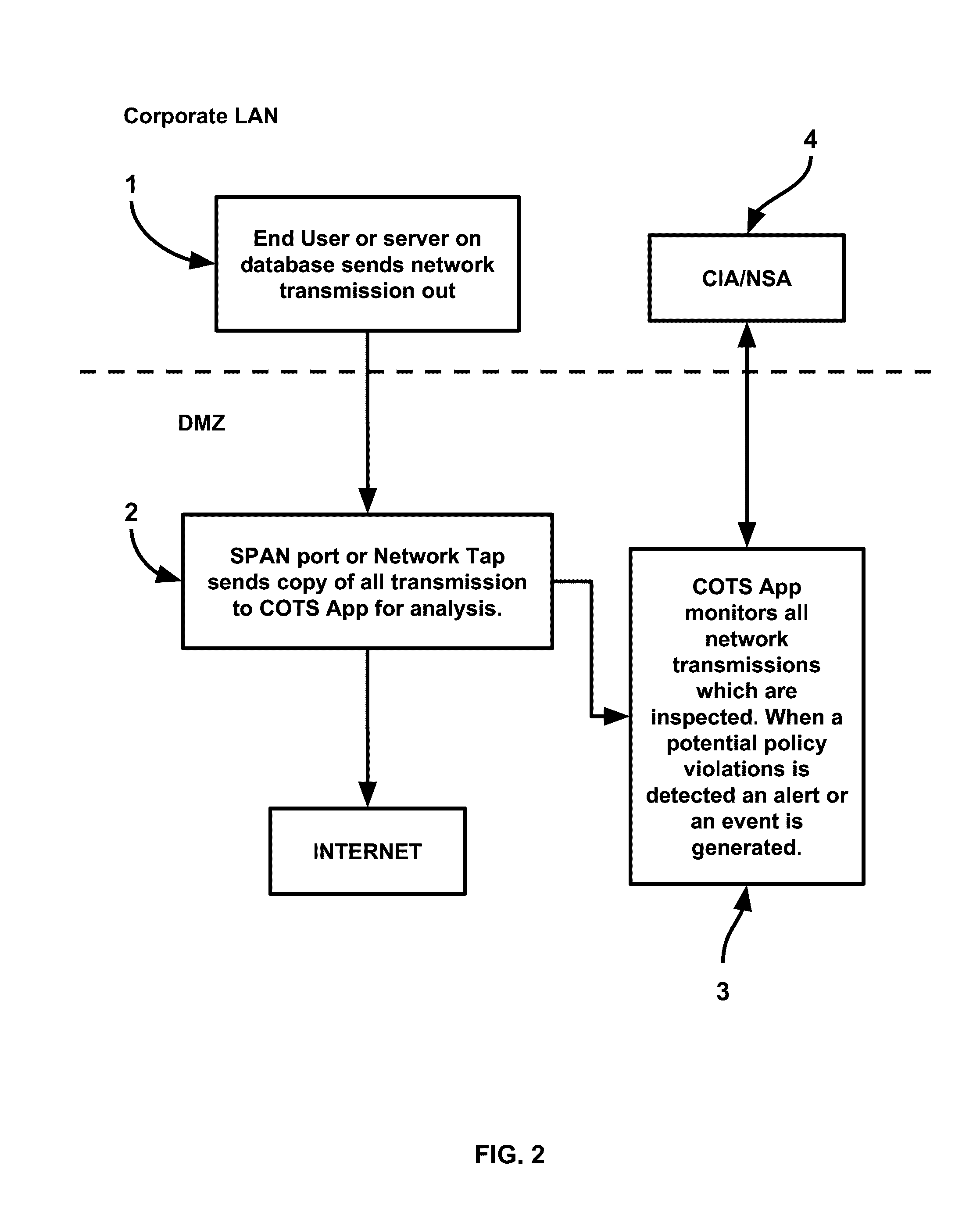
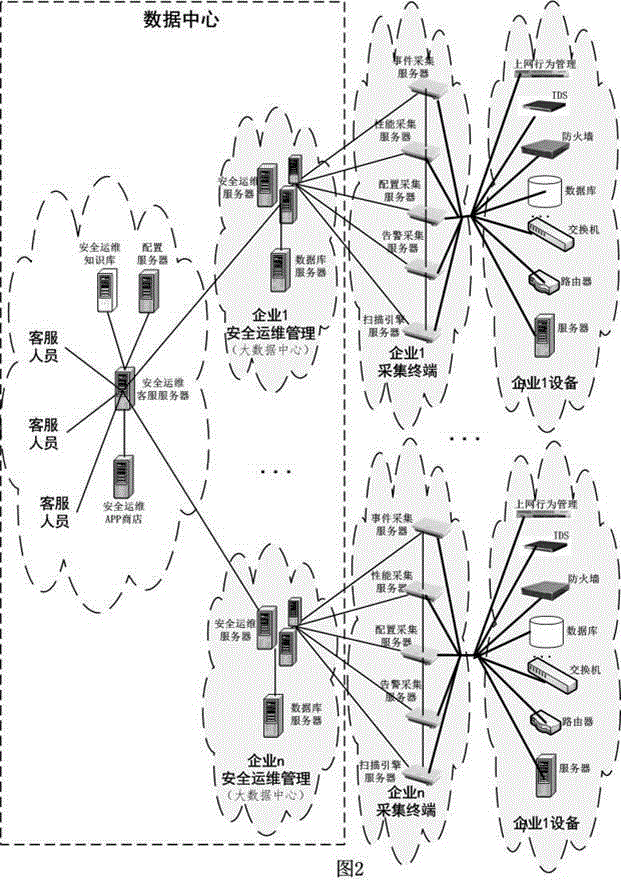
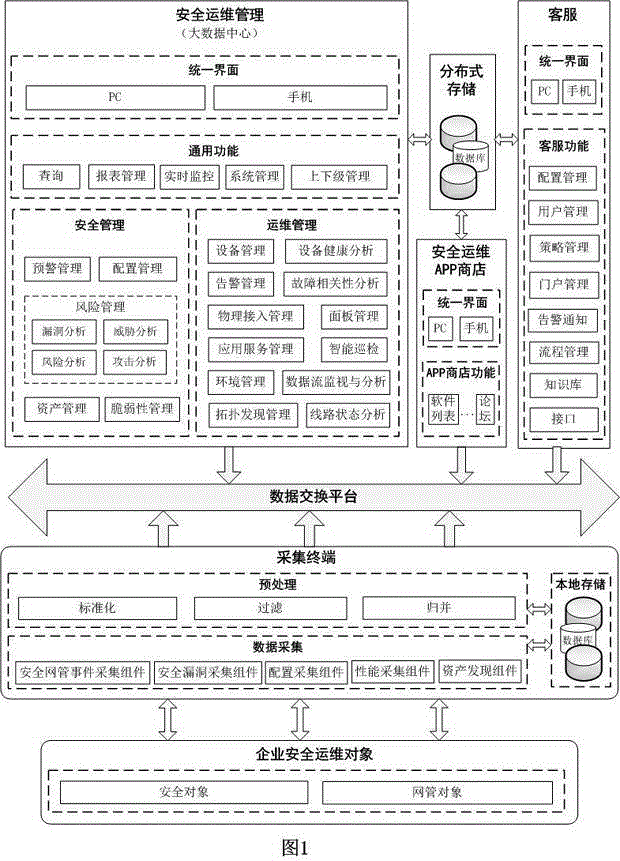
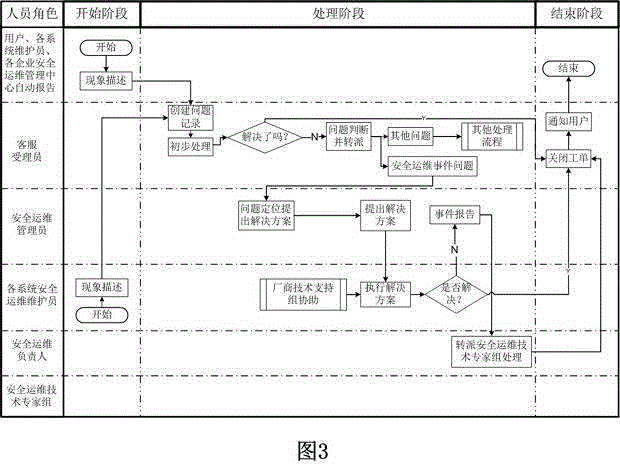
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
12980 results about "Information security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information security, sometimes shortened to infosec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or at least reducing the probability of unauthorized/inappropriate access, use, disclosure, disruption, deletion/destruction, corruption, modification, inspection, recording or devaluation, although it may also involve reducing the adverse impacts of incidents. Information may take any form, e.g. electronic or physical., tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves...
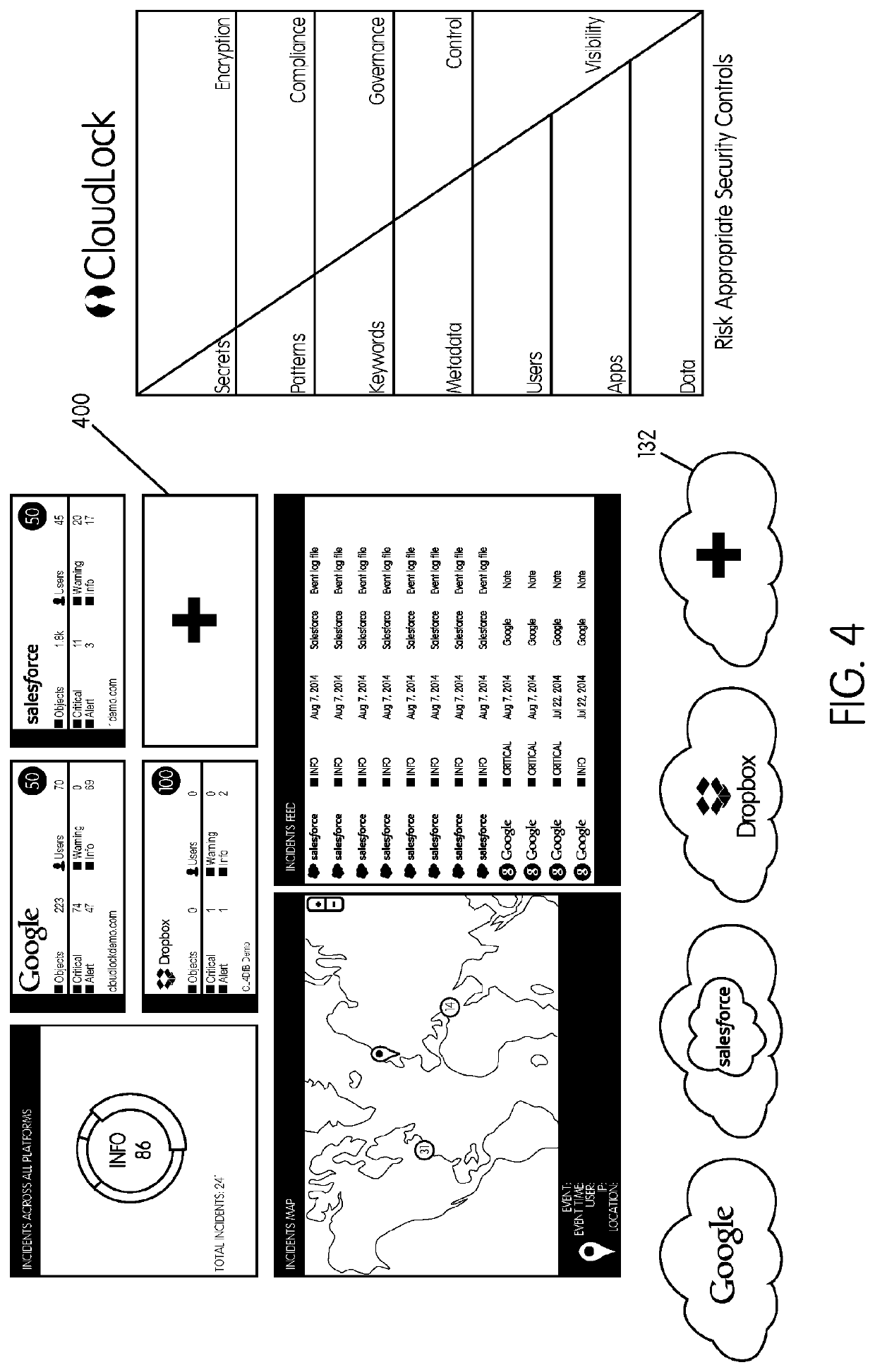
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
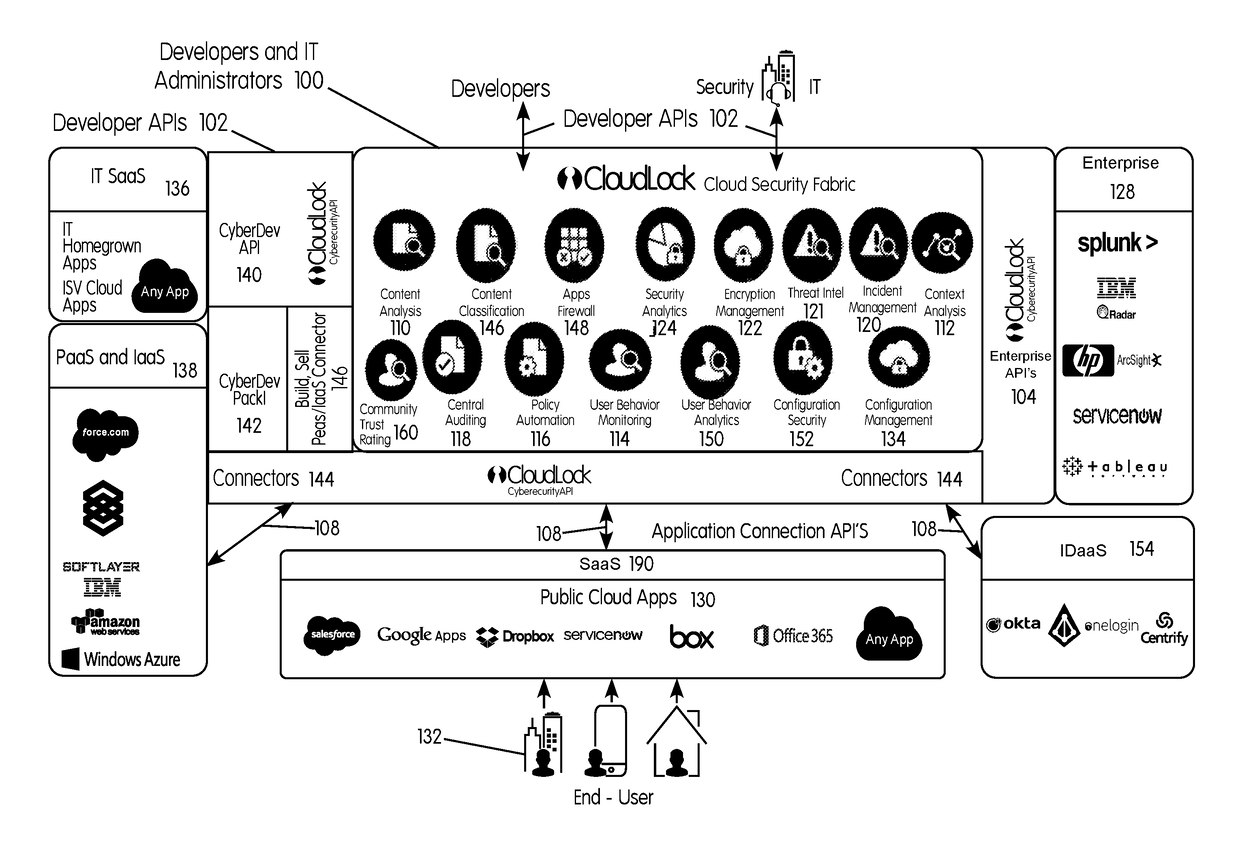
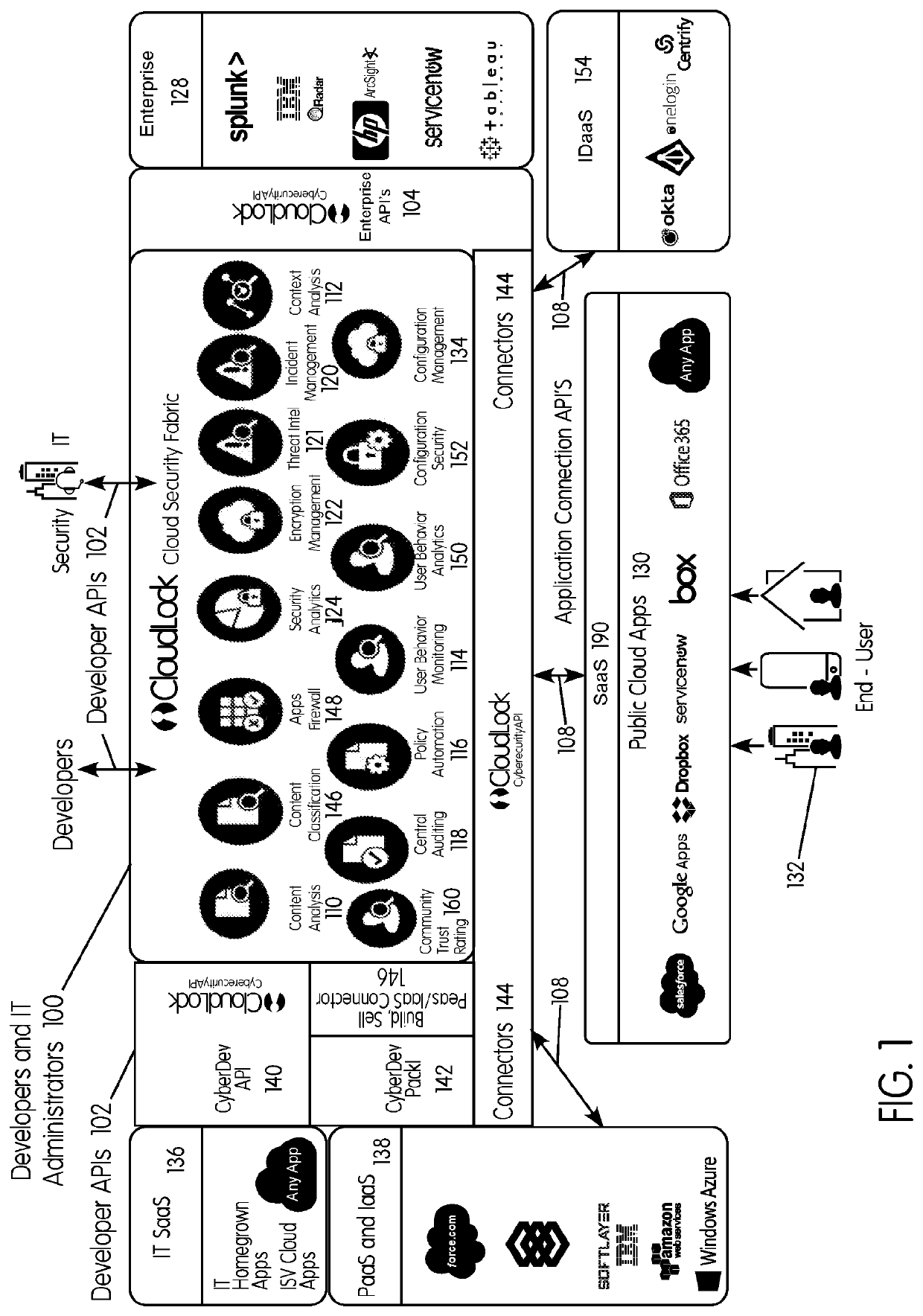
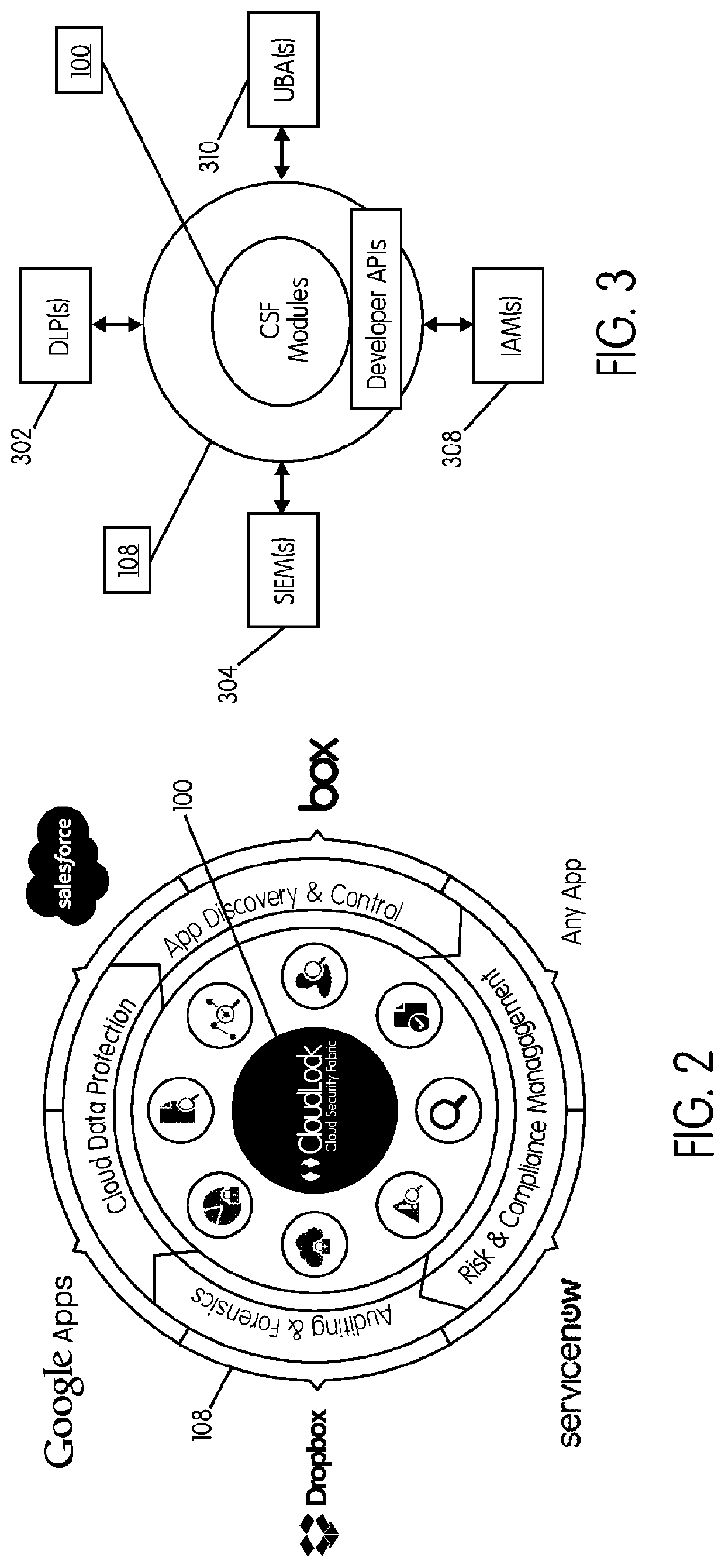
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
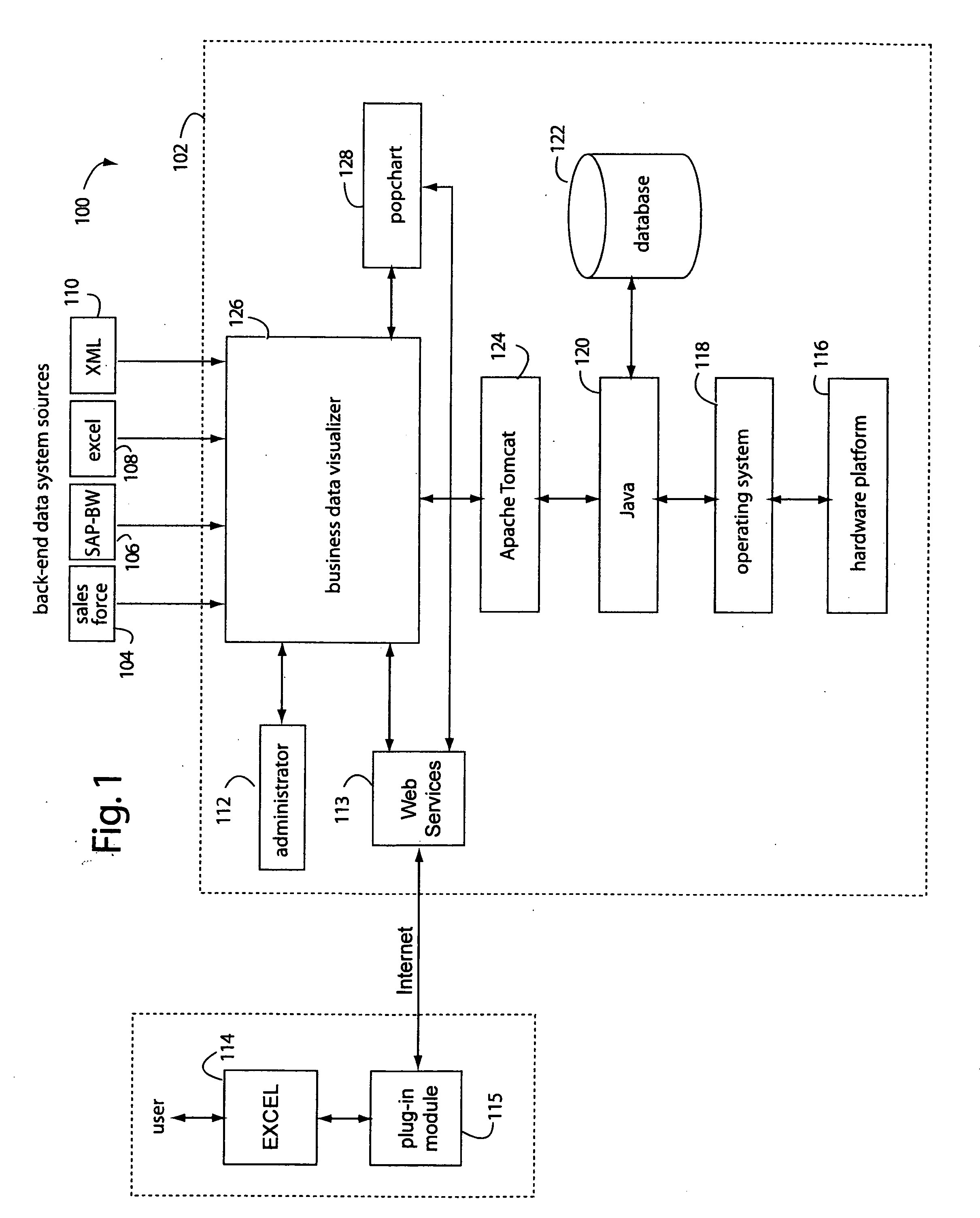
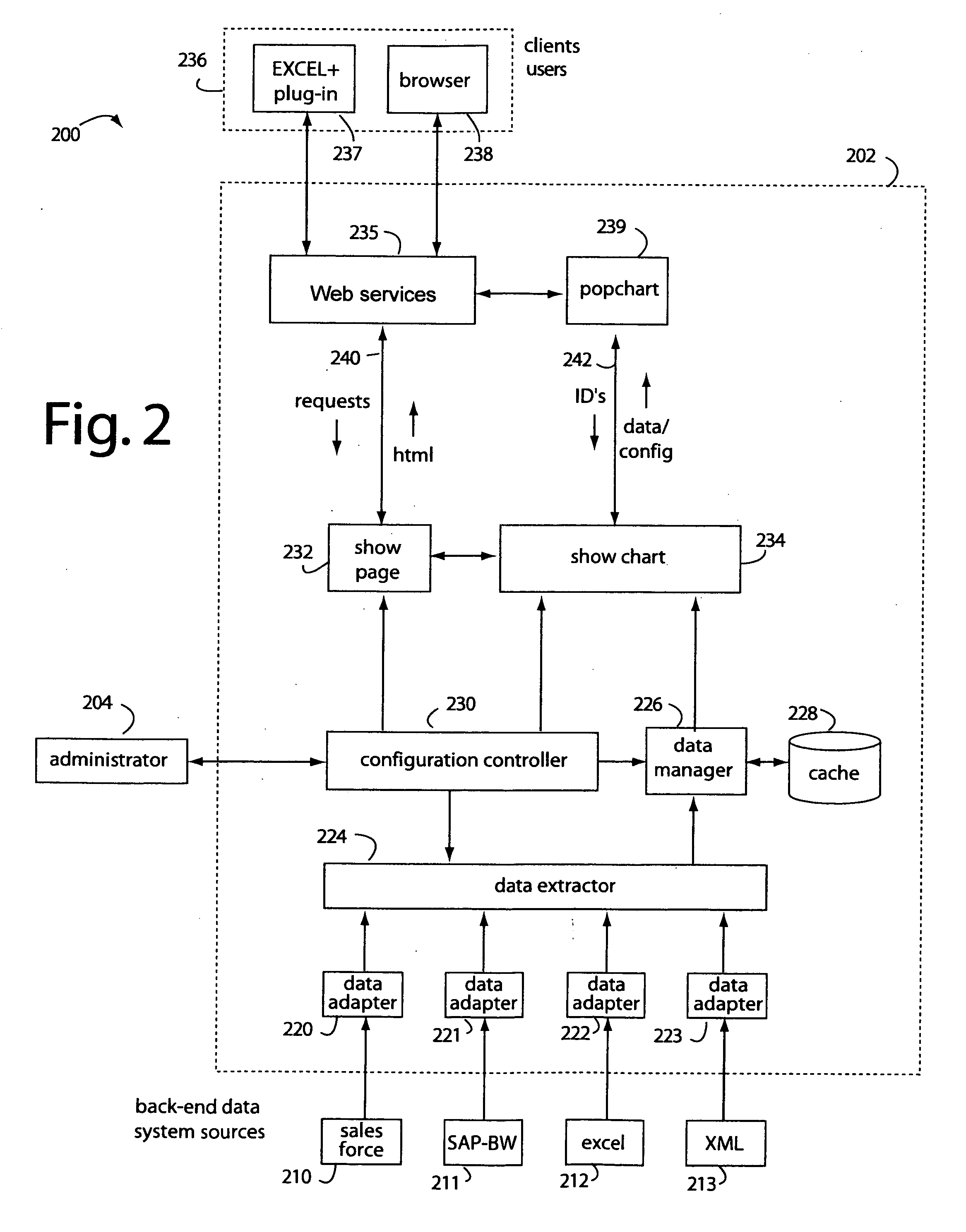
Spreadsheet user-interfaced business data visualization and publishing system
InactiveUS20060112123A1Improve strategic decisionFacilitate communicationDigital data processing detailsText processingDashboardData set
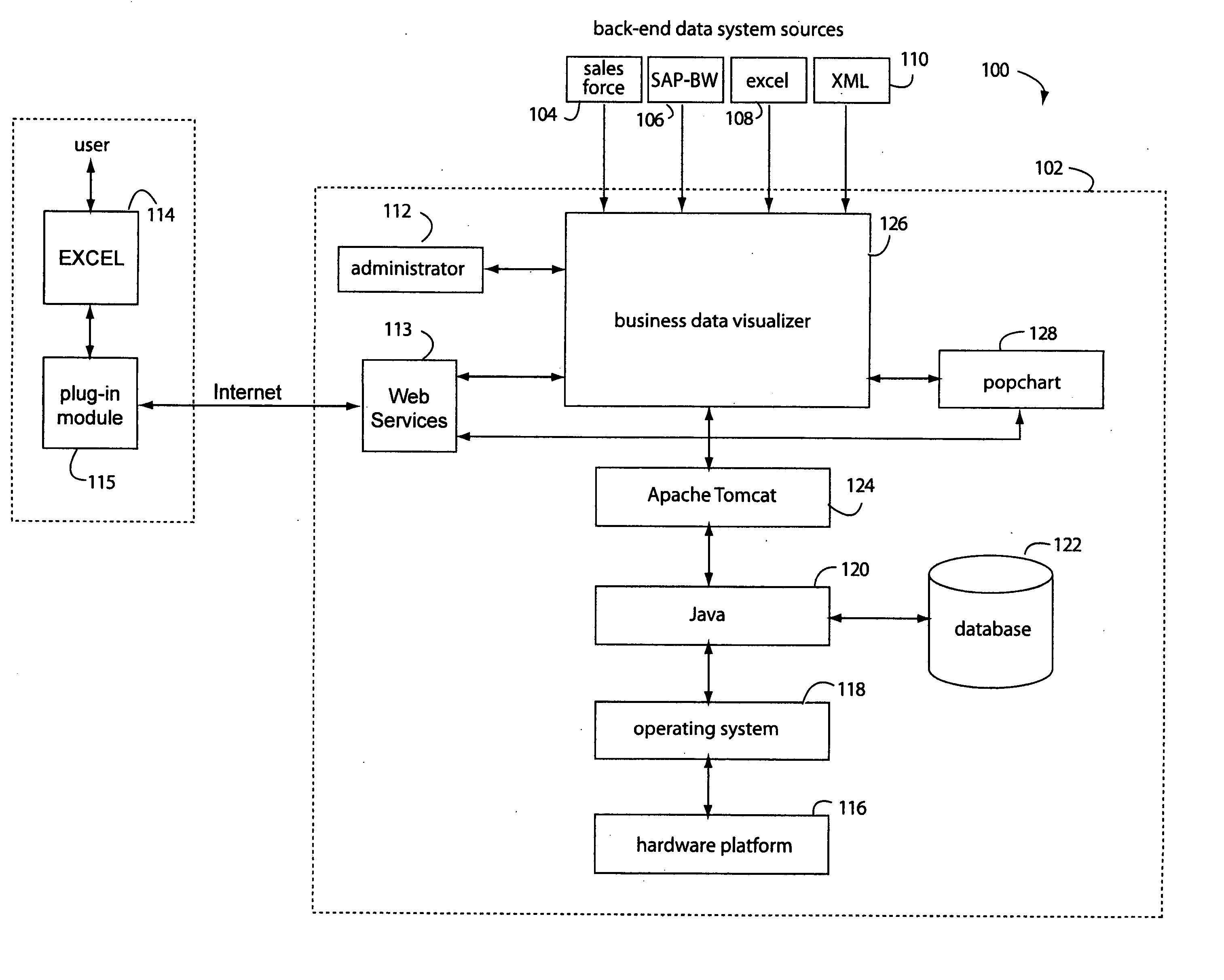
A spreadsheet user-interfaced web-based business data publishing system allows users to input and visualize field data and analytical results with interactive charts through a familiar MS-EXCEL user interface. A plug-in module associated with the user's browser and EXCEL application enables a background, web-services connection over the Internet to a management sub-system which extracts, transforms, and publishes data. Charts are customized using a WYSIWYG interface, and business dashboards are constructed through a simple drag-n-drop process. An account management system is included with access control to protect information security. The system is used for visualizing data managing reports, providing special tools to use SAP data, access Query Cubes in SAP BW, and standard and custom R / 3 reports. Once data has been extracted from SAP, it is transformed, merged with other data sources, and published as a dashboard or in a business portal. Its management and configuration functions are suited for enterprise reporting and sharing business data.
Owner:MACNICA
Method, system and computer program product for assessing information security
A method, system and computer program product for assessing information security interviews users regarding technical and non-technical issues. In an embodiment, users are interviewed based on areas of expertise. In an embodiment, information security assessments are performed on domains within an enterprise, the results of which are rolled-up to perform an information security assessment across the enterprise. The invention optionally includes application specific questions and vulnerabilities and / or industry specific questions and vulnerabilities. The invention optionally permits users to query a repository of expert knowledge. The invention optionally provides users with working aids. The invention optionally permits users to execute third party testing / diagnostic applications. The invention, optionally combines results of executed third party testing / diagnostic applications with user responses to interview questions, to assess information security. A system in accordance with the invention includes an inference engine, which may include a logic based inference engine, a knowledge based inference engine, and / or an artificial intelligence inference engine. In an embodiment, the invention includes an application specific tailoring tool that allows a user to tailor the system to assess security of information handled by a third party application program.
Owner:SAFEOPERATIONS
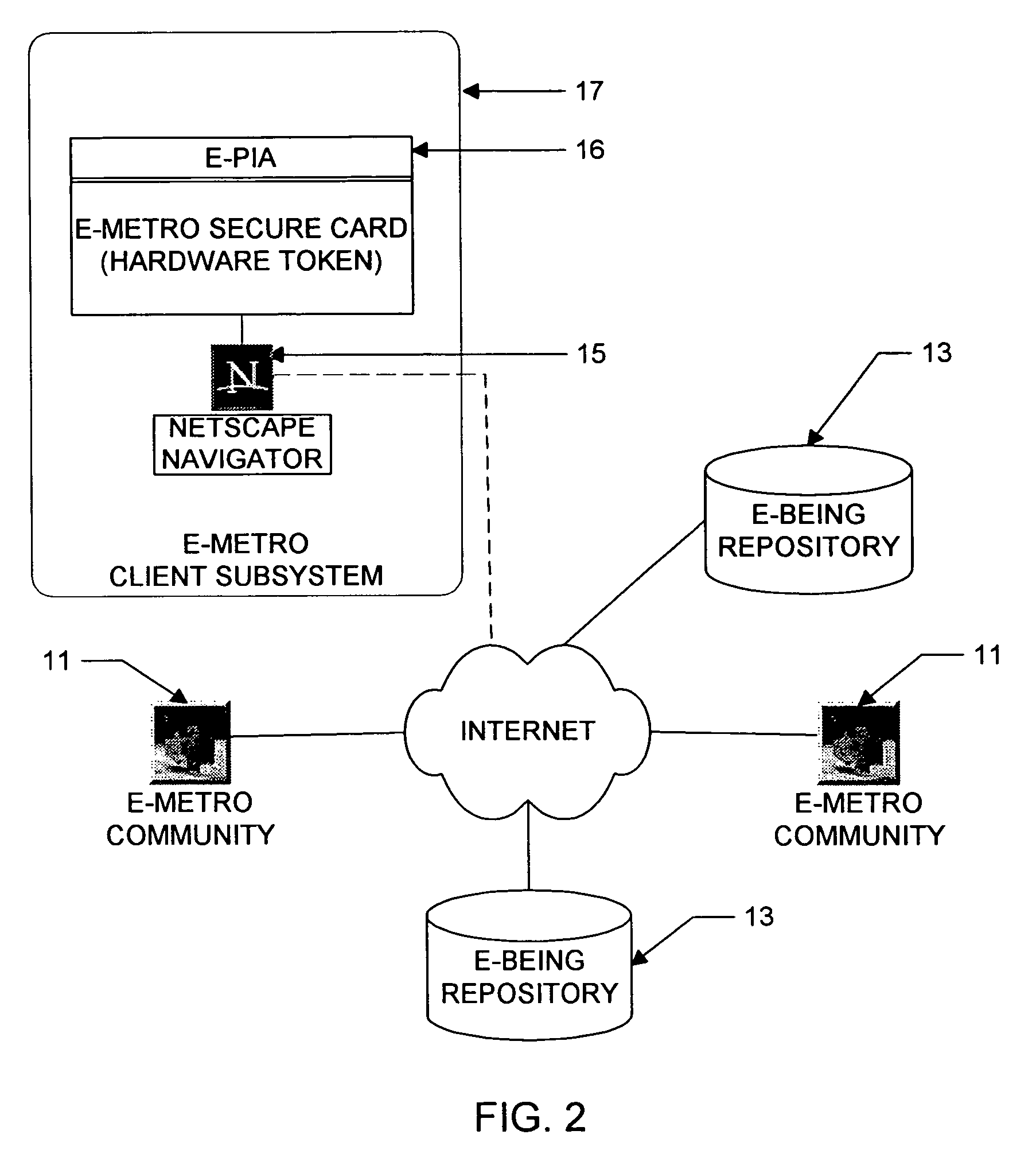
Personal information security and exchange tool
InactiveUS7289971B1Facilitates formation and useEasy to useFinanceComputer security arrangementsCommand and controlElectricity market
Utilization of the E-Metro Community and Personal Information Agents assure an effective and comprehensive agent-rule based command and control of informational assets in a networked computer environment. The concerns of informational privacy and informational self-determination are addressed squarely by the invention affording persons and entities a trusted means to author, secure, search, process, and exchange personal and / or confidential information in a networked computer environment. The formation of trusted electronic communities wherein members command and control their digital persona, exchanging or brokering for value the trusted utility of their informational assets is made possible by the invention. The present invention provides for the trusted utilization of personal data in electronic markets, providing both communities and individuals aggregate and individual rule-based control of the processing of their personal data.
Owner:CYVA RES HLDG
Methods for rights enabled peer-to-peer networking
InactiveUS20030120928A1User identity/authority verificationUnauthorized memory use protectionDigital rights managementRights management
The present invention relates to digital rights management. In one embodiment, persons, processes, and / or computers and appliances locate, share, publish, retrieve, and use all kinds of digital information that has been protected using digital rights management technologies. Rights management includes securely associating rules for authorized use with the digital information. Rules and / or digital information may be encapsulated in a cryptographically secure data structure or "container" ("CSC") to protect against unauthorized use, to ensure secrecy, to maintain integrity, and to force the use of a rights management system to access the protected information. Attributes or metadata information describing at least some of the rules ("rules-metadata information") and optionally any associated rule parameter data with respect to the protected information are created. This rules-metadata information may be organized, structure, encoded, and / or presented using a self-defining data structure such as those created using Extensible Markup Language (XML). In one embodiment, the XML-encoded rules-metadata information is also made available unencrypted, in plain text, to facilitate P2P search and file transfer. Having at least some of the rules-metadata information outside or external to a CSC allows greater flexibility in searching based at least in part upon the rules-metadata information. Some embodiments may hold the rules-metadata information in a separate CSC. Putting the rules-metadata information in a separate CSC more easily allows authentication and maintains the integrity of the rules-metadata information. In another embodiment, the rules metadata may be in an unencrypted portion of a CSC itself or concatenated with a CSC in a single file.
Owner:CATO MILES +2
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
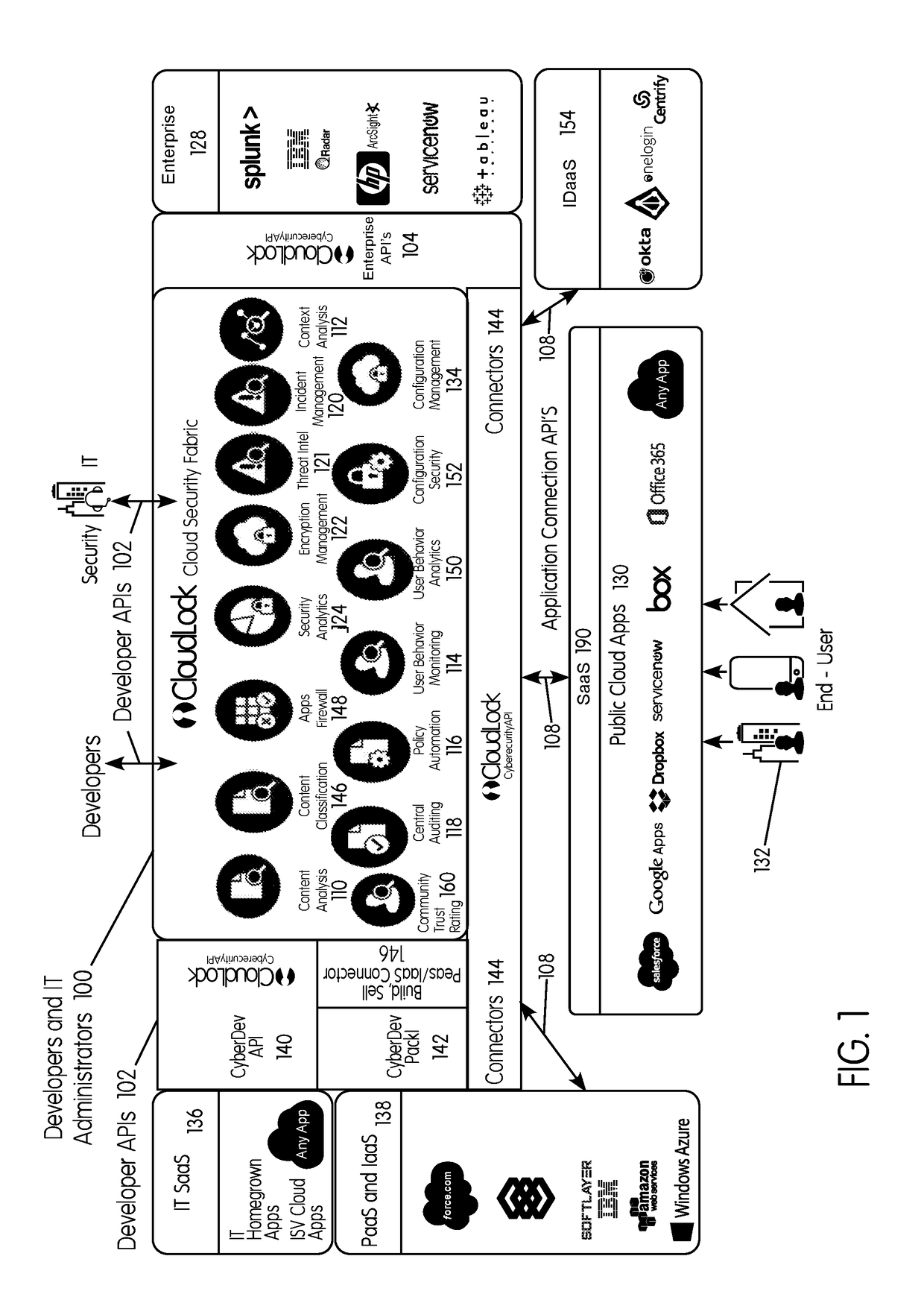
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
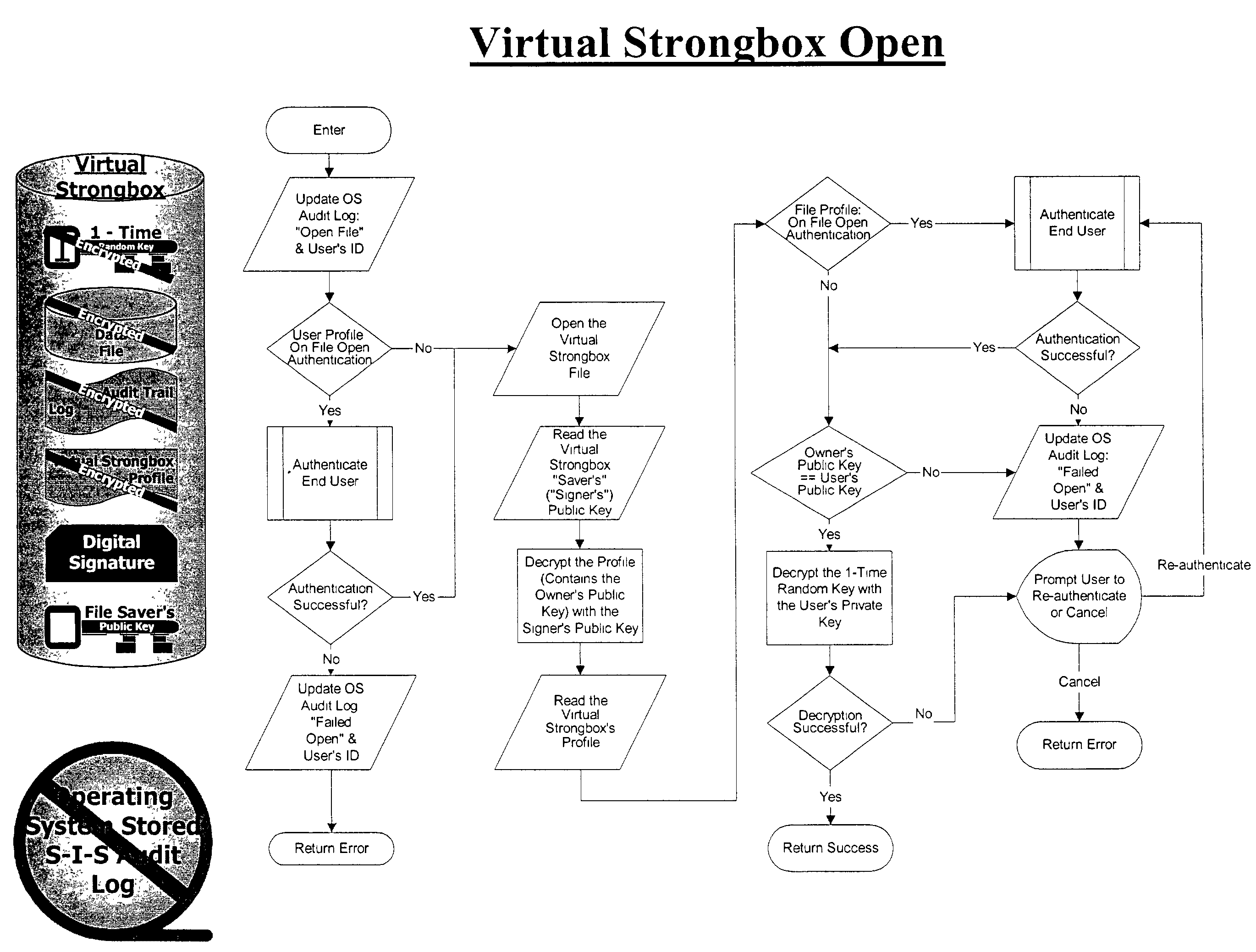
Methods, software programs, and systems for electronic information security
InactiveUS7395436B1Digital data processing detailsUser identity/authority verificationConfidentialityDigital signature
The present invention relates to various methods, software programs, and systems for electronic information security. More particularly, these various methods, software programs, and systems may serve to protect information security by providing an integrated system that helps ensure confidentiality, integrity, accountability, and ease of use. Certain embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a file container for storing: (a) a data file, which data file is encrypted with a one-time random encryption key; (b) the one-time random encryption key, which one-time random encryption key is encrypted with a public key portion of a public key / private key pair associated with an owner of the file container; (c) an audit trail log of the history of the file container, which audit trail log is encrypted with the one-time random encryption key with which the data file is encrypted; (d) a digital signature based upon a hash of the combined data file and the audit trail log, which hash is encrypted with a private key portion of a public key / private key associated with a writer / creator of the file container; and (e) a profile associated with the file container. Additional embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a fully integrated system for user authentication, virus scanning, time / date certification, encryption / decryption, digital signatures, stored document protection, transmitted document protection, and delivery verification.
Owner:KENEISYS
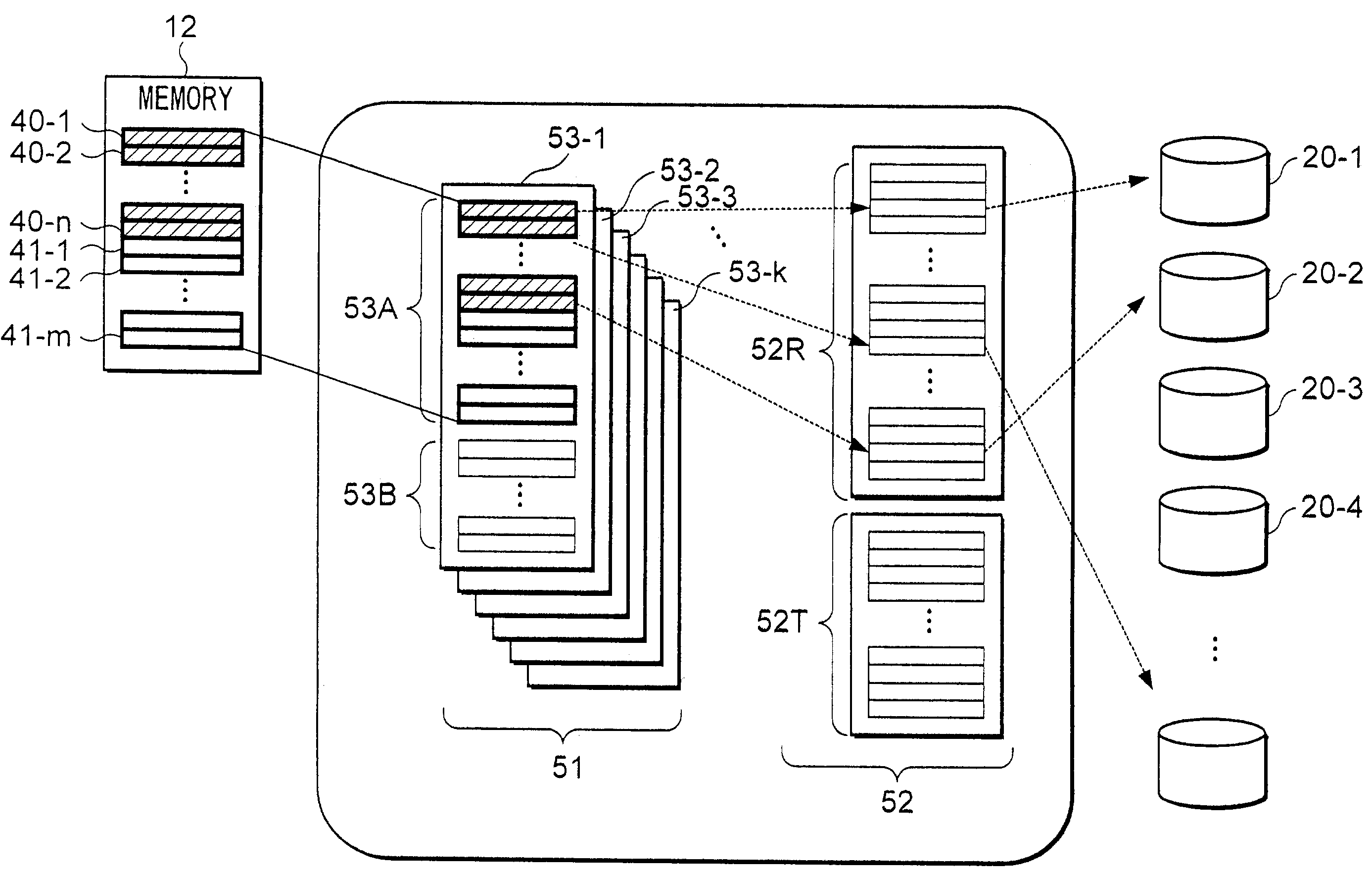
System for managing program applications storable in a mobile terminal
ActiveUS7379731B2Ensure safetyLow reliabilityProgram control using stored programsMultiple digital computer combinationsComputer terminalApplication software
Management server 16 may obtain application programs from content server 20 in response to requests of mobile terminal 11. Management server 16 may transmit the obtained application programs to mobile terminal 11 with information concerning reliabilities of the application programs. After mobile terminal 11 receives the application programs from management server 16, mobile terminal 11 manages operations of the application programs. Operations of the application programs are coordinated with operations of other programs using the information concerning the reliabilities corresponding to the application programs. Management of the coordinated operations of the application programs avoids problems concerning information security, where valuable information may be distributed unexpectedly because of operations of low reliable application programs. As a result, convenience of users of mobile terminals 11 can be improved without deteriorating the information security of mobile terminals 11.
Owner:NTT DOCOMO INC
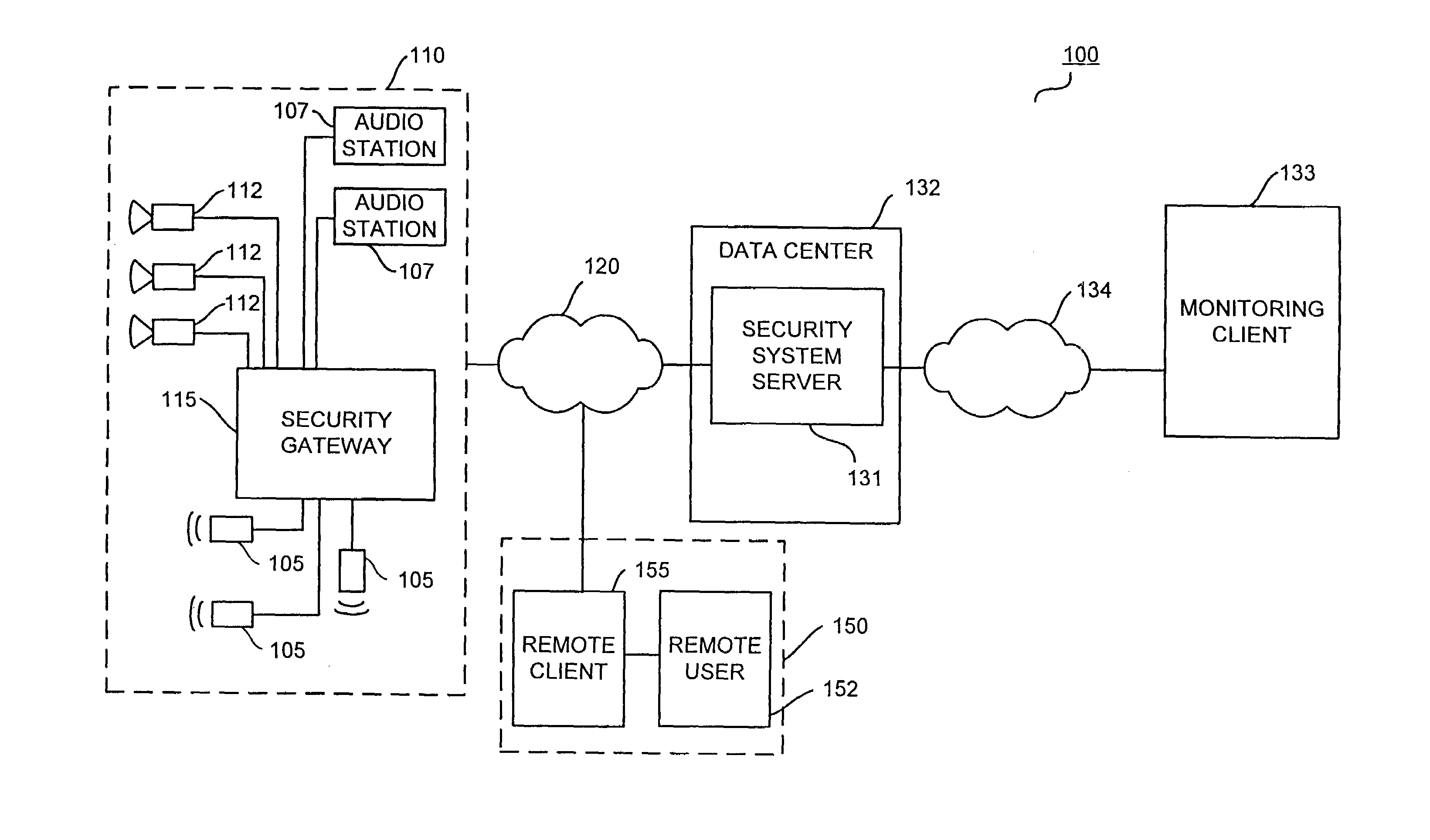
Lifestyle multimedia security system
InactiveUS7119609B2Facilitate communicationTransmission systemsTelephonic communicationInternet privacyEngineering
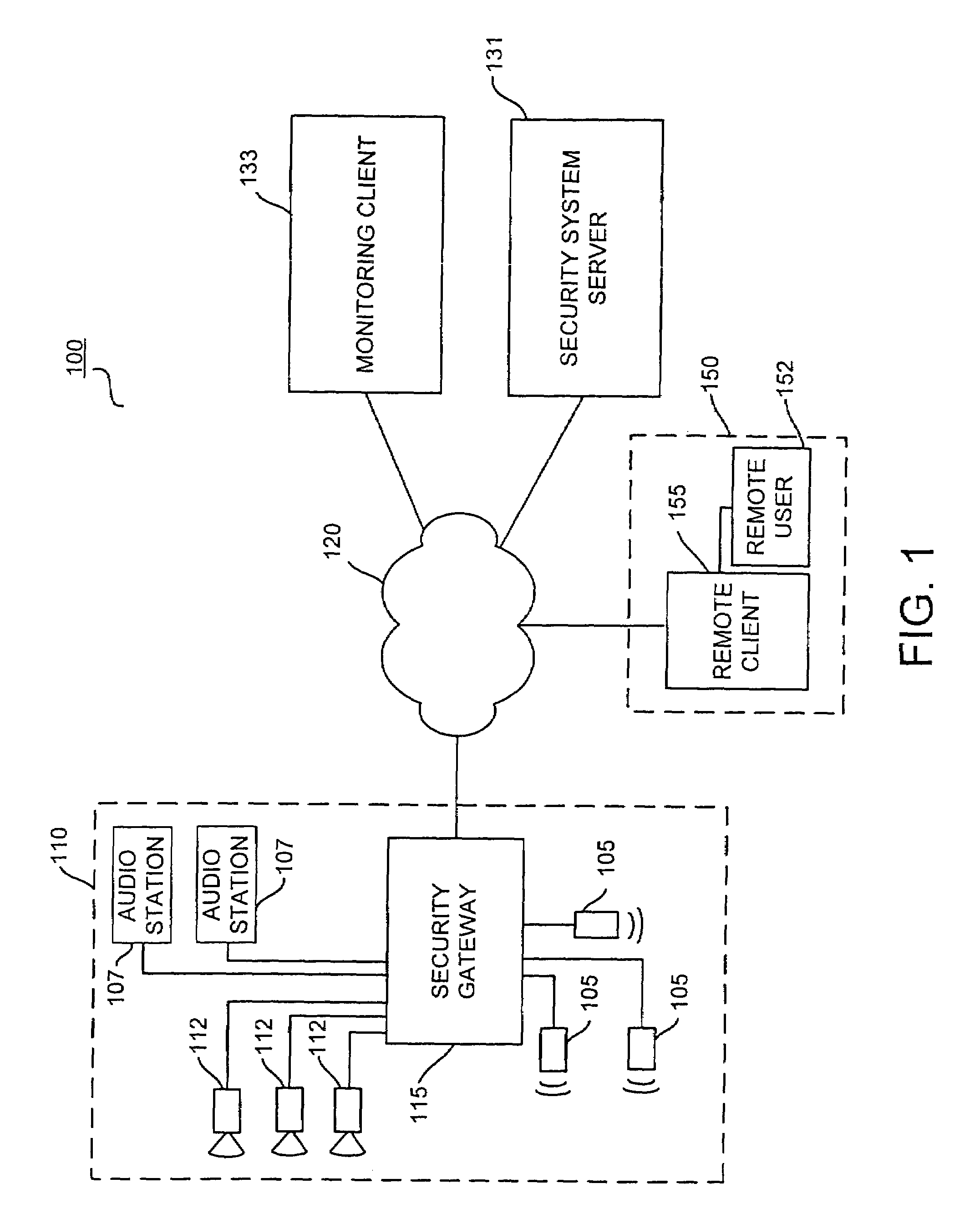
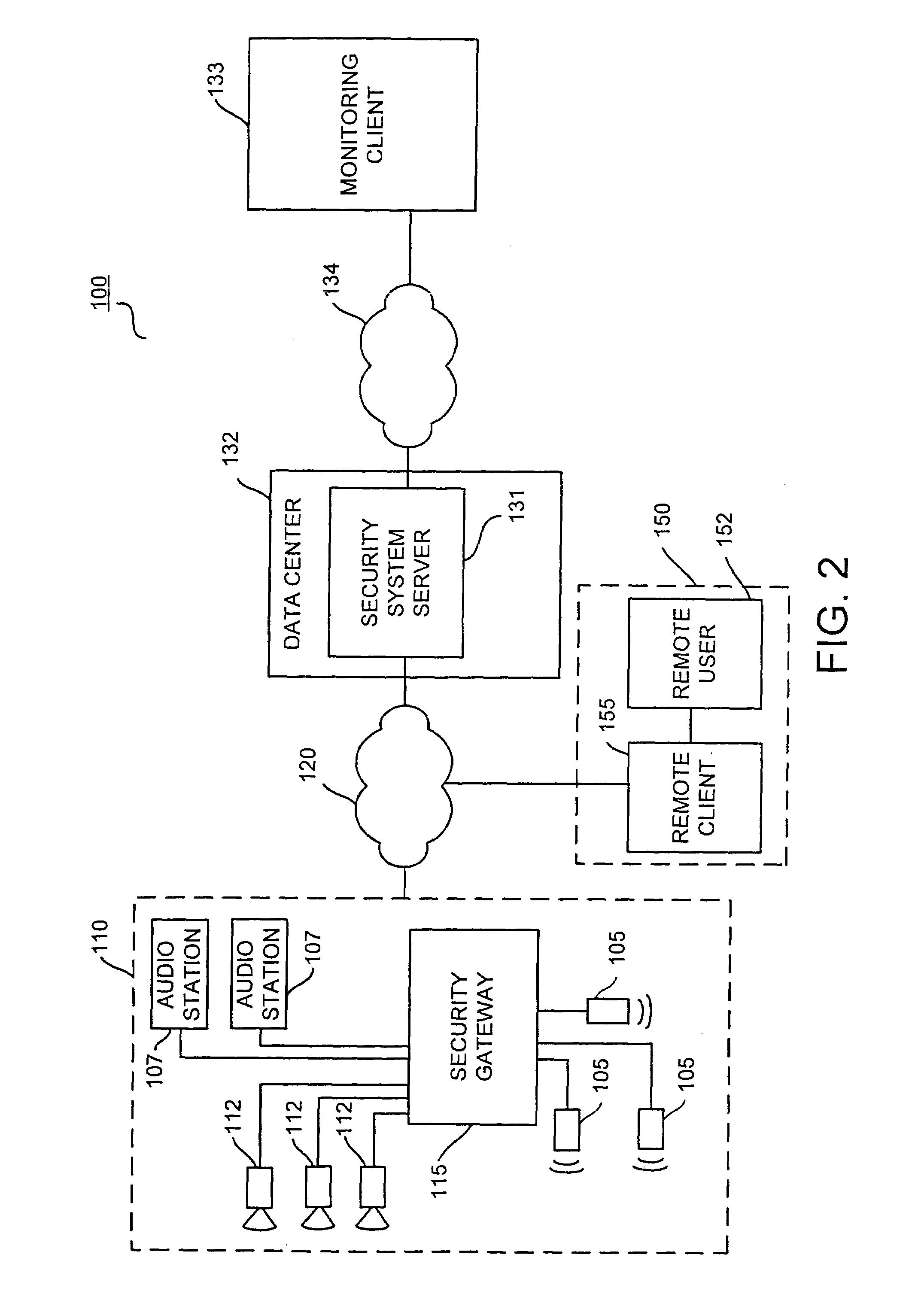
A method for remote monitoring of a premises. A geographically remote client is operatively coupled to a security system server capable of authenticating a user of the remote client. The remote client is then operably coupled to a security gateway capable of managing the monitoring of the premises, activating a signal at the premises for notifying an occupant at the premises that remote monitoring is occurring, and transferring information between the security gateway and the remote client. The transfer of information between the security gateway and the remote client is controlled by the user of the remote client. The security gateway may be operably coupled to at least one camera at the premises and to at least one audio station at the premises.
Owner:COMCAST CABLE COMM LLC
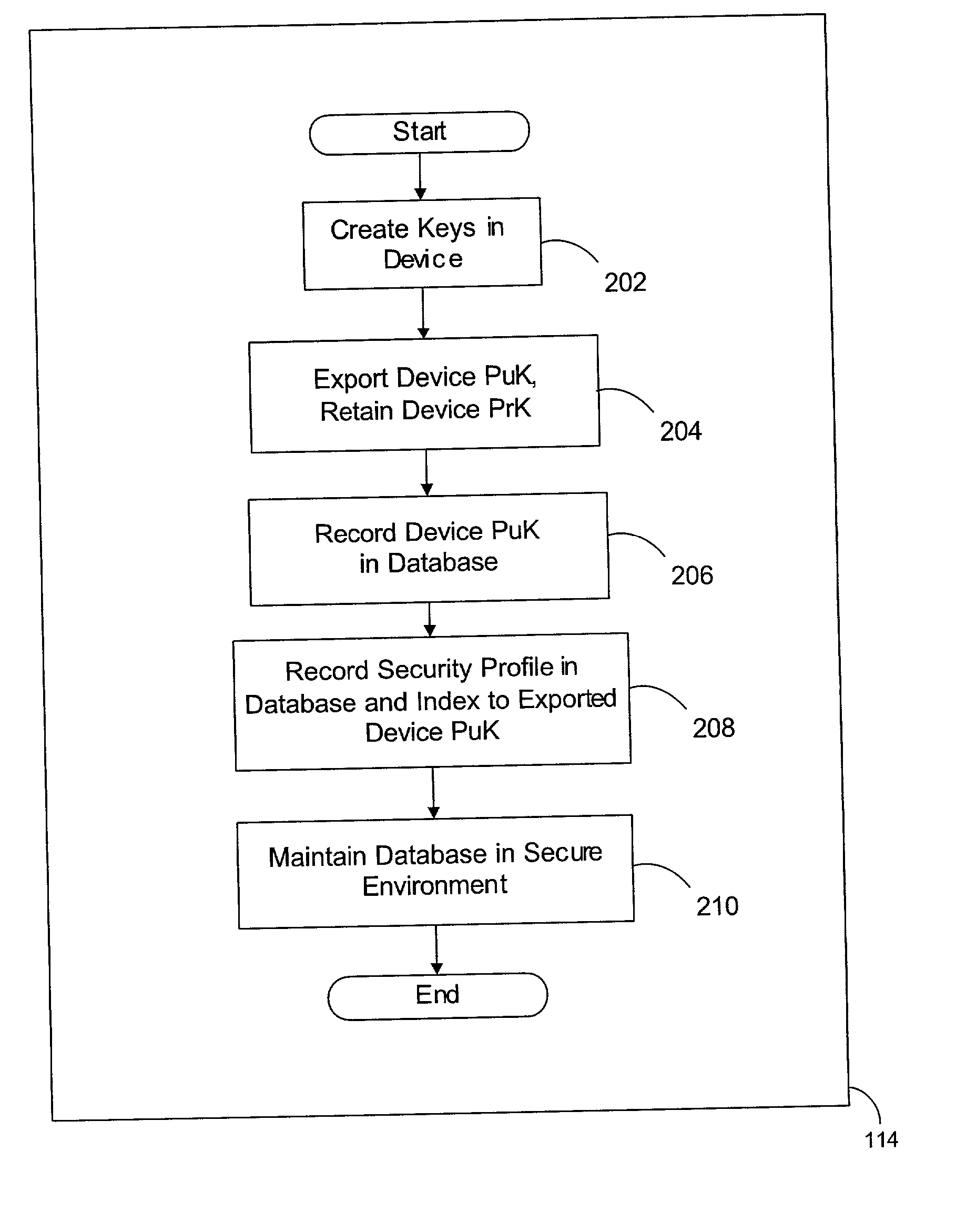
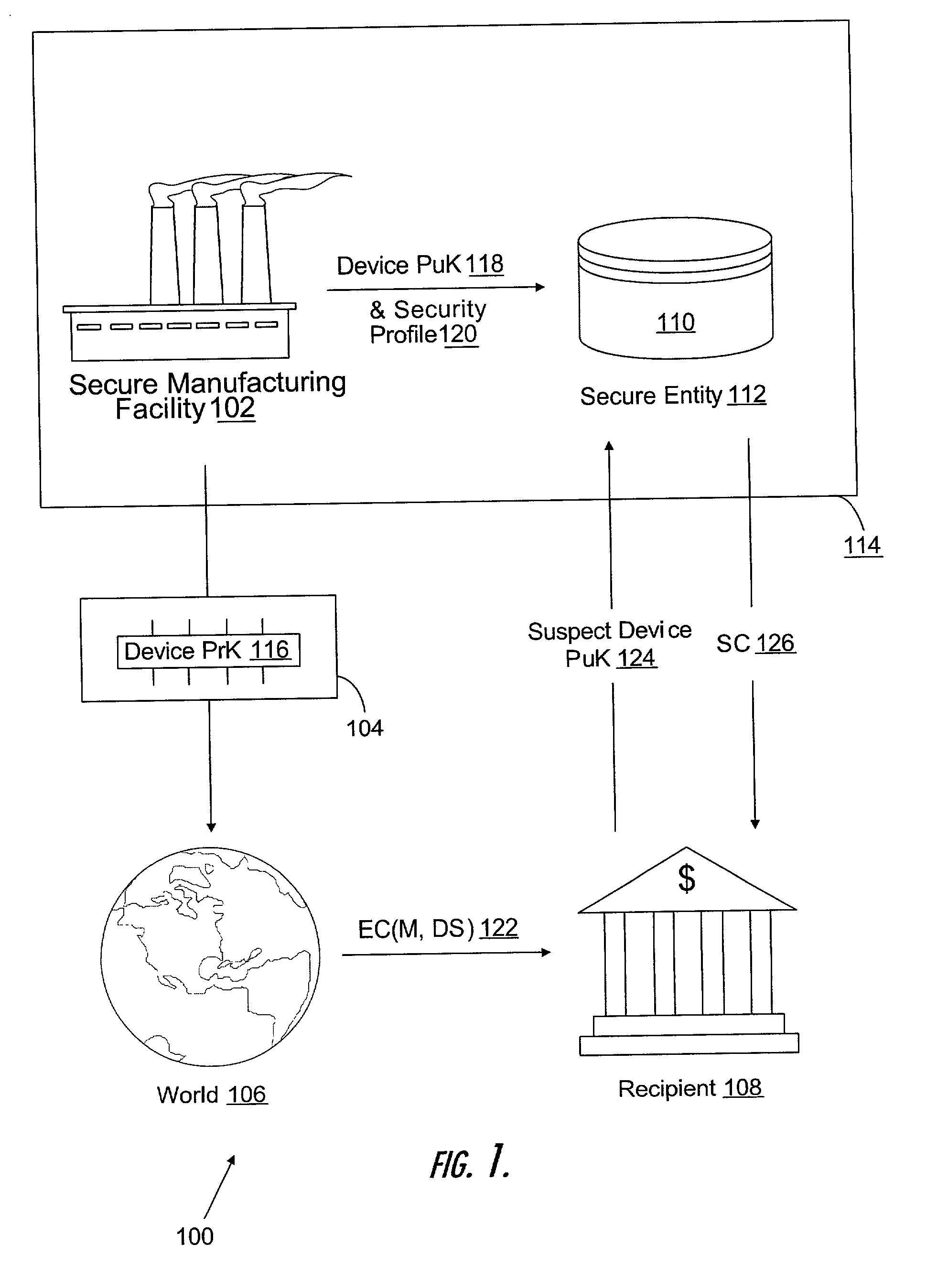
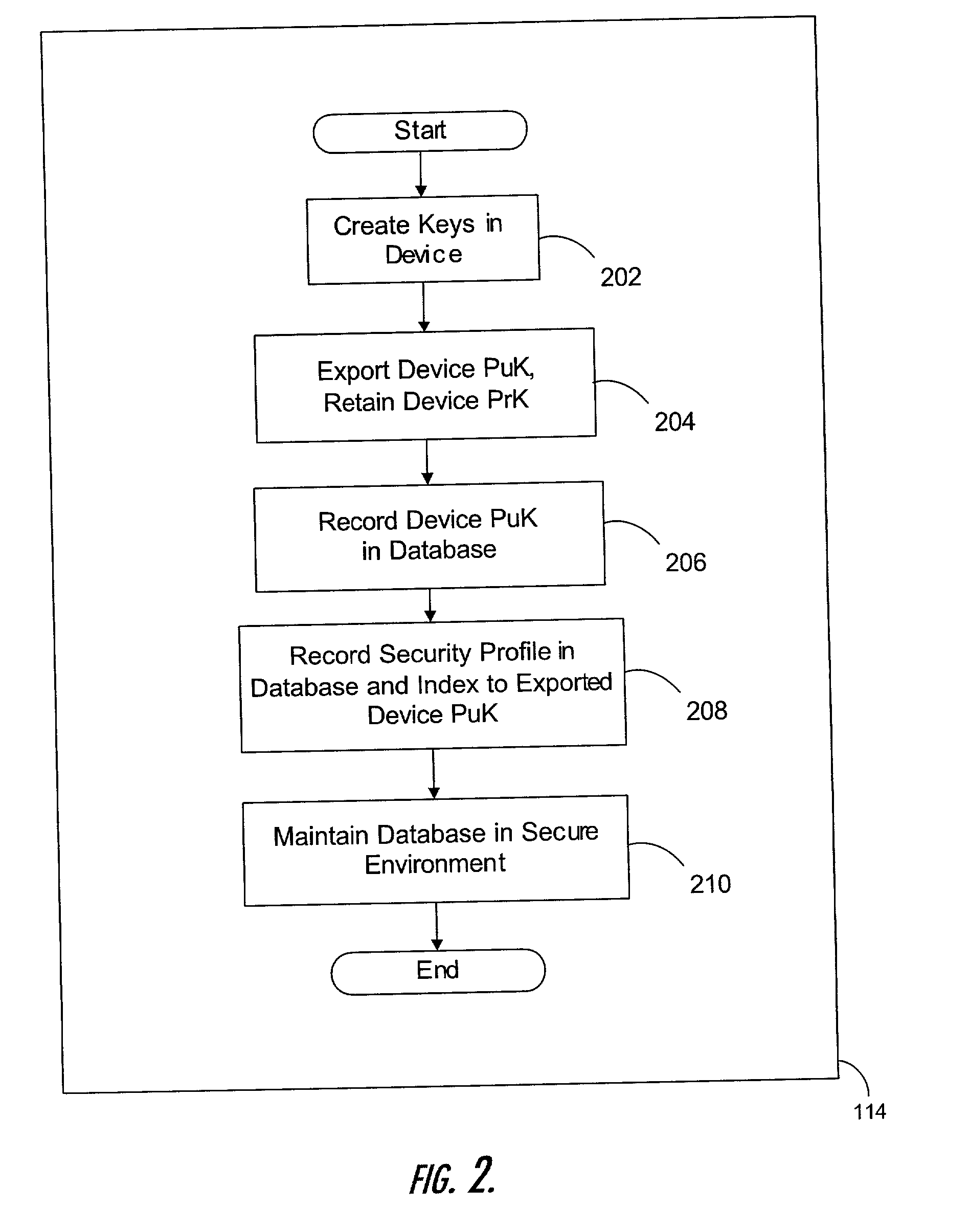
Manufacturing unique devices that generate digital signatures
InactiveUS20020023217A1User identity/authority verificationUnauthorized memory use protectionThird partyDigital signature
A method of manufacturing devices that generate digital signatures such that each device may be reliably and uniquely identified includes creating a public-private key pair within each device during manufacture; exporting only the public key from the device; retaining the private key within the device against the possibility of divulgement thereof by the device; and securely linking said exported public key with other information within the environment of the manufacture of the device, whereby each device is securely bound with its respective public key. A database of PuK-linked account information of users is maintained. The PuK-linked account information for each user includes a public key of such a device; information securely linked with the public key during manufacture; and third-party account identifiers, each of which identifies an account to a third-party of the user maintained with the third-party that has been associated with the user's public key by the third-party.
Owner:FIRST DATA
Systems and methods for identifying and mitigating information security risks
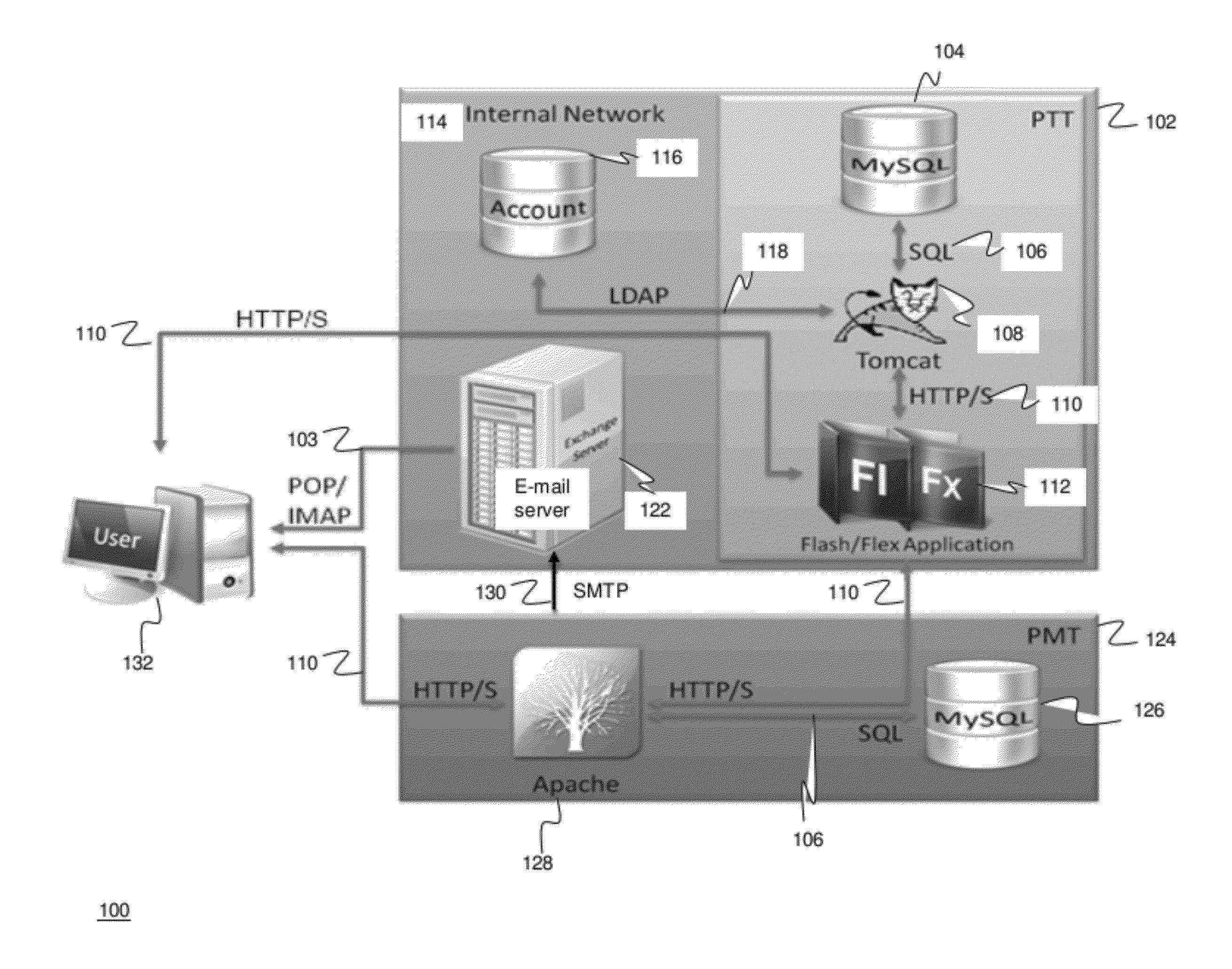
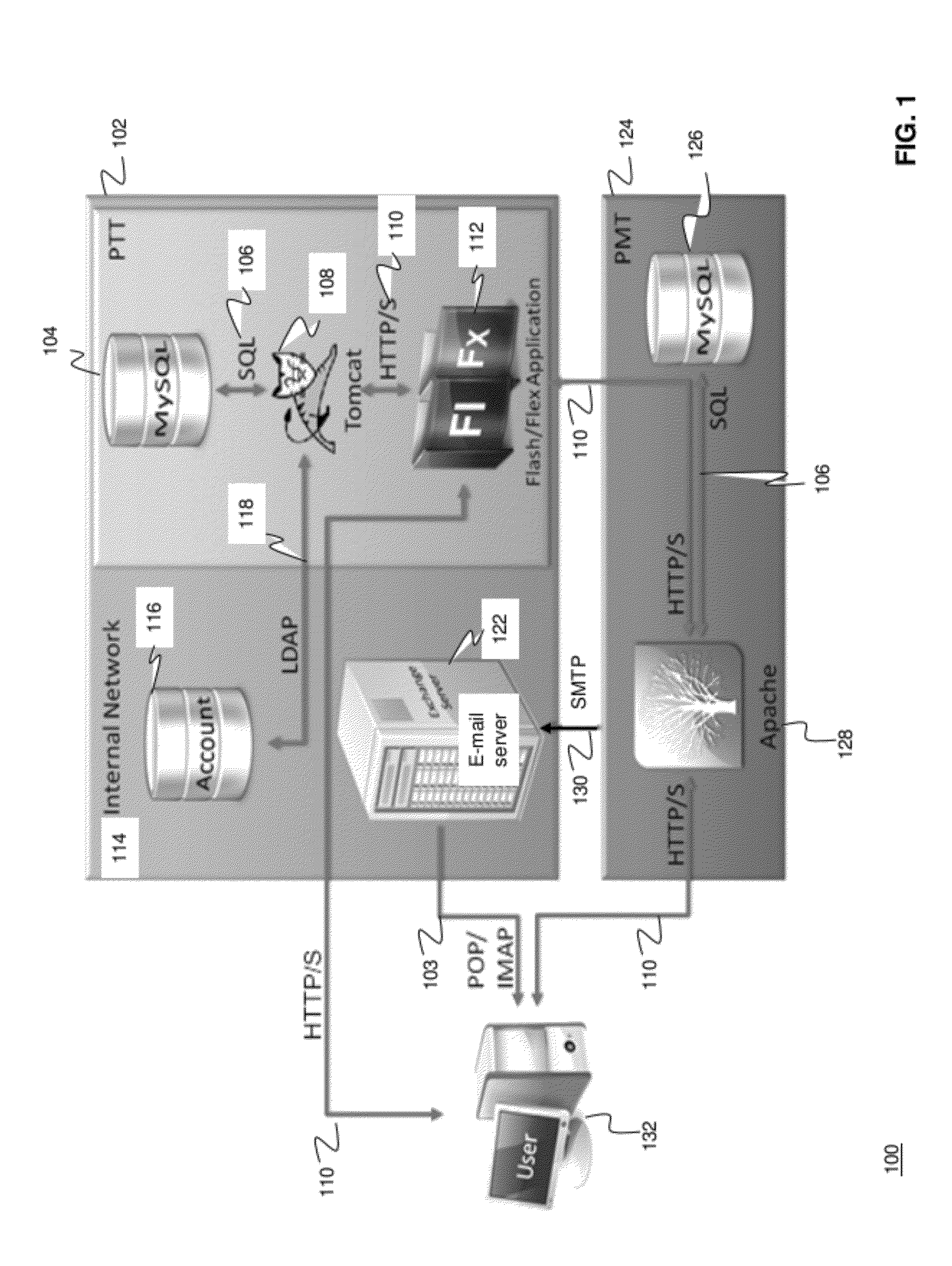
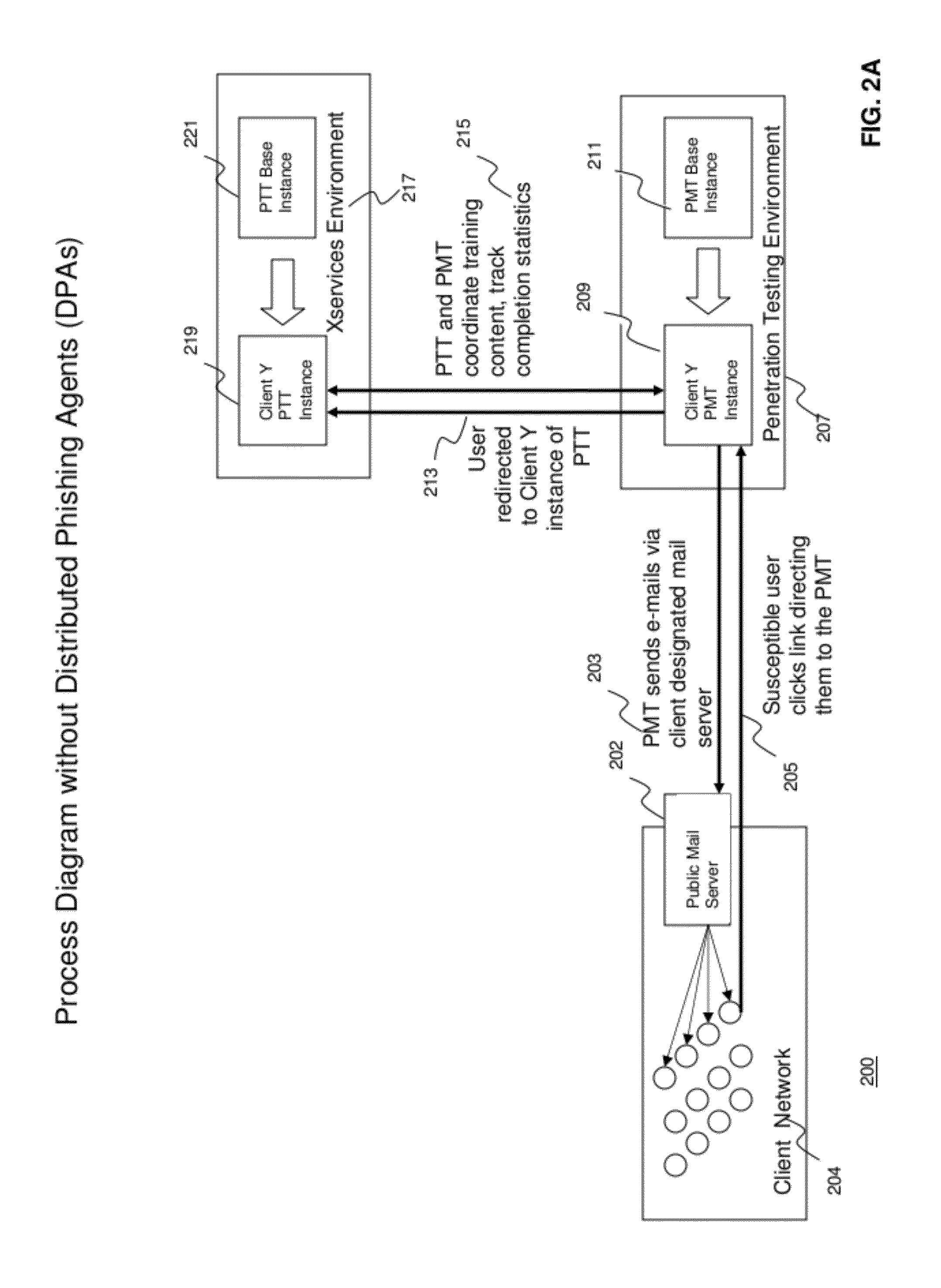
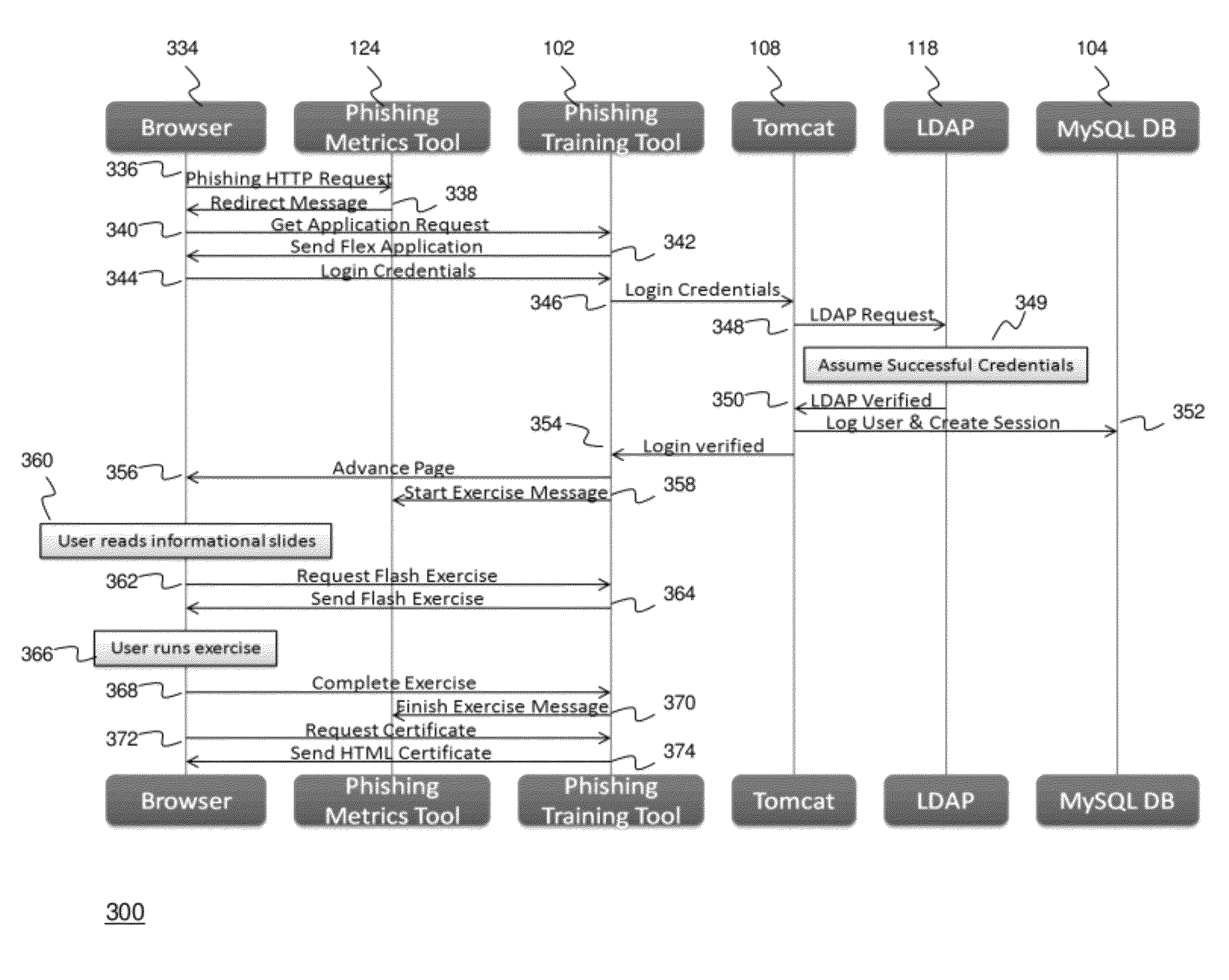
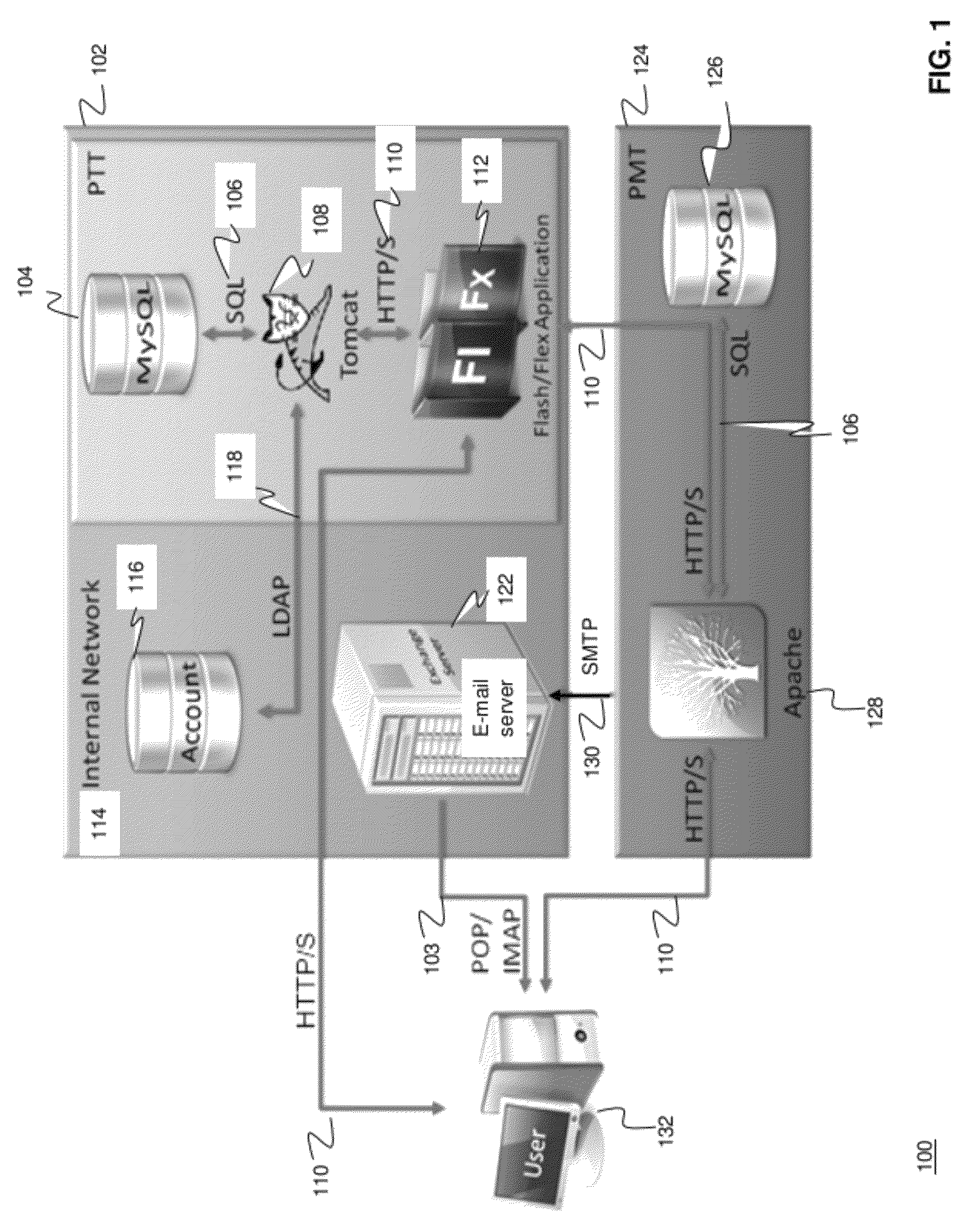
ActiveUS20120124671A1High level of realismRaise the possibilityDigital data processing detailsAnalogue secracy/subscription systemsUnique identifierPhishing
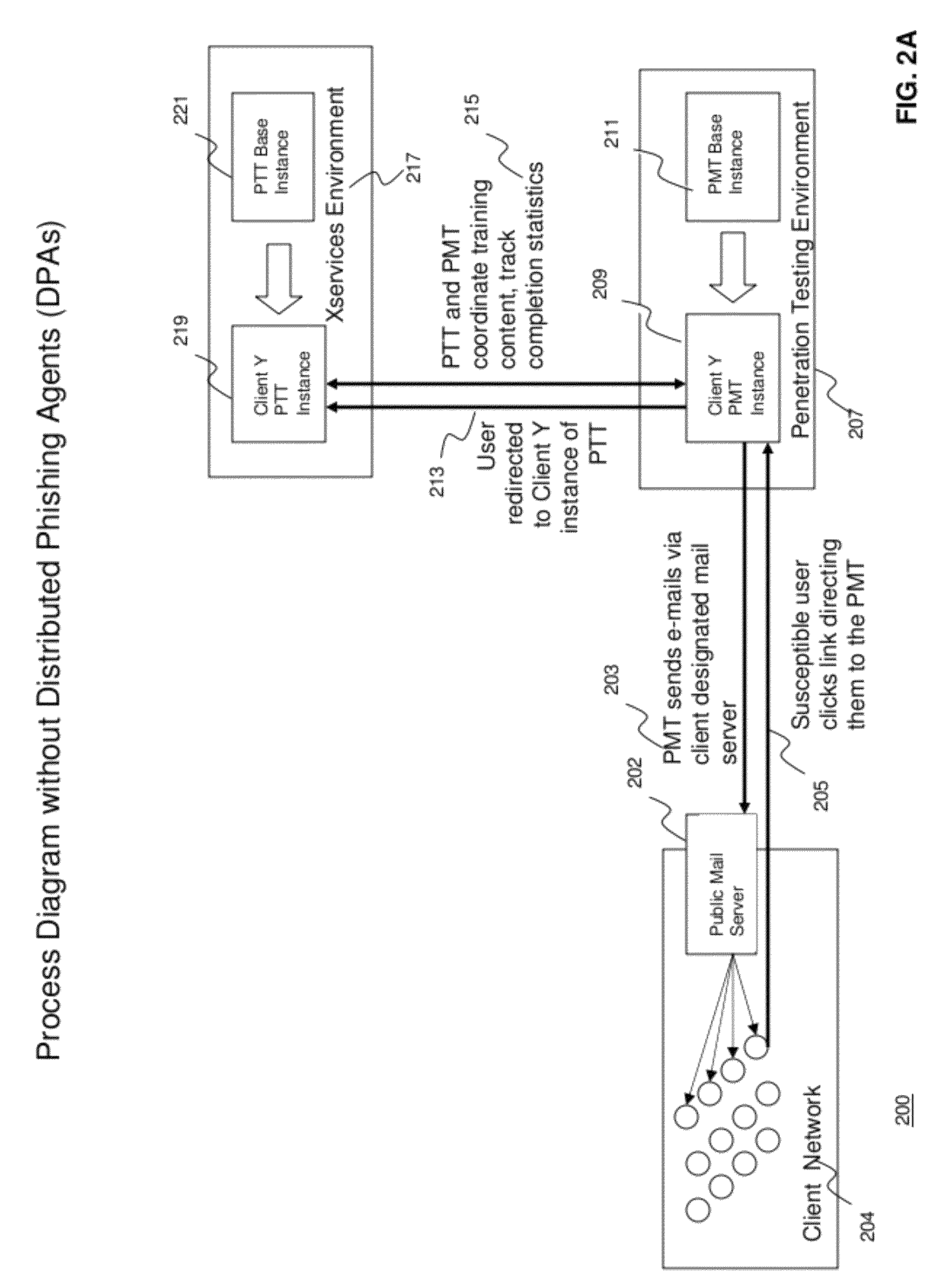
Methods and systems for Sustained Testing and Awareness Refresh against Phishing threats (STAR*Phish™) are disclosed. In an embodiment, a method assigns schemes and unique identifiers to target e-mail addresses associated with a user accounts. The method delivers e-mail messages to the targeted e-mail addresses, the e-mail messages comprising an HTTP request and a unique identifier associated with each of the user accounts. The method then receives, at a Phishing Metric Tool (PMT), a response including the unique identifier. The PMT logs training requirements for the user accounts, tracks response metrics for the training requirements, and redirects the respective HTTP requests to a phishing training tool (PTT). The PTT sends a notification of the user account identities and the unique identifiers to the PMT and returns a status for the training requirements for the user accounts. Upon completion of the training, the PMT sends completion notifications for the user accounts.
Owner:BOOZ ALLEN HAMILTON INC
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
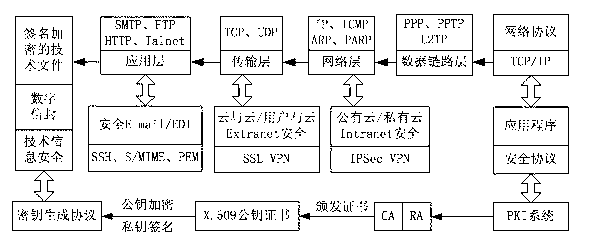
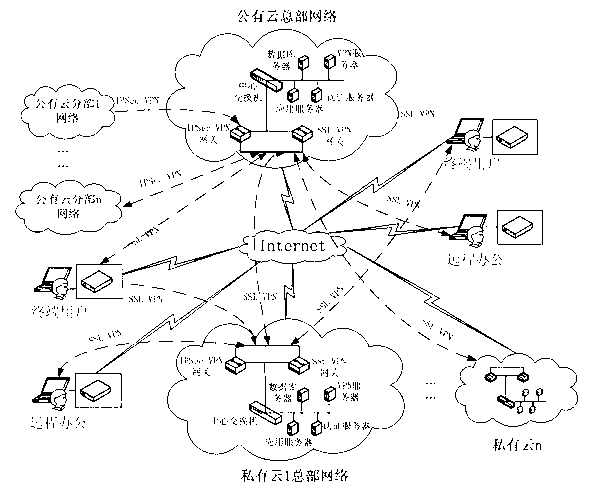
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
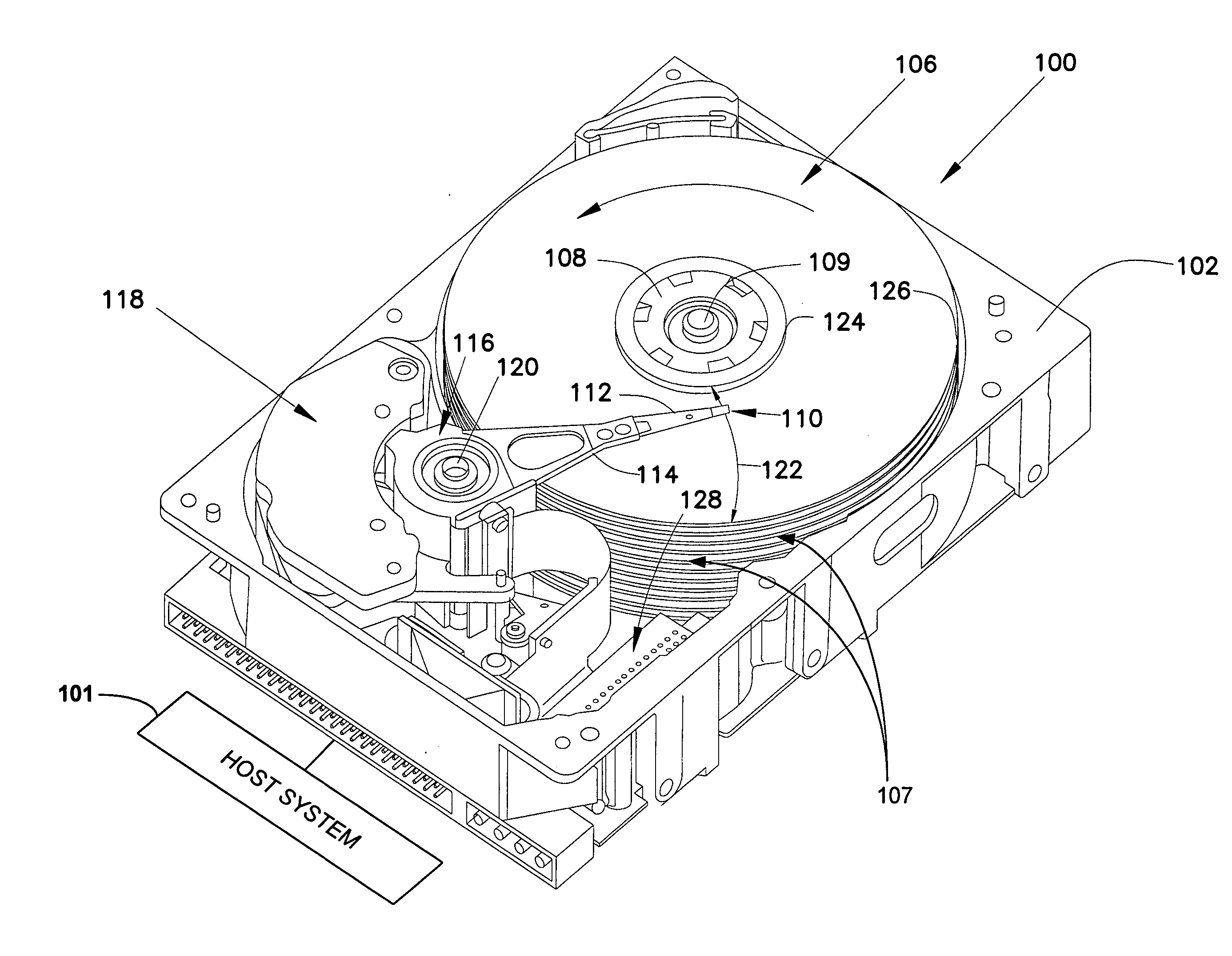
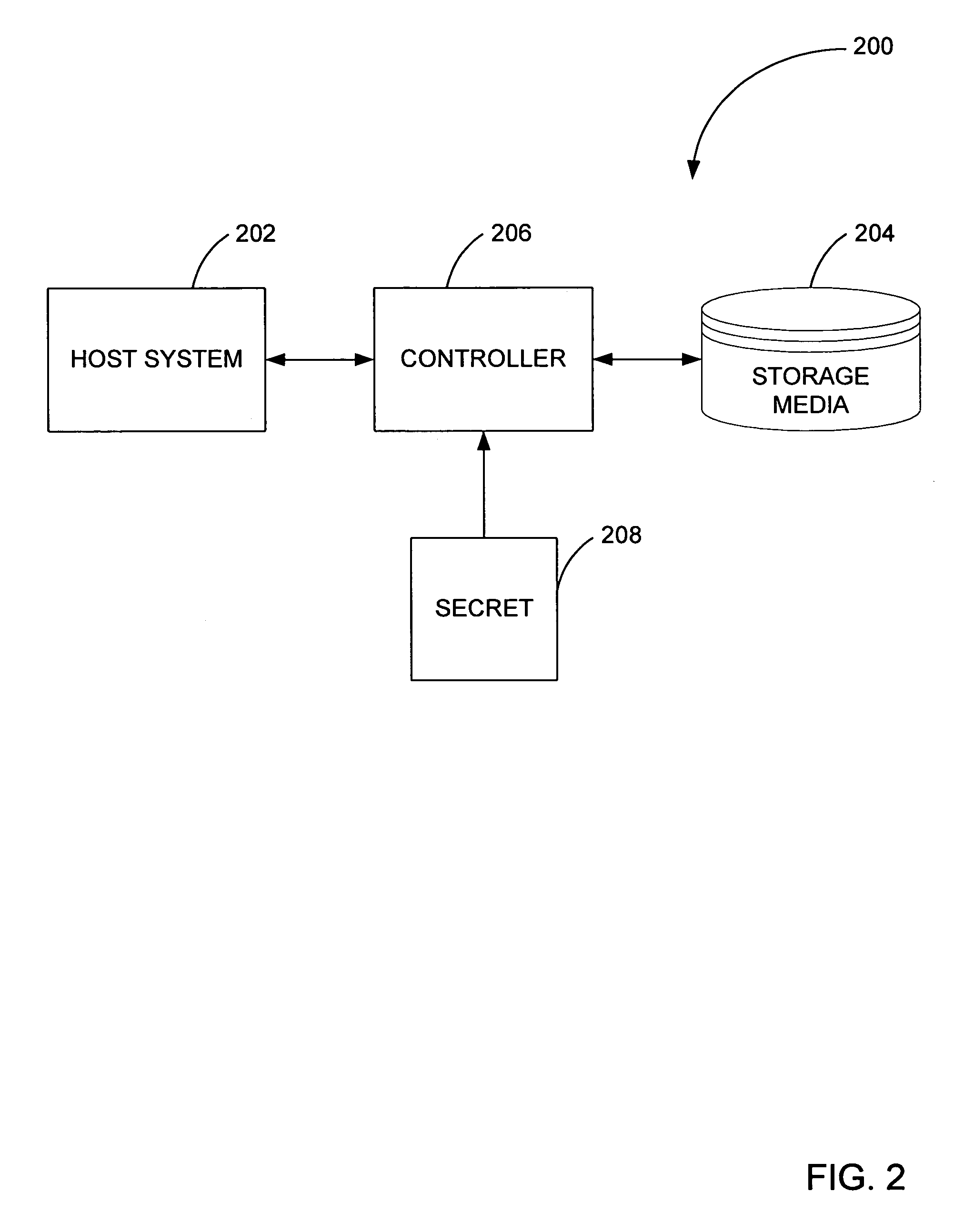
System and method for magnetic storage disposal
InactiveUS20050262361A1User identity/authority verificationUnauthorized memory use protectionMagnetic storageInformation security
A storage system has integrated information security features adapted to interact with a host system. The storage system includes a storage media, controller firmware and a controller. The storage media is adapted to store data. Controller firmware stores a secret. The controller controls data transfers between the host system and the storage media, and is adapted encrypt and decrypt data written to or read from the storage media using an encryption key based on the secret.
Owner:SEAGATE TECH LLC
Method and device for managing security in a computer network
InactiveUS20160330219A1Speed up iterationShorten the timeNavigation instrumentsKnowledge representationInteraction systemsInformation type
Method and device for managing security in a computer network include algorithms of iterative intelligence growth, iterative evolution, and evolution pathways; sub-algorithms of information type identifier, conspiracy detection, media scanner, privilege isolation analysis, user risk management and foreign entities management; and modules of security behavior, creativity, artificial threat, automated growth guidance, response / generic parser, security review module and monitoring interaction system. Applications include malware predictive tracking, clandestine machine intelligence retribution through covert operations in cyberspace, logically inferred zero-database a-priori realtime defense, critical infrastructure protection & retribution through cloud & tiered information security, and critical thinking memory & perception.
Owner:HASAN SYED KAMRAN
Distributed information security operation and maintenance management platform based on massive data
The invention discloses a distributed information security operation and maintenance management platform based on massive data. The distributed information security operation and maintenance management platform supports a single-user mode and a multi-user mode and comprises a customer service module, a security operation and maintenance management module, an acquisition terminal module, a distributed storage module and a security operation and maintenance APP store module. In the multi-user mode, the security operation and maintenance management module of each enterprise is autonomous; and one customer service module can simultaneously provide security operation and maintenance management services for a plurality of enterprises. APPs provided by the security operation and maintenance APP store on the platform include those cooperating with various information security operation and maintenance service providers together; and the distributed information security operation and maintenance management platform is convenient for users to use and can help the enterprises to rapidly position and solve problems.
Owner:NANJING LIANCHENG TECH DEV
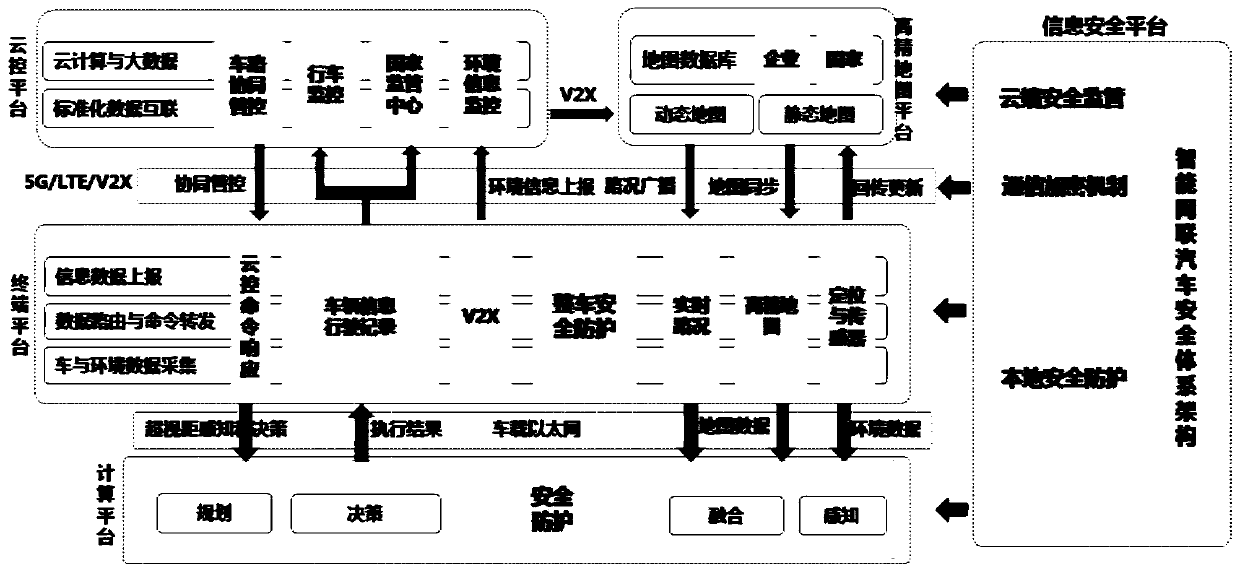
An intelligent network-connected automobile operation system based on vehicle-road collaboration
ActiveCN109714421ARealize data standardization and interconnectionMeet different applicationsParticular environment based servicesDetection of traffic movementHorizonVehicle driving
The invention discloses an intelligent network-connected automobile operation system based on vehicle-road collaboration. The intelligent networked automobile operation system comprises a high-precision map platform, a cloud control platform, a vehicle-mounted terminal platform, a vehicle-mounted computing platform and an information security platform. The high-precision map platform provides a real-time dynamic high-precision map; the cloud control platform and the vehicle-mounted terminal platform are subjected to cooperative management and control through a communication network; the cloudcontrol platform executes data storage, cloud computing and standardized data interconnection; the vehicle-mounted terminal platform executes information reporting; wherein the vehicle-mounted computing platform is connected with the vehicle-mounted terminal platform through the vehicle-mounted Ethernet, over-the-horizon perception data, map data, environment data and the like are obtained, a vehicle driving scheme is formulated through fusion calculation, and the cloud control platform, the vehicle-mounted terminal platform, the vehicle-mounted computing platform and the map platform are allprovided with safety monitors. Common basic services are provided for operation of the intelligent network connection automobile, and national and industrial development requirements are met.
Owner:CHINA INTELLIGENT & CONNECTED VEHICLES (BEIJING) RES INST CO LTD +1
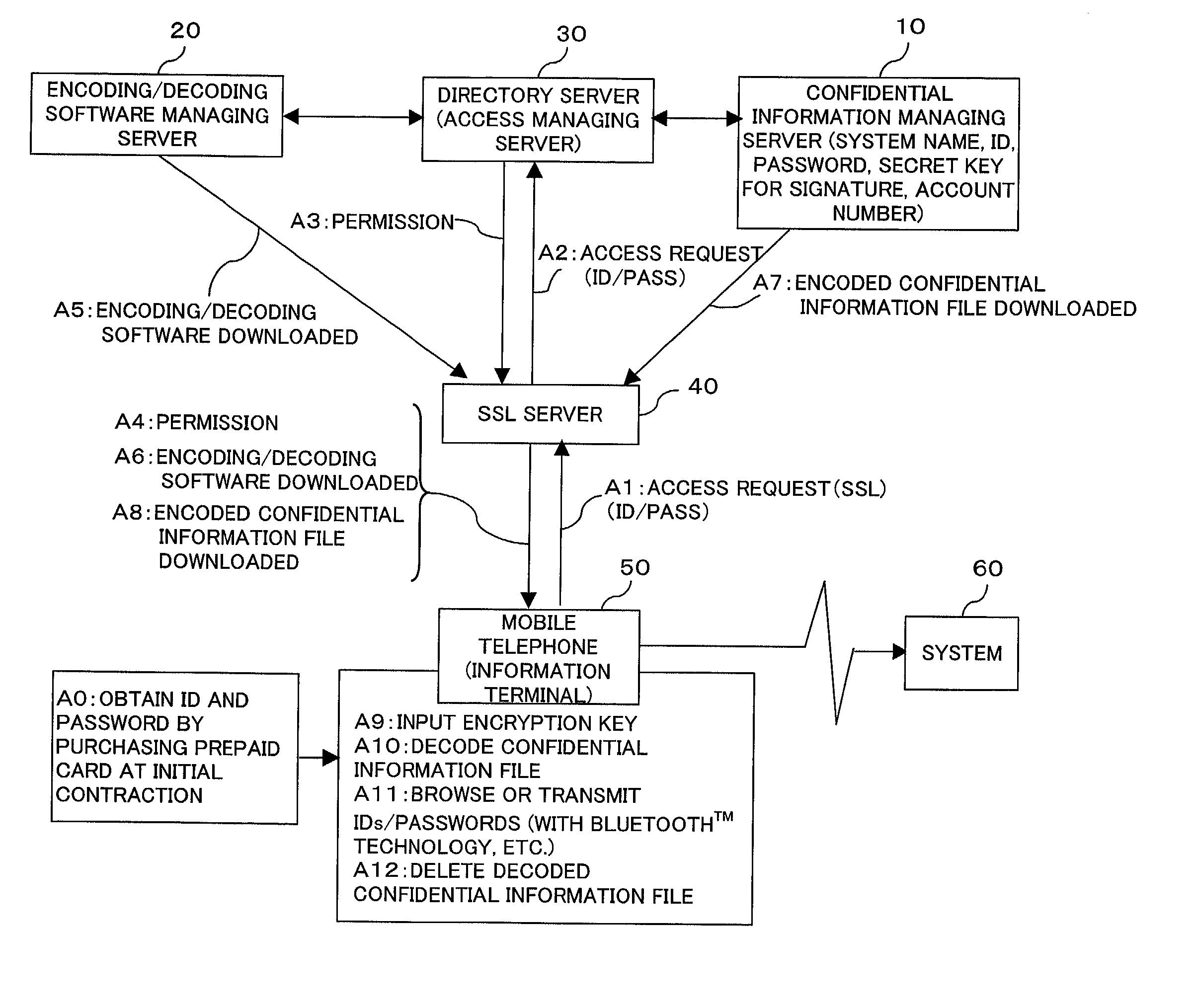
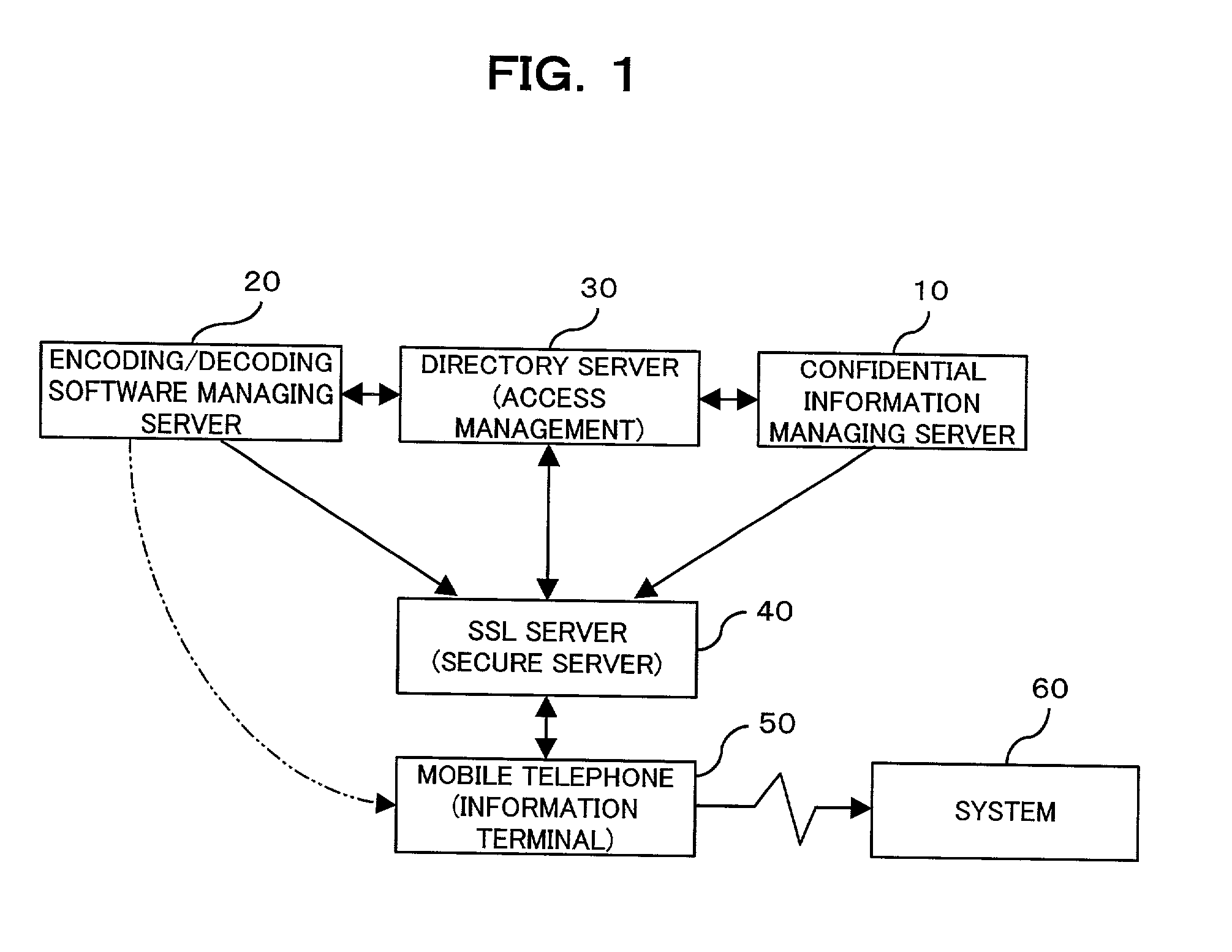
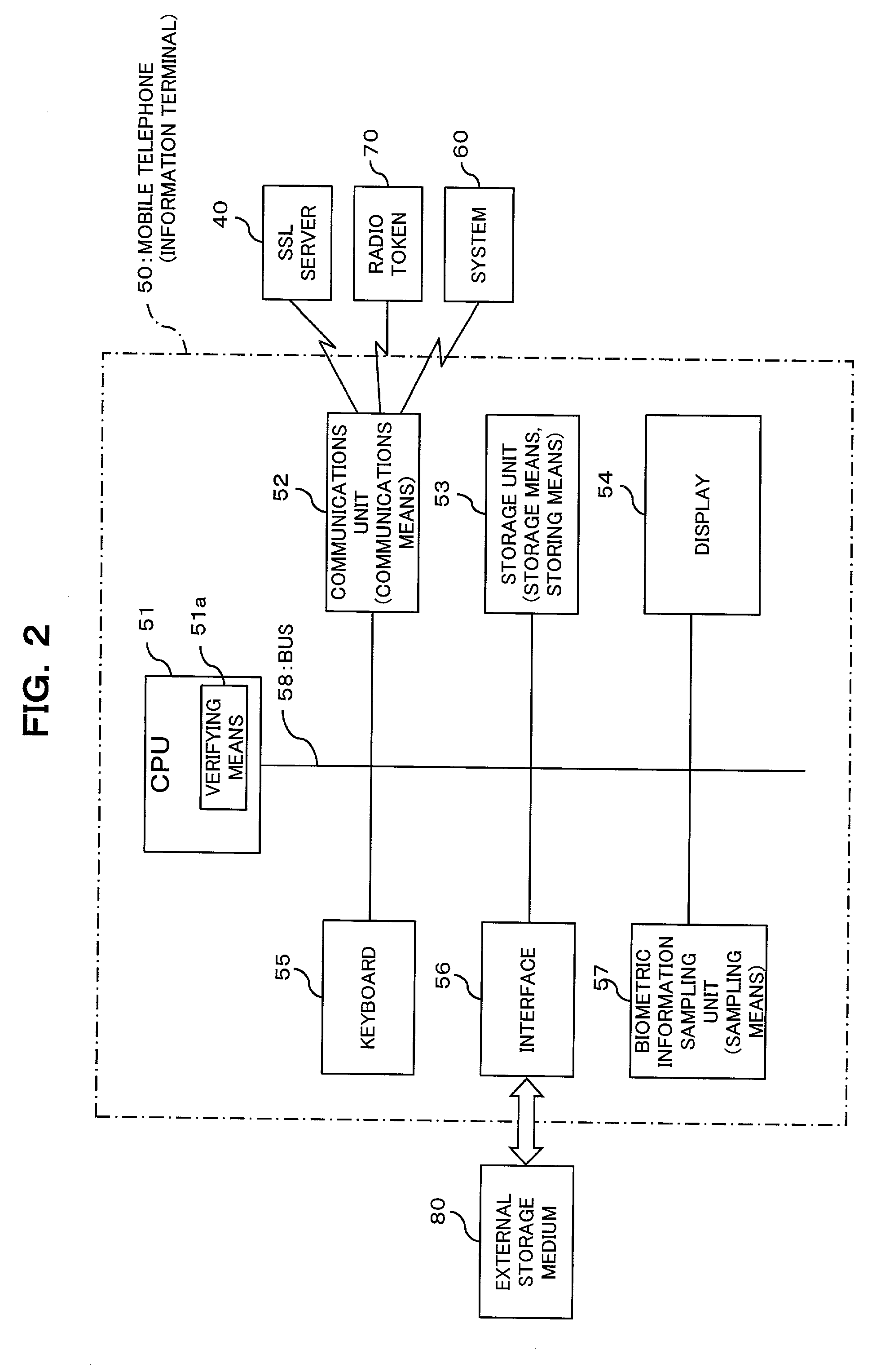
Confidential information management system and information terminal for use in the system
InactiveUS20030004881A1Simplify user operationsAvoid problemsUser identity/authority verificationUnauthorized memory use protectionUser verificationInternet privacy
The present invention provides a confidential information management system which allows users to securely obtain confidential information files containing various confidential information, which files are securely stored in the present system, anywhere and anytime, using a minimum of confidential information. A confidential information file and encoding / decoding software are downloaded to an information terminal from a confidential information managing server and an encoding / decoding software managing server, respectively, so that the confidential information file is decoded on the information terminal by using the encoding / decoding software. The present system is applicable to various (computer) systems which store and manage confidential information (ID numbers, passwords, encryption keys, digital certificates, etc.) for use in user verification.
Owner:FUJITSU LTD
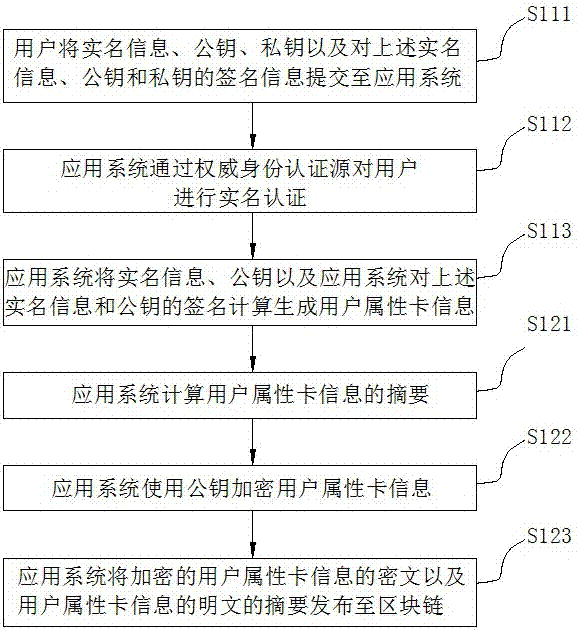
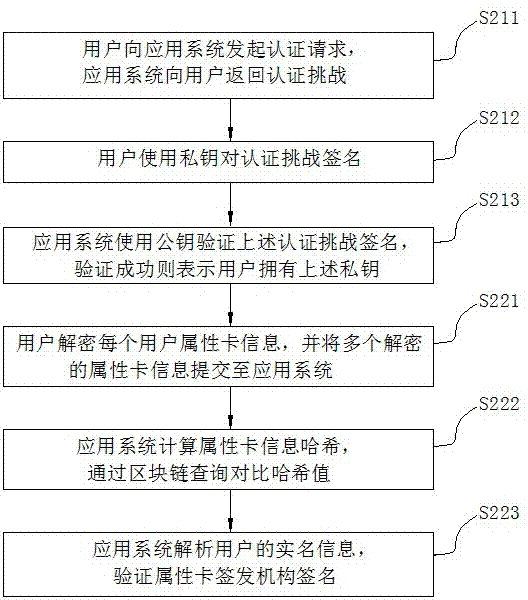
Multi-party trusted identity authentication method and system based on block chain
ActiveCN107196966AEnsure authenticityClear and unambiguous identityKey distribution for secure communicationMultiple keys/algorithms usageApplication serverThe Internet
The invention discloses a multi-party trusted identity authentication method and system based on a block chain, and belongs to the field of Internet identity authentication. The technical problem to be solved is to realize identity authentication of a user in a plurality of application systems based on the block chain, securely store the user information in the identity authentication process through the block chain and really and completely verify the user identity. The method comprises the following steps: an application system generates user attribute card information according to a received registration request, encrypts the user attribute card information and issues the user attribute card information to the block chain, wherein a plurality of application systems are provided, and the encrypted user attribute card information corresponding to each application system is stored in the block chain; each application system verifies the user identity based on the block chain. The system structurally comprises a block chain network, a client authentication module configured in a client and an application server authentication module configured in the application system. By adoption of the multi-party trusted identity authentication method and system, the real name information of the user is stored in the block chain securely and reliably, and the identity authentication of the user is implemented really and completely through the block chain.
Owner:北京信任度科技有限公司
Identity-based-encryption system with district policy information
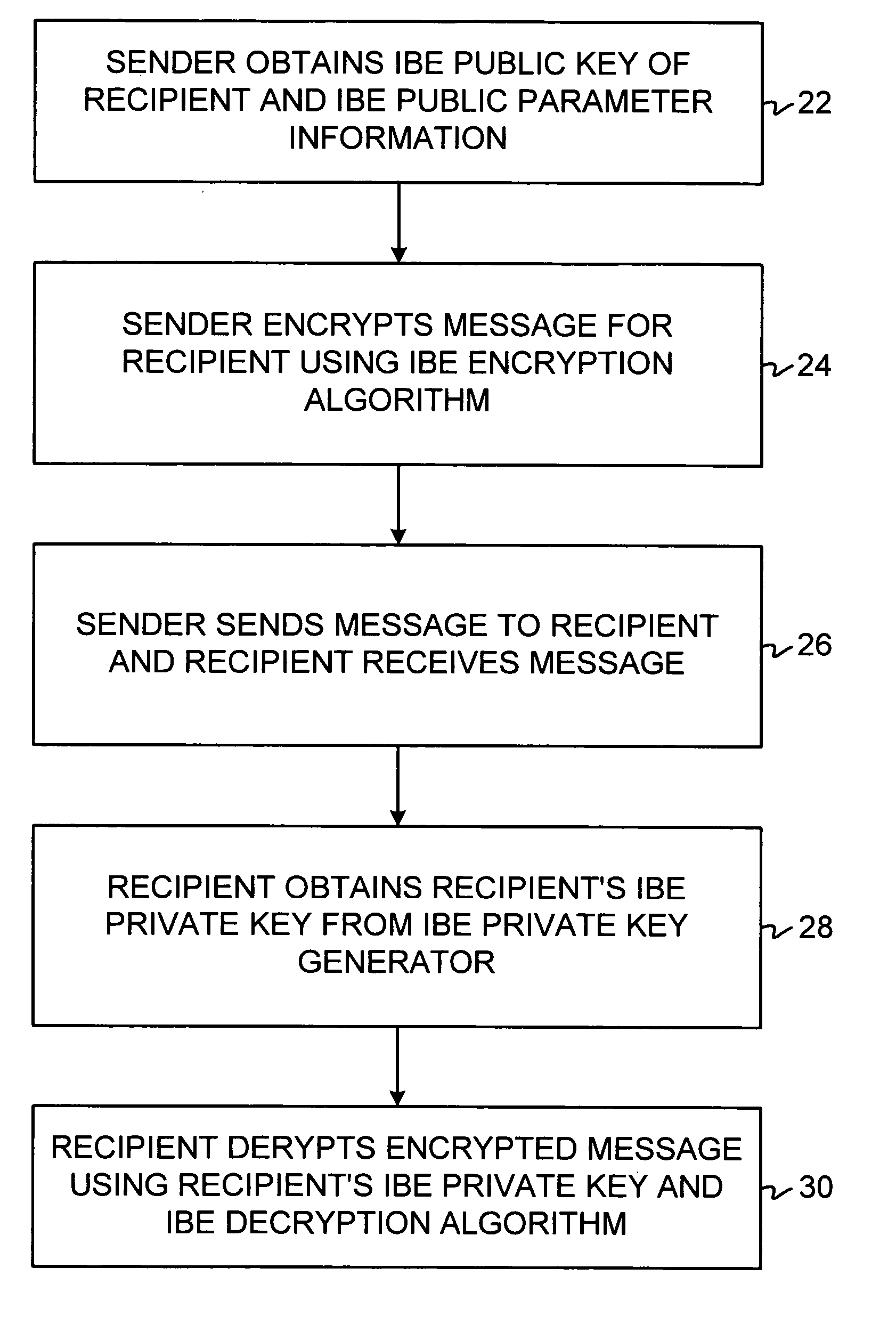
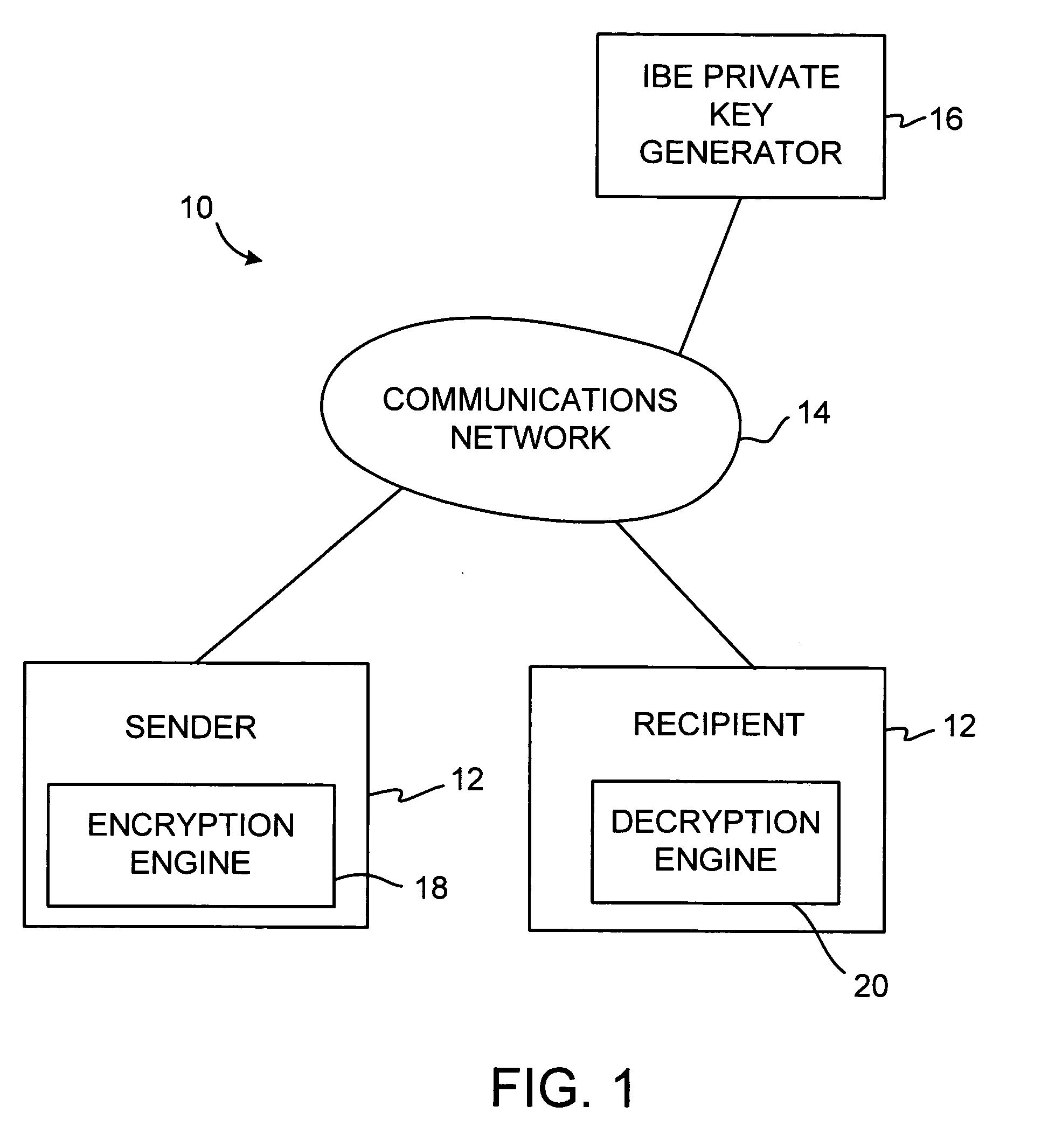
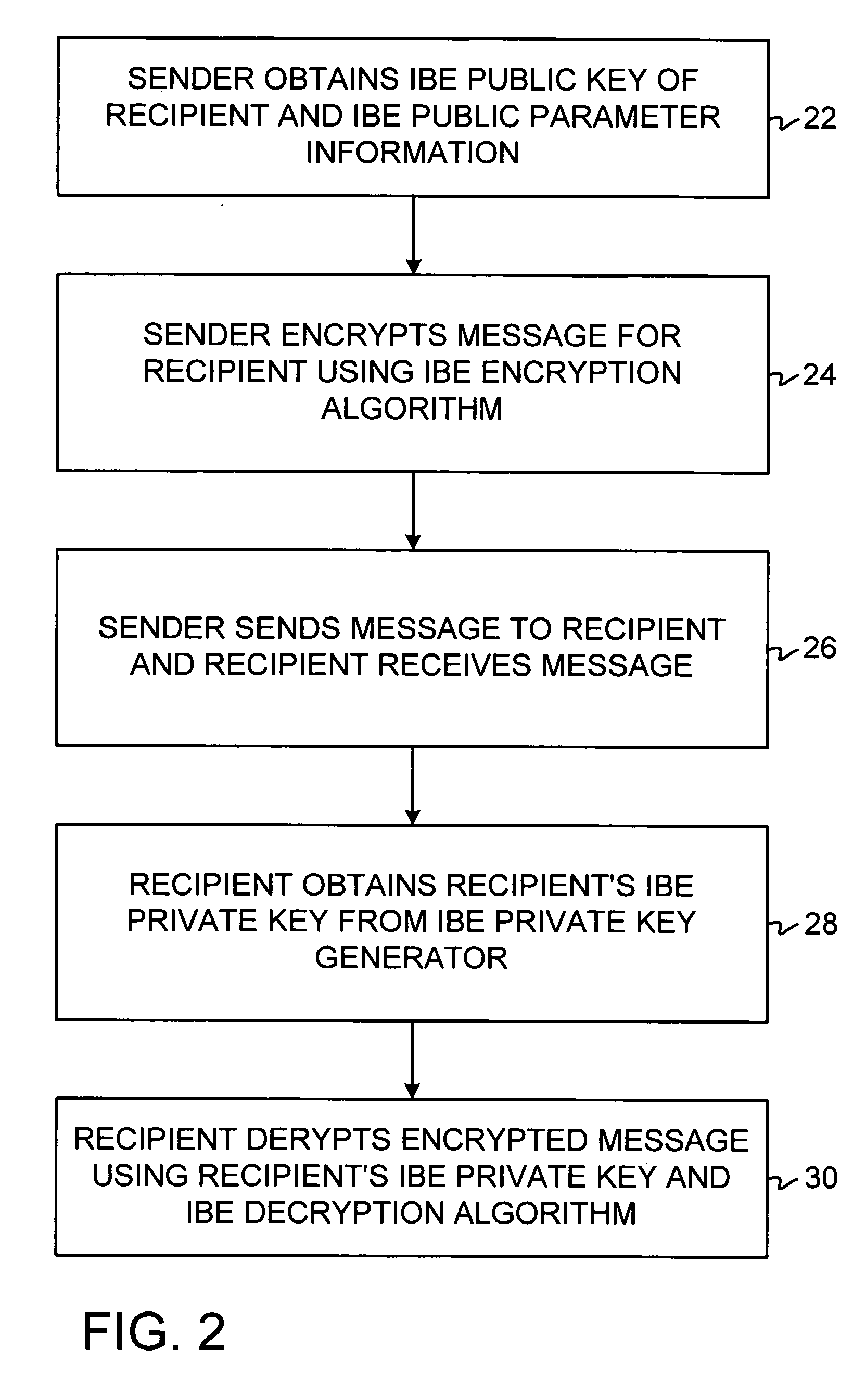
ActiveUS20050084100A1Public key for secure communicationSecret communicationNetwork Communication ProtocolsInformation security
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. The IBE private keys may be provided to message recipients by an IBE private key generator. The IBE private key generator and the recipients who obtain their IBE private keys from that generator form a district. District policy information may be provided by the IBE private key generator that specifies which encryption and communications protocols are used by the district. The district policy information may also specify which authentication protocols are used by the district and may set forth how content-based protocols are implemented. This information may be used by senders in sending messages to recipients.
Owner:MICRO FOCUS LLC
Terminal -to-terminal communication connection control method using IP transfer network
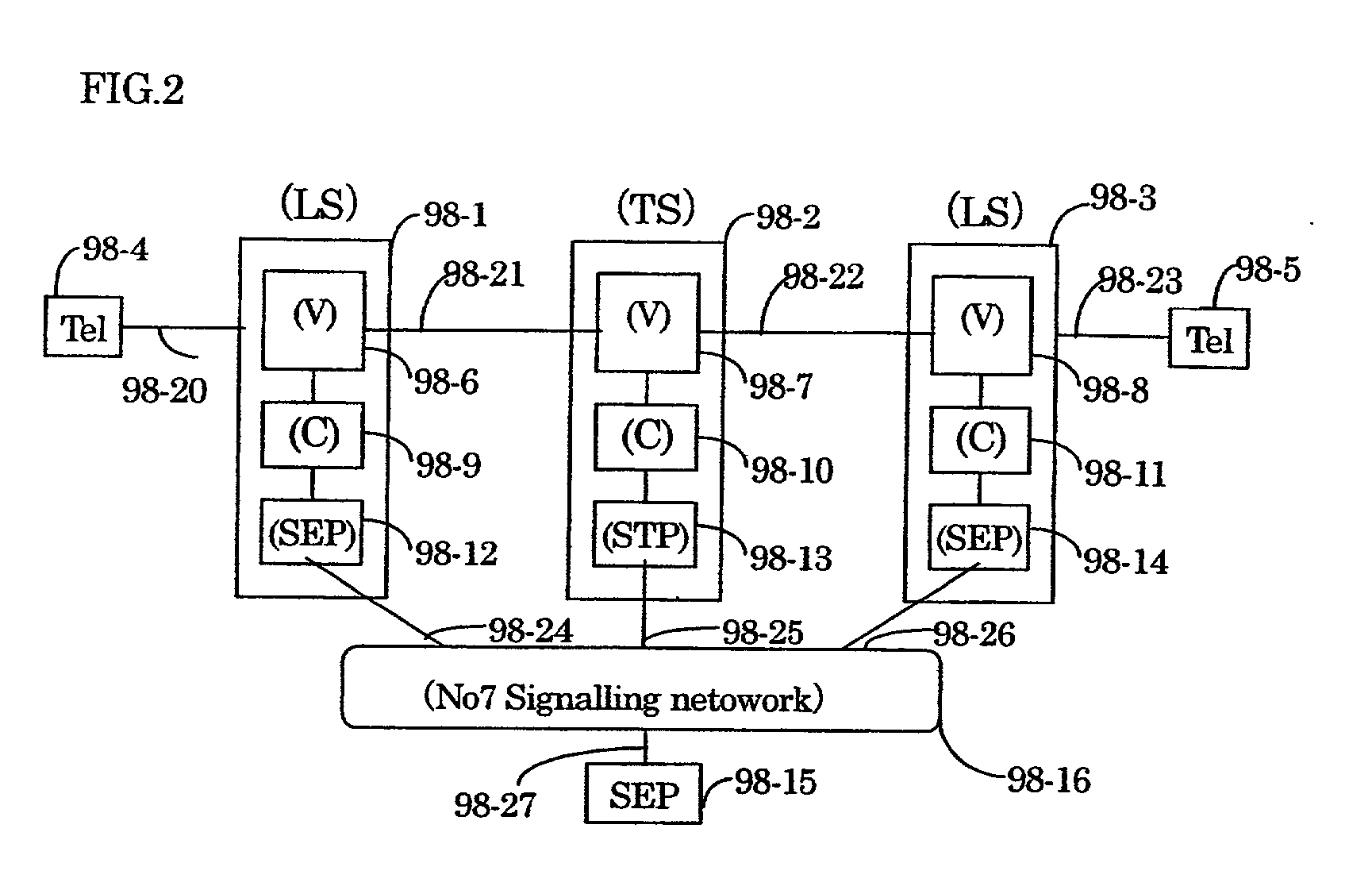
InactiveUS20020009073A1Special service provision for substationData switching by path configurationPacket communicationSignaling system
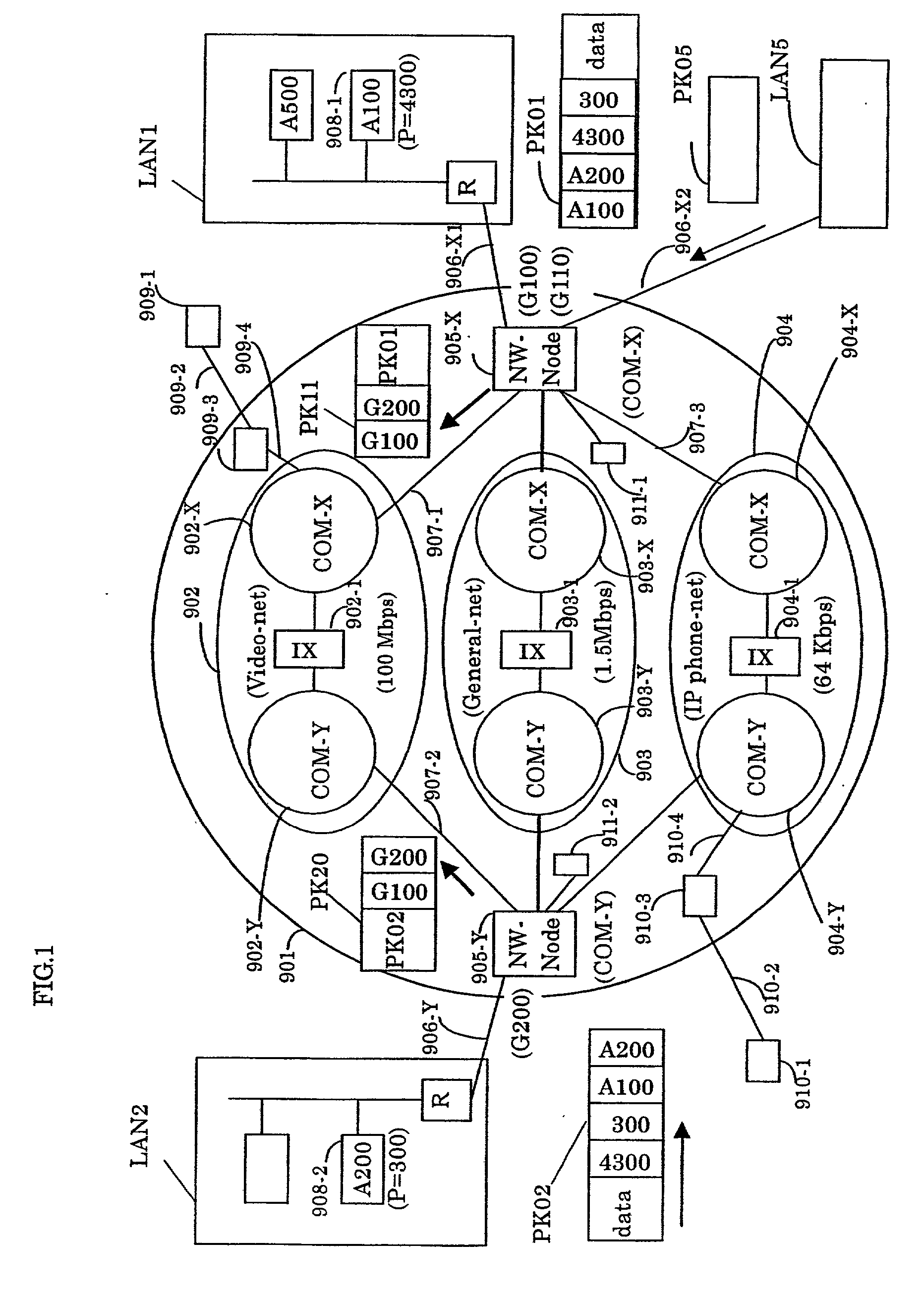
Both a connection server and a relay connection server are installed in an IP transfer network; a function similar to a line connection control of a subscriber exchanger is applied to a connection server; a function similar to a line connection control of a relay exchanger is applied to the relay connection server; and a terminal-to-terminal communication connection control method with using the IP transfer network is realized in such a manner that a telephone set and a terminal such as an IP terminal and a video terminal transmit / receive an initial address message, an address completion message, a call pass message, a response message, a release message and a release completion message, which can be made in a 1-to-1 correspondence relationship with line connection control messages of the common line signal system. Furthermore, while an address administration table is set to a network node apparatus of an IP transfer network, means for registering addresses of the terminals into this address administration table is employed, so that an IP packet communication by a multicast manner can be realized with improving information security performance.
Owner:DISTRIBUTION SYST RES INST THE AN UNDIVIDED 60 INTEREST +1
Systems and methods for identifying and mitigating information security risks
ActiveUS8793799B2High level of realismRaise the possibilityMemory loss protectionDigital data processing detailsUnique identifierPhishing
Methods and systems for Sustained Testing and Awareness Refresh against Phishing threats (STAR*Phish™) are disclosed. In an embodiment, a method assigns schemes and unique identifiers to target e-mail addresses associated with a user accounts. The method delivers e-mail messages to the targeted e-mail addresses, the e-mail messages comprising an HTTP request and a unique identifier associated with each of the user accounts. The method then receives, at a Phishing Metric Tool (PMT), a response including the unique identifier. The PMT logs training requirements for the user accounts, tracks response metrics for the training requirements, and redirects the respective HTTP requests to a phishing training tool (PTT). The PTT sends a notification of the user account identities and the unique identifiers to the PMT and returns a status for the training requirements for the user accounts. Upon completion of the training, the PMT sends completion notifications for the user accounts.
Owner:BOOZ ALLEN HAMILTON INC
RFID transponder information security methods systems and devices
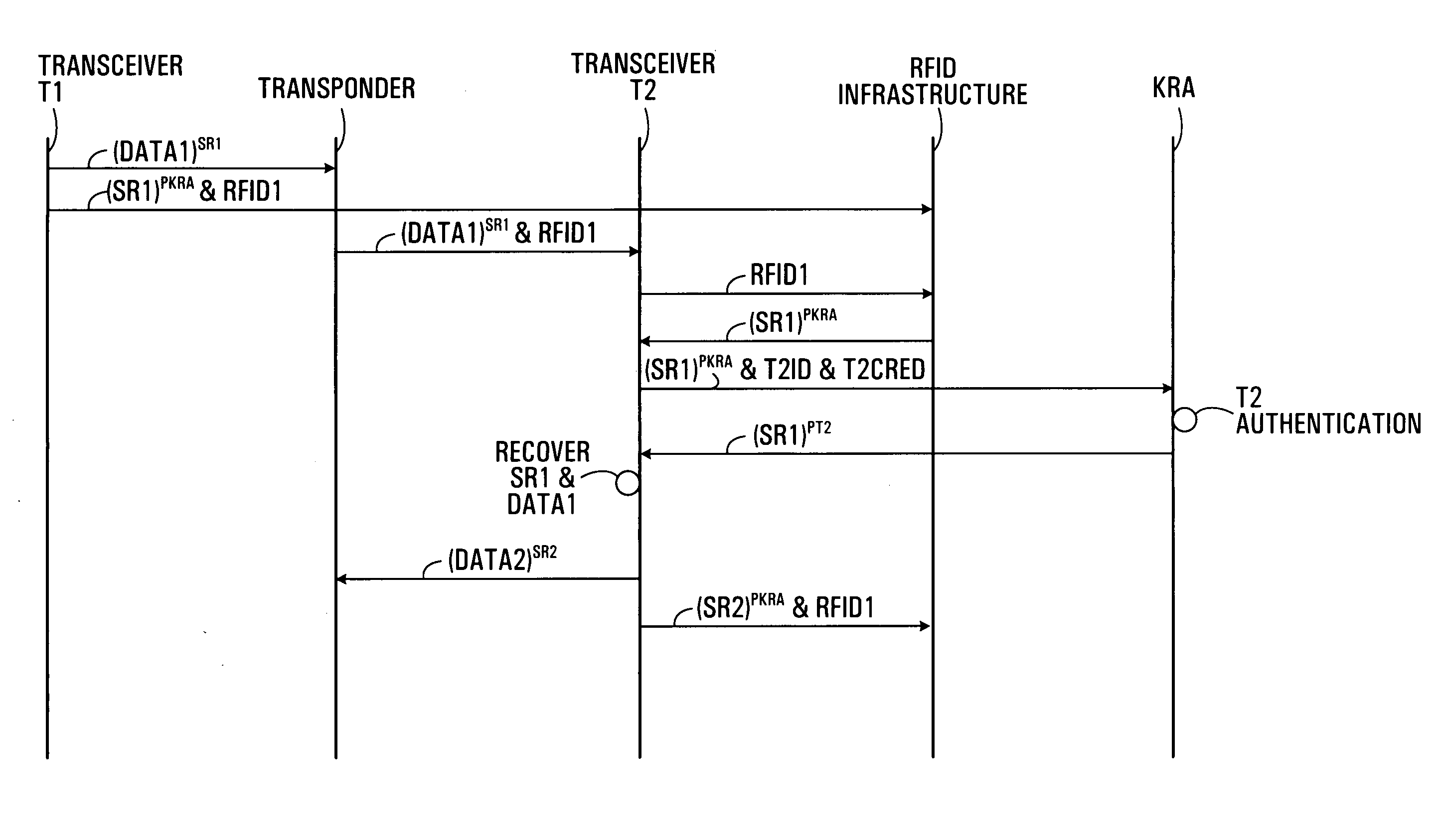
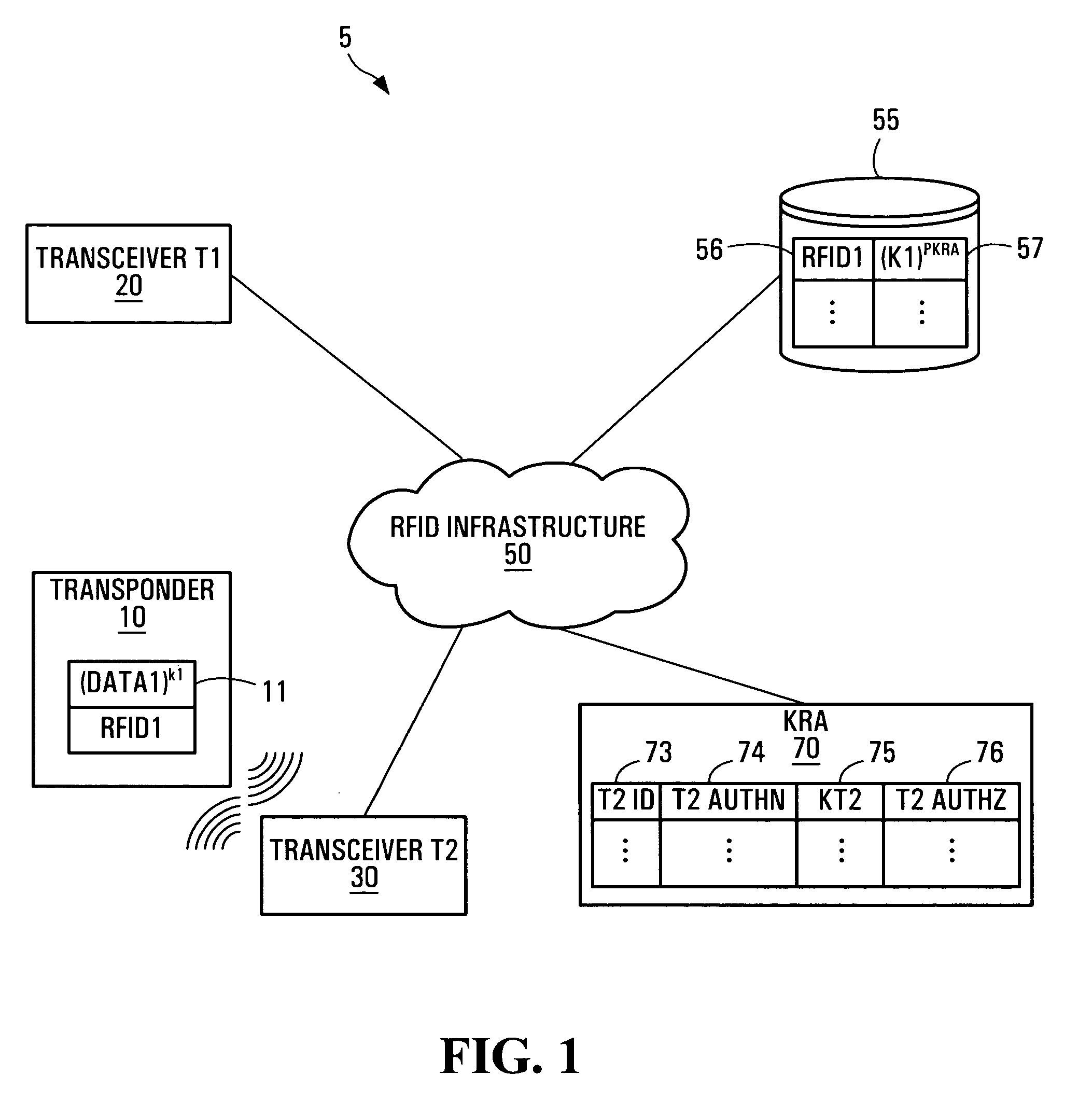
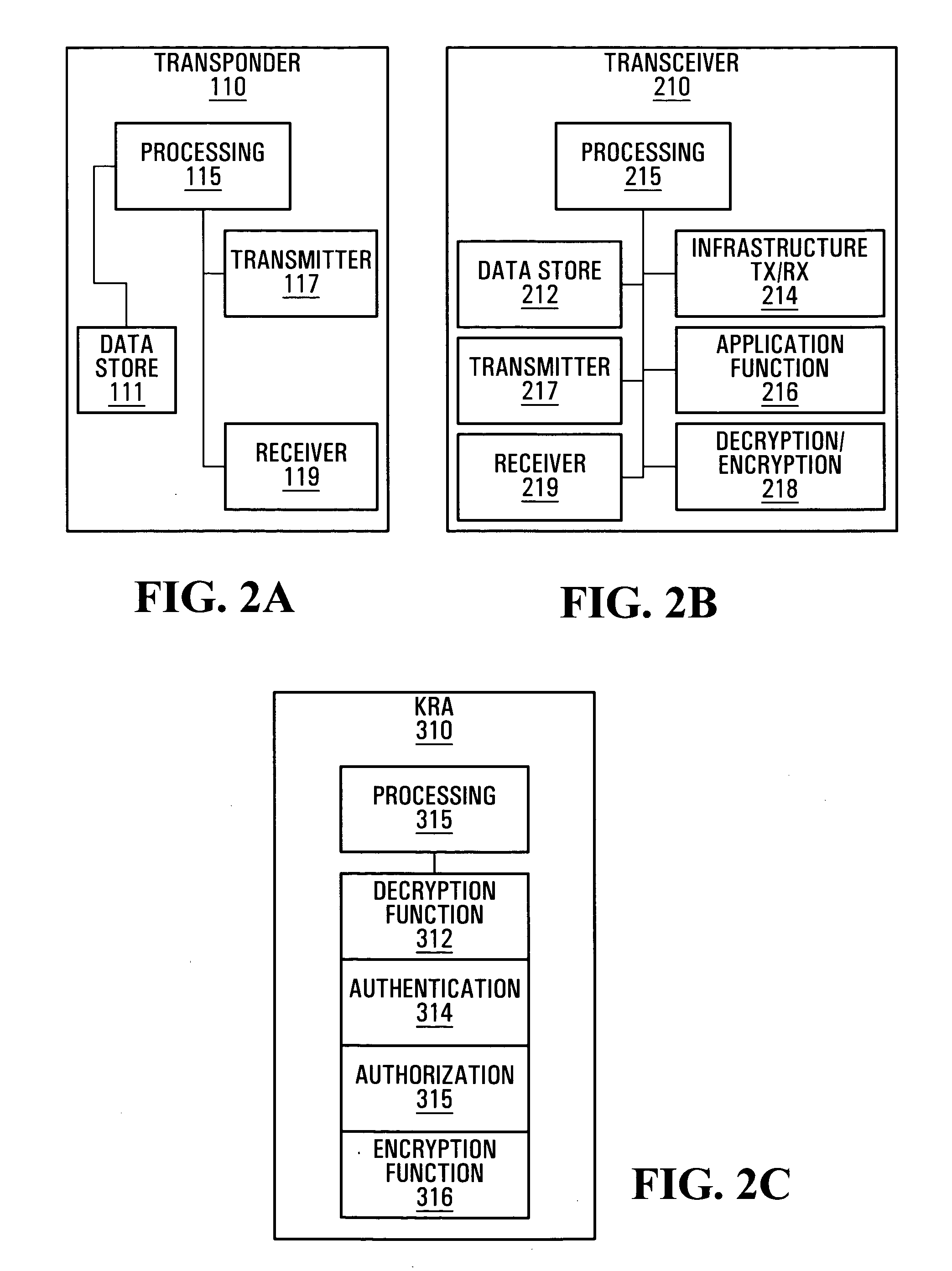
ActiveUS20060077034A1Electric signal transmission systemsMultiple keys/algorithms usageTransceiverInformation security
Methods, systems and devices for providing RFID system security are provided that involve cryptographically encrypting data on a transponder and managing the release of the decryption information, decryption keys, or the data itself to a transceiver having a transaction with the transponder.
Owner:ENTRUST
Enterprise service-to-service trust framework
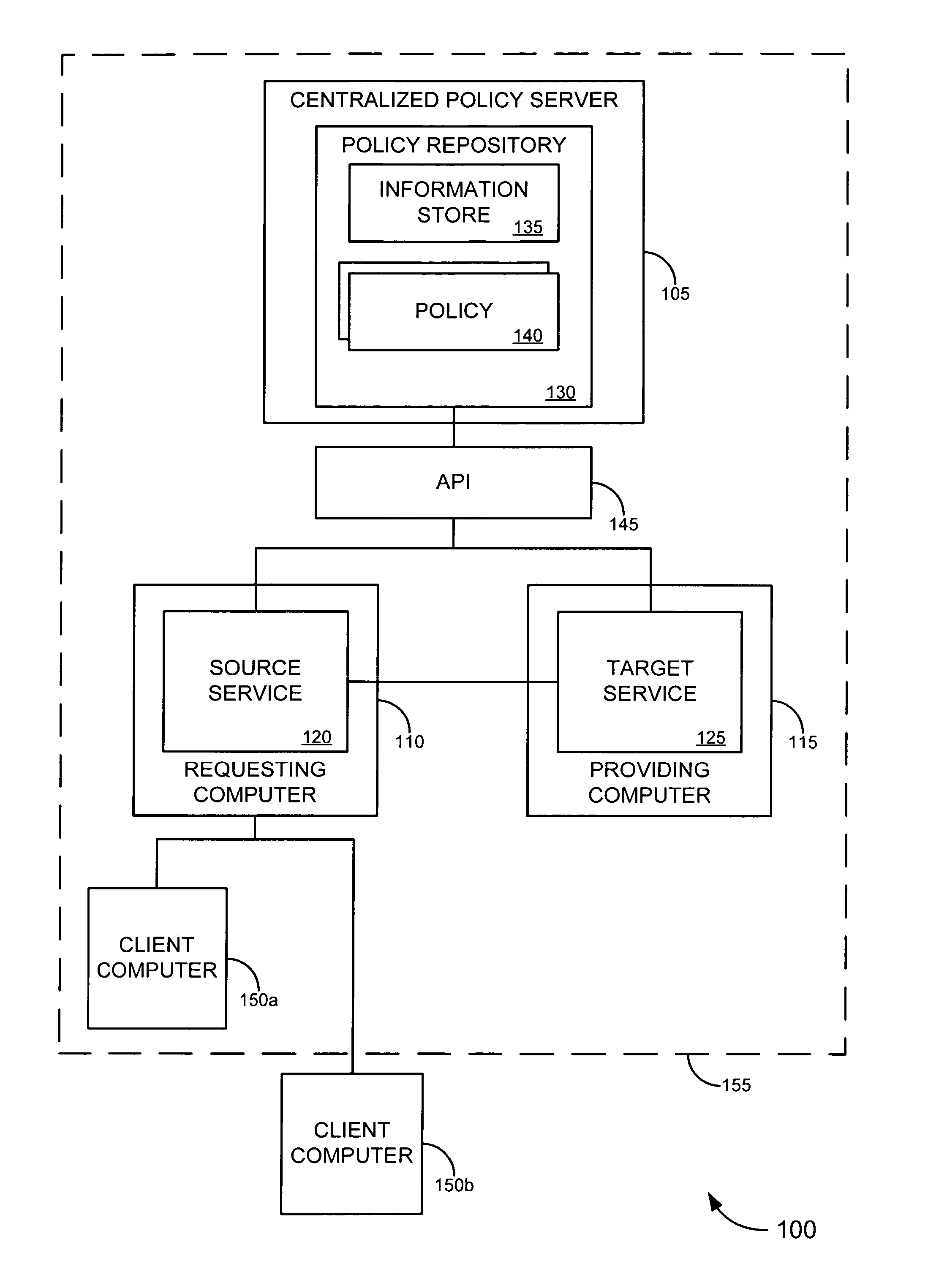
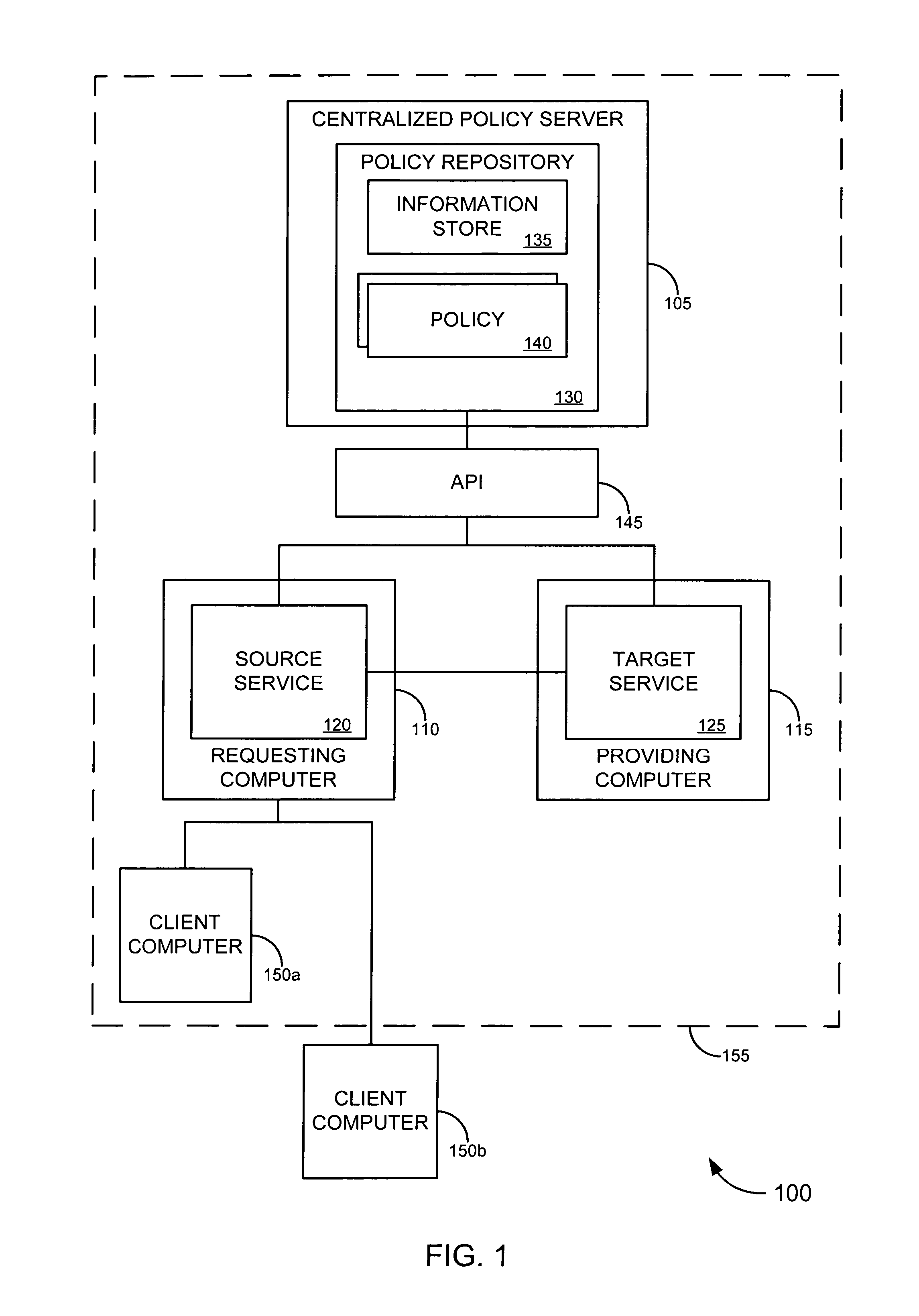
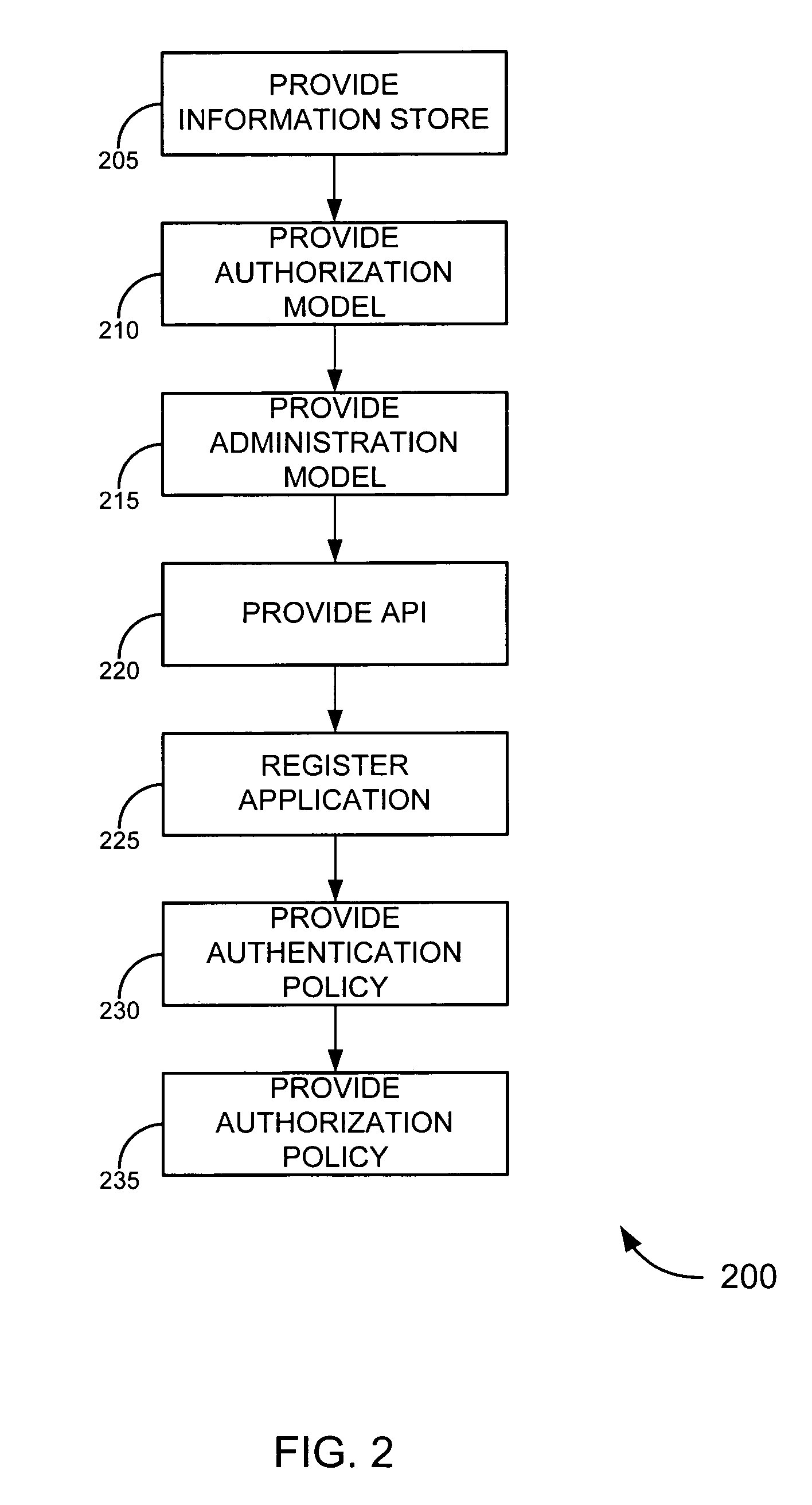
ActiveUS7721322B2Improve manageabilityImprove securityDigital data processing detailsMultiple digital computer combinationsEnterprise servicesInformation security
Embodiments of the invention provide a trust framework for governing service-to-service interactions. This trust framework can provide enhanced security and / or manageability over prior systems. Merely by way of example, in some cases, an information store can be used to store information security information (such as trust information, credentials, etc.) for a variety of services across an enterprise. In other cases, the trust framework can provide authentication policies to define and / or control authentication between services (such as, for example, types of authentication credentials and / or protocols are required to access a particular service—either as a user and / or as another service—and / or types of authentication credentials and / or protocols a service may be enabled to use to access another service). Alternatively and / or additionally, the trust framework can provide authorization policies to define and / or control authorization between services.
Owner:ORACLE INT CORP
Data processing method, device and system, and information acquisition device
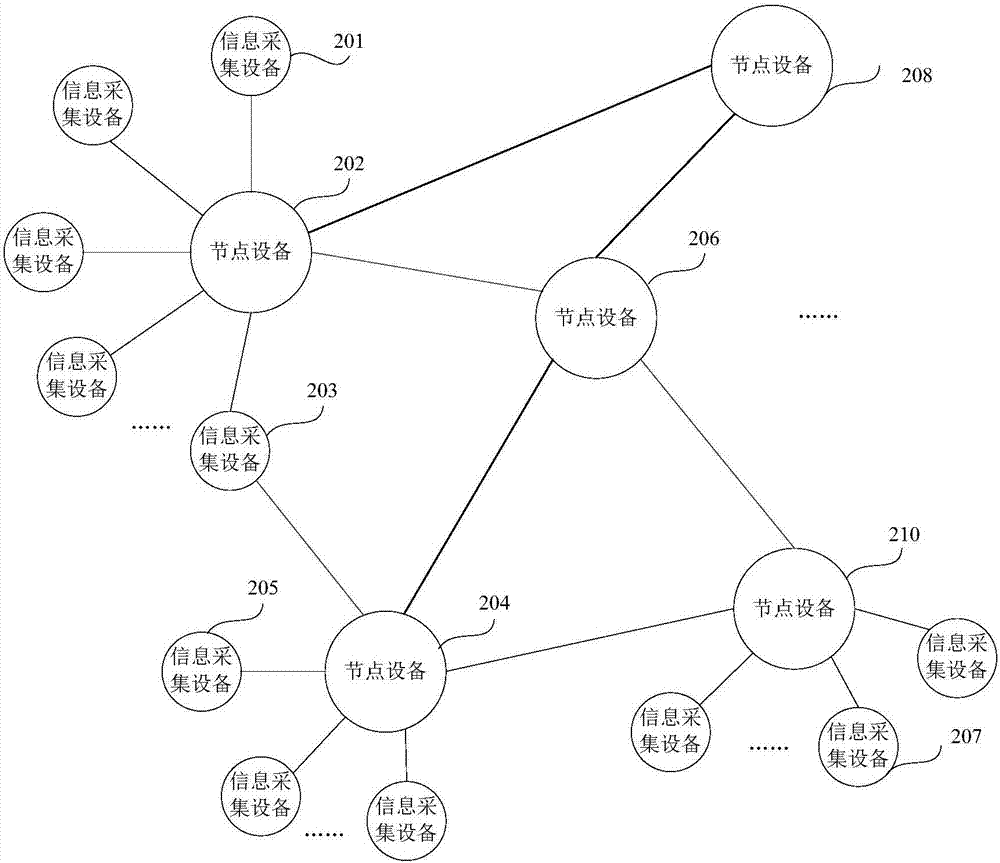
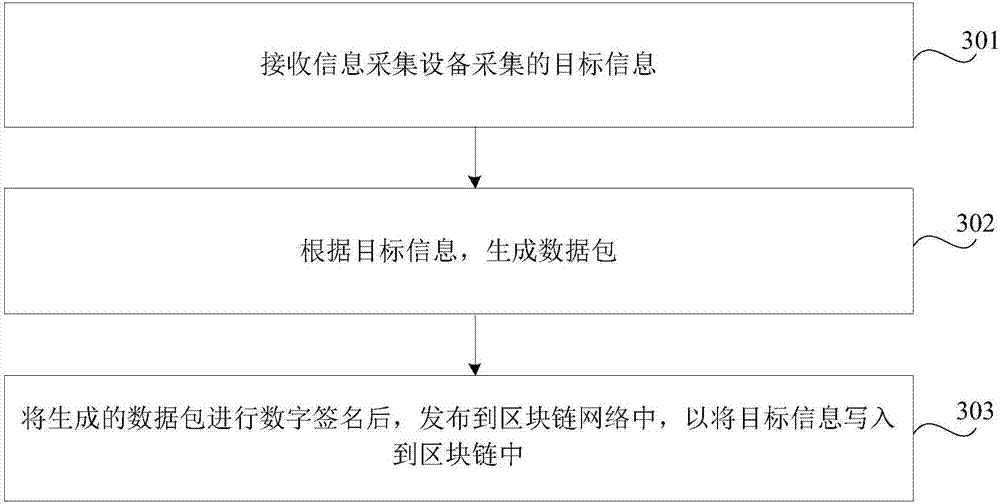
InactiveCN107135661AEnsure safetyIntegrity guaranteedInput/output to record carriersTransmissionData informationDigital signature
The invention discloses a data processing method, device and system, and an information acquisition device. The data processing method comprises receiving target information acquired by the information acquisition device; generating a data package in dependence on the target information; carrying out digital signature on the generated data package, then issuing the data package to a block chain network in order to write the target information into the block chain. All urban data information is recorded through the block chain, the safety and integrity of information storage are guaranteed, information is prevented from being tampered, and the information querying efficiency is improved; for information with large data volume, a Hash value storing mode is employed, and the storage space is saved; the information querying log can be stored in the block chain, subsequent recognition of the querying log is facilitated, and the information safety is improved.
Owner:CLOUDMINDS (SHENZHEN) ROBOTICS SYST CO LTD
Network user identifying method and system
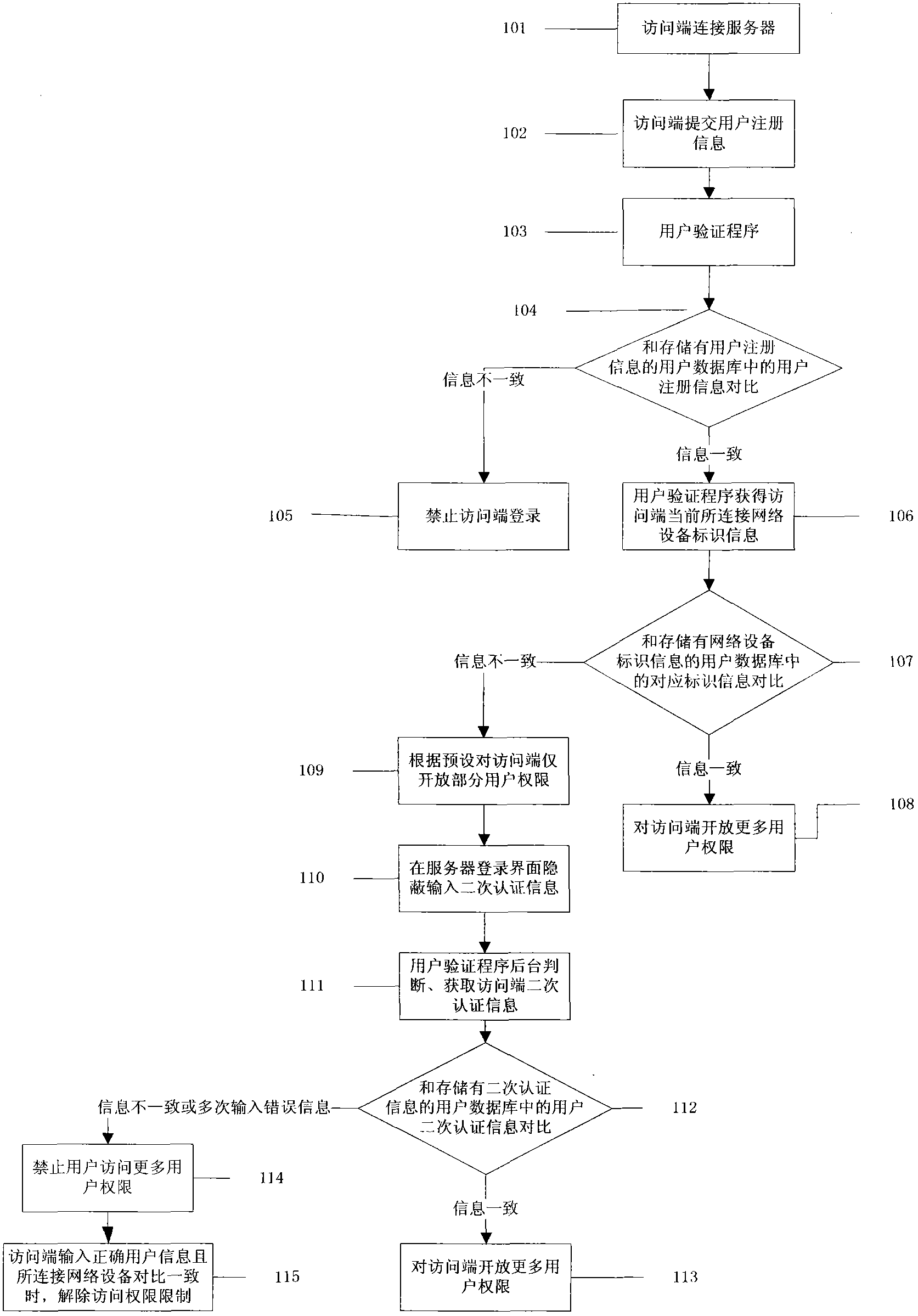
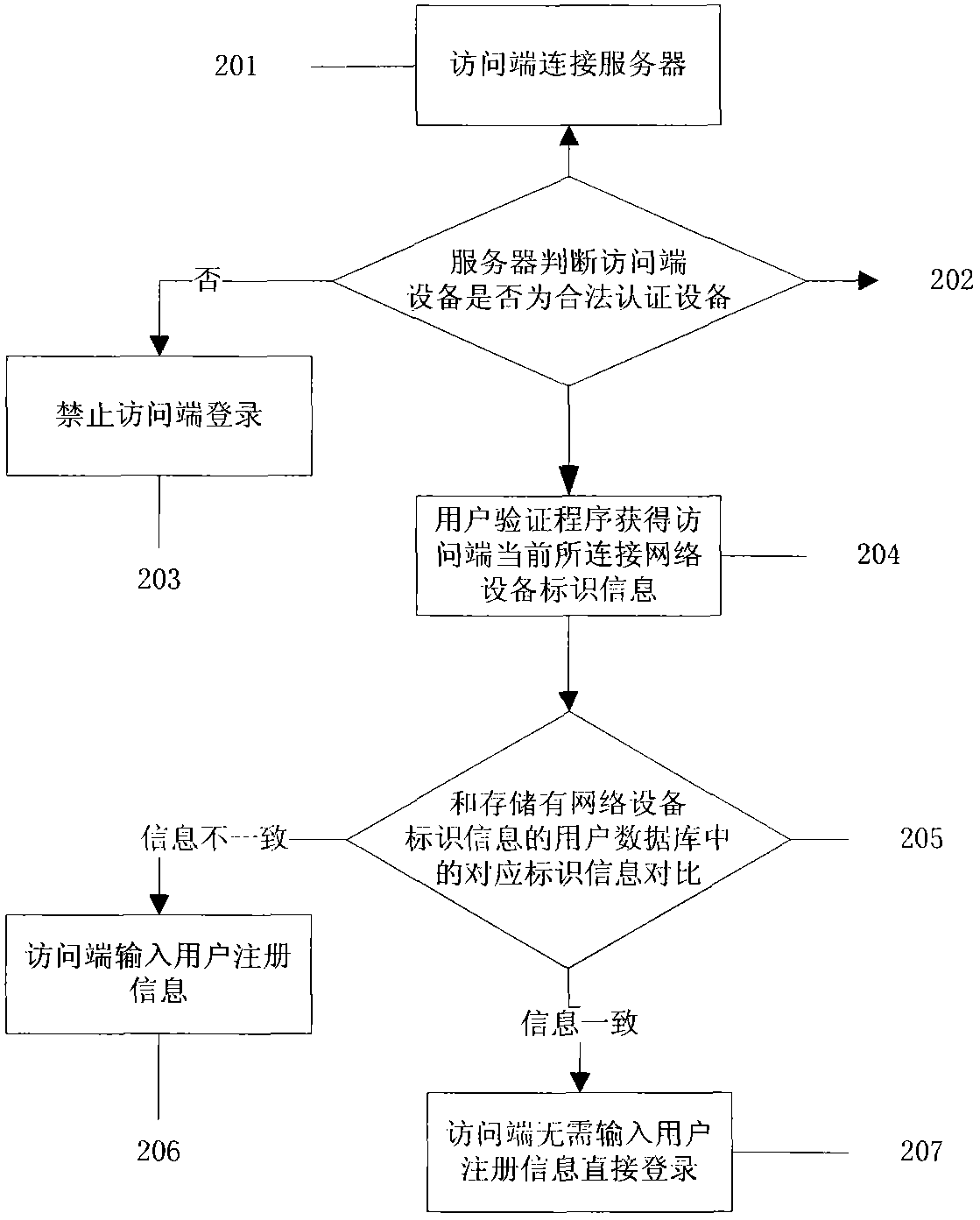
The invention discloses a network user identifying method and system, which belong to the technical field of information safety. The system comprises an access terminal, a network server, a user identifying program and a user database, wherein the user identifying program is installed in a network server end. The method comprises the following steps: when the access terminal accesses the network server, the user identifying program compares relevant user information submitted by using access terminal input equipment of the access terminal with user information stored in the user database for identifying, acquires the identification information of network connecting equipment which is directly connected with the access terminal at present, and compares with relevant identification information of the network connecting equipment which is directly connected with the access terminal acquired by using the server during previous submission of user registration information by an access terminal stored in the user database for identifying; and the user identifying program performs corresponding preset operation on a data operation permission which can be acquired by the access terminal according to an identification result of the user registration information and an identification result of the identification information of the network connecting equipment which is directly connected with the access terminal. Due to the adoption of the system and the method, a user identifying interface is not displayed, input of secondary identifying information is hidden, a server user identifying program background is used for identifying input identifying information, and different user permissions are open to the user according to identification results.
Owner:李明
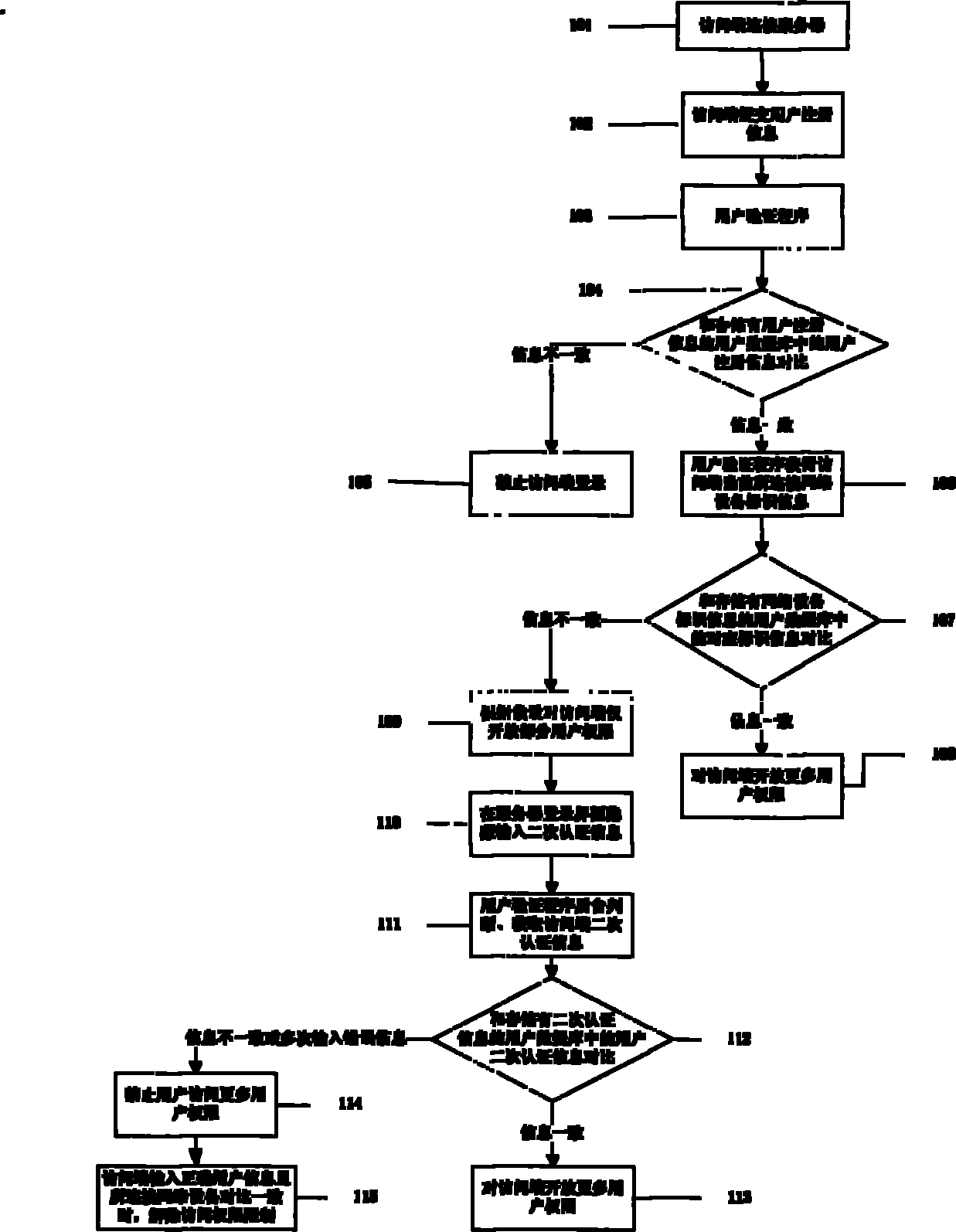
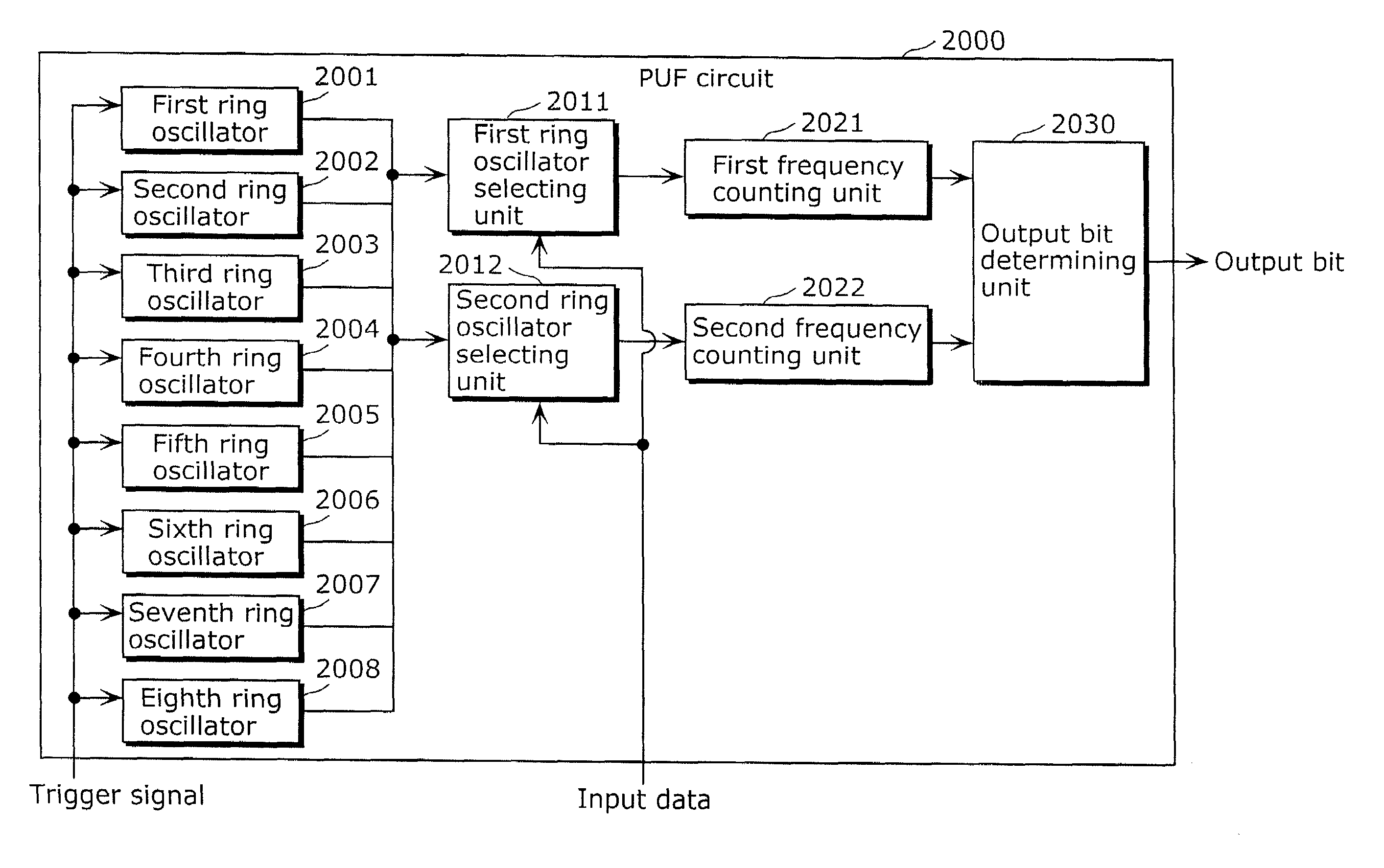
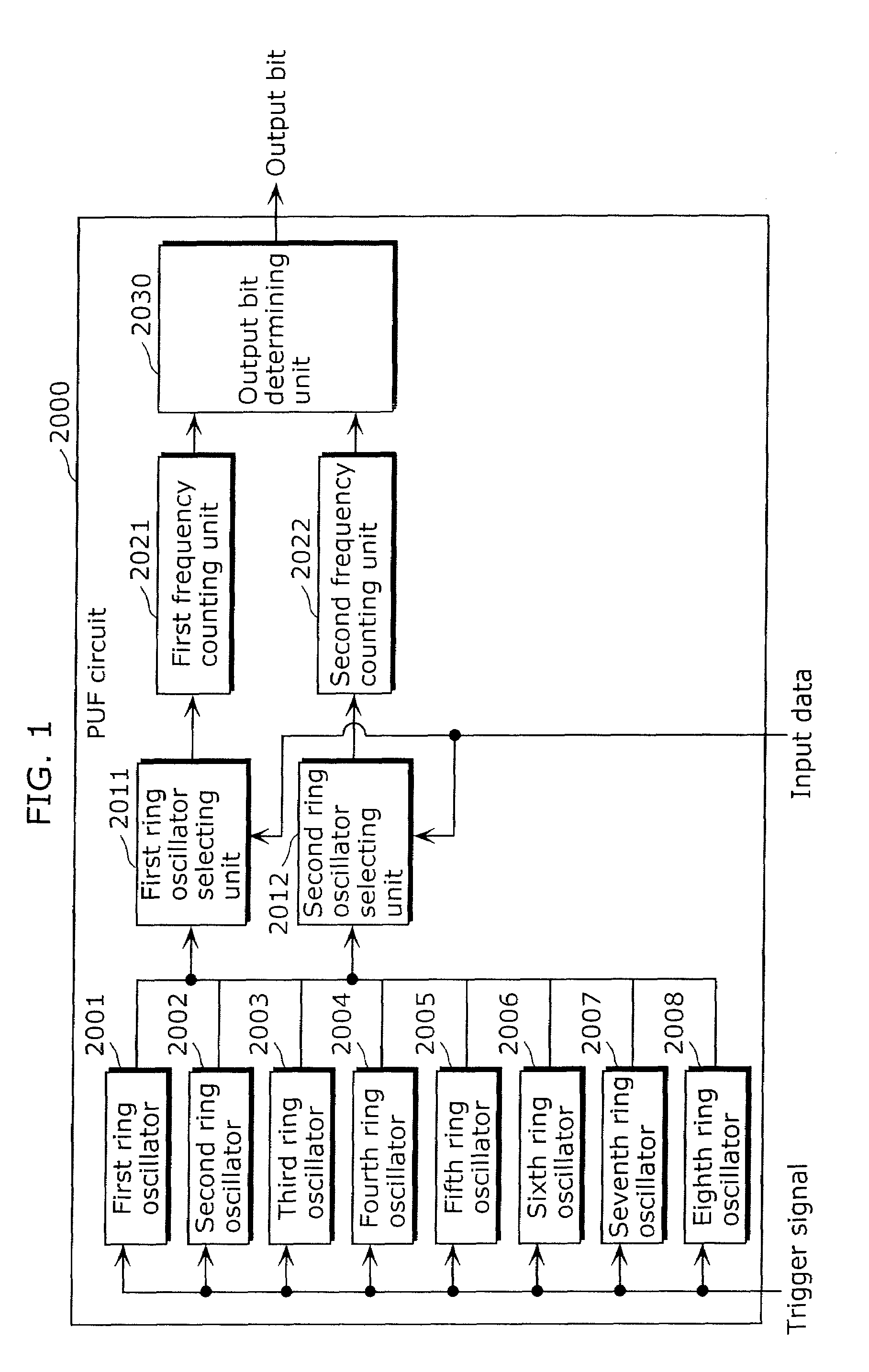
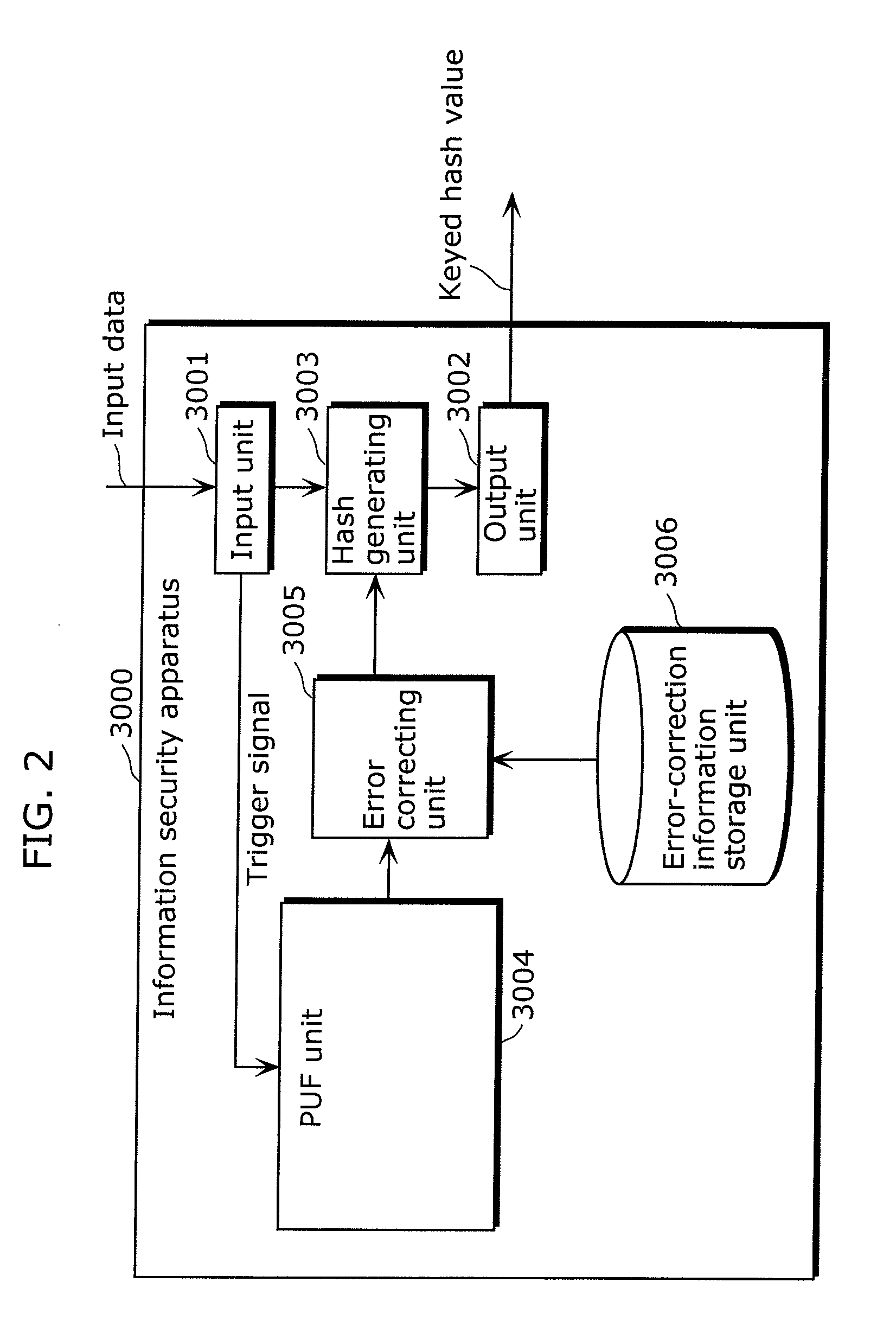
Information security apparatus
ActiveUS20100031065A1Low costImprove output stabilityError preventionRandom number generatorsComputer hardwareTamper resistance
Provided is an information security apparatus (1100) that has enhanced stability and confidentiality of a hash key. The information security apparatus (1100) includes an information generating PUF unit (1104) that has tamper resistance set, using physical characteristics, so as to output a preset hash key, a partial error-correction information storage unit (1107) that stores partial error-correction information, an error correcting PUF unit (1106) that has tamper-resistance set, using physical characteristics, so as to output error-correcting PUF information, an error-correction information generating unit (1108) that generates error-correction information using partial correction information and the error-correcting PUF information, and an error correcting unit (1105) that corrects an error for the hash key outputted from the information generating PUF unit (1104) and outputs an error-corrected hash key.
Owner:PANASONIC CORP
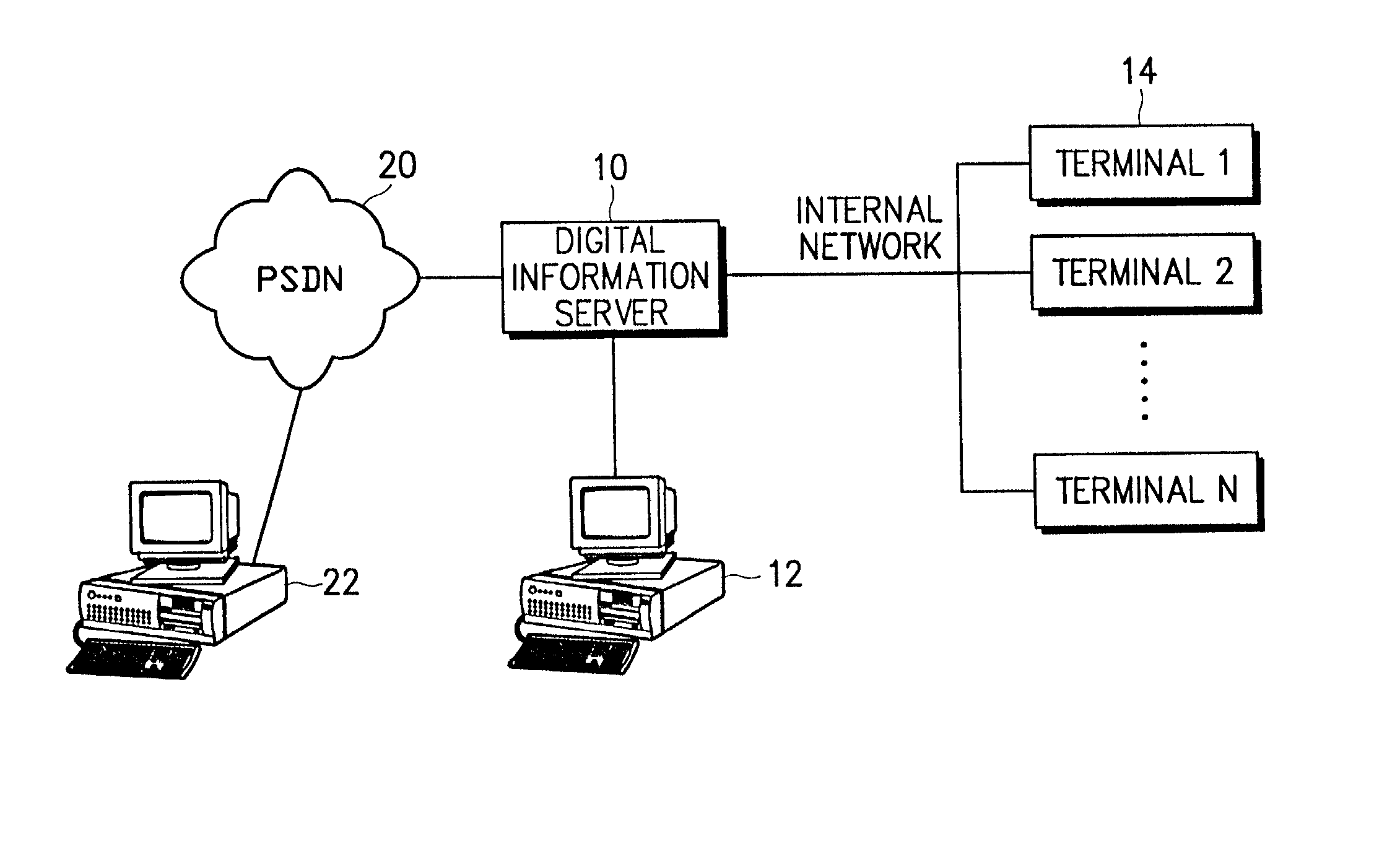
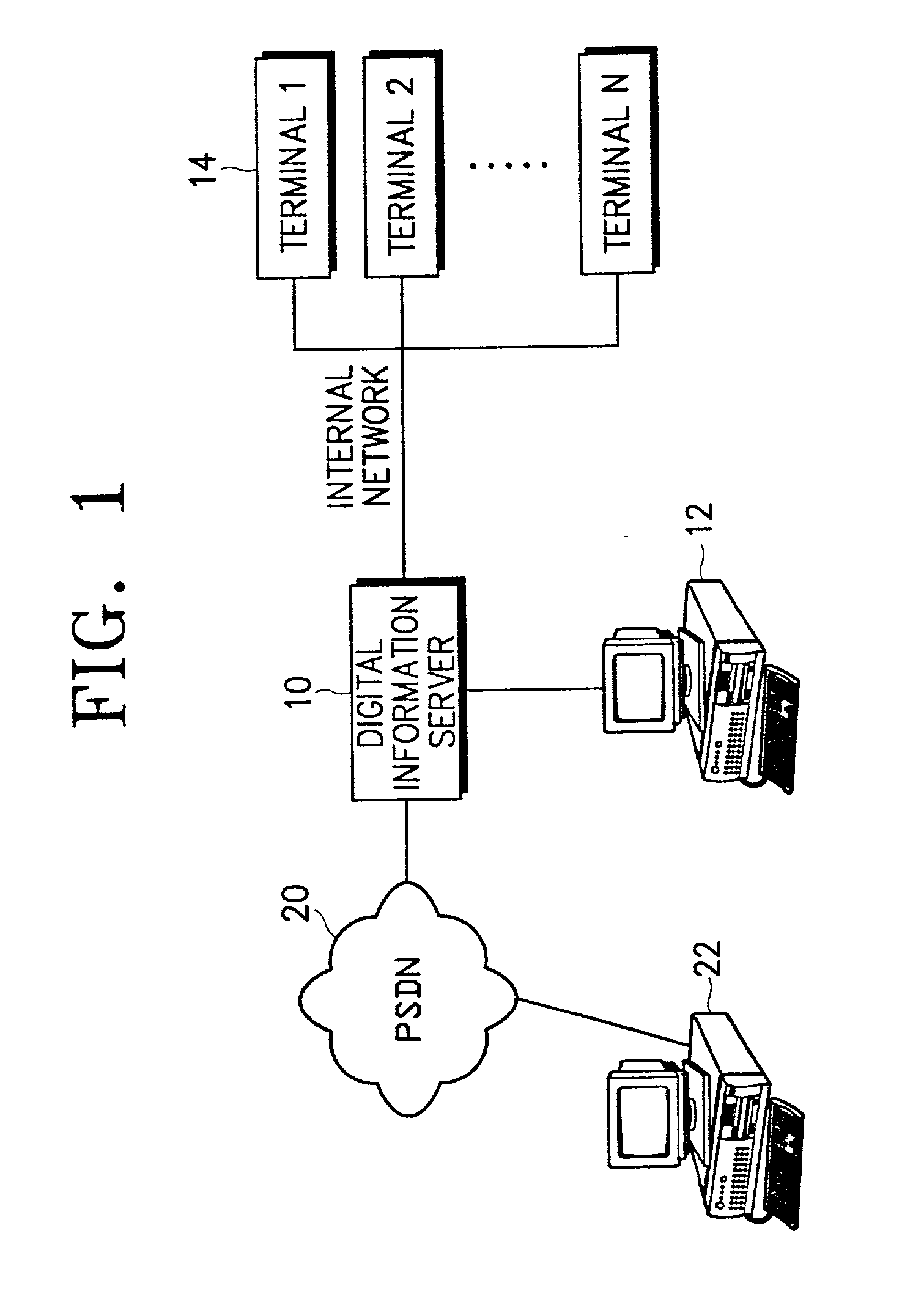
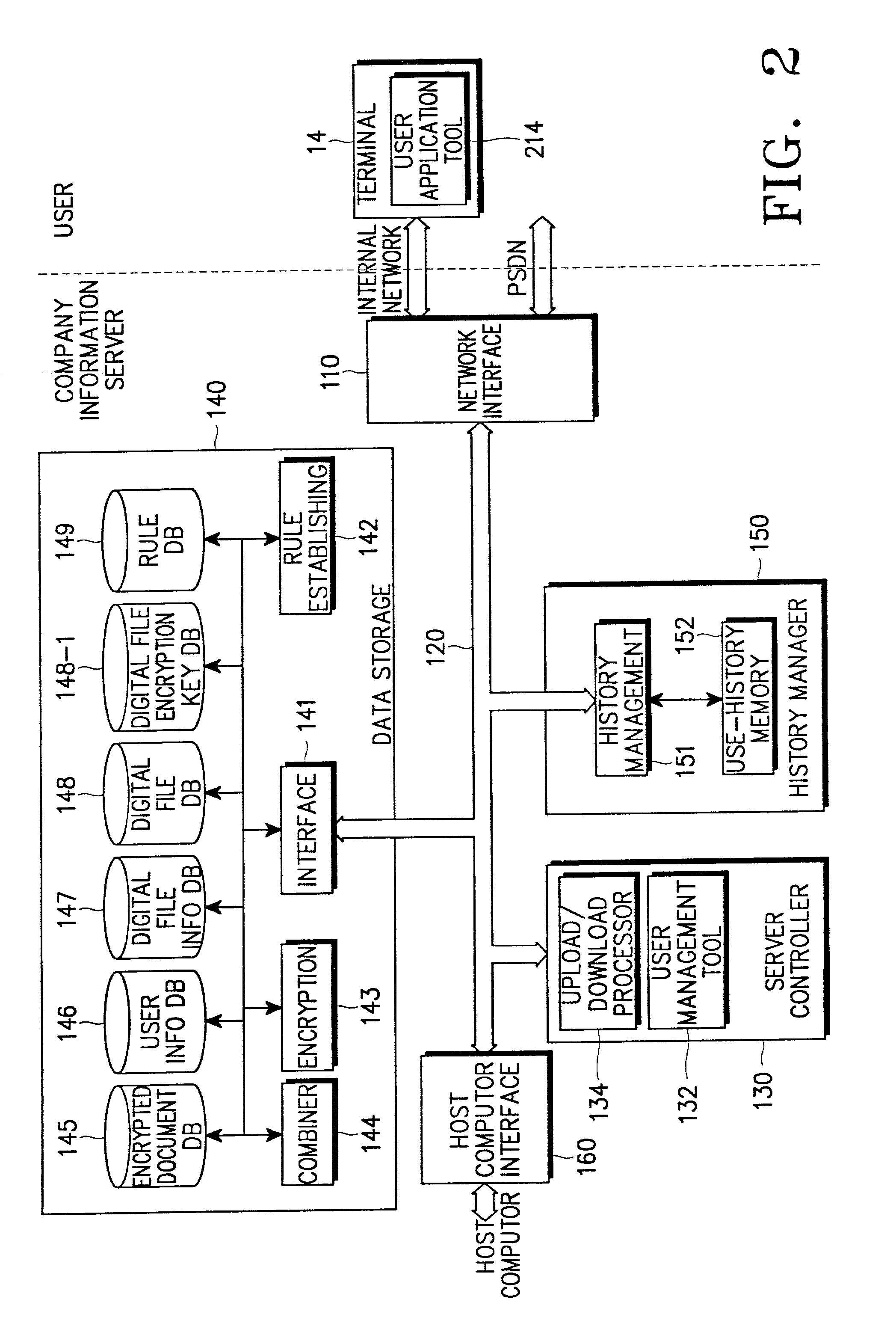
Method for securing digital information and system therefor
InactiveUS20030023559A1Key distribution for secure communicationData taking preventionUser authenticationInformation security
A digital information security system is disclosed. A user application tool installed in a user terminal, creates a unique user key using unique system information of the user terminal. A data storage unit stores user information and digital information. A user management tool installed in a server, receives the unique user key created by the user application tool, stores the received unique user key in the data storage unit as part of the user information, and compares, during user authentication, the stored unique user key with a unique user key provided from the user application tool of a user currently being subjected to authentication.
Owner:MARKANY
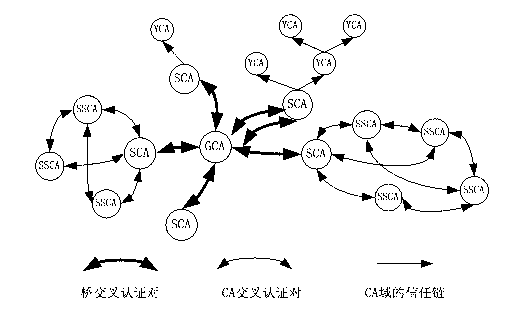
Digital certificate management method and system
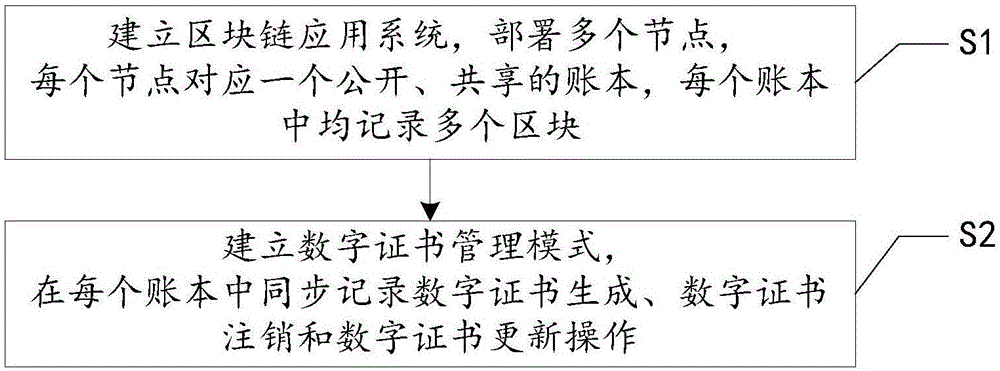
ActiveCN106385315AIncrease the difficultyImprove securityUser identity/authority verificationSelf maintenanceComputer module
The invention relates to a digital certificate management method and system, belongs to the field of information security, and aims at solving the problem that application for a digital certificate is low in autonomous flexibility and high in cost at present. The method comprises that a block chain application system is established; and a digital certificate management mode including certificate generation, cancellation and update is established. Digital certificates can be managed in a distributed, self-maintenance and auditable manner, and the safety and reliability of the whole digital certificate system are improved. The digital certificate management system comprises a block chain application system establishing module for disposing nodes, each node corresponds to a public and shared account book, and each account book records multiple blocks; and the digital certificate management system also comprises a digital certificate management mode establishing module for carrying out autonomous digital certificate generation, digital certificate cancellation and digital certificate update operations on each account book.
Owner:BEIJING SANSEC TECH DEV
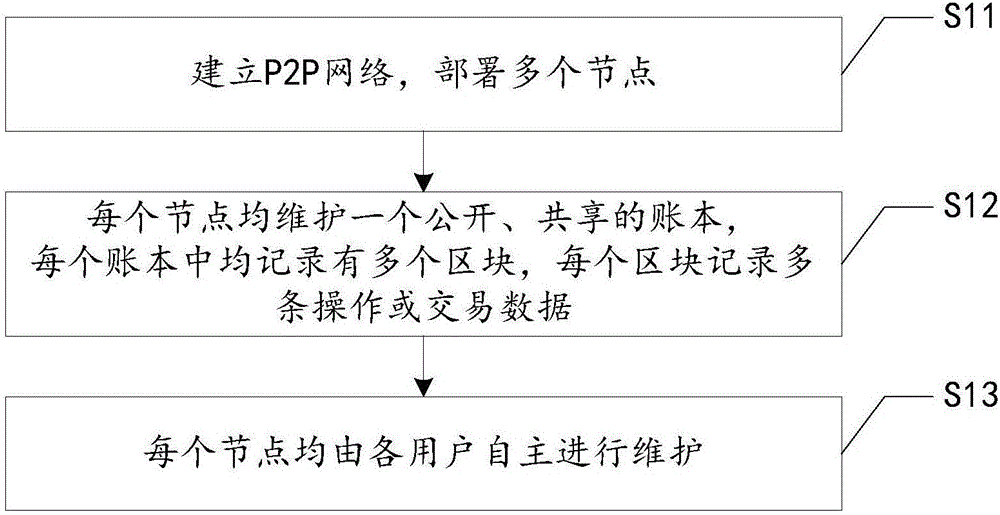
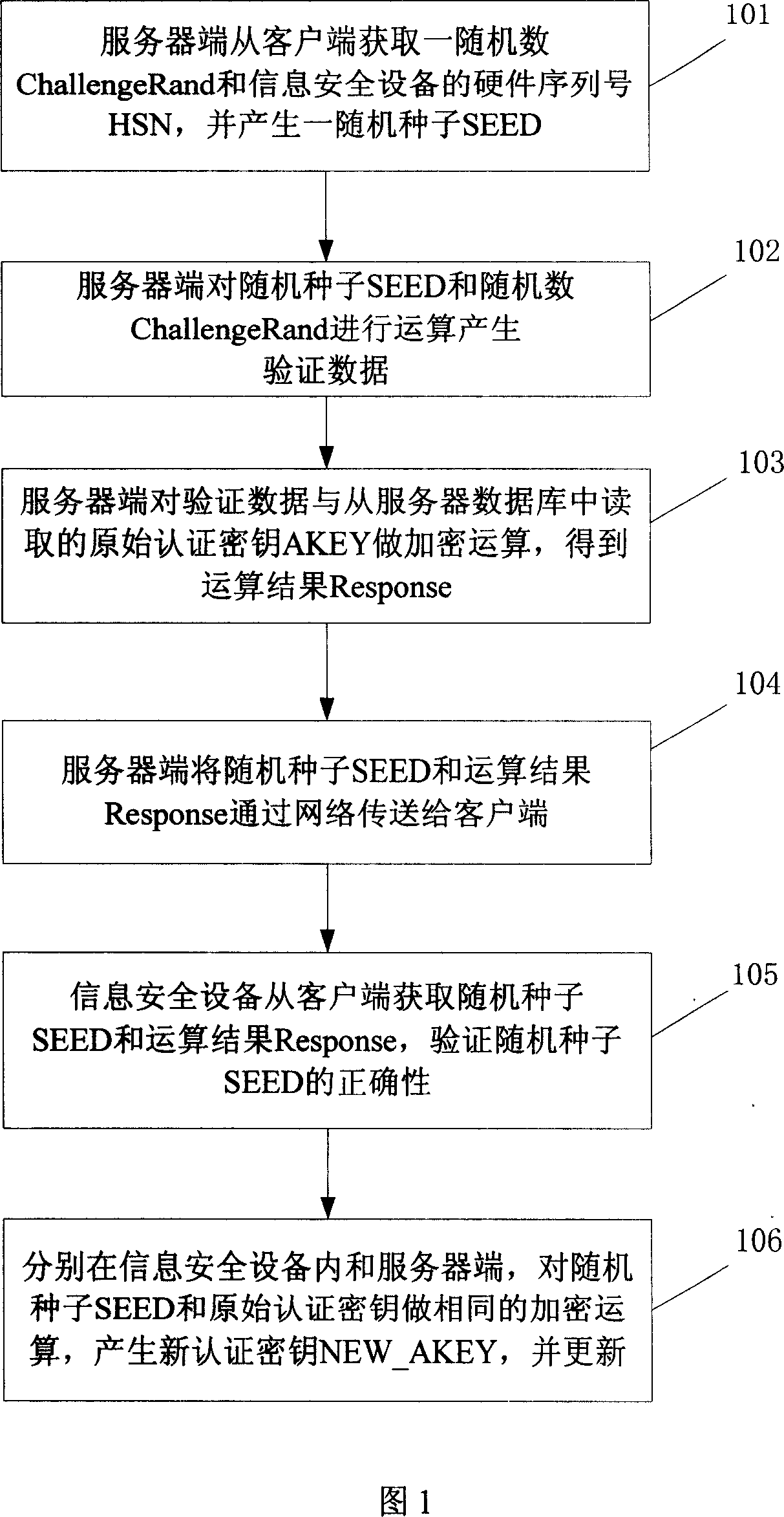
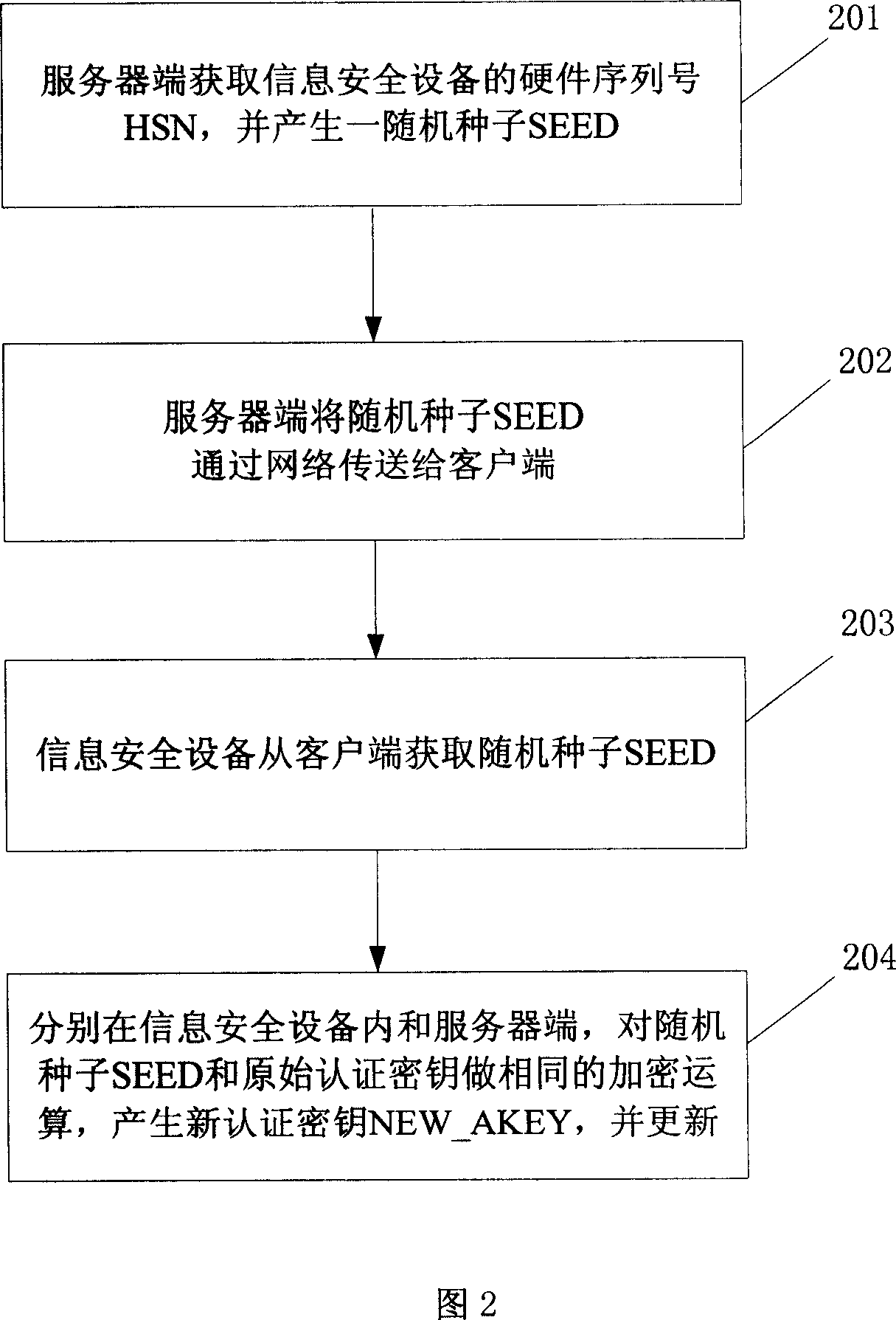
Method and system for updating certification key
The invention is to solve issues: not security of transferring authentication cipher key through network by using plaintext; and managing bother, and high cost by using cryptograph format to transfer authentication cipher (AC). The disclosed method for updating AC remotely includes steps: server end calculates random seed and random number to generate verification data; server end carries out encryption operation for original AC and verification data, and transfers random seed and result of encryption operation to client end; information security equipment validates correctness of random seed; carrying out same encryption operation for random seed and original AC inside the information security equipment, and at server end so as to generate new AC, which is in use for updating AC inside the information security equipment, and database in server. The invention also discloses system for updating AC.
Owner:FEITIAN TECHNOLOGIES
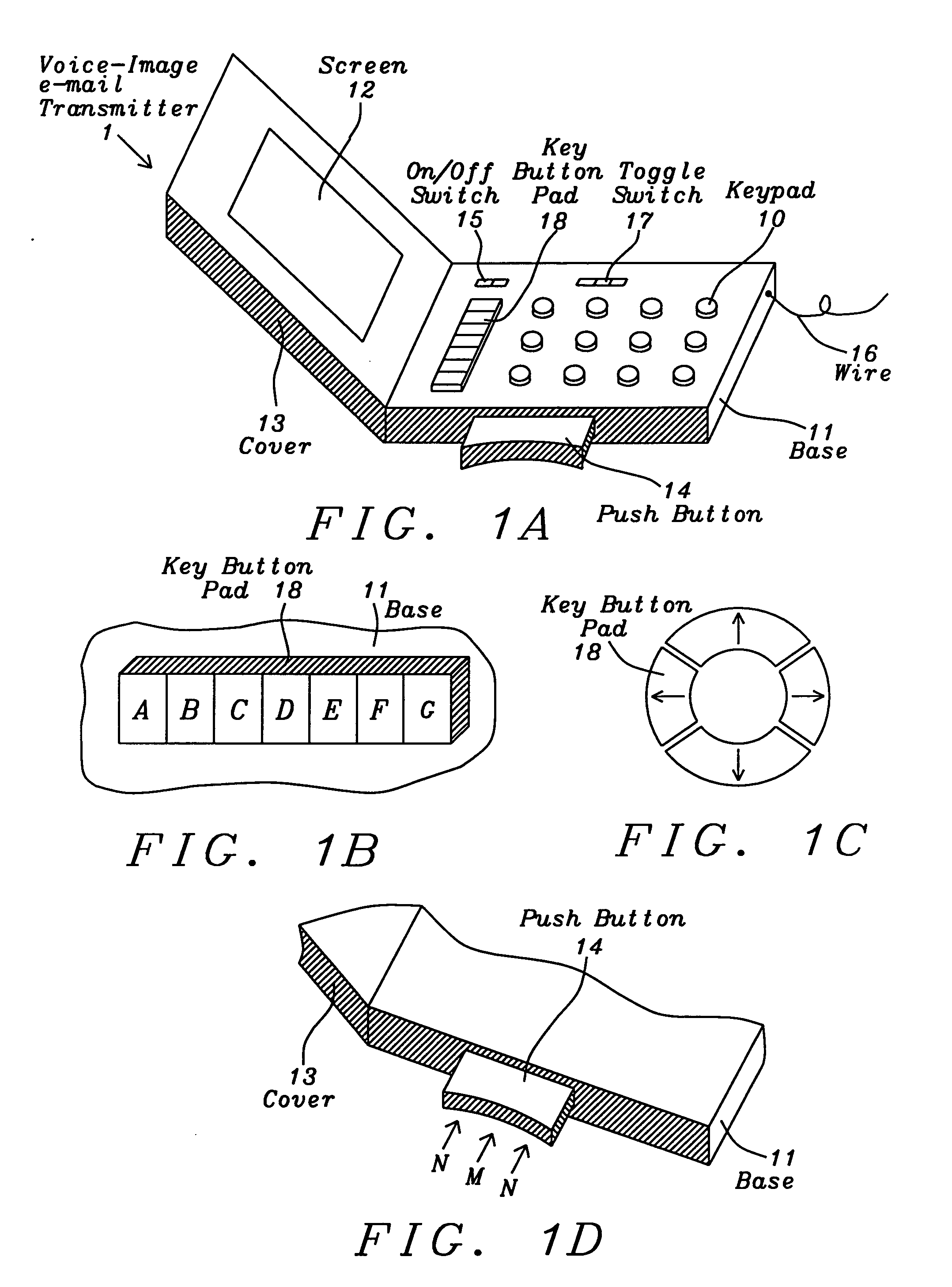
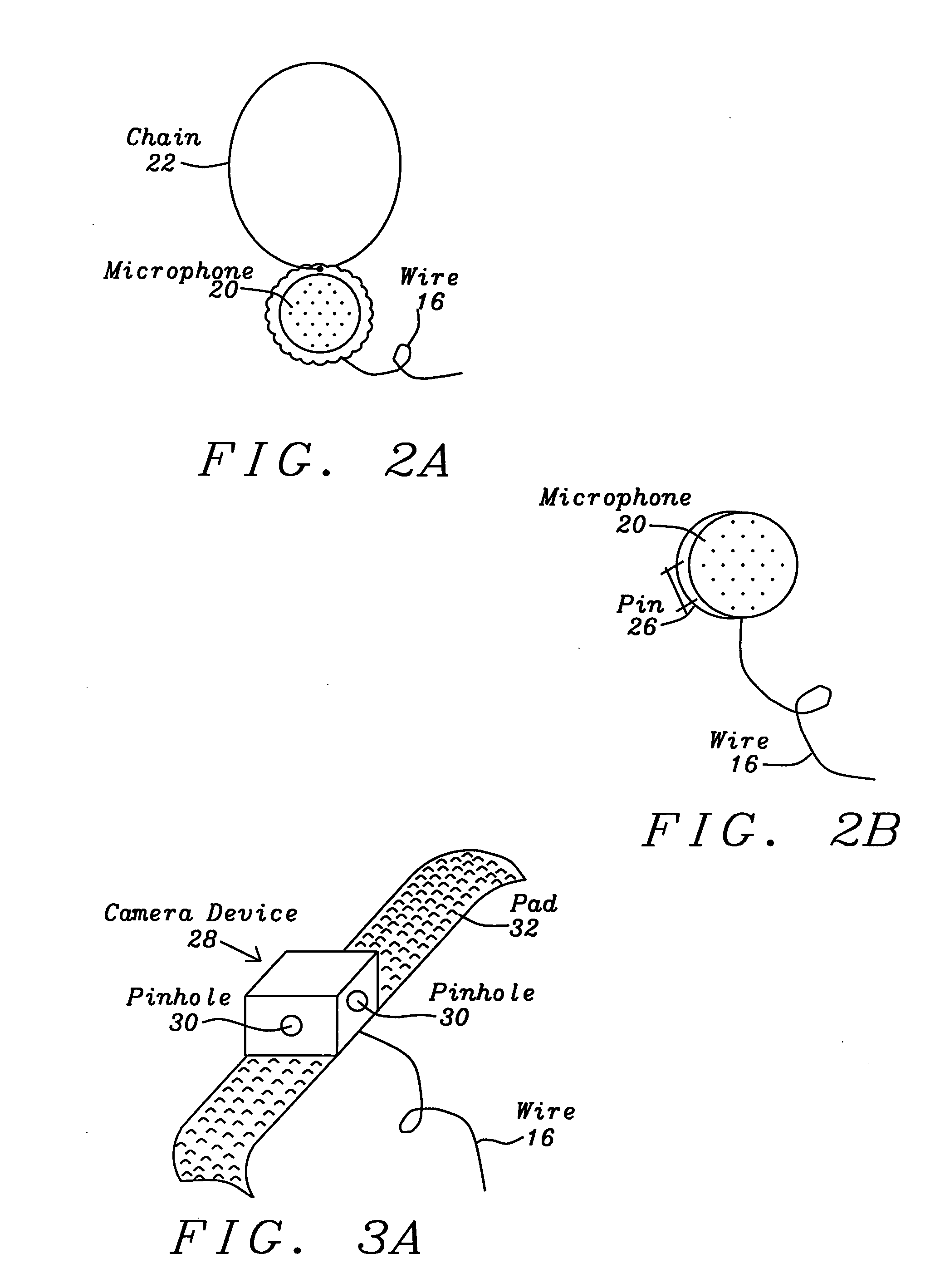
System and method for the emergency voice and image e-mail transmitter device
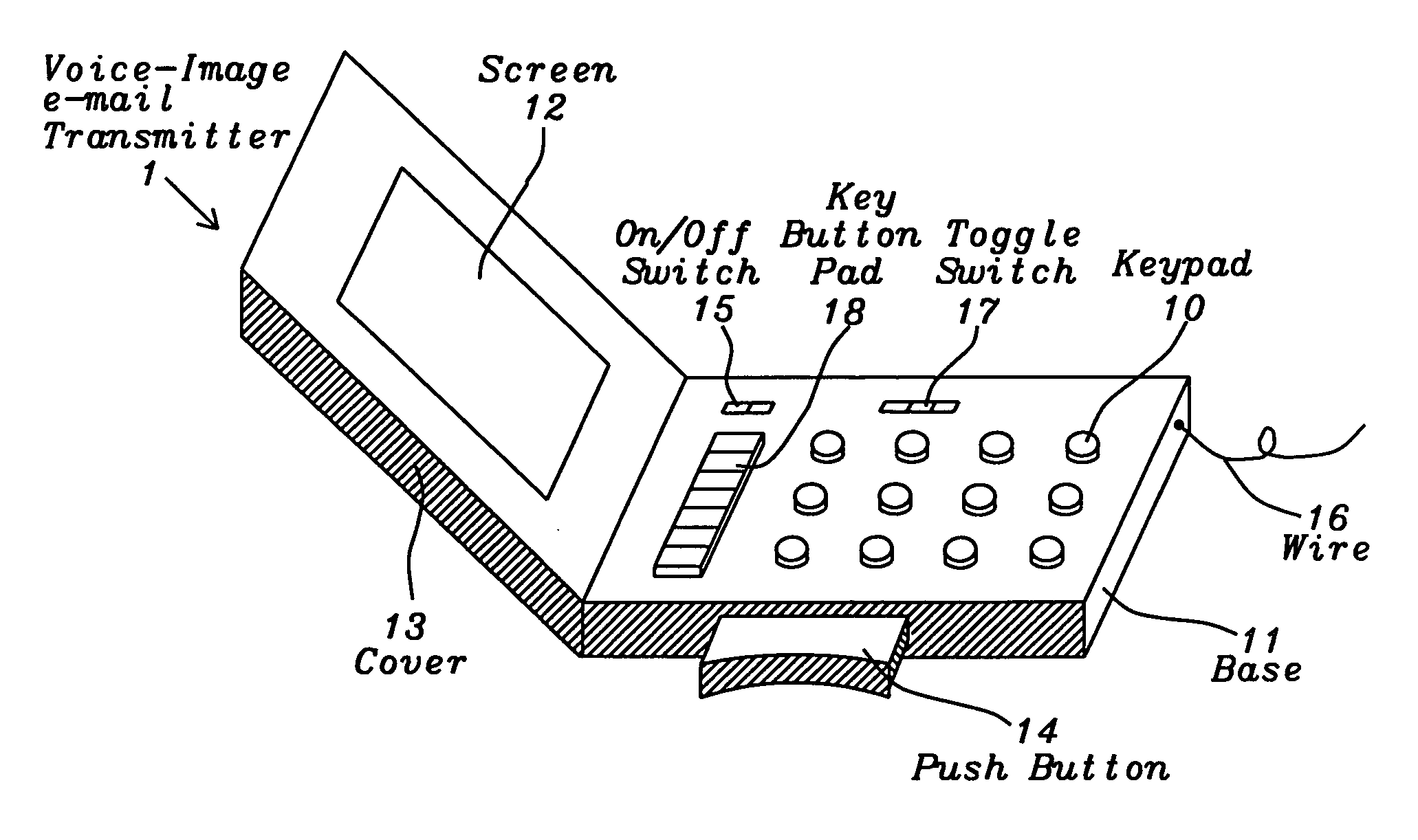
InactiveUS20120282884A1Justice be serveEasy and fastDevices with GPS signal receiverSubstation equipmentElectronic equipmentDigital signal
A voice and image e-mail transmitter device with an external camera attachment that is designed for the emergency and surveillance purposes is disclosed. The device converts voice signals and photo images into digital format, which are transmitted to the nearest voice-image message receiving station from where the digital signal strings are parsed and converted into voice, image, or video message files which are attached to an e-mail and delivered to user pre-defined destination e-mail addresses and a 911 rescue team. The e-mail also includes the caller's voice and personal information, photo images of a security threat, device serial number, and a GPS location map of the caller's location. The digital signal data may be recorded and transmitted within few seconds. The victim's family or police may either check the GPS location map in an e-mail or apply a new GPS based people tracking system of the present invention to search for a missing victim.
Owner:SUN NICHOLAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com