Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
461 results about "Software agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a software agent is a computer program that acts for a user or other program in a relationship of agency, which derives from the Latin agere (to do): an agreement to act on one's behalf. Such "action on behalf of" implies the authority to decide which, if any, action is appropriate. Agents are colloquially known as bots, from robot. They may be embodied, as when execution is paired with a robot body, or as software such as a chatbot executing on a phone (e.g. Siri) or other computing device. Software agents may be autonomous or work together with other agents or people. Software agents interacting with people (e.g. chatbots, human-robot interaction environments) may possess human-like qualities such as natural language understanding and speech, personality or embody humanoid form (see Asimo).
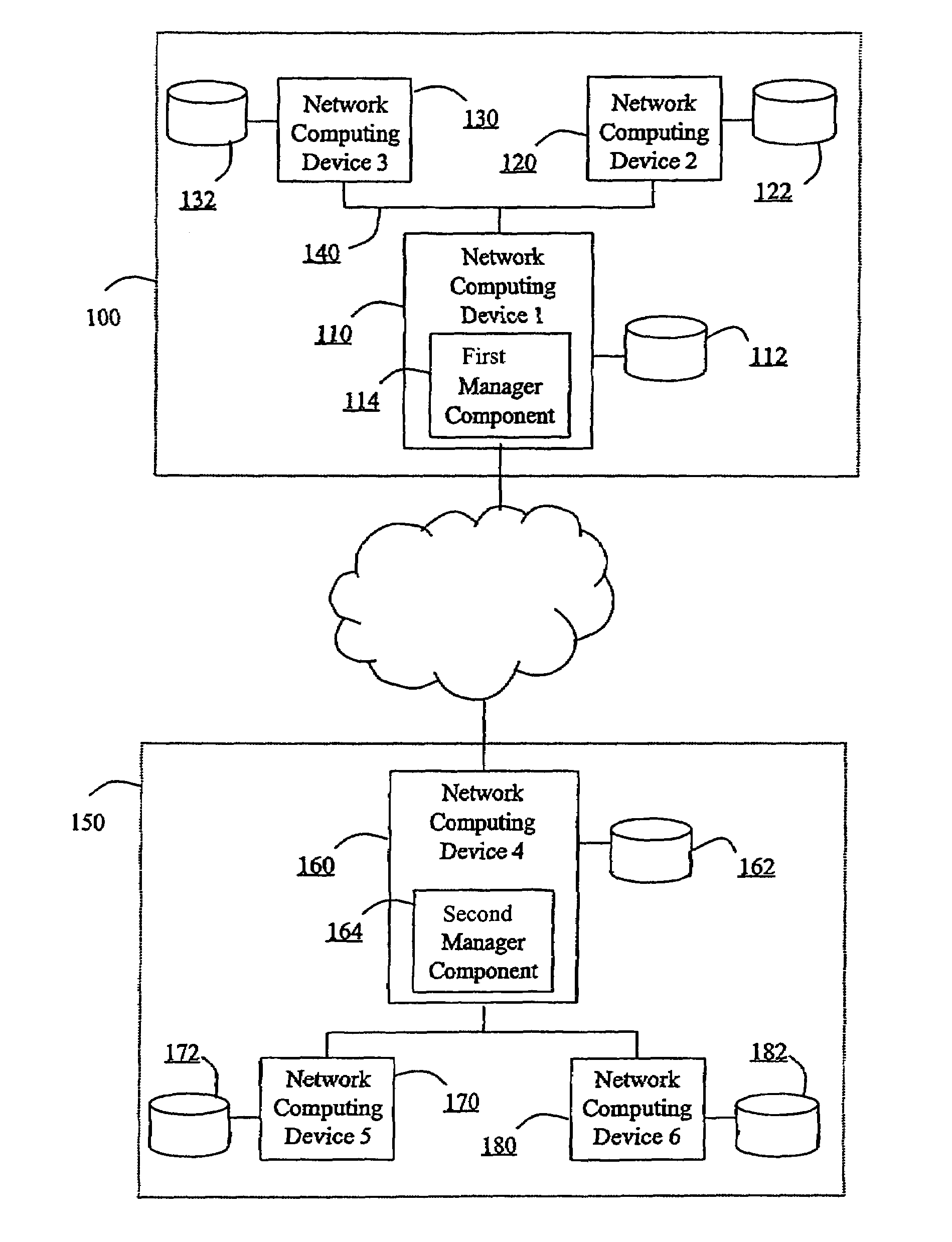
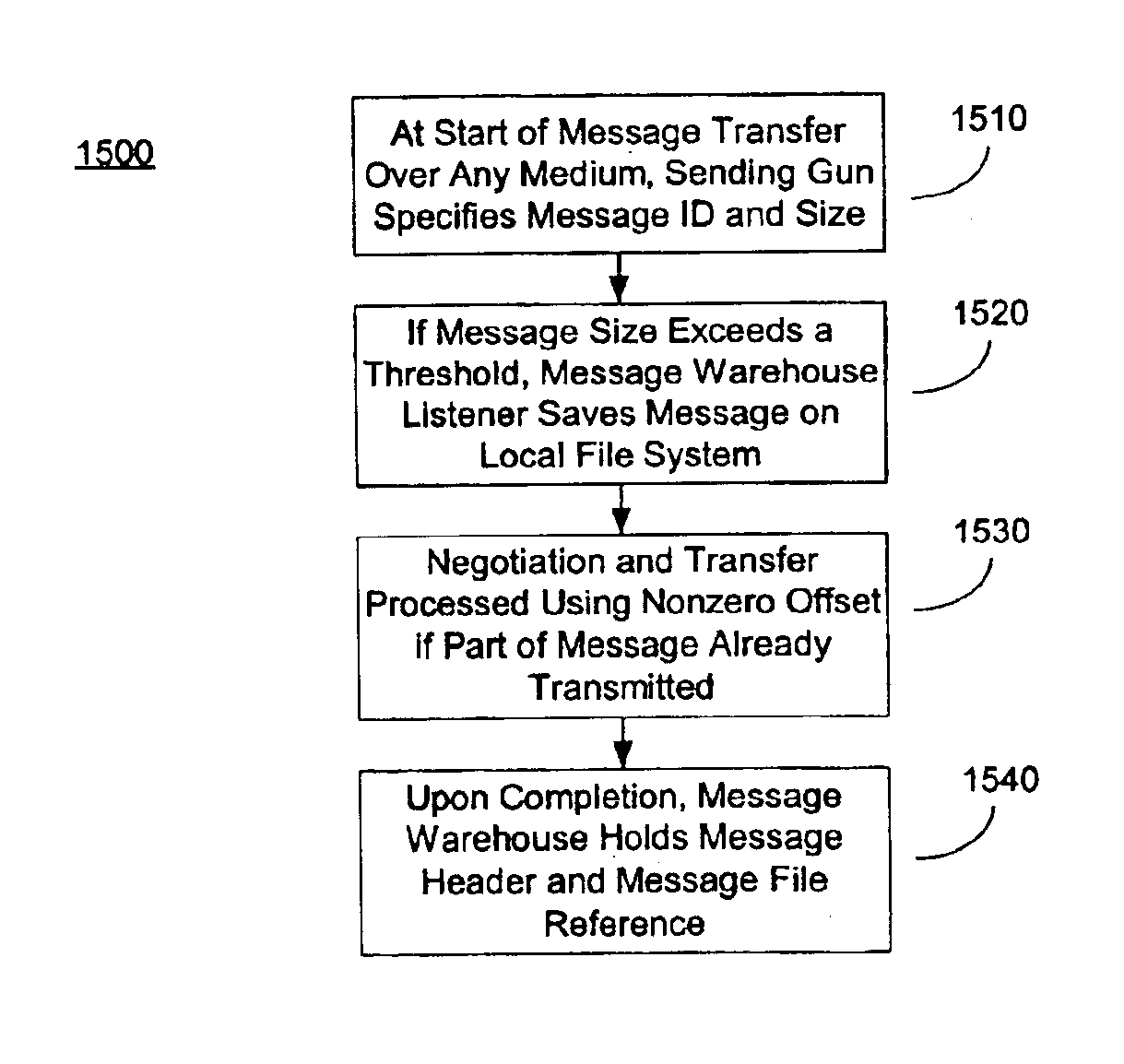
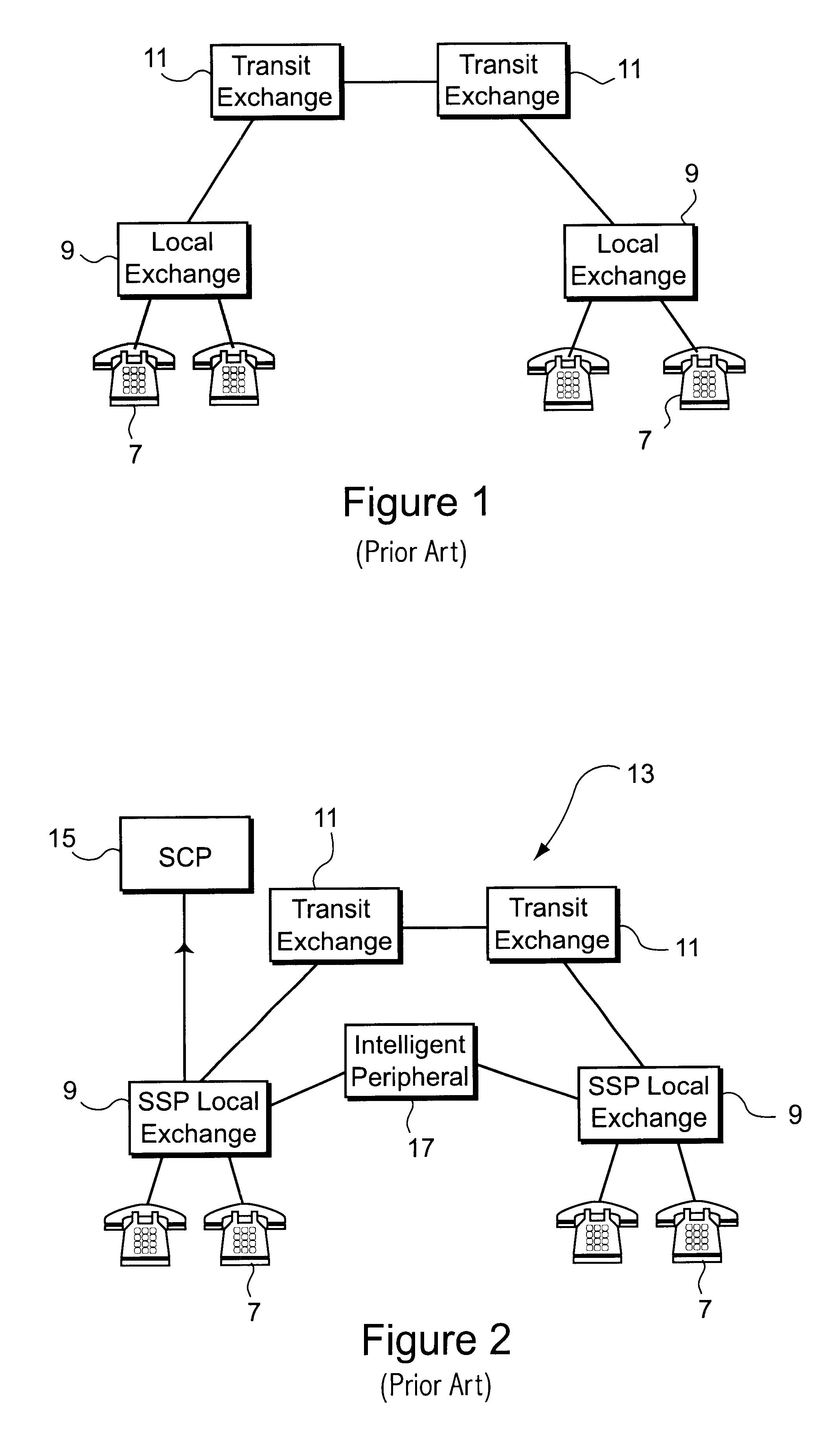
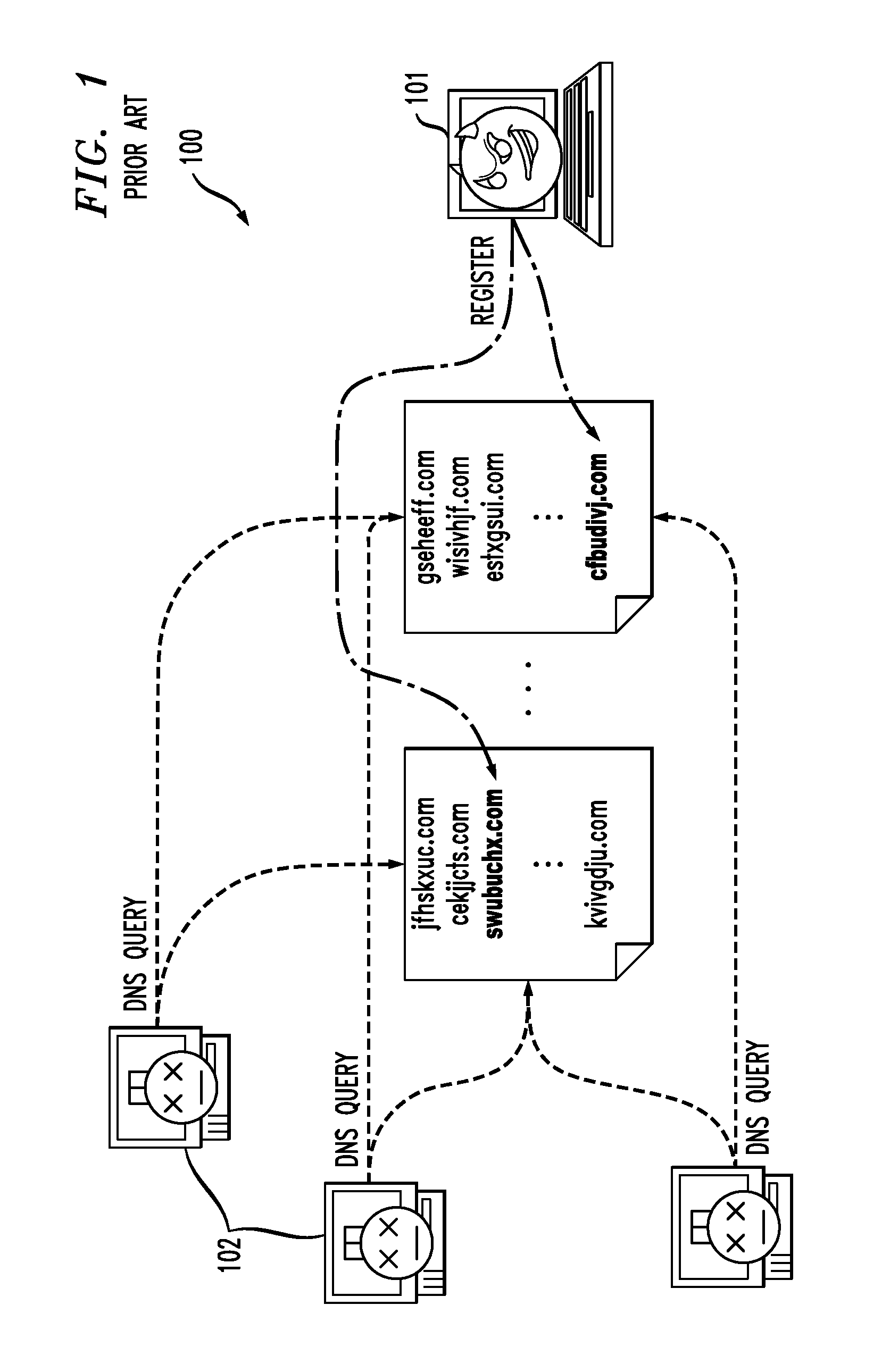
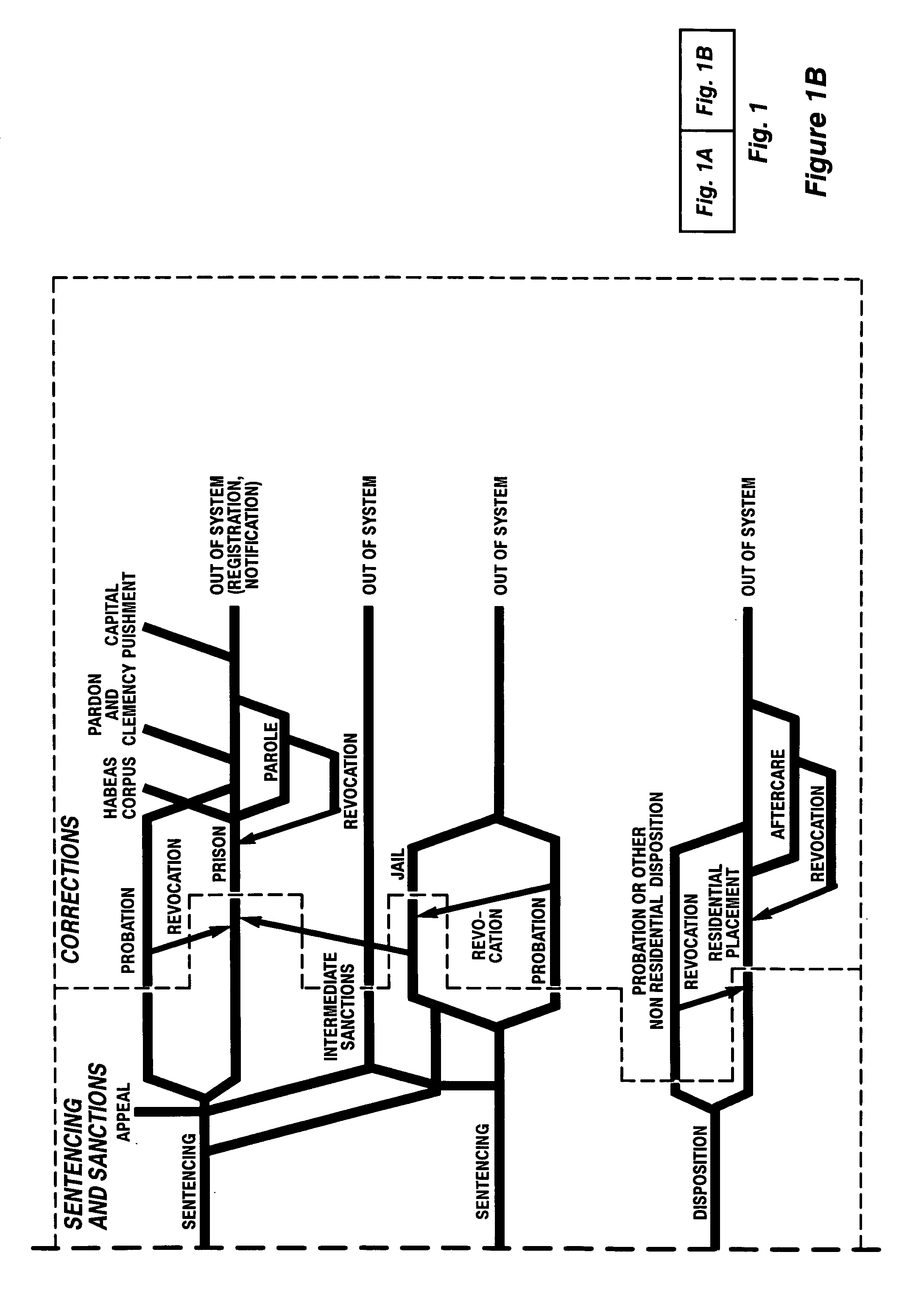
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
System and method for use of mobile policy agents and local services, within a geographically distributed service grid, to provide greater security via local intelligence and life-cycle management for RFlD tagged items
InactiveUS20070112574A1Low costIntegration costMultiple digital computer combinationsProgram controlDistributed servicesRadio frequency
This invention provides a system, method, and software program for providing software intelligence to Radio Frequency Identity (RFID) tags. Utilizing the unique characteristics of the Service Grid, mobile software agents can relocate in close proximity to RFID tagged items. Once associated with the tag, these RFID agents migrate near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history. These RFID agents respond to events as circumstances require. They transport data and policy between supply-chain partners when the partners participate in a secure extranet. Enhanced service grids composed of distributed agents, comprising numerous services, facilitates supply-chain security and integration as virtual software service agents, including virtual RFID tags, are directed from one computer to another computer in response to changing conditions.
Owner:GREENE WILLIAM SPROTT
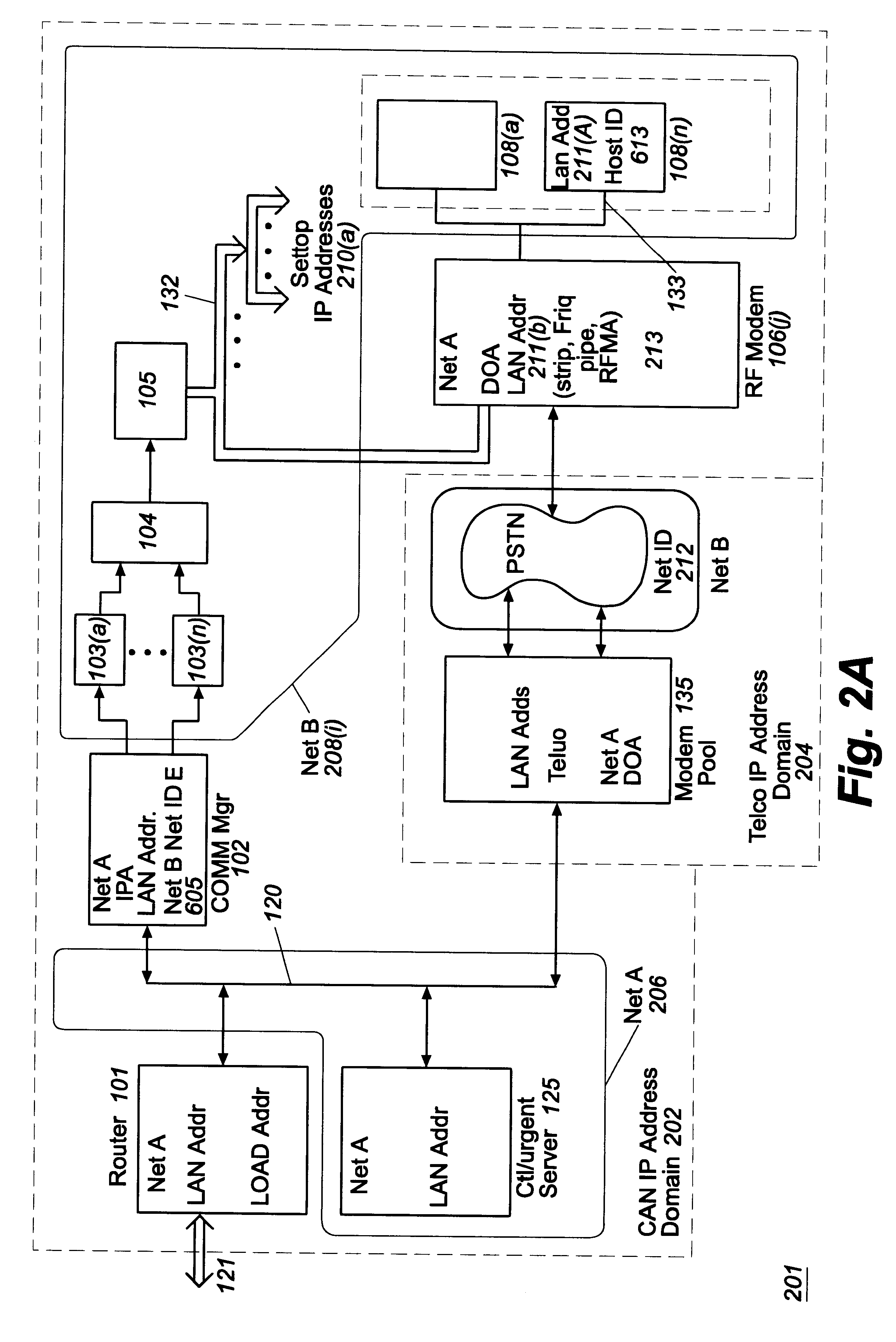
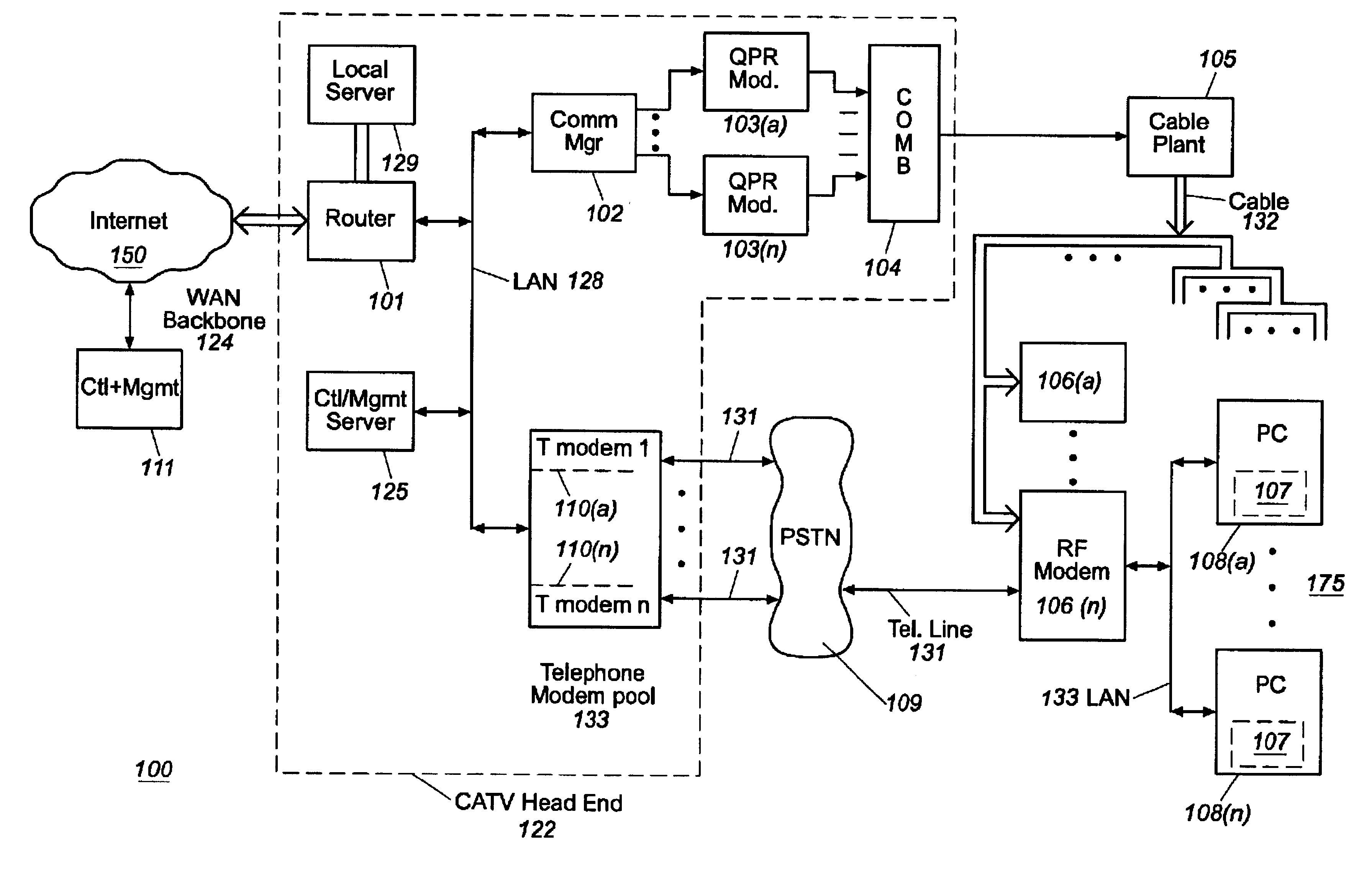
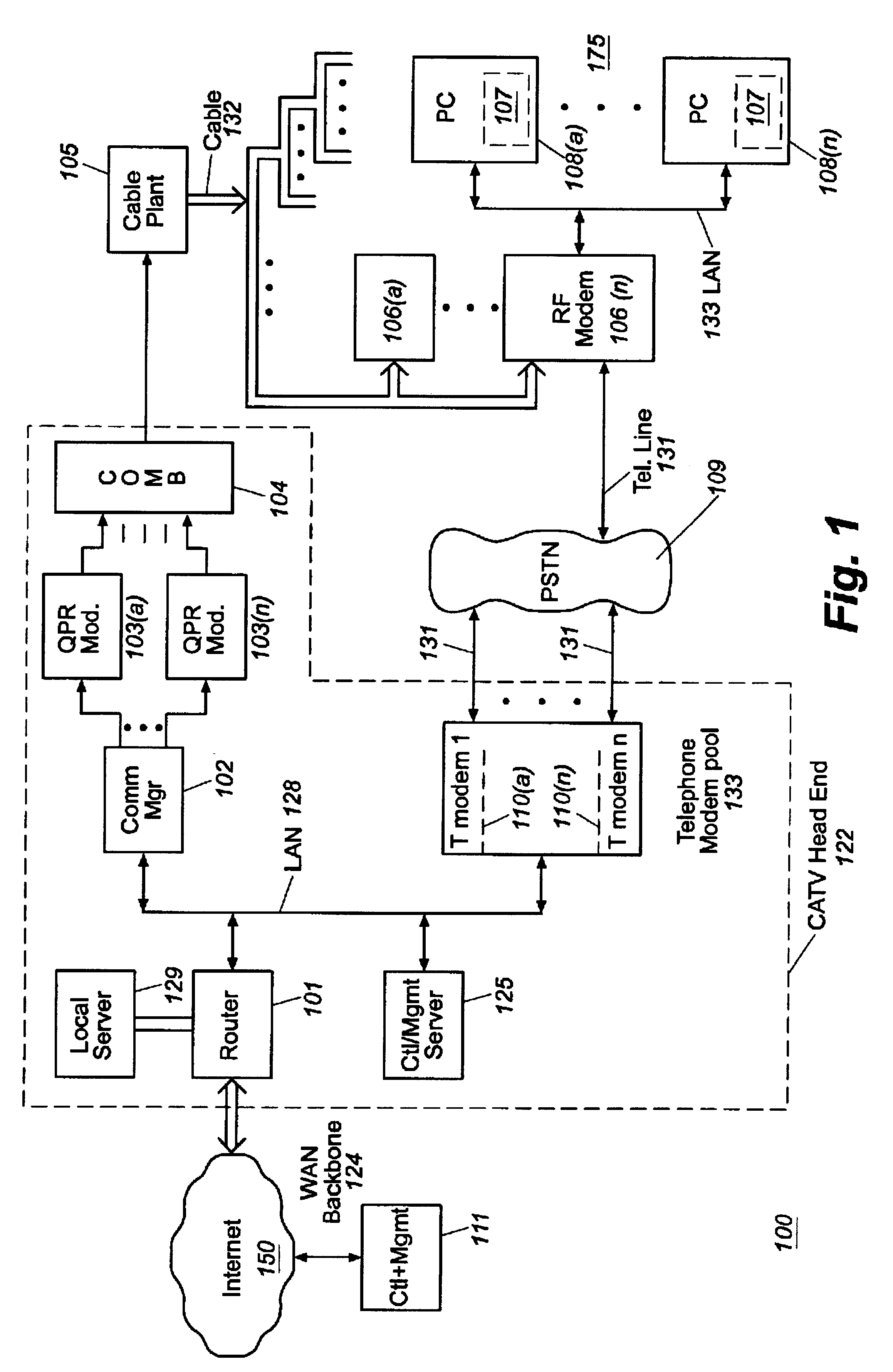
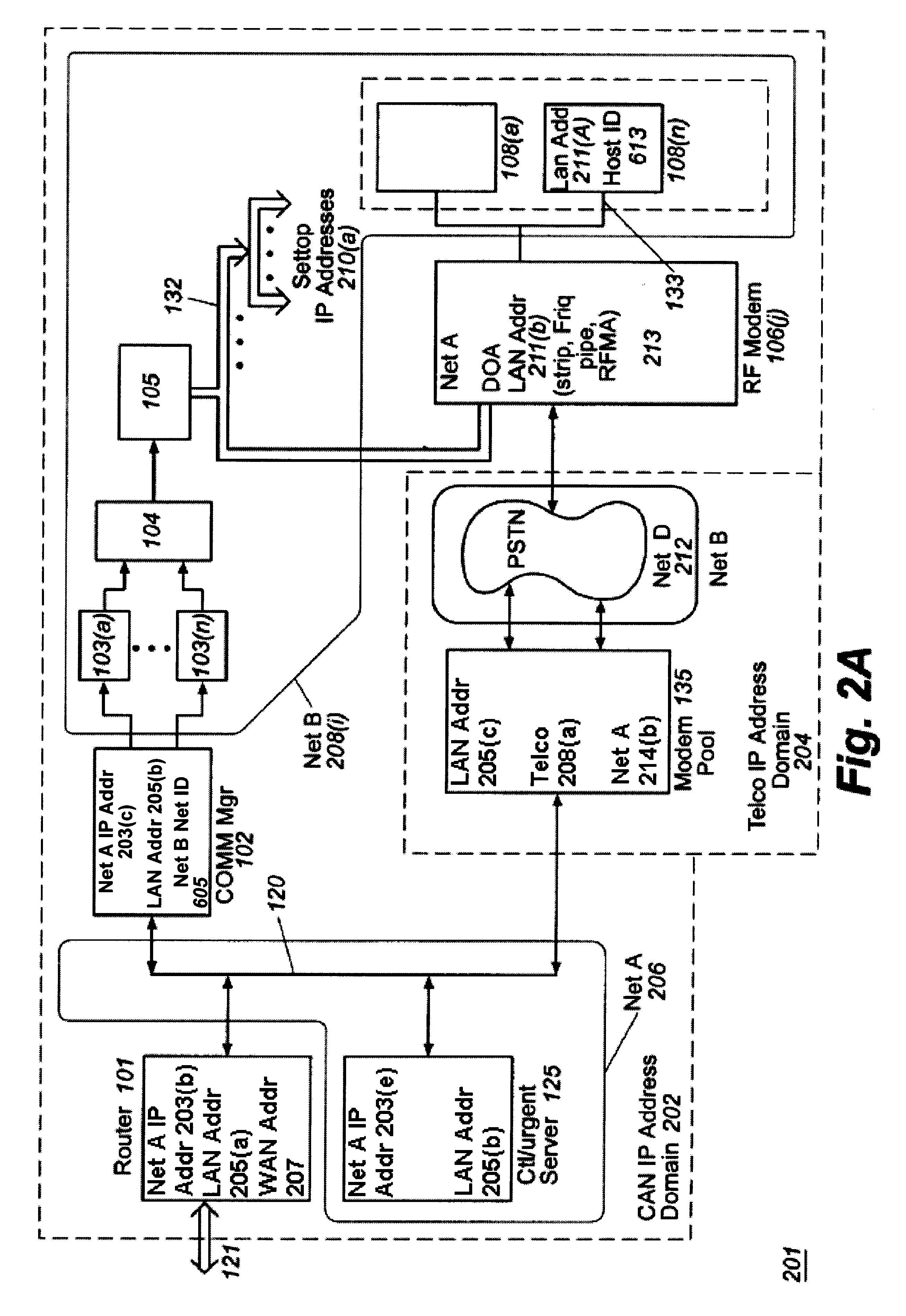
Cable modem map display for network management of a cable data delivery system
InactiveUS6272150B1Broadband local area networksBroadcast-related systemsTransport systemModem device
Apparatus for recording and collecting the installed location of cable modems in a cable data network comprises a network manager for maintaining and collecting cable modem location information. Components of the network manager maintains a software agent that manages a database of modem installation and status information. Responsive to a manager request, the component software agent provides the installation and status information to the network manager. The information is displayed as a map which can show the topology of the cable modem's location in the network with respect to other modems and other components of the network.
Owner:CISCO TECH INC
Method for Voice Activation of a Software Agent from Standby Mode
InactiveUS20140214429A1Save energyPower managementDigital data processing detailsDialog systemBiological activation
A method for voice activation of a software agent from a standby mode. In one embodiment, an audio recording (2) is buffered in an audio buffer (6) and at the same time, the audio recording is input to a secondary voice recognition process (7) which is economical in terms of energy and has an increased false positive rate. When a keyword is recognized, a primary voice recognition process (8) is activated from an inactive state, which converts the audio buffer to text and inputs it to a dialog system (9) which analyzes as to whether there is a relevant question made by the user. If this is the case, the user gets an acoustic reply (3), and if this is not the case, the dialog system and the primary voice recognition process immediately return to the inactive state and transfer the control to the secondary voice recognition process.
Owner:INODYN NEWMEDIA
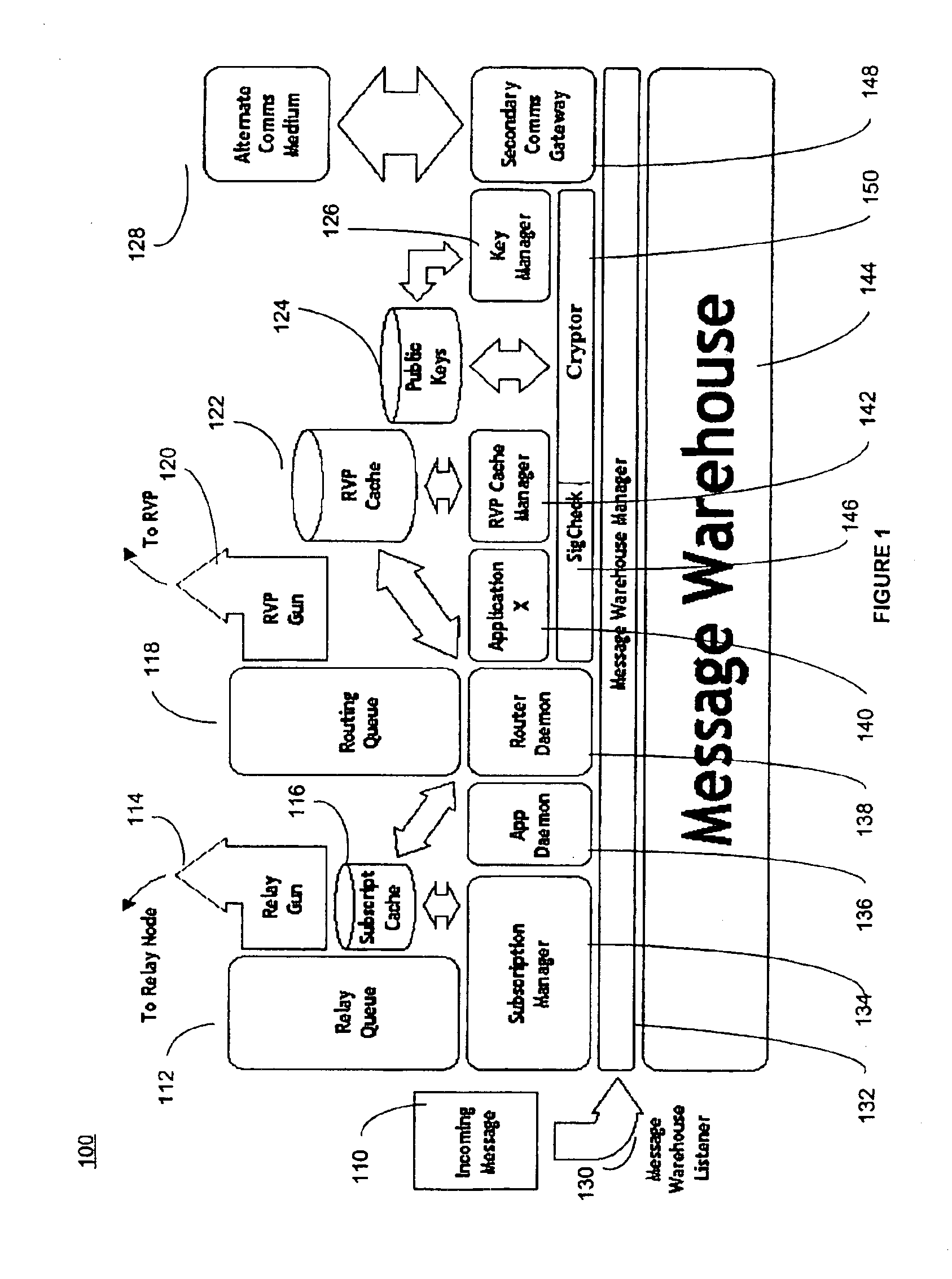
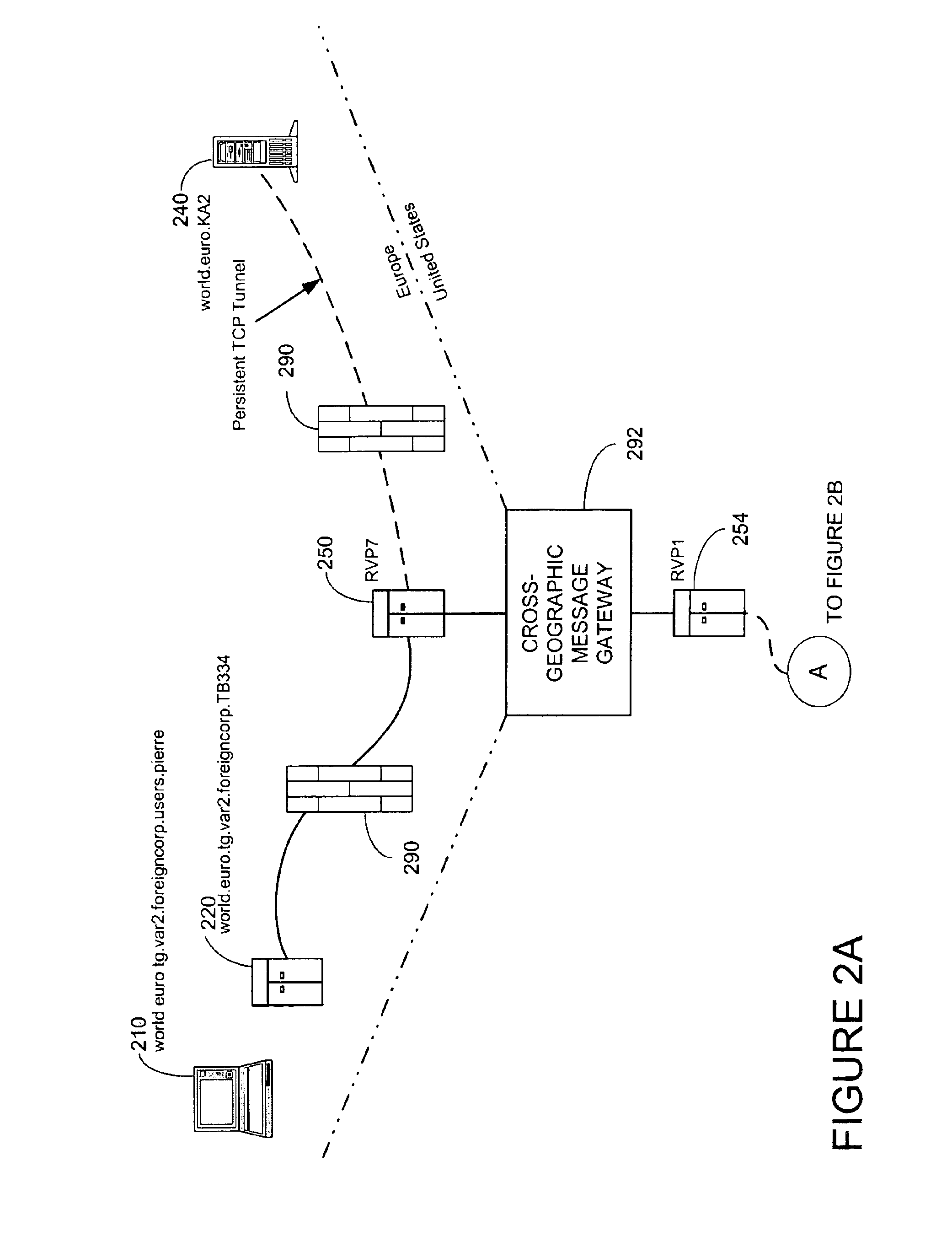
System and method for secure message-oriented network communications
InactiveUS6959393B2Minimize threatFacilitate and control accessKey distribution for secure communicationDigital data processing detailsSecurity MeasureNetwork communication
The present invention provides a message-oriented middleware solution for securely transmitting messages and files across public networks unencumbered by intervening network barriers implemented as security measures. It also provides a dynamic, dedicated, application level VPN solution that is facilitated by the message-oriented middleware. Standard encryption algorithms are used to minimize the threat of eavesdropping and an Open-Pull Protocol (OPP) that allows target nodes to pull and verify the credentials of requestors prior to the passing of any data. Messaging can be segregated into multiple and distinct missions that all share the same nodes. The security network's architecture is built to resist and automatically recover from poor, slow, and degrading communications channels. Peers are identifiable by hardware appliance, software agent, and personally identifiable sessions. The security network provides a dynamic, private transport for sensitive data over existing non-secure networks without the overhead and limited security associated with traditional VPN solutions.
Owner:THREATGUARD
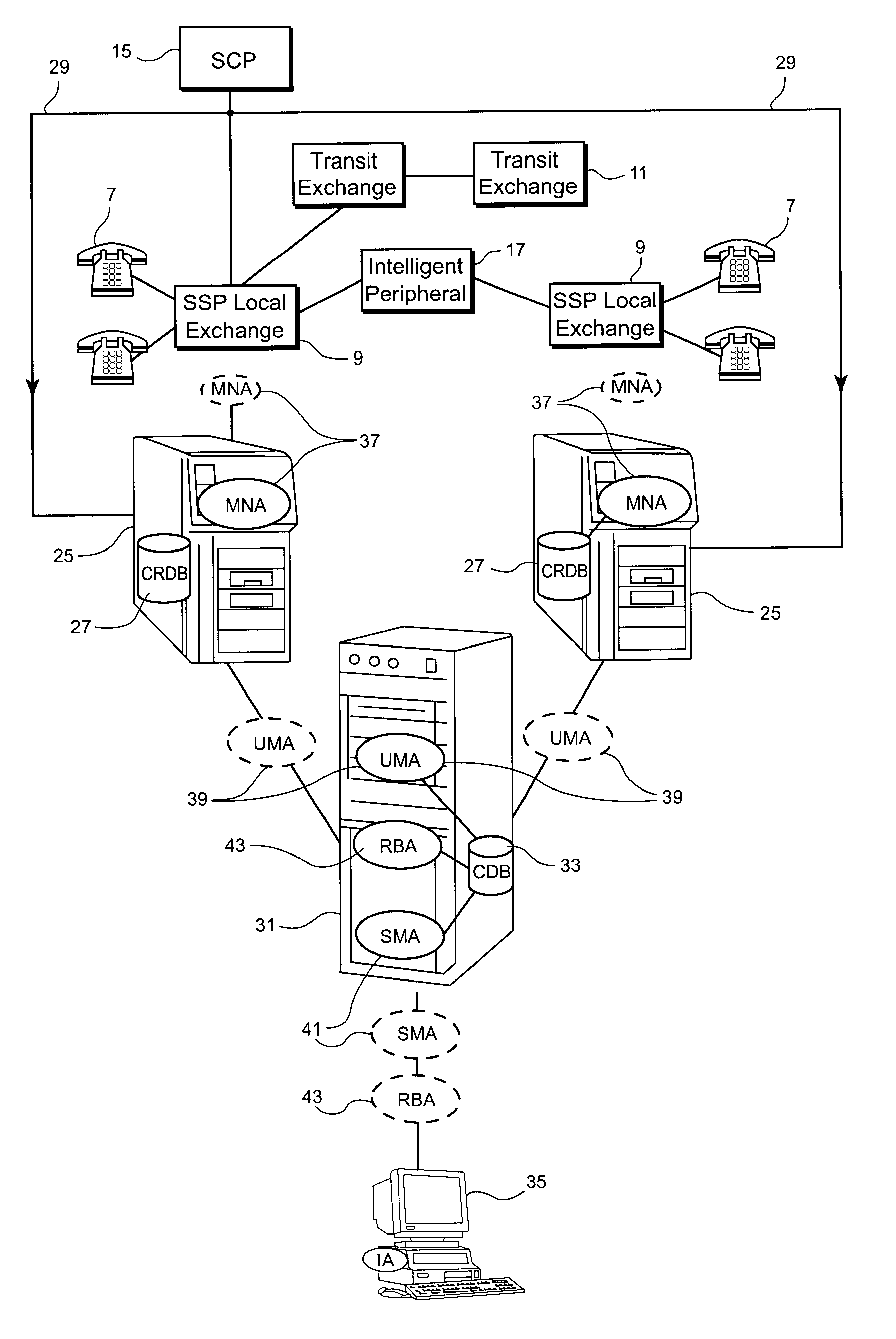
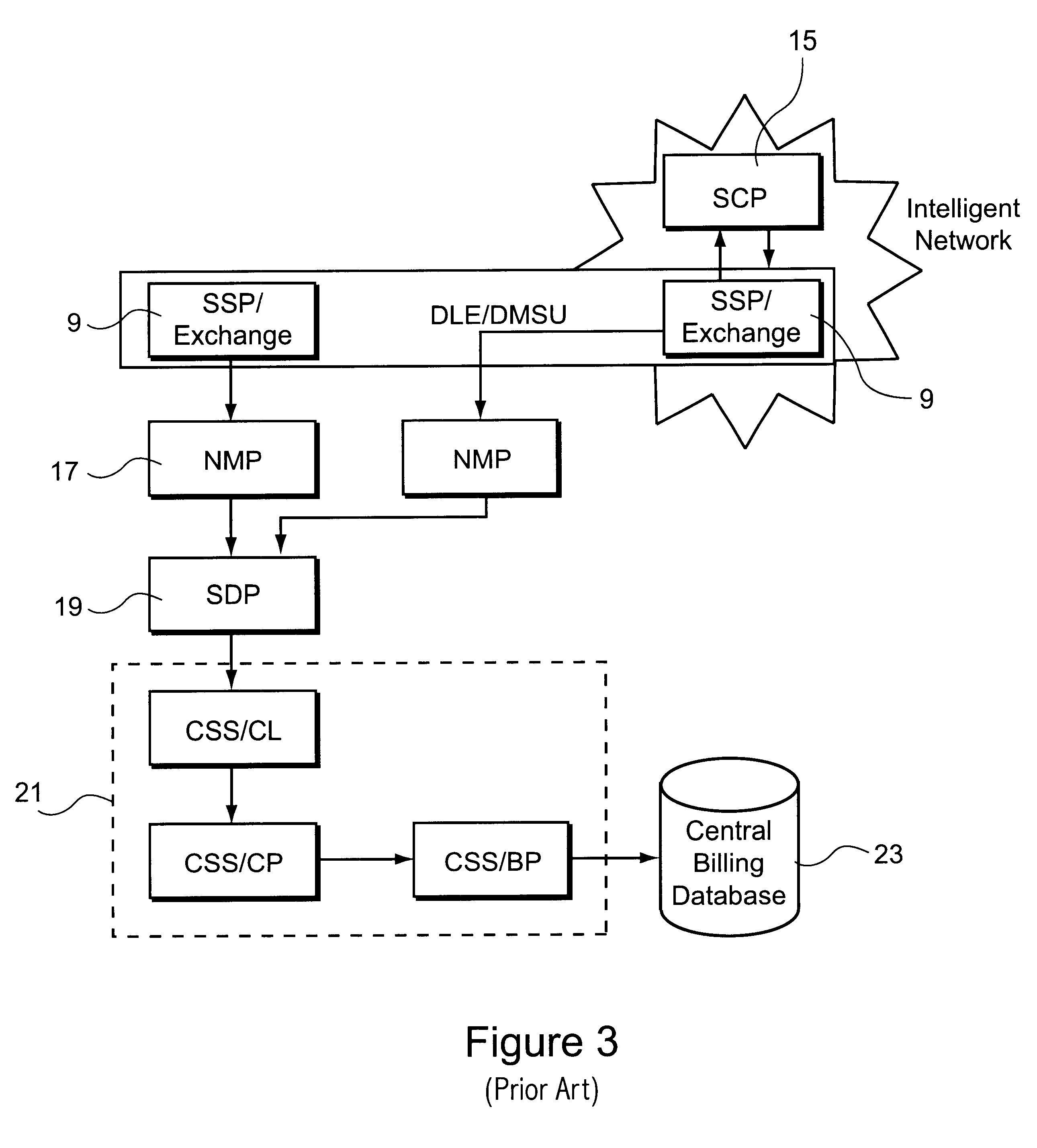
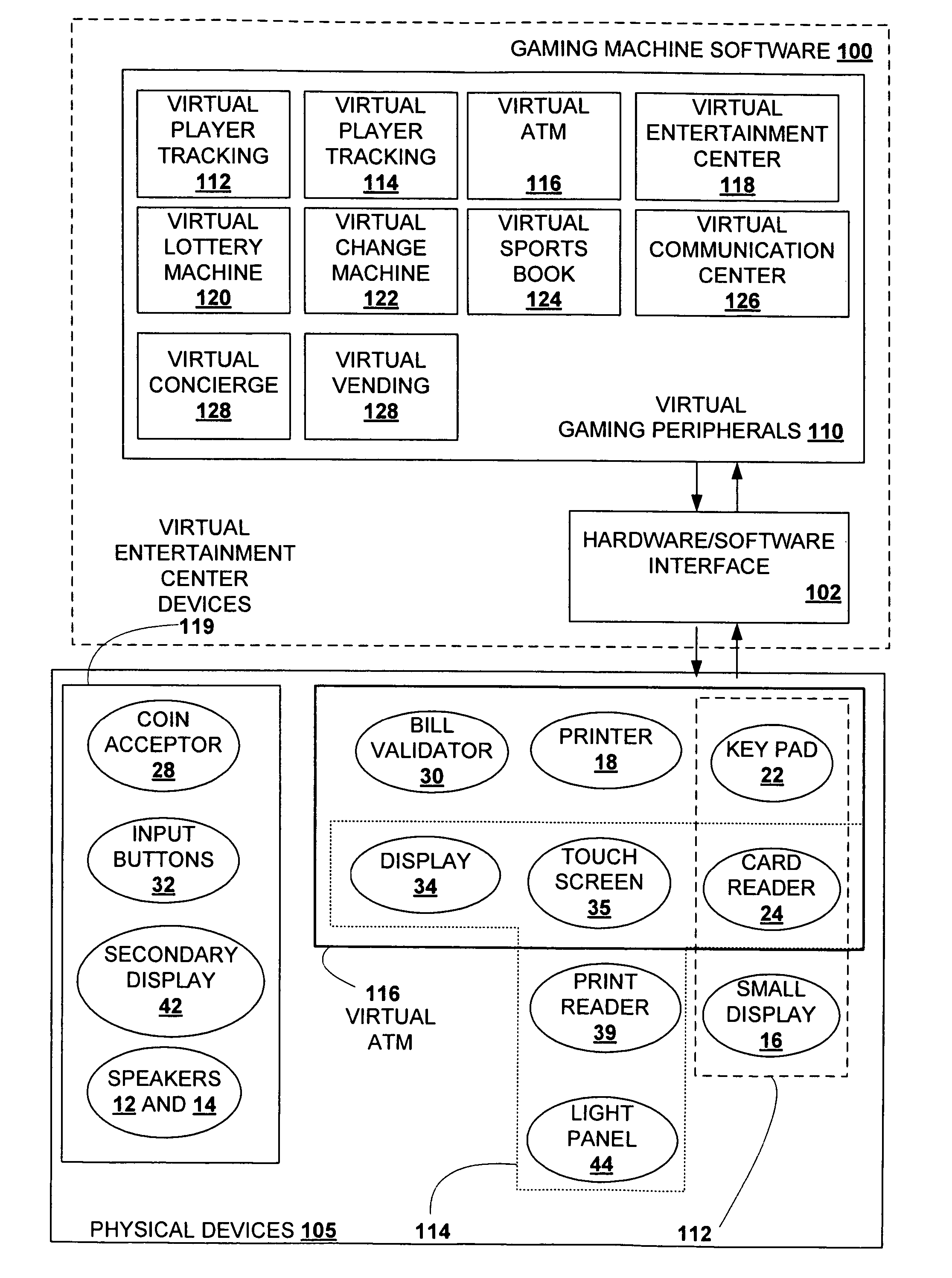
Billing system
A billing system for a telecommunications network uses a monitoring software agent to monitor messages, indicative of individual calls on the network, passing between a service switching point and a service control point. Call record information is extracted and is stored in a local call record database. Information from each call record database is then passed on to a central database, using updating mobile agents, the central database being accessible to such agents and report building agents which can extract billing information as requested by an operator. By monitoring the messages as they pass, the system can provide real time billing information without needing to poll the switch at the service switching point.
Owner:BRITISH TELECOMM PLC
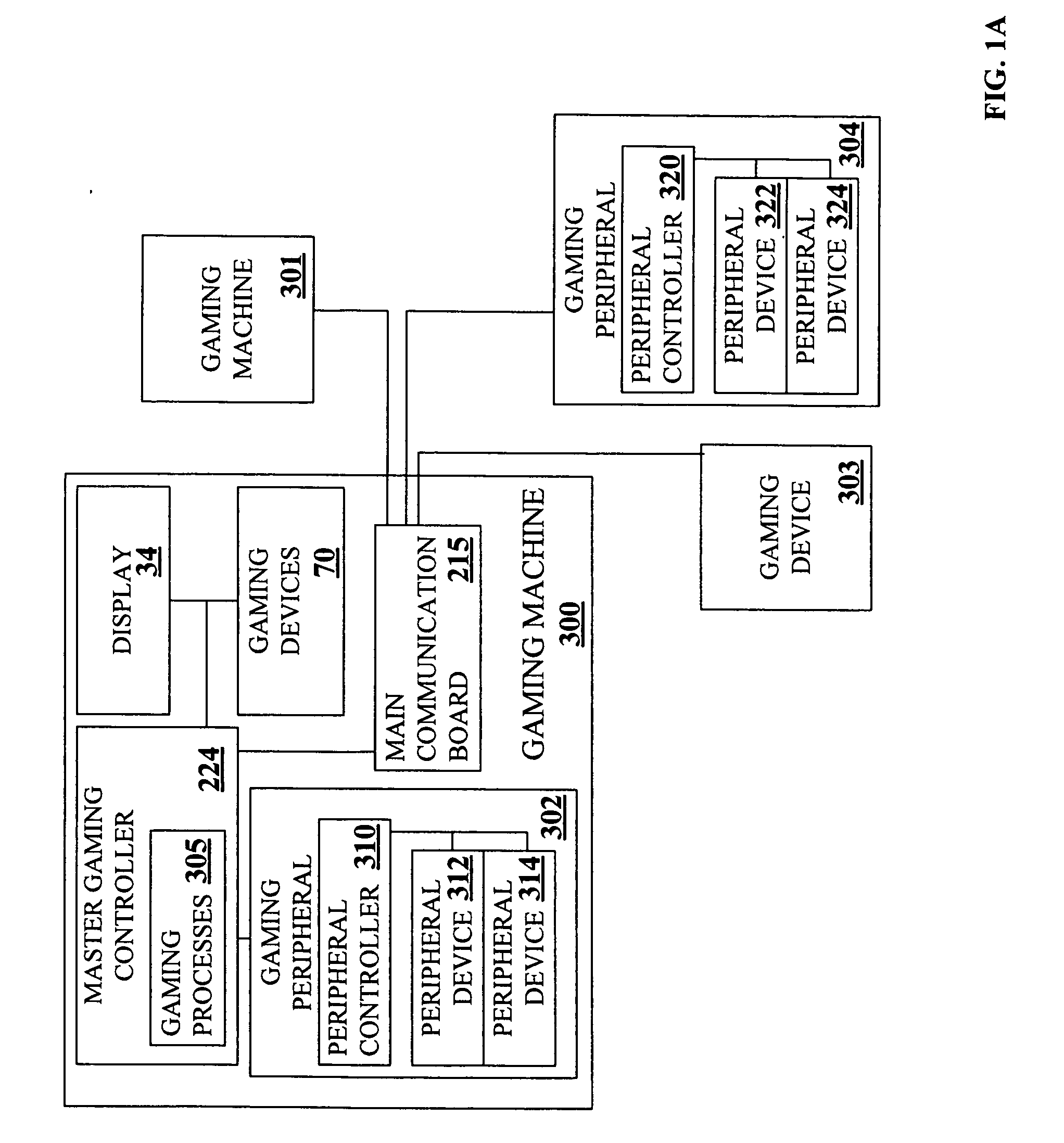
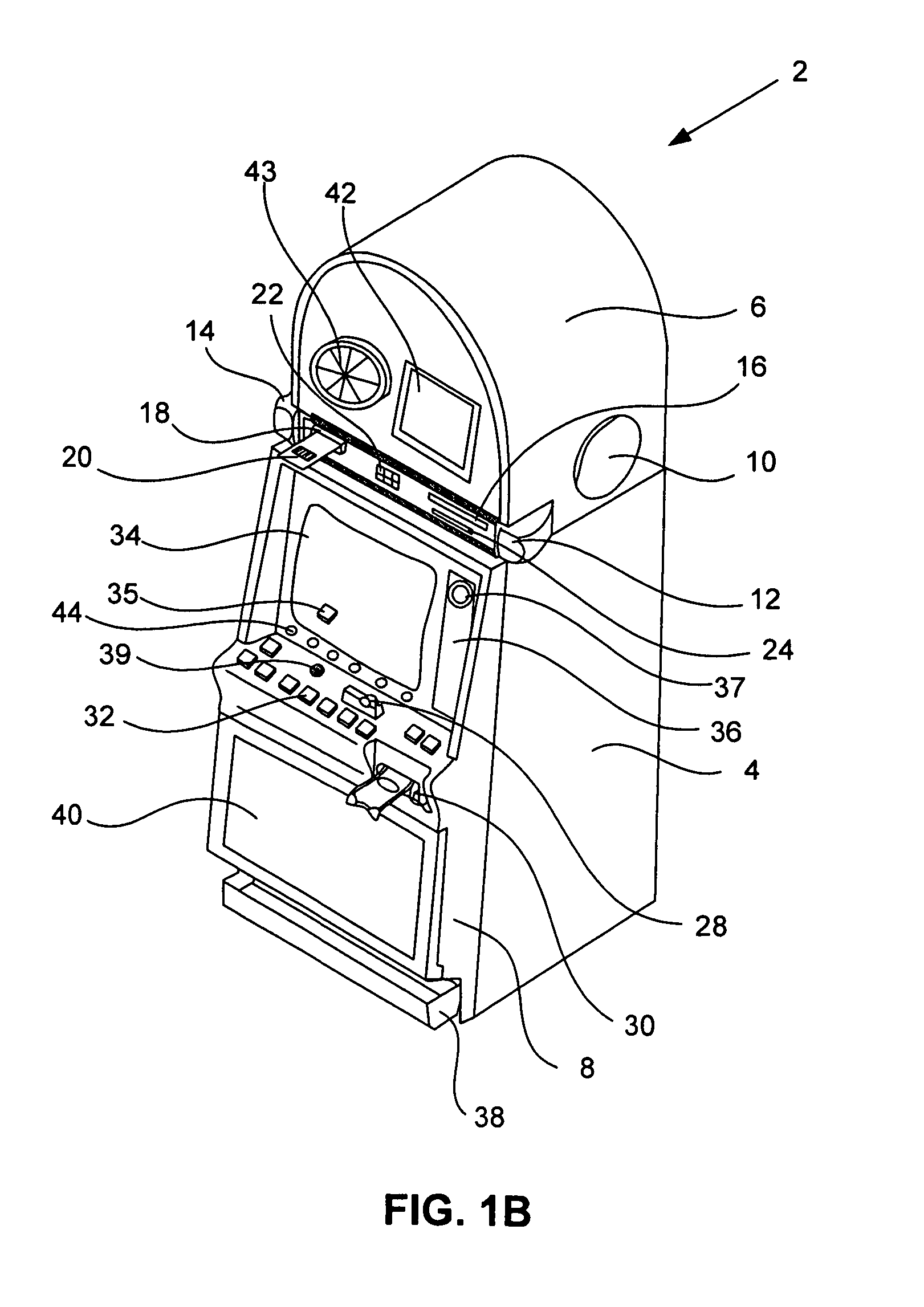
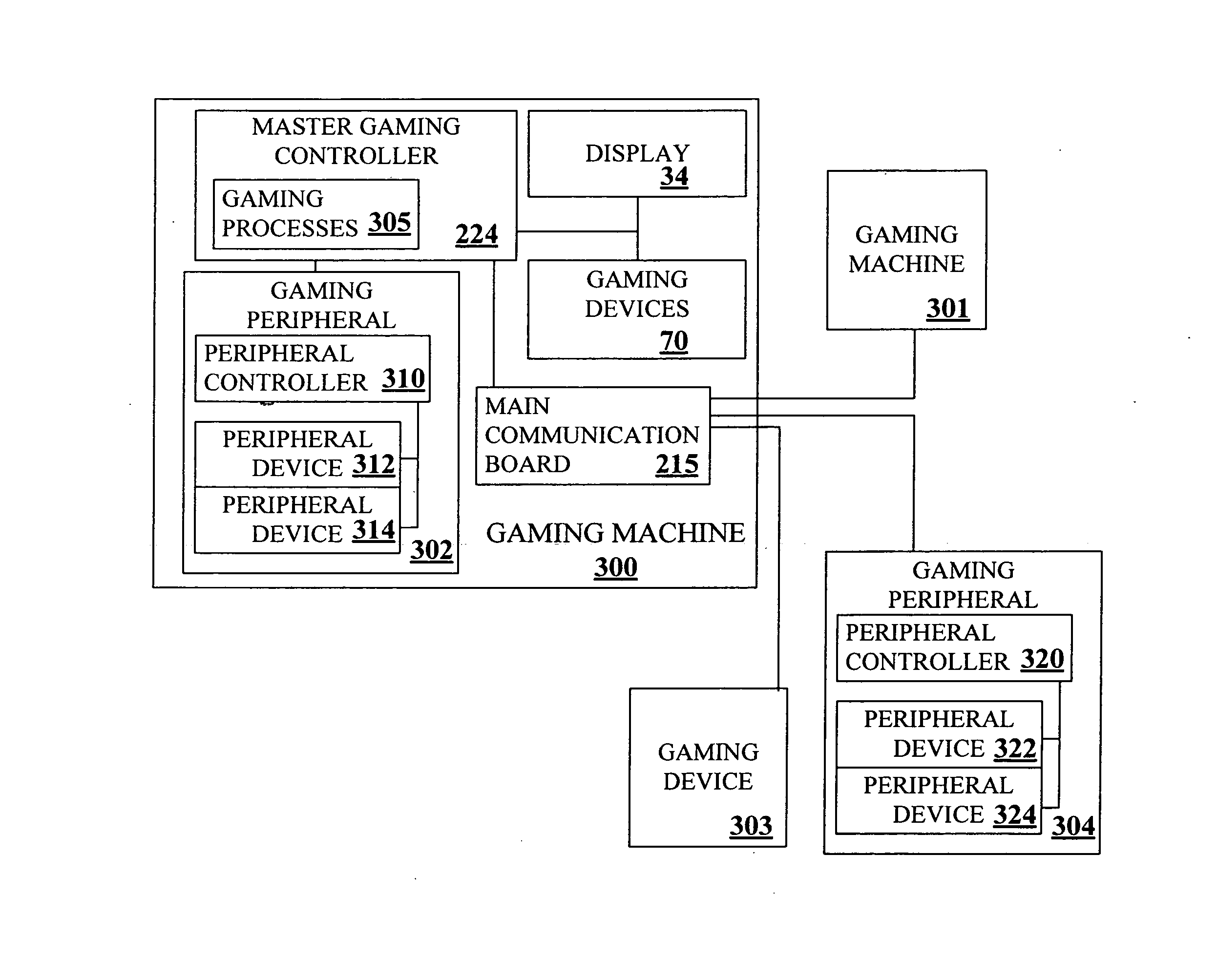
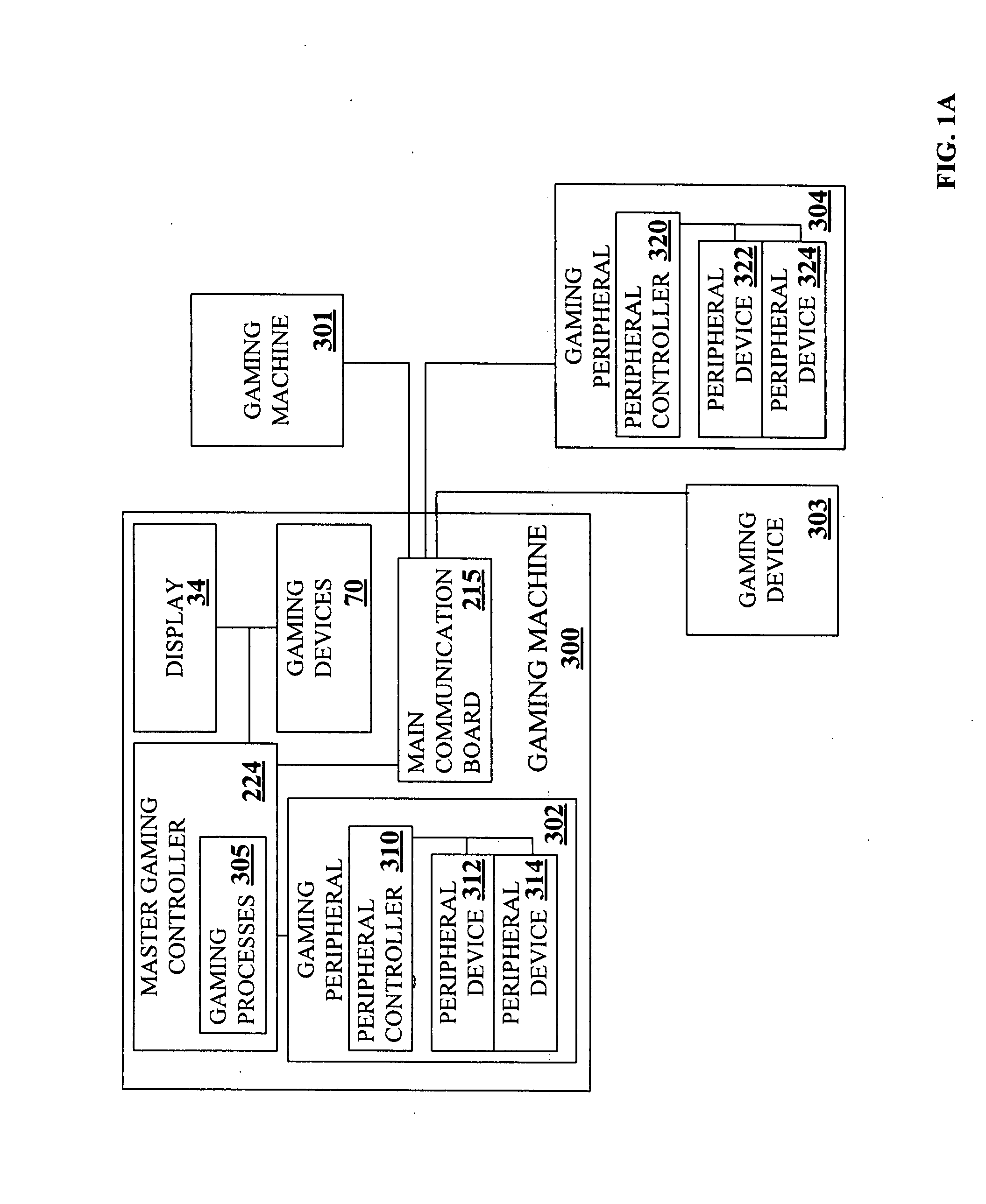
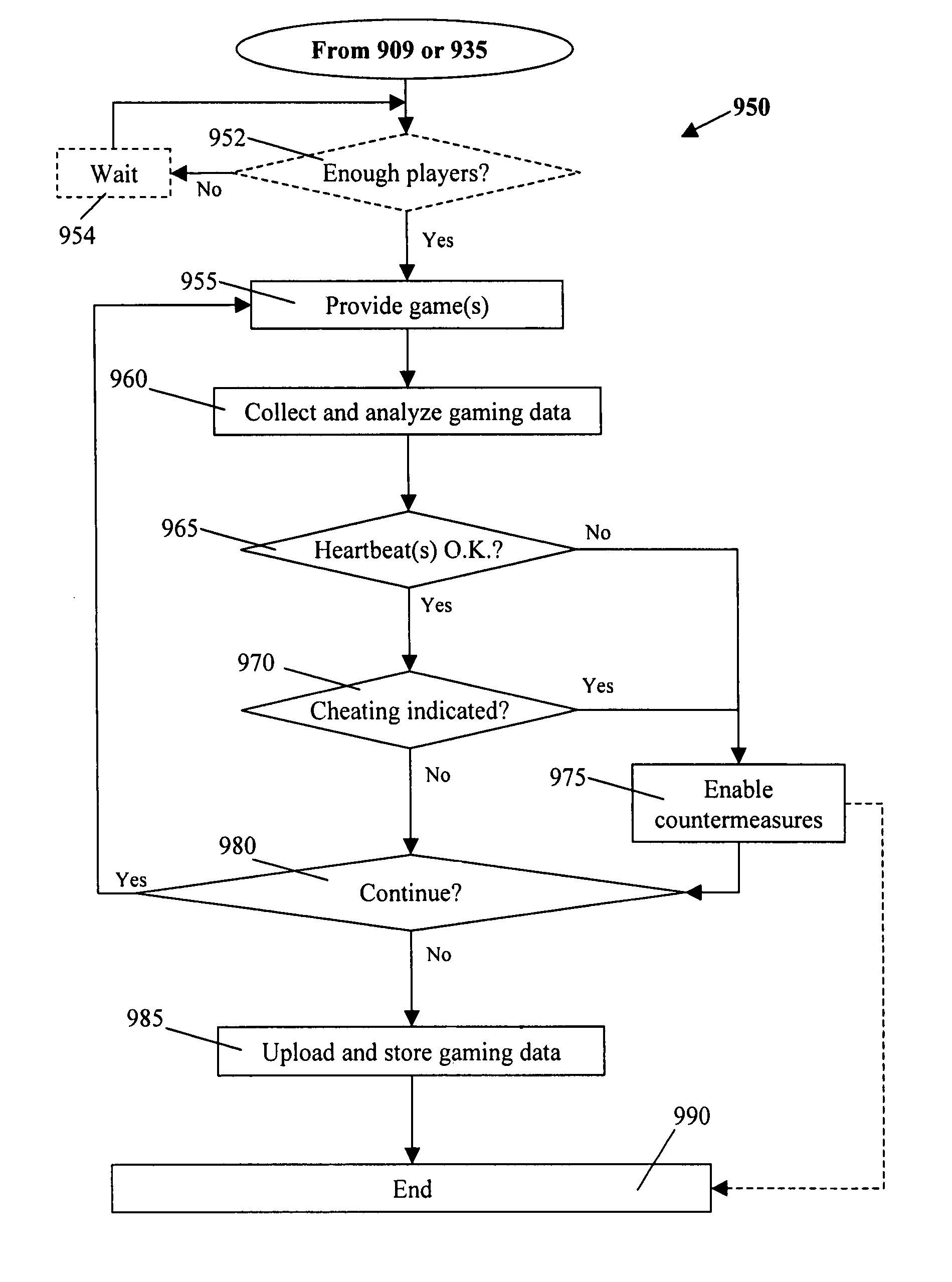
Virtual player tracking and related services
ActiveUS20060281541A1Apparatus for meter-controlled dispensingVideo gamesOperational systemSoftware agent
Various gaming-related services are provided, including but not limited to security services, harm minimization services, player identification services, bonusing / progressive services, accounting services, financial / banking services, network tunneling services, cheating detection services, etc. Such services may be provided, at least in part, by software agents that can be configured for different platforms and / or operating systems. Some software-based player tracking methods of the invention can aggregate data from multiple devices used by a player for gaming.
Owner:IGT
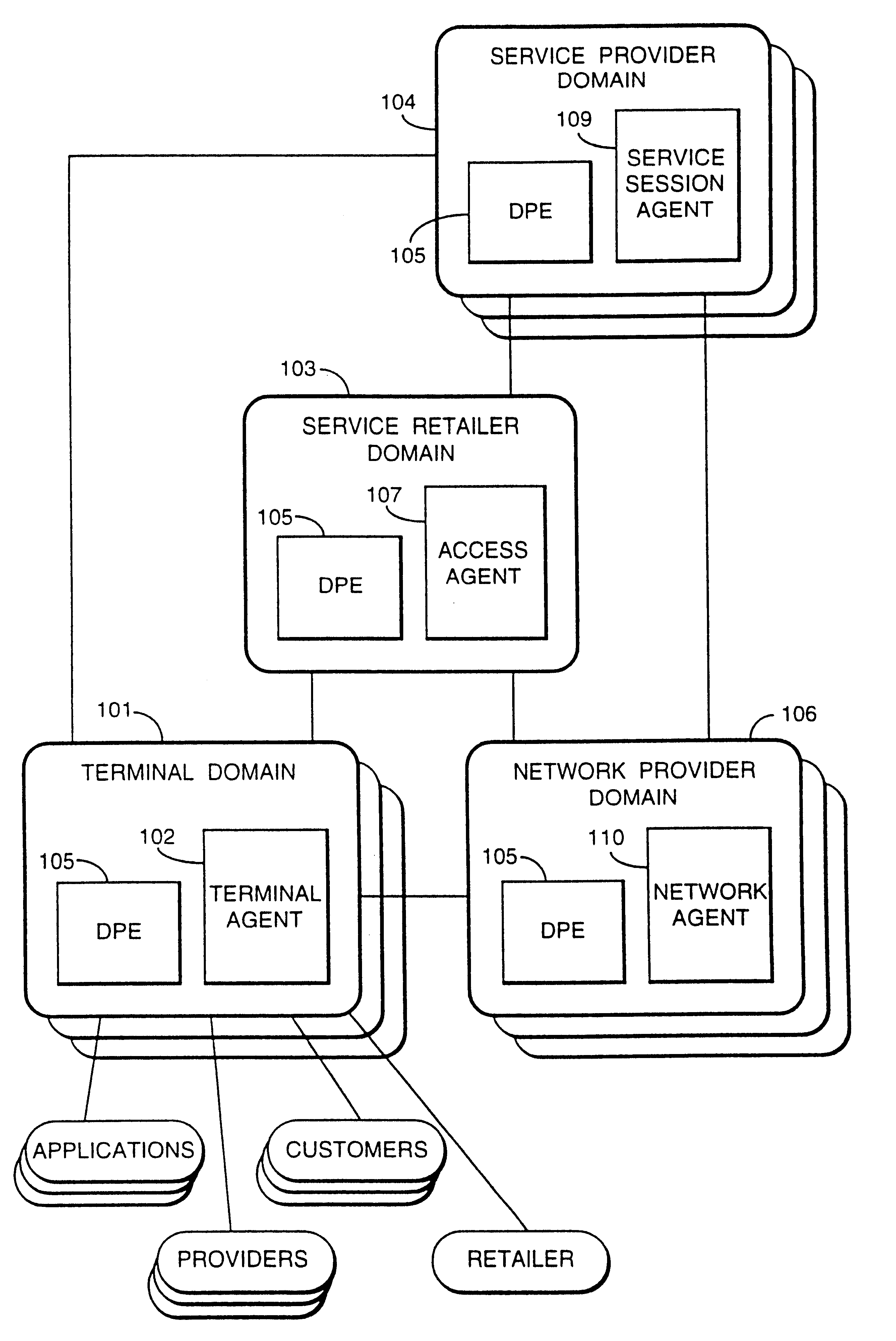
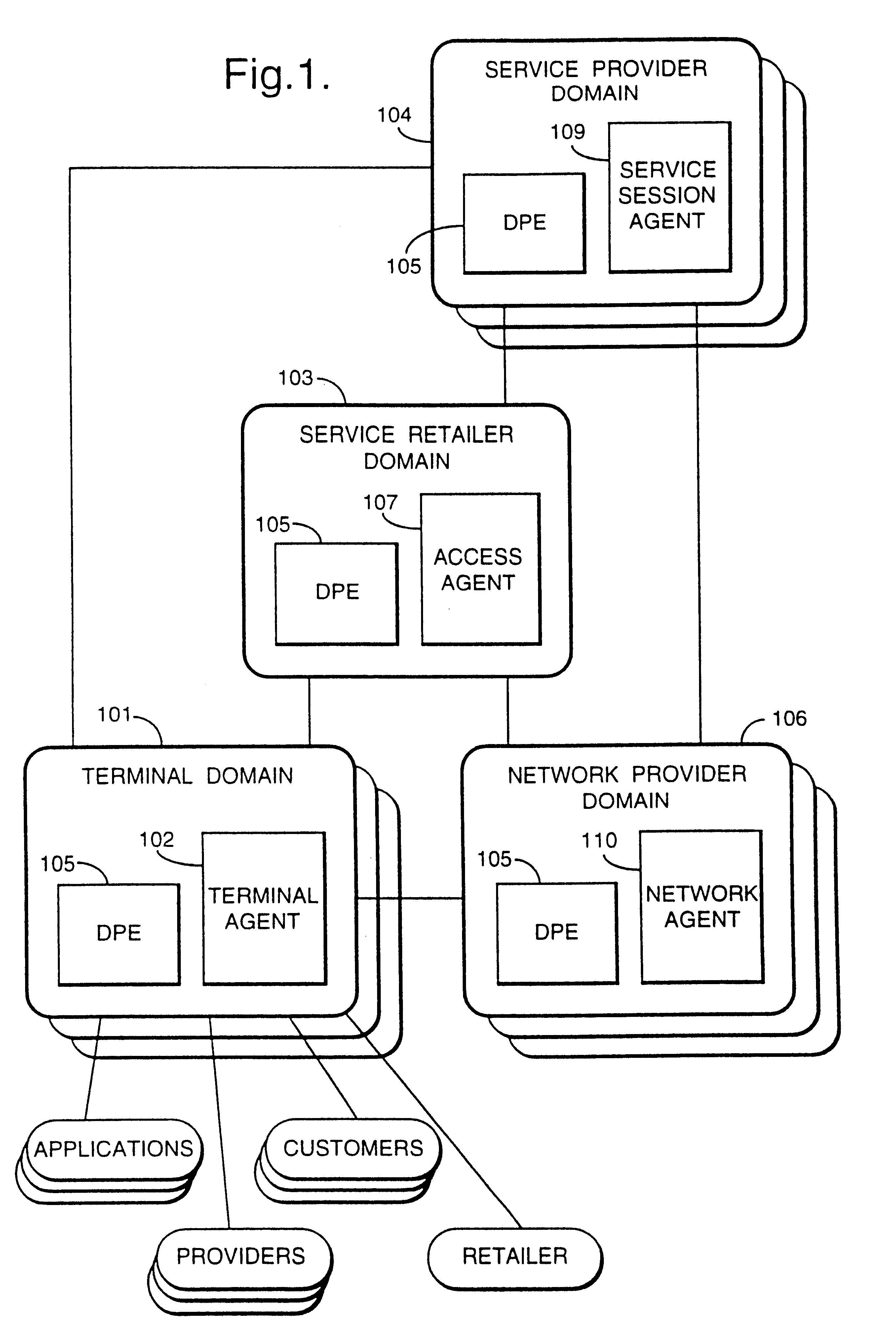
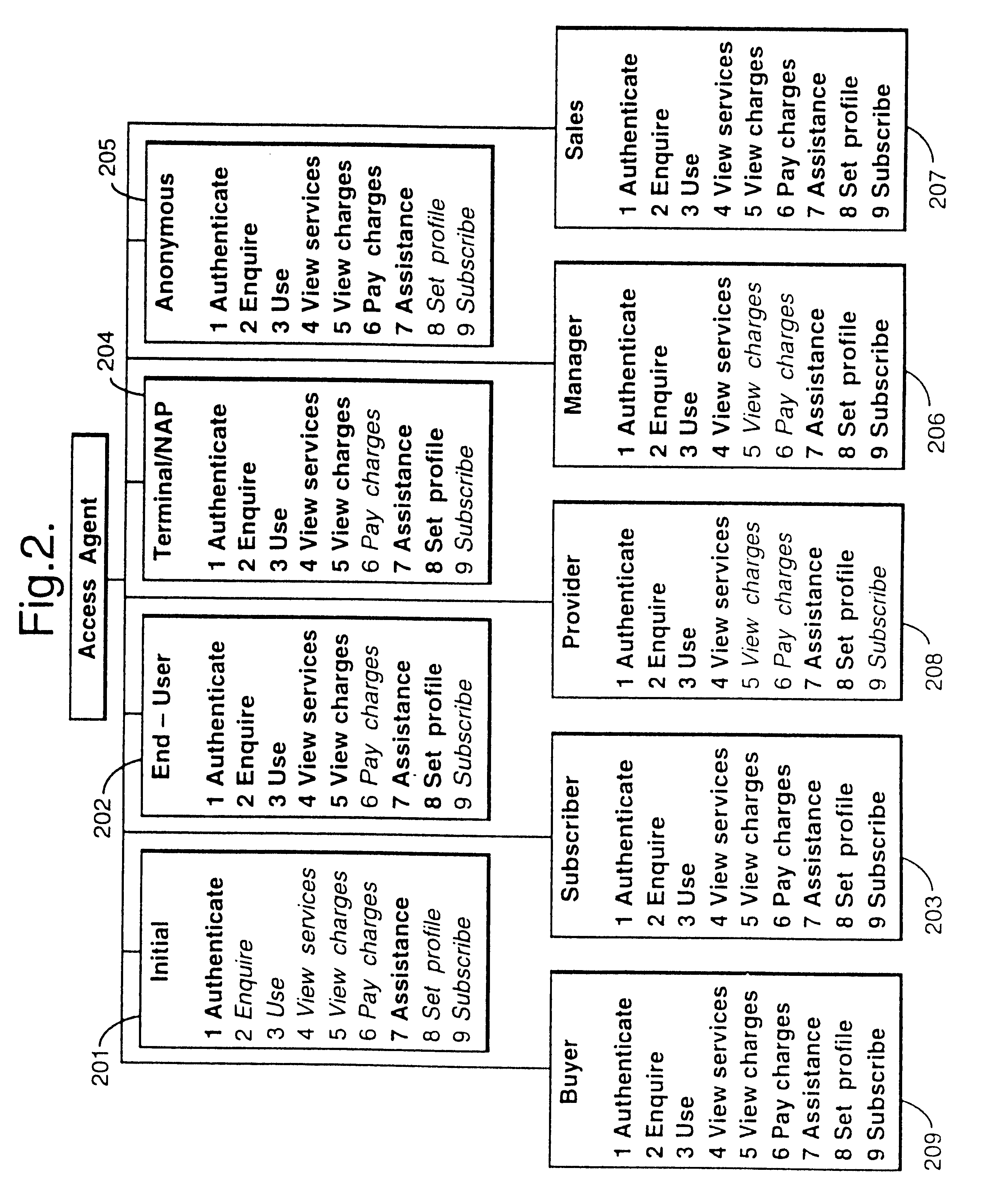
Reconfigurable service provision via a communication network
InactiveUS6330586B1Customer base for information services is particularly wideLarge capacityMultiplex system selection arrangementsData processing applicationsReconfigurabilityReusable software
A services provision system provides information services over one or more communications networks and has a software infrastructure divided into domains. Each domain has an intelligent software agent and this community of agents sits in a computing environment represented in each domain by a DPE kernel. The community of agents co-operates to provide service and service management functionality to a user. At least one of the agents is reconfigurable to change the functionality the system makes available. Reconfigurability is based on the use of a plurality of reusable software modules, the agent reconfiguring by selecting a new combination of modules. The software modules themselves incorporate rules, or policies, which determine process steps offered by the modules at run-time. These policies are external to the modules and may be loaded at run-time, allowing dynamic modification to functionality of the system. The system as a whole offers functionality associated with using services, providing them and managing them and the reconfigurability allows it to offer the different types of functionality in an efficient way. It also allows access control to functionality at different levels with particularly good security against fraudulent use.
Owner:BRITISH TELECOMM PLC
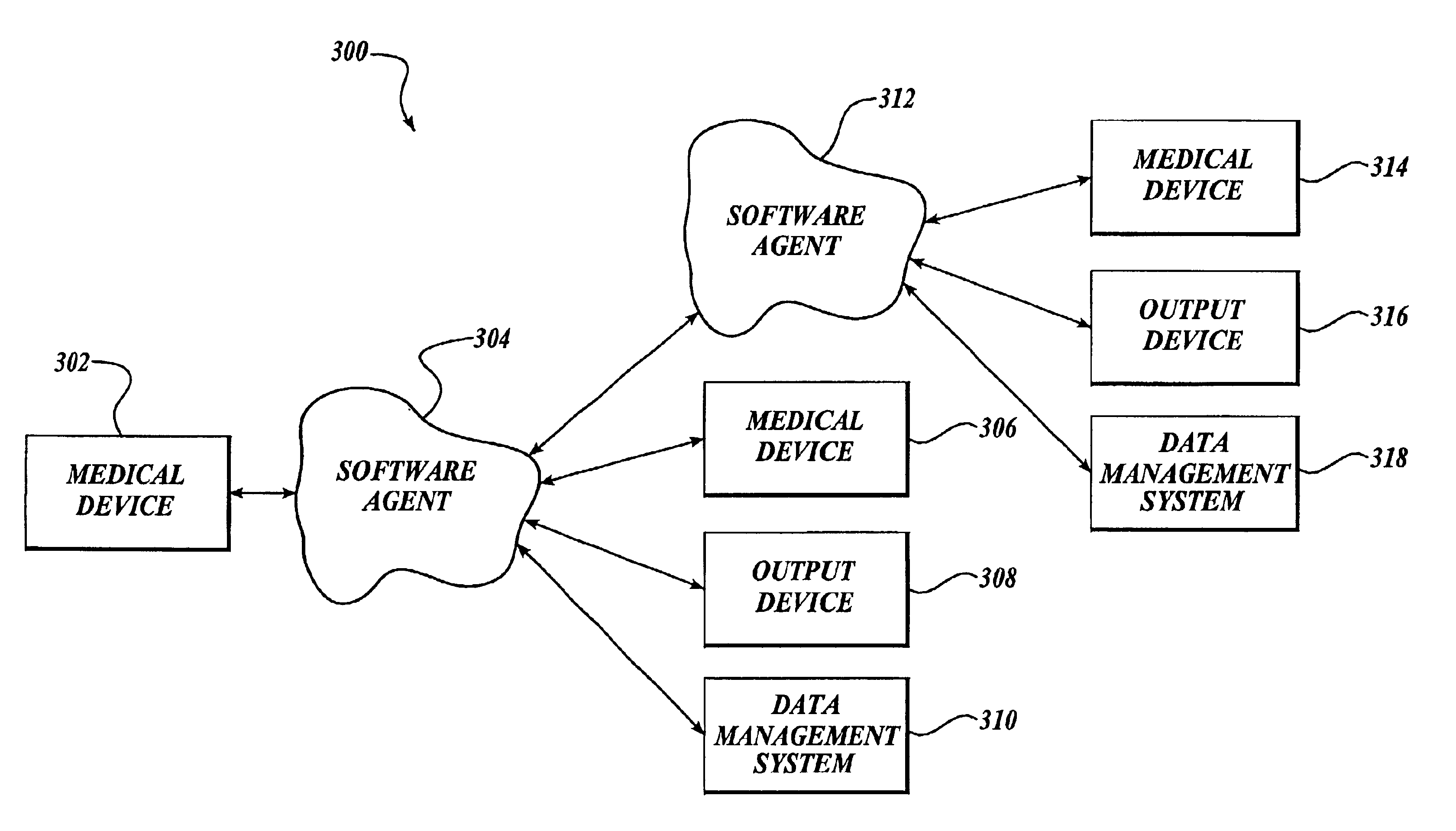
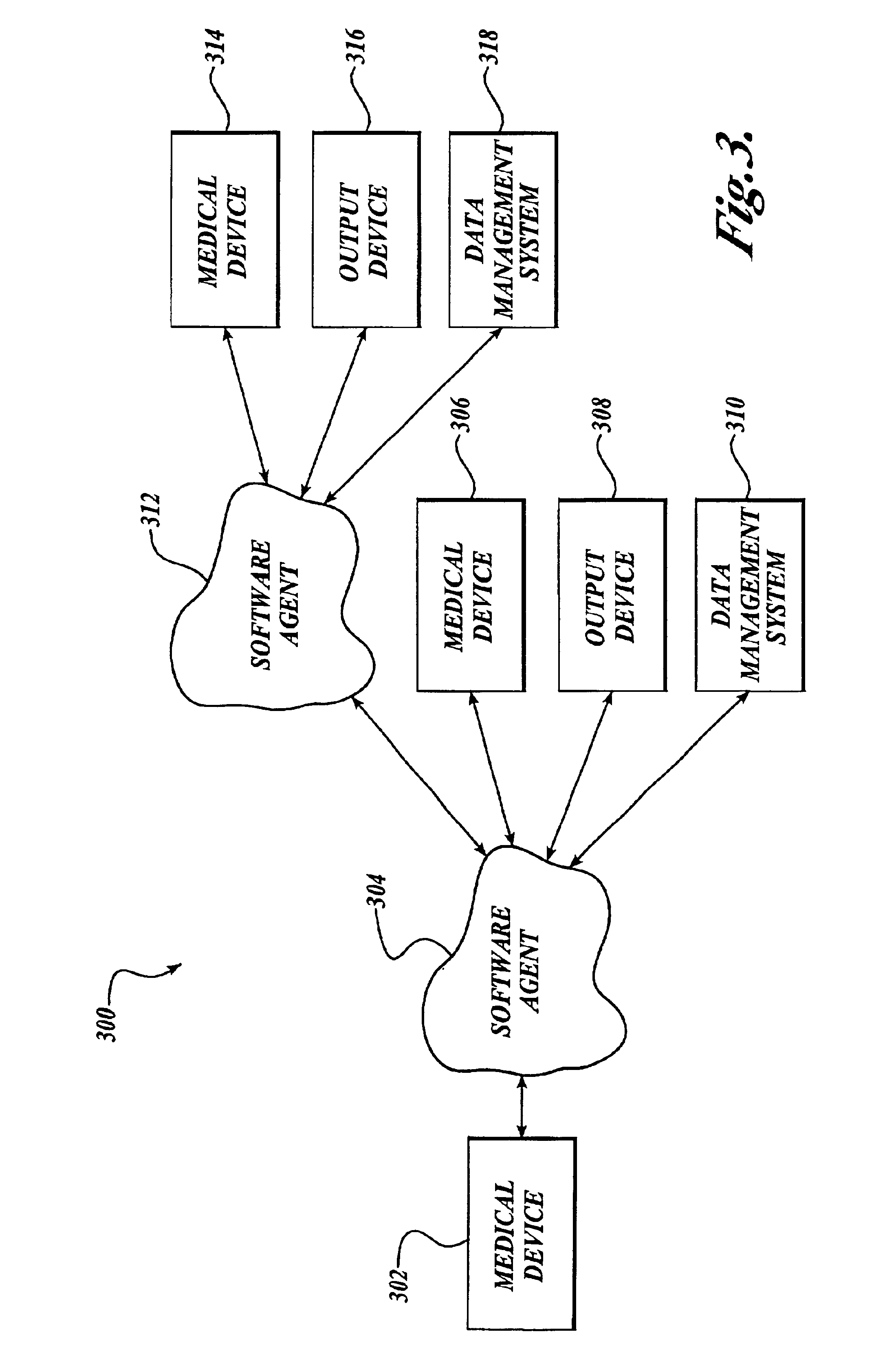
Enhanced interface for a medical device and a terminal
InactiveUS6957102B2Facilitate communicationElectrotherapyMechanical/radiation/invasive therapiesComputer terminalData storing
A system is described that comprises a medical device on which is installed a version of software and a software agent communicatively coupled to the medical device without regard to the version of software installed on the medical device. An example of the medical device includes a defibrillator. The software agent may reside in a personal digital assistant and can be operated to communicate with the defibrillator to access the data stored in the defibrillator irrespective of the version of software of the defibrillator.
Owner:PHYSIO CONTROL INC
Usage statistics collection for a cable data delivery system
InactiveUS6308328B1Broadband local area networksBroadcast transmission systemsData connectionNetwork management
Apparatus for recording and collecting usage and other statistical data from components of a cable data network comprises a network manager for maintaining and collecting the statistics. Internet protocol addresses are associated with components of the network. The component maintains a software agent that manages a statistics database. Responsive to a manager request generated at a service provider defined time interval, the component software agent provides the usage statistics to the network manager in real-time during an Internet session with a host. When the host to Internet or other data connection is torn down due to failure, disconnect or inactivity time-out, remaining usage statistics data is collected and the session duration updated with the time of tear down. Usage statistics collected include the amount of data transferred to / from a host, the amount of data that is discarded due to insufficient resource capacity and amount of data that cannot be corrected despite forward error correction used in a downstream high capacity channel to the host. Data traps may be defined and downloaded to components of the network for implementation. As a result, billing of users of the cable data network can be usage sensitive and determined based on actual data transferred (including credit given for errored data) and / or time sensitive based on session duration.
Owner:CISCO TECH INC
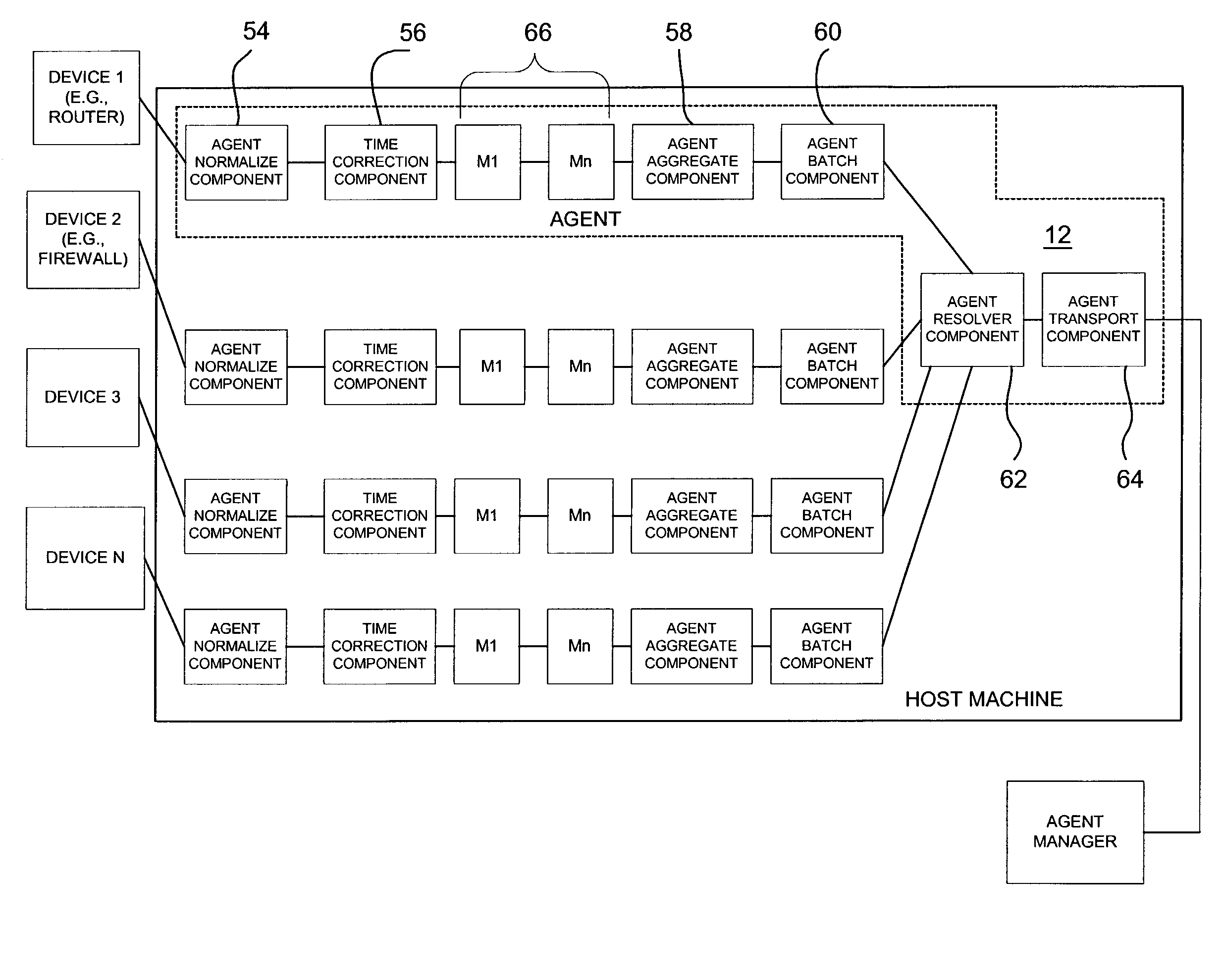
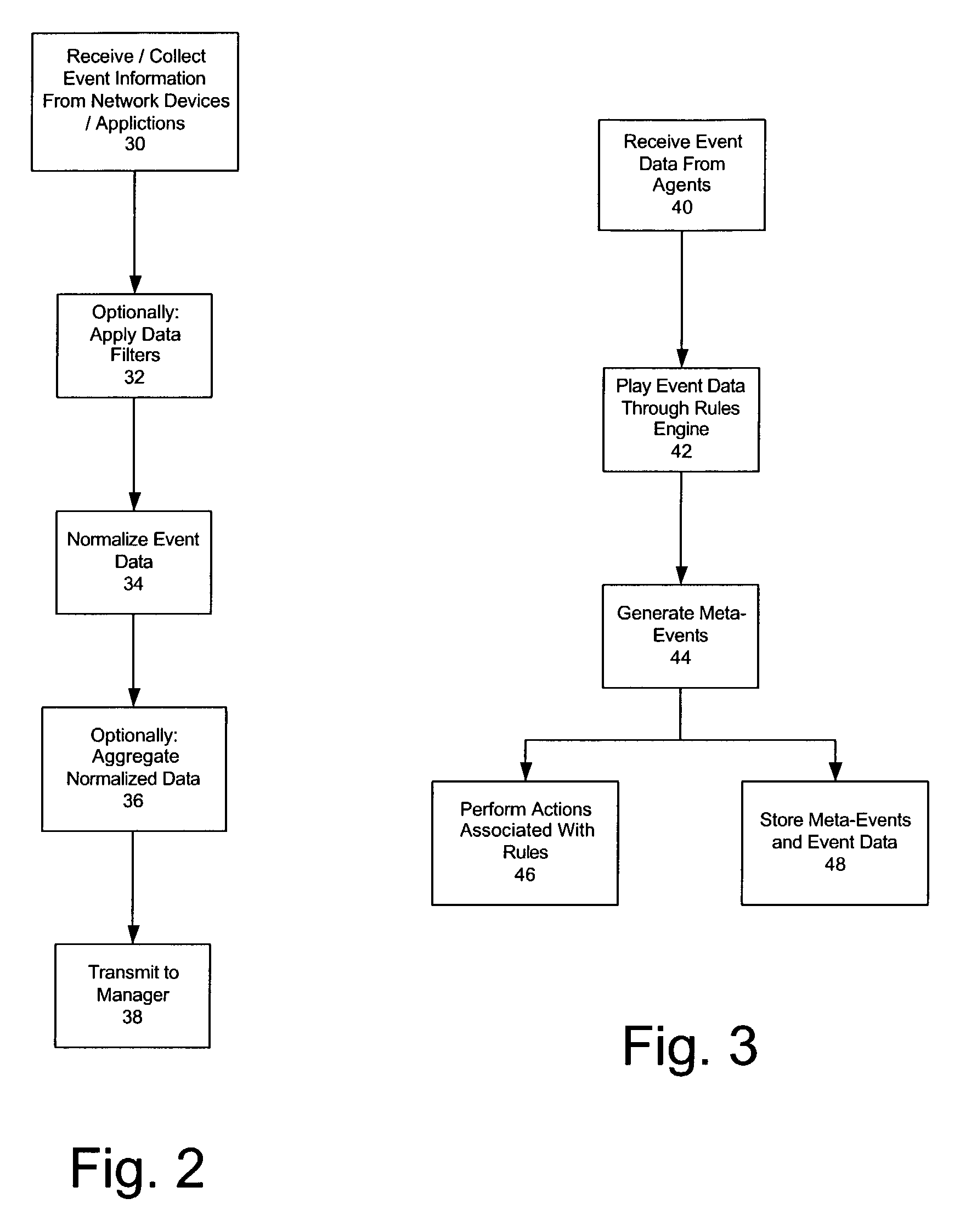
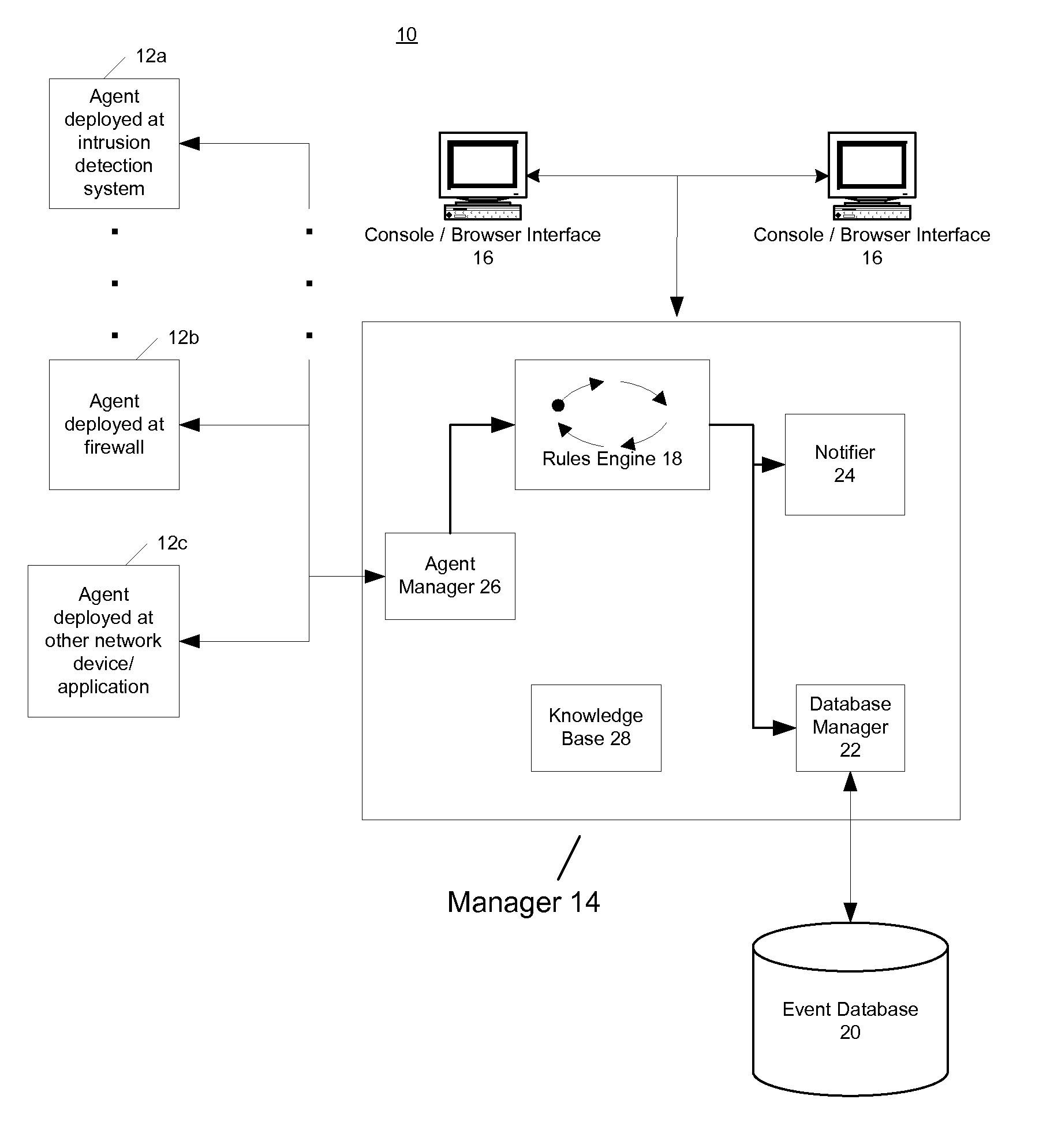
Method for batching events for transmission by software agent
ActiveUS7219239B1Memory loss protectionDigital data processing detailsSoftware agentComputer science
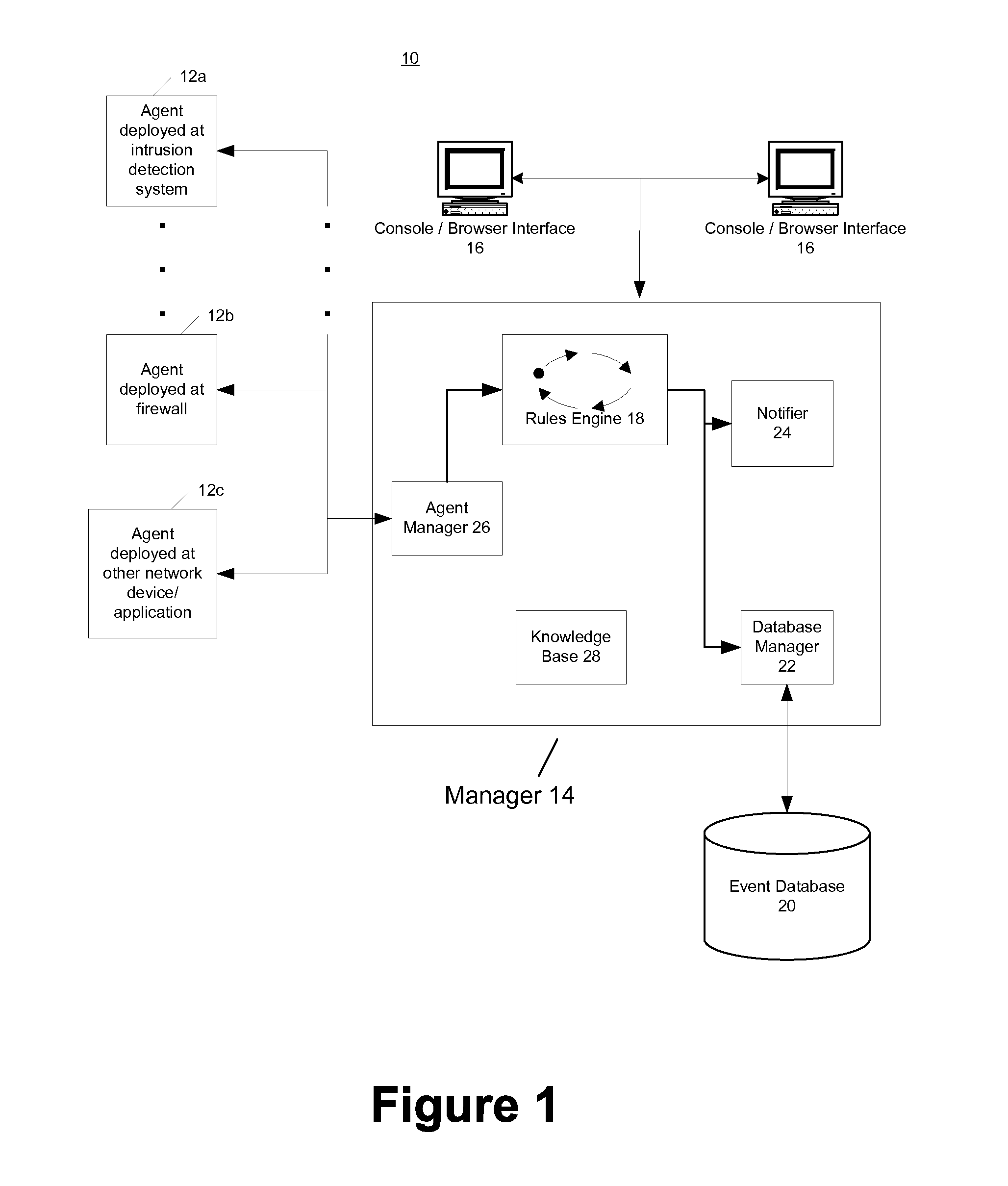
In one embodiment, the present invention provides for receiving security events from a network device by a distributed software agent of a network security system, determining a priority of each received security event, and storing the security events in a plurality of prioritized event buffers based on the determined priorities for a period of time determined by a timer. Upon expiration of the timer, a batch of security events for transport to a security event manager of the network security system can be created by including security events in the batch in order of priority until the batch is full.
Owner:MICRO FOCUS LLC
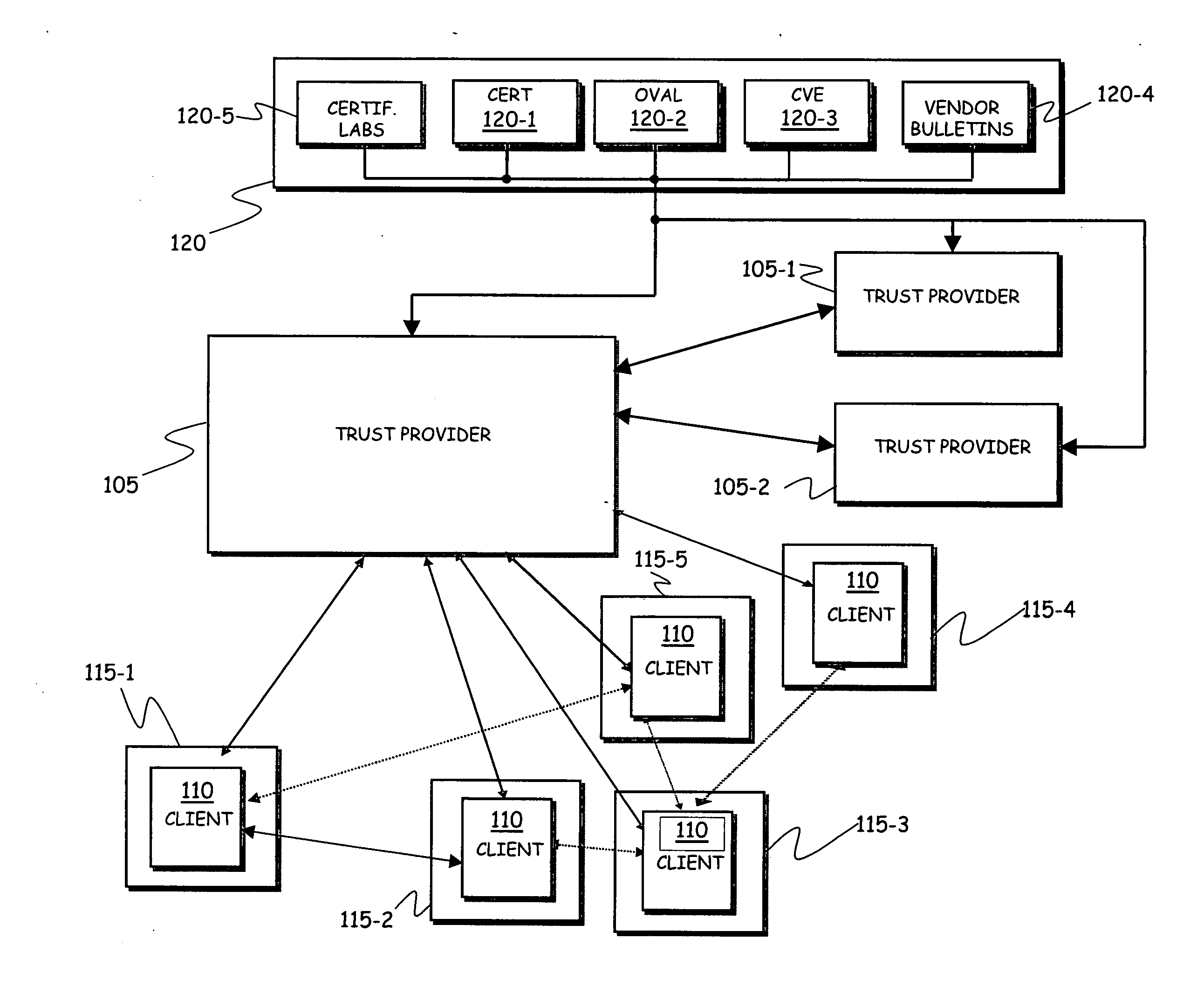
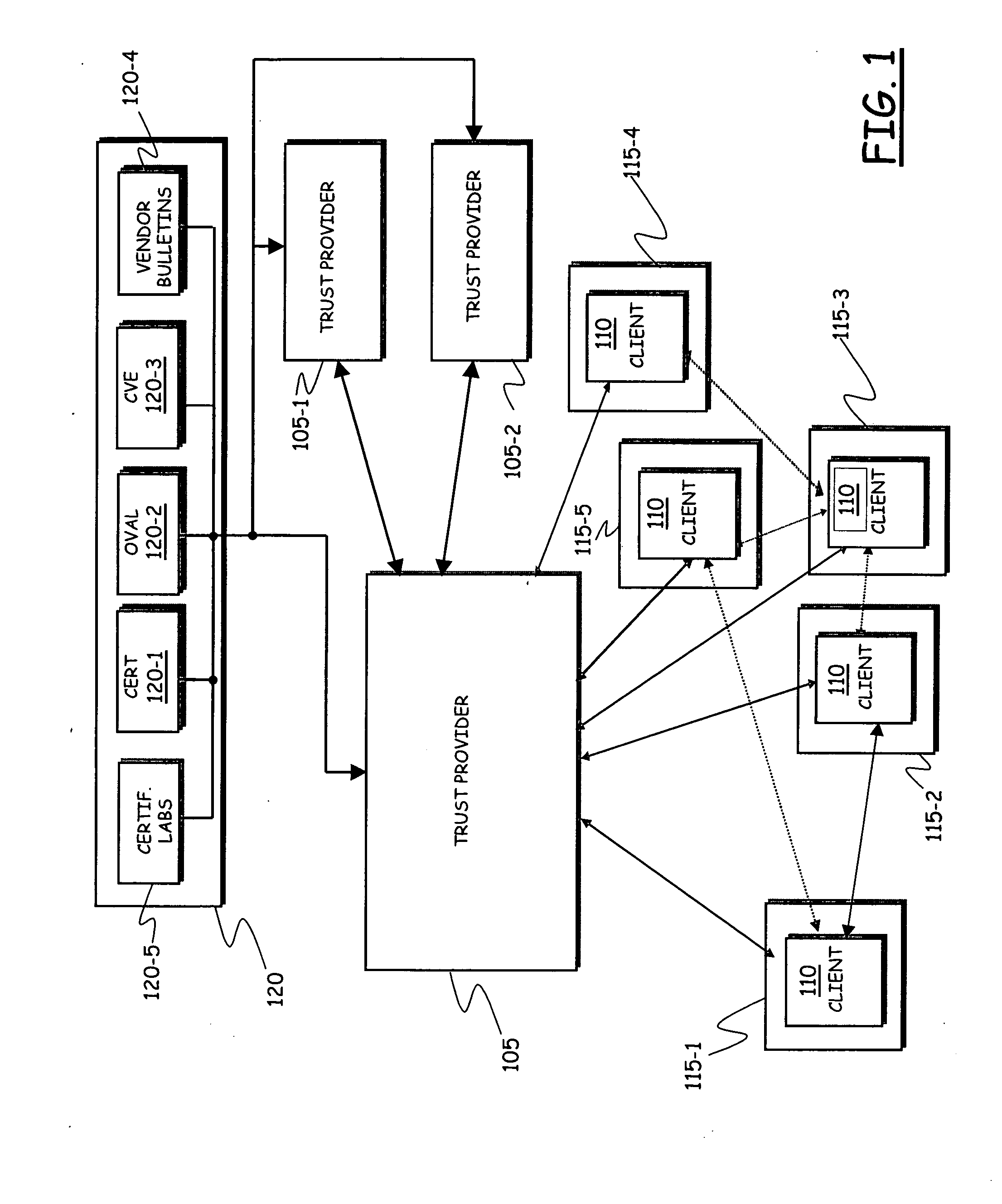
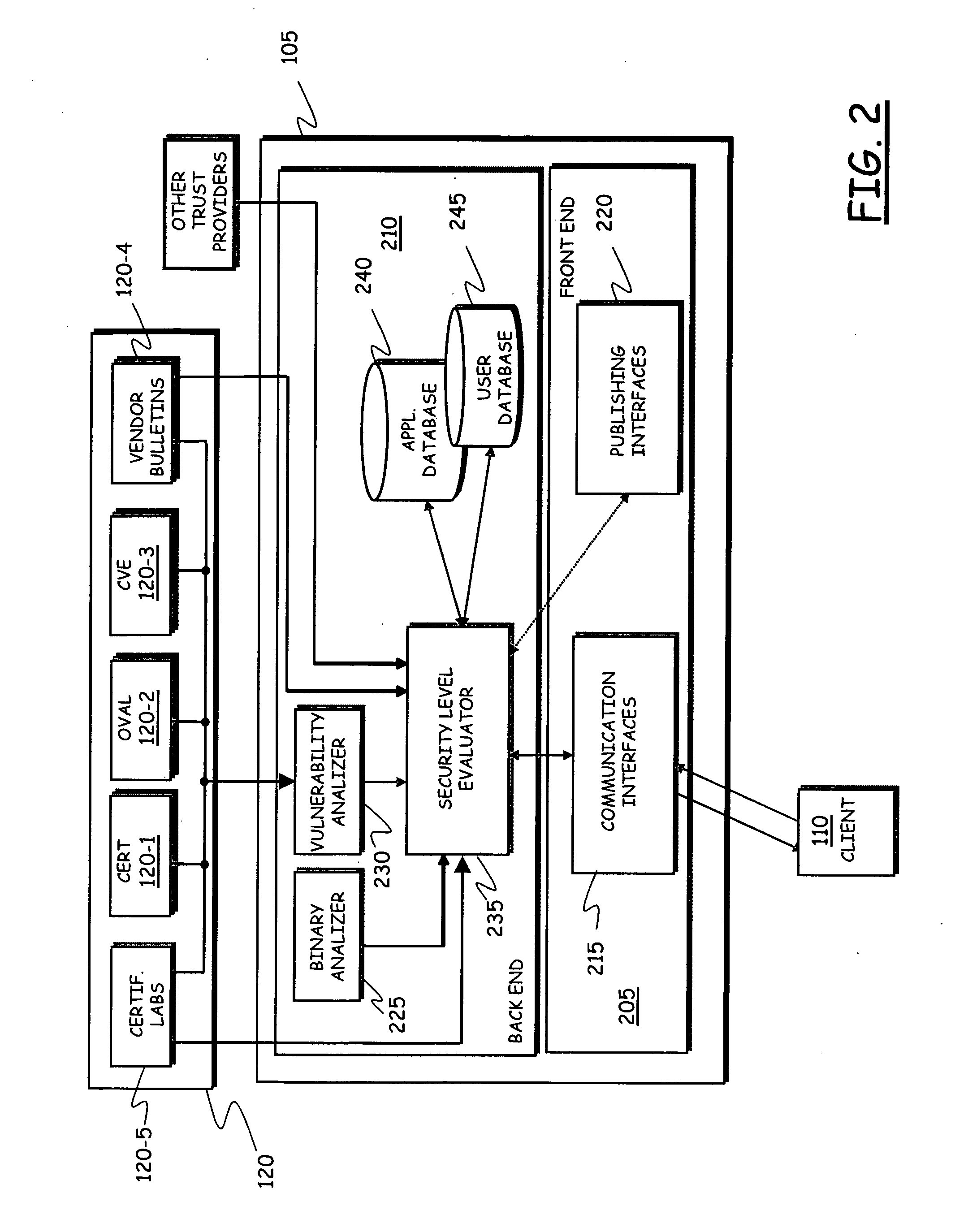
System for implementing security on telecommunications terminals
ActiveUS20090254993A1Improve securityOvercome problemsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkComputer terminal
A system includes at least one telecommunications terminal having data processing capabilities, the telecommunications terminal being susceptible of having installed thereon software applications, wherein each software application has associated therewith a respective indicator adapted to indicate a level of security of the software application, the level of security being susceptible of varying in time; a software agent executed by the at least one telecommunications terminal, the software agent being adapted to conditionally allow the installation of software applications on the telecommunications terminal based on the respective level of security; a server in communications relationship with the software agent, the server being adapted to dynamically calculate the level of security of the software applications, and to communicate to the software agent the calculated level of security of the software applications to be installed on the telecommunications terminal.
Owner:TELECOM ITALIA SPA
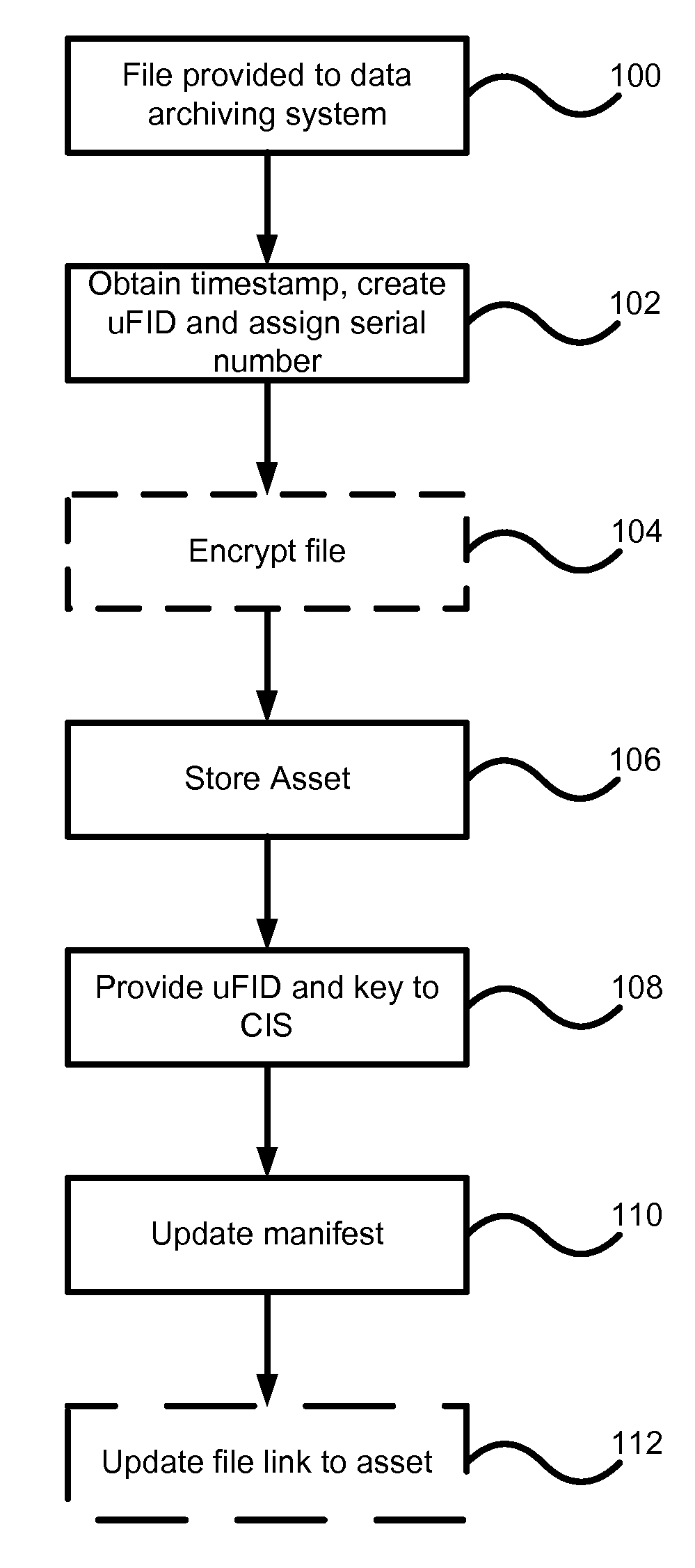
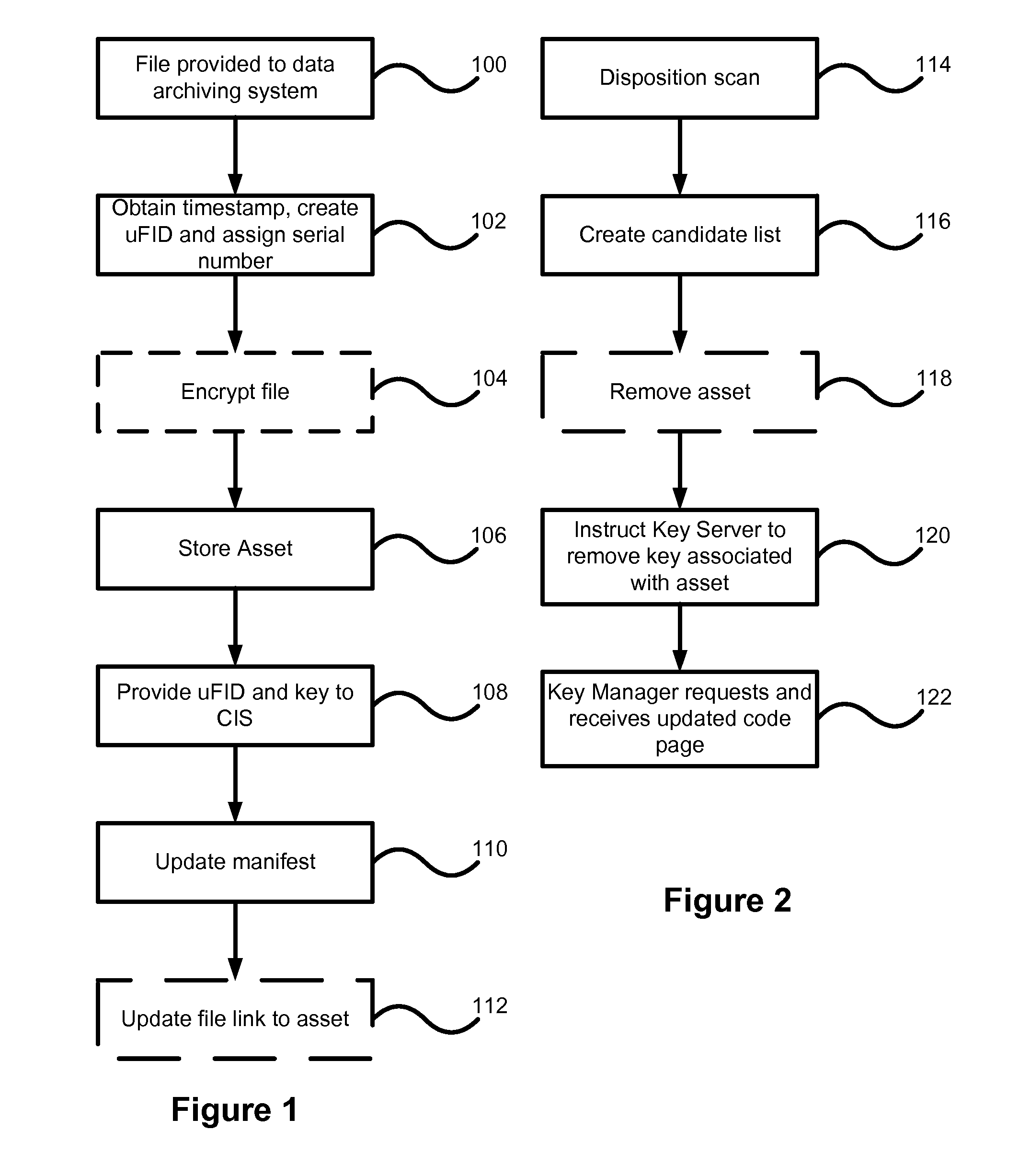
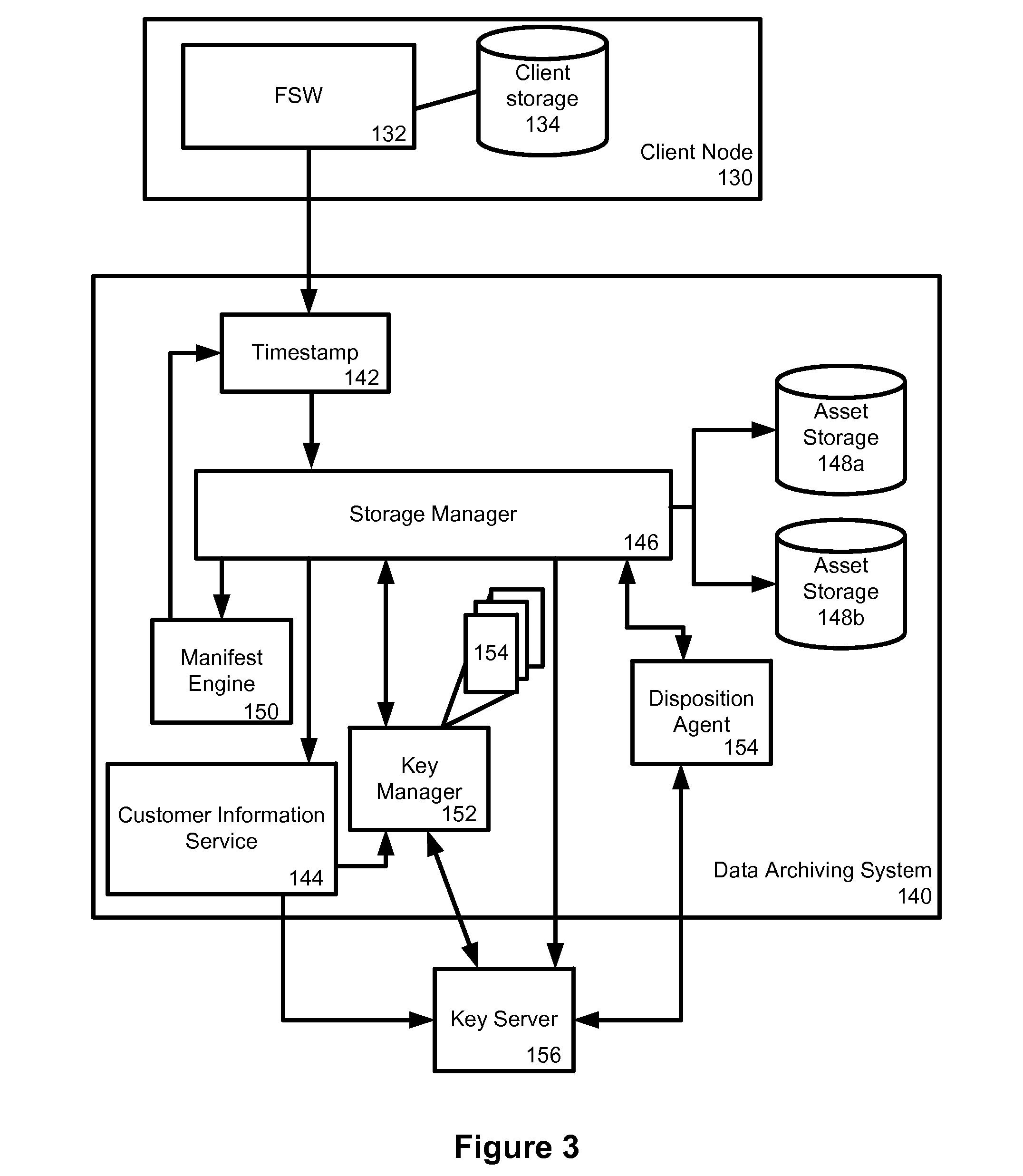
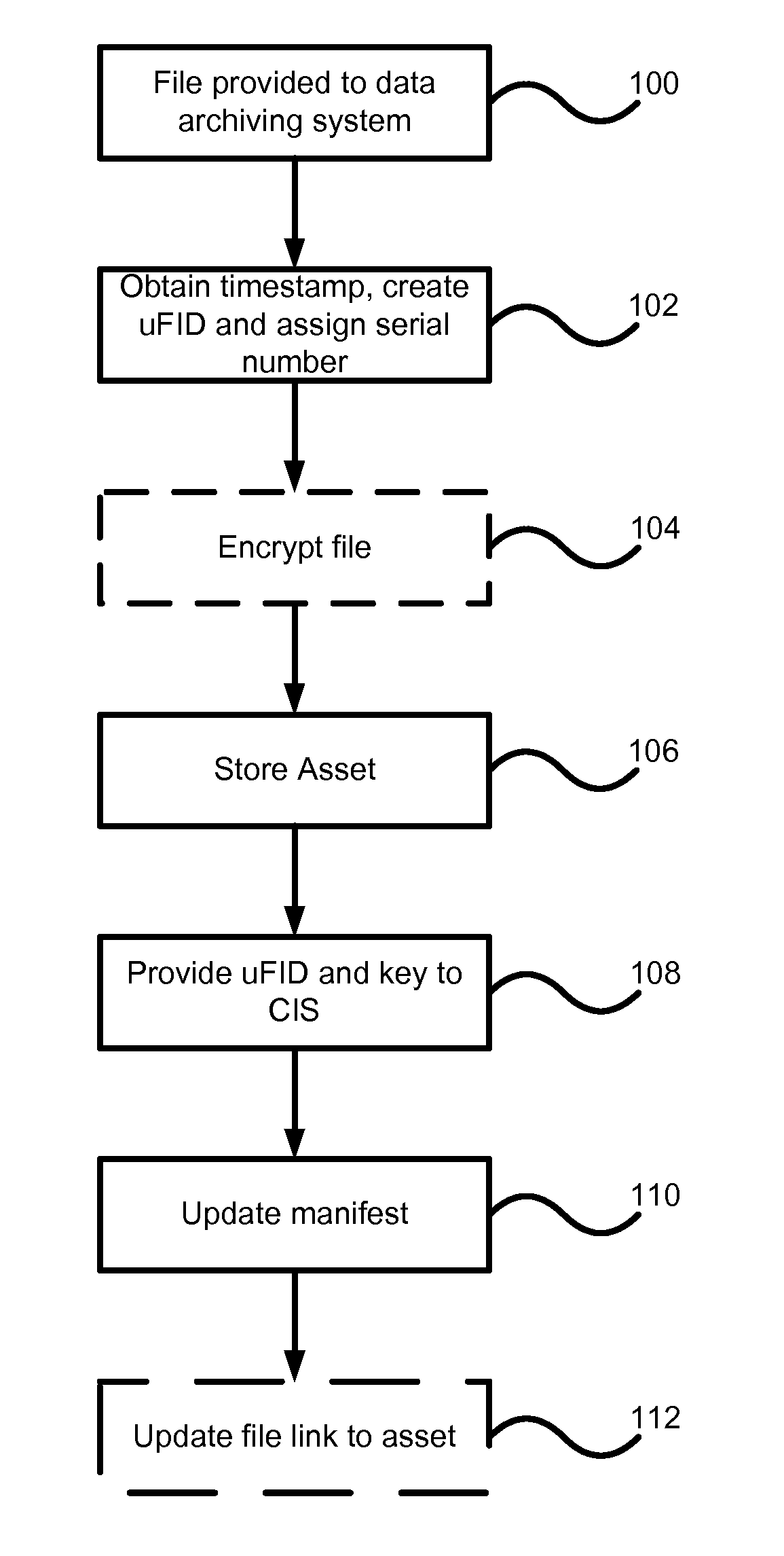
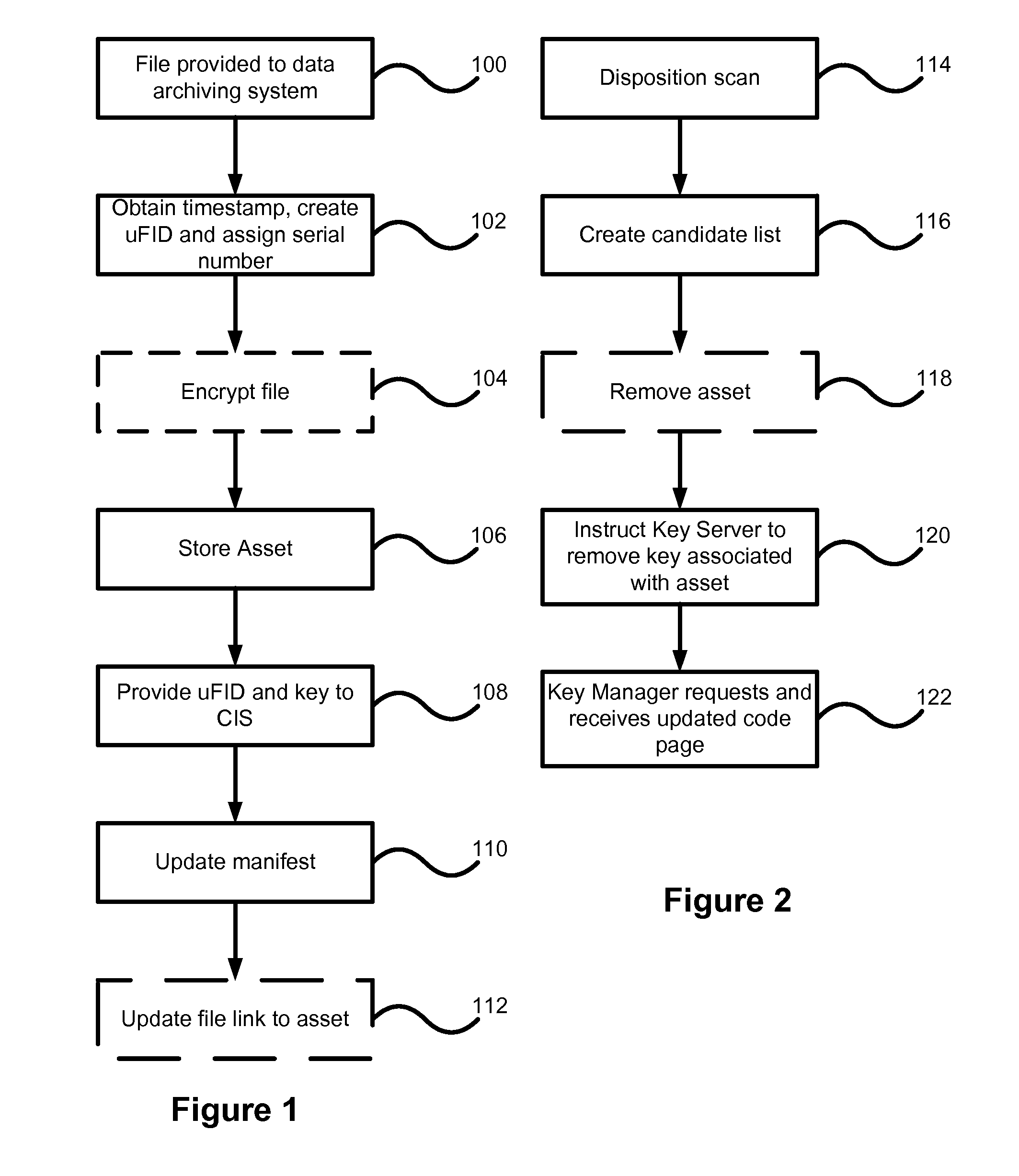
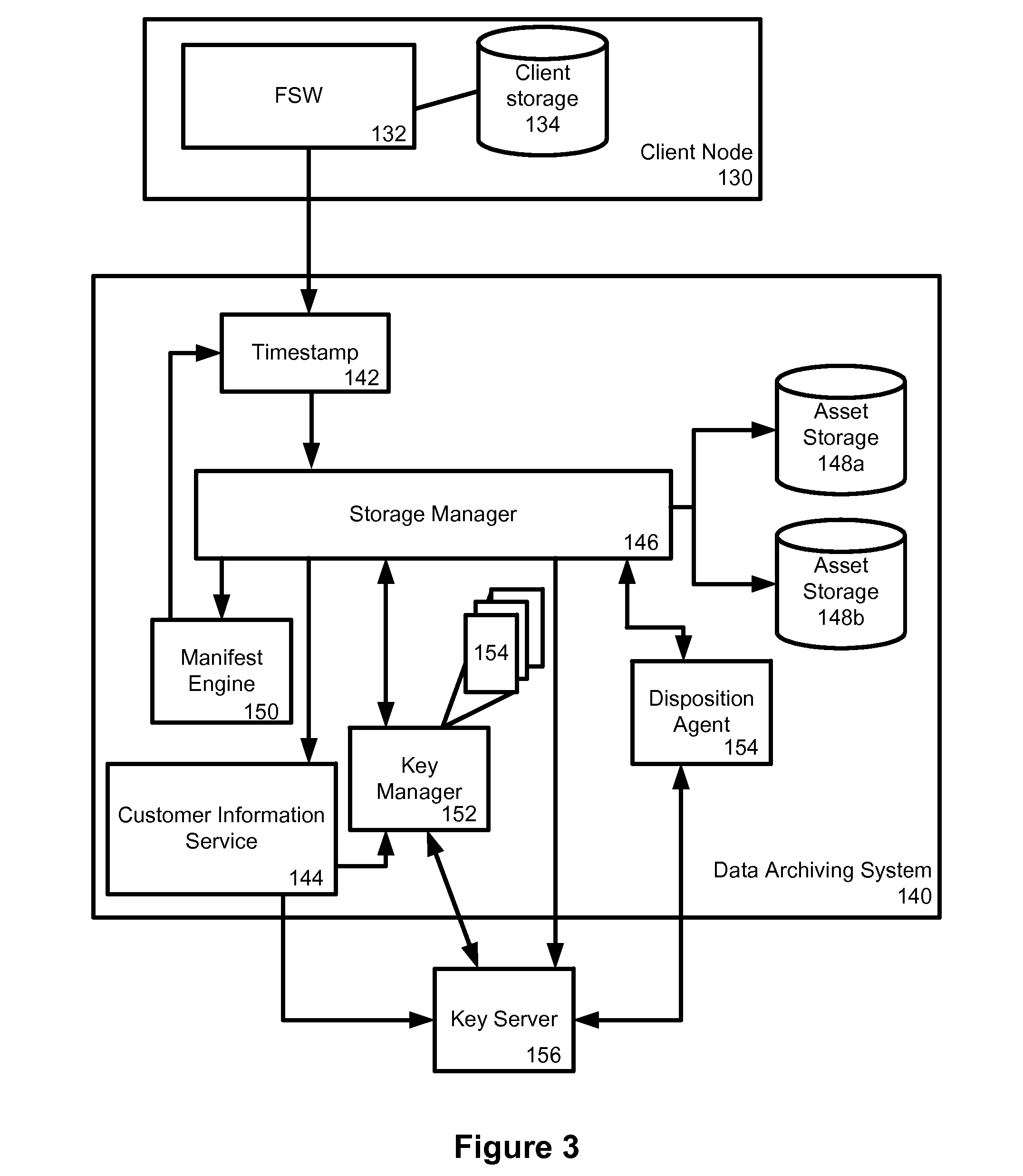
Data archiving system
ActiveUS7801871B2Digital data processing detailsComputer security arrangementsFault toleranceApplication server
An encrypted file storage solution consists of a cluster of processing nodes, external data storage, and a software agent (the “File System Watcher”), which is installed on the application servers. Cluster sizes of one node up to many hundreds of nodes are possible. There are also remote “Key Servers” which provide various services to one or more clusters. The preceding describes a preferred embodiment, though in some cases it may be desirable to “collapse” some of the functionality into a smaller number of hardware devices, typically trading off cost versus security and fault-tolerance.
Owner:STORCENTRIC DIP LENDER LLC +1
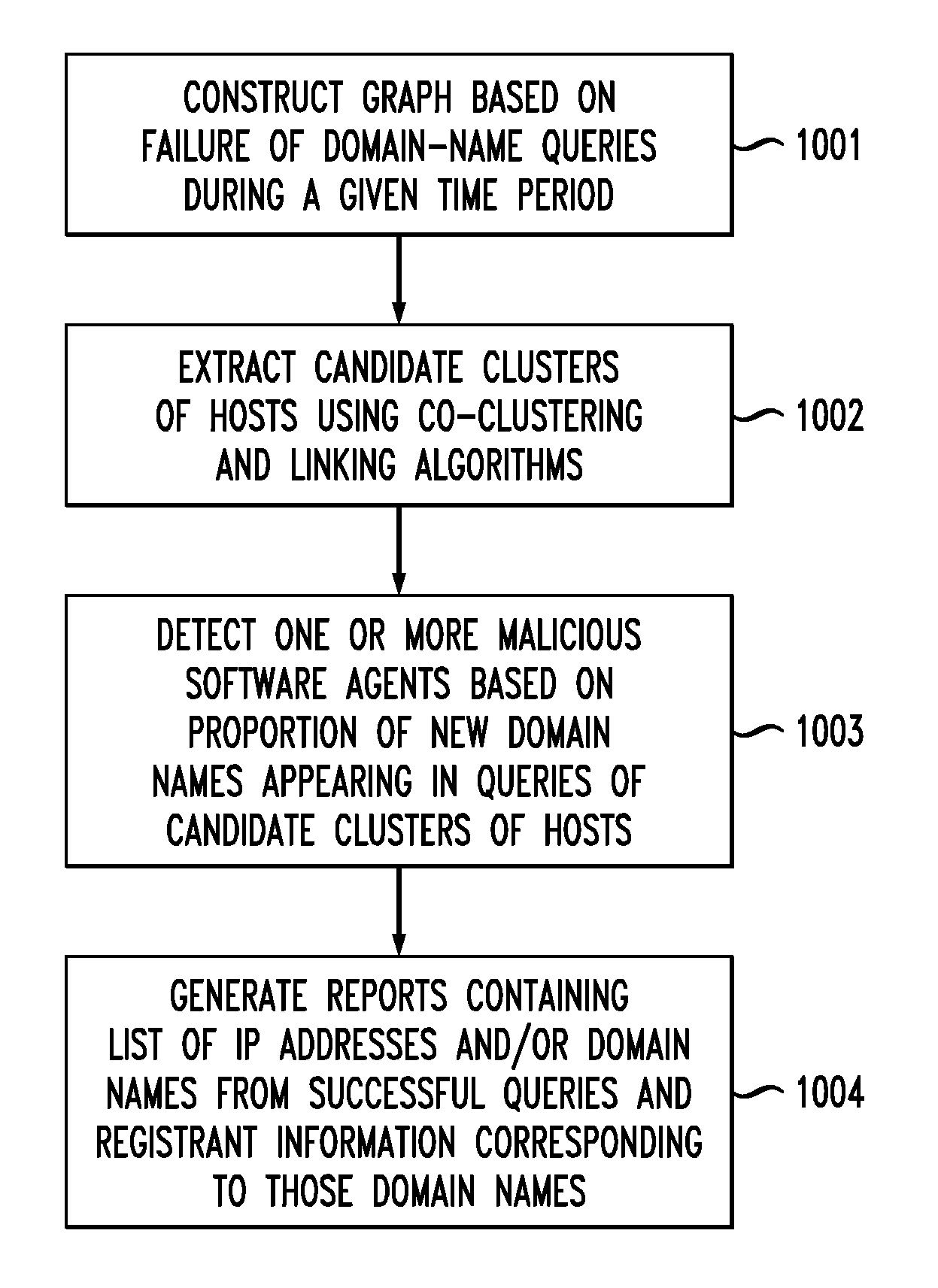
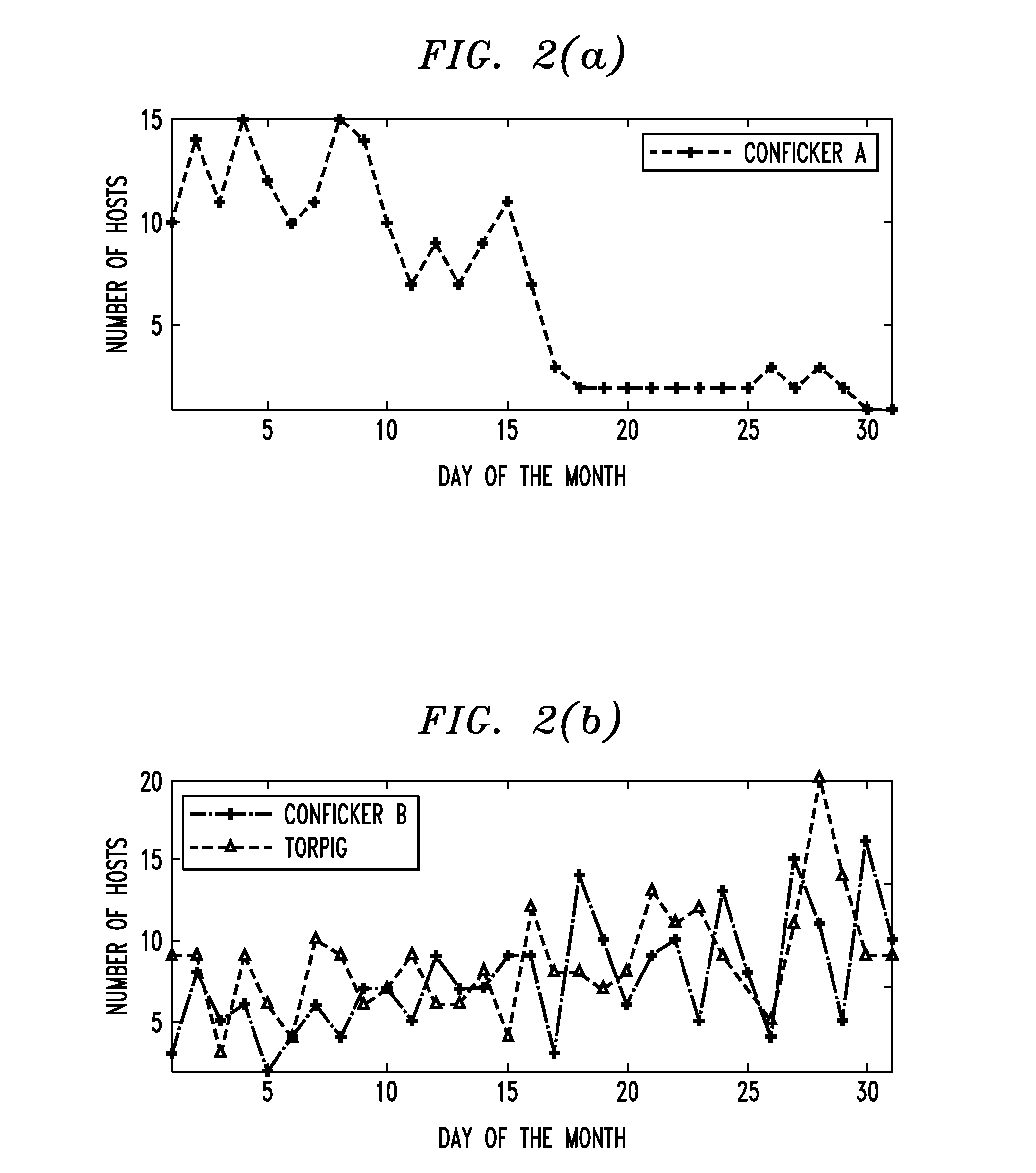
System and method for detection of domain-flux botnets and the like
ActiveUS20120084860A1Memory loss protectionUnauthorized memory use protectionDomain nameCluster algorithm
In one embodiment, a method for detecting malicious software agents, such as domain-flux botnets. The method applies a co-clustering algorithm on a domain-name query failure graph, to generate a hierarchical grouping of hosts based on similarities between domain names queried by those hosts, and divides that hierarchical structure into candidate clusters based on percentages of failed queries having at least first- and second-level domain names in common, thereby identifying hosts having correlated queries as possibly being infected with malicious software agents. A linking algorithm is used to correlate the co-clustering results generated at different time periods to differentiate actual domain-flux bots from other domain-name failure anomalies by identifying candidate clusters that persist for relatively long periods of time. Persistent candidate clusters are analyzed to identify which clusters have malicious software agents, based on a freshness metric that characterizes whether the candidate clusters continually generate failed queries having new domain names.
Owner:RPX CORP
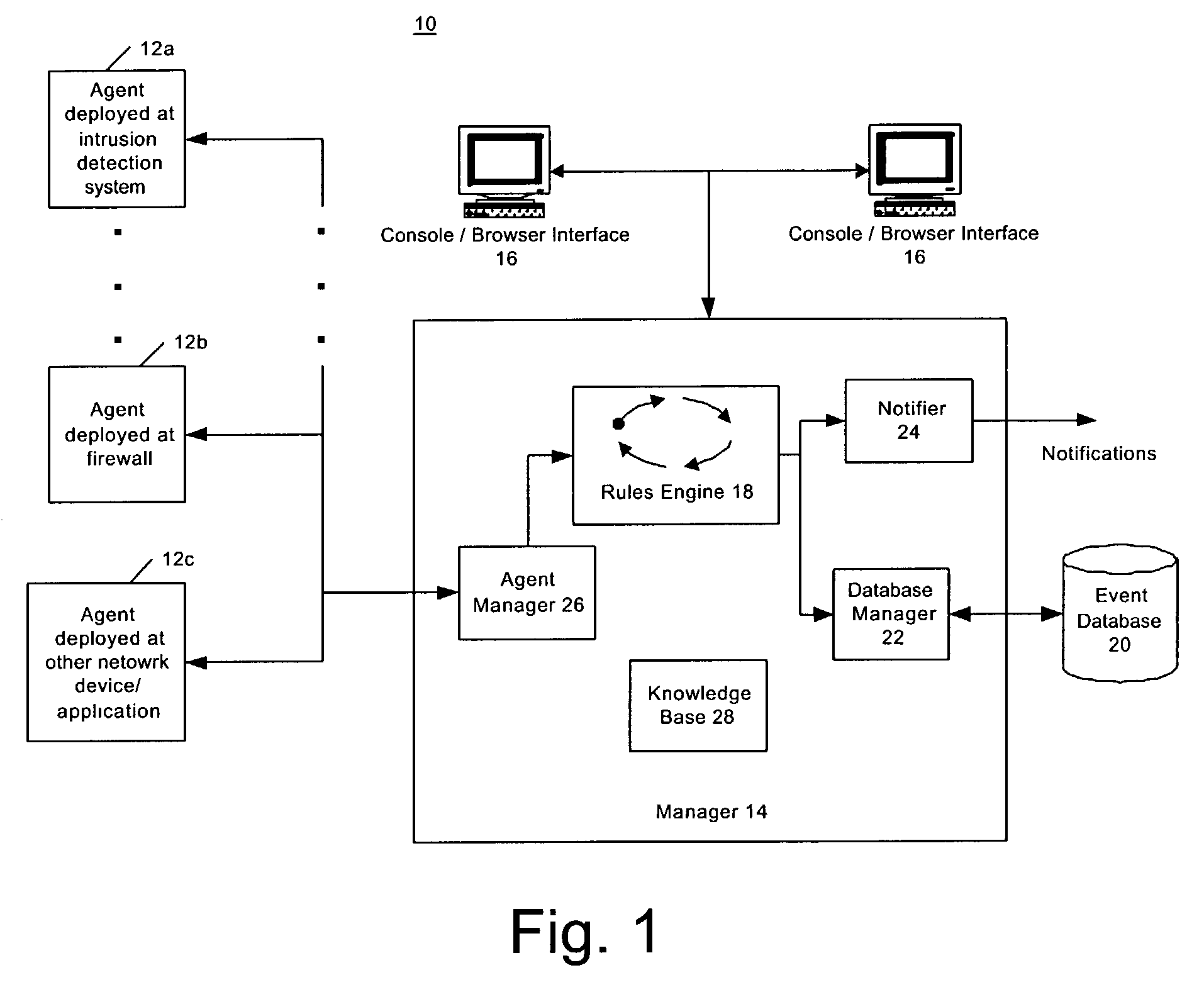
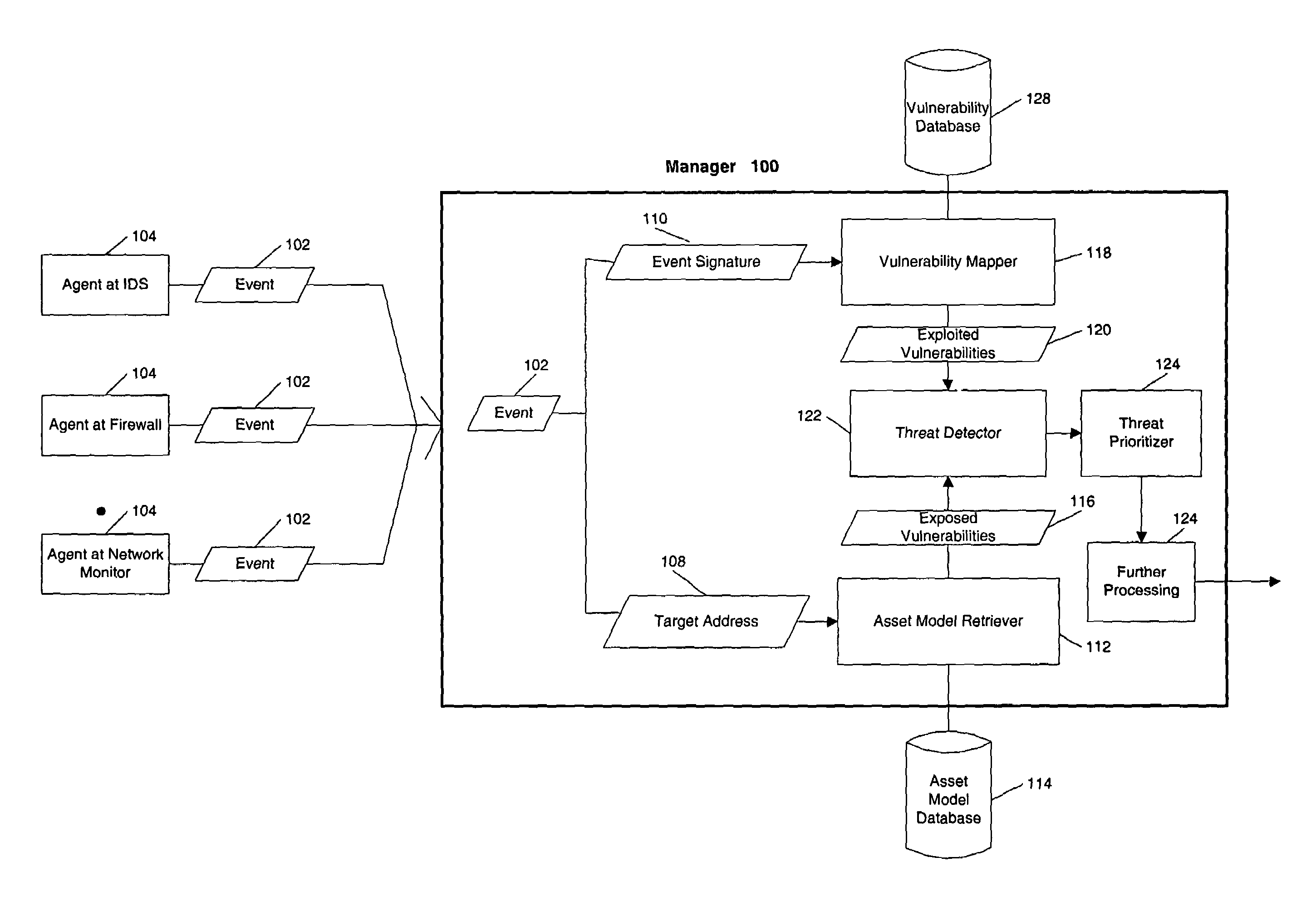
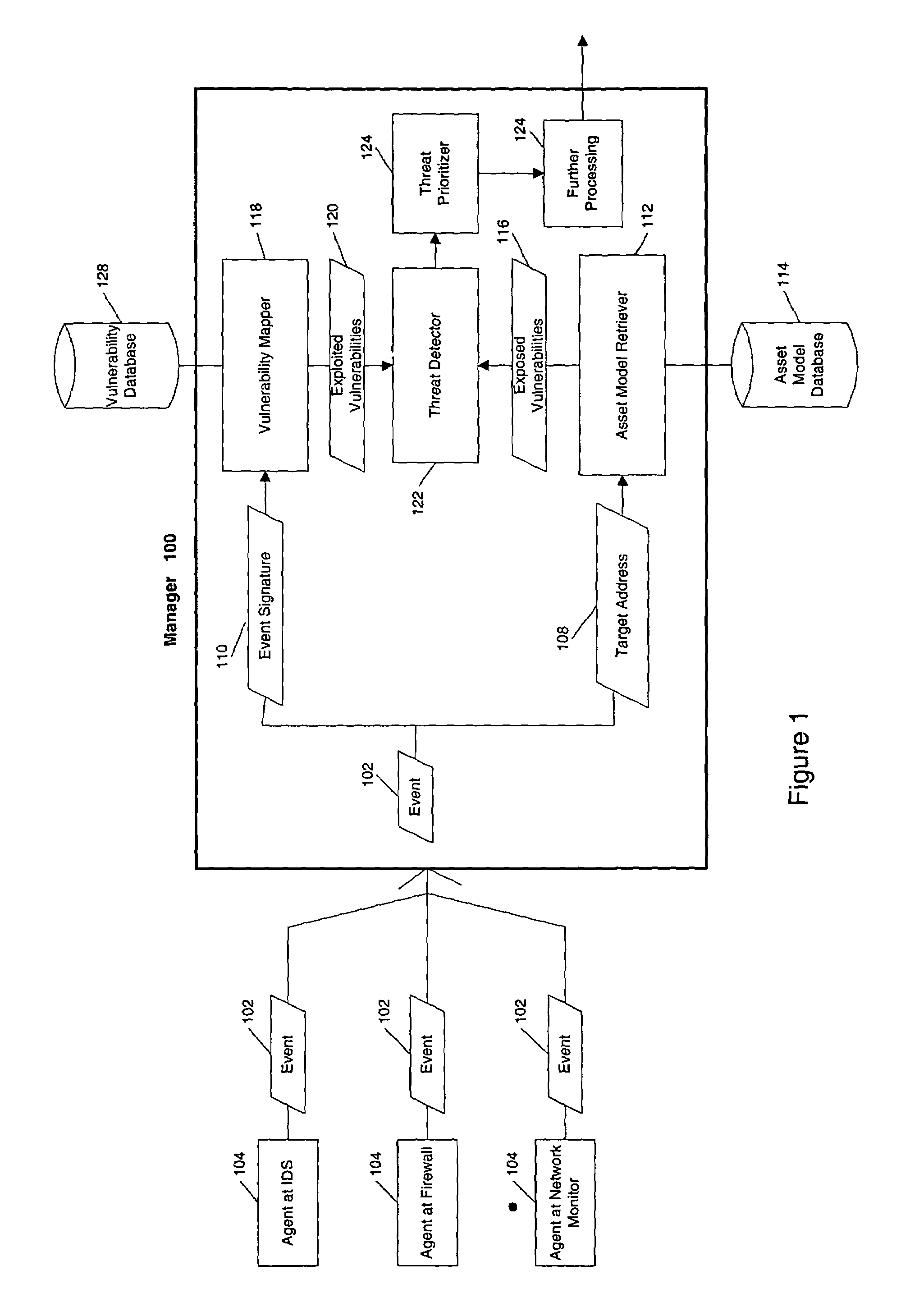
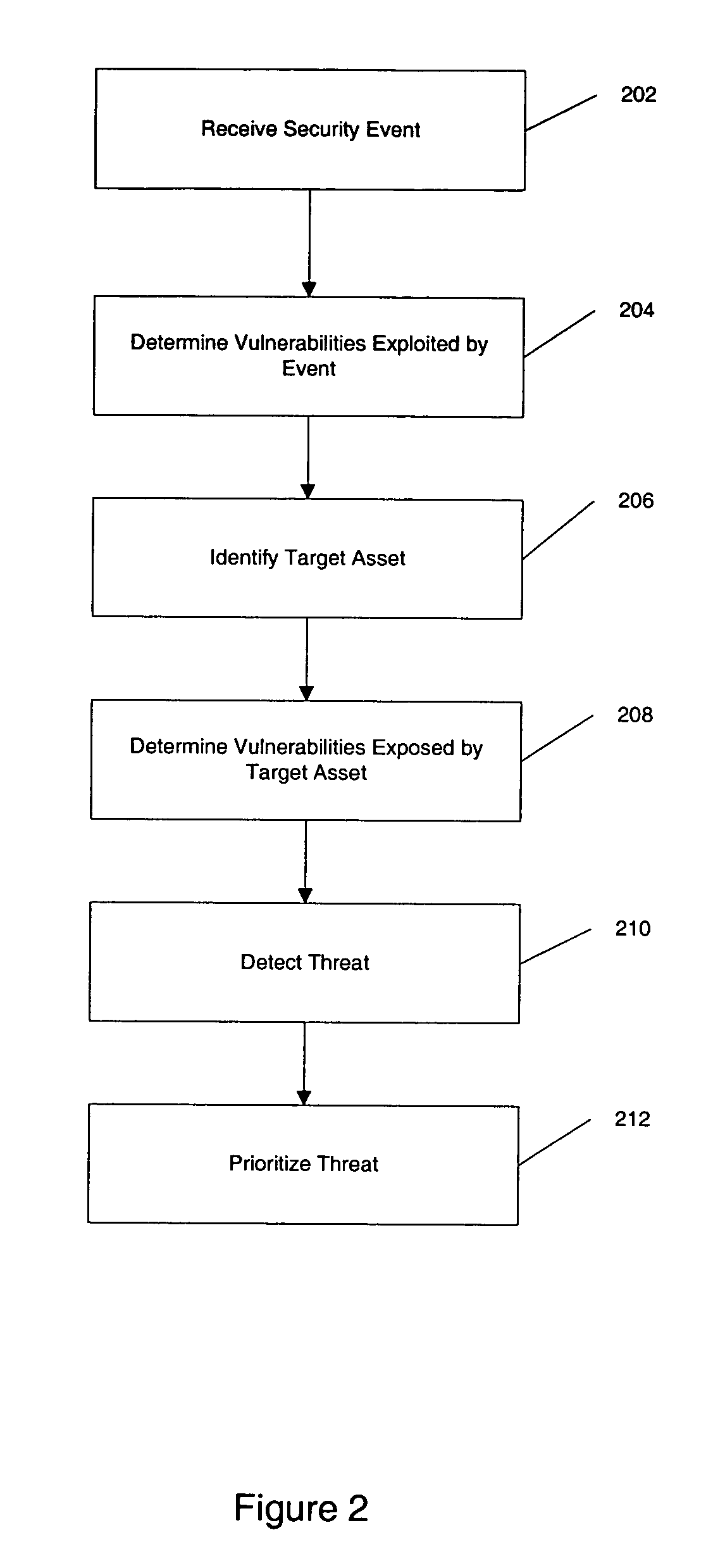
Threat detection in a network security system
A network security system is provided that receives information from various sensors and can analyse the received information. In one embodiment of the present invention, such a system receives a security event from a software agent. The received security event includes a target address and an event signature, as generated by the software agent. The event signature can be used to determine a set of vulnerabilities exploited by the received security event, and the target address can be used to identify a target asset within the network. By accessing a model of the target asset, a set of vulnerabilities exposed by the target asset can be retrieved. Then, a threat can be detected by comparing the set of vulnerabilities exploited by the security event to the set of vulnerabilities exposed by the target asset.
Owner:MICRO FOCUS LLC
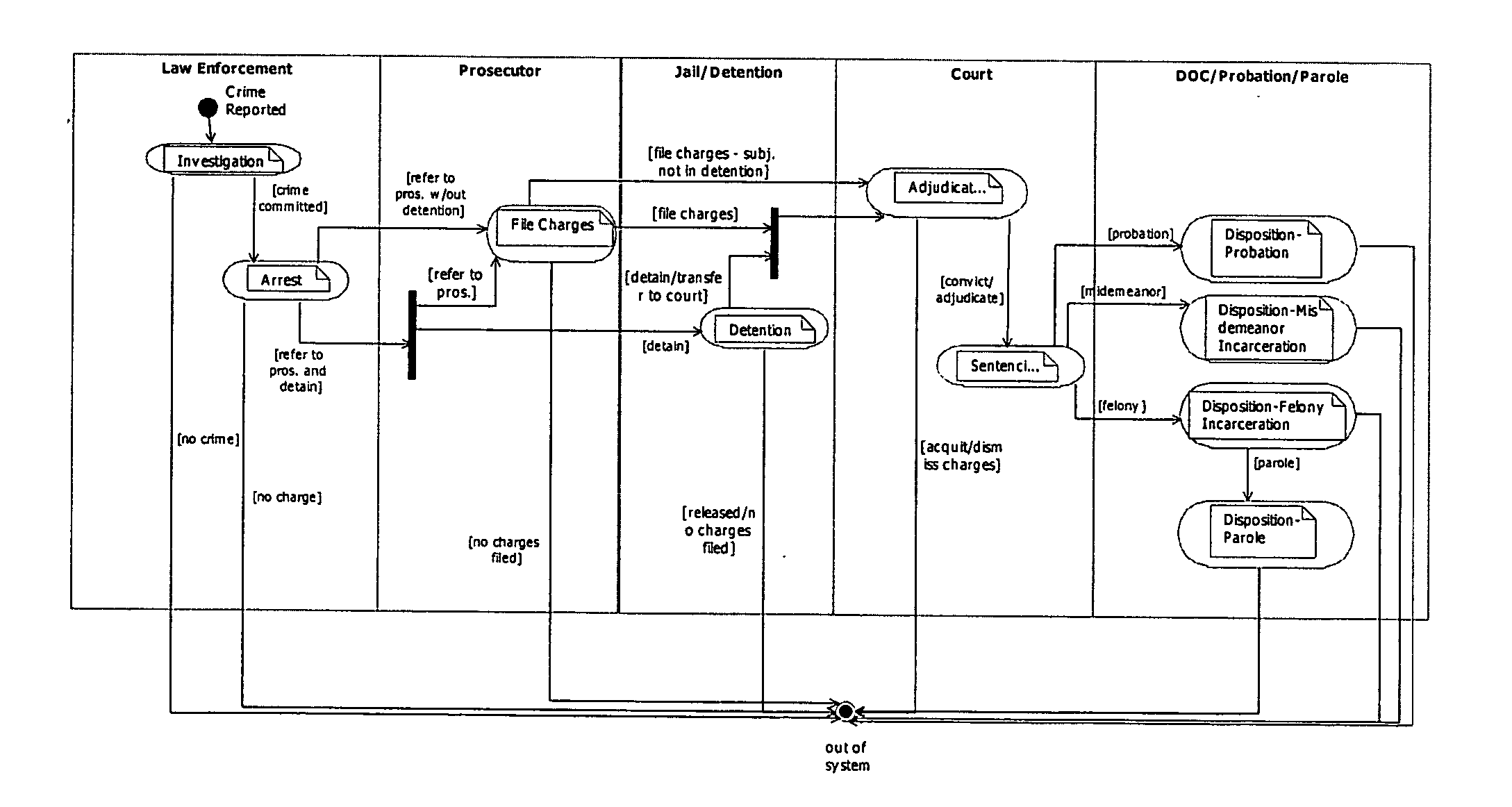
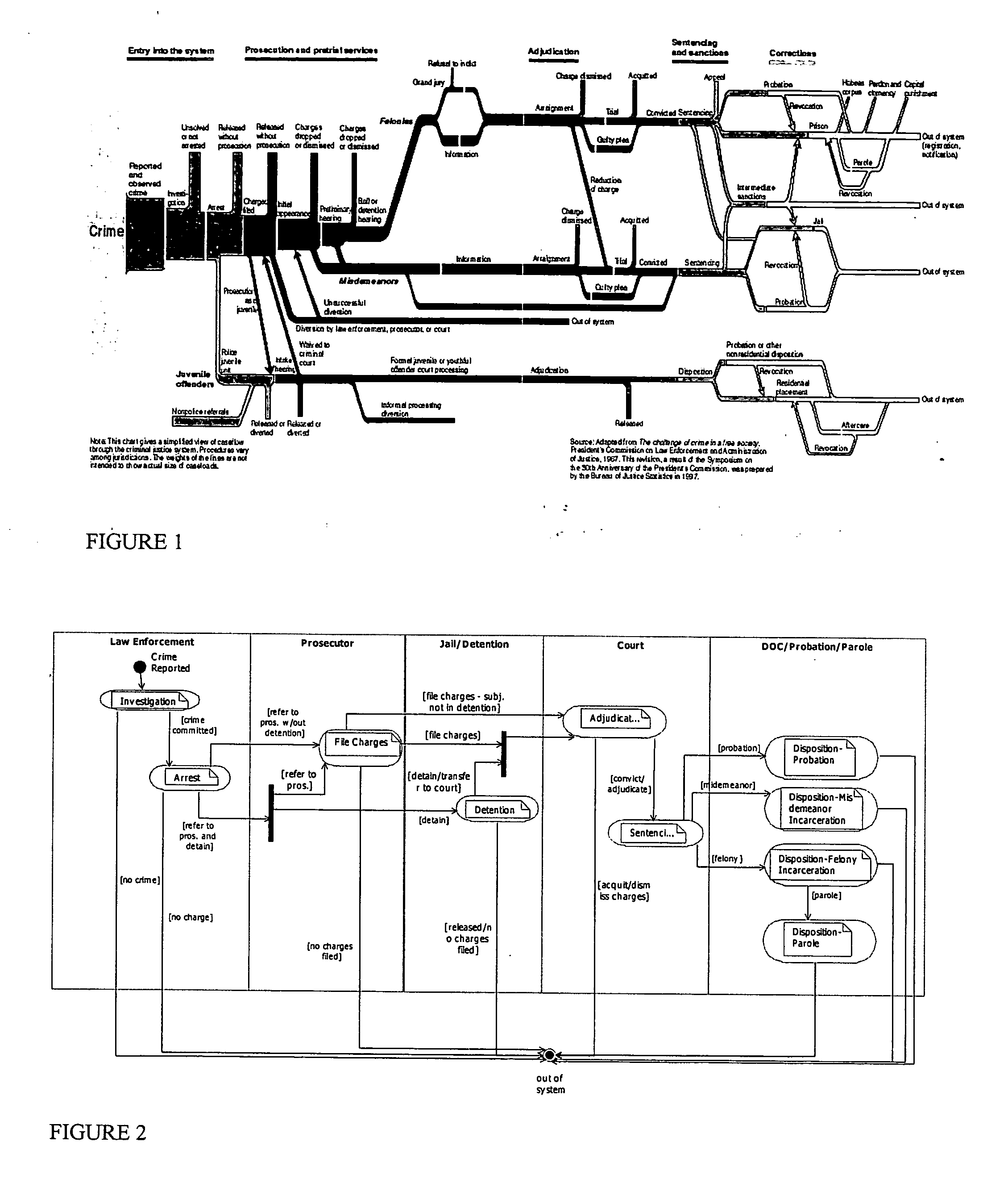
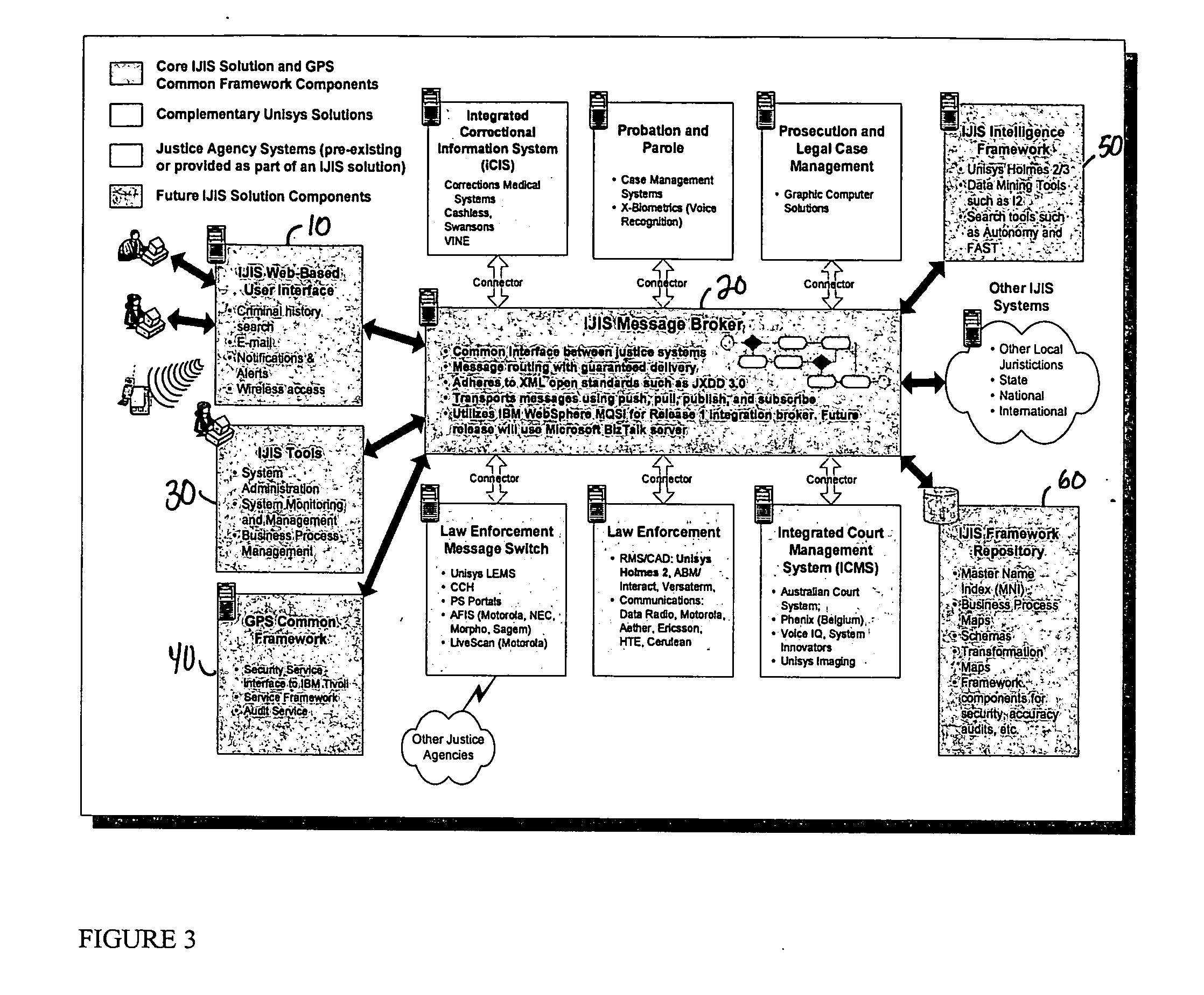
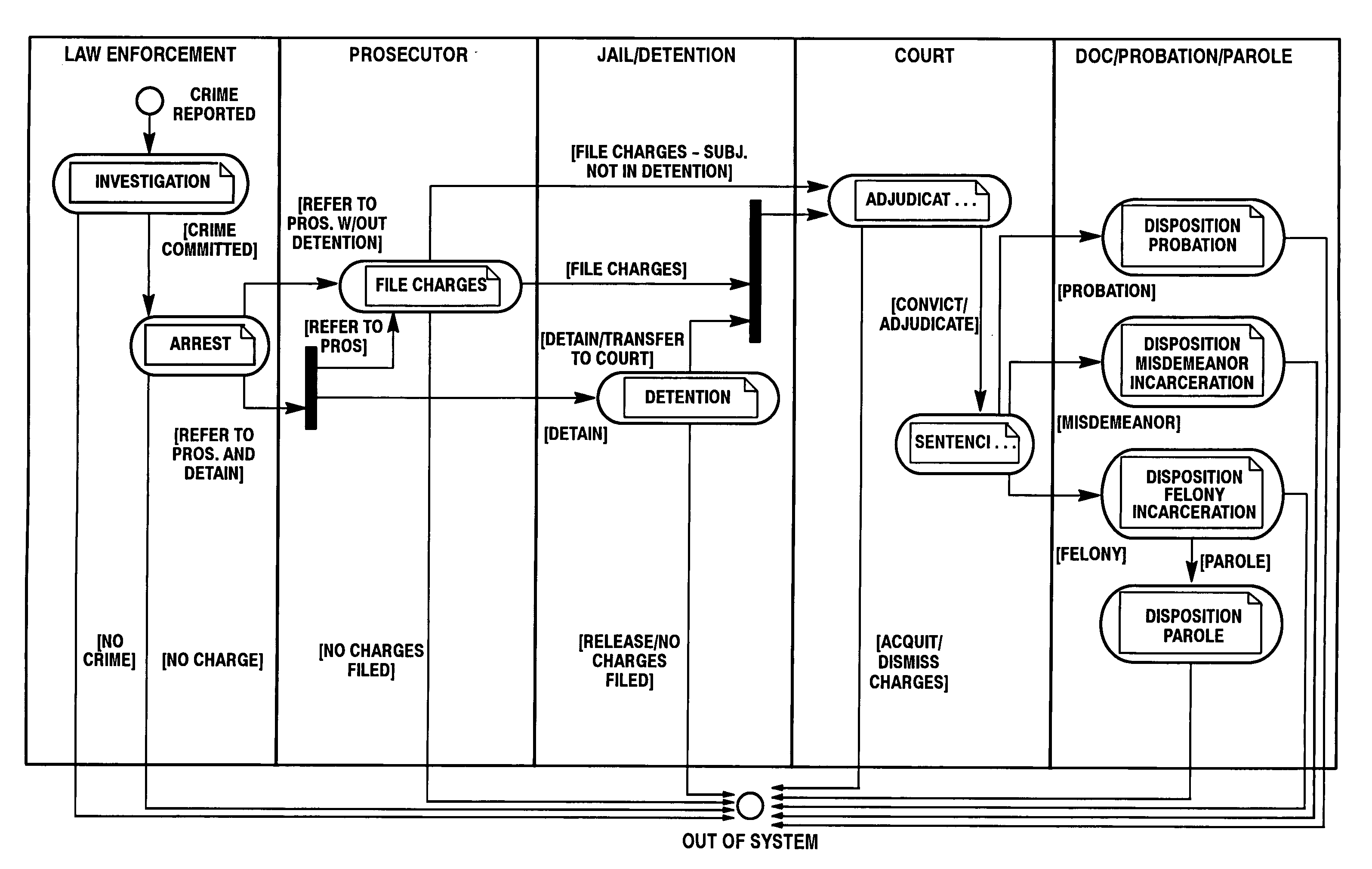
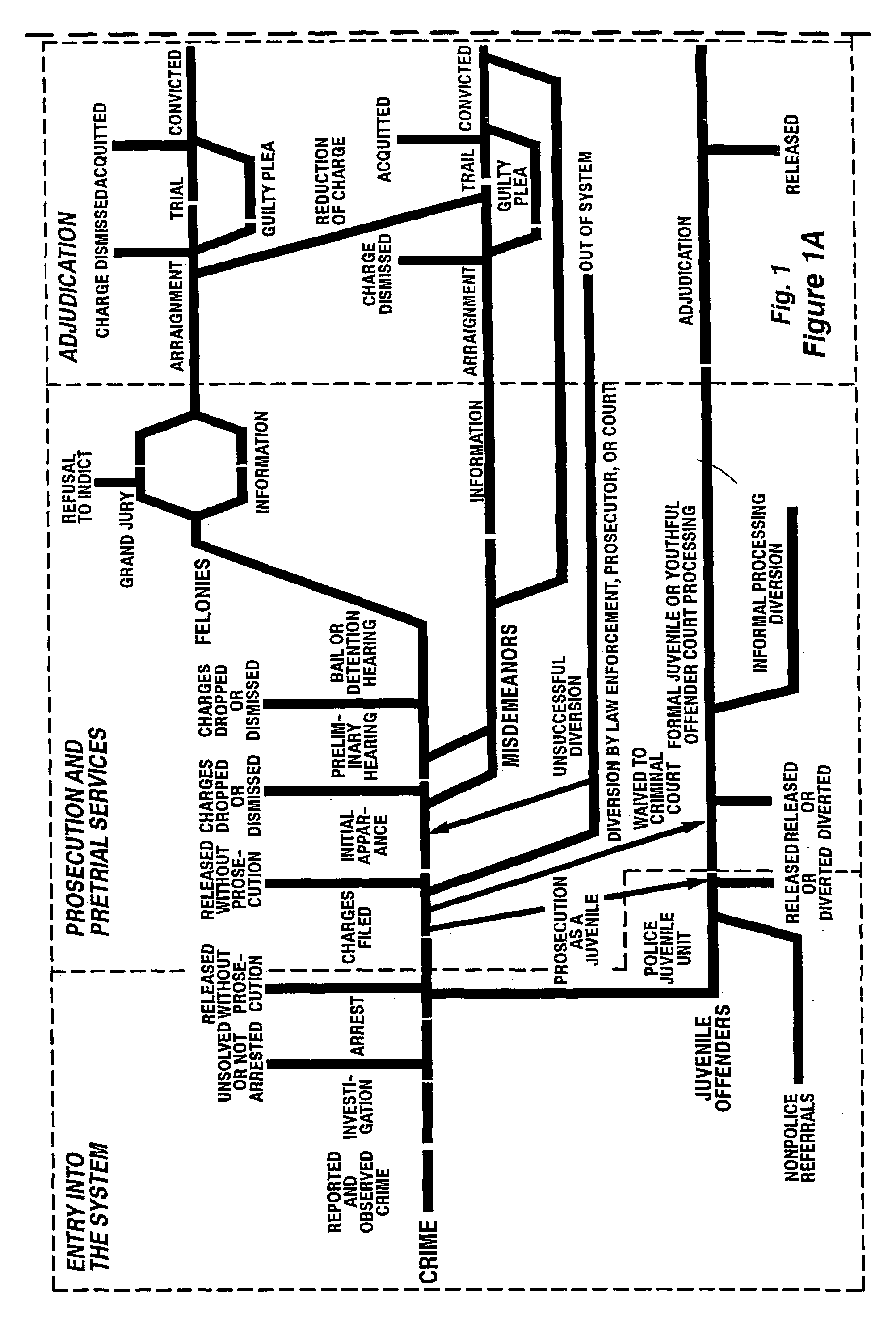
Platform independent model-based framework for exchanging information in the justice system
InactiveUS20050216555A1Guaranteed message deliveryData processing applicationsMultiple digital computer combinationsCost effectivenessSoftware agent
A platform independent model for exchanging information among numerous entities in a justice system with diverse system components is implemented in a hub and spoke arrangement. Each spoke includes a software agent that communicates with a system component of an entity of the justice system, translates from a common communication format to a communication format of the system component, and manages the timing of the flow of information to / from the system component. The hub includes an information broker that communicates with each agent in the common communication format, determines what information is needed by which entity, and routes the needed information to / from respective agents for the entities that need the information. The platform independent model includes a plurality of traceable and linked UML models that define the information broker from a business use case model through to a platform independent solution model for implementation on a given solution platform. Since these UML models are readily modifiable and traceable for changes to the justice system, they facilitate implementation of the system in a cost-effective manner from one customer to the next without requiring system redesign.
Owner:UNISYS CORP
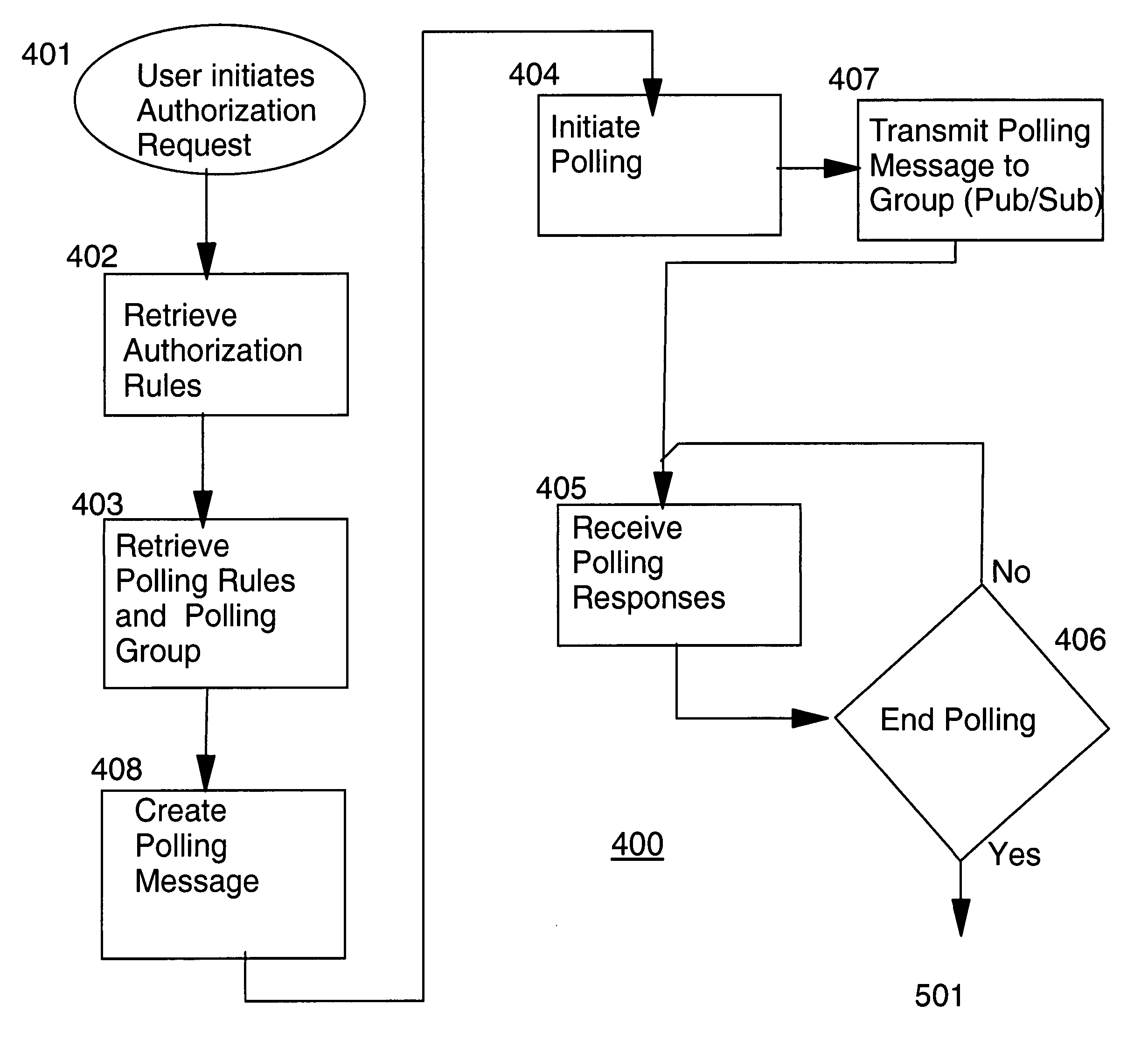
Real-time voting based authorization in an autonomic workflow process using an electronic messaging system
ActiveUS20060021023A1Simple processMinimal human interactionDigital data processing detailsUser identity/authority verificationSoftware engineeringSoftware agent
In a network of computer systems having a group of users subscribing to a service comprising restricted channels, a user applies for an action to be performed by an automated software agent. The agent initiates a poll of a predetermined group of subscribers soliciting votes for approving the action. When the poll is complete, the votes are tallied by the agent and compared with predetermined authorization rules. If the votes pass the rules test, the action is approved and performed by a software agent. The user in one embodiment is an automated software agent.
Owner:IBM CORP
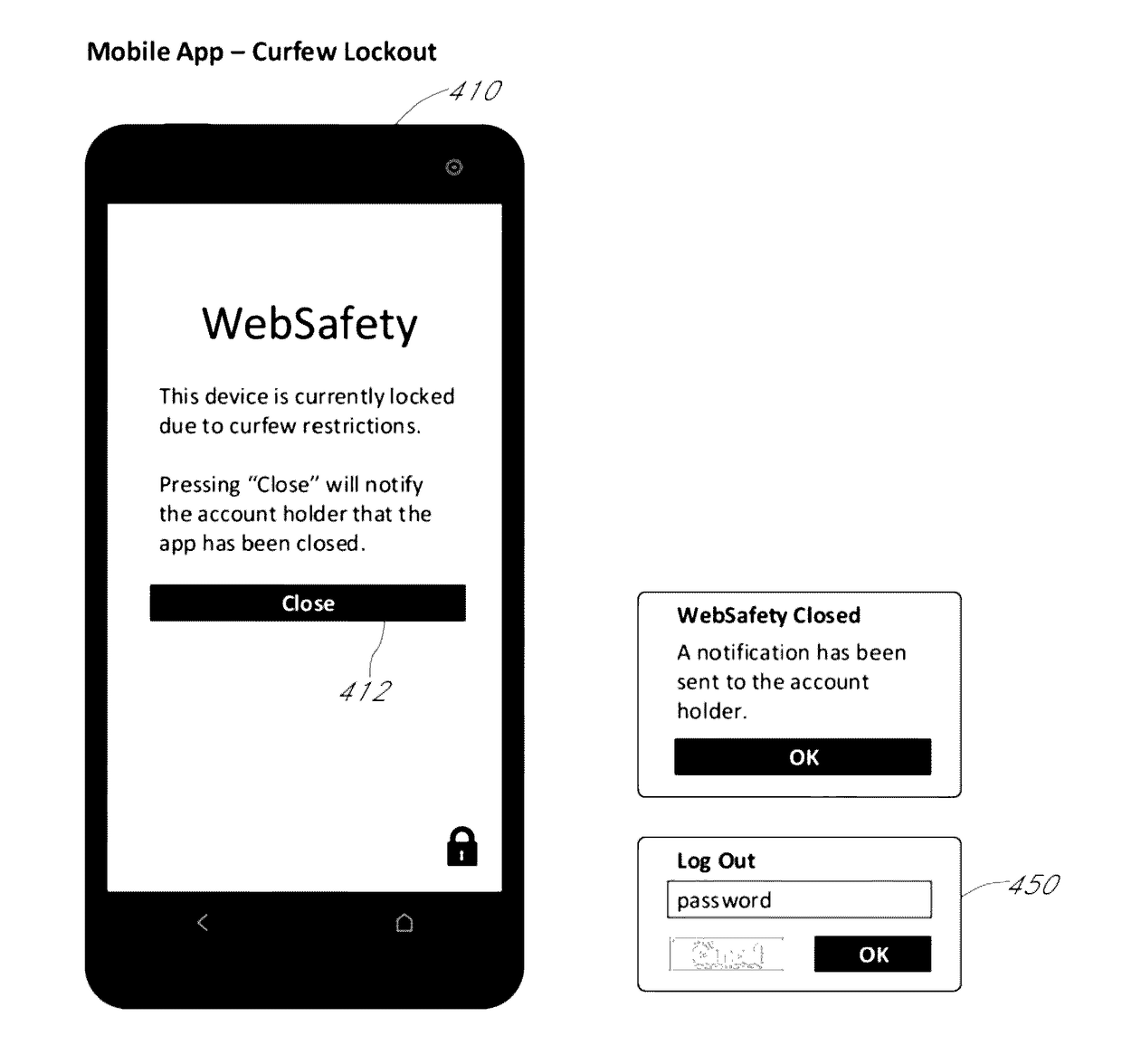
Management and control of mobile computing device using local and remote software agents
ActiveUS20170149795A1Computer security arrangementsLocation information based serviceSocial mediaWeb browser
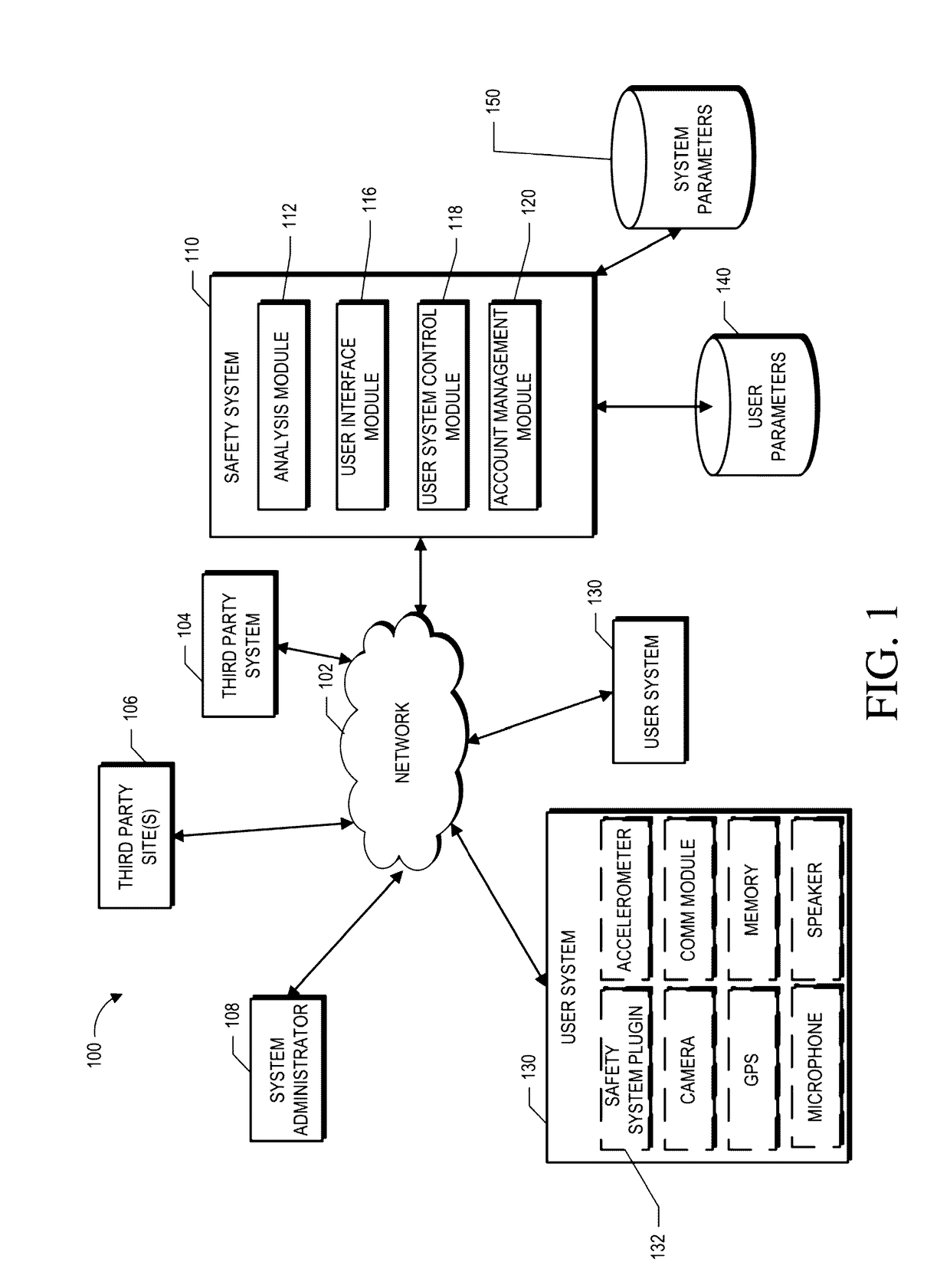
Devices, systems, and methods for allowing parents to view and track smart phone activities of their children can include one or more child software modules. The module can be installed on each child's smart phone. The module can access and extract data from or about more than one of the smart phone's other software applications, including at least two of the following: a texting application, a social media application, an image application that facilitates transmission or reception of images, and a web browser application. The module can further send the extracted data to an analysis server. The module can also monitor location data. Moreover, the system can include an analysis server that can identify potentially harmful language, images, and websites. Further, the system can include a parent portal. The parent portal can receive results from the analysis server.
Owner:WEBSAFETY
Software agent for facilitating electronic commerce transactions through display of targeted promotions or coupons
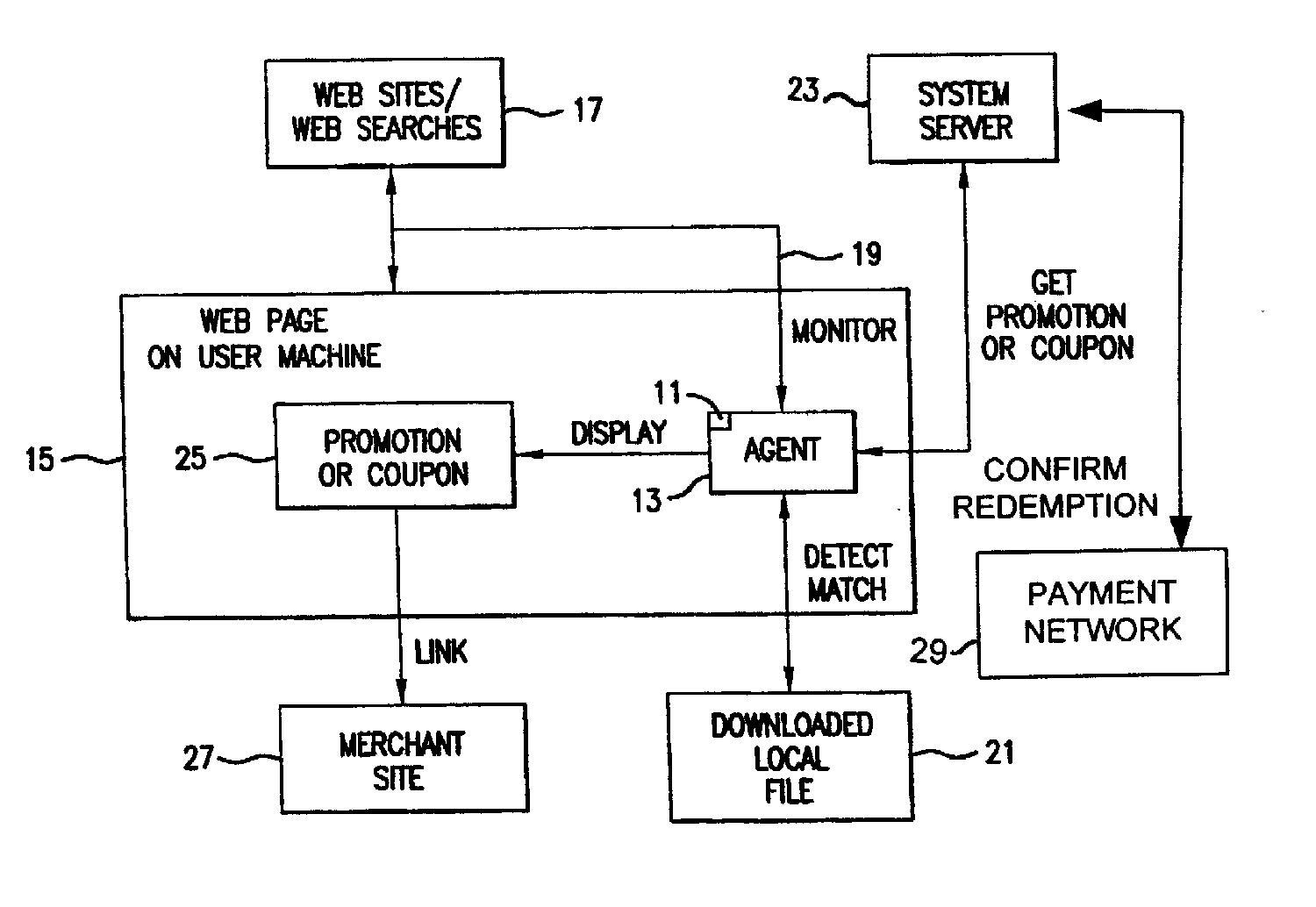
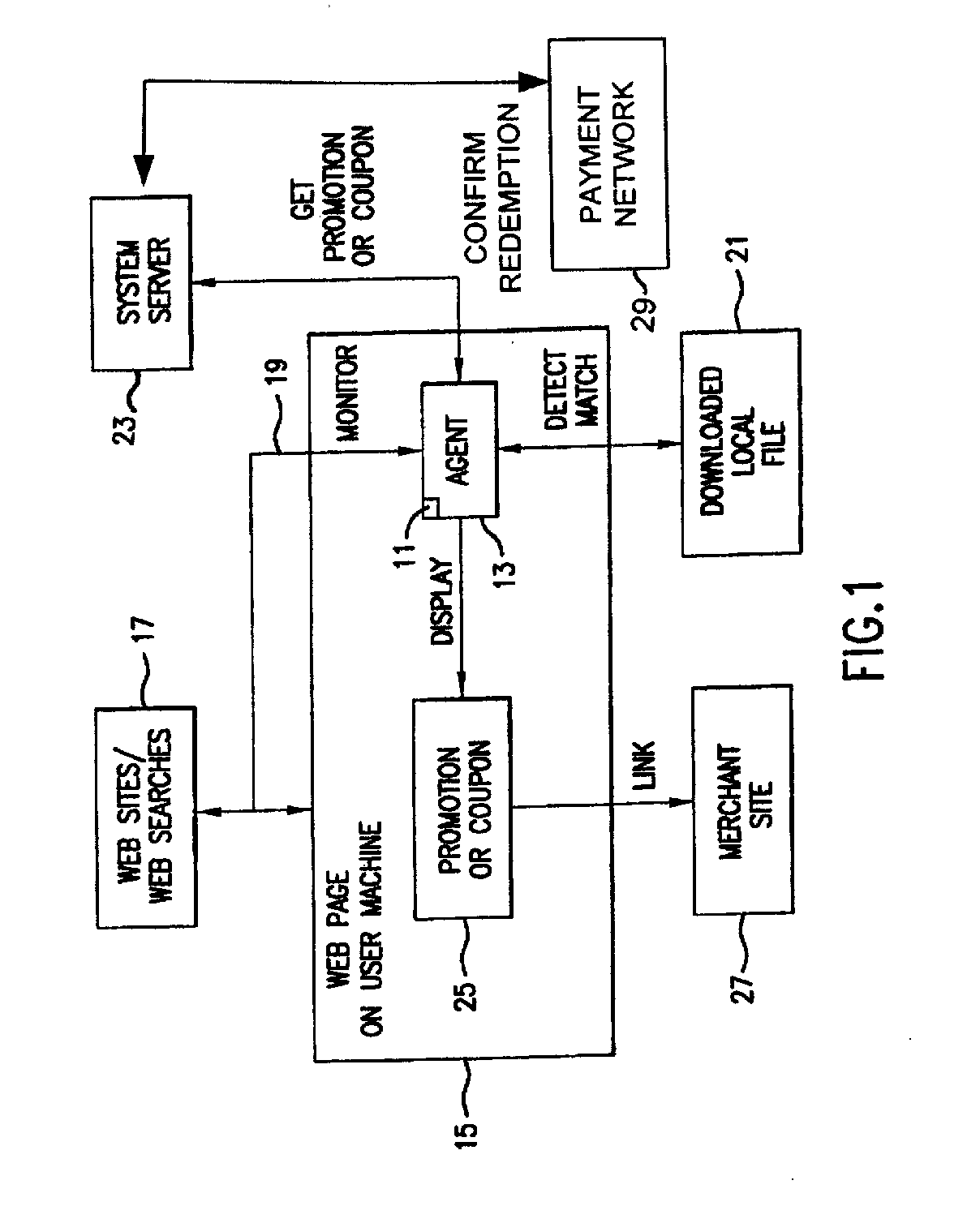
InactiveUS20060015405A1Easy to confirmAdvertisementsBroadcast information monitoringNetwork addressSoftware
A software agent for locally tracking a user's network interaction, such as web browsing, and providing targeted promotions with optional coupons to the user. The monitoring involves use of a downloaded file of network addresses and words potentially tailored to each individual user. The software agent locally compares network addresses and content of web sites accessed and search terms entered against the stored addresses and key words in the file. Upon detecting a match, the software agent contacts a system server to obtain a promotion with an optional coupon for the match, and displays an indication of the promotion or coupon to the user, providing the user with the option to view, decline, save, or defer the promotion. The user is provided with redeemable credits for viewing promotions, visiting the site of a merchant offering the promotion, completing a transaction, and spending at least a threshold dollar amount. The coupons can include coupons targeted to users geographically close to particular merchants so that the coupons can be printed and redeemed at the merchant's establishment. Transactions related to the promotions, whether completed online or in-store, are confirmed to demonstrate the efficacy of the promotions, award additional loyalty rewards to a user's account, or to compensate an advertiser or affiliate. Confirmation of in-store transactions may be accomplished by accessing transaction data routed through third-party payment networks used for credit and debit card transactions and cellular phone transactions and the like.
Owner:KNOWLEDGEFLOW
Real time context learning by software agents
InactiveUS7296007B1Cathode-ray tube indicatorsKnowledge representationTheoretical computer scienceEngineering
Owner:YEN WEI
Method and system for monitoring environmental conditions
InactiveUS20060187017A1Telephonic communicationElectric testing/monitoringTelecommunications linkCommunication link
A system for detecting the occurrence of anomalies includes a plurality of spaced apart nodes, with each node having adjacent nodes, each of the nodes having one or more sensors associated with the node and capable of detecting anomalies, and each of the nodes having a controller connected to the sensors associated with the node. The system also includes communication links between adjacent nodes, whereby the nodes form a network. At least one software agent is capable of changing the operation of at least one of the controllers in response to the detection of an anomaly by a sensor.
Owner:UT BATTELLE LLC
Platform independent model-based framework for exchanging information in the justice system
InactiveUS7181493B2Data processing applicationsDigital data processing detailsSoftware agentInformation agents
A platform independent model for exchanging information among numerous entities in a justice system with diverse system components is implemented in a hub and spoke arrangement. Each spoke includes a software agent that communicates with a system component of an entity of the justice system, translates from a common communication format to a communication format of the system component, and manages the timing of the flow of information to / from the system component. The hub includes an information broker that communicates with each agent in the common communication format, determines what information is needed by which entity, and routes the needed information to / from respective agents for the entities that need the information. The platform independent model includes a plurality of traceable and linked UML models that define the information broker from a business use case model through to a platform independent solution model for implementation on a given solution platform. Since these UML models are readily modifiable and traceable for changes to the justice system, they facilitate implementation of the system in a cost-effective manner from one customer to the next without requiring system redesign.
Owner:UNISYS CORP
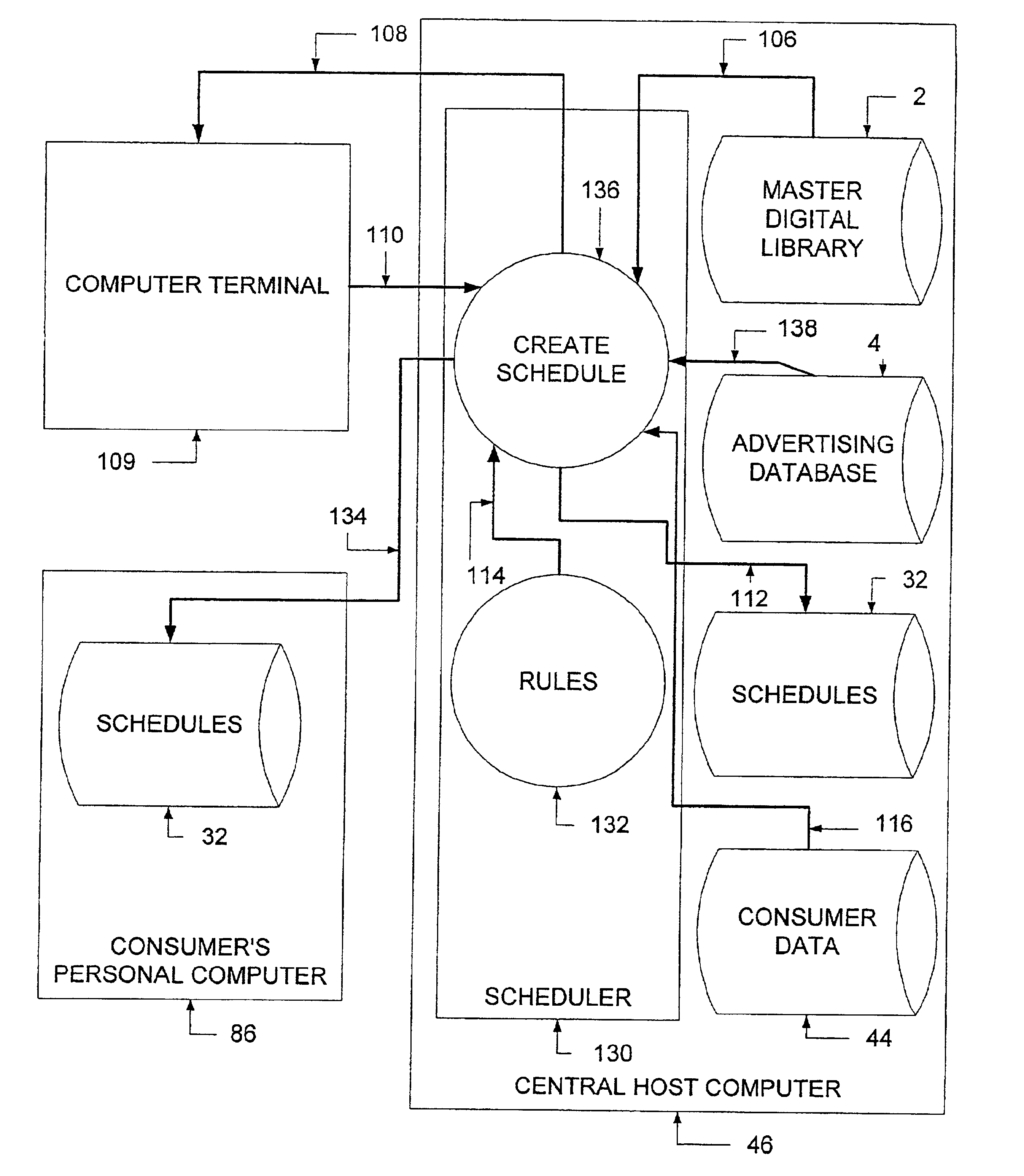
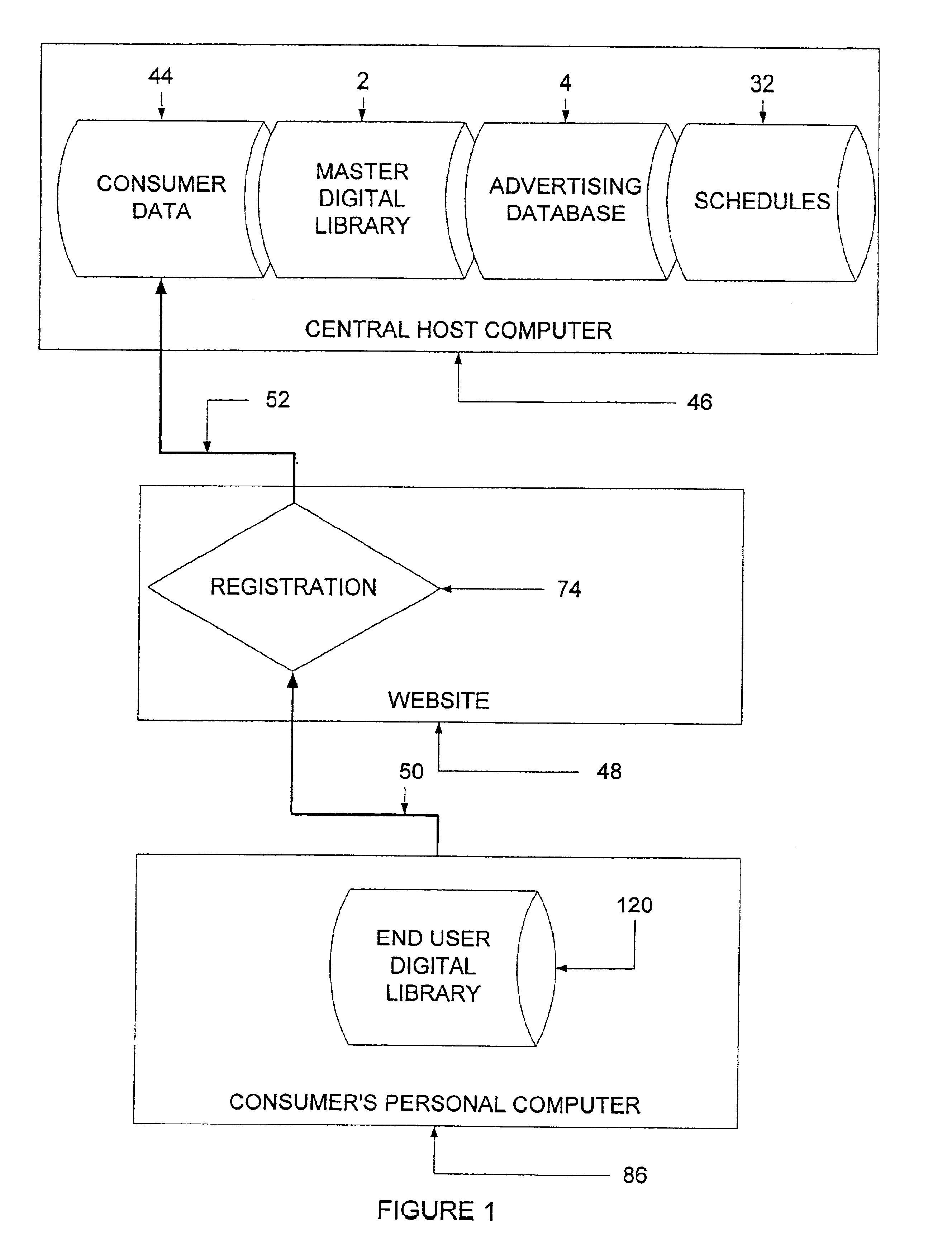
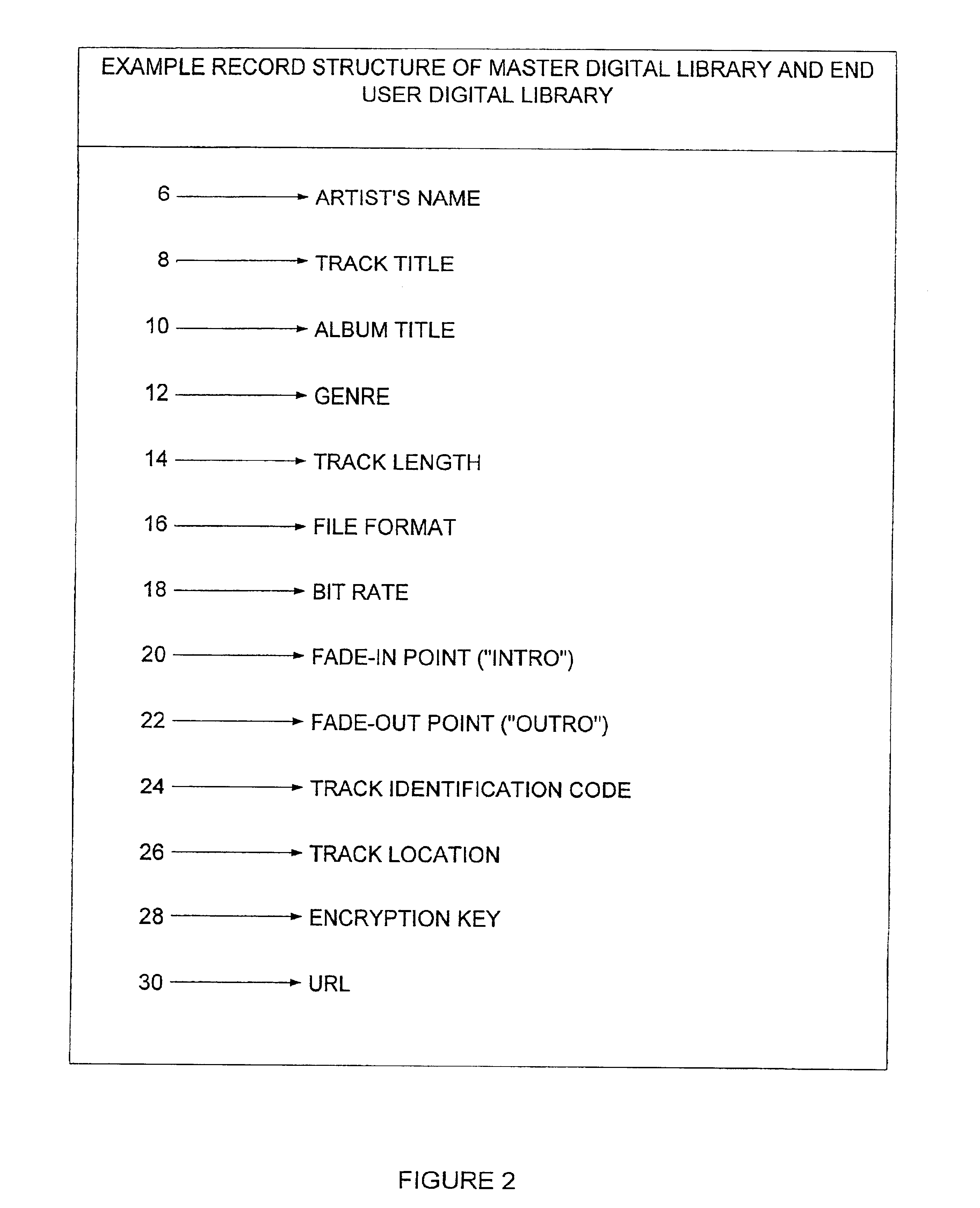
Personal digital content system
InactiveUS6842604B1Implement economyAdvertisementsBroadcast transmission systemsTime schedulePersonalization
An Internet-enabled means of distributing entertainment programming with embedded advertising in which the entertainment programming is customized according to consumers' stated preferences and the advertising is customized according to consumer demographics and also according to consumers' stated preferences. A computing system usable to create and distribute personalized entertainment and advertising content comprising computer hosts having software agents acting to administer a master digital library as well as end users' digital libraries, establish advertising bookings and insert advertising content, establish schedules of digital content for distribution to end users, identify digital content listed on a schedule but missing from the end user's digital library, distribute across a communications network digital content to end users, and decrypt and play or display the digital entertainment and advertising content. A communications network for exchanging information and data among said computer hosts and agents.
Owner:RPX CORP
Virtual player tracking and related services
InactiveUS20070270213A1Apparatus for meter-controlled dispensingVideo gamesOperational systemSoftware agent
Various gaming-related services are provided, including but not limited to security services, harm minimization services, player identification services, bonusing / progressive services, accounting services, financial / banking services, network tunneling services, cheating detection services, etc. Such services may be provided, at least in part, by software agents that can be configured for different platforms and / or operating systems. Some software-based player tracking methods of the invention can aggregate data from multiple devices used by a player for gaming.
Owner:IGT
Virtual player tracking and related services
InactiveUS8057298B2Apparatus for meter-controlled dispensingVideo gamesComputer networkSoftware agent
Various gaming-related services are provided, including but not limited to security services, harm minimization services, player identification services, bonusing / progressive services, accounting services, financial / banking services, network tunneling services, cheating detection services, etc. Such services may be provided, at least in part, by software agents that can be configured for different platforms and / or operating systems. Some software-based player tracking methods of the invention can aggregate data from multiple devices used by a player for gaming.
Owner:IGT
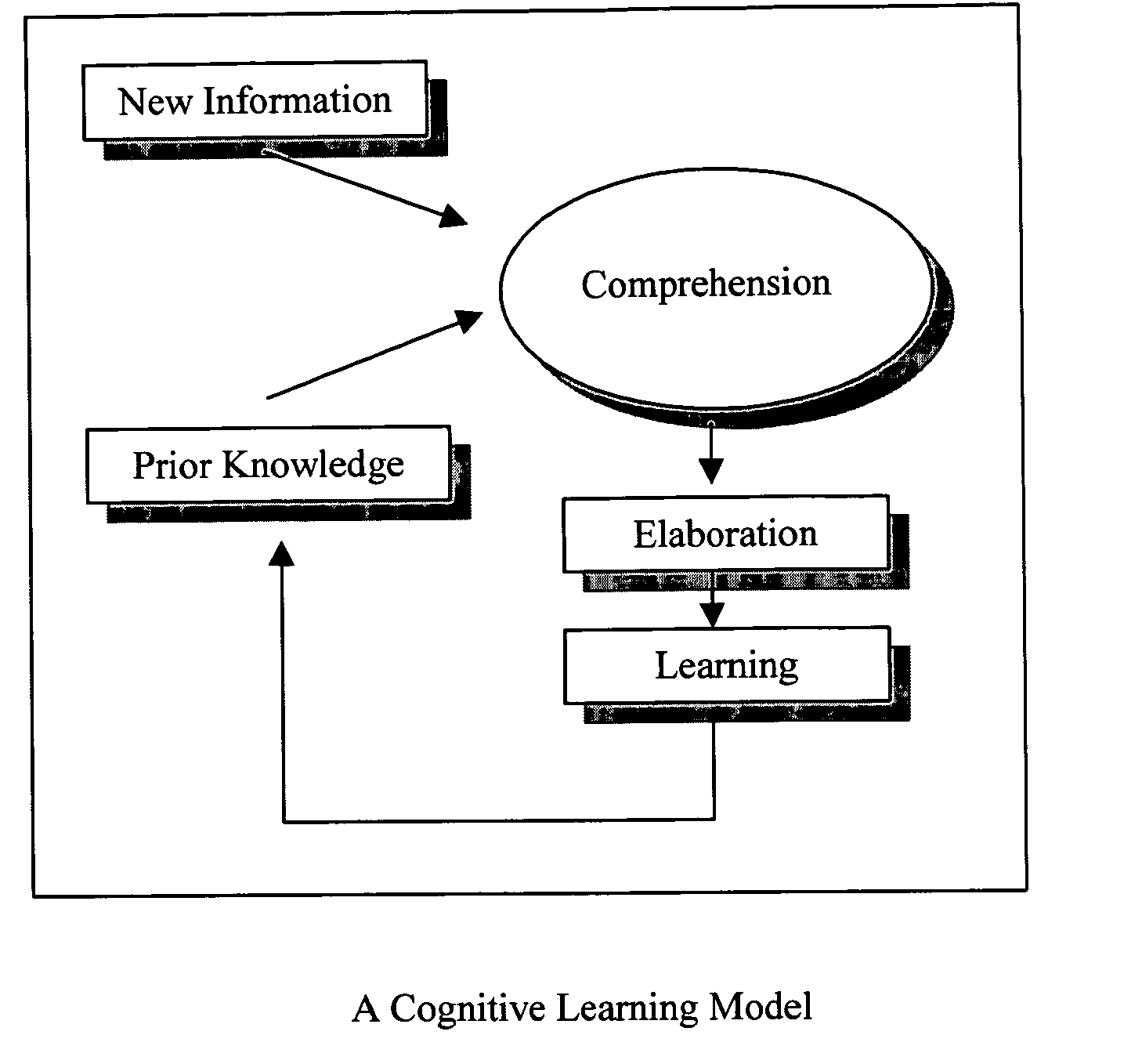
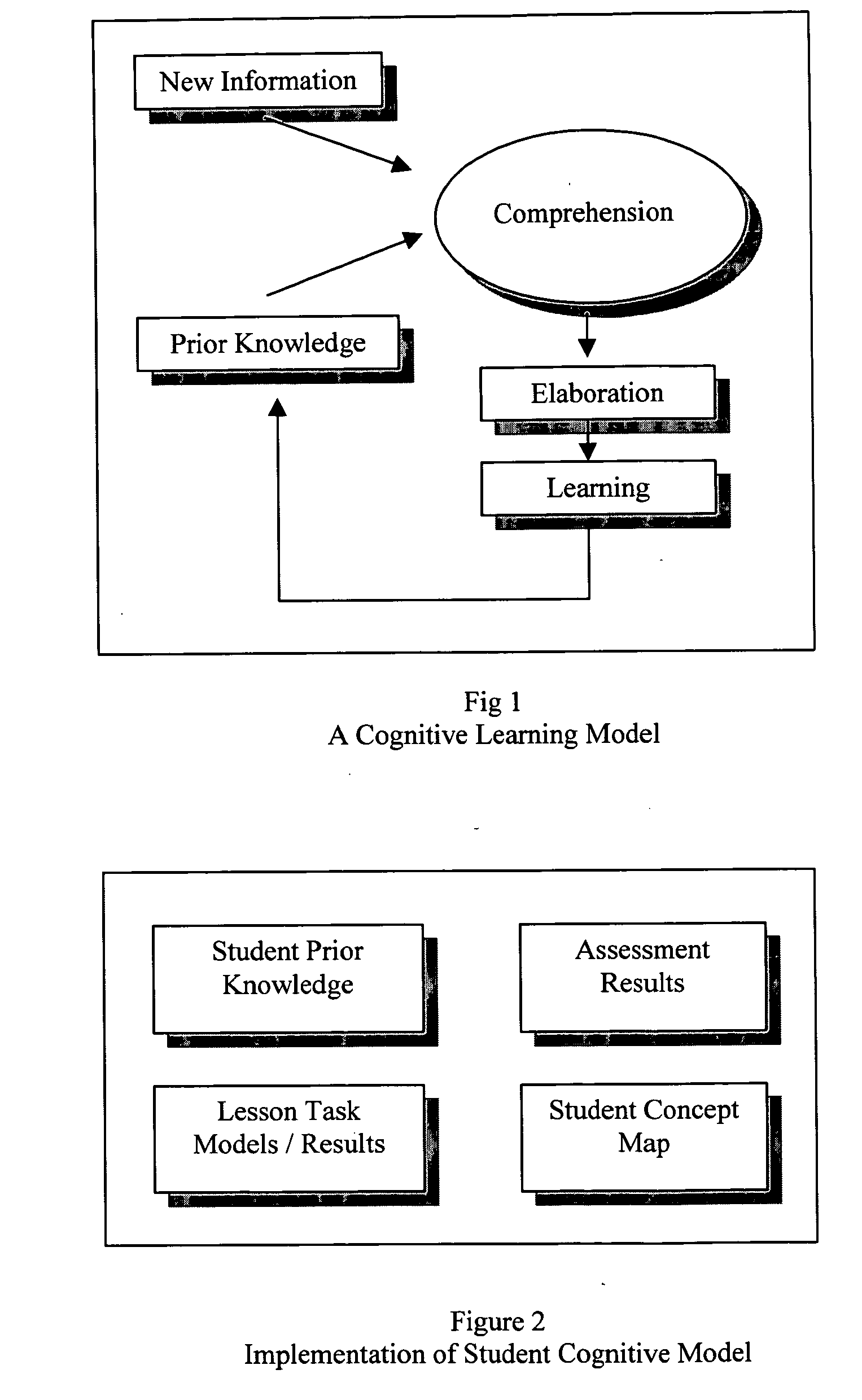
Predictive artificial intelligence and pedagogical agent modeling in the cognitive imprinting of knowledge and skill domains
InactiveUS20060166174A1Accurate predictionNew informationReadingElectrical appliancesPredictive learningAnimation
Owner:ROWE T PETER +2
Data archiving system
ActiveUS20070038857A1Digital data processing detailsComputer security arrangementsFault toleranceExternal storage
An encrypted file storage solution consists of a cluster of processing nodes, external data storage, and a software agent (the “File System Watcher”), which is installed on the application servers. Cluster sizes of one node up to many hundreds of nodes are possible. There are also remote “Key Servers” which provide various services to one or more clusters. The preceding describes a preferred embodiment, though in some cases it may be desirable to “collapse” some of the functionality into a smaller number of hardware devices, typically trading off cost versus security and fault-tolerance.
Owner:STORCENTRIC DIP LENDER LLC +1
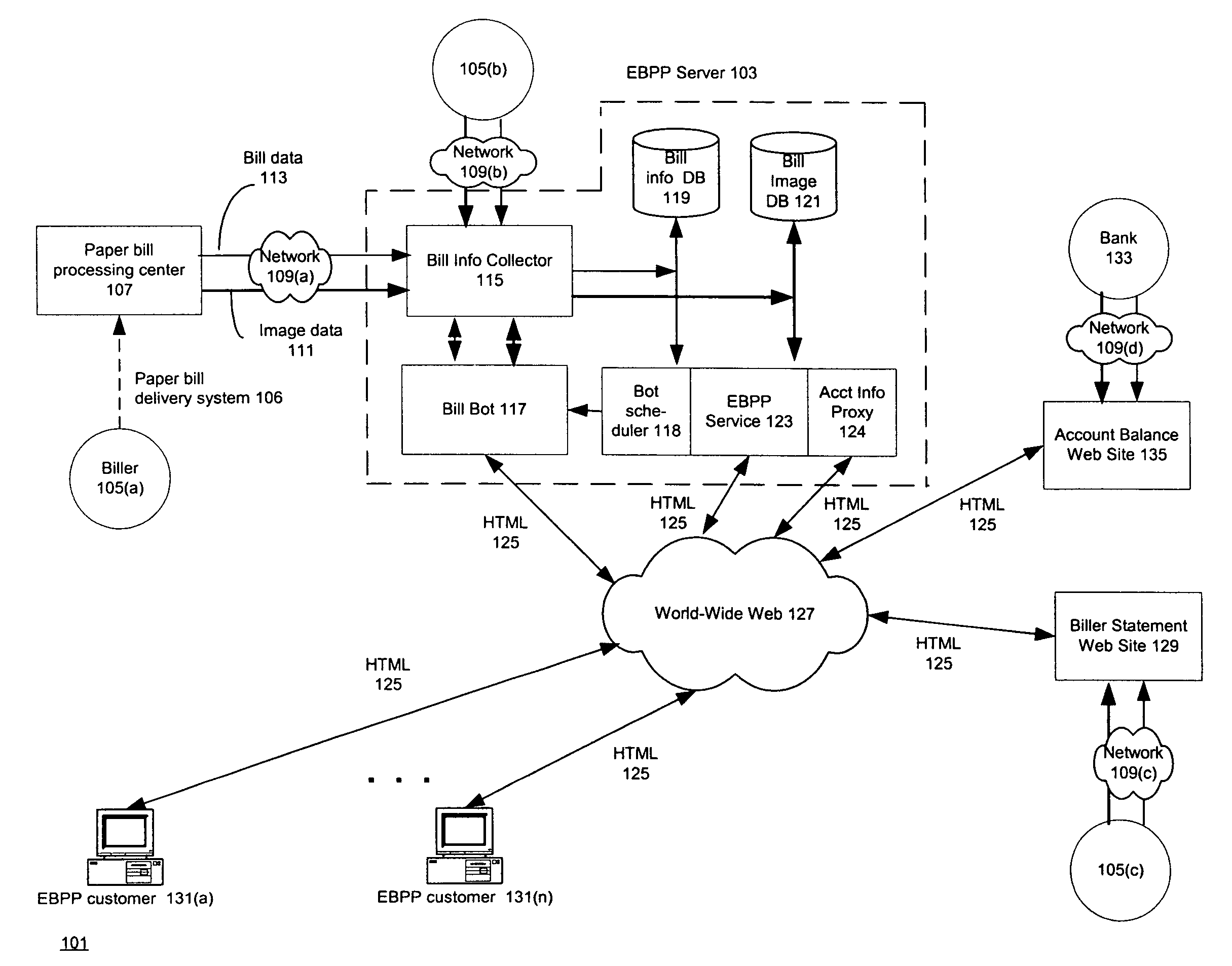
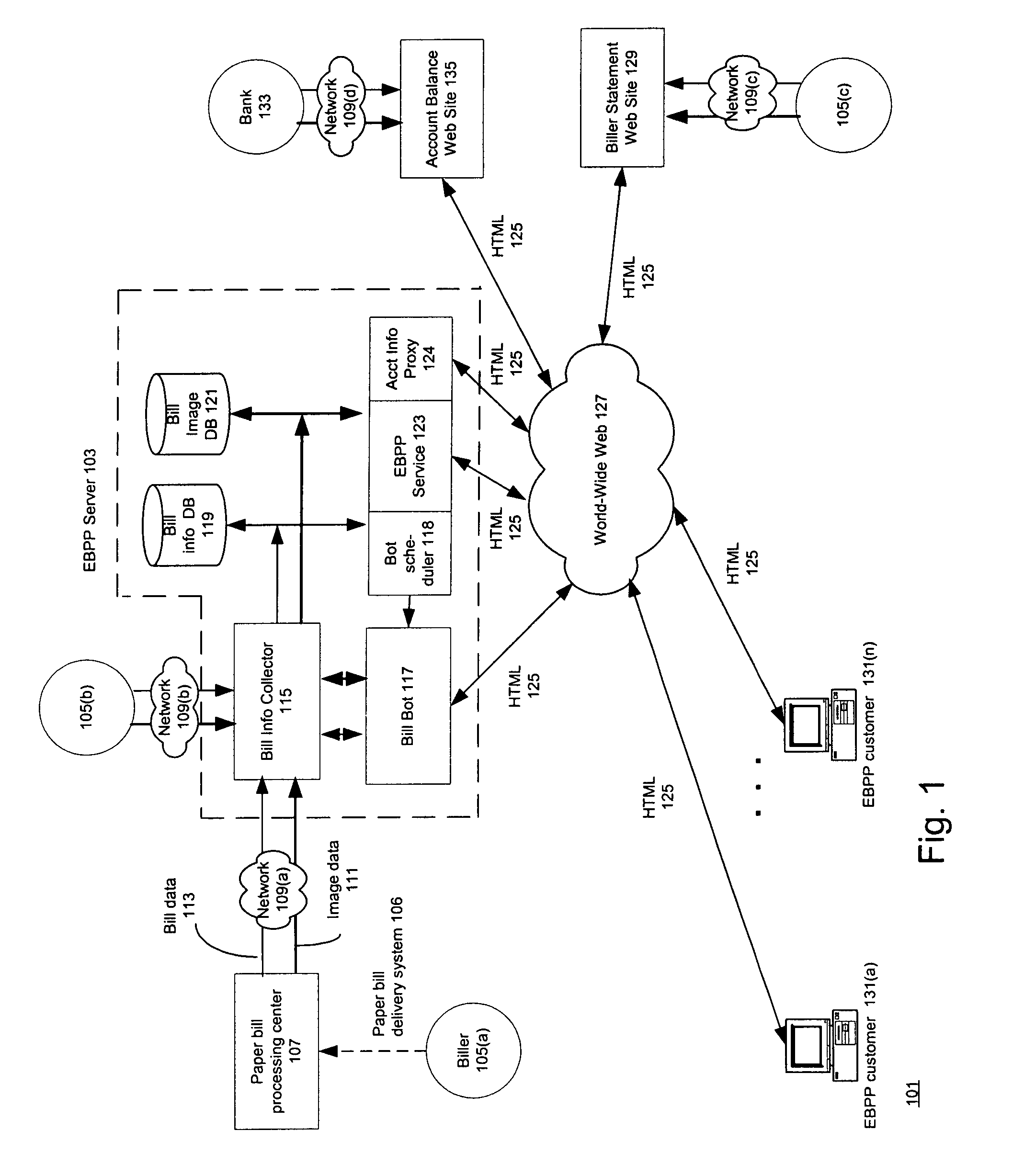
Electronic bill presentment and payment system that obtains user bill information from biller web sites
An electronic bill presentation and payment (EBPP) system that is able to obtain bills for its customers from scrape-enabled biller Web sites. The EBPP system has an interface which permits a customer to specify that the customer wishes the EBPP system to retrieve a customer's bills from a biller Web site at which the customer may access them. The customer provides his or her access information for the biller Web site to the EBPP system, which then uses a software agent to make scheduled scrapes of the biller Web site to obtain the customer's bill. The software agent scrapes not only bill summary information such as the account number, the statement date, the bill amount, the payment due date, the minimum amount and / or total amount due from the biller Web site, but also scrapes display information for the bill. The display information is the HTML that the biller Web site itself uses to display the bill. The agent cleans the HTML so that it can be displayed in the environment provided by the EBPP system. Both the bill summary information and the display information are incorporated into databases maintained by the EBPP system, which treats bills obtained from scrape-enabled Web sites in the same fashion as bills obtained from other sources.
Owner:FIDELITY INFORMATION SERVICES LLC
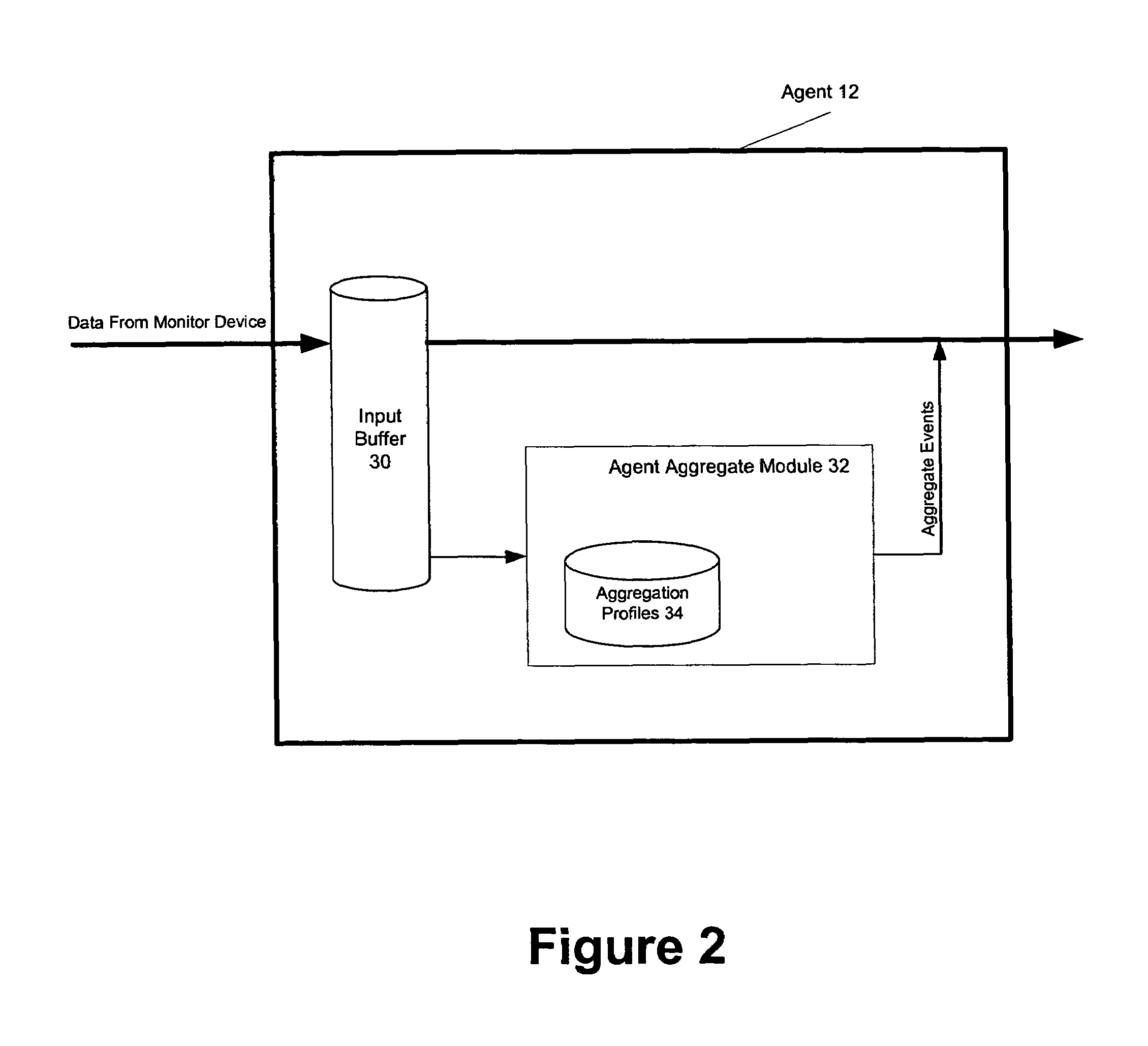
Security event aggregation at software agent
InactiveUS7644438B1Memory loss protectionError detection/correctionNetwork security policySoftware agent
A network security system can have a plurality of distributed software agents configured to collect security events from network devices. In one embodiment, the agents are configured to aggregate the security events. In one embodiment of the present invention, an agent includes a device interface to receive a security event from a network device, a plurality of aggregation profiles, and an agent aggregate module to select one of the plurality of aggregation profiles, and increment an event count of an aggregate event representing the received security event using the selected aggregation profile.
Owner:MICRO FOCUS LLC
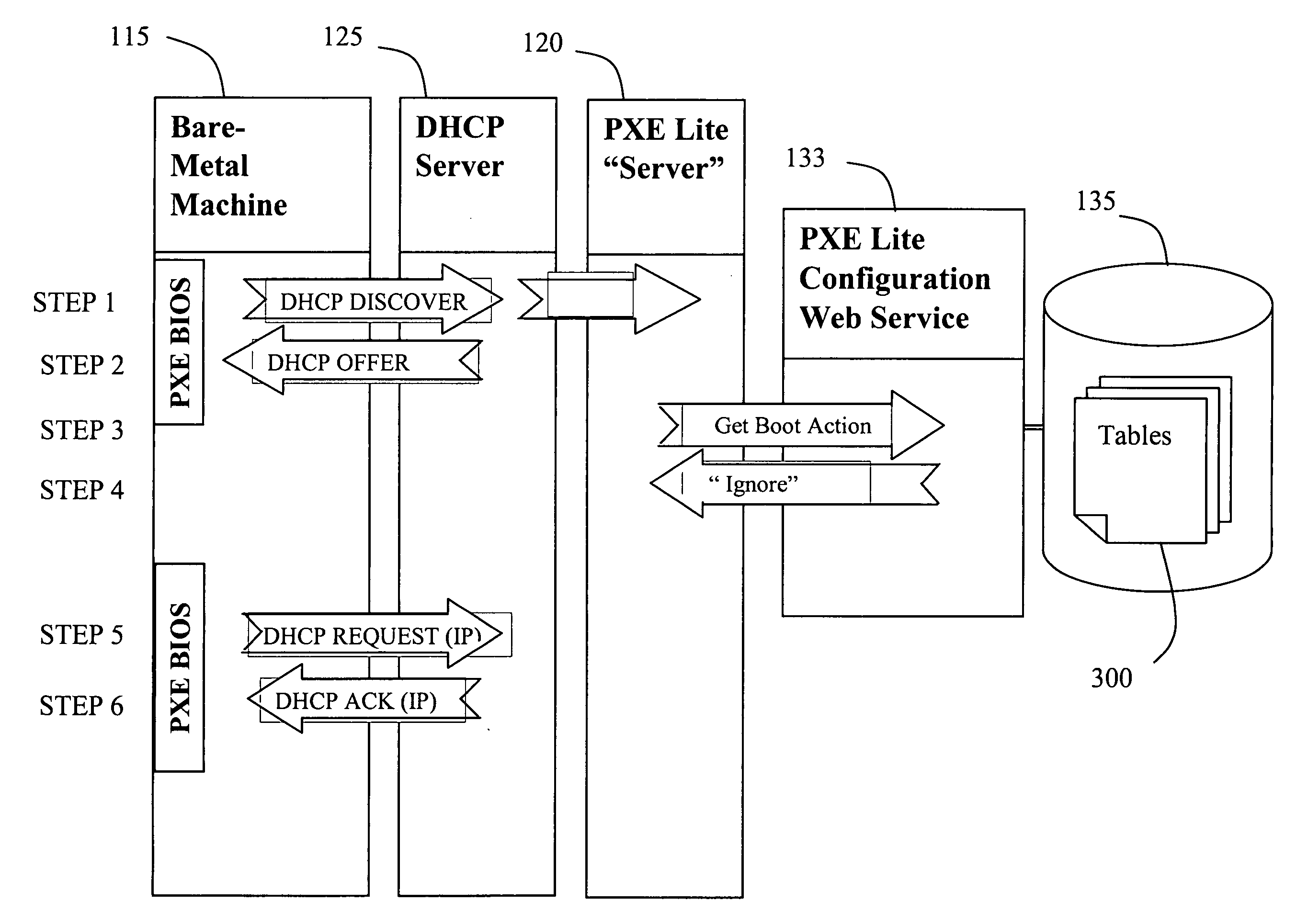
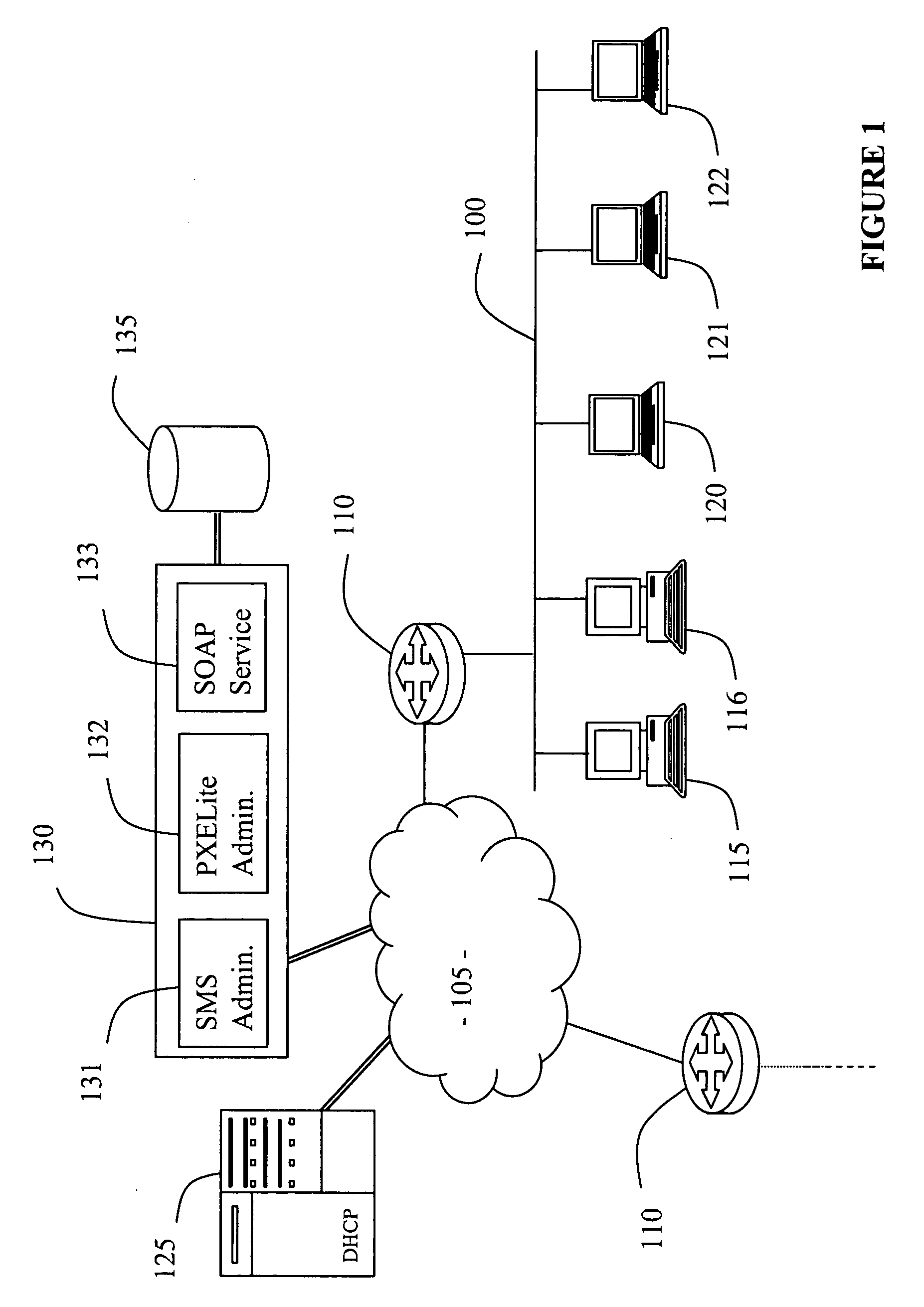
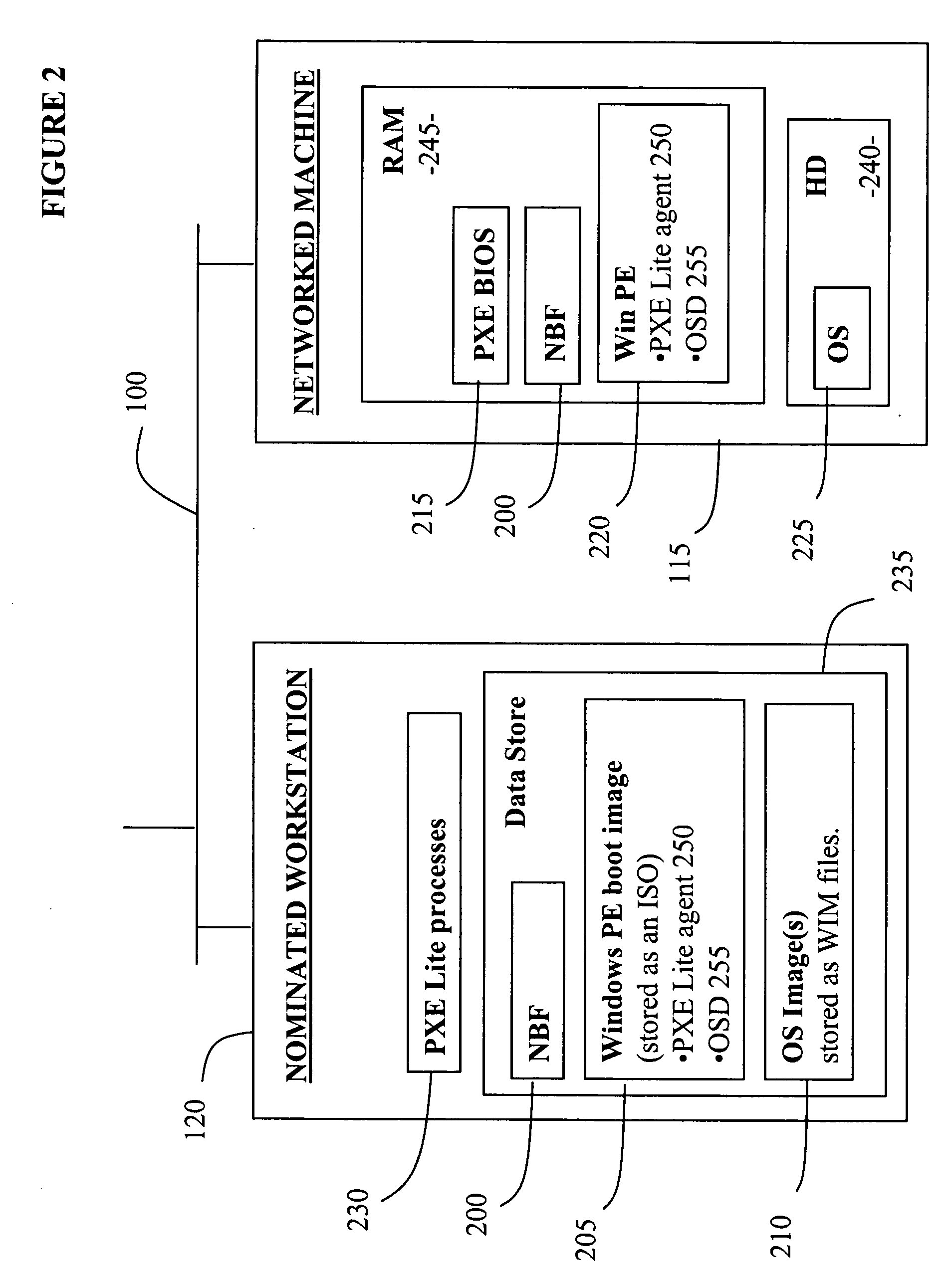
Network booting apparatus and method
ActiveUS20080155245A1Avoid problemsEasy to solveDigital computer detailsProgram controlOperational systemNetwork booting
An operating system deployment arrangement provides a database connected to a network for use in monitoring the boot status of machines connected to sub-networks of the network. A workstation connected to a sub-network is adapted to act as a server for a pre-installation environment to machines newly connecting to the sub-network or at the same geographical location. The workstation carries a program for detecting boot initiation messages broadcast on the sub-network and for progressing booting of newly connecting machines in accordance with boot action data held by the database. In particular, the workstation also sends a software agent and operating system deployment processes to a newly connected machine and the agent takes over progression of the booting process from the workstation. The data held in the database for any one machine is updated as booting progresses. Flexibility is provided both in administration of the boot action data held in the database and by means of user interaction software loaded to a newly connected machine in the course of booting.
Owner:1E LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com