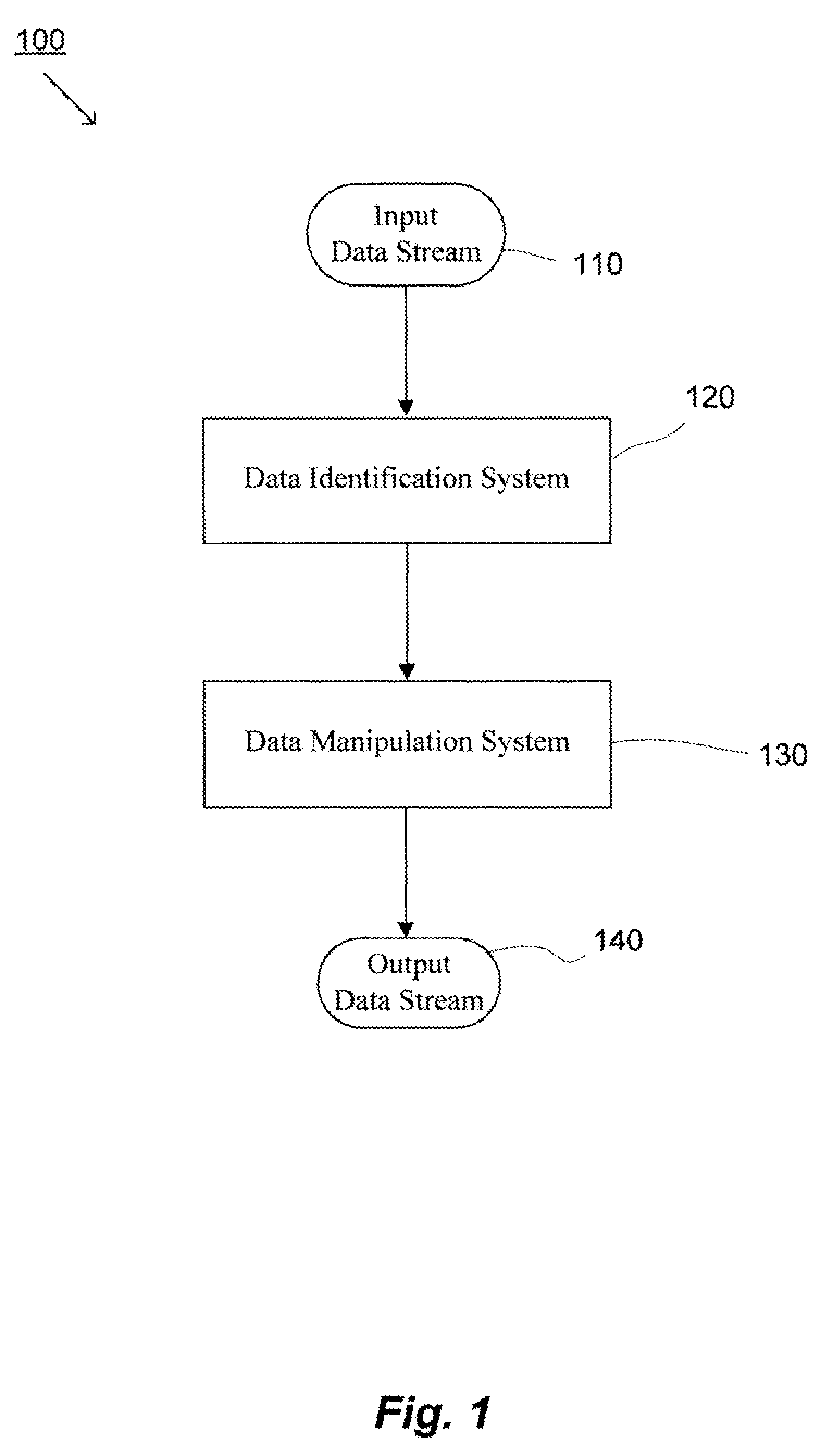
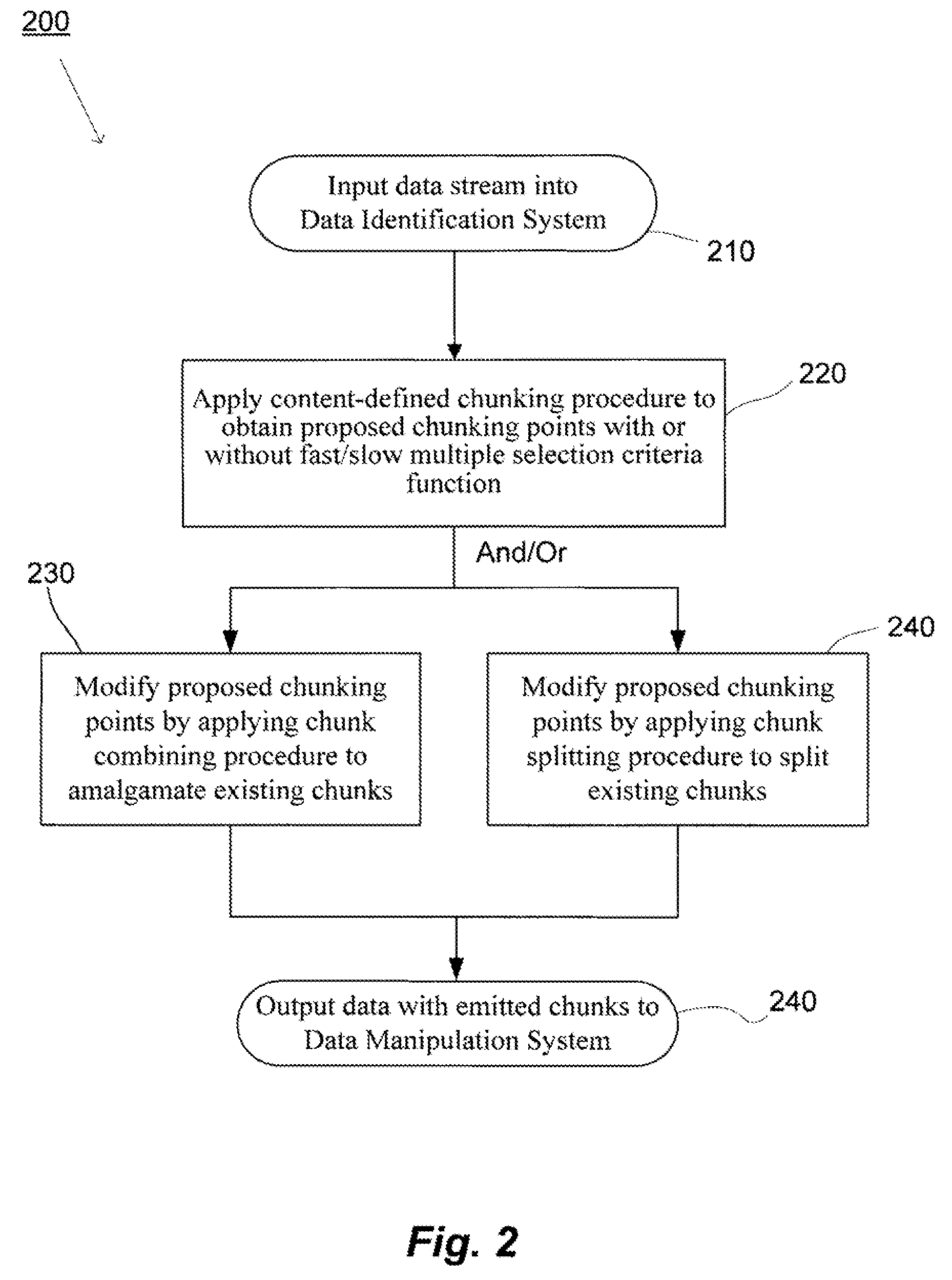
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2905results about "Program control using stored programs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
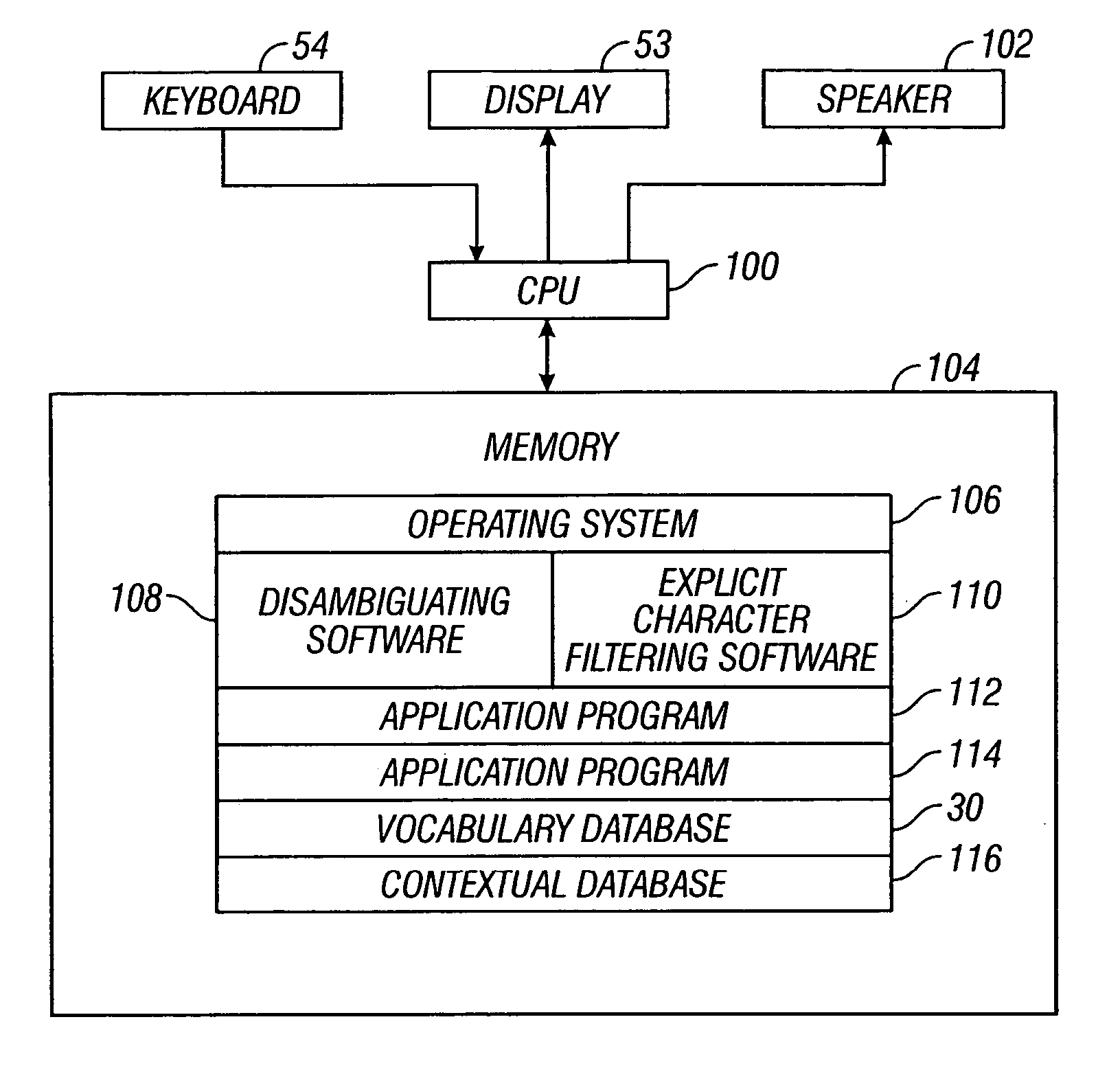
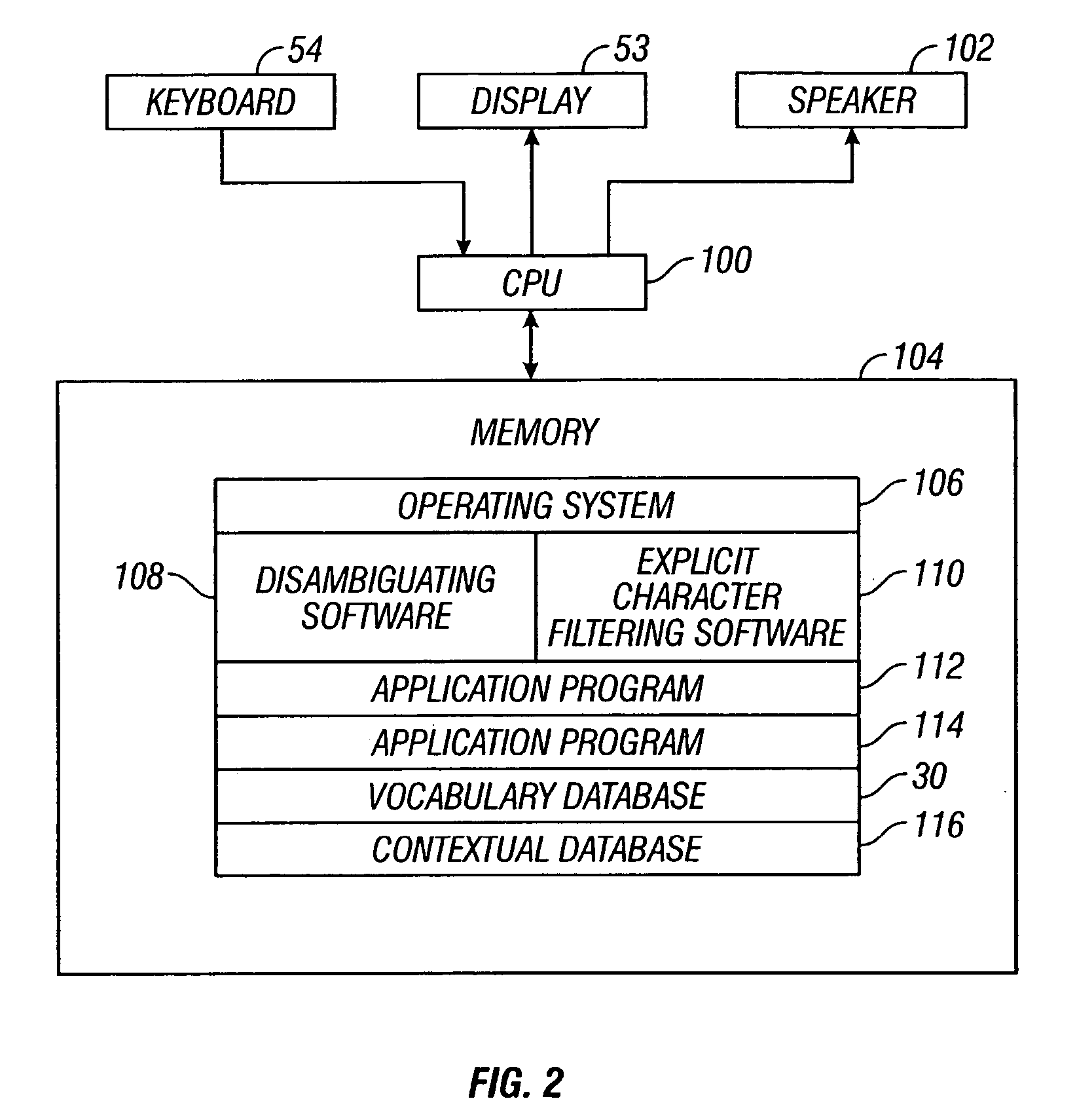
Contextual prediction of user words and user actions
InactiveUS7679534B2Increase volumeHigh levelInput/output for user-computer interactionProgram control using stored programsWord listPhrase
Owner:TEGIC COMM +1
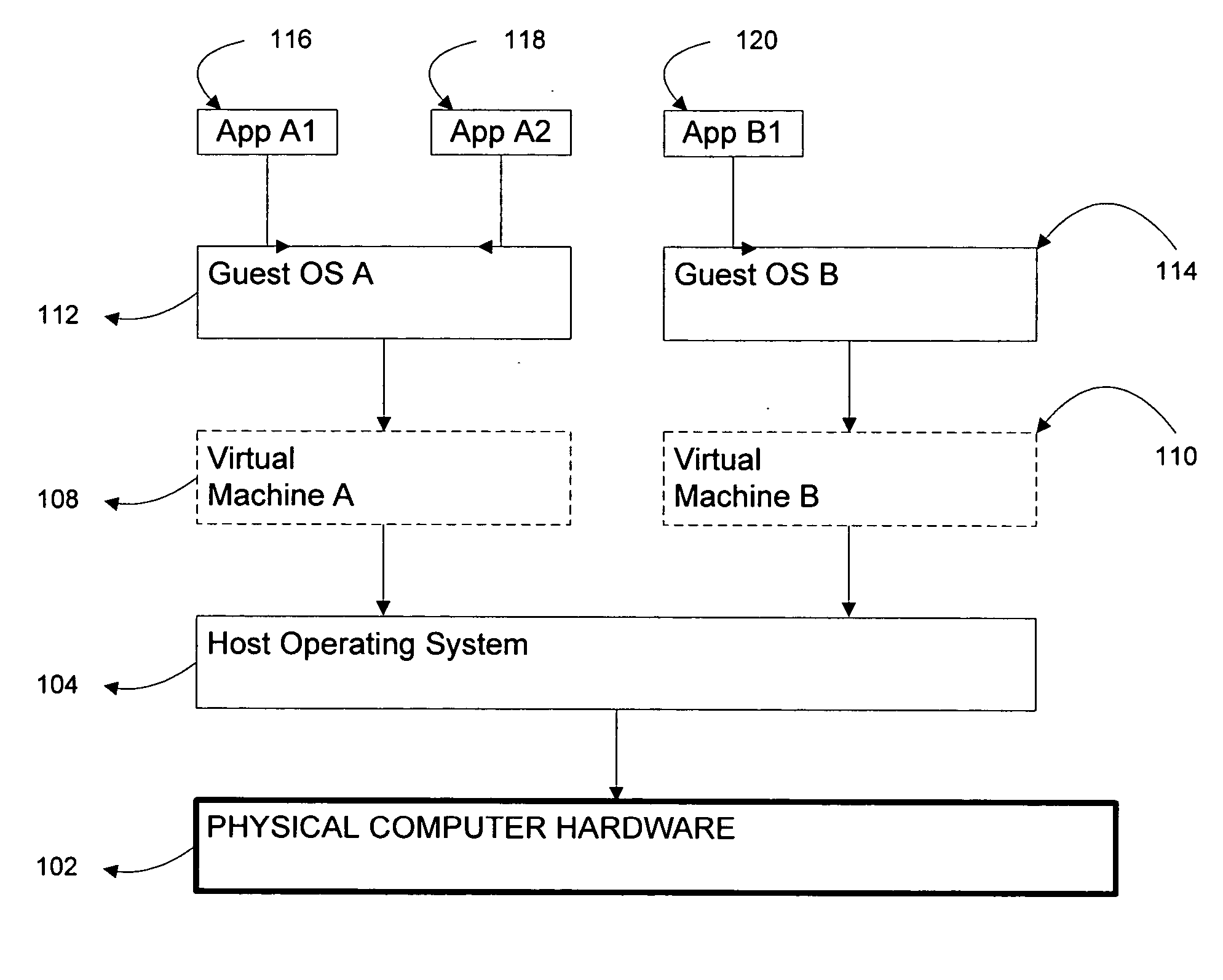
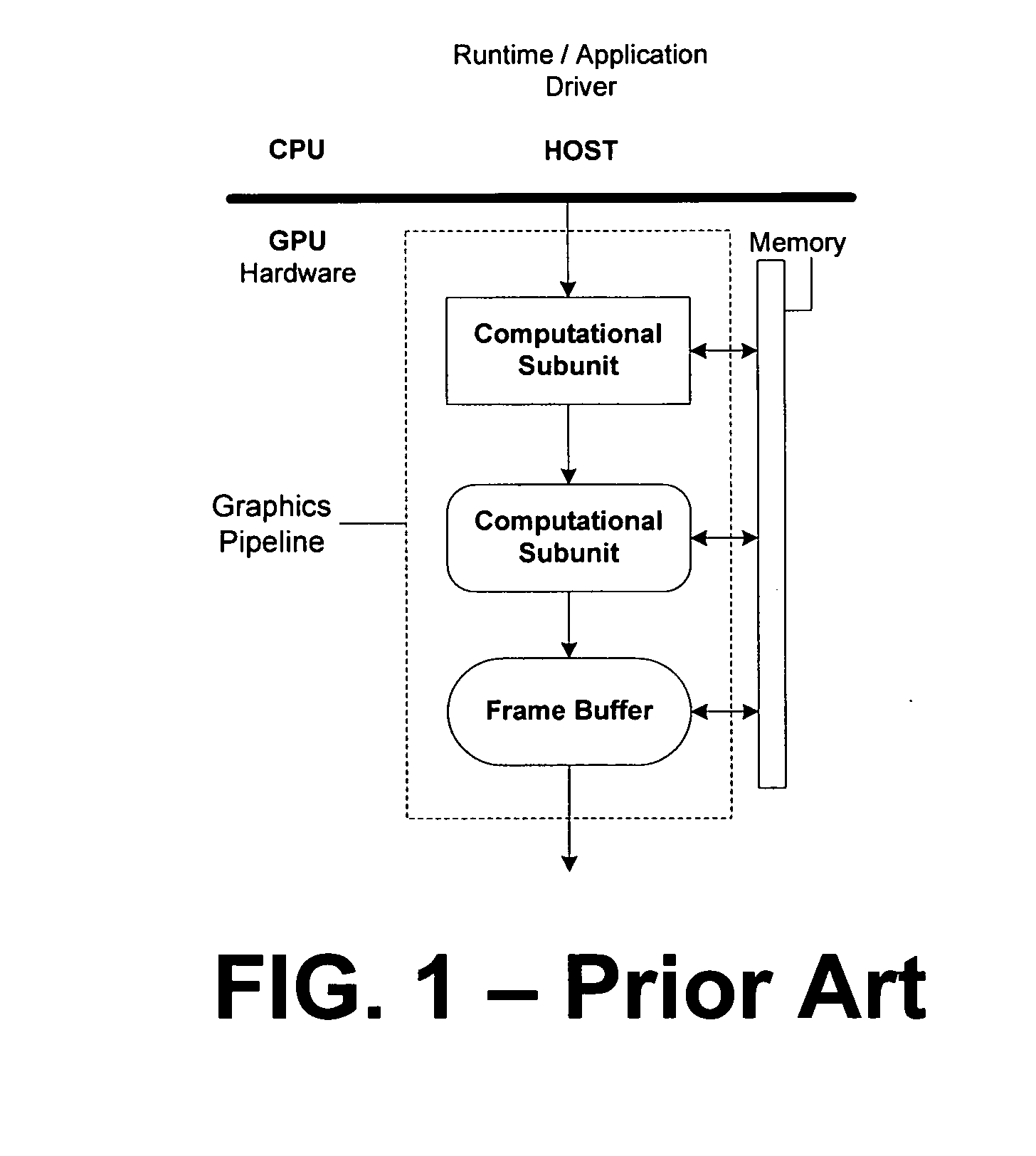
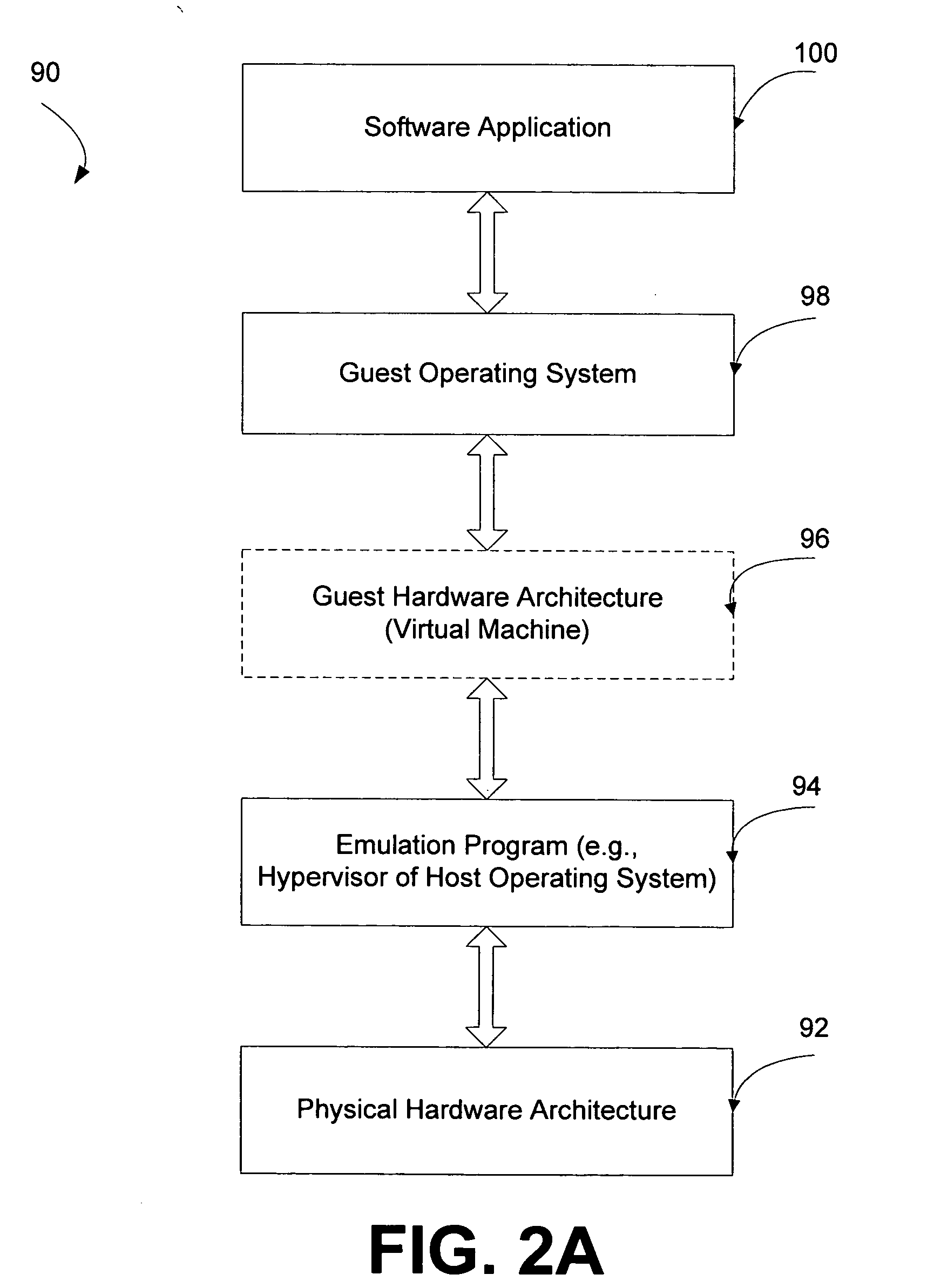
Systems and methods for virtualizing graphics subsystems
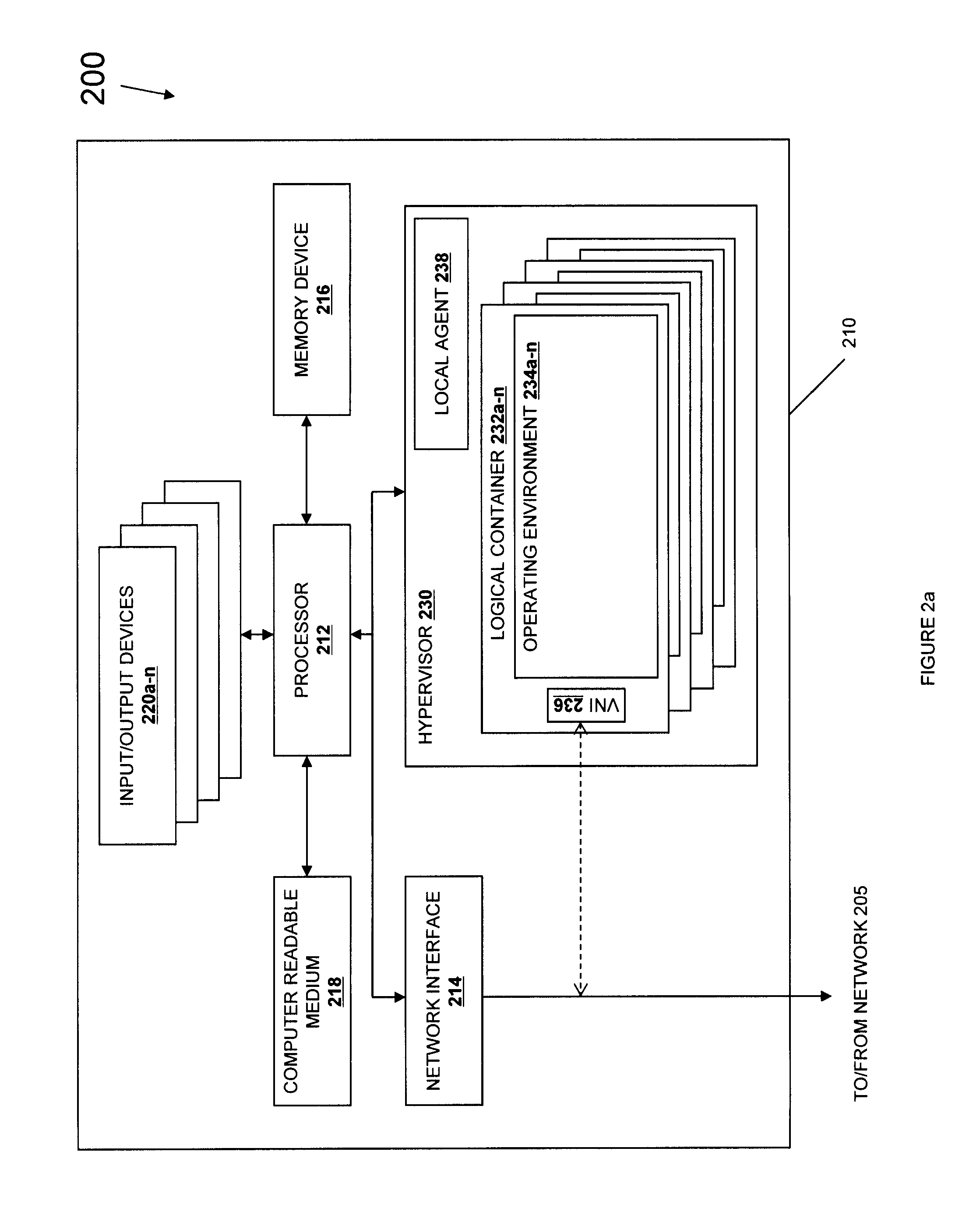
ActiveUS20060146057A1Program control using stored programsProcessor architectures/configurationVirtualizationOperational system
Systems and methods for applying virtual machines to graphics hardware are provided. In various embodiments of the invention, while supervisory code runs on the CPU, the actual graphics work items are run directly on the graphics hardware and the supervisory code is structured as a graphics virtual machine monitor. Application compatibility is retained using virtual machine monitor (VMM) technology to run a first operating system (OS), such as an original OS version, simultaneously with a second OS, such as a new version OS, in separate virtual machines (VMs). VMM technology applied to host processors is extended to graphics processing units (GPUs) to allow hardware access to graphics accelerators, ensuring that legacy applications operate at full performance. The invention also provides methods to make the user experience cosmetically seamless while running multiple applications in different VMs. In other aspects of the invention, by employing VMM technology, the virtualized graphics architecture of the invention is extended to provide trusted services and content protection.
Owner:MICROSOFT TECH LICENSING LLC
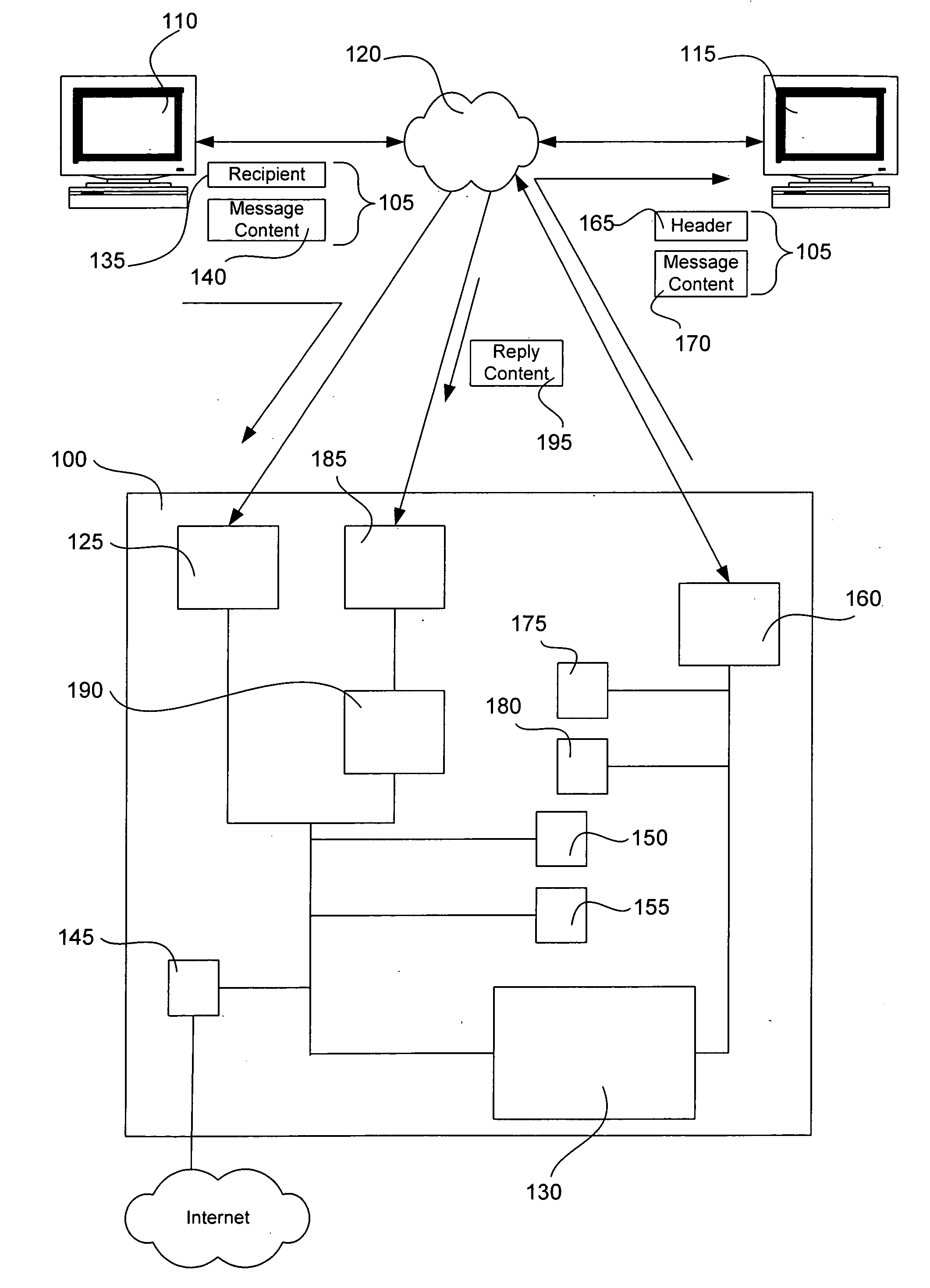
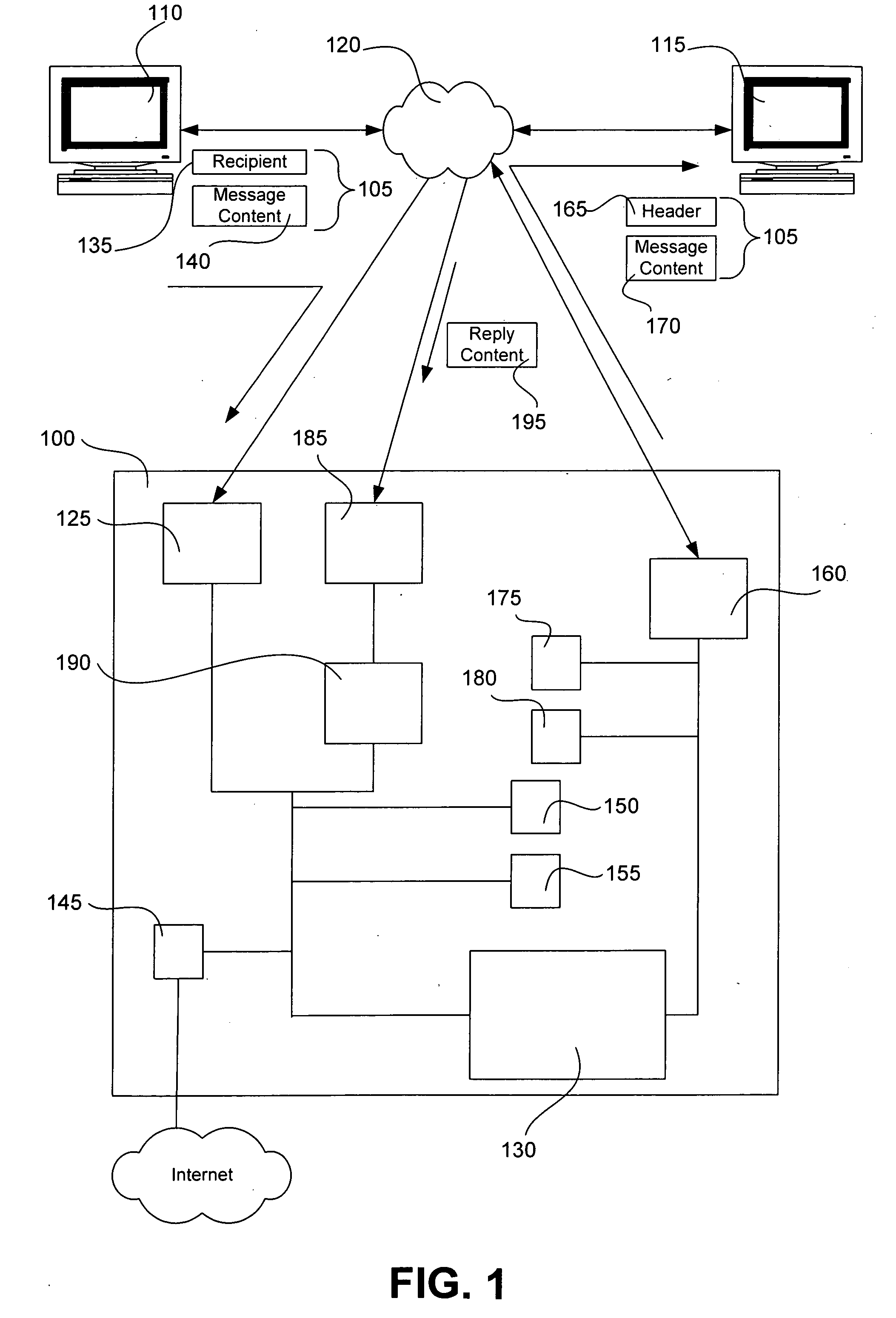
Reduced traceability electronic message system and method
ActiveUS20070038715A1Reduced traceabilityProgram control using stored programsMultiple digital computer combinationsElectronic messagingTraceability
An electronic messaging system and method with reduced traceability. An electronic message is separated into a message content and container (header) information. In one aspect, the message content and header information are displayed separately. In another aspect, an electronic message is permanently automatically deleted from the system at a predetermined time.
Owner:VAPORSTREAM
Application program prediction method and mobile terminal
ActiveUS20060156209A1Appropriately predict operation modeAppropriately predictInput/output for user-computer interactionInstruments for road network navigationMultiple applicationsControl unit
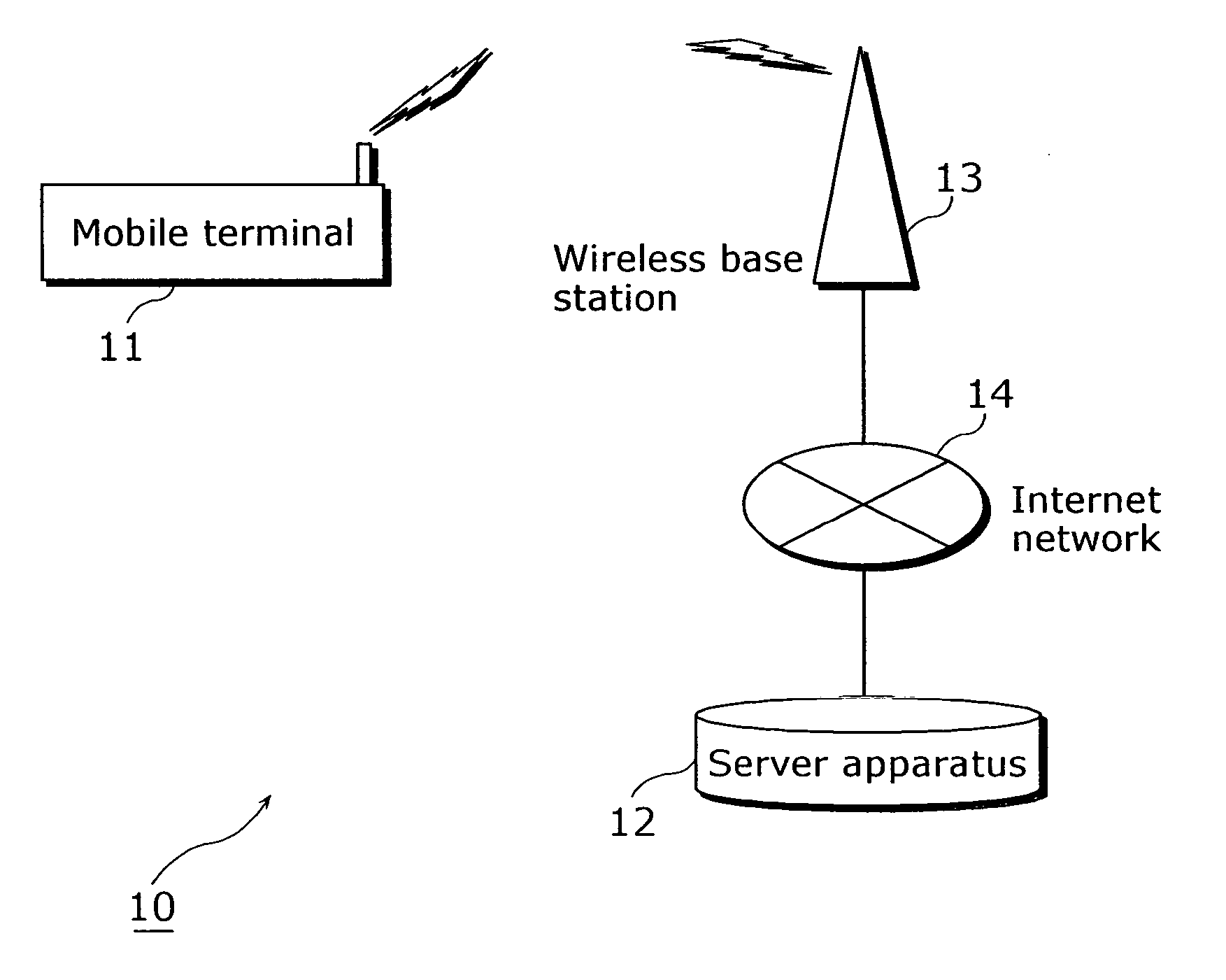
A mobile terminal (21) that appropriately predicts an application that a user is likely to use includes: an input device (106) that selects and executes any of two or more applications; a GPS reception unit (108); a behavior pattern extraction unit (205) that creates a usage prediction rule of the application executed on the input device (106), in association with a usage location detected by the GPS reception unit (108); and an information display control unit (204) that specifies, based on the usage prediction rule, an application corresponding to the current location detected by the GPS reception unit (108), and causes a display (105) to display the specified application as a prediction result.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
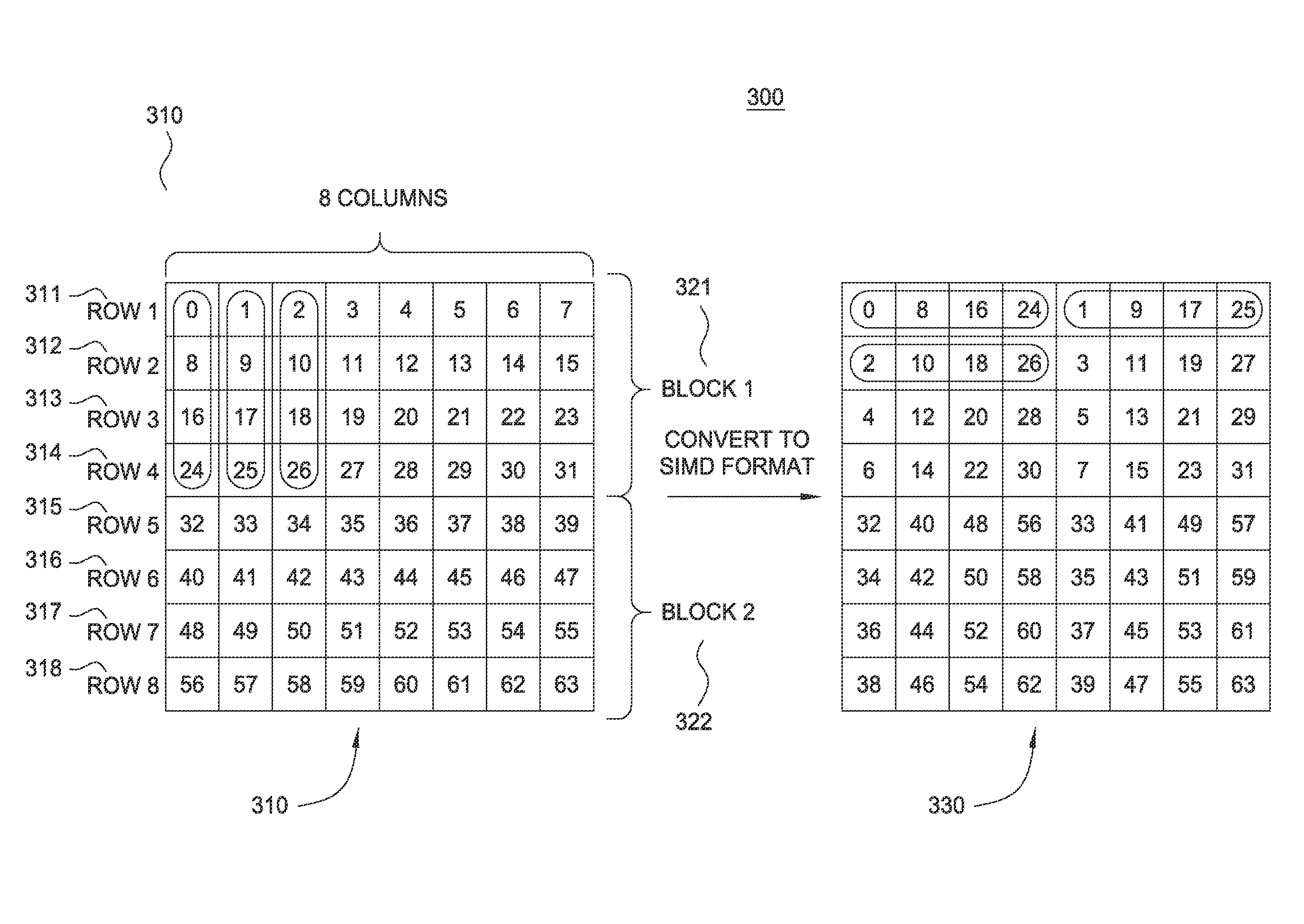
Processing array data on SIMD multi-core processor architectures
InactiveUS8484276B2Program control using stored programsGeneral purpose stored program computerFast Fourier transformFourier transform on finite groups
Owner:INT BUSINESS MASCH CORP
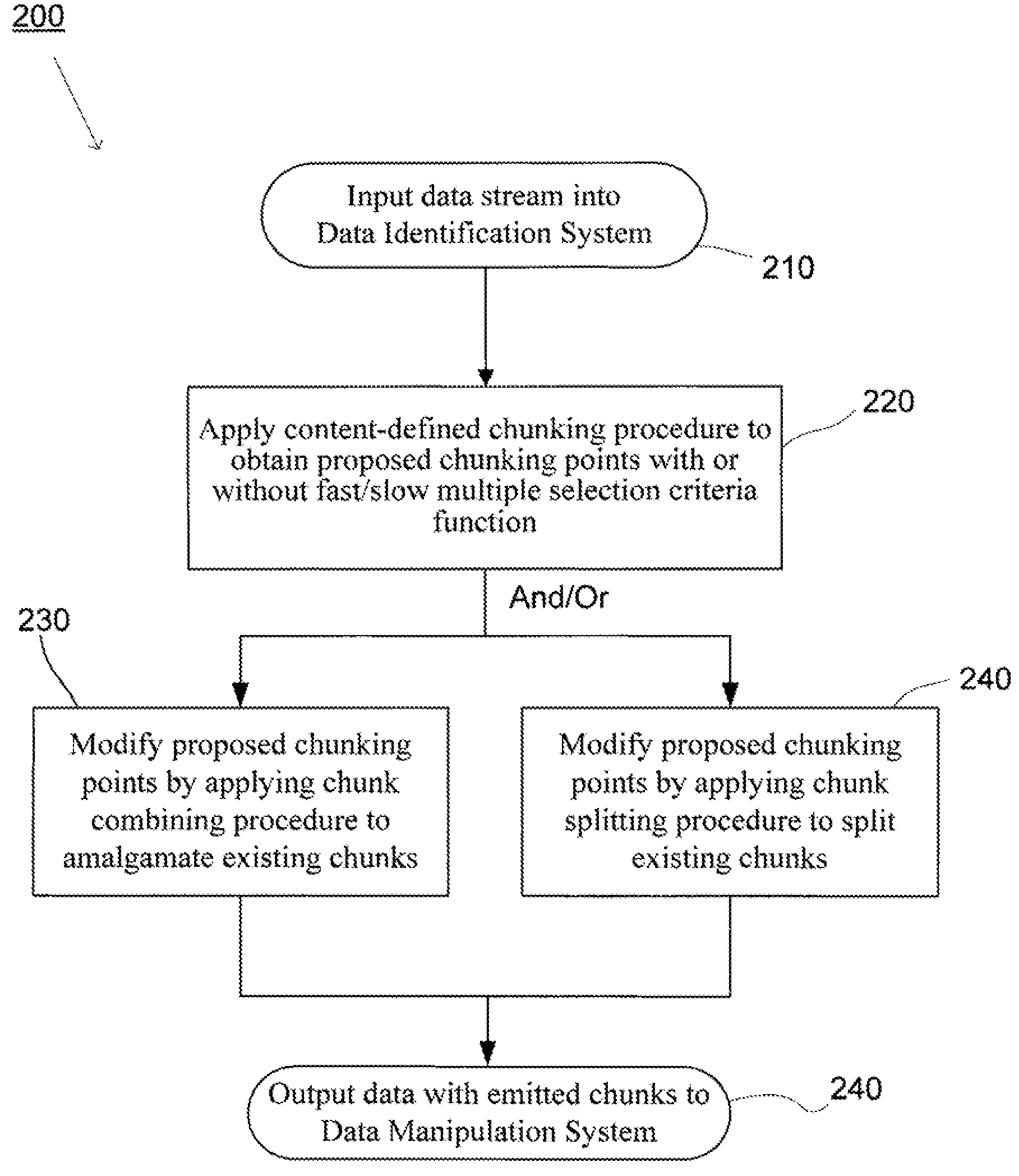
Methods and systems for quick and efficient data management and/or processing
ActiveUS20080133561A1Improve data processing efficiencyReduce quality problemsDigital data information retrievalProgram control using stored programsData managementCombined technique
System(s) and method(s) are provided for data management and data processing. For example, various embodiments may include systems and methods relating to relatively larger groups of data being selected with comparable or better performing selection results (e.g., high data redundancy elimination and / or average chunk size). In various embodiments, the system(s) and method(s) may include, for example a data group, block, or chunk combining technique or / and a data group, block, or chunk splitting technique. Various embodiments may include a first standard or typical data grouping, blocking, or chunking technique and / or data group, block, or chunk combining technique or / and a data group, block, or chunk splitting technique. Exemplary system(s) and method(s) may relate to data hashing and / or data elimination. Embodiments may include a look-ahead buffer and determine whether to emit small chunks or large chunks based on characteristics of underlying data and / or particular application of the invention (e.g., for backup).
Owner:NEC CORP
Market-Based Virtual Machine Allocation
InactiveUS20130304903A1Program control using stored programsDigital computer detailsMarket placeMarket based
A cloud computing system management system including a plurality of computing devices configured to host virtual machine instances, each computing device in the plurality of computing devices including a local agent that continuously evaluates the observed load relative to a utility maximization function. If observed load is higher than a calculated optimal level, individual loading processes are offered for “sale” via a market scheduler. If observed load is lower than a calculated optimal level, then available capacity is offered as a bid via the market scheduler. The market scheduler matches bids with available processes and coordinates the transfer of load from the selling device to the buying device. The offered prices and utility maximization functions can be employed to optimize the performance of the cloud system as a whole.
Owner:RACKSPACE US
System for monitoring and reporting performance of hosts and applications and selectively configuring applications in a resource managed system
ActiveUS7051098B2Program initiation/switchingResource allocationResource Management SystemMonitoring system
A monitoring system for a distributed environment including a plurality of hosts capable of executing multiple copies of a scalable application includes a first device for generating first data corresponding to performance of all copies of the scalable application; a second device for generating second data corresponding to performance of all host in the distributed environment; and a third device for generating performance metrics based on the first and second data.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
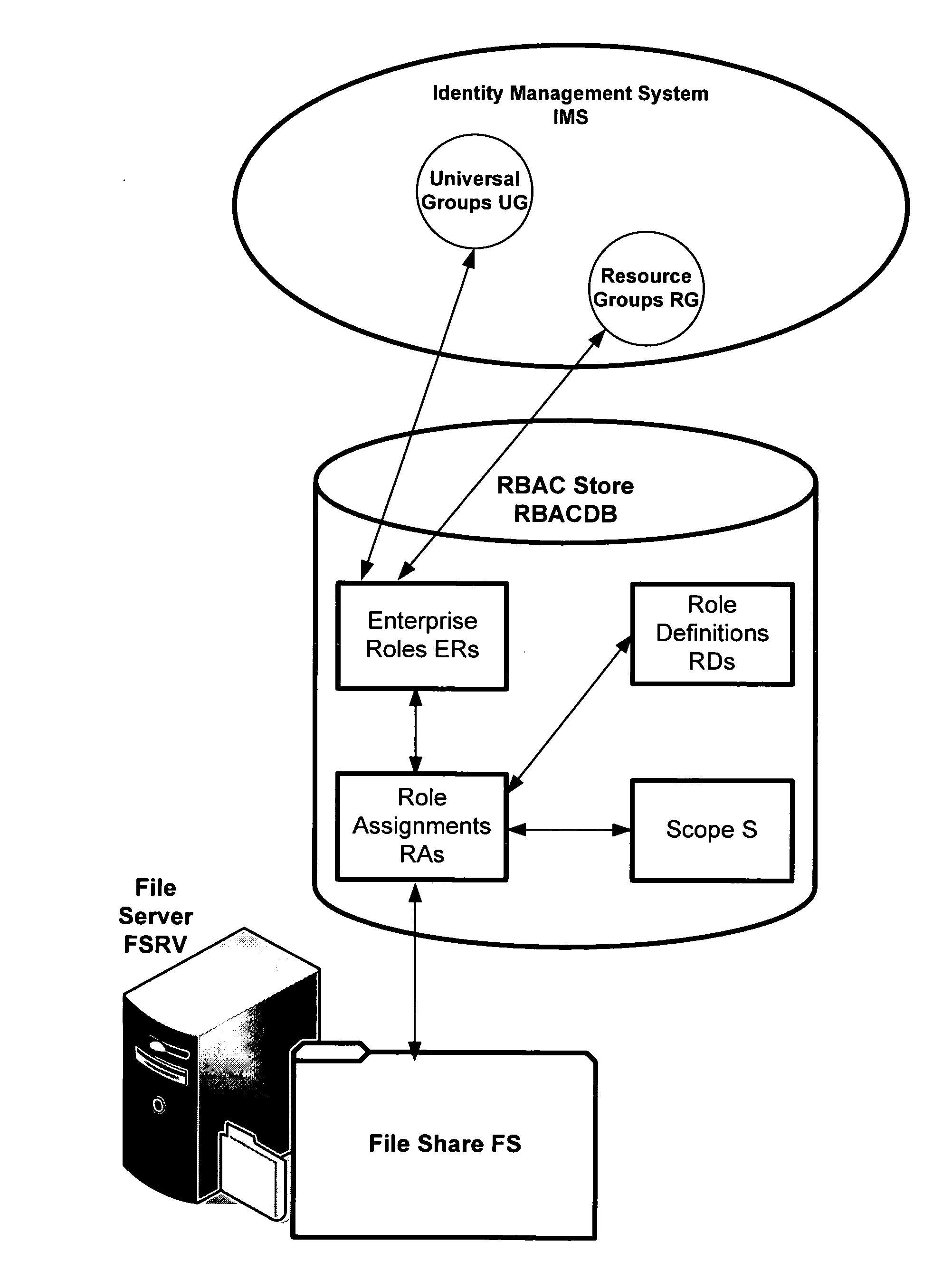
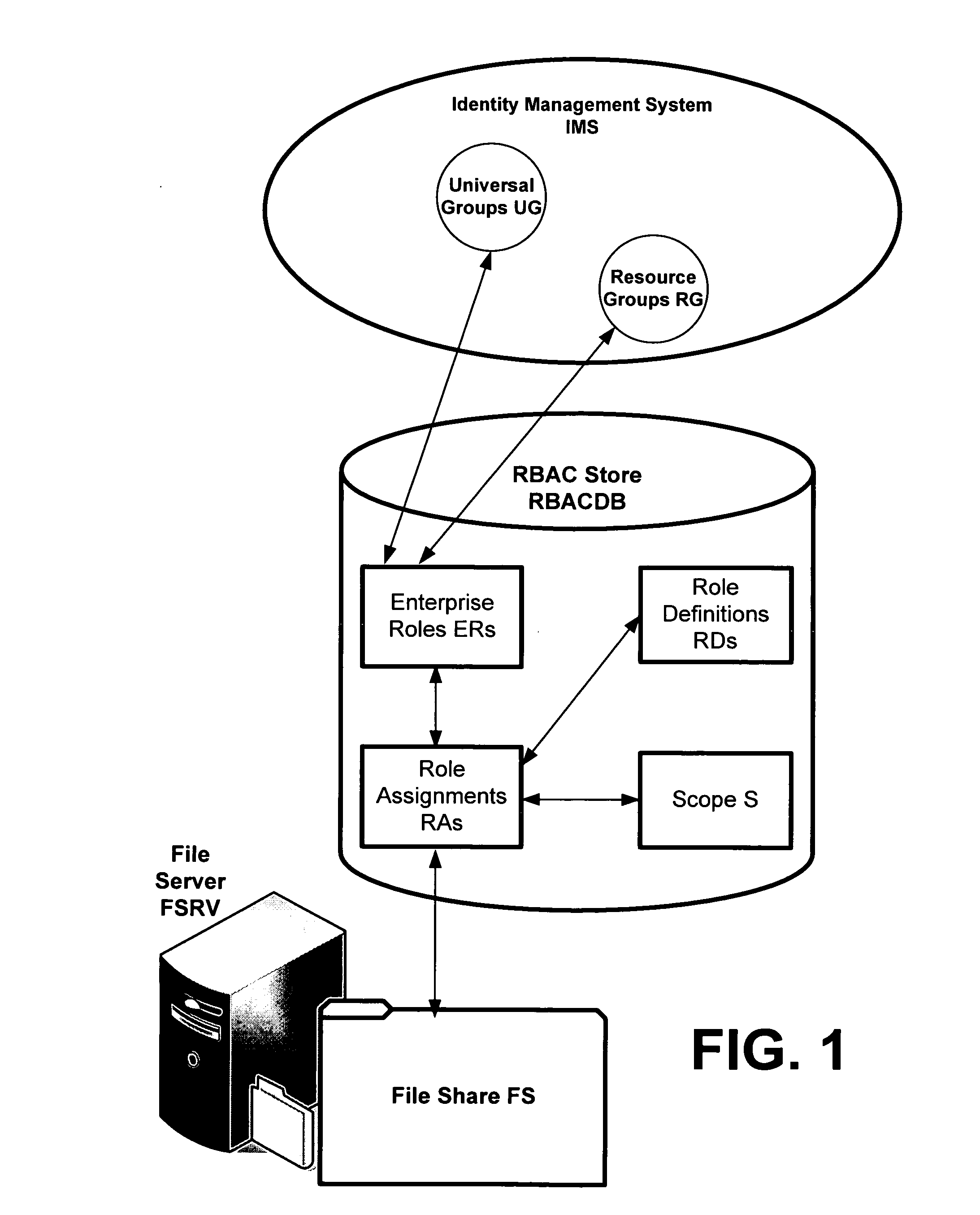
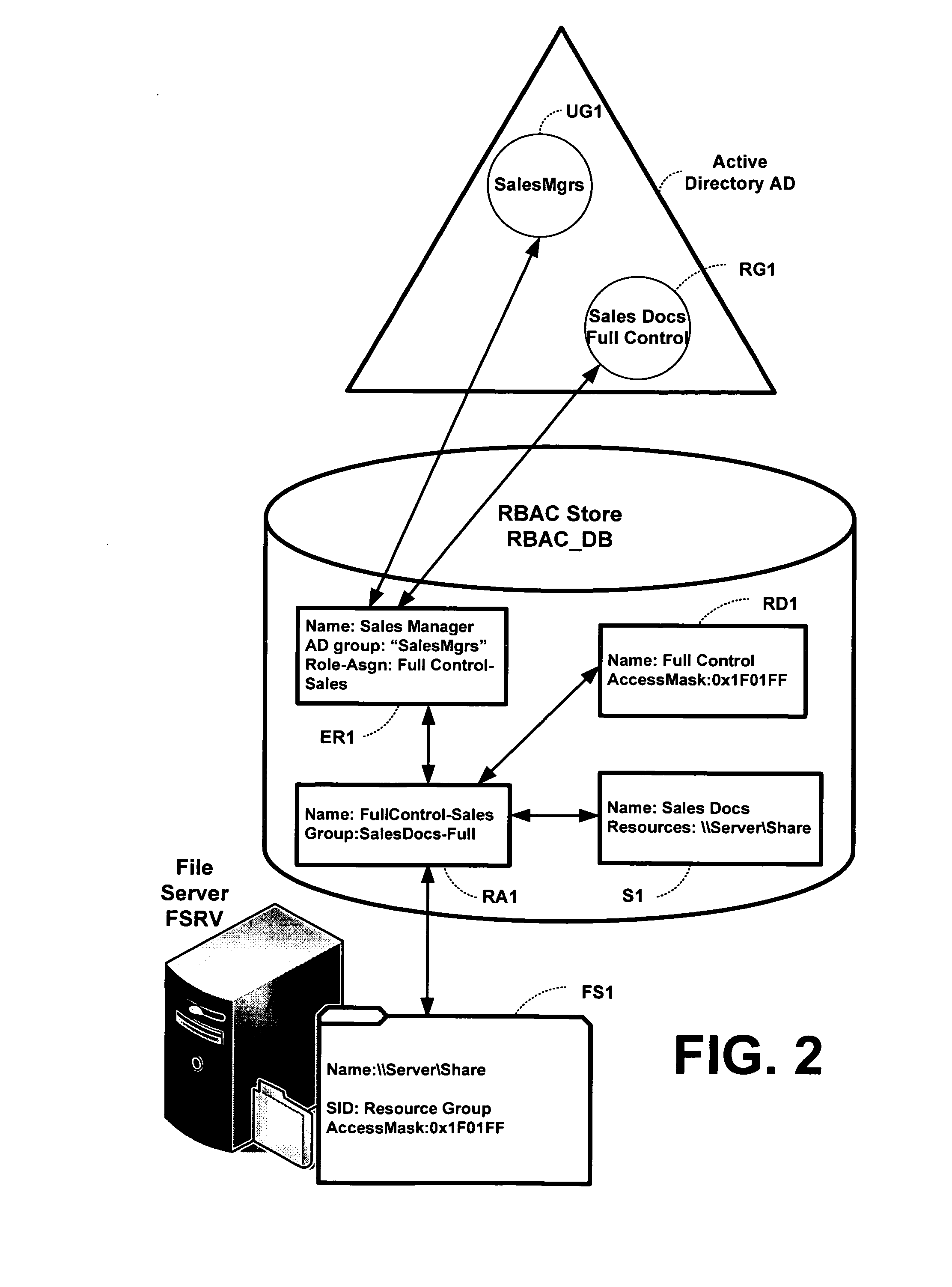
Translating role-based access control policy to resource authorization policy
ActiveUS20070283443A1Program control using stored programsDigital data processing detailsFile systemManaged object
Translation of role-based authoring models for managing RBAC “roles” to resource authorization policy (RAP), such as ACL-based applications, is provided. A generic RBAC system is defined from which mappings to other authorization enforcement mechanism make possible the translation of RBAC “roles” to resource authorization policies applied to resources managed by a resource manager, e.g., a file system resource manager. An implementation is described that uses Windows Authorization Manager as a storage mechanism and object model to manage object types and relationships translated from an RBAC system.
Owner:MICROSOFT TECH LICENSING LLC
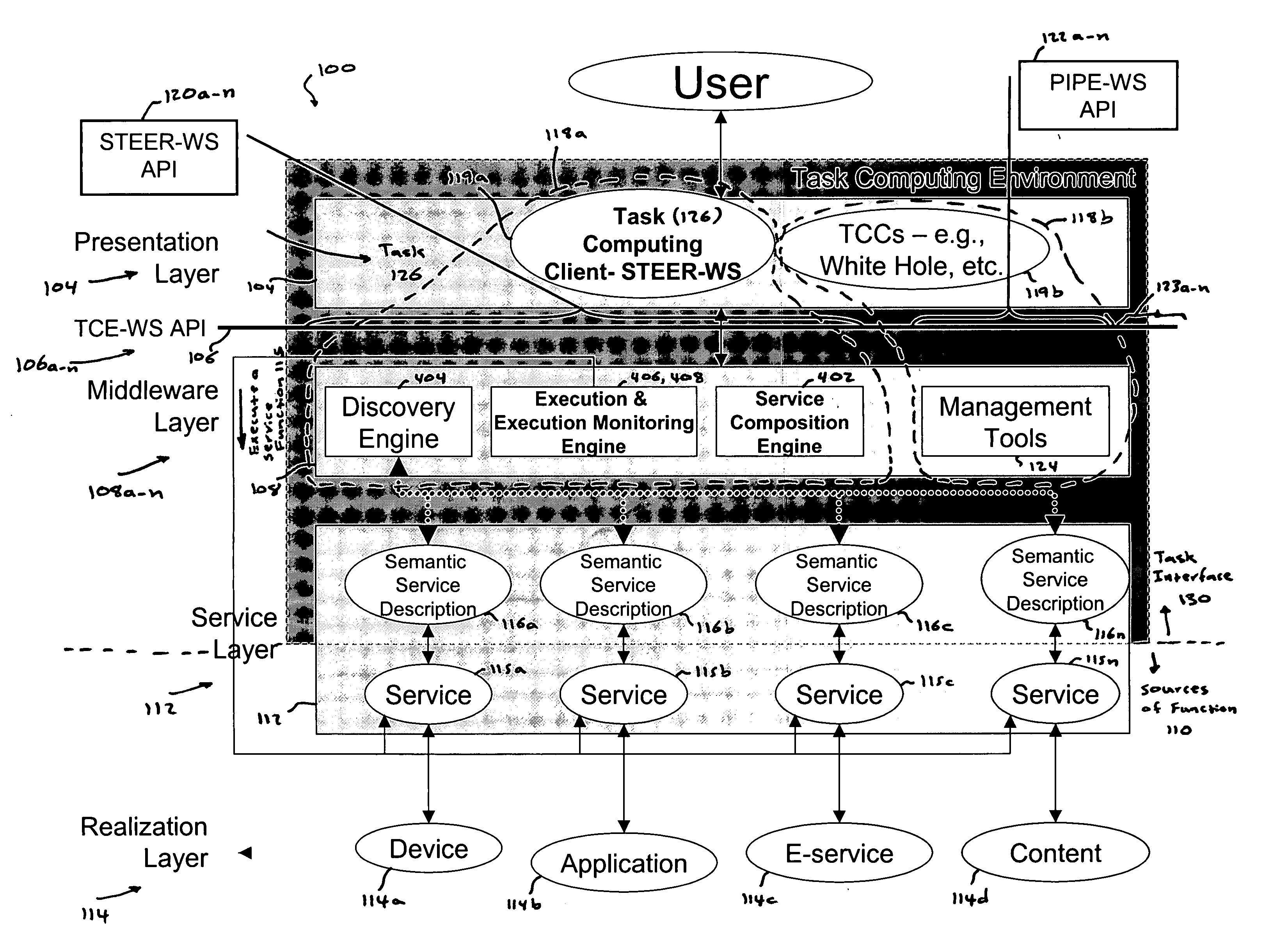
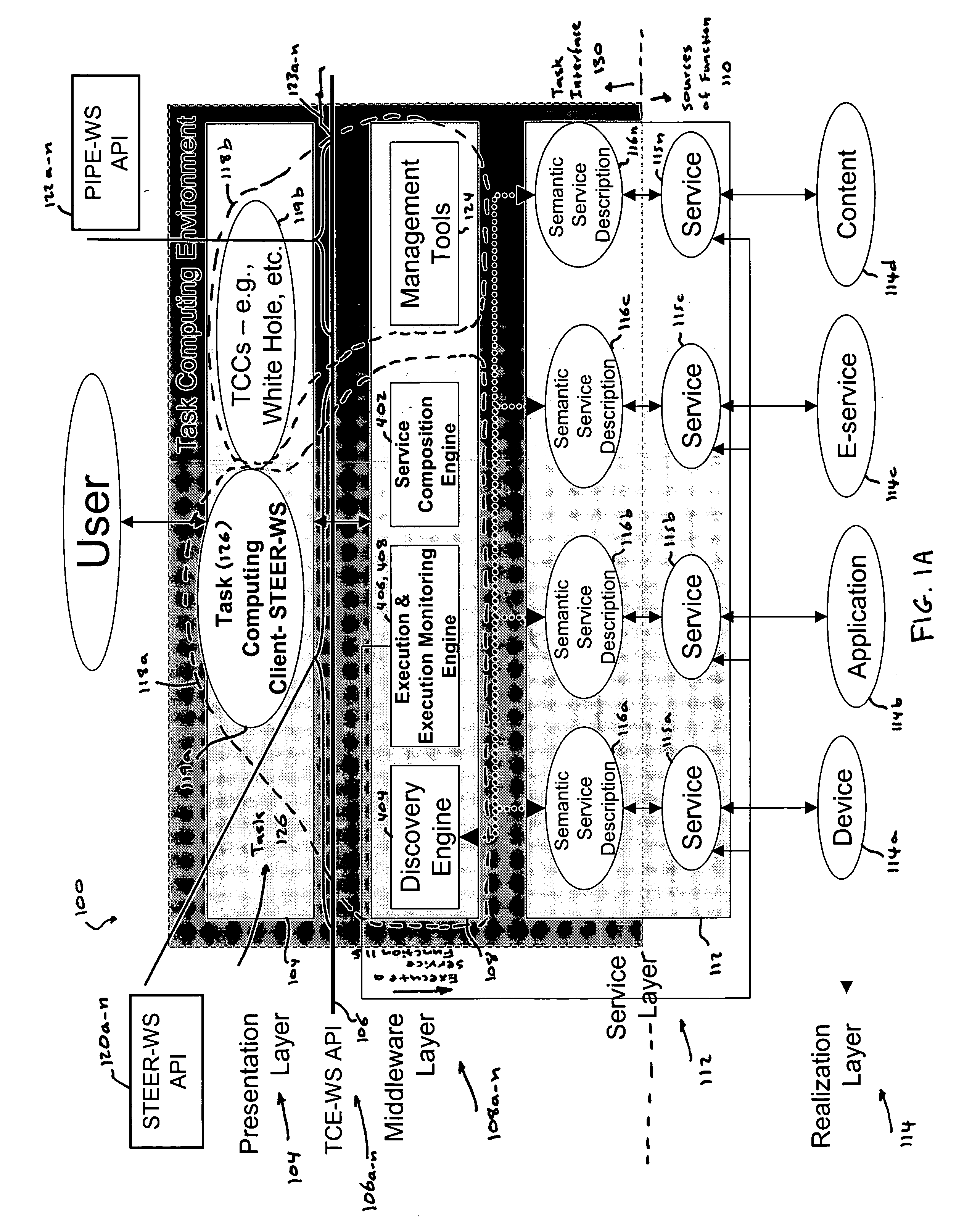
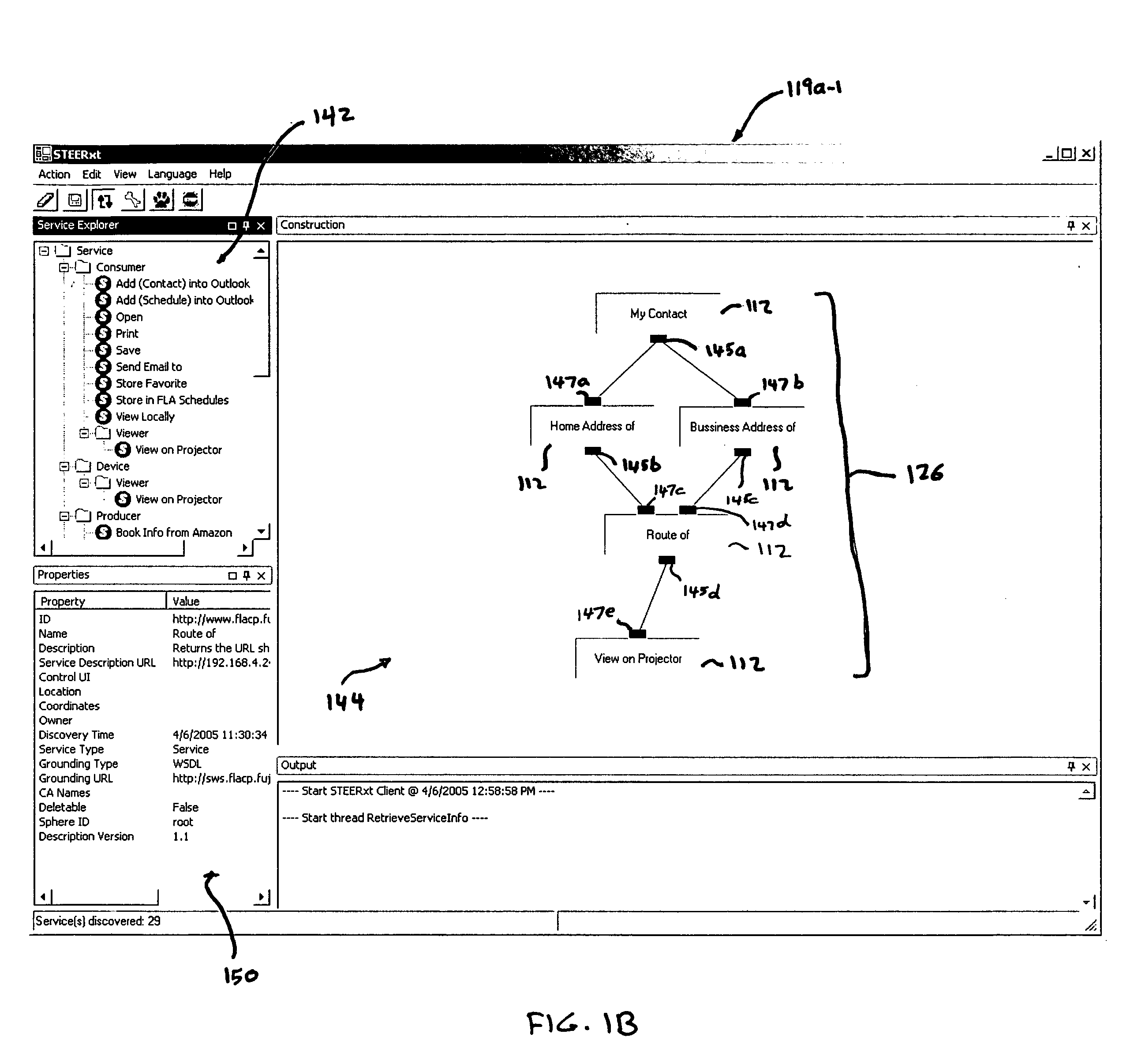
Task computing
InactiveUS20050246726A1Program control using stored programsConcurrent instruction executionLayer interfaceProcedure calls
Task Computing computer system by segmenting the system into a plurality of implementation tiers of a presentation layer, a remote procedure call programming interface (API), a middleware layer to which the presentation layer interfaces via the remote procedure call API to real-time, dynamically generate a computer implemented task interface at the presentation layer to a semantically described source of function as a service on a computer system, and a service layer and a function source realization layer providing the semantically described source of function as the service on the computer system to which the middleware layer interfaces. Real-time and dynamically composing an executable task that comprises one or more services using the generated task interface at the presentation layer to one or more services on the computer based upon the semantically described application-, device- and service-rich computer.
Owner:FUJITSU LTD
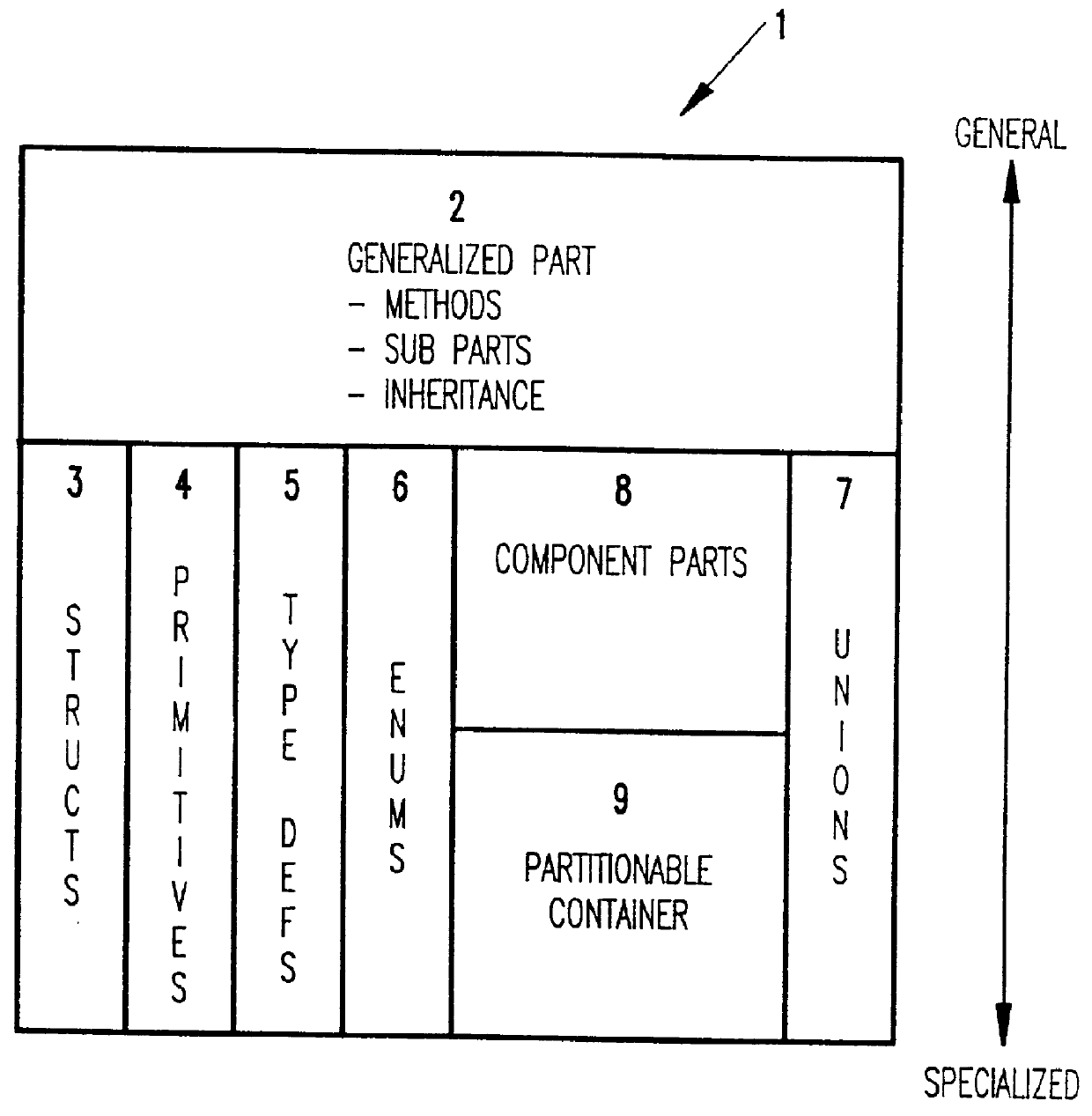
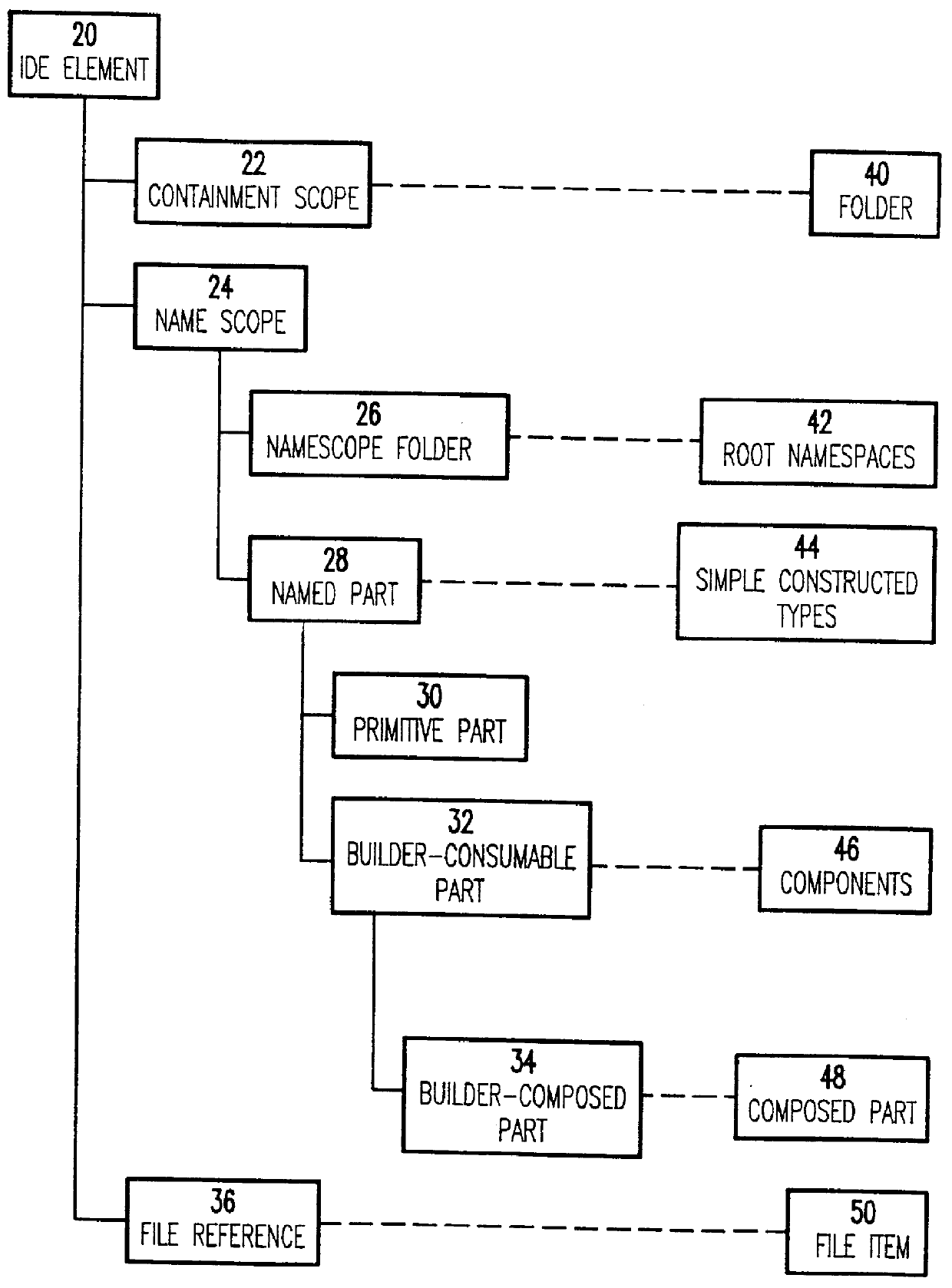
Hierarchical metadata store for an integrated development environment
InactiveUS6044217AData processing applicationsProgram control using stored programsApplication softwareData store
A metadata repository for use in an integrated development environment is provided. The metadata repository is layered to define levels of common behaviour useful to different types of application development tools. The most general use tools have access to metadata at the level of simple constructed types; more specialised tools have access to components that contain properties of a target language; highly specialised tools have access to composed partitionable part metadata that can be used for constructing distributed applications.
Owner:IBM CORP
Method and apparatus for a process and project management computer system
InactiveUS6023702AReduce storageImprove performanceProgram control using stored programsResourcesDigital dataModularity
PCT No. PCT / EP95 / 03289 Sec. 371 Date Dec. 10, 1998 Sec. 102(e) Date Dec. 10, 1998 PCT Filed Aug. 18, 1995 PCT Pub. No. WO97 / 07472 PCT Pub. Date Feb. 27, 1997The inventive concept comprises a system platform for a synergistic, role modular work process environment. A work process object (WPO) (1001) is created, residing in a data base, and stored in a memory of the process and project management computer system (1030). All data concerning the process and project management are reported to said work process object (WPO) (1001) and said work process object (WPO) (1001) is used as a common data base. According to the inventive concept, each view must be supported by a specific workplace, represented by digital data and enforcing the rules for the specific role. A work process information model supports the dynamic definition and use of a data base object representing a work process, boch in its process and project planning modes and its execution. According to the inventive concept, one object supports simultaneously all modes delimited by dynamically moving boundaries. Workplace implementation enforces over-all rules for each role in the inventive system.
Owner:IBM CORP
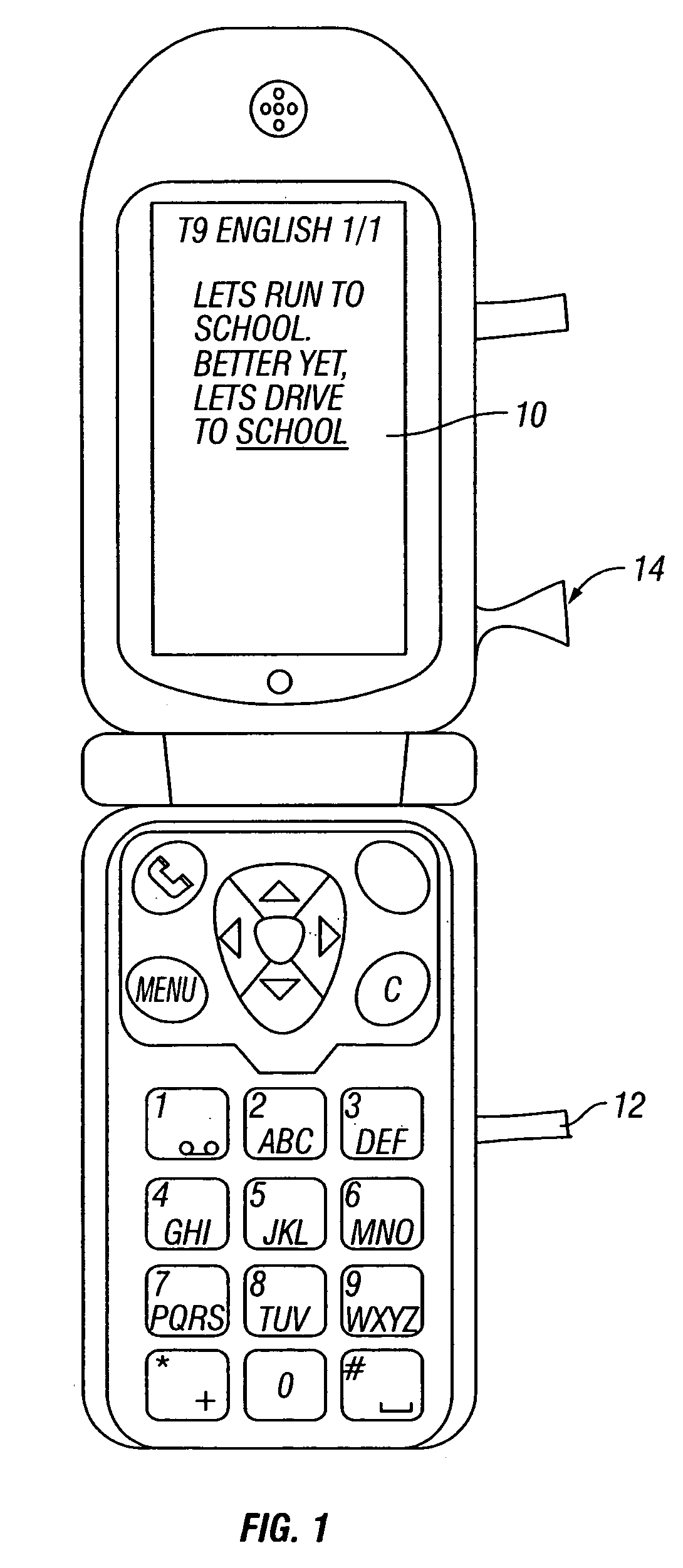
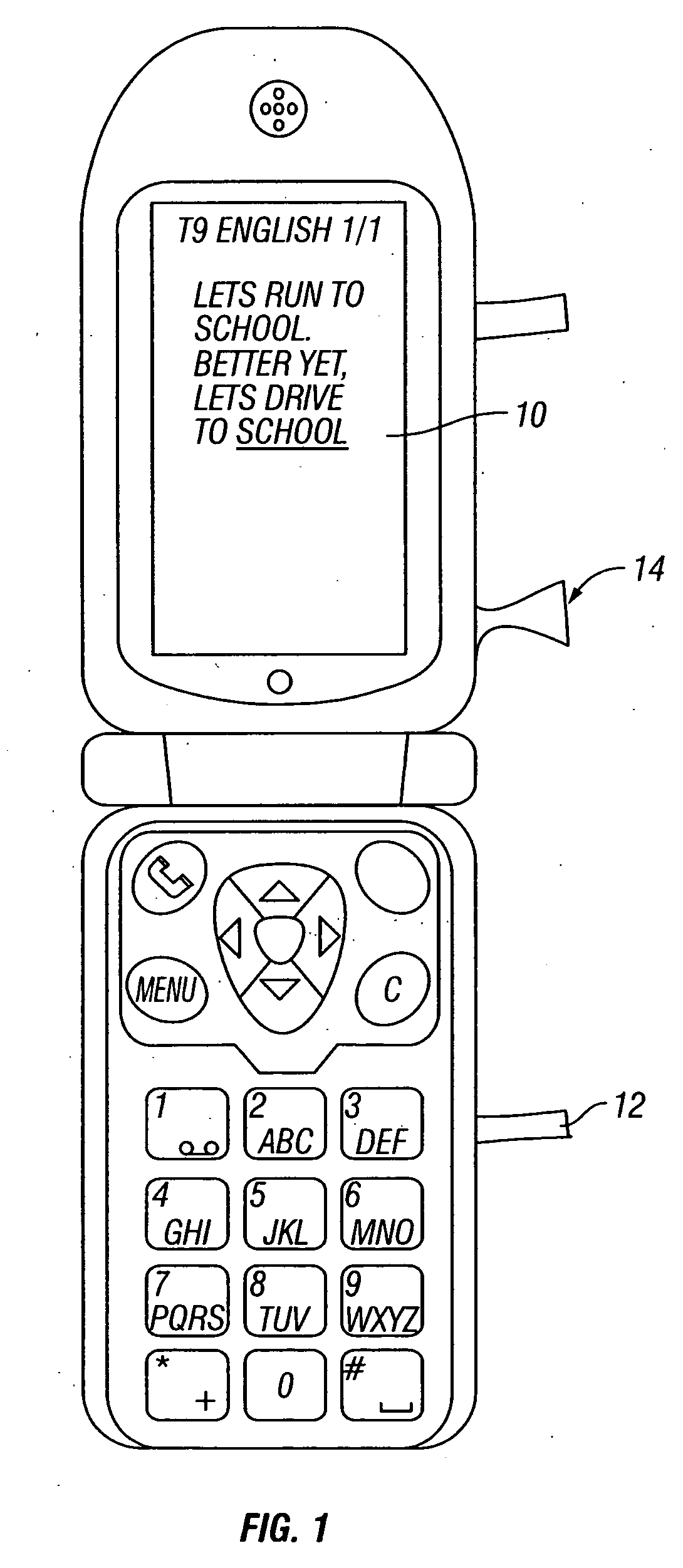
Contextual prediction of user words and user actions
InactiveUS20050017954A1Increase volumeHigh levelInput/output for user-computer interactionProgram control using stored programsUser inputWord list
The invention concerns user entry of information into a system with an input device. A scheme is provided in which an entire word that a user wants to enter is predicted after the user enters a specific symbol, such as a space character. If the user presses an ambiguous key thereafter, rather than accept the prediction, the selection list is reordered. For example, a user enters the phrase “Lets run to school. Better yet, lets drive to “.””” After the user presses the space, after first entering the second occurrence of the word “to,” the system predicts that the user is going to enter the word “school” based on the context in which the user has entered that word in the past. Should the user enter an ambiguous key after the space, then a word list which contains the word “school” is reordered and other options are made available to the user. The invention can also make predictions on context, such as the person to whom the message is sent, the person writing the message, the day of the week, the time of the week, etc. Other embodiments of the invention contemplate anticipation of user actions, as well as words, such as a user action in connection with menu items, or a user action in connection with form filling.
Owner:TEGIC COMM +1
Data run programming
ActiveUS20050144367A1Reduce the impactReduce impactMemory architecture accessing/allocationProgram control using stored programsData storeNon-volatile memory
Data in data runs are stored in a non-volatile memory array in adaptive metablocks that are configured according to the locations of data boundaries. A serial flash buffer is used to store some data, while other data are directly stored in non-volatile memory. Data may be stored with alignment to data boundaries during updating of the data to improve efficiency of subsequent updates.
Owner:SANDISK TECH LLC
Apparatus and method for synchronizing software between computers
InactiveUS6425126B1Data processing applicationsProgram control using stored programsSoftware engineeringModel system
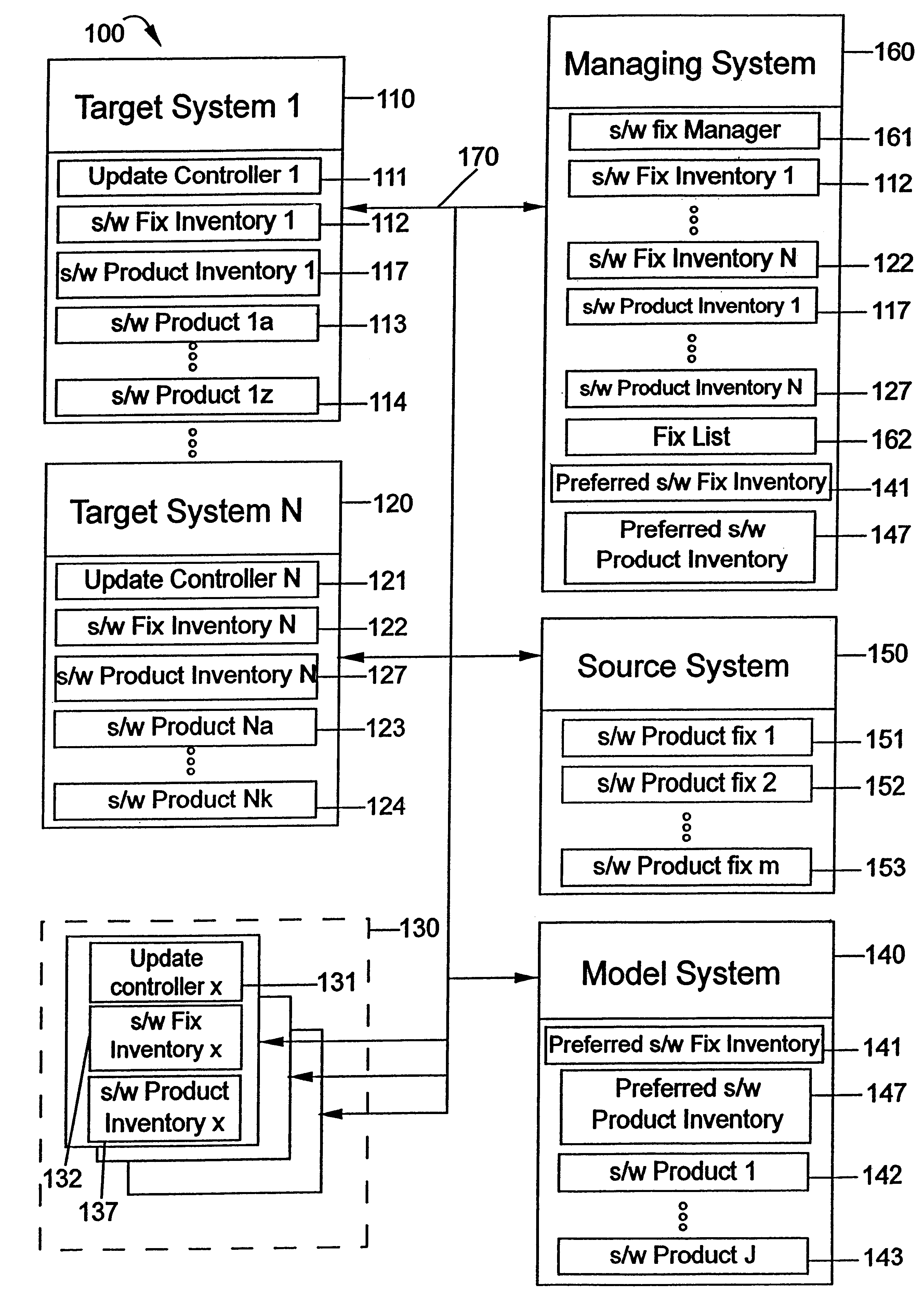
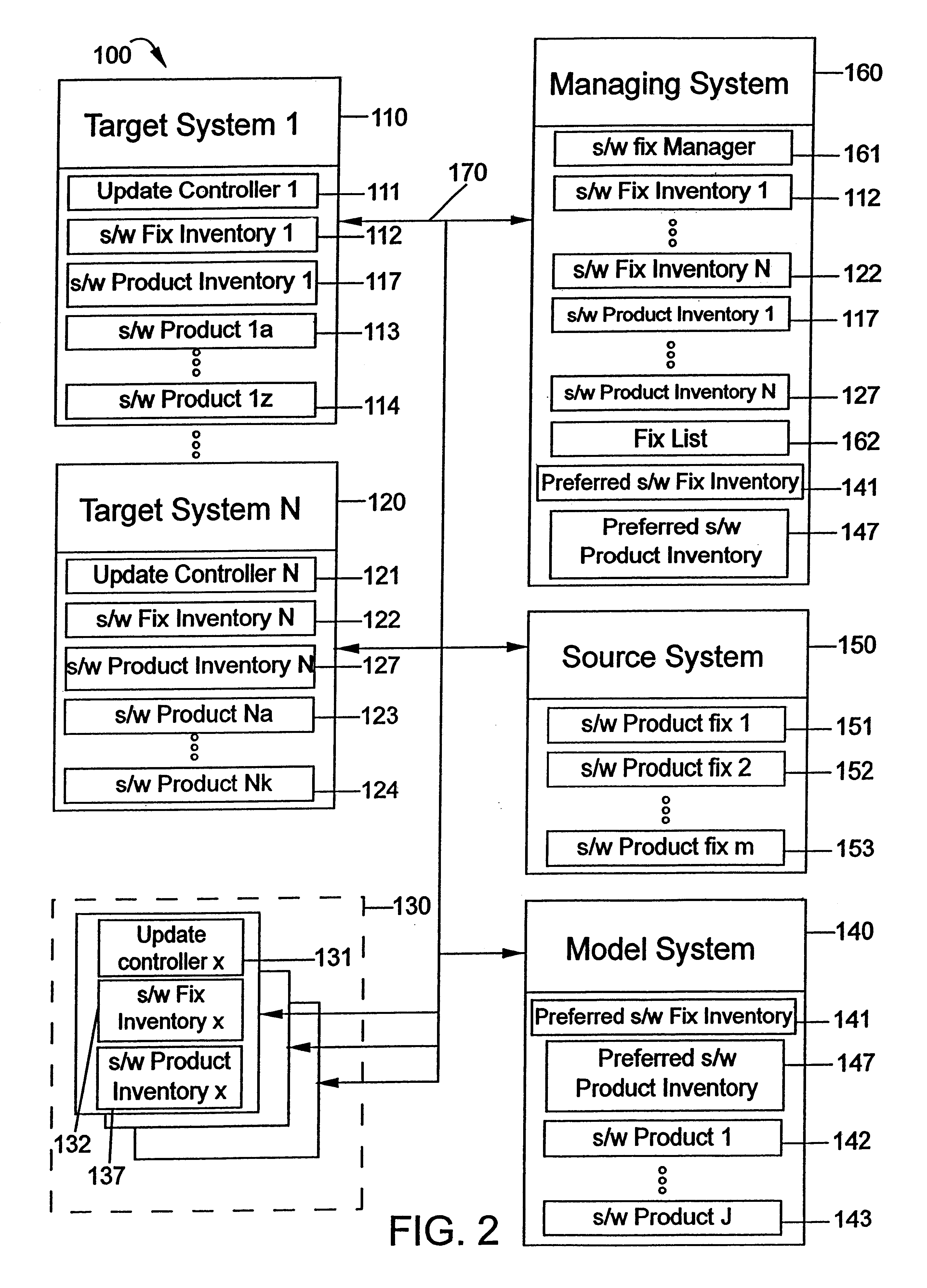
A method and apparatus for synchronizing software between computers are disclosed. A software fix manager compares a preferred software inventory with a software inventory from a computer that is to be synchronized and, from this comparison, creates a number of software product synchronizations. An update manager uses the software fix list to apply software product synchronizations to the computer. Preferably, the computer can be brought to the same fix level or product level, if desired, as the preferred software inventory through this process. The software fix manager can place synchronizations in a fix list. There can be multiple software product synchronizations per software product, and the synchronizations can be applied to a computer by removing a software product fix or installing a product software fix. The current invention may also be applied to software products themselves, by installing or removing software products. The present invention potentially has its best application in networks, as numerous target computers or groups of target computers may be synchronized with a preferred software inventory of a model system.
Owner:IBM CORP
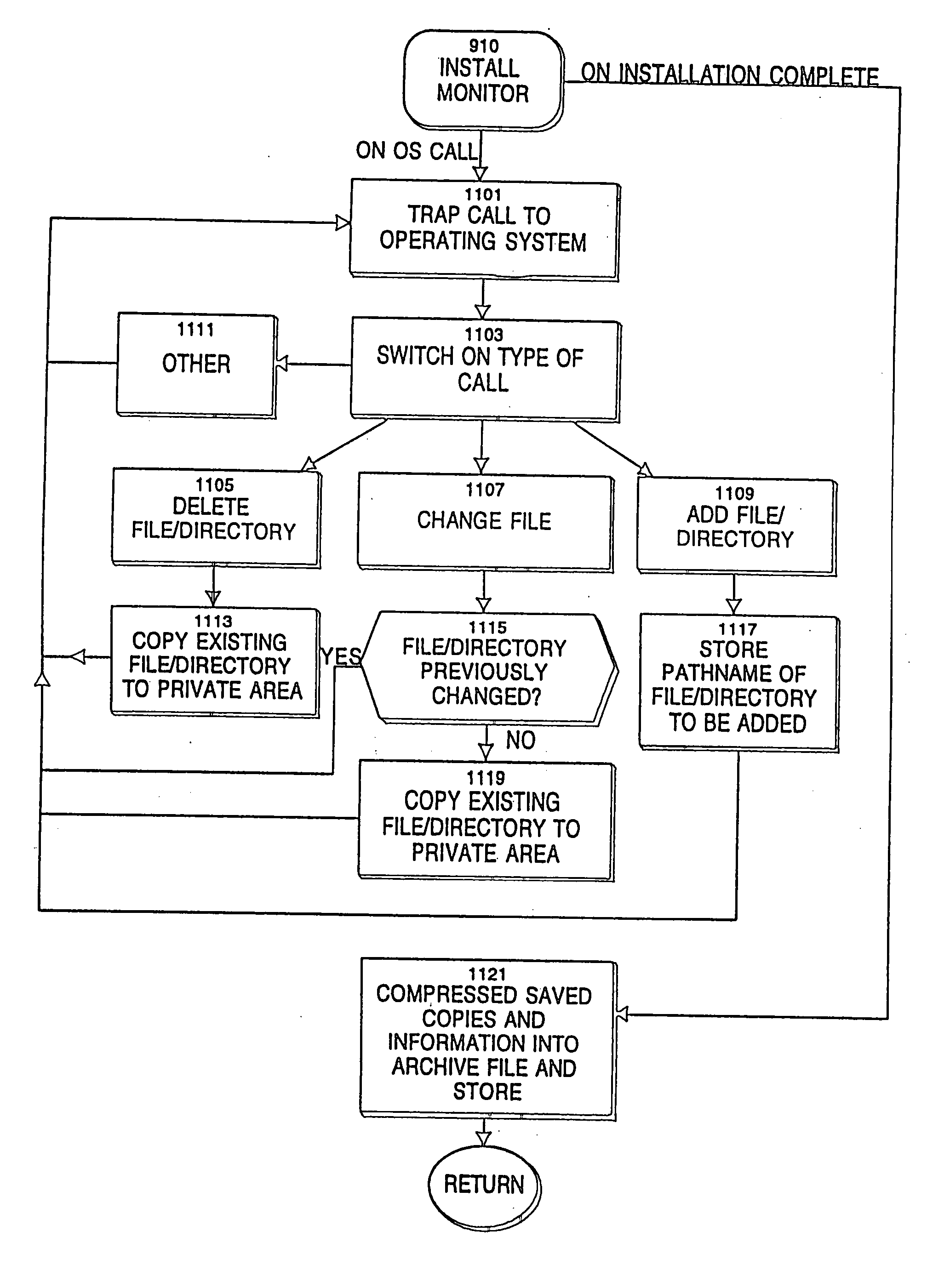
Method and system for reversible installation of software applications in a data processing system utilizing an automated archival process
InactiveUS6430738B1Program control using stored programsProgram loading/initiatingData processing systemRemovable media
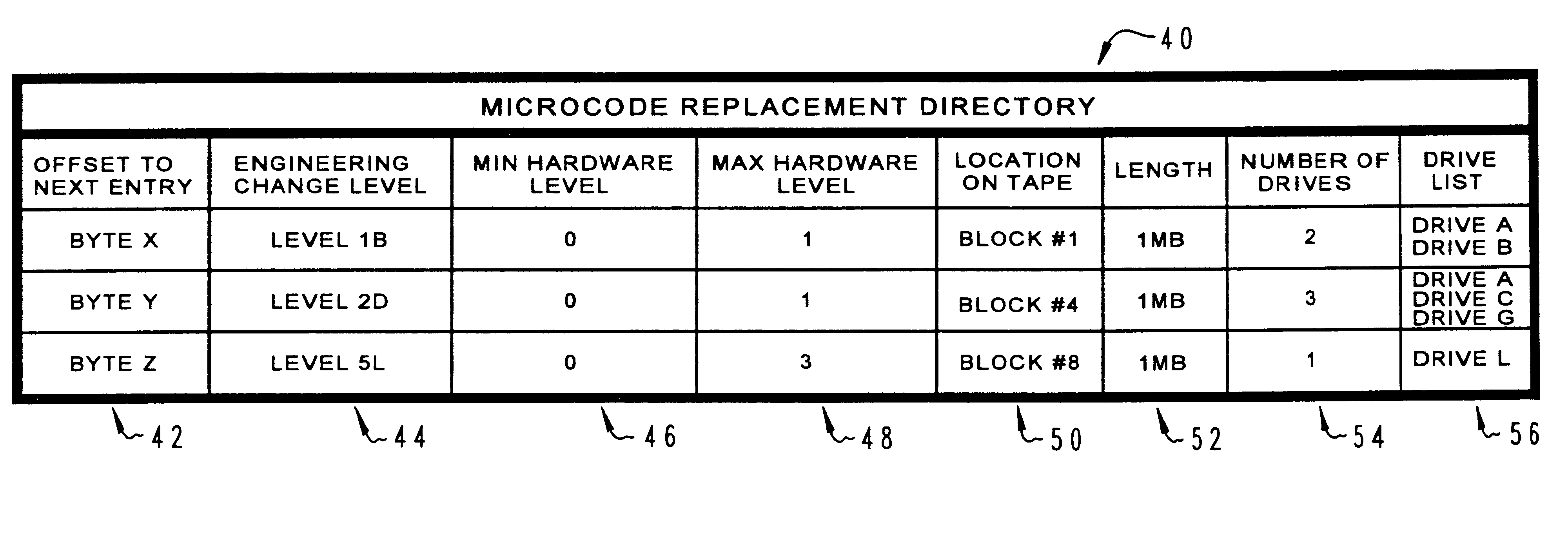
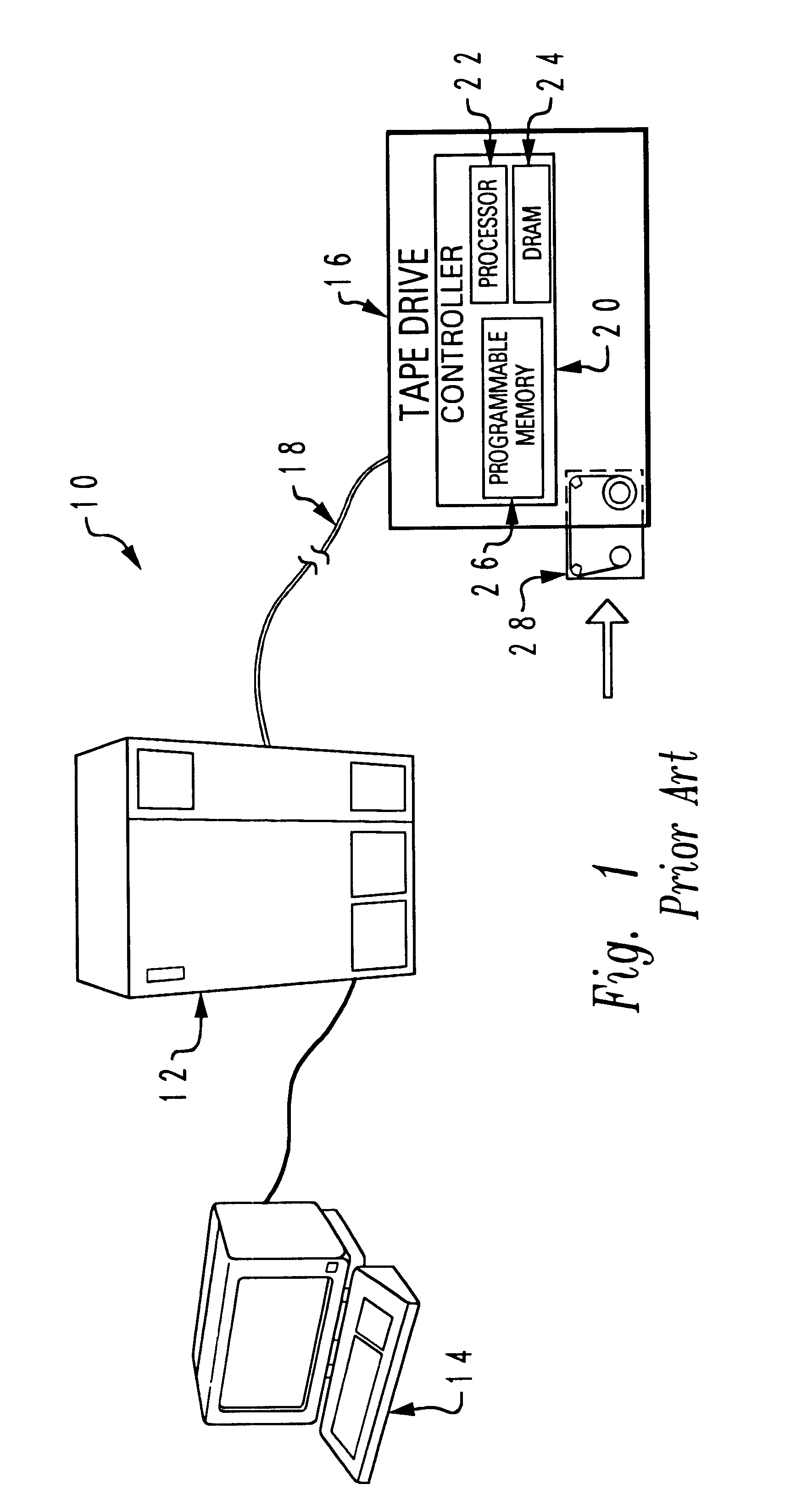
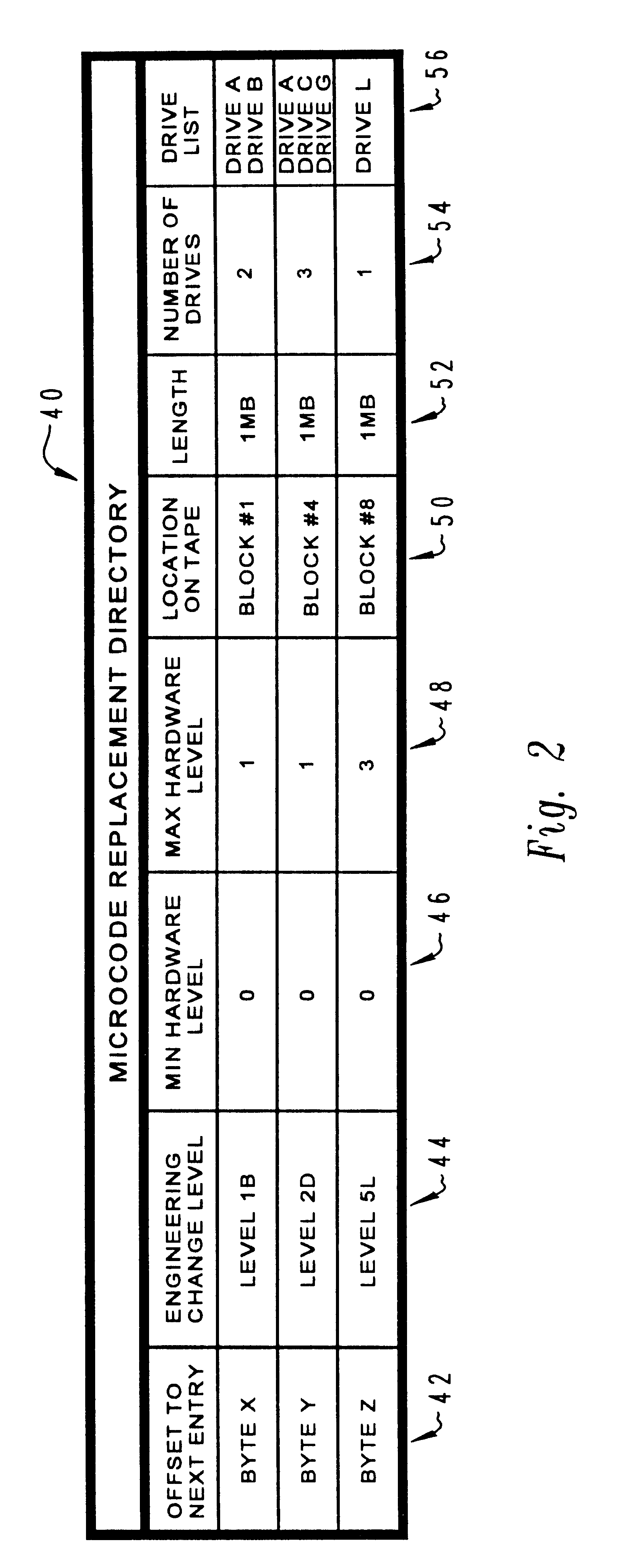
A method and system for permitting reversible installation of software applications in a data processing system which includes a processor, memory containing a first version of a selected software application and a storage system for receiving a removable storage medium. A removable storage medium which includes at least one alternate version of a selected software application is inserted into the storage system and a user is then prompted to select an alternate version of the selected software application for installation within the data processing system. The existing version of the selected software application within the data processing system is then automatically copied from memory to the removable storage medium prior to initiation of installation of the alternate version of the selected software application in response to a selection of the alternate version, such that the installation may be selectively reversed. A directory within the removable storage medium is automatically created and updated each time an application is copied from or to the removable storage medium with a listing of each alternate version of the selected software application, a required hardware level for utilization with each version of the selected software application and a listing of each data processing system within the enterprise which has utilized that version.
Owner:IBM CORP
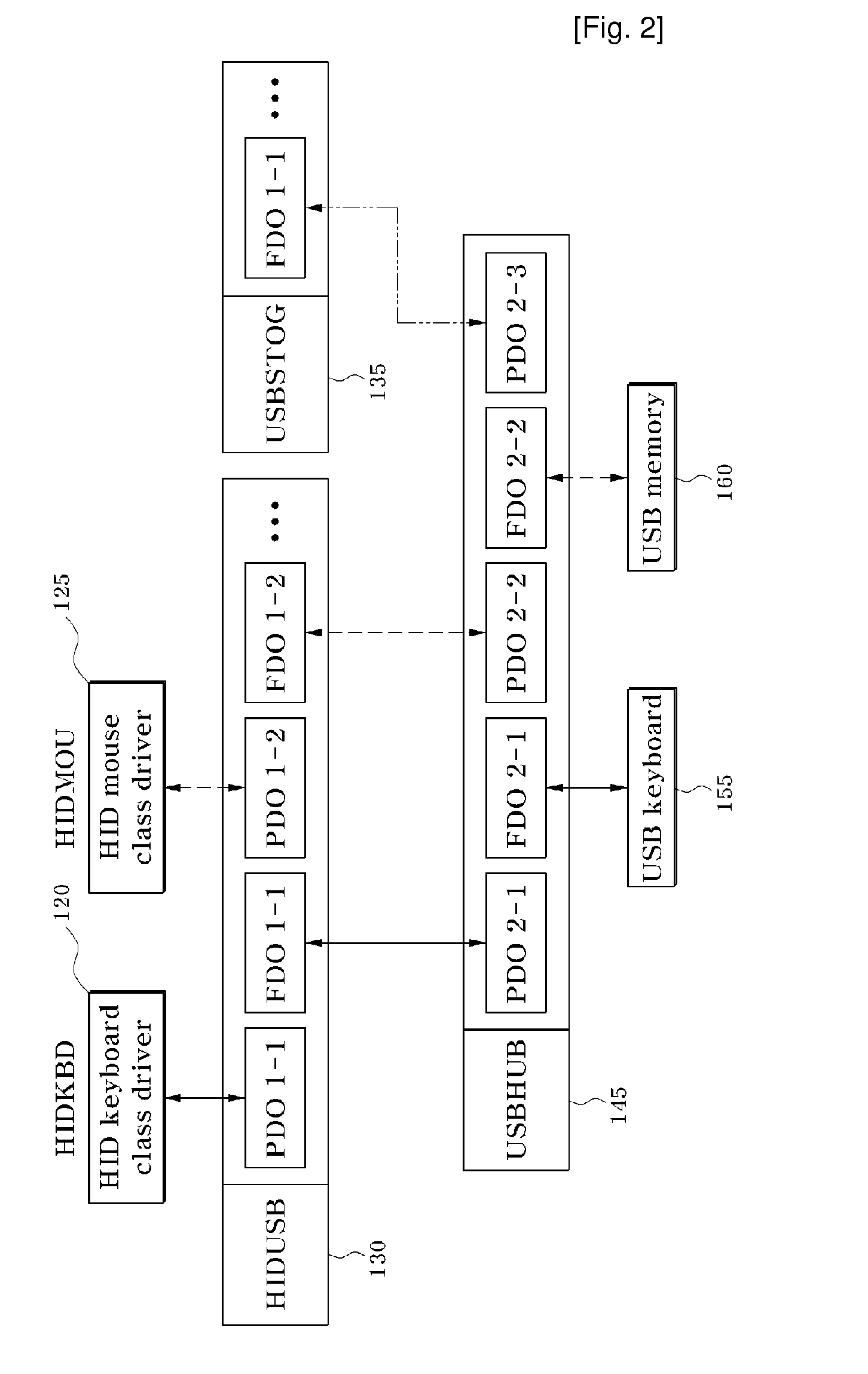
Apparatus and Method for Preservation of USB Keyboard
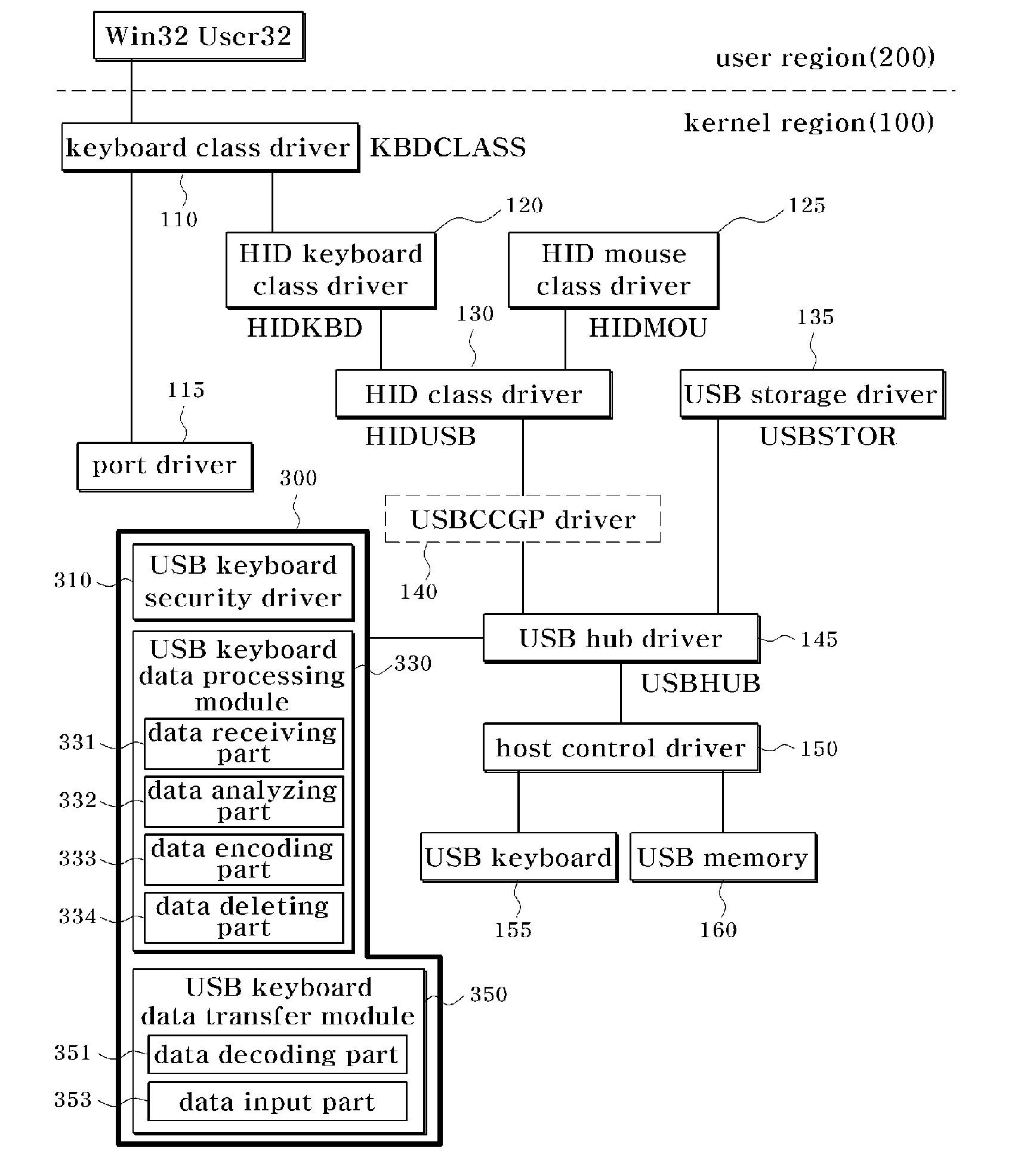
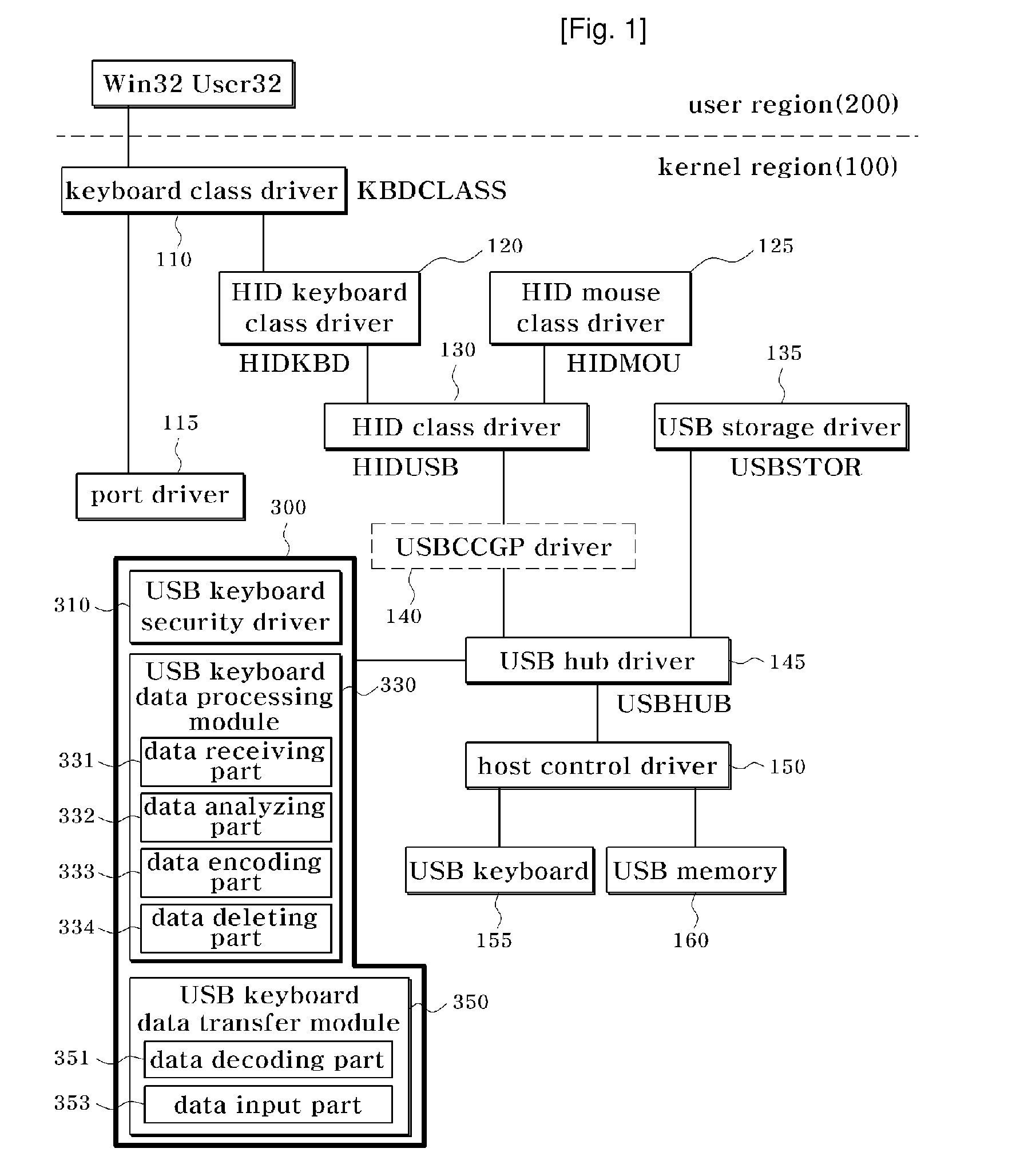
InactiveUS20090172705A1Inhibit inputInput/output for user-computer interactionProgram control using stored programsUSB hubPersonal computer
Provided are a data security apparatus and method for a USB keyboard. The data security apparatus includes: a USB keyboard security driver for selecting a driver for a USB keyboard from USB devices connected to a personal computer, and replacing a data processing function address in a USB hub driver with a function address of the selected USB keyboard driver to acquire input data input by the USB keyboard; a USB keyboard data processing module for preferentially receiving the input data acquired from the USB keyboard security driver, and processing the input data through analysis, encoding and deletion processes; and a USB keyboard data transfer module for decoding the input data processed by the USB keyboard USB keyboard data processing module and outputting the decoded input data to a user's desired location. Thus, data input by a malicious program from a keyboard in communication with a main body of a personal computer (PC) through USB to transmit data can be protected from being transmitted to the external.
Owner:KING INFORMATION & NETWORK
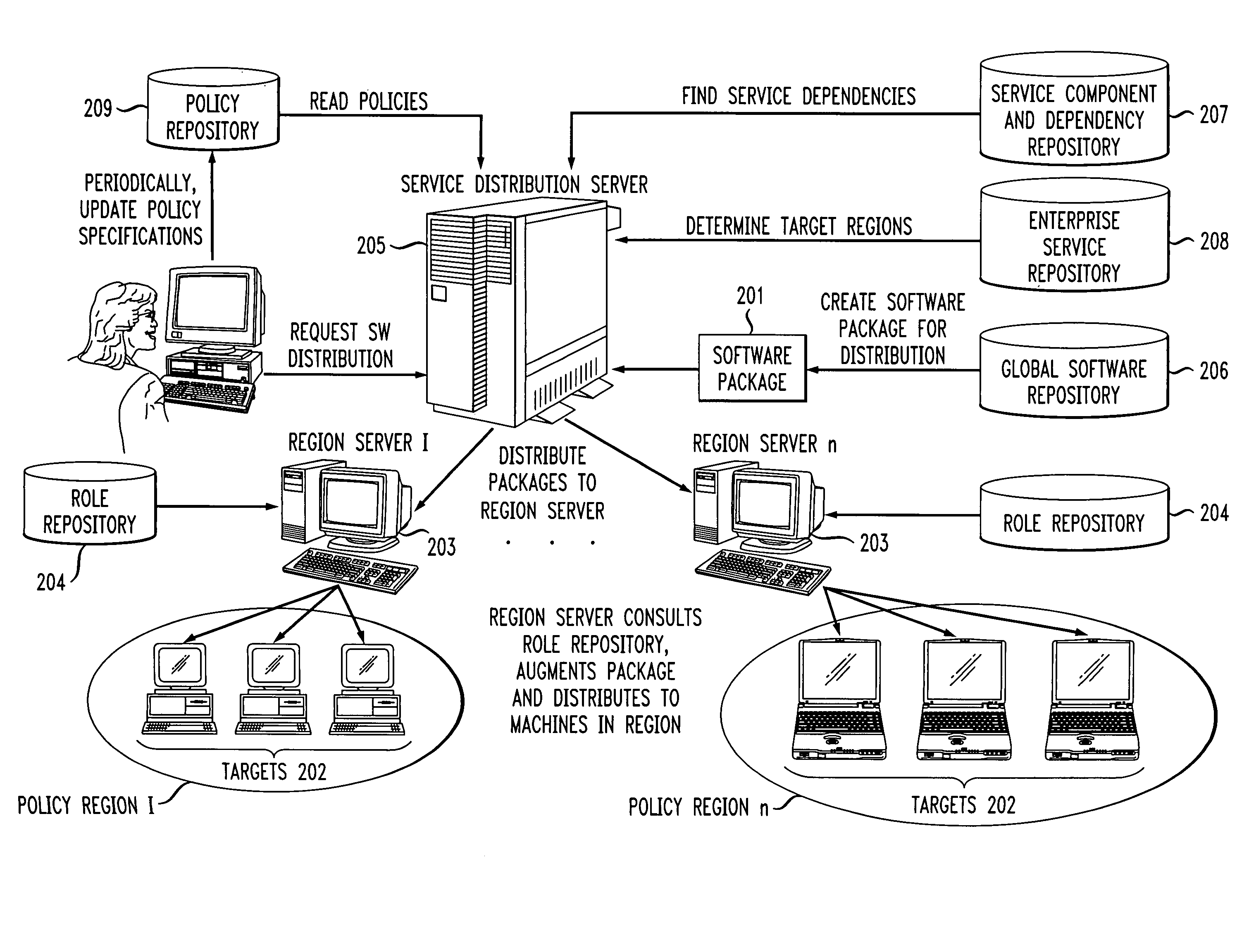
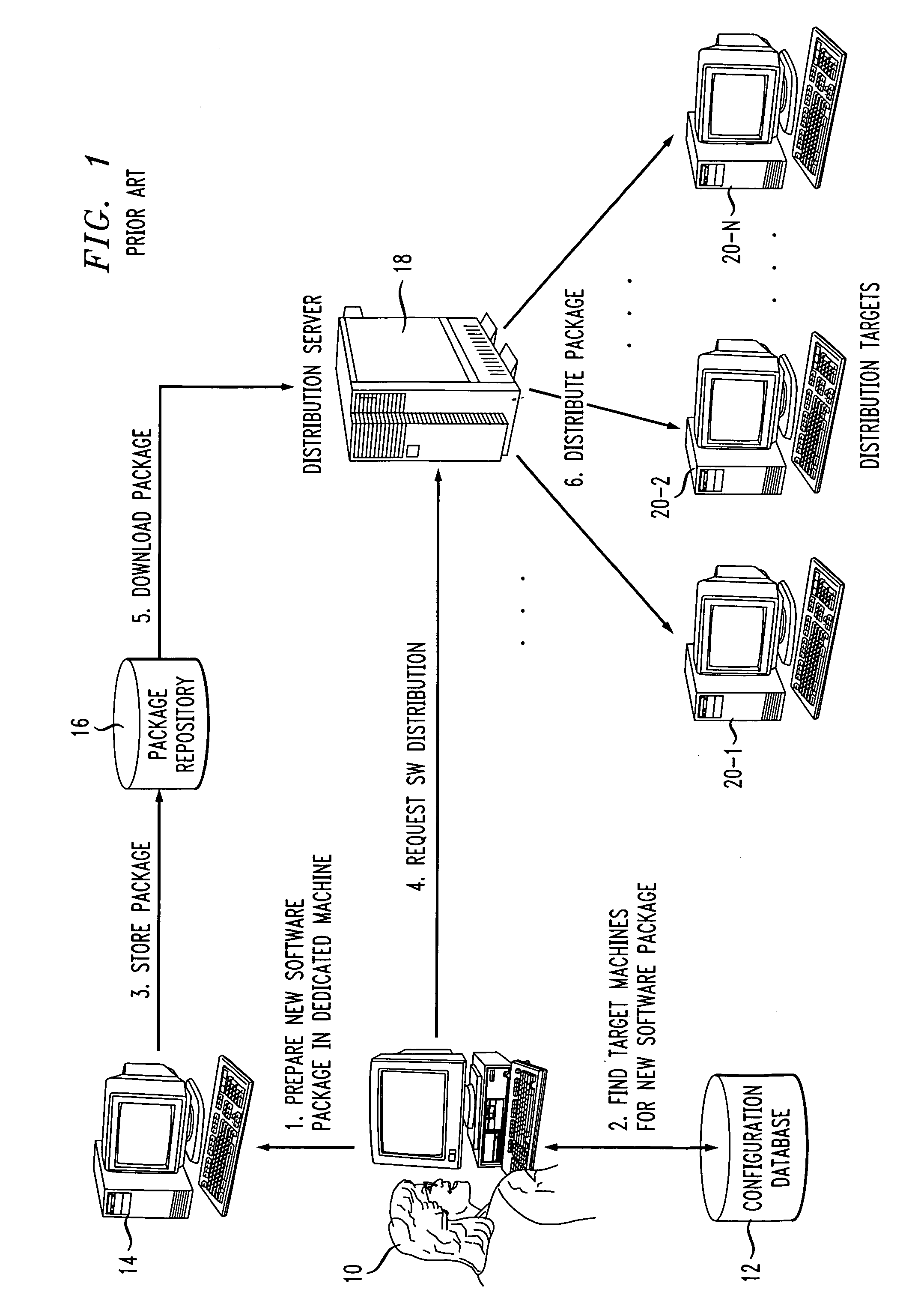
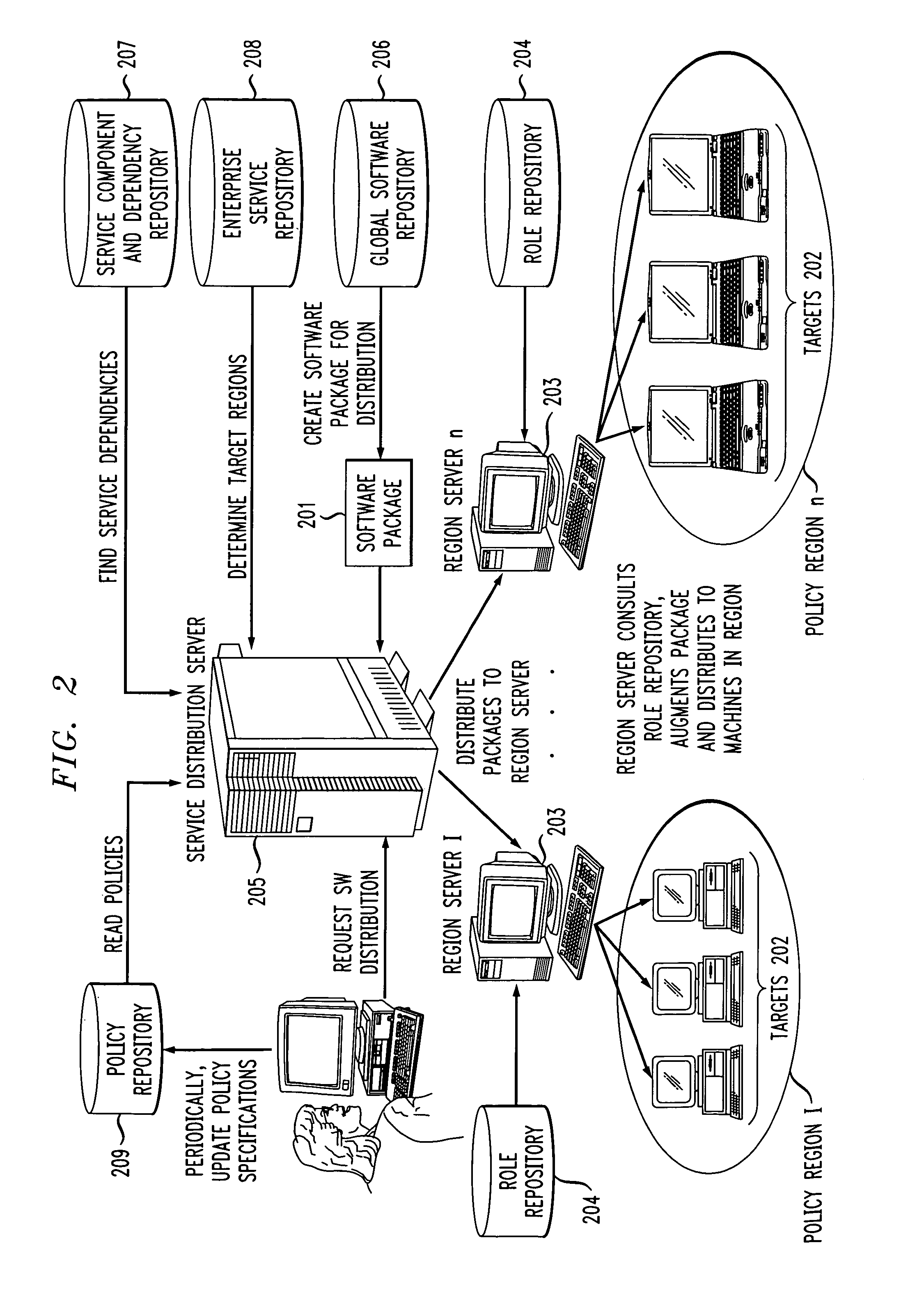
Systems and methods for service and role-based software distribution
InactiveUS7013461B2Good and more scaleable distributionMinimization requirementsProgram control using stored programsDigital computer detailsSoftware distributionSoftware package
Computer-based methods and systems for performing automated distribution of a software package to one or more target machines in one or more regions of a distributed network of target machines, comprises the following steps. First, a base software package is prepared for each of the one or more regions based on at least one of: (i) policy data indicating which of the one or more regions are candidates for receiving the software package, (ii) dependency information indicating requisites for a service provided by the software package, and (iii) configuration information for each of the candidate regions. The base software package is then distributed to each of the candidate regions of the distributed network. The base software package received at each of the candidate regions is then customized based on at least one of: (i) regional distribution policies, (ii) dependency information specific to one or more roles performed by the target machines in that region, and (iii) individual target machine configuration information. Lastly, the software package customized in each of the candidate regions is distributed to at least one of the target machines in the candidate regions of the distributed network.
Owner:INT BUSINESS MASCH CORP
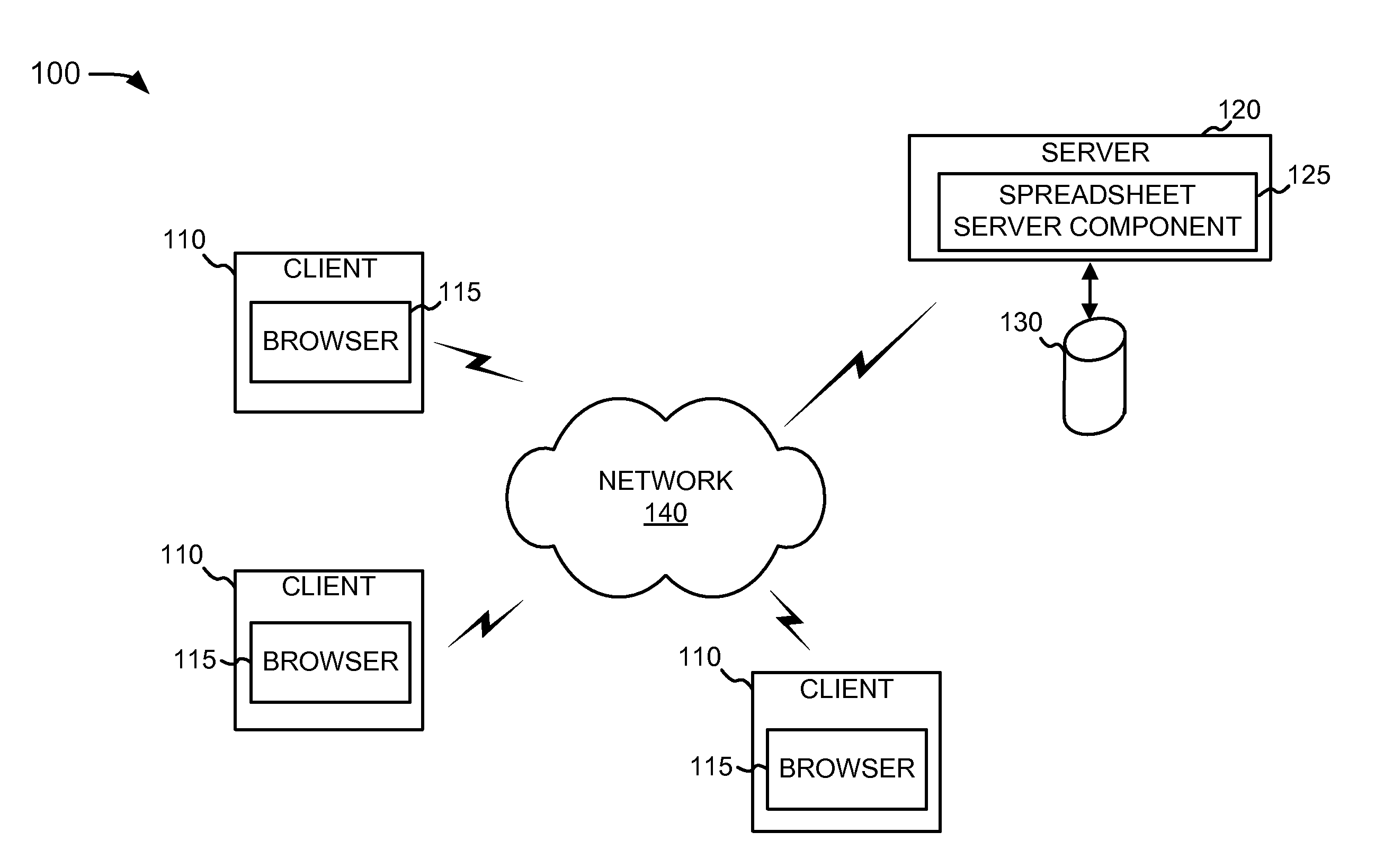
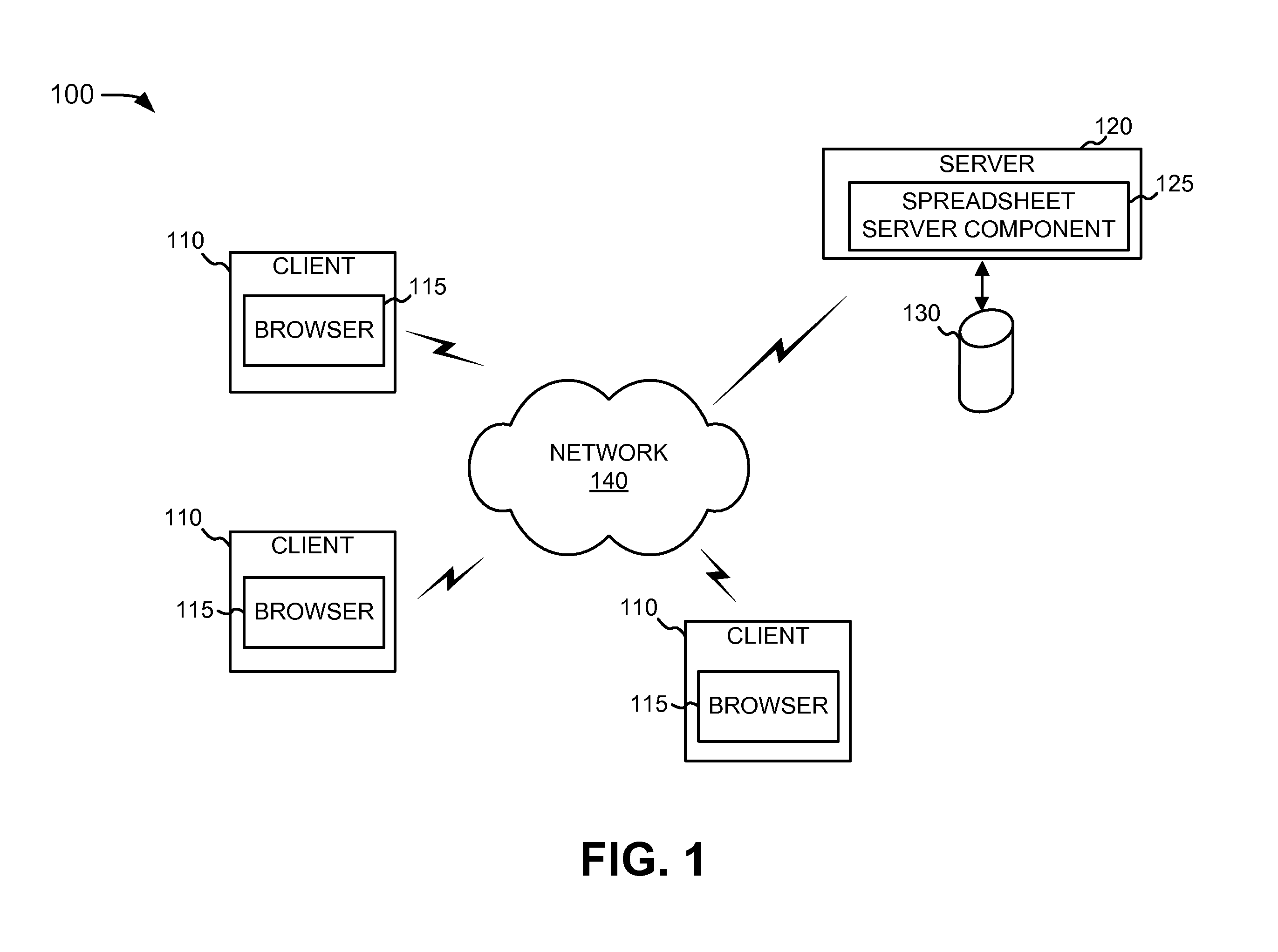
Collaborative online spreadsheet application
ActiveUS20070233811A1Program control using stored programsText processingElectronic formApplication software
A distributed spreadsheet application executes at a server and a client in a network. The networked spreadsheet application can generally be used without requiring a user to install any specific spreadsheet software prior to using the application. In one implementation, the spreadsheet application may include a client engine that executes within browser programs of a plurality of client computing devices and server logic. The server logic may be configured to distribute the client engines to the plurality of client computing devices of the spreadsheet application when requested through the browser programs of each of the plurality of client computing devices. The server logic synchronizes a single spreadsheet document that is simultaneously open at the plurality of client computing devices.
Owner:GOOGLE LLC
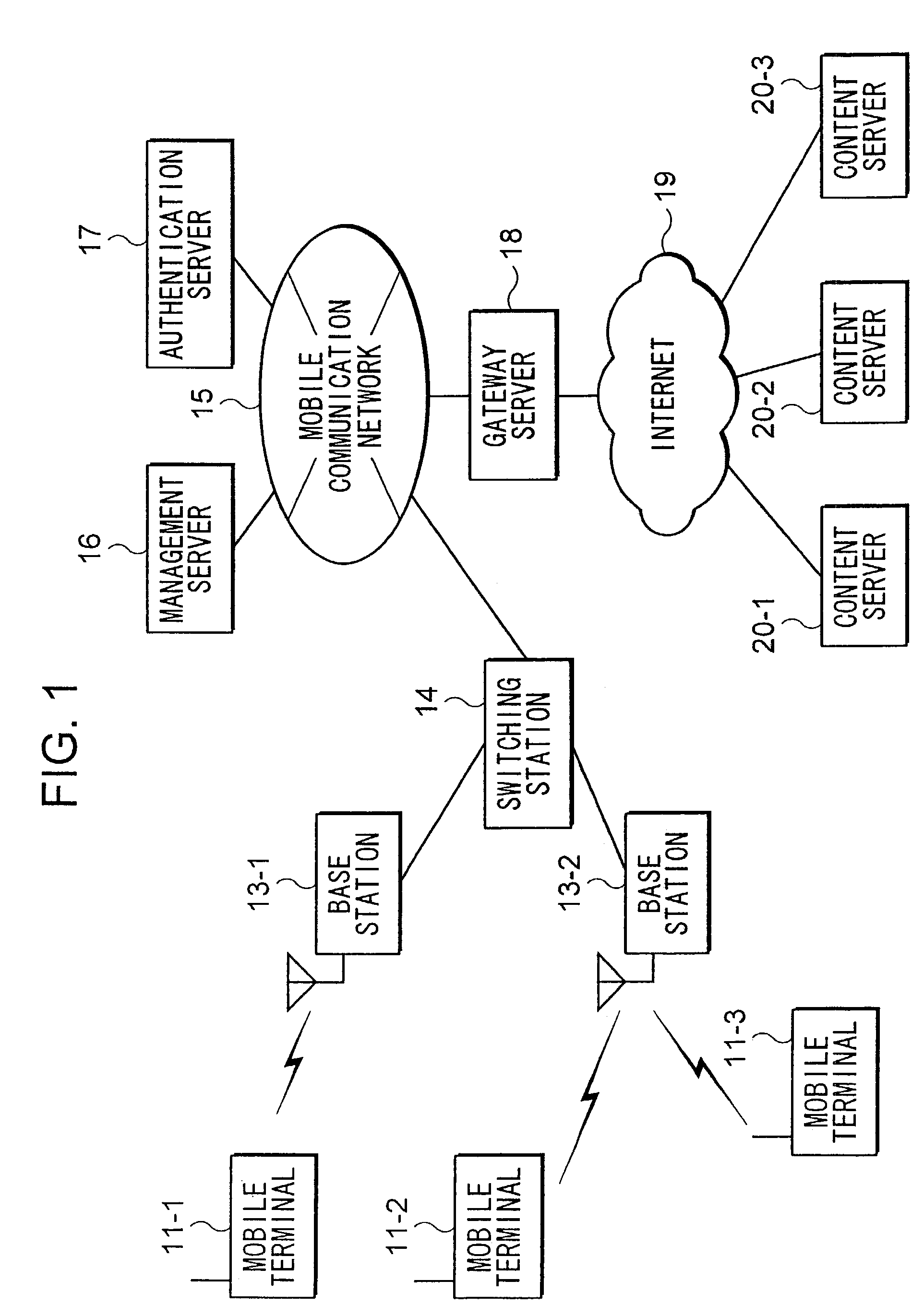
System for managing program applications storable in a mobile terminal
ActiveUS7379731B2Ensure safetyLow reliabilityProgram control using stored programsMultiple digital computer combinationsComputer terminalApplication software
Management server 16 may obtain application programs from content server 20 in response to requests of mobile terminal 11. Management server 16 may transmit the obtained application programs to mobile terminal 11 with information concerning reliabilities of the application programs. After mobile terminal 11 receives the application programs from management server 16, mobile terminal 11 manages operations of the application programs. Operations of the application programs are coordinated with operations of other programs using the information concerning the reliabilities corresponding to the application programs. Management of the coordinated operations of the application programs avoids problems concerning information security, where valuable information may be distributed unexpectedly because of operations of low reliable application programs. As a result, convenience of users of mobile terminals 11 can be improved without deteriorating the information security of mobile terminals 11.
Owner:NTT DOCOMO INC
Systems and methods for providing conflict handling for peer-to-peer synchronization of units of information manageable by a hardware/software interface system
InactiveUS20050044187A1Efficient application developmentFacilitate data sharingDigital data information retrievalData processing applicationsThree stageUsability
Various embodiments of the present invention are directed to conflict handling for conflicts that occur in a peer-to-peer synchronization system, where the ability to correctly and efficiently handle conflicts minimizes data loss while retaining good usability and reduces the need for user intervention during synchronization. Conflict handling in the synchronization service is divided into three stages: (1) conflict detection; (2) automatic conflict resolution and logging; and (3) conflict inspection and resolution. Certain embodiments are directed to a conflict handling schema comprising one or more of the follow conflict handling elements: (a) schematized representation of conflicts; (b) detection of conflicts; (c) logging of conflicts into a durable store; (d) automatic resolution of conflicts according to a flexible and configurable azqsxqxwdconflict resolution policy; (e) composable and extensible conflict handlers to filter and resolve conflicts; (f) automatic detection and removal of obsolete conflicts; and (g) programmatic conflict resolutions.
Owner:MICROSOFT TECH LICENSING LLC
Module class objects in a process plant configuration system
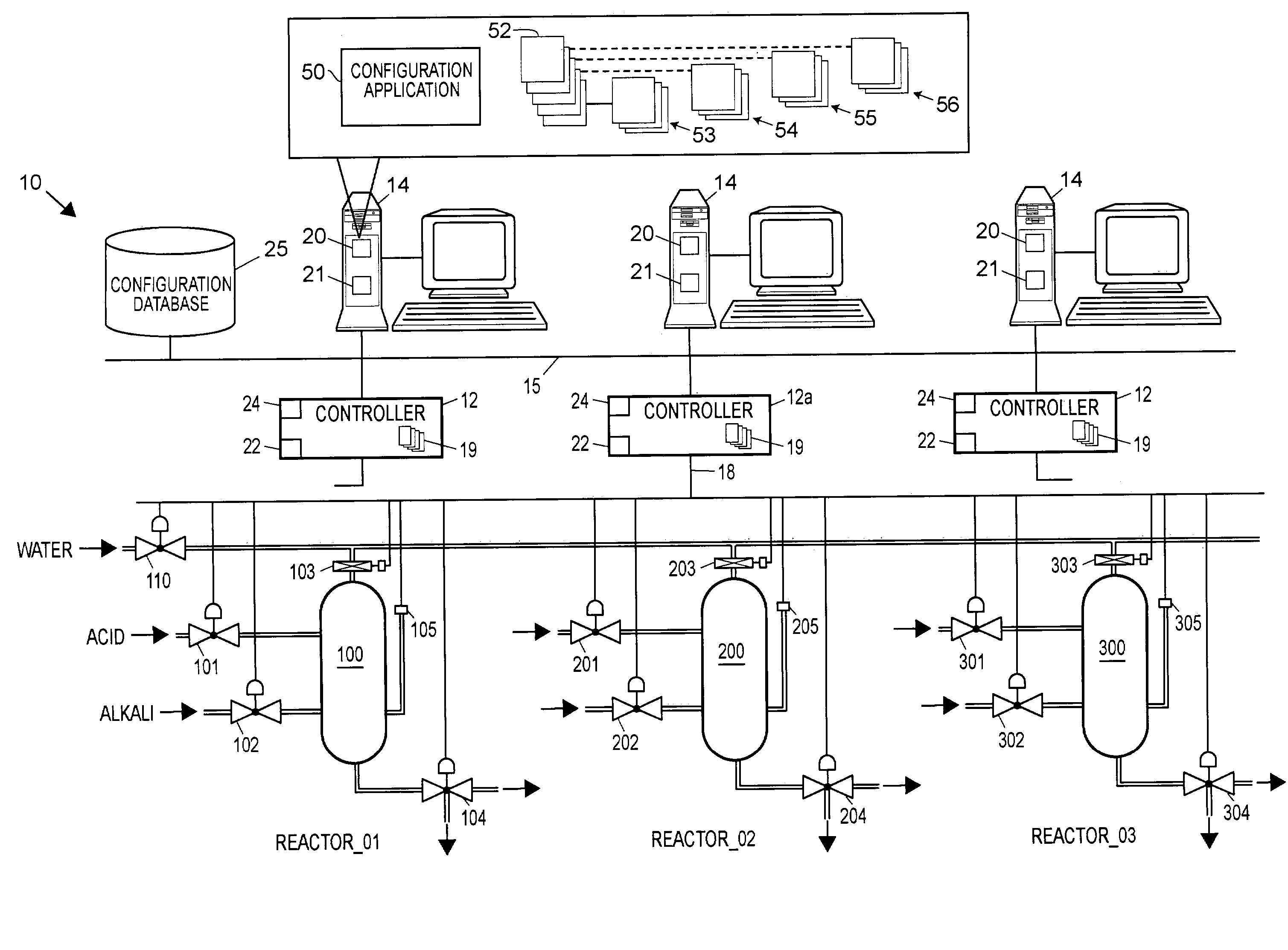
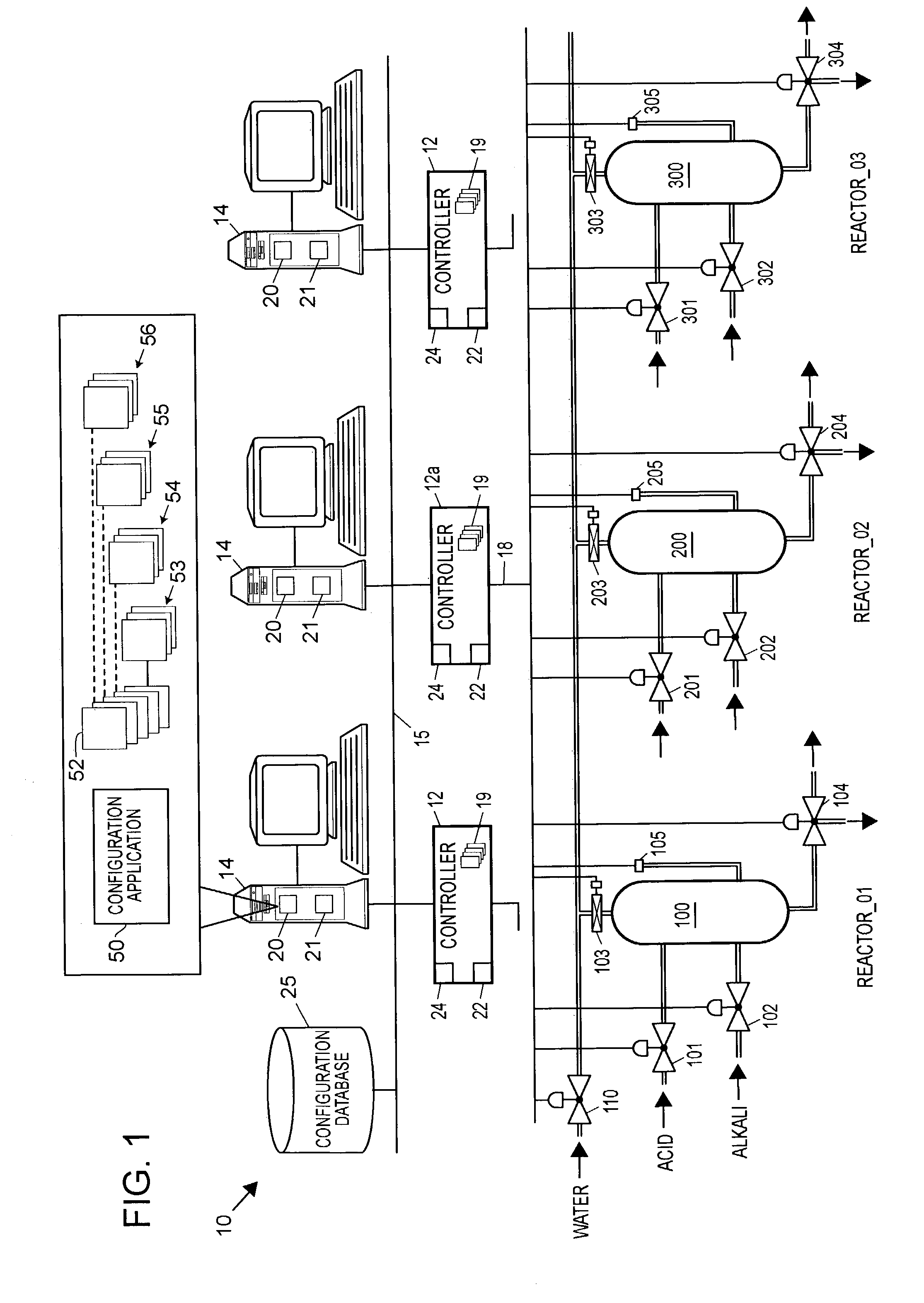
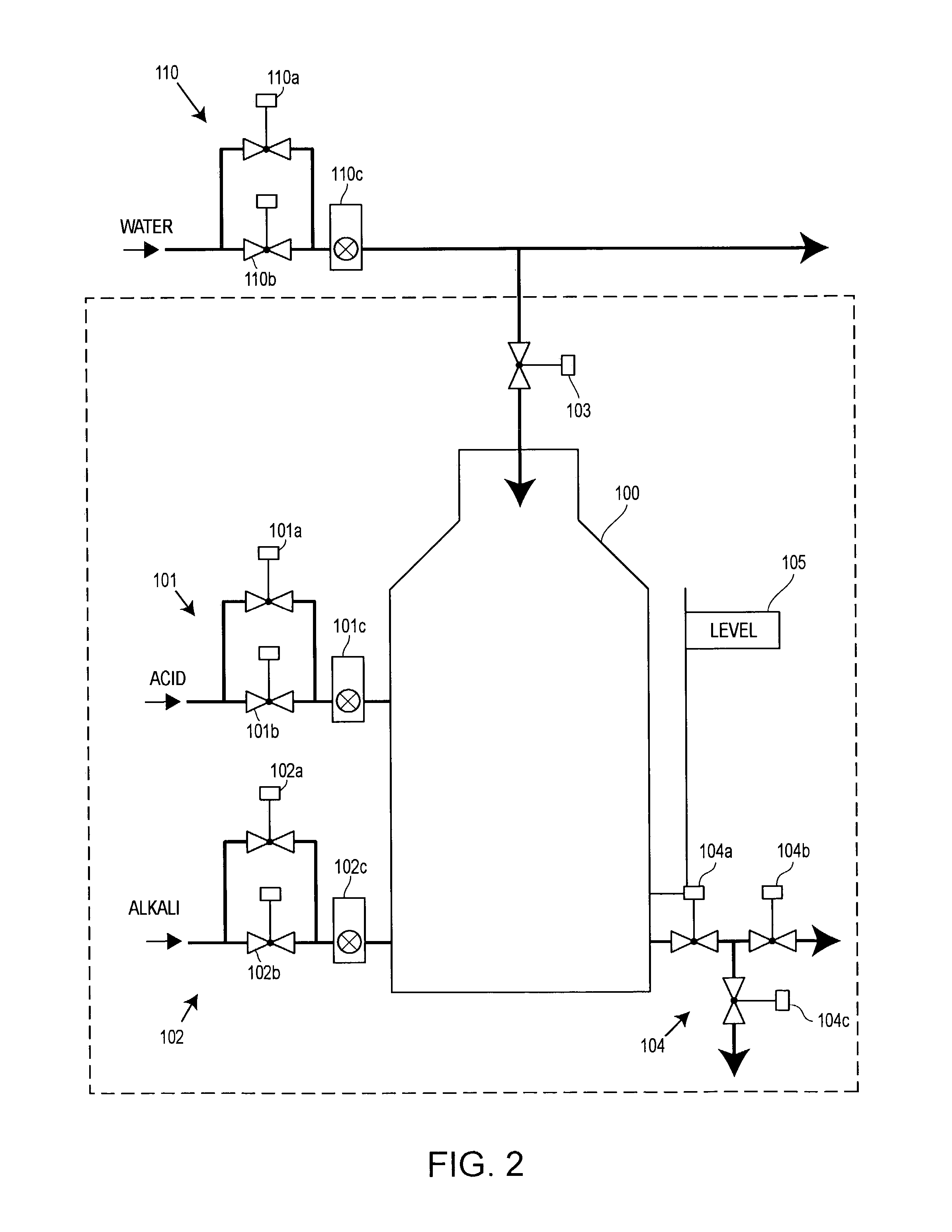
ActiveUS7043311B2Configuration of process easyLess time-consumingProgram control using stored programsComputer controlComputer scienceTime-Consuming
A configuration system for a process plant uses module class objects to assist in configuring, organizing and changing the control and display activities within the process plant. Each module class object generically models or represents a process entity, such as a unit, a piece of equipment, a control activity, etc., and may be used to create instances of the object, called module objects, which represent and are tied to specific equipment within the process plant. The module class objects may represent process entities of any desired scope, which means that a single module class object may be used to configure the control and display activities of process entities of any desired scope within the process plant, instead of just at a control module level. In particular, module class objects of a large scope may be used to configure large sections or portions of the process plant, which makes configuration of the process plant easier and less time consuming. A module class object may be a unit module class object reflecting a physical unit within the process plant, an equipment module class object reflecting a physical piece of equipment within the process plant, a control module class object reflecting a control module or scheme within the process plant, or a display module class object reflecting a display routine that provides information to a user within the process plant.
Owner:FISHER-ROSEMOUNT SYST INC
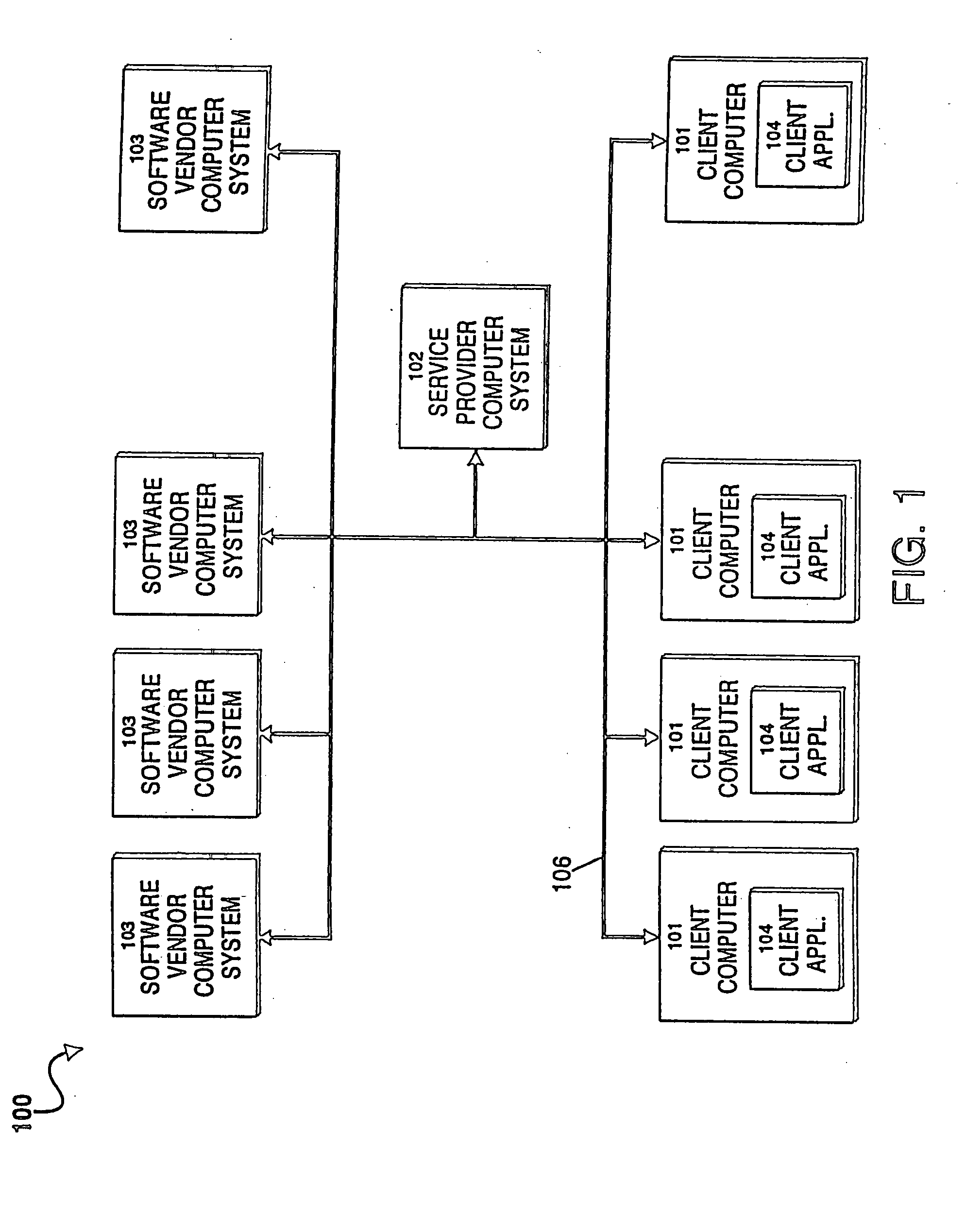
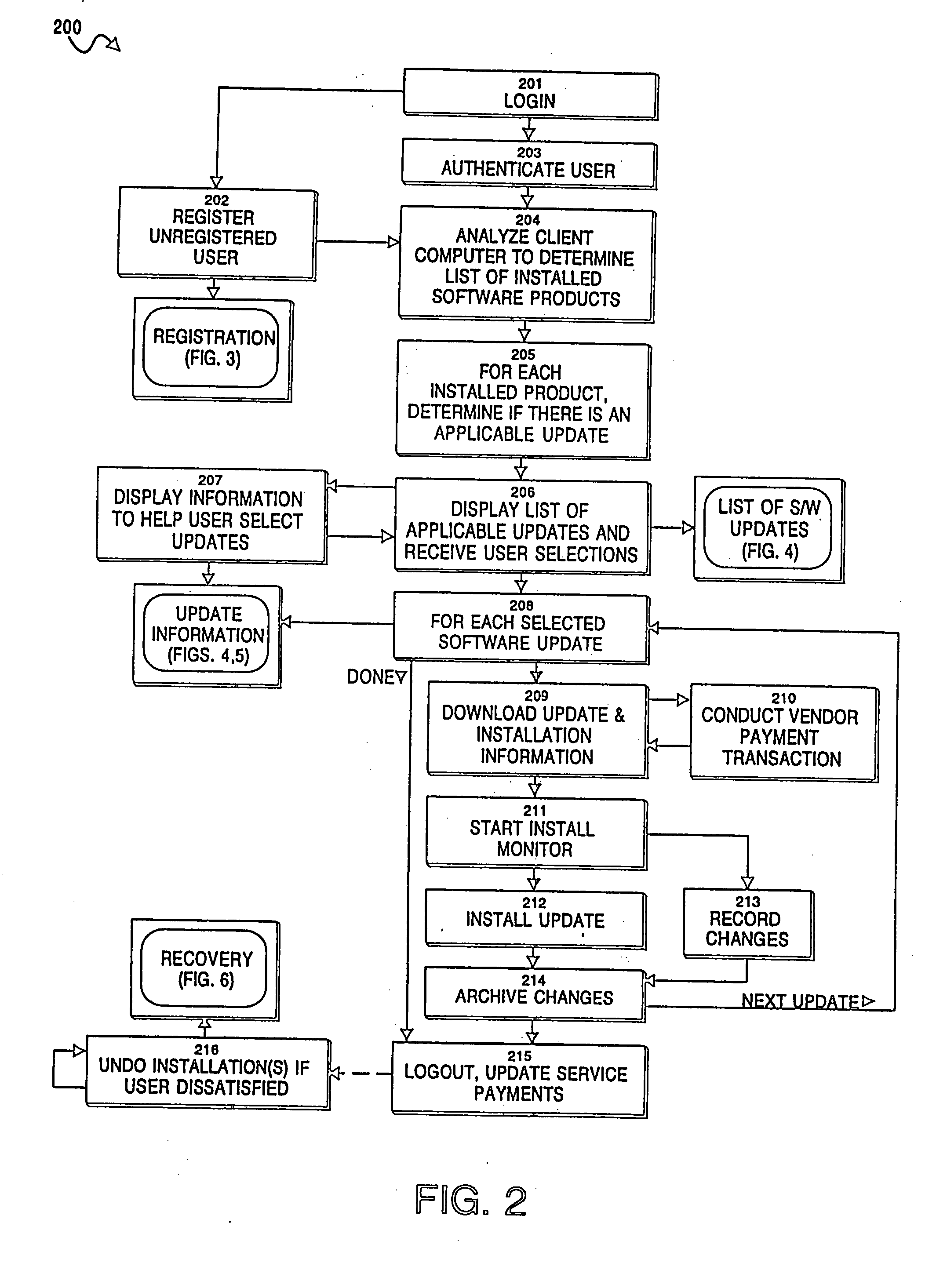
Automatic updating of diverse software products on multiple client computer systems
InactiveUS20050273779A1Program control using stored programsBuying/selling/leasing transactionsPaymentSoftware update
A system and method update client computers of various end users with software updates for software products installed on the client computers, the software products manufacturered by diverse, unrelated software vendors. The system includes a service provider computer system, a number of client computers and software vendor computer systems communicating on a common network. The service provider computer system stores in an update database information about the software updates of the diverse software vendors, identifying the software products for which software updates are available, their location on the network at the various software vendor computer systems, information for identifying in the client computers the software products stored thereon, and information for determining for such products, which have software updates available. Users of the client computers connect to the service provider computer and obtain a current version of portions of the database. The client computer determines that software products stored thereon, and using this information, determines from the database, which products have updates available, based on product name and release information for the installed products. The user selects updates for installation. The selected updates are downloaded from the software vendor computer systems and installed on the client computer. Payment for the software update and the service is mediated by the service provider computer. Authentication of the user ensures only registered users obtain software updates. Authentication of the software updates ensures that the software updates are virus free and uncorrupted. Changes to the client computer during installation are monitored and archived, allowing the updates to be subsequently removed by the user.
Owner:MCAFEE LLC
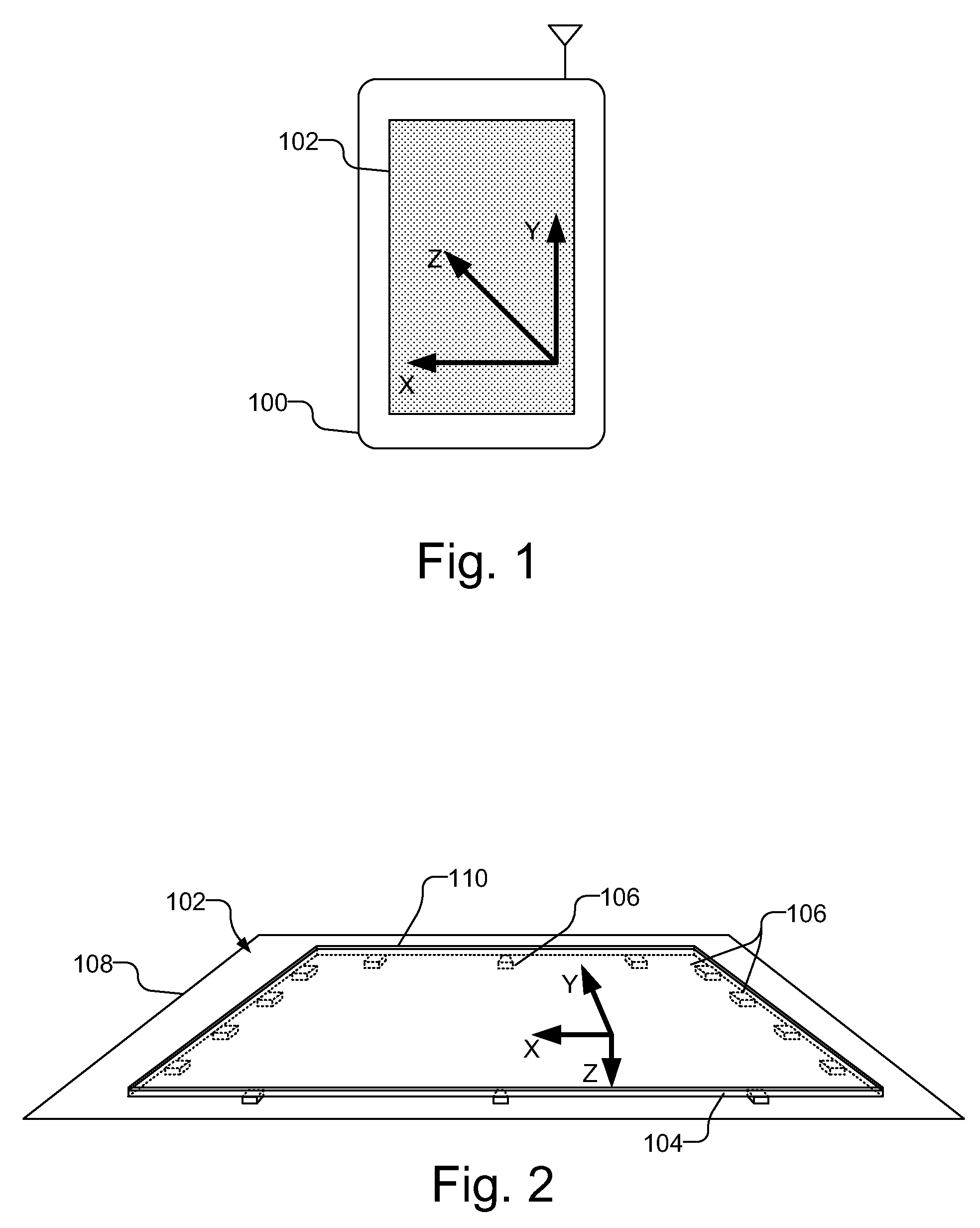
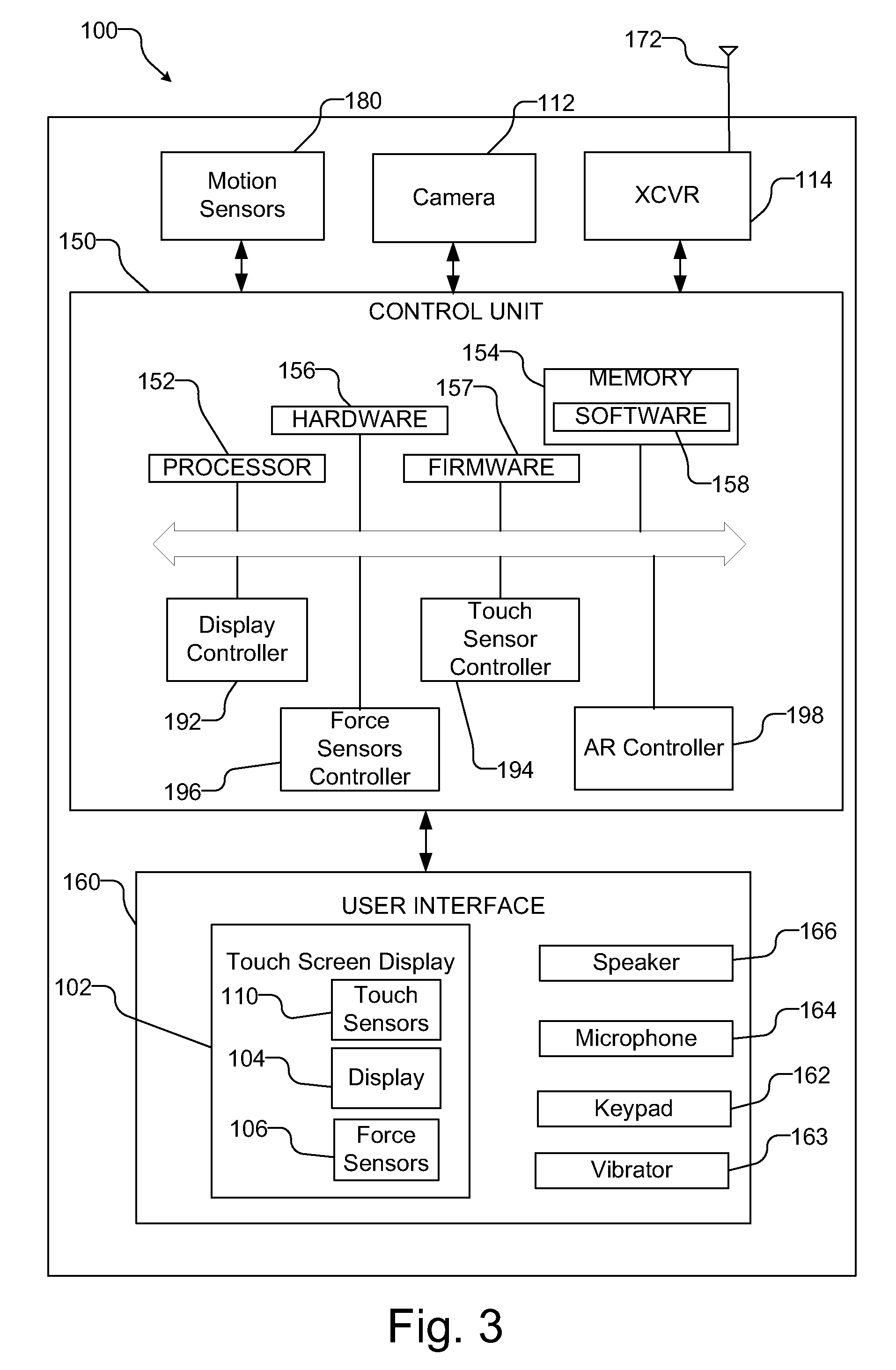
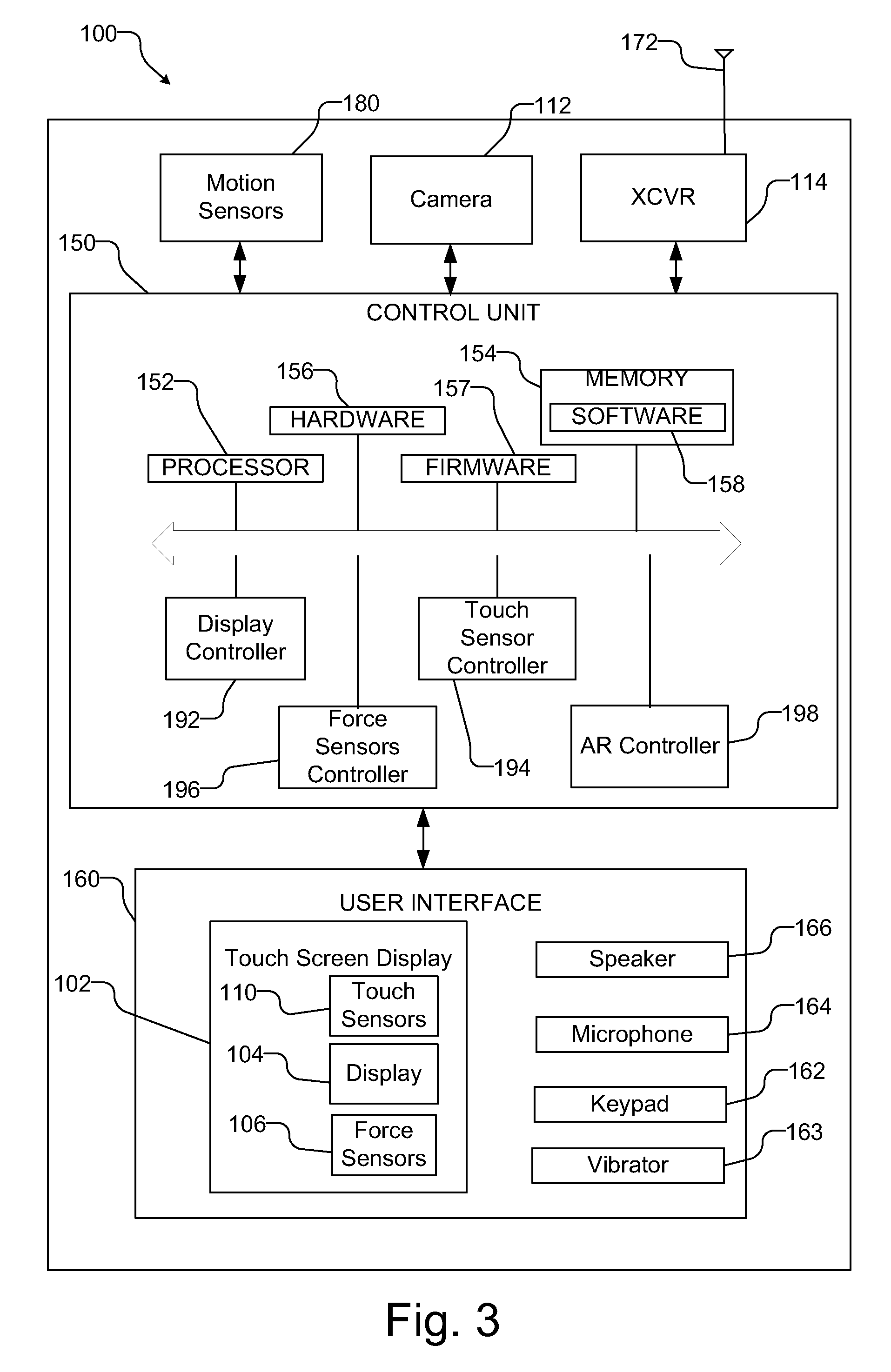
User interface elements augmented with force detection
ActiveUS8952987B2Inhibition of activationProgram control using stored programsCathode-ray tube indicatorsDisplay deviceBiological activation
A computing device includes a touch screen display with at least one force sensor, each of which provides a signal in response to contact with the touch screen display. Using force signals from the at least one force sensor that result from contact with the touch screen, the operation of the computing device may be controlled, e.g. to select one of a plurality of overlaying interface elements, to prevent the unintended activation of suspect commands that require secondary confirmation, and to mimic the force requirements of real-world objects in augmented reality applications.
Owner:QUALCOMM INC
Efficient use of hybrid media in cache architectures
ActiveUS8397016B2Memory architecture accessing/allocationProgram control using stored programsParallel computingCache management
A multi-tiered cache manager and methods for managing multi-tiered cache are described. Multi-tiered cache manager causes cached data to be initially stored in the RAM elements and selects portions of the cached data stored in the RAM elements to be moved to the flash elements. Each flash element is organized as a plurality of write blocks having a block size and wherein a predefined maximum number of writes is permitted to each write block. The portions of the cached data may be selected based on a maximum write rate calculated from the maximum number of writes allowed for the flash device and a specified lifetime of the cache system.
Owner:INNOVATIONS IN MEMORY LLC
Configuring client software using remote notification
InactiveUS6219698B1New informationEasy to installProgram control using stored programsDigital computer detailsClient-sideHandling system
To maintain communications between first and second processing systems interconnected by a communications network, computer programing having first and second sets of instructions are stored at the first processing system. The computer programing is initialized at the first processing system to perform a task associated with the first set of instructions. In accordance with the second set of instructions, a first signal is automatically transmitted from the first processing system to the second processing system responsive to the initialization of the computer programming.
Owner:GOOGLE LLC
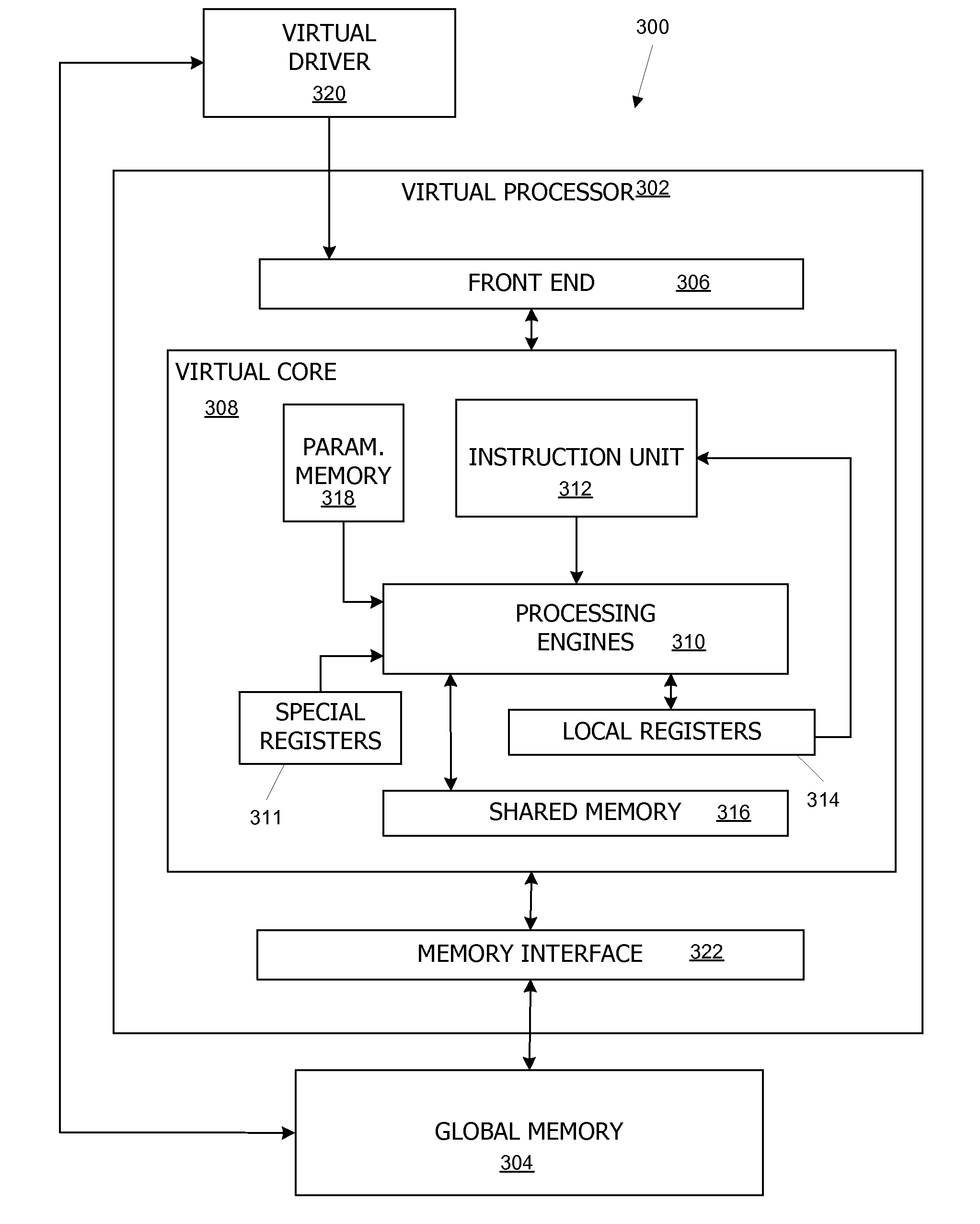
Virtual architecture and instruction set for parallel thread computing
ActiveUS20080184211A1Improve developmentImprove portabilityProgram control using stored programsSoftware engineeringApplication softwareData sharing
A virtual architecture and instruction set support explicit parallel-thread computing. The virtual architecture defines a virtual processor that supports concurrent execution of multiple virtual threads with multiple levels of data sharing and coordination (e.g., synchronization) between different virtual threads, as well as a virtual execution driver that controls the virtual processor. A virtual instruction set architecture for the virtual processor is used to define behavior of a virtual thread and includes instructions related to parallel thread behavior, e.g., data sharing and synchronization. Using the virtual platform, programmers can develop application programs in which virtual threads execute concurrently to process data; virtual translators and drivers adapt the application code to particular hardware on which it is to execute, transparently to the programmer.
Owner:NVIDIA CORP
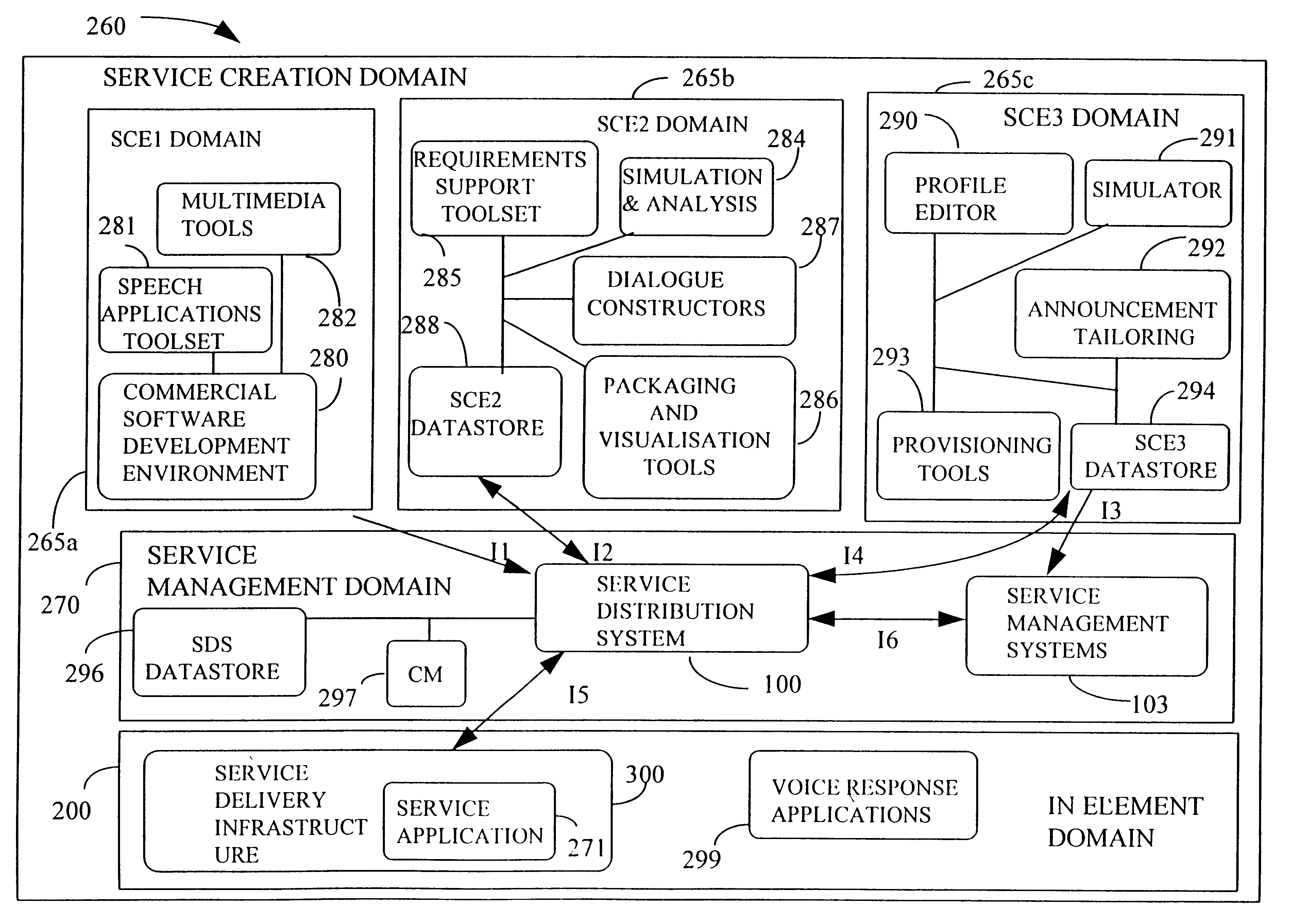
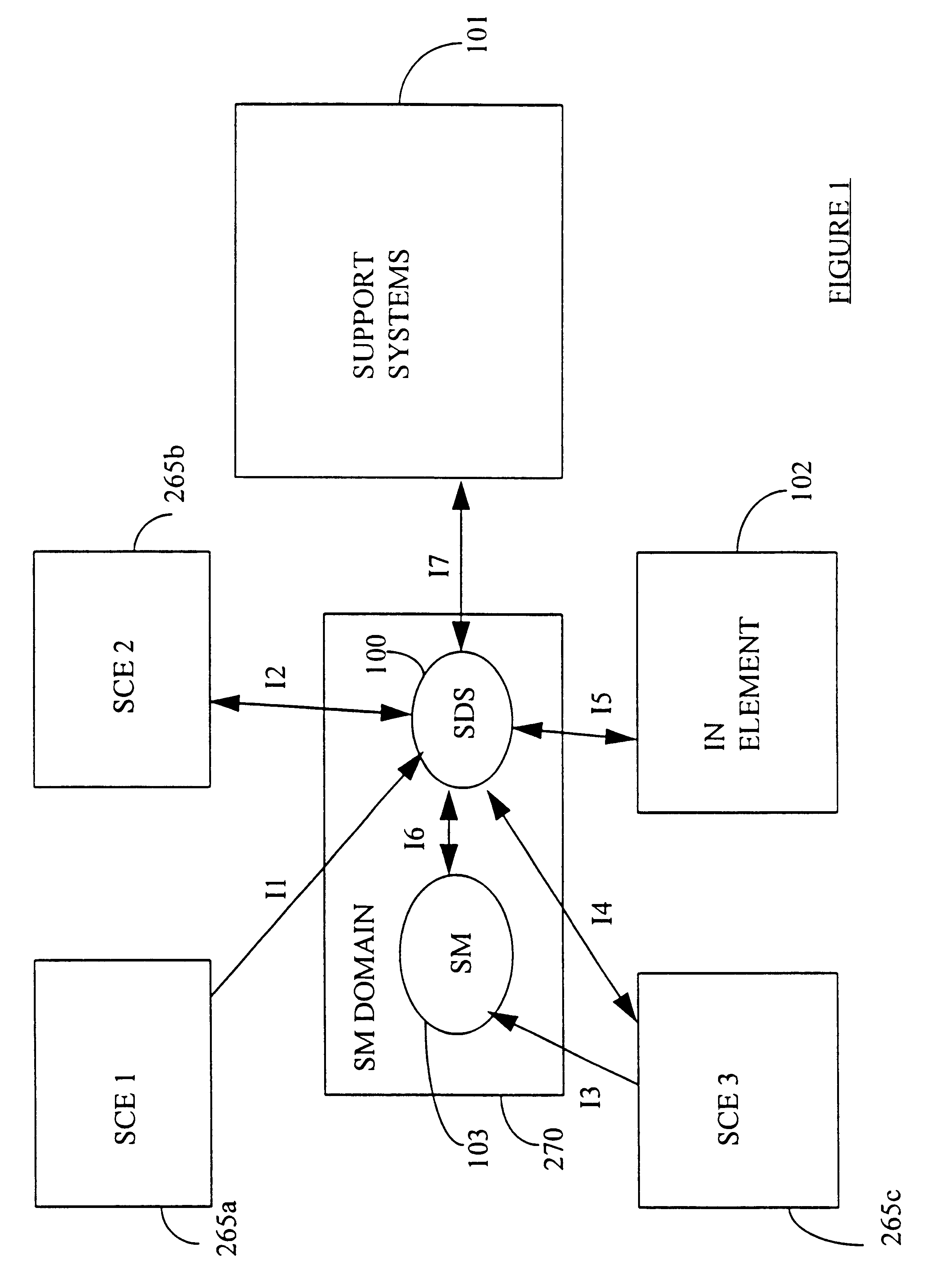
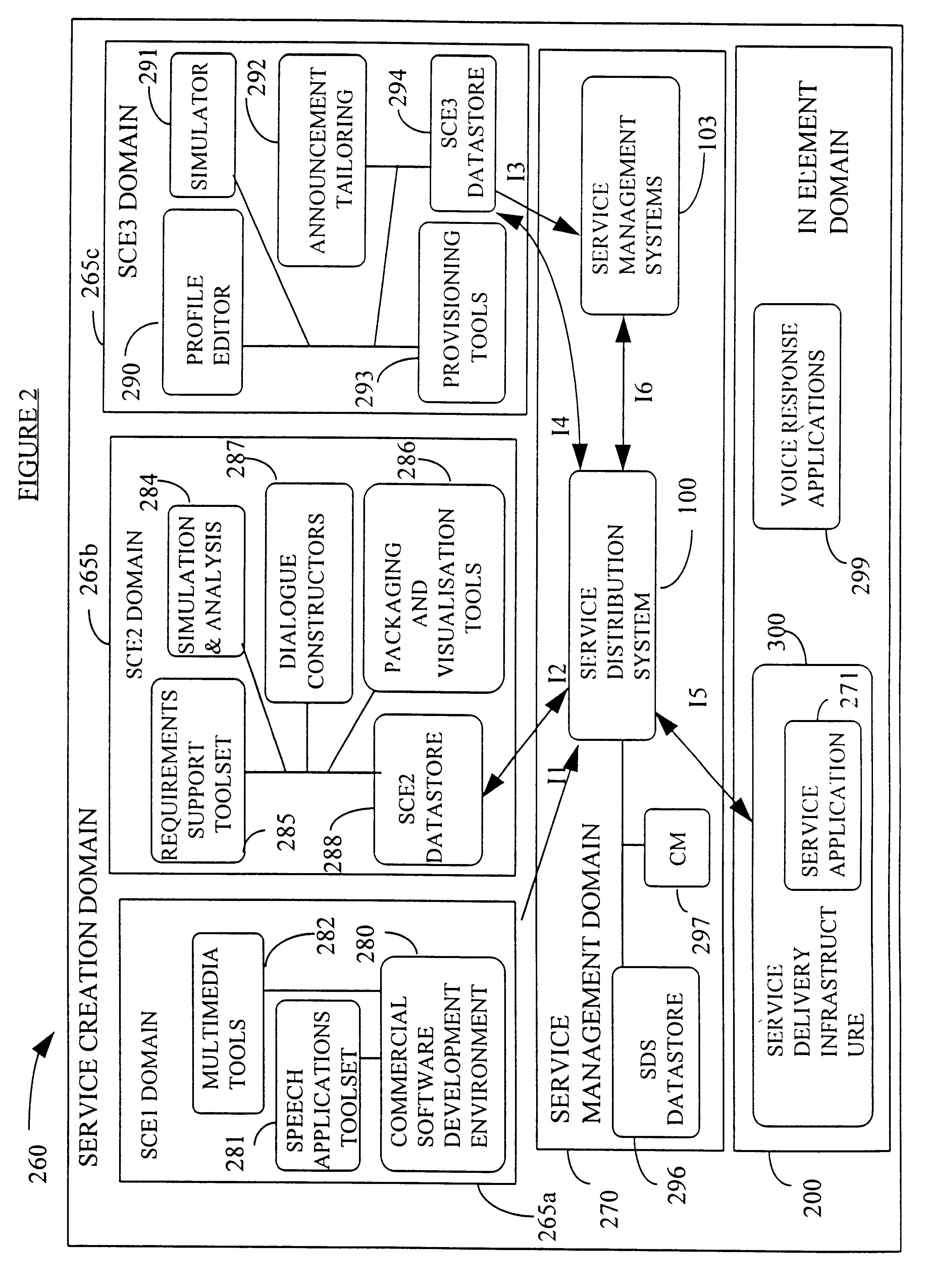
Service creation apparatus for a communications network
InactiveUS6338088B1Multiplex system selection arrangementsProgram control using stored programsIntelligent NetworkService provision
A service creation system for a communications network of the intelligent network type has 3 different levels at which service creation activities can be carried out, these being SCE1, SCE2 and SCE3. The use of separate levels allows access to the service creation system to be kept functionally separate for users having different interests in the network. Hence, features which have to be installed at the network element level for a selected service to be available can be created in SCE1. Marketable service features, which give a view of features in that they encapsulate call handling logic thereof together with support and management descriptions of the feature, can be created in SCE2. Service packages, which permit collection of marketable service features to meet requirements of a service together with servicespecific support and management information, can be created in either of SCE2 or SCE3. The service provider at SCE2 creates and tests edit graphs which comprise ordered sequences of marketable service features. These are then made available to the customer at SCE3. Profiles, which list the features relevant to a service for a user and provide data slots for the data necessary to each feature, can be provisioned and modified in SCE3 by the creation of execute graphs from edit graphs. In addition to marketable service features, metafeatures can be embedded in edit graphs. These are similar to marketable service features but have no associated screen information. This allows the user to generate execute graphs from what appears to be a blank screen but in practice has embedded constraints by means of the metafeatures, thus ensuring that the execute graph is still within tested constraints.
Owner:BRITISH TELECOMM PLC
Server side configuration management
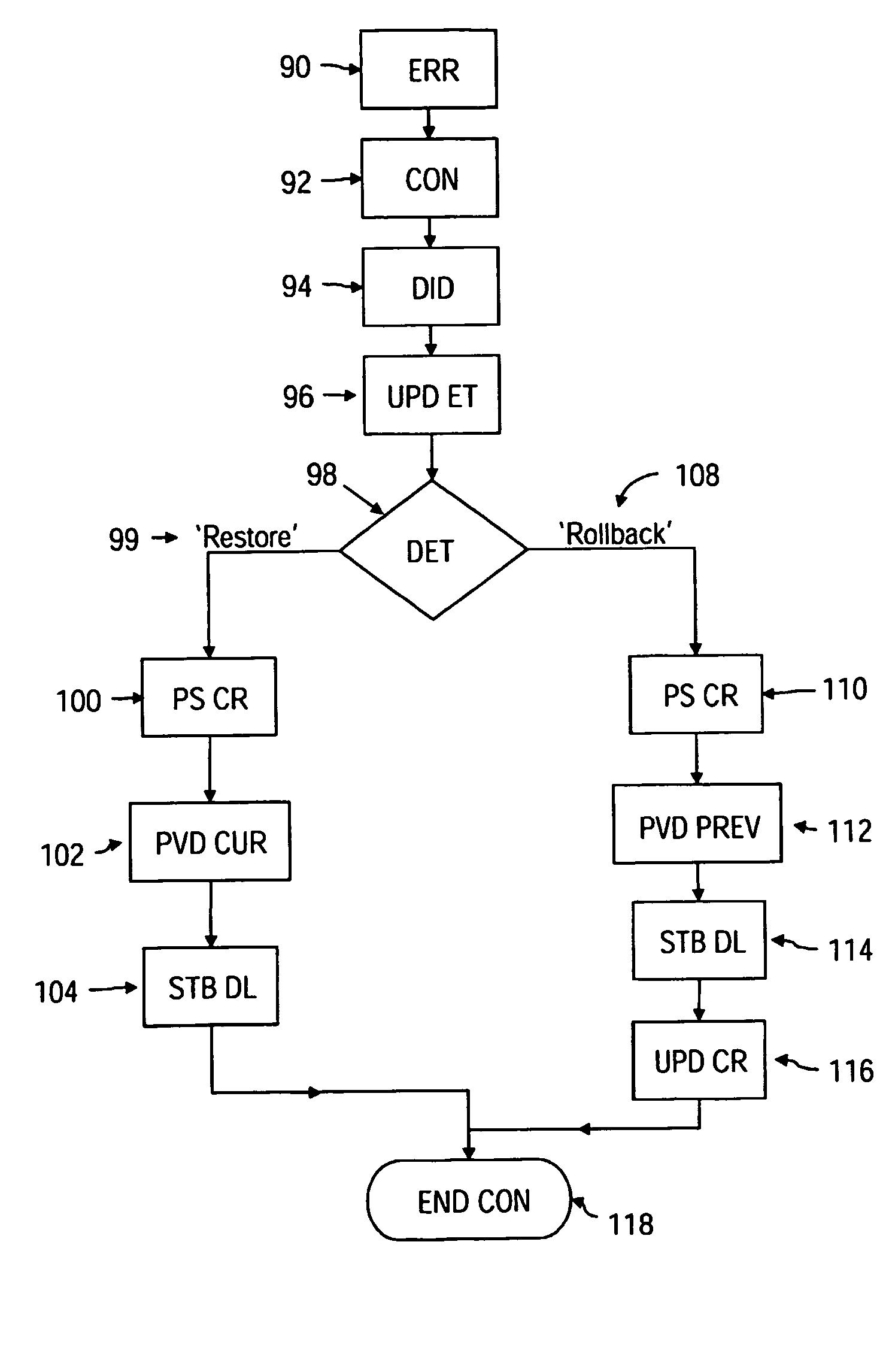
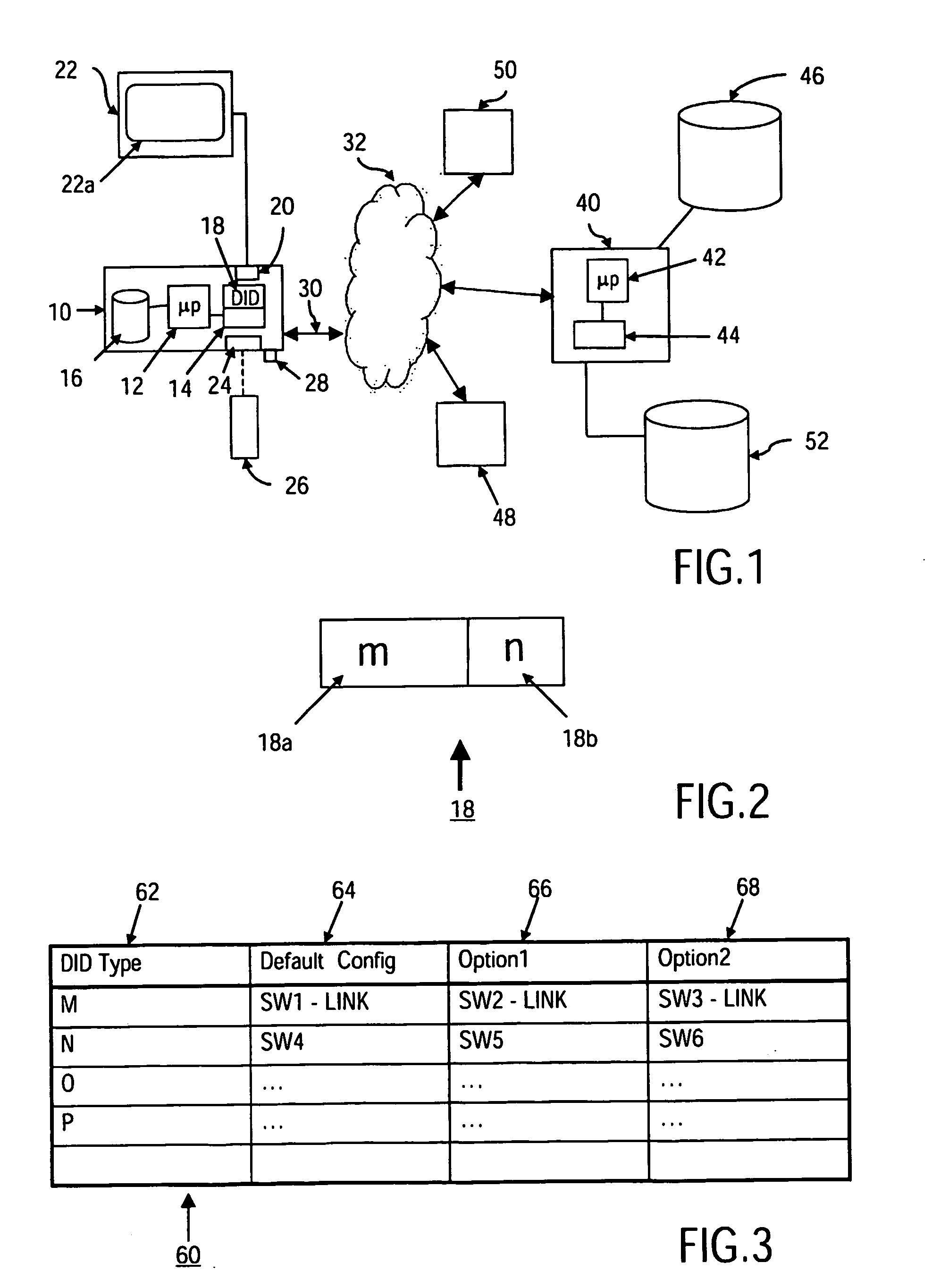
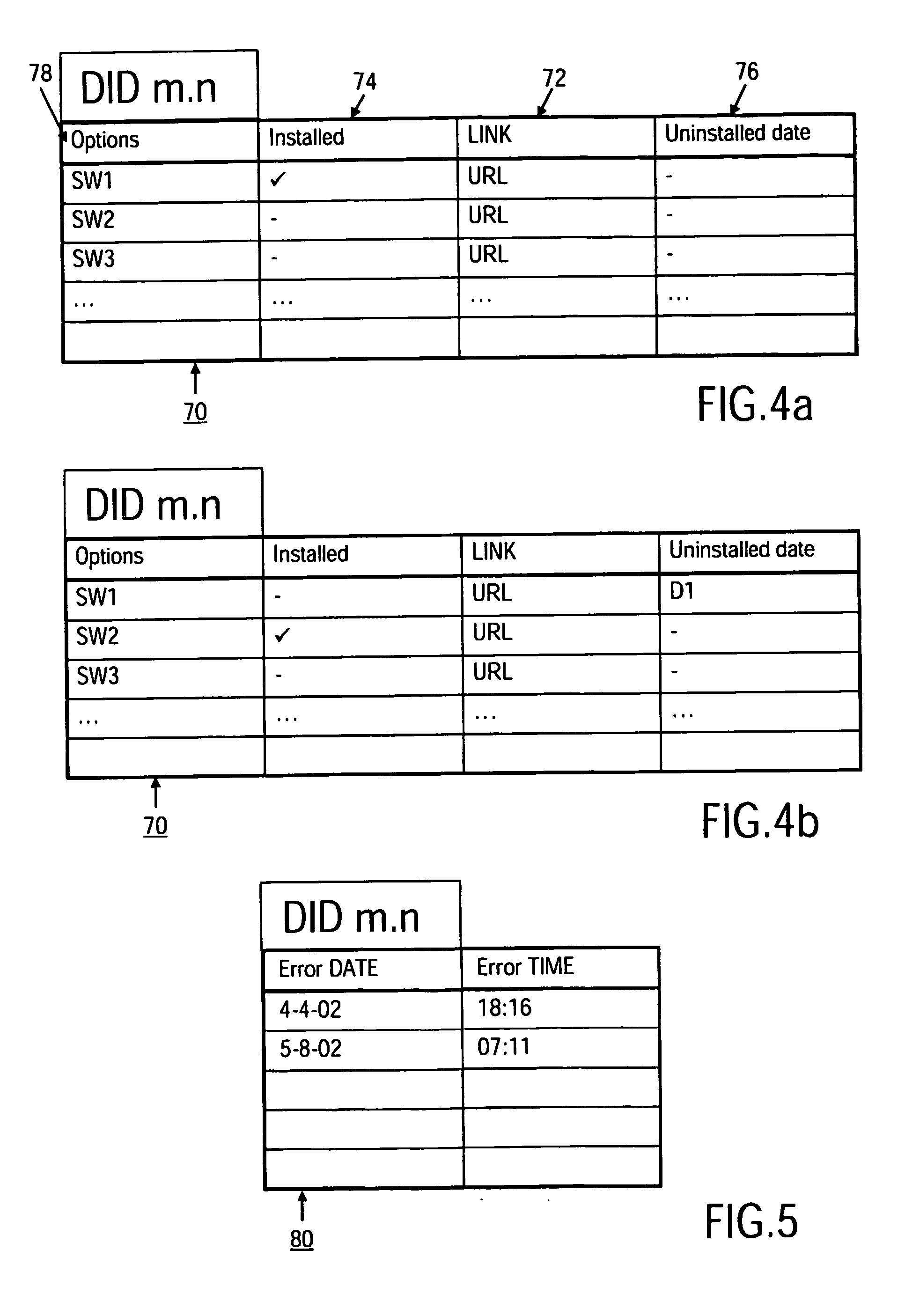
InactiveUS20050223374A1Improve stabilityFaster bug-fix and upgrade cycleProgram control using stored programsError detection/correctionDevice typeUnique identifier
A method and system for managing differing software configurations of Consumer Electronic (CE) devices (10) having a unique identifier (18) and network communication means (30) is described. Software options (60, 78) for types of CE device are stored in a software configuration database (46) comprising individual configuration records (70) for each identified CE device (10). The identifier (18) enables a configuration server (40) to look up that devices associated configuration record (70) and installable software options, and provide such options for download to a user's device. The server maintains the record according to user choices, and furthermore upgrades, restores or rolls back software configurations for the CE device(s) according to error detection and / or user preference.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
User interface elements augmented with force detection
ActiveUS20120293551A1Inhibition of activationProgram control using stored programsCathode-ray tube indicatorsDisplay deviceBiological activation
A computing device includes a touch screen display with at least one force sensor, each of which provides a signal in response to contact with the touch screen display. Using force signals from the at least one force sensor that result from contact with the touch screen, the operation of the computing device may be controlled, e.g. to select one of a plurality of overlaying interface elements, to prevent the unintended activation of suspect commands that require secondary confirmation, and to mimic the force requirements of real-world objects in augmented reality applications.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com