Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6728 results about "Transaction data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
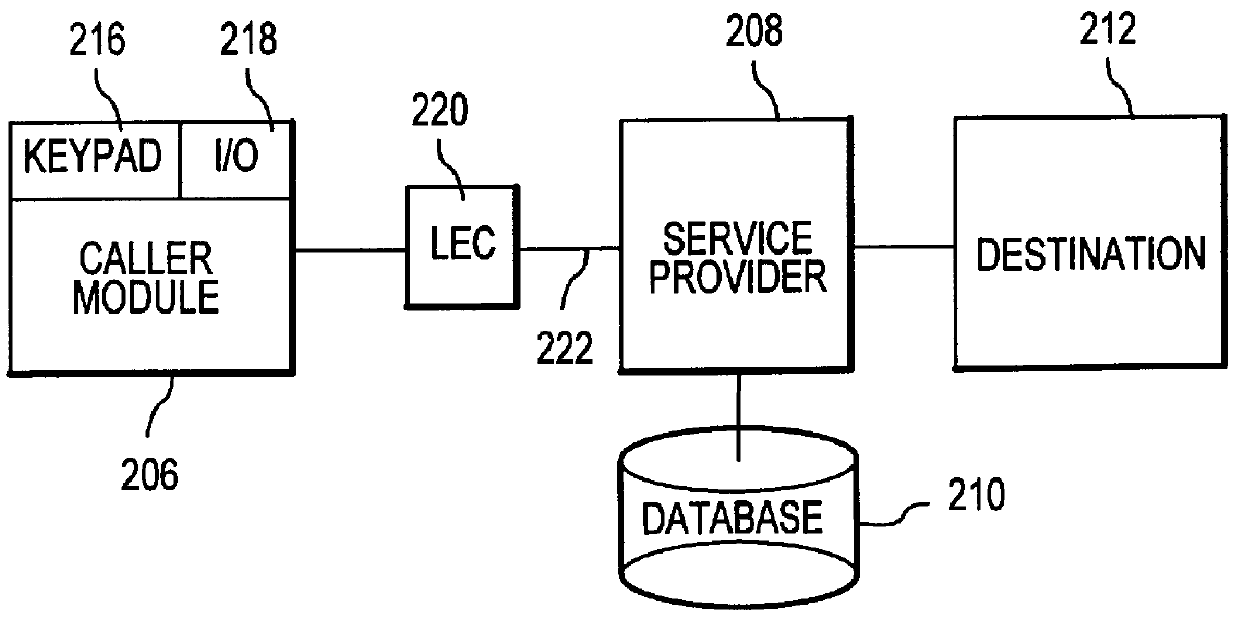
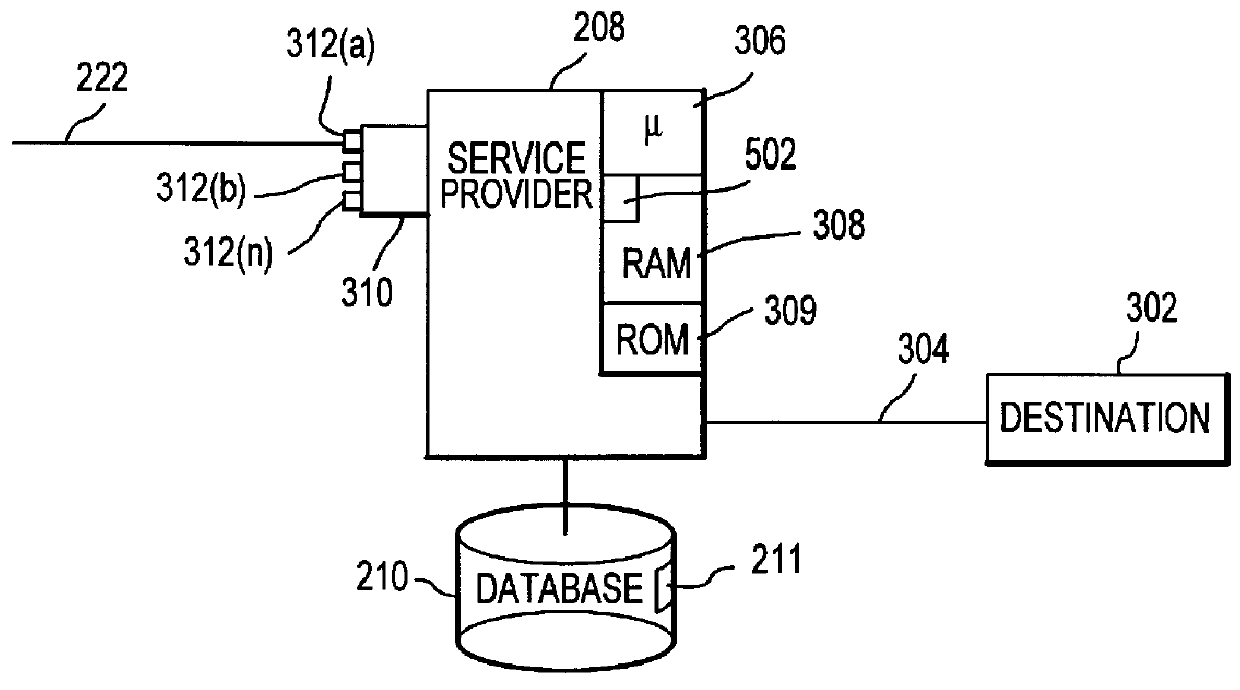
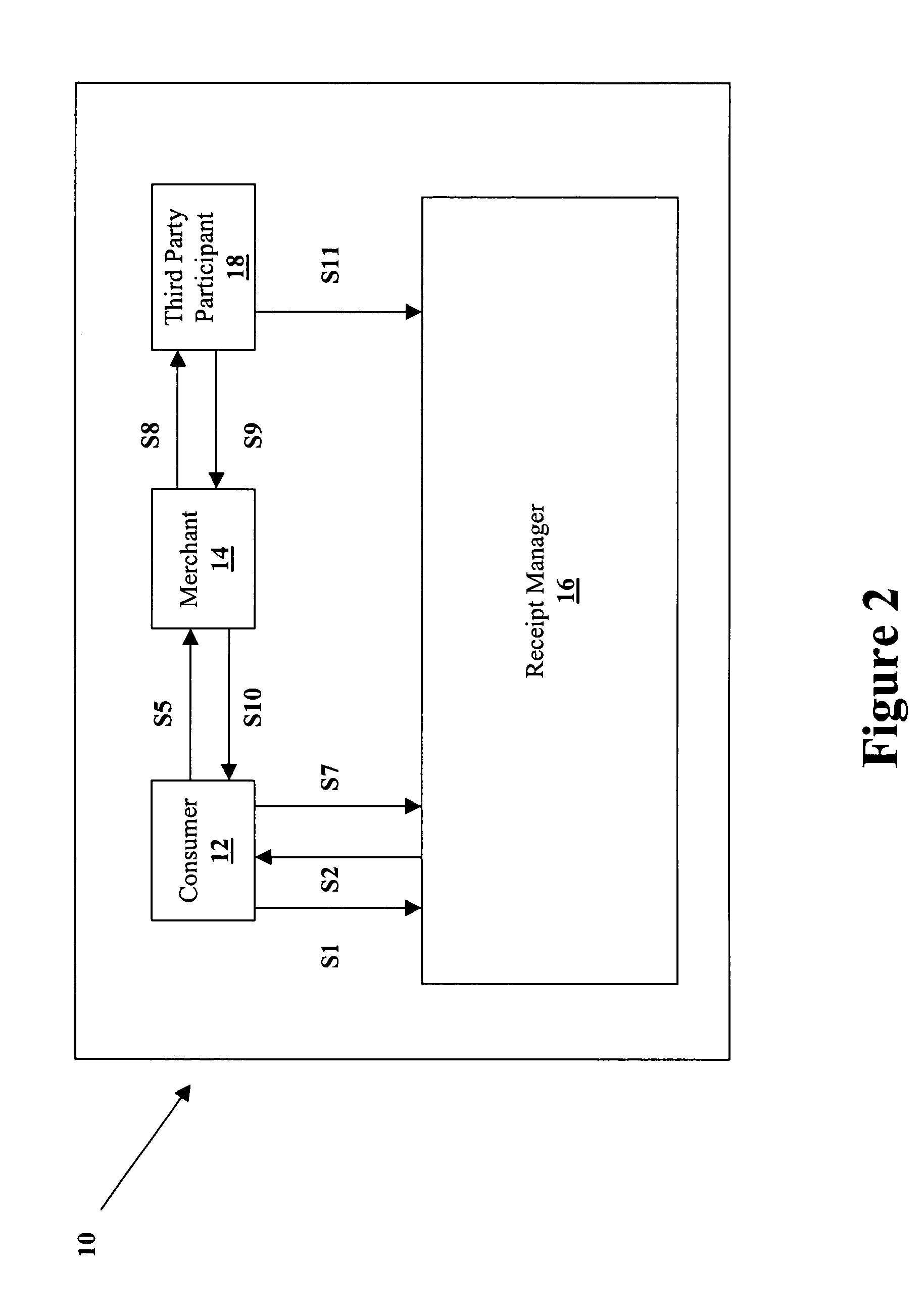
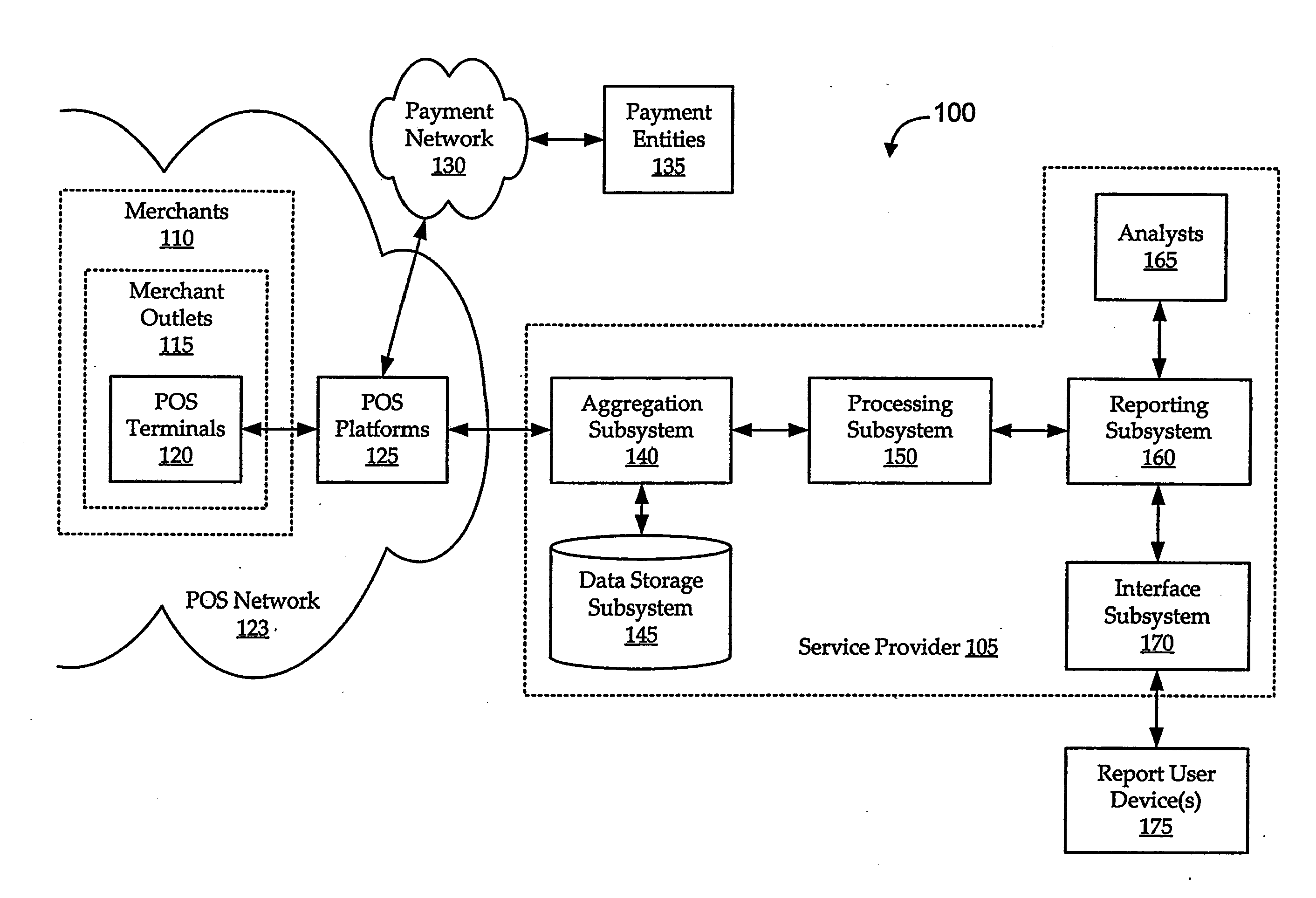
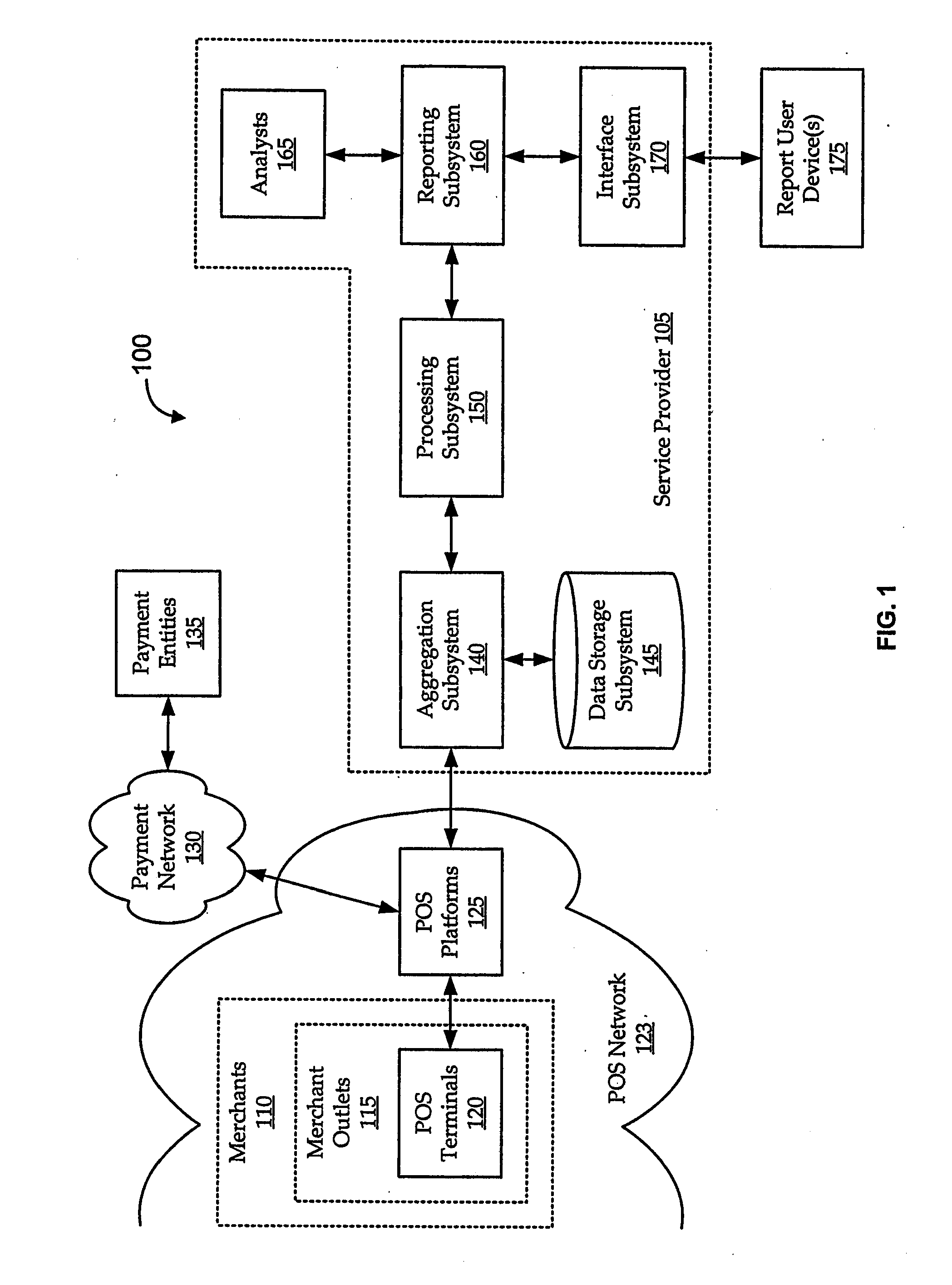
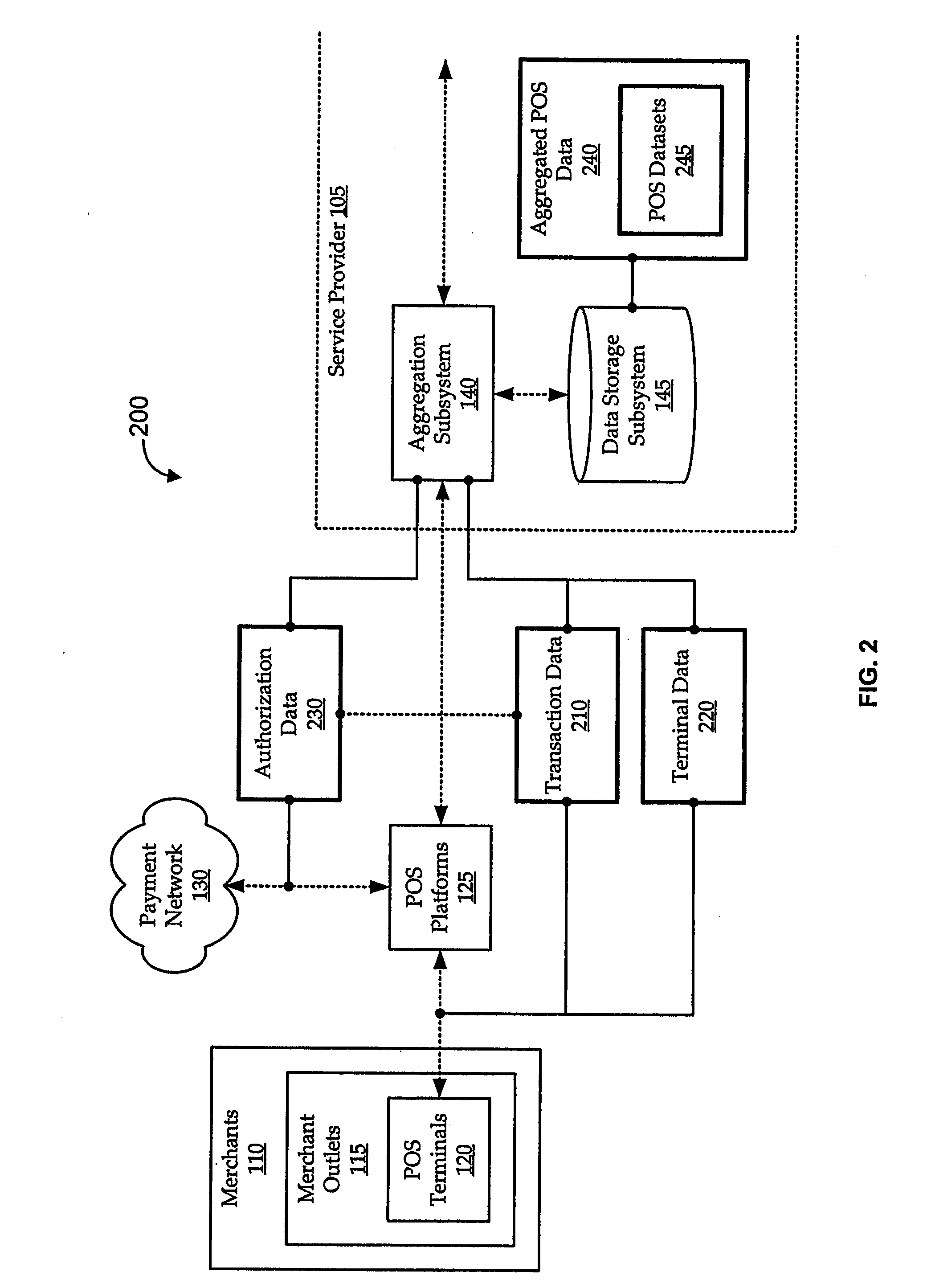
Transaction data is data describing an event (the change as a result of a transaction) and is usually described with verbs. Transaction data always has a time dimension, a numerical value and refers to one or more objects (i.e. the reference data).
Predictive modeling of consumer financial behavior using supervised segmentation and nearest-neighbor matching
InactiveUS6839682B1Specific accurate targetingIncrease valueDiscounts/incentivesDigital computer detailsPredictive modellingAlgorithm
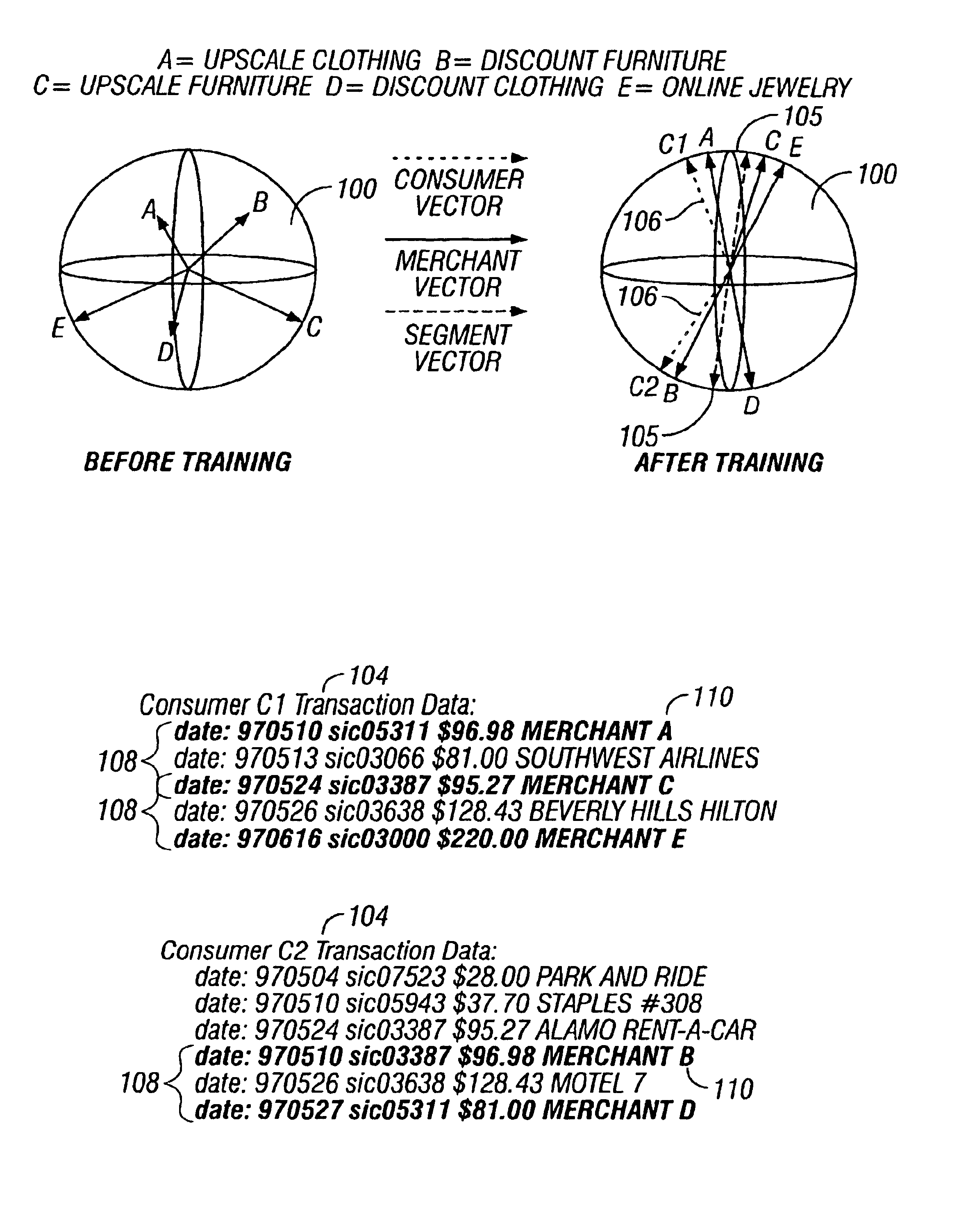
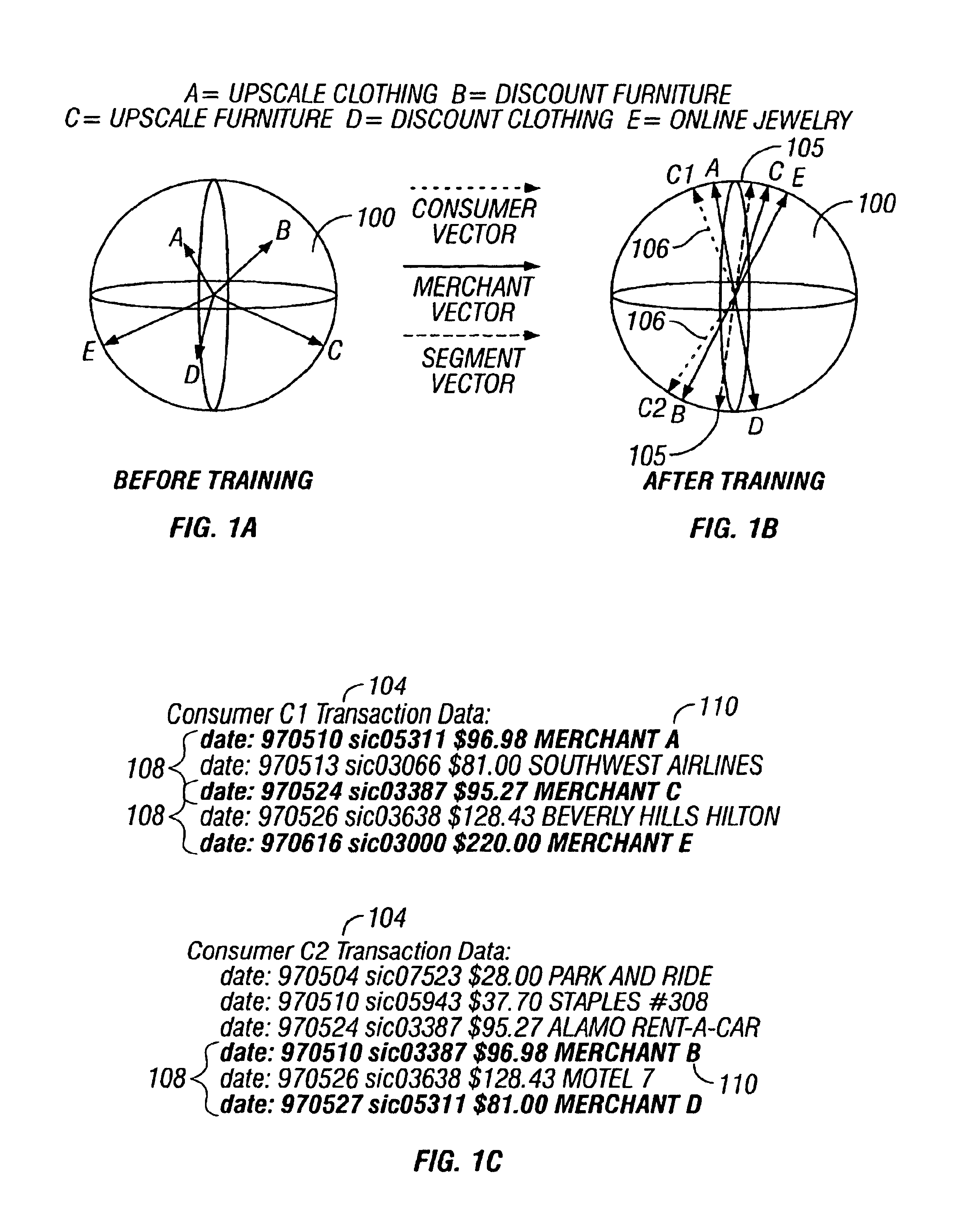
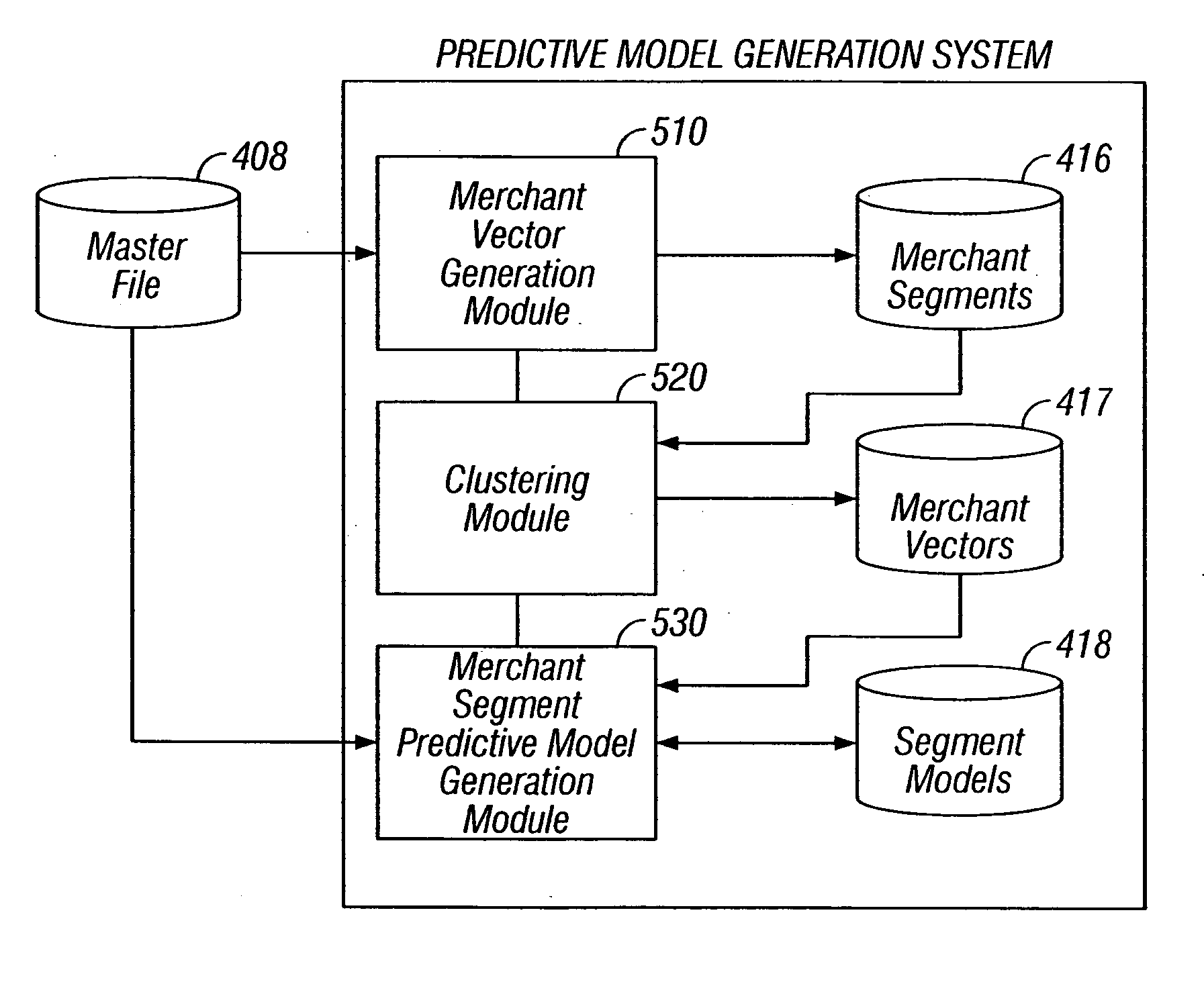
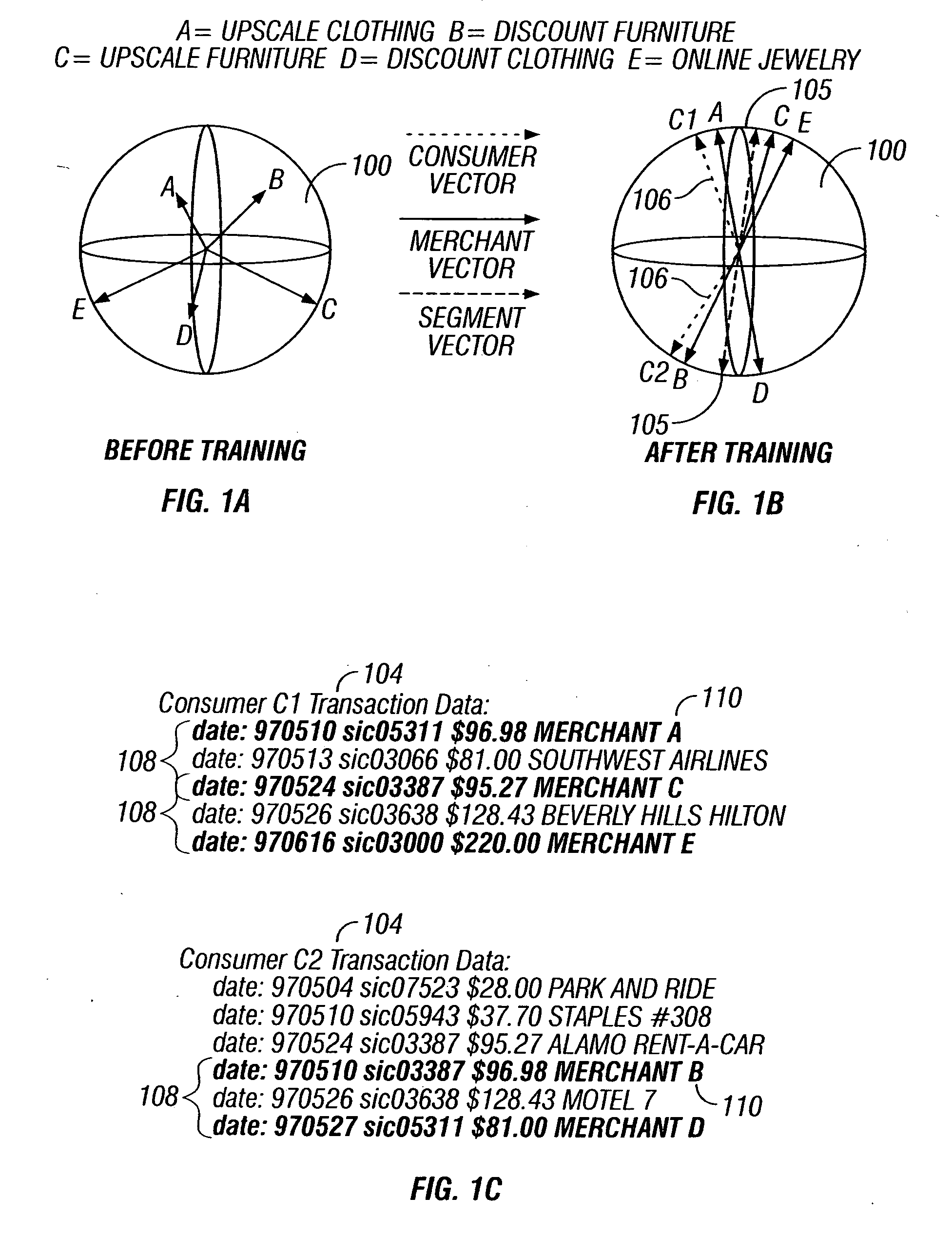
Predictive modeling of consumer financial behavior, including determination of likely responses to particular marketing efforts, is provided by application of consumer transaction data to predictive models associated with merchant segments. The merchant segments are derived from the consumer transaction data based on co-occurrences of merchants in sequences of transactions. Merchant vectors represent specific merchants, and are aligned in a vector space as a function of the degree to which the merchants co-occur more or less frequently than expected. Consumer vectors are developed within the vector space, to represent interests of particular consumers by virtue of relative vector positions of consumer and merchant vectors. Various techniques, including clustering, supervised segmentation, and nearest-neighbor analysis, are applied separately or in combination to generate improved predictions of consumer behavior.
Owner:CALLAHAN CELLULAR L L C
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
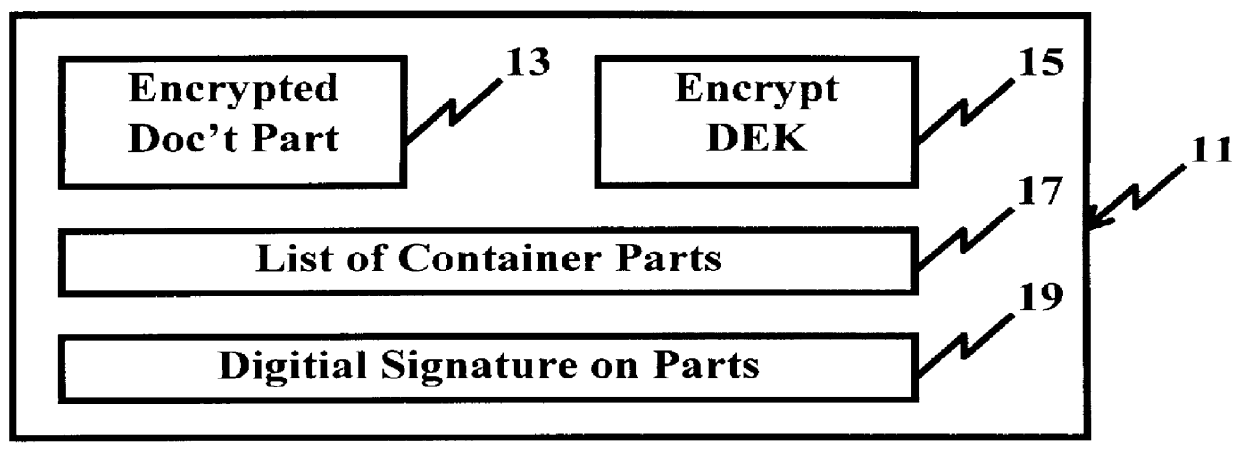
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
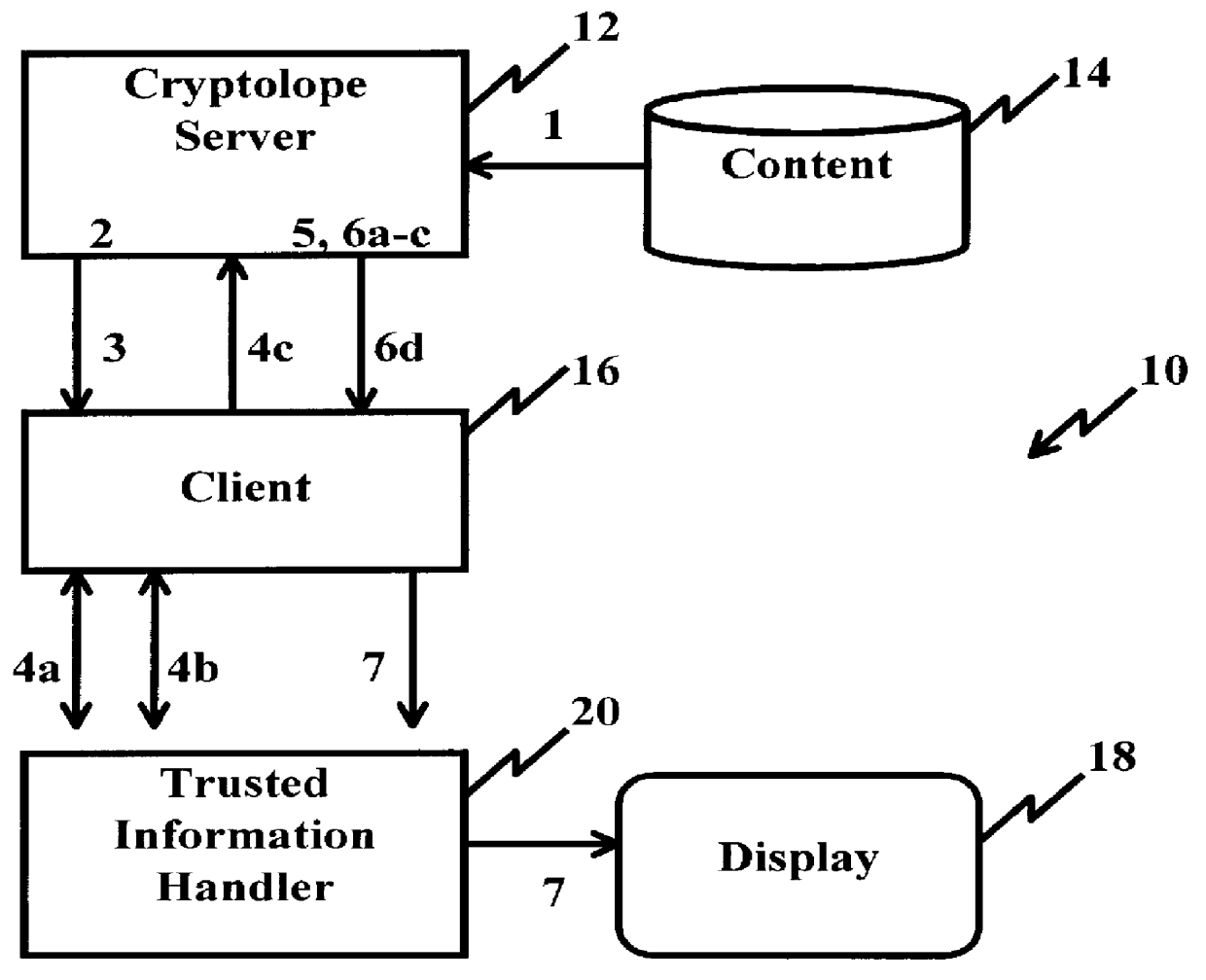
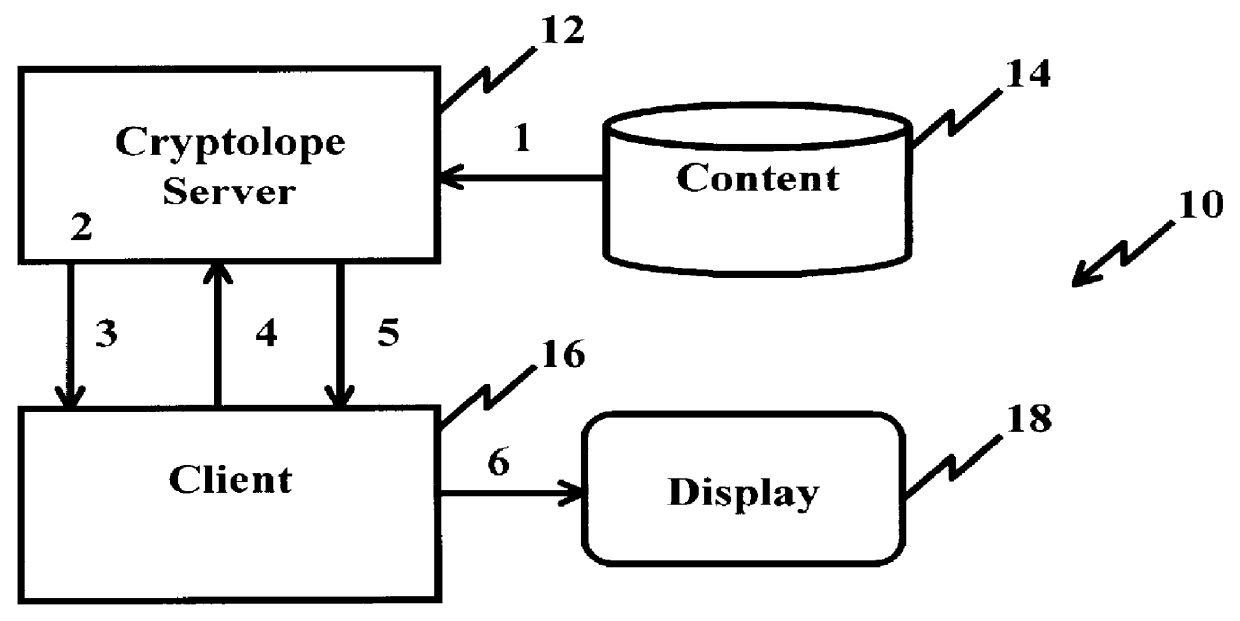
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
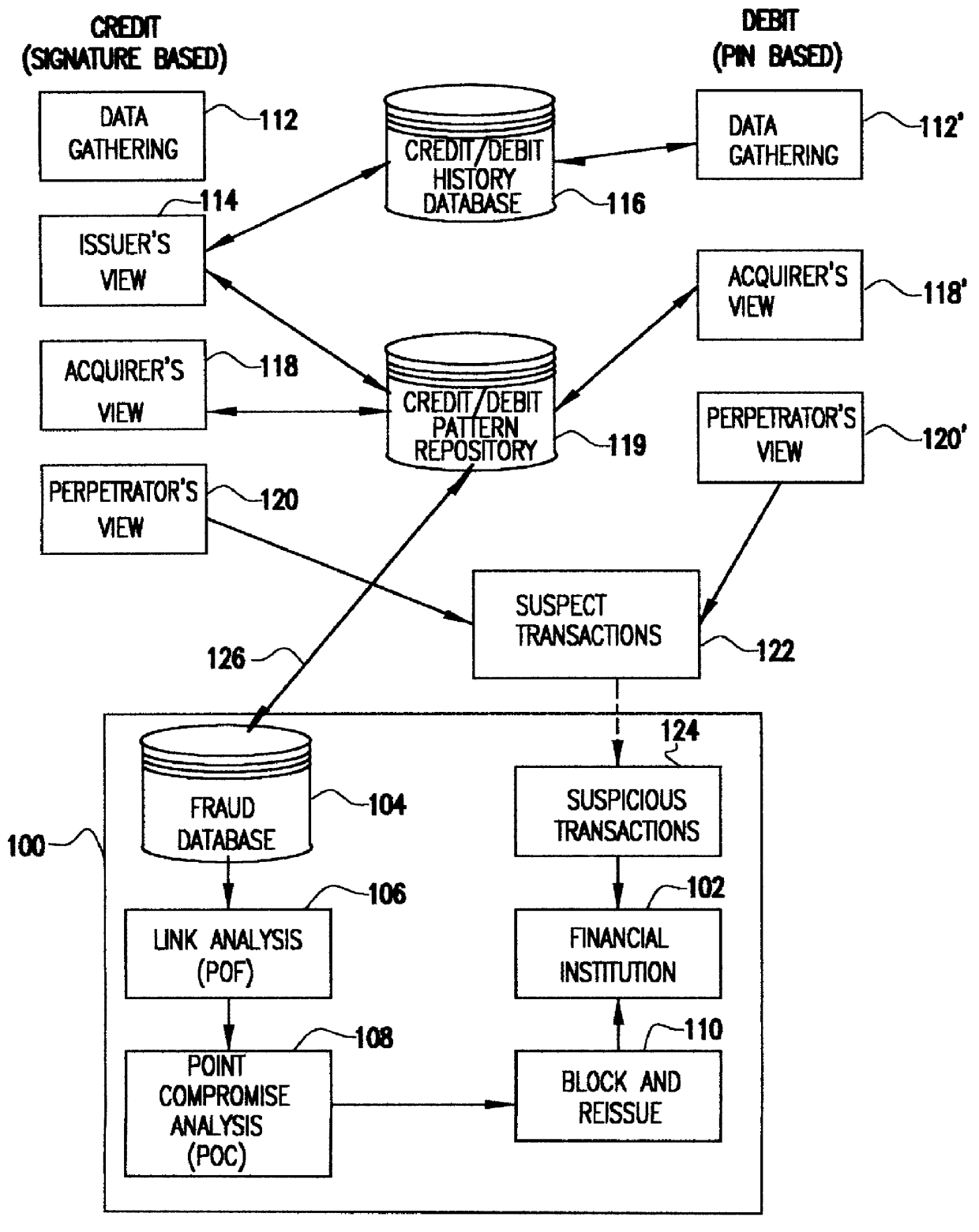
System for detecting counterfeit financial card fraud
Counterfeit financial card fraud is detected based on the premise that the fraudulent activity will reflect itself in clustered groups of suspicious transactions. A system for detecting financial card fraud uses a computer database comprising financial card transaction data reported from a plurality of financial institutions. The transactions are scored by assigning weights to individual transactions to identify suspicious transactions. The geographic region where the transactions took place as well as the time of the transactions are recorded. An event building process then identifies cards involved in suspicious transactions in a same geographic region during a common time period to determine clustered groups of suspicious activity suggesting an organized counterfeit card operation which would otherwise be impossible for the individual financial institutions to detect.
Owner:FAIR ISAAC & CO INC
Predictive modeling of consumer financial behavior using supervised segmentation and nearest-neighbor matching
InactiveUS20050159996A1Improve efficiencyDiscounts/incentivesSpecial data processing applicationsPredictive modellingCo-occurrence
Predictive modeling of consumer financial behavior, including determination of likely responses to particular marketing efforts, is provided by application of consumer transaction data to predictive models associated with merchant segments. The merchant segments are derived from the consumer transaction data based on co-occurrences of merchants in sequences of transactions. Merchant vectors represent specific merchants, and are aligned in a vector space as a function of the degree to which the merchants co-occur more or less frequently than expected. Supervised segmentation is applied to merchant vectors to form the merchant segments. Merchant segment predictive models provide predictions of spending in each merchant segment for any particular consumer, based on previous spending by the consumer. Consumer profiles describe summary statistics of each consumer's spending in the merchant segments, and across merchant segments. The consumer profiles include consumer vectors derived as summary vectors of selected merchants patronized by the consumer. Predictions of consumer behavior are made by applying nearest-neighbor analysis to consumer vectors, thus facilitating the targeting of promotional offers to consumers most likely to respond positively.
Owner:CALLAHAN CELLULAR L L C
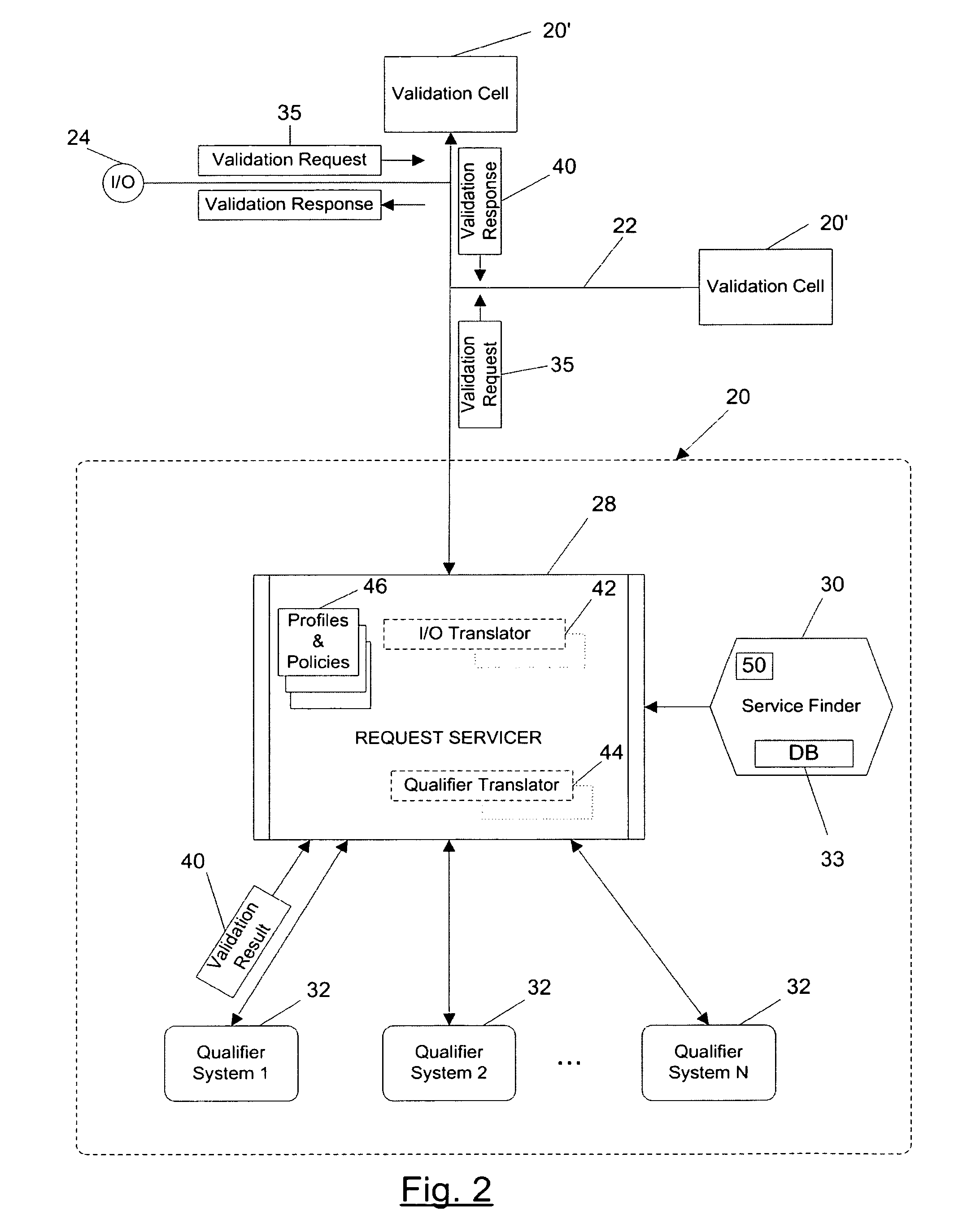
Payment validation network
ActiveUS7004382B2Easy to analyzeReduce riskComplete banking machinesSpecial service provision for substationPaymentTransaction data
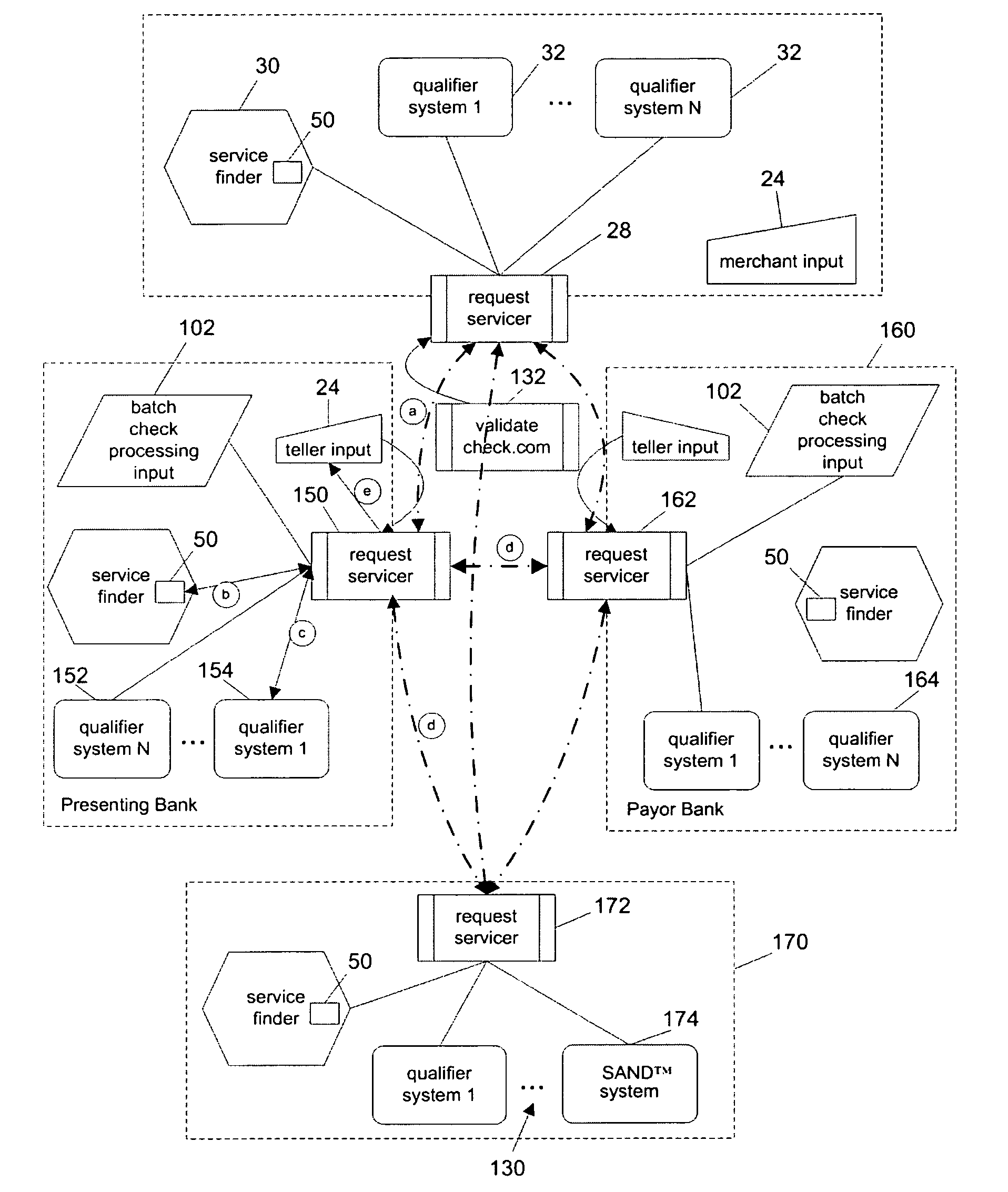
A payment validation network having network of payment validation cells, each of which includes: one or more local qualifier systems for assessing the risk of loss in accepting a check; a service finder for identifying the scope of coverage provided by each of the local qualifier systems and for identifying the scope of coverage provided by other cells; and one or more input / output (I / O) sources for obtaining transaction data associated with a check at a point of presentment. The request servicer interfaces with the I / O sources, service finder and the qualifier systems in order to (i) receive transaction data from an I / O source in connection with the check, including the routing / transit number, (ii) maintain a user profile for the I / O source, (iii) consult the service finder to identify which local qualifier systems cover the routing / transit (R / T) number associated with the check, (iv) transmit a payment validation request to the identified local qualifier systems and at least one other remote request servicer in accordance with the user profile, (v) receive one or more validation results from local qualifier systems or remote request servicers, and (vi) process said results to provide a homogeneous validation assessment to the requesting I / O source.
Owner:ADVANCED SOFTWARE DESIGN
System and method using merchant token
A merchant computer generates a token including a “pay-me” merchant account identifier and transaction data for a transaction conducted by a consumer. The merchant token can be obtained by a mobile communication device and transmitted to a payment processing network along with a device identifier for the mobile communication device and an authentication token provided by the consumer. The payment processing network can authenticate the device using the authentication token, retrieve a consumer account number based on the device identifier, and complete the transaction by pushing money into the merchant “pay-me” account from the consumer account.
Owner:VISA INT SERVICE ASSOC
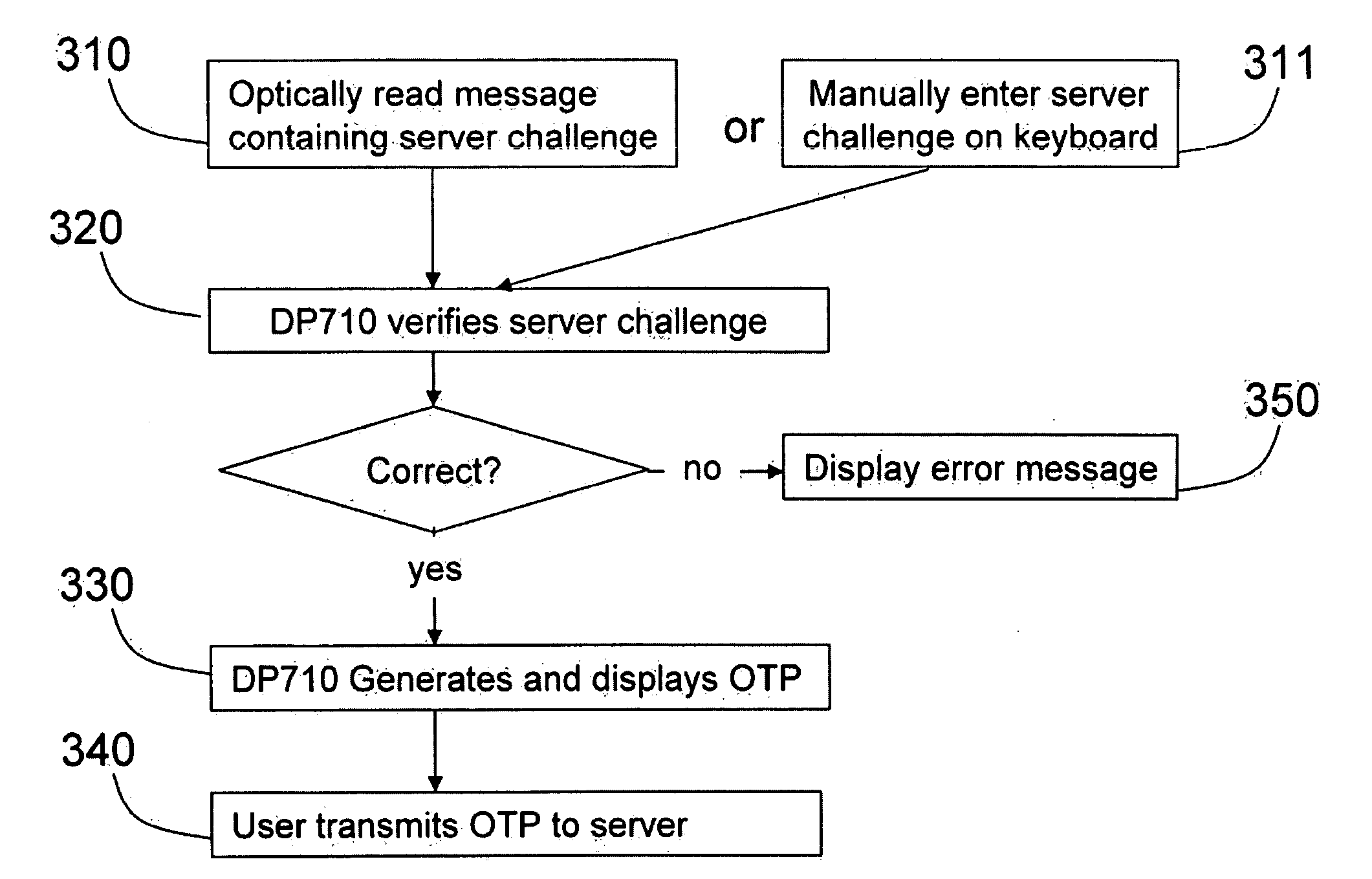
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS20090235339A1Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces
Owner:ONESPAN NORTH AMERICA INC
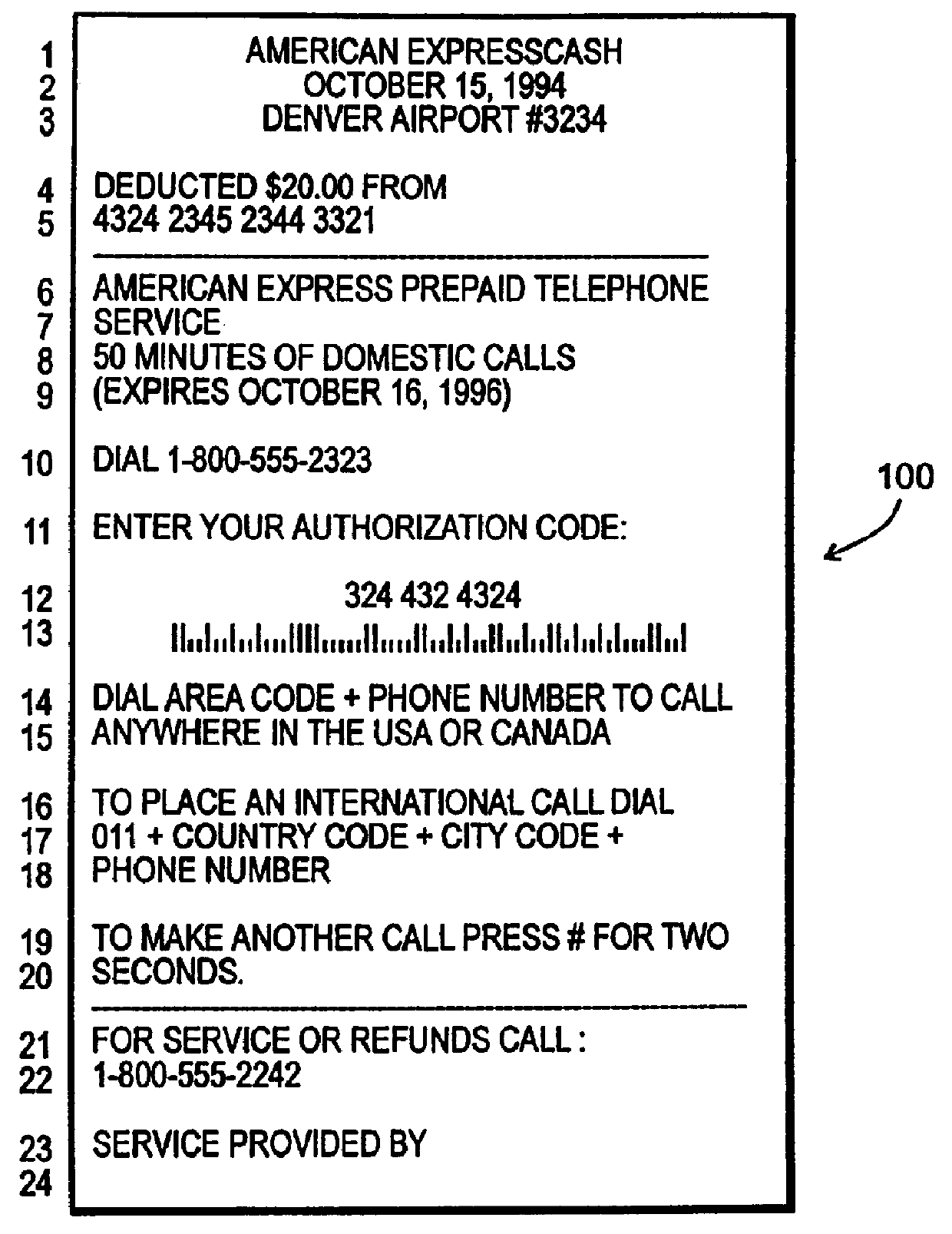
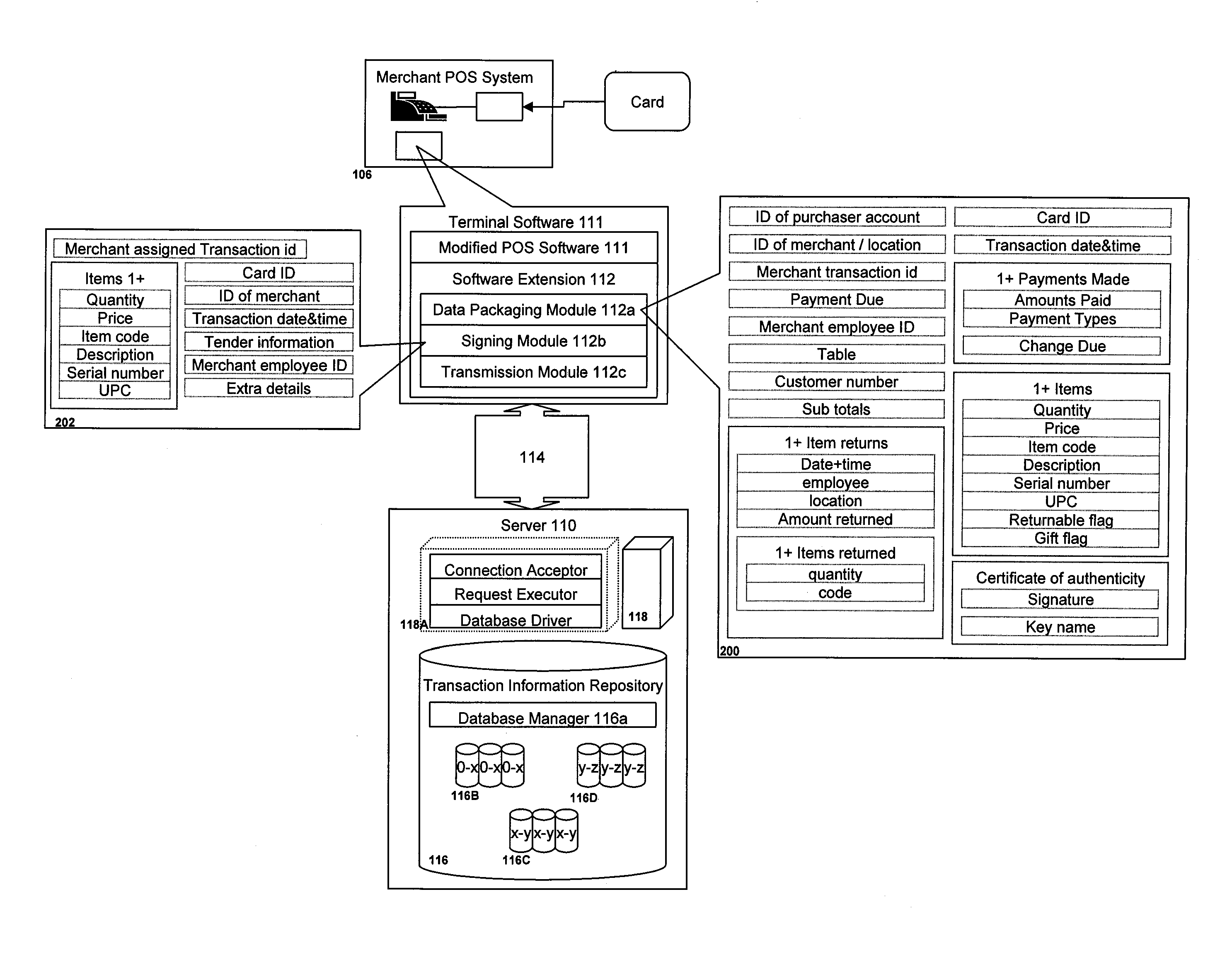
Method and apparatus for summaries of prepaid instrument transaction activity
InactiveUS6115458AConveniently and efficiently generatingConveniently and efficiently and transmittingPayment circuitsVerifying markings correctnessCredit cardSummary data
A system for generating and transmitting summary transaction data includes a computer database from which information is compiled and forwarded to a requesting party automatically, i.e., without the need to interface with a human operator. A party having access to a prepaid transaction account number may access the host computer from a remote location and interactively request transaction information pertaining to the account using virtually any communication modality. The computer is suitably configured to communicate with one or more of the foregoing communication modalities and to automatically compile and transmit the summary data to a requested destination, for example, to a PC. The computer may further be configured to allow the requesting party to select among various formats to configure the form of the summary data. Summary transaction data may be generated and transmitted for virtually any type of prepaid transaction card, including phone cards, travel, credit cards, stored value (e.g., smart cards) cards, and the like.
Owner:LIBERTY PEAK VENTURES LLC +1
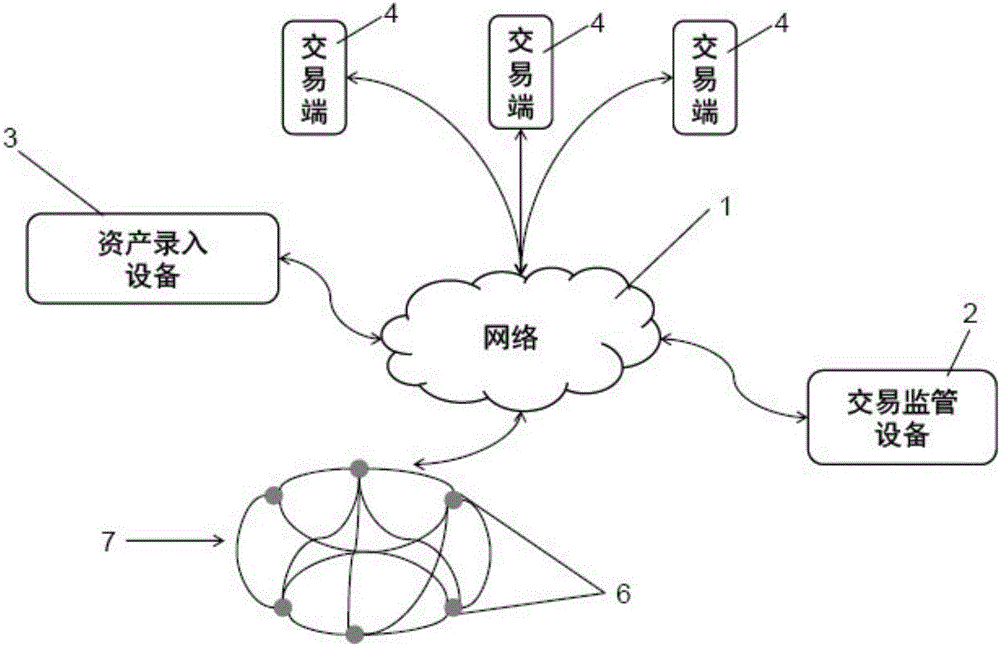
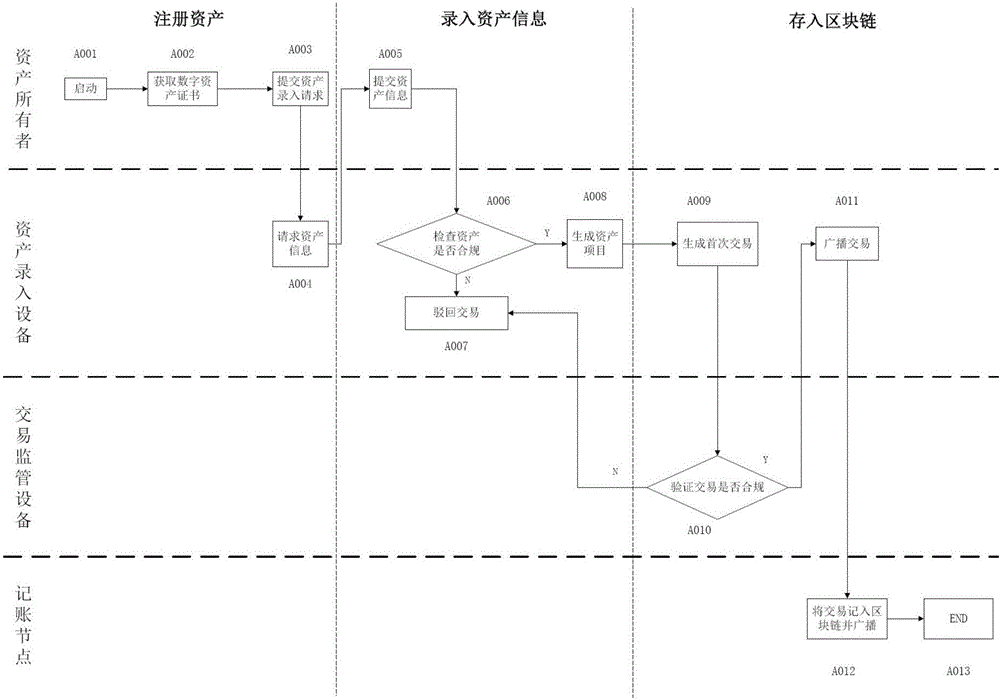
Asset transaction platform and digital certification and transaction method for assets
ActiveCN105956923AAchieve decentralizationGuarantee authenticityFinanceData synchronizationDigital identity
The present invention relates to a digital asset transaction platform, comprising an asset entry device and a distributed accounting network. An asset is validated by the asset entry device. When compliance is achieved, asset project information is generated and is input to the asset transaction platform, wherein the asset project information includes a hash value of a digital asset certificate of the asset. The distributed accounting network comprises a plurality of accounting nodes, which are connected in a point-to-point manner and each store a transaction data information general ledger which is synchronized with each other and is based on a block chain database. The asset transaction platform supports mutual transaction of at least two different types of assets. The asset transaction platform provided by the invention adopts the block chain technology and the digital identity identification technology of assets and realizes de-centralization and trusted quick transaction of various assets.
Owner:上海如鸽投资有限公司
Merchant scoring system and transactional database
A merchant scoring system predicts and reports the likelihood that a merchant is reliable (e.g., trustworthy, honest, and reputable), which is expected to translate into a positive consumer experience. The system collects data from a variety of data sources, including combinations of the merchant, third-parties, and / or customers who have transacted with the merchant. A scoring model is executed on this collected data to determine an independent and objective merchant reliability metric that predicts the expected reliability of a merchant within a range. The system may also track transactions of individual merchants, populating a transaction history database with information about each merchant for use in this collection and scoring process. The transaction history data and other data may also be accessible to a prospective customer to build his or her confidence in and understanding of the merchant reliability metric and his or her trust of the merchant.
Owner:GOOGLE LLC
Method for customizing payment card transactions at the time of the transactions
InactiveUS20050086177A1Anonymous user systemsRecord carriers used with machinesThird partyTransaction data
A user can customize use of a payment card, which can be an electronic card, by selecting a customization variable for any given transaction. The customization variable involves at least one of the following steps: (1) customizing generation of a one-time card number; (2) customizing a user identifier; or (3) inclusion of a customization variable with information transmitted to a verification agency for validation of the given use. Multiple payment card transactions can be processed differently depending upon which customization variable is chosen for a given transaction. Different customization variables can be used for different accounts, different types of transactions, or to classify the transactions. A user can receive one bill, or multiple bills. Different levels of privacy can be accorded to transactions that use different customization variables. A user may pay the issuer for increased security, or the user may be paid by the issuer to allow transaction data to be distributed to third parties.
Owner:ANDERSON ROY L +2
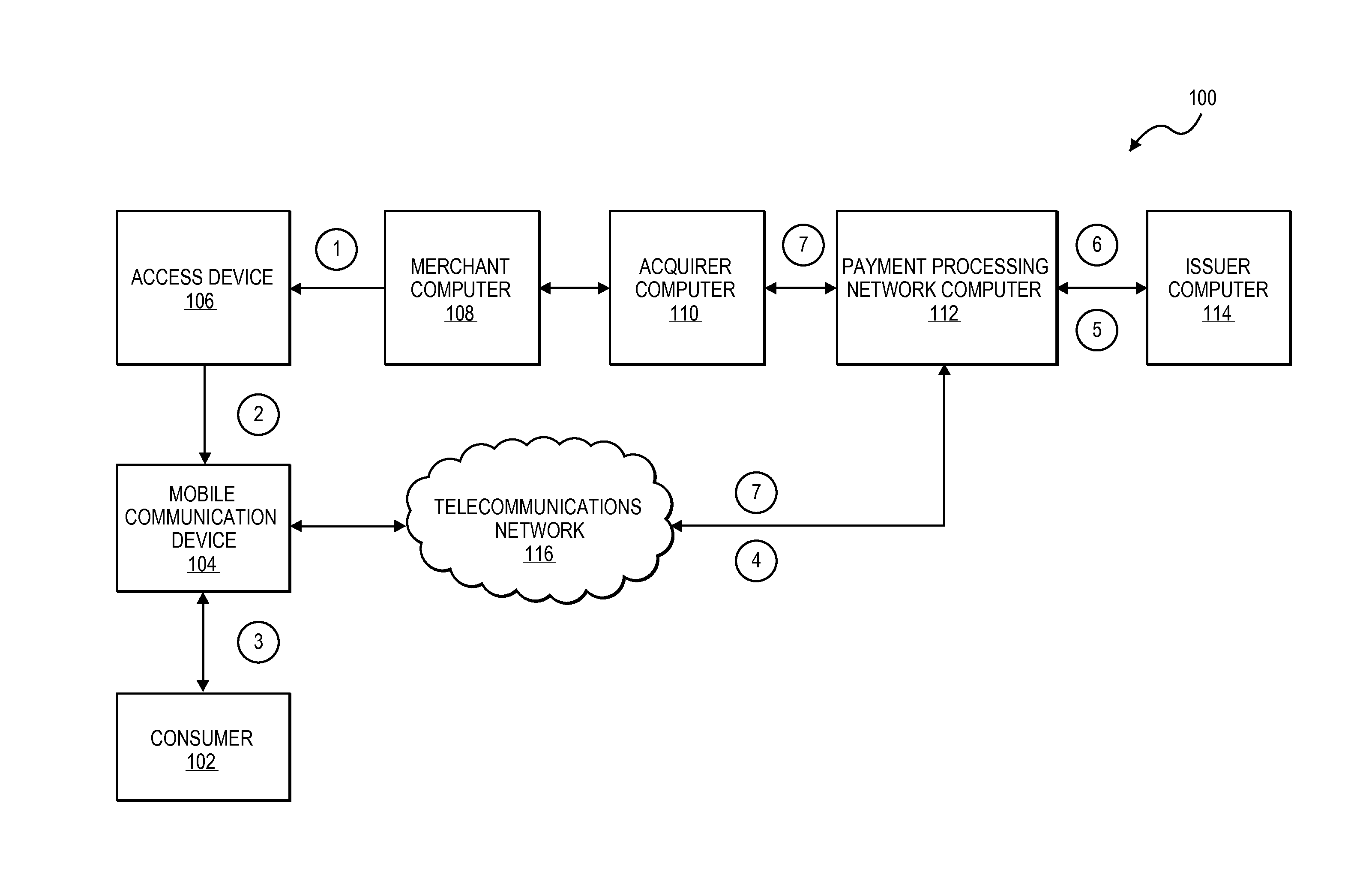
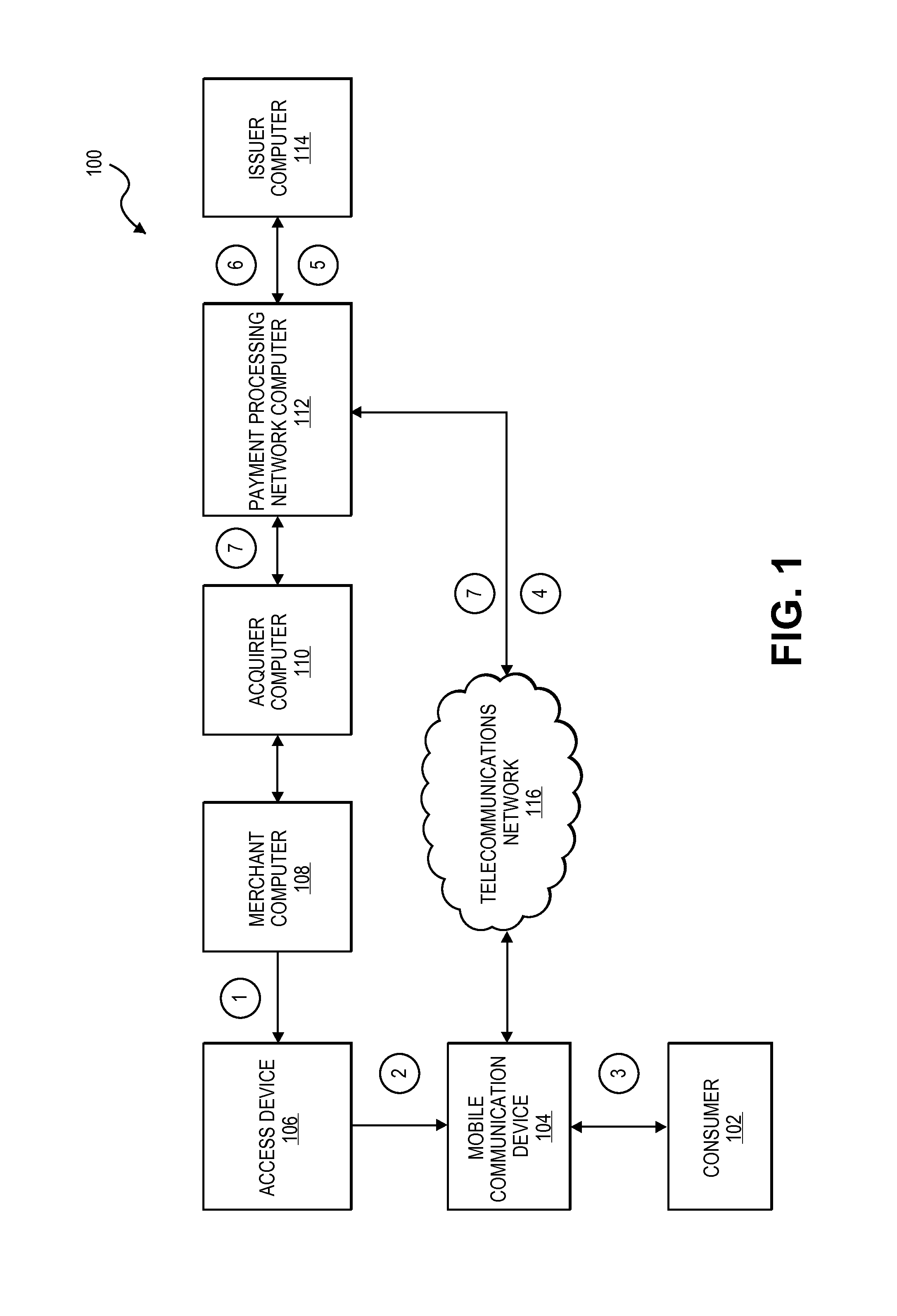
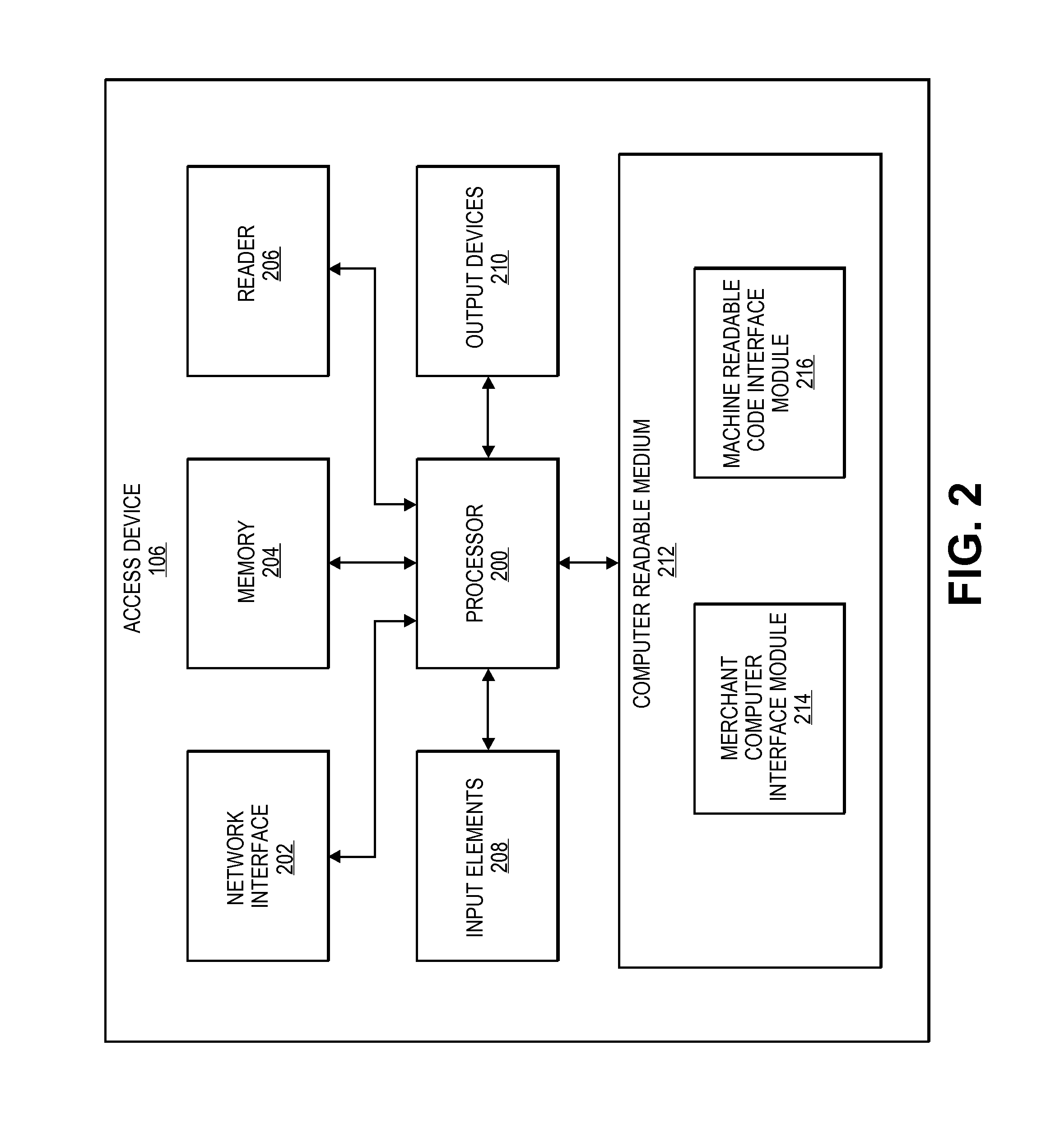
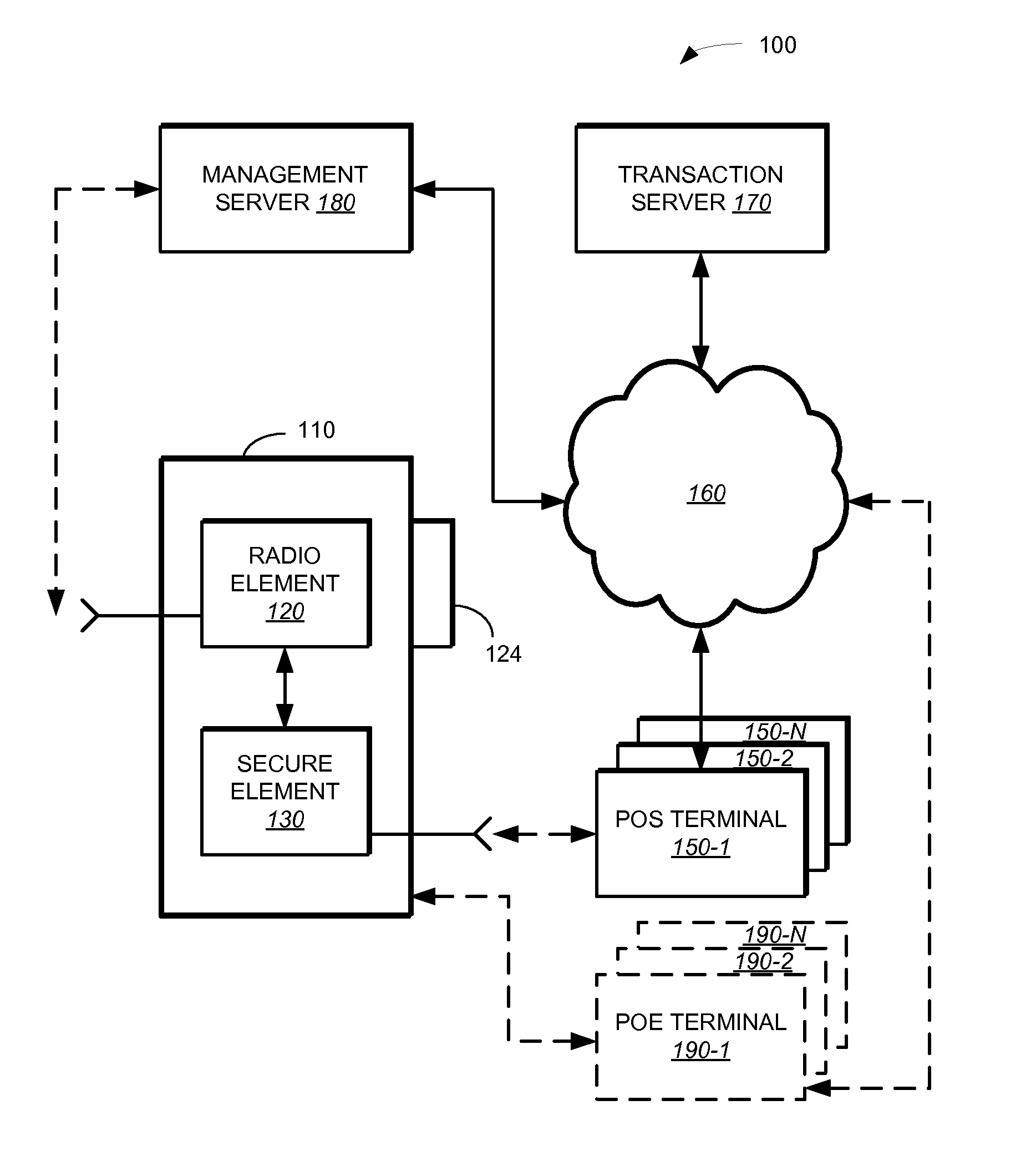
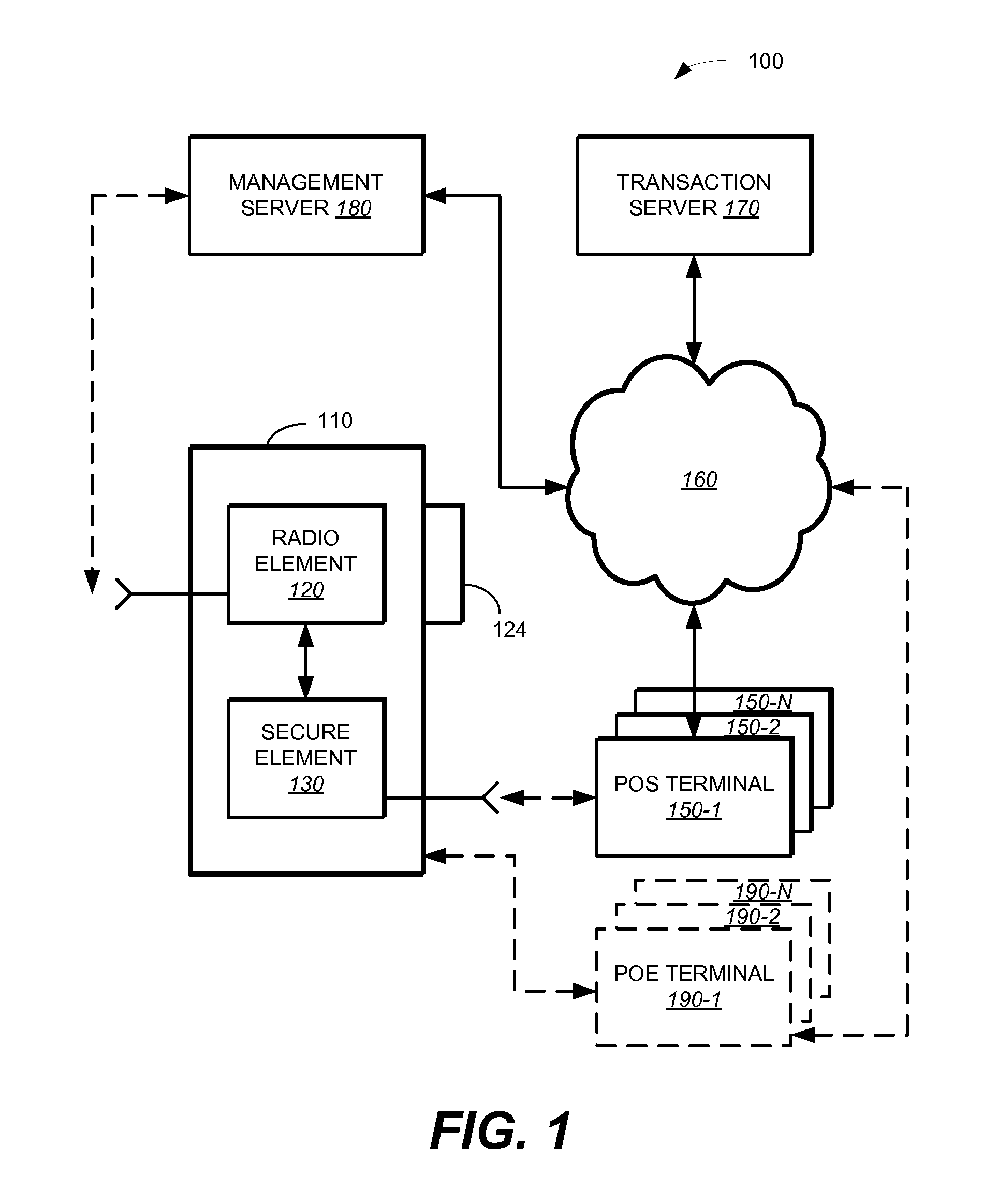
Method and system for adapting a wireless mobile communication device for wireless transactions
ActiveUS20080051059A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareTransceiver
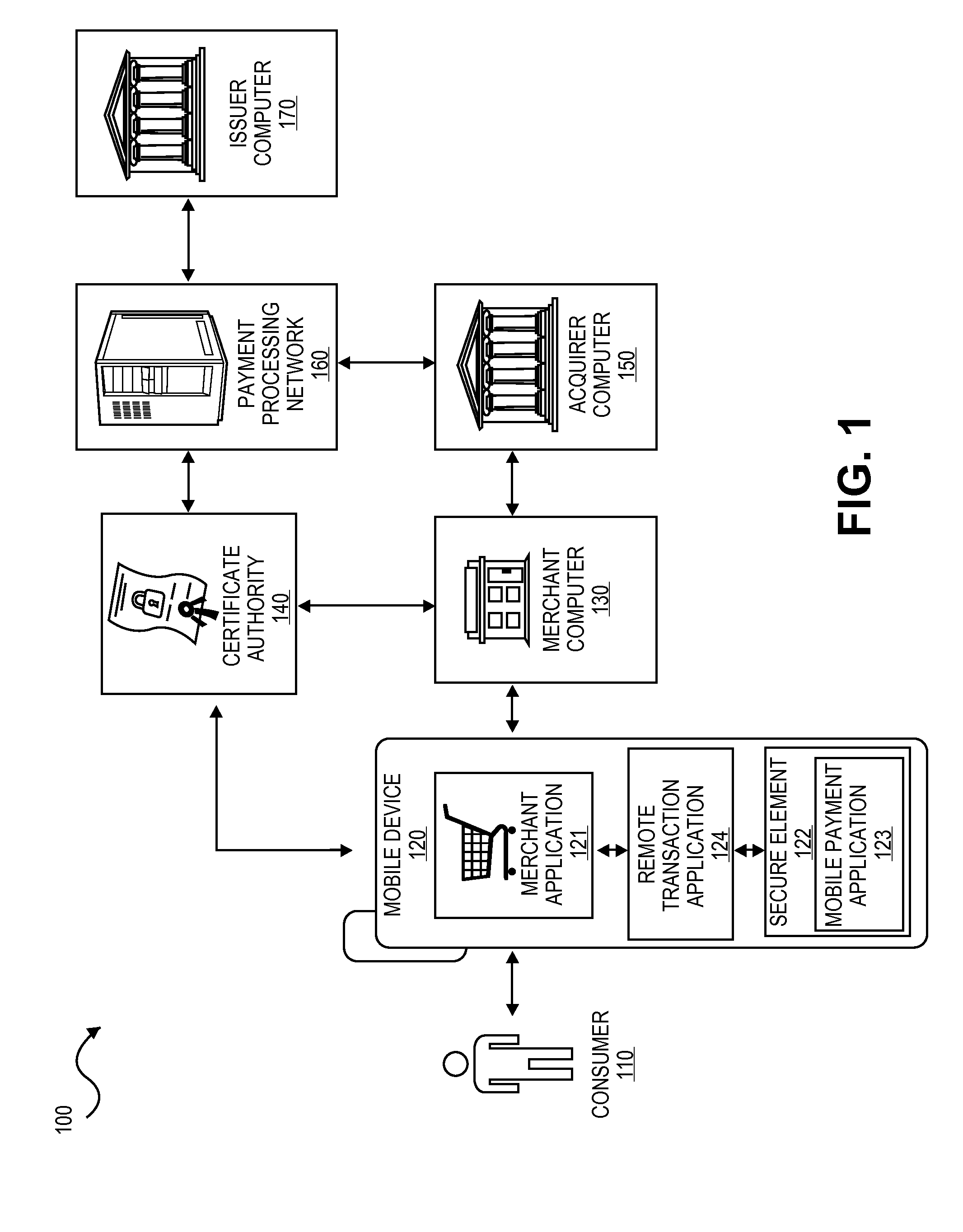
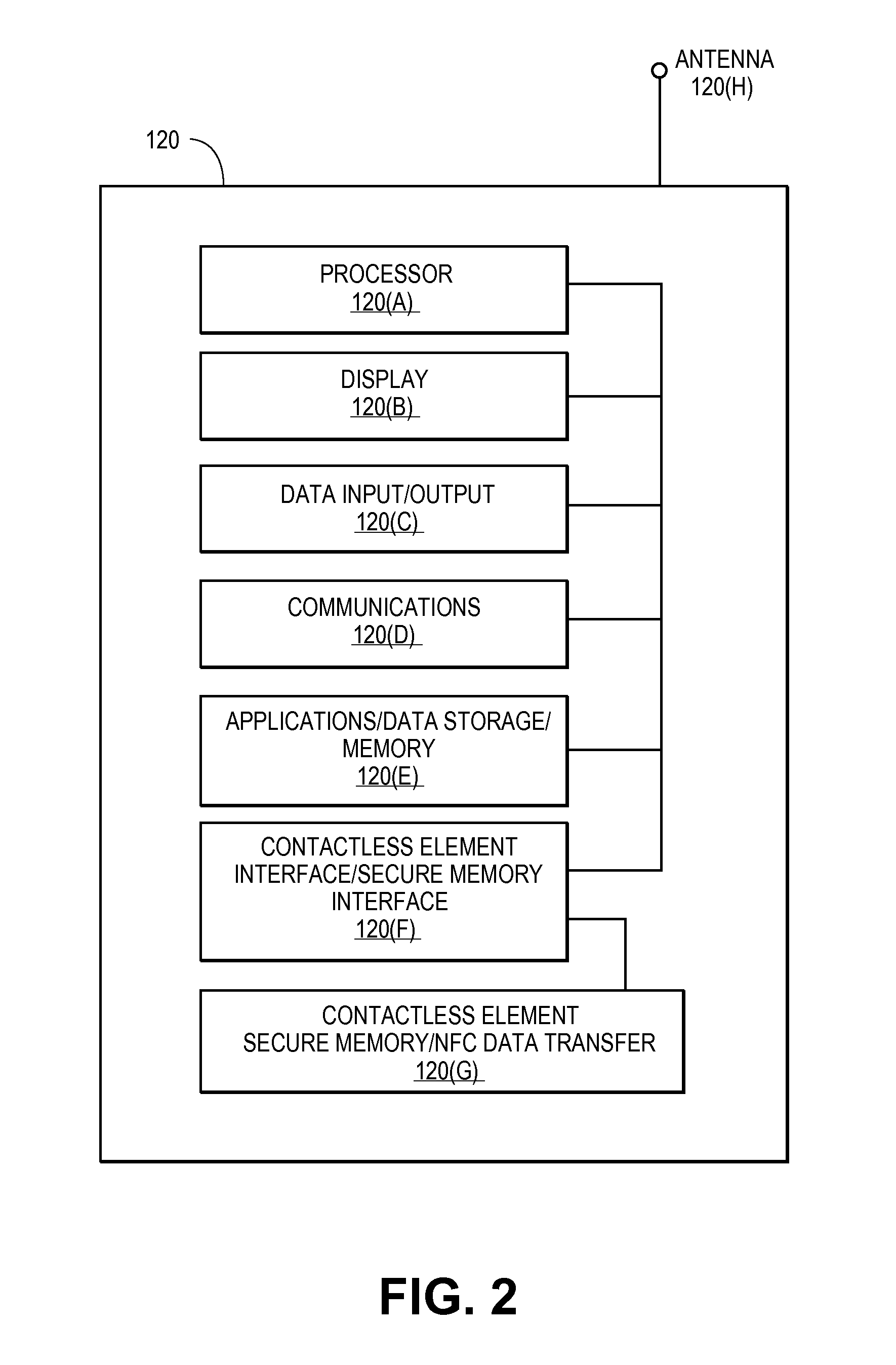
A method for configuring a mobile communication device to perform transactions using a second communication channel that is different from a first communication channel through which the mobile communication device sends voice data. The method includes attaching a secure element to the mobile communication device. The secure element includes a memory storing an application, a processor configured to execute the application stored in the memory; and a wireless transceiver configured to send transaction data associated with the executed application through the second communication channel to a terminal that is remote from the mobile communication device.
Owner:BLAZE MOBILE
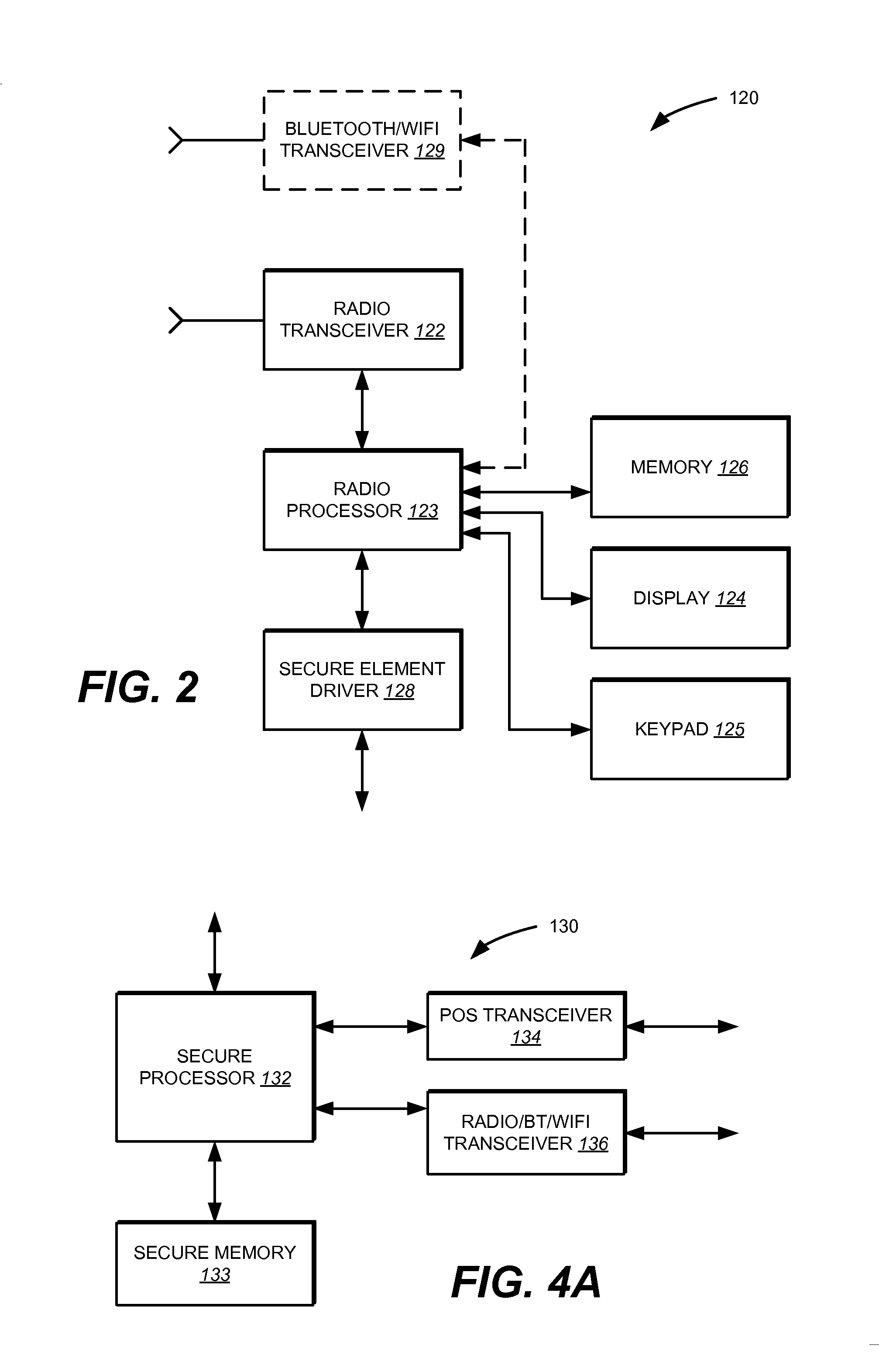
Secure Remote Payment Transaction Processing Using a Secure Element
ActiveUS20150052064A1Improve security levelImprove securityPayment protocolsSecuring communicationPayment transactionTransaction data
Embodiments of the present invention are directed to methods, apparatuses, computer readable media and systems for securely processing remote transactions. One embodiment of the invention is directed to a method of processing a remote transaction initiated by a mobile device. The method comprises receiving, by a mobile payment application on a secure memory of the mobile device, transaction data from a transaction processor application on the mobile device. The method further comprises validating that the transaction processor application is authentic and in response to validating the transaction processor application, providing encrypted payment credentials to the transaction processor application. The transaction processor application further initiates a payment transaction with a transaction processor server computer using the encrypted payment credentials.
Owner:VISA INT SERVICE ASSOC
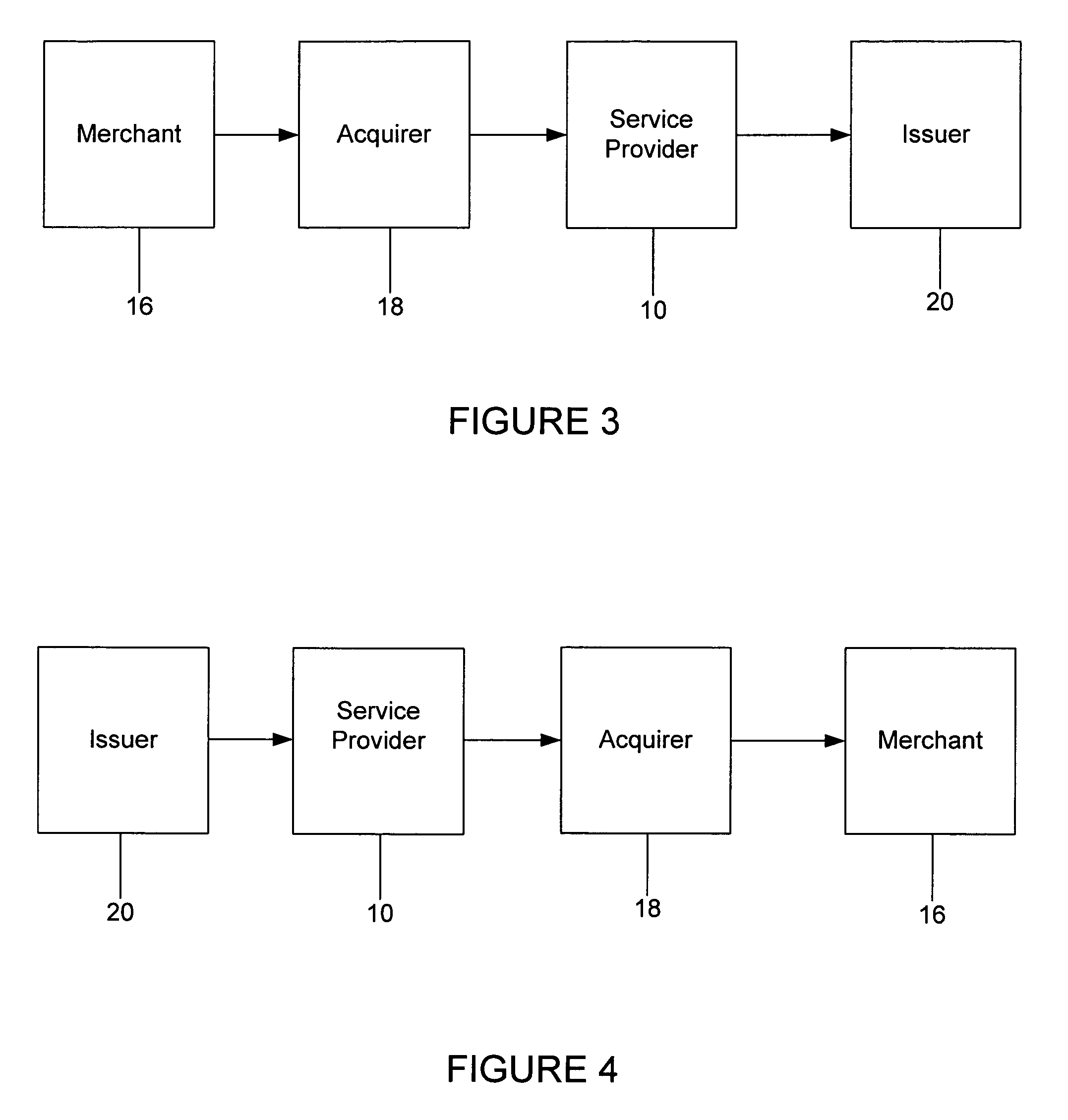
Method and system for conducting secure payments over a computer network
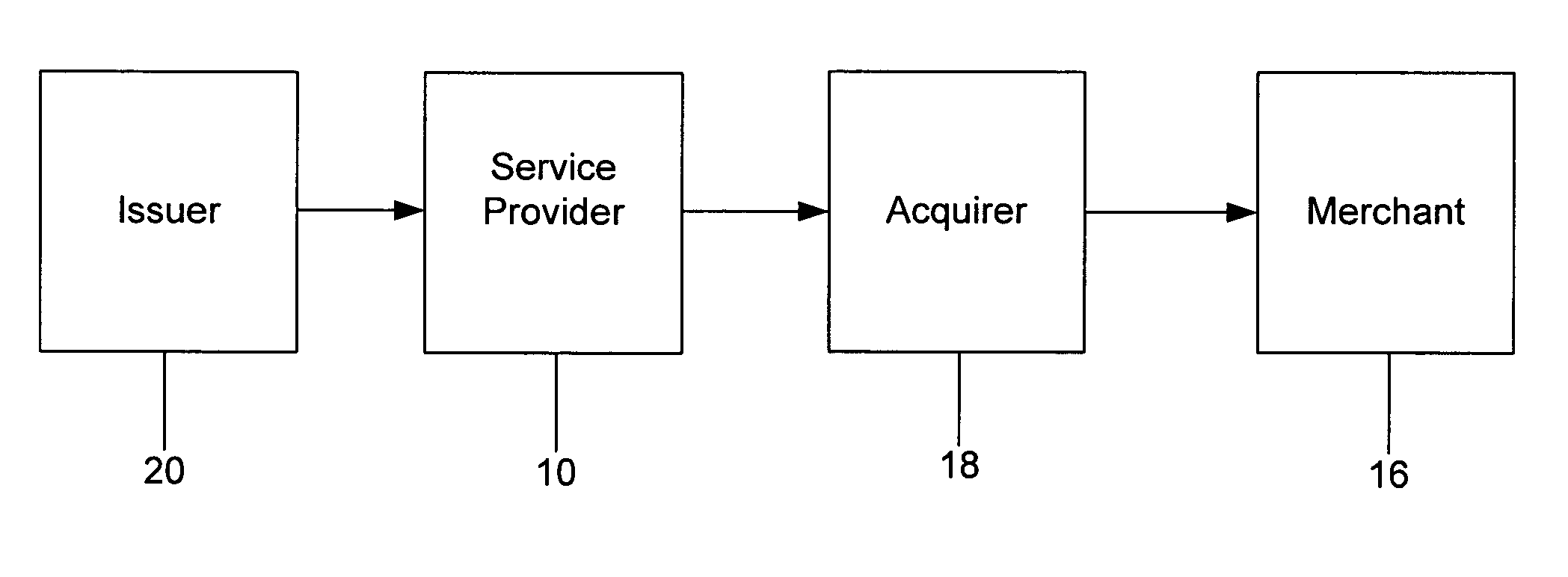
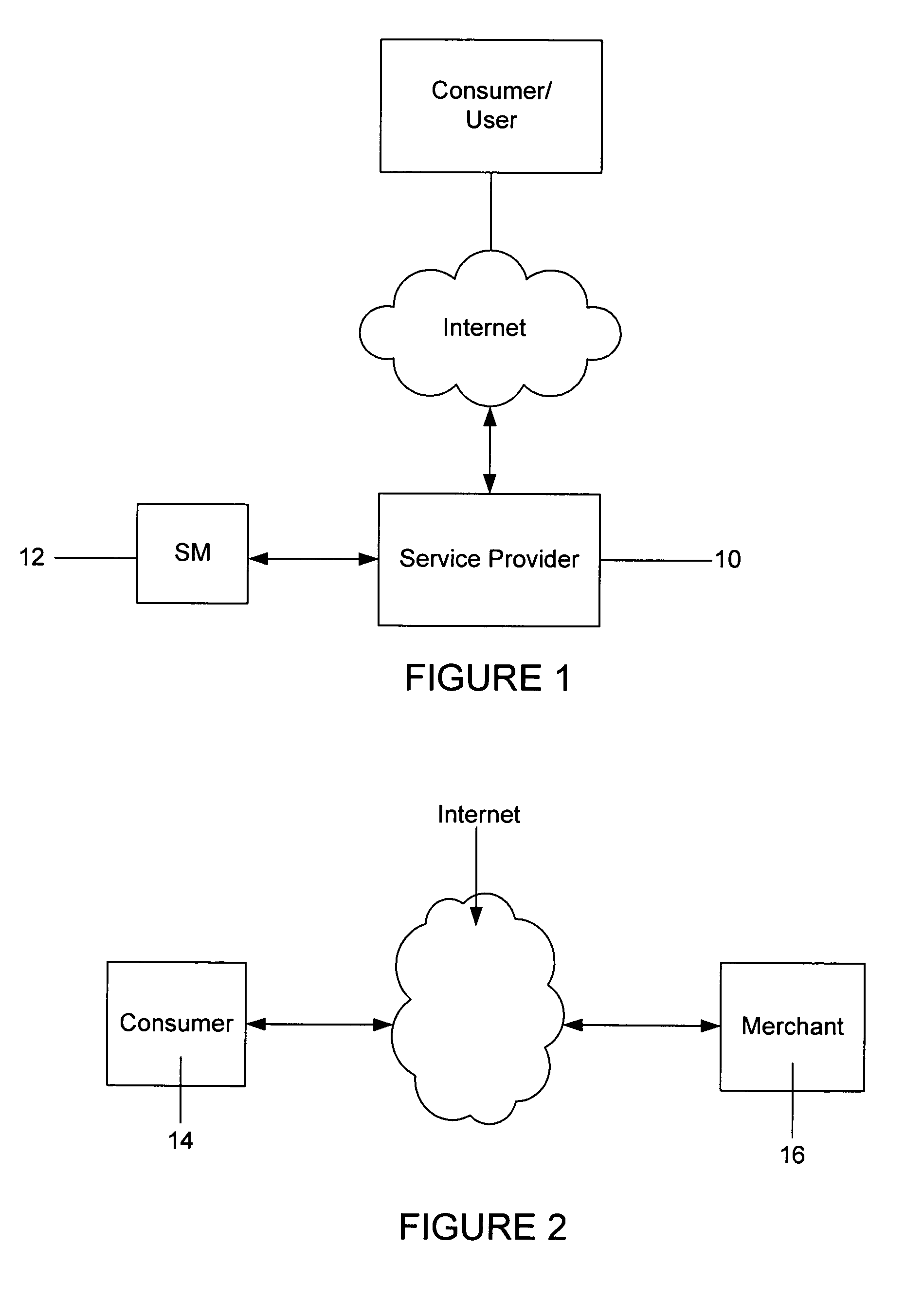
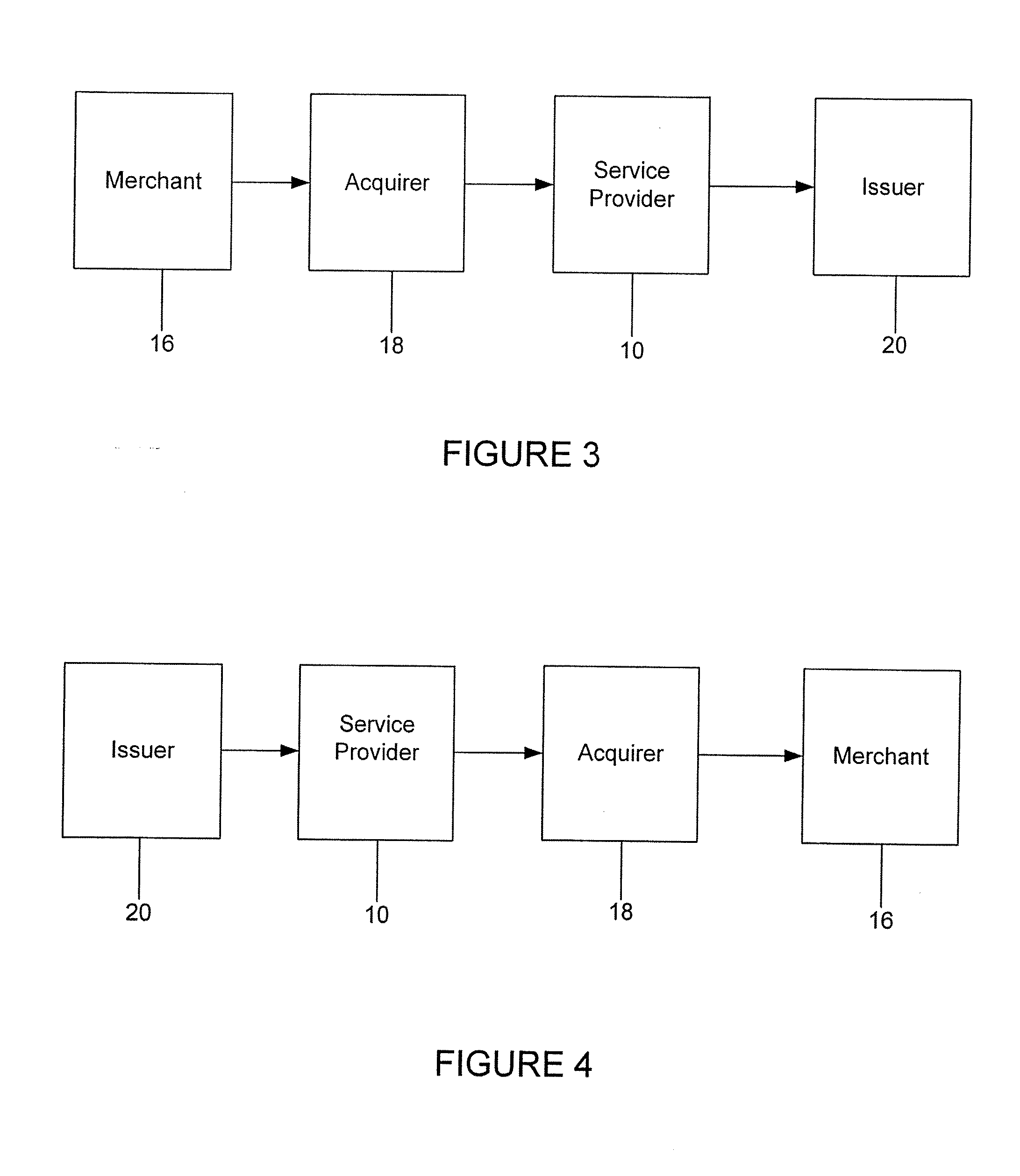
A method is provided for conducting a financial transaction by a purchaser with a merchant having an acquirer bank, over a communications network. The method includes the steps of sending a first authorization request using a pseudo account number associated with a real account number to a service provider which forwards a second authorization request to the issuer using the real account number and preferably a pseudo acquirer code associated with the service provider such that the response to the second request is based on the real account number and sent back to the service provider who preferably forwards a response to the first request preferably to the “real” acquirer. A message authentication code is further provided which includes transaction data, and where the authorization request is formatted as a standard payment card track having one or more fields including a discretionary field in which the message authentication code is placed.
Owner:MASTERCARD INT INC
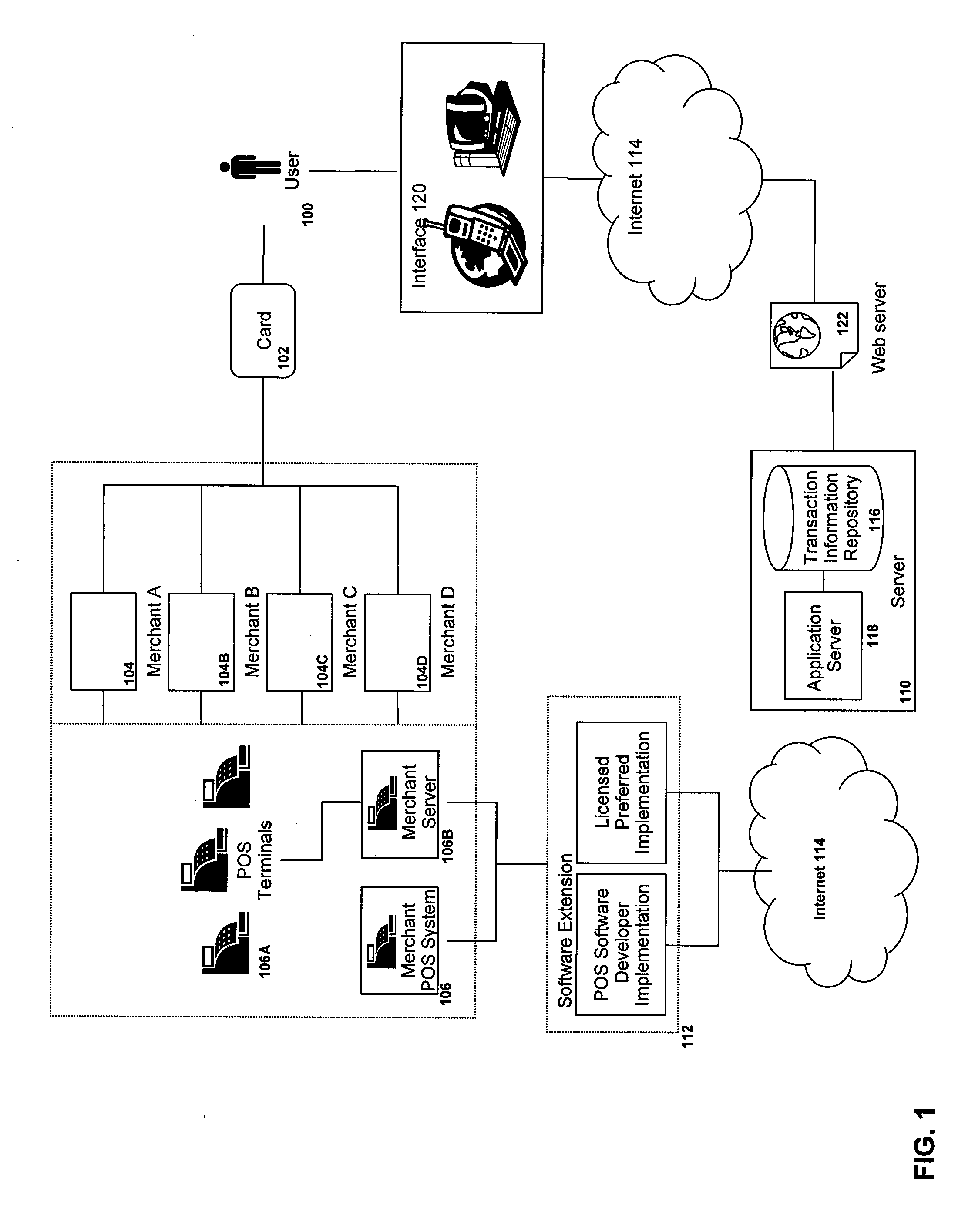
System and method for tracking transaction records in a network
The disclosure describes a database system and method for processing a transaction record of a transaction between a merchant and a user is provided. The system comprises a database and a server. The database stores and updates an account record and coupon records. The account record contains account data associated with the user and transaction data. The server provides update instructions for the account record to the database; communicates with a first terminal associated with the merchant to process the account record; builds the transaction record for the database using data relating to the transaction provided from the first terminal, the transaction record containing information relating to the transaction, the merchant and the customer; associates the transaction record with the transaction data in the account record; provides data relating to a selection of coupon records to the first terminal during a session relating to the transaction; and provides access to the account record to a requesting entity upon verification of access rights of the requesting entity to access the account record.
Owner:SMARTSLIPS
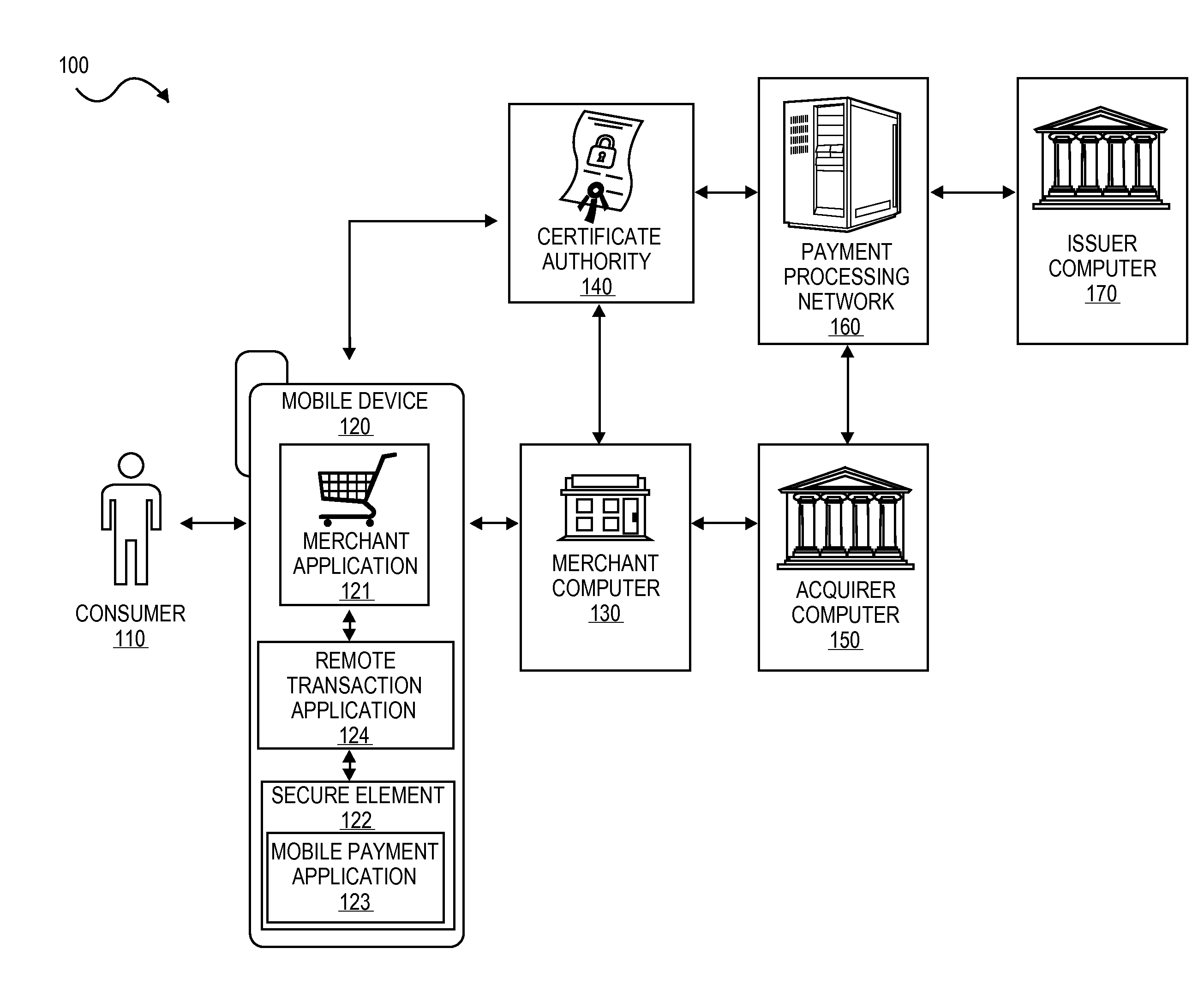
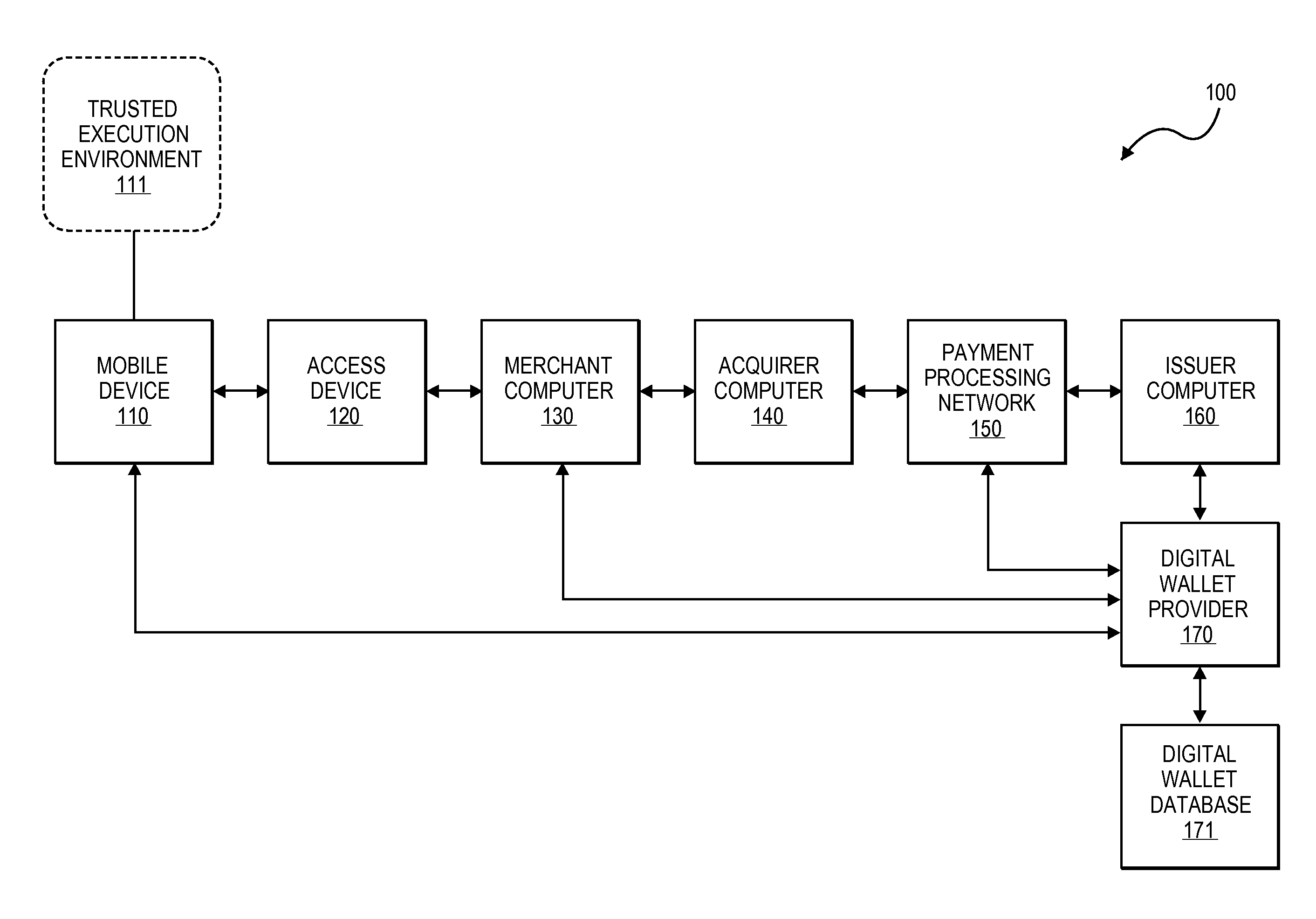
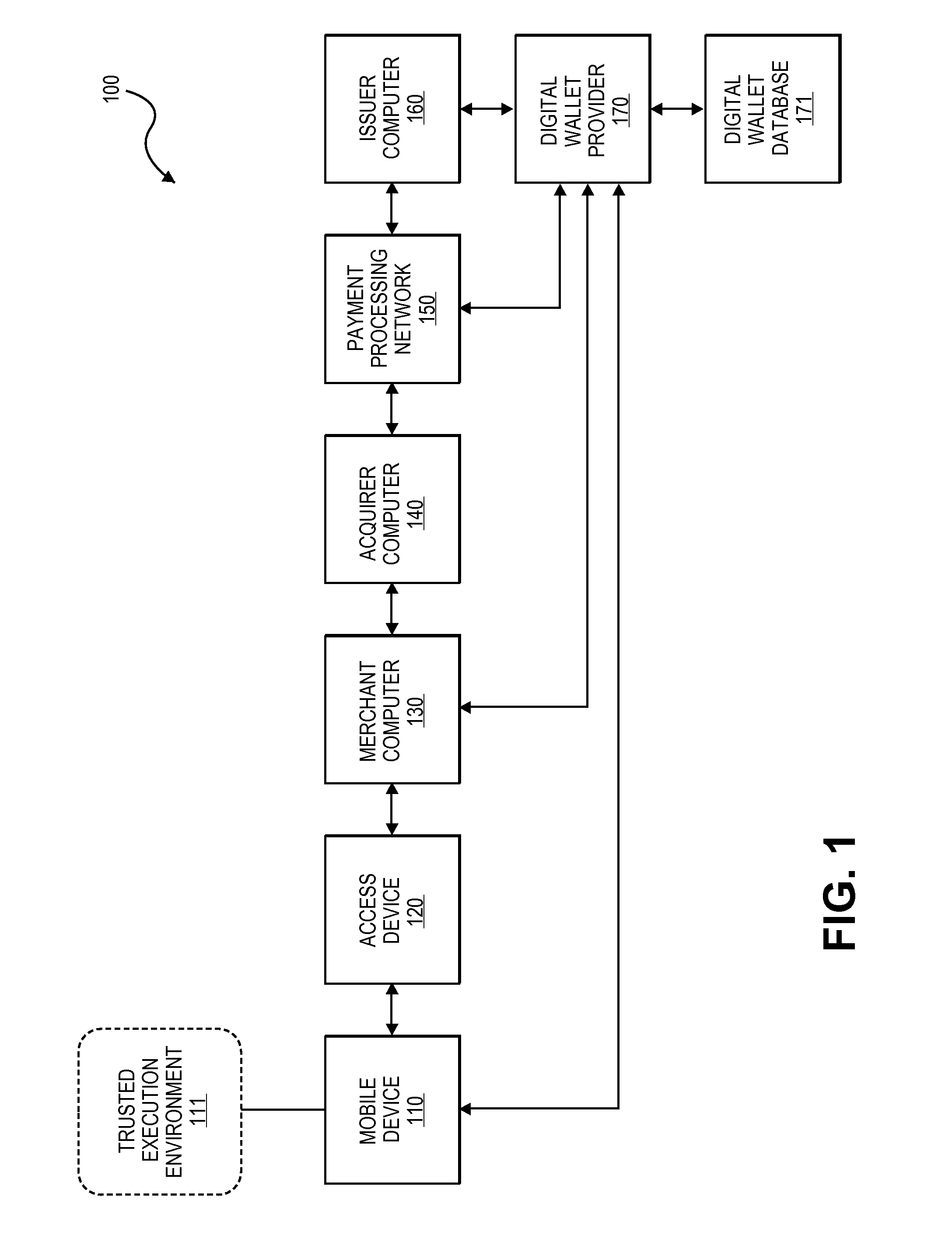
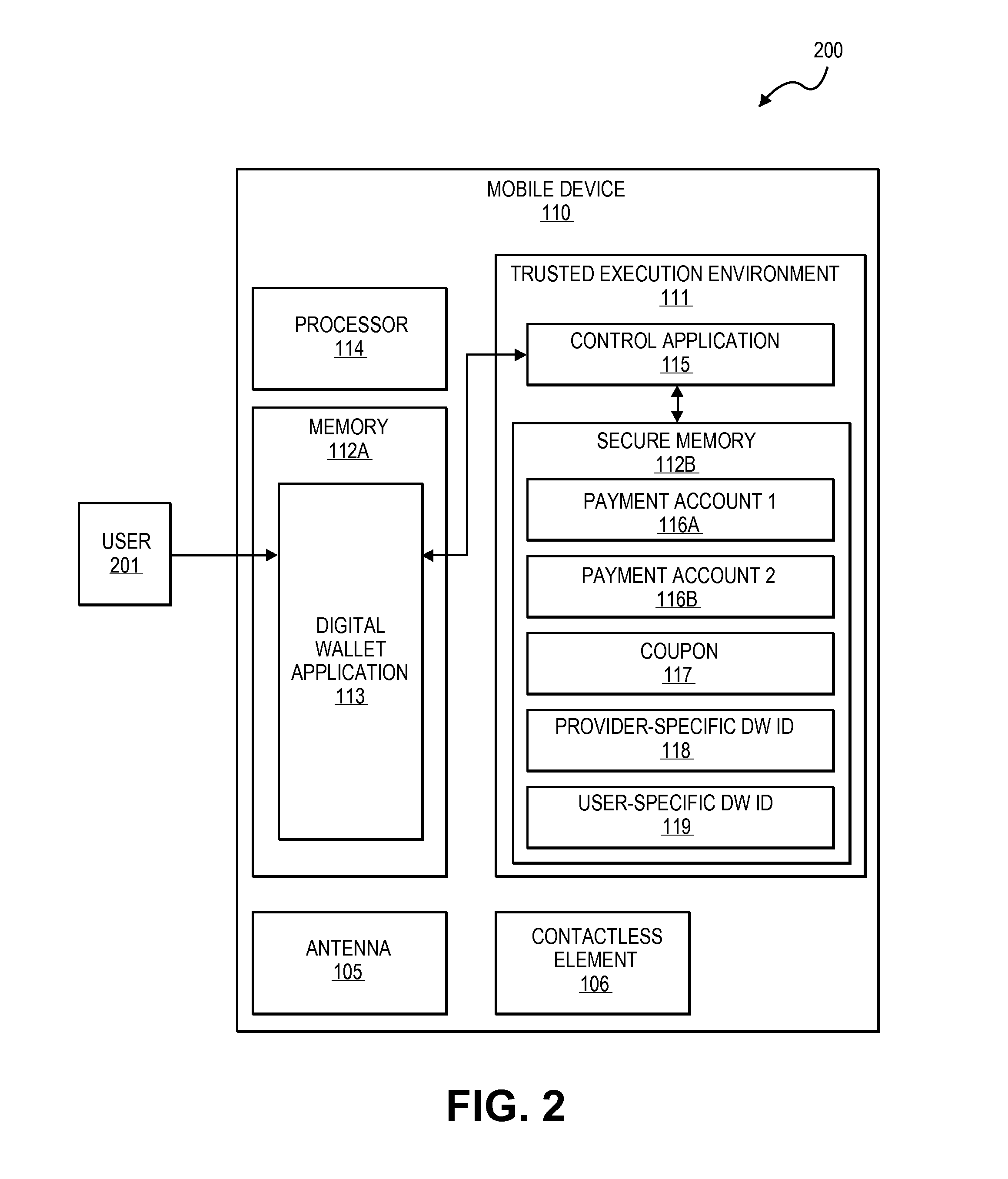
Digital wallet system and method
Embodiments of the present invention provide methods and systems to enable a digital wallet identifier to be present in communications associated with transaction data for transactions that are facilitated by a digital wallet provider. In one embodiment, a communication device of a user receives a request for payment credentials required to conduct a transaction and obtains the payment credentials. The payment credentials include a digital wallet identifier and at least some of the payment credentials are obtained from a trusted execution environment associated with the communication device. The obtained payment credentials are provided to an access device associated with a merchant. The access device is configured to initiate the transaction by generating an authorization request message including the payment credentials for onward transmission to an issuer computer.
Owner:VISA INT SERVICE ASSOC
Text mining system for web-based business intelligence applied to web site server logs
InactiveUS7330850B1Data processing applicationsMultiple digital computer combinationsClustered dataWeb site
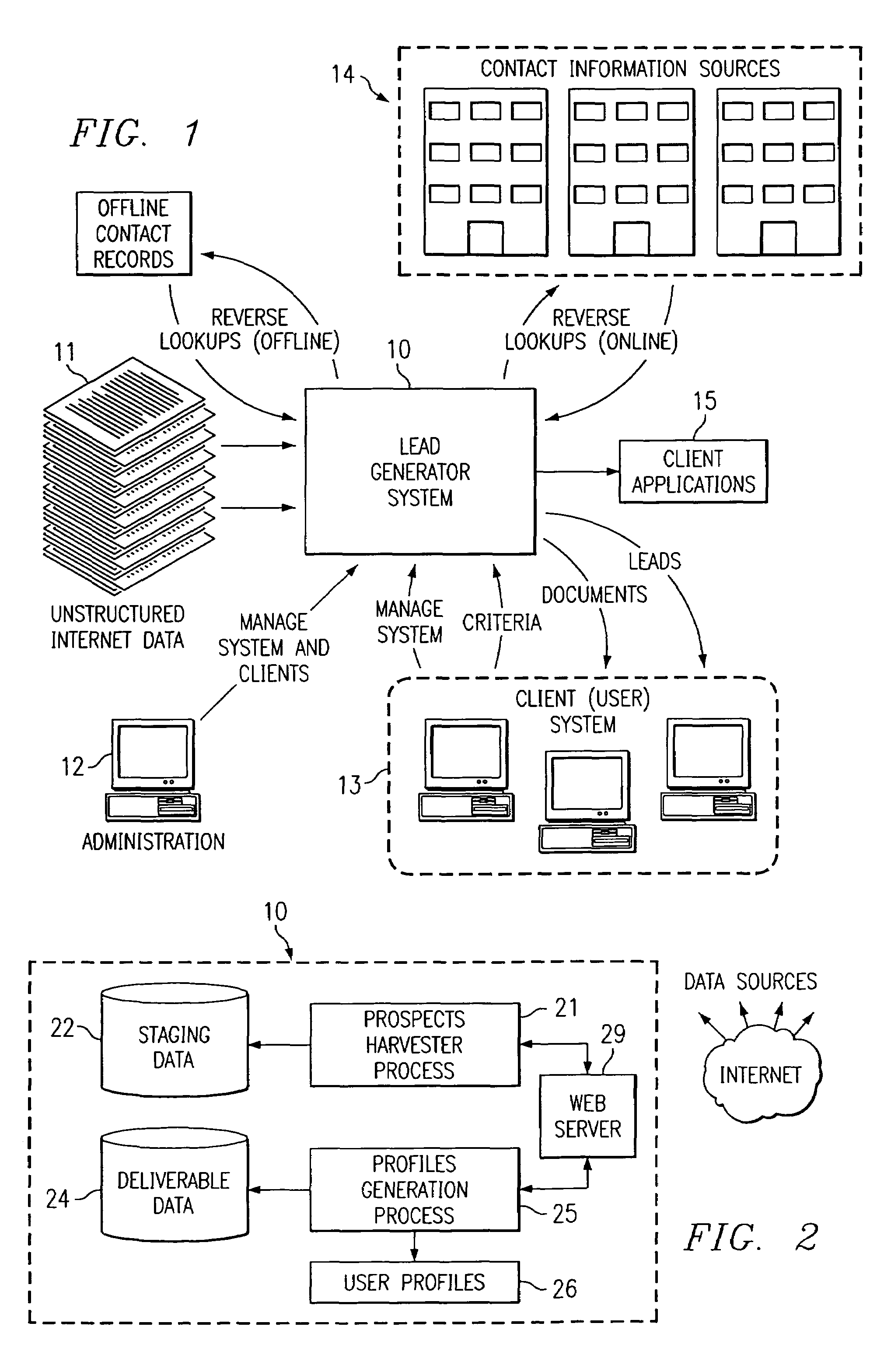
A text mining system for collecting business intelligence about a client, as well as for identifying prospective customers of the client, for use in a lead generation system accessible by the client via the Internet. The text mining system has various components, including a data acquisition process that extracts textual data from Internet web sites, including their logs, content, processes, and transactions. The system compares log data to content and process data, and relates the results of the comparison to transaction data. This permits the system to provide aggregate cluster data representing statistics useful for customer lead generation.
Owner:CALLAHAN CELLULAR L L C +1
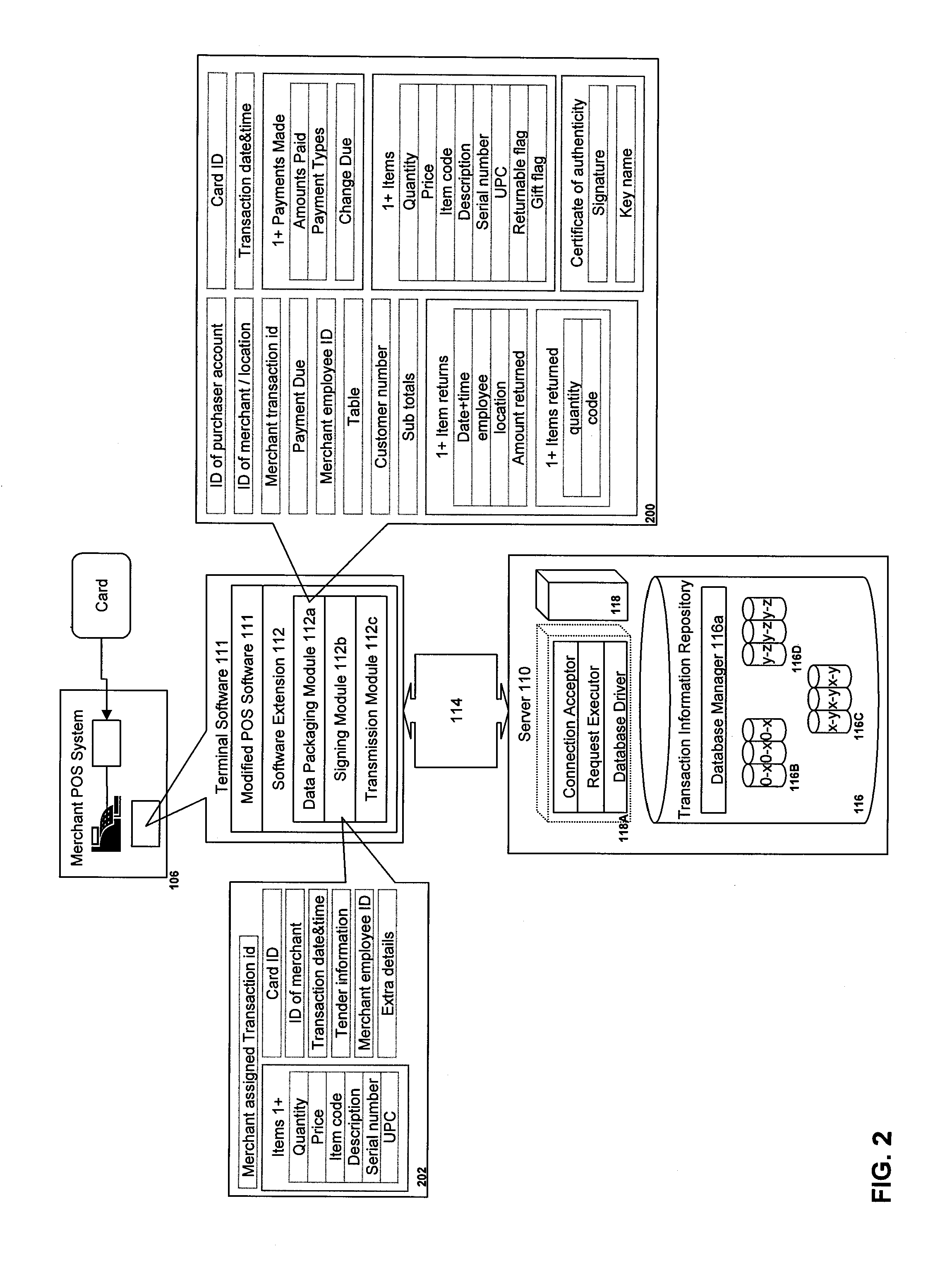
Recovering a database to any point-in-time in the past with guaranteed data consistency
ActiveUS8364648B1Digital data processing detailsStructured data retrievalTransaction dataData management
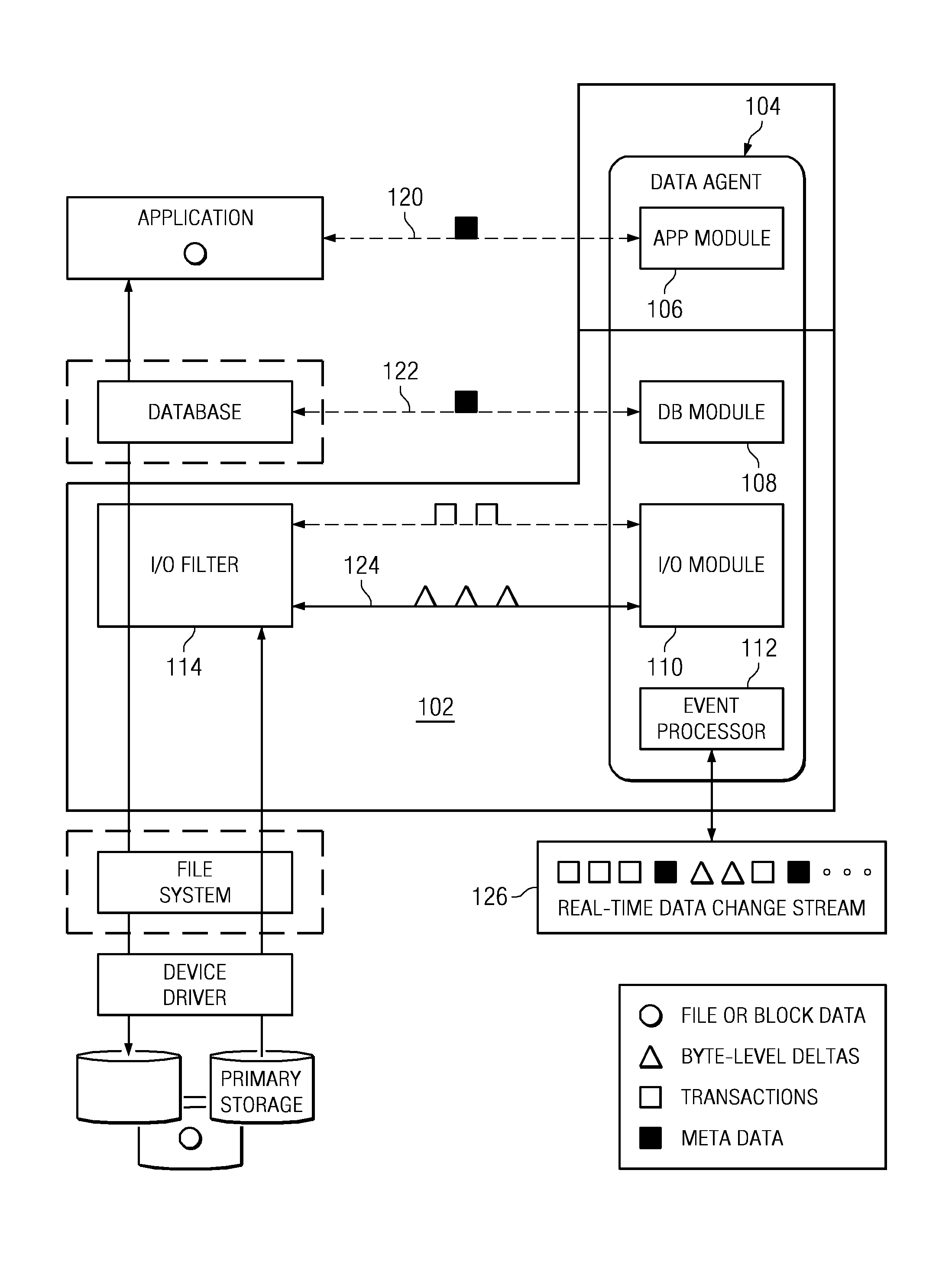
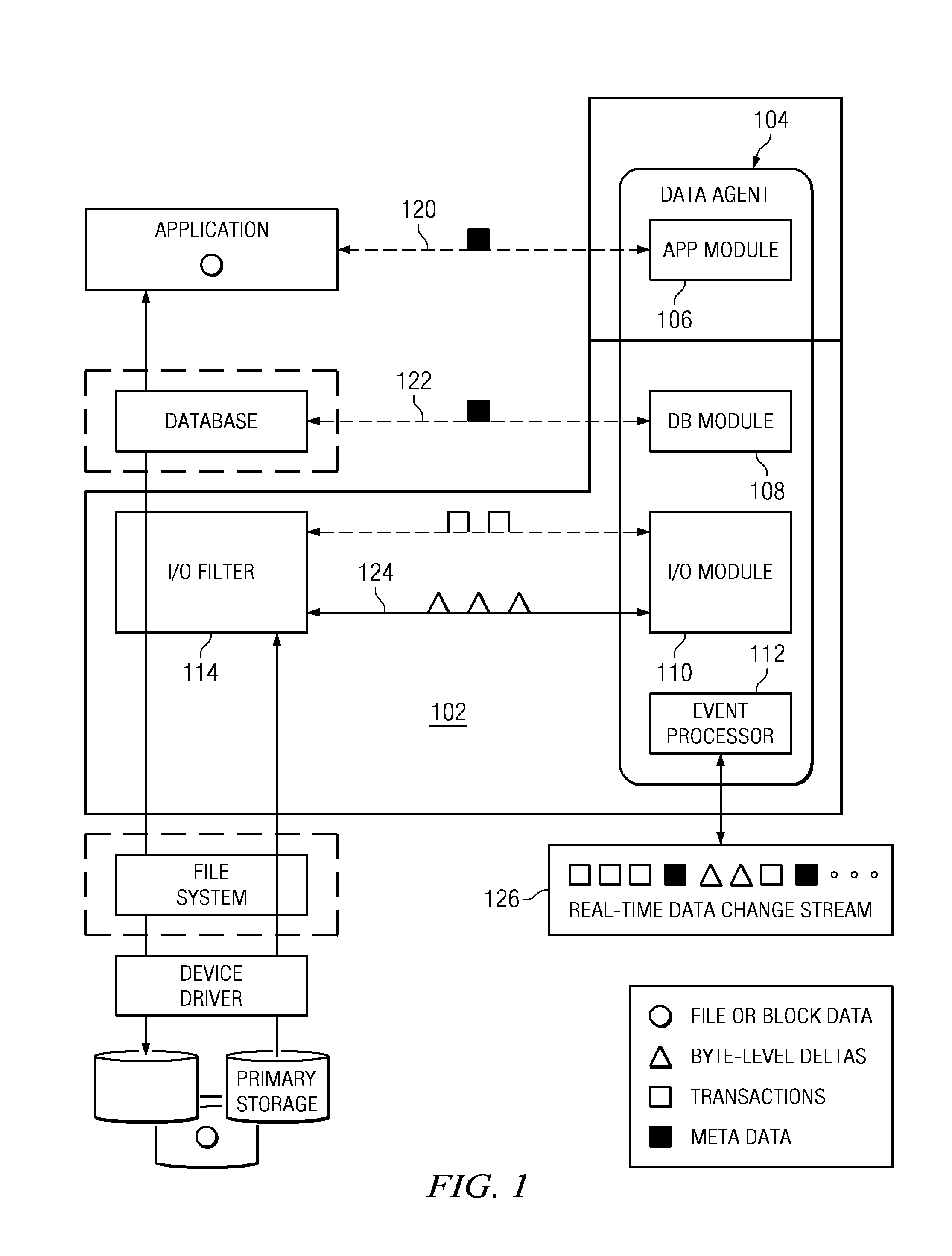
A data management method wherein a real-time history of a database system is stored as a logical representation and the logical representation is then used for any point-in-time recovery of the database system. More specifically, a method for capturing transaction data, binary data changes, metadata, and events, and for tracking a real-time history of a database system according to the events. The method enables tracking and storing of consistent checkpoint images of the database system, and also enables tracking of transaction activities between checkpoints. The database system may be recovered to any consistent checkpoint or to any point between two checkpoints.
Owner:QUEST SOFTWARE INC
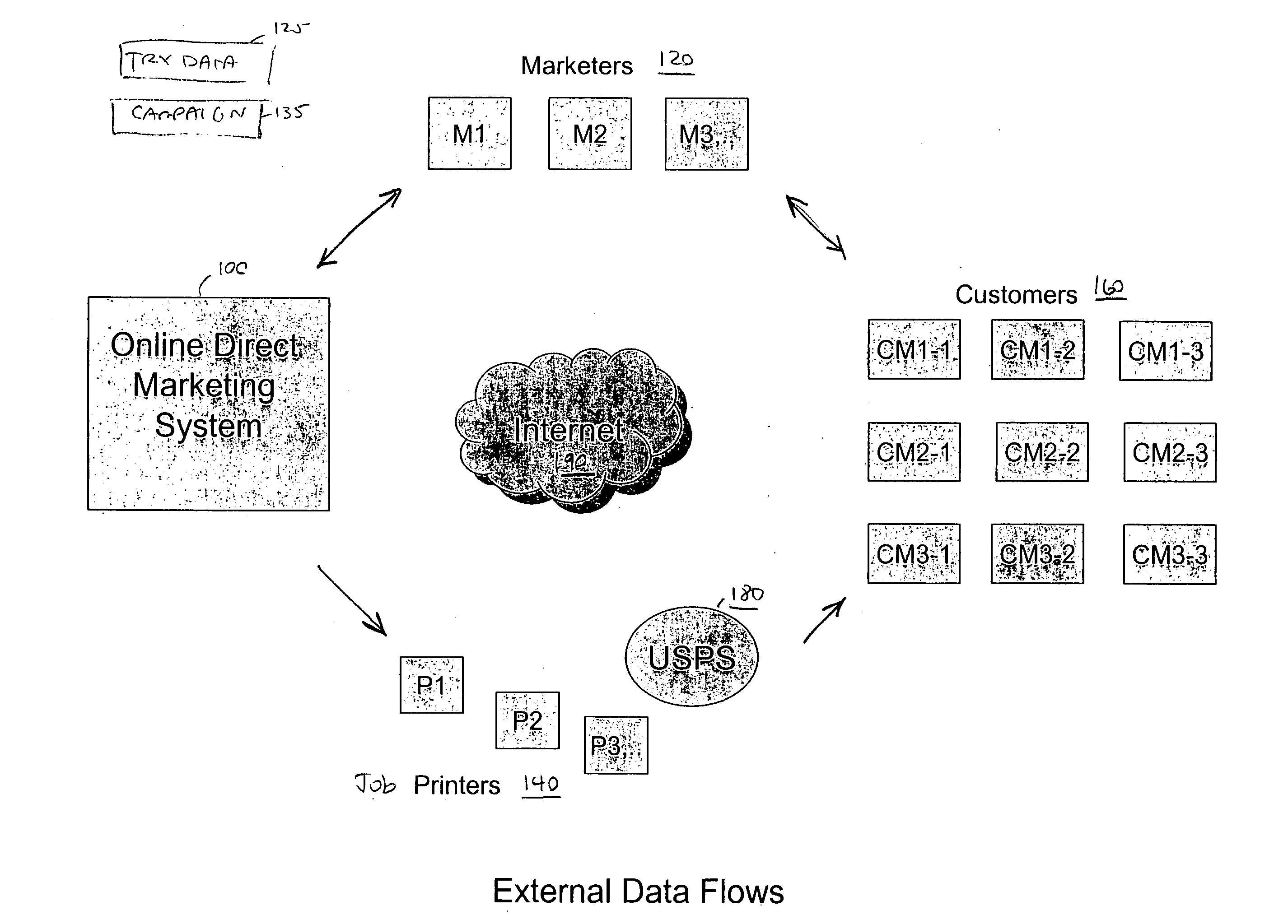
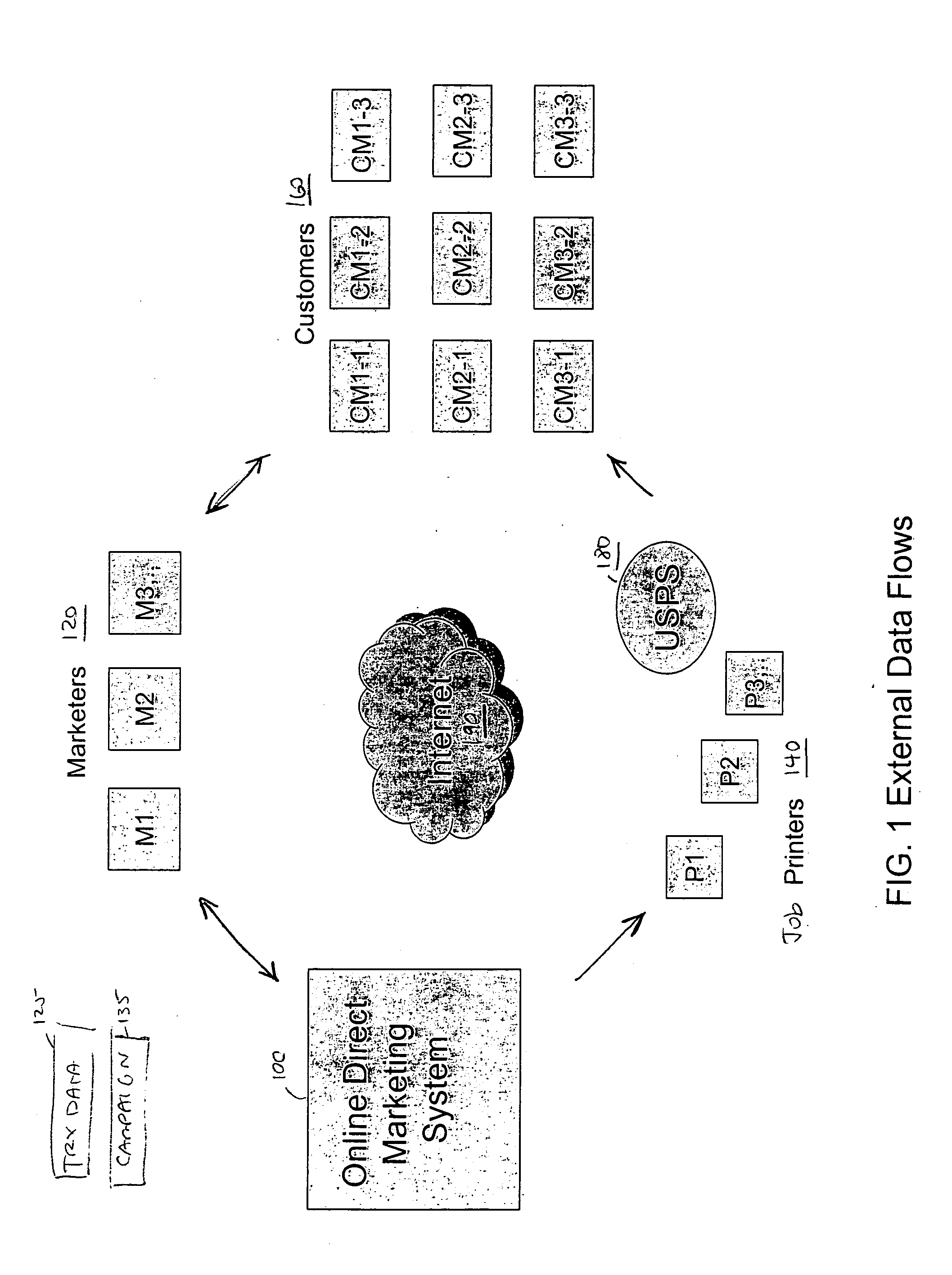
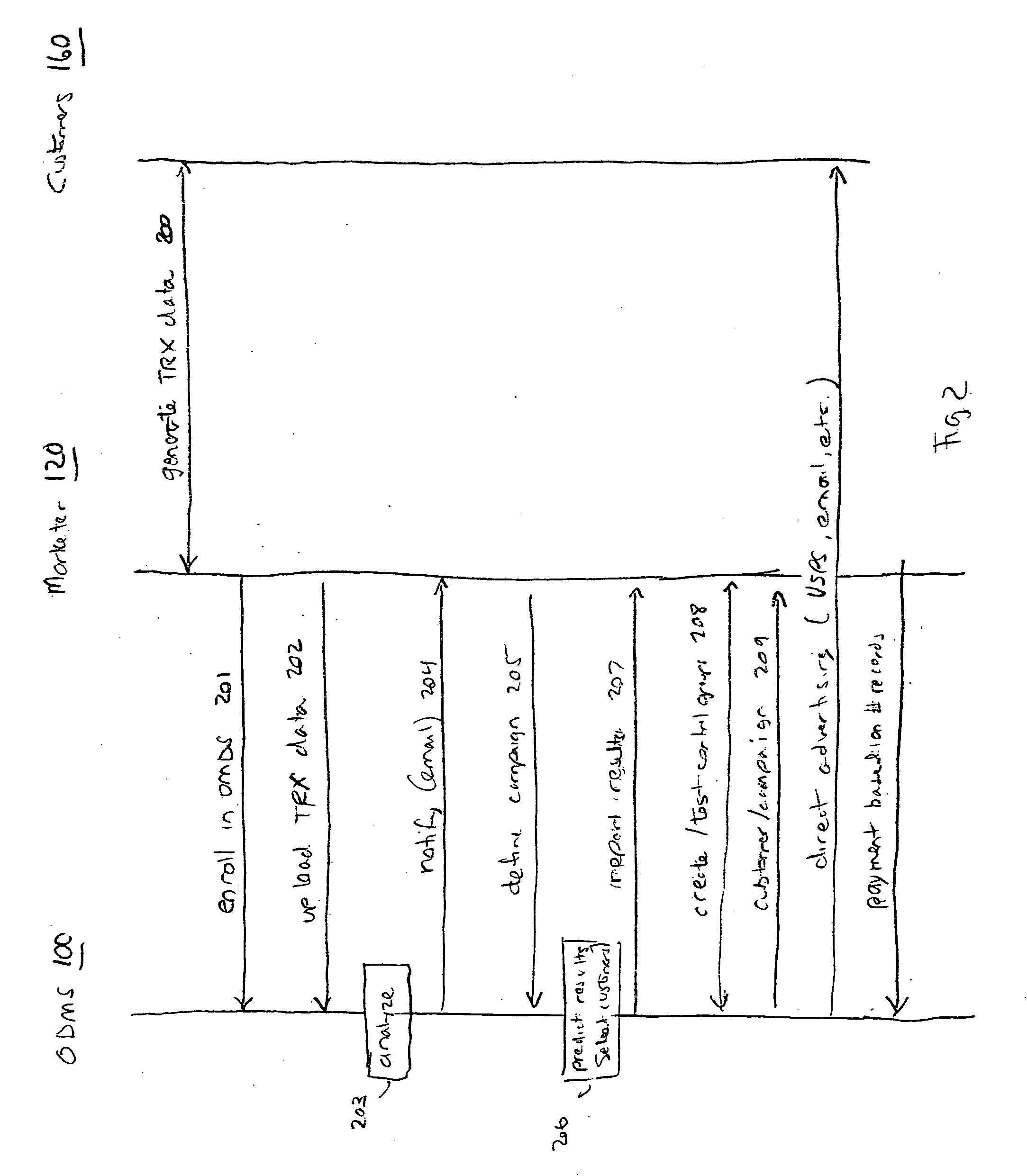
Online direct marketing system
InactiveUS20080065476A1Targeting of customers is improvedImprove accuracyAdvertisementsTransaction dataFinancial transaction
An automated, unified, interactive system and methods for marketing. After a Marketer uploads transaction and customer data, the system automatically analyzes this data to predict at least one of the group consisting of purchase probabilities, likely buyers, up-sell opportunities, cross-sell opportunities, and potential defectors; selects a marketing campaign and customers to target in that marketing campaign, the step of selecting customers being based upon results from the step of analyzing customer and transaction data; predicts anticipated response rate and / or revenue from the marketing campaign; delivers at least one list of the customers to target, wherein the list of customers further comprises customer records; supplies an expert system to test elements of the campaigns such as targeting and offers; and collects fees based on a number of the records downloaded.
Owner:LOYALTY BUILDERS
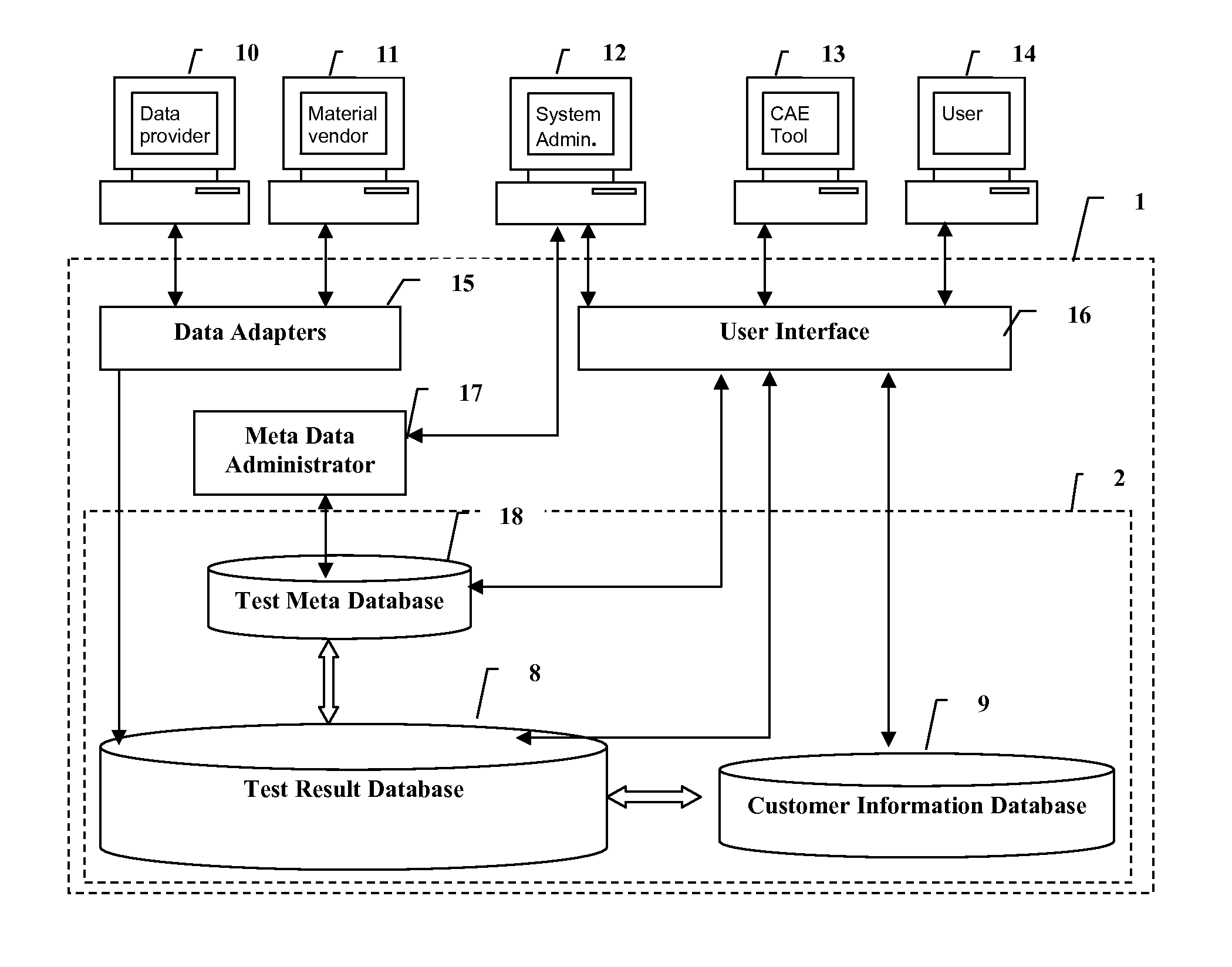
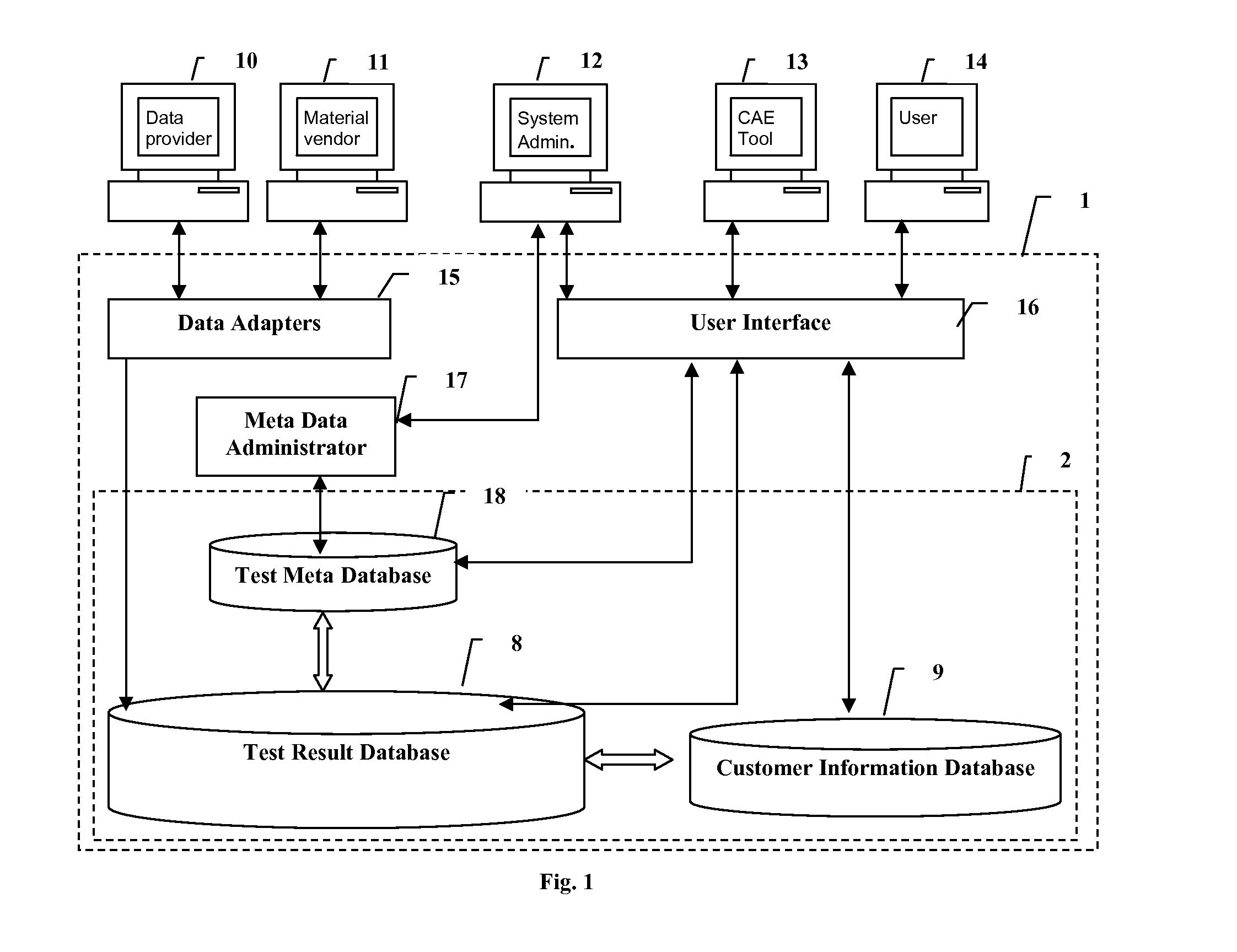
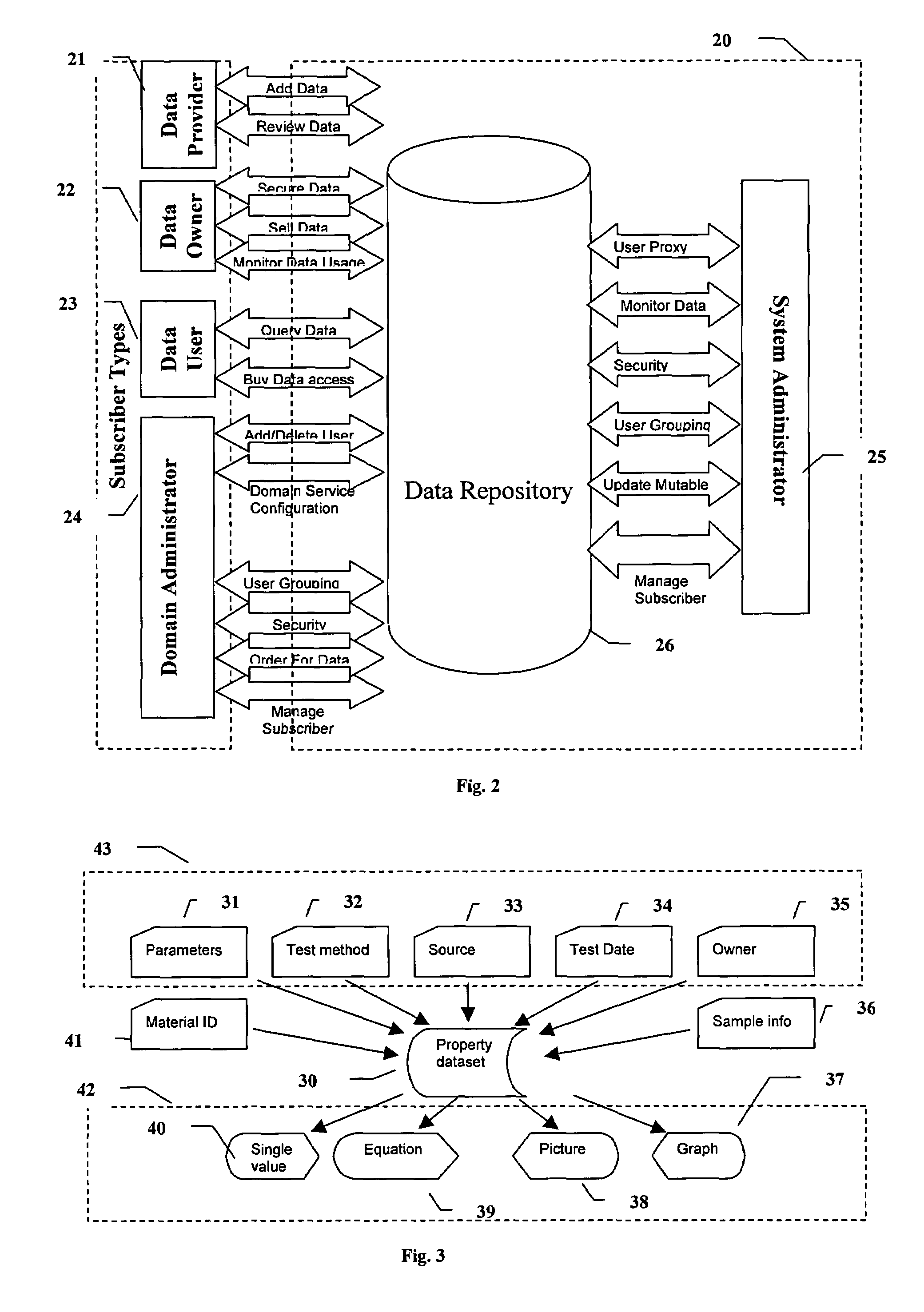
System and method for electronic submission, procurement, and access to highly varied material property data
Traceable material property data is maintained in a database and provided to users upon demand. Cohesive and logical definitions of material property datasets are provided that capture the different industry standard facets of a material property. Traceability information includes the manufacturer of the material, the source of the material, the property measuring authority, points of responsibility, facets and constraints of the measurement process. Attributes for dataset ownership and dataset access cost are maintained and only the dataset owner is allowed to update those attributes. The ability to control access to the dataset is provided to the data owner. A dataset's measuring authority is permitted to review and re-grade data. The ability to define groups of users is provided with a designated user having the ability to control group membership and set the group's policies with respect to access of datasets owned by any member of the group. The ability to transfer or trade ownership of data is permitted.
Owner:MATEREALITY
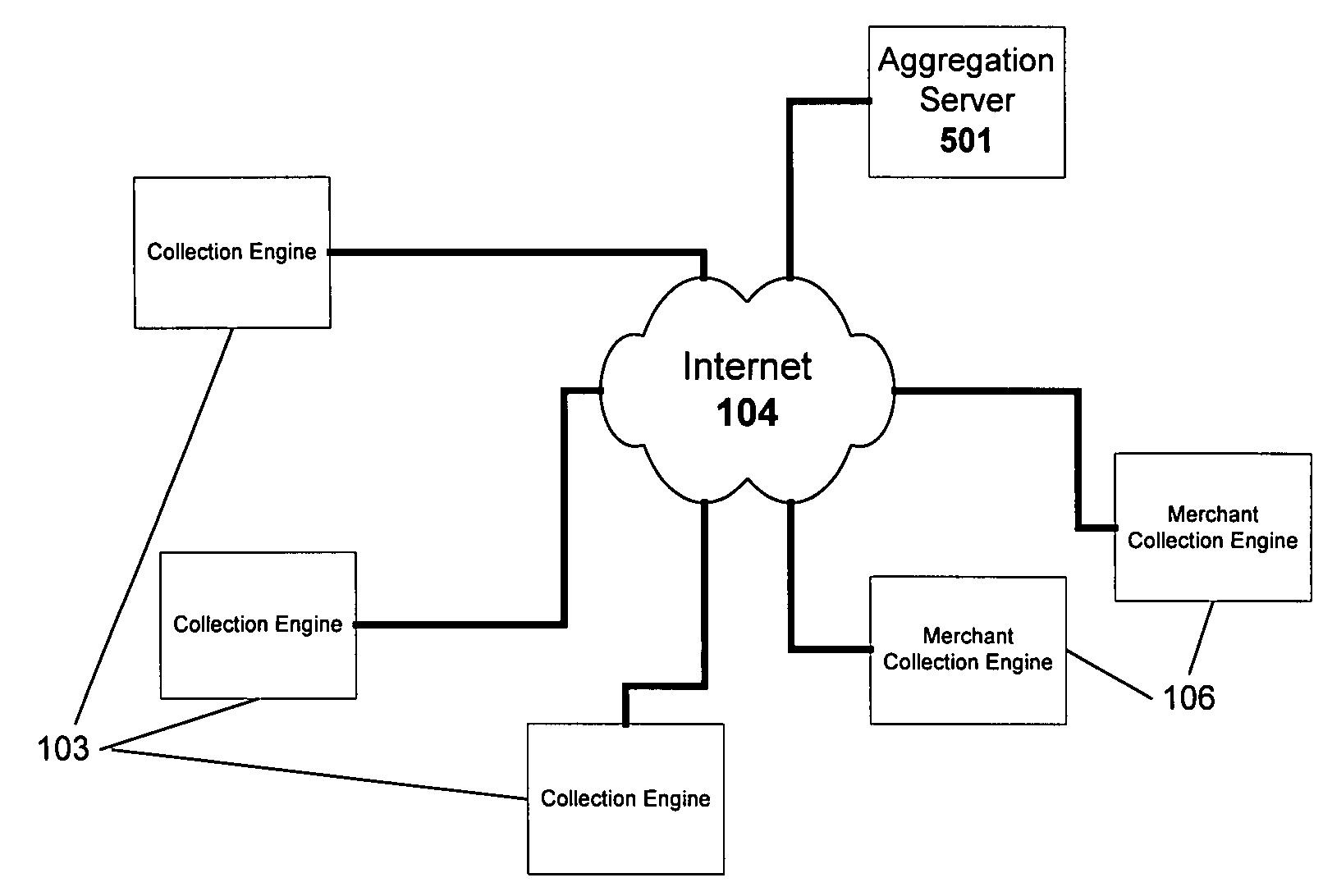
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
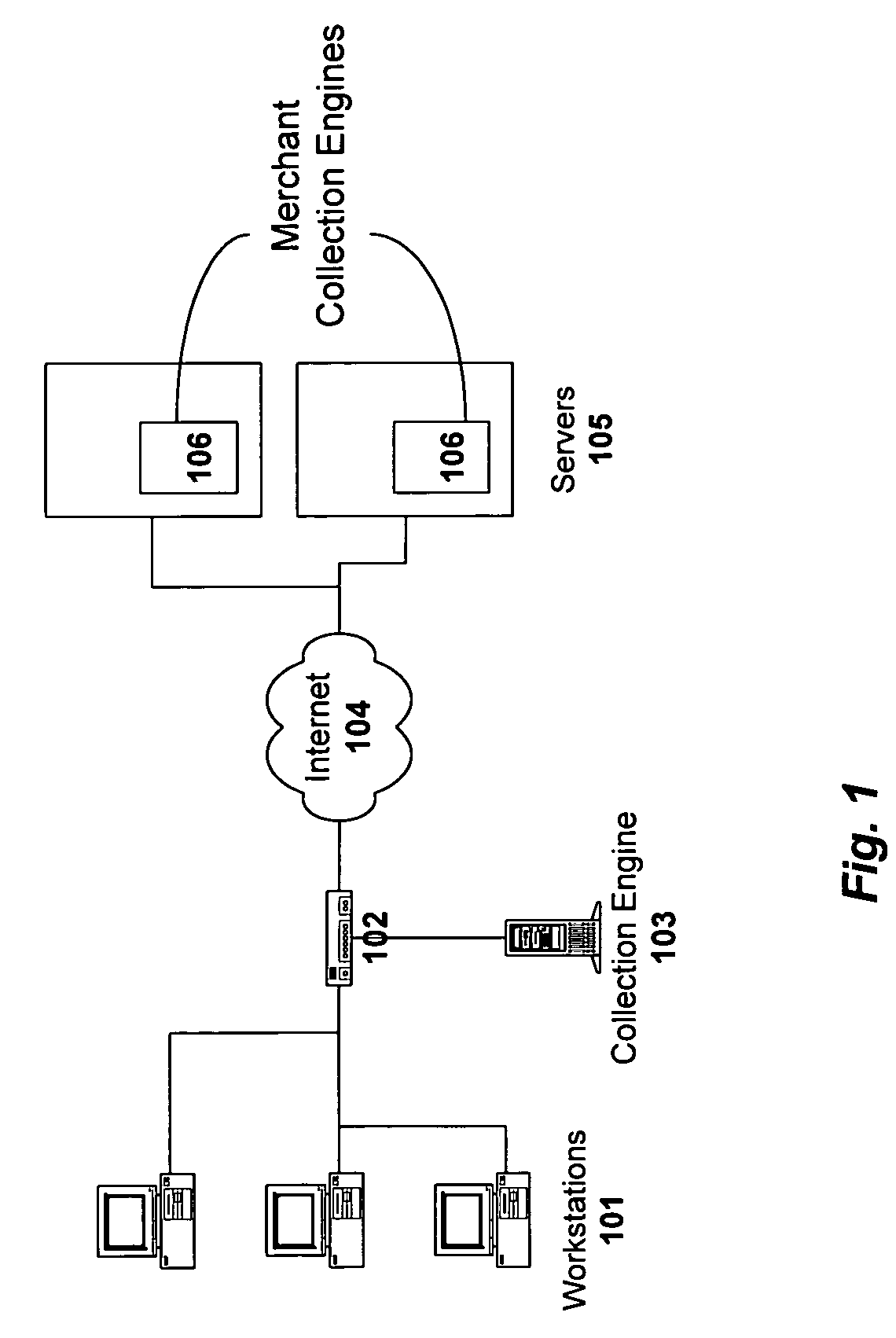
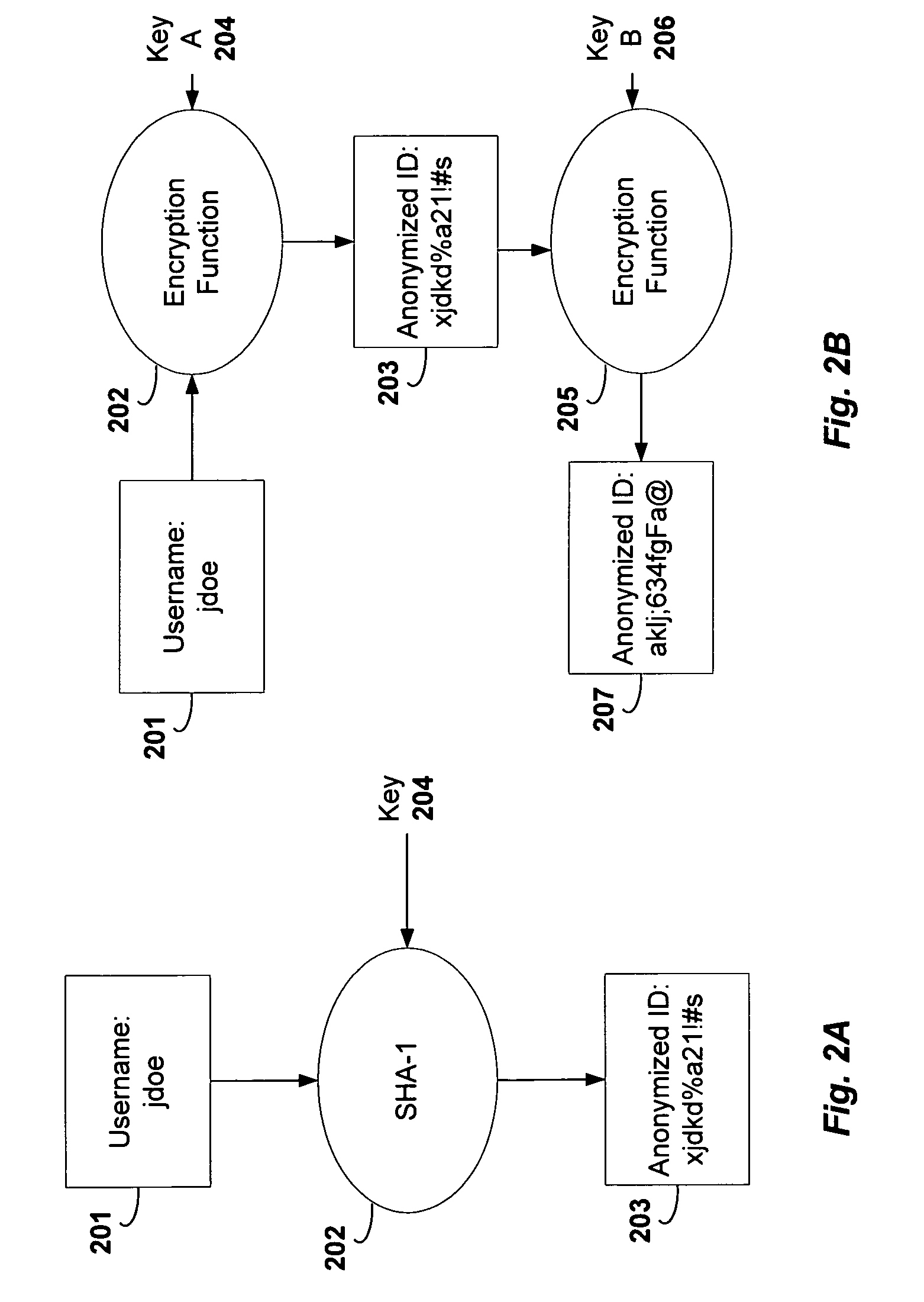
InactiveUS6983379B1Amount of timeHardware monitoringComputer security arrangementsInternet privacyTransaction data
A method and system for monitoring users on one or more computer networks, disassociating personally identifiable information from the collected data, and storing it in a database so that the privacy of the users is protected. The system includes monitoring transactions at both a client and at a server, collecting network transaction data, and aggregating the data collected at the client and at the server. The system receives a user identifier and uses it to create an anonymized identifier. The anonymized identifier is then associated with one or more users' computer network transactions. The data is stored by a collection engine and then aggregated to a central database server across a computer network.
Owner:PLURIMUS CORP +1
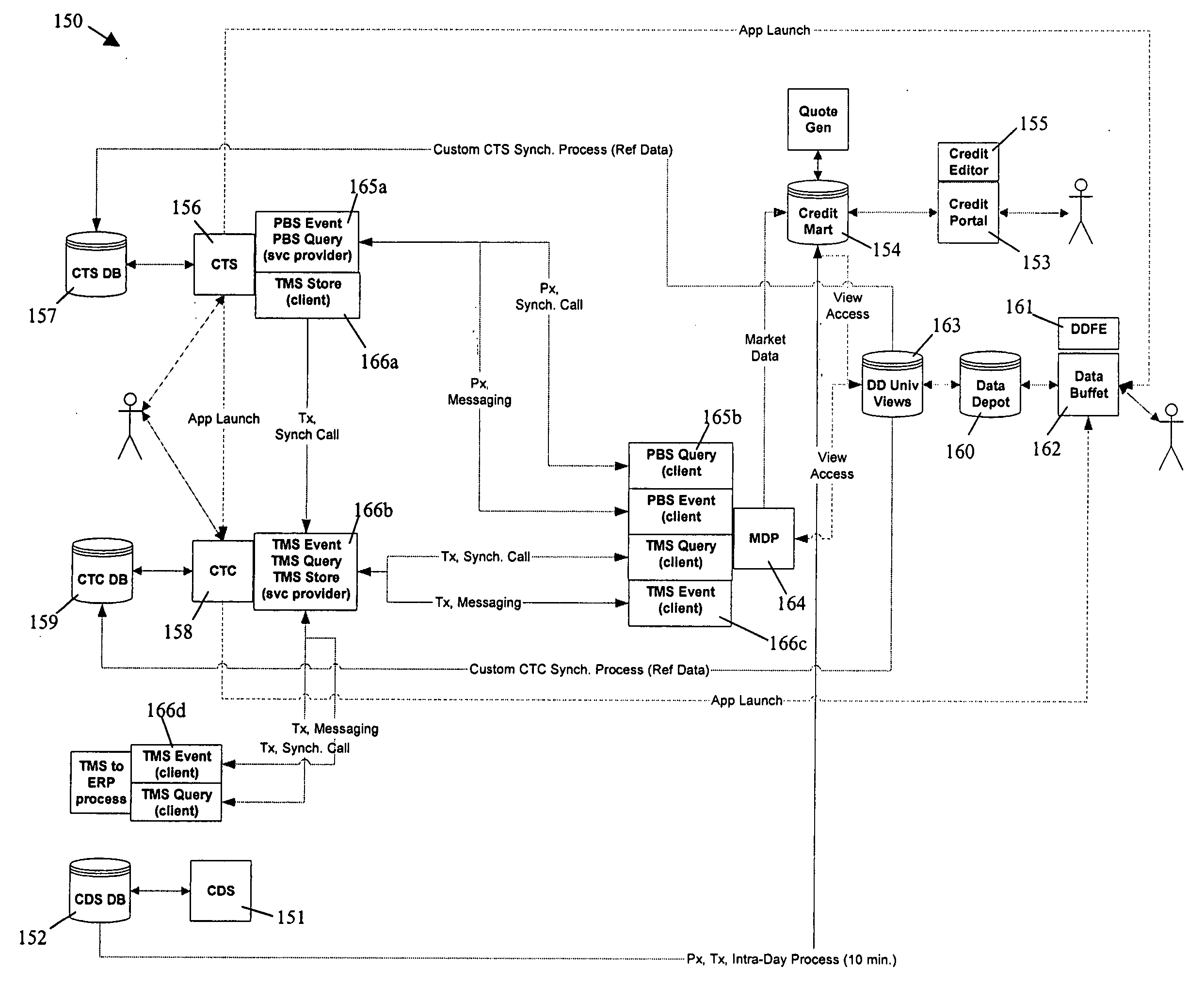
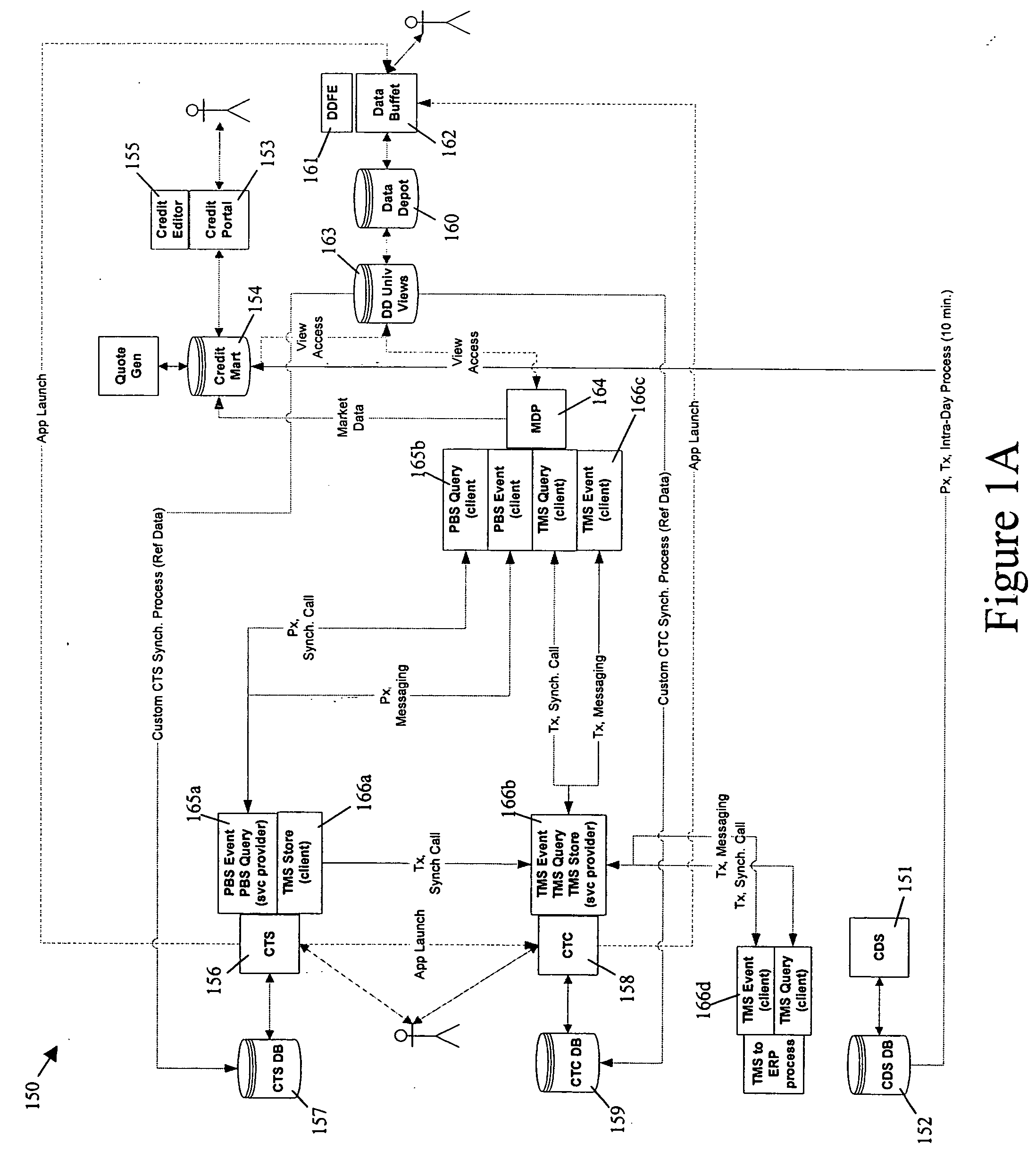
Apparatus, method and system for providing an electronic marketplace for trading credit default swaps and other financial instruments, including a trade management service system
ActiveUS20050149428A1Improve accessibilityEasy to deployFinanceCoin/paper handlersTransaction managementTransaction data
A method and system for providing integrated credit derivative brokerage services, the method or system including or using a credit trading arrangement, a credit trade capture arrangement, a trade management service arrangement to process trade data for the credit trading arrangement and the credit trade capture arrangement, and a central repository arrangement to store market data and shared reference data.
Owner:GFI GROUP INC
Pervasive, user-centric network security enabled by dynamic datagram switch and an on-demand authentication and encryption scheme through mobile intelligent data carriers
InactiveUS20040221163A1Improve reliabilityIncrease flexibilityKey distribution for secure communicationUnauthorised/fraudulent call preventionNetwork connectionEngineering
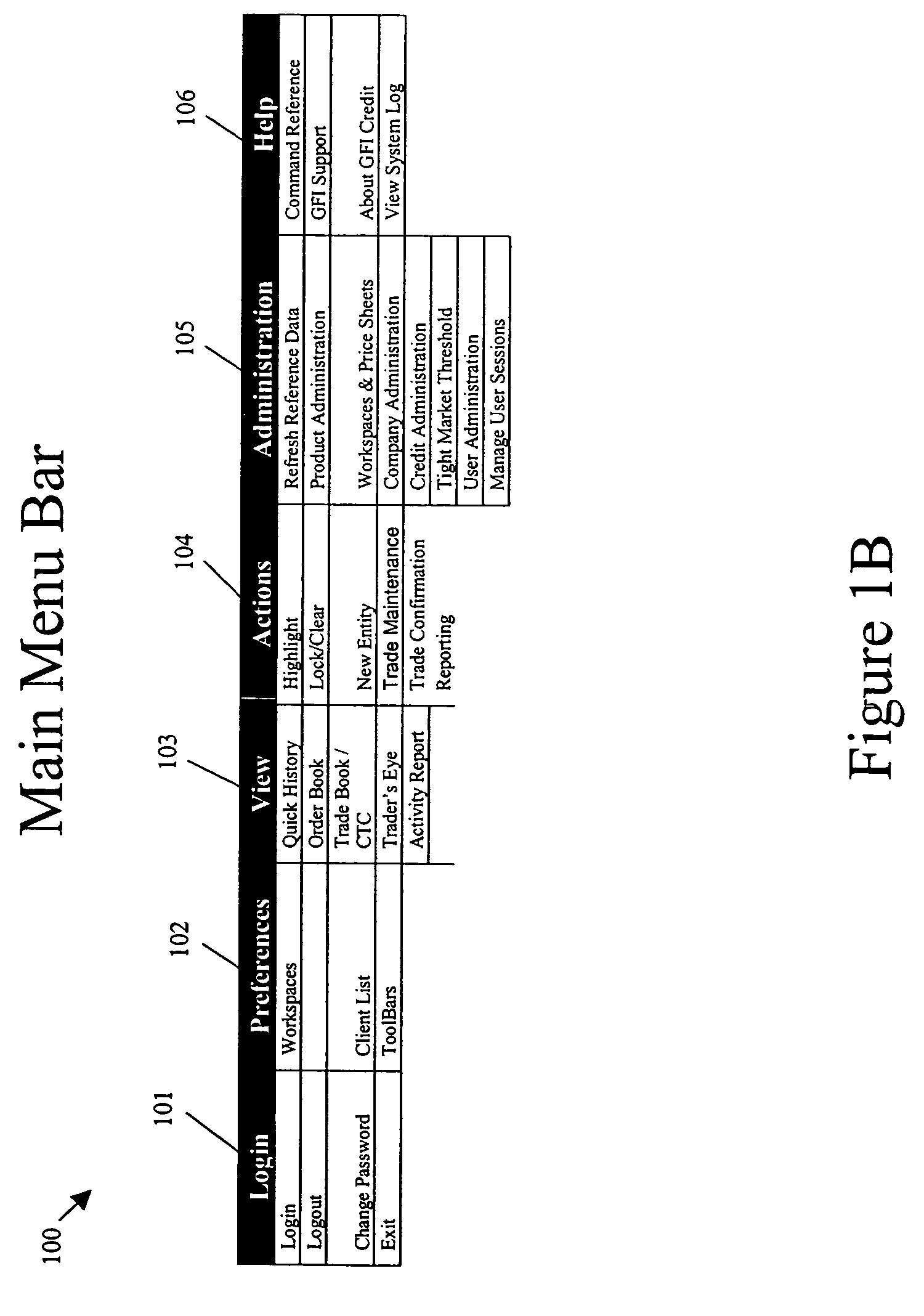
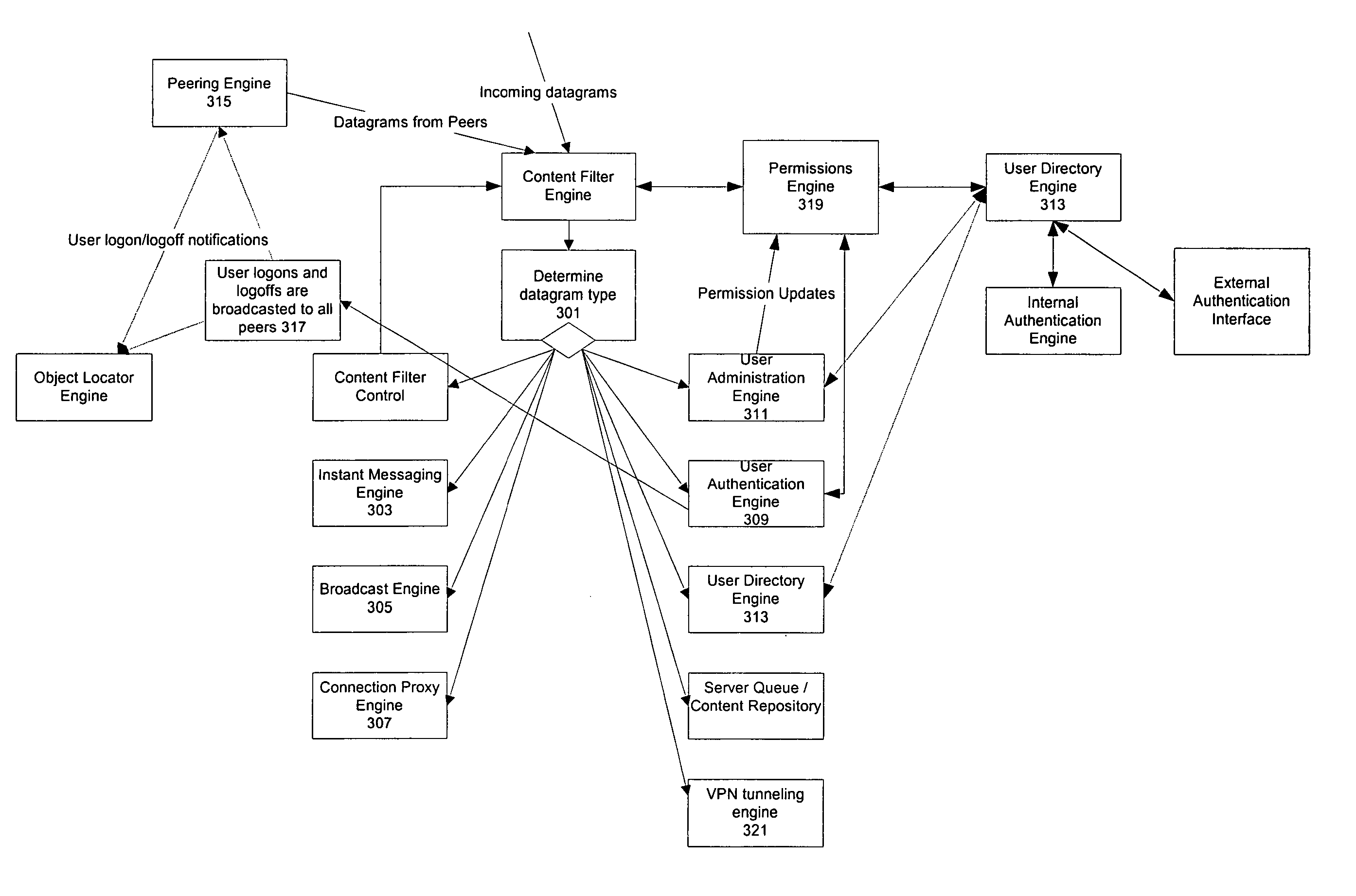
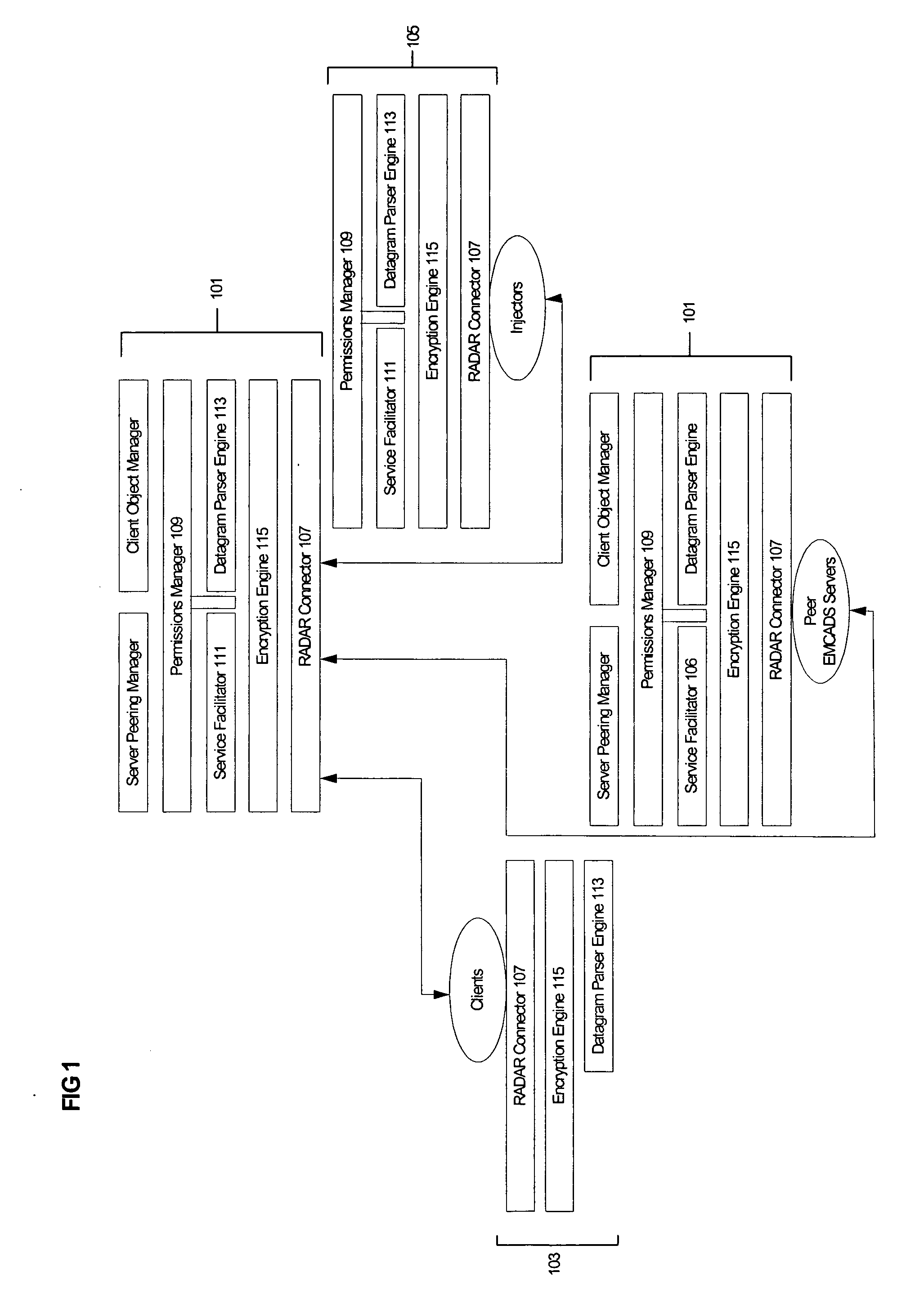
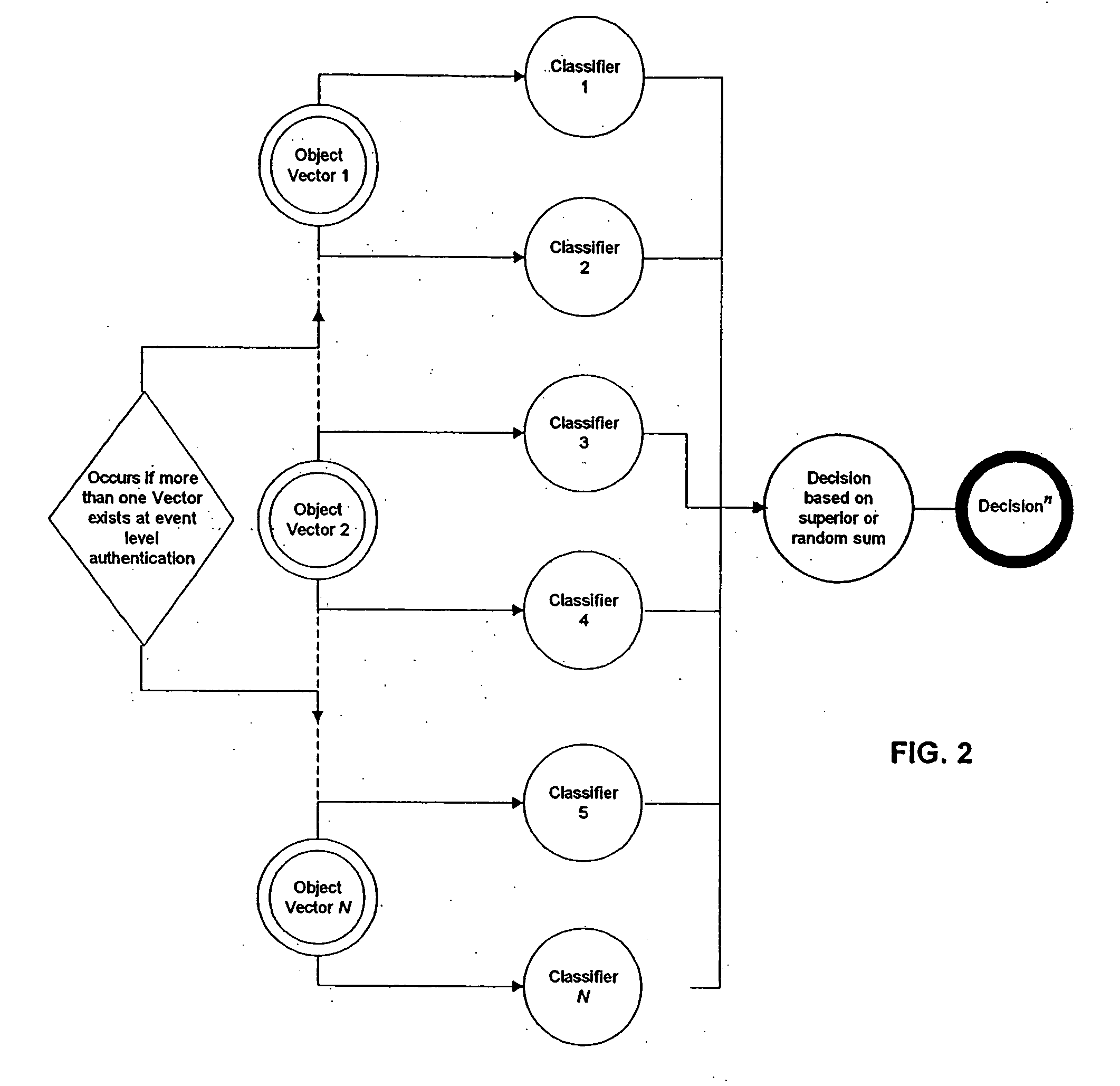
Methods and systems are provided for improving access control, administrative monitoring, reliability, as well as flexibility of data transmission and remote application sharing over a network. Secure, stable network connections and efficient network transactions among multiple users are supported by an open and distributed client-server architecture. A datagram schema is adapted to enable dynamic datagram switching in support of a multitude of applications and network services. Mobile intelligent data carriers are provided that allow for the implementation of an authentication and encryption scheme. The intelligent data carriers are adapted to target deliver applications to authorized users, thereby achieving access control to not only data but also applications. The authentication and encryption scheme in one embodiment is based on physical or performance biometrics. The methods and systems of this disclosure may be advantageously deployed in an enterprise network environment to support a wide spectrum of business, research, and administrative operations.
Owner:GIRITECH APS
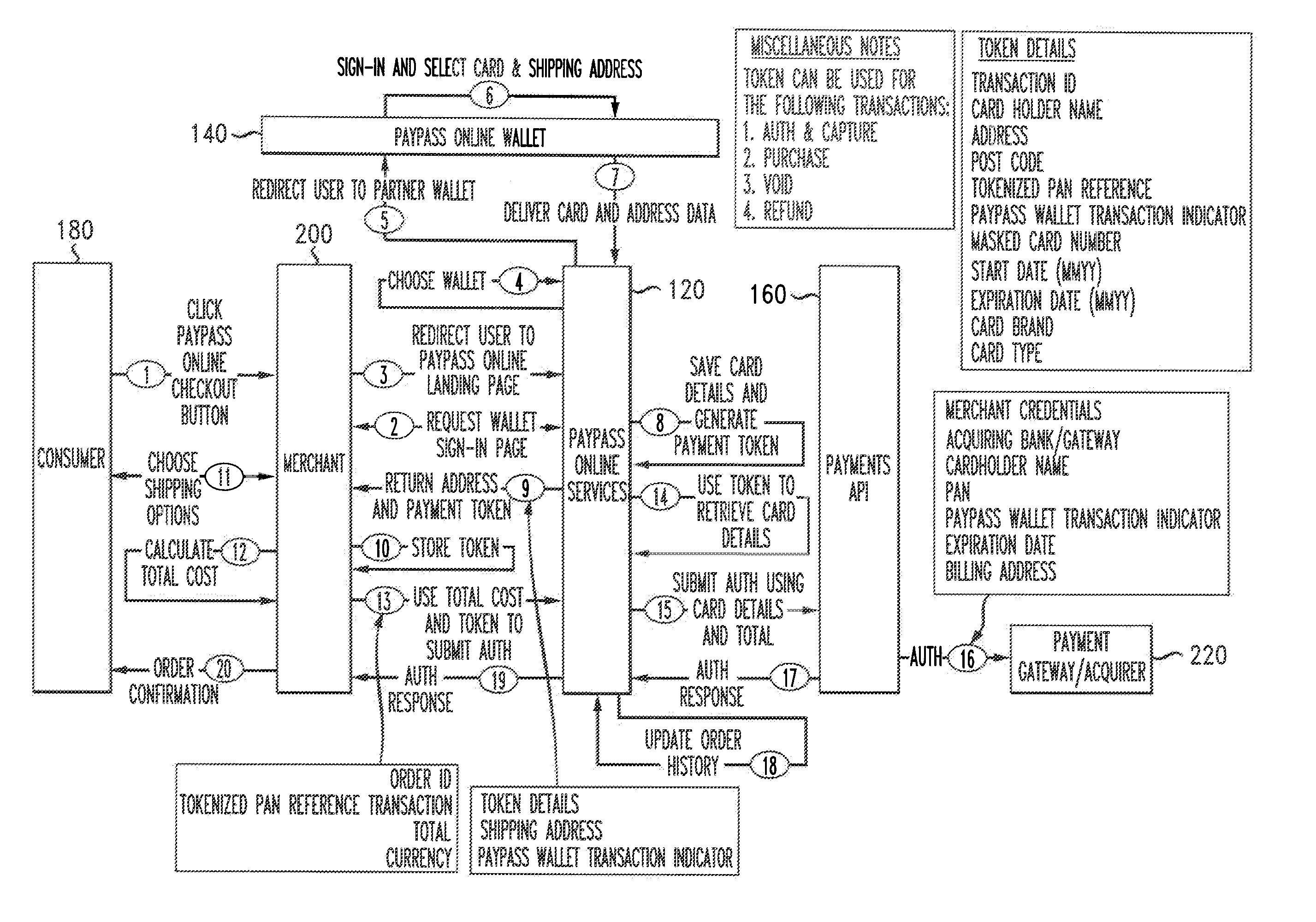
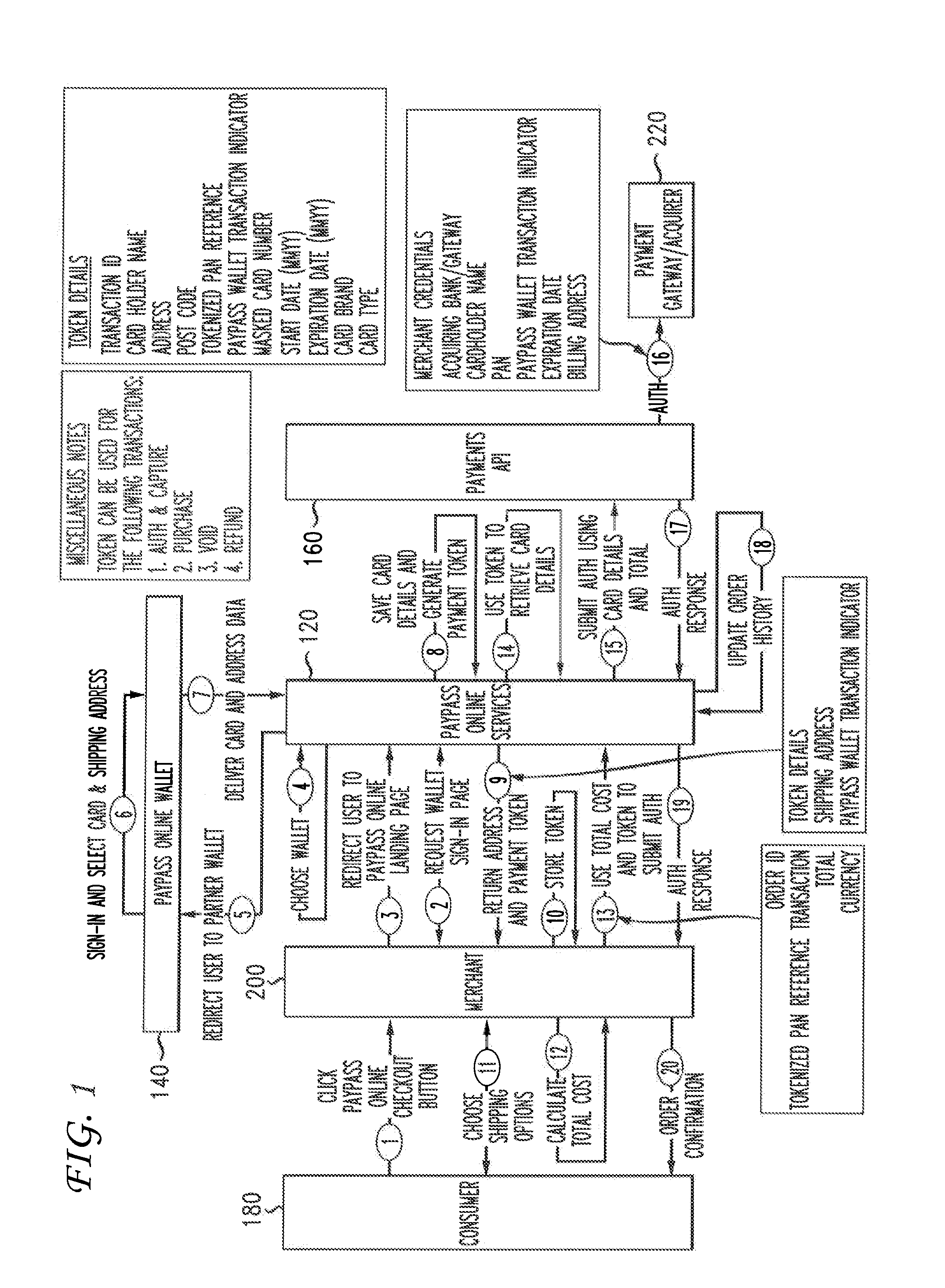
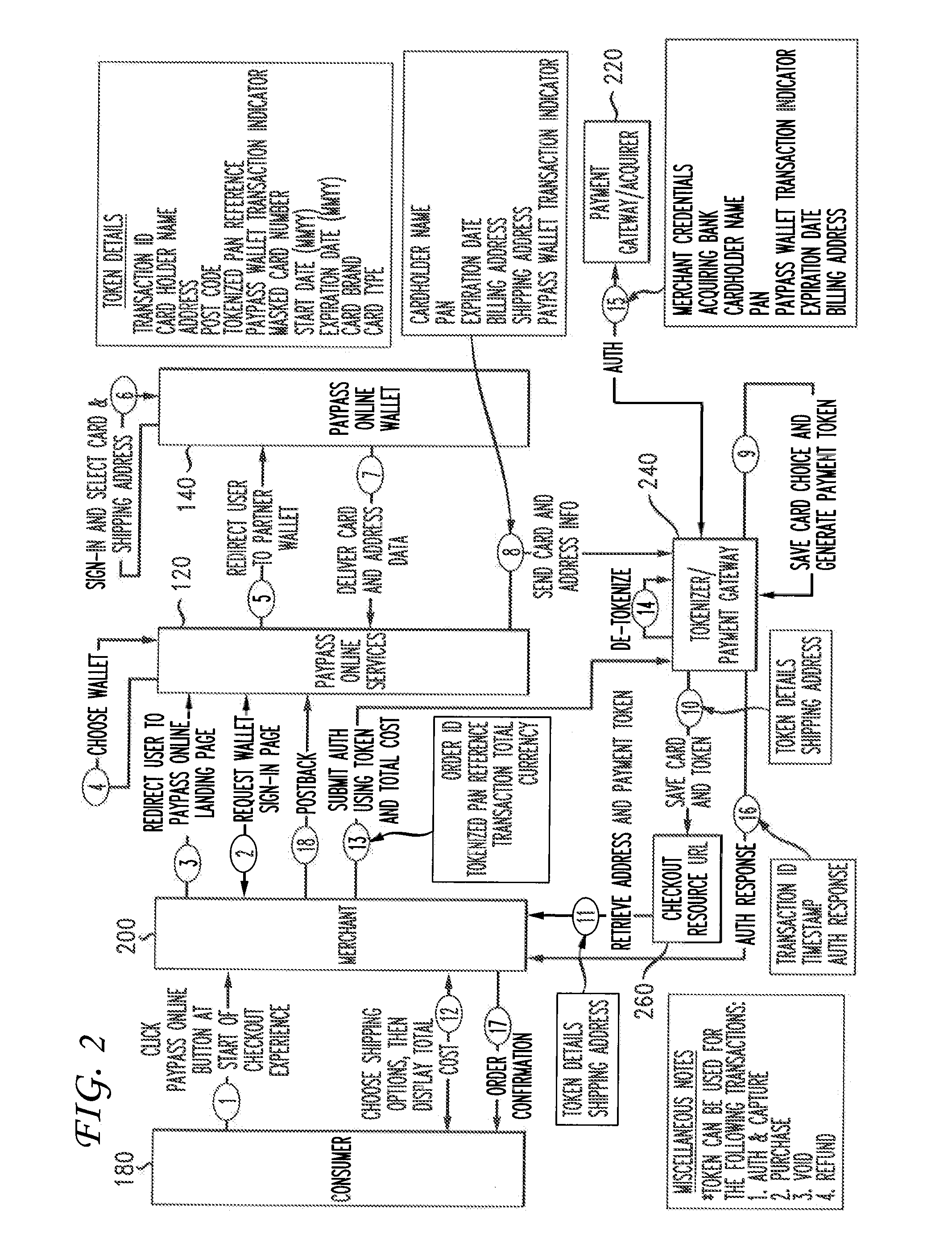
Transaction data tokenization
A system and method of tokenizing sensitive cardholder payment information for use in cashless transactions includes receiving a request to process a cashless transaction between a merchant and a purchaser using first payment data stored with an electronic wallet provider on behalf of the purchaser. First payment data is retrieved from the electronic wallet provider. The first payment data is tokenized into a payment token, and provided to the merchant for use in completing the cashless transaction. The merchant issues a request to process payment for the cashless transaction using the payment token. The payment token is detokenized into second payment data, with correspondence between the first and second payment data being indicative of payment token authenticity. Payment for the cashless transaction is processed using the second payment data, and the merchant is provided with a response indicating either the success or failure of the payment processing.
Owner:MASTERCARD INT INC
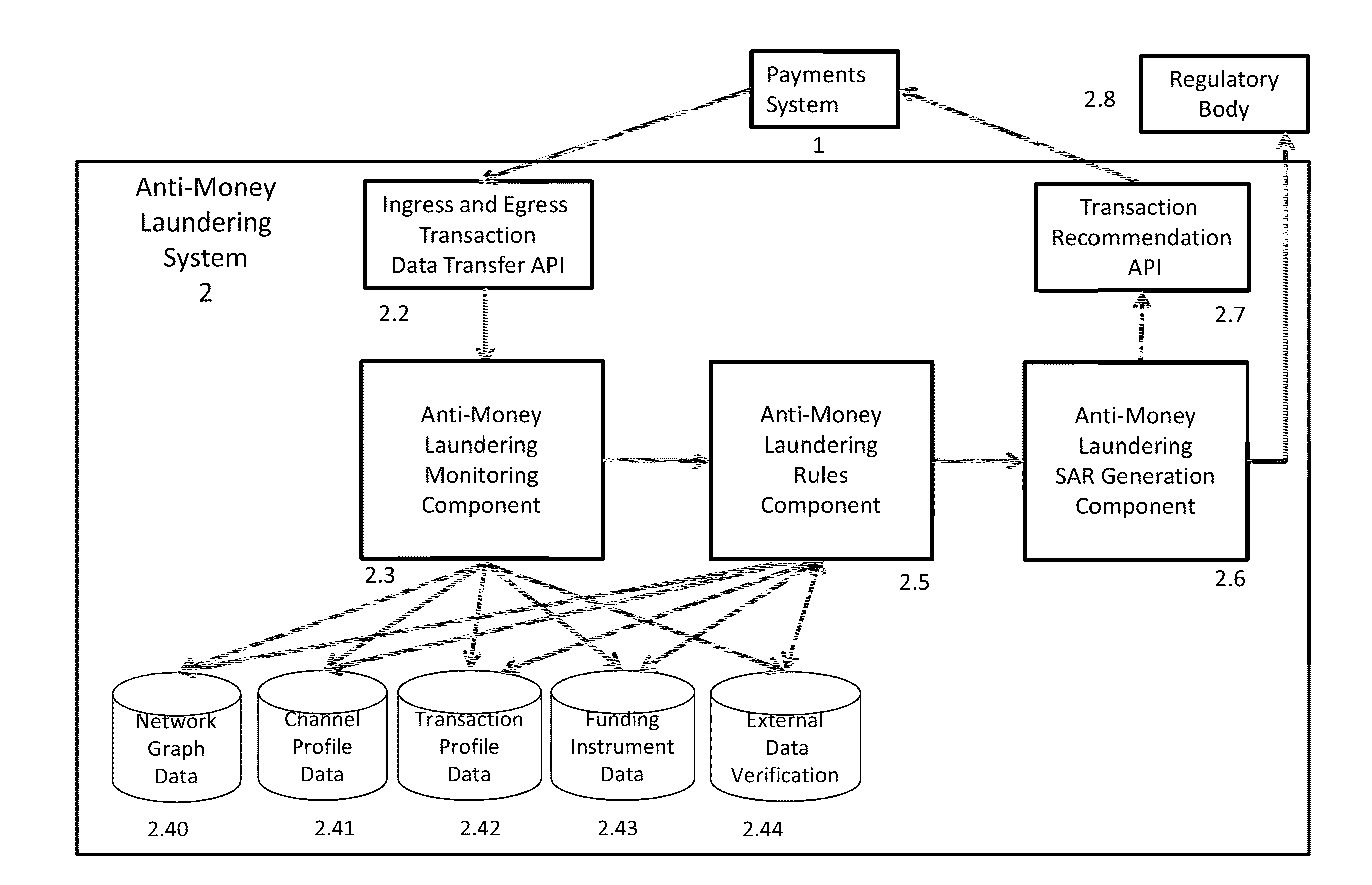
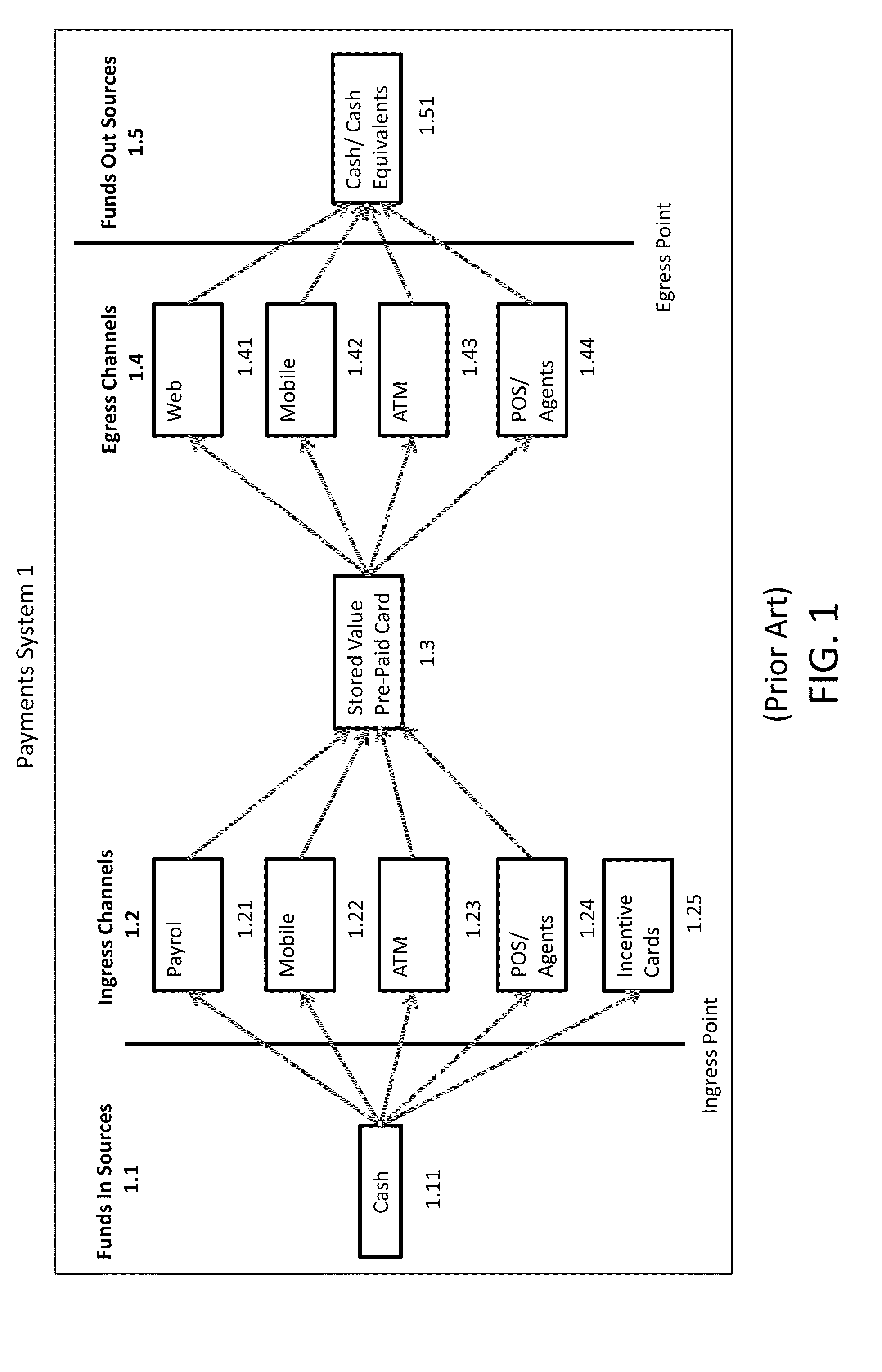
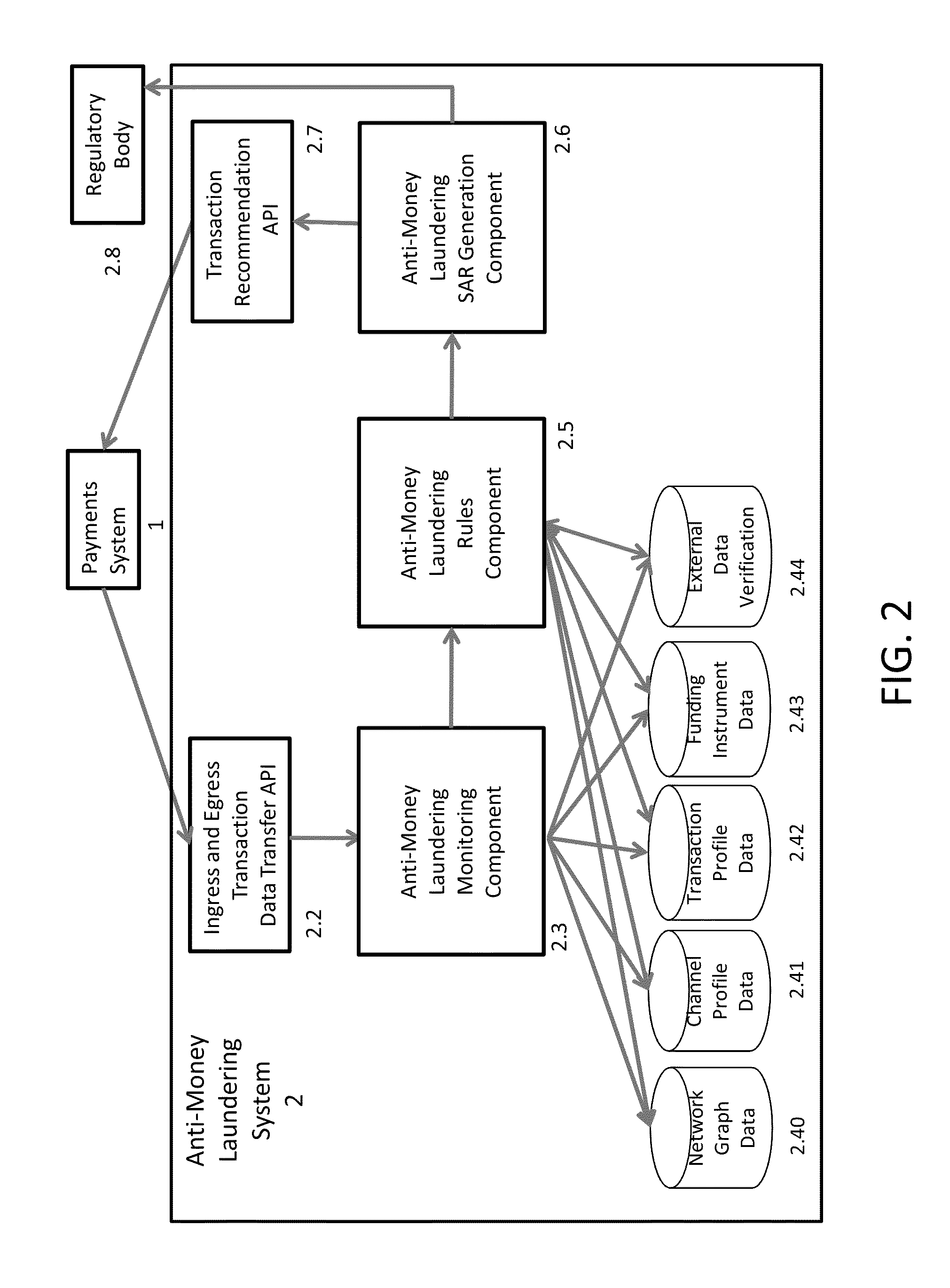
Multi-Channel Data Driven, Real-Time Anti-Money Laundering System For Electronic Payment Cards
Electronic payment card money laundering detection includes receiving real-time payment card transaction data from ingress channels and an egress channels of at least one payment card system through a first API; generating transactional profiles for each of at least payment cards, the ingress channel, the egress channels, and funding sources of the payment cards; in response to receiving transaction data for a current payment card transaction, evaluating the transaction data using a predictive algorithm that compares the transaction data to the transactional profiles to calculate a probabilistic money laundering score for the current transaction; evaluating the probabilistic money laundering score and current transaction data based on a set of rules to generate a suspicious activity report that recommends whether to approve or report the current transaction; and transmitting the suspicious activity report back to the payment card system and transmitting the suspicious activity report to an identified regulatory body.
Owner:WALMART APOLLO LLC
Method and system for associating consumers with purchase transactions
A system and method for associating consumers with their purchases so that consumer transactions can be tied back to a particular consumer is described. More particularly, a central transaction entity as part of a larger network collects, aggregates, manages and mines consumer transaction data from at least consumer and merchant members of the network for the purpose of routing electronic purchase history to consumers and allowing merchant analysis of consumer behavior in order to create consumer profiles to better service consumers and provide more personalized offers.
Owner:CITICORP CREDIT SERVICES INC (USA)
Transaction location analytics systems and methods
One embodiment provides a method for evaluating transaction data to determine point of location usage. This could be, for example, to determine where customers are mostly likely to shop before or after shopping at a given merchant. For instance, the method could show the percentage of customers that shop at certain types of stores during a time period right before or after shopping at the merchant's location. As another example, the method could be used to determine when a merchant's customer makes a purchase at the merchant's store, then makes a purchase at a competing merchant's store within a specified time.
Owner:FIRST DATA
System and method for determining vehicle price adjustment values
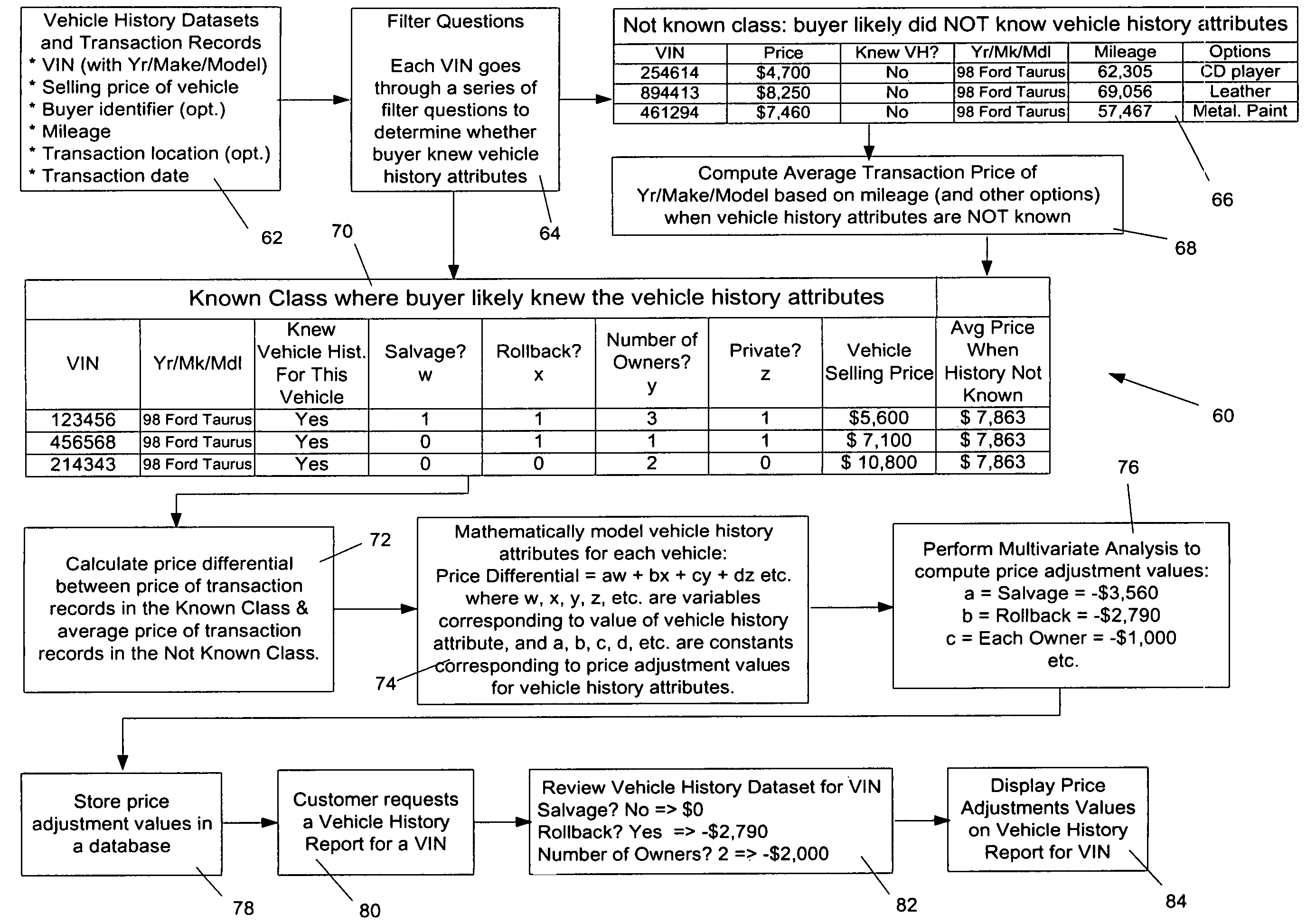
InactiveUS7596512B1Minimal user inputGenerates adjustment valueFinanceMarketingData setTransaction data
System and method for computing price adjustment values associated with vehicle history attributes including a vehicle history database with vehicle history datasets, a transaction database, a vehicle history knowledge determination module adapted to determine whether a sale transaction related to a transaction record occurred with buyer's knowledge of the vehicle history attributes associated with the vehicle of the transaction record and to classify each transaction record based on whether buyer possessed knowledge of the vehicle history attributes, and a price adjustment module adapted to determine price adjustment values for the vehicle history attributes based on the vehicle history datasets and classification of the plurality of transaction records. In accordance with one aspect, the present invention may be implemented as a computer readable medium with instructions.
Owner:CARFAX
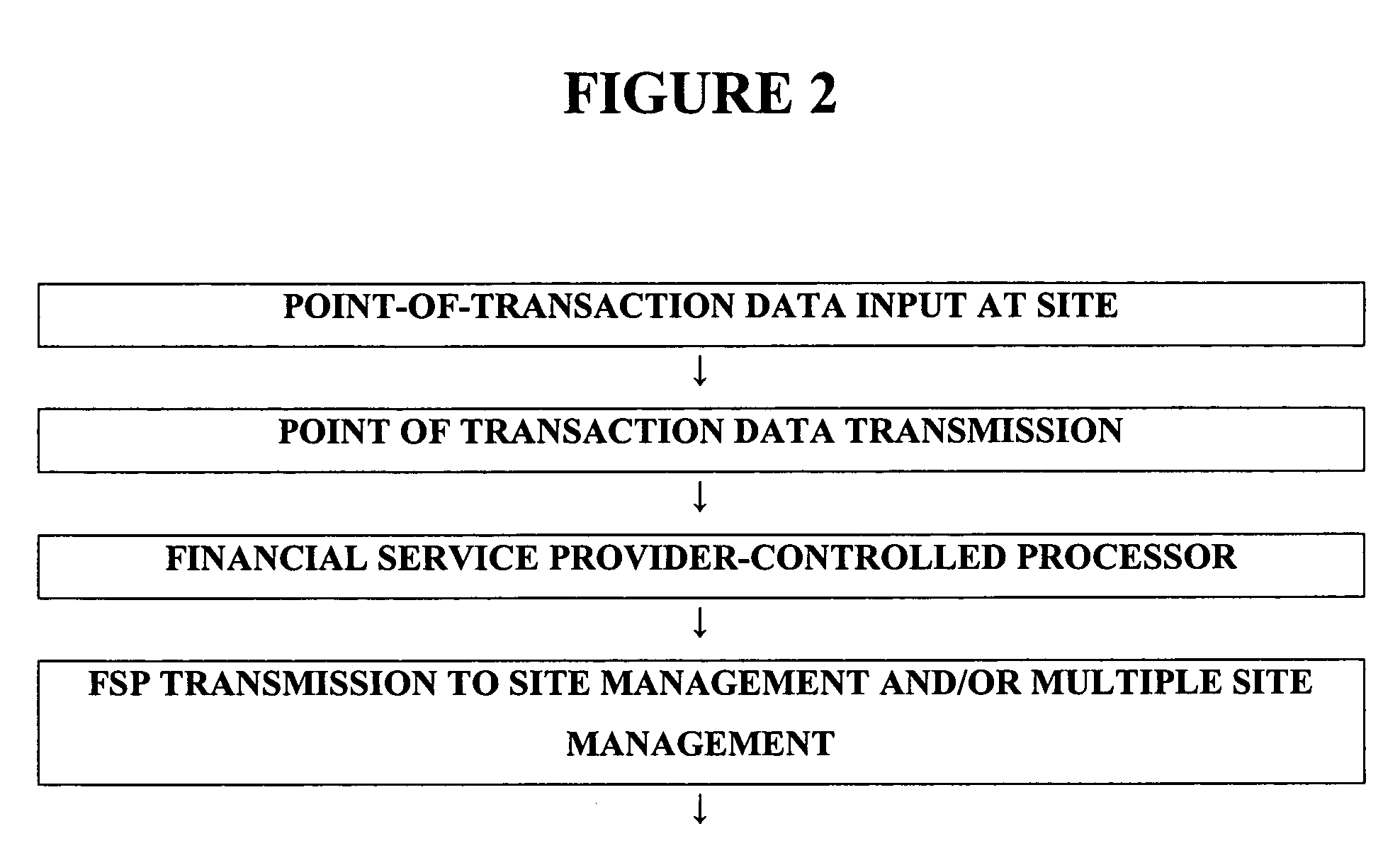
Point-of-sale provider evaluation
A system provides information indicative of customer satisfaction respecting at least one service or sales provider, the system including at least one customer information entry component that provides customer input to a database supported by a financial service provider that assists point-of-sales or point-of-service payment to a site. The system can segregate or aggregate accumulated customer input data according to at least business one customer of the financial service provider. At least one business customer can access information from the accumulated customer input data that relates to data relating to that specific business customer. The system can provide alerts and / or can relate the data in its variance to the customer's historical average scores. A method of providing information to a master business site regarding a subordinate business site comprises providing the subordinate business site with a point-of-sales or point-of-service data input for local customer site evaluation data to be provided by a local on-site primary customer, data input and data reception being directly associated with a financial service provider electronically supported economic transactions and transmitting data relating to both the economic service and the local customer site evaluation data to a processor that receives both the economic transaction data and the local customer site evaluation data.
Owner:FOSS SWIM SCHOOL LLC
Method and system for conducting secure payments over a computer network
A method is provided for conducting a financial transaction by a purchaser with a merchant having an acquirer bank, over a communications network. The method includes the steps of sending a first authorization request using a pseudo account number associated with a real account number to a service provider which forwards a second authorization request to the issuer using the real account number and preferably a pseudo acquirer code associated with the service provider such that the response to the second request is based on the real account number and sent back to the service provider who preferably forwards a response to the first request preferably to the “real” acquirer. A message authentication code is further provided which includes transaction data, and where the authorization request is formatted as a standard payment card track having one or more fields including a discretionary field in which the message authentication code is placed.
Owner:HOGAN EDWARD J +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com