Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6192results about How to "Increased complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
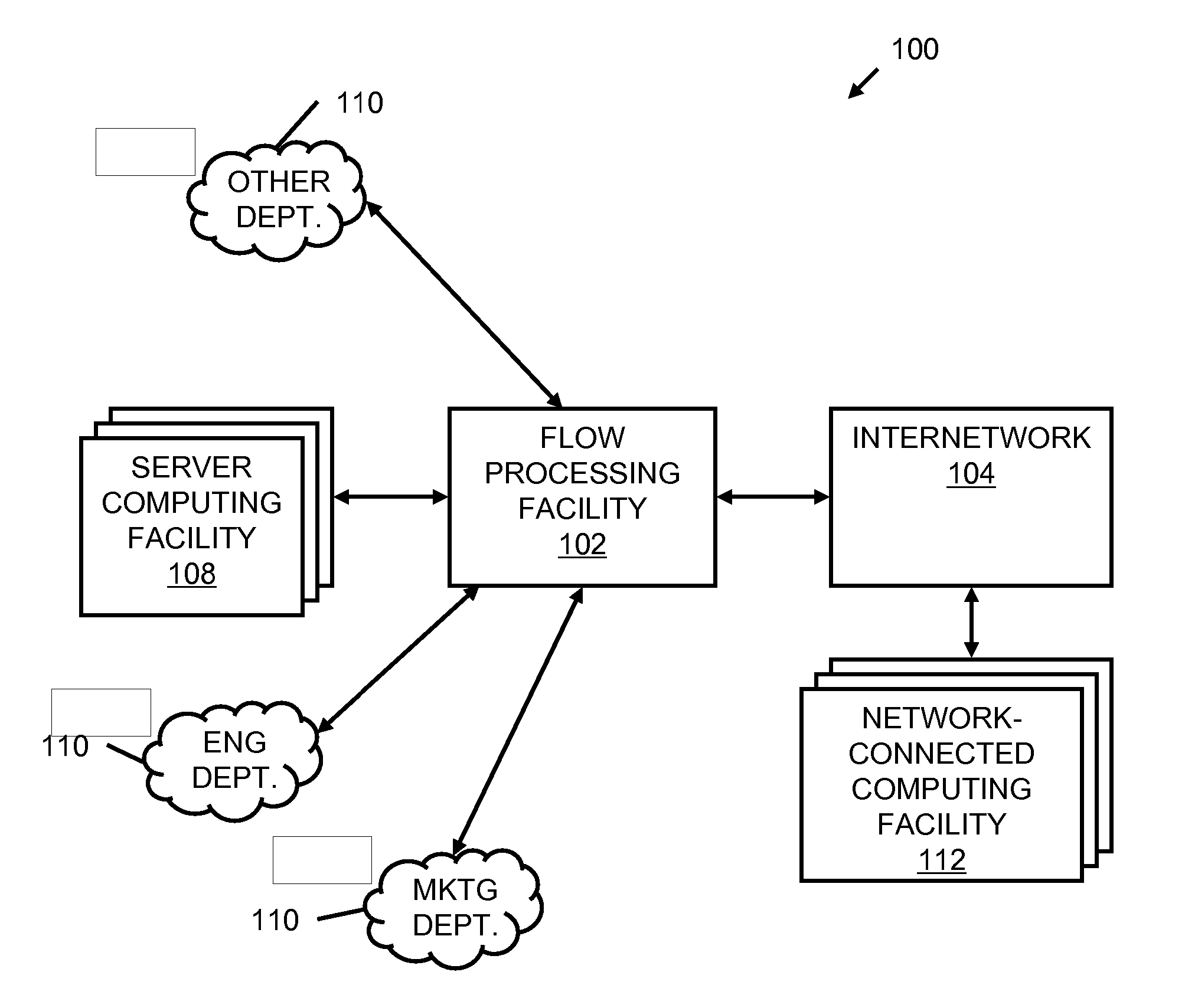
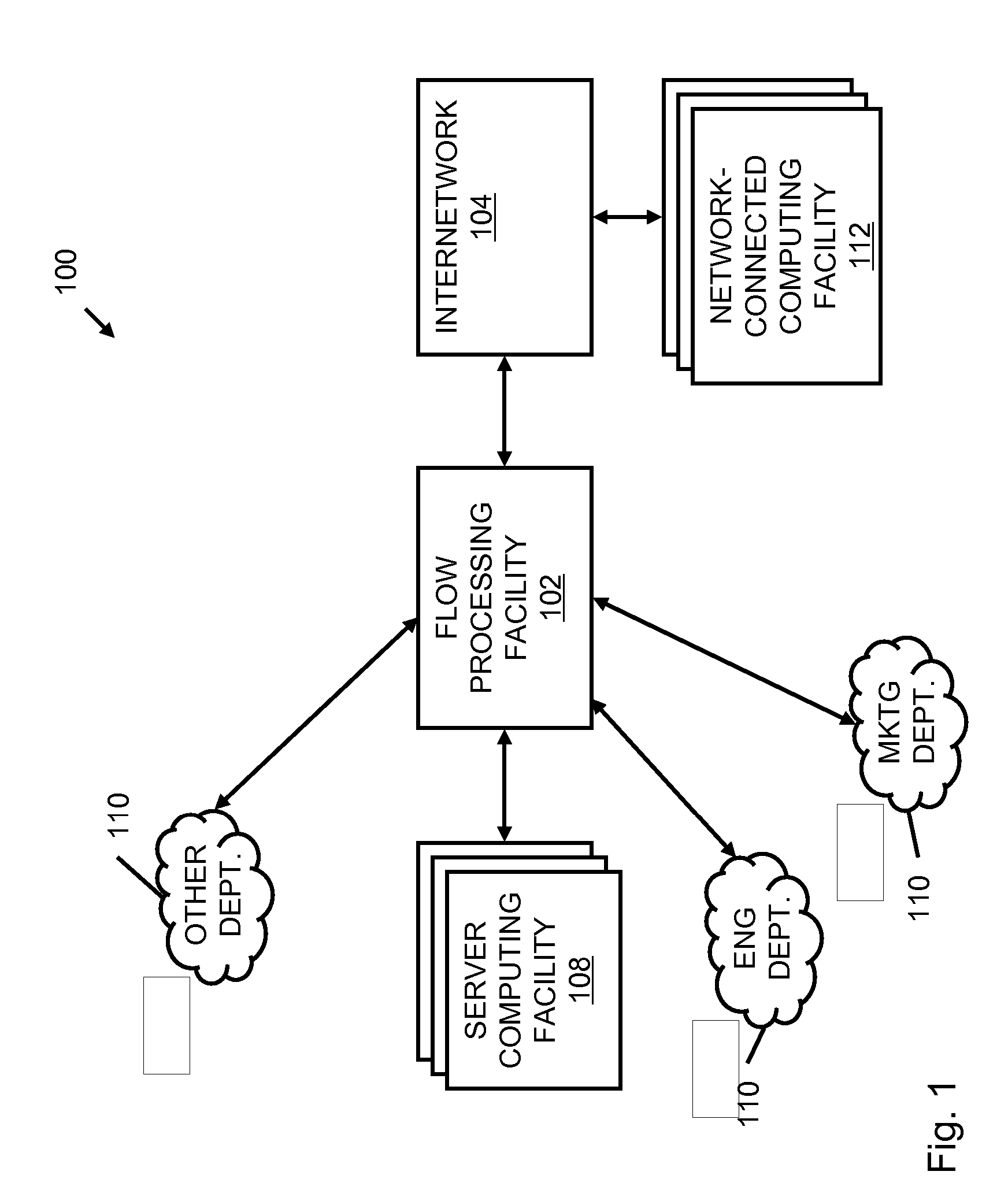
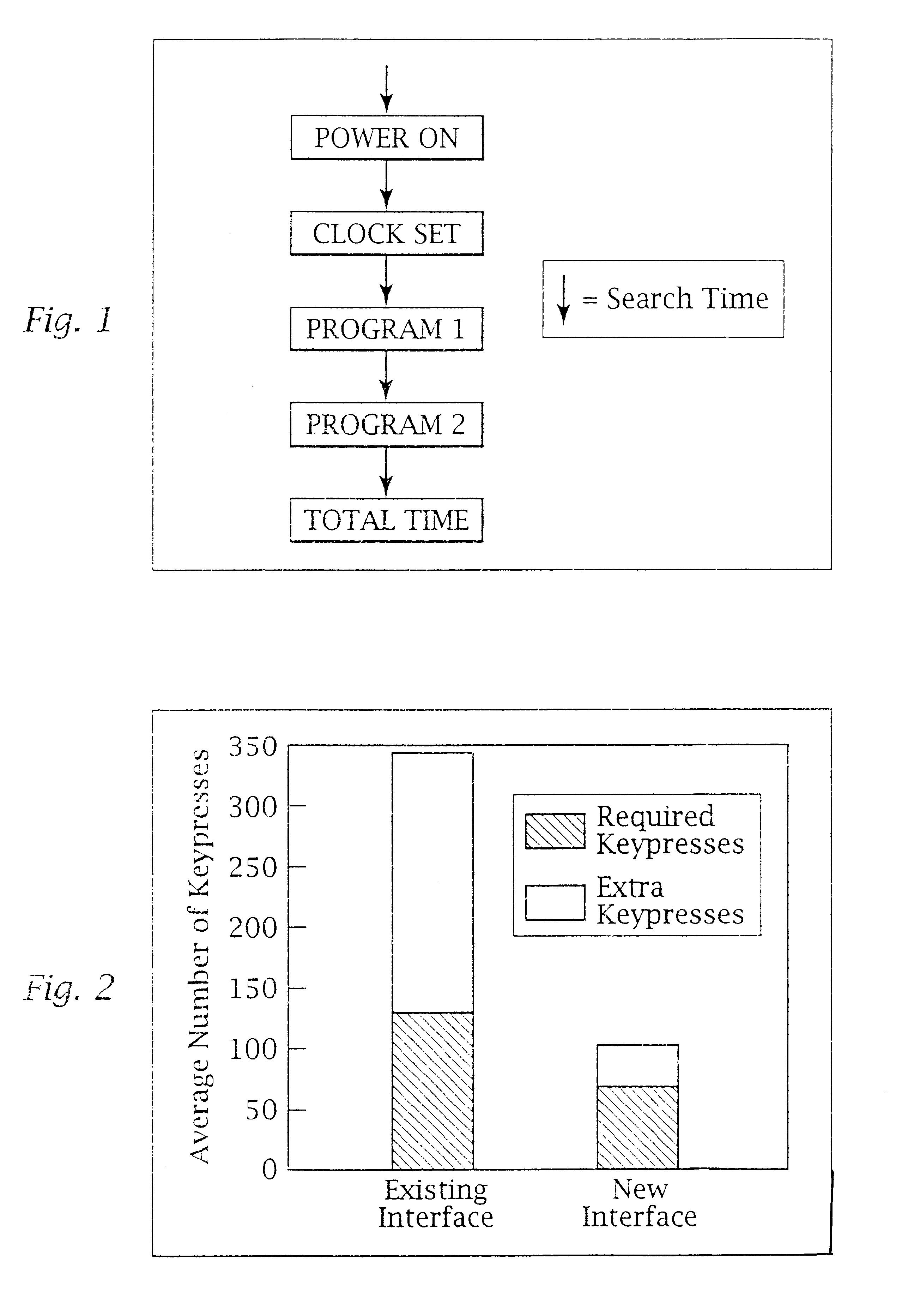
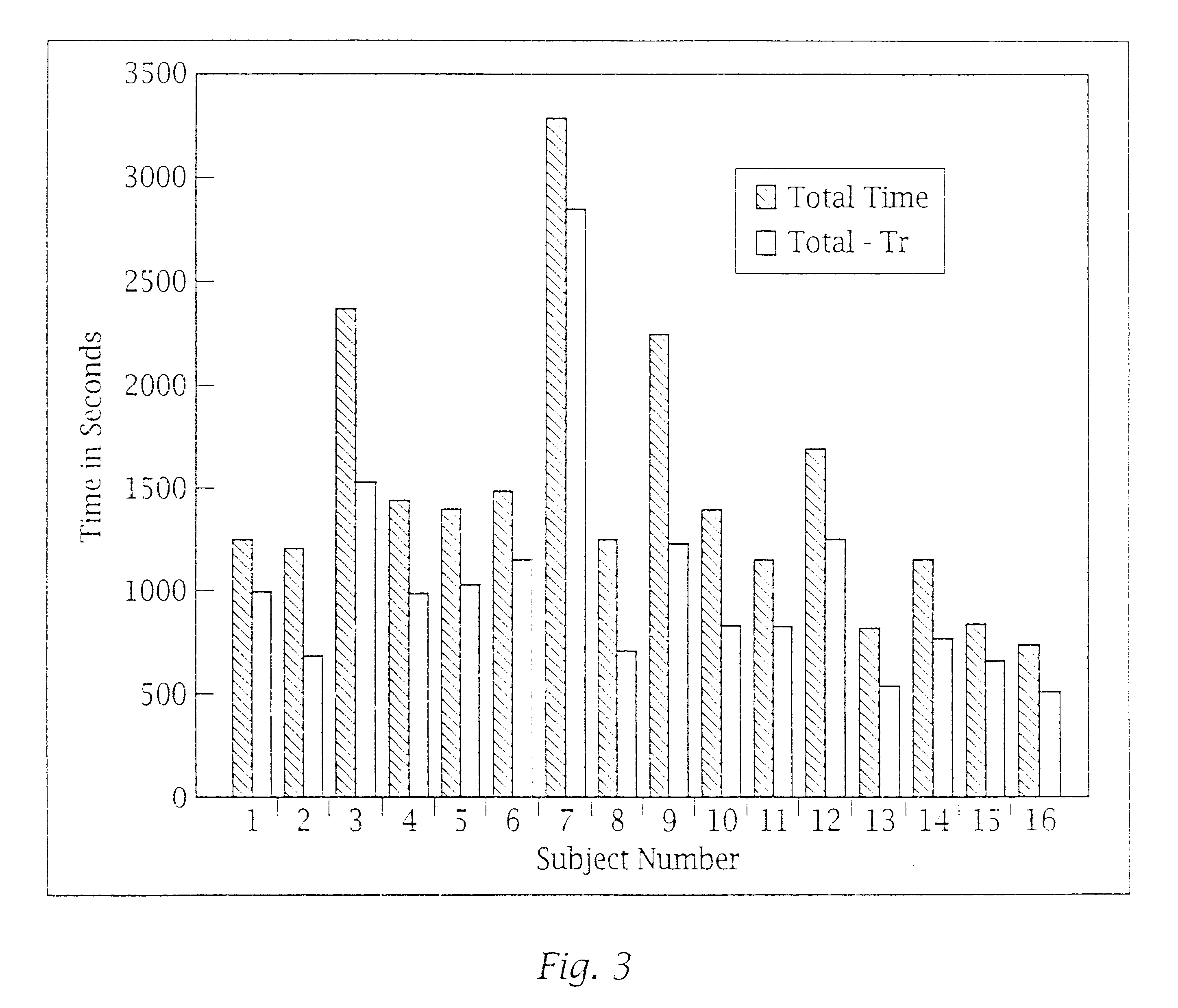
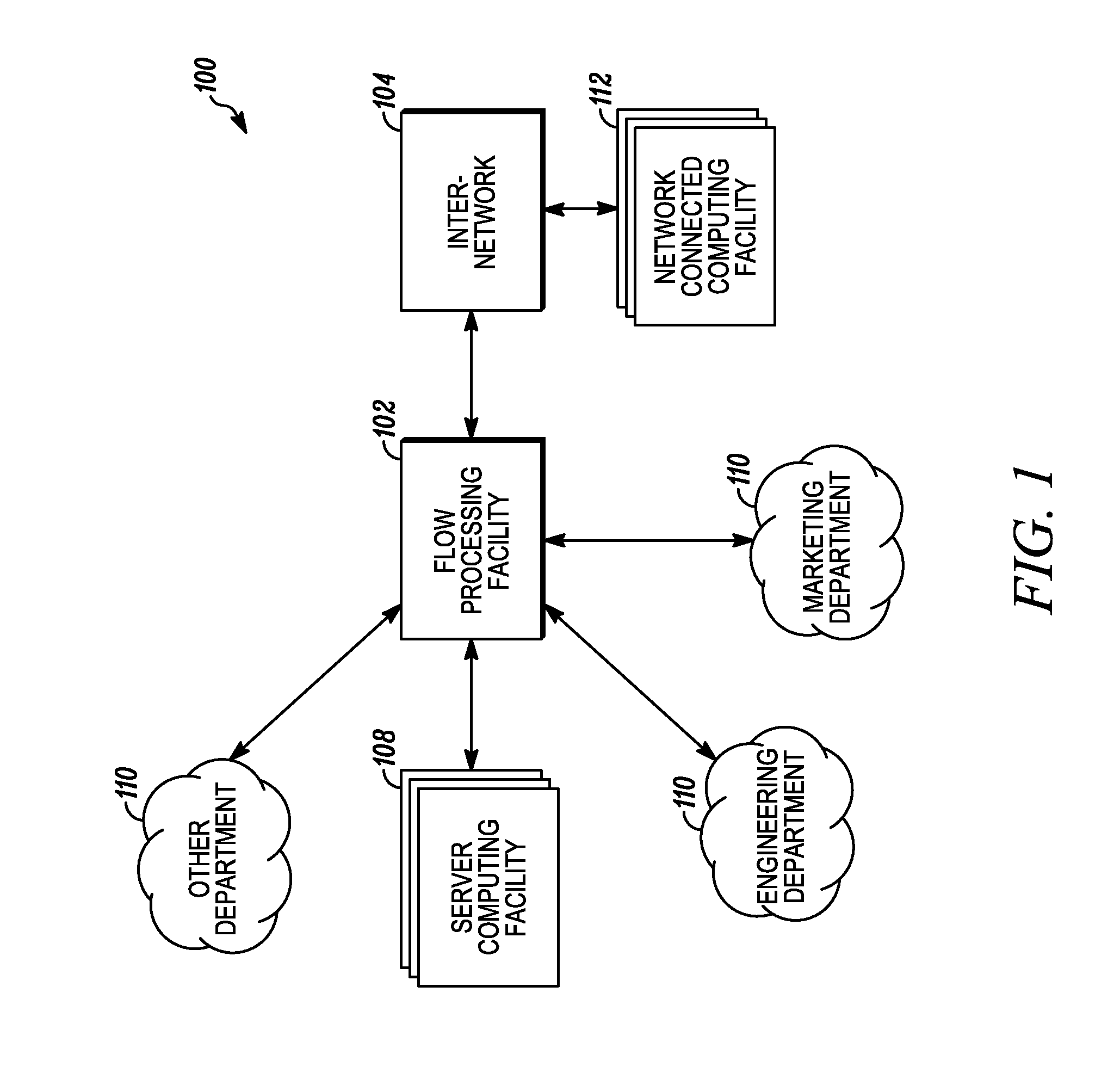
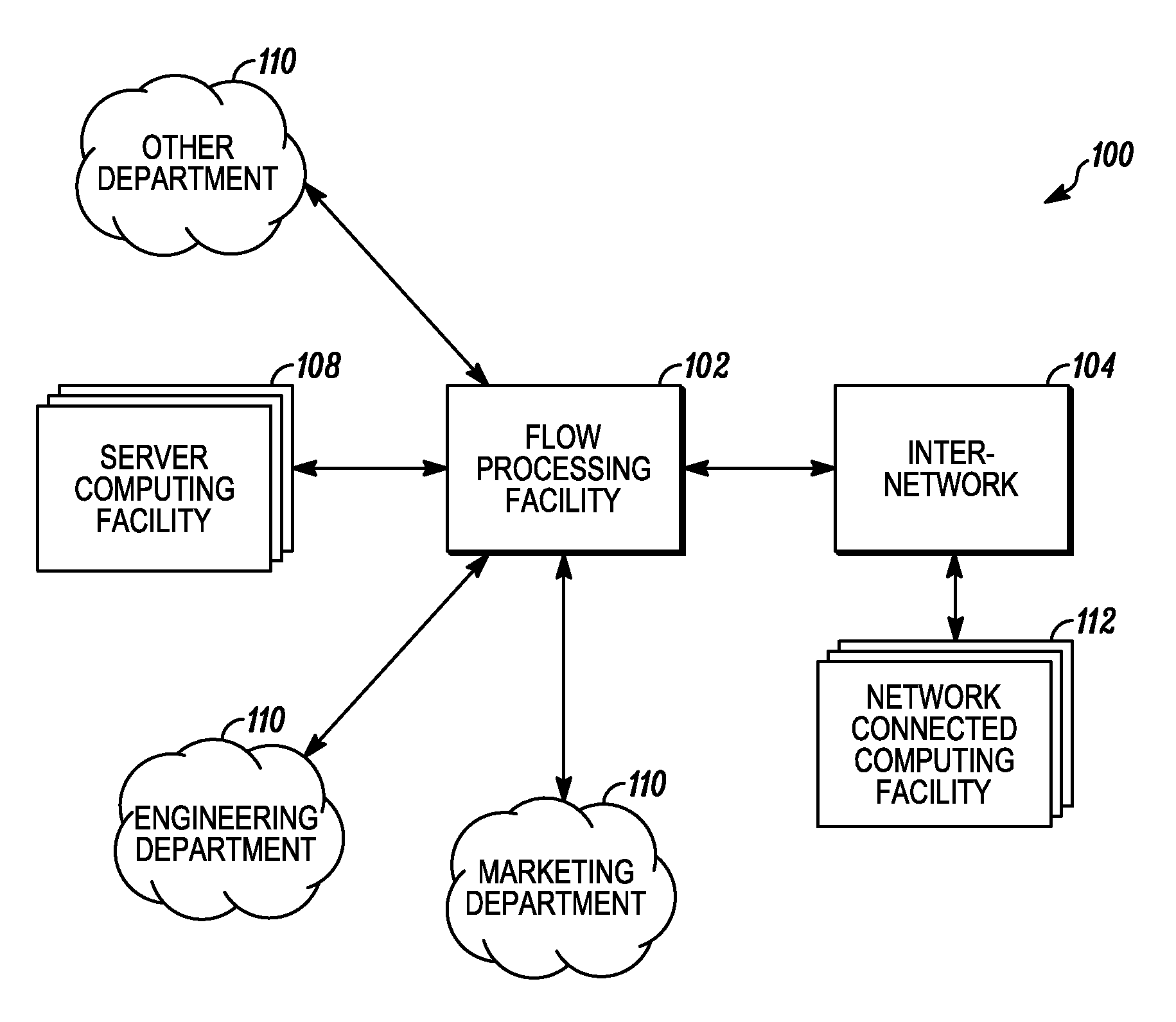
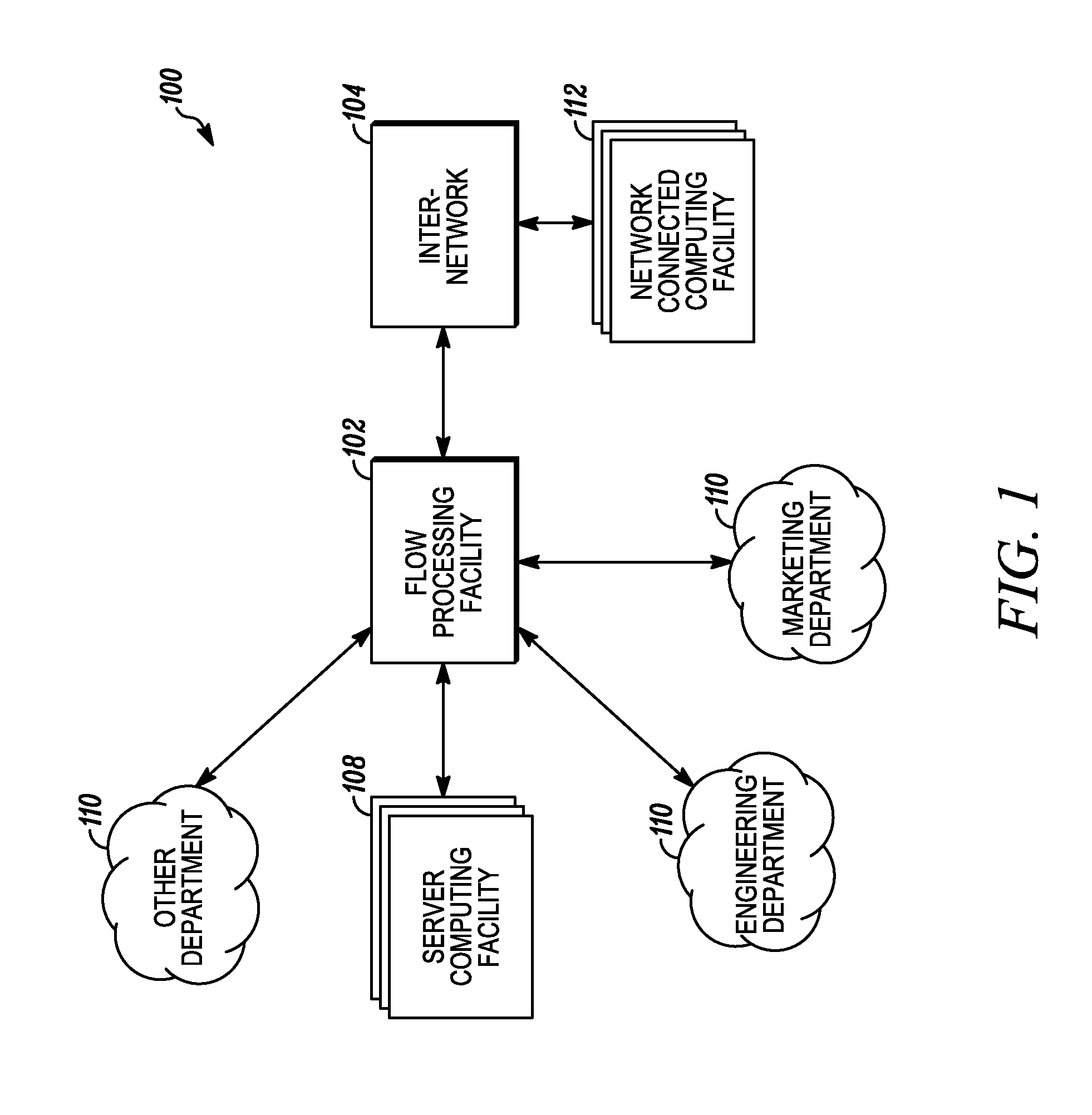
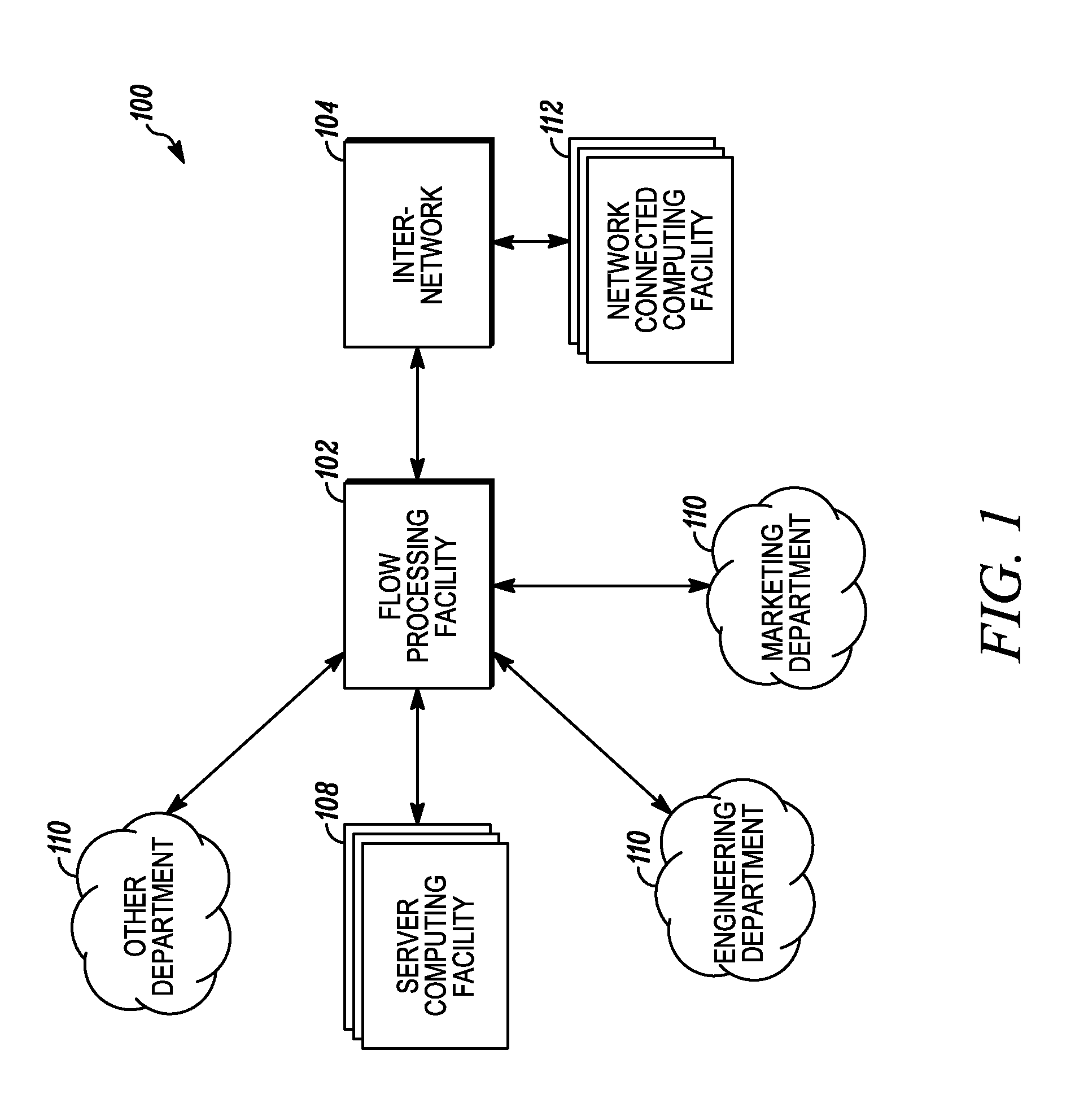
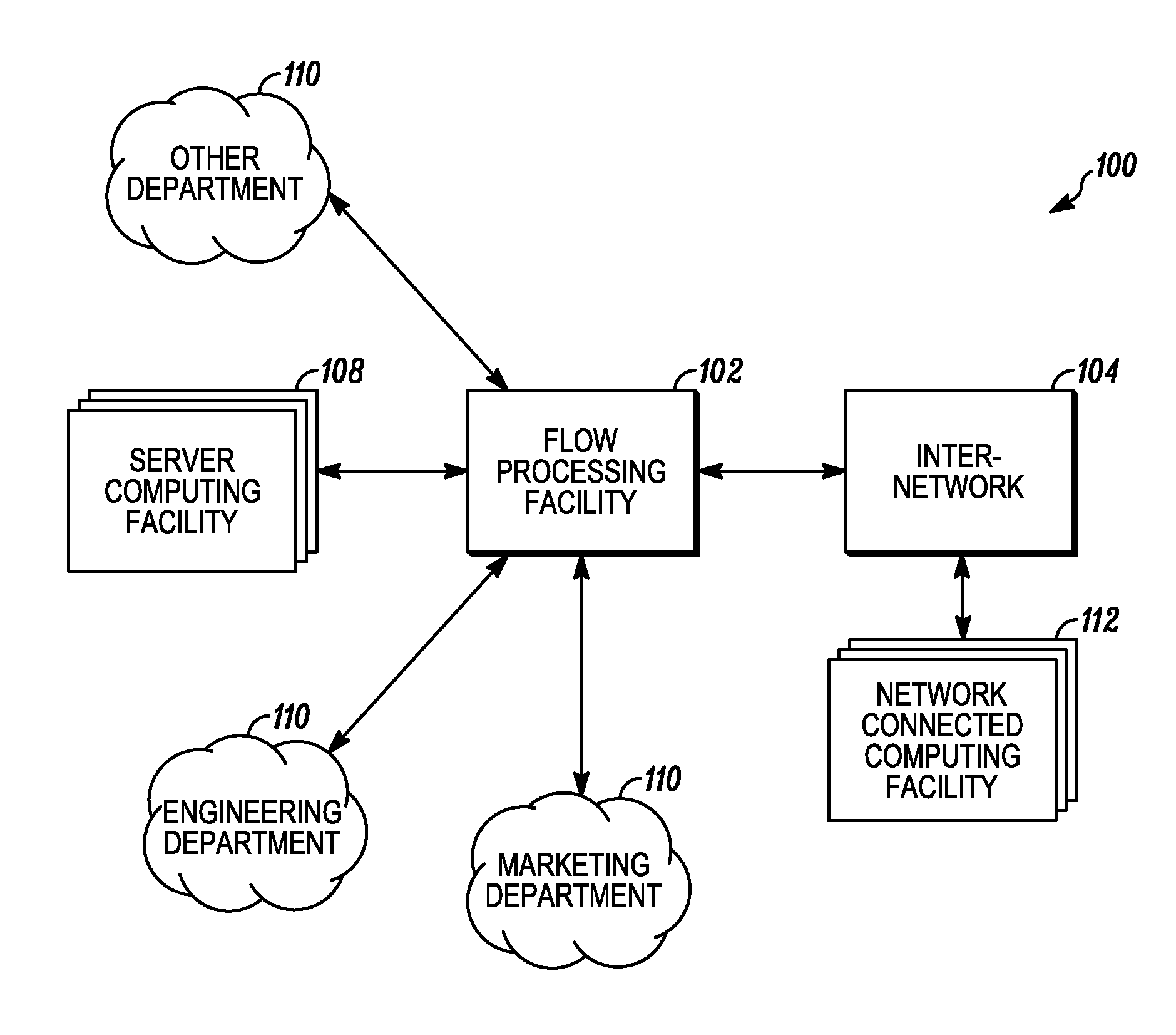
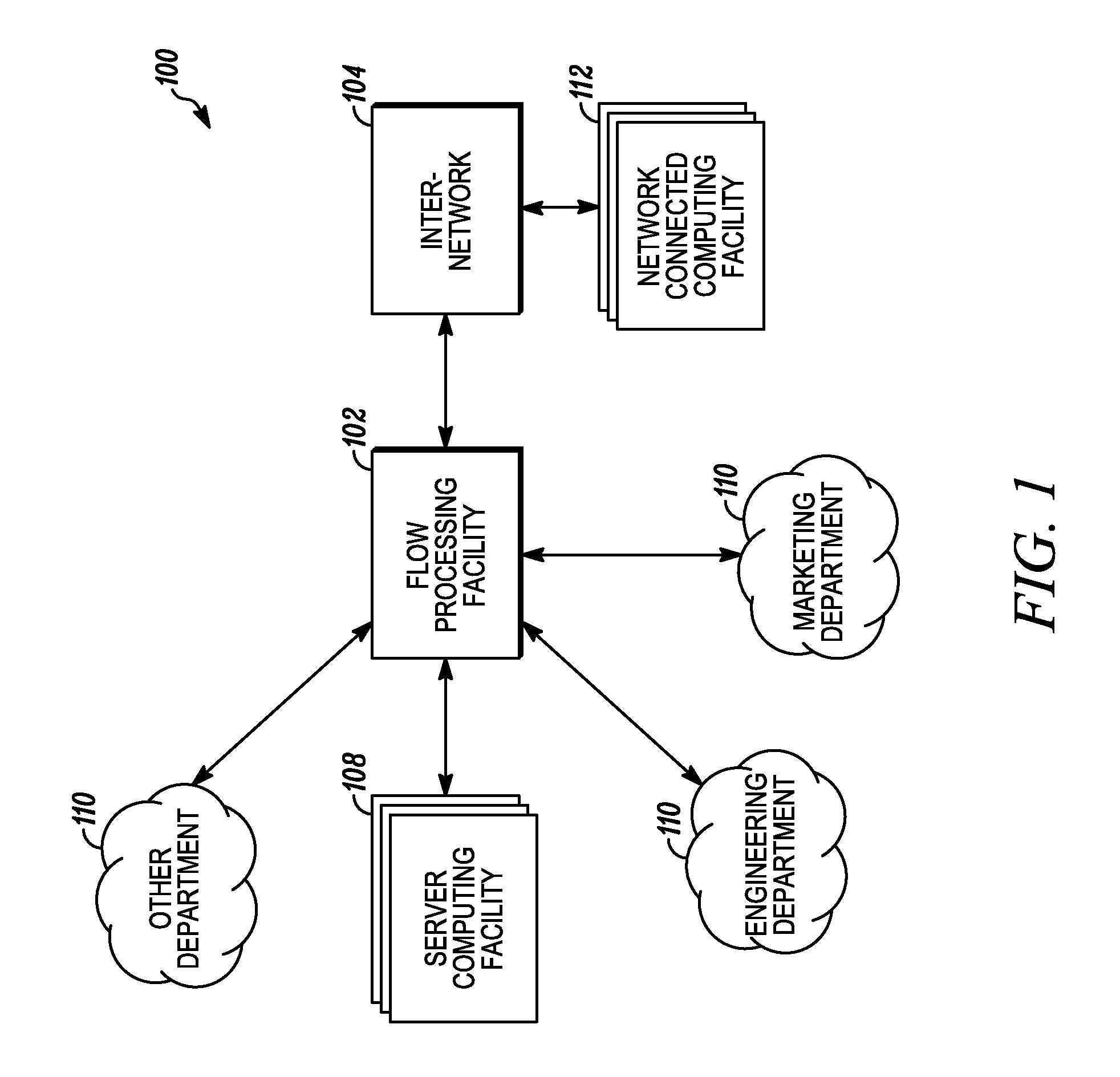
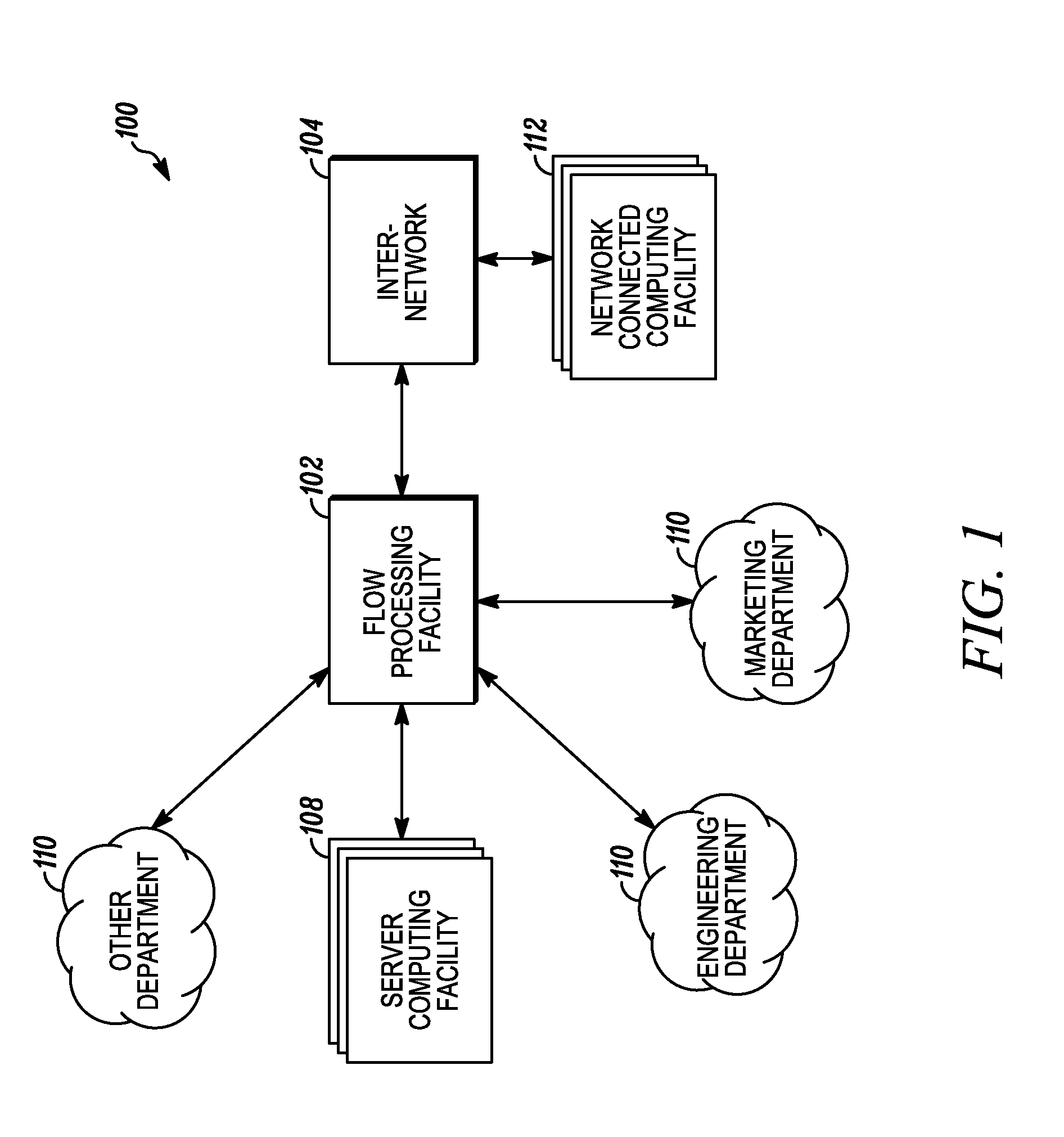
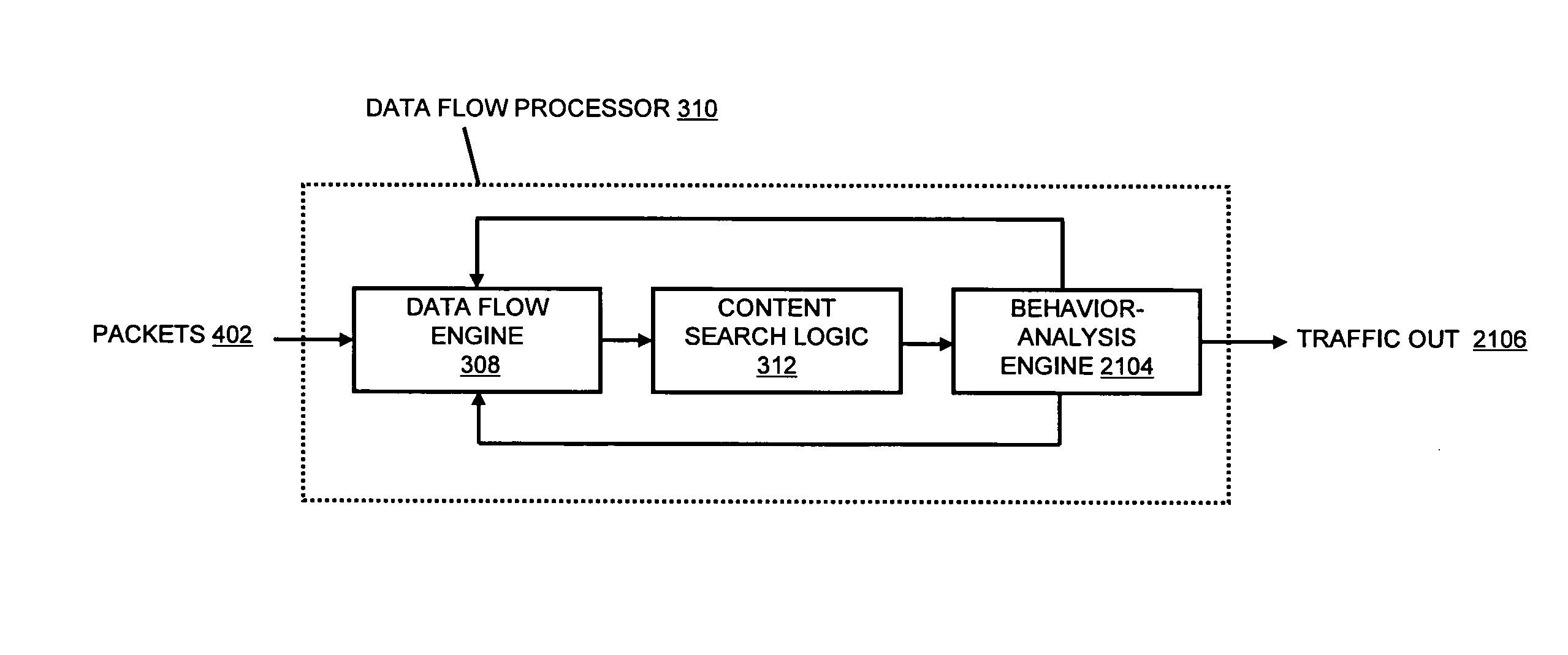
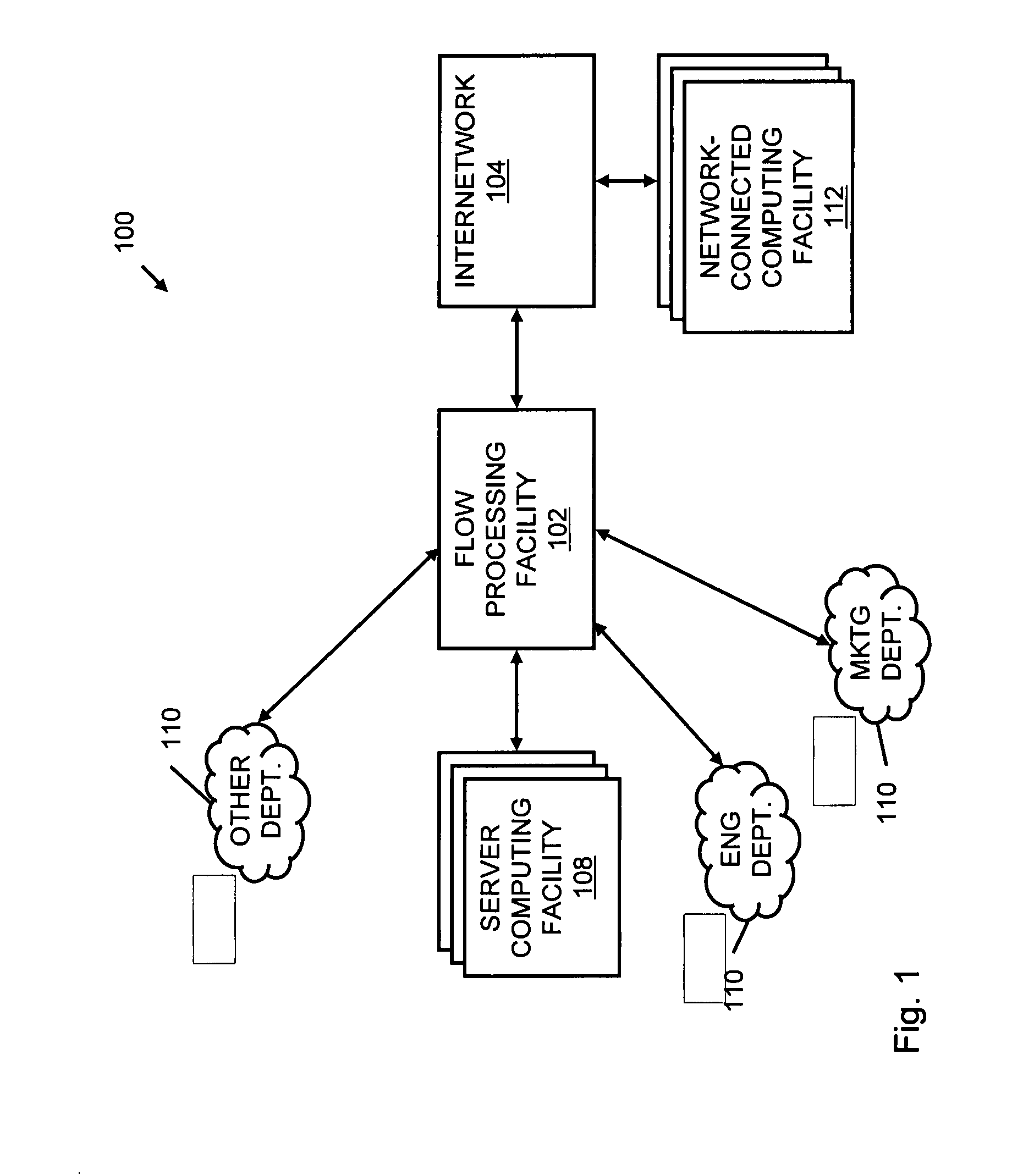
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
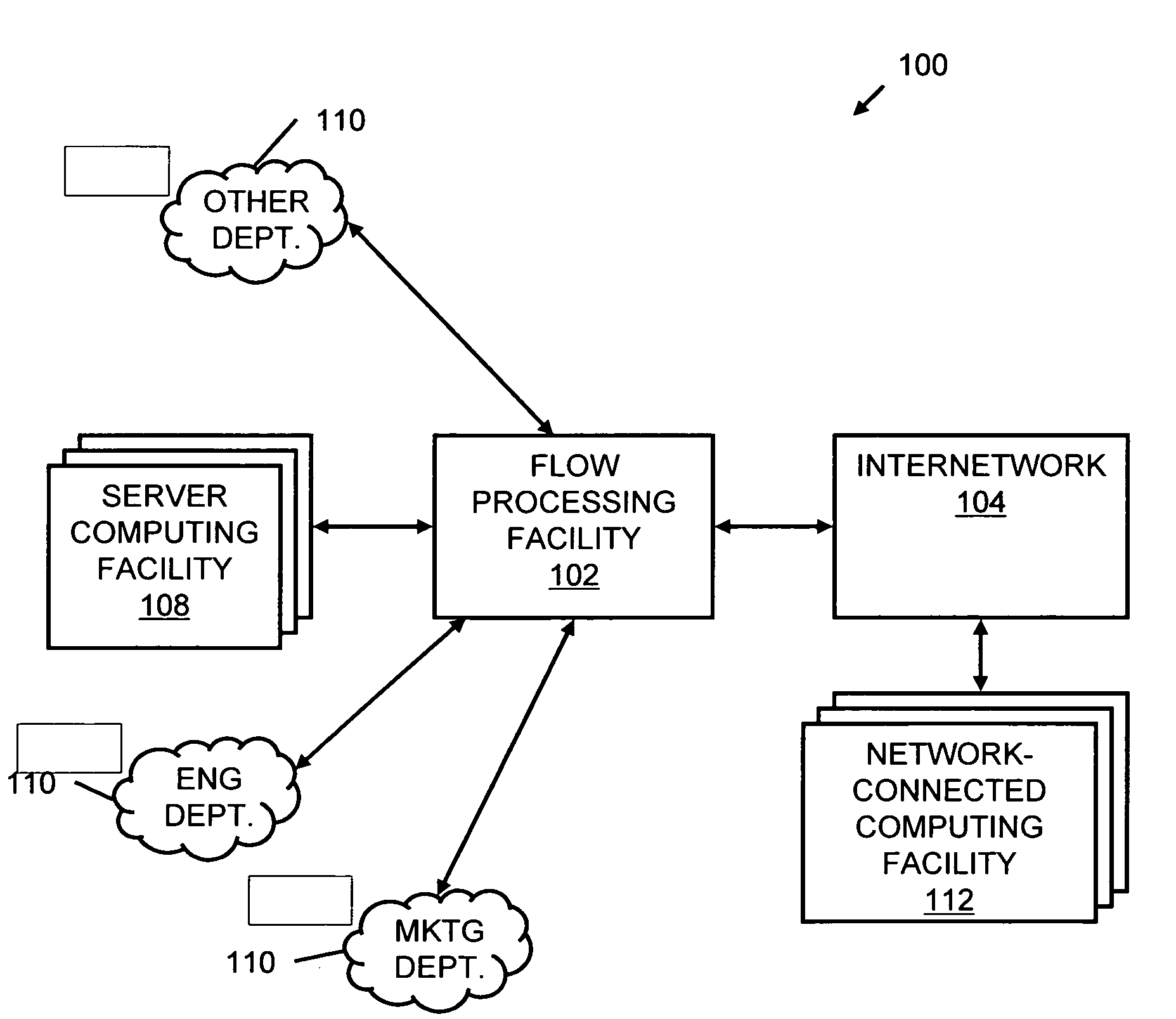
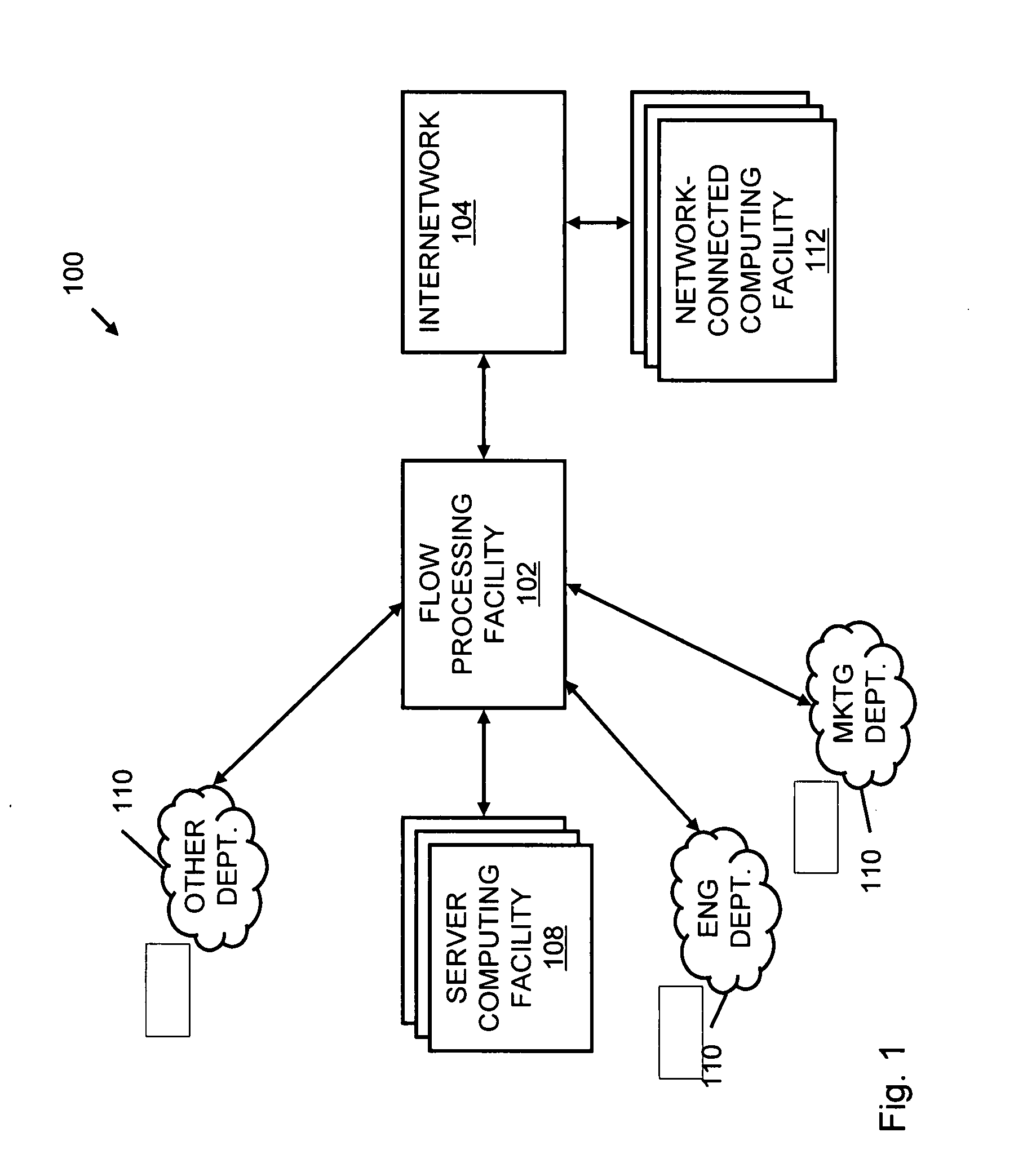
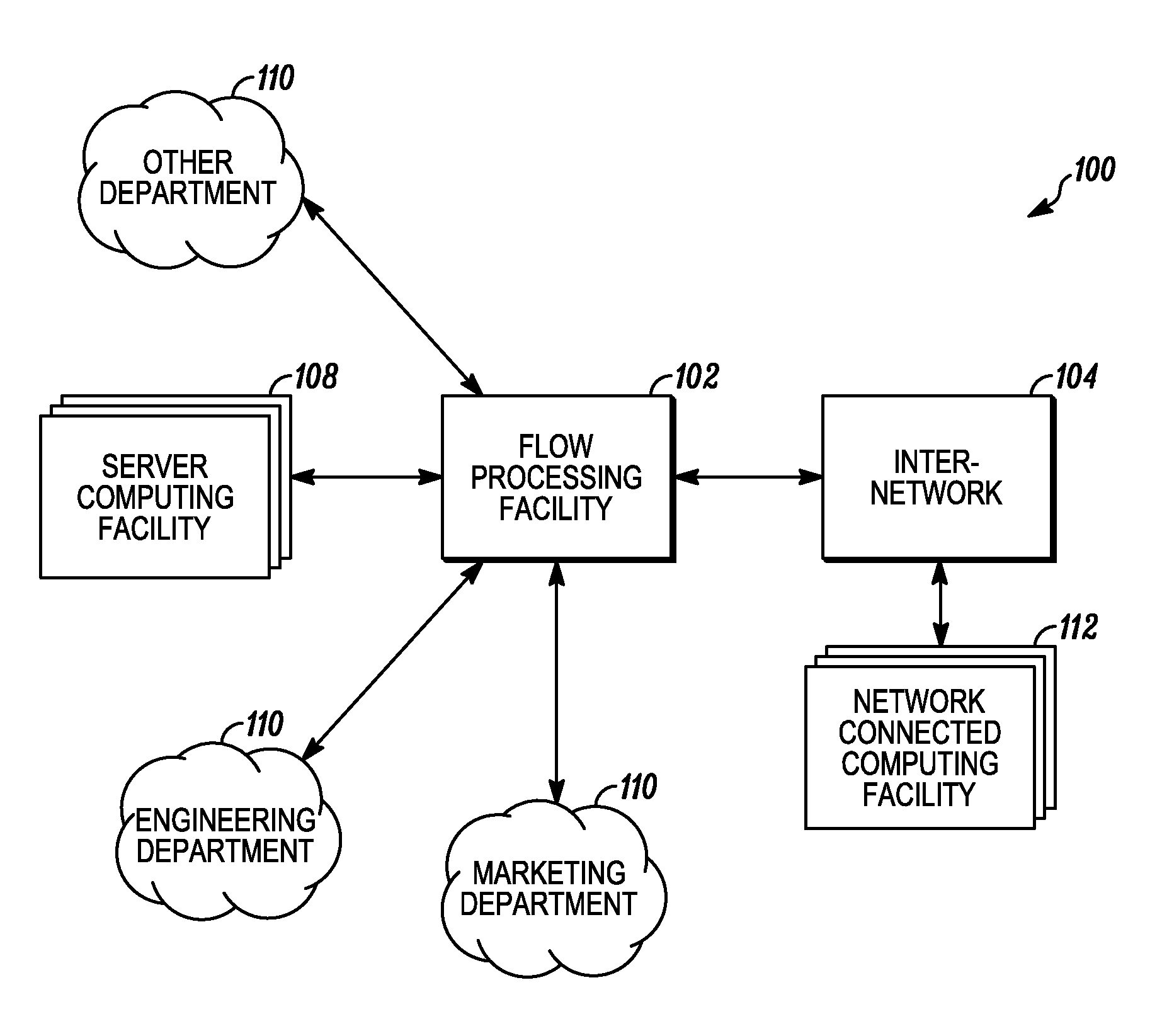
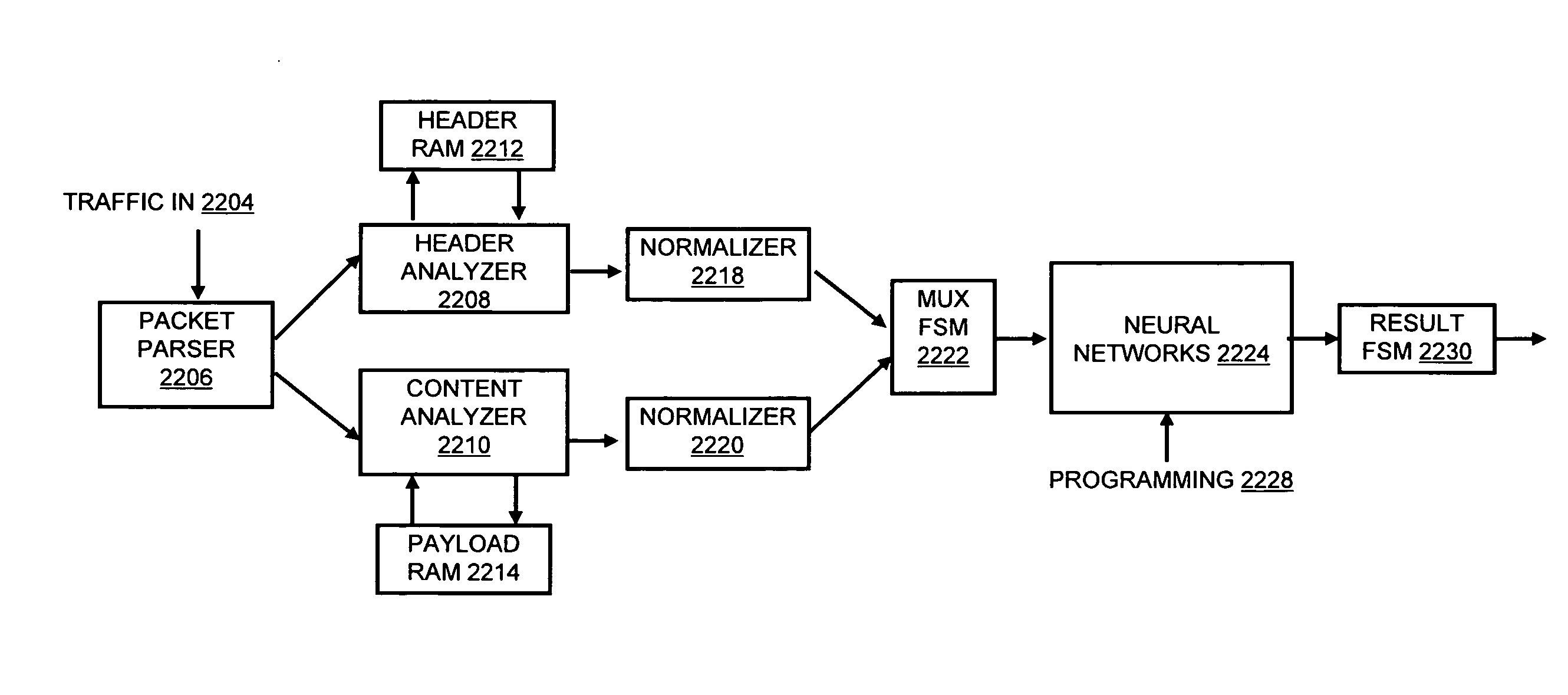
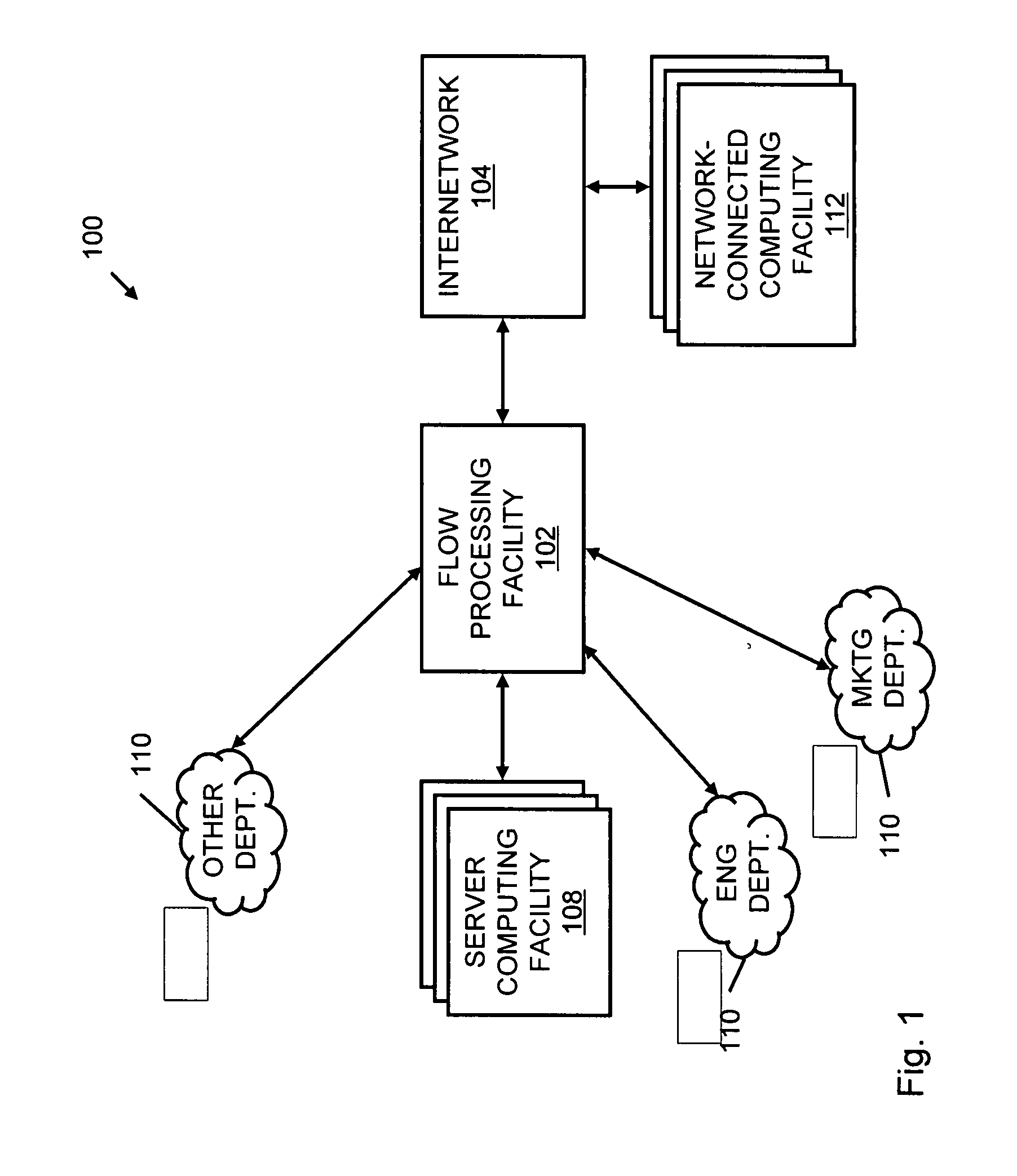
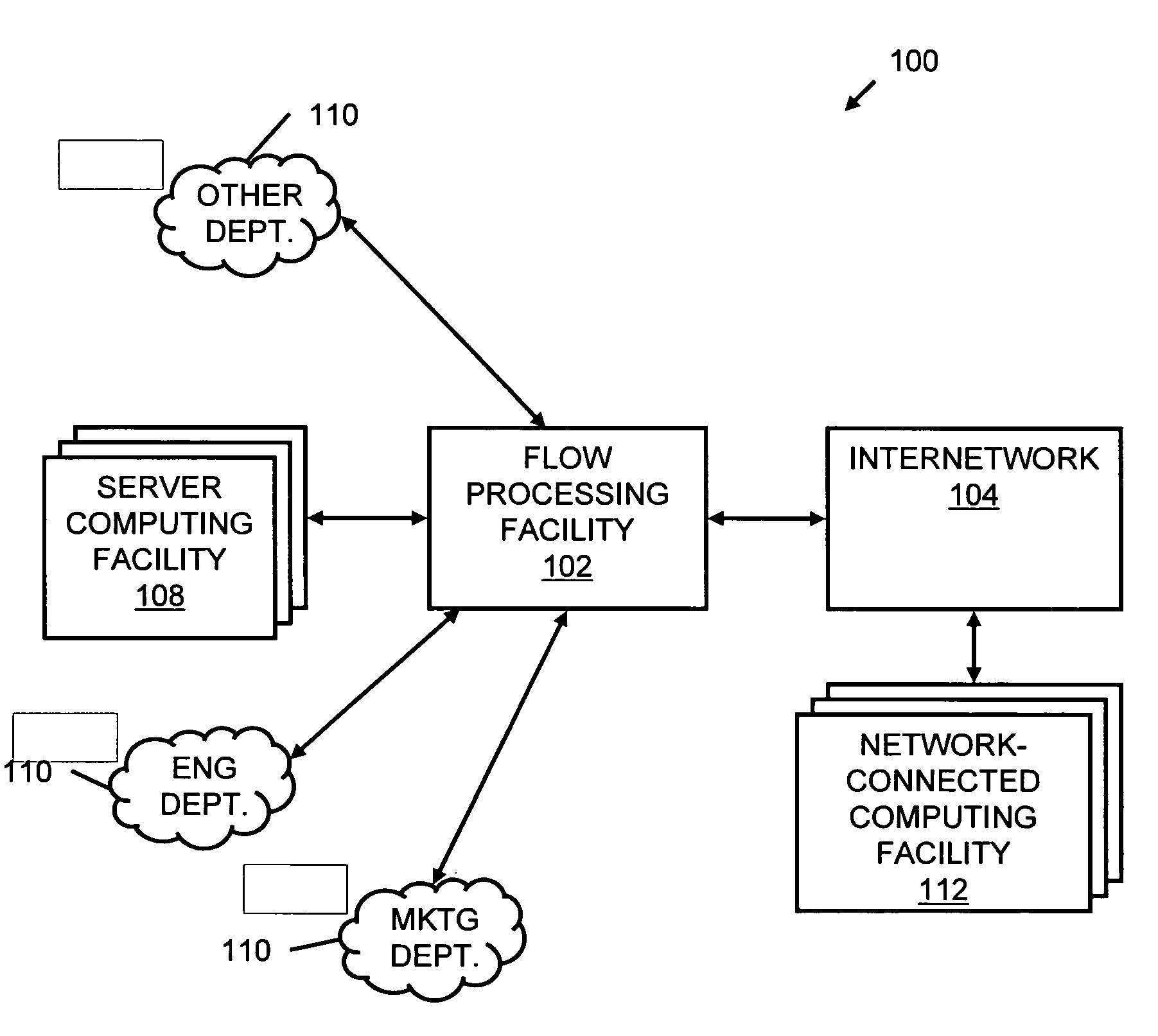
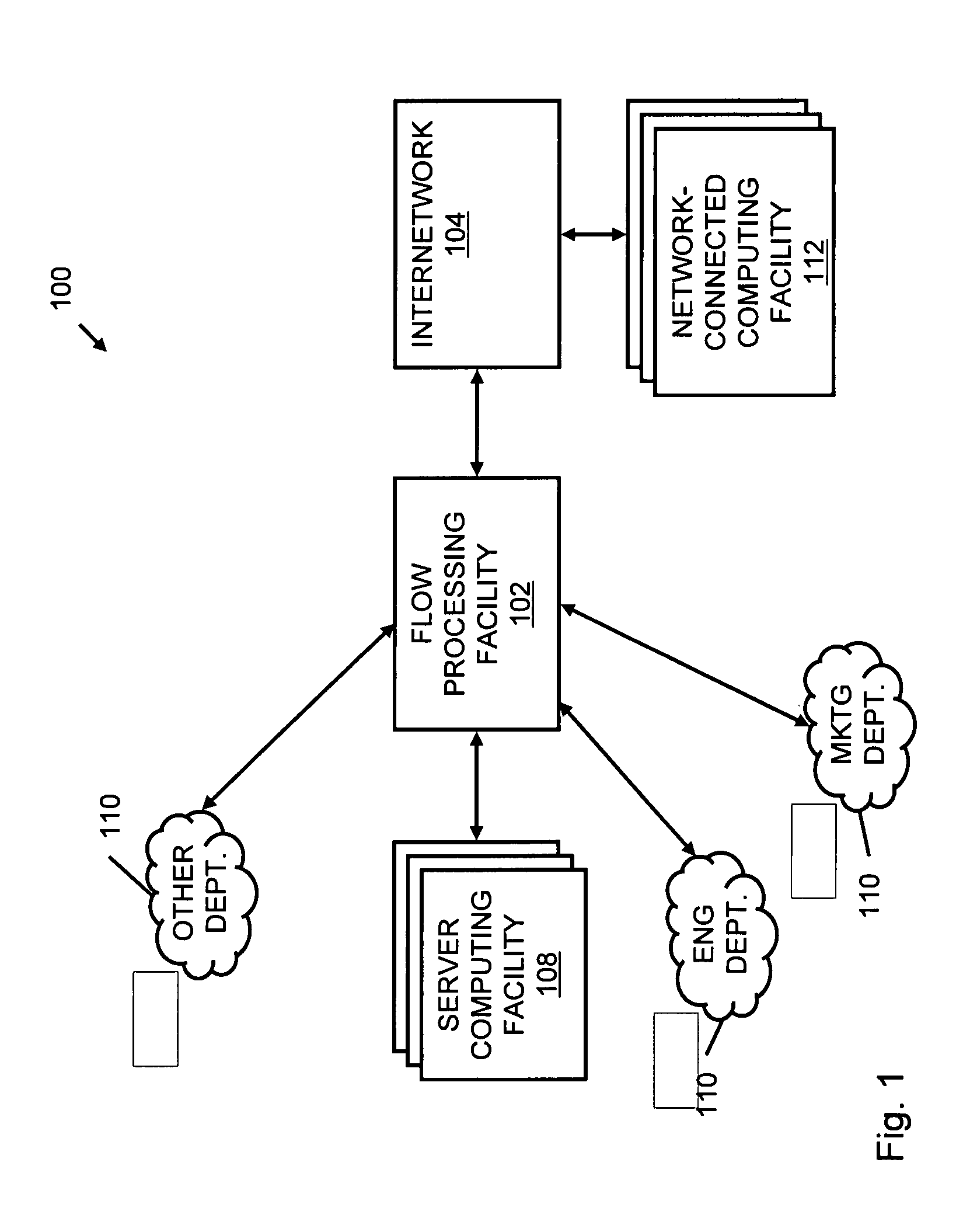
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
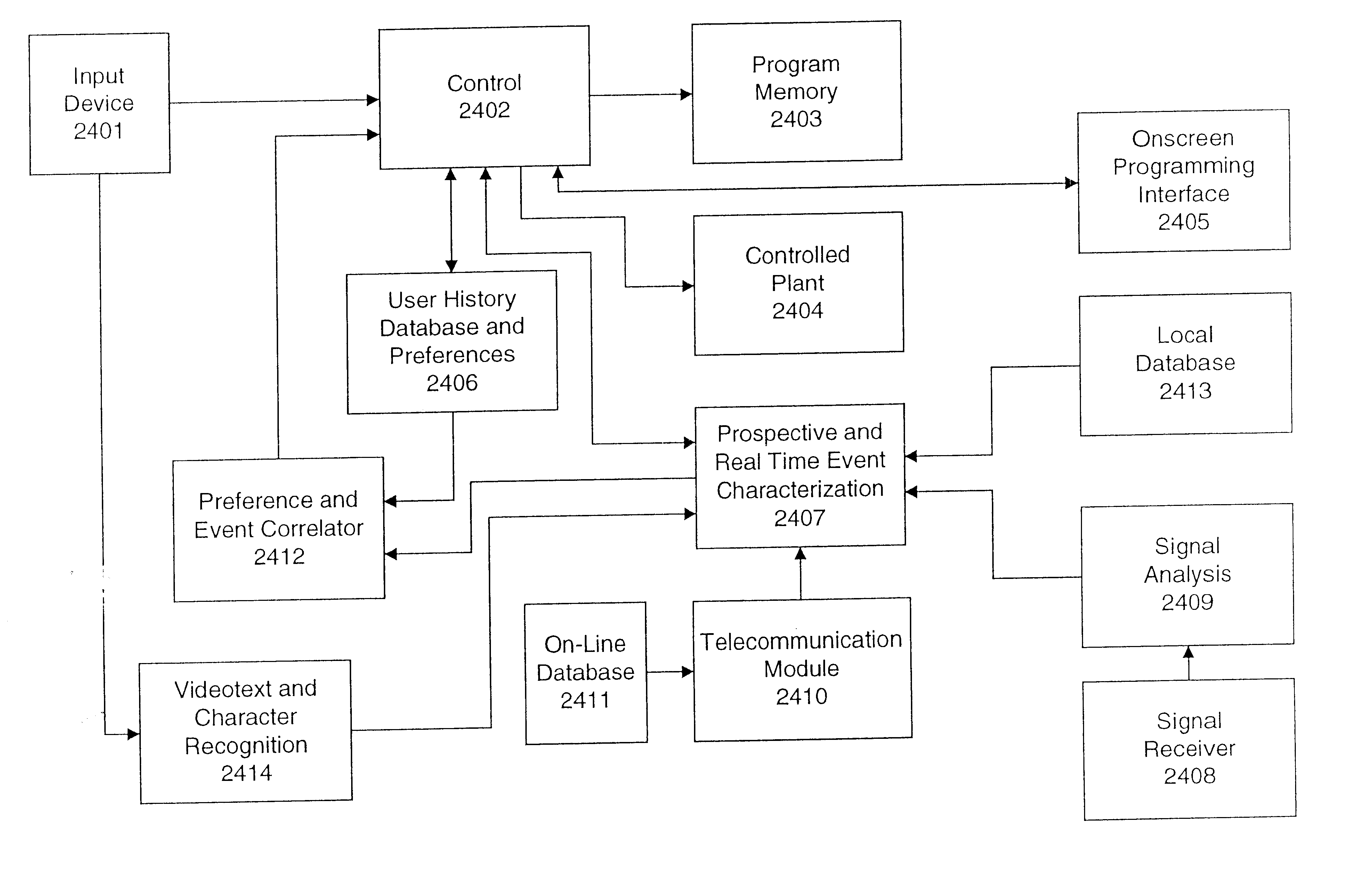
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6418424B1Minimal costAvoid the needTelevision system detailsDigital data processing detailsHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Systems and methods for processing data flows
ActiveUS20120240185A1Facilitate detectionIncreased complexityComputer security arrangementsTransmissionPacket payloadUnified threat management
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Method and system for wireless instant messaging
InactiveUS7058036B1Increase demandIncreased complexityAutomatic call-answering/message-recording/conversation-recordingData switching by path configurationText entryComputer terminal
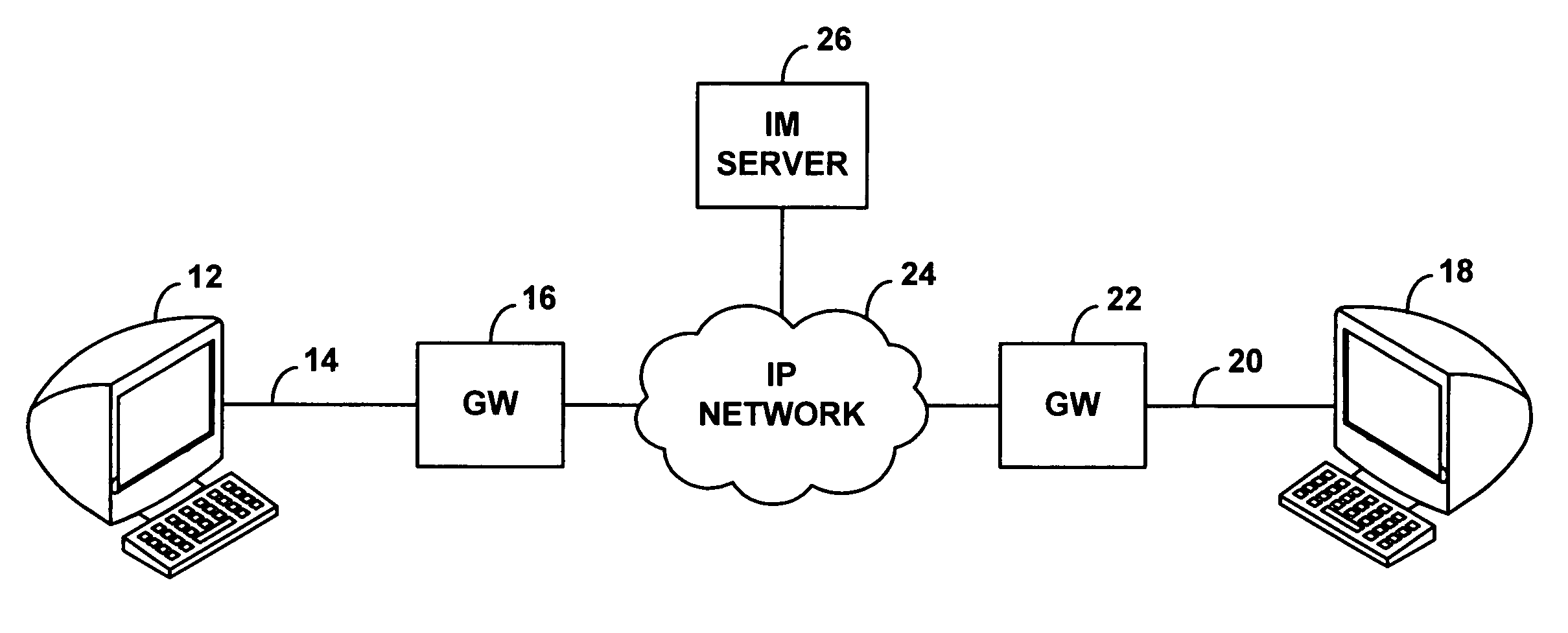
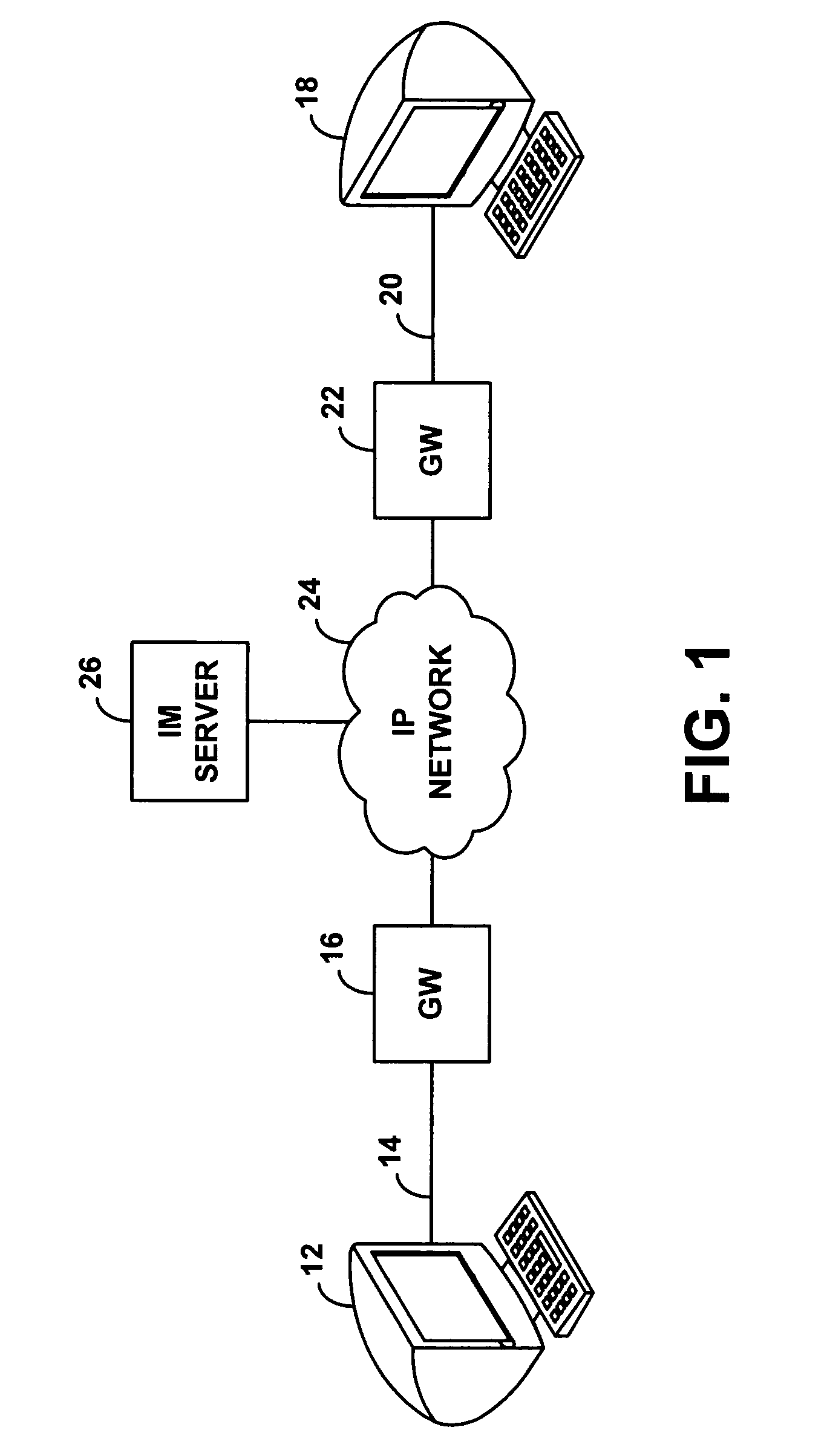
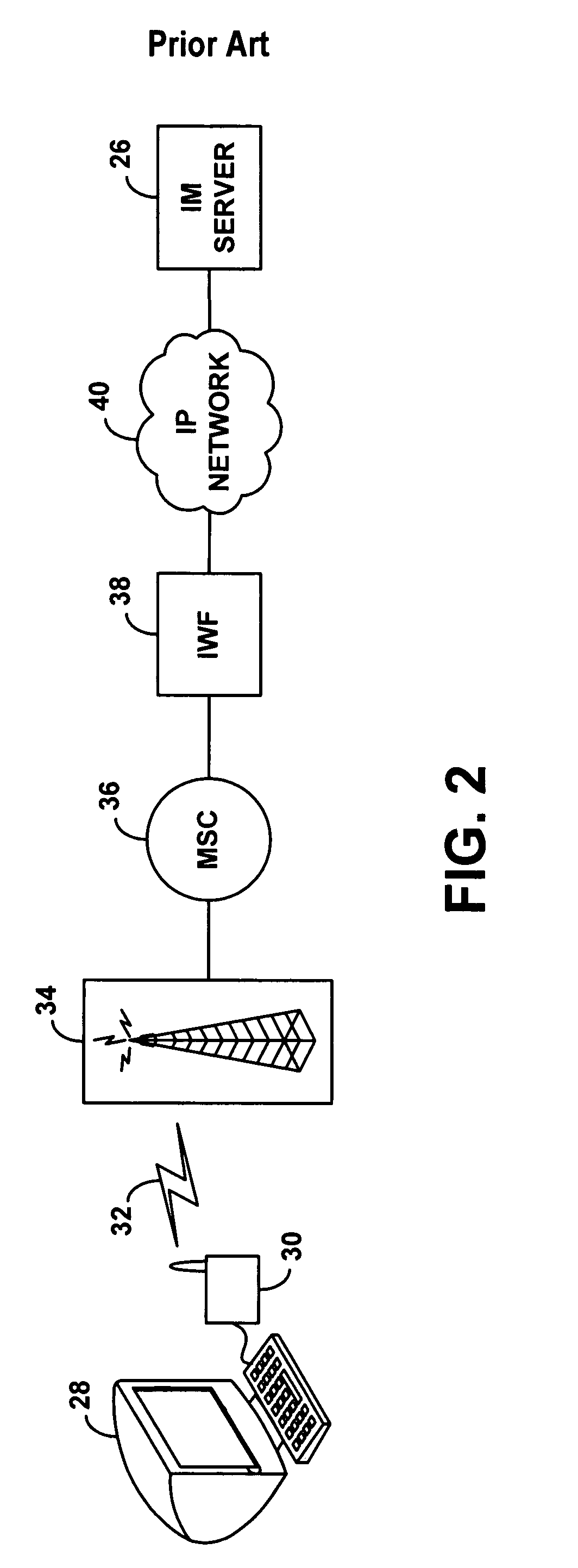
A wireless instant messaging system is disclosed. A mobile station (MS), such as a cellular telephone for instance, may be registered with an instant messaging (IM) server as being available to receive instant messages via an IM proxy. A user at an IM client terminal may then send an instant message destined for a user at the MS. The IM server may direct the message to a service node (SN), which may convert the message into an industry standard SMS message and send the SMS message to the MS. At the MS, a user may read the SMS message and engage a callback feature, which will establish a dial-up voice connection between the MS and the SN. The user at the MS may then speak an instant message response, and the SN may record the response as a compressed audio file. The SN may then send the compressed audio file as an attachment to an instant message back to the user at the IM client terminal. The IM client terminal may then play the spoken response message. The invention facilitates robust instant messaging communication, while avoiding the need for a user at the mobile station to engage in cumbersome text entry via a numeric keypad.
Owner:SPRING SPECTRUM LP
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
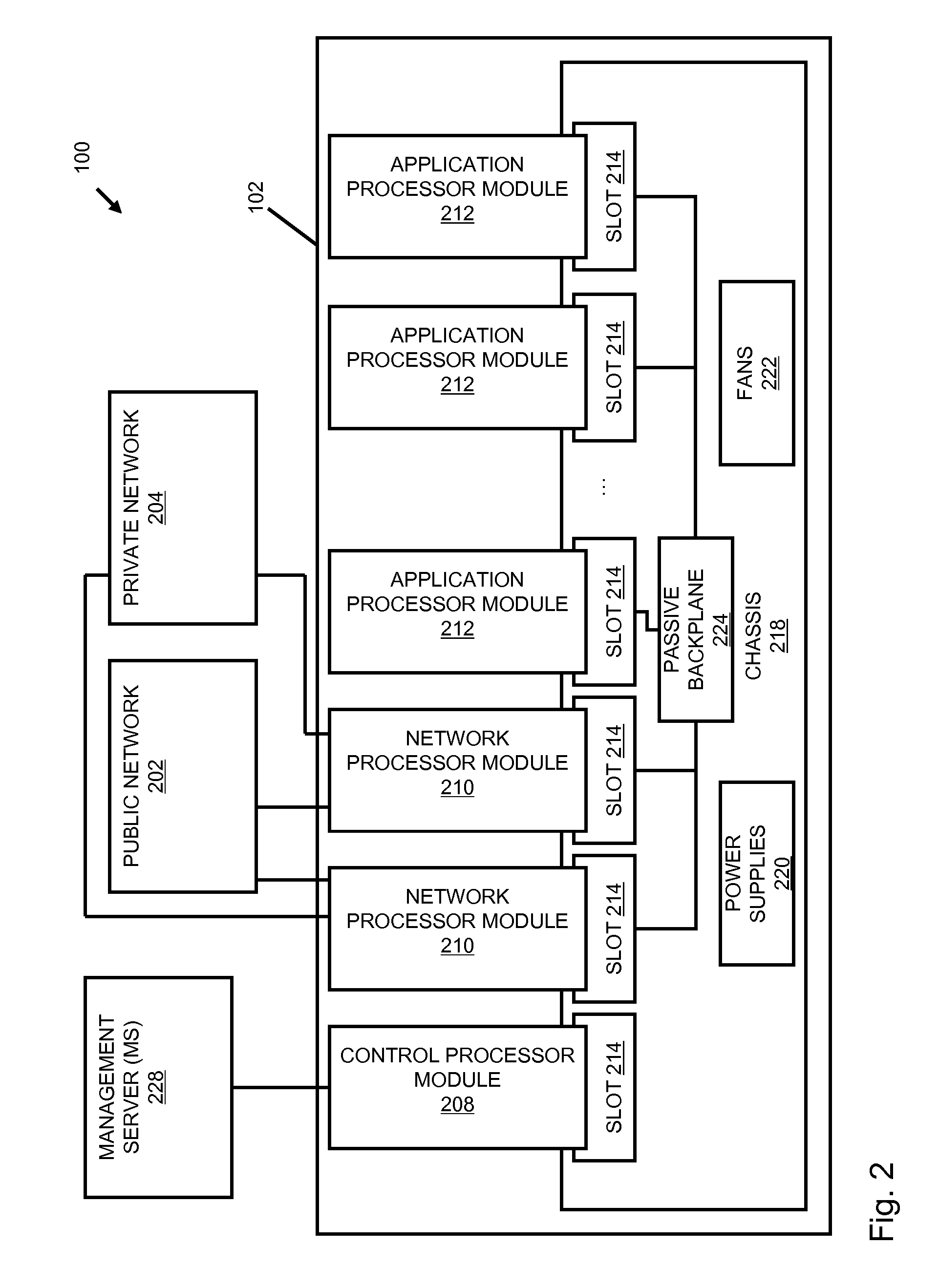
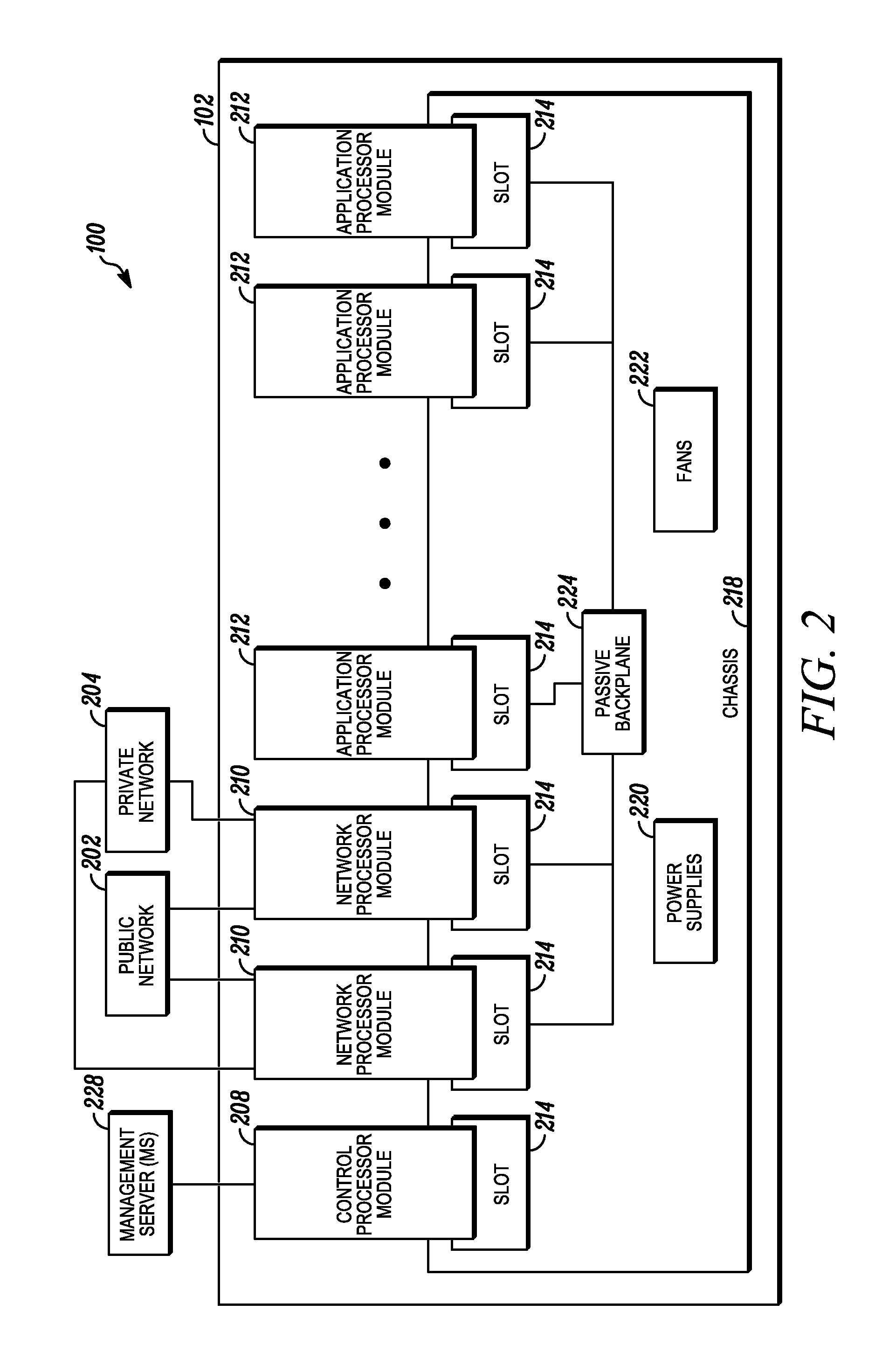
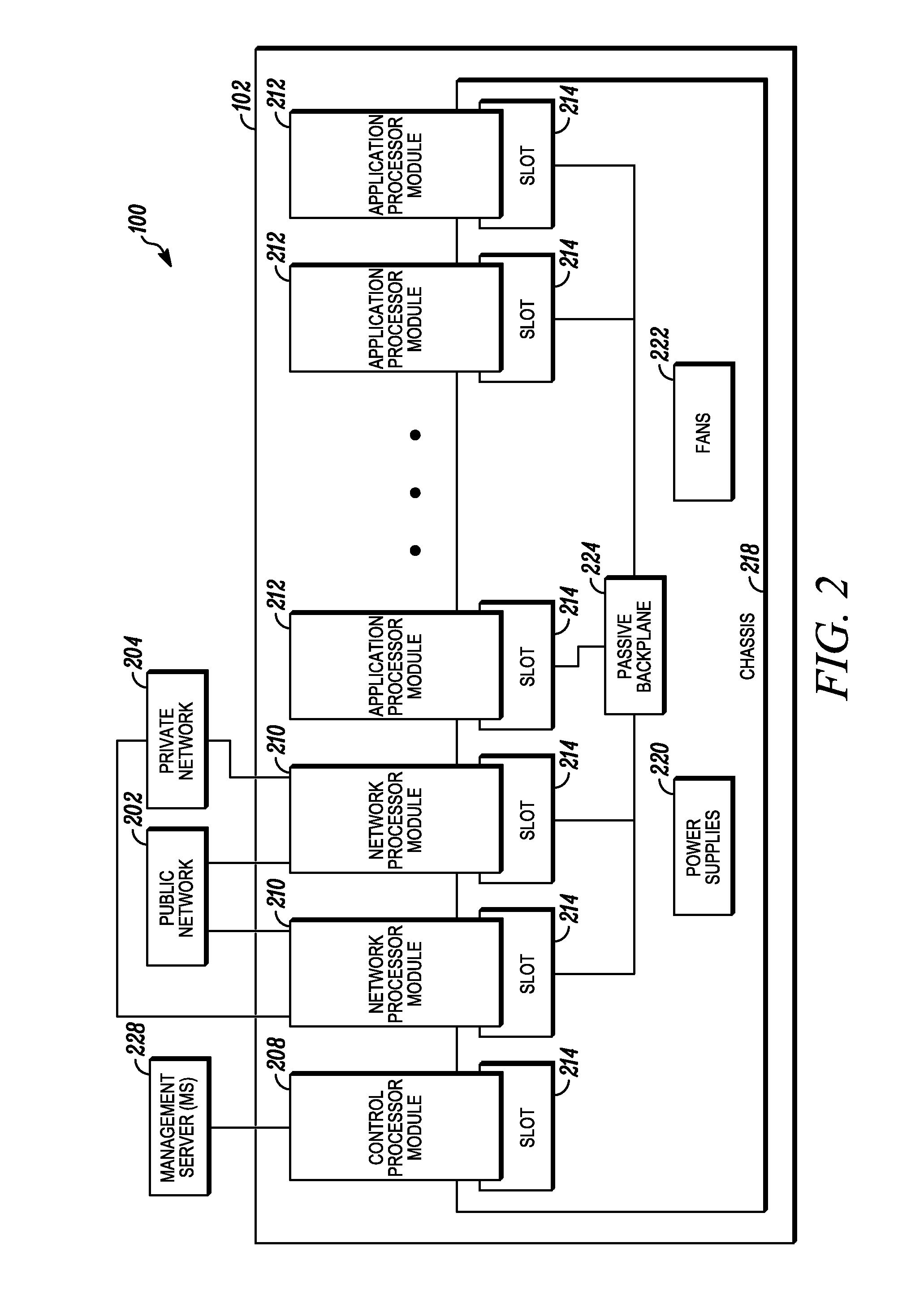
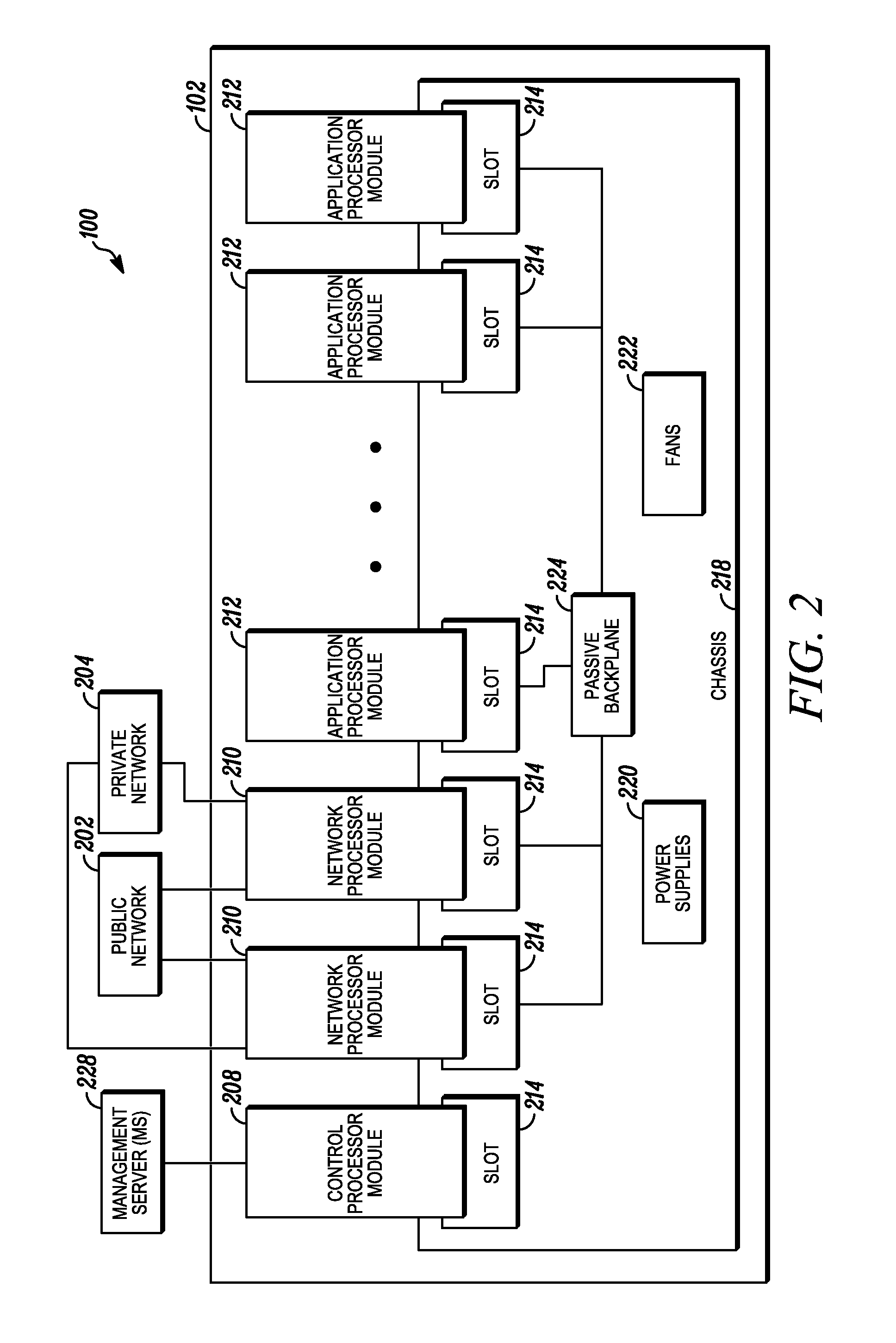
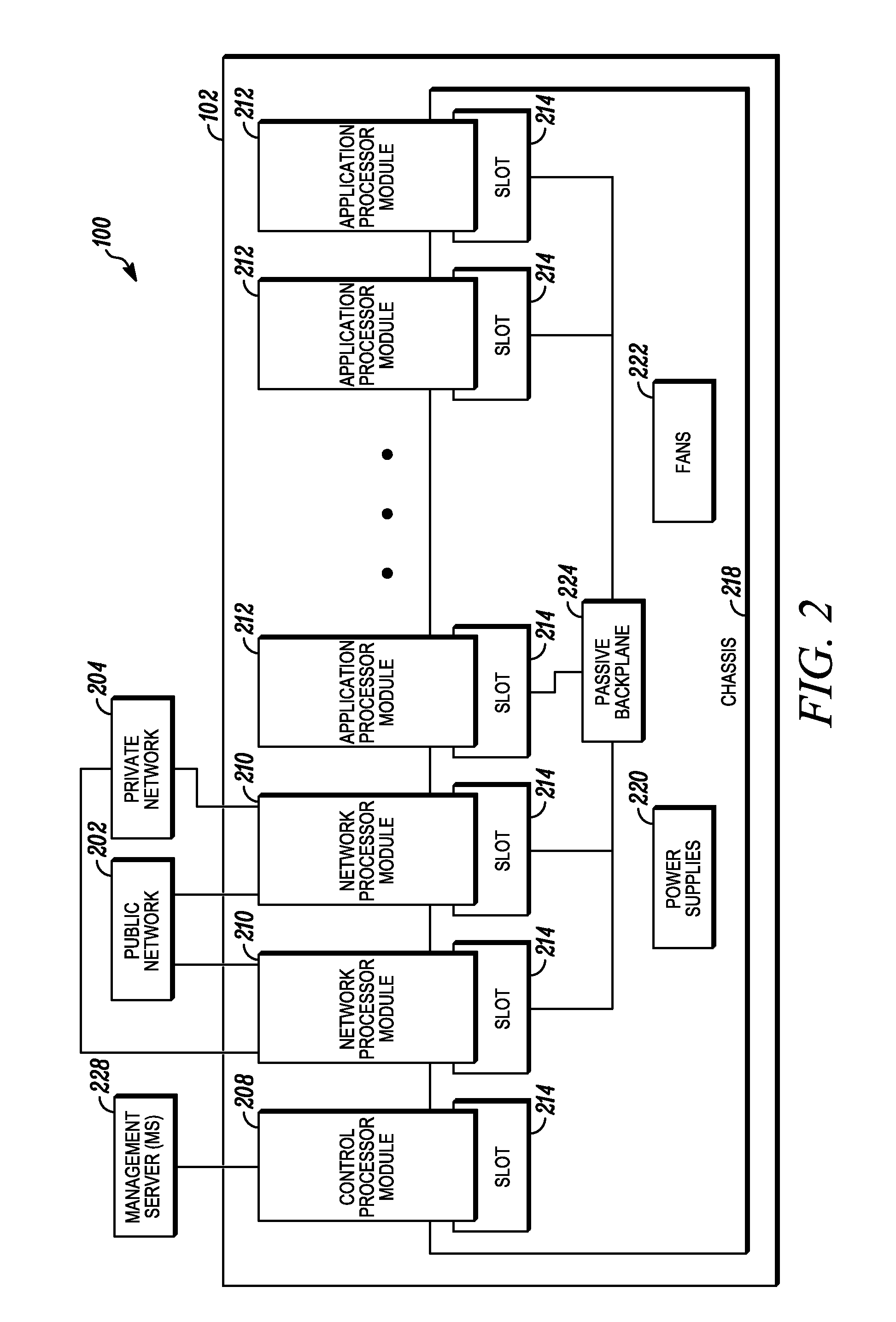
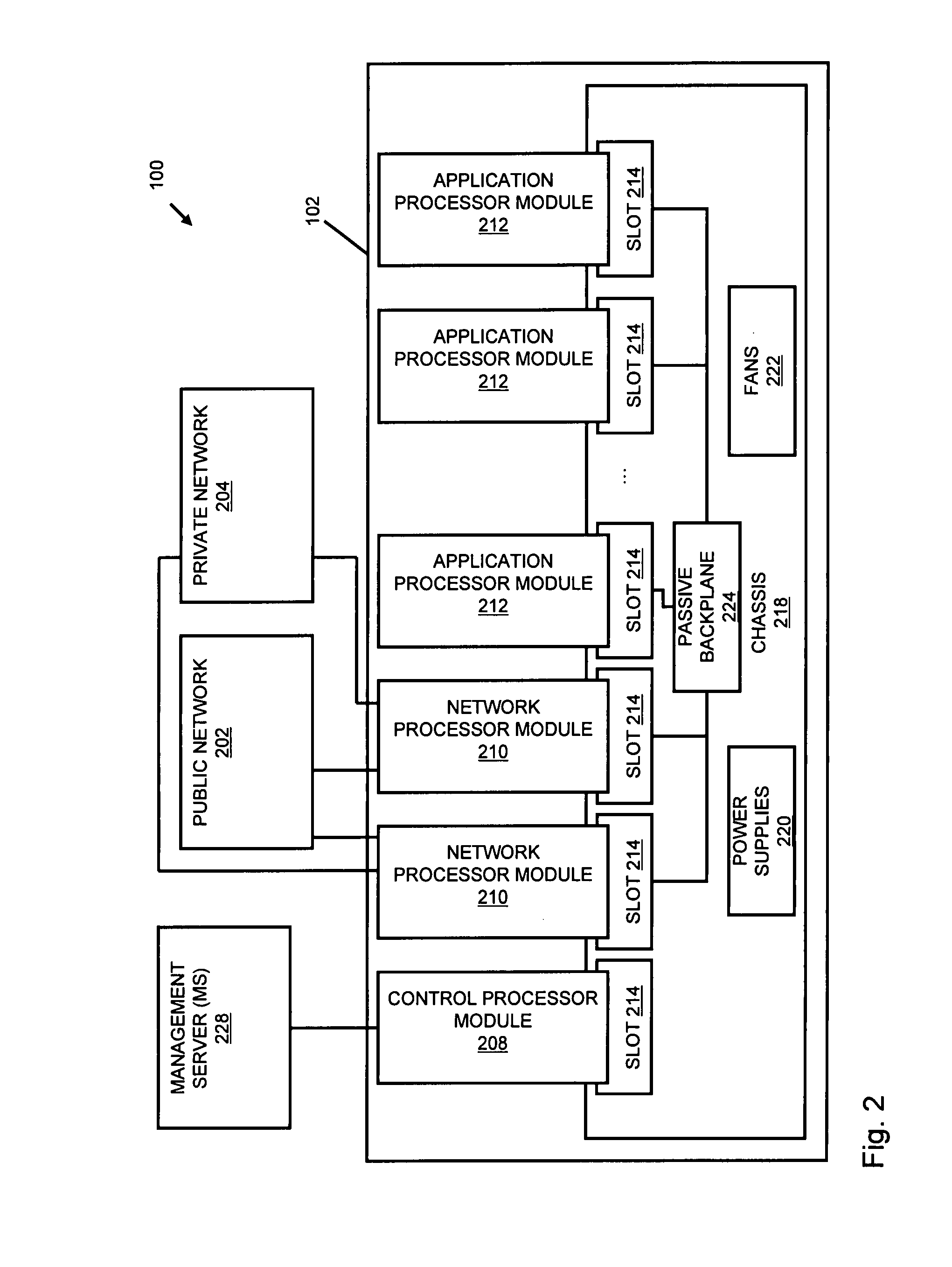
Processing data flows with a data flow processor
InactiveUS20110238855A1Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData controlConfigfs
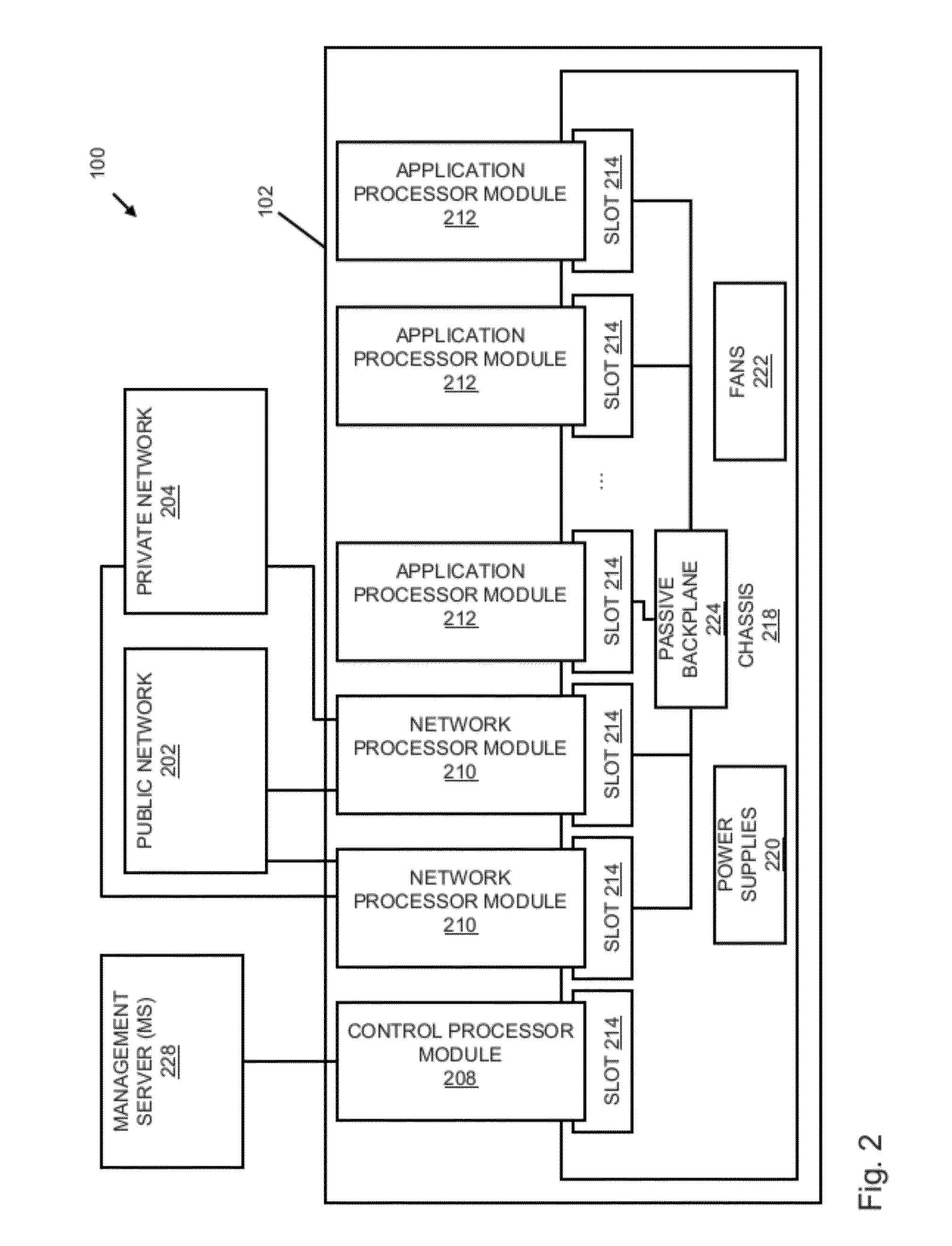
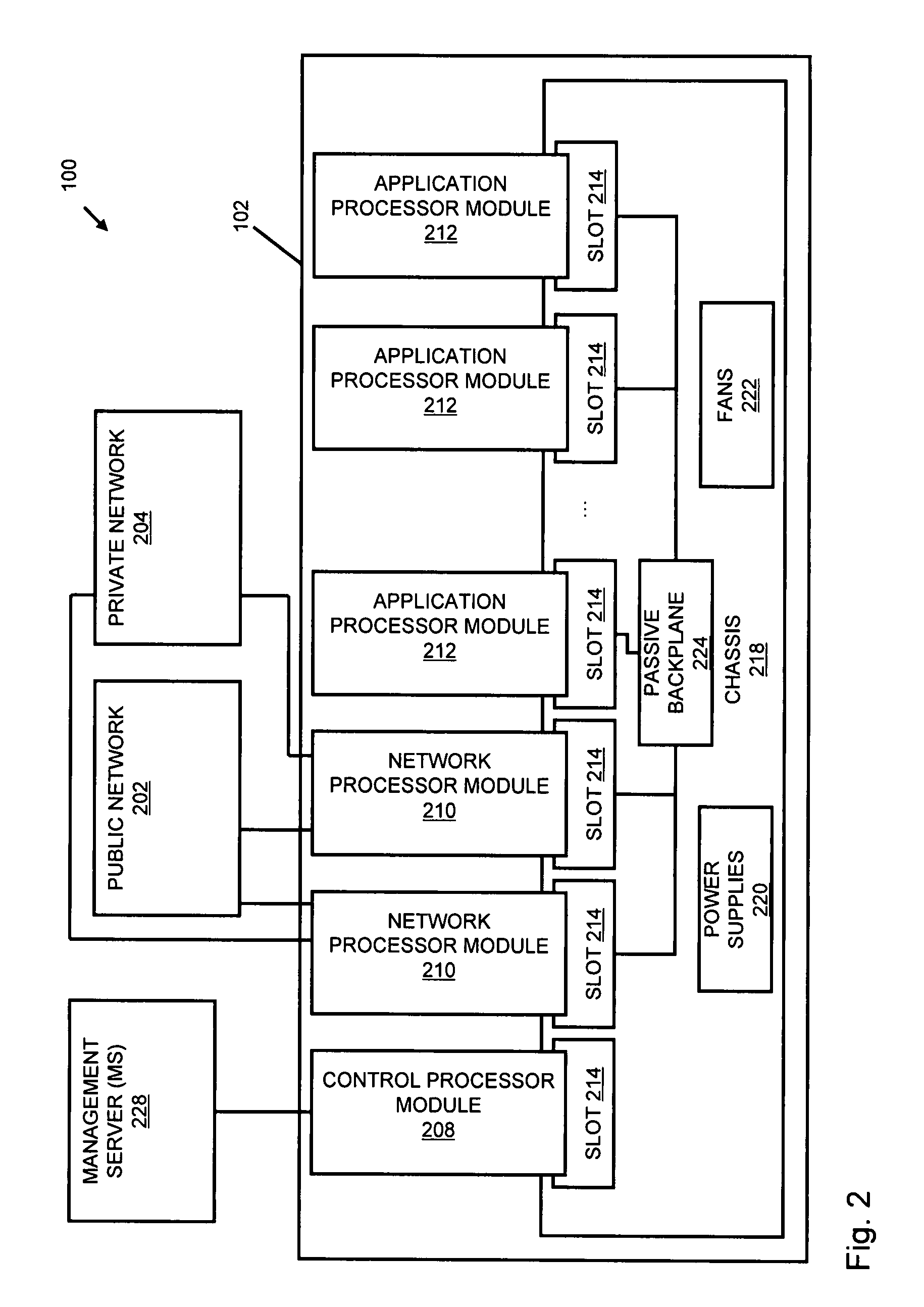
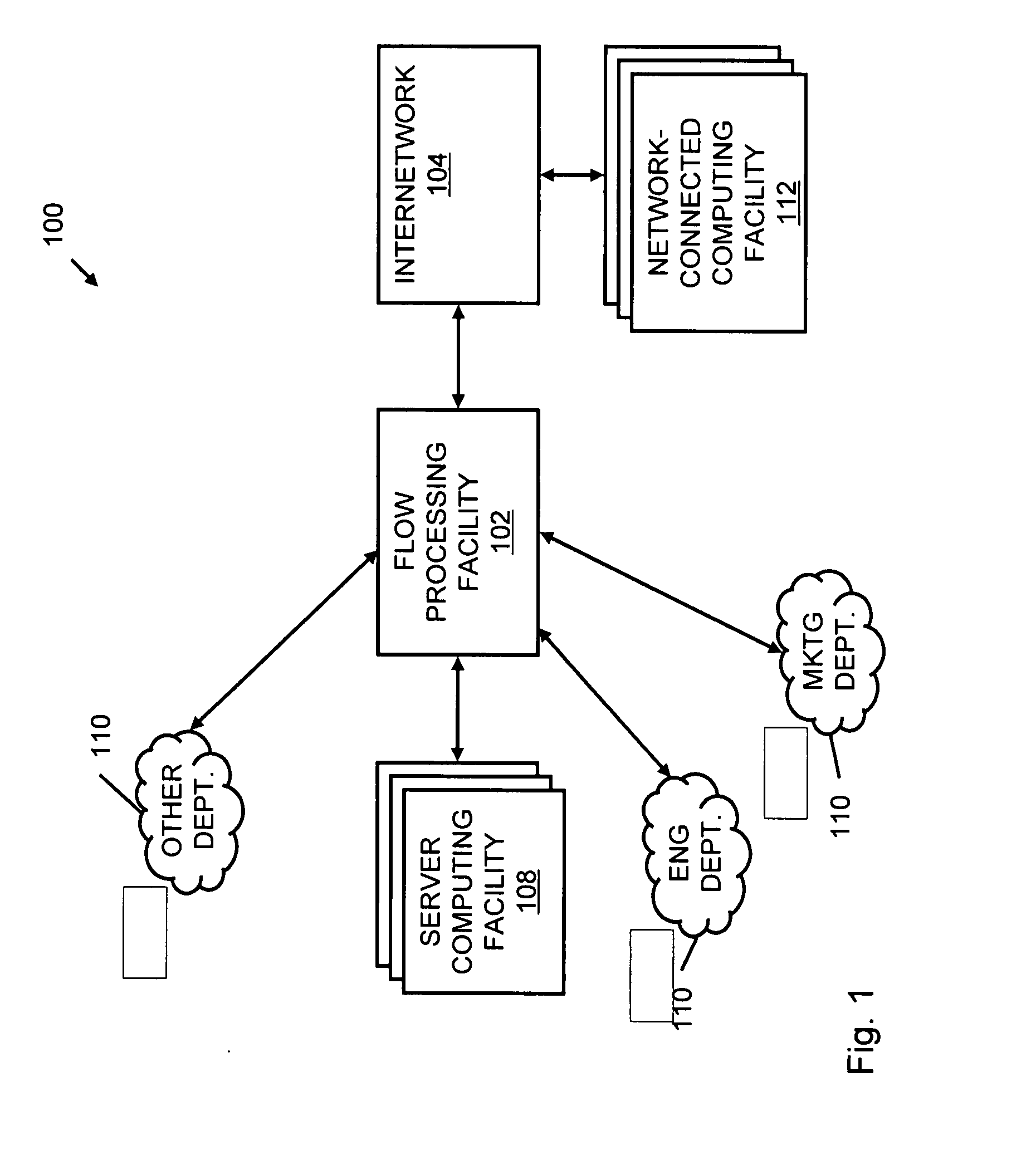
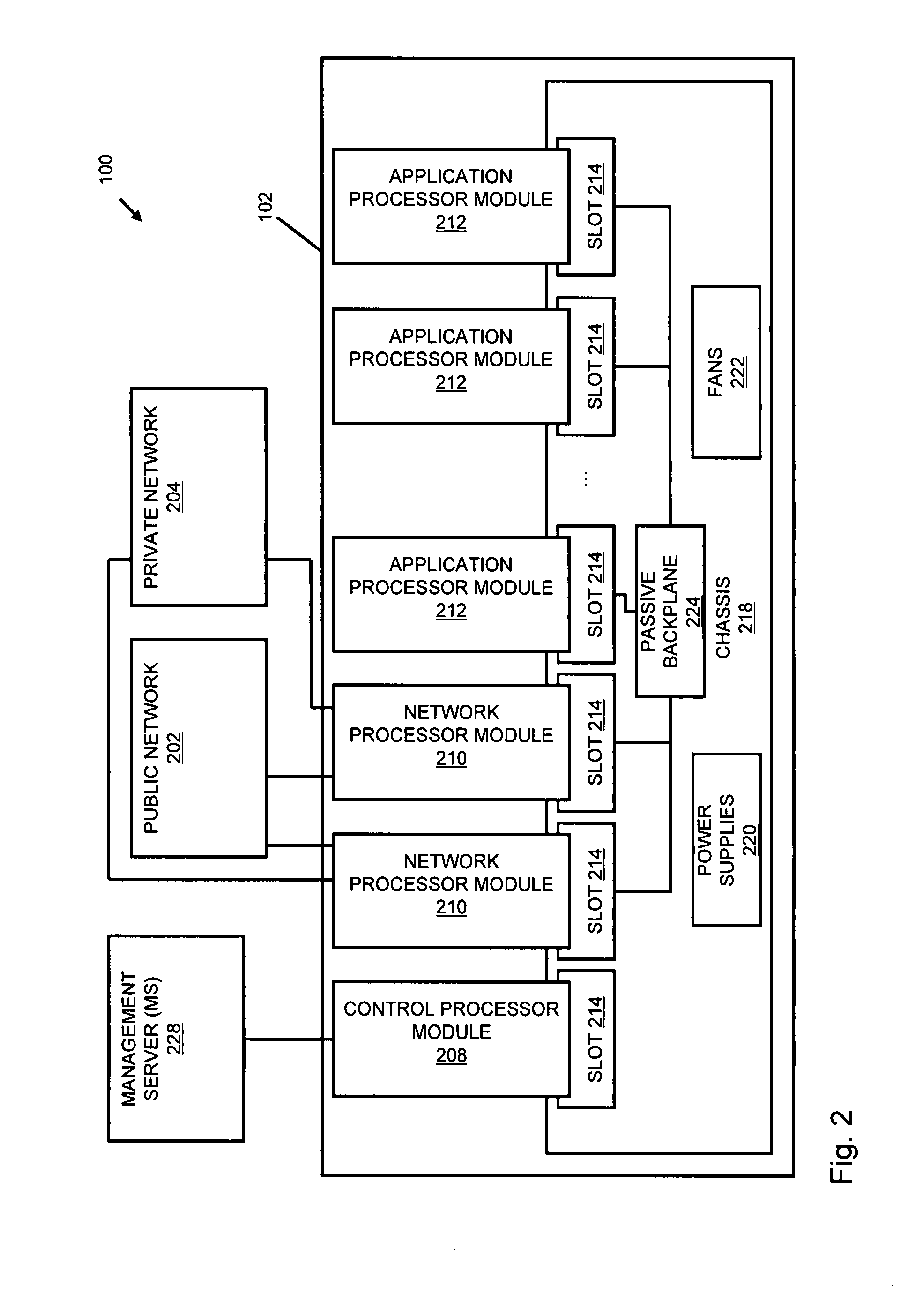
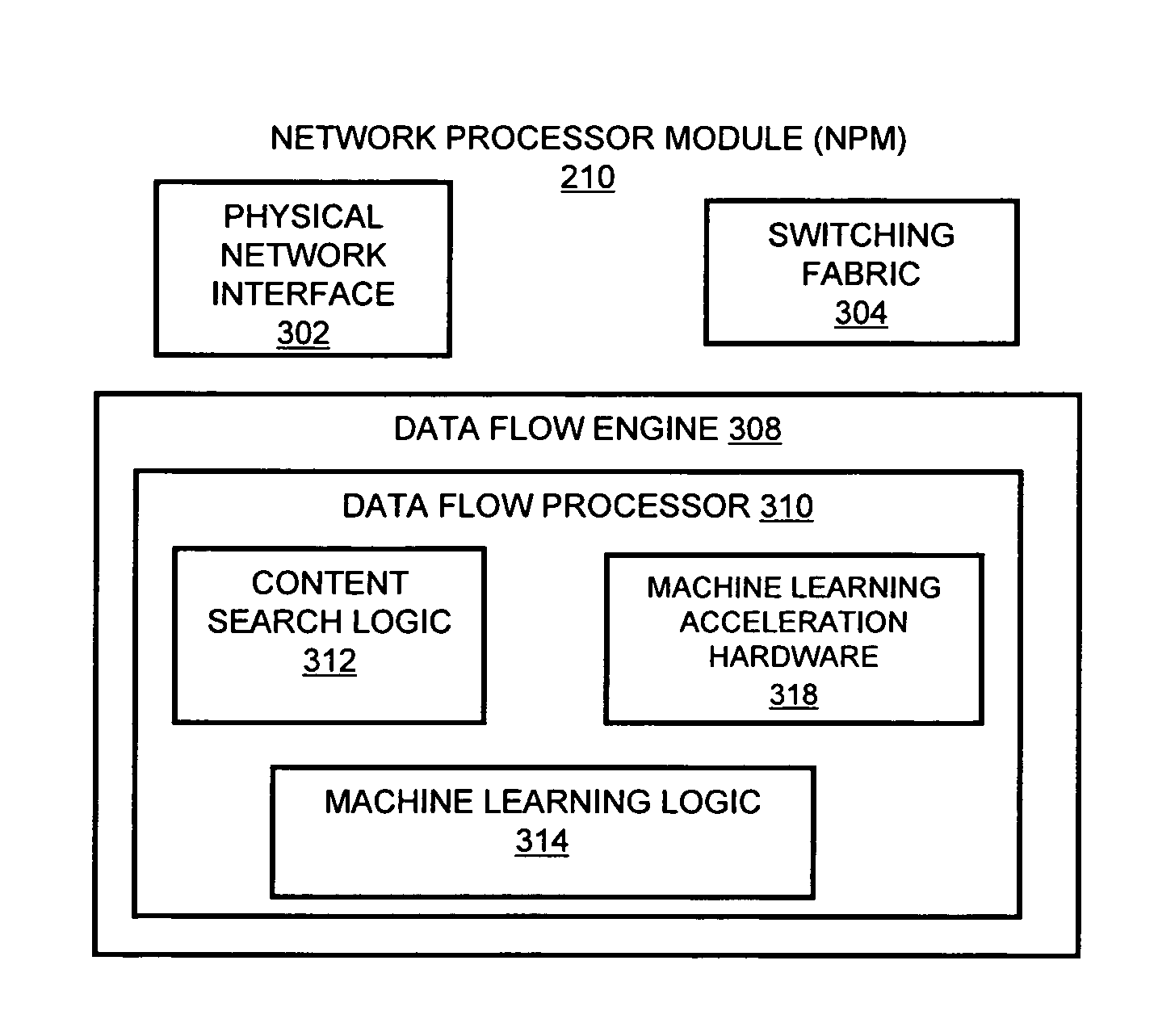
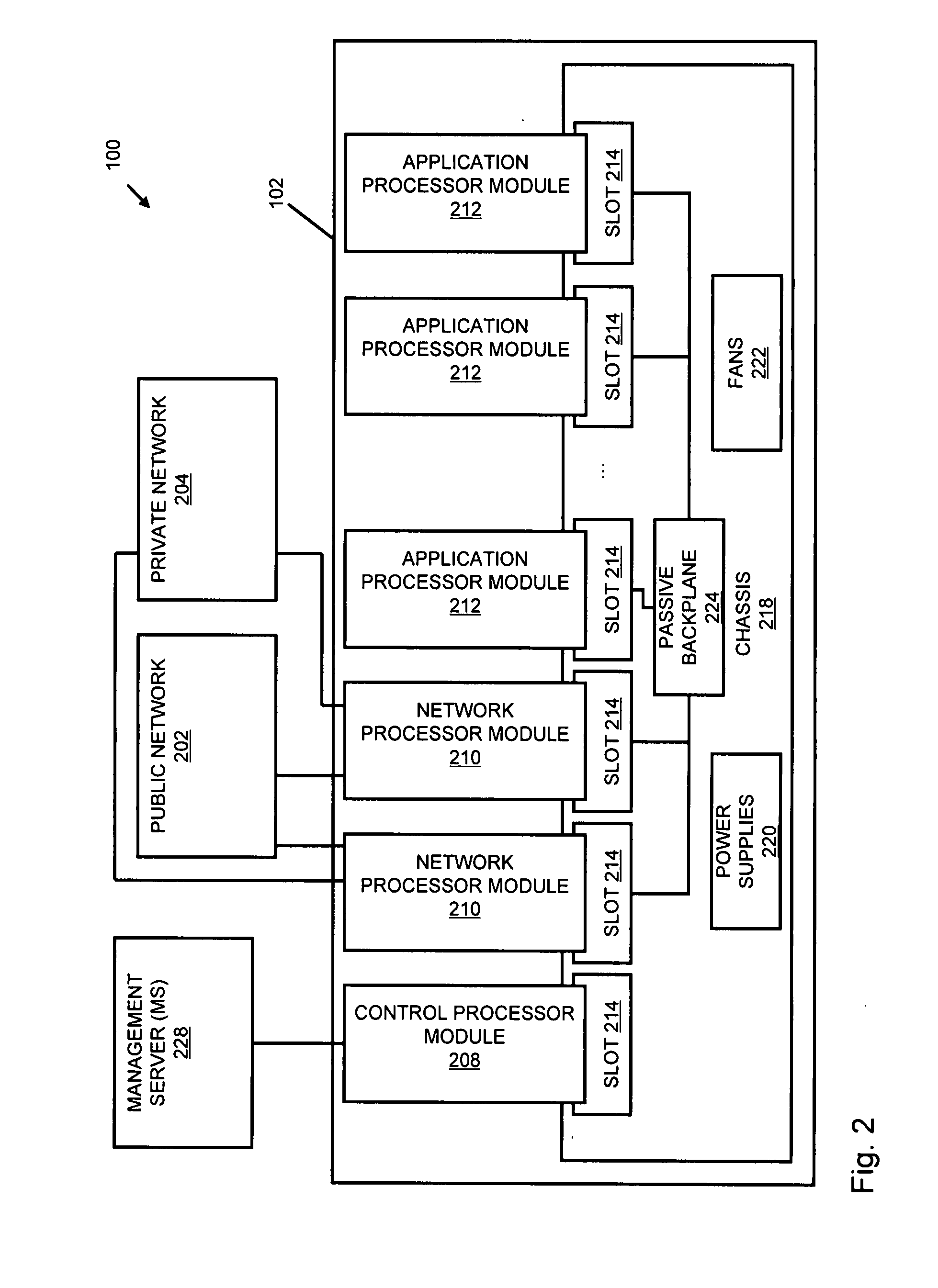
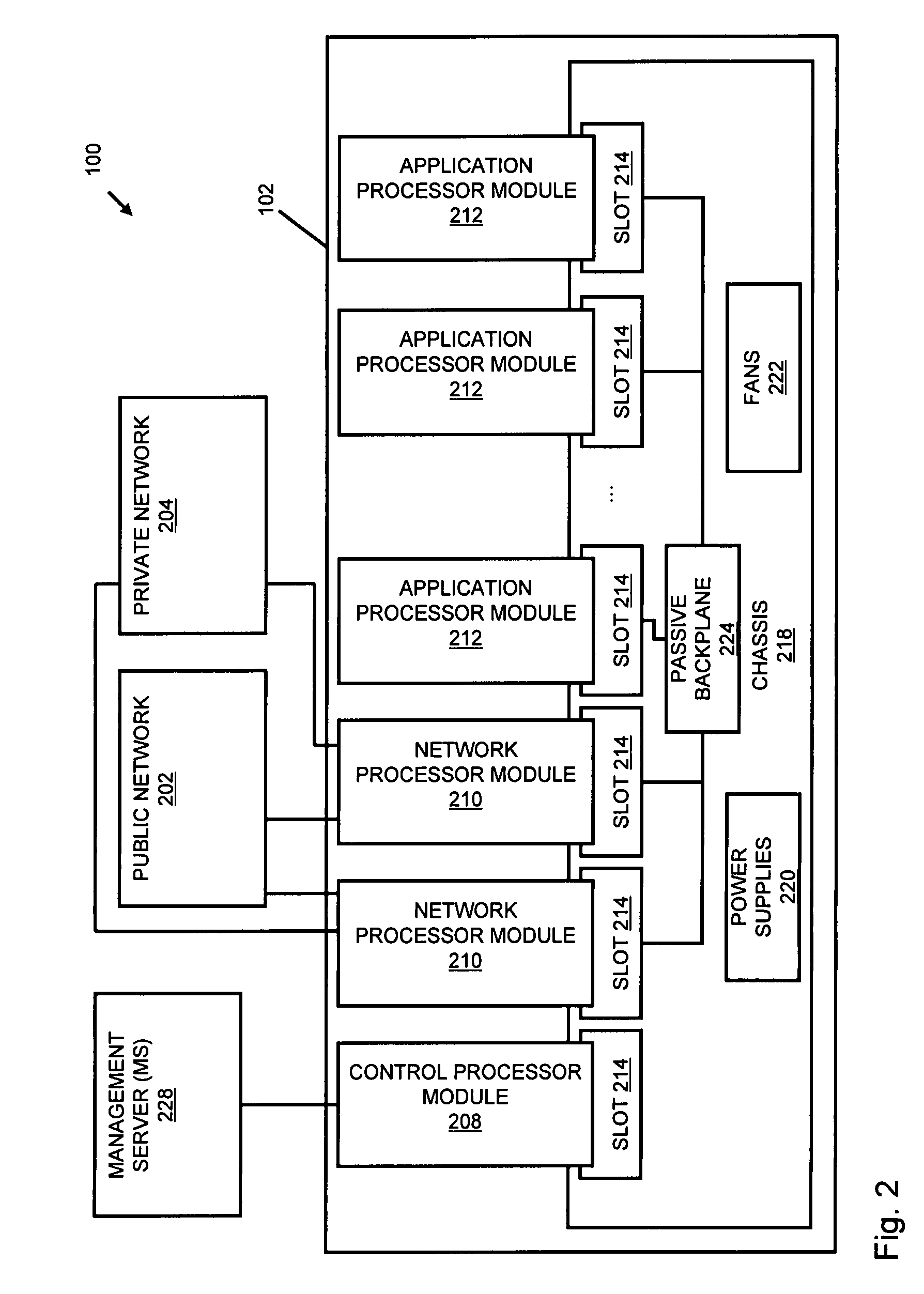
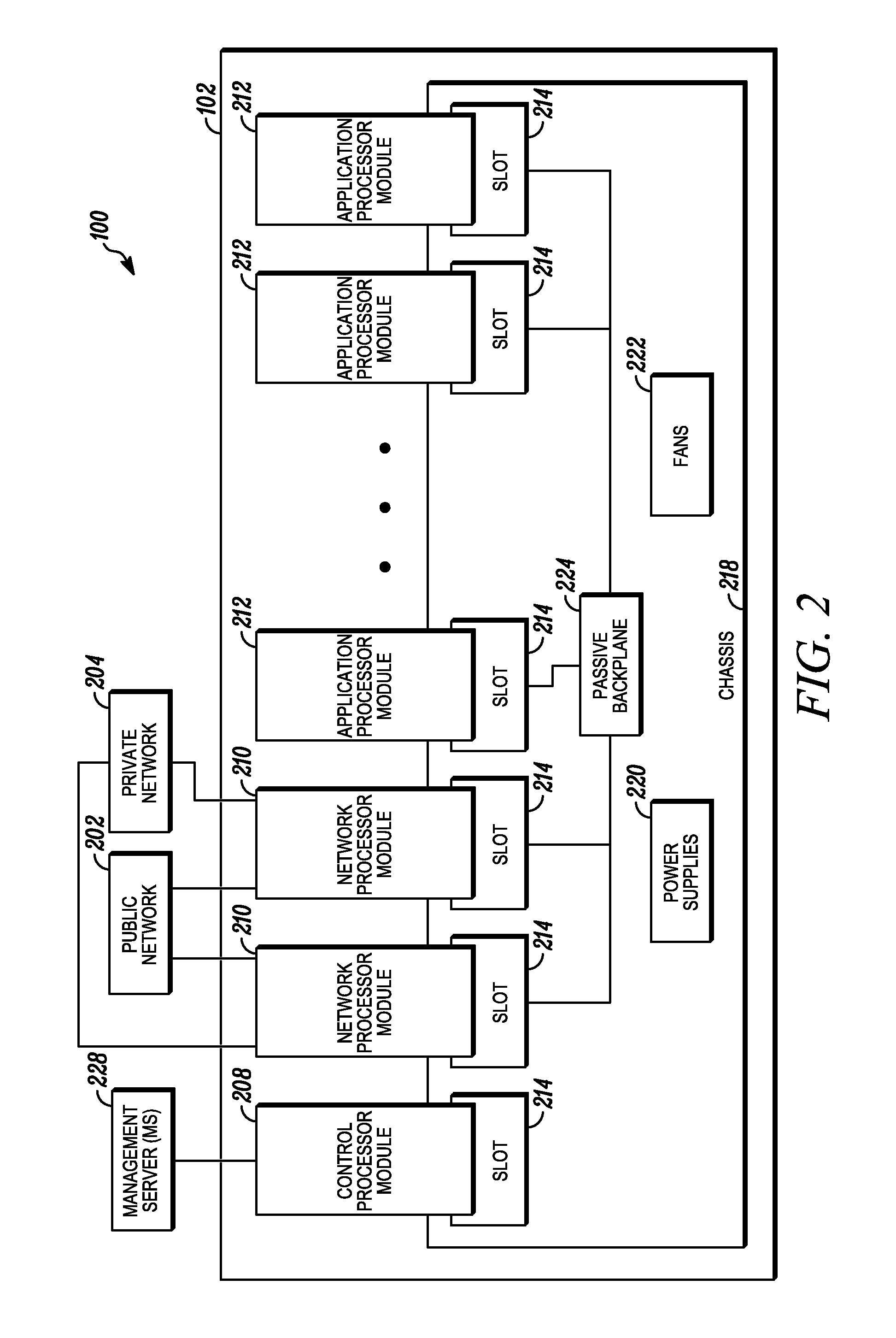
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
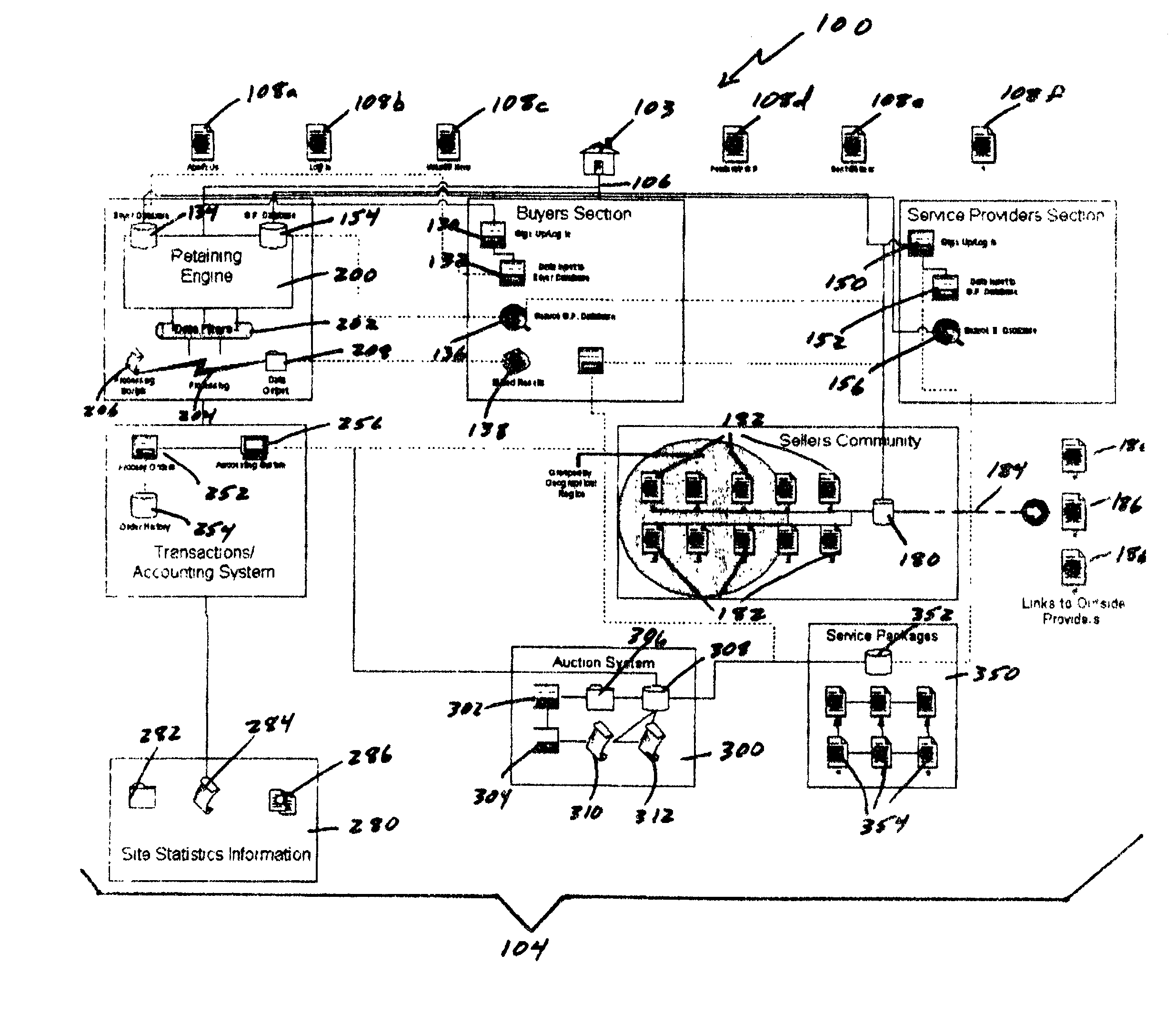
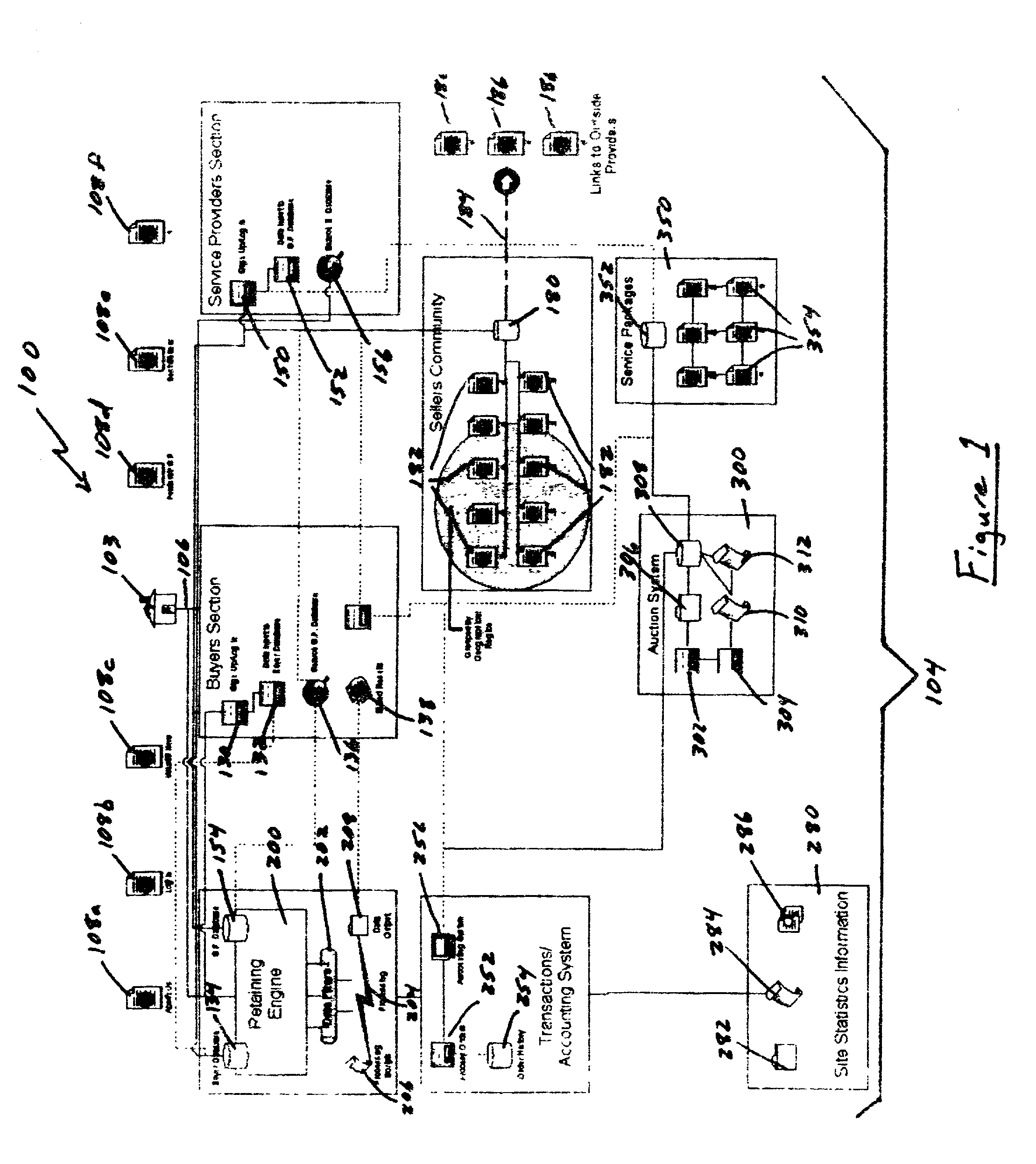
Auction, imagery and retaining engine systems for services and service providers
InactiveUS20020120554A1Facilitates in efficiently accessing latent demandEliminate riskFinancePayment architectureGroup PurchasingService provision
The present disclosure provides a computer-implemented method / system for facilitating communications between service providers and potential customers for services. The computer-implemented method / system provides a marketplace for interactions, both online and off-line, between service providers and potential customers, including purchasing groups, particularly buyer-driven service-related interactions. The marketplace advantageously allows categorization, key word searching, group purchasing, service packaging, data mining, auctions and other commercial features and functionality. The computer-implemented method / system also supports holographic imagery, e.g., in the form of virtual assistants, that facilitates marketplace-related activities. Based on the computer-implemented method / system, service providers are able to efficiently and cost effectively extend the reach of their marketing and promotional activities to a wide range of additional customers, and customers are able to initiate access service providers ideally suited to meet their needs, i.e., buyer-driven commerce, at desirable prices and according to required timeframes.
Owner:VEGA LILLY MAE
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
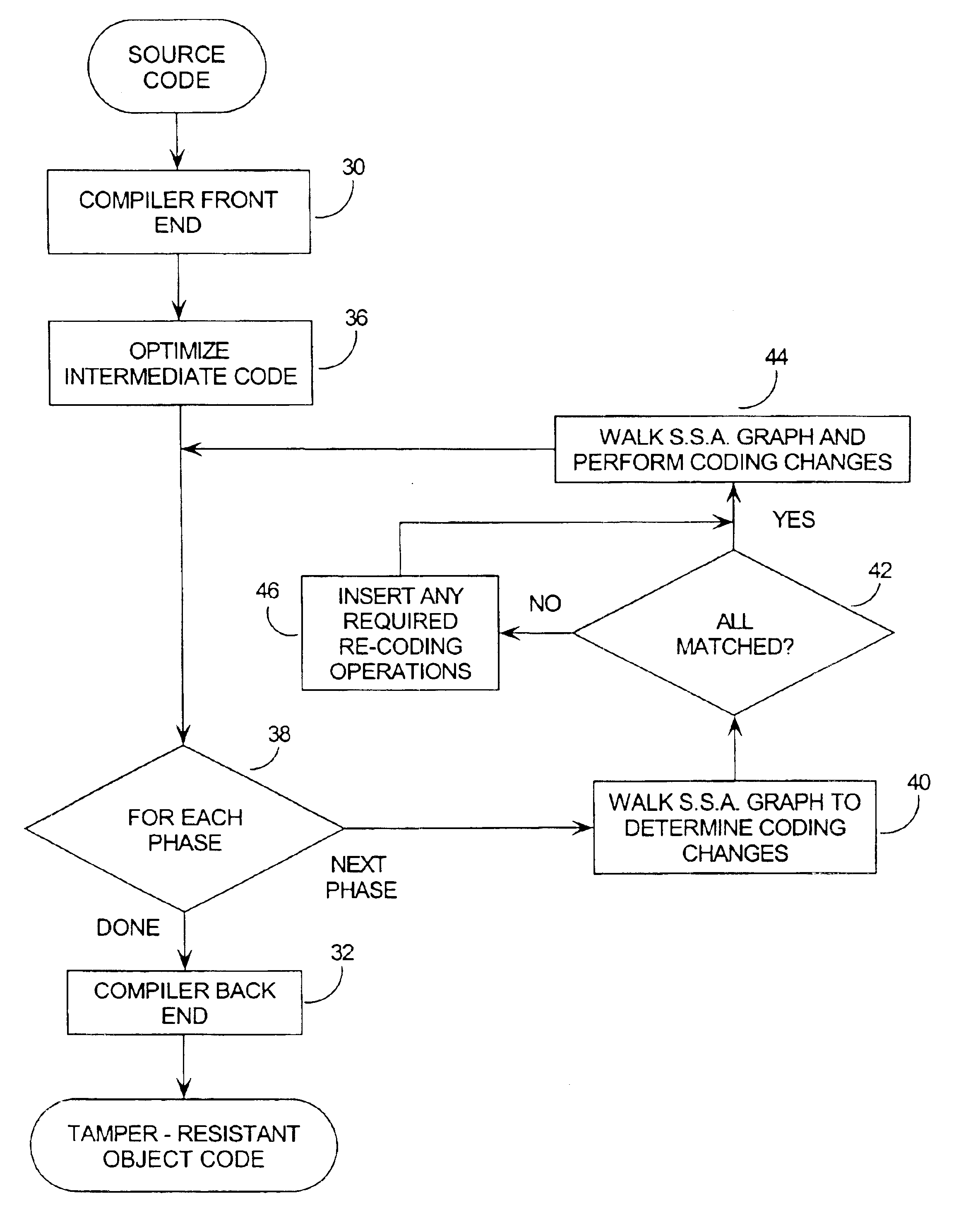
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
Method and apparatus for selective blocking of radio frequency identification devices
ActiveUS6970070B2Enhanced consumer privacyIncreased complexityMemory record carrier reading problemsTime-division multiplexComputer hardwareRadio-frequency identification
Techniques are disclosed for providing enhanced privacy in an RFID system comprising a plurality of RFID devices, each having an associated identifier, and at least one reader which communicates with one or more of the devices. A blocker device is operative to receive a communication directed from the reader to one or more of the RFID devices, and to generate, possibly based on information in the received communication, an output transmittable to the reader. The output simulates one or more responses from at least one of the RFID devices in a manner which prevents the reader from determining at least a portion of the identifier of at least one of the RFID devices. The blocker device may itself comprise one of the RFID devices. In an illustrative embodiment, the output generated by the blocker device interferes with the normal operation of a singulation algorithm implemented by the reader.
Owner:EMC IP HLDG CO LLC
Method for facilitating pathogen resistance
InactiveUS20030150017A1Convenient researchImprove developmentClimate change adaptationOther foreign material introduction processesDNA constructNucleotide
Methods are provided for the genetic control of pathogen infestation in host organisms such as plants, vertebrate animals and fungi. Such methods utilize the host as a delivery system for the delivery of genetic agents, preferably in the form of RNA molecules, to a pathogen, which agents cause directly or indirectly an impairment in the ability of the pathogen to maintain itself, grow or otherwise infest a host plant, vertebrate animal or fungus. Also provided are DNA constructs and novel nematode nucleotide sequences for use in same, that facilitate pathogen resistance when expressed in a genetically-modified host. Such constructs direct the expression of RNA molecules substantially homologous and / or complementary to an RNA molecule encoded by a nucleotide sequence within the genome of a pathogen and / or of the cells of a host to effect down-regulation of the nucleotide sequence. Particular hosts contemplated are plants, such as pineapple plants, and particular pathogens are nematodes.
Owner:THE UNIV OF QUEENSLAND +1
Securing a network with data flow processing
InactiveUS20110214157A1Easy to detectPreventing data flowPlatform integrity maintainanceTransmissionData stream processingApplication software
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:CA TECH INC
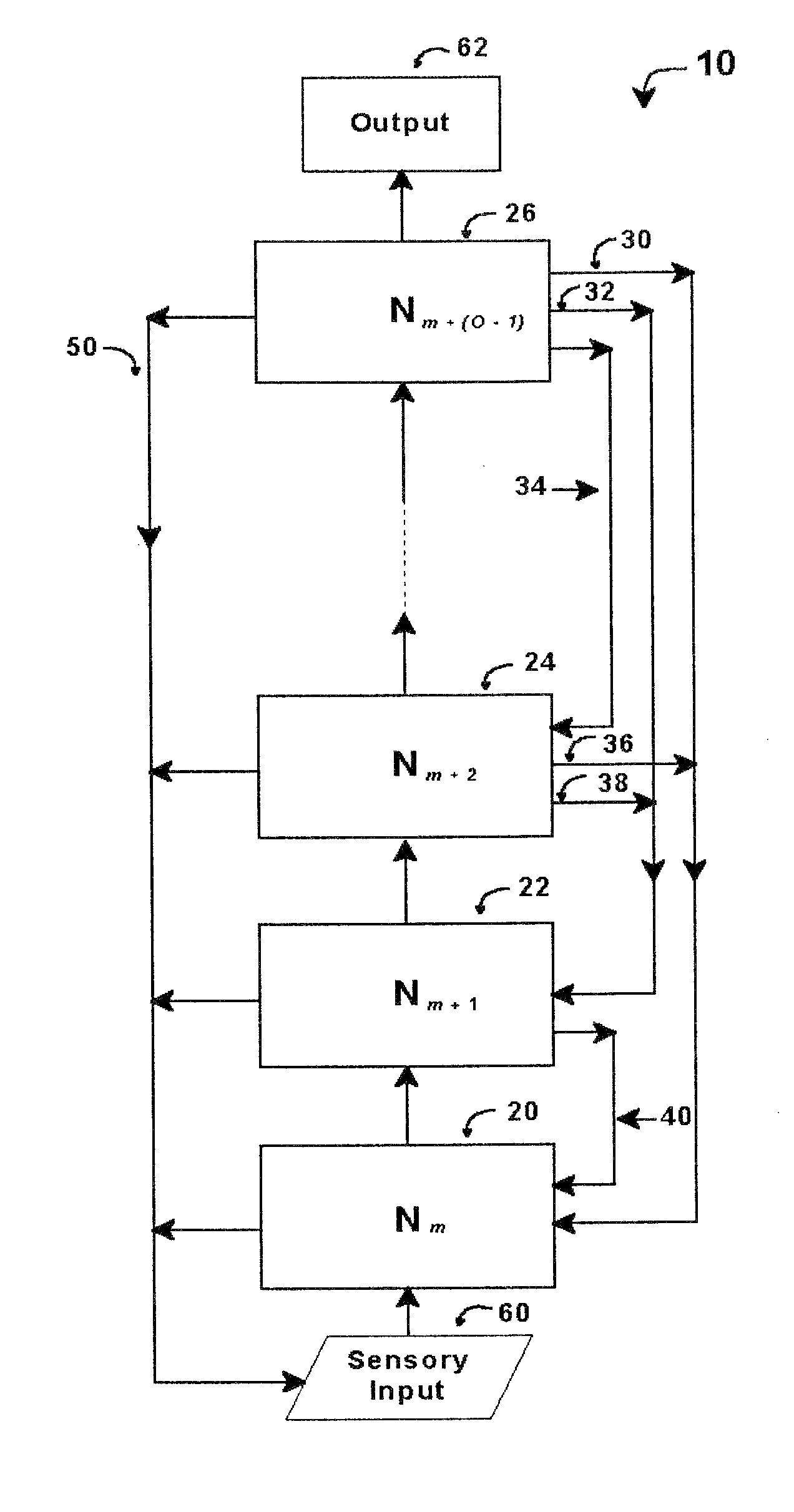
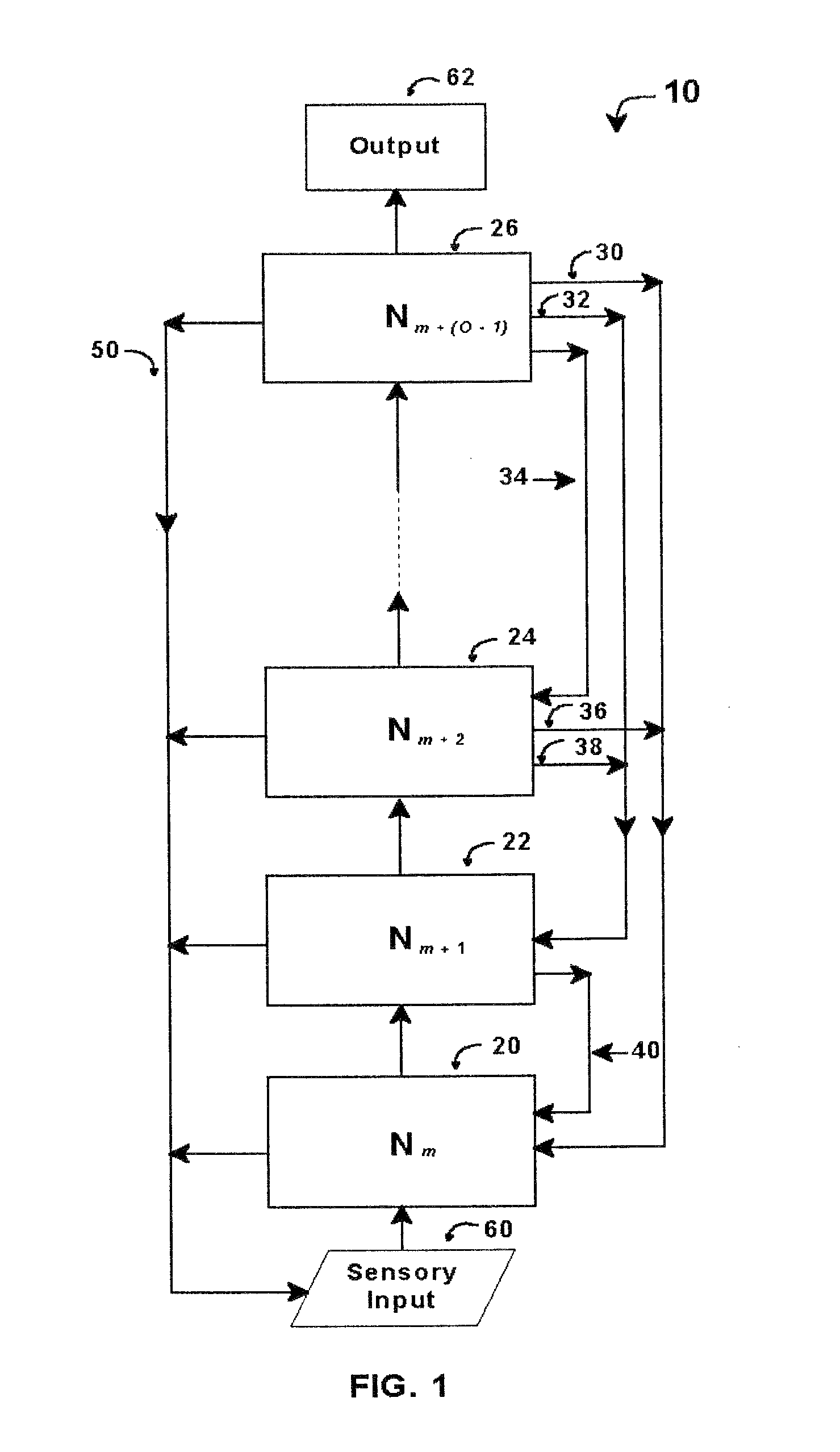
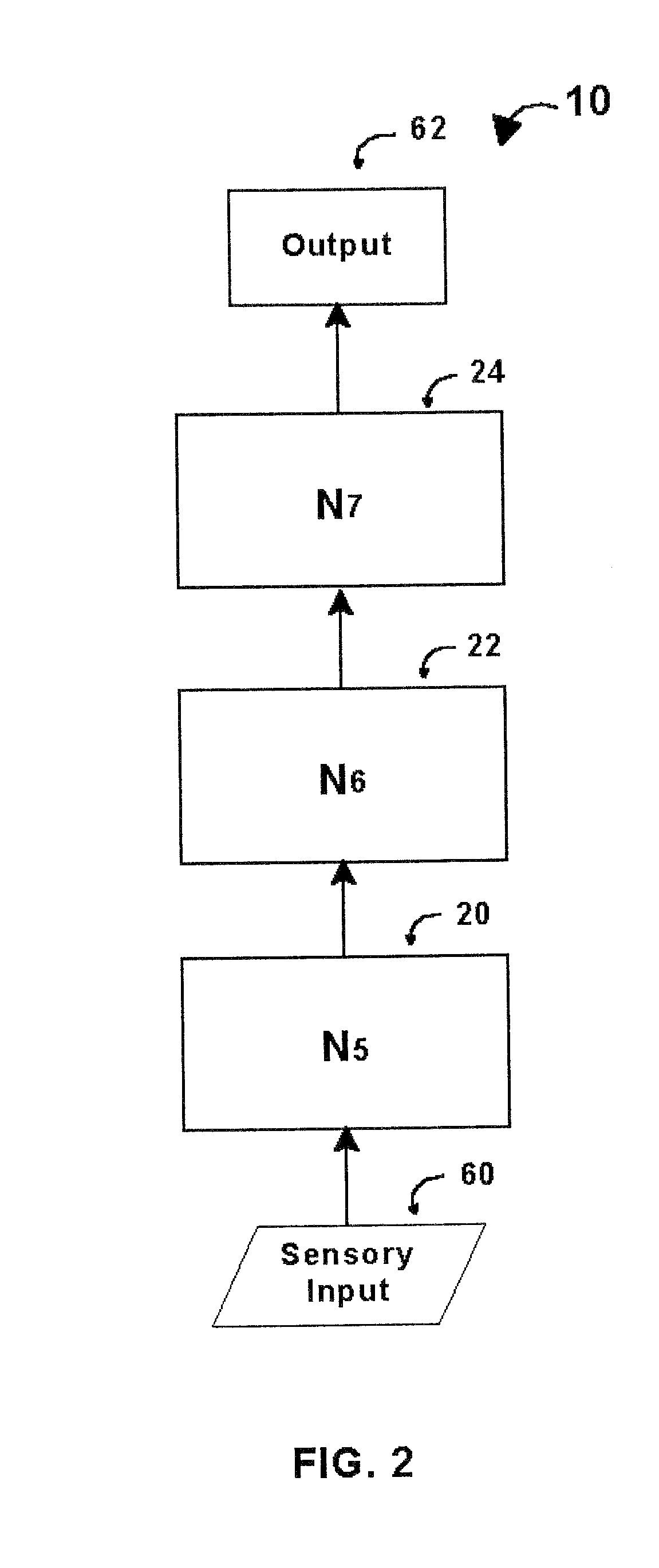
Intelligent control with hierarchical stacked neural networks
ActiveUS8775341B1Increased complexityComplex mathematical operationDigital data information retrievalSemantic analysisSemantic propertyNerve network
A system and method of detecting an aberrant message is provided. An ordered set of words within the message is detected. The set of words found within the message is linked to a corresponding set of expected words, the set of expected words having semantic attributes. A set of grammatical structures represented in the message is detected, based on the ordered set of words and the semantic attributes of the corresponding set of expected words. A cognitive noise vector comprising a quantitative measure of a deviation between grammatical structures represented in the message and an expected measure of grammatical structures for a message of the type is then determined. The cognitive noise vector may be processed by higher levels of the neural network and / or an external processor.
Owner:COMMONS MICHAEL LAMPORT
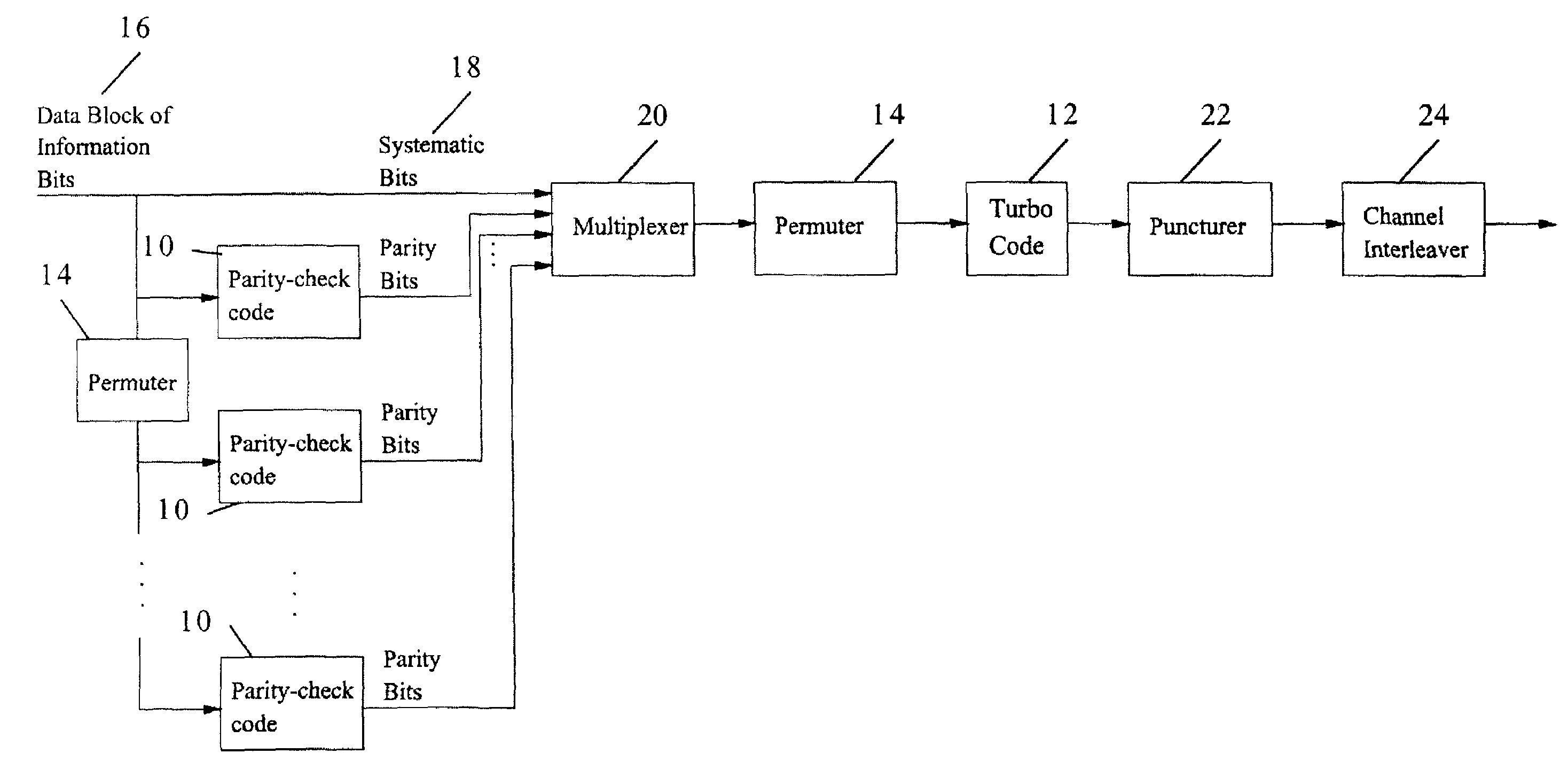
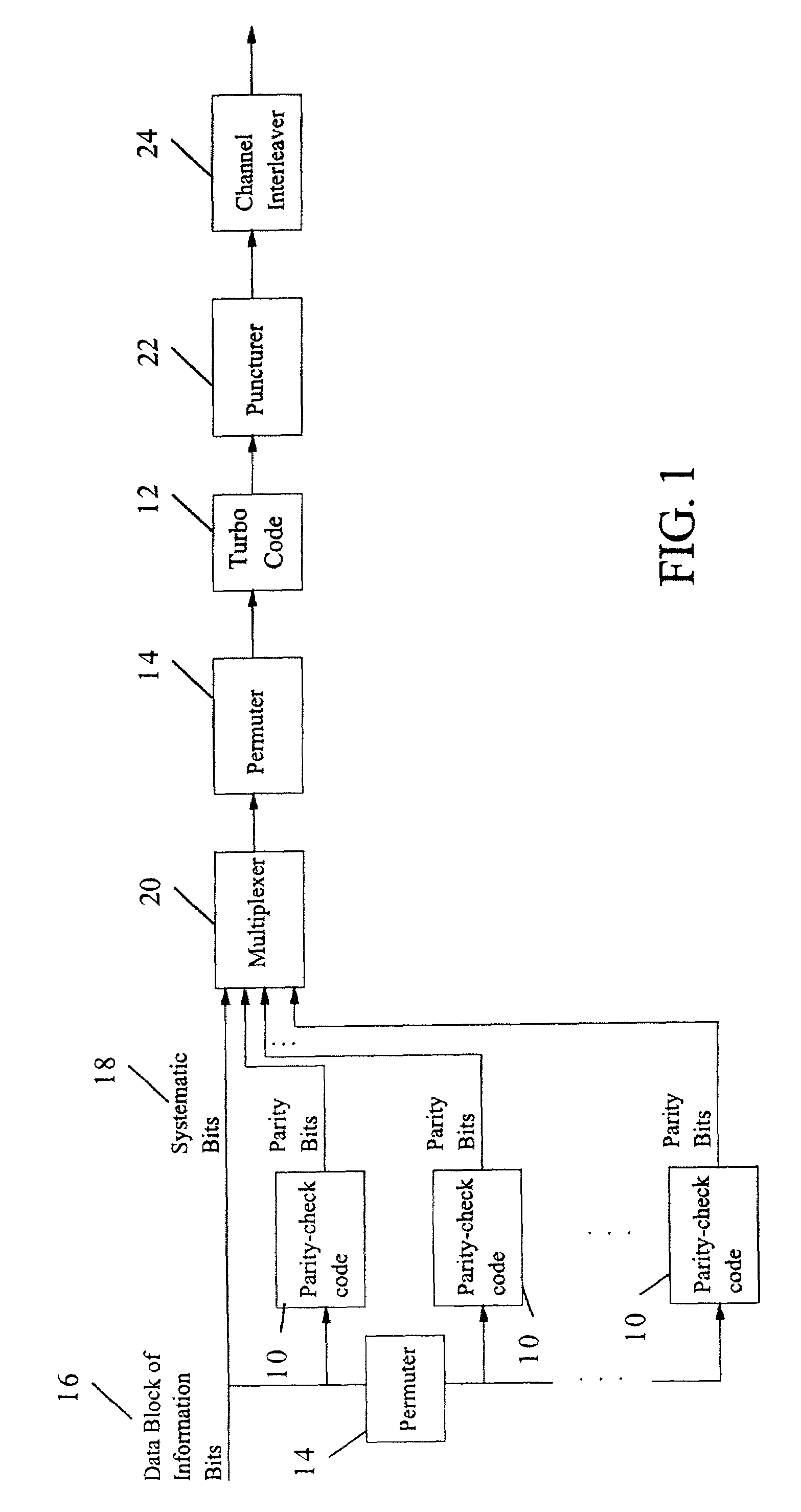
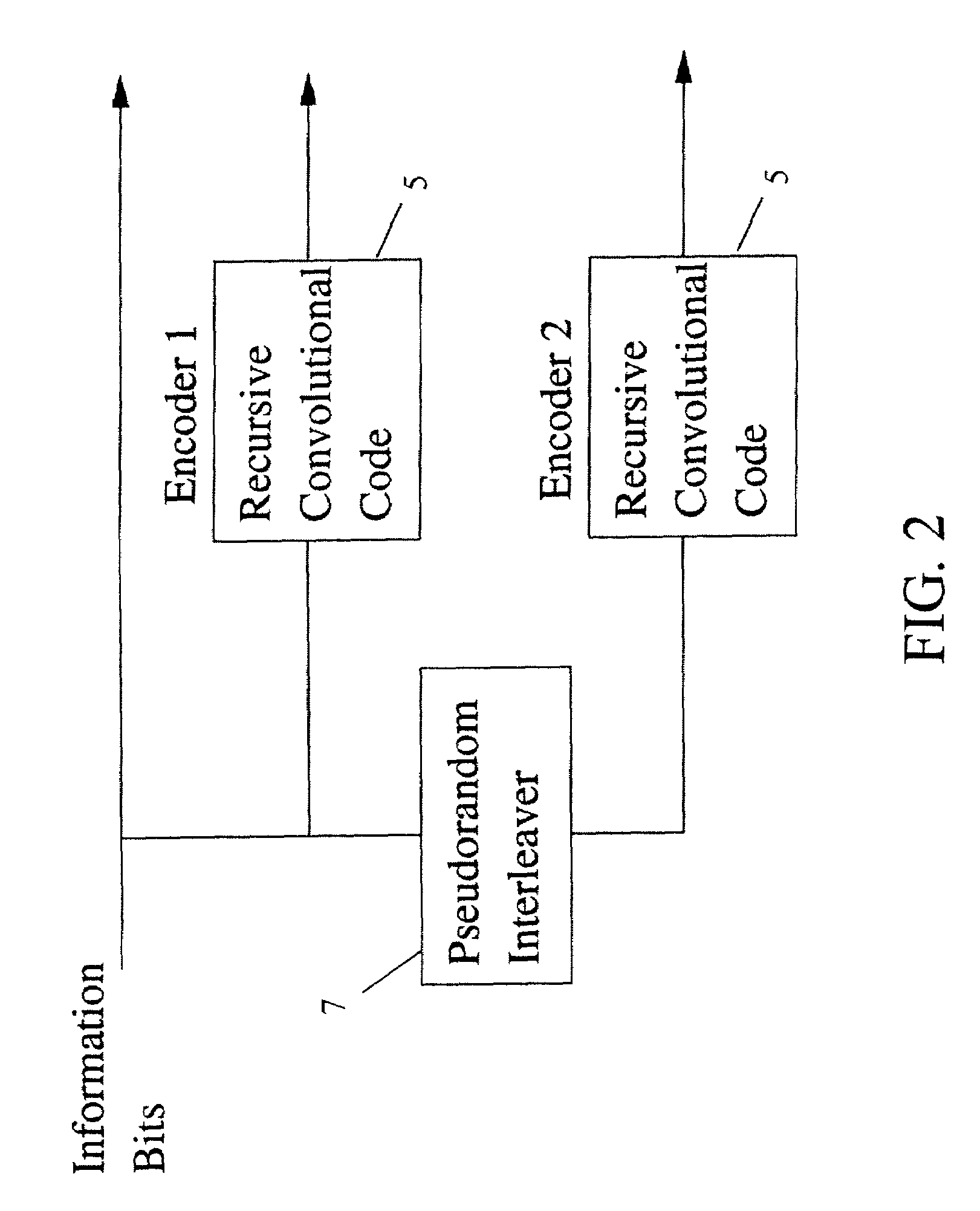
Method and coding means for error-correction utilizing concatenated parity and turbo codes
InactiveUS7093179B2Reduction in rateImprove overall utilizationError preventionError detection/correctionParallel computingTurbo coded
A method and apparatus for encoding and decoding data using an overall code comprising an outer parity-check and an inner parallel concatenated convolutional, or turbo code. The overall code provides error probabilities that are significantly lower than can be achieved by using turbo codes alone. The output of the inner code can be punctured to maintain the same turbo code rate as the turbo code encoding without the outer code. Multiple parity-check codes can be concatanated either serially or in parallel as outer codes. Decoding can be performed with iterative a posteriori probability (APP) decoders or with other decoders, depending on the requirements of the system. The parity-check code can be applied to a subset of the bits to achieve unequal error protection. Moreover, the techniques presented can be mapped to higher order modulation schemes to achieve improved power and bandwidth efficiency.
Owner:FLORIDA UNIV OF A FLORIDA +1
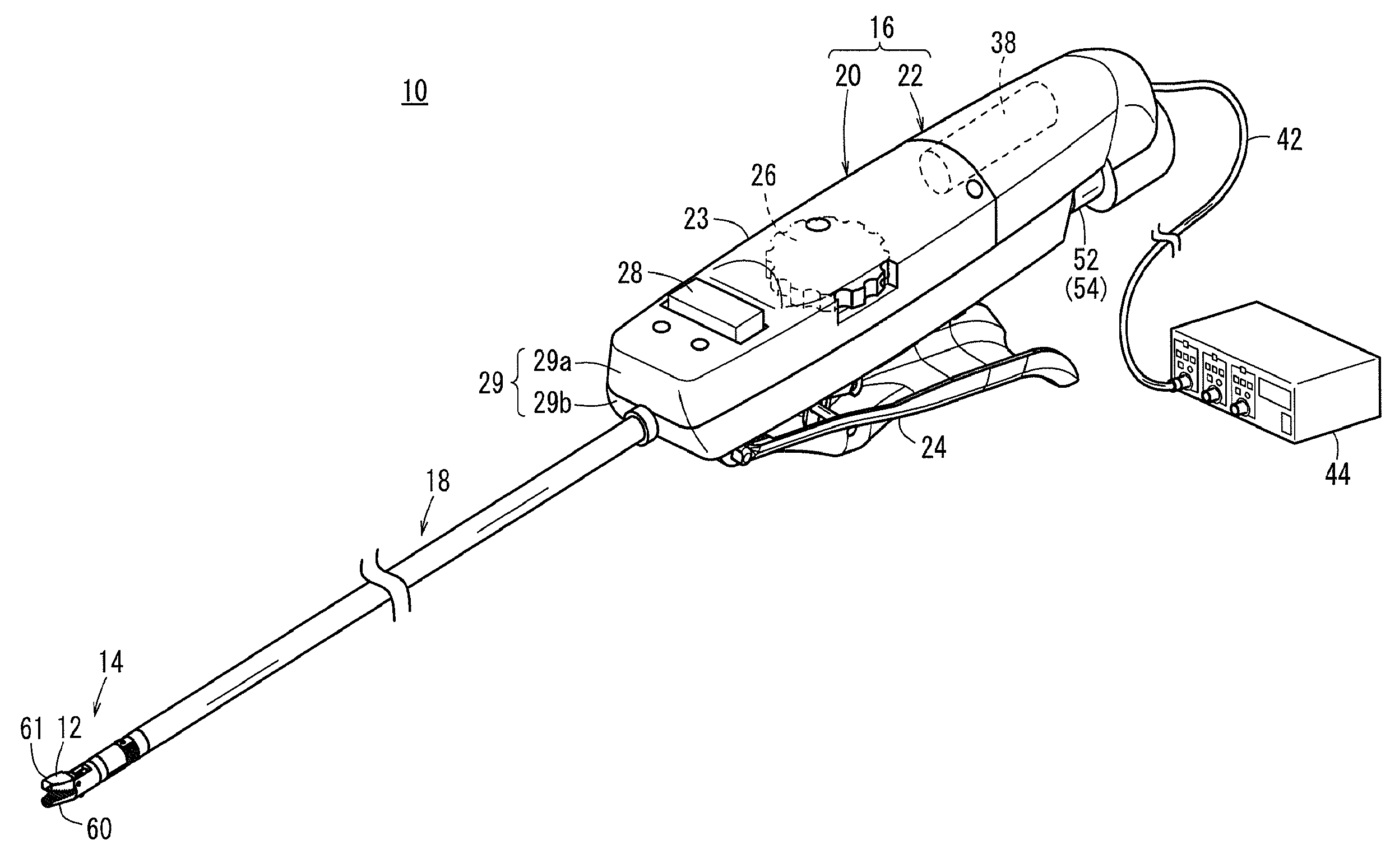
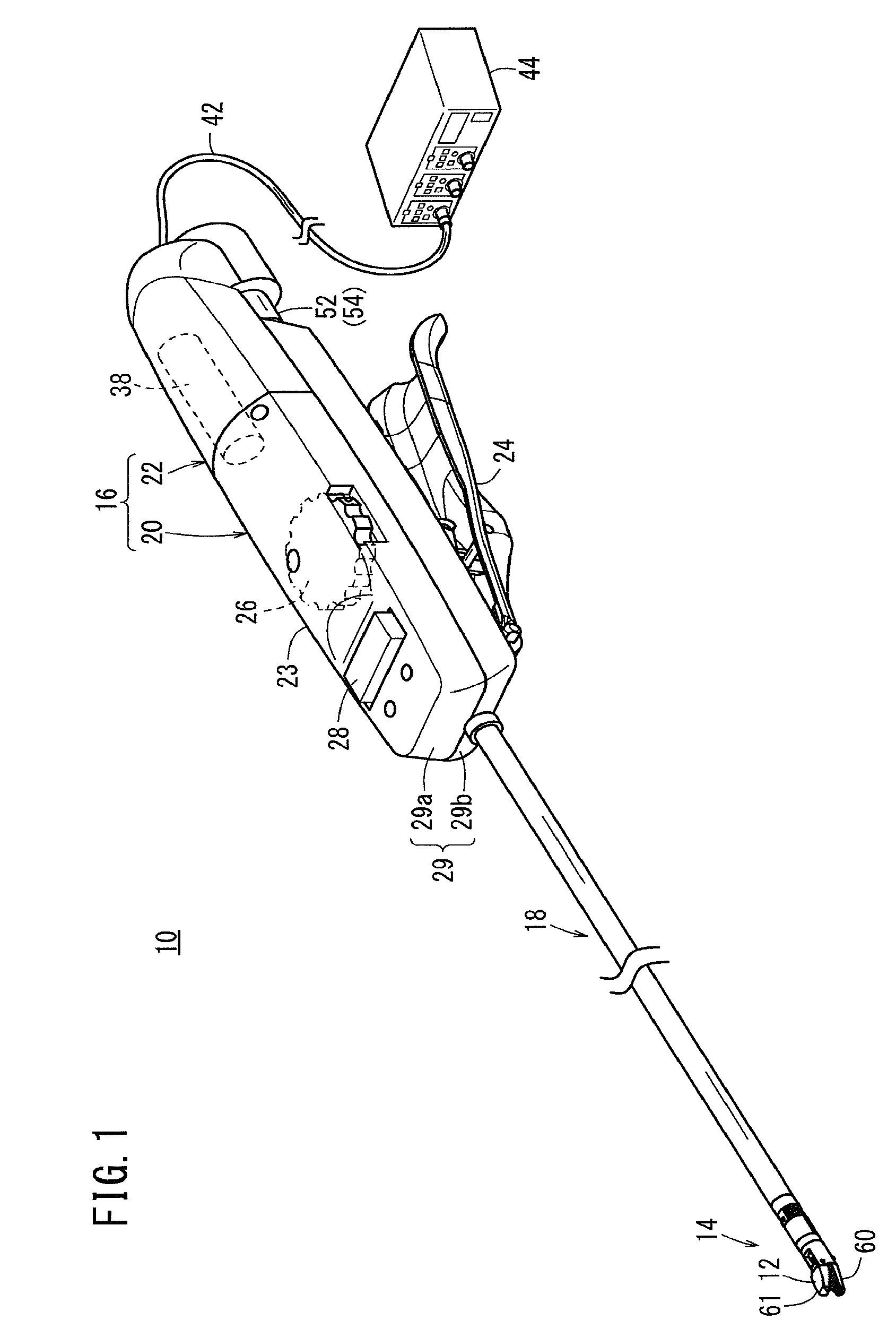
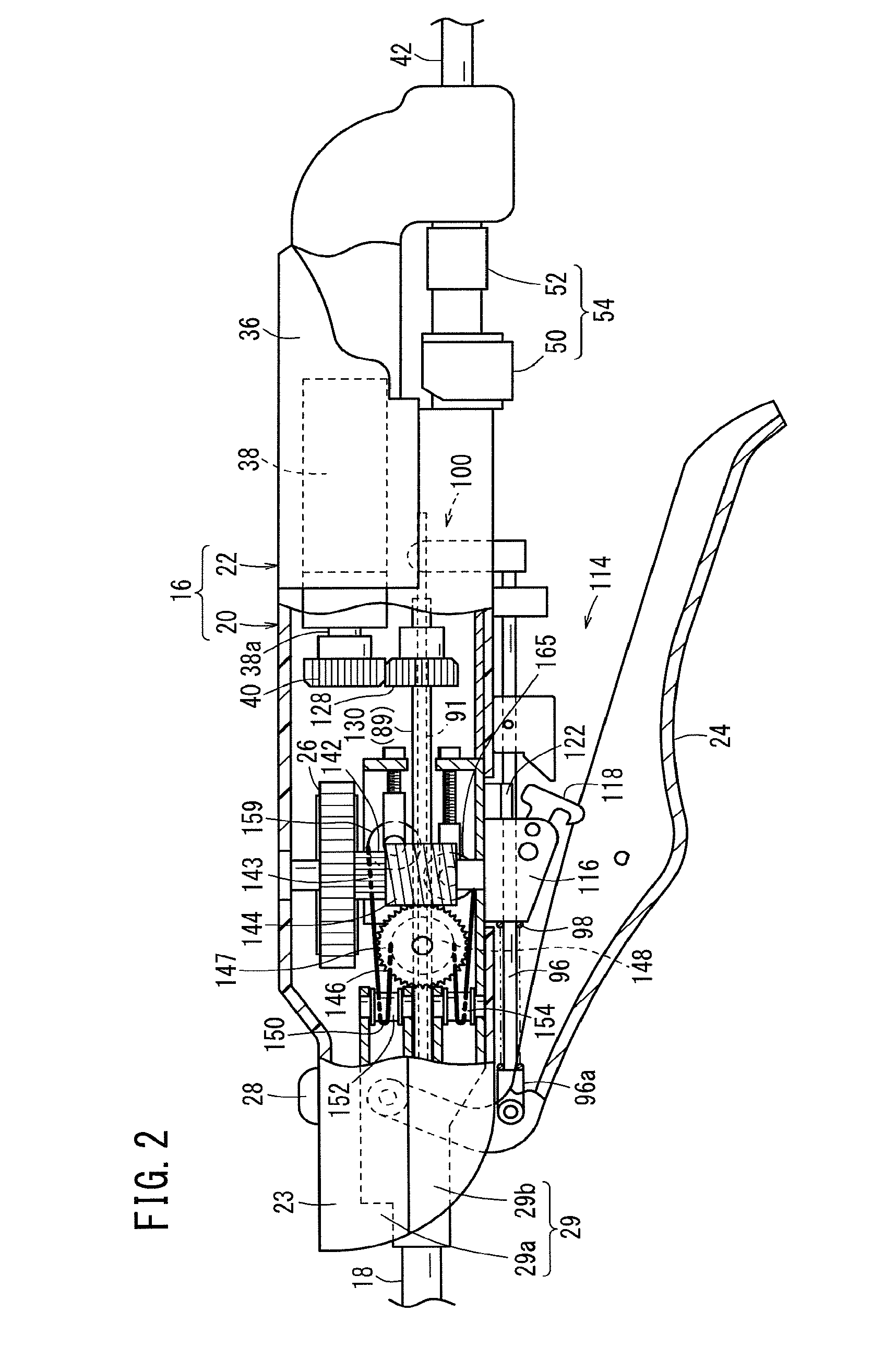
Medical Manipulator
ActiveUS20150025571A1Increase freedomImprove stabilityDiagnosticsSurgical manipulatorsManipulatorMedical treatment
This medical manipulator is provided with a distal-end moving section including an end effector. The distal-end moving section includes a rotating sleeve (a distal-end rotator) which is able to rotate integrally with the end effector about a roll axis and has a hollow cylindrical portion, and a distal-end fulcrum block (rotary support cylinder) which is provided so as to be able to change orientation in relation to the axial direction of a shaft and rotatably supports the rotating sleeve at an inner peripheral section. A part of an opening / closing driving transmission section (actuating means) for transmitting an opening / closing driving force to the end effector is disposed inside of the distal-end moving section.
Owner:KARL STORZ GMBH & CO KG
Emitter driver for noninvasive patient monitor
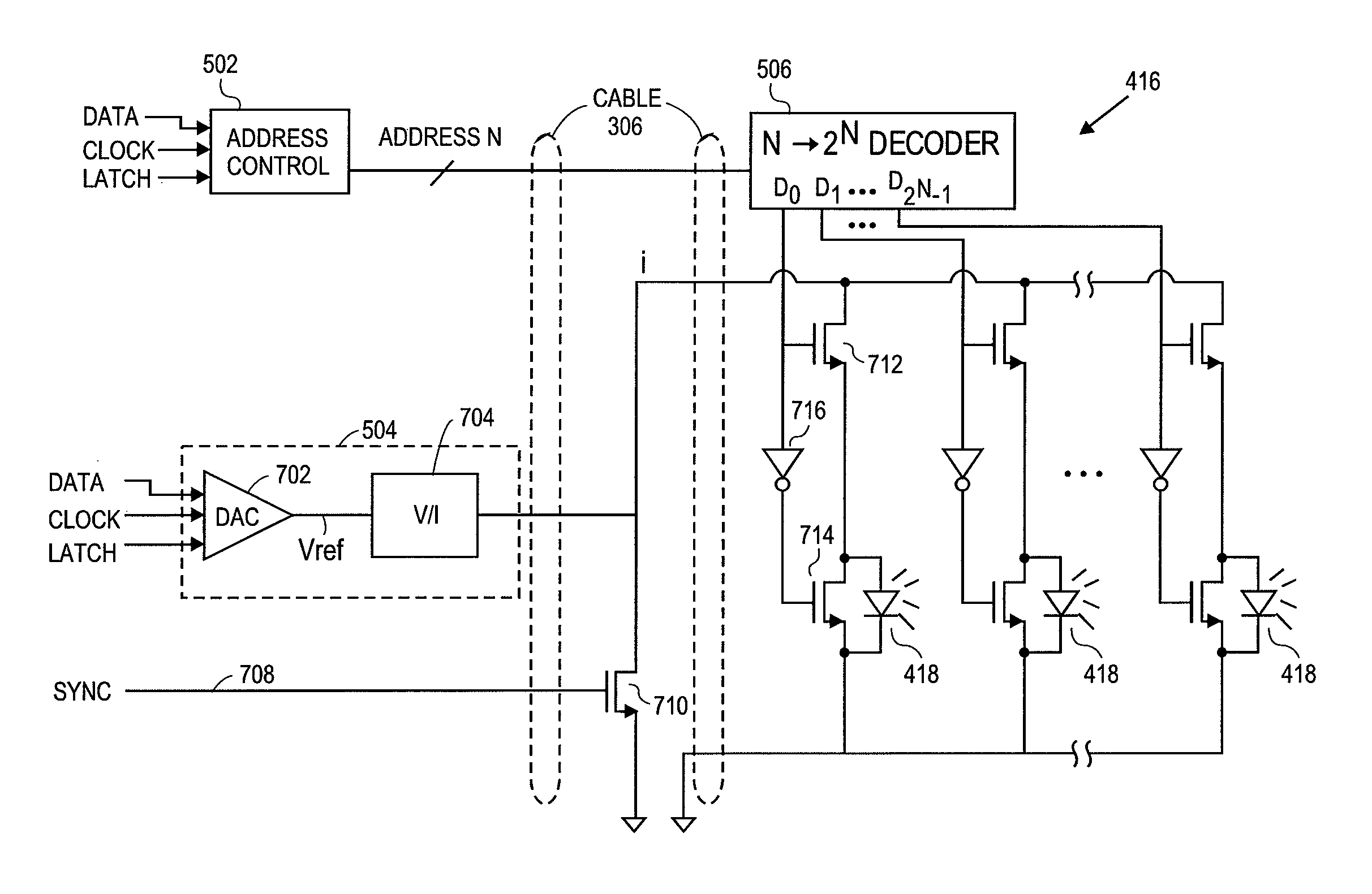
ActiveUS8688183B2Raise the possibilityIncreased complexityDiagnostics using lightOptical sensorsElectrical conductorEngineering
Embodiments of the present disclosure include an emitter driver configured to be capable of addressing substantially 2N nodes with N cable conductors configured to carry activation instructions from a processor. In an embodiment, an address controller outputs an activation instruction to a latch decoder configured to supply switch controls to activate particular LEDs of a light source.
Owner:MASIMO CORP
Processing data flows with a data flow processor
InactiveUS20110213869A1Easy to detectPreventing data flowDigital computer detailsPlatform integrity maintainanceData stream processingApplication software
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
Database security via data flow processing
InactiveUS20110219035A1Easy to detectPreventing data flowDigital data information retrievalDigital data processing detailsComputer moduleData stream processing
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
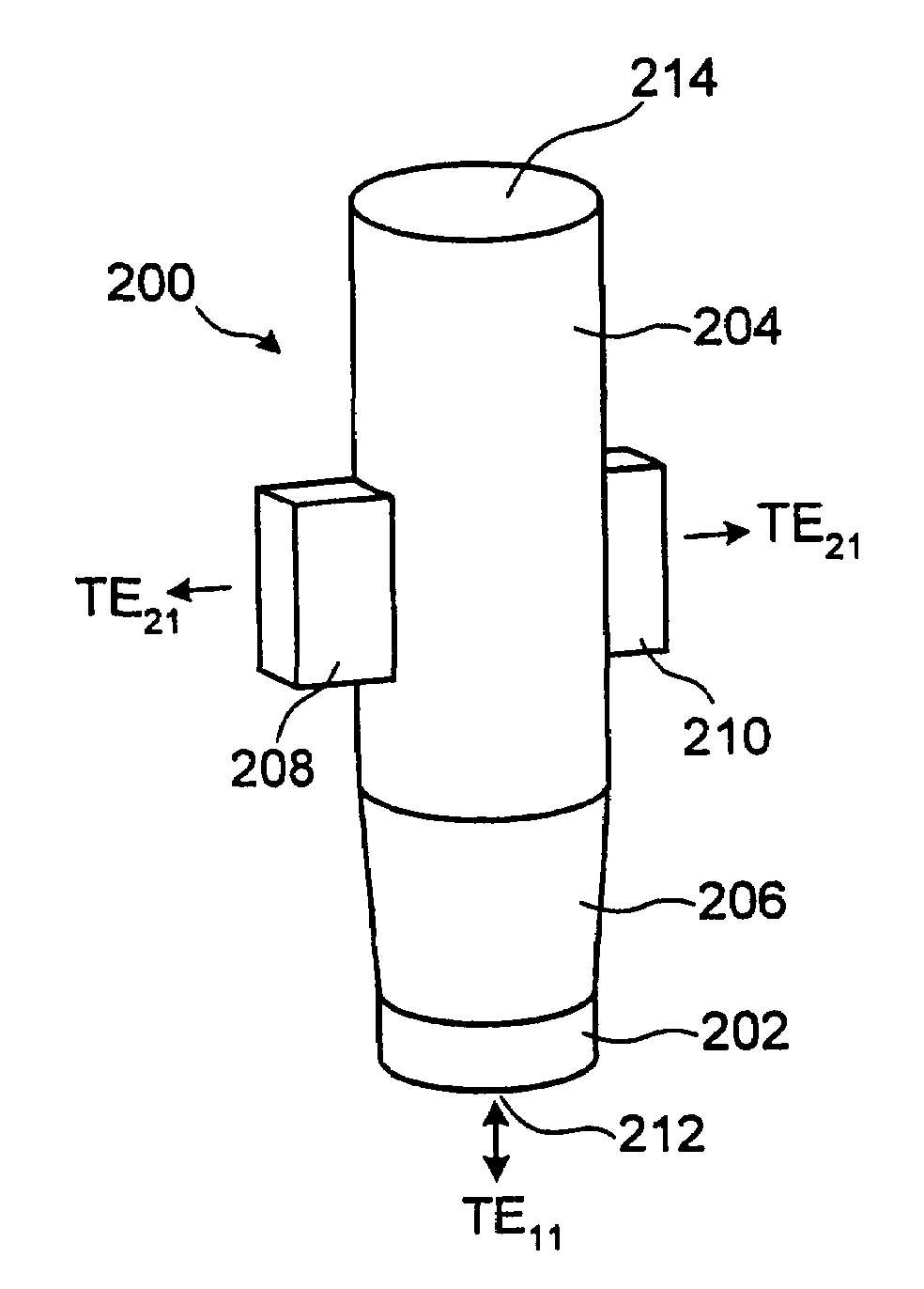
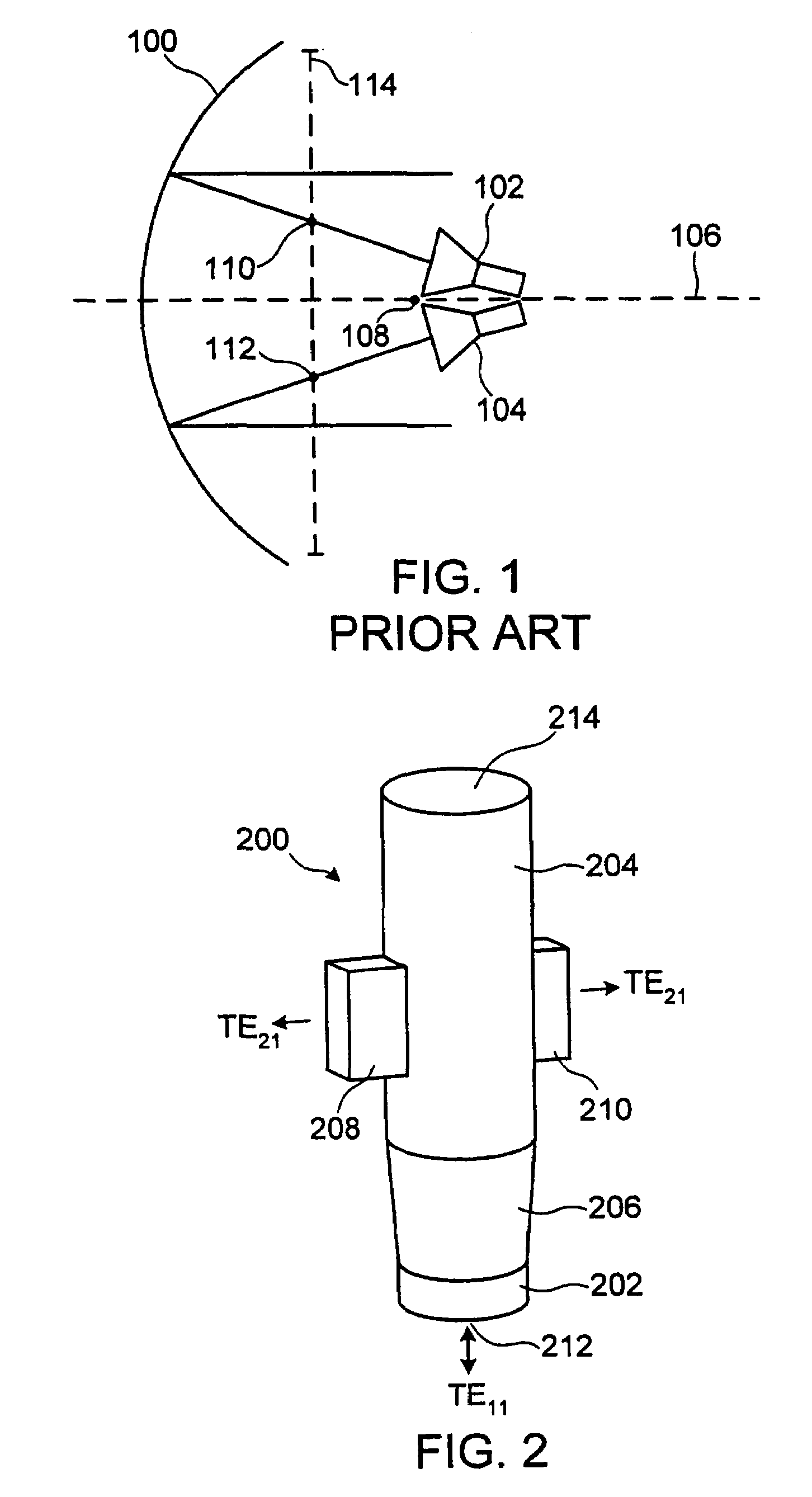
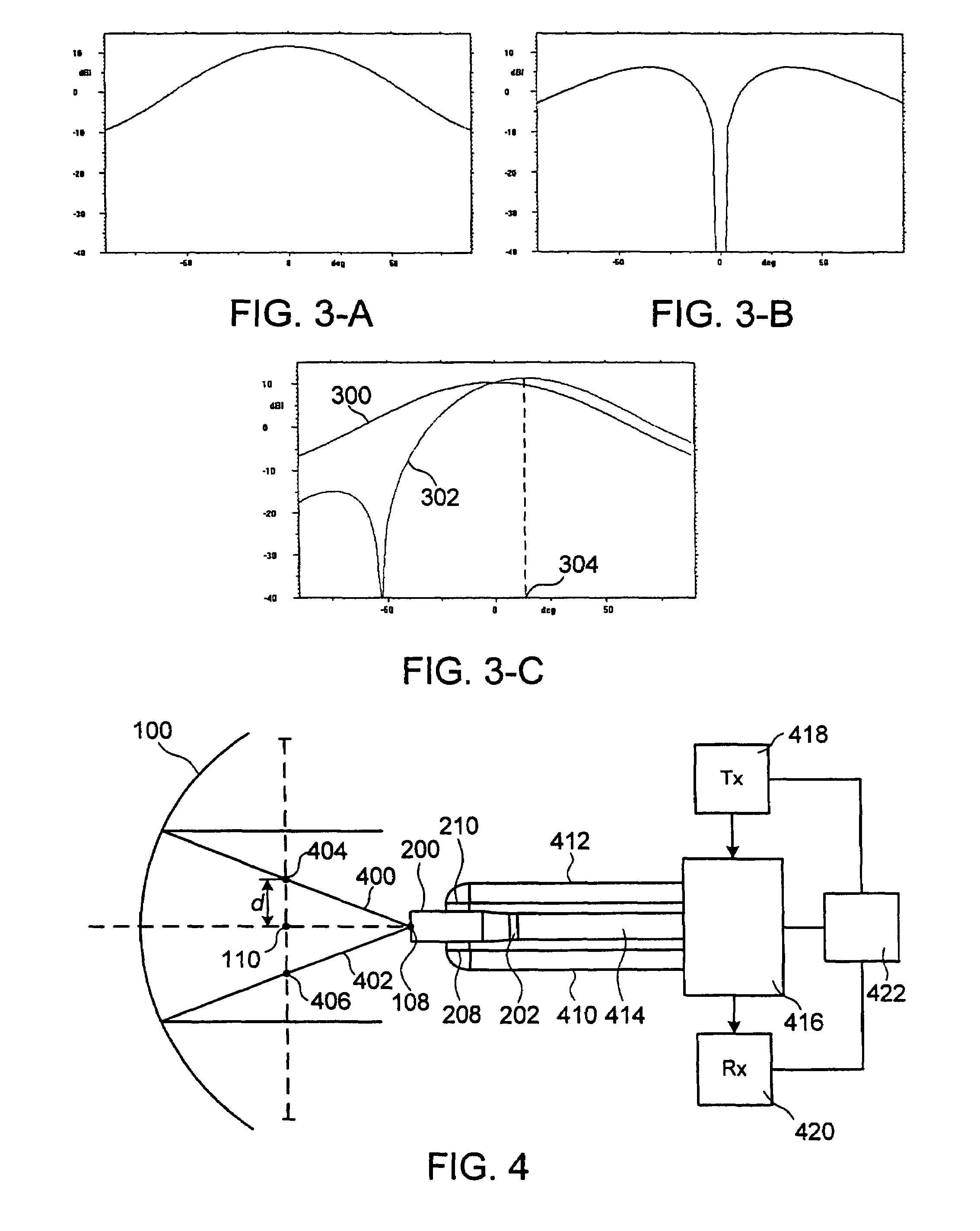
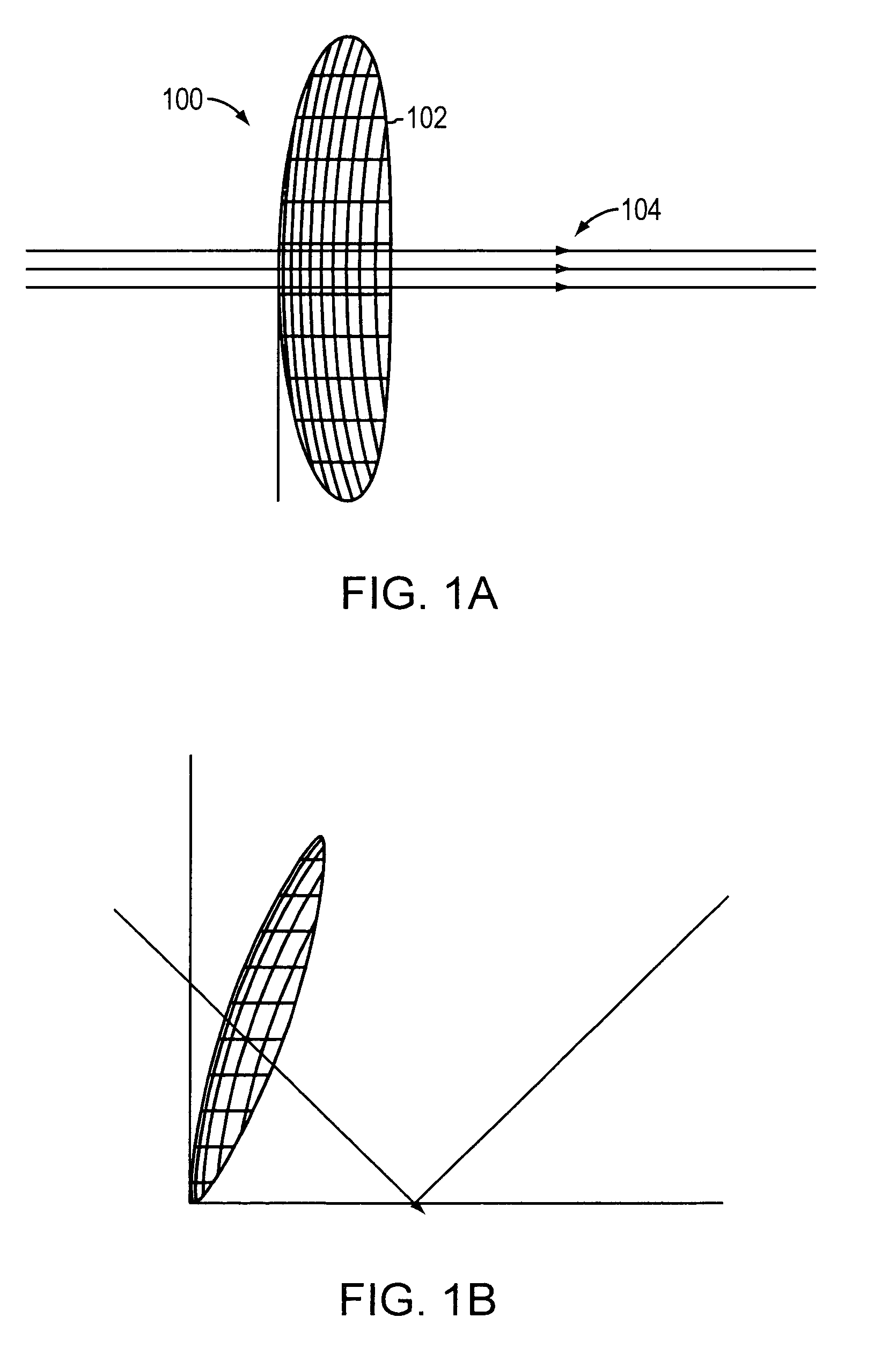
Multiple phase center feedhorn for reflector antenna
A feedhorn driving method and apparatus allows the establishment of multiple phase centers using only a single multimode feedhorn. At least two higher-order modes are extracted from the feedhorn and weighted in amplitude and phase. The phase center separation is established in accordance with an assigned weights. The feedhorn has application in i.a. moving target indication systems.
Owner:HER MAJESTY THE QUEEN AS REPRESENTED BY THE MINIST OF NAT DEFENCE OF HER MAJESTYS CANADIAN GOVERNMENT
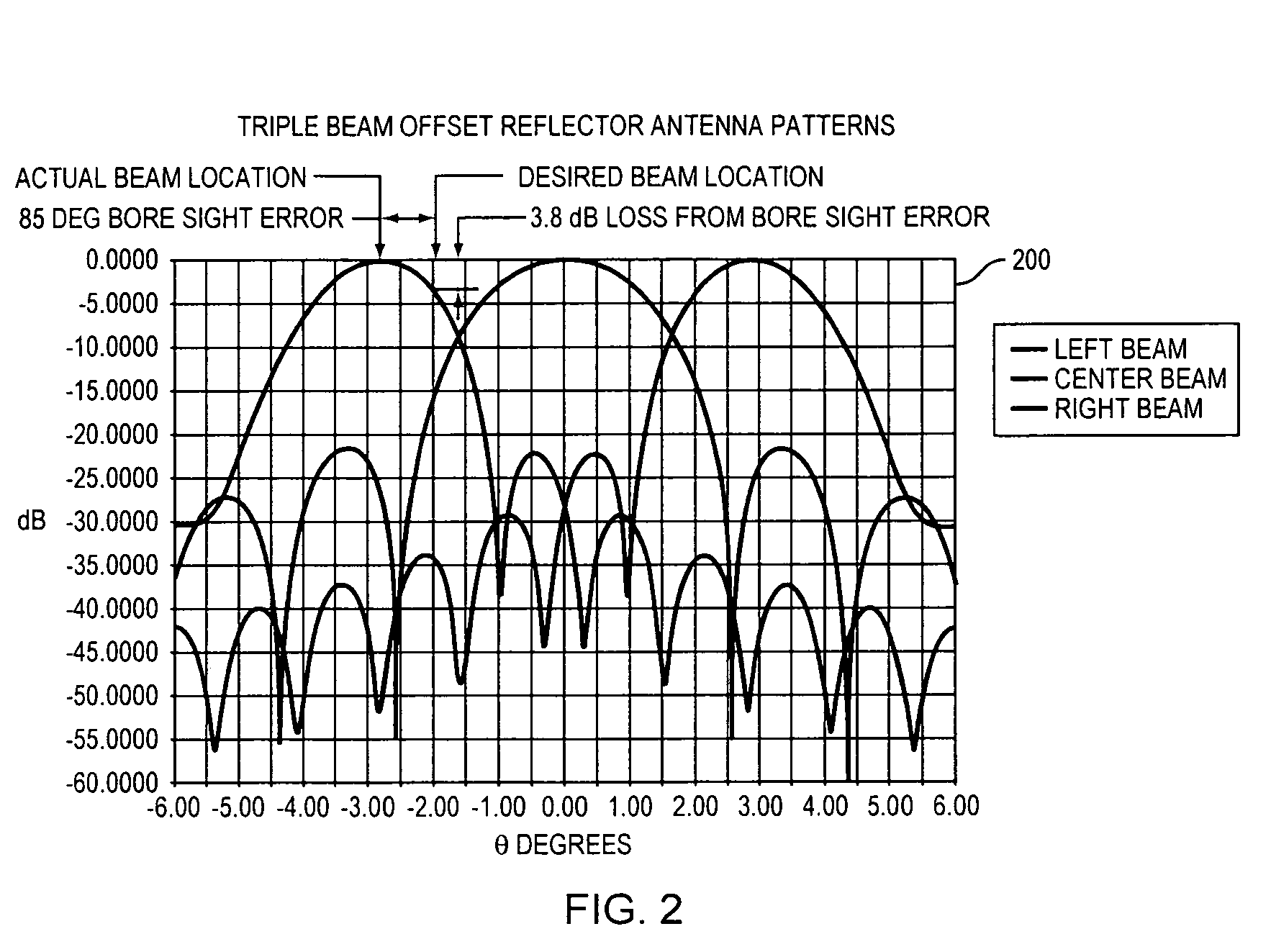
Method and system for controlling medium access in a wireless network
InactiveUS20060164969A1Simple designEasy to manufactureEnergy efficient ICTSpatial transmit diversityFrequency spectrumSpectral efficiency
A method and system are disclosed that can be applied to achieve high-throughput in a WLAN. Central to the present invention is the use of an SDMA compatible multi-beam antenna system by a WLAN access point. A system based on two types of antennas-dynamic beam forming and fixed beam antennas—is described. A mechanism and protocol are described that implement simultaneous transmissions with respect to an SDMA compatible access point and thereby improve spectral efficiency, and by extension achieve higher throughput. Based on the recognition that current WLAN MAC has major limitations in throughput, certain MAC extensions (that can be applied independently of SDMA) are described. Also disclosed are power-saving and power control techniques that improve battery performance and contribute to a reduction in station size, and a means of reducing channel interference. The present invention also deals with the problem of backward compatibility with conventional devices that implement the protocol that is a subset covered by the present invention.
Owner:SOVEREIGN PEAK VENTURES LLC
Small wave-guide radiators for closely spaced feeds on multi-beam antennas
Owner:PRO BRAND INT
Processing data flows with a data flow processor
ActiveUS20110231510A1Easy to detectPreventing data flowDigital computer detailsPlatform integrity maintainanceData stream processingComputer module
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:CA TECH INC
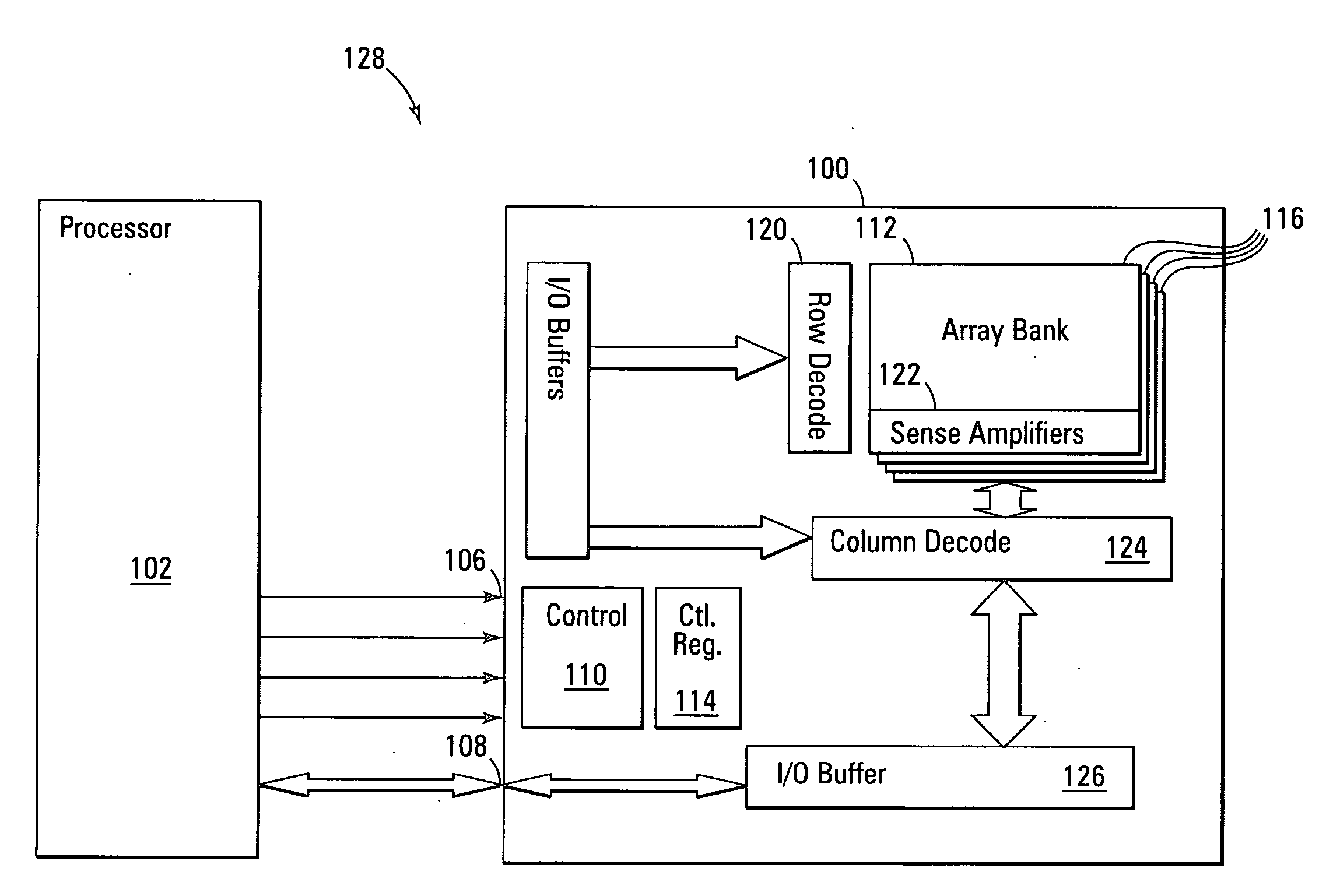
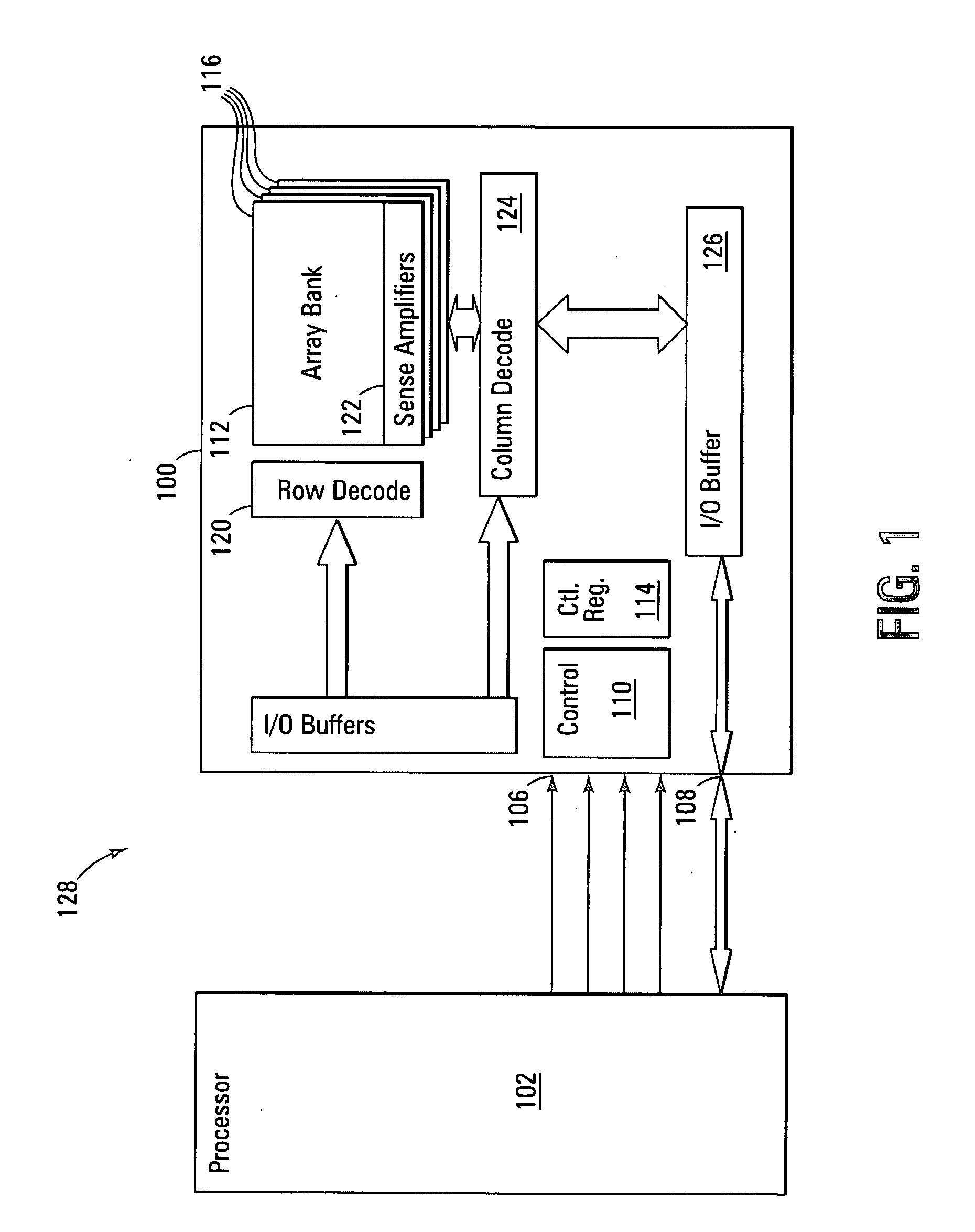
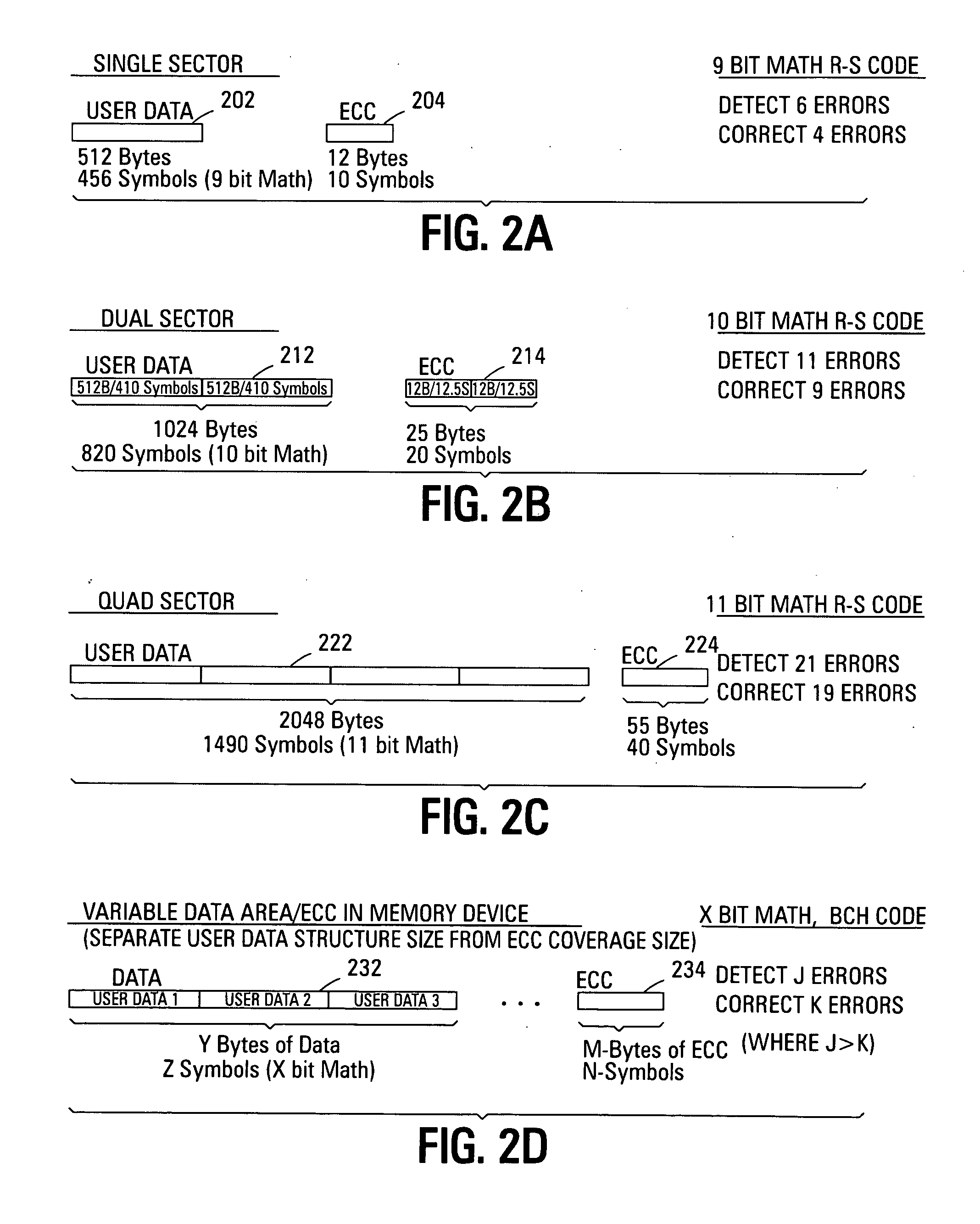
Variable sector-count ECC
ActiveUS20070226592A1Easy to detectEasy to correctError detection/correctionCode conversionData typeMemory systems
Improved memory devices, circuitry, and data methods are described that facilitate the detection and correction of data in memory systems or devices by increasing the data area of user data being covered by the ECC code. This averages any possible bit errors over a larger data area and allows a greater number of errors to be corrected by a combining the ECC codes in the coverage area without substantially changing the overall size of ECC codes being stored over a single sector approach. In one embodiment of the present invention, the size of the data block utilized for ECC coverage is variable and can be selected such that differing areas of the memory array or data types can have a differing ECC data coverage sizes. It is also noted that the ECC algorithm, math base or encoding scheme can also be varied between these differing areas of the memory array.
Owner:MICRON TECH INC
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
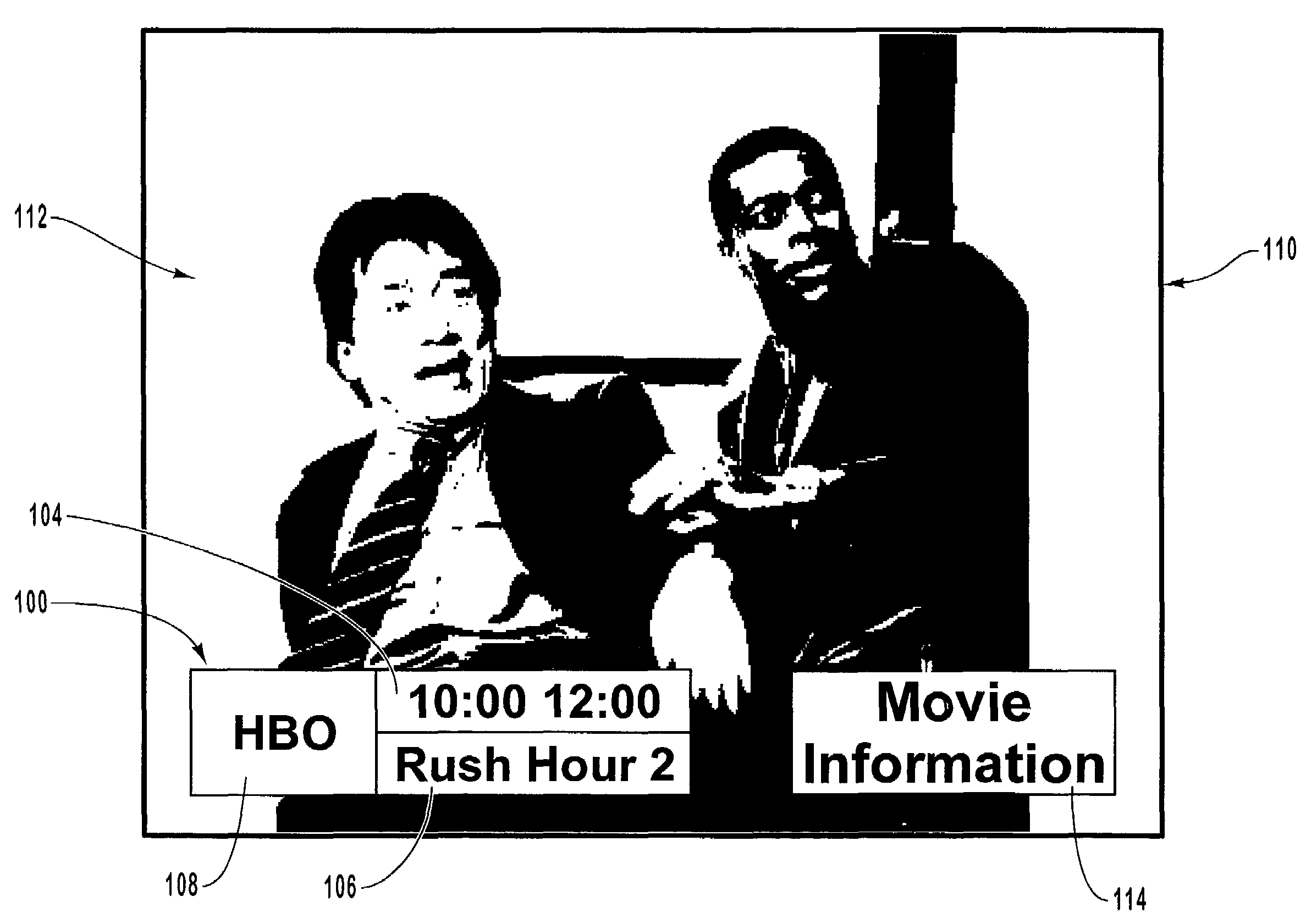
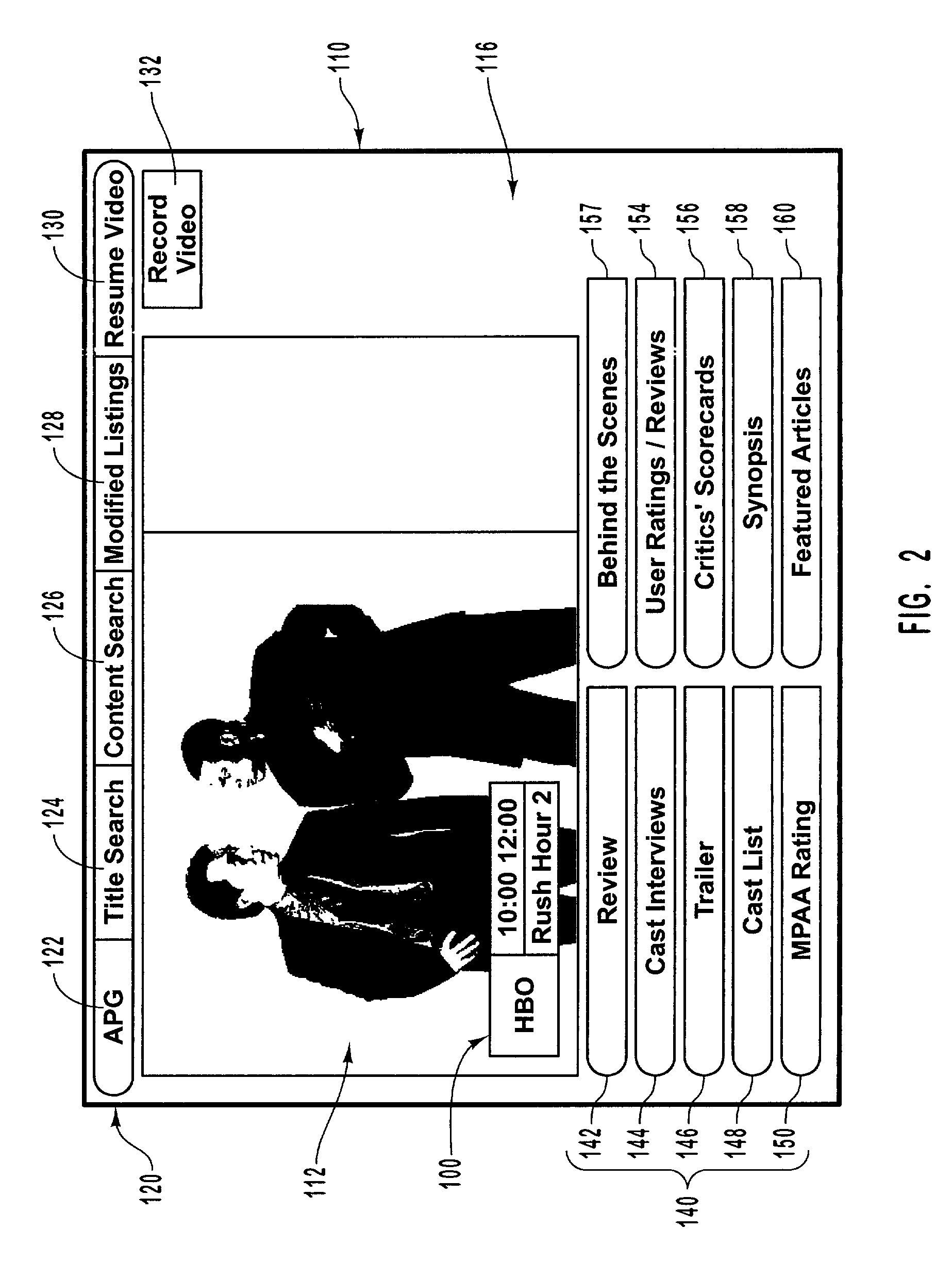
Enhanced video content information associated with video programs
InactiveUS7293275B1Improve viewing experienceProvide goodTelevision system detailsColor television detailsComputer graphics (images)Display device
Providing interactive access to video programming and video content information in a multimedia system. A processing device of the multimedia system receives video content information associated with video programming that is to be broadcast. The video content information includes at least video identification information and video content information. The display device of the multimedia system presents a first interface image that presents the video content information for one of the video programs of the video programming. In response to viewer input, a second interface image is displayed on the display device presenting video content information for another one of the video programs of the video programming or for more detailed information associated with the video program. In this manner, the viewer can conveniently navigate through the video content information and identify information that is useful in selecting a program to watch.
Owner:MICROSOFT TECH LICENSING LLC
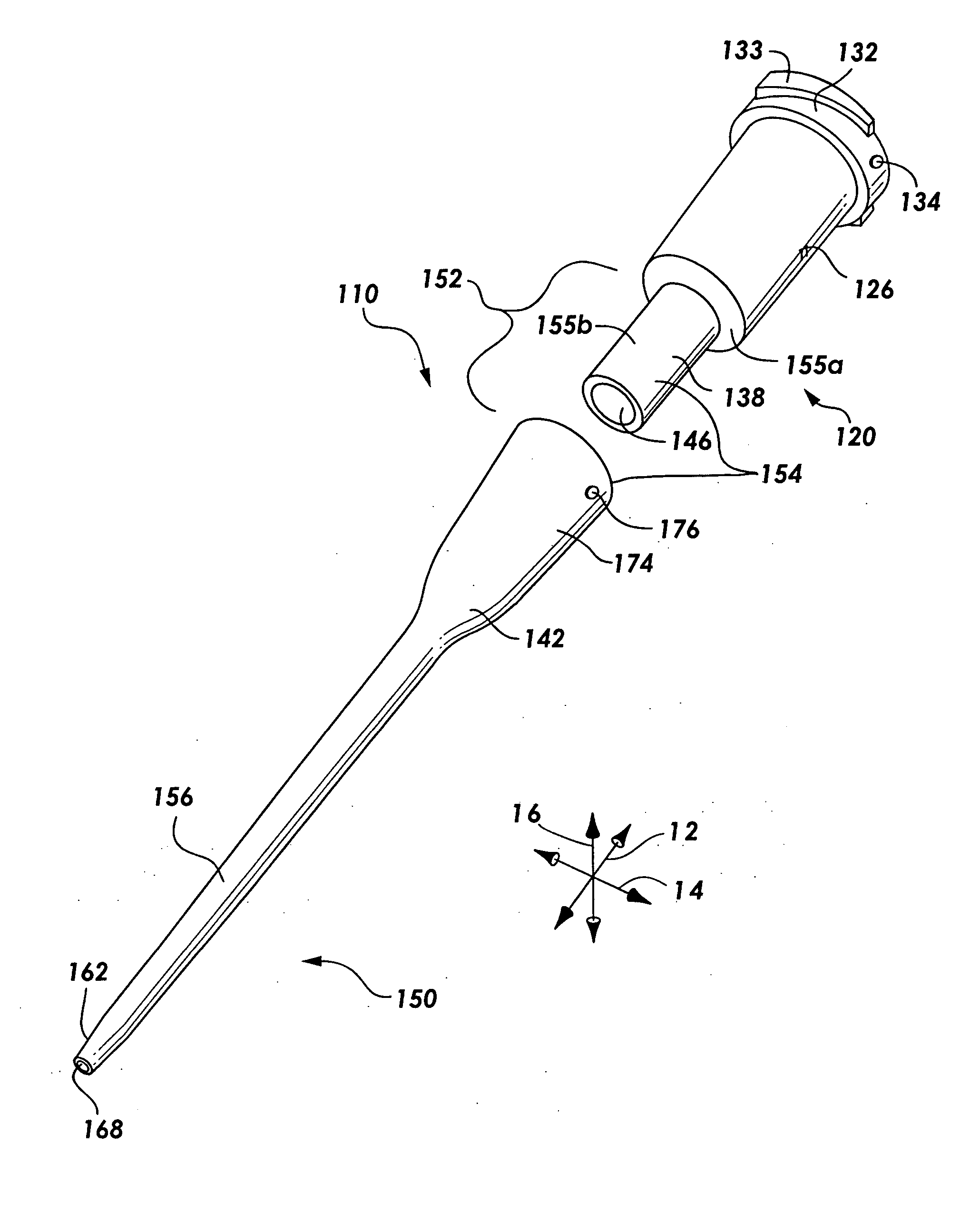
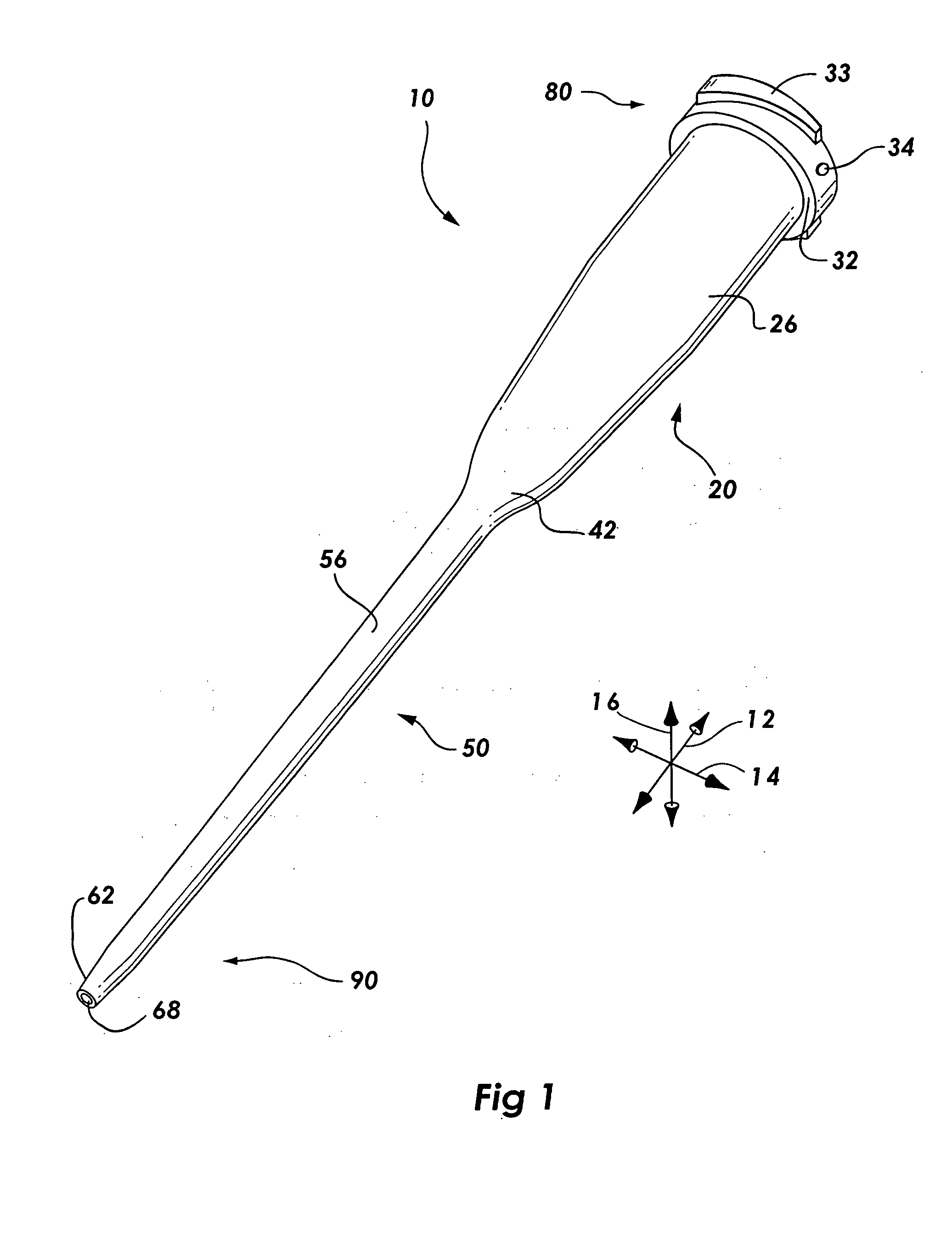
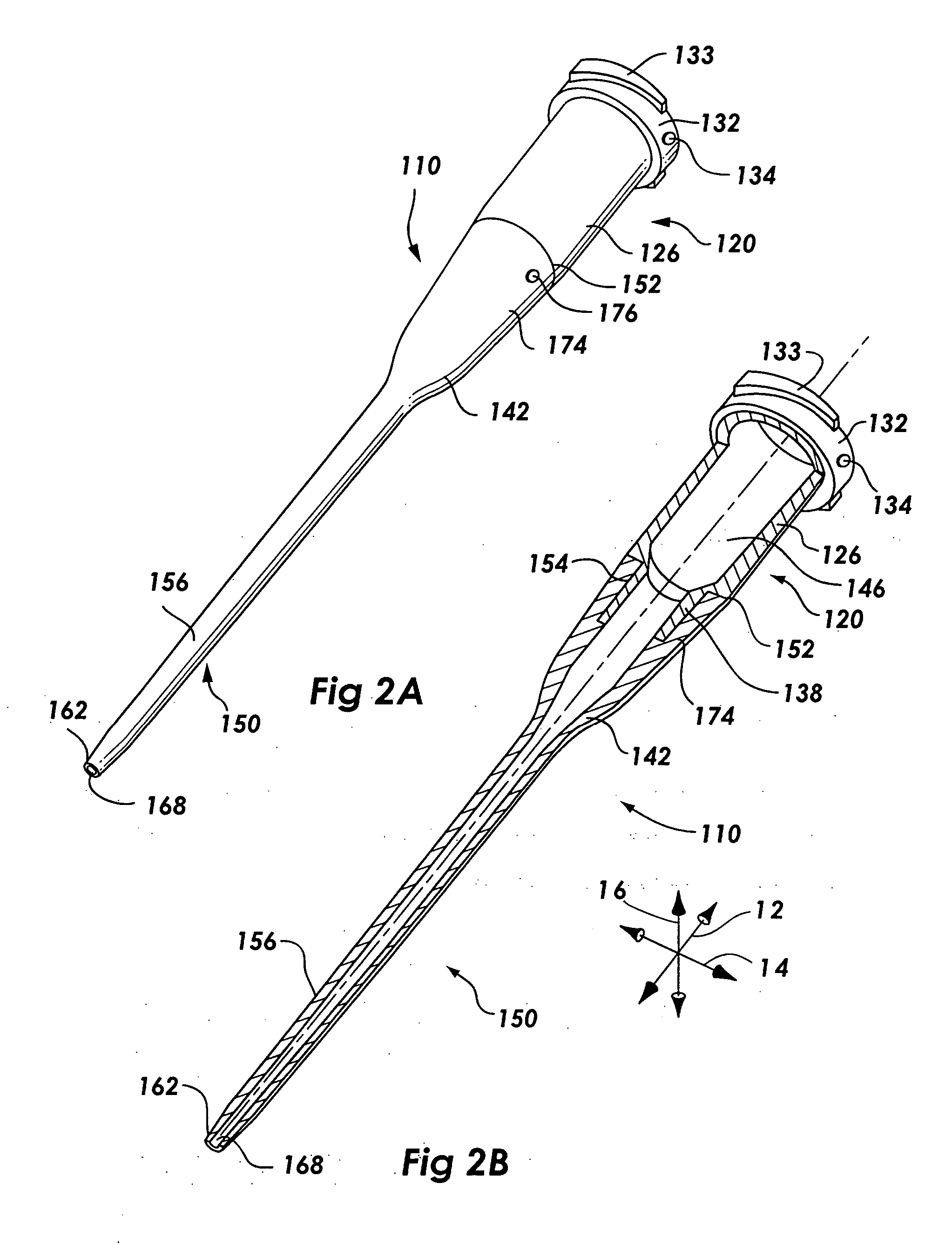
Catheter assemblies and injection molding processes and equipment for making the same
InactiveUS20050033237A1Increased complexityExtension of timeMouldsInfusion syringesMulti materialCatheter hub
Various single-part catheter assemblies, multi-part integrated catheter assemblies, and methods and apparatus for making the same are disclosed. The single-part catheter assemblies include a catheter hub integrally formed with a catheter tube for insertion into the bloodstream of a patient. The multi-part integrated catheter assemblies include a catheter hub integrally formed to a catheter tube for insertion into the bloodstream of a patient. The catheter assemblies of the invention may be injection molded in a single step or in multiple steps by injecting flows of molten plastic into a cavity of molds provided herein such that the flows converge into an even distribution about the circumference of the sleeve. The mold may have a core pin designed to fit into the cavity. Through the use of the even distribution of flows, the core pin may be seated within the cavity in an untensioned manner. The catheter assemblies of the invention may be produced of a single material or of multiple materials.
Owner:BECTON DICKINSON & CO
Speech enhancement techniques on the power spectrum
The method provides a spectral speech description to be used for synthesis of a speech utterance, where at least one spectral envelope input representation is received. In one solution the improvement is made by manipulation an extremum, i.e. a peak or a valley, in the rapidly varying component of the spectral envelope representation. The rapidly varying component of the spectral envelope representation is manipulated to sharpen and / or accentuate extrema after which it is merged back with the slowly varying component or the spectral envelope input representation to create an enhanced spectral envelope final representation. In other solutions a complex spectrum envelope final representation is created with phase information derived from one of the group delay representation of a real spectral envelope input representation corresponding to a short-time speech signal and a transformed phase component of the discrete complex frequency domain input representation corresponding to the speech utterance.
Owner:CERENCE OPERATING CO
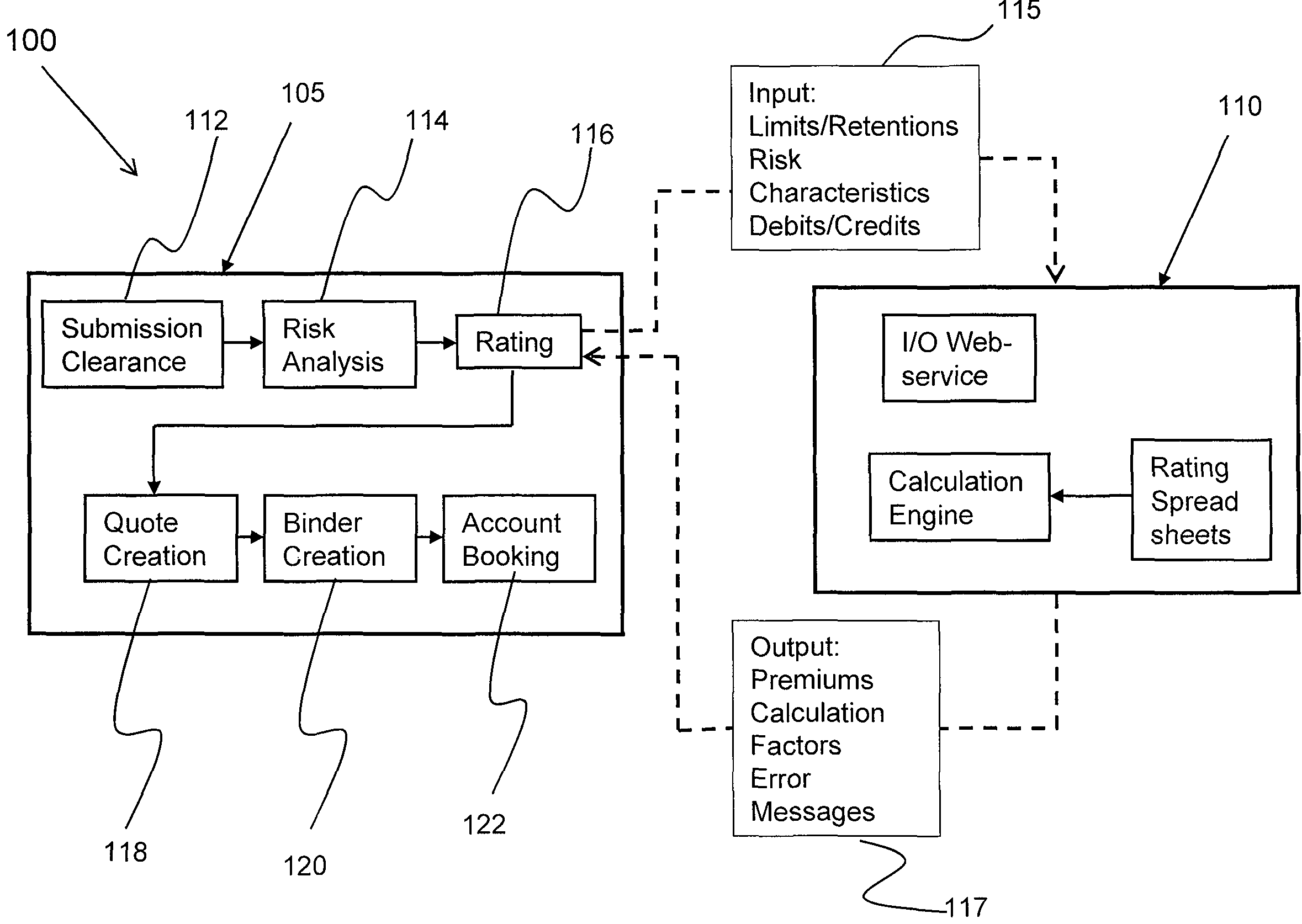
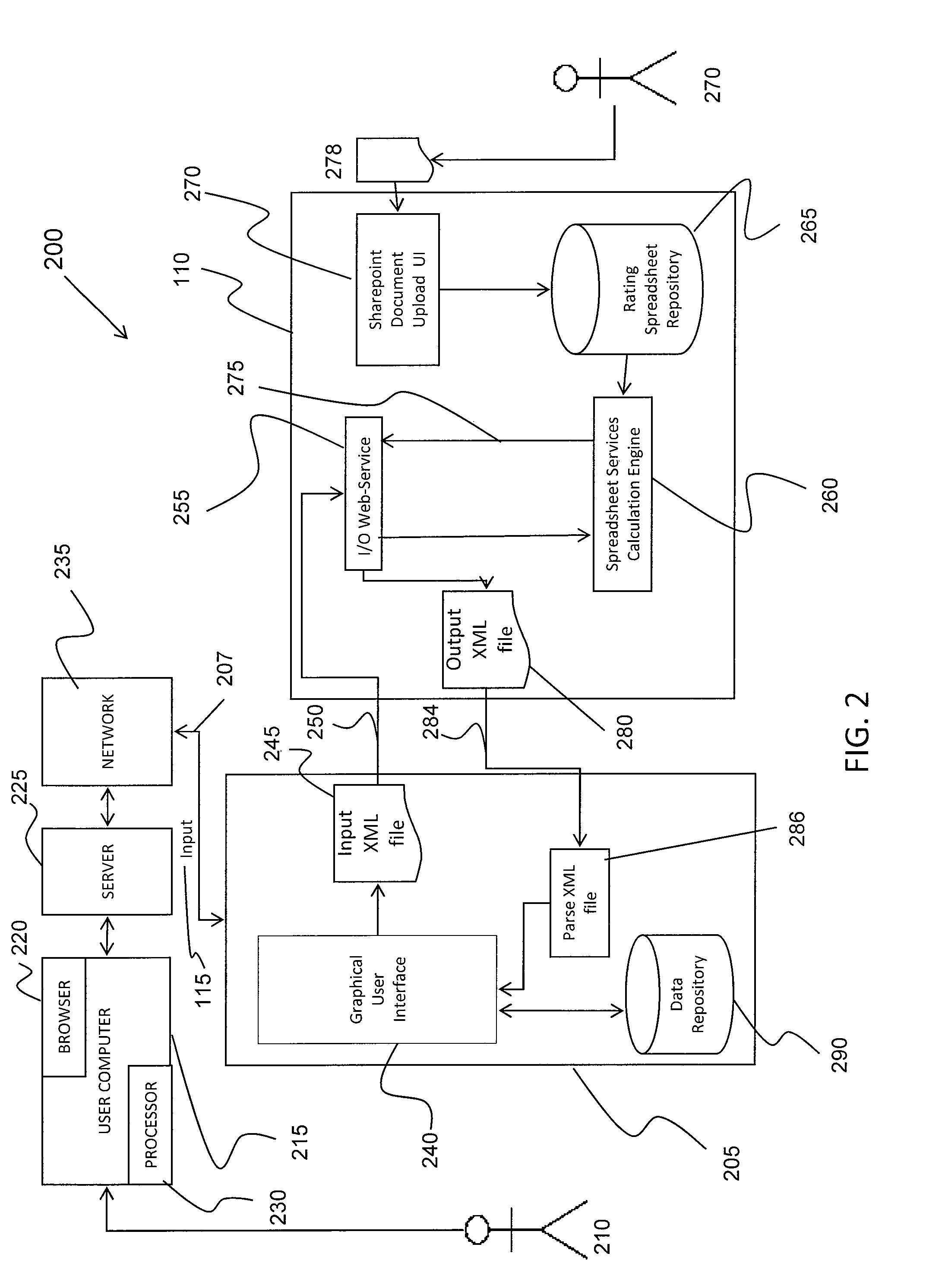
System and method for computerized insurance rating
InactiveUS7783505B2Short response timeIncreased complexityFinanceOffice automationRating systemWeb service
The invention relates generally to a computer system and method for integrating insurance policy underwriting. In one aspect, it integrates an older legacy insurance policy generating system to on-line rating systems where users access the system through browsers. The computer system to perform the process of dynamically rating includes generating an input XML file of risk information that is sent to a web service and calculated in a calculation engine. The processed data is retrieved by the web service and transmitted as an XML file to a user interface that parses the rating information and displays the data.
Owner:HARTFORD FIRE INSURANCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com