Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
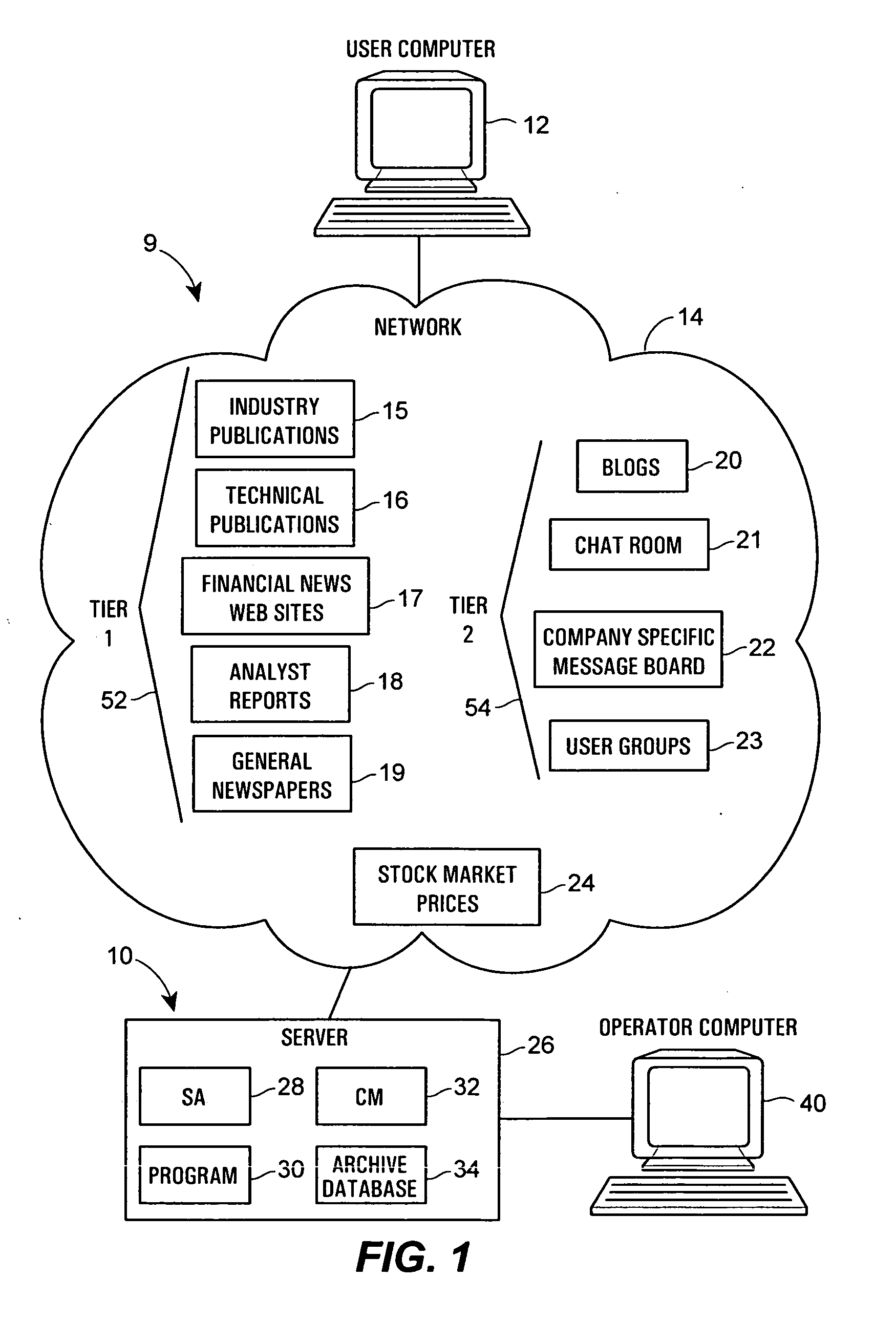
2975 results about "Electronic data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
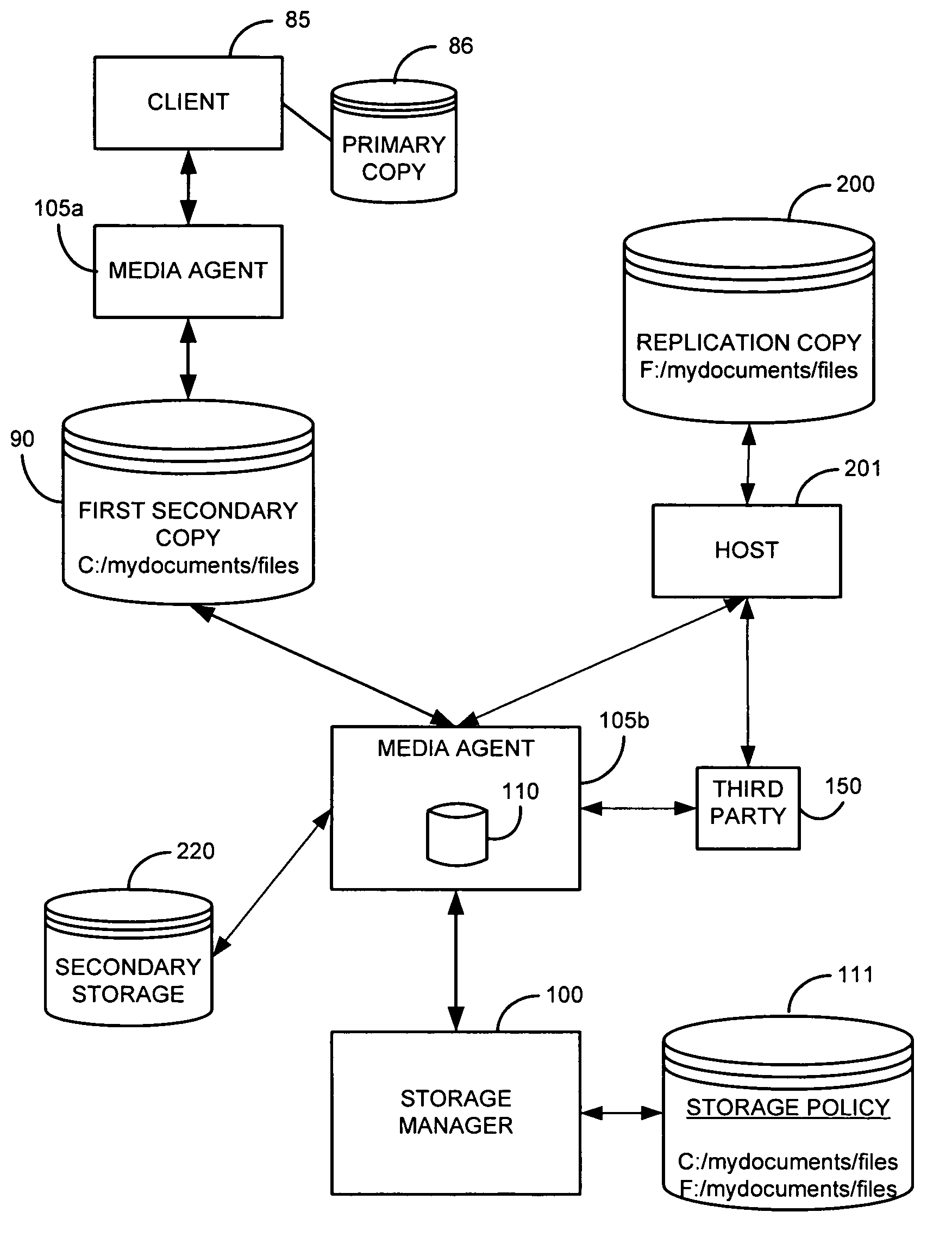
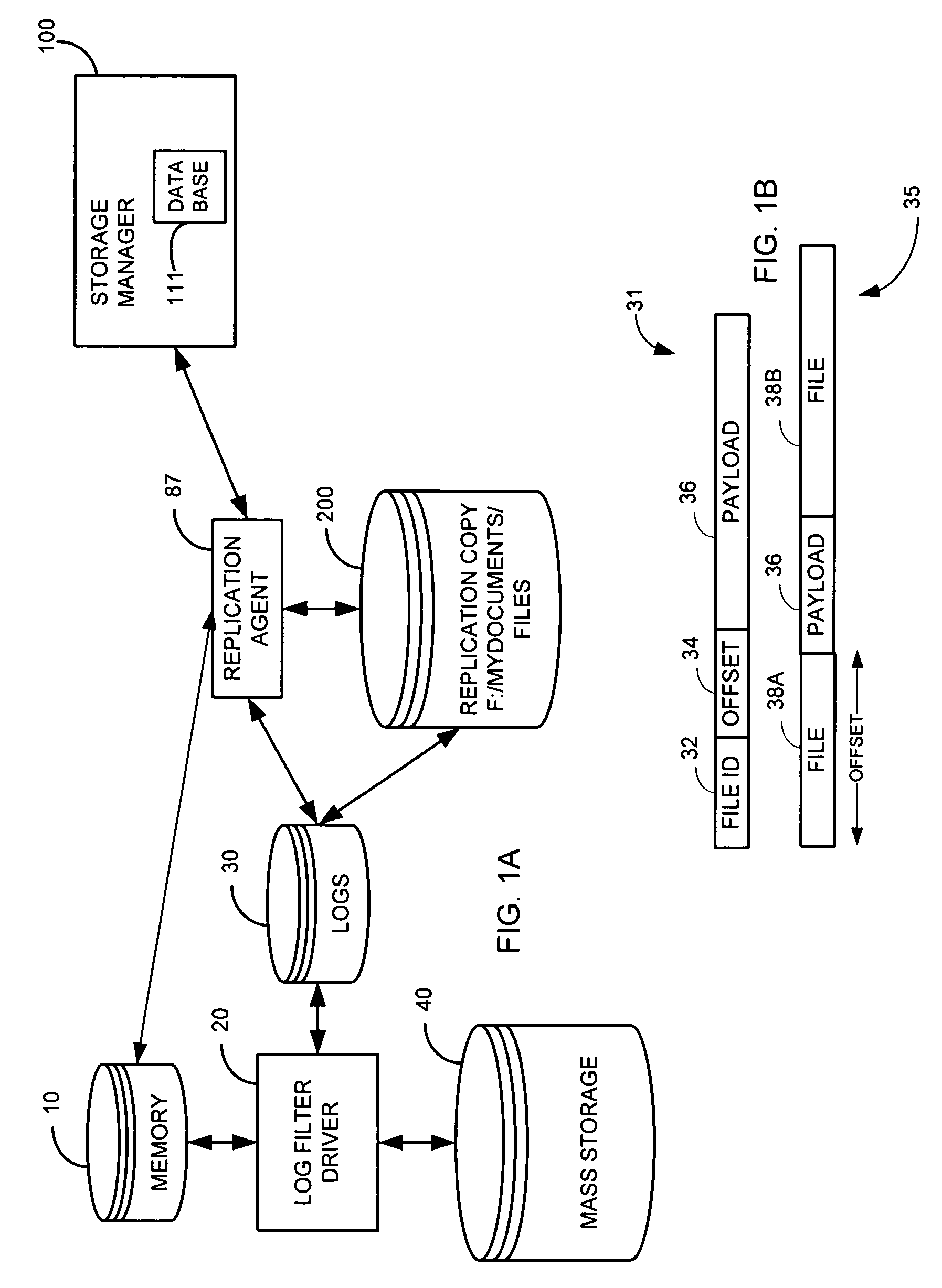
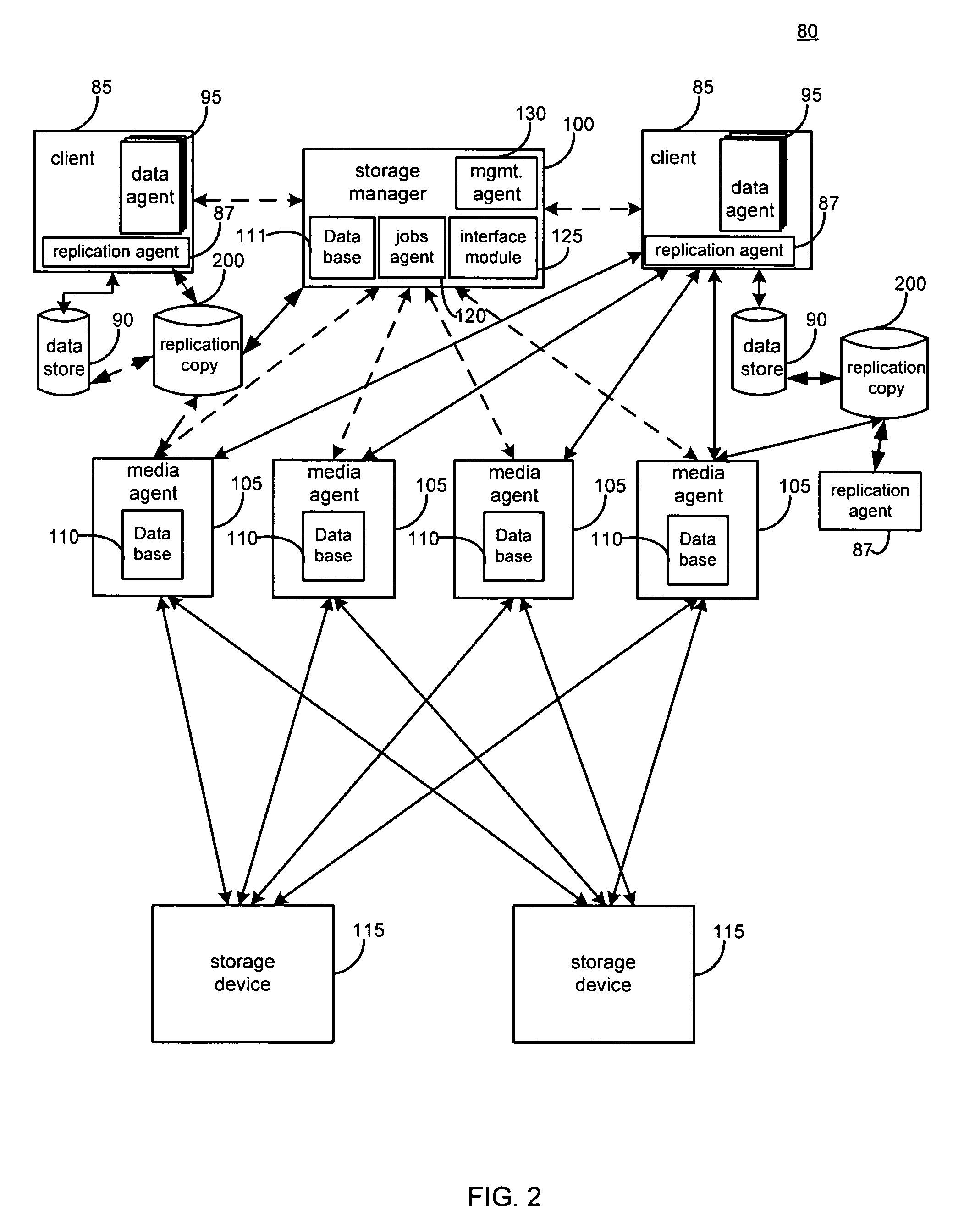
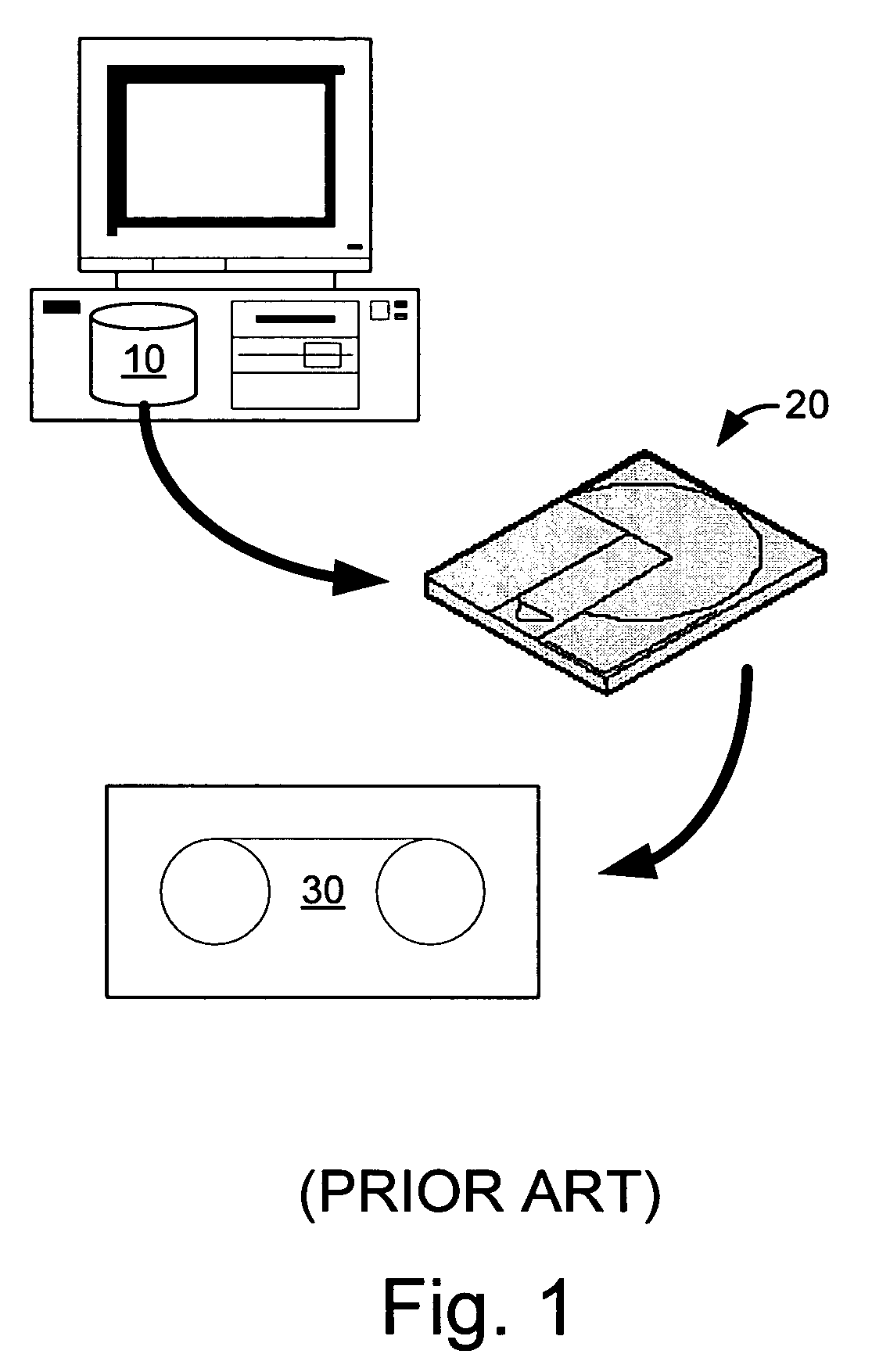
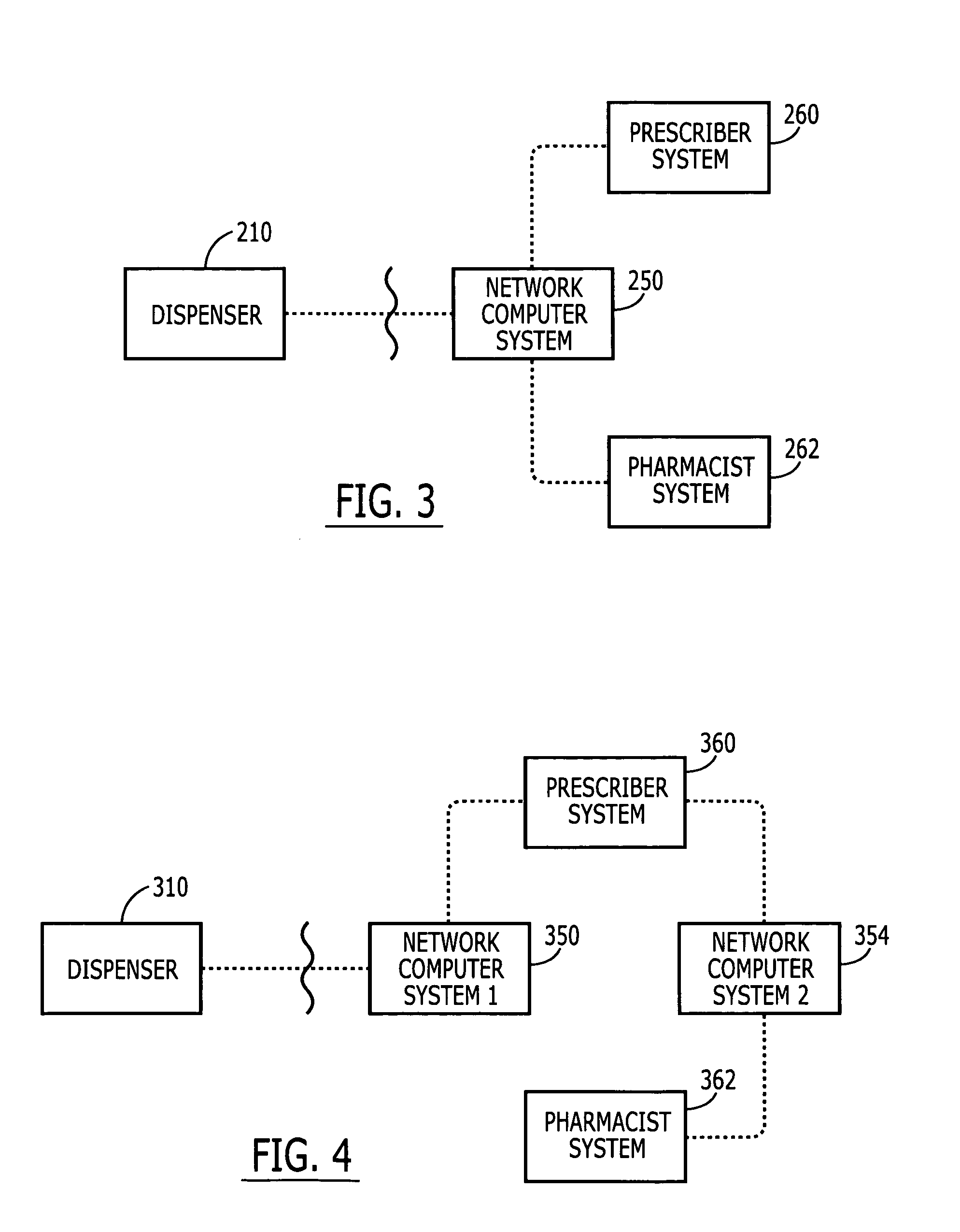
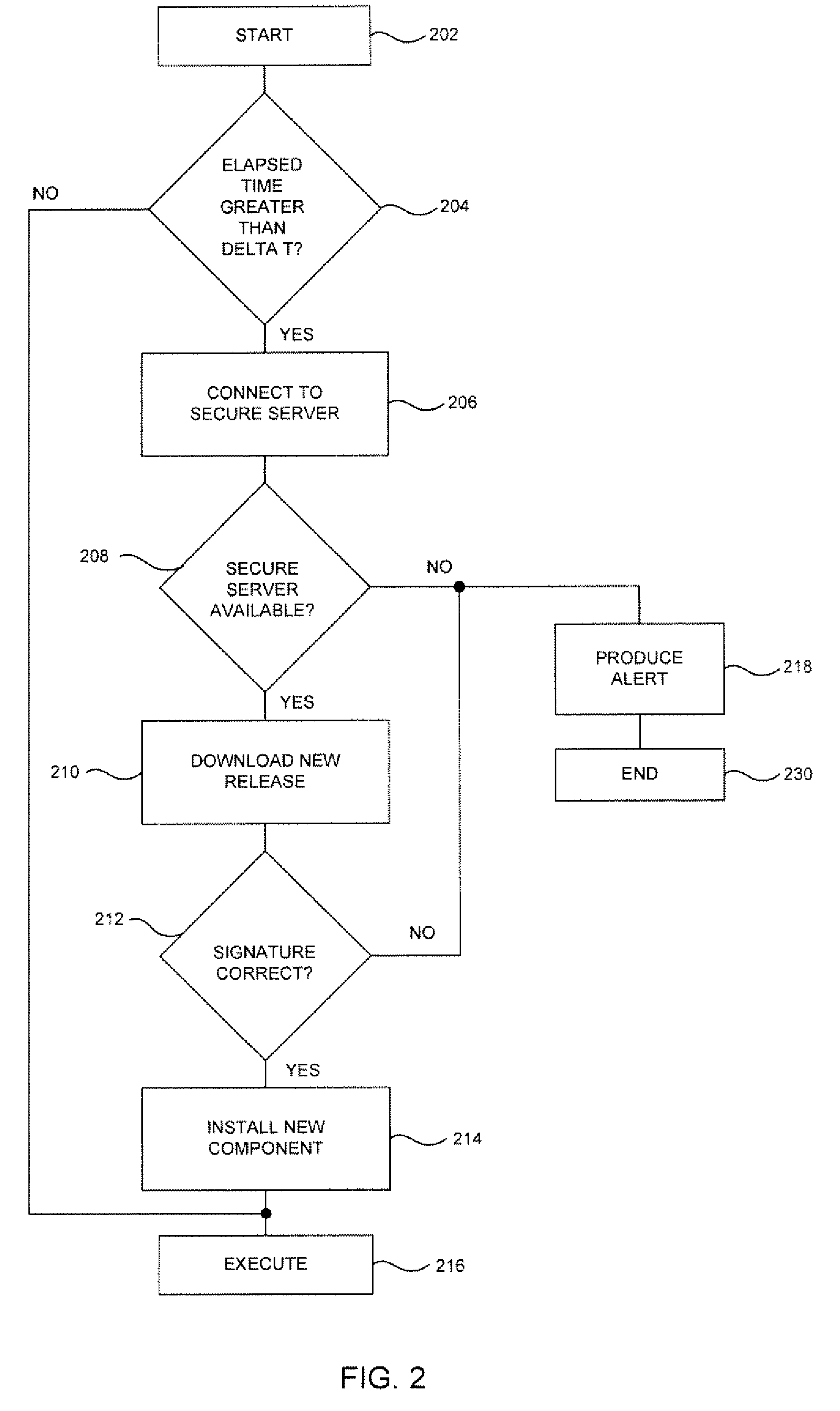
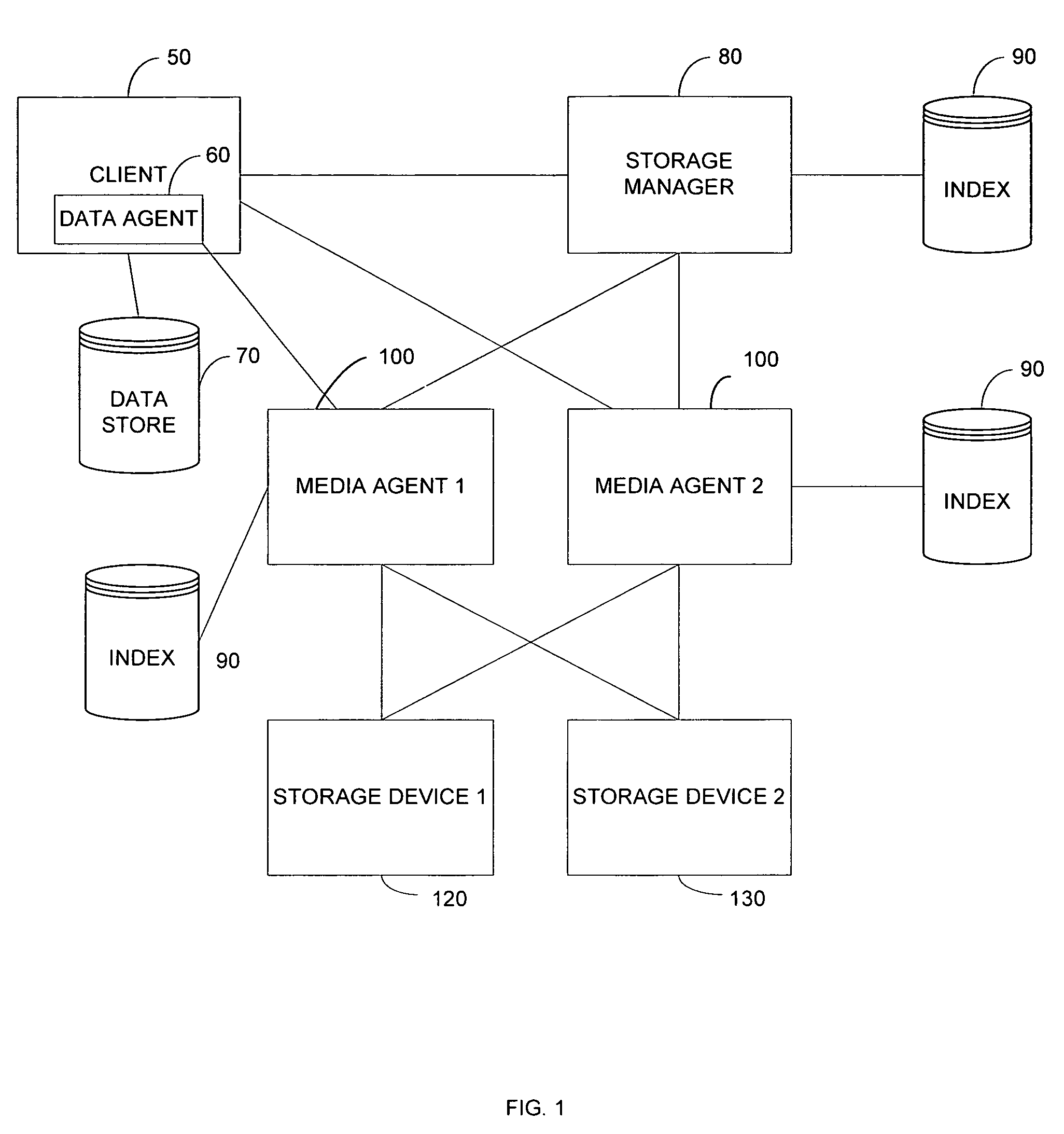
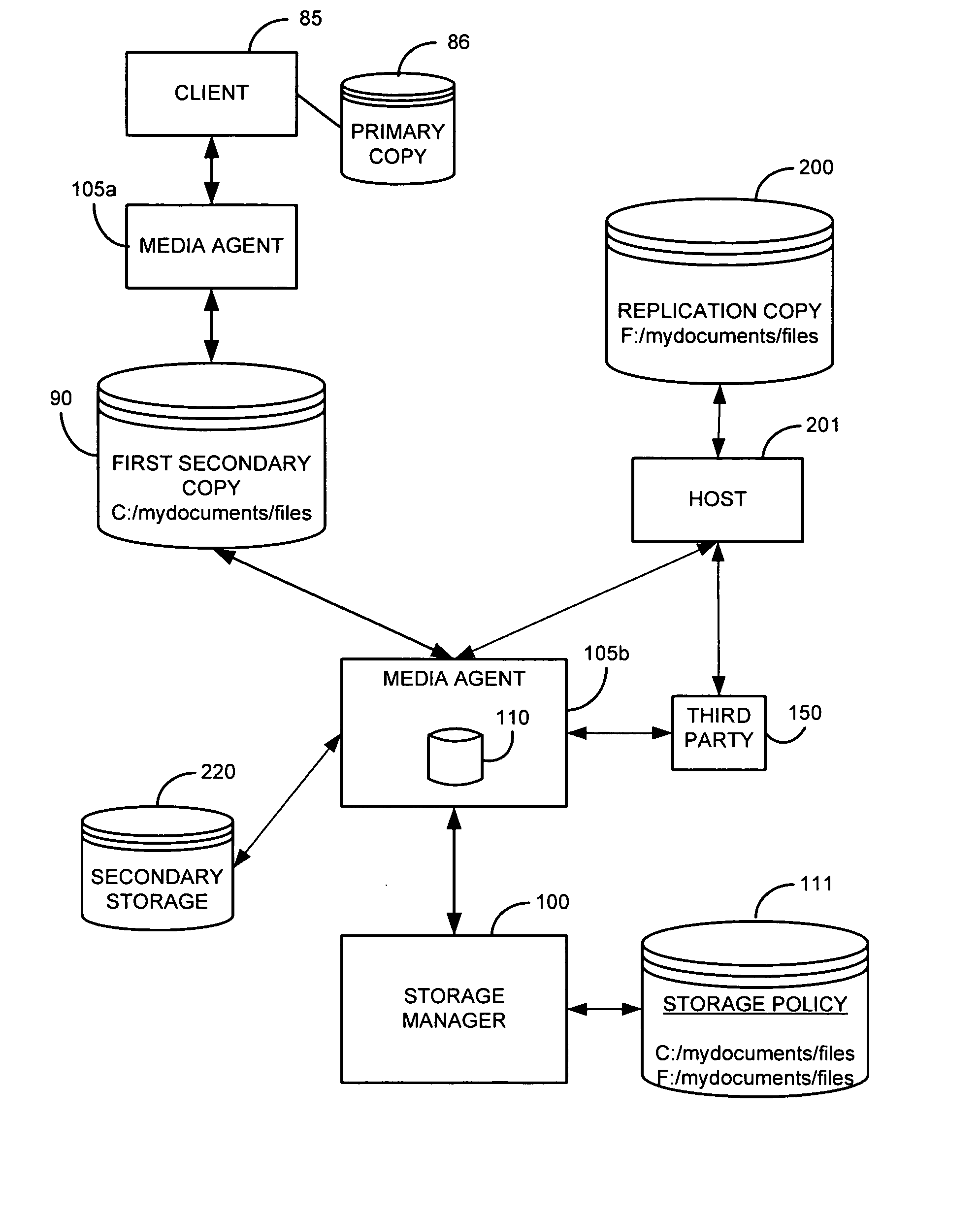
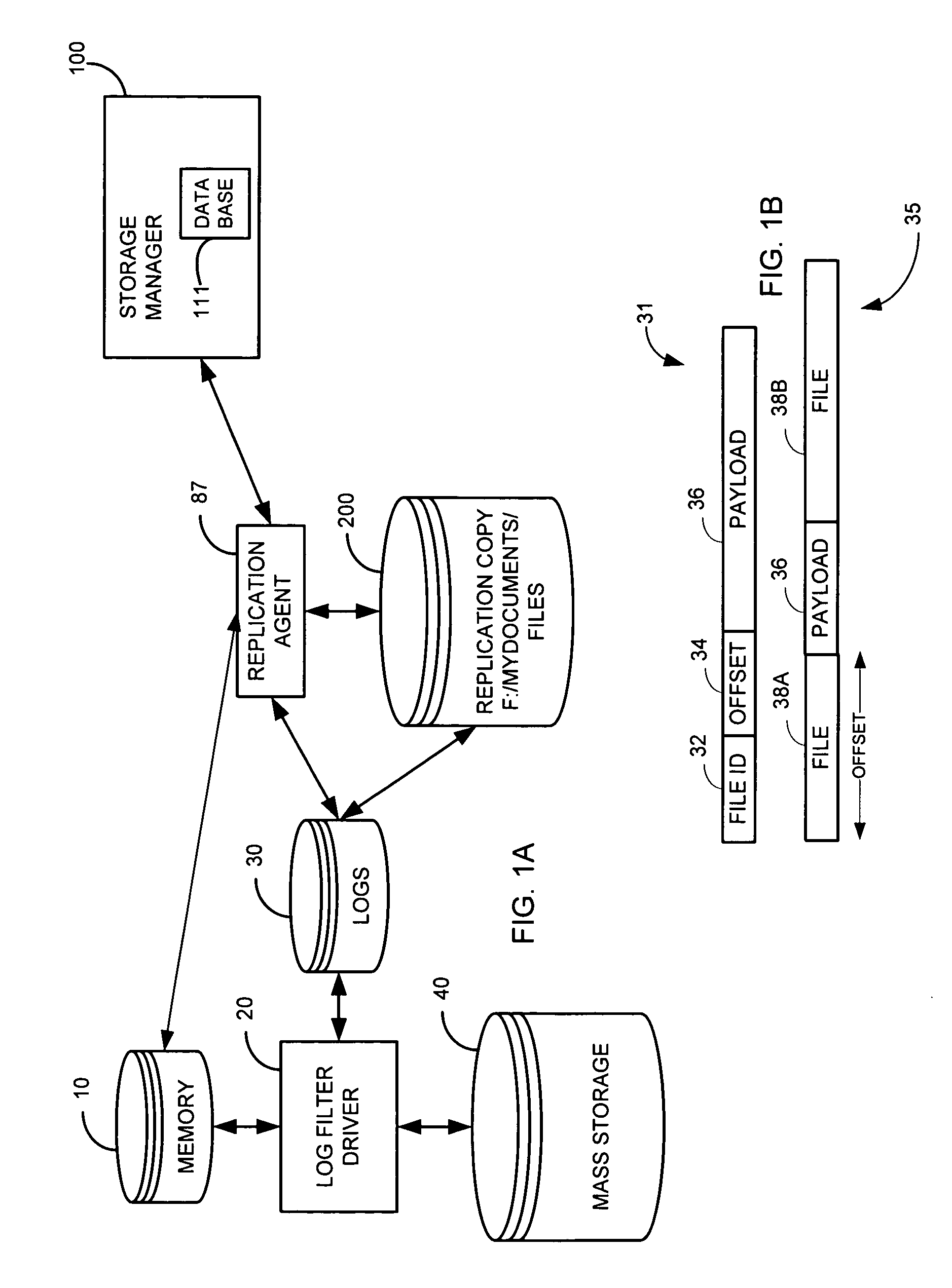
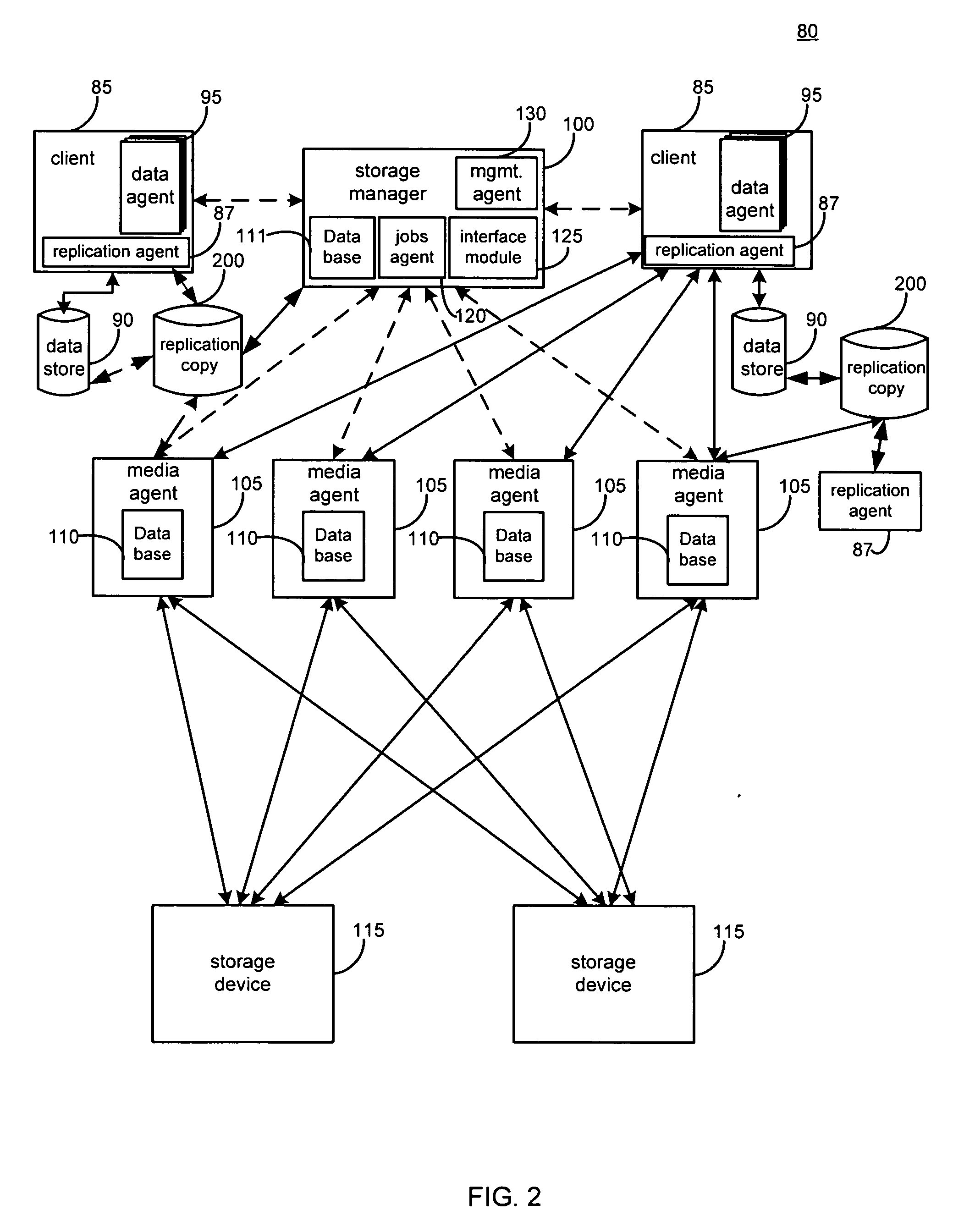
System and method for performing replication copy storage operations
InactiveUS7606844B2Data processing applicationsDatabase distribution/replicationThird partyEngineering
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
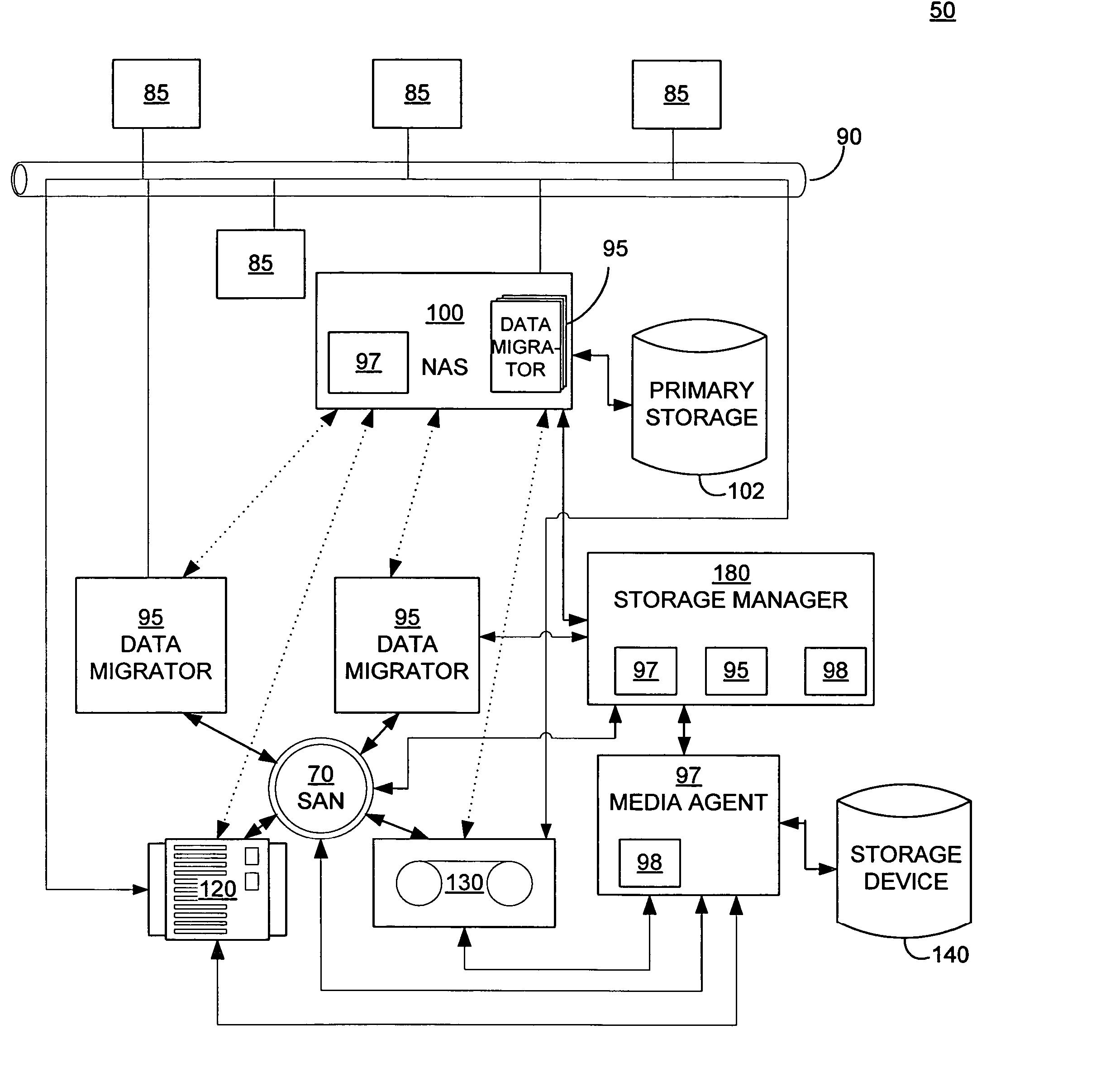
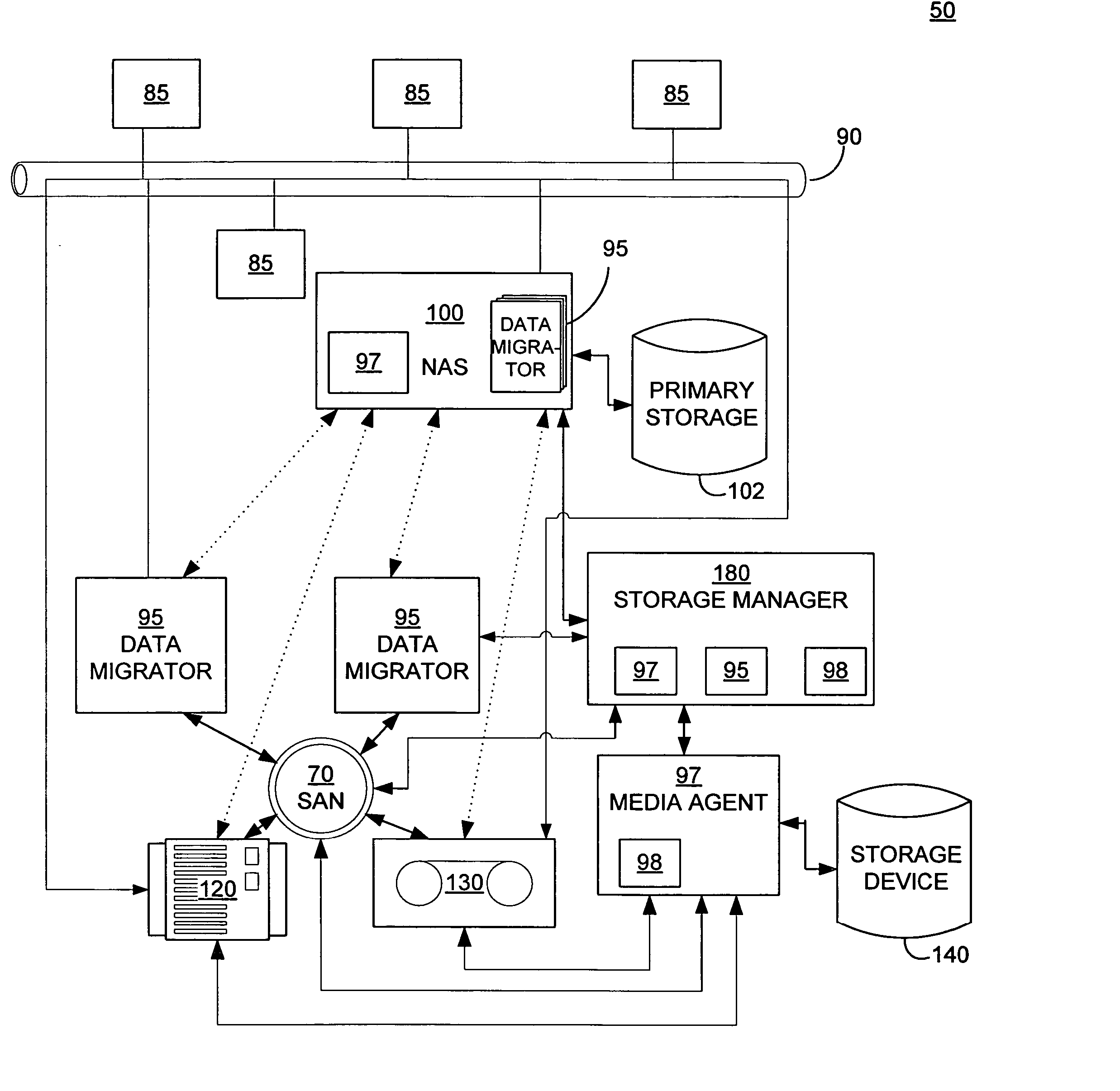
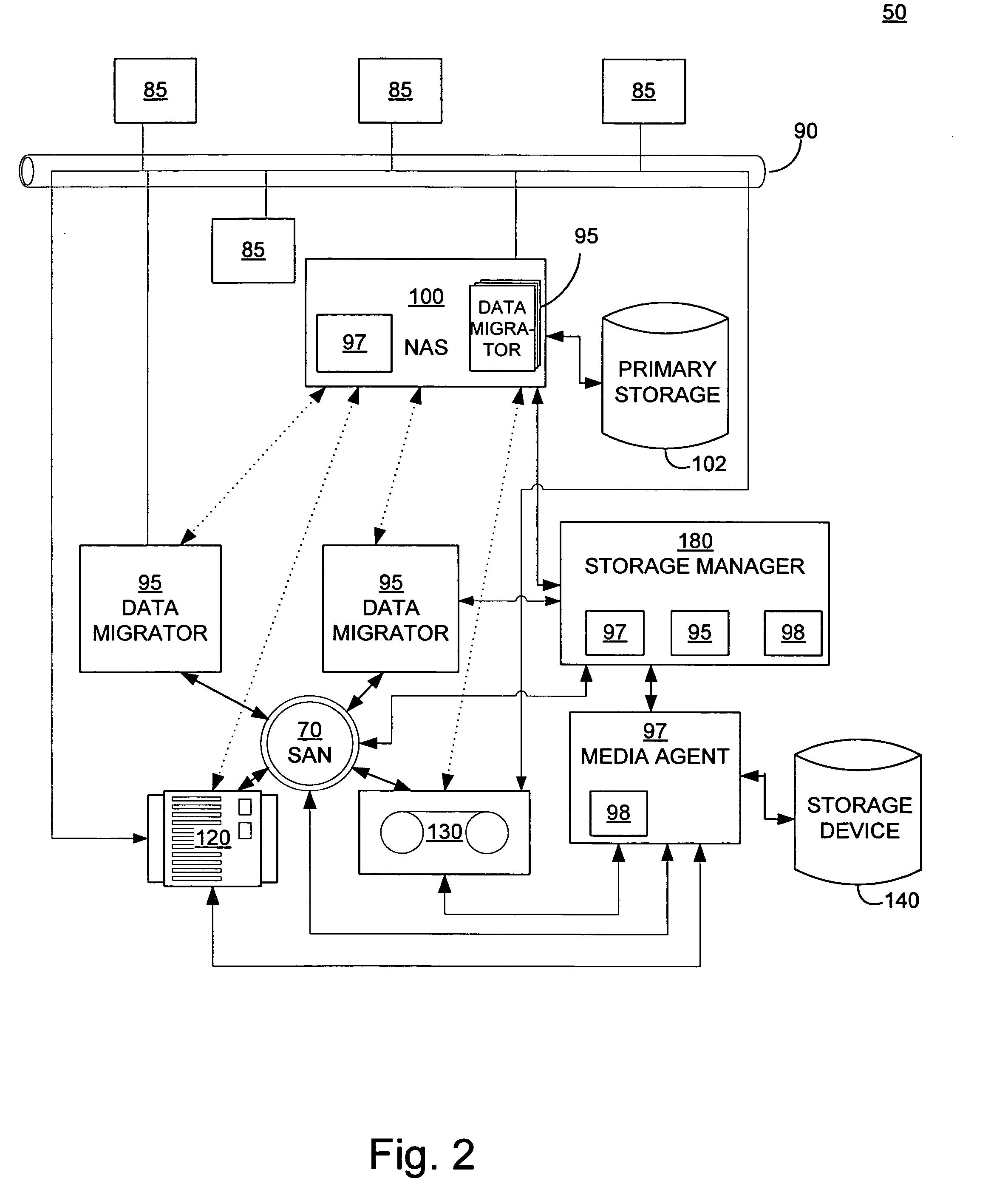
Systems and methods for performing storage operations using network attached storage
ActiveUS7546324B2More processedData processing applicationsDigital data information retrievalAuxiliary memoryData storing
Systems and methods for performing hierarchical storage operations on electronic data in a computer network are provided. In one embodiment, the present invention may store electronic data from a network device to a network attached storage (NAS) device pursuant to certain storage criteria. The data stored on the NAS may be migrated to a secondary storage and a stub file having a pointer pointing to the secondary storage may be put at the location the data was previously stored on the NAS. The stub file may redirect the network device to the secondary storage if a read request for the data is received from the network device.
Owner:COMMVAULT SYST INC
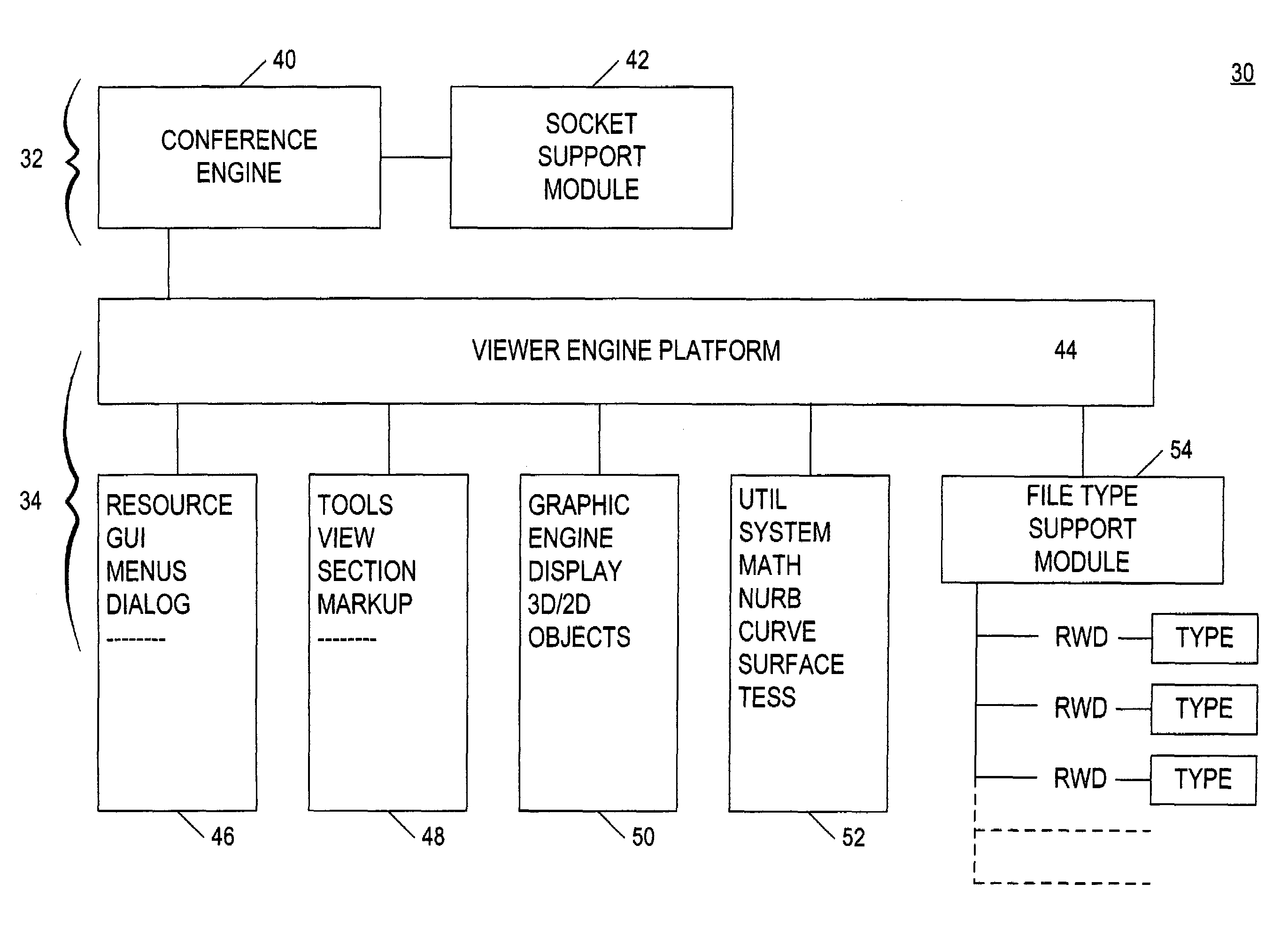
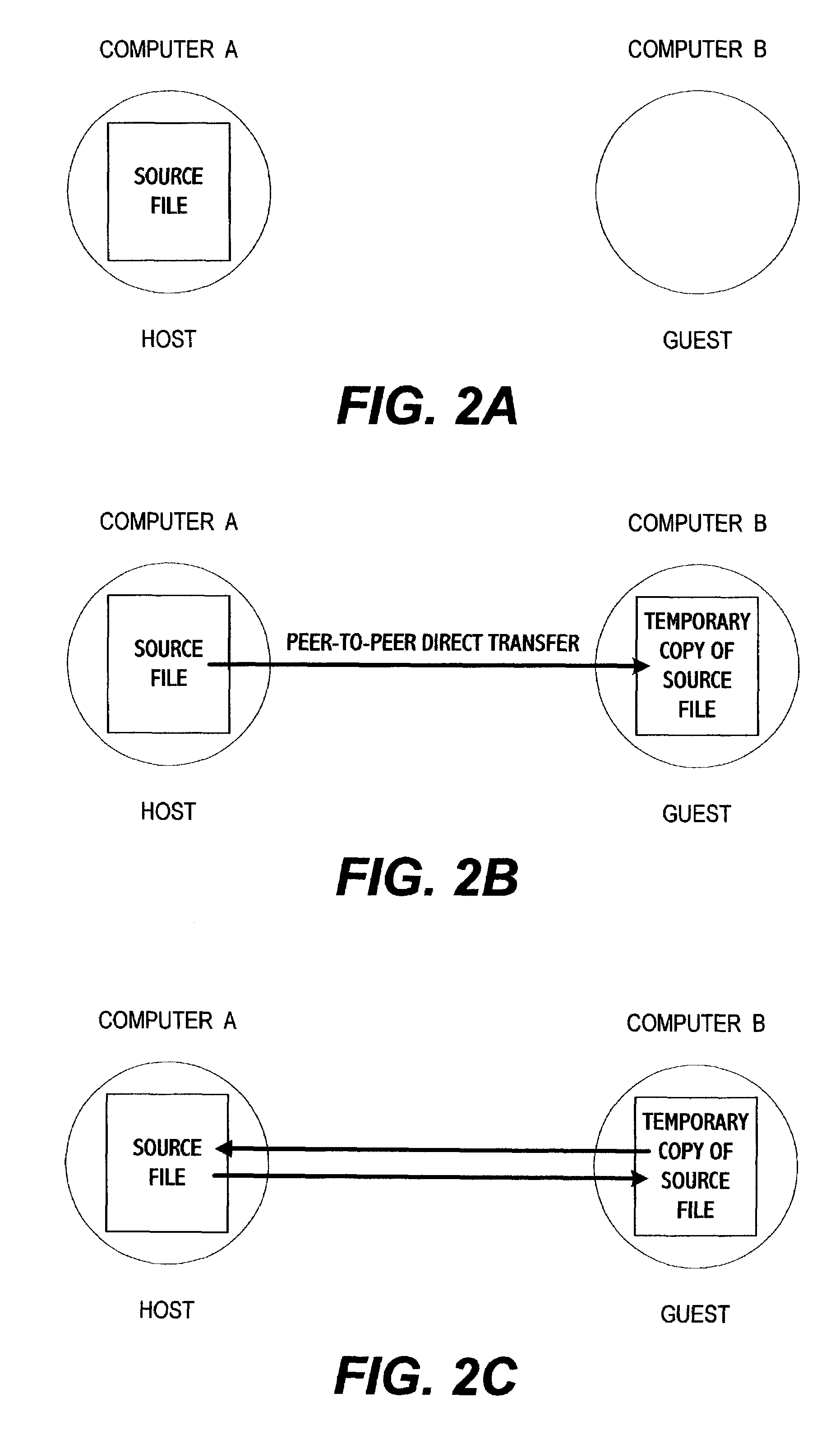
System for electronic file collaboration among multiple users using peer-to-peer network topology
InactiveUS7353252B1Avoid storage problemsMultiple digital computer combinationsOffice automationDocumentation procedurePrivate network
A system for electronic file collaboration among multiple users is implemented using command messages transmitted on dedicated network channels established between conference participants in a peer-to-peer architecture with total autonomy from a central server. The system employs owner-in-control methodology to allow direct transmission of copies of documents among participants by permission, and to prevent storage of copies of documents used in a conference by participants. Mark-ups, additions, and other actions occurring on a conference document can only be saved by the document owner. An advanced viewer engine is provided for reading, displaying and manipulating electronic data in texts, tables, vectors and 3D model formats, as well as common raster images. A proxy module allows data transmitted through IPFW routers or firewall devices with sufficient authentications and security measures.
Owner:SIGMA DESIGNS
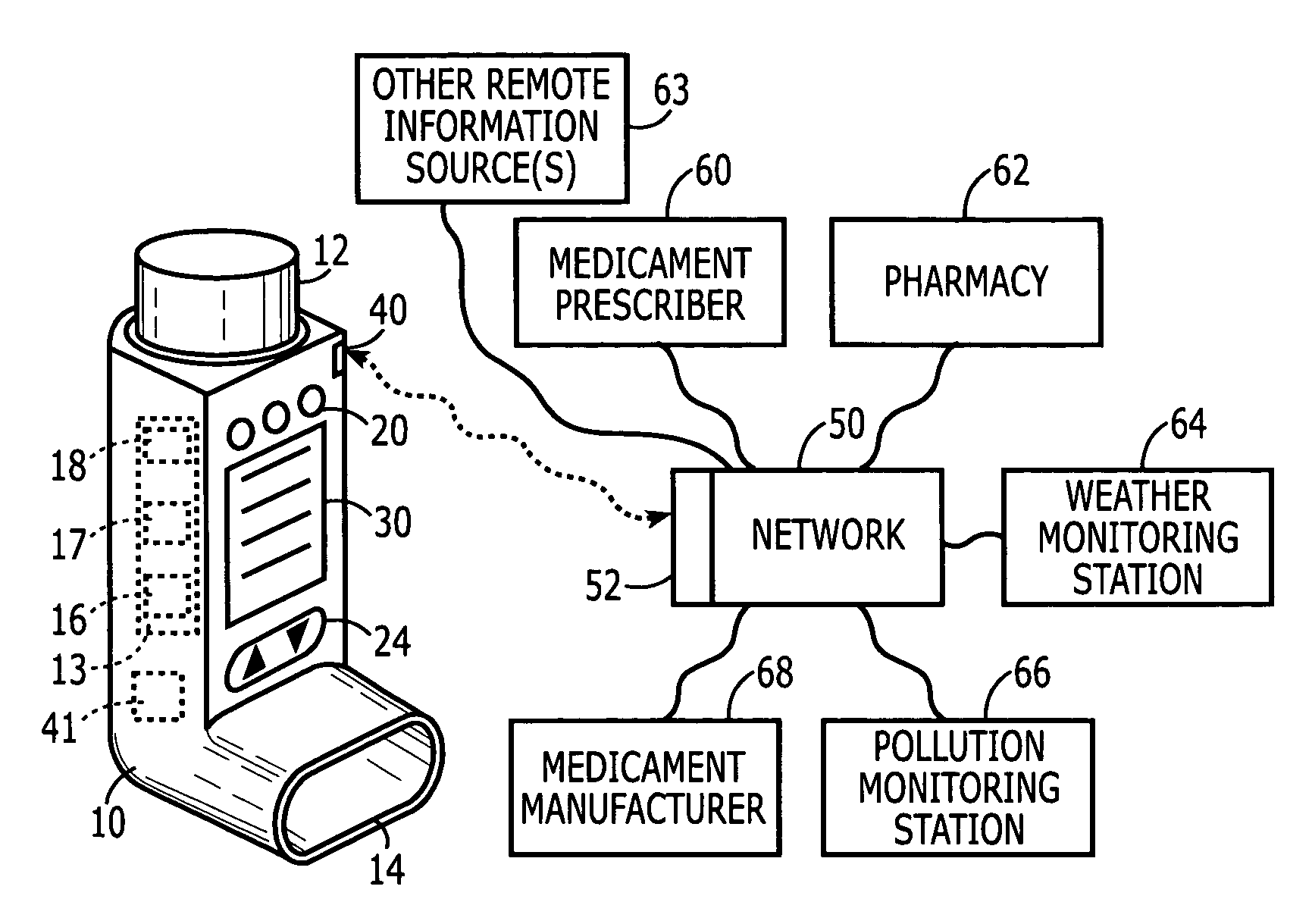
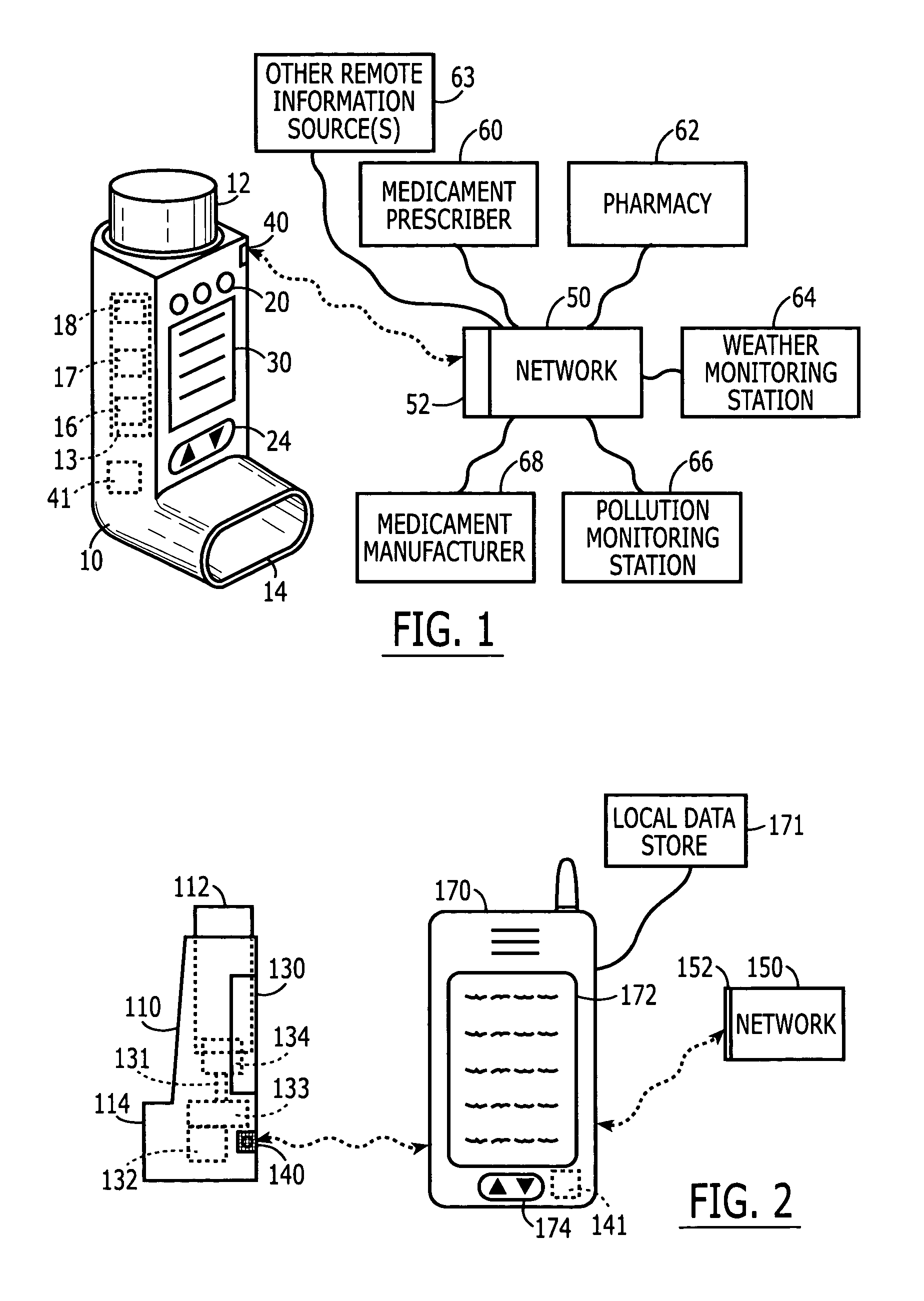
Medicament delivery system
InactiveUS6958691B1Simple systemEasy accessDigital data processing detailsDrug and medicationsComputer scienceDelivery system
There is provided a system for the delivery of medicament comprising a medicament container; a dispensing mechanism for dispensing medicament from the medicament container; an electronic data management system; and a communicator for wireless communication with a network computer system to enable communication of data between the network computer system and the electronic data management system. The electronic data management system comprises a memory for storage of data; a microprocessor for performing operations on the data; and a transmitter for transmitting a signal relating to the data or the outcome of an operation on the data.
Owner:GLAXO WELLCOME INC
Secured data format for access control
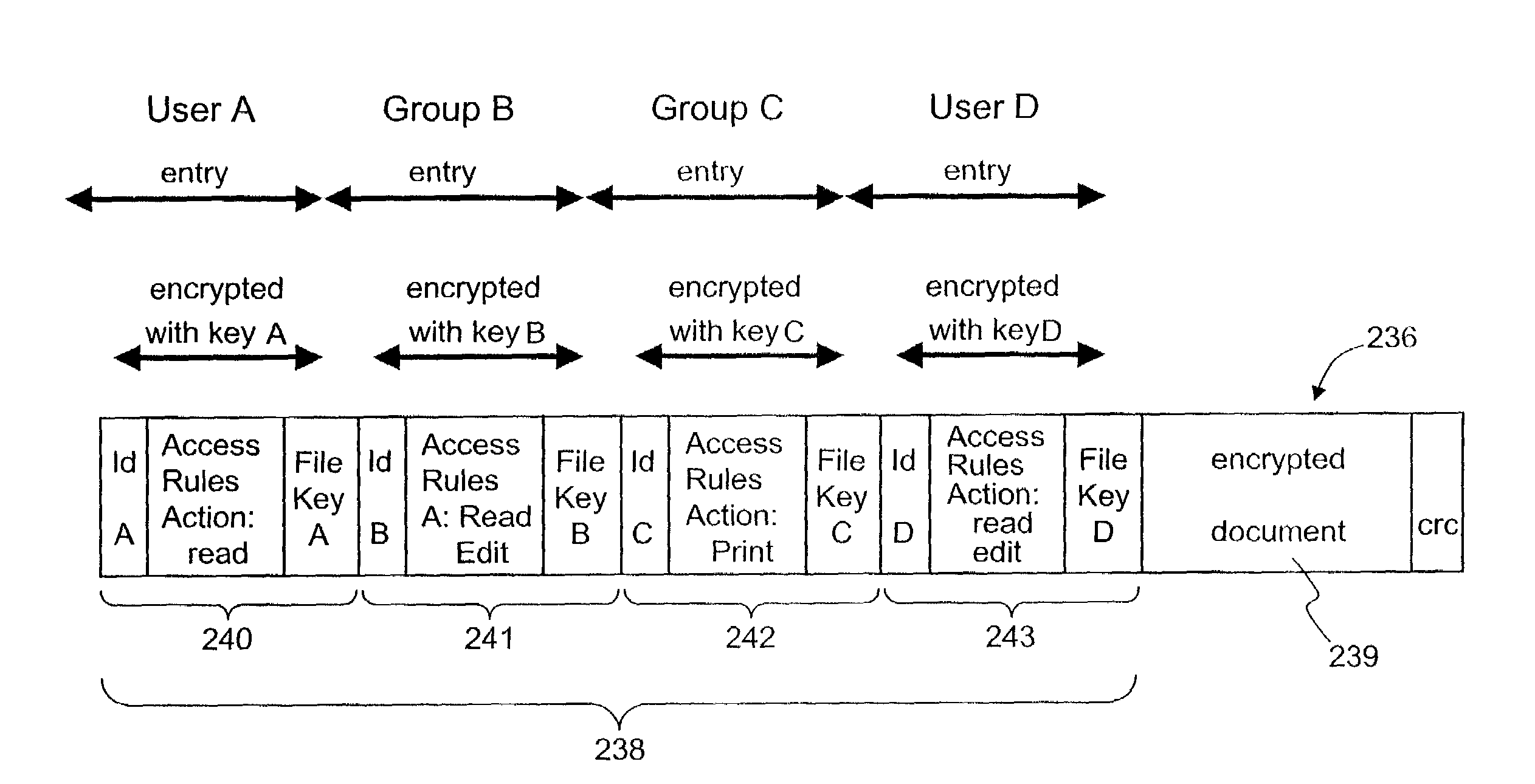
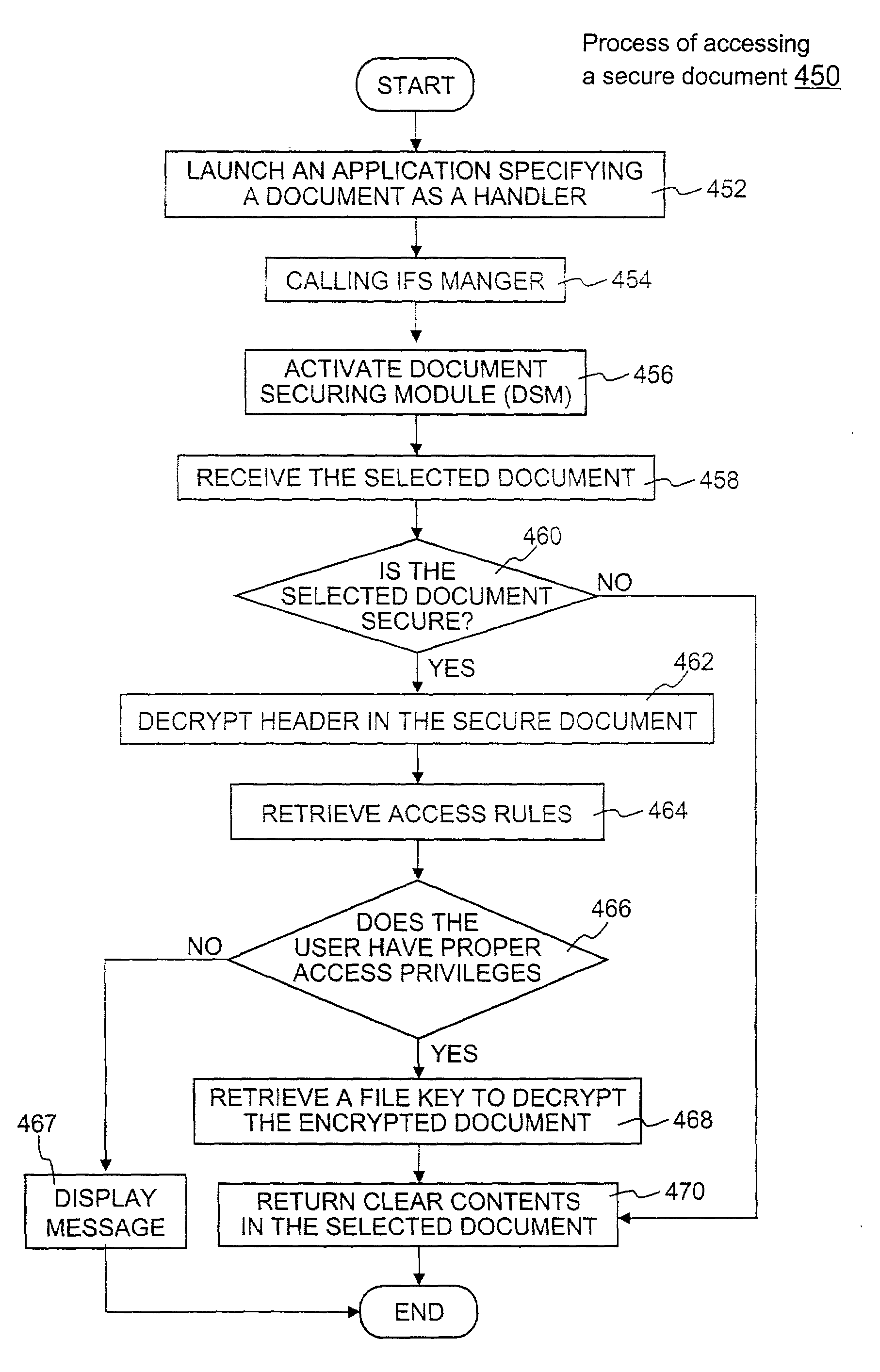
ActiveUS7380120B1Facilitate access control managementGood synchronizationDigital data processing detailsUser identity/authority verificationMedia access controlDocumentation
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
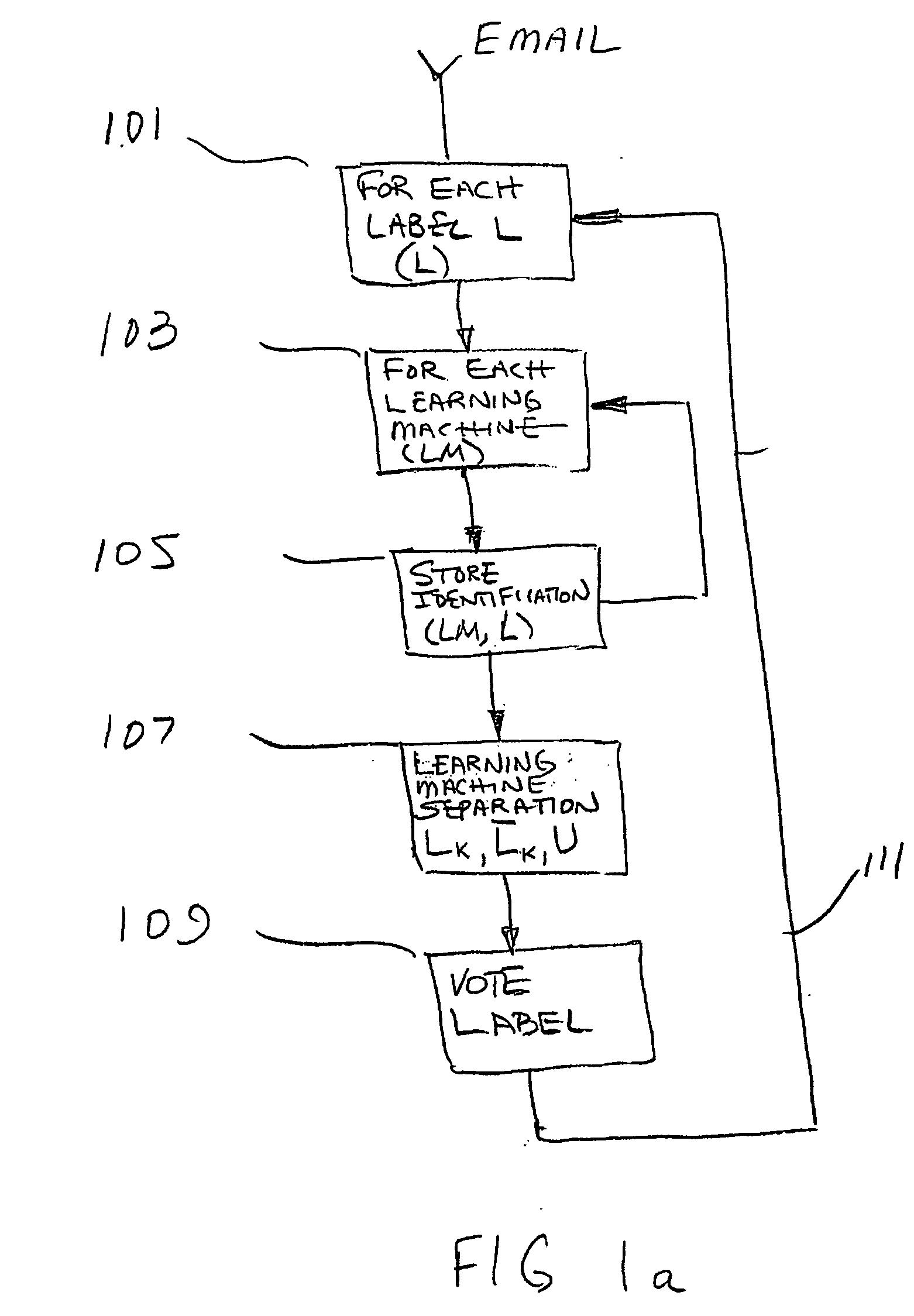
Method, apparatus, and system for clustering and classification
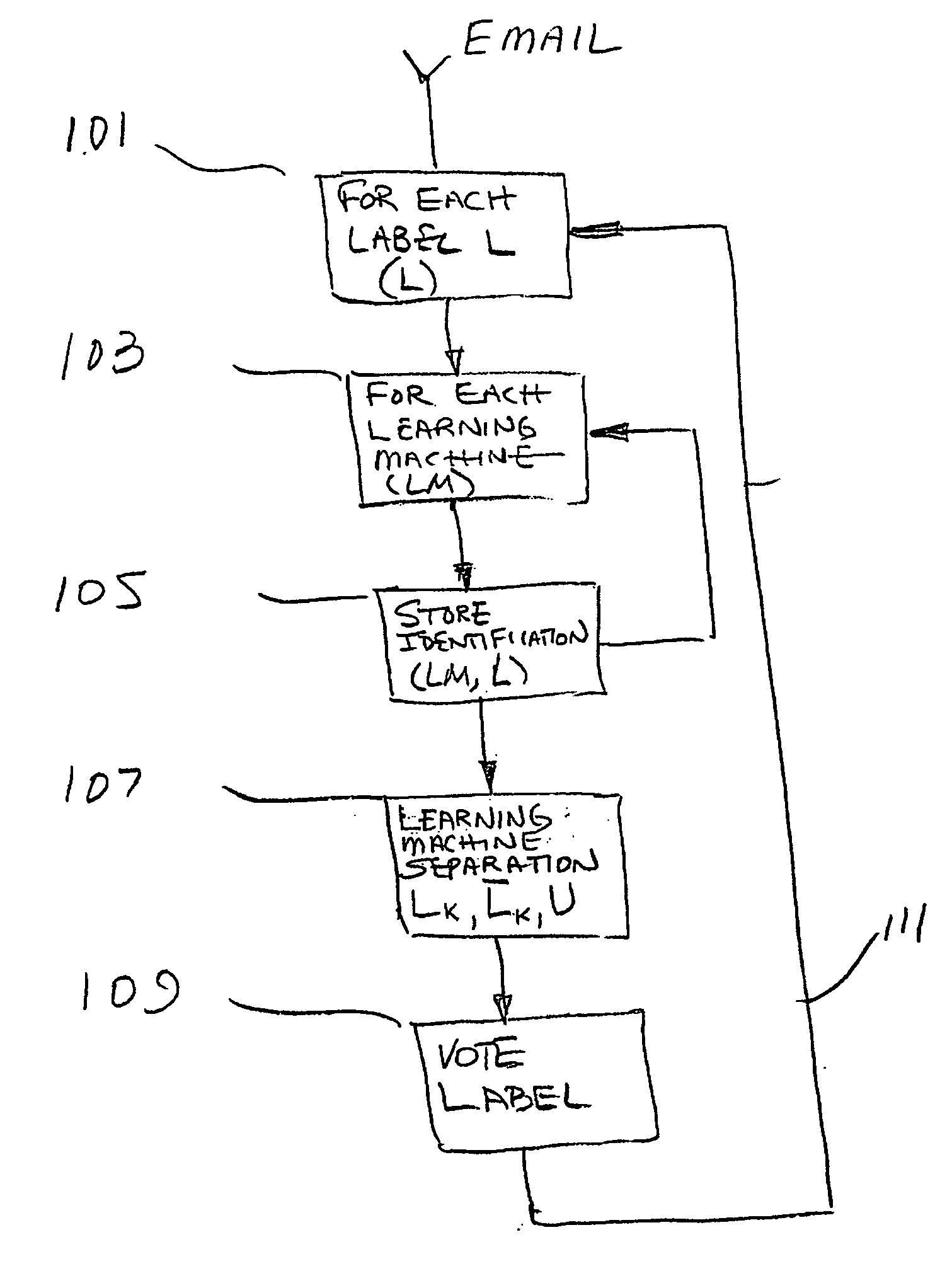
ActiveUS20060095521A1Multiple digital computer combinationsData switching networksLearning machineData stream
The invention provides a method, apparatus and system for classification and clustering electronic data streams such as email, images and sound files for identification, sorting and efficient storage. The inventive systems disclose labeling a document as belonging to a predefined class though computer methods that comprise the steps of identifying an electronic data stream using one or more learning machines and comparing the outputs from the machines to determine the label to associate with the data. The method further utilizes learning machines in combination with hashing schemes to cluster and classify documents. In one embodiment hash apparatuses and methods taxonomize clusters. In yet another embodiment, clusters of documents utilize geometric hash to contain the documents in a data corpus without the overhead of search and storage.
Owner:SYSXNET
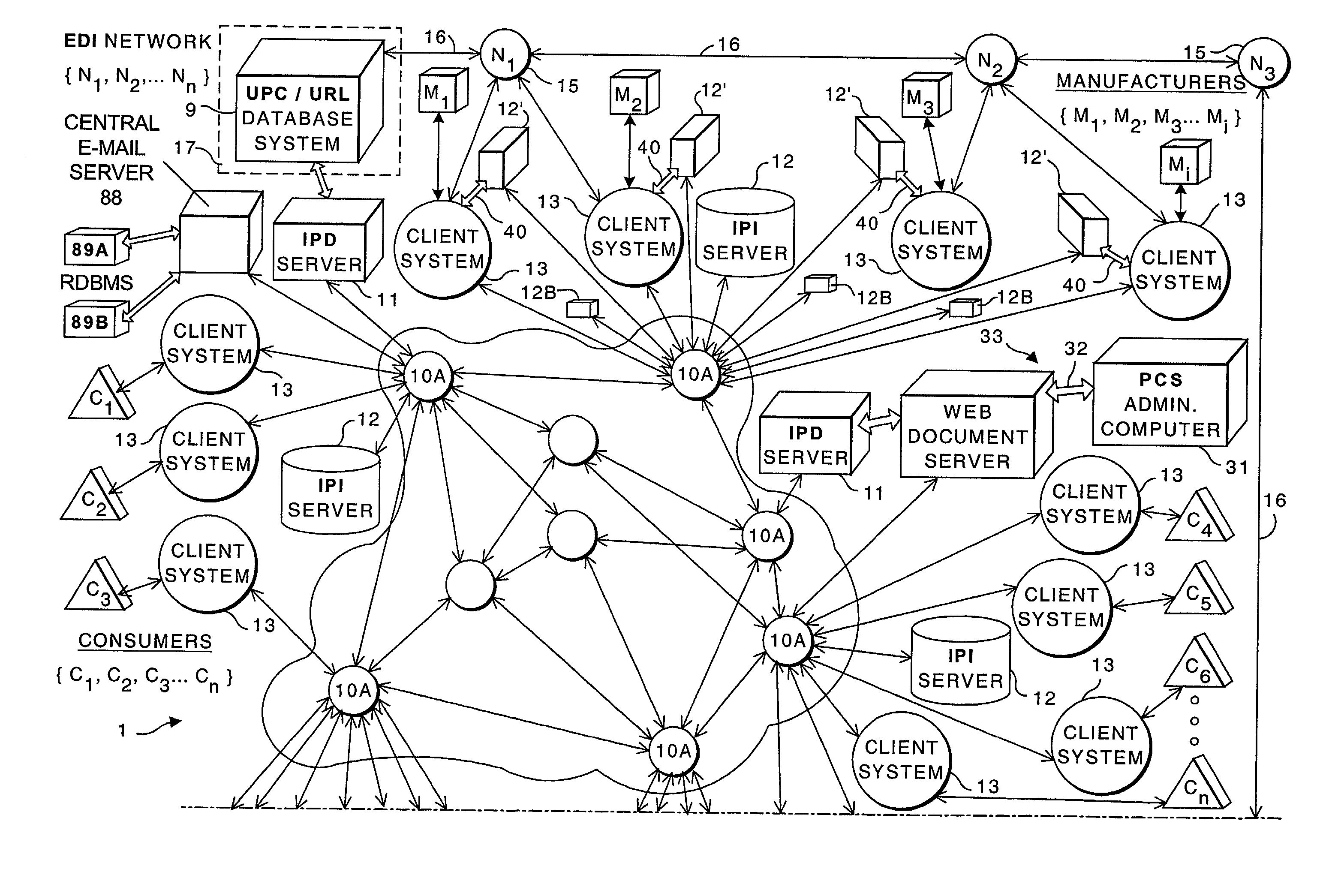
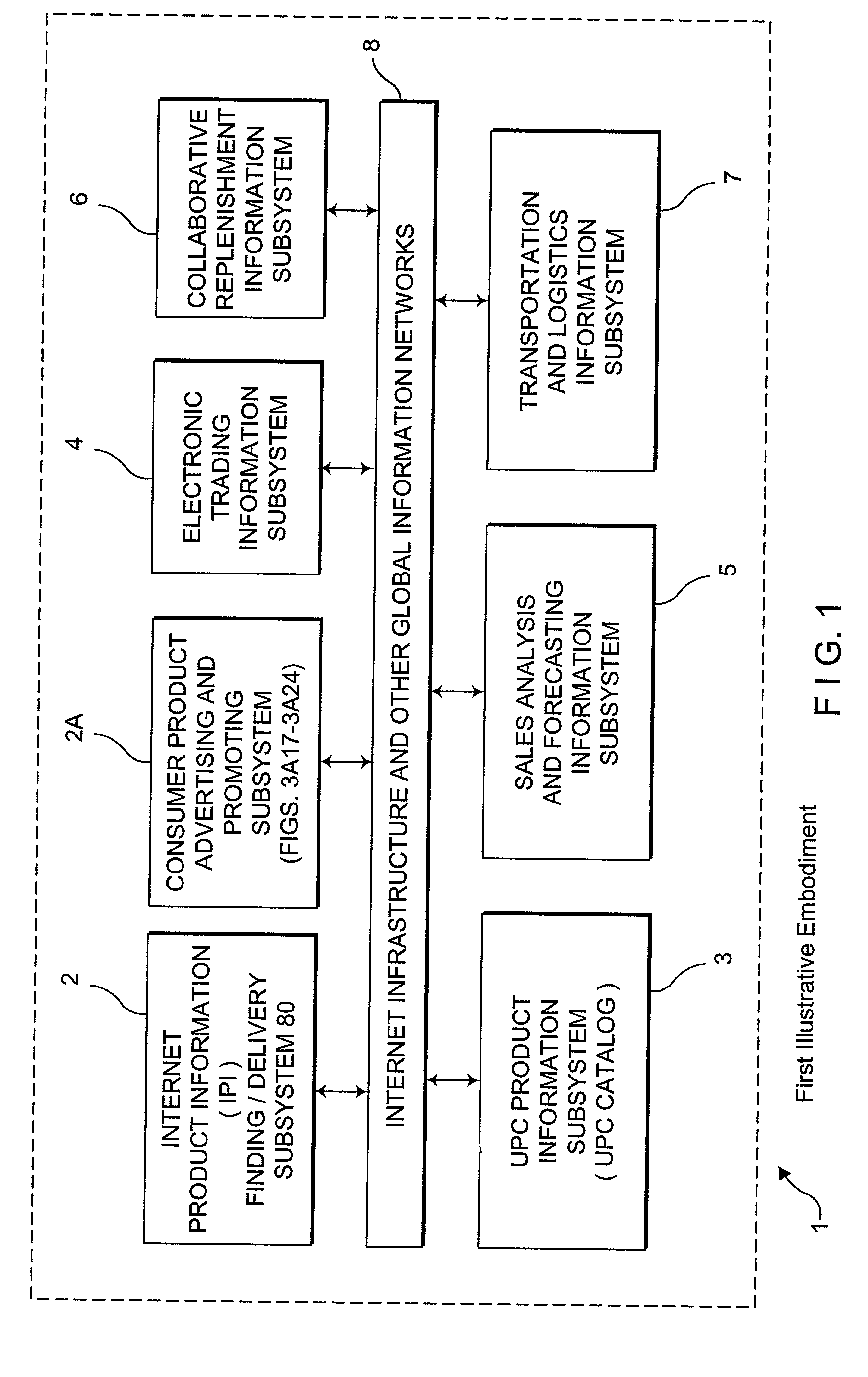
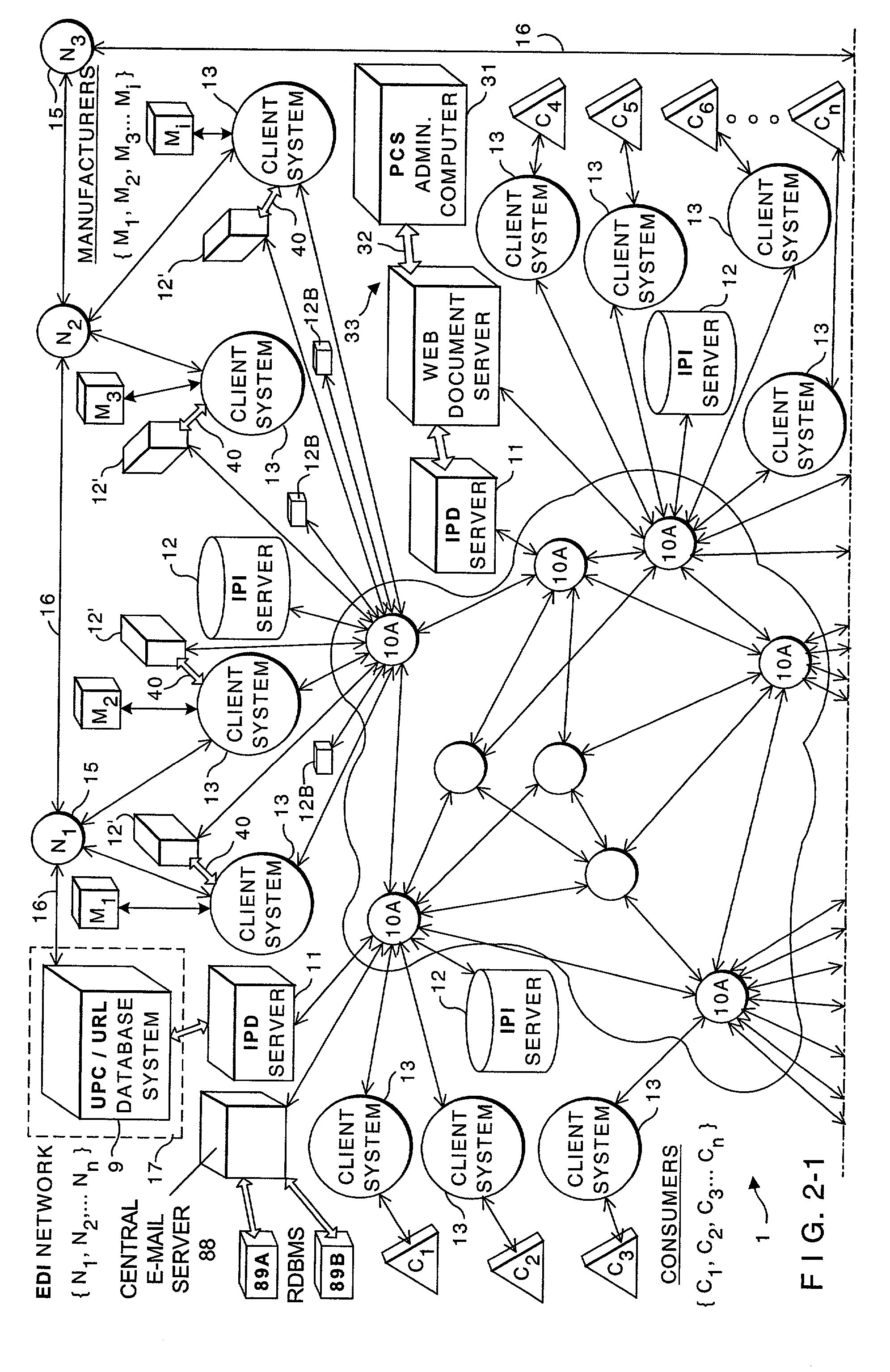
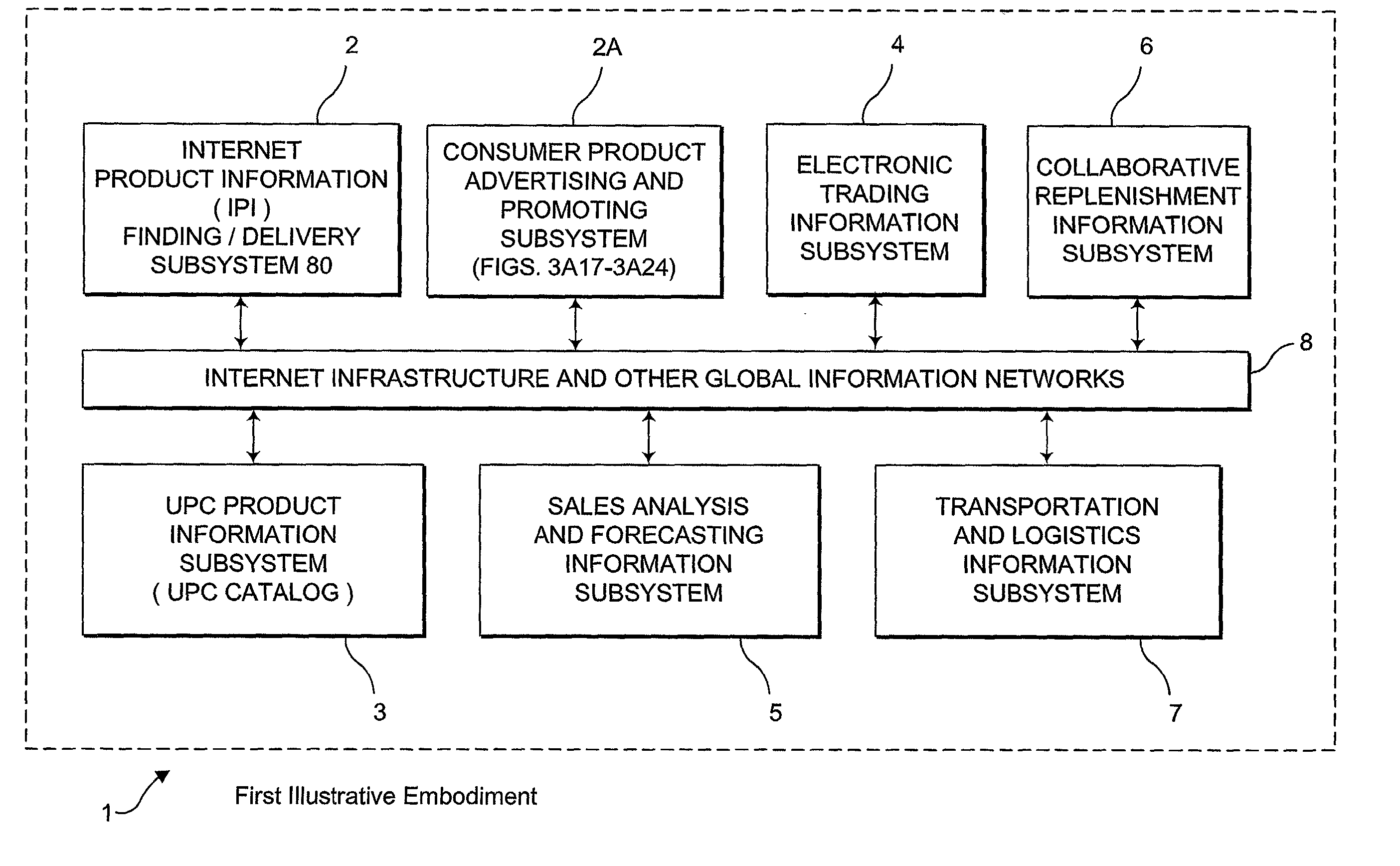
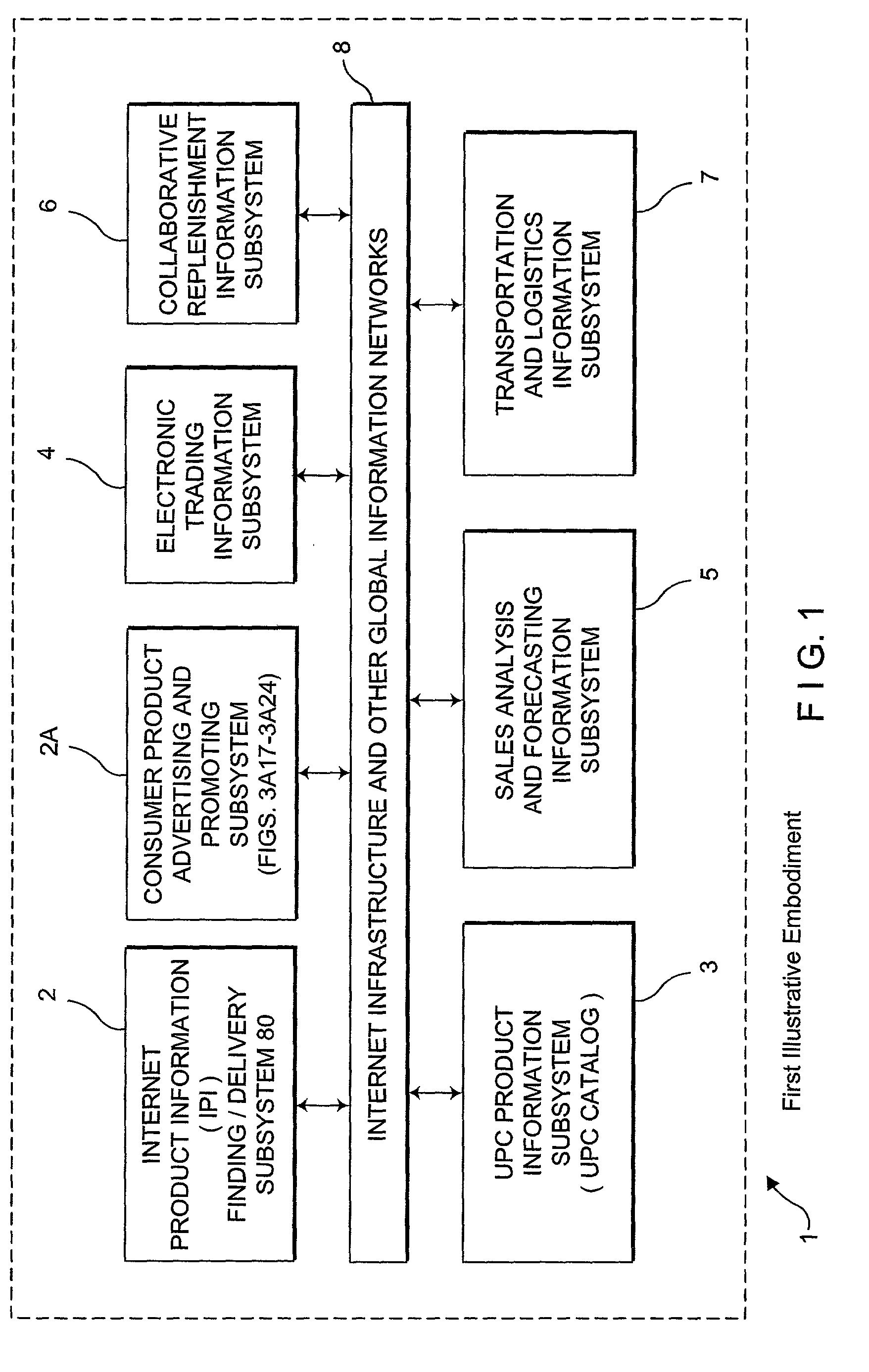
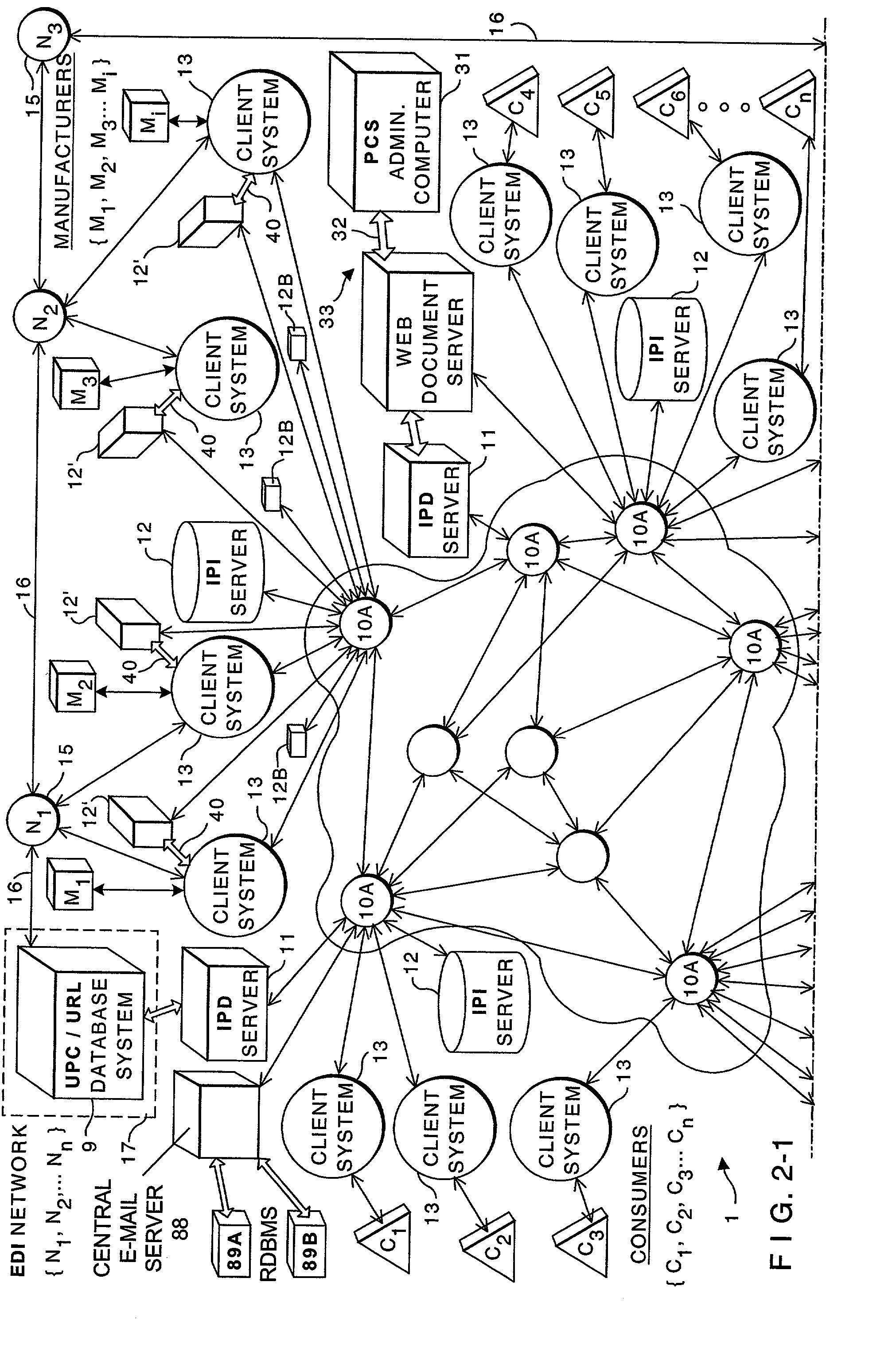
Internet-based consumer service brand marketing communication system which enables service-providers, retailers, and their respective agents and consumers to carry out service-related functions along the demand side of the retail chain in an integrated manner
InactiveUS20020194081A1Easy accessEasy alignmentDigital data information retrievalData switching by path configurationUniversal serviceCommunications system
An Internet-based consumer service marketing, merchandising and education / information system which enables service-providers, retailers and their respective agents, and consumers to carry out service-related functions along the demand side of the retail chain. A central USN / SM / SN / URL RDBMS stores a central database of USN / SM / SN / URL links, wherein the USN represents a Universal Service Number assigned to a particular service offered by a service-provider, the SM represents a Service Mark used in connection with the particular service, the SD is representative of one or more Universal Resource Locators pointing to information resources on the WWW relating to the particular service. A first subsystem enables a service-provider's marketing, brand and / or service managers to create and manage a local database of USN / SM / SN / URL links related to the consumer services of the service-provider being offered for sale in both physical and / or electronic marketplaces, and periodically transport the local database of USN / SM / SN / URL links to the central USN / SM / SN URL RDBMS by electronic data transport techniques. The local database of USN / SM / SN / URL links is managed with a local USN / SM / SN / URL RDBMS, and selected by the service-provider's marketing, brand and / or service managers so as to create a desired brand image for each consumer service of the service-provider. A second subsystem enables consumers to access one or more USN / SM / SN / URL links in the central USN / SM / SN / URL RDBMS, to request and obtain information about a service-provider's consumer service so as to make informed / educated purchases along the demand side of the retail chain. A third subsystem enables service-providers and their advertising and marketing agents to access one or more USN / SM / SN / URL links in the central USN / SM / SN / URL RDBMS, to display consumer service advertisements to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to project the desired brand image to consumers. A fourth subsystem enables retailers and their marketing and promotional agents to access one or more USN / SM / SN / URL links in the central USN / SM / SN / URL RDBMS, to promote consumer services to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to promote the sale of such services.
Owner:PERKOWSKI THOMAS J
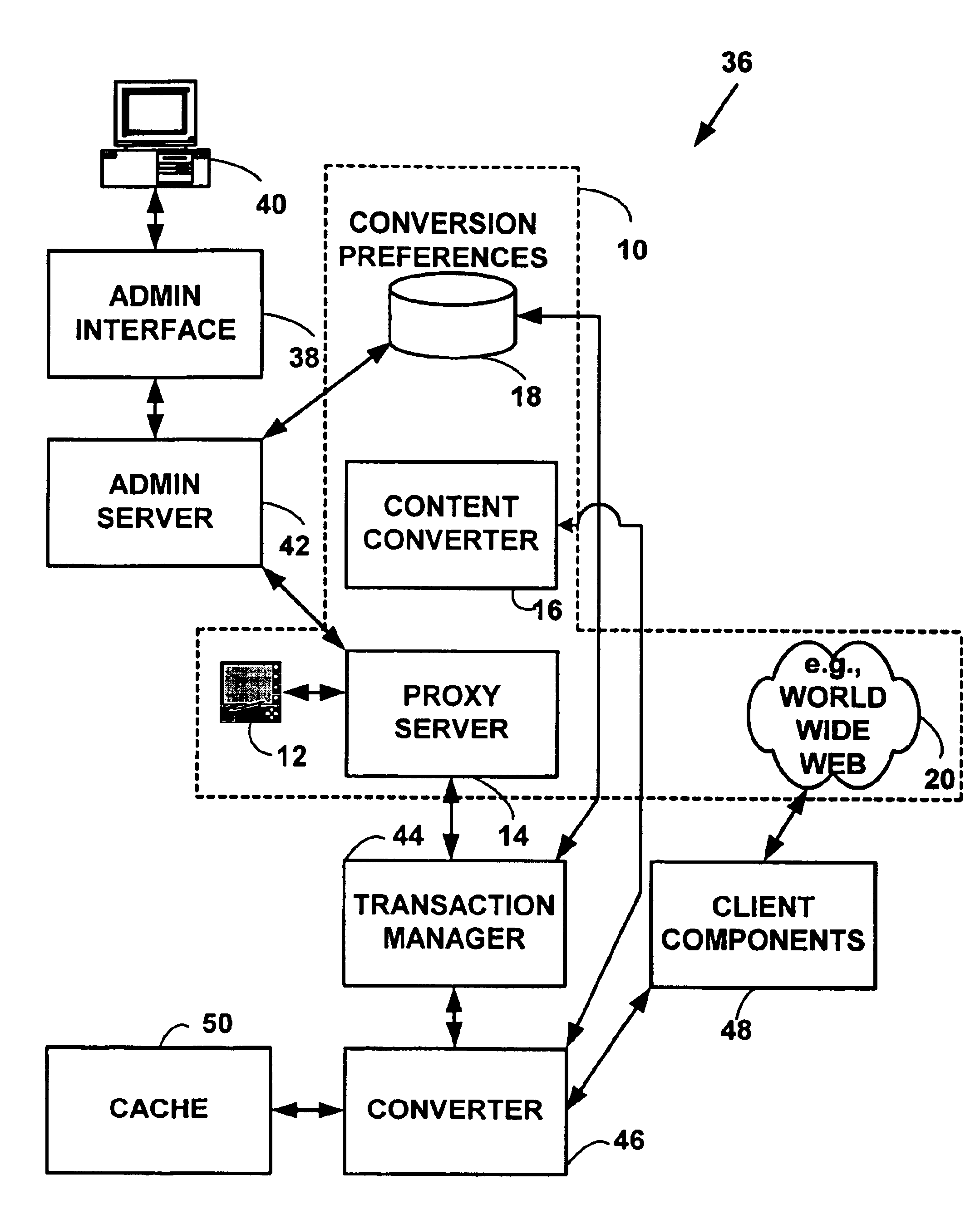
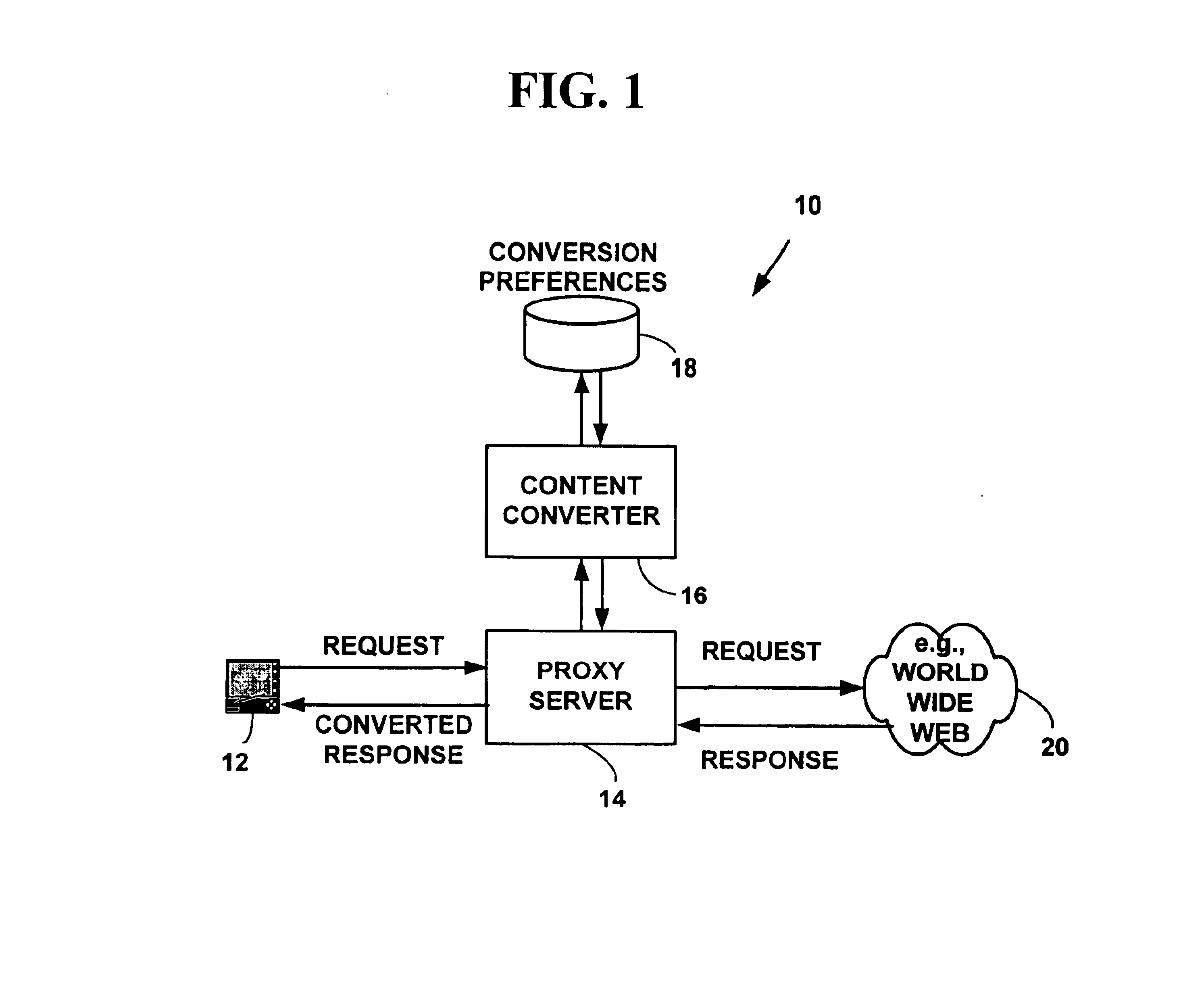
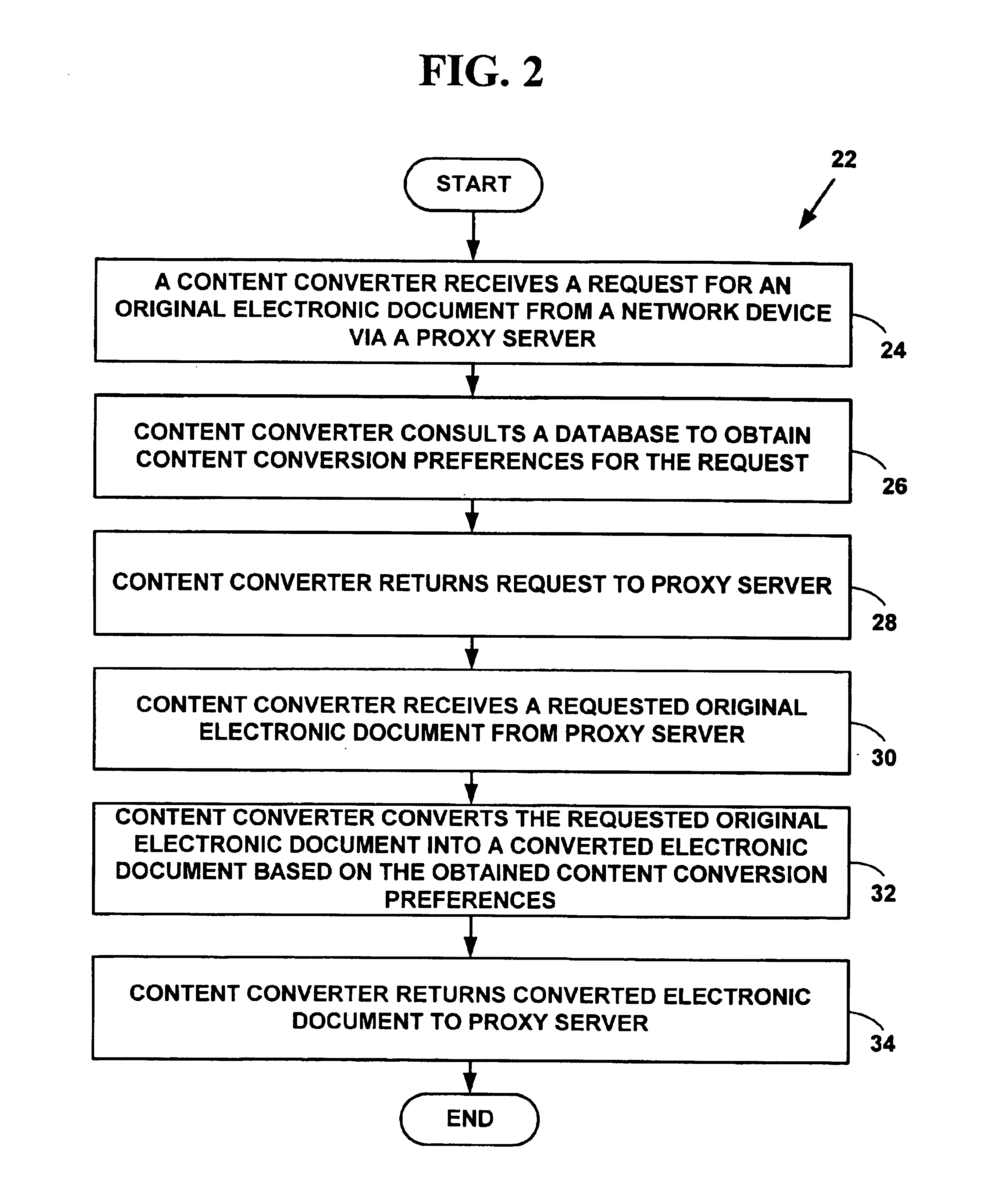
Method and system for content conversion of hypertext data using data mining
InactiveUS6925595B1Digital data information retrievalData processing applicationsElectronic documentUser device
Method and system for content conversion of electronic data using data mining. A user is able select one or more hypertext elements from one or more hypertext electronic document for conversion based on user conversion preferences. For example, a user selects one or more display elements from one or more “web-pages” from the World-Wide-Web on the Internet or an intranet. The hypertext elements are extracted from one or more hypertext electronic documents and converted into a format suitable for display on a user device based on user conversion preferences. Selected hypertext elements are extracted and converted using data mining conversion operations. The data mining conversion operations allow a user to extract only desired display information displayed from a hypertext element and convert the display information into a format different than that defined for the original electronic document. The converted display information is appropriate for a user device such as hand-held, wireless phone, personal digital assistant, or other device.
Owner:OPEN TV INC
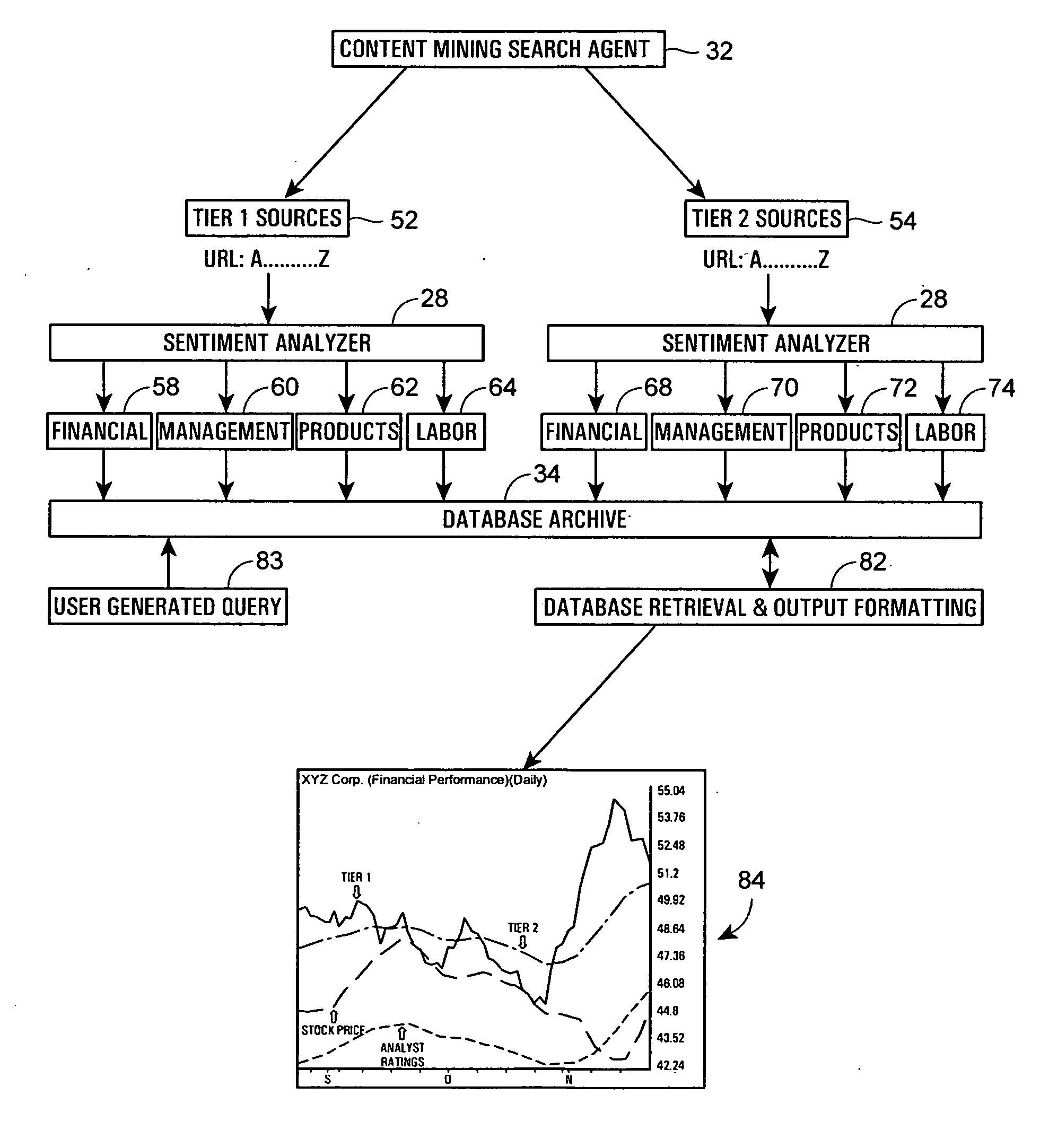
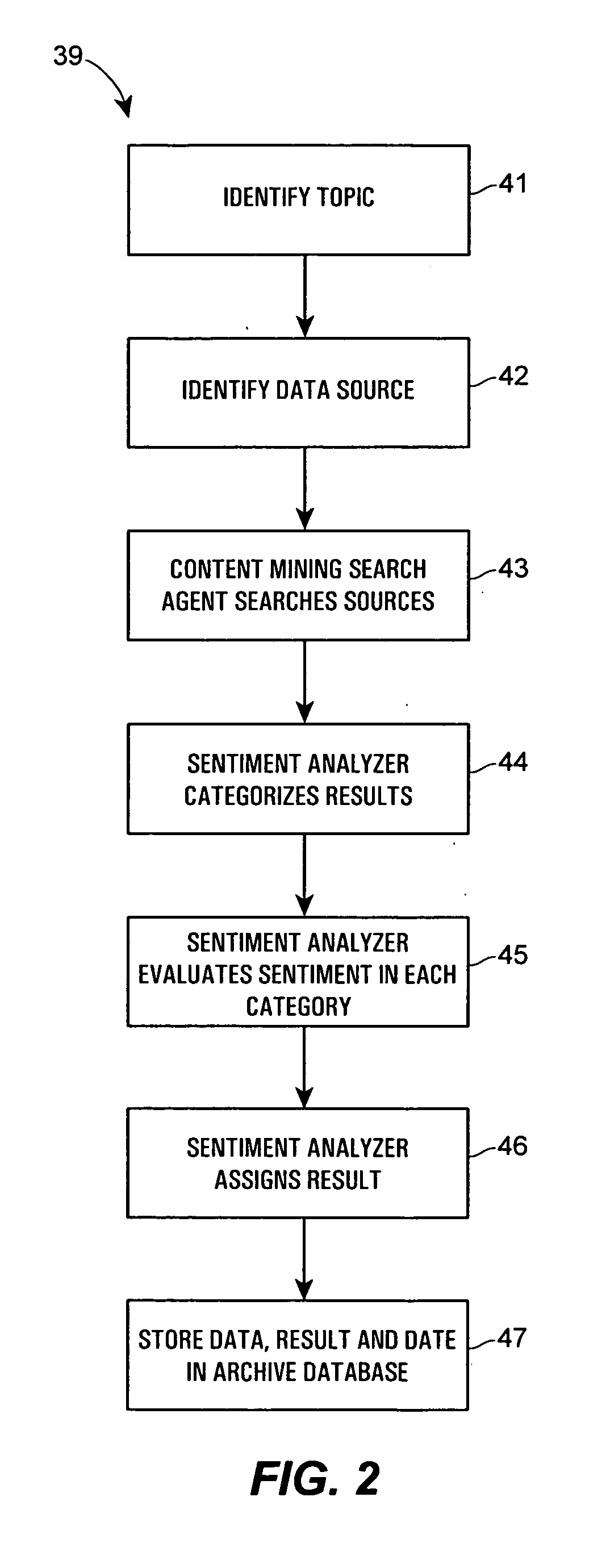
Method and system for conducting sentiment analysis for securities research
A computer system performs financial analysis on one or more financial entities, which may be corporations, securities, etc., based on the sentiment expressed about the one or more financial entities within raw textual data stored in one or more electronic data sources containing information or text related to one or more financial entities. The computer system includes a content mining search agent that identifies one or more words or phrases within raw textual data in the data sources using natural language processing to identify relevant raw textual data related to the one or more financial entities, a sentiment analyzer that analyzes the relevant raw textual data to determine the nature or the strength of the sentiment expressed about the one or more financial entities within the relevant raw textual data and that assigns a value to the nature or strength of the sentiment expressed about the one or more financial entities within the relevant raw textual data, and a user interface program that controls the content mining search agent and the sentiment analyzer and that displays, to a user, the values of the nature or strength of the sentiment expressed about the one or more financial entities within the data sources. This computer system enables a user to make better decisions regarding whether or not to purchase or invest in the one or more financial entities.
Owner:AIM HLDG LLC
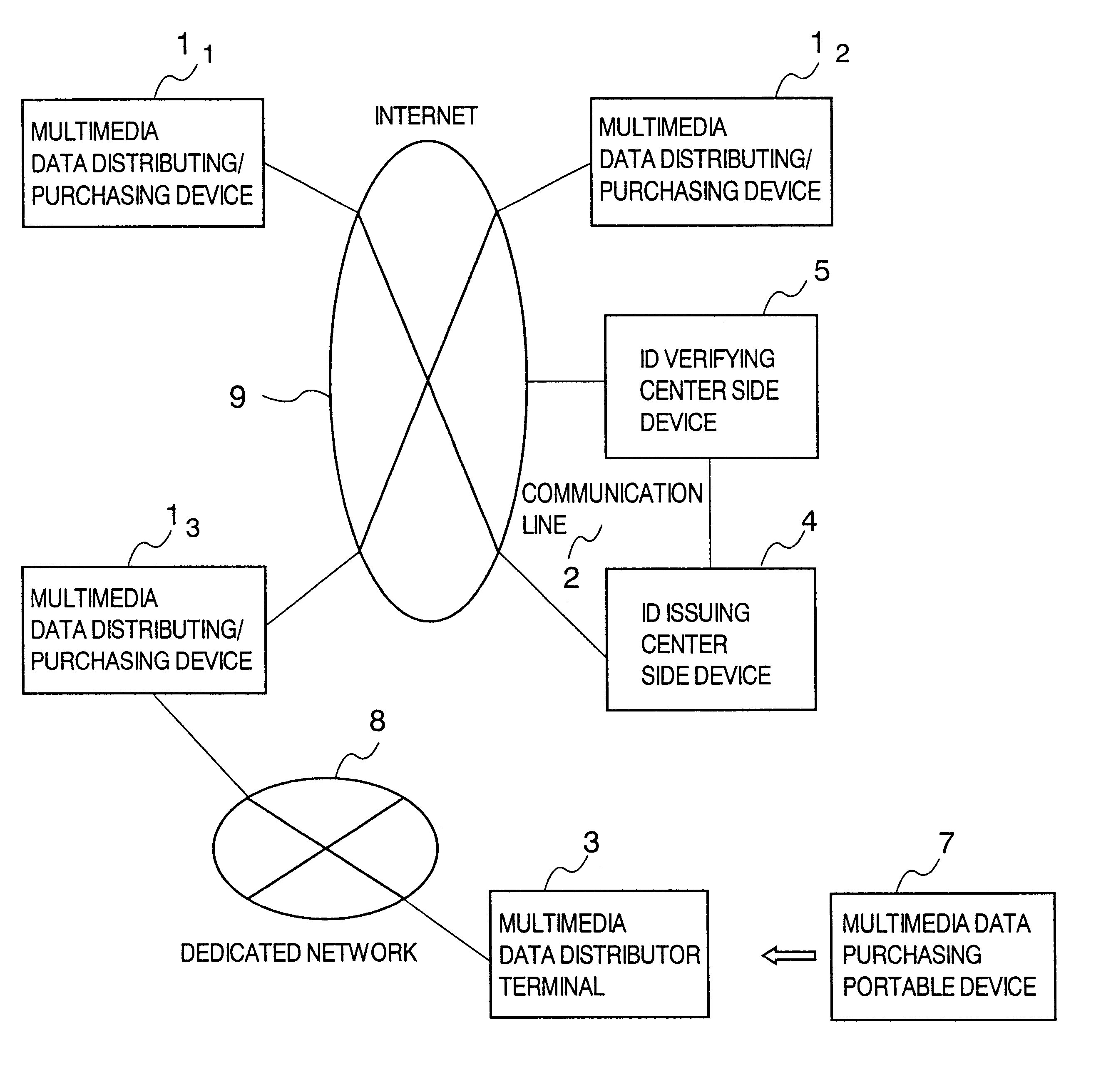
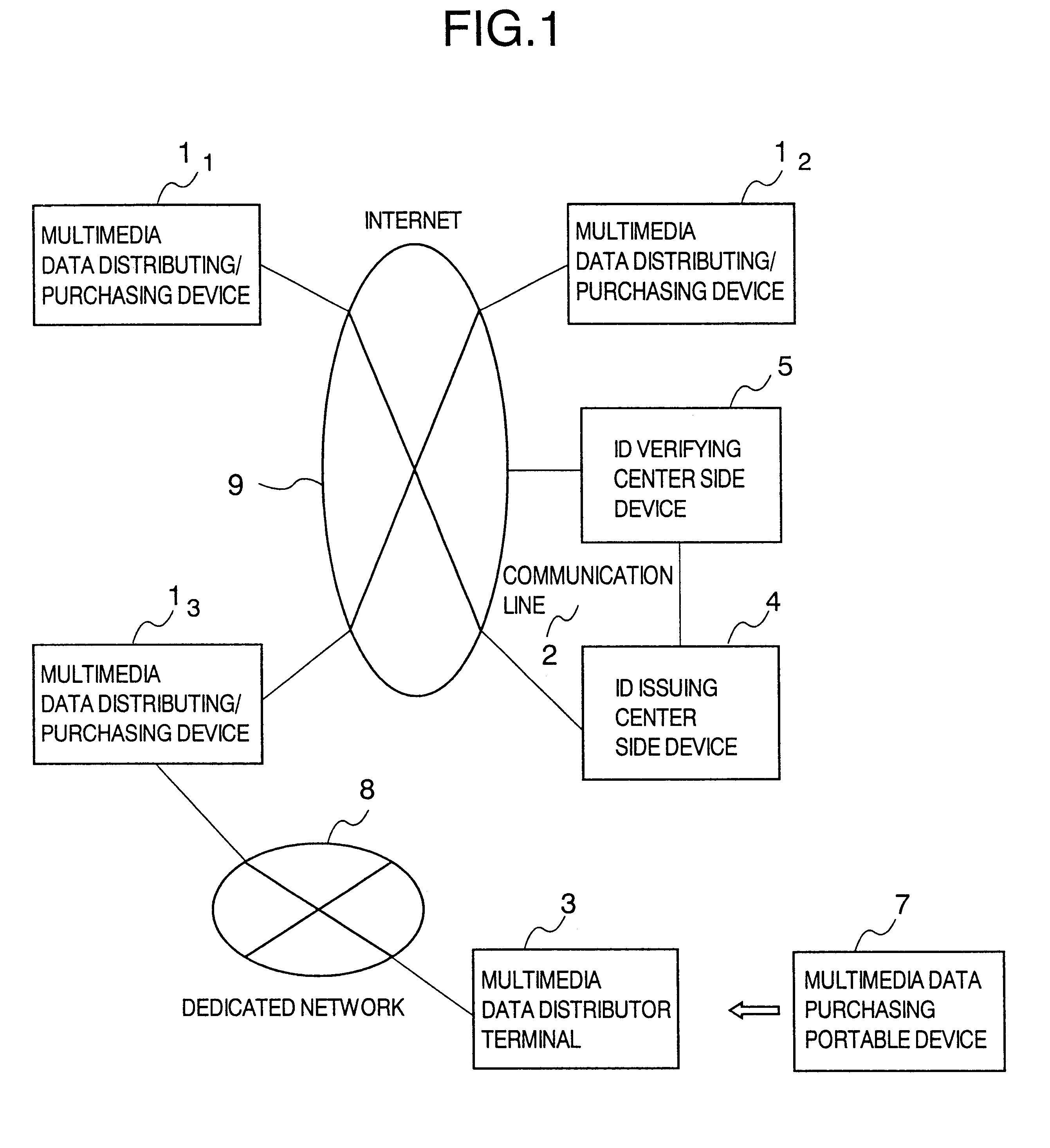
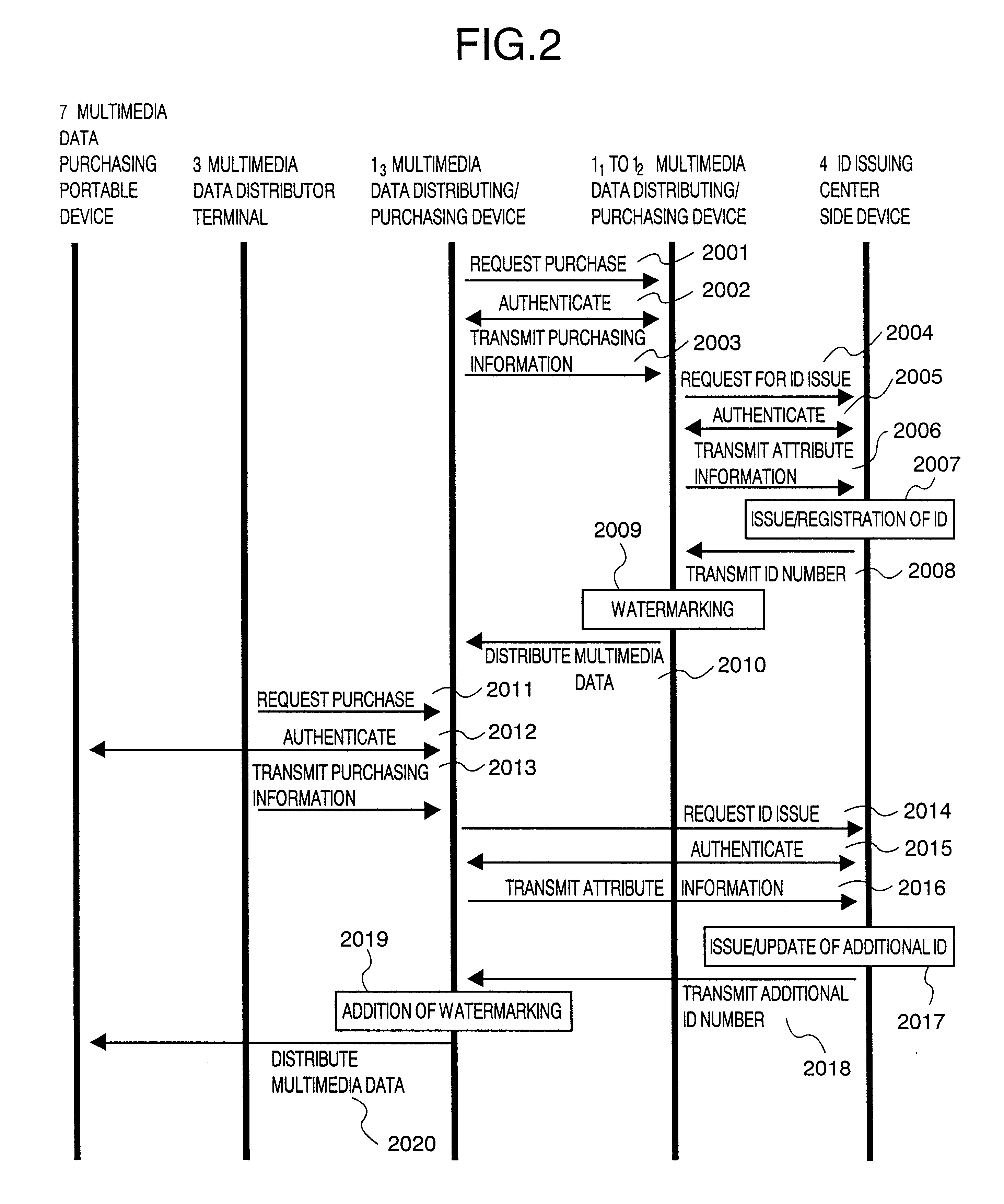
Method and system for distributing multimedia data with management information
InactiveUS6889211B1Data processing applicationsDigital data protectionInformation embeddingManagement information systems
A multimedia data distributing system comprising an ID issuing center side device and a multimedia data distributor side device for distributing multimedia data as electronic data to a purchaser of the multimedia data. The multimedia data distributor device includes: an attribute information transmitting unit that transmits attribute information of the electronic data indicating the multimedia data to be distributed, to the ID issuing center side device; a watermark information embedding unit that embeds information specifying the ID number transmitted from the ID issuing center side device in response to the attribute information transmitted to the attribute information transmitting unit, as an watermark information in the electronic data indicating the multimedia data to be distributed; and a distribution unit that distributes the electronic data indicating the multimedia data, in which the information specifying the ID number is embedded as the watermark information by the watermark information embedding unit, to the purchaser of the multimedia data. The ID issuing center side device includes: an ID number generating unit that generates a unique ID number and registering the generated ID number in a database in a manner to correspond to the attribute information transmitted by the distributor of the multimedia data; and an ID number transmitting unit that transmits the information specifying the generated ID number to the multimedia data distributor device.
Owner:HITACHI LTD
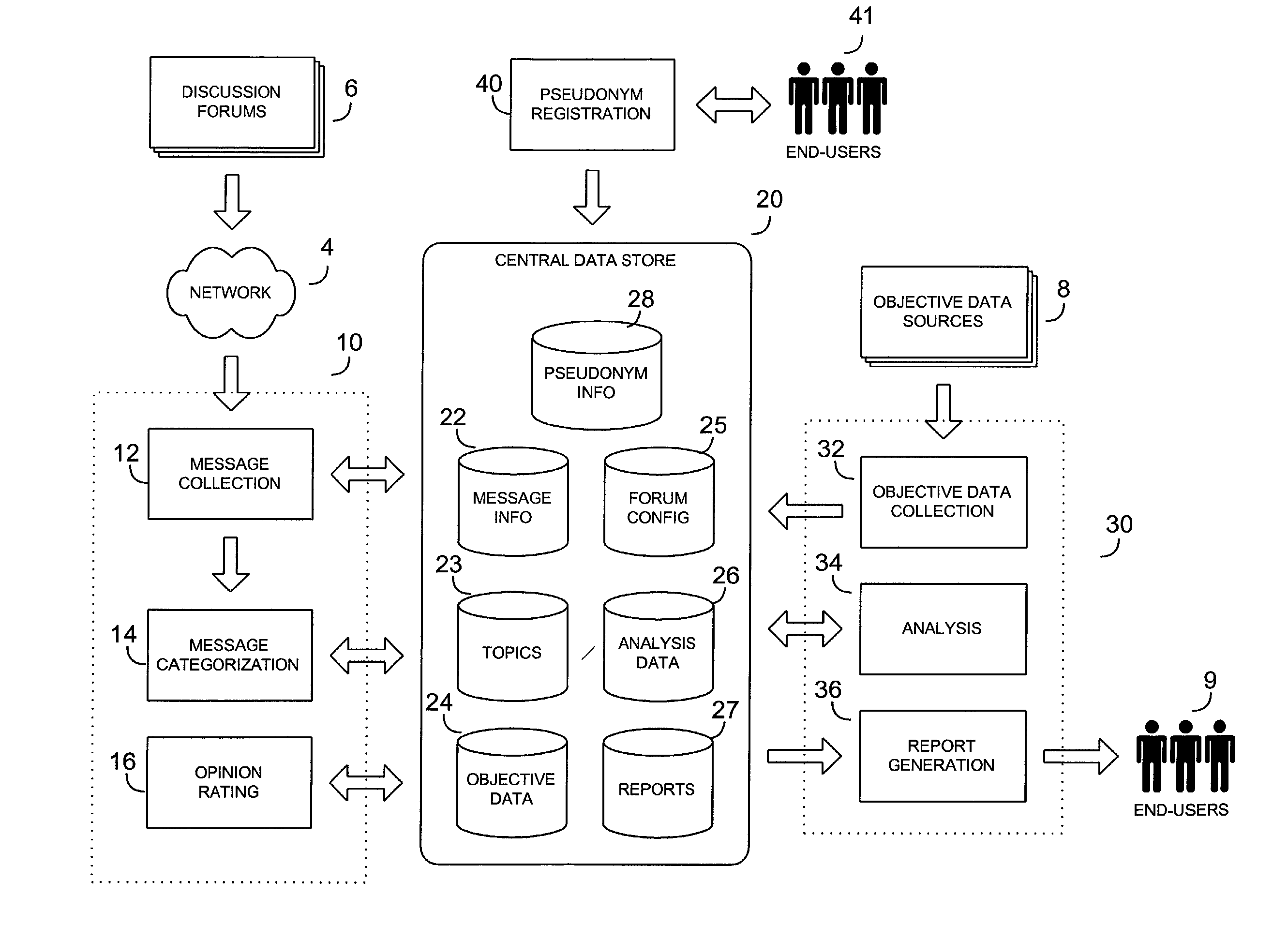
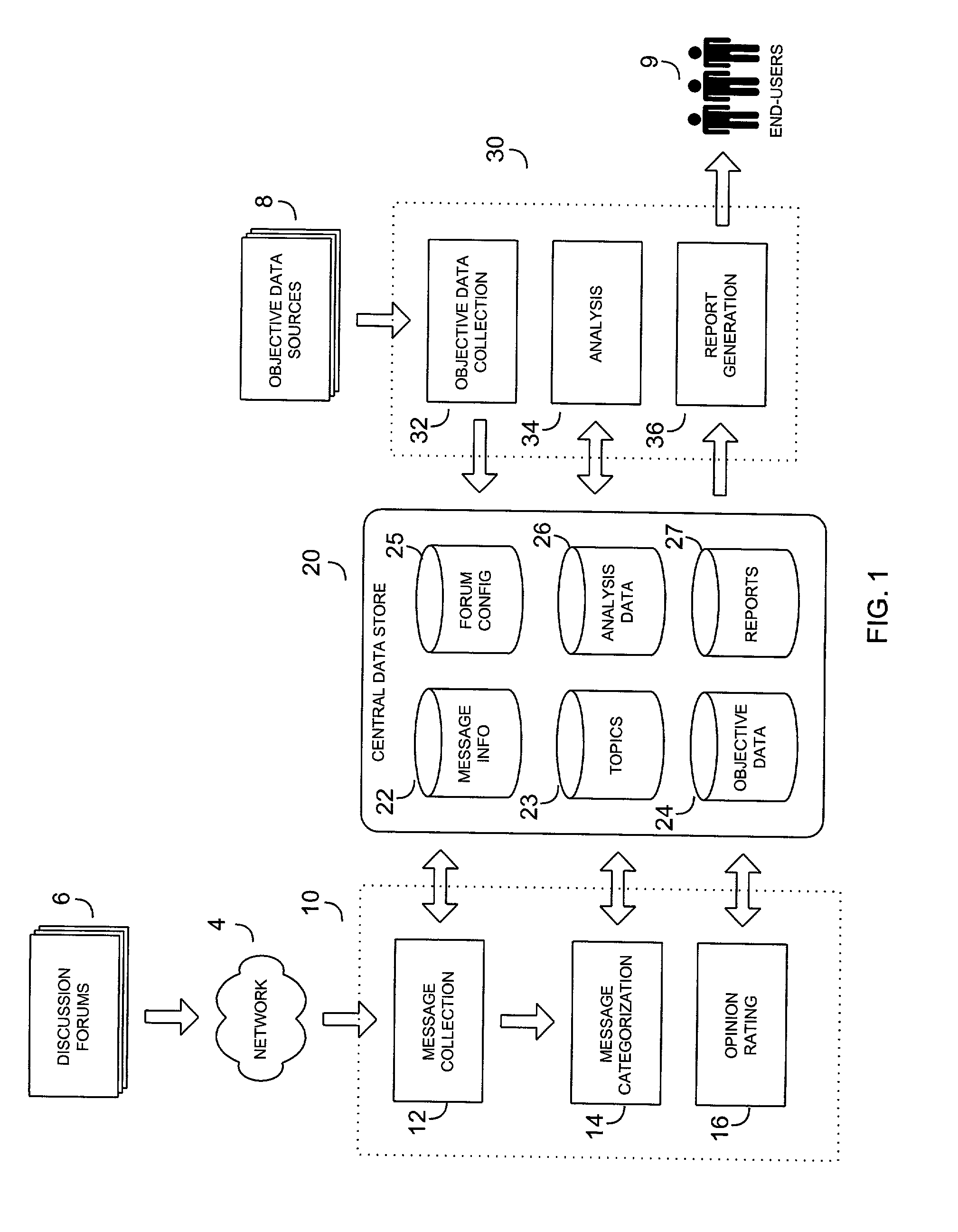
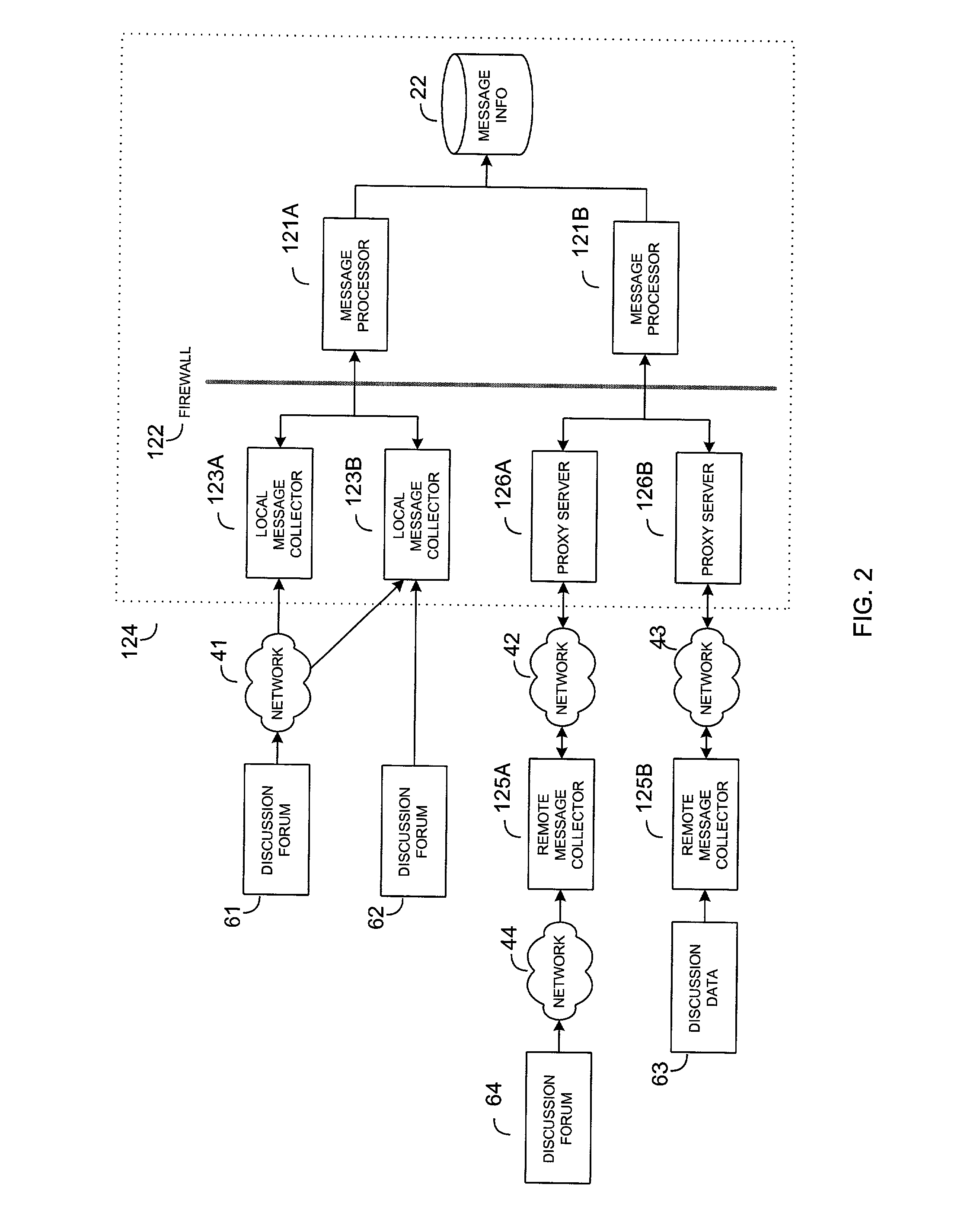
System and method for scoring electronic messages
A system and method for collecting and analyzing electronic discussion messages to categorize the message communications and the identify trends and patterns in pre-determined markets. The system comprises an electronic data discussion system wherein electronic messages are collected and analyzed according to characteristics and data inherent in the messages. The system further comprises a data store for storing the message information and results of any analyses performed. Objective data is collected by the system for use in analyzing the electronic discussion data against real-world events to facilitate trend analysis and event forecasting based on the volume, nature and content of messages posted to electronic discussion forums.
Owner:BUZZMETRICS
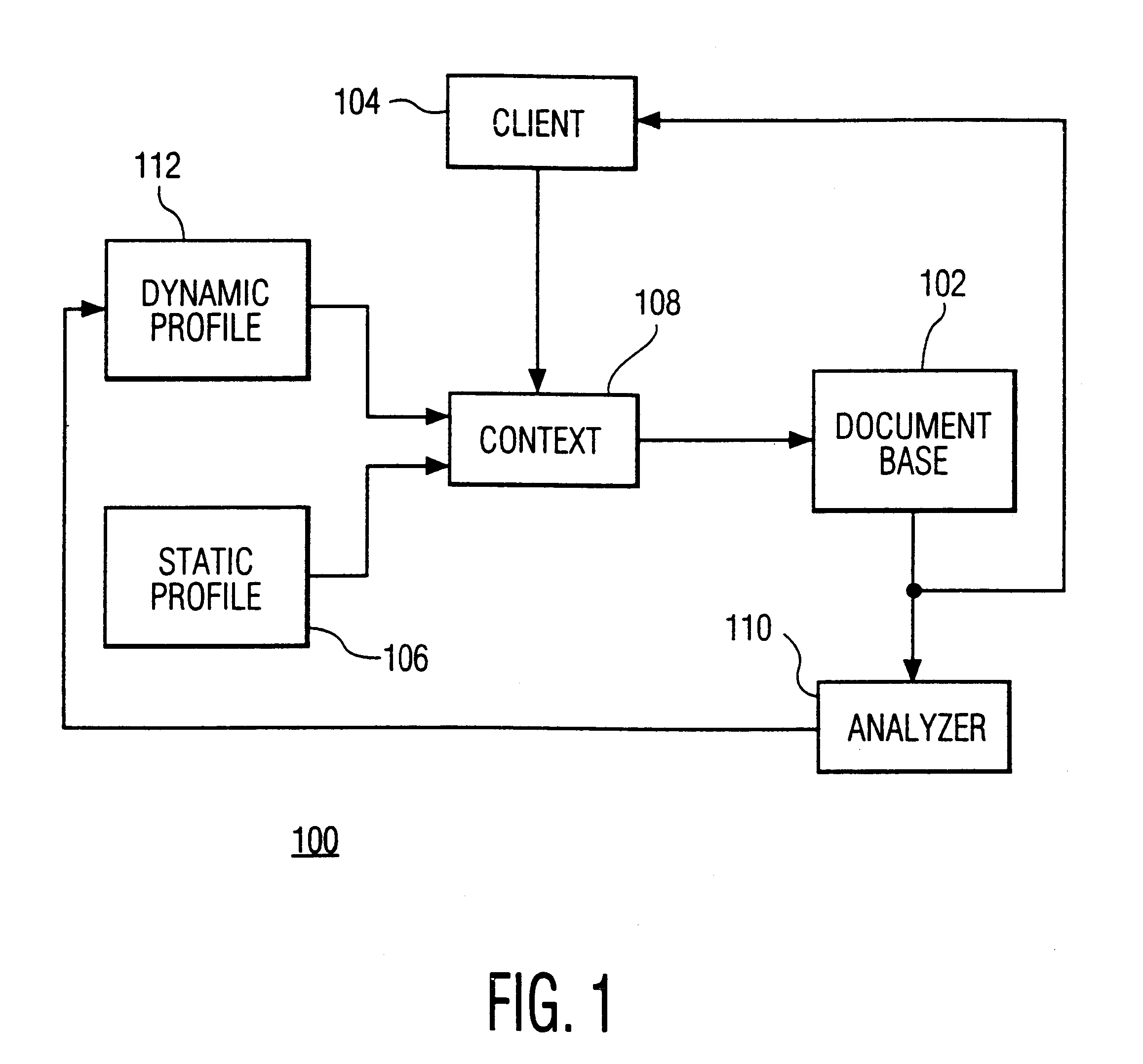
Context-based and user-profile driven information retrieval
InactiveUS6256633B1Quality improvementImprove efficiencyData processing applicationsDigital data information retrievalPersonalizationContext based
A user is enabled to navigate through an electronic data base in a personalized manner. A context is created based on a profile of the user, the profile being at least partly formed in advance. Candidate data is selected from the data base under control of the context and the user is enabled to interact with the candidates. The profile is based on topical information supplied by the user in advance and a history of previous accesses from the user to the data base.
Owner:U S PHILIPS CORP
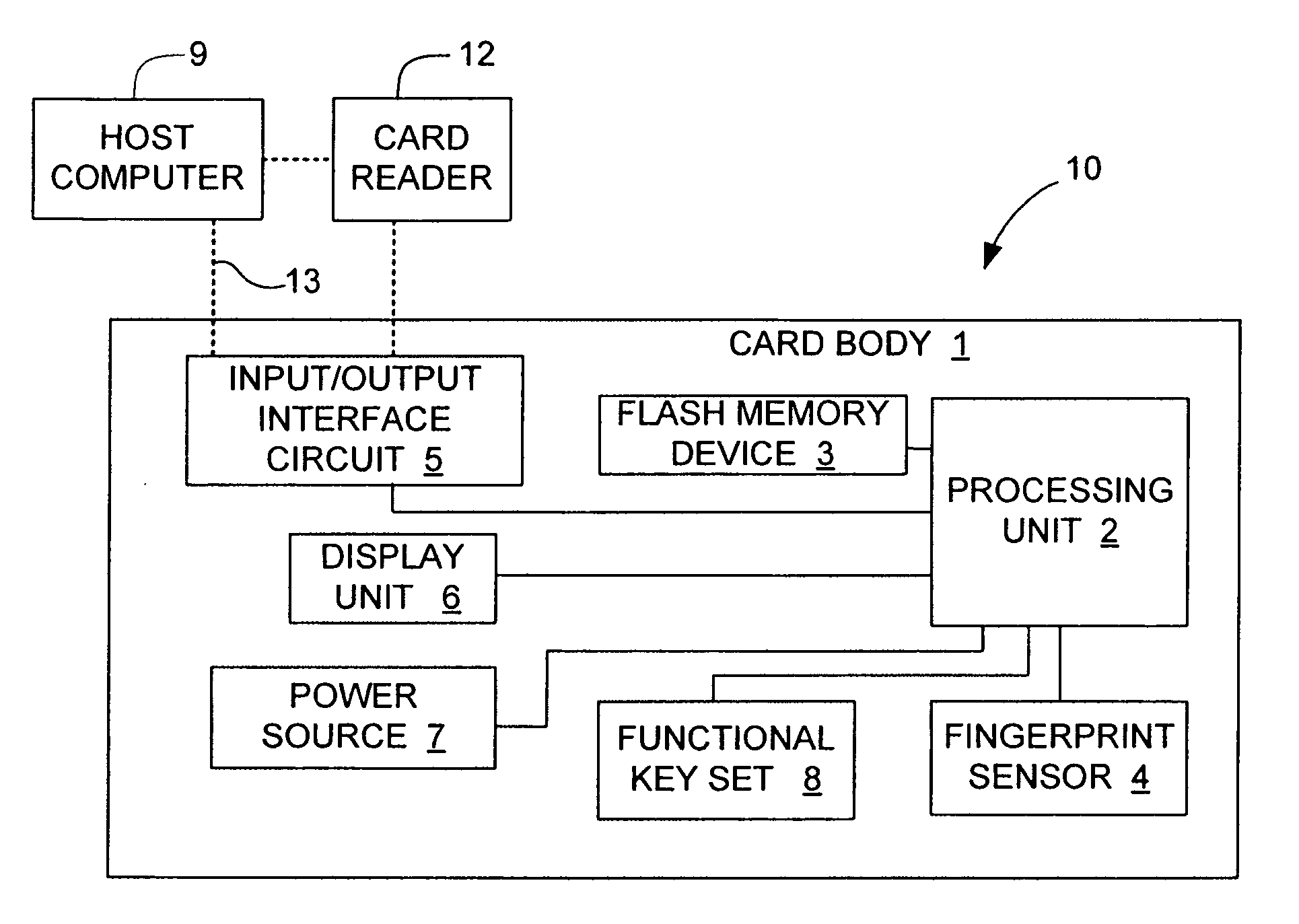
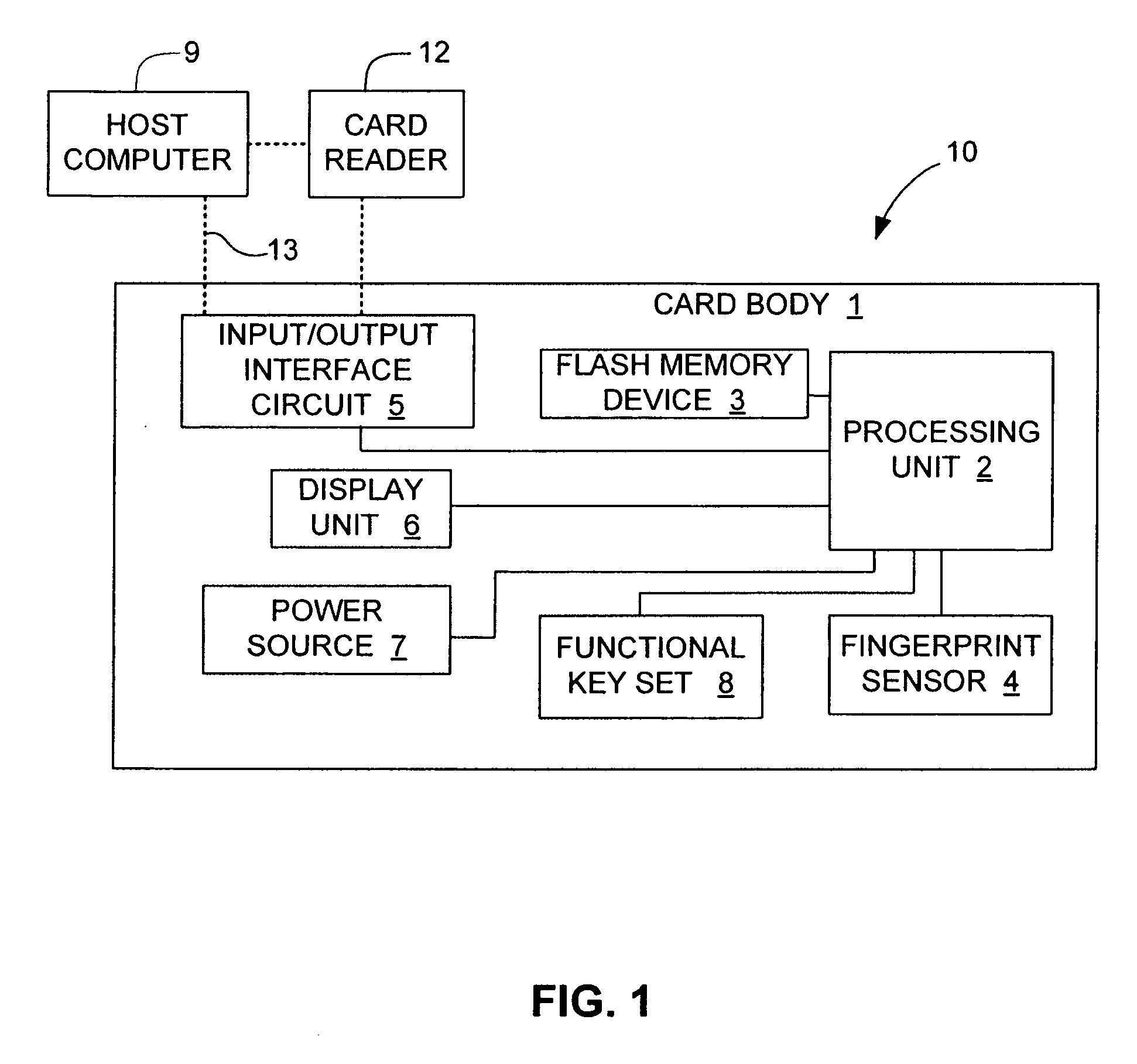
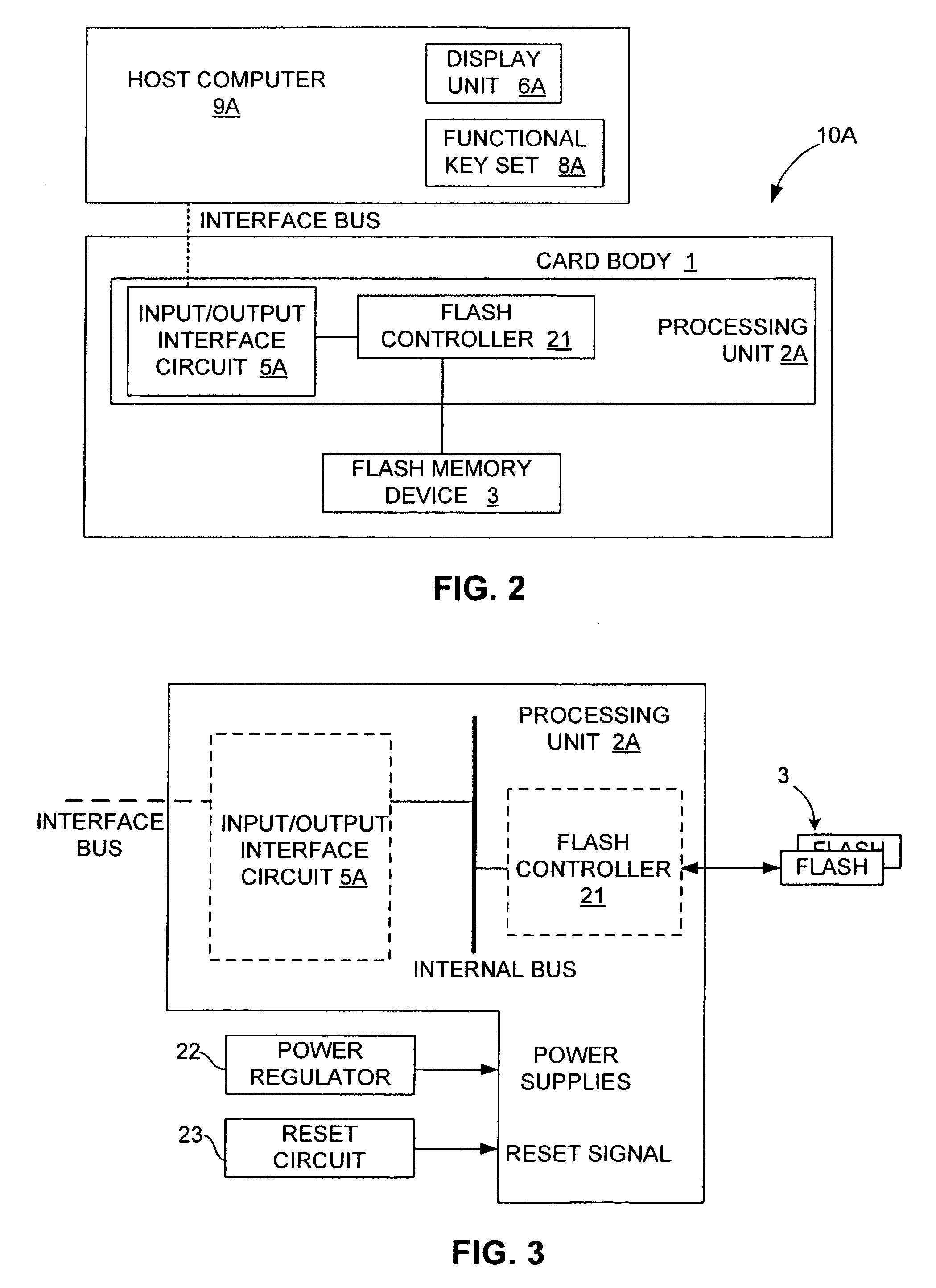
Managing bad blocks in various flash memory cells for electronic data flash card
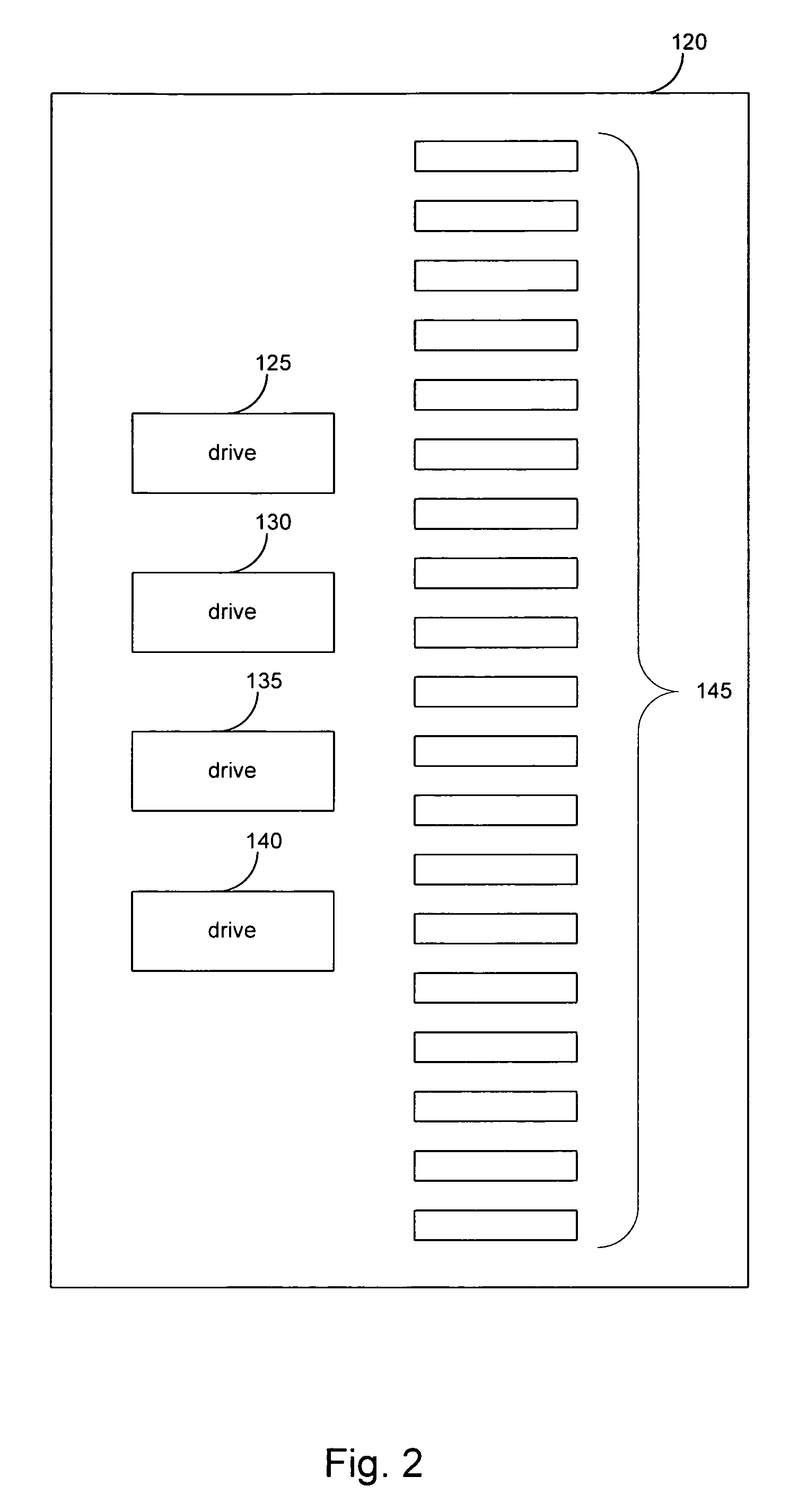
InactiveUS20080082736A1Small sizeLow costMemory architecture accessing/allocationMemory systemsComputer accessFlash memory controller
An electronic data flash card accessible by a host computer, includes a flash memory controller connected to a flash memory device, and an input-output interface circuit activated to establish a communication with the host. In an embodiment, the flash card uses a USB interface circuit for communication with the host. A flash memory controller includes an arbitrator for mapping logical addresses with physical block addresses, and for performing block management operations including: storing reassigned data to available blocks, relocating valid data in obsolete blocks to said available blocks and reassigning logical block addresses to physical block addresses of said available blocks, finding bad blocks of the flash memory device and replacing with reserve blocks, erasing obsolete blocks for recycling after relocating valid data to available blocks, and erase count wear leveling of blocks, etc. Furthermore, each flash memory device includes an internal buffer for accelerating the block management operations.
Owner:SUPER TALENT ELECTRONICS
Cryptographic method and system
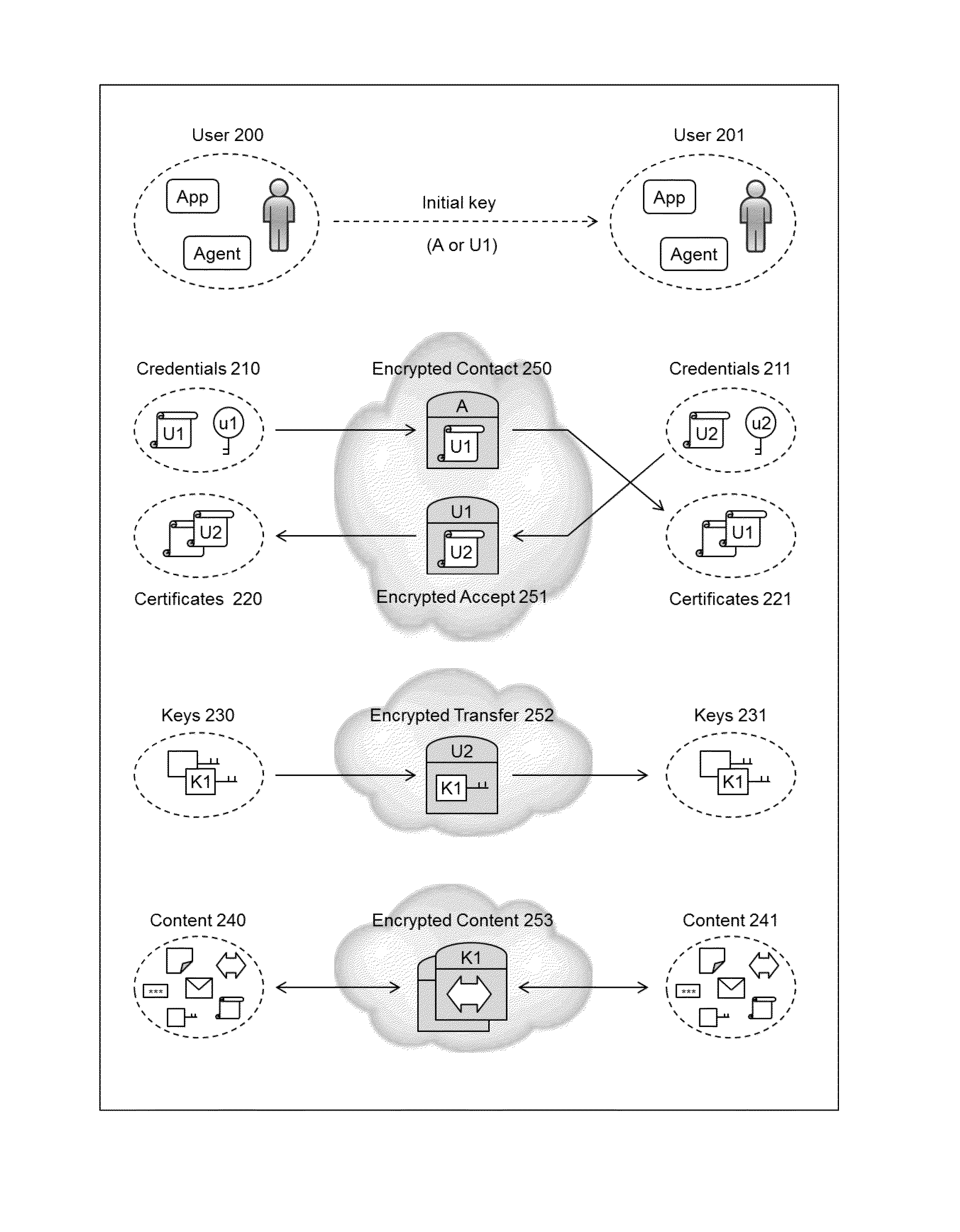
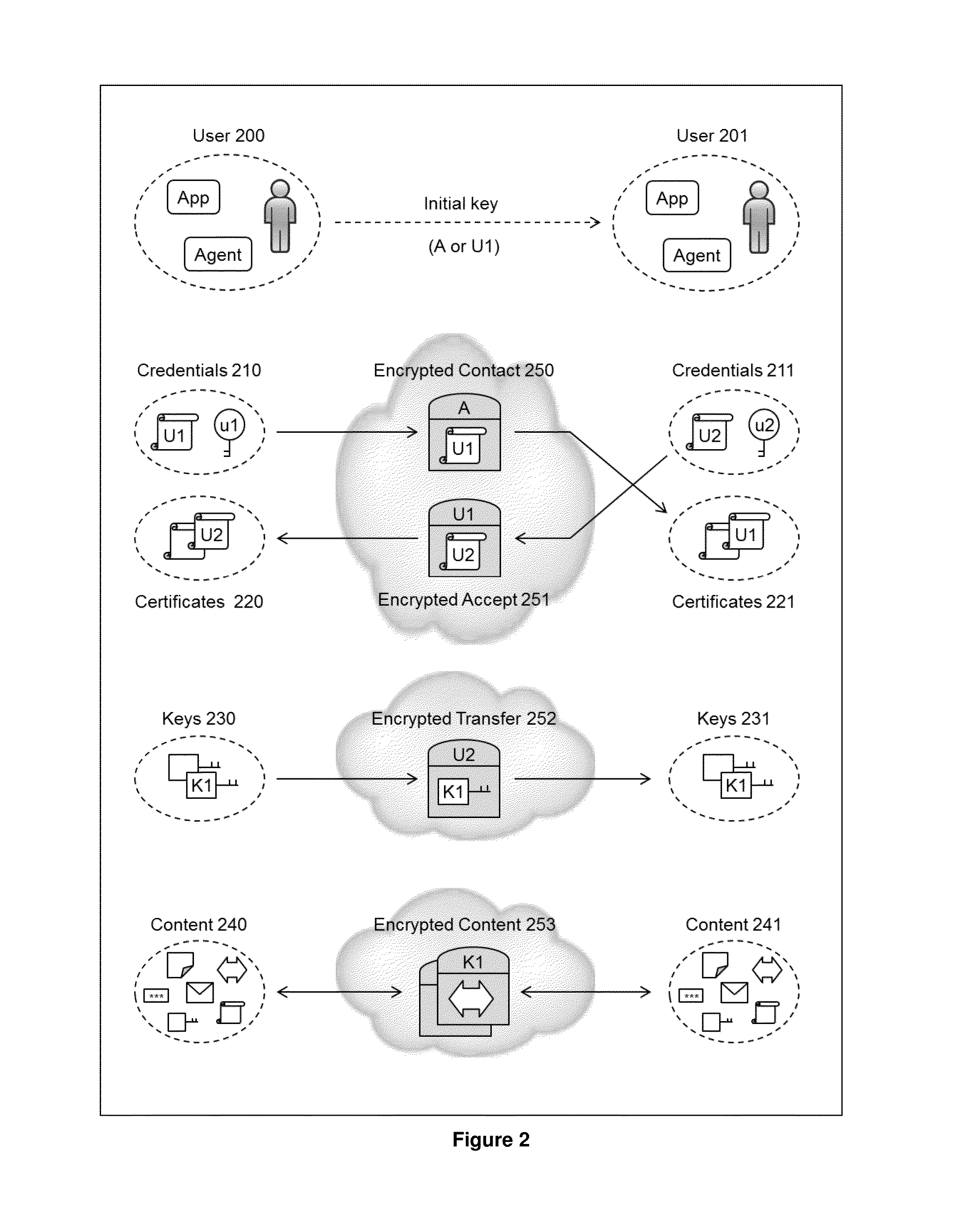
InactiveUS20140164776A1Easy to useImprove abilitiesKey distribution for secure communicationMultiple keys/algorithms usageInformation sharingInternet privacy
The present invention relates to the field of security of electronic data and / or communications. In one form, the invention relates to data security and / or privacy in a distributed and / or decentralised network environment. In another form, the invention relates to enabling private collaboration and / or information sharing between users, agents and / or applications. Embodiment(s) of the present invention enable the sharing of key(s) and / or content between a first user and / or agent and a second user and / or agent. Furthermore, embodiment(s) of the present invention have application in sharing encrypted information via information sharing services.A number of inventions, aspects and embodiments are disclosed herein.
Owner:LOCK BOX
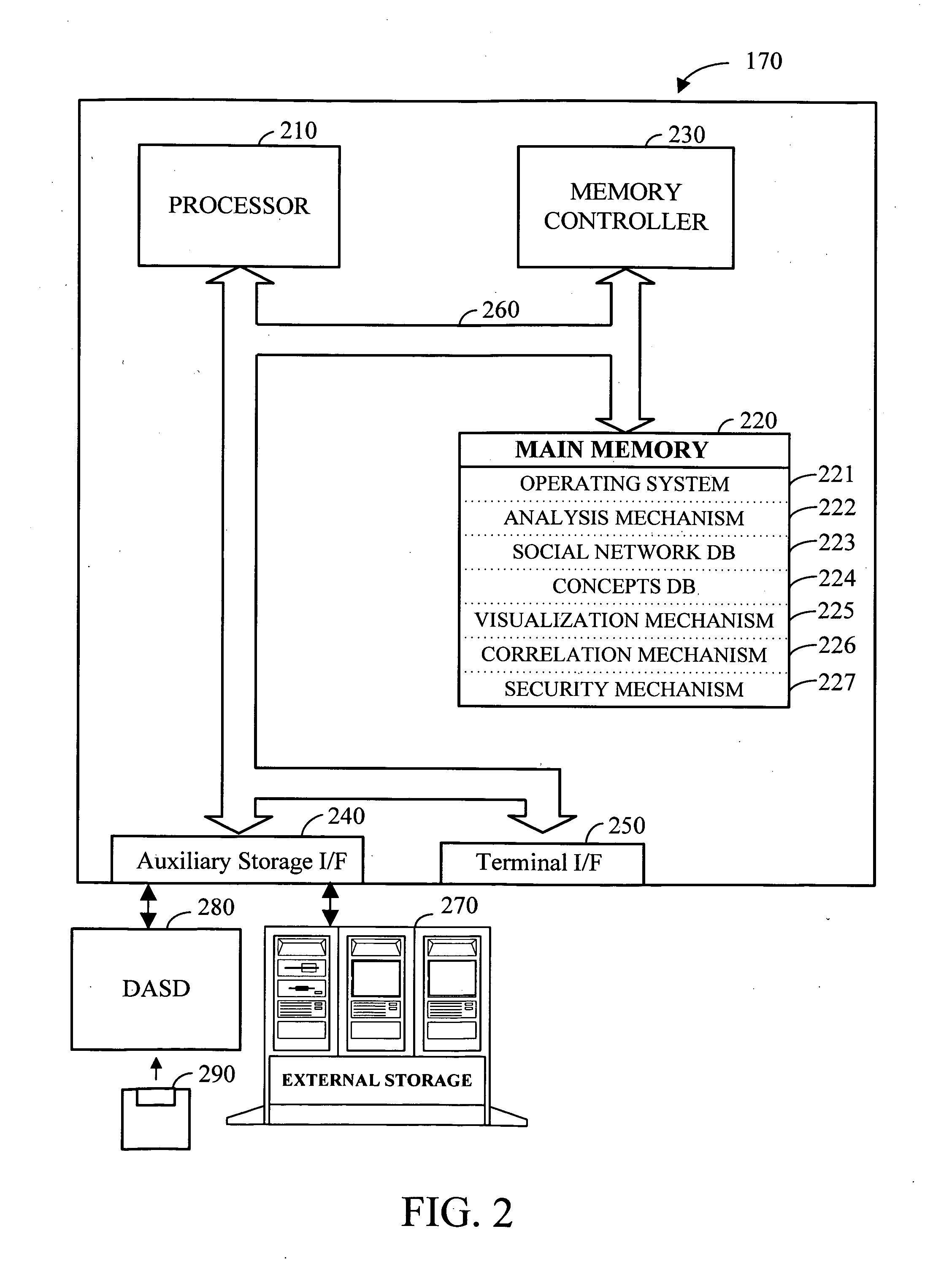
Apparatus and method for message-centric analysis and multi-aspect viewing using social networks
ActiveUS20060173957A1Data switching by path configurationMultiple digital computer combinationsReference modelMulti aspect
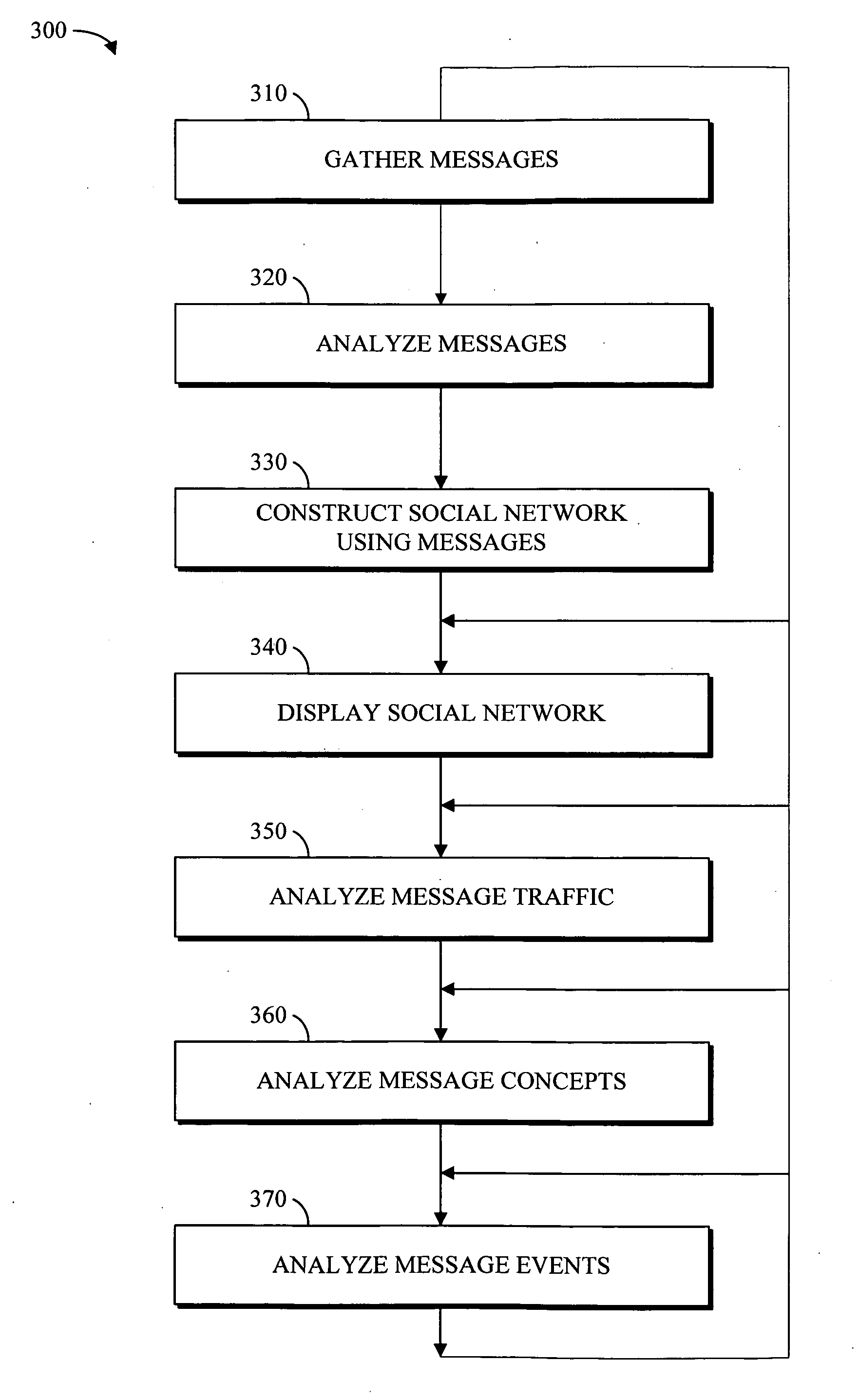
Electronic data files are broadly characterized as “messages” and a social network is constructed by analyzing one or more messages exchanged between various entities. Additionally, messages from structured and / or unstructured data stores are correlated using one or more common / related data elements from two or more messages. Further, the social network and the concepts contained in the exchanged messages (i.e. semantic network) can be visualized using a series of multi-aspect viewing tools. Finally, in conjunction with the social network and the semantic network, a message network based on the chronological relationship of the messages (event network) can be constructed to analyze and visualize how the messages relate to each other in a time-based reference model. Once visualized, the relationship of the concepts contained in the messages as well as the relationship between the entities and the timing involved in the exchange of messages can be analyzed for desired information.
Owner:NUIX NORTH AMERICA
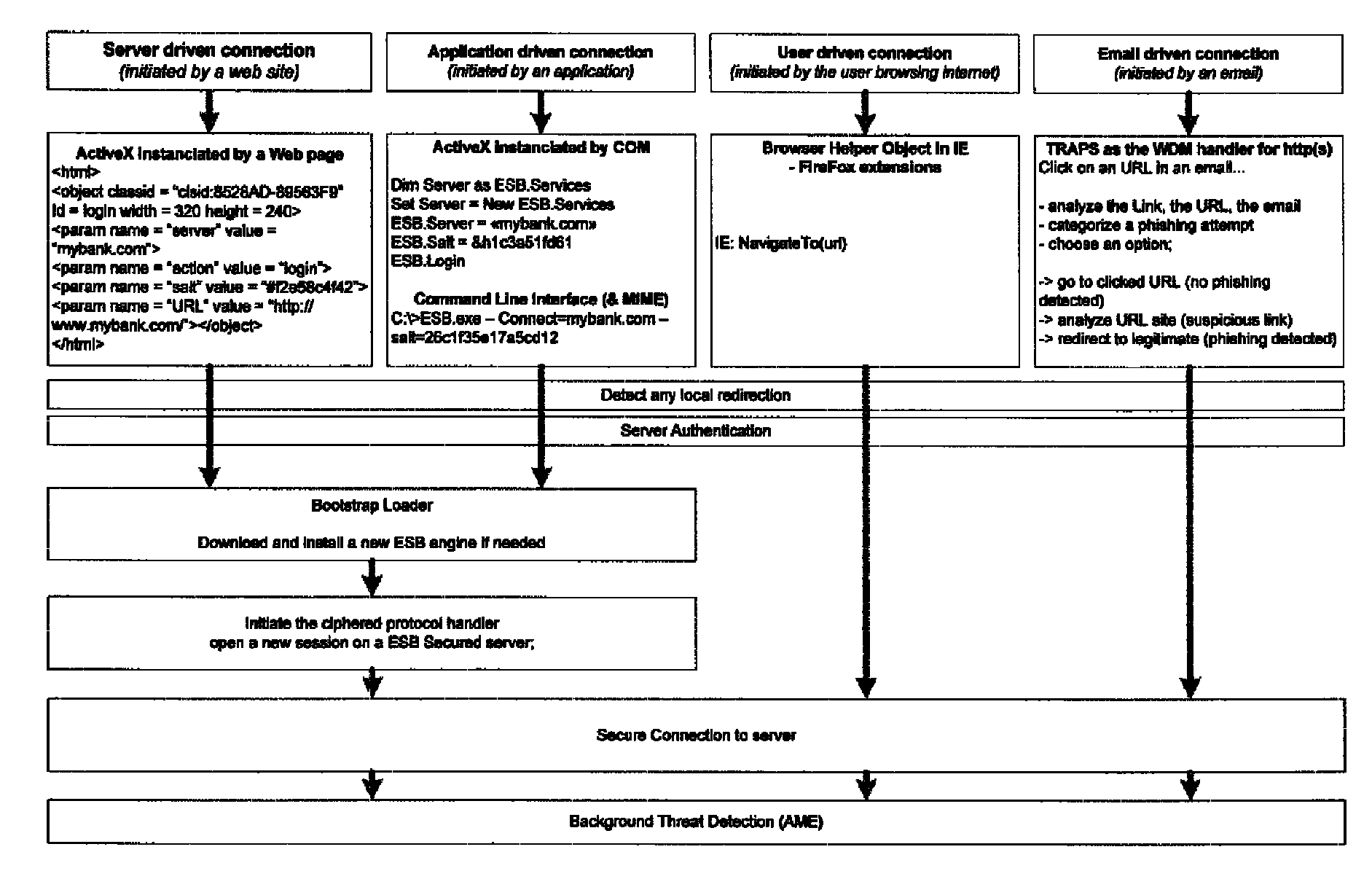
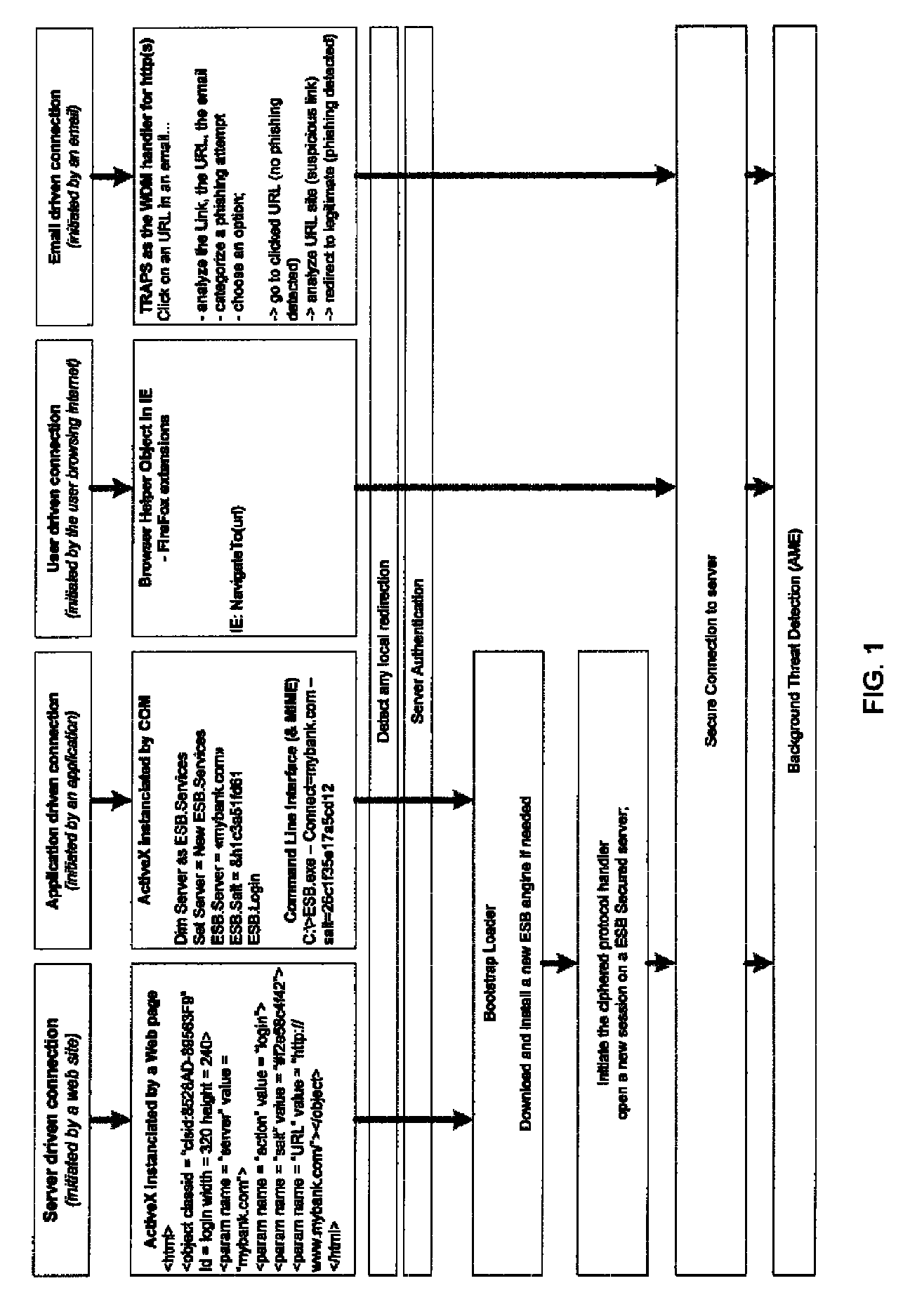
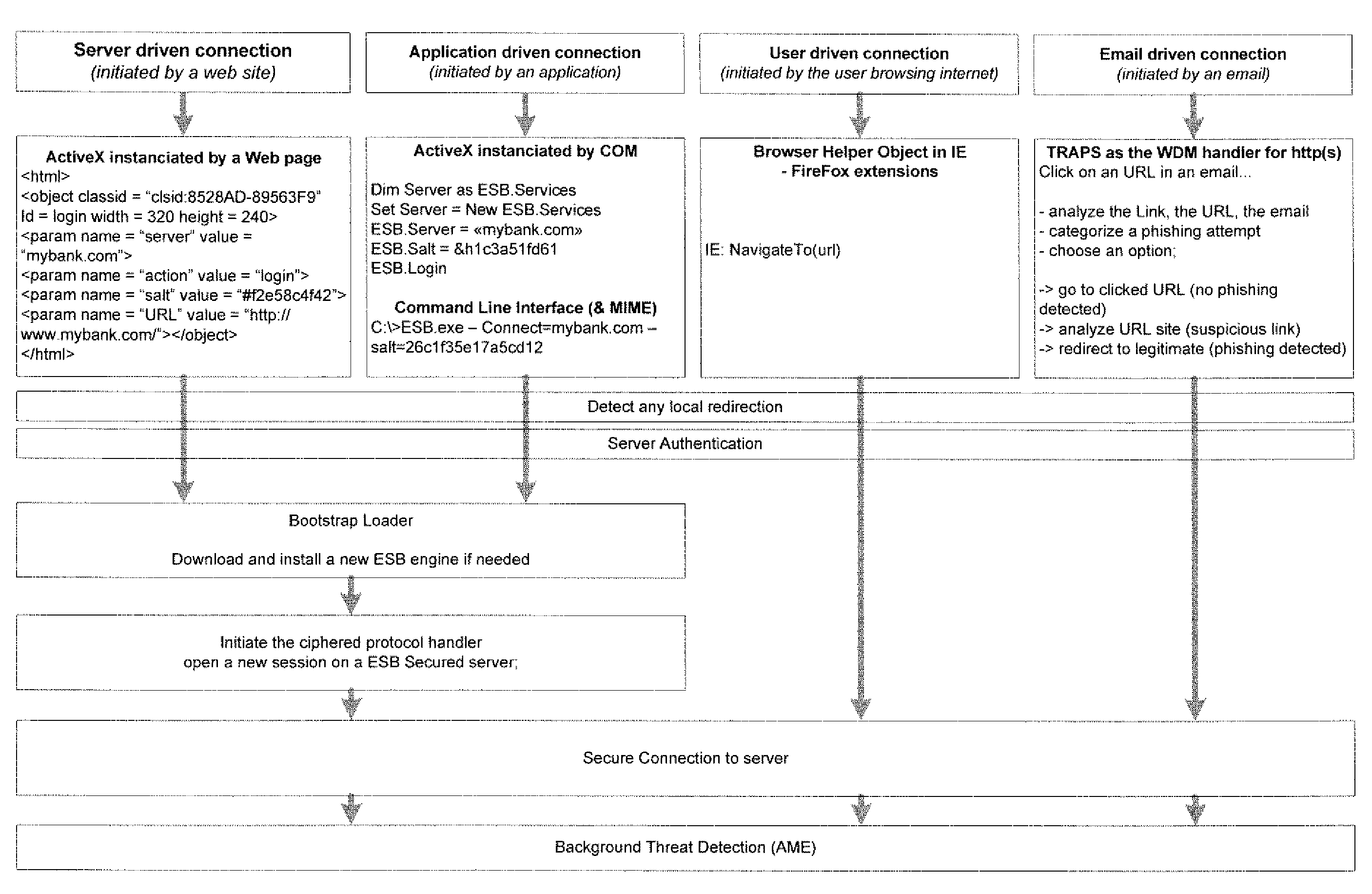
System and method for authentication, data transfer, and protection against phishing
ActiveUS8578166B2Key distribution for secure communicationDigital data processing detailsElectronic communicationStructure of Management Information
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
Selective data replication system and method
InactiveUS7287047B2Input/output to record carriersData processing applicationsData setSelection criterion
The invention relates generally to copying electronic data. More particularly, the invention provides a computerized method for identifying, in a first backup data set, a data item satisfying a selection criterion, and copying to a second backup data set at least a portion of the data item.
Owner:COMMVAULT SYST INC
Method, apparatus, and system for clustering and classification
The invention provides a method, apparatus and system for classification and clustering electronic data streams such as email, images and sound files for identification, sorting and efficient storage. The inventive systems disclose labeling a document as belonging to a predefined class though computer methods that comprise the steps of identifying an electronic data stream using one or more learning machines and comparing the outputs from the machines to determine the label to associate with the data. The method further utilizes learning machines in combination with hashing schemes to cluster and classify documents. In one embodiment hash apparatuses and methods taxonomize clusters. In yet another embodiment, clusters of documents utilize geometric hash to contain the documents in a data corpus without the overhead of search and storage.
Owner:SYSXNET
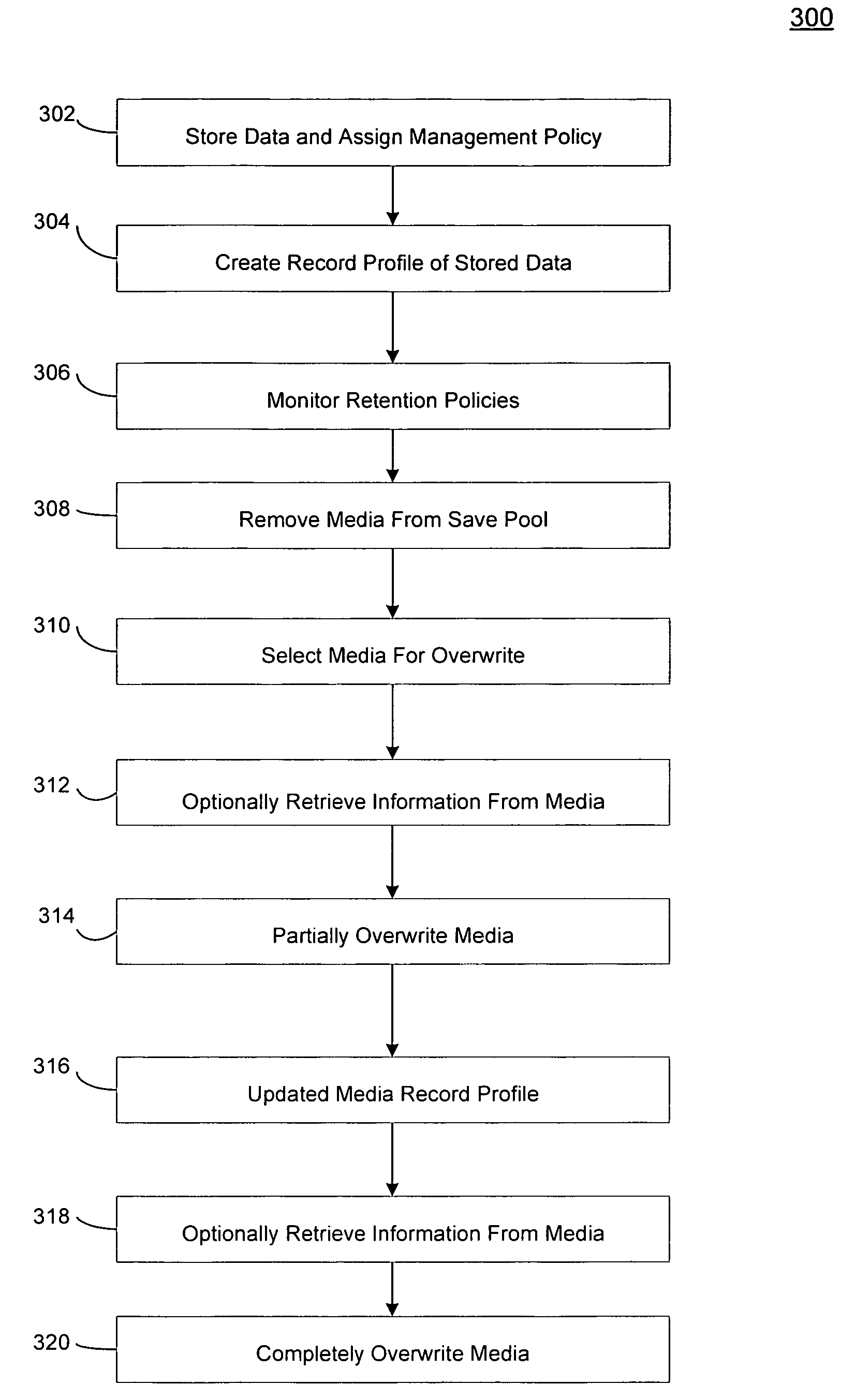
Systems and methods for recovering electronic information from a storage medium
ActiveUS7472238B1Error detection/correctionMemory adressing/allocation/relocationSystems managementEngineering
In one embodiment of the invention, a method is provided for retrieving certain electronic information previously stored on certain storage media after a threshold set in the storage retention criteria has been exceeded in an electronic information storage system that stores electronic information on storage media in accordance with a storage retention criteria is provided. The method includes storing a record in a memory associated with a system manager that assigns the storage retention criteria to the certain electronic data, designating the storage media available for overwrite after the threshold set in the storage retention policy has been exceeded, identifying the certain storage media available for overwrite, and retrieving information from the certain media after the threshold set in the storage retention policy has been exceeded.
Owner:COMMVAULT SYST INC
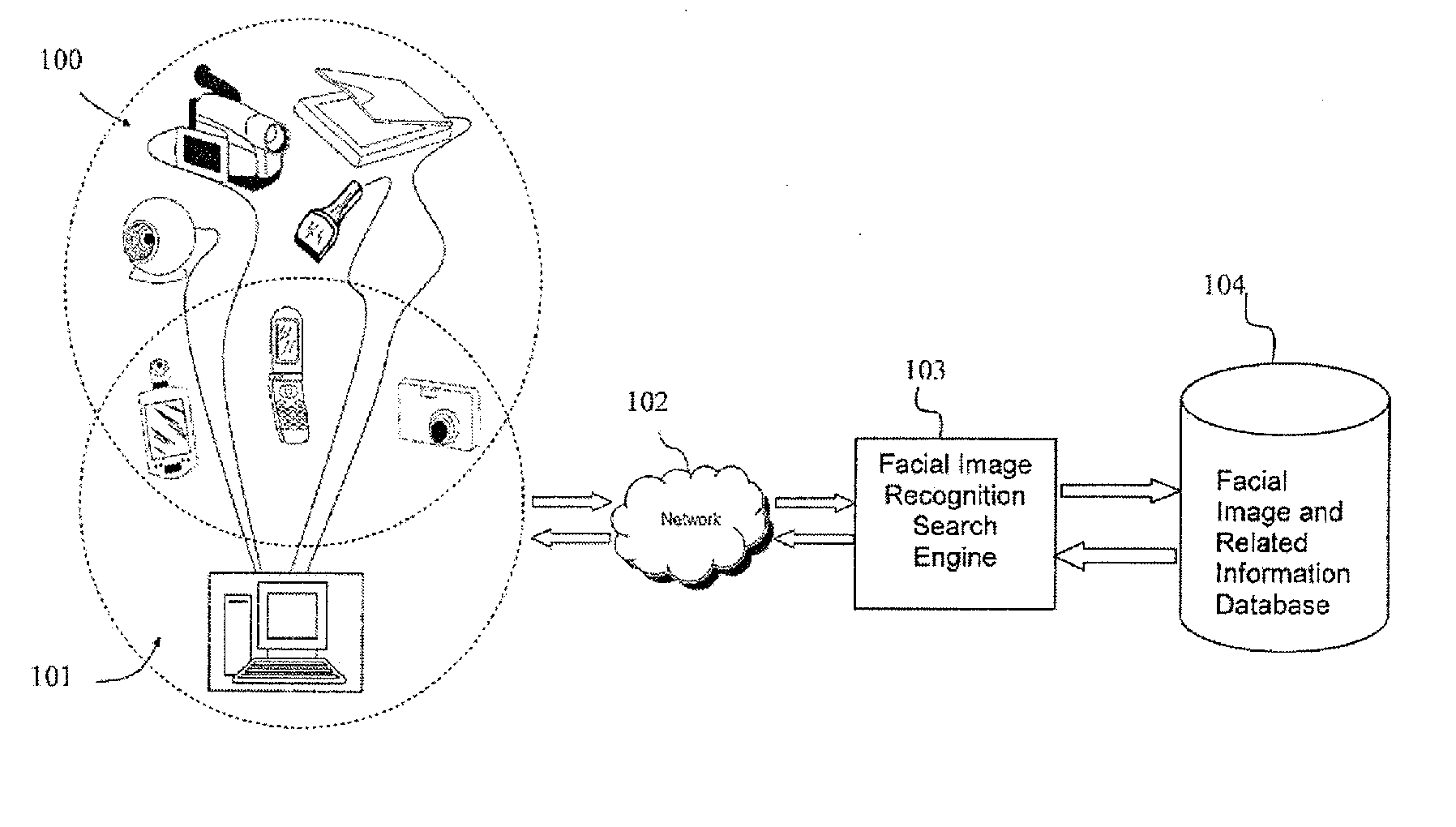
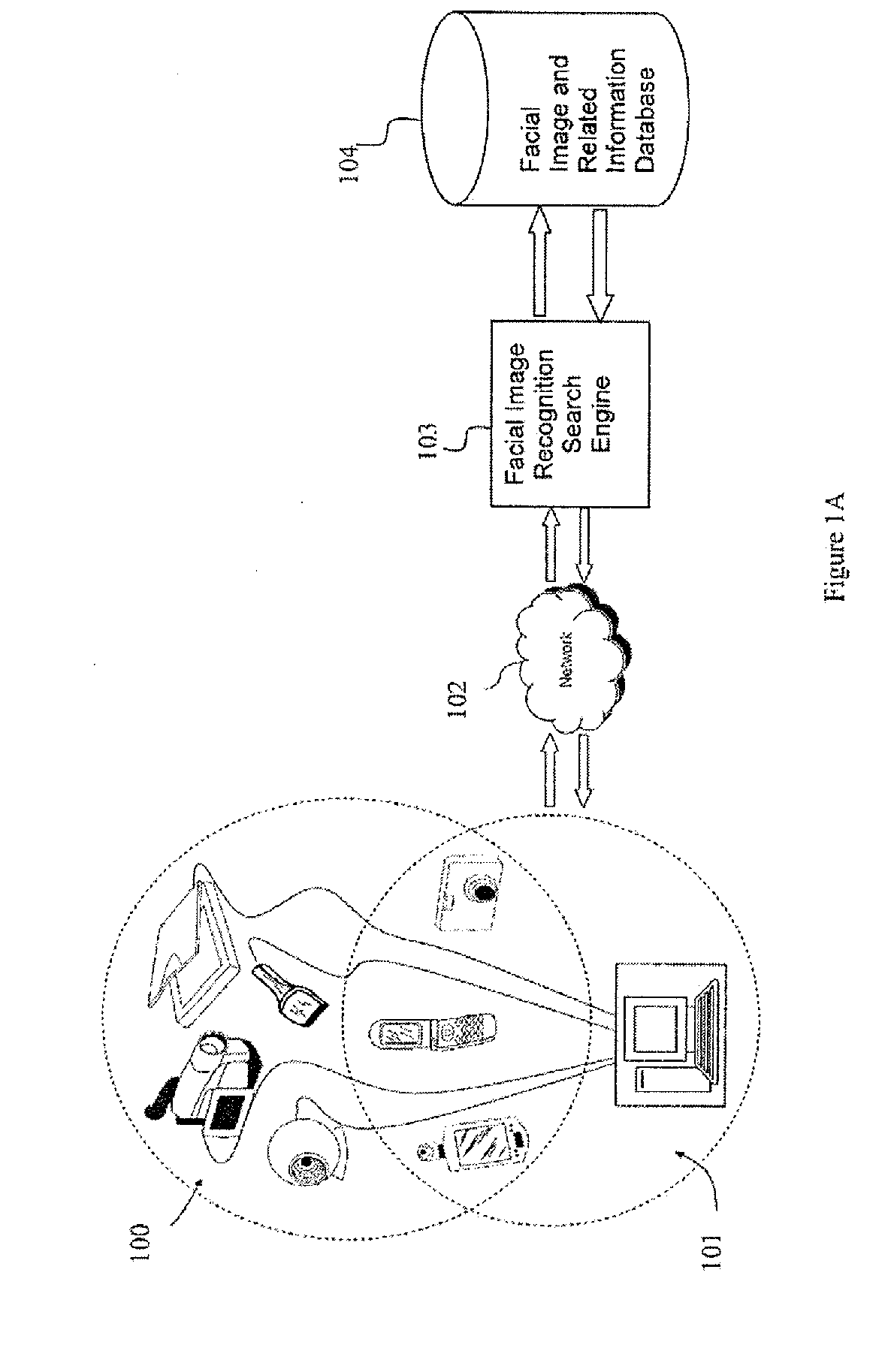
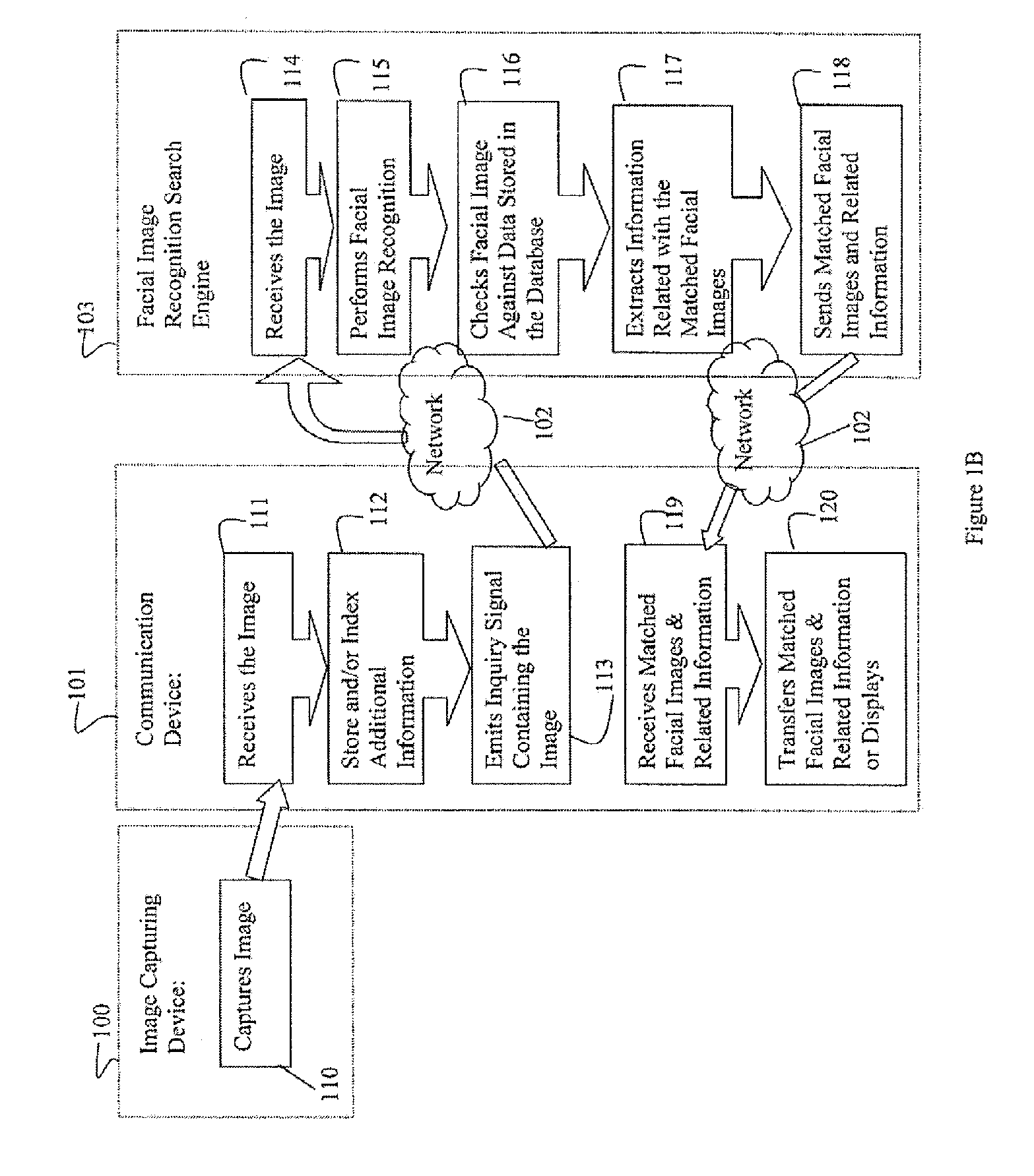
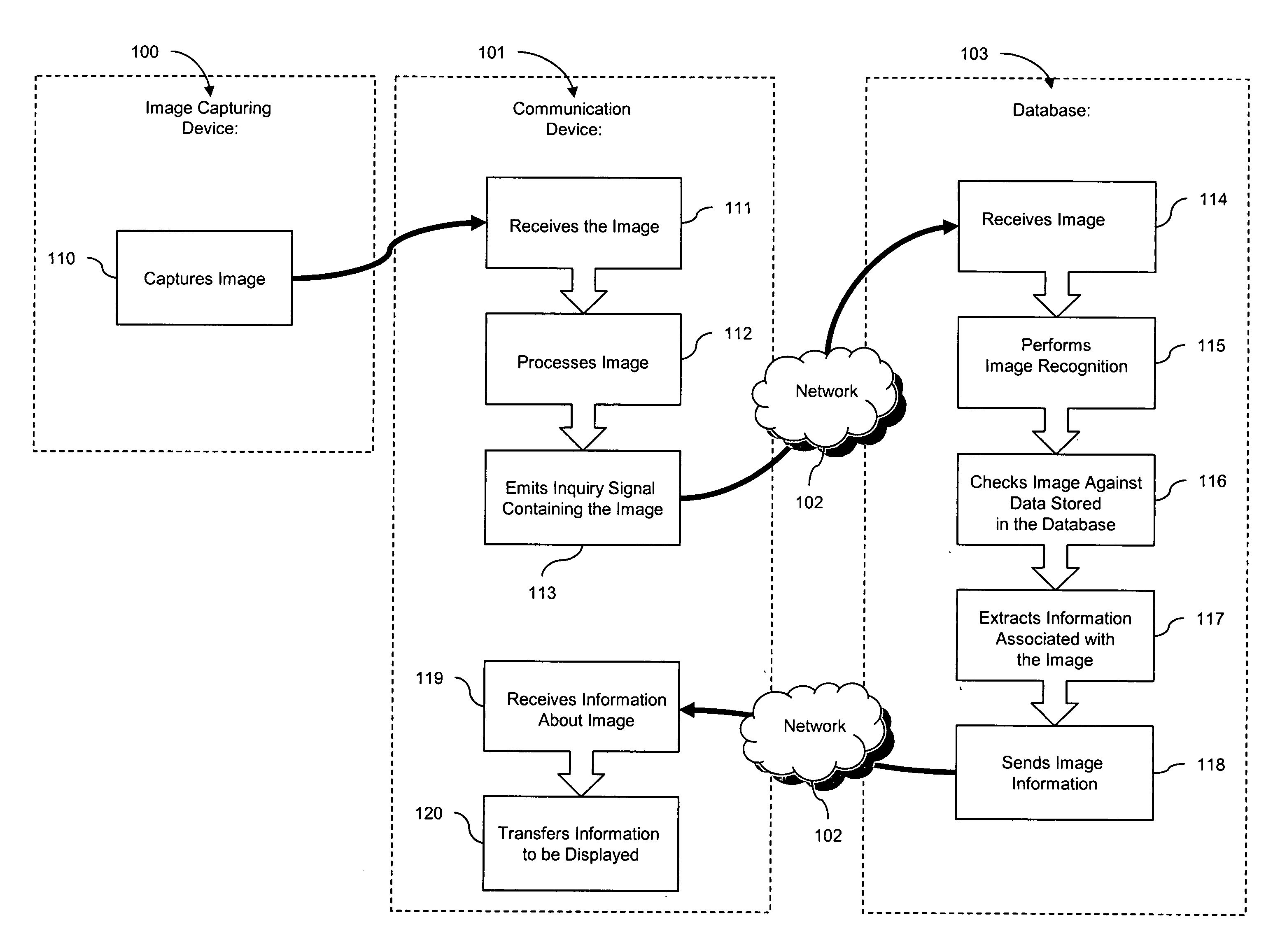
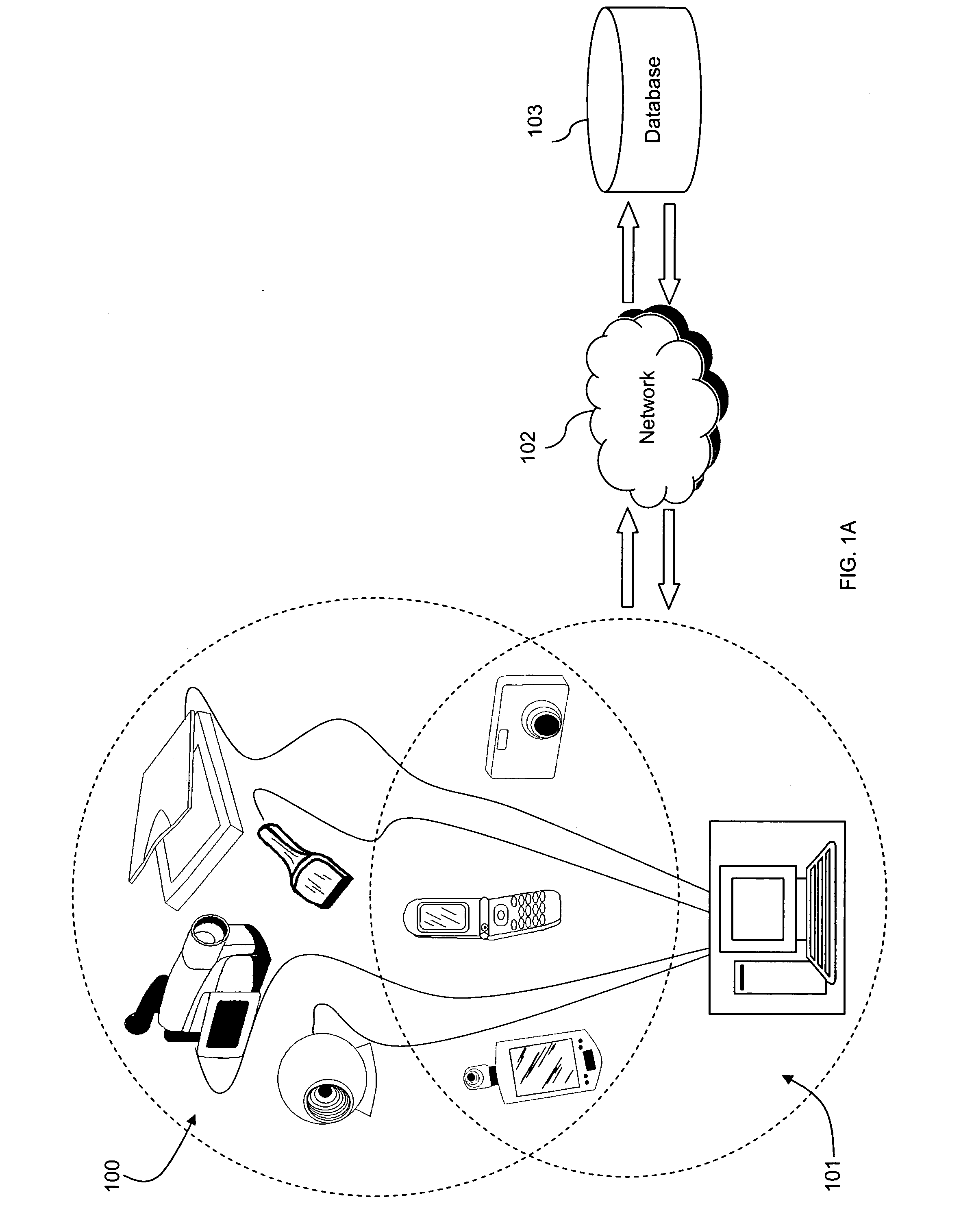
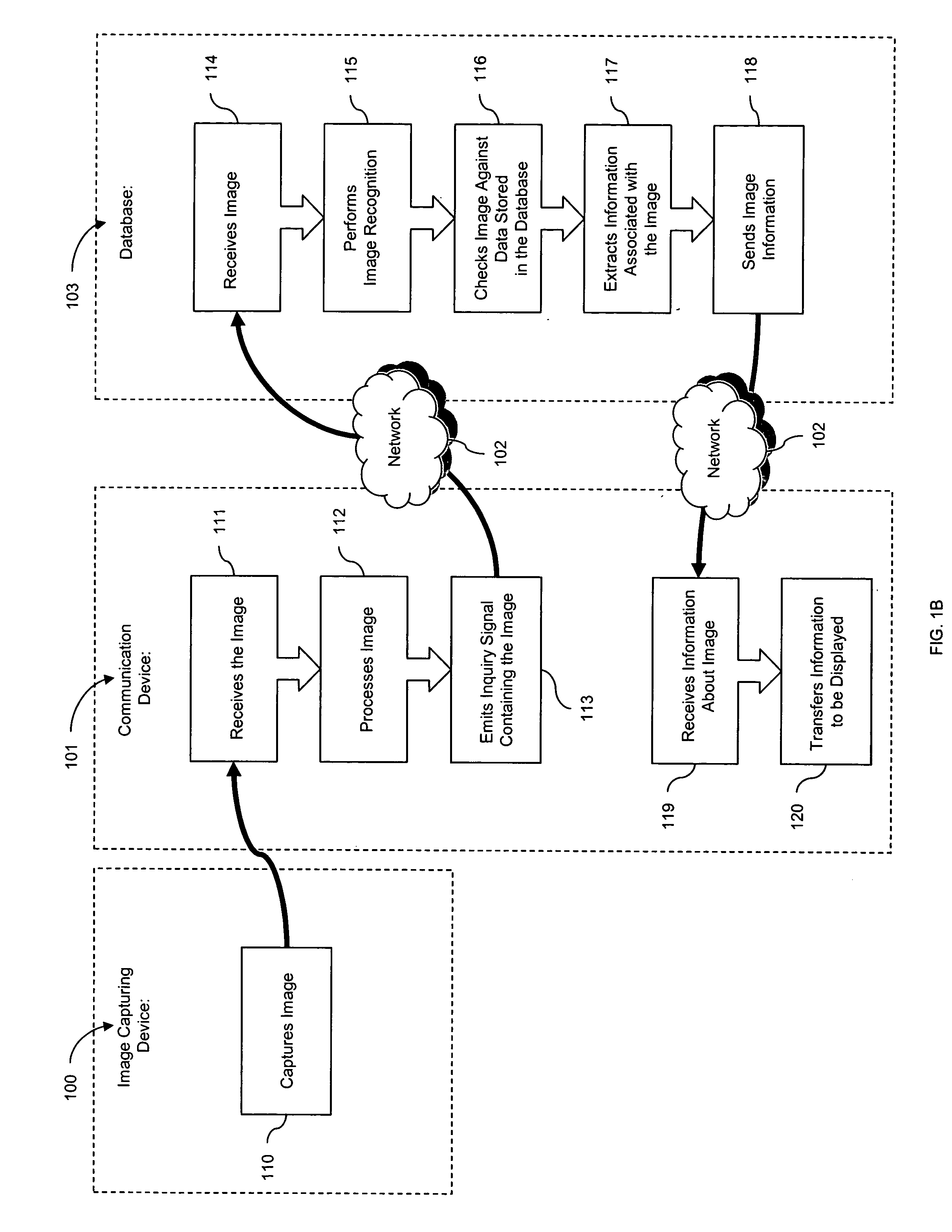
Photo Automatic Linking System and method for accessing, linking, and visualizing "key-face" and/or multiple similar facial images along with associated electronic data via a facial image recognition search engine
ActiveUS20070172155A1Quick searchEnhanced and improved organization, classification, and fast sorts and retrievalDigital data information retrievalCharacter and pattern recognitionHealth professionalsWeb crawler
The present invention provides a system and method for input of images containing faces for accessing, linking, and or visualizing multiple similar facial images and associated electronic data for innovative new on-line commercialization, medical and training uses. The system uses various image capturing devices and communication devices to capture images and enter them into a facial image recognition search engine. Embedded facial image recognition techniques within the image recognition search engine extract facial images and encode the extracted facial images in a computer readable format. The processed facial images are then entered for comparison into at least one database populated with facial images and associated information. Once the newly captured facial images are matched with similar “best-fit match” facial images in the facial image recognition search engine's database, the “best-fit” matching images and each image's associated information are returned to the user. Additionally, the newly captured facial image can be automatically linked to the “best-fit” matching facial images, along with comparisons calculated, and / or visualized. Key new use innovations of the system include but are not limited to: input of user selected facial images for use finding multiple similar celebrity look-a-likes, with automatic linking that return the look-a-like celebrities' similar images, associated electronic information, and convenient opportunities to purchase fashion, jewelry, products and services to better mimic your celebrity look-a-likes; health monitoring and diagnostic use by conveniently organizing and superimposing periodically captured patient images for health professionals to view progress of patients; entirely new classes of semi-transparent superimposed training your face to mimic other similar faces, such as mimic celebrity look-a-like cosmetic applications, and or facial expressions; intuitive automatic linking of similar facial images for enhanced information technology in the context of enhanced and improved organization, classification, and fast retrieval objects and advantages; and an improved method of facial image based indexing and retrieval of information from the web-crawler or spider searched Web, USENET, and other resources to provide new types of intuitive easy to use searching, and / or combined use with current key-word searching for optimized searching.
Owner:VR REHAB INC +2
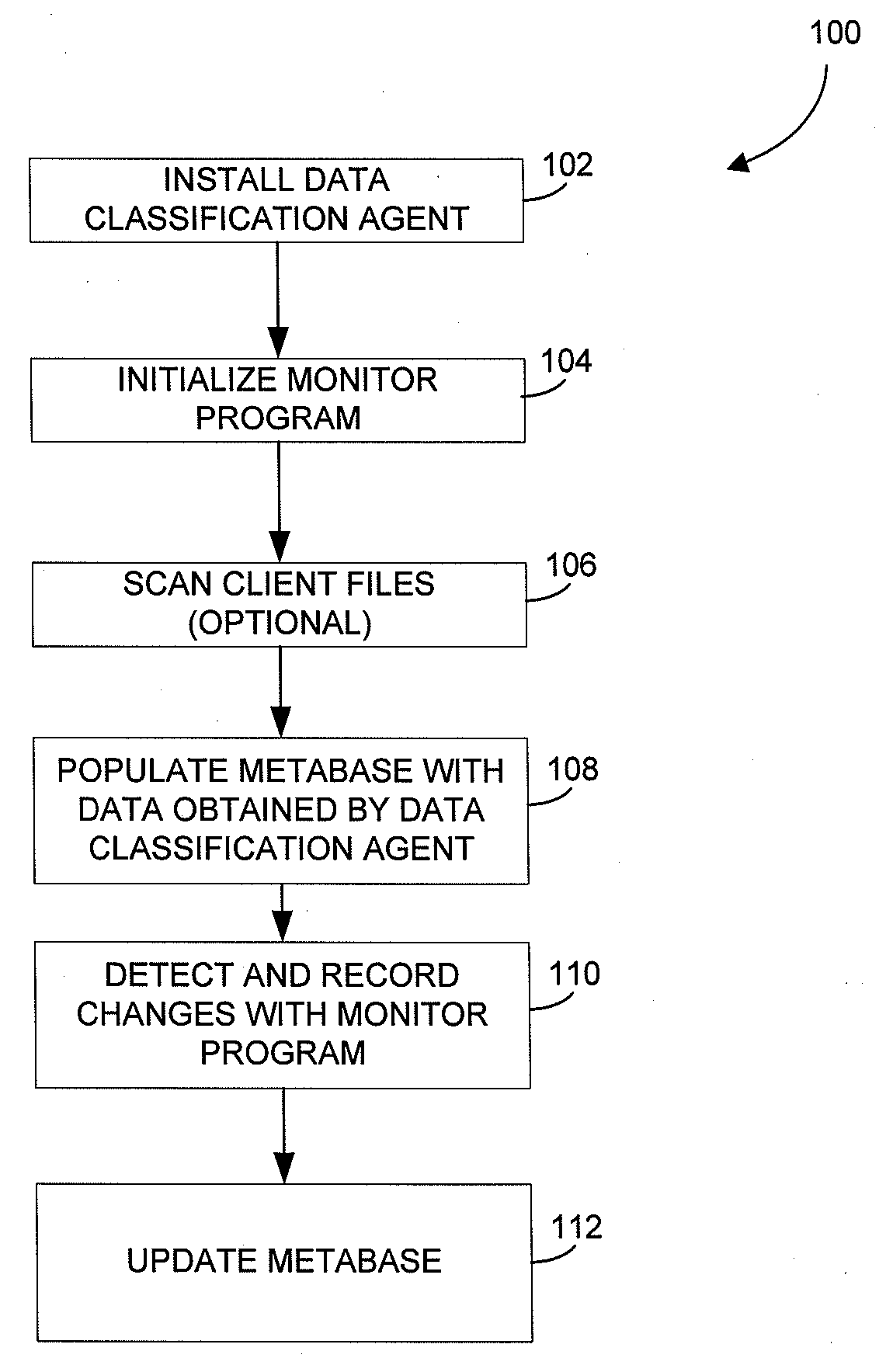
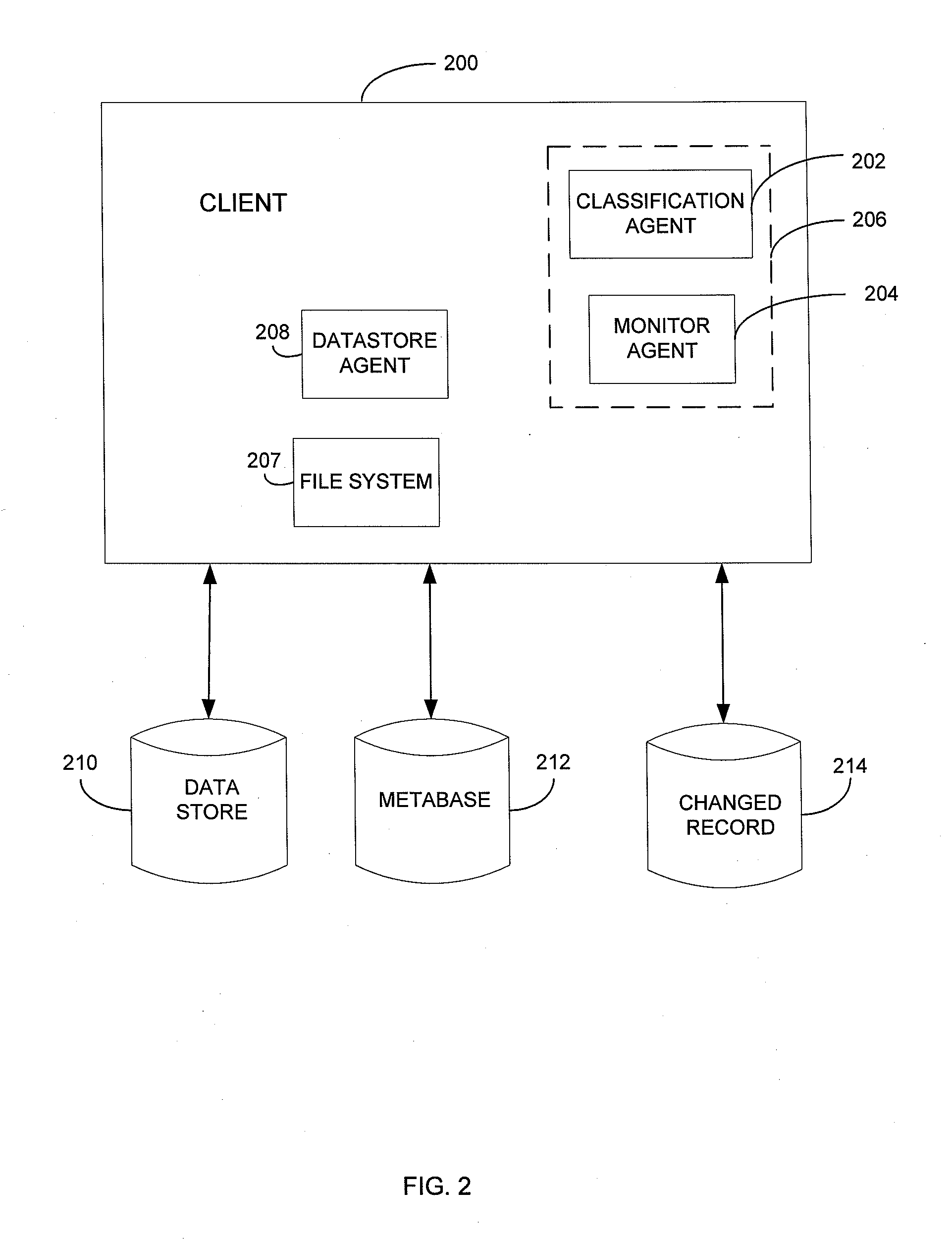
Metabase for facilitating data classification
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
Internet-based consumer product brand marketing communication system which enables manufacturers, retailers and their respective agents, and consumers to carryout product-related functions along the demand side of the retail chain in an integrated manner
InactiveUS20030009392A1Easy accessEasy alignmentDigital data information retrievalData switching by path configurationInformation resourceGeneric Product
An Internet-based consumer product brand marketing communication system which enables manufacturers, retailers and their respective agents, and consumers to carryout product-related functions along the demand side of the retail chain. A central RDBMS (i.e. data warehouse) stores a central database of consumer product related information resource files (IRFs) each IRF being indexed with a Universal Product Number (UPN) assigned thereto by the manufacturer of the consumer product, or its designated agent, which relates to the consumer product. A first subsystem enables a manufacturer's marketing, brand and / or product managers to create and manage a local RDBMS containing UPN-indexed IRFs related to the consumer products of the manufacturer being offered for sale in both physical and / or electronic marketplaces, and periodically transport the local RDBMS of UPN-indexed IRFs to the central RDBMS by electronic data transport techniques. The local RDBMS of UPN-indexed IRFs is selected by the manufacturer's marketing, brand and / or product managers so as to create a desired brand image for each the consumer product of the manufacturer. A second subsystem enables consumers to access one or more UPN-indexed IRFs in the central RDBMS, to request and obtain information about a manufacturer's consumer product so as to make informed / educated purchases along the demand side of the retail chain. A third subsystem enables manufacturers and their advertising and marketing agents to access one or more UPN-indexed IRFs in the central RDBMS to display consumer product advertisements to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to project the desired brand image to consumers. A fourth subsystem enables retailers and their marketing and promotional agents to access one or more UPN-indexed IRFs in the central RDBMS, to promote consumer products to consumers, at or near the point of purchase or sale within both physical and / or electronic retail shopping environments so as to promote the sale of such products in inventory.
Owner:PERKOWSKI THOMAS J
System and method for accessing electronic data via an image search engine
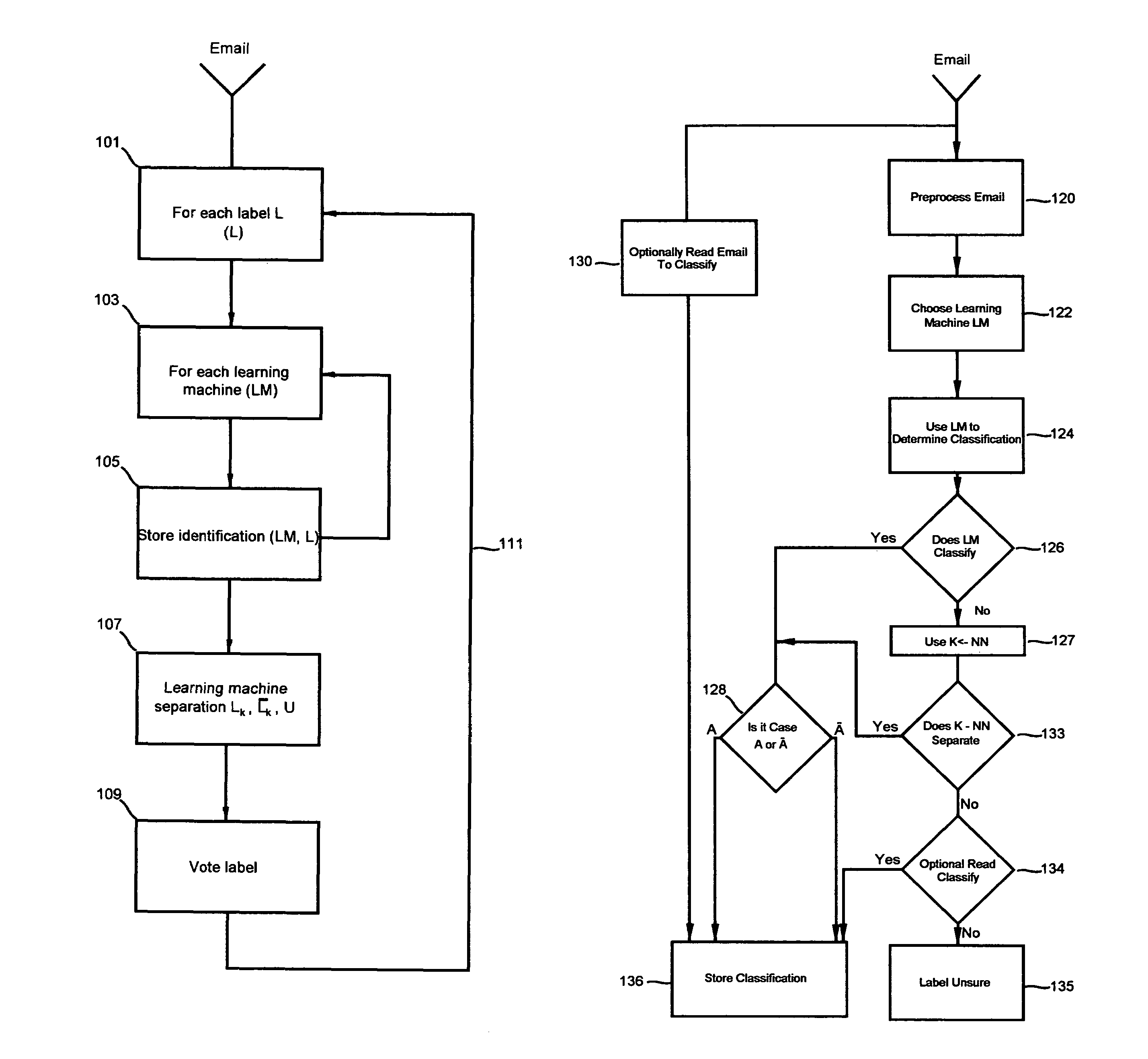
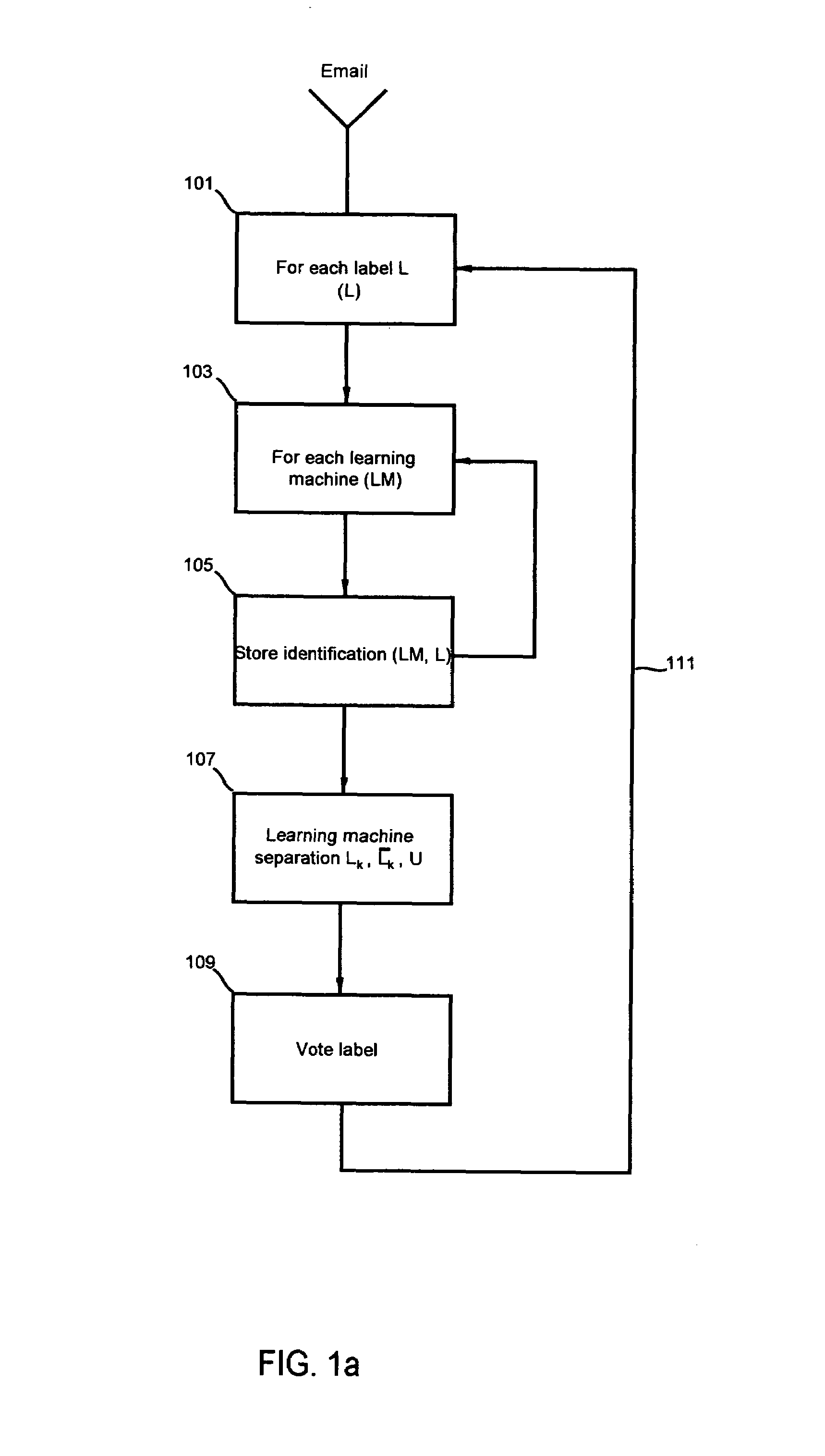
InactiveUS20060227992A1Extraction of informationStill image data retrievalDigital data processing detailsRelevant informationImage matching
The present invention provides a system and method for accessing electronic data through entry of images as queries in search engine. The system uses various image capturing devices and communication devices to capture images and enter them into image database. Image recognition techniques encode images in a computer readable format. The processed image is then entered for comparison into at least one database populated with images and associated information. Once the newly captured image is matched with an image in the database, the information linked with that image is returned to the user.
Owner:HYDRA GRP HLDG LLC
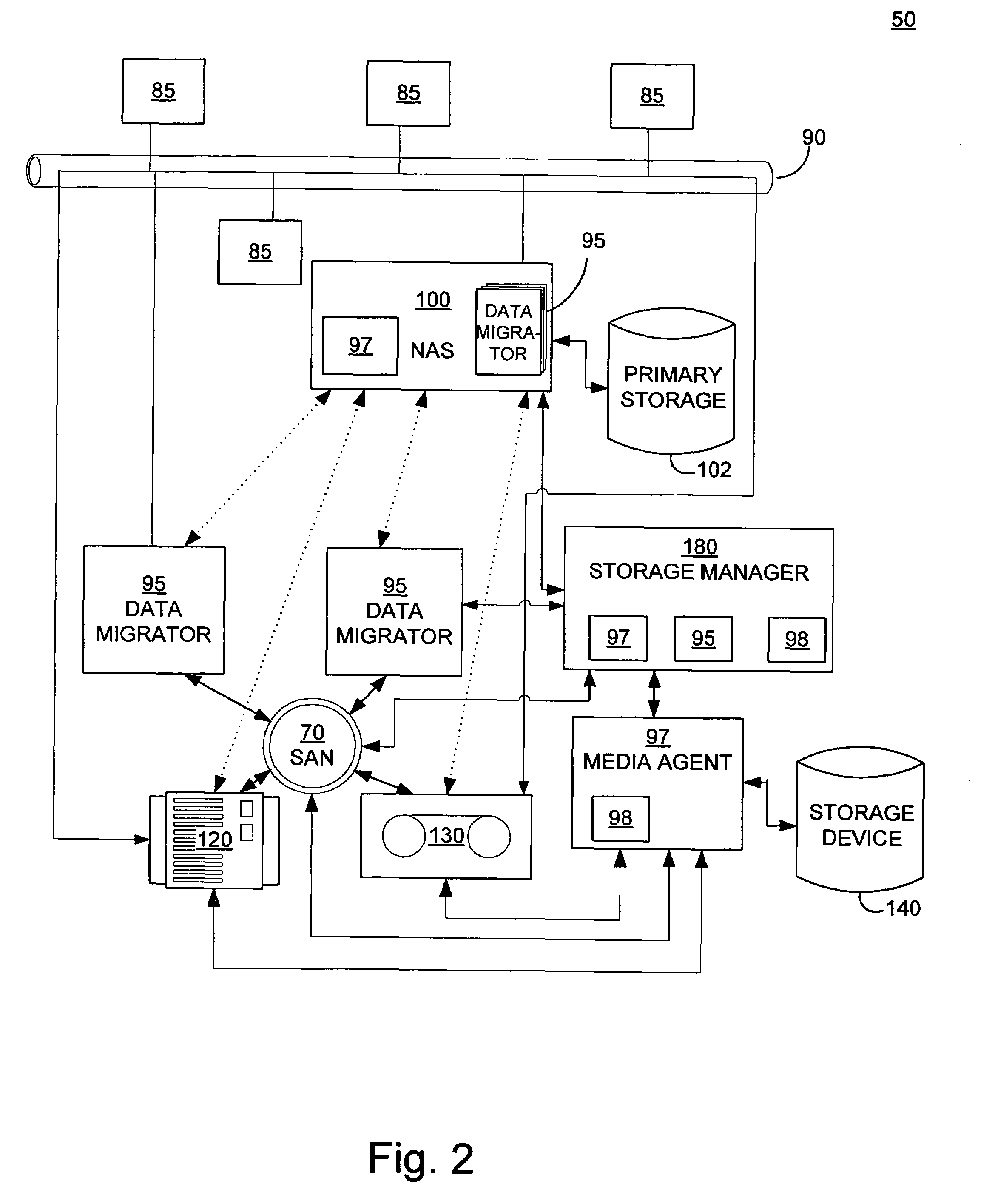
Systems and methods for performing storage operations using network attached storage
ActiveUS20060010154A1More processedData processing applicationsDigital data information retrievalAuxiliary memoryData storing
Systems and methods for performing hierarchical storage operations on electronic data in a computer network are provided. In one embodiment, the present invention may store electronic data from a network device to a network attached storage (NAS) device pursuant to certain storage criteria. The data stored on the NAS may be migrated to a secondary storage and a stub file having a pointer pointing to the secondary storage may be put at the location the data was previously stored on the NAS. The stub file may redirect the network device to the secondary storage if a read request for the data is received from the network device.
Owner:COMMVAULT SYST INC
Apparatus for analyzing biologic fluids
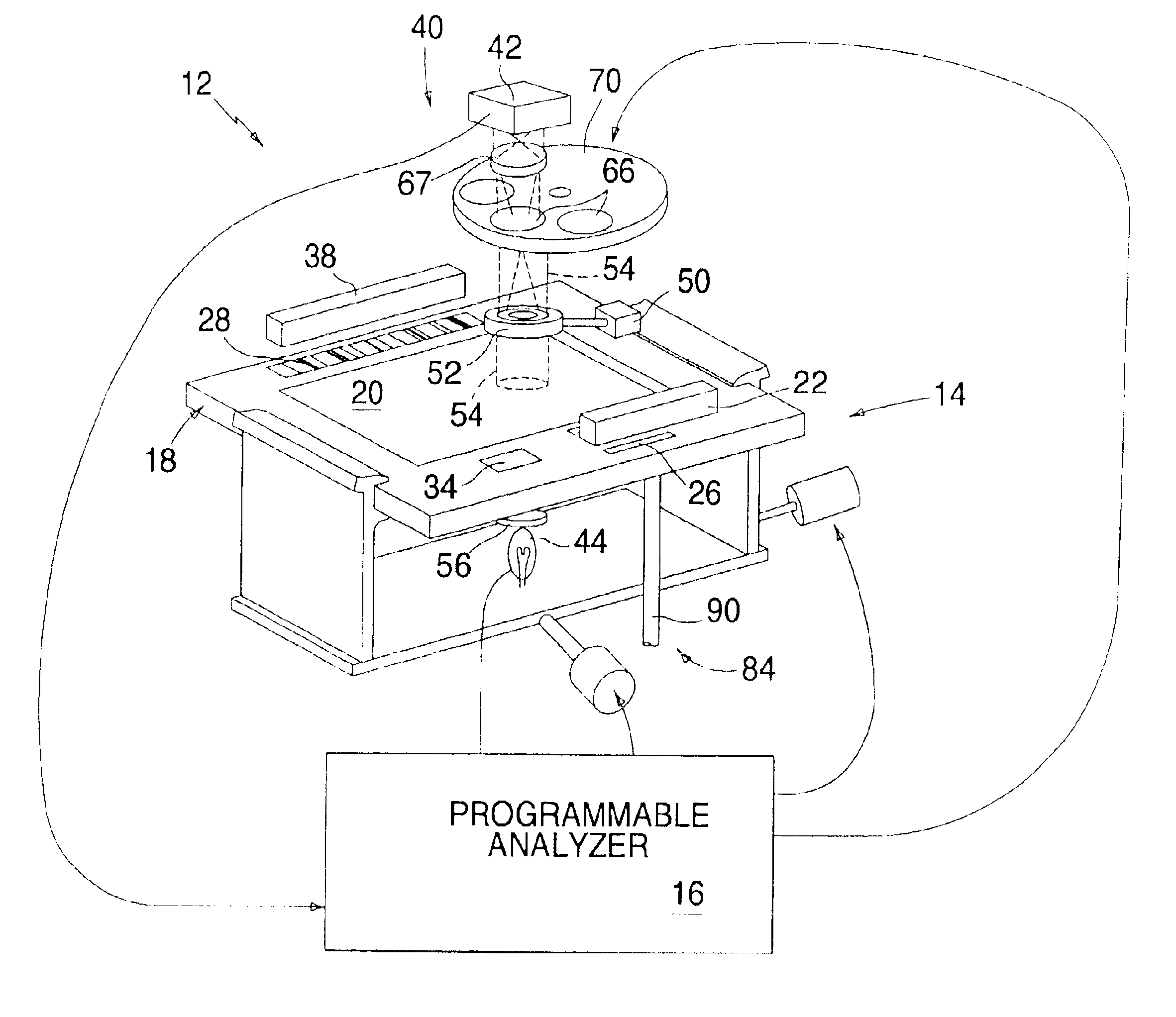
InactiveUS6866823B2Low costReduce spacingMaterial analysis by observing effect on chemical indicatorChemiluminescene/bioluminescenceImage dissectorImage conversion
An apparatus for analyzing a sample of biologic fluid quiescently residing within a chamber is provided. The apparatus includes a light source, a positioner, a mechanism for determining the volume of a sample field, and an image dissector. The light source is operable to illuminate a sample field of known, or ascertainable, area. The positioner is operable to selectively change the position of one of the chamber or the light source relative to the other, thereby permitting selective illumination of all regions of the sample. The mechanism for determining the volume of a sample field can determine the volume of a sample field illuminated by the light source. The image dissector is operable to convert an image of light passing through or emanating from the sample field into an electronic data format.
Owner:WARDLAW PARTNERS +2
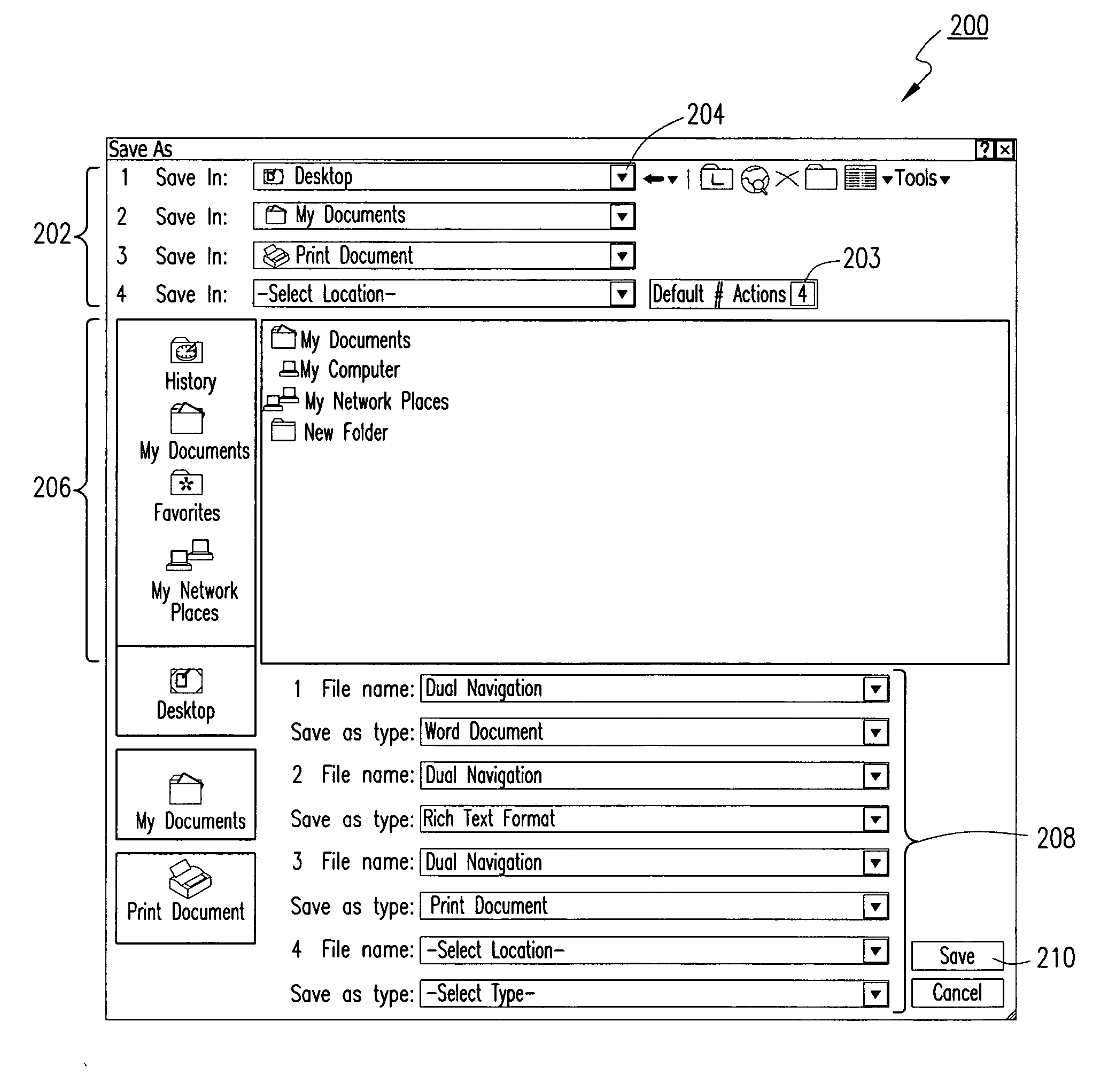
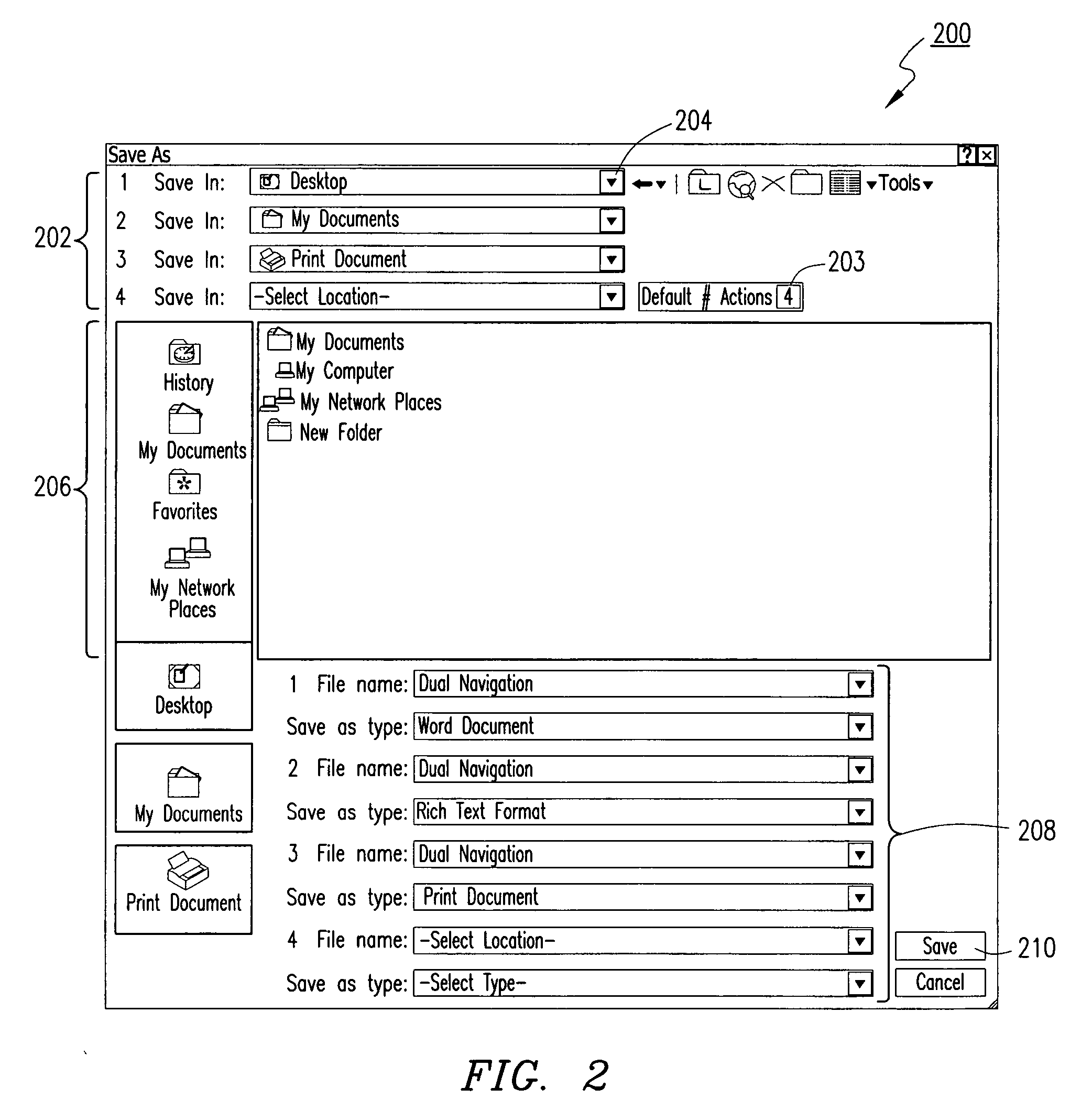
Method and graphic interface for storing, moving, sending or printing electronic data to two or more locations, in two or more formats with a single save function
InactiveUS20060129746A1Shorten the timeProgram loading/initiatingExecution for user interfacesGraphicsComputer users
A single graphic user interface enabling a computer user to store, print, back up or send an electronic file to multiple locations. The electronic file can be sent on multiple paths to multiple devices in multiple formats.
Owner:ITHINK
Method and apparatus for securing electronic data
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
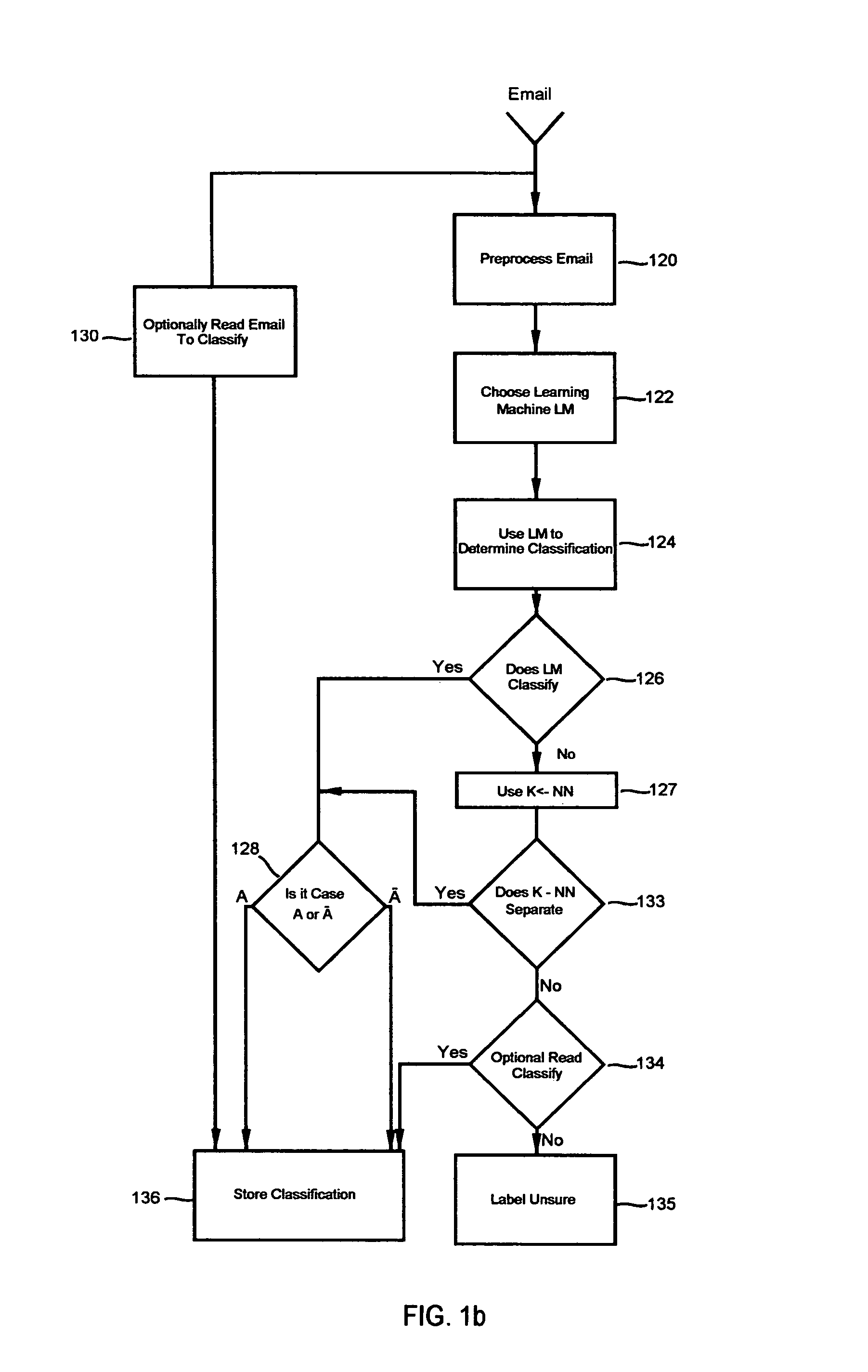
Networked personal customized information and facility services
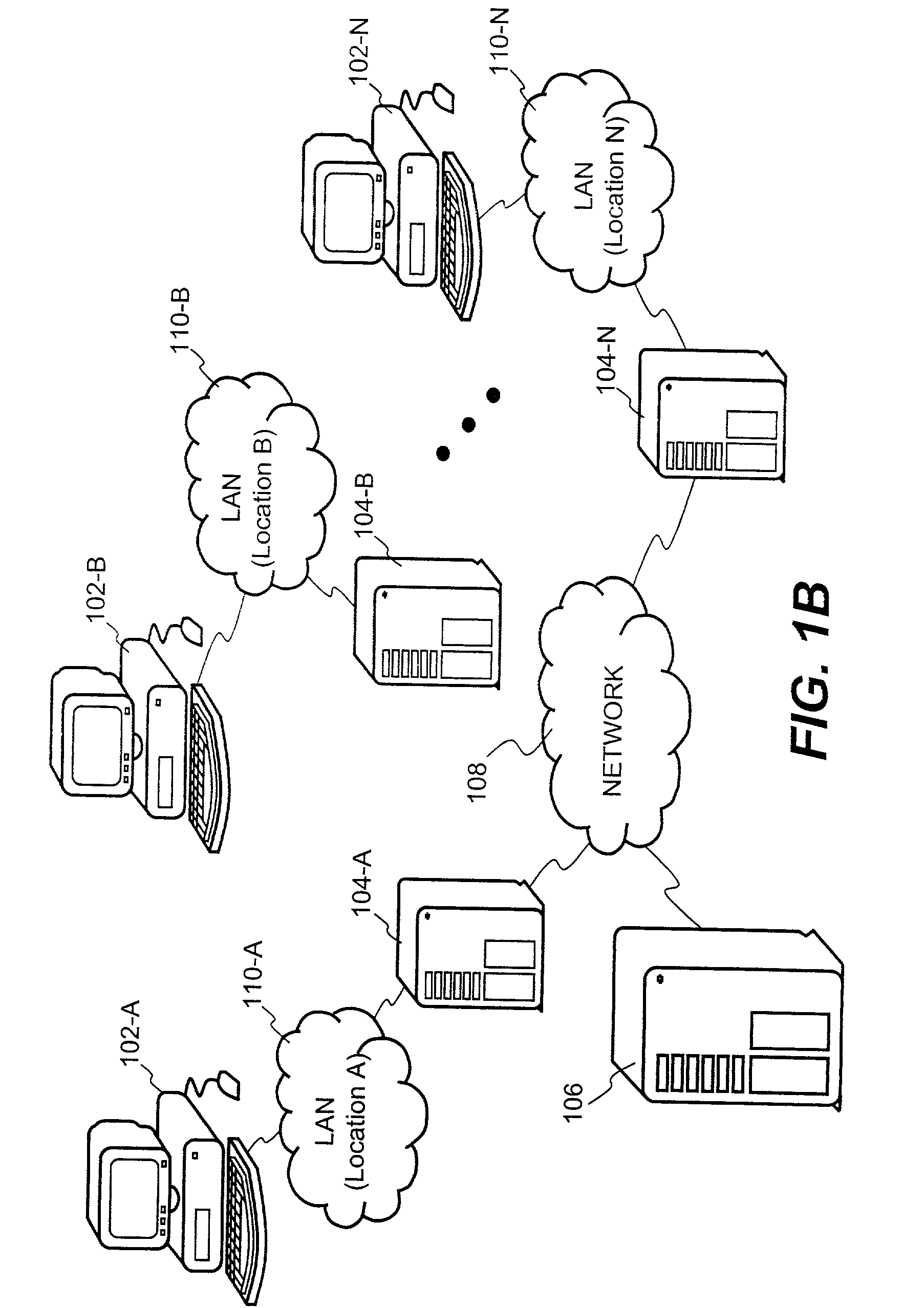
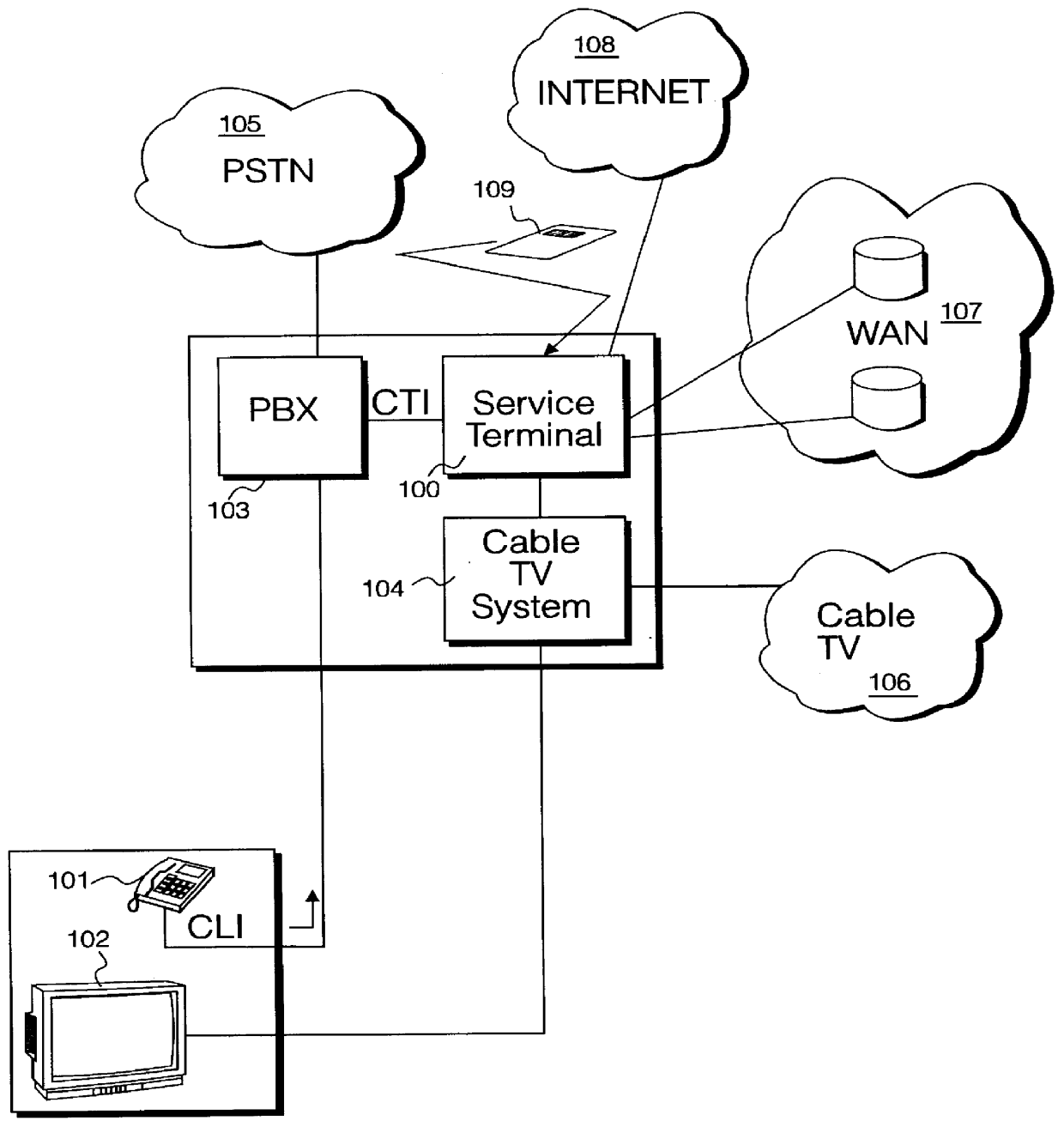
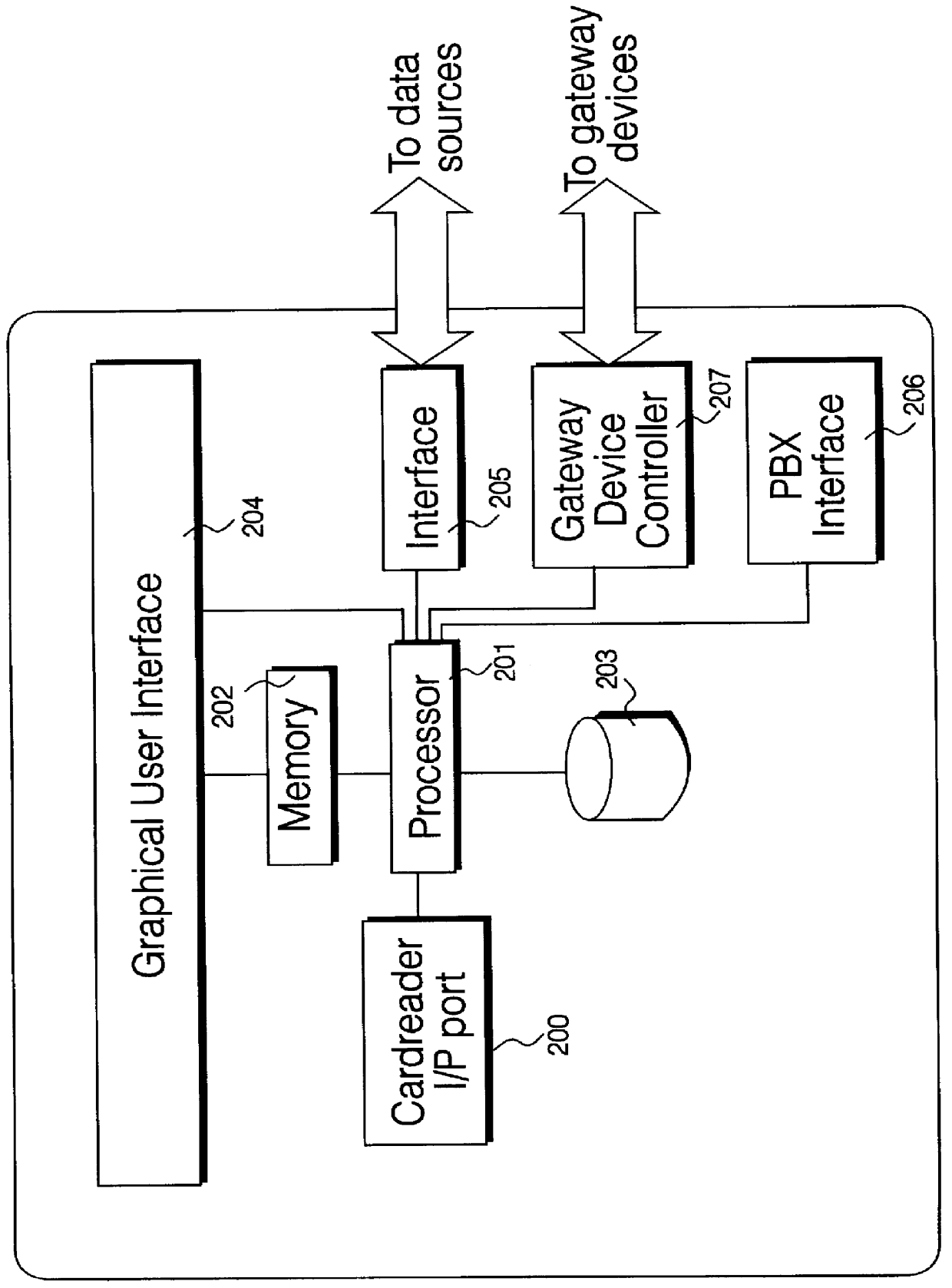
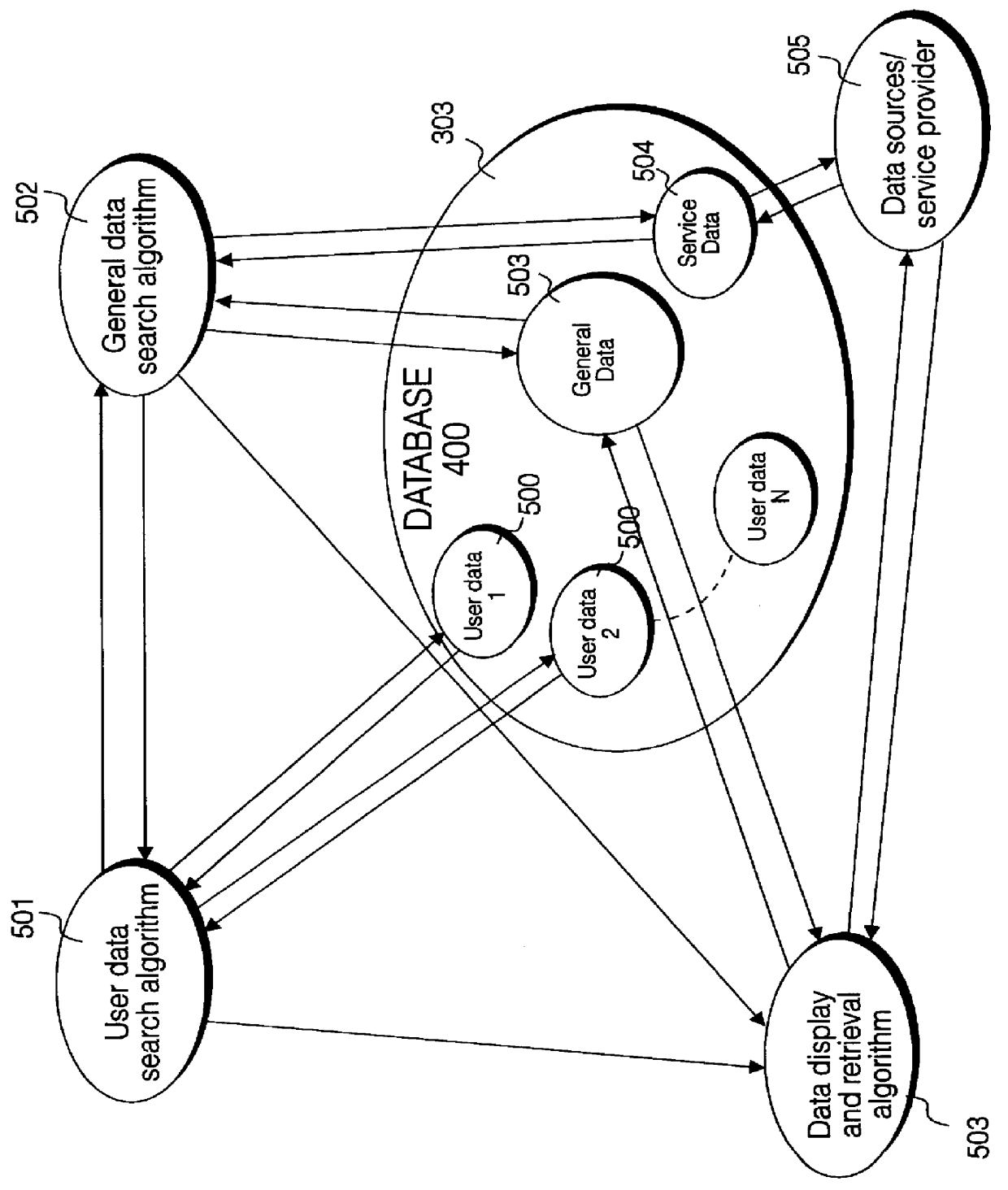
InactiveUS6055512AMultiple digital computer combinationsBuying/selling/leasing transactionsData displayPersonal details
A service terminal facility is provided at a public access location, for example in a hotel, hospital or airport, the service terminal facility available for providing electronic information services to users, in response to input of a portable data storage medium, for example a smart card or the like. A smart card contains stored data describing user specified information such as contacts names, personal details and medical information and personal interest information. The service terminal comprises a search engine for searching the user data and comparing data types within the user data with general data stored locally at the service terminal. The service terminal selects data corresponding to data types specified in the user data and displays these on the graphical user interface at the service terminal, or at a user interface connected with the service terminal. The user data may specify one or more data sources or service providers from which electronic data services of interest to the user can be obtained. The service terminal may obtain listings of data from remote data sources and / or service providers and display these on the graphical user interface and / or user interface. The user may instruct downloading of electronic data or electronic information services from remote data sources or service providers from the service terminal for delivery to the graphical user interface or the user interface.
Owner:NORTEL NETWORKS LTD
System and method for performing replication copy storage operations
InactiveUS20070143371A1Data processing applicationsDatabase distribution/replicationThird partyStorage management
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
System and method for authentication, data transfer, and protection against phishing
ActiveUS20090077383A1Key distribution for secure communicationDigital data processing detailsElectronic communicationPhishing
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com