Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
94results about How to "Reduce certification time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
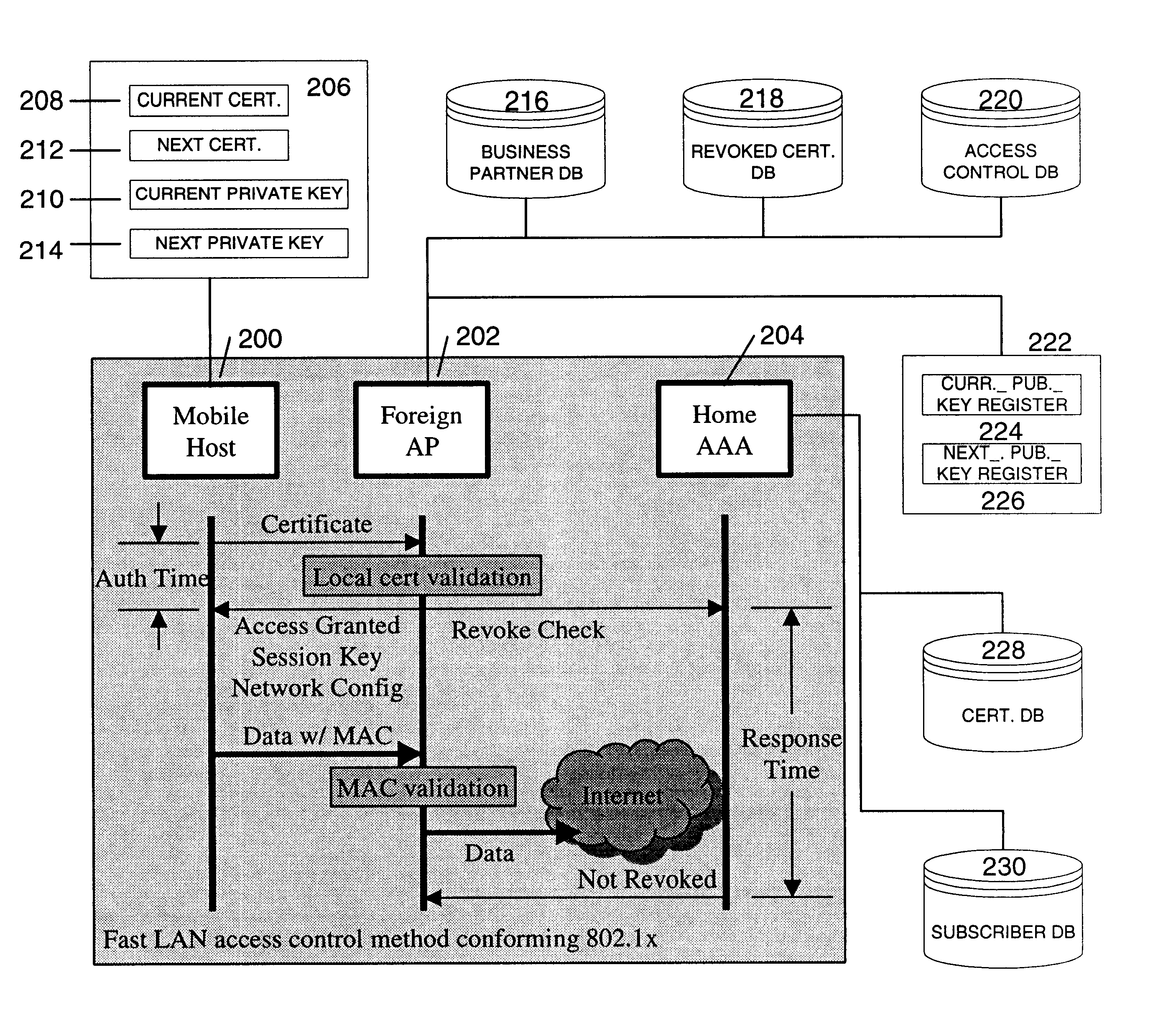
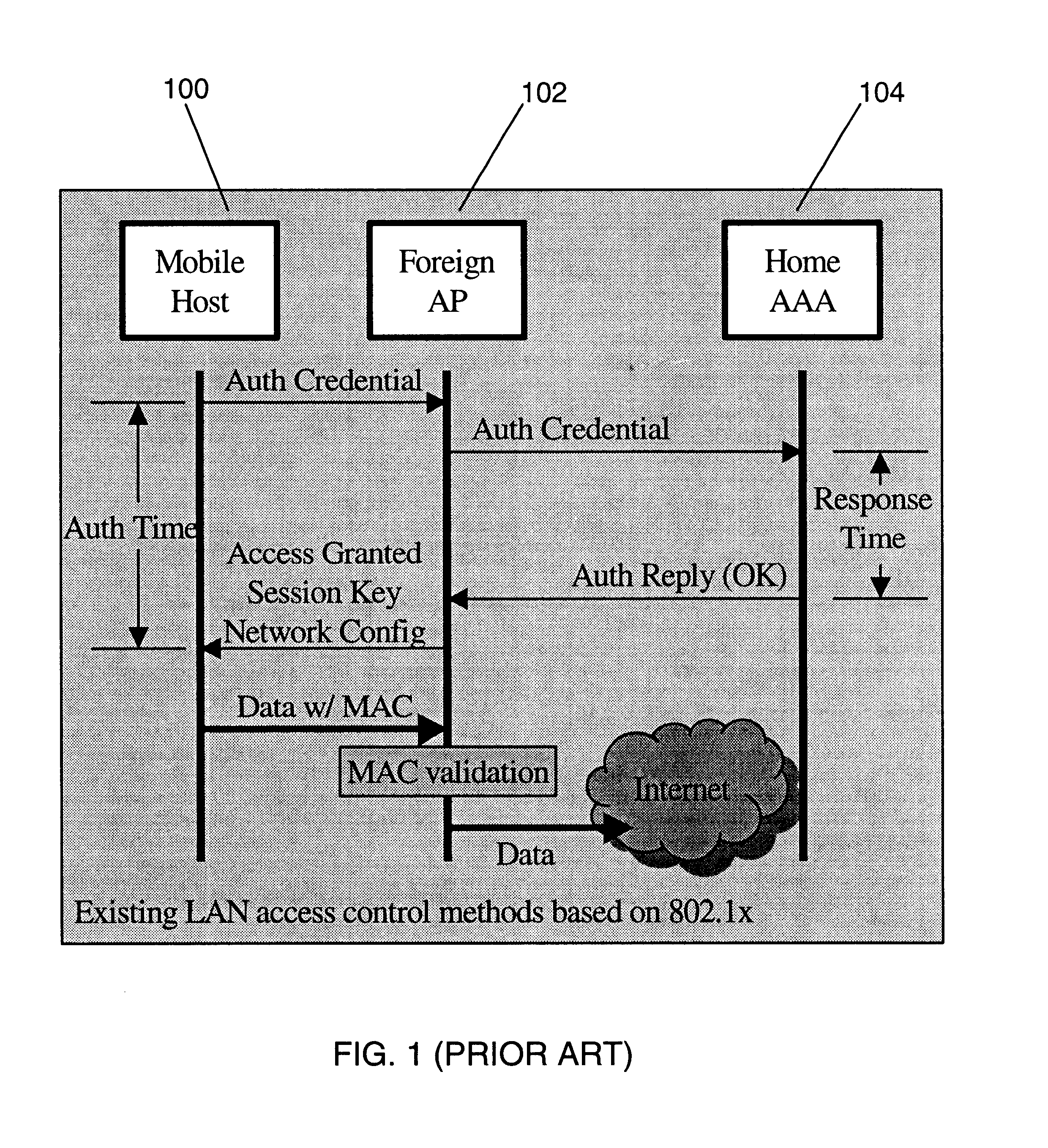
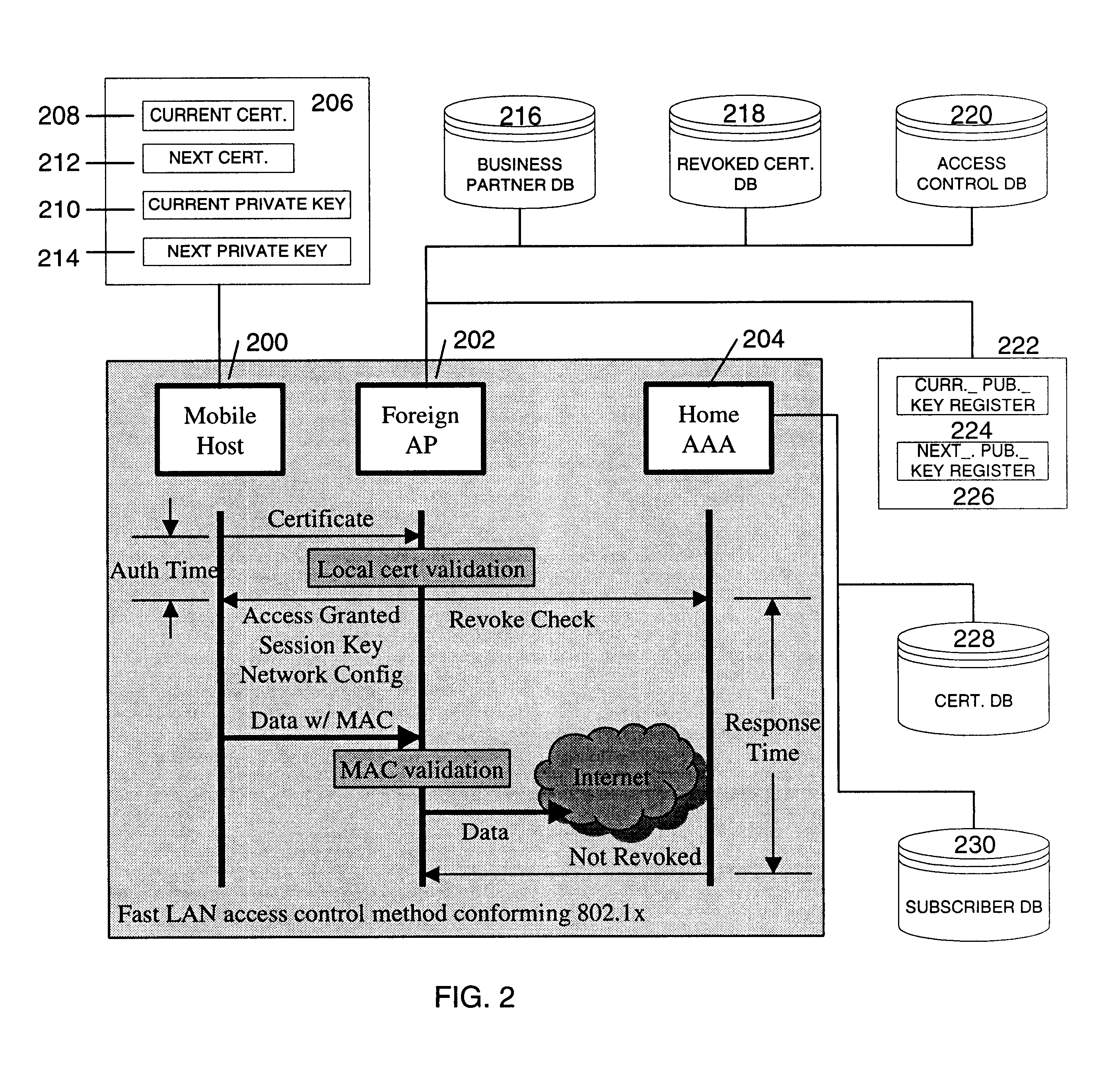
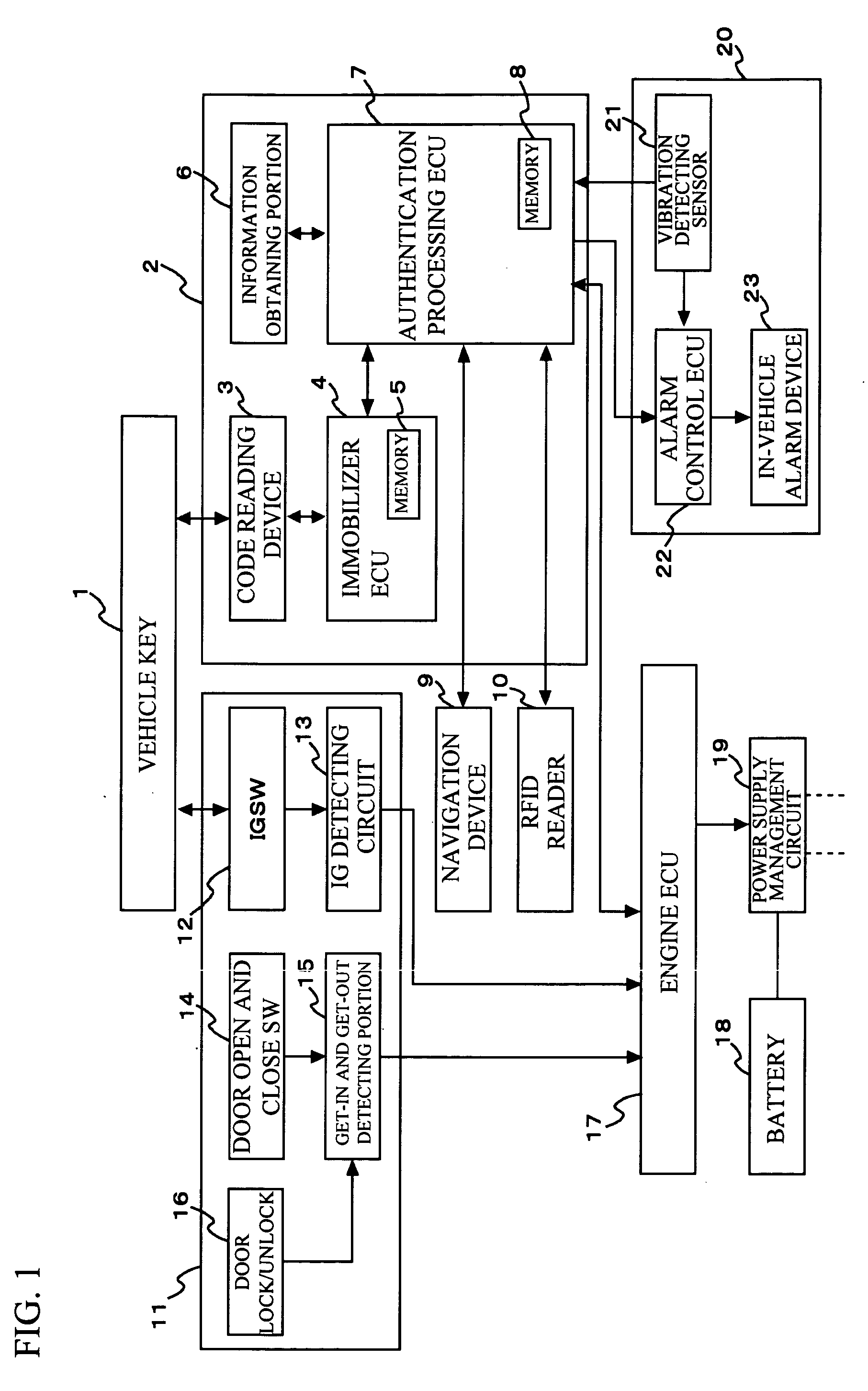
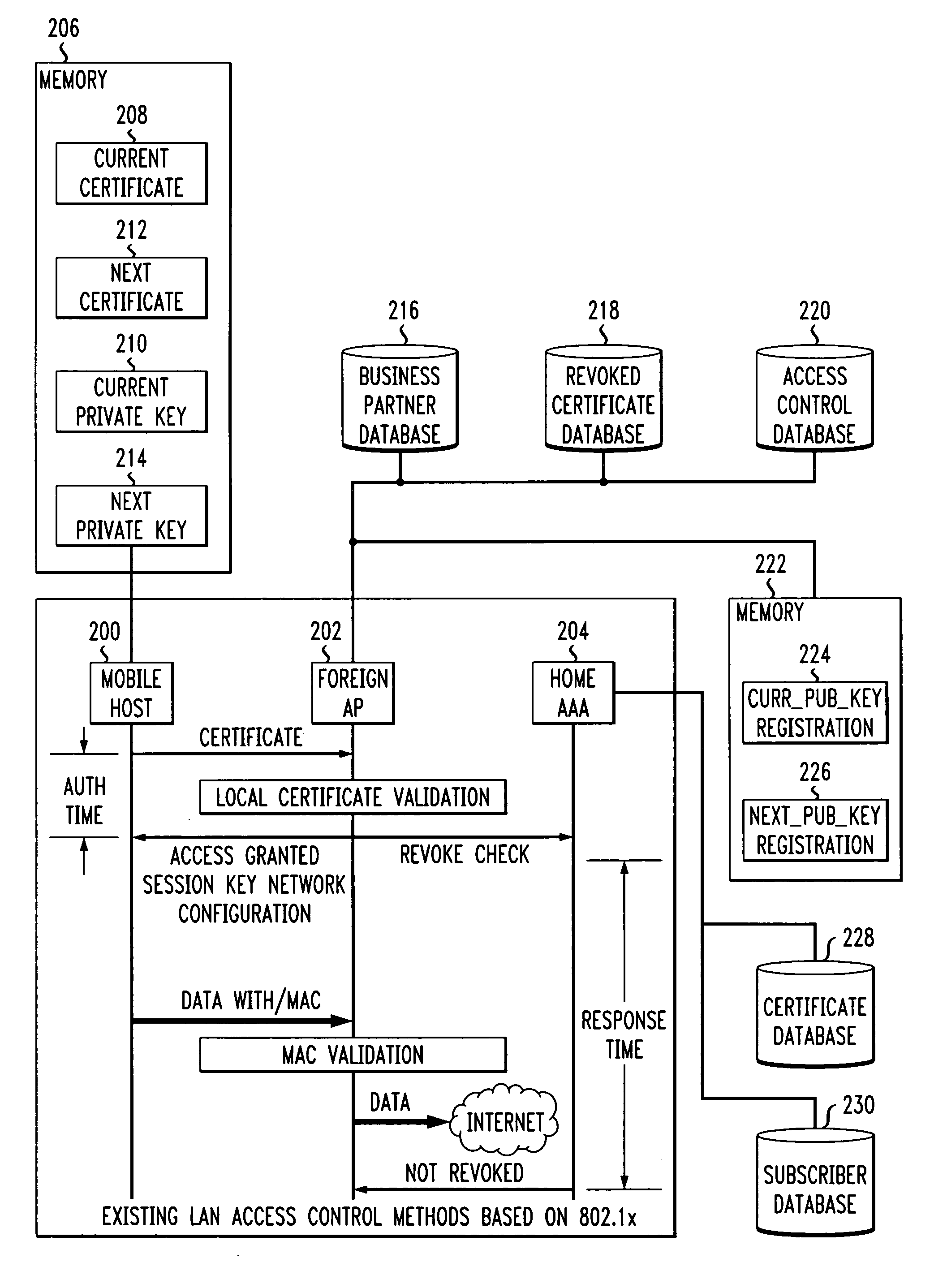
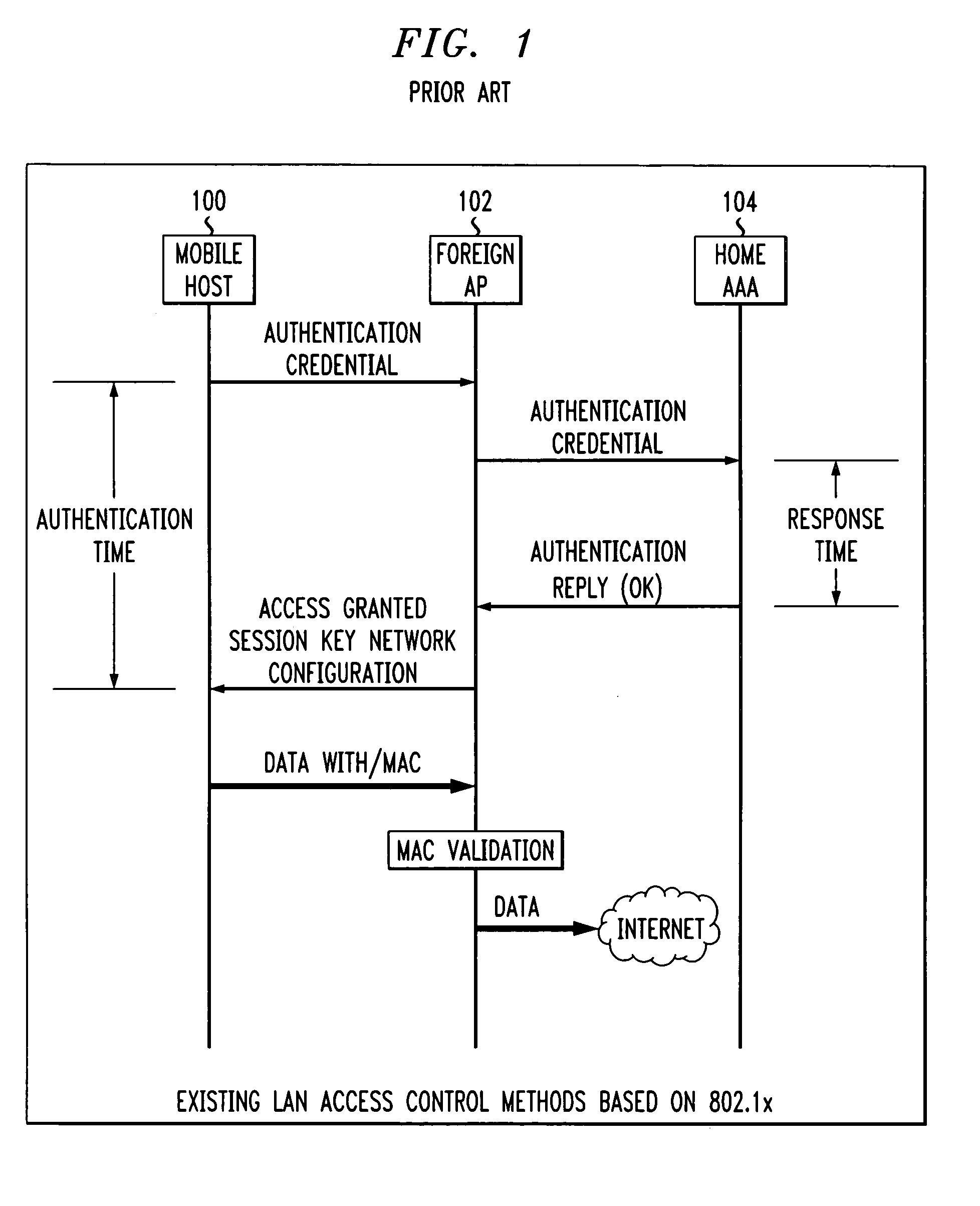
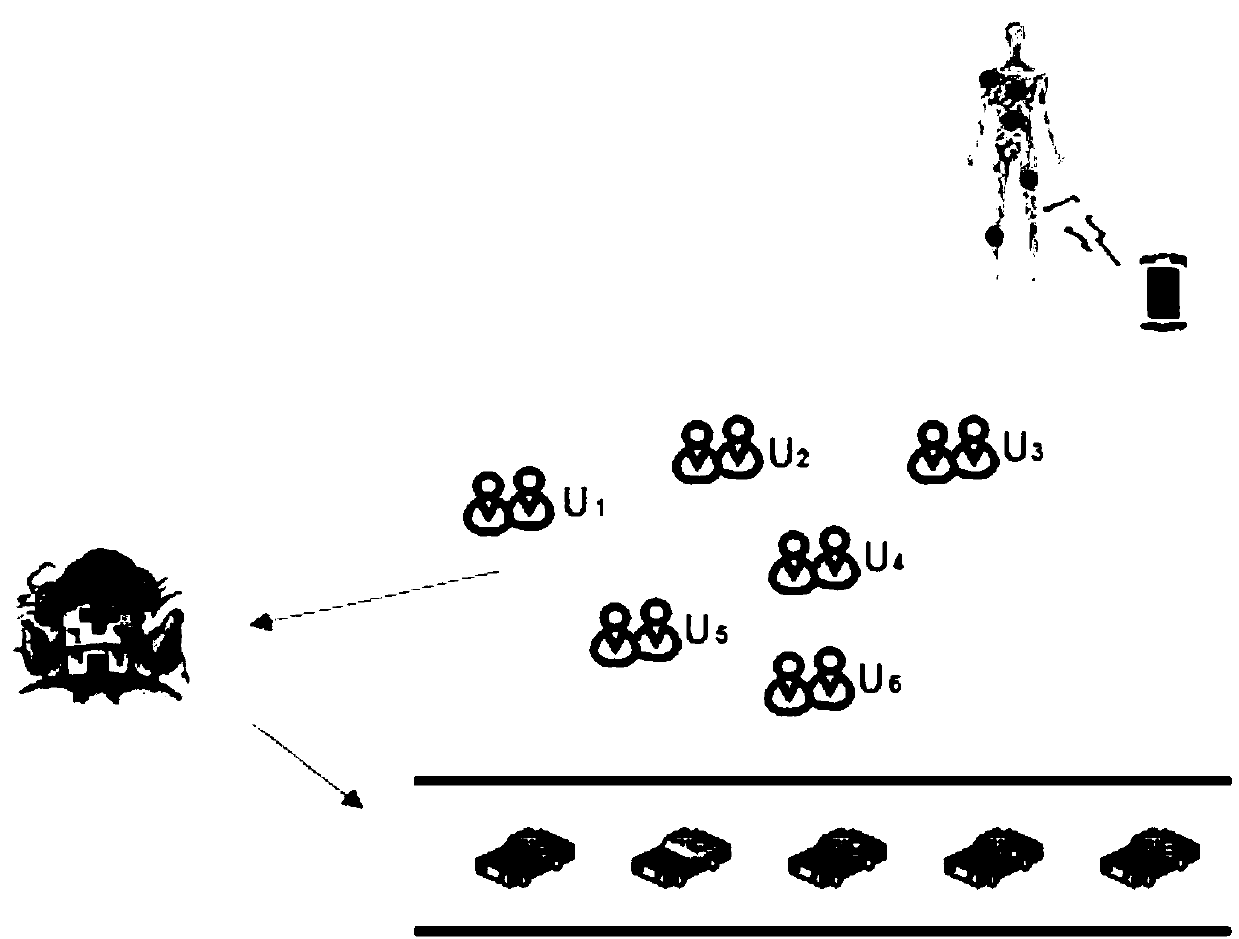
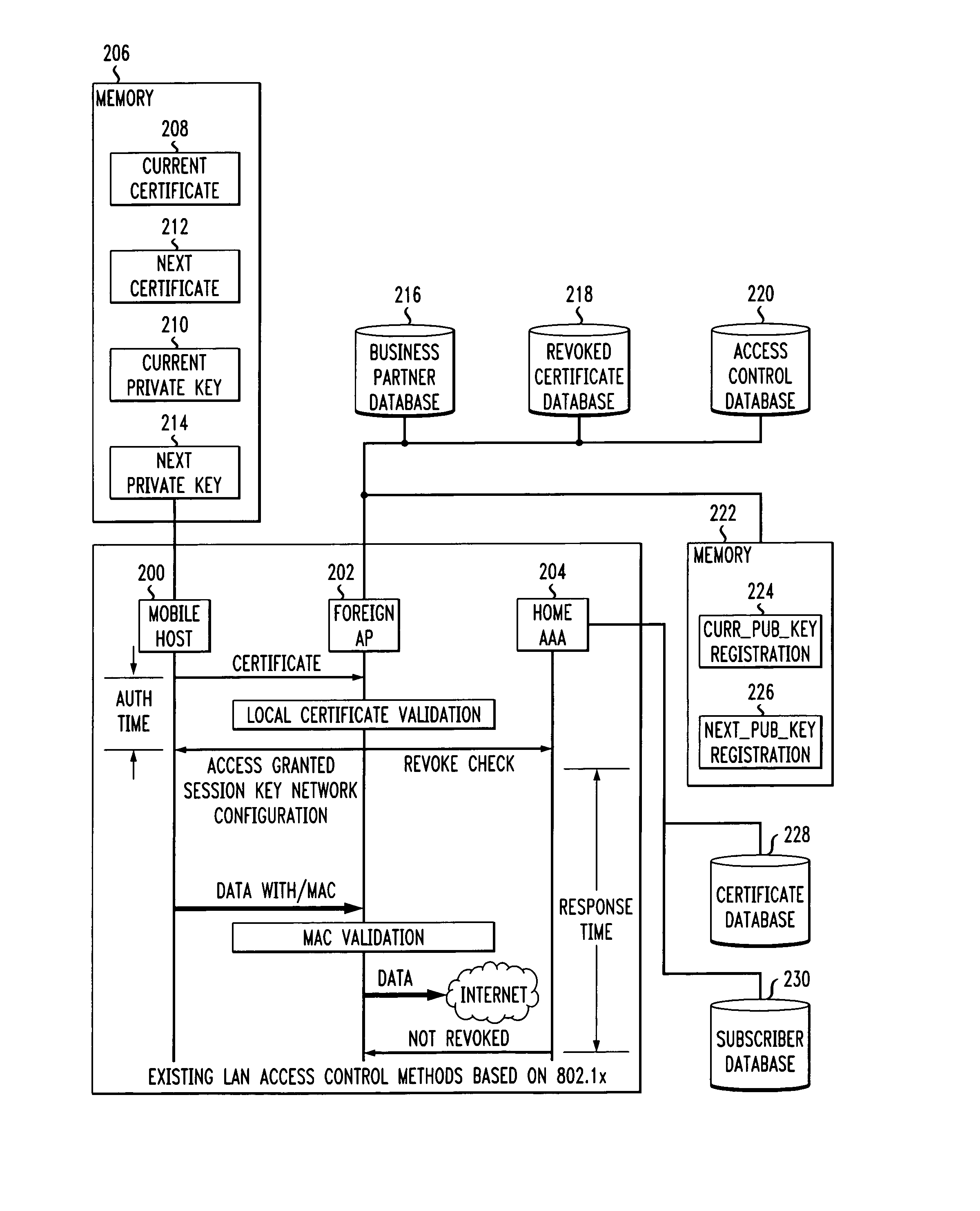
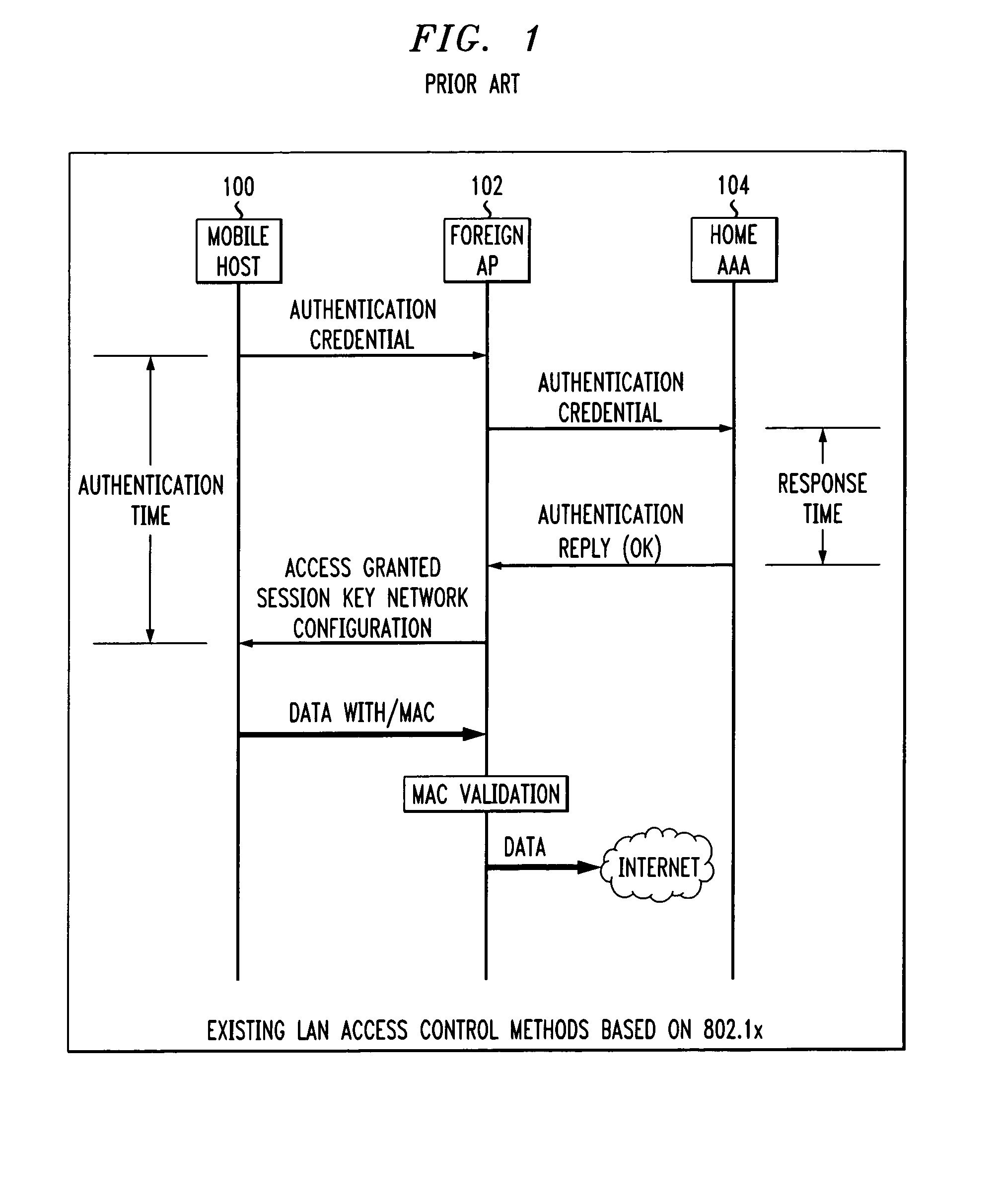
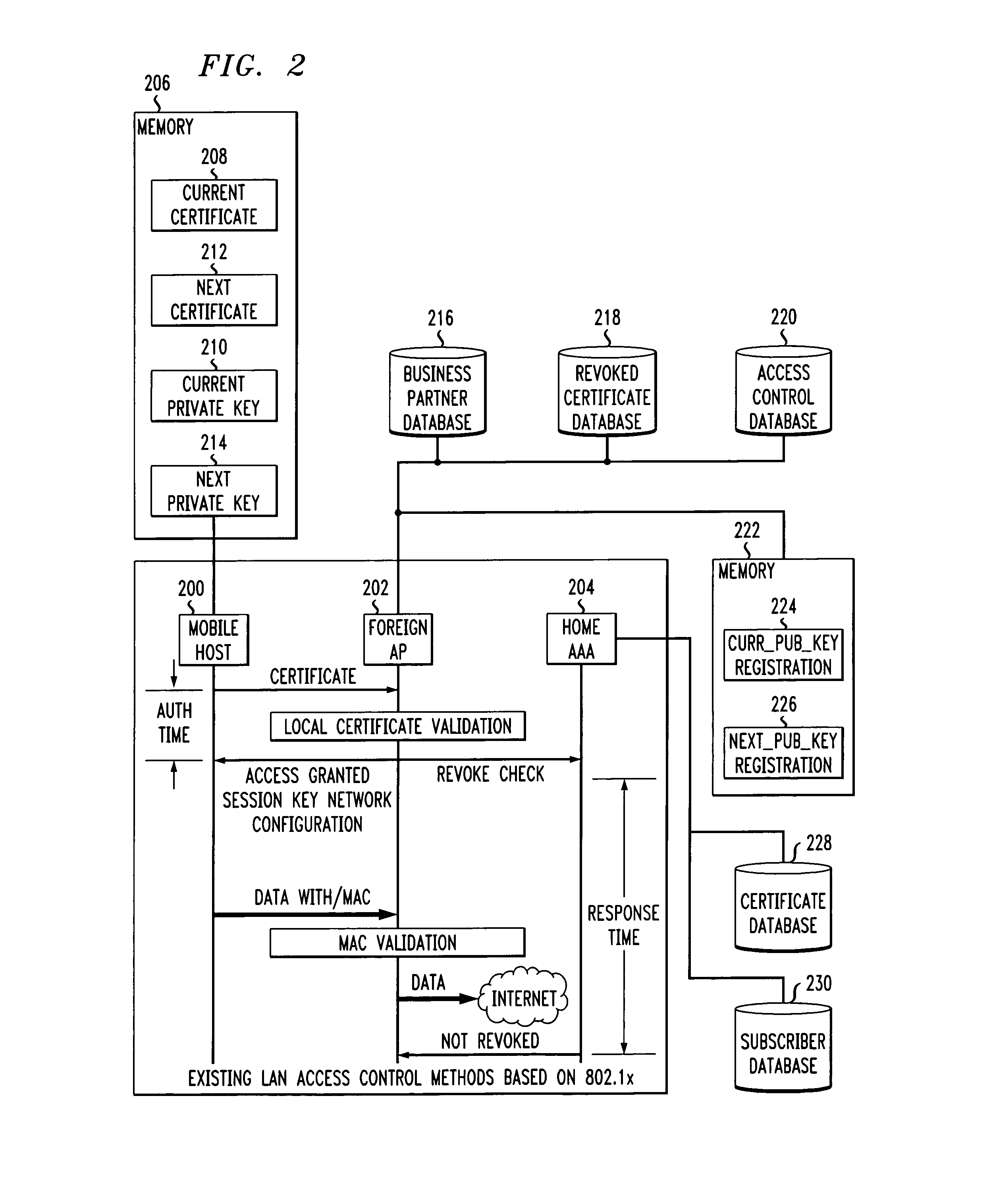
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
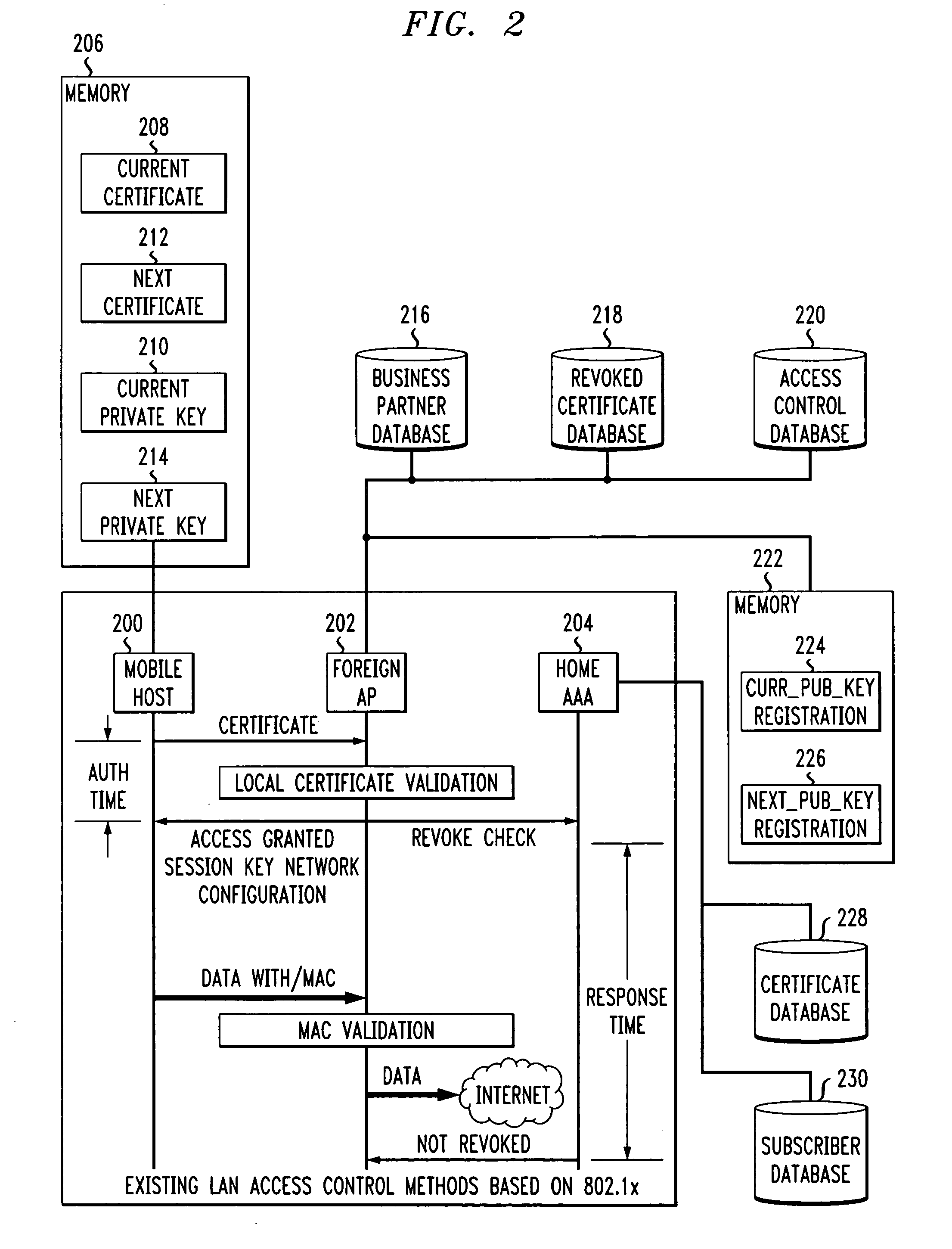
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
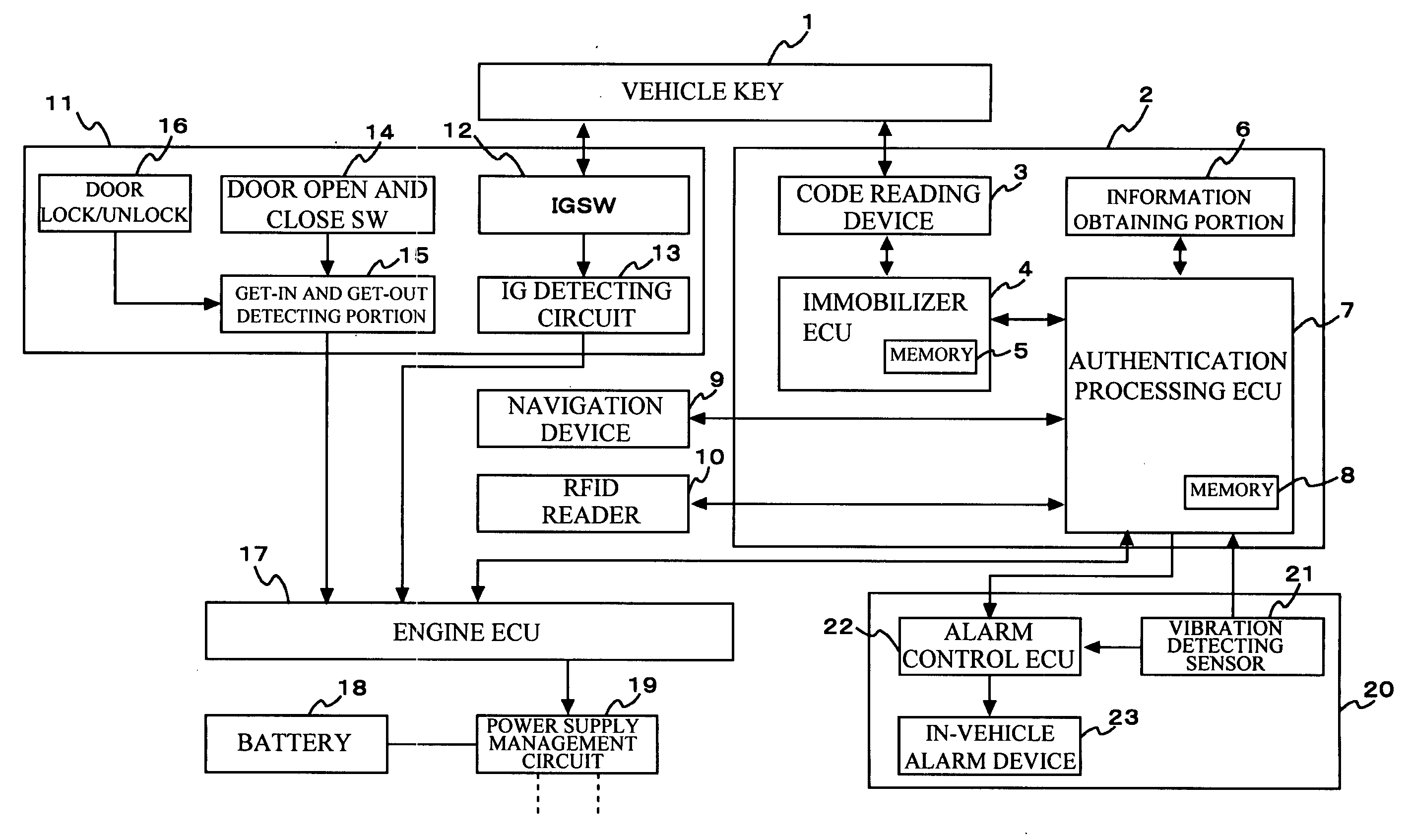
Authentication apparatus and method for use in vehicle
InactiveUS20070124599A1Increasing authentication levelReduce certification timeRandom number generatorsAnti-theft devicesComputer hardwareRisk level
An authentication method for use in a vehicle includes identifying validity by use of identification information stored, detecting an unauthorized use risk level predicted by a state of a vehicle, changing an authentication level according to an identification result and the unauthorized use risk level at the time of processing a biometric authentication, calculating a matching level between first biometric characteristic information of a vehicle passenger and second biometric characteristic information stored, and comparing the matching level calculated and an authentication level to output an authentication result at the time of processing the biometric authentication.
Owner:FUJITSU GENERAL LTD
Fast authentication and access control method for mobile networking
InactiveUS7174456B1Easy to switchReduce certification timeDigital data processing detailsUser identity/authority verificationExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Identity authentication method of fee payment via mobile communication terminal
The invention discloses an ID authentication method using mobile communication terminal to pay expenses, where mobile payment platform allocates graphic mark information to a mobile communication terminal user when the mobile communication terminal user registers, and the ID authentication process comprises the steps of: A. seller terminal obtains the graphic mark information of a mobile communication terminal user to pay expenses and sending this information to the mobile payment platform; B. the mobile payment platform compares the received graphic mark information with the stored graphic mark information: if they are the same, the ID authentication passes; otherwise does not pass. And it can be convenient for users and shorten mobile payment authentication time.
Owner:POTEVIO INFORMATION TECH
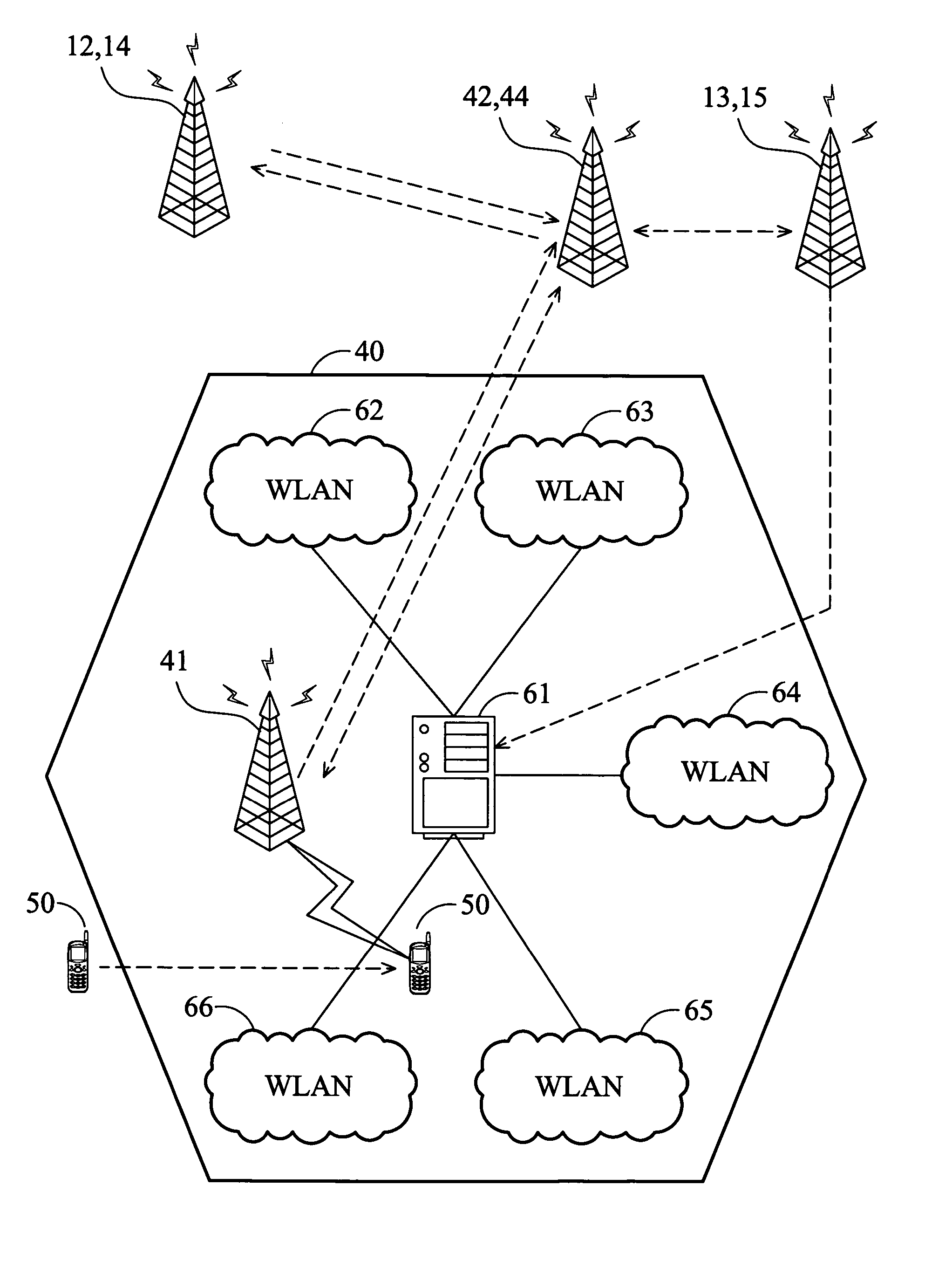
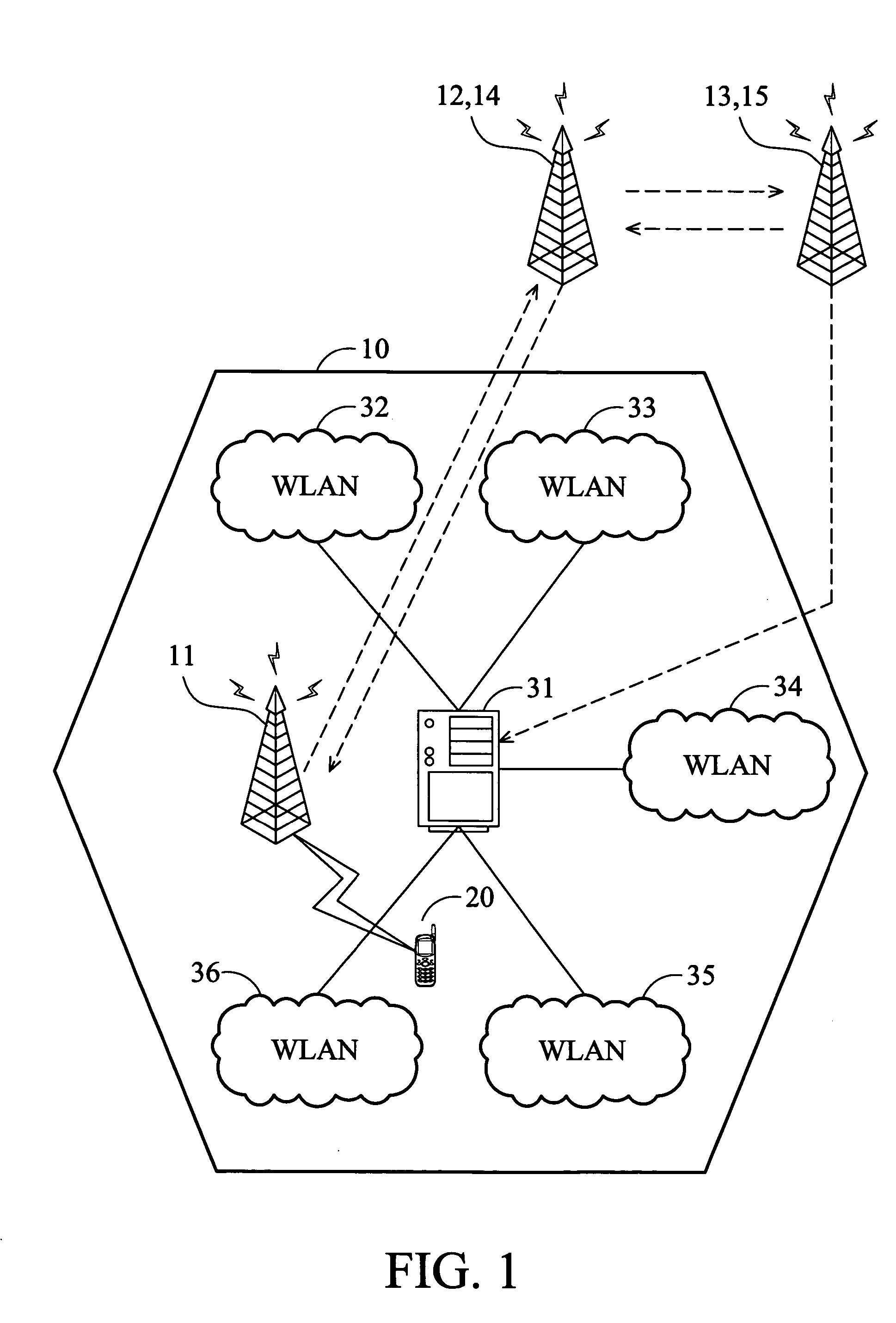
System and method for data communication handoff across heterogeneous wireless networks
ActiveUS20050122941A1Reduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelephone networkWireless lan
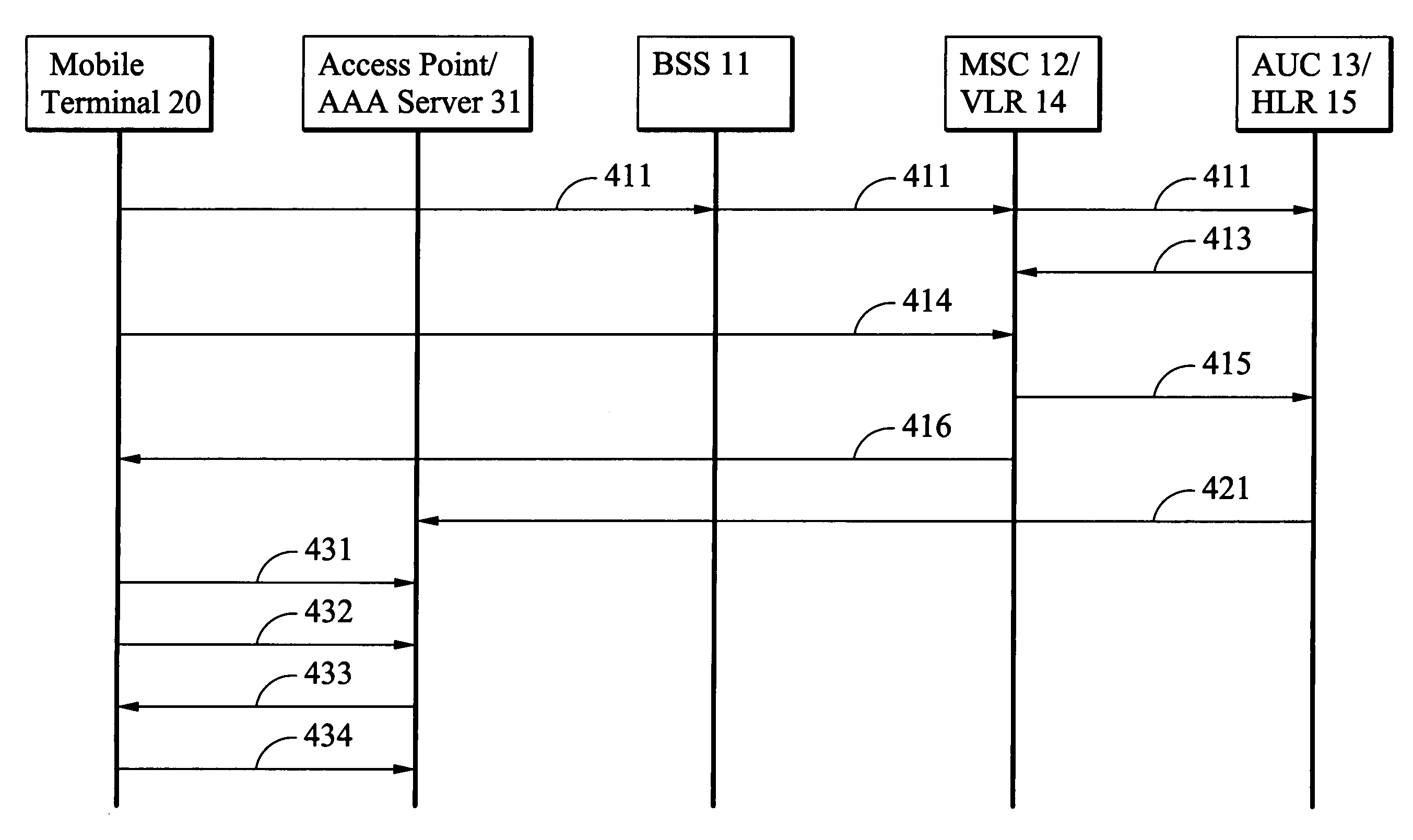
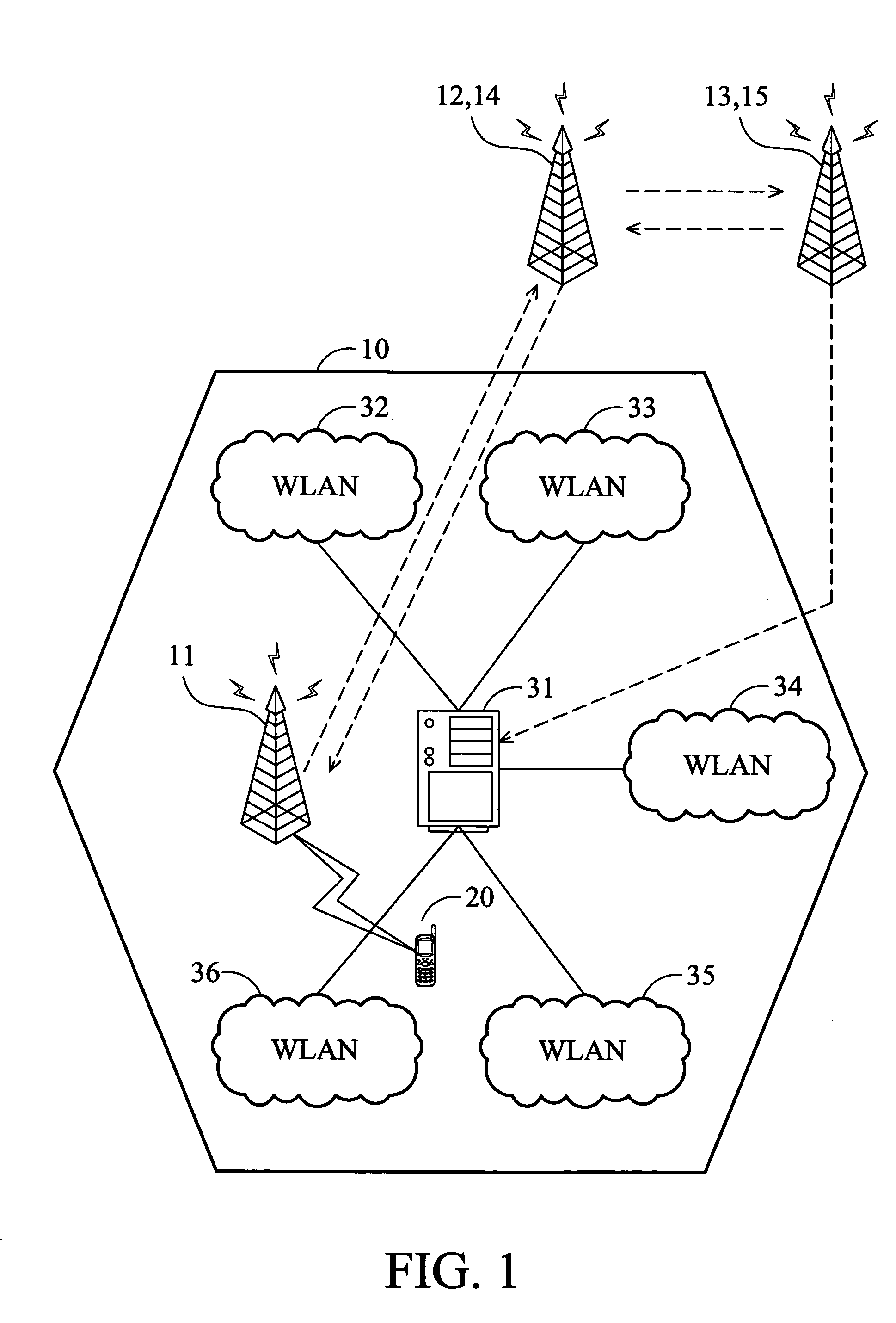
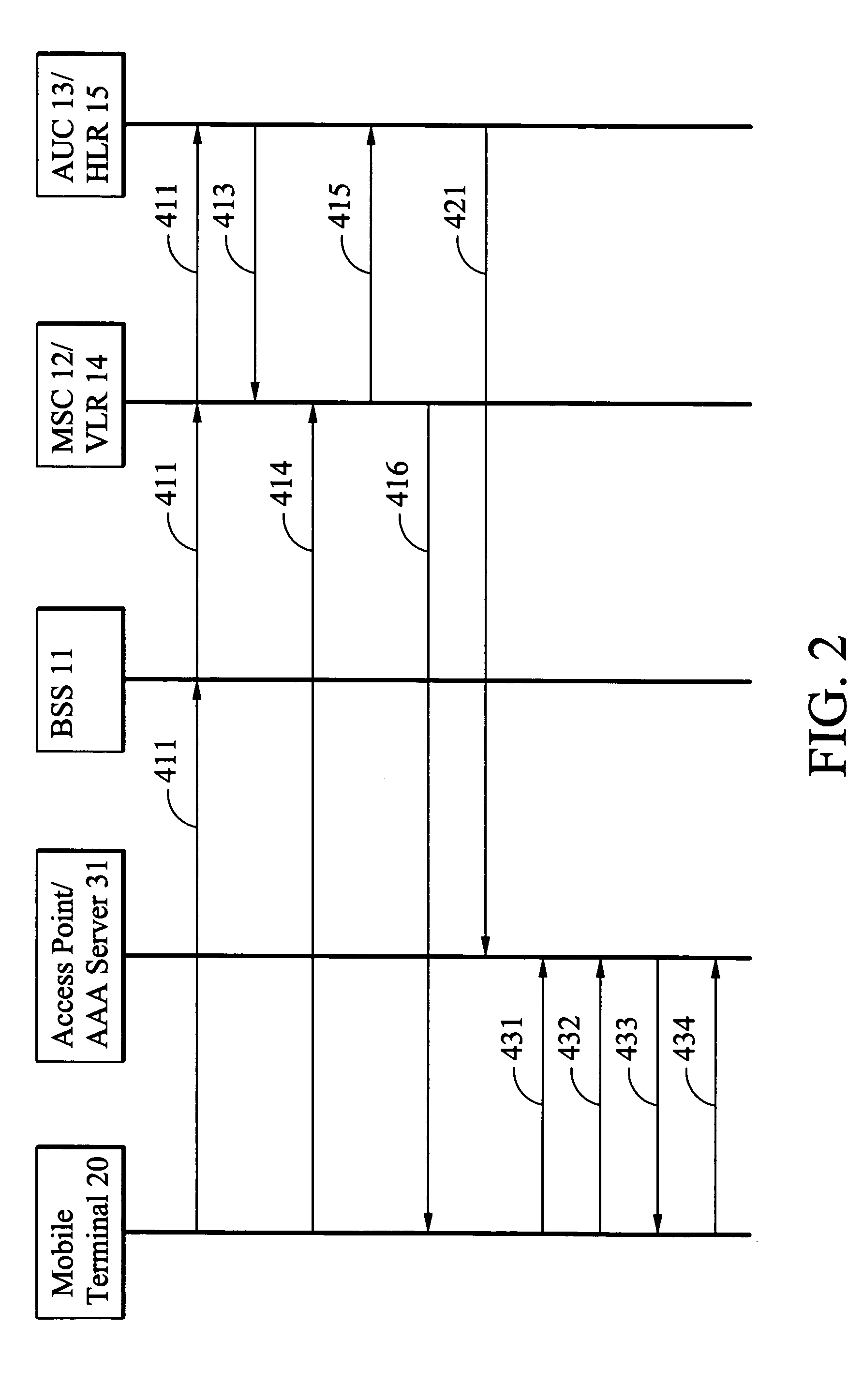
A system and method of data communication handoff across heterogeneous wireless networks. A wireless telephony network comprises a base station system (BSS) and a visit location register (VLR). The BSS manages data communication in a cell. The VLR generates a temporary authentication identity applicable in the cell when a mobile terminal is successful authentication for data communication via the wireless telephony network, and transmits the temporary authentication identity to the mobile terminal. A wireless local area network (WLAN) located in the cell comprises an access point. The access point receives the temporary authentication identity from the wireless telephony network and authenticates the mobile terminal for data communication via the WLAN by verifying the temporary authentication identity upon the mobile terminal associates with the access point.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
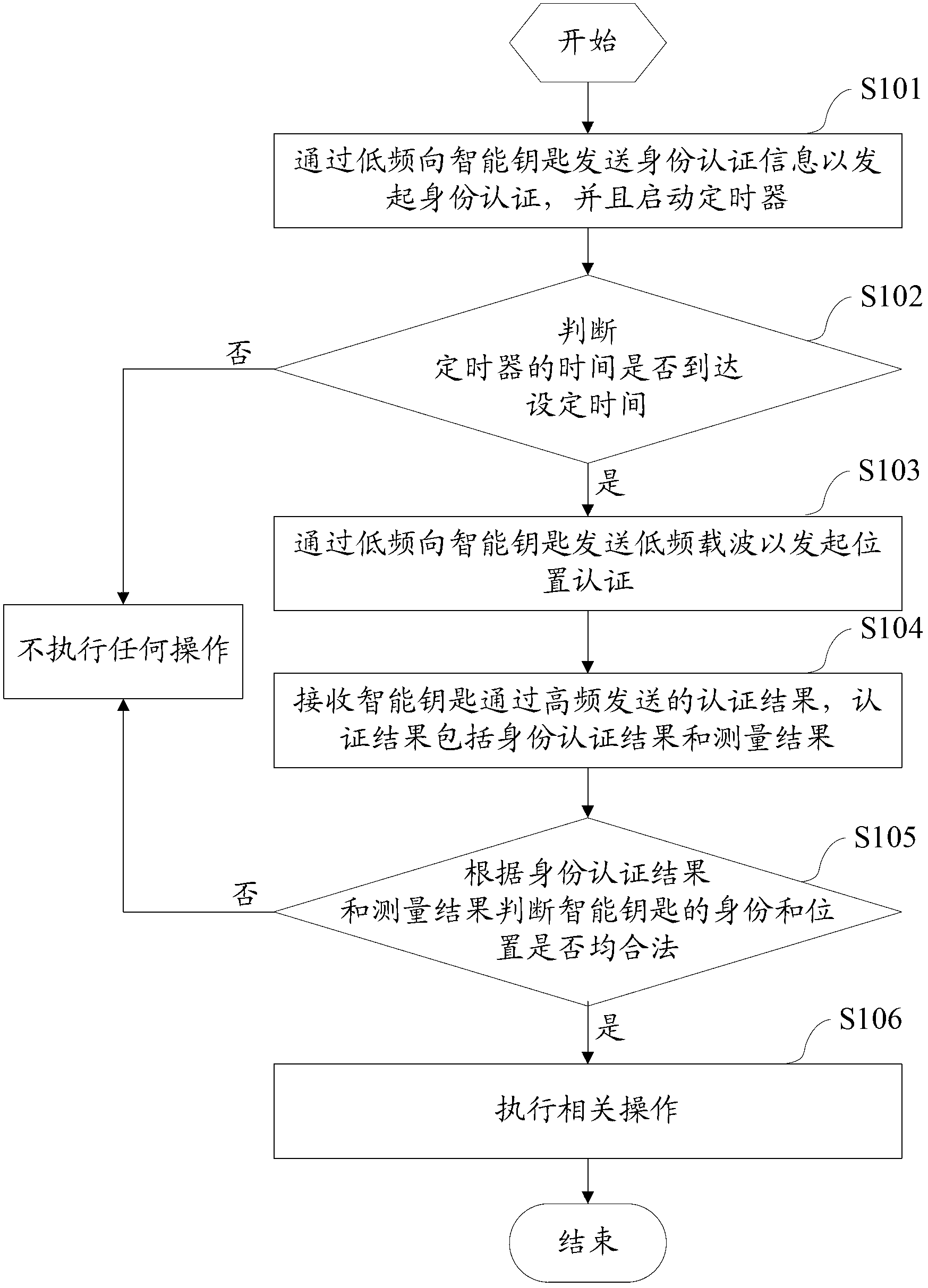
KPD (key position detection) authentication method and system for vehicle and smart key and vehicle base station
ActiveCN103178966AReduce certification timeImprove practicalityAnti-theft devicesUser identity/authority verificationCarrier signalField intensity
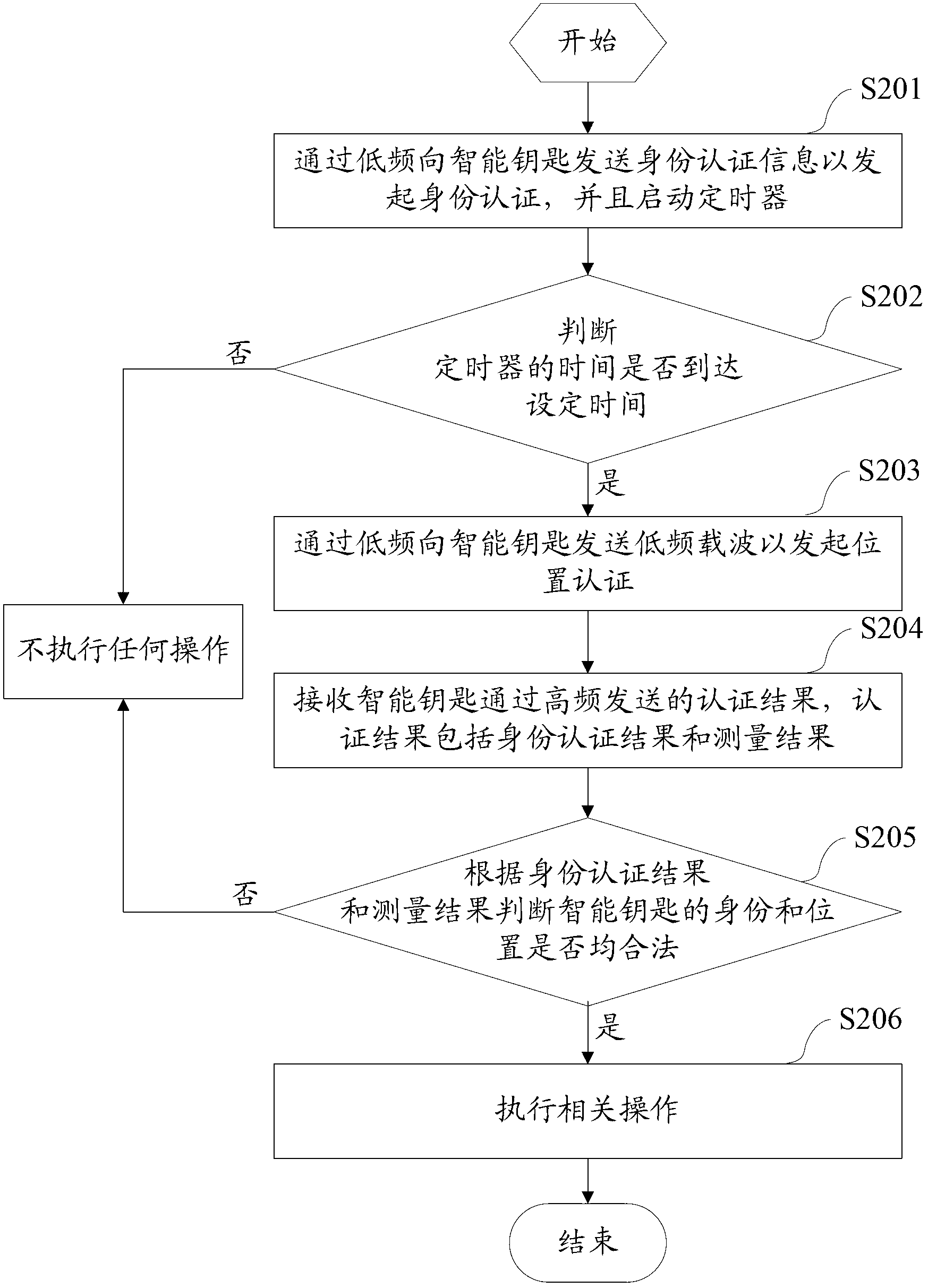
The invention provides a KPD (key position detection) authentication method and system for a vehicle and a smart key and a vehicle base station. The method comprises the following steps of: sending encrypted and coded identity authentication information to the smart key through low frequency so as to initiate identity authentication and starting a timer; when the time of the timer reaches set time, sending a low-frequency carrier wave to the smart key through low frequency so as to initiate position authentication; receiving authentication results sent by the smart key through high frequency, wherein the authentication results include an identity authentication result obtained in a manner that the smart key decrypts and decodes the identity authentication information and a measurement result obtained through measuring the field intensity of the low-frequency carrier wave; and judging whether the identity and position of the smart key are legal or not according to the identity authentication result and the measurement result, and executing related operations when the identity and position of the smart key are legal. The method, the system and the vehicle base station, provided by the invention, have the advantages that the time for KPD authentication is greatly shortened, the probability that unstable factors appear in a communication process is reduced, and the practicability of PEPS (Passive Entry & Push Start Systems) is enhanced.
Owner:天津经纬恒润科技有限公司
Distributed cloud authentication system based on random instruction, apparatus and method thereof
InactiveCN105915542AReduce occupancyRun fastTransmissionAuthentication systemAuthentication information
A distributed cloud authentication system based on a random instruction comprises a terminal, a root node, a distributed node and a local node. The system is characterized in that the root node does not authenticate authentication information sent by a terminal, a random instruction distributed node carries out authentication and sends the authentication information to the distributed node; the distributed node sends an authentication result to the root node; and the root node determines the result sent by the distributed node according to a preset threshold and sends a determination result to the terminal. Further, a process that the root node determines the result sent by the distributed node according to a preset threshold comprises the following steps that the root node carries out determination according to an assigned authenticated distributed node number; if the authenticated distributed node number is greater than a half of an assigned distributed node number, authentication is performed continuously; and if the authenticated distributed node number is less than a half of the assigned distributed node number, the authentication is terminated.
Owner:惠众商务顾问(北京)有限公司
System and method for data communication handoff across heterogenous wireless networks
ActiveUS7206301B2Reduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsHeterogeneous wireless networkAuthentication
A system and method of data communication handoff across heterogeneous wireless networks. A wireless telephony network comprises a base station system (BSS) and a visit location register (VLR). The BSS manages data communication in a cell. The VLR generates a temporary authentication identity applicable in the cell when a mobile terminal is successful authentication for data communication via the wireless telephony network, and transmits the temporary authentication identity to the mobile terminal. A wireless local area network (WLAN) located in the cell comprises an access point. The access point receives the temporary authentication identity from the wireless telephony network and authenticates the mobile terminal for data communication via the WLAN by verifying the temporary authentication identity upon the mobile terminal associates with the access point.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Copyright authentication method and device based on block chain, equipment and storage medium
ActiveCN110598376APrevent tamperingImprove securityDigital data protectionDigital data authenticationInformation processingUser authentication
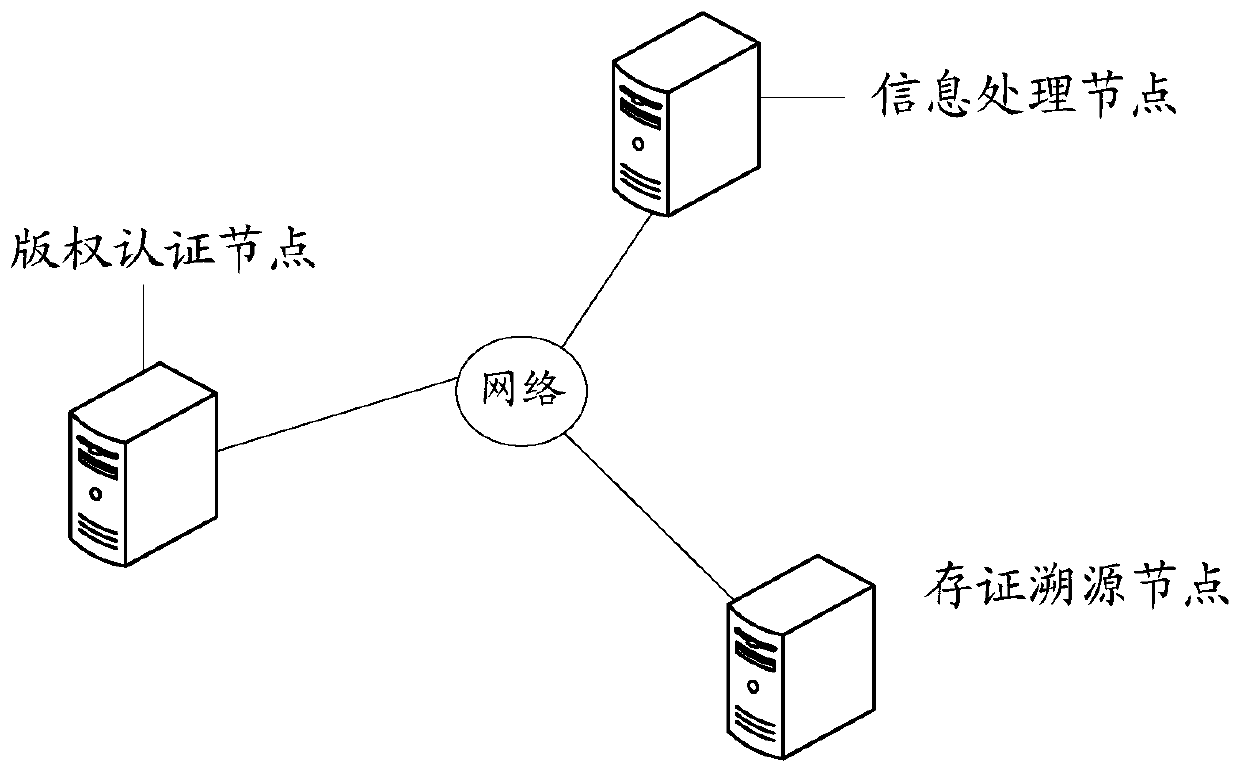
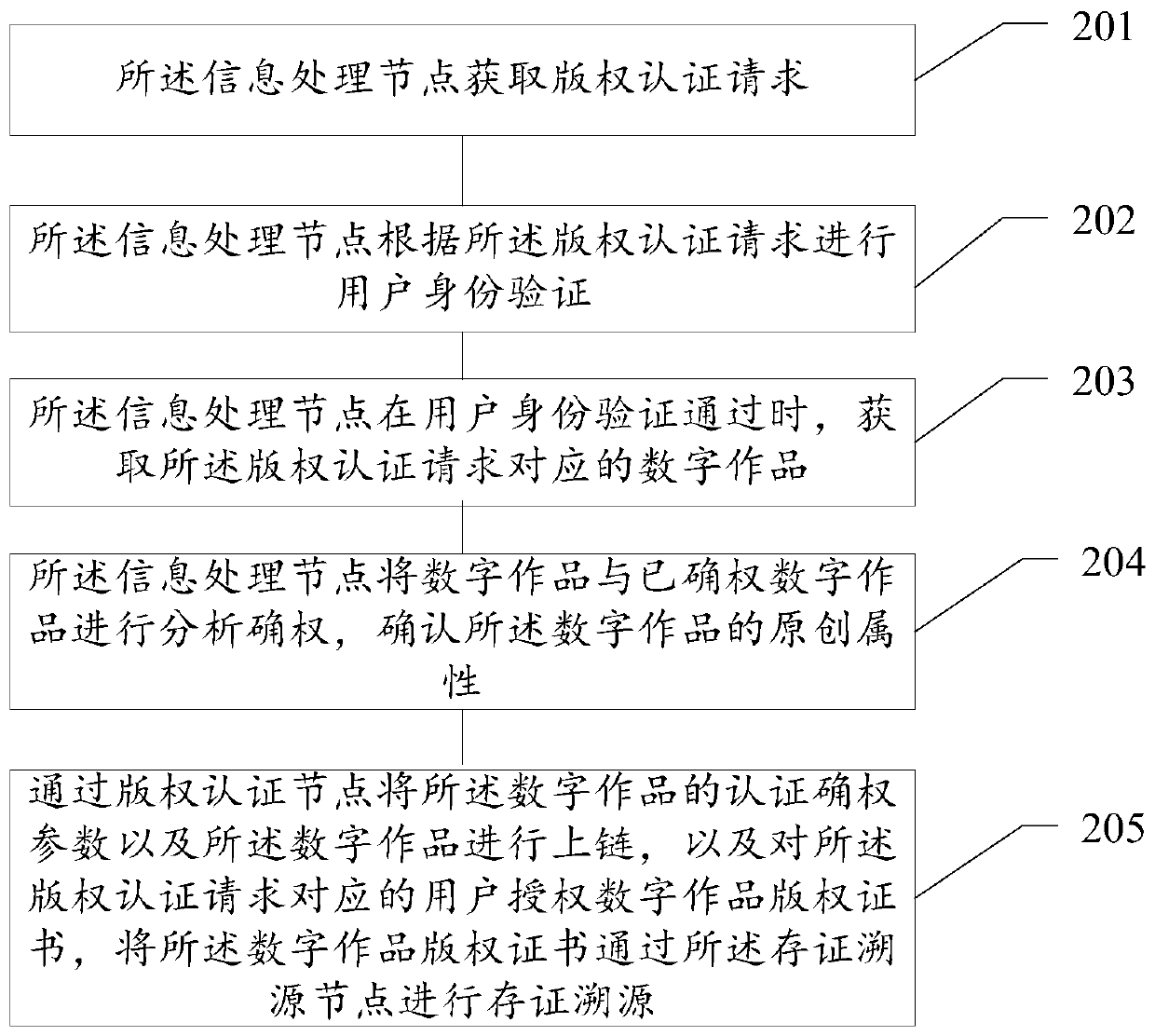
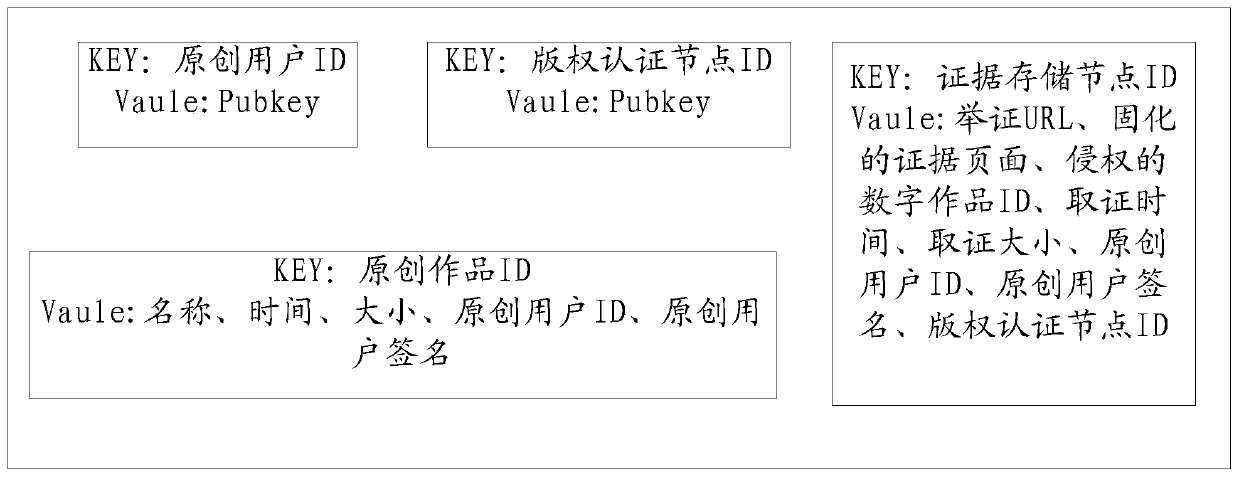
The embodiment of the invention discloses a copyright authentication method, device and equipment based on a block chain and a storage medium. The copyright authentication method comprises the steps of obtaining a copyright authentication request through an information processing node; the information processing node performing user identity authentication according to the copyright authenticationrequest; the information processing node acquiring a digital work corresponding to the copyright authentication request when the user identity authentication is passed; the information processing node analyzing and determining the right of the digital work and the right-determined digital work to determine the original attribute of the digital work; and uploading the authentication right confirmation parameter of the digital work and the digital work through a copyright authentication node, authorizing a digital work copyright certificate for a user corresponding to the copyright authentication request, and carrying out evidence storage tracing on the digital work copyright certificate through an evidence storage tracing node. According to the scheme, the copyright authentication efficiency and safety can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
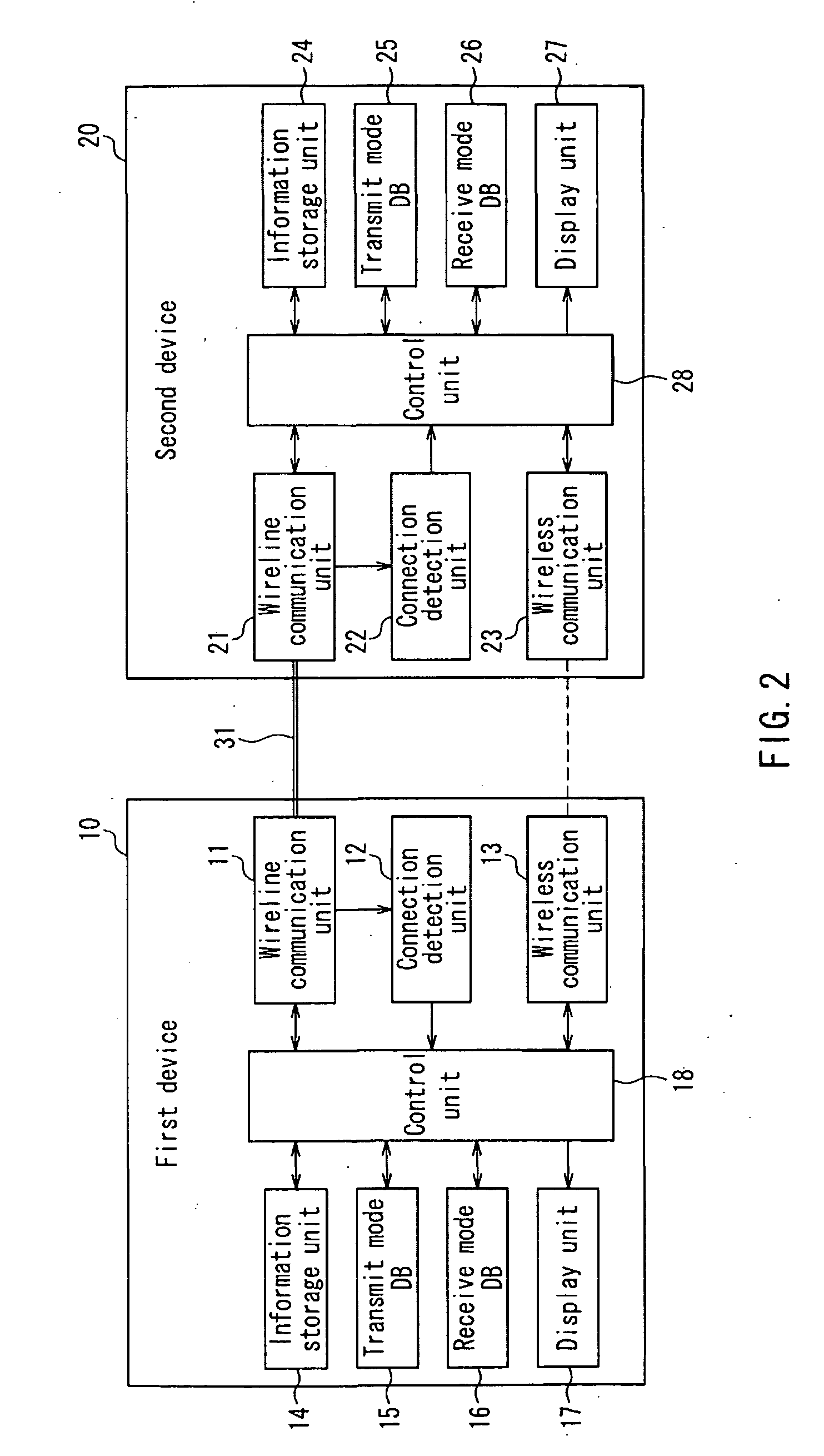
Information communication device
InactiveUS20090017755A1Improve ease of useEasy to operateNetwork topologiesRadio transmissionOperabilityBluetooth
In the information communication device of the present invention, the first device and the second device are arranged to be connected by wired and exchange device information with each other, as a result of which the first device and the second device can be placed into a state permitting Bluetooth-based wireless communication between the two even without performing a Bluetooth pairing process. Accordingly, the user can enable Bluetooth-based wireless communication simply by inserting the portable audio device 2, i.e. the second device, into the slot 3 in the audio system 1, i.e. the first device, which allows operability to be improved.
Owner:PANASONIC CORP
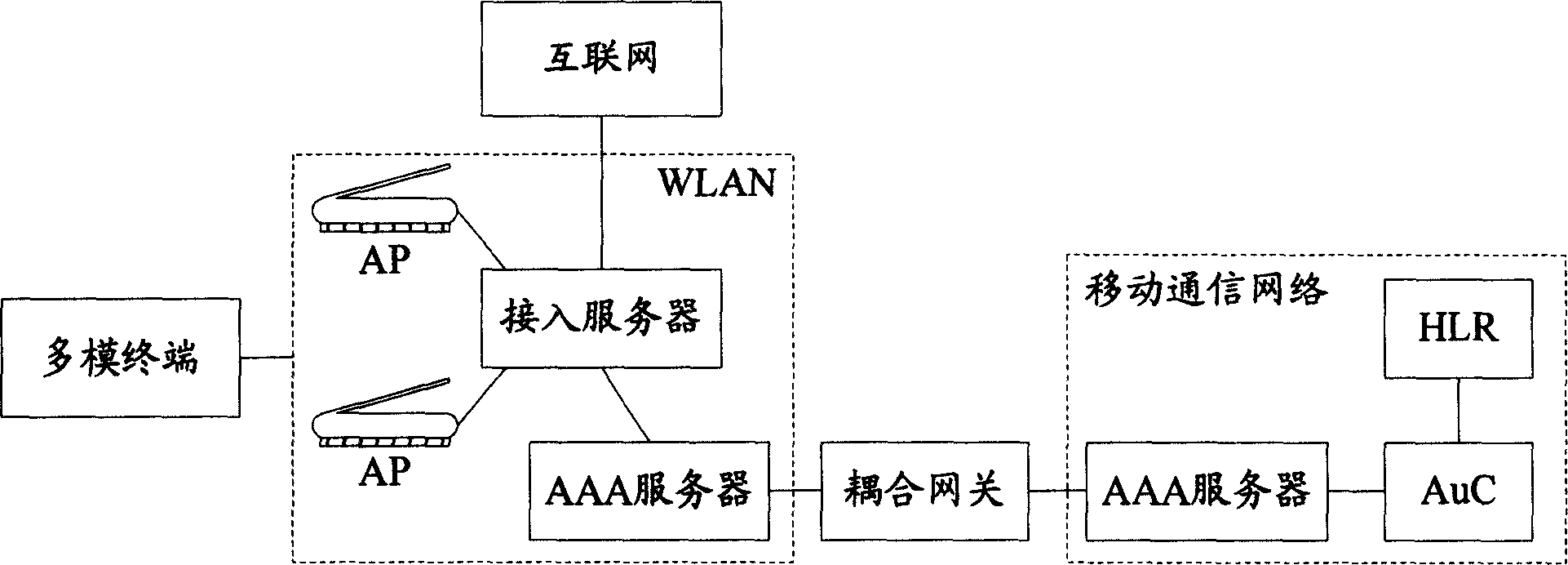
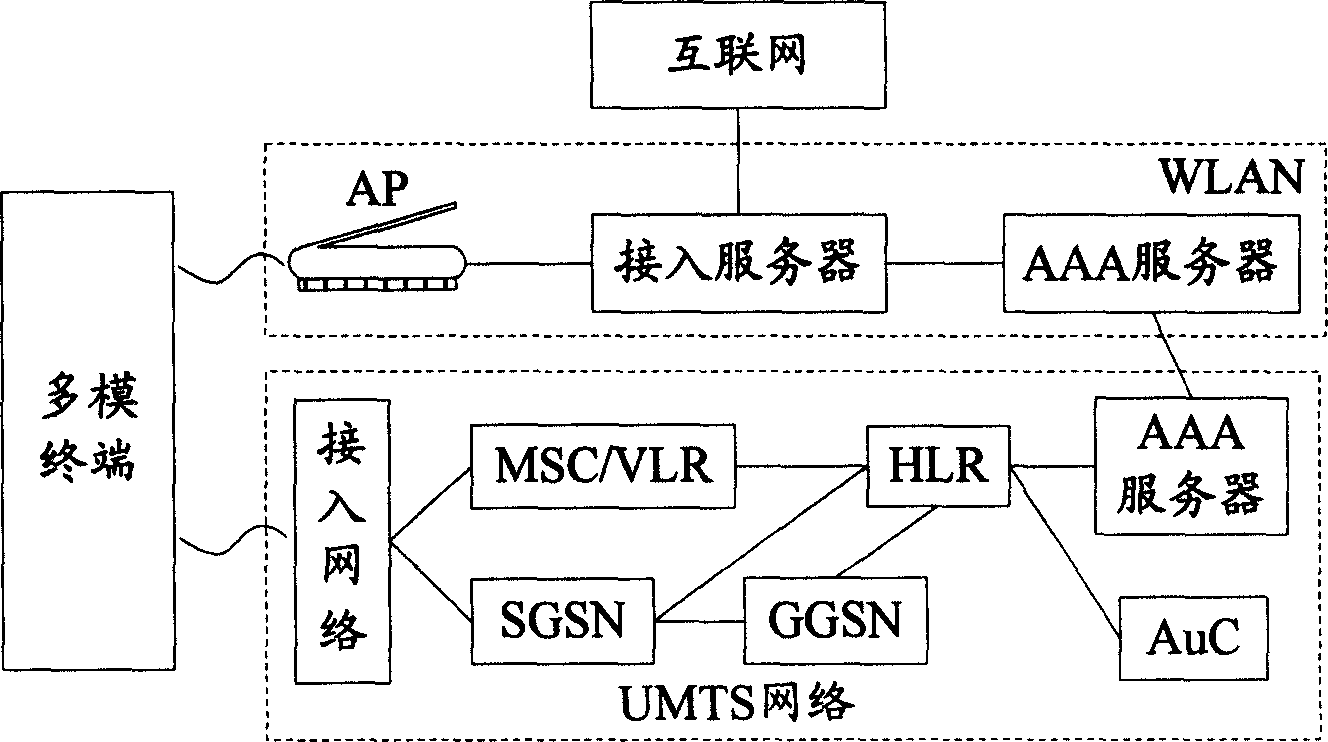
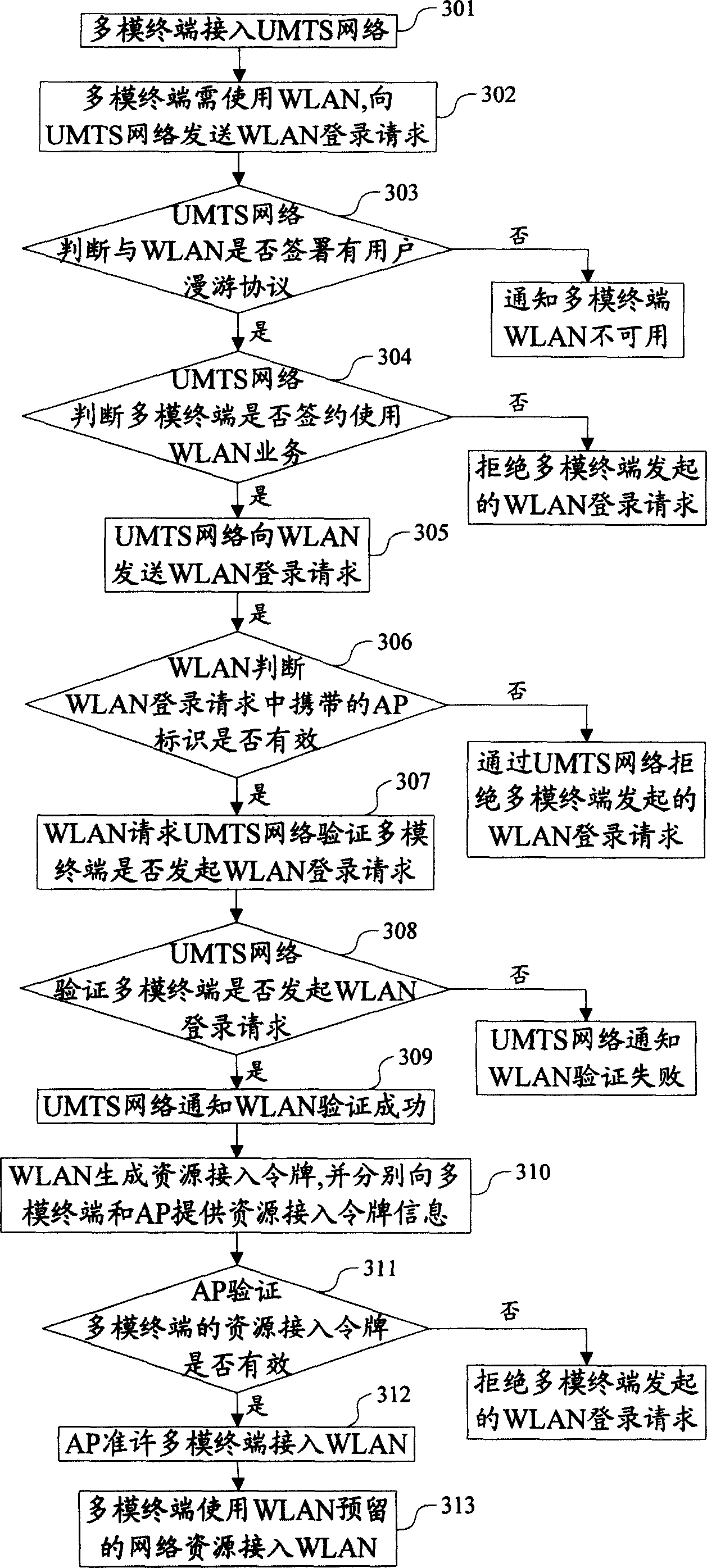
Identification method for multi-mode terminal roaming among heterogenous inserting technology networks
ActiveCN1889781AImprove securityAvoid Malicious Billing FraudAssess restrictionRadio/inductive link selection arrangementsTelecommunicationsEnd user
Owner:DATANG MOBILE COMM EQUIP CO LTD
Authentication method between client and server, machine-readable storage medium, client and server
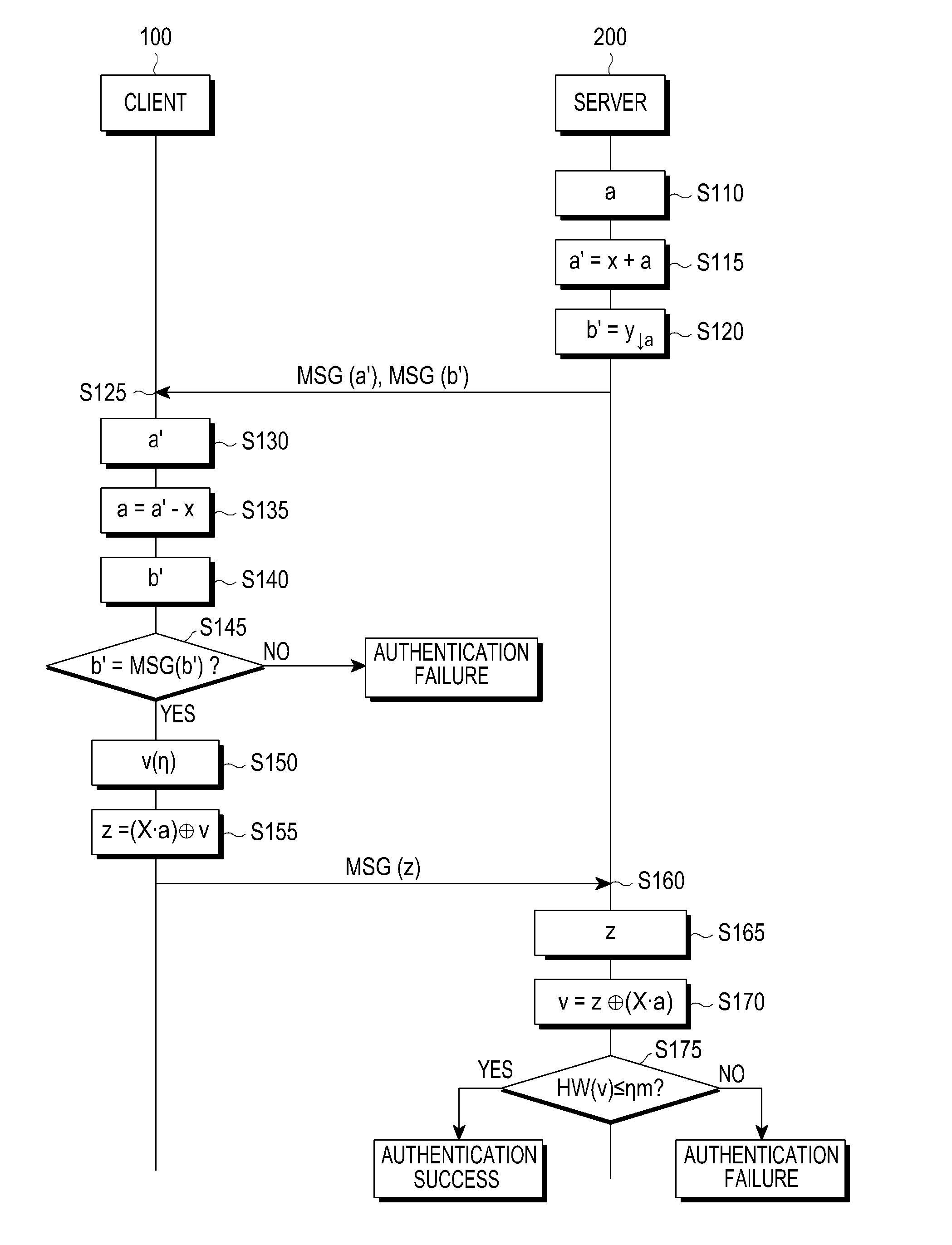
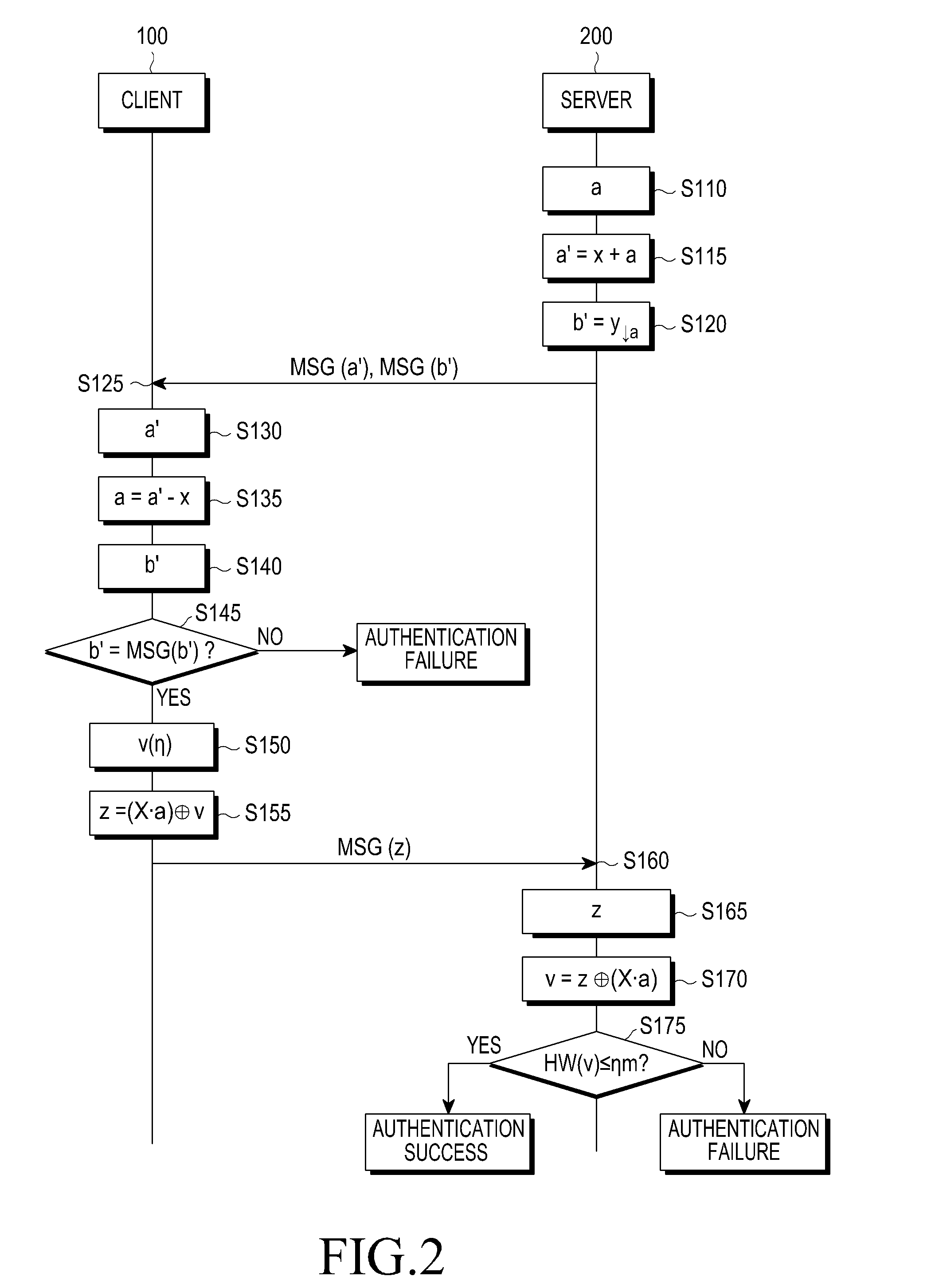
ActiveUS20130205379A1Efficiently usReduce certification timeKey distribution for secure communicationDigital data processing detailsClient-sideKey generation
An authentication method between a server and a client is provided. The authentication method includes transmitting, to the client, an inquiry message including a first modified secret key generated based on a first secret key and a first blinding value, receiving, from the client, a response message including a response value generated based on the first blinding value, a second secret key, and an error value, calculating the error value from the response value, and determining whether authentication of the client has succeeded based on the error value.
Owner:SAMSUNG ELECTRONICS CO LTD +1
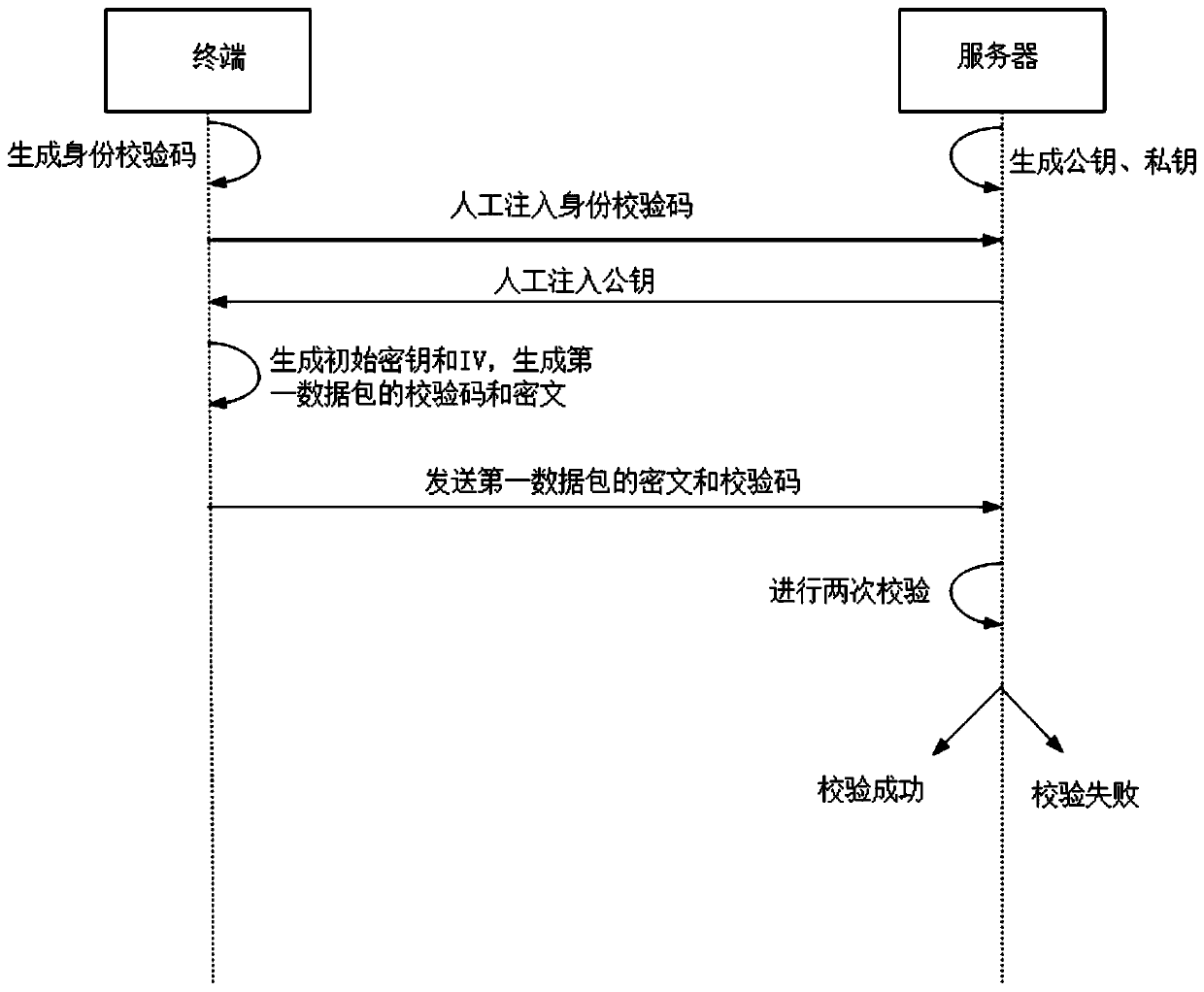
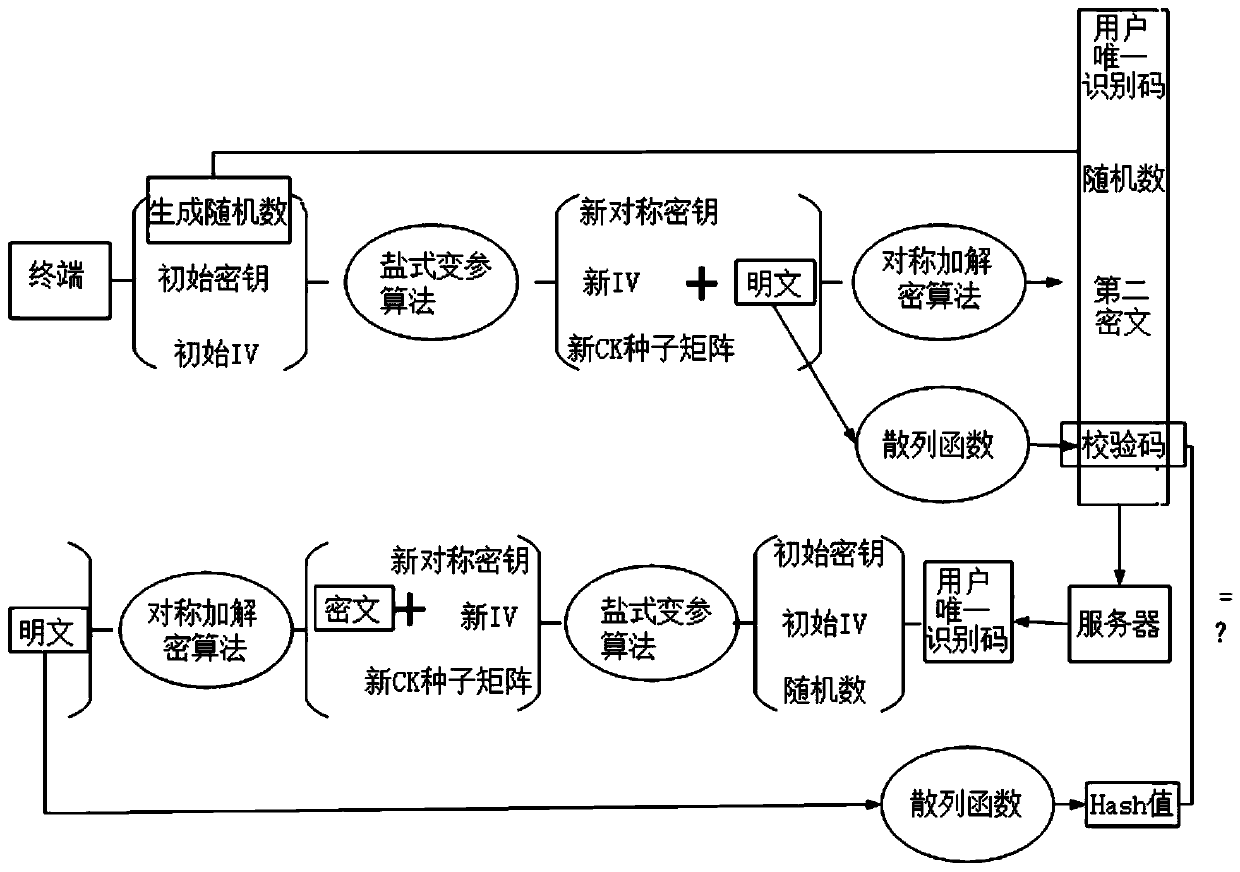
Security hybrid encryption method based on narrowband Internet of Things
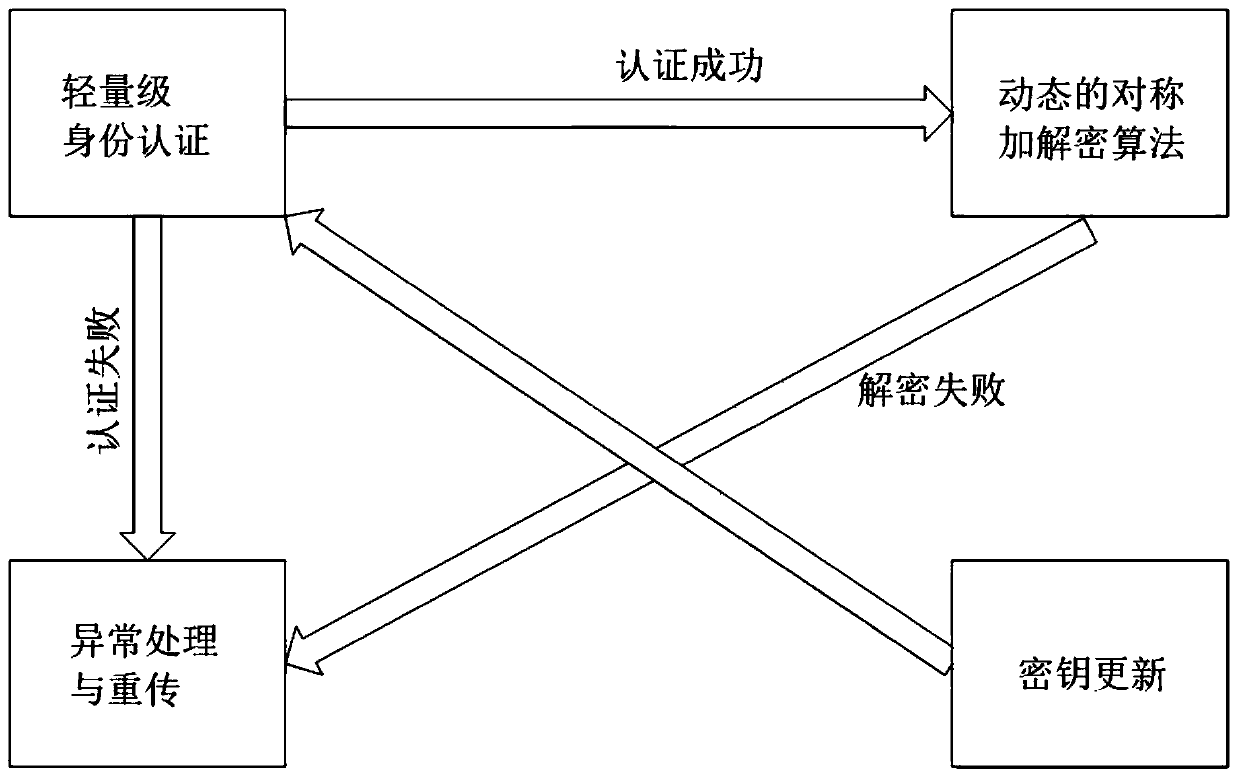
ActiveCN111541677AIncrease aggressivenessEasy to primeKey distribution for secure communicationMultiple keys/algorithms usageIdentity recognitionEngineering
The invention provides a security hybrid encryption method based on narrowband Internet of Things, which comprises the following steps of carrying out lightweight identity authentication on each terminal and a server, and realizing the identity authentication of the terminal and the transmission of an initial key and an initial IV vector by using unidirectional asymmetric encryption in the lightweight identity authentication, and after the identity authentication of the terminal succeeds, performing encryption communication between the terminal and the server by adopting a dynamic symmetric encryption and decryption algorithm, so that the symmetric encryption and decryption algorithm uses different symmetric keys and different structural parameters in each time of encryption communicationof each terminal. Lightweight identity recognition is adopted; on the basis of ensuring the security, the authentication time and the calculation consumption are greatly reduced, a dynamic symmetric encryption and decryption algorithm is adopted, a symmetric key and a set of structural parameters are ensured to be set at a time, the structural parameters of the algorithm are changed in a nonlinearmode under the condition that the large structure is not changed, and the capacity of the algorithm for resisting side channel attacks such as energy analysis is improved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
PMIPv6 network bidirectional access authentication system and method based on classification identity signature
ActiveCN103957524AEliminate message interactionFunction increaseSecurity arrangementNetwork data managementAuthentication systemTrust third party
The invention provides a PMIPv6 network bidirectional access authentication system and method based on a classification identity signature. The system comprises a plurality of mobile access gateways, a plurality of local mobile anchors, a trusted third party server and a plurality of mobile nodes. The method comprises the steps that trusted channels are built through the mobile access gateways and the local mobile anchors corresponding to the mobile access gateways; system public parameters are generated by the trusted third party server and published; when the mobile nodes are in a home network, the trusted third party server distributes private keys to the local mobile anchors, and the local mobile anchors distribute private keys to the mobile nodes or the mobile access gateways; when a certain mobile node leaves the home network and has access to a certain mobile access gateway of a foreign network for the first time, bidirectional access authentication is carried out; the mobile nodes are in the current access foreign network, and authentication is switched when the current mobile access gateway is switched into another mobile access gateway. According to the system and method, message exchange between the mobile nodes having access between the foreign network and the home network can be eliminated, and the bidirectional access authentication of the mobile nodes and the mobile access gateways is achieved.
Owner:NORTHEASTERN UNIV
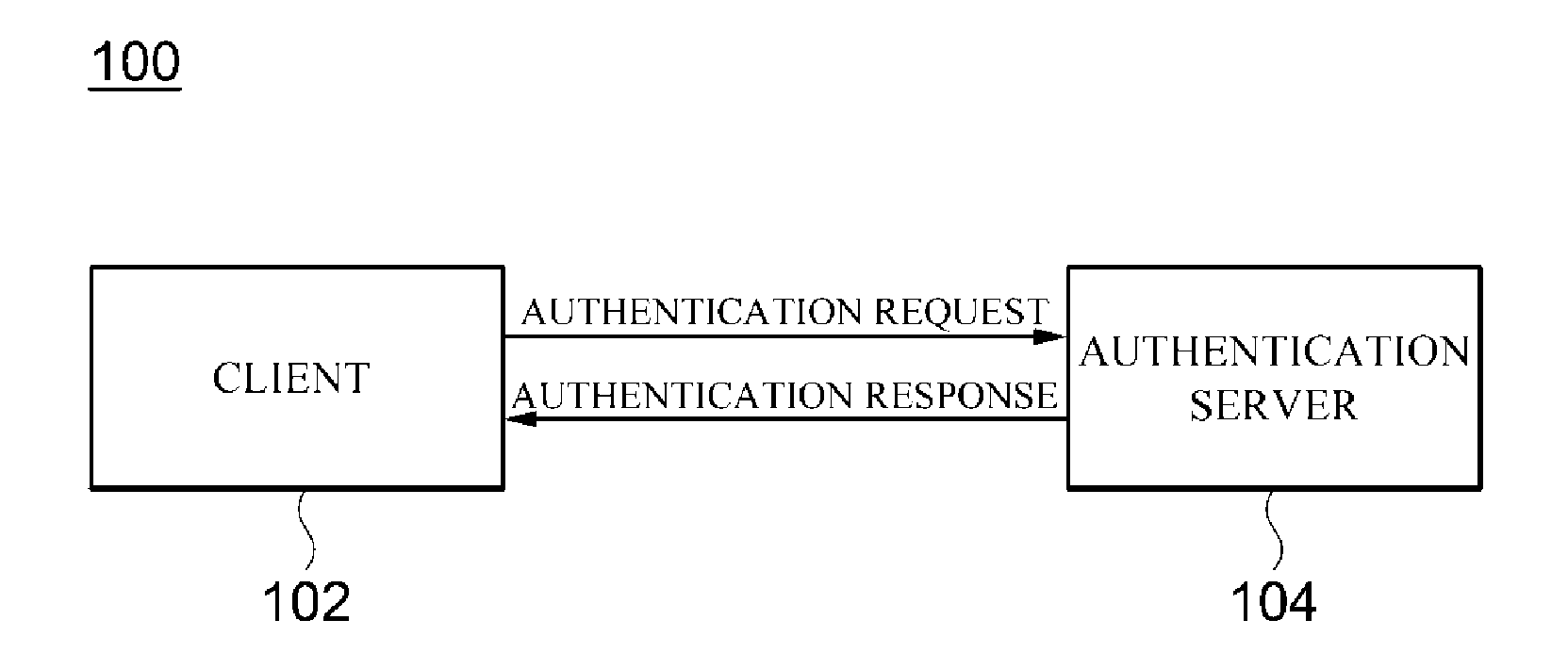
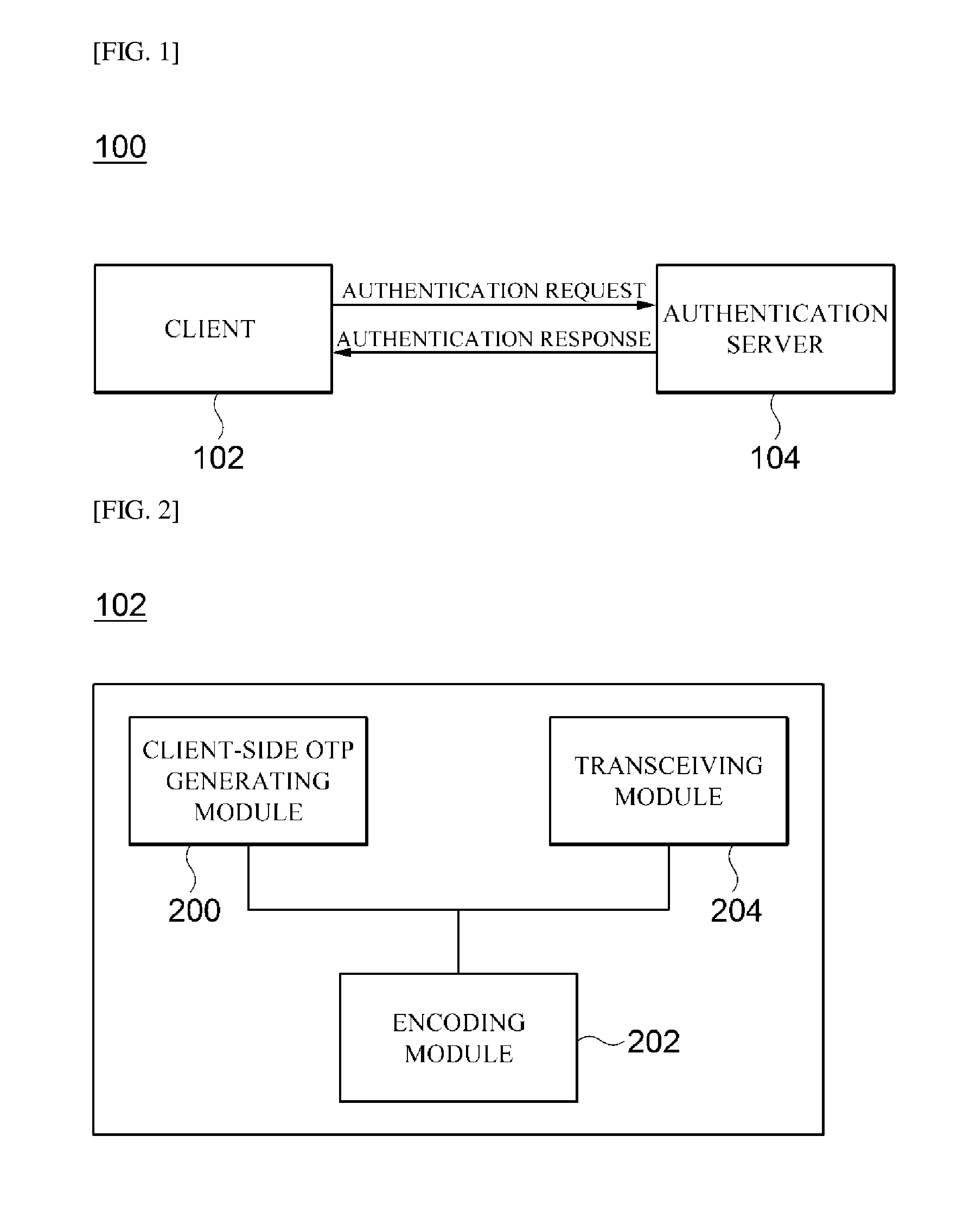
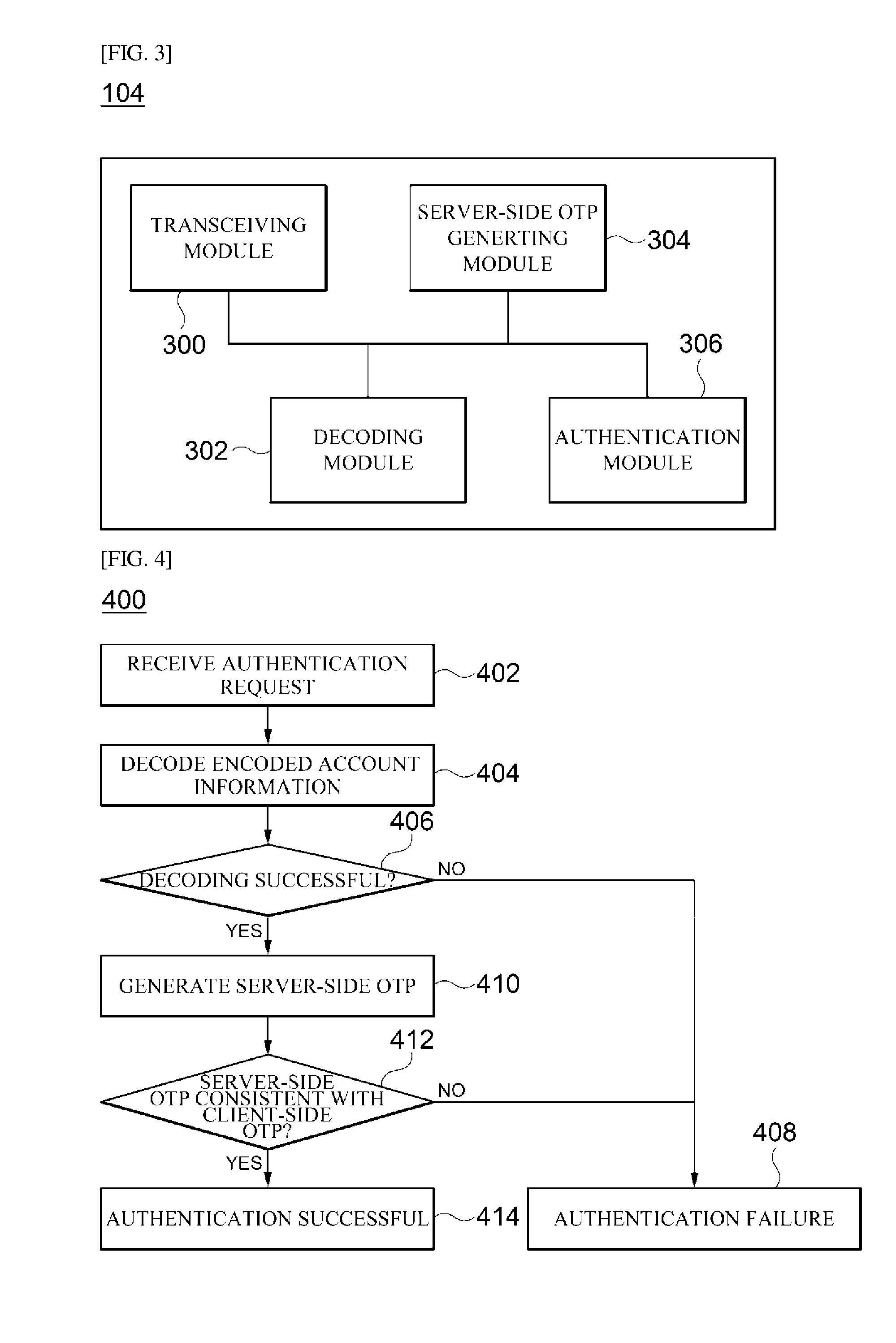
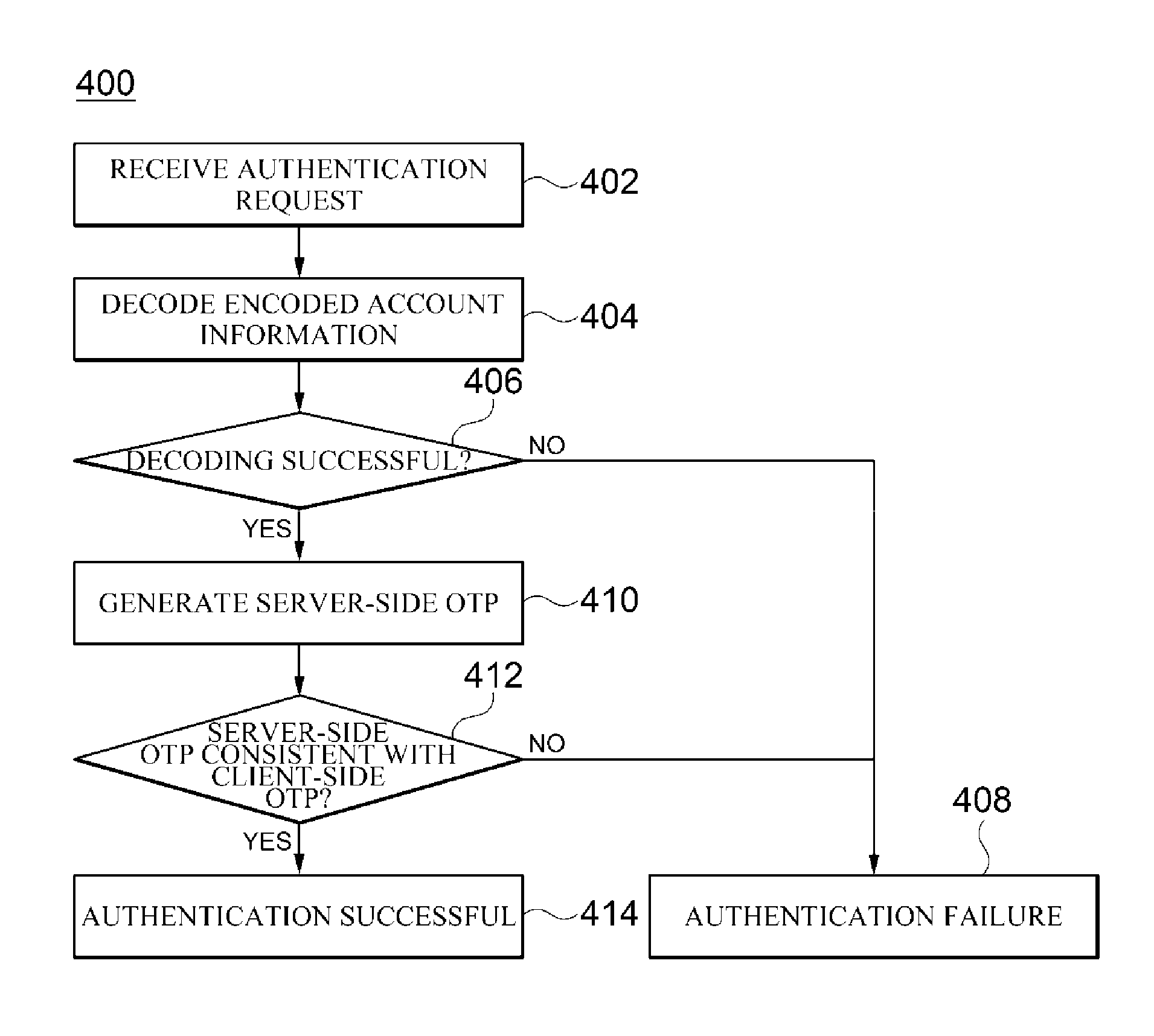
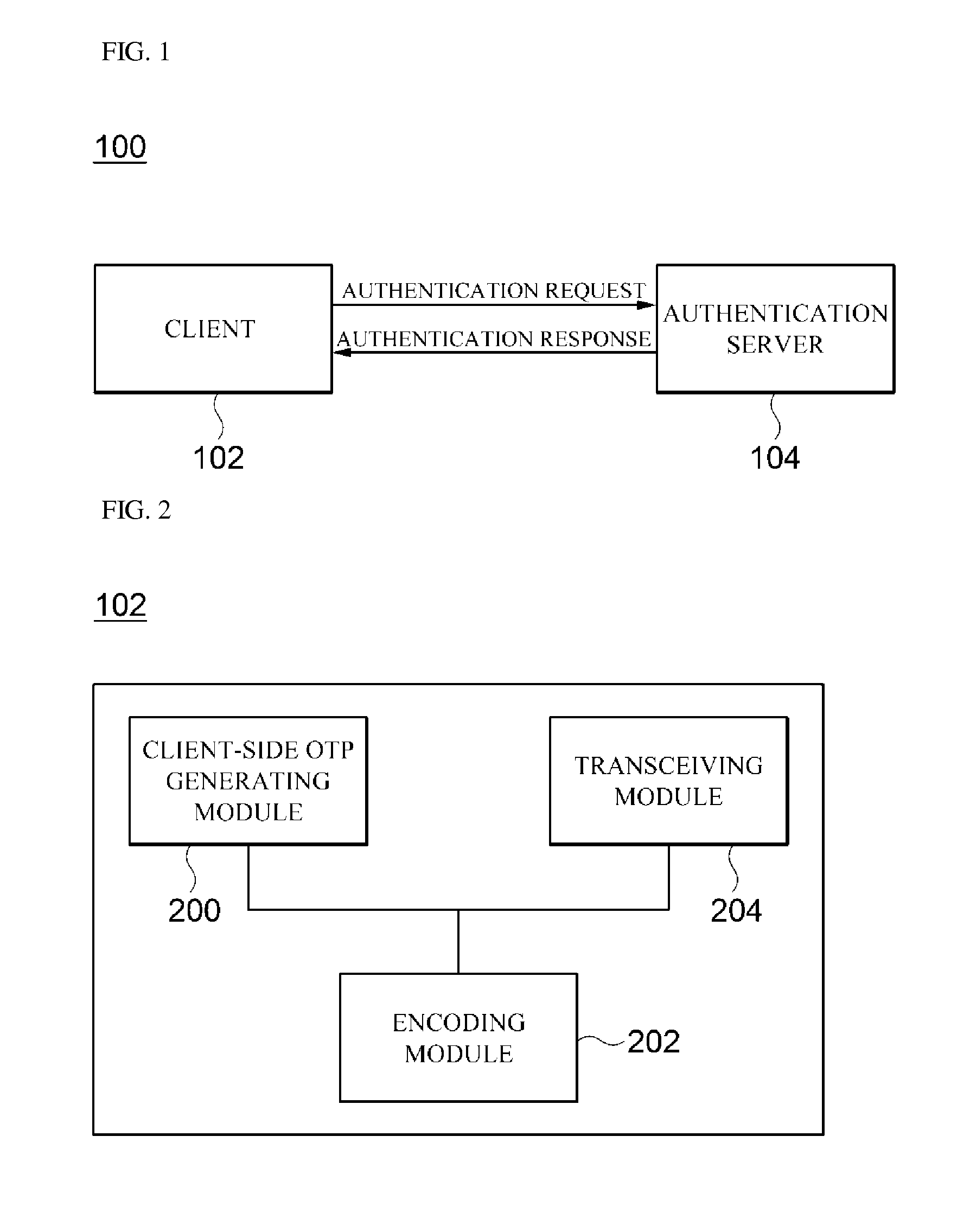
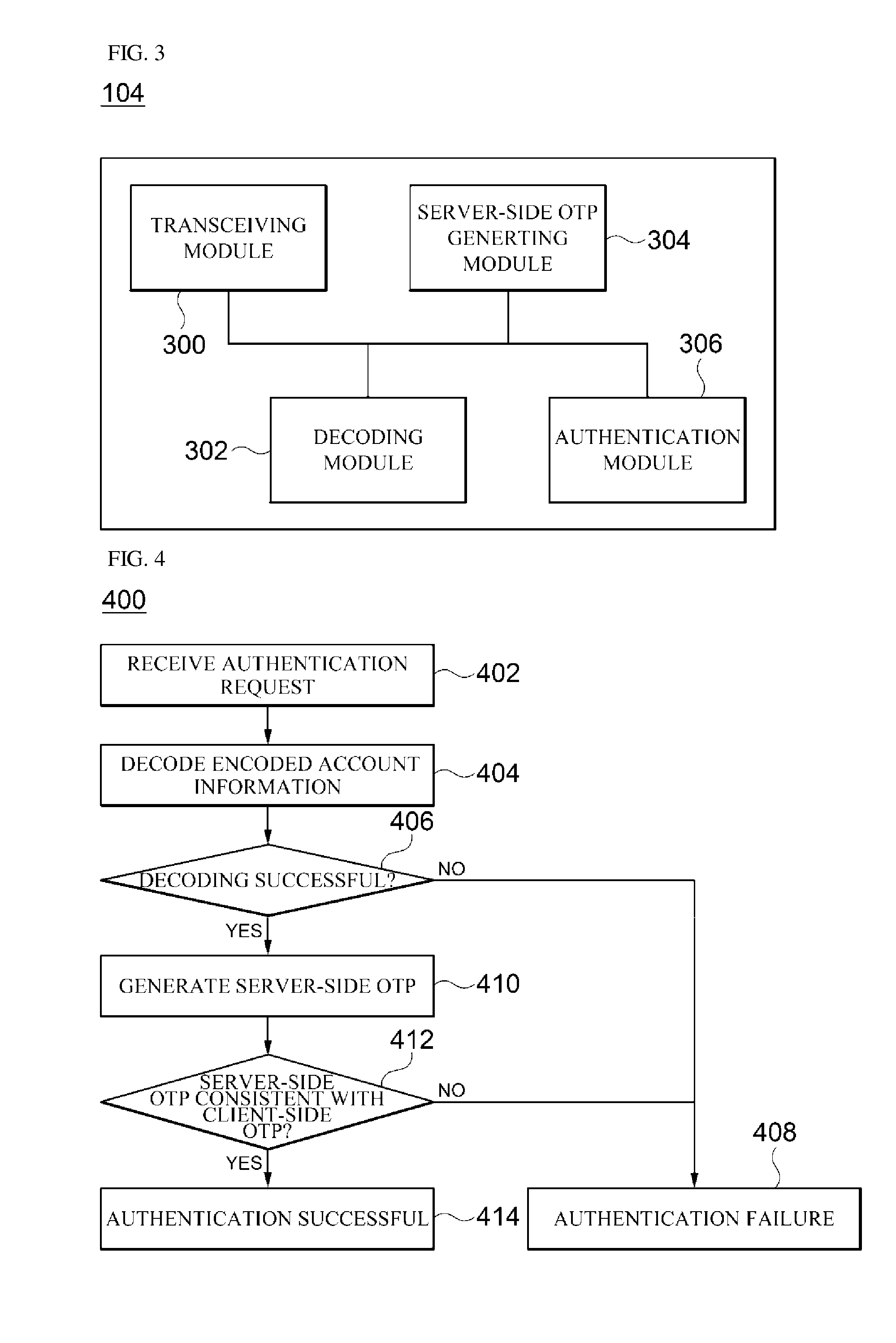
Otp-based authentication system and method
ActiveUS20150172280A1Shorten the timeAccurate timingSynchronising transmission/receiving encryption devicesDigital data processing detailsTransceiverAuthentication server
Disclosed is an authentication system and method. The authentication system according to one embodiment of the present disclosure comprises a transceiver for receiving an authentication request including a client-side OTP and encoded account information from a client, and transmitting the result of the authentication performed in accordance with the authentication request to the client; a decoder for decoding the encoded account information so as to compute the account information of the client and an authentication request time; a server-side OTP generator for generating a server-side OTP using the computed account information of the client and authentication request time; and an authenticator for comparing the client-side OTP included the authentication request and the server-side OTP in order to authenticate the client.
Owner:SAMSUNG SDS CO LTD
Subway riding system and method based on two-dimensional code and face image intercommunication
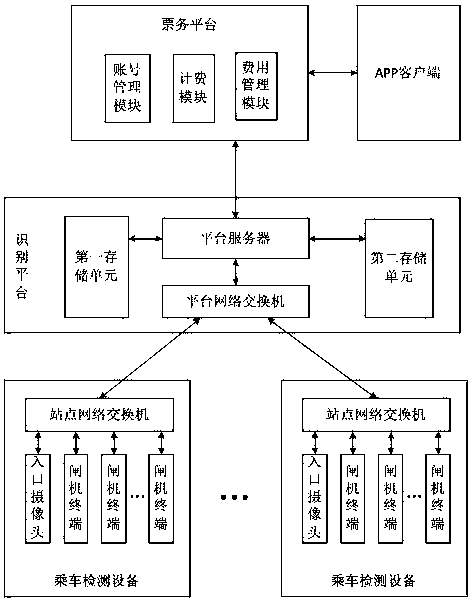
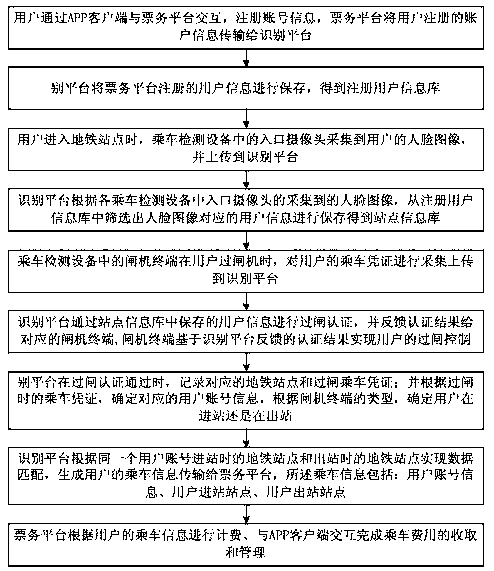
InactiveCN110659705ASave transit timeEasy rideData processing applicationsCo-operative working arrangementsSubway stationNetwork switch
The invention discloses a subway riding system and method based on two-dimensional code and face image intercommunication. The system comprises a ticket service platform, a recognition platform, riding detection devices located at different subway stations and an APP client installed on a user handheld mobile terminal, wherein the recognition platform is connected with the ticket service platformand the riding detection equipment of each subway station, and the ticket service platform is also connected with the APP client; the riding detection device comprises a station network switch, an entrance camera located at the entrance of a station, and a plurality of gate terminals. The recognition platform comprises a platform network switch, a platform server, a first storage unit and a secondstorage unit. Based on intercommunication of the face image and the two-dimensional code, the station-crossing time of the user can be saved, and much convenience is brought to riding of the user.
Owner:CHENGDU ZHIYUANHUI CULTURE & MEDIA CO LTD
A hybrid method based on simulation and experimental data to normalize PET data
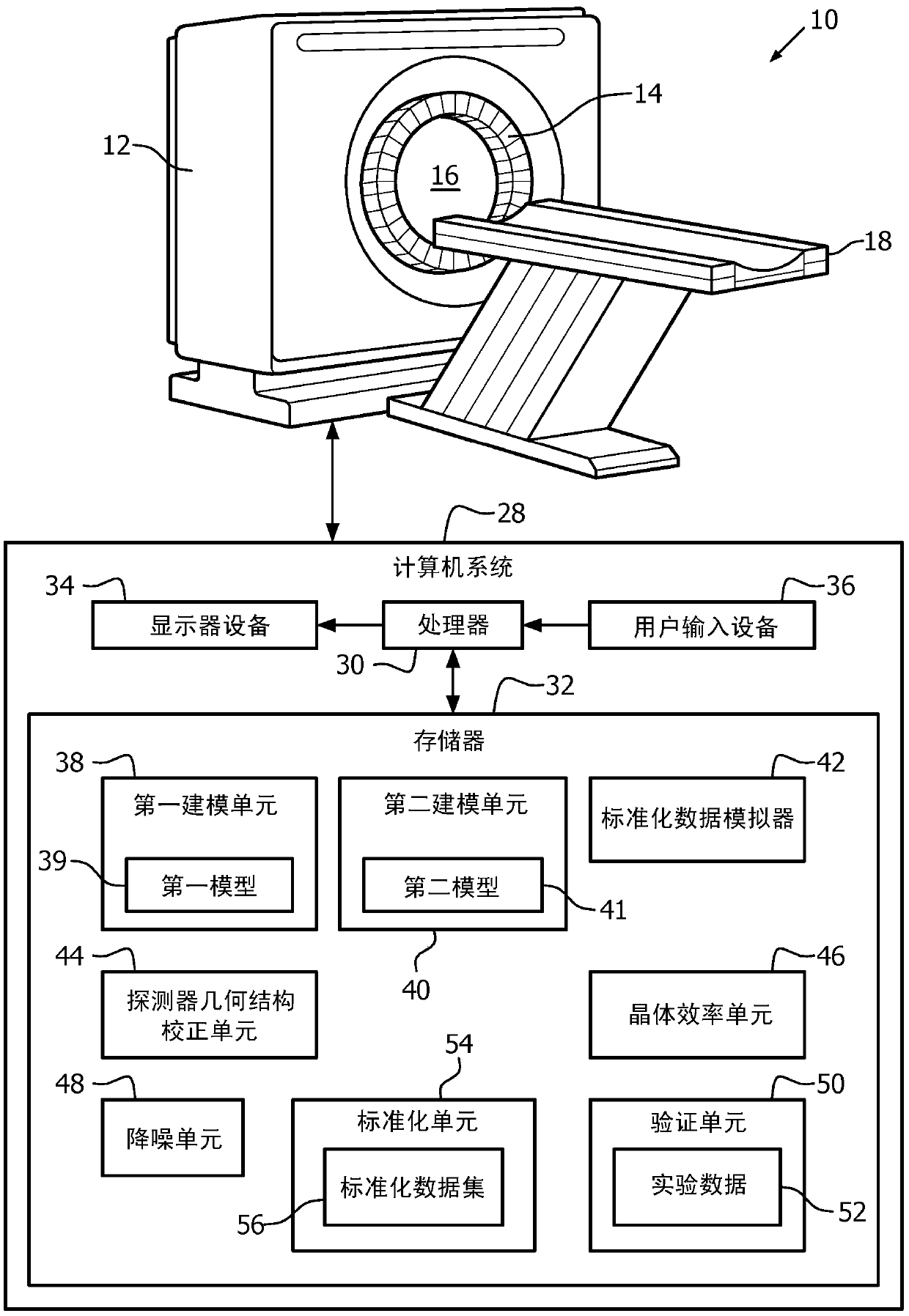
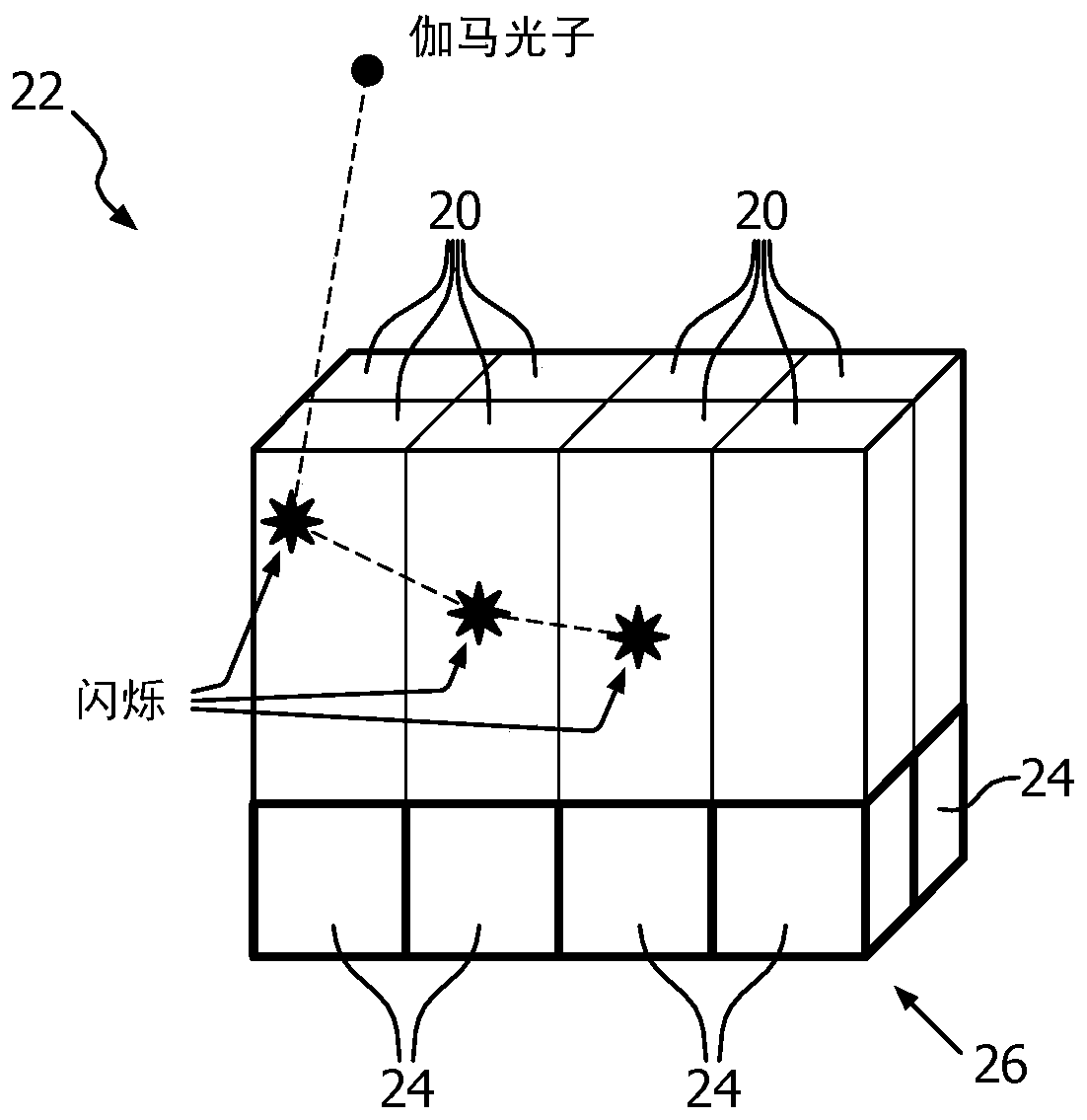
ActiveCN105556342AShorten the timeReduce certification timeTomographyX/gamma/cosmic radiation measurmentData setStructure of Management Information
A medical system (28) for normalization correction of an imaging system (10) includes a detector geometry correction unit (44), a crystal efficiency unit (46), and a normalization unit (54). The detector geometry correction unit (44) mathematically calculates a detector geometry correction component for a type of scanner (12) of interest. The crystal efficiency unit (46) configured to empirically determine a crystal efficiency component for at least one individual scanner (12). The normalization unit (54) generates a normalization data set (56) which corresponds to a normalization correction factor of the at least one individual scanner (12) in accordance with the detector geometry correction component and the crystal efficiency component.
Owner:KONINKLJIJKE PHILIPS NV
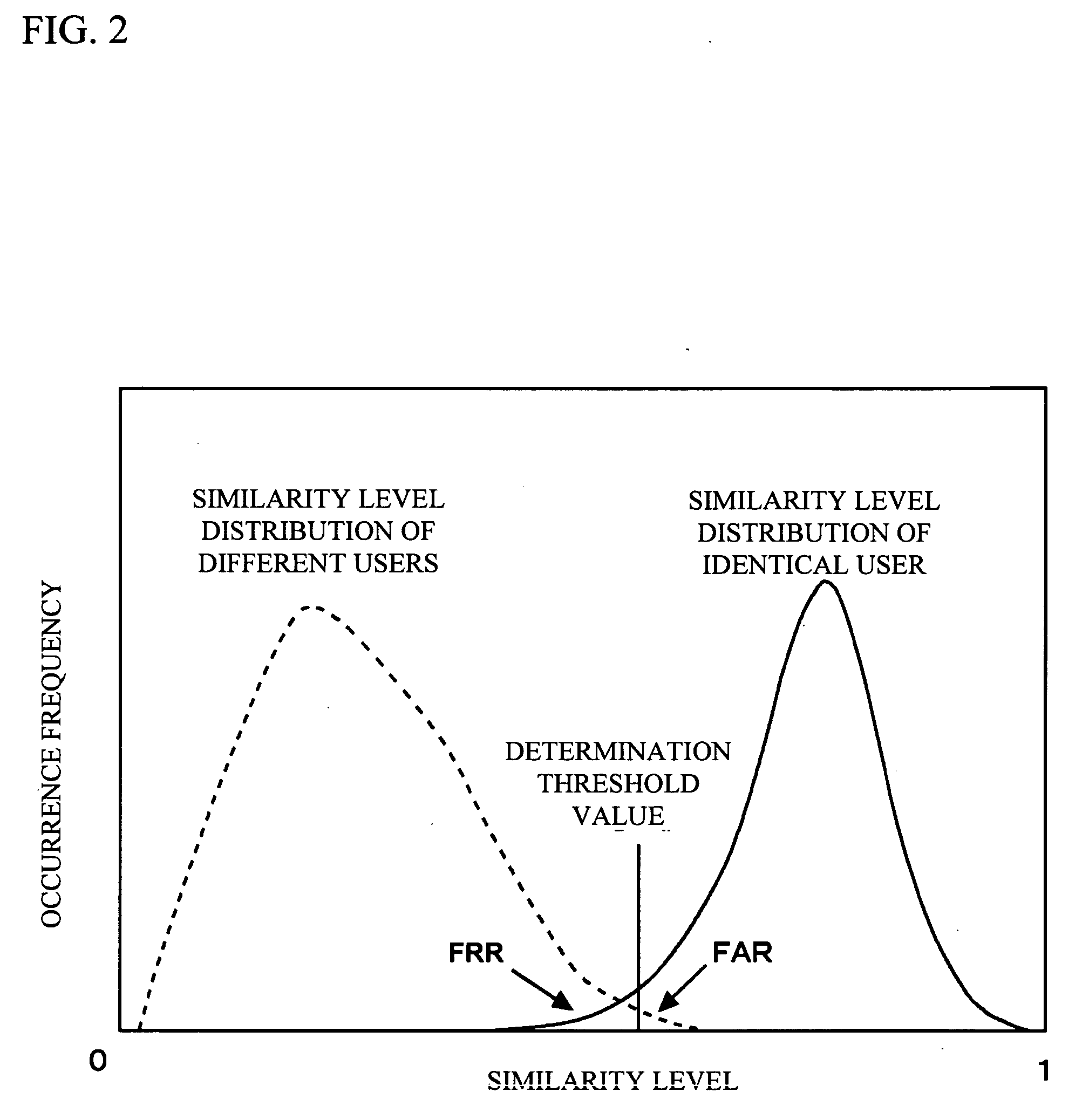
Biometric Authentication System and Biometric Authentication Method
ActiveUS20100158323A1Reduce certification timeCharacter and pattern recognitionInternal/peripheral component protectionInformation processingAuthentication system
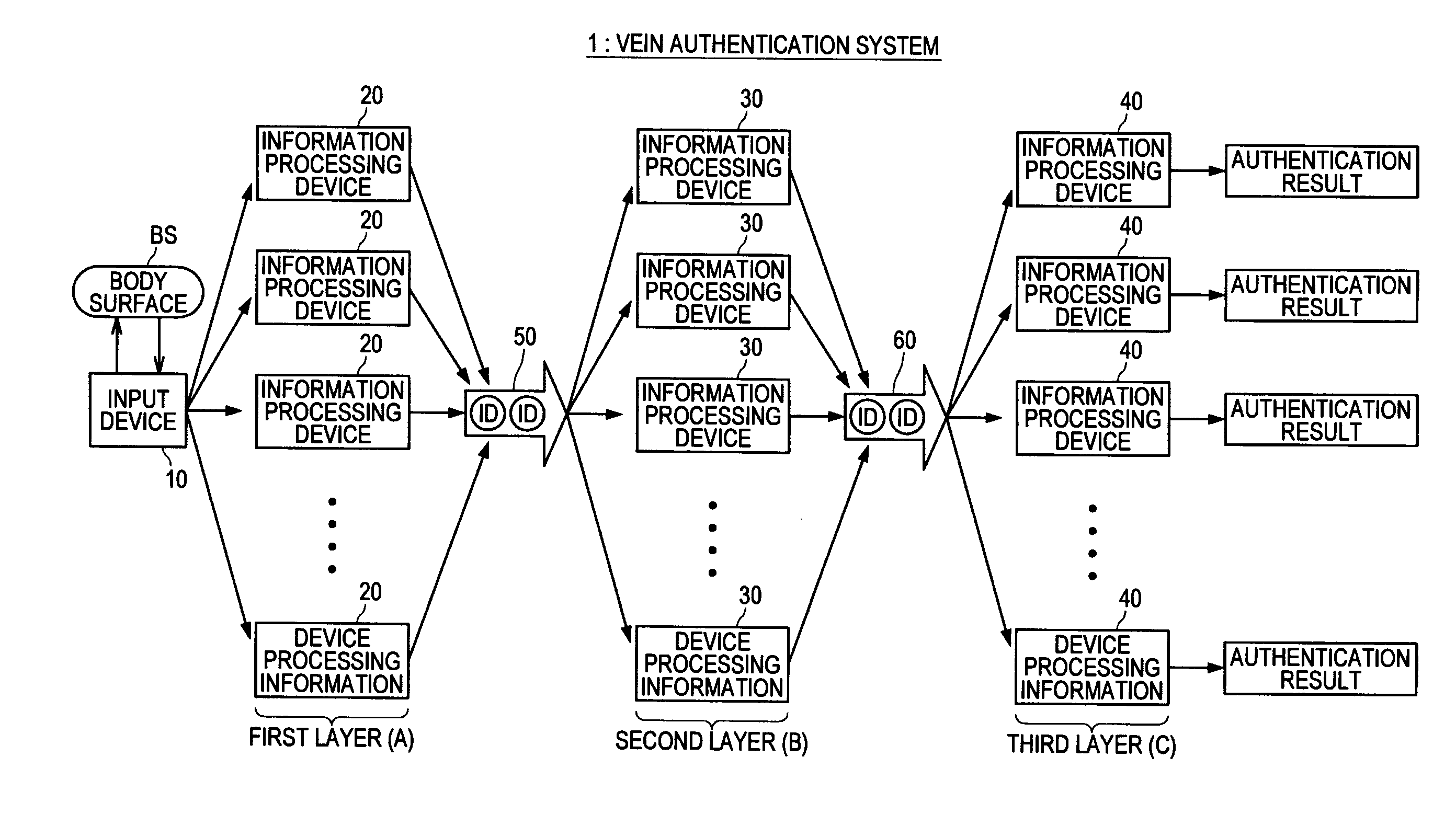
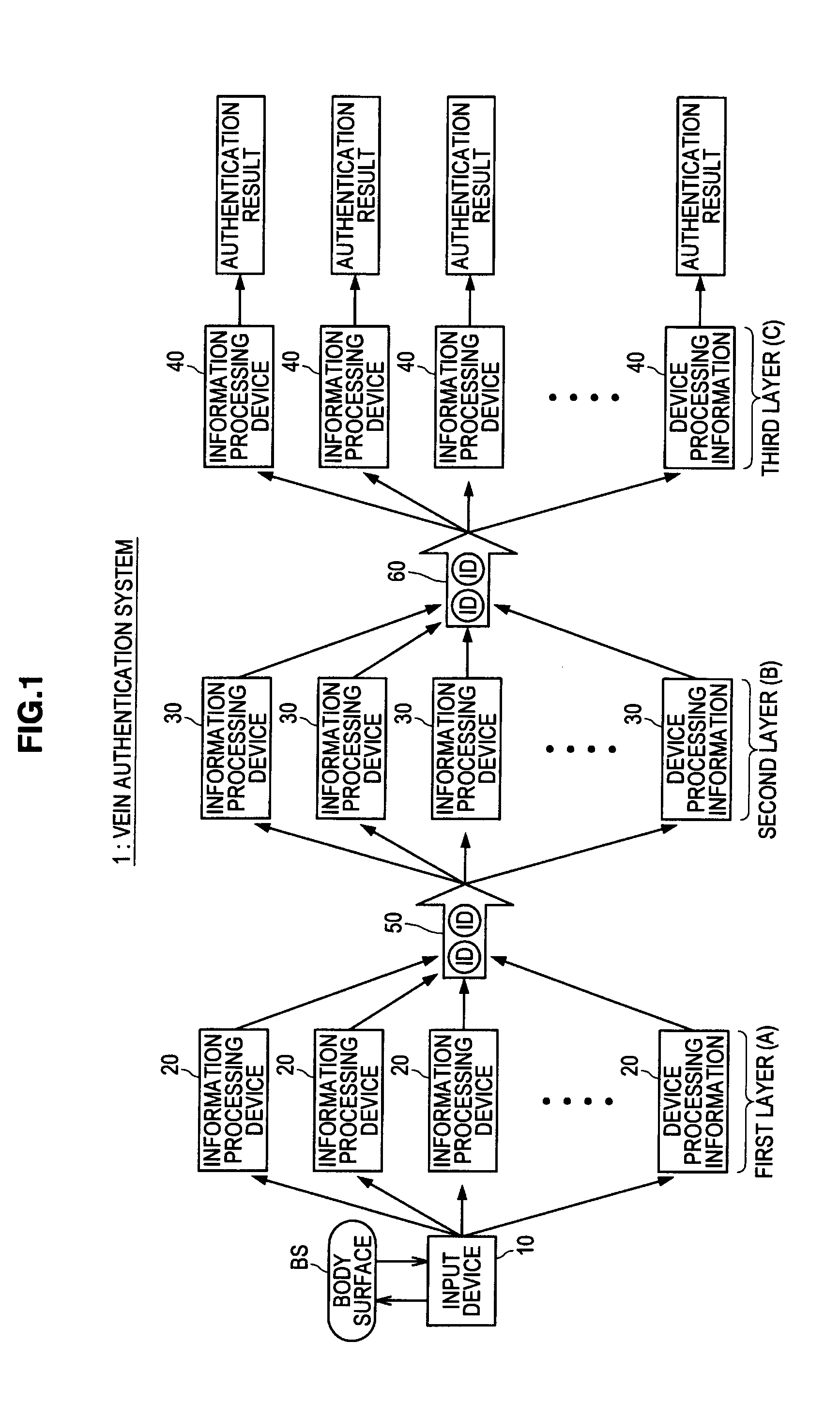
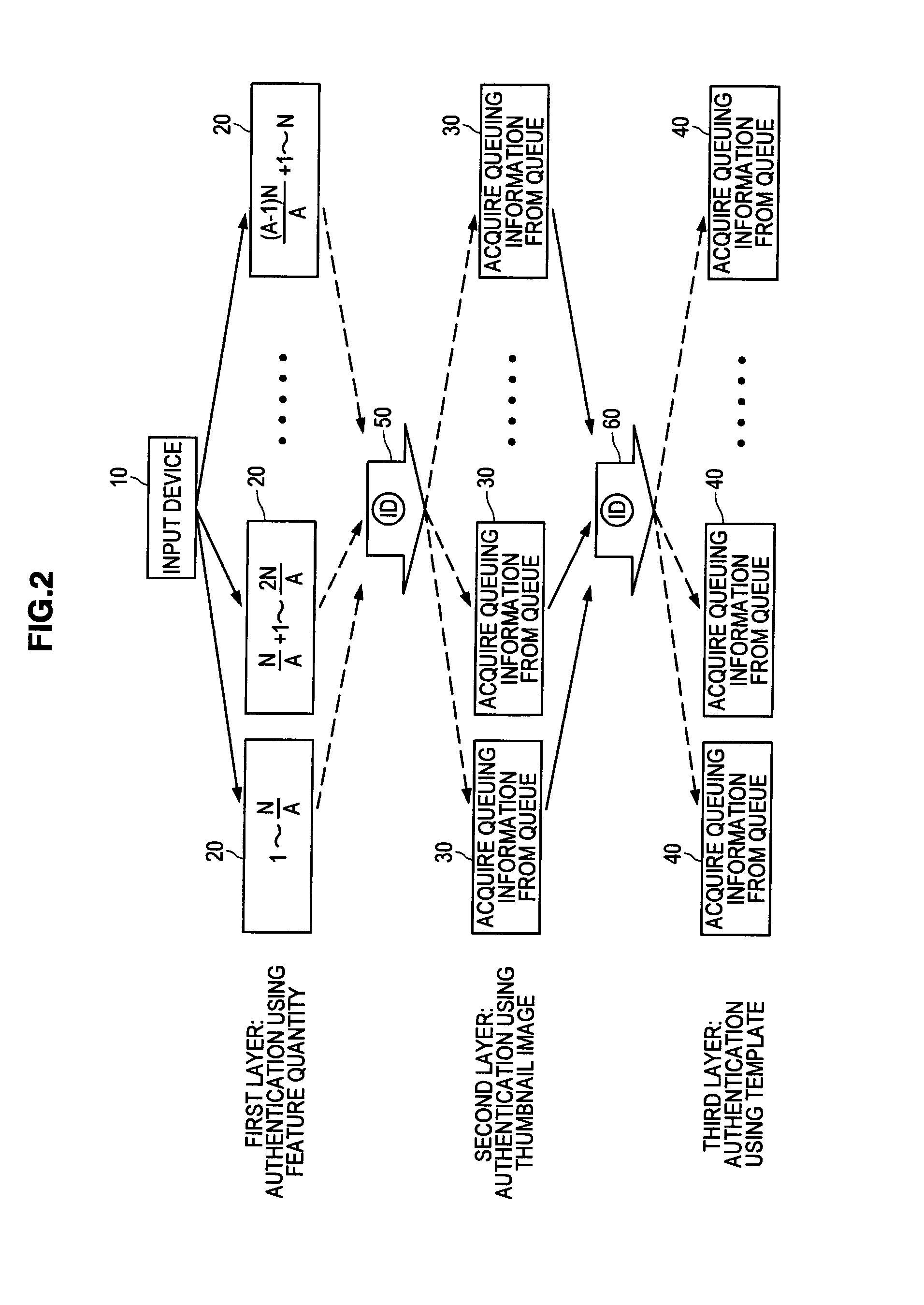
There is provided a biometric authentication system including a plurality of information processing devices divided to a first group for performing a primary authentication based on feature quantity information unique to a biological pattern of a user associated with biological information, and specifying an identification number assigned to the user, and a second group for performing a secondary authentication on the biological information that succeeded in the primary authentication based on the identification number and registered biological information registered in advance. The input biological information is transmitted to all information processing devices belonging to the first group, the biological information that succeeded in the primary authentication is added as queuing information to a queue, and each of the information processing devices belonging to the second group acquires the queuing information positioned at a head of the queue when the secondary authentication process being executed in the own device is terminated.
Owner:SONY CORP
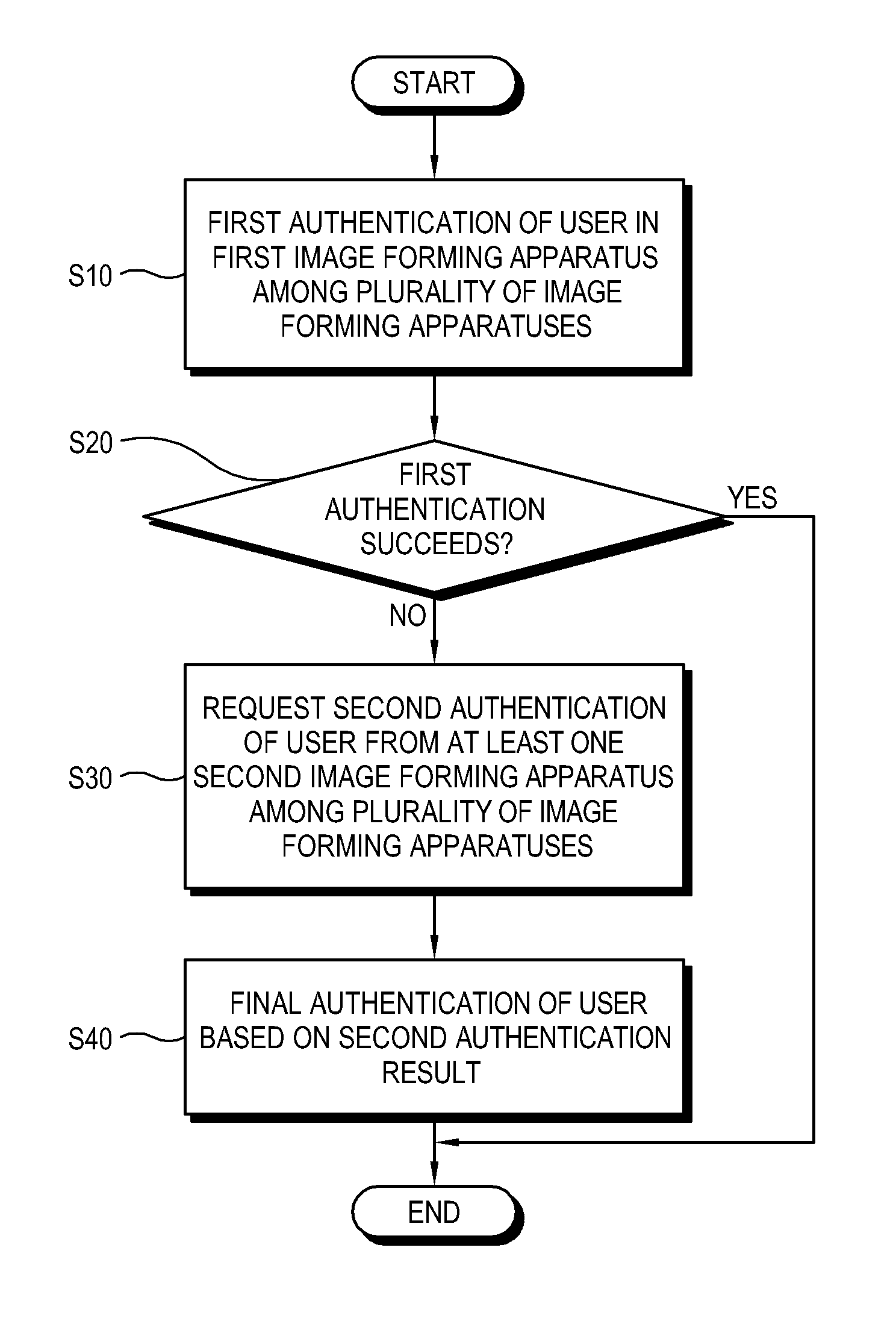
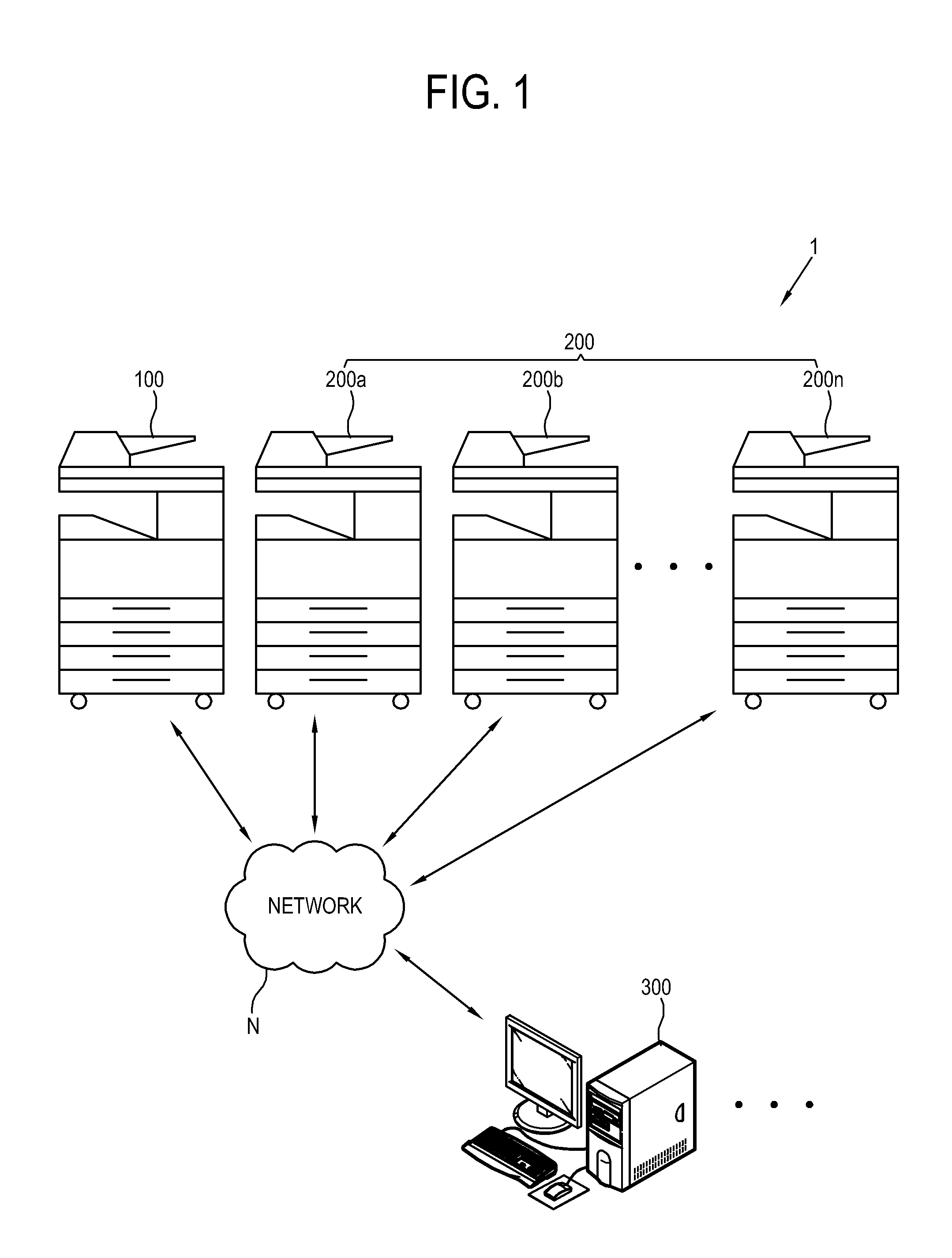
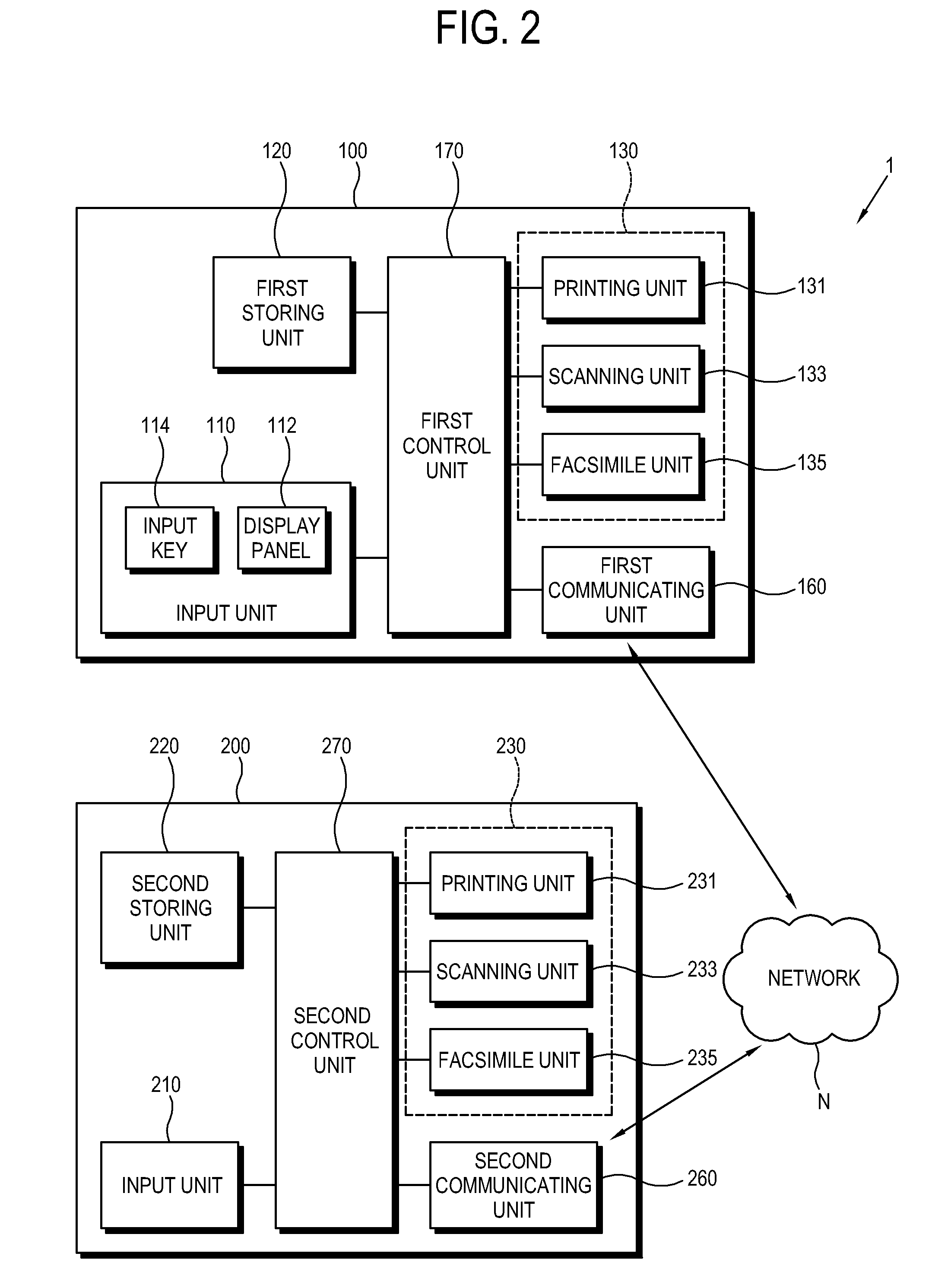
Image forming system, user authenticating method thereof, and control method thereof
ActiveUS8433214B2Improve convenienceImprove securityUser identity/authority verificationElectrographic process apparatusImage formationComputer science
An image forming system, and a user authenticating method and a control method thereof, the image forming system including a plurality of image forming apparatuses communicably connected and performing a first authentication of a user in a first image forming apparatus of the plurality of image forming apparatuses; requesting a second authentication of the user from at least one second image forming apparatus of the plurality of image forming apparatuses in response to the first authentication failing in the first image forming apparatus; and finally authenticating the user based on a result of the second authentication.
Owner:HEWLETT PACKARD DEV CO LP
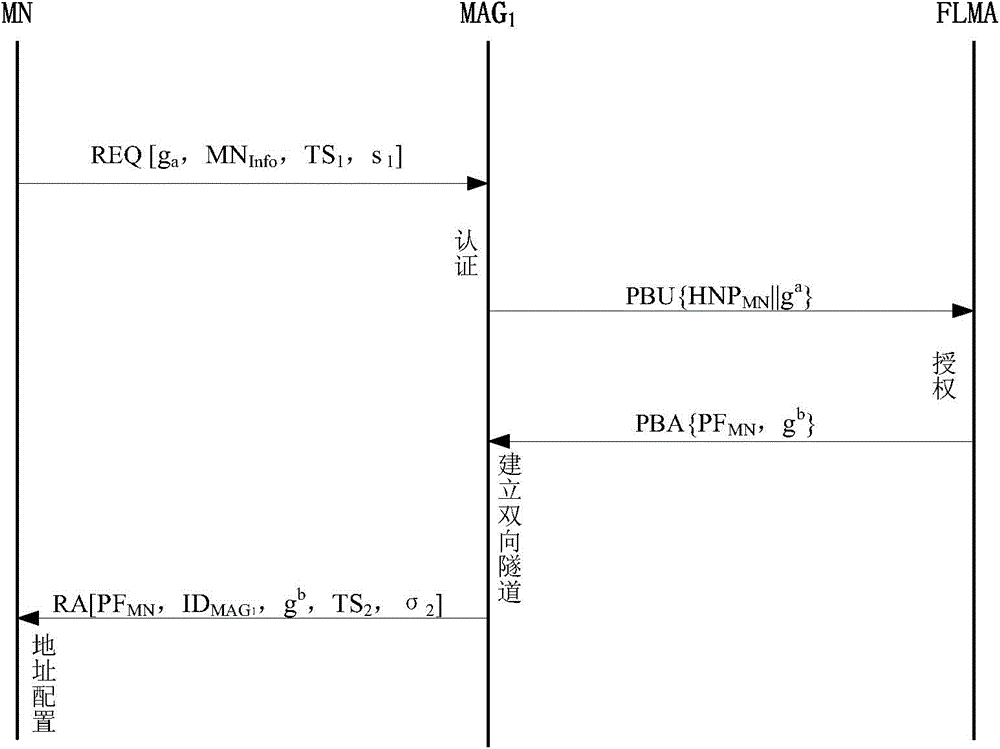
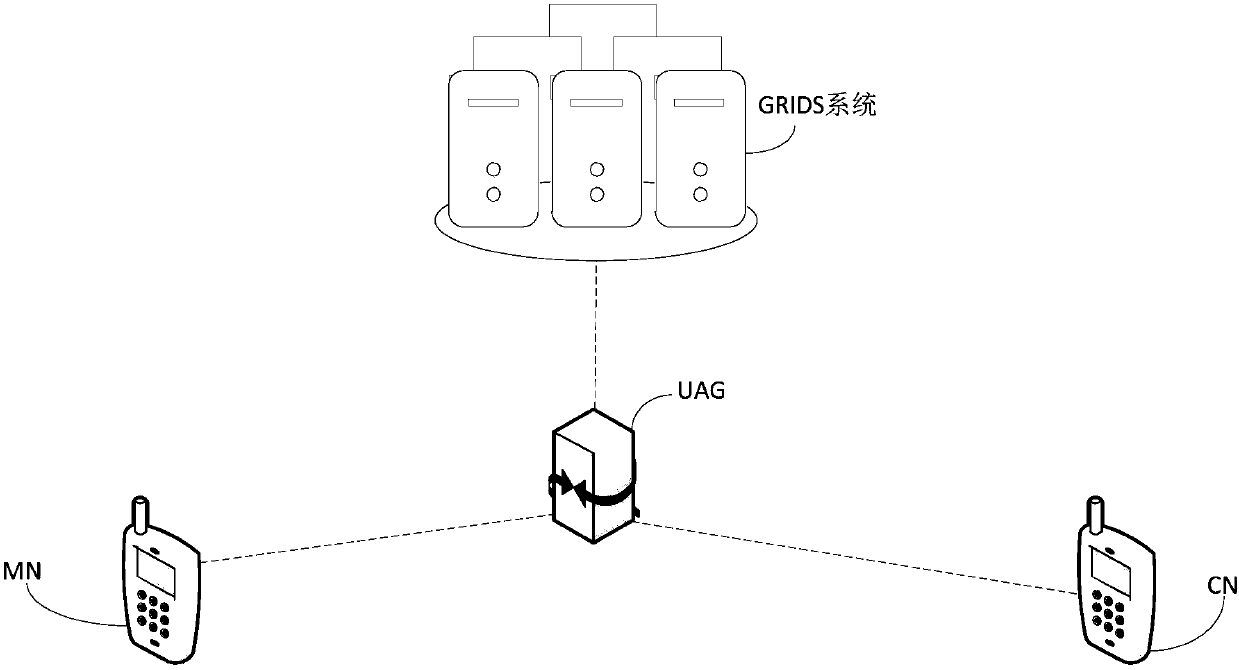
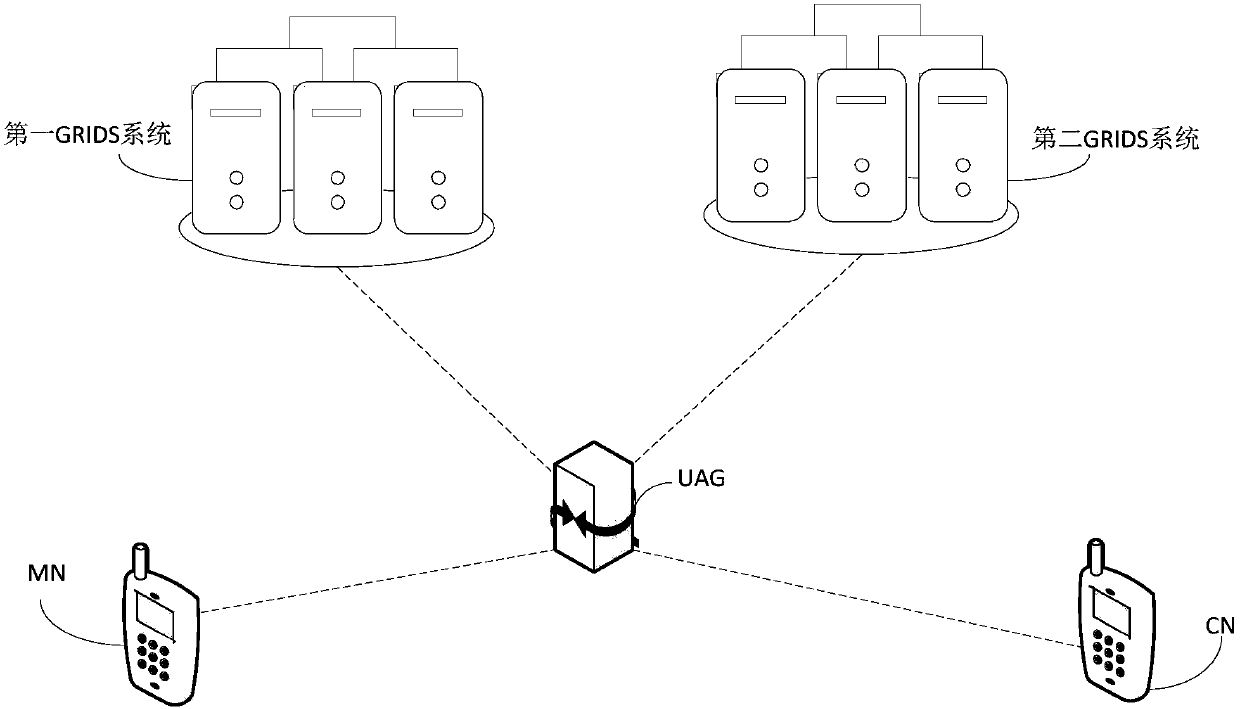
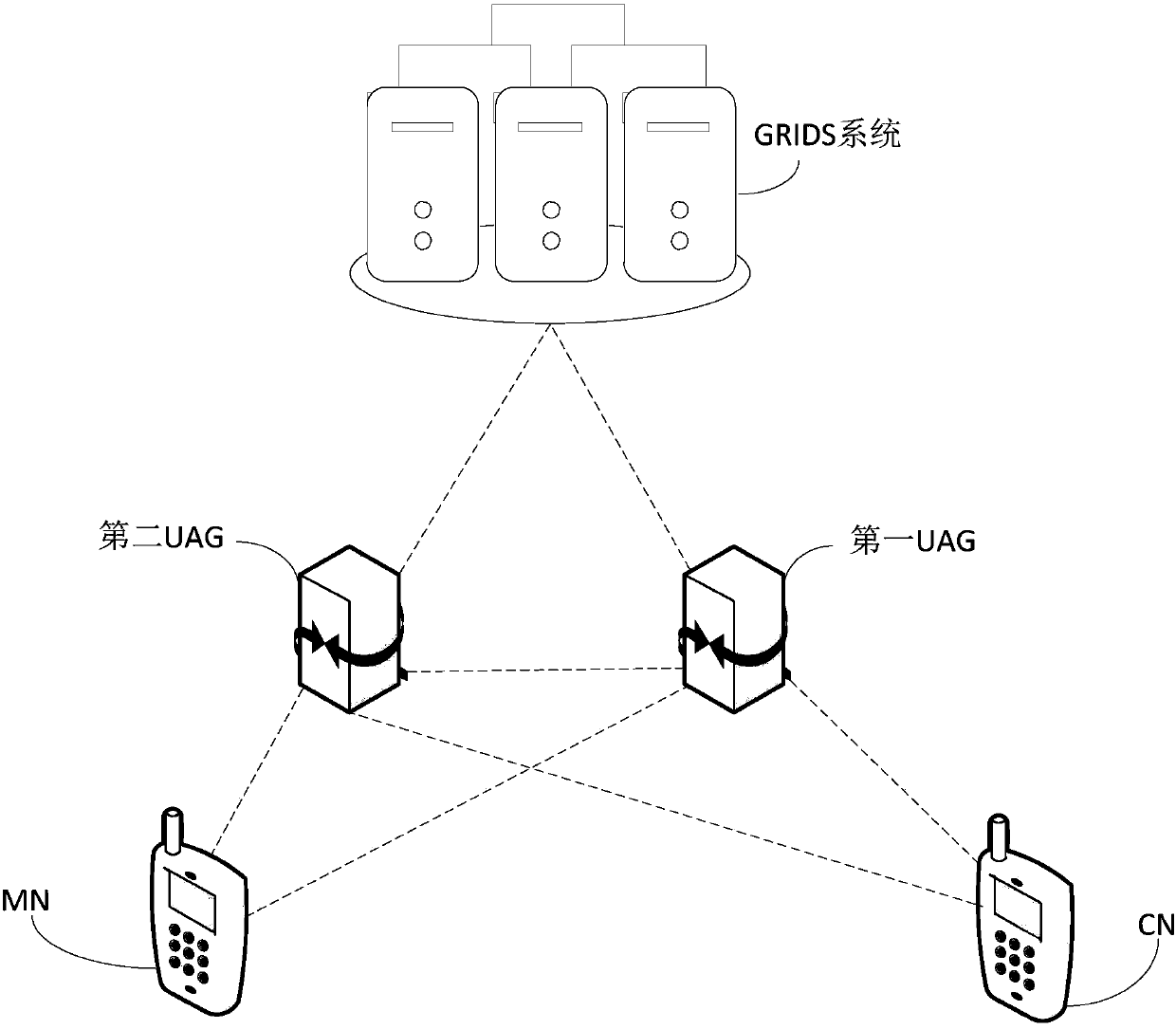
Security authentication method, related equipment and system
ActiveCN110035037AShort processReduce latencyUser identity/authority verificationSecurity arrangementCommunications systemSecurity authentication
The invention discloses a security authentication method, related equipment and a communication system. The communication system comprises MN, CN, UAG and GRIDS systems. The method comprises: the UAGreceiving a BU message sent by the MN and a signature of the MN, and the signature of the MN being obtained by calculating the BU message by using a private key of the MN; calculating the BU message,the signature of the MN and the identifier of the UAG by using the private key of the UAG to obtain the signature of the UAG; sending the BU message, the signature of the MN and the signature of the UAG to the CN; receiving a BU response message and a signature of the CN sent by the CN, wherein the BU response message comprises a result obtained by verifying the signatures of the UAG and the MN; and sending the BU response message and the signature of the CN to the MN. By implementing the method and the device, the security authentication problem after the ID is added to the network layer canbe solved, rapid authentication and network switching based on the ID are realized, the authentication process is simplified, the authentication efficiency is improved, and the switching time delay isreduced.
Owner:HUAWEI TECH CO LTD
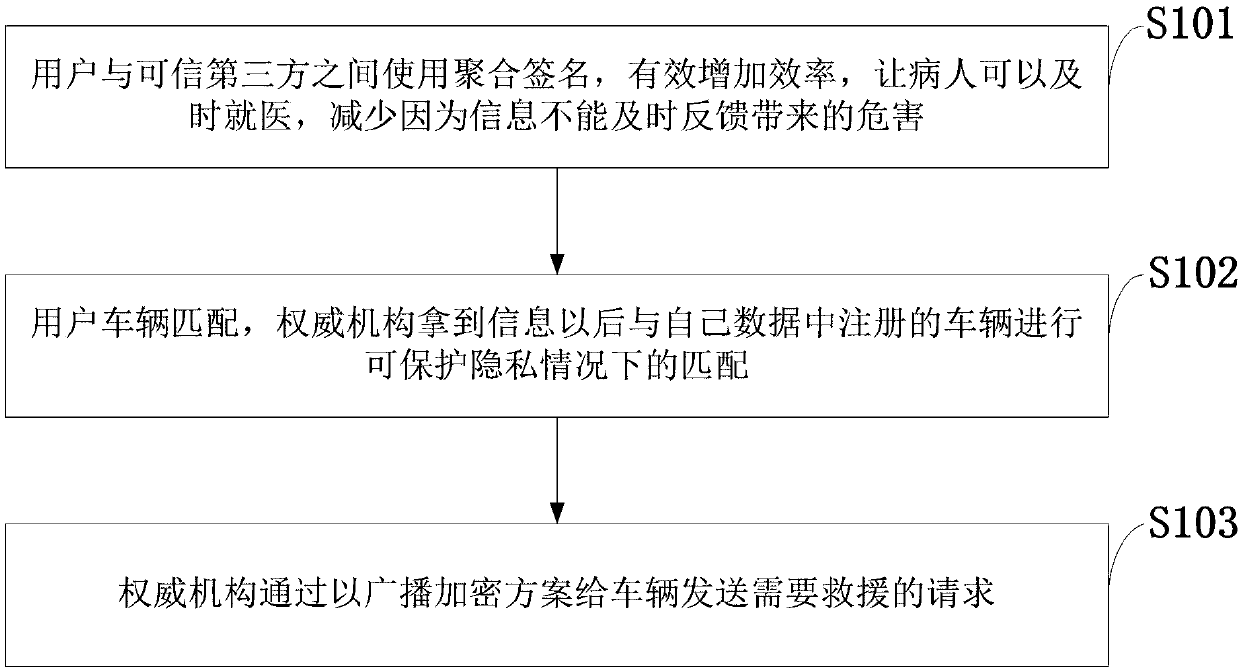
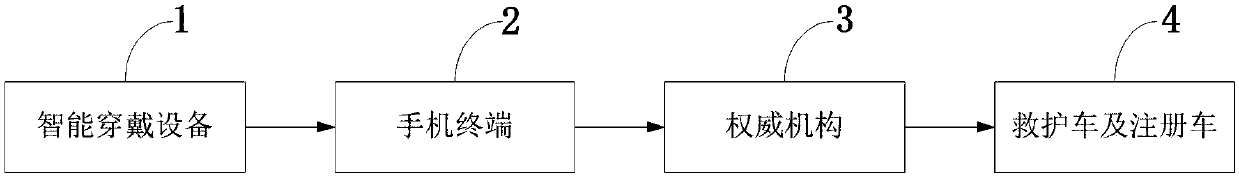
Intelligent medical assistance method and system based on IoV (Internet of Vehicles)
ActiveCN108401010ASafe and fast authenticationFast authenticationMedical communicationUser identity/authority verificationThe InternetTrusted third party
The invention belongs to the technical field of a transmission control procedure, such as a data chain level control procedure, and discloses an intelligent medical assistance method and system basedon the IoV (Internet of Vehicles). The intelligent medical assistance method based on the IoV comprises the steps that: an aggregate signature is used between a user and a trusted third party; user vehicle matching is carried out, and after receiving information, an authority carries out matching in a case that privacy can be protected with a vehicle registered in data of the authority; and the authority sends a rescue request to the vehicle by a broadcast encryption scheme. Verification between a patient and the authority is carried out in a mode of the aggregate signature; the authority carries out matching with the registered vehicle in a case of not leaking privacy of the patient by a matching algorithm; and the authority notifies the registered vehicle to carry out rescue in a broadcast encryption mode. According to the invention, the intelligent medical assistance method and system are developed on the basis of cryptography; the user can be checked anytime and anywhere and can berescued at the critical moment, and meanwhile, privacy safety of the user is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
Fast authentication and access control system for mobile networking
InactiveUS8065518B1Easy to switchReduce certification timeSecurity arrangementSecuring communicationExpiration TimeConditional access
Owner:AT & T INTPROP II LP
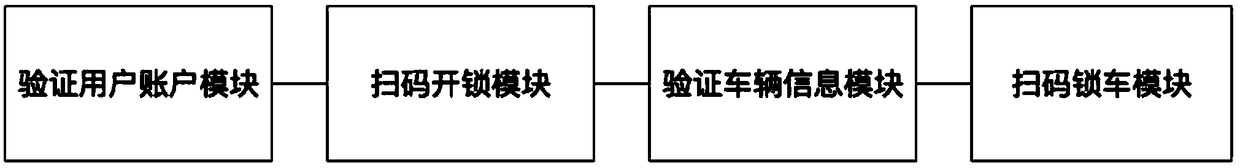
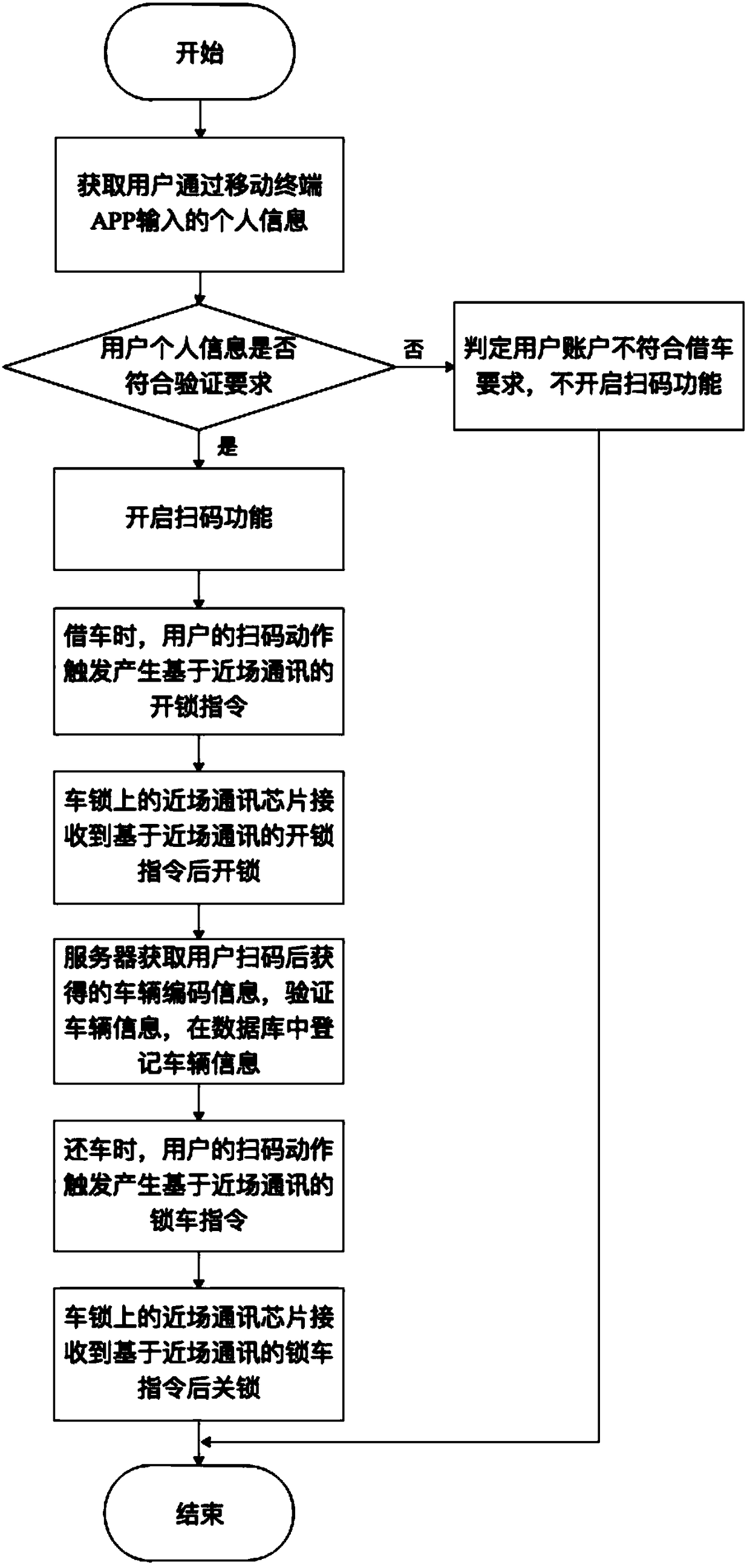
Shared bicycle borrowing and returning method and system based on account authentication
InactiveCN108961583AReduce certification timeAvoid unrecognizedApparatus for meter-controlled dispensingIndividual entry/exit registersSingle vehicleBicycle sharing
The invention discloses a shared bicycle borrowing and returning method and system based on account authentication. The shared bicycle borrowing and returning system comprises a user account verification module, a code-scanning unlocking module and a code-scanning bicycle locking module. By means of the method and the system, the technical problem that the bicycle borrowing time is long since thetime of authenticating a two-dimensional code of a shared bicycle is long and the two-dimensional code cannot be recognized is solved.
Owner:HANGZHOU HOUBO TECH CO LTD
Partitioned backing store implemented in a distributed database
PendingUS20210365477A1Reduce certification timeReduce dataDatabase updatingDatabase management systemsEngineeringTimestamping
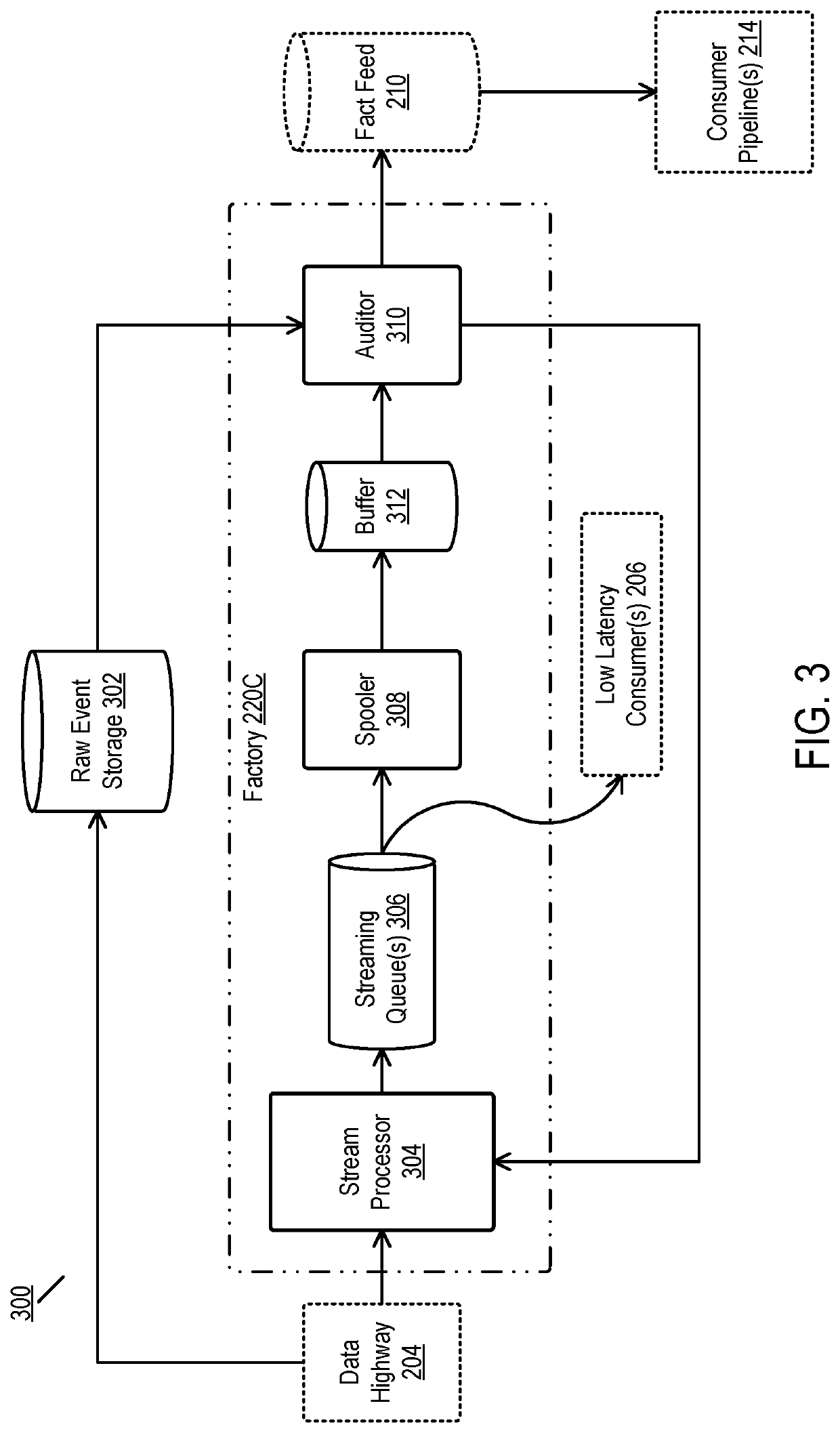
Disclosed are embodiments for providing batch performance using a stream processor. In one embodiment, a method is disclosed comprising receiving an event that includes an event key and a timestamp. The method then generates a partition value and time bucket value, the partition value generated based on the event key and the time bucket value generated based on the timestamp. The event key, partition value, and time bucket value are then combined to form a database key and used in a command to a database.
Owner:YAHOO ASSETS LLC
Identity authentication method, system and device and computer storage medium
ActiveCN111552942AReduce processing burdenReduce the likelihood of authentication failuresFinanceDigital data authenticationEngineeringAuthentication server
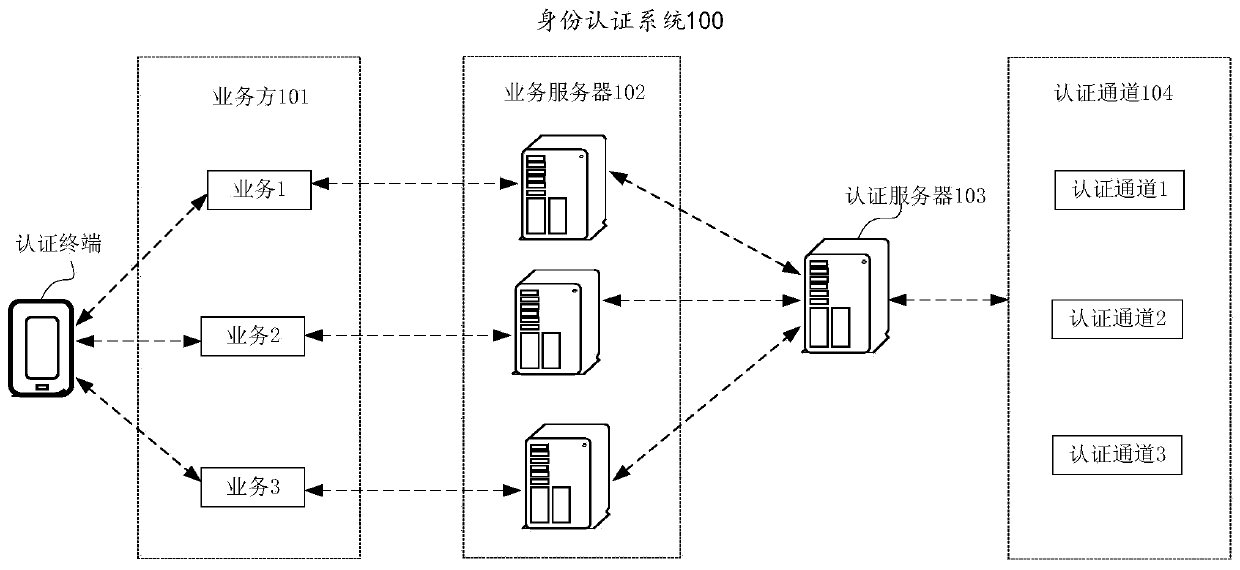
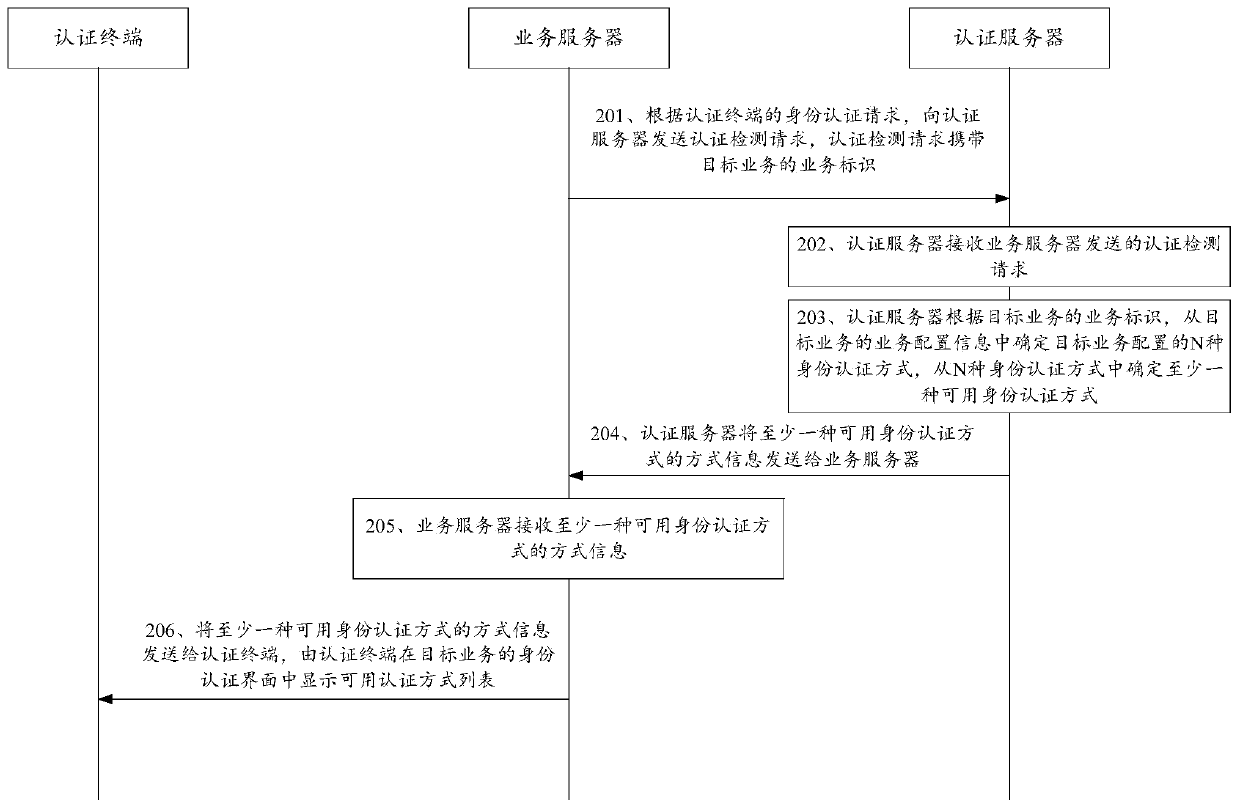
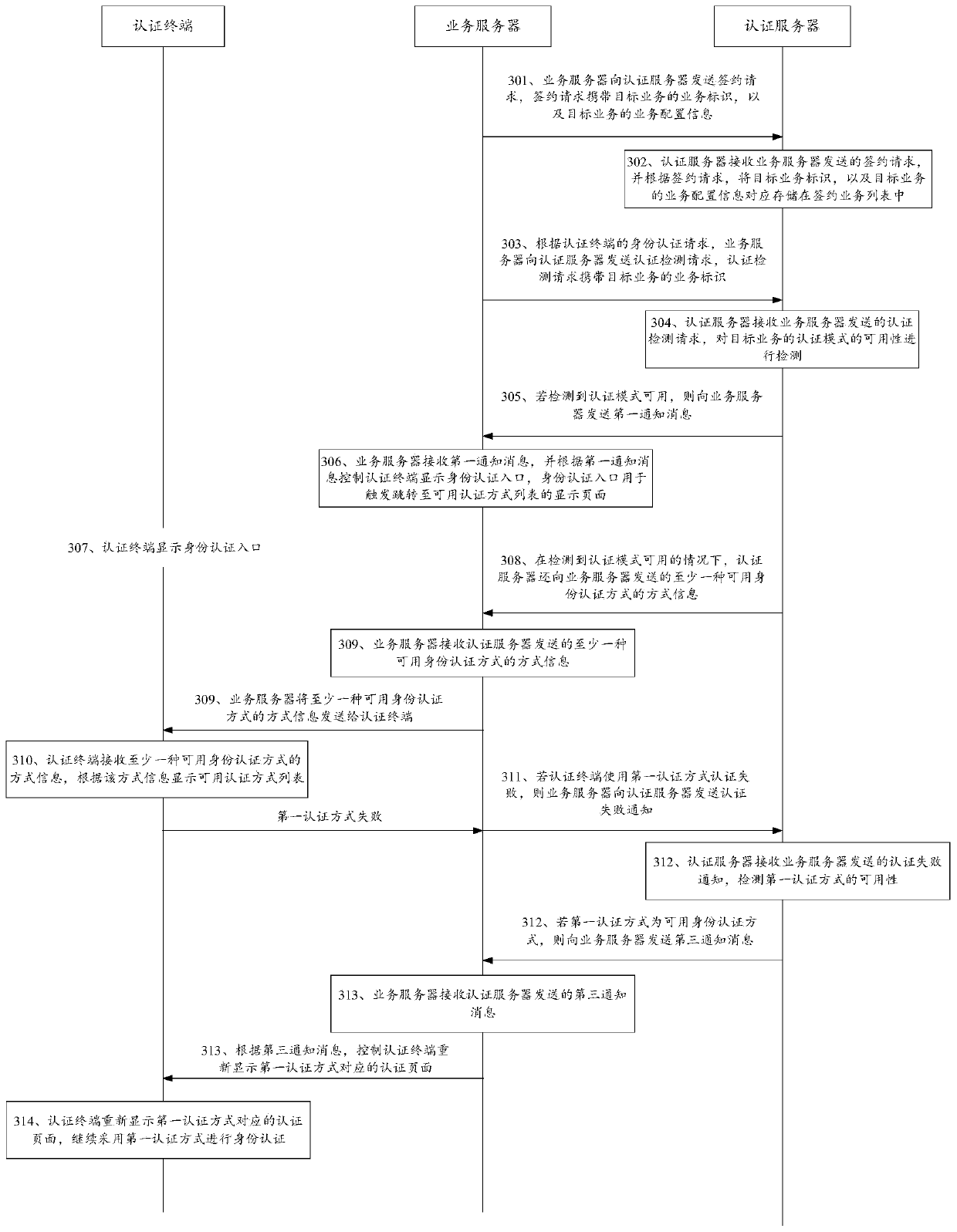
The invention discloses an identity authentication method, system and device and a computer storage medium, and belongs to the field of business processing, wherein the method comprises the followingsteps: forming a substrate; the authentication server receives an authentication detection request sent by the service server, according to a service identifier of a target service carried by the authentication detection request, determining N identity authentication modes configured by the target service from the service configuration information of the target service, at least one available identity authentication mode is determined from the N identity authentication modes, mode information of the at least one available identity authentication mode is sent to the authentication terminal through the service server, the authentication terminal displays an available authentication mode list, and the available authentication mode list comprises the at least one available identity authentication mode. That is to say, the authentication server performs availability detection on the identity authentication modes in a unified manner; unavailable authentication modes can be screened out; onlythe available authentication modes are presented to the user; the possibility of authentication failure is reduced; and the authentication time is saved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
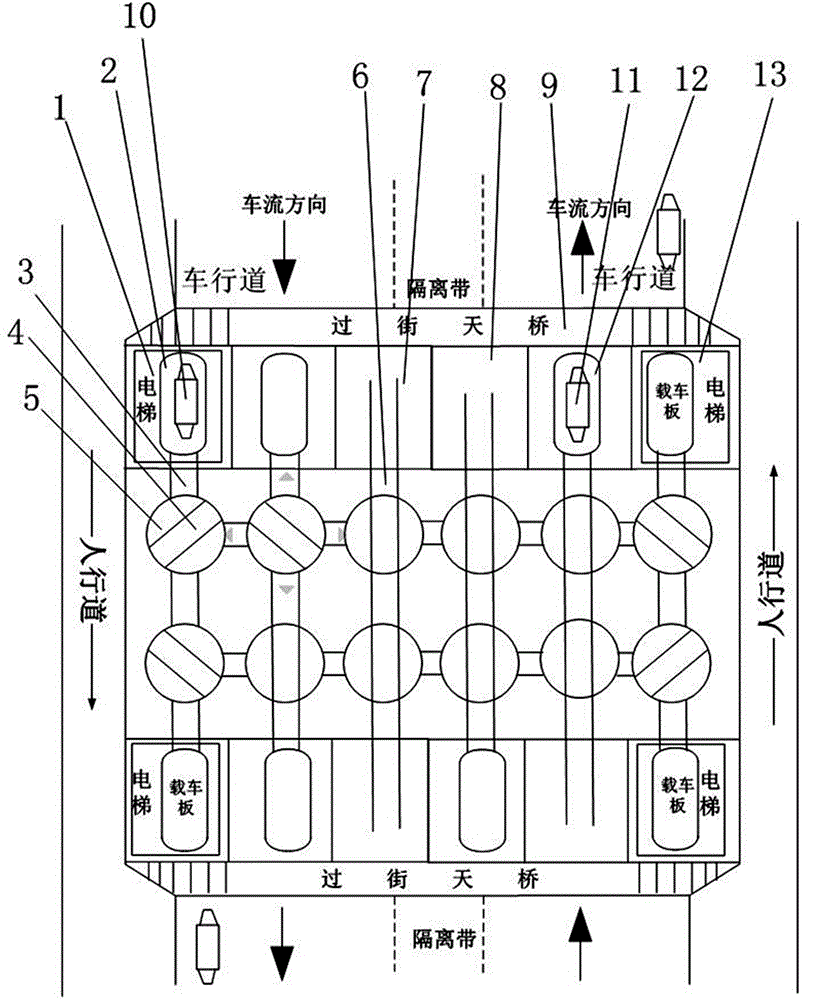
Three-dimensional garage for road parking
InactiveCN104806056AImprove building utilizationImprove the efficiency of inbound and outboundParkingsAuthentication systemAutomotive engineering
The invention discloses a three-dimensional garage for road parking. The vehicle garage entering and exiting can be directly realized on a traffic road while the traffic safety is ensured; the garage comprises a vehicle receiving and sending system, a rail system, an elevator system and a safety protection system, wherein the vehicle receiving and sending system comprises a vehicle carrying plate, a shielding part, a vehicle detection device and a parking space; the vehicle carrying plate is arranged in the garage and along the road; the elevator system is in butt joint with the vehicle receiving and sending system through the rail system; the rail system comprises a carrying rail, a steering device and a rail positioning device; the vehicle carrying plate does reciprocating movement between the elevator system and the parking space through being guided by the rail system; the safety protection system comprises a receiving and sending authentication system, a monitoring system and a warning system; the receiving and sending authentication system is used for verifying and authorizing the vehicle storing and taking behaviors; the vehicle detection device of the vehicle receiving and sending system detects the state of the vehicle entering the garage and the traffic conditions around the garage. The garage has the advantages that the vehicle garage entering and exiting can be carried out on the road.
Owner:FUJIAN AGRI & FORESTRY UNIV
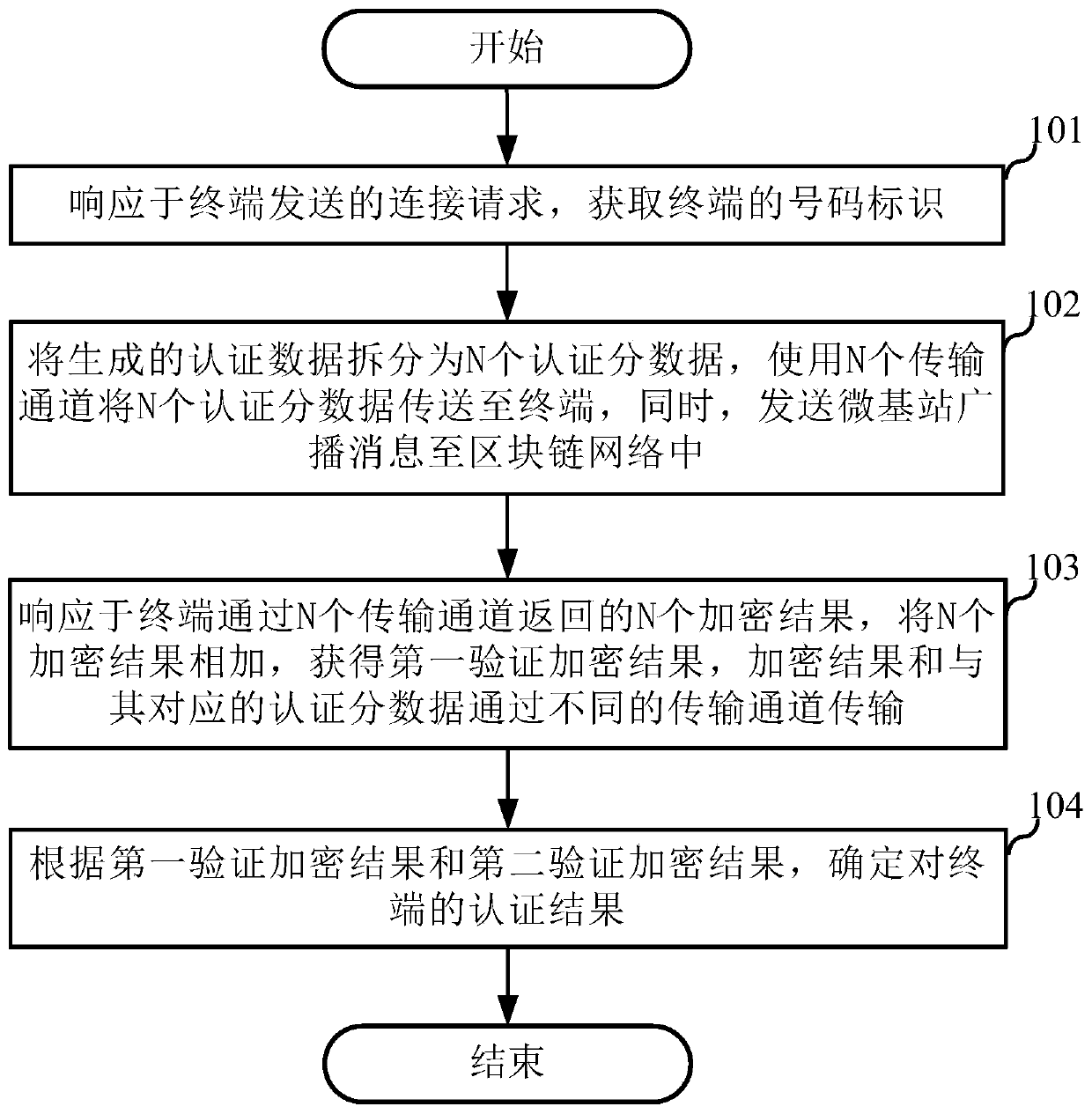
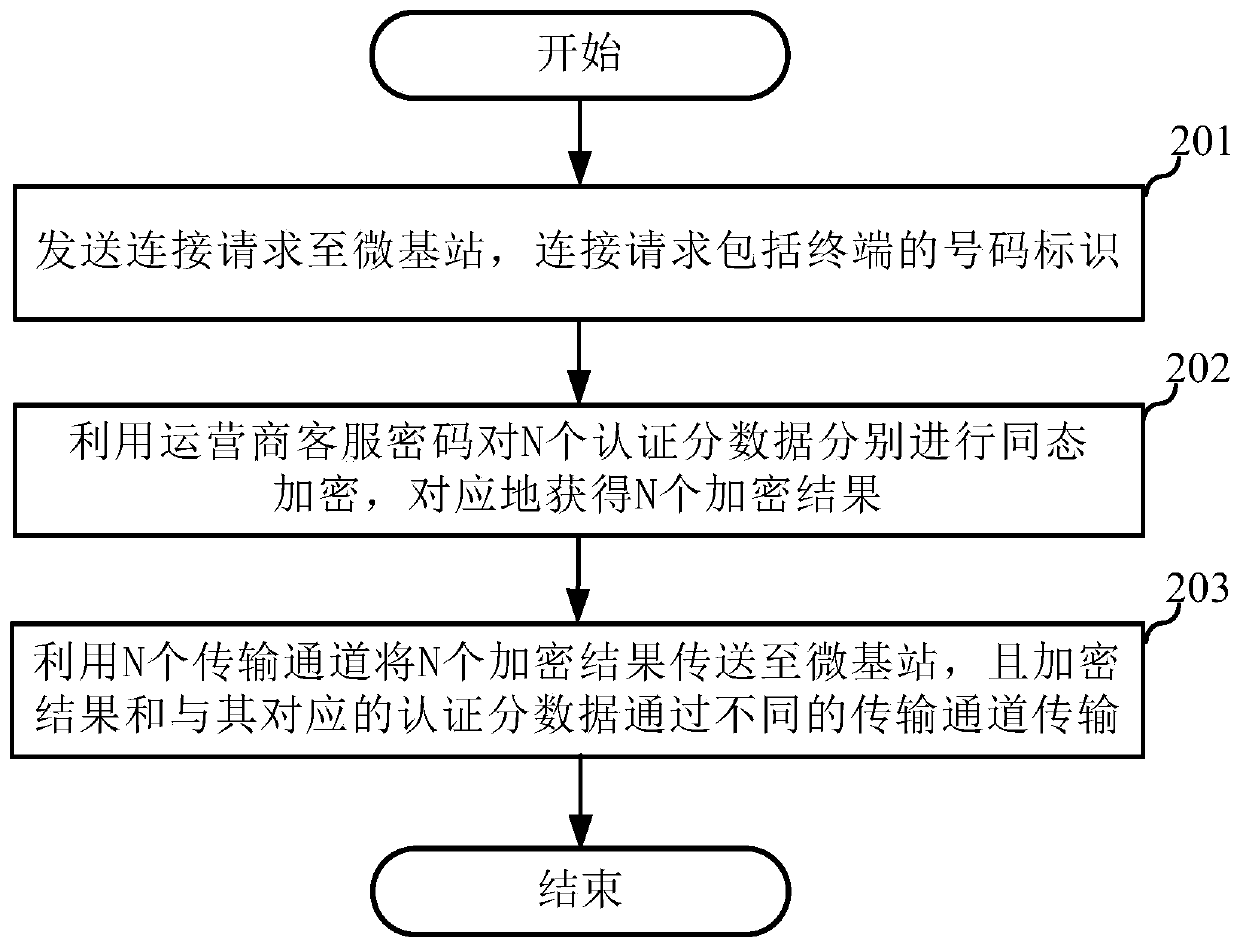
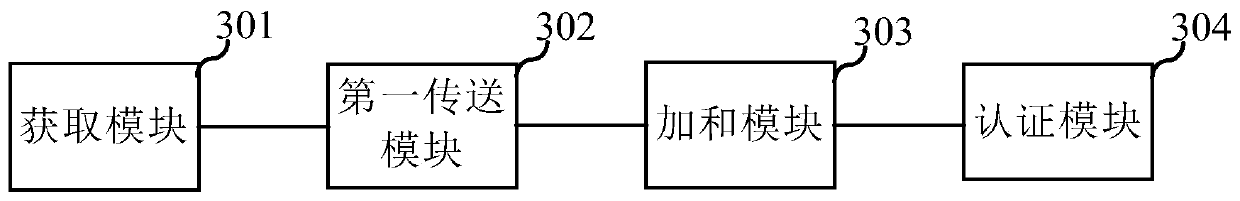
Authentication method, micro base station and terminal
ActiveCN111212422AReduce certification timeAvoid customer service password situationsUser identity/authority verificationBroadcast service distributionPasswordTransmission channel
The invention discloses an authentication method, a micro base station and a terminal, and the method comprises the steps: responding to a connection request transmitted by the terminal, and obtaininga number identification of the terminal; splitting the generated authentication data into N pieces of authentication sub-data, transmitting the N pieces of authentication sub-data to a terminal by using N transmission channels, and sending a micro base station broadcast message to a blockchain network, the micro base station broadcast message comprising the authentication data, a number identifier and a blockchain identifier of a micro base station, and N being an integer greater than or equal to 2; in response to N encryption results returned by the terminal through the N transmission channels, adding the N encryption results to obtain a first verification encryption result, and transmitting the encryption result and the authentication sub-data corresponding to the encryption result through different transmission channels; and determining an authentication result of the terminal according to the first verification encryption result and the second verification encryption result, wherein the second verification encryption result is a result obtained by performing homomorphic encryption on the operator customer service password and the authentication data by the operator server obtained from the blockchain network.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
OTP-based authentication system and method
ActiveUS9503453B2Shorten the timeAccurate timingKey distribution for secure communicationSynchronising transmission/receiving encryption devicesTransceiverClient-side
Owner:SAMSUNG SDS CO LTD
Beidou second-generation system anti-cheating method based on domestic password and spread spectrum information protection
InactiveCN109995531AReduce certification timePublic key for secure communicationPasswordNavigation system
The invention relates to the technical field of information security, and designs a beidou D2 navigation message anti-cheating scheme based on domestic passwords and spread spectrum information protection. In recent years, the Beidou navigation system serves as a new member of the GNSS, and the positioning principle of the Beidou navigation system is similar to that of the GPS. Signal parameters and information structures of civil signals are disclosed to the public through related files, so that a deception party can easily manufacture the deception signal and initiate a deception attack, thereby controlling a positioning result of a receiver and causing extremely serious consequences. According to the invention, domestic cryptographic algorithms (SM2, SM3 and SM4) are adopted to generateauthentication information, so that spoofing attacks are detected. In addition, the signature and other authentication information are subjected to information protection in a spread spectrum modulation mode, and therefore the authentication information is prevented from being tampered. According to the invention, a simulation experiment is carried out through MATLAB and OpenSSL platforms, and experiment results show that the method can resist spoofing attacks.
Owner:CIVIL AVIATION UNIV OF CHINA
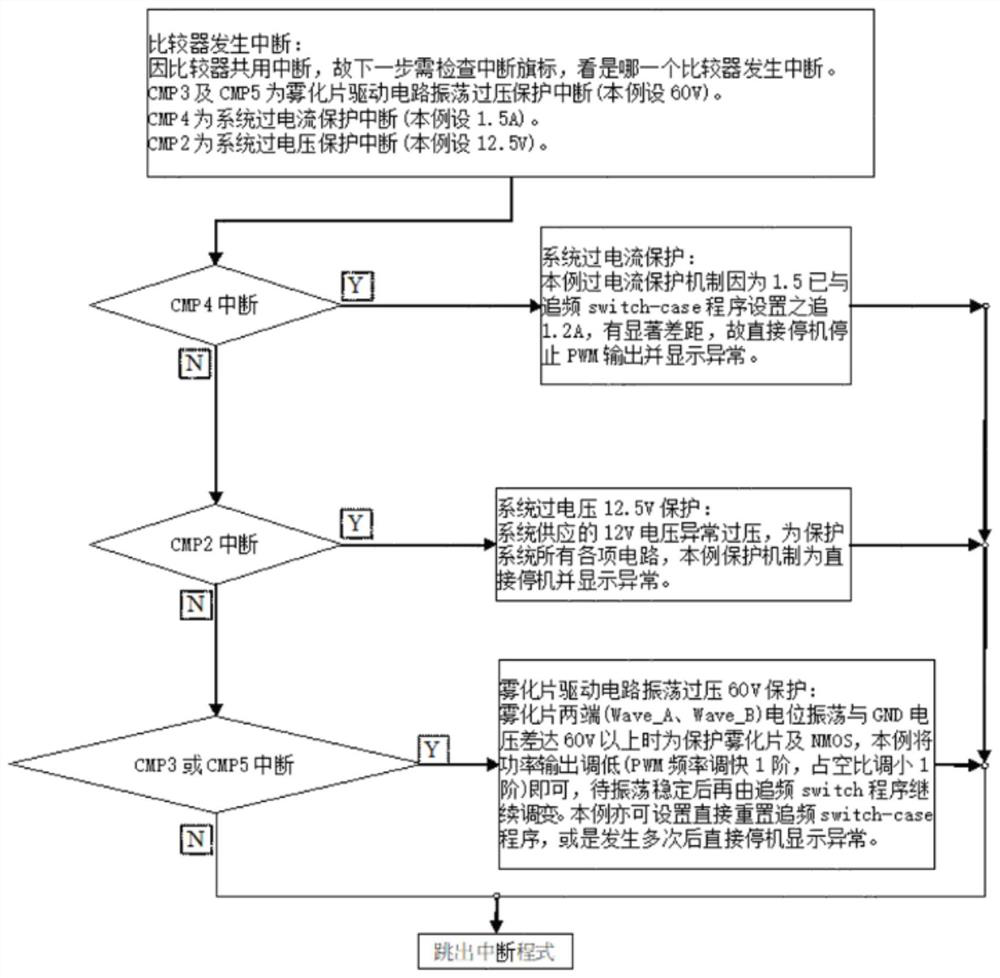
Atomizing sheet driving framework and driving method
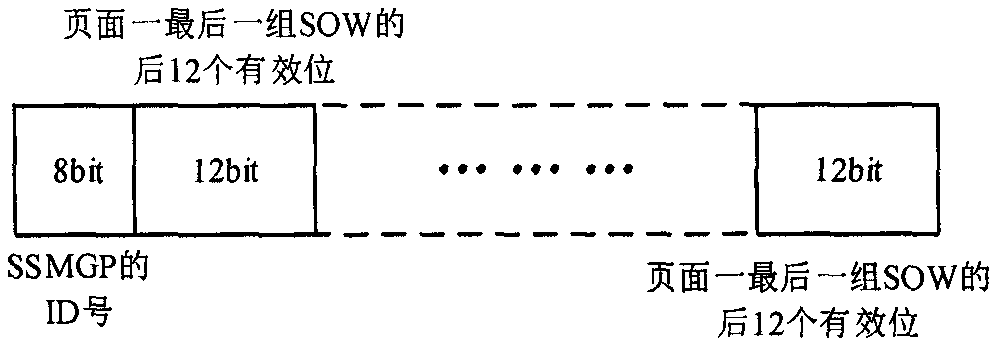
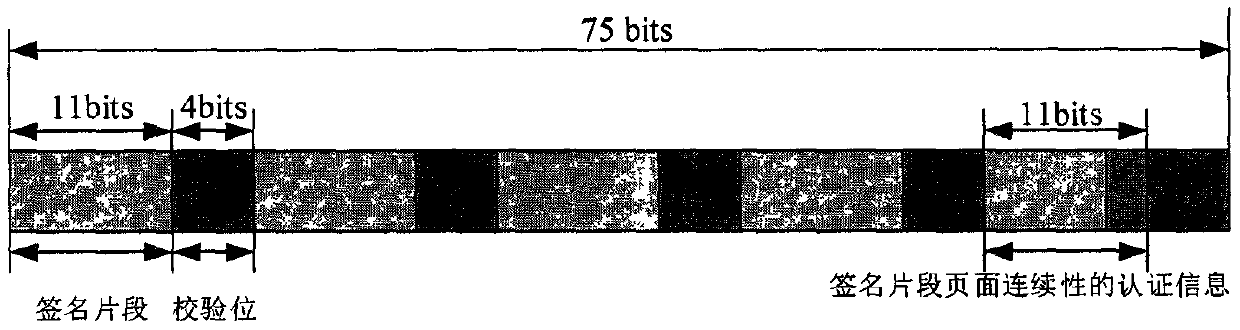
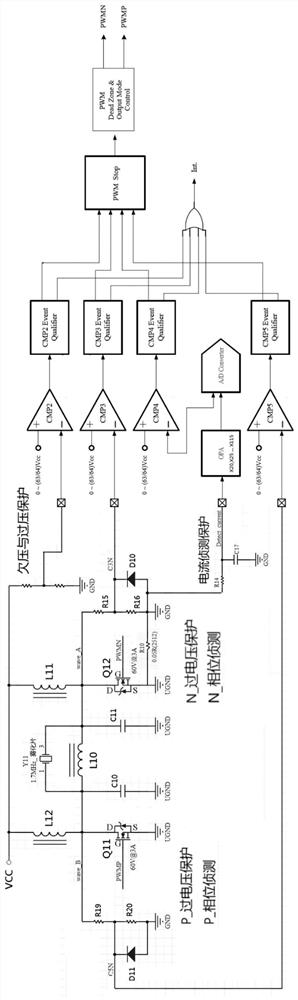
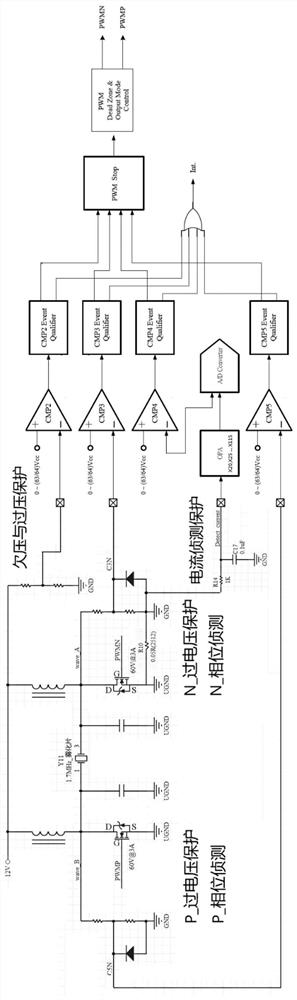
ActiveCN112503669AReduce certification timeLow costAC motor controlSpace heating and ventilation safety systemsTransformerOvercurrent
The invention discloses an atomizing sheet driving framework and a driving method. The atomizing sheet driving framework comprises a driving device and an atomizing sheet, the atomizing sheet drivingframework belongs to the technical field of atomizing sheet driving frameworks, the driving device pushes the atomizing sheet to reach the vibration frequency in an excitation vibration manner, the driving device adopts a single power supply to drive the atomizing sheet, and the atomizing sheet driving framework is scientific, reasonable, and safe and convenient to use. The driving device uses thesingle power supply without a built-in switching power supply transformer; the driving device comprises various voltage protection frameworks, a phase detection protection framework and an over-current protection framework, the voltage protection frameworks carry out voltage detection, the phase detection protection framework carries out phase detection, the over-current protection framework carries out potential monitoring and over-current protection, and the various voltage protection frameworks, the phase detection protection framework and the over-current protection frameworks can protecta humidifier.
Owner:HITENX (WUXI) TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com