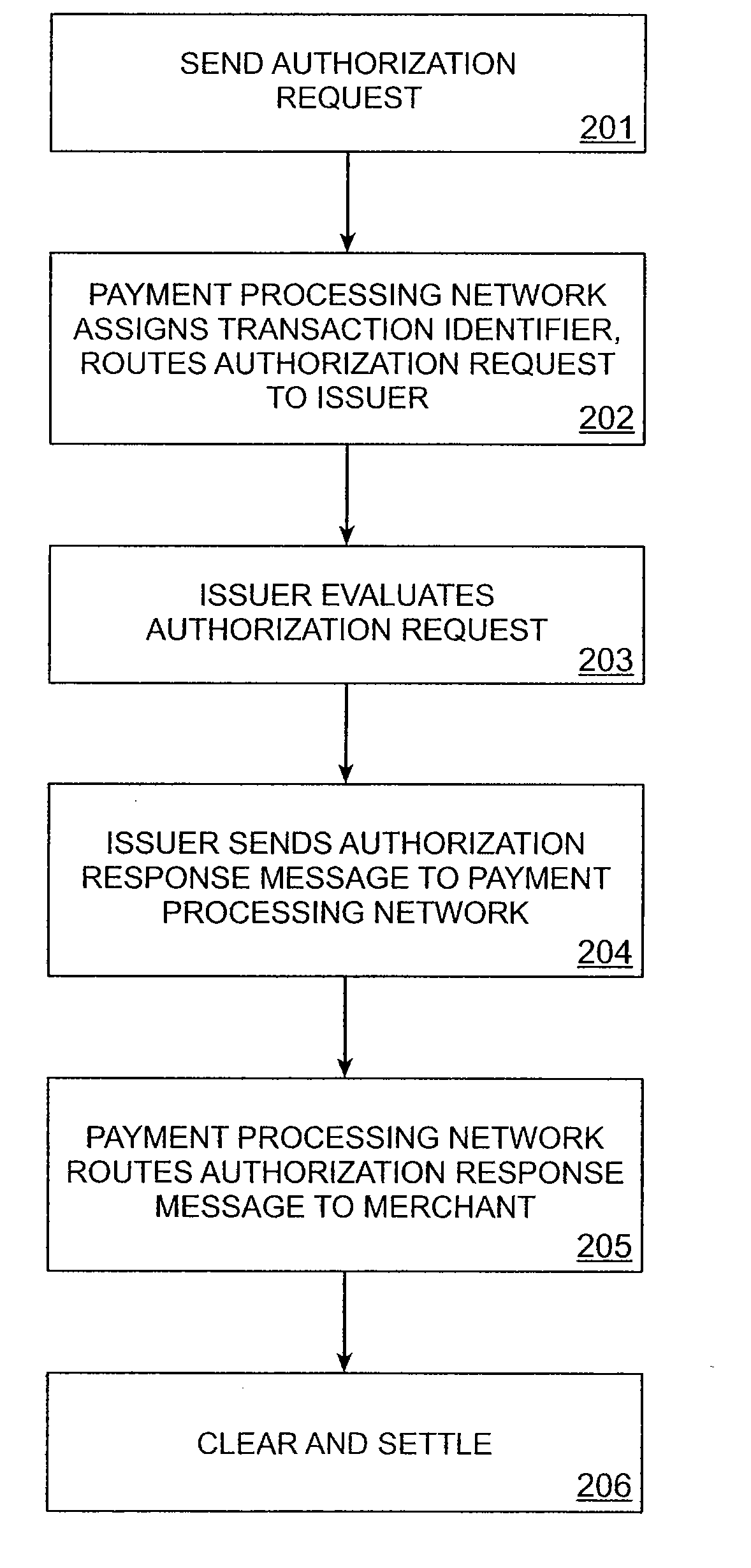
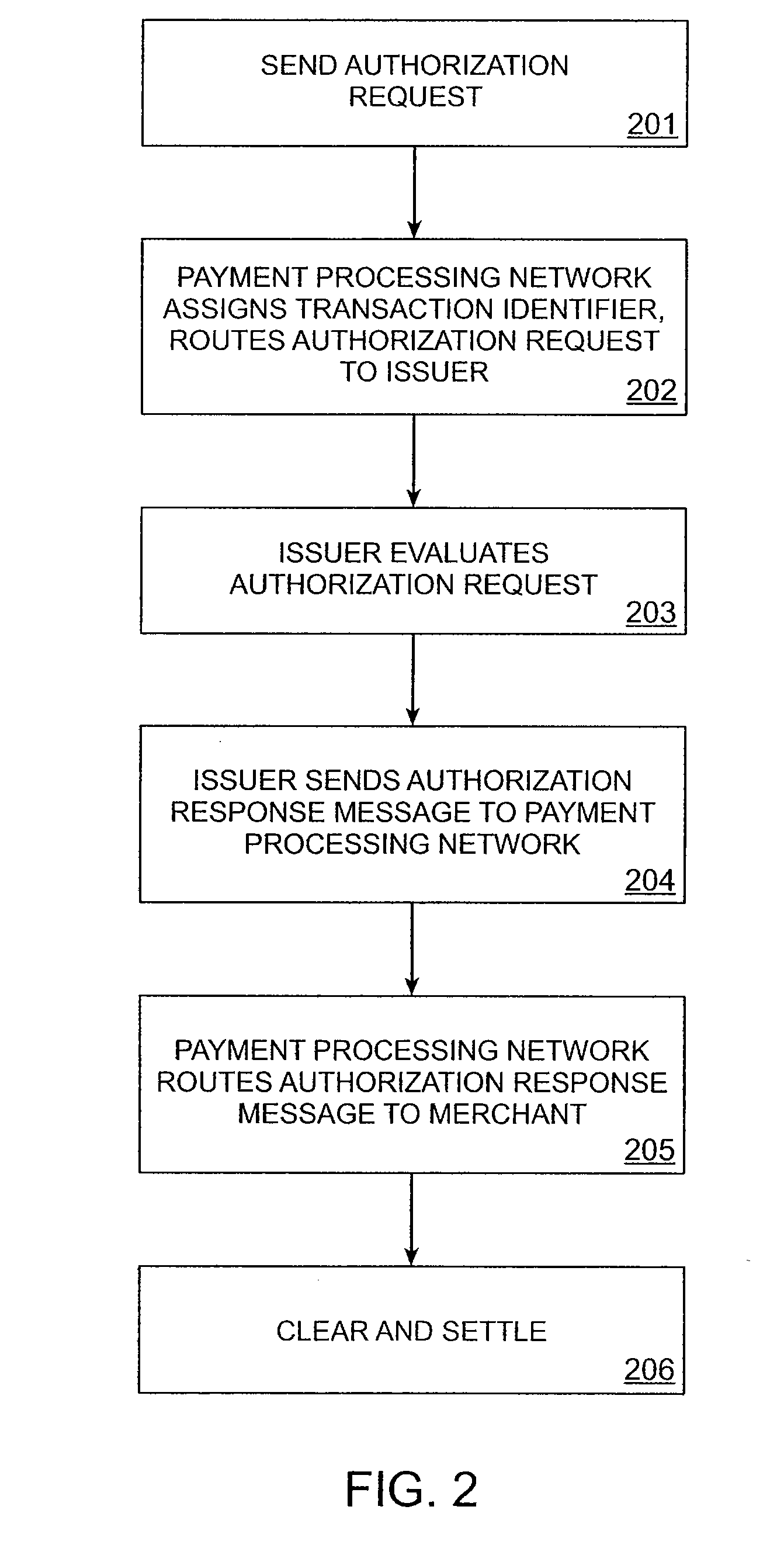
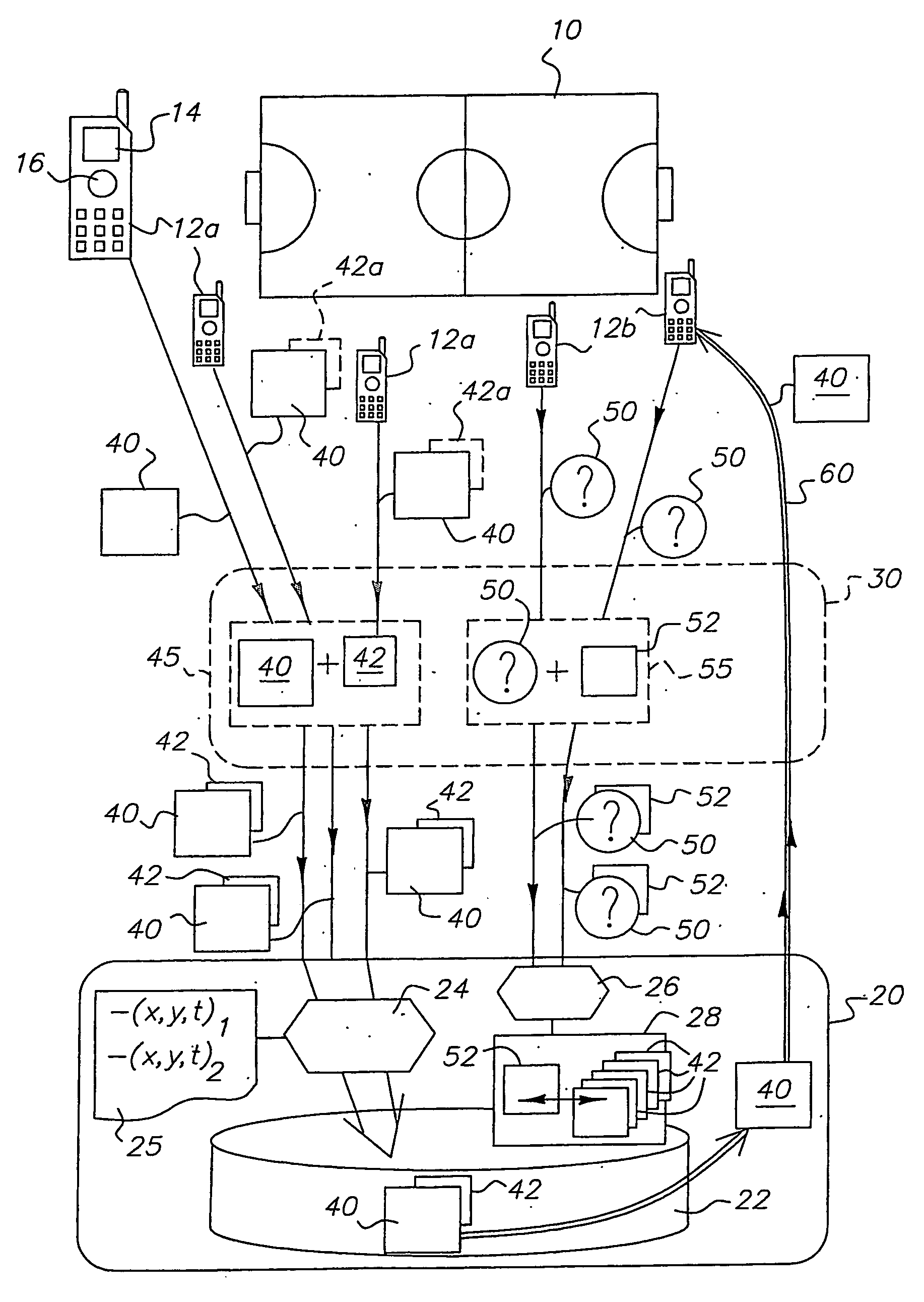
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
202results about How to "Avoid storage problems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System for electronic file collaboration among multiple users using peer-to-peer network topology
InactiveUS7353252B1Avoid storage problemsMultiple digital computer combinationsOffice automationDocumentation procedurePrivate network
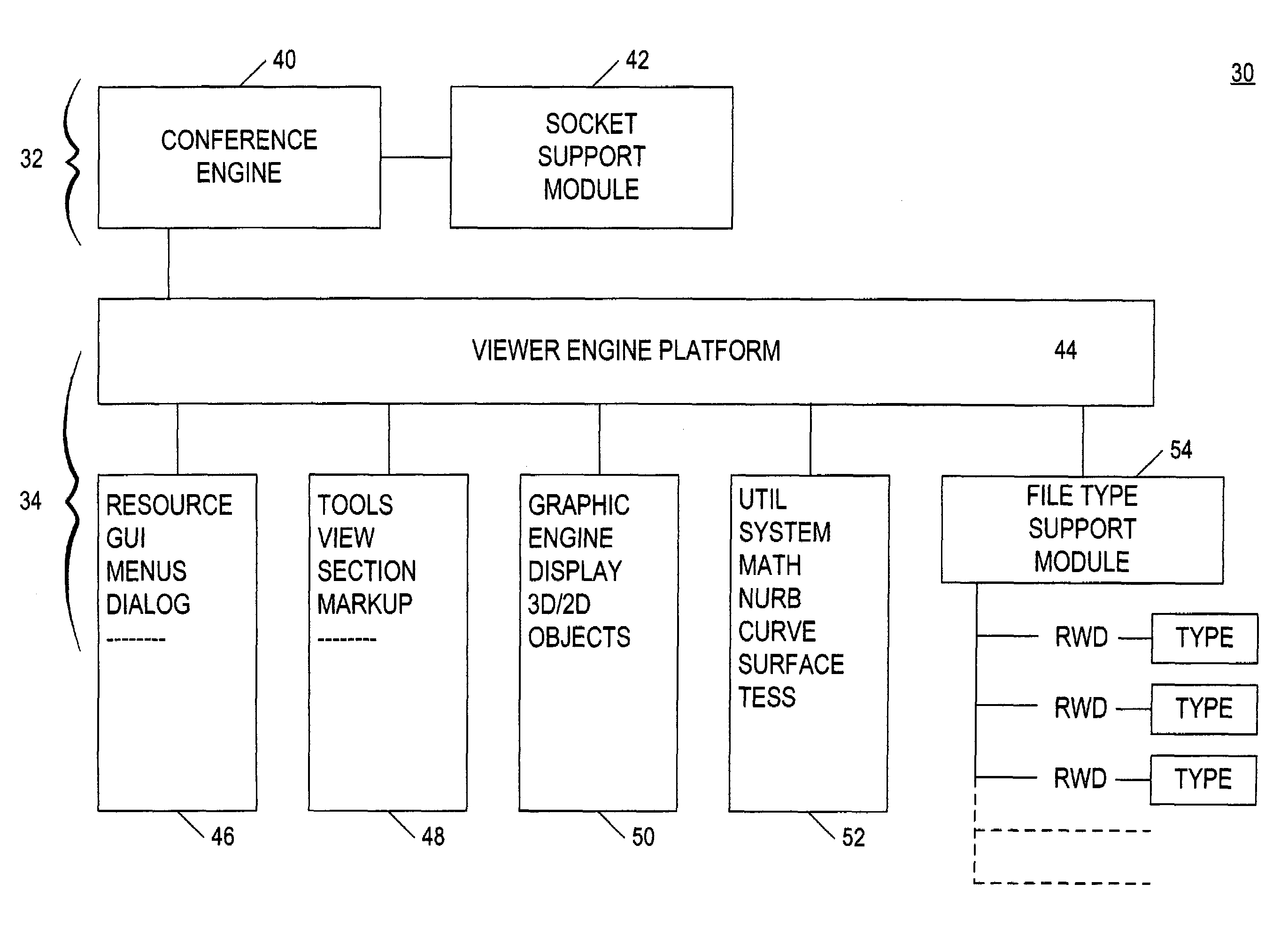
A system for electronic file collaboration among multiple users is implemented using command messages transmitted on dedicated network channels established between conference participants in a peer-to-peer architecture with total autonomy from a central server. The system employs owner-in-control methodology to allow direct transmission of copies of documents among participants by permission, and to prevent storage of copies of documents used in a conference by participants. Mark-ups, additions, and other actions occurring on a conference document can only be saved by the document owner. An advanced viewer engine is provided for reading, displaying and manipulating electronic data in texts, tables, vectors and 3D model formats, as well as common raster images. A proxy module allows data transmitted through IPFW routers or firewall devices with sufficient authentications and security measures.
Owner:SIGMA DESIGNS
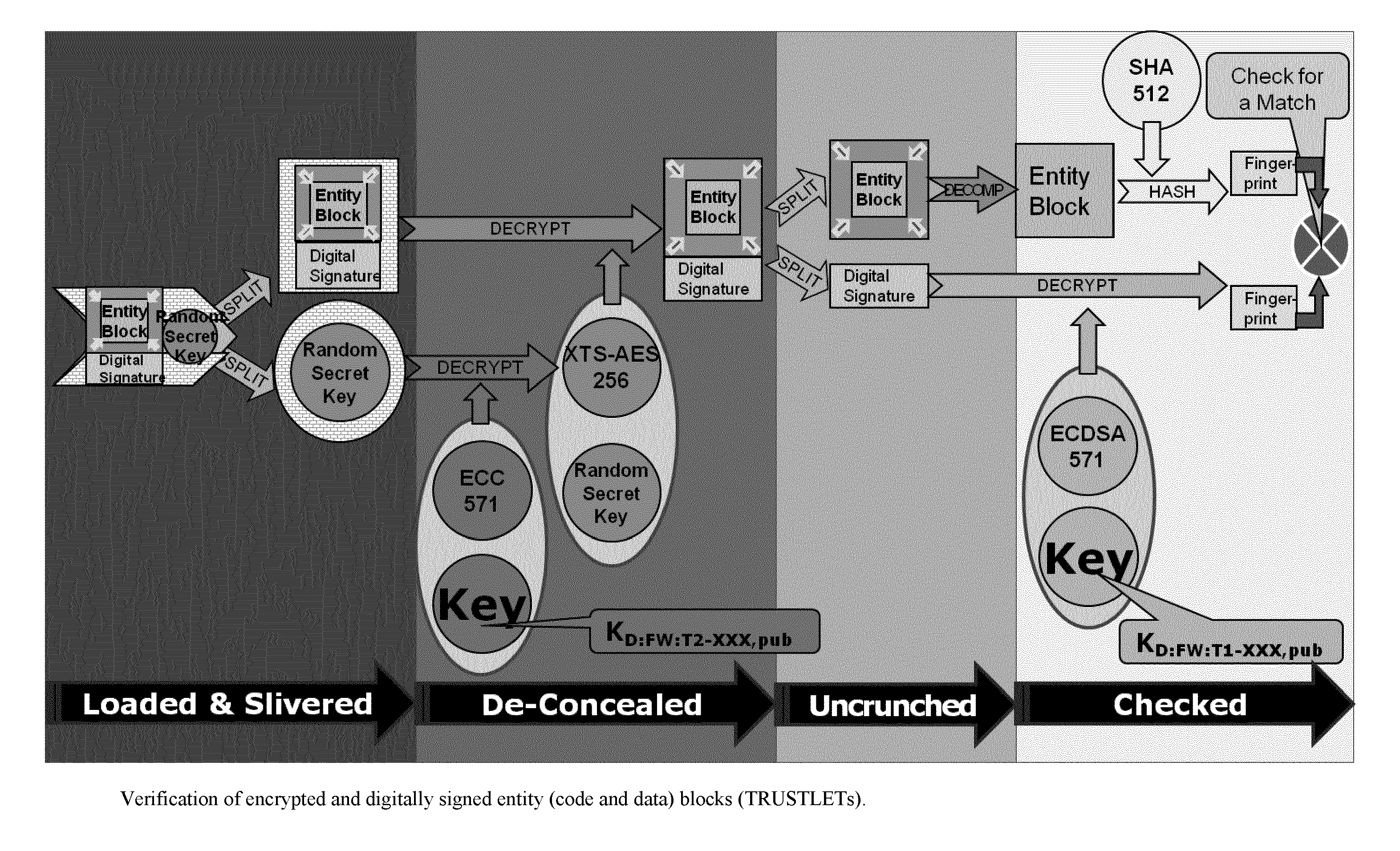
Tamper-protected hardware and method for using same
ActiveUS20140108786A1Execution of malicious code is preventedPreventing executionKey distribution for secure communicationMultiple keys/algorithms usageTamper proof hardwareComputer module
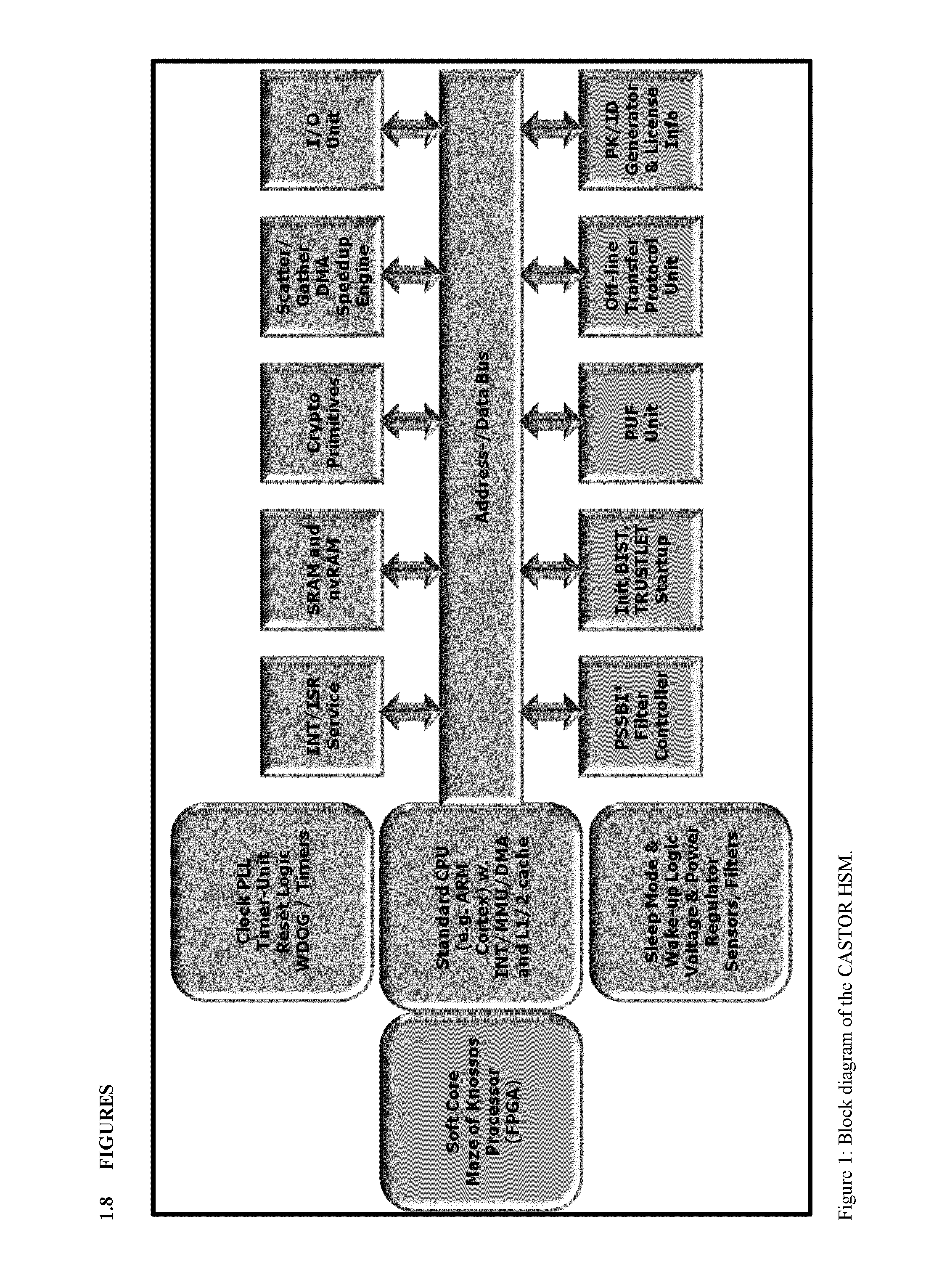
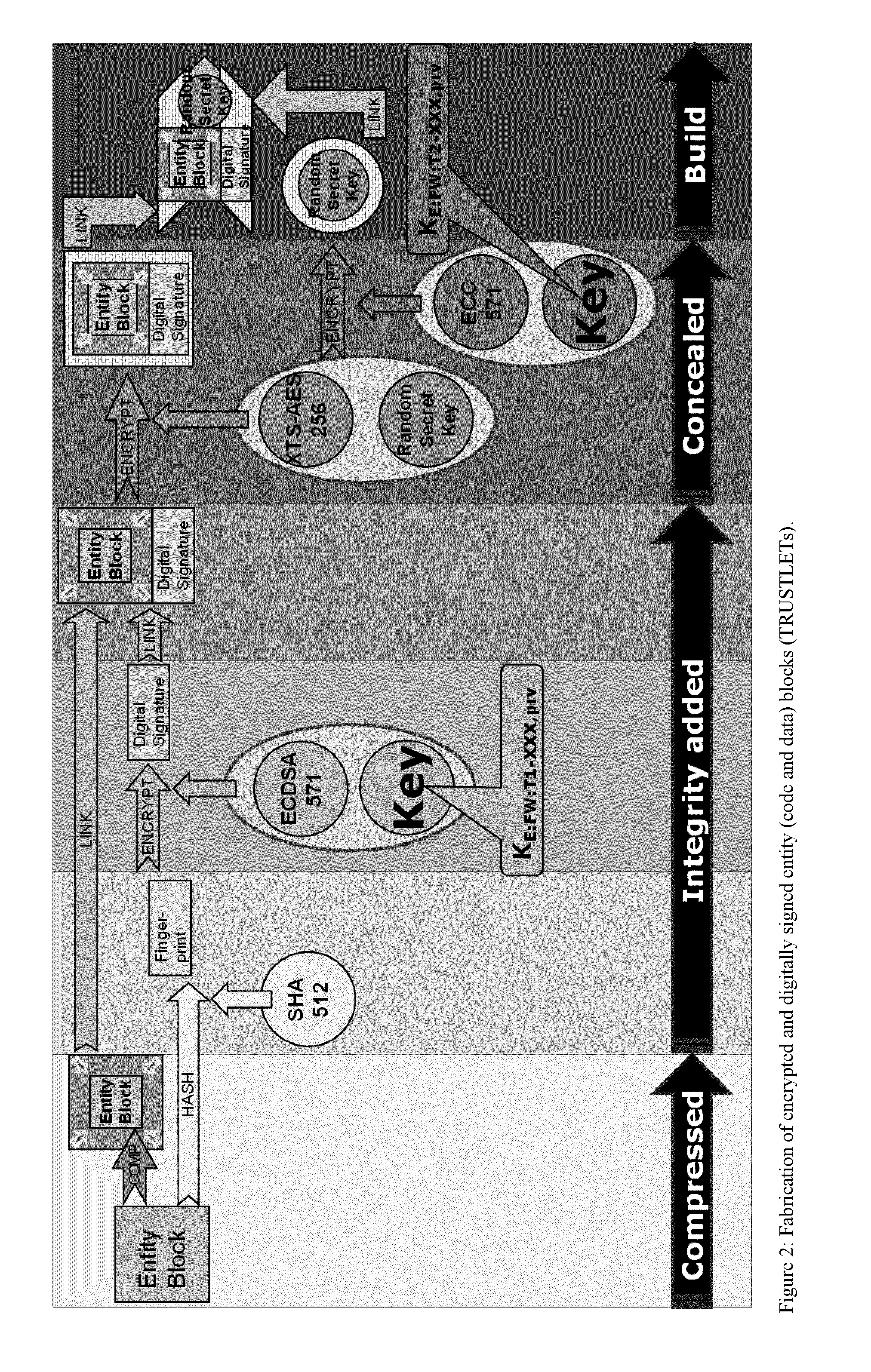
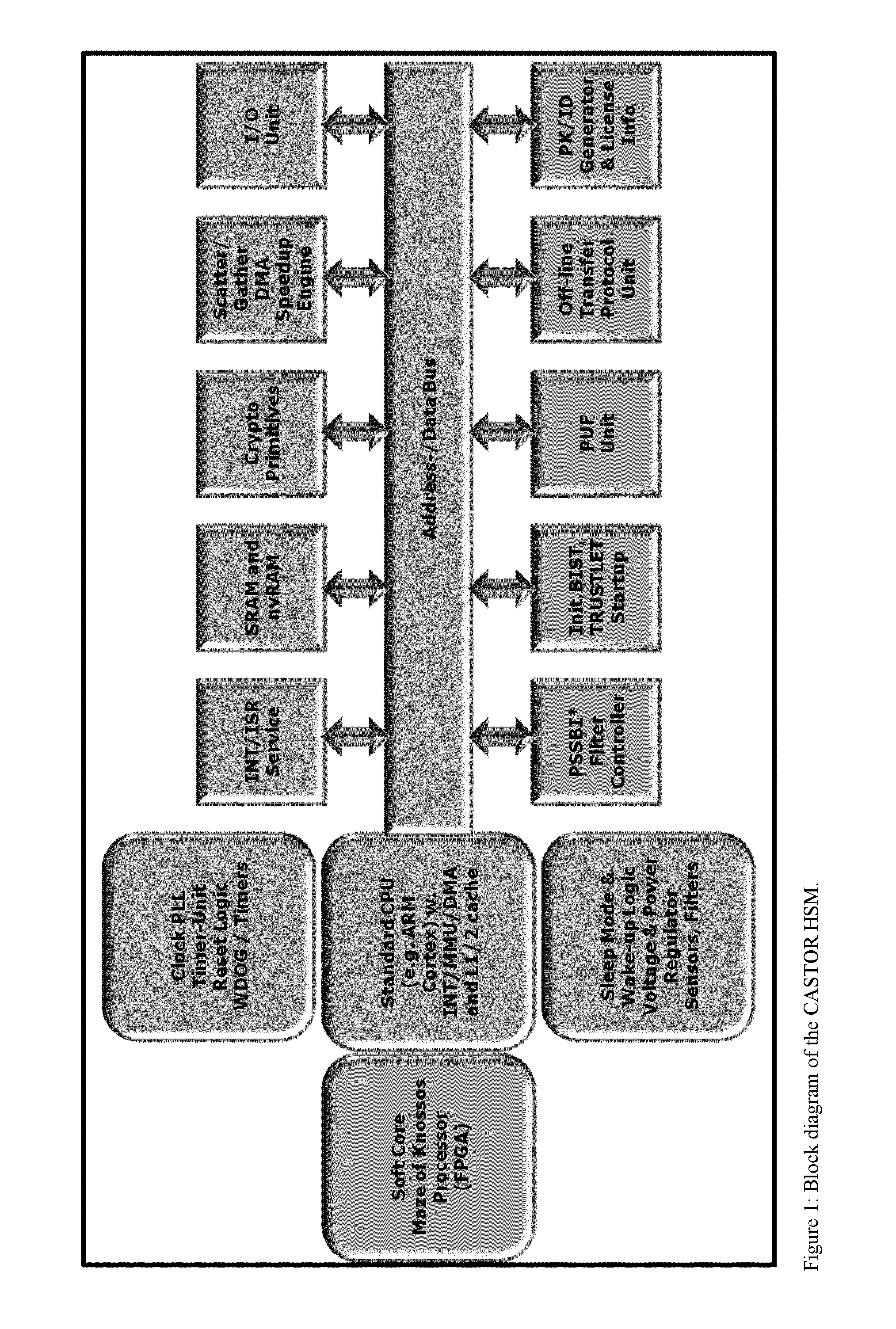
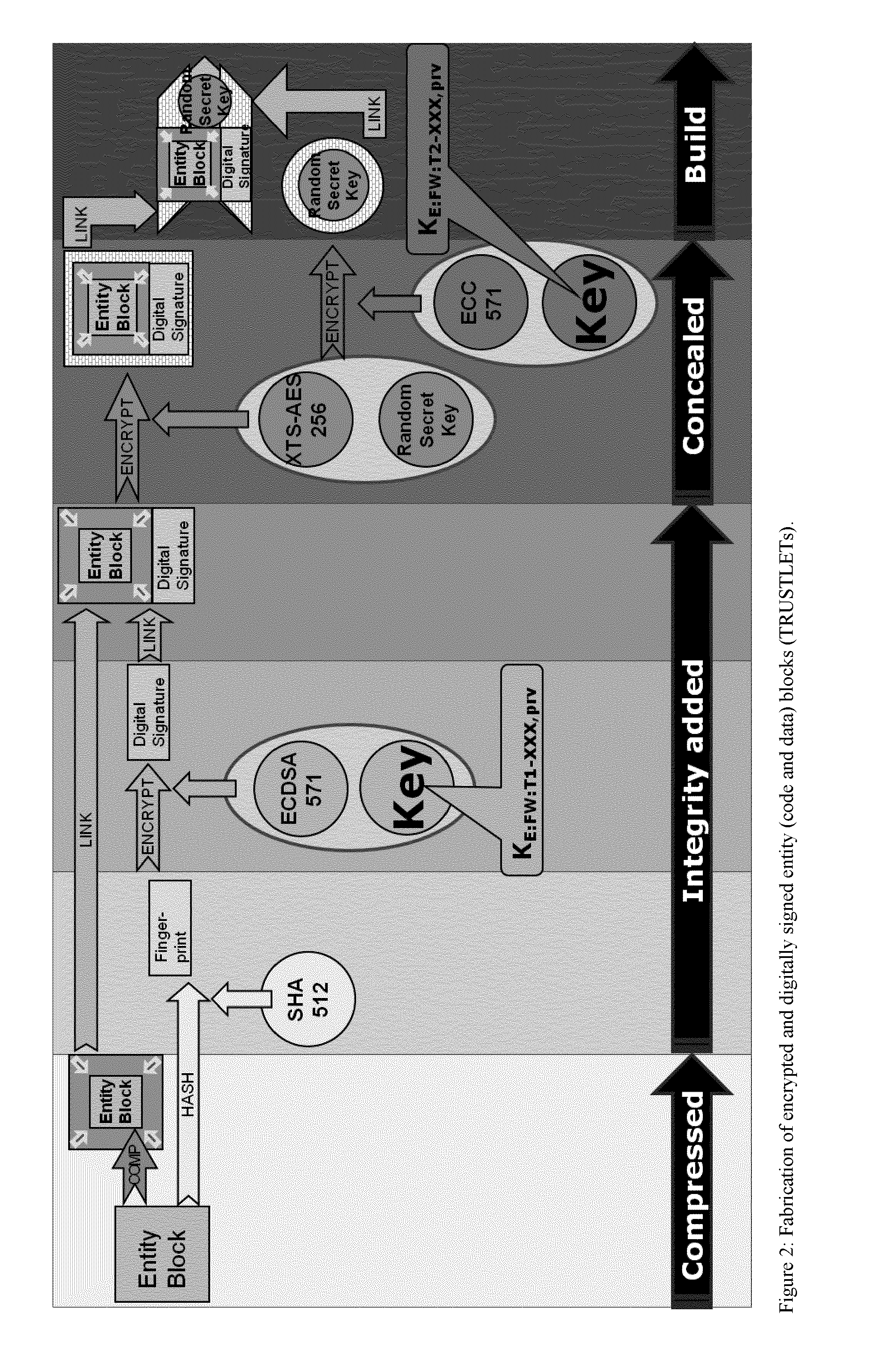
One of the various aspects of the invention is related to suggesting various techniques for improving the tamper-resistibility of hardware. The tamper-resistant hardware may be advantageously used in a transaction system that provides the off-line transaction protocol. Amongst these techniques for improving the tamper-resistibility are trusted bootstrapping by means of secure software entity modules, a new use of hardware providing a Physical Unclonable Function, and the use of a configuration fingerprint of a FPGA used within the tamper-resistant hardware.
Owner:EMSYCON
Apparatus and method for managing access to a memory
ActiveUS20040177269A1Performance is not affectedEasy to operateMemory architecture accessing/allocationDigital data processing detailsManagement unitMultiple modes
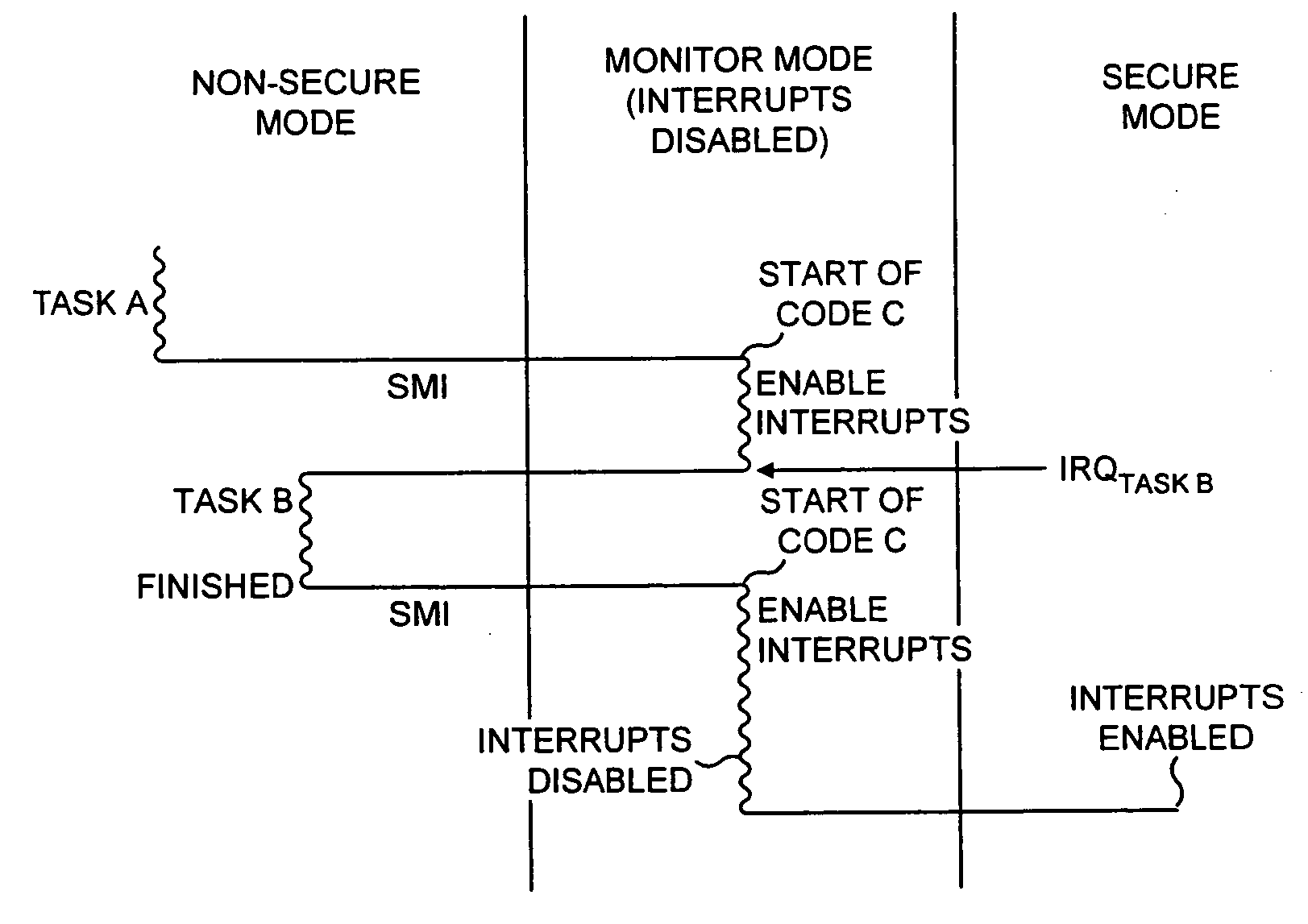
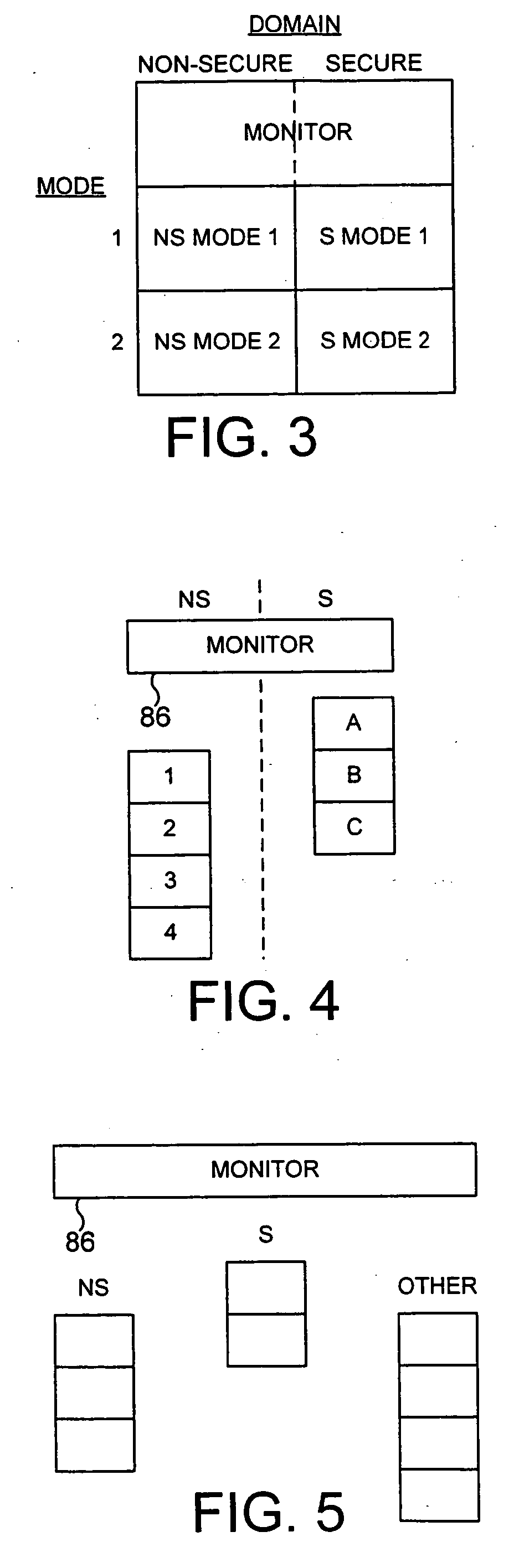
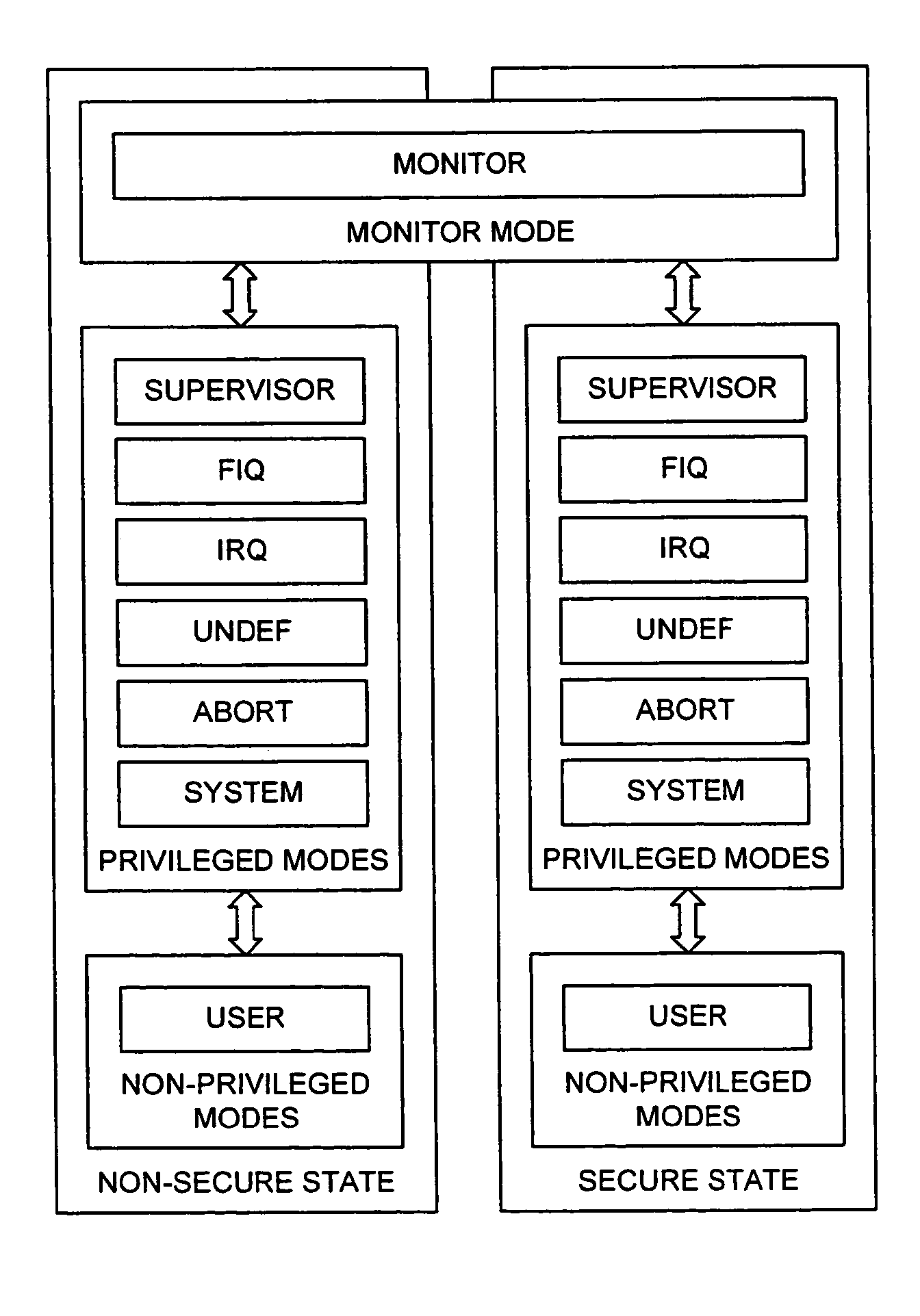
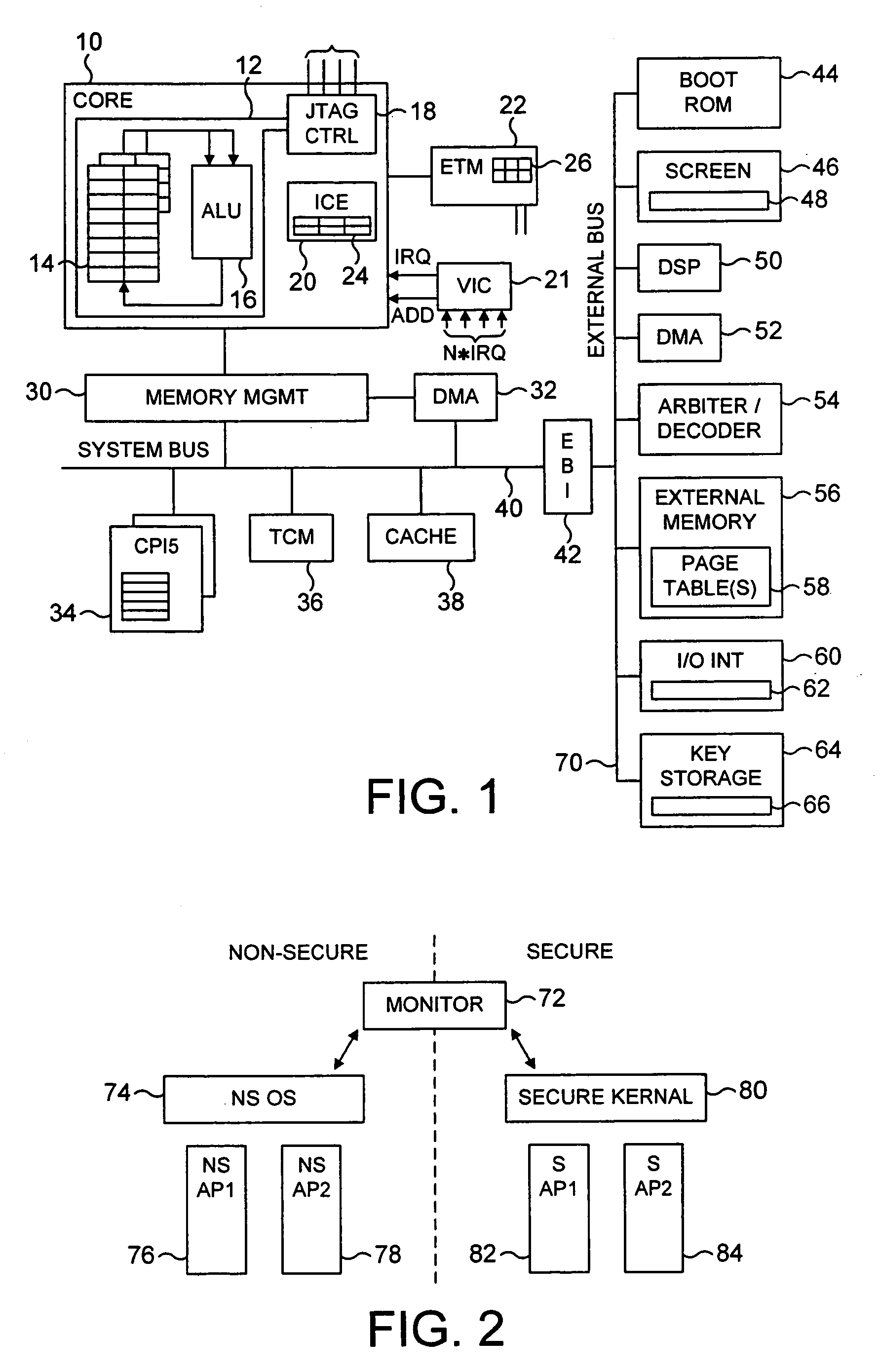
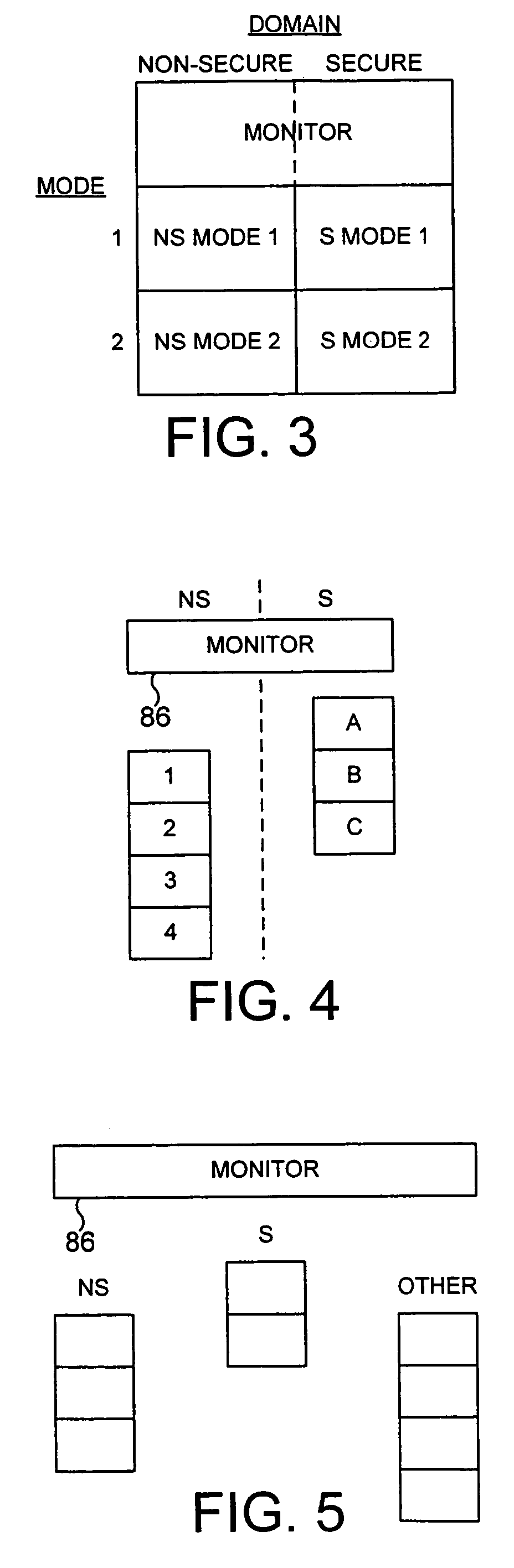
The present invention provides a data processing apparatus and method for managing access to a memory within the data processing apparatus. The data processing apparatus comprises a processor operable in a plurality of modes and a plurality of domains, said plurality of domains comprising a secure domain and a non-secure domain, said plurality of modes including at least one non-secure mode being a mode in the non-secure domain and at least one secure mode being a mode in the secure domain, said processor being operable such that when executing a program in a secure mode said program has access to secure data which is not accessible when said processor is operating in a non-secure mode. Further, a memory is provided for storing data required by the processor, and consists of secure memory for storing secure data and non-secure memory for storing non-secure data. The memory further contains a non-secure table and a secure table, the non-secure table being within the non-secure memory and arranged to contain for each of a number of first memory regions an associated descriptor, and the secure table being within the secure memory and arranged to contain for each of a number of second memory regions an associated descriptor. When access to an item of data in the memory is required by the processor, the processor issues a memory access request, and a memory management unit is provided to perform one or more predetermined access control functions to control issuance of the memory access request to the memory. The memory management unit comprises an internal storage unit operable to store descriptors retrieved by the memory management unit from either the non-secure table or the secure table, and in accordance with the present invention the internal storage unit comprises a flag associated with each descriptor stored within the internal storage unit to identify whether that descriptor is from the non-secure table or the secure table. By this approach, when the processor is operating in a non-secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the non-secure table. In contrast, when the processor is operating in a secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the secure table. This approach enables different descriptors to be used for the control of accesses to memory in either the secure domain or the non-secure domain, whilst enabling such different descriptors to co-exist within the memory management unit's internal storage unit, thereby avoiding the requirement to flush the contents of such an internal storage unit when the operation of the processor changes from the secure domain to the non-secure domain, or vice versa.
Owner:ARM LTD
Receiver and method for synchronizing and aligning serial streams
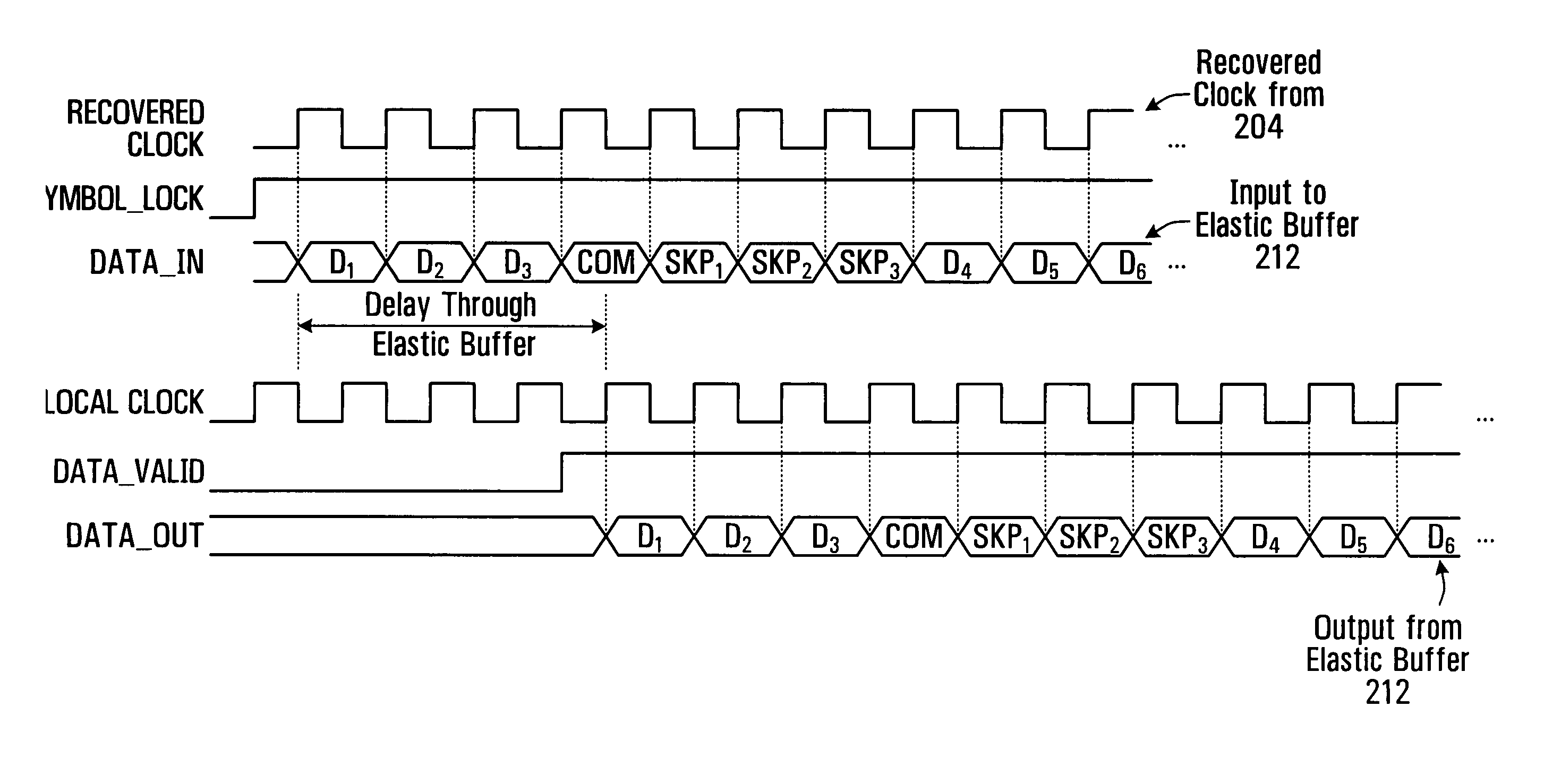
ActiveUS20070177701A1Avoid the needAvoid storage problemsTime-division multiplexSynchronising arrangementClock ratePCI Express
A receiver for receiving a stream of symbols clocked at a first rate, and providing the symbols at a second clock rate uses two buffers. Incoming symbols are written to a first dual clock buffer at the first rate, and read from the first and second buffer, at the second rate. Underflow of the first buffer is signaled to the second buffer, thereby avoiding the need to insert defined clock compensation symbols at the second rate. Symbols received at the second buffer while underflow is signaled may be ignored. Conveniently, the second buffer may also be used to align symbol data across multiple symbol streams using periodic alignment symbols. An exemplary embodiment conforms to the PCI Express standard.
Owner:ATI TECH INC
Solid formulations of crystalline compounds
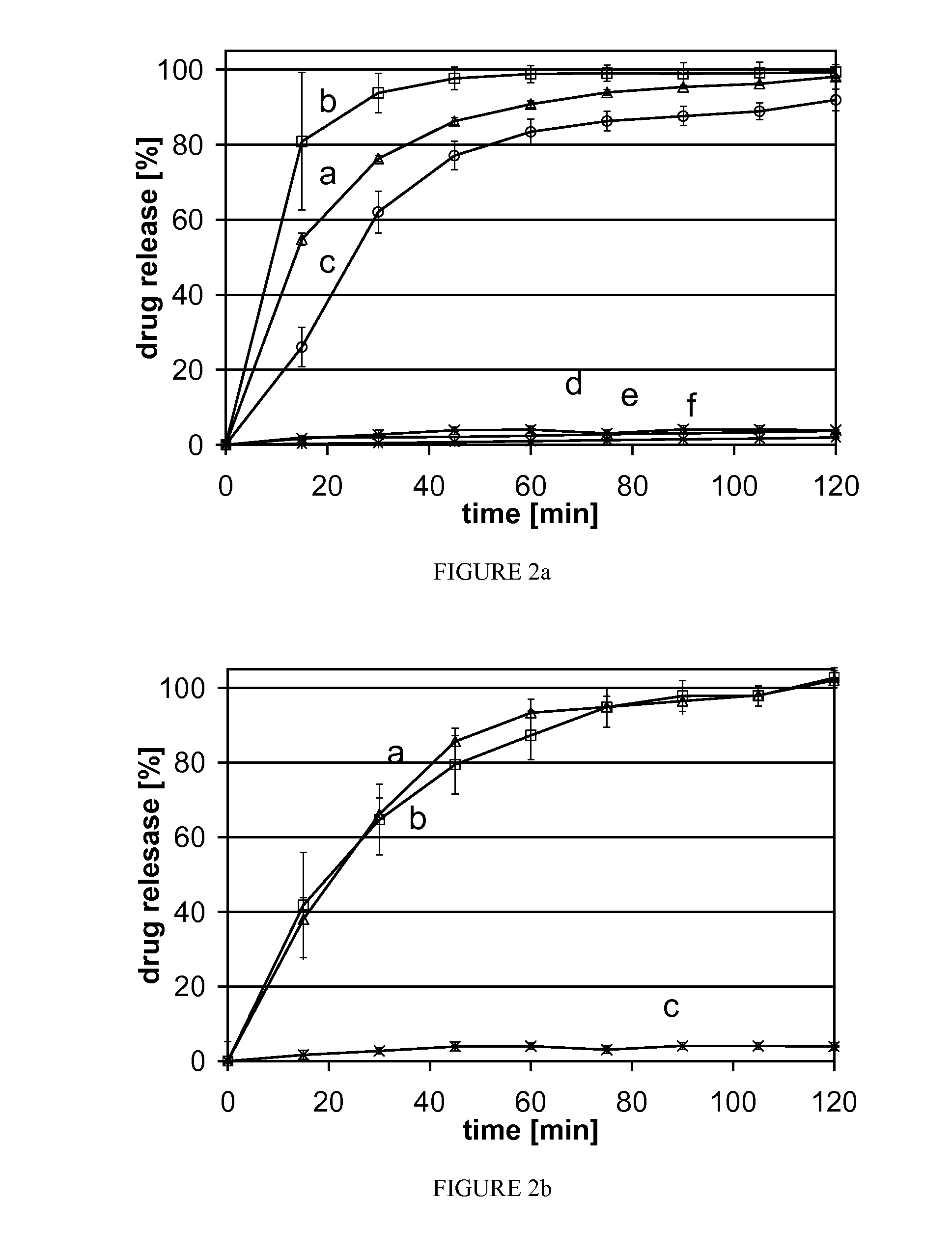
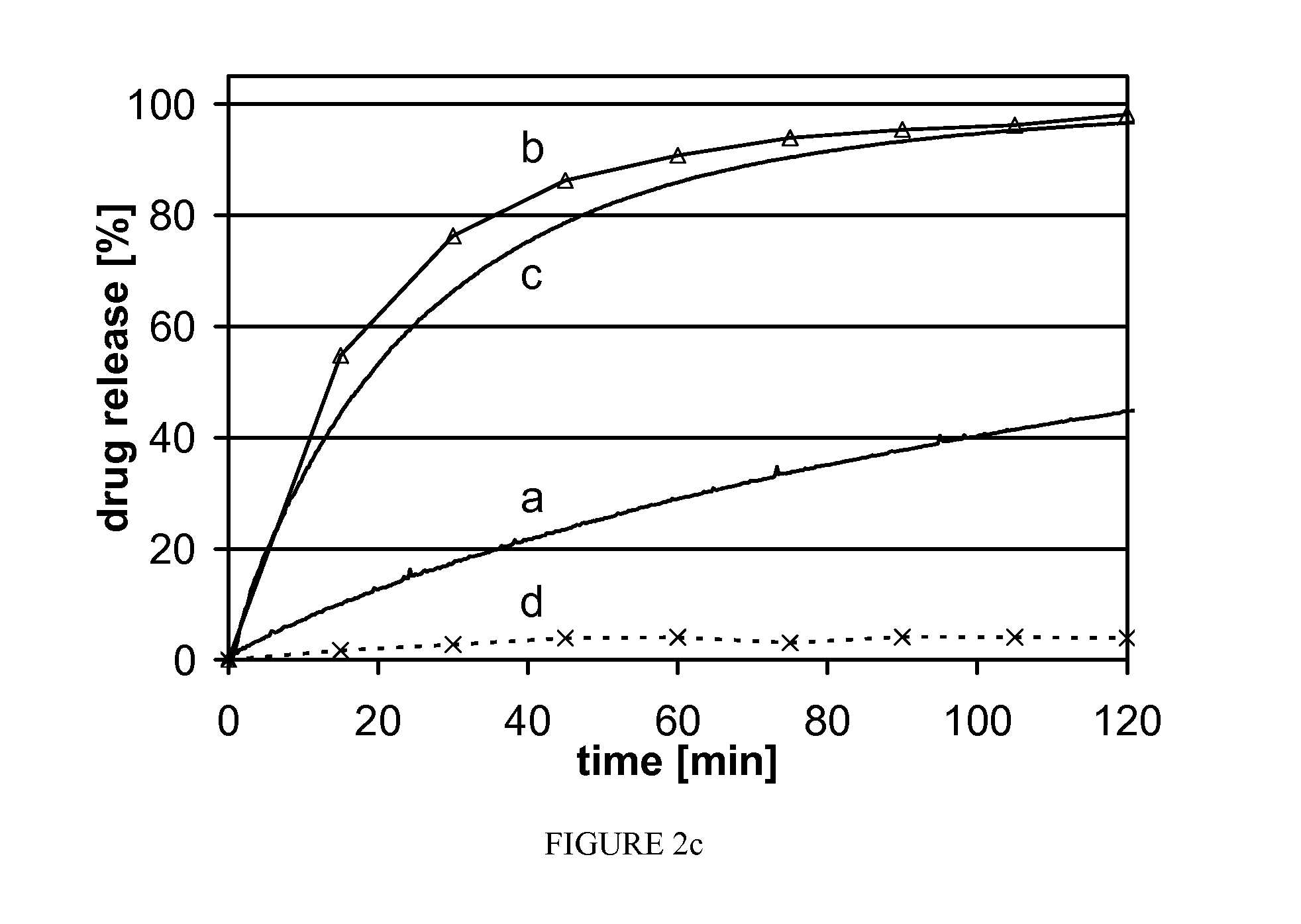
InactiveUS20100222311A1Fast dispersionFast dissolutionBiocidePowder deliverySolubilityAdditive ingredient
Described herein are formulations of active pharmaceutical ingredients, where the active pharmaceutical ingredients or drugs are included in a solid suspension with one or more solid additives. The formulations described herein are useful for formulating any drug or active pharmaceutical ingredient, including those that have limited solubility in organic and / or aqueous solvent systems.
Owner:PURDUE RES FOUND INC
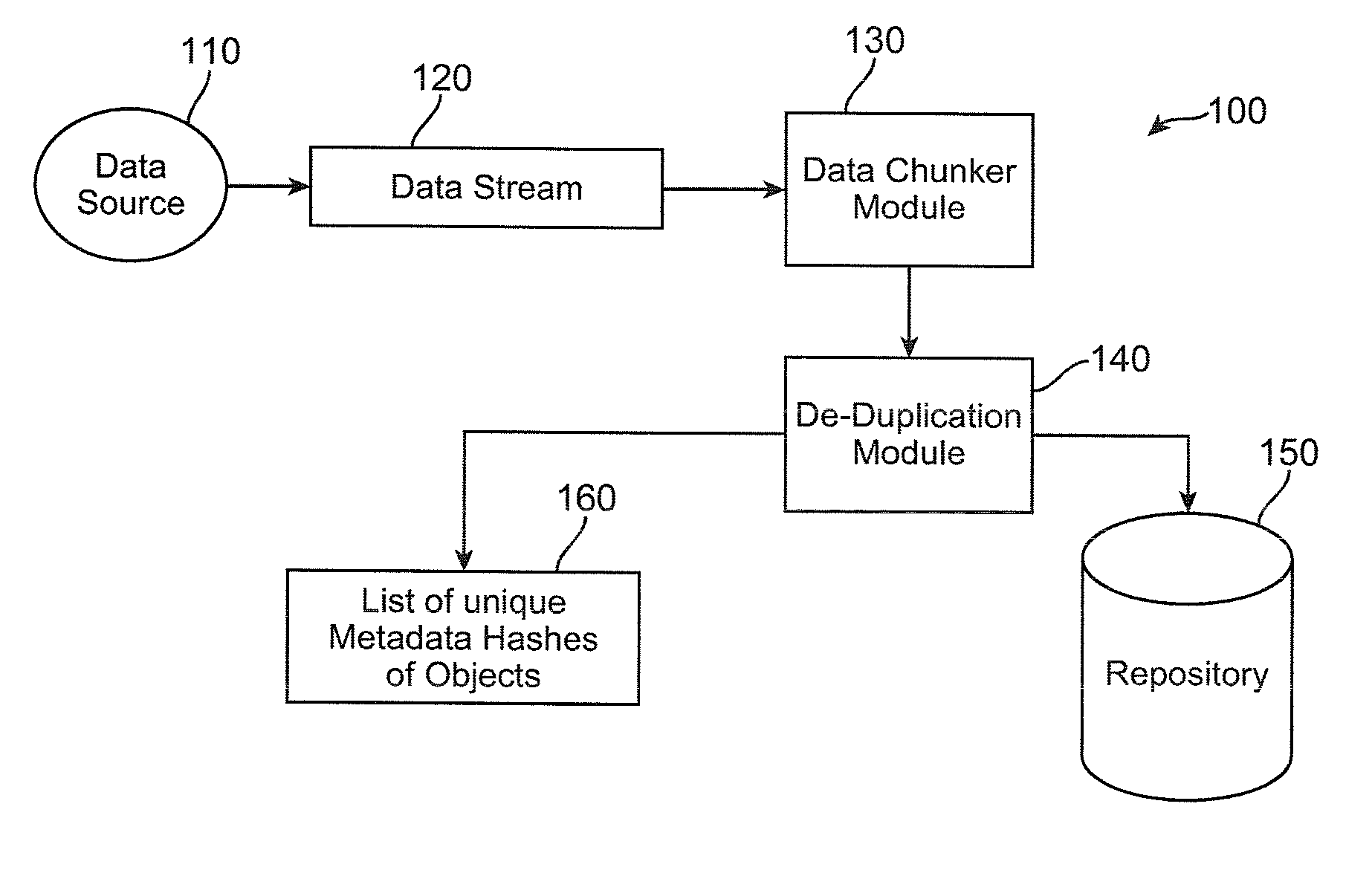
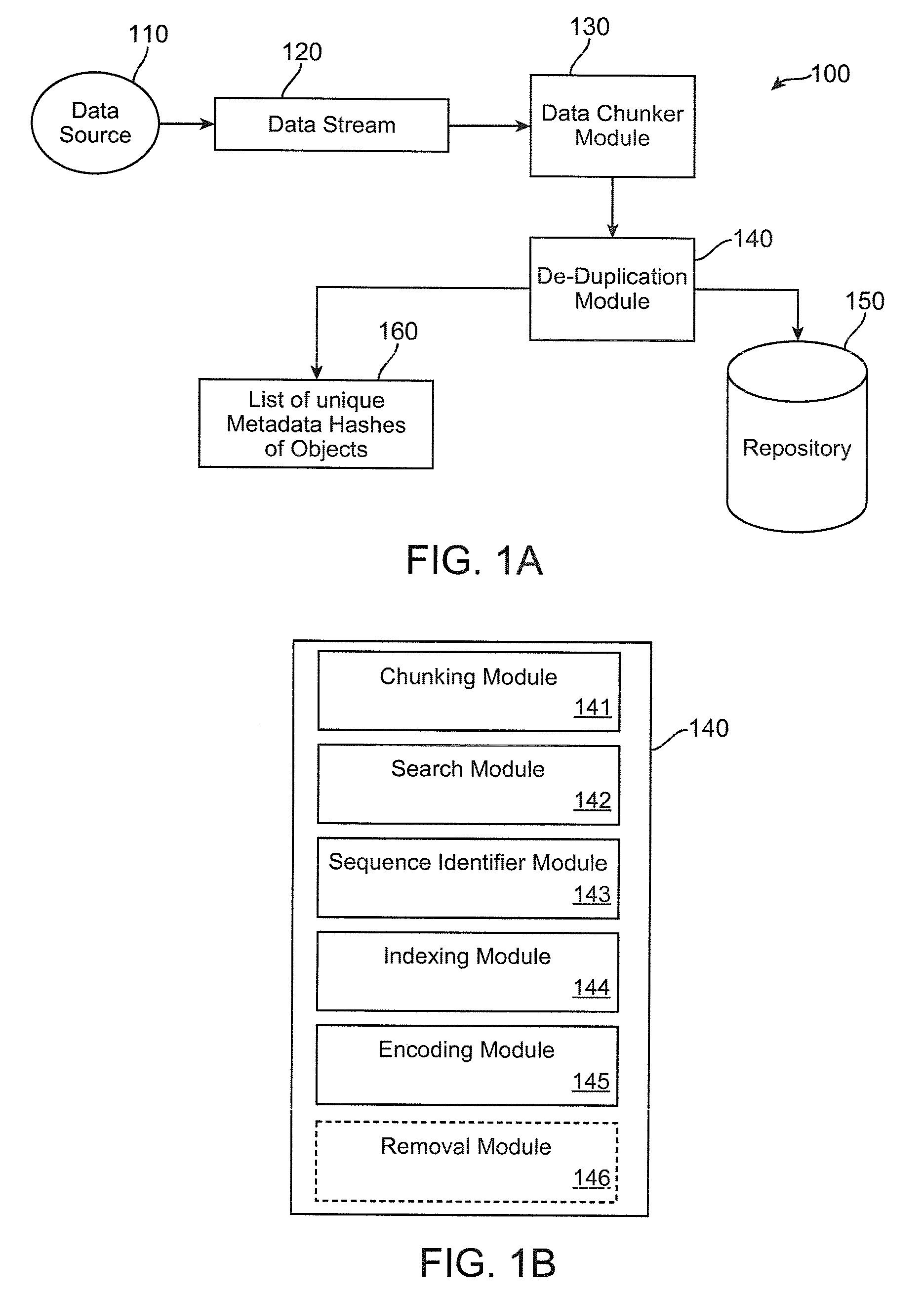
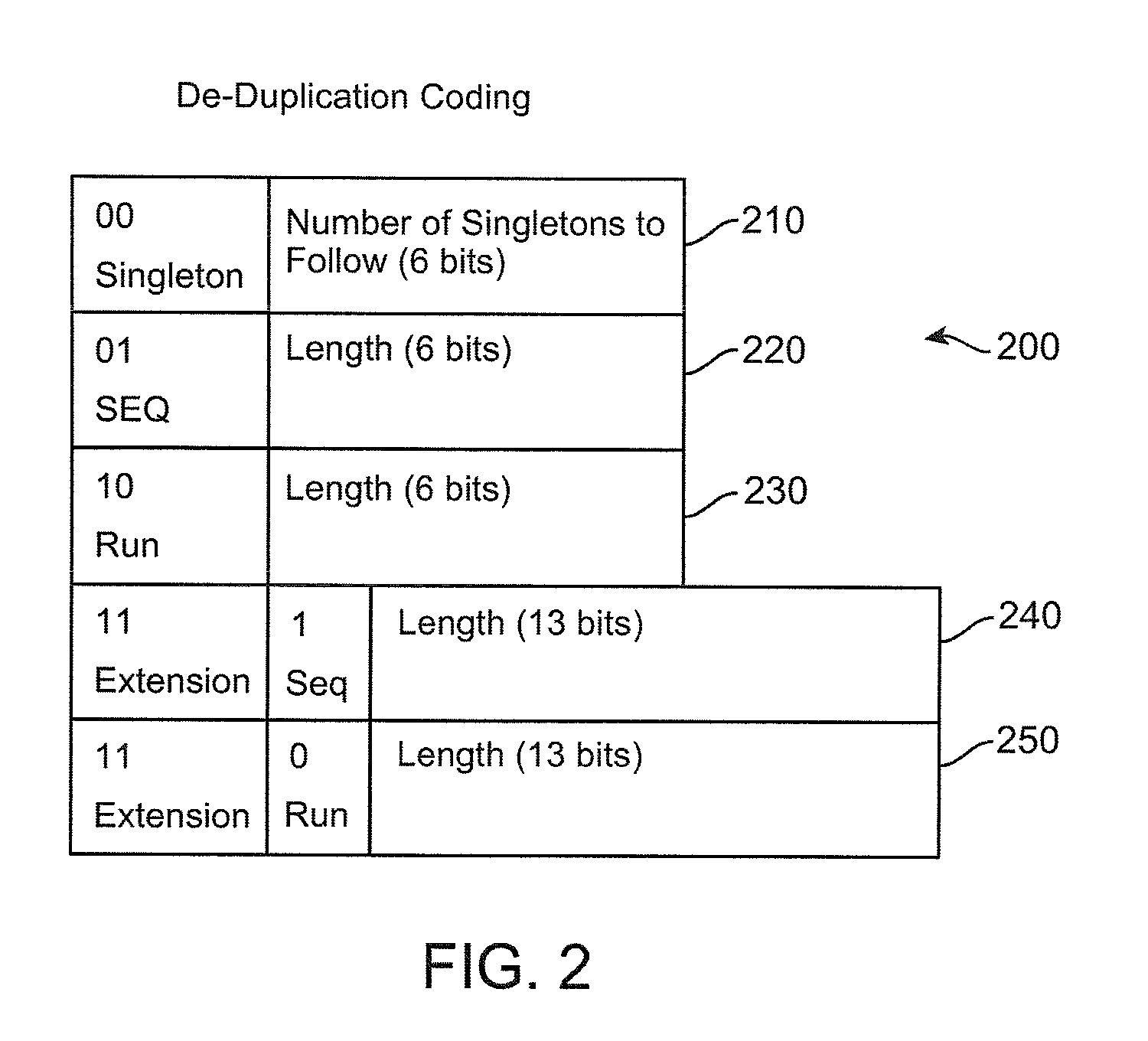
Method and apparatus to minimize metadata in de-duplication
ActiveUS20090300321A1Reduce recognitionAvoiding repeated stored identificationMemory systemsMicro-instruction address formationRecognition sequenceComputer science
Owner:IBM CORP
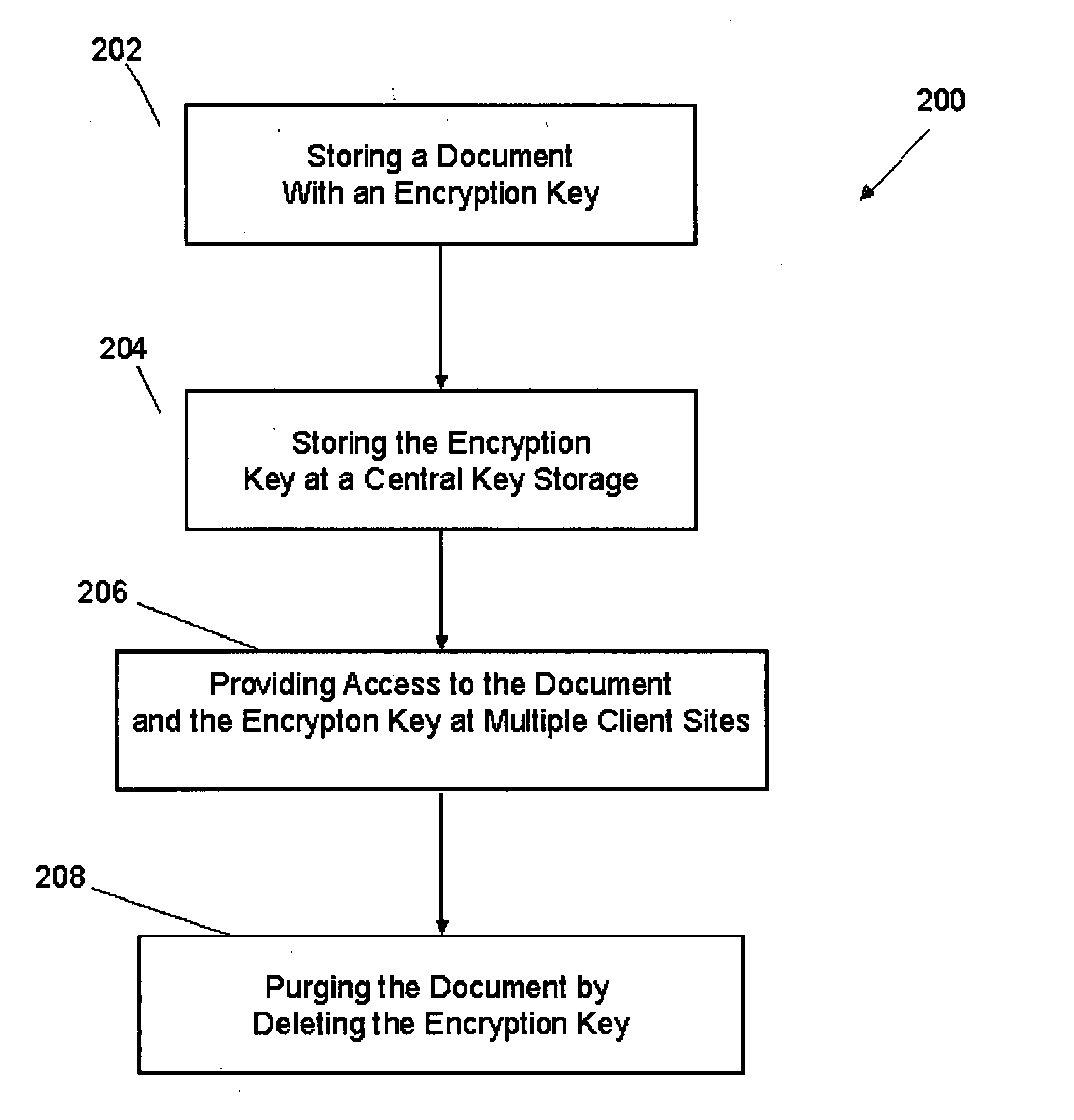
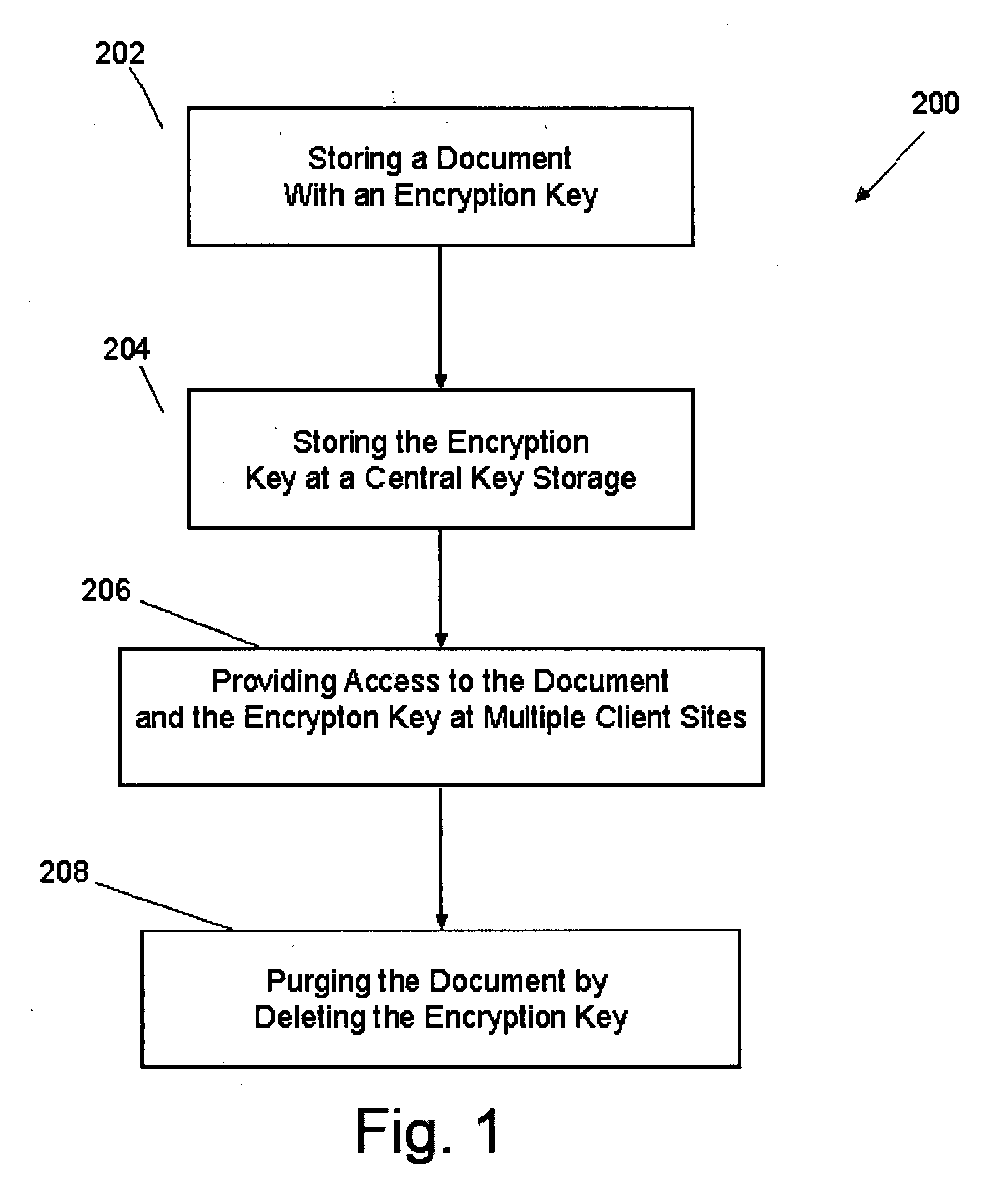
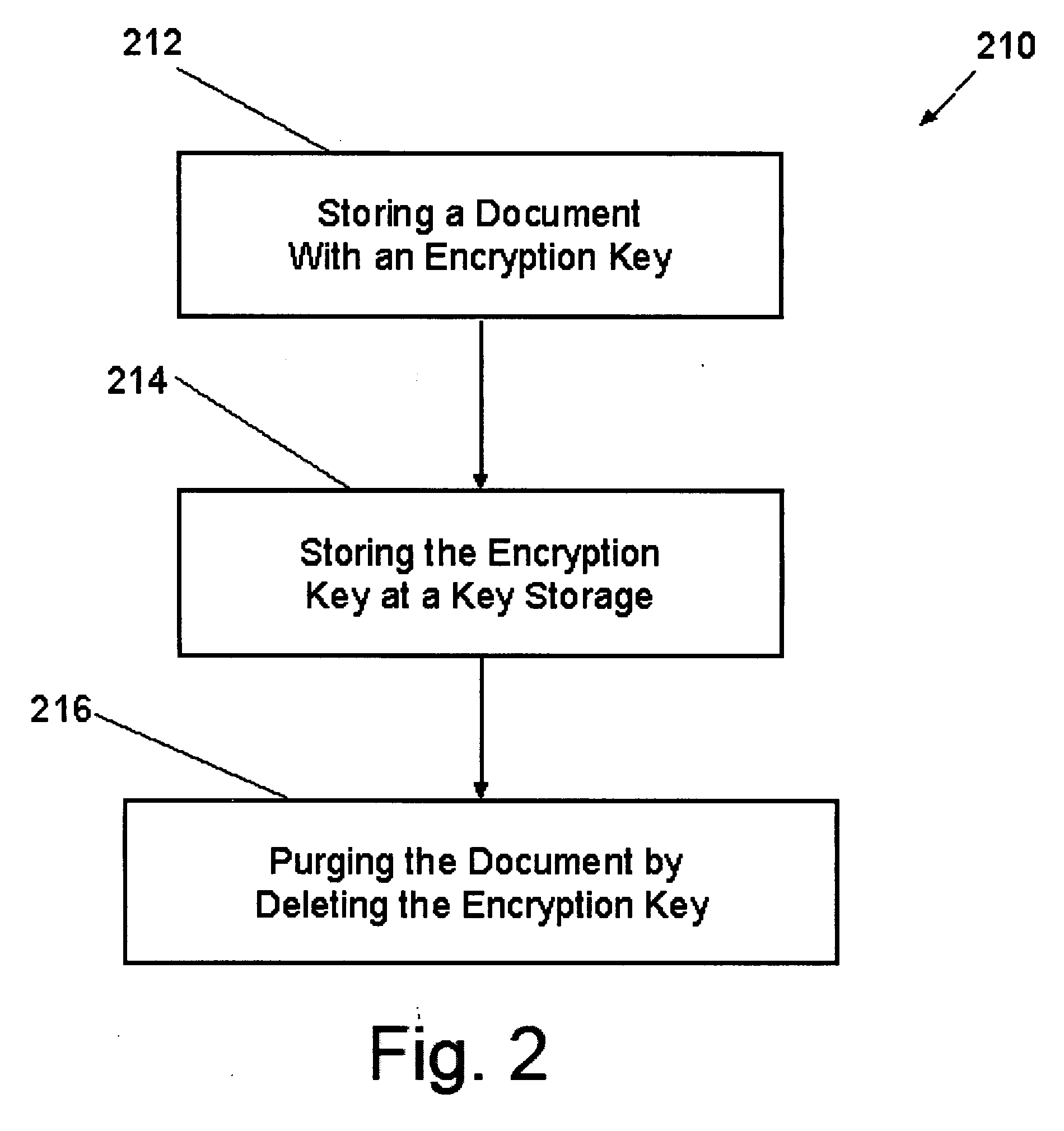
Method, system, and computer-readable medium to maintain and/or purge files of a document management system
InactiveUS20080002830A1Avoid storage problemsImprove securityMetadata multimedia retrievalSpecial data processing applicationsKey storageDocumentation
A method and corresponding apparatus and computer-readable medium to effect maintenance and / or purging of a document file in a multi-user document of file management system operating over a network. The document management system stores all document files in encrypted form. An exemplary method to assure full and complete purging of a document comprises generating an encryption key for the document, storing the encryption key in a central key storage accessible over the network by multiple users, producing an encrypted version of the document using the encryption key, storing the encrypted document in a central file storage medium, enabling a user to retrieve the document using the encryption key to decrypt the encrypted document when accessing the central file storage medium, and when necessary purging all copies of the document from the document management system by purging or deleting the encryption key.
Owner:VERTAFORE
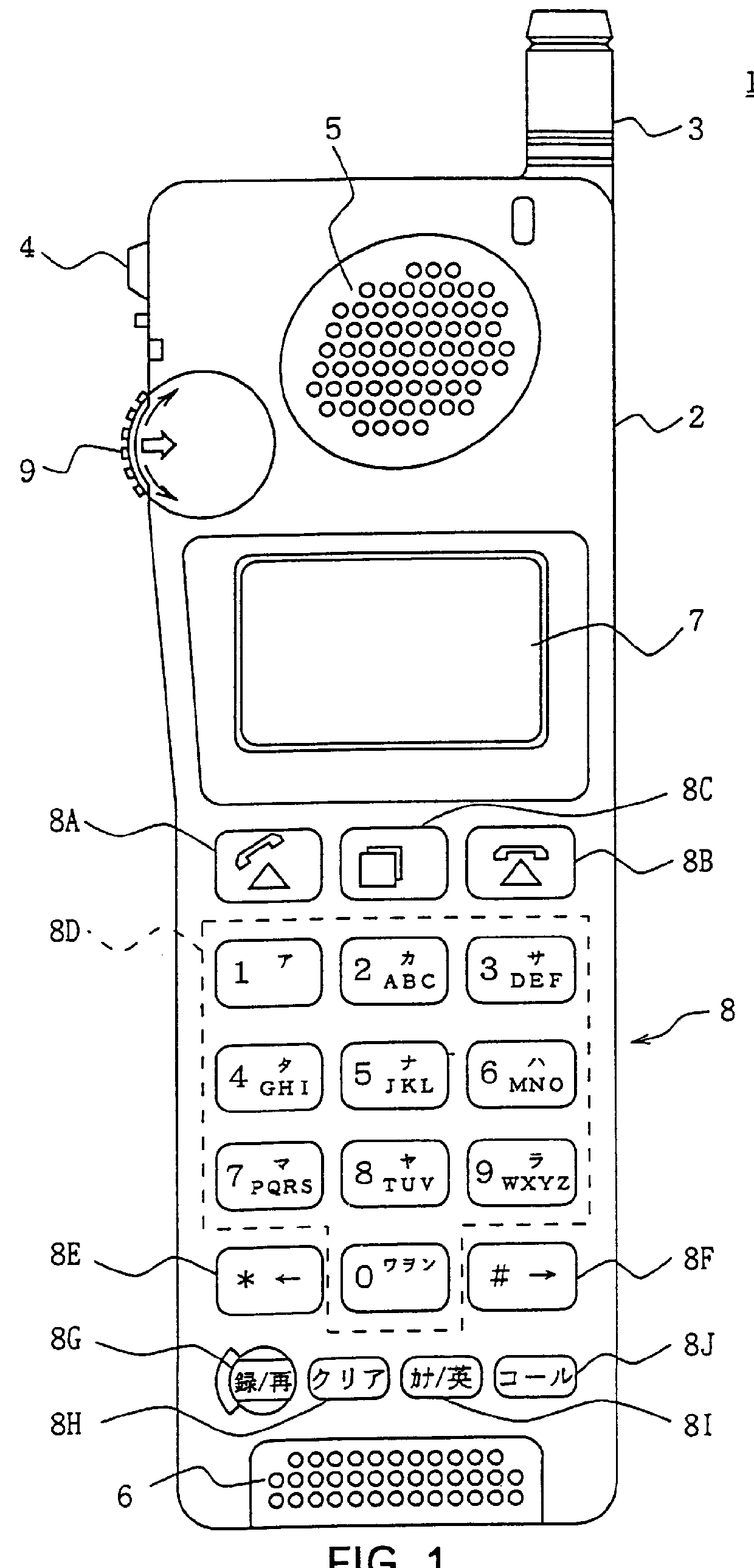
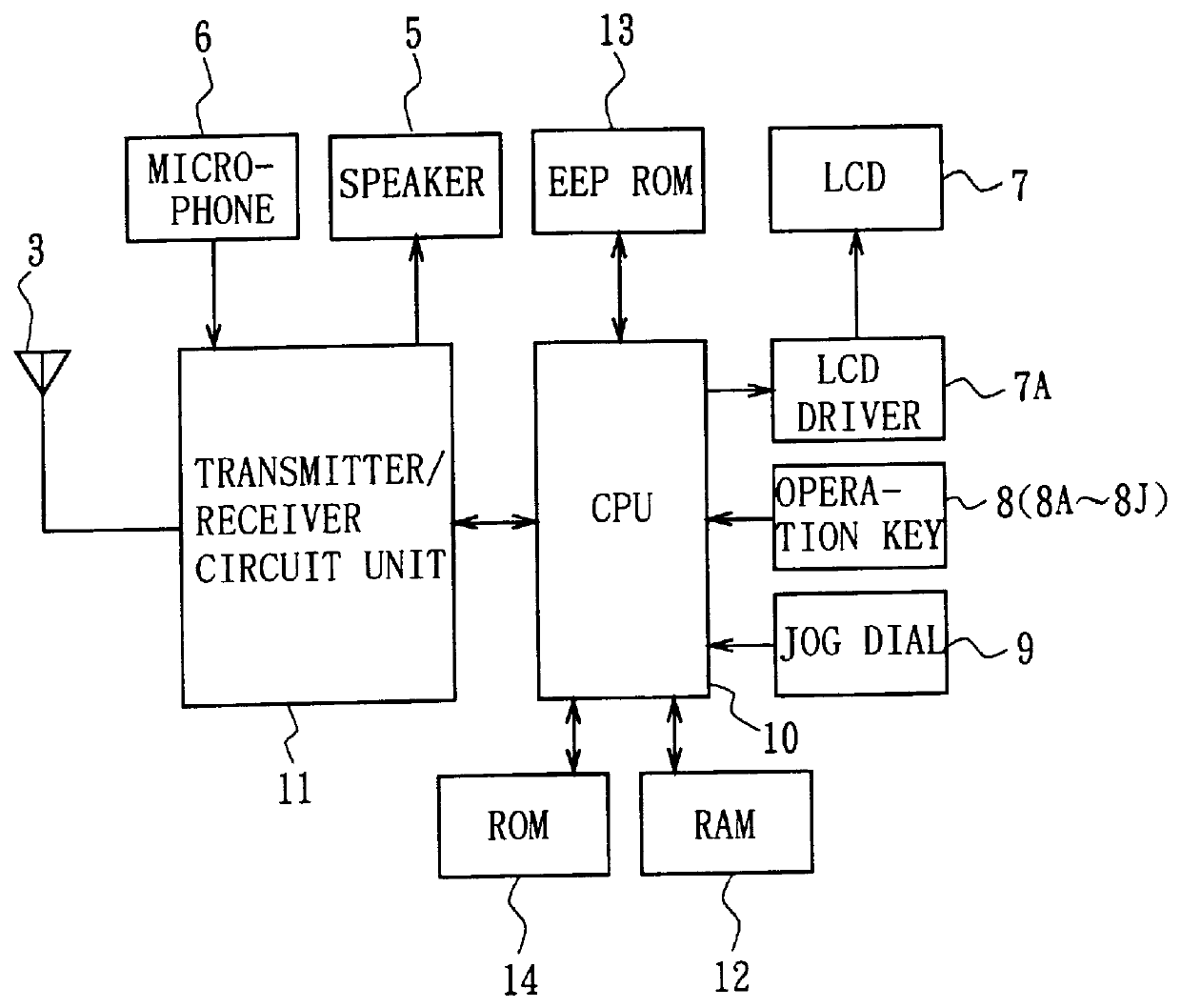
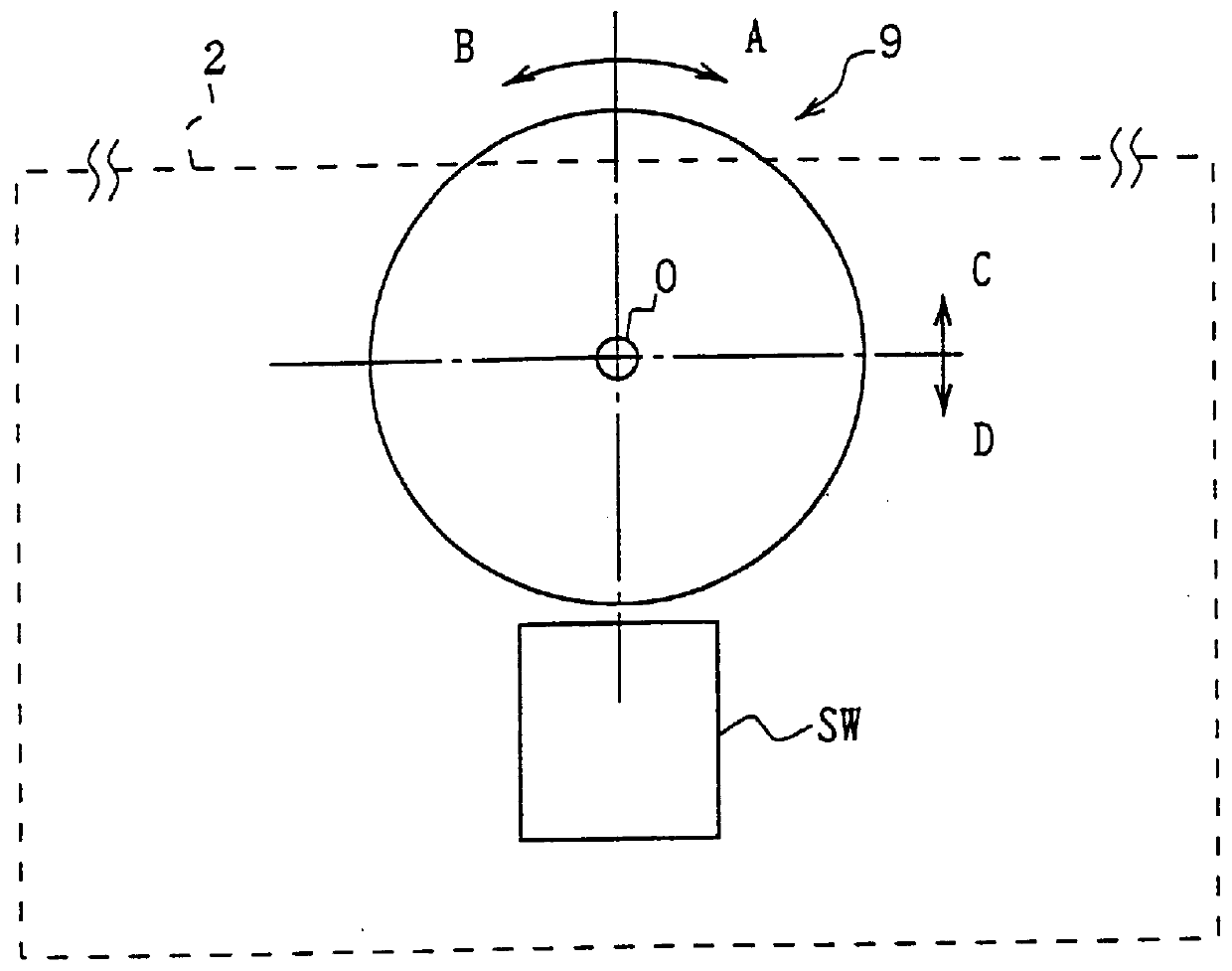
Communication terminal device, call-history memory method and call-history display method
InactiveUS6064725AAvoid storage problemsIncrease the number ofAutomatic exchangesCalled number recording/indicationTerminal equipmentUsability
A communication terminal device which easily provides a call-history function with superior usability. a call history having the same telephone number as the telephone number call-originated has been stored. If it has been stored, the past call history is canceled and the telephone number call-originated is stored as a call history. Thereby, storing call histories from the same party can be prevented increasing the actual number of storable files as call histories.
Owner:SONY CORP
Tamper-protected hardware and method for using same
ActiveUS9071446B2Improve robustnessSuitable for useKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareTamper proof hardware
Owner:EMSYCON
Authenticated program execution method
InactiveUS20050138397A1Guaranteed reputationImprove responsivenessUnauthorized memory use protectionHardware monitoringBiological activationAuthentication
According to a conventional technique, in the case where a program is stored into a non-volatile memory once and then activated, authentication of the program is performed immediately before such activation. However, calculations such as decryption of encrypted values are required before the activation of the program starts, which causes the problem that responsiveness is decreased in proportion to the time required for calculations. In order to solve this problem, authentication of a program is performed immediately before such program is stored, so that no authentication is performed or only a part of the authentication is performed to verify the validity of certificates at program activation time.
Owner:PANASONIC CORP
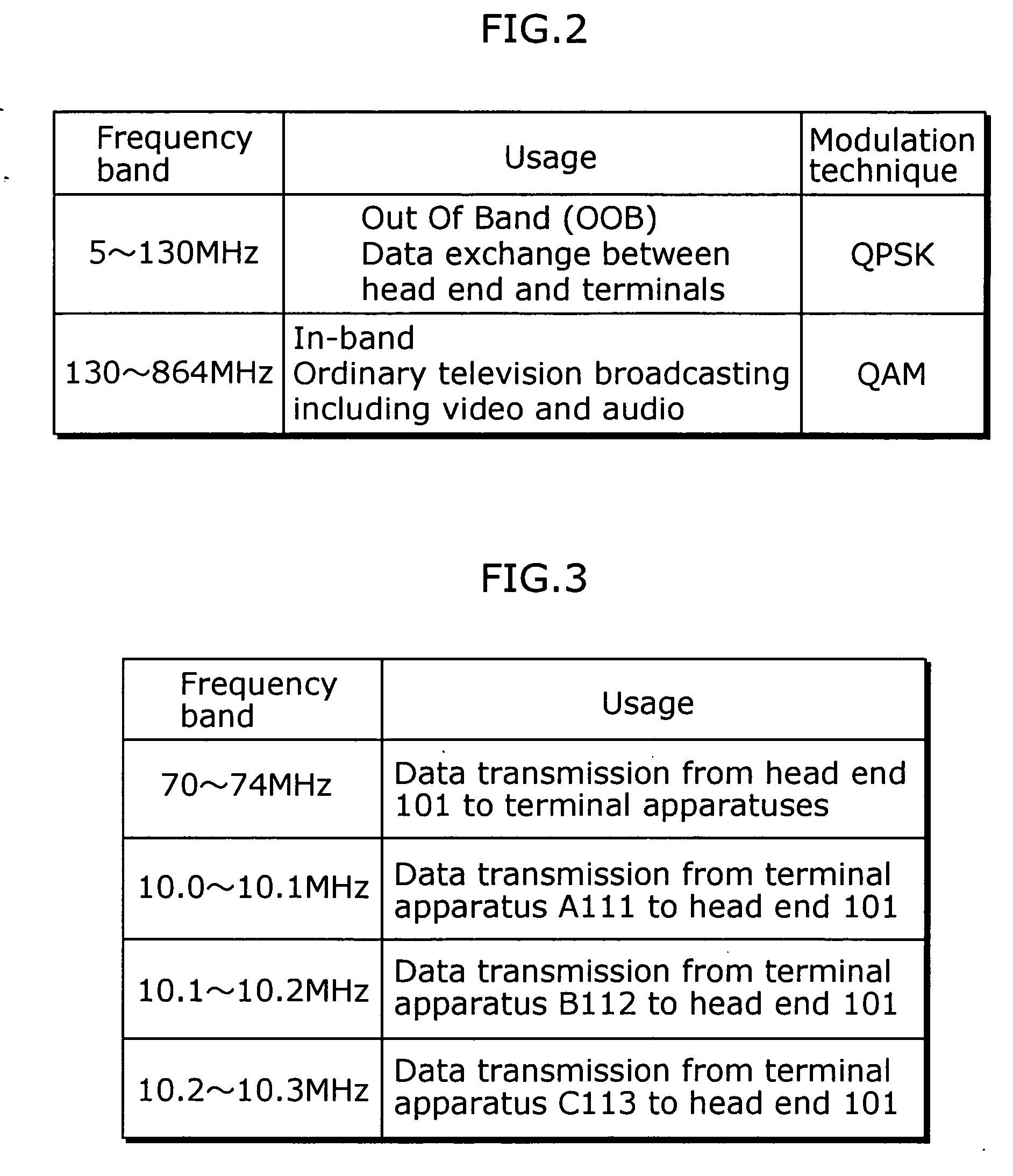
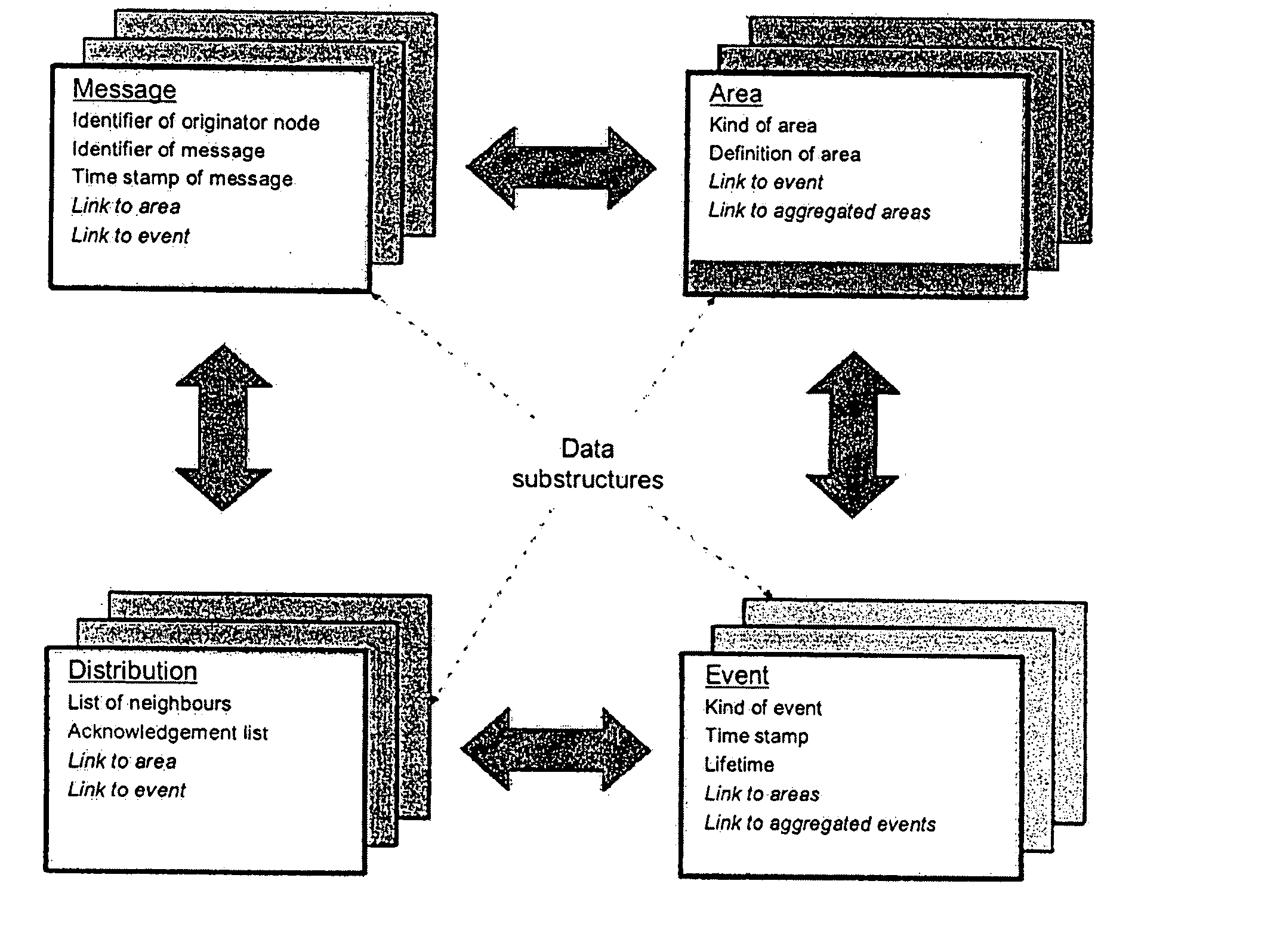
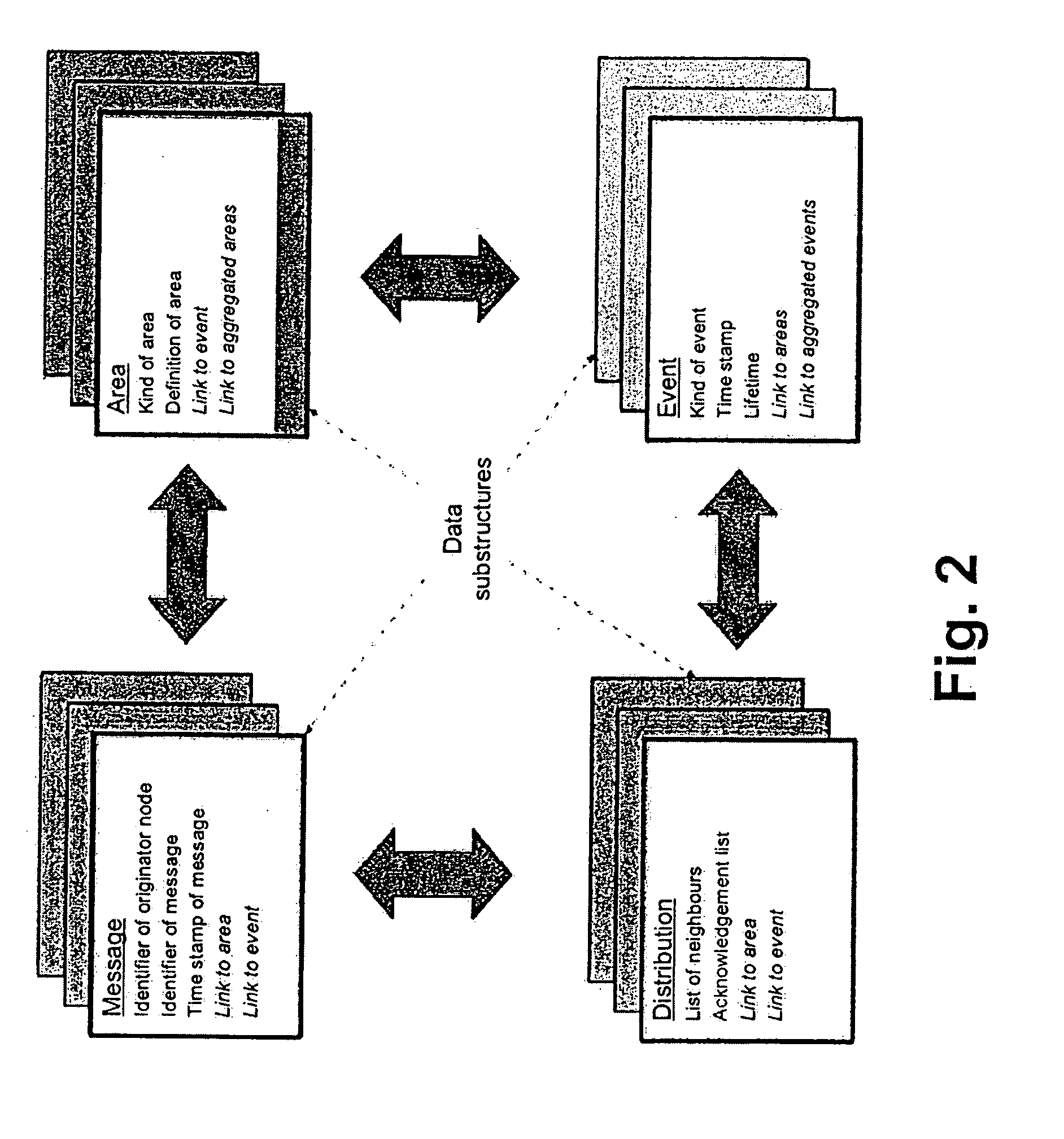
Information distribution with improved reliability and efficiency for mobile ad hoc networks
InactiveUS20060221891A1Improve efficiencyImprove reliabilityNetwork topologiesData switching by path configurationMobile WebSelf-organizing network
Information is distributed to nodes of a mobile ad hoc network, wherein the nodes dispose of position sensing elements, wherein a predeterminable geographic target area is defined and every information is assigned a pre-determinable lifetime, and wherein an information is distributed during its lifetime to all of the nodes being positioned within the target area and to nodes entering the target area by adding a list of correspondingly neighbored nodes in the target area to the broadcast message by which a node sends the information, and wherein nodes, which receive the message, only re-transmit the message if they have further neighboring nodes in the target area that are not contained in the received list.
Owner:NEC CORP
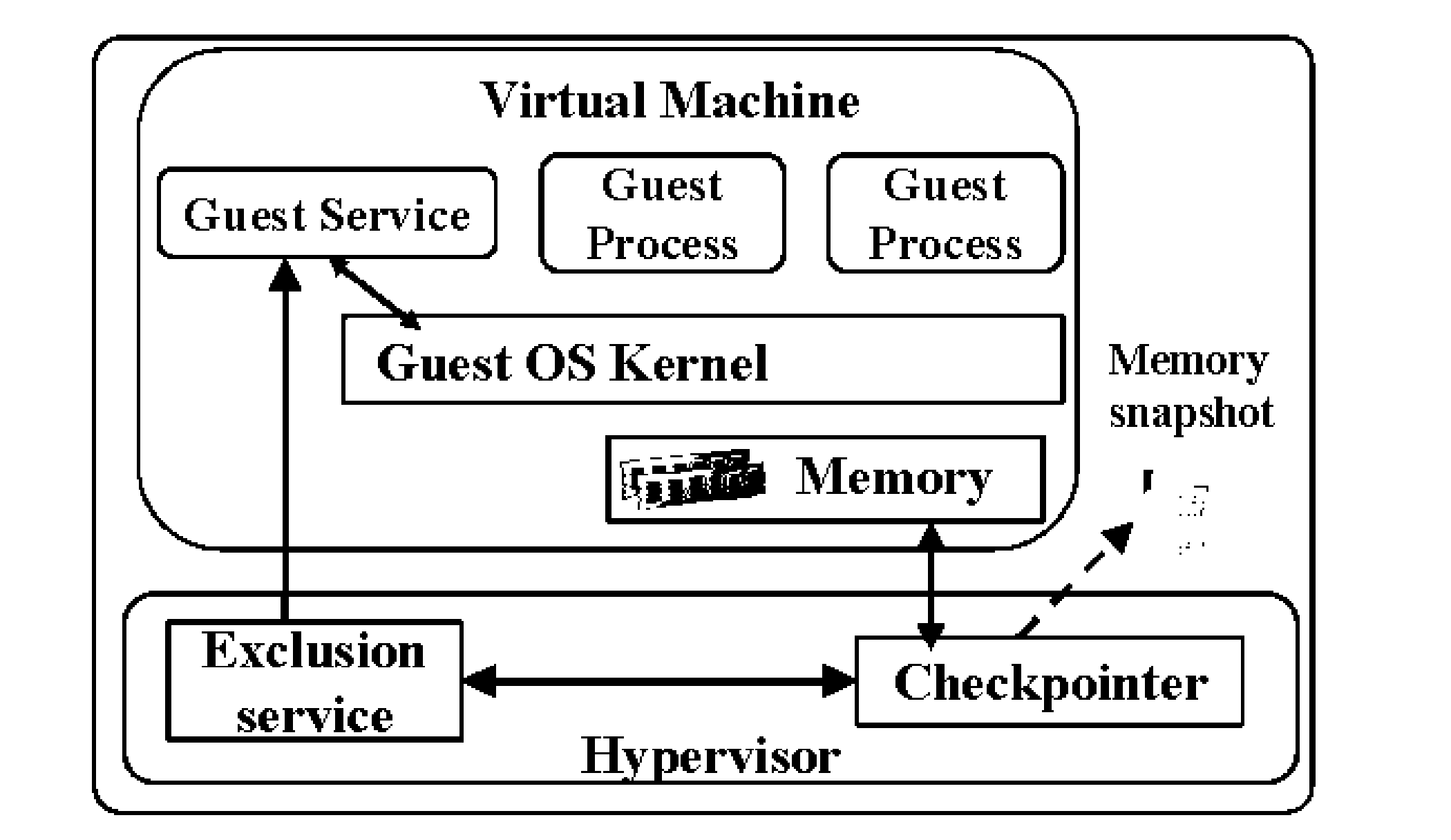
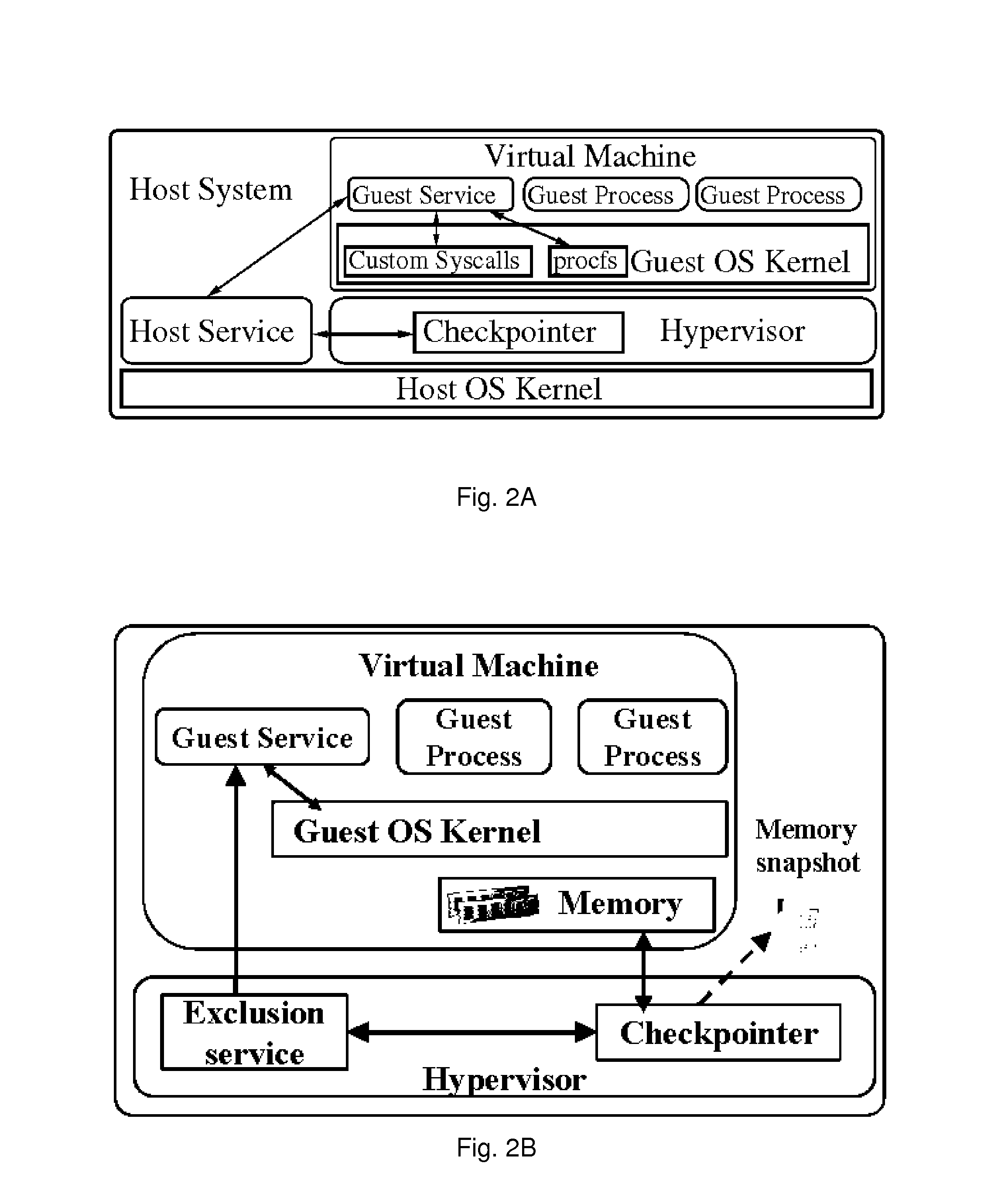
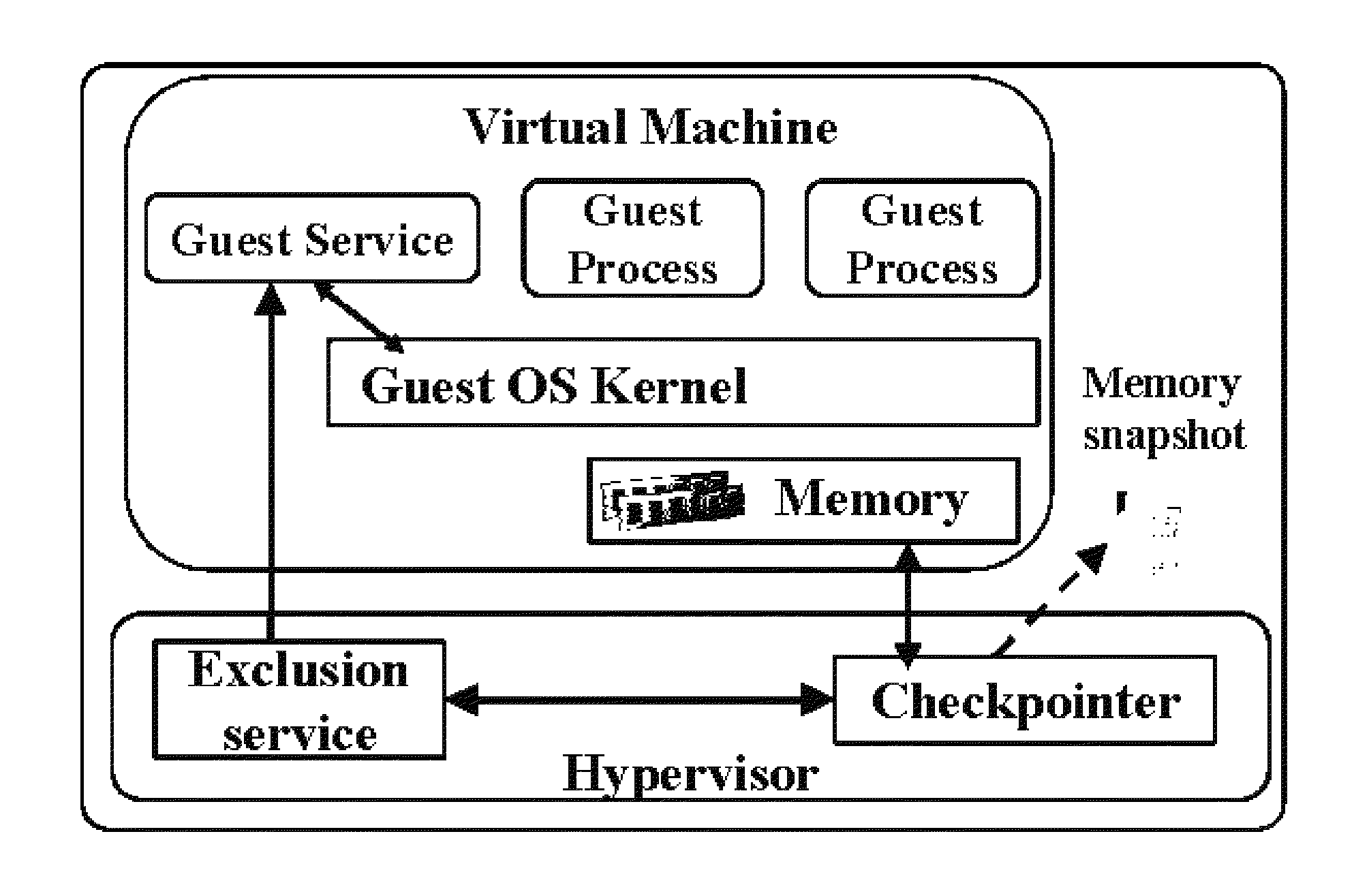
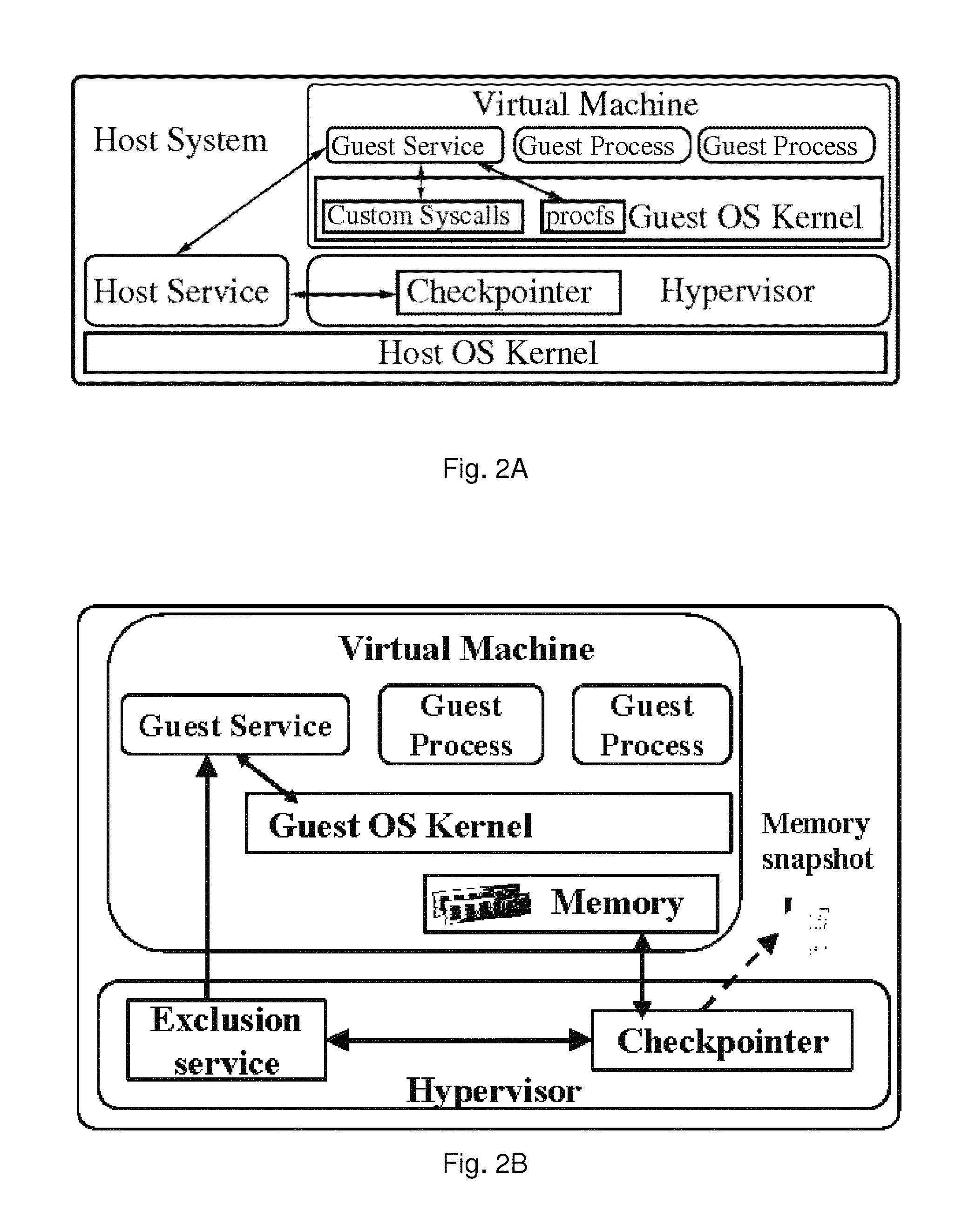
System and method for security and privacy aware virtual machine checkpointing
ActiveUS20140095821A1Avoid data breachesImprove latencyError detection/correctionInternal/peripheral component protectionApplication programming interfaceData storing
A checkpointing method for creating a file representing a restorable state of a virtual machine in a computing system, comprising identifying processes executing within the virtual machine that may store confidential data, and marking memory pages and files that potentially contain data stored by the identified processes; or providing an application programming interface for marking memory regions and files within the virtual machine that contain confidential data stored by processes; and creating a checkpoint file, by capturing memory pages and files representing a current state of the computing system, which excludes information from all of the marked memory pages and files.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Real-time near duplicate video clip detection method
InactiveUS20090028517A1Avoid storage problemsTelevision system detailsCharacter and pattern recognitionFeature vectorFeature extraction
There is provided a near duplicate video detection system. The system includes (a) a video clip acquisition module arranged to produce a video clip in machine readable data format defining a plurality of frames, (b) an image feature extractor in communication with the video clip acquisition module arranged to perform image feature extraction in respect of the frames and produce corresponding image feature extraction data in electronic format, (c) a feature vector generator in communication with the image feature extractor arranged to process the image feature extraction data to produce feature vector data in an electronic format corresponding to each of the frames, and (d) a summarization module responsive to the feature vector generator and arranged to convert the feature vector data into a summarization of the video clip in machine readable format.
Owner:THE UNIV OF QUEENSLAND
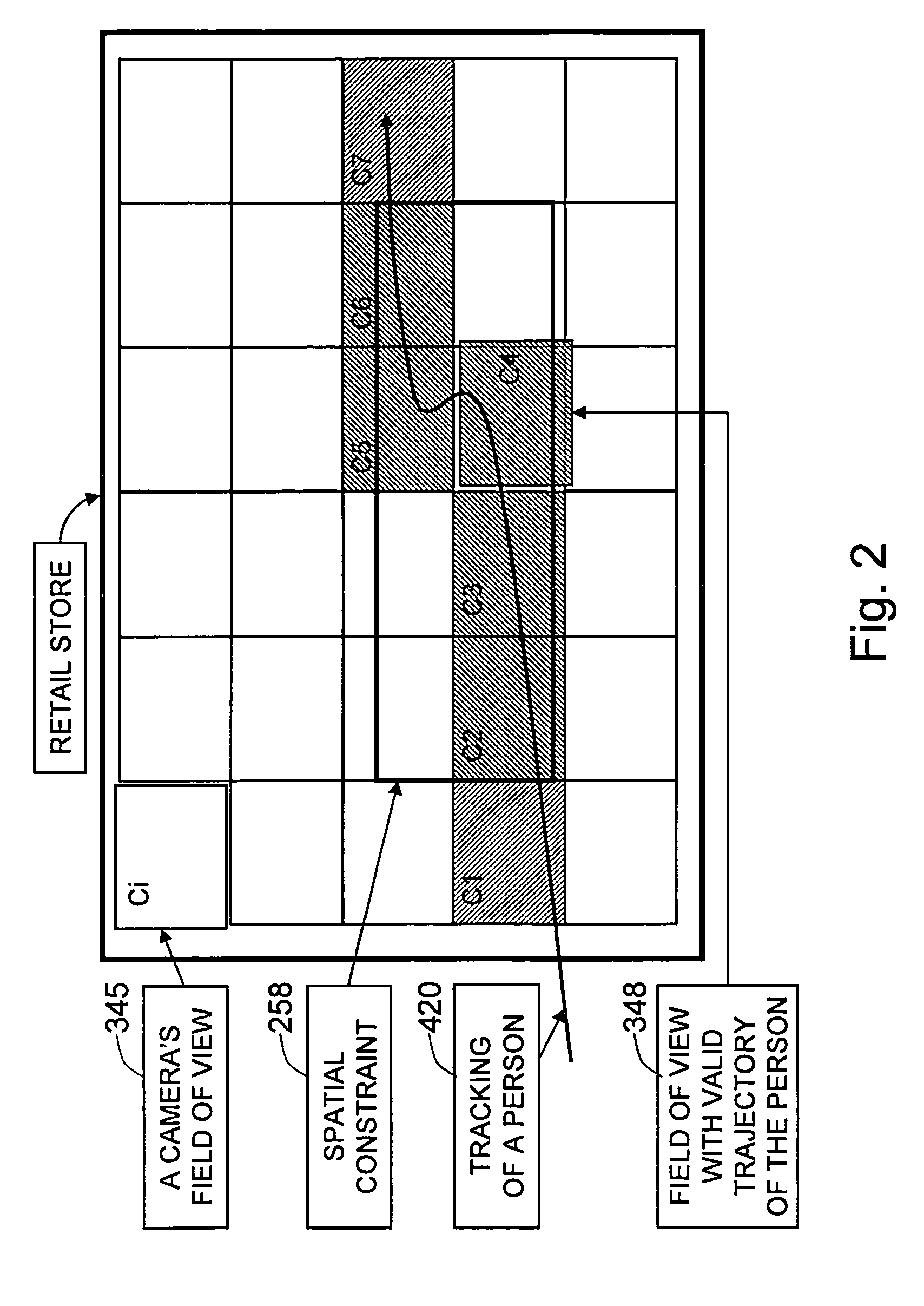
Method and system for efficient sampling of videos using spatiotemporal constraints for statistical behavior analysis
ActiveUS8570376B1Effective long-term storageSmall sizeCharacter and pattern recognitionClosed circuit television systemsComputer graphics (images)Statistical analysis
The present invention is a method and system for selecting and storing videos by applying semantically-meaningful selection criteria to the track sequences of the trips made by people in an area covered by overlapping multiple cameras. The present invention captures video streams of the people in the area by multiple cameras and tracks the people in each of the video streams, producing track sequences in each video stream. The present invention determines a first set of video segments that contains the trip information of the people, and compacts each of the video streams by removing a second set of video segments that do not contain the trip information of the people from each of the video streams. The present invention selects video segments from the first set of video segments based on predefined selection criteria for the statistical behavior analysis. The stored video data is an efficient compact format of video segments that contain the track sequences of the people and selected according to semantically-meaningful and domain-specific selection criteria. The final storage format of the videos is a trip-centered format, which sequences videos from across multiple cameras, and it can be used to facilitate multiple applications dealing with behavior analysis in a specific domain.
Owner:MOTOROLA SOLUTIONS INC
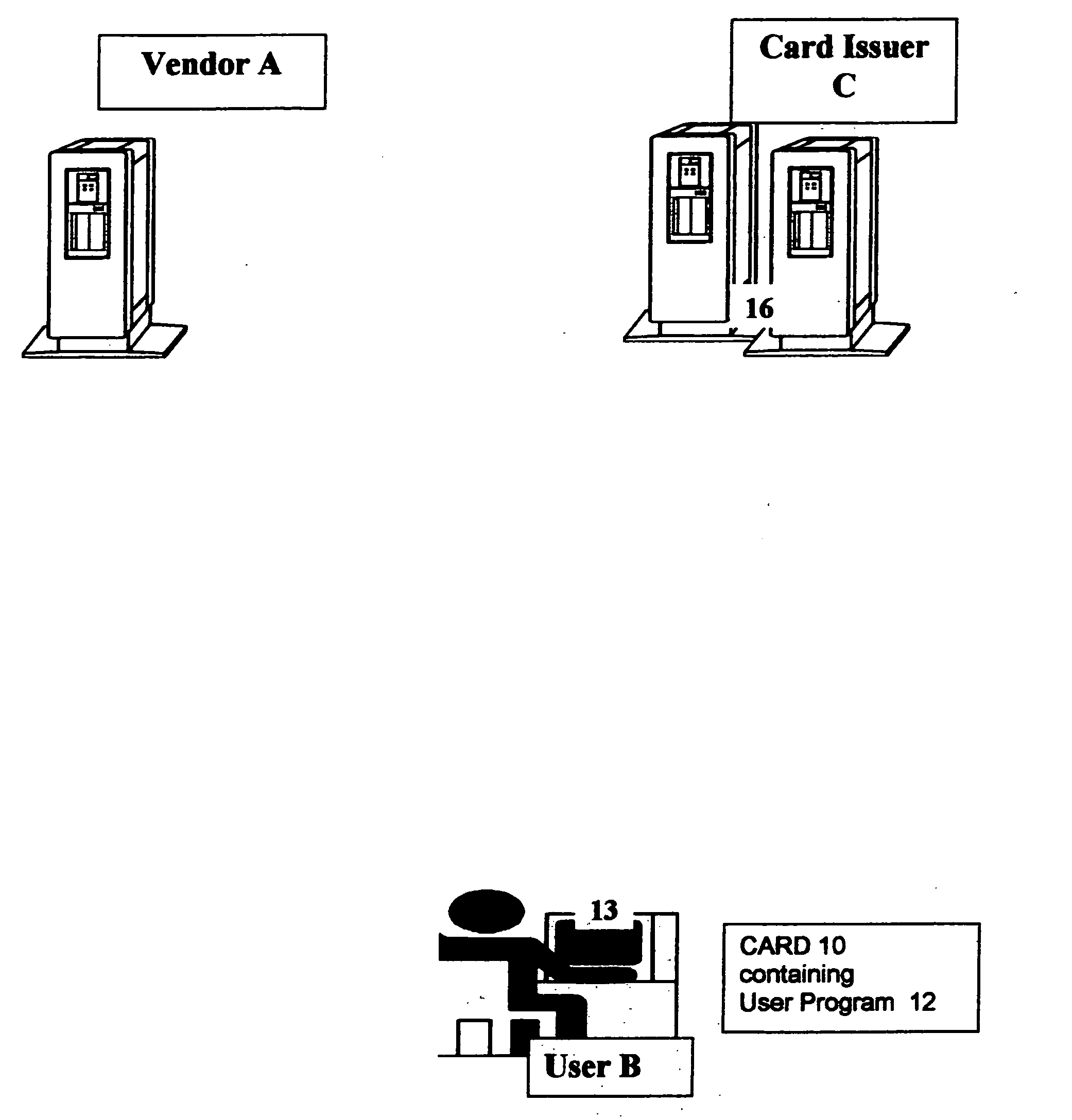
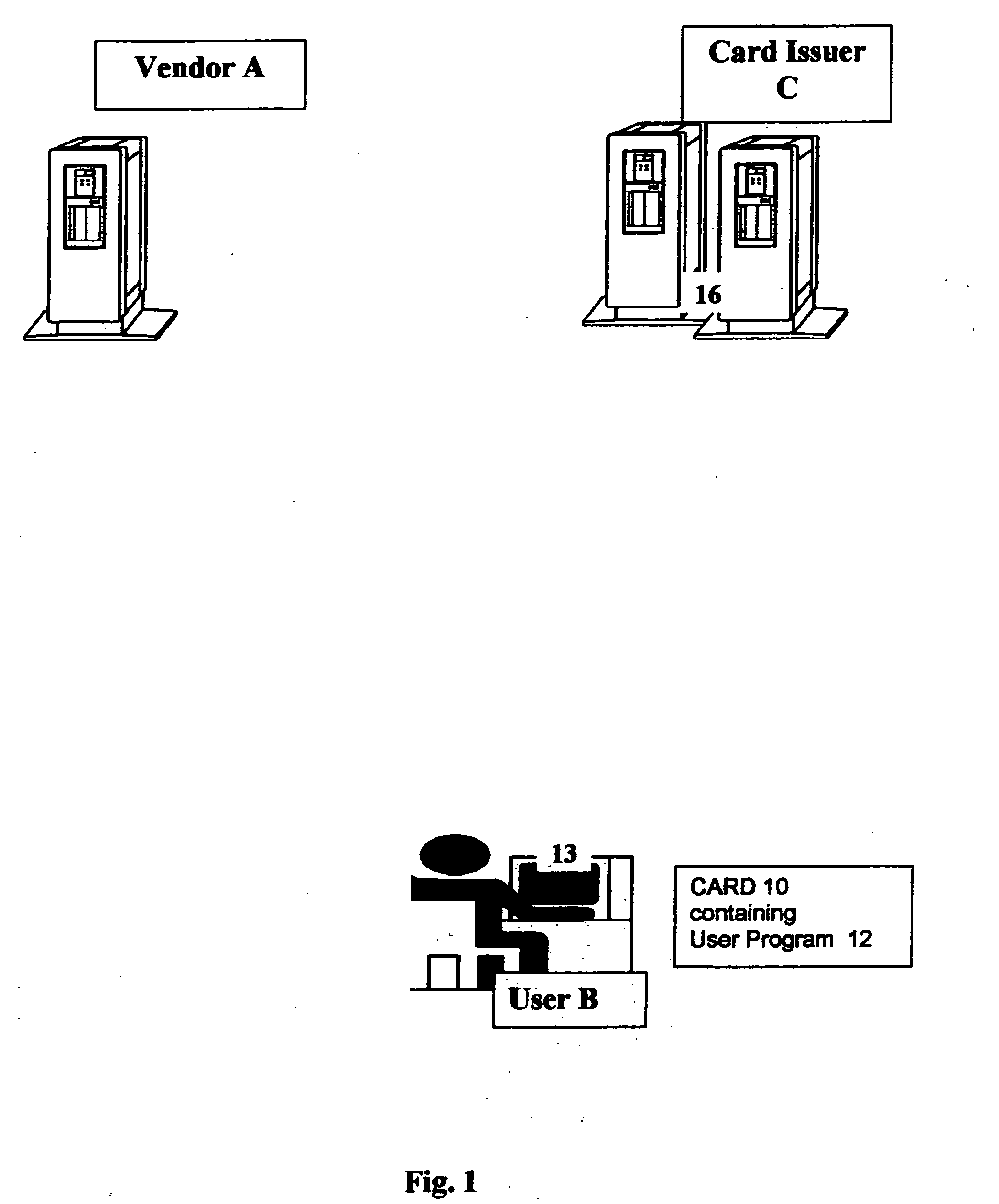
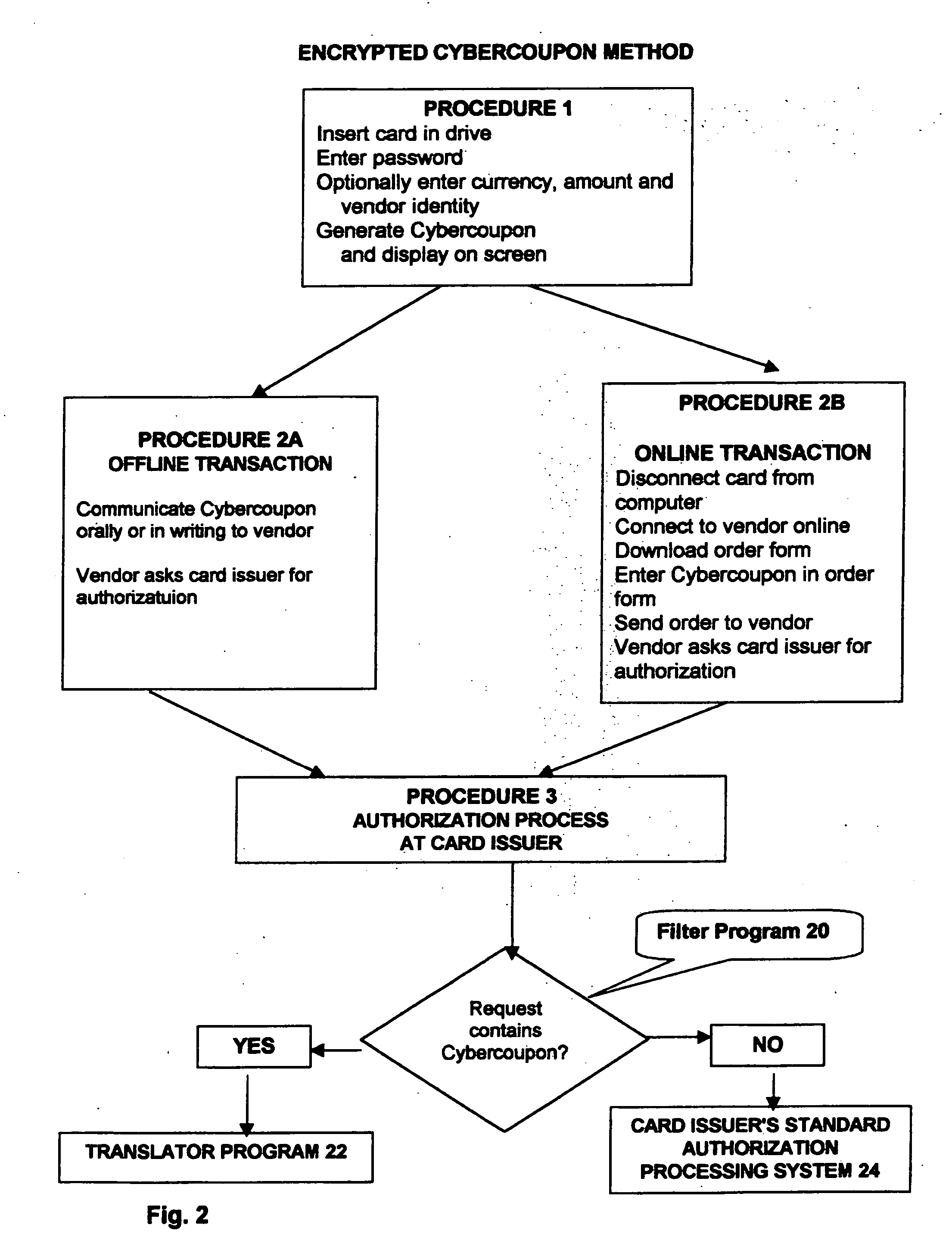
Method and system for preventing fraudulent use of credit cards and credit card information, and for preventing unauthorized access to restricted physical and virtual sites
InactiveUS20060190412A1Preventing fraudulent card transactionOvercome disadvantagesLock-out/secrecy provisionPayment circuitsCredit cardInternet privacy
A method and system for preventing fraudulent card transactions and unauthorized access to computers and physical and virtual sites online and offline whether or not involving payment. A physical card, identified by a unique identification number (ID) is issued to the user. The method provides a system of password-protected, single-use, disposable Cybercoupons for secure, authenticated on-line credit transactions, each of the Cybercoupons comprising a personal user identification number (ID) modified by combination with a one-time Cybercode selected from a number of numeric or alphanumeric codes allocated by a credit supplier.
Owner:OSTROFF MAURICE
Apparatus and method for managing access to a memory
ActiveUS7487367B2Performance is not affectedEasy to operateMemory architecture accessing/allocationEncryption apparatus with shift registers/memoriesManagement unitComputer science
The present invention provides a data processing apparatus and method for managing access to a memory within the data processing apparatus. The data processing apparatus comprises a processor operable in a plurality of modes and a plurality of domains, said plurality of domains comprising a secure domain and a non-secure domain, said plurality of modes including at least one non-secure mode being a mode in the non-secure domain and at least one secure mode being a mode in the secure domain, said processor being operable such that when executing a program in a secure mode said program has access to secure data which is not accessible when said processor is operating in a non-secure mode. Further, a memory is provided for storing data required by the processor, and consists of secure memory for storing secure data and non-secure memory for storing non-secure data. The memory further contains a non-secure table and a secure table, the non-secure table being within the non-secure memory and arranged to contain for each of a number of first memory regions an associated descriptor, and the secure table being within the secure memory and arranged to contain for each of a number of second memory regions an associated descriptor. When access to an item of data in the memory is required by the processor, the processor issues a memory access request, and a memory management unit is provided to perform one or more predetermined access control functions to control issuance of the memory access request to the memory. The memory management unit comprises an internal storage unit operable to store descriptors retrieved by the memory management unit from either the non-secure table or the secure table, and in accordance with the present invention the internal storage unit comprises a flag associated with each descriptor stored within the internal storage unit to identify whether that descriptor is from the non-secure table or the secure table. By this approach, when the processor is operating in a non-secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the non-secure table. In contrast, when the processor is operating in a secure mode, the memory management unit is operable to perform the predetermined access control functions for the memory access request with reference to access control information derived from the descriptors in the internal storage unit retrieved from the secure table. This approach enables different descriptors to be used for the control of accesses to memory in either the secure domain or the non-secure domain, whilst enabling such different descriptors to co-exist within the memory management unit's internal storage unit, thereby avoiding the requirement to flush the contents of such an internal storage unit when the operation of the processor changes from the secure domain to the non-secure domain, or vice versa.
Owner:ARM LTD
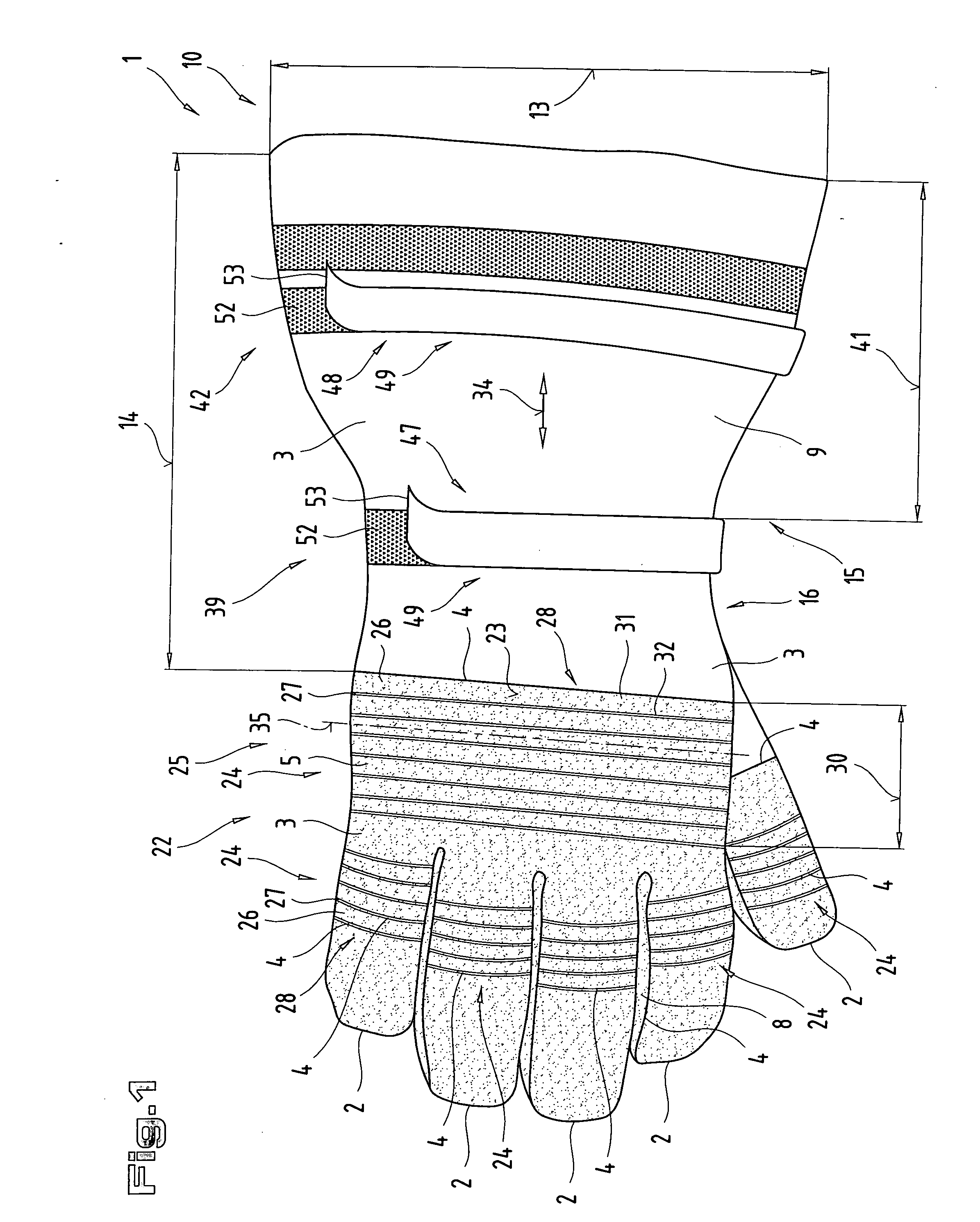
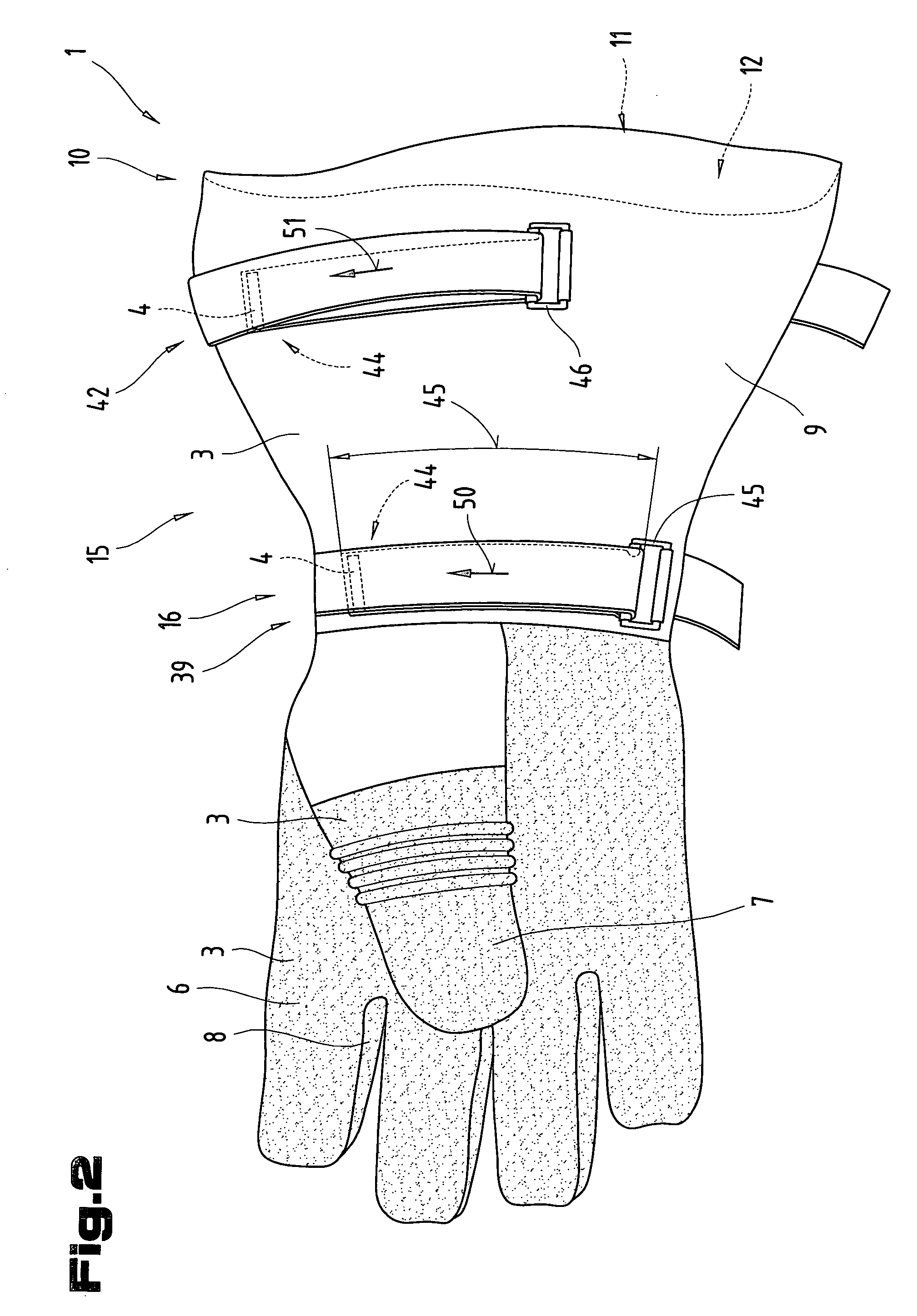
Glove
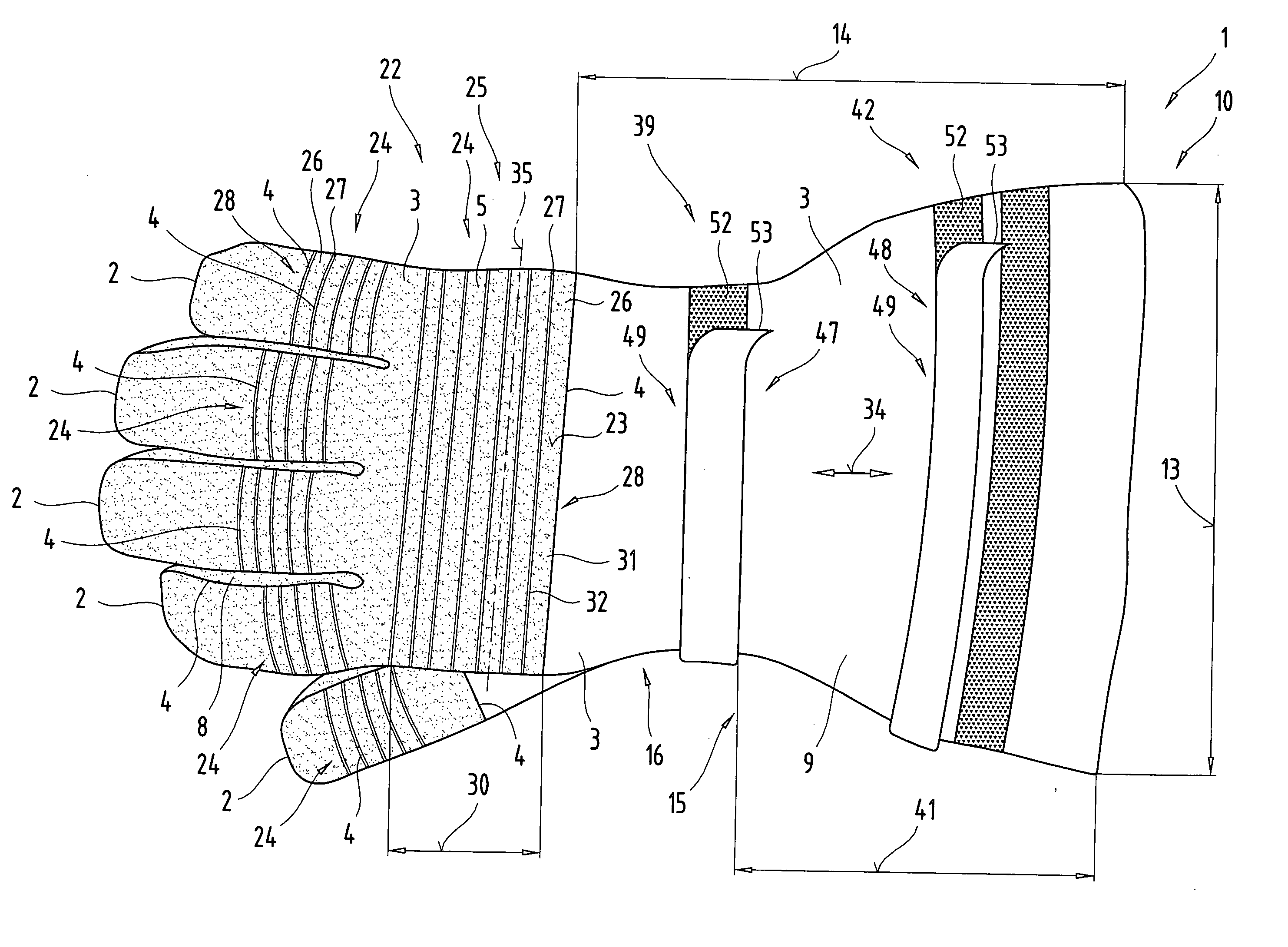
InactiveUS20060048268A1Improve fitImprove protectionGlovesGarment fastenersEngineeringBiomedical engineering
The invention describes a fireproof glove (1) with a layered structure comprising at least one liquid-tight functional layer (18) and a heat-resistant and / or fire-retarding layer (20) with low thermal conductivity. Furthermore, the invention describes a glove (1) comprising a material precut (3) with one or more reinforced areas (24). Moreover, the invention describes a glove (1) with a shaft (15) extending over a wrist area (16) and conically widening in the direction of the open face end area (10) of the shaft, whereby provision is made in the area of the shaft (15) for a first and one other adjusting device (39, 42). Furthermore, the invention describes a glove (1) that is formed by at least one material layer (17) consisting of an inelastic and non-expanding material, and comprising a tubular and cylindrical shaft (15). In its face end area (10) with a slip-in opening (11), said shaft has a circumference on the external surface (23) in the range of from 20 cm to 40 cm.
Owner:ESKA LEDERHANDSCHUHFAB & CO
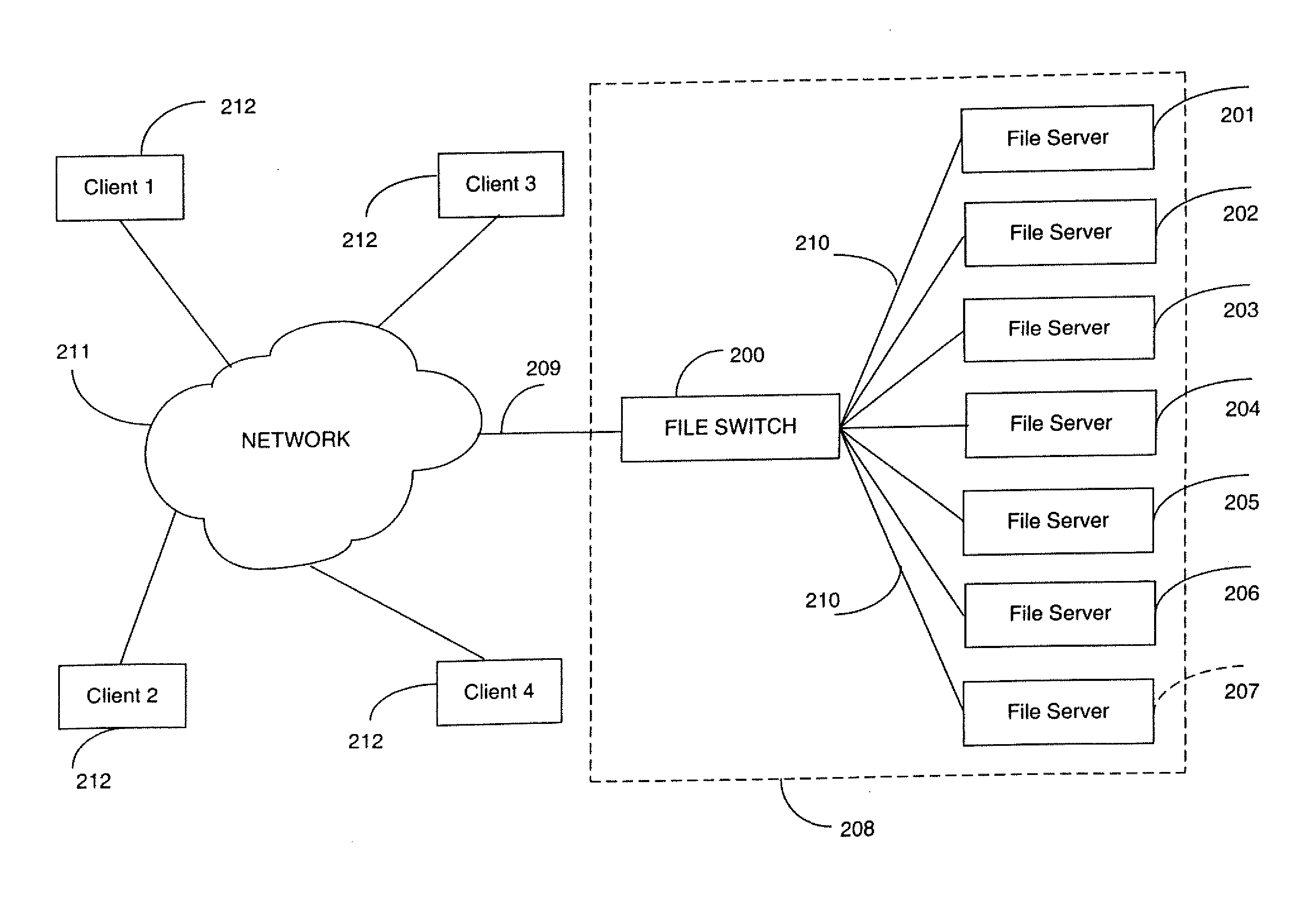
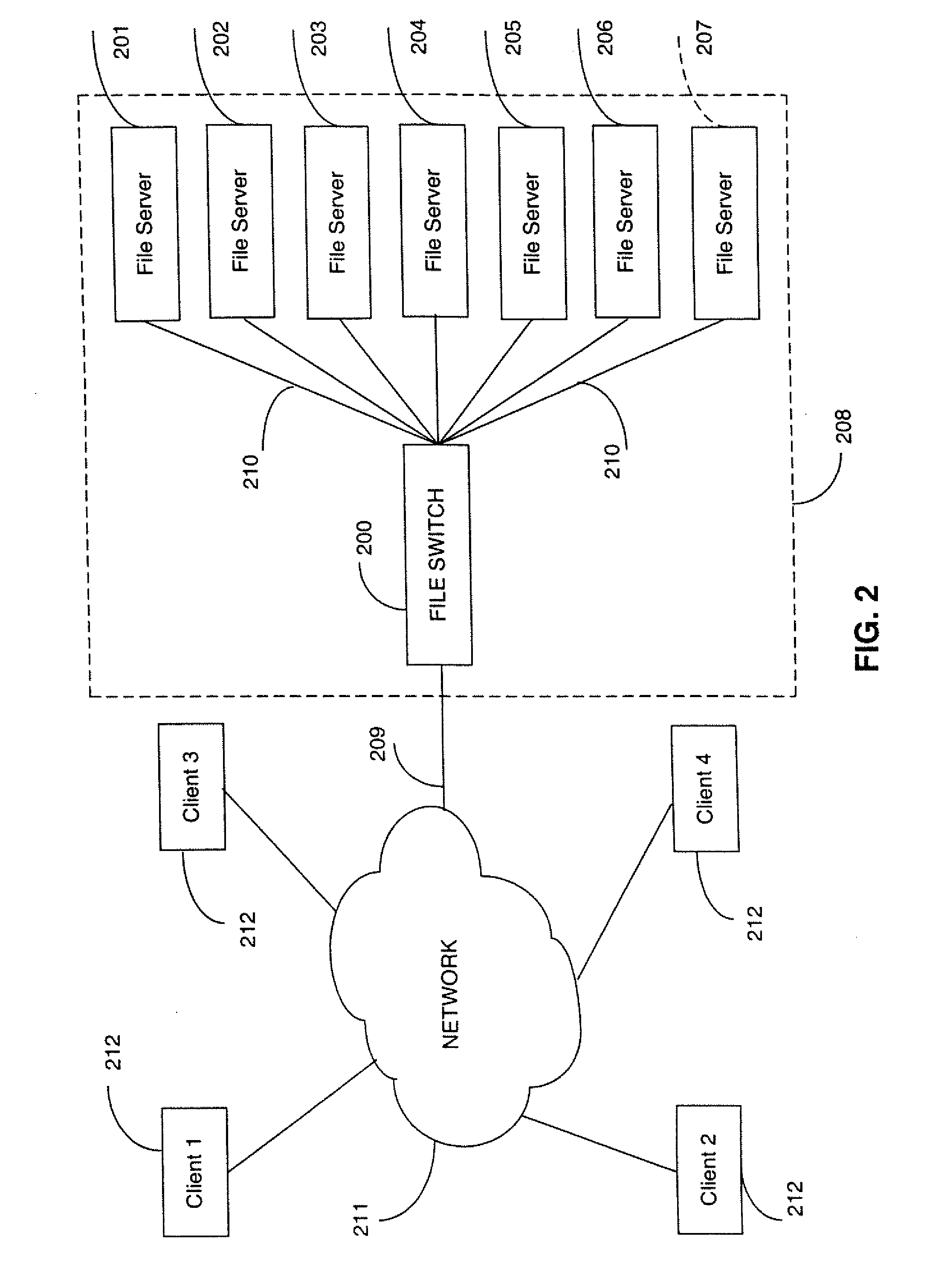
Rule based aggregation of files and transactions in a switched file system
InactiveUS20090292734A1Improve performanceLoad balancingMultiple digital computer combinationsLocation information based serviceFile systemData file
A switched file system, also termed a file switch, is logically positioned between client computers and file servers in a computer network. The file switch distributes user files among multiple file servers using aggregated file, transaction and directory mechanisms. The file switch distributes and aggregates the client data files in accordance with a predetermined set of aggregation rules. Each rule can be modified independently of the other rules. Different aggregation rules can be used for different types of files, thereby adapting the characteristics of the switched file system to the intended use and to the expected or historical access patterns for different data files.
Owner:RPX CORP
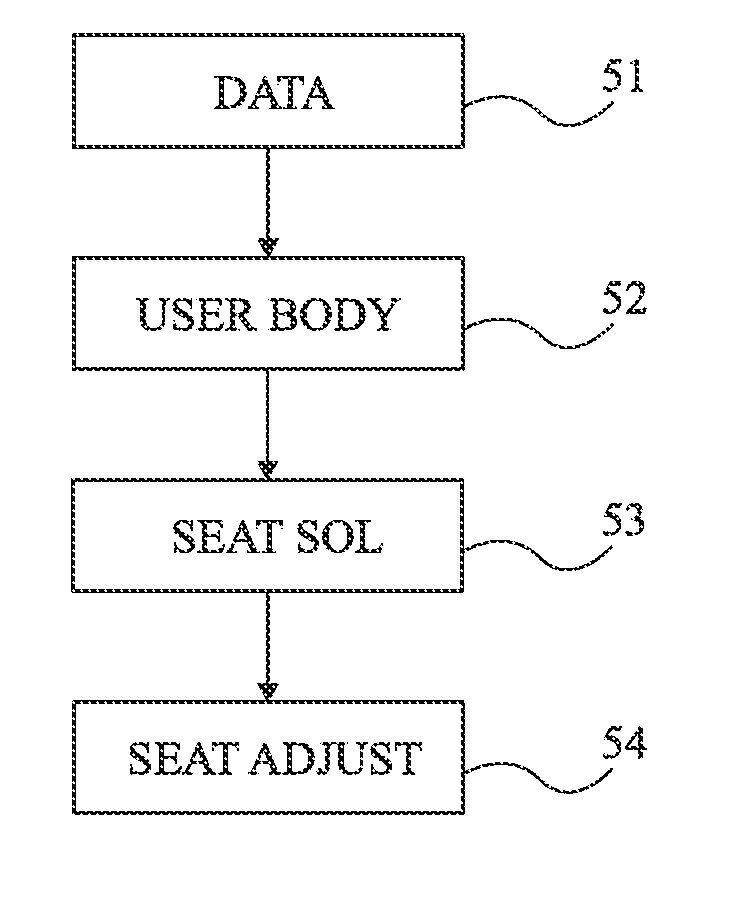
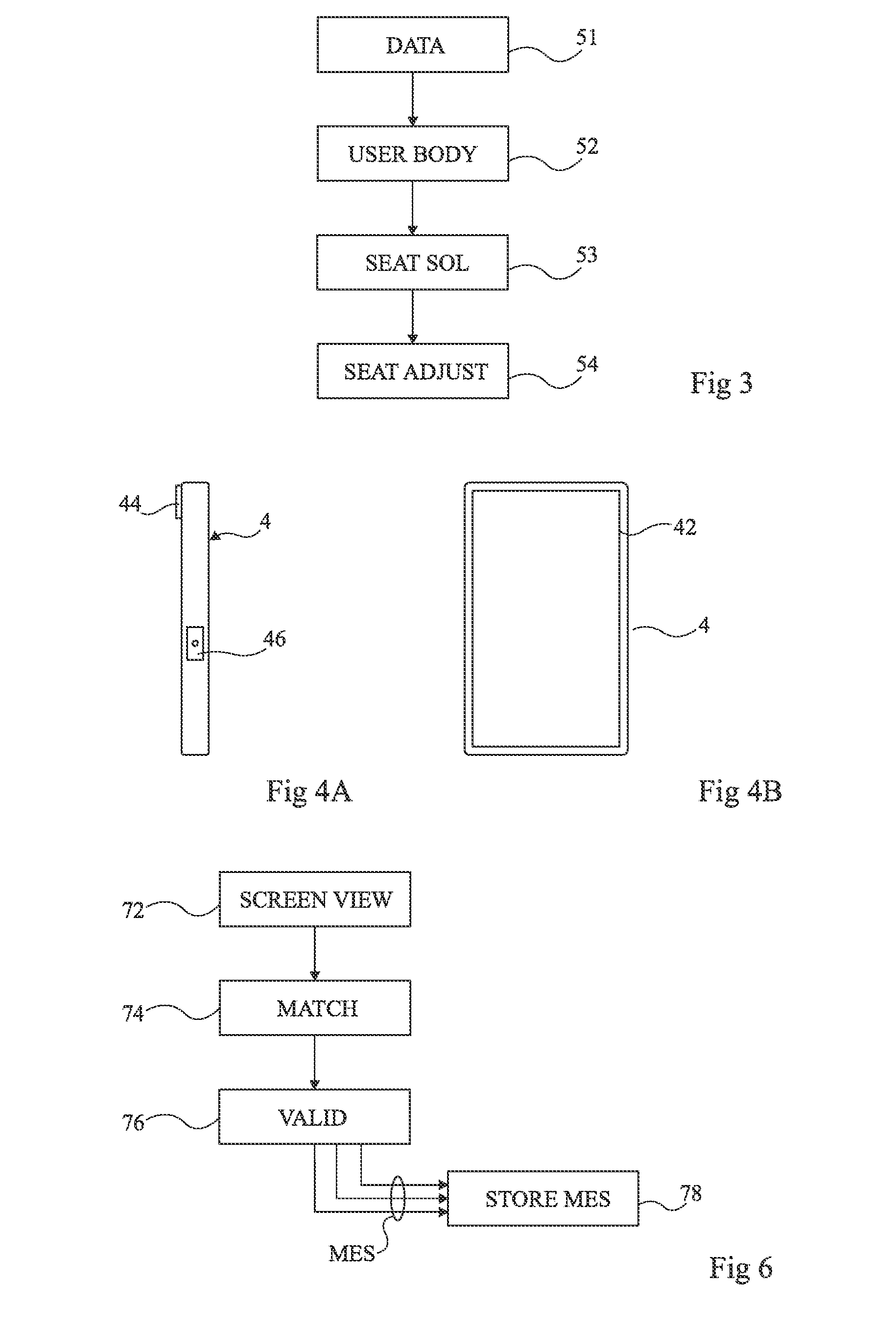
Seat adjustment for a motor vehicle
InactiveUS20150084985A1Overcome disadvantagesAvoid storage problemsCathode-ray tube indicatorsBiometric pattern recognitionComputer visionComputer graphics (images)
Owner:FAURECIA
Host capture
ActiveUS20090070171A1Improve protectionAvoid storage problemsFinanceBuying/selling/leasing transactionsDatabase
A system and method for processing transactions. A unique transaction identifier is generated for each transaction. Processing of the transaction utilizes the unique transaction identifier.
Owner:VISA USA INC (US)
Method for sharing multimedia data
InactiveUS20060216021A1Avoid storage problemsQuality improvementDigital data information retrievalPrintersEvent dataDigital image
Method for sharing multimedia data and especially images captured by many cameras provided with image transmission means, comprising: the reception of digital image routing messages that include image data (40) and at least some event data (42); the linking to each image of an identifier according to the event data, and the saving of said digital images; the reception of image requests (50) also comprising at least some event data (52); the search for at least one saved image, linked to an identifier according to an event data (42) corresponding to the event data (52) of the request, and if the search finds at least one image, the transmission of the images to an addressee.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
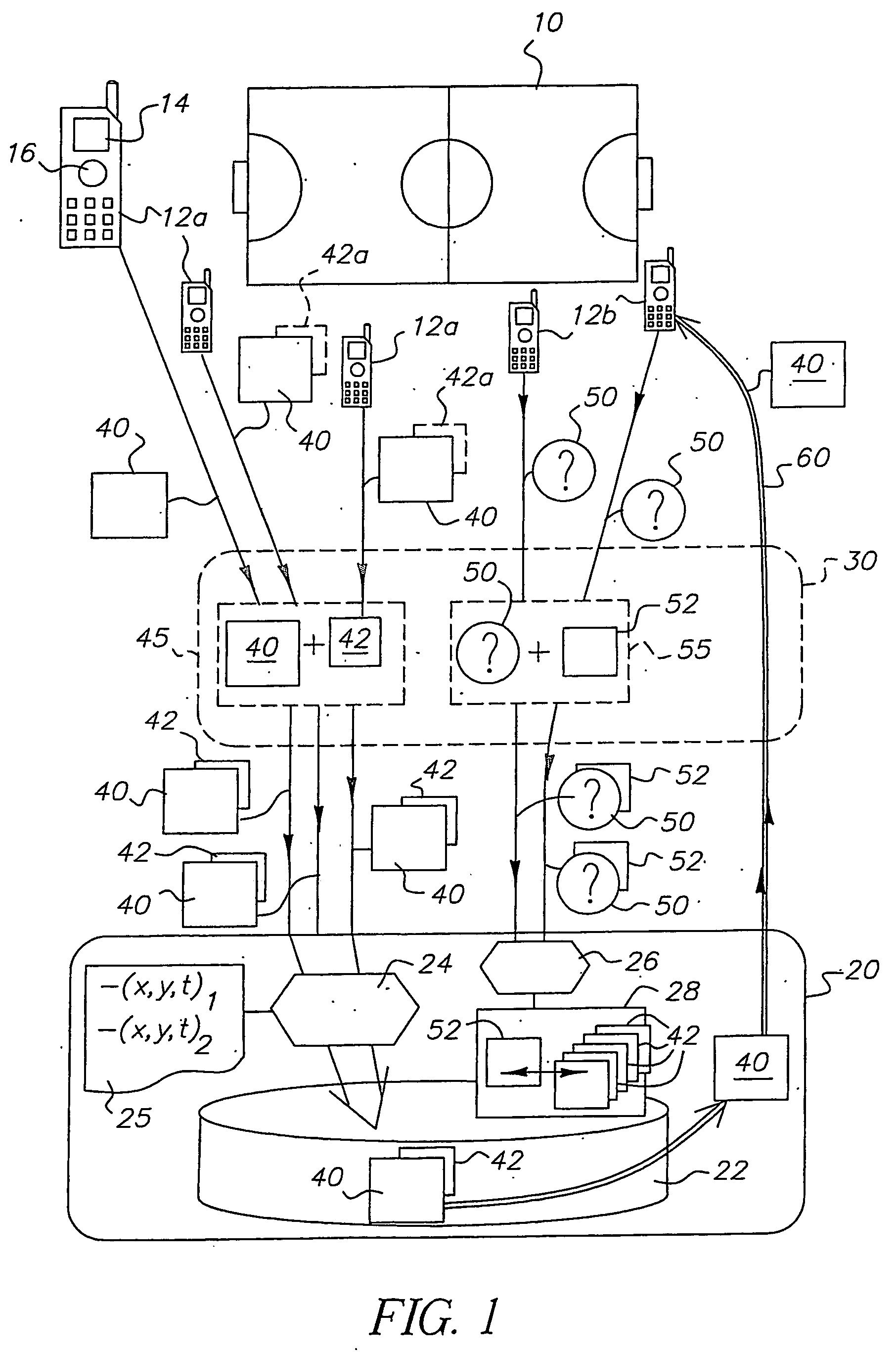
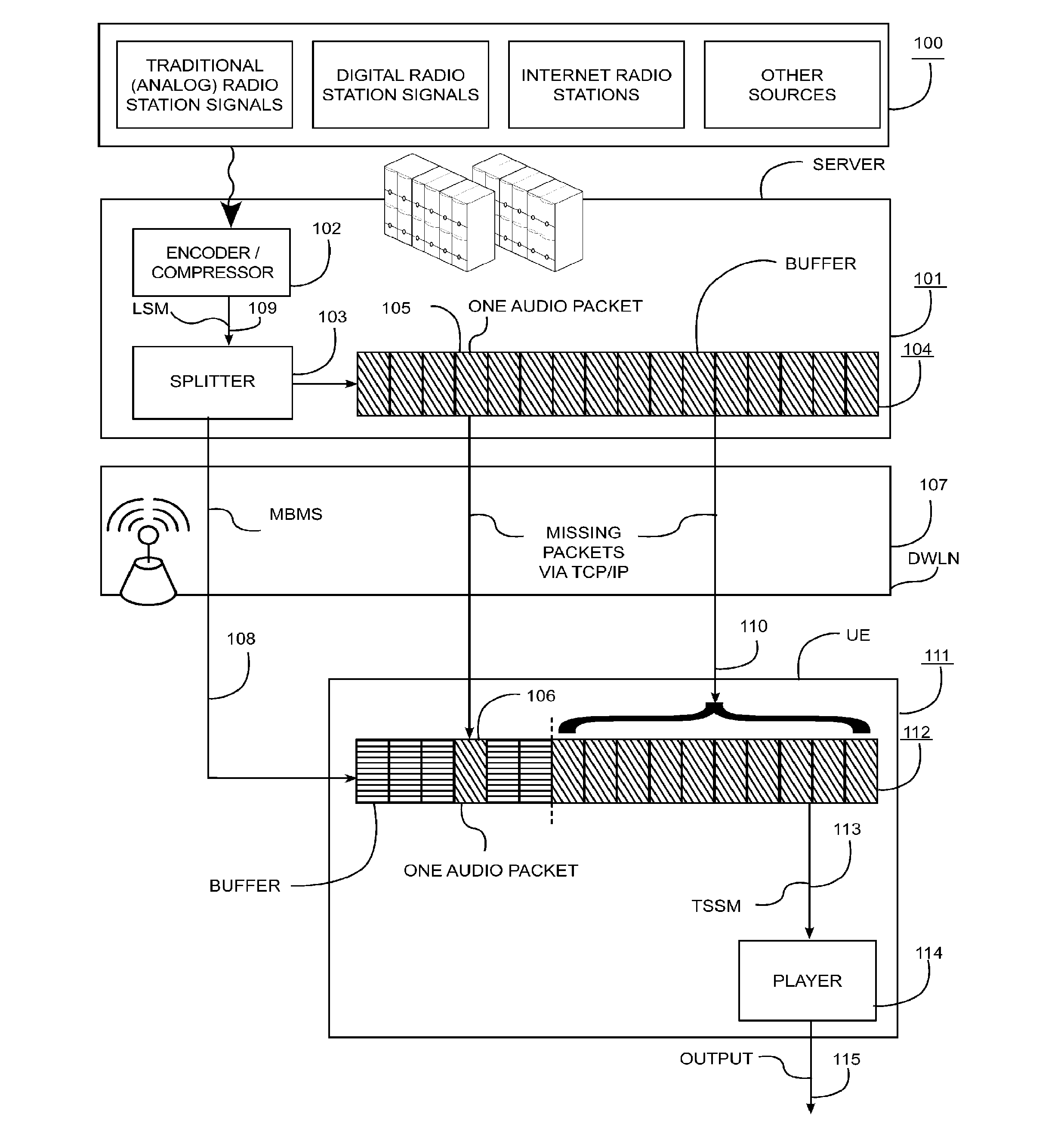
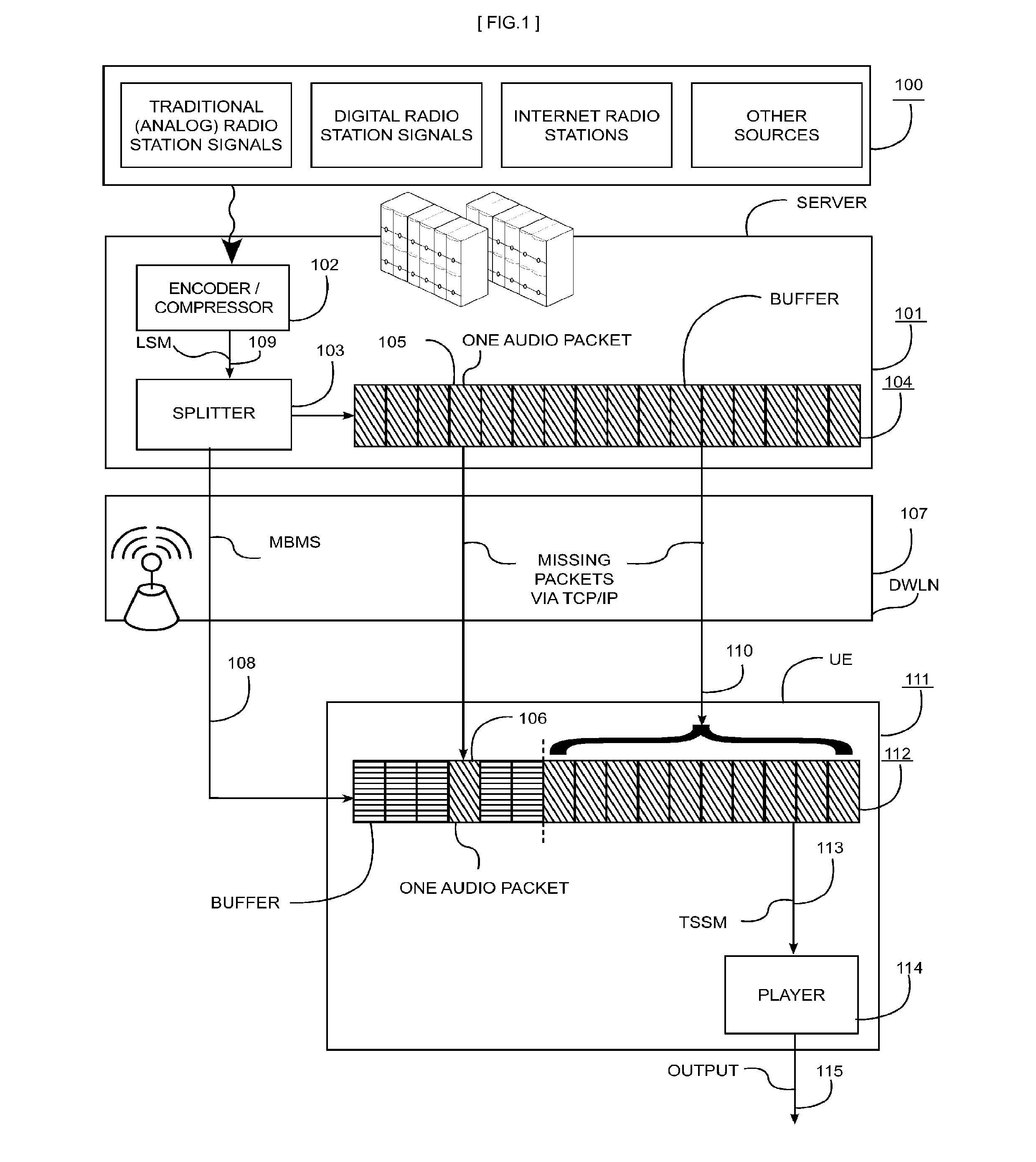
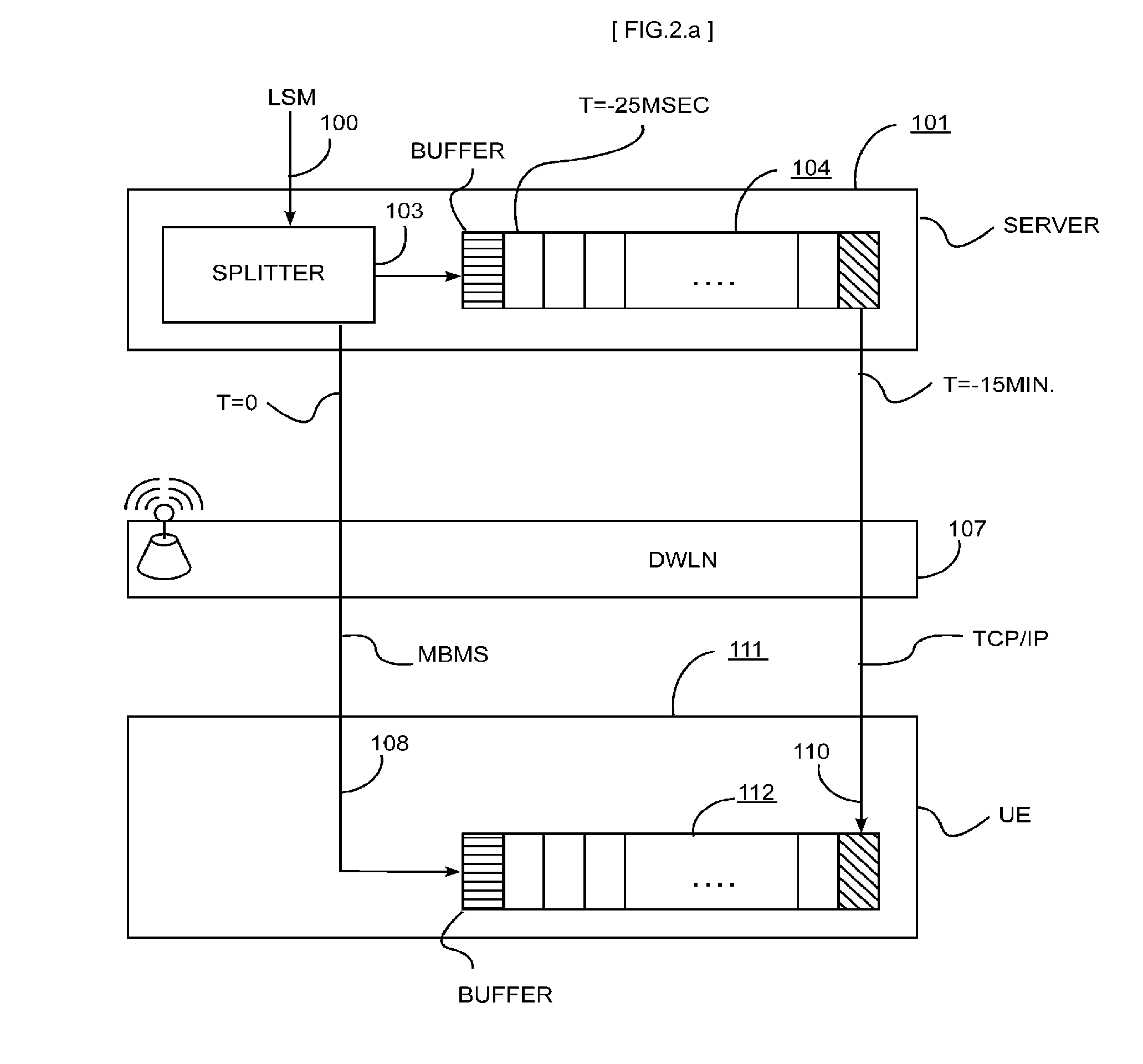
Systems and methods for transmission of uninterrupted radio, television programs and additional data services through wireless networks
ActiveUS20120099514A1Quality improvementIncrease the number ofError preventionBroadcast transmission systemsAviationStreaming data
A method and system for In-Dash Multimedia Players or Portable Multimedia Players for automotive, aviation, boating, and personal use that, exploiting the services and capabilities of the Digital Wireless Network DWLN (107), such as 3G network, and buffering the live stream data on both the Server (101) and User Equipment (111), combines in a novel synergistic integration a suite of new and known features such as: immediate and uninterrupted listening / viewing of Live Streaming Media LSM (109) by the user with or without optimization of the data bandwidth, and the provision to customize the commercial messages according to the user location, and the capability of reporting the customer choices and habits, and the automatic deletion of LSM after the time-shift time to benefit from copyright agreements.
Owner:FOSCO BIANCHETTI
Digital Rights Management System
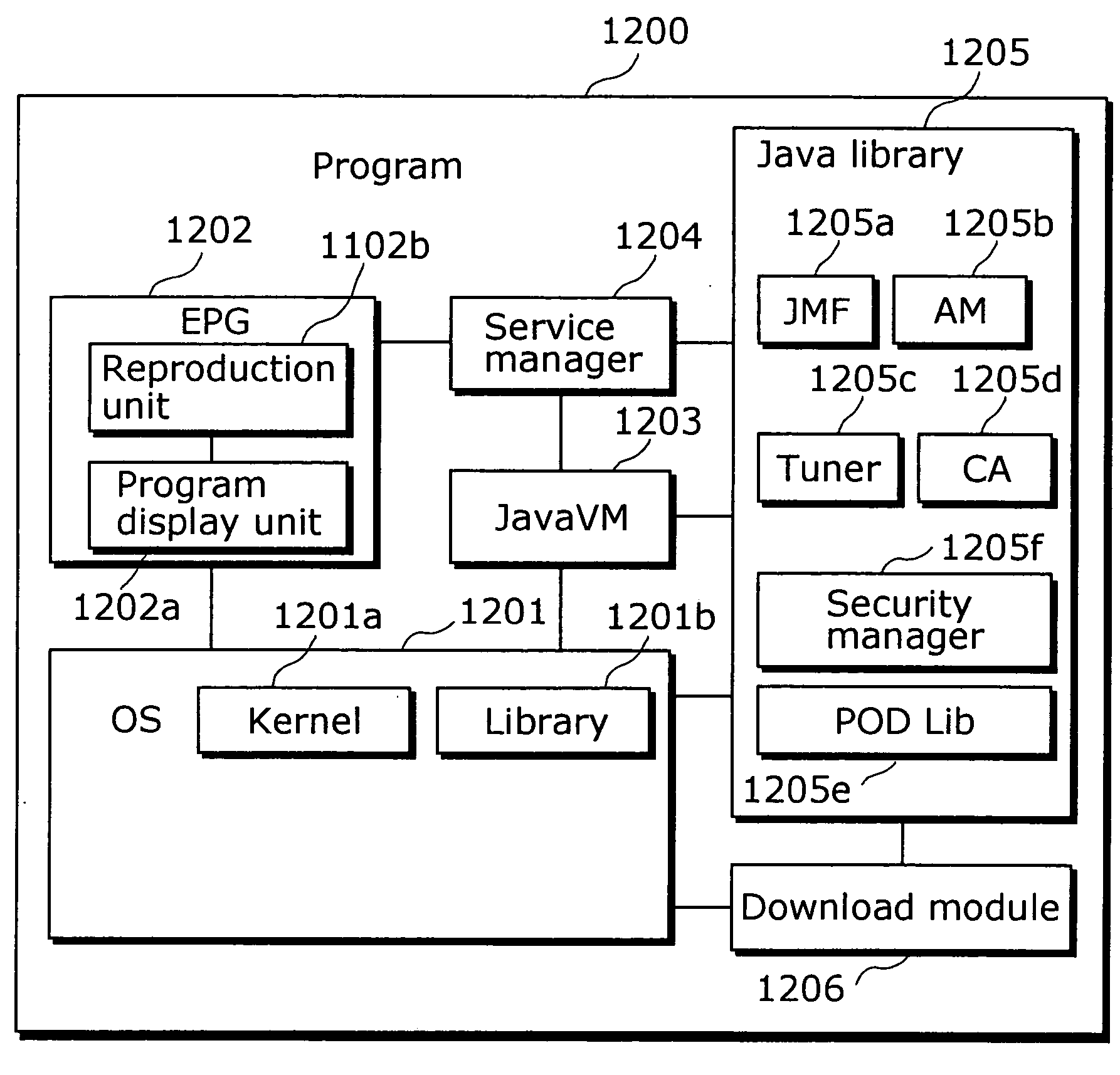
ActiveUS20080052781A1Avoid storage problemsEnough timeDigital data processing detailsUnauthorized memory use protectionDigital rights management systemManagement system
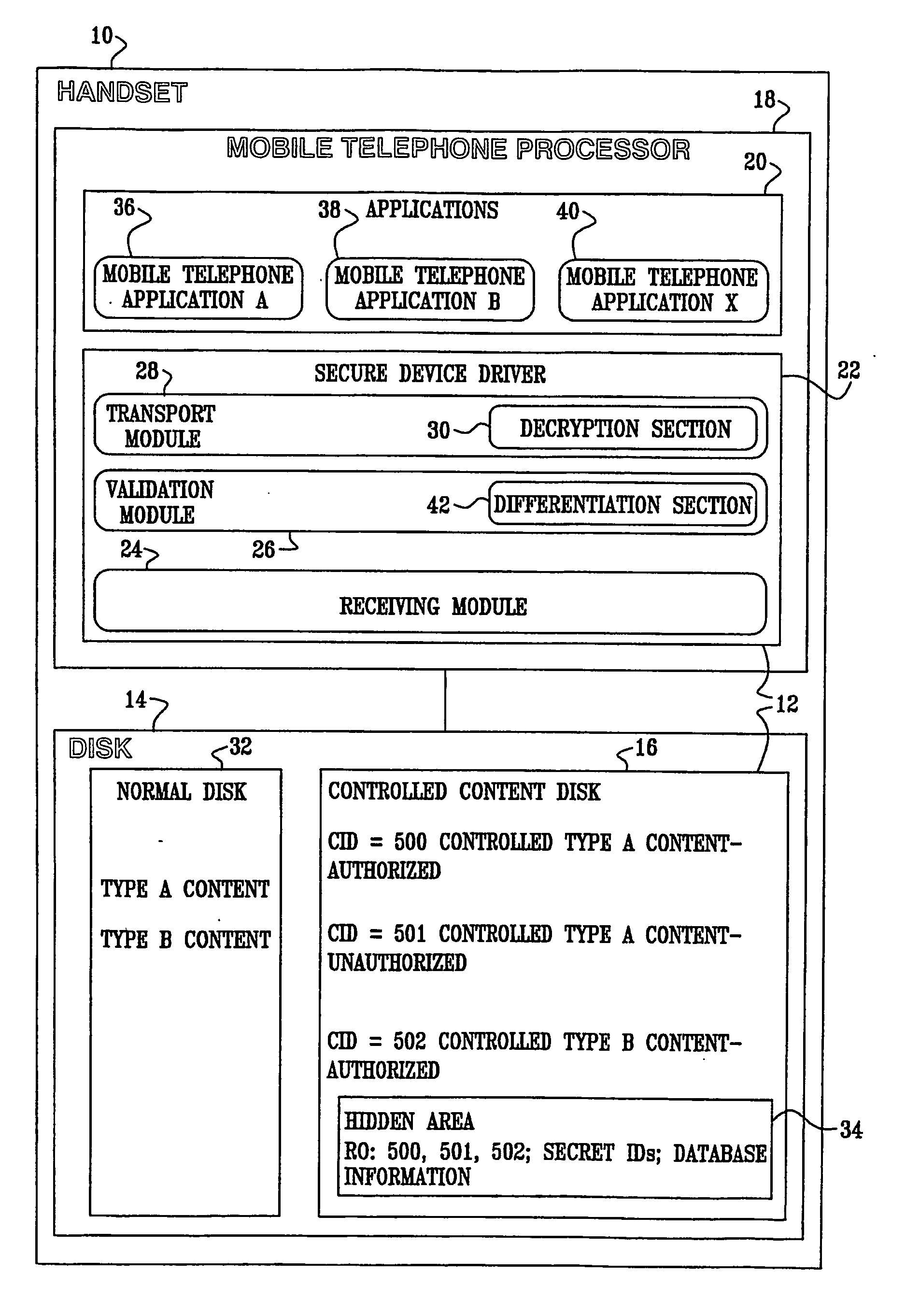
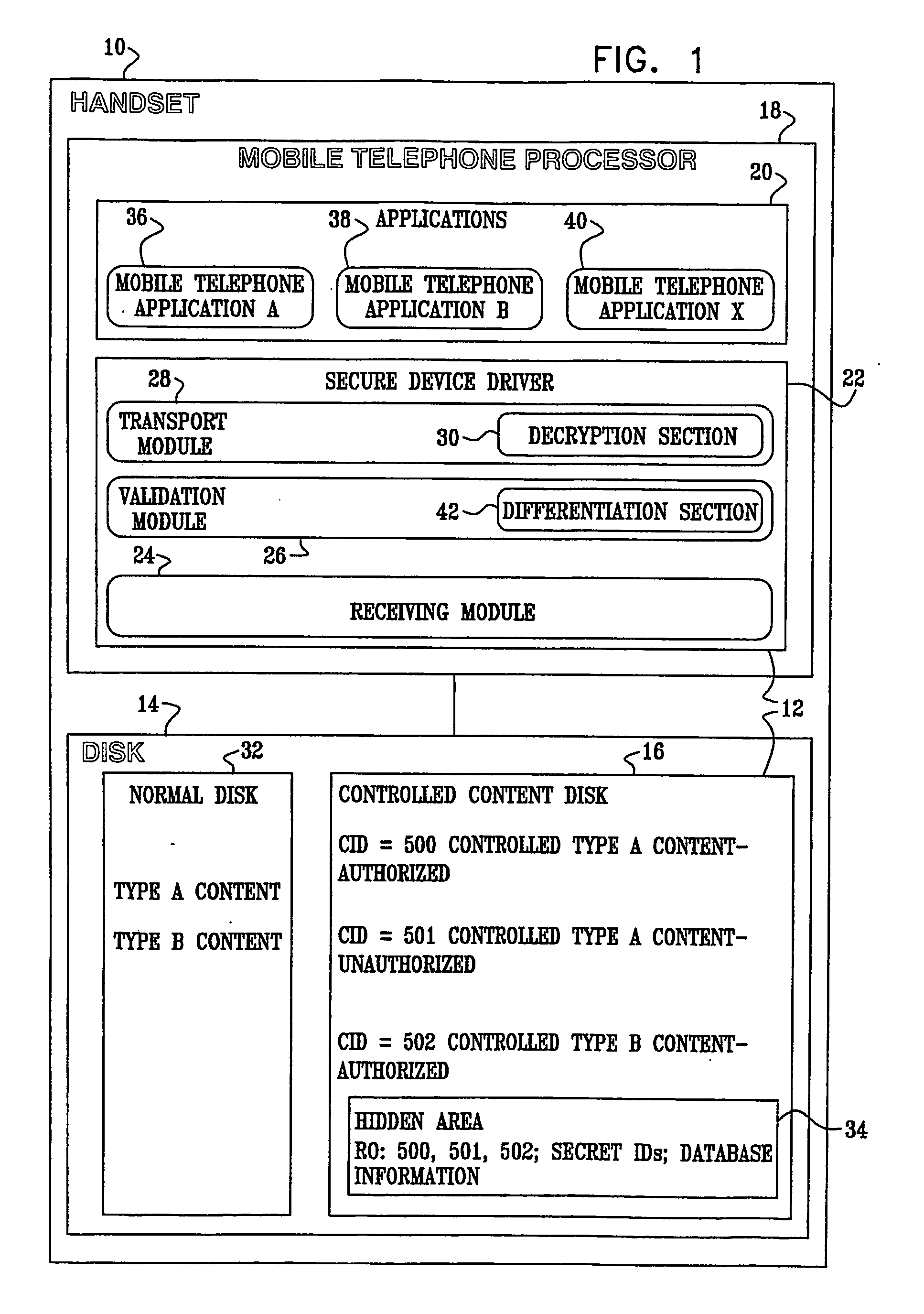
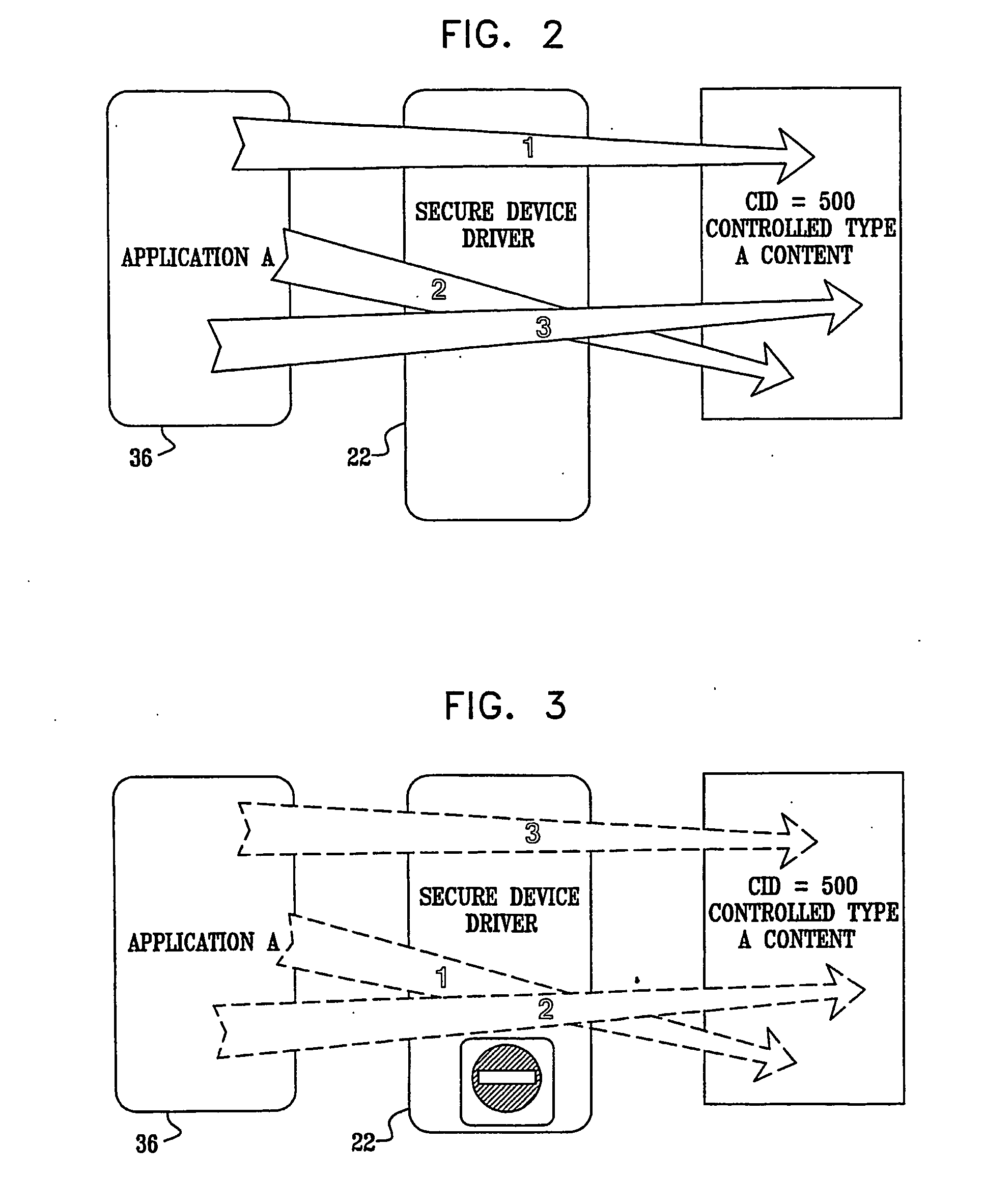
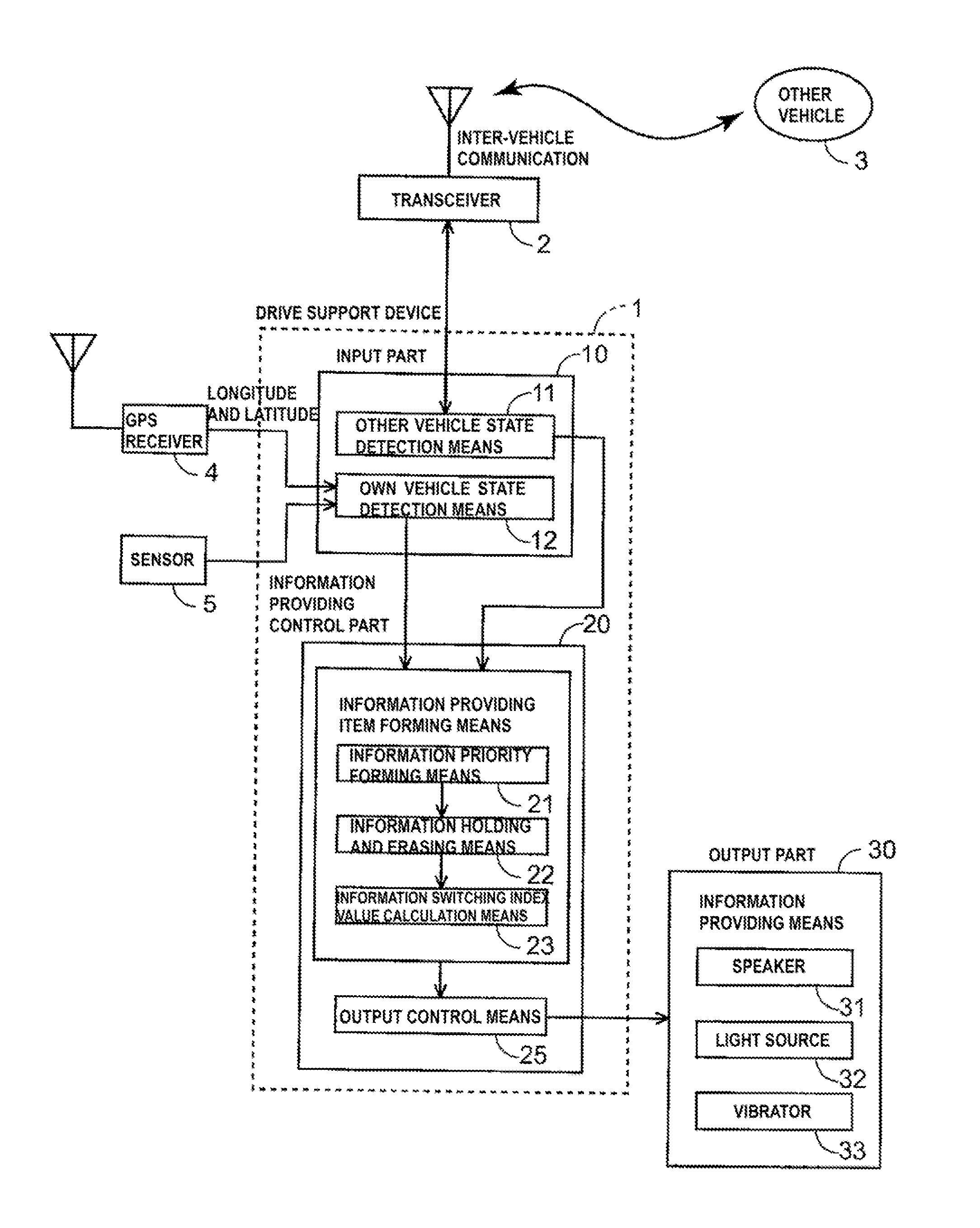
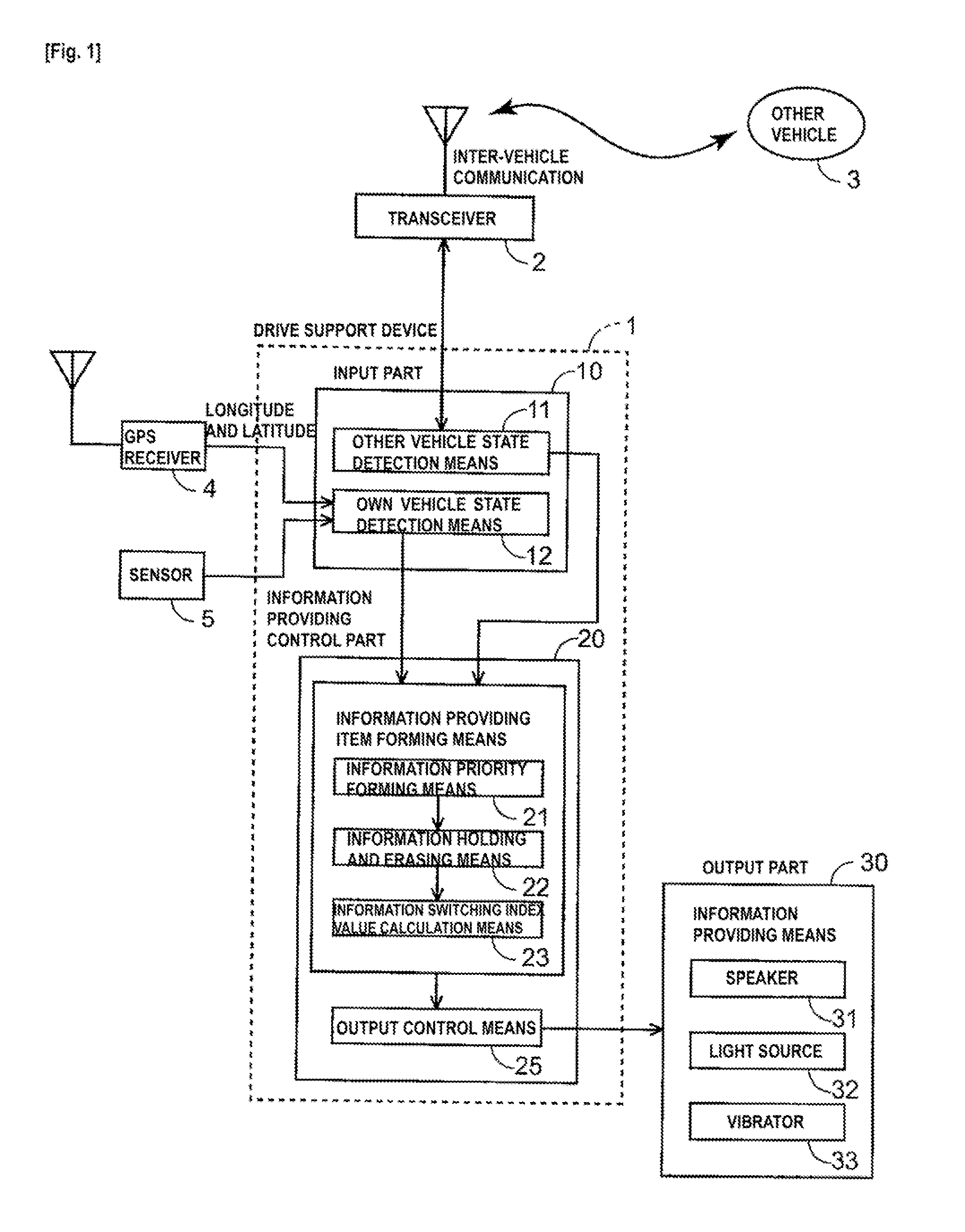
A digital rights management system (FIG. 1) for a mobile telephone (10), including a controlled content disk (16) to store content in an encrypted format, and a mobile telephone processor (18) to run a plurality of mobile telephone applications (36, 38, 40) and a secure device driver (22) thereon, the mobile telephone processor (18) being operationally associated with the controlled content disk (16), the mobile telephone applications (36, 38, 40) being unable to decrypt content from the encrypted format, the secure device driver (22) having a receiving module (24) to receive a request from one of the mobile telephone applications (36, 38, 40) to access the content, a validation module (26) to validate the request, and a transport module (28) to substantially directly transfer the content to the one mobile telephone application, contingent upon a positive result of the validating of the validation module (26). Related apparatus and methods are also described.
Owner:SYNAMEDIA LTD
Method and system for secure flexible software licensing
InactiveUS20100031373A1Avoid storage problemsDigital data processing detailsAnalogue secracy/subscription systemsData retrievalApplication software
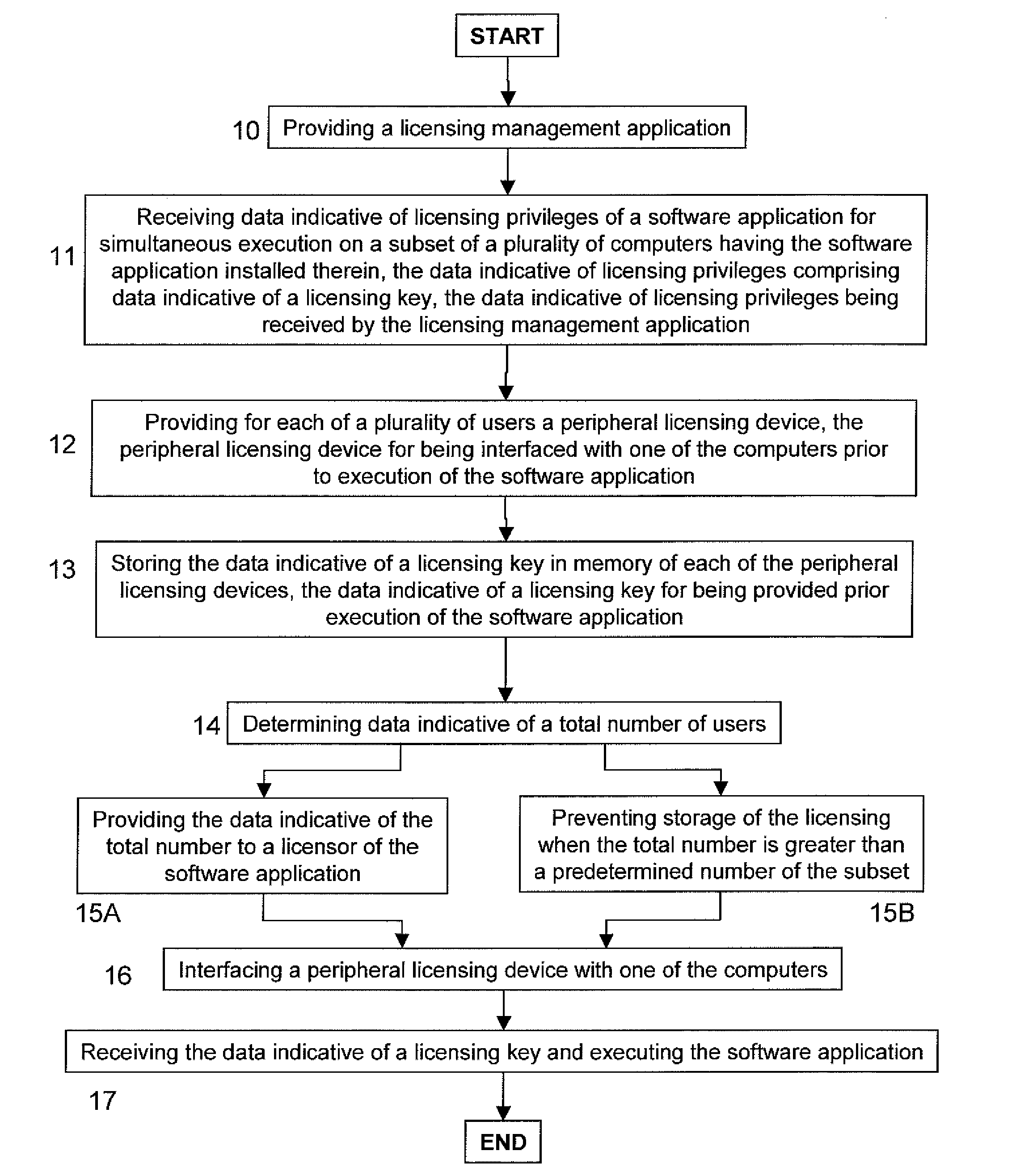
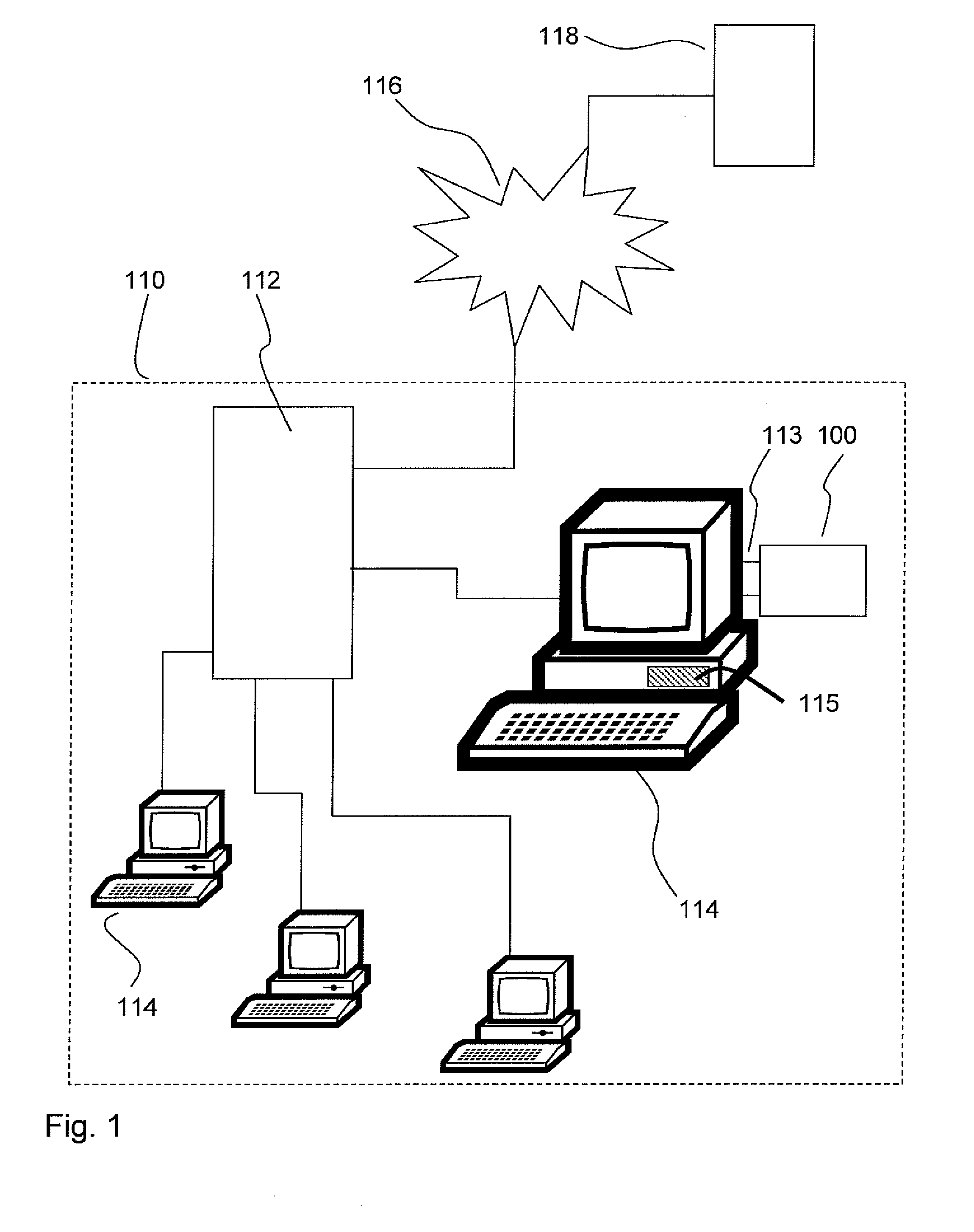
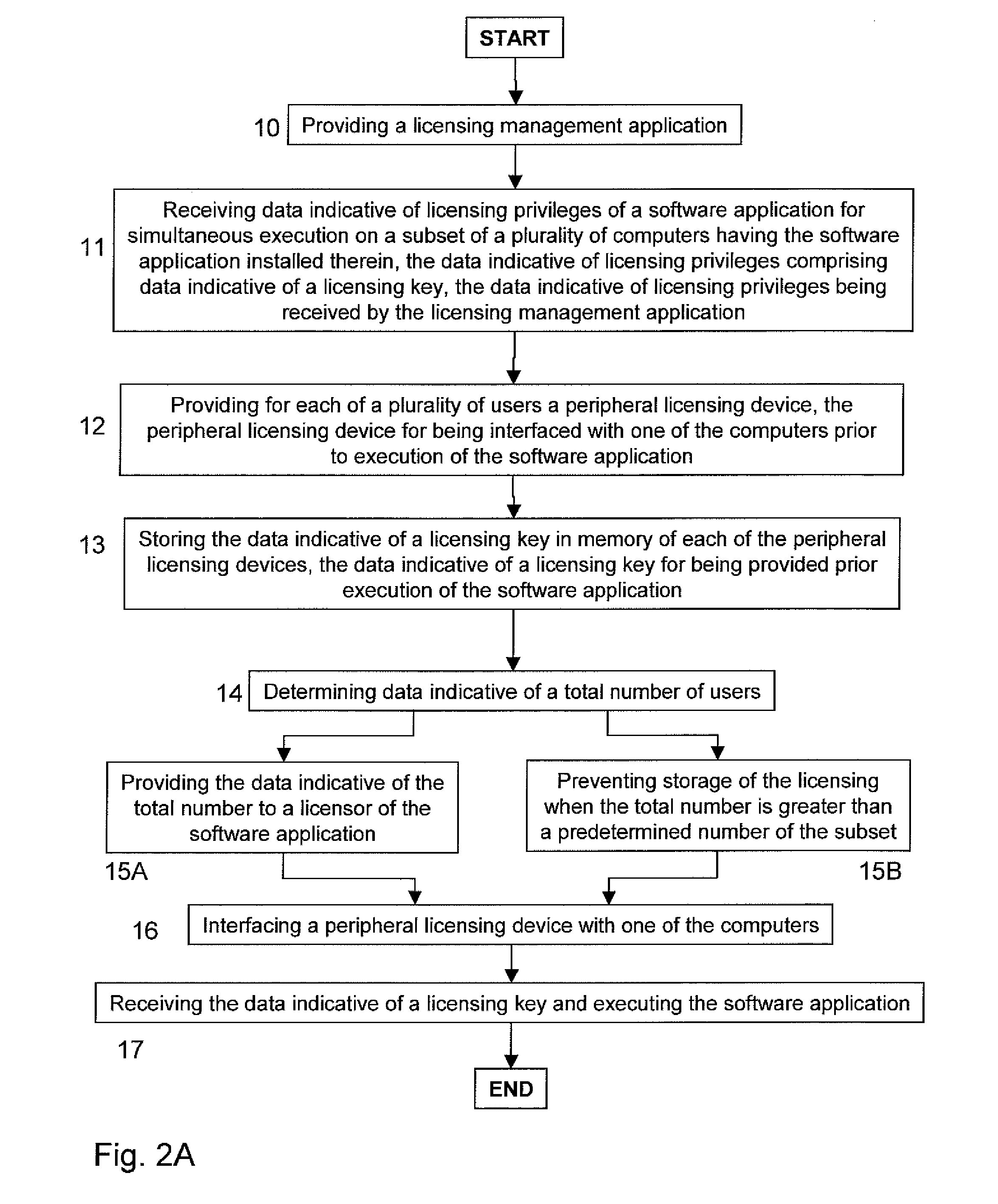
When executing a licensing management application, data indicative of licensing privileges of a software application for simultaneous execution on a subset of a plurality of computers are received from a licensor of the software application. The data indicative of licensing privileges comprise data indicative of a licensing key. For each of a plurality of users a peripheral licensing device is provided and the data indicative of a licensing key are then stored in memory thereof. Data indicative of a total number of users—equal to a number of the subset—are determined and provided to the licensor, or storage of the licensing key is prevented, when the total number is greater than a predetermined number of the subset. After execution of the licensing management application and provision of each of the users with a respective peripheral licensing device, each of the users is enabled to execute the software application by interfacing the peripheral licensing device with one of the computers, after which the data indicative of a licensing key are retrieved and the software application is executed.
Owner:IMATION
Tamper-protected hardware and method for using same
ActiveUS20150161415A1Improve robustnessSuitable for useMultiple keys/algorithms usagePublic key for secure communicationComputer hardwareTamper resistance
One of the various aspects of the invention is related to suggesting various techniques for improving the tamper-resistibility of hardware. The tamper-resistant hardware may be advantageously used in a transaction system that provides the off-line transaction protocol. Amongst these techniques for improving the tamper-resistibility are trusted bootstrapping by means of secure software entity modules, a new use of hardware providing a Physical Unclonable Function, and the use of a configuration fingerprint of a FPGA used within the tamper-resistant hardware.
Owner:EMSYCON
System and method for security and privacy aware virtual machine checkpointing
ActiveUS9069782B2Avoid storage problemsInput/output to record carriersError detection/correctionApplication programming interfaceApplication software
A checkpointing method for creating a file representing a restorable state of a virtual machine in a computing system, comprising identifying processes executing within the virtual machine that may store confidential data, and marking memory pages and files that potentially contain data stored by the identified processes; or providing an application programming interface for marking memory regions and files within the virtual machine that contain confidential data stored by processes; and creating a checkpoint file, by capturing memory pages and files representing a current state of the computing system, which excludes information from all of the marked memory pages and files.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
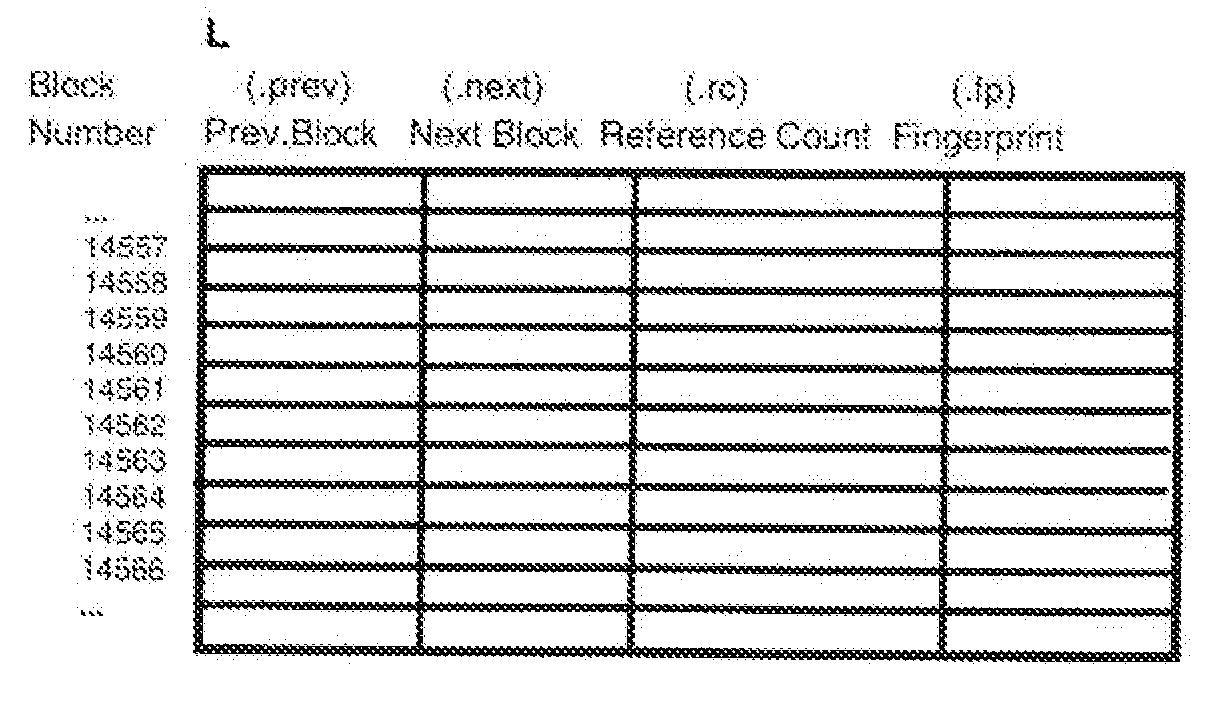
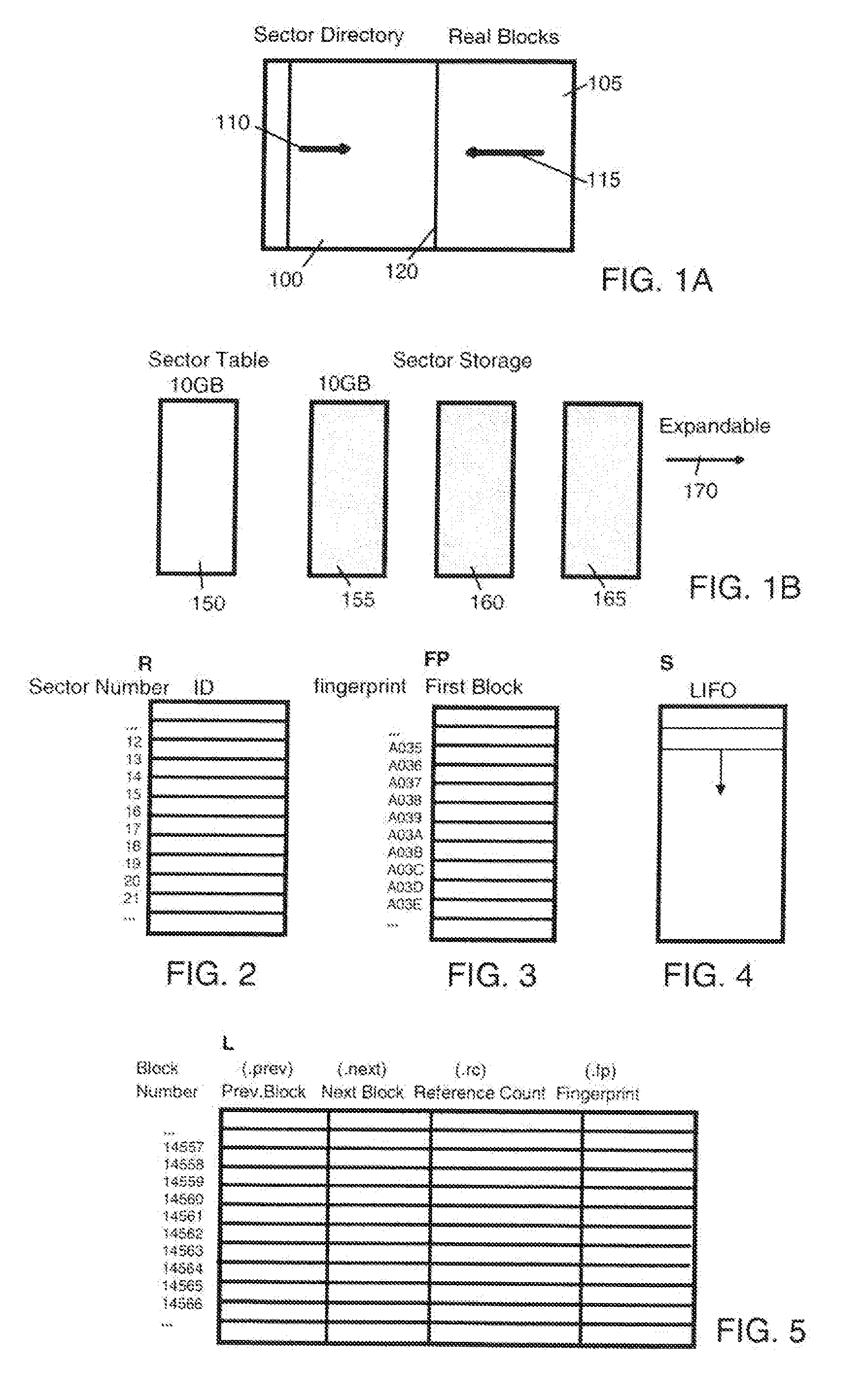
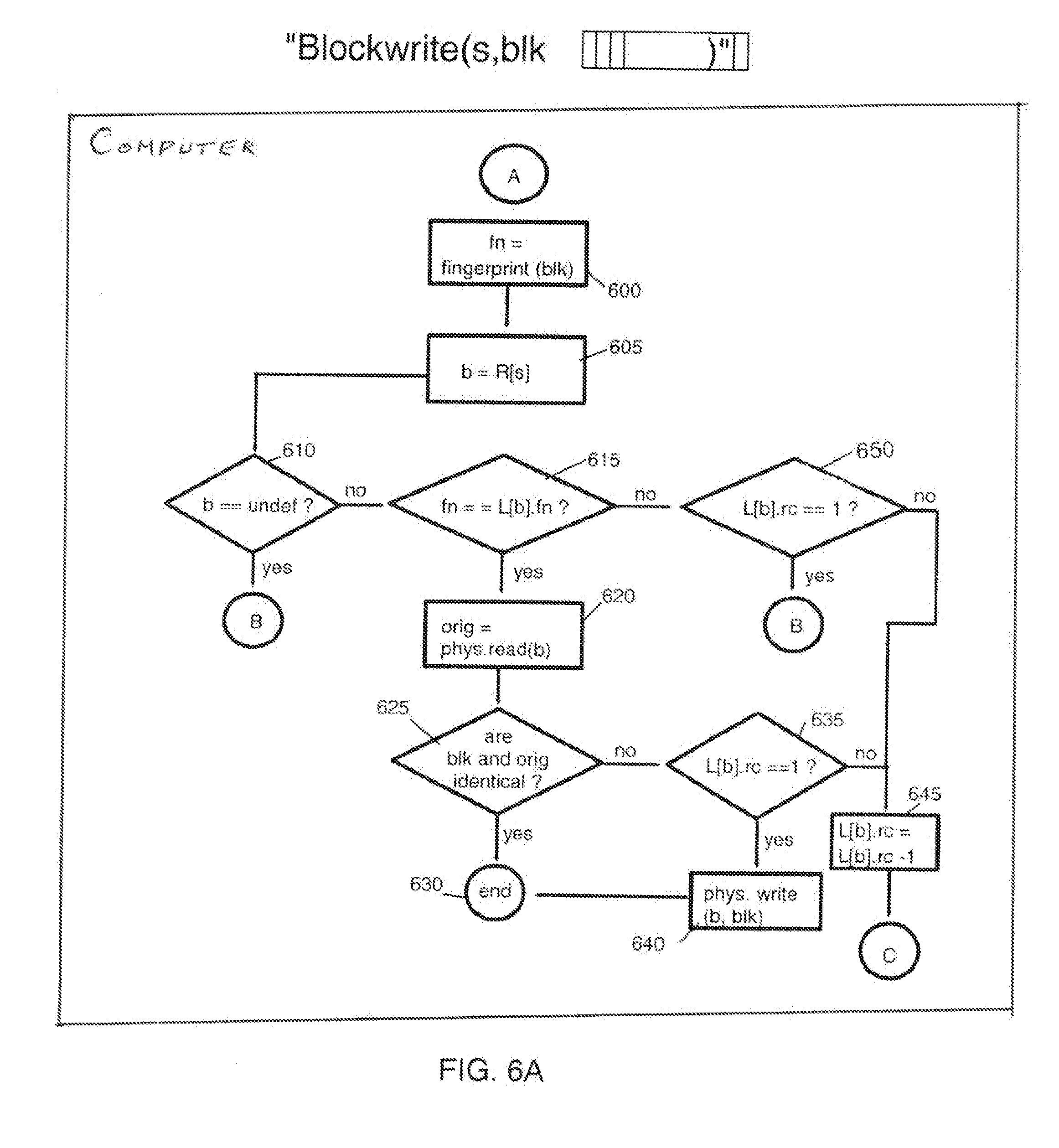
Reducing occupancy of digital storage devices
InactiveUS20110082998A1Minimizing dataOptimization mechanismDigital data processing detailsMemory adressing/allocation/relocationOperational systemMagnetic tape
A digital data storage device physically stores blocks of identical data only once on its storage medium wherein a second or even further identical blocks are stored only as reference referring to the first block of these identical blocks. By this technique, storage of duplicate data is most effectively avoided on the lowest storage level of the disk storage device, even in cases where identical blocks are written by different operating Systems. In the preferred embodiment, the underlying storage medium (magnetic hard disk, optical disk, tape, or M-RAM) is segmented into two areas, the first area particularly comprising a relatively small block reference table and the remaining physical storage area for storing real blocks of information.
Owner:IBM CORP
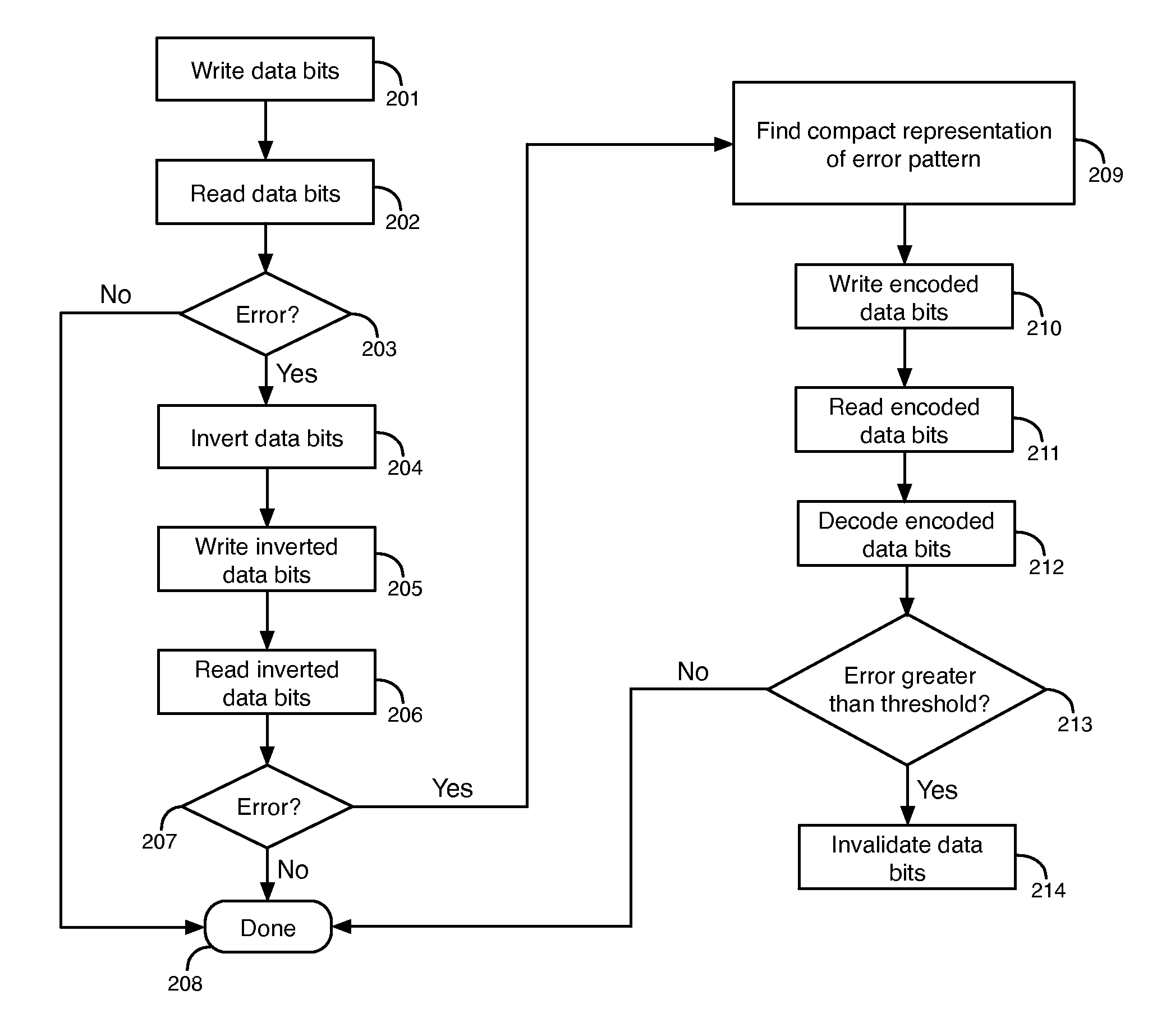
Techniques For Storing Data in Stuck and Unstable Memory Cells
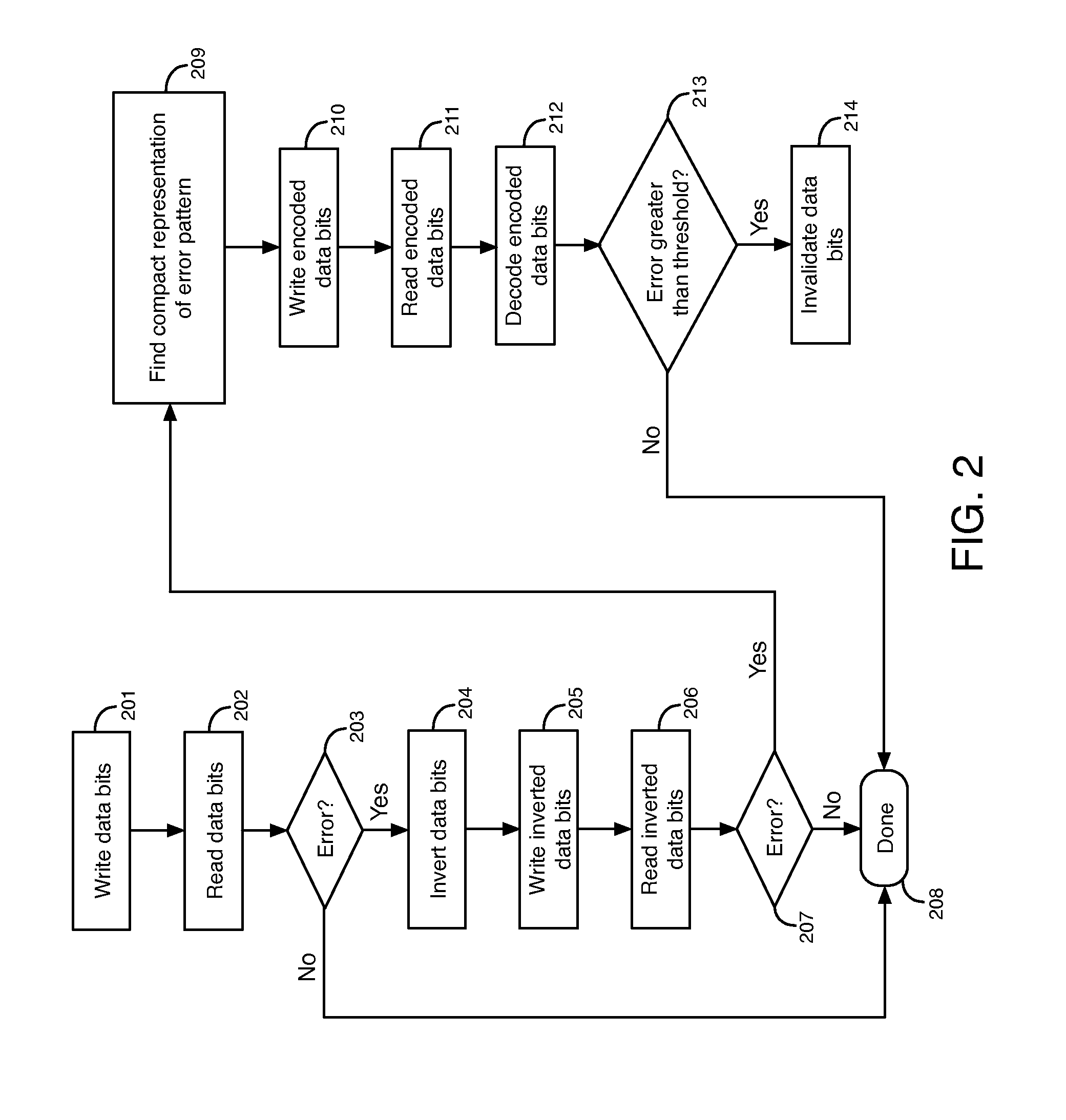
ActiveUS20130124942A1Avoid storage problemsError correction/detection using linear codesStatic storageData bitsData storage system
A data storage system includes a memory circuit and a control circuit. The control circuit is operable to receive data bits provided for storage in memory cells of the memory circuit. The control circuit is operable to compare each of the data bits provided for storage in a corresponding one of the memory cells having a stuck-at fault value to the stuck-at fault value. The control circuit is operable to generate encoded data bits by inverting each of the data bits having a different value than the stuck-at fault value of the corresponding one of the memory cells and by maintaining a digital value of each of the data bits having the stuck-at fault value of the corresponding one of the memory cells. The control circuit is operable to prevent any of the data bits from being stored in the memory cells determined to have unstable values. The control circuit is operable to generate redundant bits that indicate at least one operation to perform on the encoded data bits to regenerate the data bits.
Owner:WESTERN DIGITAL TECH INC
Method and apparatus handling radioactive waste material
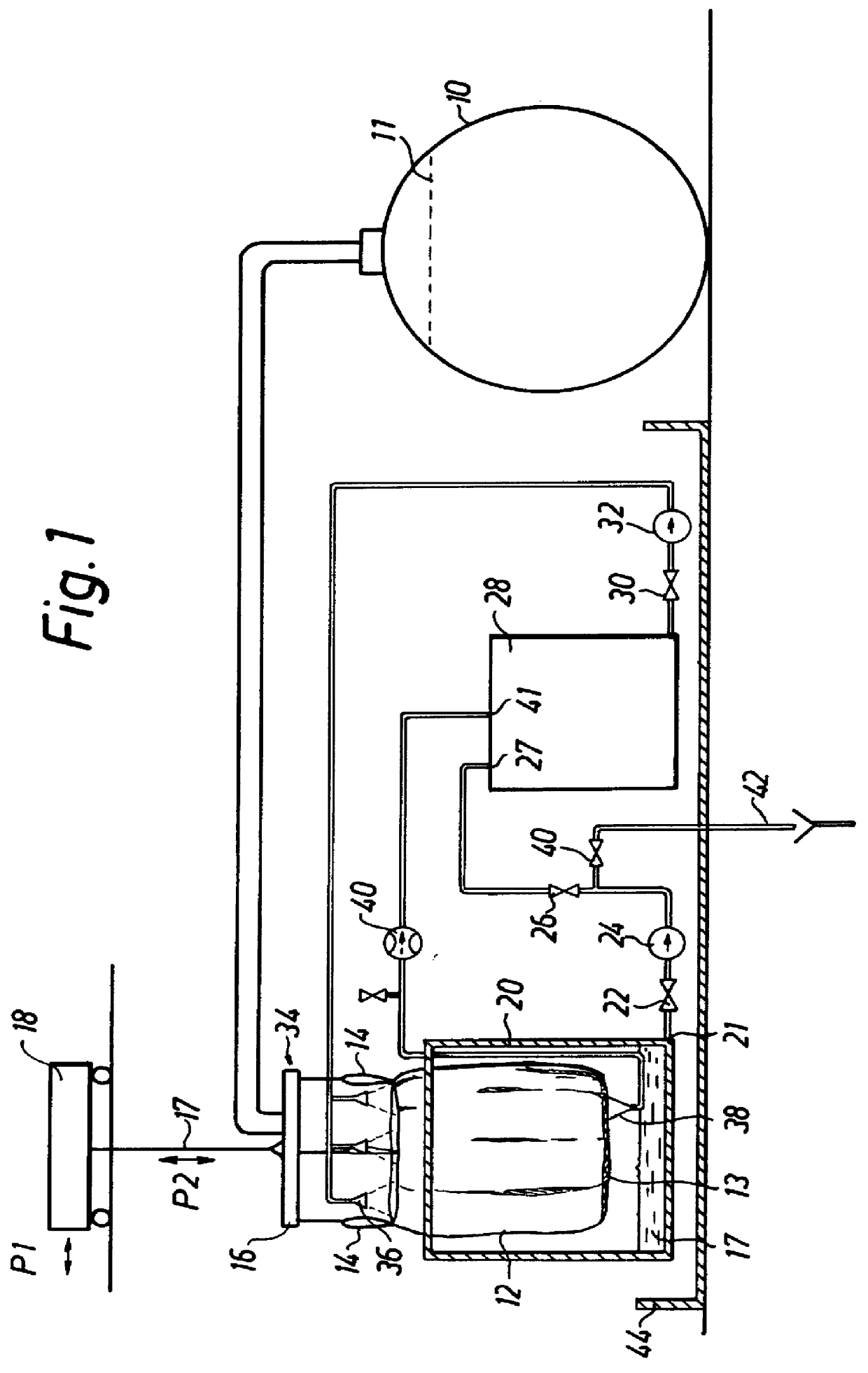
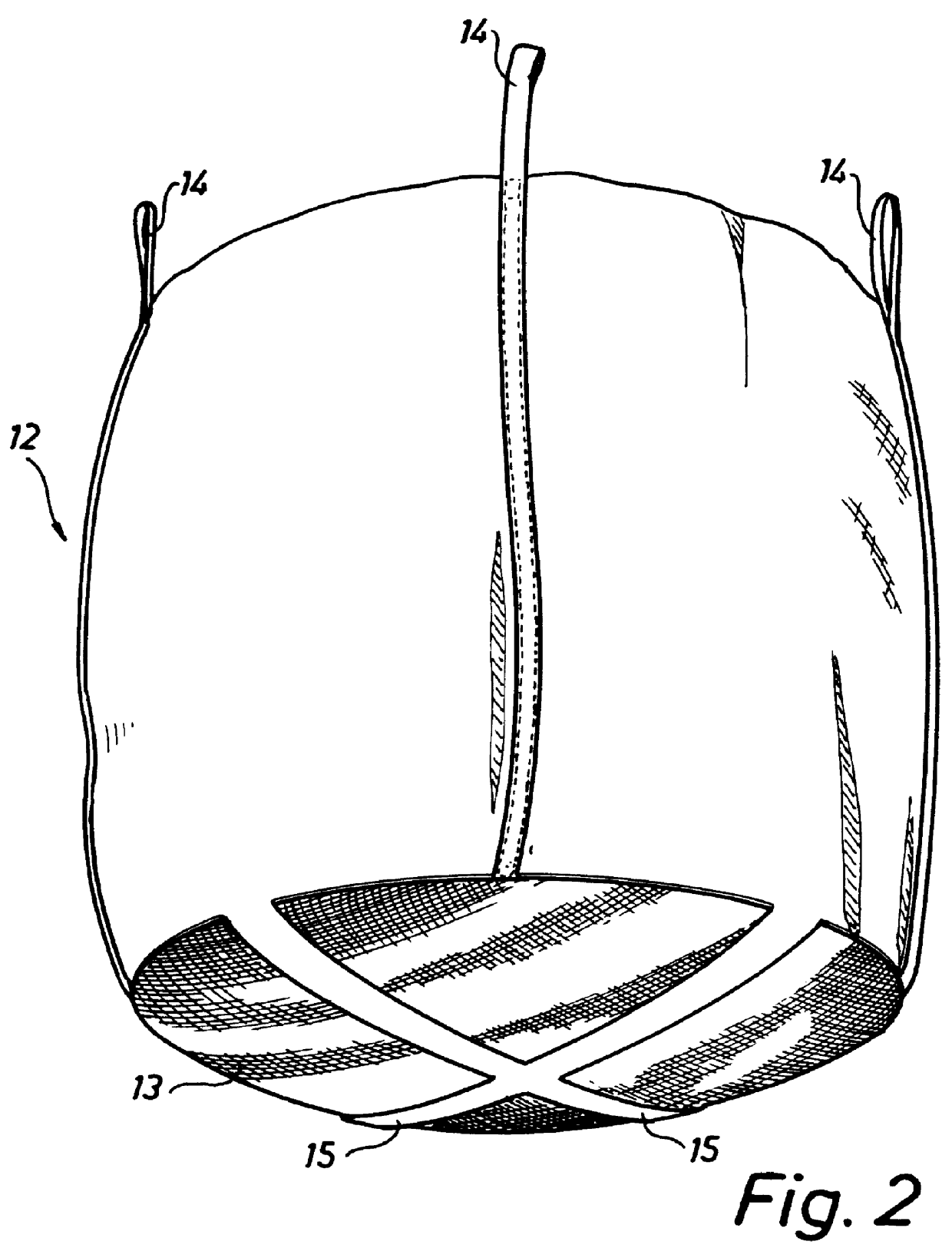
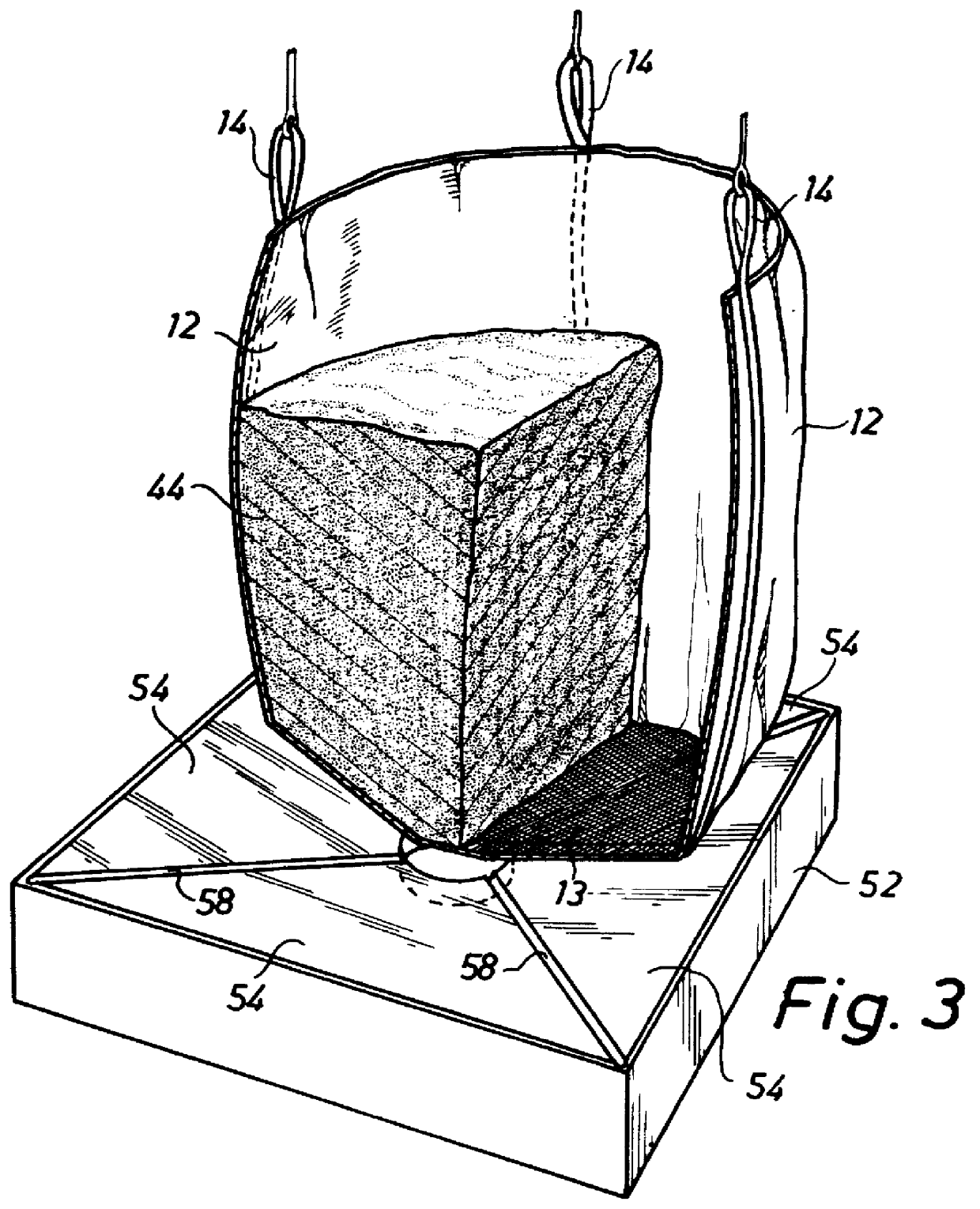
InactiveUS6040491AInexpensive and effective dewateringStorage of such void water being thus avoidedLiquid separation auxillary apparatusSolid waste disposalFiltrationRadioactive waste
PCT No. PCT / SE96 / 00306 Sec. 371 Date Sep. 30, 1997 Sec. 102(e) Date Sep. 30, 1997 PCT Filed Mar. 7, 1996 PCT Pub. No. WO96 / 28828 PCT Pub. Date Sep. 19, 1996In a method and an apparatus for dewatering and containing radioactive, aqueous waste (44), the latter is introduced into a filtration container (12) and is ultimately disposed of in a disposable container structure (12, 48, 50), which comprises the filtration container (12) holding the dewatered waste (44), as well as an outer container (50) enclosing the filtration container (12). The filtration container is an inner sack (12) having a bottom (13) which is provided with a straining cloth and through which essentially all the dewatering is carried out. After the dewatering operation has been completed, the inner sack (12) is sealed and placed in the outer container (50) in order to be ultimately disposed of. For purposes of cleaning, the filtration water (17) may be recirculated through the waste during the dewatering operation.
Owner:VATTENFALL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com