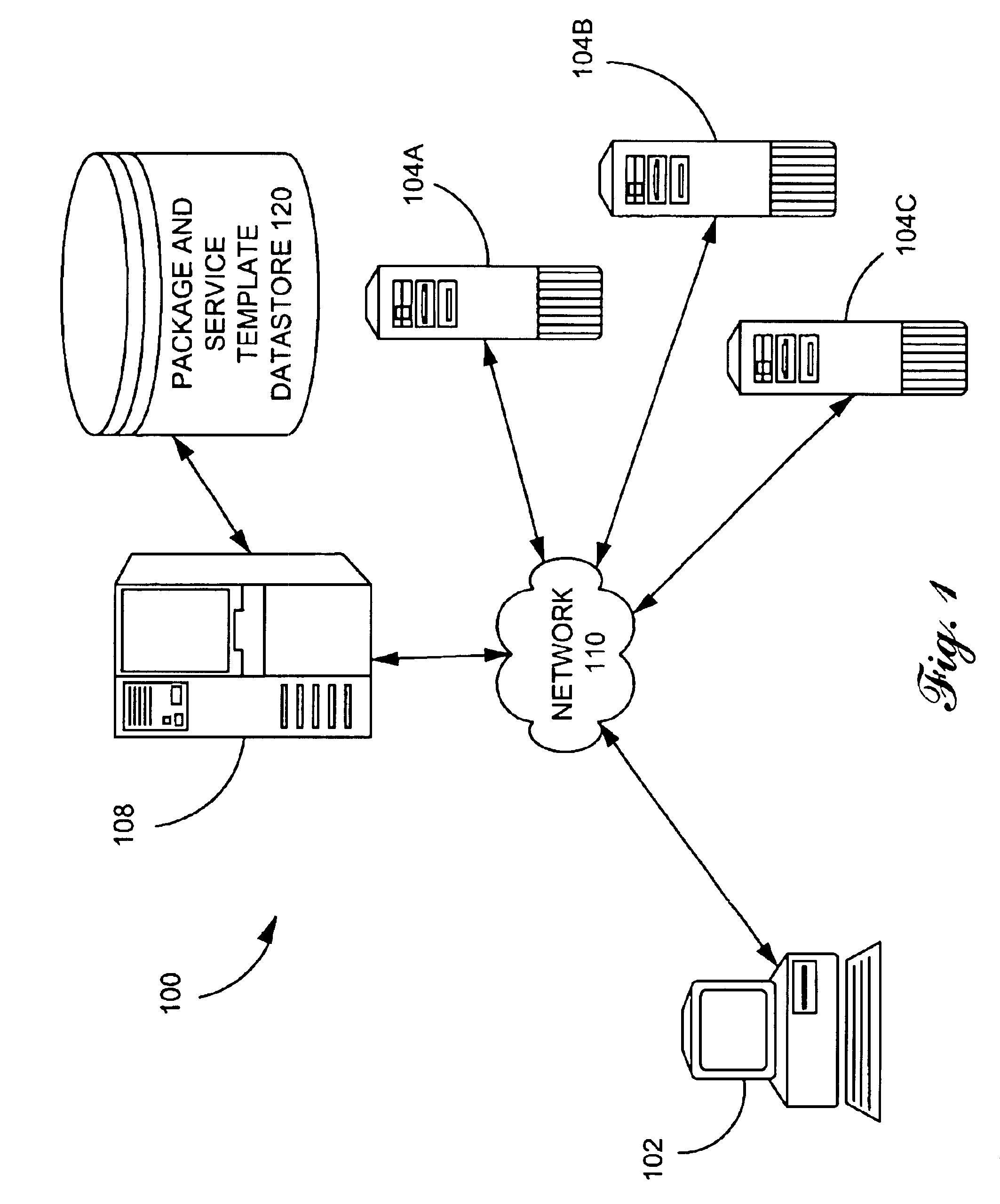
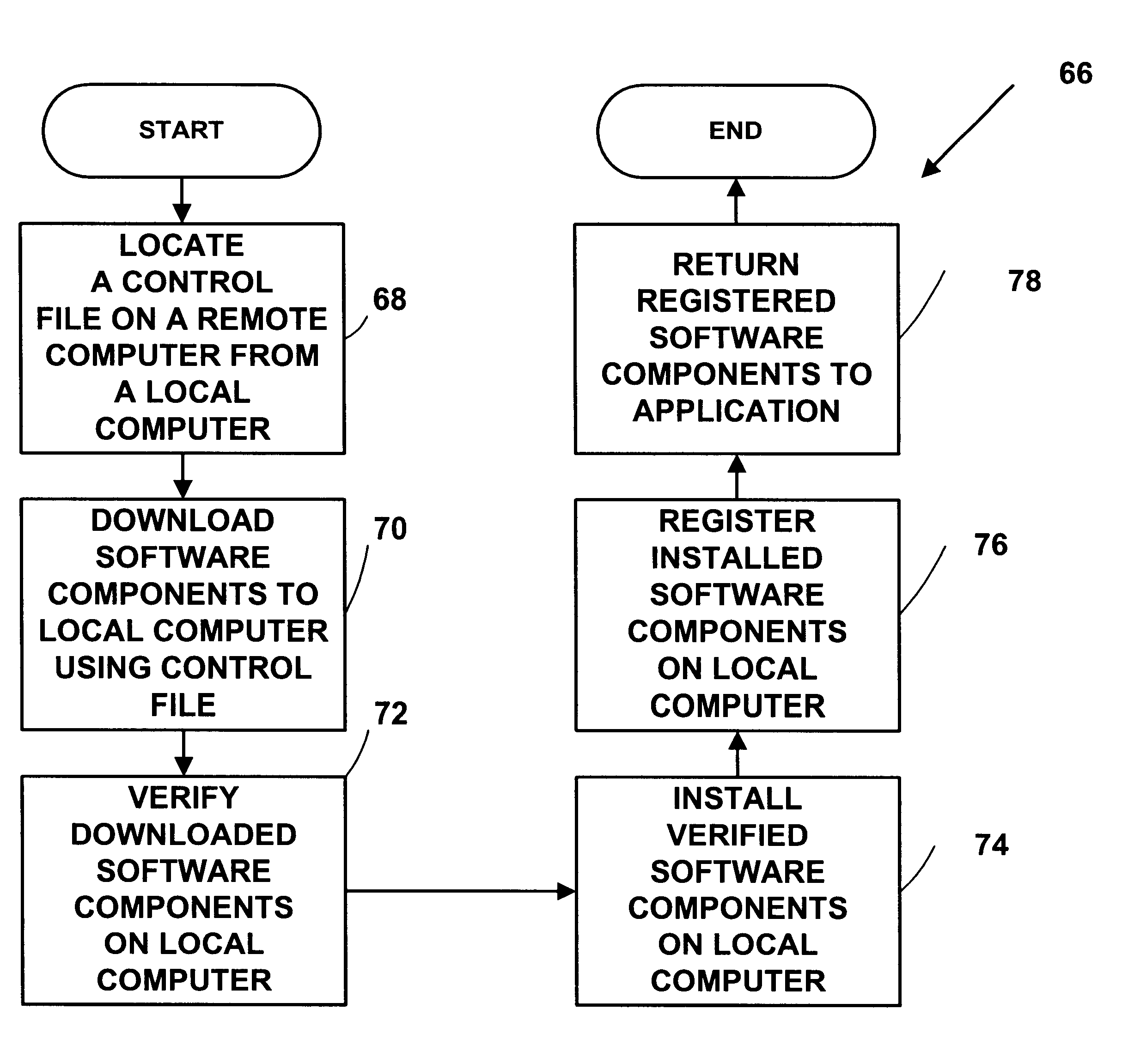
Remote software installation and maintenance
InactiveUS6865737B1Accurately easily initiateGood chanceProgram loading/initiatingSoftware reuseData fileComputerized system
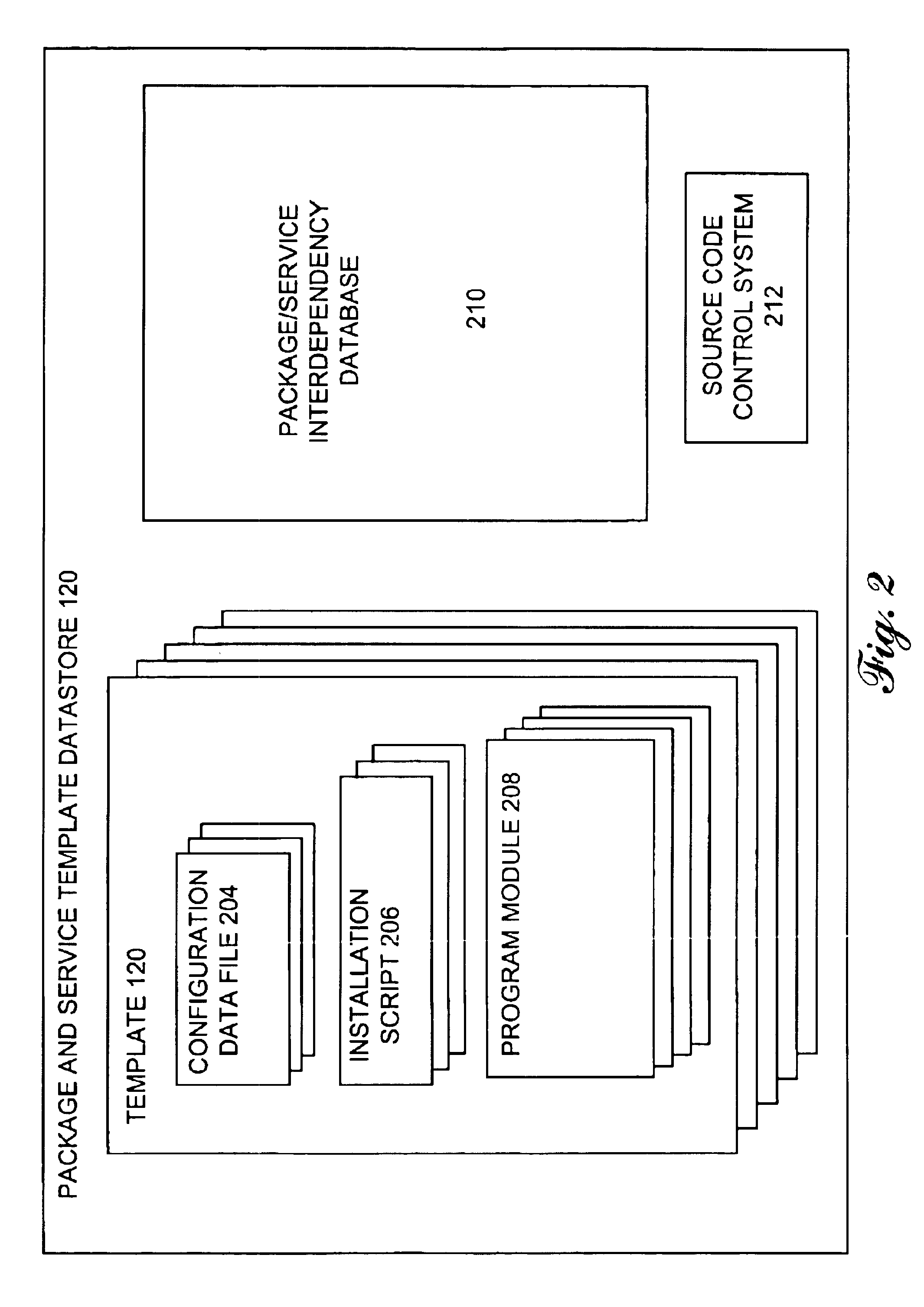
A human engineer using a computer system can maintain numerous software services and packages installed on a number of servers through a single master server and a computer network. Each software service and package is represented in a package and service template datastore 120 in templatized form. The installation template includes placeholder data which represents server-specific information used to install the computer software. The placeholder is included in program modules, configuration data files, and / or installation scripts. To install the computer software on the selected server computer, a master server retrieves server-specific information for the selected server, substitutes the retrieved server-specific data for the placeholder data to form server-specific installation data, and transports the server-specific installation data to the selected server for execution.
Owner:MICROSOFT TECH LICENSING LLC
System and method for global group reporting
ActiveUS20060123389A1Efficient flexibleEfficient and flexibleError detection/correctionResourcesProject managementSoftware development
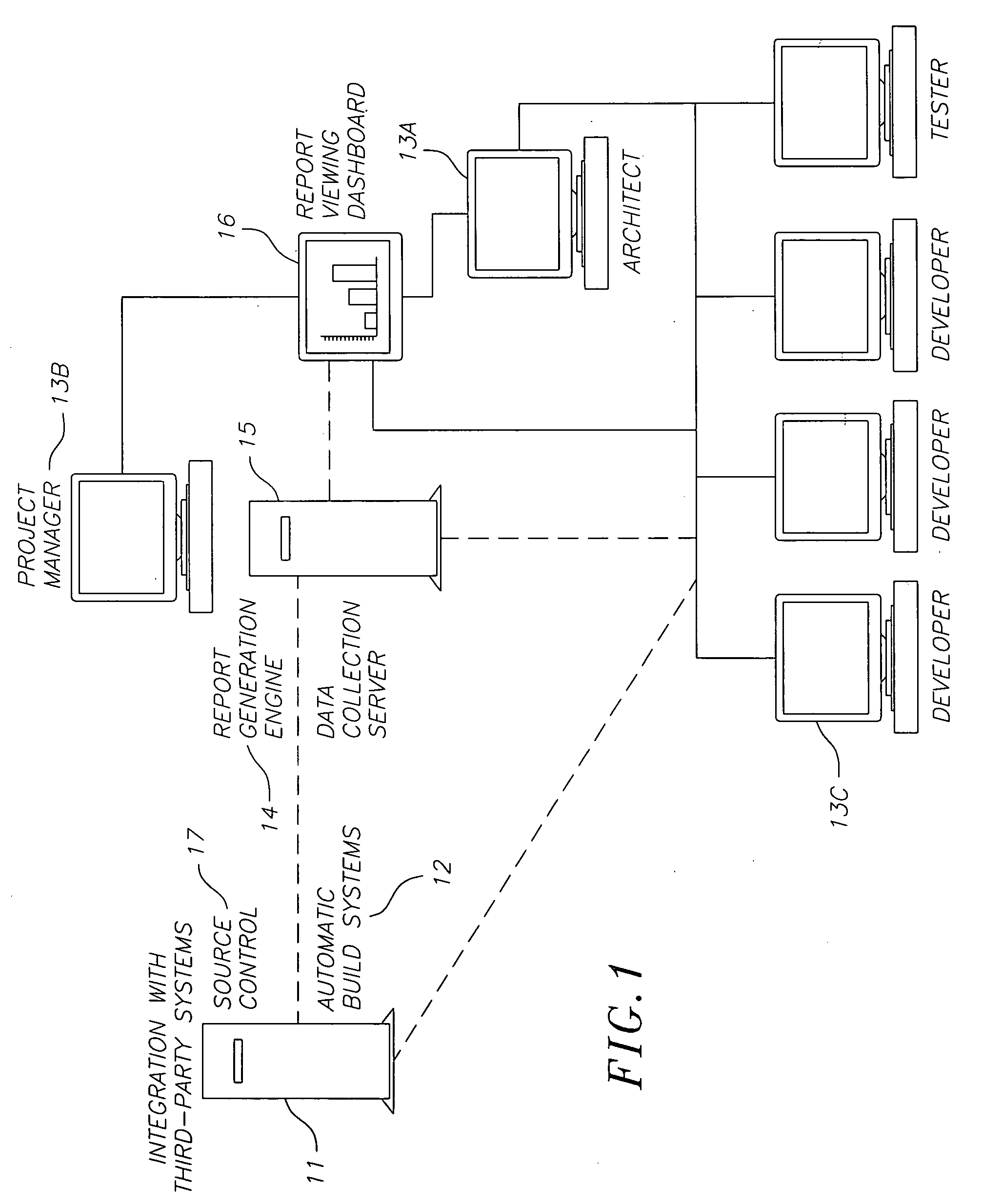
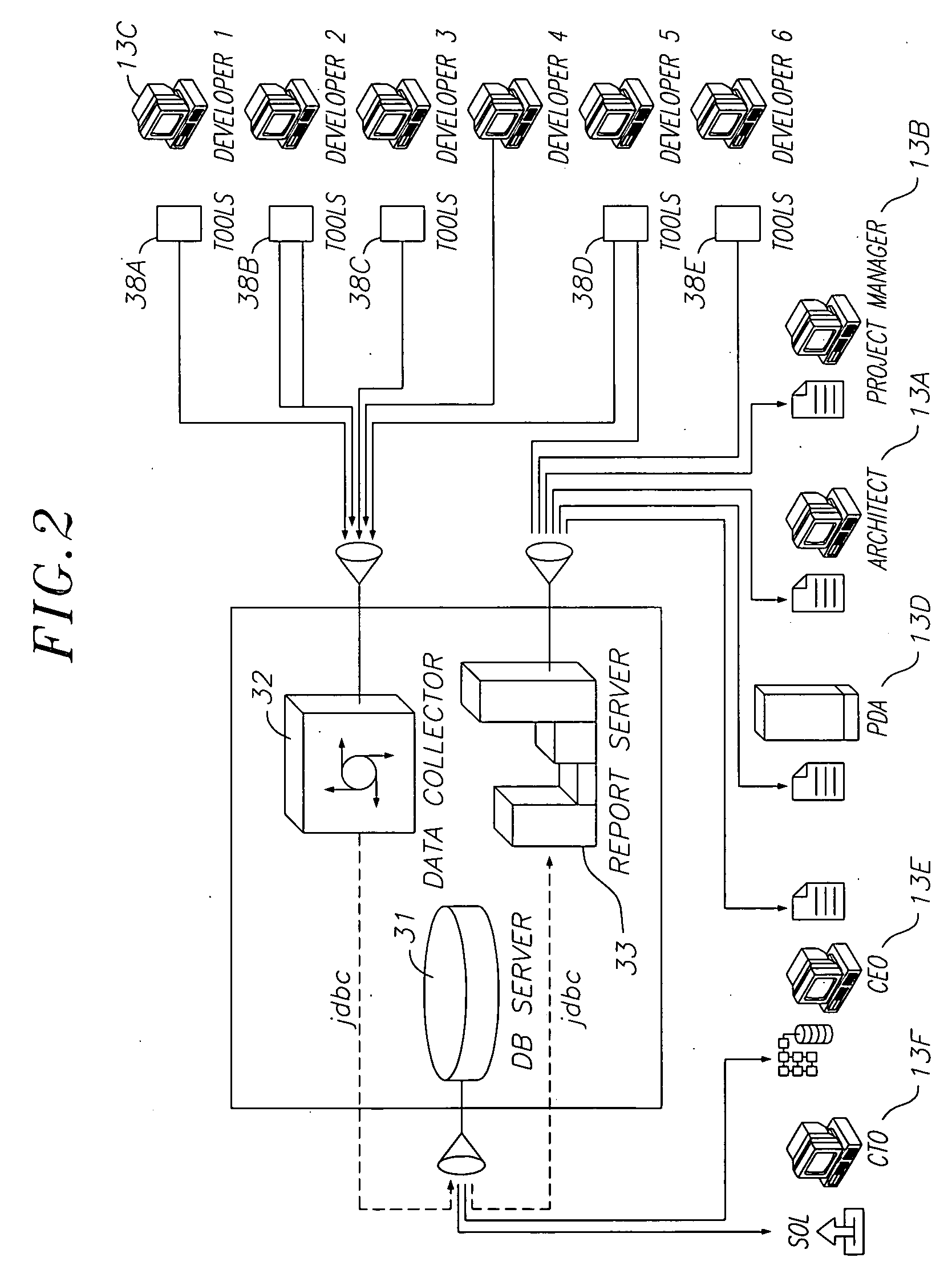
A system and method for collecting and correlating information about development of a computer software, including software tools reports. The system and method provides overview of entire software development lifecycle, provides decision support engine for project management, allows estimation of project timelines based upon empirical data, allows evaluation of project quality based upon empirical data, and correlates information from previous projects to estimate progress of current project (confidence factors). The system and method for collecting and correlating information about development of a computer software include collecting data from a plurality of software tools during each point in lifecycle of the computer software; storing the collected data in a database; and correlating the stored collected data to monitor the development of the computer software.
Owner:PARASOFT
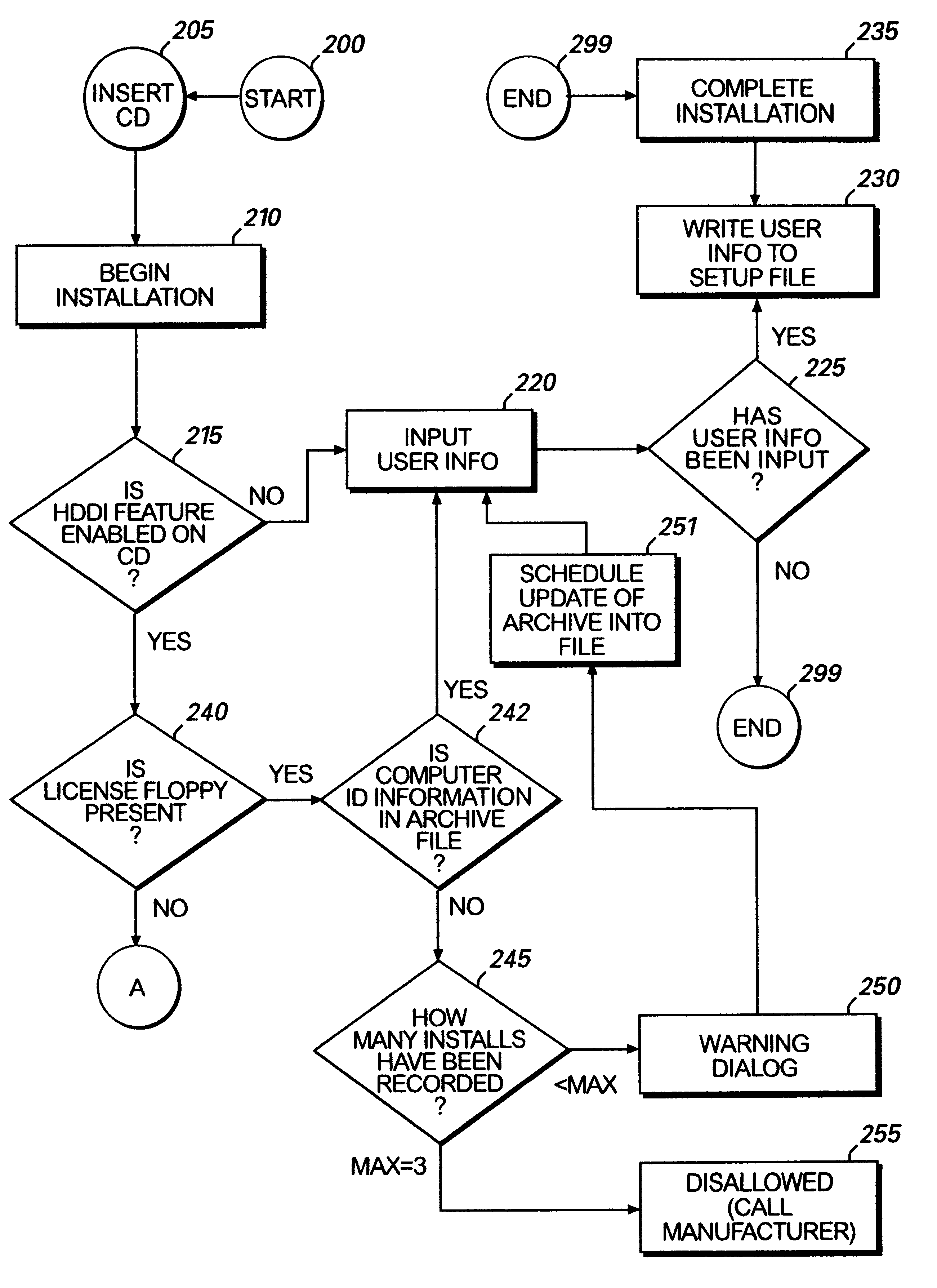
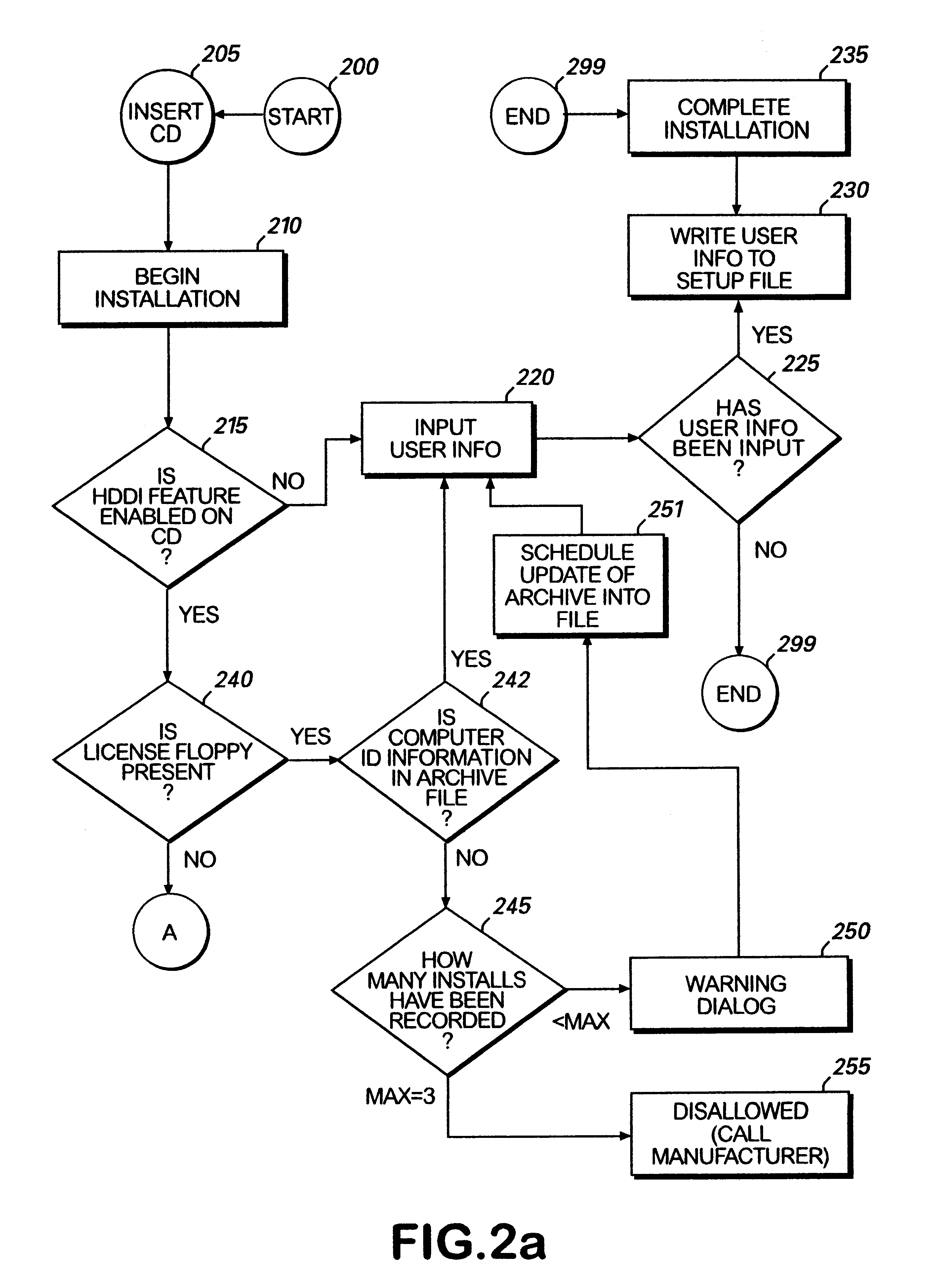
Method for preventing software piracy during installation from a read only storage medium
InactiveUS6226747B1Easy to installDigital data processing detailsRecord information storageSoftware licenseComputer software
The method and system for limiting the number of installations of a computer software program located on a read only disk from the read only disk to a computer. The read only disk is linked to a removable read / write memory by data on the removable read / write memory corresponding to data on the read only disk. Prior to installation of the computer software program from the read only disk to the computer, software residing on the removable read / write memory determines whether the installation is authorized. Such determination is made by comparing identification information corresponding to computers on to which the computer software program has previously been installed to installation limitations dictated by a software license agreement.
Owner:MICROSOFT TECH LICENSING LLC
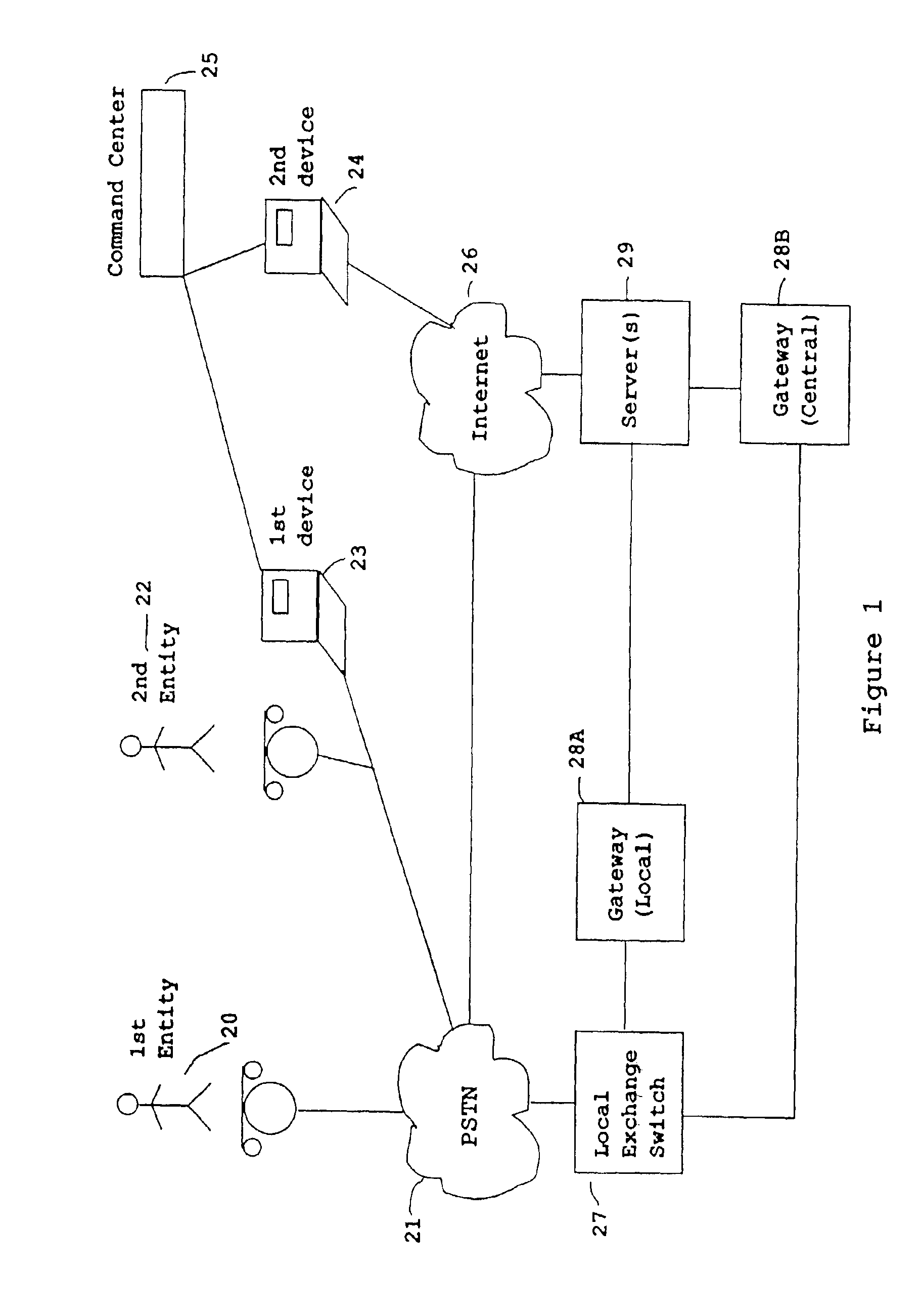
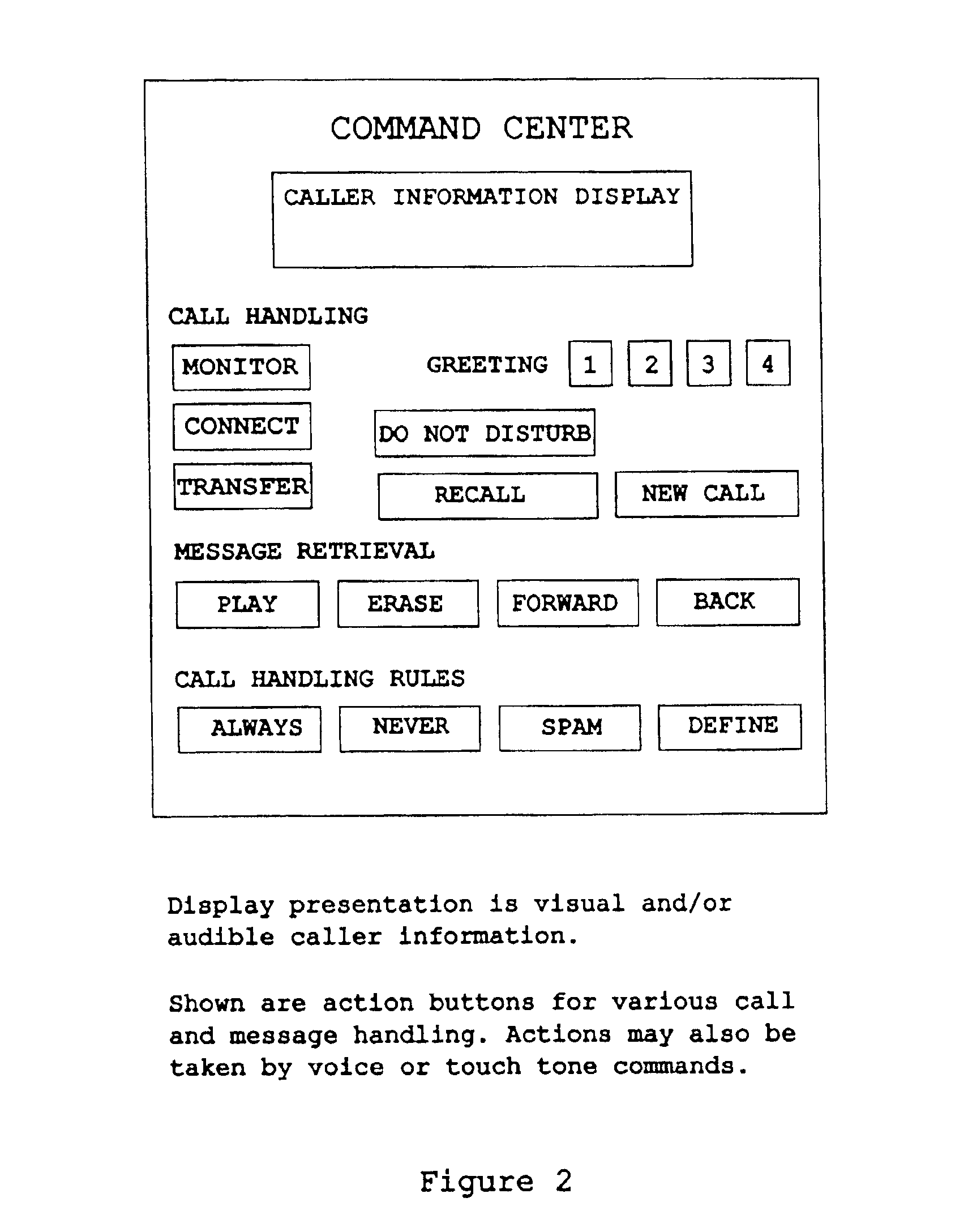
Method and apparatus for providing expanded telecommunications service
InactiveUS6898275B2Add featureAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersTelecommunications linkMultiplexer
System and method for putting control of incoming telephone calls in the hands of subscribers with the aid of computer software and the Internet. In effect, a very efficient multiplexer is provided that does not require a change in the behavior of the called party or the calling party. This system permits the called party to hear a spoken message by the calling party in real time, and the content of the spoken message permits the called party to decide how to handle the call. The system adaptively learns and captures the rules of the called party for handling calls, and learns which callers the called party always wishes to talk to. The system uses special control software on the called party's computer which is connected to the Internet. The system employs a central server in which all of the required intelligence is resident. Audio signals are exchanged via non-data channels provided by the telephone companies and by the Internet. Either a very simple Internet busy pick-up is provided, or a very complex messaging system is provided, as desired. A feature is the monitoring and screening of incoming calls before deciding how to handle them. Another feature is the capturing and storage of the decision making profile.
Owner:CALLWAVE COMM
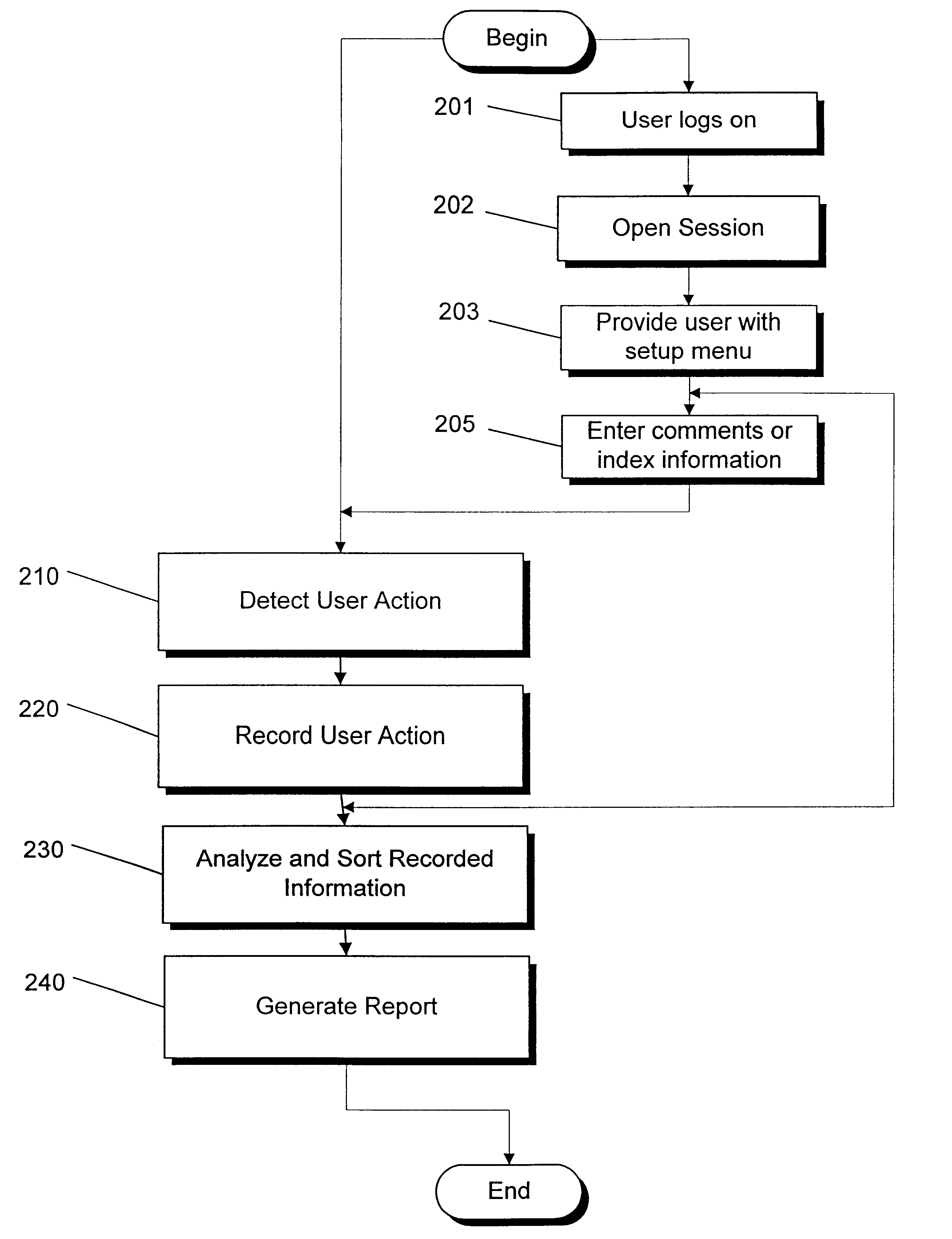
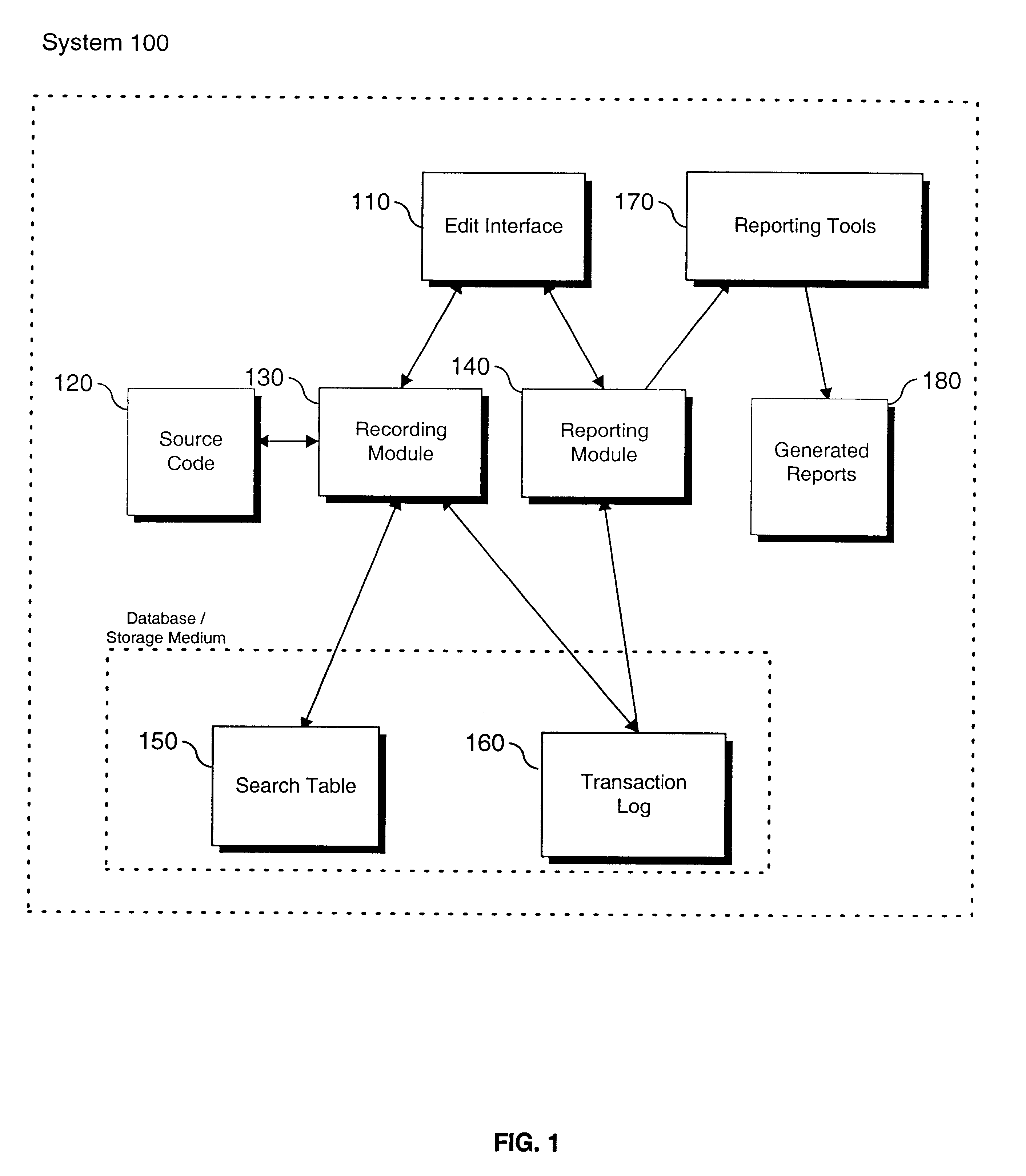
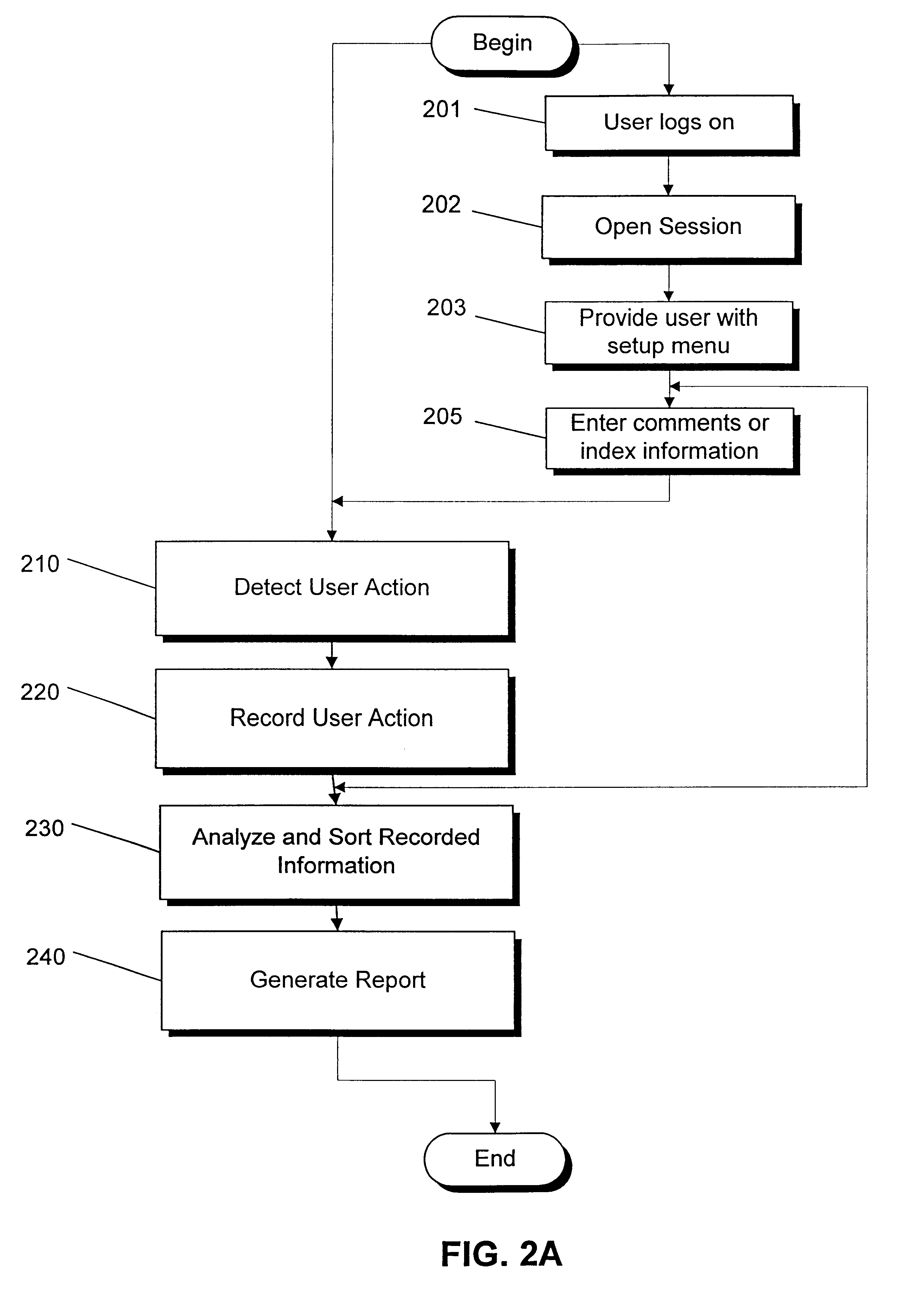
Real time monitoring system for tracking and documenting changes made by programmer's during maintenance or development of computer readable code on a line by line basis and/or by point of focus
InactiveUS6698013B1Version controlSpecific program execution arrangementsMonitoring systemComputer software
A method and system for documenting and tracking user interaction with computer readable code during modification or development of computer software is described. The invention provides a controlled environment for recording detailed information about user actions and events that occur during the maintenance and development of computer readable code. Features of the invention facilitate the entry of comments, review, and modification of the computer readable code. Embodiments of the invention, in real time, monitor, record, and report changes made to software modules at a line-by-line level. The nature and context of changes made to lines of code and any search requests are identified and recorded in one or more databases for review and reporting.
Owner:MINTAKA TECH GROUP
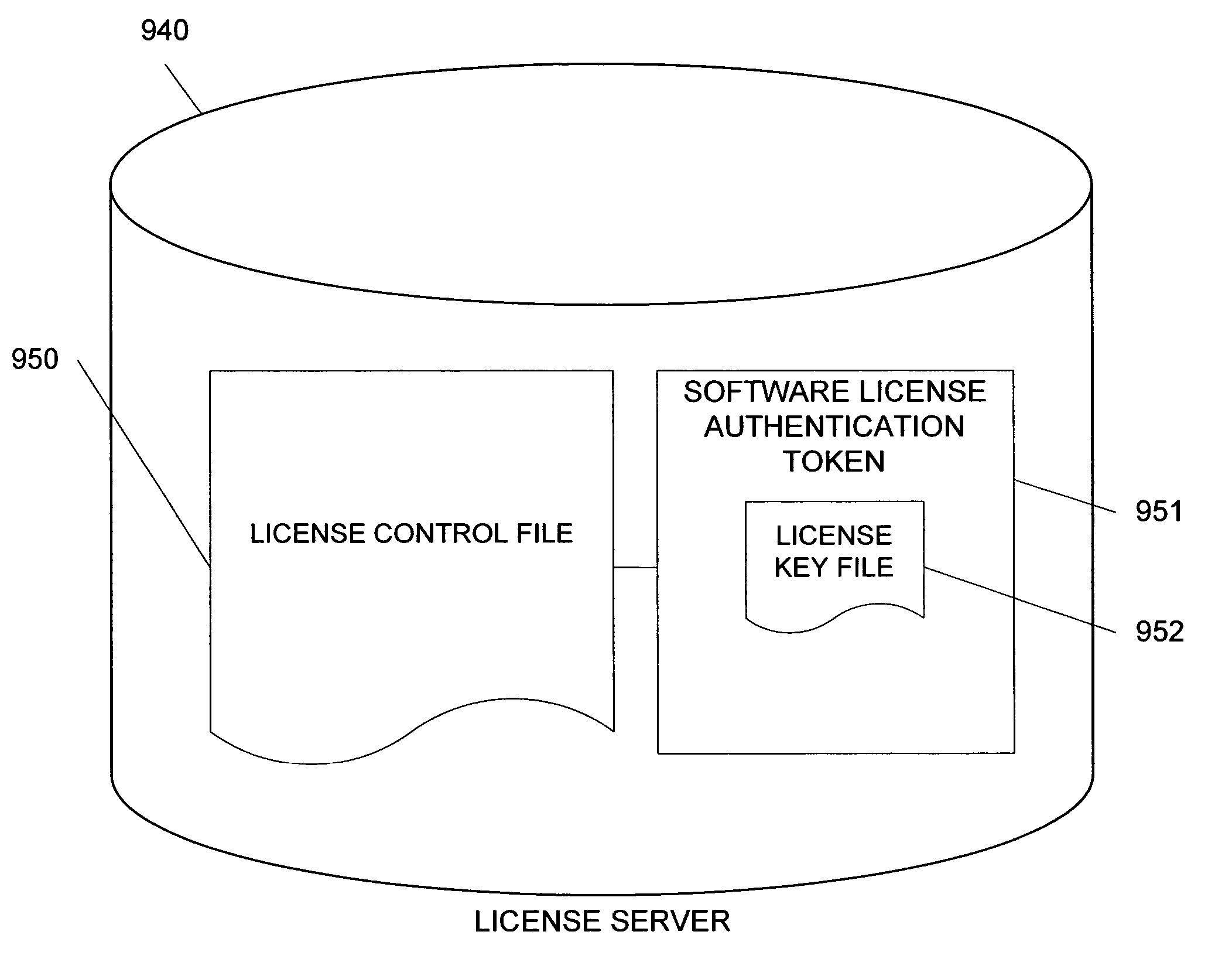
Methods and systems for licensing computer software
InactiveUS20060179058A1Computer security arrangementsInference methodsLicense controlBiological activation
Methods and systems for determining whether a component defined in a computer program is authorized to activate. One method can include receiving an activation authorization request from the component; accessing a license control file defining a plurality of mappings, each of the plurality of mappings associating at least one of a plurality of components defined in the computer program to at least one required license; determining if the component is associated with at least one required license based on the plurality of mappings; and providing a response to the component.
Owner:FIDELITY INFORMATION SERVICES LLC
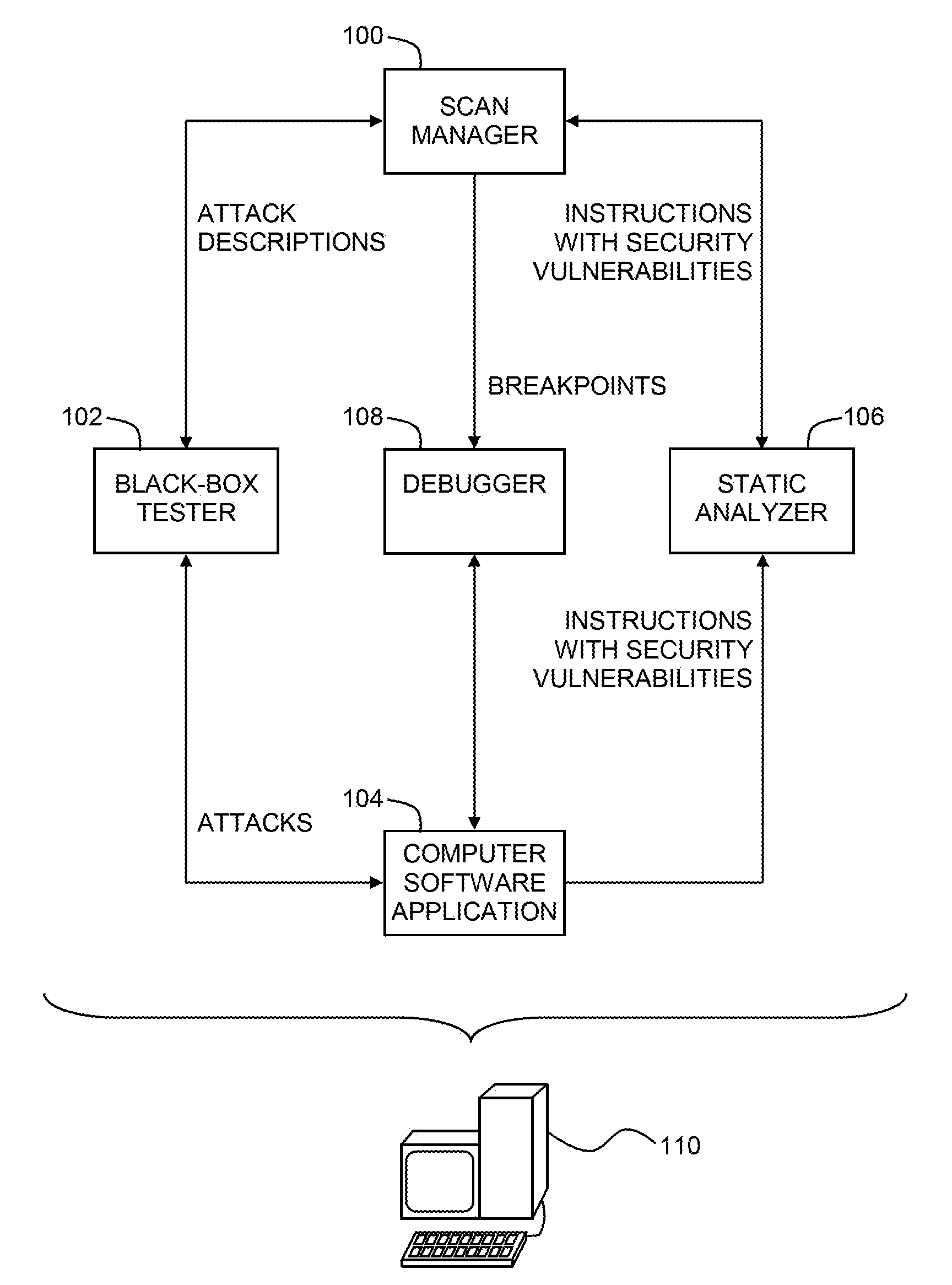
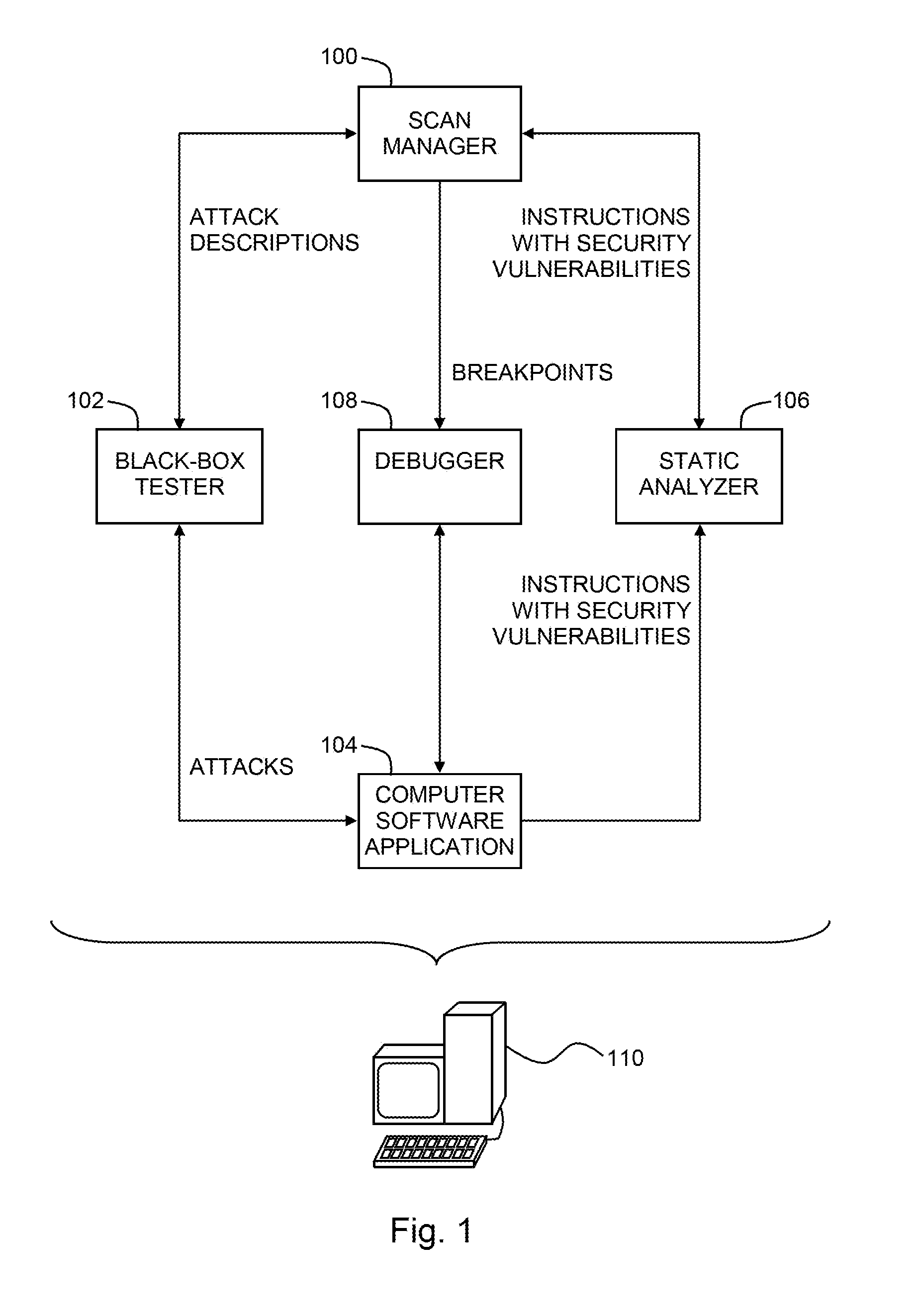
System and method for identifying and eliminating vulnerabilities in computer software applications
ActiveUS7284274B1Memory loss protectionError detection/correctionParallel computingApplication software
Owner:SYNOPSYS INC
Software and hardware analysis test
InactiveUS20060217823A1Easy pairingEasy to operateComputer controlError detection/correctionComputer softwareRapid response
Embodiments described herein relate to techniques, tools and processes for analyzing a computer system and determining the type and capabilities of hardware and software components resident on the computer system. This information can then be used for multiple different purposes. For example, the information may be used for (1) communicating an individual computer's ability to effectively operate a specific computer software and / or computer hardware product, (2) relaying the information to a technical support operation to allow a more rapid response, or (3) making a simple evaluation of the stand alone performance of a computer. These processes can be used for analyzing an individual computer's system inventory (computer hardware components and system software components) against a static set of manufacturer validated requirements for a hardware or software product.
Owner:HUSDAWG
Mobile Telephone Firewall and Compliance Enforcement System and Method
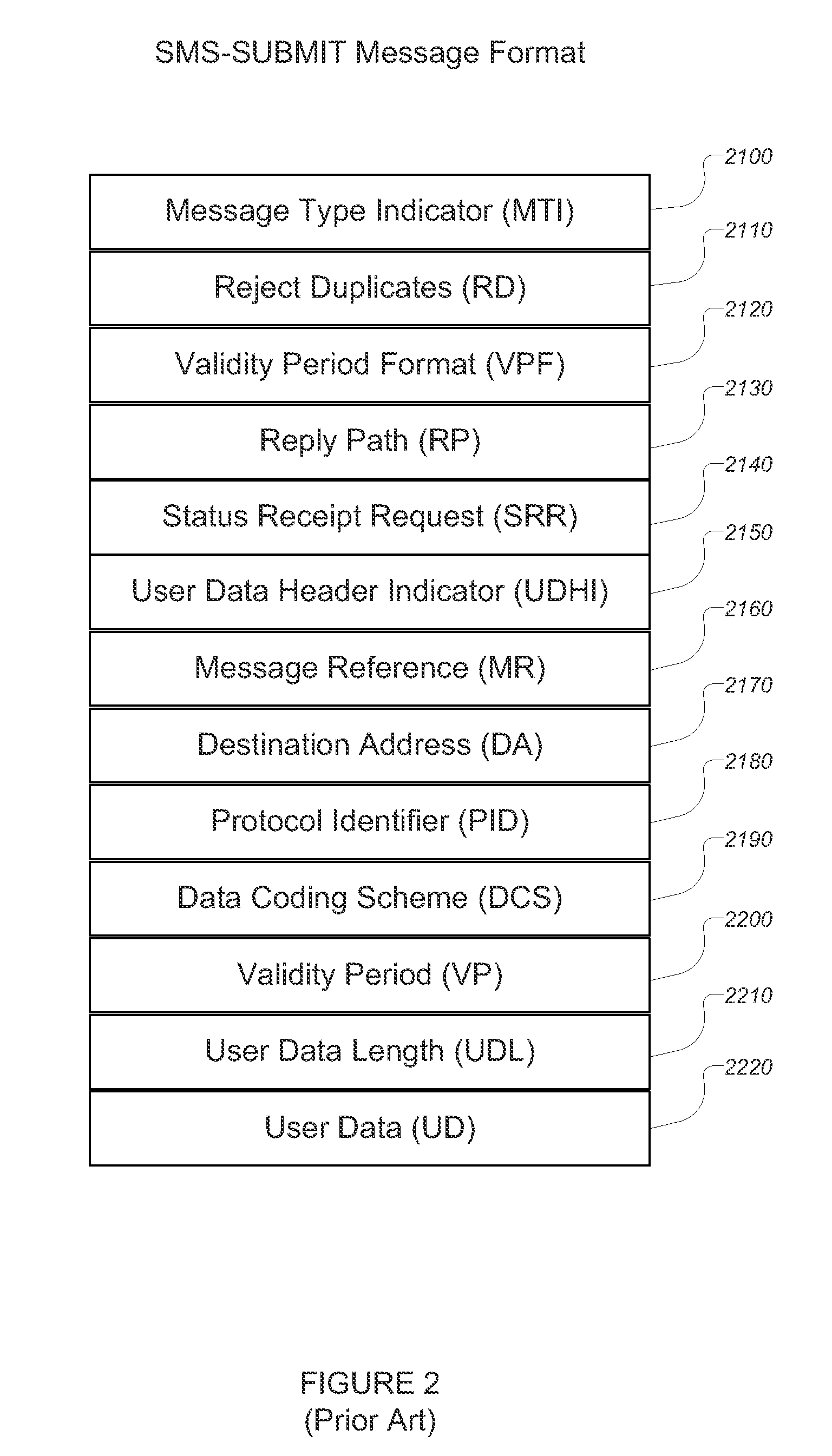
ActiveUS20090325615A1Improve protectionSubstation equipmentMessaging/mailboxes/announcementsComputer softwareSubscriber identity module
Methods, systems, and software for mediating SMS messages, and especially type 0 SMS messages, in a wireless mobile communications device configured to send and receive data using a GSM protocol and including a subscriber identity module (“SIM”) including electronic hardware and computer software executed by the hardware such that the SIM is configured to send, receive, and process messages using a Short Message System (“SMS”) between the wireless mobile communications device and a communications network. One aspect includes a method for mediating SMS messages comprising: configuring electronic hardware on the wireless mobile communications device to implement a firewall on the wireless mobile communications device, the firewall configured to identify and optionally mediate infrastructure SMS messages.
Owner:MANTECH ADVANCED SYST INT
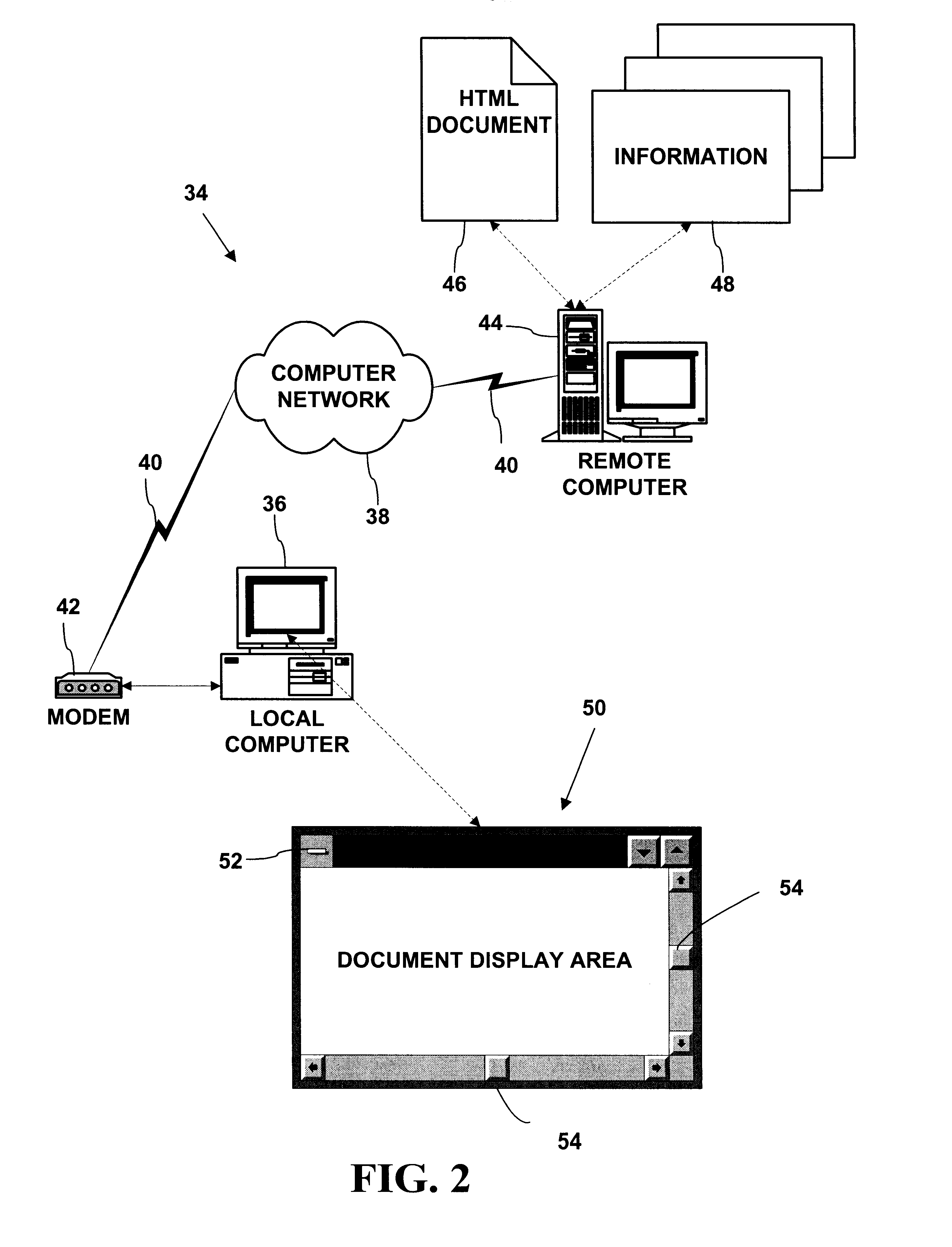
Automatic software downloading from a computer network
Methods and systems automatically download computer software components from a computer network like the Internet or an intranet. The methods and systems can be used to provide dynamic or interactive multimedia components in HTML documents with HTML <OBJECT> tags. The HTML <OBJECT> tags can contain parameters including uniform resource locators (URLs) which reference dynamic or interactive multimedia components on remote computers. Network browsers and other applications can obtain computer software components from a computer network like the Internet or an intranet in a uniform, portable, architecture-neutral, robust manner. The computer software components obtained can be used to provide a variety of new multimedia functionality to an application program.
Owner:MICROSOFT TECH LICENSING LLC
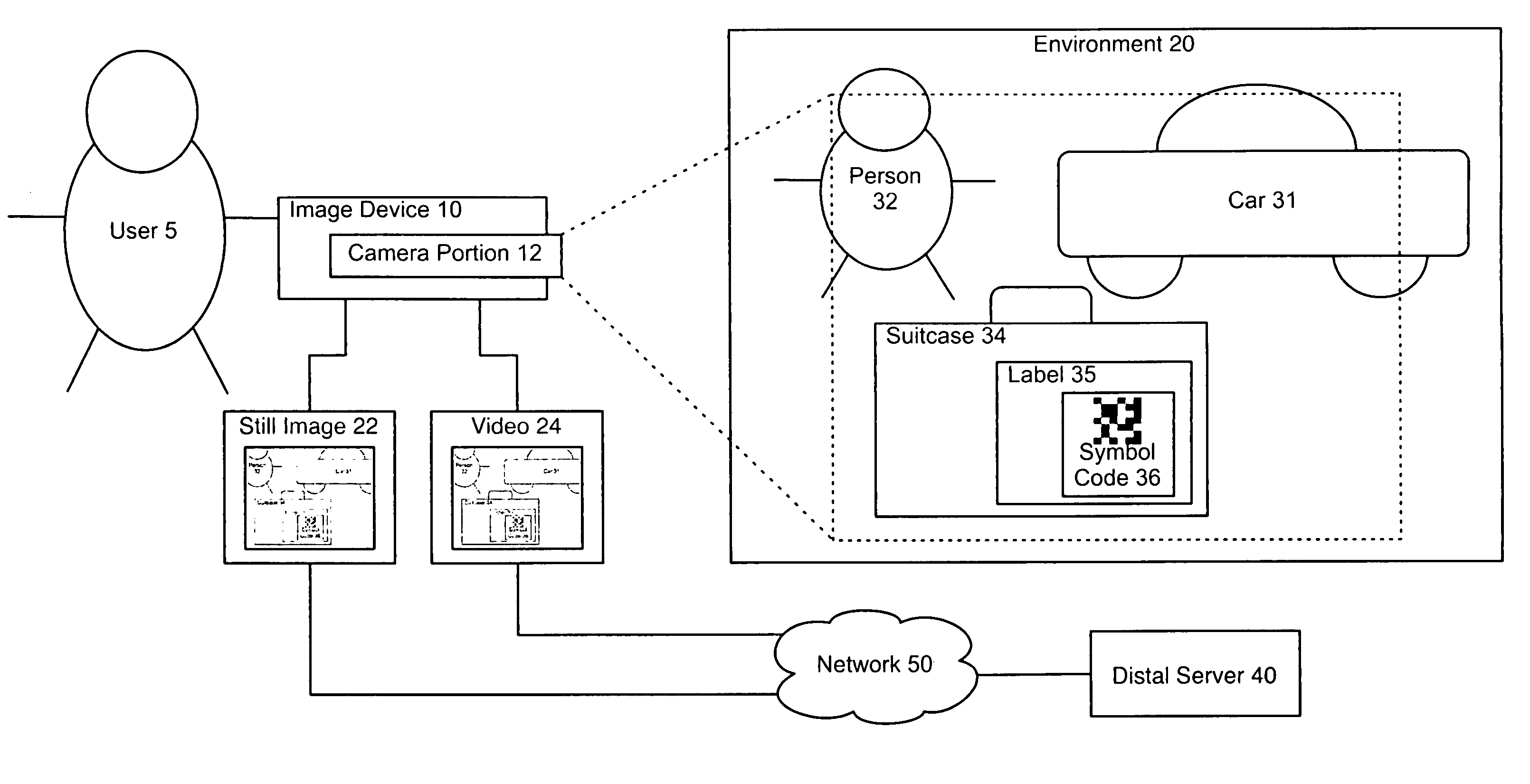
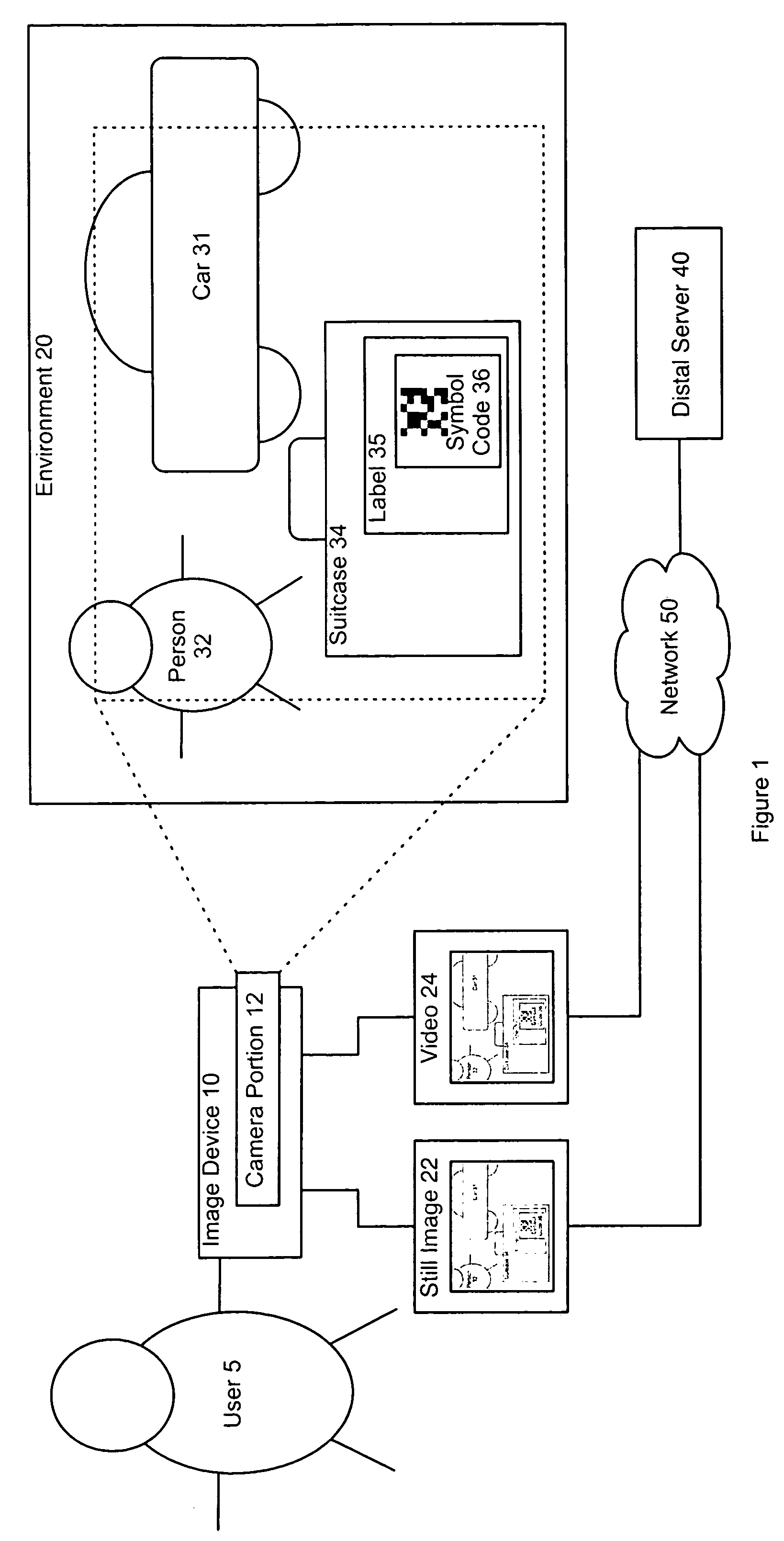
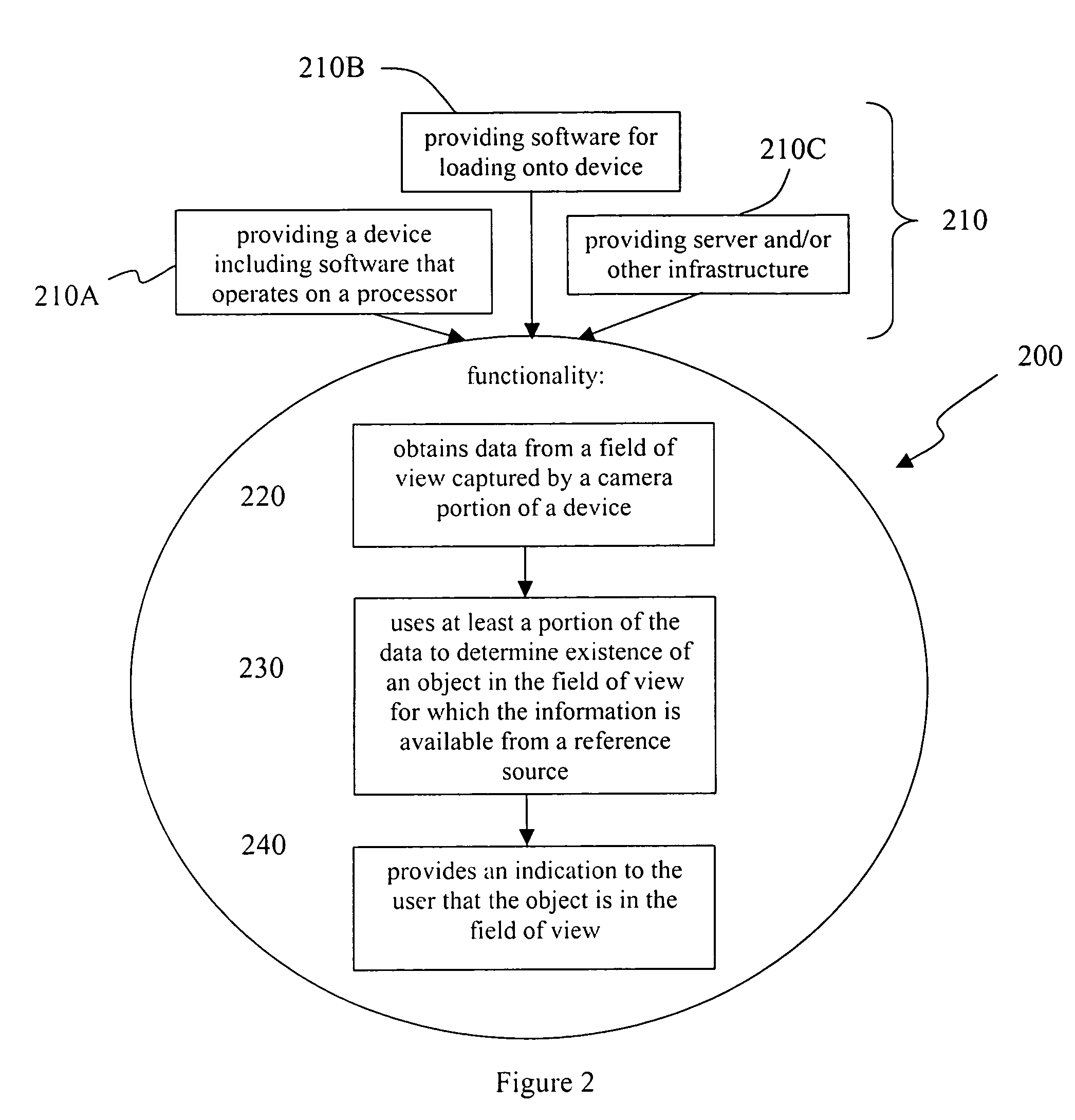
Methods and devices for detecting linkable objects
ActiveUS7775437B2Television system detailsFrequency-division multiplex detailsComputer softwareTrial and error
A camera portion of a portable consumer device obtains data from a field of view, and at least a portion of the data is used to determine existence of an object in the field of view for which the information is available from a reference source. An indication is then provided to the user that the object is in the field of view. This can all be accomplished by a functionality, such as computer software, that executes on one or both of the device and a distal server. Objects within the field that the system can identify and provide information are deemed “linkable.” Once a user is presented with an indication of which objects around him are linkable, he can then directly point and click on the linkable objects without the “trial-and-error” process of pointing and clicking on non-linkable objects.
Owner:NANT HLDG IP LLC
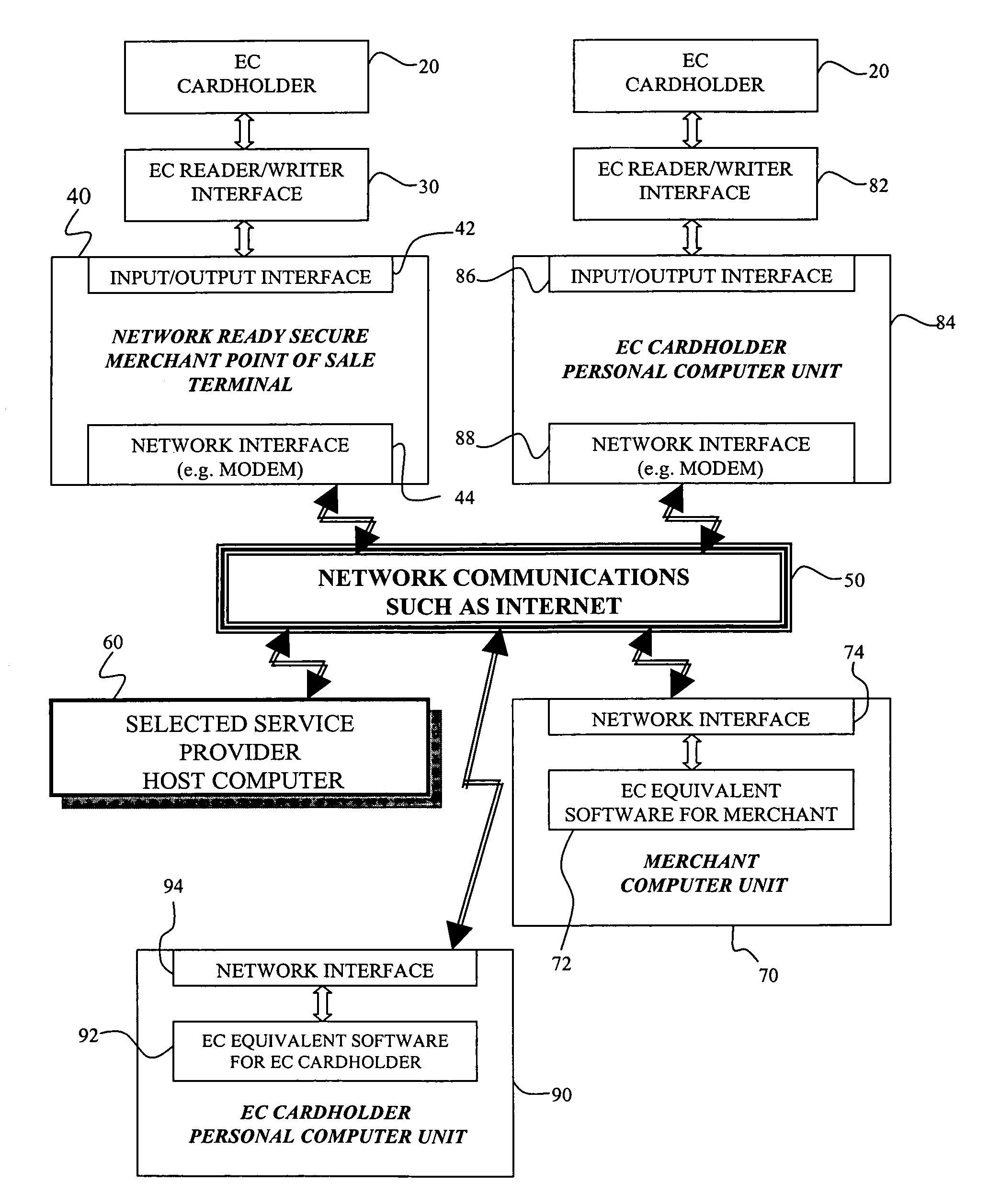
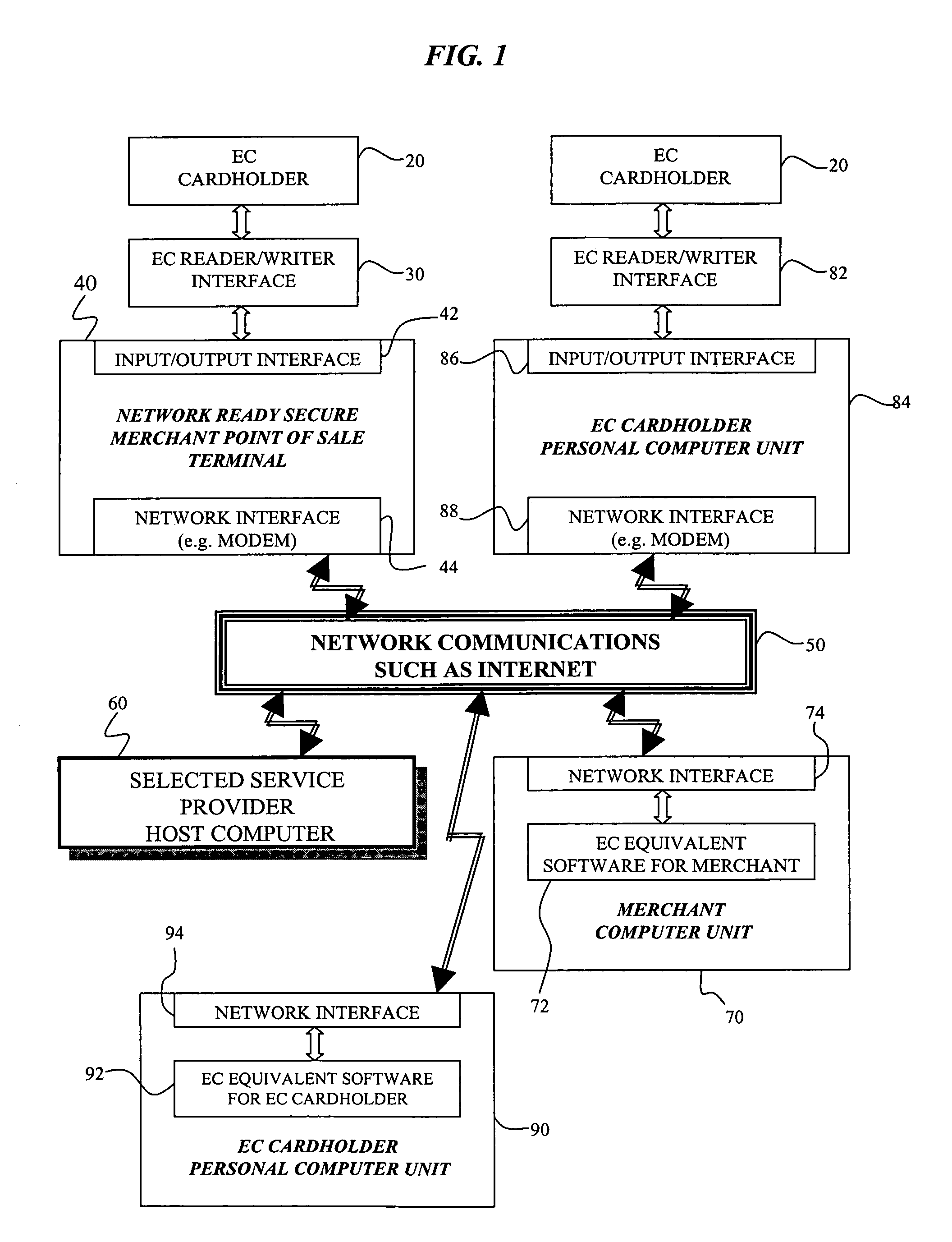
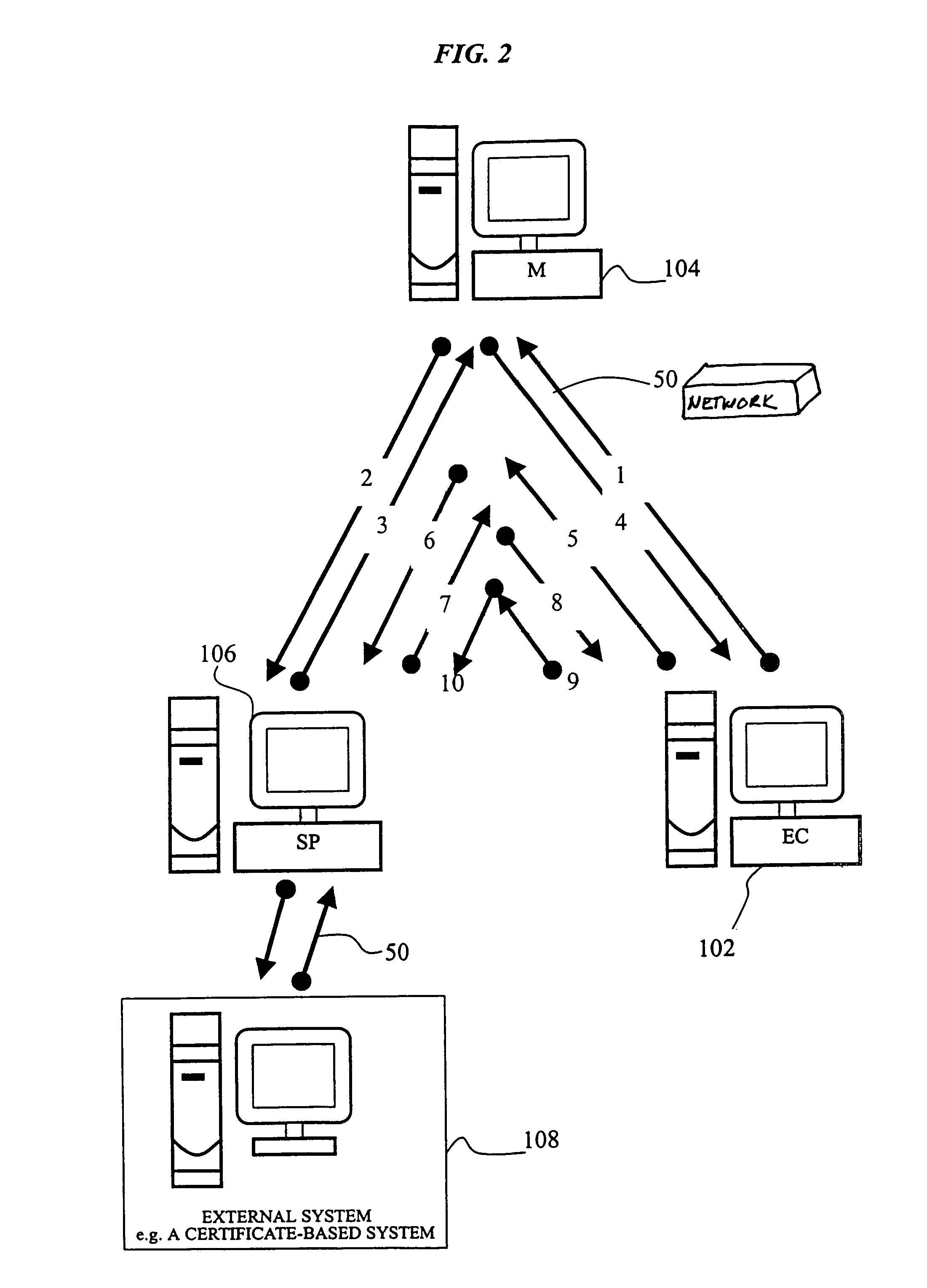
Cryptographic system and method for electronic transactions
InactiveUS7096494B1Key distribution for secure communicationFinanceCredit cardSecure Electronic Transaction
An electronic transaction system, which facilitates secure electronic transactions among multiple parties including cardholders, merchants, and service providers (SP). The system involves electronic cards, commonly known as smart cards, and their equivalent computer software package. The card mimics a real wallet and contains commonly seen financial or non-financial instruments such as a credit card, checkbook, or driver license. A transaction is protected by a hybrid key cryptographic system and is normally carried out on a public network such as the Internet. Digital signatures and challenges-responses are used to ensure integrity and authenticity. The card utilizes secret keys such as session keys assigned by service providers (SPs) to ensure privacy for each transaction. The SP is solely responsible for validating each participant's sensitive information and assigning session keys. The system does not seek to establish a trust relationship between two participants of a transaction. The only trust relationship needed in a transaction is the one that exists between individual participants and the SP. The trust relationship with a participant is established when the SP has received and validated certain established account information from that particular participant. To start a transaction with a selected SP, a participant must have the public key of the intended SP. Since the public key is openly available, its availability can be easily established by the cardholder. The SP also acts as a gateway for the participants when a transaction involves interaction with external systems.
Owner:CINGULAR WIRELESS II LLC
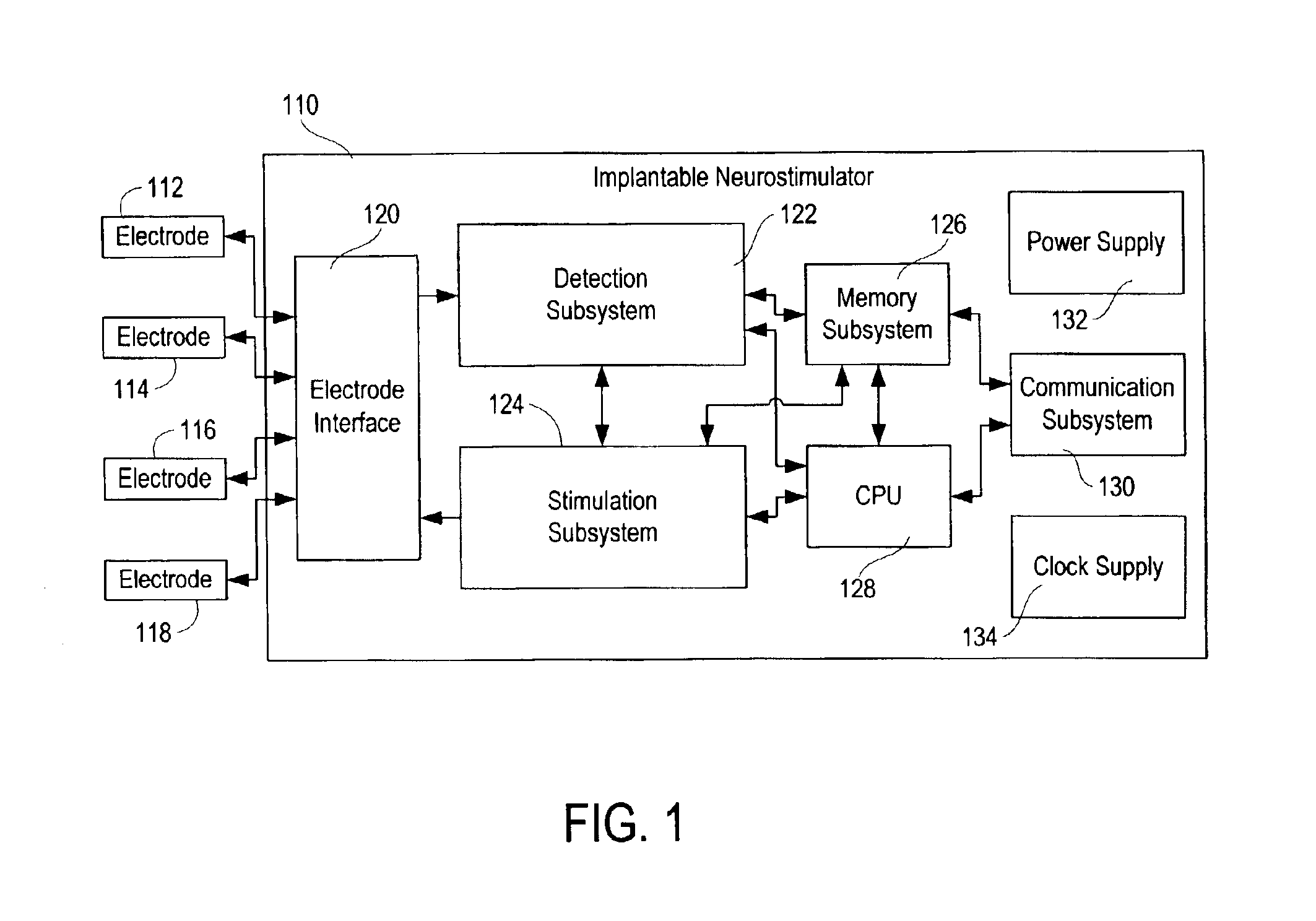
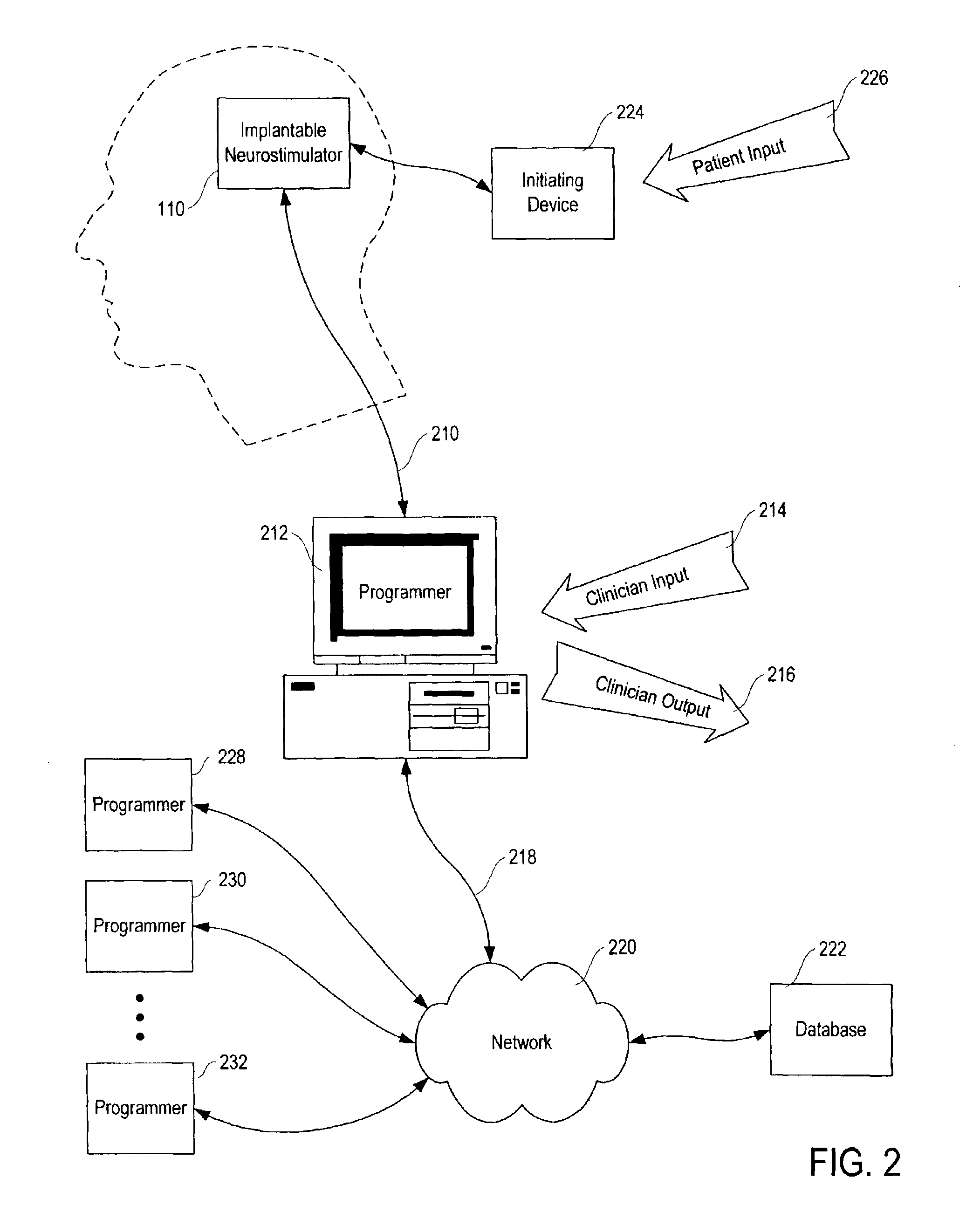
Patient-specific parameter selection for neurological event detection
InactiveUS7177674B2Efficient developmentPhysical therapies and activitiesElectroencephalographyEeg dataLine search
An epileptiform activity patient-specific template creation system permits a user to efficiently develop an optimized set of patient-specific parameters for epileptiform activity detection algorithms. The epileptiform activity patient template creation system is primarily directed for use with an implantable neurostimulator system having EEG storage capability, in conjunction with a computer software program operating within a computer workstation having a processor, disk storage and input / output facilities for storing, processing and displaying patient EEG signals. The implantable neurostimulator is operative to store records of EEG data when neurological events are detected, when it receives external commands to record, or at preset or arbitrary times. The computer workstation operates on stored and uploaded records of EEG data to derive the patient-specific templates via a single local minimum variant of a multidimensional greedy line search process and a feature overlay process.
Owner:NEUROPACE
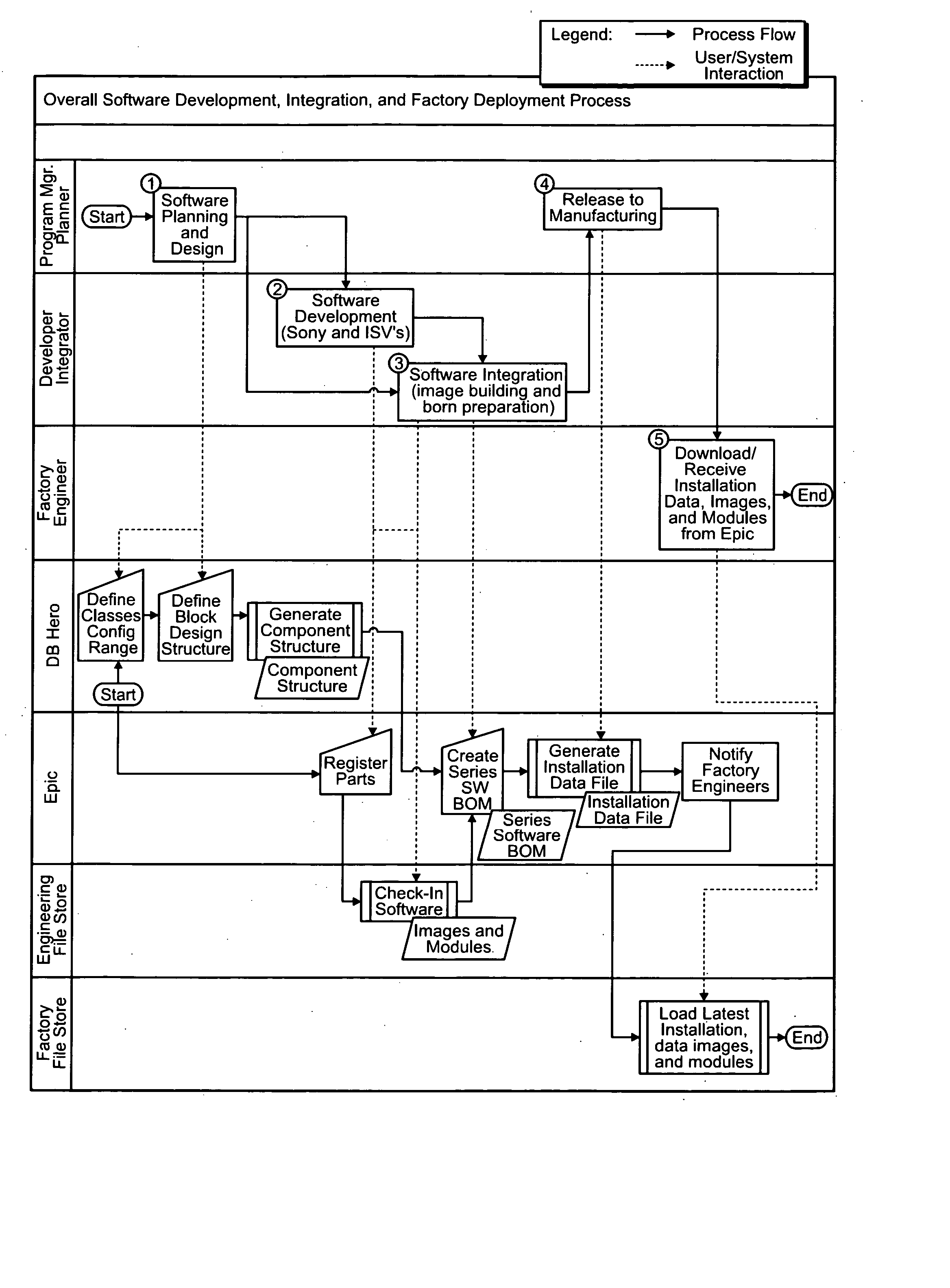
System and method for software integration and factory deployment
InactiveUS20070240154A1Easy to createReduce errorsHand manipulated computer devicesAnimal feeding devicesOperational systemSoftware engineering
A software management database contains data structures supporting computer software provisioning for a range of CTO / BTO variations, language variations, region variations, and operating system variations.
Owner:SONY CORP +1
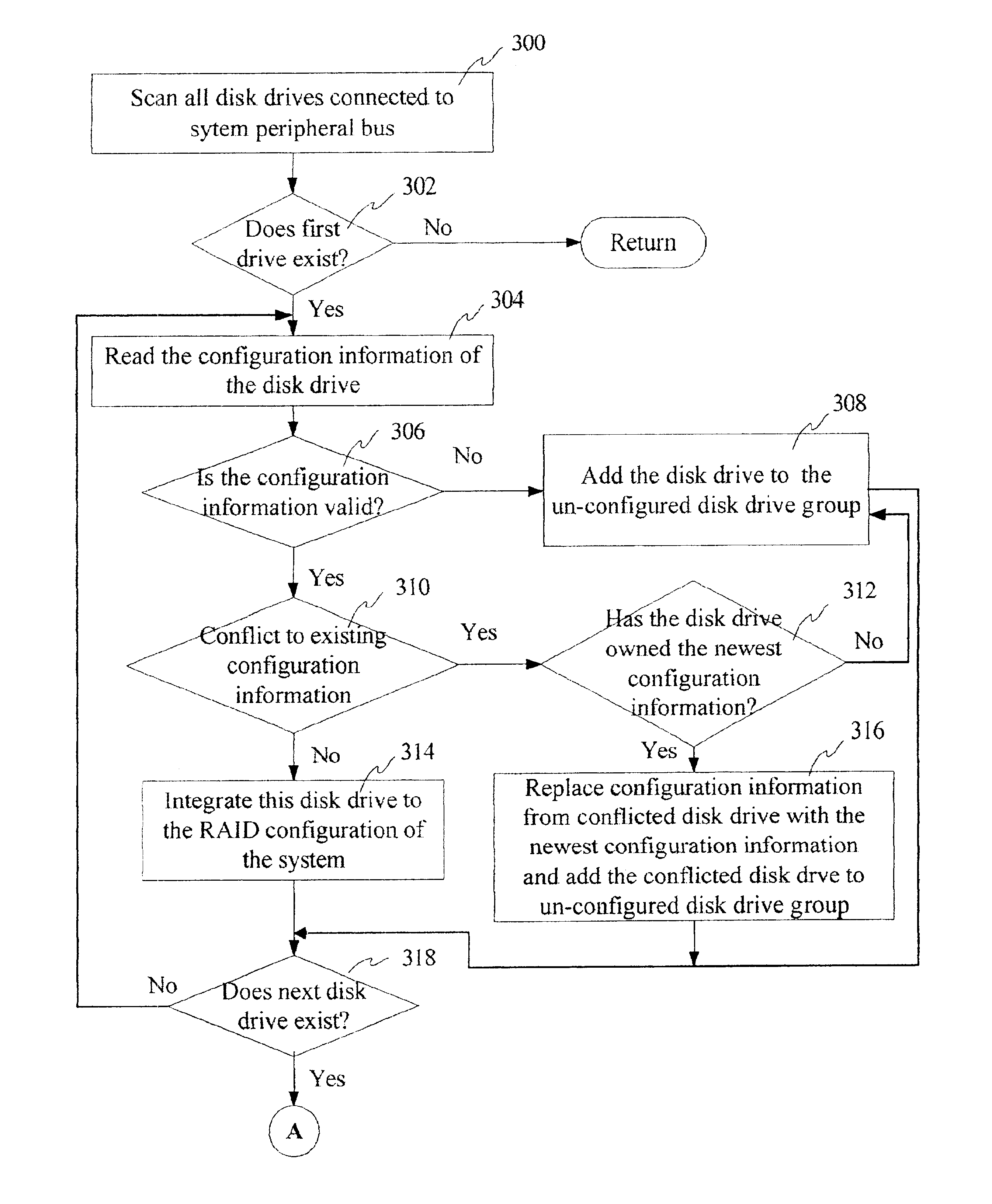
Method, system and apparatus for scanning newly added disk drives and automatically updating RAID configuration and rebuilding RAID data
InactiveUS6952794B2Raise countMaximum countInput/output to record carriersRedundant data error correctionRAIDOperational system
The present invention pertains to a computer software implemented method, system, and apparatus for automatic updating disk drive configuration and rebuilding RAID data to assure proper data storage in a RAID configured system. The computer software implemented configuration mechanism utilizing CPU and memory of a computer system automatically generates a full configuration of the disk drives connected to system peripheral bus both at system initialization time and runtime. The configuration mechanism uses a computer-implemented procedure for scanning a newly added disk drive, detecting conflict to the existing configuration, resolving conflicts, finding a proper target referenced or ruined disk drive, replacing this target disk drive with the newly added disk drive, rebuilding the RAID data into the added disk drive, updating RAID configuration with the added disk drive, and presenting to the host operating system the current configuration information.
Owner:SYNOLOGY INC
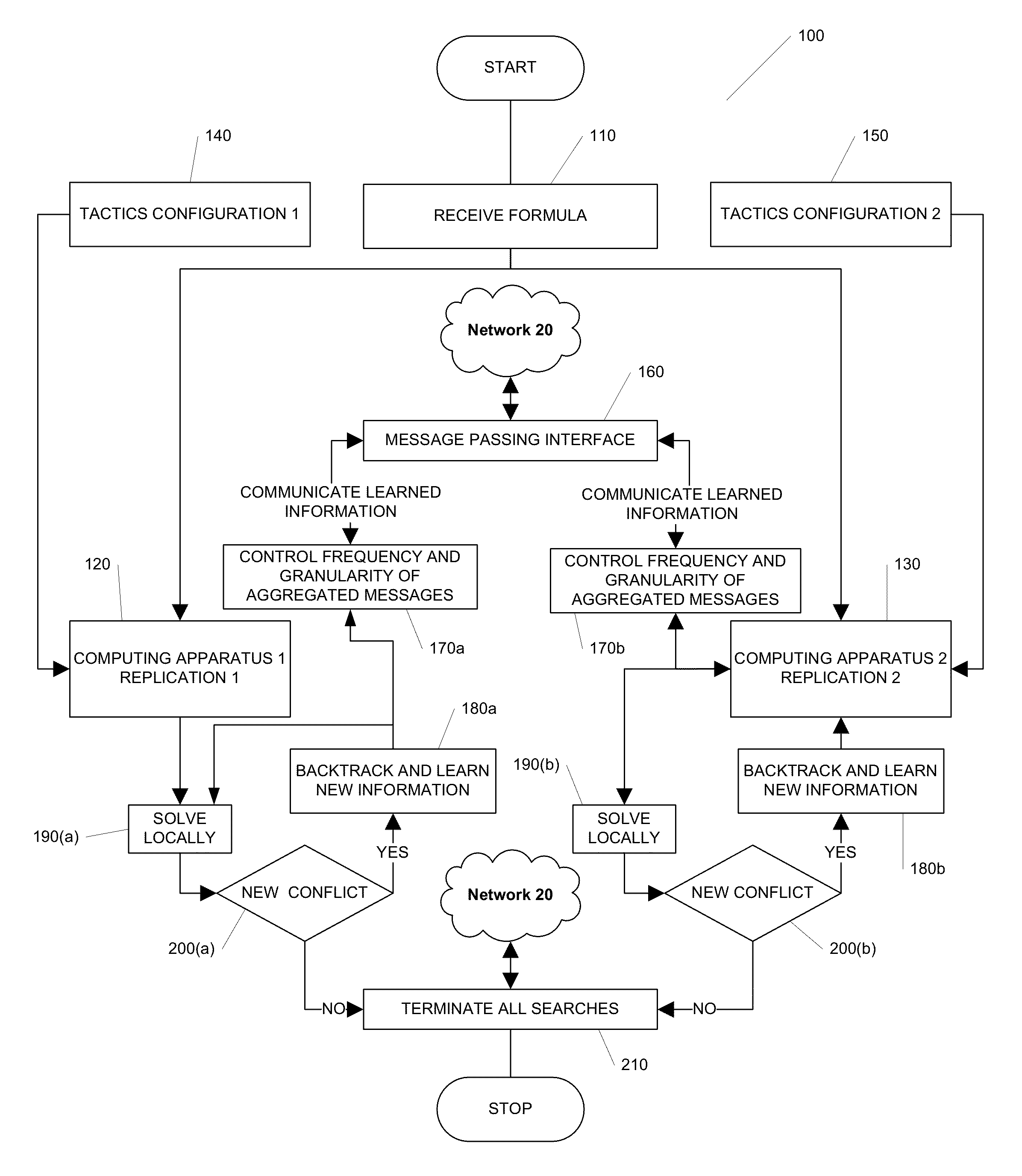
Systems, methods and apparatus for distributed decision processing
Methods, apparatus, and computer software product for making a decision based on the semantics of formal logic are provided. In an exemplary embodiment, two custom computing apparatuses are used to resolve the satisfiability of a logical formula and provide an example. In this embodiment, the two custom computing apparatuses operate in concert to explore the space of possible satisfying examples. This Abstract is provided for the sole purpose of complying with the Abstract requirement rules. This Abstract is submitted with the explicit understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:QUALCOMM TECHNOLOGIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com