Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
816 results about "Plain text" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, plain text is a loose term for data (e.g. file contents) that represent only characters of readable material but not its graphical representation nor other objects (floating-point numbers, images, etc.). It may also include a limited number of characters that control simple arrangement of text, such as spaces, line breaks, or tabulation characters (although tab characters can "mean" many different things, so are hardly "plain"). Plain text is different from formatted text, where style information is included; from structured text, where structural parts of the document such as paragraphs, sections, and the like are identified); and from binary files in which some portions must be interpreted as binary objects (encoded integers, real numbers, images, etc.).
Methods for rights enabled peer-to-peer networking
InactiveUS20030120928A1User identity/authority verificationUnauthorized memory use protectionDigital rights managementRights management
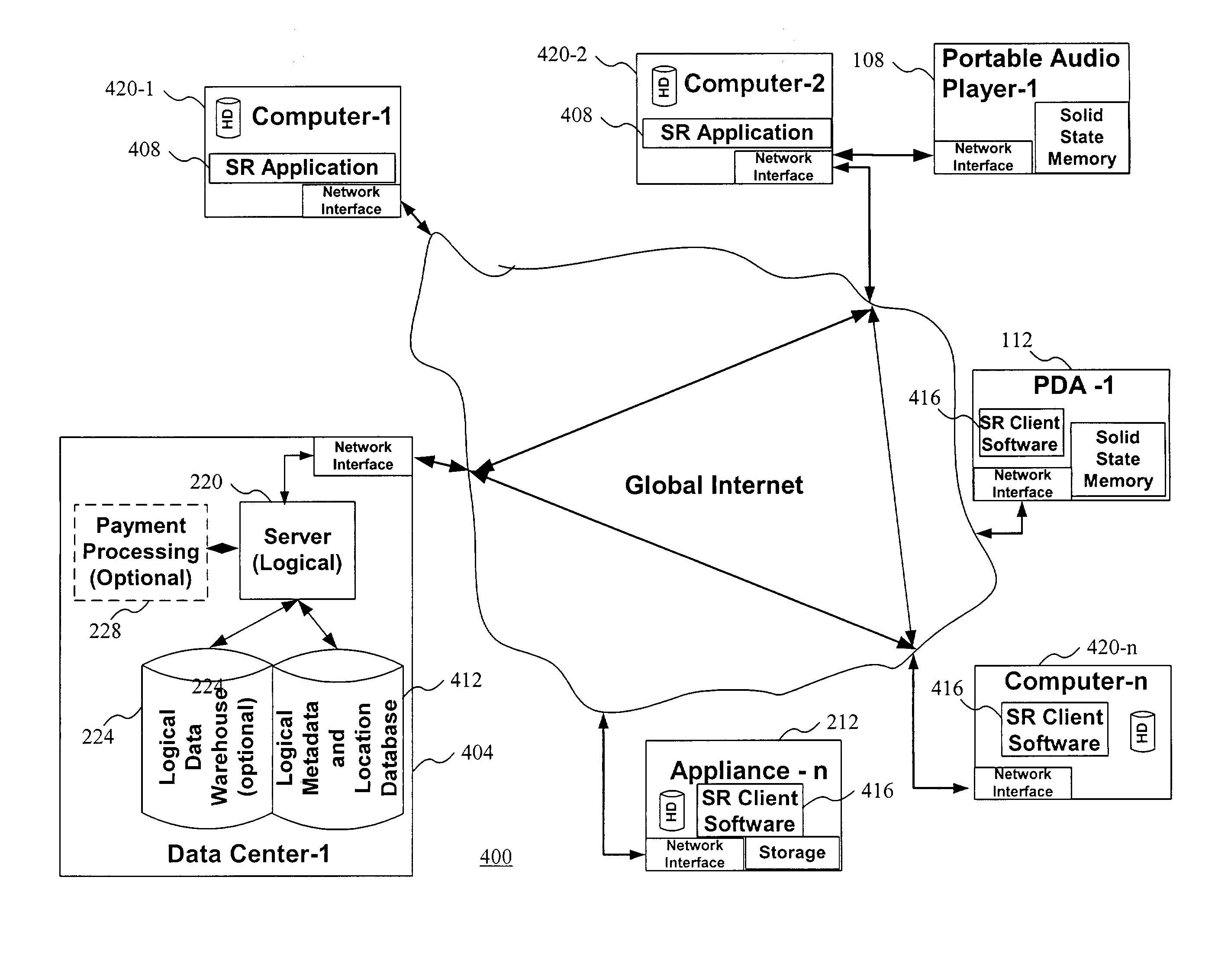
The present invention relates to digital rights management. In one embodiment, persons, processes, and / or computers and appliances locate, share, publish, retrieve, and use all kinds of digital information that has been protected using digital rights management technologies. Rights management includes securely associating rules for authorized use with the digital information. Rules and / or digital information may be encapsulated in a cryptographically secure data structure or "container" ("CSC") to protect against unauthorized use, to ensure secrecy, to maintain integrity, and to force the use of a rights management system to access the protected information. Attributes or metadata information describing at least some of the rules ("rules-metadata information") and optionally any associated rule parameter data with respect to the protected information are created. This rules-metadata information may be organized, structure, encoded, and / or presented using a self-defining data structure such as those created using Extensible Markup Language (XML). In one embodiment, the XML-encoded rules-metadata information is also made available unencrypted, in plain text, to facilitate P2P search and file transfer. Having at least some of the rules-metadata information outside or external to a CSC allows greater flexibility in searching based at least in part upon the rules-metadata information. Some embodiments may hold the rules-metadata information in a separate CSC. Putting the rules-metadata information in a separate CSC more easily allows authentication and maintains the integrity of the rules-metadata information. In another embodiment, the rules metadata may be in an unencrypted portion of a CSC itself or concatenated with a CSC in a single file.
Owner:CATO MILES +2
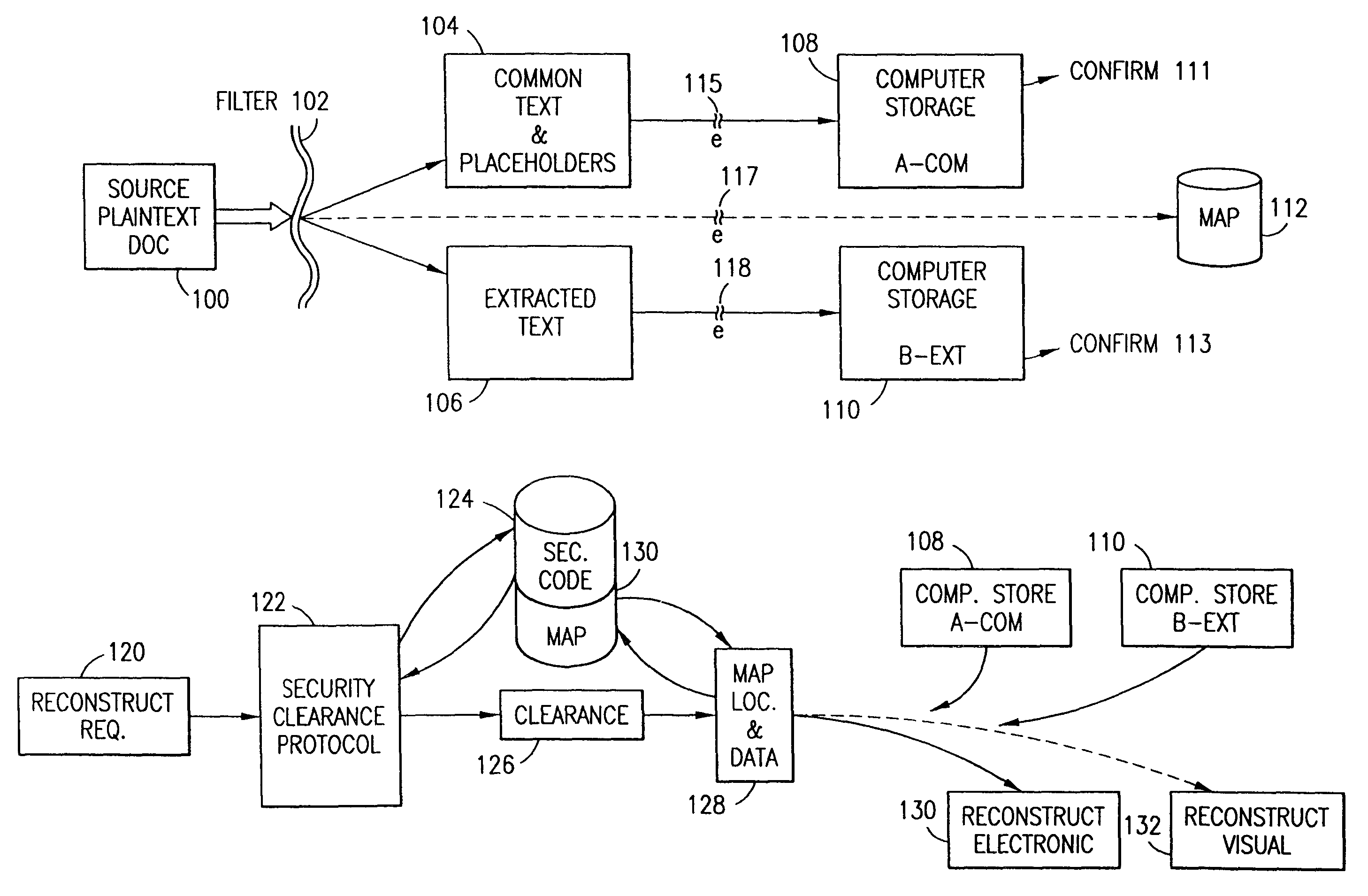
Data security system and method associated with data mining
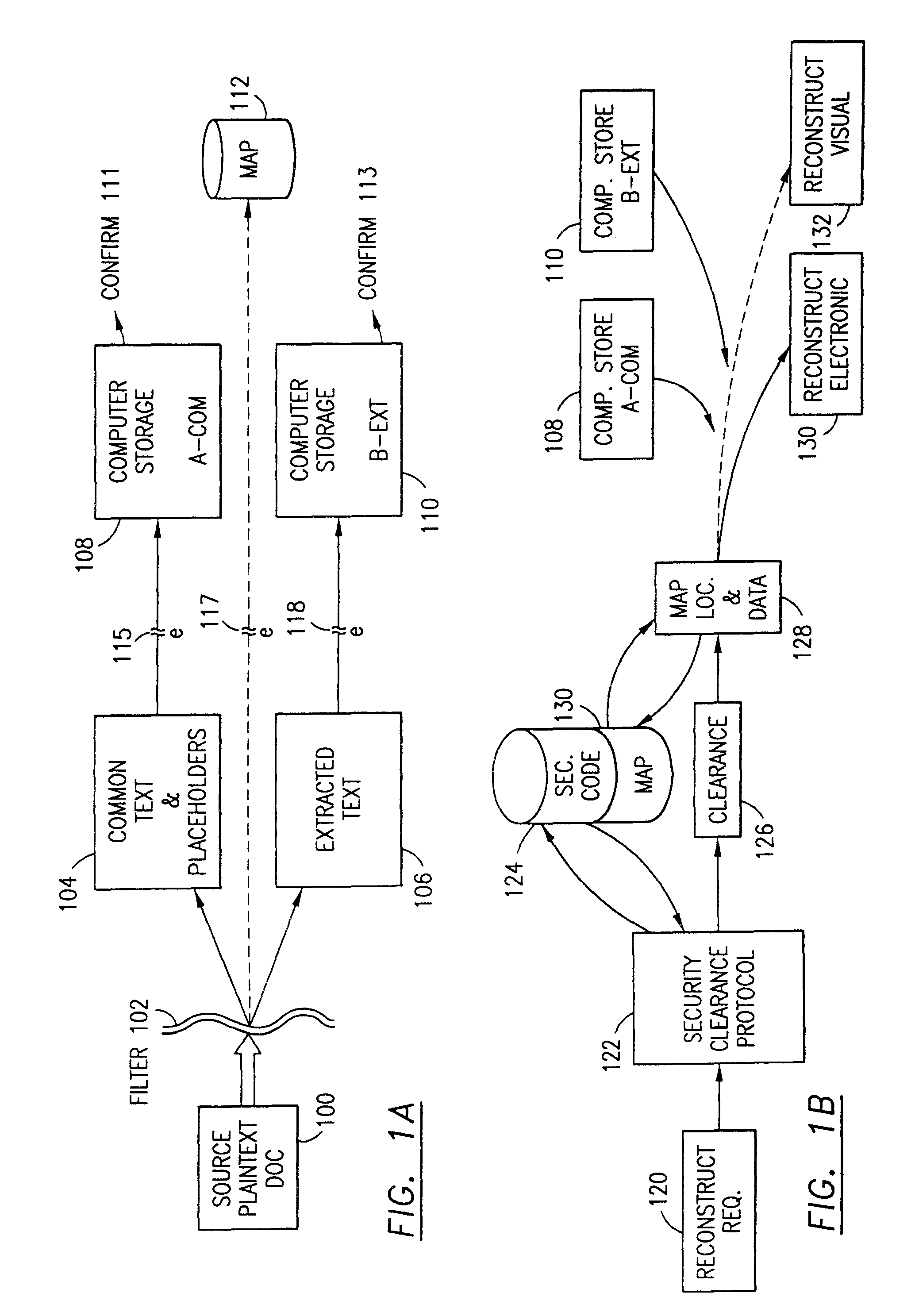
ActiveUS7322047B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsMultiple keys/algorithms usagePlaintextInternet privacy
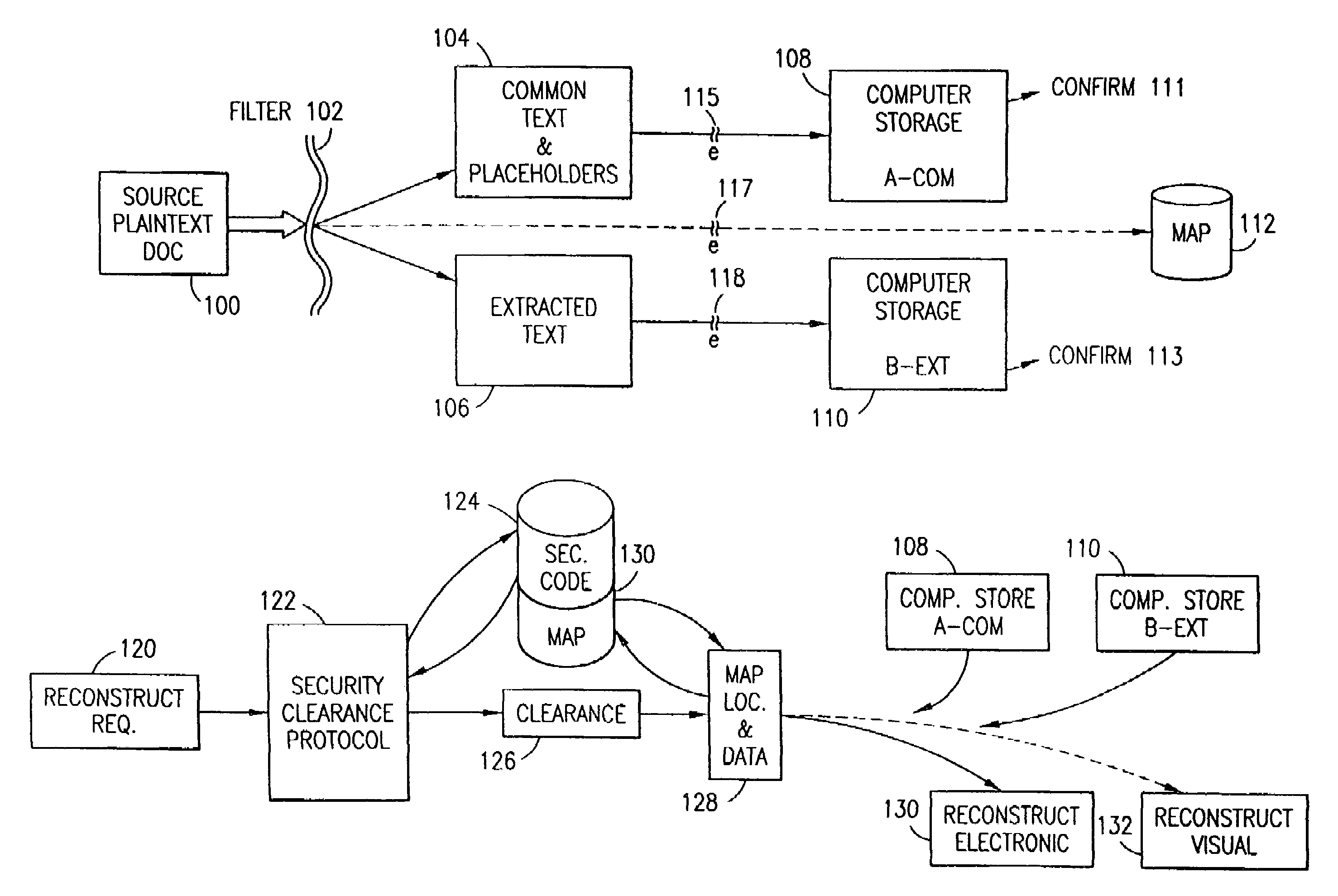
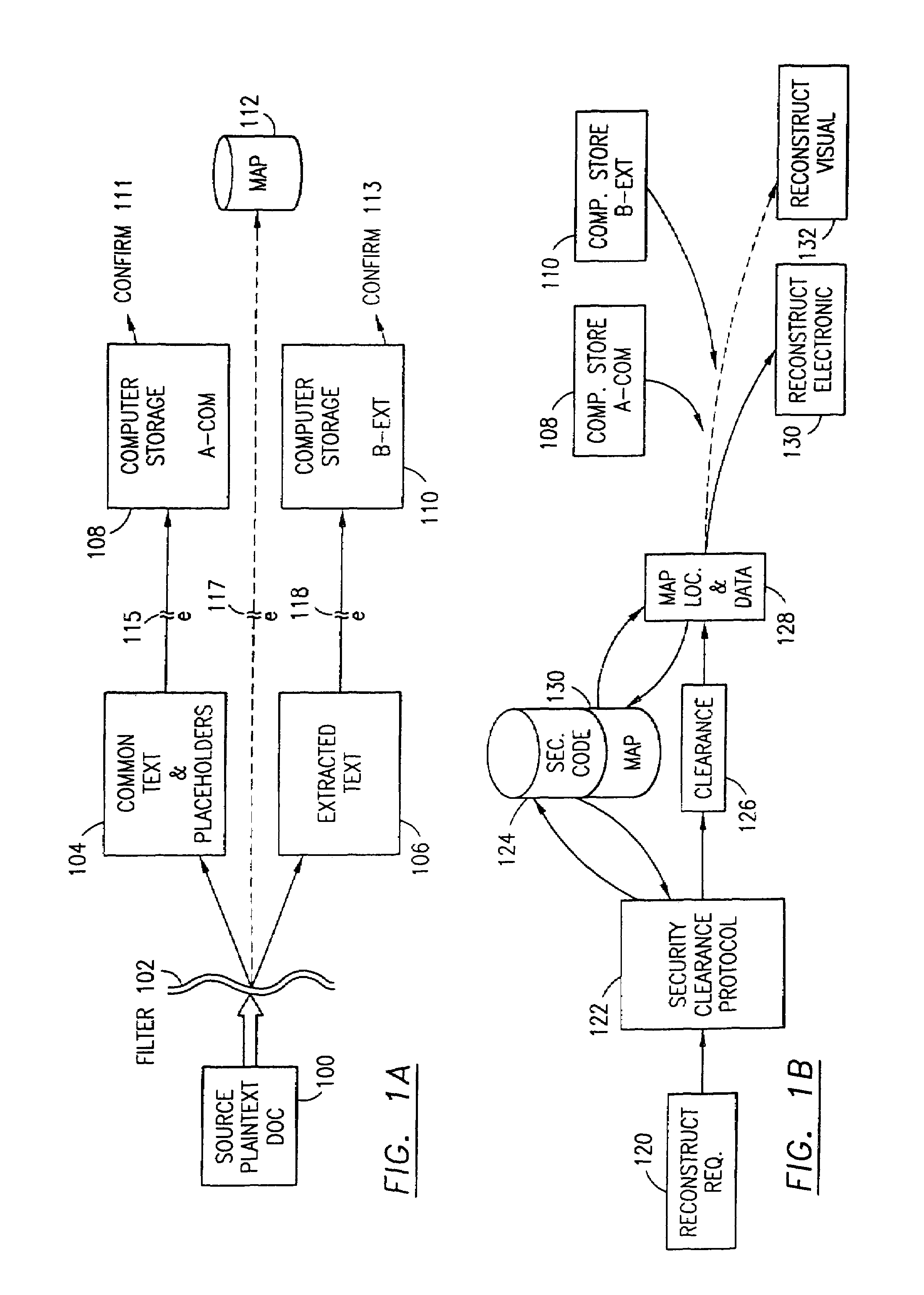
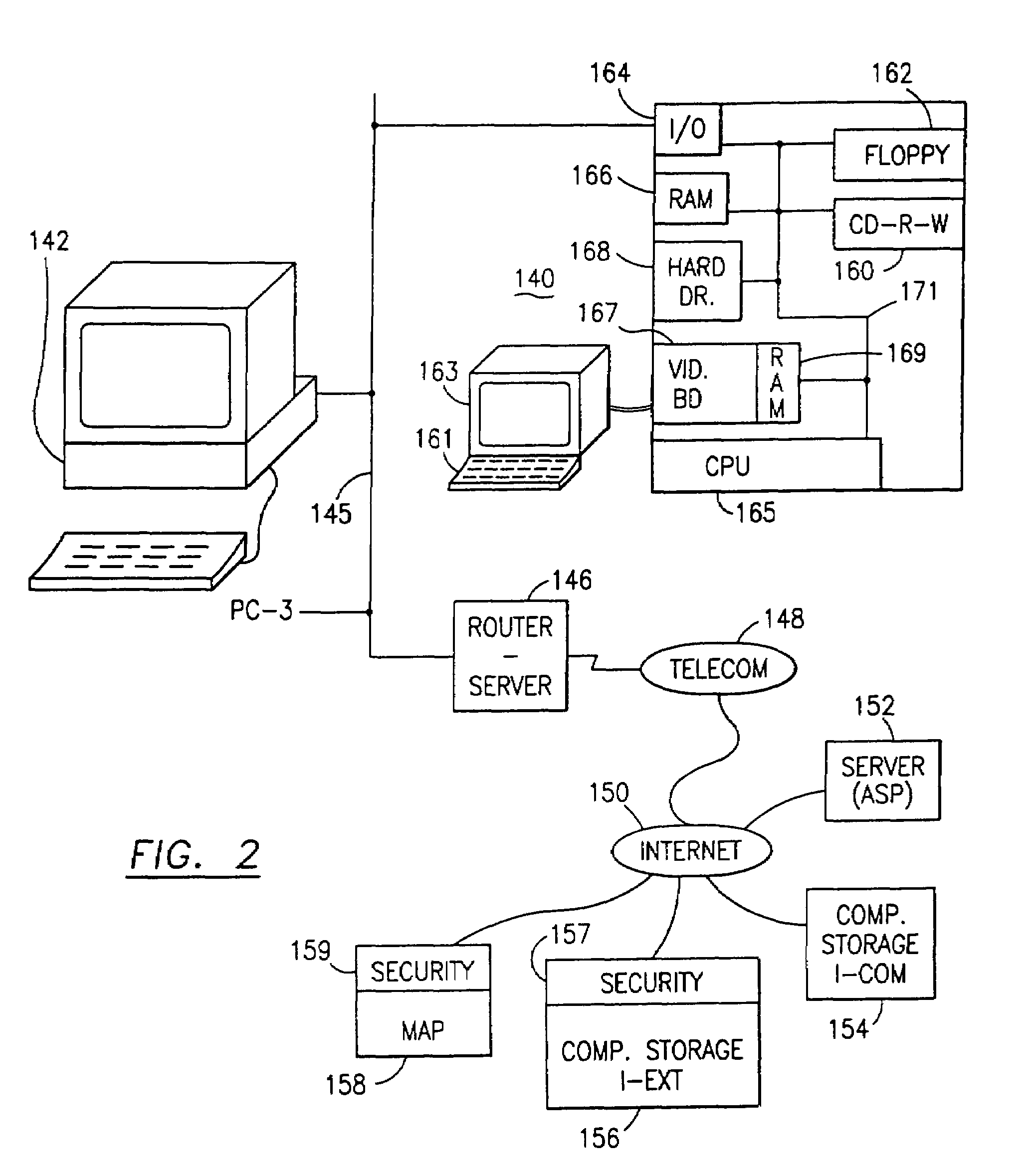
The data security method, system and associated data mining enables multiple users, each having a respective security clearance level to access security sensitive words, data objects, characters or icons. The method extracts security sensitive words, data objects, characters or icons from plaintext or other source documents to obtain (a) subsets of extracted data and (b) remainder data. The extracted data is, in one embodiment, stored in a multilevel security system (MLS) which separates extract data of different security levels with MLS guards. Some or all of the original data is reconstructed via one or more of the subsets of extracted data and remainder data only in the presence of a predetermined security level. In this manner, an inquiring party, with the proper security clearance, can data mine the data in the MLS secured storage.
Owner:DIGITAL DOORS
Interactive on line code inspection process and tool
InactiveUS6275223B1Data processing applicationsSpecific program execution arrangementsOnline codesDisplay device
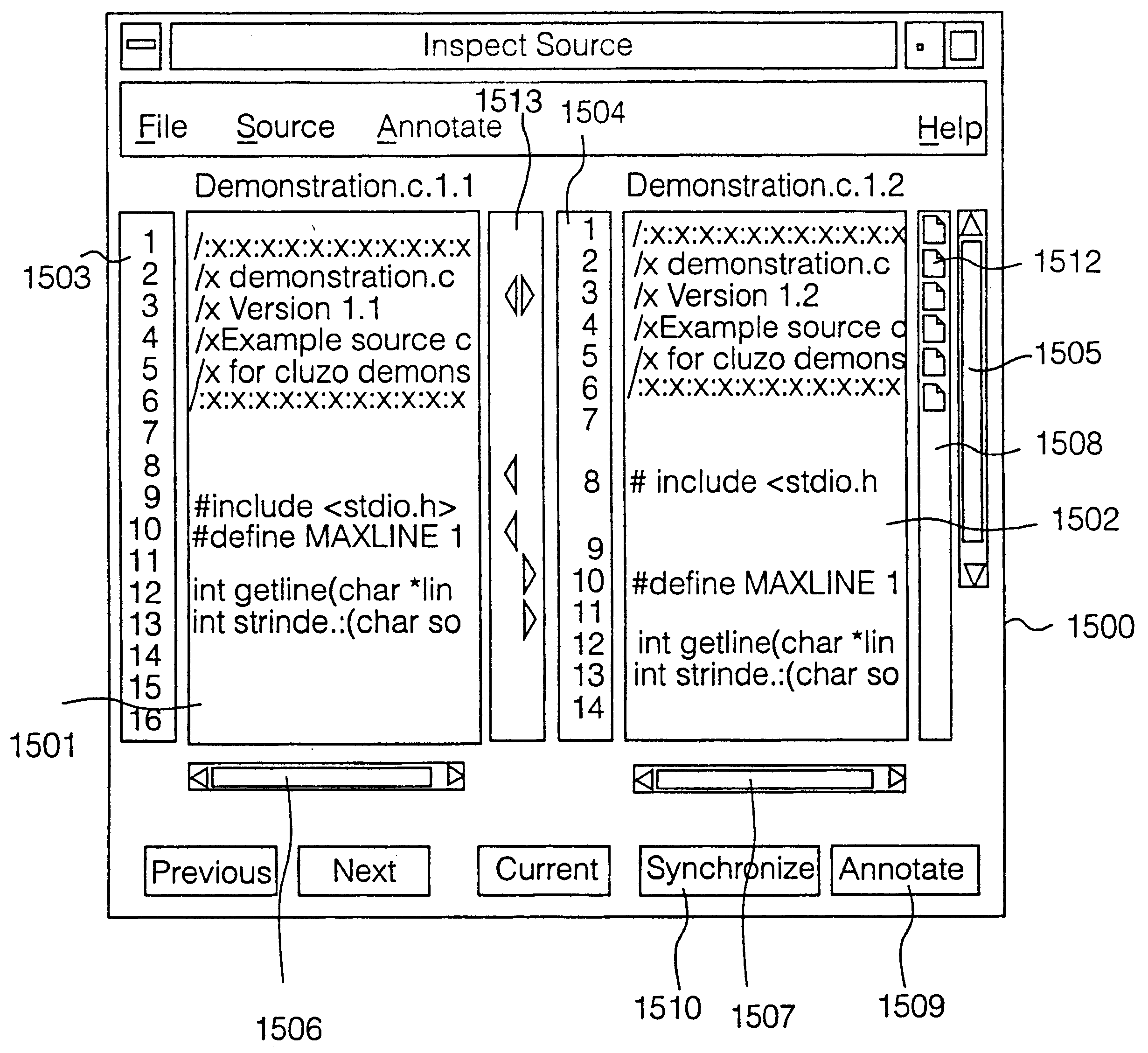
A code inspection tool comprises a plurality of physical computing resources connected by a network facility, eg an LAN, intranet or internet, and a voice conferencing communications facility. The code inspection tool interfaces with a known configuration management system to load a quantity of original source code. A group of developers use a plurality of graphical user interfaces to inspect the code. All graphical user interfaces log into display views generated on a main graphical user interface, which is operated by a human controller of a code inspection session. The code inspection tool comprises means for allowing developers to compile annotation data and forward the annotation data from their respective graphical user interfaces to a centralized data store. Internal algorithms of the code inspection tool compile markers relating the annotation data files to individual lines of source code. During a code inspection session, all developers view a same display, which sets out original source code, side by side with new source code on a line by line basis, matching the line numbers of the original source code with those of the new source code. Changes to the original source code and new source code are visually identified by automatic generation of icons next to the appropriate source code lines on the display. Annotations to the source code lines are indicated by further icons next to the appropriate lines. The tool automatically generates data describing statistics of a code inspection process, for example number of lines inspected, during of a code inspection session, proportion of original and new code lines inspected. Code inspection reports may be generated in a variety of formats, eg plain text or HTML, and automatically distributed to individual developers over the networked facility.
Owner:RPX CLEARINGHOUSE
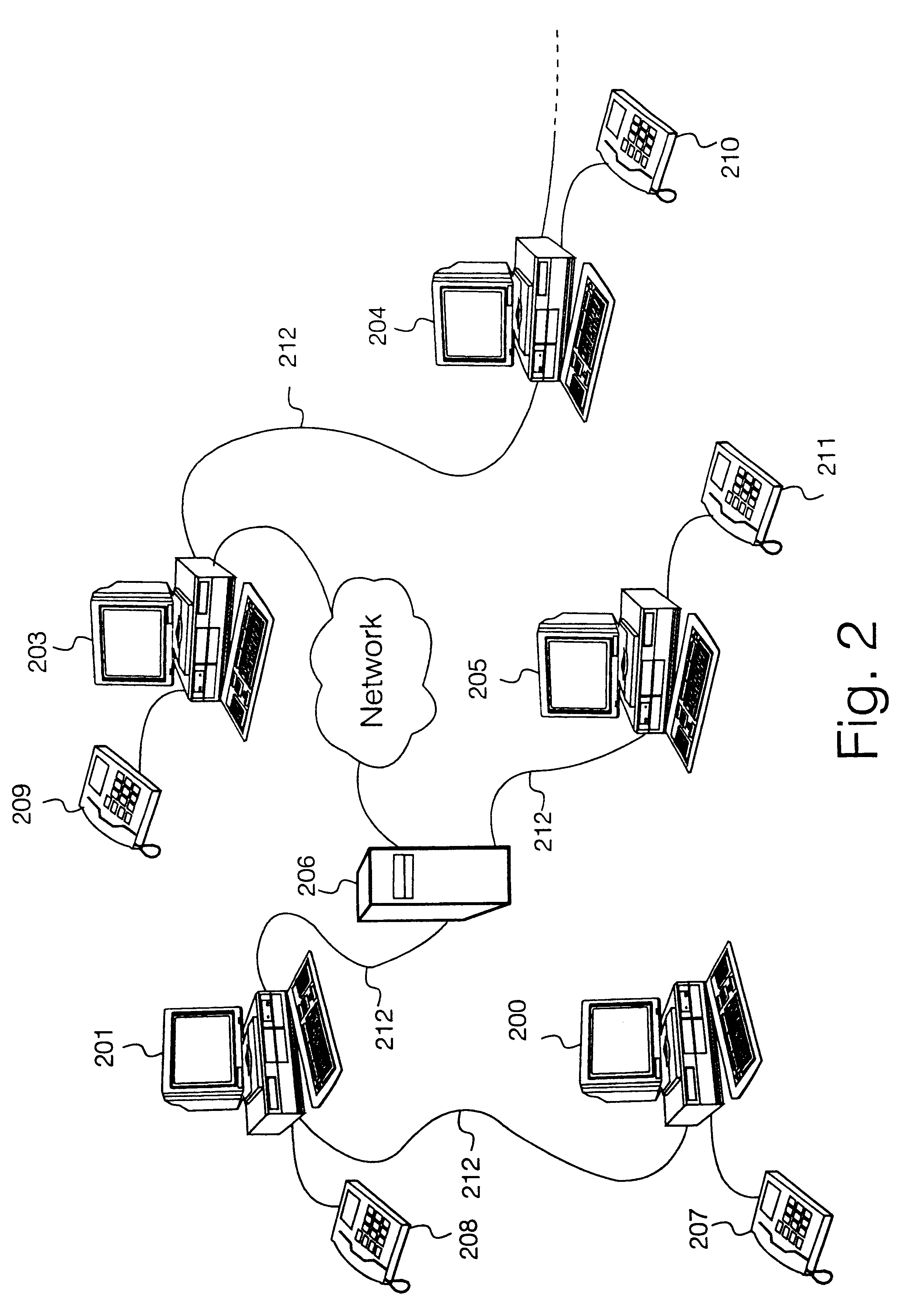
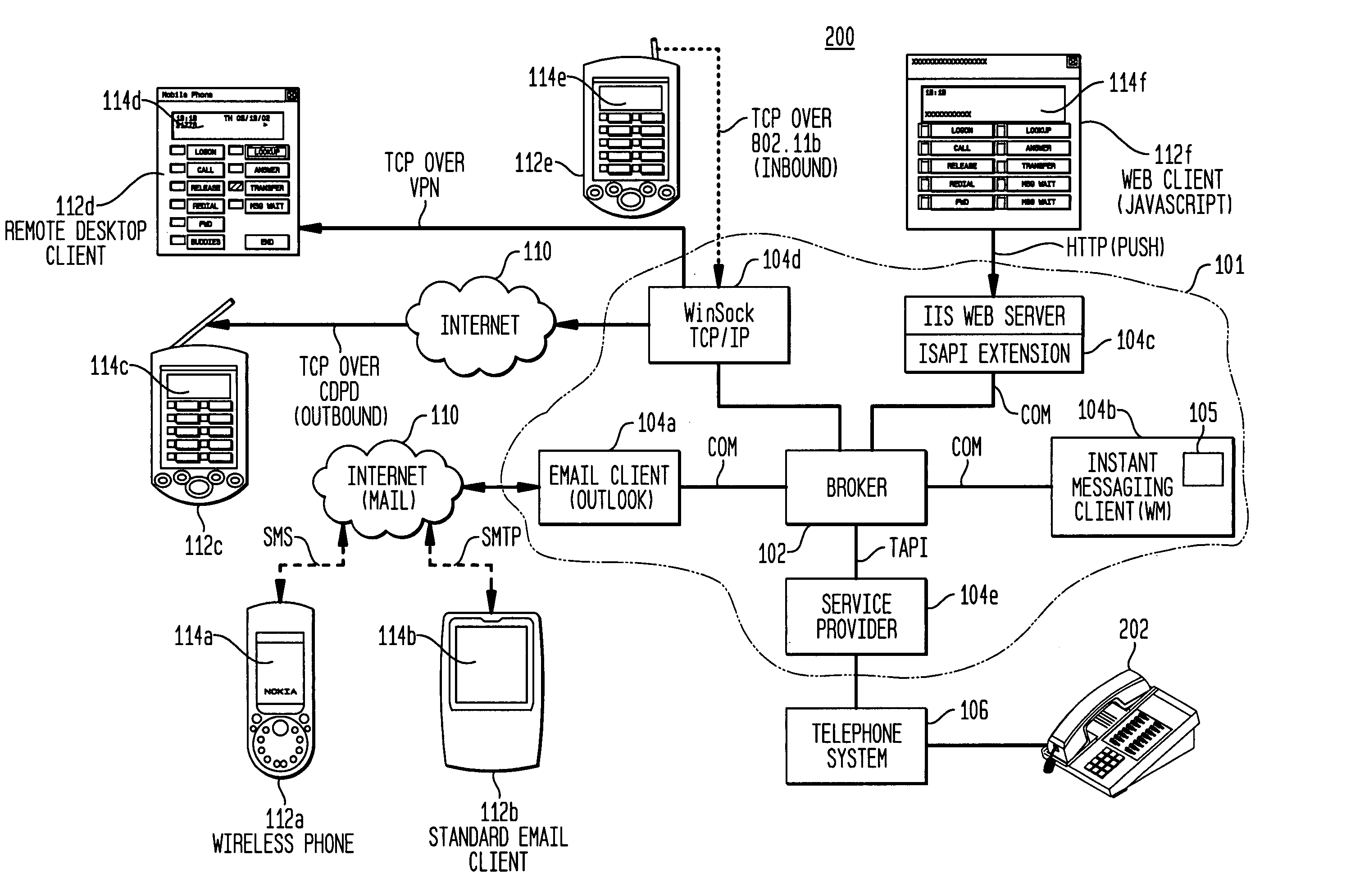
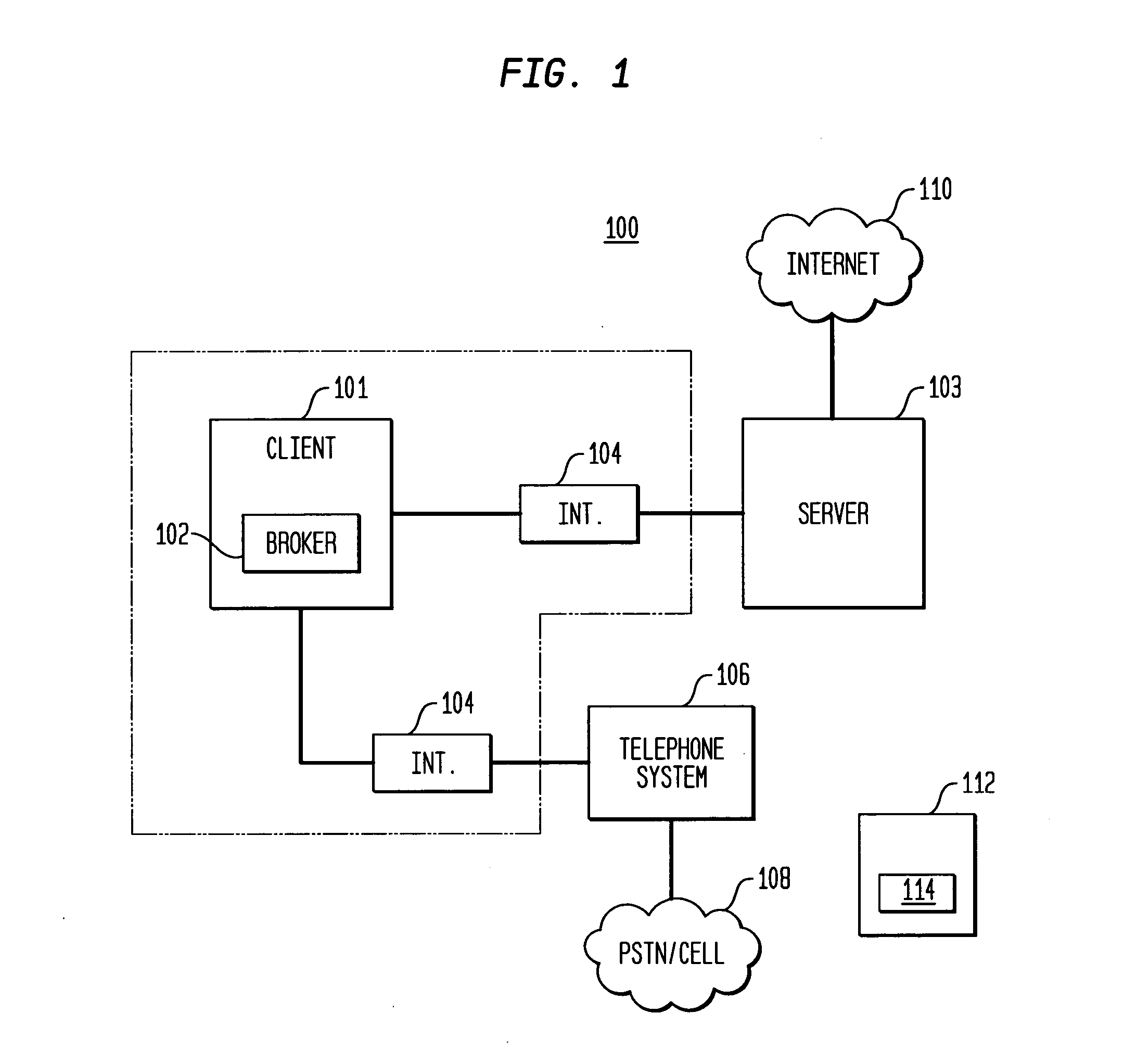
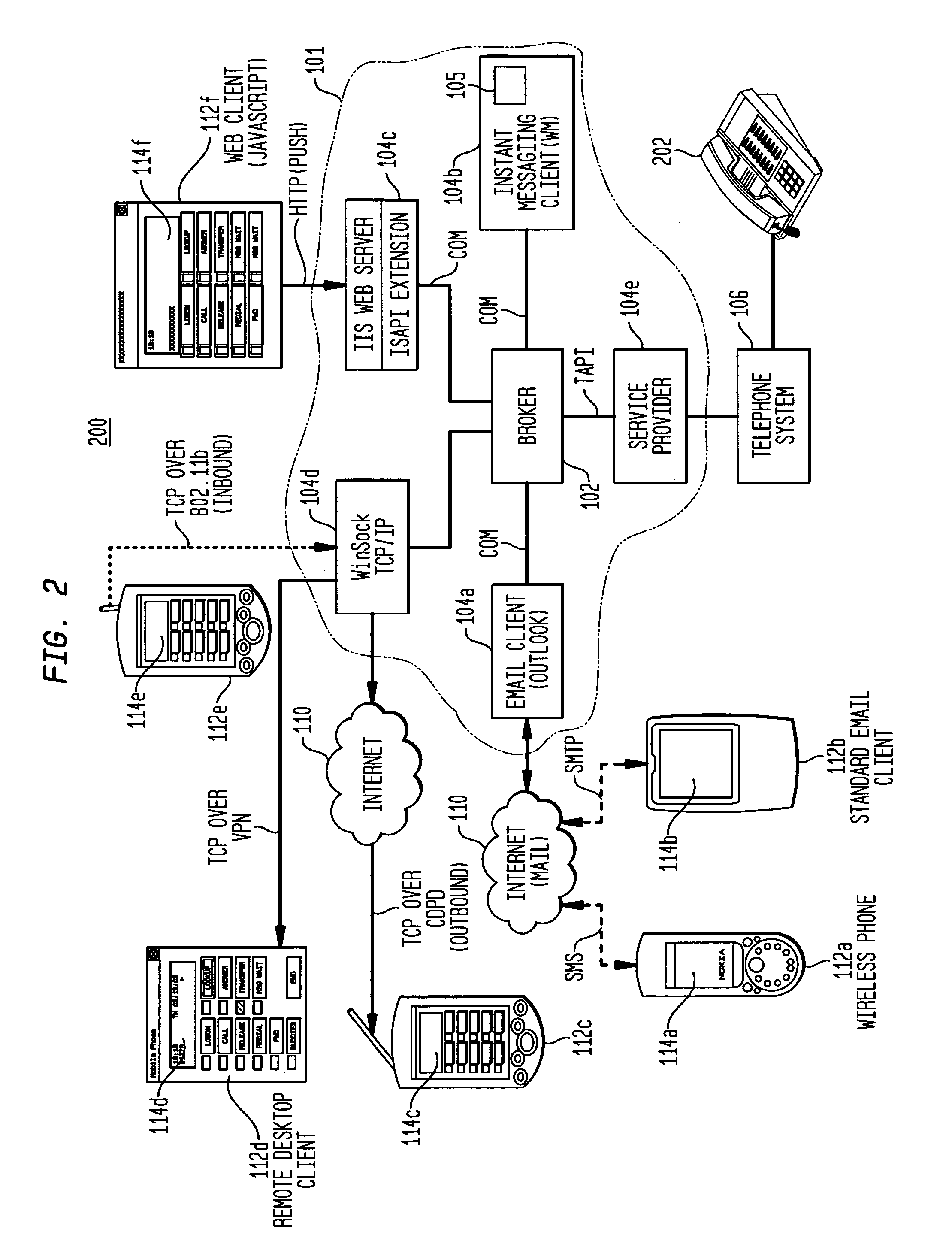
System and method for telephonic presence via e-mail and short message service
InactiveUS20050037741A1Increase delayHigh-cost IPInformation formatSpecial service for subscribersLow speedShort Message Service
A telecommunications device includes a broker module that translates telephone, mail and presence status information into short coded plain-text strings suitable for transmission over low-speed, high latency, high-cost IP networks. The broker module further transmits and receives such messages, to allow a user to monitor voicemail, e-mail, IM, and presence status, as well as control various telephone functions remotely.
Owner:SIEMENS INFORMATION & COMM NEWTWORKS INC
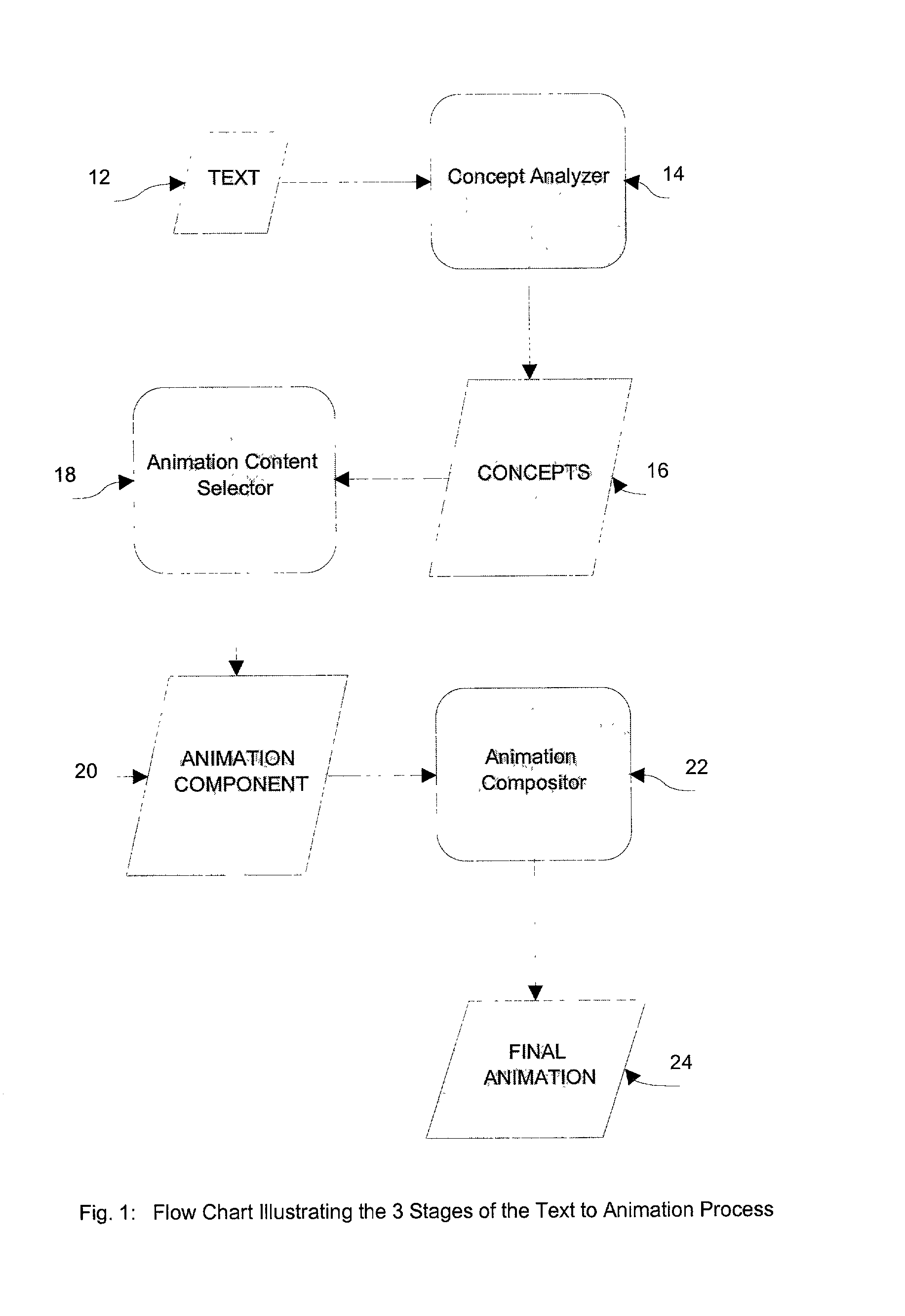
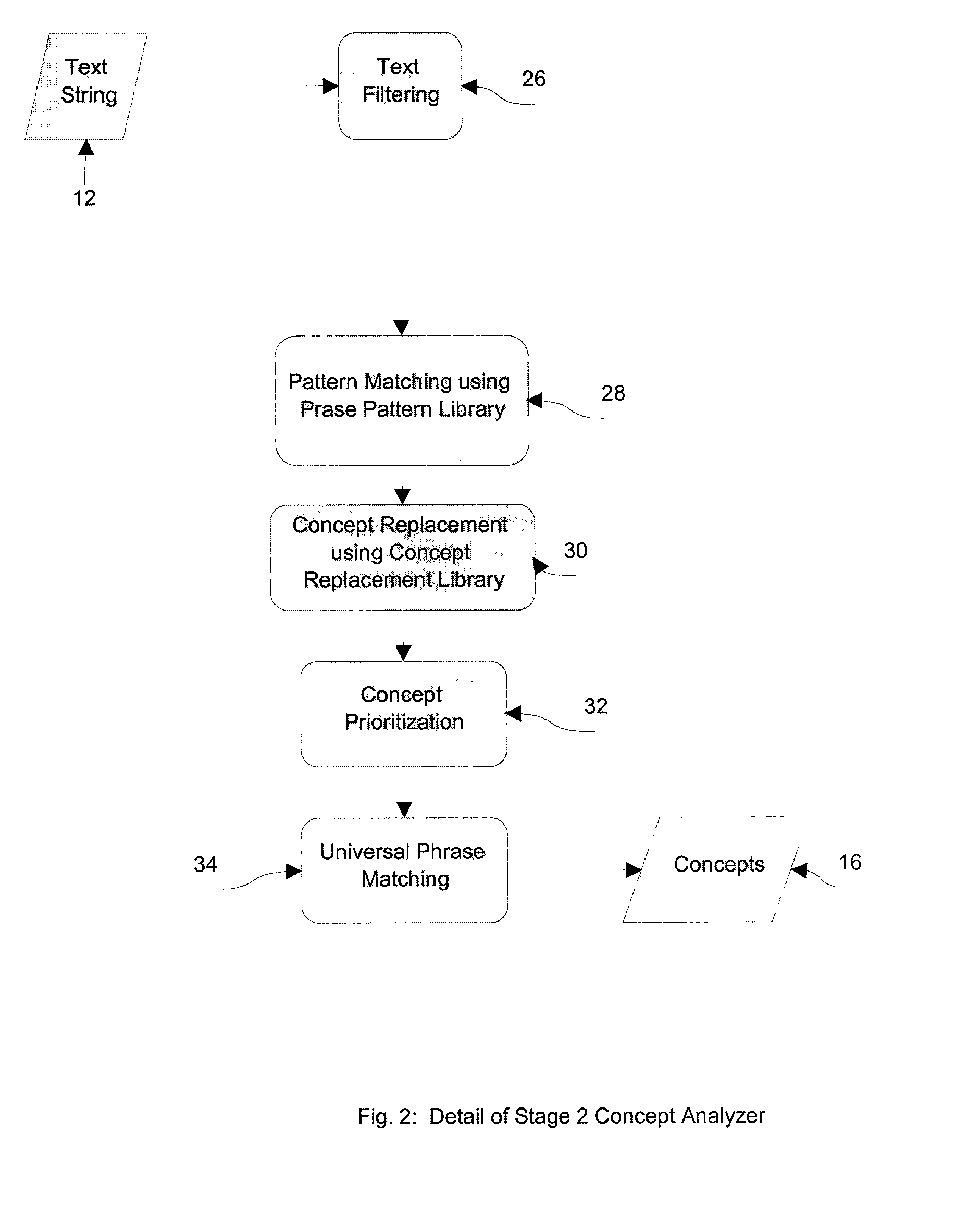
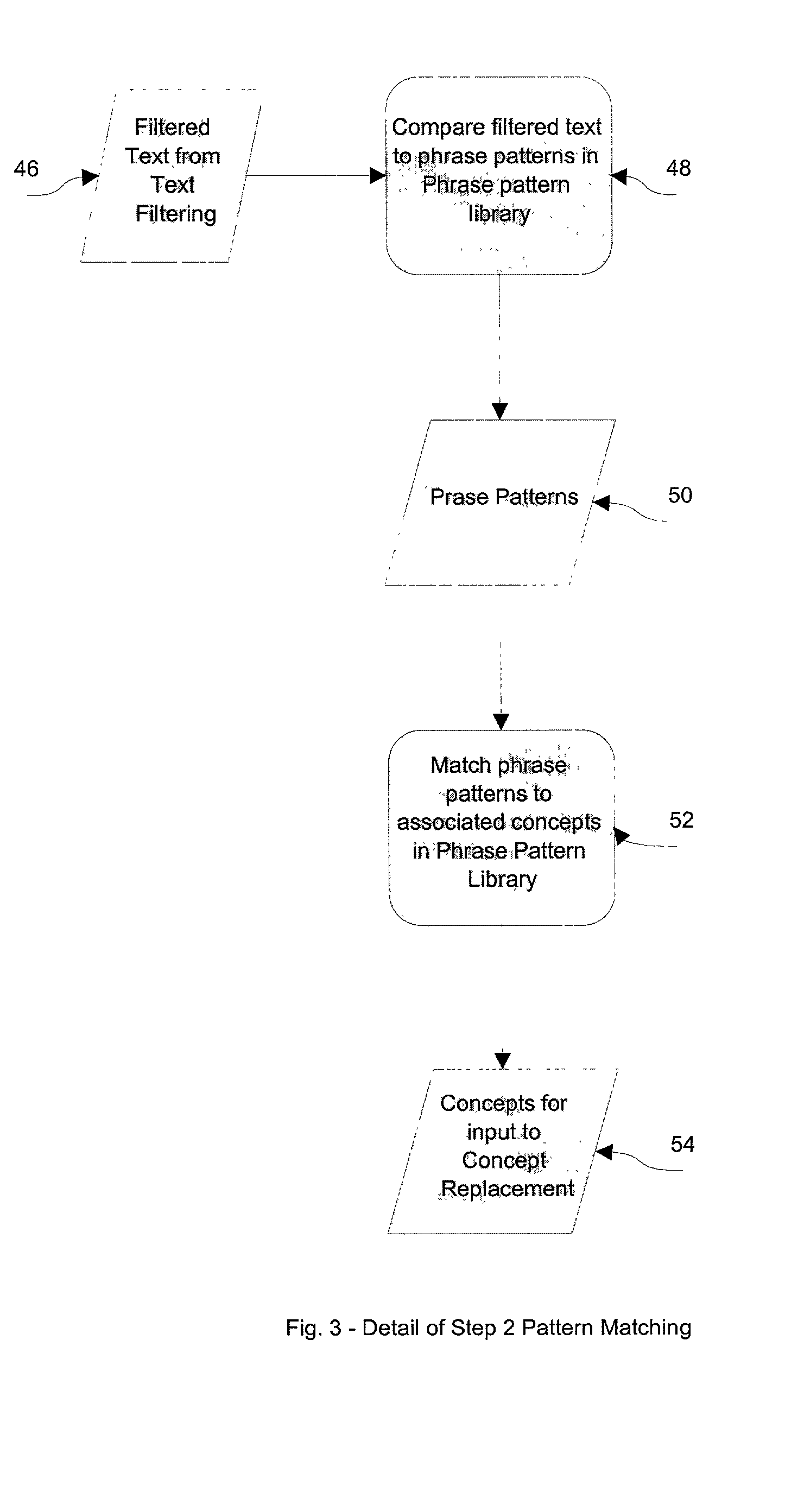
Text to animation process
The process of turning plain text into animated sequences using a digital image generator, which can be a computer or digital video system is disclosed. A text string is analyzed to determine the concepts contained in the string. An Animation Compositor is used to compose an animated sequence based on the selected concept. The disclosed invention combined with the animation compositor can take a text string and display an animated story, which is conceptually related to the text.
Owner:FUNMAIL
Data security system and method with parsing and dispersion techniques
ActiveUS7349987B2Ease overhead performanceHigh overhead performanceDigital data processing detailsUser identity/authority verificationOriginal dataInternet privacy
A data security having parsing and dispersion aspects enables the user to parse, disperse and reconstruct the original, plain text data or data object, thereby enabling secure storage of the data. The original data may be maintained in its original state, encrypted or it may be destroyed. For example, financial data maintained by an institute, stored as is customary, be parsed with an algorithm, the parsed segments dispersed off-site (that is, separated and stored in extract and remainder stores or computer memories) and away from the financial institute, and, upon appropriate security clearance, the dispersed data can be reconstructed to duplicate the data. Large distribution of parsed data is contemplated by the system. The original data remains stable, operable and immediately useful in its customary storage location (or alternatively destroyed). The secured dispersed data is a back-up of the original data.
Owner:DIGITAL DOORS
Information processing apparatus, information processing method, and program
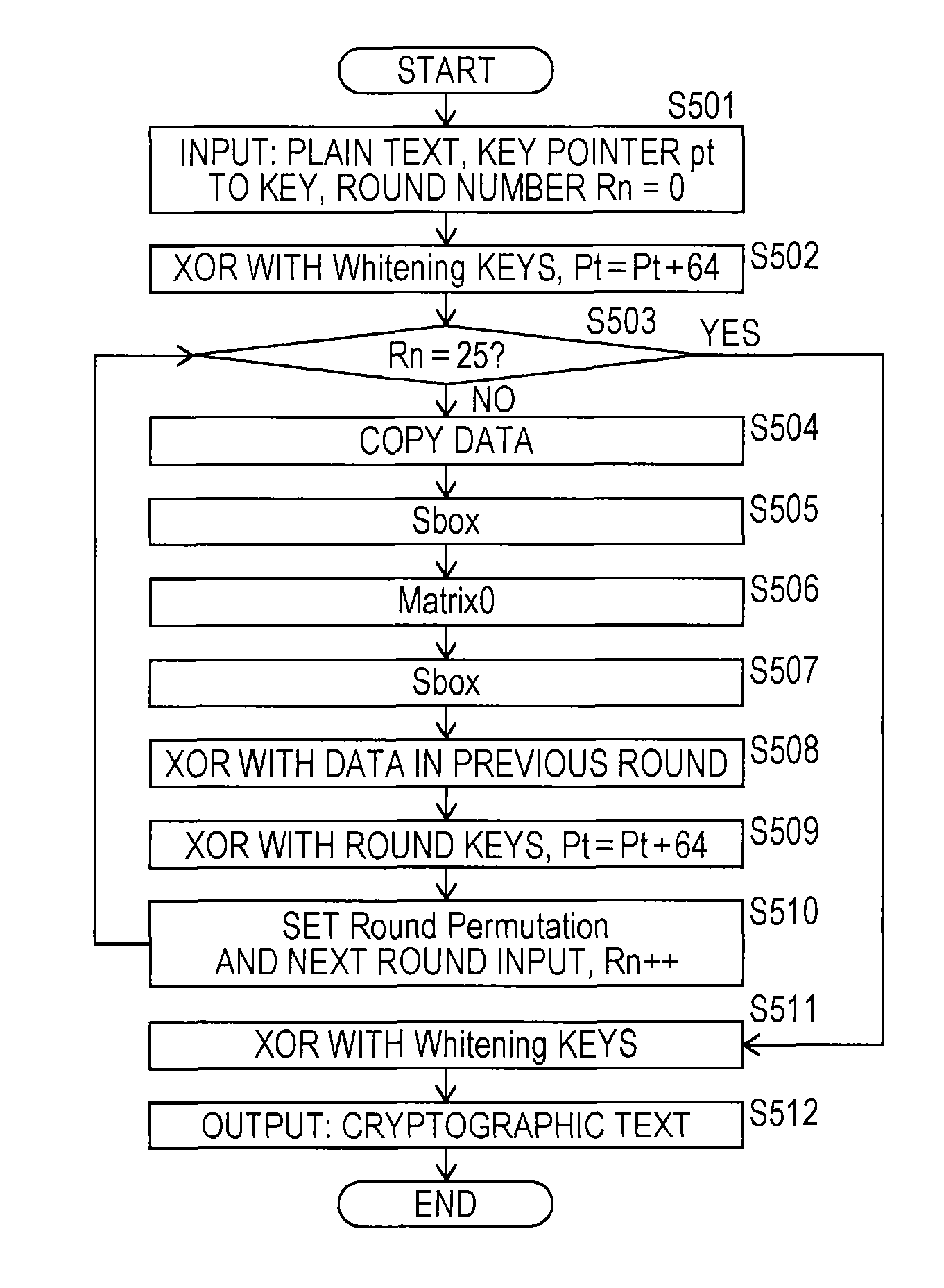
ActiveUS9281940B2Fast processingHigh-speed performanceEncryption apparatus with shift registers/memoriesInternal/peripheral component protectionComputer hardwareInformation processing
Speed-up of a cryptographic process by software (program) is realized. A data processing unit which executes a data process according to a program defining a cryptographic process sequence is included, and the data processing unit, according to the program, generates a bit slice expression data based on a plurality of plain text data items which are encryption process targets and a bit slice expression key based on a cryptographic key of each plain text data item, generates a whitening key and a round key based on the bit slice expression key, executes the cryptographic process including operation and movement processes of a block unit of the bit slice expression data, and an operation using the round key, as a process according to a cryptographic algorithm Piccolo, and generates the plurality of encrypted data items corresponding to the plurality of plain text data items by the reverse conversion of the data with respect to the cryptographic process results.
Owner:SONY CORP
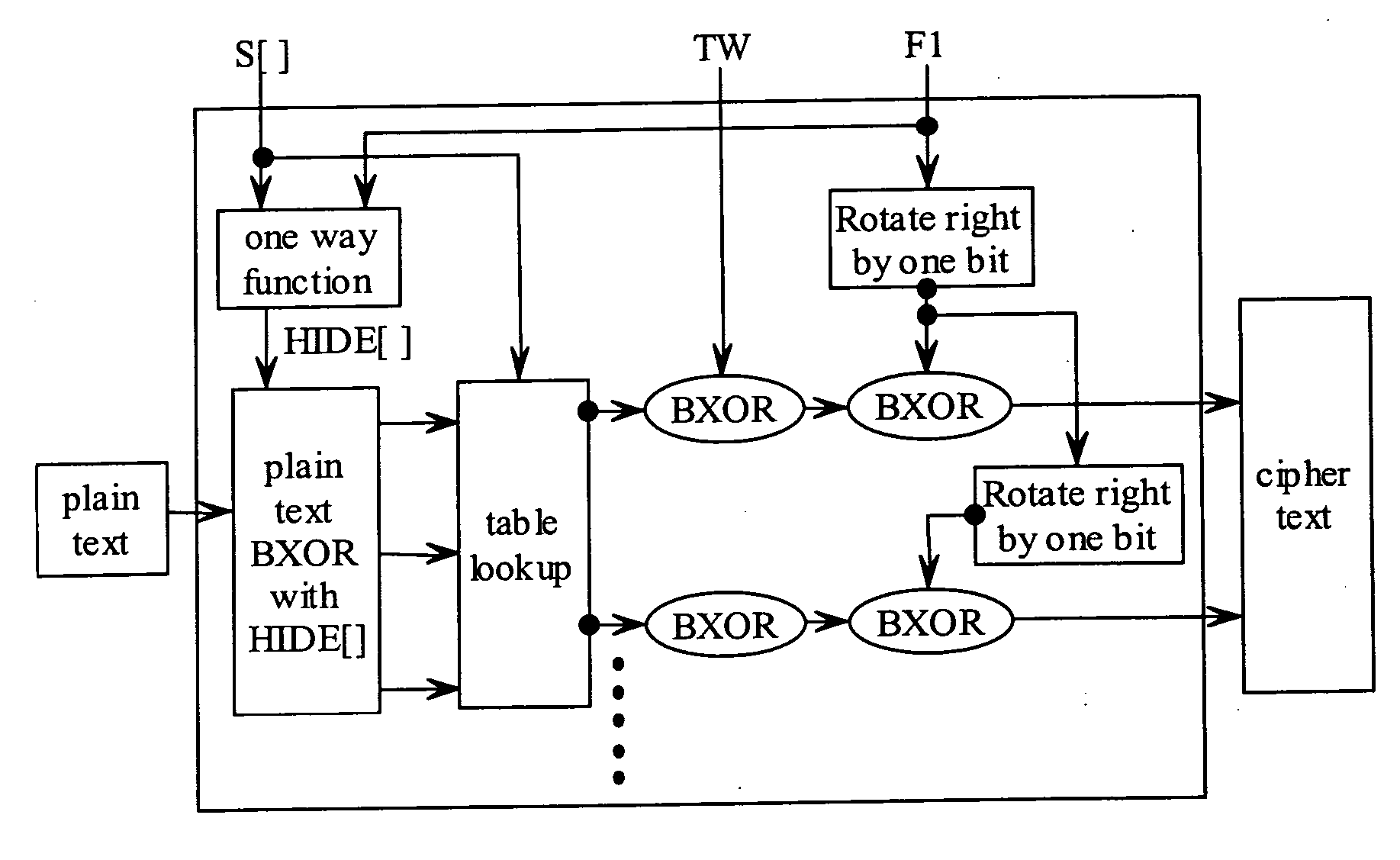
State-varying hybrid stream cipher
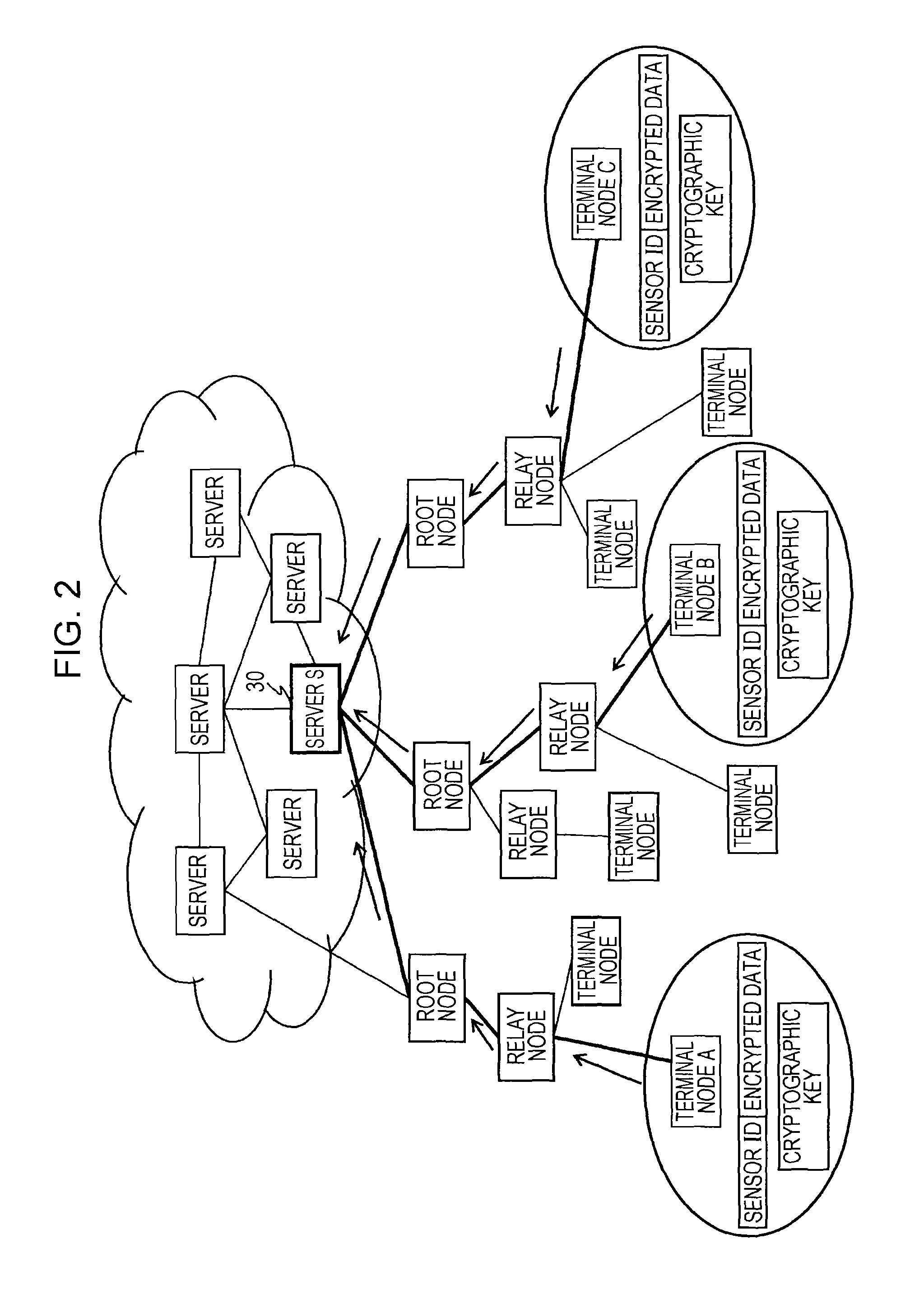
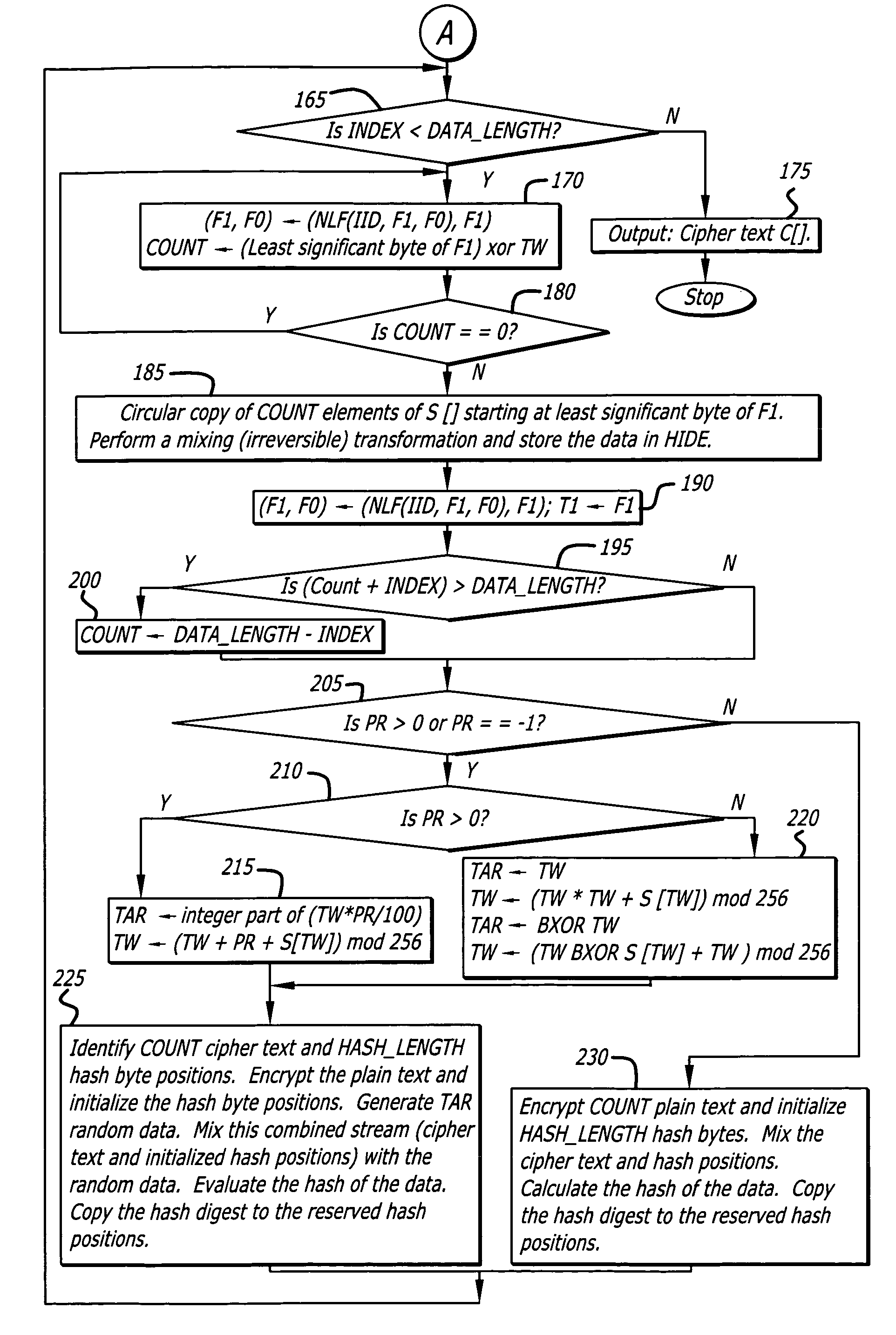
InactiveUS7103181B2Data stream serial/continuous modificationSecret communicationAlgorithmCiphertext
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
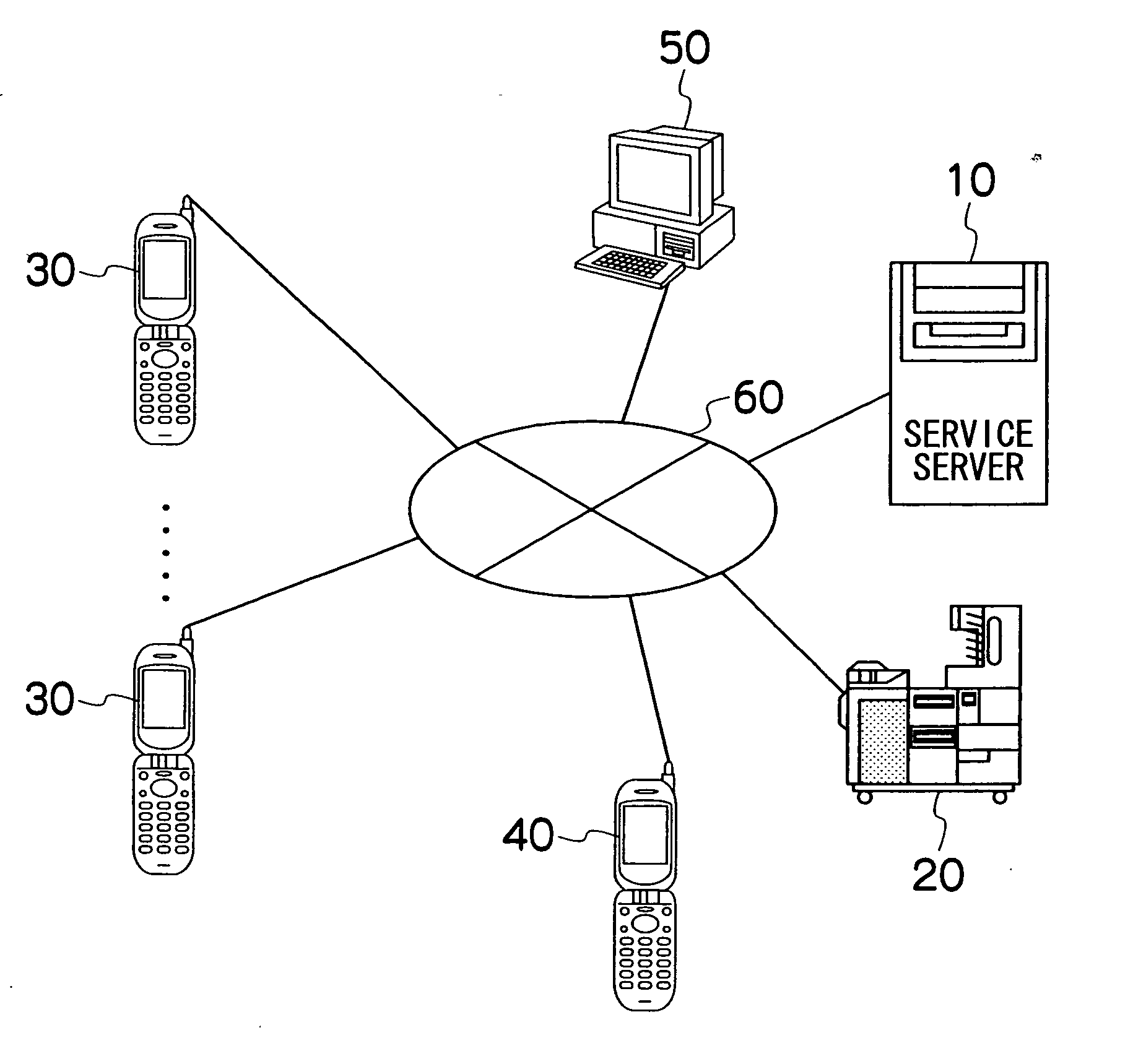
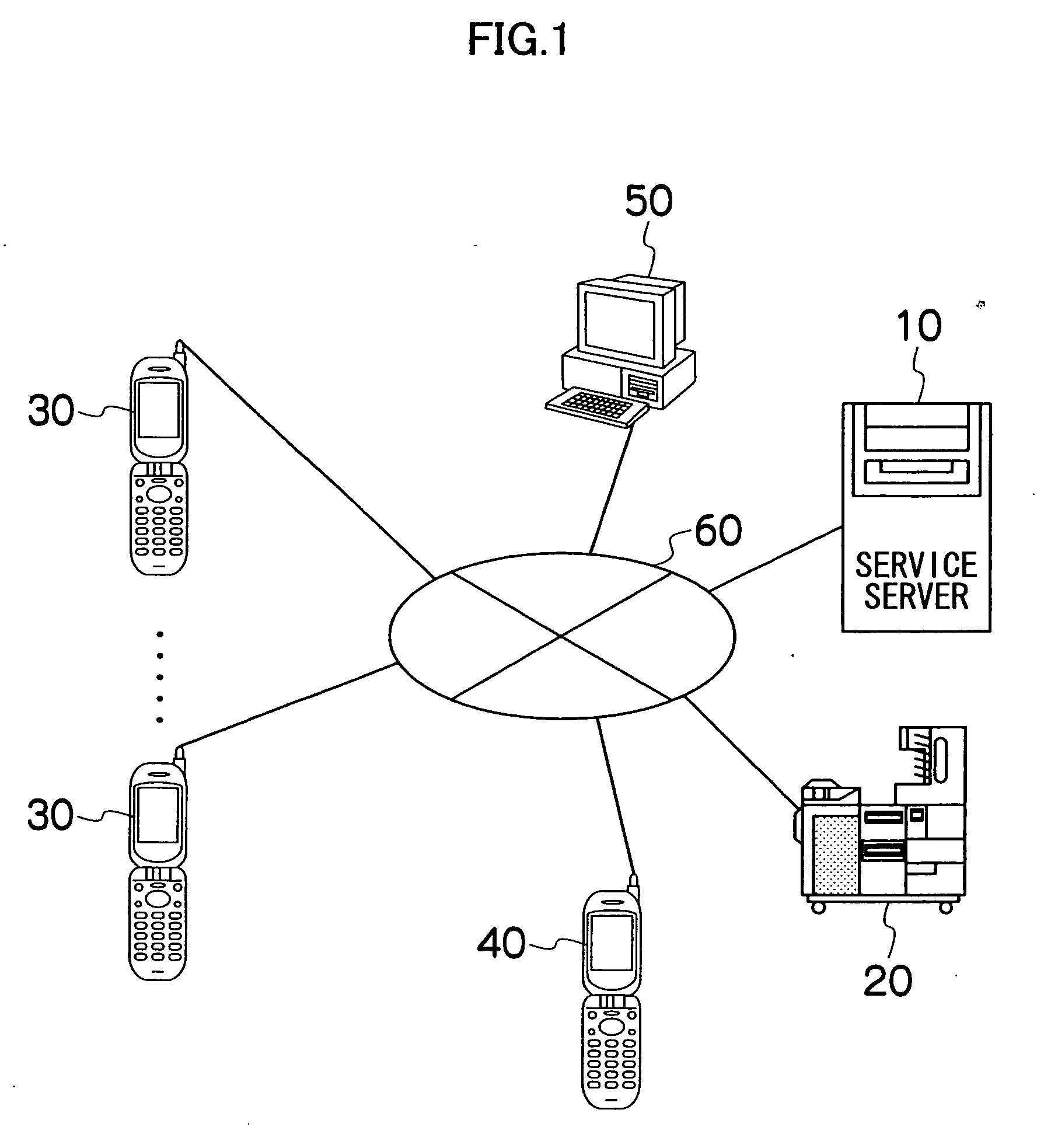
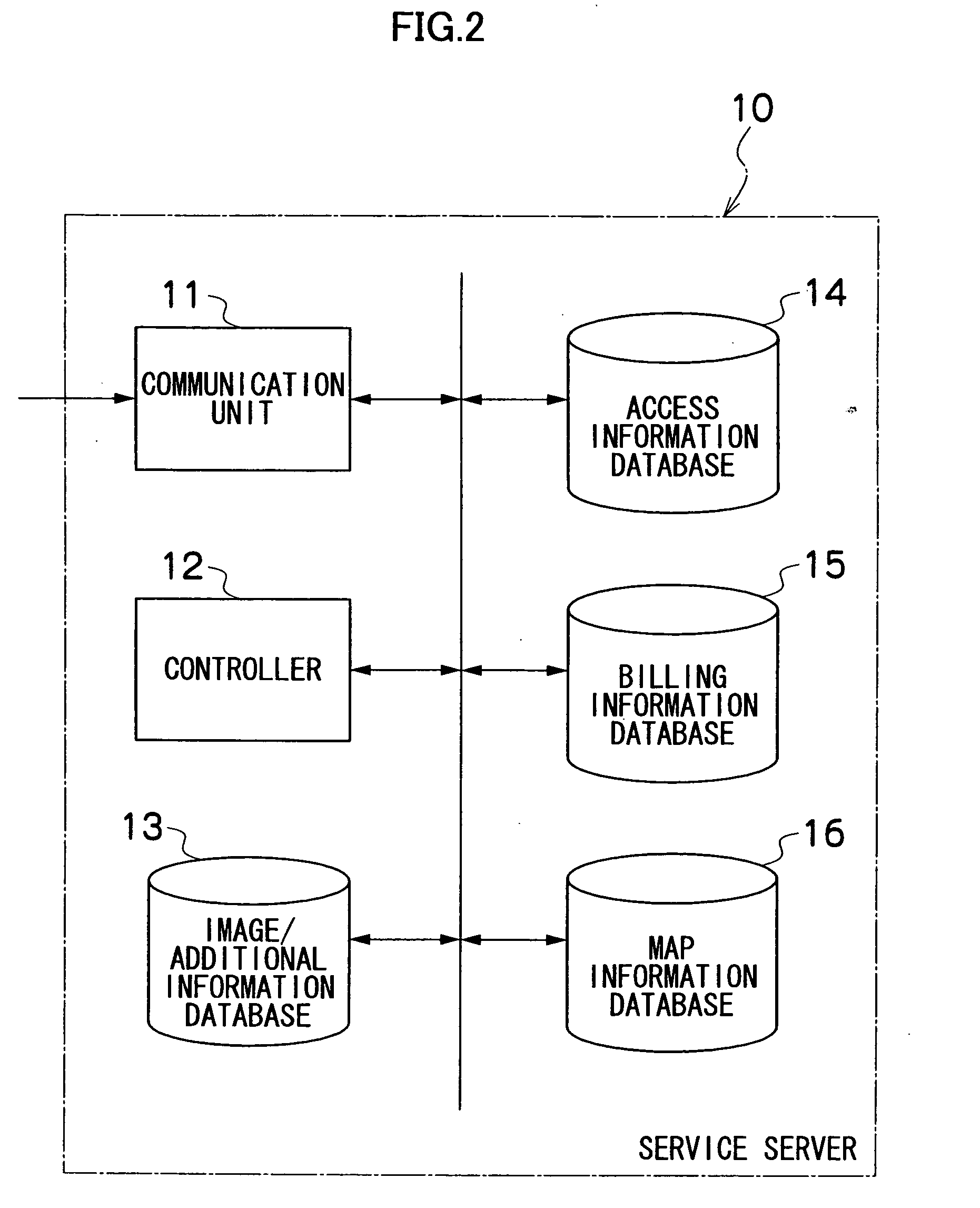
Server, mobile terminal, and service method
ActiveUS20050277405A1Inhibition of informationAvoid accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwarePlaintext
The server which provides at least one of an image and additional information of the image via a network to a mobile terminal of an access source when access is received from the mobile terminal via the network using access information recorded together with the image on a prescribed print medium, the server comprises: an encrypting device which encrypts identification information corresponding to the image; an access information generating device which generates the access information containing a plain text URL required for access to the server and the encrypted identification information; a print instruction information creating device which creates instruction information that the access information is recorded together with the image onto a print medium by a prescribed printer; a receiving device which receives the encrypted identification information contained in the access information from the mobile terminal when the access information recorded on the print medium is inputted to the mobile terminal; a decrypting device which decrypts the encrypted identification information that is received; and a transmitting device which transmits at least one of the image and the additional information of the image that correspond to the decrypted identification information to the mobile terminal.
Owner:FUJIFILM CORP +1
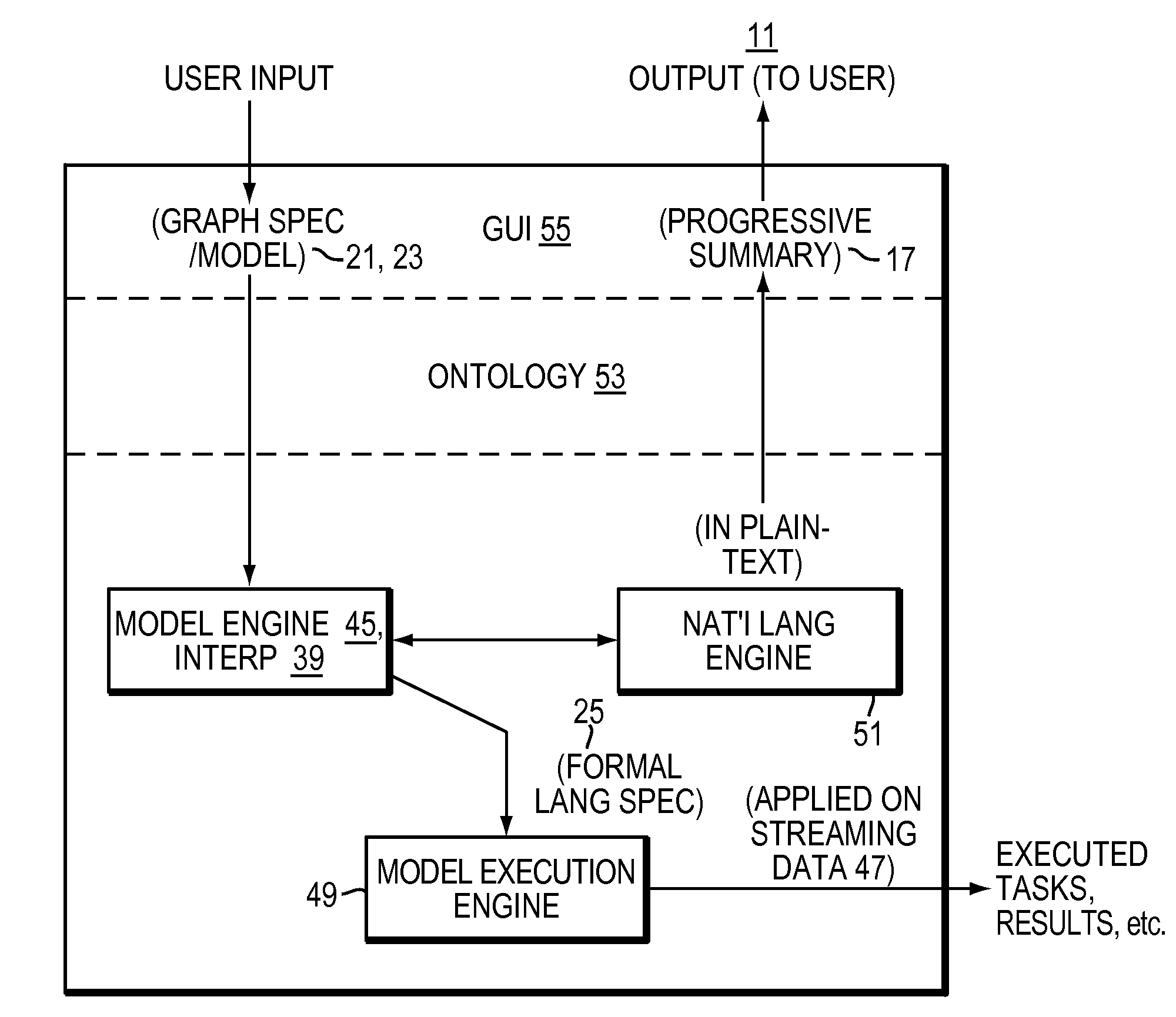
Computer method and apparatus for graphical inquiry specification with progressive summary
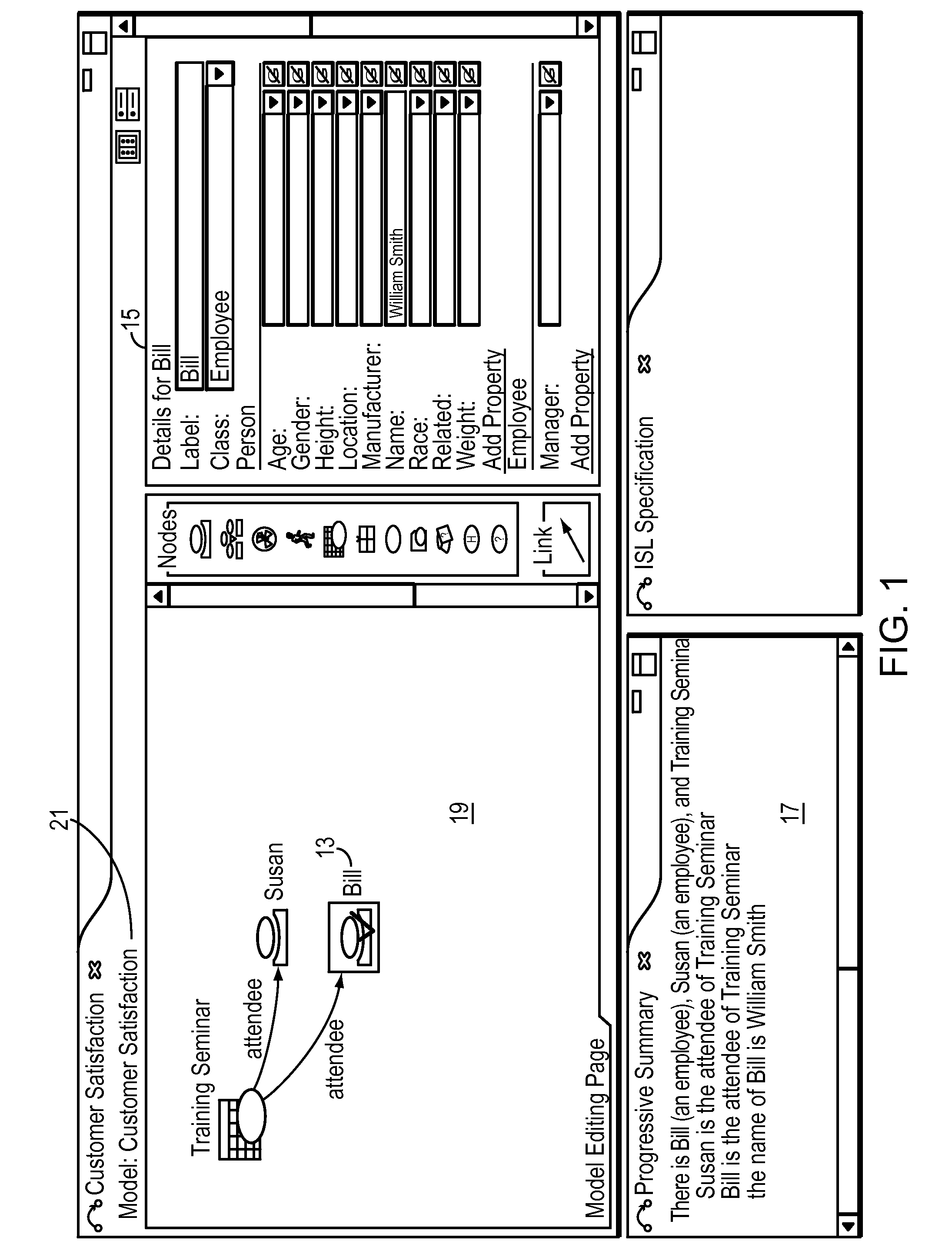
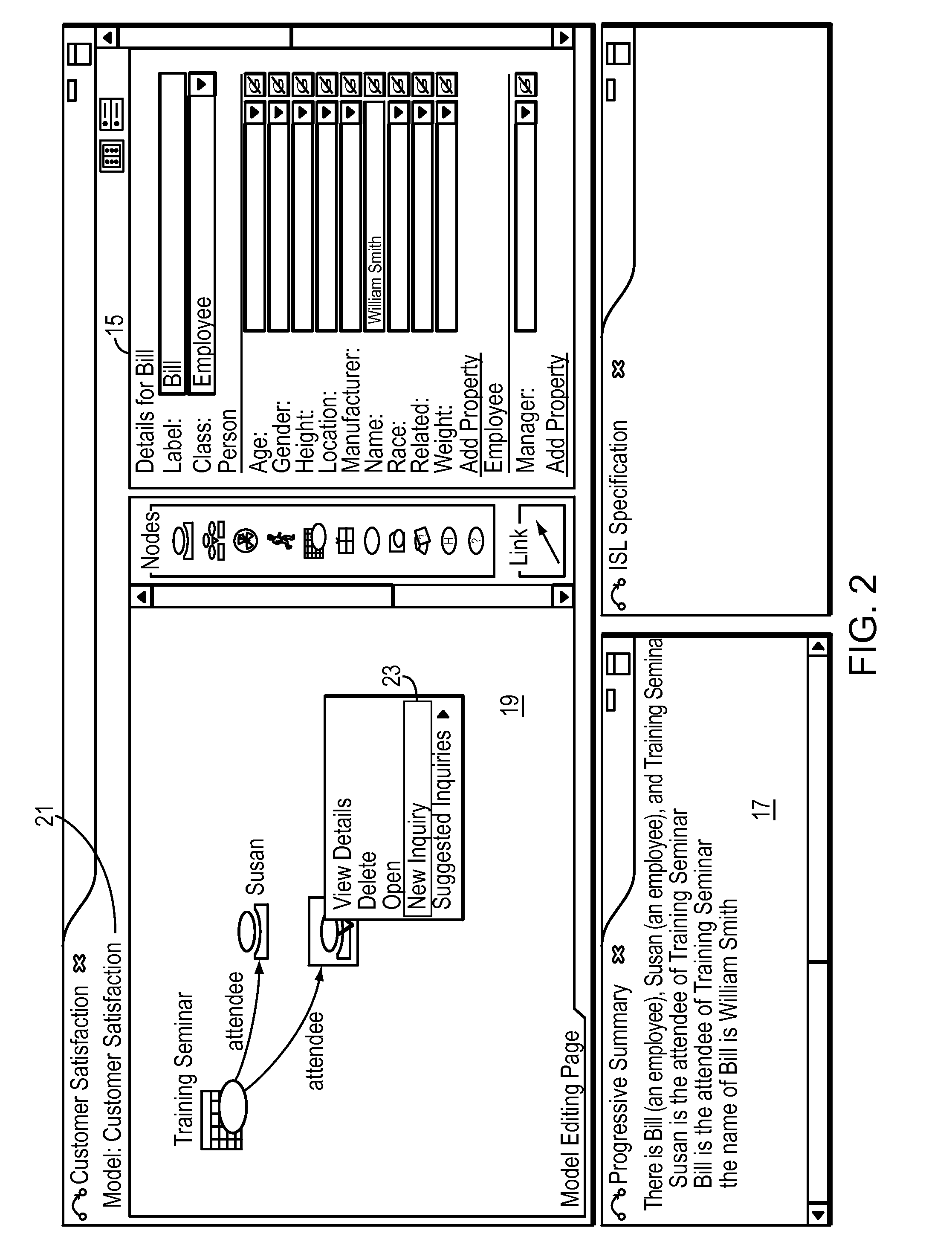
InactiveUS20090187556A1Easy to specifyDigital data information retrievalDigital data processing detailsGraphical specificationStreaming data
A computer method and system provides for graphical specification of inquiries and includes a corresponding progressive summary. The inquiries operate on stream data. Users graphically specify an inquiry in a graphical user interface according to an ontology. The invention system generates a plain-text translation of the graphical description of the inquiry and displays the generated plain-text description in a progressive summary in the graphical user interface. The system continually updates and generates the display of the plain-text description during user construction of the inquiry. This provides feedback to the user for improved construction of the inquiry.
Owner:IBM CORP
Symmetric key authenticated encryption schemes
InactiveUS6963976B1Low costSame level of securityData processing applicationsEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
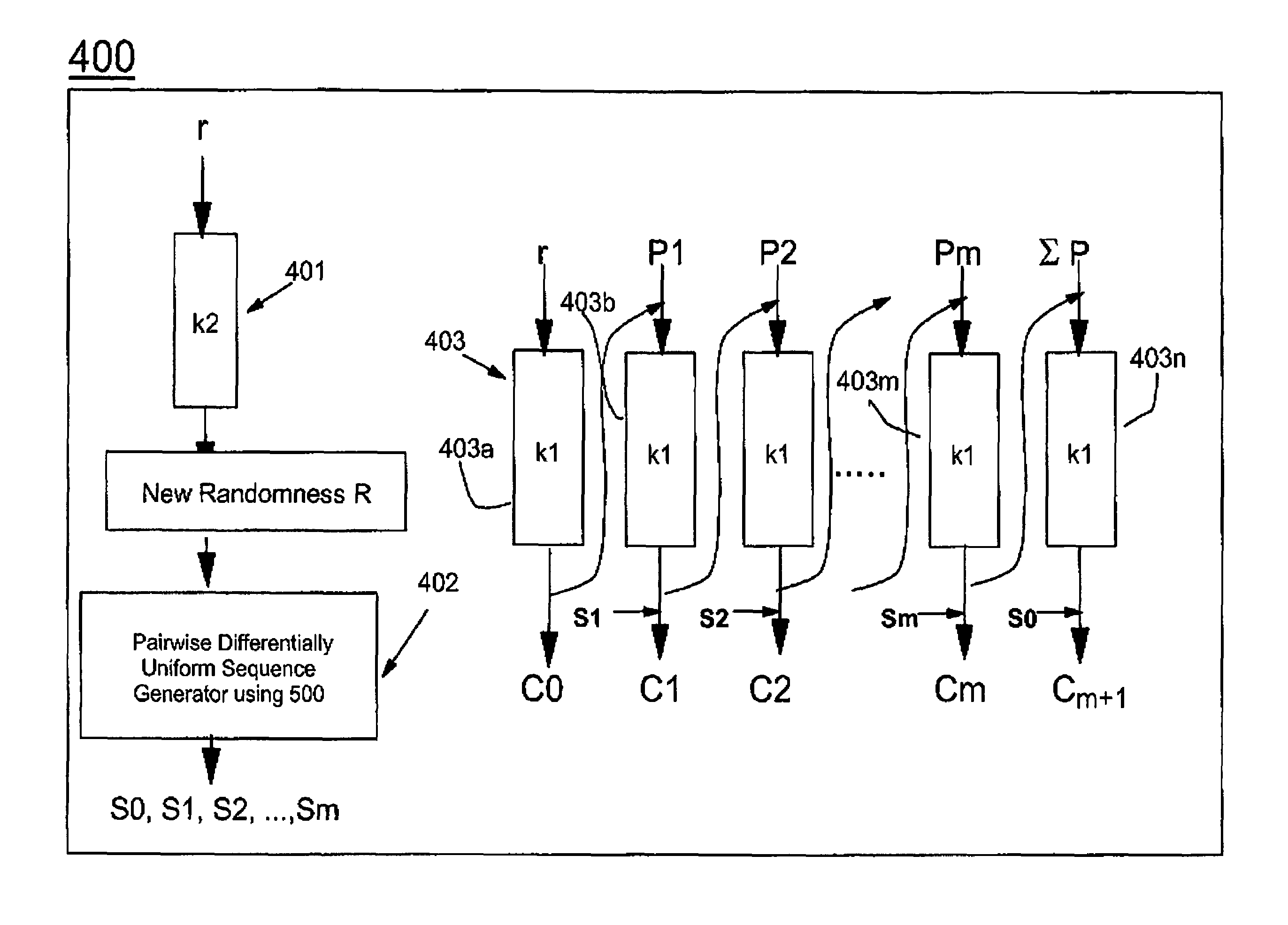
The present invention provides encryption schemes and apparatus which securely generate a cipher-text which in itself contains checks for assuring message integrity. It also provides compatible decryption schemes confirming message integrity. The encryption scheme generates a cipher-text with message integrity in a single pass with little additional computational cost, while retaining at least the same level of security as schemes based on a MAC. One embodiment encrypts a plain-text message by dividing the plain-text message into a multitude of plain-text blocks and encrypting the plain-text blocks to form a multitude of cipher-text blocks. A single pass technique is used in this process to embed a message integrity check in the cipher-text block. A message integrity check is embedded in the cipher-text blocks by embedding a set of pseudo random numbers, which may be dependent, but are pair-wise differentially uniform. We also describe an embodiment which is highly parallelizable.
Owner:IBM CORP +1
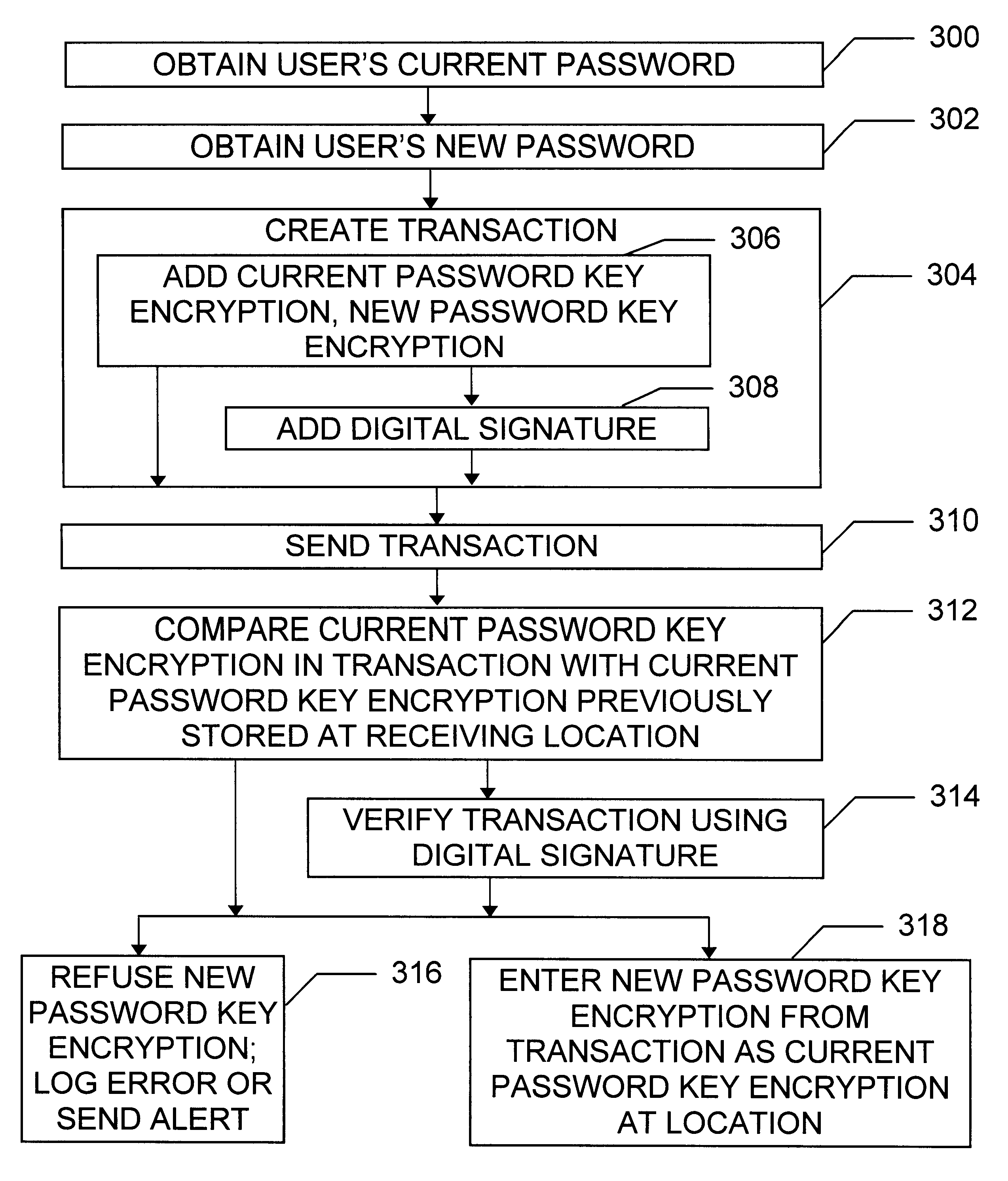
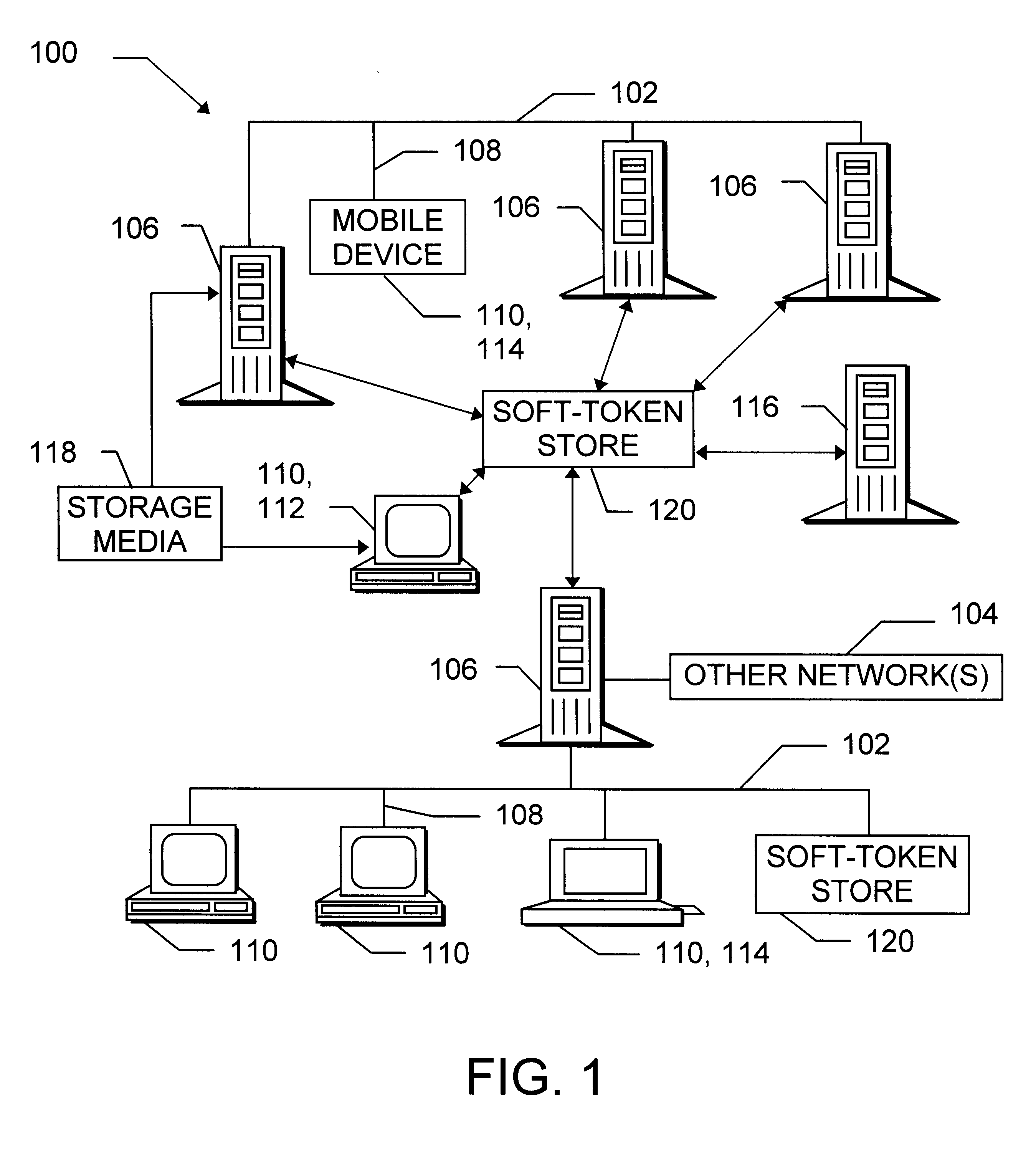
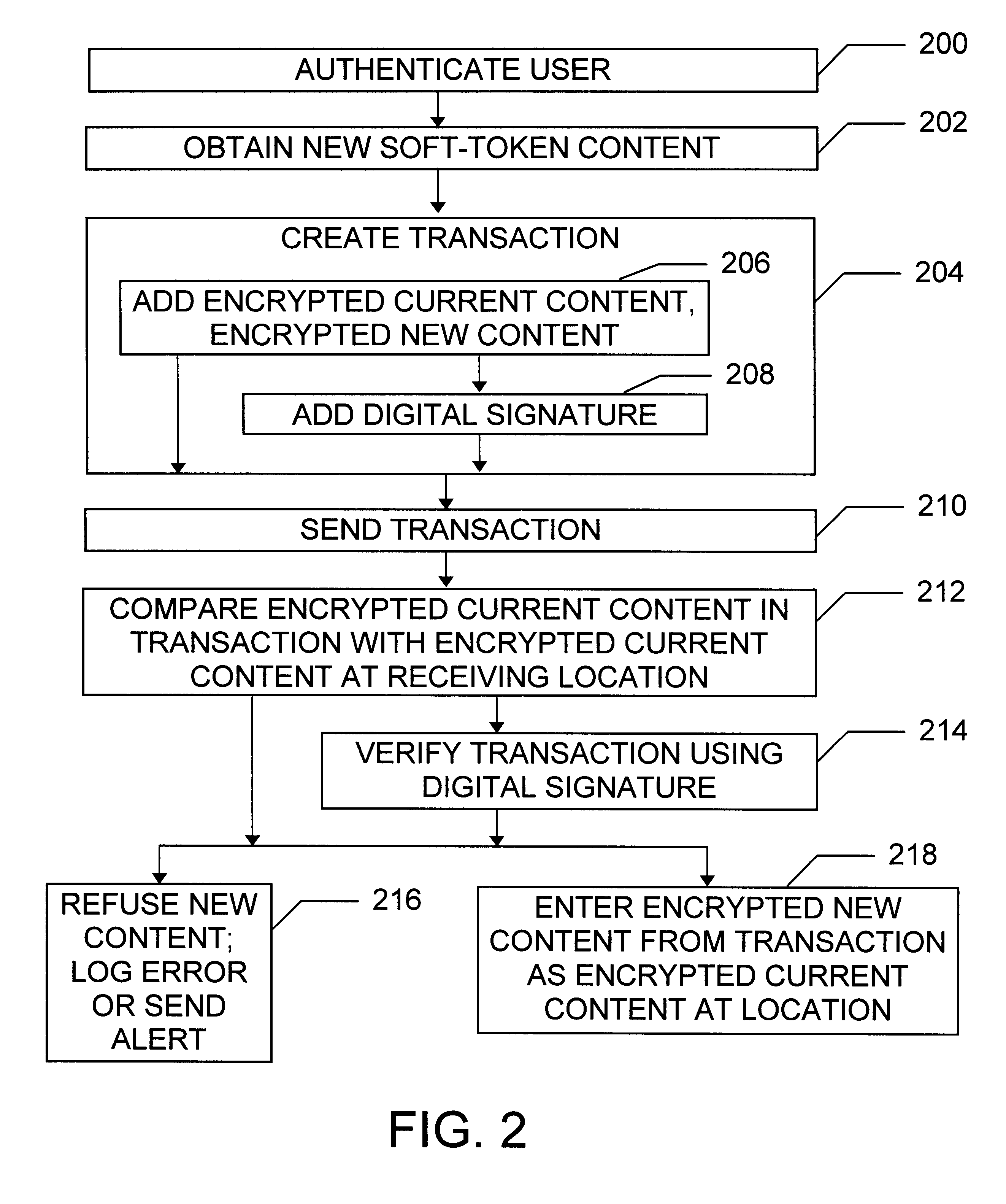
Maintaining a soft-token private key store in a distributed environment
InactiveUS6738907B1Key distribution for secure communicationDigital data processing detailsPasswordSecret code
Methods, systems, and devices are provided for securely updating private keys, key pairs, passwords, and other confidential information in a distributed environment. A transaction is created including appropriate encrypted soft-token content, and then transmitted to a new location. Comparisons are made to determine whether the new soft-token content should be recognized as authentic and entered at the new location. Updates are accomplished without ever sending the plain text form of a key or a password across the wire between the distributed locations.
Owner:RPX CORP
Scalable and Secure Key Management For Cryptographic Data Processing
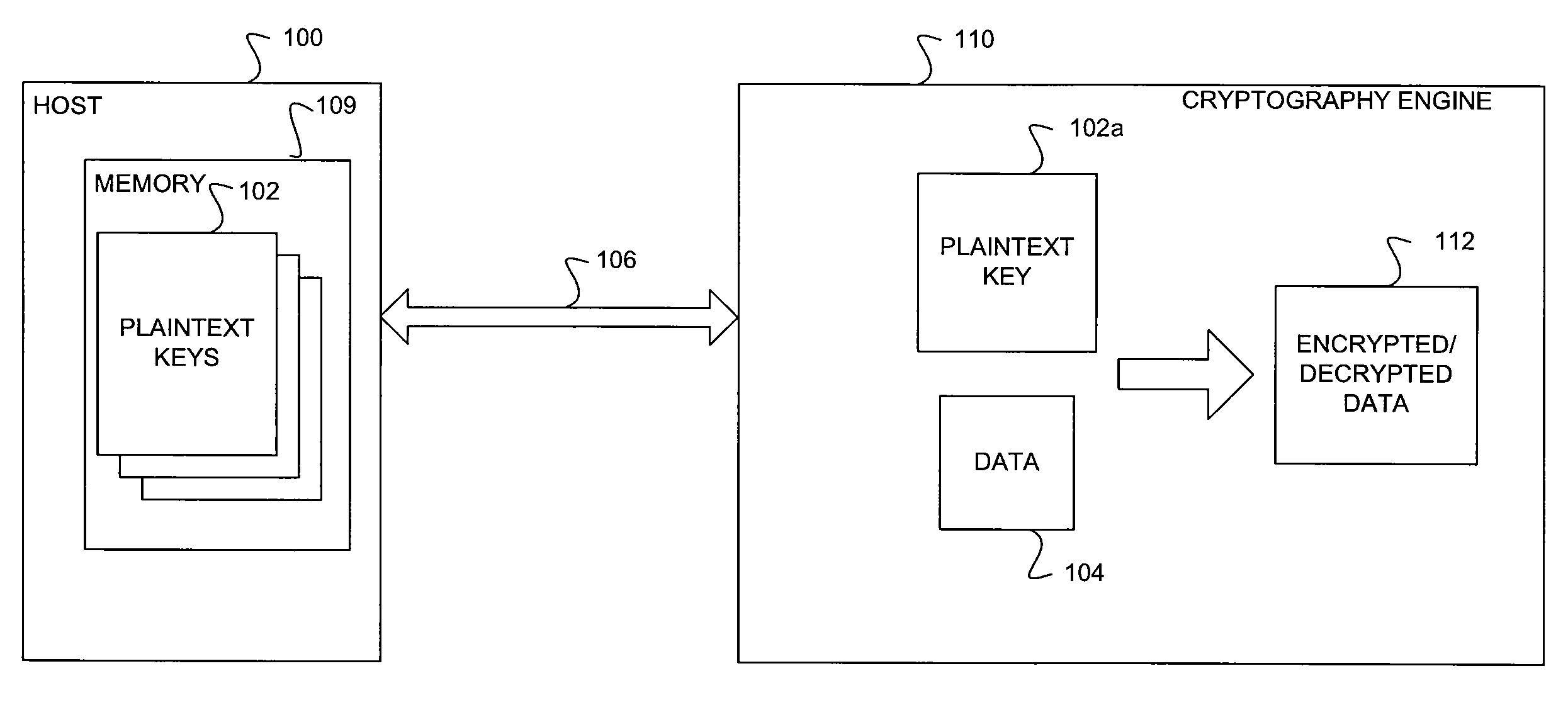
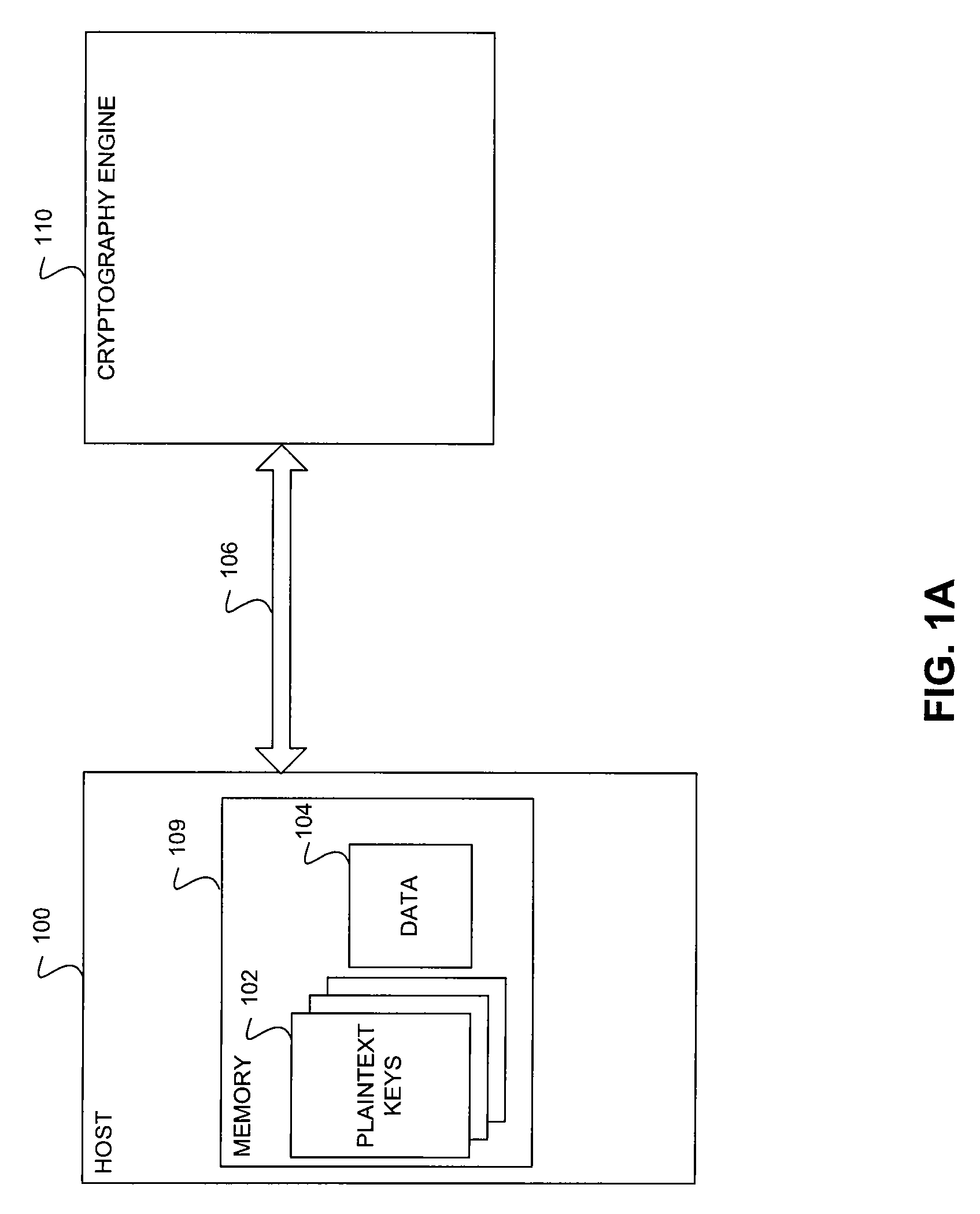
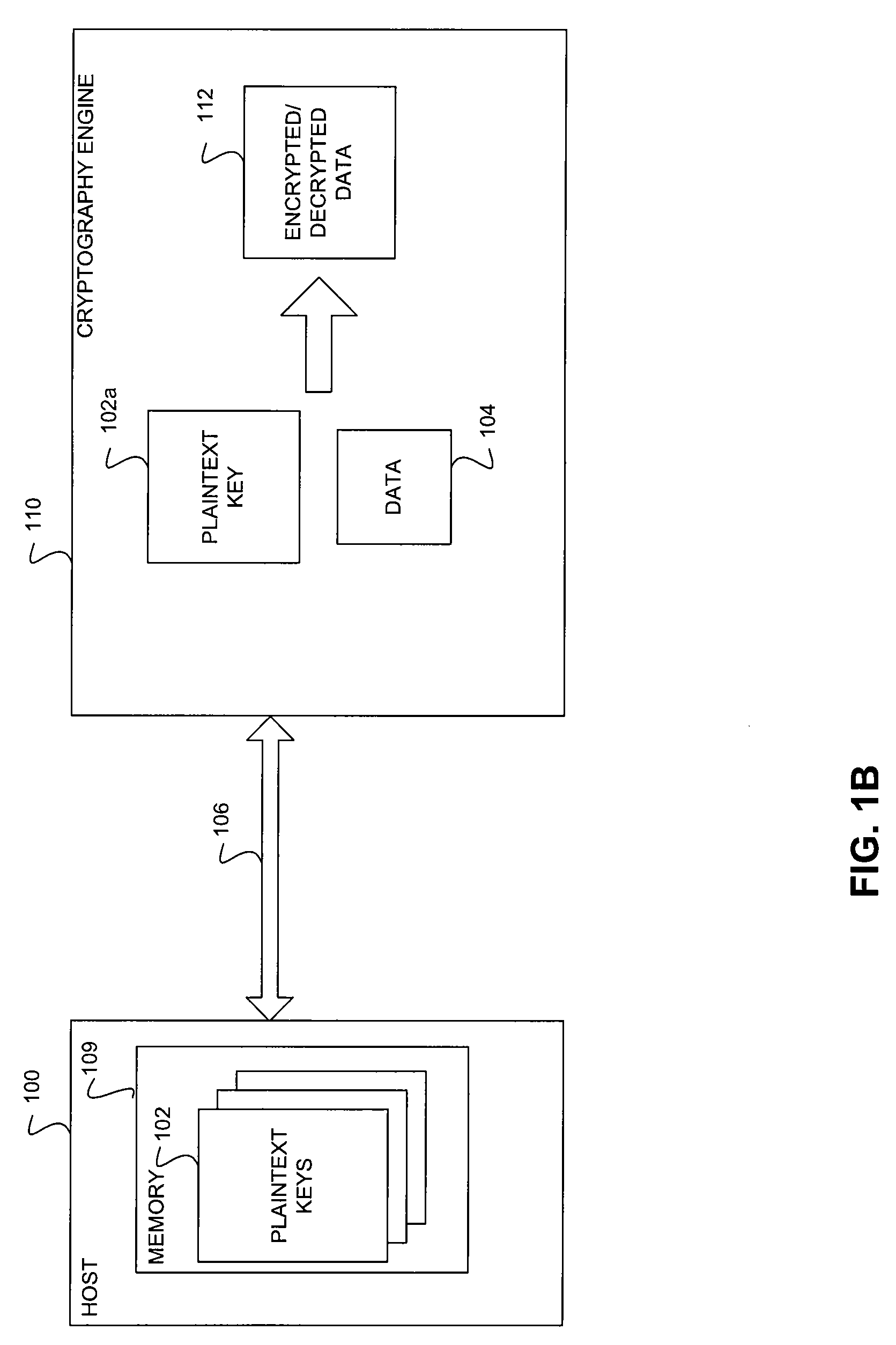
ActiveUS20100254537A1Key distribution for secure communicationDigital data processing detailsGeneral purposePlaintext
A method and system for secure and scalable key management for cryptographic processing of data is described herein. In the method, a General Purpose Cryptographic Engine (GPE) receives key material via a secure channel from a key server and stores the received Key encryption keys (KEKs) and / or plain text keys in a secure key cache. When a request is received from a host to cryptographically process a block of data, the requesting entity is authenticated using an authentication tag included in the request. The GPE retrieves a plaintext key or generate a plaintext using a KEK if the authentication is successful, cryptographically processes the data using the plaintext key and transmits the processed data. The system includes a key server that securely provides encrypted keys and / or key handles to a host and key encryption keys and / or plaintext keys to the GPE.
Owner:AVAGO TECH INT SALES PTE LTD
Creation of structured data from plain text
InactiveUS7324936B2Functionality availableEfficient storageData processing applicationsDigital data information retrievalProgramming languageApplication software
A method and system for converting plain text into structured data. Parse trees for the plain text are generated based on the grammar of a natural language, the parse trees are mapped on to instance trees generated based on an application-specific model. The best map is chosen, and the instance tree is passing to an application for execution. The method and system can be used both for populating a database and / or for retrieving data from a database based on a query.
Owner:SOFTFACE
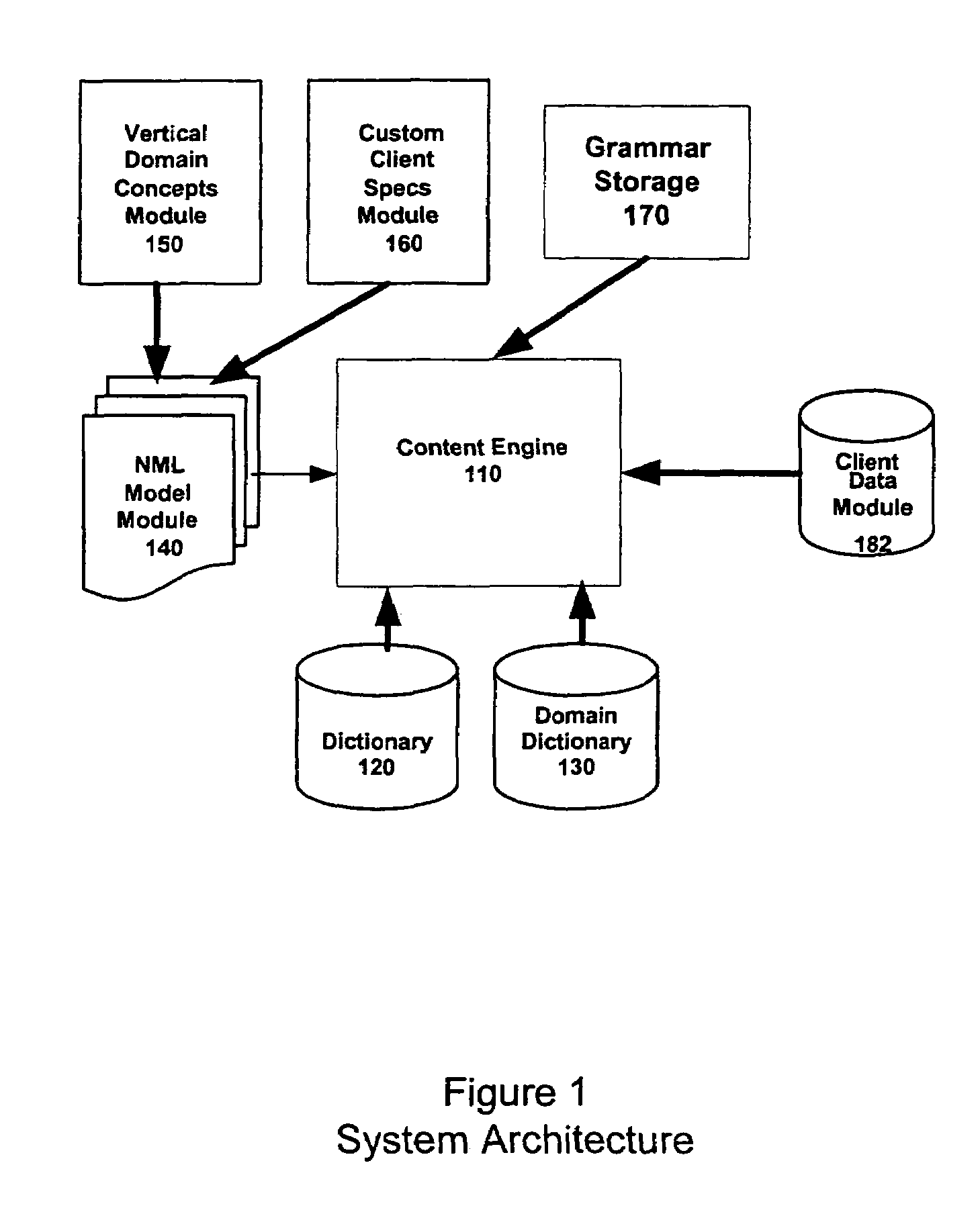
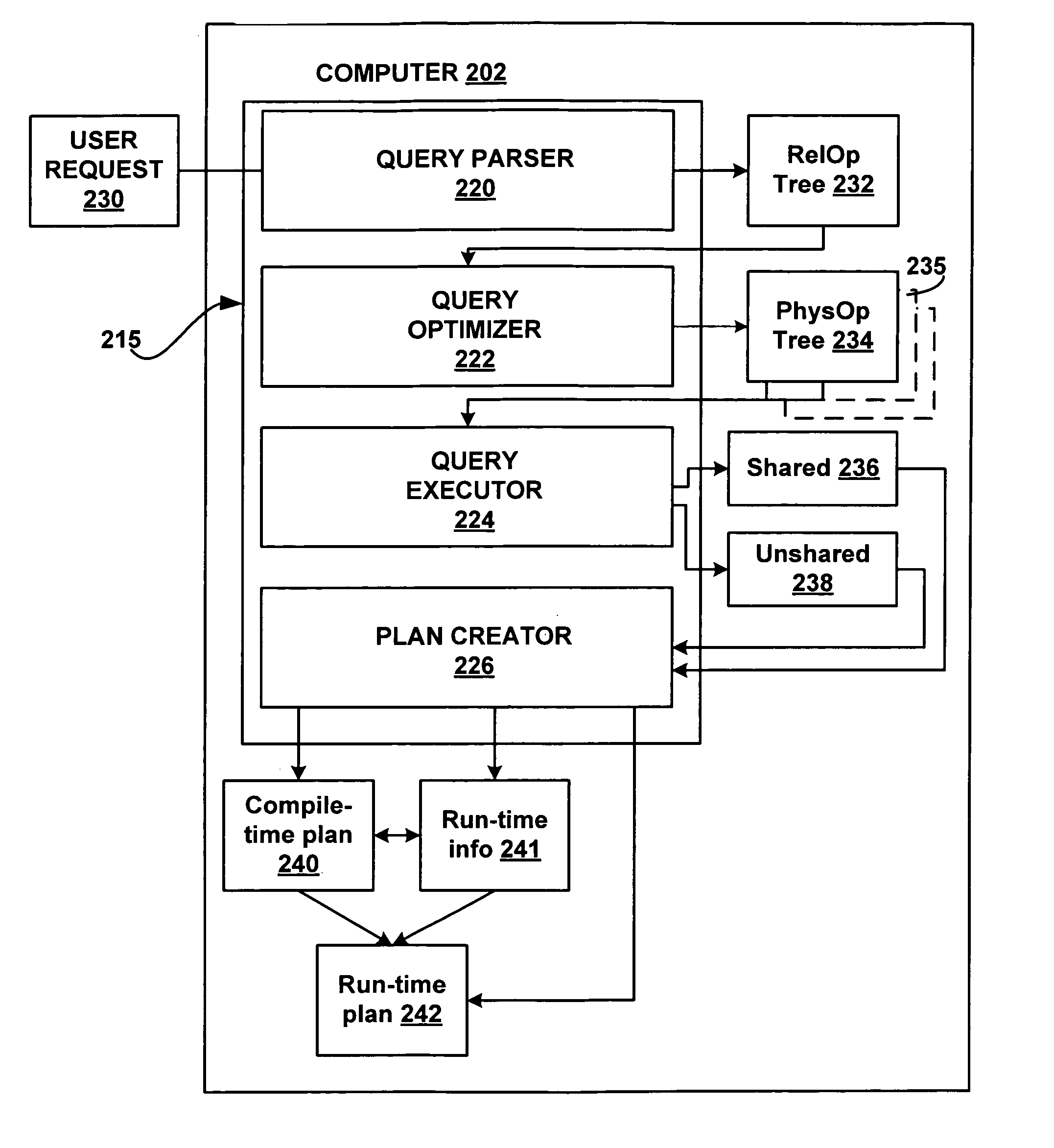
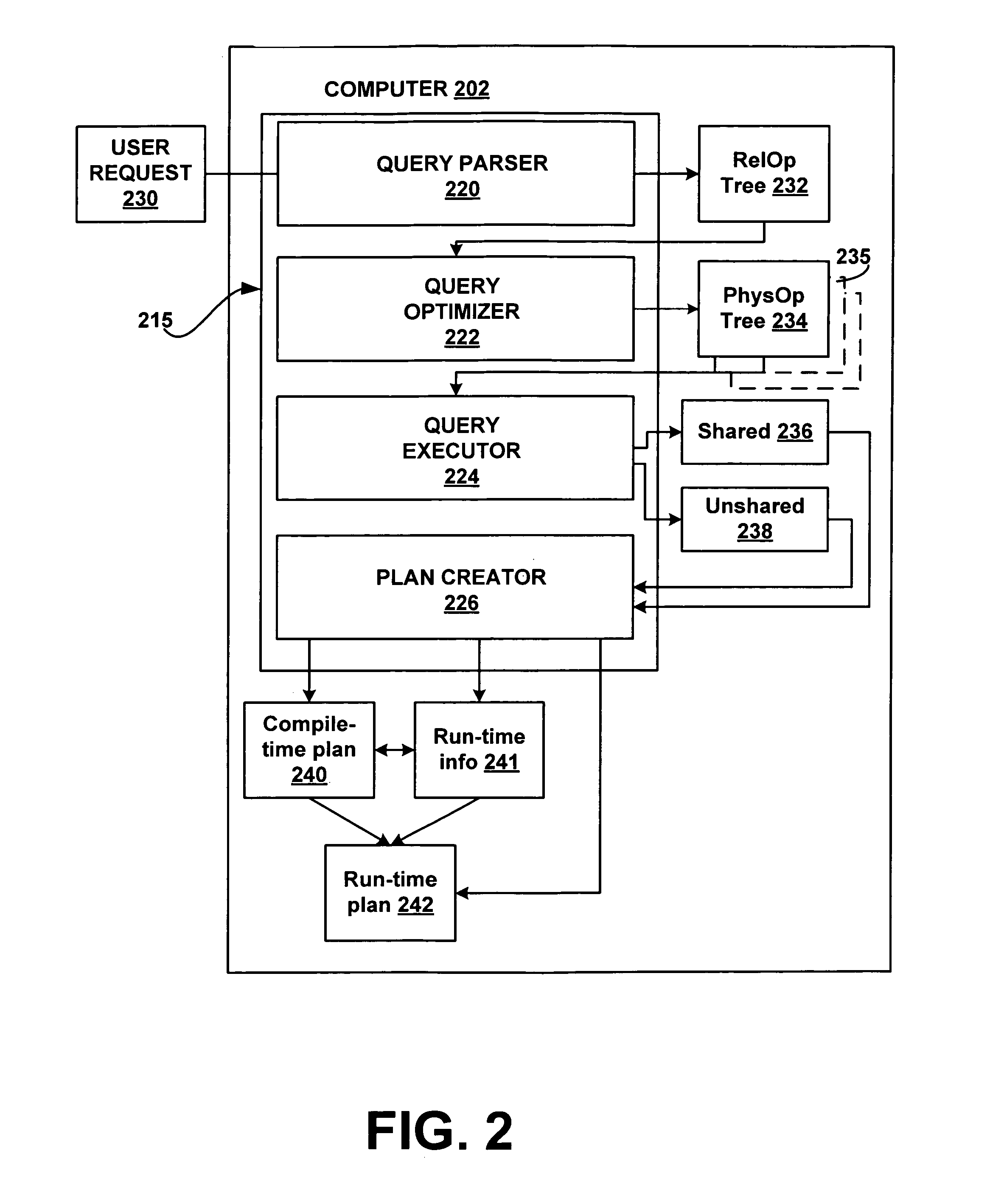
Generating a hierarchical plain-text execution plan from a database query
A system, method and computer-readable medium containing computer-executable instructions for tuning queries is provided. A query processor converts a query into an execution plan in a hierarchical format that conforms to a standardized schema. In one embodiment of the invention, the hierarchical format employed is XML.
Owner:MICROSOFT TECH LICENSING LLC
State-varying hybrid stream cipher
InactiveUS20060291650A1Data stream serial/continuous modificationUser identity/authority verificationState variationCiphertext
In one embodiment, a state-varying hybrid stream cipher operating within a computing device. The state-varying hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:ANANTH VISWANATH
Data cipher processors, AES cipher systems, and AES cipher methods using a masking method
ActiveUS20050207571A1Small sizeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesOriginal dataAdvanced Encryption Standard
Data cipher processors, advanced encryption standard (AES) cipher system, and AES cipher methods using a masking method perform round operations using a round key, a plain text, a cipher text, and masking data. Some of the round operations are implemented over a composite Galois Field GF(•). Original data and predetermined masking data are processed according to a predetermined rule. Sub-byte transformation operations used in the cipher method and system may include an affine transformation, an inverse affine transformation, an isomorphic transformation, and an inverse isomorphic transformation which are linear transformations, and an inverse transformation that is a non-linear transformation.
Owner:SAMSUNG ELECTRONICS CO LTD
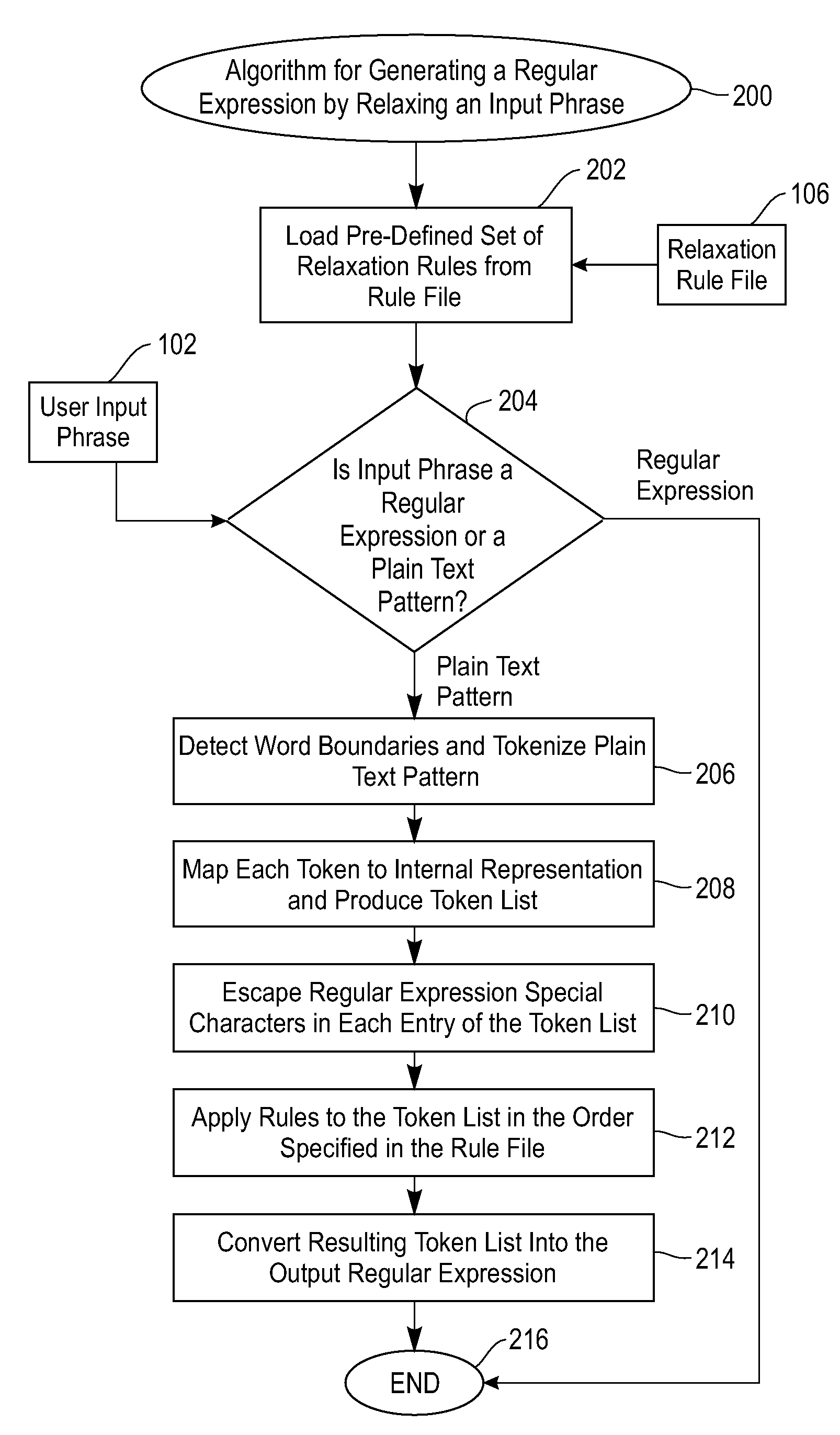
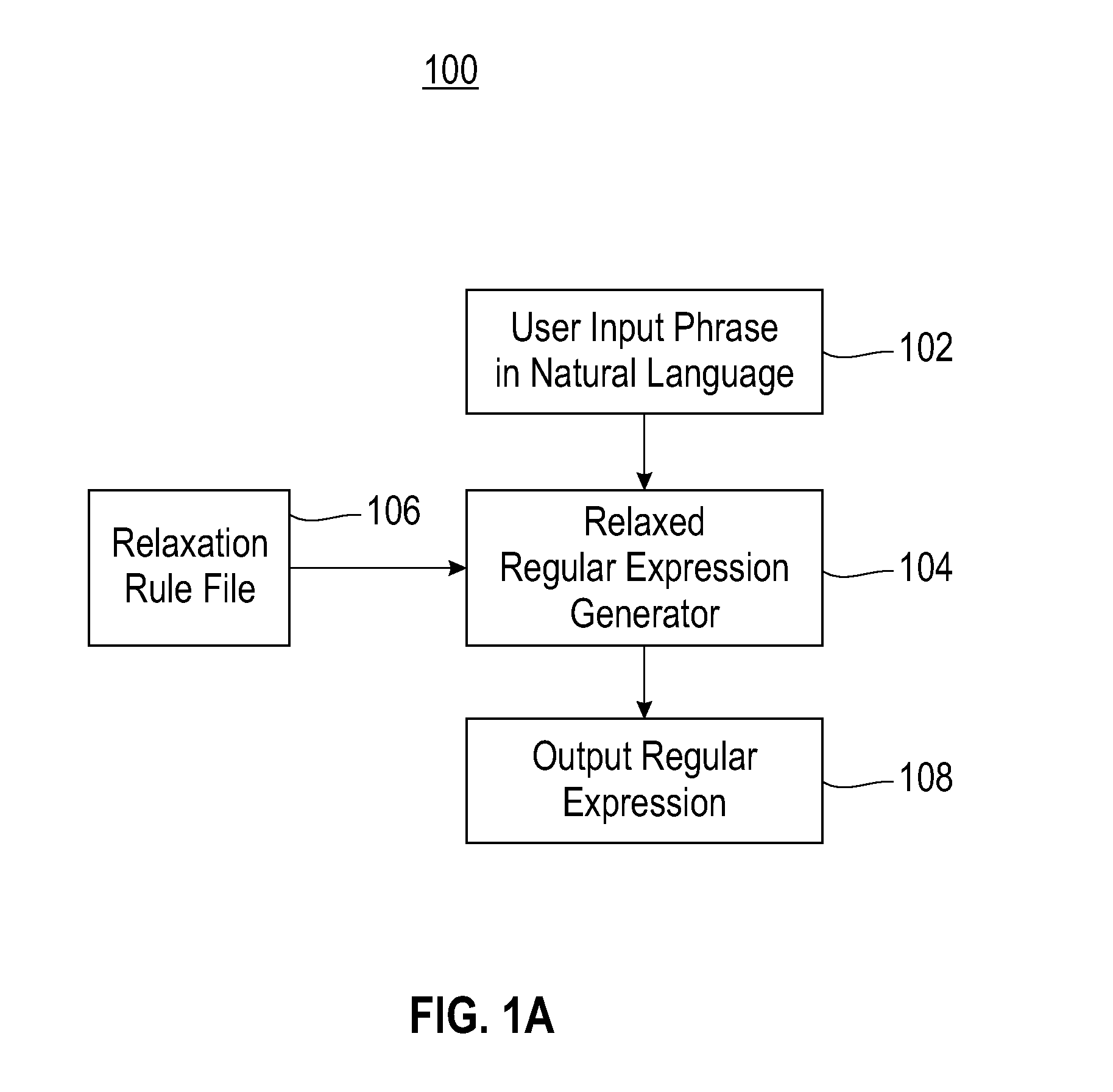
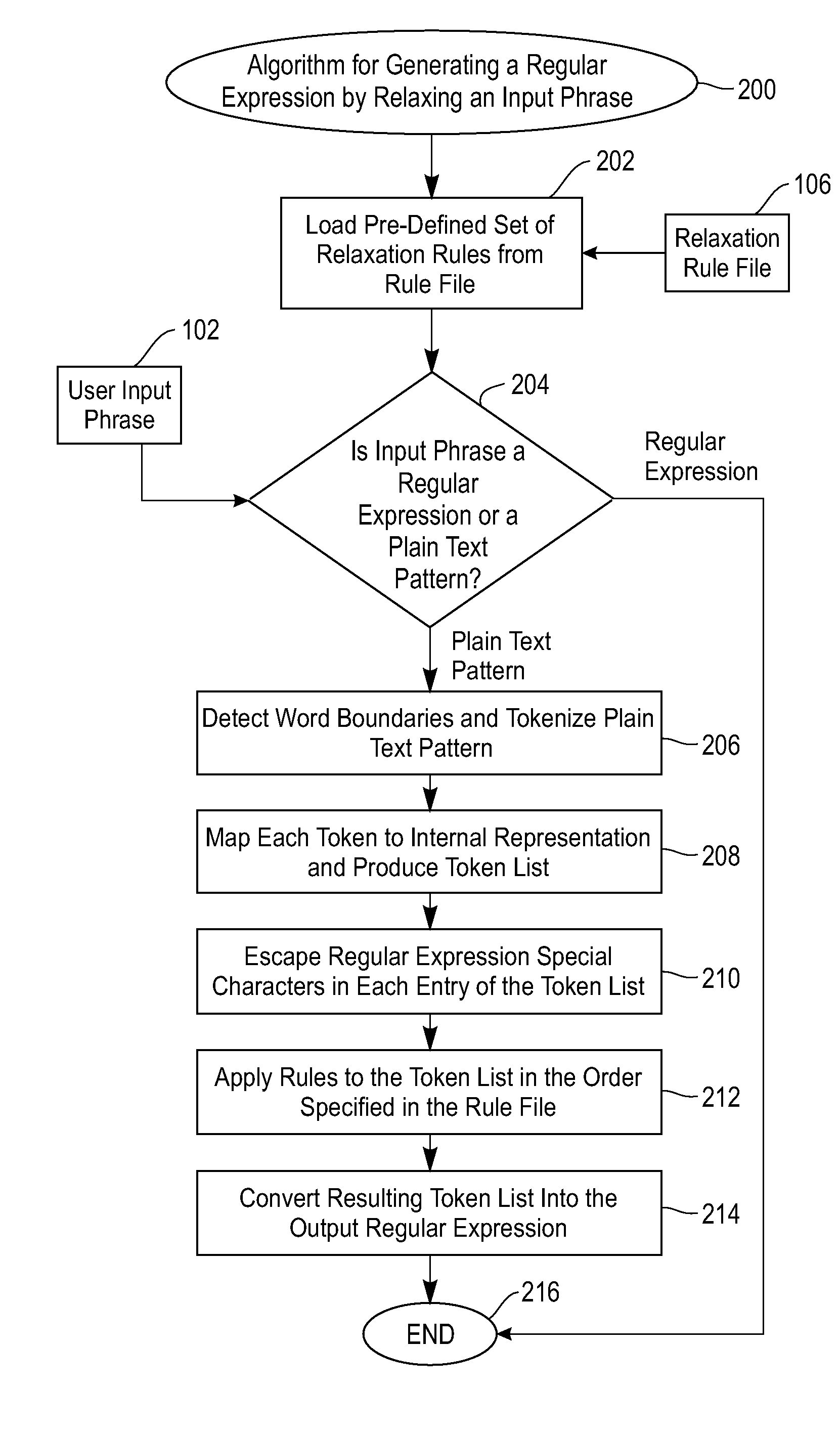
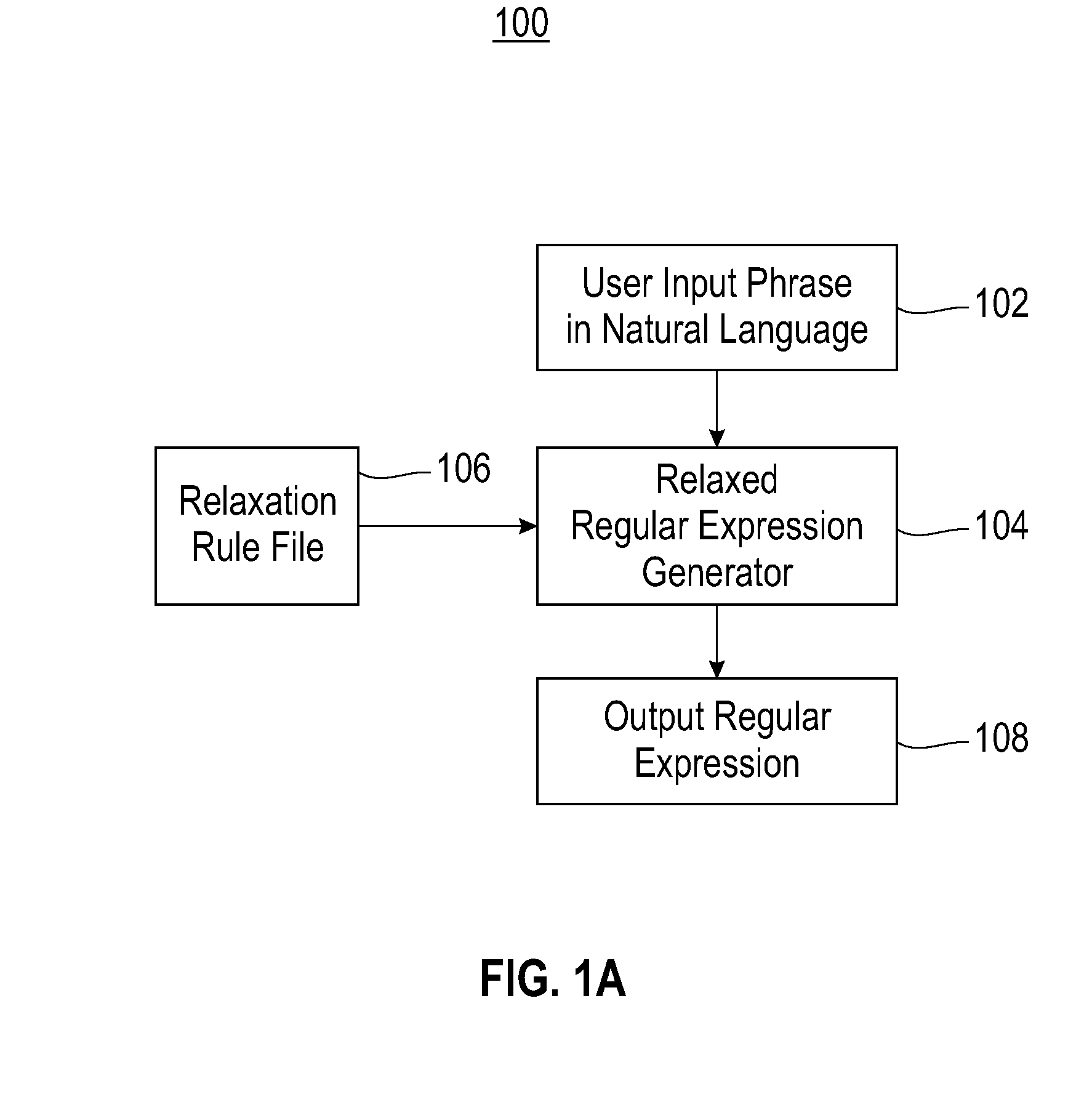
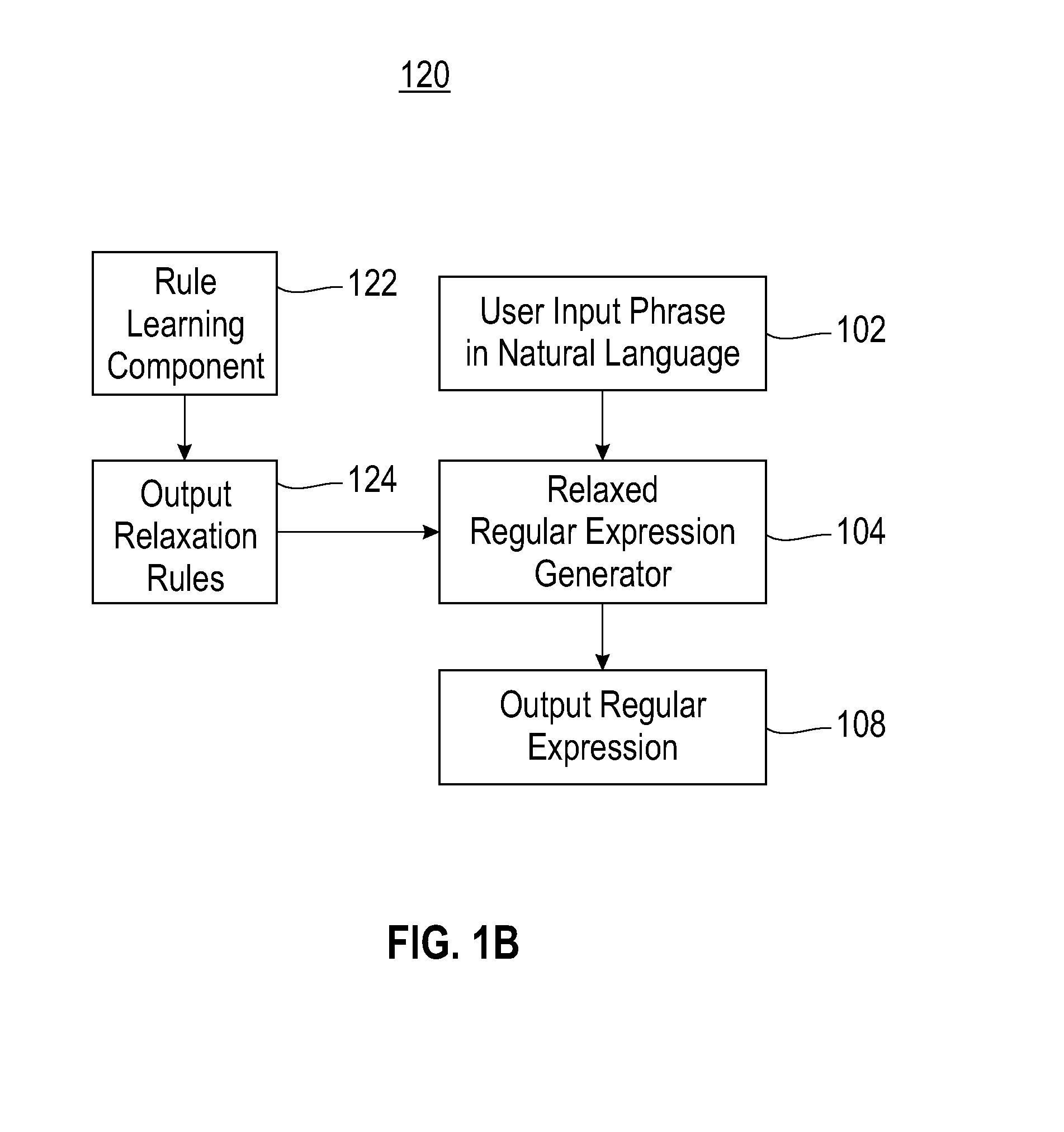
Method for automatically generating regular expressions for relaxed matching of text patterns
InactiveUS20090070327A1Digital data information retrievalSpecial data processing applicationsText modeRegular expression
A method for automatically generating regular expressions for relaxed matching of text patterns. A received input phrase expressed in a natural language is determined to be a plain text pattern. The plain text pattern is automatically tokenized, thereby generating a first token list. Rules loaded from a predefined rule set are automatically applied to the first token list in an order specified by the predefined rule set to automatically modify a token list by applying a replace word, split-at-character or whitespace operator. The modified token list is automatically converted into a regular expression that matches the plain text pattern and one or more variations of the plain text pattern. A utilization of the regular expression for an information extraction facilitates a recall and a precision of the information extraction.
Owner:IBM CORP
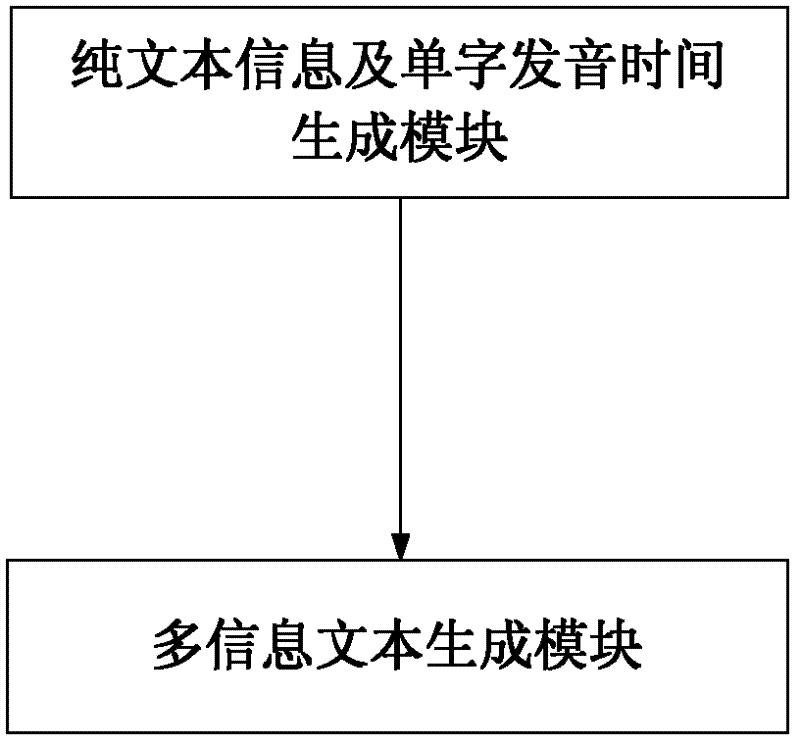
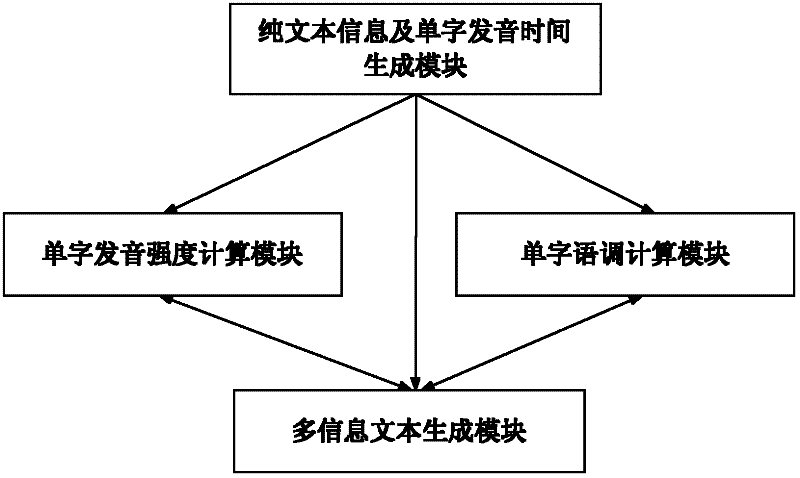
Device and method for acquiring speech recognition multi-information text
The invention provides a device and a method for acquiring a speech recognition multi-information text. After a speech audio frequency is converted into pure text information by speech recognition, individual character pronunciation speed, individual character pronunciation strength and individual character pronunciation intonation in the speech audio frequency are integrated into the initially-generated pure text information in a certain expression way to generate multi-information text information. The device and the method for acquiring the speech recognition multi-information text can be widely used for information release platforms such as micro blogs, short messages, signature files and the like.
Owner:SHANGHAI GUOKE ELECTRONICS
Control of data linkability
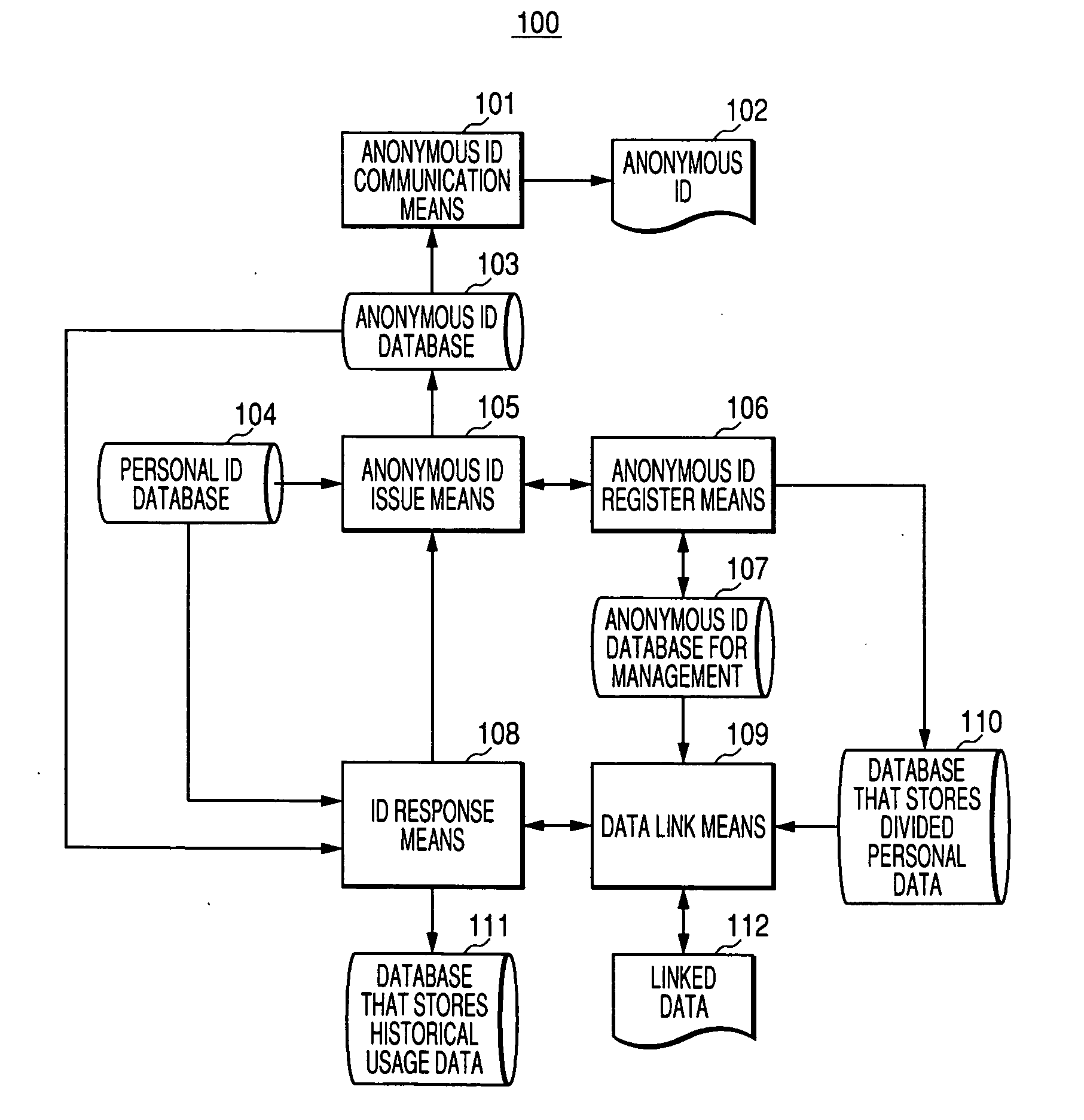
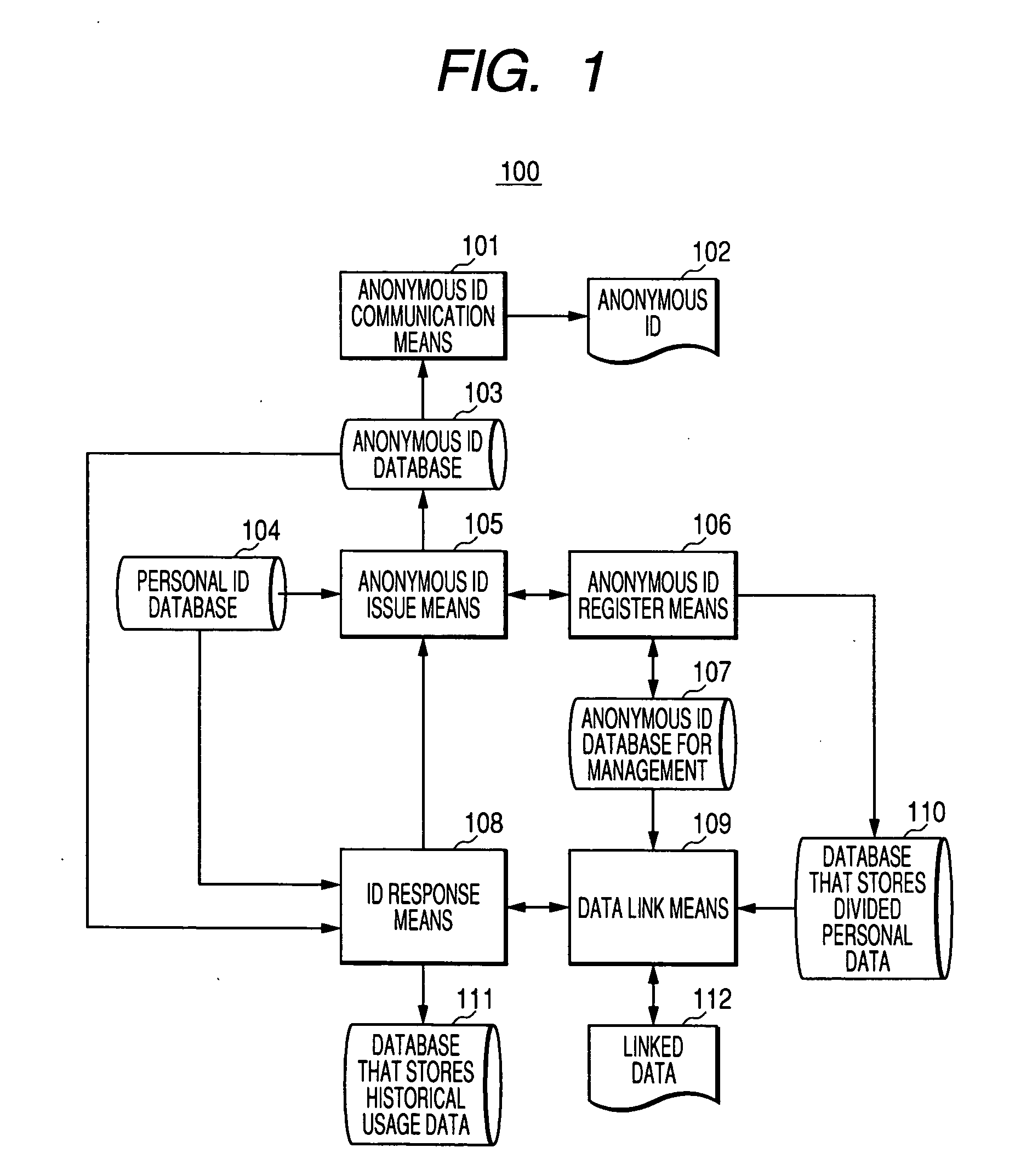
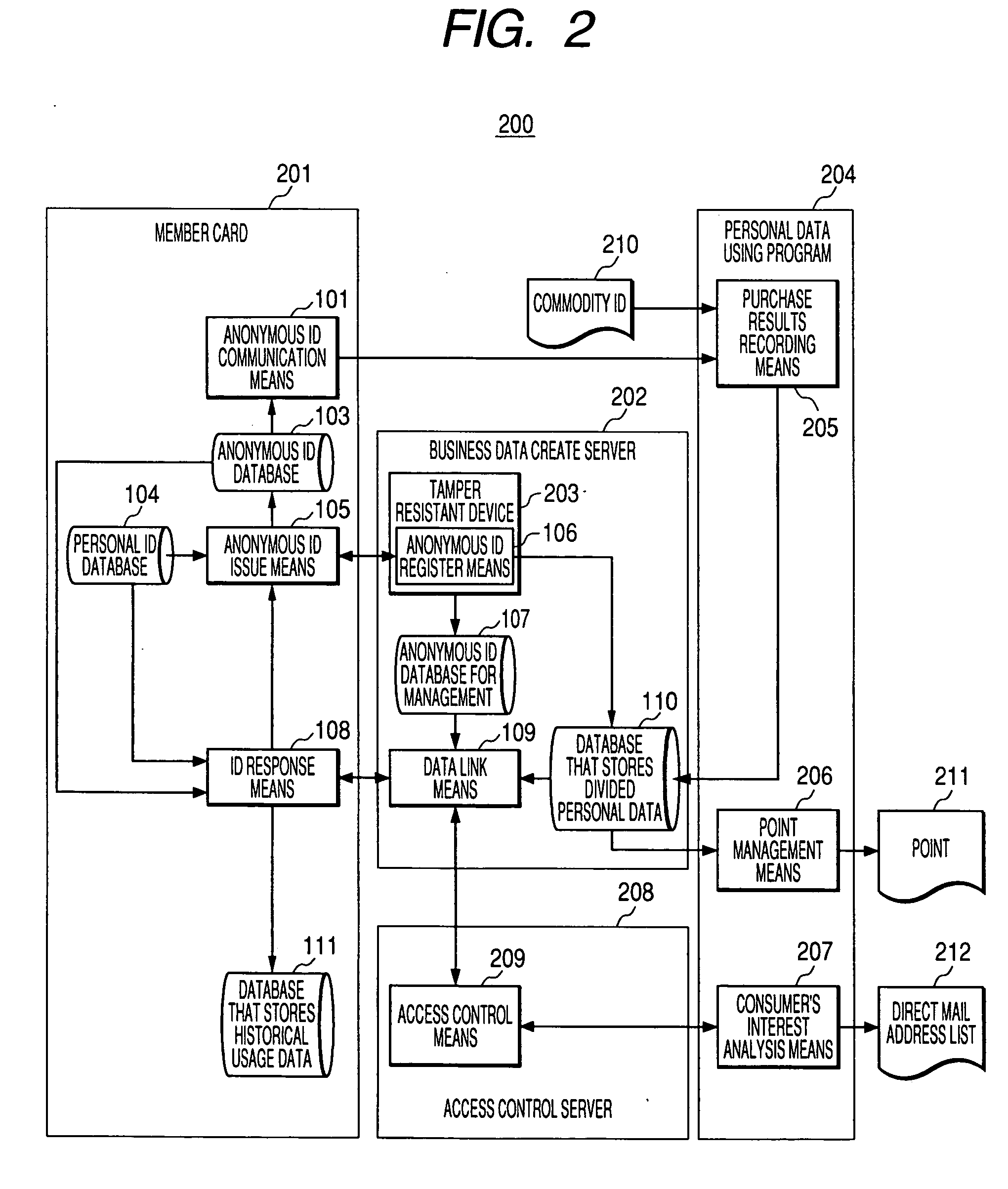
InactiveUS20050283621A1Permit useOvercome problemsKey distribution for secure communicationDigital data processing detailsPlaintextInternet privacy
In the conventional technique for mainly performing access control, an entity (an individual) which provides information cannot grasp a state of use of personal information. In the conventional technique for encrypting stored data, a decryption key is always required when personal data is used and the personal data is not protected once decrypted. The invention constitute a system such that a purchase history is collected according to an anonymous ID and a response from a member card or an agent server is required for operation for associating the anonymous ID with a personal ID. Personal data itself is not encrypted but stored in a plain text with the personal ID and the anonymous ID as keys such that the anonymous ID is regenerated every time the anonymous ID is associated with the personal ID on a server side. At this point, the anonymous ID serving as a collection key for the purchase history, which is accumulated concurrently, is also regenerated.
Owner:HITACHI LTD
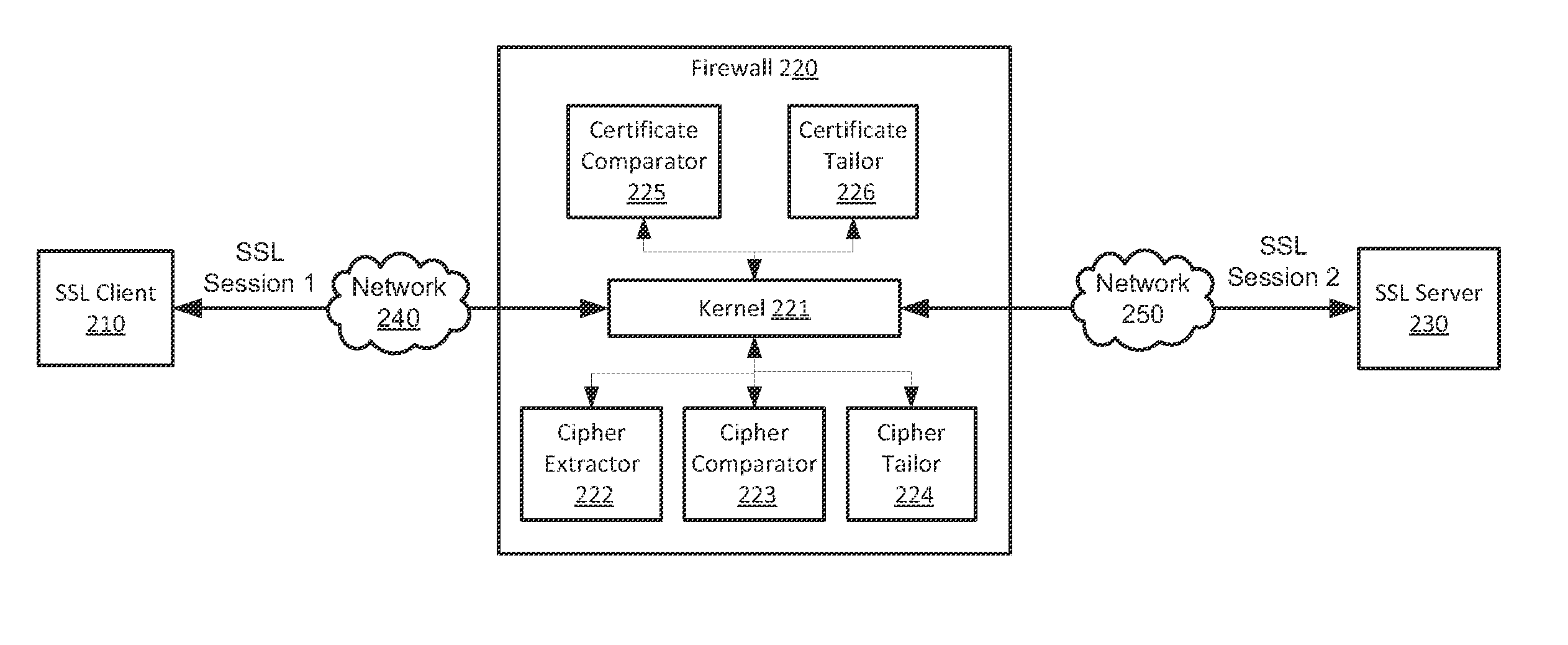
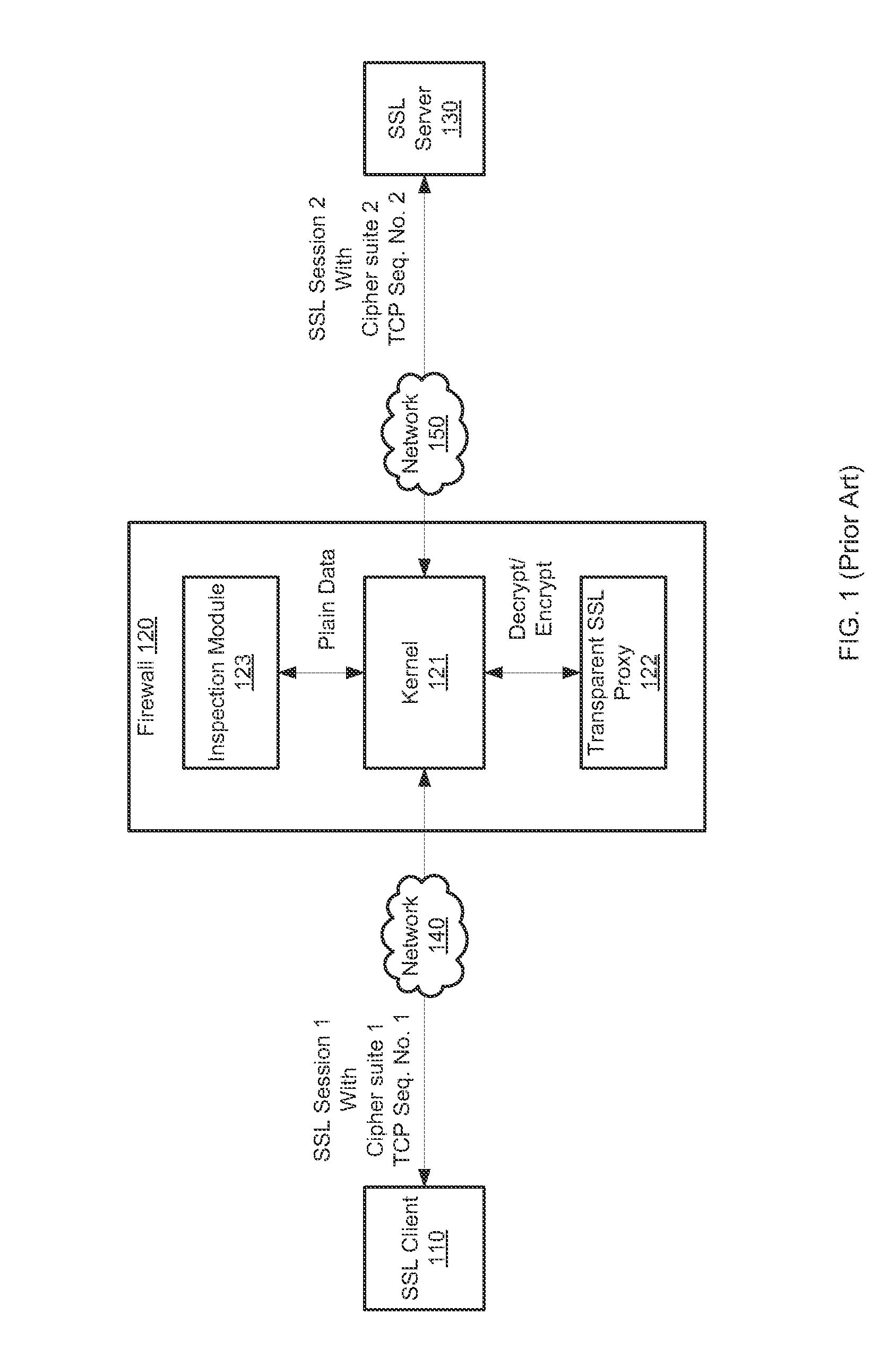
Inline inspection of security protocols
Systems and methods for inline security protocol inspection are provided. According to one embodiment, a security device receives an encrypted raw packet from a first network appliance and buffers the encrypted raw packet in a buffer. An inspection module accesses the encrypted raw packet from the buffer, decrypts the encrypted raw packet to produce a plain text and scans the plain text by the inspection module.
Owner:FORTINET
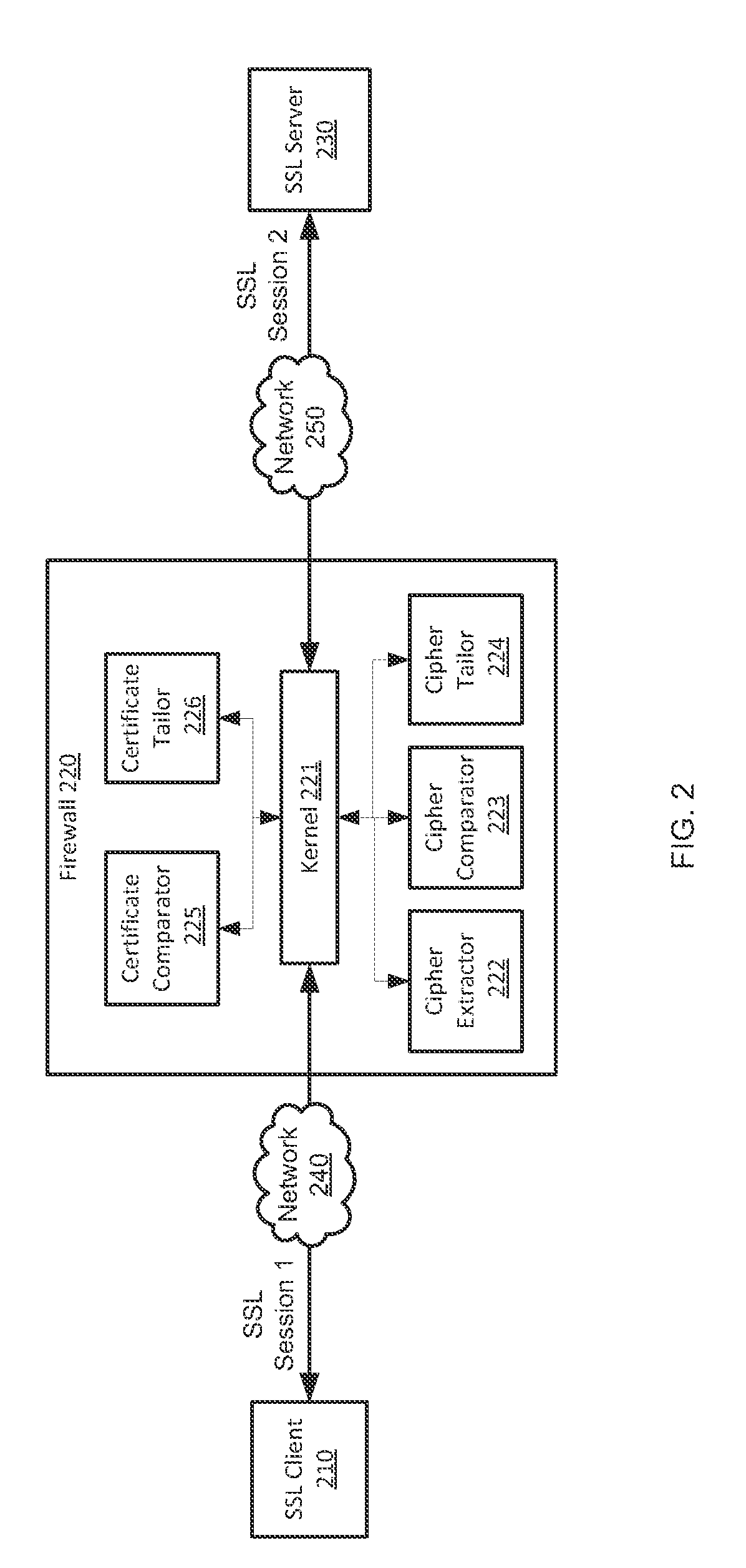
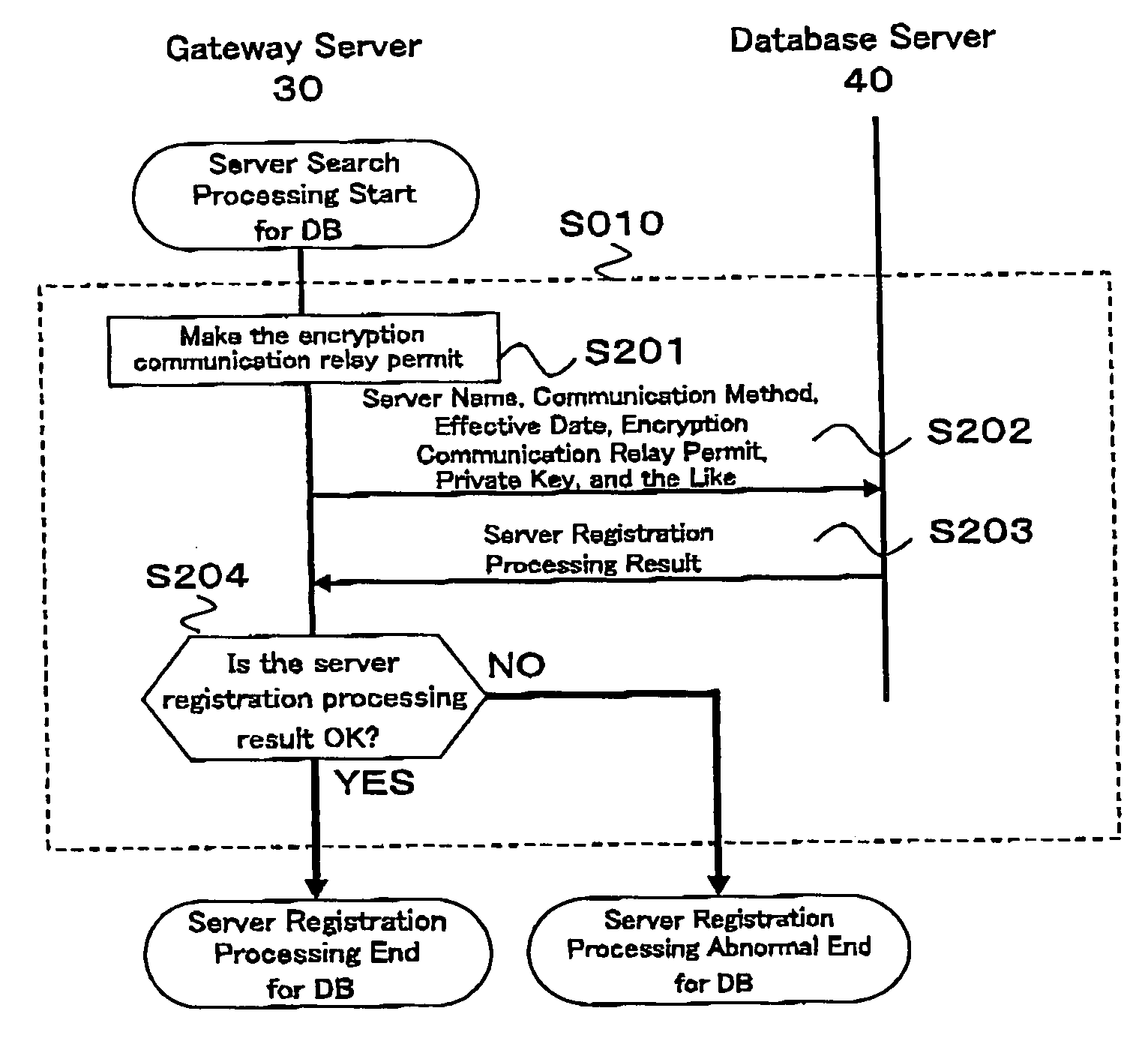
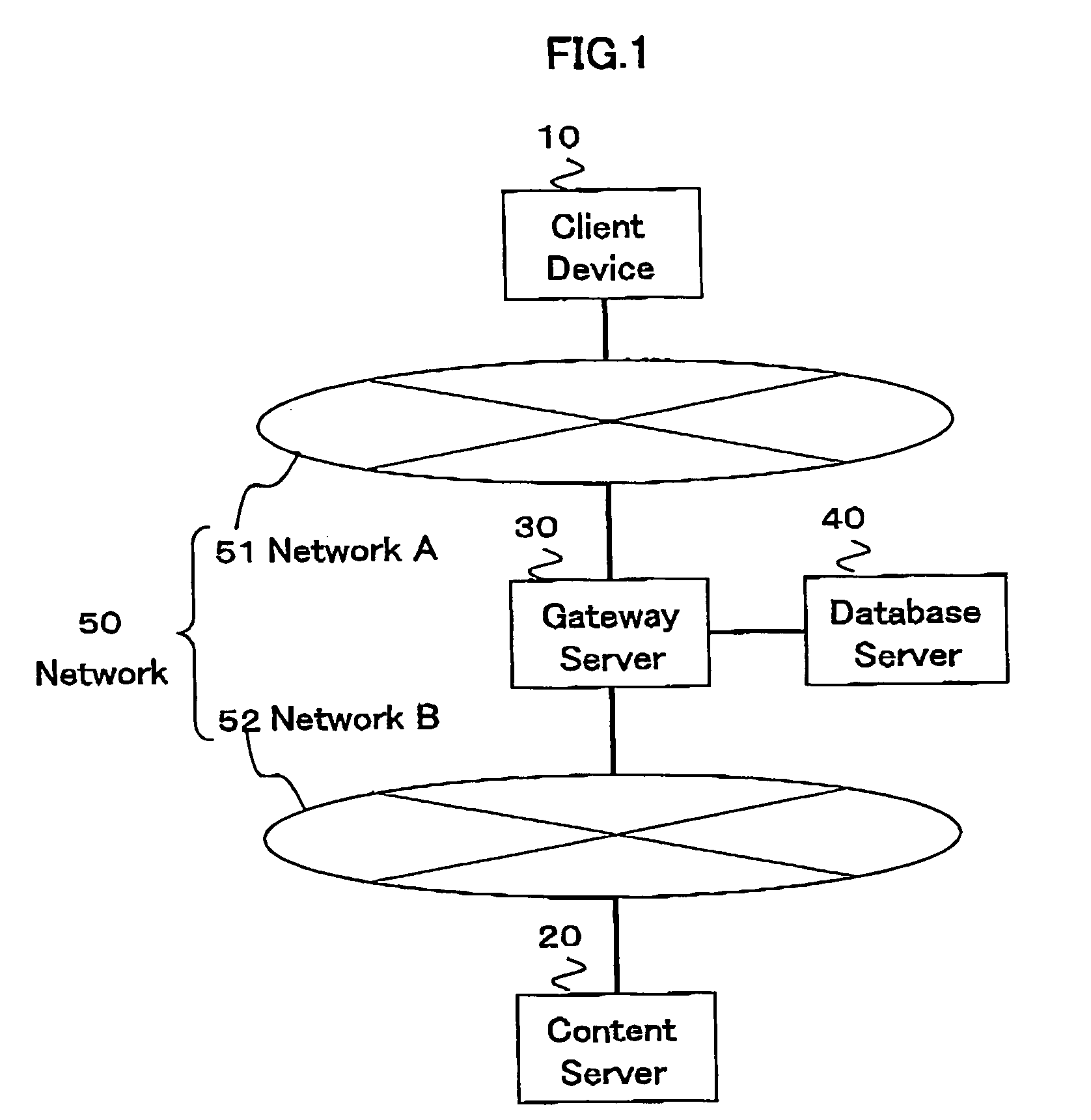
Relay method of encryption communication, gateway server, and program and program memory medium of encryption communication
InactiveUS20060136724A1User identity/authority verificationMultiple digital computer combinationsPlaintextEnd-to-end encryption
The relay method for relaying an encryption communication in a gateway server between a client device and a content server includes the steps of receiving an encryption communication connection message to the content server from the device; producing a temporary encryption communication permit and a private key of its counterpart for the content server of a destination server name included in the connection message; sending the permit to the device; performing an End-End encryption communication with the device, receiving an encrypted access request message sent by the device, and decrypting and converting the request message to an access request message of a plain text; performing an End-End encryption communication with the content server, and acquiring content information instructed by the access request message; and performing value added processing for the acquired content information and its communication header, encrypting the information and the header, and sending them to the device.
Owner:HITACHI LTD
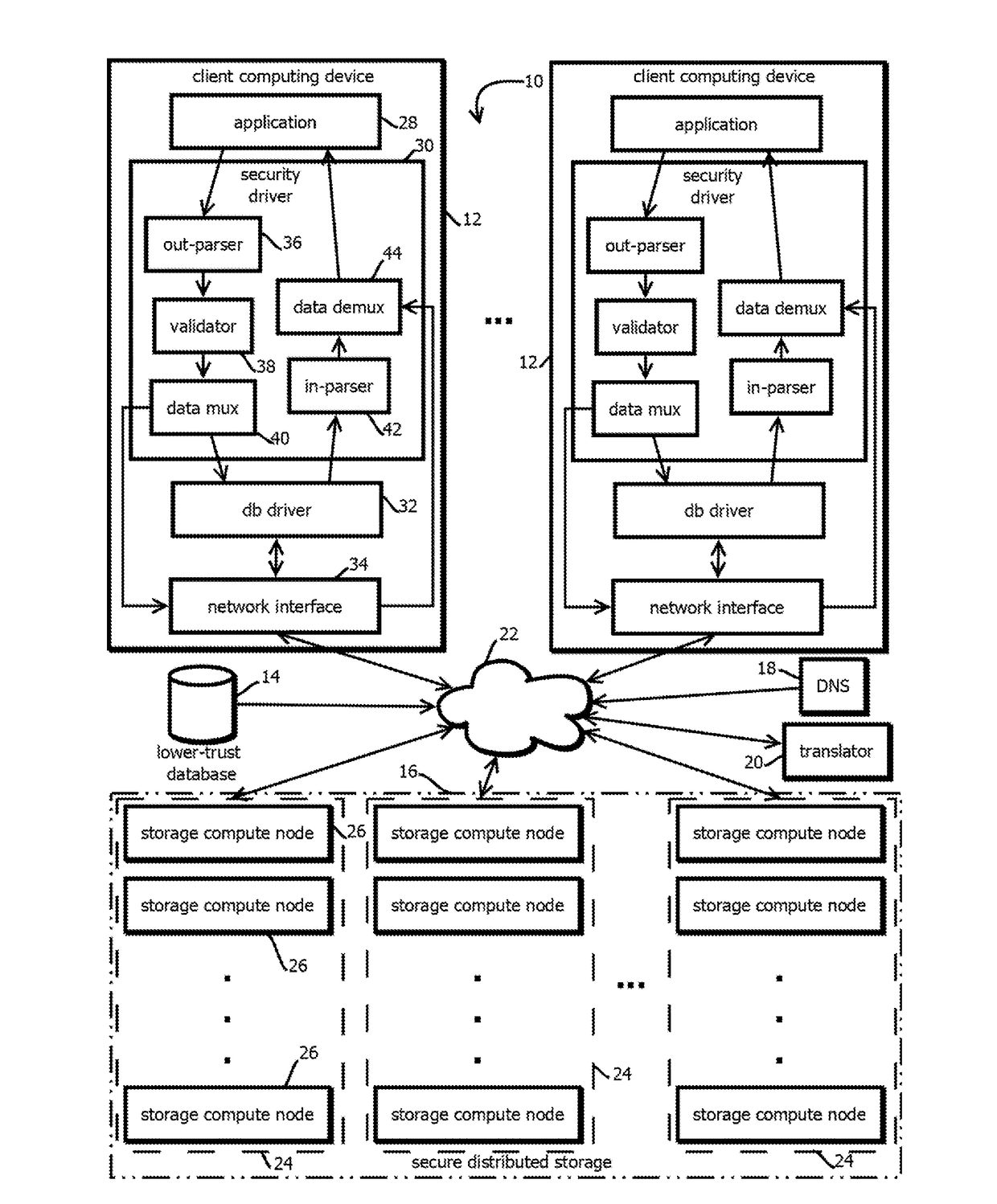
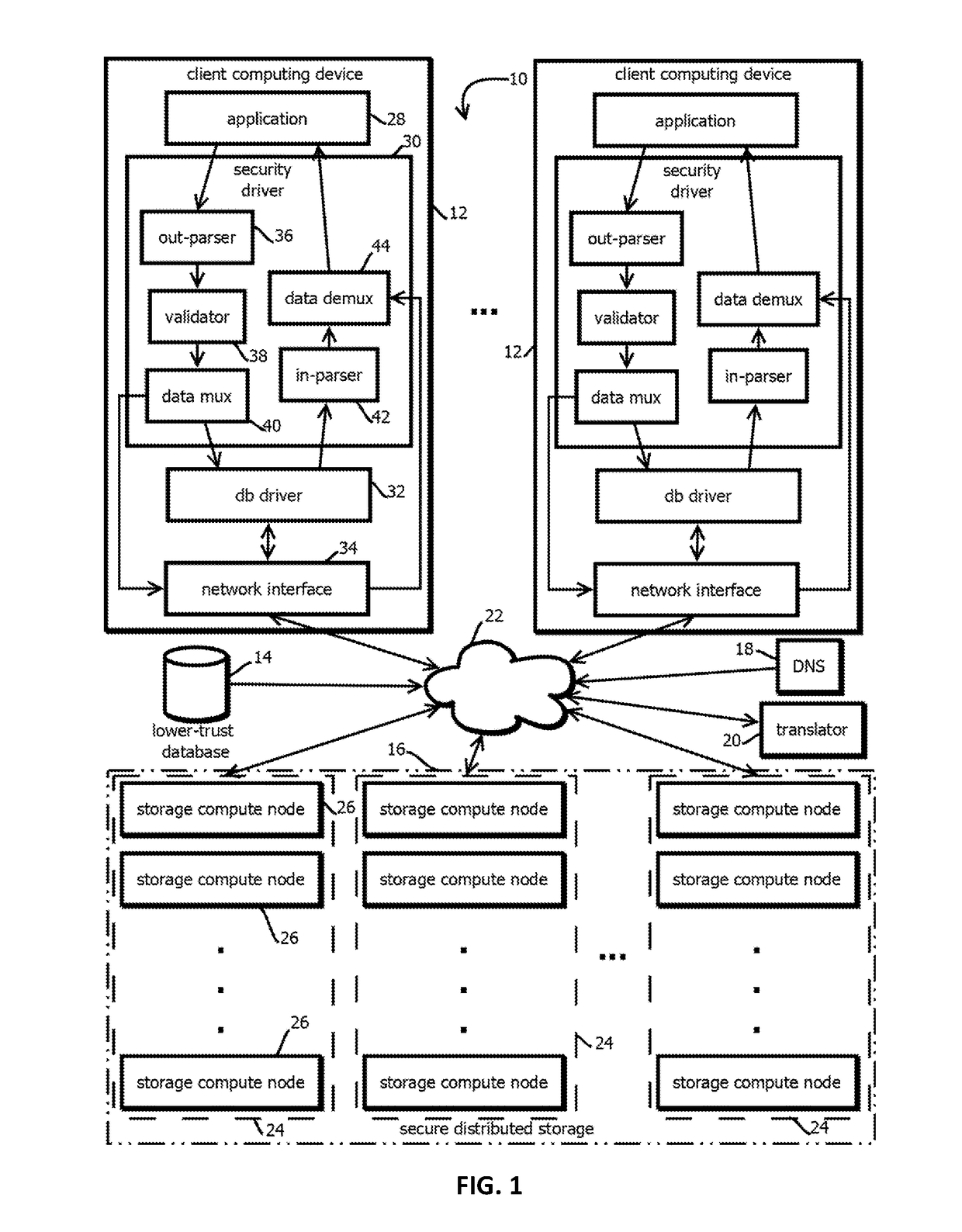
Replacing distinct data in a relational database with a distinct reference to that data and distinct de-referencing of database data
ActiveUS20180307857A1Digital data information retrievalUser identity/authority verificationPlaintextRelational database
Provided is a process including: obtaining criteria to select plain-text values in a lower-trust database; selecting, based on the criteria, a first plain-text value; in response, determining a first reference value; storing the first plain-text value in a higher-trust database in a second entry identified by the first reference value; storing the first reference value in the first entry of the lower-trust database; selecting another instance of the first plain-text value stored requested to be stored in a third entry in the lower-trust database; and in response, storing the first reference value in the third entry.
Owner:ALTR SOLUTIONS INC
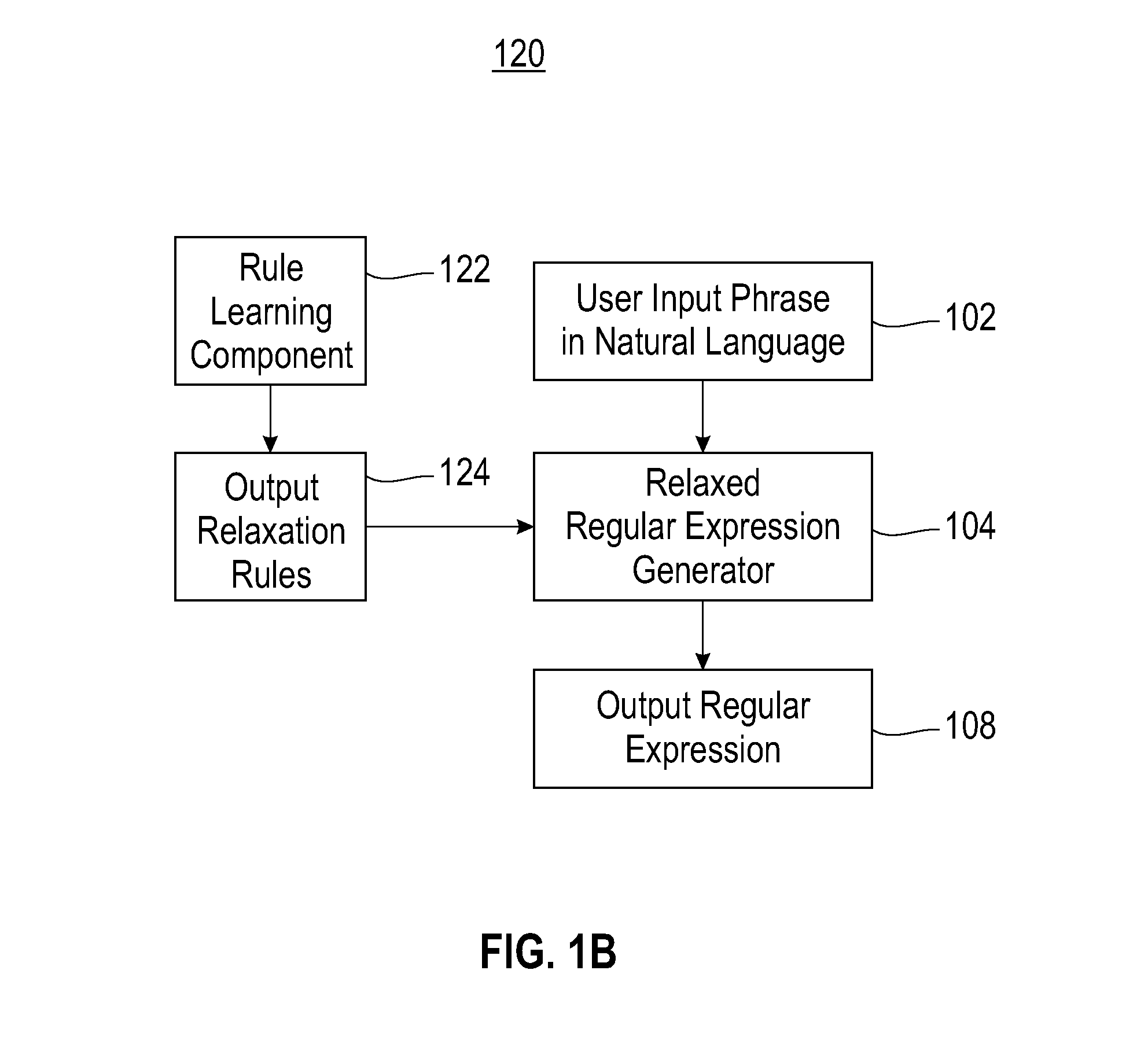
Method and system for automatically generating regular expressions for relaxed matching of text patterns
InactiveUS20090070328A1Digital data information retrievalDigital data processing detailsText modeRegular expression
A method and system for automatically generating regular expressions for relaxed matching of text patterns. A received input phrase expressed in a natural language is determined to be a plain text pattern. The plain text pattern is automatically tokenized, thereby generating a first token list. Rules loaded from a predefined rule set are automatically applied to the first token list to automatically generate a modified token list. The order of the rules being applied to the first token list is specified by the rule set. The modified token list is automatically converted into a regular expression that matches the plain text pattern and one or more variations of the plain text pattern. A utilization of the regular expression for an information extraction facilitates a recall and a precision of the information extraction.
Owner:IBM CORP
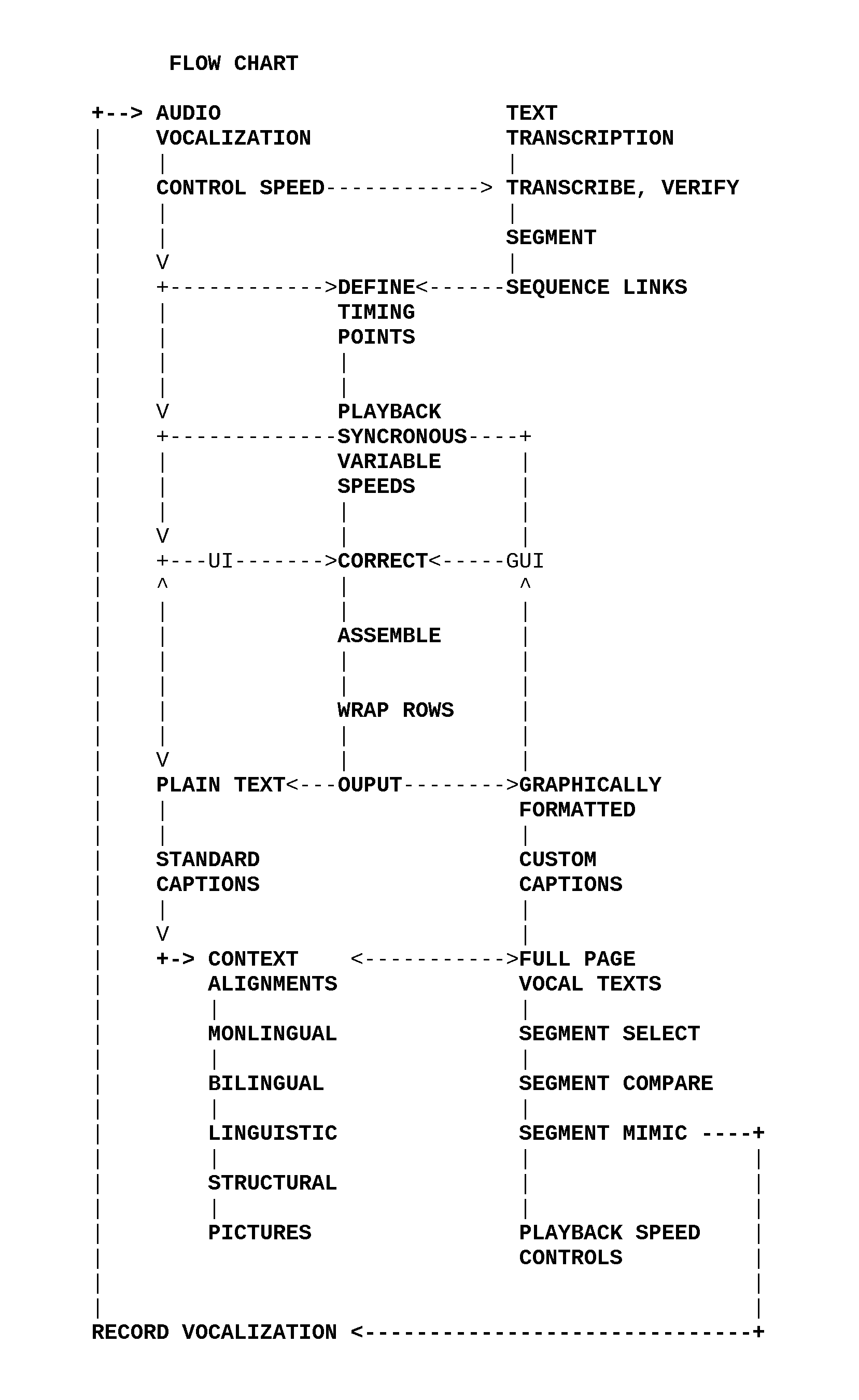
Synchronous Texts
InactiveUS20140039871A1Enhanced touch controlEasy to controlNatural language translationSpecial data processing applicationsPersonalizationProgramming language
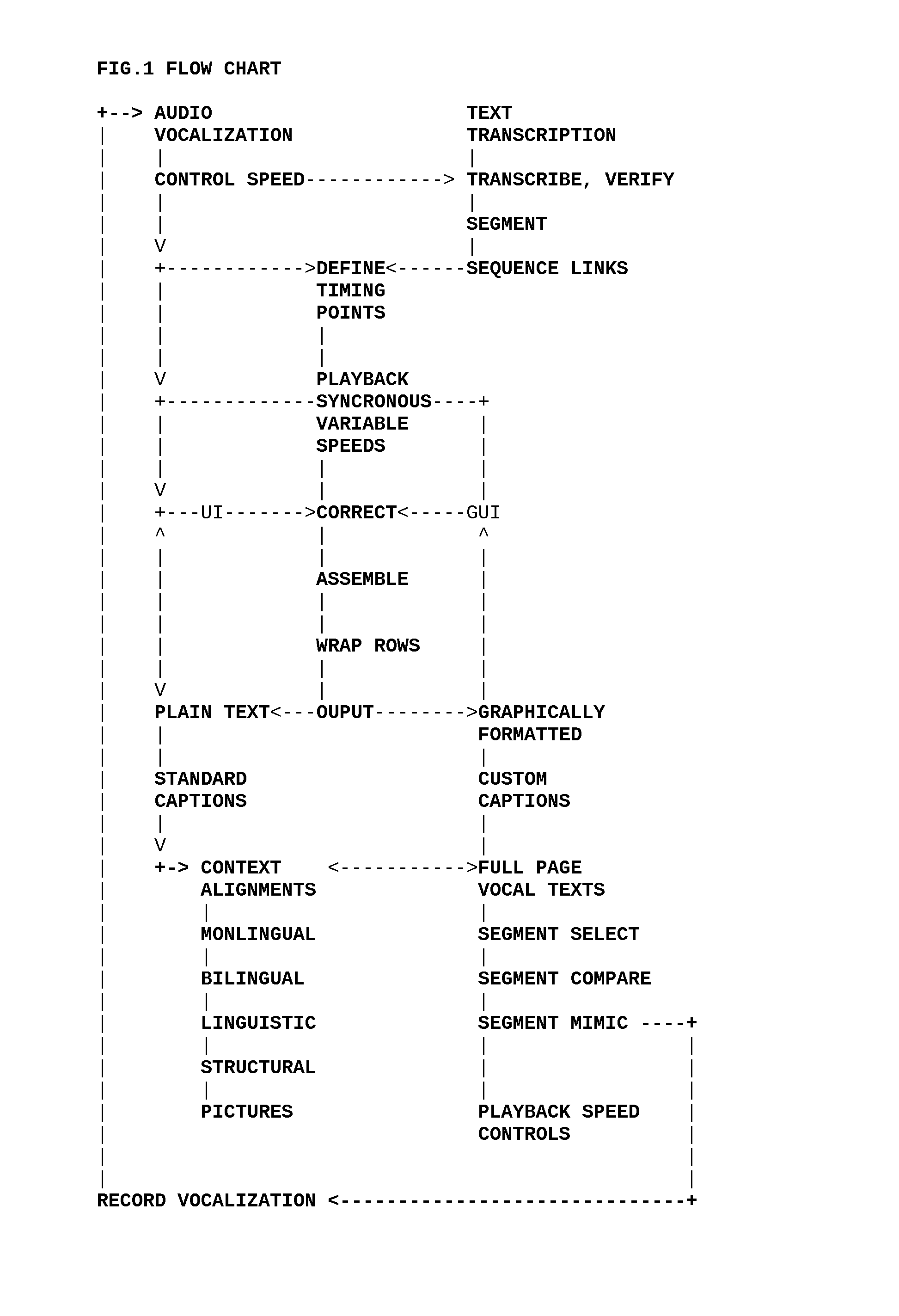
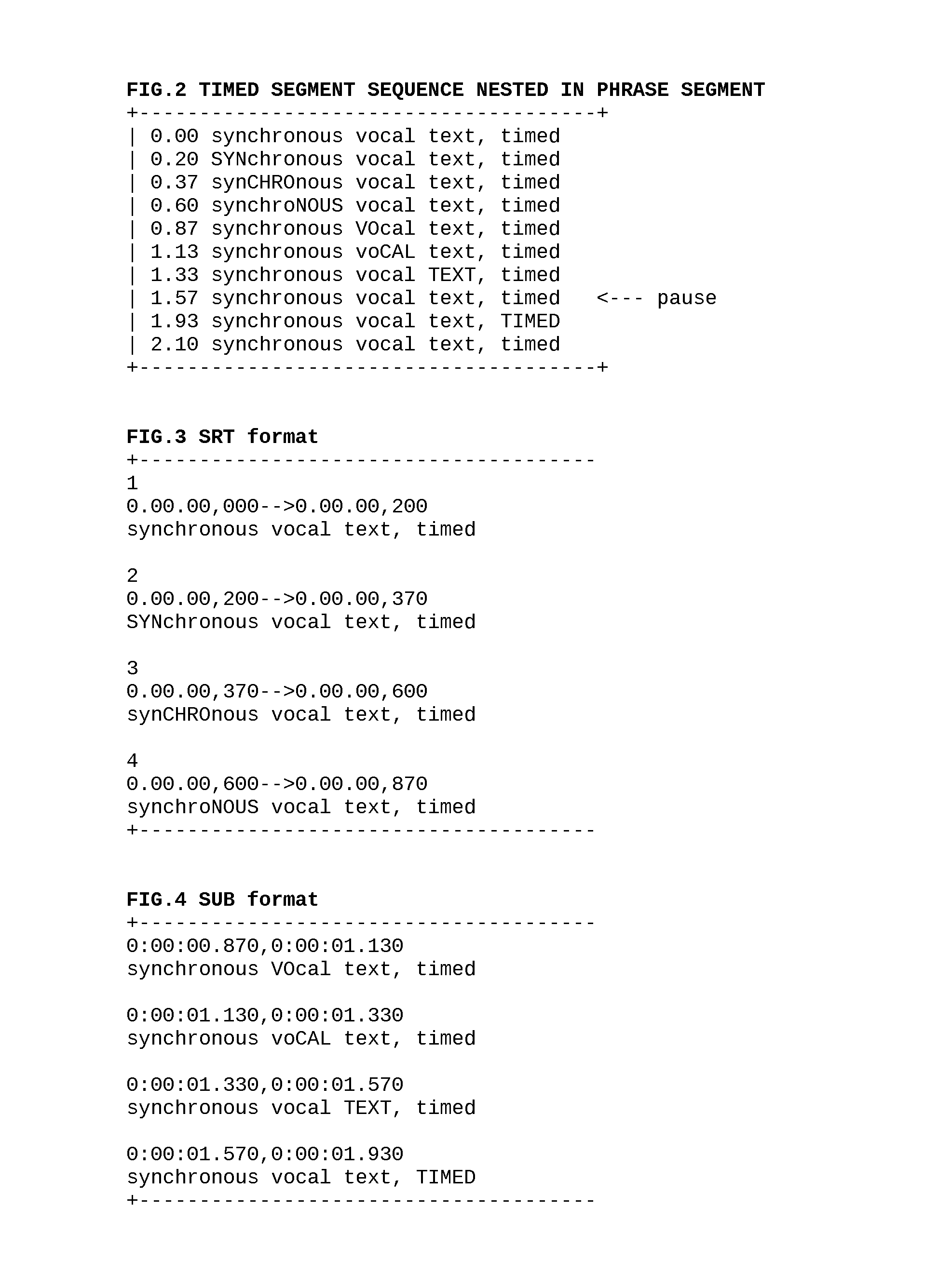
A method and apparatus to synchronize segments of text with timed vocalizations. Plain text captions present syllabic timings visually while their vocalization is heard. Captions in standard formats are optionally used. Synchronous playback speeds are controlled. Syllabic segments are aligned with timing points in a custom format. Verified constant timings are variably assembled into component segments. Outputs include styled custom caption and HTML presentations. Related texts are aligned with segments and controlled in plain text row sets. Translations, synonyms, structures, pictures and other context rows are aligned. Pictures in sets are aligned and linked in tiered sorting carousels. Alignment of row set contents is constant with variable display width wraps. Sorting enables users to rank aligned contexts where segments are used. Personalized contexts are compared with group sorted links. Variable means to express constant messages are compared. Vocal language is heard in sound, seen in pictures and animated text. The methods are used to learn language.
Owner:CRAWFORD RICHARD HENRY DANA
Hybrid stream cipher
InactiveUS7003107B2Data stream serial/continuous modificationSecret communicationCiphertextInternal identifier
In one embodiment, a hybrid stream cipher operating within a computing device. The hybrid stream cipher comprises at least two software routines. A first routine is responsible for dividing incoming plain text into variable-sized blocks. A second software routine is for converting the plain text into cipher text based on an encryption key, an internal identifier and perhaps a percentage of random data value.
Owner:MAINSTREAM ENCRYPTION
Recombinant DNA technology based information encrypting and hiding method and application
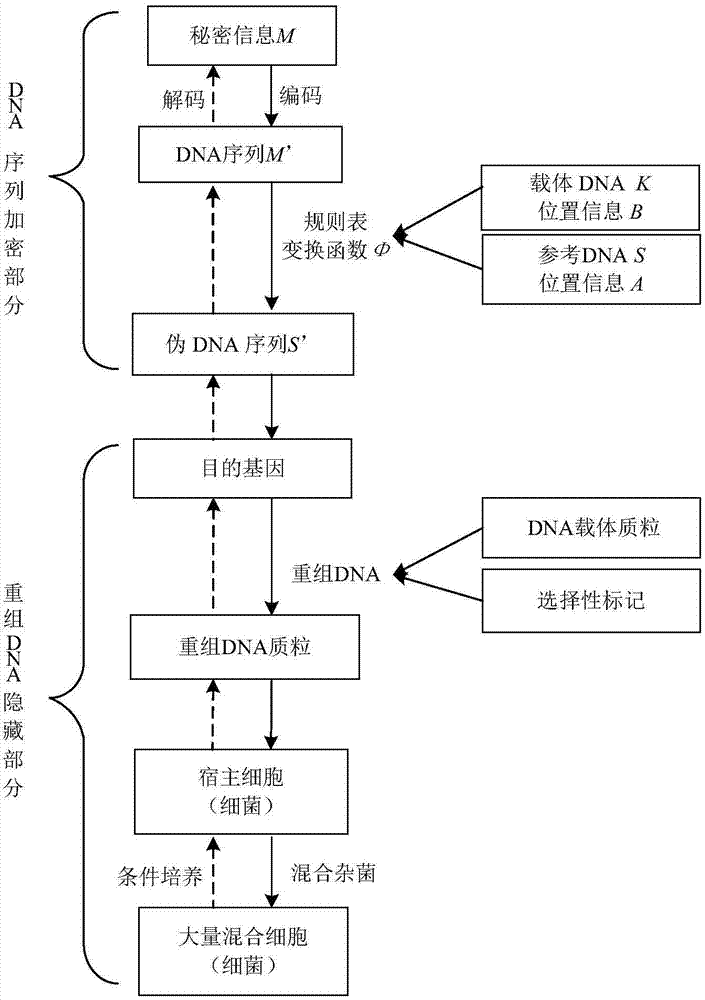
InactiveCN104734848AMeet safety requirementsIncrease the difficulty of crackingVector-based foreign material introductionSecuring communicationPlasmid VectorDNA fragmentation
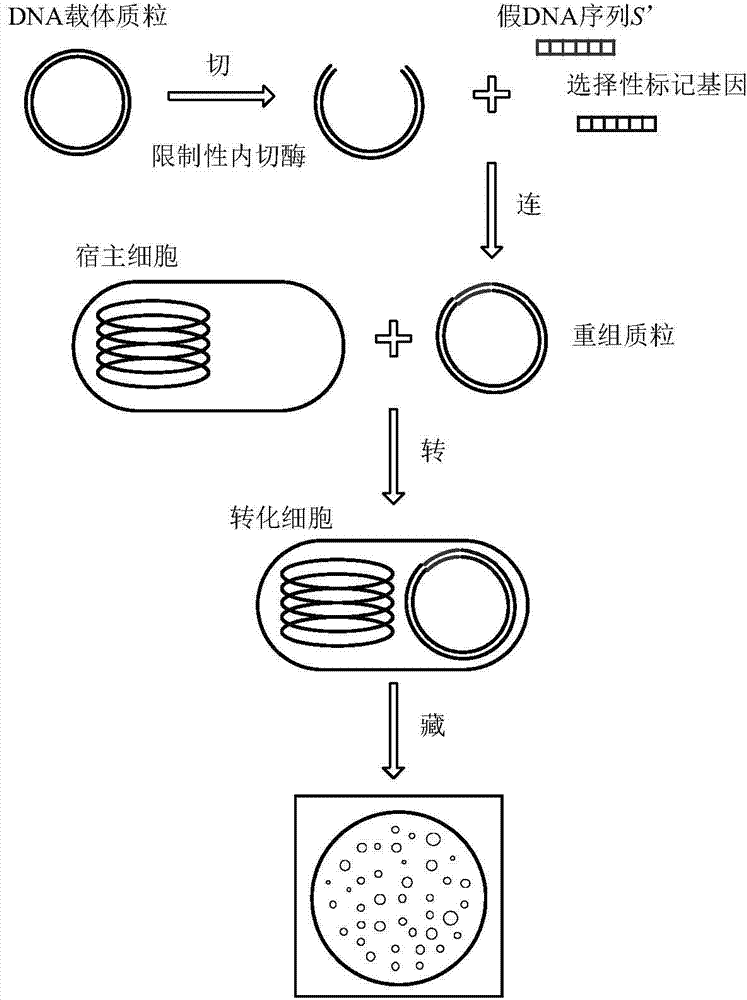
The invention provides a recombinant DNA technology based information encrypting and hiding method and an application. Firstly, a plain text is coded into a DNA sequence, preprocessing is carried out on the DNA sequence by adopting the encryption algorithm, and a pseudo-DNA segment is generated; and then the pseudo-DNA segment and a marker gene segment are connected to a DNA plasmid vector by using the restriction enzyme and the ligase, and an obtained recombinant plasmid is further hided into a germ body; finally, a cell which contains confidential information is hided into a large number of irrelevant pseudo-cells, and the hided cells can be screened out by the selective cultivation. The encrypting and hiding method is applied to the authentication and signature technology. Encrypting, hiding and transmitting of the confidential information are achieved, and the cracking difficulty of a system is enhanced.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
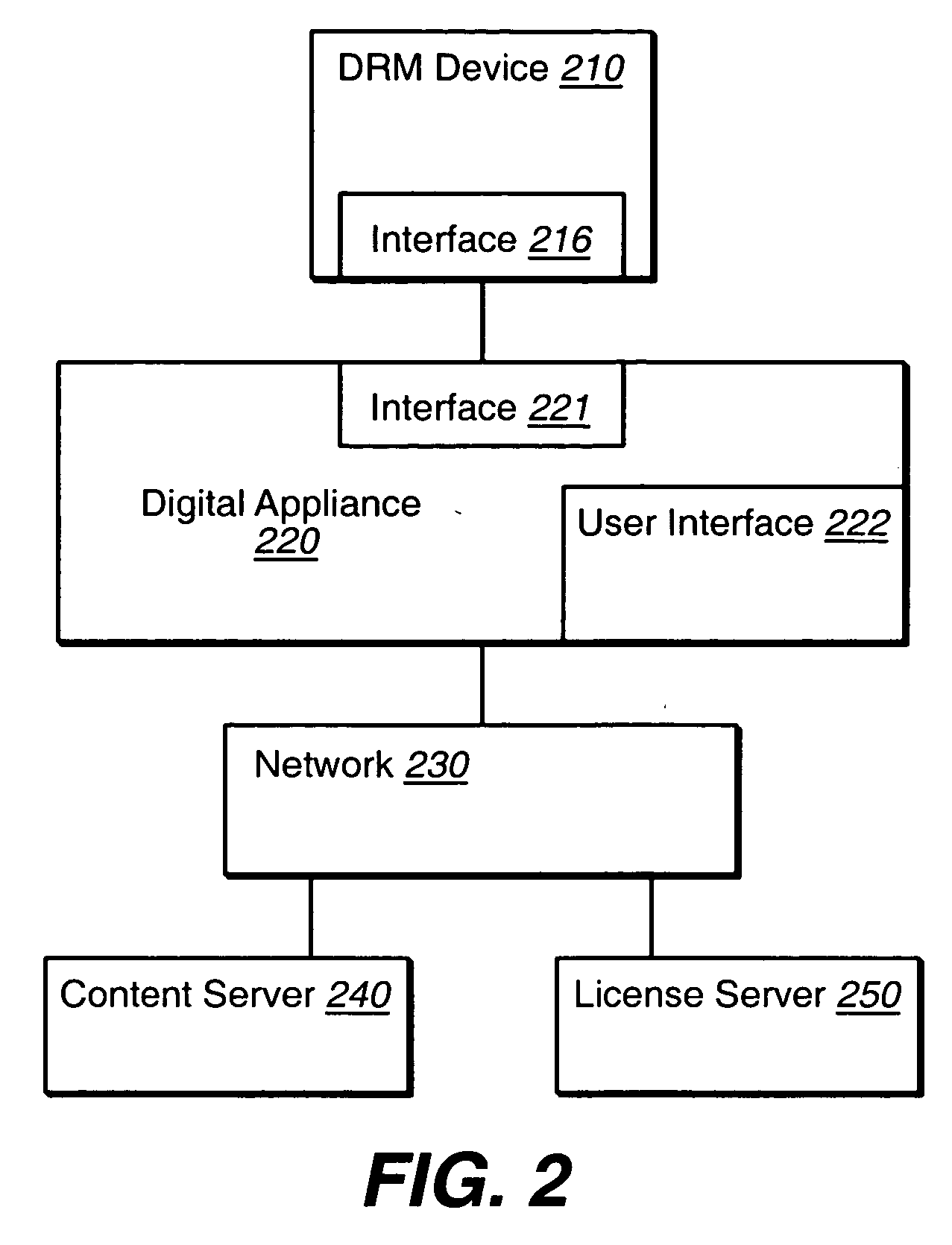
Apparatus, system and method for securing digital documents in a digital appliance
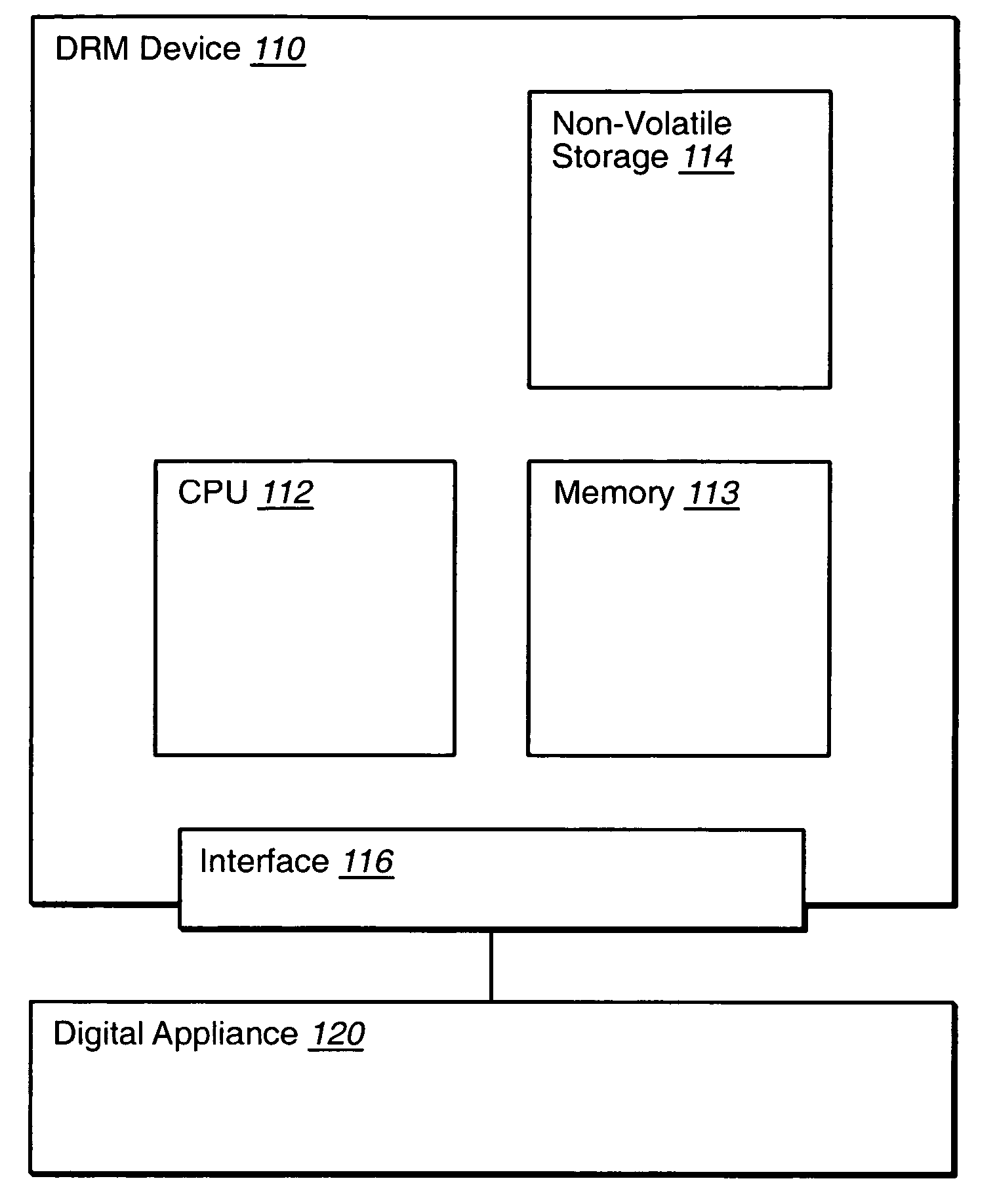
InactiveUS20060080535A1Protect environmentNot provideData processing applicationsMultiple keys/algorithms usageGraphicsWeb site
Various embodiments include an apparatus and a method to secure protected digital document content from tampering by their user, such as unauthenticated use or use violating a policy of the digital document. The digital document file can be transferred from a network node such as a web site server to a digital appliance, such as a computer, in encrypted form. The digital document file can be resident already on a device, and / or be transferred into a device that is connected to the digital appliance. The device (hereafter a DRM device) can internally store the digital document or part of the document. The DRM device may decrypt the digital document when requested to do so. The device may further format the content for usage, for example, convert text into its graphic bitmap representation. Device formatting can include sending plain text data to the digital appliance. The device may further process degradation to the resulted file, for example, reduce the resolution of the graphic representation. The digital appliance uploads the result of the processing or sections of the result of the processing for user access via the digital appliance.
Owner:SANDISK TECH LLC
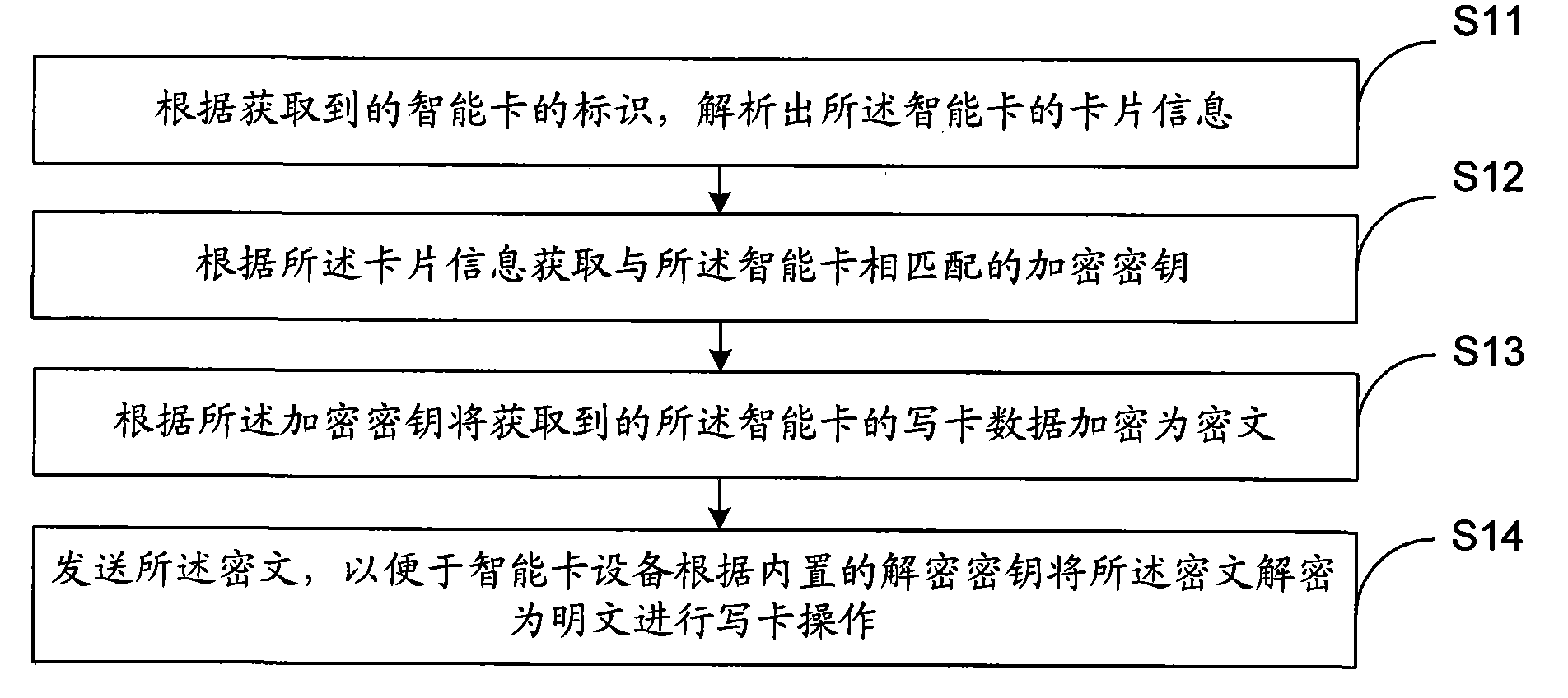
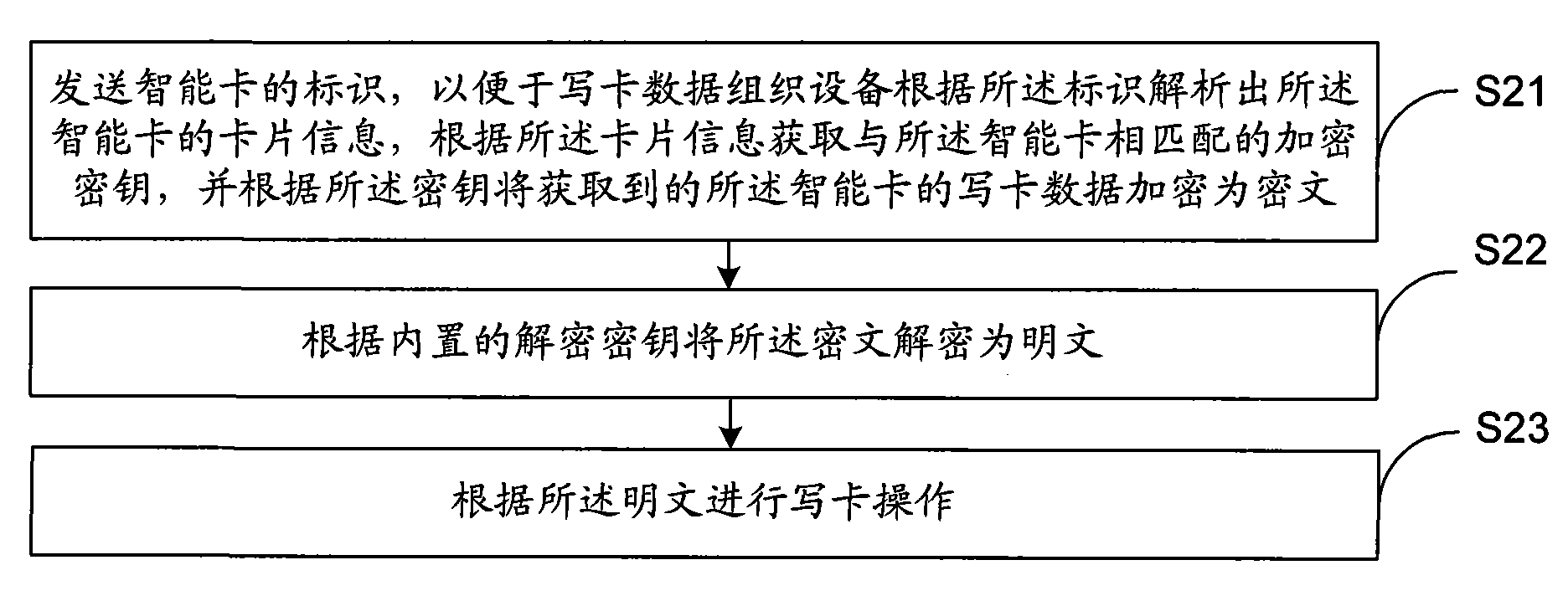
Intelligent card and card writing method, equipment and system thereof
ActiveCN101667240AAvoid dependencyReduce management costsDigitally marking record carriersKey distribution for secure communicationCiphertextSmart card
The invention discloses an intelligent card and a card writing method, equipment and a system thereof, relating to the field of intelligent cards, and aiming to enhance the information safety in the card writing process of the intelligent card. The card writing method of the intelligent card comprises the following steps: analyzing the card information of the intelligent card according to an acquired mark of the intelligent card; acquiring an encryption key matching with the intelligent card according to the card information; encrypting the acquired card writing data of the intelligent card to a cipher text through the encryption key; and transmitting the cipher text so that the intelligent card deciphers the cipher text to a plain text through the encryption key for card writing operation. The invention is applied to the card writing operation of the intelligent card.
Owner:BEIJING WATCH DATA SYST
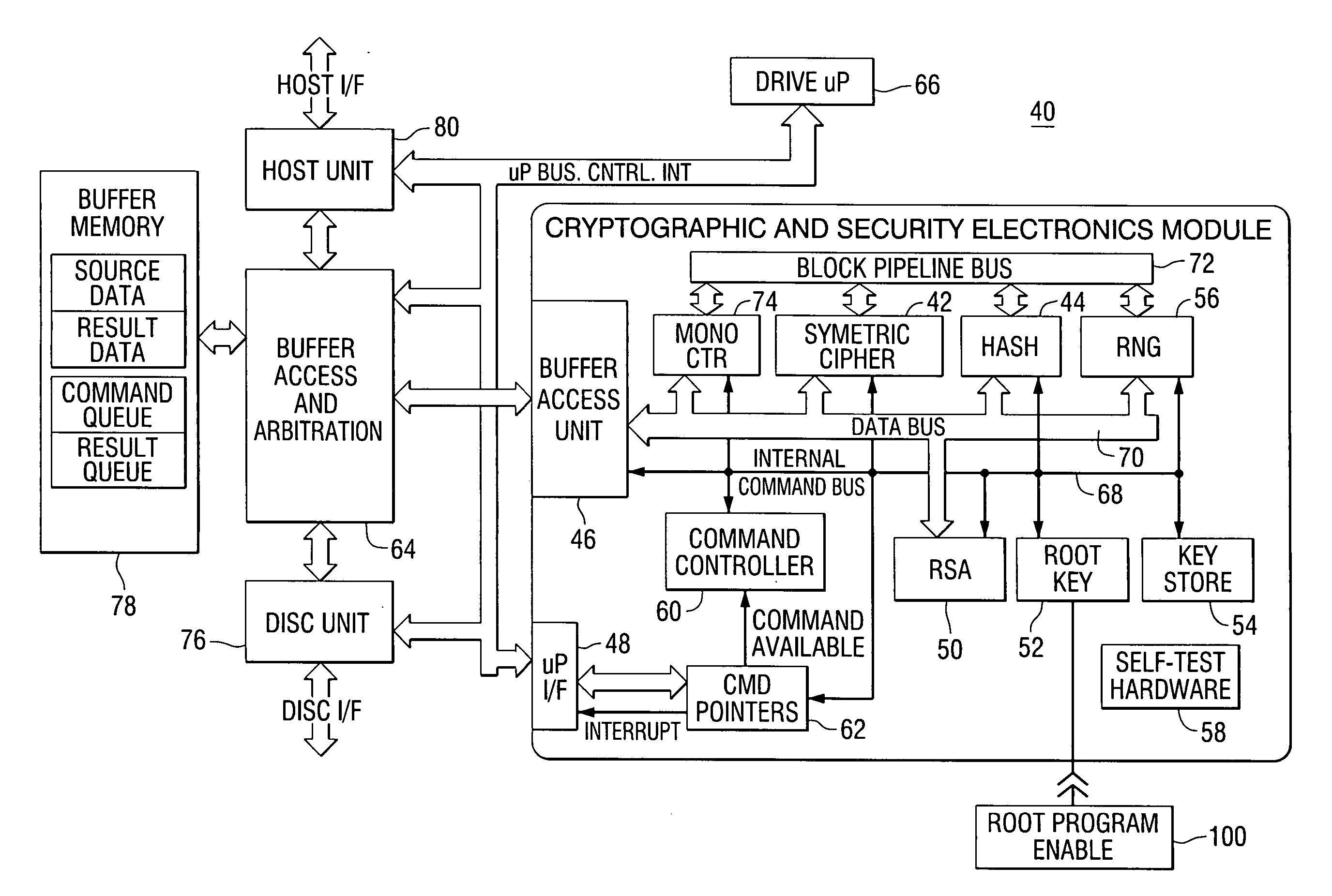
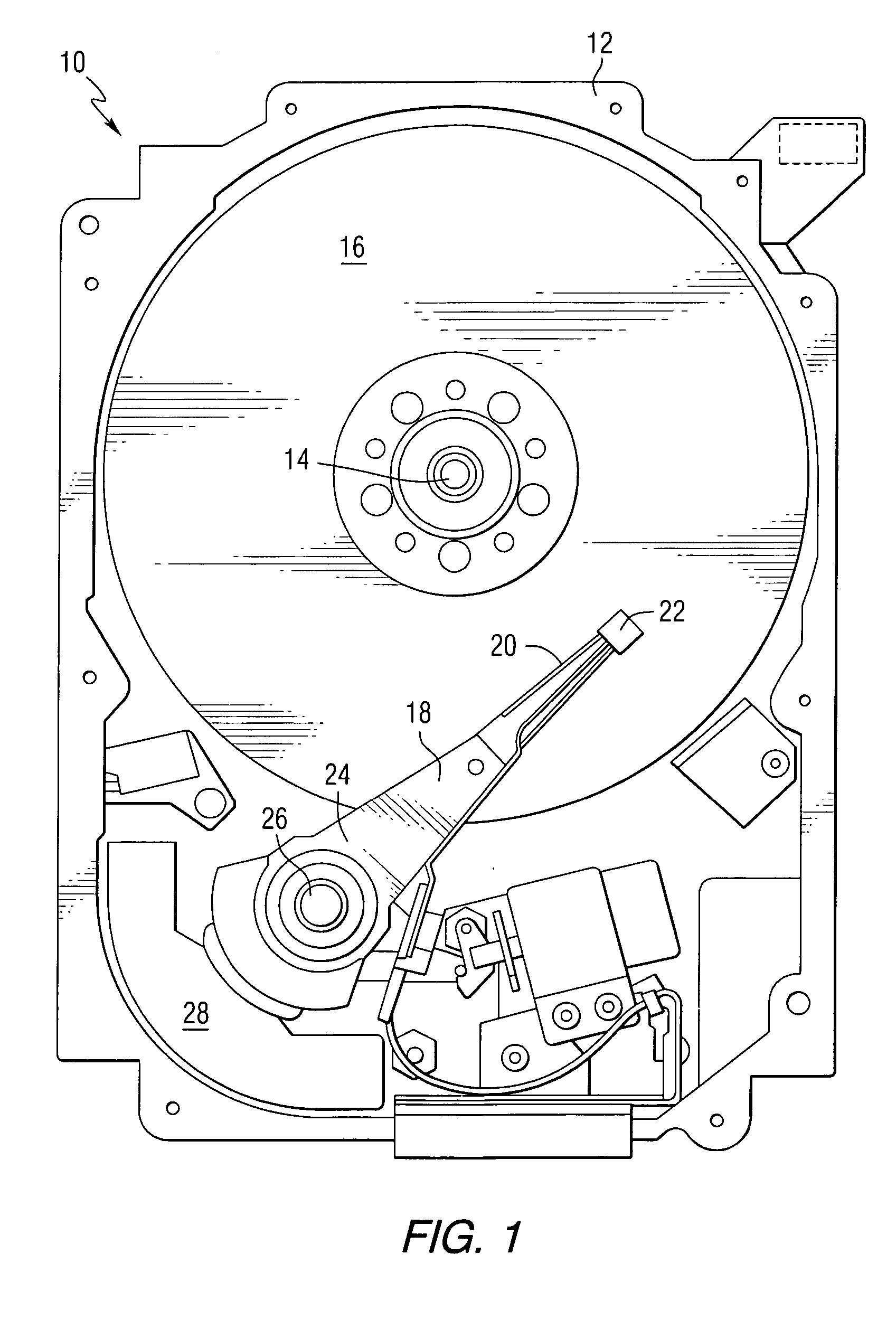
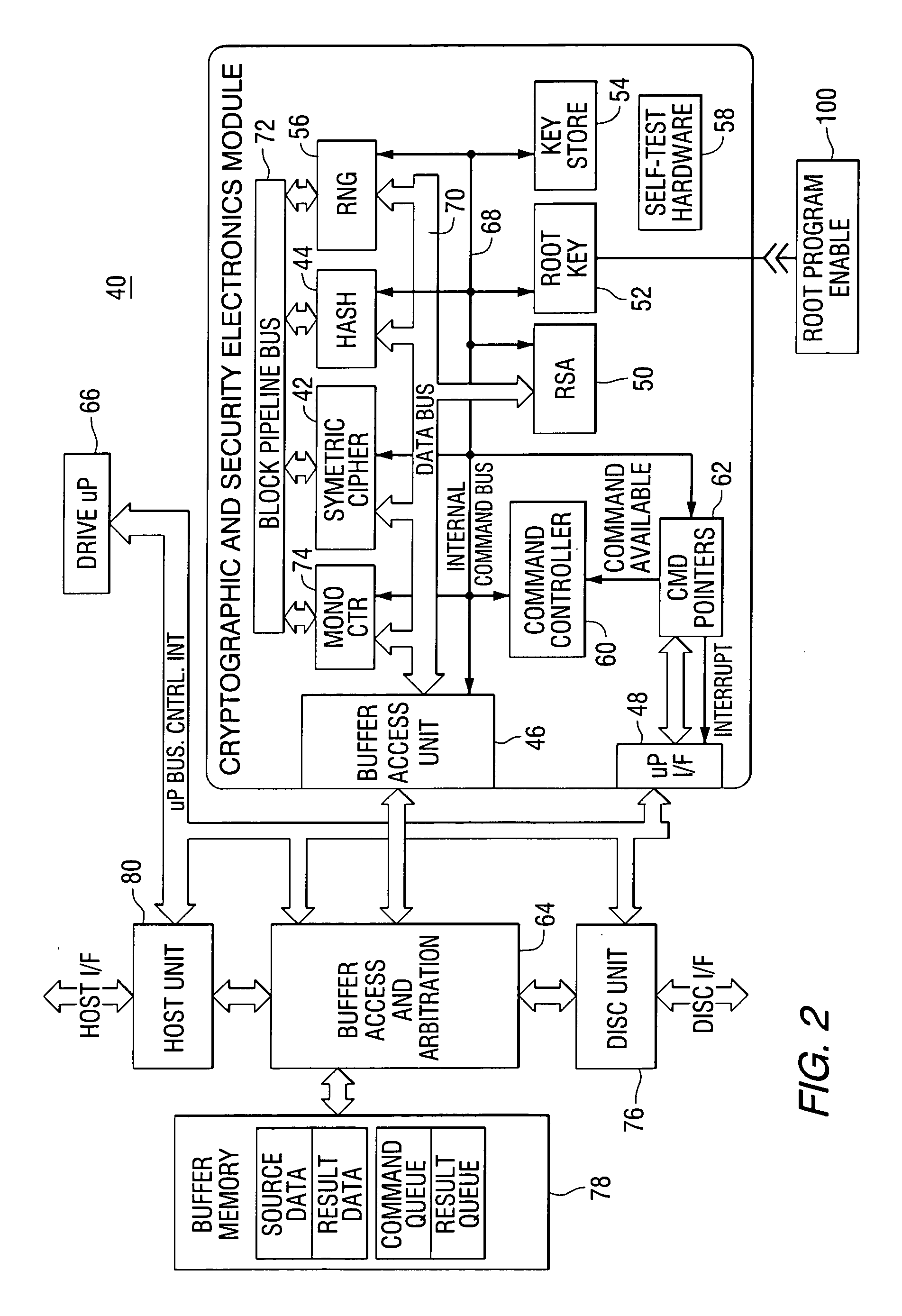
Secure disc drive electronics implementation
InactiveUS20060198515A1Internal/peripheral component protectionSecret communicationVisibilityComputer hardware
A data storage device comprises a storage medium and a controller including a cryptographic and security module for encrypting and decrypting data to be stored in and retrieved from the storage medium. The cryptographic and security module includes an interface for receiving commands from a processor, a secret root key, an encryption and decryption unit for encrypting and decrypting data using the secret root key, a buffer access unit for receiving encrypted data from and sending encrypted data to a memory, and a command controller for controlling the encryption and decryption unit and the buffer access unit in response to commands from the processor. The command controller implements mechanisms for movement of intermediate results within the cryptographic and security module to protect intermediate and plain text results from visibility outside the cryptographic and security module.
Owner:SEAGATE TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com