Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
201 results about "Modes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
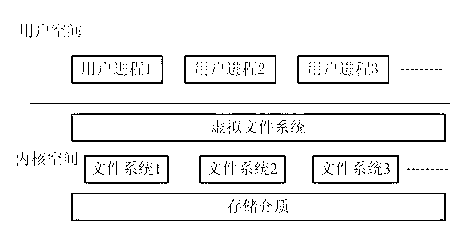
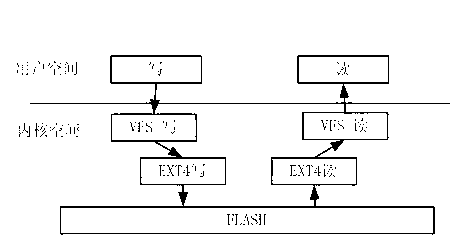
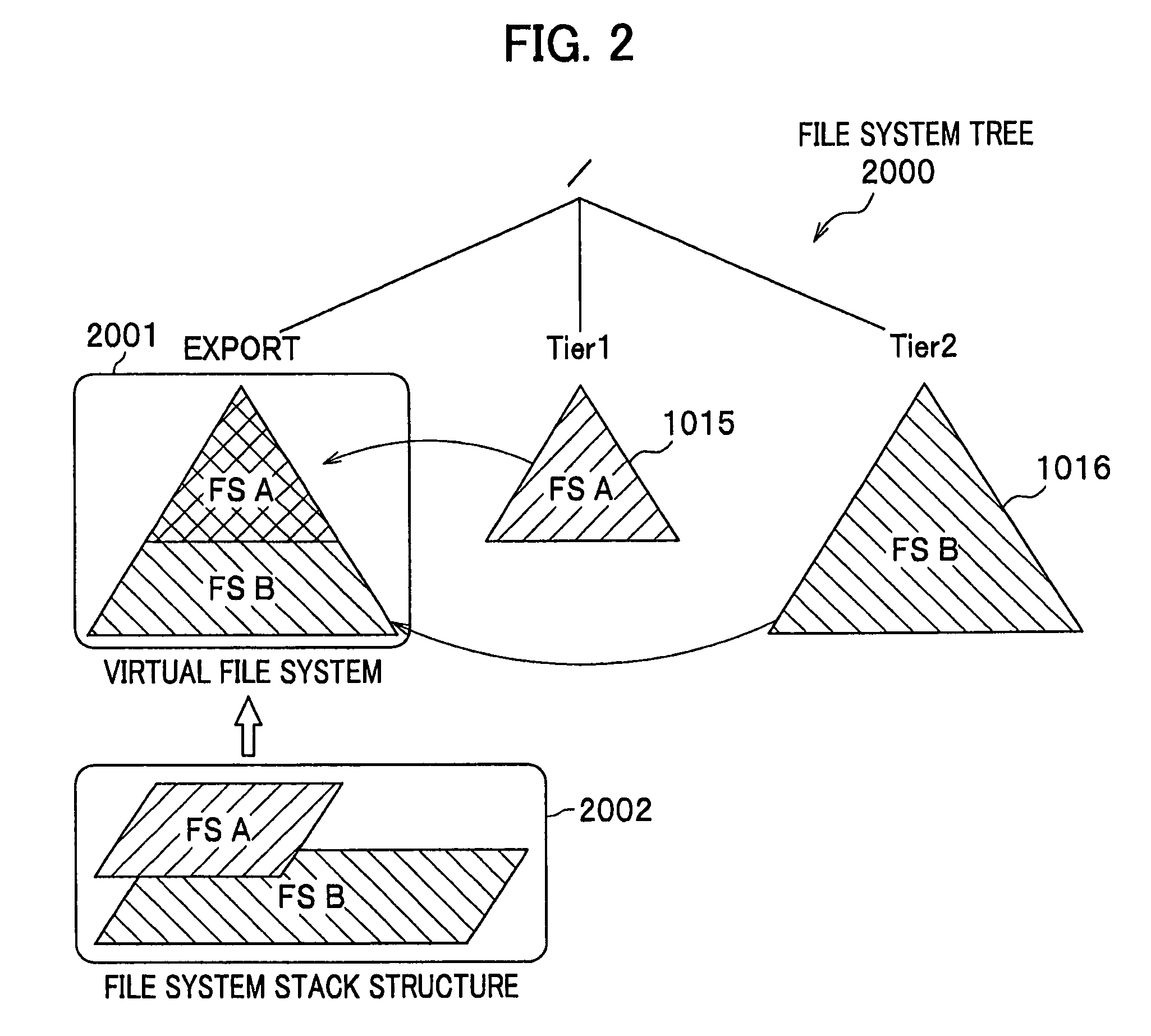
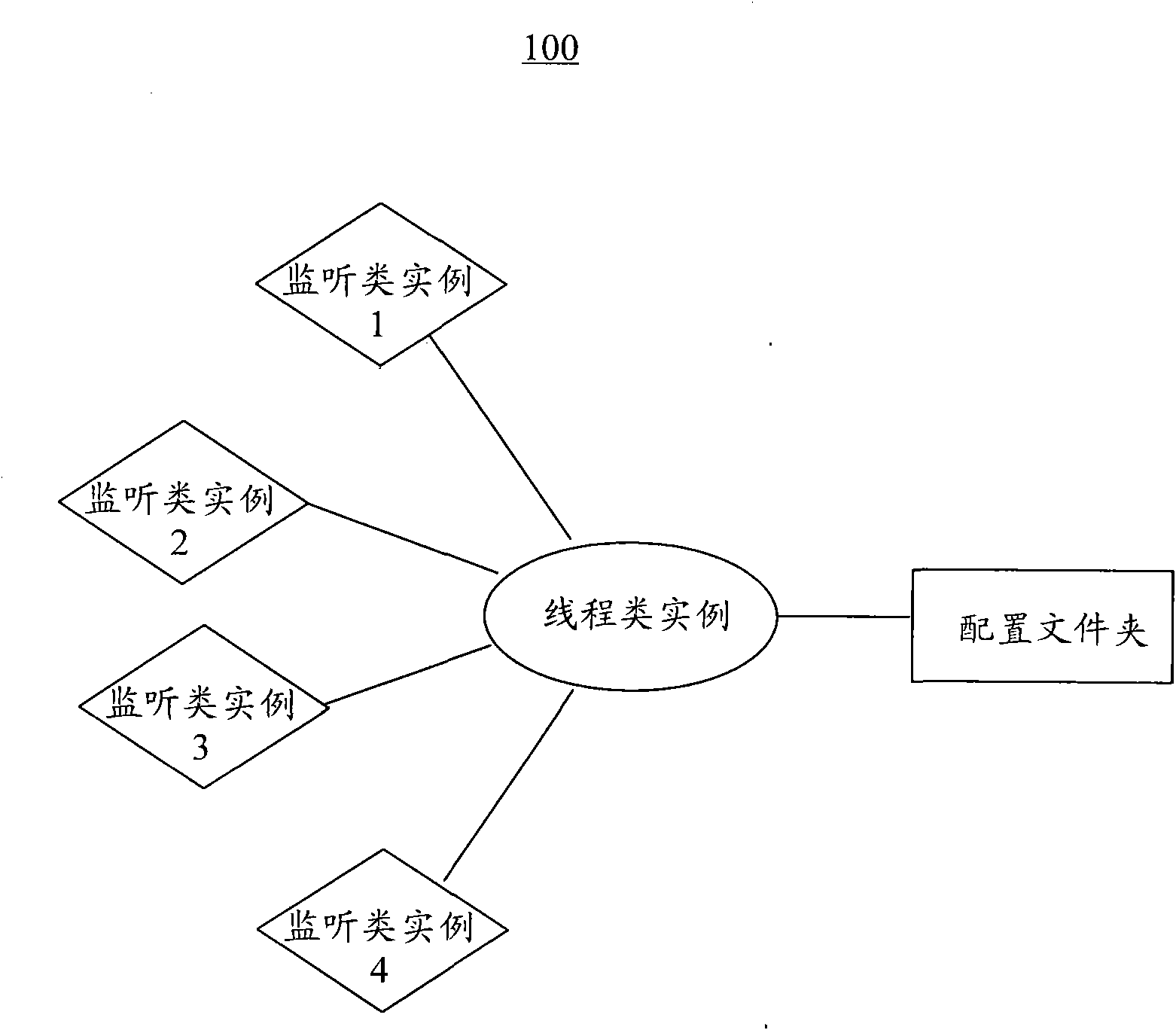
Modes are the file system permissions given to "user", "group" and "others" classes to access files under Unix. They are shown when listing files in long format, or, if access control lists are in use, using getfacl. Modes can be changed with chmod (for traditional Unix permissions) or with setfacl (for access control lists).
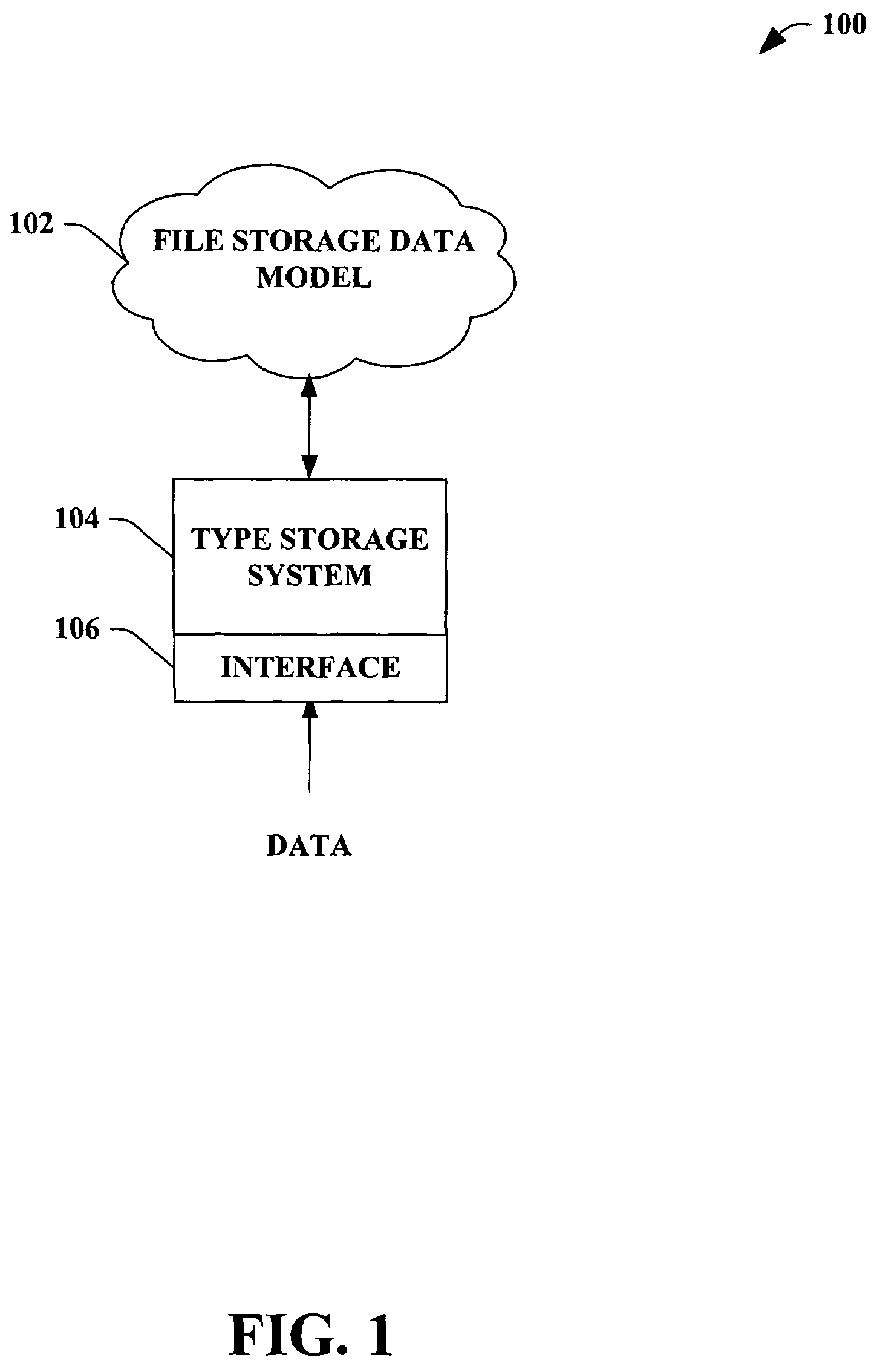
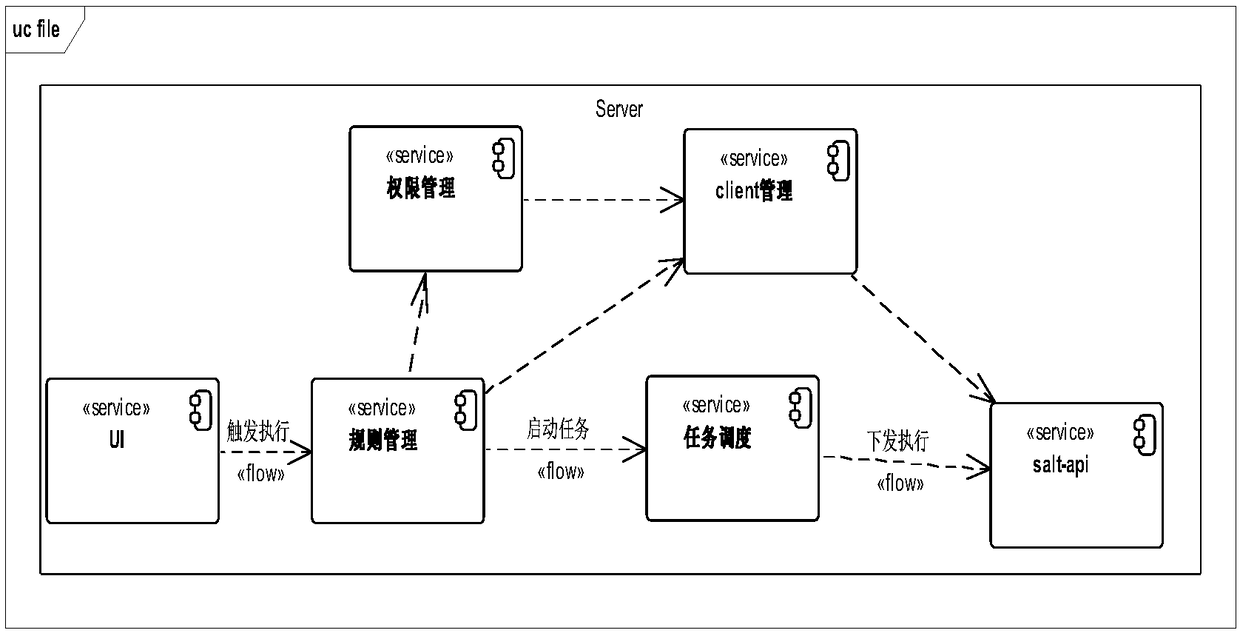
System for collaborative engineering using component and file-oriented tools
InactiveUS6341291B1Improve the level ofHigh currentData processing applicationsCAD network environmentSoftware engineeringIdenticon
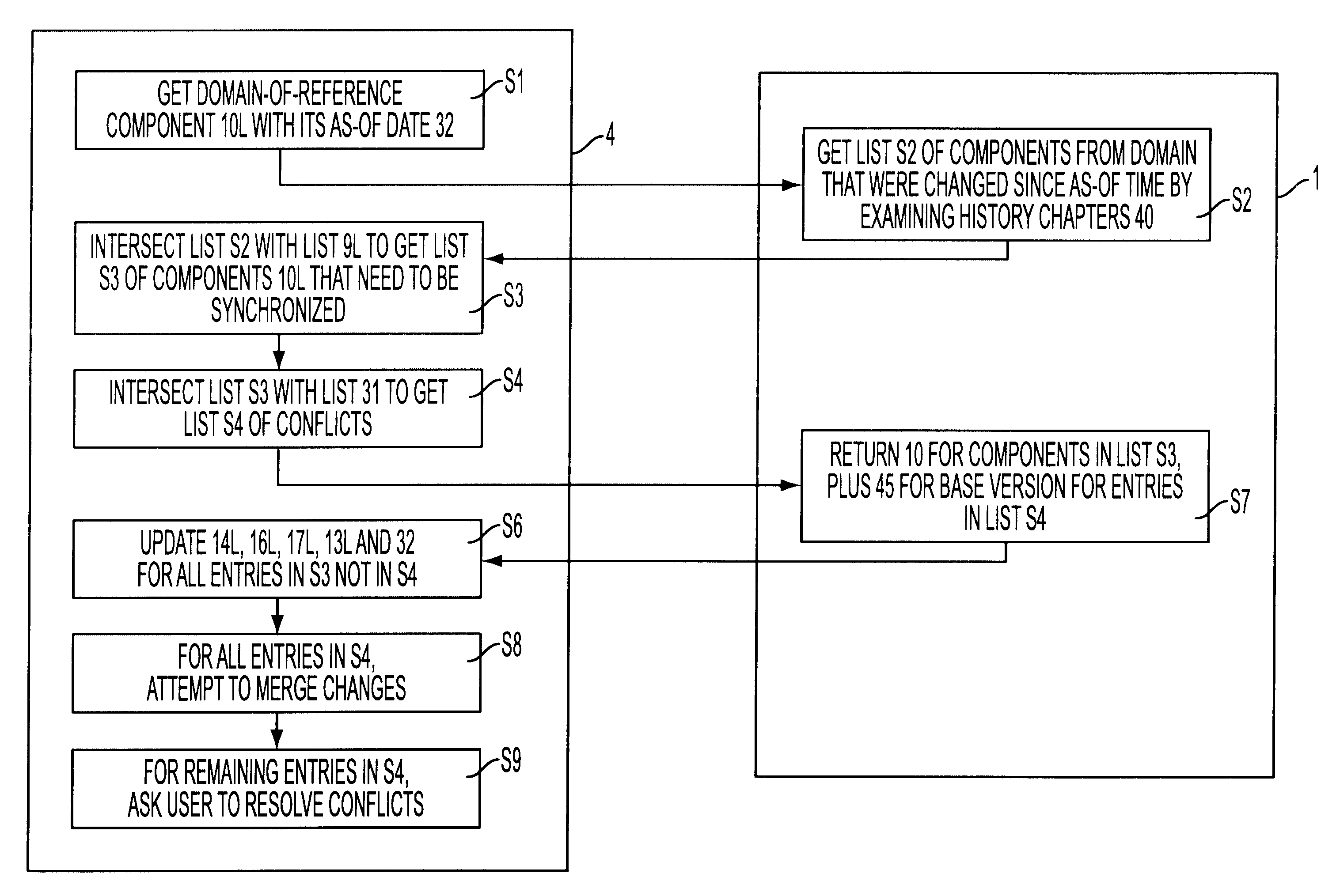
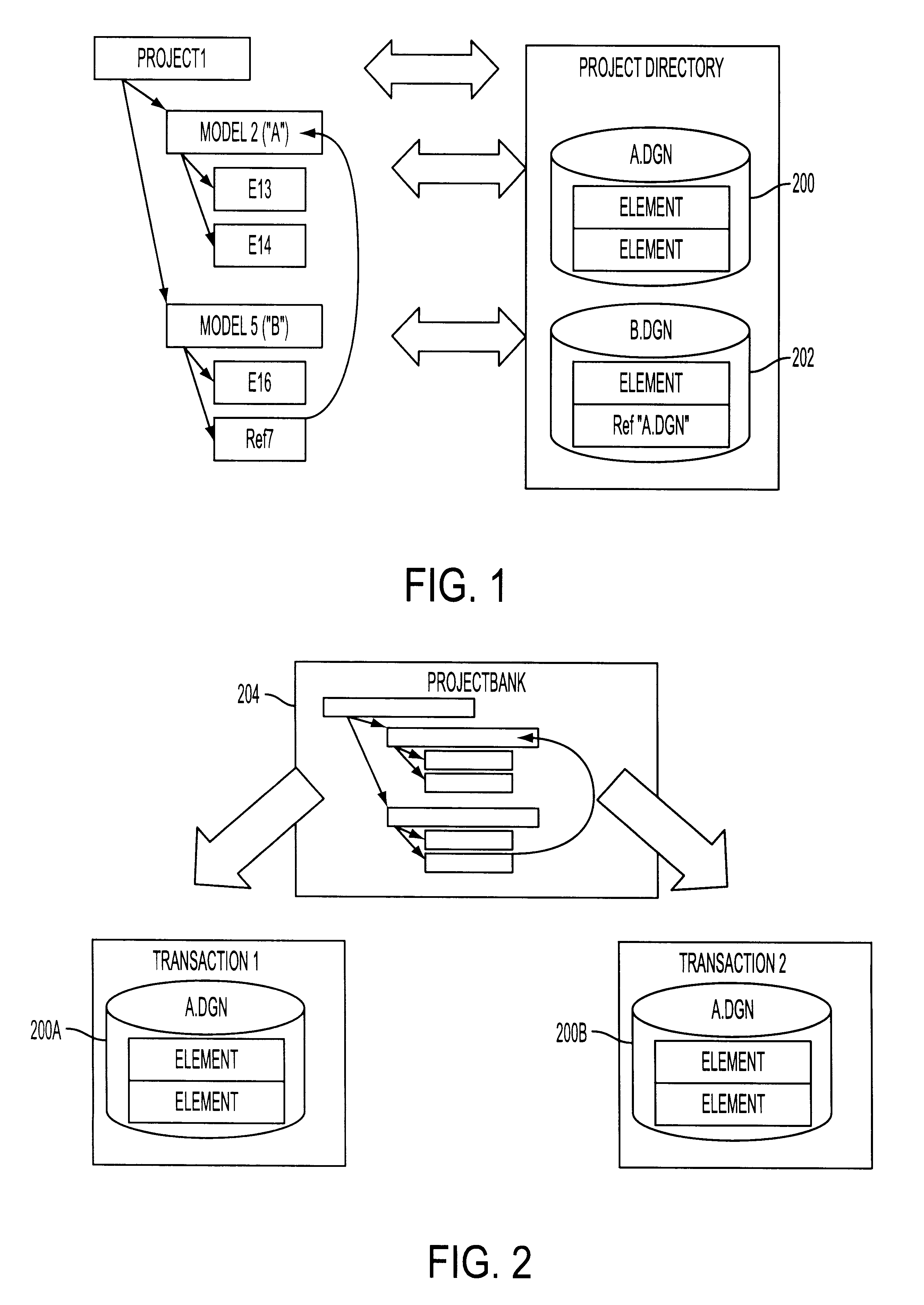
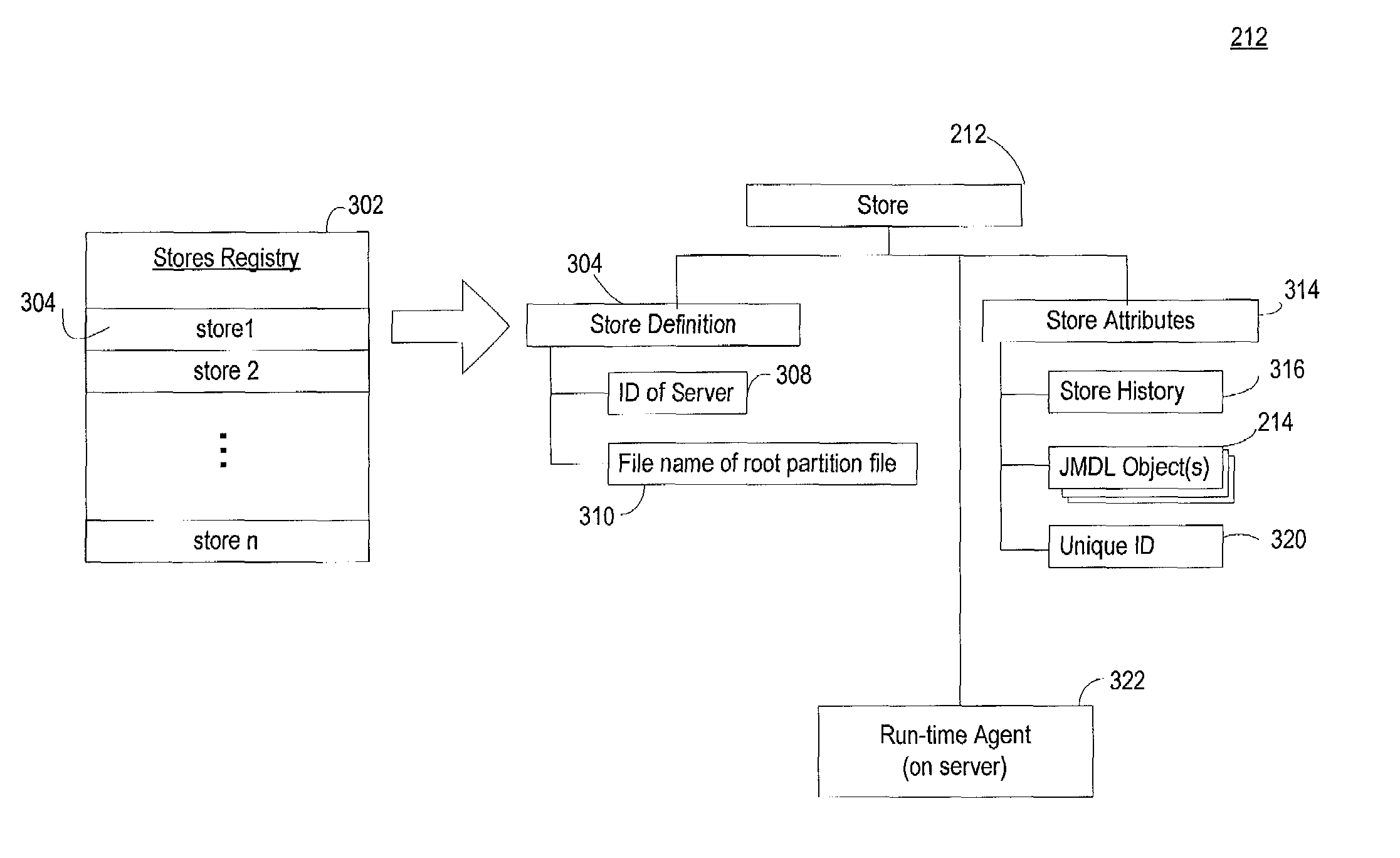
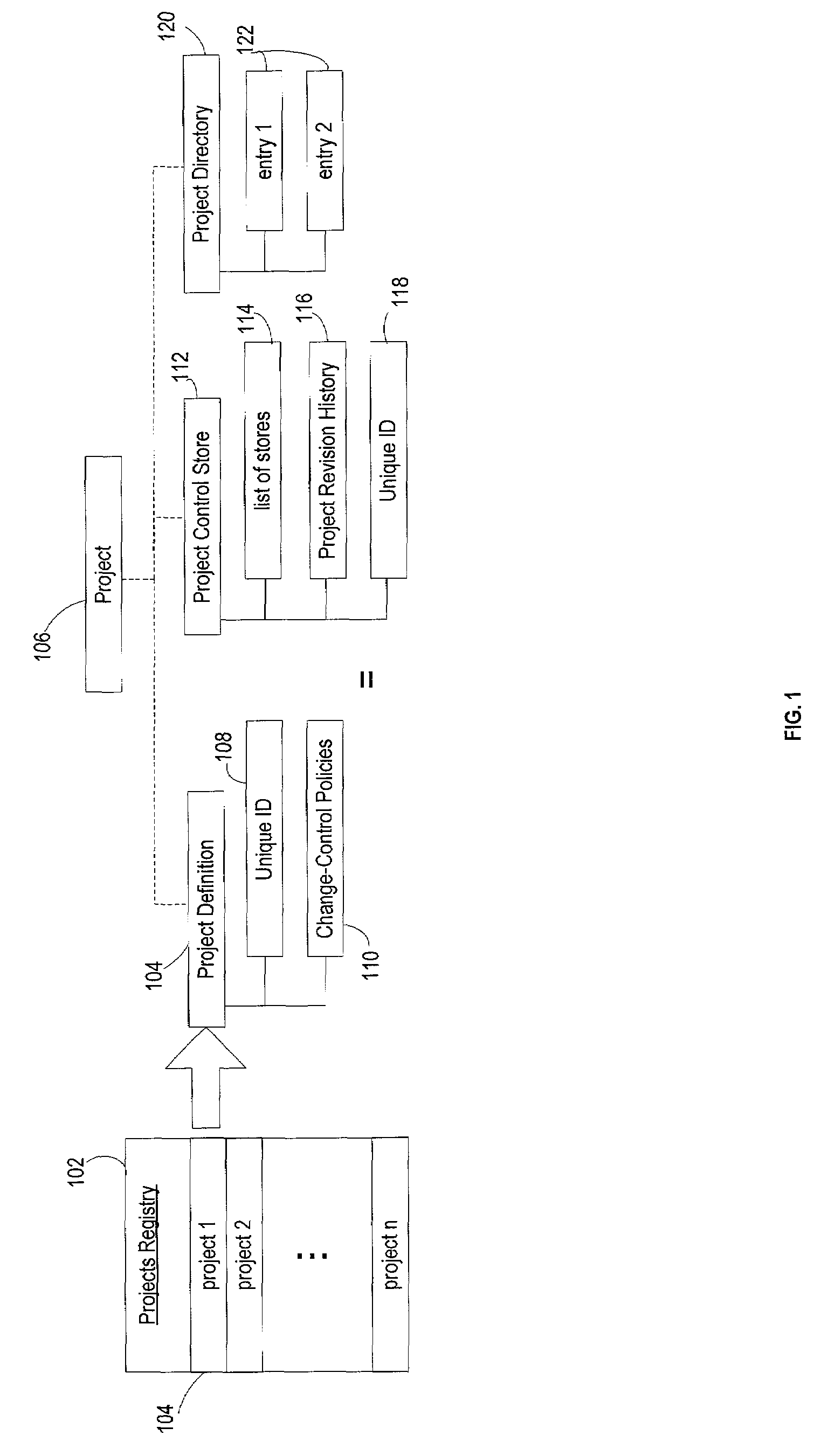
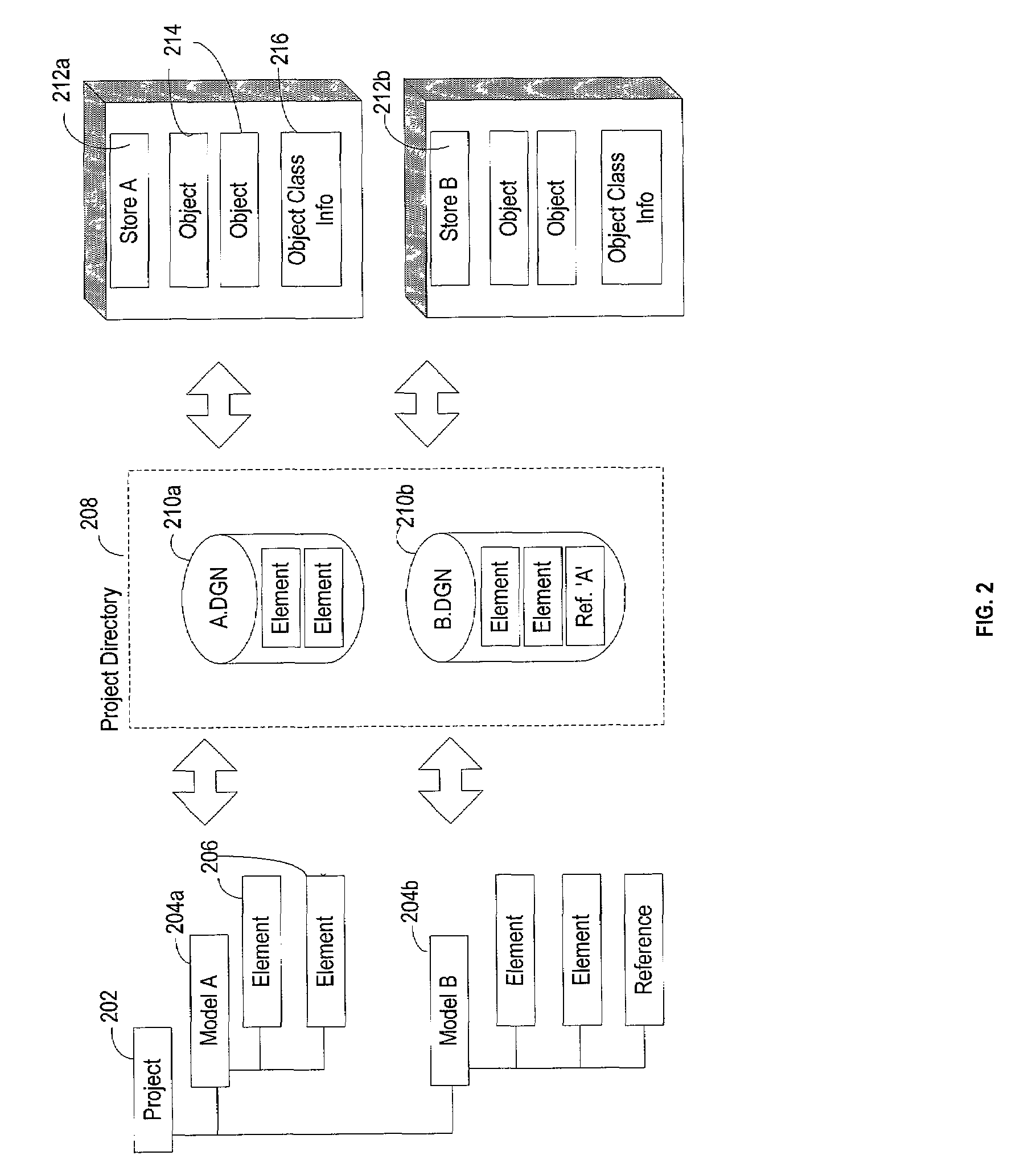
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. Each component has a unique identifier, a set of fields, each field having a data type and a data value, and a program which interprets and modifies the fields. The plurality of components are stored in a repository of a server. The repository also stores a history of any changes made to the components. A plurality of client computers are bidirectionally connected to the server. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the server to replace the current versions in the repository. At the client computer, the user interacts with the components using conventional file-based software. Before locally edited versions of the components are committed to the server to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts therebetween. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to "wrap" each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
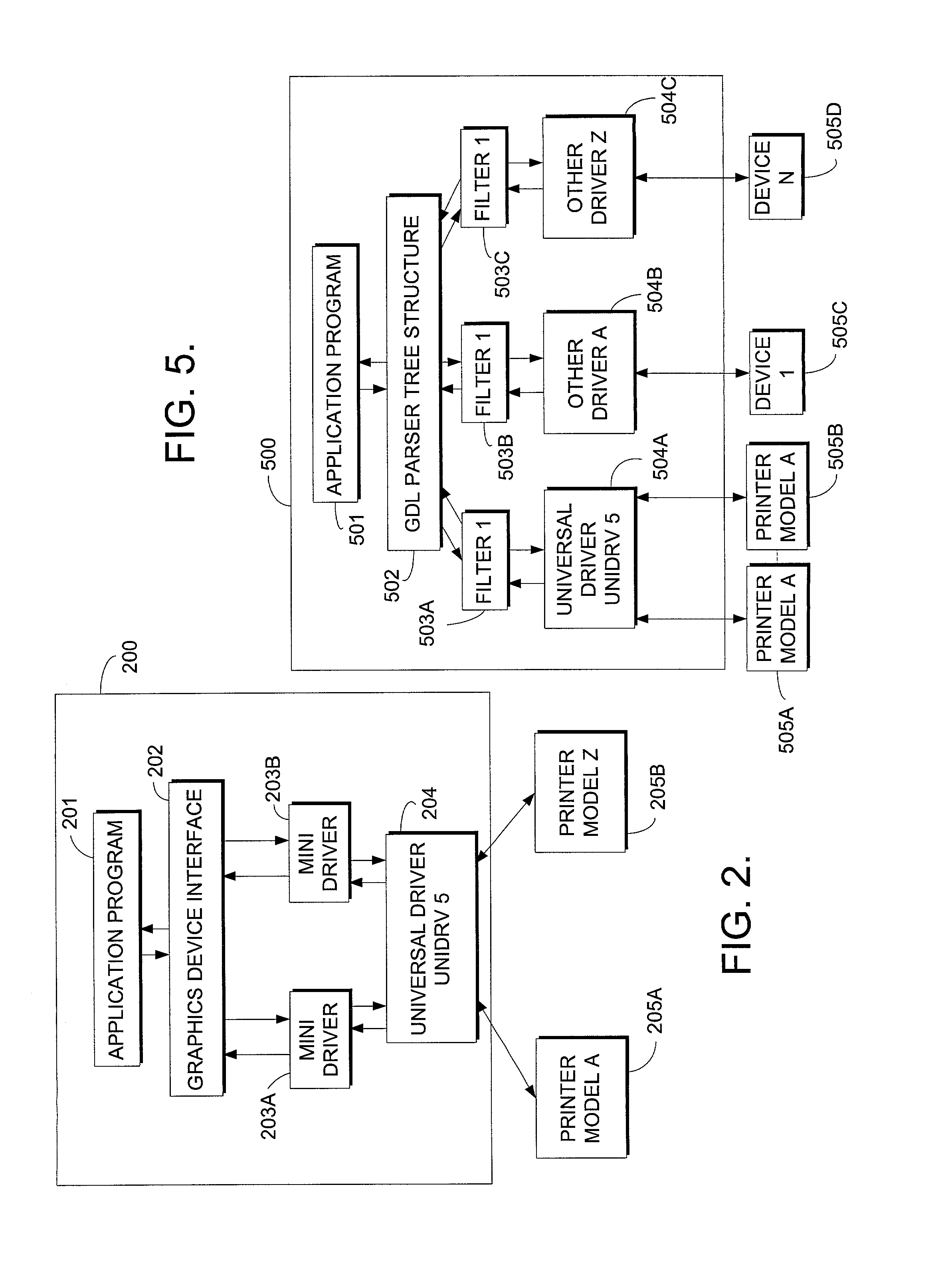
Method for generic object oriented description of structured data (GDL)
InactiveUS7092950B2Facilitate semanticFacilitate definitional information verificationData processing applicationsDigital data processing detailsText entryComputerized system
A method is provided for use in a computer system to describe and obtain arbitrary data relating to a subject. The method provides a meta-language “Generic Object Oriented Description of Structured Data (GDL)” and a Parser. GDL allows a user to organize, define and describe subjects through the use of a schema known as a Template. Templates can be used to define the semantics for each subject element as well as, to define how each element fits into a larger data framework. Through the concept of Inheritance, Templates can be extended and defined to various levels of nesting, while still having a common core of properties. GDL allows the features and attributes of a subject to be quickly and readily extended or modified by altering a source file. A GDL parser provides a structured and hierarchical representation of the information, validation of text-entry semantics and a means to traverse through information obtained from the source file.
Owner:MICROSOFT TECH LICENSING LLC
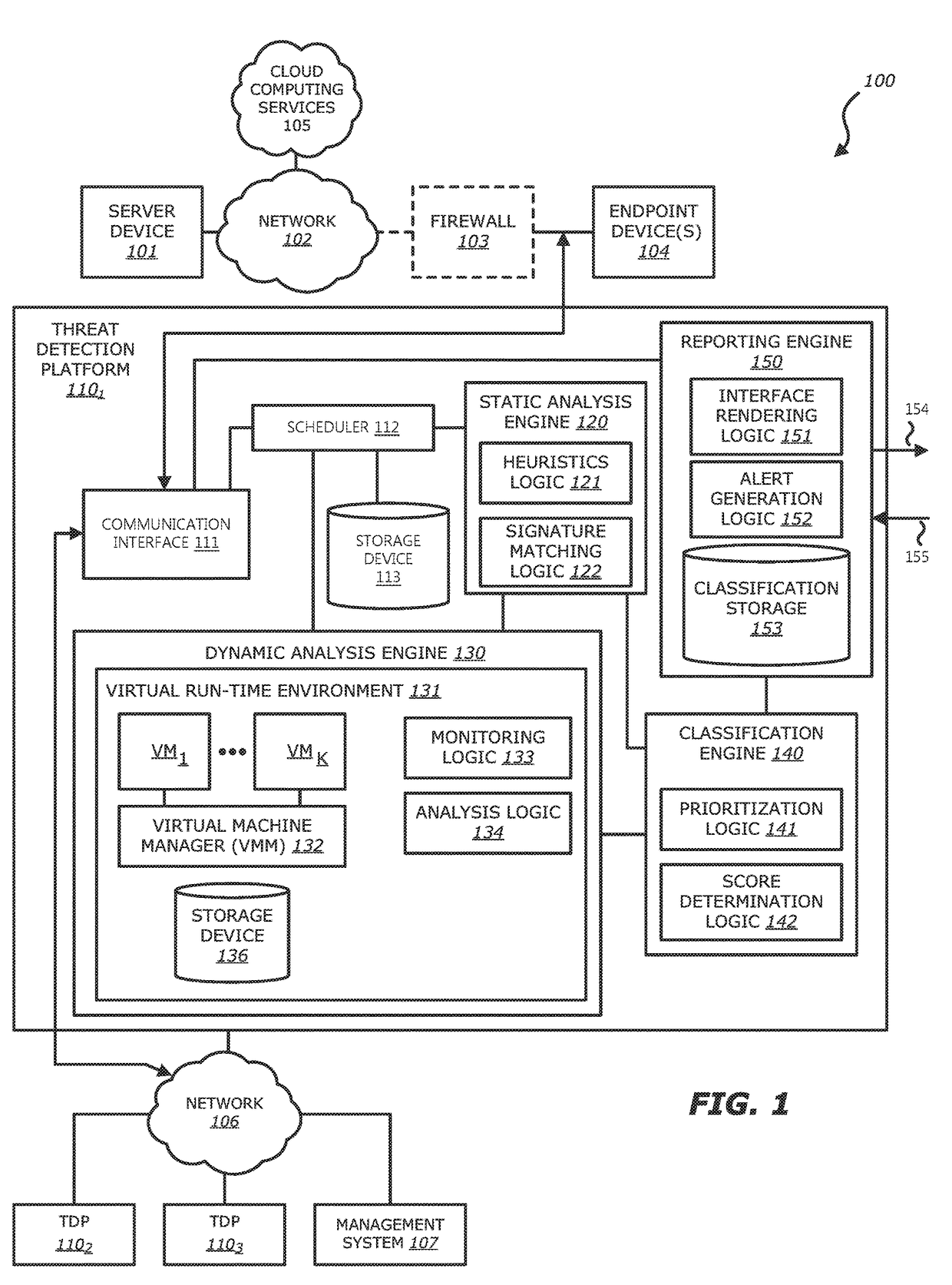
System and method for detecting file altering behaviors pertaining to a malicious attack
ActiveUS9846776B1Digital data information retrievalPlatform integrity maintainanceData informationAttack
Owner:FIREEYE SECURITY HLDG US LLC
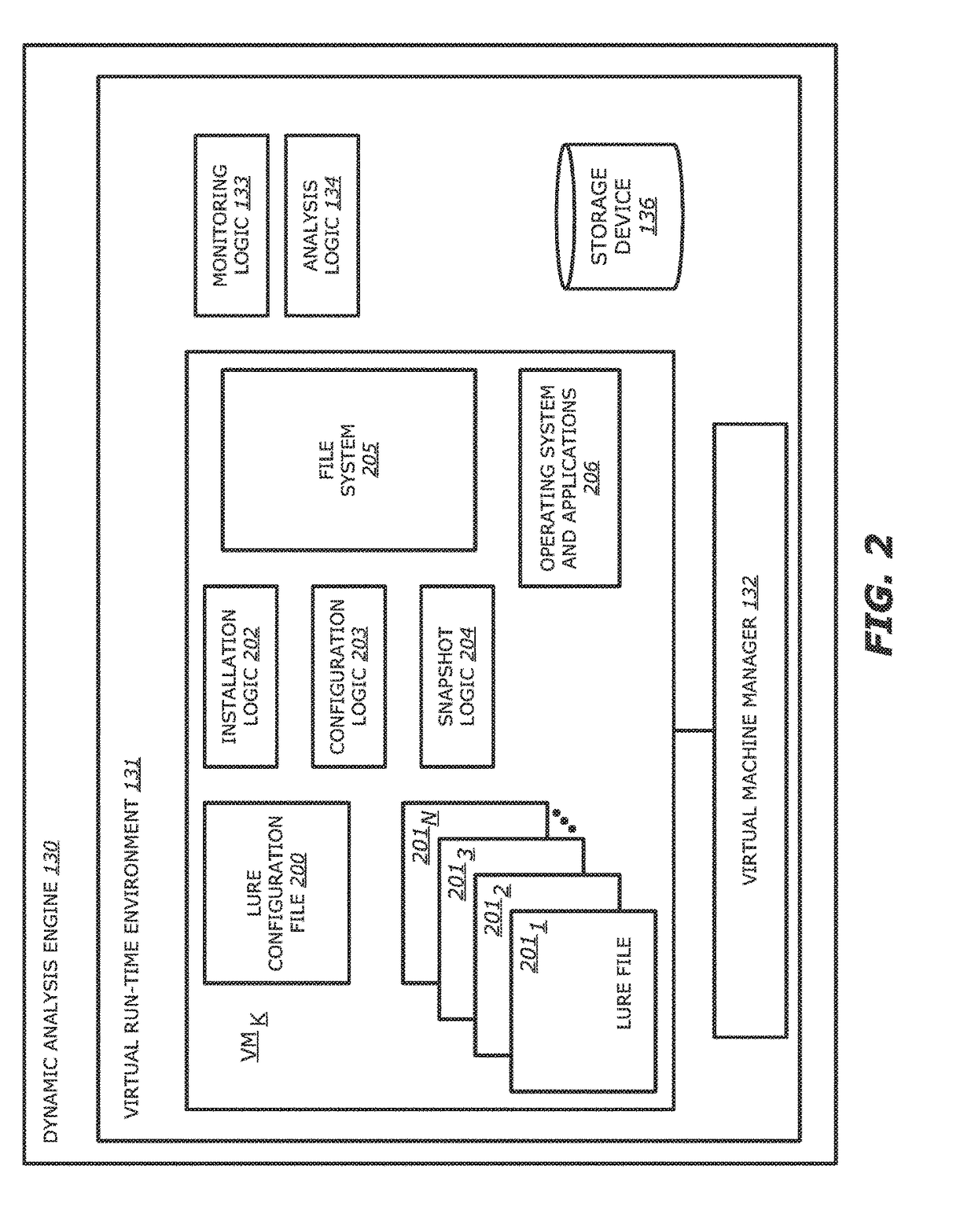
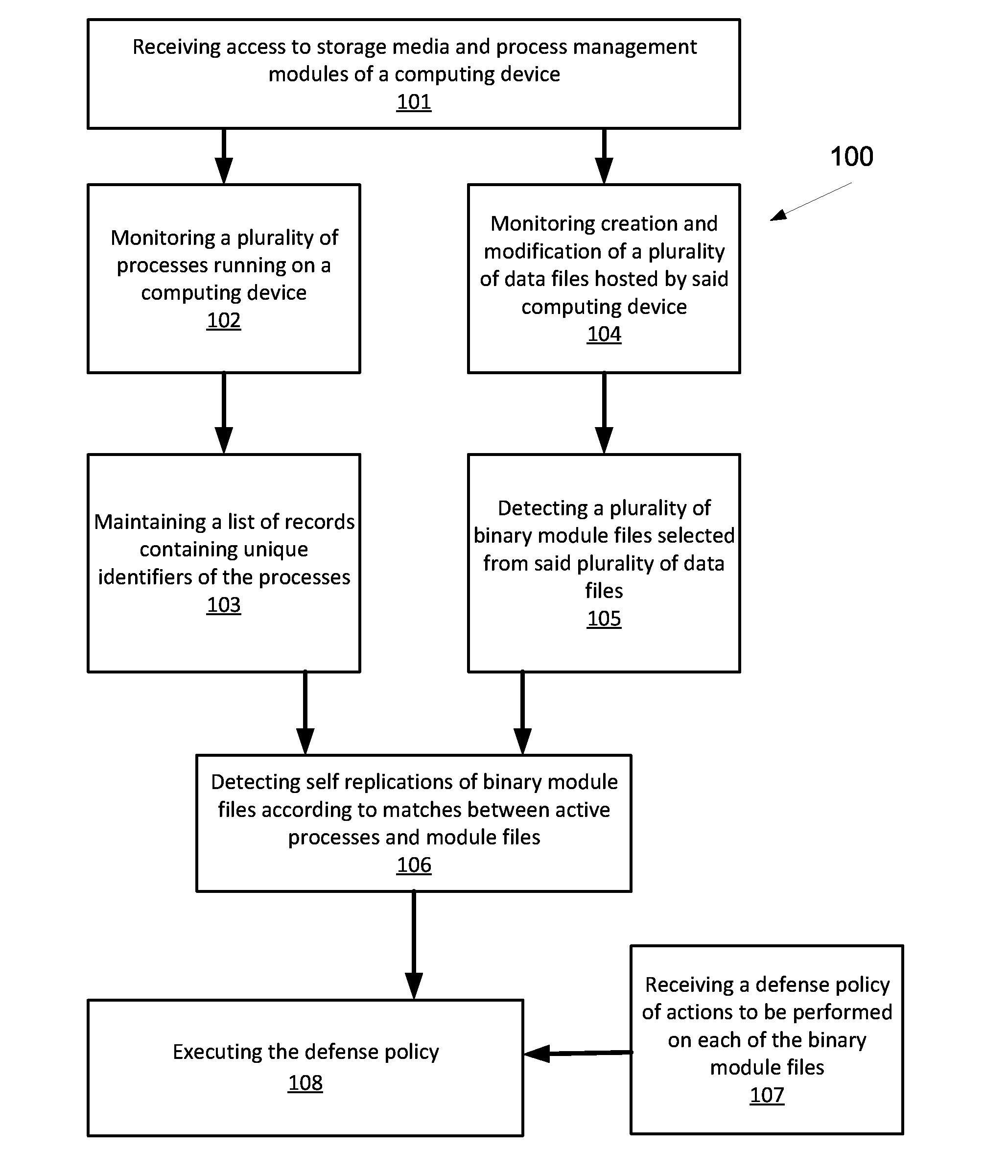
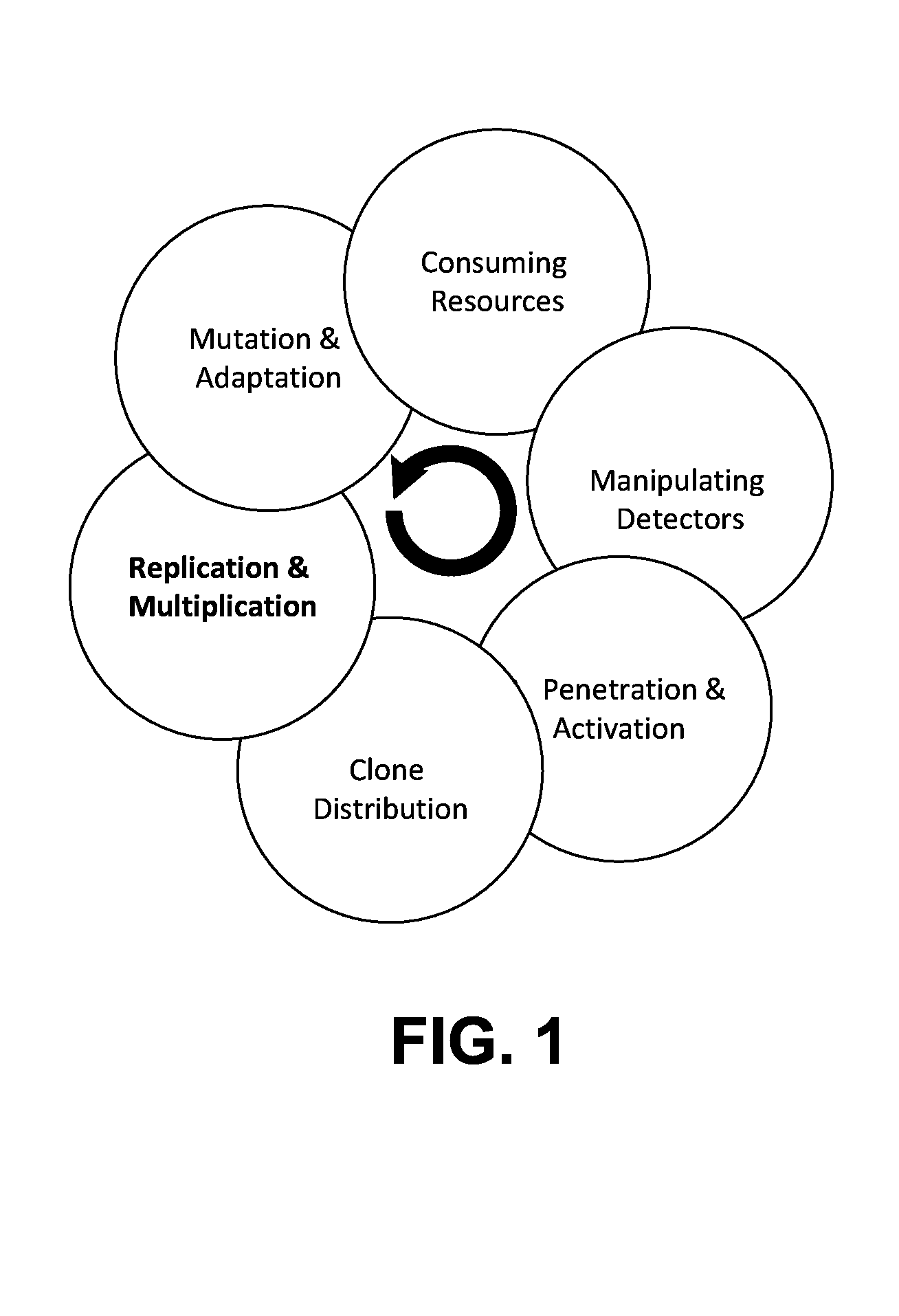
Runtime detection of self-replicating malware
ActiveUS20140123280A1Memory loss protectionUnauthorized memory use protectionTheoretical computer scienceUnique identifier
A method for detecting malicious active processes and self replicating executable binary files on a computing device. The method comprises monitoring in runtime active processes running on a computing device, extracting unique identifier(s) of each of the active processes which maps the active process to executable binary file(s) containing executable code of the active process, monitoring in runtime creation and modification of data files hosted by the computing device, identifying executable binary files among the data files, monitoring concurrent operation of logical sensors which detect malicious behavioral patterns of the active processes and maintain one or more lists of malicious behavioral pattern findings, and detecting malicious active process(es) of a malware from the active processes and self-replicating executable binary file(s) of the malicious active process(es) according to a match between the respective unique identifier(s), the malicious behavioral pattern findings and at least one the executable binary files.
Owner:KEDMA GABRIEL +1
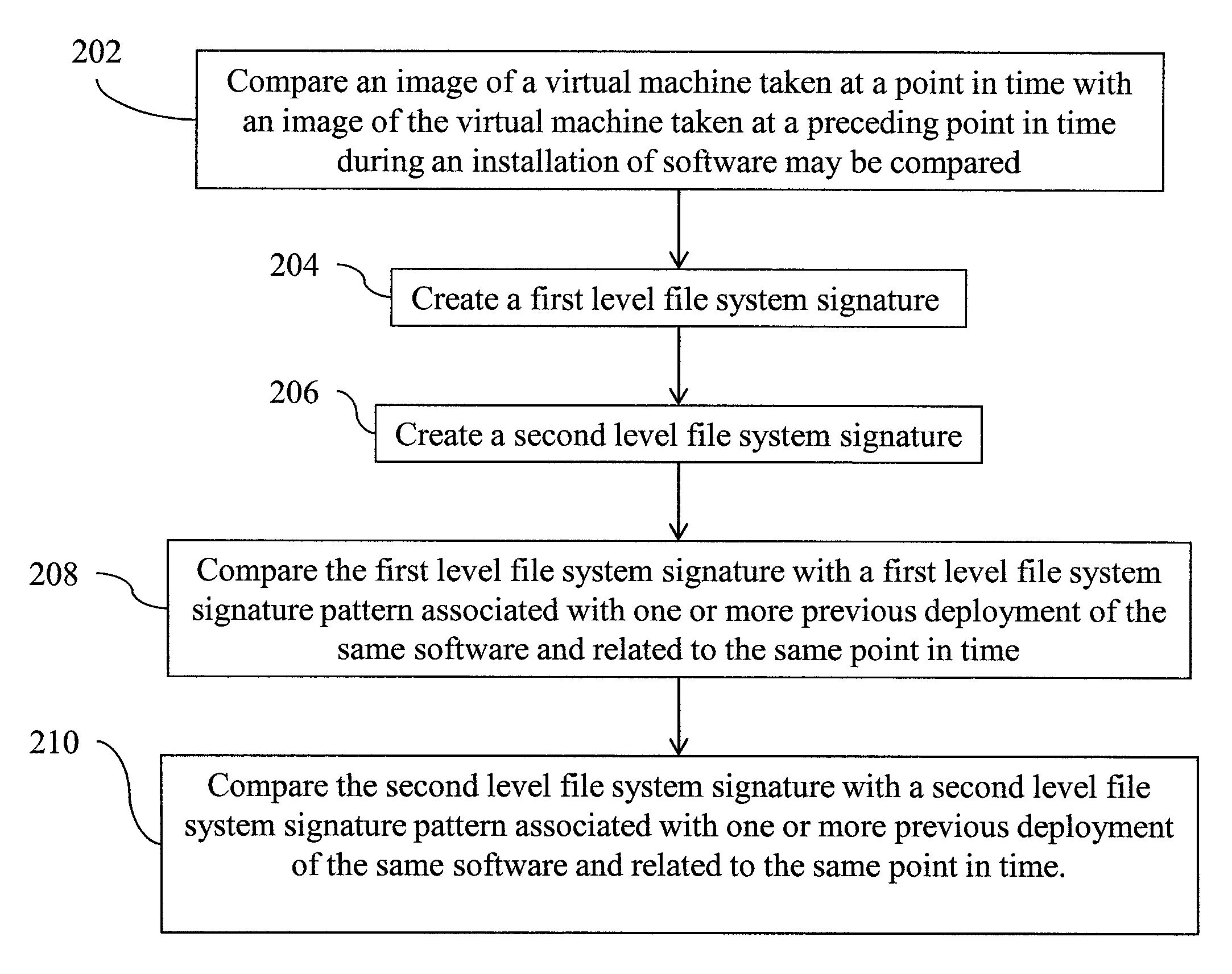
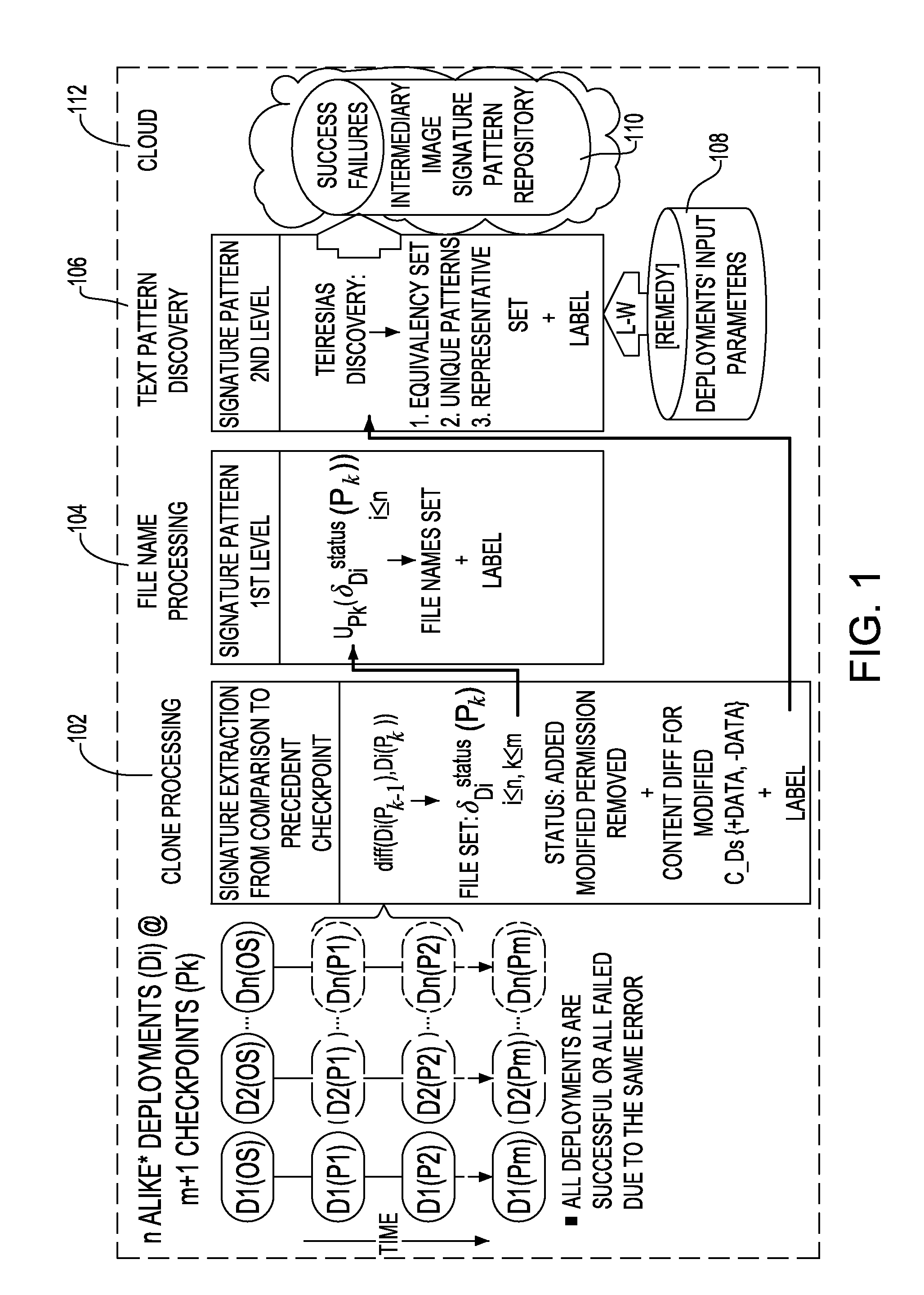
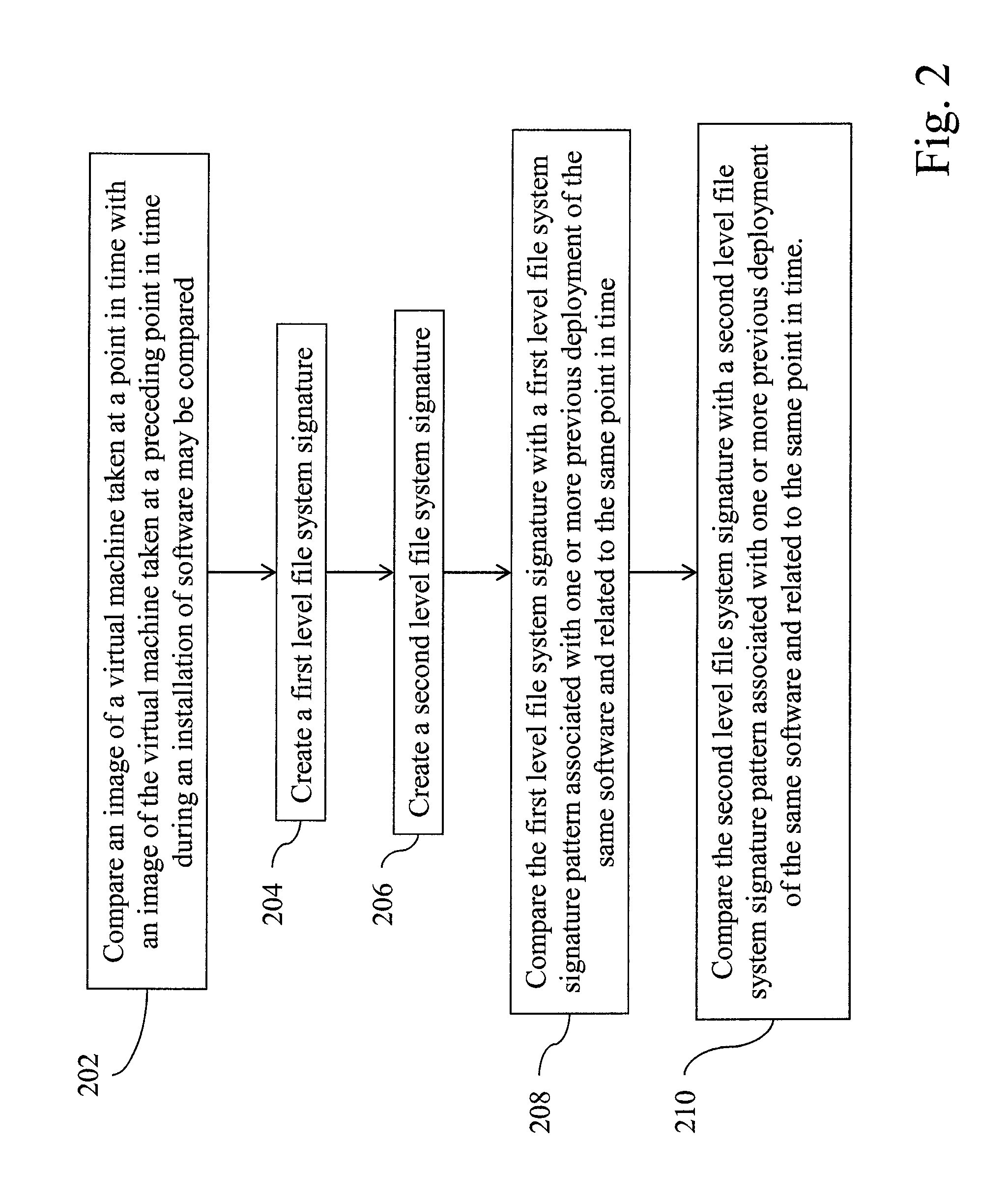
Accelerated virtual environments deployment troubleshooting based on two level file system signature
Troubleshooting virtual environment deployment based on two level file system signatures, in one aspect, may include creating a first level file system signature including a set of file names of files in an image of a virtual machine taken at a point in time and associated status of the files as compared with an image of the virtual machine taken at a preceding point in time. A second level file system signature may be created using file content differences of the files having modified status in the set of file names. The first level file system signature may be compared with a first level file system signature pattern associated with one or more previous deployment of the same software and related to the same point in time. Optionally, the second level file system signature may be compared with a second level file system signature pattern.
Owner:IBM CORP
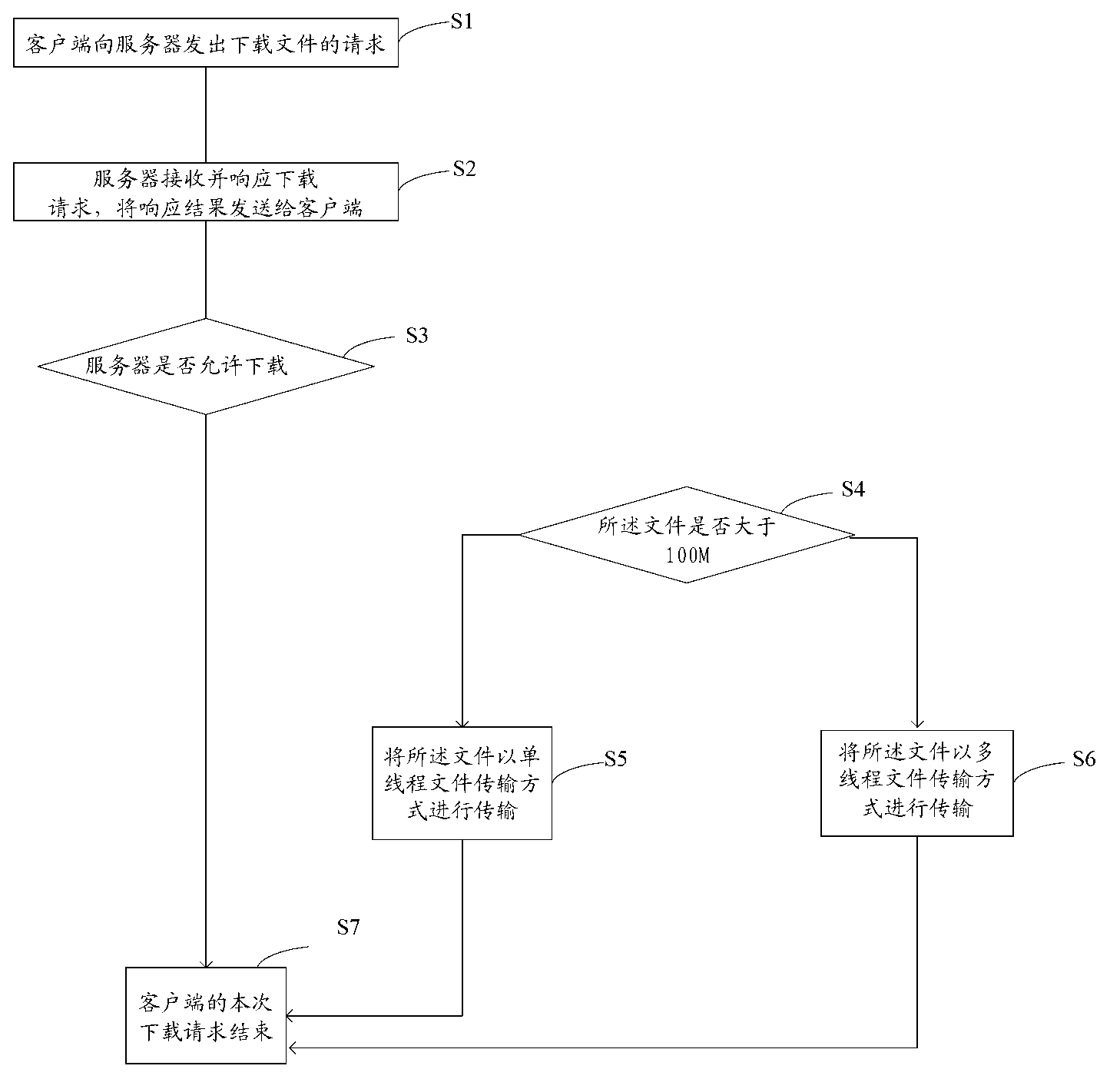
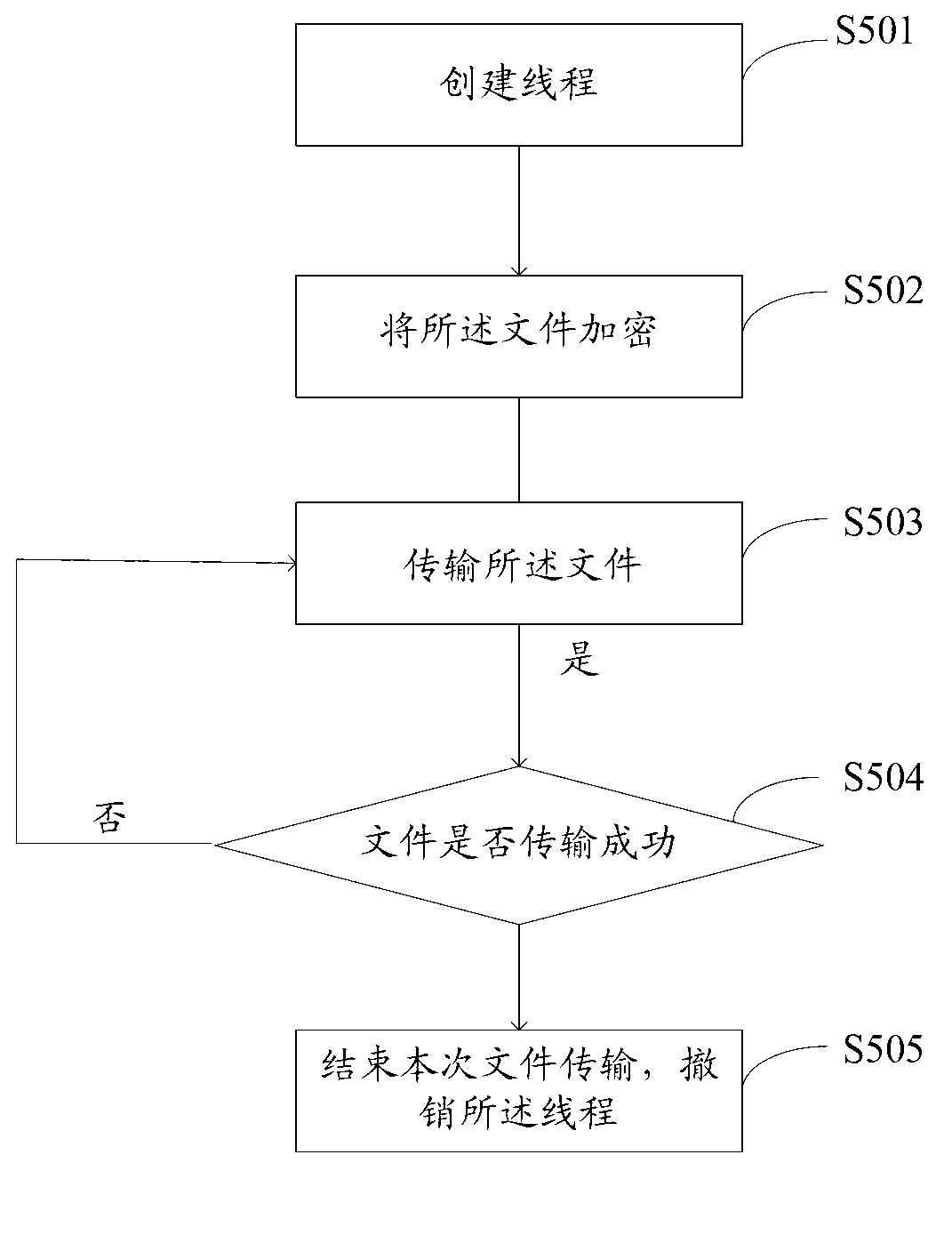
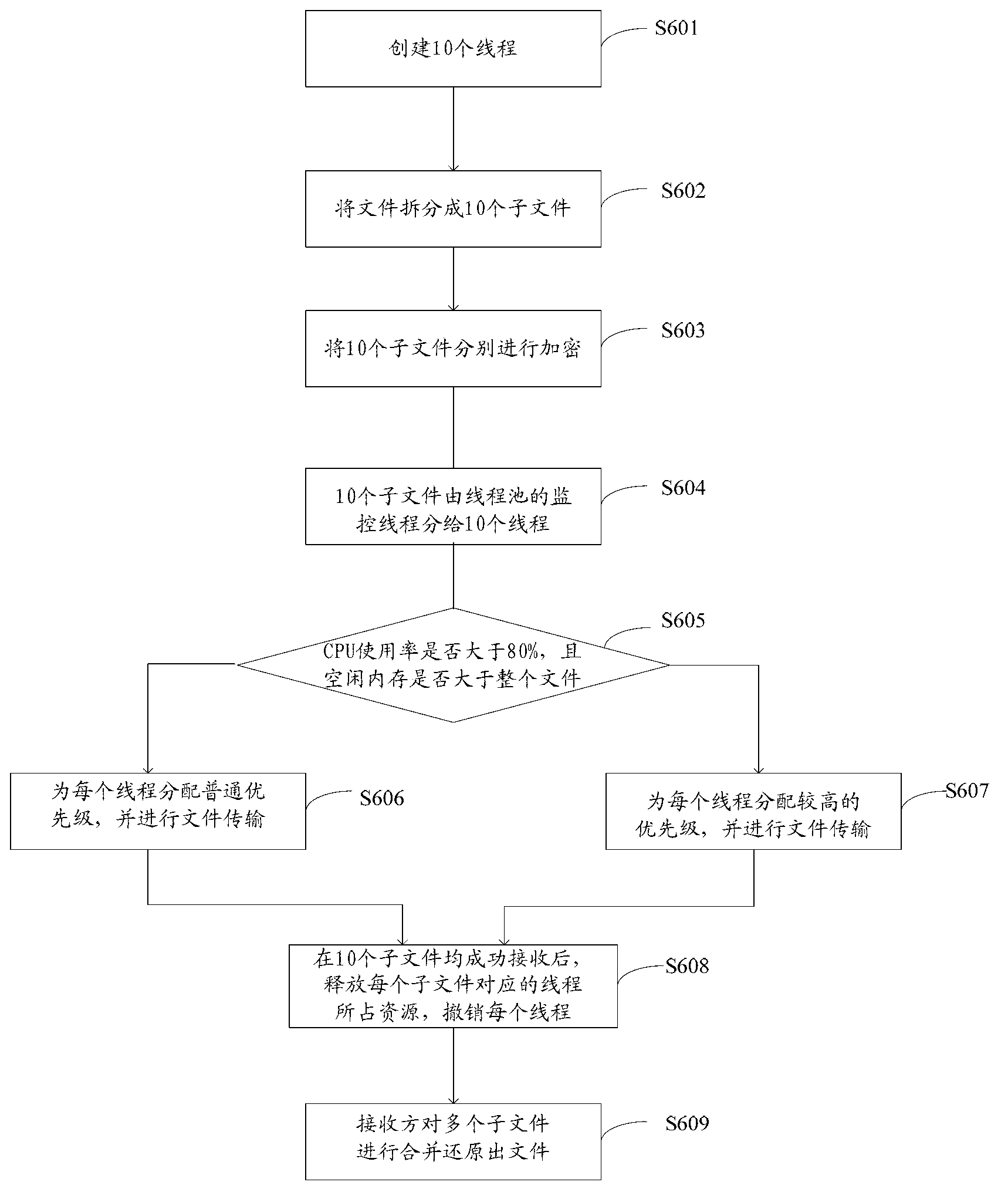
File transfer method and device
InactiveCN103237049AImprove transmission efficiencyFull transmissionError prevention/detection by using return channelTransfer modeMultithreading
The invention discloses file transfer method and device. The method includes following steps: 1, sending a file transfer request to a server by a client side; 2, receiving and responding to the request by the server; 3, receiving response results by the client side, judging whether the server accepts the request or not, if yes, executing step 4; if not, executing step 5; 4, judging whether a file is larger than 100M or not, if yes, transferring in a multithreading manner; if not, transferring in a single-thread file transfer manner; and 5, finishing transfer of the request of the client side, wherein transfer includes uploading and downloading. By the file transfer method and device, when the file is large, the multithreading transfer mode is adopted, so that a CPU (central processing unit) can be utilized to the greatest extent; when the file is small, the single-thread transfer mode is adopted, so that overmuch time consumed during switching among threads can be avoided; by adopting the different transfer modes according to different sizes of the file, file transfer efficiency of the whole file transfer method and the transfer device can be improved.
Owner:BEIJING E HUALU INFORMATION TECH
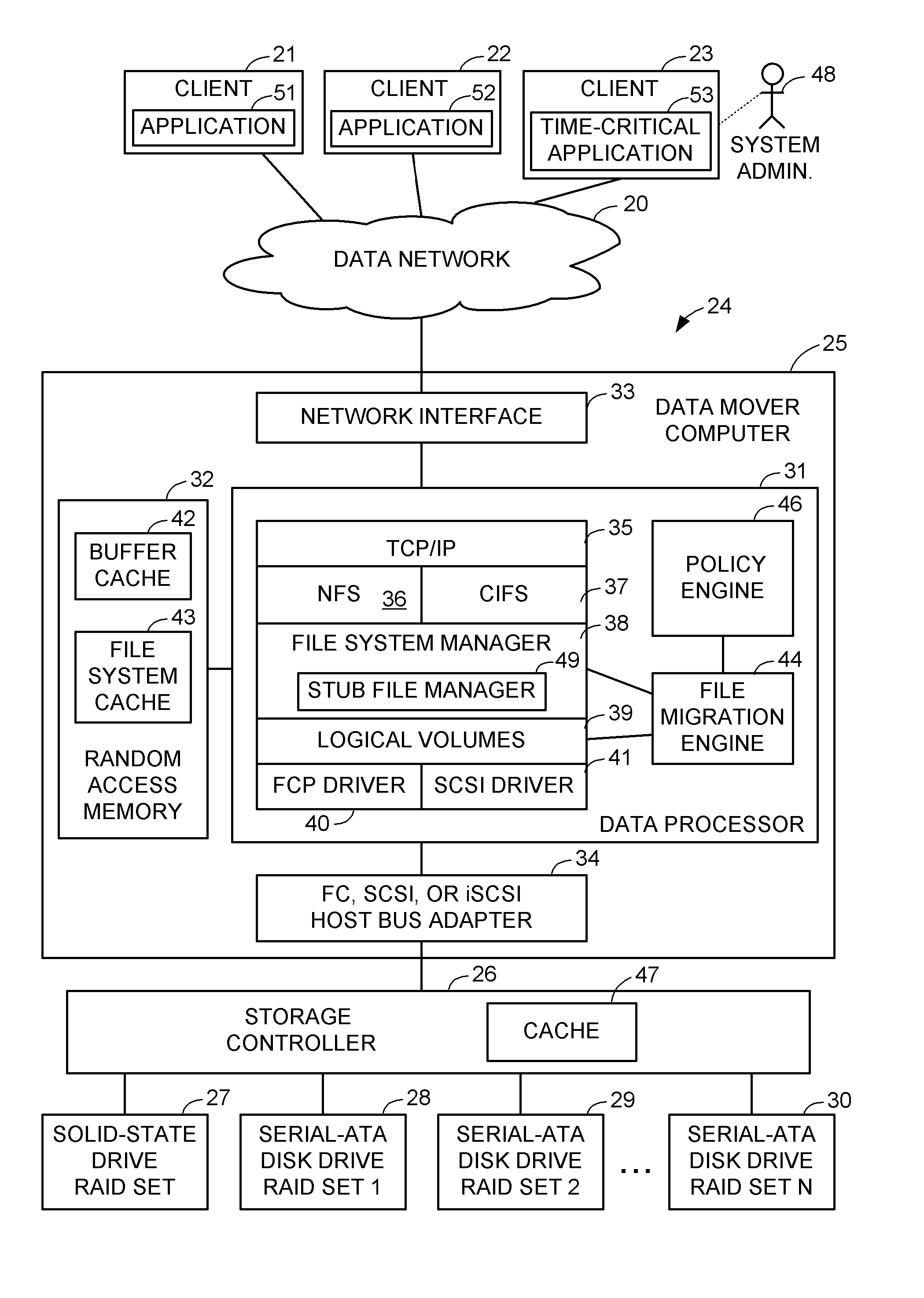
File server system having tiered storage including solid-state drive primary storage and magnetic disk drive secondary storage
ActiveUS9213721B1Digital data information retrievalDigital data processing detailsLoad SheddingFile system
A file server system having solid-state drive primary storage and magnetic disk drive secondary storage aggressively moves newly created files from the primary storage to selected file systems in the secondary storage to match expected access patterns upon the files to different configurations of the file systems and for load balancing upon the file systems in the secondary storage. Upon read access to a file that has been moved to the secondary storage, or upon migration of a newly created file that was read in primary storage after creation, a corresponding stub file containing file mapping metadata is created in the primary storage. The file mapping metadata in the stub file maps the extent of the file to logical storage addresses in the secondary storage.
Owner:EMC IP HLDG CO LLC
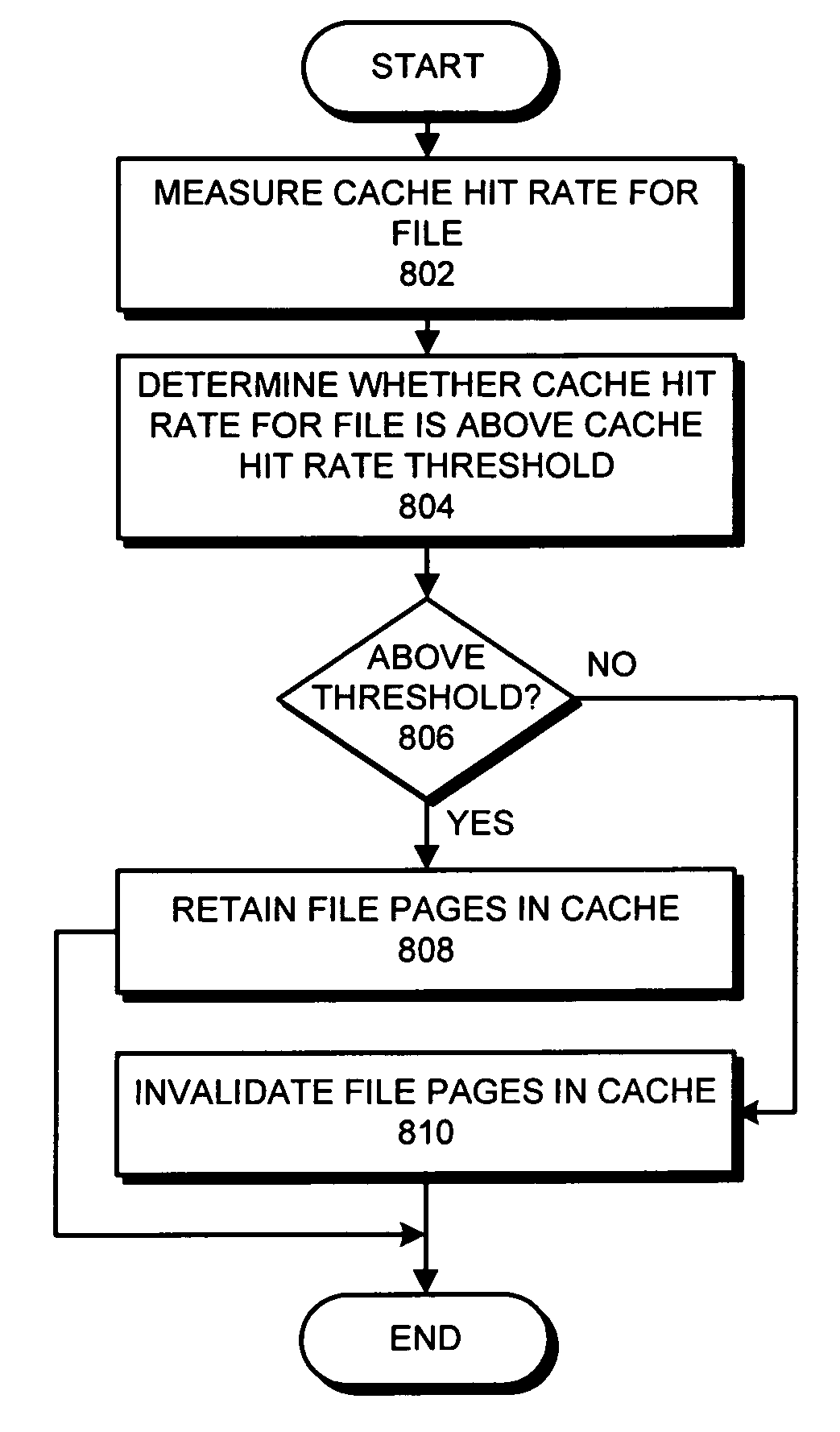
Method and apparatus for performing caching in a file system
ActiveUS20080086600A1Easy to useReduces cache hit rate thresholdDigital data information retrievalSpecial data processing applicationsSystem usageSystem monitor
A system that caches a file within a computer system. During operation, the system monitors accesses to the file, wherein the file is located on a storage device. Next, the system analyzes the monitored accesses to determine an access pattern for the file. The system then uses the determined access pattern to adjust a caching policy for the file.
Owner:ORACLE INT CORP
Expandable storage system and control method based on objects
ActiveCN1728665AEasy to expandImprove scalabilityData switching by path configurationSpecial data processing applicationsObject basedAdaptive management
Combining file with block mode, the invention puts forward a brand new object interface in order to overcome disadvantages of system structure and mode of user service in current mass storage system. The system includes I pieces of metadata server, N pieces of object storage node, and M pieces of client end connected to each other. Three parties among client ends, object storage node and severs are realized. The system provides high expandability, and synchronous growth of memory capacity and collective bandwidth of data transmission. Changing traditional data management and control mode, object storage node OSN executes fussy functions for managing data at bottom layer of file system, and MS implements management of metadata. Based on object storage, the system realizes adaptive management function.
Owner:HUAZHONG UNIV OF SCI & TECH
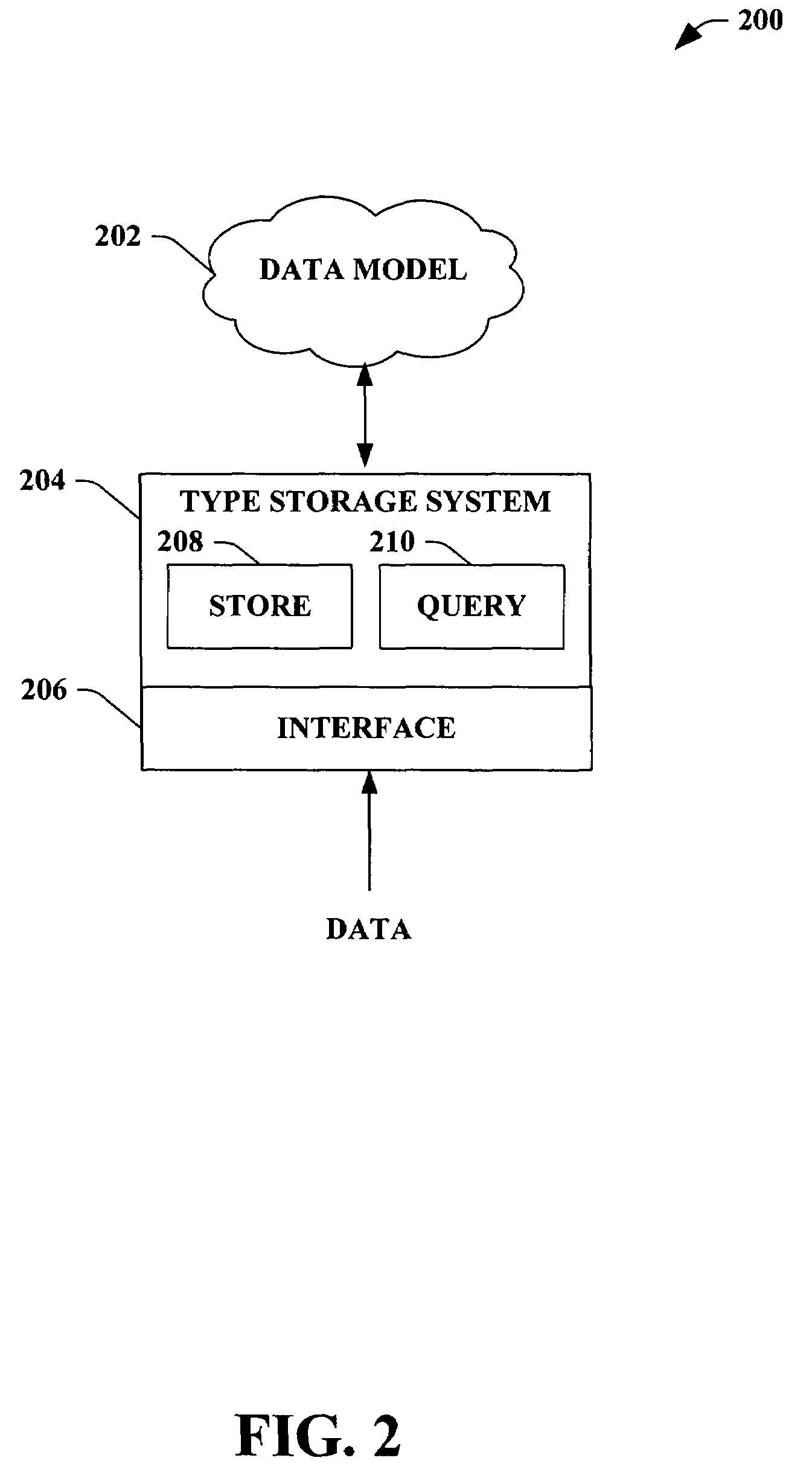
System, method and computer program product for collaborative engineering using component and file oriented tools
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. The plurality of components are kept in stores, which reside on servers. Each store contains the components that correspond to the elements of one design file. The stores also maintain a history of changes made to the components. A plurality of client computers are bidirectionally connected to the servers. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the servers to replace the current versions in the stores. At the client computer, the user interacts with the components using conventional file-based software. Before the locally edited versions of the components are committed to the servers to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to “wrap” each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
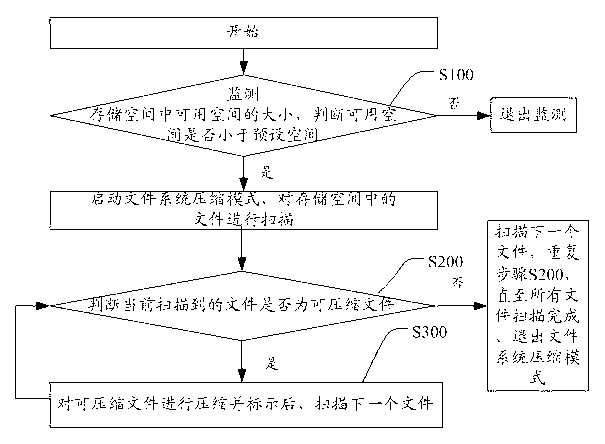
Method and terminal for improving utilization ratio of memory space
ActiveCN103218224AShorten the timeEasy to operateSpecific program execution arrangementsFile systemComputer terminal
The invention discloses a method and a terminal for improving the utilization ratio of a memory space. The method comprises steps of A, monitoring the available space in the memory space, judging whether the available space is smaller than a preset space or not; if yes, starting a file system compression mode, and scanning files in the memory space; if not, stopping monitoring; B1, judging whether the currently scanned file is a compressible file or not; if yes, executing step C1; if not, scanning the next file, repeating step B1 until all the files are completely scanned, and exiting from the file system compression mode; and C1, compressing and marking the compressible file, scanning the next file, and returning to step B1. All the files in the memory space are appropriately and selectively compressed through the method, the utilization ratio of the memory space is improved, and a user does not need to select the files to perform a plurality of times of compression, so that the use by users is facilitated, and a user experience effect is improved.
Owner:DONGGUAN YULONG COMM TECH +1
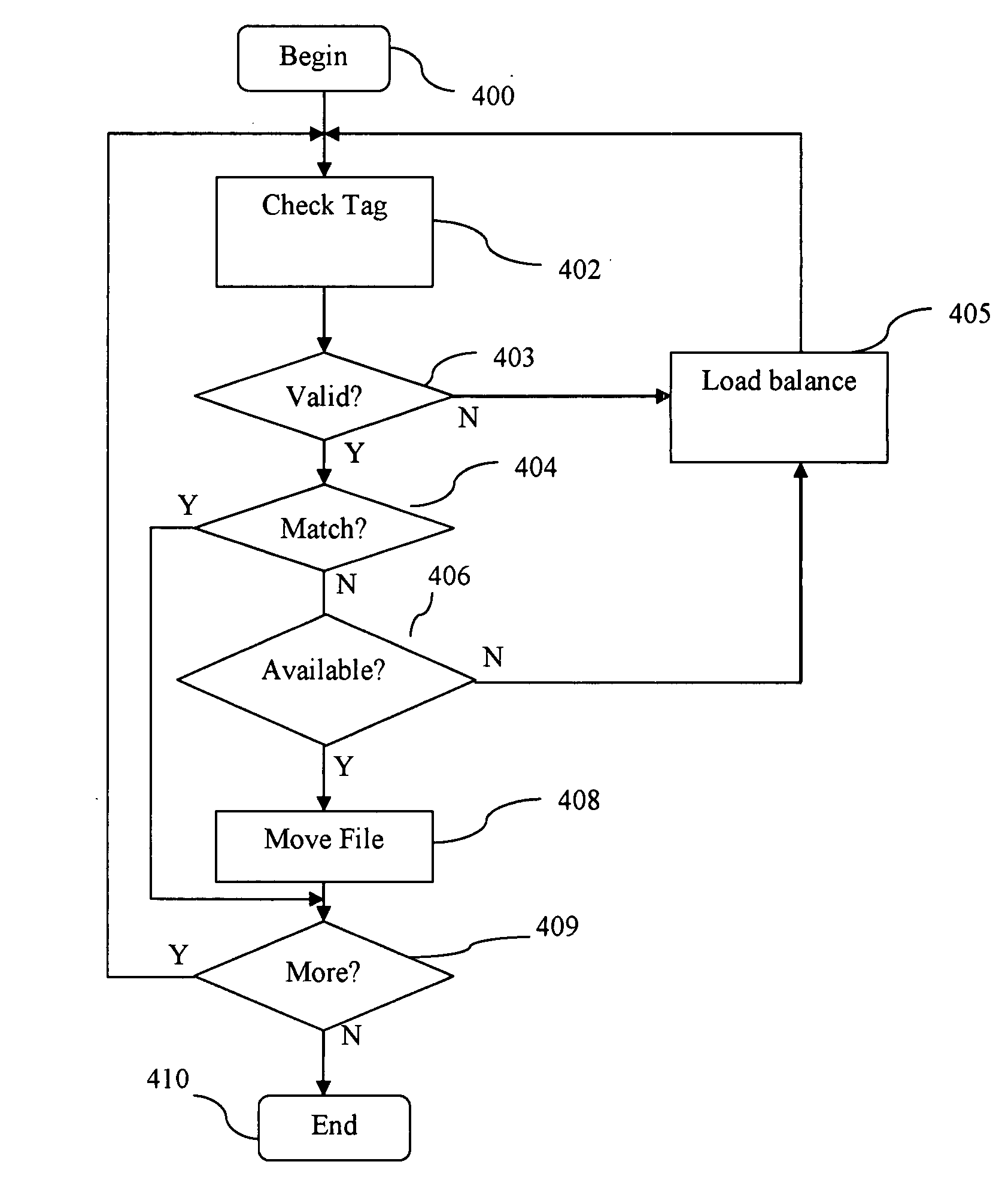
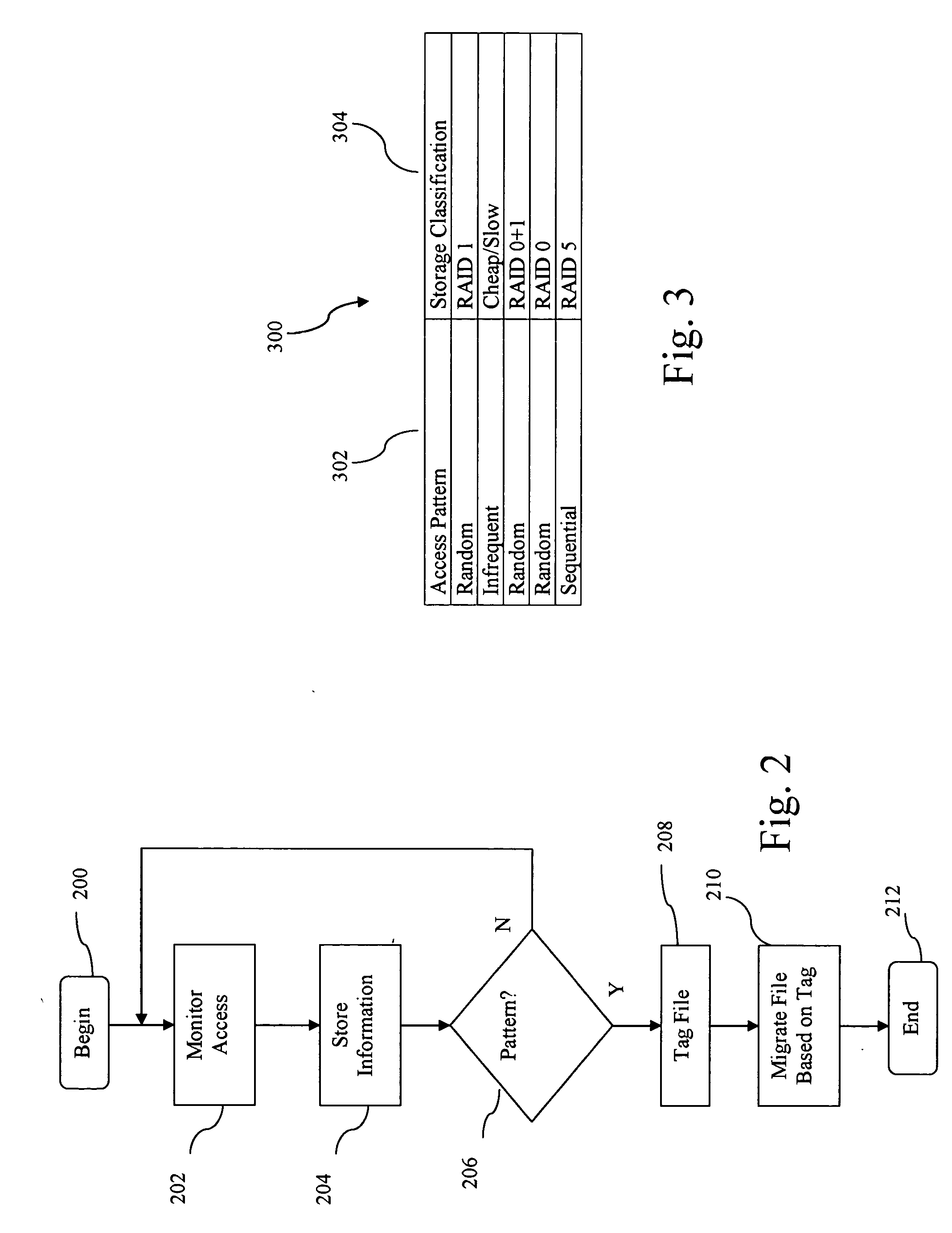
Transparent migration of files among various types of storage volumes based on file access properties
In one embodiment, a method and system for storing a file in a storage domain is provided. The method includes monitoring access to a file to determine a file access pattern, tagging the file to indicate the identified access pattern and using the tag to identify an appropriate storage medium in a storage domain for the file, when available, based on the access pattern.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
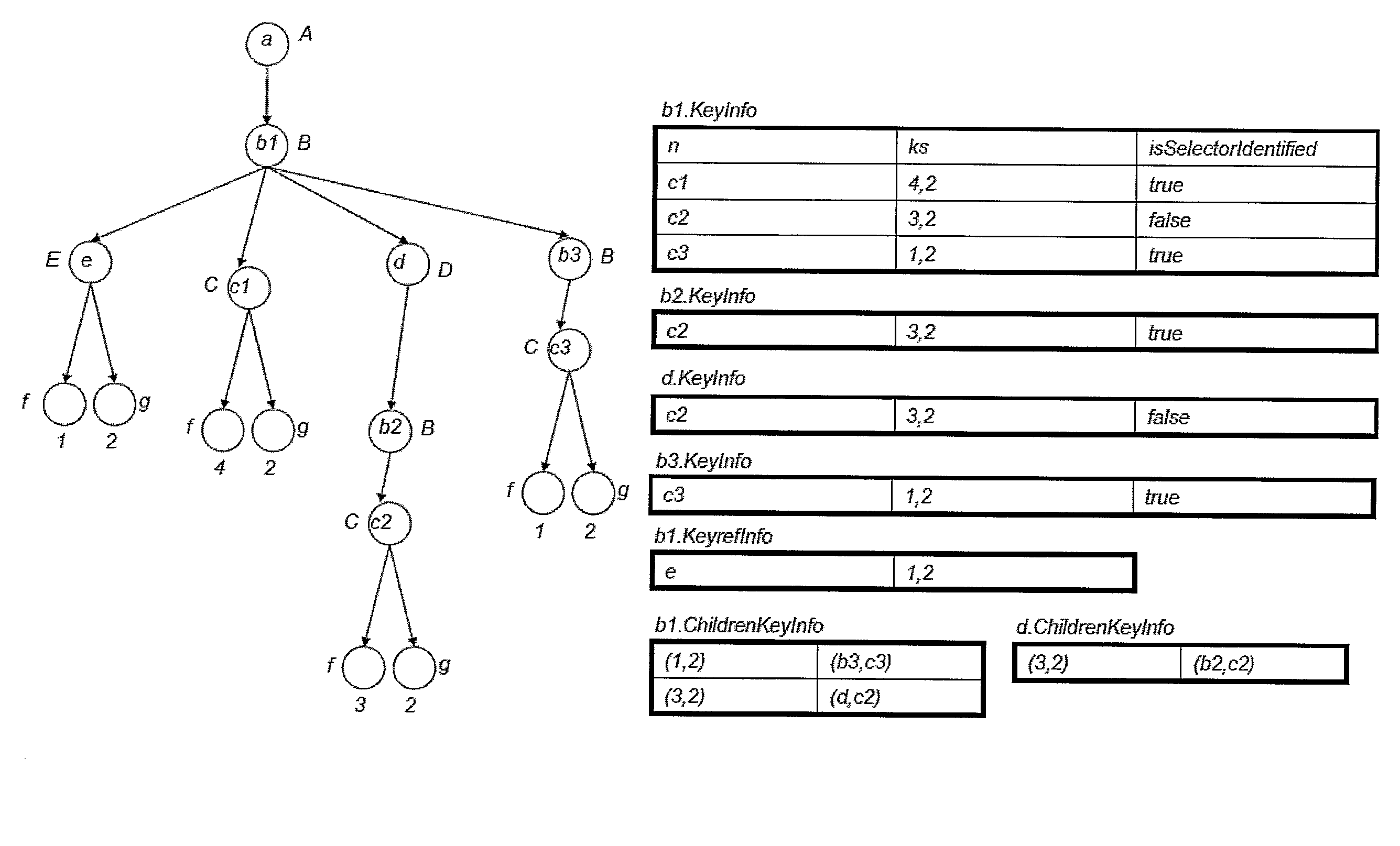
Incremental Validation of Key and Keyref Constraints
InactiveUS20080235251A1Easy to updateEffective monitoringNatural language data processingSpecial data processing applicationsXML schemaEngineering
The present invention relates to a method, and system for implementing the method, for performing incremental validation of an XML document with respect to XML Schema key and keyref constraints, and handling the semantics dictated by the XML Schema specification. Several operations are defined that change the content of a document, i.e., add or remove nodes, or change the value of existing nodes. The present invention verifies whether performing such an operation would violate key or keyref constraints, and allows changing the document only if the operation maintains the validity of the document with respect to the constraints. The verification traverses only the parts of the document that may be affected by the change operation, and not the whole document. The invention maintains, in an efficient manner, data structures that hold information relevant to the validation of key and keyref constraints.
Owner:TECHNION RES & DEV FOUND LTD
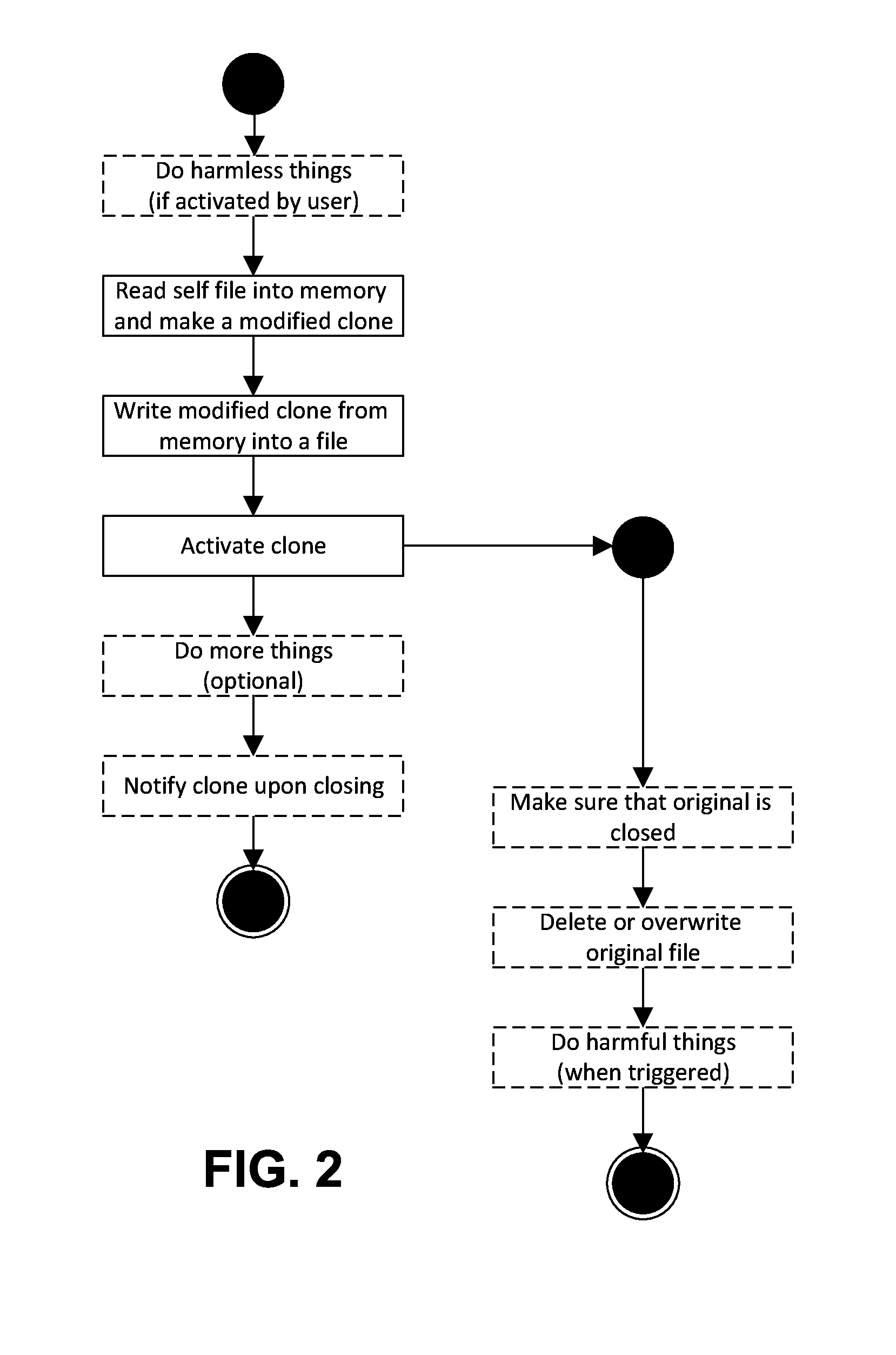
Nullification of malicious code by data file transformation
To nullify any malicious code potentially contained within a data file. a transformation engine randomly selects a transformation from a number of available file transformations each arranged to alter the bit pattern of a file to which it is applied while still enabling manifestation of at least some of the file's semantic content to a user. The selected transformation is then applied to the data file to produce a transformed file. Preferably, the transformation engine runs in a dedicated virtual machine of a computing platform.
Owner:HEWLETT PACKARD DEV CO LP
File access method and system
InactiveUS20100138406A1Improve performanceProgram control using stored programsDigital data processing detailsFile systemAccess method
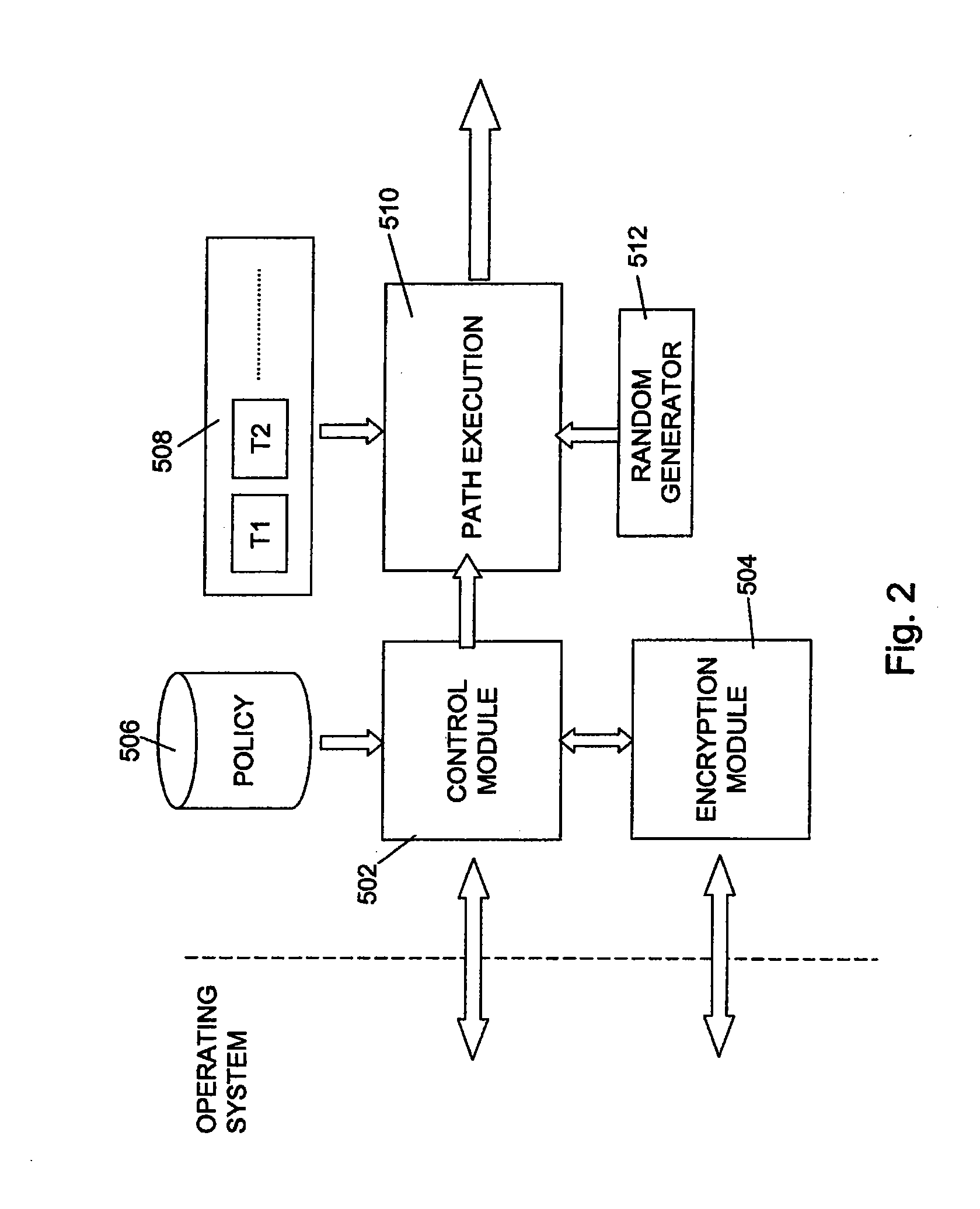
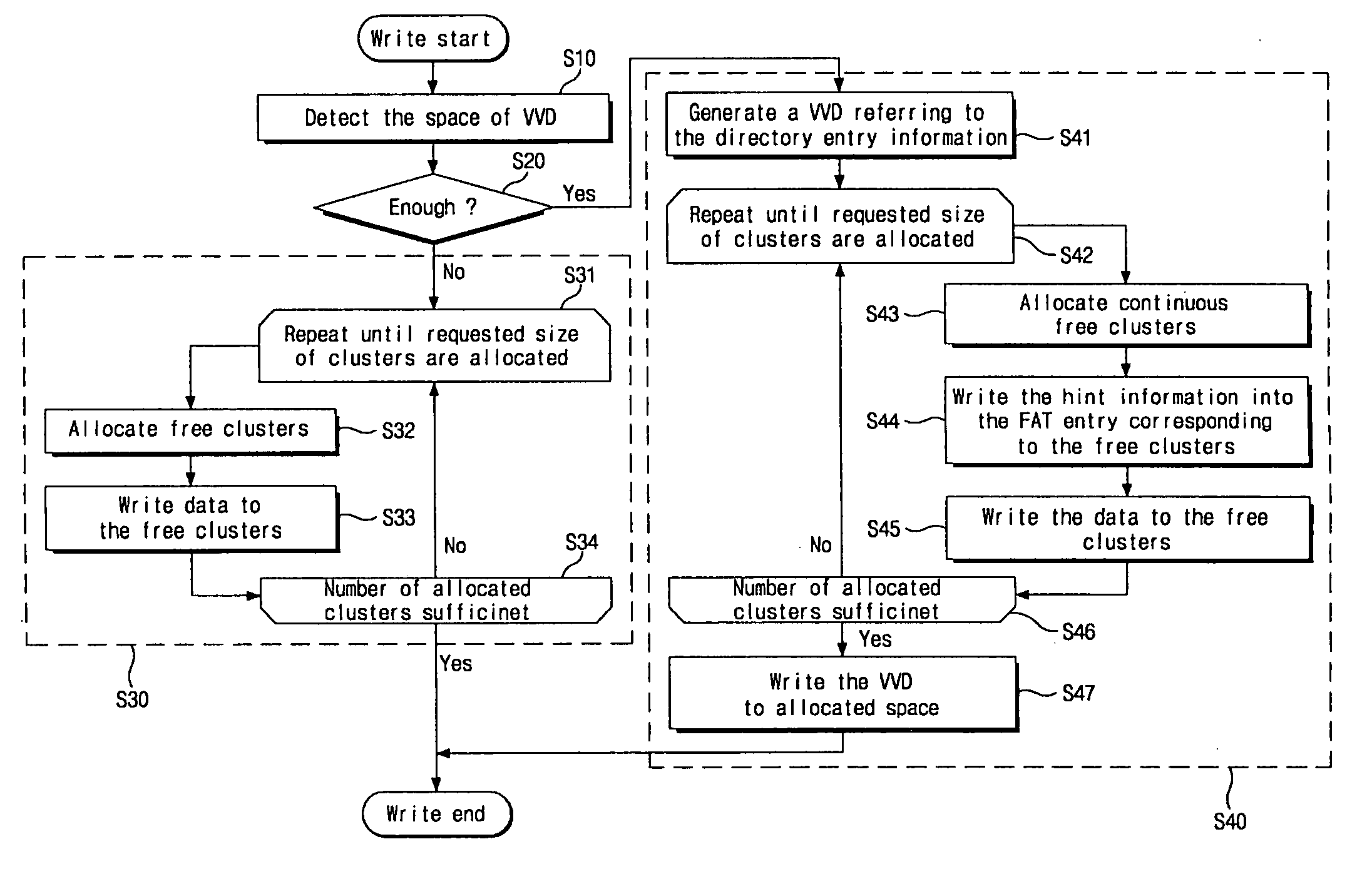
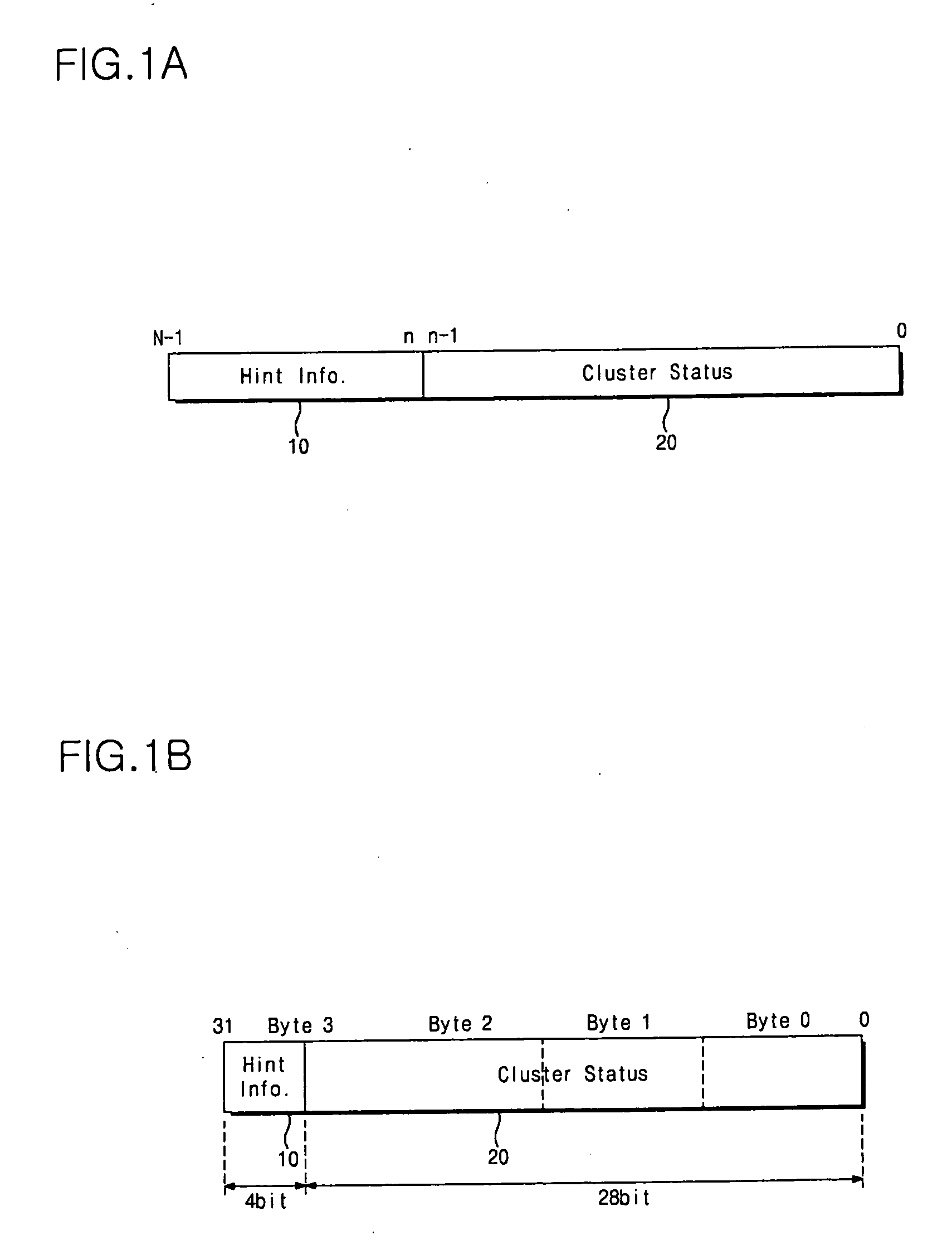
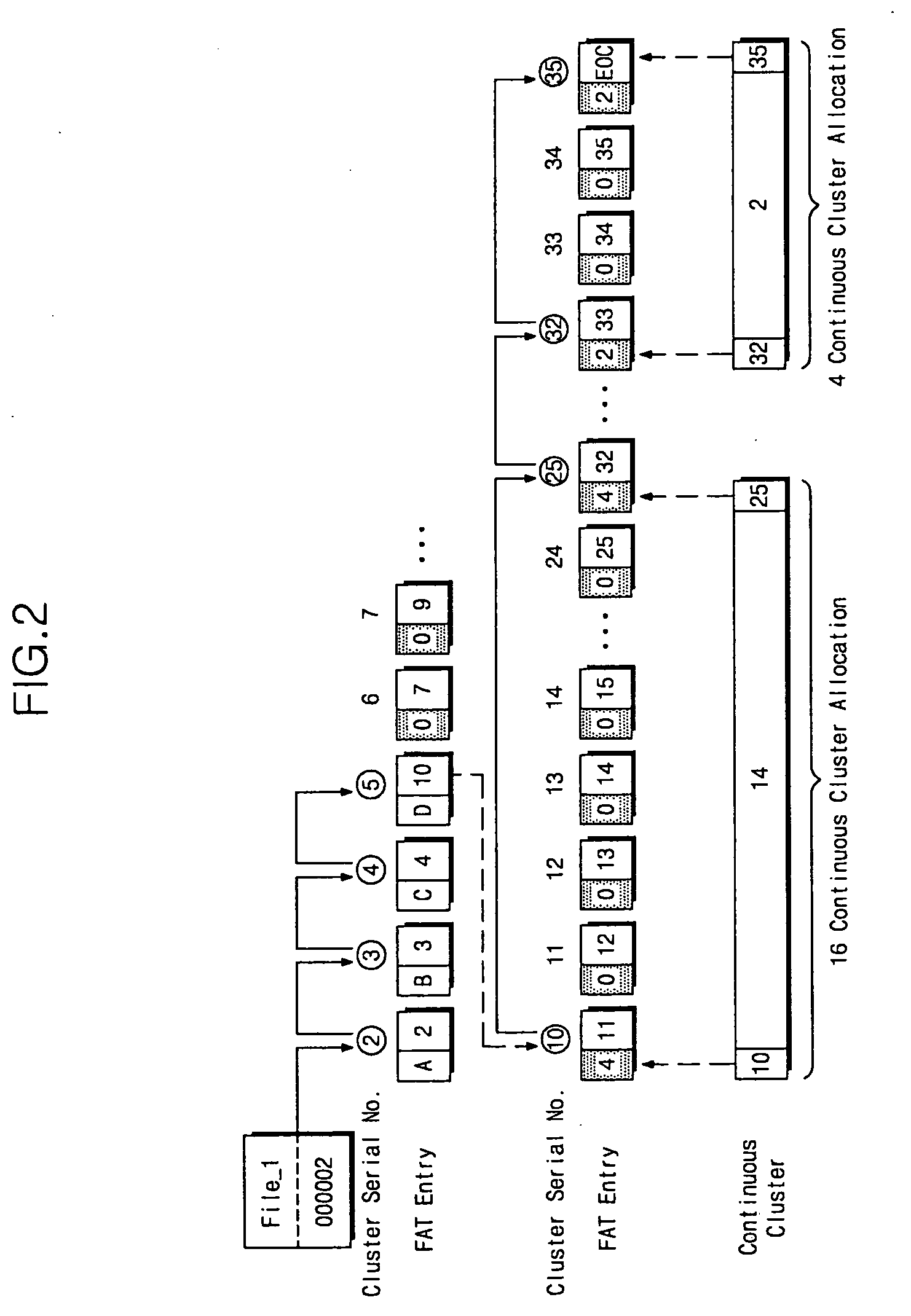
Disclosed is a file accessing method of a file system which manages data by a block unit of a fixed size having an index and provides information associated with a file via a plurality of entries having an index and linked information of each of blocks forming the file. The file accessing method includes providing a hint information area to each of the plurality of entries so as to record an access mode or continuous allocation information for the file, allocating the plurality of blocks to record contents of the file, and recording the access mode in each of the hint information areas of entries corresponding to a first chain group of the allocated blocks and the continuous allocation information in the hint information area of at least one entry corresponding to a second chain group of the allocated blocks.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system of caching management in cluster file system
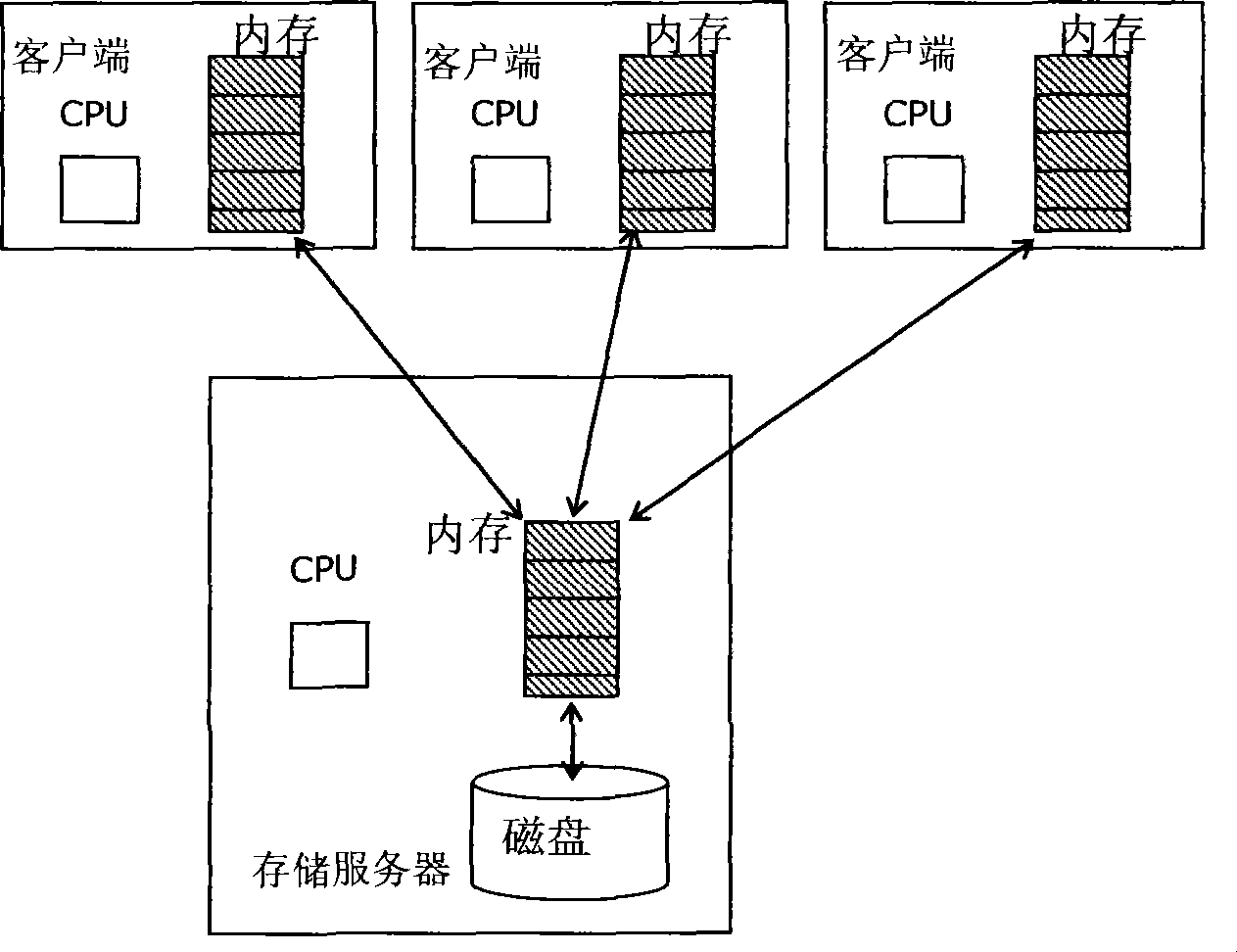
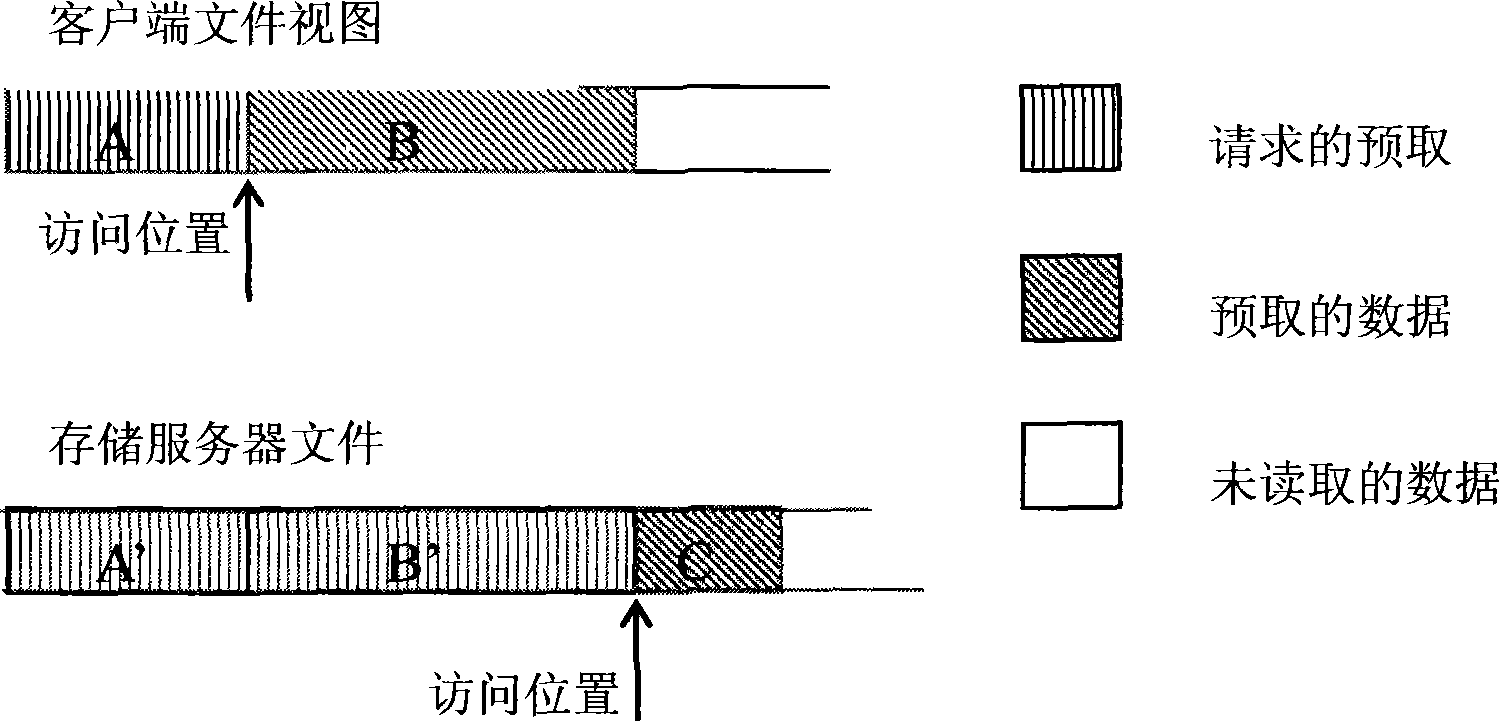
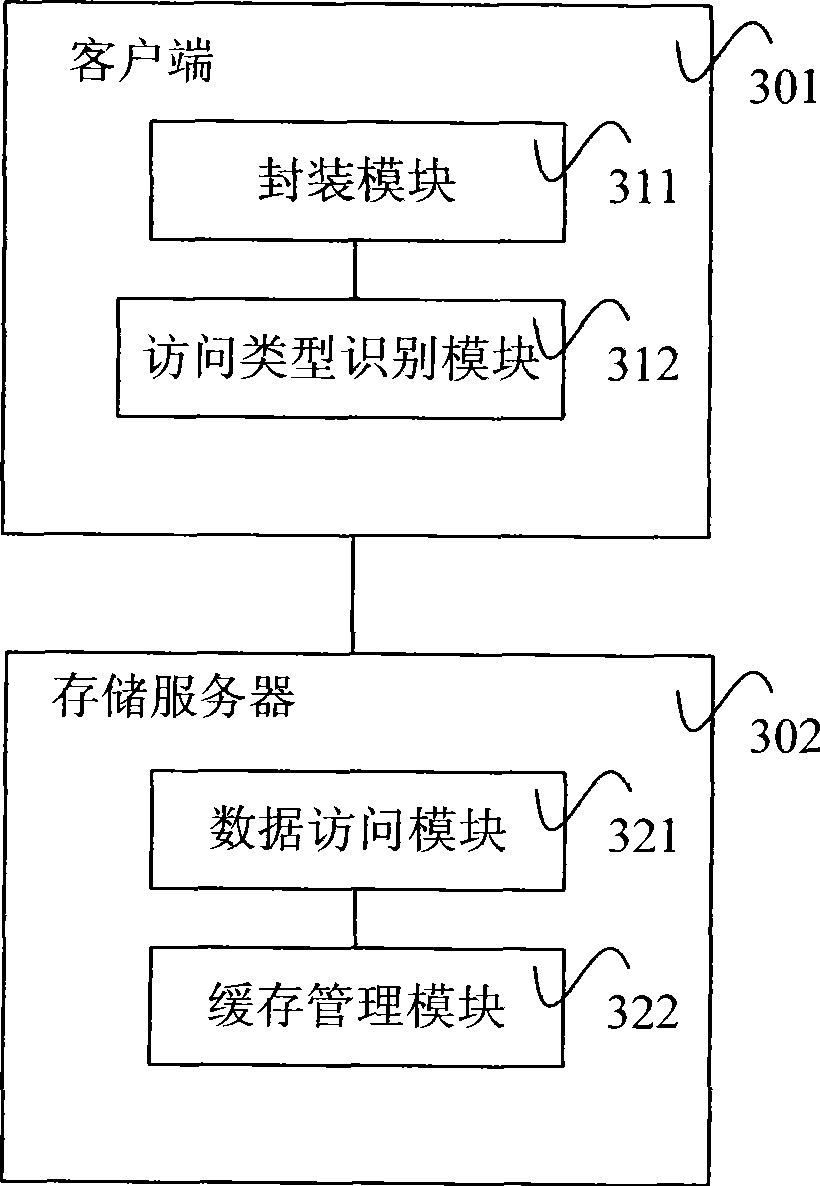
InactiveCN101377788AAvoid Data OverlapImprove overall utilizationMemory adressing/allocation/relocationSpecial data processing applicationsClient-sideClustered file system
The invention relates to a method for cache management in a cluster file system and a system thereof. The method comprises the steps of receiving a request for accessing files on an application layer by a client end and encapsulating the request for accessing files into the read request information. The method further comprises the following steps: step 1. the client end identifies the access module information corresponding to the read request; step 2. the client end encapsulates the access model information into the read request information, and sends the read request information to a storage server; step 3, the storage server receives the read request information, and reads the data to be accessed from the storage server by read request information from the disk of the storage server, and sends the data to the client end through a response message; step 4, the storage server acquires the access model information through resolution from the read request information. The caching of the data accessed by the read request information in a server-end memory is managed according to the access module information. In this way, the caching hit ratio of the storage server end is improved; repeated caching of sequentially prefetched data in memories of all levels is eliminated.
Owner:INST OF COMPUTING TECHNOLOGY - CHINESE ACAD OF SCI
Unified storage method supporting various storage modes
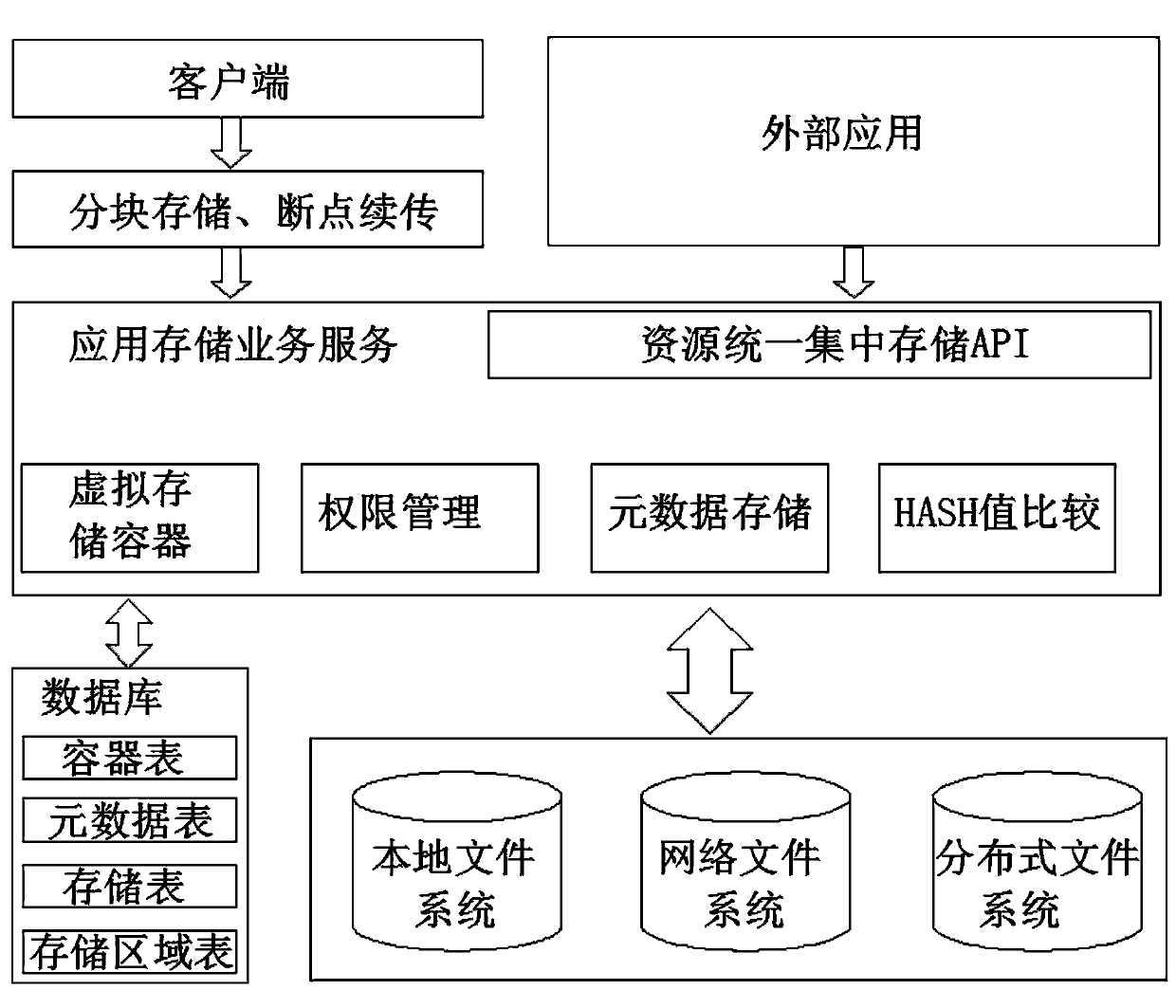
InactiveCN104182487AExpandable and flexibleFlexible switchingSpecial data processing applicationsTable (database)Datasheet
The invention discloses a unified storage method supporting various storage modes. The specific implementation process comprises the following steps: setting a database which comprises four tables: a container table, metadata table, a storage table and a storage region table; accessing the database into a client side, setting a threshold value according to the file size on the client side, dividing a file into N parts, starting a plurality of line paths, and simultaneously uploading all parts of the file; after file uploading, setting a file storage path with id built therein, wherein url is unique; configuring the file, determining the file storage mode, configuring the default virtual space of a storage container, integrating the parts of the file and storing the parts of the file in the database. Compared with the prior art, the unified storage method supporting various storage modes adapts to unified and centralized storage of data resources of different scales, different scenes and different data amounts and is relatively low in maintenance cost and strong in practicability.
Owner:INSPUR SOFTWARE CO LTD
Coordinated access to a file system's shared storage using dynamic creation of file access layout
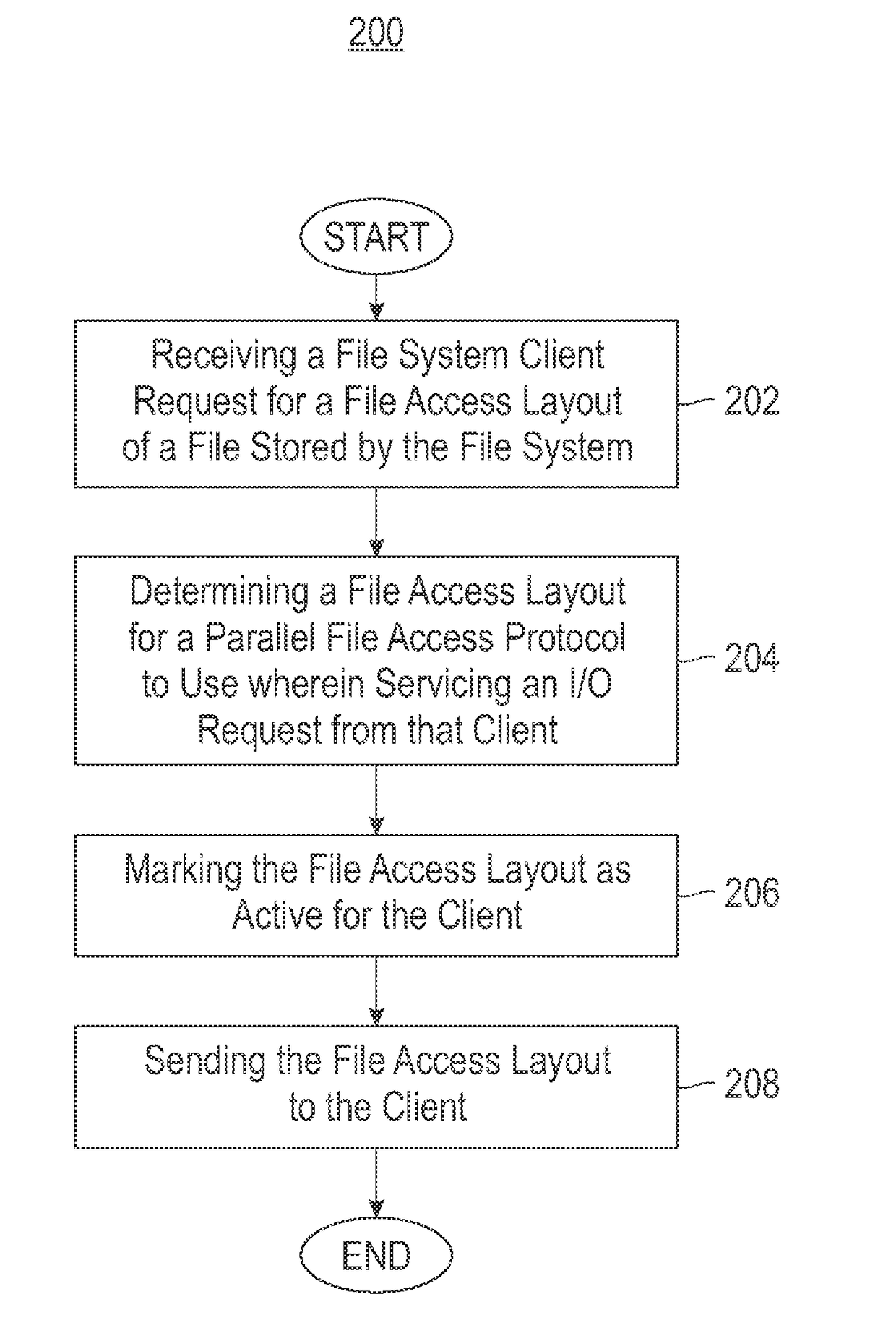
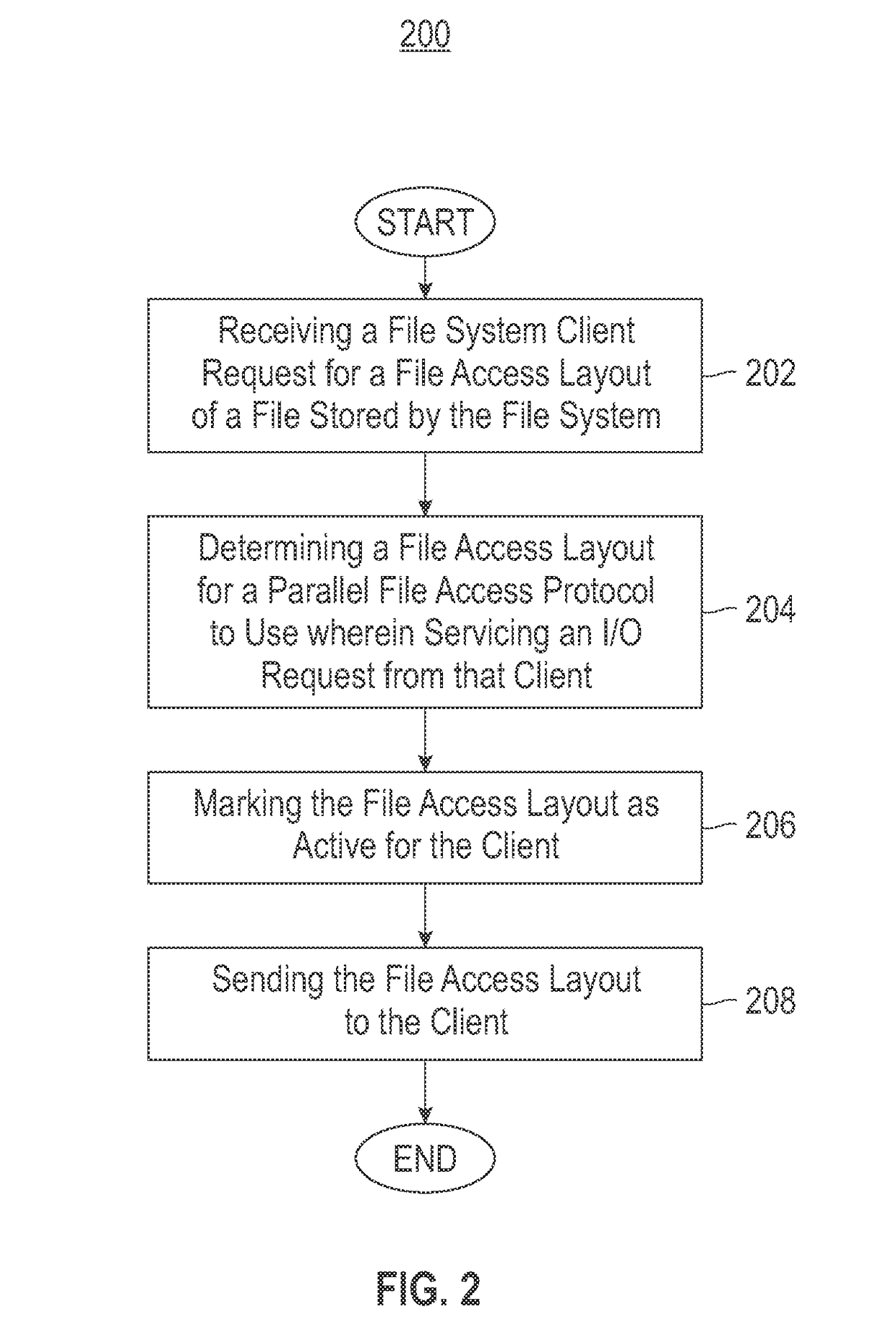
InactiveUS9727578B2Input/output to record carriersDatabase distribution/replicationClustered file systemFile system
Embodiments of the invention relate to supporting coordinated access to a clustered file system's shared disk storage subsystem by using dynamic creation of file access layout for different workloads and access patterns. Active file servers in the cluster have equivalent access to shared data of said file system. In one embodiment, a particular file server in the cluster is configured to coordinate the file system's layout. The particular file server, in response to a particular client's request for a layout of a file stored by said file system in said subsystem determines a file access layout for a parallel file access protocol to use when servicing an I / O request by said client, marks said layout as active for the client, and sends the layout to the client. The file access layout is determined based on one or more of current file system resources, a specific workload type and a specific byte-range of the file included in the client request, and properties of the file. The layout includes a set of file servers in said cluster and byte ranges of the file, and the byte-range being associated with a particular server among the set.
Owner:IBM CORP
Automated database creation
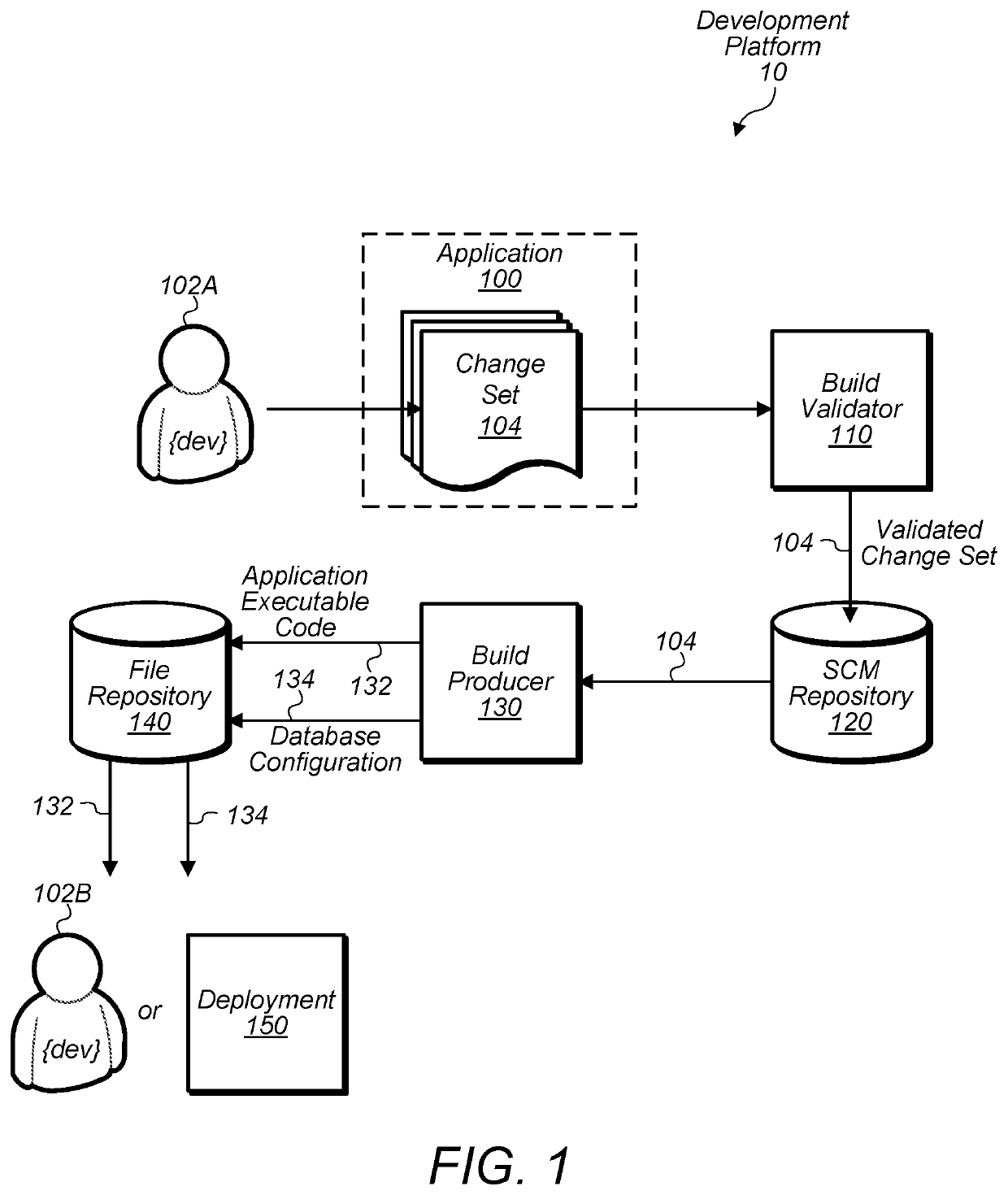
ActiveUS20200004849A1Error detection/correctionVersion controlProgram instructionSoftware engineering
Techniques are disclosed relating to create a configuration for a database system. In some embodiments, program instructions of a change set for an application are received from a source code management (SCM) repository. In response to the receiving, a build process is performed that includes causing compilation of the received program instructions to produce program instructions executable to run the application. The build process also includes provisioning the configuration with a schema by retrieving a first set of metadata defining the schema and issuing corresponding data definition language (DDL) instructions to create the schema in the configuration. The build process includes provisioning the configuration with data by retrieving a second set of metadata defining the data and issuing corresponding data manipulation language (DML) instructions to insert the data into the configuration and storing the provisioned configuration in a repository as one of multiple configurations associated with multiple received change sets.
Owner:SALESFORCE COM INC
Program white list generation method and device and program updating method and device
PendingCN111914249AAvoid spreadingEnsure safetyPlatform integrity maintainanceSoftware deploymentSoftware engineeringModes
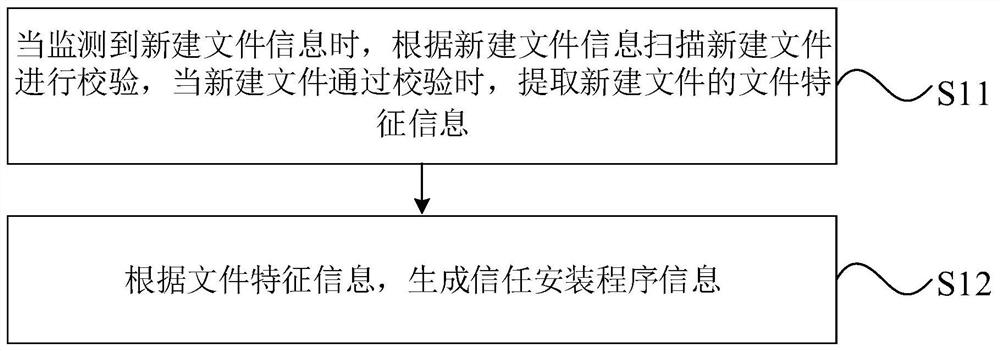
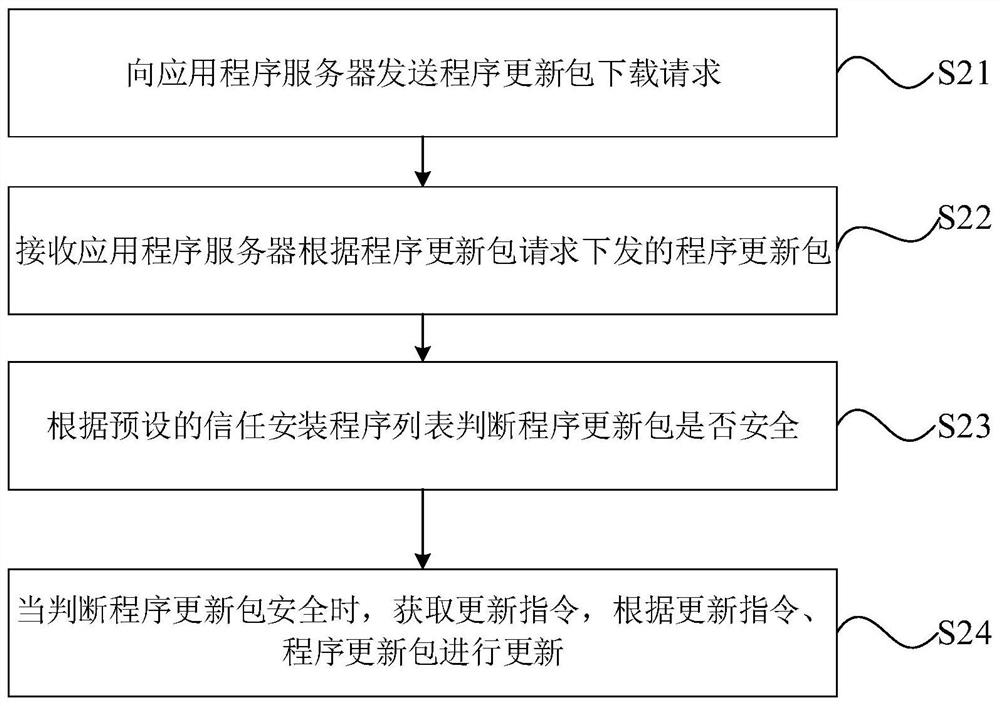
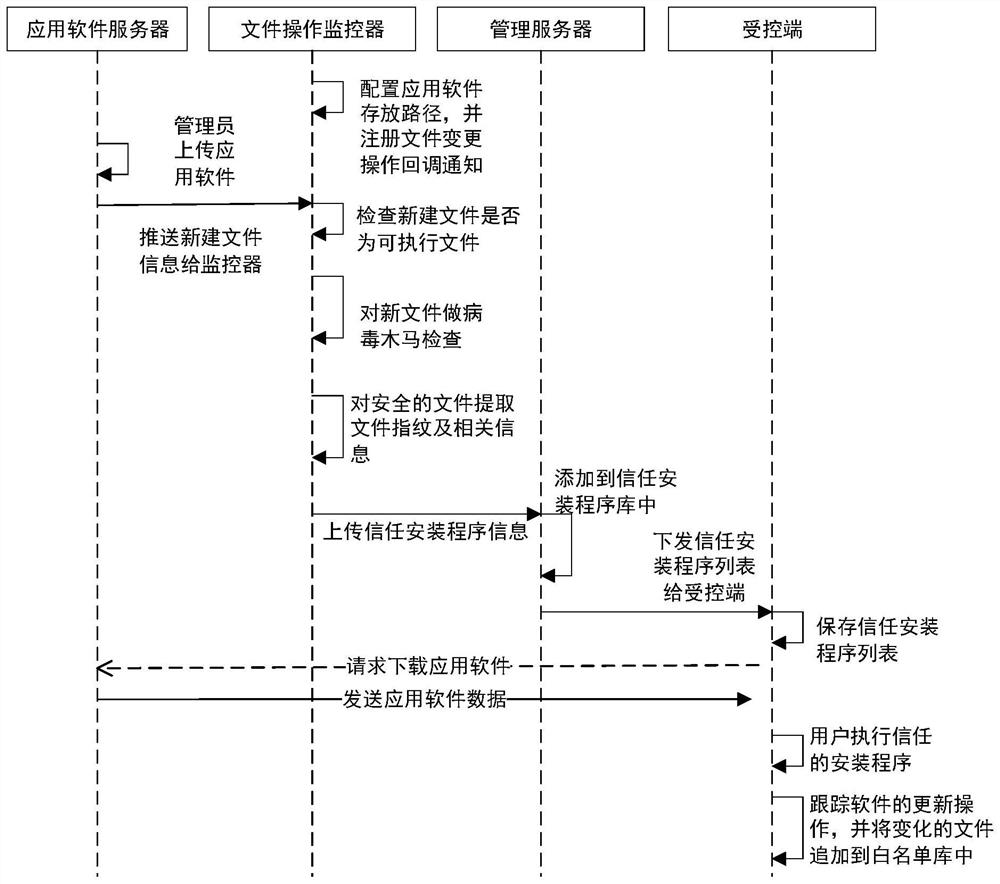
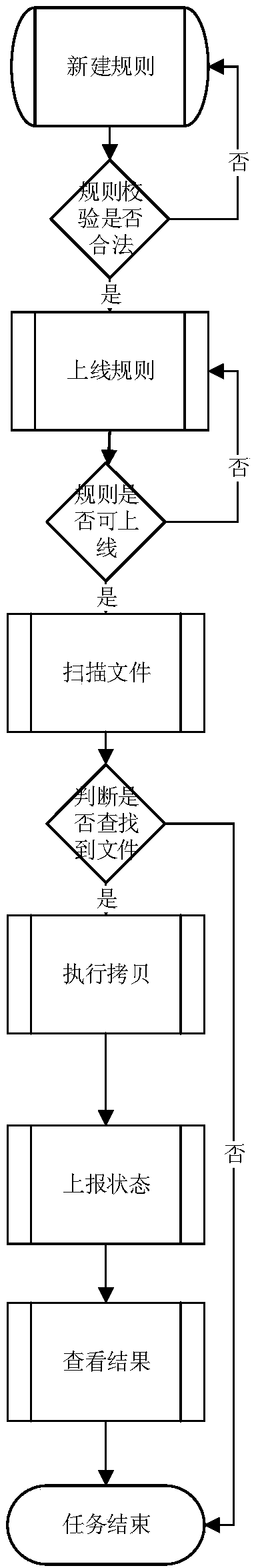
The invention discloses a program white list generation method and device and a program updating method and device, and the method comprises the steps: monitoring a target file storage directory basedon a file change notification mechanism, scanning a newly-built file for verification when the information of the newly-built file is monitored, and updating the newly-built file when the newly-builtfile passes the verification; extracting file feature information; and generating trust installation program information according to the file feature information. The problem of potential safety hazards caused by the fact that the industrial control host updates a program update package without checking the program update package is solved, the security of the program update package is ensured by automatically scanning the newly-built file and searching and killing a virus Trojan, and the propagation of the virus Trojan in an industrial control network is avoided; and the full-automatic processing flow of the program from downloading to installation in the program white list control mode is realized, and the safe updating of the program is realized on the premise of not changing the usehabit of the user.
Owner:北京珞安科技有限责任公司
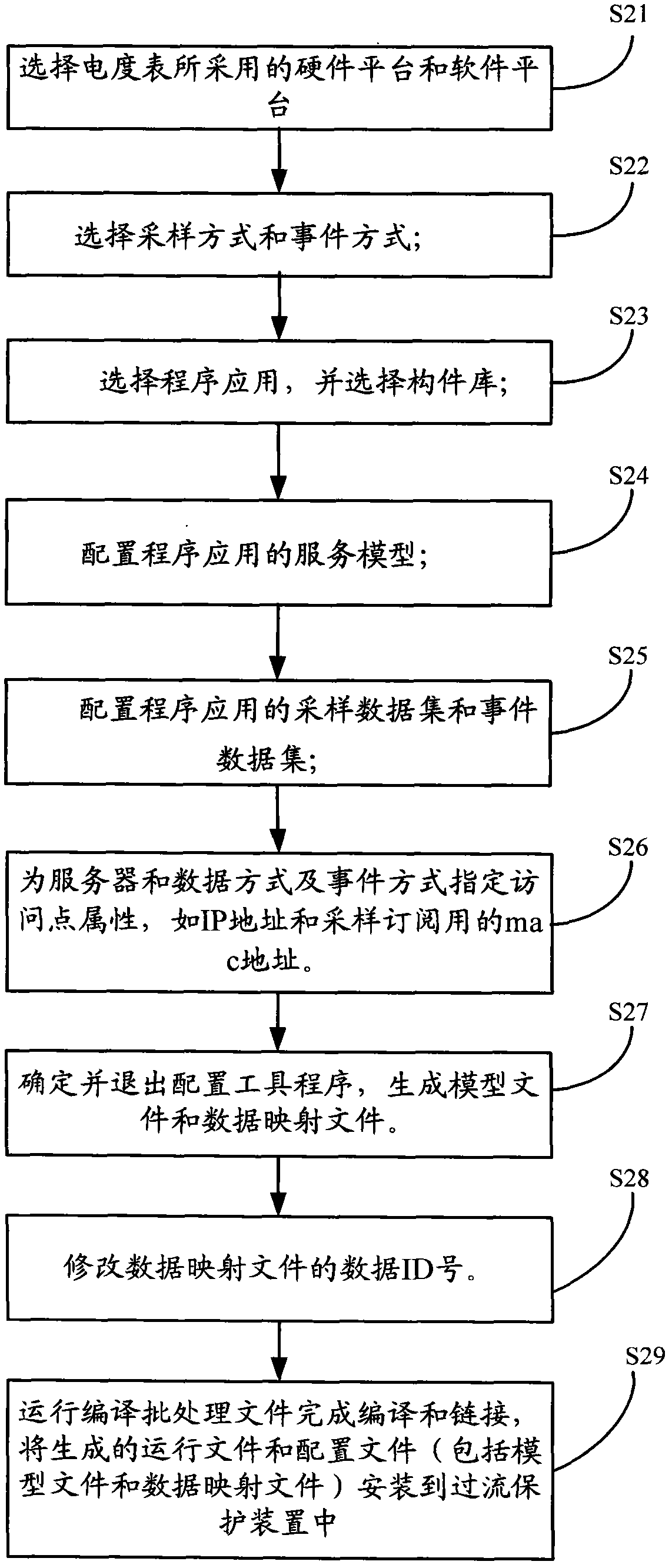
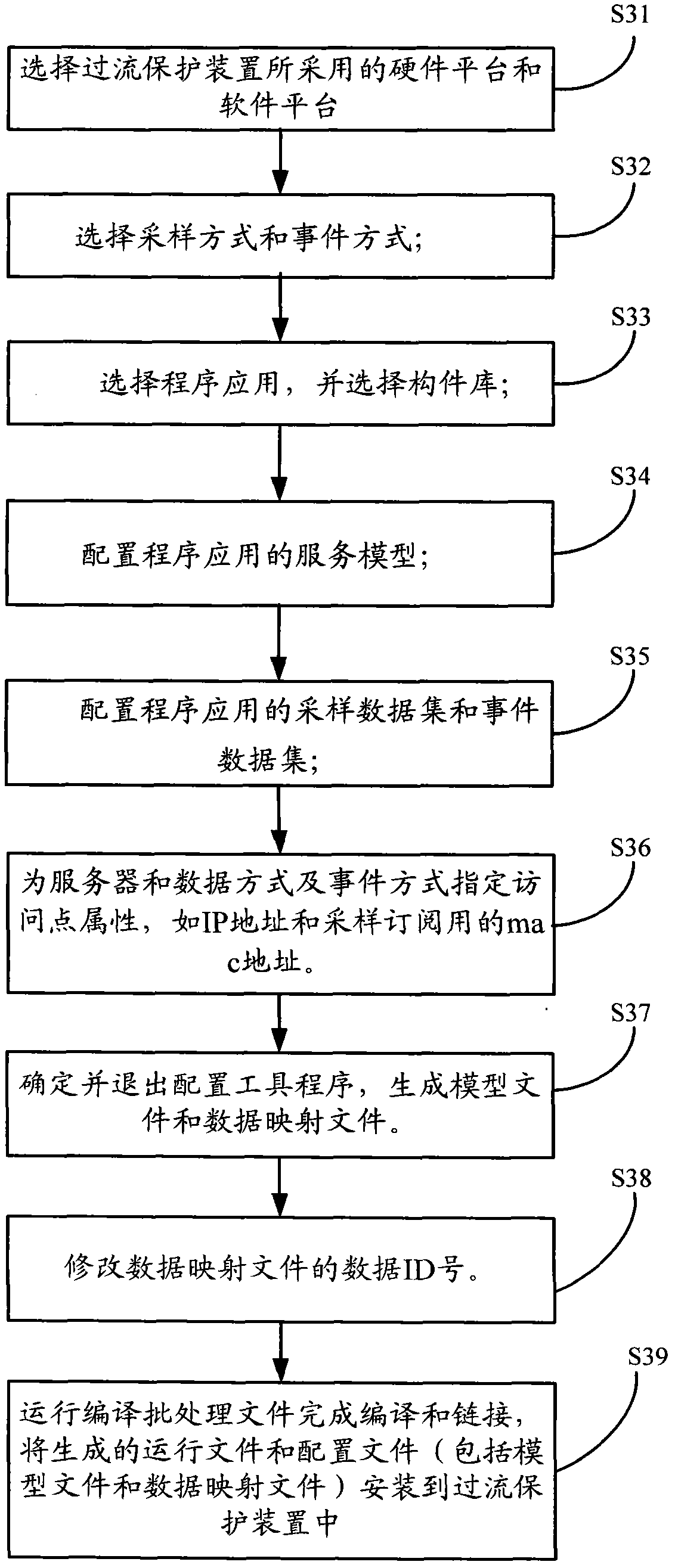
Method for generating programs on basis of IEC (international electrotechnical commission) 61850
ActiveCN103425467ASimplify the development processImprove development efficiencySpecific program execution arrangementsSoftware engineeringSource code
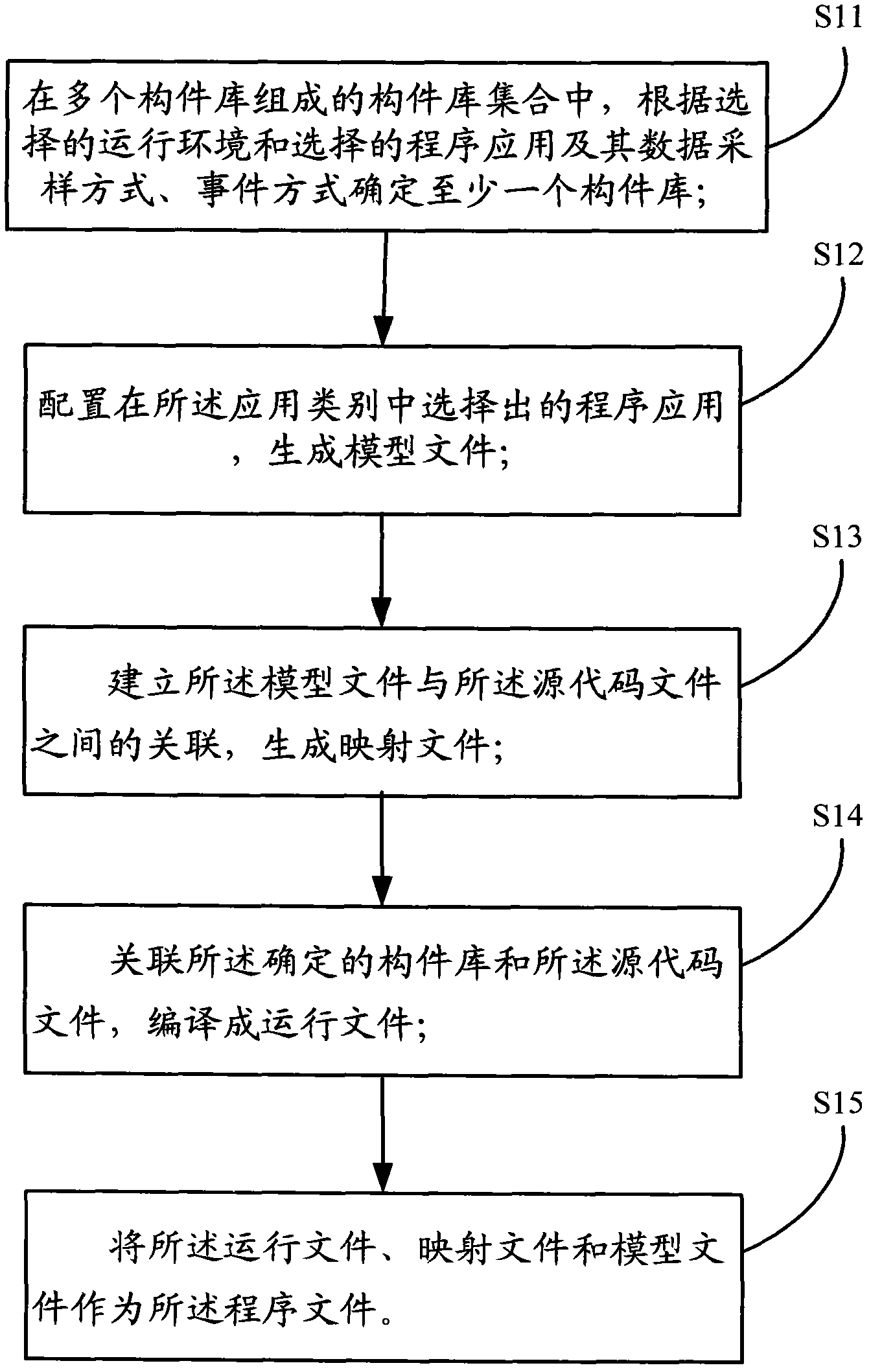
The invention discloses a method for generating program files on the basis of the IEC (international electrotechnical commission) 61850. The method includes determining at least one component library among a plurality of component libraries according to program application, sampling modes, event modes and running environments; configuring the program application to generate model files; establishing relations among the model files and source codes of the program application to generate mapping files; correlating the determined component libraries with the source codes, and compiling the component libraries and the source codes to generate running files; using the running files, the mapping files and the model files as the program files. The component libraries are operating function sets with APIs (application program interfaces). The method has the advantages that IEC61850-related functions are packaged in component library and selection configuration procedures in advance, so that the running files, the mapping files and the model files which are used as the program files can be acquired via a few steps, a program development procedure is simplified, and the program development efficiency is improved.
Owner:汪巨森
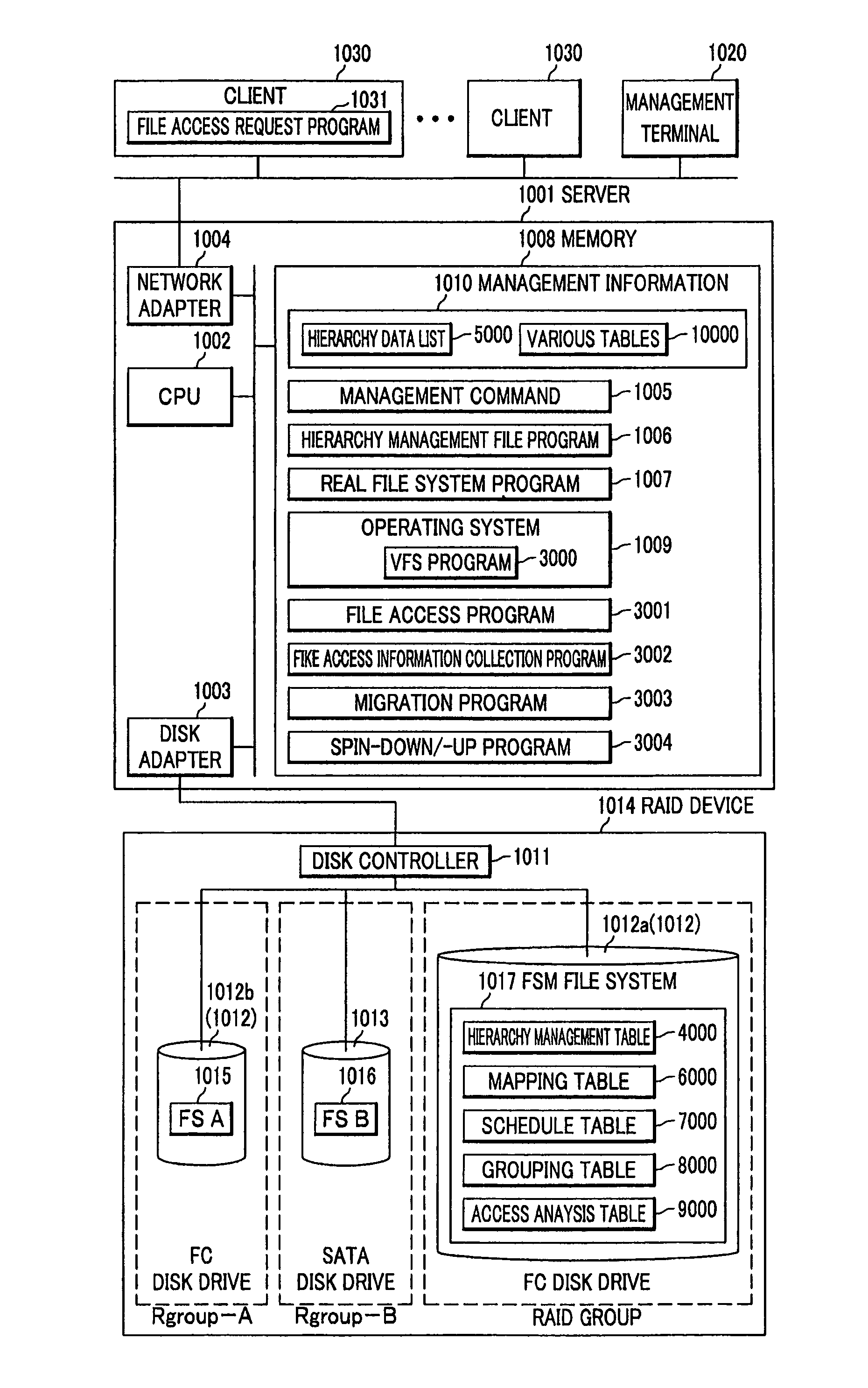
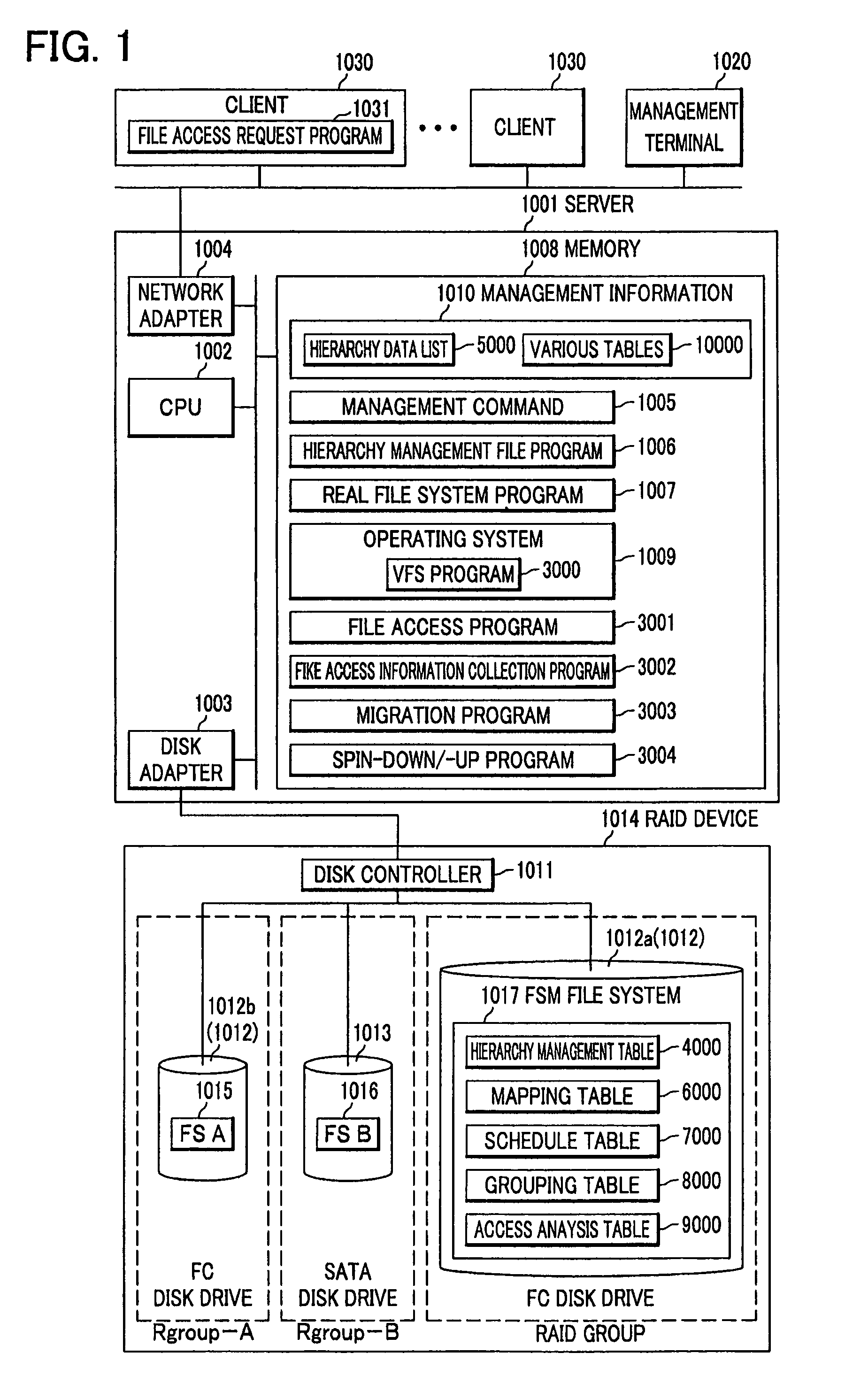
File server, file management system and file management method
Owner:HITACHI LTD
Method, system and apparatus for defending bypassing of file uploading verification, and medium
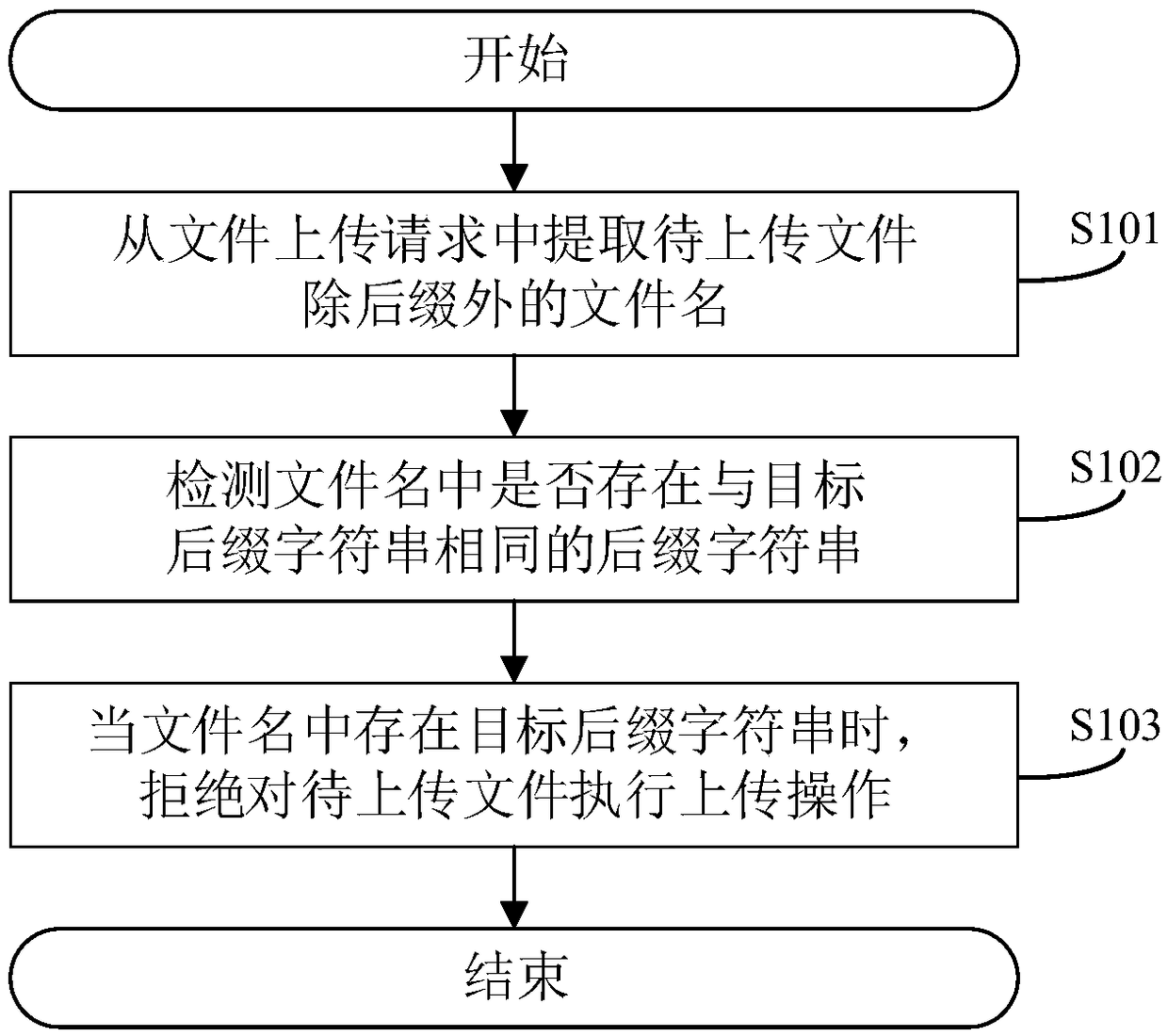
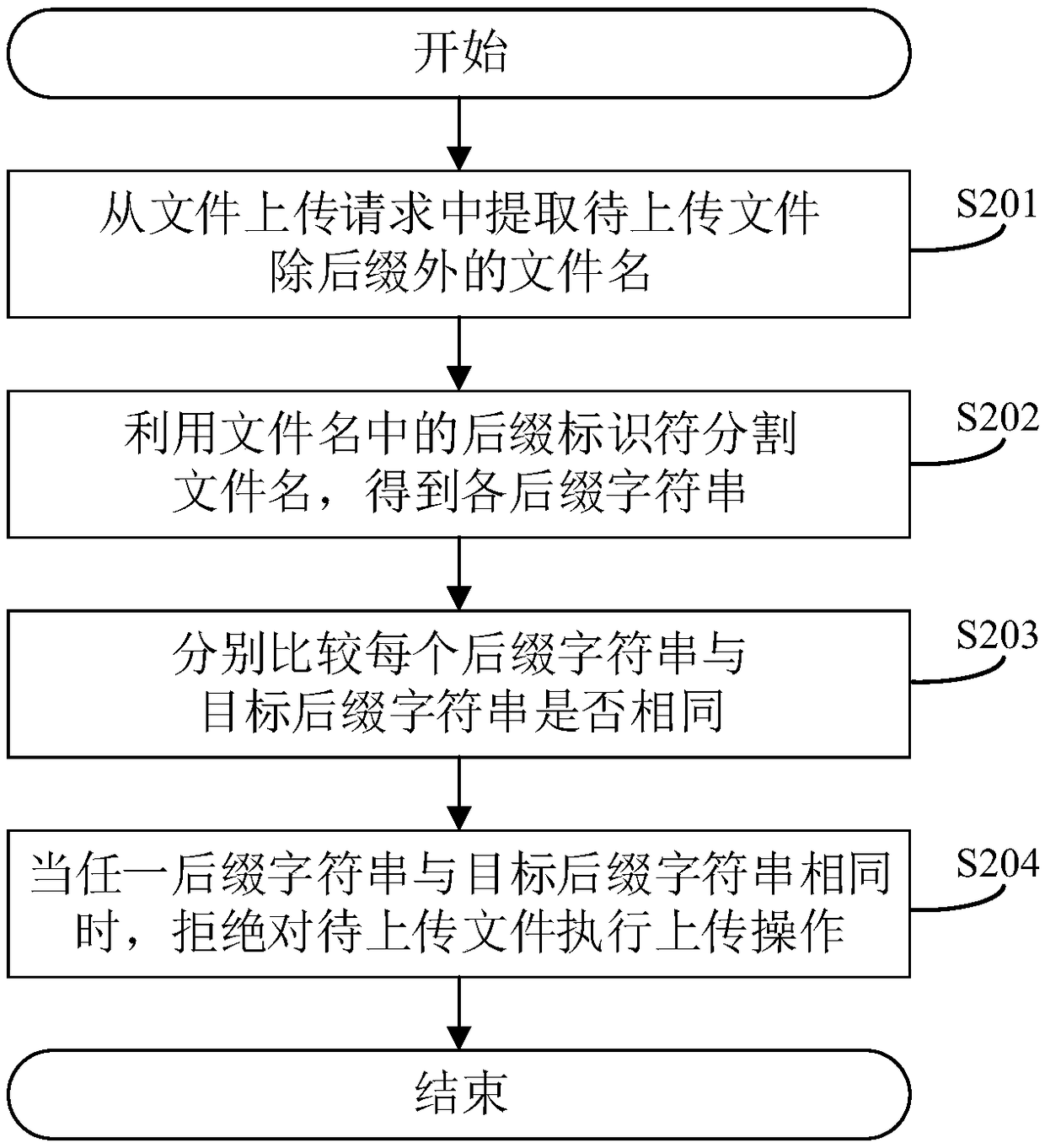
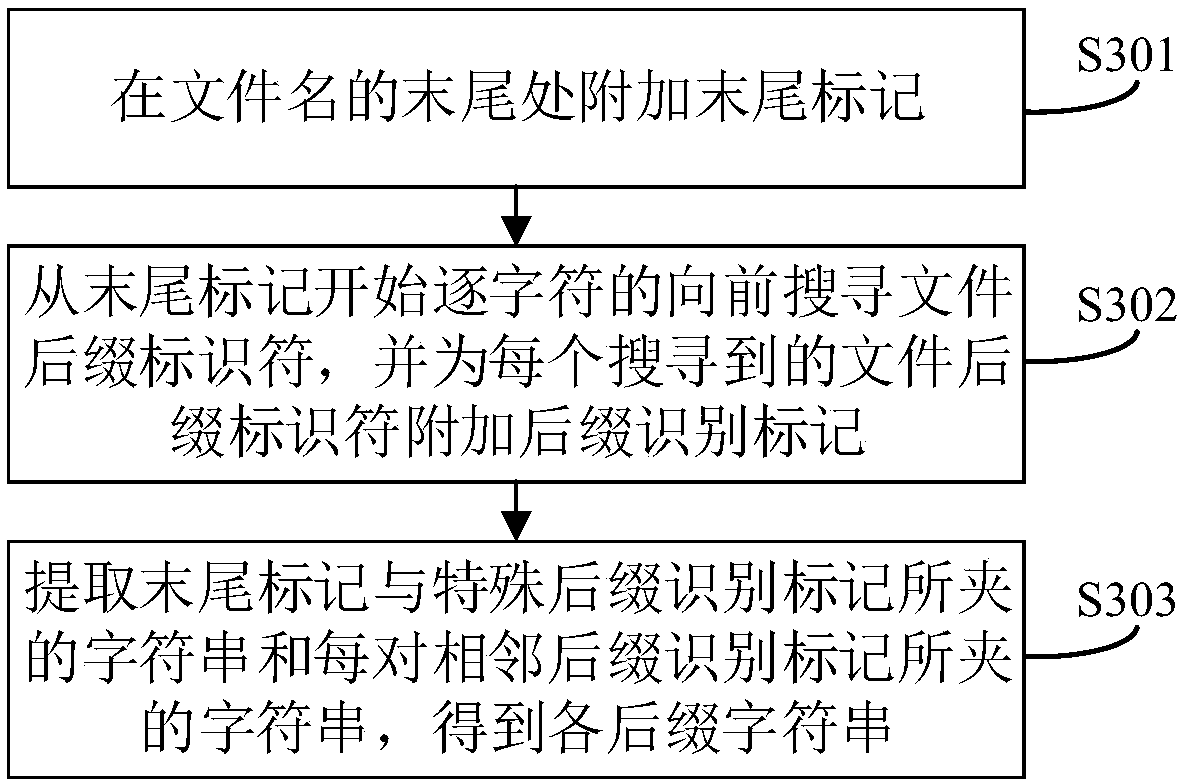
The invention discloses a method for defending bypassing of file uploading verification. The method comprises the following steps: when uploading verification is performed on a file to be uploaded, firstly obtaining a file name with a removed suffix, detecting whether the file name contains a suffix character string the same as a target suffix character string, and refusing the uploading of the file to be uploaded when the suffix character string the same as the target suffix character string is discovered. Different from the manner of only performing the uploading verification on the last suffix in the prior art, according to the method disclosed by the invention, the suffix character string hidden in the file name is also detected, so that accurate detection can be performed effectivelyon a plurality of existing bypassing manners, the method is applicable to the modes of multiple kinds of server management software to parse files, and the possibility of jeopardizing a server and thedata in the server by the file uploading vulnerability can be greatly reduced, so that the security is higher. The invention further discloses a system and apparatus for defending bypassing of file uploading verification, and a computer readable storage medium, which have the above beneficial effects.
Owner:SANGFOR TECH INC
Configuration file control method and device in program development process
InactiveCN102012807AProgram behavior takes effect immediatelySpecific program execution arrangementsSoftware development processProgram behavior
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
Mapping of a file system model to a database object
InactiveUS7478102B2Easy to storeData processing applicationsDigital data information retrievalFile systemModes
Owner:MICROSOFT TECH LICENSING LLC
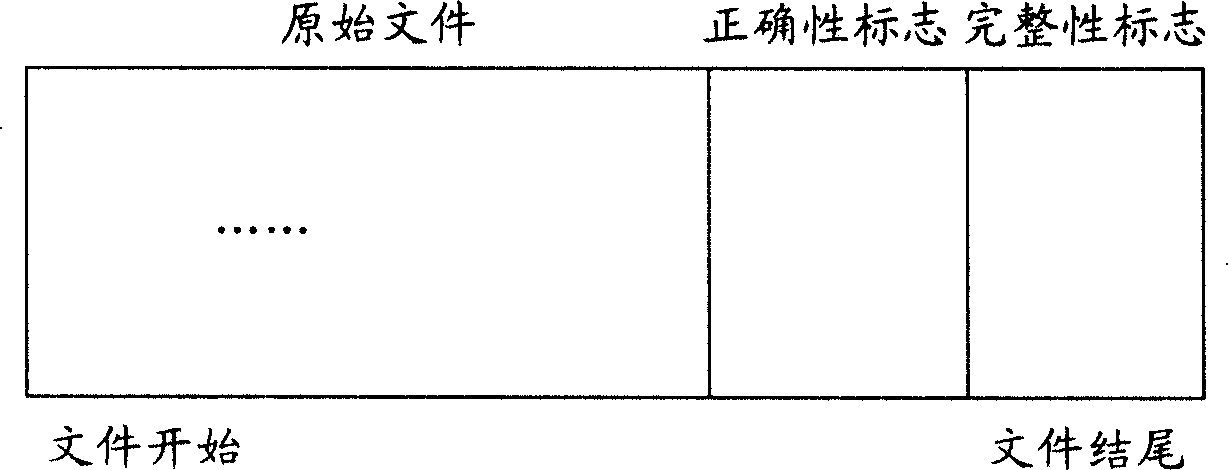
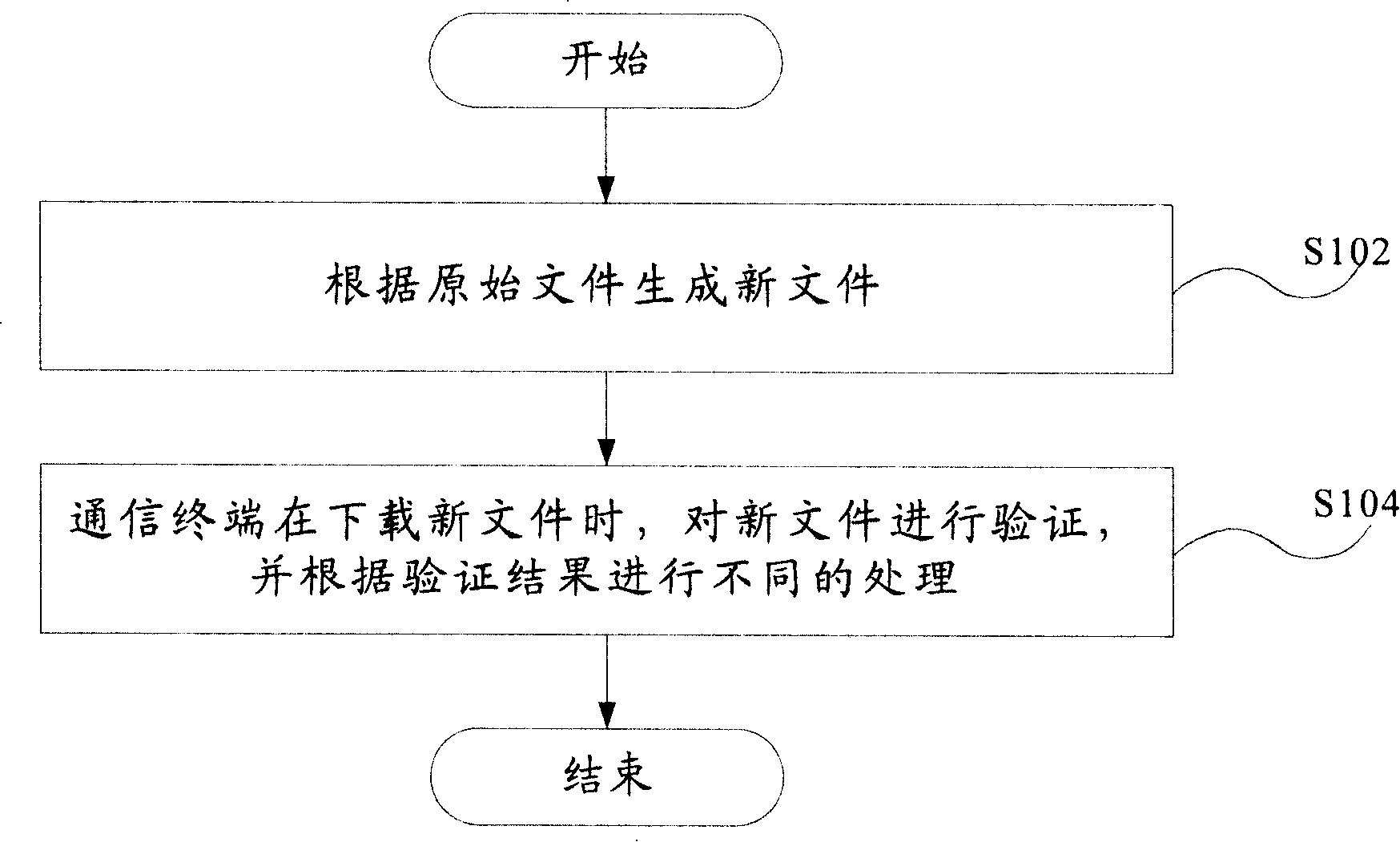
Method and apparatus for avoiding downloading error document
The invention provides a download method as well as a device for avoiding downloading error files. The method comprises the following steps: the step S102, a new file is generated according to a primary file; the step S104, the new file is verified when a communication terminal downloads the new file, and different processing modes are carried out according to the verification result; thus the error files can be prevented from being downloaded through the invention, thereby effectively guaranteeing to only download correct and complete files to a veneer, and further ensuring the reliability of downloading and upgrading.
Owner:ZTE CORP
Protection method and system for HDFS access mode
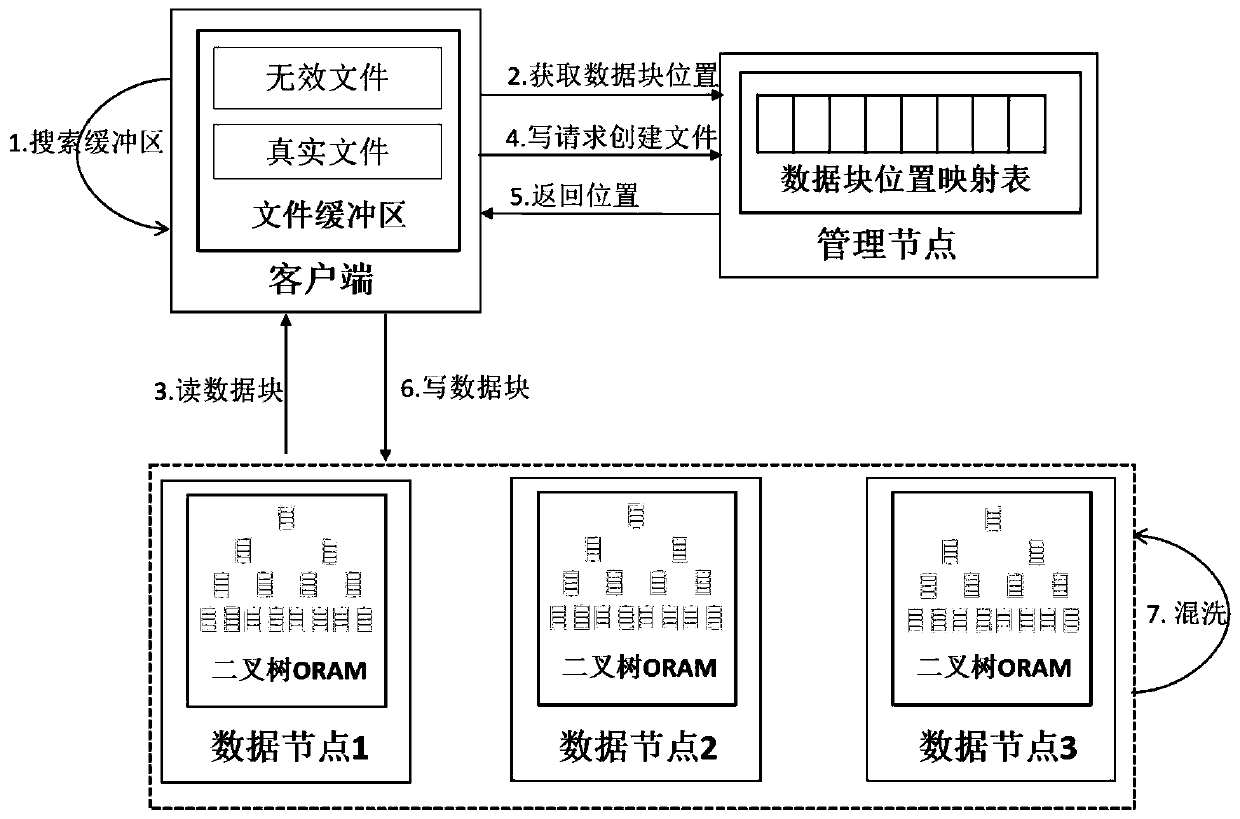
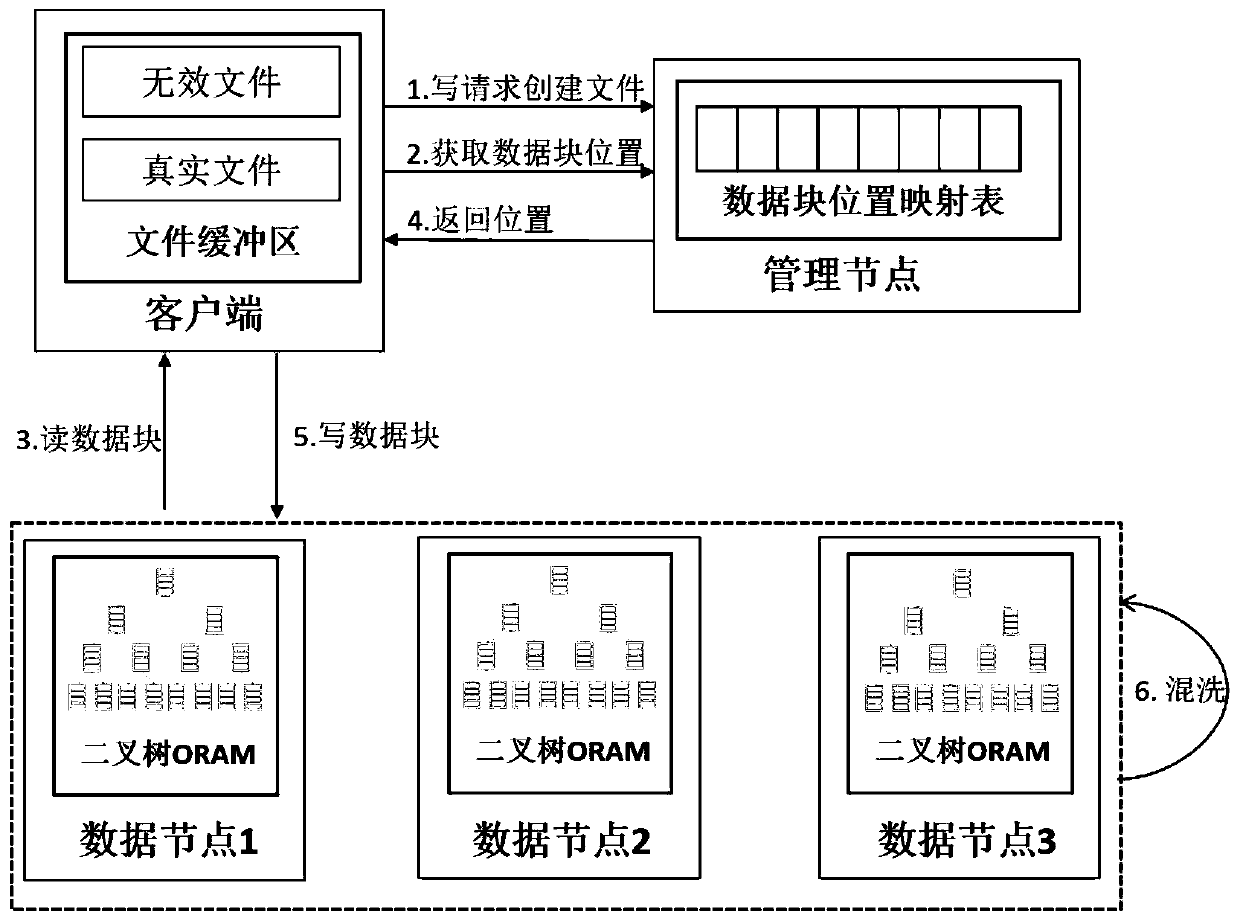
ActiveCN110245515AProtected Access ModeImprove securityDigital data protectionAccess frequencyComputer science
The invention relates to a protection method and system for an HDFS access mode. The method comprises the following steps: decomposing a reading operation and a writing operation on a data node of an HDFS cluster into two atomic operations of reading first and writing second so as to hide an operation type of a file; adding obfuscated data blocks for the file before writing the file to the data node so as to hide the number of blocks of the file; deleting the file from the data node after reading the file each time, and randomly selecting one file in the file buffer area of the client to write back to the data node so as to hide the position of the data node stored in the file; and hiding the access frequency and the access sequence of the file through the continuous change of the storage position of the file. According to the invention, the design and implementation of the HDFS access mode protection scheme based on the ORAM technology are provided, the blank of HDFS access mode protection is filled, and the brought performance overhead is in an acceptable range while the HDFS security is enhanced.
Owner:PEKING UNIV
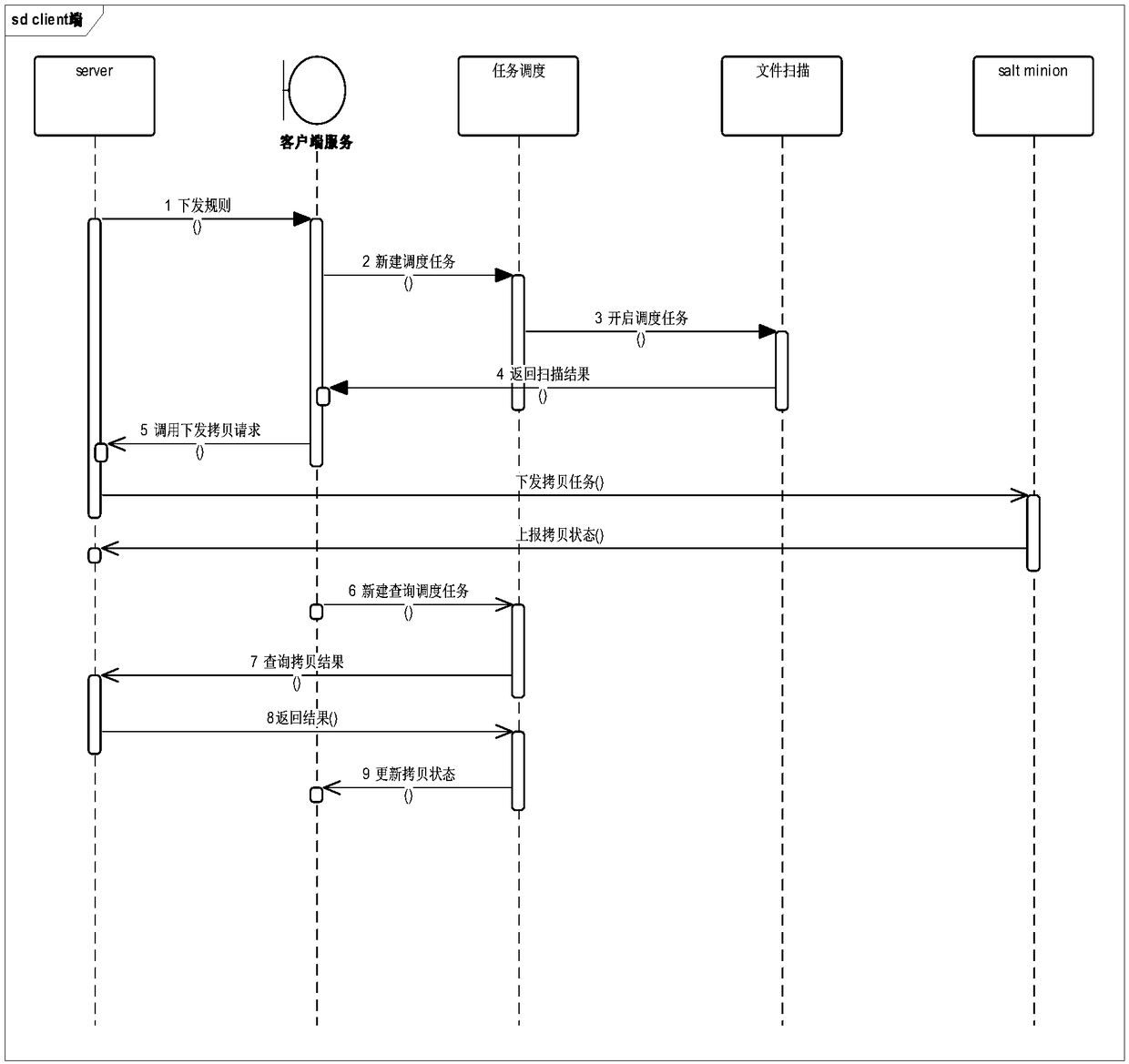
File distribution method and system based on micro-service architecture mode
ActiveCN108234607ASupport copyFully decoupledTransmissionSpecial data processing applicationsDistribution methodDistribution system
The invention discloses a file distribution method and system based on a micro-service architecture mode, which is designed and developed combined with the open source system software saltstack on thebasis of the micro-service distributed architecture. The scene for the invention is file copy between different network mapping disks (including physical disks) of a single file server; wherein the file servers are existed in the form of clusters, no central server exists, and no correlation and influence is existed among the servers. The schemes in the prior art are looked up, and no scheme cansatisfy the scene better. The file distribution method and system based on the micro-service architecture mode is used as a scene supplement to the schemes in the prior art; not only the schemes in the prior art are enriched, but also optimization and innovation are carried out on the architecture; the micro-service architecture which is popular currently is used for decoupling among services adequately, therefore, the stability and reliability of the system are greatly improved, and the file distribution systems and methods in the prior art are enriched.
Owner:上海中畅数据技术有限公司
System and method for real-time detection of computer system files intrusion
InactiveUS20080010681A1Memory loss protectionUnauthorized memory use protectionOperational systemSystem call
Owner:TREND MICRO INC
Performing live updates to file system volumes
ActiveCN107870968AReduce the amount of timeEliminate downtimeSoftware engineeringRedundant operation error correctionOperational systemFile system
The present invention provides 'performing live updates to file system volumes'. The described embodiments set forth techniques for performing live updates to file system volumes (e.g., operating system (OS) file system volumes) of computing devices through the utilization of snapshots. In particular, the techniques enable a computing device to remain active while a majority of an update process is performed, which eliminates the considerable functional downtime that is normally imposed when implementing conventional update techniques. Moreover, the overall robustness of the update process isenhanced as the techniques described herein reduce the amount of time that is required for the computing device to remain in the above-described specialized update mode.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com