Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
25353 results about "Financial transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A financial transaction is an agreement, or communication, carried out between a buyer and a seller to exchange an asset for payment. It involves a change in the status of the finances of two or more businesses or individuals. The buyer and seller are separate entities or objects, often involving the exchange of items of value, such as information, goods, services, and money. It is still a transaction if the goods are exchanged at one time, and the money at another. This is known as a two-part transaction: part one is giving the money, part two is receiving the goods.
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
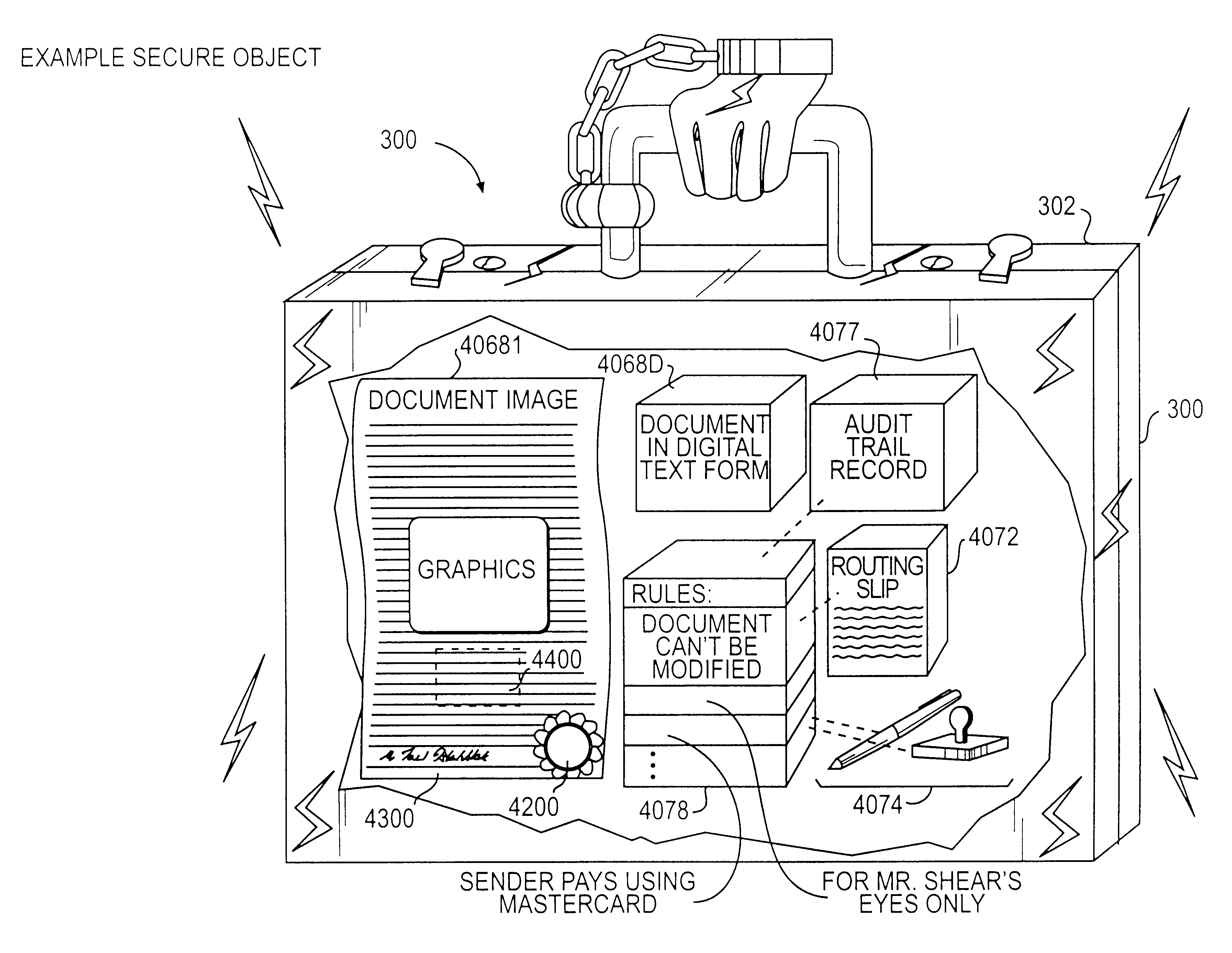
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
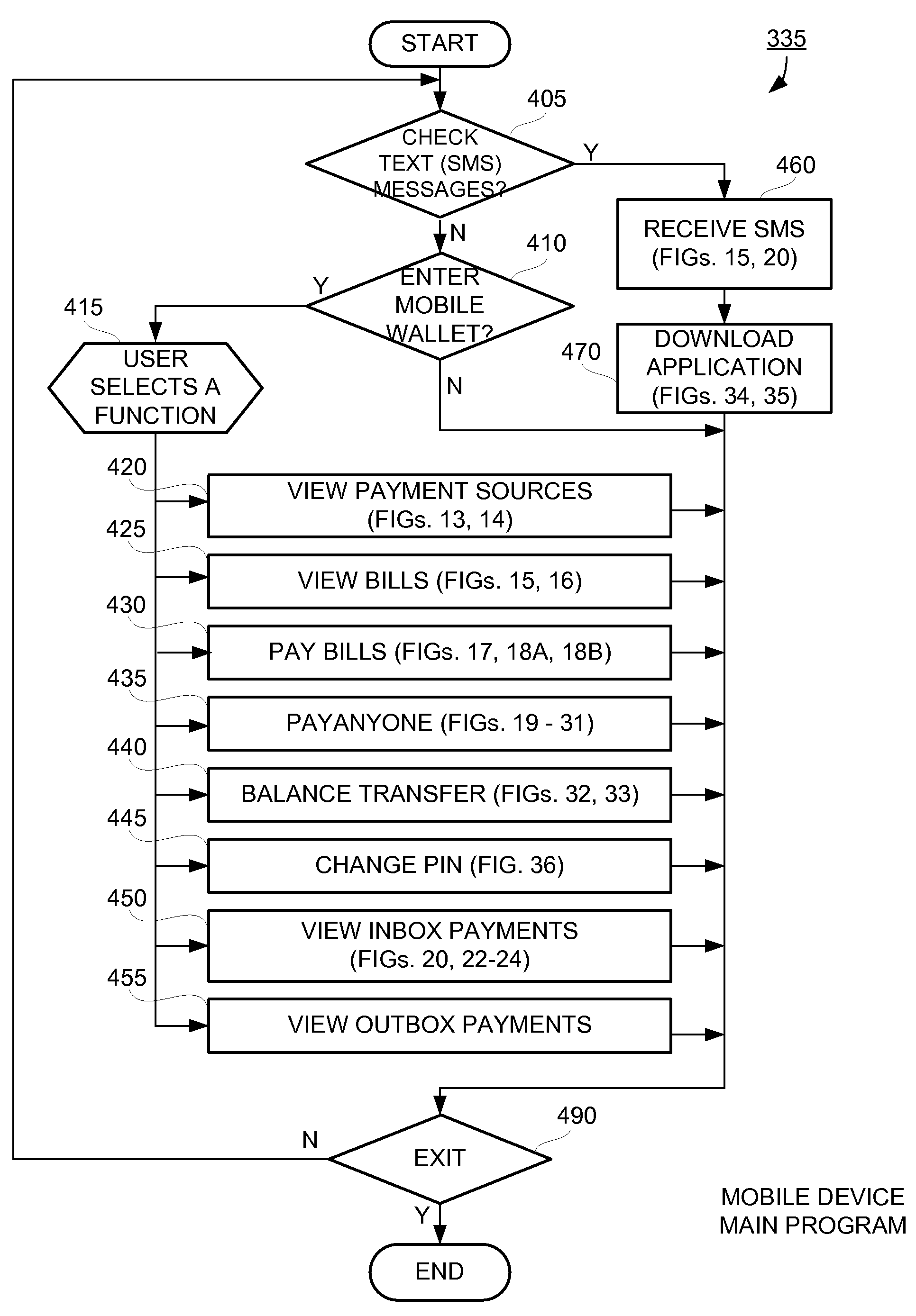
Mobile Person-to-Person Payment System
InactiveUS20070255653A1Easy to useFraudulent transaction is minimizedFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions can be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions can be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
System and method for an automated benefit recognition, acquisition, value exchange, and transaction settlement system using multivariable linear and nonlinear modeling
A system and process that provides an on-line, interactive, and fully integrated benefit-driven value exchange and settlement program that monitors, evaluates, and manages economic and personal benefits and executes functions to produce and acquire the maximum or preferred benefit items for users by guiding and automating appropriate payment and settlement actions. The present invention finds useful patterns in data; produces conclusions based on rules and experience; responds to environmental changes with or without human intervention; and, may evolve through selecting the best results from random mutations all of which are intended to maximise user value.
Owner:IANNACCI GREGORY FX
Method of and system for uniquely responding to code data captured from products so as to alert the product handler to carry out exception handling procedures
InactiveUS20120203647A1Avoid disadvantagesEffectively reliably informCash registersPayment architectureLogistics managementSoftware engineering
A code reading system capable of signaling exception handling procedures for products being handled in a work environment, such as, for example, consumer product being purchased in a retail store or a product or package being sorted by a logistics company. The system includes a system housing containing one or more one or more signal sources for generating distinctive visual and / or audible exception handling signals for special classes of products identified in the environment. Such special products may include: EAS tagged products requiring EAS tag deactivation: alcohol and tobacco products requiring proof of age; controlled products requiring additional customer tracking; age restricted products requiring identification; product purchases requiring personnel to show up and approve or assist in a product transaction; and the like.
Owner:METROLOGIC INSTR
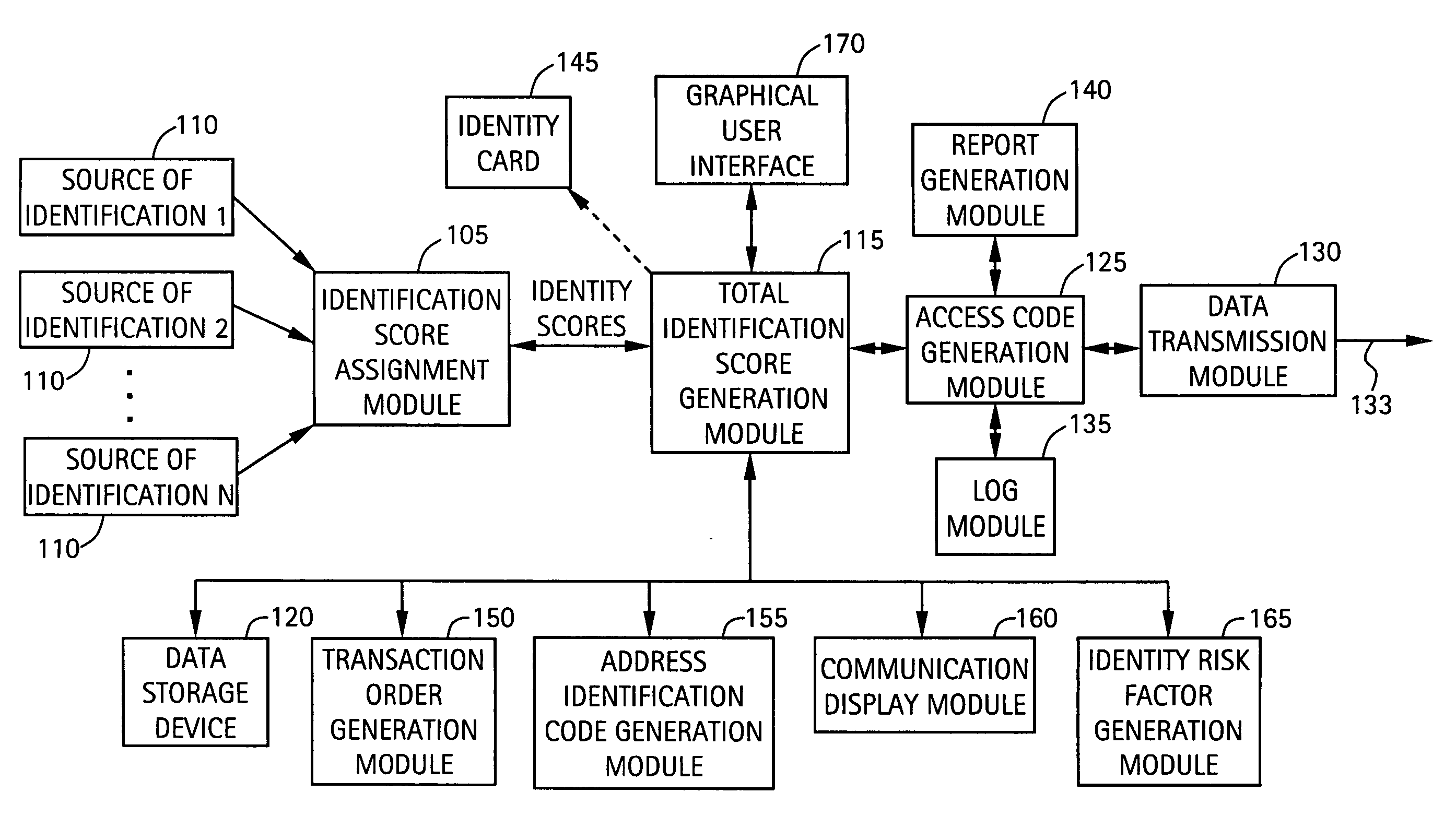
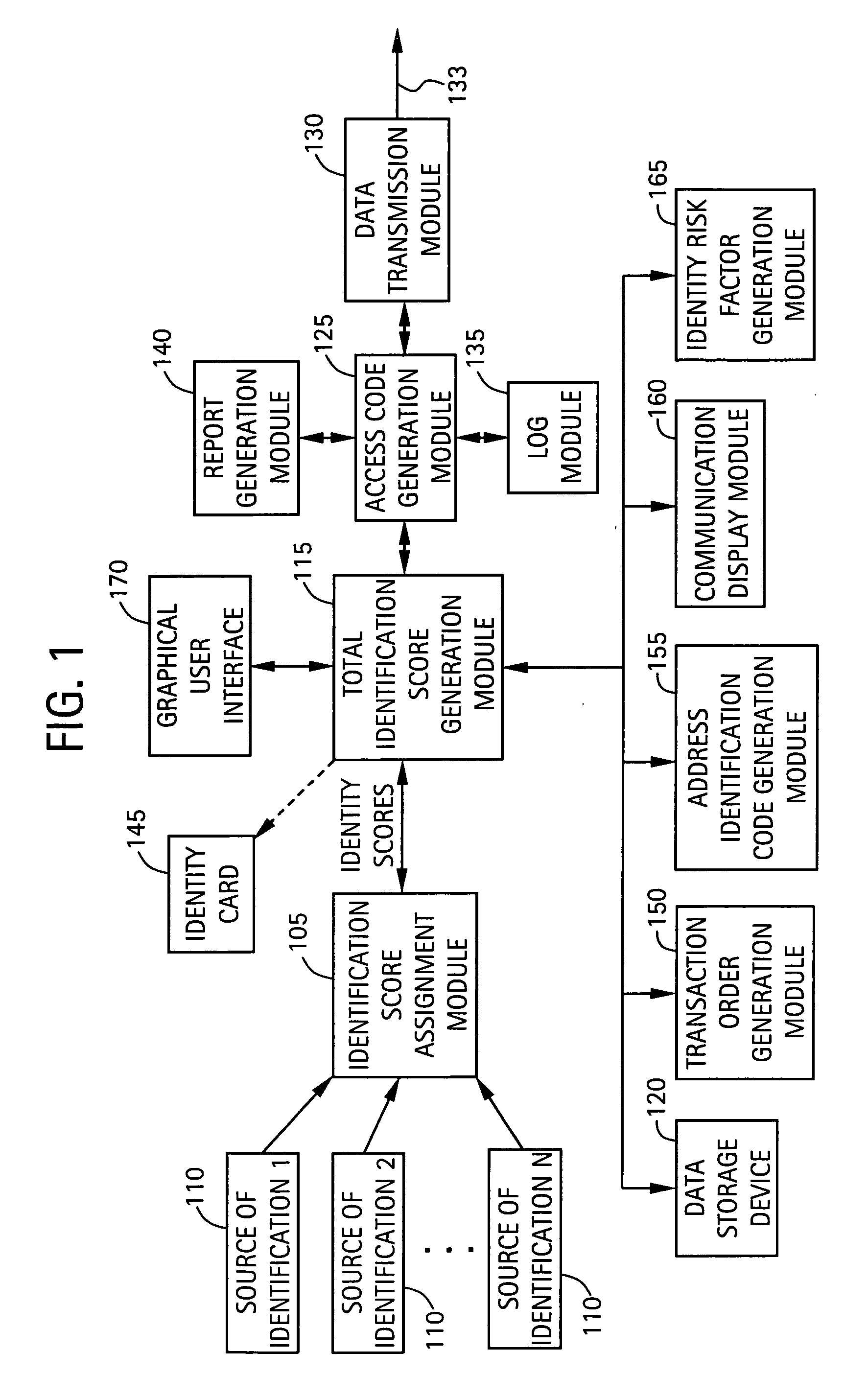
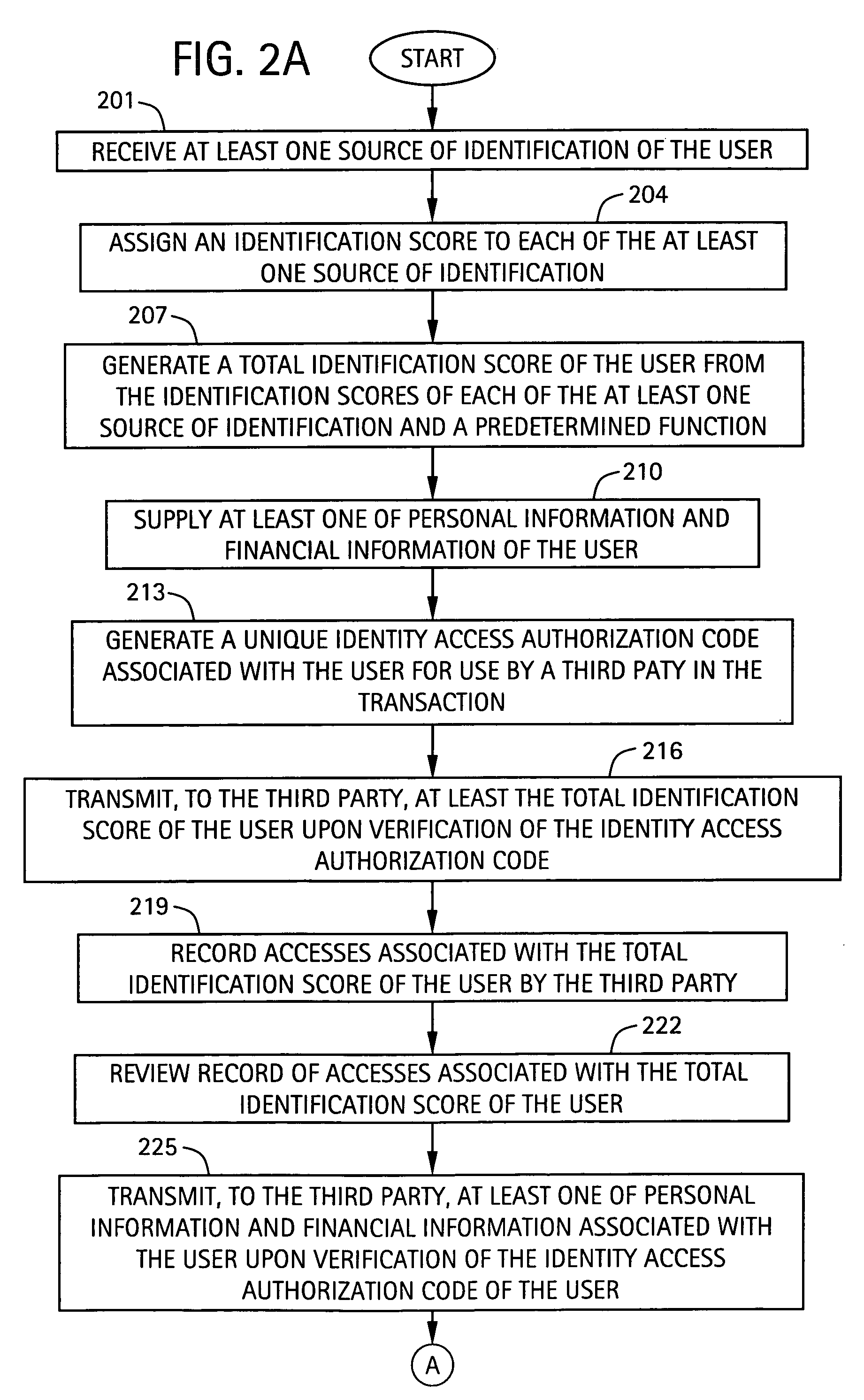
System and method for identity verification and management
ActiveUS20060161435A1Identity confidence factor of be increaseIncrease length of timeElectric signal transmission systemsDigital data processing detailsComputer scienceAuthentication
A system for verifying the identity of a user includes an identification score assignment module configured to receive at least one source of identification of the user and to assign an identification score to each of the at least one source of identification. The system includes a total identification score generation module, in communication with the identification score assignment module, configured to generate a total identification score of the user from the identification scores of each of the at least one source of identification and a predetermined function. The total identification score of the user is associated with a level of verification of the identity of the user, and compared to a minimum identification score associated with a transaction. The transaction is performed when the total identification score of the user is greater than or equal to the minimum identification score.
Owner:ATEF FARSHEED +1
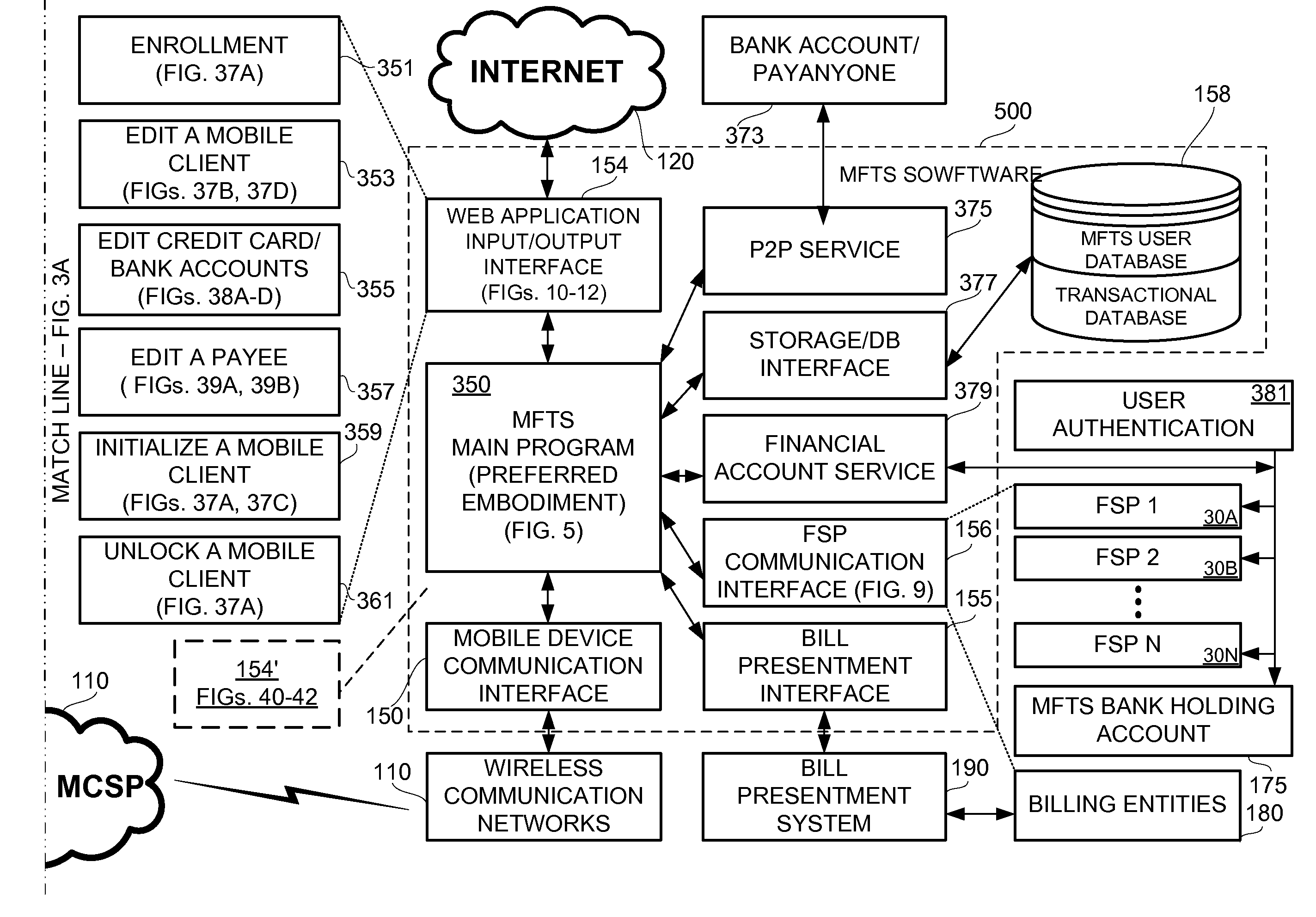
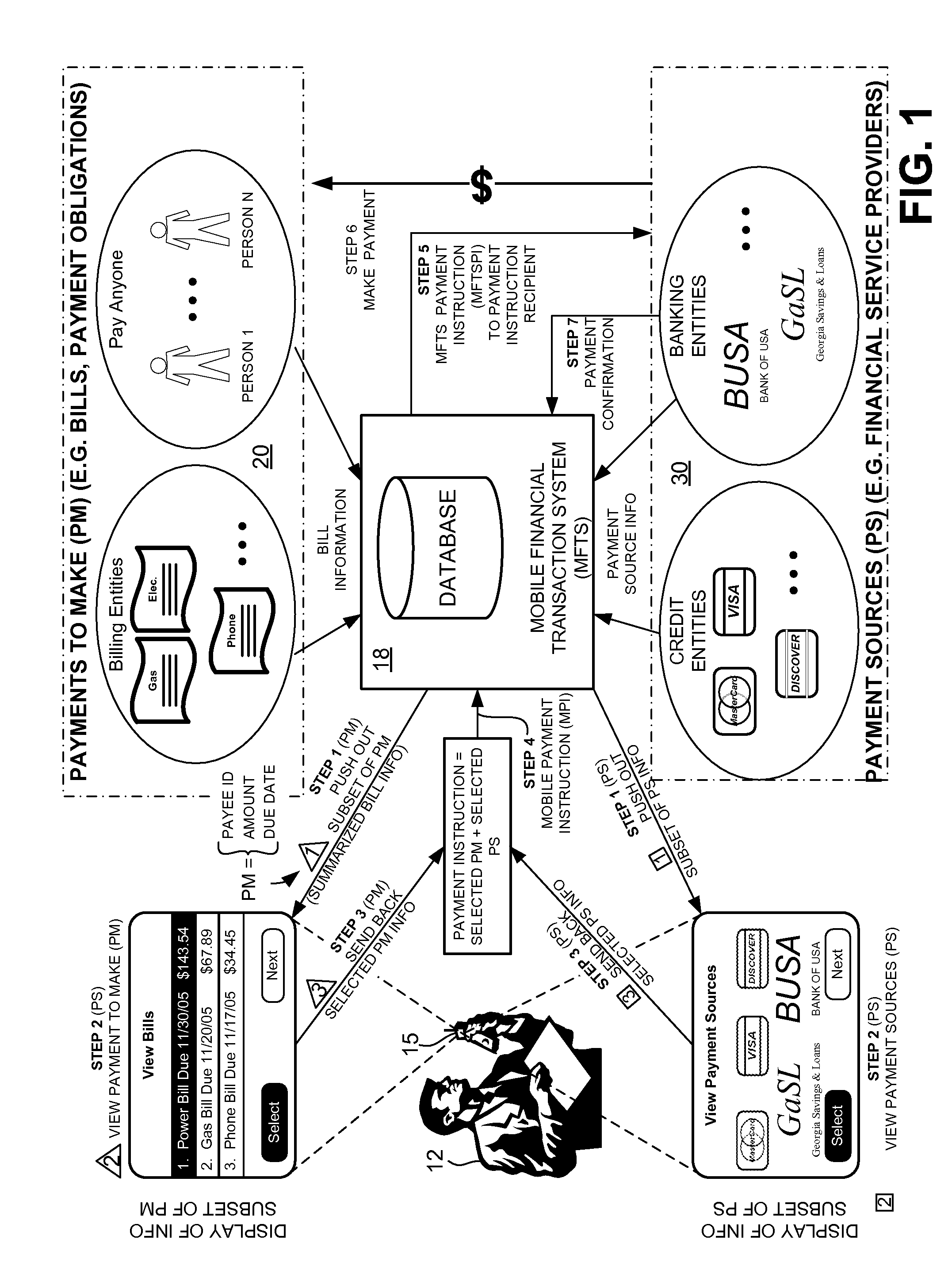
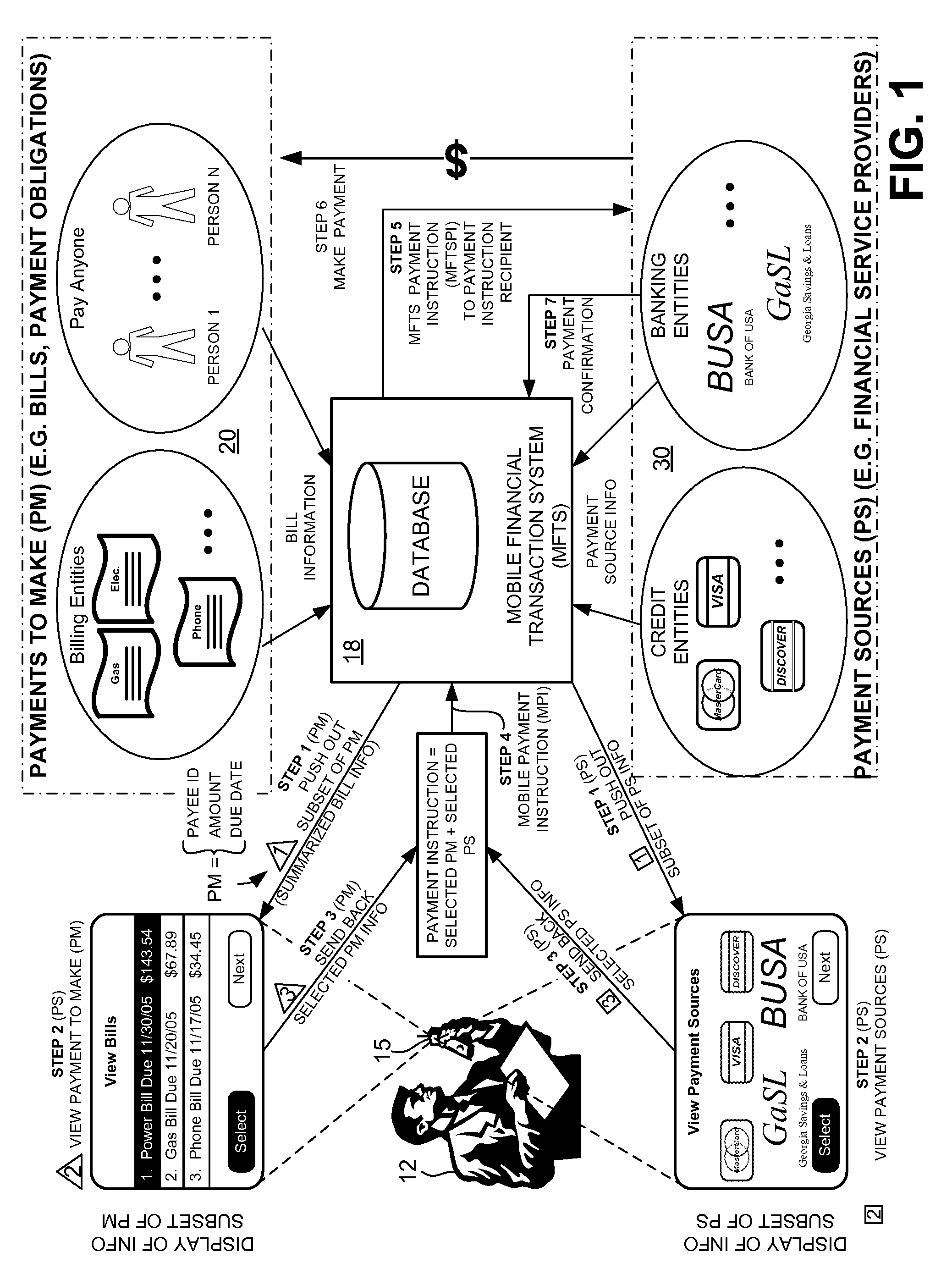
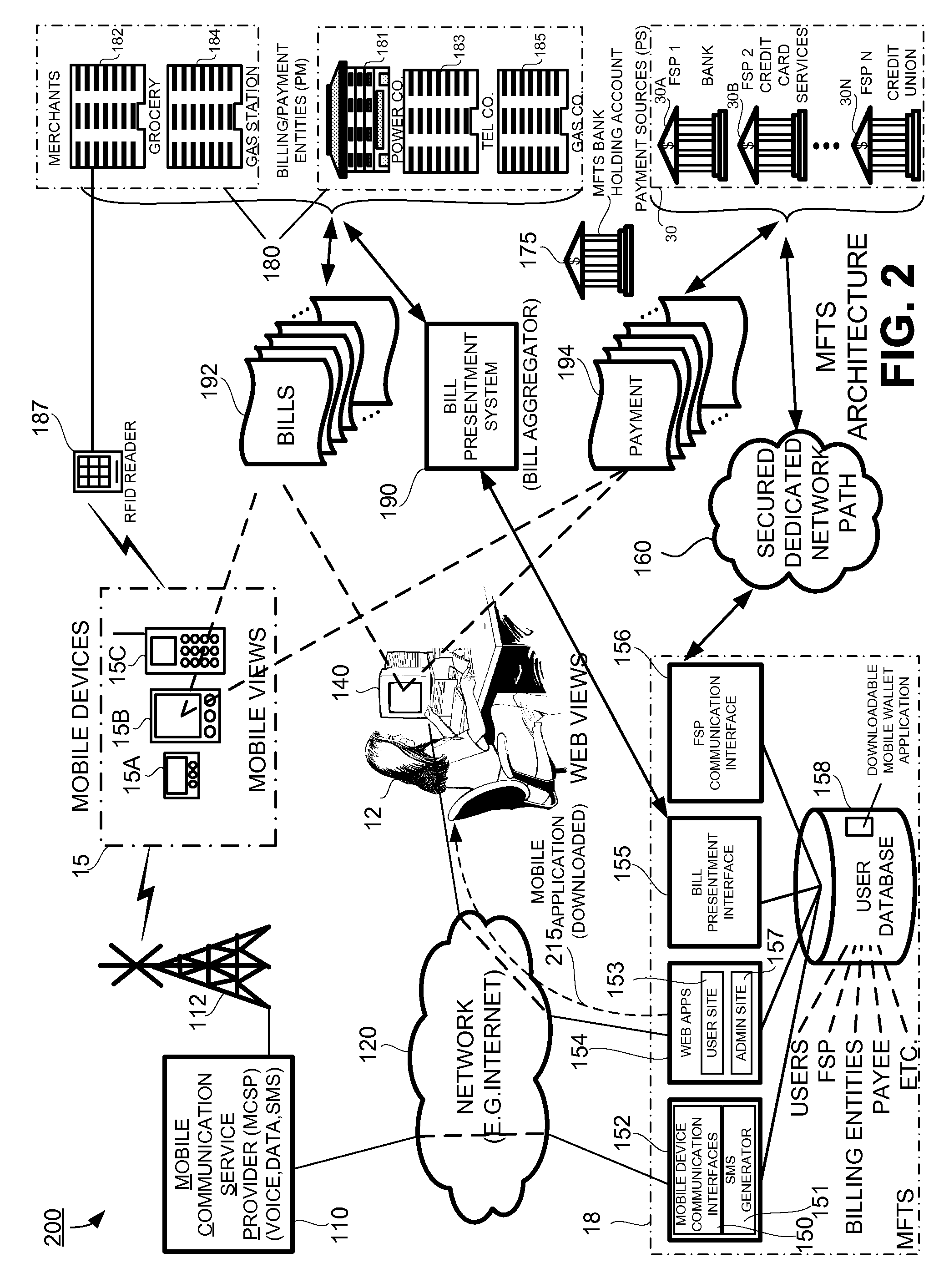
Methods and Systems For Making a Payment Via A Stored Value Card in a Mobile Environment
ActiveUS20080040265A1Unprecedented convenienceUnprecedented flexibilityFinanceBilling/invoicingFinancial transactionMobile context
Methods and systems for making a financial payment to a payee via a stored value (SV) card utilizing a mobile device such as a mobile telephone (cellphone) or wireless connected personal digital assistant (PDA). The mobile device communicates wirelessly with a mobile financial transaction system (MFTS) that stores user information and transaction information. A user enters information via the mobile device identifying a payee and indicating a stored value card payment method. The mobile device generates a mobile payment instruction that includes information corresponding to the identified payee and indicating a stored value card payment method. The mobile payment instruction is wirelessly communicated to the MFTS. The MFTS generates an MFTS payment instruction to a payment instruction recipient that can issue a new stored value card and / or reload funds onto a pre-existing stored value card. The MFTS communicates the MFTS payment instruction to the payment instruction recipient, which arranges for payment to the identified payee by issuing a new stored value card or reloading funds onto a pre-existing stored value card.
Owner:QUALCOMM INC
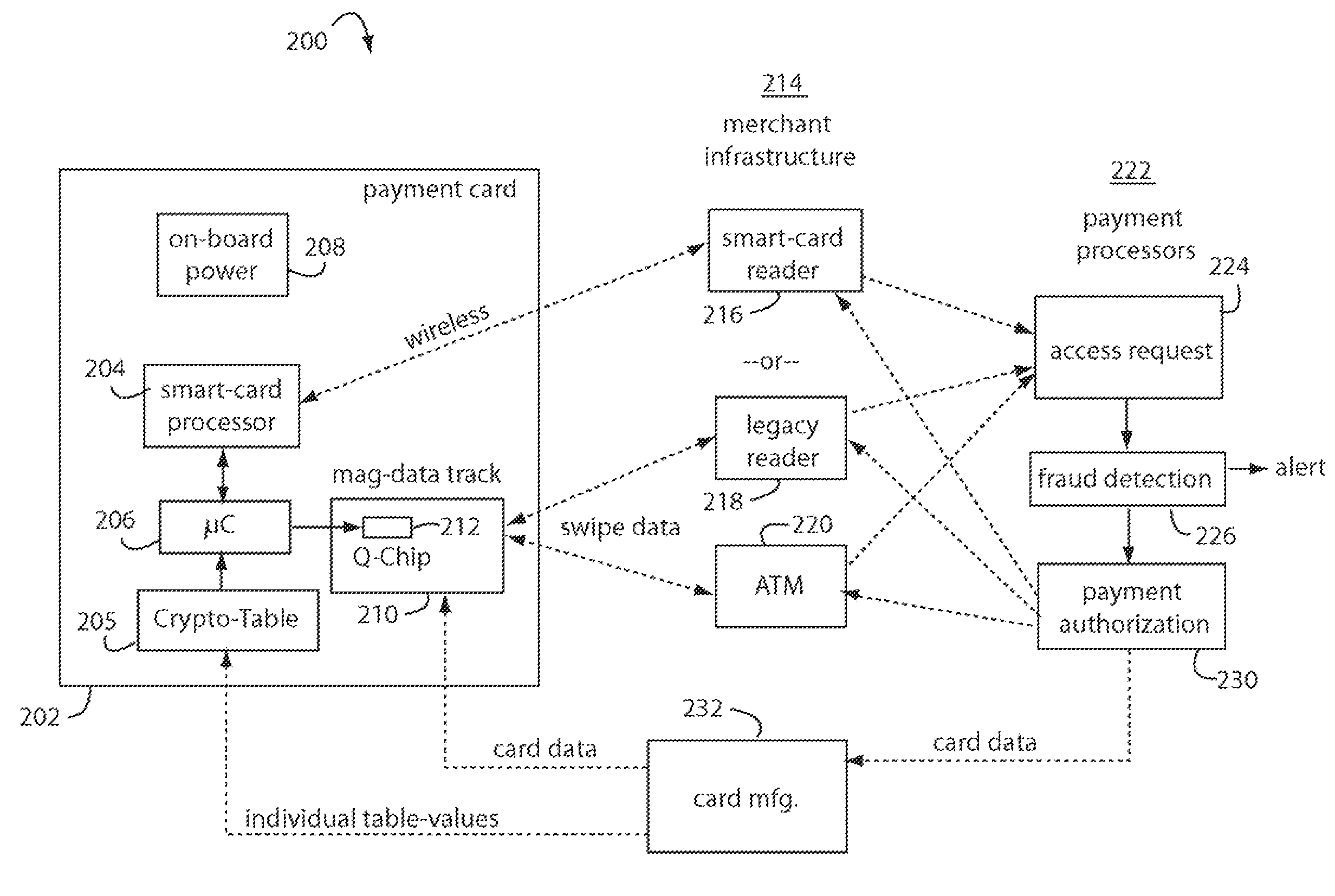
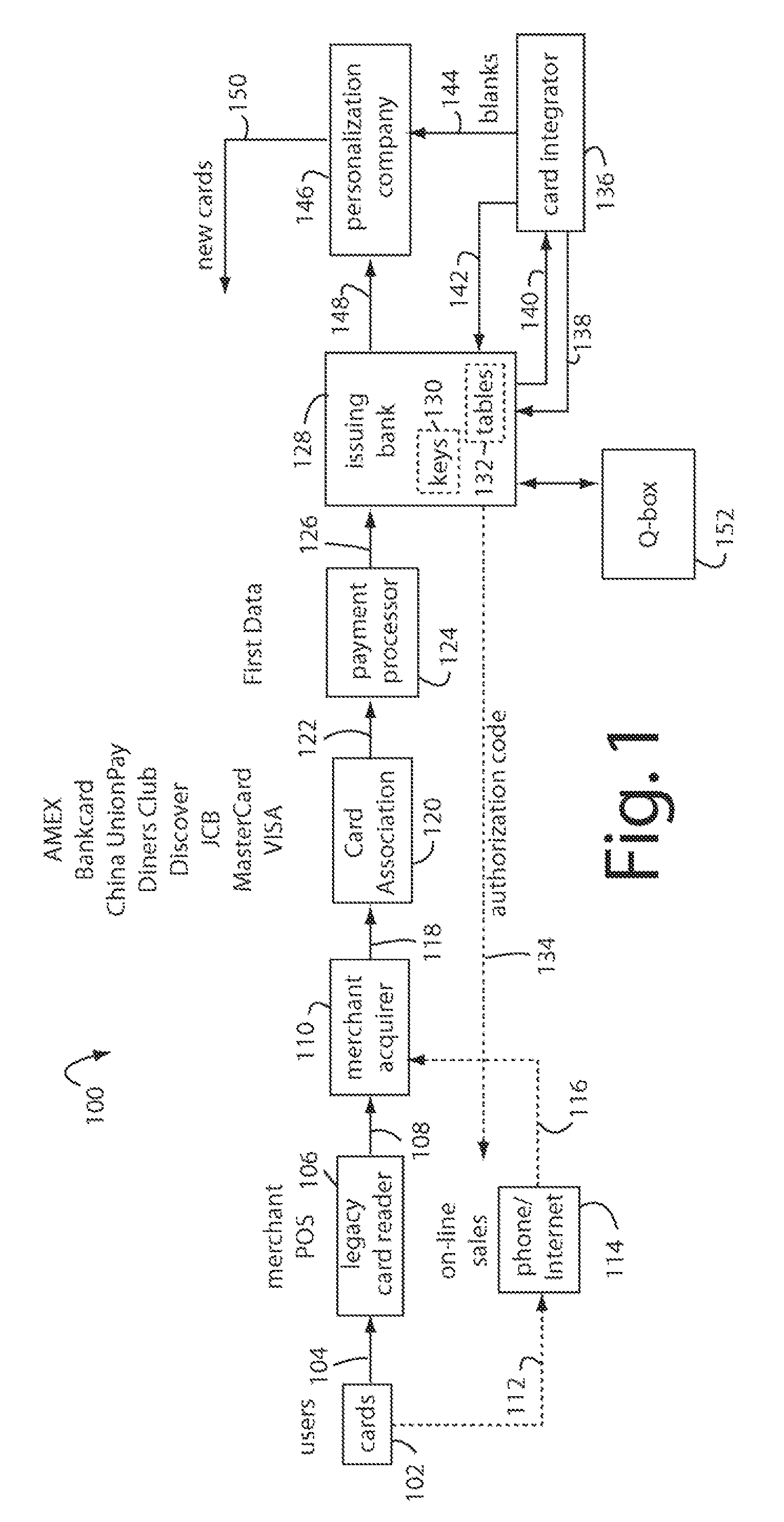
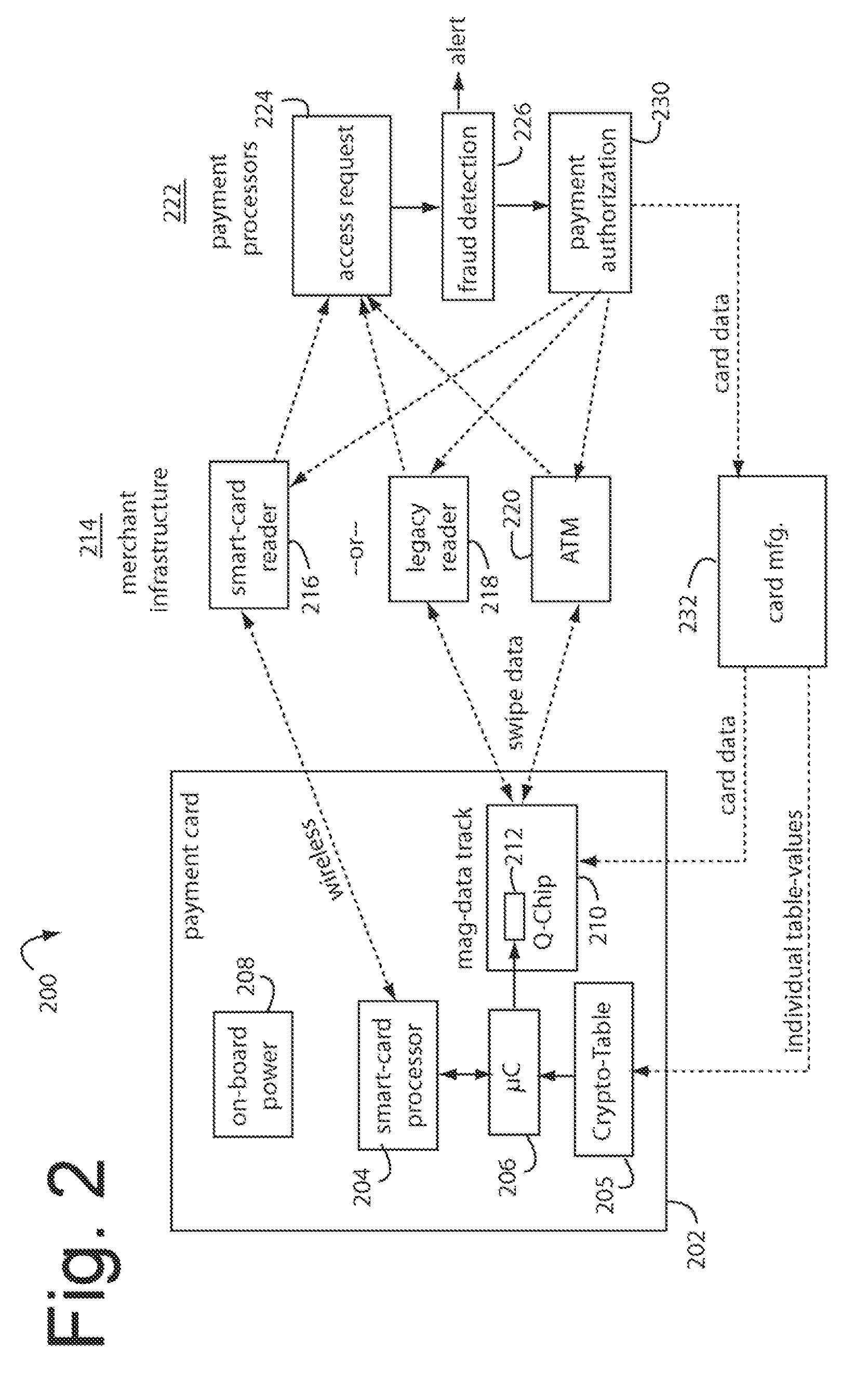
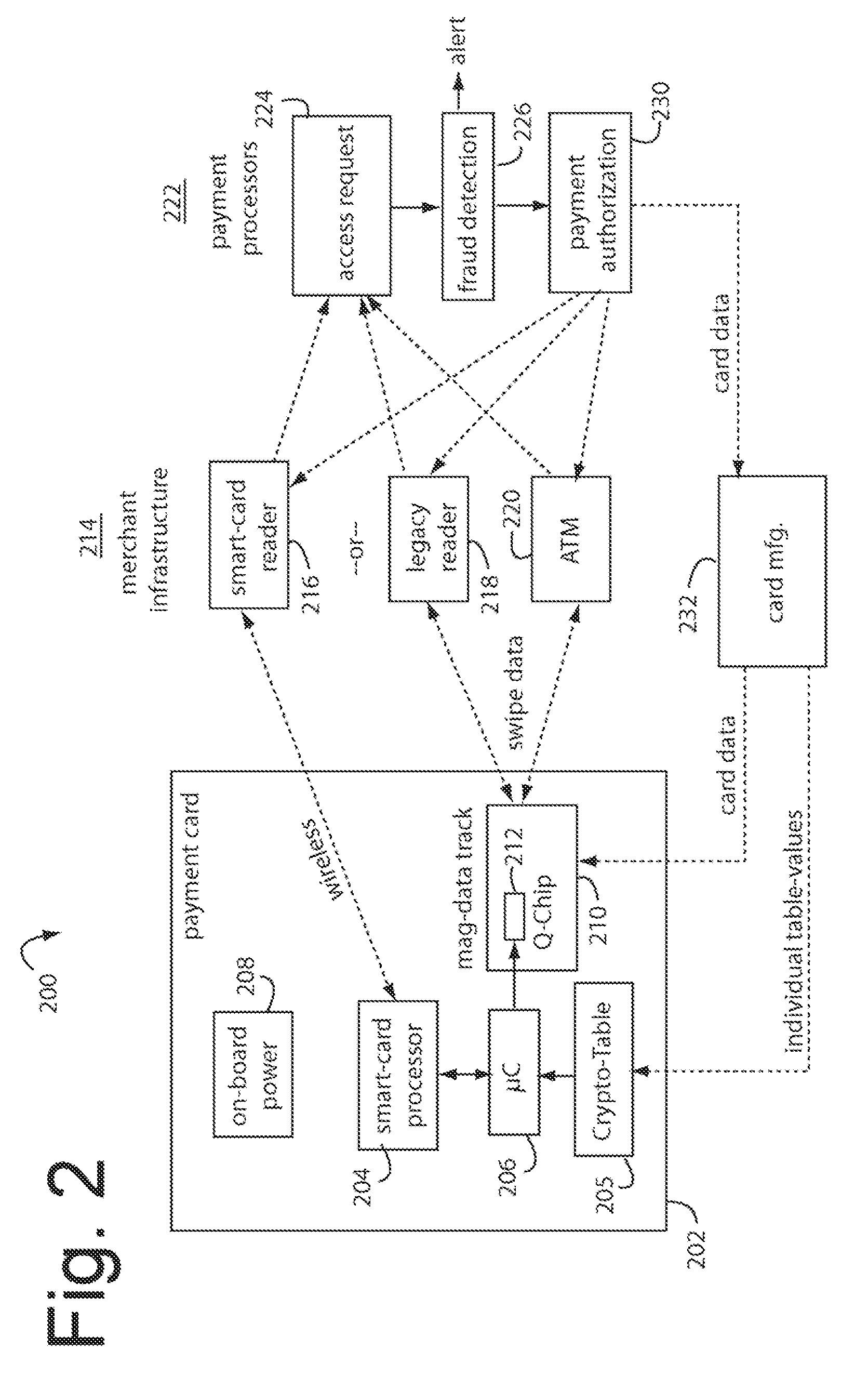
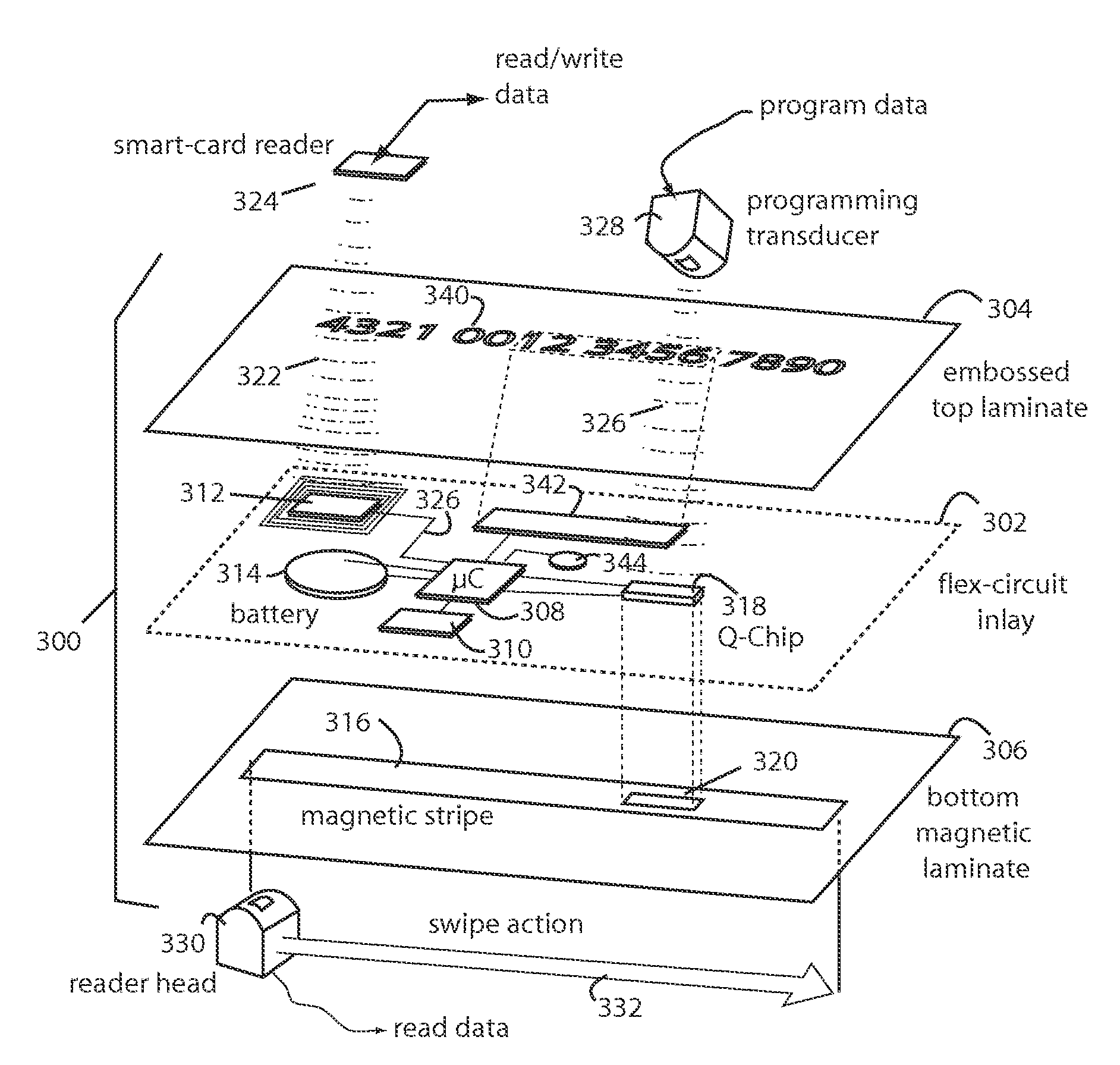
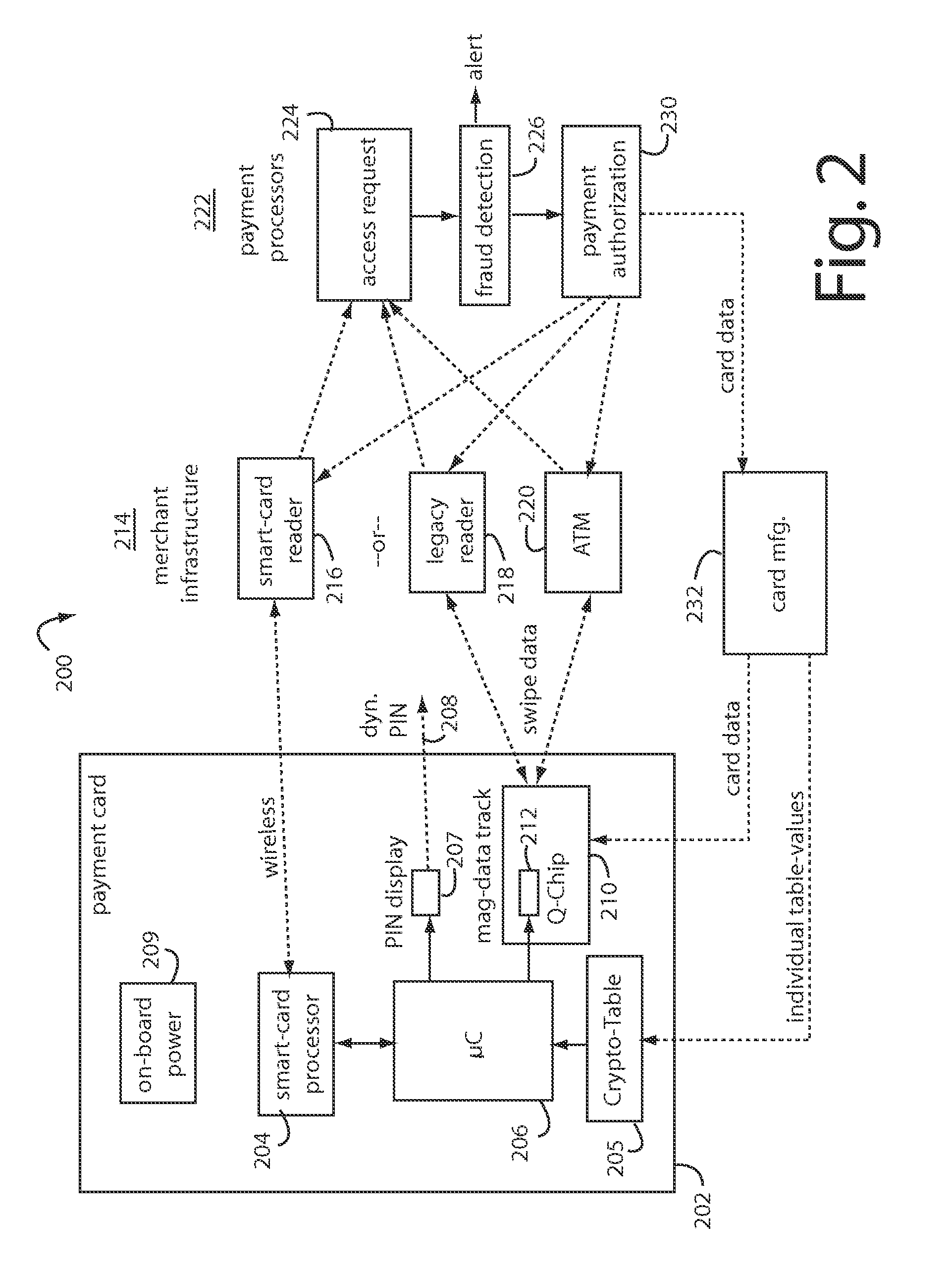
Financial transactions with dynamic card verification values
ActiveUS7584153B2Sufficient dataComputer security arrangementsPayment architectureUser needsDisplay device
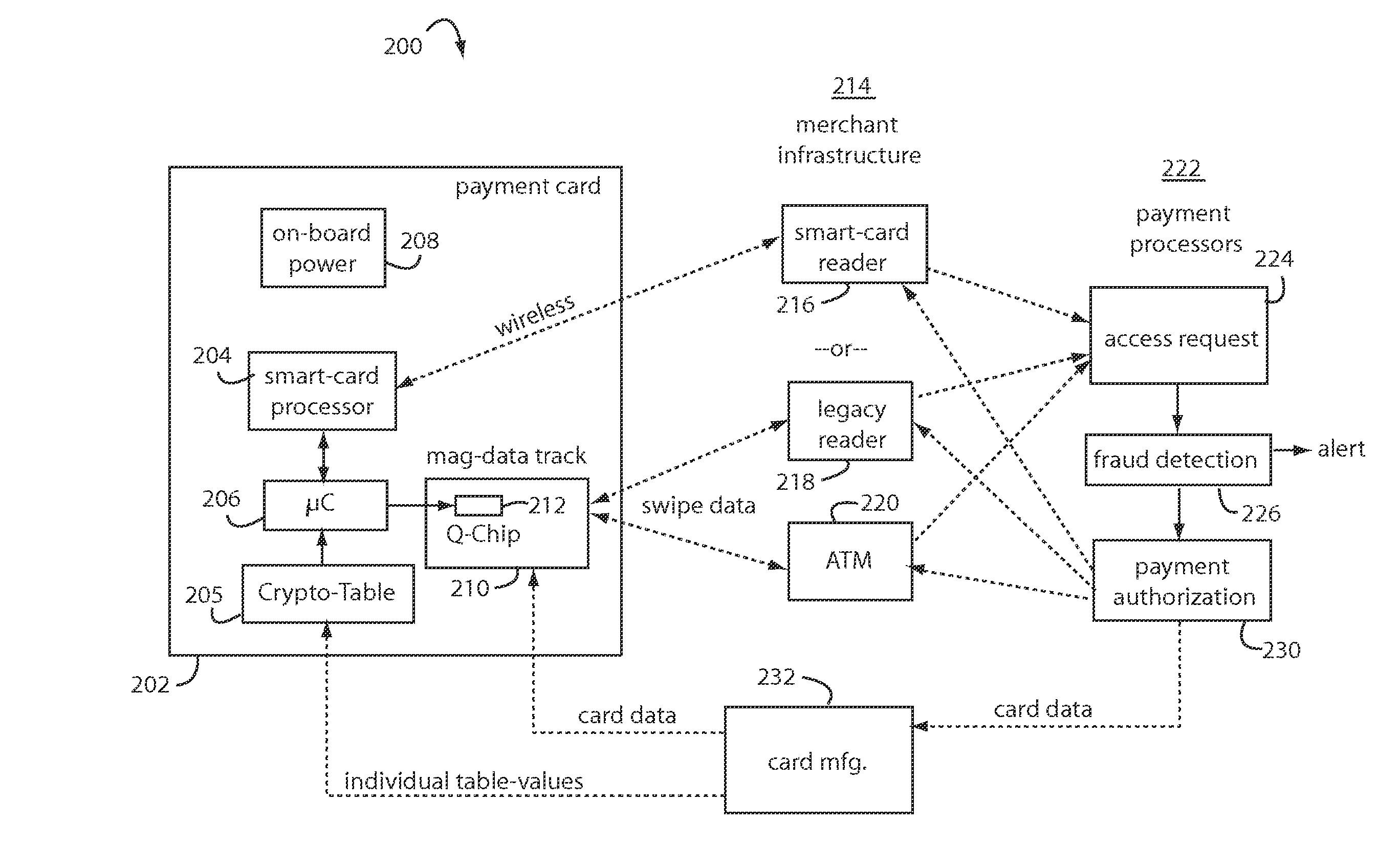
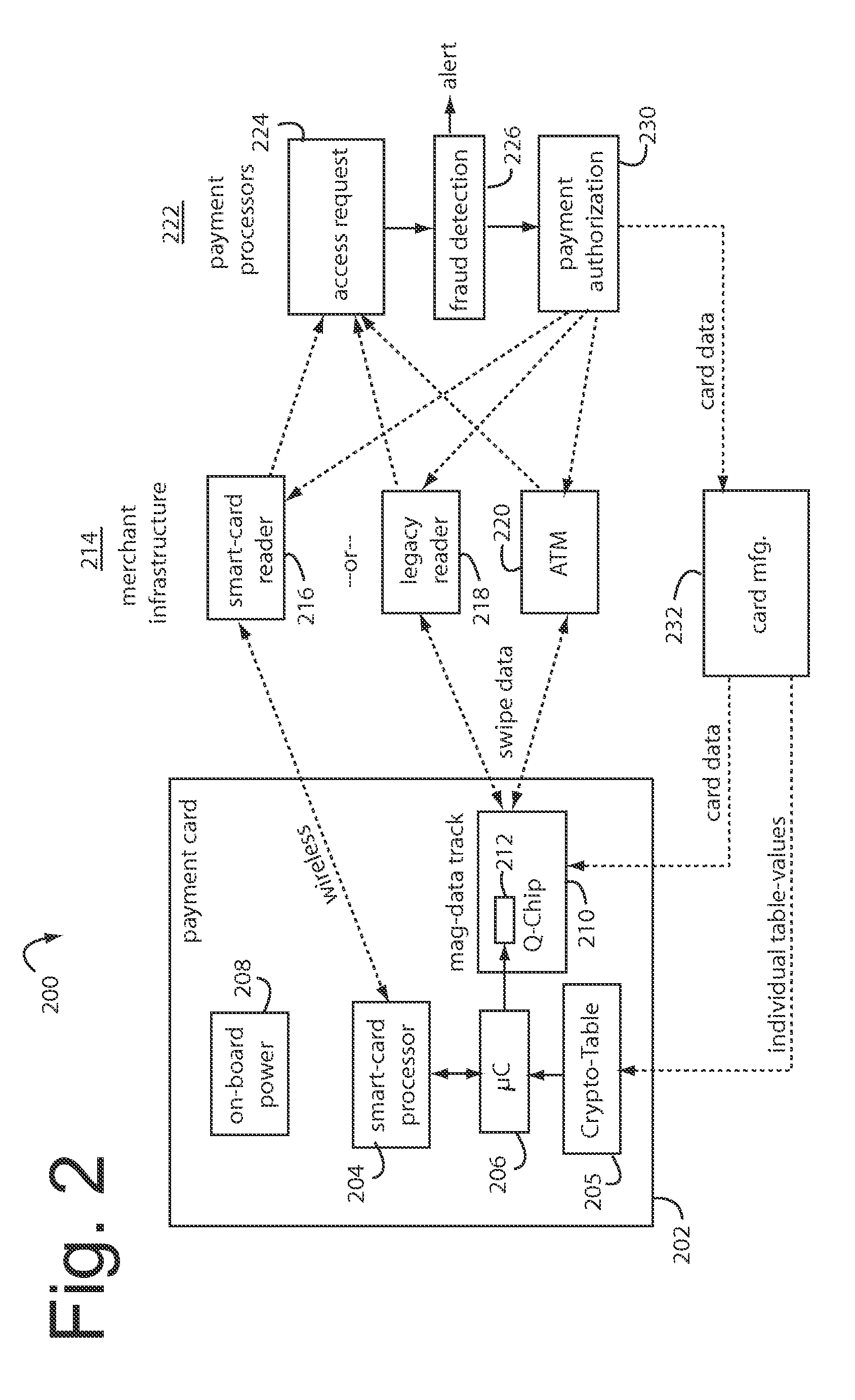
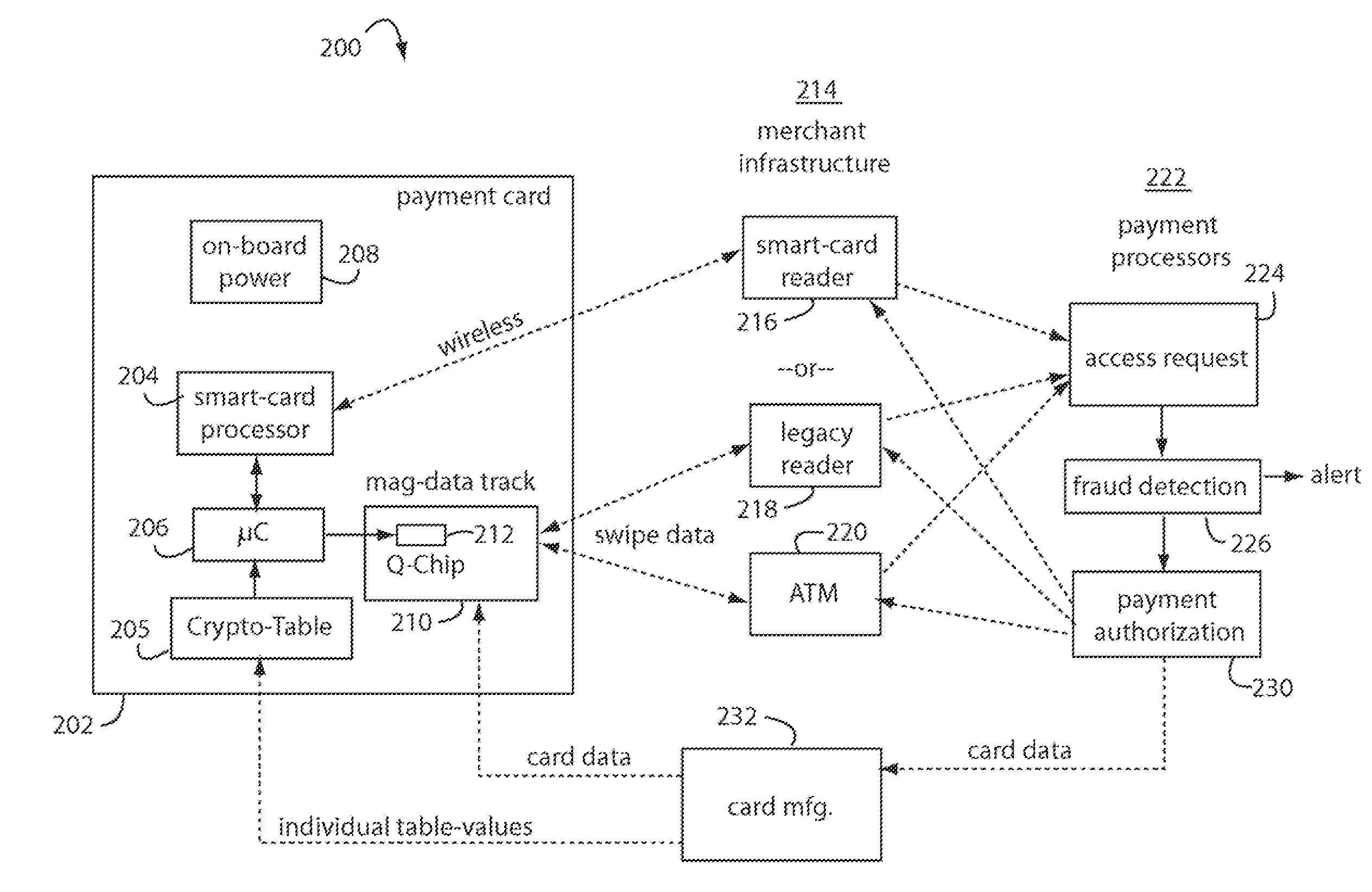
A payment card comprises an internal dynamic card verification value (CVV) generator and a user display for card-not-present transactions. Card-present transactions with merchant card readers are enabled by a dynamic magnetic array internally associated with the card's magnetic stripe. The user display and a timer are triggered by the user when the user needs to see the card verification value and / or begin a new transaction. A new card verification value is provided for each new transaction according to a cryptographic process, but the timer limits how soon a next new card verification value can be generated.
Owner:FITBIT INC
Method of buying or selling items and a user interface to facilitate the same
InactiveUS20060069635A1Easy to useFast and efficient and intuitive and user friendlySpecial service provision for substationFinanceMarket placeFinancial transaction
A method of buying or selling items having at least one market and its associated processes are disclosed. The method includes the steps of, under control of a client system, displaying information identifying at least one item and a bid and / or ask price for the item in the market; and specifying transaction conditions based on a user directed position of a moveable icon, where the transaction conditions are related to the buying or selling of the identified item in the active market. Then, in response to an action of the user sending a user transaction request at the transaction conditions displayed at the time of said action, facilitating financial transactions for the user in accordance with the transaction conditions to complete the transaction. In this manner, the item may be bought or sold by the user at the transaction conditions specified. A user interface to facilitate this method is also disclosed. A quantity recommendation system to facilitate the quantity decision of a financial transaction is further disclosed.
Owner:RAM PRANIL
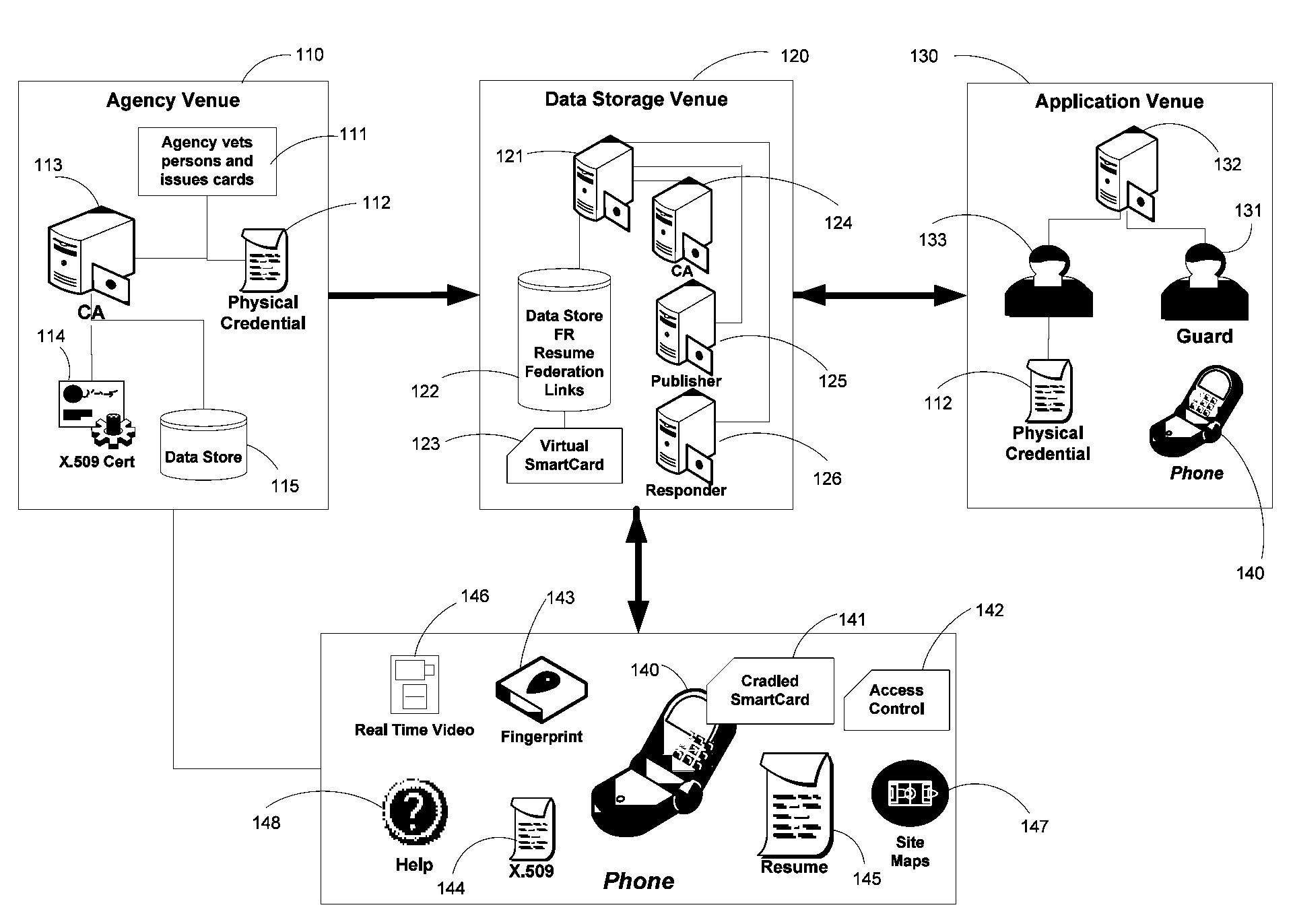
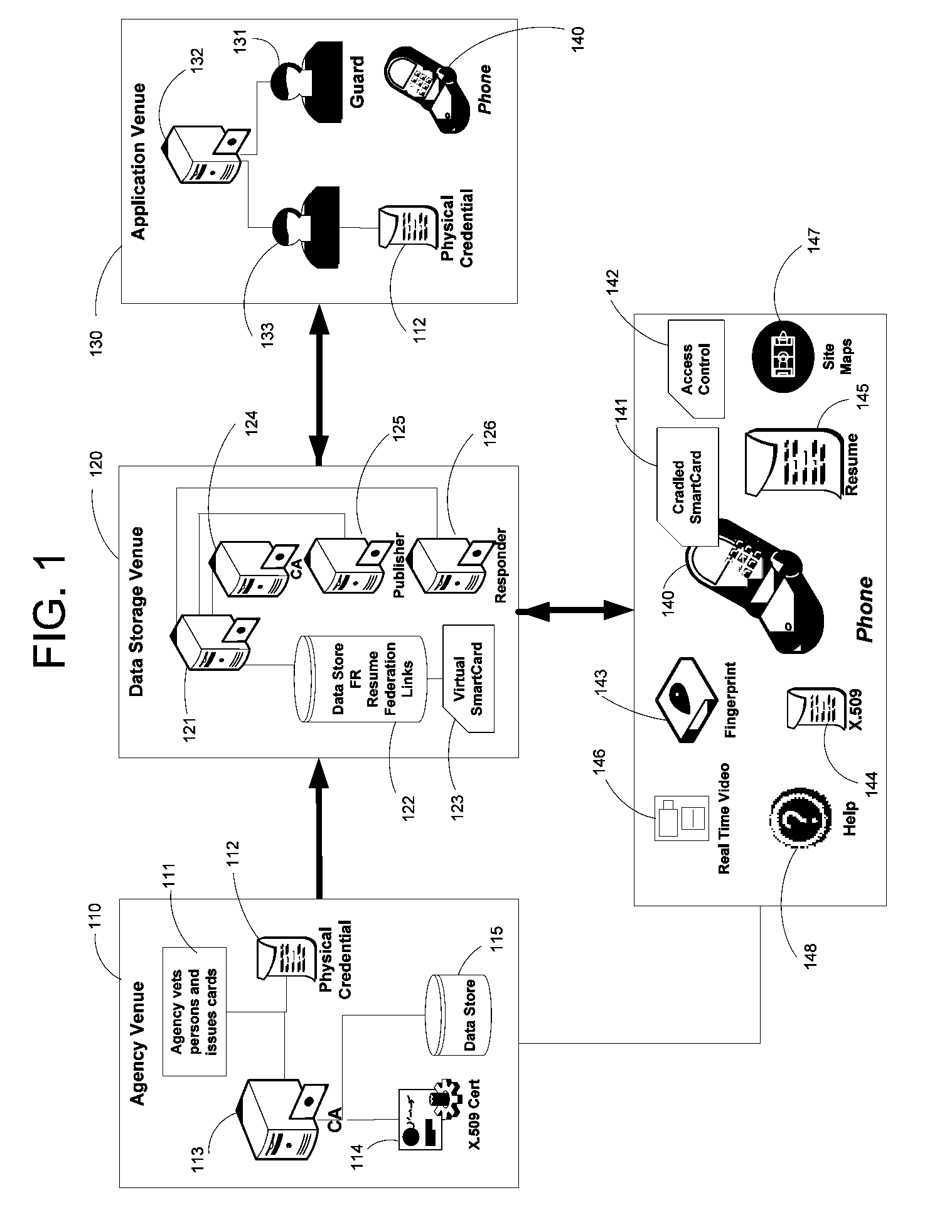
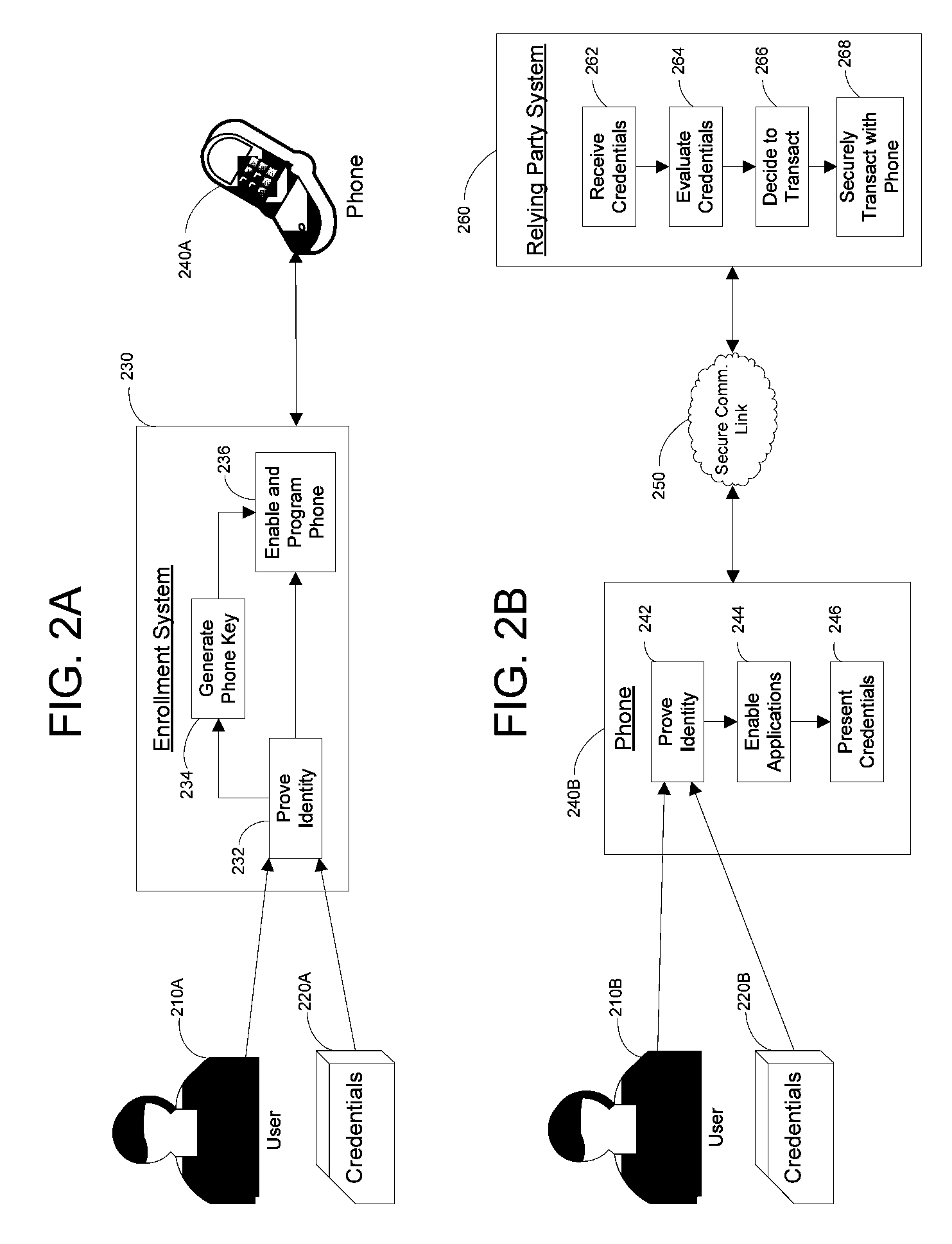
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
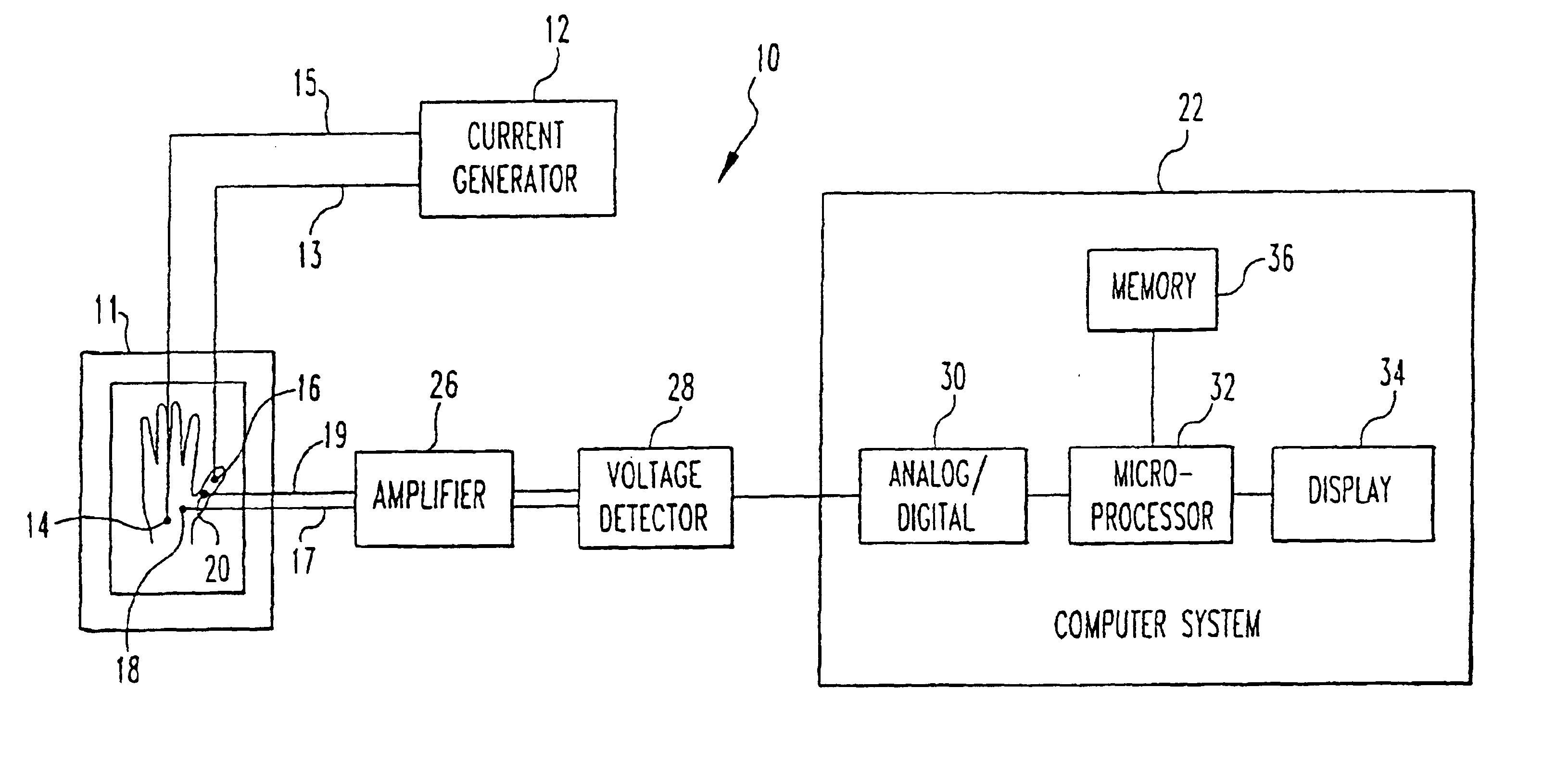
Method and system for biometric recognition based on electric and/or magnetic characteristics
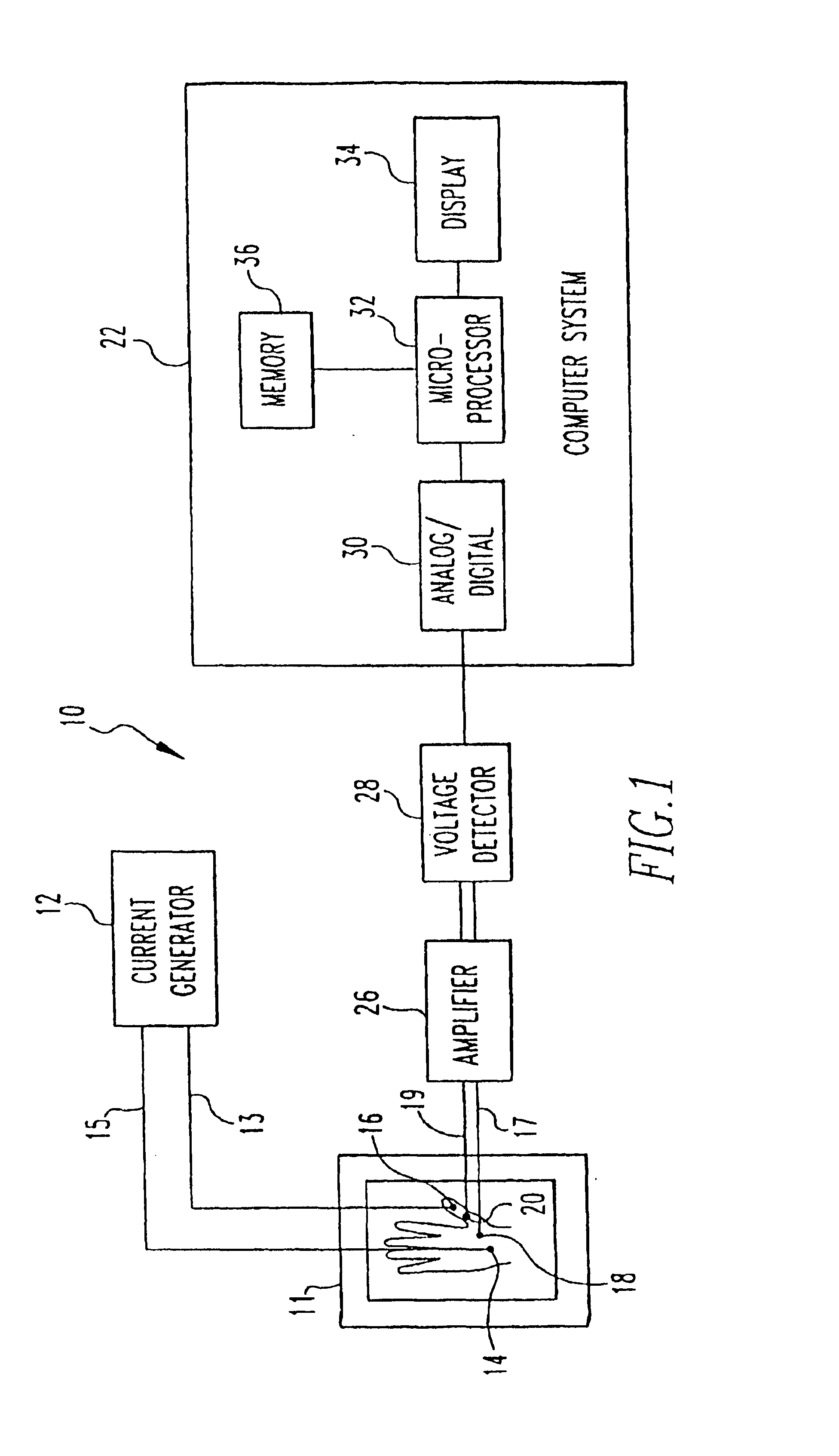
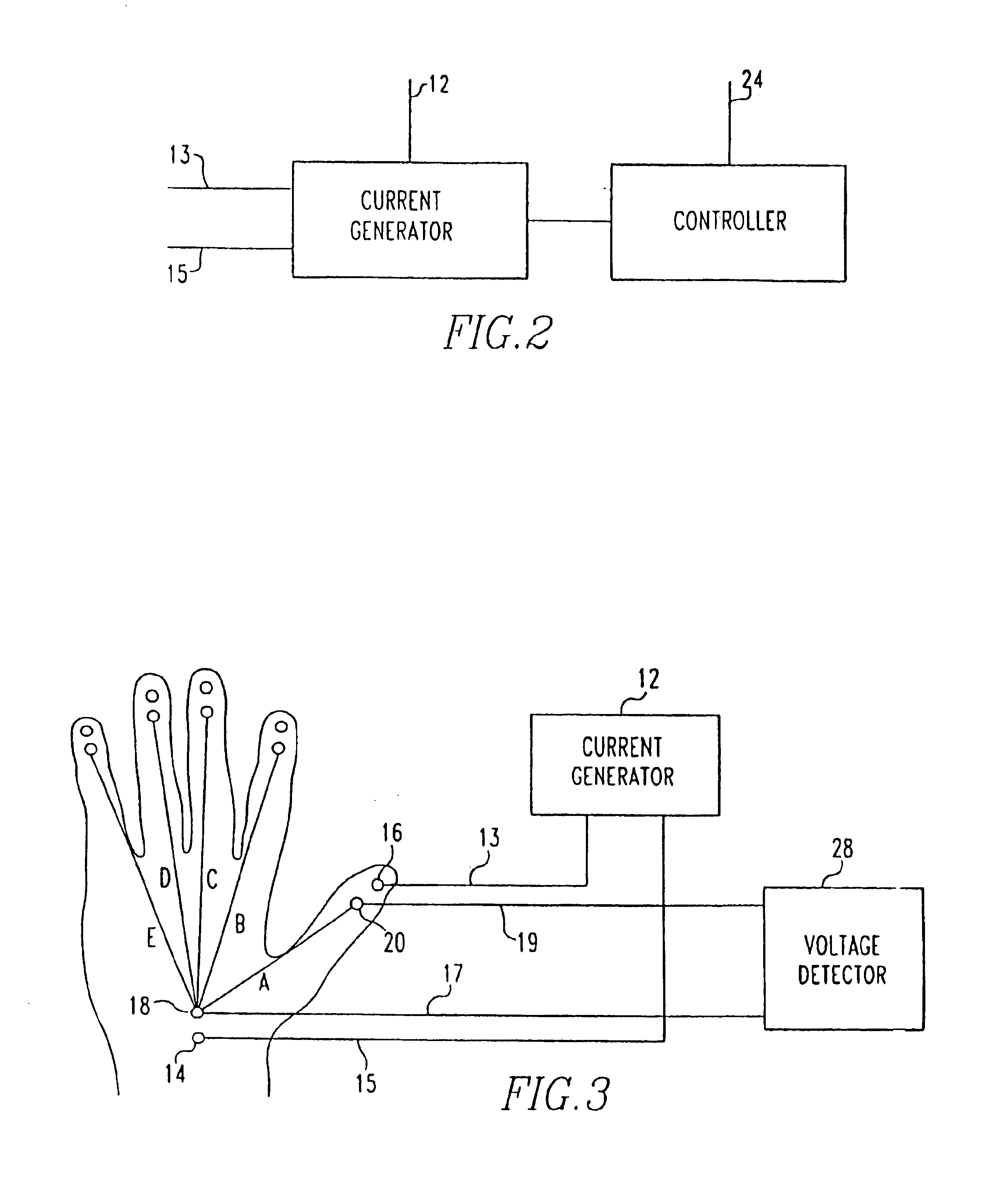
InactiveUS6898299B1Electric signal transmission systemsDigital data processing detailsElectricityBiological body
A method and apparatus for authenticating an individual living organism by recognizing a unique internal electric and / or magnetic and / or acoustic characteristic, which comprises a biometric signature, involve presenting a body part to a sensing device that senses the signature. The sensed presented biometric signature is compared to a known biometric signature to authenticate the individual. This authentication can then be used to authorize any of a wide variety of actions by the individual, such as accessing equipment or an area, or to perform actions, such as conducting financial transactions. A card having sensors is used to sense the biometric signature which is read by a card reader and sent to a local or remote reader for biometric signature comparison.
Owner:GR INTELLECTUAL RESERVE LLC
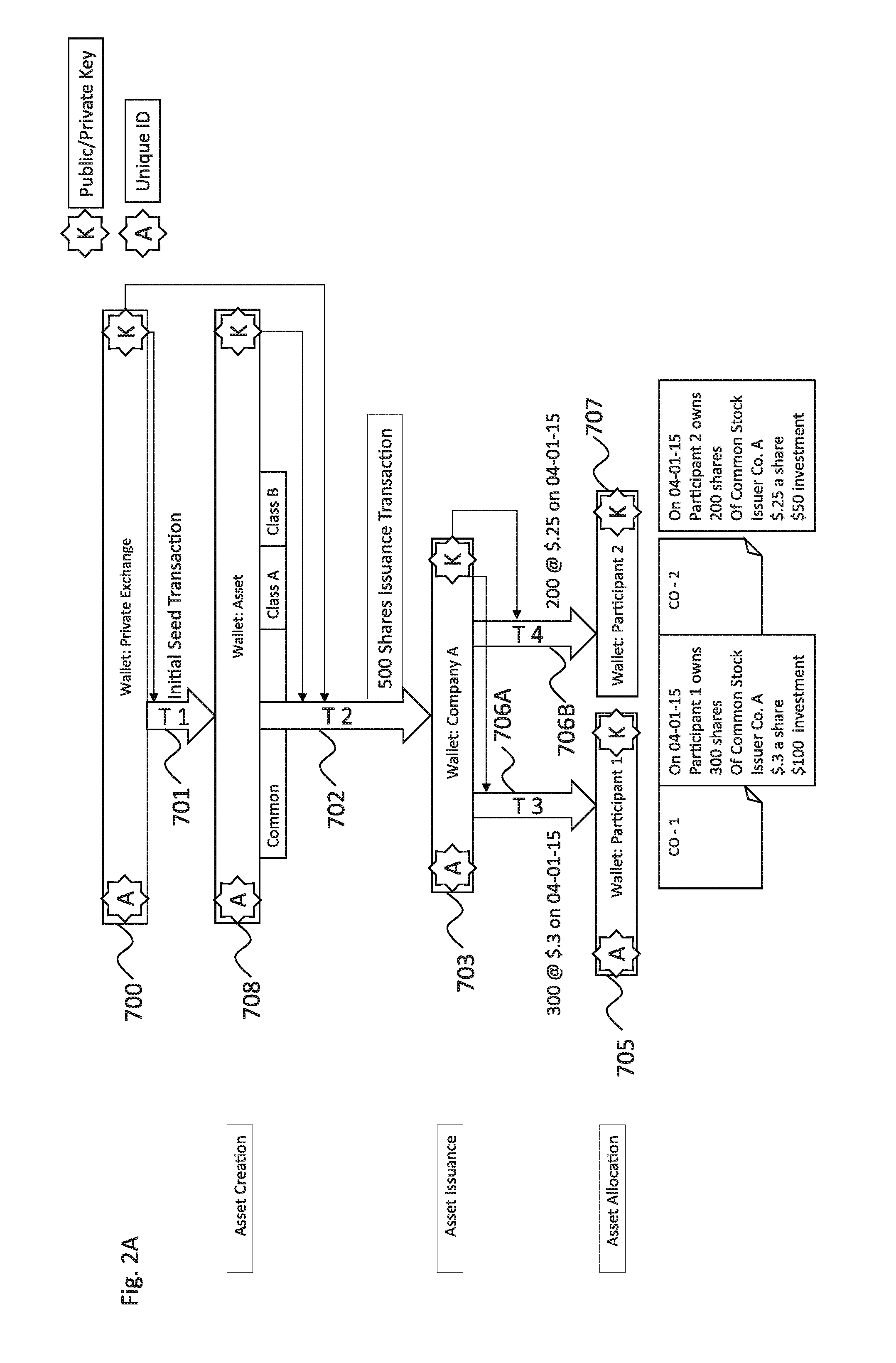
Systems and methods of secure provenance for distributed transaction databases
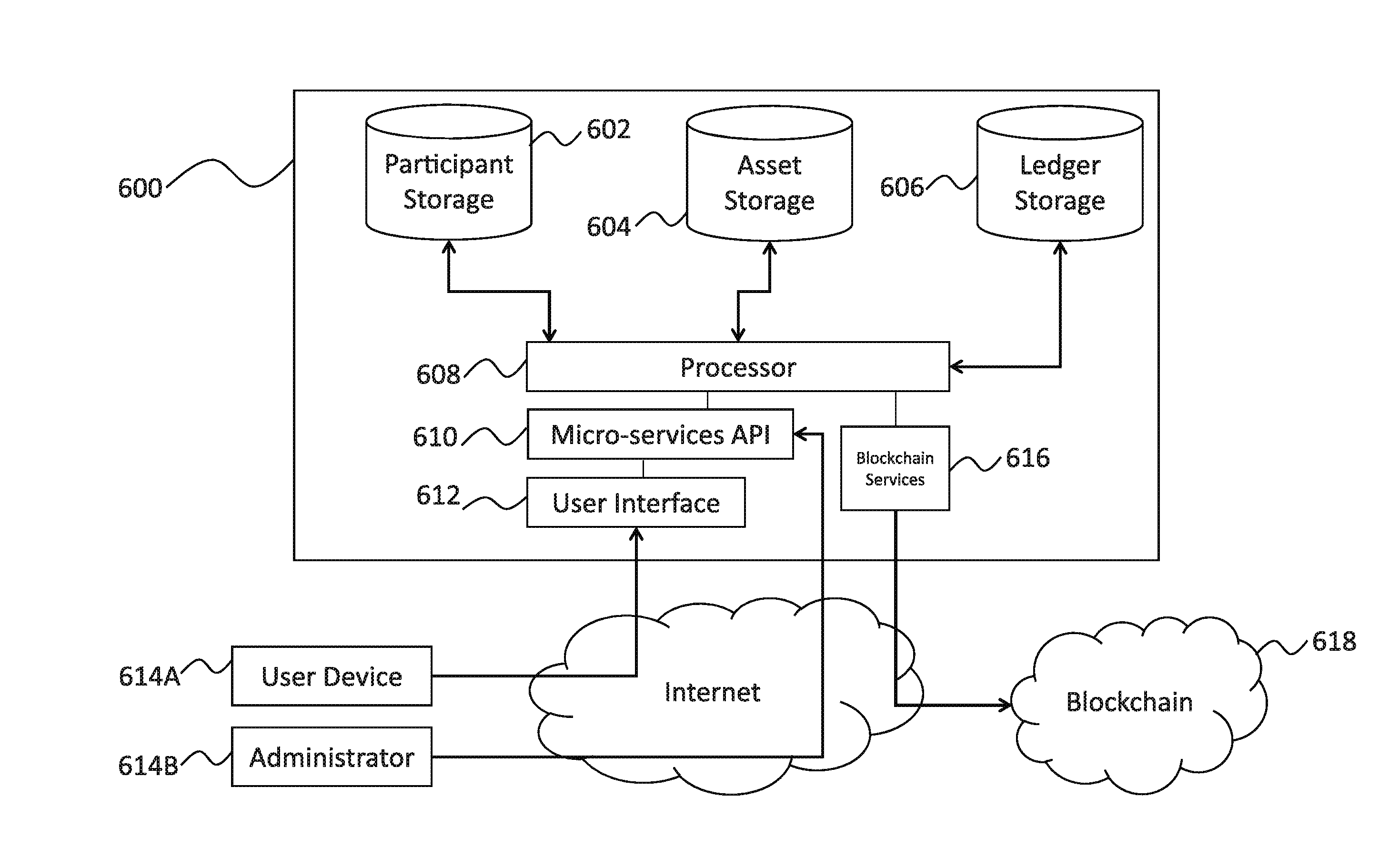
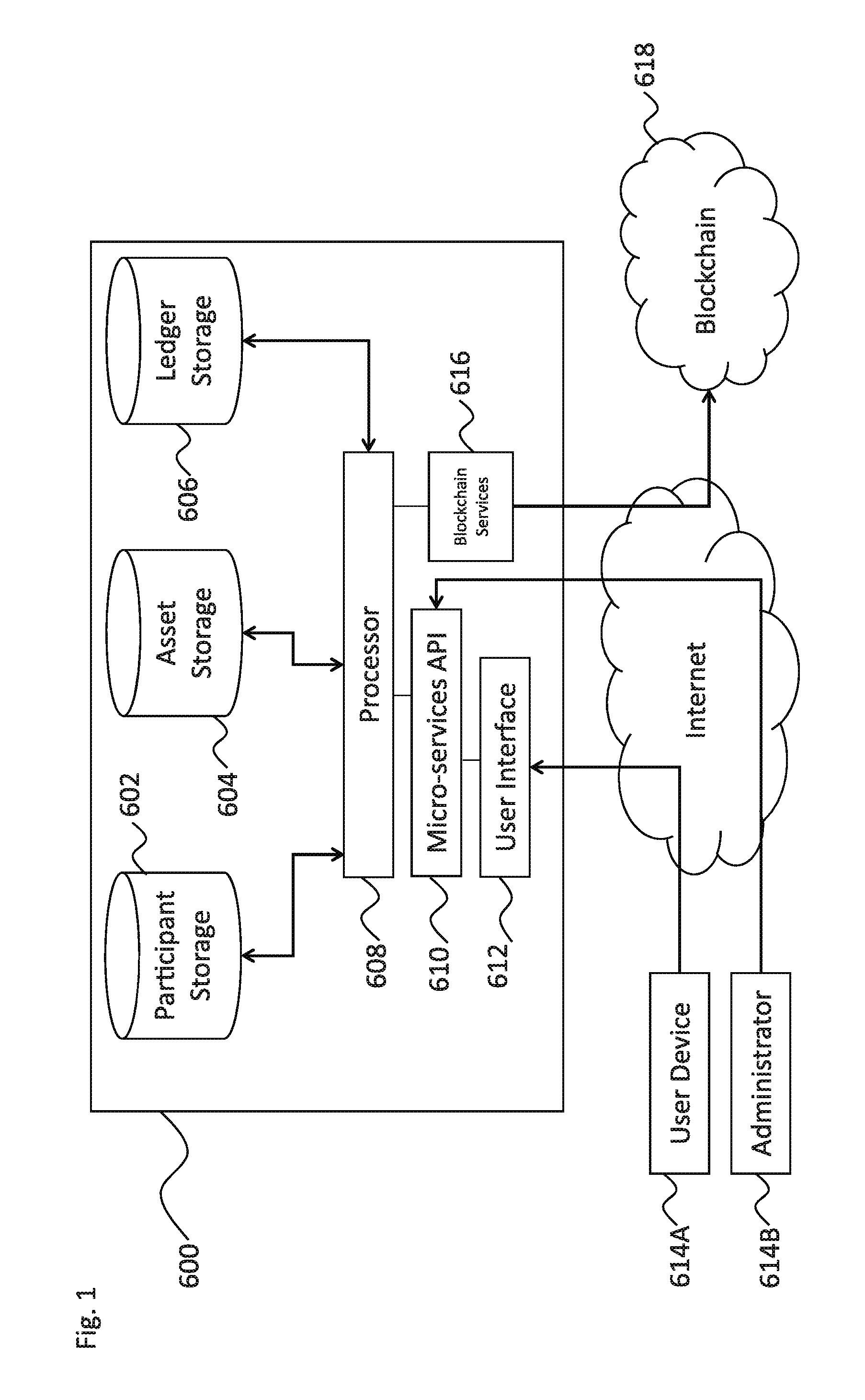
ActiveUS20170005804A1Direct accessImprove usabilityUser identity/authority verificationDigital data protectionFinancial transactionHandling system
An electronic resource tracking and storage computer system is provided that communicates with a distributed blockchain computing system that includes multiple computing nodes. The system includes a storage system, a transceiver, and a processing system. The storage system includes an resource repository and transaction repository that stores submitted blockchain transactions. A new resource issuance request is received, and a new resource is added to the resource repository in response. A new blockchain transaction is generated and published to the blockchain. In correspondence with publishing to the blockchain, the transaction storage is updated with information that makes up the blockchain transaction and some information that was not included as part of the blockchain transaction. The transaction storage is updated when the blockchain is determined to have validated the previously submitted blockchain transaction.
Owner:NASDAQ INC
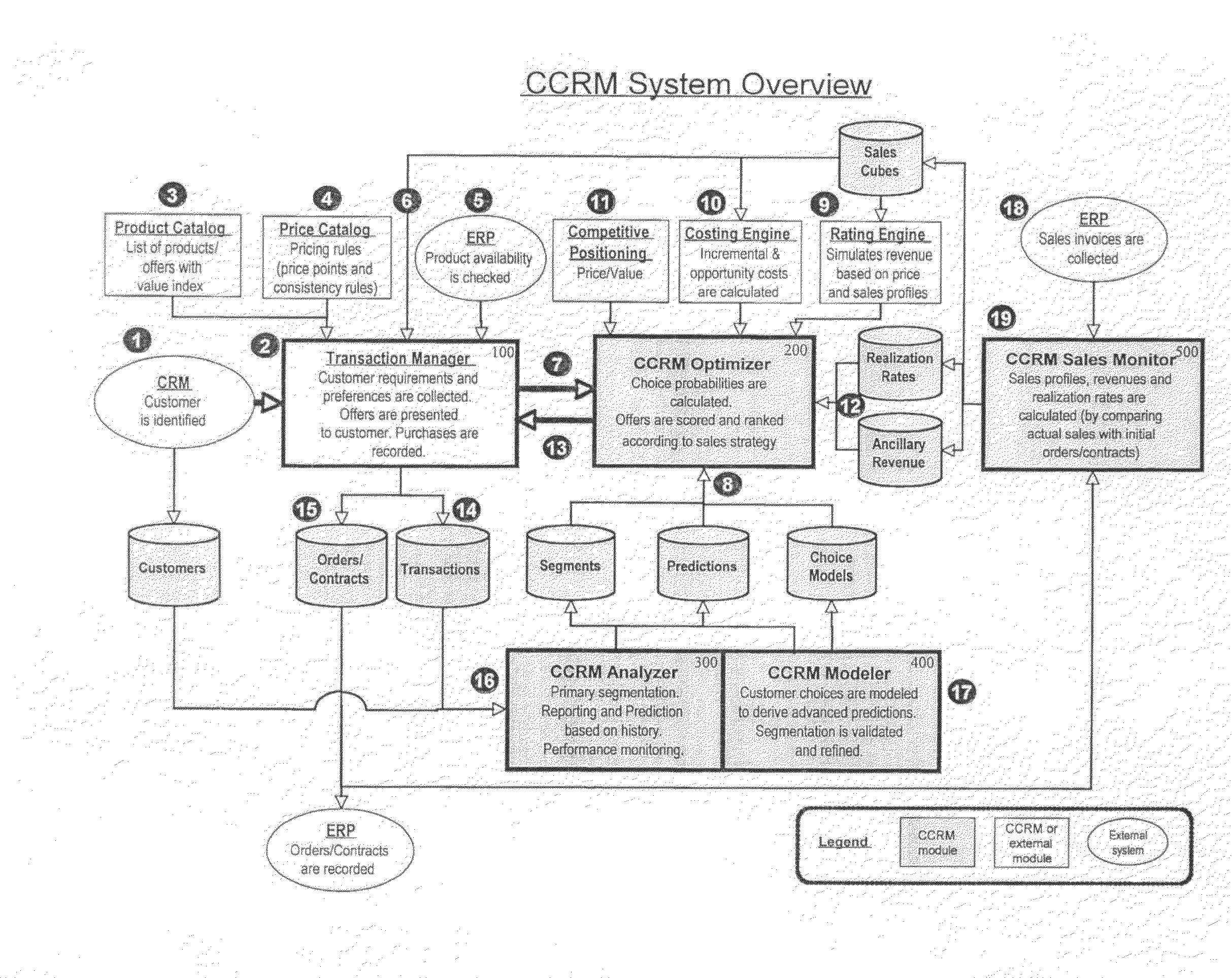
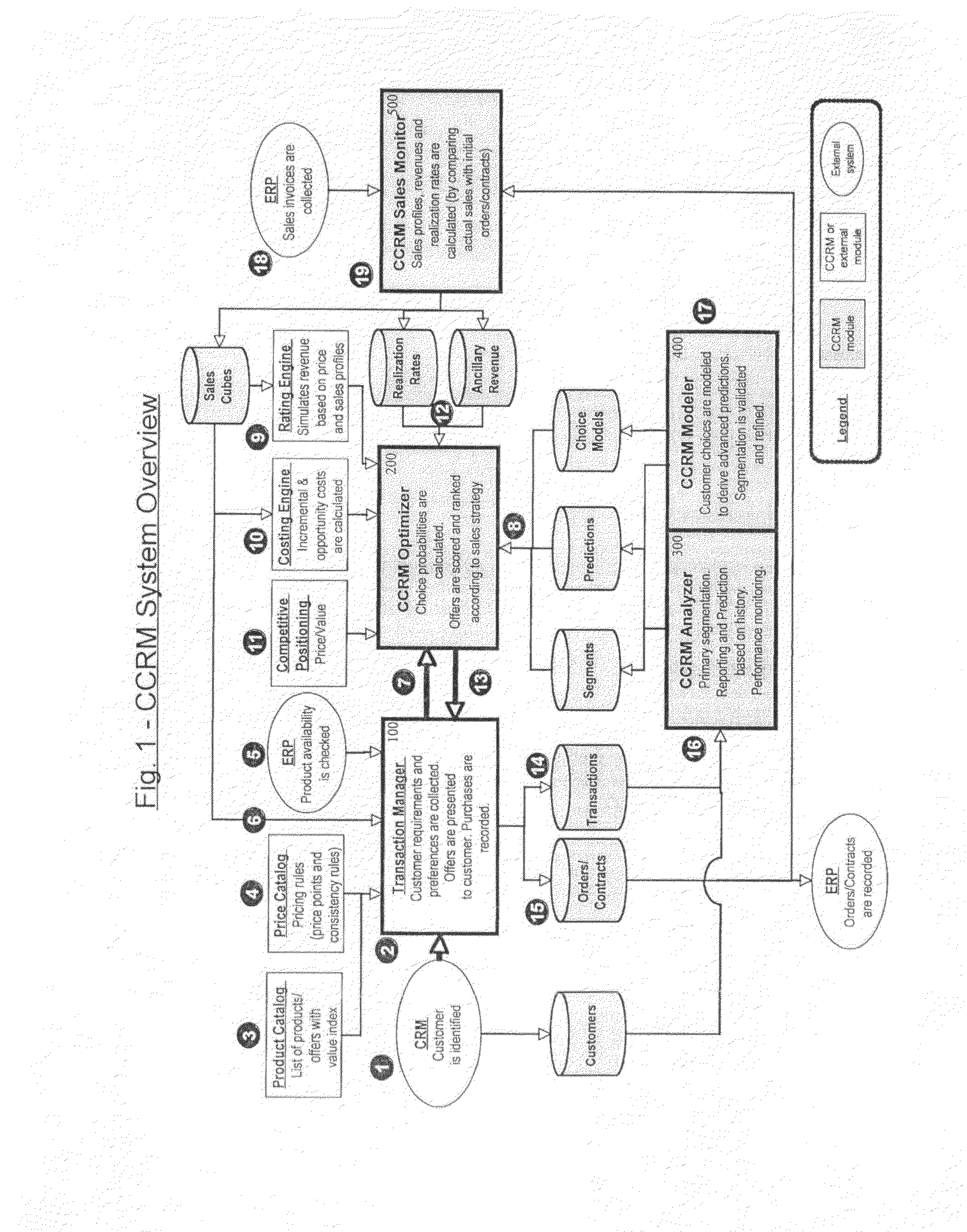
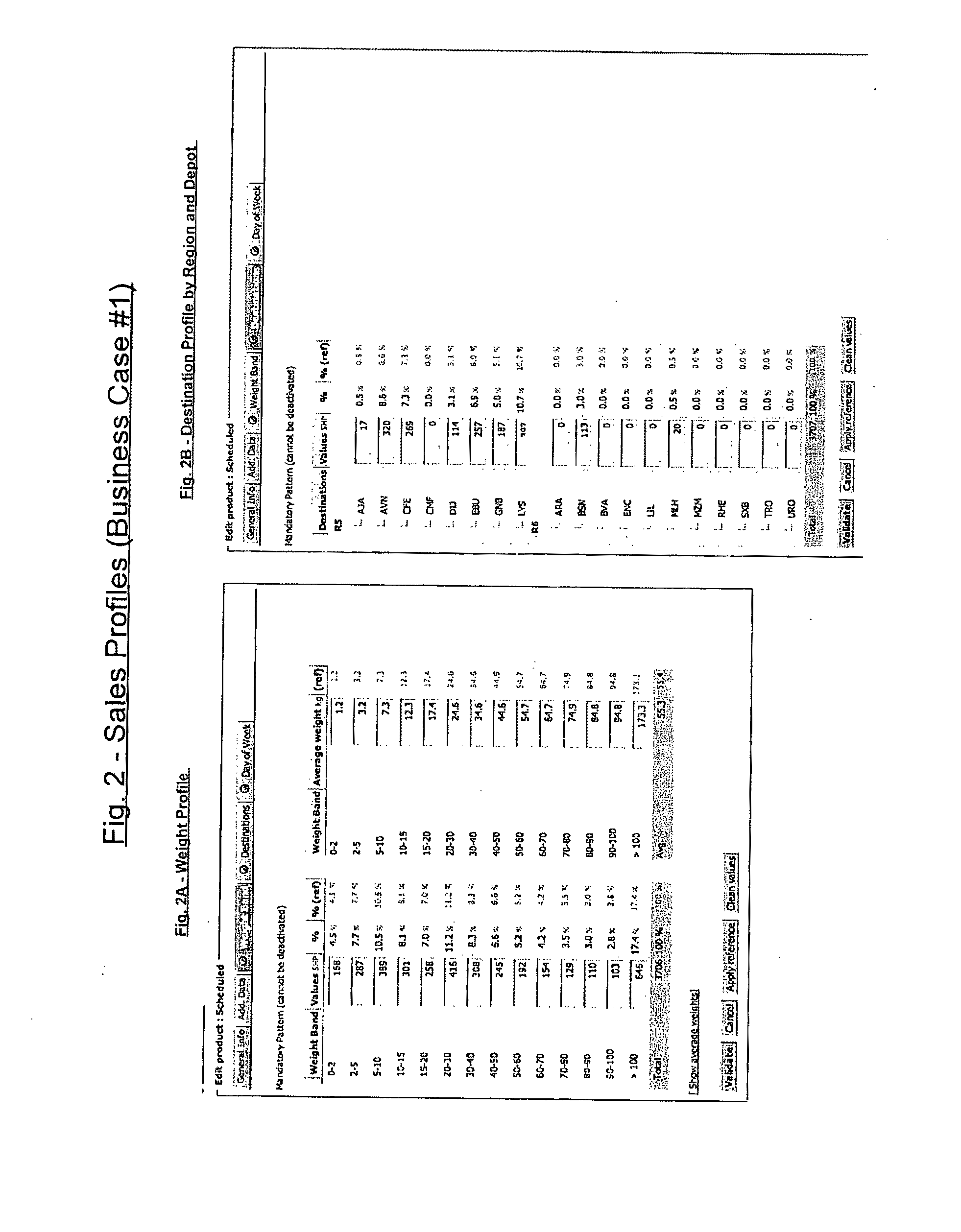
Customer centric revenue management
InactiveUS20090234710A1Improve recommendationsImprove definitionMarket predictionsSpecial data processing applicationsCustomer centricSoftware
CCRM is a business method and computer software system, to be used by Enterprises selling portfolios of products / services, aiming to optimize the expected value of transactions (or contracts) with consumers or business customers. At a transaction level, CCRM estimates the probability of choice of potential offers by the customer. These offers may be presented alone with possible variation of their attributes (such as price), or in combinations / sets, or in sequences. CCRM calculates the probability of consequent conversion and realization of the sale. Probabilities of choice and conversion are forecasted based on a disaggregated customer choice model, taking into account customer characteristics and stated preferences as well as product / service attributes such as price. Offers are then scored and ranked by expected value based on their revenue, cost and choice probability. Finally, CCRM recommends which offer(s) to present to the customer, at which price(s) and in which display / sequence order, to maximize a business objective function such as the expected value of the transaction / contract.
Owner:OPEN PRICER
Limited-use keys and cryptograms
ActiveUS20150178724A1Promote generationImprove securityMultiple keys/algorithms usageCryptography processingCryptogramCommunication device
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include encrypting account information with a first encryption key to generate a second encryption key, and encrypting key index information using the second key to generate a limited-use key (LUK). The key index information may include a key index having information pertaining to generation of the LUK. The LUK and the key index can be provided to the communication device to facilitate generation of a transaction cryptogram for a transaction conducted using the communication device, and the transaction can be authorized based on the transaction cryptogram generated from the LUK.
Owner:VISA INT SERVICE ASSOC
System and method for processing peer-to-peer financial transactions
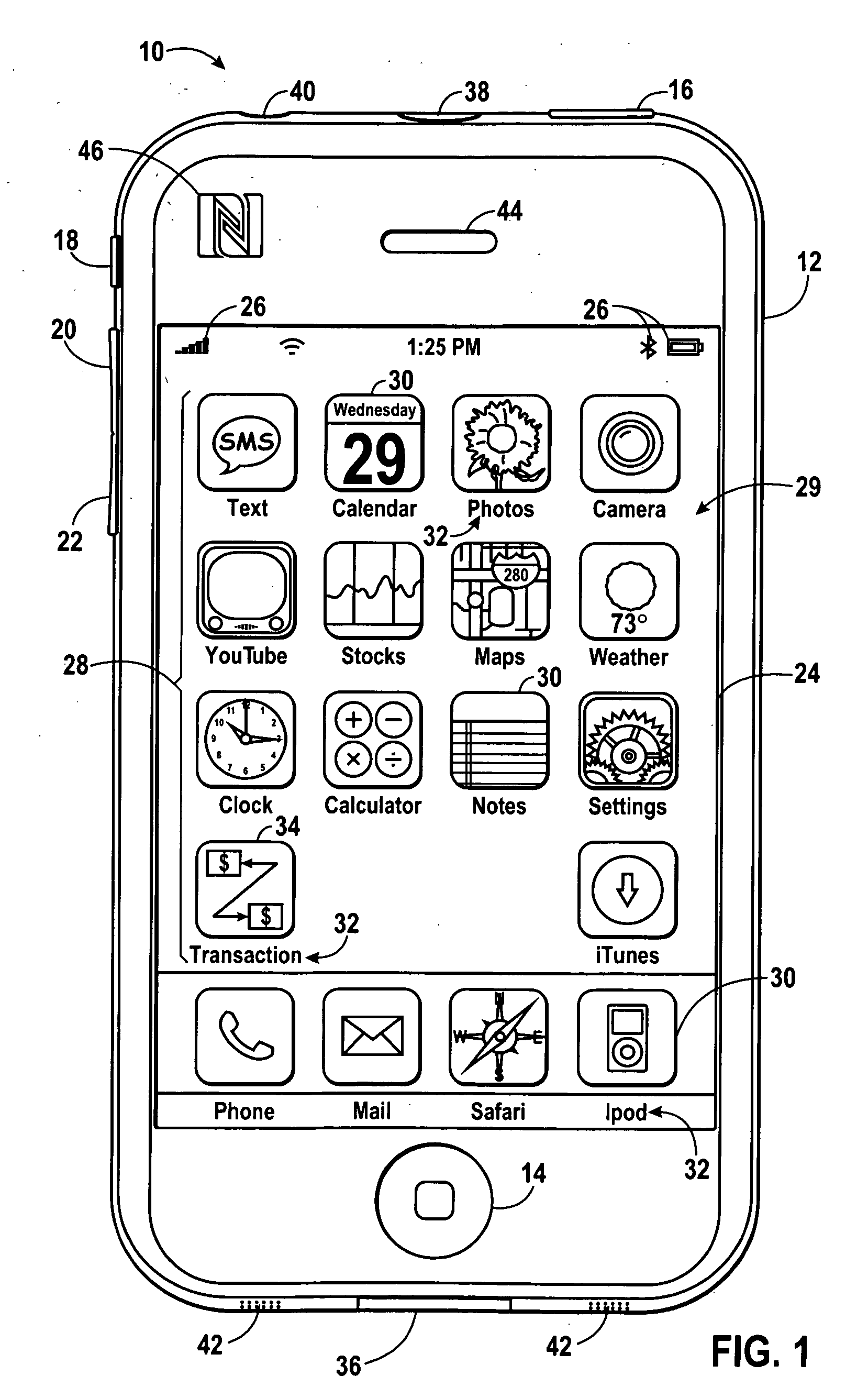
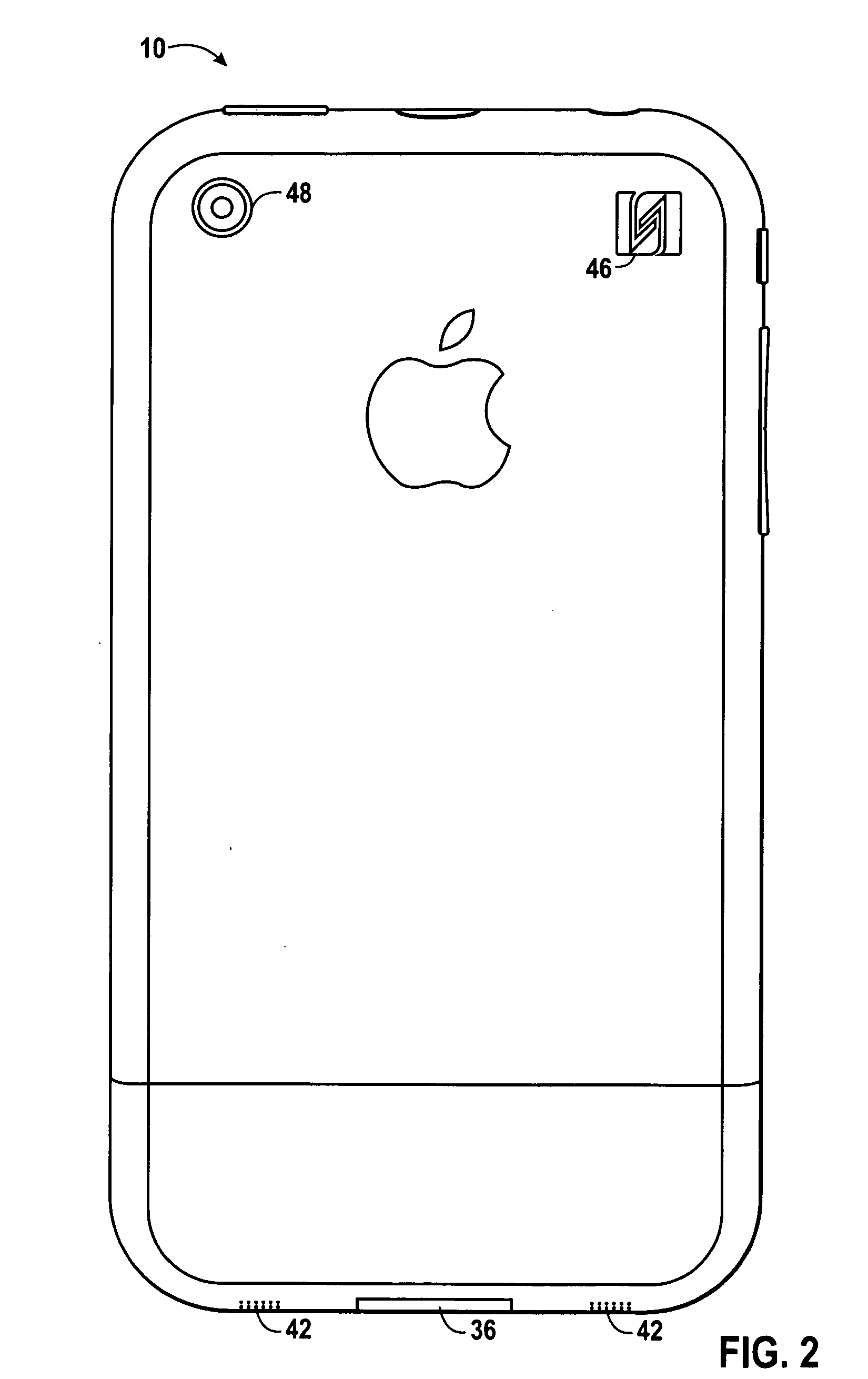
Various techniques are provided for carrying out peer-to-peer financial transactions using one or more electronic devices. In one embodiment, a request for payment is transmitted from a first device to a second device using a near field communication (NFC) interface. In response to the request, the second device may transmit payment information to the first device. The first device may select a crediting account and, using a suitable communication protocol, may communicate the received payment information and selected crediting account to one or more external financial servers configured to process and determine whether the payment may be authorized. If the payment is authorized, a payment may be credited to the selected crediting account. In a further embodiment, a device may include a camera configured to obtain an image of a payment instrument. The device may further include an application to extract payment information from the acquired image.
Owner:APPLE INC
Parimutuel wagering system with opaque transactions
InactiveUS20050096124A1Apparatus for meter-controlled dispensingBuying/selling/leasing transactionsDeposit accountCredit union
A seamless ledger-based wagering system is provided wherein a secure, flexible and automated database method and apparatus is used for retrieving information and accounting for wagers in an electronic wagering format. The accounting system can be a ledger wherein funds are accounted for by a financial structure (e.g., financial institution such as a bank, credit union, savings and loan, deposit account, and the like) so that funds may be transferred through an intermediate transaction (e.g., the electronic wager entered onto the account) on the ledger and committed to payment at the ultimate target of the transfer (e.g., the pari-mutuel site, and ancillary recipients of wagering monies, such as horseman's associations, totalisator companies, automated machine lessors, track association, governmental agencies and the like). As the financial records from the financial structure never ‘sees’ the wagering facility in the transaction, transferring funds or guaranteeing funds to the intermediate transaction on a ledger, the entire transaction is in compliance with state and national regulations prohibiting or limiting or rendering illegal the availability of funds in the wagering transaction or transferring funds into a wagering account.
Owner:ASIP HLDG INC
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
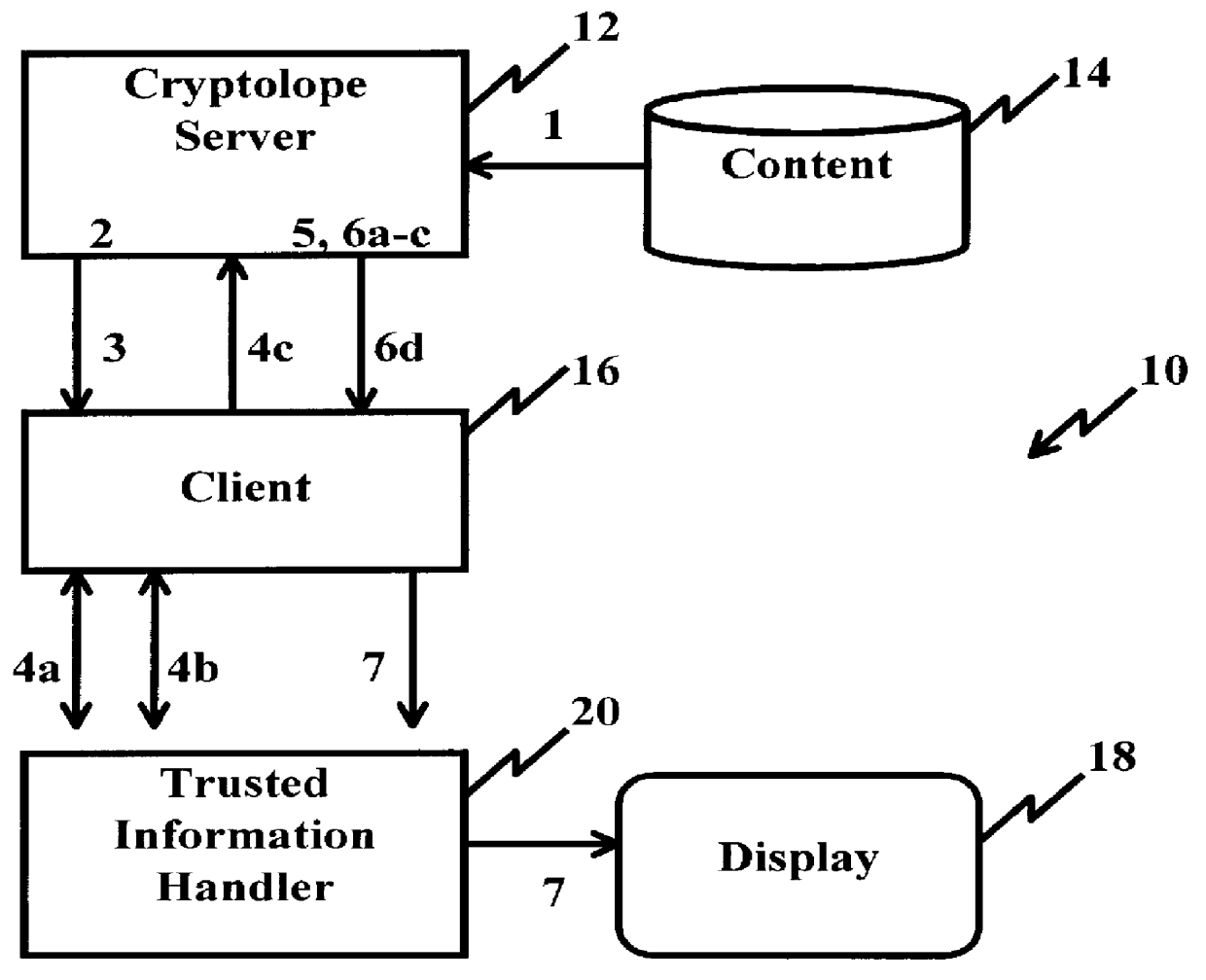
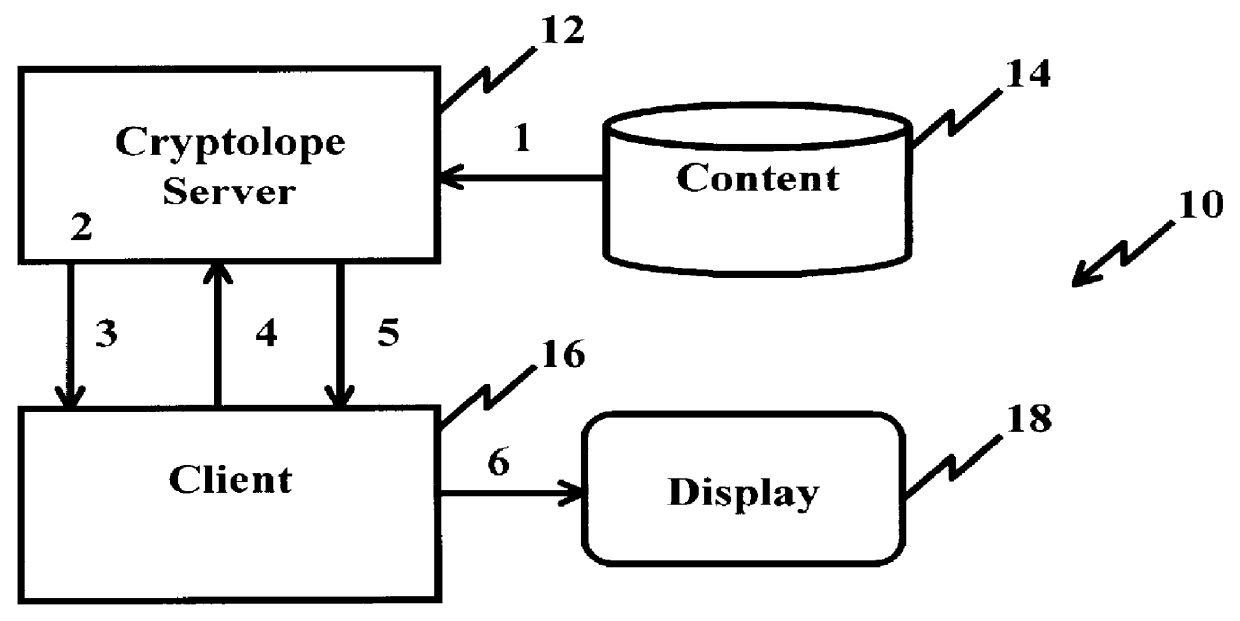
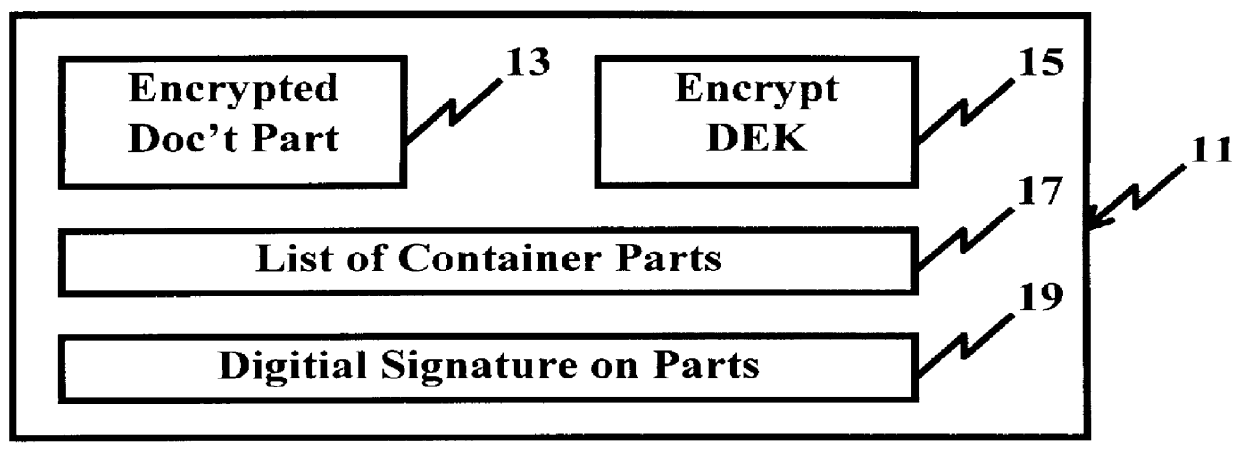
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Peer-to-peer financial transaction devices and methods
Various techniques are provided for carrying out peer-to-peer financial transactions using one or more electronic devices. In one embodiment, a request for payment is transmitted from a first device to a second device using a near field communication (NFC) interface. In response to the request, the second device may transmit payment information to the first device. The first device may select a crediting account and, using a suitable communication protocol, may communicate the received payment information and selected crediting account to one or more external financial servers configured to process and determine whether the payment may be authorized. If the payment is authorized, a payment may be credited to the selected crediting account. In a further embodiment, a device may include a camera configured to obtain an image of a payment instrument. The device may further include an application to extract payment information from the acquired image.
Owner:APPLE INC
System and method for processing financial transactions
InactiveUS7571139B1Improve securityGreat degree of convenienceFinanceCash registersPaymentFinancial transaction
A network for processing retail sales transactions includes a customer transceiver with a unique customer number, a reader receiving the customer number and sending it to a point-of-sale device where it is combined with transaction information to form a transaction entry. The transaction entry is sent through a merchant computer to a transaction processing system having a customer database. The transaction processing system references an entry in the customer database corresponding to the customer / transmitter ID number and routes the transaction entry to a payment processing system specified in the customer database entry.
Owner:EXXON RES & ENG CO +1
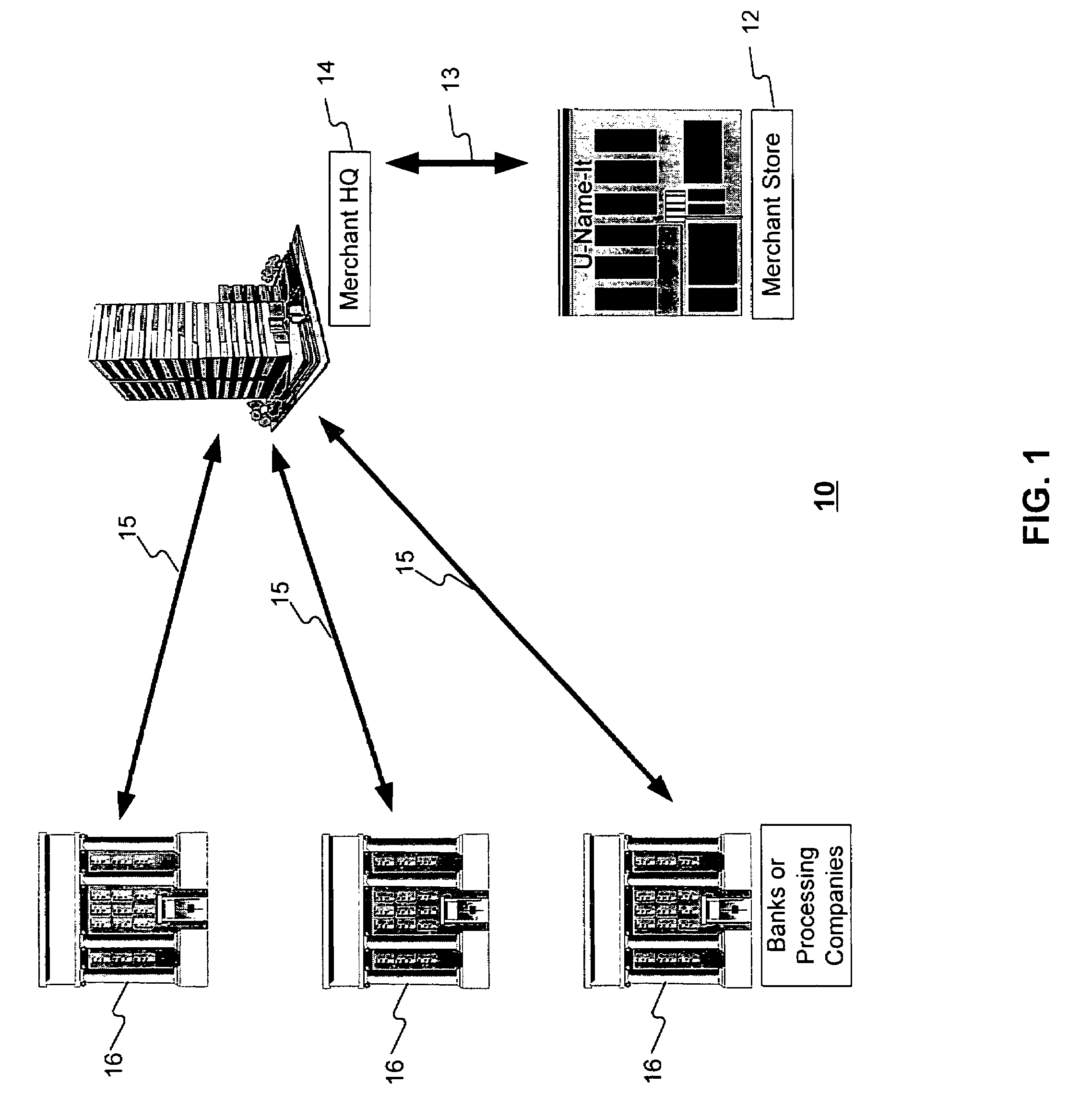
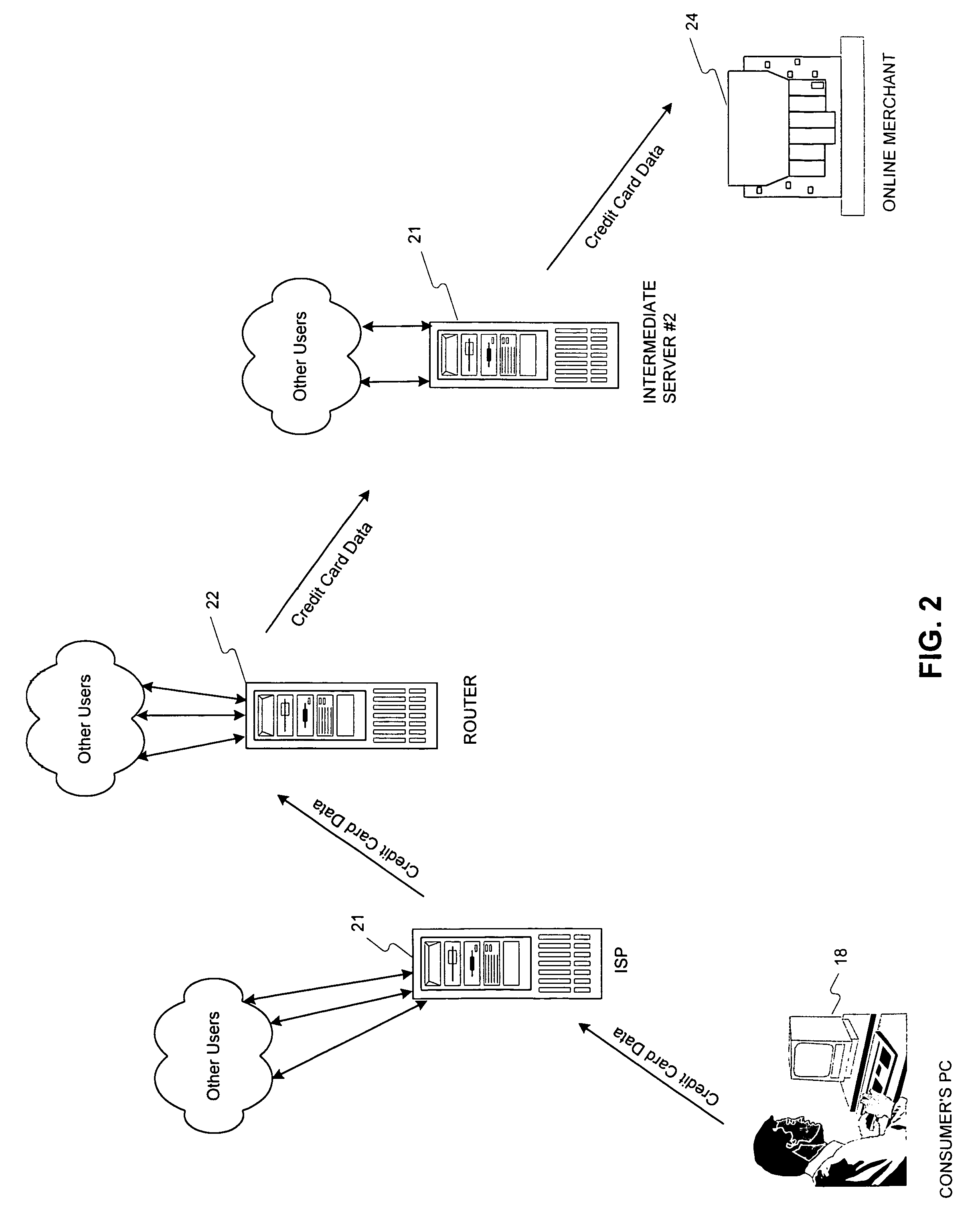
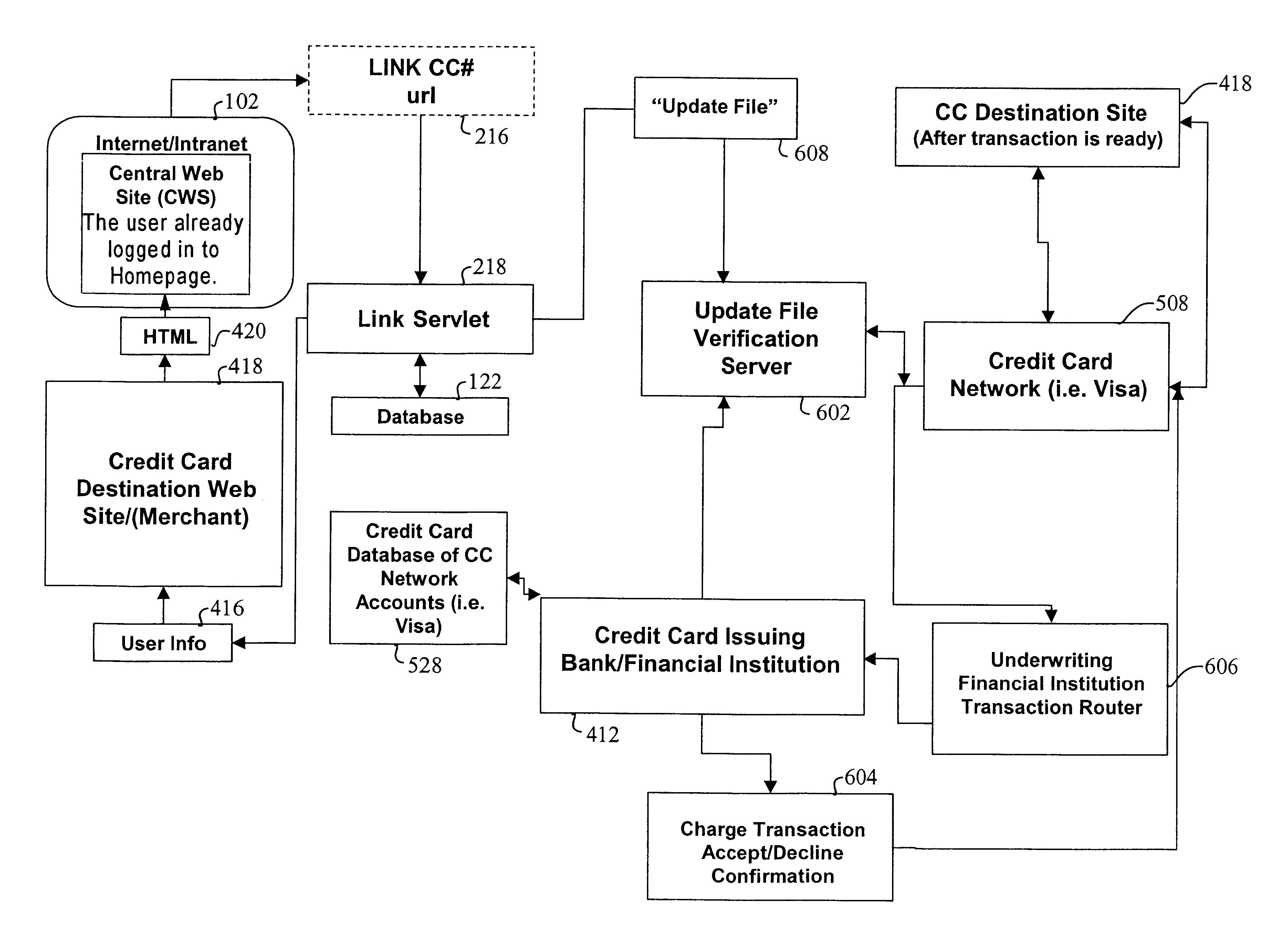
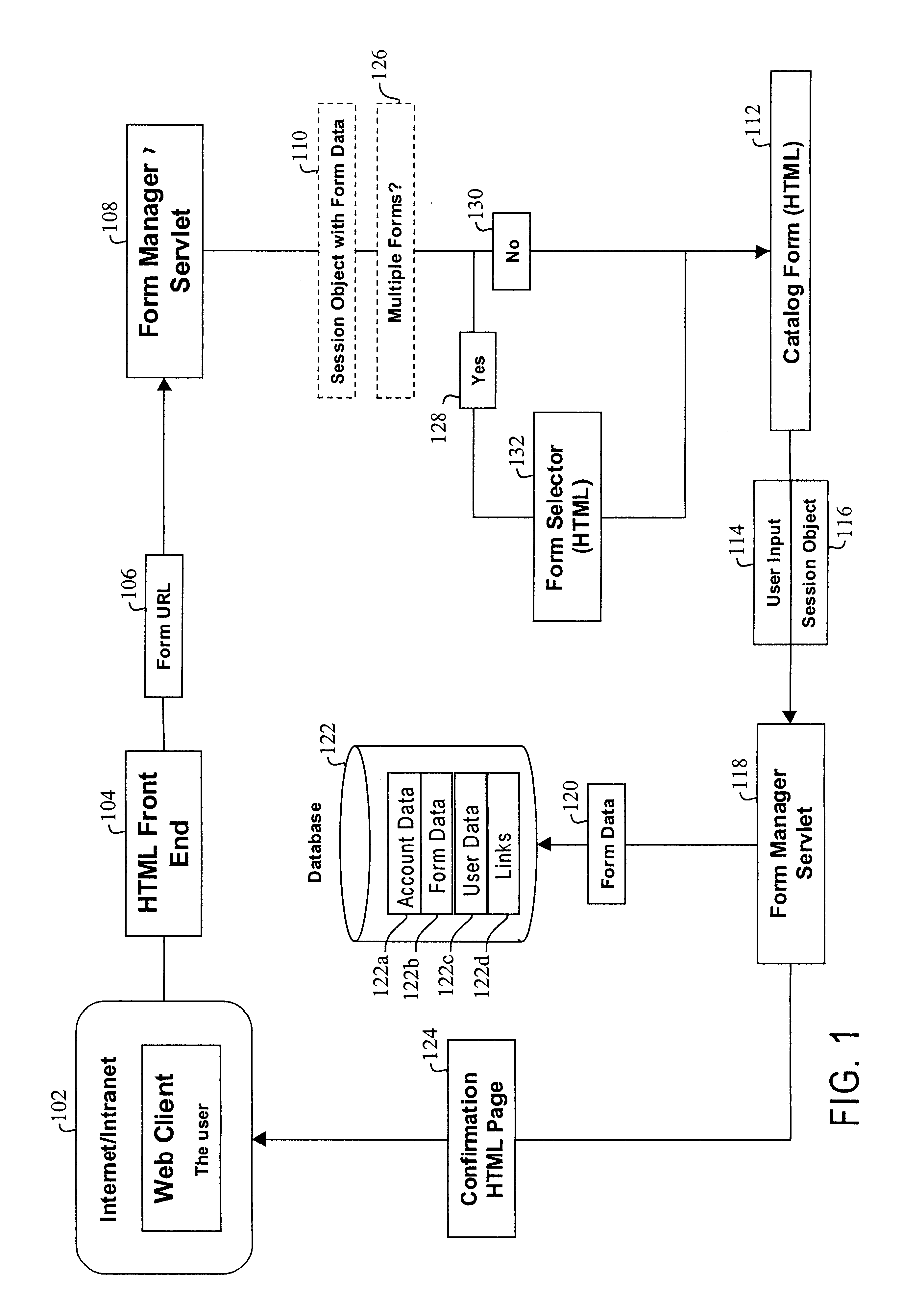
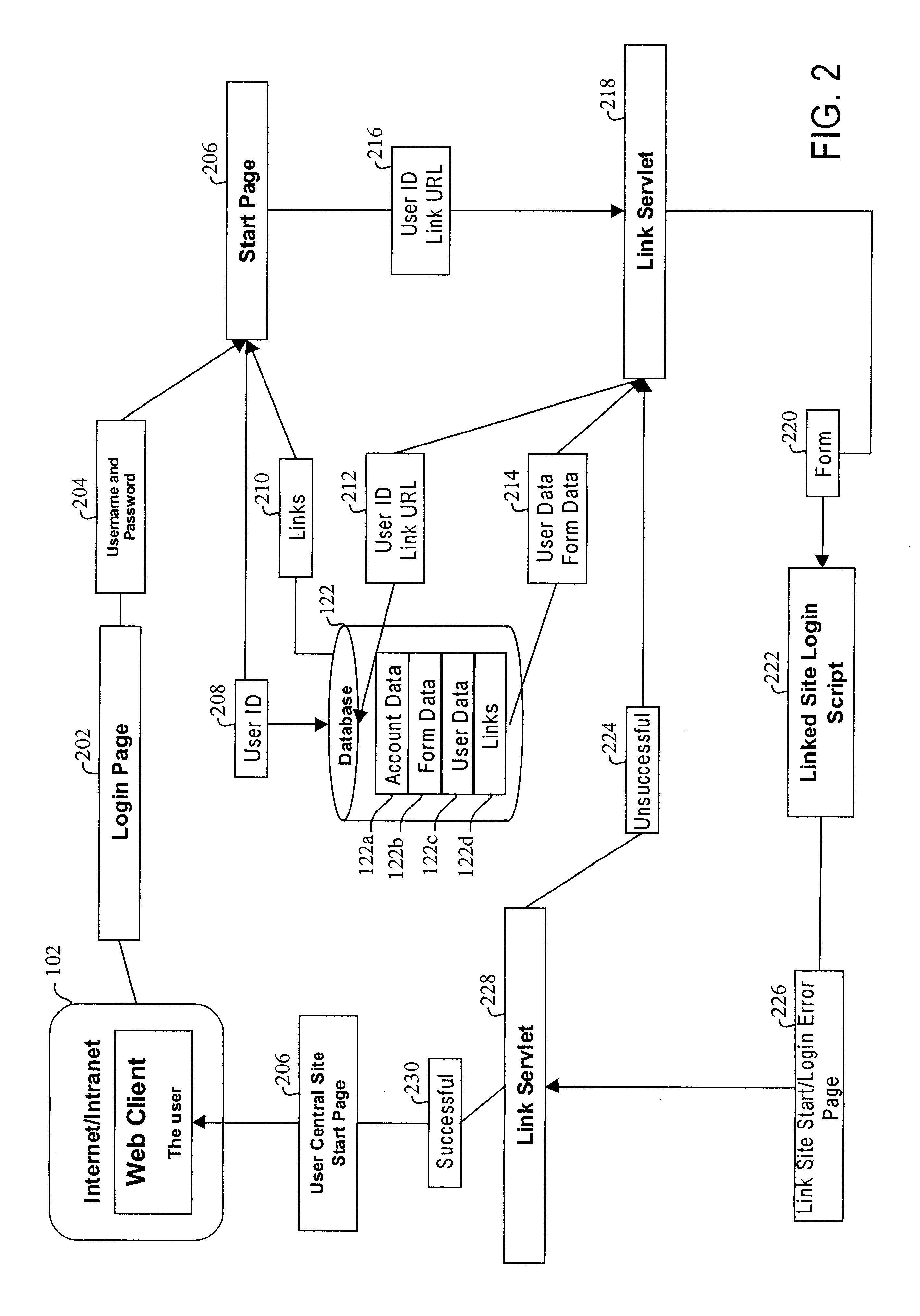
Method, system and computer readable medium for web site account and e-commerce management from a central location
InactiveUS6879965B2Minimizing activation timeMinimizing financial exposureComplete banking machinesAcutation objectsWeb siteData field
A method, system and computer readable medium for, from a central Web site, performing at least one of registering a user at a destination Web site, logging in a user at a destination Web site and managing an online financial transaction at a destination Web site, including parsing a form Web page of the destination Web site to extract form data fields therefrom; mapping form data fields of a central Web site form to corresponding extracted form data fields of the form Web page of the destination Web site; and using the mapped form data fields to perform at least one of registering a user at the destination Web site, logging in a user at the destination Web site and managing an online financial transaction of a user at the destination Web site. In another aspect, there is provided a method, system and computer readable medium for managing an online or offline financial transaction of a user, from a central Web site, including generating financial transaction account information for a user based on existing credit or debit card information; gathering from the user one or more limits that are applied to a financial transaction performed based on the financial transaction account information; receiving from a source information indicating that an online or offline financial transaction using the financial transaction account information is in progress; applying the one or more limits gathered from the user to approve or disapprove the online or offline or online financial transaction that is in progress; and transmitting an approval or disapproval signal to the source based on a result of the applying step.
Owner:SLINGSHOT TECH LLC
Mobile Person-to-Person Payment System
InactiveUS20070255652A1The process is simple and fastSimple accessFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions may be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions may be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
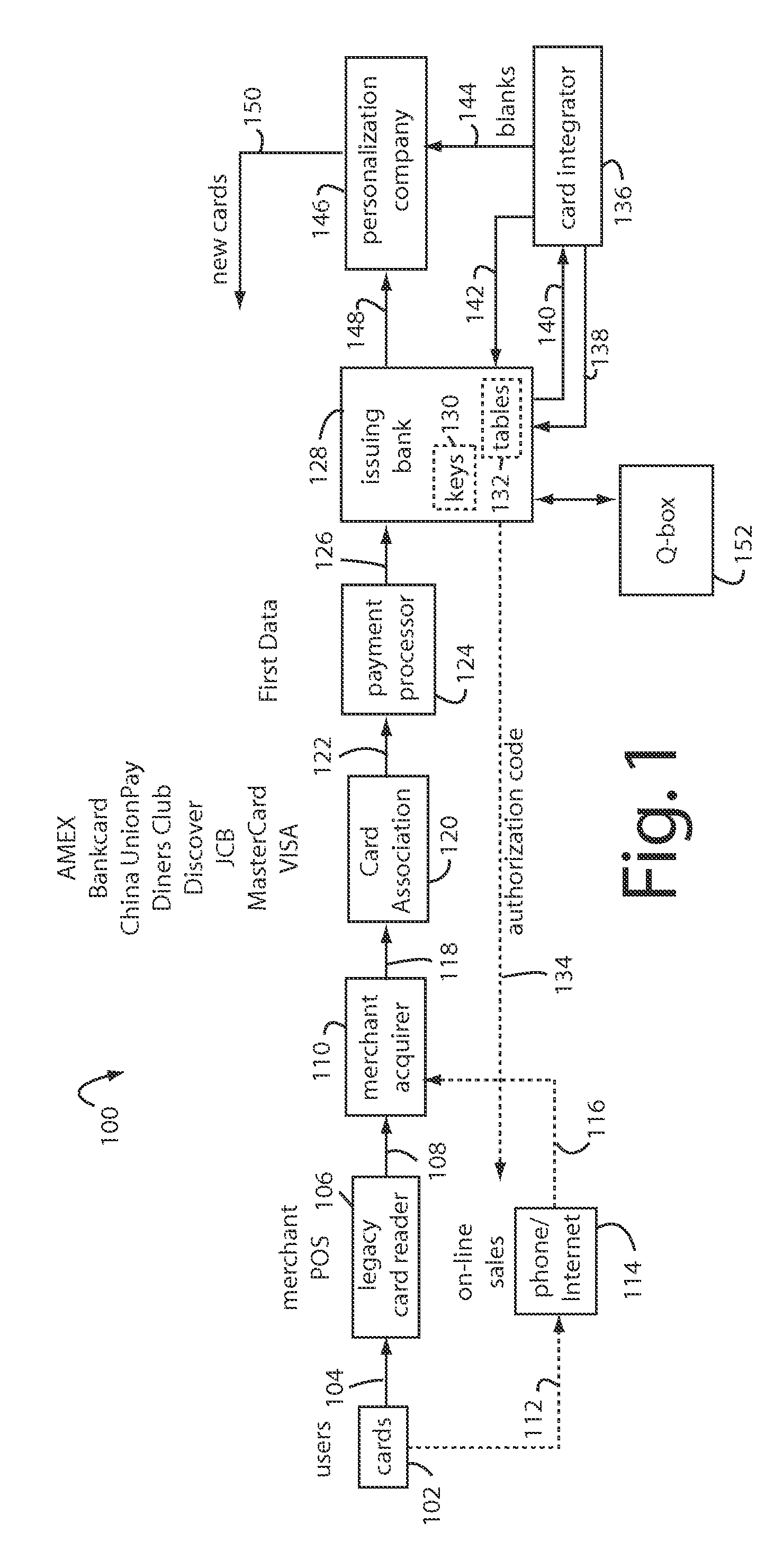
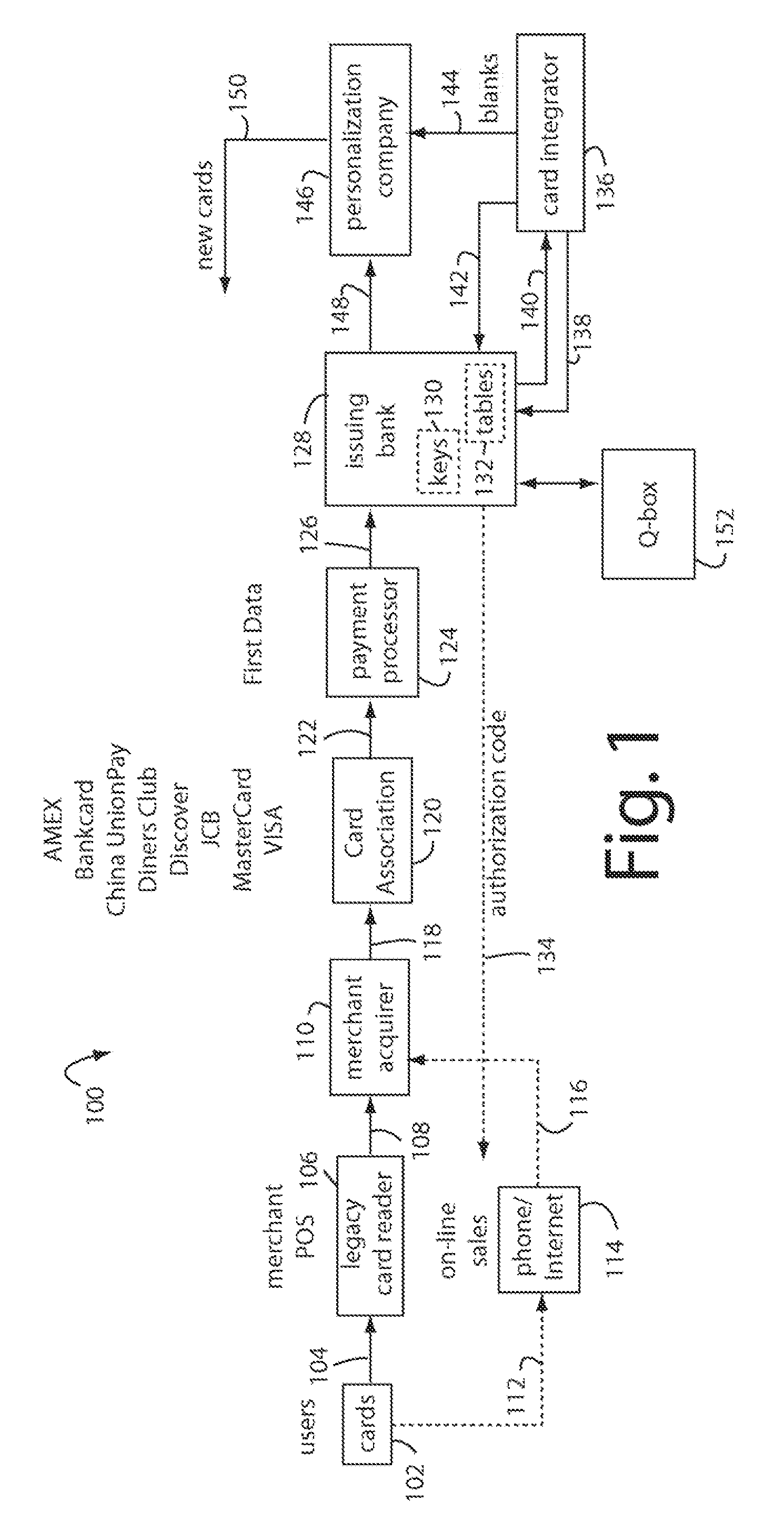
Financial transactions with dynamic personal account numbers
ActiveUS7580898B2Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
Financial transactions with dynamic card verification values
ActiveUS20070136211A1Sufficient dataComputer security arrangementsPayment architectureUser needsPower user
A payment card comprises an internal dynamic card verification value (CVV) generator and a user display for card-not-present transactions. Card-present transactions with merchant card readers are enabled by a dynamic magnetic array internally associated with the card's magnetic stripe. The user display and a timer are triggered by the suer when the user needs to see the card verification value and / or begin a new transaction. A new card verification value is provided for each new transaction according to a cryptographic process, but the timer limits how soon a next new card verification value can be generated.
Owner:FITBIT INC
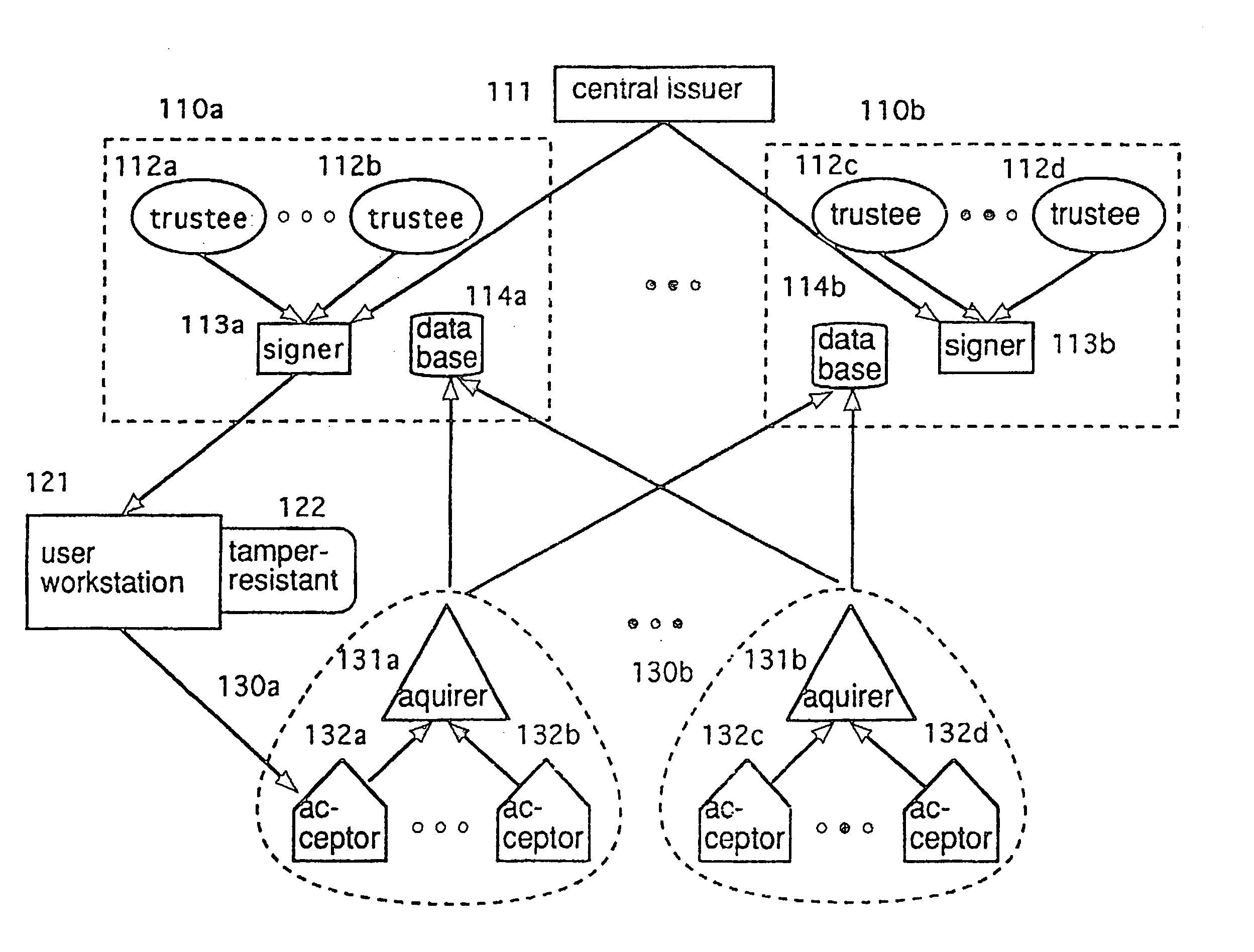
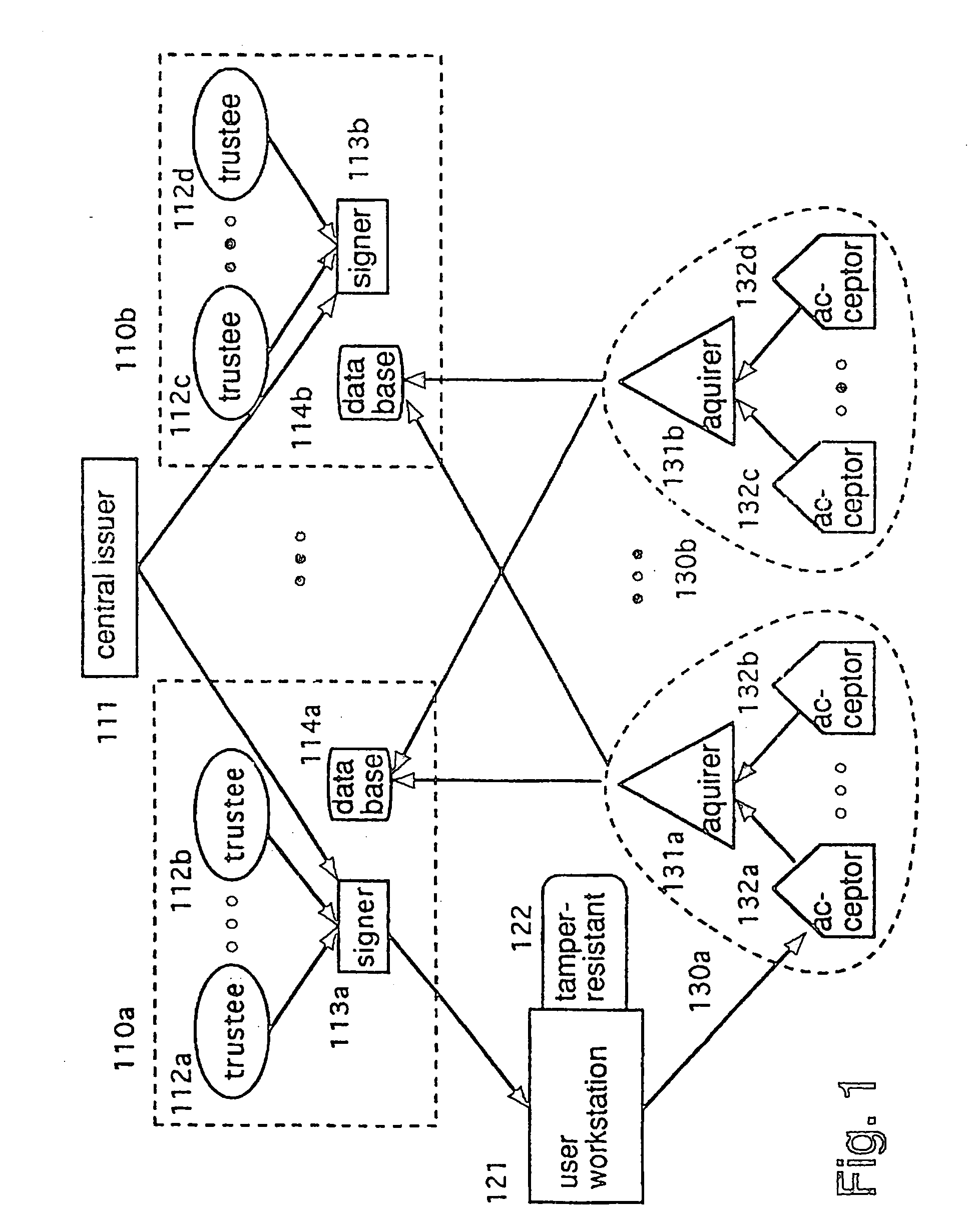
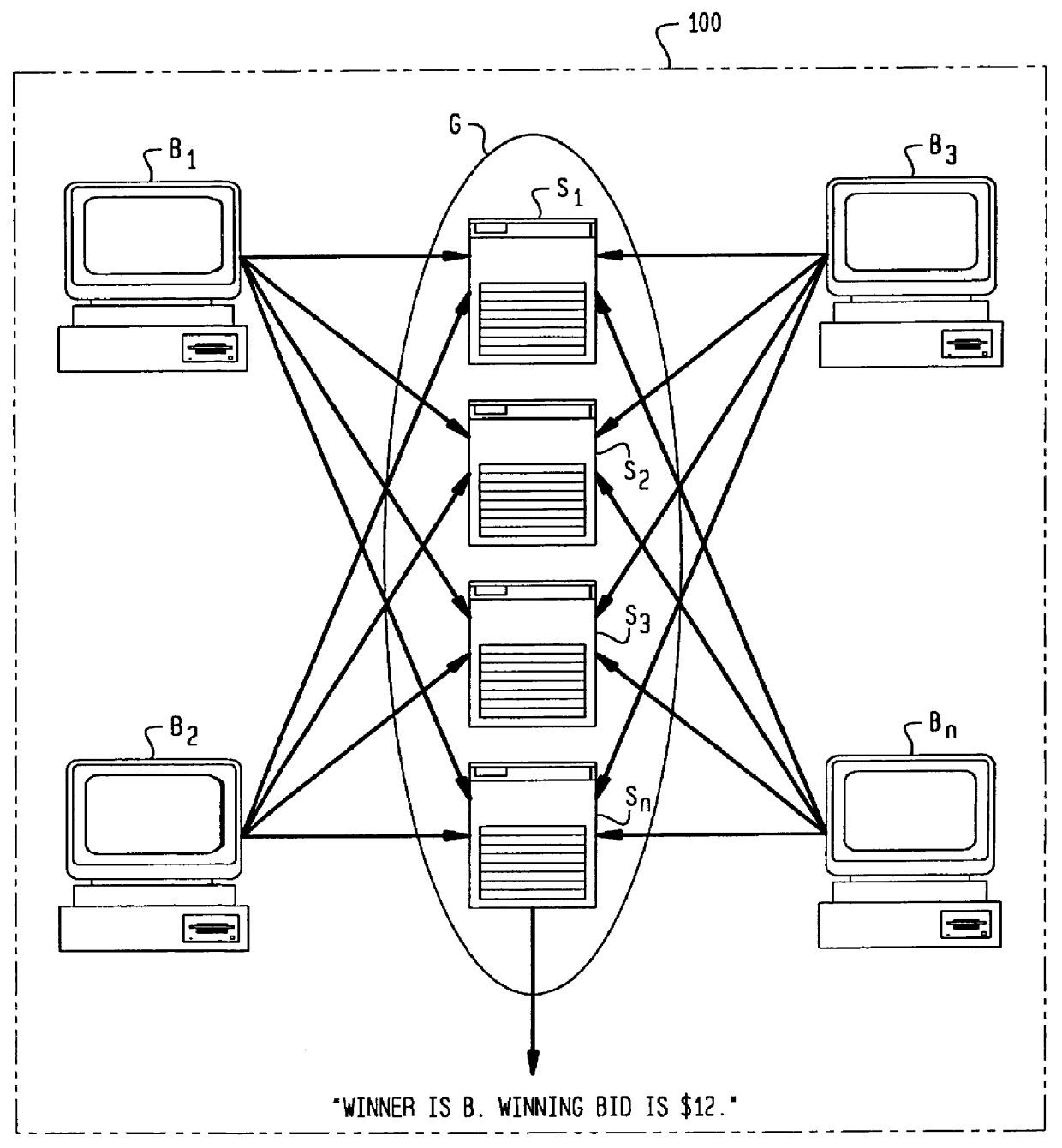
Secure auction systems
InactiveUS6055518AEasy to rebuildFinanceUser identity/authority verificationFinancial transactionMonetary value
The apparatus and method of the present invention provide secure auction service for use in a network having servers and bidding terminals. The auction service makes transactions among servers and bidding terminals subject to a distributed protocol. The distributed protocol distributes submitted bids among the multiple servers, closes a bidding period, verifies validity of monetary value of each submitted bid by utilizing said distributed protocol and determines a winning bidder.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
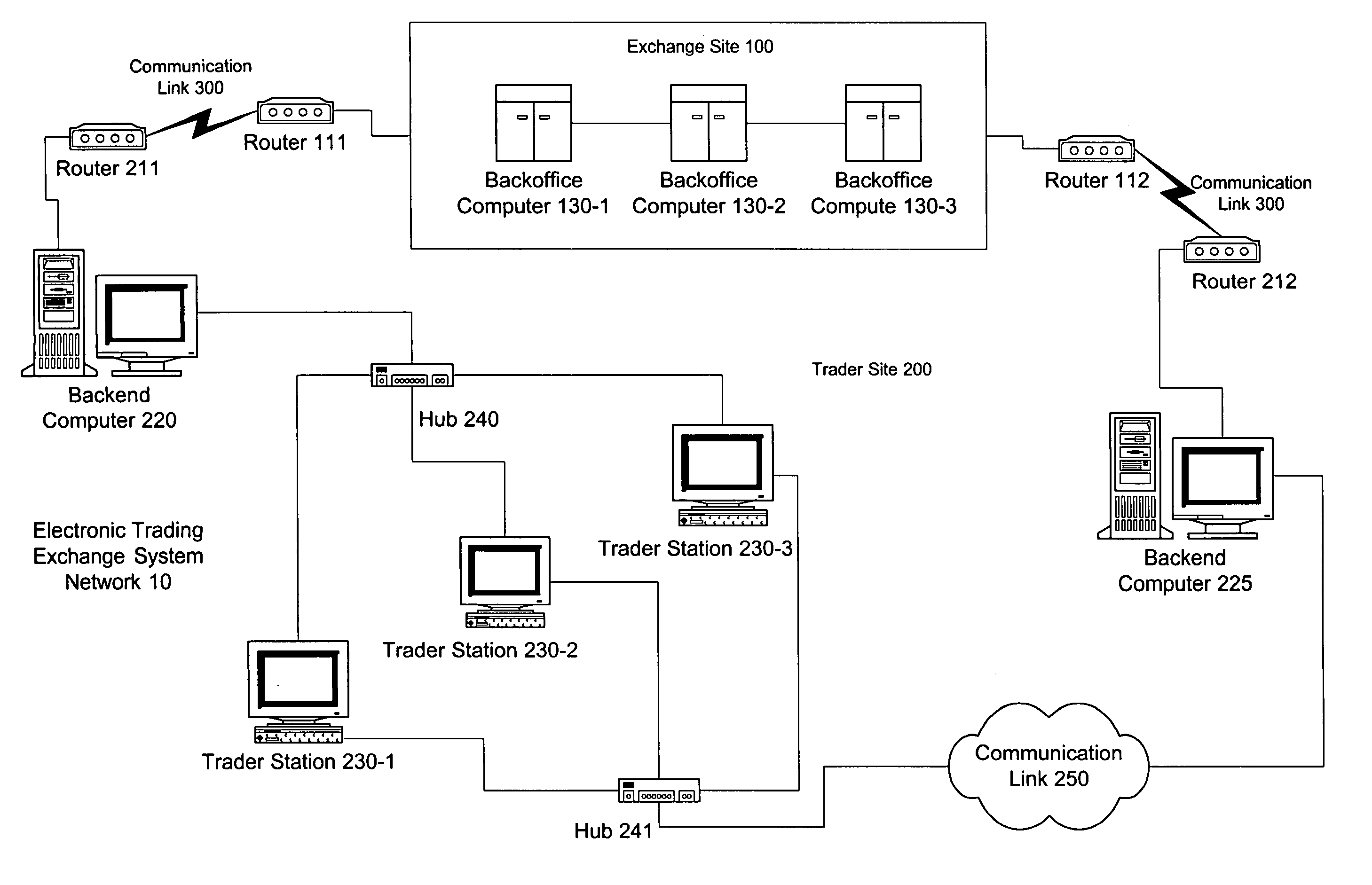
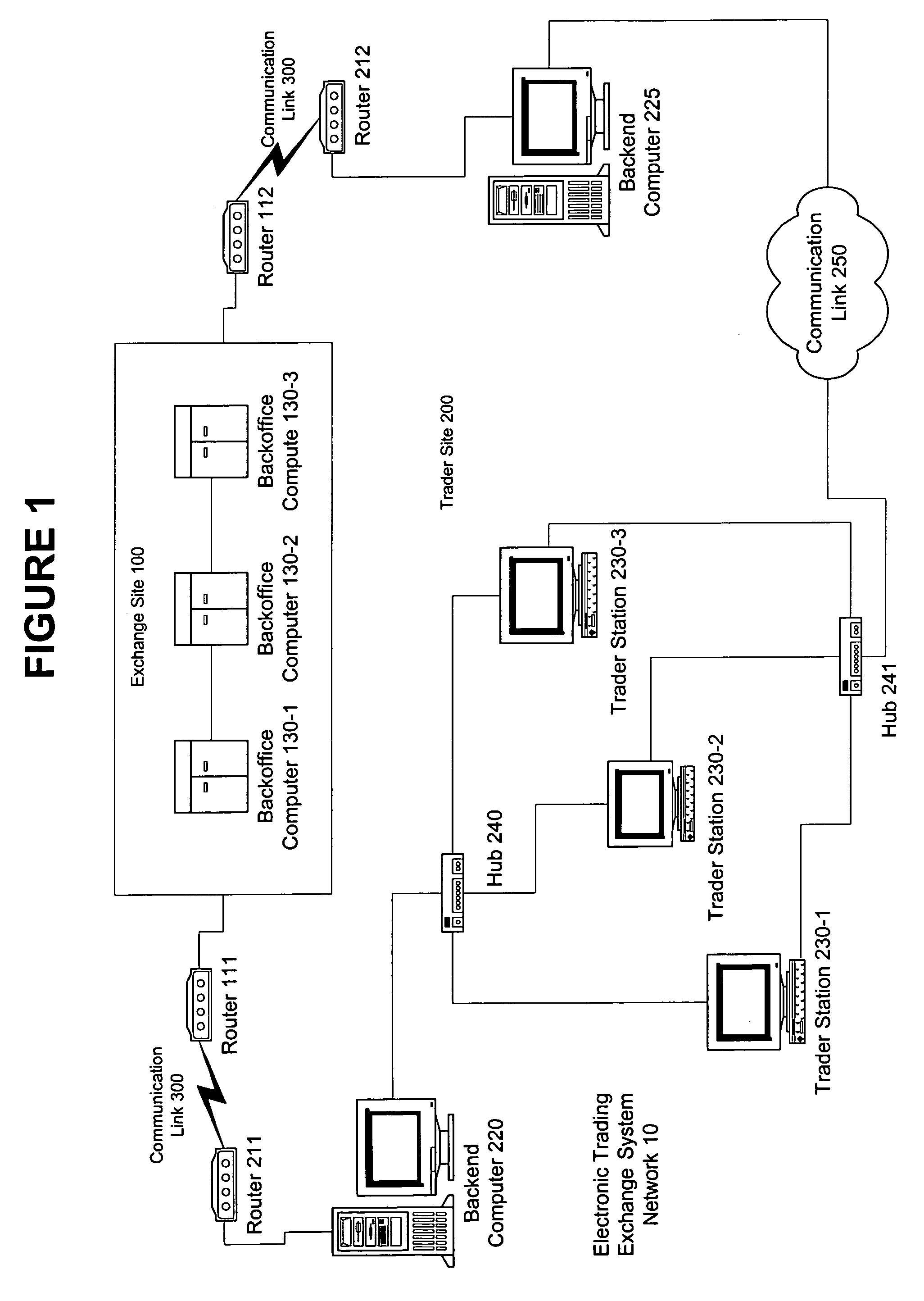
Automated trading system in an electronic trading exchange
An electronic exchange system network includes a trader site having an automated trading system capable of submitting orders and / or quotes to an exchange site. The automated trading system determines whether an order or quote should be submitted based on, for example, the current market price of an option and theoretical buy and sell prices. The theoretical buy and sell prices are derived from, among other things, the current market price of the security underlying the option. The theoretical buy and sell prices are calculated when underlying factors that contribute to the theoretical prices change. Computation times of the theoretical prices may be reduced by using precalculated values and / or using interpolation and extrapolation. Other techniques may be used in addition or in the alternative to speed automatic decision-making. In addition, a system of checks may be conducted to ensure accurate and safe automated trading. The automated trading system may be capable of automatically submitting orders in connection with the underlying security in order to hedge part of the delta risk associated with the automated option trades.
Owner:DCFB
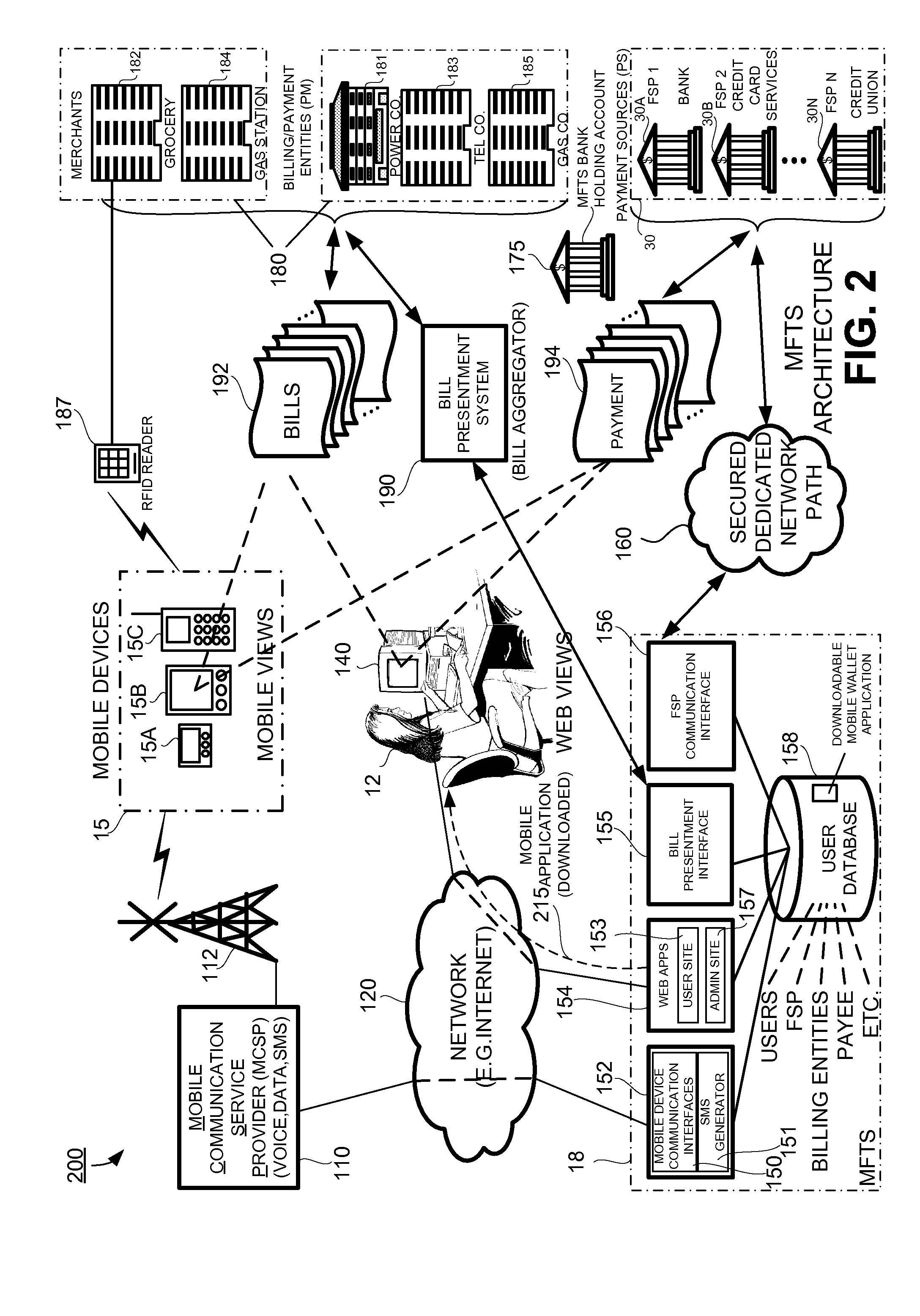
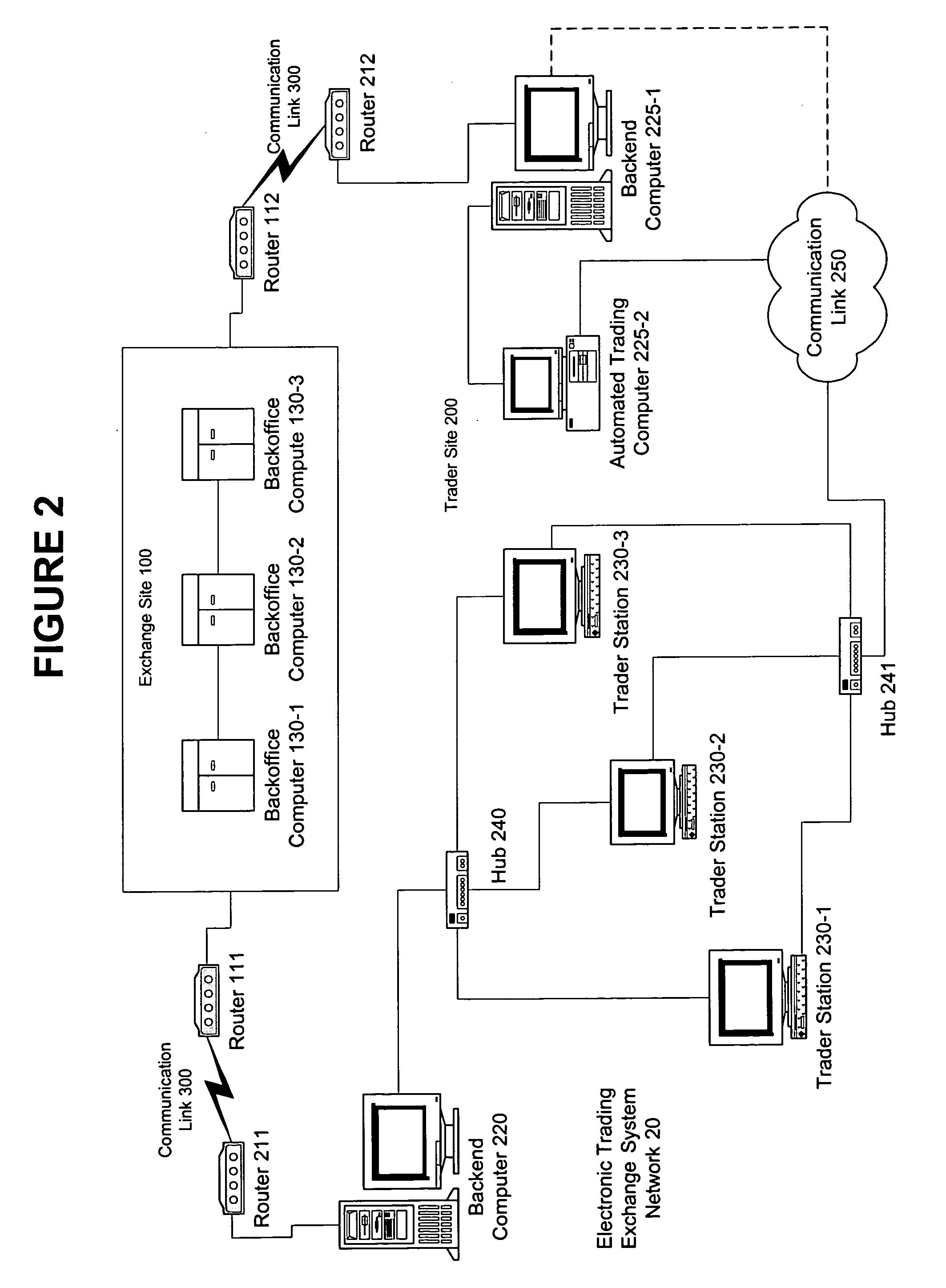
Methods and Systems For Distribution of a Mobile Wallet for a Mobile Device
InactiveUS20080126145A1Financial transaction facilitatedPromote disseminationFinanceTelephonic communicationPaymentWireless mobile devices
Methods and systems for distributing a mobile device application for use in making and receiving payments utilizing a mobile device such as a mobile telephone (cellphone) or wireless connected personal digital assistant (PDA). A downloadable mobile device application, when installed on a compatible mobile device, is operative for communicating with a mobile financial transaction system (MFTS) that facilitates the making and receiving of payments via wireless mobile devices. The downloadable mobile device application is provided via a download system that downloads the application to mobile devices according to download procedures appropriate for a particular type of mobile device. When a payment is made to a payee having a mobile device, system communicates a message to the payee's mobile device that informs that a payment has been made and instructs the payee about the downloadable mobile device application. If the mobile device user / payee downloads and installs the mobile device application on his or her mobile device and provides enrollment information, interaction between the MFTS and the mobile device user / payee is permitted, and payment is provided to the mobile device user as user / payee.
Owner:QUALCOMM INC
Payment card financial transaction authenticator
InactiveUS20080201264A1Sufficient dataAcutation objectsFinanceCryptographic nonceFinancial transaction
A payment card financial transaction authenticates for providing overall financial network security computes a number of results from a cryptographic key that match values that were selectively used to personalize individual payment cards with their individual user identification and account access codes. An account access code is later presented daring a financial transaction involving at least one of those individual payment cards. A dynamic portion is included in a merchant's magnetic reading of the payment card. Then authenication can proceed by matching it with values computed from the cryptographic key.
Owner:FITBIT INC
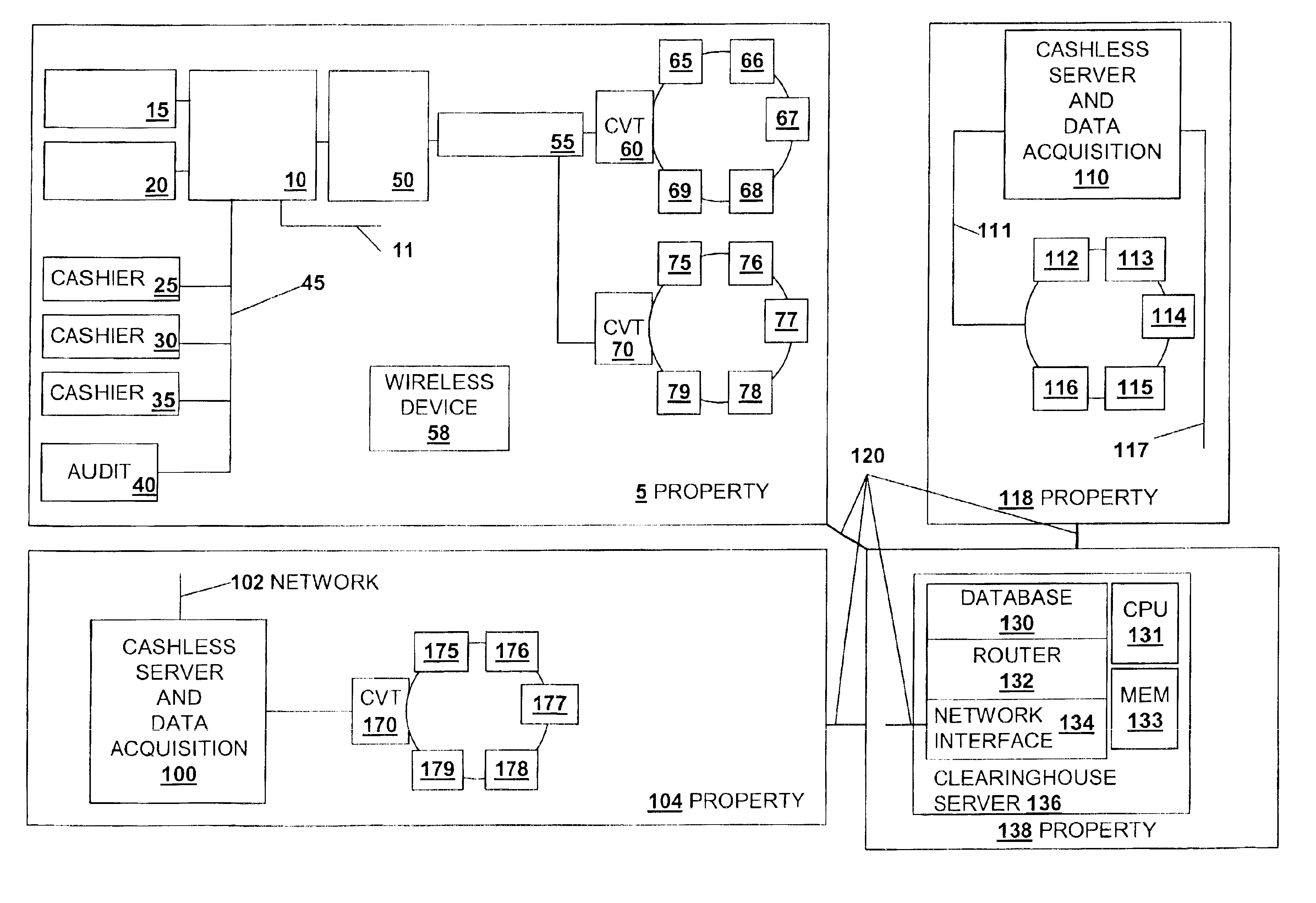
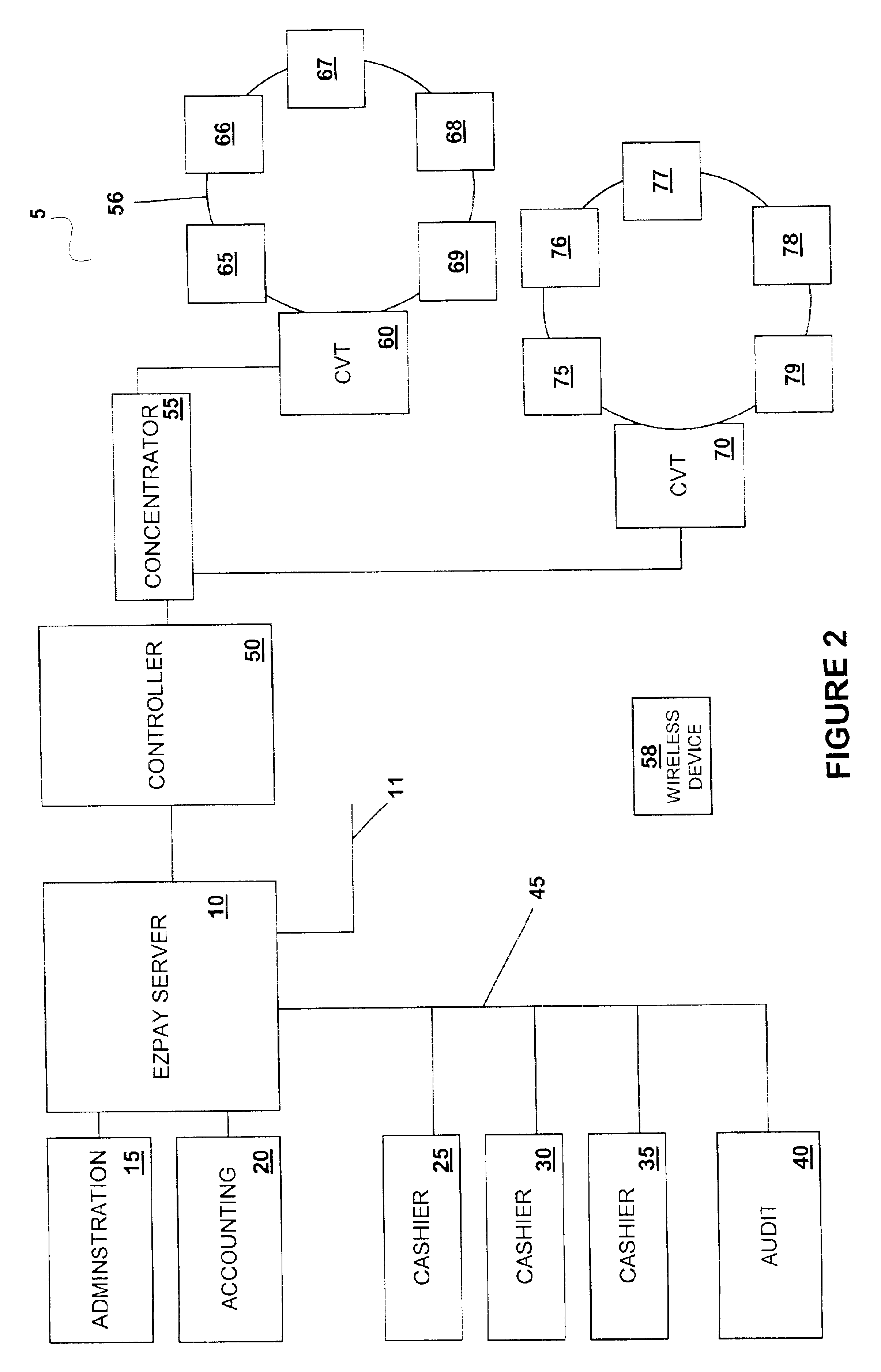
Cashless transaction clearinghouse
InactiveUS6866586B2Reduce the possibilityApparatus for meter-controlled dispensingPre-payment schemesEngineeringFinancial transaction
A disclosed cashless instrument transaction clearinghouse provides clearinghouse server including a network interface allowing the cashless instrument transaction clearinghouse to communicate with a number of gaming properties and a processor configured to enable the validation of cashless instruments at a gaming property different from where the cashless instrument was generated. Methods are provided that allow a plurality of cashless gaming devices located at different gaming properties to communicate with one another via the cashless instrument transaction clearinghouse in a secure manner using symmetric and asymmetric encryption techniques. Further, to reduce the possibilities of theft and fraud, the methods allow a receiver of a message to authenticate an identity of a sender of a message.
Owner:IGT
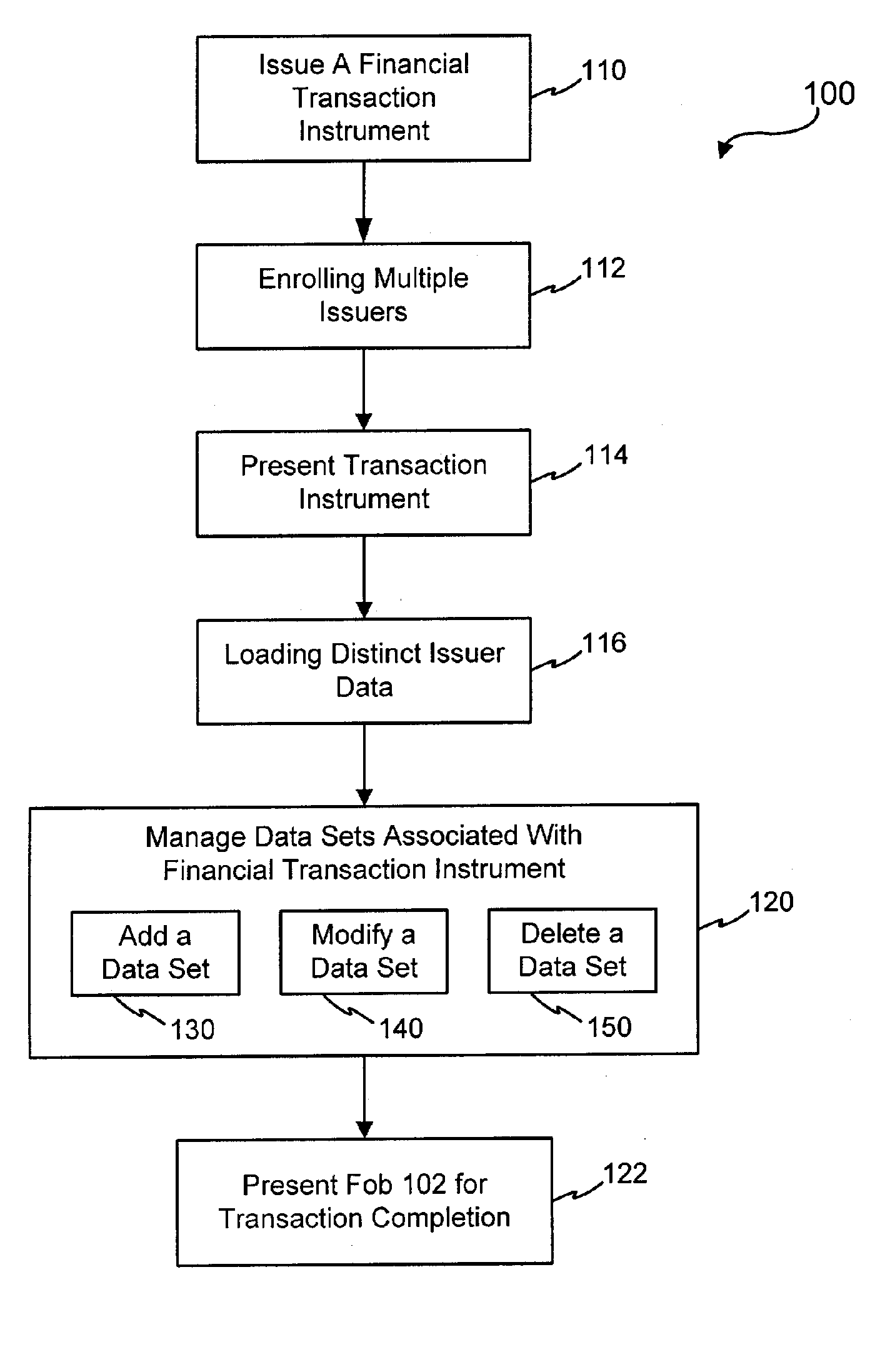
Systems and methods for managing multiple accounts on a RF transaction device using secondary identification indicia
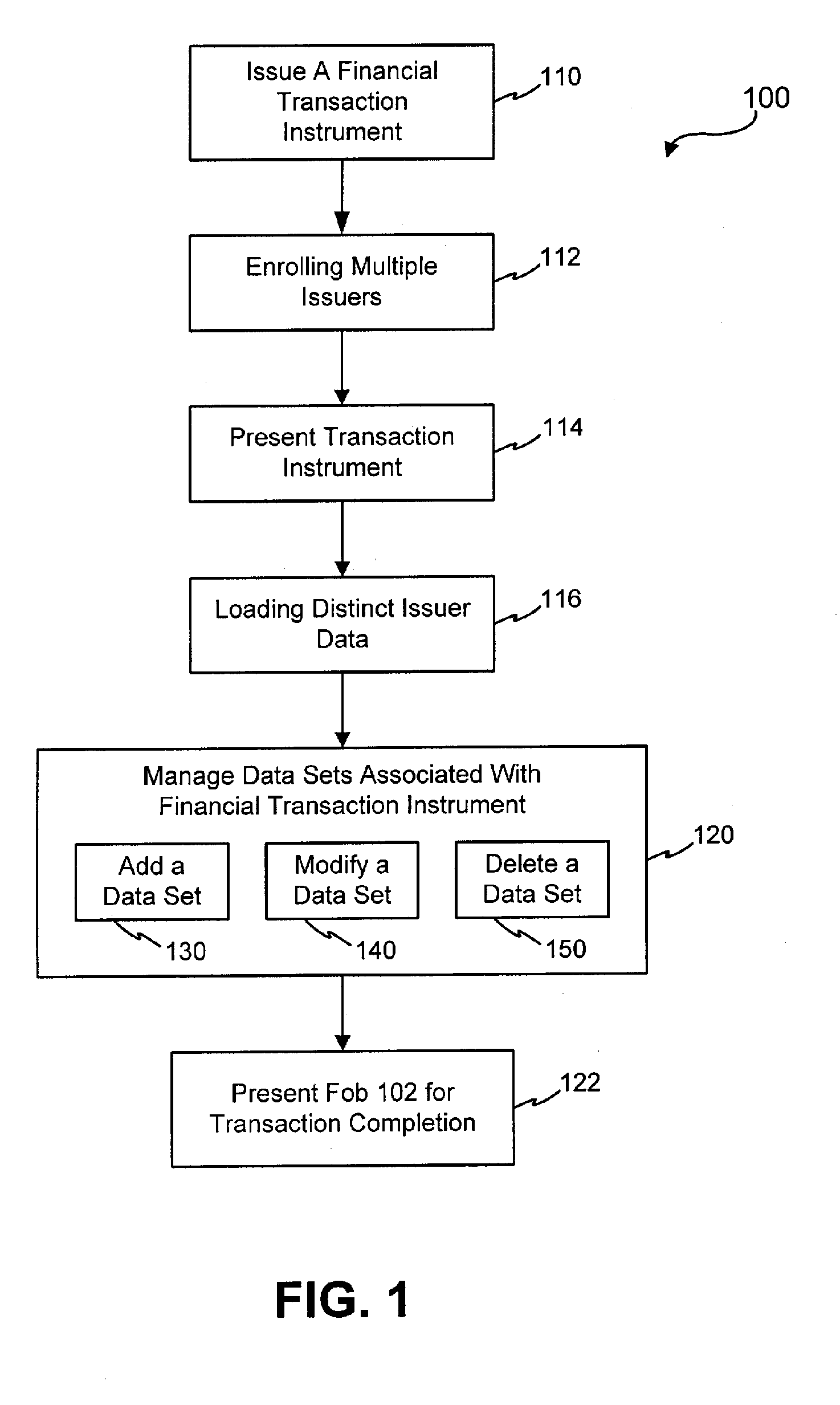
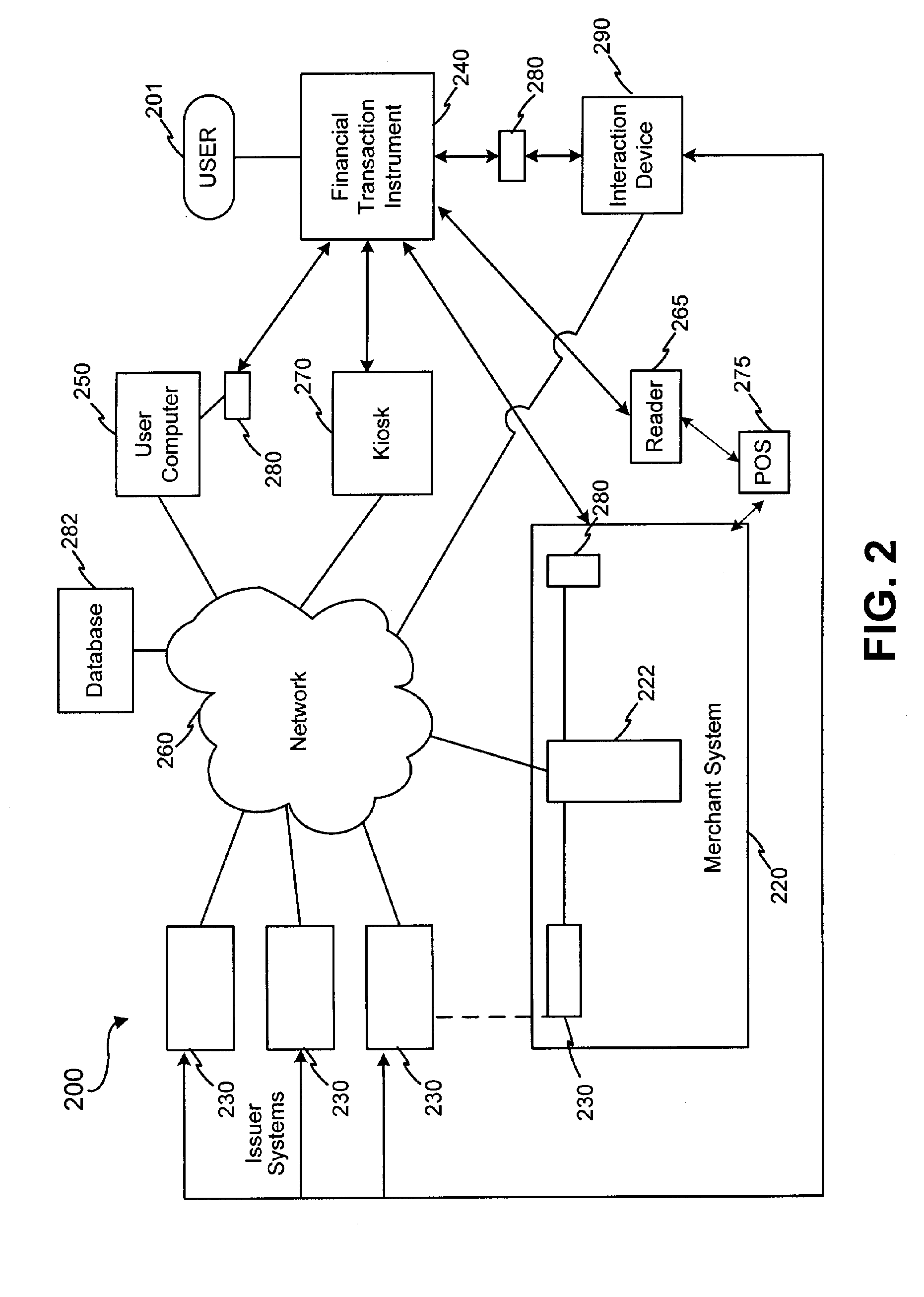
InactiveUS20050171898A1Easy to manageEliminate needAcutation objectsFinanceData setFinancial transaction
Systems and methods are configured to manage data sets associated with a transaction device. For example, a method is provided for facilitating the management of distinct data sets on a transaction device that are provided by distinct data set owners, wherein the distinct data sets may include differing formats. The method includes the steps of: adding, by a read / write, a first data set to the financial transaction device, wherein the first data set is owned by a first owner; adding, by the read / write device, a second data set to the financial transaction device, wherein the second data set is owned by a second owner; and storing the first data set and the second data set on the financial transaction device in accordance with an owner defined format. The first and second data sets are associated with first and second owners, respectively, and are configured to be stored independent of each other The transaction device user may be permitted to select at least one of the multiple data sets for transaction completion using a secondary identifier indicia. Where the user selects multiple accounts for transaction completion, the user may be permitted to allocate portions of a transaction to the selected transaction accounts. The transaction request may be processed in accordance with the user's allocations.
Owner:LIBERTY PEAK VENTURES LLC
Method and system for a virtual safe
Owner:SARCANIN BRANKO
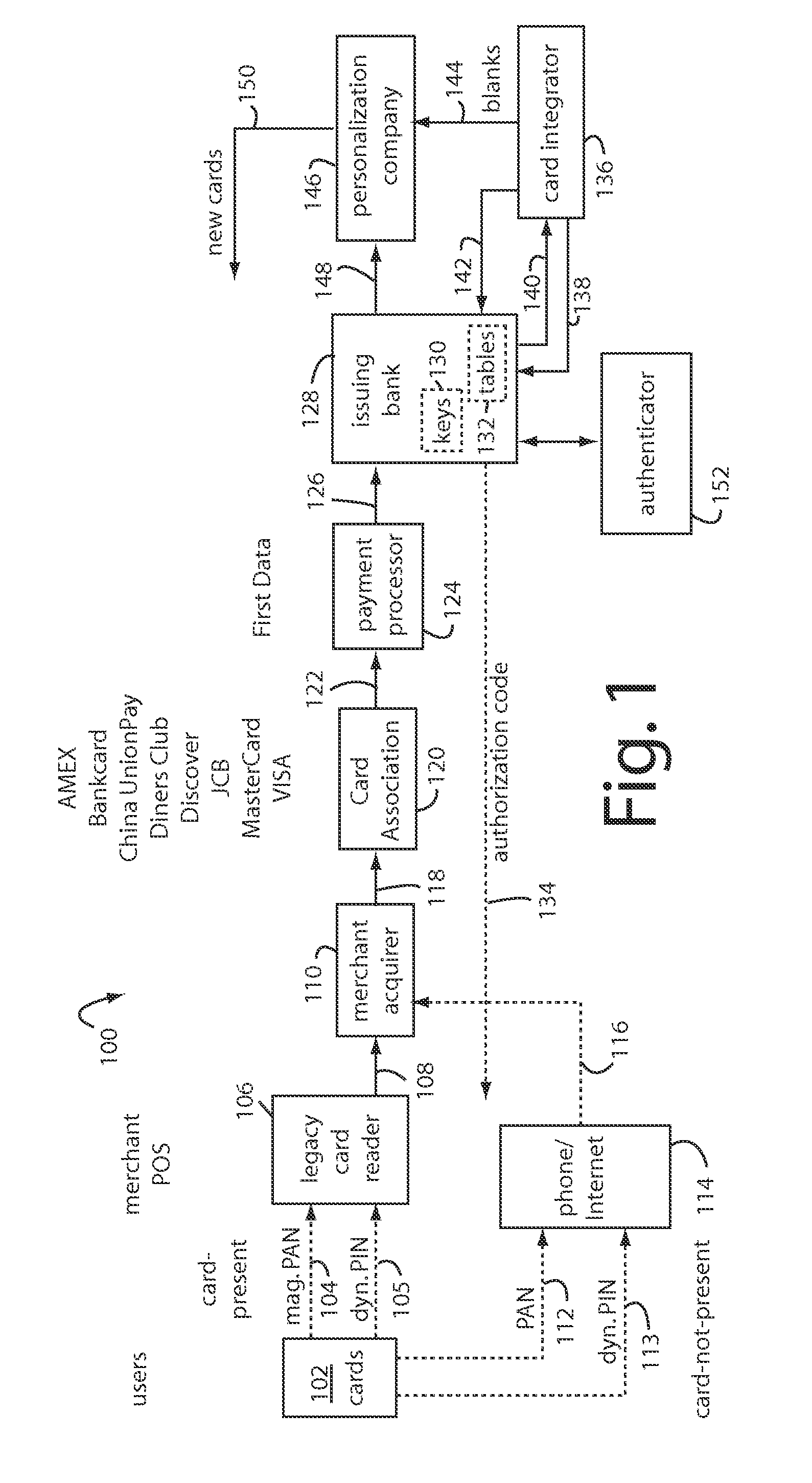
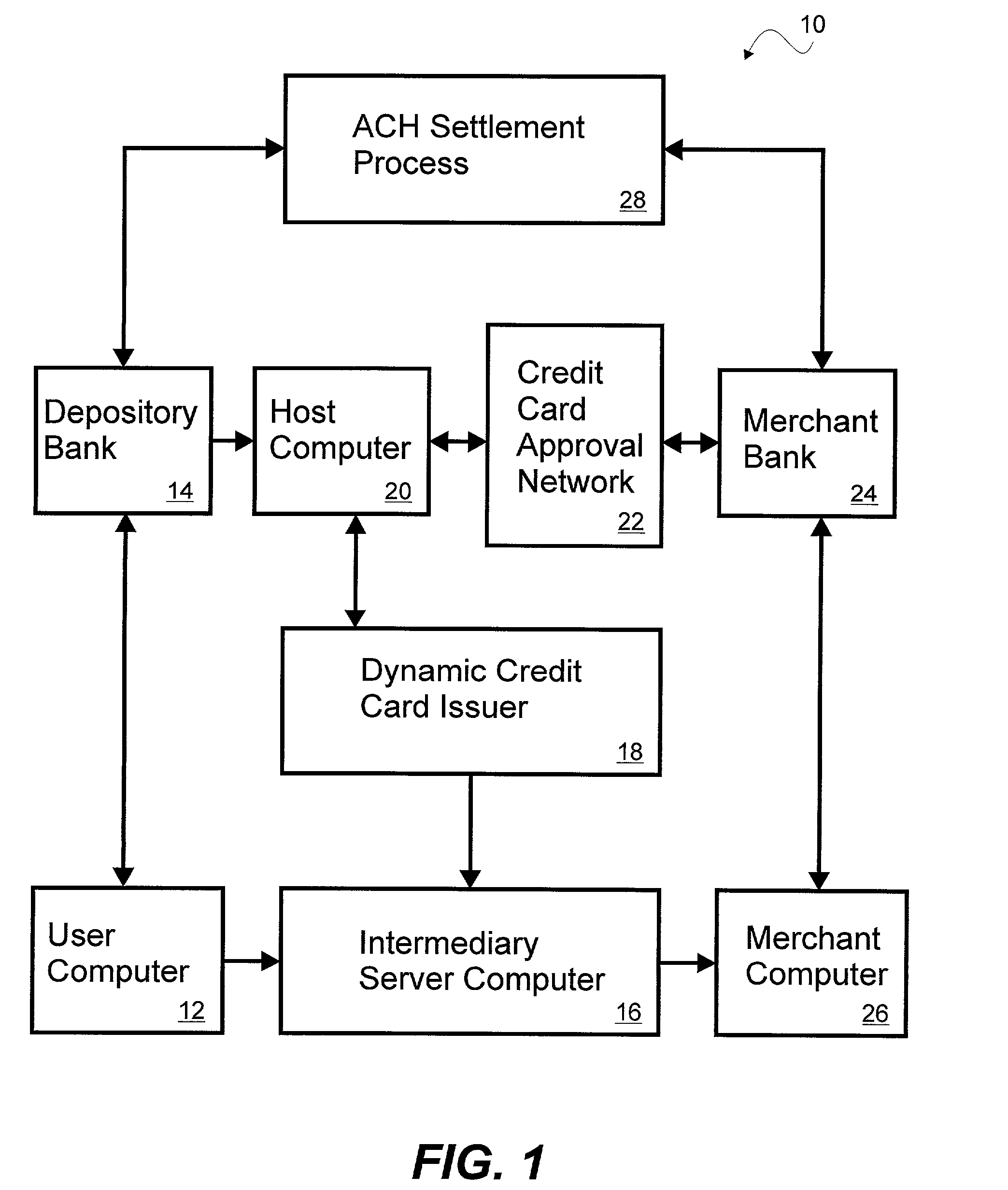
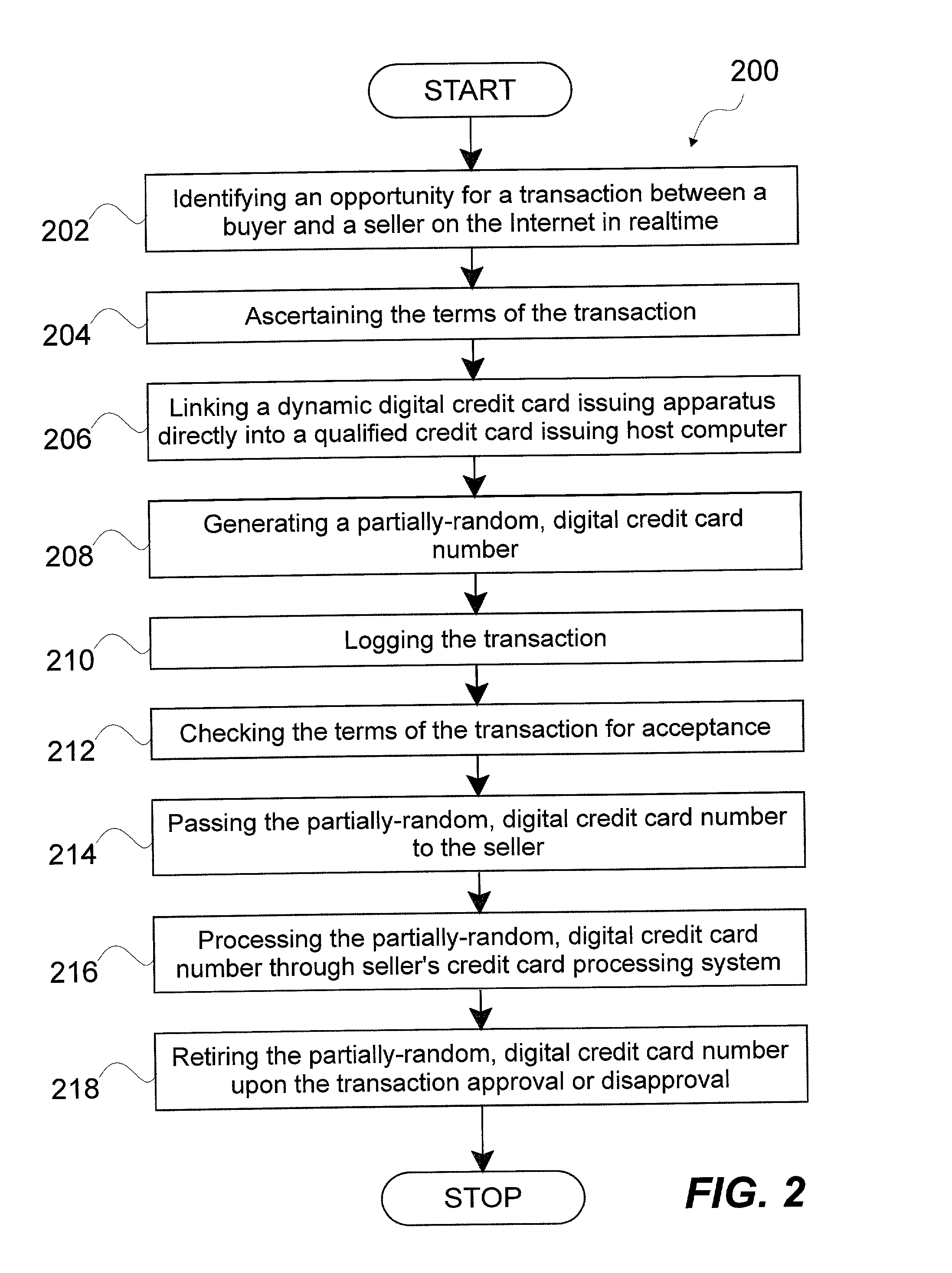
System and method for dynamically issuing and processing transaction specific digital credit or debit cards
A system and method of dynamically issuing credit card numbers and processing transactions using those credit card numbers is disclosed. A method according to the invention includes digitally recognizing a transaction opportunity on the Internet in real-time, recognizing the terms of the transaction, linking a dynamic digital credit card issuing apparatus directly into a qualified credit card issuing host, generating a partially random digital credit card number, logging the transaction, checking the terms of the transaction for acceptance, passing the dynamically issued digital credit card number to the merchant, processing the digital credit card number through the merchant's card processing system, receiving the transaction approval request, participating in credit card validity checking systems, processing the approval request in real-time, sending the requesting party a legitimate authorization code, and retiring the digital credit card number immediately upon transaction approval or disapproval. A system according to the invention implements the method of the invention.
Owner:ORANGATANGO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com