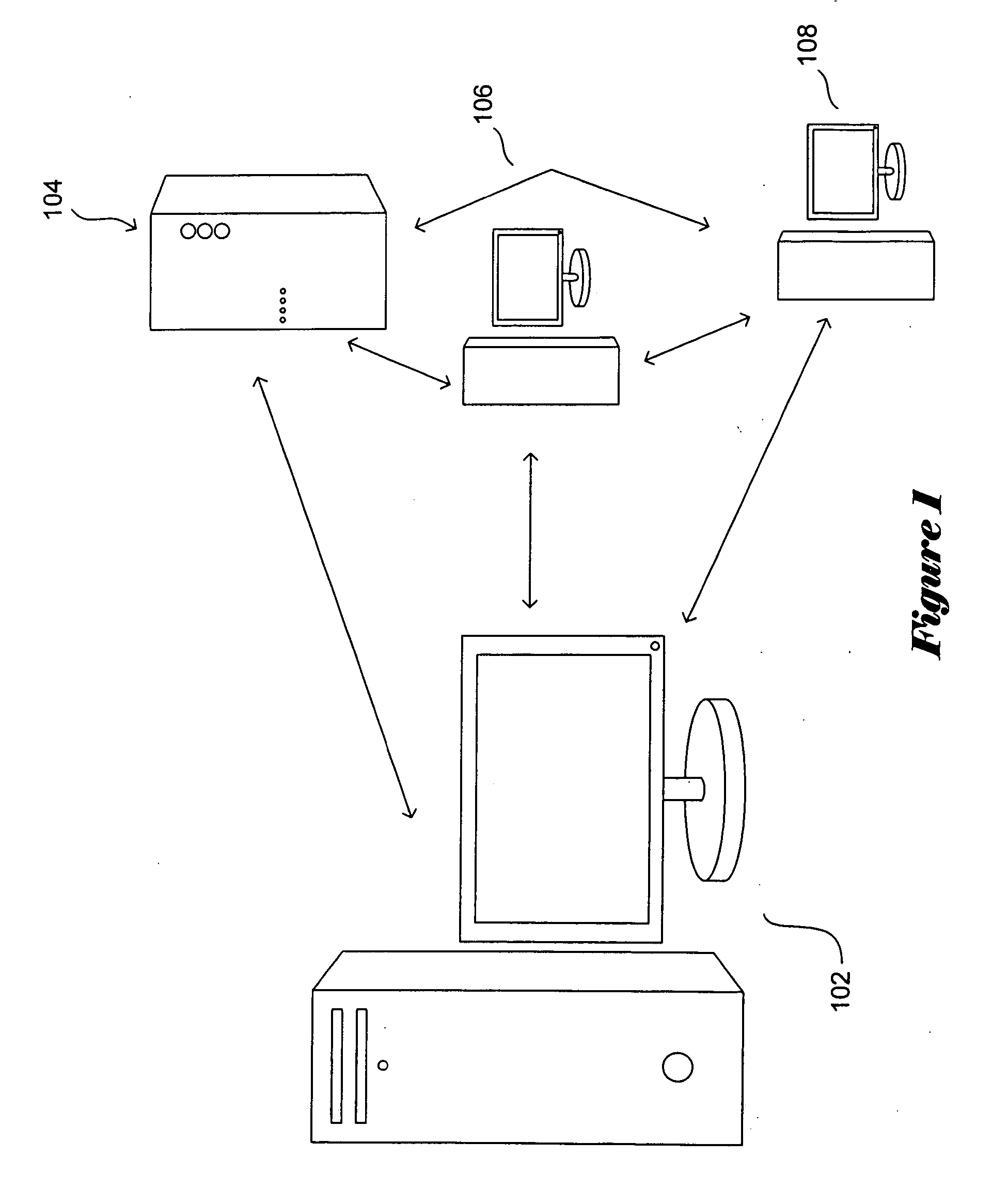
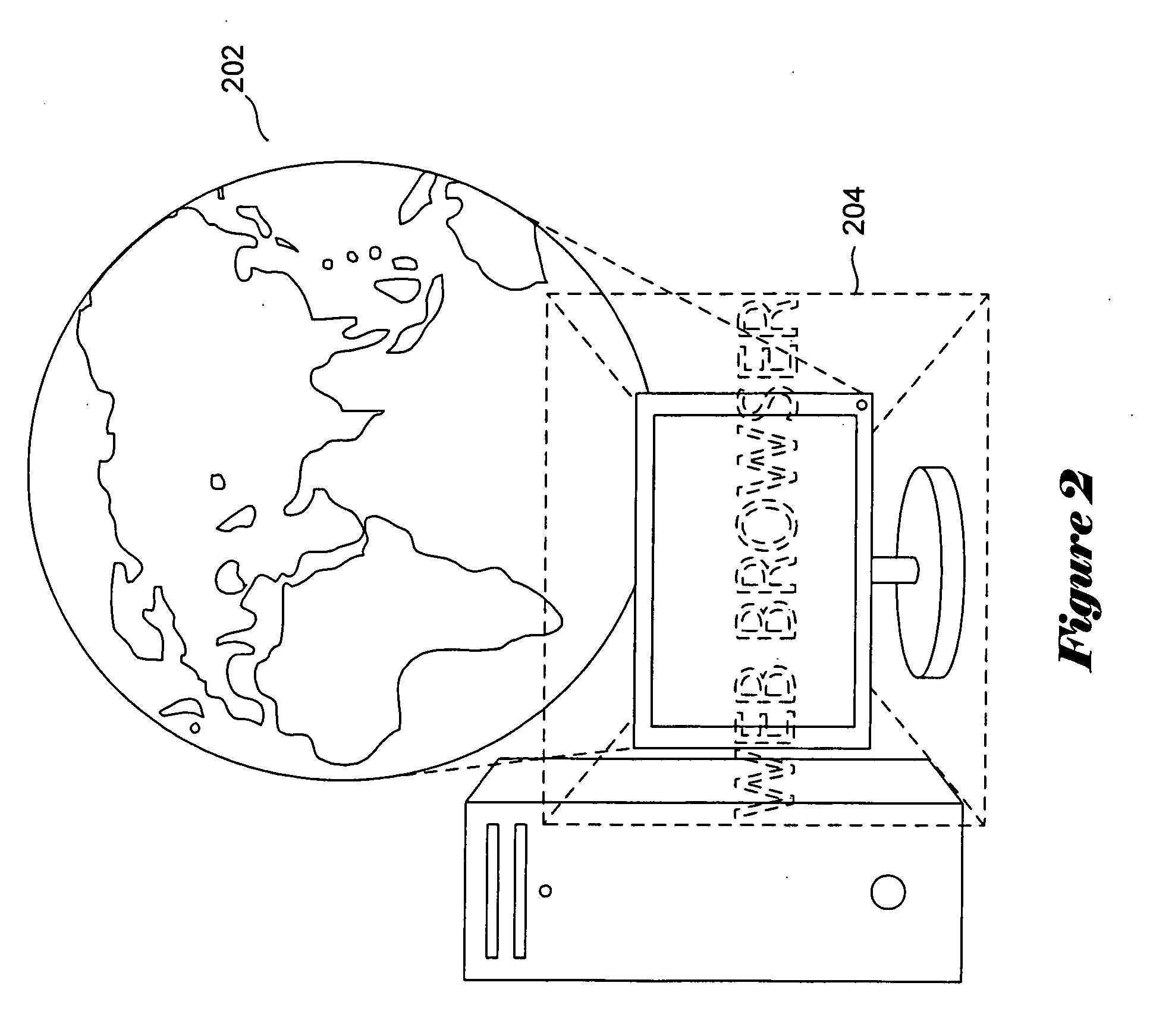
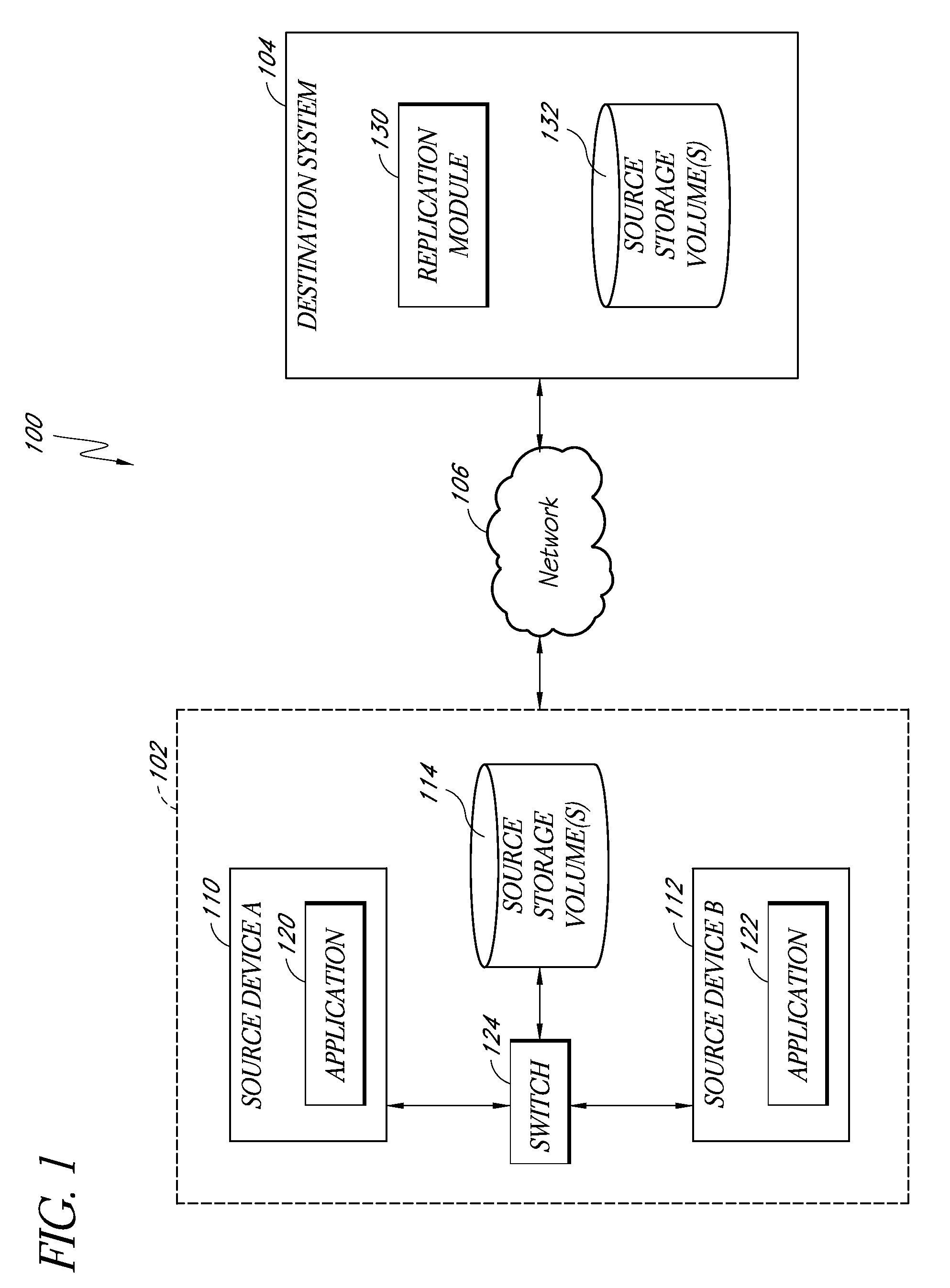
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
17759 results about "Backup" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
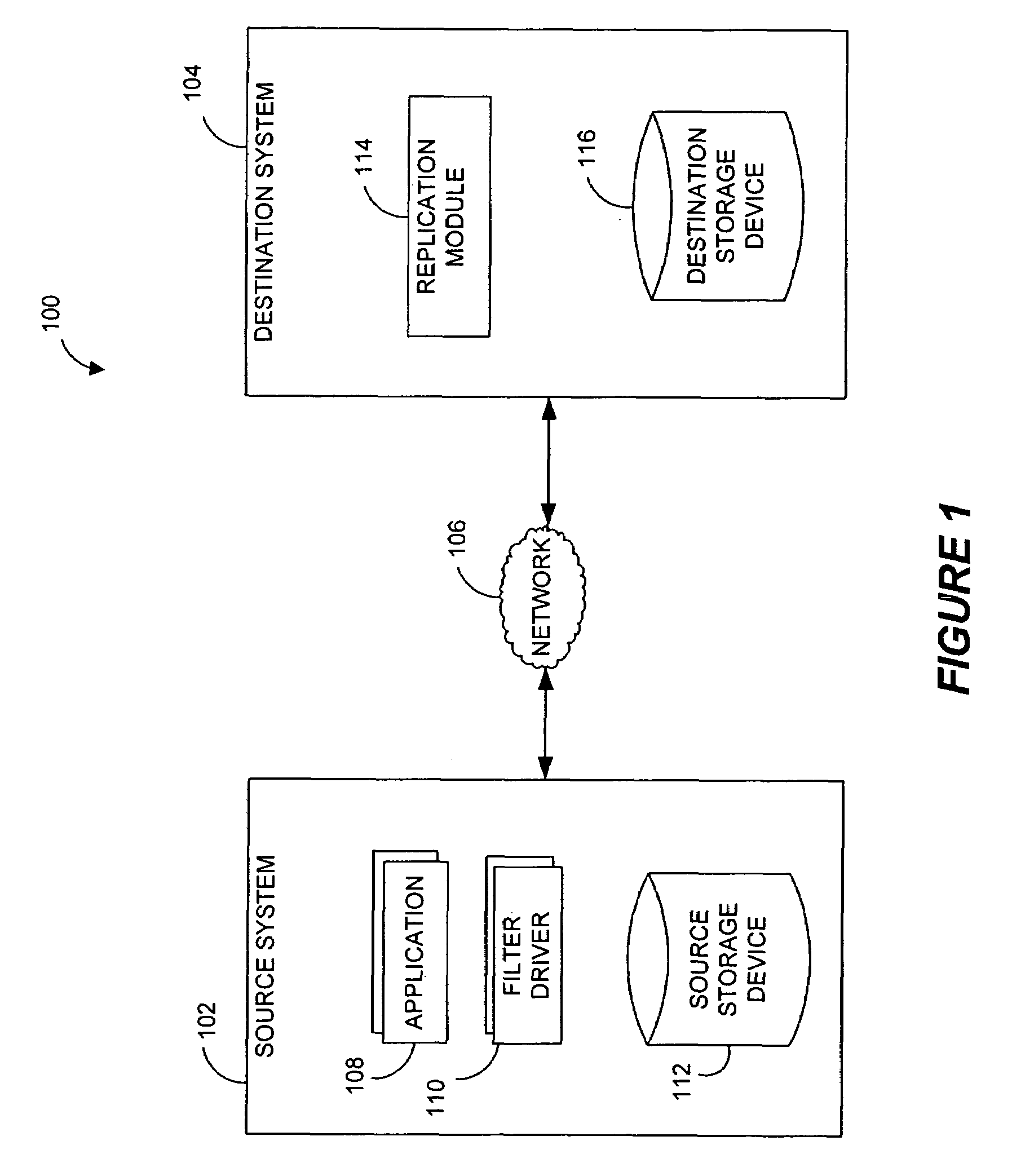
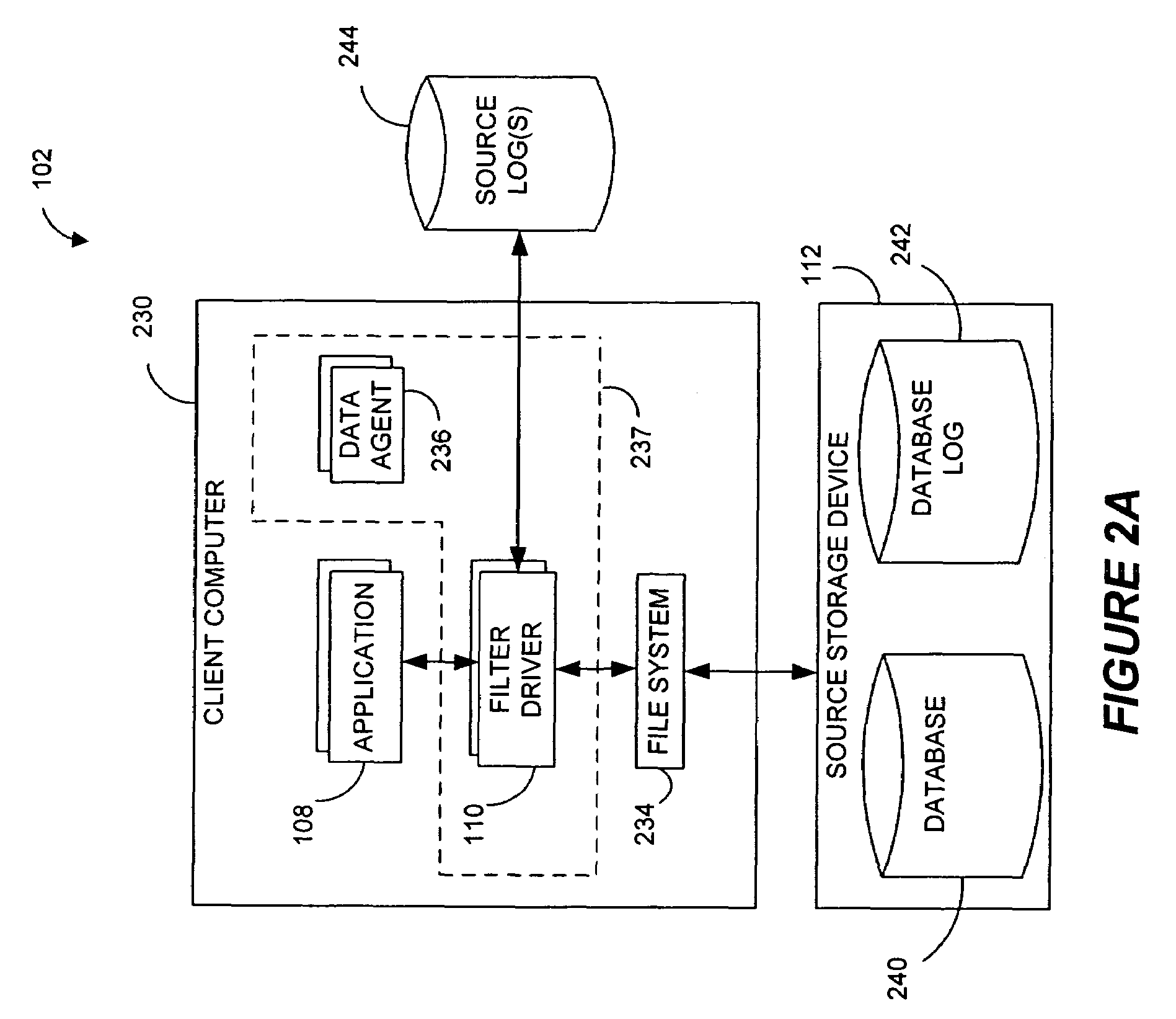
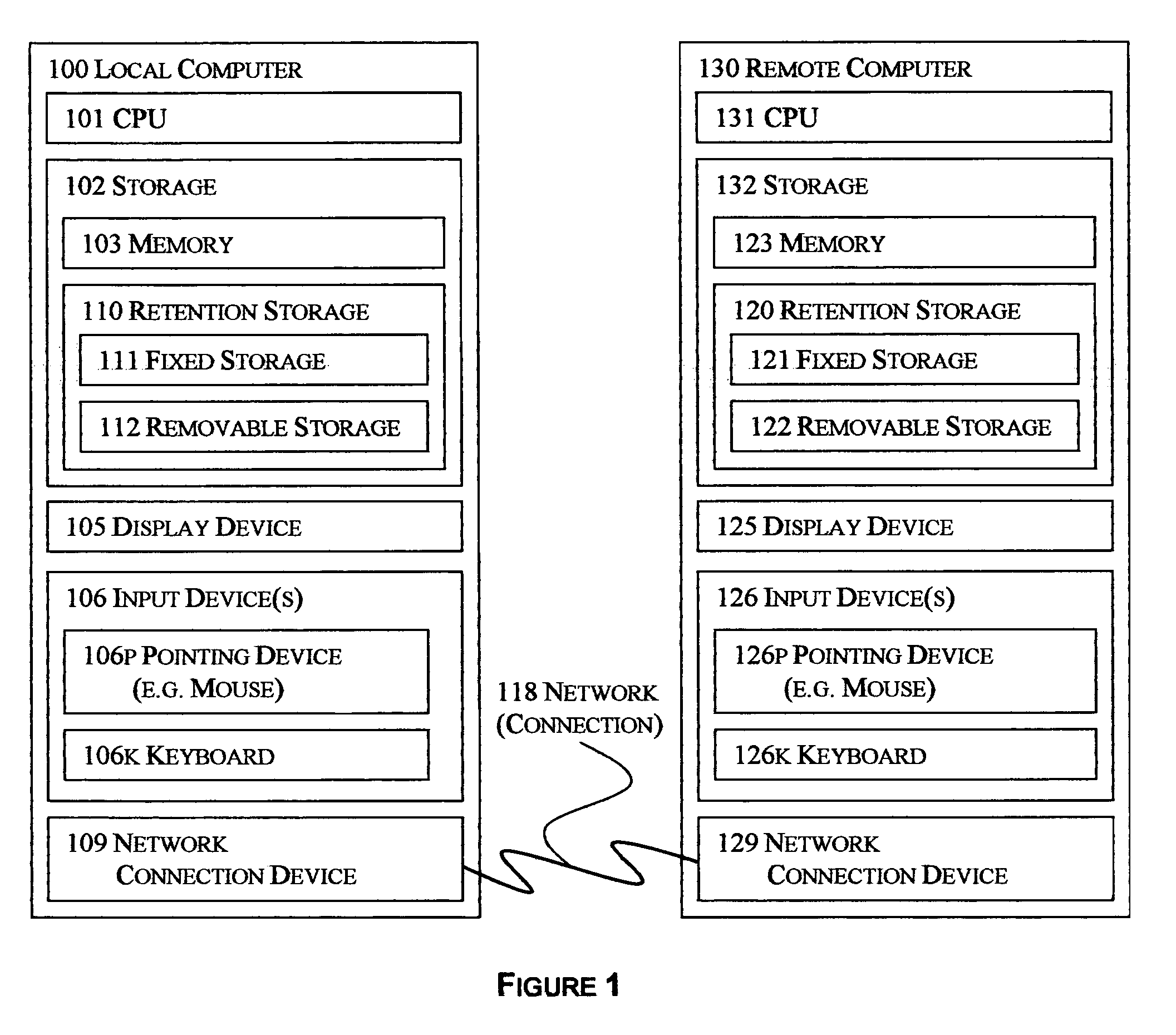
In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is "back up", whereas the noun and adjective form is "backup". Backups can be used to recover data after its loss from data deletion or corruption, or to recover data from an earlier time. Backups provide a simple form of disaster recovery; however not all backup systems are able to reconstitute a computer system or other complex configuration such as a computer cluster, active directory server, or database server.
Method for reducing database recovery time
ActiveUS7222133B1Reduce database recovery timeShorten recovery timeData processing applicationsError detection/correctionComplete dataComputer science
Owner:UNISYS CORP
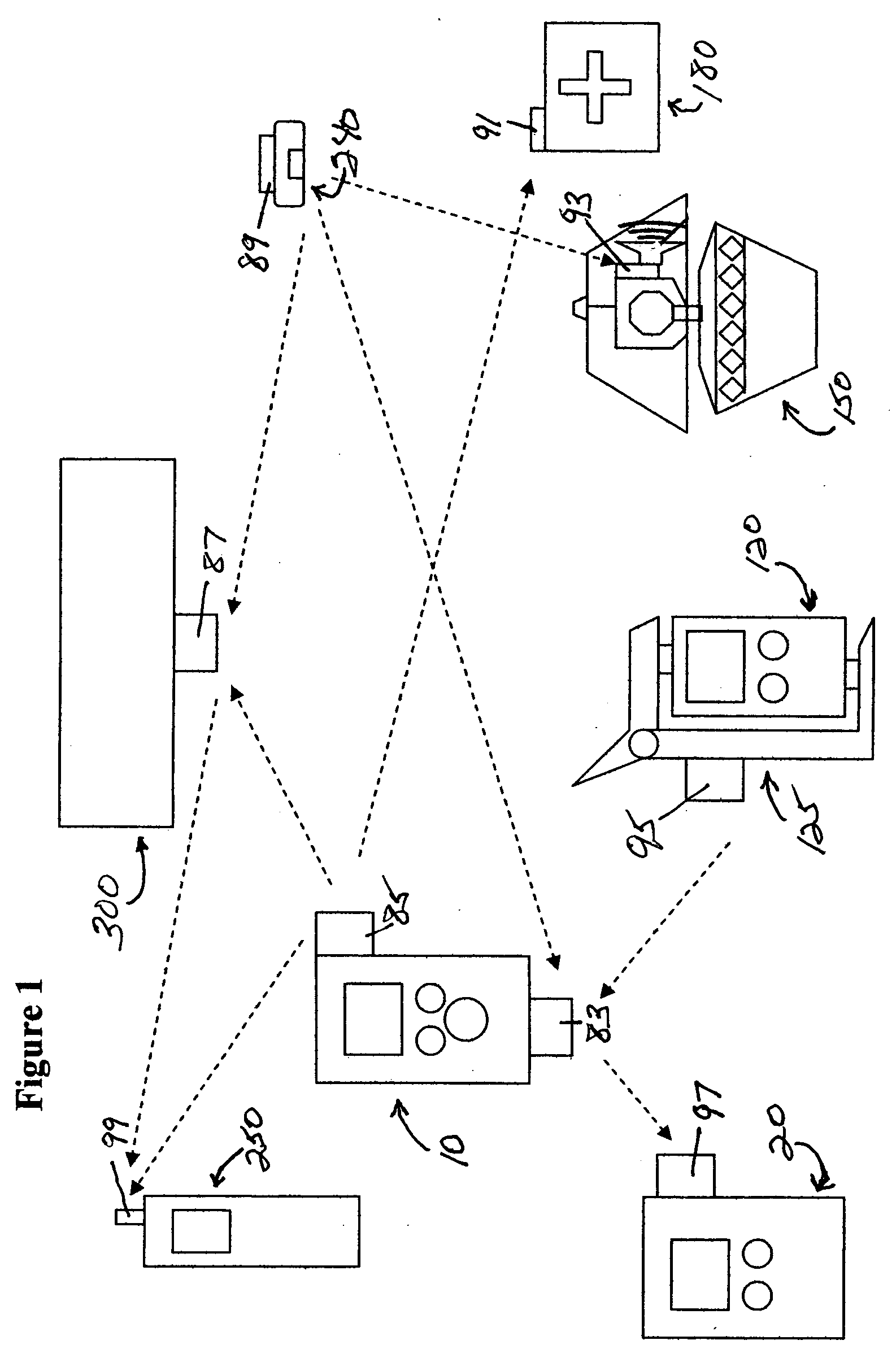
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
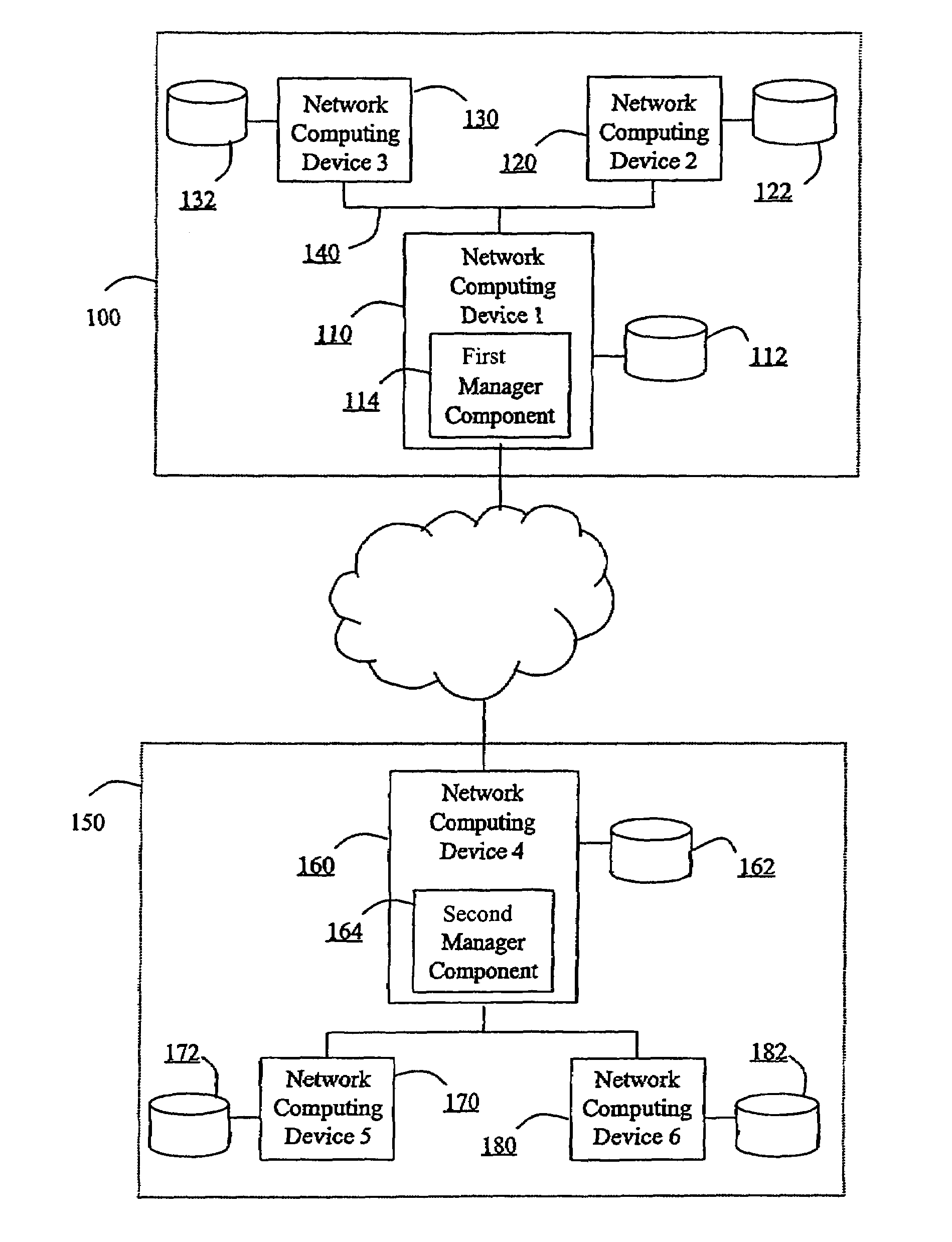
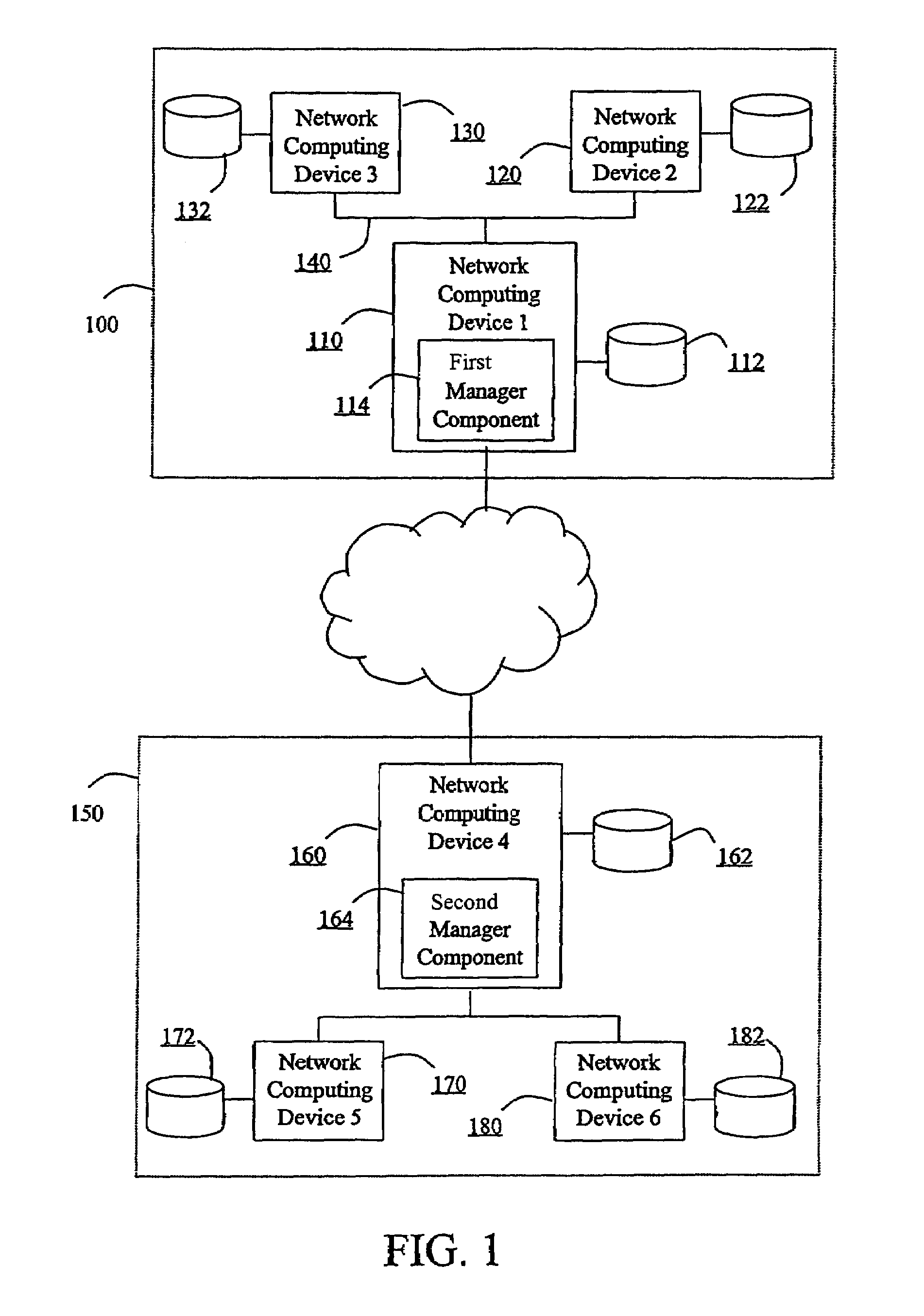
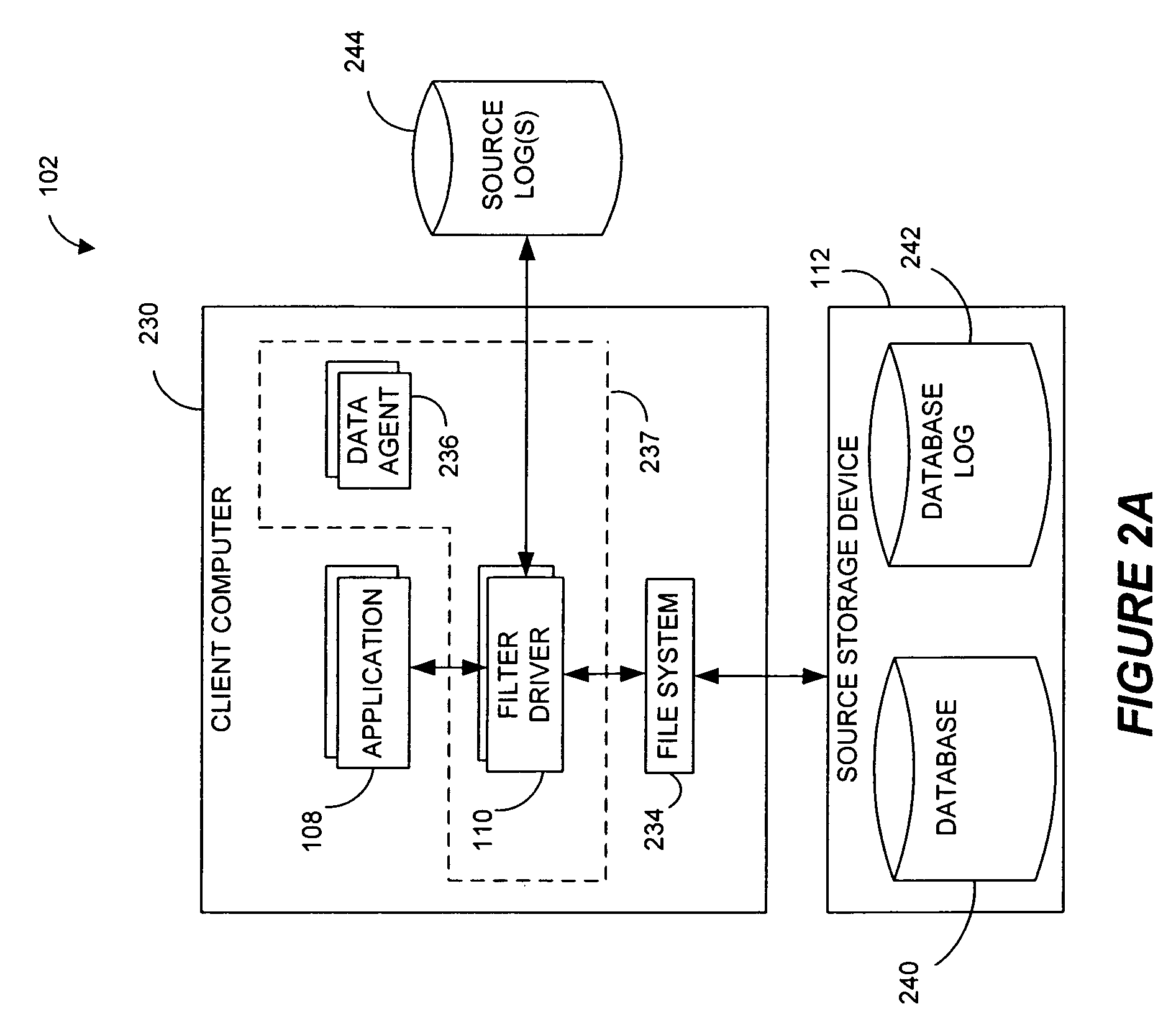
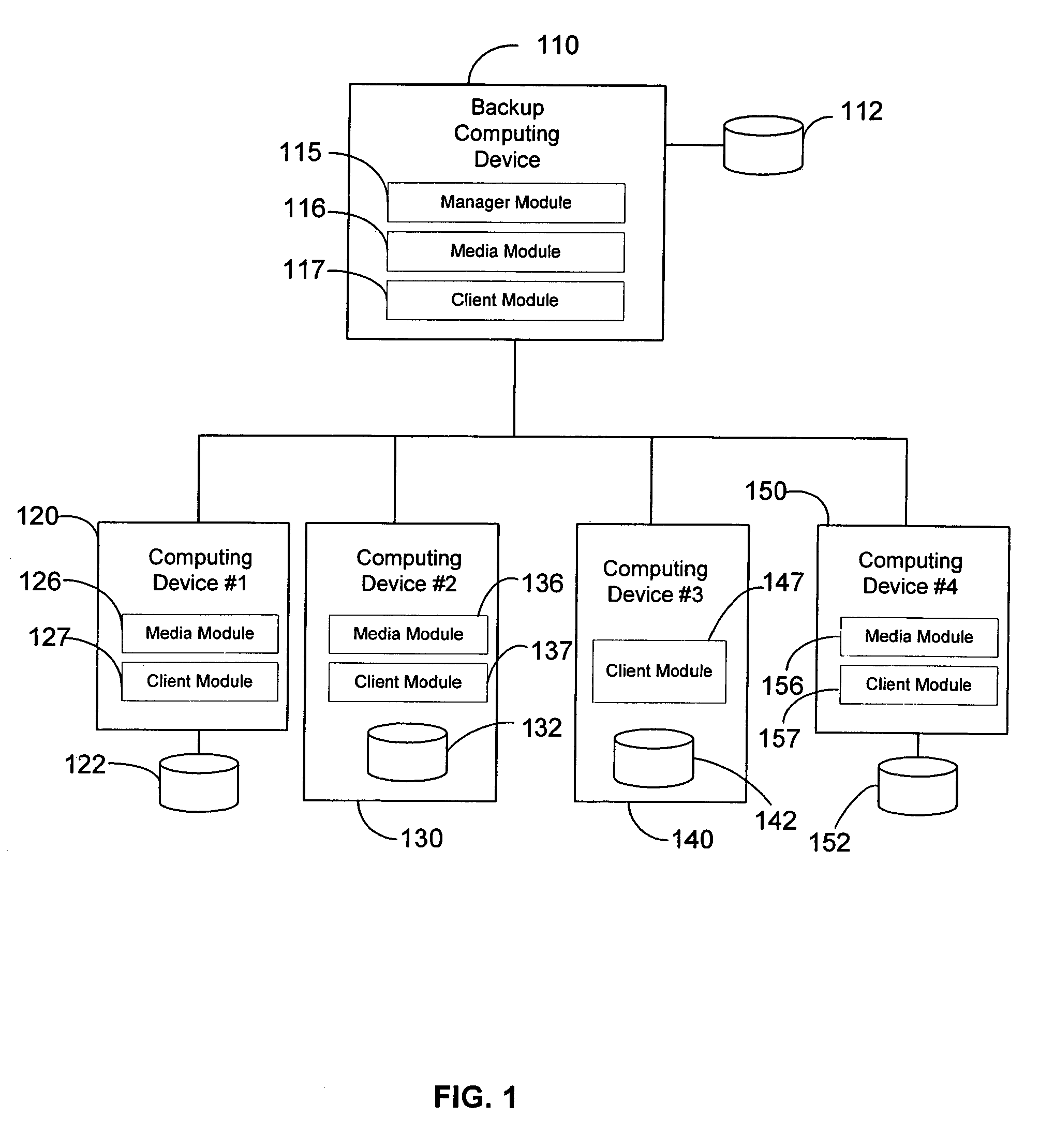
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
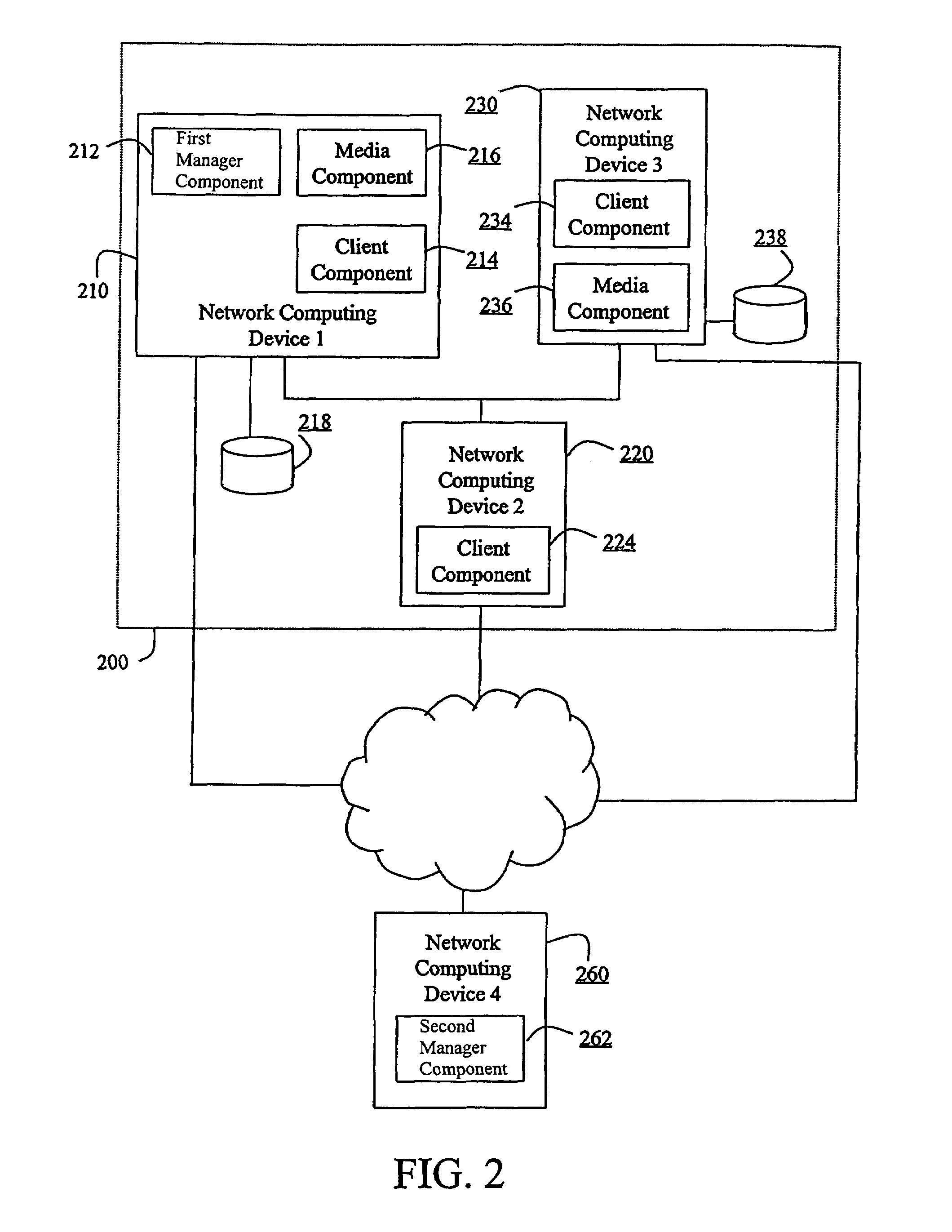
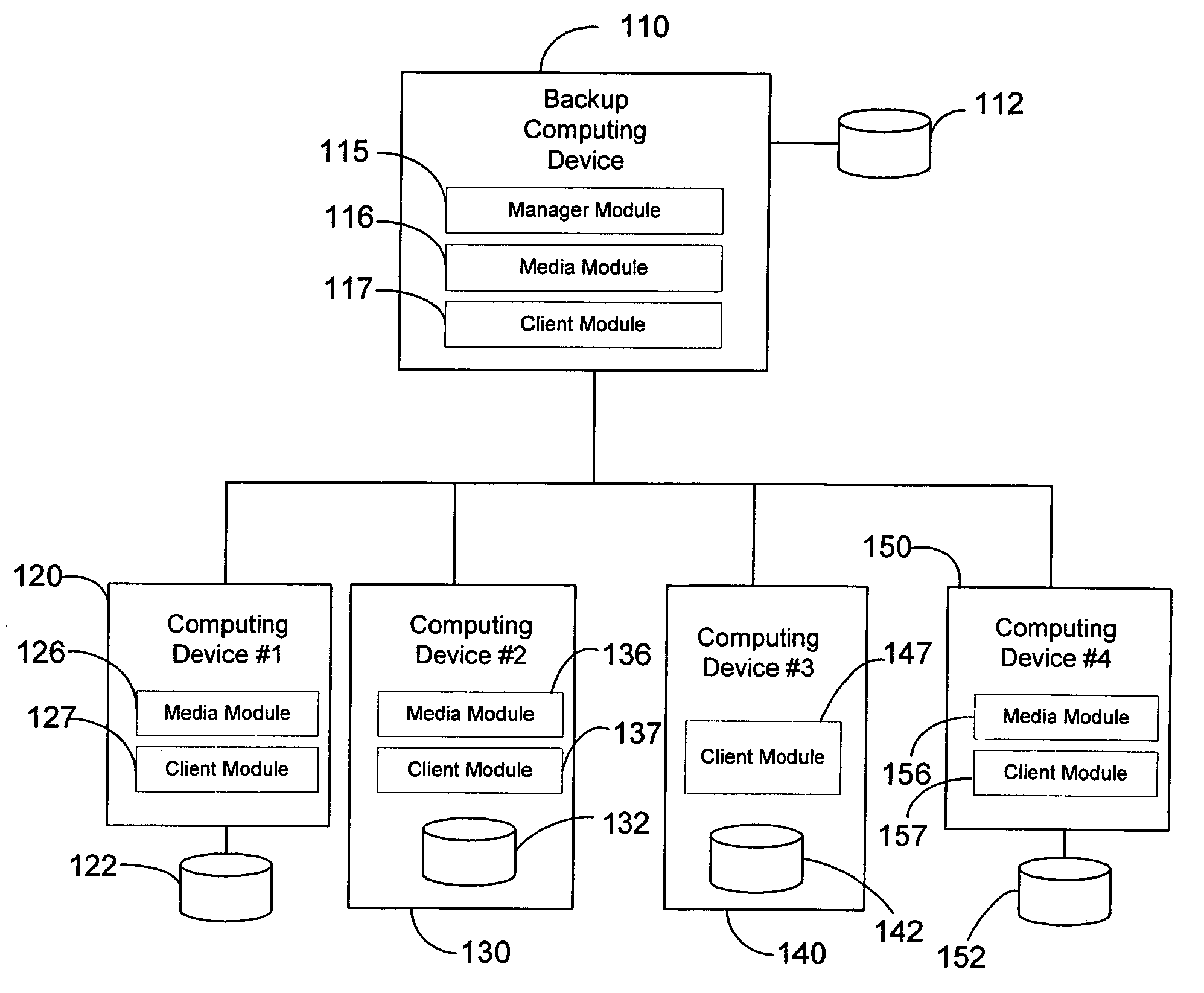
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
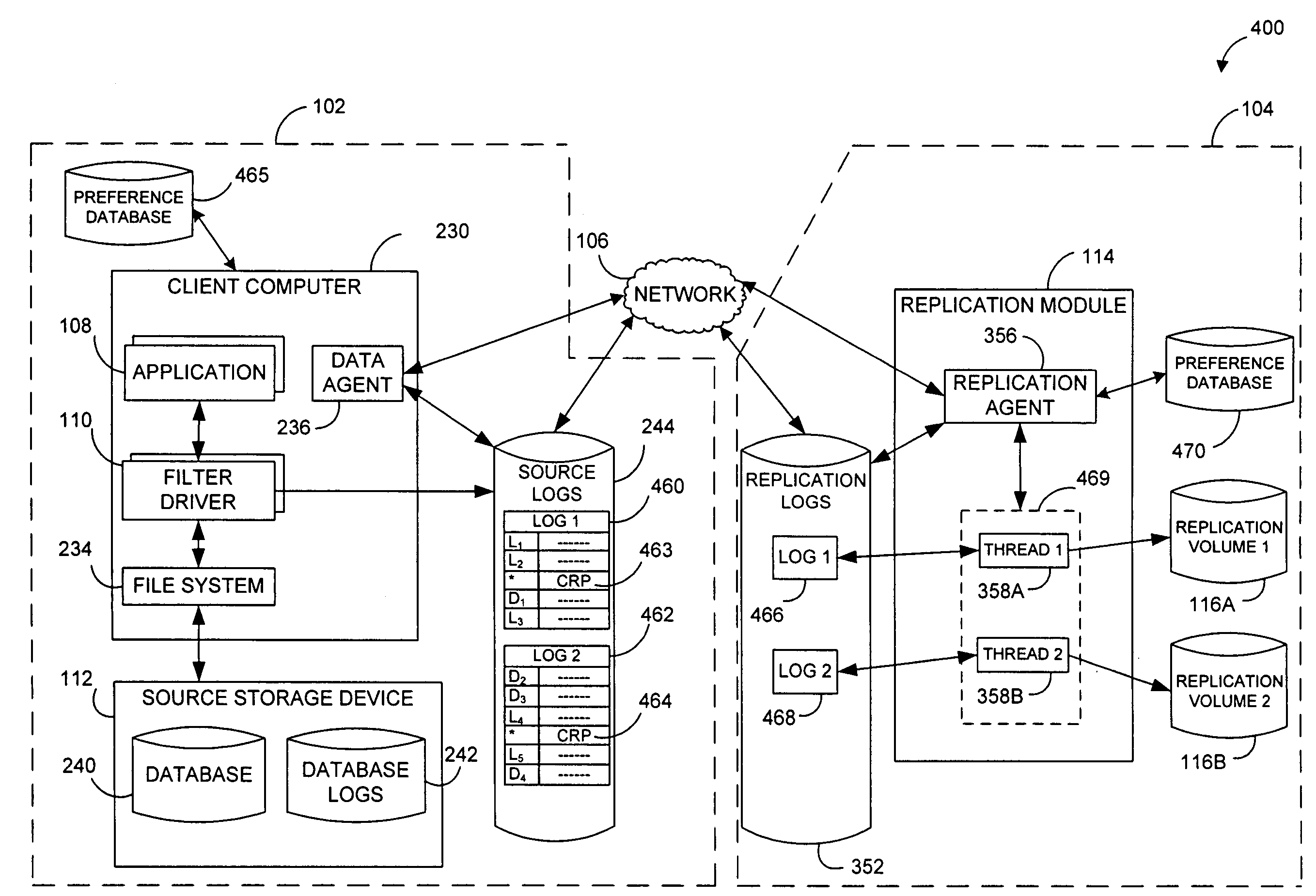
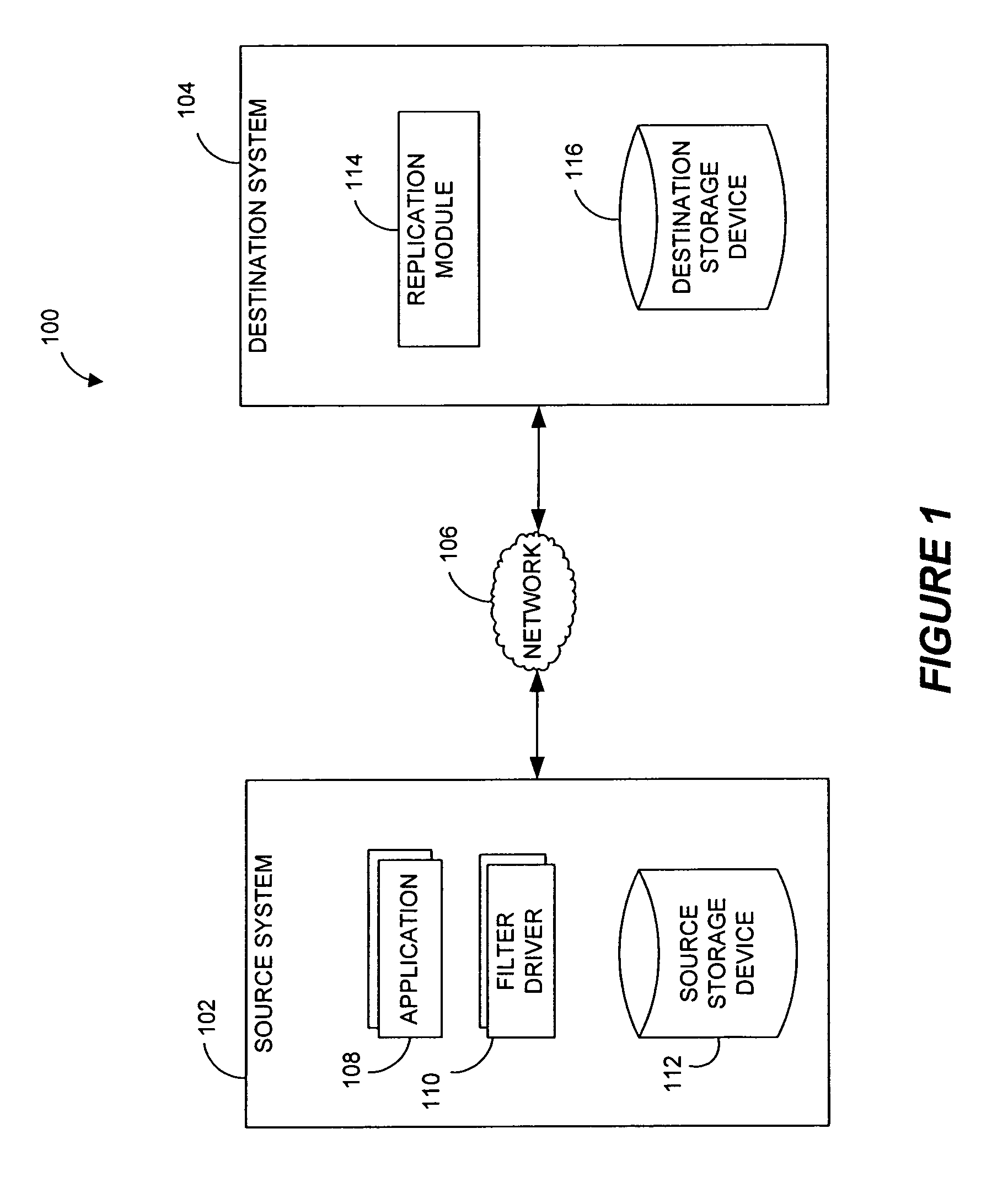
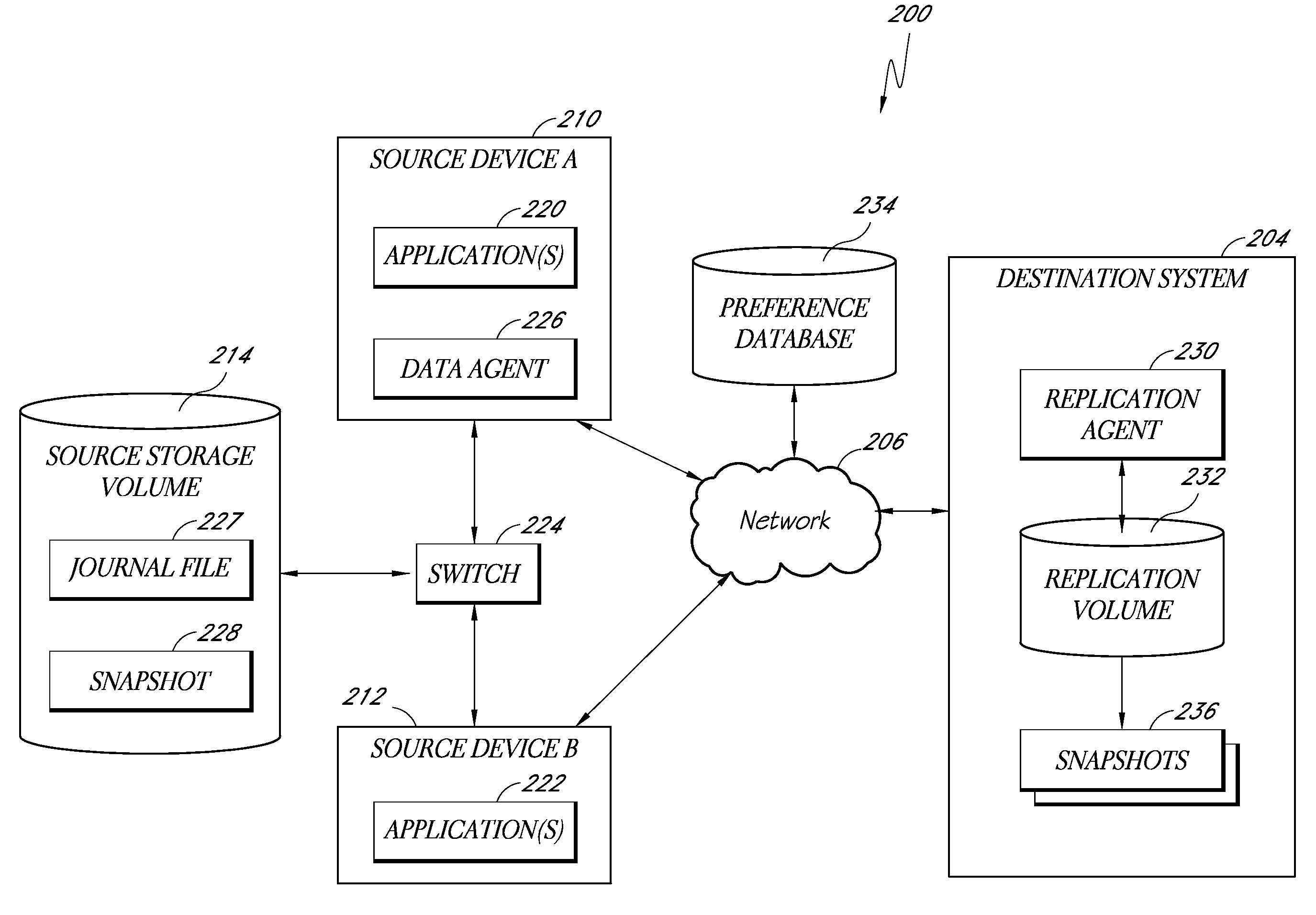
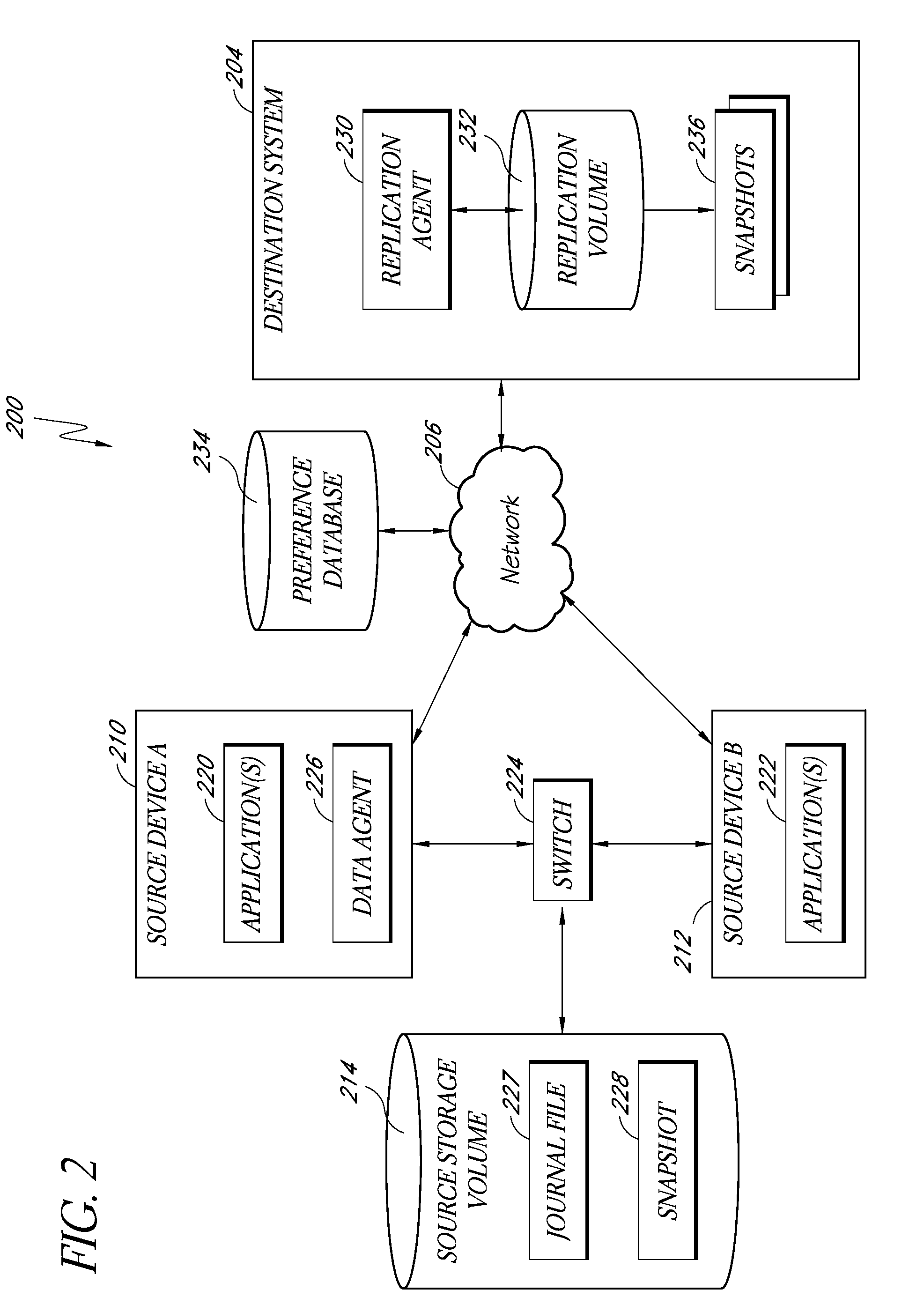
Systems and methods for monitoring application data in a data replication system
InactiveUS7617262B2Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationData management
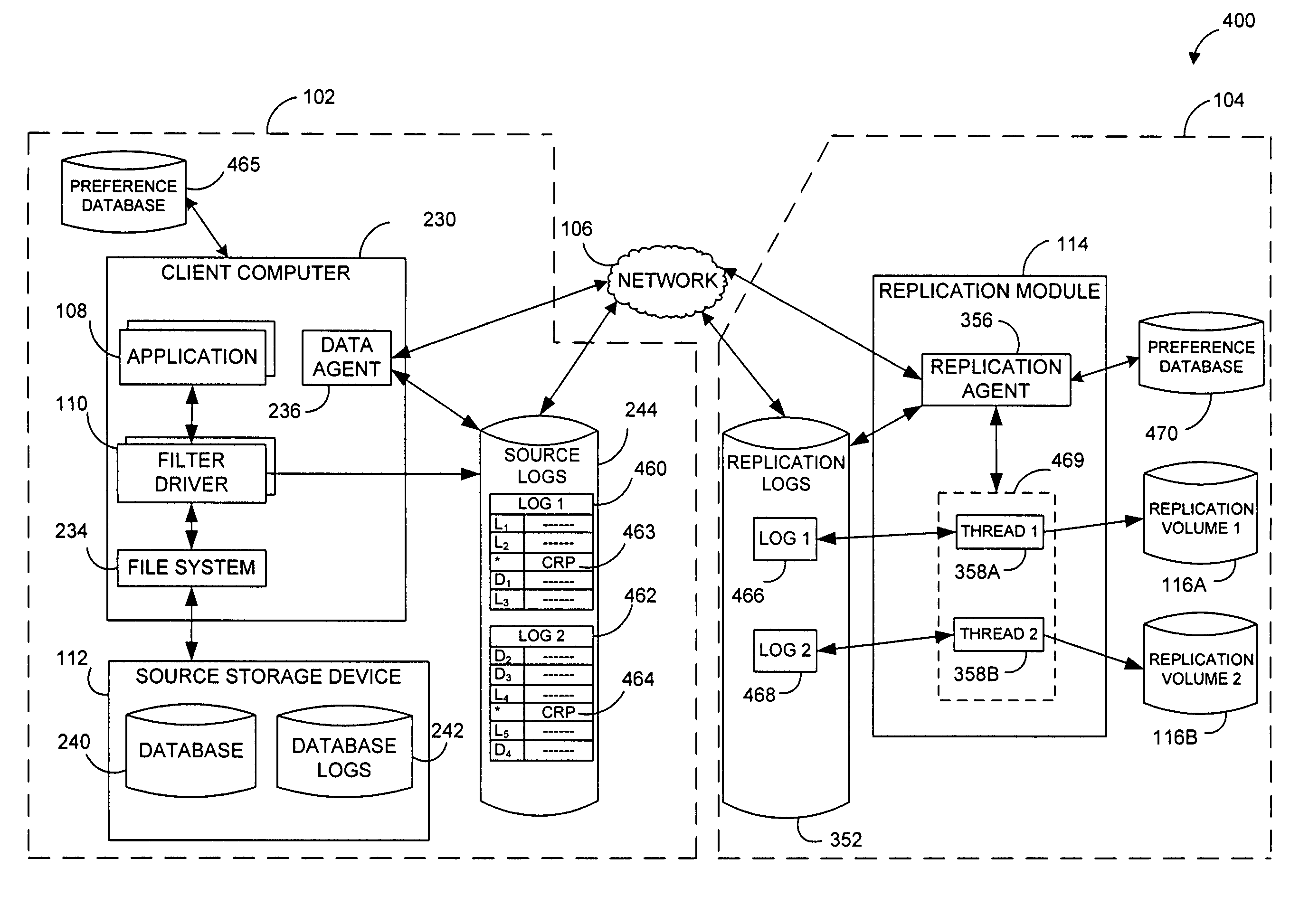
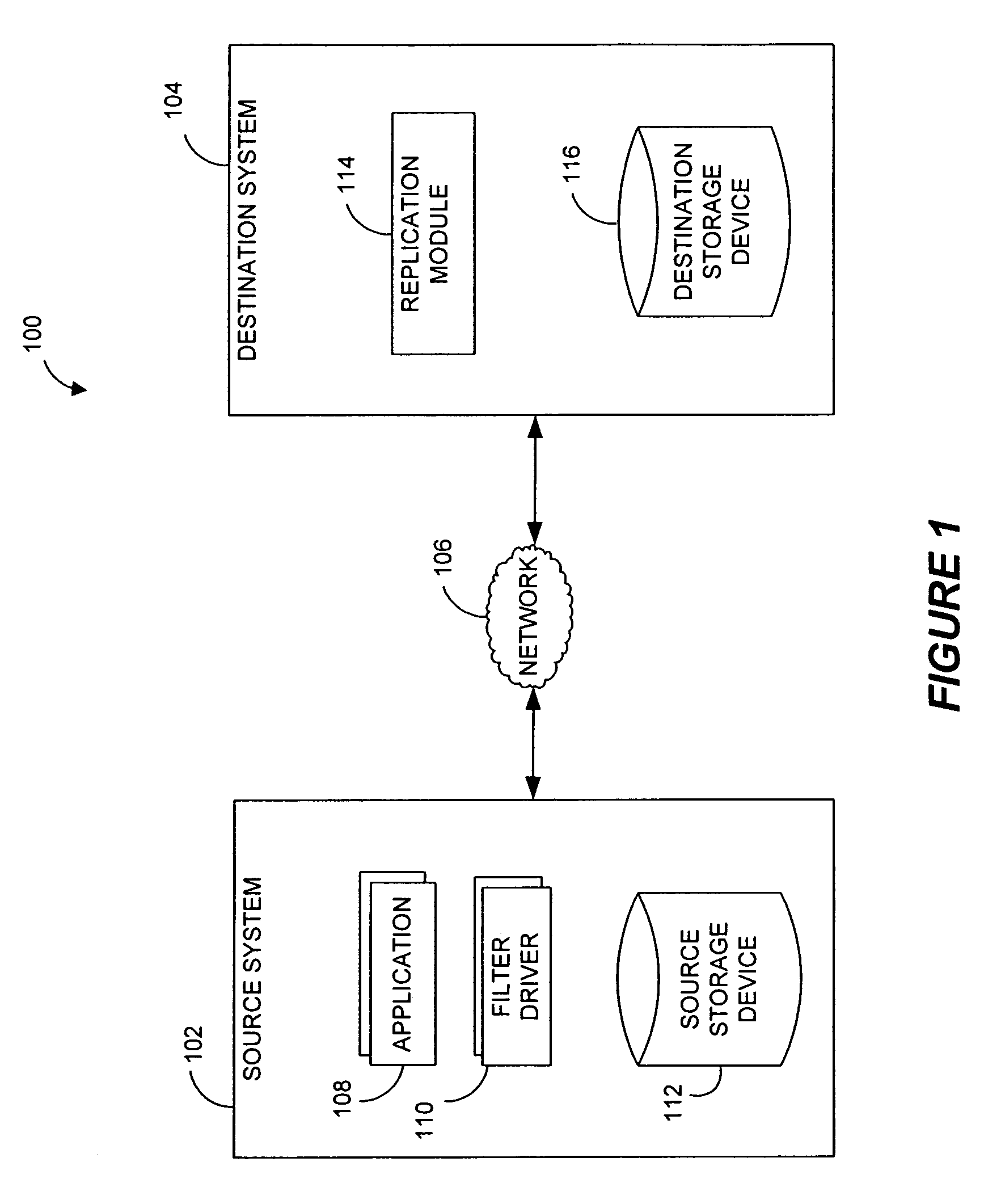
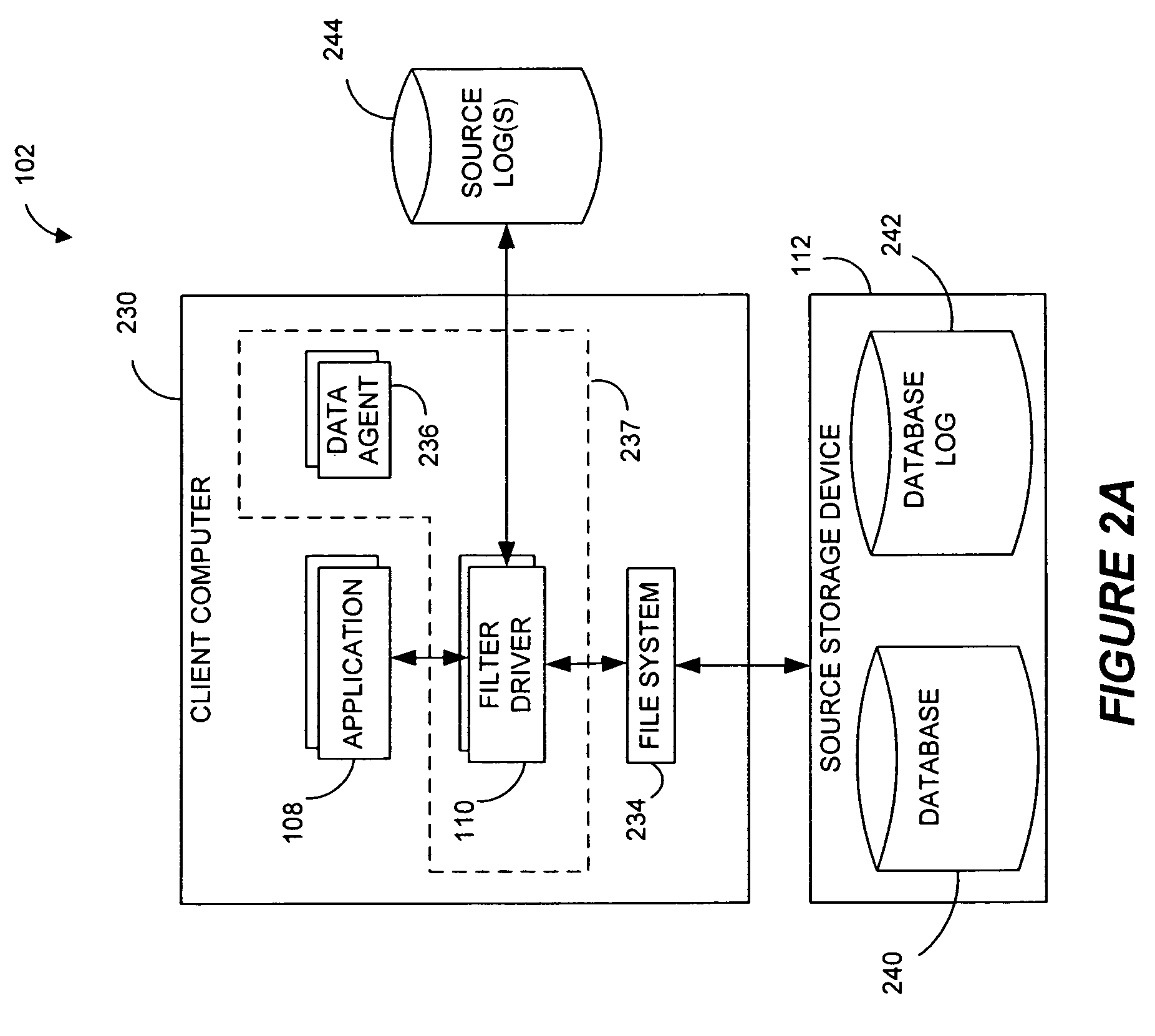
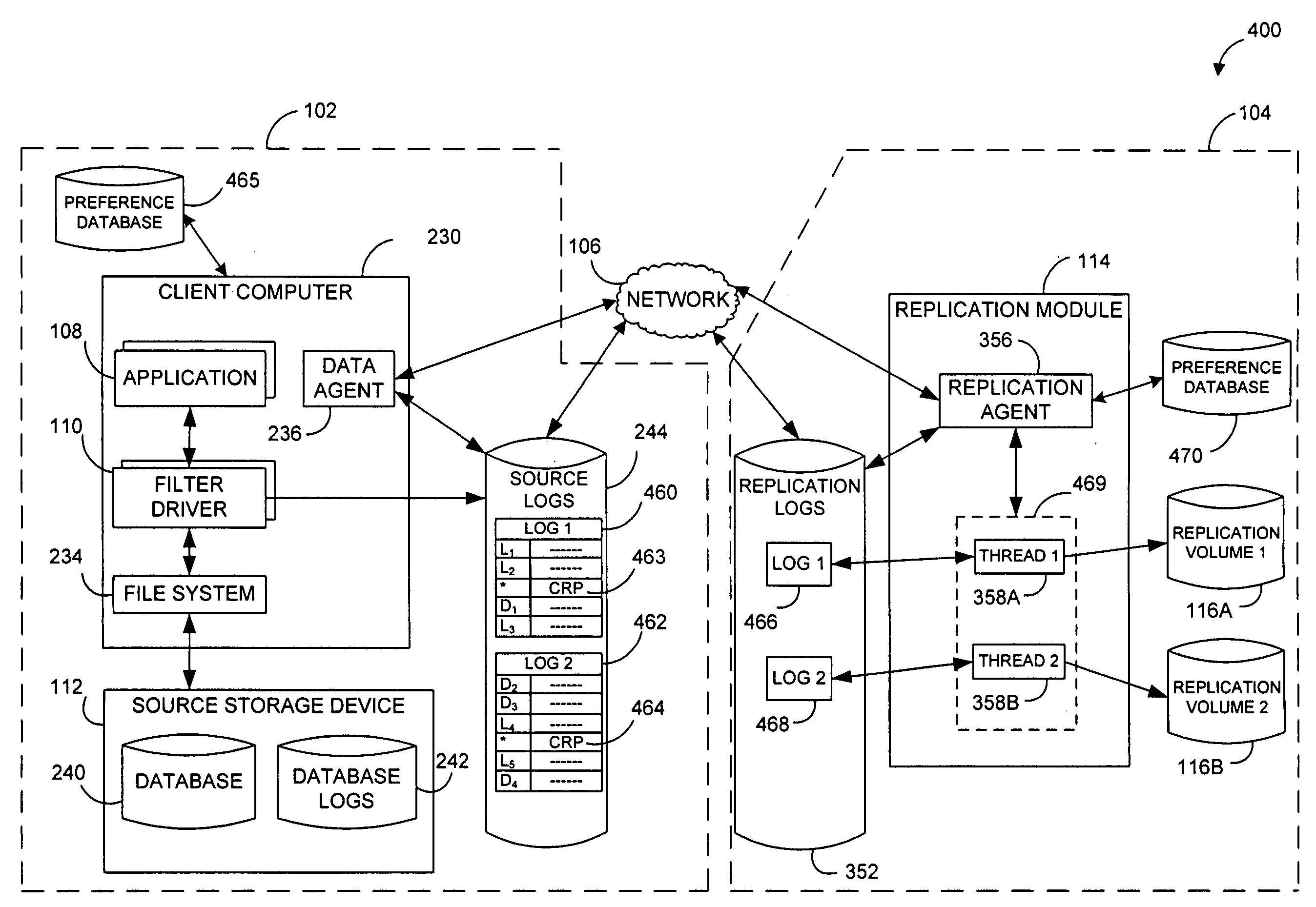
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
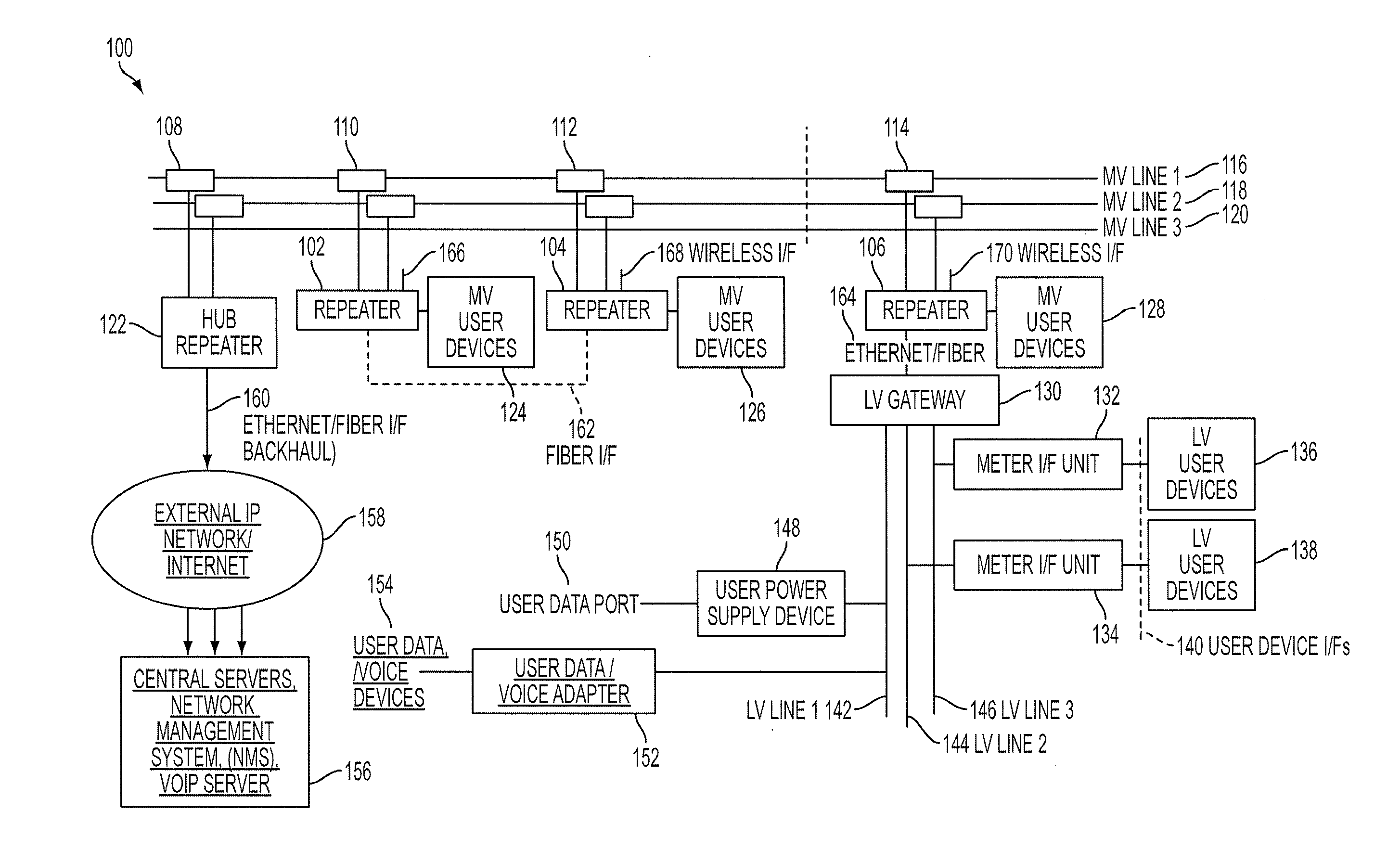
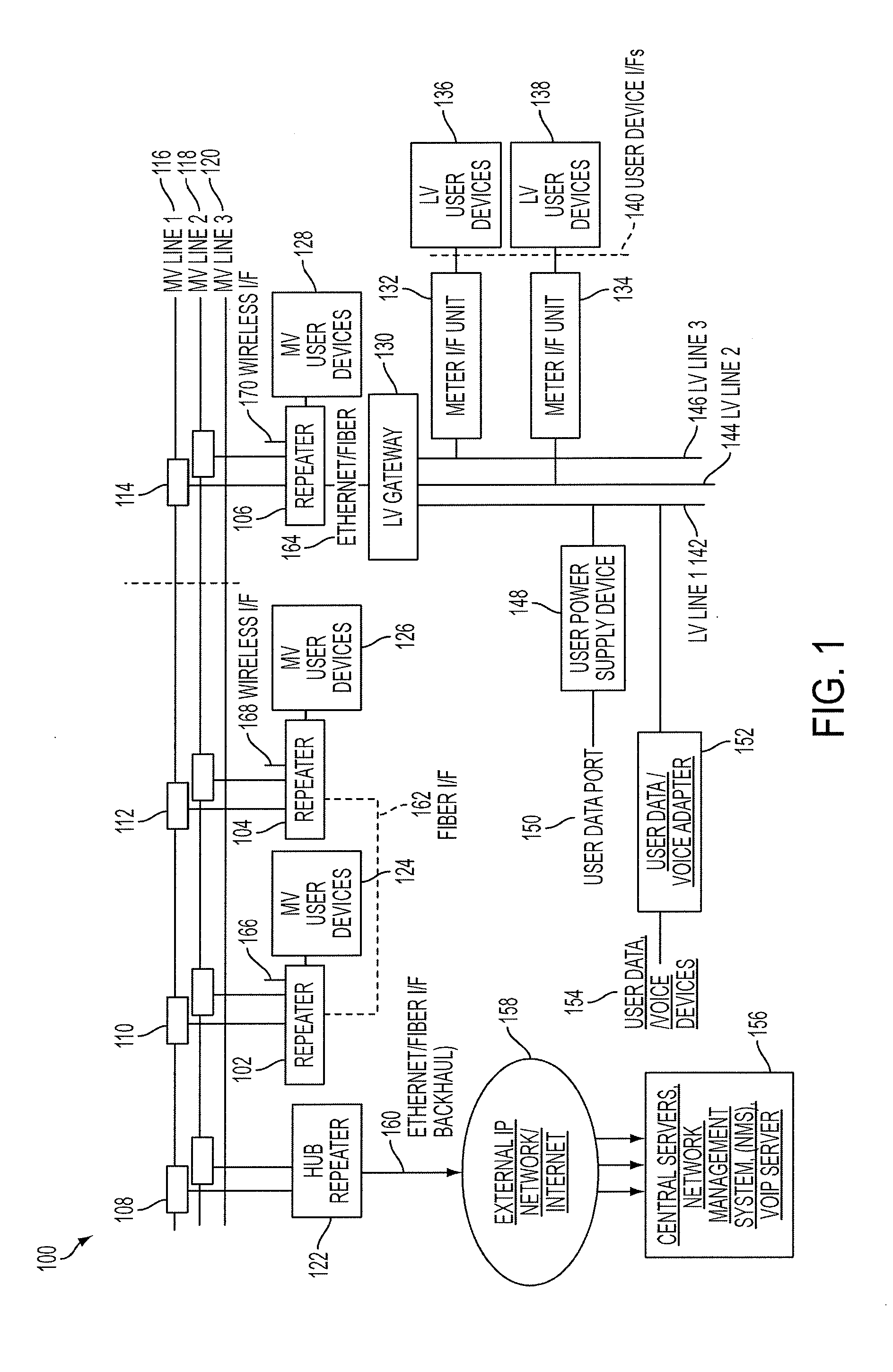
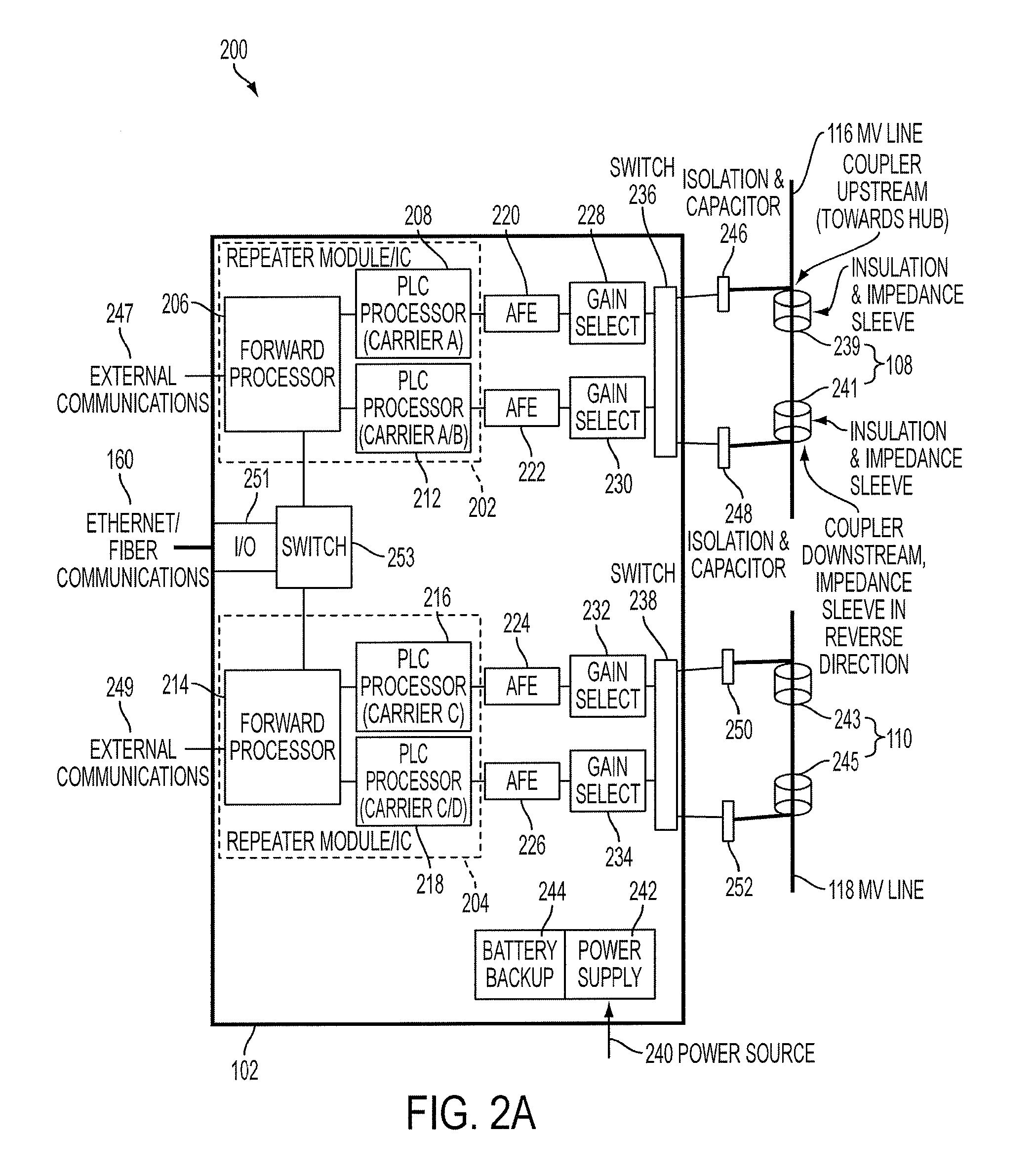
Reliable, long-haul data communications over power lines for meter reading and other communications services
InactiveUS20110140911A1Highly long-haulImprove reliabilityElectric signal transmission systemsPower distribution line transmissionPower qualitySignal quality
A system, method and computer program product provides for power line communications (PLC) over electric power lines includes a device mountable near an electrical distribution transformer (DT) to provide a high speed interface and communicates with one or multiple access devices, which provide low speed interfaces for analog signals or digital signals over RS 232, RS 485, optical, wireless and Ethernet. The device transmits data to / from these access devices over the electric lines to other repeaters over one or more wires of an electrical line or over multiple lines, and serves to strengthen and improve signal quality. Upon detecting a wire or line is having problems carrying data, the data is sent over other wires, and upon power line failures, wireless backup to mobile / GSM and WiMax networks is utilized. The device permits utilities and others to read electric meters, monitor the power quality of the distribution grid and detect power losses / failures / outages, and permits telecom service providers and others to provide a communications link to cell phone towers, WiFi Access Points and enable broadband Internet and telephony in rural, remote or sparely populated areas.
Owner:POWERMAX GLOBAL
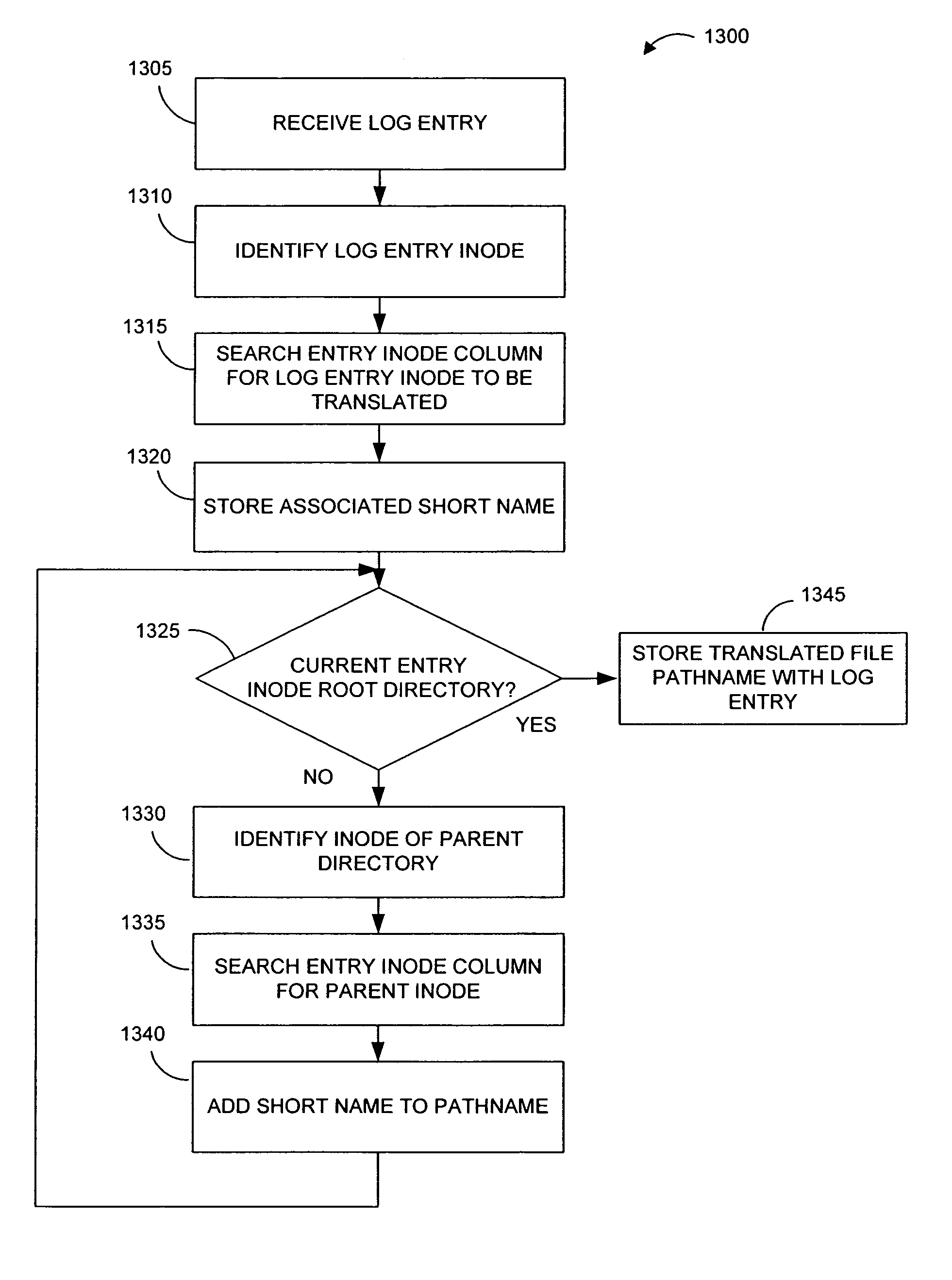
Pathname translation in a data replication system
InactiveUS7636743B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Owner:COMMVAULT SYST INC
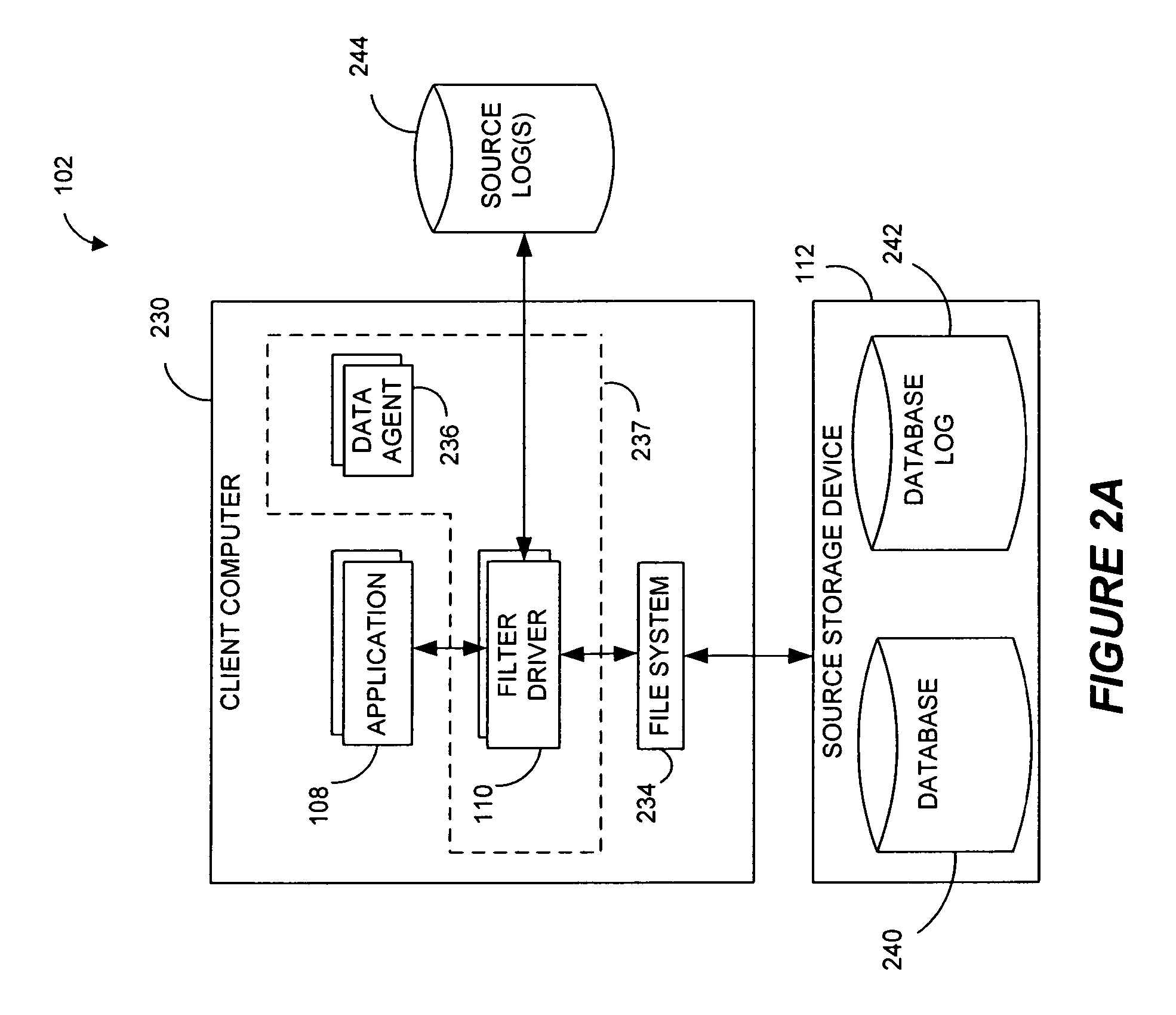
Backup mechanism for a multi-class file system
ActiveUS7103740B1Reduce in quantityData processing applicationsError detection/correctionFile systemComputer science
System and method for performing backups of a multi-class file system are described. In one embodiment, more recently modified data may be assigned and / or migrated to higher storage classes and less recently modified data may be migrated at time intervals to lower storage classes in the multi-class file system. Backups of each of the storage classes may be performed at time intervals. In one embodiment, the backups may be image-based backups of the storage devices in the storage classes. In one embodiment, the lower storage classes may include one or more read-only storage classes including less-recently modified data that are backed up less frequently than higher storage classes including more-recently modified data. In one embodiment, files migrated to lower storage class(es) may be compressed.
Owner:SYMANTEC OPERATING CORP
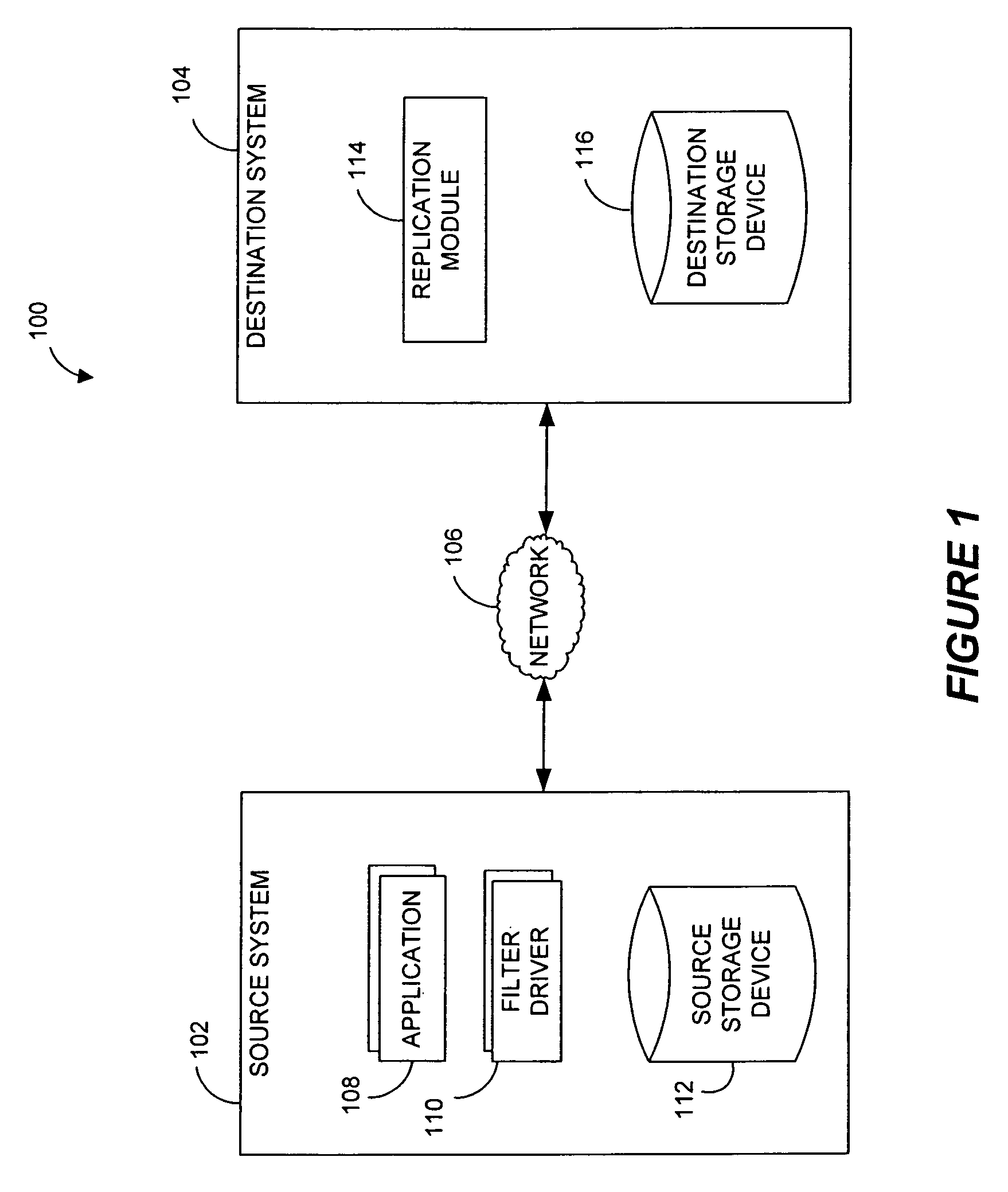
Destination systems and methods for performing data replication
InactiveUS7617253B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Modular backup and retrieval system
InactiveUS7389311B1Data processing applicationsDigital data processing detailsSystems managementModularity
Owner:COMMVAULT SYST INC
Methods and apparatus for accessing data from a primary data storage system for secondary storage
InactiveUS20060010227A1Error detection/correctionMultiple digital computer combinationsMachine instructionLogical view
A system for providing secondary data storage and recovery services for one or more networked host nodes includes a server application for facilitating data backup and recovery services; a first data storage medium accessible to the server application; a second data storage medium accessible to the server application; at least one client application for mapping write locations allocated by the first data storage medium to write locations represented in a logical view of the first data storage medium; and at least one machine instruction enabling direct read capability of the first data storage medium by the server application for purposes of subsequent time-based storage of the read data into the secondary data storage medium.
Owner:MICROSOFT TECH LICENSING LLC
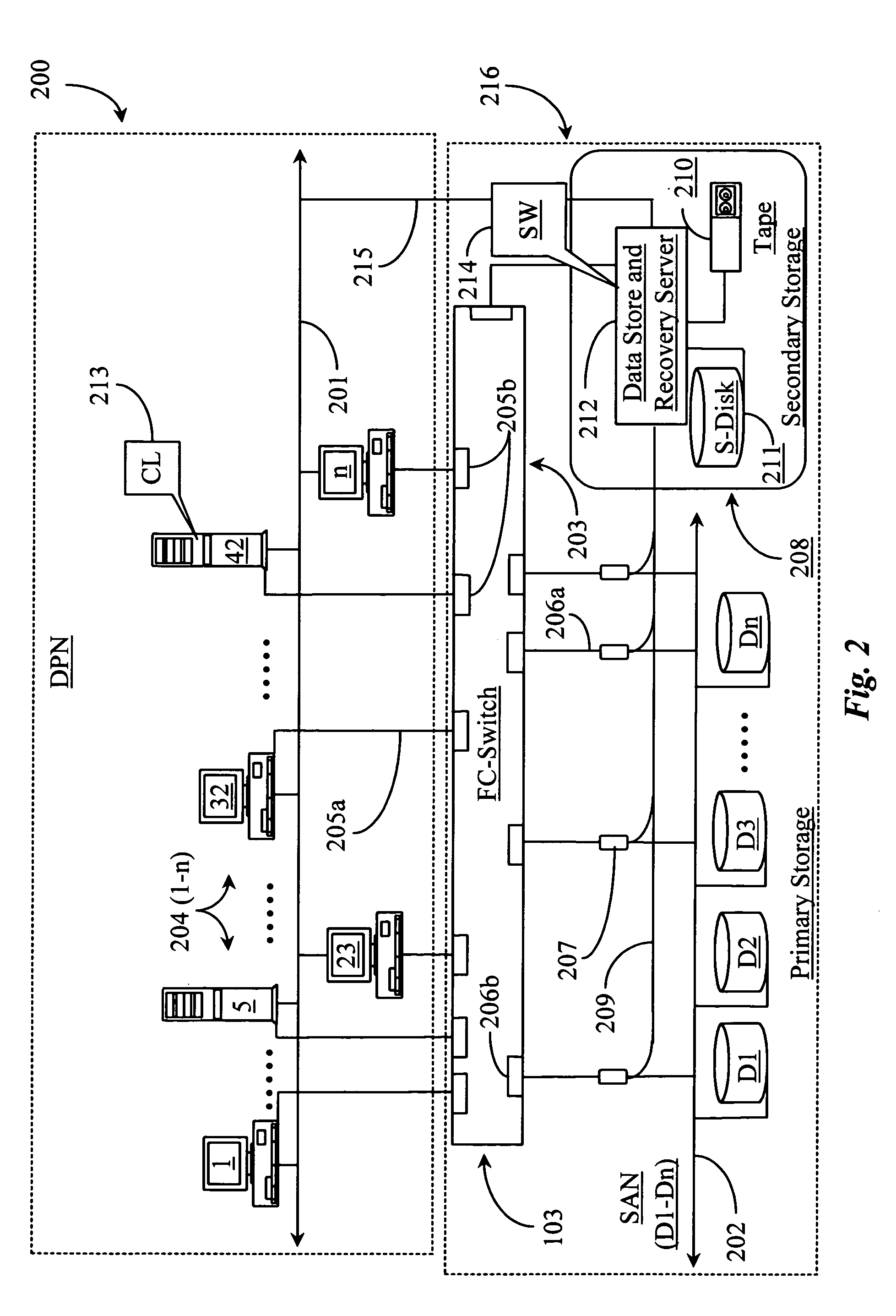
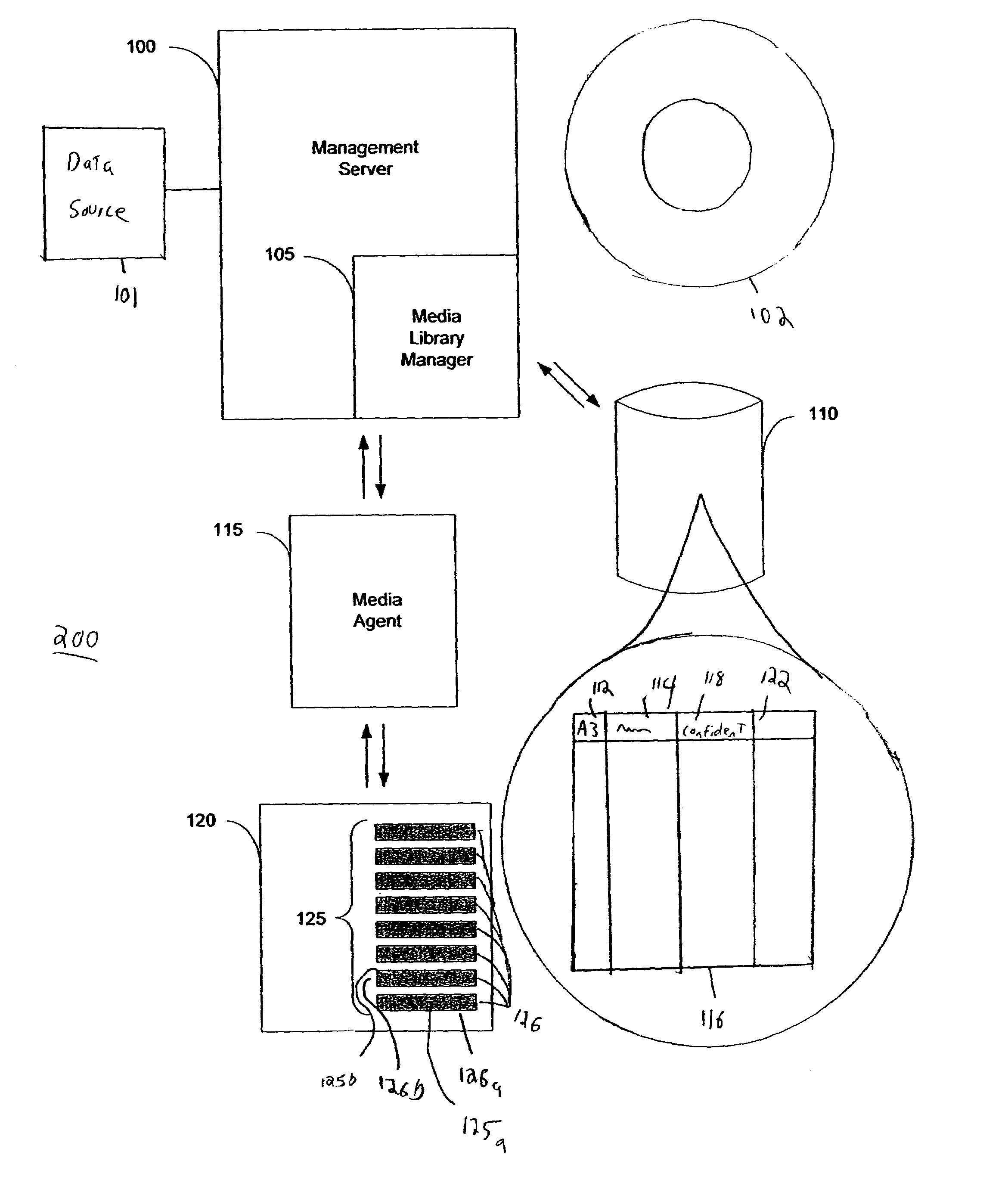
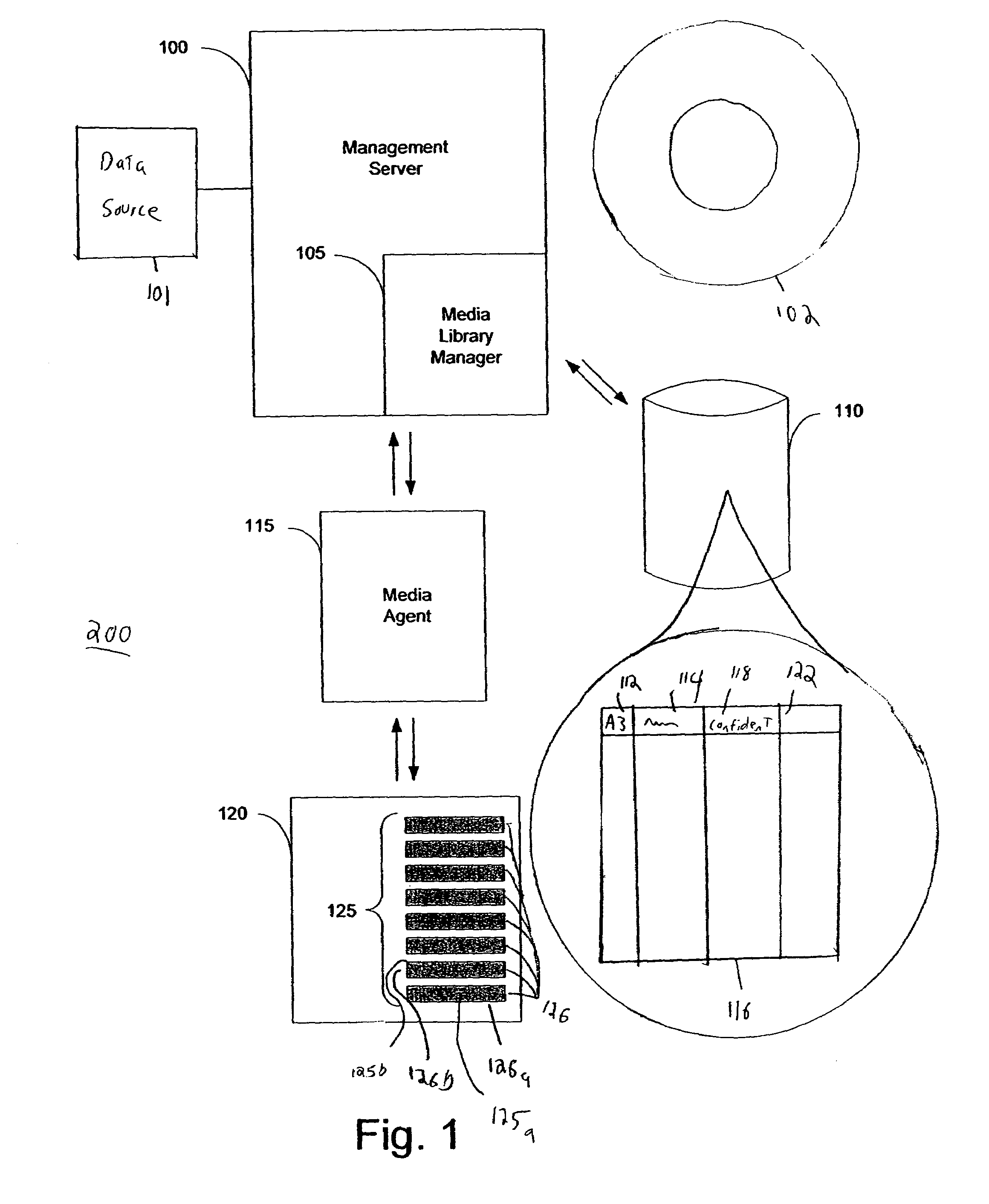
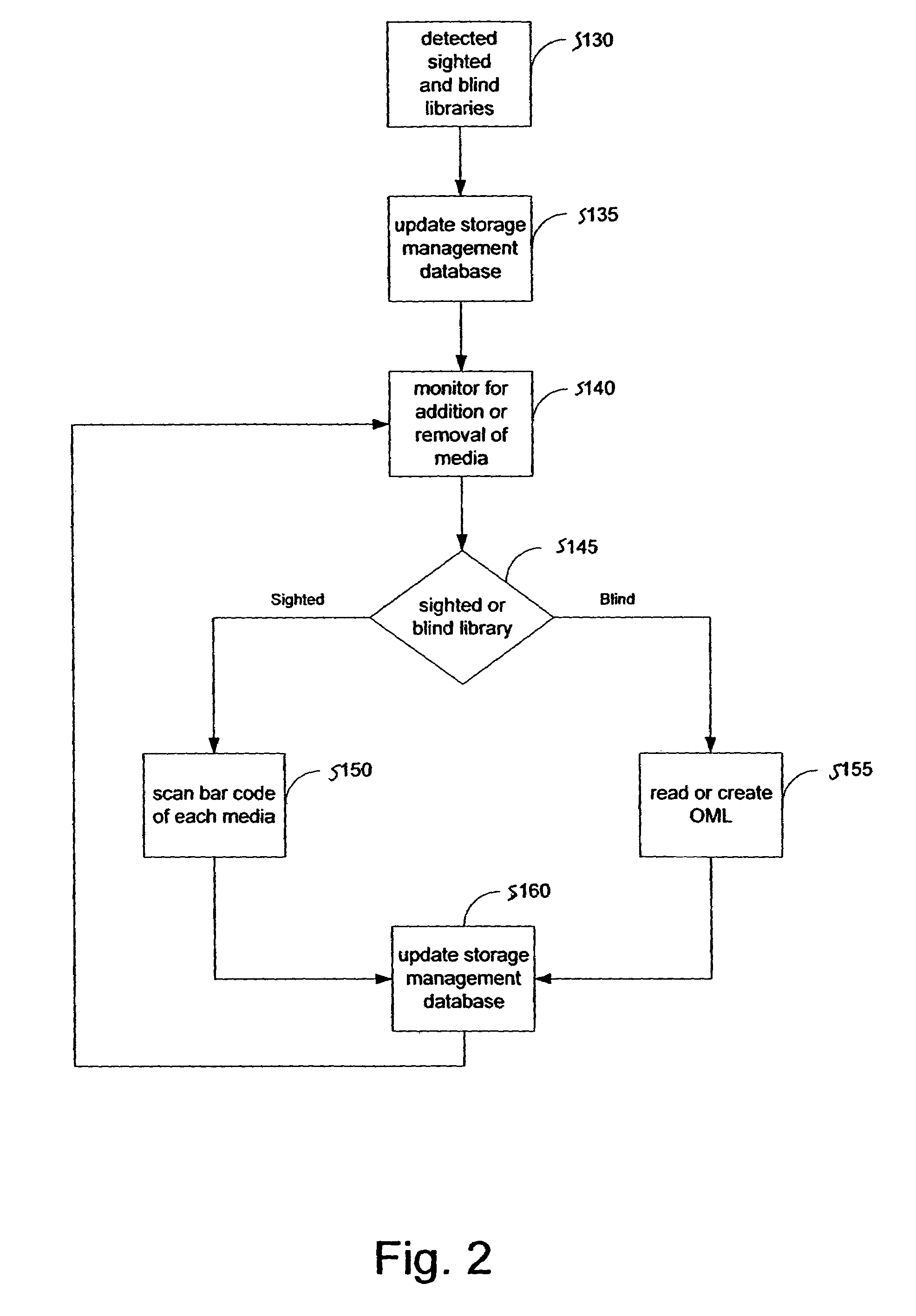
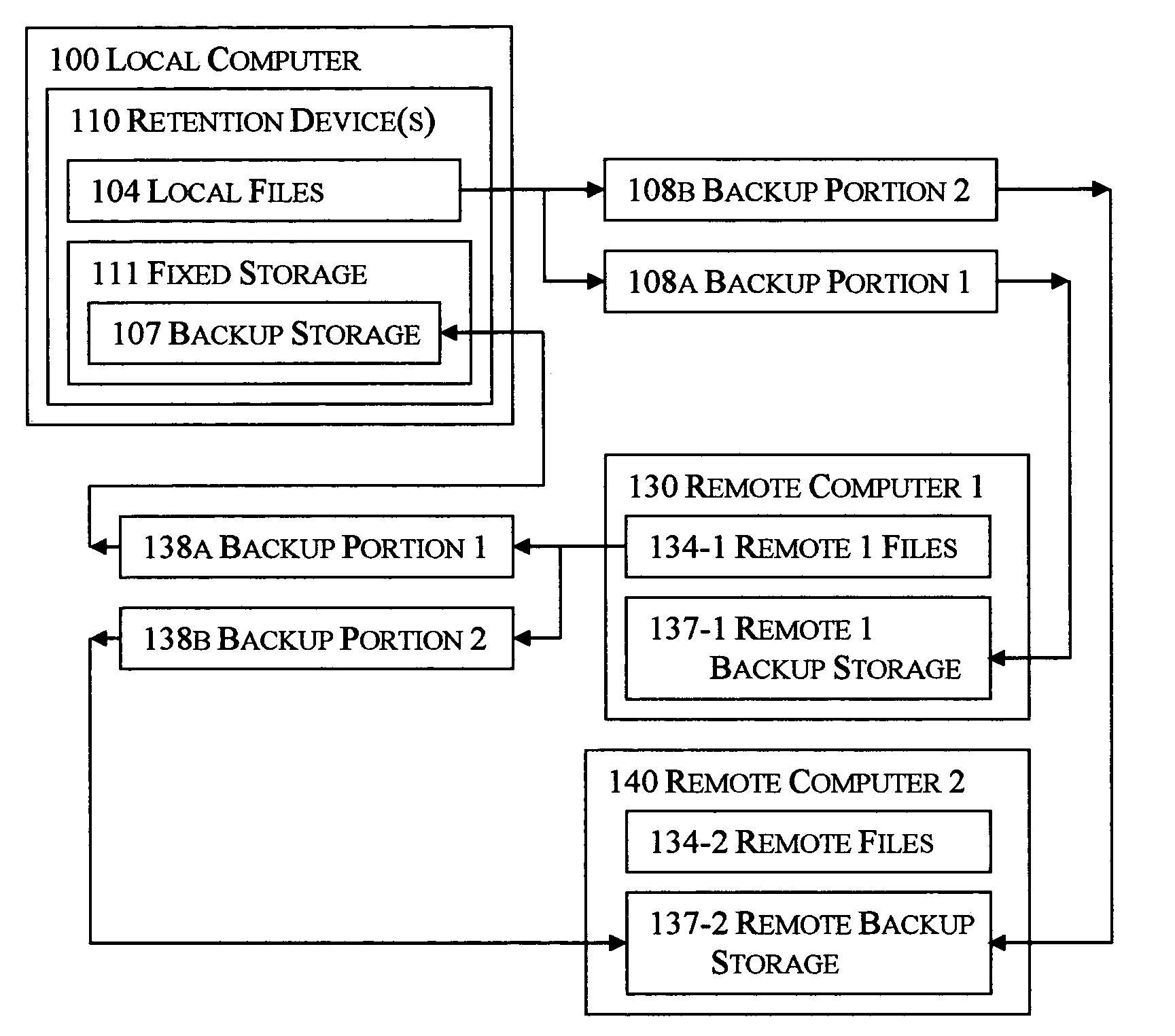
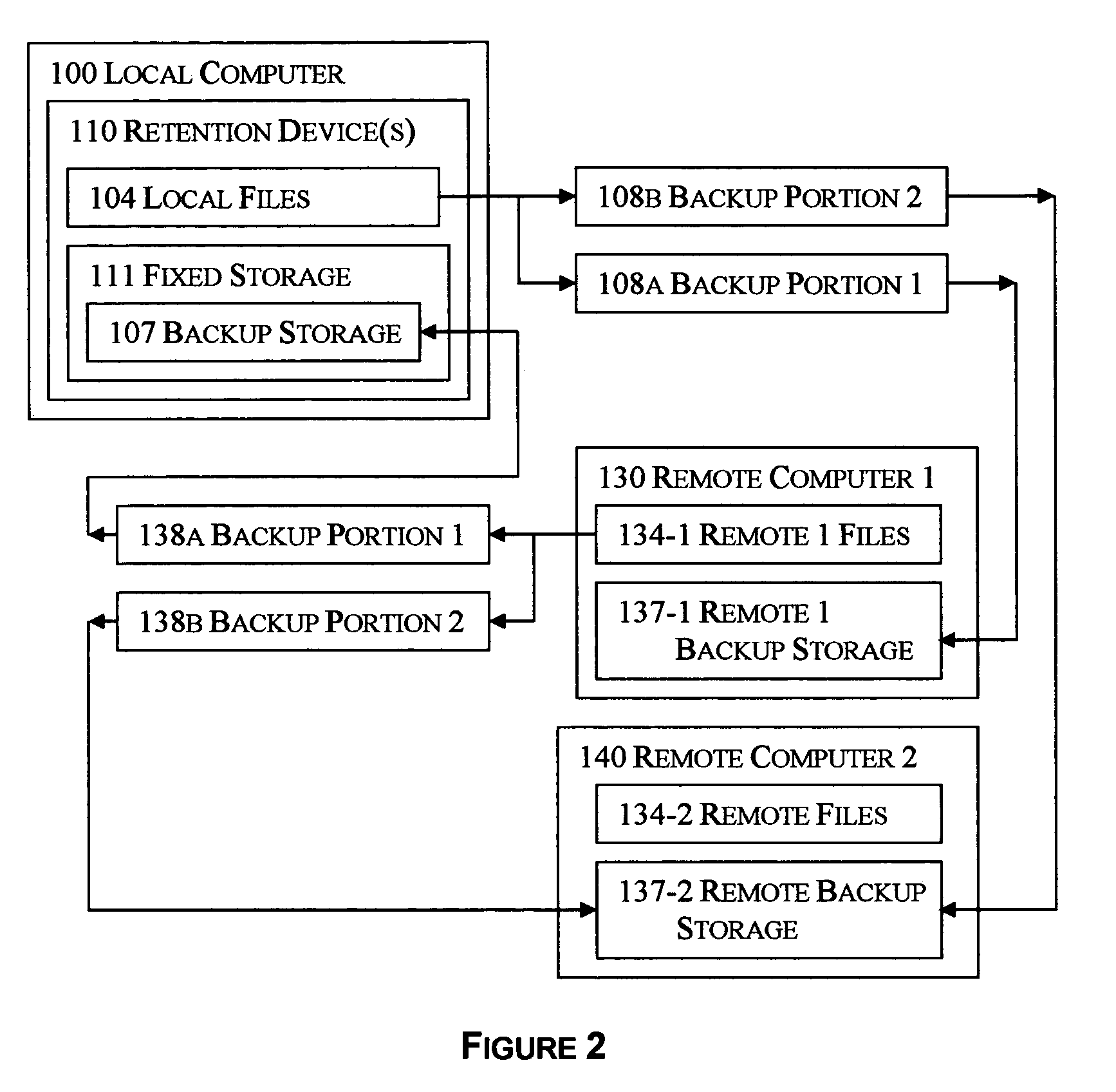
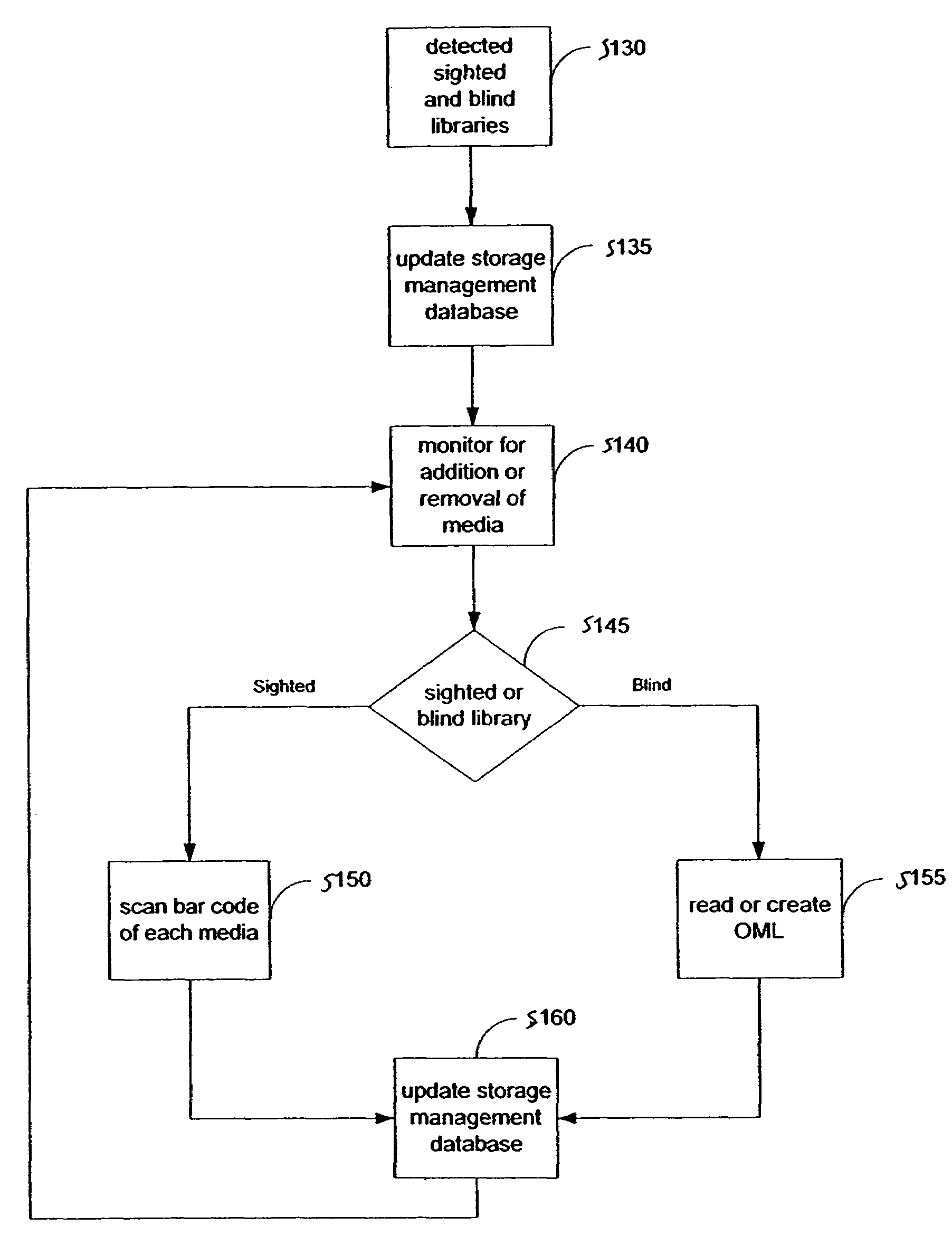
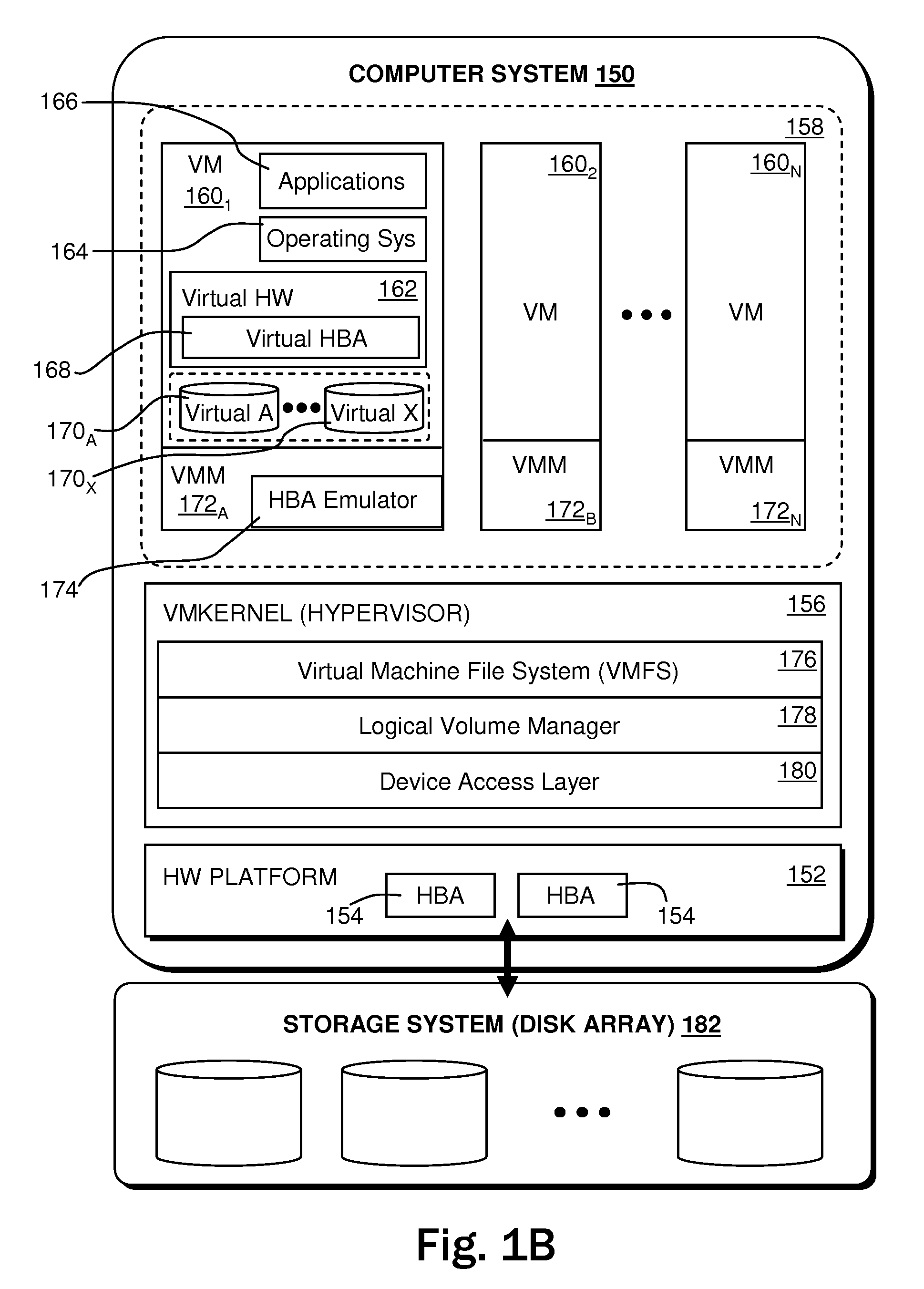
System and method for blind media support
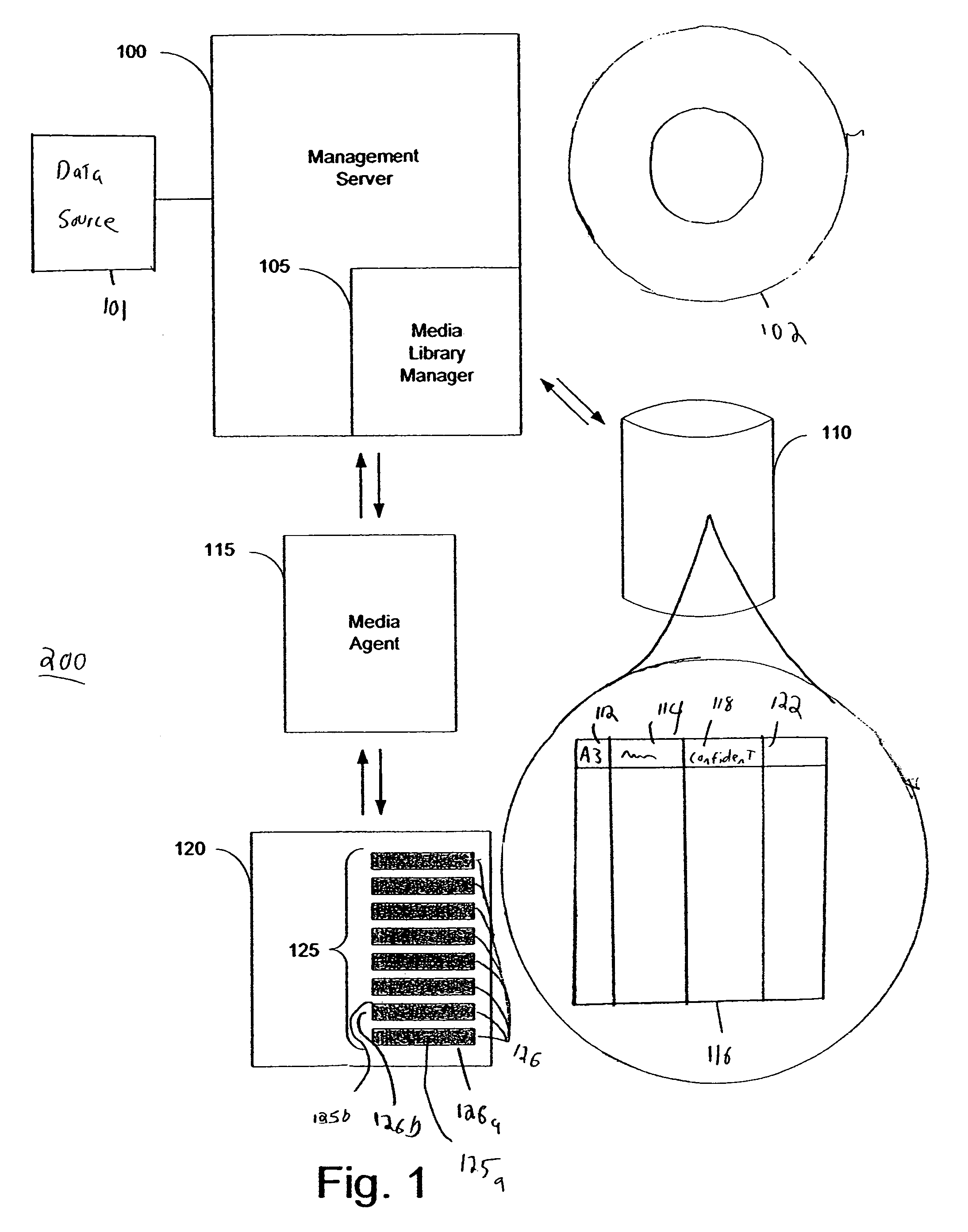
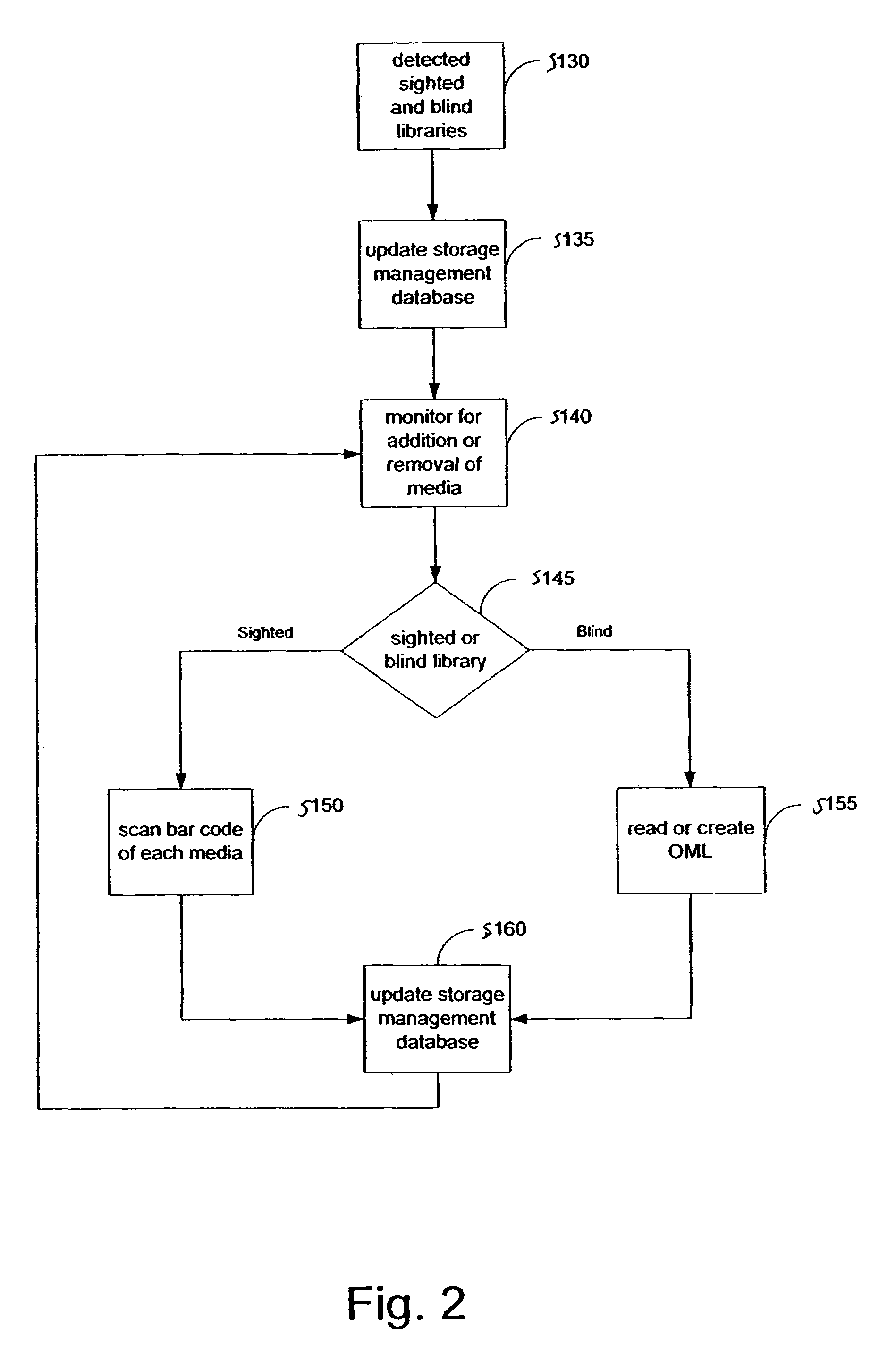
A system and method for operating a storage library. The system comprises a management server, a media agent connected to the management server, a library connected to the media agent and a database connected to the management server. The management server controls the media agent to monitor for the addition or removal of a piece of media in the library. When the media agent determines that the piece of media has been added to the library or removed from the library, the media agent causes the library to read a media label stored as data on the piece of media, the media label including an identifier identifying the piece of media. When a backup or restore is performed, the system checks the media label to ensure that the correct media is being used. Inventory procedures are disclosed. Media labels are stored in a database along with an indication of the corresponding slot where the media is stored, a time when the label was put on the medium, and a confidence parameter indicating how confident the system is that the particular medium is stored in the respective slot.
Owner:COMMVAULT SYST INC
Selective reciprocal backup
InactiveUS7330997B1Risk minimizationIncrease probabilityError detection/correctionMemory systemsNetwork connectionApplication software
The disclosed technology applies the principle of anonymous reciprocity to facilitate remote backups. A local computer stores other computer's backup files, while storing backup copies of local files on other computers connected through a network. Each computer may securely maintain and manage storage for other computers' files. Application may be constrained to a local area network, or work on the Internet. The disclosed technology works in a peer-to-peer environment; no central server is required. The same disclosed technology may also apply to file sharing.
Owner:ODOM GARY
Systems and methods for managing location of media in a storage system
InactiveUS7603386B2Input/output to record carriersData processing applicationsHybrid storage systemWorld Wide Web
Owner:COMMVAULT SYST INC
Storage system and method for backup
InactiveUS7085904B2Easy to getReduce the burden onData processing applicationsInput/output to record carriersDisk controllerStorage pool
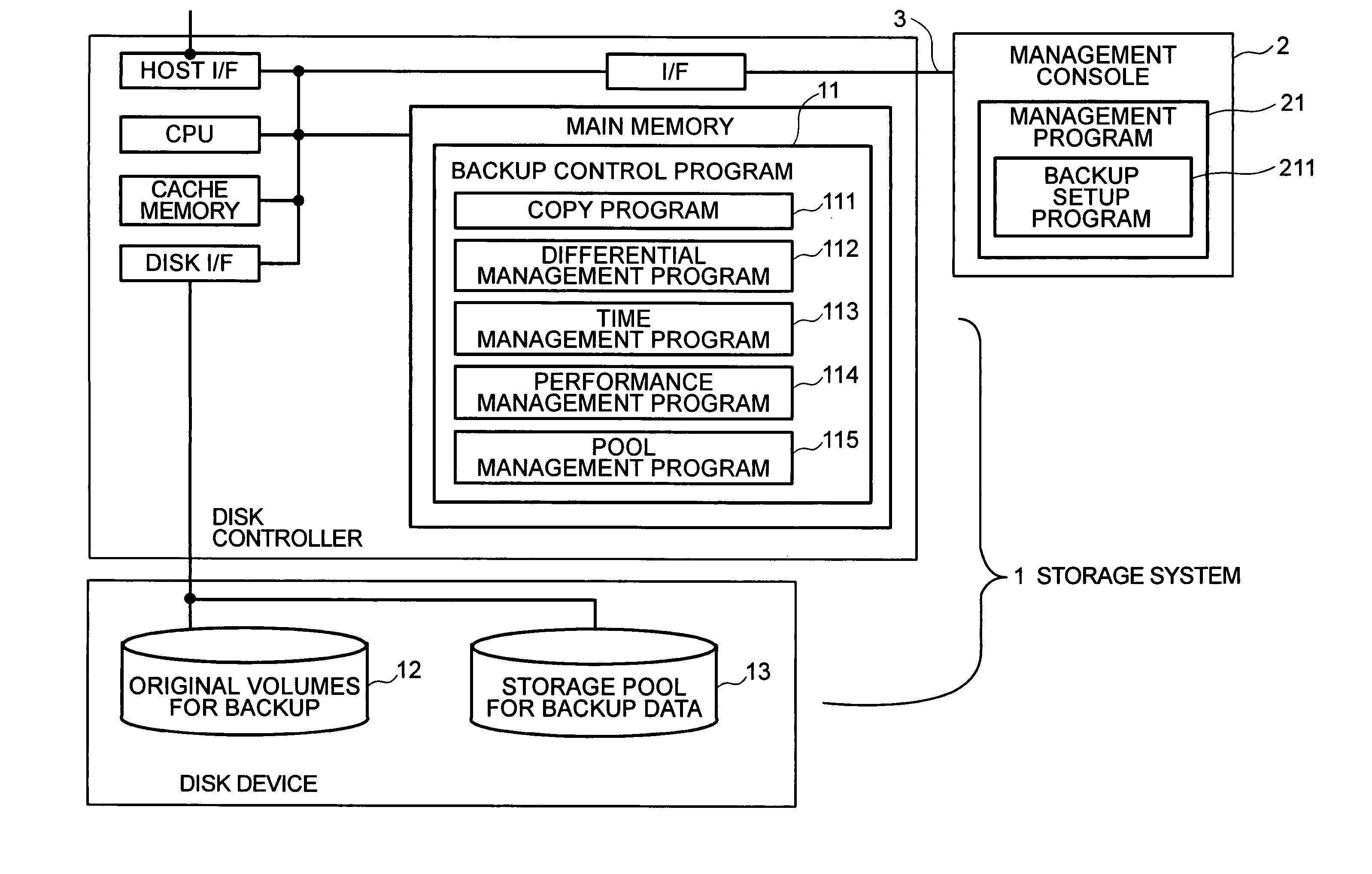
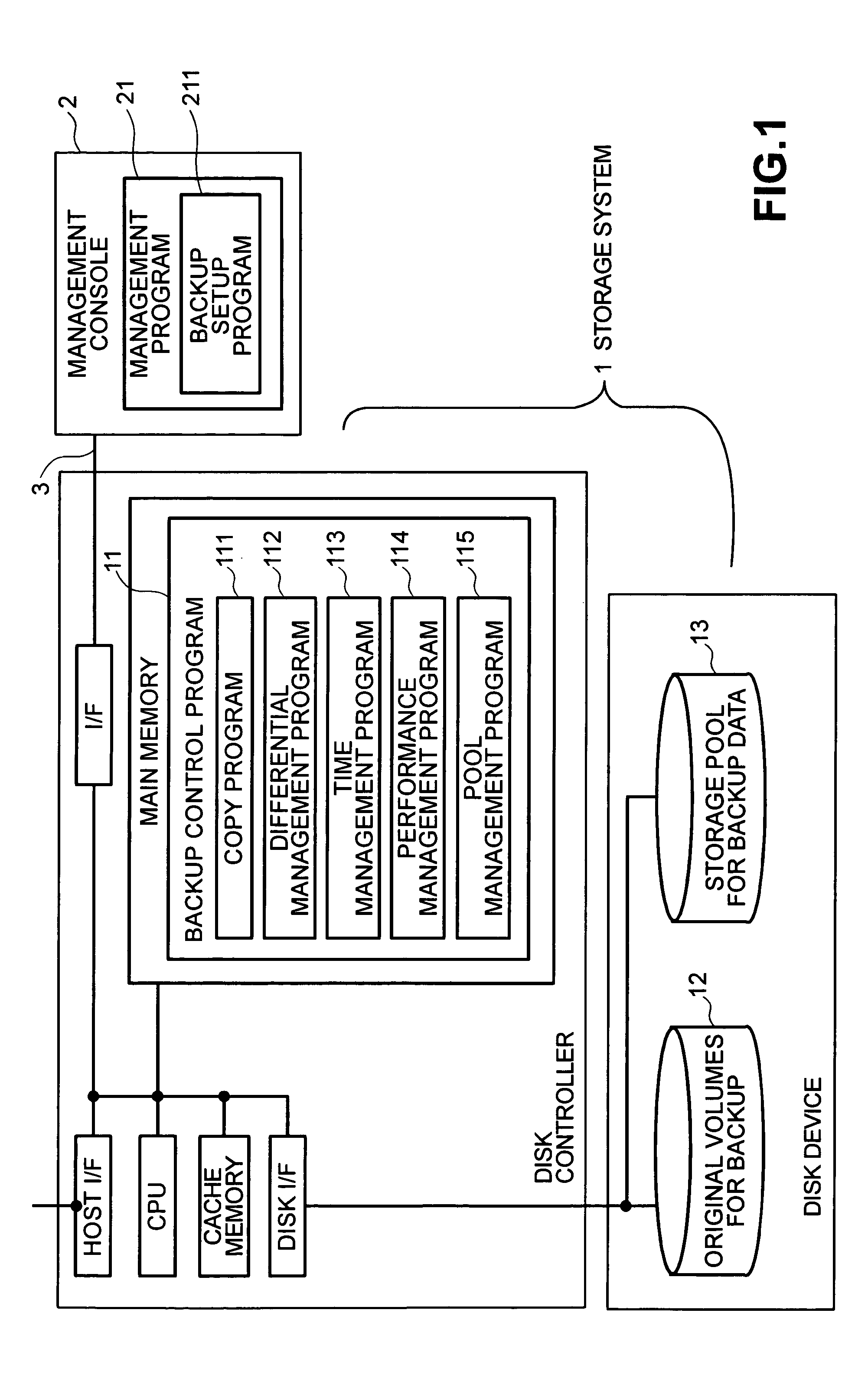
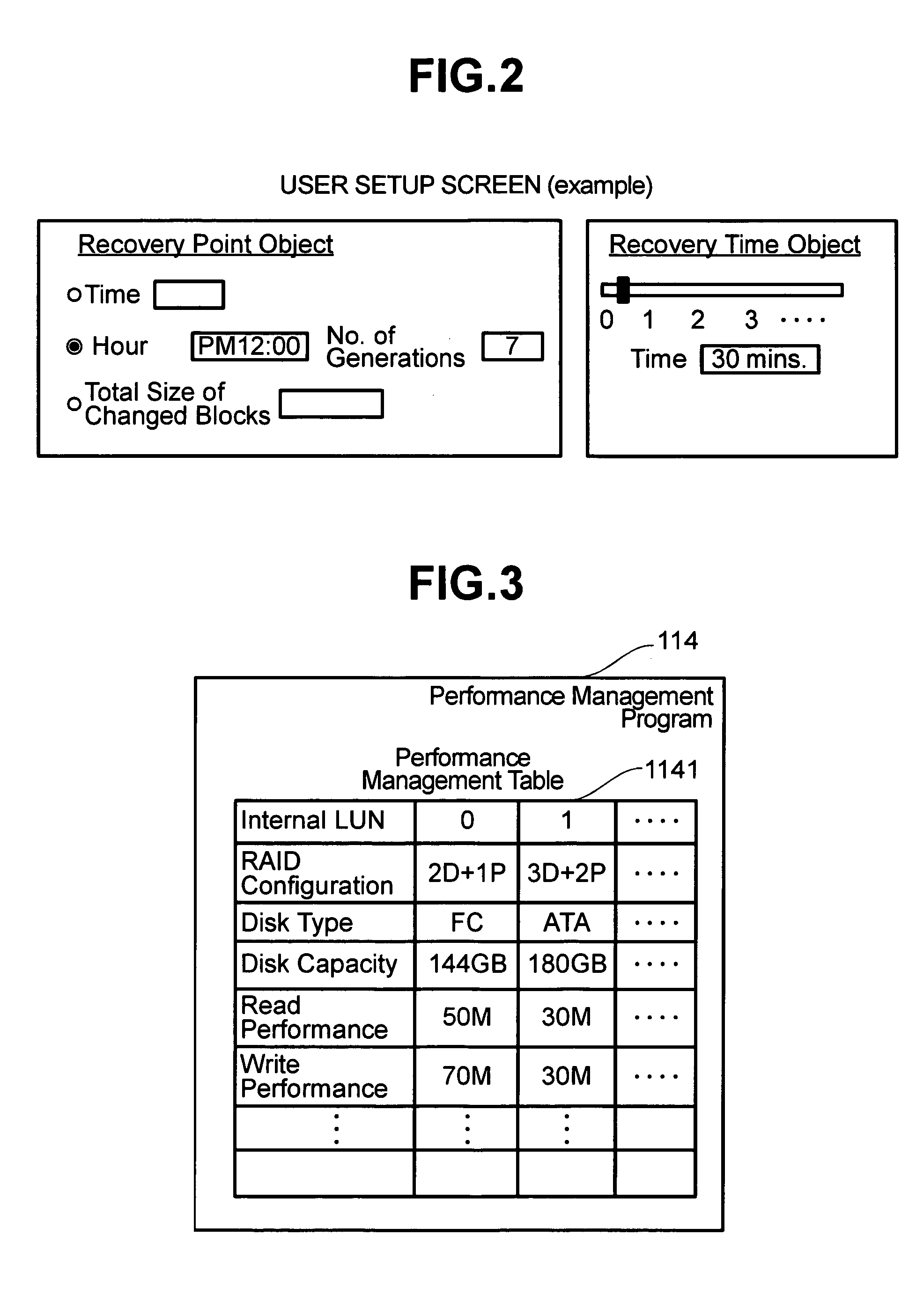
A storage system includes a disk controller and a disk device having original volumes for backup and a storage pool for backup data. It incorporates a differential management program which checks whether the original volumes for backup are updated or not; a pool management program which allocates a disk area to the storage pool for backup data; a performance management program which manages the performance of each volume; and a backup control program which performs total backup control. A backup method by which recovery within a user-specified recovery object time is possible is selected according to the restore performance calculated by the performance management program and the total size of changed blocks after backup acquisition as counted by the differential management program.
Owner:HITACHI LTD
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
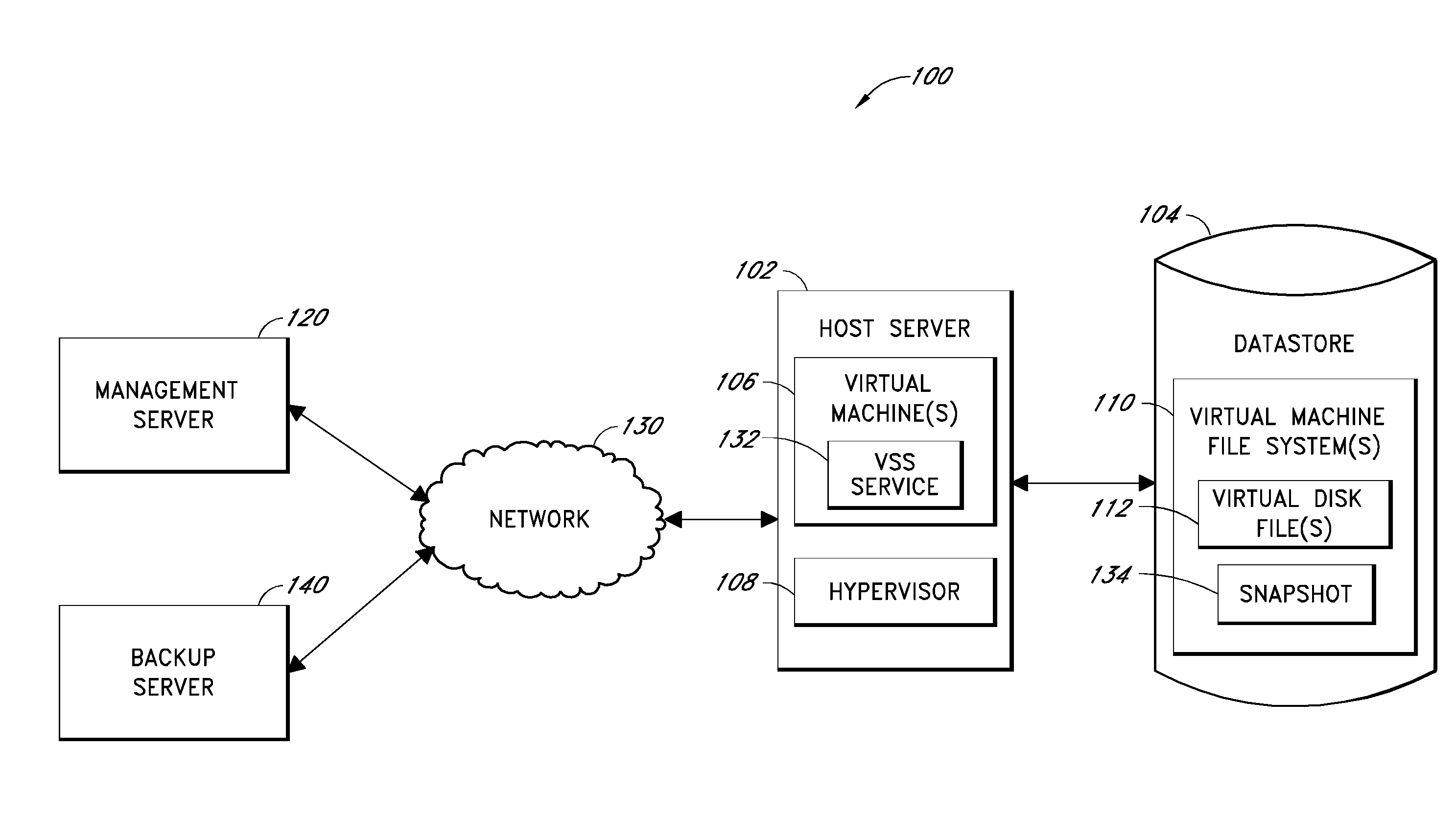
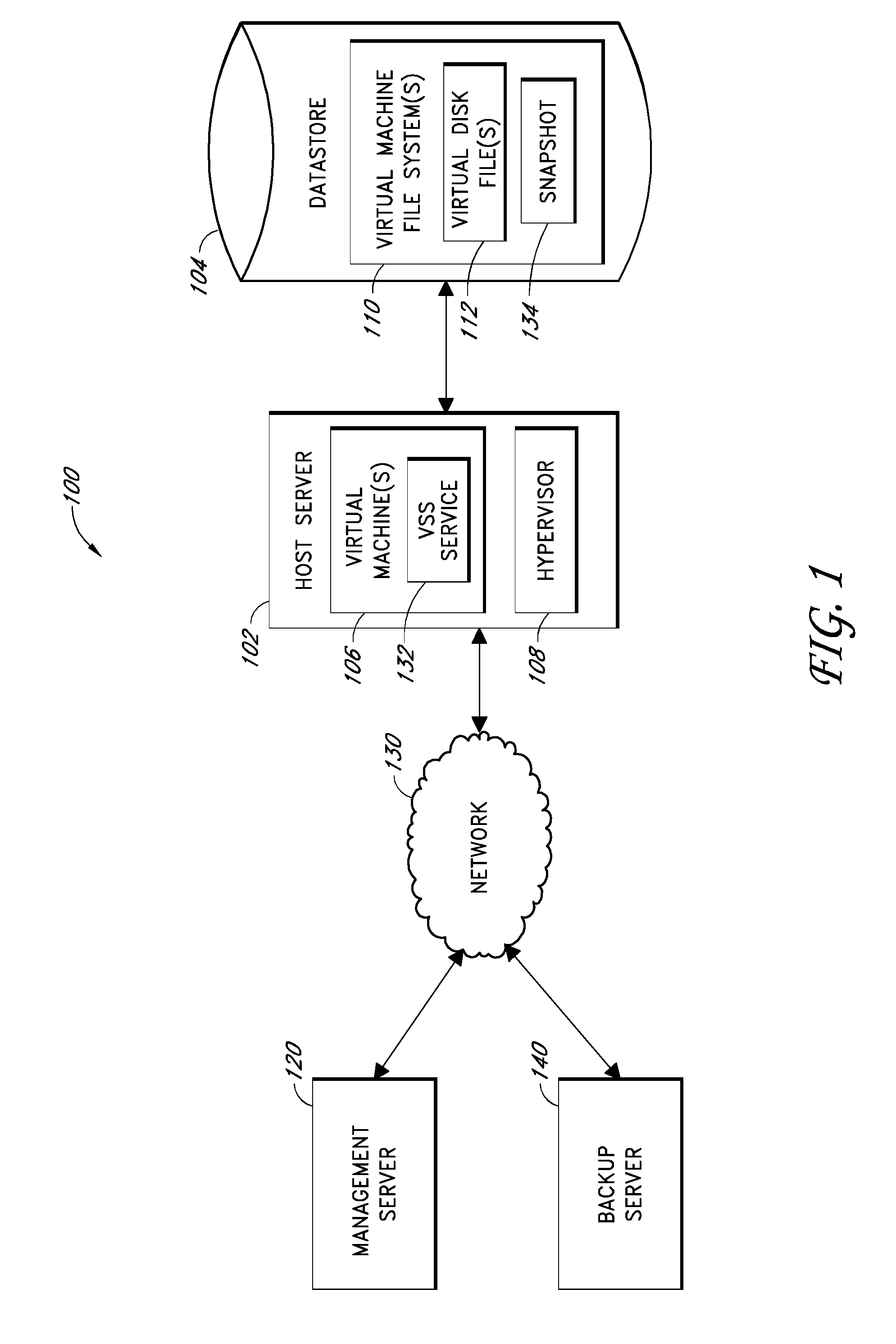
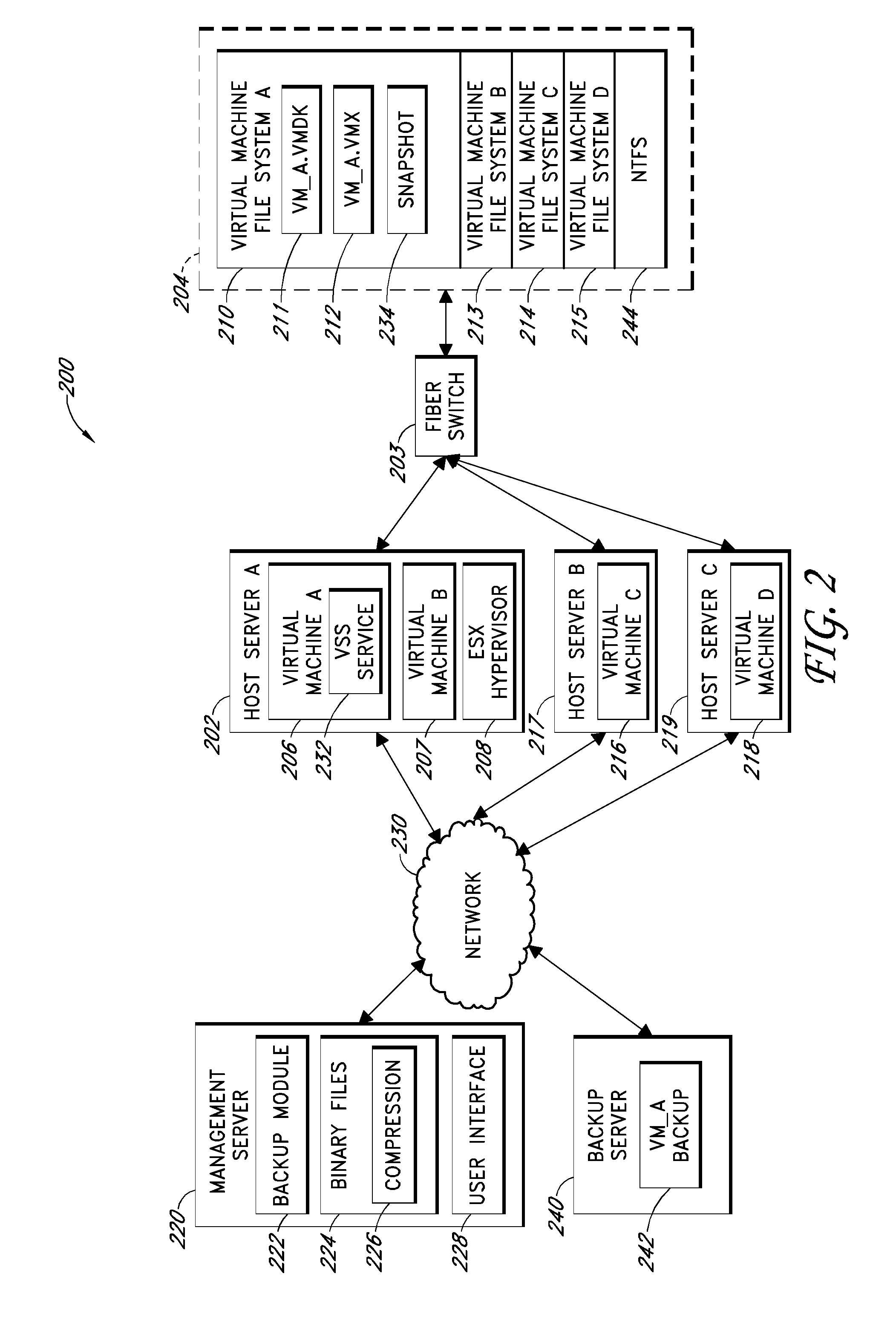
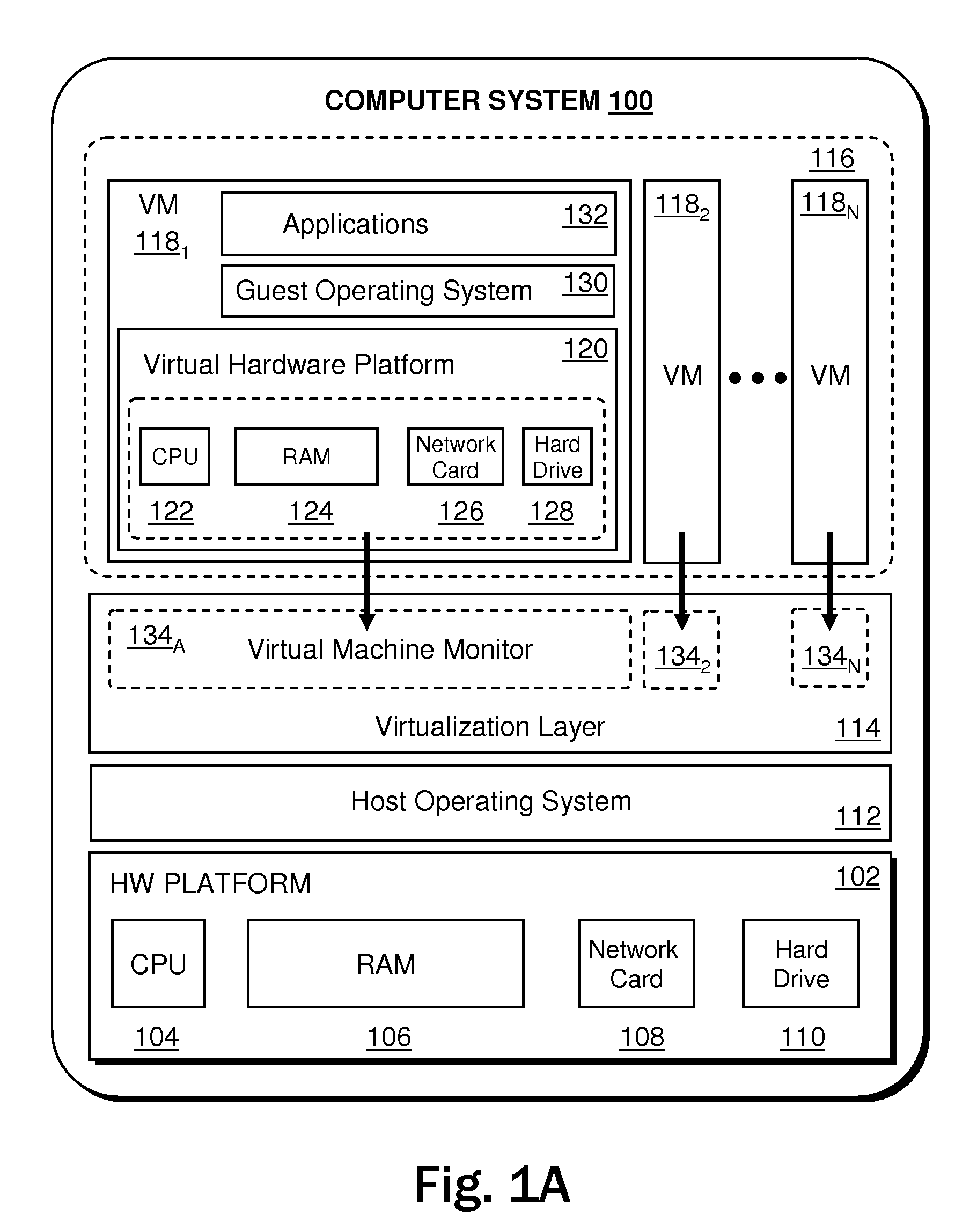
Systems and methods for performing backup operations of virtual machine files
ActiveUS20100011178A1Memory loss protectionError detection/correctionCommunications managementOperational system
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
Method and system for data backup
ActiveUS20070100913A1Cost-effectiveAvoid accessMemory loss protectionError detection/correctionWeb serviceApplication software
Embodiments of the present invention are directed to Web-Services-based data backup and data-archiving applications that provide remote data backup and data archiving to private individuals, small businesses, and other organizations that need reliable, secure, geographically remote, and cost-effective data backup, data archiving, and backed-up and archived-data retrieval. In one embodiment of the present invention, a private or small-business client contracts with a service provider for data-backup and data-archiving services. The service provider, in turn, contracts with a remote data-storage facility to provide secure, reliable data backup and data archiving to the personal or small-business client. A client-side application is downloaded to the client computer and configured to allow the client to store locally encrypted data at the remote, data-storage facilities. Neither the service provider nor the data-storage facility can decrypt or otherwise access the information stored by the client. In addition, the encryption key or encryption keys used by the client to encrypt the data for remote storage are securely stored at the remote, data-storage facility for subsequent recovery by the client, should the client suffer damage or loss to a local computer system. However, the client encryption key is stored in a doubly encrypted fashion, preventing access to the client's encryption key by either the service provider or the data-storage facility. Certain embodiments of the present invention also provide local indexing for remotely stored, encrypted data and efficient storage of updates to already remotely stored data.
Owner:CARBONITE GMBH
Systems and methods for performing discrete data replication
ActiveUS20100179941A1Reduce data volumeReduce consumptionDigital data information retrievalDigital data processing detailsBlock levelSource system
Systems and methods for performing intelligent replication of production data on a source storage device. In certain examples, a full backup of the production data is first performed and stored on a destination system. A journal module on the storage device (e.g., a shared storage device), or on at least one source system, tracks files on the storage device that change during a particular period of time. Following this period, a snapshot is taken of the production data. Upon mounting the snapshot, the replication system uses the journal information to identify modified files, conduct a block-level comparison of only the modified files with corresponding files on the destination system, and identify the particular data blocks that changed. The replication system then replicates only the changed blocks to the destination system. Certain systems further store information indicating a source system time of a known good state of the production data.
Owner:COMMVAULT SYST INC
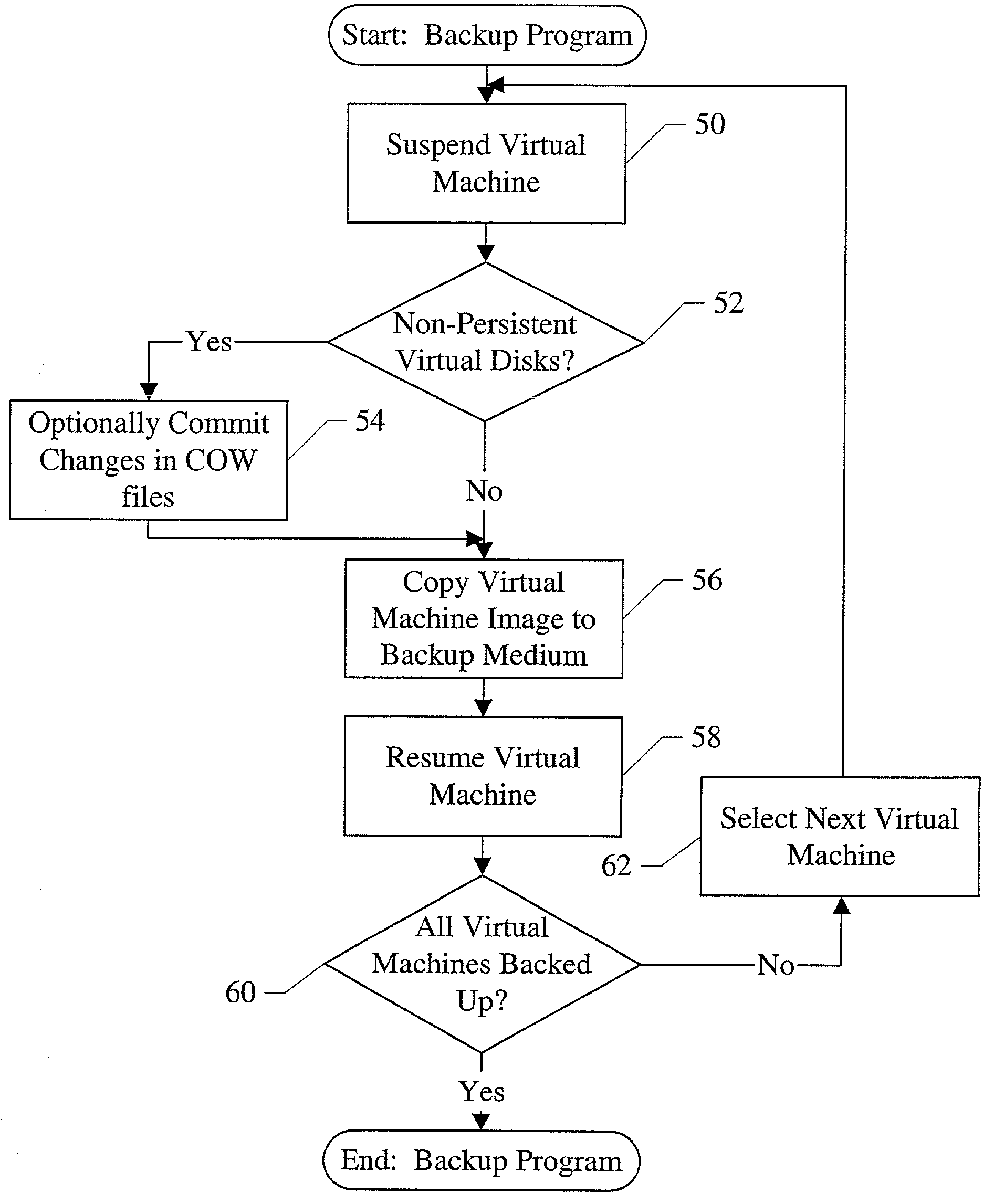
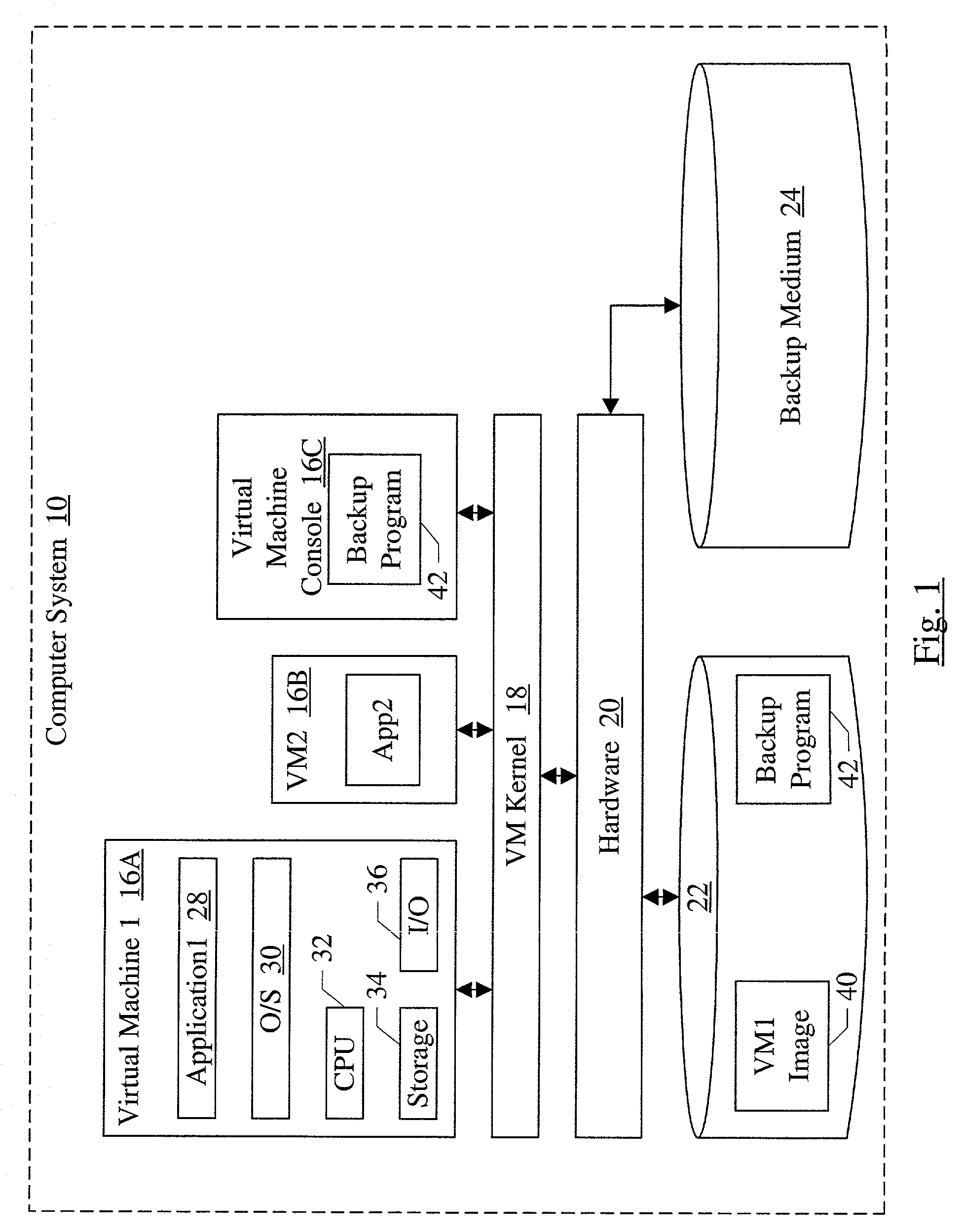
Disaster recovery and backup using virtual machines
One or more computer systems, a carrier medium, and a method are provided for backing up virtual machines. The backup may occur, e.g., to a backup medium or to a disaster recovery site, in various embodiments. In one embodiment, an apparatus includes a computer system configured to execute at least a first virtual machine, wherein the computer system is configured to: (i) capture a state of the first virtual machine, the state corresponding to a point in time in the execution of the first virtual machine; and (ii) copy at least a portion of the state to a destination separate from a storage device to which the first virtual machine is suspendable. A carrier medium may include instructions which, when executed, cause the above operation on the computer system. The method may comprise the above highlighted operations.
Owner:VERITAS TECH
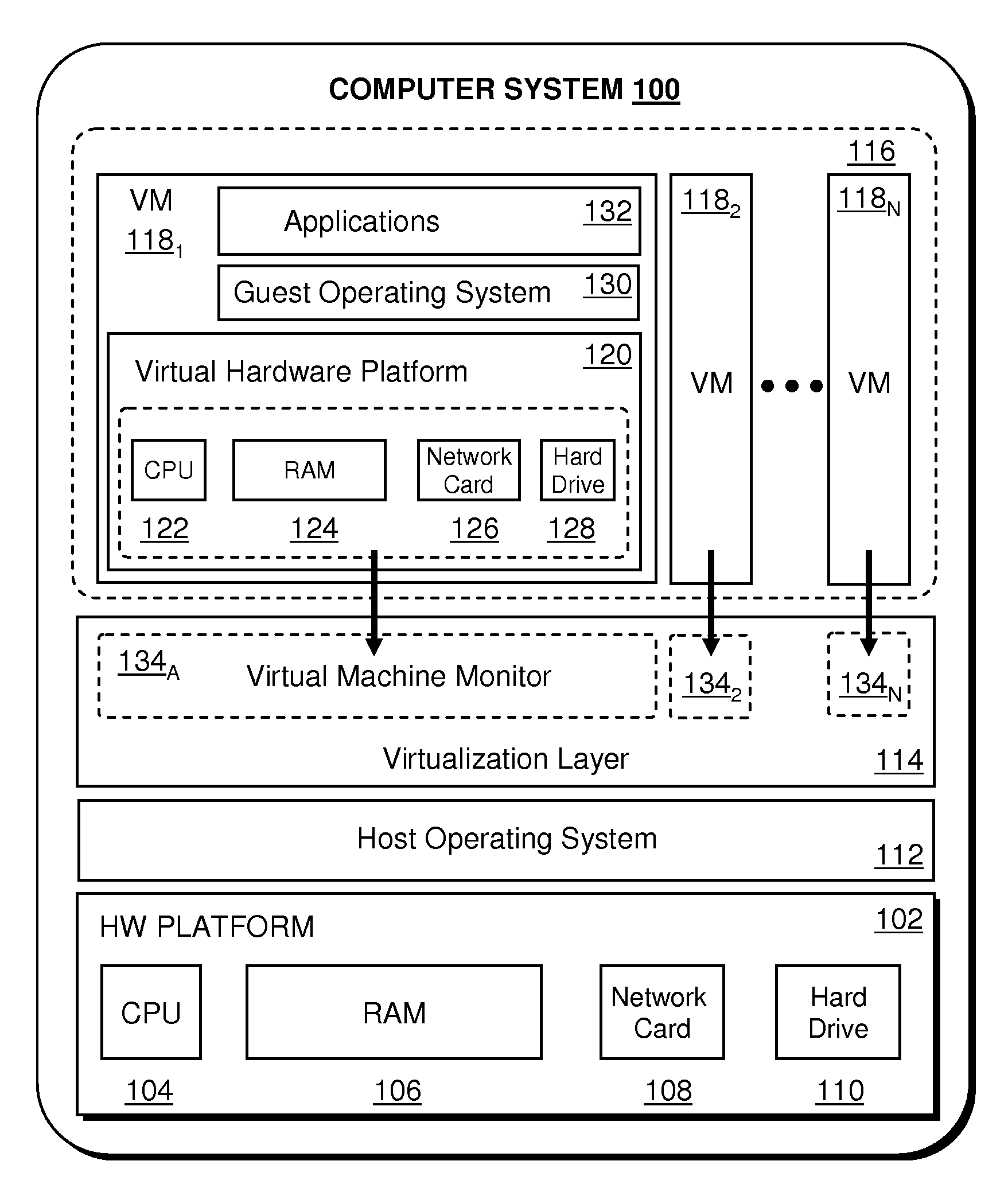
Low overhead fault tolerance through hybrid checkpointing and replay
ActiveUS20100107158A1Reduce overheadReduce needSoftware simulation/interpretation/emulationSpecial data processing applicationsVirtualizationLow overhead
A virtualized computer system provides fault tolerant operation of a primary virtual machine. In one embodiment, this system includes a backup computer system that stores a snapshot of the primary virtual machine and a log file containing non-deterministic events occuring in the instruction stream of the primary virtual machine. The primary virtual machine periodically updates the snapshot and the log file. Upon a failure of the primary virtual machine, the backup computer can instantiate a failover backup virtual machine by consuming the stored snapshot and log file.
Owner:VMWARE INC
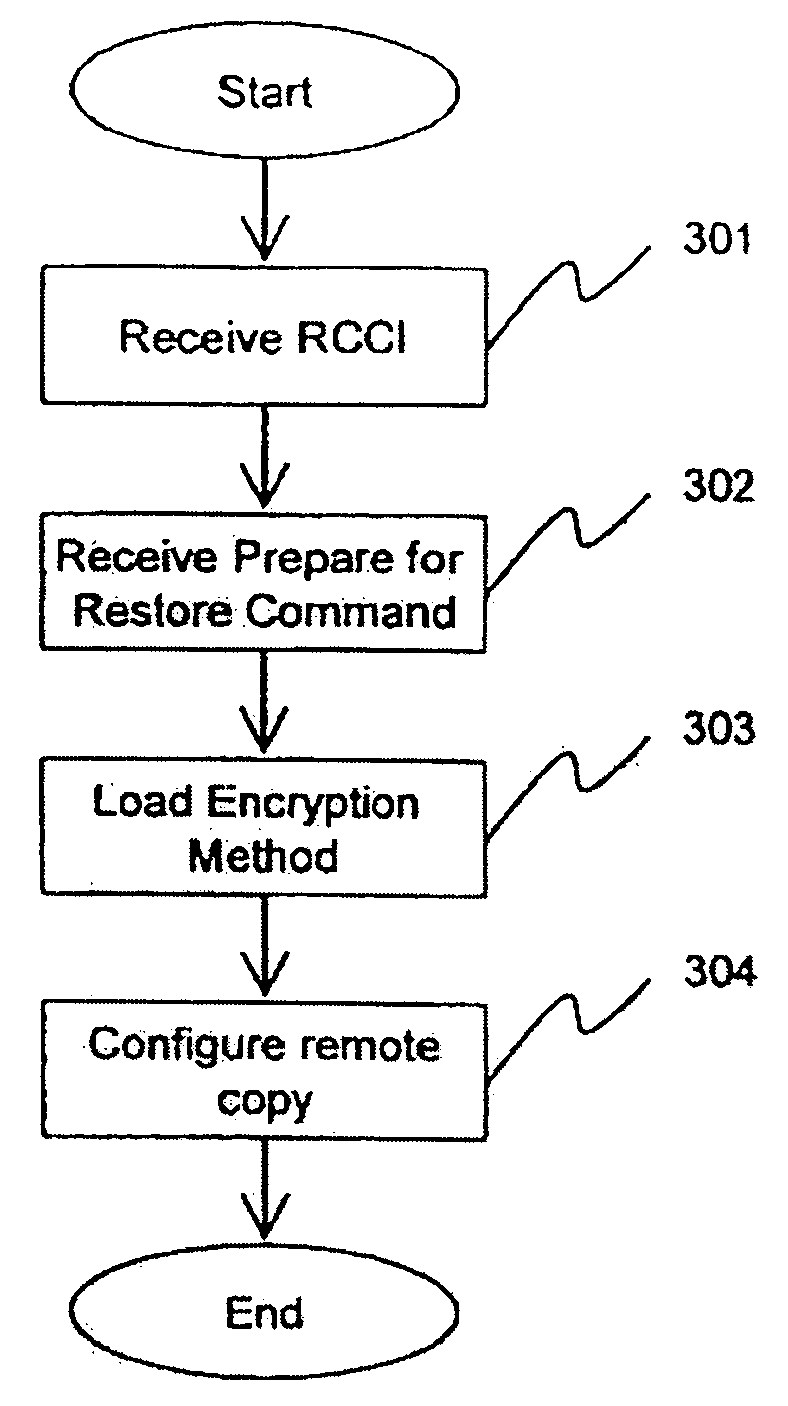
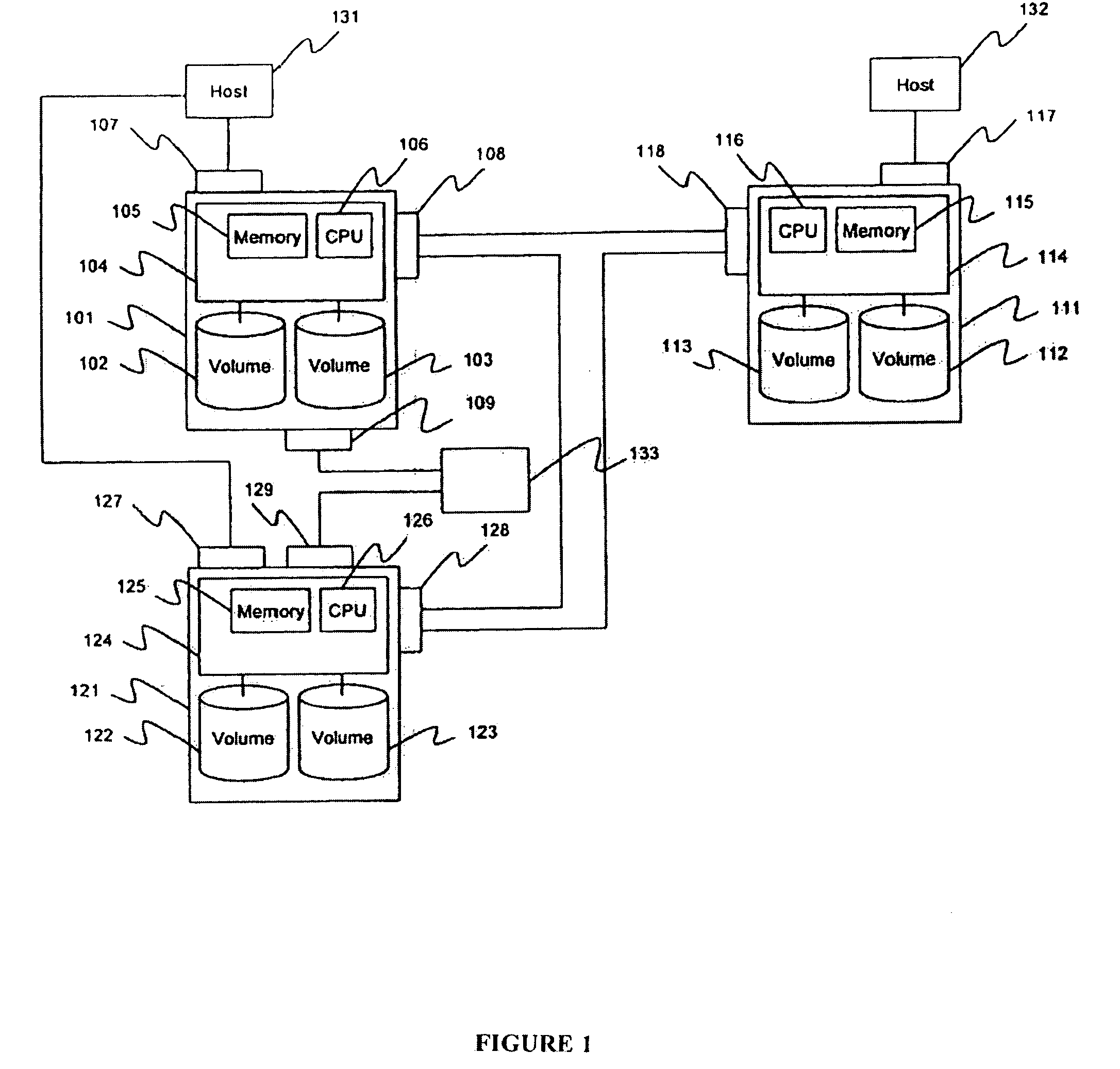
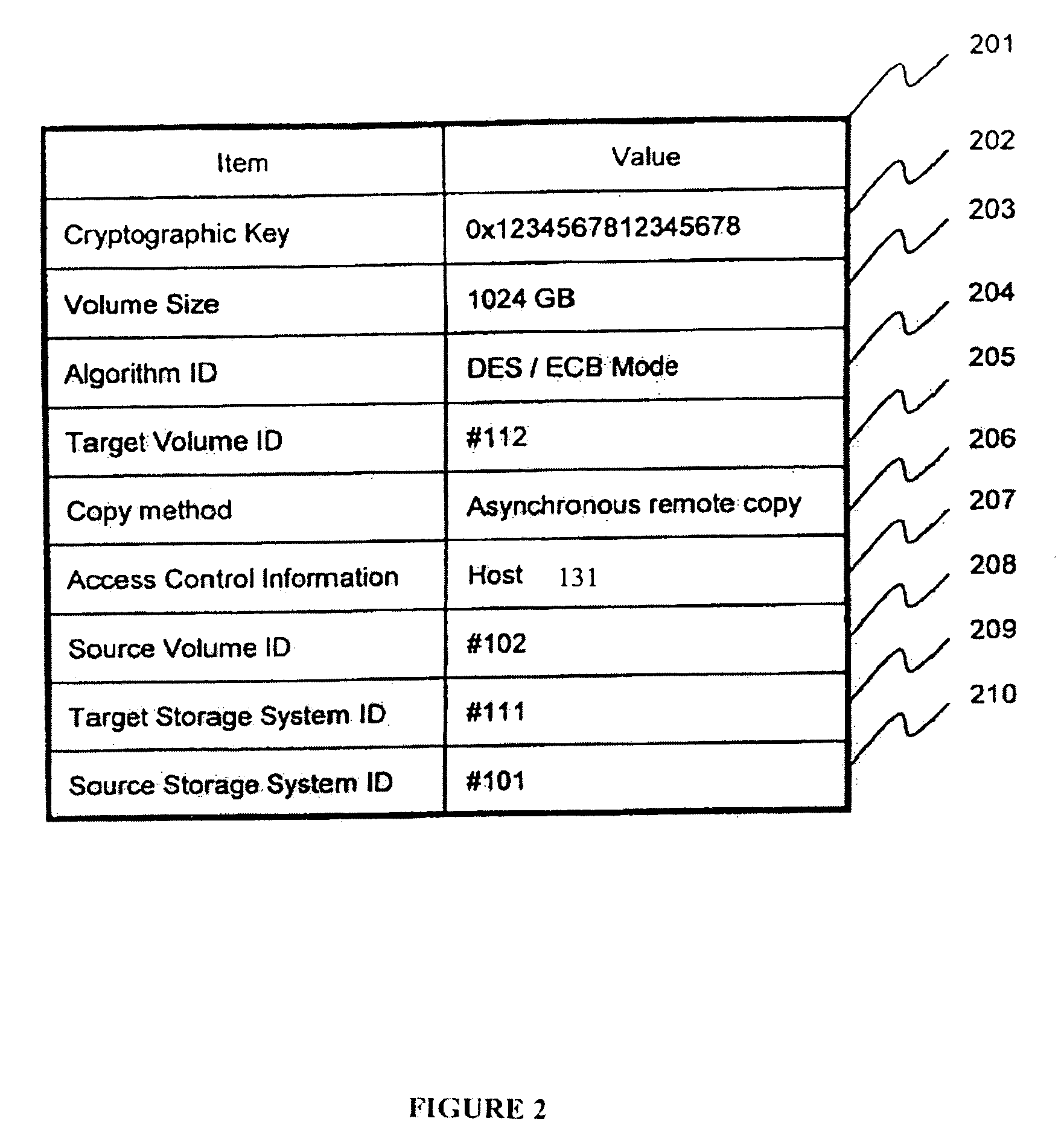
Method and apparatus for encrypted remote copy for secure data backup and restoration
InactiveUS20060005048A1Conveniently implemented in programmingDigital data processing detailsUser identity/authority verificationThird partyData source
Data at a primary storage system is encrypted and remote copied to a secondary storage system. A Remote Copy Configuration Information (RCCI) is created that identifies the encryption mechanism, keys, data source volume, and target volume for the remote copy. The RCCI is backed up on a trusted computer system. In one embodiment, the secondary storage system is an off-site data storage system managed by a third party. Upon detection of a failure in the primary storage system, the encrypted data and RCCI are transferred to a tertiary server, which is optionally created upon detection of the failure, and operations of the failed primary server are resumed by the tertiary server. In one embodiment, the failure is detected by loss of a heart beat signal transmitted from the primary storage system to a management server that initiates the transfers to the tertiary server.
Owner:HITACHI LTD
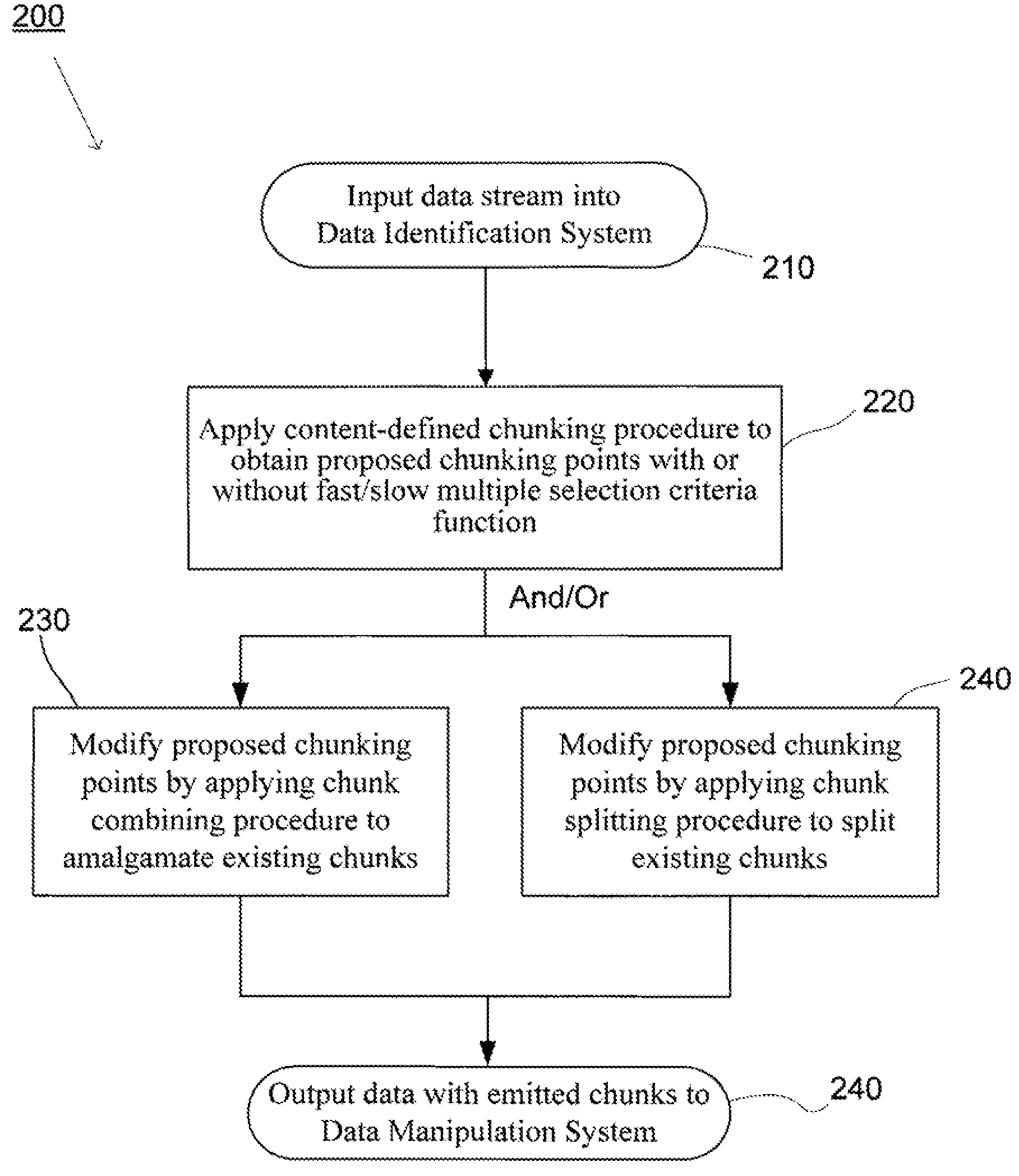
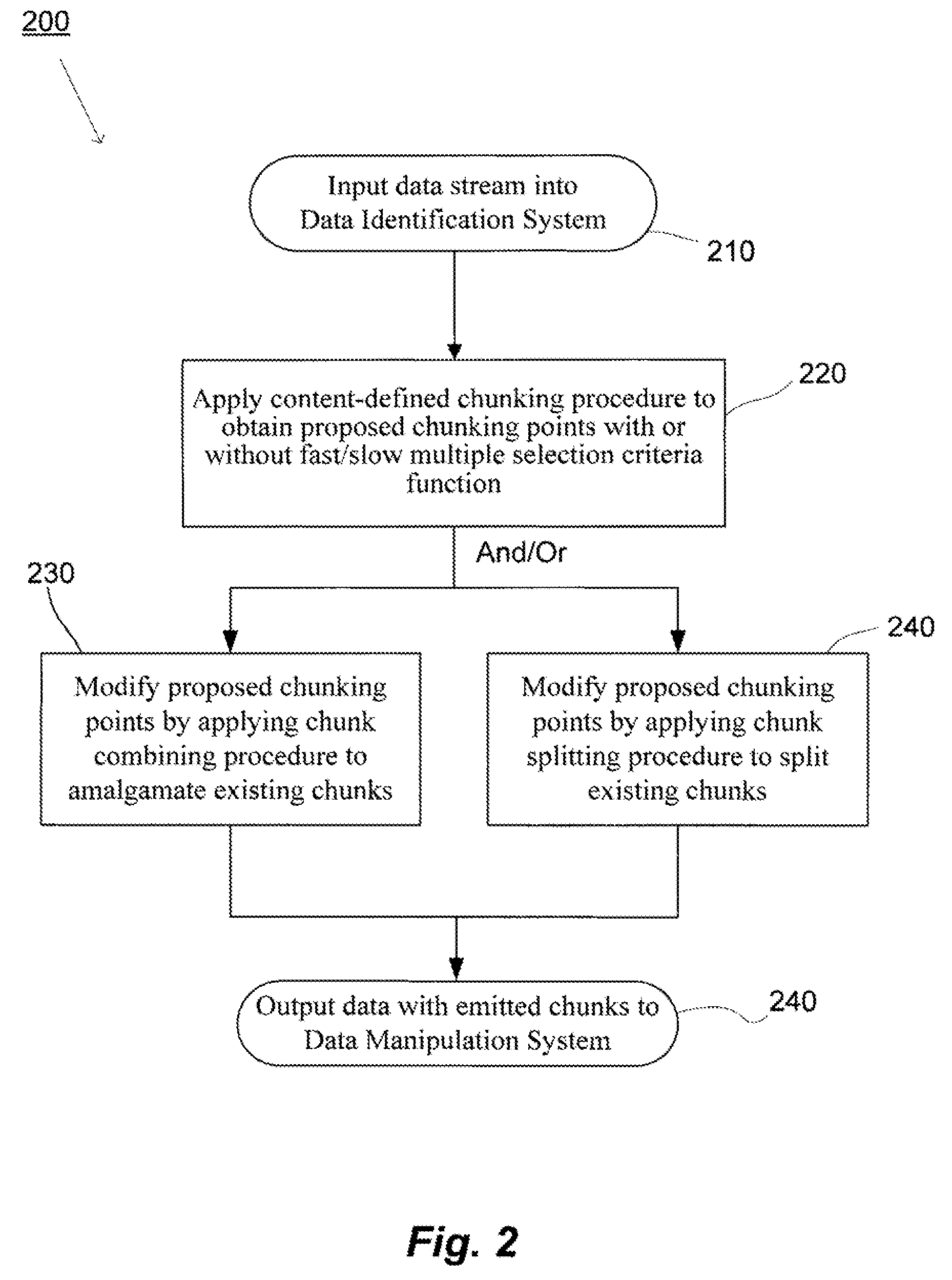
Methods and systems for quick and efficient data management and/or processing
ActiveUS20080133561A1Improve data processing efficiencyReduce quality problemsDigital data information retrievalProgram control using stored programsData managementCombined technique
System(s) and method(s) are provided for data management and data processing. For example, various embodiments may include systems and methods relating to relatively larger groups of data being selected with comparable or better performing selection results (e.g., high data redundancy elimination and / or average chunk size). In various embodiments, the system(s) and method(s) may include, for example a data group, block, or chunk combining technique or / and a data group, block, or chunk splitting technique. Various embodiments may include a first standard or typical data grouping, blocking, or chunking technique and / or data group, block, or chunk combining technique or / and a data group, block, or chunk splitting technique. Exemplary system(s) and method(s) may relate to data hashing and / or data elimination. Embodiments may include a look-ahead buffer and determine whether to emit small chunks or large chunks based on characteristics of underlying data and / or particular application of the invention (e.g., for backup).
Owner:NEC CORP
Vehicle backup monitoring and alarm system
InactiveUS6693524B1Reduce manufacturing costImprove product reliabilityAnti-collision systemsColor television detailsMobile vehicleDriver/operator
A vehicle backup monitoring and alarm system which comprises a system of three closed circuit video cameras, three laser-based distance detection systems and an associated monitor is disclosed. A camera and a laser-based distance detection system are mounted on each side, as well as the rear of the motor vehicle or large truck, and coupled to one monitor, located by the driver, which displays all three images simultaneously. The distance to the closest object, displayed by each camera, as determined by the laser-based distance detection system, is superimposed over the respective object in the monitor. If any of these said distances fall below a minimum predetermined distance, the numeric representation will flash and an audible alarm will sound.
Owner:PAYNE GEORGE R
Method and system for asynchronous transmission, backup, distribution of data and file sharing
InactiveUS6662198B2Easy to shareSolve the real problemDigital data information retrievalData processing applicationsOperational systemFile sharing
A system and method is provided for asynchronously sharing, backing up, and distributing data based on immutable entries. The system which is layered upon an existing operating system automatically stores, queues and distributes requested data among users.
Owner:ZOTECA
System and methods providing automatic distributed data retrieval, analysis and reporting services
InactiveUS6944662B2Increasing computationalIncreasing storage burdenMultiple digital computer combinationsWebsite content managementData processing systemPush and pull
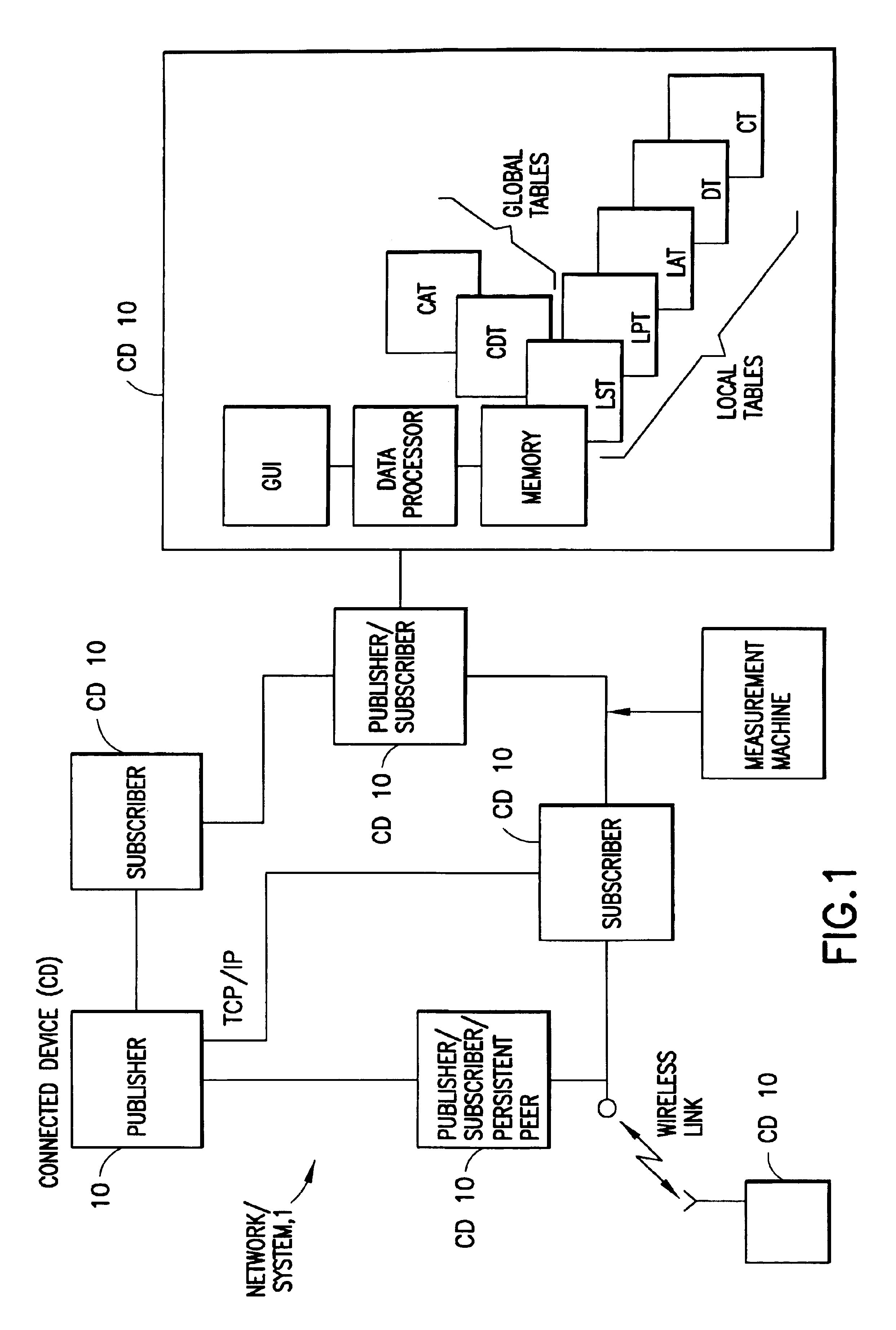
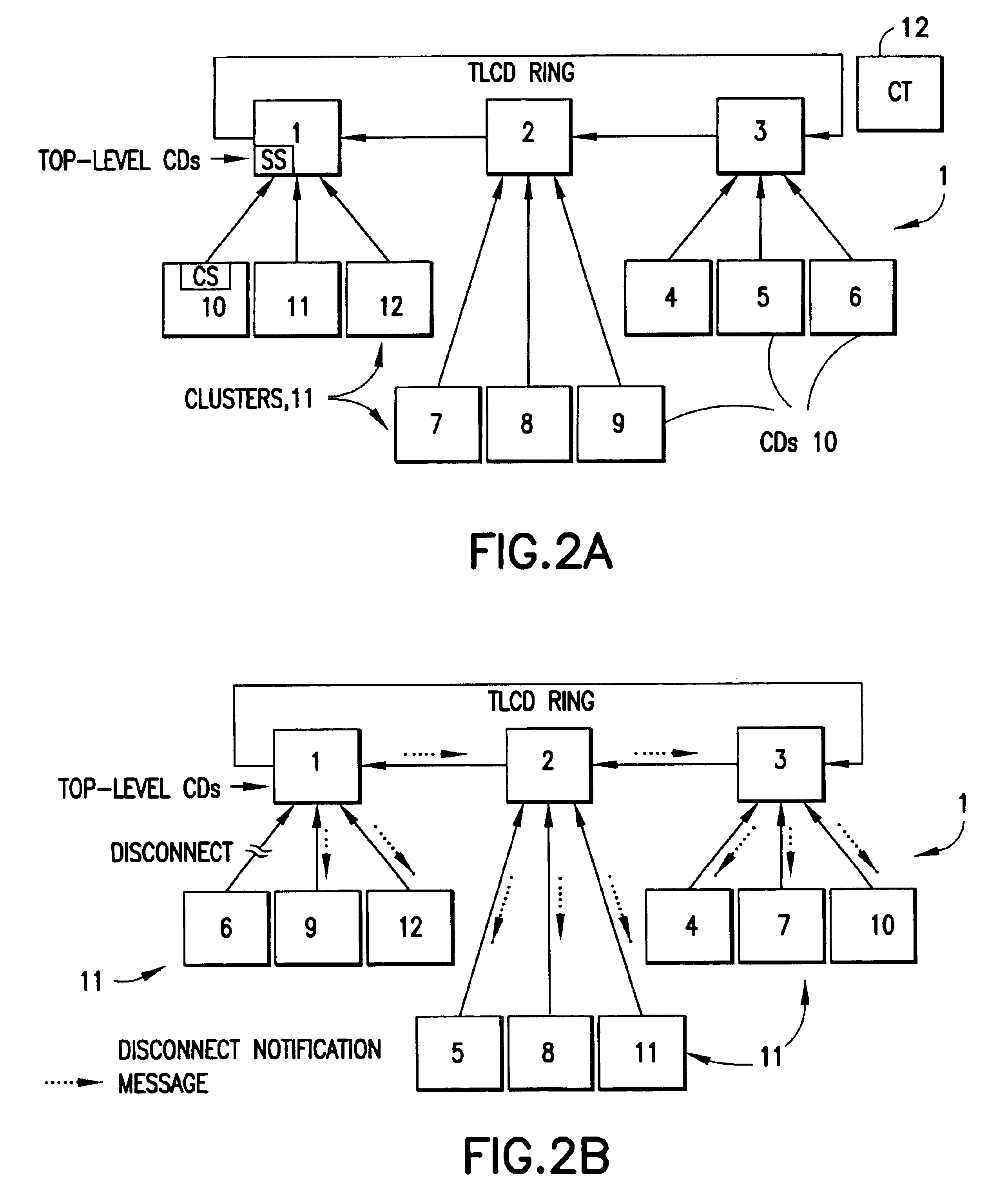
A data processing system includes a network containing of a set of connected devices, where individual ones of the connected devices include a data processor that executes a program for connecting to and disconnecting from the network and for maintaining a first list descriptive of other connected devices and a second list descriptive of at least some user-defined services published by individual ones of publisher connected devices that form a first sub-set of the connected devices. Individual ones of the publisher connected devices maintain a third list descriptive of an individual one or individual ones of registered service subscriber connected devices that form a second sub-set of connected devices. The publisher connected devices provide a service output to registered service subscriber connected devices upon an occurrence of at least one predetermined triggering event, which may be a push trigger, a pull trigger, or a combination of push and pull triggers. A given one of the connected devices may be a member of only the first sub-set of connected devices, or may be a member of only the second sub-set of connected devices, or may be a member of both the first sub-set of connected devices and the second sub-set of connected devices. The set of connected devices are logically organized into a plurality of clusters each having a top level connected device (TLCD), where the plurality of TLCDs are coupled together in a ring for propagating system administration information between the plurality of clusters. Services remain operative even after the connected device on which they initially reside becomes inoperative. This is accomplished by migrating the publication function to at least one other connected device when a current publisher's connected device becomes inoperative for any reason. A backup of last resort is referred to as a persistent connected device.
Owner:TAIWAN SEMICON MFG CO LTD
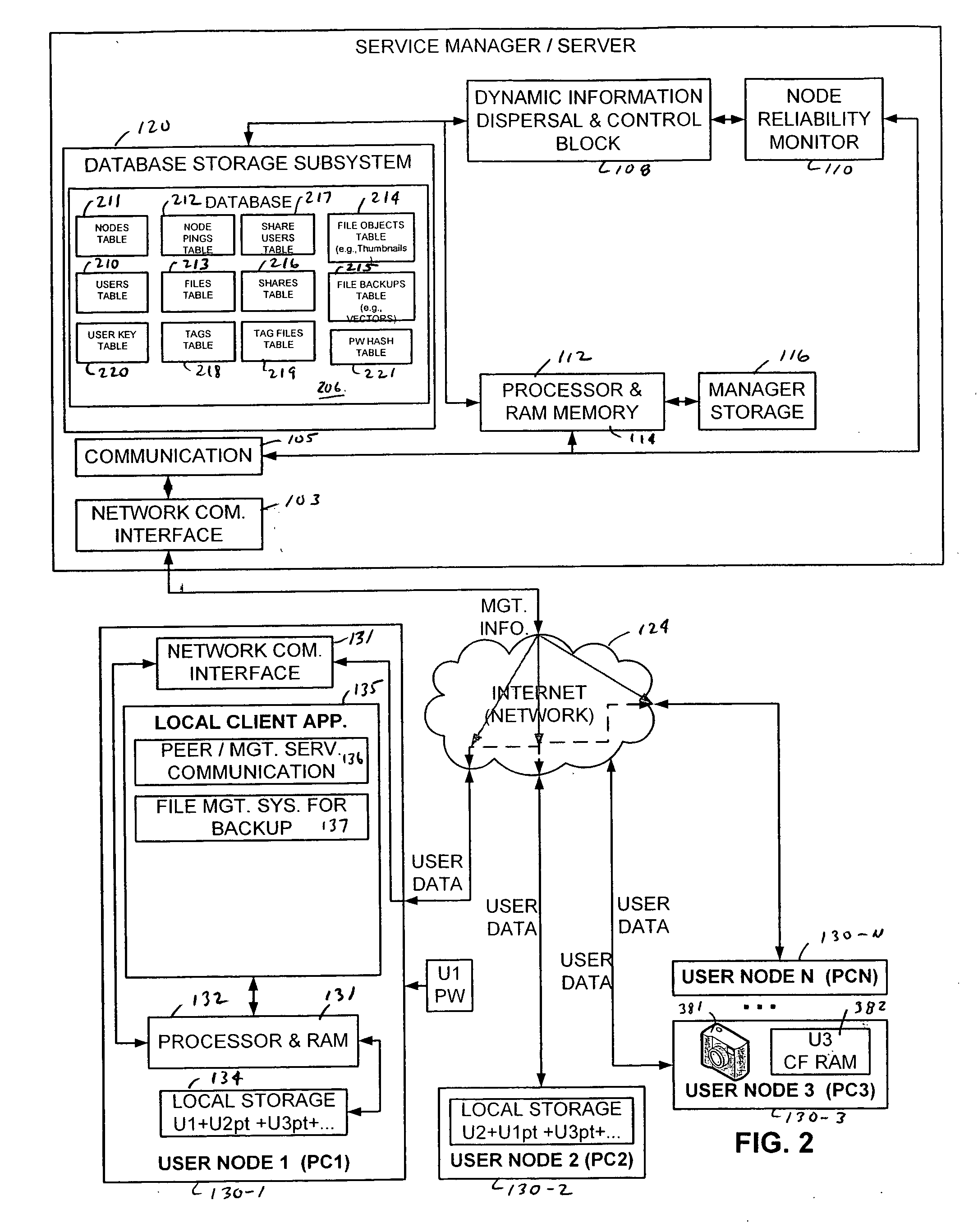
Managed peer-to-peer content backup service system and method using dynamic content dispersal to plural storage nodes
InactiveUS20080147821A1Generating monetary revenueDigital data information retrievalDigital computer detailsDigital dataDynamic management
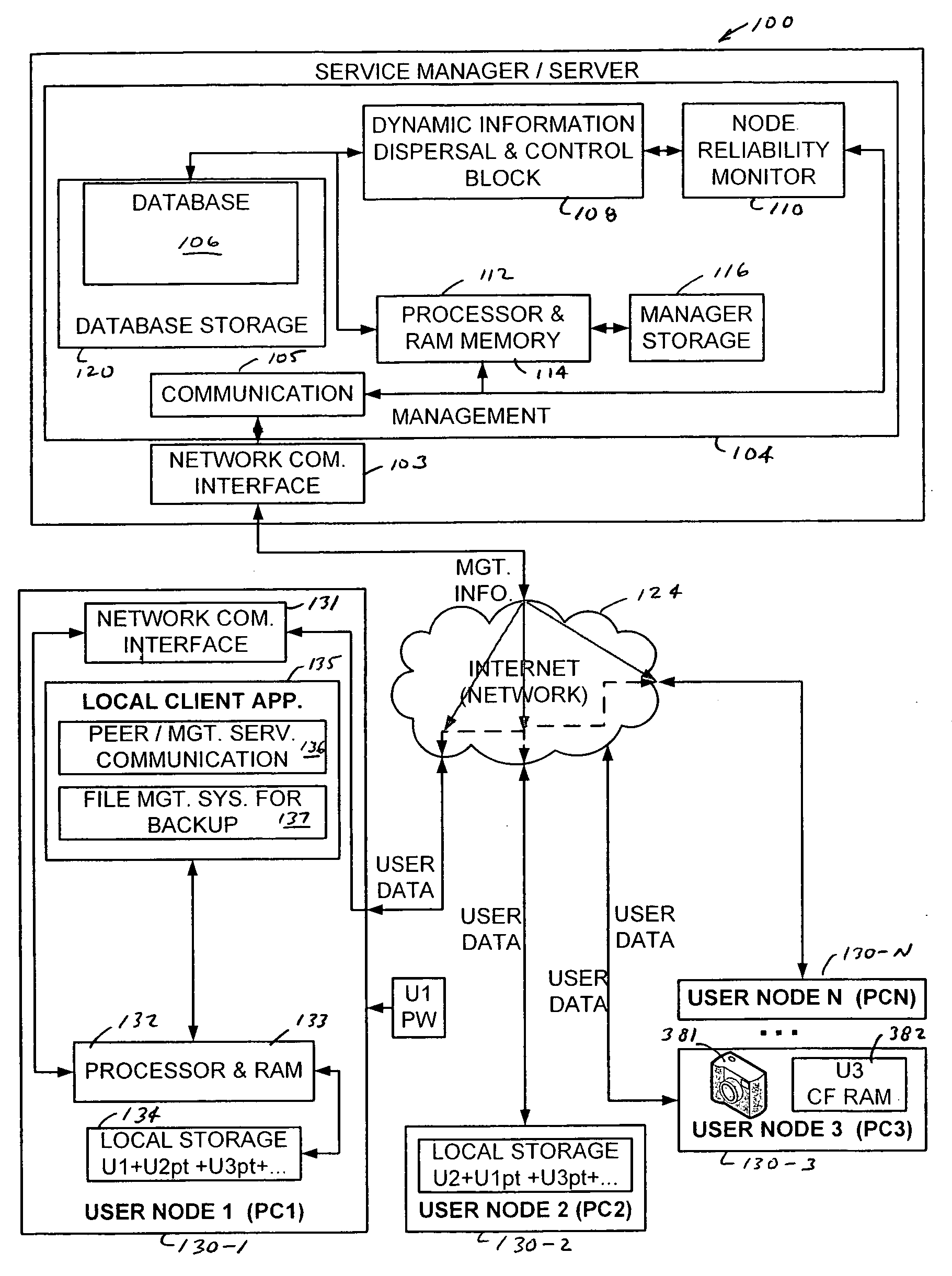
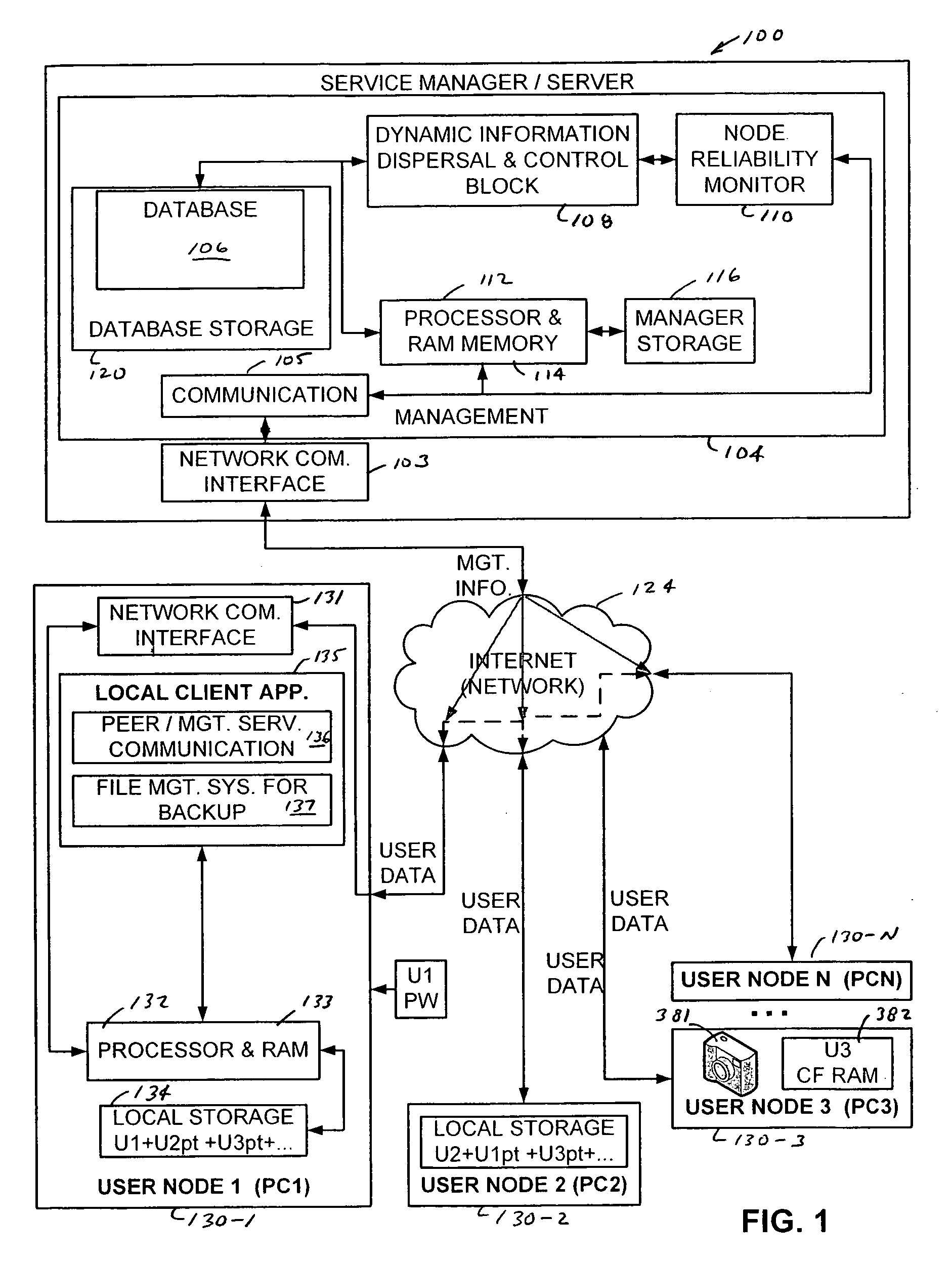
Systems, method, computer program stored on computer readable media, and business method for providing and operating a distributed network based secure storage of business or consumer digital data or content. System, method, computer program stored on computer readable media and business model for dynamically managed peer-to-peer media content backup that uses a plurality of subscriber personal computer based storage devices to store backups of other subscriber data in a manner that is secure and redundant.
Owner:CLOUD ENGINES
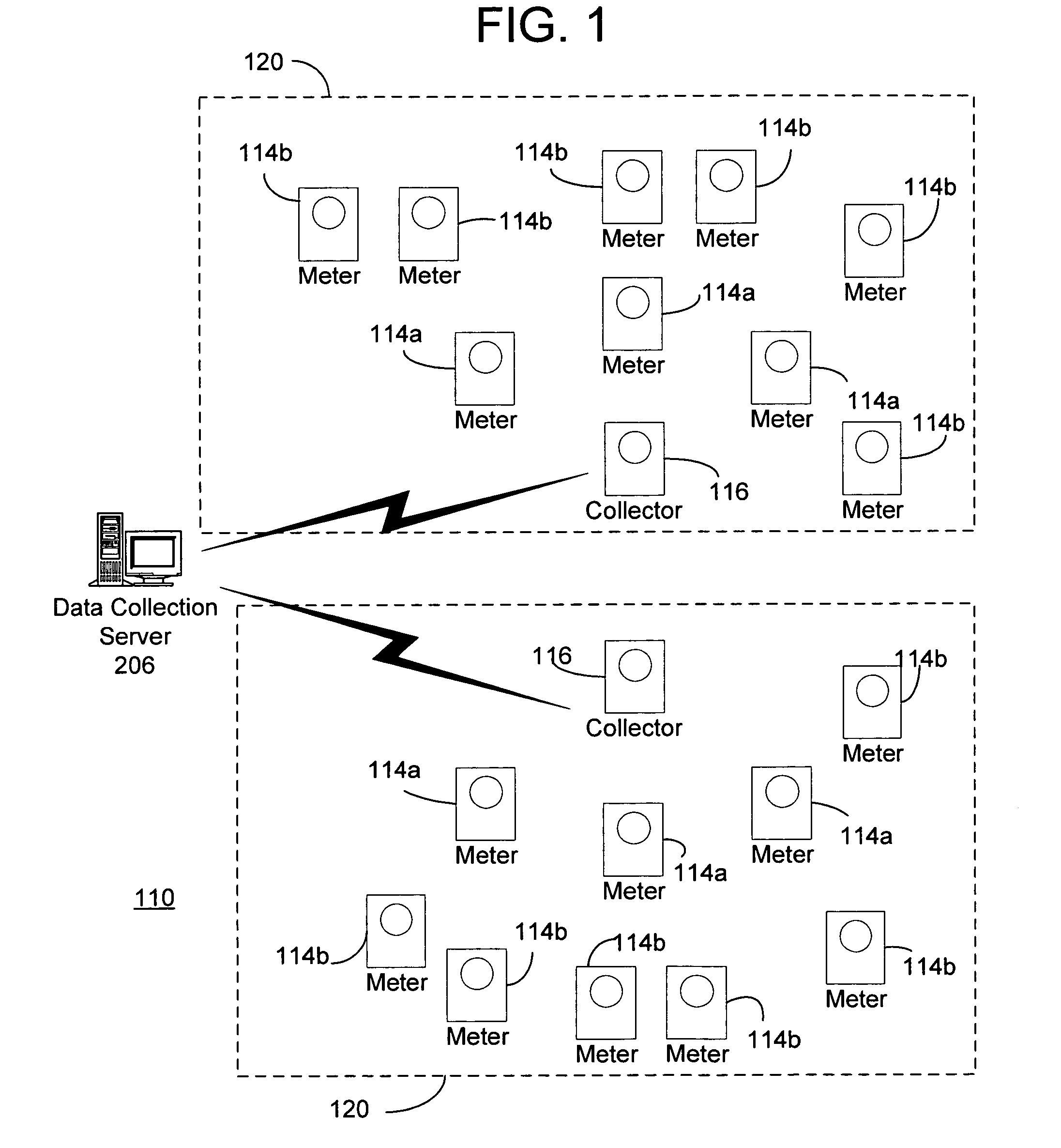
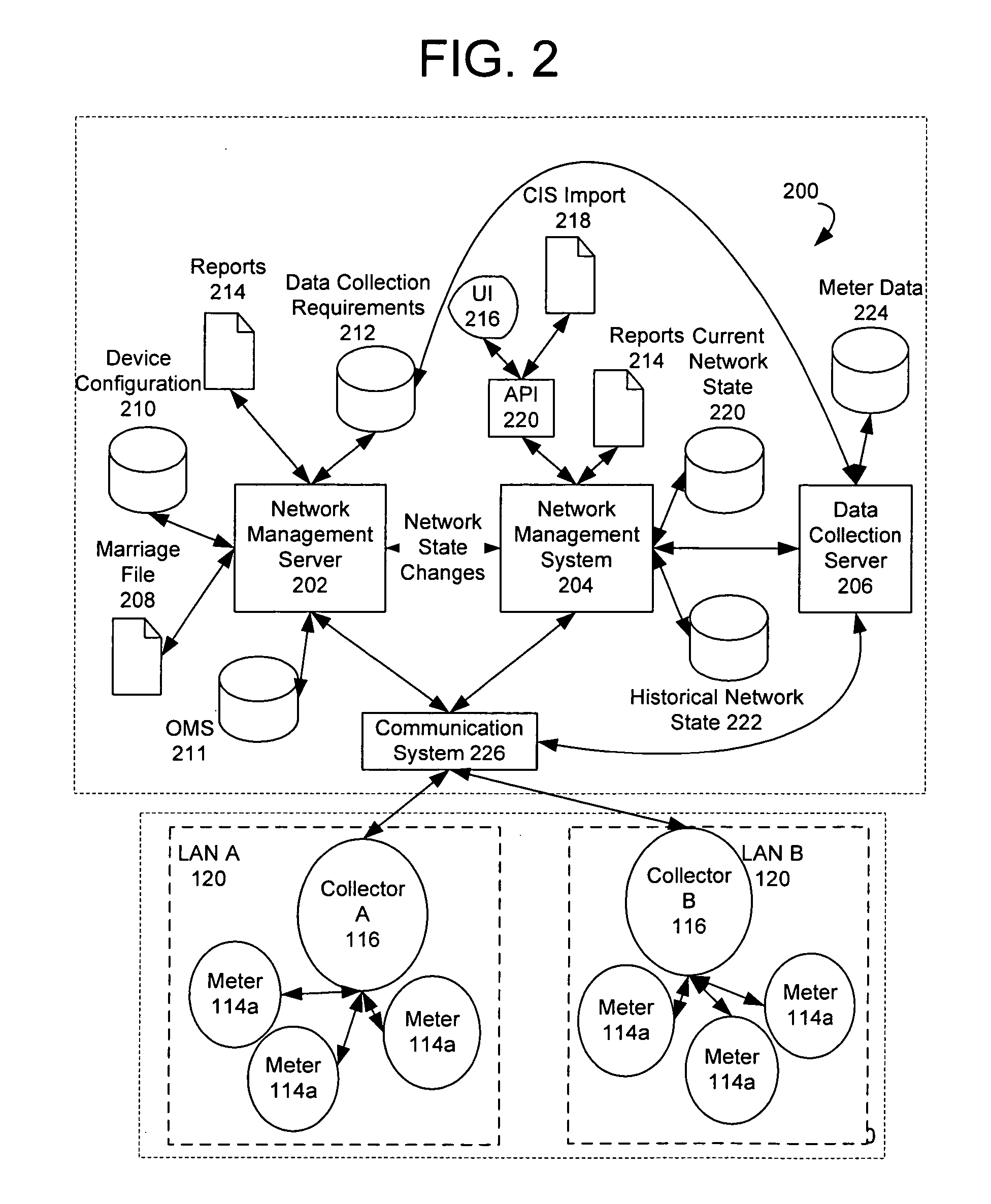
Using a fixed network wireless data collection system to improve utility responsiveness to power outages
ActiveUS7308370B2Good serviceElectric signal transmission systemsElectrical testingCollection systemWireless data
A system for determining service outages and restorations includes an outage management server (OMS) that generates reports of outages and restoration information for metering endpoints. The outages may be caused by faults at various locations in the distribution network. The metering endpoint may include a transmitter having a battery backup that transmits the outage information upon a failure to detect a voltage at the endpoint. The transmission of the information may be filtered based on configurable criteria. The metering endpoints may also inform the OMS when power is restored.
Owner:ELSTER ELECTRICTY LLC
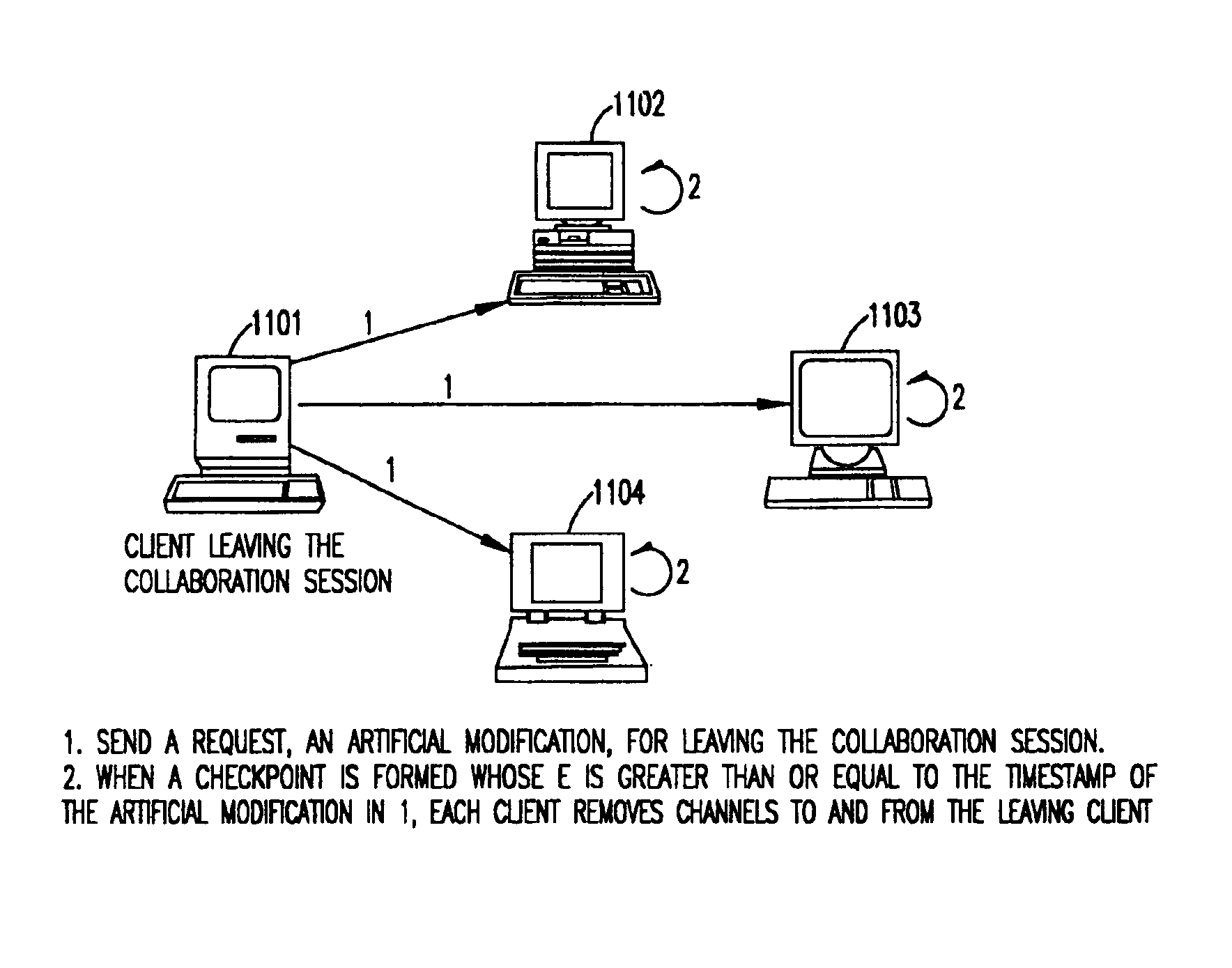
Synchronous collaboration based on peer-to-peer communication
InactiveUS6898642B2Eliminate useFully treatDigital data information retrievalMultiple digital computer combinationsTimestampWorkspace
A peer-to-peer protocol is based on the use of global timestamps and client priorities in serializing modifications to a shared workspace of real-time collaboration. The method caters to dynamic clients wherein a client can leave or join an ongoing collaboration session as long as there is always at least one client present / remaining in the collaboration session. The method can support multiple definitions of a modification, including partitioning-based definitions, wherein the method provides full support for locking of partitions, and a full treatment of inter-partition synchronization via a modification definition over multiple partitions. The method is capable of utilizing the many standard methods of creating a global, distributed, synchronized clock for the global timestamps utilized by it. The method is rollback-based for correcting tentative but incorrect serializations, and provides additional backup in terms of checkpoints for additional safety and for the support of lightweight, pervasive clients. The method includes many optimizations for efficiency, and includes a method of switching to and back from distributed server-based serialization for the periods when the network response is better suited to a distributed server than the peer-to-peer protocol.
Owner:INT BUSINESS MASCH CORP
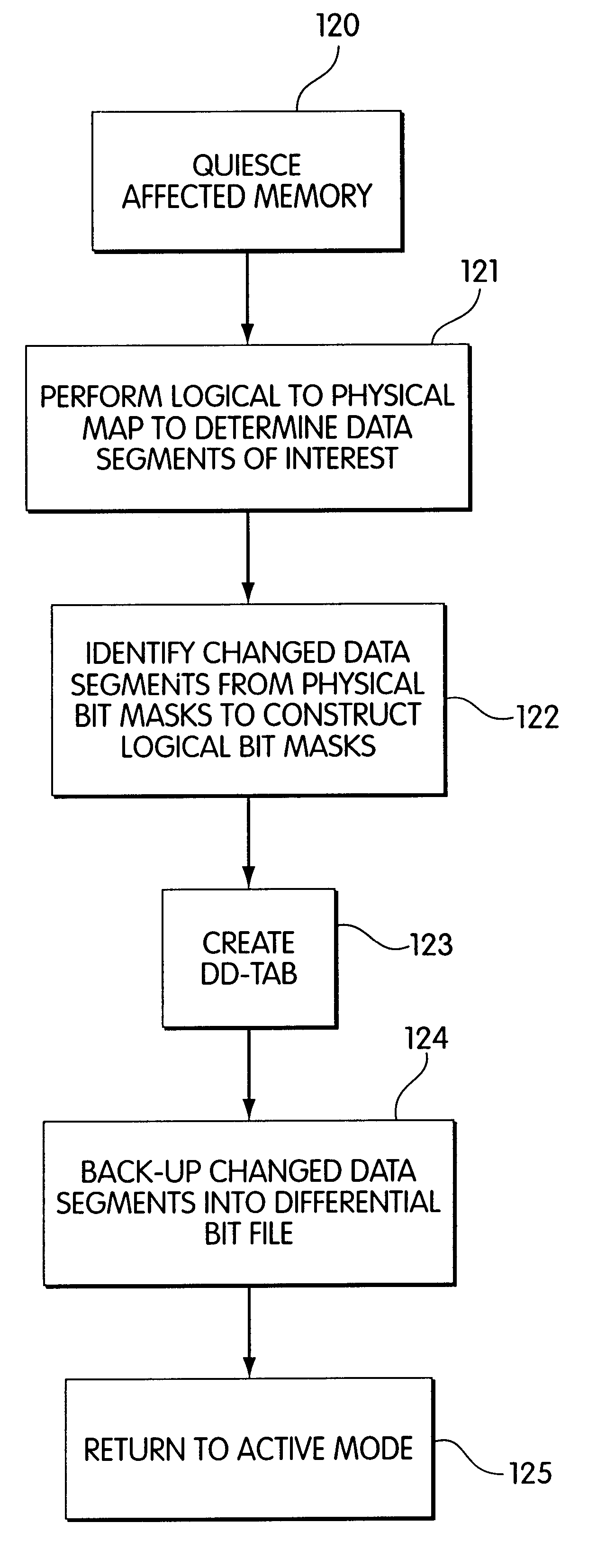
Method and apparatus for differential backup in a computer storage system
InactiveUS6366986B1Memory loss protectionRedundant operation error correctionComputer hardwareComputerized system
Method and apparatus for backup in restoring data on a computer system are disclosed. Backups may include a differential backup. In a differential backup, only some (but not all) segments of data in a primary copy are backed up. The segments may correspond to physical segments of storage in a storage system, rather than logical level segments of storage. The method and apparatus may include constructing a complete copy of a backed up element from an earlier fill backup and a subsequent differential backup.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com