Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6522 results about "Mobile Web" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
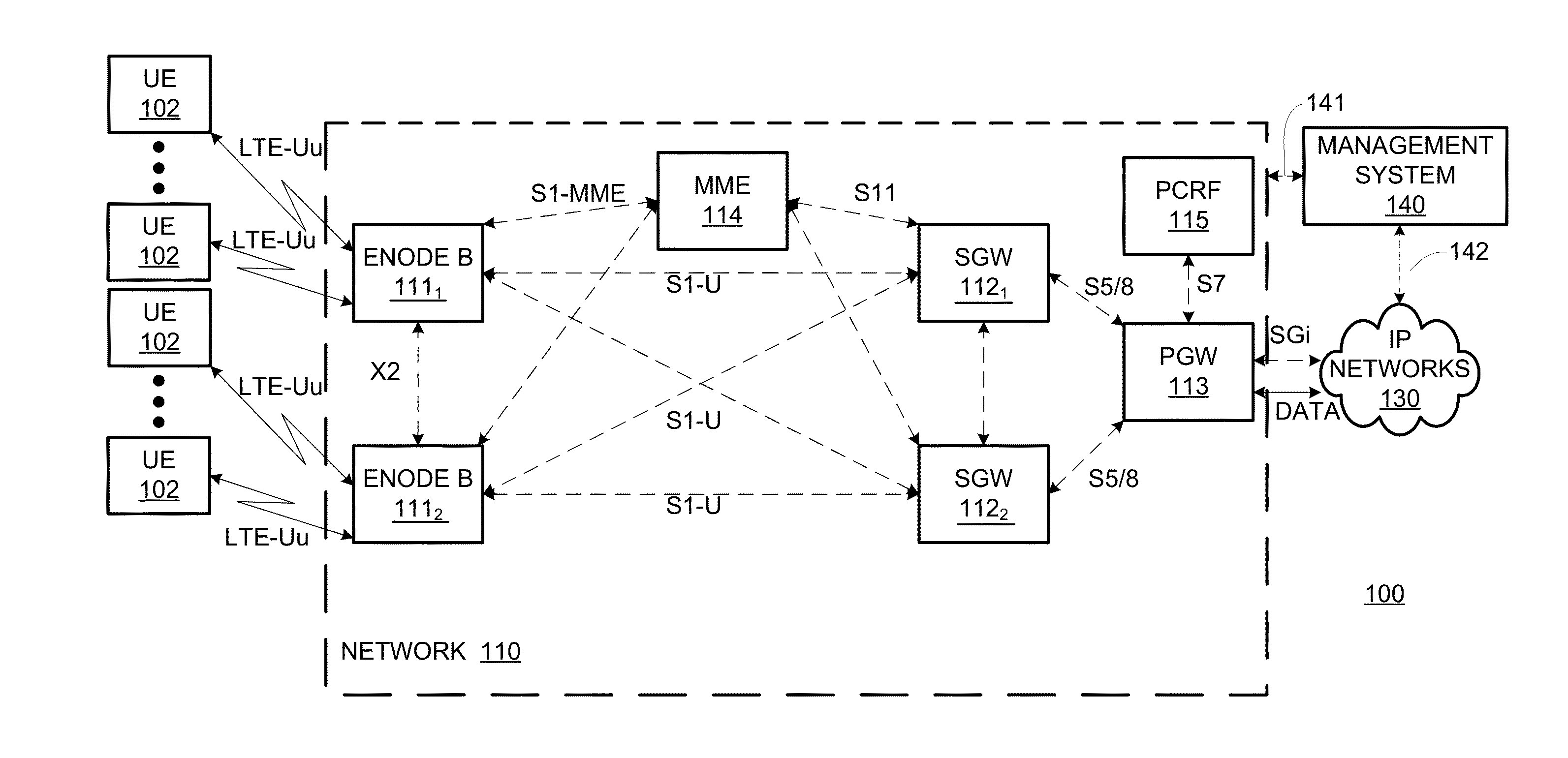
The mobile web refers to browser-based World Wide Web services accessed from handheld mobile devices, such as smartphones or feature phones, through a mobile or other wireless network. Traditionally, the World Wide Web has been accessed via fixed-line services on laptops and desktop computers. However, the web is now more accessible by portable and wireless devices. An early 2010 ITU (International Telecommunication Union) report said that with current growth rates, web access by people on the go – via laptops and smart mobile devices – is likely to exceed web access from desktop computers within the next five years. In January 2014, mobile internet use exceeded desktop use in the United States. The shift to mobile web access has accelerated since 2007 with the rise of larger multitouch smartphones, and since 2010 with the rise of multitouch tablet computers. Both platforms provide better Internet access, screens, and mobile browsers, or application-based user web experiences than previous generations of mobile devices. Web designers may work separately on such pages, or pages may be automatically converted, as in Mobile Wikipedia. Faster speeds, smaller, feature-rich devices, and a multitude of applications continue to drive explosive growth for mobile internet traffic. The 2017 Virtual Network Index (VNI) report produced by Cisco Systems forecasts that by 2021, there will be 5.5 billion global mobile users (up from 4.9 billion in 2016). Additionally, the same 2017 VNI report forecasts that average access speeds will increase by roughly three times from 6.8 Mbit/s to 20 Mbit/s in that same period with video comprising the bulk of the traffic (78%).
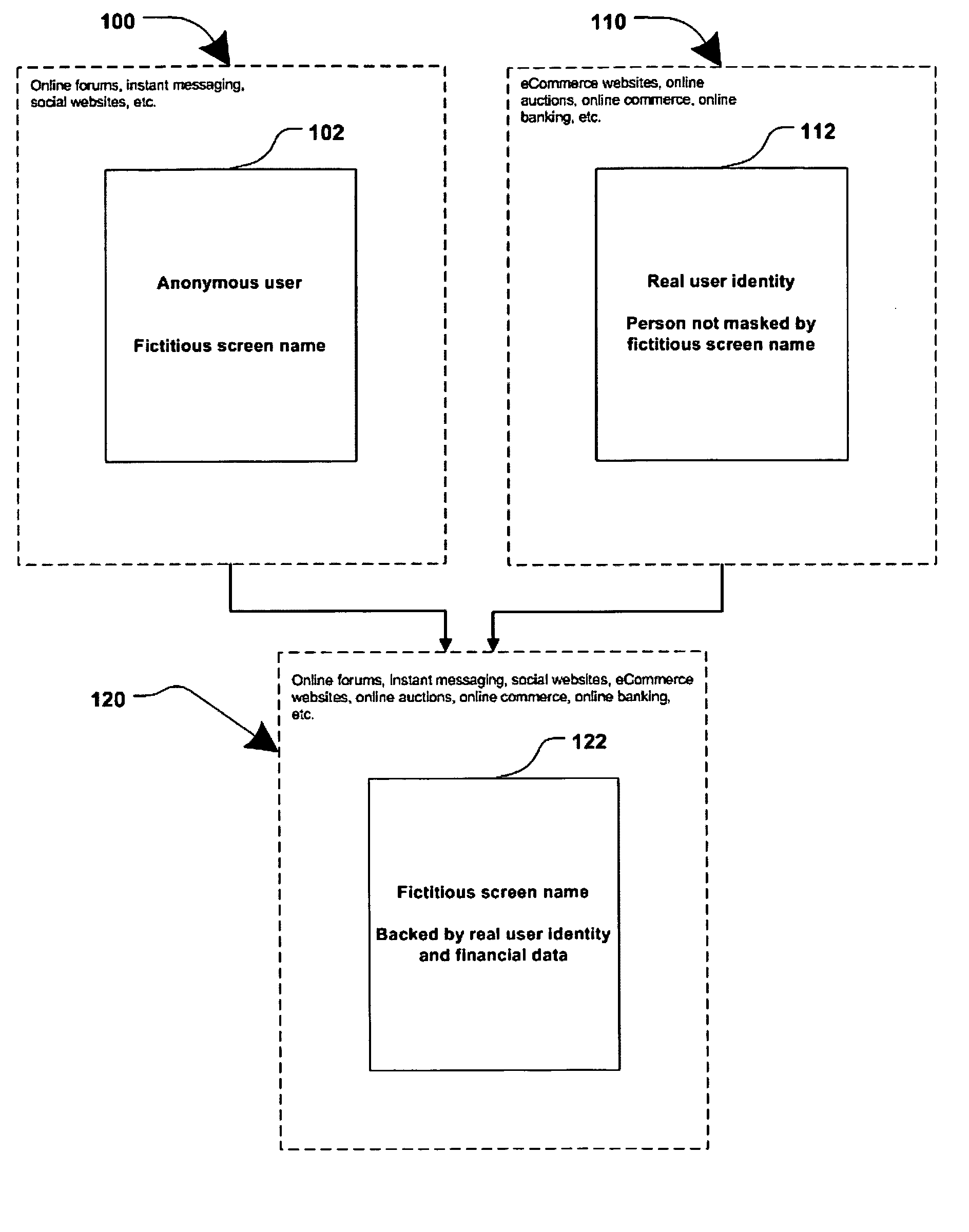
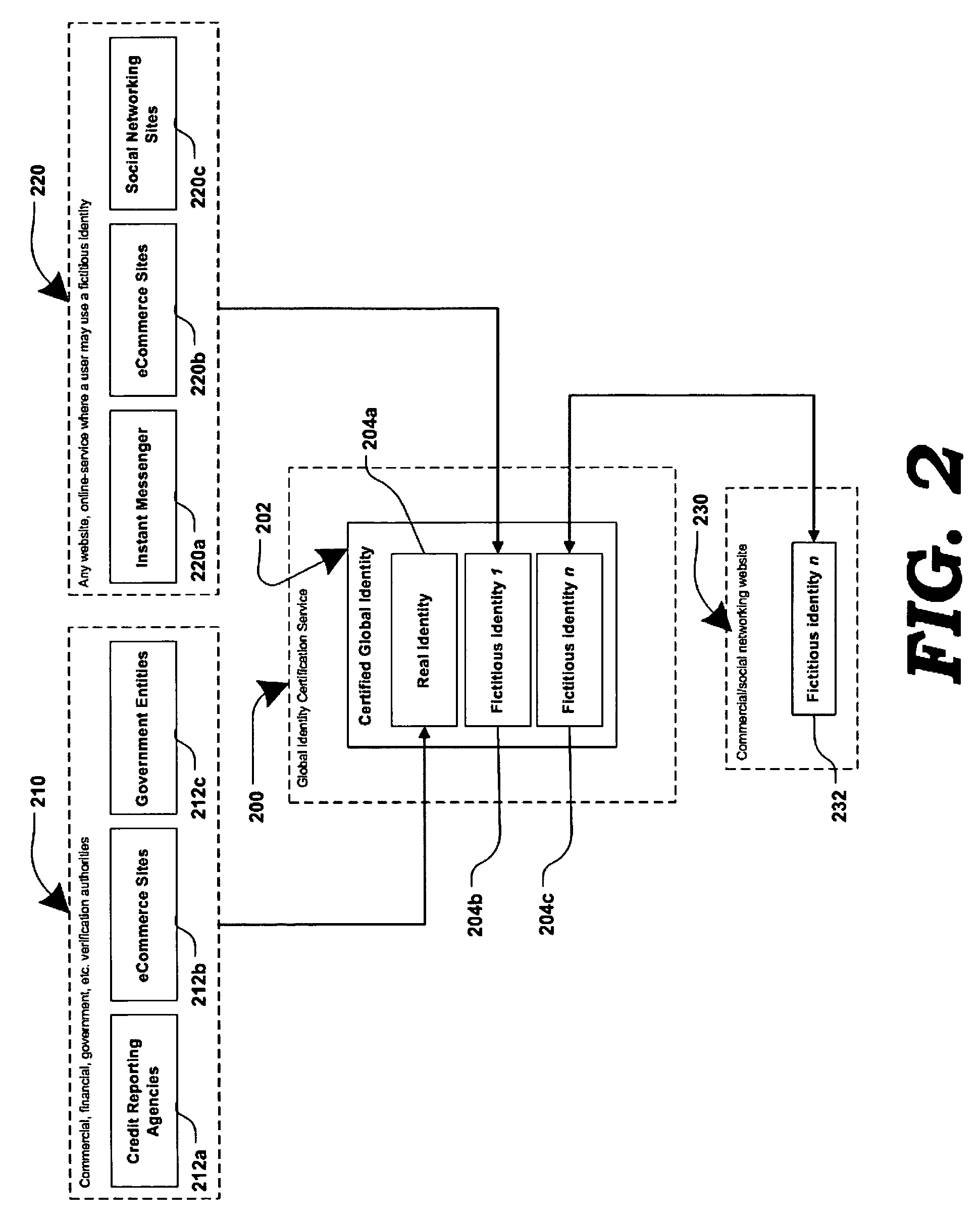
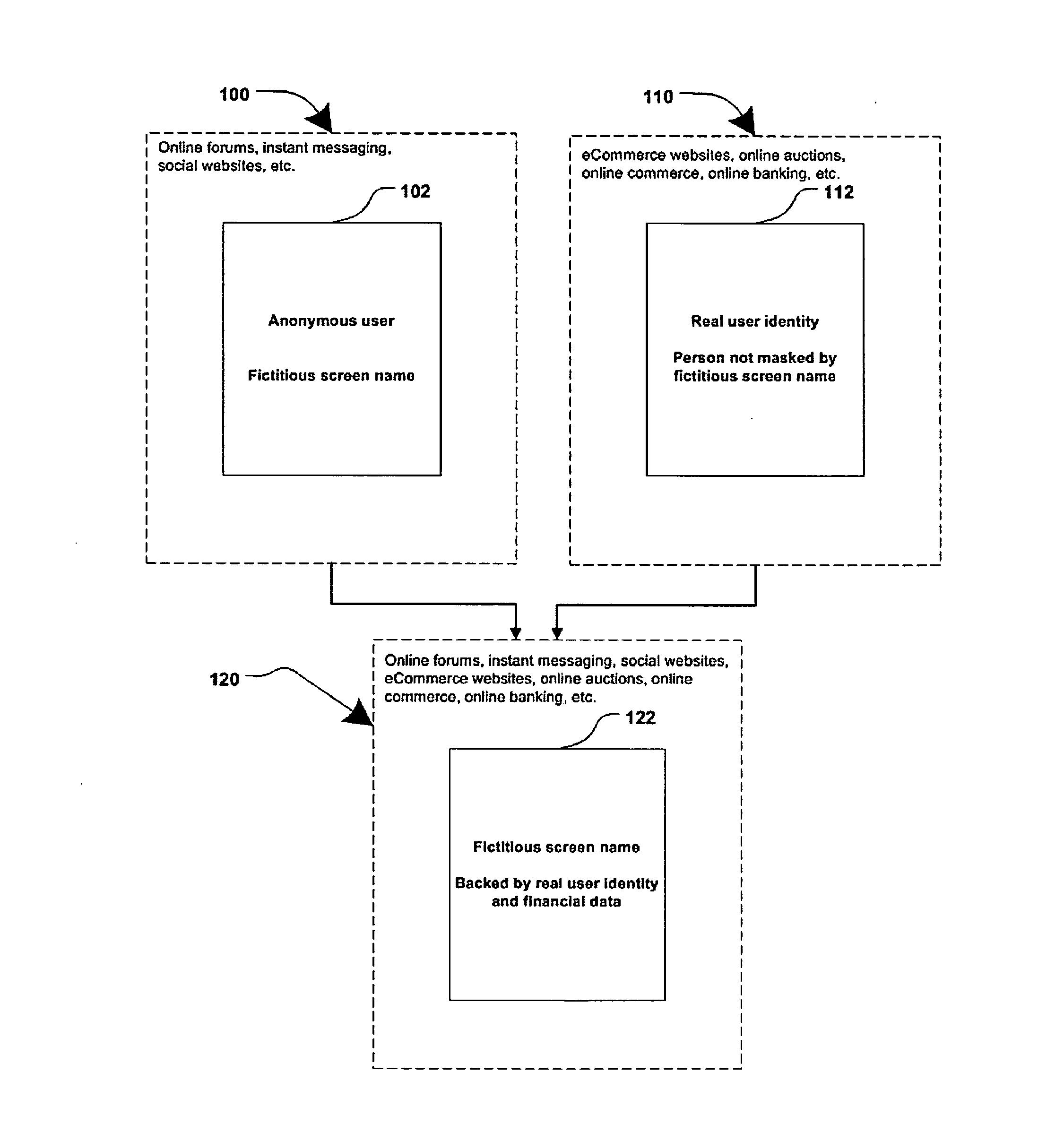
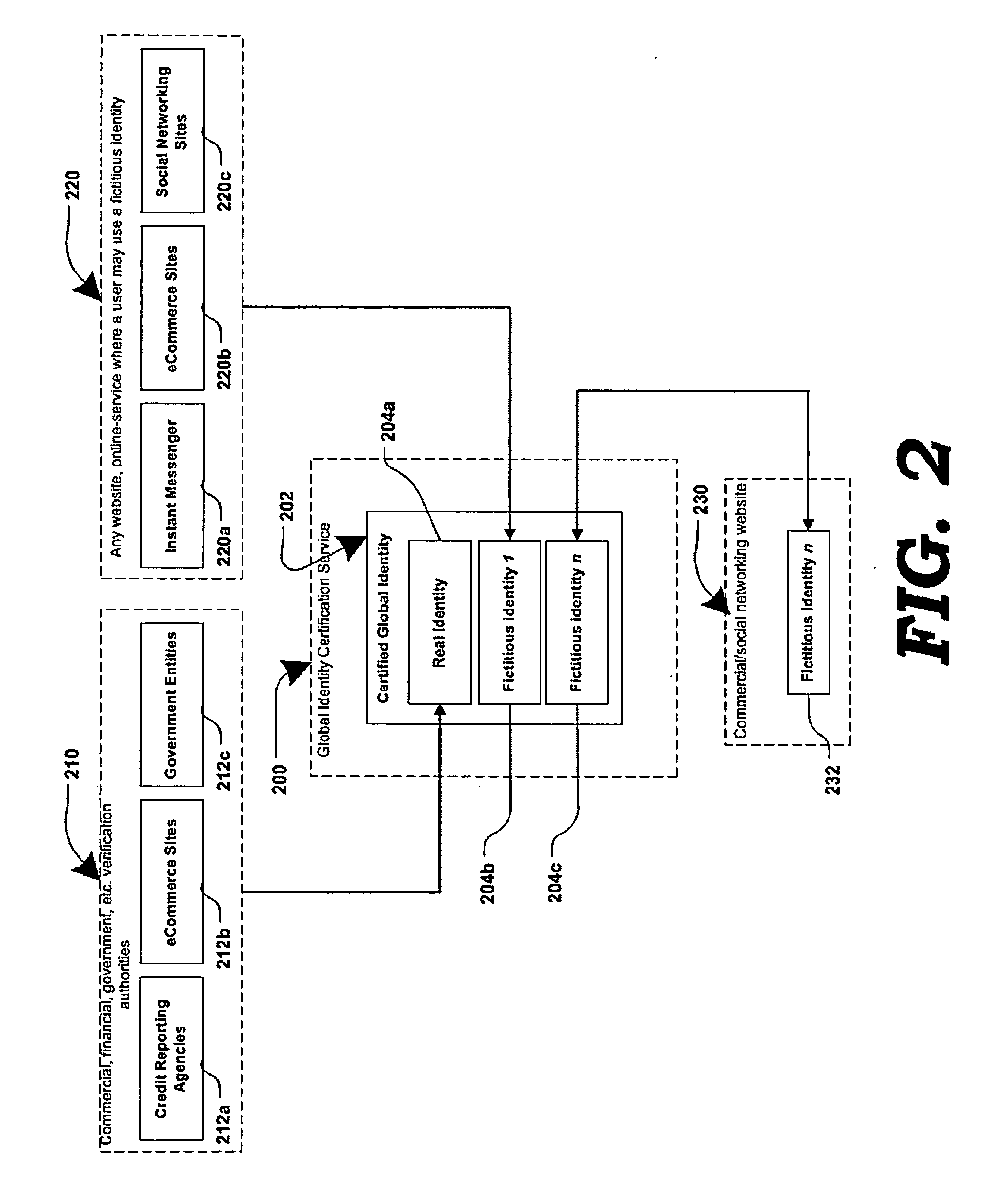
Method and system for securing online identities
InactiveUS8646103B2Targeted optimizationDigital data processing detailsUser identity/authority verificationUser verificationElectronic communication
Owner:JAKOBSON GABRIEL +1
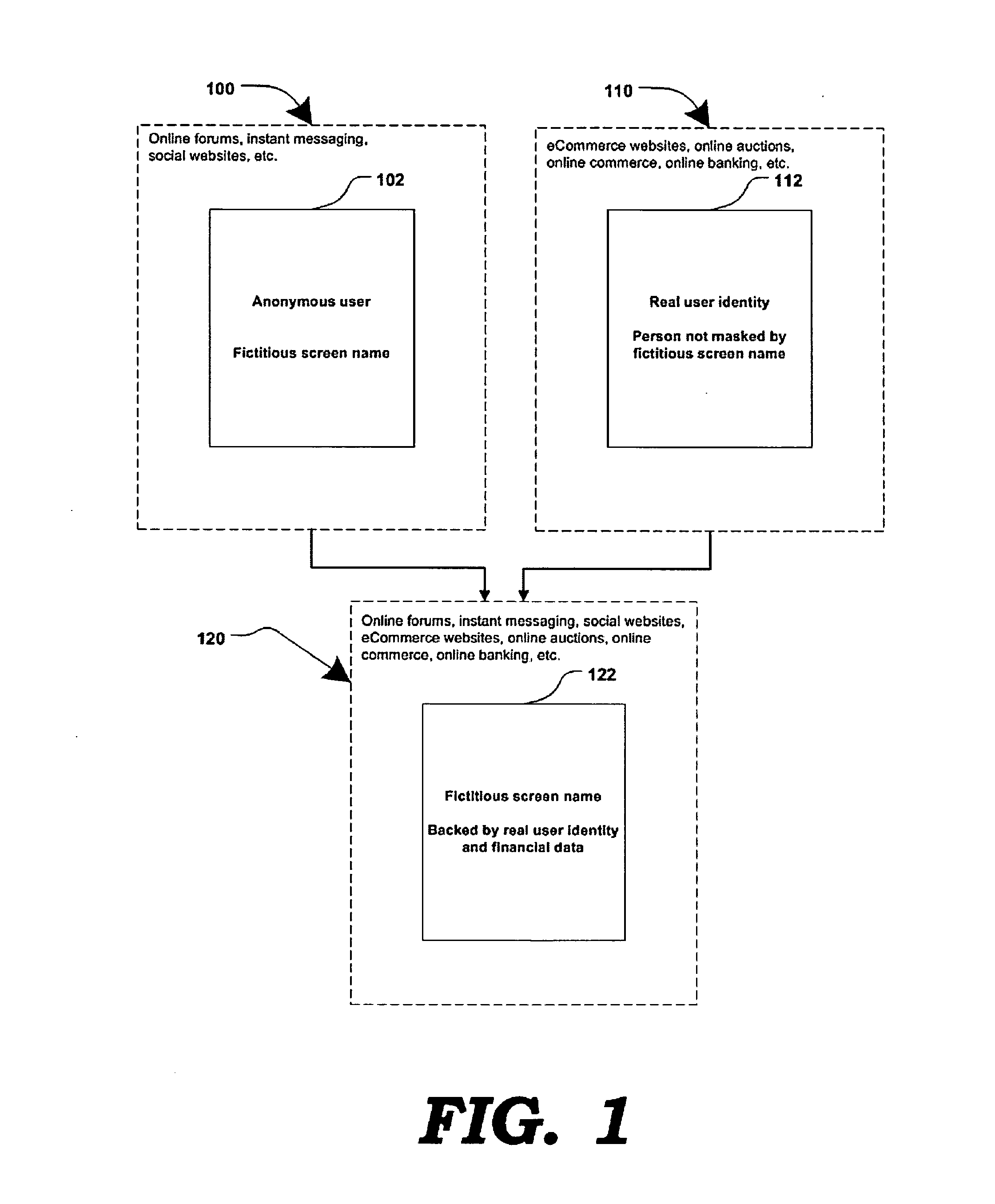
Method and systems for online advertising to users using fictitious user idetities
Various methods, systems and apparatus for associating fictitious user identities (e.g. screen names, user names, email addresses, handles, etc.) used in electronic communications (e.g. over the internet or mobile network via instant messenger, e-mail, social networks, ecommerce, auction websites, etc.) with real personal information (e.g. the true identity of an individual such as their name, address, credit score, driving record, mobile number, etc.) are disclosed. One such method may include discovering, verifying and storing real personal information, associated with fictitious user identities and email addresses. The method may further include allowing a remote user or service to submit a fictitious user identity and a query requesting real-user information associated with the submitted fictitious user identity. In one possible embodiment, a targeted-advertising service may utilize real user information, associated with a fictitious user name, to target advertisements at the user of the fictitious user name.
Owner:JAKOBSON GABRIEL +1
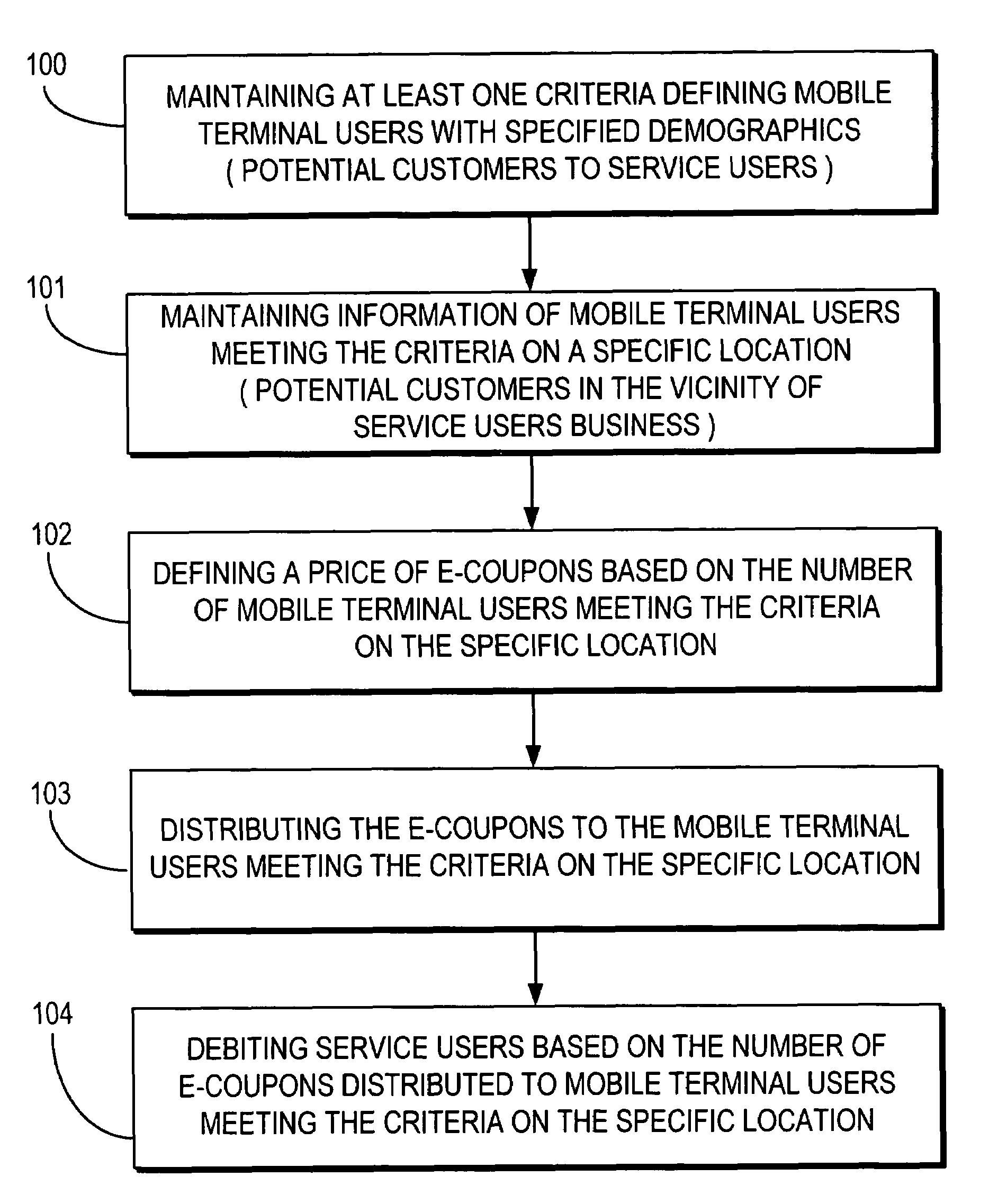
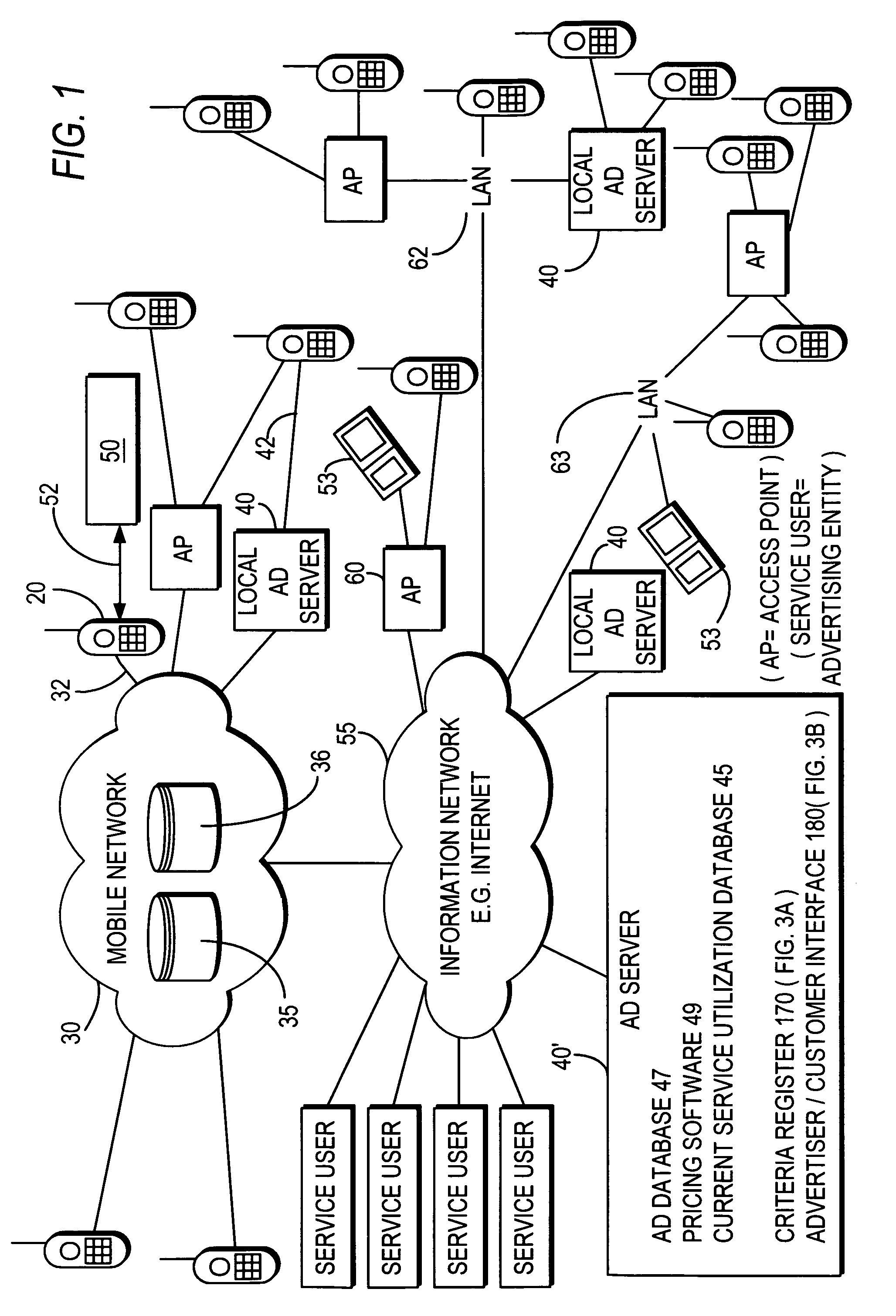
Real-time wireless e-coupon (promotion) definition based on available segment
Advertising messages are provided to mobile terminals of those users identified by user information as meeting certain criteria, such as users fitting particular user profiles and / or users located in a particular desired location. The content of the advertising messages is dynamically generated based on the number of mobile terminals to whom the advertising message is to be sent and the advertising message is sent to the identified mobile terminals over a mobile network or a short range communication signal. In the latter case, location information may be sent to the mobile terminal along with an advertising message. Where the content of an advertising message comprises an electronic coupon, the value of the coupon depends on the number of mobile terminals to whom the advertising message is to be sent. A mobile terminal user can redeem an electronic coupon by transmitting it from his mobile terminal to a coupon redemption terminal.
Owner:NOKIA TECH OY
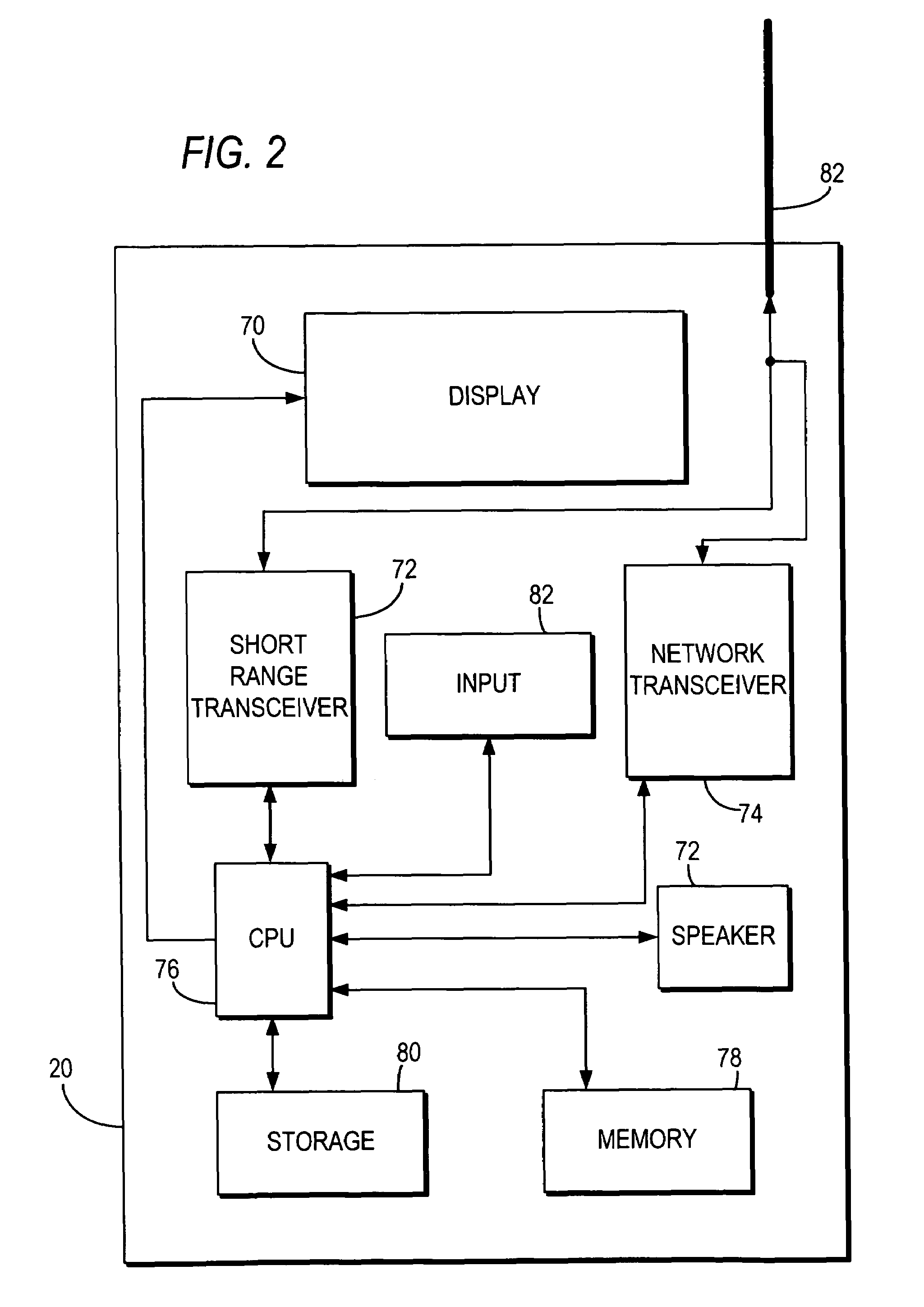
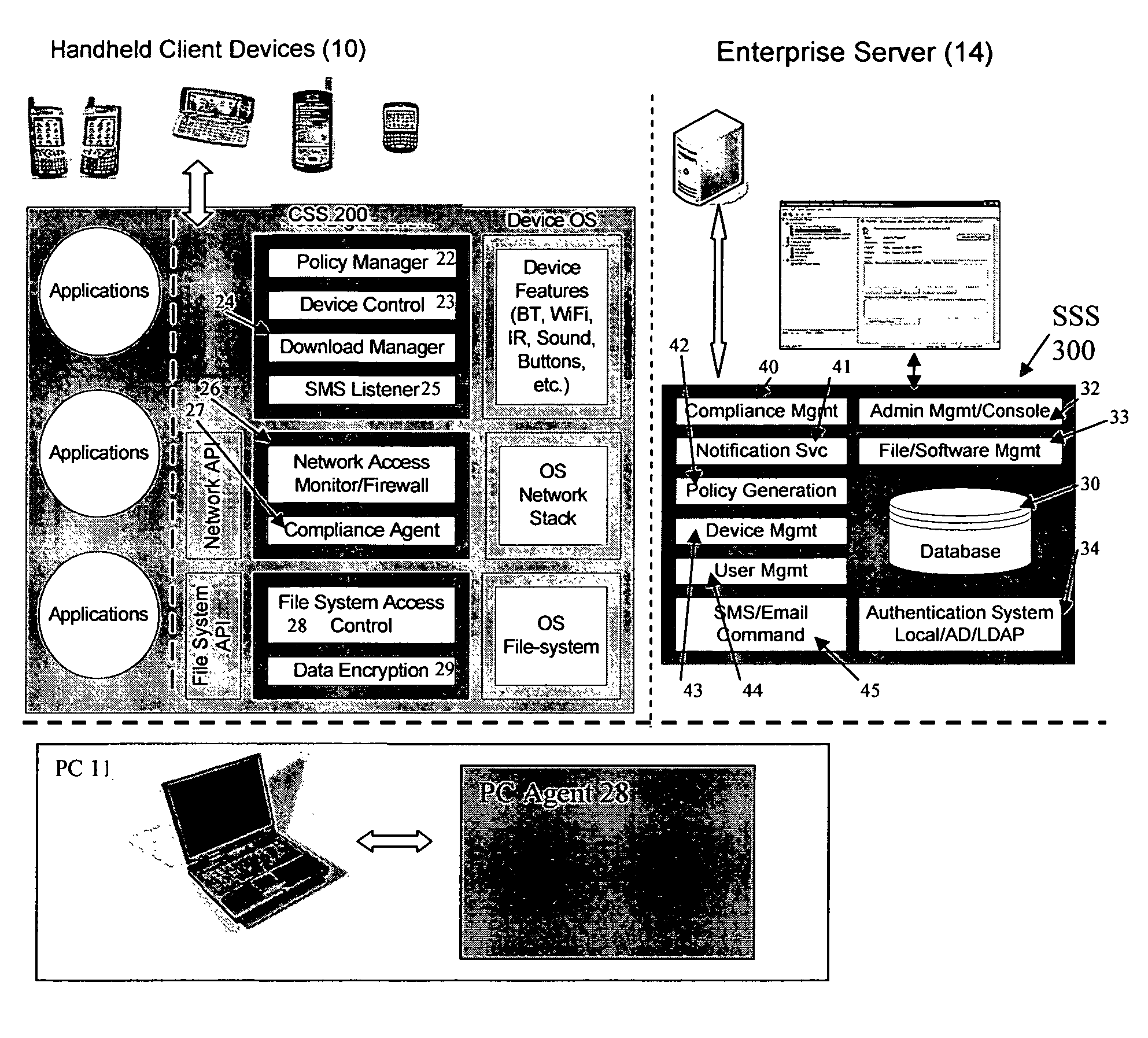
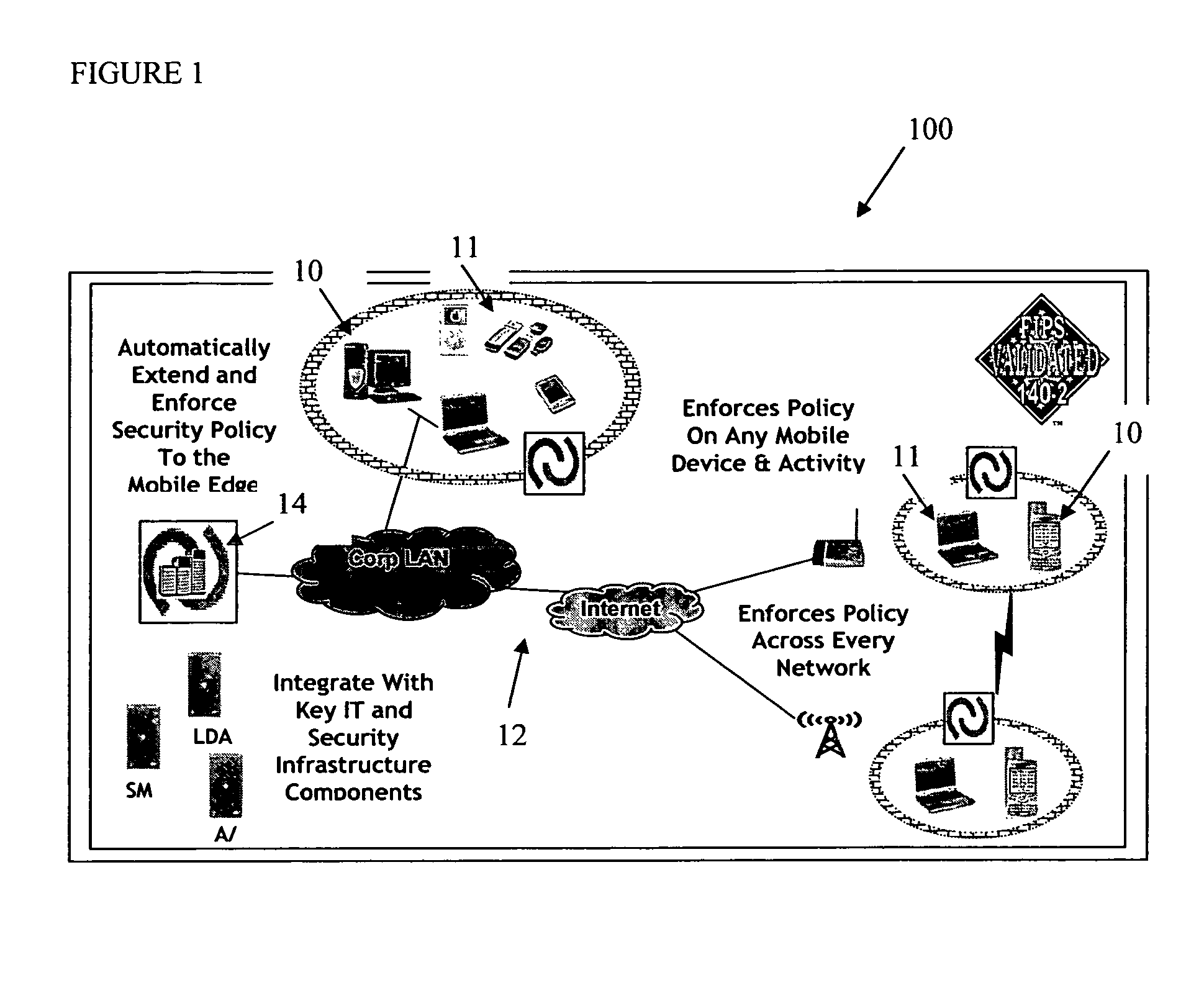
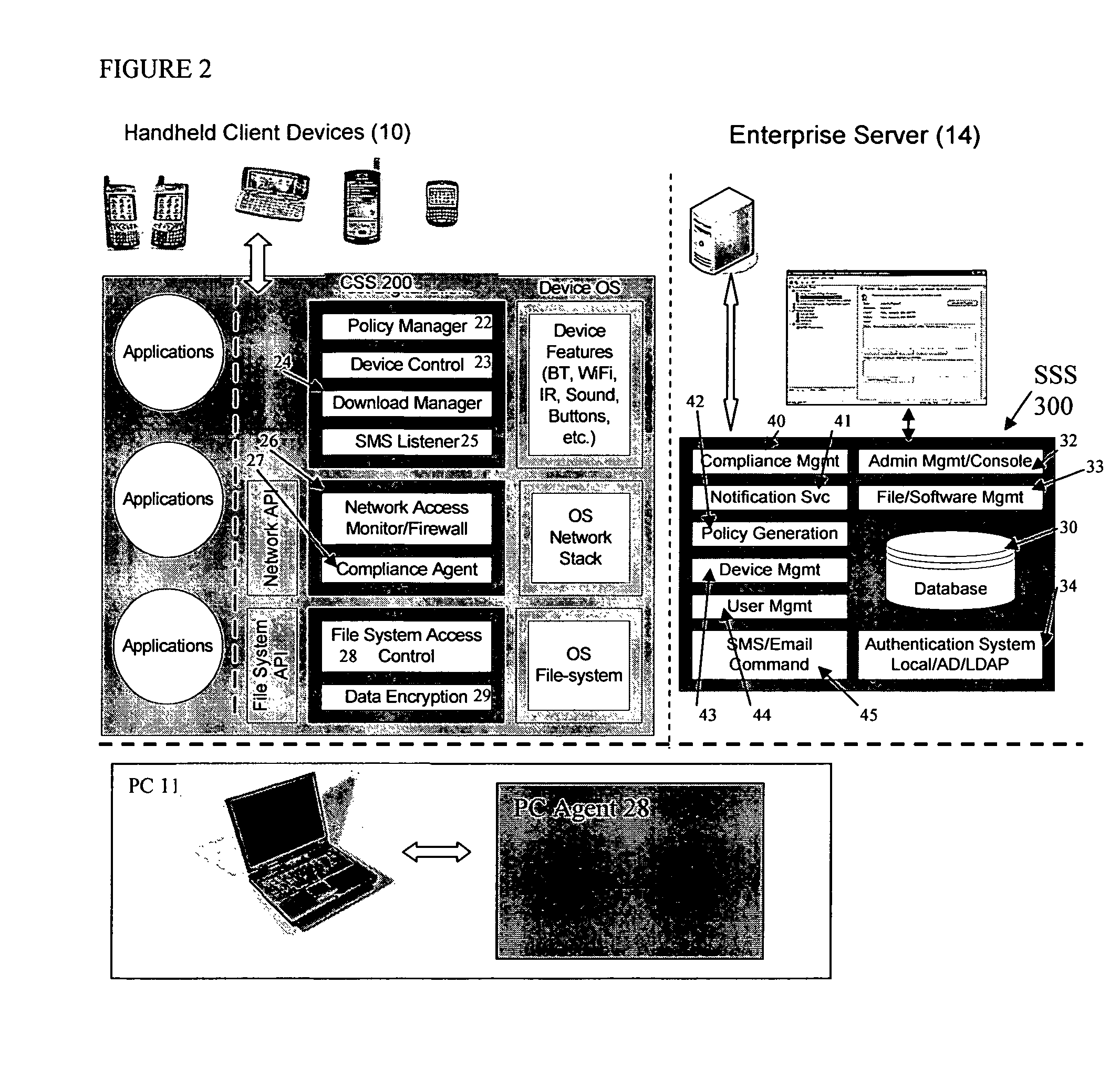
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
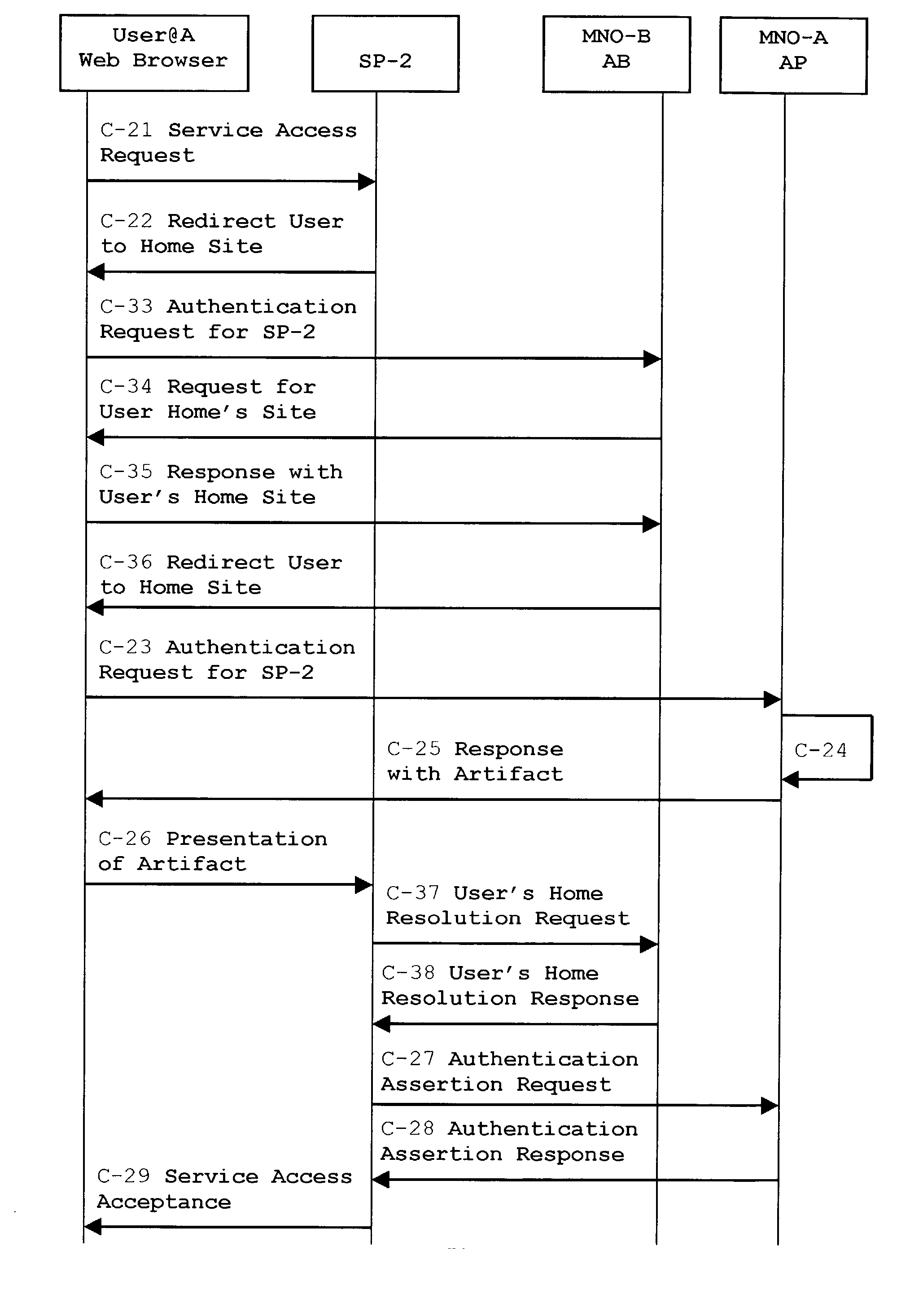
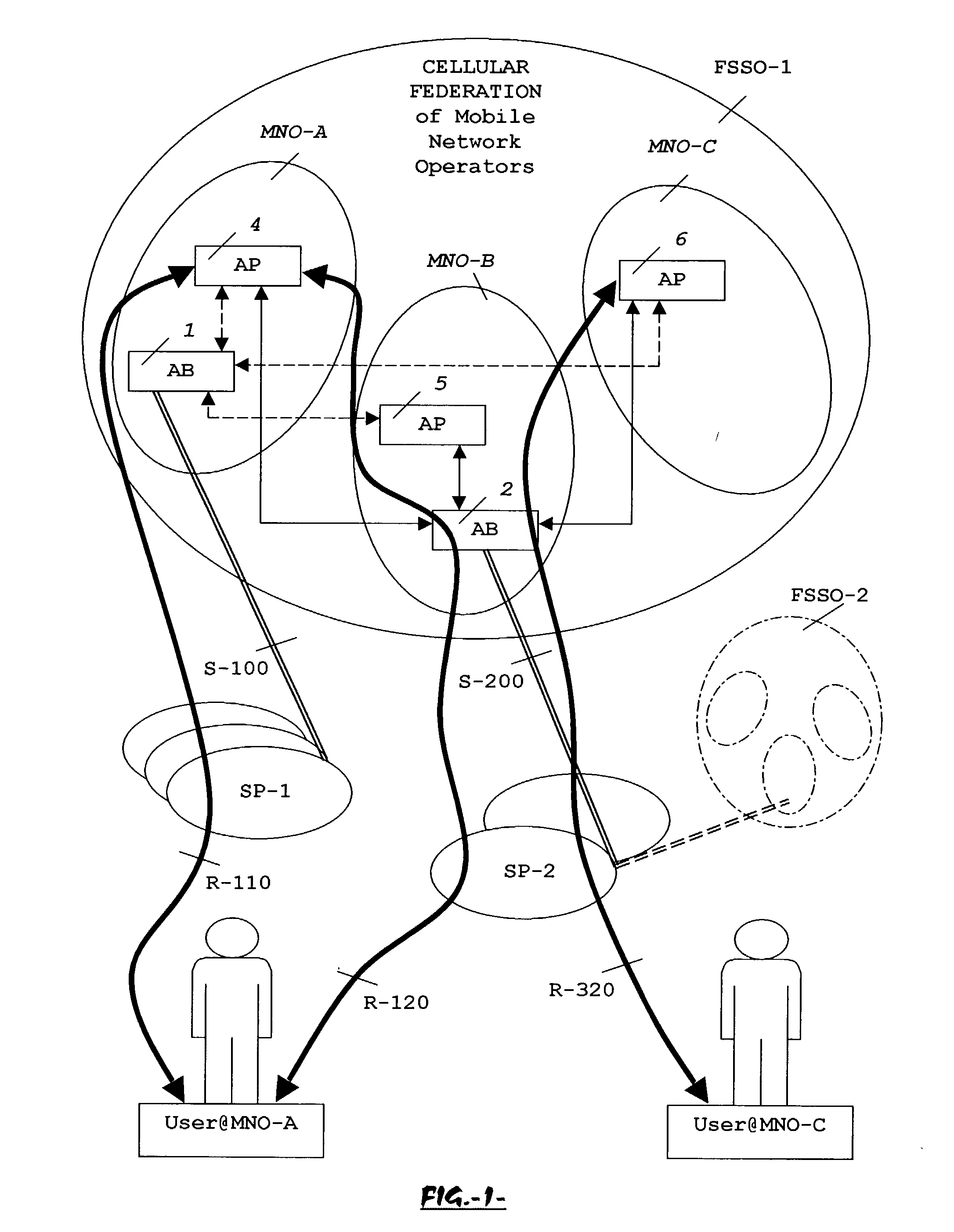
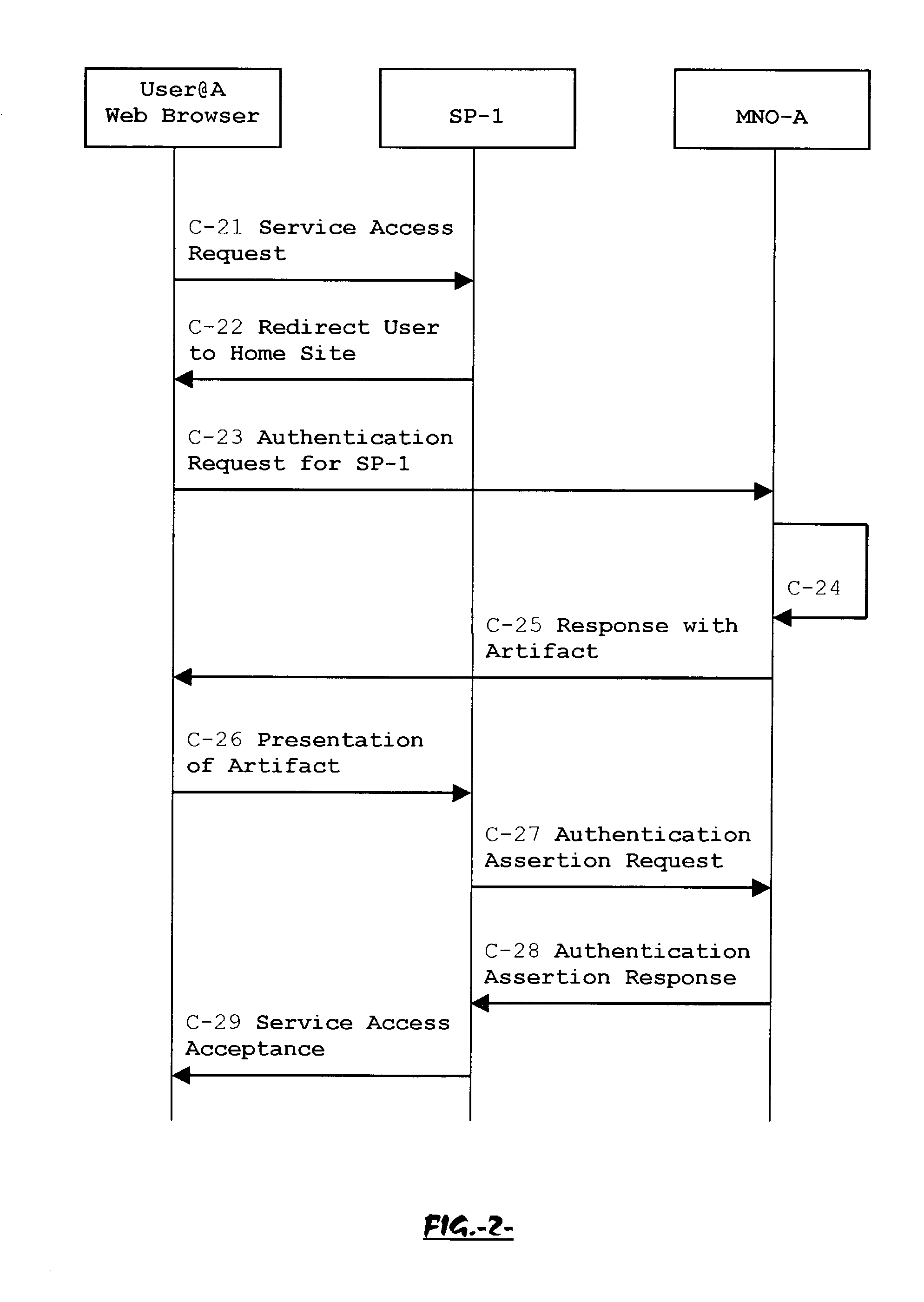
System, method and apparatus for federated single sign-on services
ActiveUS20030163733A1Unauthorised/fraudulent call preventionDigital data processing detailsCyber operationsService domain
The advent of new and sophisticated web services provided by Service Providers to users, services that individually require authentication of user and authorization of access, brings the needs for a new service to facilitate such authentication and access, a service referred to as Single Sign-On (SSO). The basic principle behind SSO is that users are authenticated once at a particular level, and then access all their subscribed services accepting that level of authentication. The present invention provides a system, method and apparatus wherein a cellular Federation of mobile network operators becomes an SSO authentication authority for subscribers of this Federation accessing Service Providers having such agreement with a mobile network operator of the Federation. In accordance with this invention, mobile network operators can leverage their operator-subscriber trust relationship in order to act as SSO authentication authority for those subscribers accessing Service Providers in a service domain other than the mobile network domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
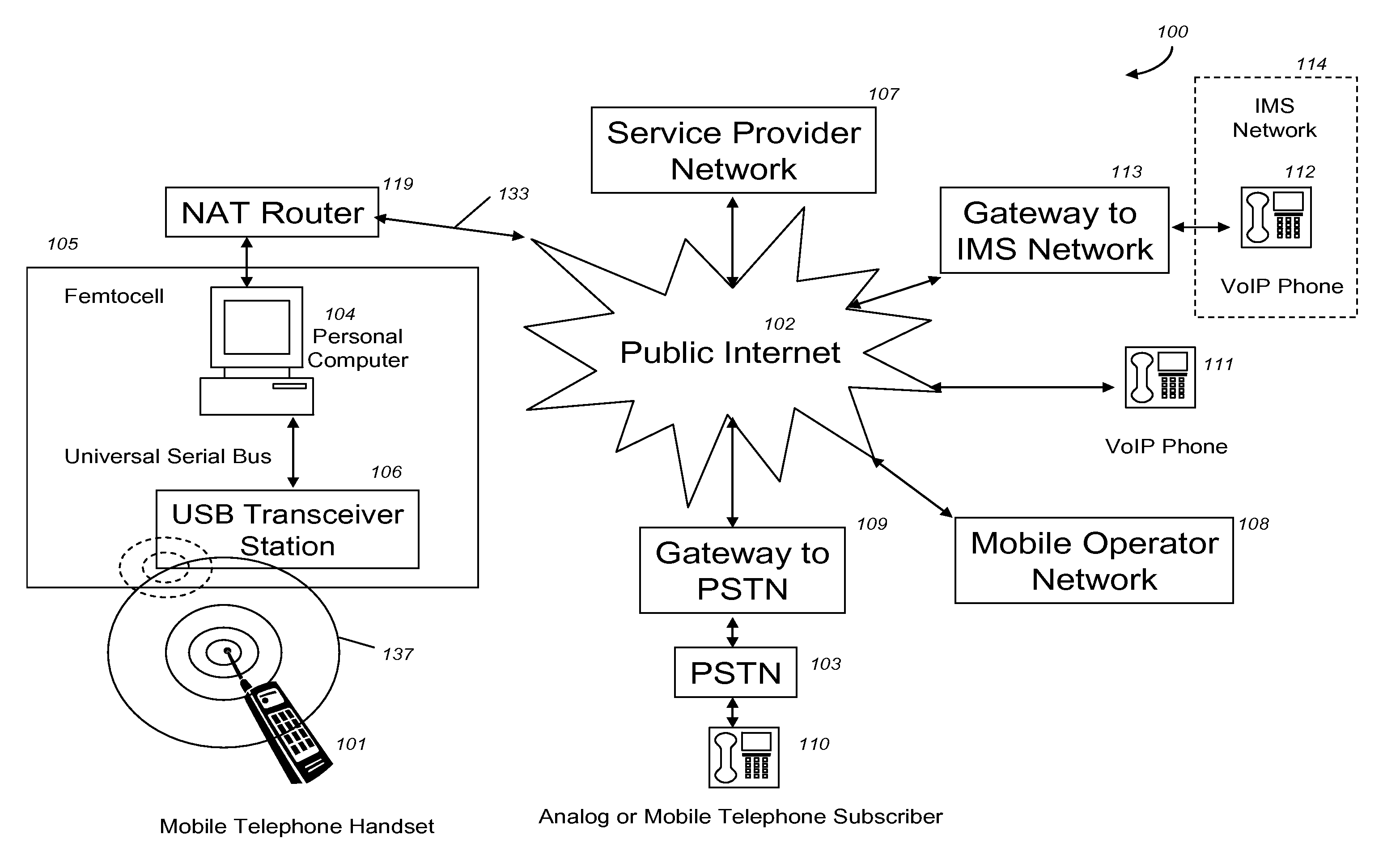
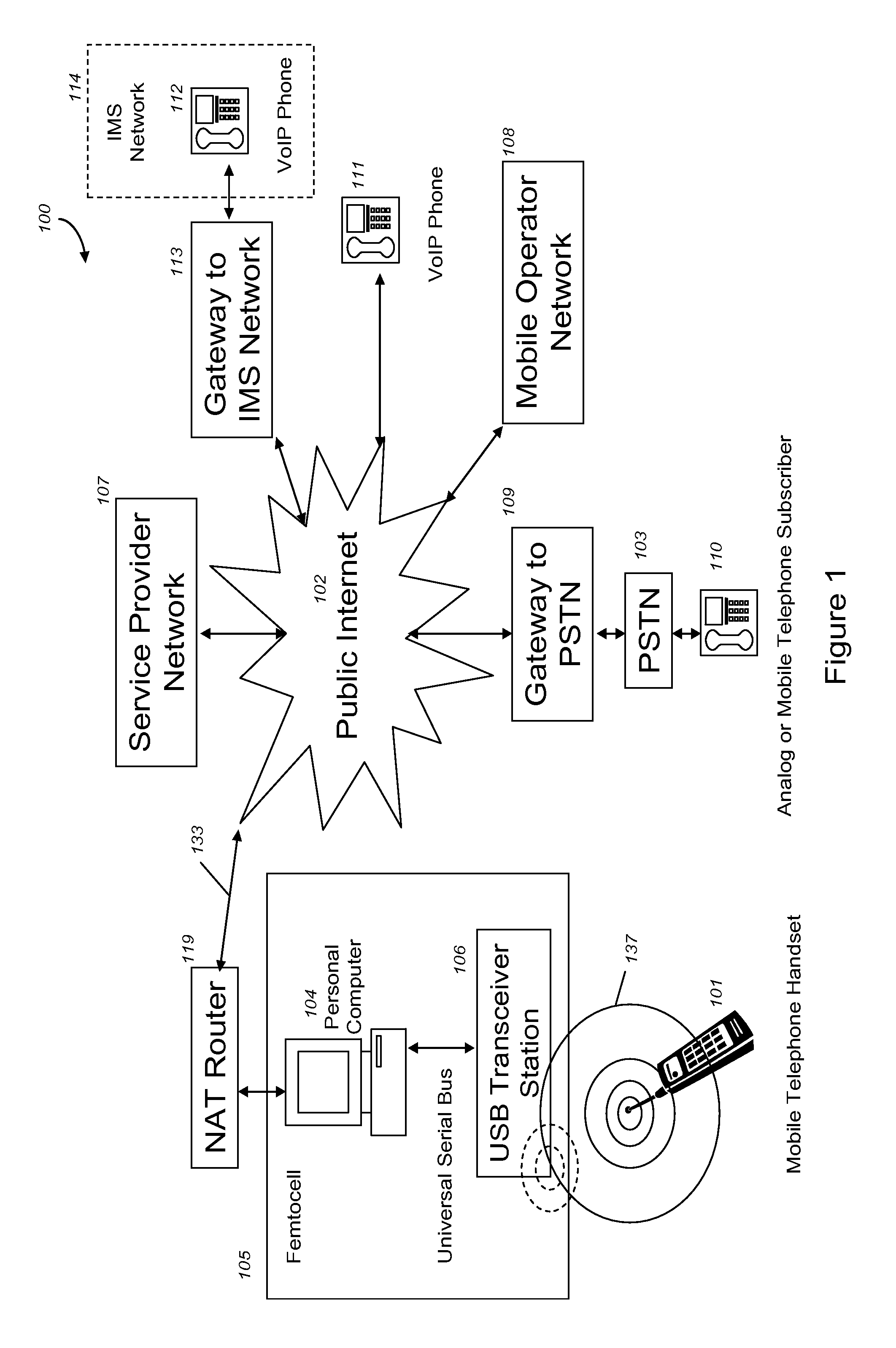
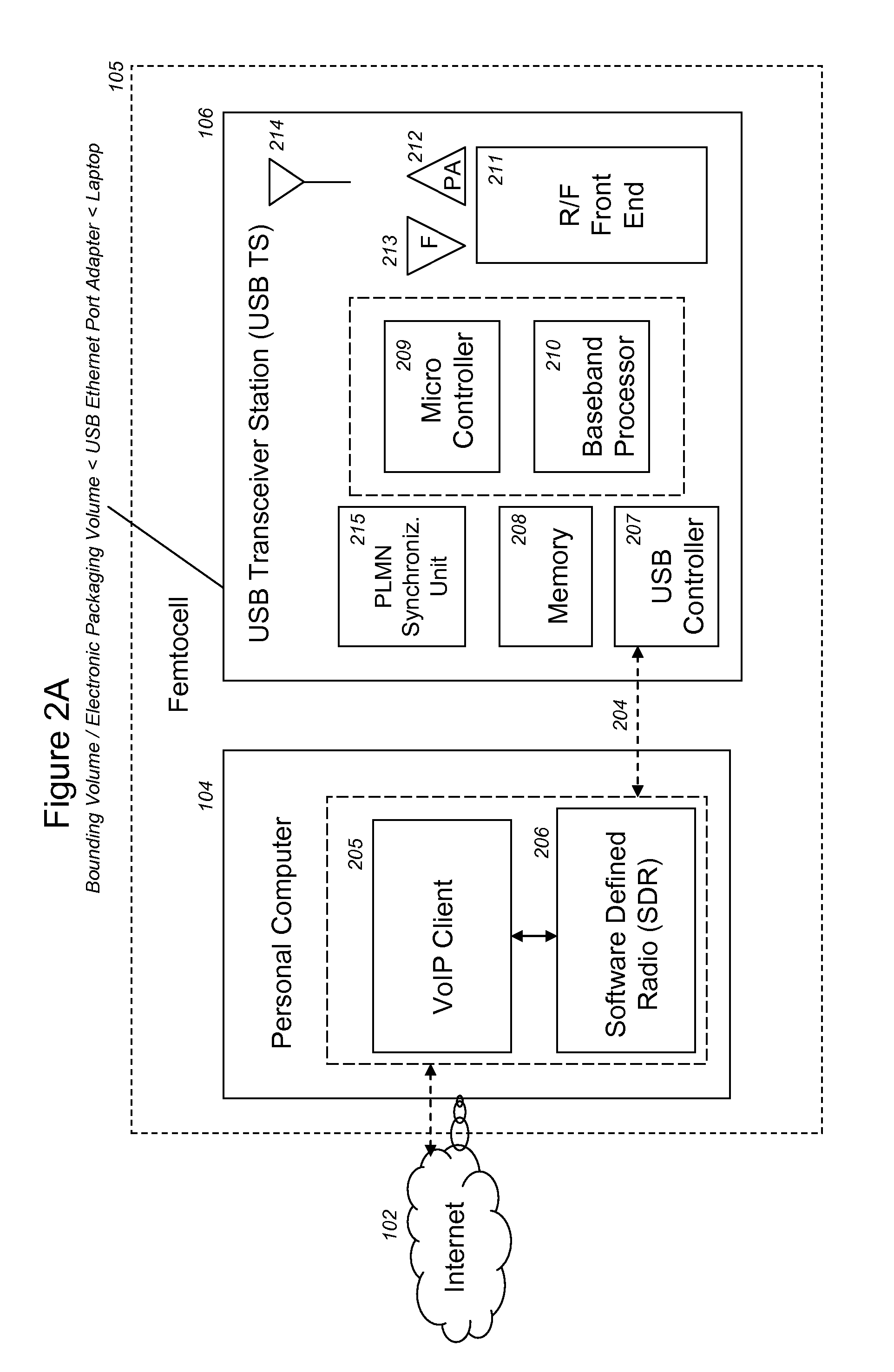
VoIP Enabled Femtocell with a USB Transceiver Station
InactiveUS20080244148A1High quality audioLow costNetwork topologiesSubstation equipmentMicrocontrollerRF front end
Telephone calls between a mobile station (MS) and the mobile network or PSTN are routed through the Internet via VoIP using a femtocell, as opposed to the traditional macrocellular network. The femtocell can comprise a USB Transceiver Station that is connected to a personal computer through a universal serial bus port, which provides both power and a multi-megabit per second connection between the personal computer and the USB transceiver station. The USB transceiver station can comprise a microcontroller to manage signaling between the RF front end / baseband processor and the personal computer, as well as a precise timing mechanism to assist the synchronization of femtocell timing with the surrounding macrocellular network, if it is present. The USB transceiver station can have a compact form factor that that facilitates a high degree of portability by the subscriber, such as being readily attachable to their keychain.
Owner:SMALL CELL INNOVATIONS
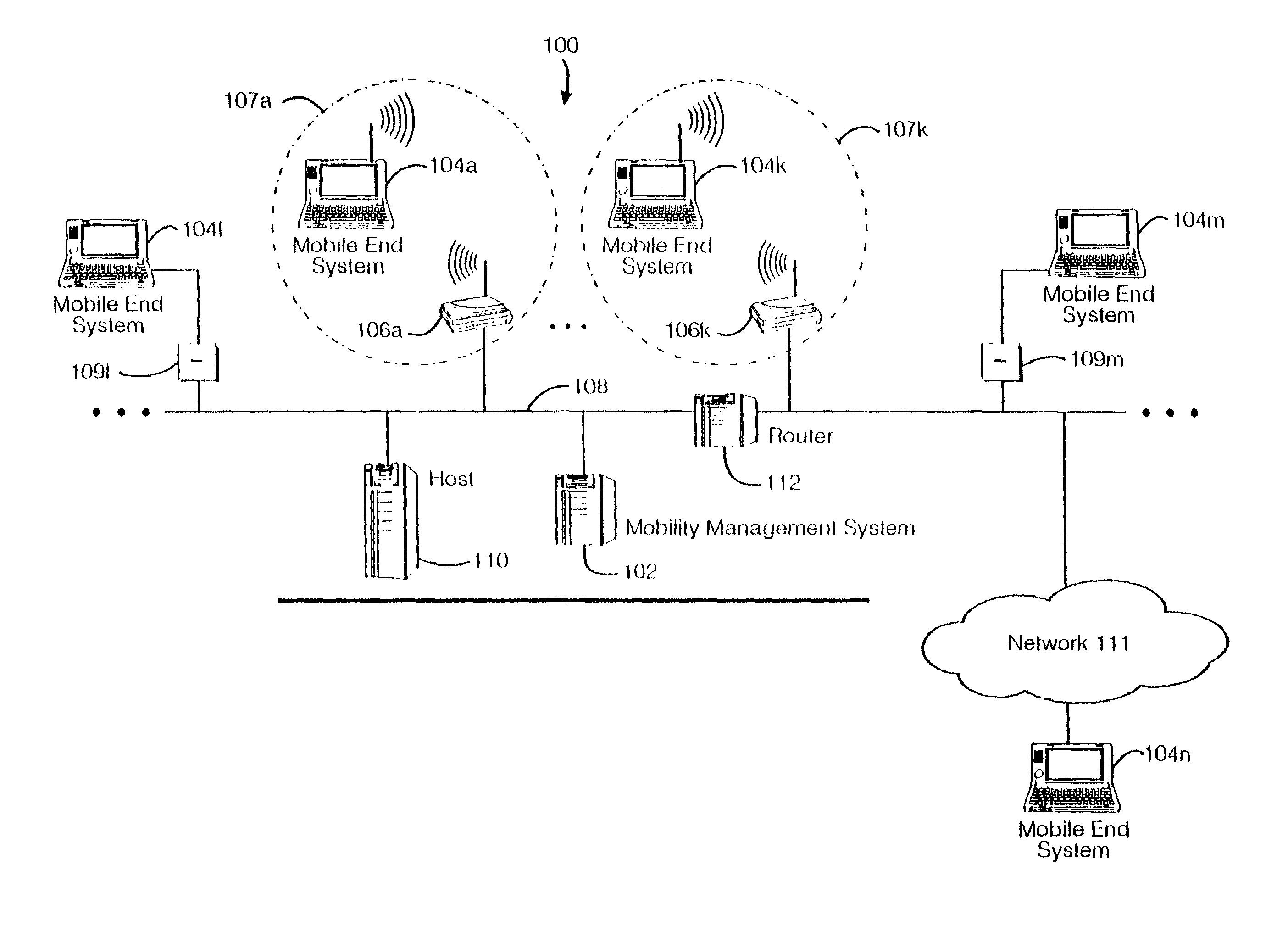
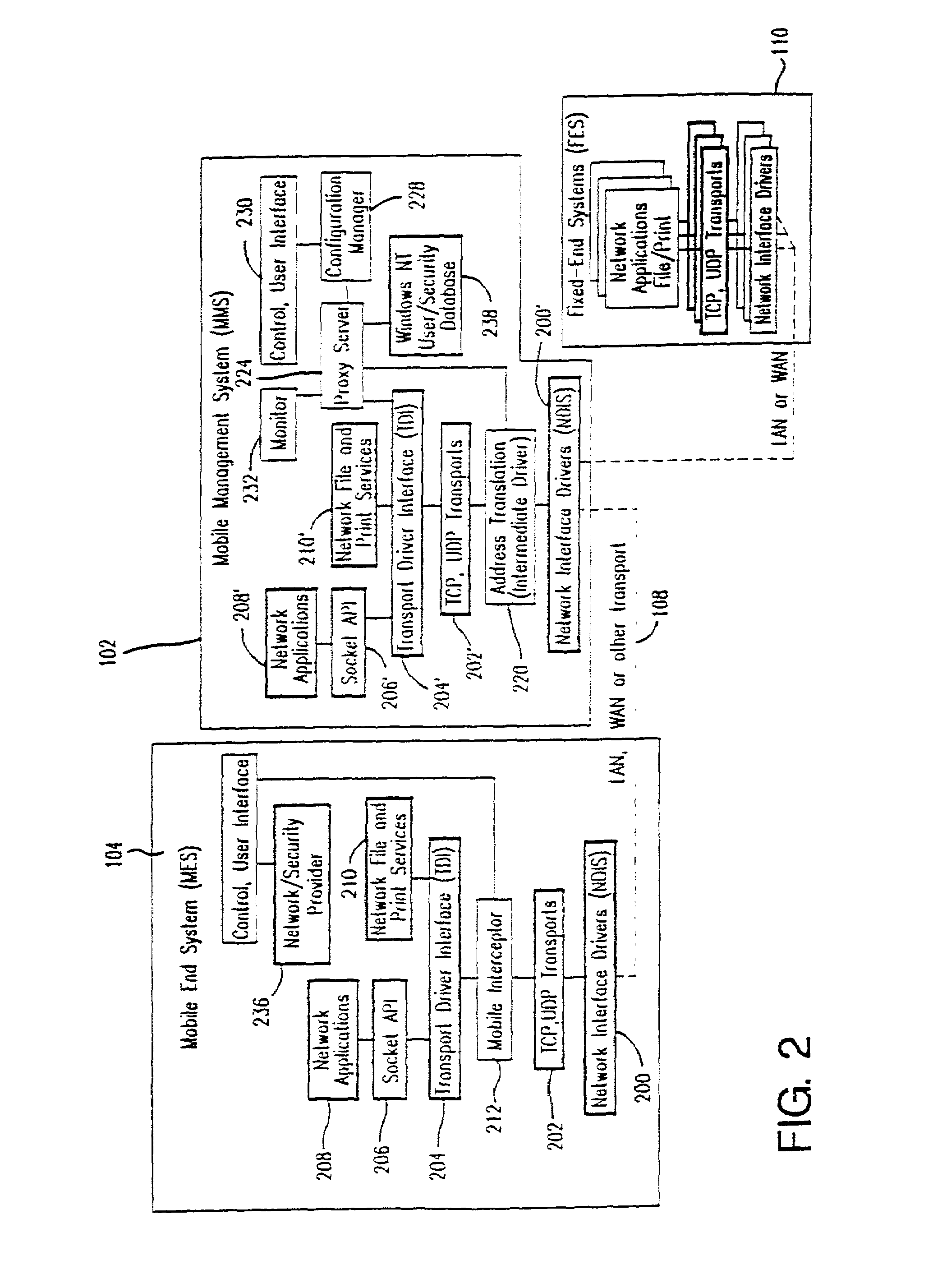
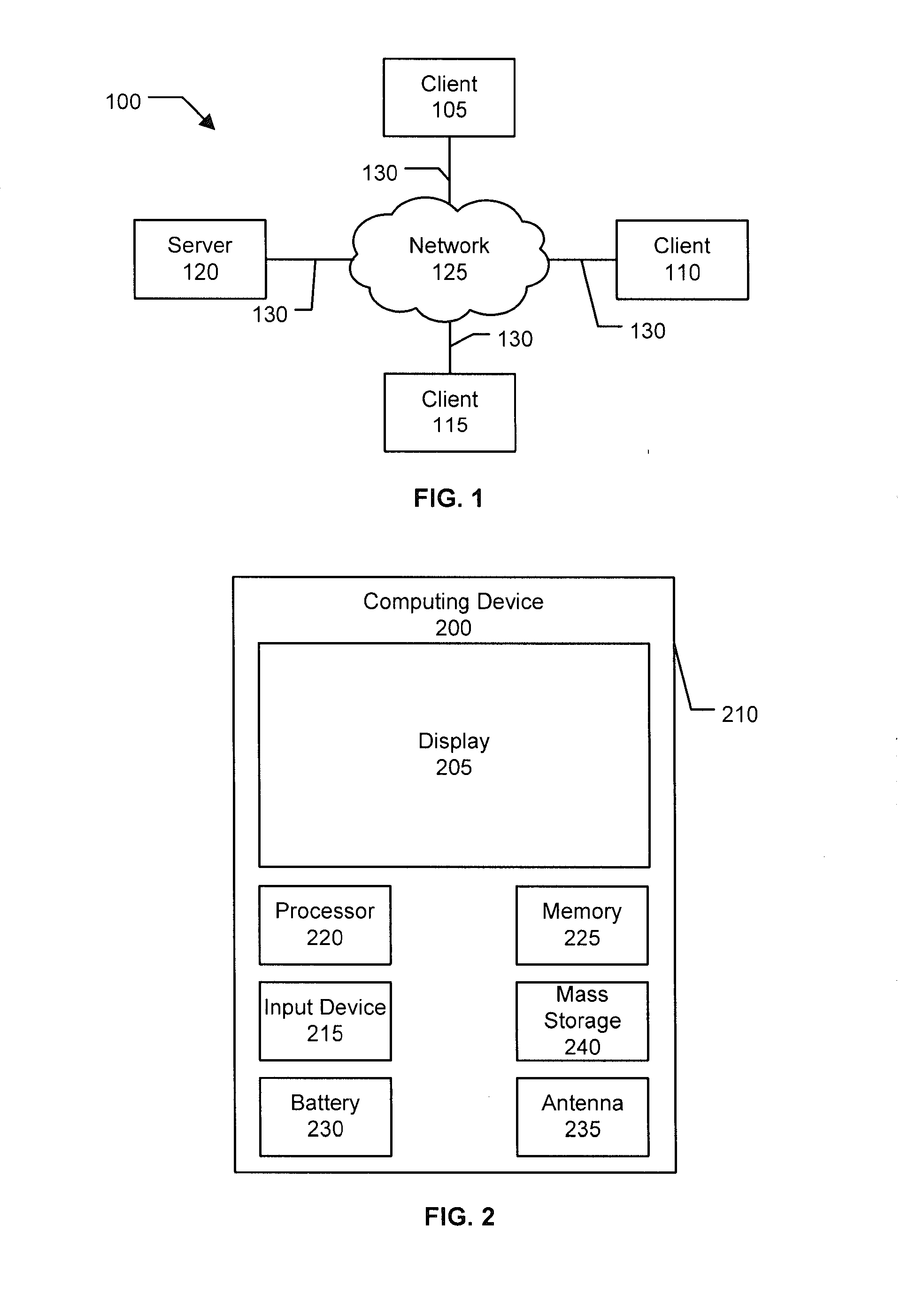
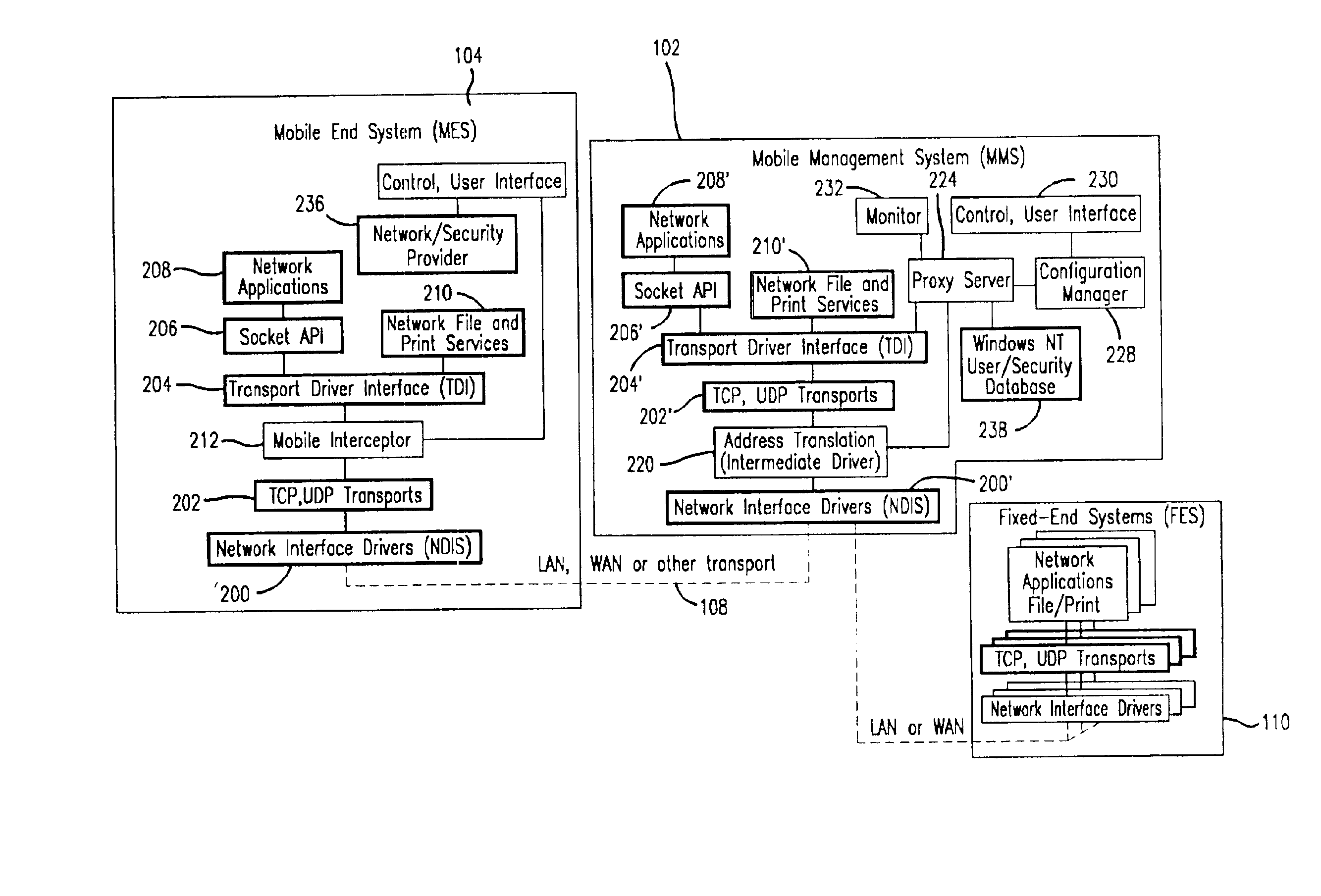
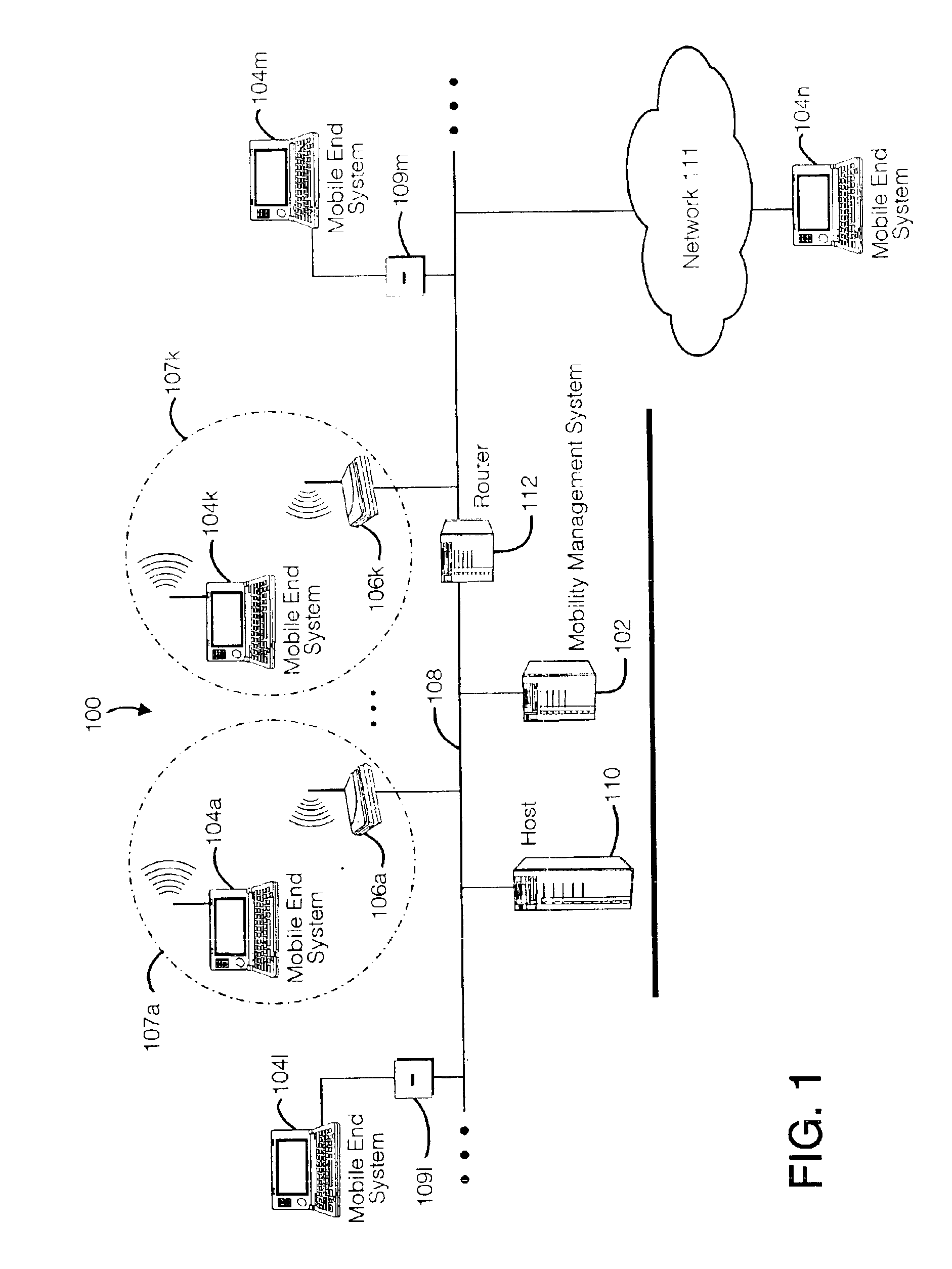
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS7136645B2Low costEasy accessError prevention/detection by using return channelNetwork traffic/resource managementNetwork connectionMobile end
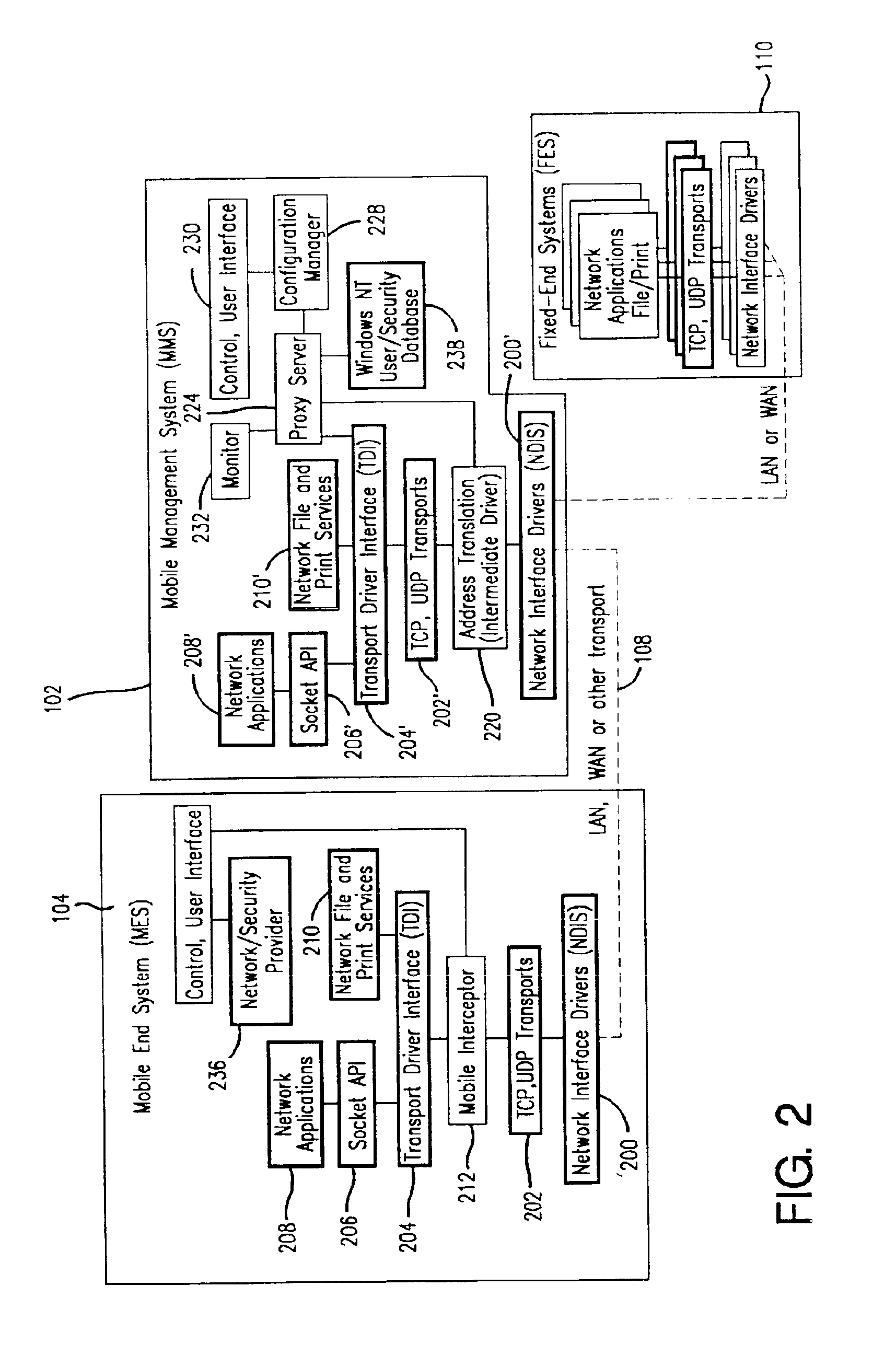
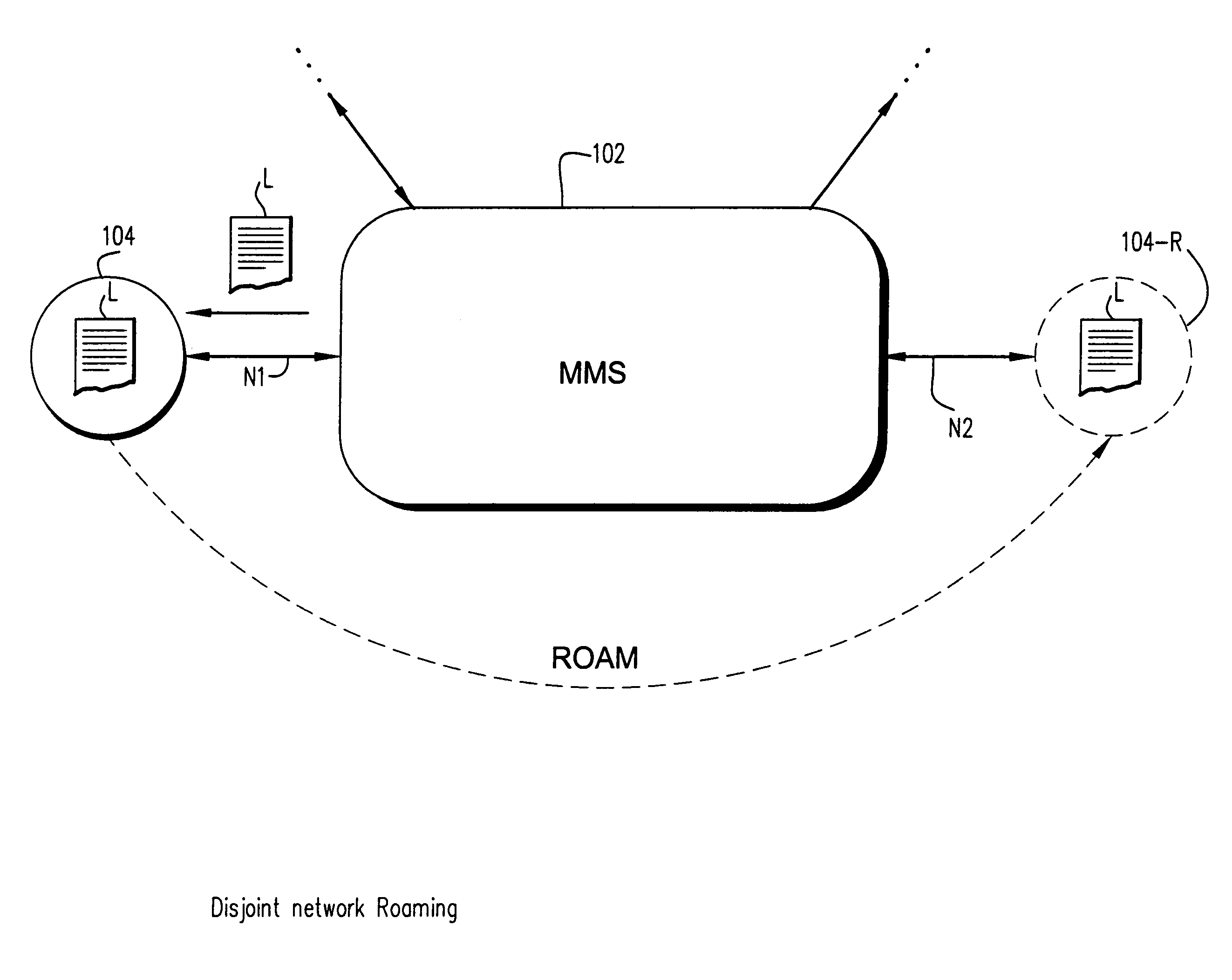
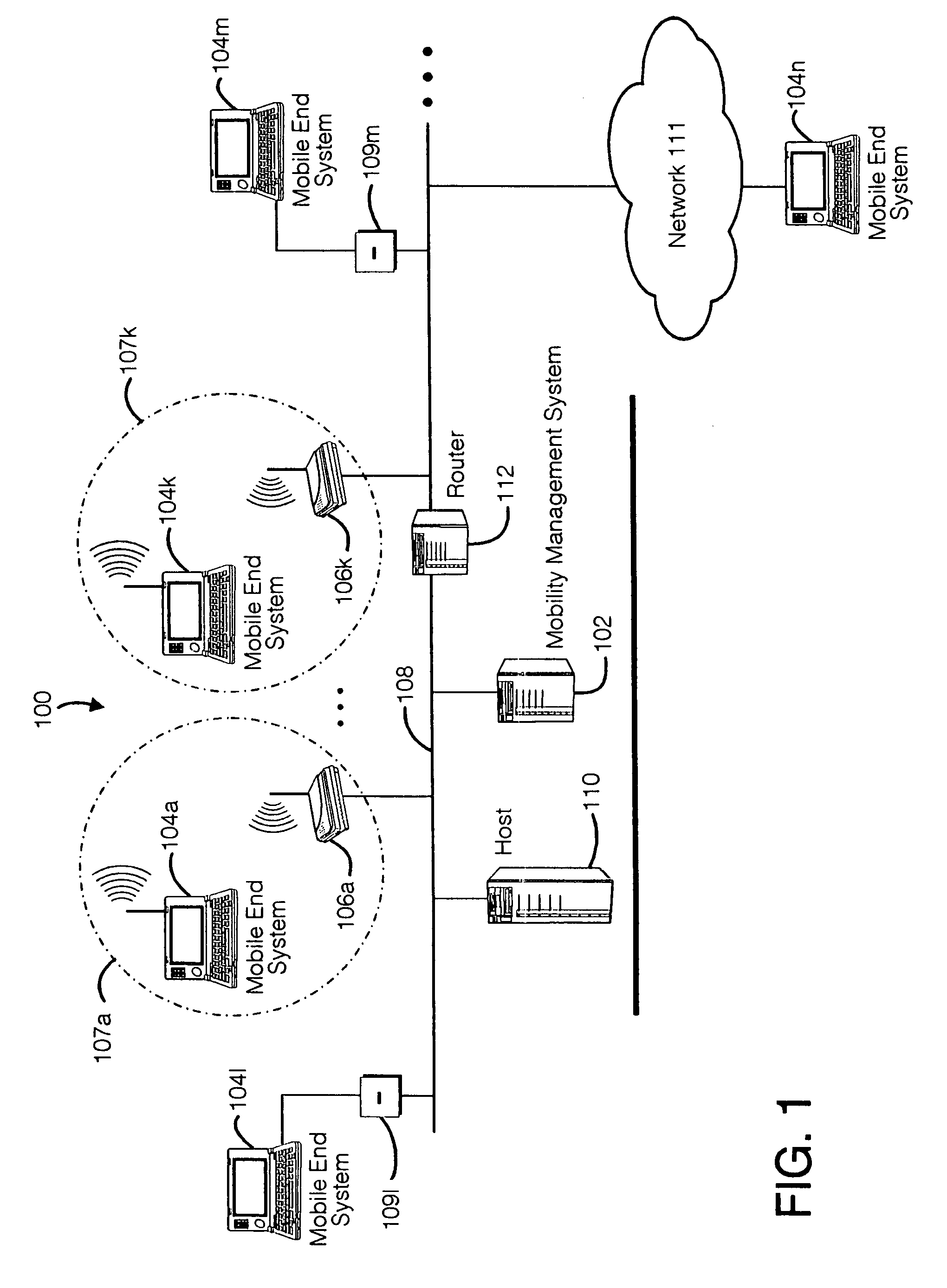
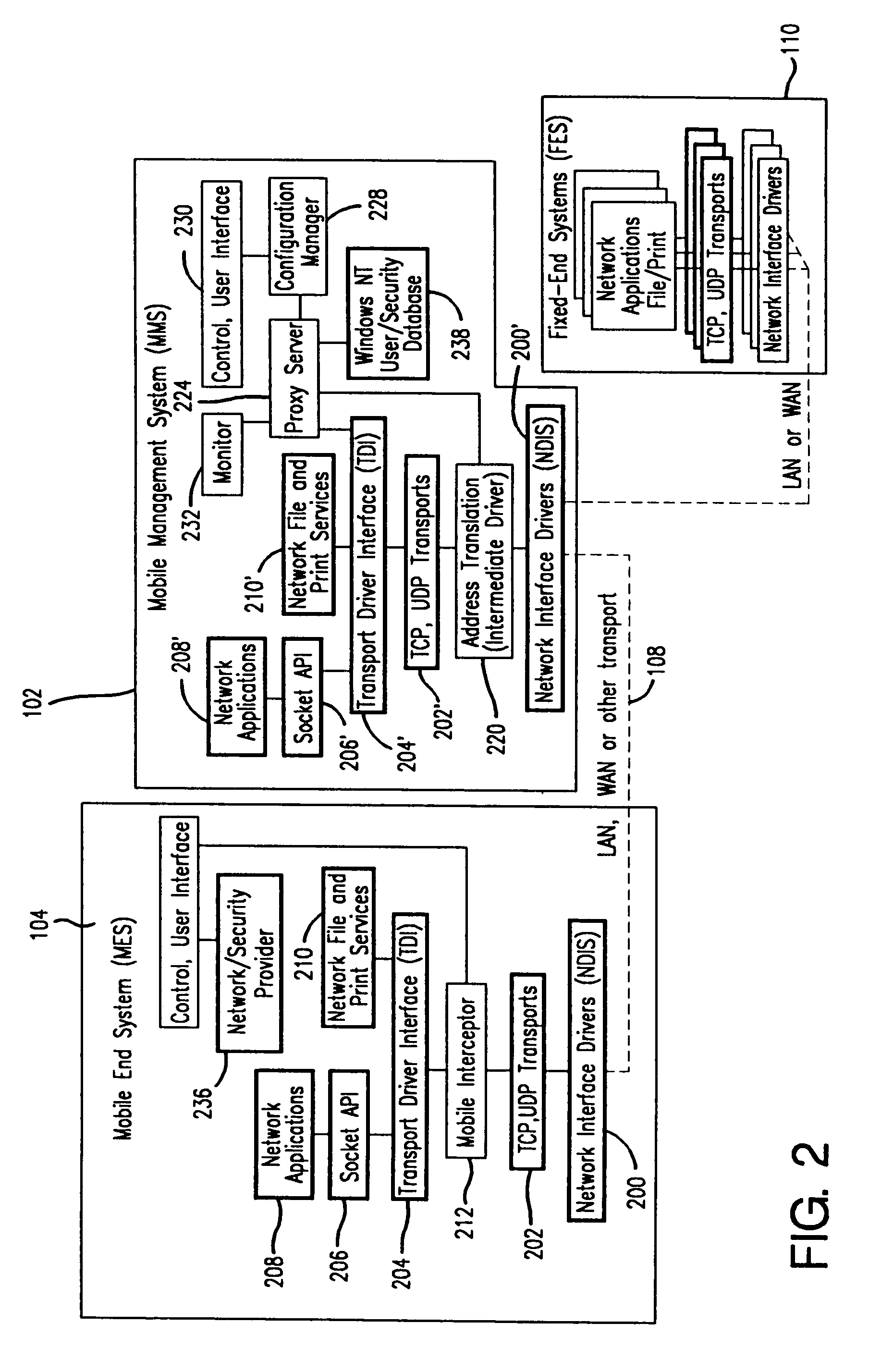
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
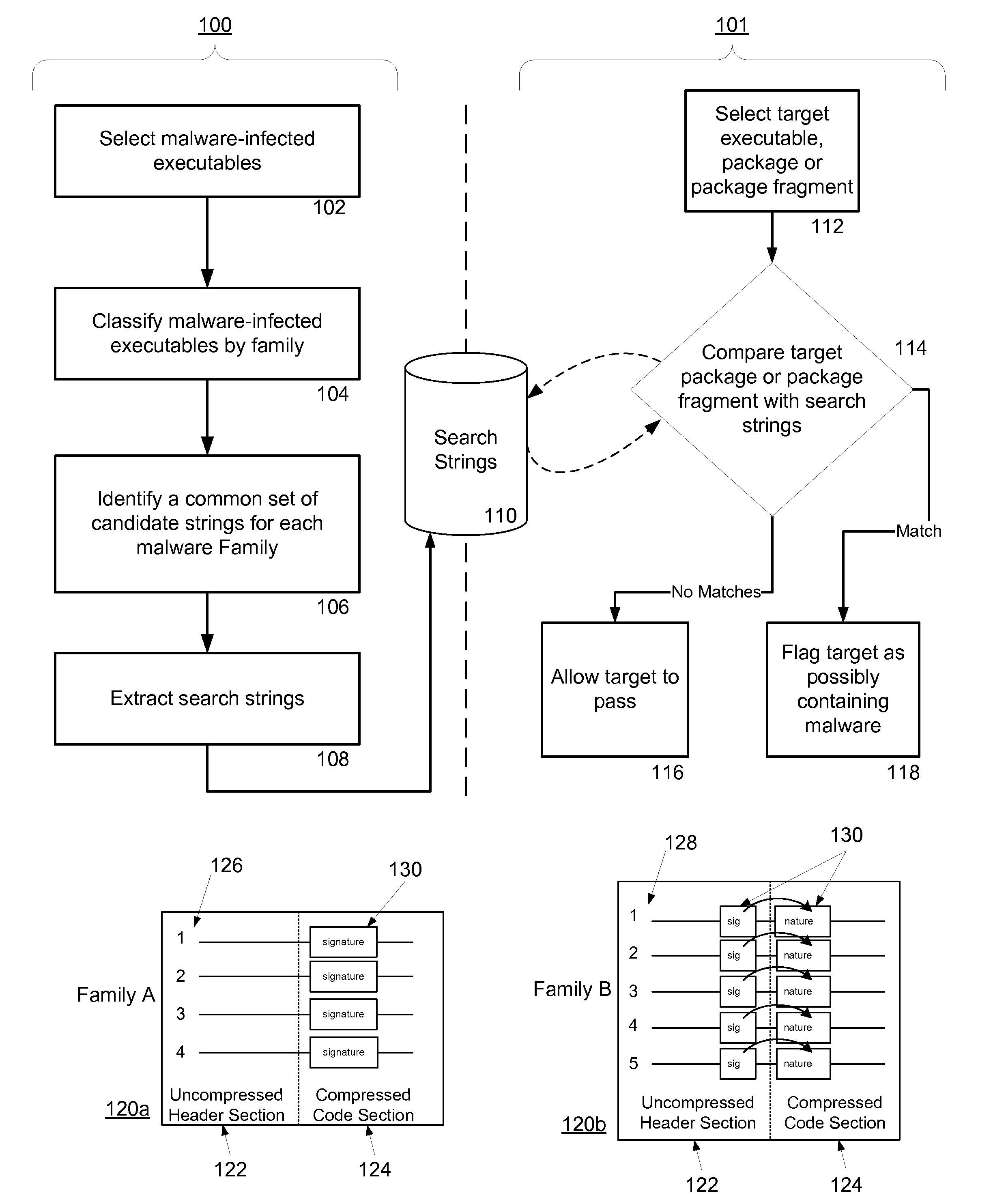
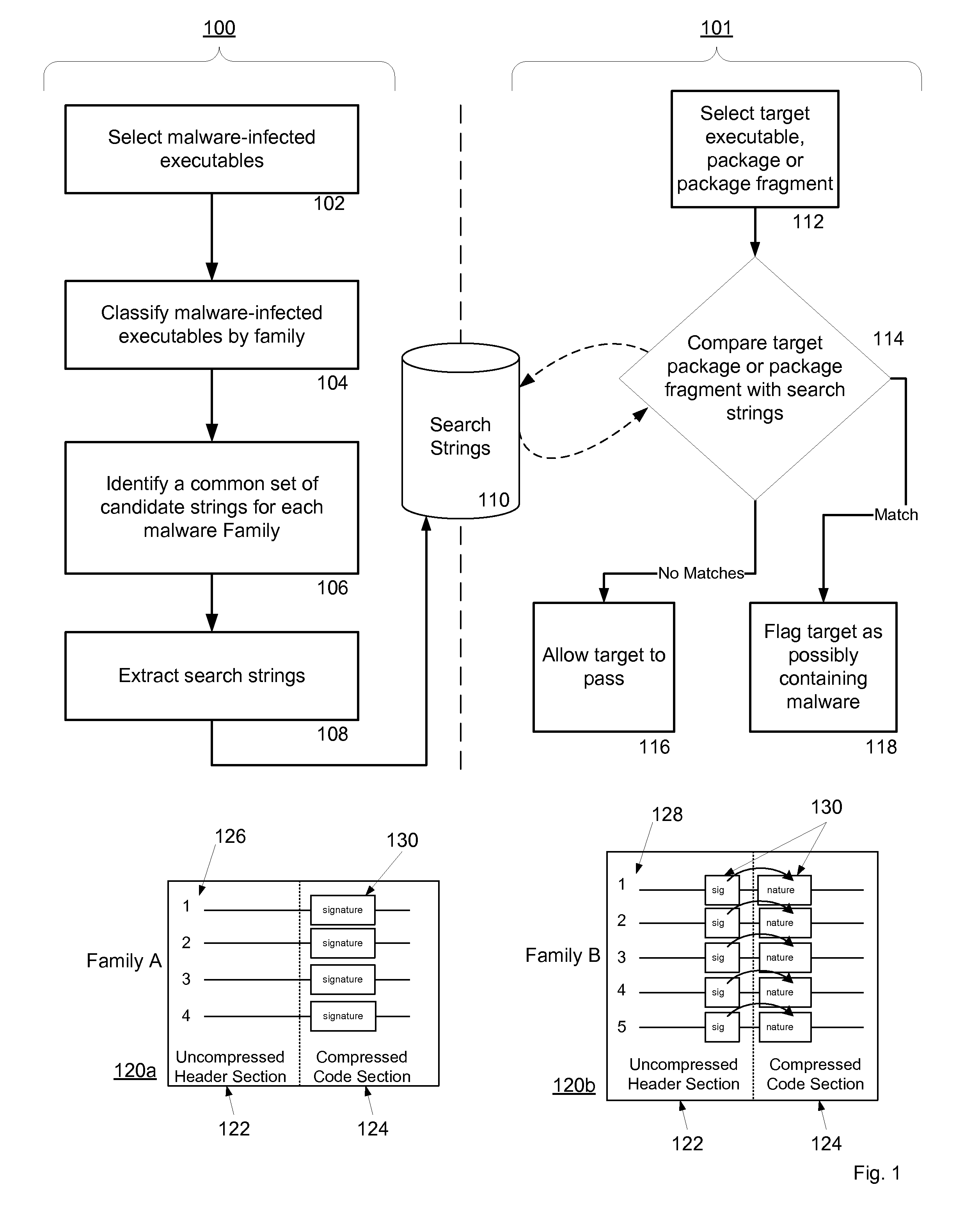
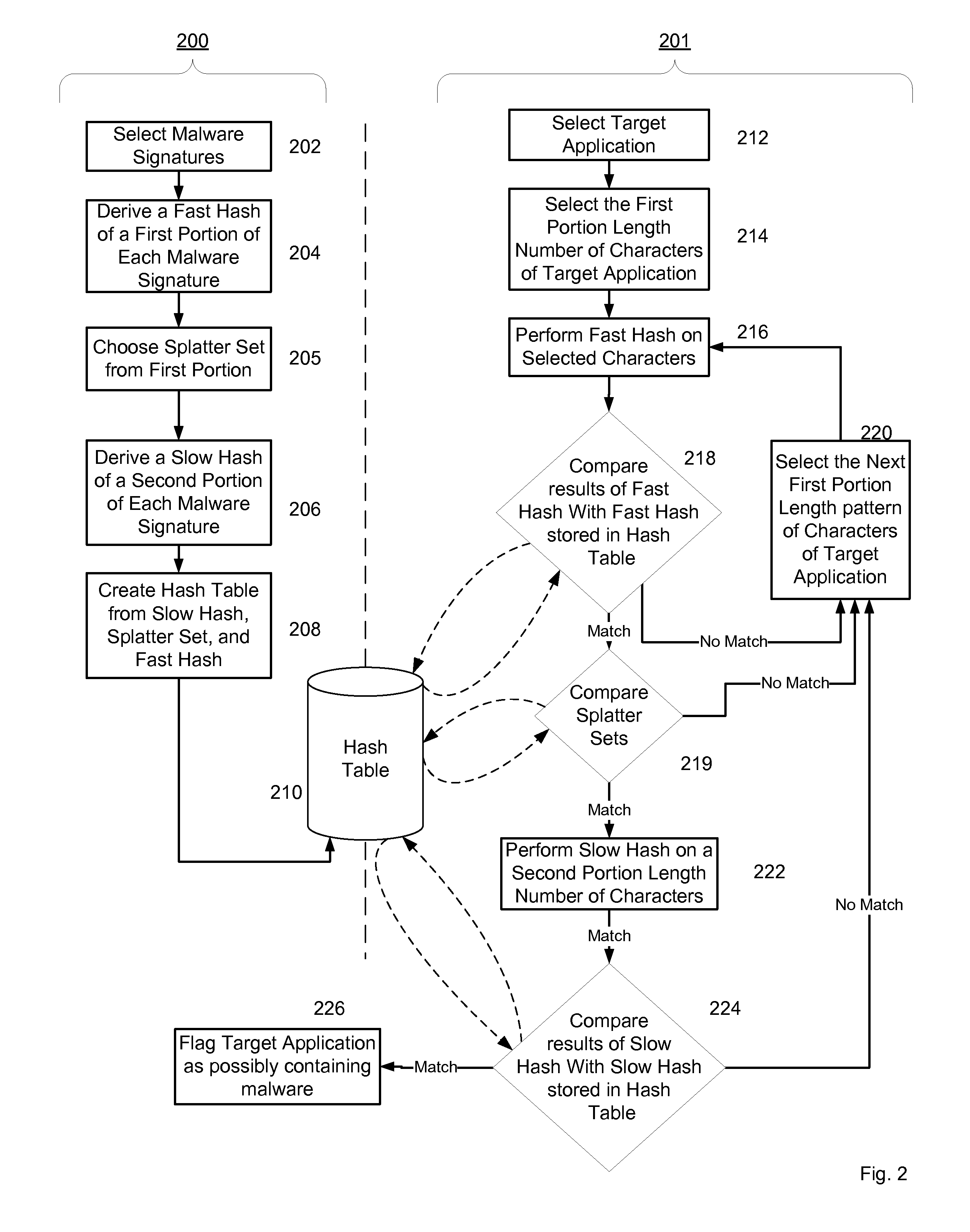
System and method for managing malware protection on mobile devices
ActiveUS20070240220A1Suitable for useReliable detectionMemory loss protectionError detection/correctionLimited accessFeature set
A system and method for detecting malware on a limited access mobile platform in a mobile network. The system and method uses one or more feature sets that describe various non-executable portions of malware-infected and malware-free applications, and compares a application on the limited access mobile platform to the features sets. A match of the features in a suspect application to one of the feature sets provides an indication as to whether the suspect application is malware-infected or malware-free.
Owner:PULSE SECURE
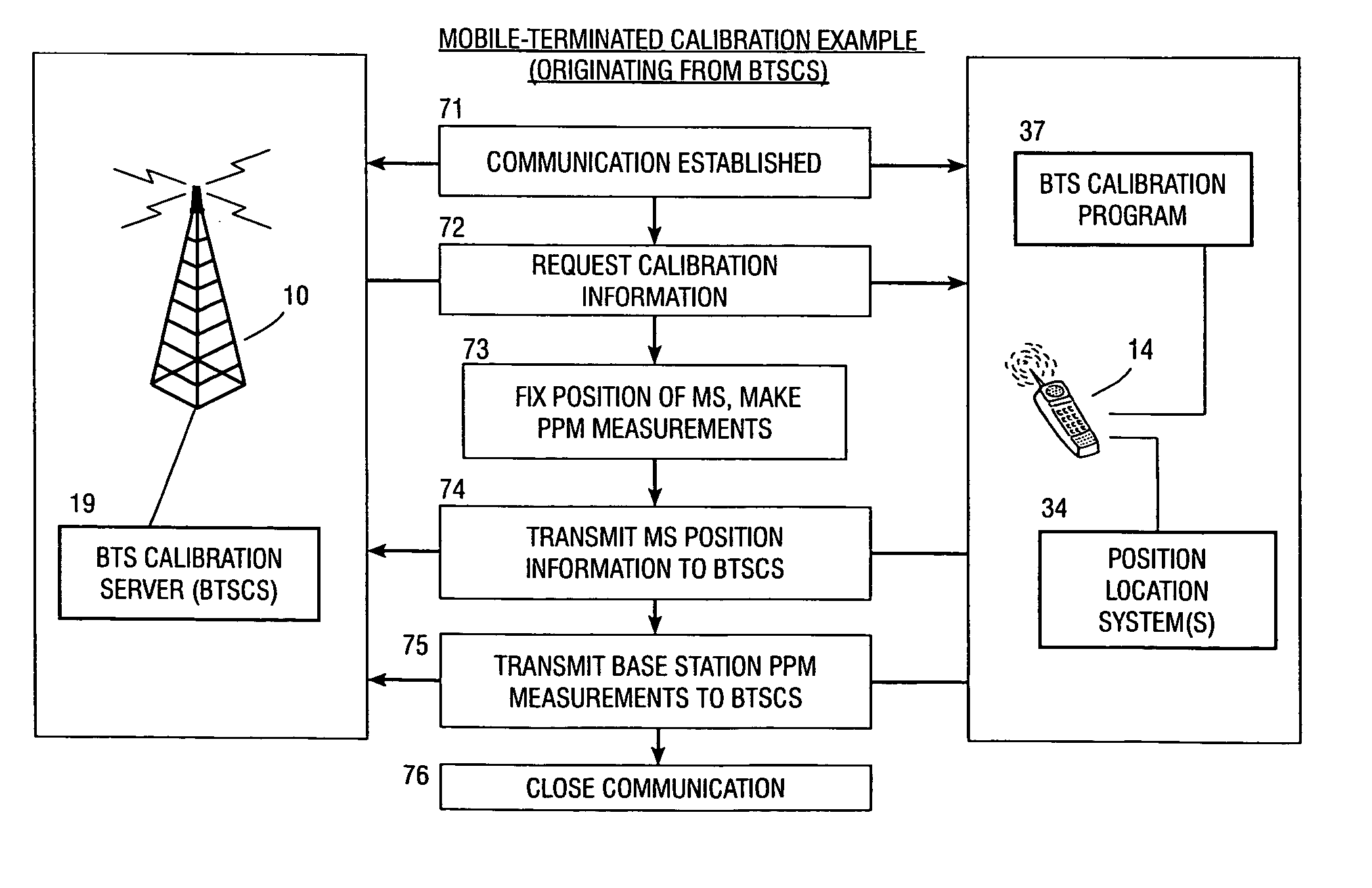
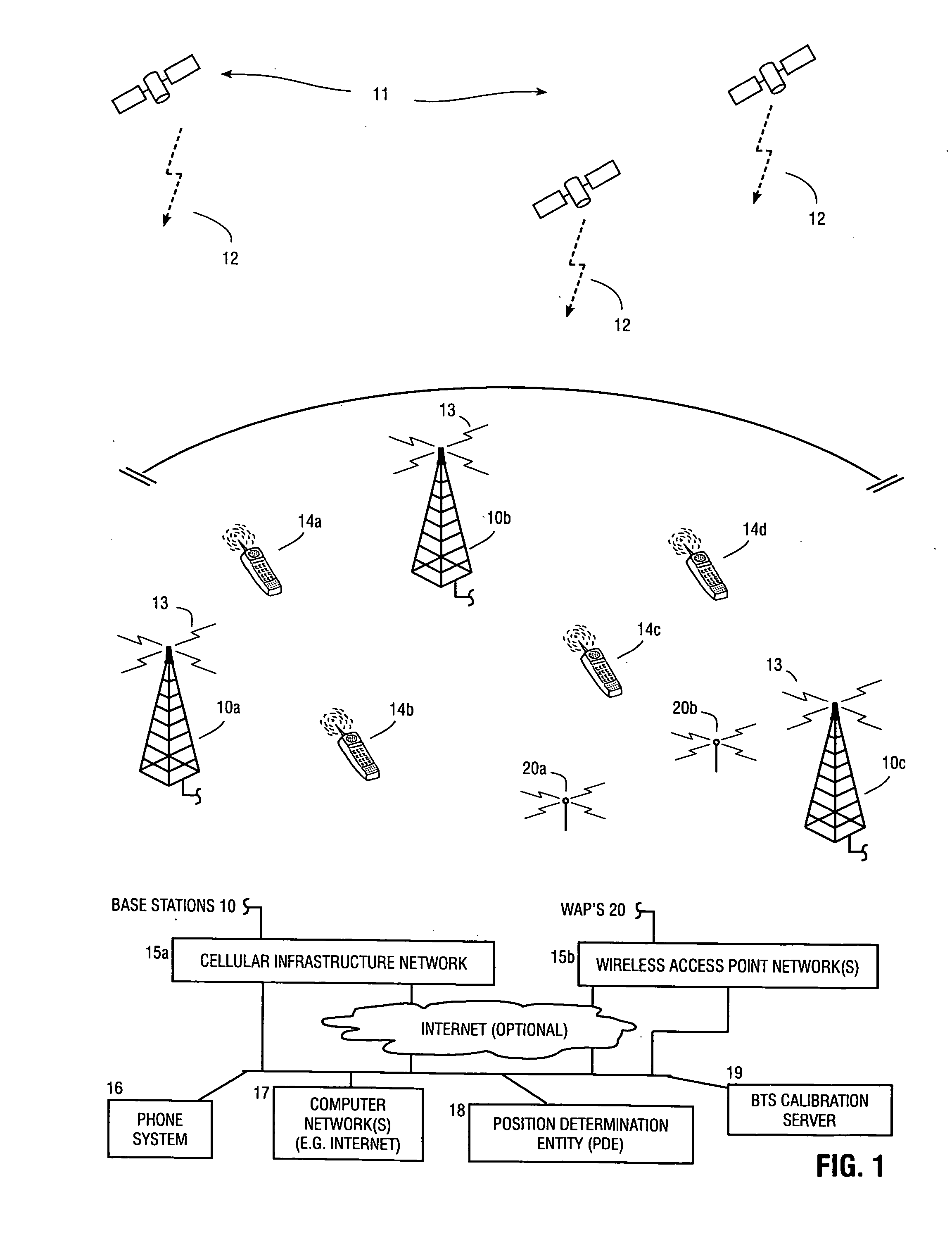
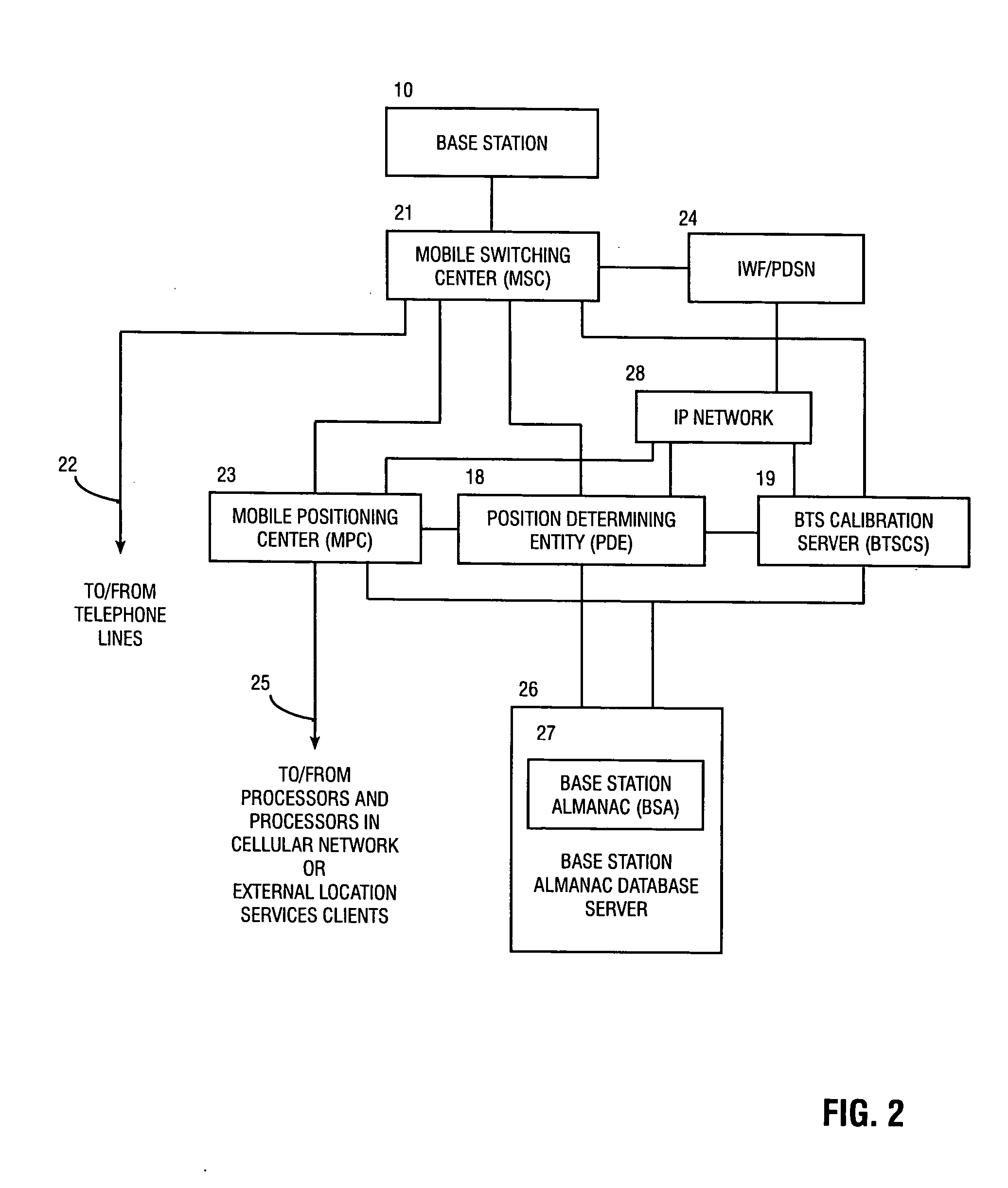
Method and apparatus for determining location of a base station using a plurality of mobile stations in a wireless mobile network
A method and apparatus for determining a position of a base station in a wireless communication network that includes a mobile station in communication with base stations. A BTS calibration server is networked with the base stations. A BTS calibration program is programmed into a group of mobile stations that have position location capabilities. Using the BTS calibration program, calibration information may be requested by the BTS calibration server, or a session may be initiated by the mobile station. The BTS calibration program also provides privacy features that allow user of the mobile station to prevent it from being used for base station location. If authorized, the BTS calibration program determines the position of the mobile station, and provides calibration information, such as position and base station phase measurements, to the server. The calibration information may be used to calibrate the base station almanac.
Owner:QUALCOMM INC
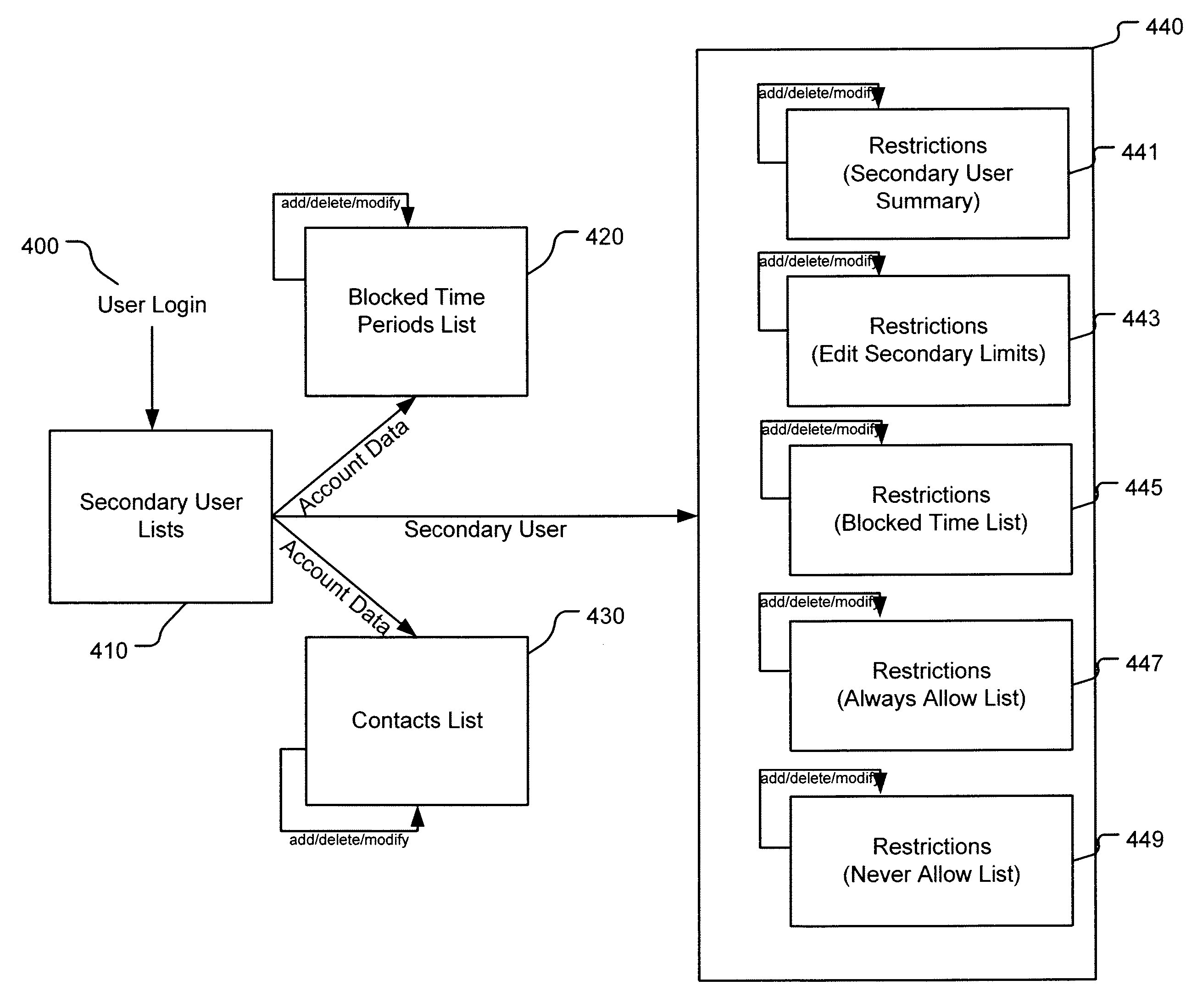
Consumer configurable mobile communication web filtering solution
InactiveUS7516219B2Multiple digital computer combinationsWireless network protocolsMobile deviceMobile Web
Consumer configurable mobile communications solution enabling web filtering based on policy-enforcement services allowing authorized users to define, manage and enforce restrictions for mobile web data and services of a secondary mobile device.
Owner:VENTRAQ CORP
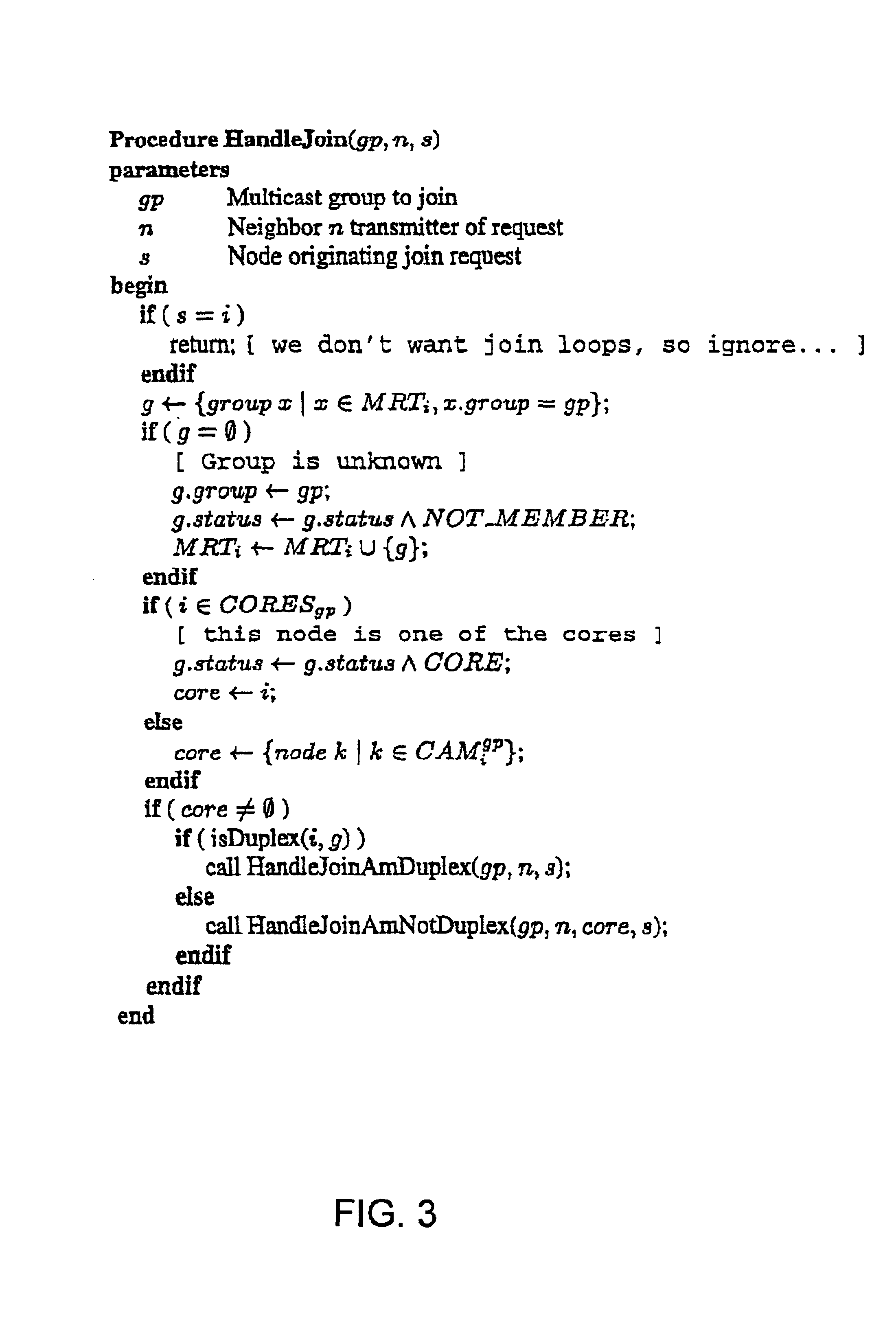
Core assisted mesh protocol for multicast routing in ad-hoc Networks
InactiveUS6917985B2Enrich connectivityStay connectedSpecial service provision for substationError preventionIP multicastBroadcasting
A method of providing multicast routing for use in ad hoc broadcast networks, such as wireless and mobile networks. The method is described within a protocol referred to as core-assisted mesh protocol, or CAMP. The method departs from traditional tree-structured multicast protocols and utilizes multicast meshes in which the network need not be flooded with control or data packets to establish routing paths. Each router configured for CAMP is capable of accepting unique packets arriving from any neighbor in the mesh, wherein packets are forwarded along reverse shortest paths to the receiver. Multiple cores may be defined for a group wherein the loss of a single core does not prevent packet flow. Routers for sender-only hosts are allowed to join the multicast mesh in simplex mode, and in certain cases may join without the sending of a join request.
Owner:RGT UNIV OF CALIFORNIA
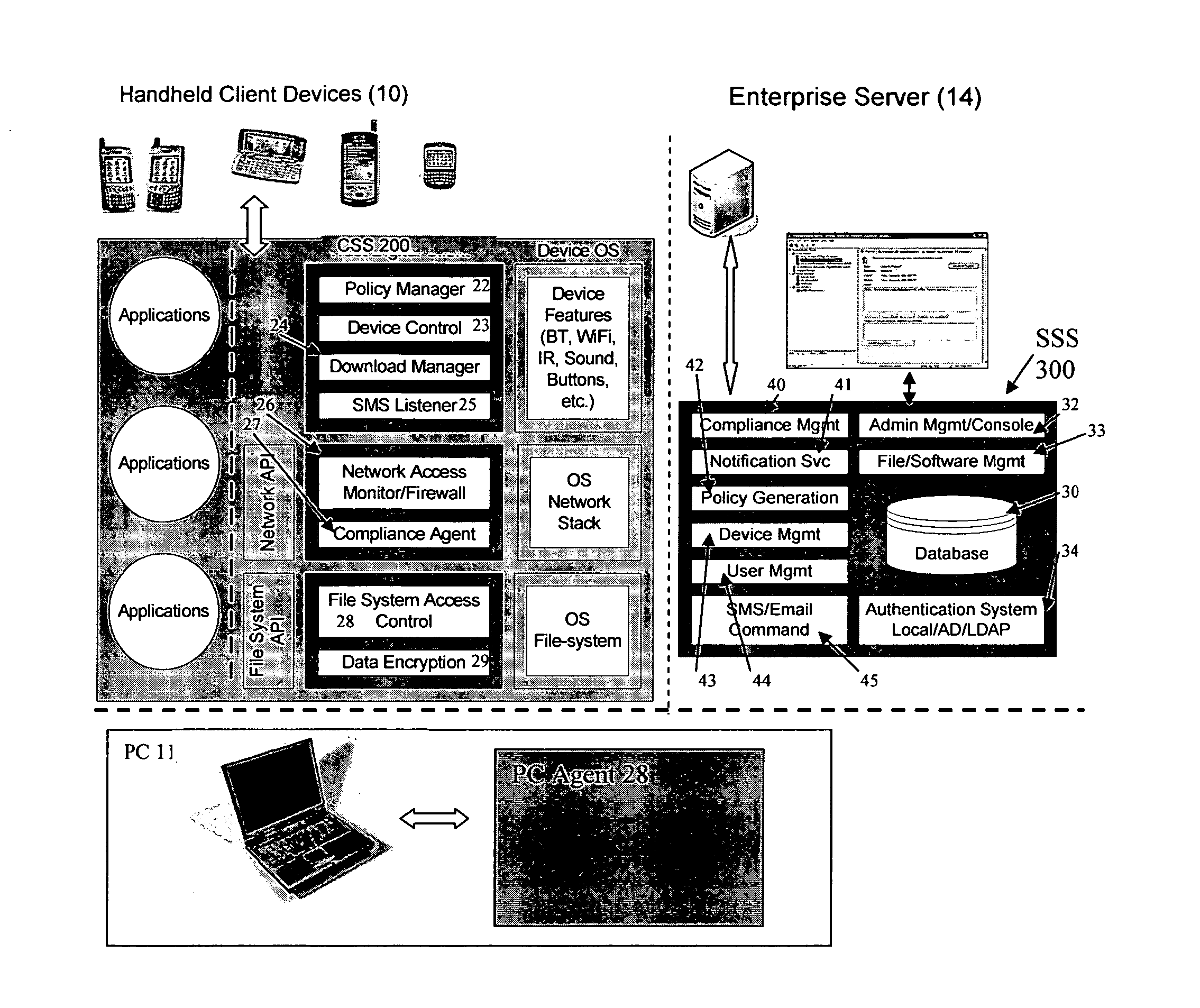
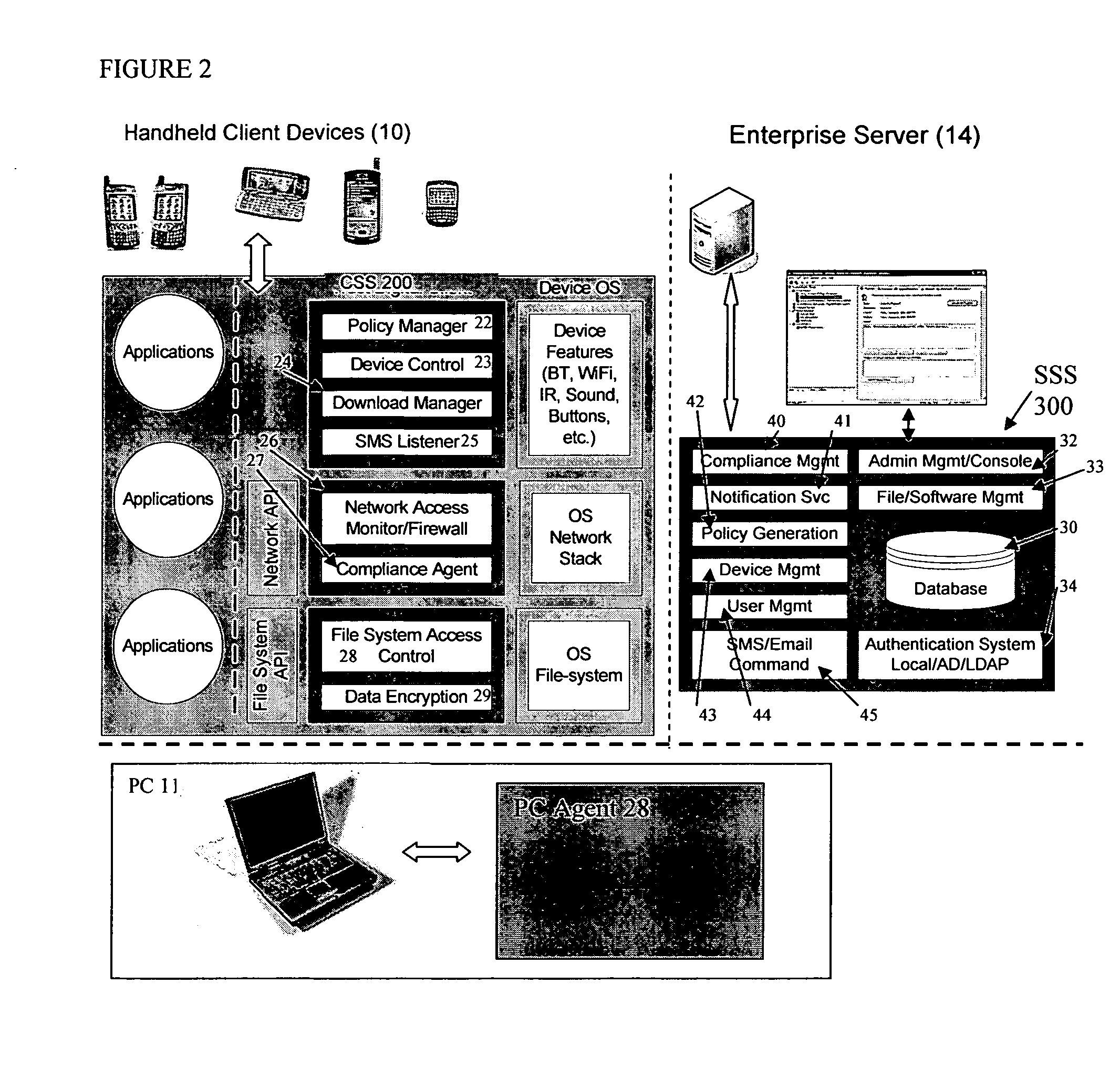
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
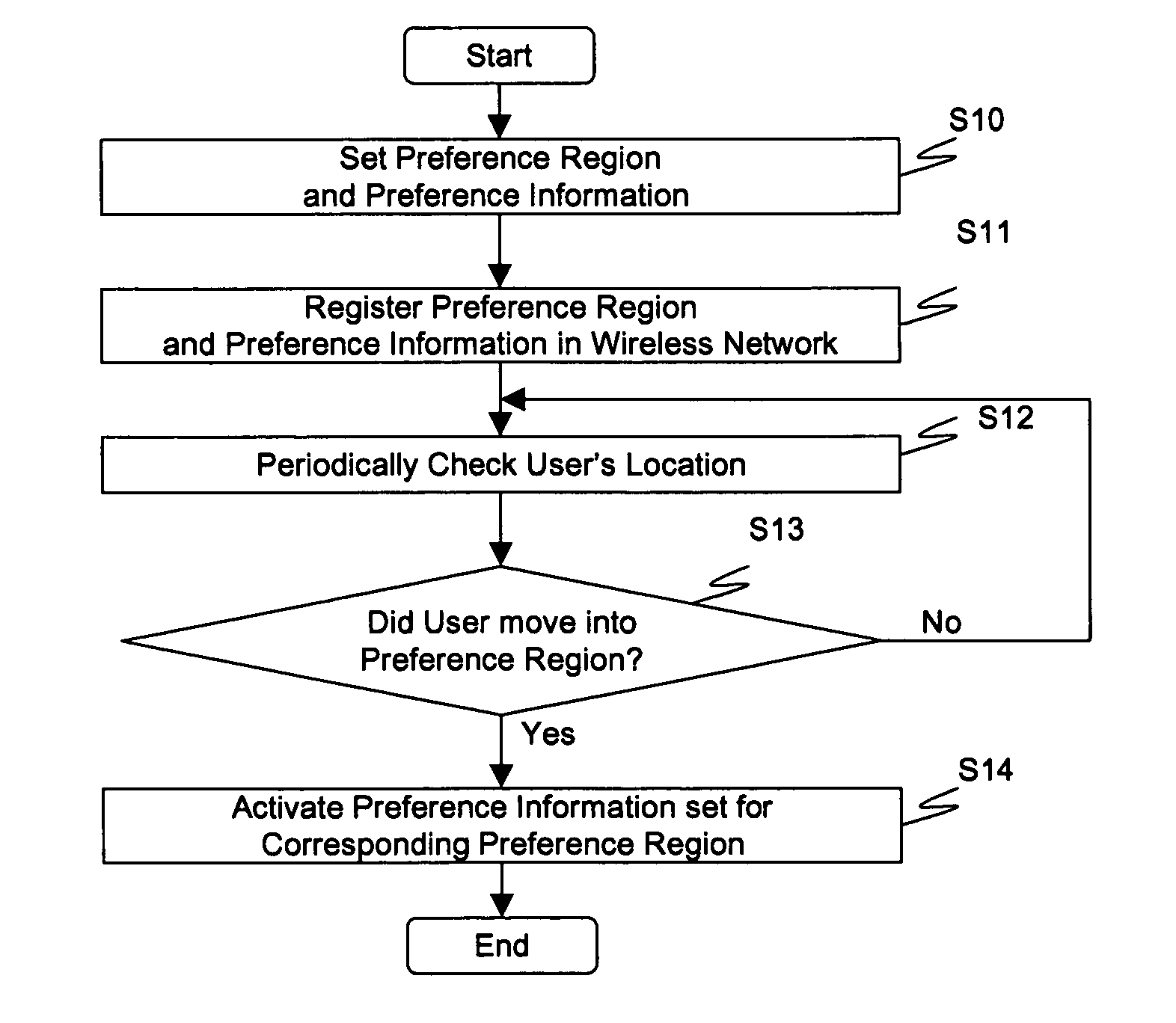
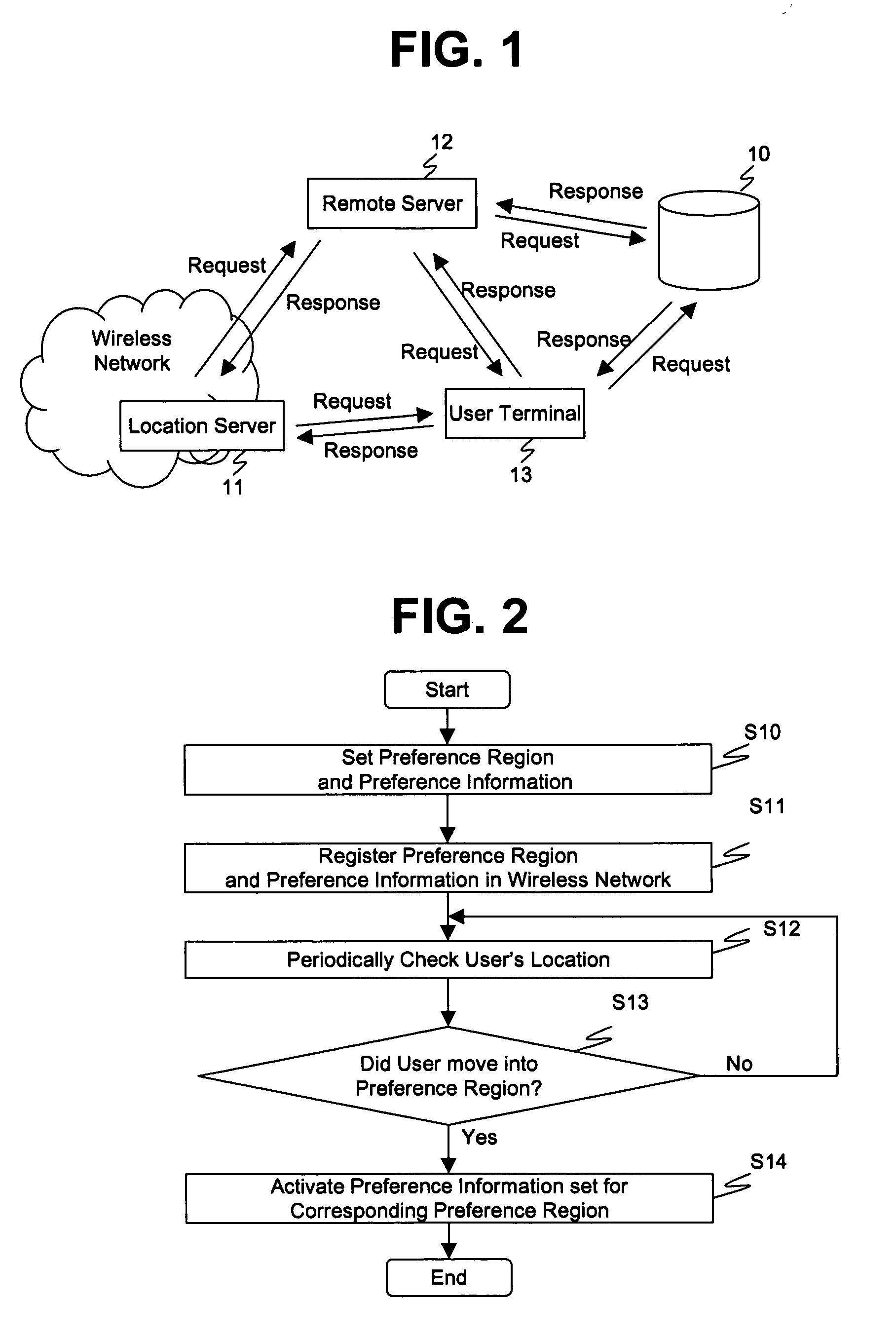
Location information system reflecting user preferences and service providing method thereof
InactiveUS20050250516A1Different operationalRadio/inductive link selection arrangementsLocation information based serviceService provisionMobile Web
For users with user terminals in a wireless or mobile network, a mechanism is provided for returning a representative location based on the user's profile settings and the user's current physical location. The representative location is not the user's actual physical location, but a conceptual location used for reporting the user's physical location in order to activate various functions and capabilities of the user terminal according to where the user is located. By employing representative locations, various necessary information and corresponding relationships between the user's actual location, which may continuously change due to the user's mobility, and the user preferences containing profile settings allowing the user's terminal to operate in a certain manner designated for certain physical locations, are more efficiently handled and managed.
Owner:LG ELECTRONICS INC
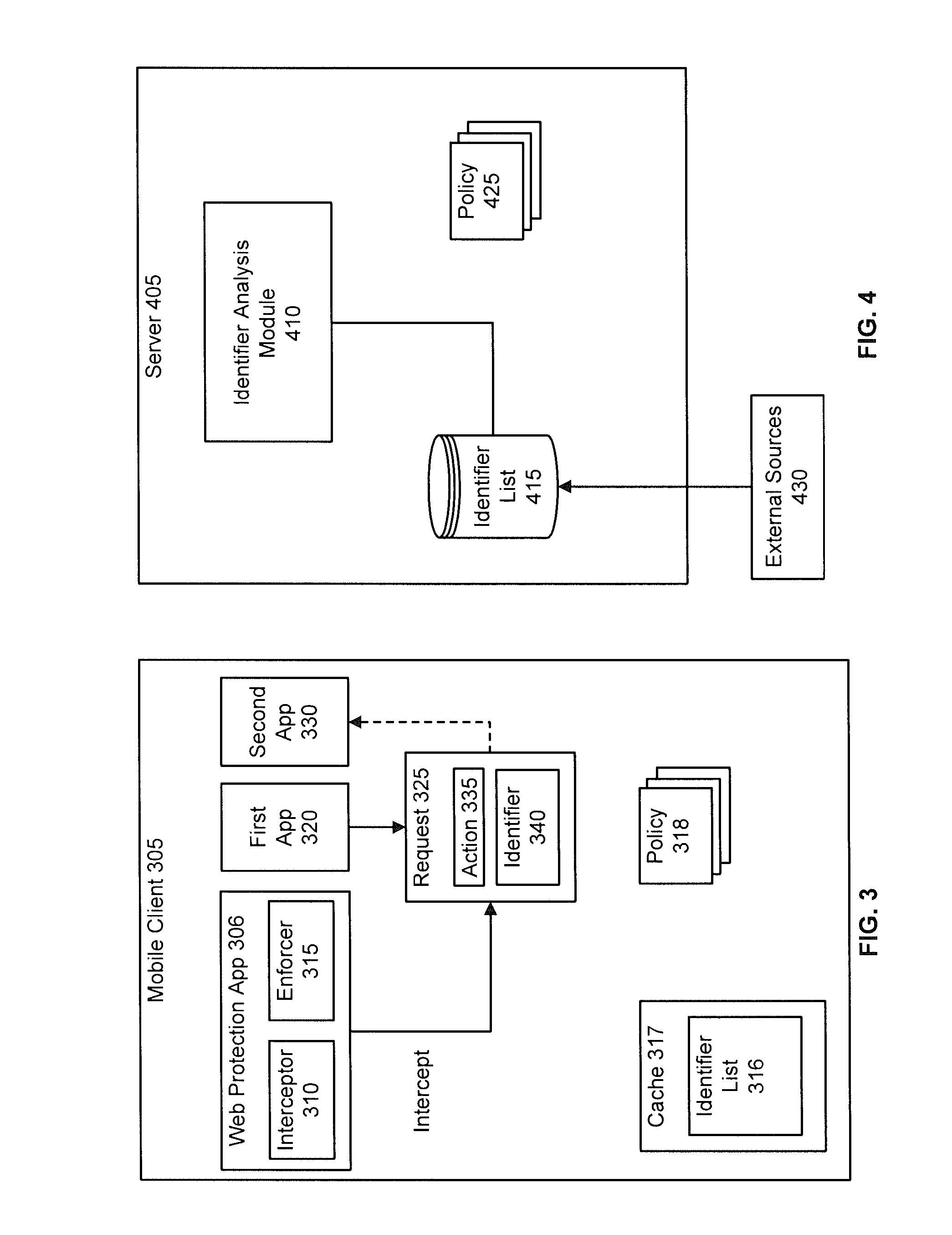
Mobile web protection
InactiveUS20120324568A1Computer security arrangementsMultiple digital computer combinationsEvaluation resultWeb browser
On a mobile communications device, visiting a link from a messaging application or web browser may result in an undesired action, such as visiting a phishing site, downloading malware, causing unwanted charges, using too much battery, or the device being exploited. In an implementation, a mobile application intercepts a request including an identifier associated with an action to be performed by another application on the device and evaluates the identifier to determine when the request should be permitted, blocked, or conditionally permitted. The client may use local data or make a request to a server to evaluate the identifier. In an implementation, server communications are optimized to minimize latency by caching evaluation results on the device, proactively priming the device's DNS cache, optimizing when DNS lookups are performed, and adapting evaluation policy based on factors such as the source of the request, and the currently active network connection.
Owner:LOOKOUT MOBILE SECURITY
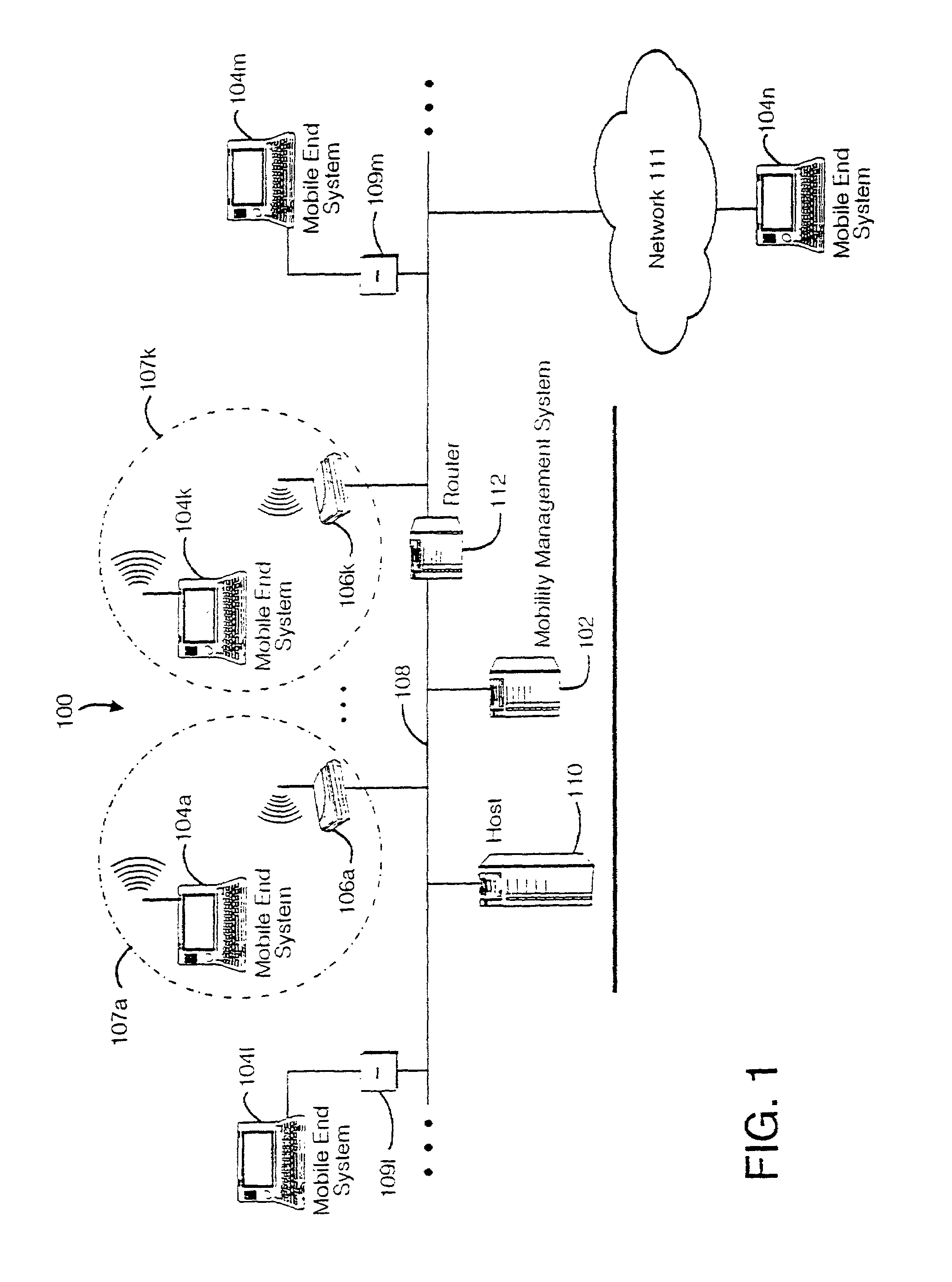
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS6981047B2Error prevention/detection by using return channelData switching by path configurationMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
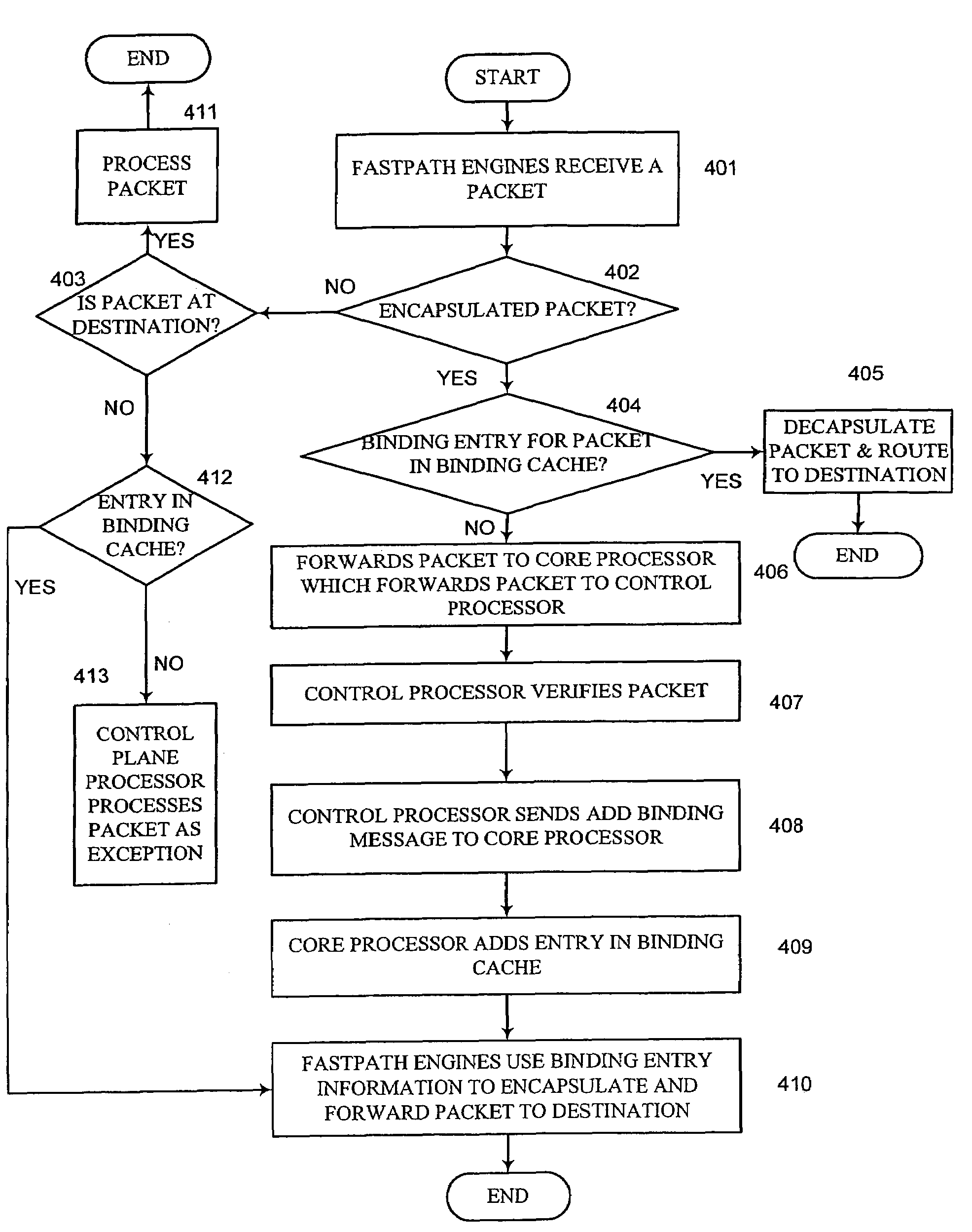
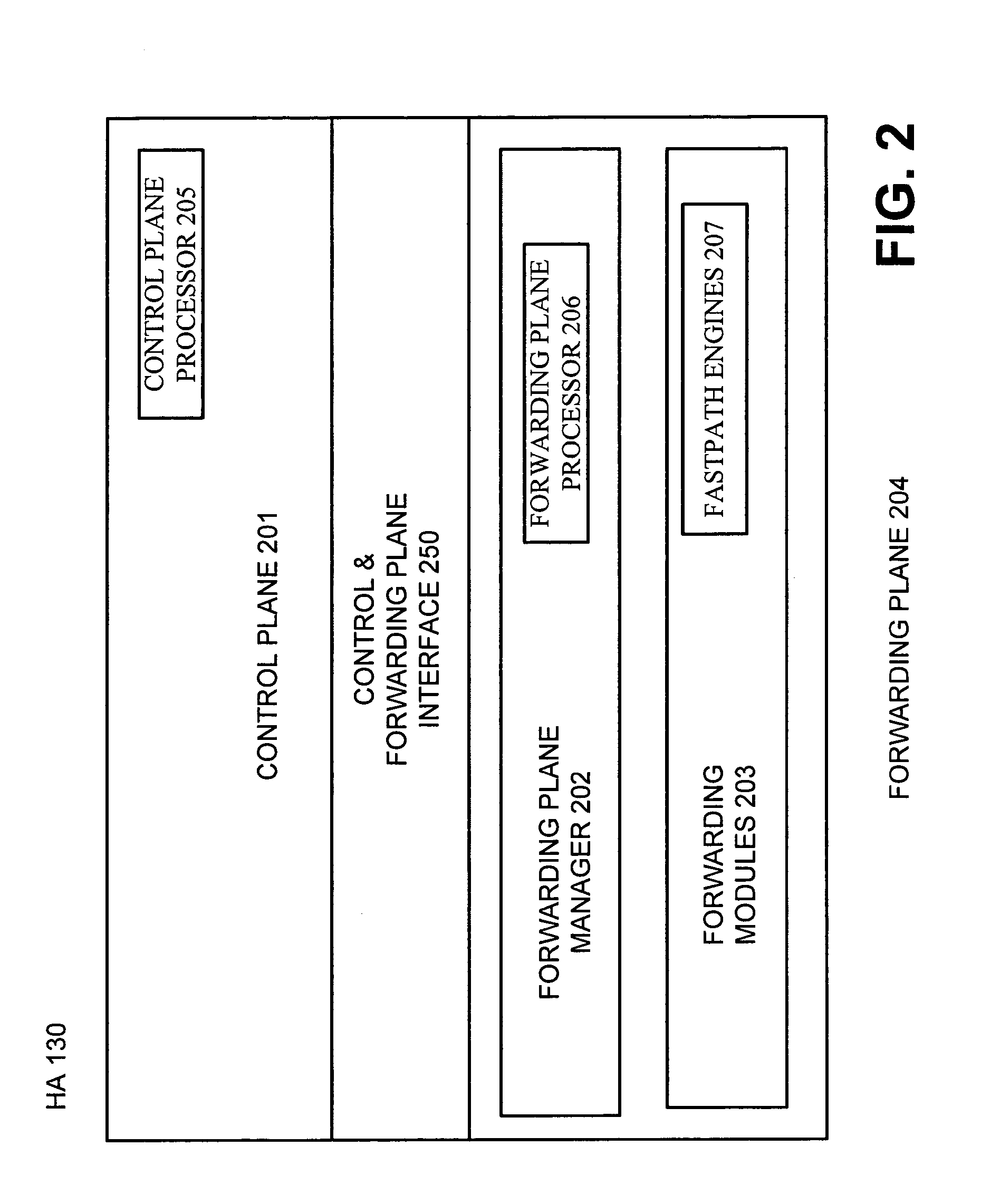
Method, apparatus and system for optimizing routing of mobile IP packets
Network devices on mobile networks may be configured to improve and optimize packet processing and routing. Specifically, a home agent device may be decomposed into its major functionality, namely processing and routing. Various processors on the device are assigned to specific tasks and each processor may be optimized for its specific tasks, thus improving packet processing and routing. The home agent device may comprise one or more physical components.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
System and method for root cause analysis of mobile network performance problems
A method and system for identifying causes of performance metric changes in a network by selecting, from a pool of network event counters, a plurality of candidate counters relevant to a performance metric; grouping the candidate counters into clusters of similar counters; selecting, from each cluster, one or more representative counters; and fitting the selected representative counters to a model of the performance metric to determine thereby a set of representative counters most relevant to the performance metric.
Owner:ALCATEL LUCENT SAS
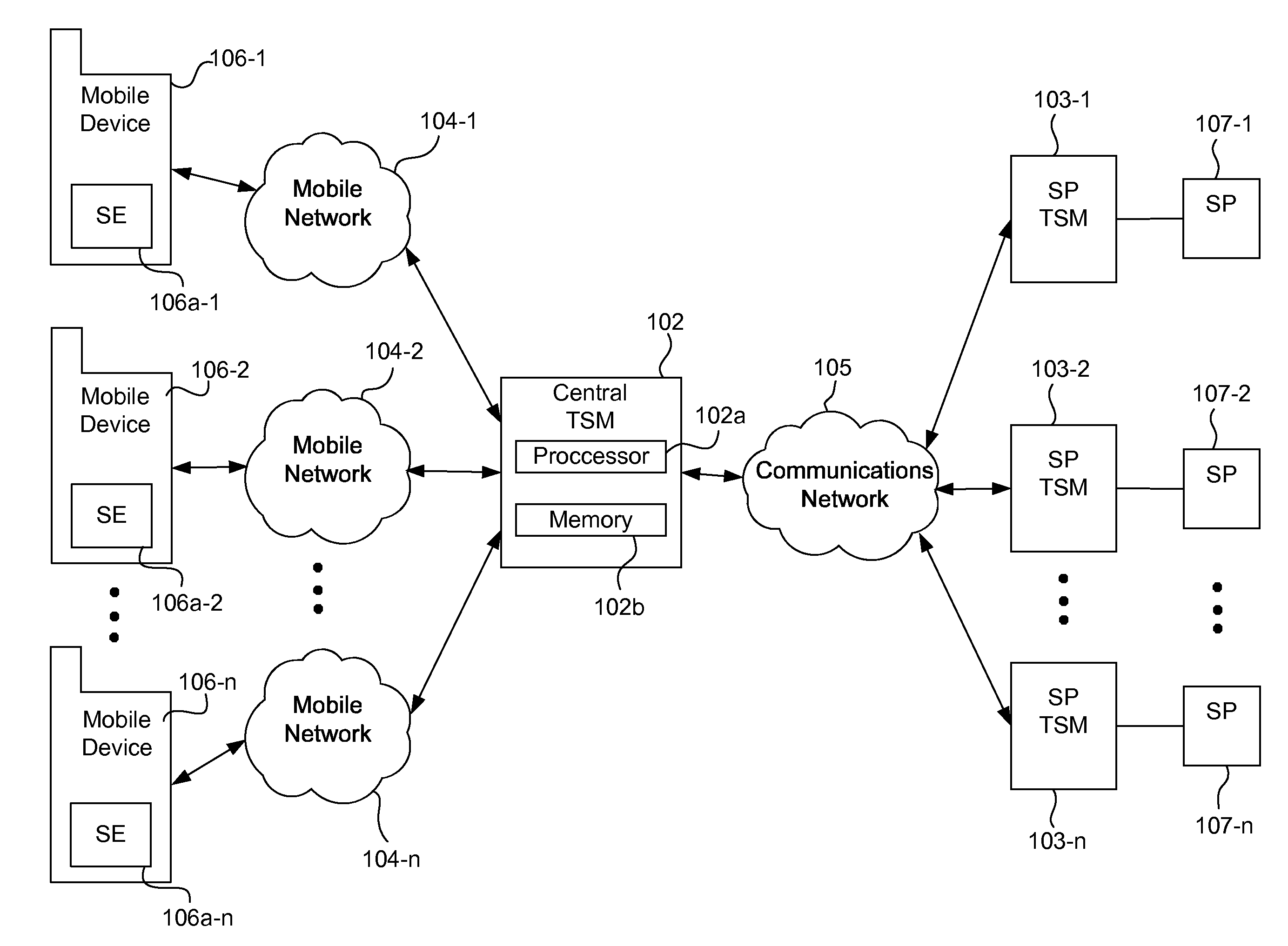
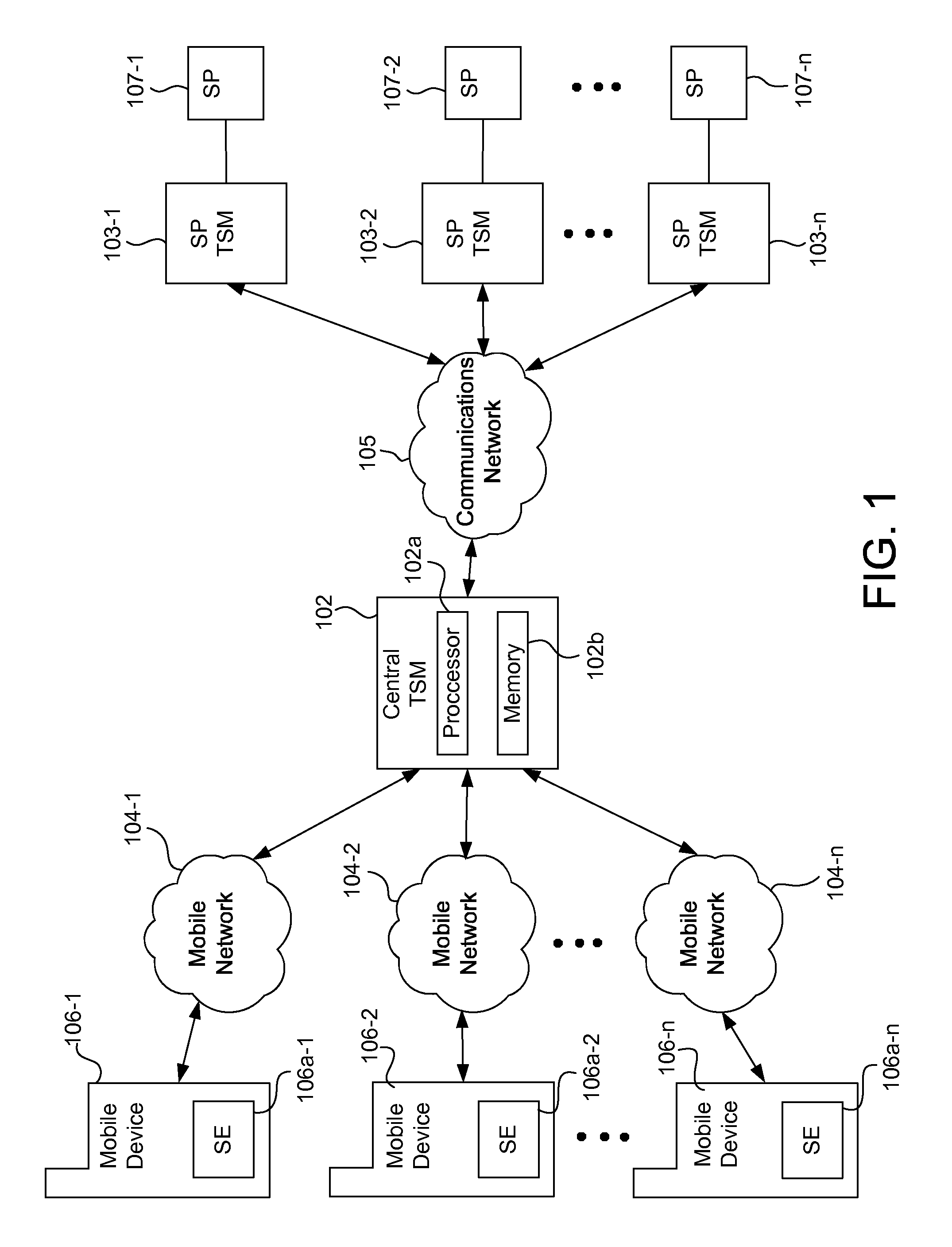
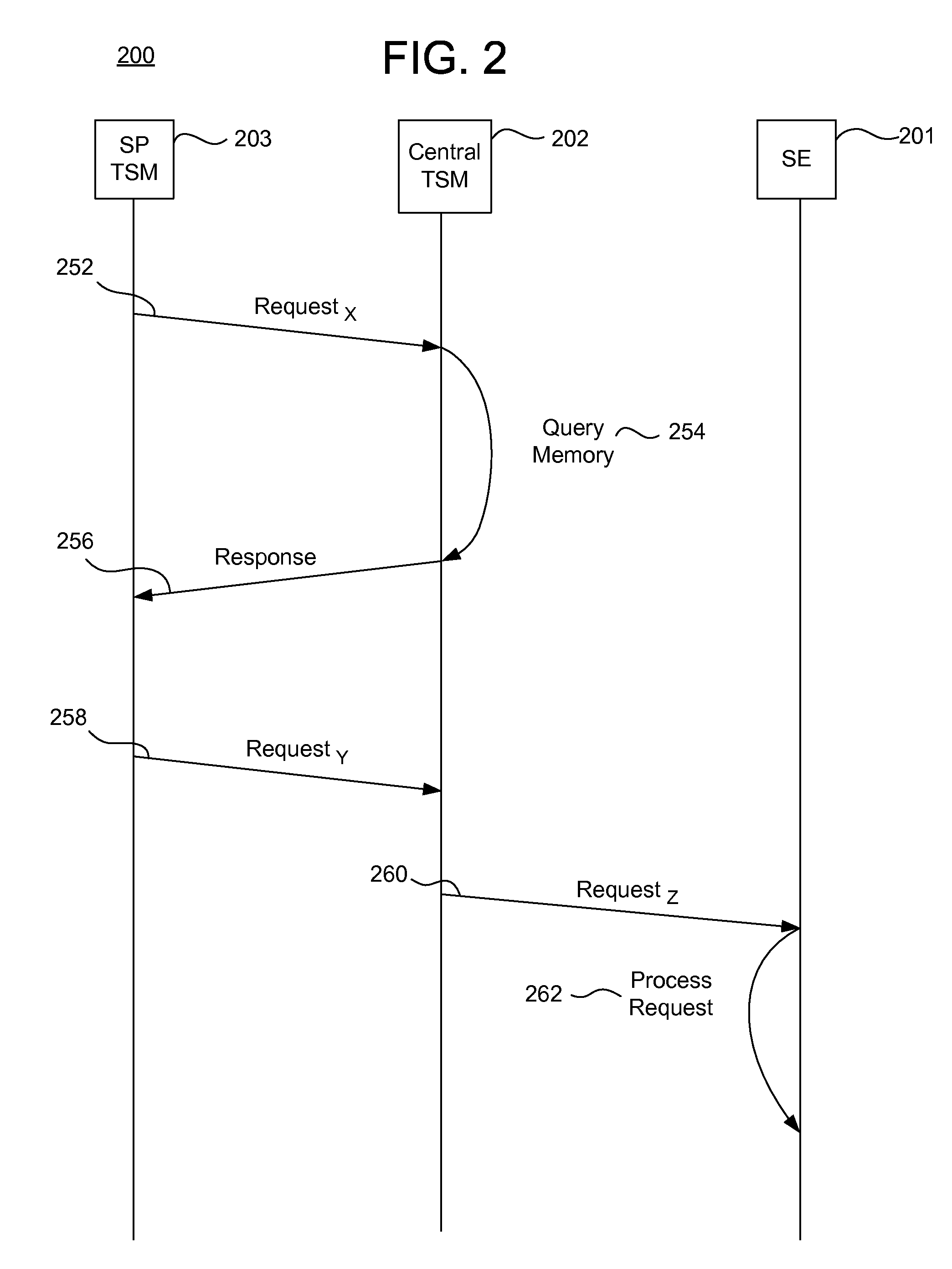
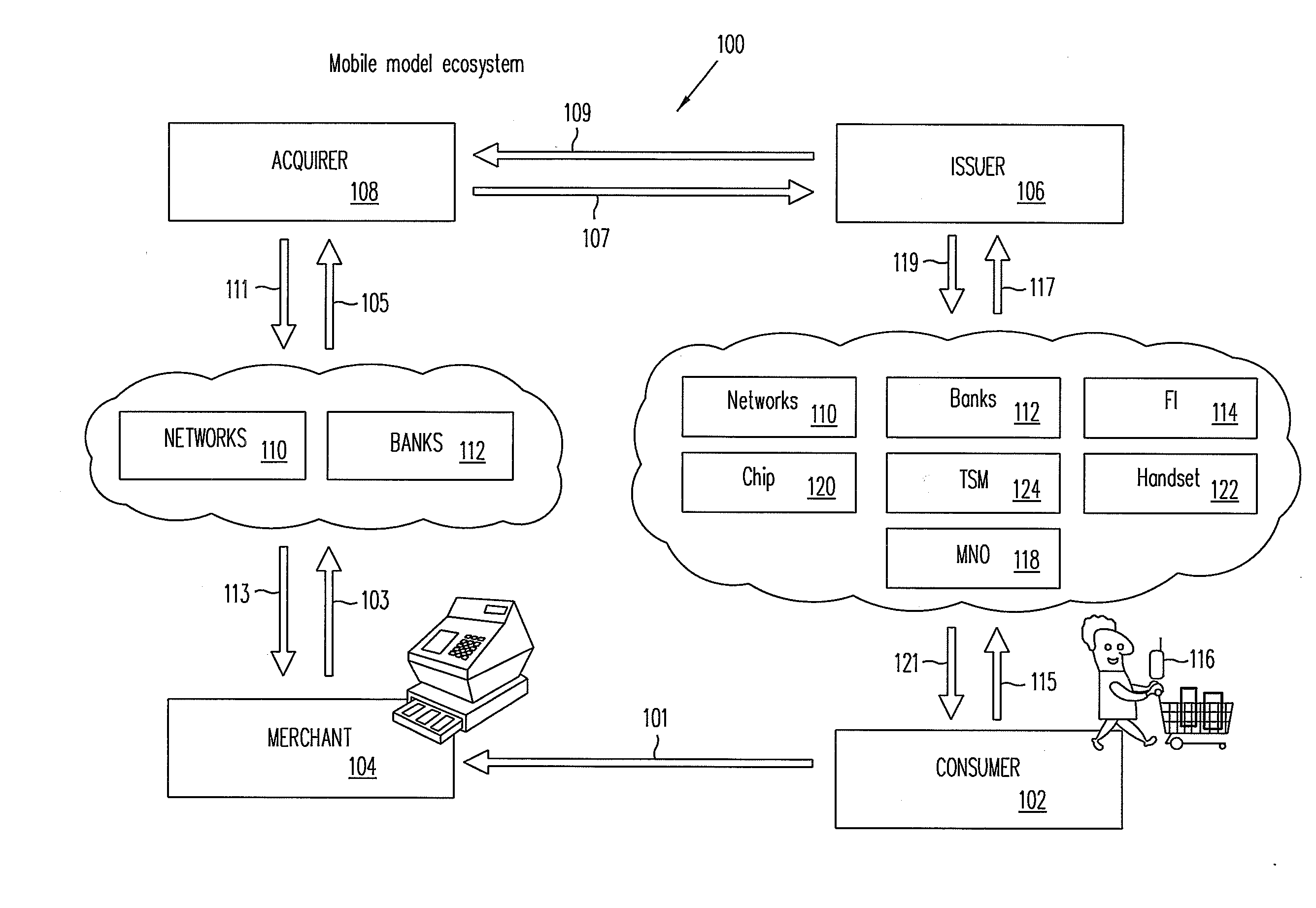
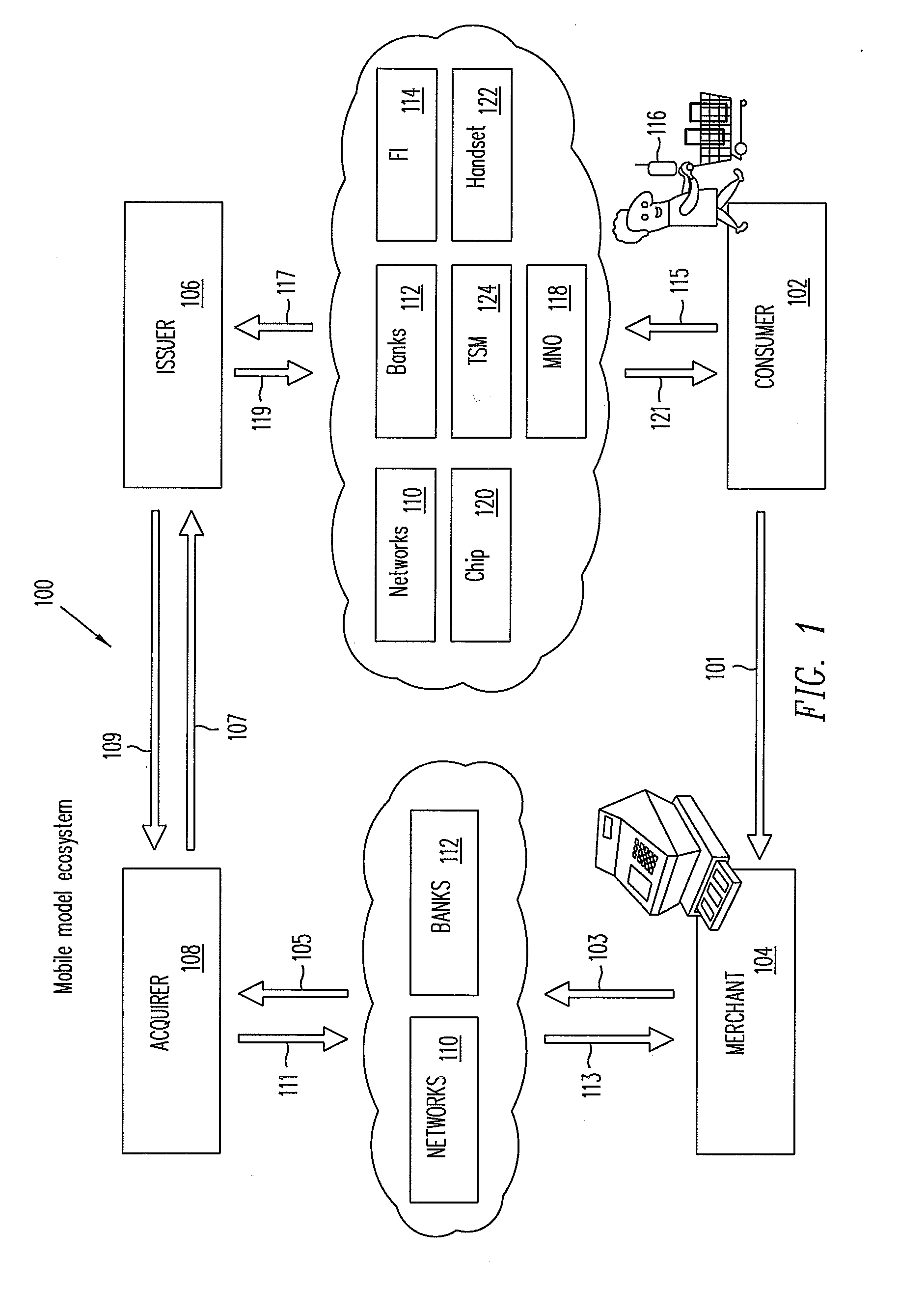
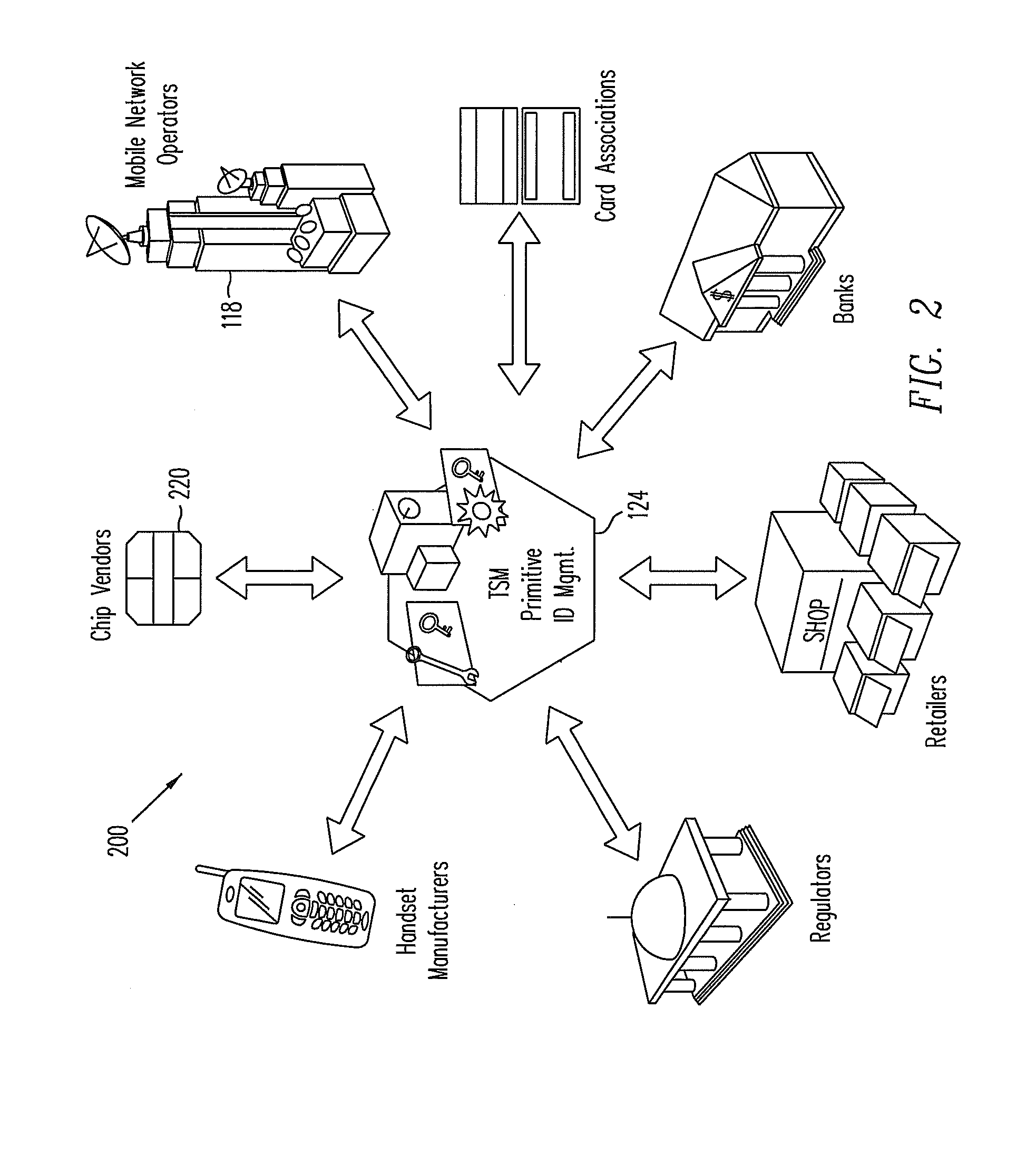
Systems, methods, and computer program products for interfacing multiple service provider trusted service managers and secure elements
ActiveUS20130111599A1Easily and securely communicateKey distribution for secure communicationDigital data processing detailsComputer networkTerm memory
System, methods, and computer program products are provided for interfacing between one of a plurality of service provider (SP) trusted service managers (TSM) and one of a plurality of secure elements (SE). A first request including a mobile subscription identifier (MSI) is received from an SP TSM over a communications network. At least one memory is queried for SE data including an SE identifier corresponding to the MSI. The SE data is transmitted to the SP TSM over the communications network. A second request based on the SE data is received from the SP TSM over the communications network. A third request, based on the second request, is transmitted, over a mobile network, to an SE corresponding to the SE data. The mobile network is selected from multiple mobile networks, and is determined based on the SE data queried from the memory.
Owner:GOOGLE LLC
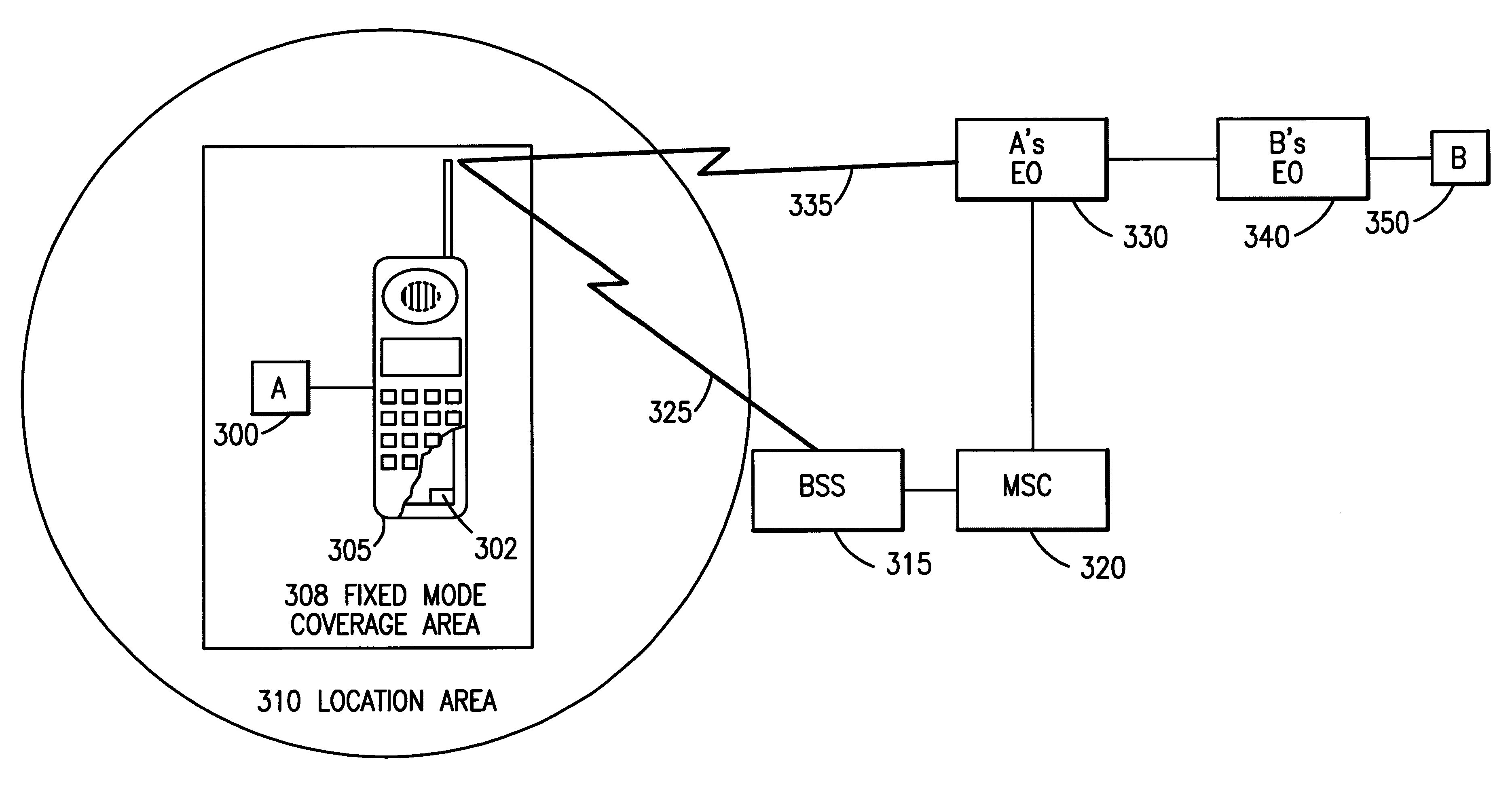
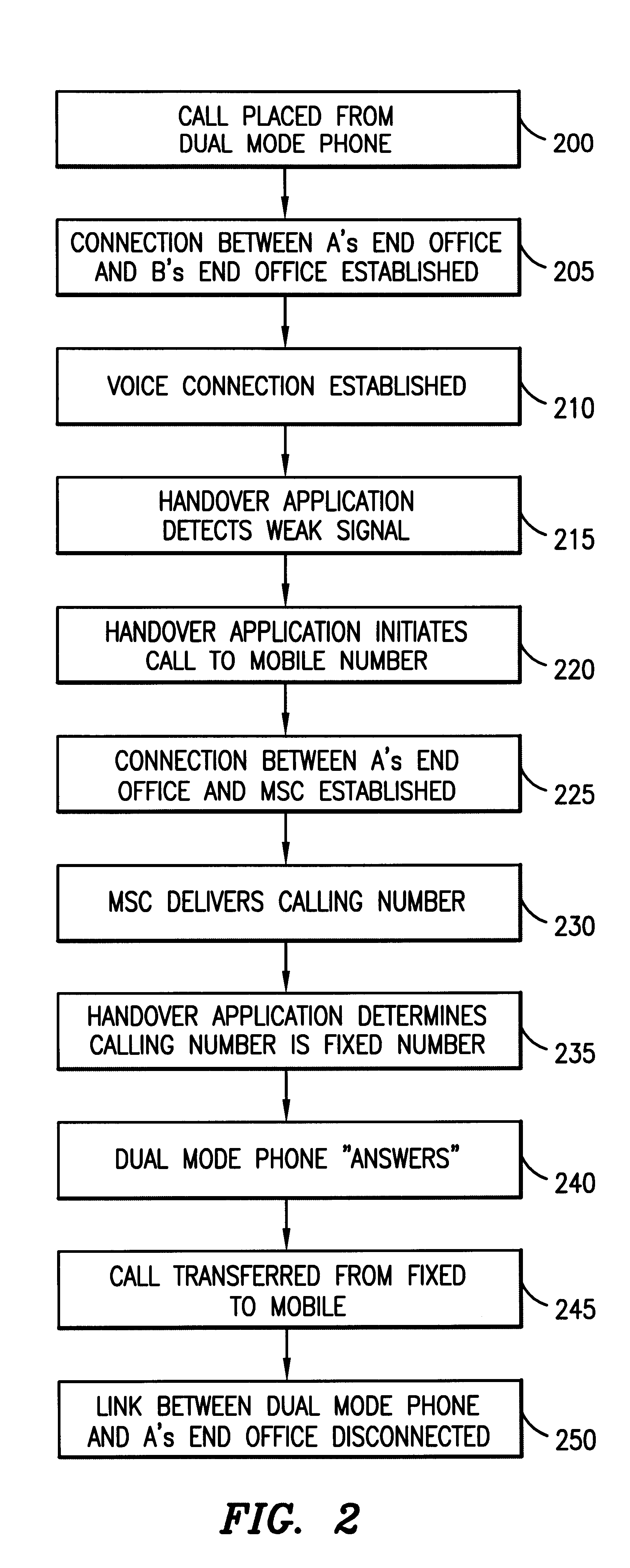
Handover between fixed and mobile networks for dual mode phones
InactiveUS6327470B1Radio/inductive link selection arrangementsWireless commuication servicesData connectionCall forwarding
A telecommunications system and method for performing a handover between the fixed (wireline) network and a mobile network during a call placed to or from a dual mode device, without any interruption in the voice or data connection. Therefore, for calls initiated in the fixed network, once the subscriber leaves the coverage area for the fixed mode of the dual mode device, the call continues as normal by transferring the call to the mobile network. Similarly, for calls initiated in the mobile network, once the subscriber moves back into the fixed mode coverage area, the call can be transferred to the fixed network in order to provide a lower rate to the subscriber, without any service interruption.
Owner:ERICSSON INC
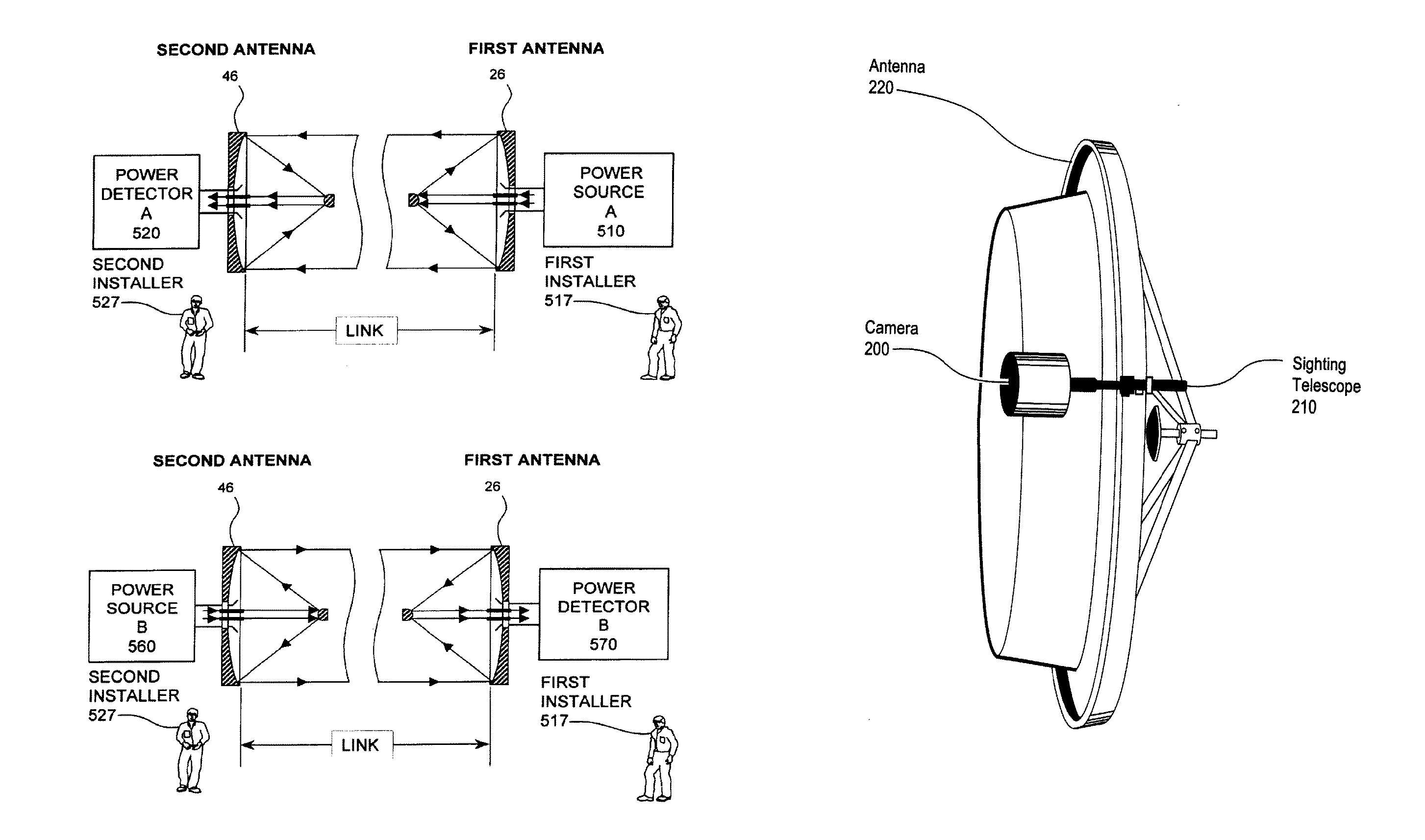
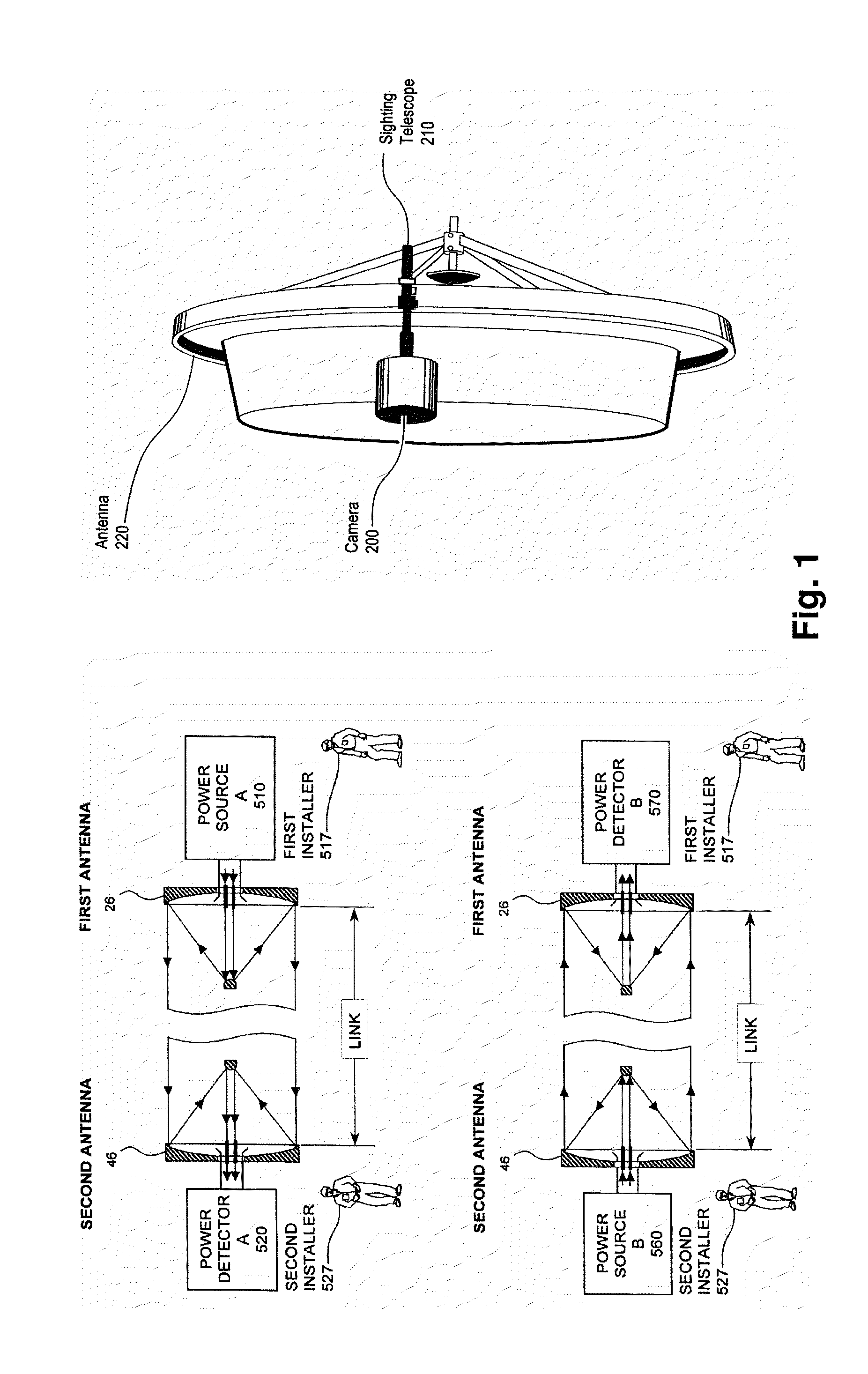
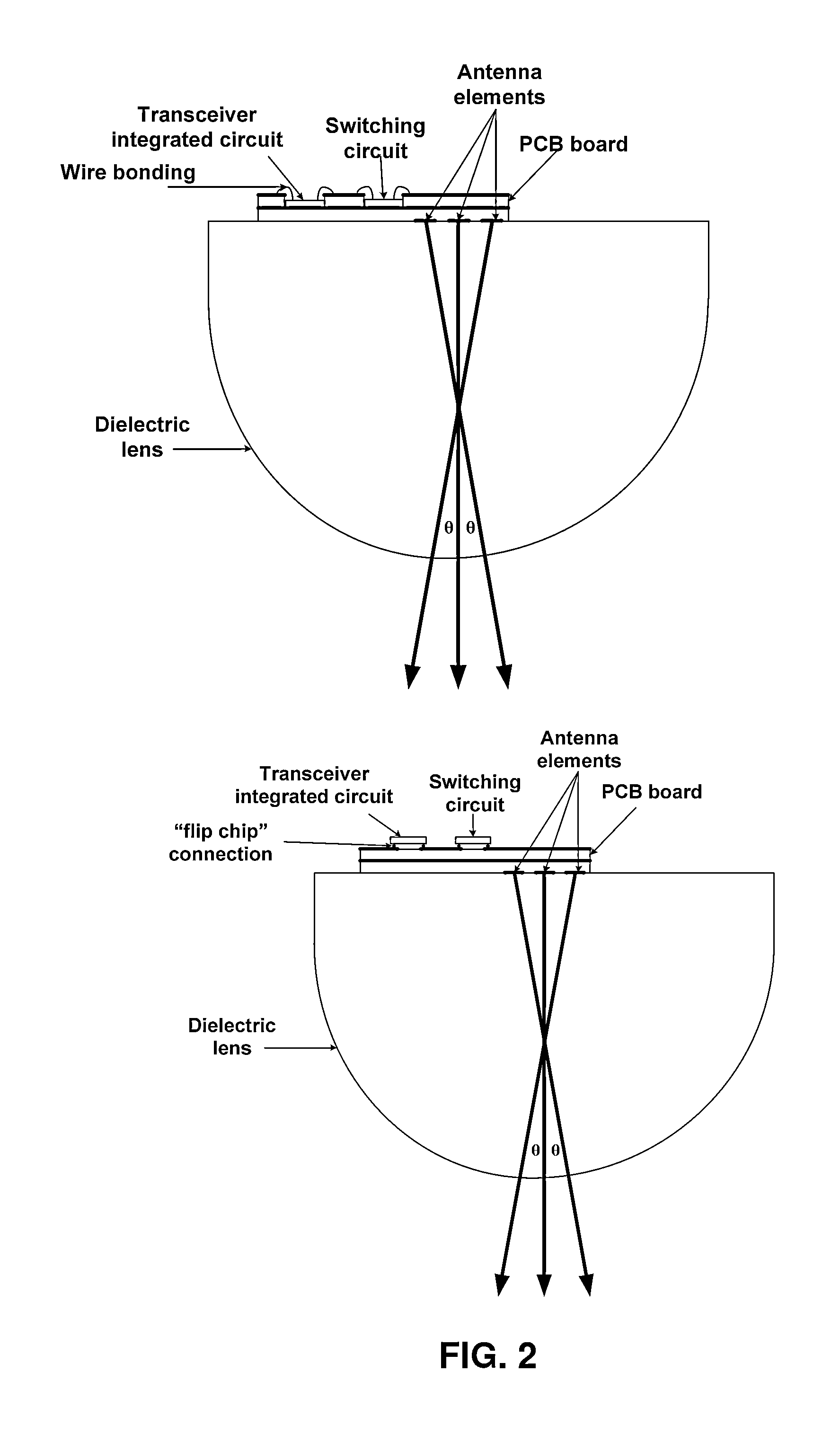
System and method of relay communication with electronic beam adjustment
ActiveUS20140227966A1Avoid the needSimple procedureAntenna supports/mountingsRadio transmissionTransceiverHigh-gain antenna
The invention relates to millimeter-wave point-to-point communication systems. A system comprises two separated millimeter-wave transceivers which provide high throughput data transmission and reception in frequency duplex mode and use high gain antennas capable of electronic scanning in some continuous angle range provided by the control module that implement control algorithms for antenna radiation pattern. Also a method based on the exploitation of scanning antennas of initial beam directions fine adjustment and subsequent beam directions tracking and readjustment when needed is proposed.The proposed system and method provide automatic recovery of failed connection in case of relay station orientation change due to influence of various external factors (wind, vibration, different intensity of heating of the bracing mountings at different time of a day and others) and can be used in backhaul systems of base station sites for mobile networks.
Owner:OBSHCHESTVO S OGRANICHENNOJ OTVETSTVENNOSTYU RADIO GIGABIT
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS7293107B1Easy accessSacrificing reliability or centralized managementNetwork traffic/resource managementMultiple digital computer combinationsNetwork connectionMobile end
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
Multiple access internet portal revenue sharing
ActiveUS7127232B2Metering/charging/biilling arrangementsAccounting/billing servicesCable Internet accessInternet access
Multiple access internet portal billing systems are provided. A representative system, among others, includes a communication facility, a wireless internet server, and a transaction billing system. The communication facility includes a billing platform, and is operable to connect to a plurality of wireless device platforms through a mobile network, and to connect to the wireless internet server. The wireless internet server provides internet access to the wireless devices and communicate at least one billing information record including a usage time to a transaction billing system. The transaction billing system receives the billing information record from the wireless internet server, formats the billing information record, and communicates the formatted record to the communication facility billing platform. Methods and other systems for multiple access internet portals are also provided.
Owner:BELLSOUTH INTPROP COR
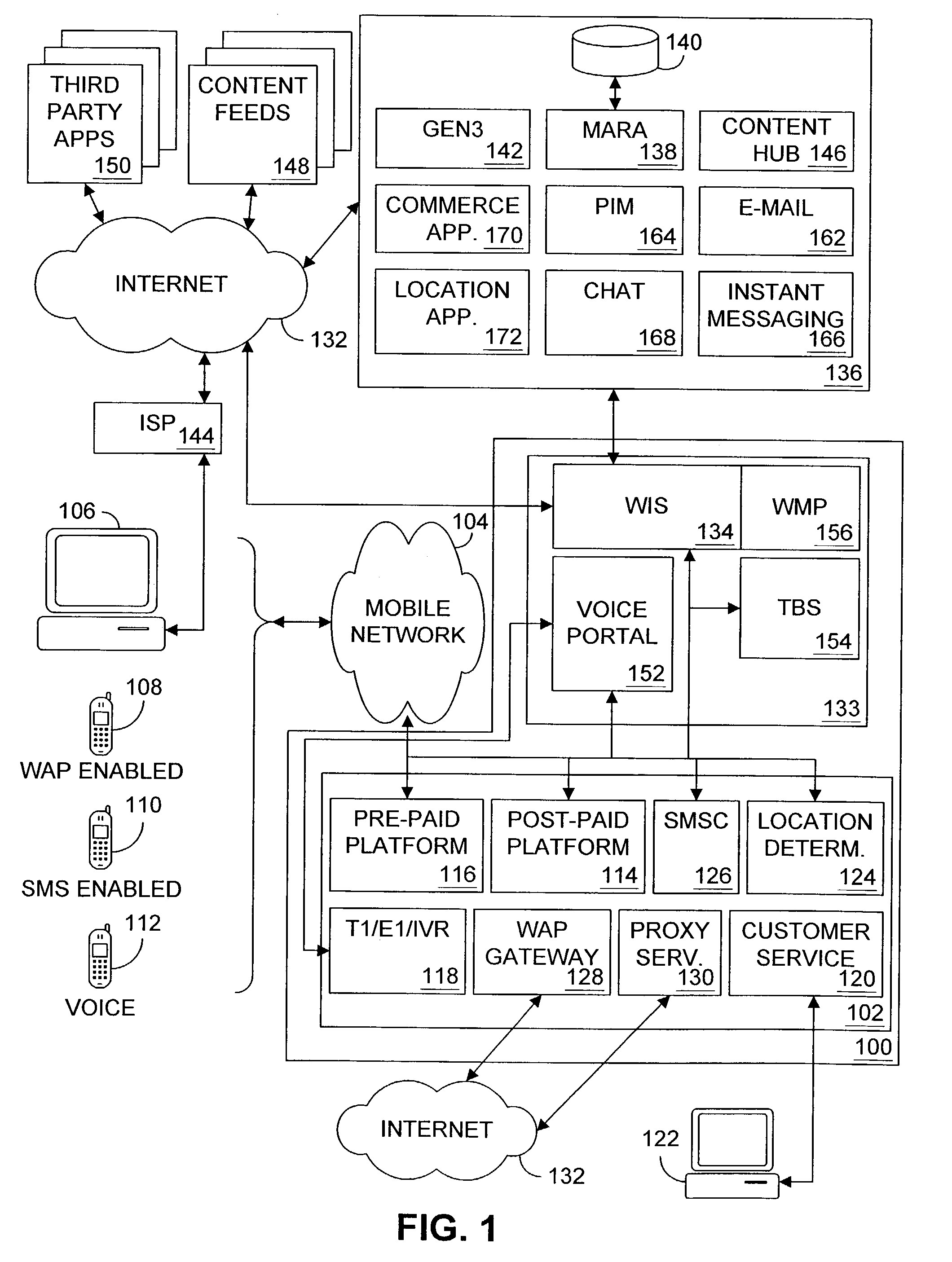
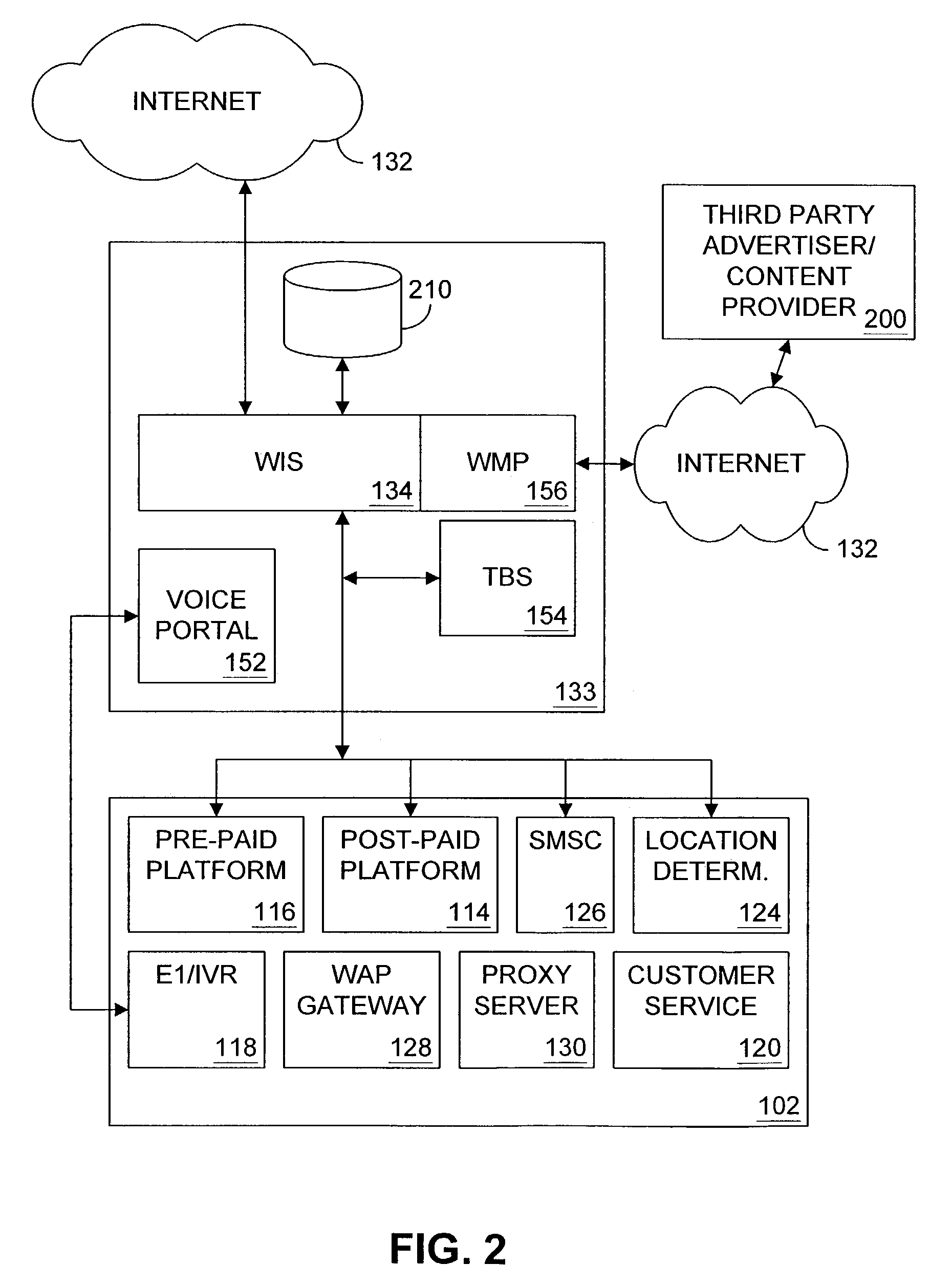
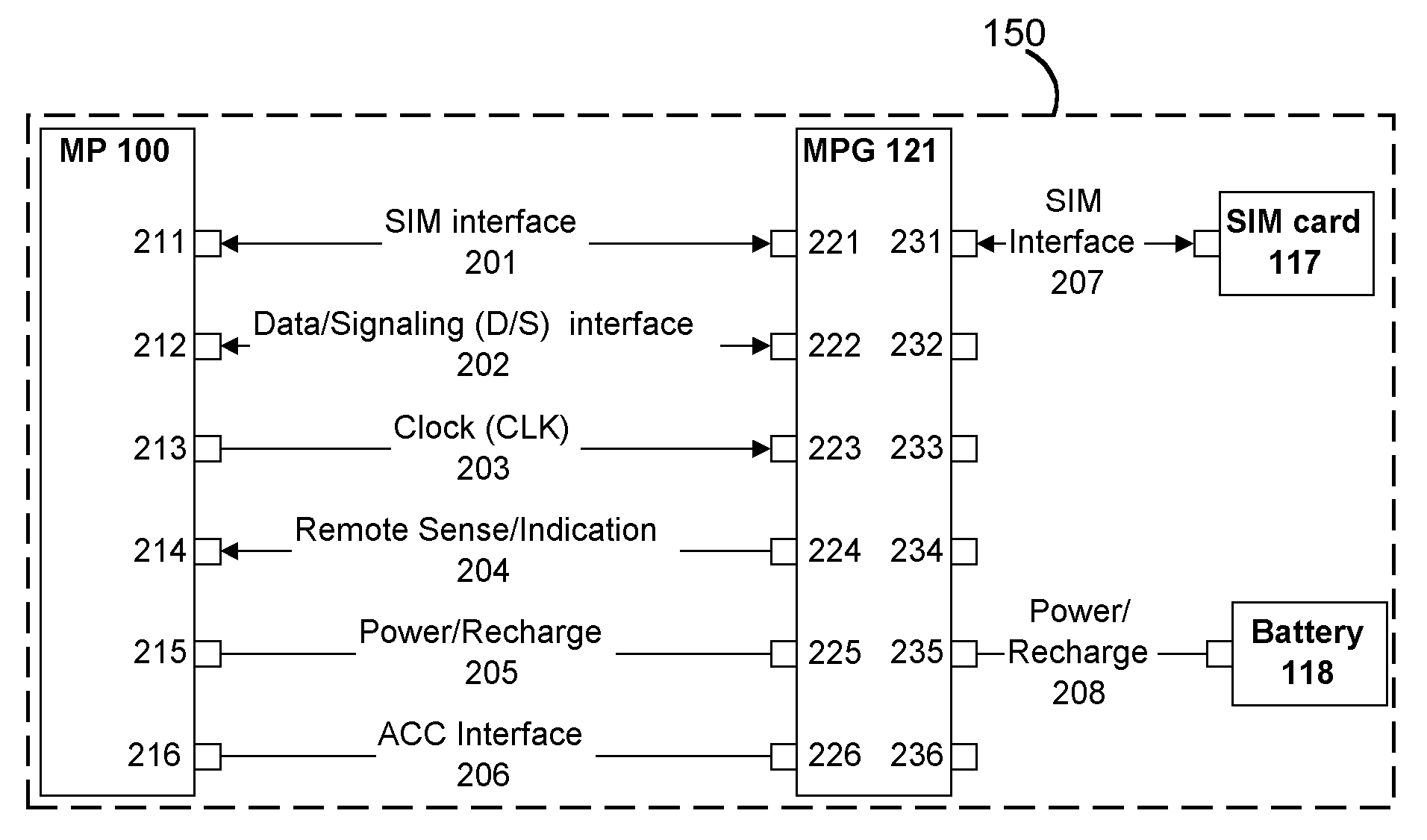
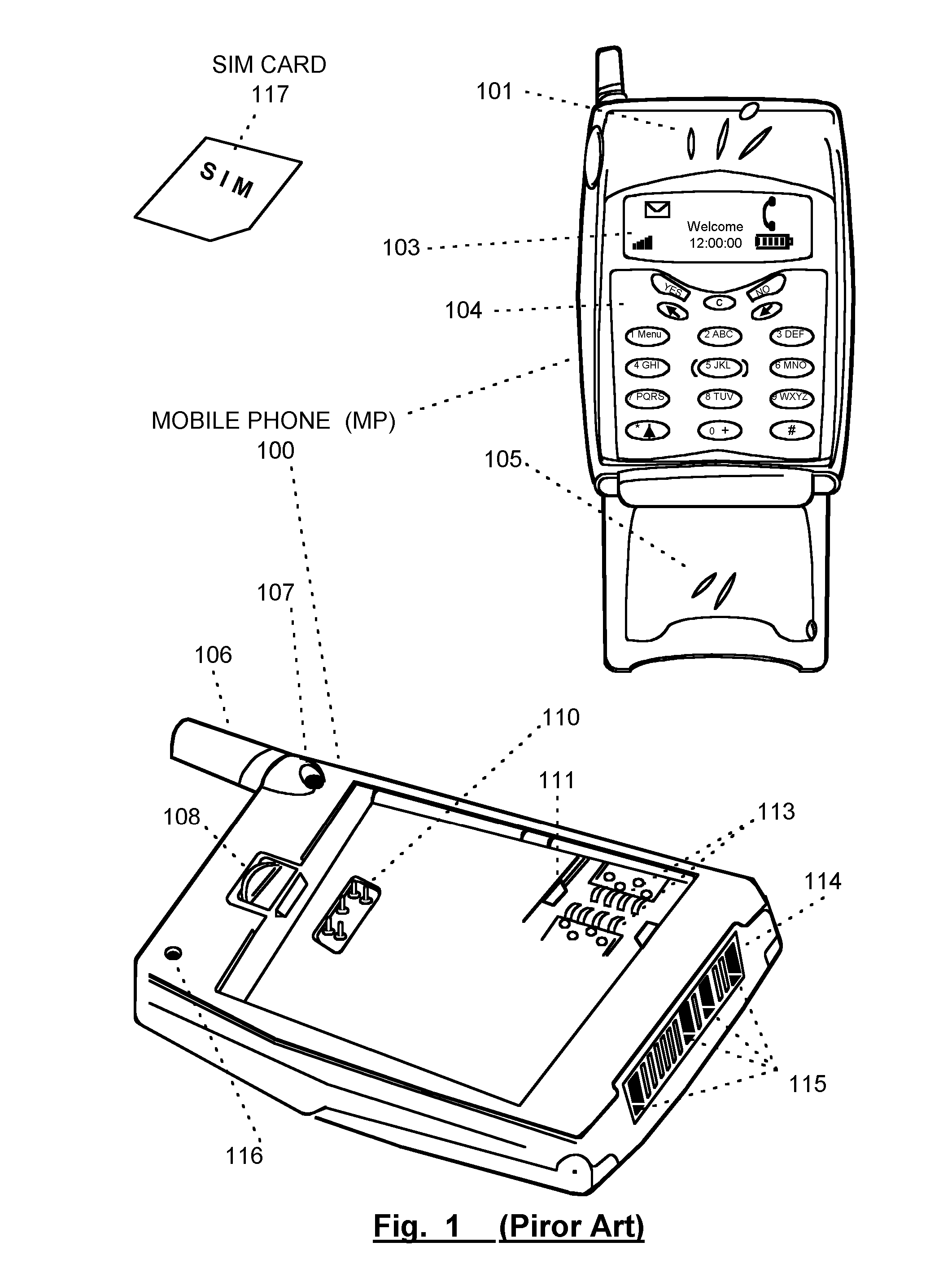
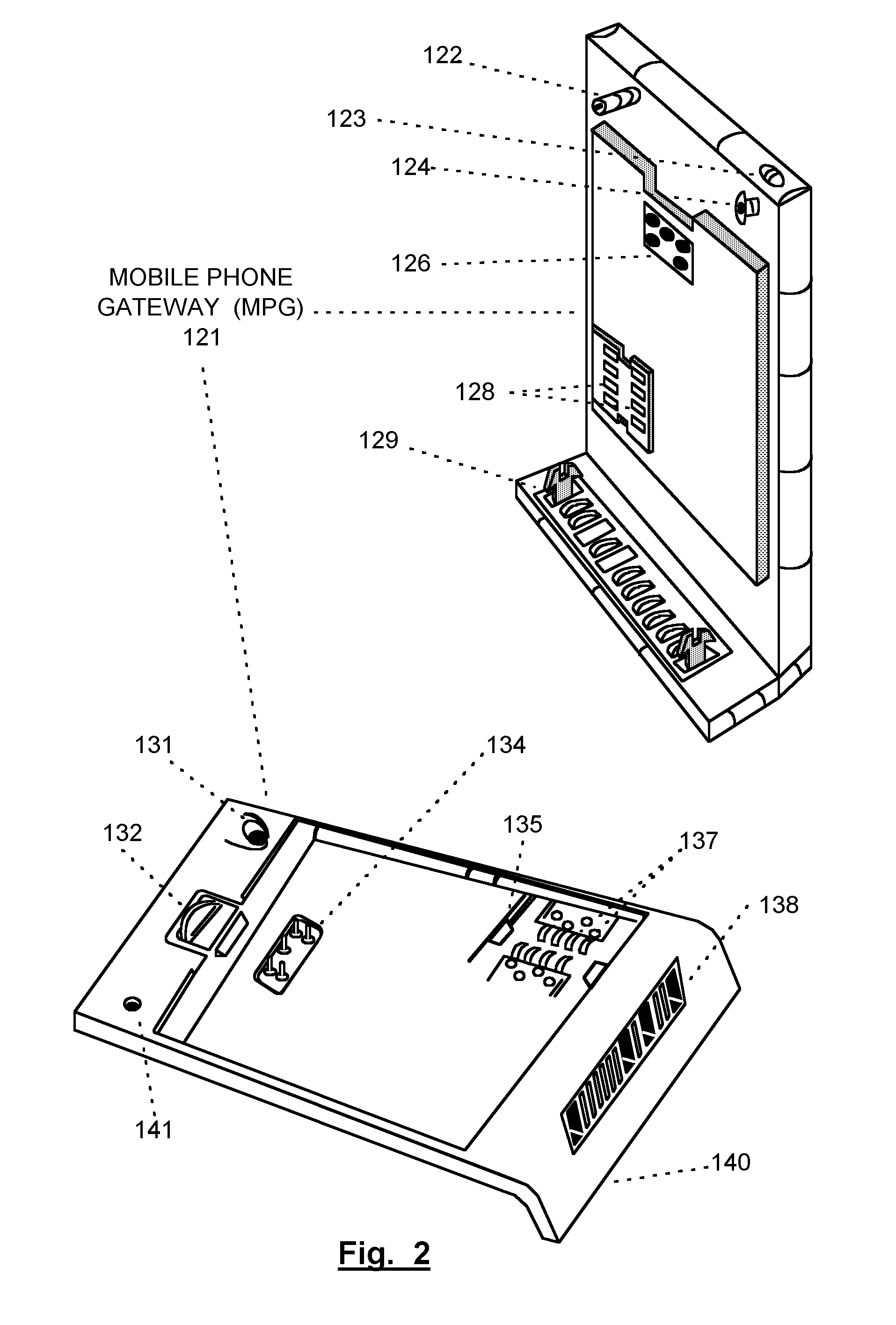
Mobile Telephone Gateway Apparatus, Communication System, and Gateway Operating System
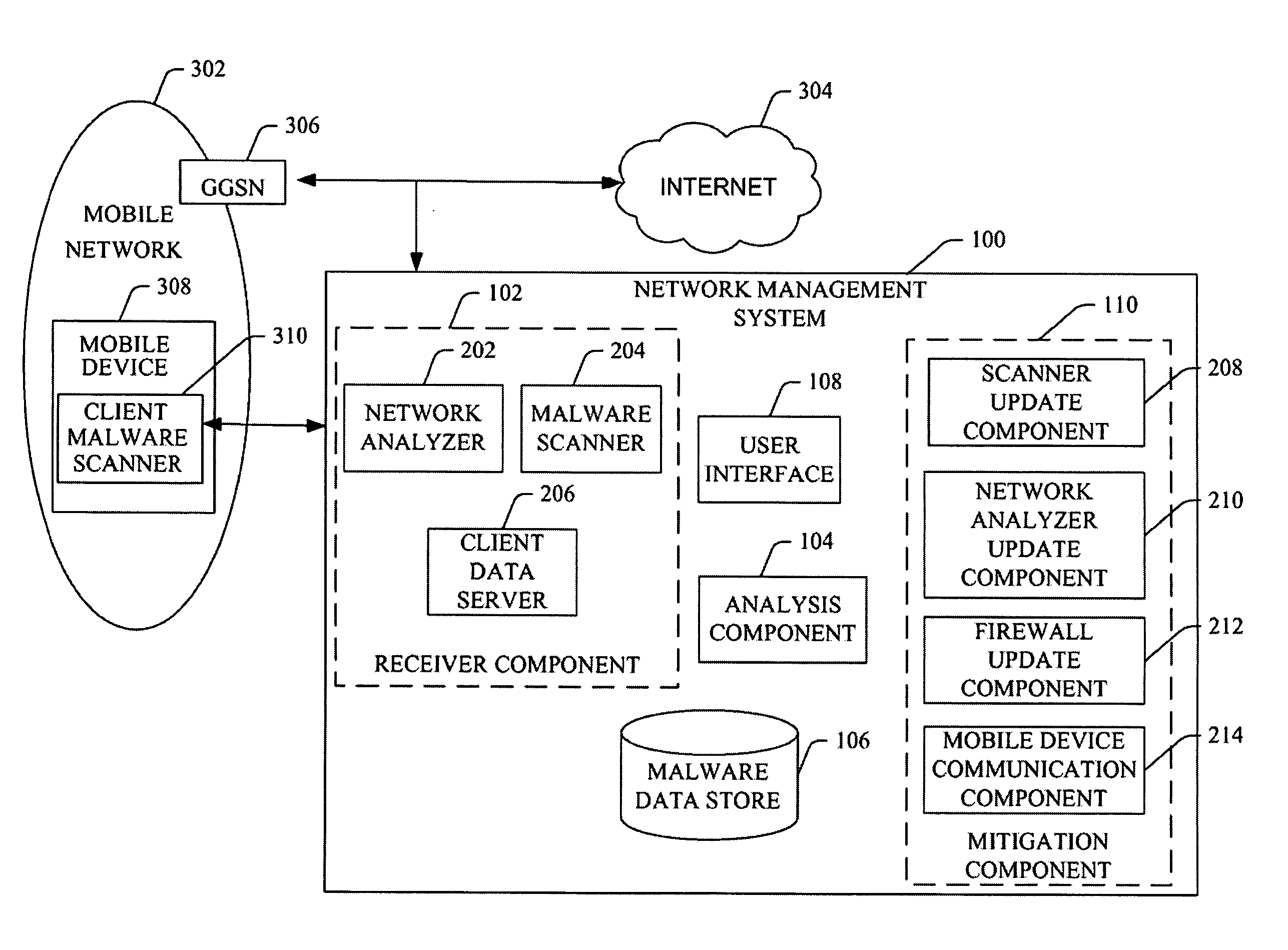
InactiveUS20060291483A1Facilitates proper initializationImprove coordinationDevices with wireless LAN interfaceData switching by path configurationOperational systemWireless data
A mobile telephone gateway and communication routing device (MPG) (121) disclosed by the present invention is coupled through an electrical signaling transmission medium with a mobile telephone (100) operative on a first communication network in accordance with a first communication protocol, for adding communication capabilities through at least a second communication network in accordance with a second communication protocol. A mobile communication system (150) is disclosed, comprising MPG (121) placed in-between mobile phone (100) and battery (118) and Subscriber Identification Module (SIM) card (117). MPG connects to the SIM interface of mobile phone (100), using which it wraps SIM functionalities and controls call management. It connects to the data / signaling interface of mobile phone (100), using which it communicates with it, while communicating with the second network using another communication means. It may optionally connects to an accessory device interface of mobile phone (100) such as a Terminal Adapter / Terminal Equipment (TA / TE) or a USB OTG interface, thereby enabling communication between the mobile phone and wireless data terminals of the second network. In a preferred embodiment of the present invention, a MPG is provided for use with a mobile phone operative on a mobile communication network such as GSM, adding communication capabilities through a wireless communication network such as Bluetooth or Wi-Fi. Furthermore, gateway applications are provided to facilitate or support communication through at least the second network in accordance with mobile web protocols and technologies such as Mobile IP, mobile SIP, and mobile VoIP.
Owner:SELA YOSSY
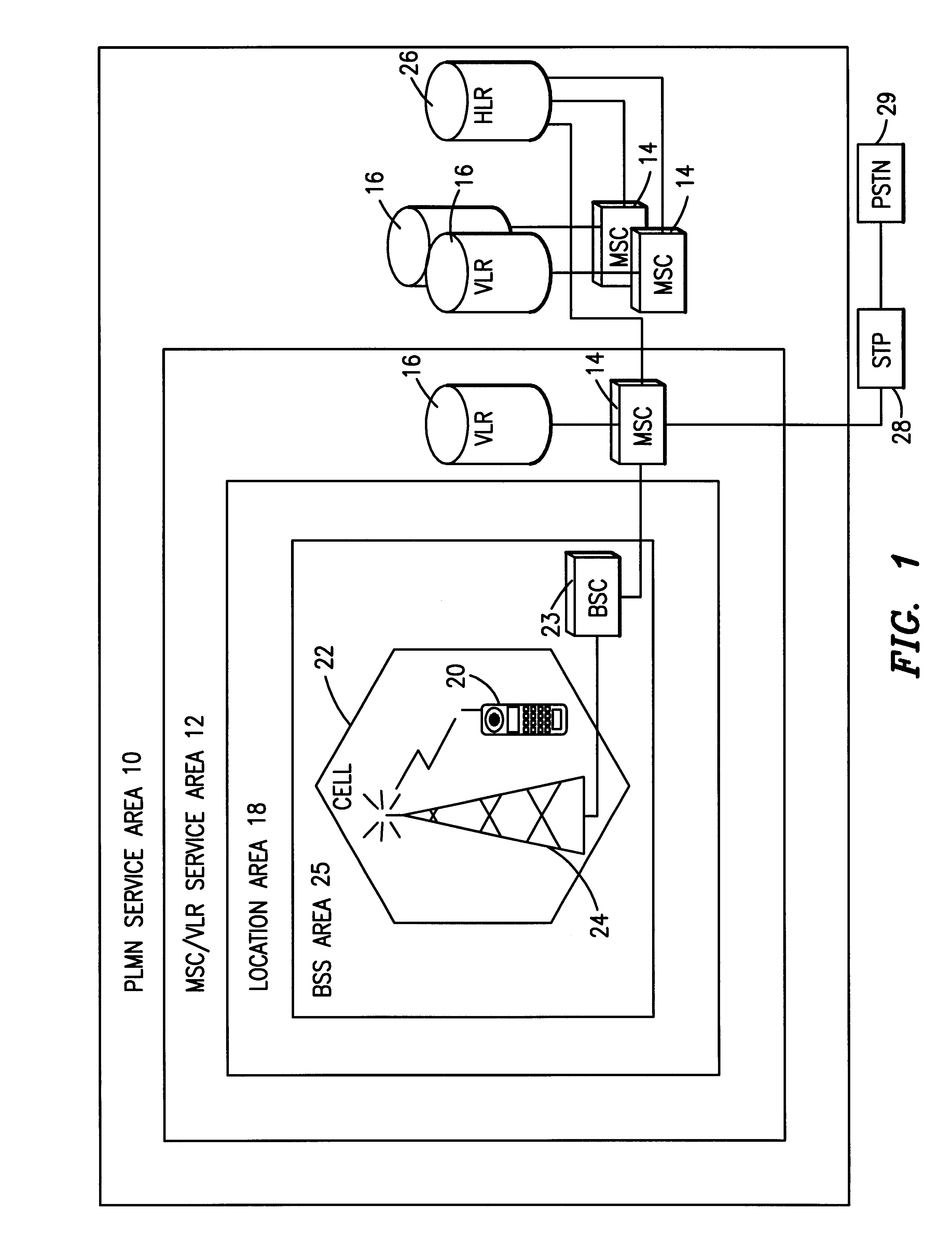
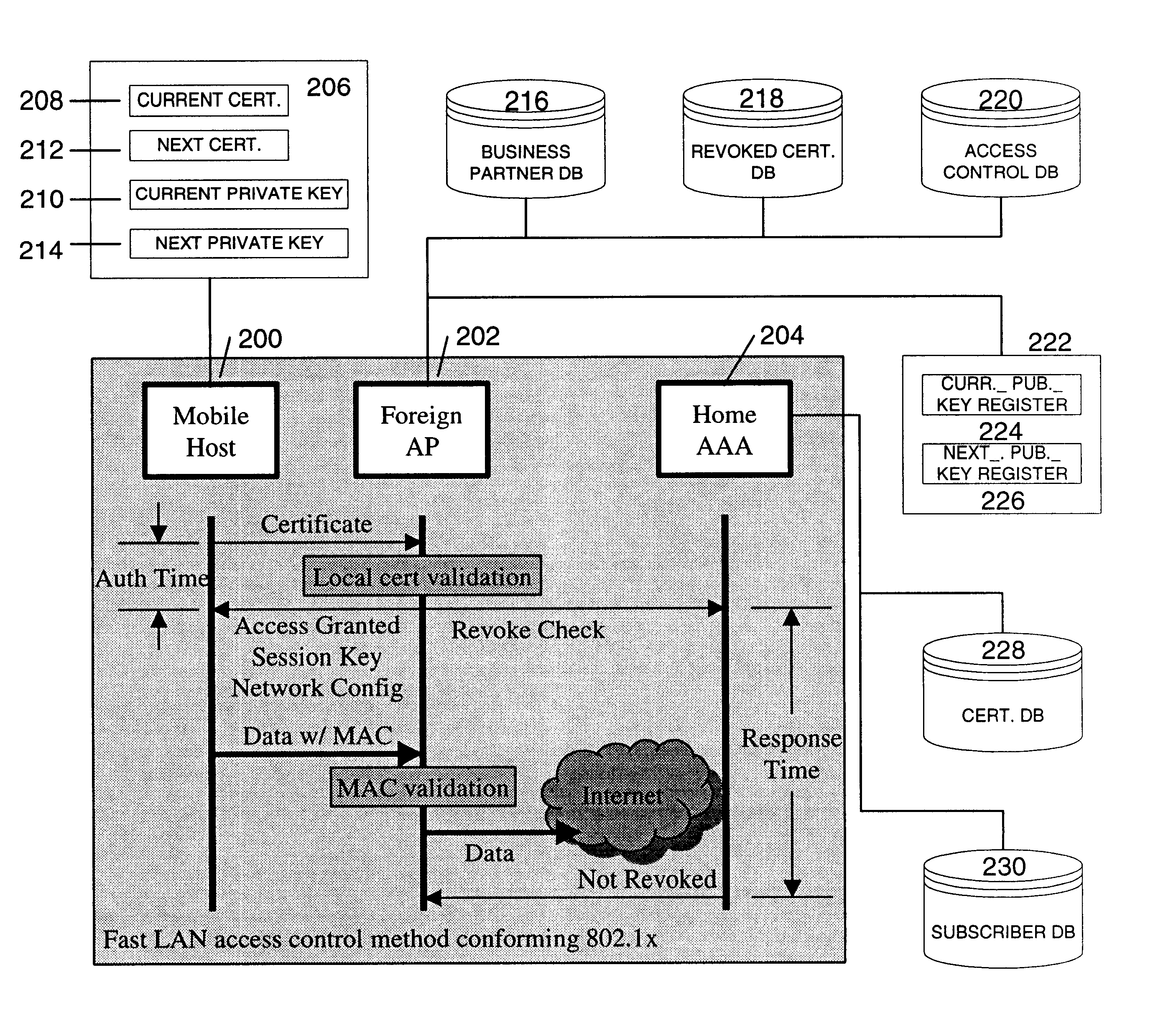
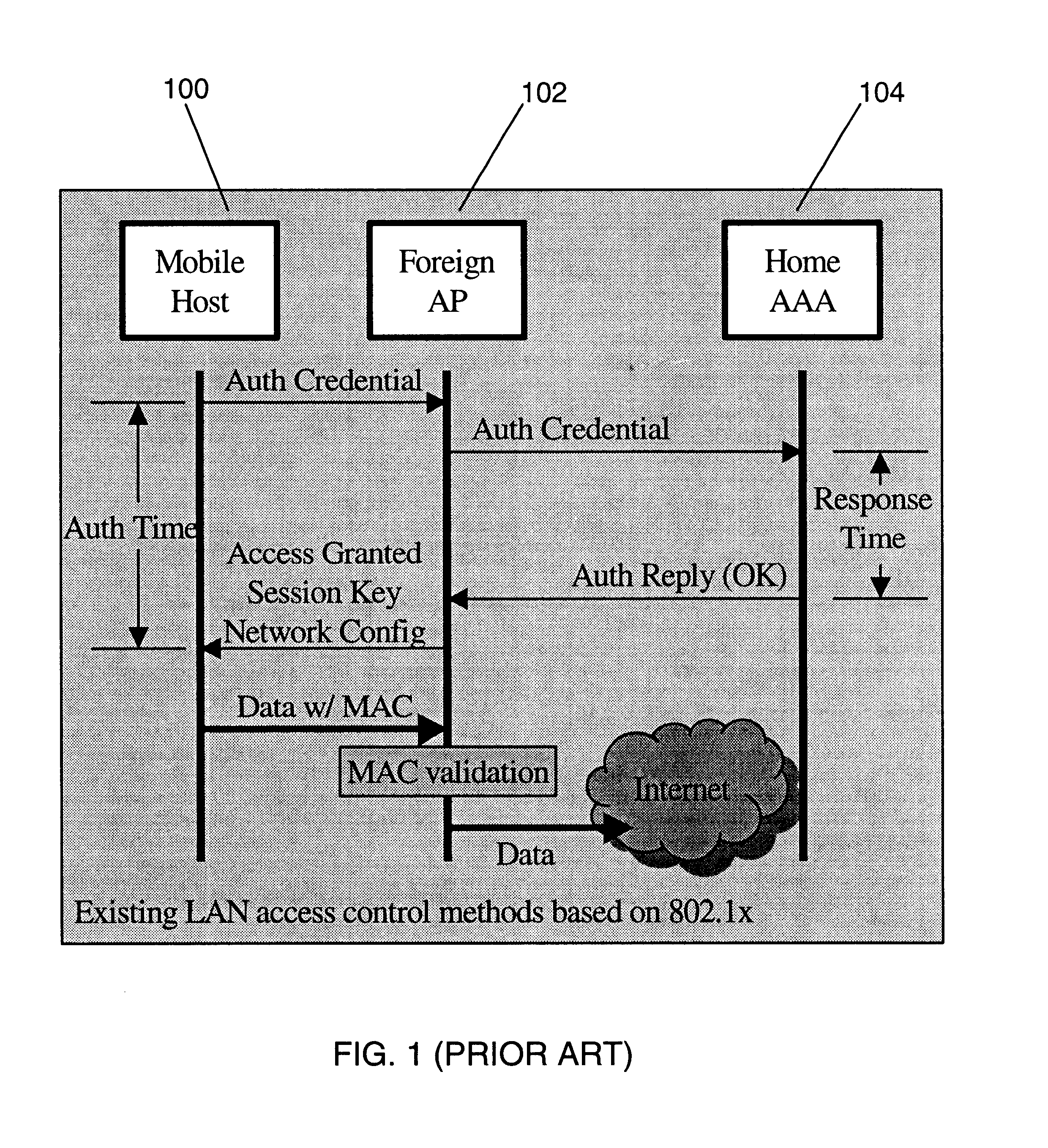
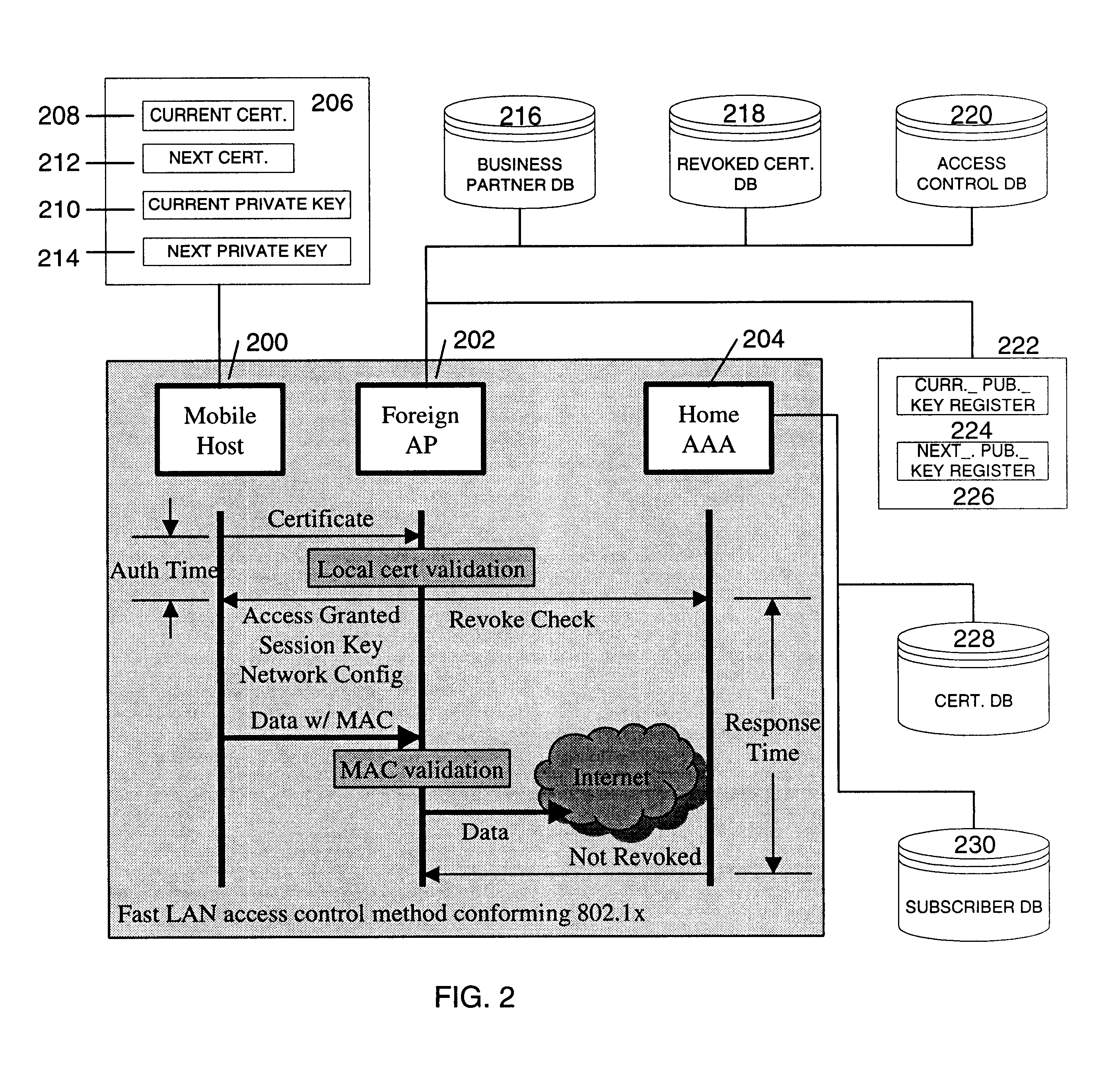
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
System and method of malware sample collection on mobile networks
ActiveUS20080086776A1Raise the possibilityMemory loss protectionError detection/correctionNetworking protocolProxify
A collection agent monitors a mobile network for data samples containing executable code. The collection agent accepts executables and forwards them to a sample collection center for further analysis, reporting, or in some instances initiating one or more mitigating actions. Depending on the network protocol being monitored, the collection agent responds to connection attempts from nearby mobile devices.
Owner:PULSE SECURE
Transparant non-disruptable ATM network
InactiveUS6011780AIncrease probabilityIncrease spare capacityError preventionTransmission systemsManagement unitTime switching
A method and apparatus for the transparent, non-disruptable transfer of data, particularly multimedia data, through any packet-based network, such as an ATM network is provided. The method of the present invention includes the step of setting a primary path and a secondary path between nodes of a network, or of a network domain. Accordingly, when a switch or node establishes a Virtual Path (VP) to another switch with specified effective bandwidth, it also has an alternate VP that is available, although no bandwidth is actually used. The method of the present invention further includes the step of optimizing the available capacity of the system through management actions. For handling congestion and resource failures, the total effective bandwidth on each physical link is categorized in terms of idle capacity (unused or available), used capacity (for existing VPs), and spare capacity. When a resource failure occurs, the idle capacity is used for real-time switching of the VP and service is not disrupted. This is accomplished by an alarm indication management cell which is delivered when a resource problem is encountered. This management cell sets forth the secondary path and the bandwidth associated therewith. On the other hand, if idle capacity does not exist, the spare capacity is used, while the bandwidth of all other VPs is reconfigured using virtual bandwidth optimization. Therefore, service disruption does not occur. In a wireless, mobile network, the present invention monitors node movement and takes management actions on the basis of such node movement to prevent service disruption.
Owner:HANGER SOLUTIONS LLC +1
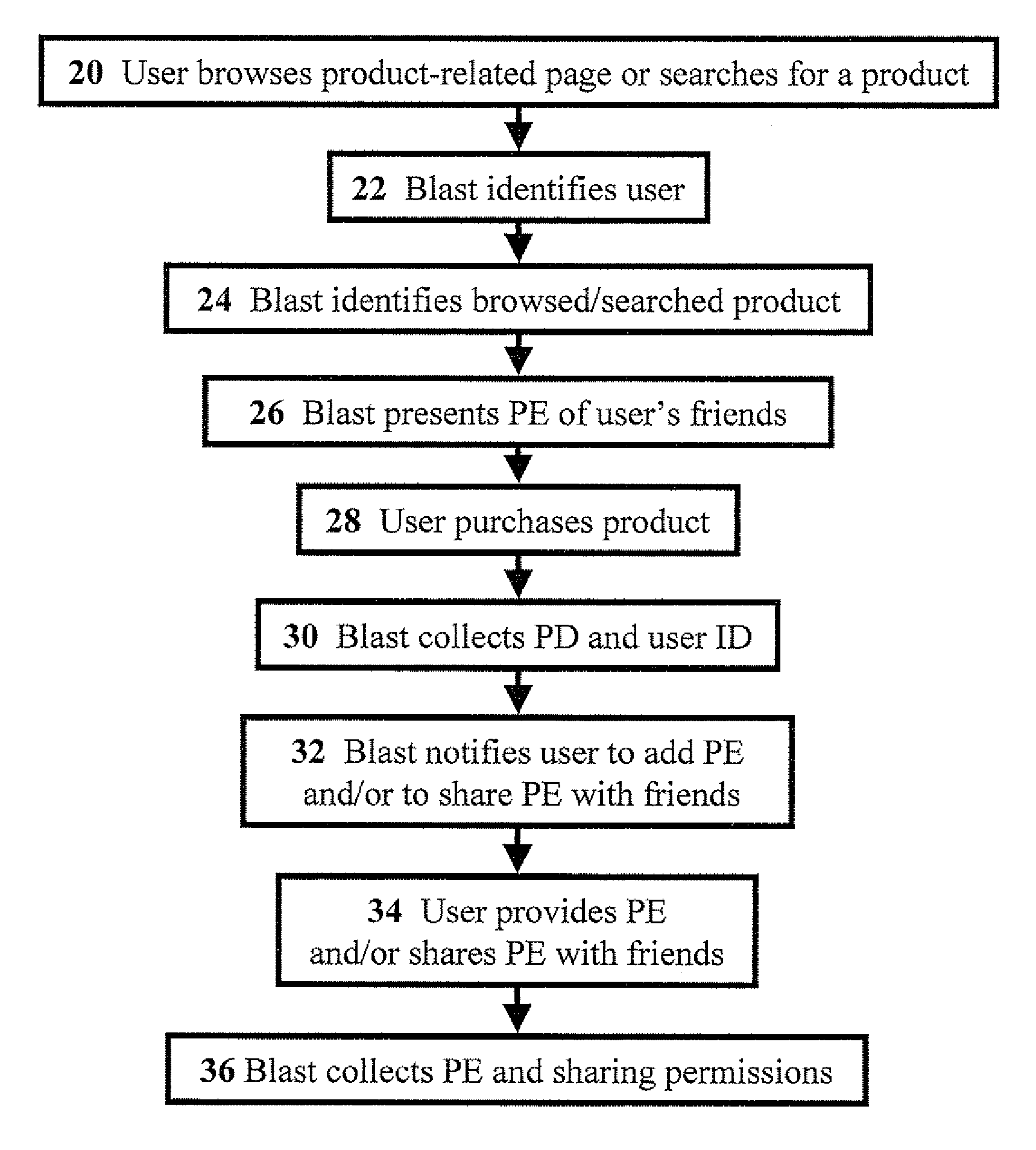
Systems and methods for e-commerce and mobile networks for providing purchase experiences of friends in a social network
InactiveUS20090070228A1Eliminate needImprove abilitiesData acquisition and loggingCommerceRelevant informationE-commerce
Methods, for facilitating electronic commerce using a social network, including: registering users on a social-network product-review site, wherein each user can be connected to other users by designating the other users as friends; identifying product purchases, of the users, made in merchant locations; collecting purchase details, and associated-user identities; sending a notification to an associated user requesting a user-specific product review from the associated user upon the associated user receiving the purchase details associated with the associated user; obtaining the user-specific product review and permissions from the associated user, wherein the permissions designate to share the user-specific product review and a relevant associated-user identity with associated-user friends; determining product-related information being accessed in various locations by a product-seeking user; ascertaining an identity of the product-seeking user; and presenting related-product reviews, based on the product-related information and related permissions, of user-related friends to the product-seeking user in the various locations.
Owner:SOCIAL FABRICS
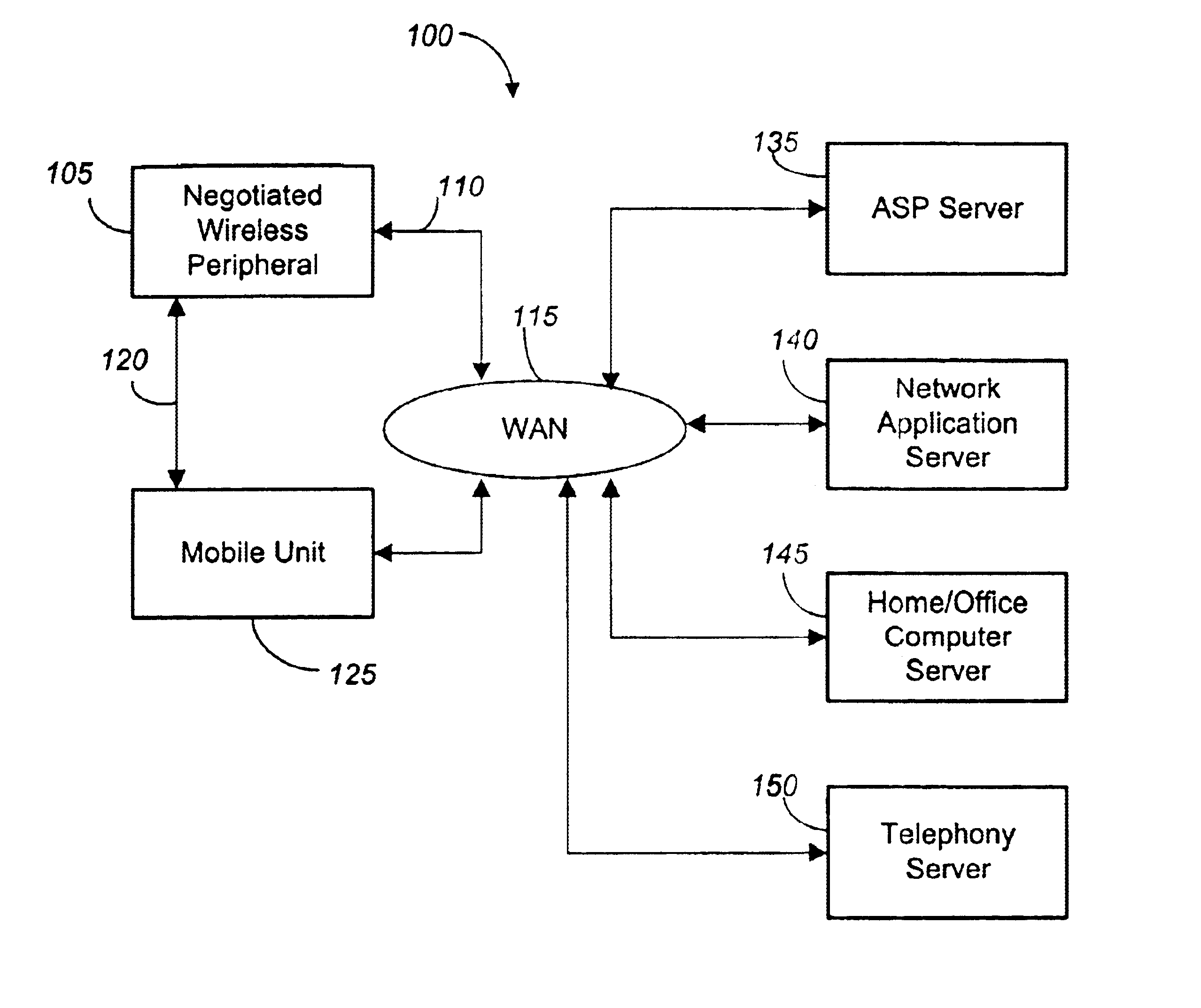
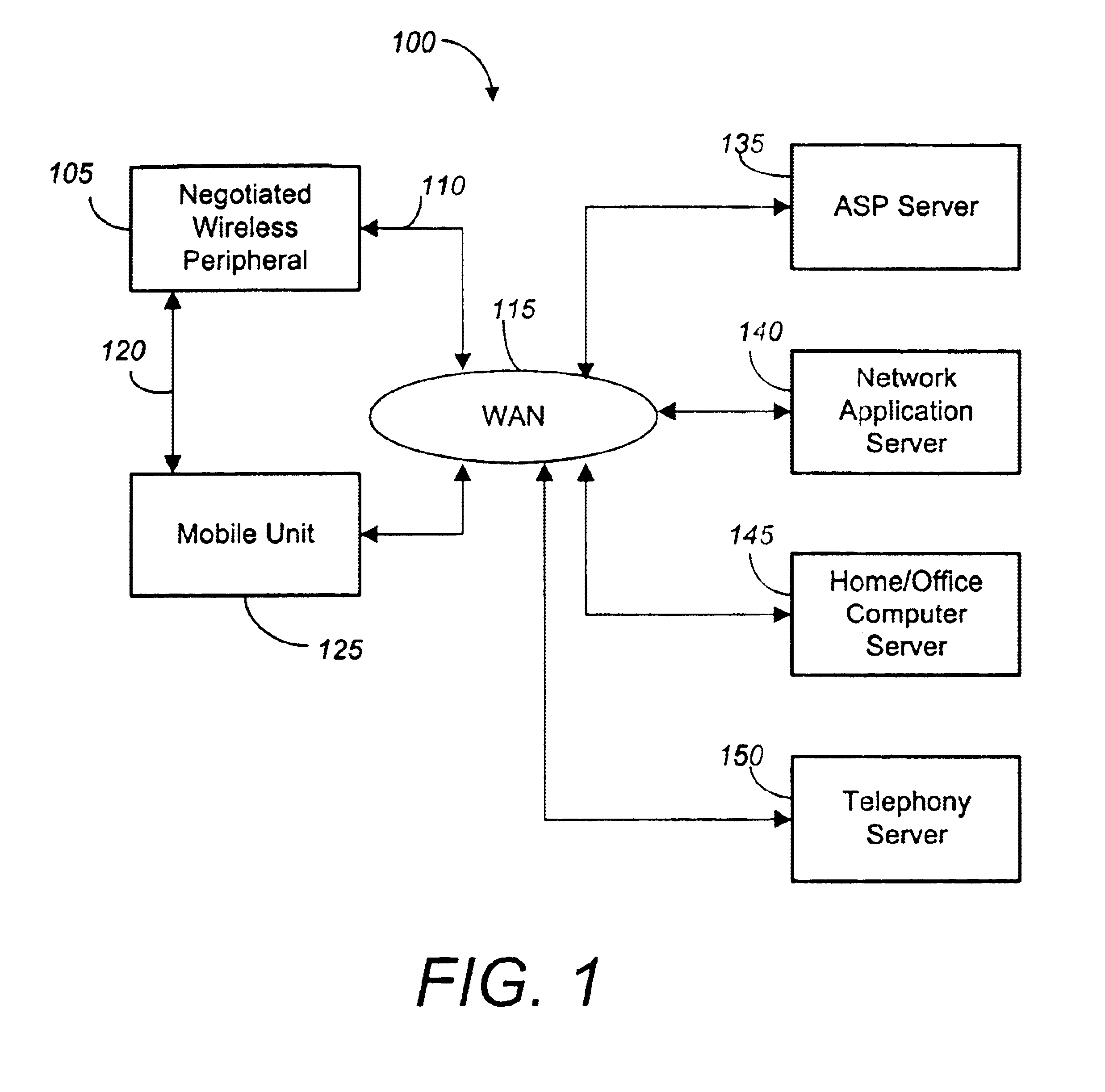
Negotiated wireless peripheral security systems
InactiveUS6901429B2Consumes more powerAvoid interceptionNetwork traffic/resource managementNetwork topologiesNetwork connectionDisplay device
Methods, apparatus, and business techniques are disclosed for use in mobile network communication systems. A mobile unit such as a smart phone is preferably equipped with a wireless local area network connection and a wireless wide area network connection. The local area network connection is used to establish a position-dependent ecommerce network connection with a wireless peripheral supplied by a vendor. The mobile unit is then temporarily augmented with the added peripheral services supplied by the negotiated wireless peripheral. Systems and methods allow the mobile unit to communicate securely with a remote server, even when the negotiated wireless peripheral is not fully trusted. Also mobile units, wireless user peripherals, and negotiated wireless peripherals that project a non-area constrained user interface image on a display surface are taught.
Owner:RPX CORP
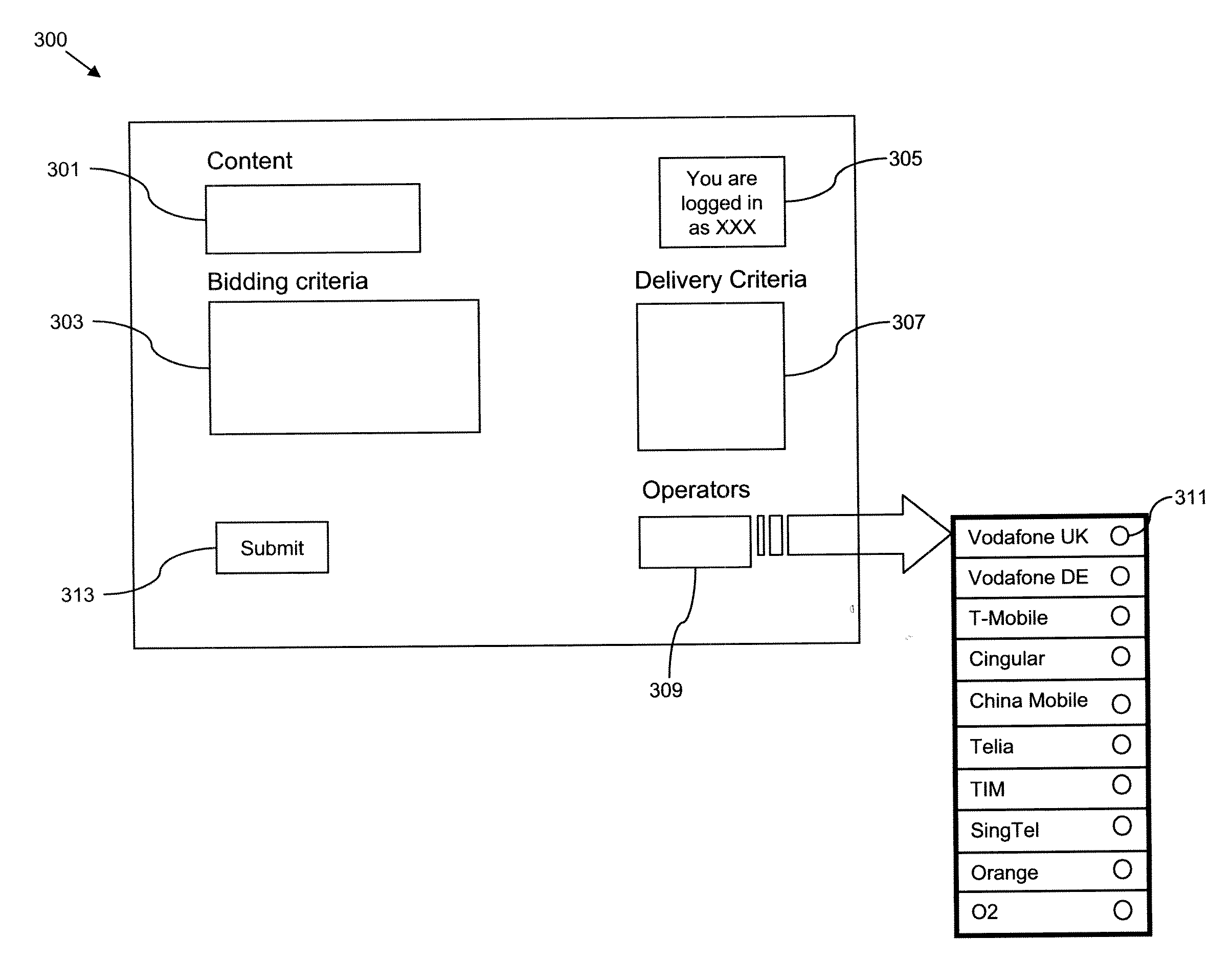
User Interface for Selecting Operators
The present invention relates generally to a method of identifying data delivery parameters relating to delivery of data accessible from a network location via a communications service provider. Embodiments of the invention are particularly well suited to identifying delivery parameters when the delivery of data is metered, such as when data are delivered to terminals connected to mobile networks.
Owner:APPLE INC
Trusted remote attestation agent (TRAA)
ActiveUS20100306107A1Reduce riskFinanceMultiple digital computer combinationsComputer hardwareRisk profiling
Systems and methods for use with a service provider and a consumer electronic device include a trusted remote attestation agent (TRAA) configured to perform a set of checking procedures or mechanisms to help ensure the security status of a consumer electronic device (e.g., a mobile terminal or phone) that holds financial instruments. The checking procedures may include: self-verifying integrity by the TRAA; checking for presence of a provisioning SIM card (one that was present when the financial instruments were enabled on the device); checking that a communication connection between the consumer electronic device and the service provider is available and active; and checking that communication connectivity to a home mobile network is available and active. The frequency of the checking mechanisms may be adjusted, for example, according to a risk-profile of a user associated with the device or the location (e.g., GPS location) of the device. The checks may be used, for example, to temporarily disable or limit the use of the financial instruments from the device.
Owner:PAYPAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com